Patents
Literature
34 results about "Border Security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Border Security may refer to: Border Security: Australia's Front Line, Australian television show Border Security: Canada's Front Line, Canadian television show
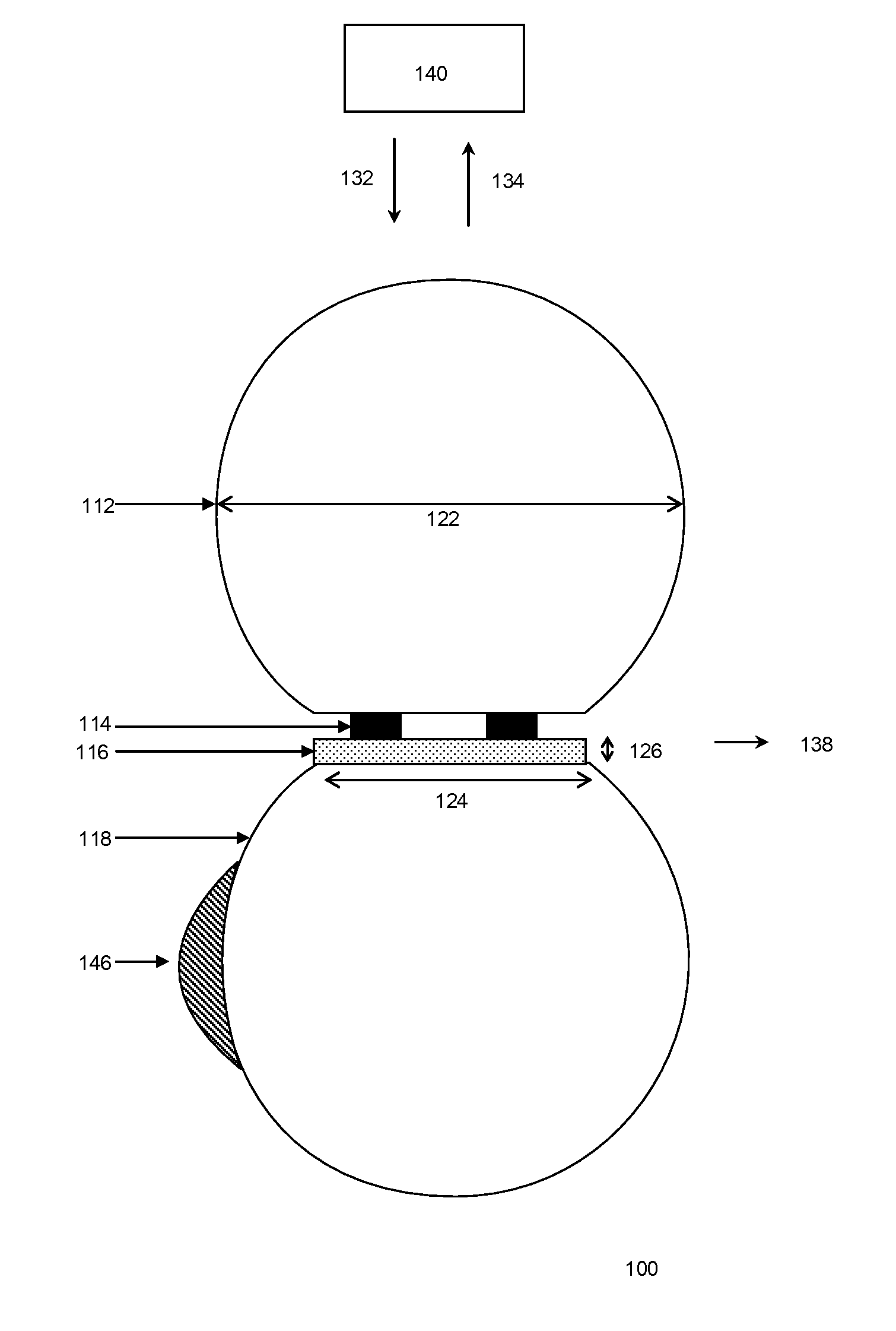
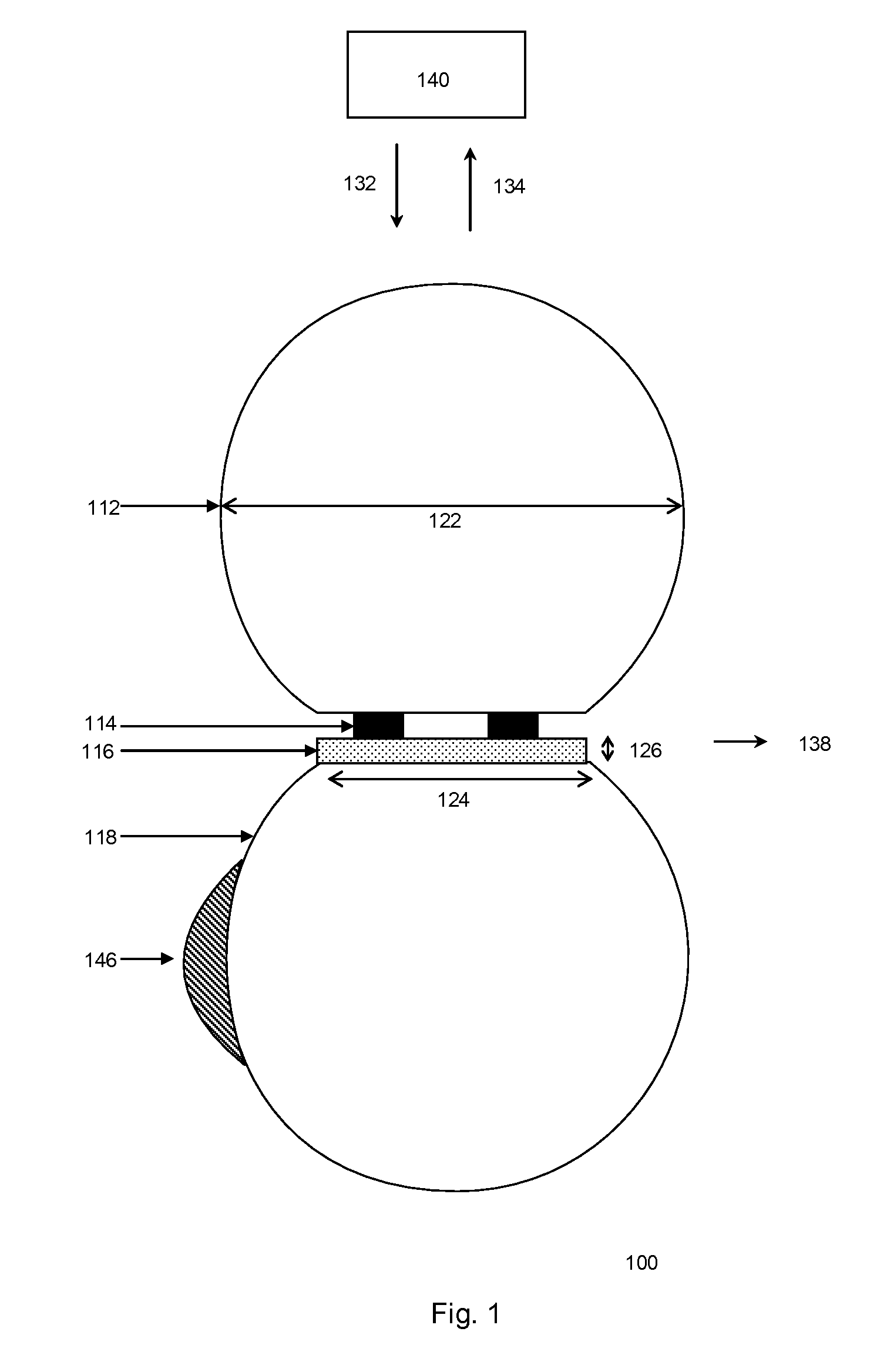
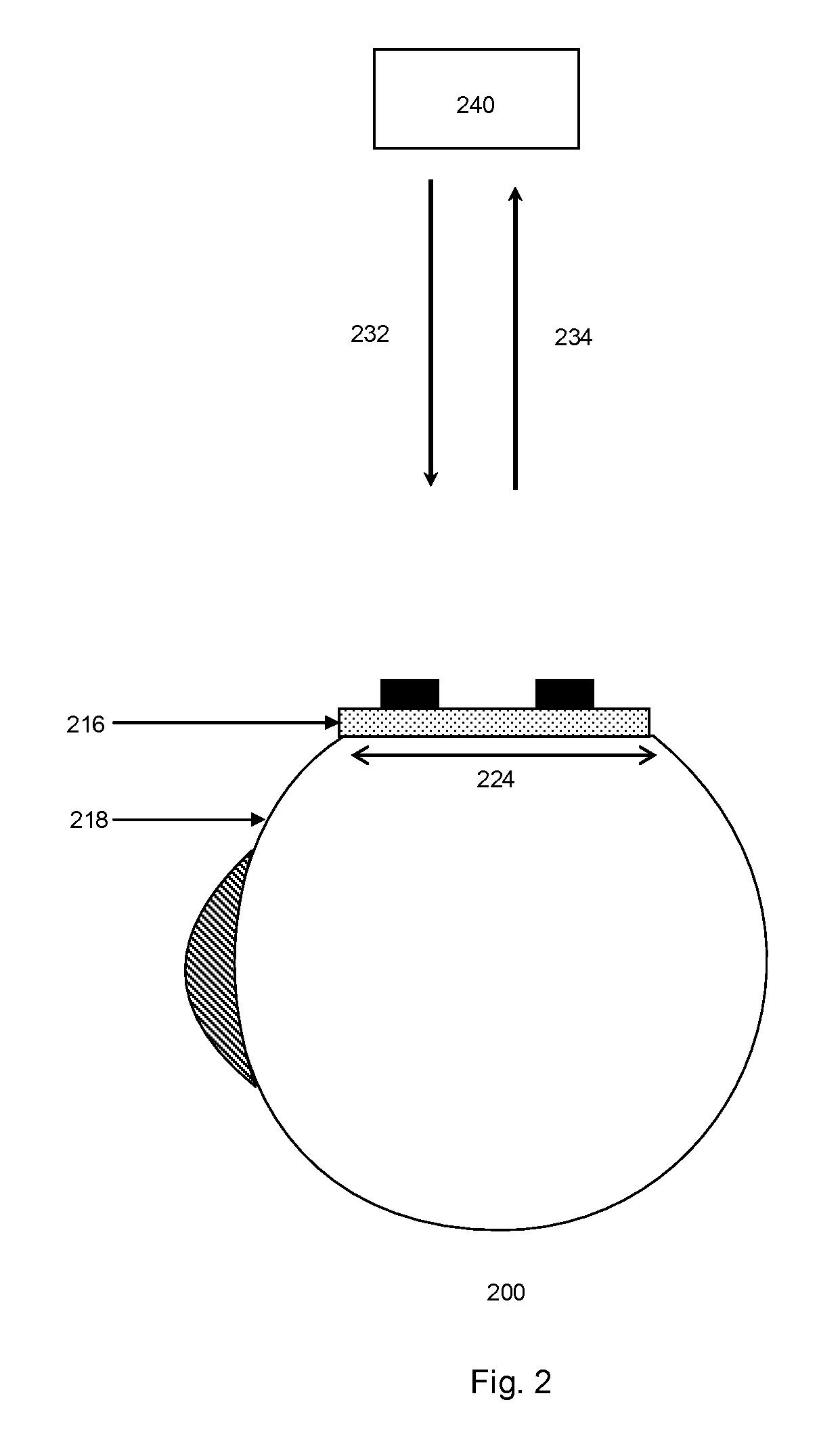
Monitoring device and security system
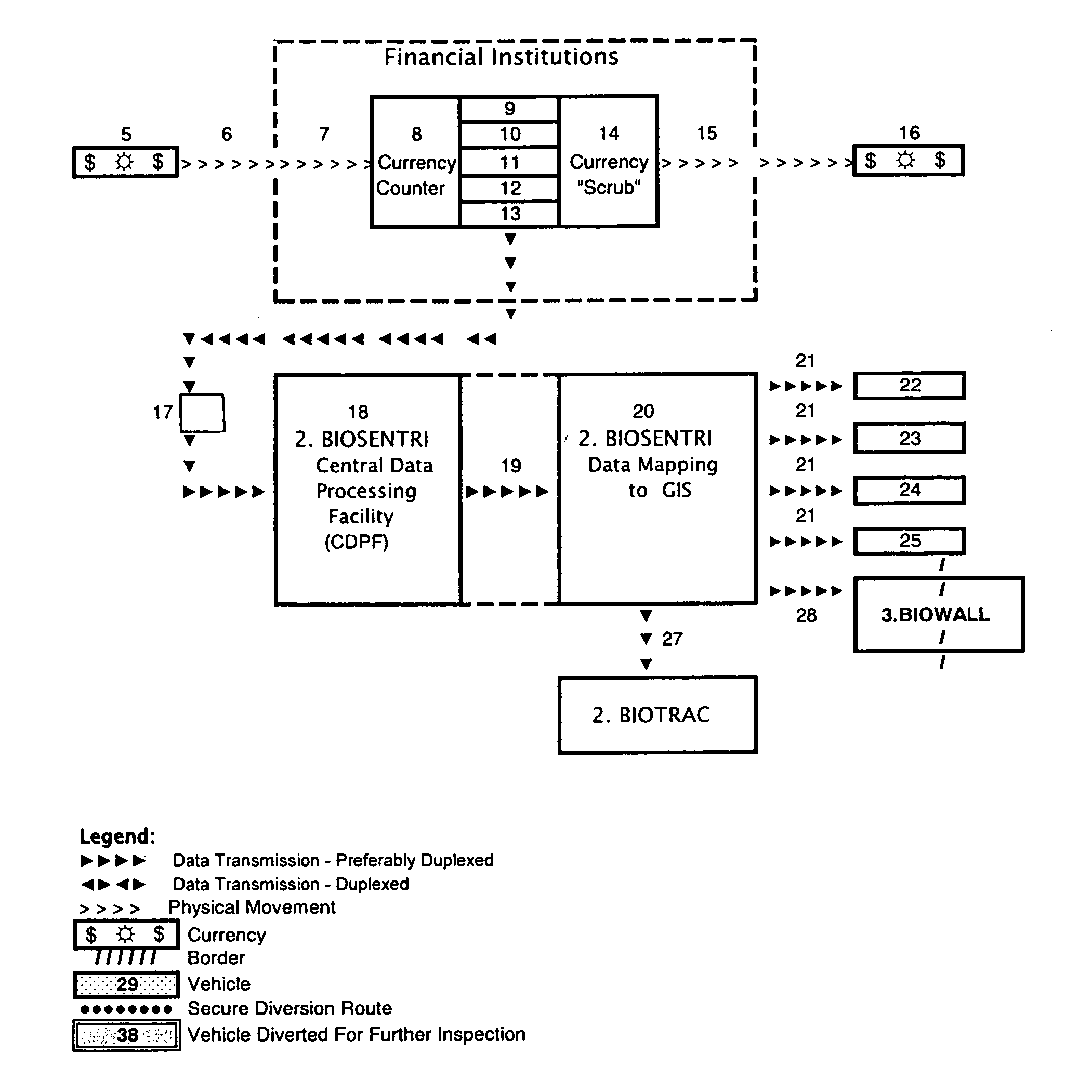
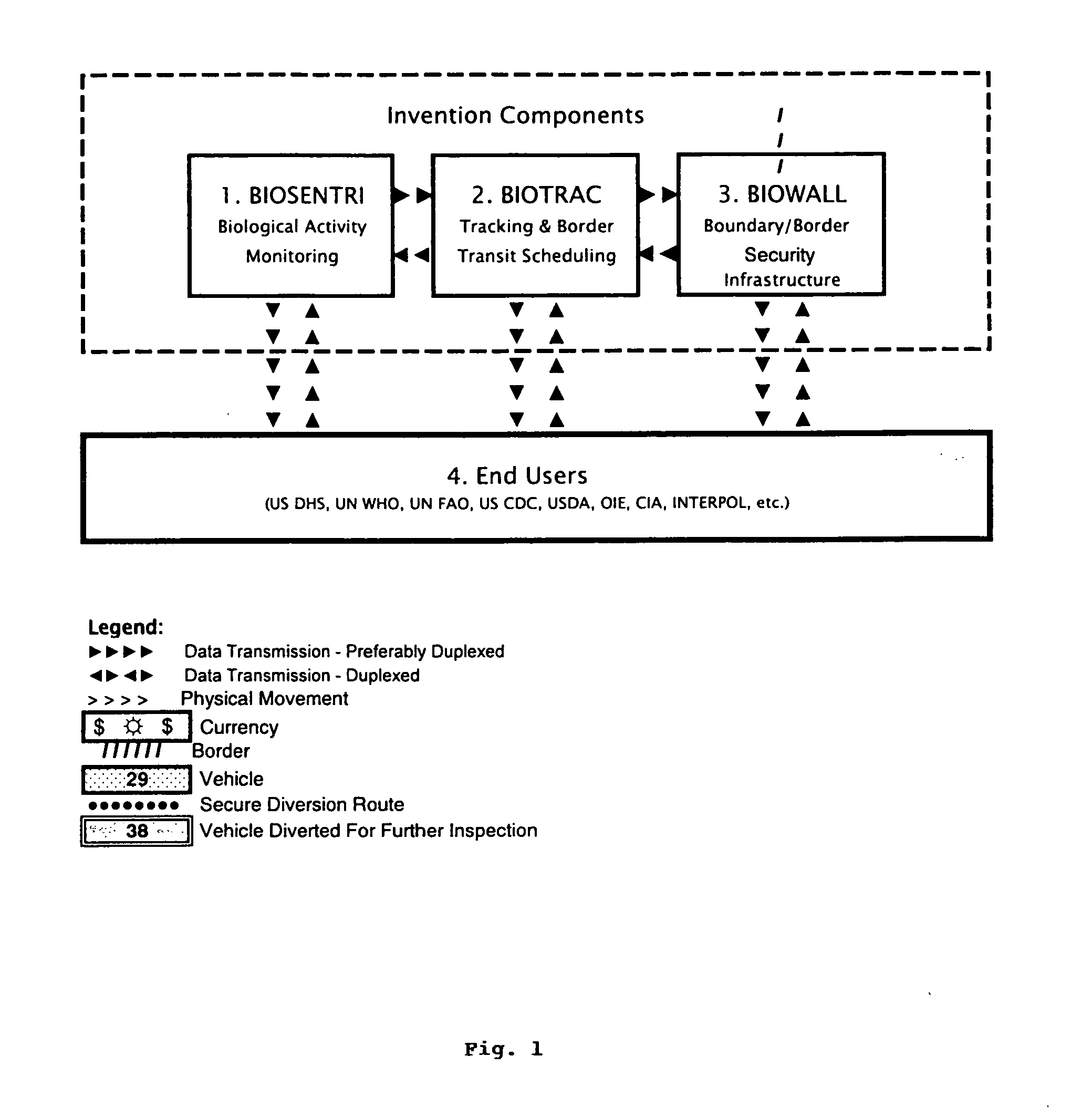
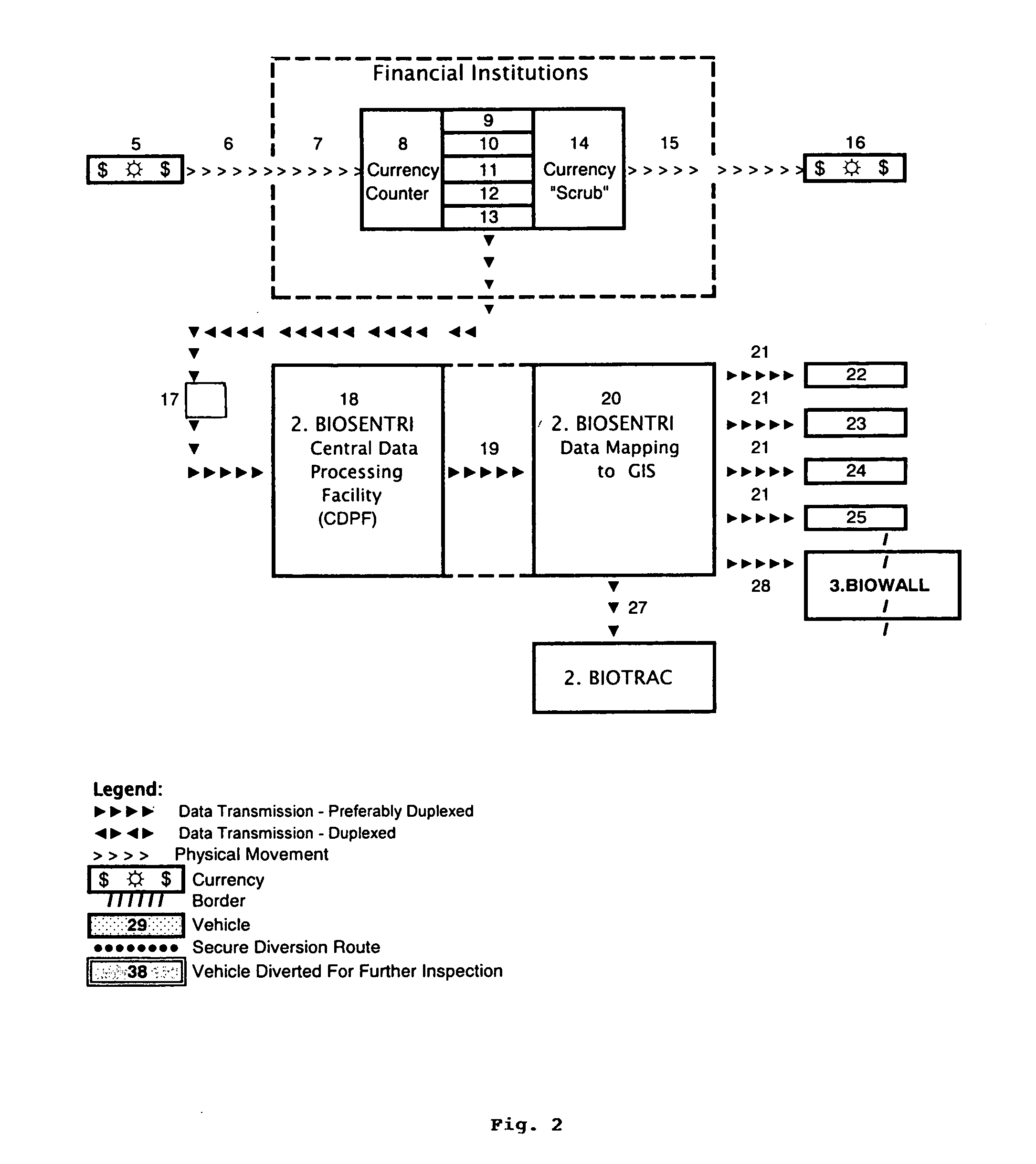
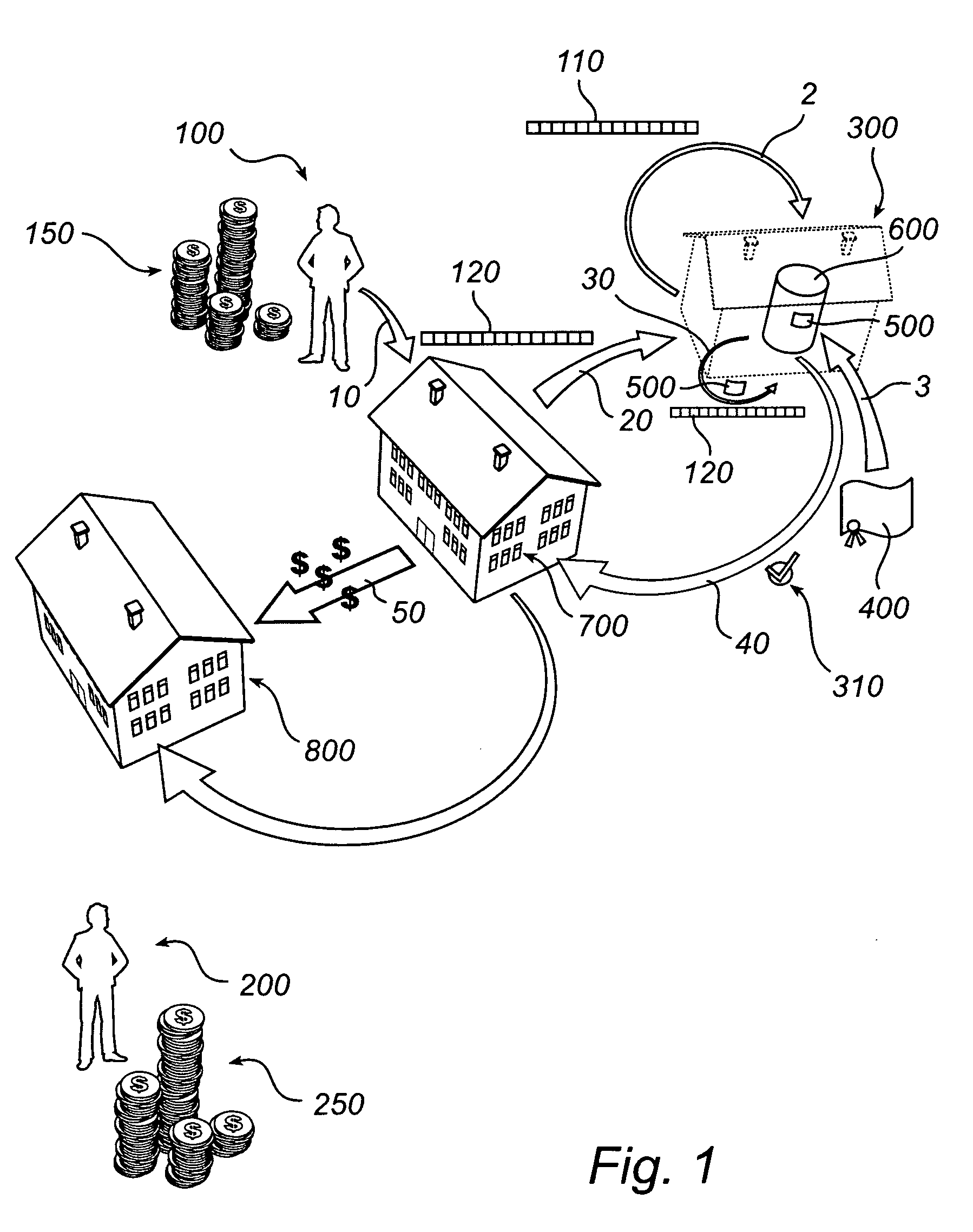
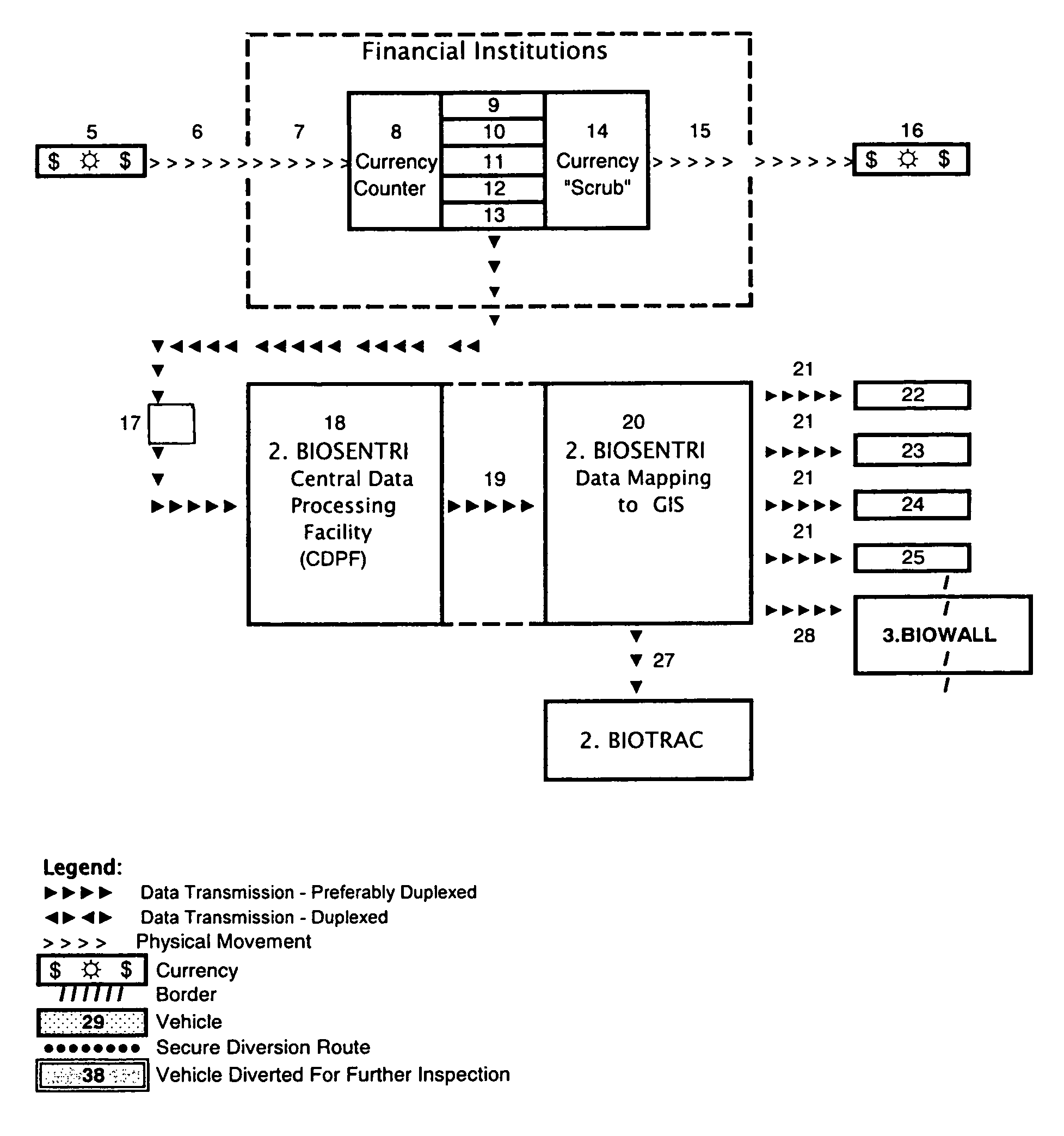
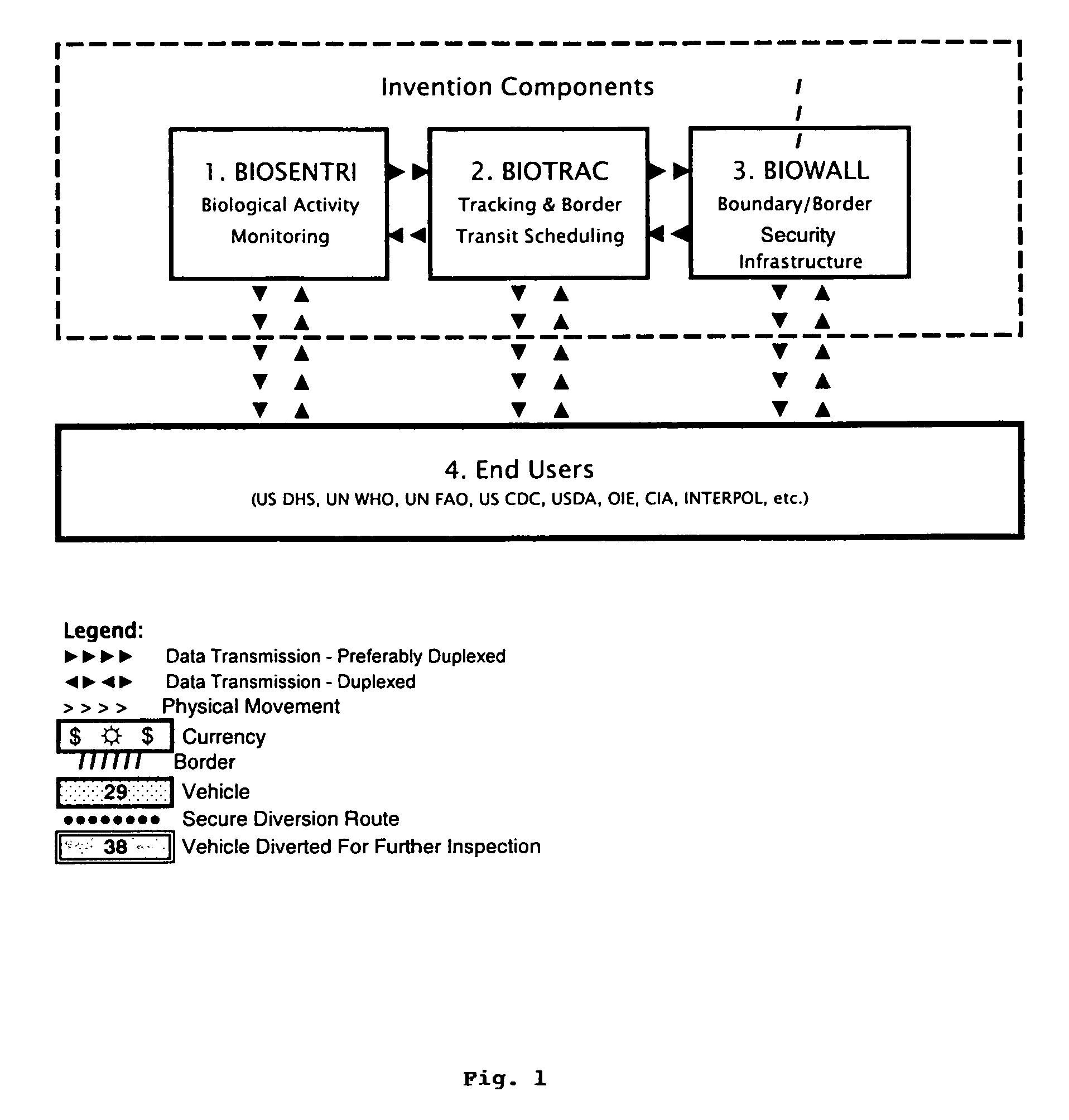
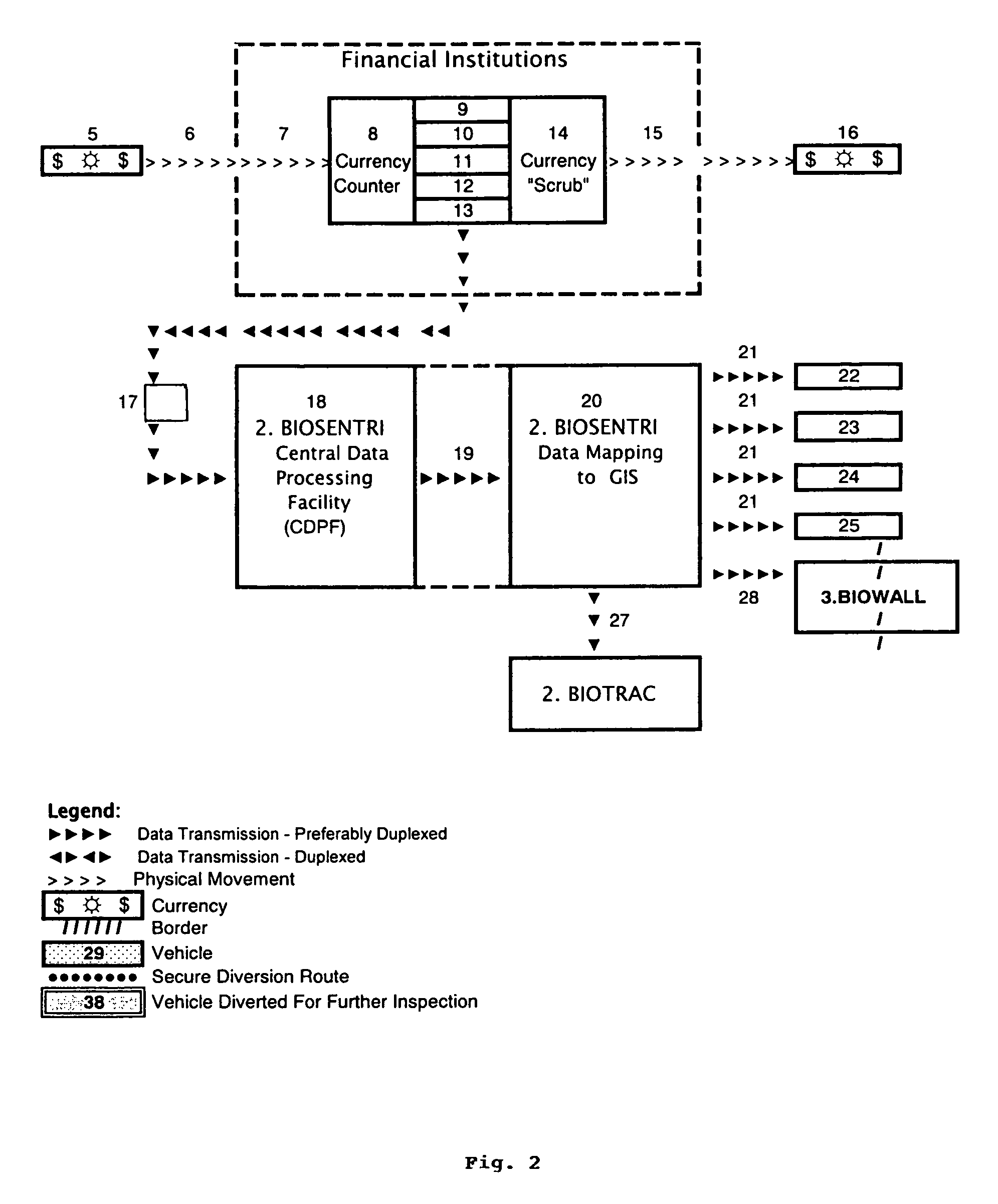
The present invention provides for an integrated global biological activity detection, traffic tracking and scheduling, and boundary / border security system. Detection apparatuses of the system are preferably placed in a stream of currency such as in financial institutions and other sites of currency exchange, and are also placed in or about transportation vehicles and linked into a data collection, analysis, and graphical information system to provide early warning for security activities. Detection apparatuses located in and about transportation vehicles are combined with a system for routing vehicles into security corridors and with a system of notification, scheduling, and monitoring to enhance the capacity of authorities to insure security and efficient trade movement particularly as it approaches boundaries and borders.
Owner:ARROWHEAD CENT
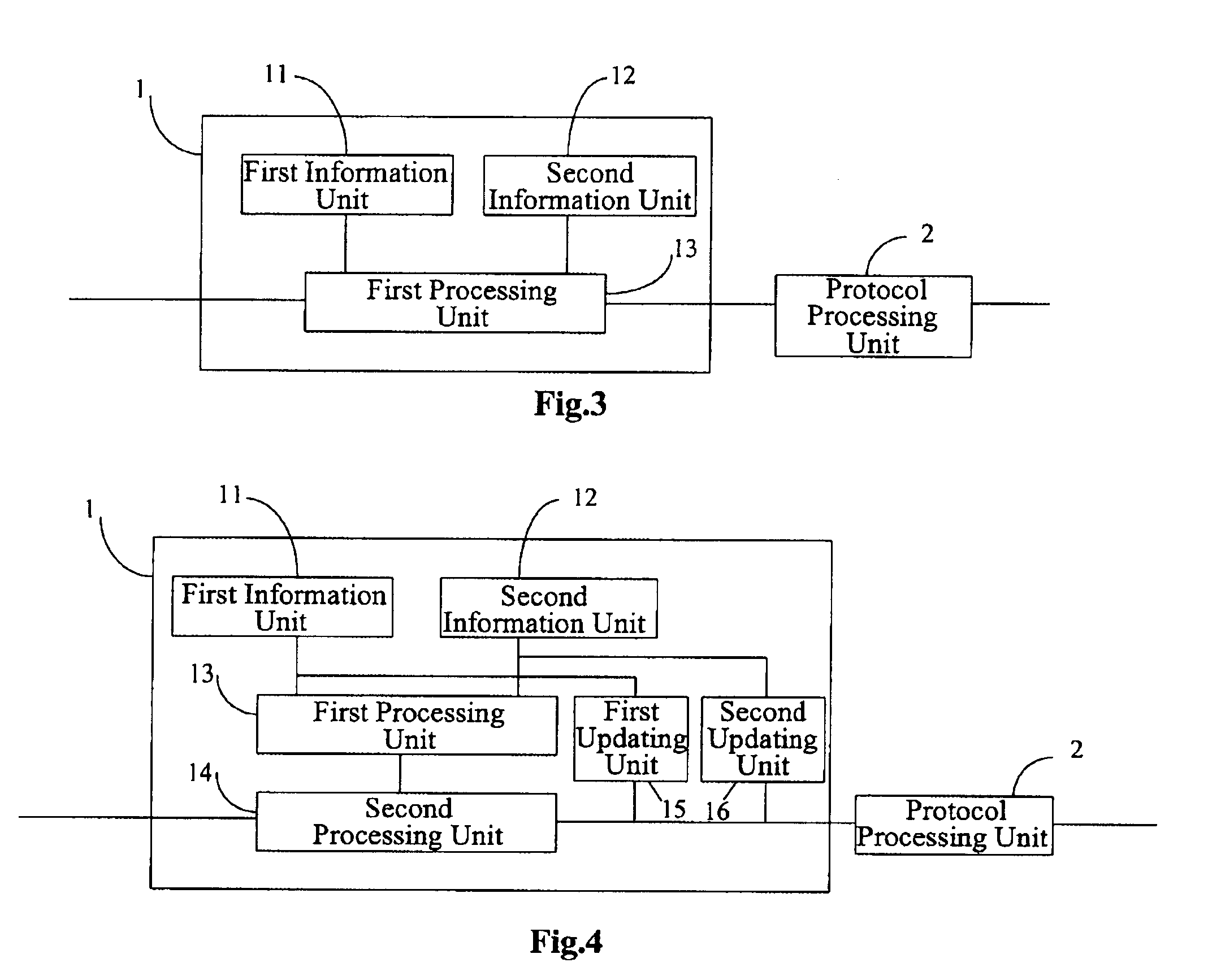
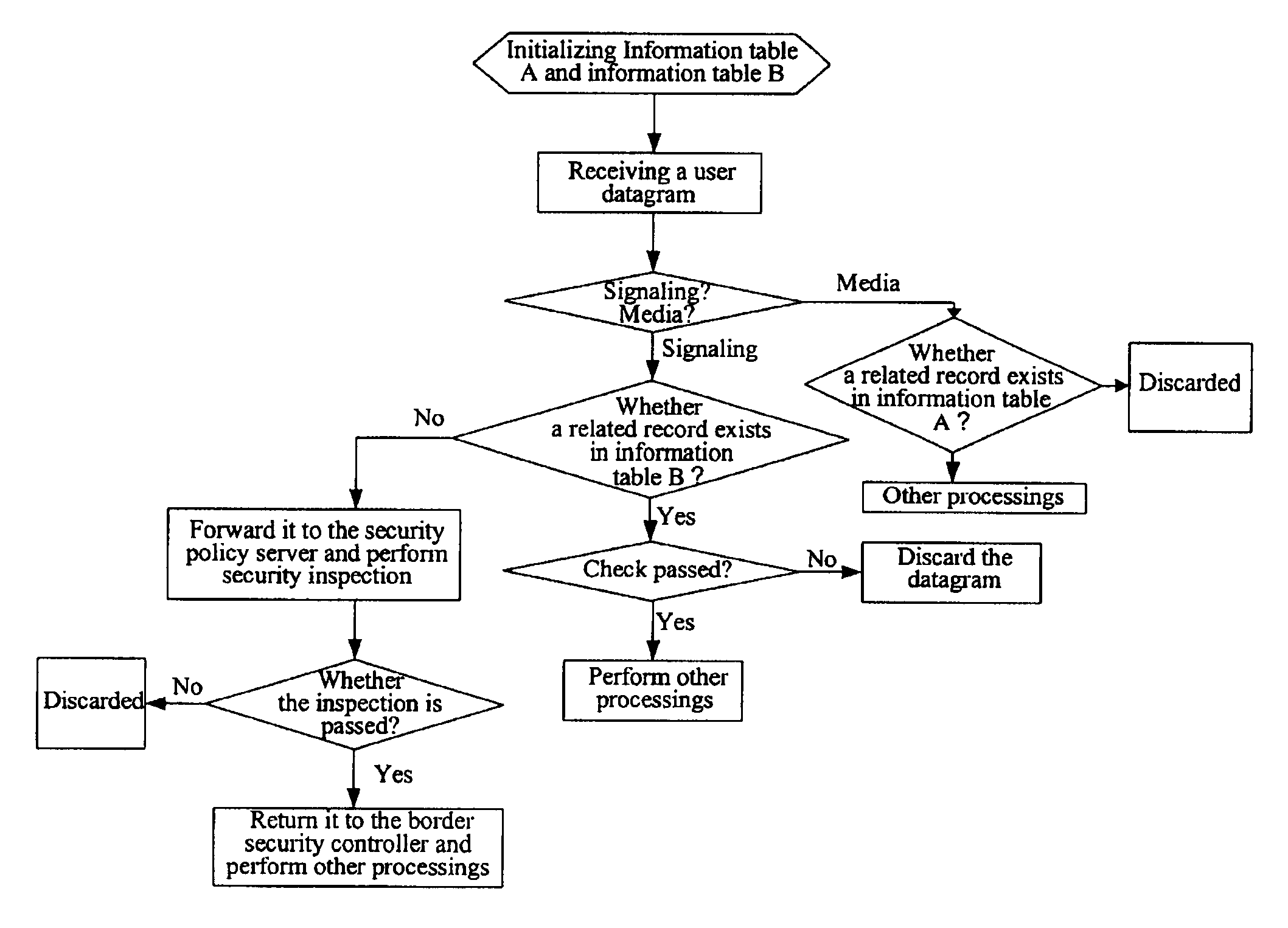
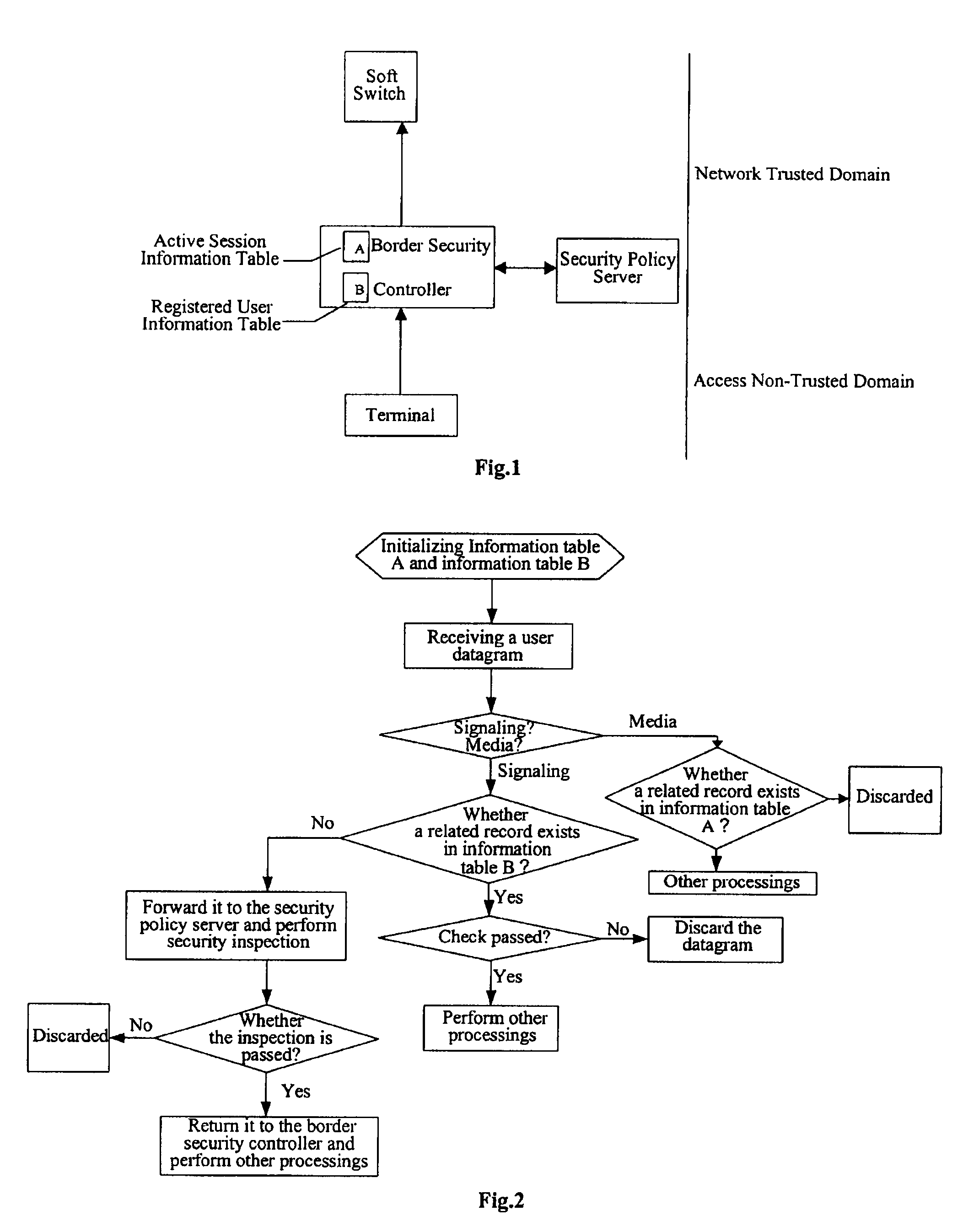
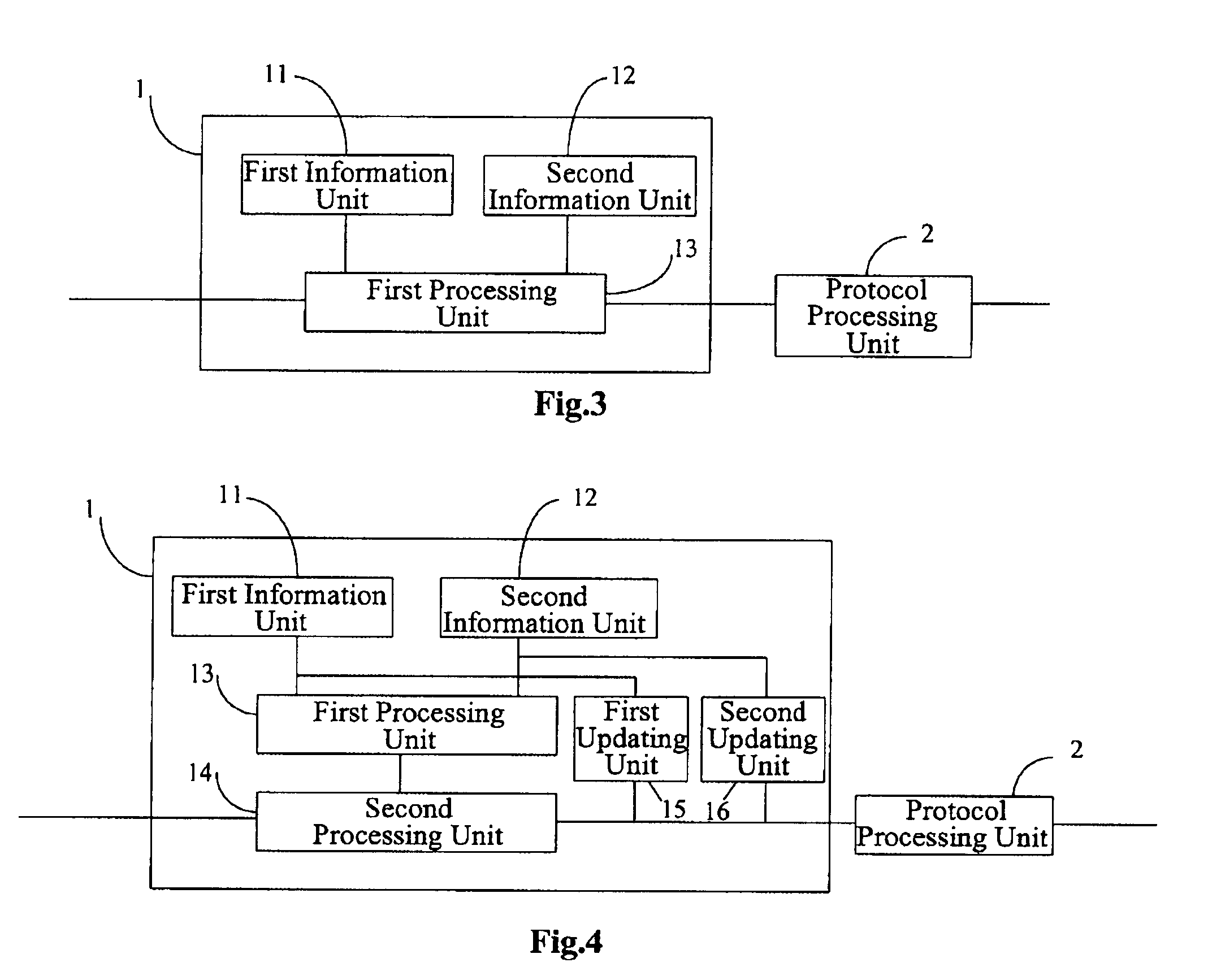
Method, device and security control system for controlling communication border security
ActiveUS20080098473A1Effective possibilityBlocking in networkMemory loss protectionError detection/correctionProtocol processingControl communications
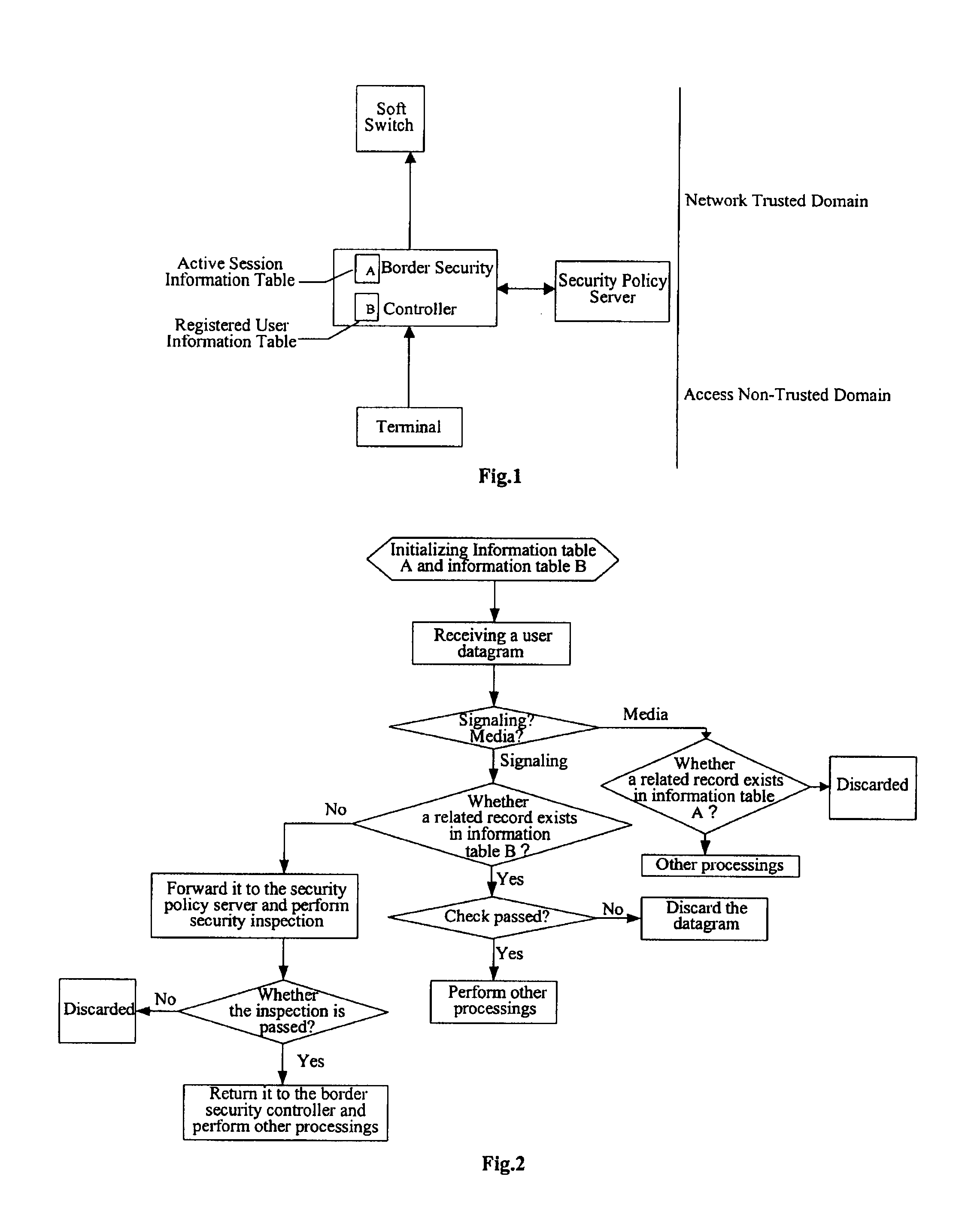
The present invention provides a method, a device and a system for controlling VoIP border security. The system includes: a border security controller, which includes two dynamic information tables, an active session information table and a registered user information table, acting as the basis of security control; and a security policy server, in communication with the border security controller, adapted to provide a security policy to the border security controller and check the security of a signaling packet forwarded by the border security controller. The border security control system first checks the security and processes the packets of a user datagram received according to the active session information table and the registered user information table, and allows a packet which passed the security processing to pass, and then performs protocol processing on the media packet and signaling packet which are allowed to pass.
Owner:HUAWEI TECH CO LTD
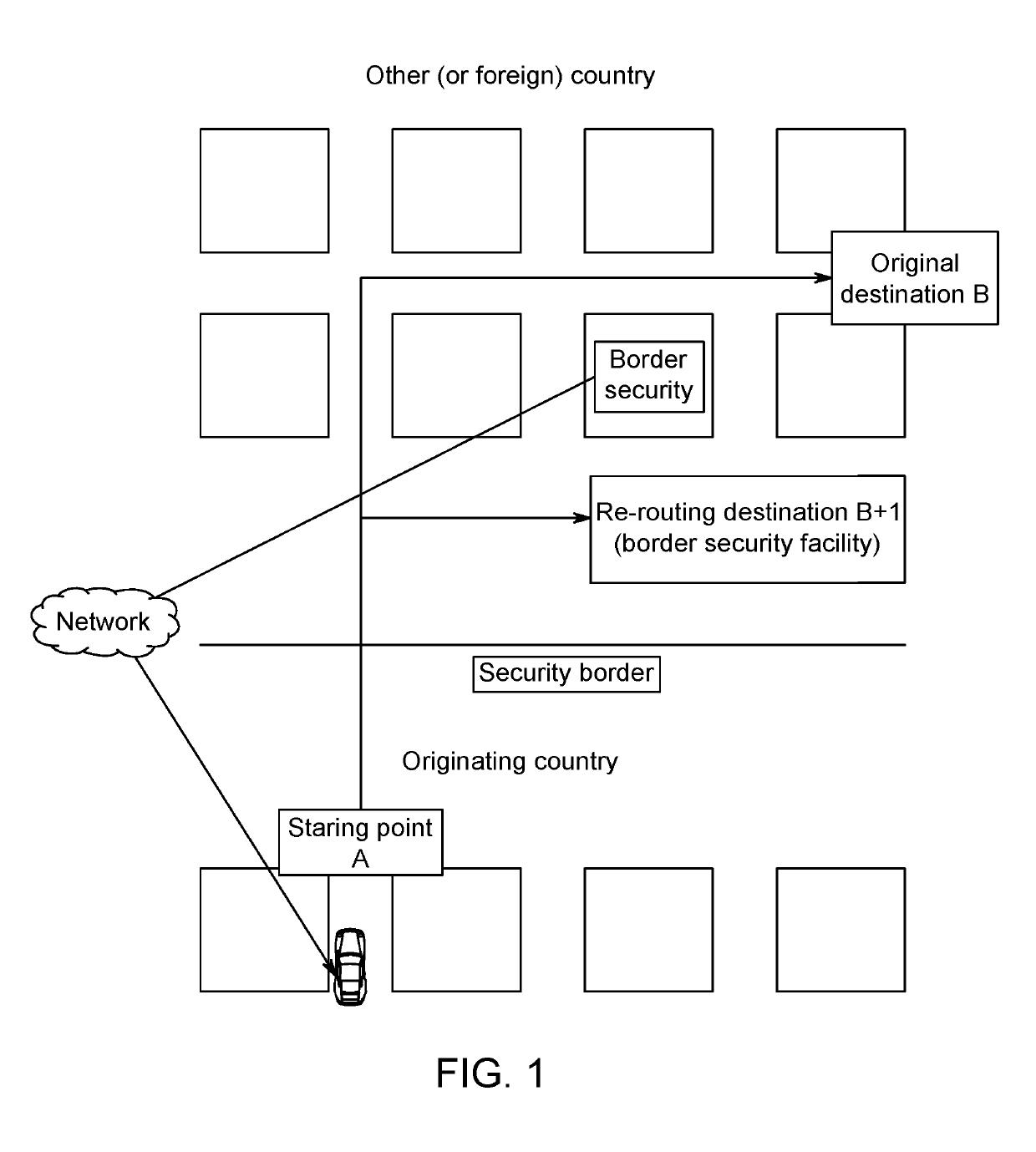
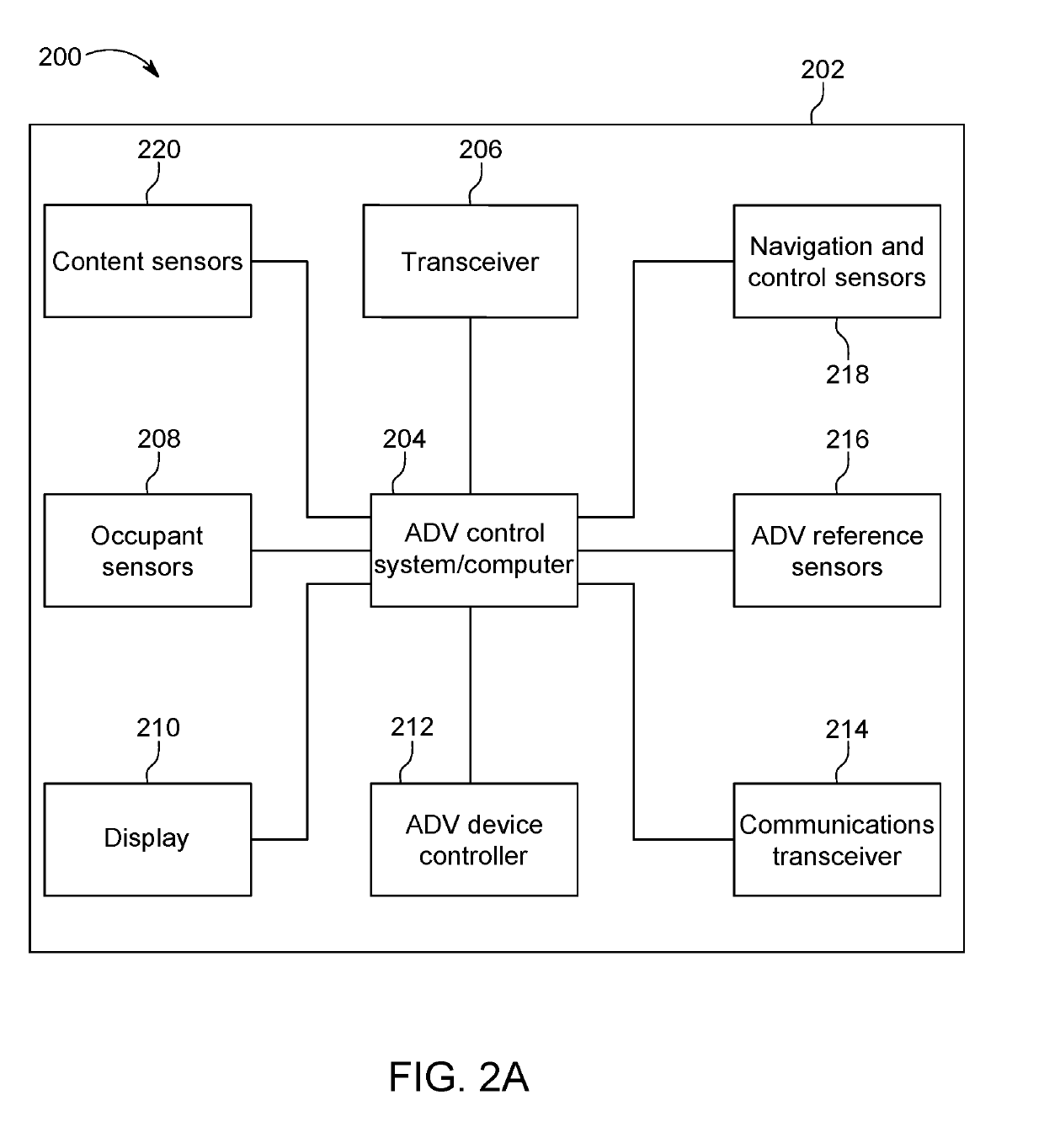
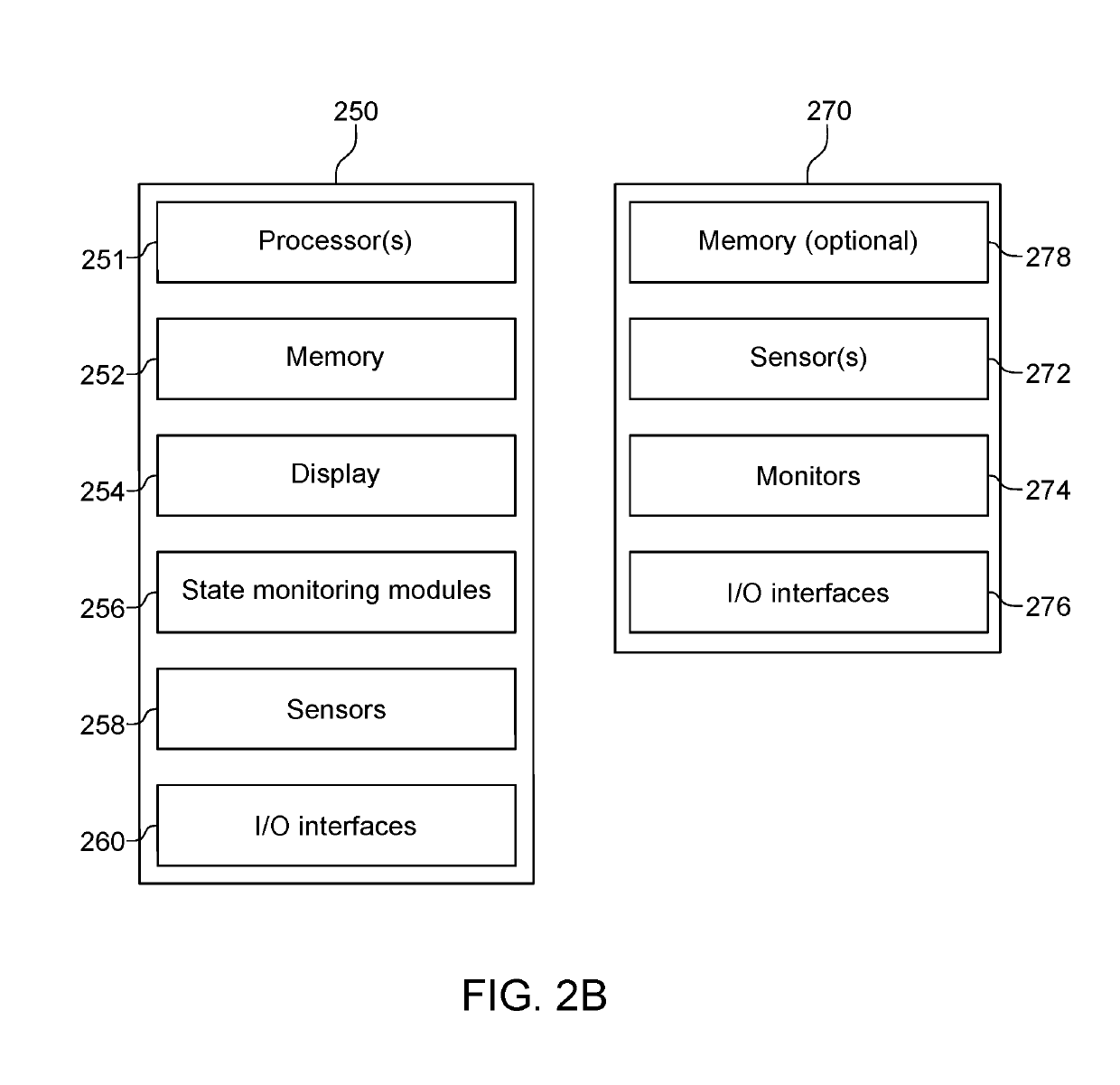
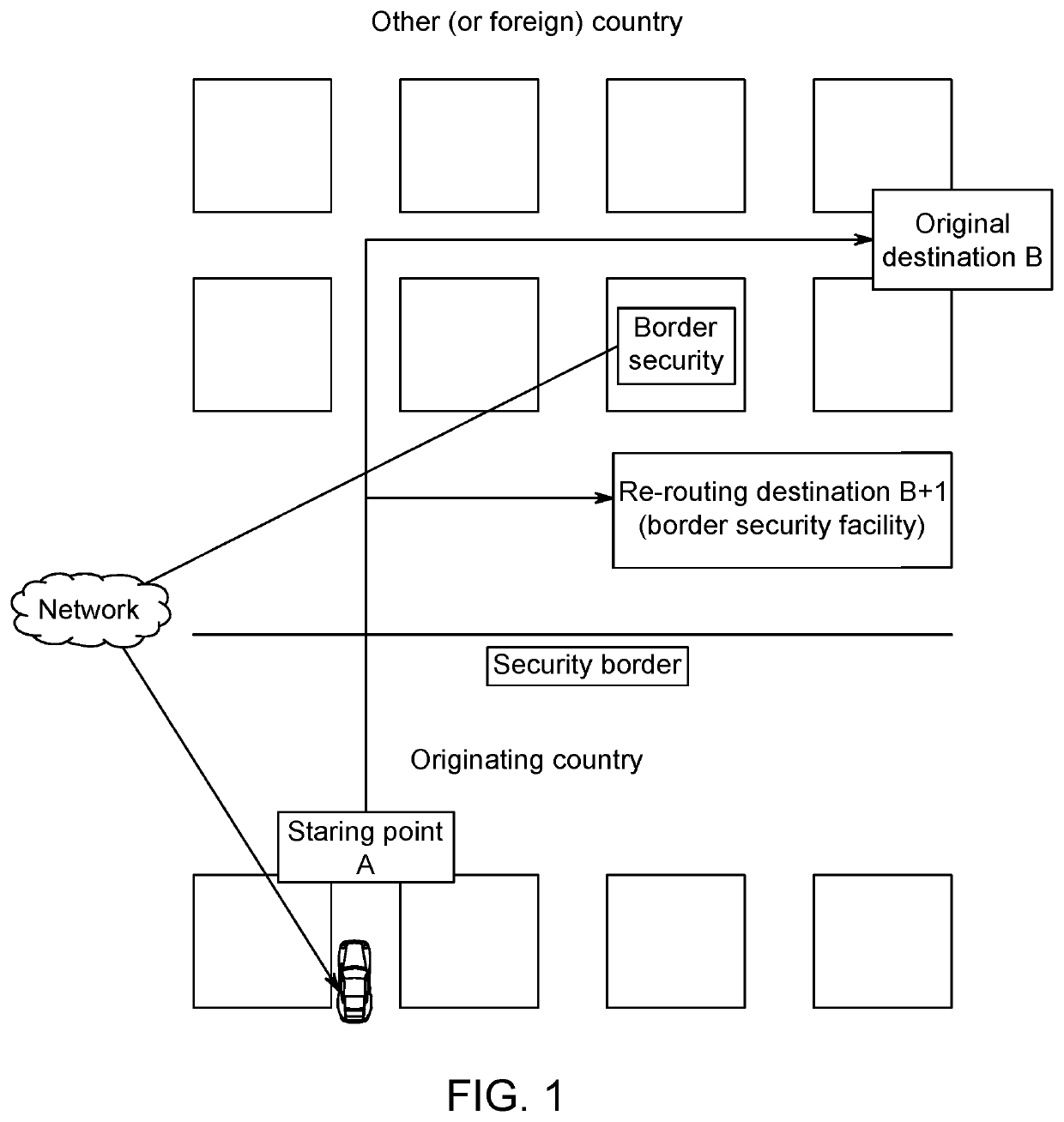
Re-routing autonomous vehicles using dynamic routing and memory management for border security purposes
ActiveUS20190293437A1Assisted identificationInstruments for road network navigationData processing applicationsOn boardControl system
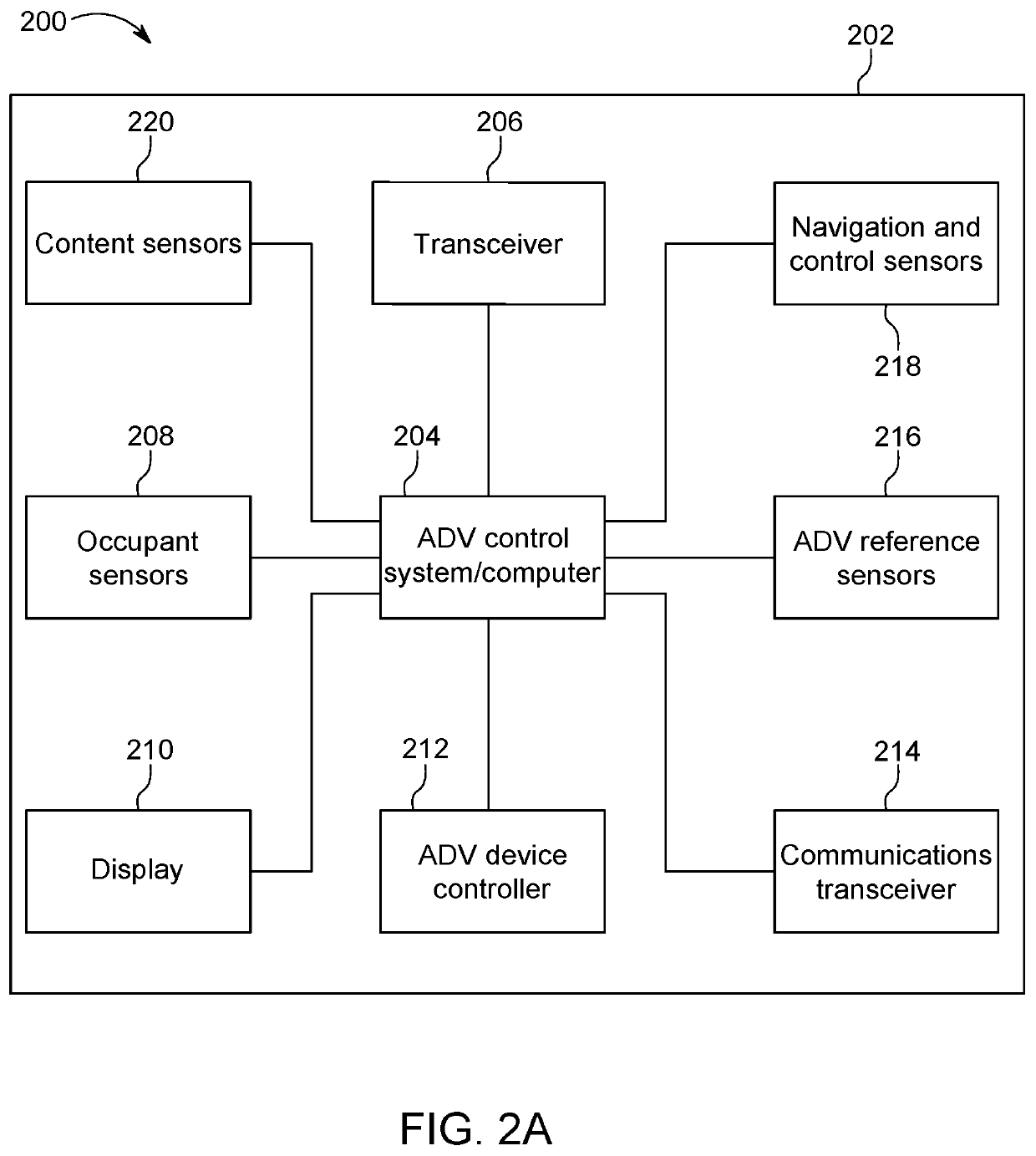
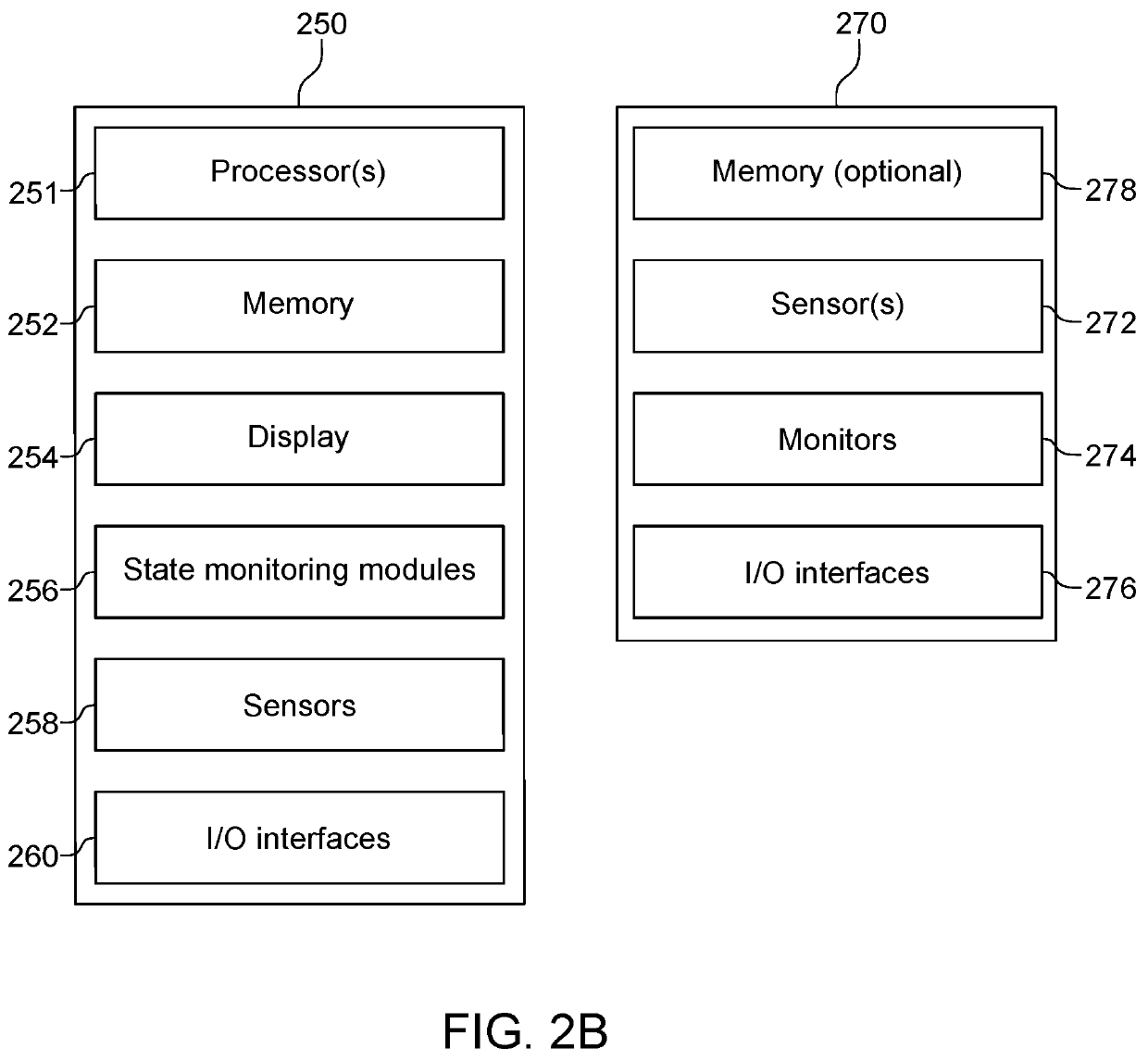
The invention relates to a system and method for navigating an autonomous driving vehicle (ADV) that utilizes an-onboard computer and / or one or more ADV control system nodes in an ADV network platform. The on-board computer receives physiological and ADV occupant identification sensor data concerning one or more occupants occupying an ADV, sensor data concerning the items being transported within the ADV, and information concerning the ADV itself to aid border security agencies in protecting their respective borders and territories (e.g., international borders, security zone borders, geographical borders, etc.). The relevant border agency can receive certain information over a network concerning one or more ADVs and make a determination if a heightened security screening should be requested. In response to a request, the on-board computer automatically initiates a dynamic routing algorithm that utilizes artificial intelligence to re-route the ADV to a predetermined destination, for example a border security facility.
Owner:MICRON TECH INC
Smart sensors for perimeter and border security
InactiveUS7893960B1Improve detection rateTelevision system detailsColor television detailsLand basedHigh probability
A border or perimeter is protected from intruders, such as illegal immigrants, terrorists with WMD or smugglers of drugs. The method comprises a detection and communication processing system capable of a high probability of detection and low probability of false positives. The system includes land-based sensor particles and sensitive airborne or land-based camera processing units. The sensors are sown over key border or perimeter landscape areas and are activated by specific pressure levels characteristic of the weight of transiting intruders whereby the sensors emit characteristic optical signals. Specific emitted indicators detect people, vehicles, or particular animals.
Owner:WALLACH MORTON L
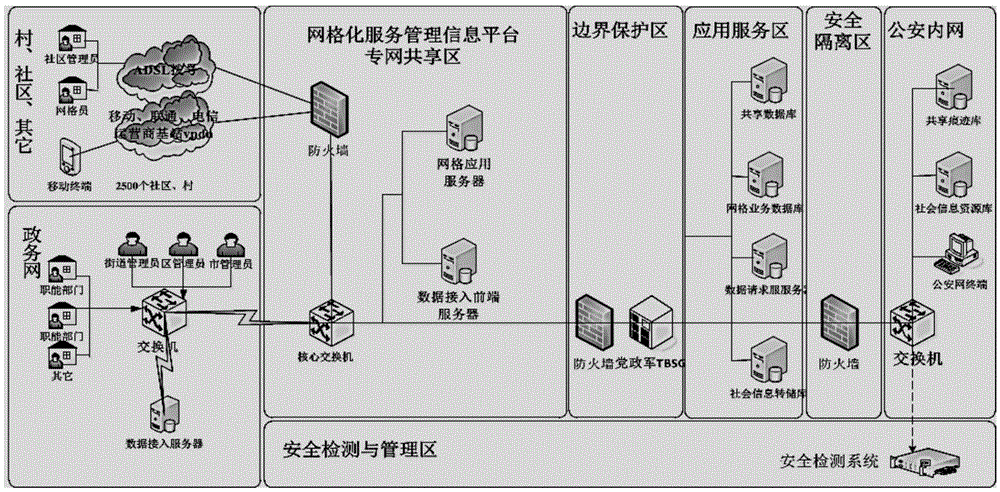
Information acquisition method in community grid management
InactiveCN105654077AEnsure safetyGuaranteed accuracyData processing applicationsCharacter and pattern recognitionInformatizationGrid management
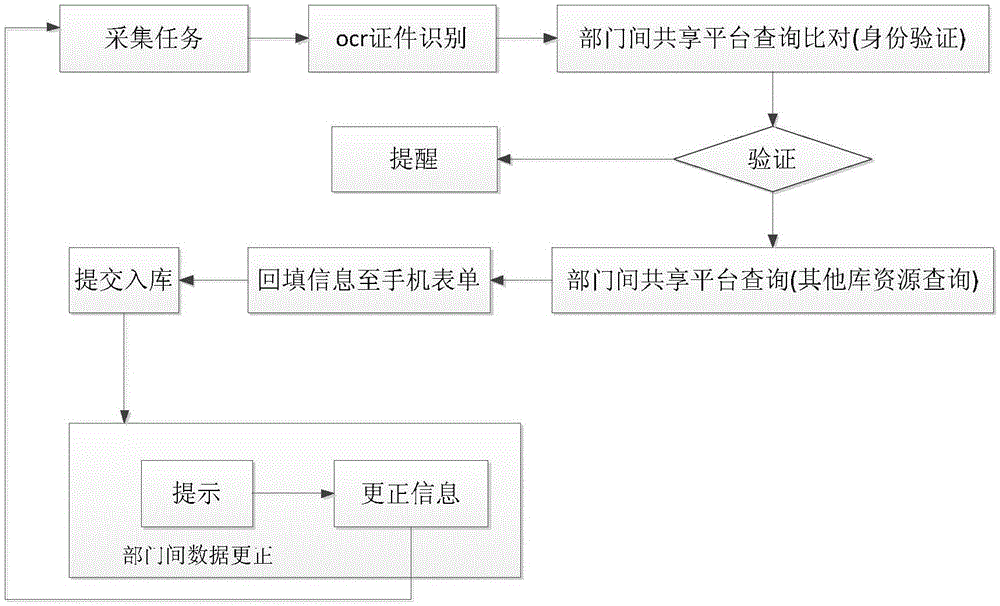
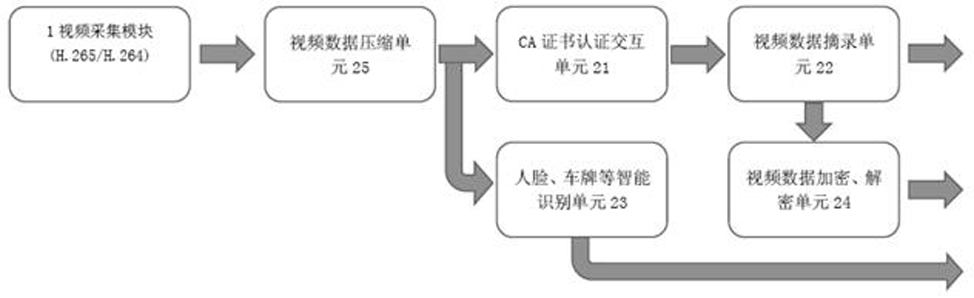
The invention provides an information acquisition method in community grid management. Acquisition information is read through an OCR certificate recognition technology. Validity of certificate information is verified through data comparison of a shared platform between departments, and the acquisition information and the shared platform between the departments are intelligently compared to prompt abnormal information and new data so that the functional departments are enabled to conveniently acquire the latest business data. Meanwhile, secondary acquisition of the data can be performed by relying on grid members or the grid members are enabled to notify acquisition objects to correct business windows and dealing information so that great channel assistance can be provided for rolling updating of the business data of the business departments, a social governance system through longitudinal and transverse directions without blind angles of social management can be formed, and flattening, linked and standardized social governance is facilitated through informatization. Data comparison of the private network of a grid service management information platform and public security population basic information on the public security network and information of other functional departments on the government affair network can be realized through public security border security equipment so that accuracy of data information acquisition can be guaranteed.
Owner:LINEWELL SOFTWARE
Respiratory protection head cover for emergency escape
InactiveCN102641563ASimple structureSmall wearing repulsionBreathing filtersBreathing masksAir filterEngineering
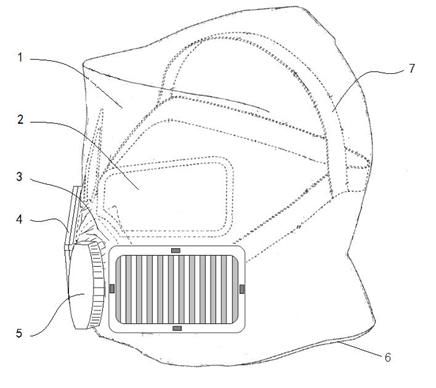
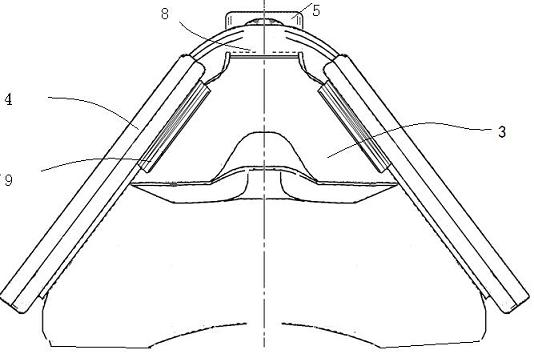
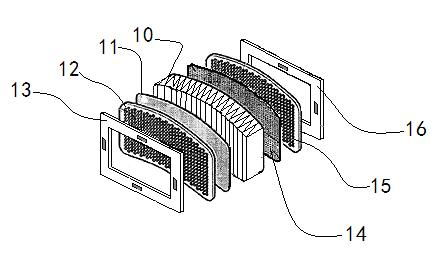
The invention discloses a respiratory protection head cover for emergency escape, which comprises a transparent cover body, a window, a fixed head belt, an oronasal cover, a high-efficiency air filter, a talker and a neck fixing ring. The window and the transparent cover body are heat-sealed into a whole, and the oronasal cover and the transparent cover body are heat-sealed and then clamped on the high-efficiency air filter on two sides of the head cover. The front end of the oronasal cover is provided with the talker, the fixed head belt is connected to two sides of the oronasal cover, and the neck fixing ring is heat-sealed at the bottom of the transparent cover body. The respiratory protection head cover for the emergency escape can serve as a respiratory protection article which is light, portable, safe and comfortable for employed persons possibly threatened by biological pollution in occasions including infectious hospitals, emergency and unexpected problem solving, disaster rescue, epidemic prevention protection, border security and the like.
Owner:SANITARY EQUIP INST ACAD OF MILITARY MEDICAL SCI PLA
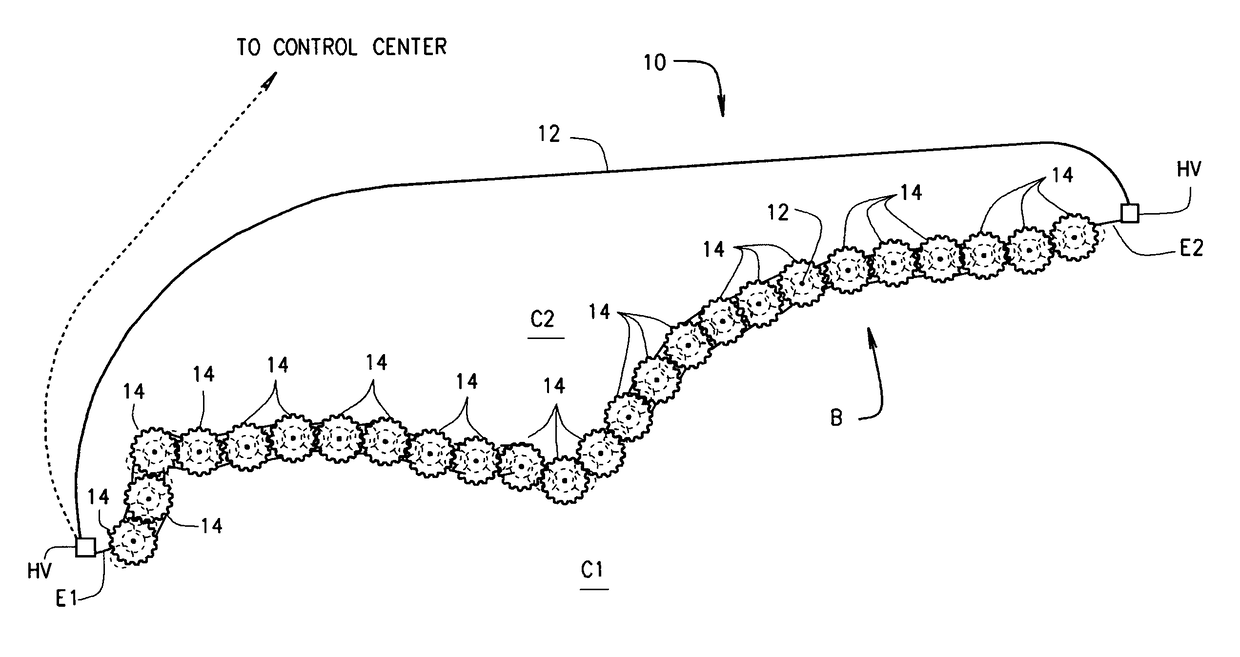
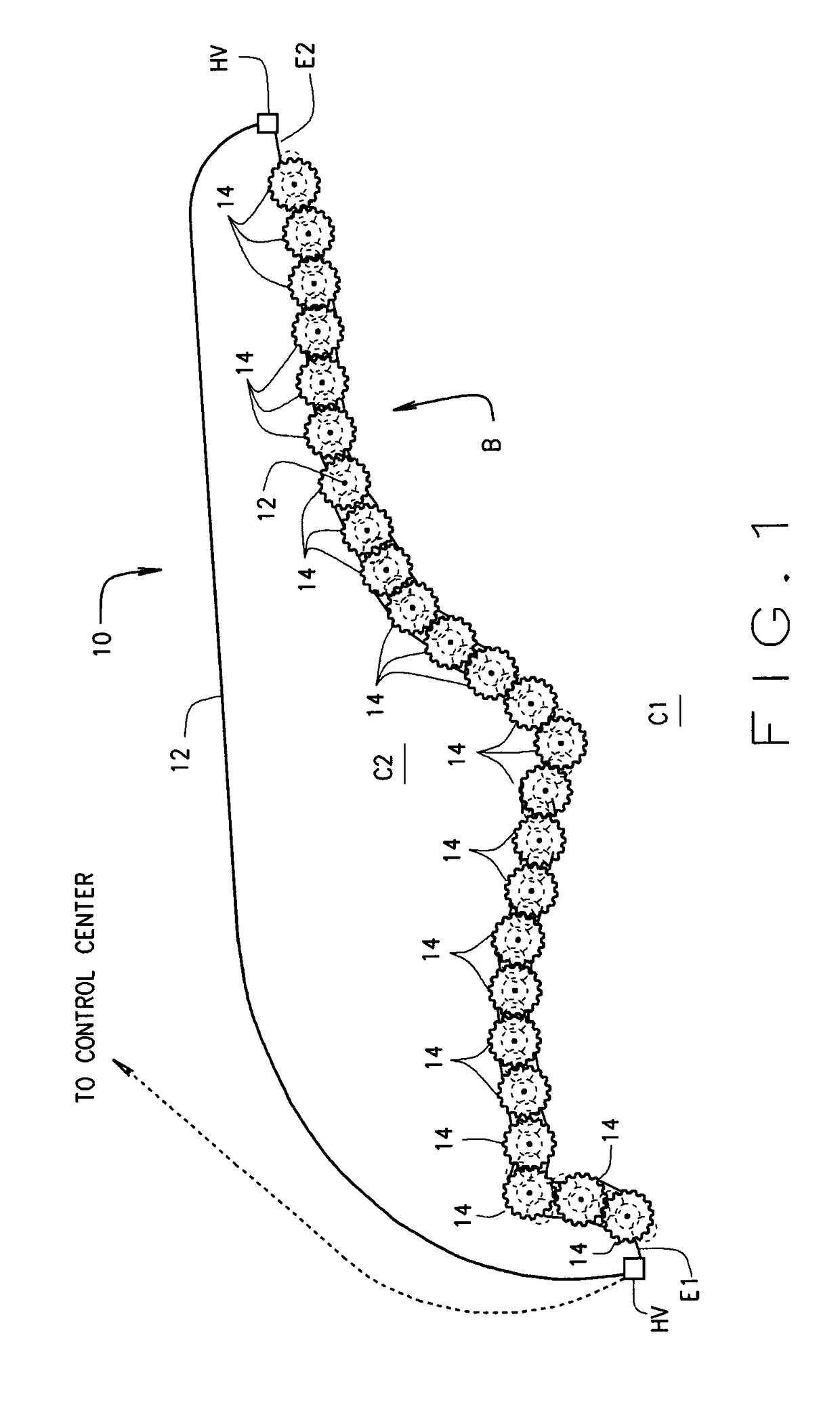
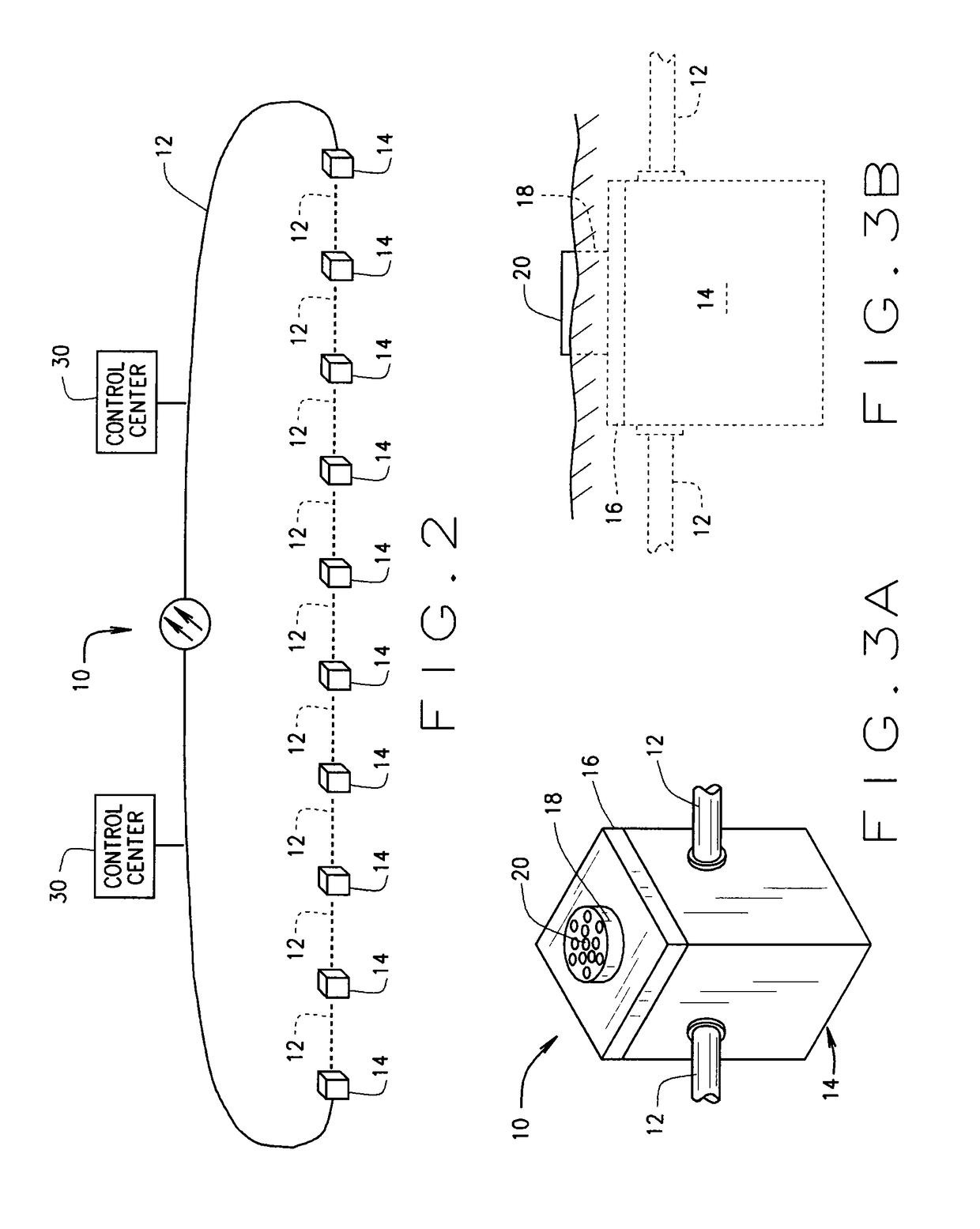
Method and system for advanced electronic border security
ActiveUS20150206403A1Improve reliabilitySensitive highFrequency-division multiplex detailsTime-division multiplexTelecommunicationsElectrical conductor
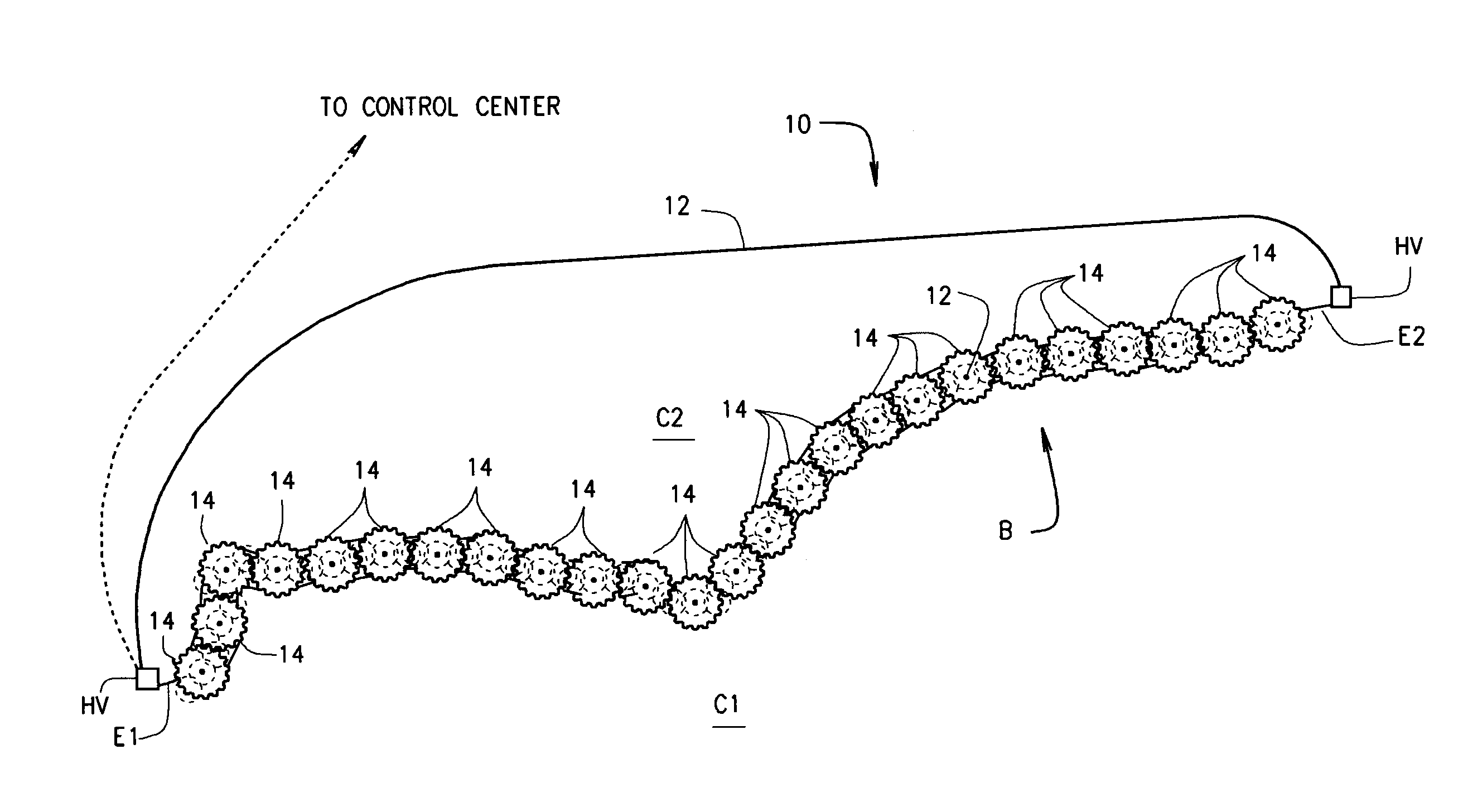
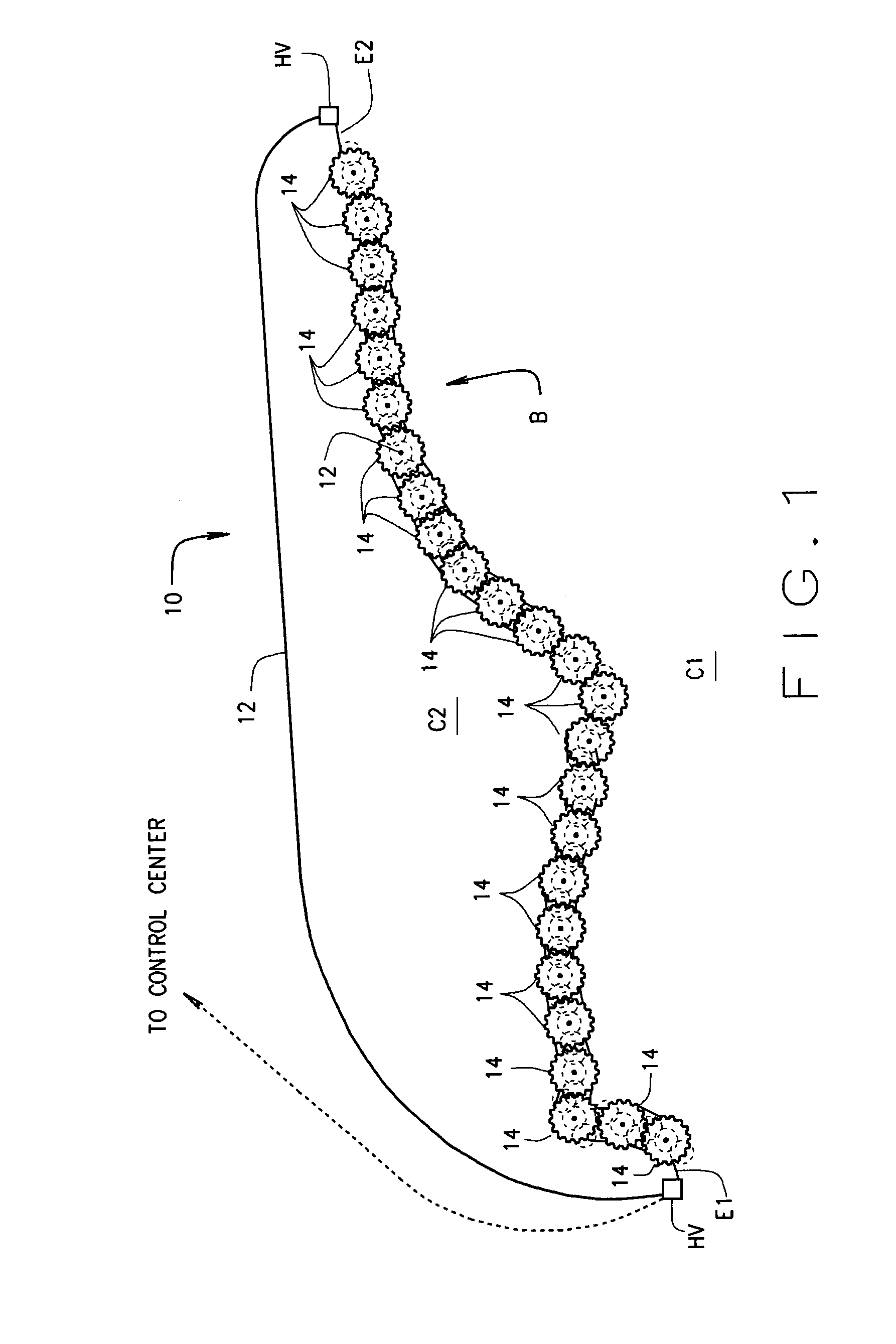
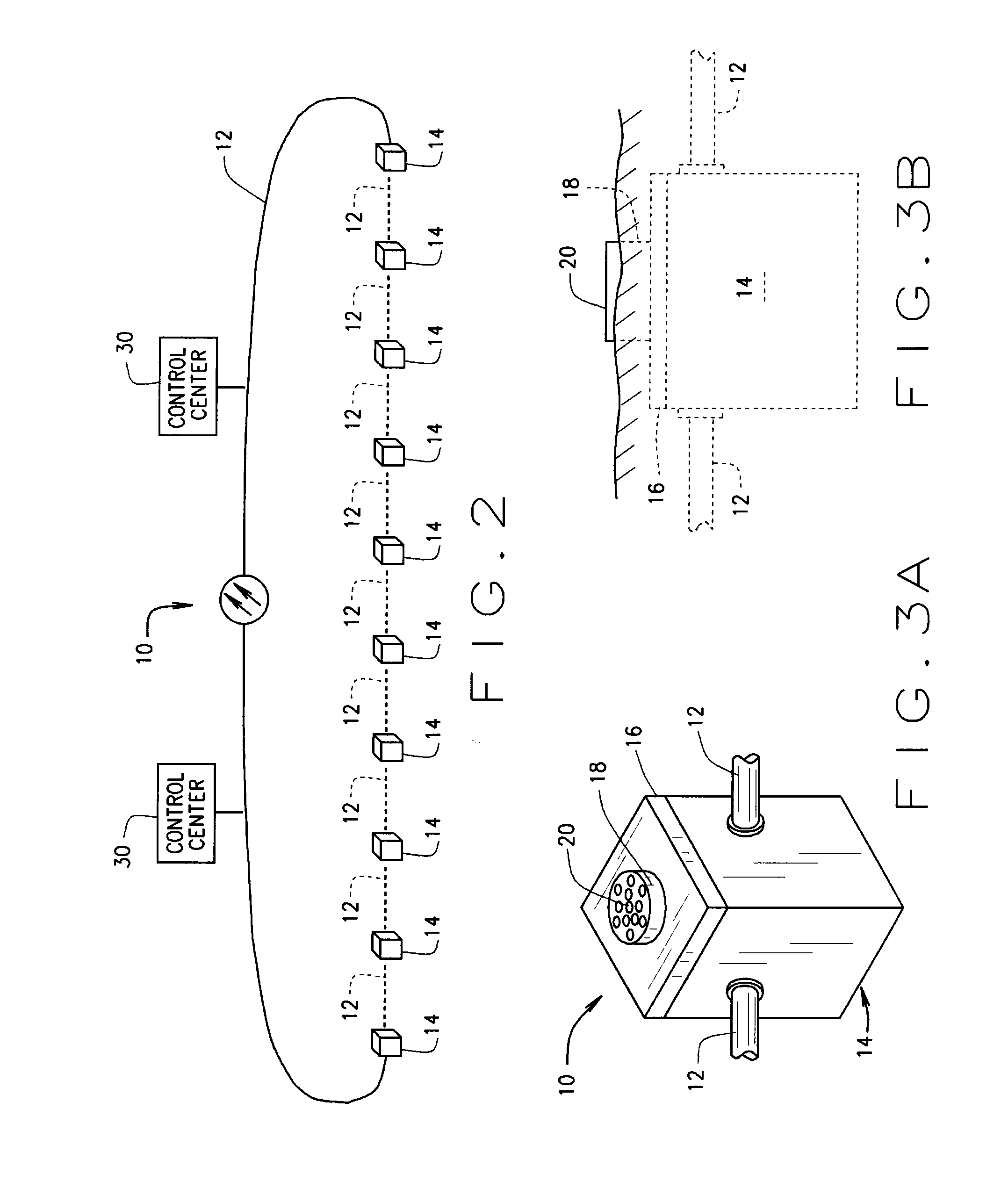
A system (10) for protecting a border (B) comprises a fiber-optic cable (12) extending from one end of a border to the other end thereof. The cable includes a bundle of optical fibers which connect to sensors placed at intervals long the border. Included within the fiber-optic cable is a high voltage conductor by which high voltage AC is introduced into, and passes through, the cable for powering the sensors. The high voltage is stepped down and rectified from AC to DC for this purpose. Various types of sensors (100-700) are arranged in pods (14) located at intervals along the length of the border. A method of border protection is also disclosed.
Owner:WEINSTEIN BRADLEY A +1
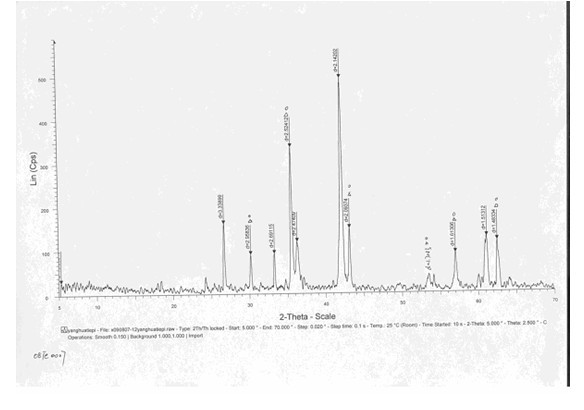
Identification method for distinguishing iron ore from oxide scale
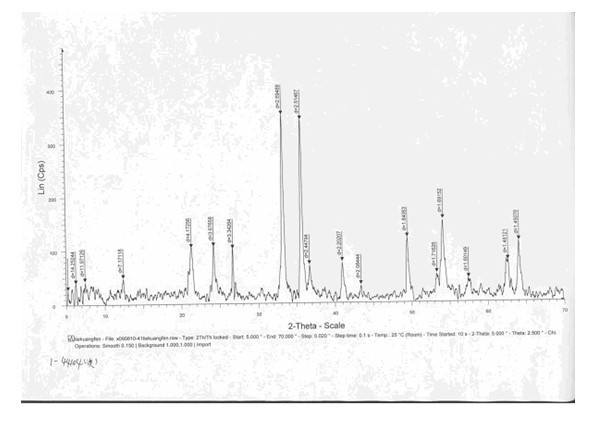
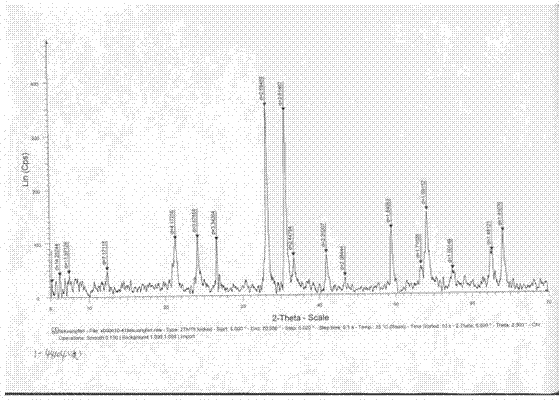
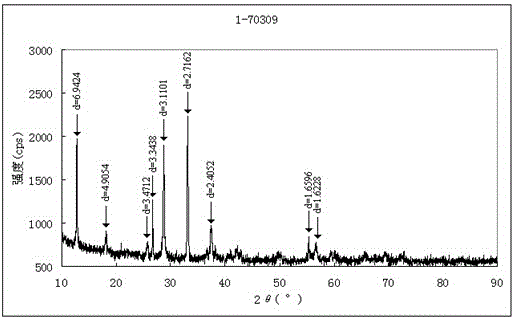
ActiveCN102095742AFind sensitivityFind reliabilityMaterial analysis using radiation diffractionX-raySpectroscopy
The invention relates to an identification method for distinguishing iron ore from oxide scale, which is used for identifying the attributes of the iron ore and the oxide scale by analyzing and comparing characteristic spectrum peaks of hematite, magnetite, ferrous oxide and pure iron by respectively adopting X-ray diffraction spectroscopy and scanning electron microscopy through X-ray diffraction spectrums and judging whether the hematite, magnetite, the ferrous oxide and the pure iron have obvious characteristics of oxide scale under an electron microscope. The identification method prevents import goods from passing through the Custom under another name in terms of the source, provides technical support for inspection and quarantine and for the Custom, provides scientific authentication reports for traders, guarantees border security, and avoids pollution to environment. The identification method discloses and establishes an identification process for the first time, standardizes the working method for identification, and is instructive for identifying the raw materials of all the imported wastes.
Owner:CHEM MINERALS & METALLIC MATERIALS INSPECTION CENT OF TIANJIN ENTRY EXIT INSPECTION & QUARANTINE BUREAU
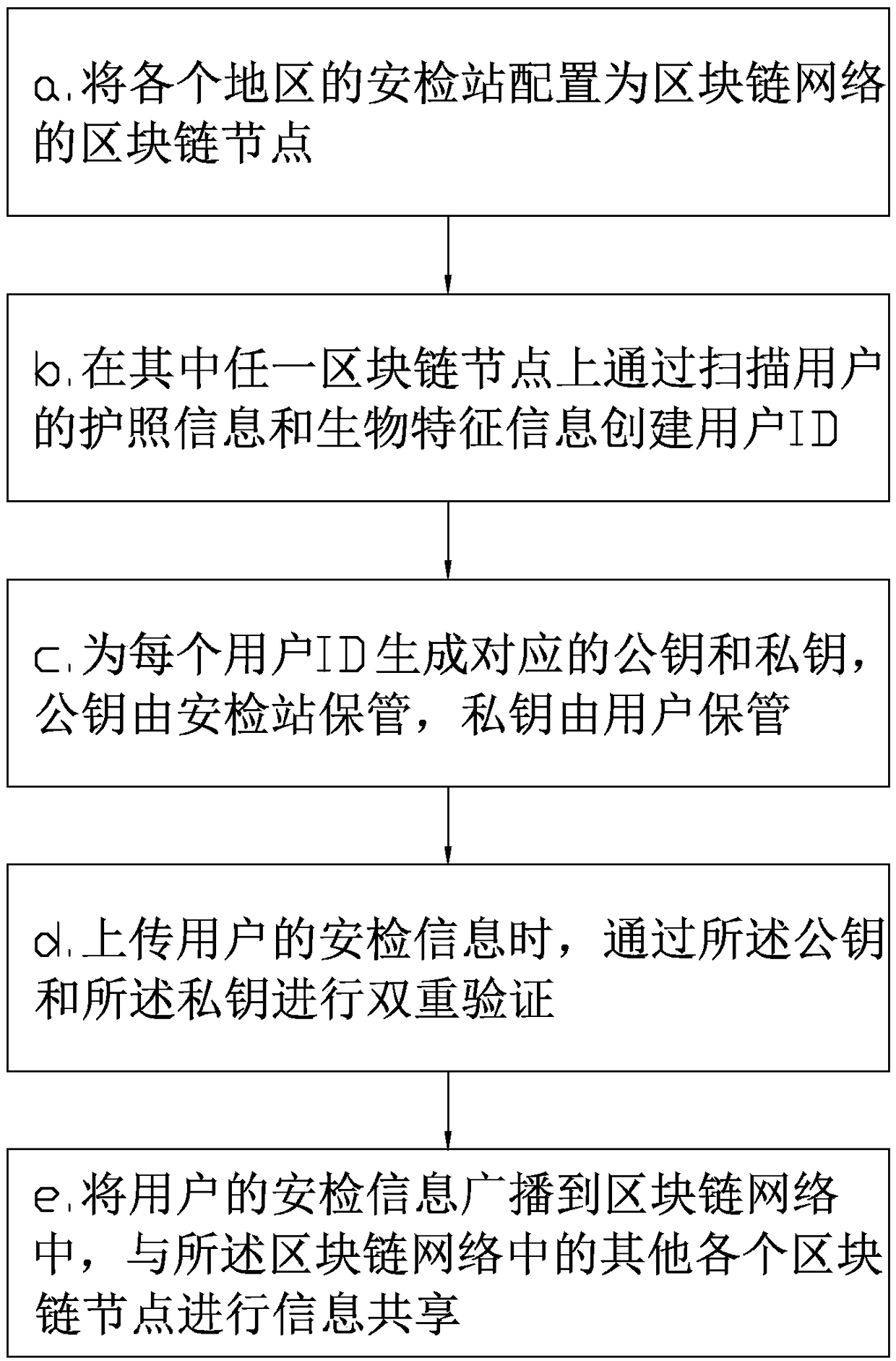
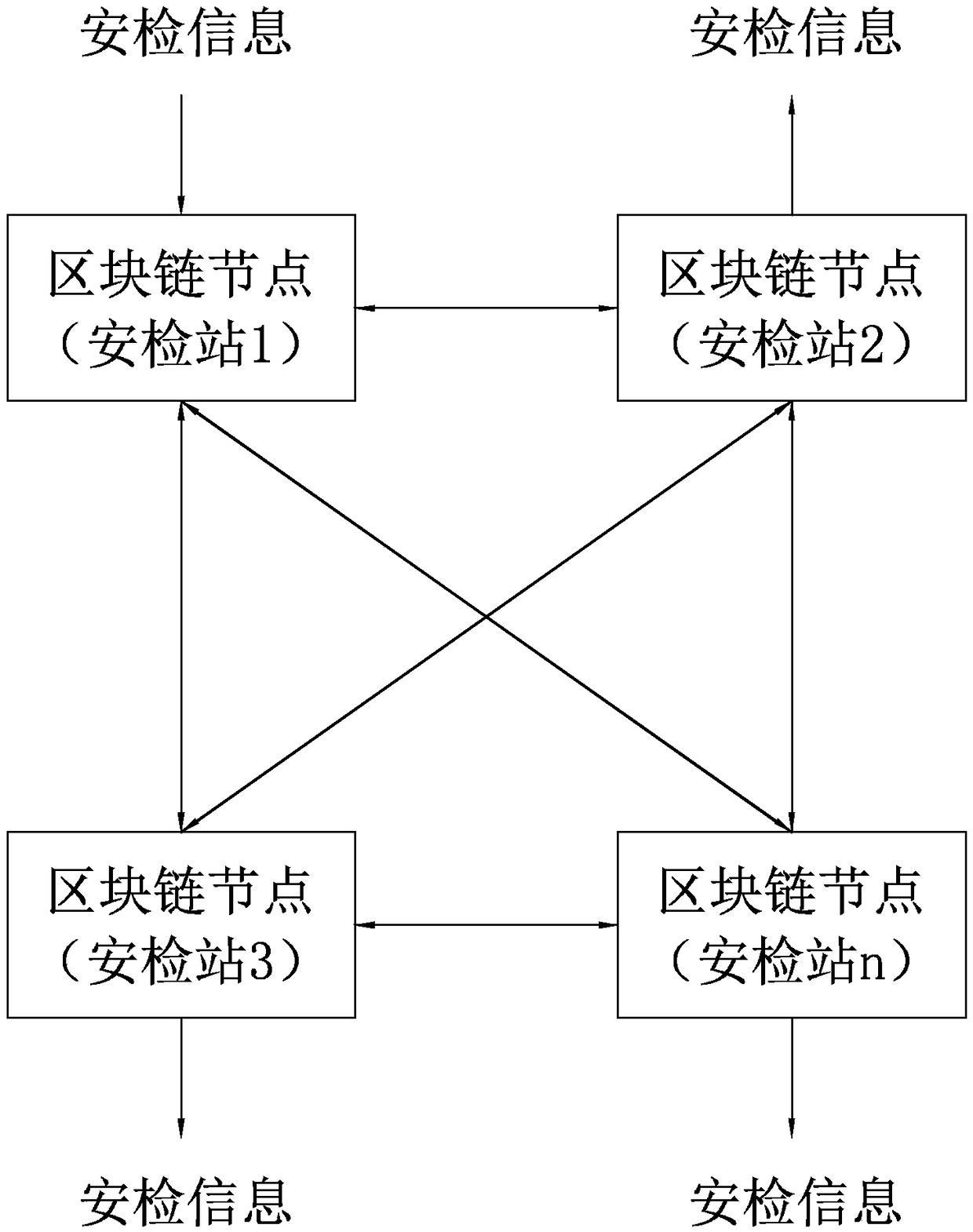
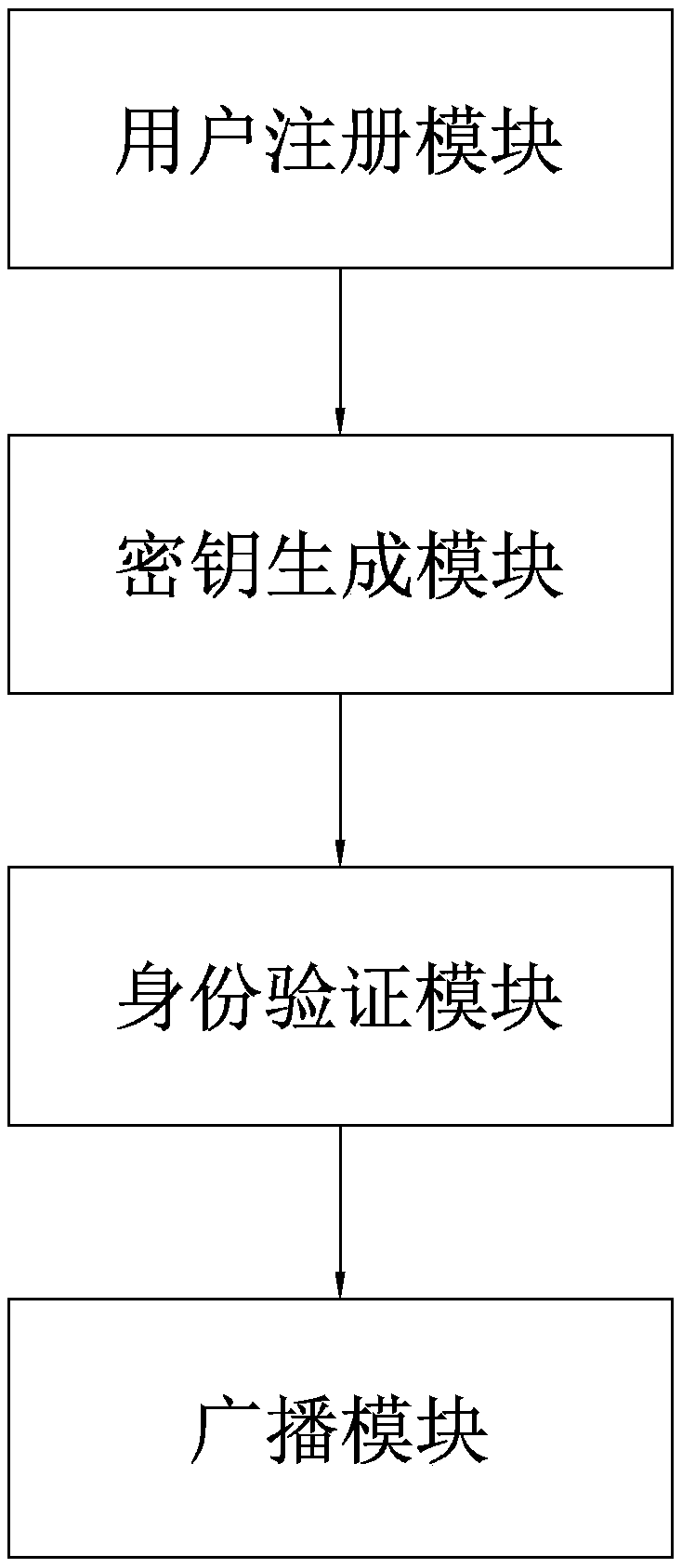
Border security check method and system based on blockchain technology
InactiveCN108650079AImprove satisfactionShorten the timeKey distribution for secure communicationData processing applicationsInformation sharingSecurity check
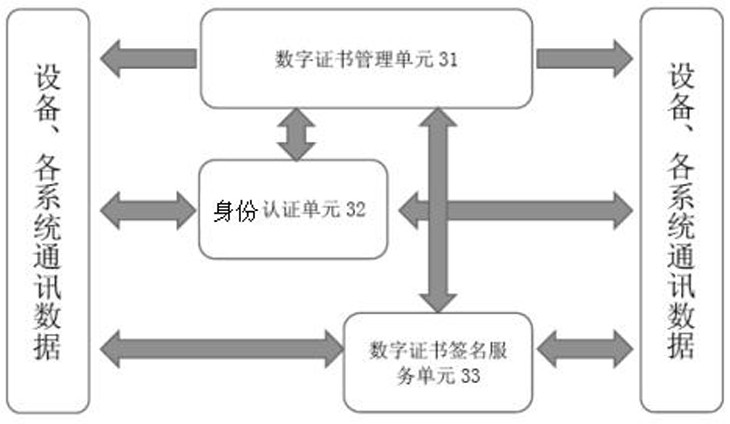
The invention discloses a border security check method and system based on a blockchain technology. The method comprises the following steps: configuring security stations of each region as a blockchain node of a blockchain network; establishing a user ID by scanning the passport information and biological feature information of a user on any blockchain node; generating a public key and a privatekey corresponding to each user ID, wherein the public key is kept by the security station, and the private key is kept by the user; when the security check information of the user is uploaded, performing double verification through the public key and the private key; broadcasting the security check information of the user to the blockchain network, and carrying out information sharing with other blockchain nodes in the blockchain network; and realizing distributed recording and distributed storage of the security check information, so that the security check information of the security stations in each region is mutually shared, thereby greatly improving the security check efficiency.
Owner:XIAMEN KUAISHANGTONG INFORMATION TECH CO LTD
Secure transmission of money transfers
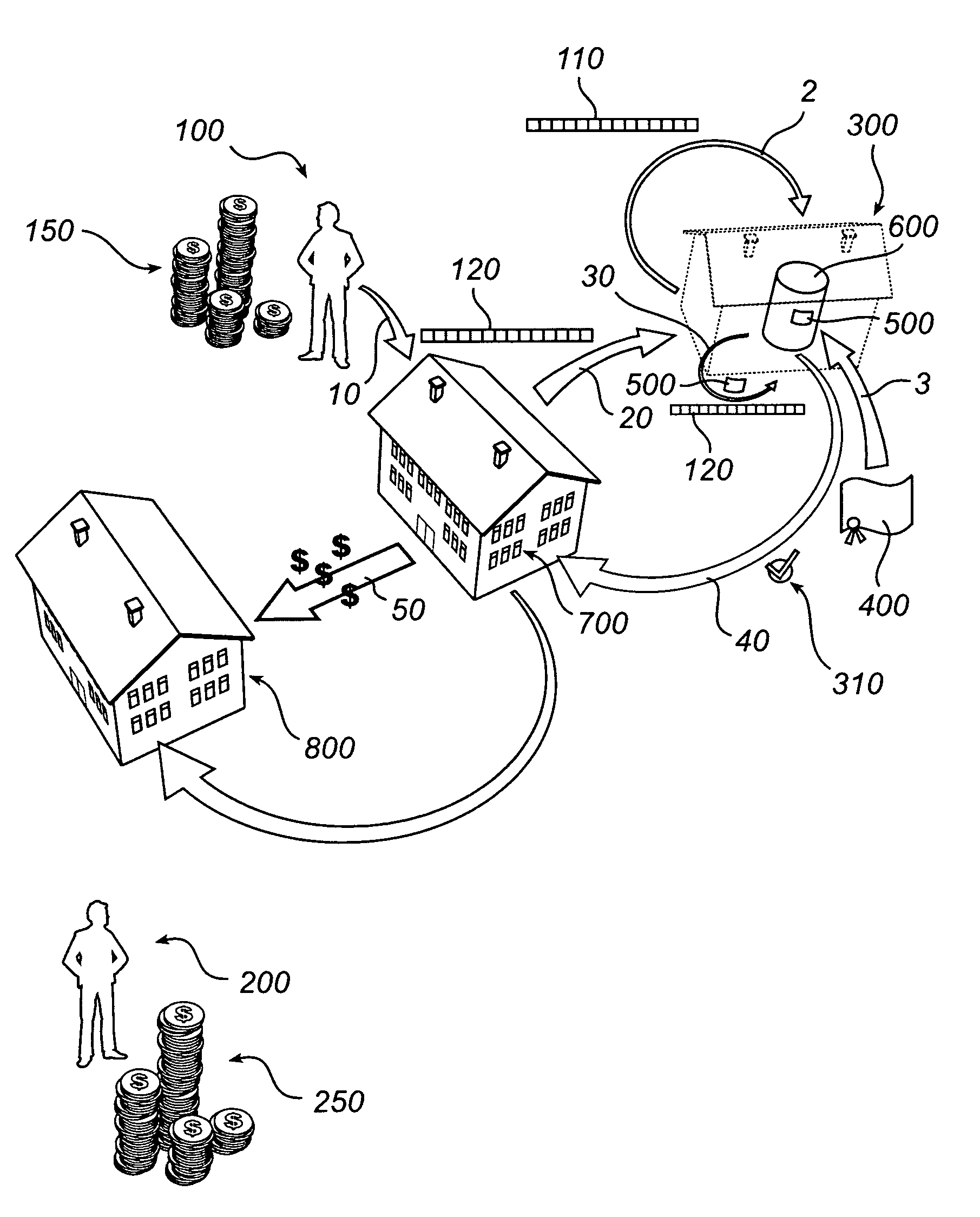
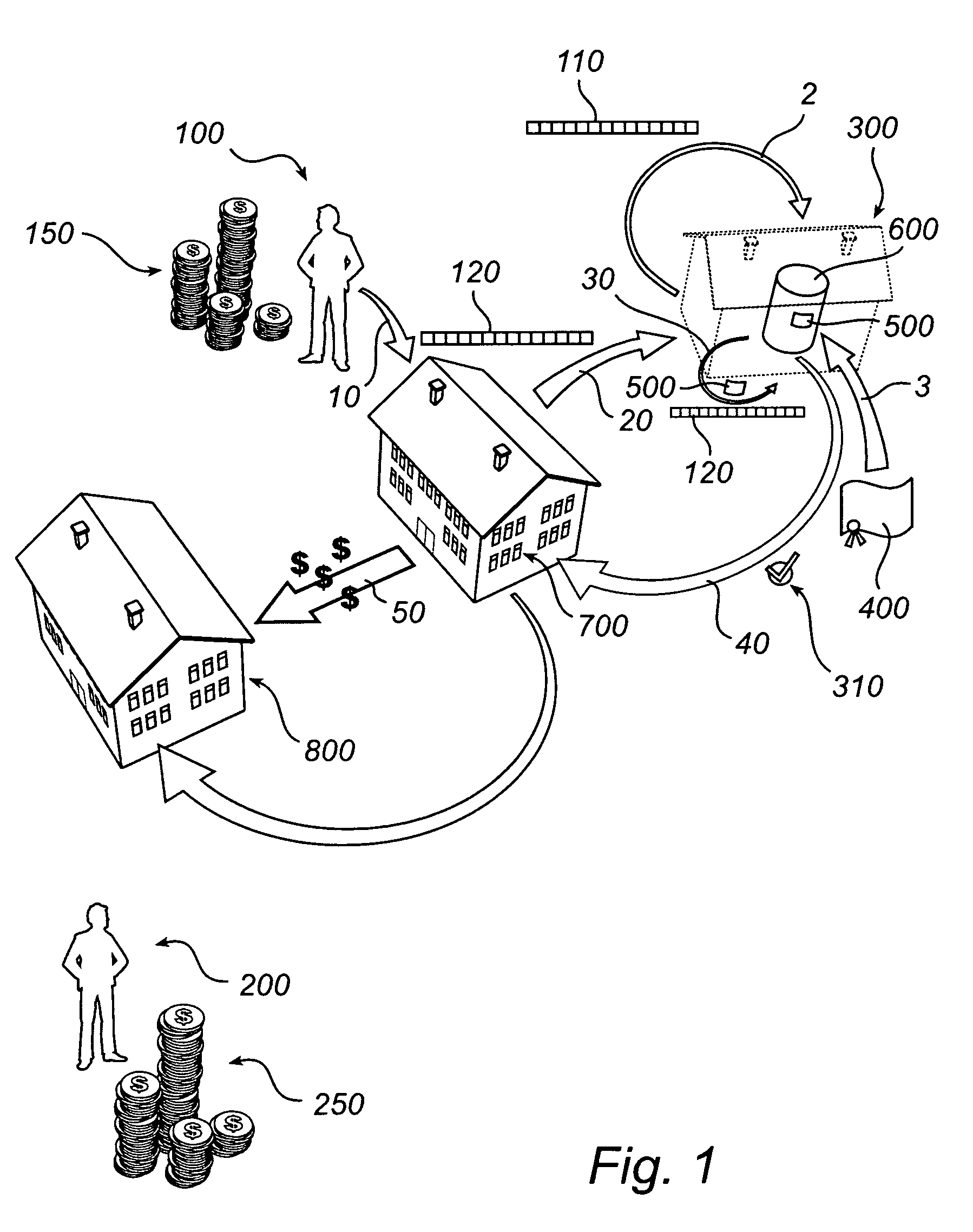
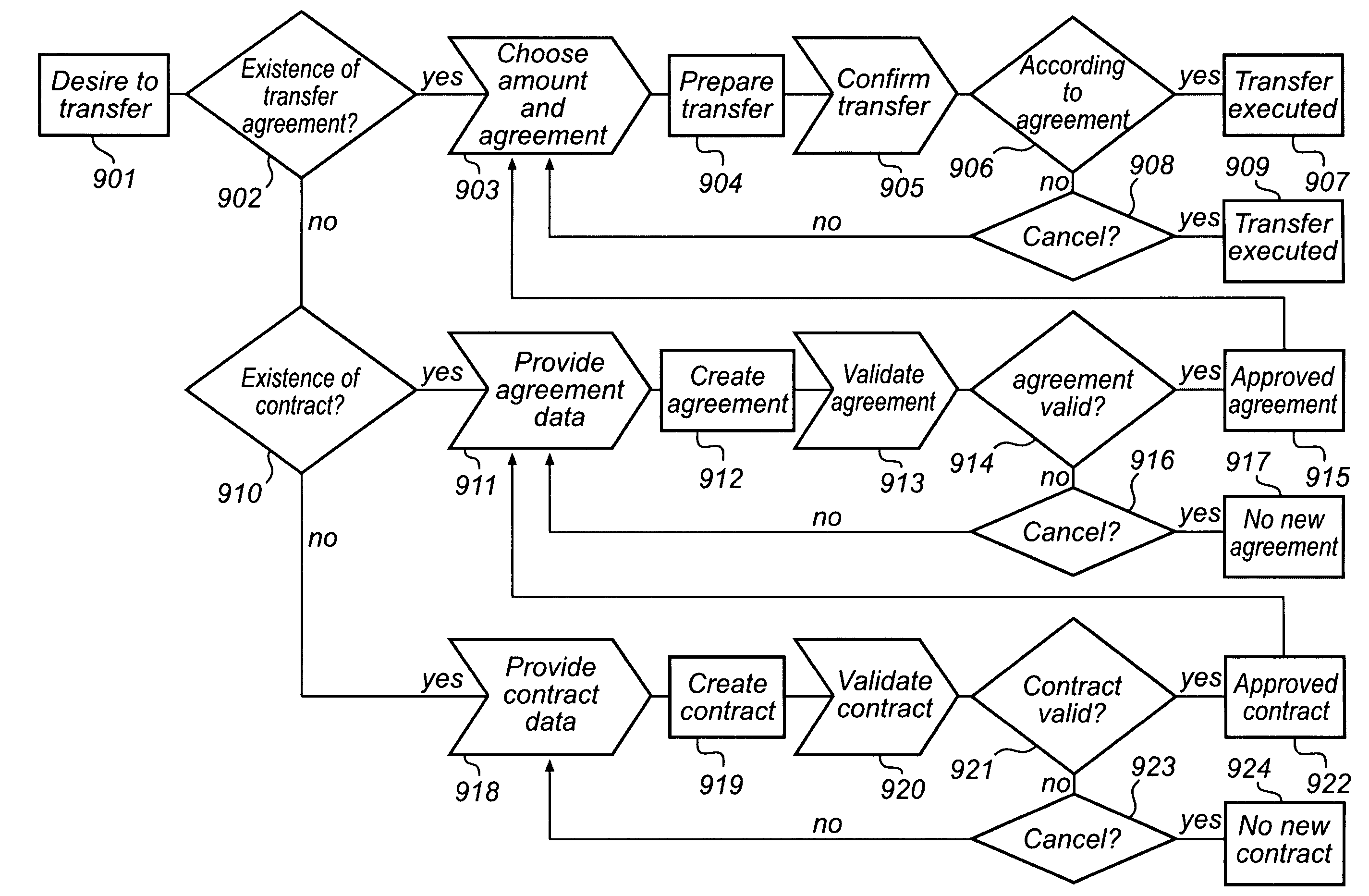
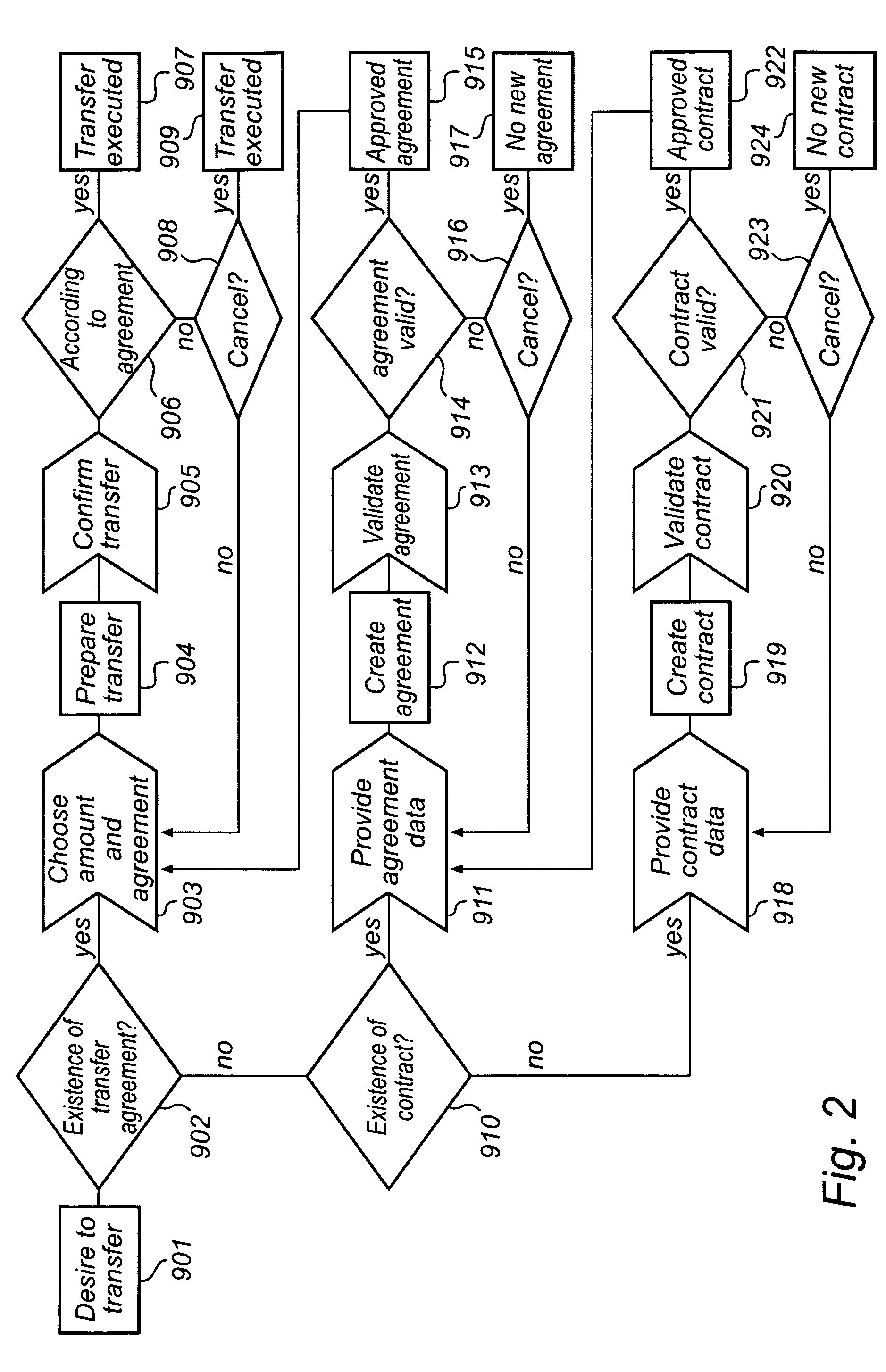
InactiveUS8032435B2More reliableMore secureFinanceProtocol authorisationSecure transmissionBorder Security
Owner:DIASPORALINK
Method and device for radar remote control
InactiveCN103257628AFor professional useUniversalFibre transmissionTotal factory controlInternational standardRadar
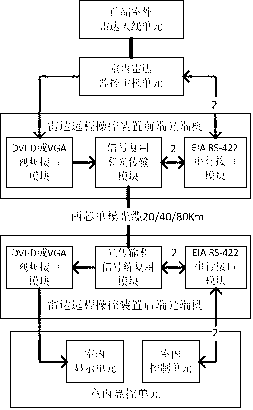
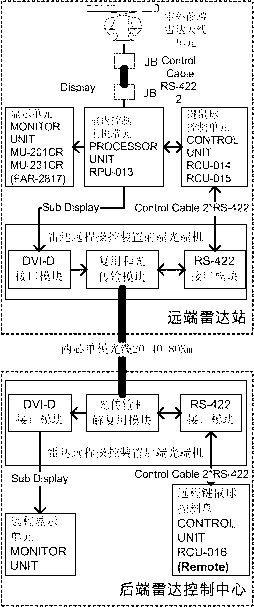
A shore radar monitoring station is an important technological means for offshore border security and protection, and a monitoring center is usually arranged at places far away from a front end radar monitoring station. The invention provides a novel and engineering method and device for radar remote control. By increasing the distance between a radar display control unit and a radar monitoring host unit and adopting the general optical fiber transmission technology and an international standard interface to transmit signals, the method and device for radar remote control realizes remote control of a radar, is simple and practical, and is operated comprehensively.
Owner:王琦
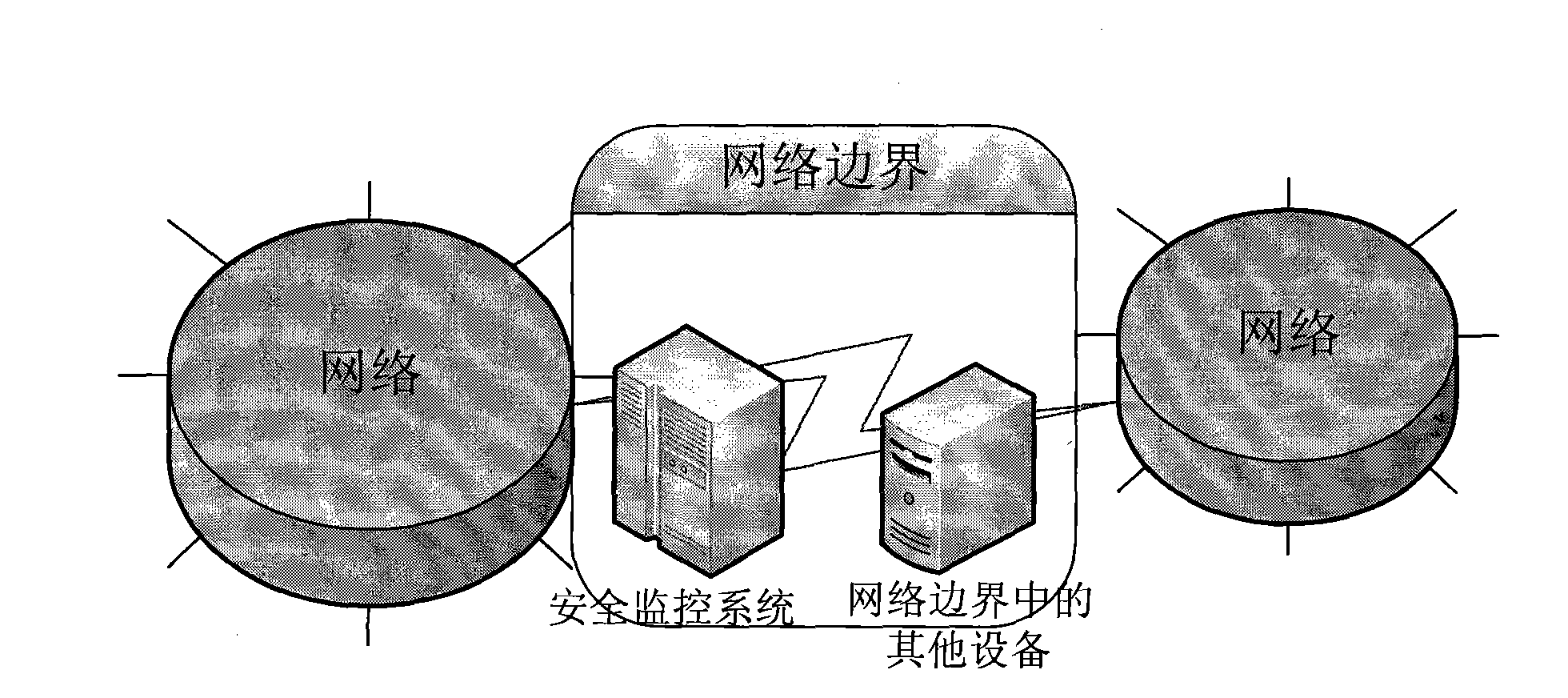
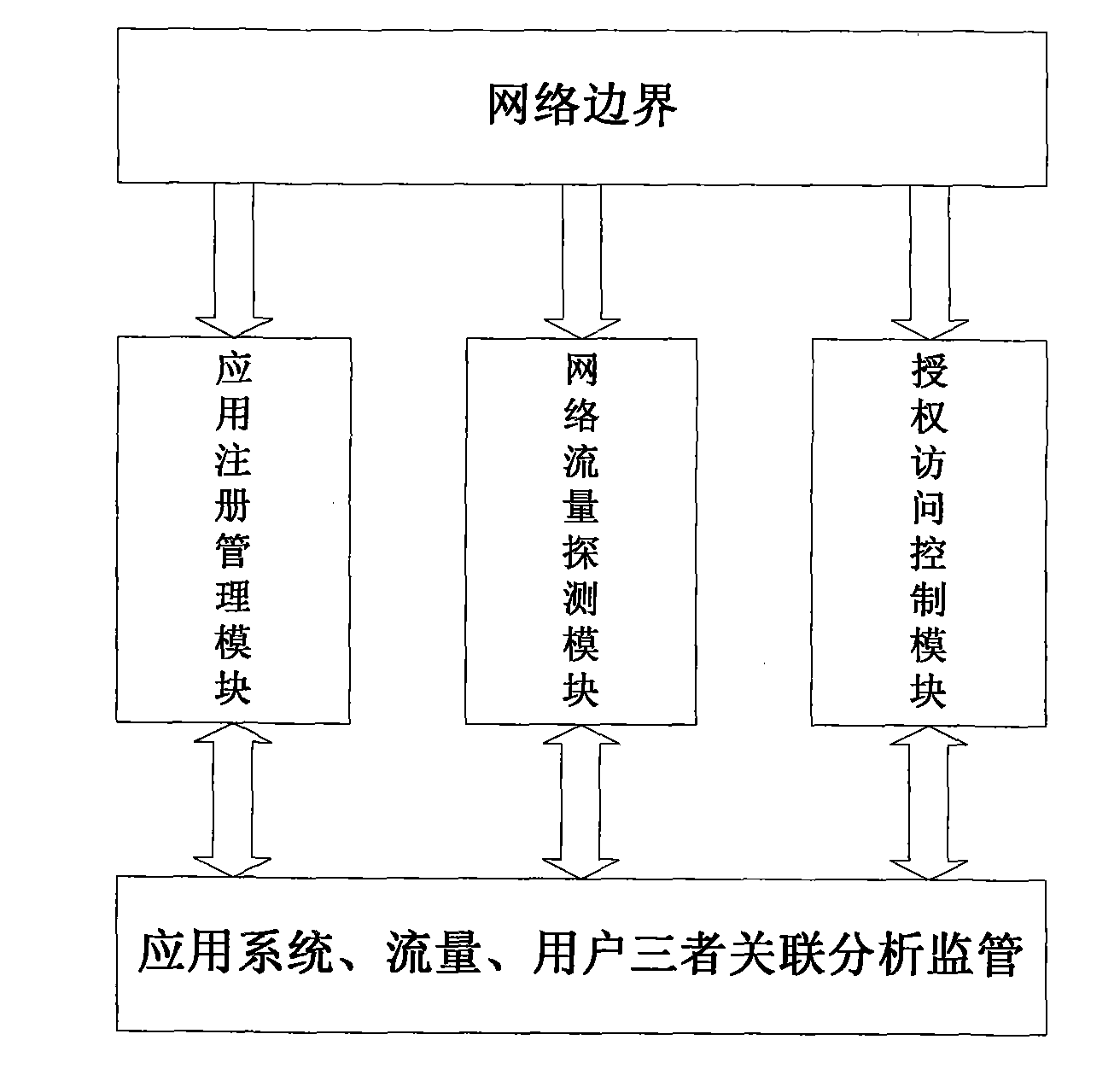
Method for monitoring network border security
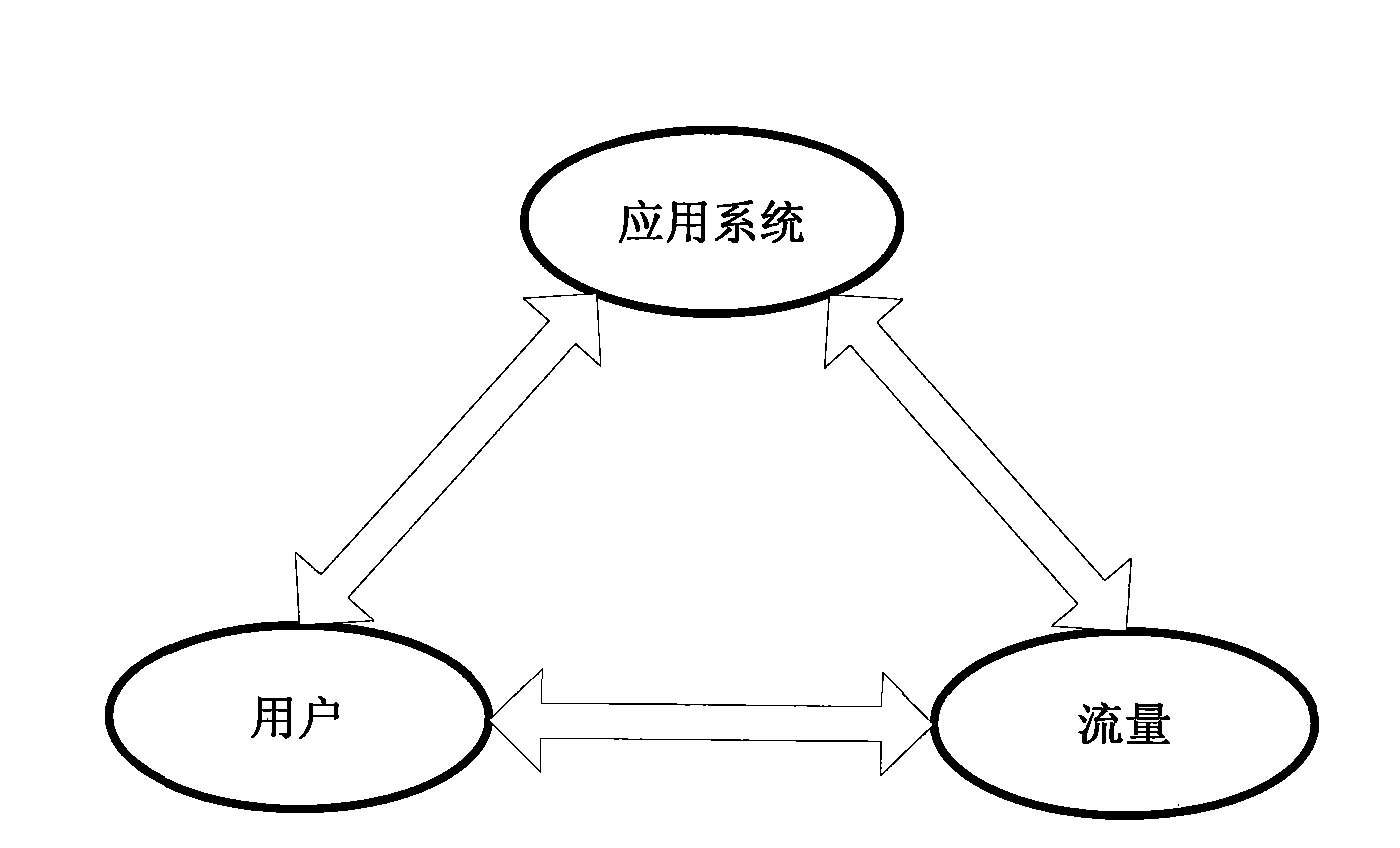
InactiveCN101667935AFull monitoring informationData switching networksTraffic capacityMonitoring system
The invention discloses a method for monitoring network border security, which monitors traffic, users and application systems of a network border respectively through a monitoring module. The information of the traffic, the users and the application systems of the network border acquired by the monitoring module is subjected to association analysis, and other monitoring information of the networkborder can be associated through information of the traffic, the users or the application systems; a relatively complete monitoring system is formed by association monitoring among the traffic, the users and the application systems of the network border; and more complete monitoring information can be acquired by associating relationships among the traffic, the users and the application systems and starting from the traffic, the users or the application systems. The method particularly has great assistance to security event processing and positioning so as to achieve aims of the invention.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Autonomous navigation system for border security unmanned patrol vehicle
PendingCN111459172ARun fastShort construction cyclePosition/course control in two dimensionsAutonomous Navigation SystemControl engineering
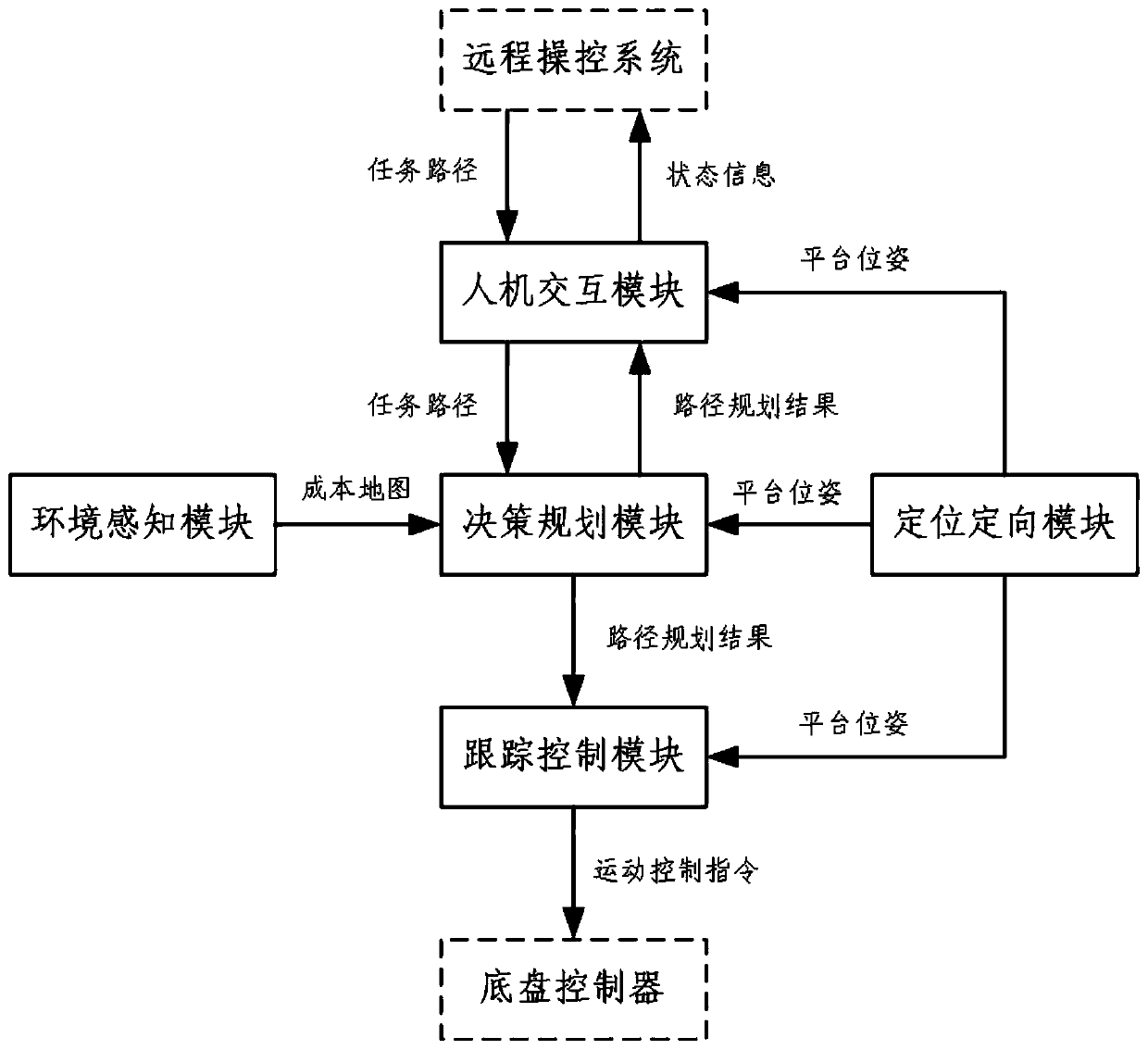
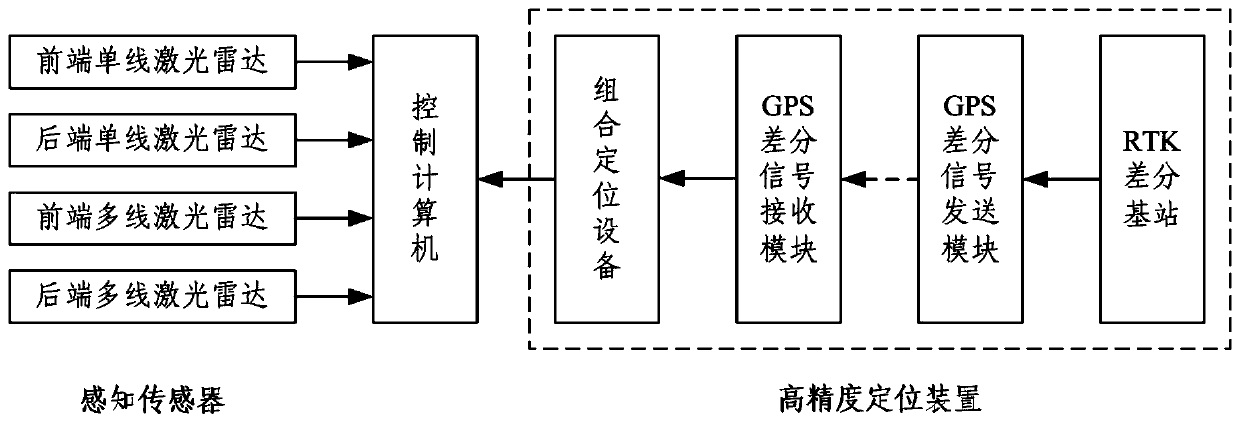
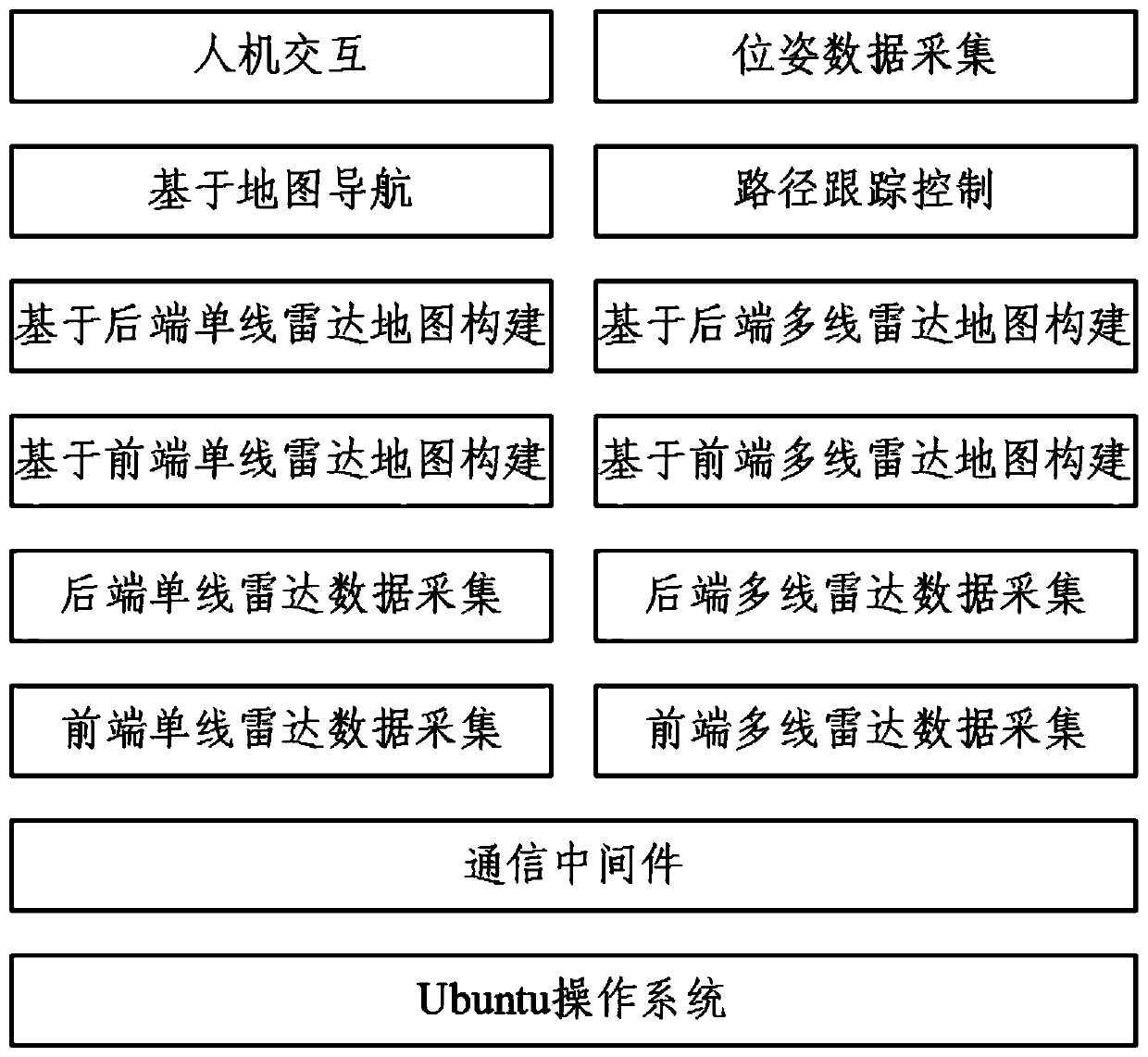
The invention belongs to the field of autonomous navigation of unmanned vehicles, and particularly relates to an autonomous navigation system for a border security unmanned patrol vehicle. The systemcomprises a man-machine interface module, an environment sensing module, a positioning and orientating module, a decision planning module and a tracking control module, wherein the environment sensingmodule adopts a calculation lightweight mapping algorithm, is short in mapping period, can support the rapid operation of an autonomous navigation system and the high-speed driving of an unmanned vehicle, and meets the requirements of large-range patrol operation; in addition, the environment sensing sensor suites are symmetrically arranged at the front end and the rear end of the unmanned vehicle body respectively, and the unmanned vehicle is supported to have forward and backward two-way autonomous driving capacity under the condition that the unmanned vehicle does not turn around; a single-line radar and a multi-line radar are arranged, so that an environment detection blind area is eliminated; an RTK differential base station is configured, so that the positioning precision is improved; an electronic fence is overlaid on a cost map, path planning is carried out in a road surface range in a constrained mode, and the measures and methods improve the safety of autonomous driving of the unmanned vehicle.
Owner:CHINA NORTH VEHICLE RES INST +1
Re-routing autonomous vehicles using dynamic routing and memory management for border security purposes
ActiveUS10690504B2Assisted identificationInstruments for road network navigationData processing applicationsInternaviEngineering
The invention relates to a system and method for navigating an autonomous driving vehicle (ADV) that utilizes an-onboard computer and / or one or more ADV control system nodes in an ADV network platform. The on-board computer receives physiological and ADV occupant identification sensor data concerning one or more occupants occupying an ADV, sensor data concerning the items being transported within the ADV, and information concerning the ADV itself to aid border security agencies in protecting their respective borders and territories (e.g., international borders, security zone borders, geographical borders, etc.). The relevant border agency can receive certain information over a network concerning one or more ADVs and make a determination if a heightened security screening should be requested. In response to a request, the on-board computer automatically initiates a dynamic routing algorithm that utilizes artificial intelligence to re-route the ADV to a predetermined destination, for example a border security facility.
Owner:MICRON TECH INC
Identification method for distinguishing iron ore from oxide scale
ActiveCN102095742BFind sensitivityFind reliabilityMaterial analysis using radiation diffractionSpectroscopyX-ray
The invention relates to an identification method for distinguishing iron ore from oxide scale, which is used for identifying the attributes of the iron ore and the oxide scale by analyzing and comparing characteristic spectrum peaks of hematite, magnetite, ferrous oxide and pure iron by respectively adopting X-ray diffraction spectroscopy and scanning electron microscopy through X-ray diffraction spectrums and judging whether the hematite, magnetite, the ferrous oxide and the pure iron have obvious characteristics of oxide scale under an electron microscope. The identification method prevents import goods from passing through the Custom under another name in terms of the source, provides technical support for inspection and quarantine and for the Custom, provides scientific authentication reports for traders, guarantees border security, and avoids pollution to environment. The identification method discloses and establishes an identification process for the first time, standardizes the working method for identification, and is instructive for identifying the raw materials of all the imported wastes.
Owner:CHEM MINERALS & METALLIC MATERIALS INSPECTION CENT OF TIANJIN ENTRY EXIT INSPECTION & QUARANTINE BUREAU
Secure transmission of money transfers
InactiveUS20090164367A1Faster and cheap and more secureMore reliableFinanceProtocol authorisationTransmission protocolSecure transmission
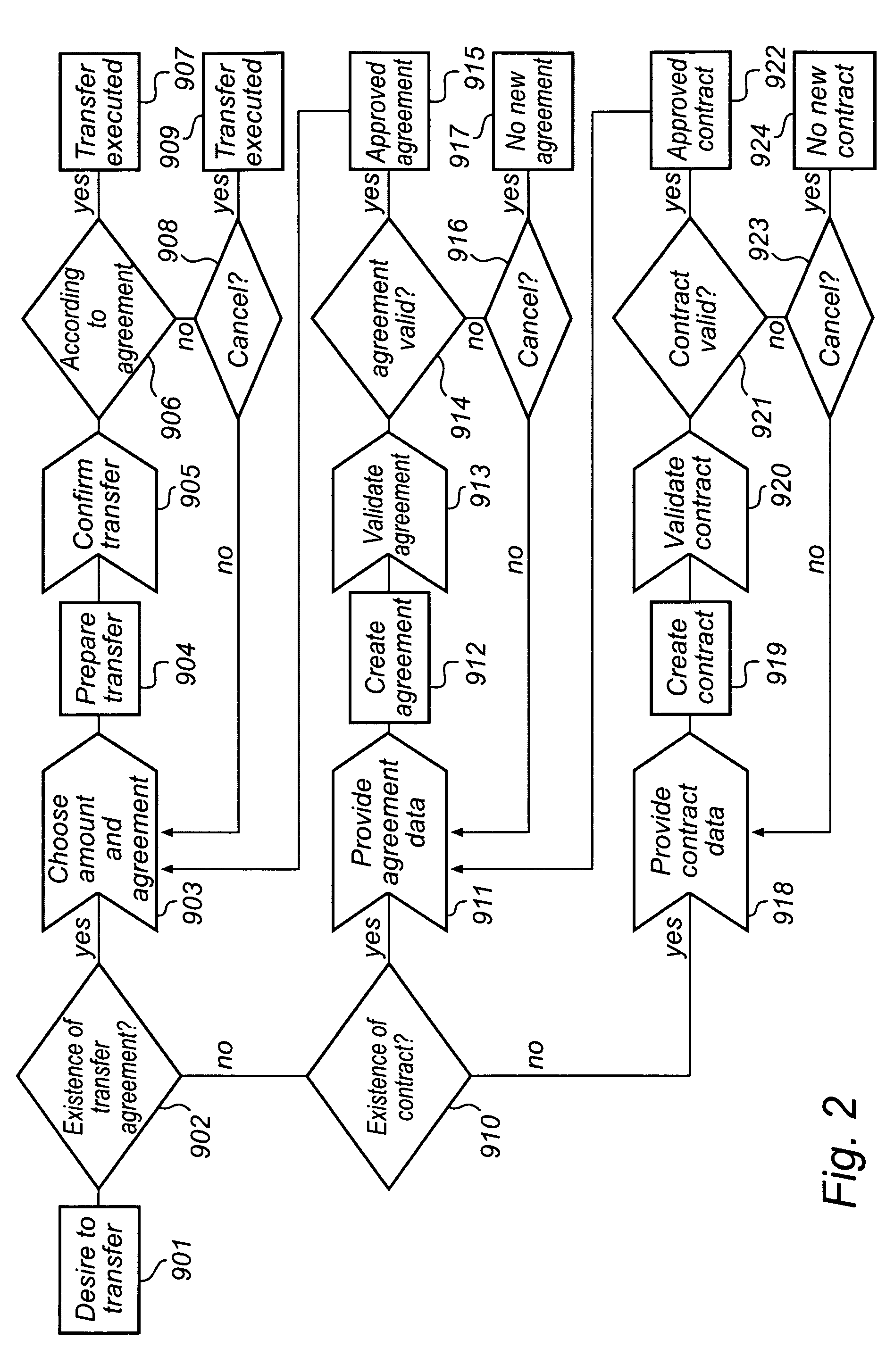
The invention relates to a method and a device for enabling a validated money transfer between a sending and a receiving person via a sending and a receiving financial institution, where a request to a validation agent for validation of a money transfer replaces normal time consuming cross border security checks. The validation agent, being unaffiliated with the sending financial institution and the receiving financial institution, administers a data base comprising validated transfer agreements, which agreements specifies at least the identity of a sending person and of a receiving person. A validation of a transfer is executed at the validation agent by comparing current transfer data with information specified in the validated transfer agreements.
Owner:DIASPORALINK
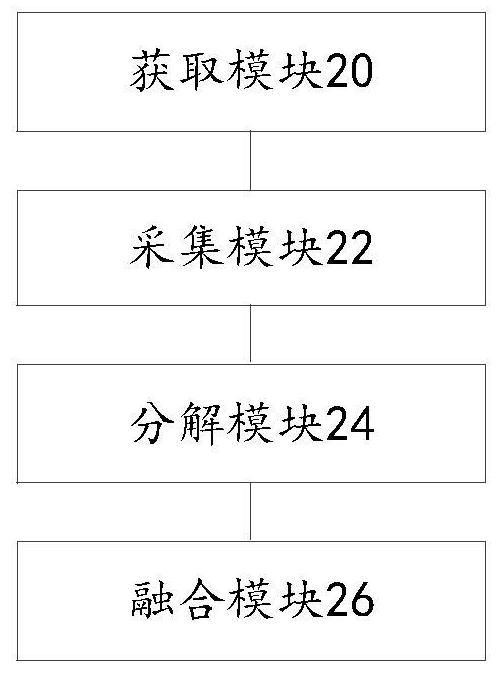
Border monitoring acquisition method and device based on multi-auxiliary linkage camera shooting technology
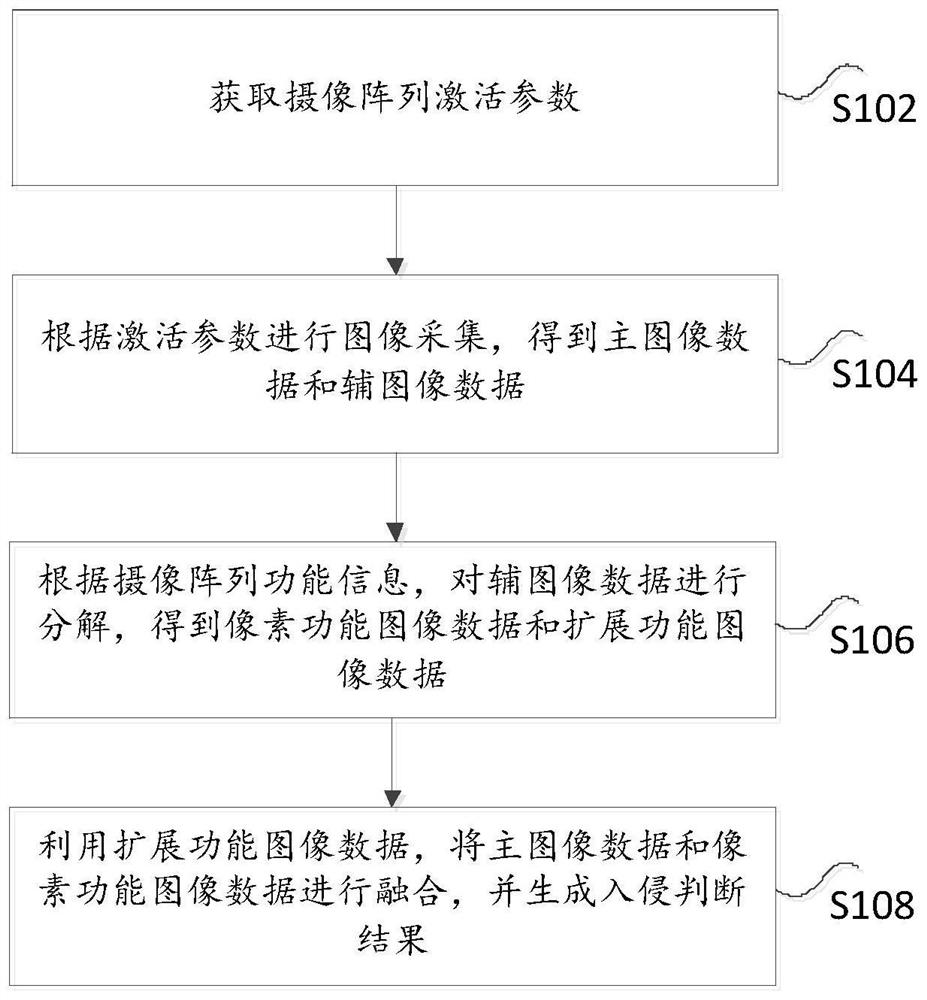
PendingCN114866702ALow efficiencyReduce quality problemsTelevision system detailsColor television detailsPattern recognitionEngineering
The invention discloses a border monitoring acquisition method and device based on a multi-auxiliary linkage camera shooting technology. The method comprises the following steps: acquiring a camera array activation parameter; performing image acquisition according to the activation parameters to obtain main image data and auxiliary image data; decomposing the auxiliary image data according to camera array function information to obtain pixel function image data and extended function image data; and fusing the main image data and the pixel function image data by using the extended function image data, and generating an intrusion judgment result. According to the method, the problems that management and analysis of border security and protection are obtained only through regional splicing processing of a single camera or a plurality of cameras, and the same placement region cannot be judged through a set of several or dozens of camera systems in the prior art are solved; and therefore, the technical problems of the efficiency and the quality of border security time judgment are reduced.
Owner:BEIJING ZOHETEC CO LTD
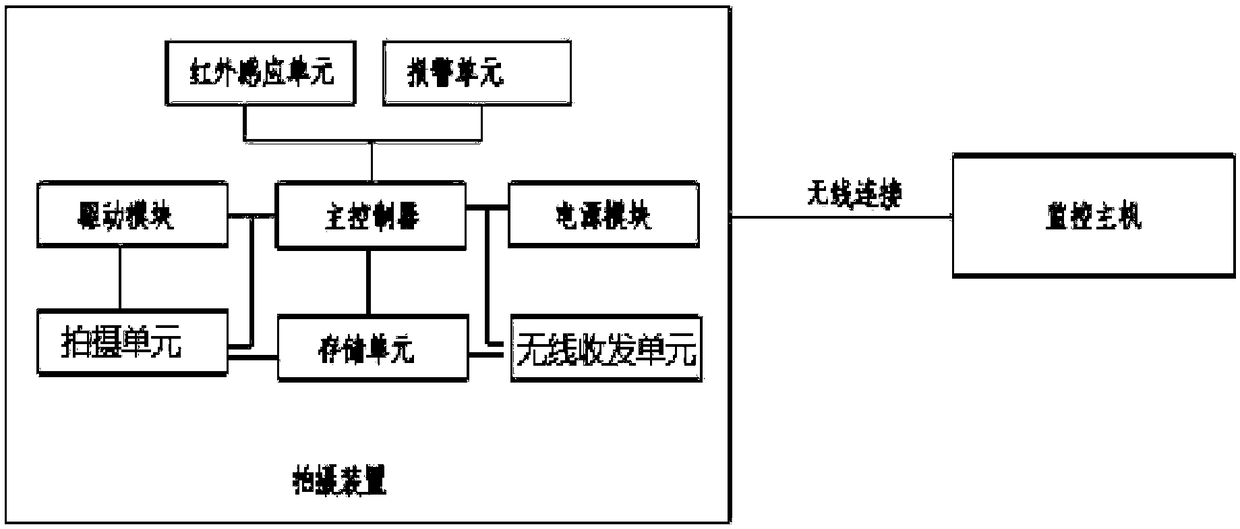
Border intelligent security and protection monitoring system and method based on Internet of Things
InactiveCN108429900AImprove work efficiencyGood practical valueClosed circuit television systemsBurglar alarm short radiation actuationWireless transceiverMonitoring system
The invention discloses a border intelligent security and protection monitoring system based on the Internet of Things. The system comprises a shooting device and a monitoring host, the shooting device is wirelessly connected with the monitoring host, when border security and protection monitoring is performed, when an infrared sensing unit in the shooting device senses a pedestrian near a borderline, a main controller controls a shooting unit to perform all-round shooting, meanwhile, shot photos or videodata are sent by a wireless transceiver unit to the monitoring host of the monitoring center through a mobile data network in real time, the monitoring personnel can obtain the video and photo information shot by a mobile shooting system in real time, and meanwhile neither large-capacitystorage card is required for storage, nor the personnel need to go to the shooting site to take the memory card of a miniature camera, thereby saving time, saving labor, greatly improving the workingefficiency and having relatively good practical value.
Owner:GUIZHOU MINZU UNIV
Method, device and security control system for controlling communication border security
ActiveUS7904954B2Avoid attackImprove self-protection performanceMemory loss protectionDigital data processing detailsProtocol processingControl system
The present invention provides a method, a device and a system for controlling VoIP border security. The system includes: a border security controller, which includes two dynamic information tables, an active session information table and a registered user information table, acting as the basis of security control; and a security policy server, in communication with the border security controller, adapted to provide a security policy to the border security controller and check the security of a signaling packet forwarded by the border security controller. The border security control system first checks the security and processes the packets of a user datagram received according to the active session information table and the registered user information table, and allows a packet which passed the security processing to pass, and then performs protocol processing on the media packet and signaling packet which are allowed to pass.
Owner:HUAWEI TECH CO LTD
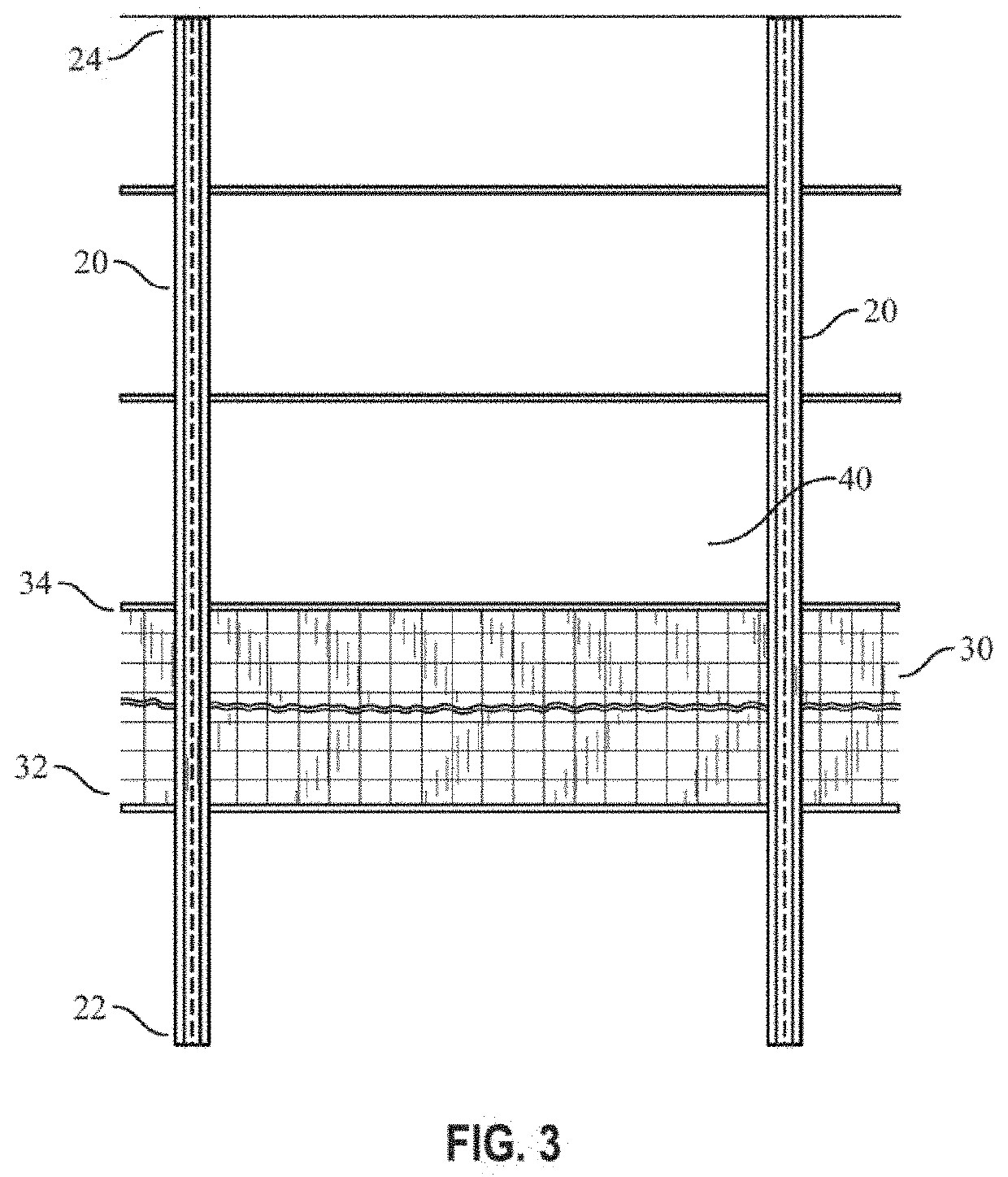
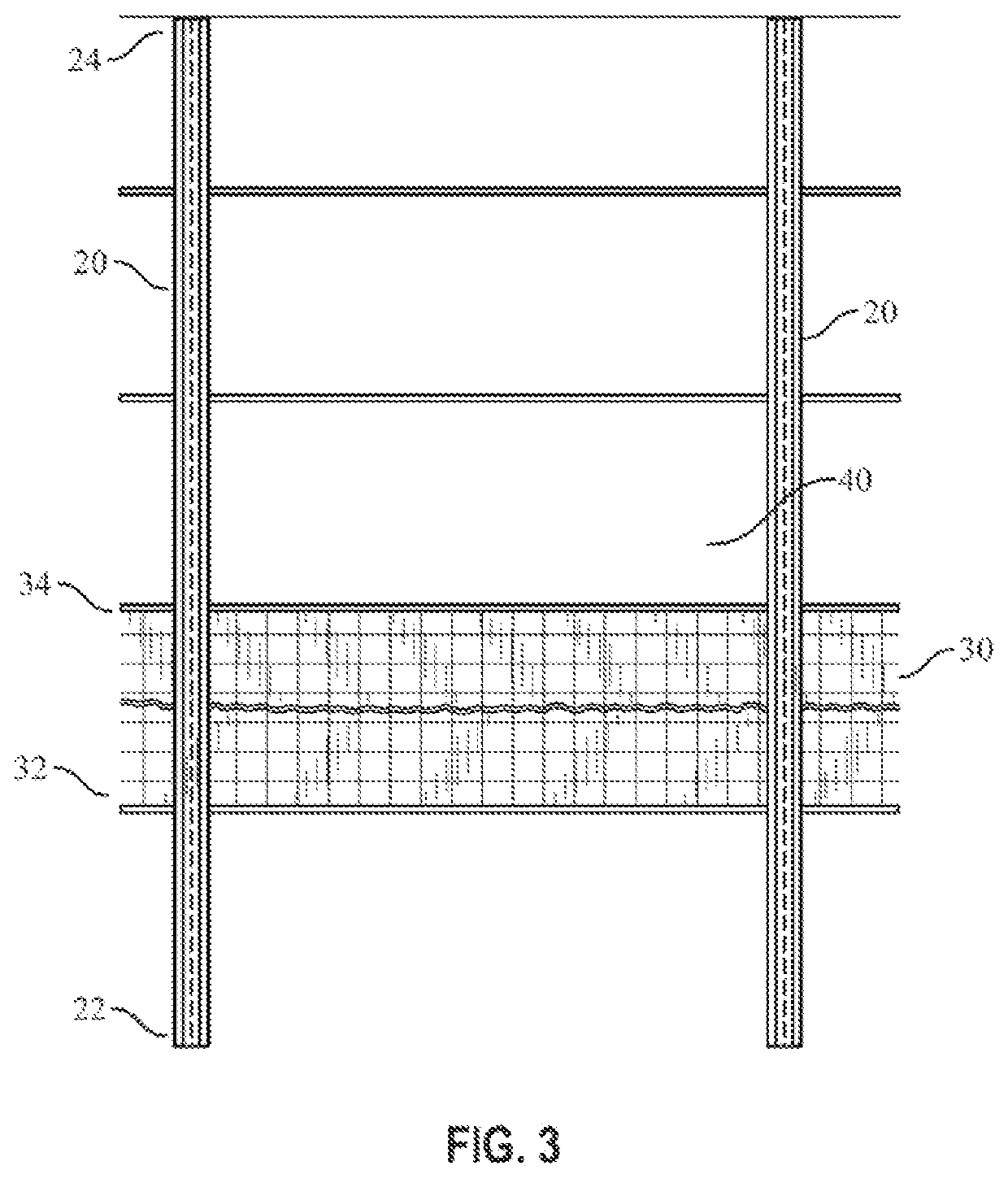
Border security barrier
A security barrier is presented for preventing unauthorized persons or vehicles from easily crossing a border. In one preferred embodiment, the security barrier is suitable for installation in a waterway and comprises: (1) a plurality of piles, each pile having a bottom end embedded into the earth and a top end extending vertically upward; (2) an open security grid juxtaposed between and secured by the piles, wherein the grid preferably has a bottom end that extends downward below the surface between the piles toward the earth; (3) at least one rigid wall panel also juxtaposed between and secured by the piles on top of the open security grid, thereby forming a security barrier that allows water, air, aquatic life, and birds to pass through the barrier, but restricts the movement of humans and vehicles across the barrier.
Owner:A H BECK FOUND CO INC
Border Security Barrier
A security barrier is presented for preventing unauthorized persons or vehicles from easily crossing a border. In one preferred embodiment, the security barrier is suitable for installation in a waterway and comprises: (1) a plurality of piles, each pile having a bottom end embedded into the earth and a top end extending vertically upward; (2) an open security grid juxtaposed between and secured by the piles, wherein the grid preferably has a bottom end that extends downward below the surface between the piles toward the earth; (3) at least one rigid wall panel also juxtaposed between and secured by the piles on top of the open security grid, thereby forming a security barrier that allows water, air, aquatic life, and birds to pass through the barrier, but restricts the movement of humans and vehicles across the barrier.
Owner:A H BECK FOUND CO INC
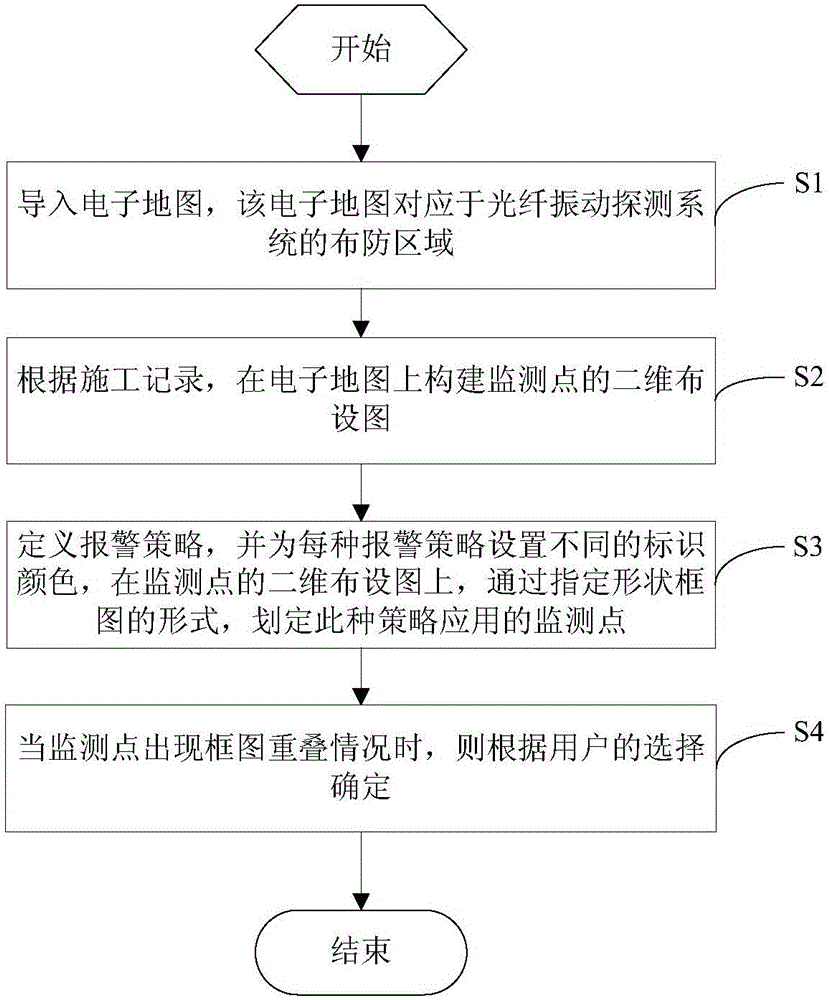
Graphical strategy configuration method for fiber sensing border security system
InactiveCN105701934AGuaranteed validityGuaranteed correctnessBurglar alarm by disturbance/breaking stretched cords/wiresFiberVibration detection
The invention discloses a graphical strategy configuration method for a fiber sensing border security system. The method includes the steps of importing an electronic map corresponding to a deployment region of a fiber vibration detection system, constructing a two-dimensional monitoring point distribution graph on the electronic map according to a construction record, defining alarm strategies, setting different marking colors for different alarm strategies, and marking the monitoring points that a certain strategy applies through a block diagram with a specific shape on the two-dimensional monitoring point distribution graph. When block diagrams overlap on one monitoring point, determination is made according to a user's choice. The alarm strategy configuration for lots of monitoring points is carried out in a graphical way, and the configuration method is visible and highly effective.
Owner:WUHAN WUTOS
Method and system for advanced electronic border security
ActiveUS9633535B2High detectionCost effectiveSignalling system detailsBurglar alarm electric actuationFiberElectrical conductor
A system (10) for protecting a border (B) comprises a fiber-optic cable (12) extending from one end of a border to the other end thereof. The cable includes a bundle of optical fibers which connect to sensors placed at intervals long the border. Included within the fiber-optic cable is a high voltage conductor by which high voltage AC is introduced into, and passes through, the cable for powering the sensors. The high voltage is stepped down and rectified from AC to DC for this purpose. Various types of sensors (100-700) are arranged in pods (14) located at intervals along the length of the border. A method of border protection is also disclosed.
Owner:WEINSTEIN BRADLEY A +1
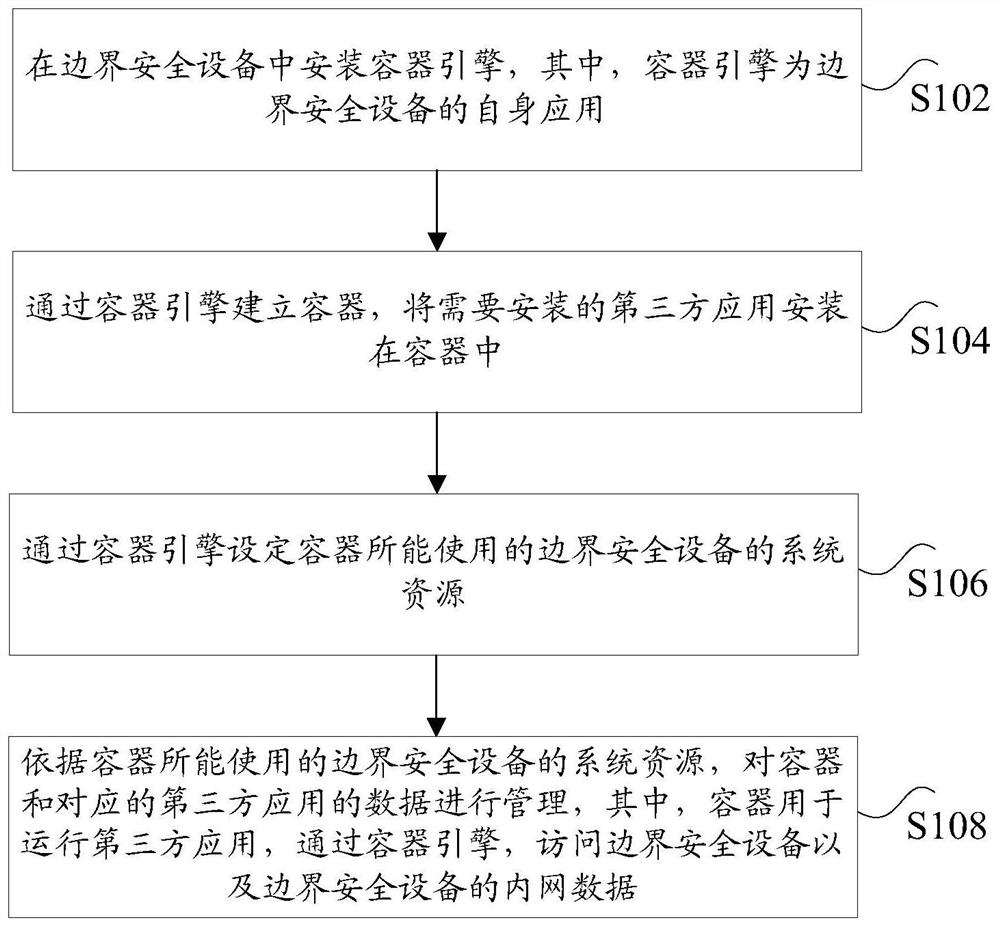
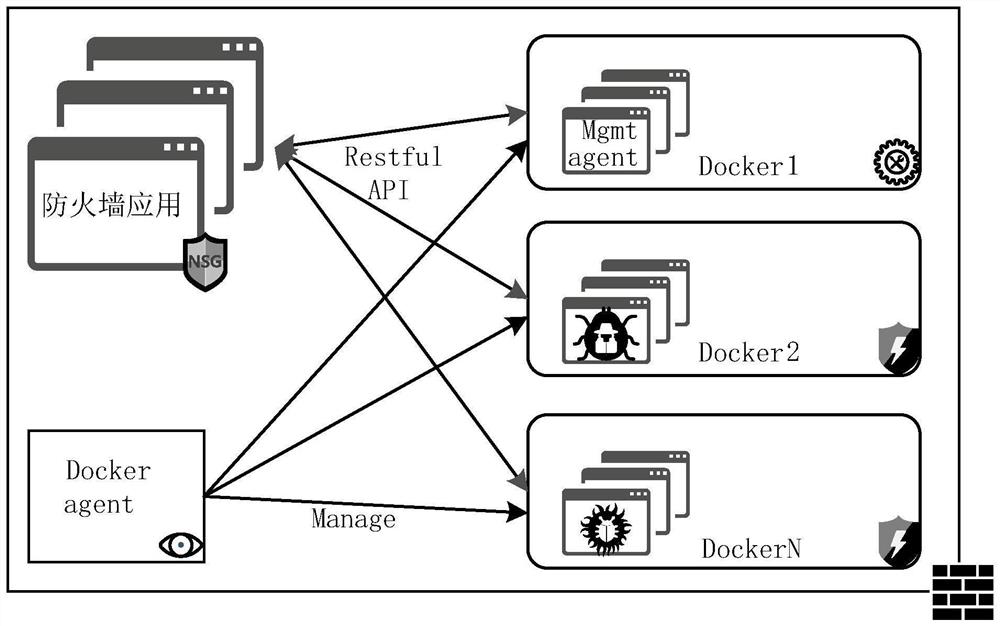
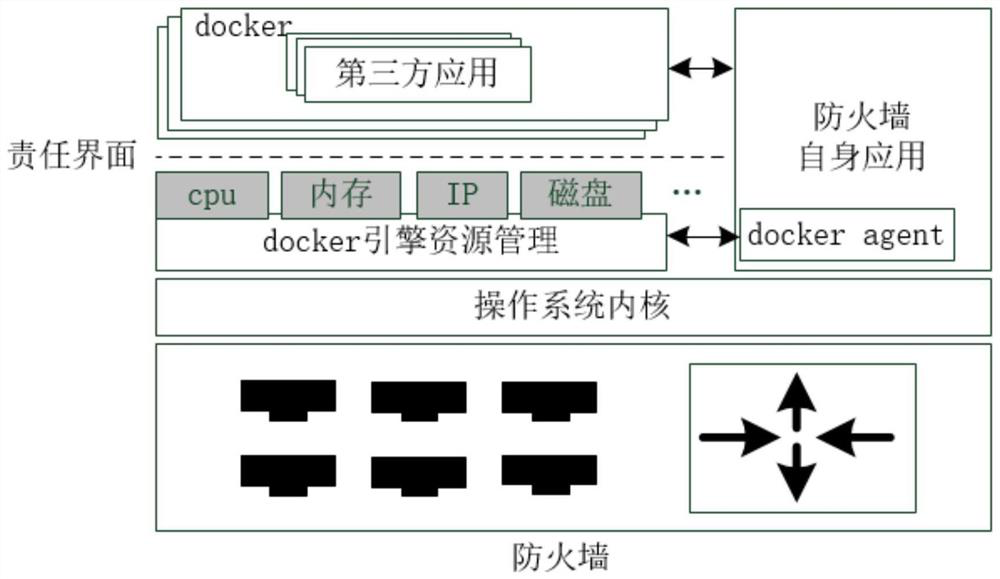
Data processing method and device for boundary security equipment
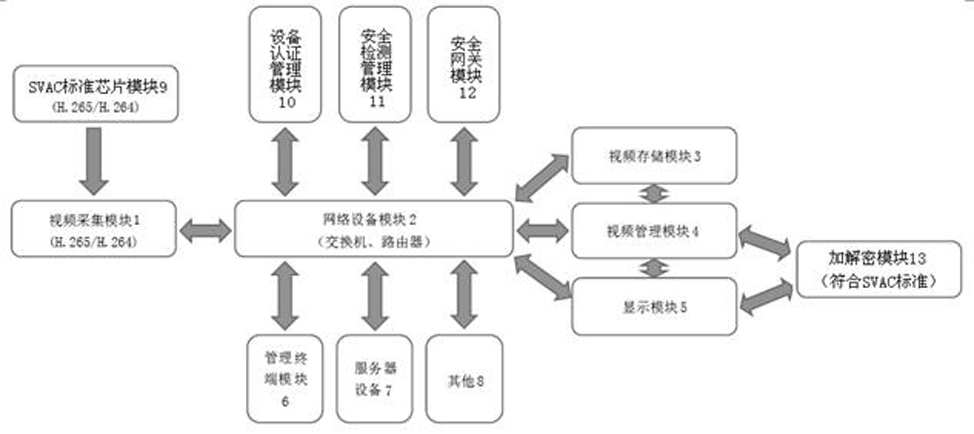
PendingCN113608821AImprove management efficiencyReduce management difficultySoftware simulation/interpretation/emulationThird partyManagement process
The invention discloses a data processing method and device for boundary security equipment. The method comprises the following steps: installing a container engine in the boundary safety equipment; establishing a container through a container engine, and installing a third-party application needing to be installed in the container; setting system resources of the boundary safety equipment which can be used by the container through a container engine; according to the system resources of the boundary safety equipment which can be used by the container, managing the data of the container and the corresponding third-party application, wherein the container is used for operating the third-party application and accessing the boundary safety equipment and the intranet data of the boundary safety equipment through the container engine. According to the method and the device, the technical problems that the system operation of the boundary security equipment is influenced, the management process is complicated, and the development and maintenance processes of the third-party application are complicated because the third-party application needs to be newly added in the boundary security equipment in related arts are solved.
Owner:HILLSTONE NETWORKS CORP
Monitoring device and security system
The present invention provides for an integrated global biological activity detection, traffic tracking and scheduling, and boundary / border security system. Detection apparatuses of the system are preferably placed in a stream of currency such as in financial institutions and other sites of currency exchange, and are also placed in or about transportation vehicles and linked into a data collection, analysis, and graphical information system to provide early warning for security activities. Detection apparatuses located in and about transportation vehicles are combined with a system for routing vehicles into security corridors and with a system of notification, scheduling, and monitoring to enhance the capacity of authorities to insure security and efficient trade movement particularly as it approaches boundaries and borders.
Owner:ARROWHEAD CENT
Identification method of properties of manganese ore and manganese smelting slag
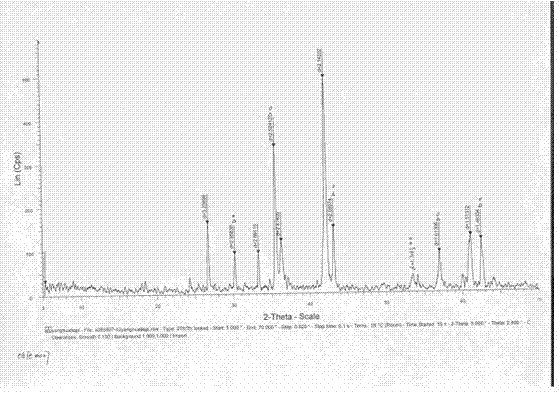
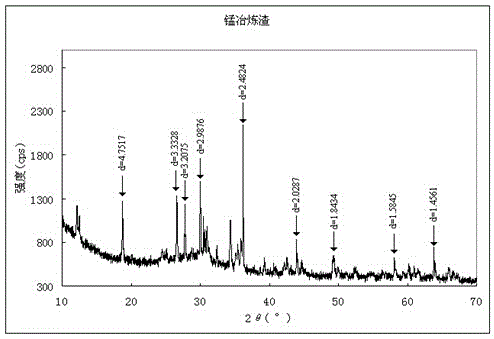
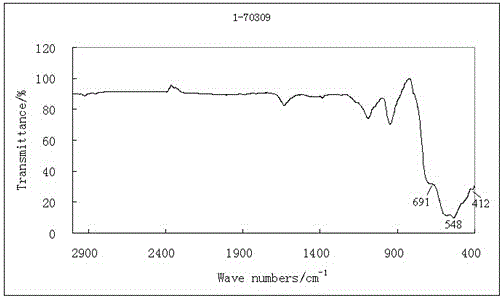
ActiveCN104198514BEnsure safetyAvoid pollutionMaterial analysis by optical meansMaterial analysis using radiation diffractionMetallurgical slagPyrolusite
The invention relates to a method for identifying the attributes of manganese ore and manganese smelting slag. The method uses X-ray diffraction spectroscopy and infrared spectroscopy to identify the attributes of manganese ore and manganese smelting slag. Search for characteristic peaks of manganese oxide, bistrosite, rhodochrosite, etc., and analyze and compare with characteristic peaks such as iron silicate in manganese smelting slag to identify the properties of manganese ore. At the same time, it can be proved by infrared spectrum characteristics. ~400cm ‑1 There are two strong absorption bands in the range, and they are separately or simultaneously at 1420cm ‑1 There is a characteristic absorption peak at , and the manganese smelting slag is at 960cm ‑1 The nearby wide and strong absorption peaks can confirm and identify the properties of manganese ore at the same time. This identification method provides technical support for inspection and quarantine and customs, and provides scientific identification reports for traders to ensure border security and avoid environmental pollution and trade fraud.
Owner:CHEM MINERALS & METALLIC MATERIALS INSPECTION CENT OF TIANJIN ENTRY EXIT INSPECTION & QUARANTINE BUREAU
Energy-saving quick wireless imaging method
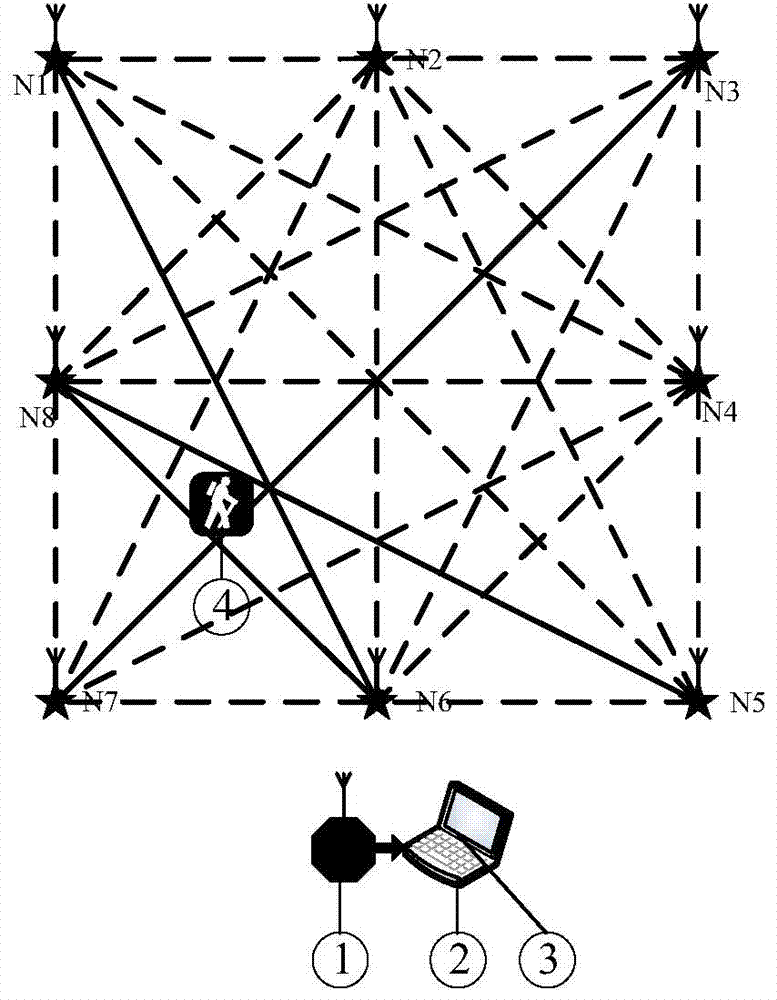
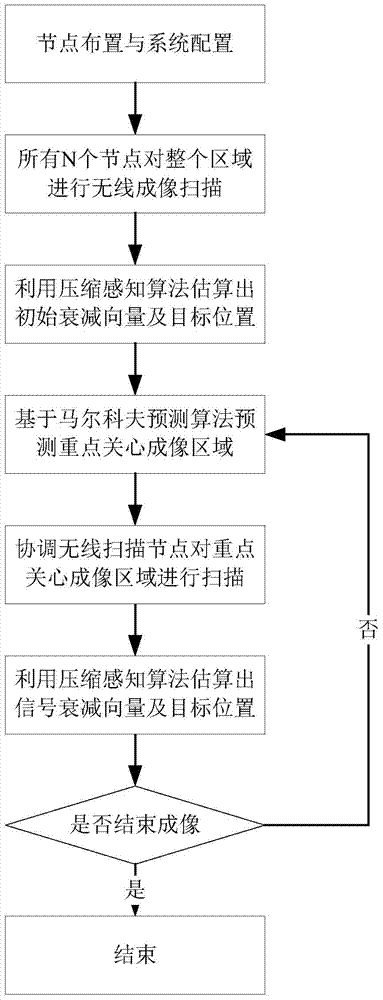
InactiveCN104502884AReduce energy consumptionIncreased wireless scanning speedBeacon systems using radio wavesPosition fixationWireless controlPersonal computer
The invention discloses an energy-saving quick wireless imaging method, and relates to an energy-saving quick wireless imaging method based on the markov process theory, belonging to the technical field of test and measurement technology and wireless network. The wireless imaging method comprises the following steps: predicating a key concerned imaging area through a markov process, coordinating each wireless scanning node to perform wireless link scanning only on the key concerned imaging area; according to wireless link measuring information, reconstructing shielding characteristics of the key concerned imaging area by a wireless imaging system through a compressed sensing algorithm, wherein the wireless imaging system comprises N wireless scanning nodes, a wireless control node, a general PC (personal computer) and intelligent processing softwares operated on the general PC. The energy-saving quick wireless imaging method can be used for expanding the scope of application of the wireless imaging technology, so that the wireless imaging technology can be applied to a battery-powered portable monitoring application occasion and a wireless imaging monitoring for a large-scale area and has a wide application prospect in the fields such as border security and protection monitoring and animal monitoring.
Owner:DALIAN UNIV OF TECH
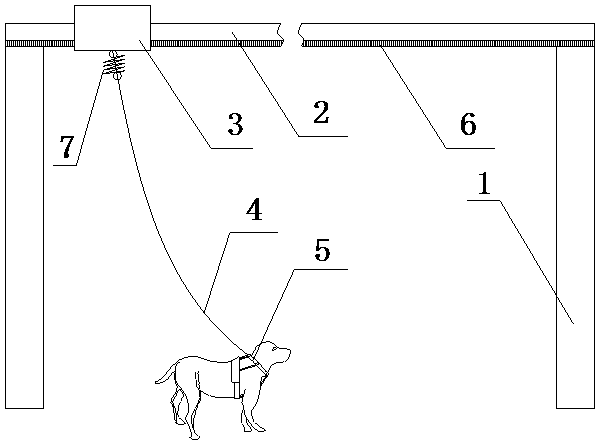
Intelligent remote dog defense system
InactiveCN109143898ARealize feeding managementReduce human resource costsAnimal watering devicesAnimal feeding devicesElectromagnetic clutchEngineering
The invention relates to an intelligent remote dog defense system. The system comprises support columns, a rail and a rail car. A traction rope is connected to the rail car, and a dog collar is connected to a tail end of the traction rope. A microphone and a communication circuit are arranged on the dog collar, and the microphone is connected to a remote computer through a communication circuit. An automatic feeder is near the rail which is provided with a rack, and the rail car has a first gear which engages with the rack and a motor. An output shaft of the motor is equipped with a speed reduction box which is connected to the first gear through an electromagnetic clutch. The motor and the electromagnetic clutch are controlled by the remote computer. The rail car has a first battery for supplying power to the electromagnetic clutch and the motor. A second battery supplying power to the microphone and the communication circuit is in the dog collar. According to the intelligent remote dog defense system provided by the invention, the behavior principle of dog active defense is used, at the same time, an automatic facility is arranged for dog control management, and border security situations are timely discovered and timely processed.
Owner:NANJING POLICE DOG RES INST OF MINIST OF PUBLIC SECURITY
Intelligent security check equipment for border security
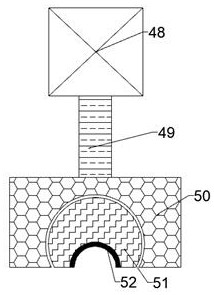
InactiveCN112363240APrevent forced escapeGeological measurementsTraffic restrictionsScannerPosition check
The invention discloses intelligent security check equipment for border security. The equipment comprises a check box, a security check mechanism is arranged in a check bin, the security check mechanism comprises a check plate, six check scanners are arranged on the check plate, the six check scanners are fixedly connected to the inner wall of the lower side of the check plate, and the check plateis slidably connected with the inner wall of the check movable bin. The equipment can provide a channel through which a to-be-detected person can pass, the to-be-detected person needs to be checked if entering the channel, the to-be-detected person needs to place the hands and the feet at specific positions according to operation procedures after entering the checking channel, then the checking equipment starts to check the to-be-detected person, the detection equipment can check the whole body of the to-be-detected person, if dangerous equipment displays the position of a dangerous article,the hands and feet are limited by the equipment, and the equipment cuts off the back path of the to-be-detected person to prevent the to-be-detected person from forcibly escaping.
Owner:WENZHOU SHANHENG LOCKS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com