Patents
Literature
2980 results about "Safety Equipment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
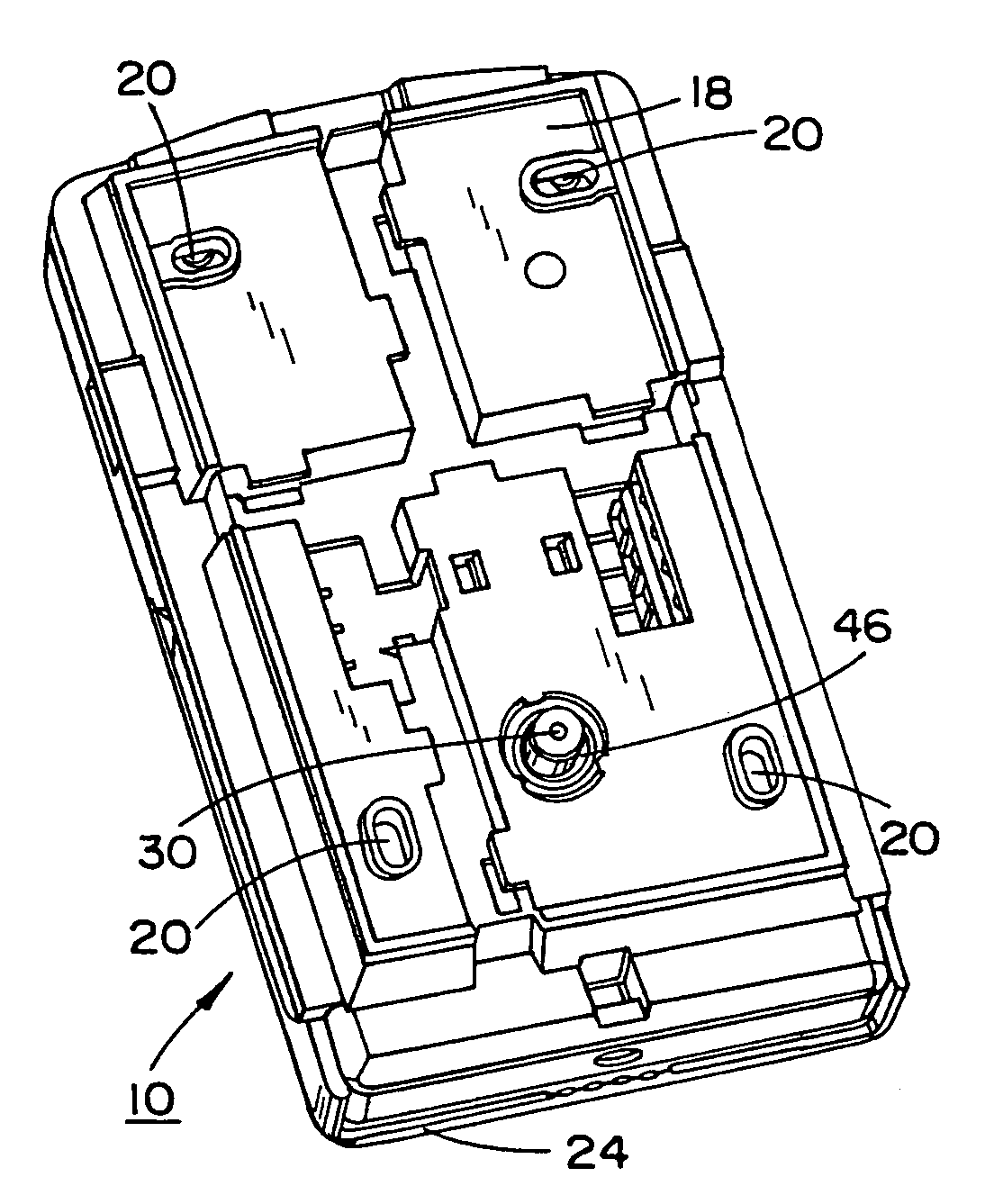
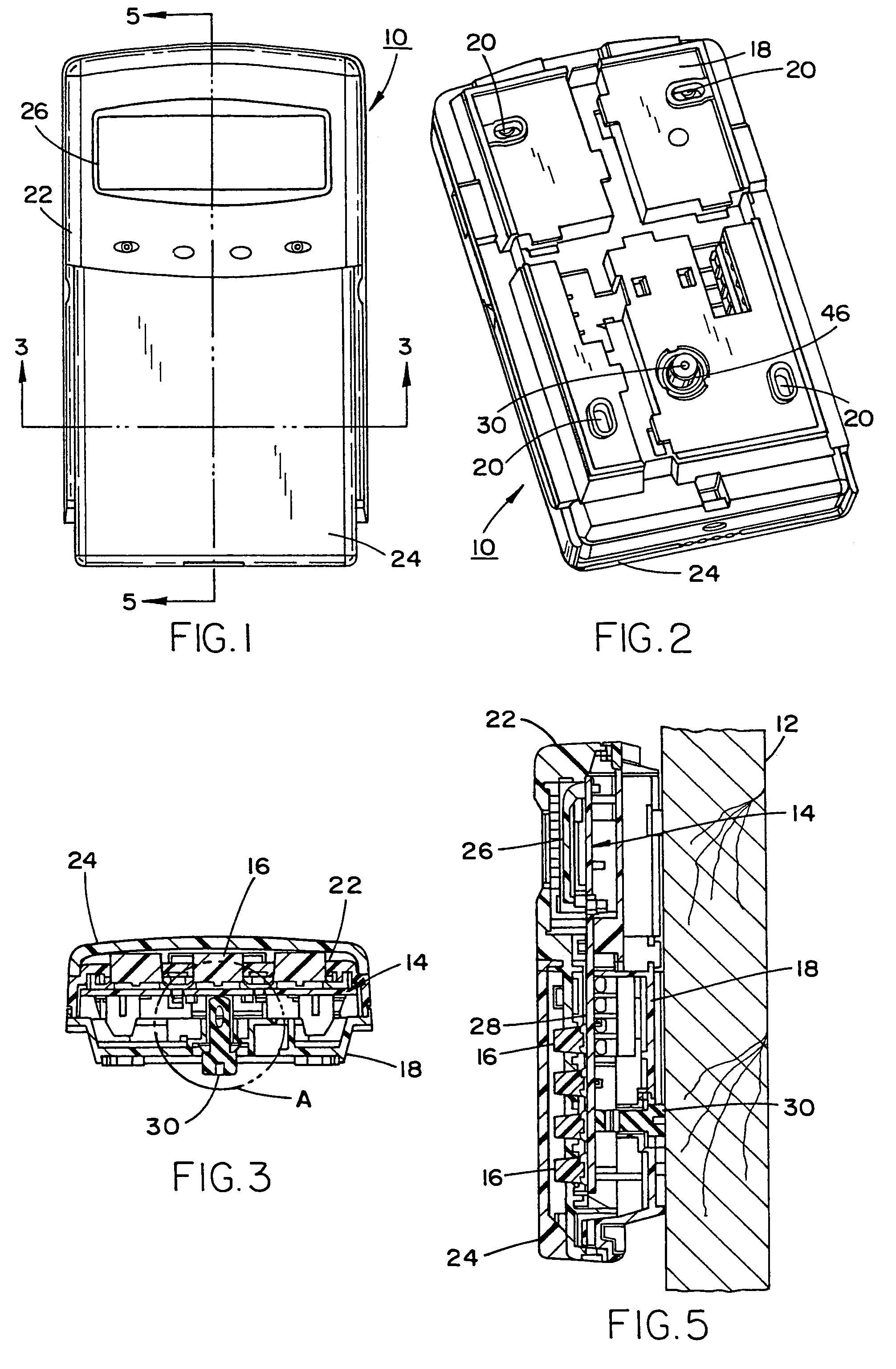
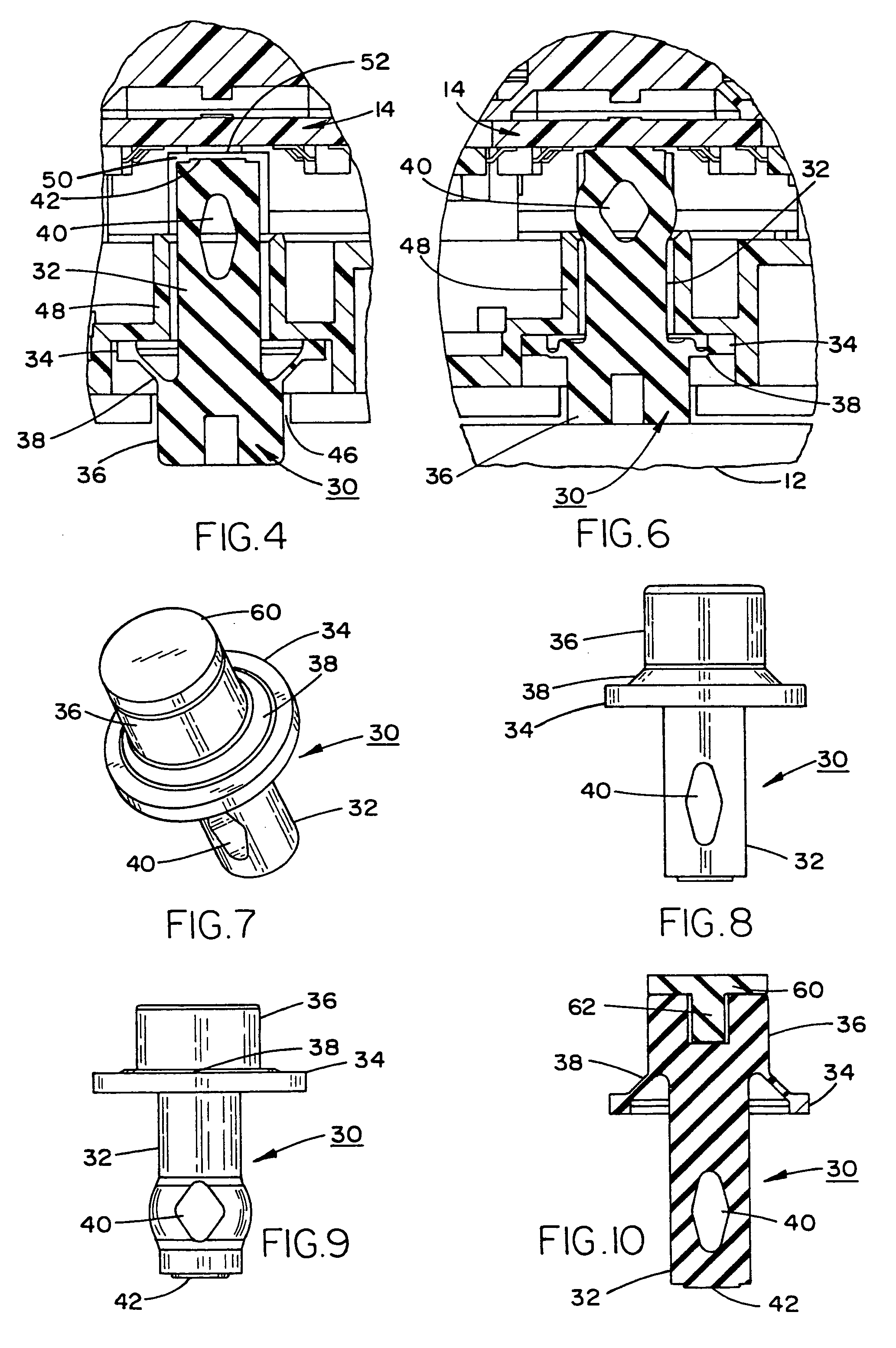
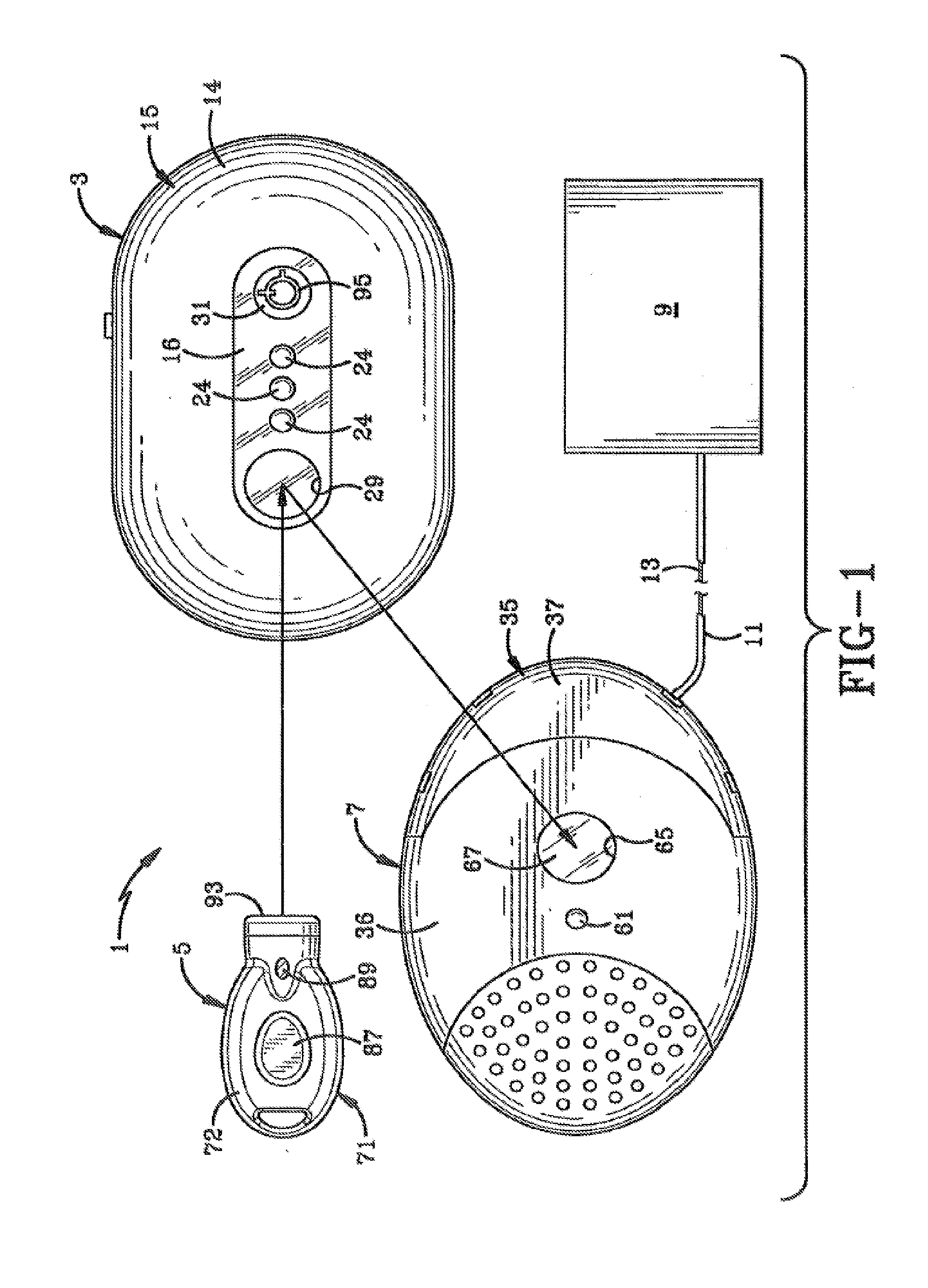
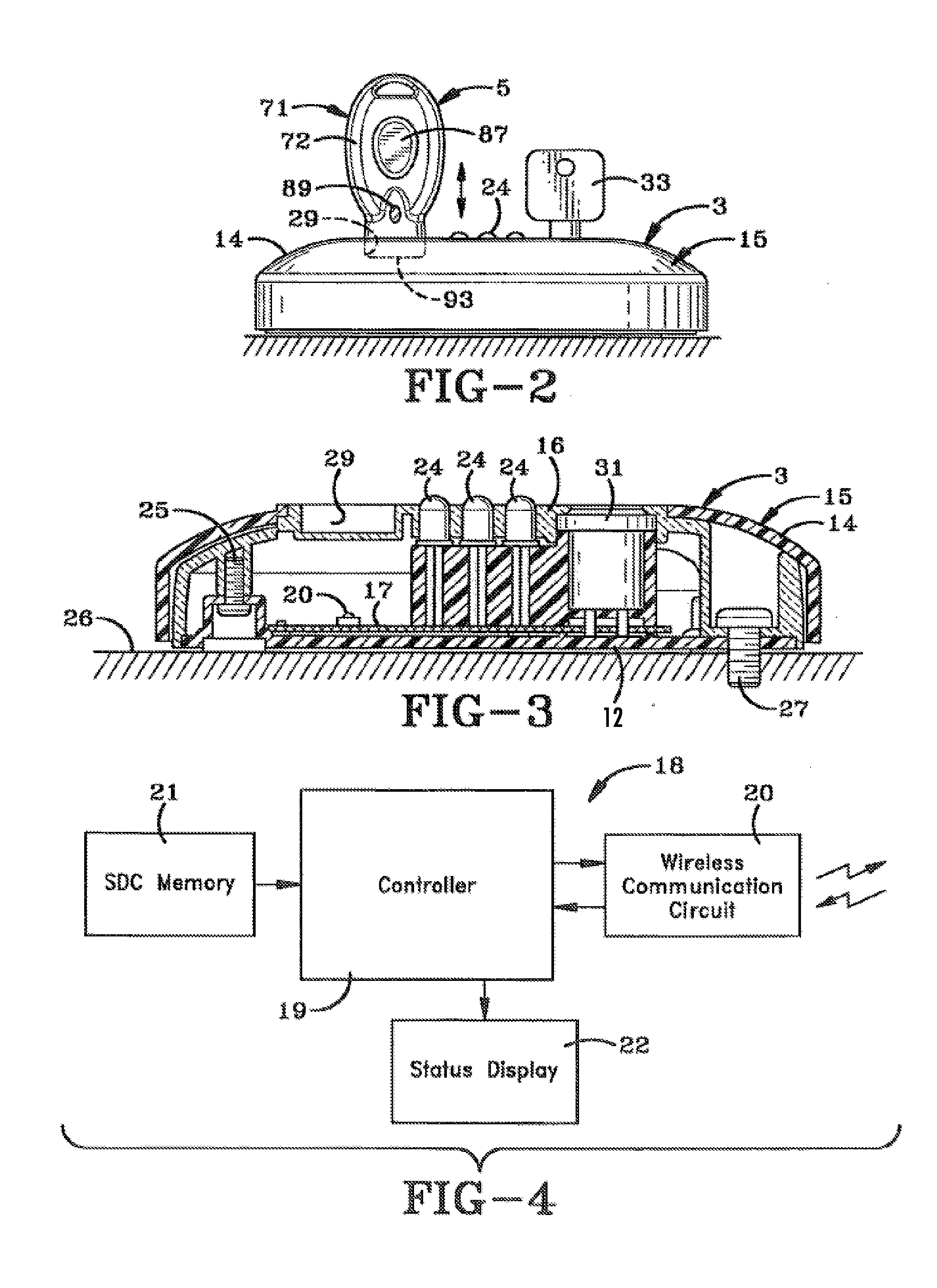
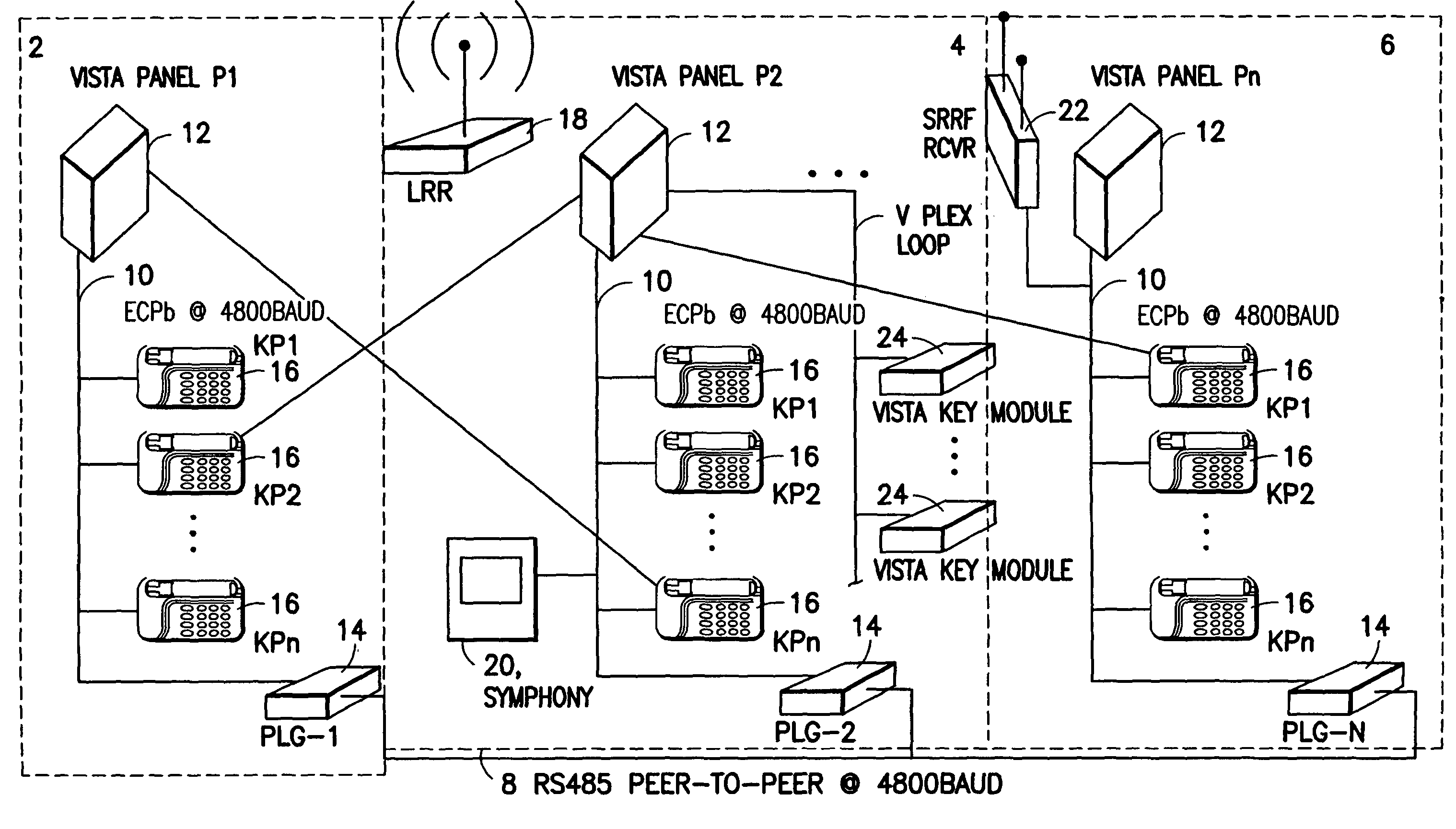
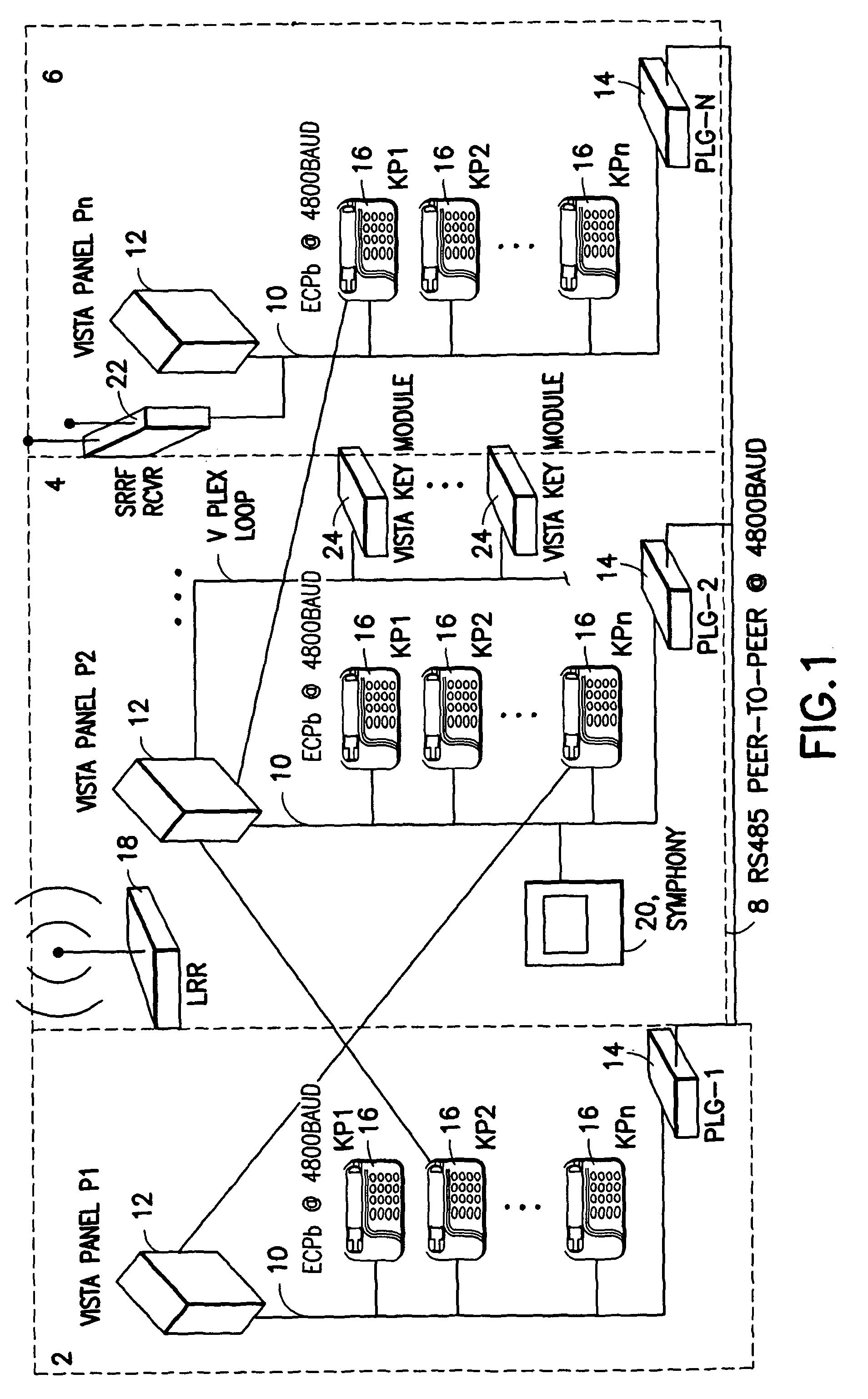
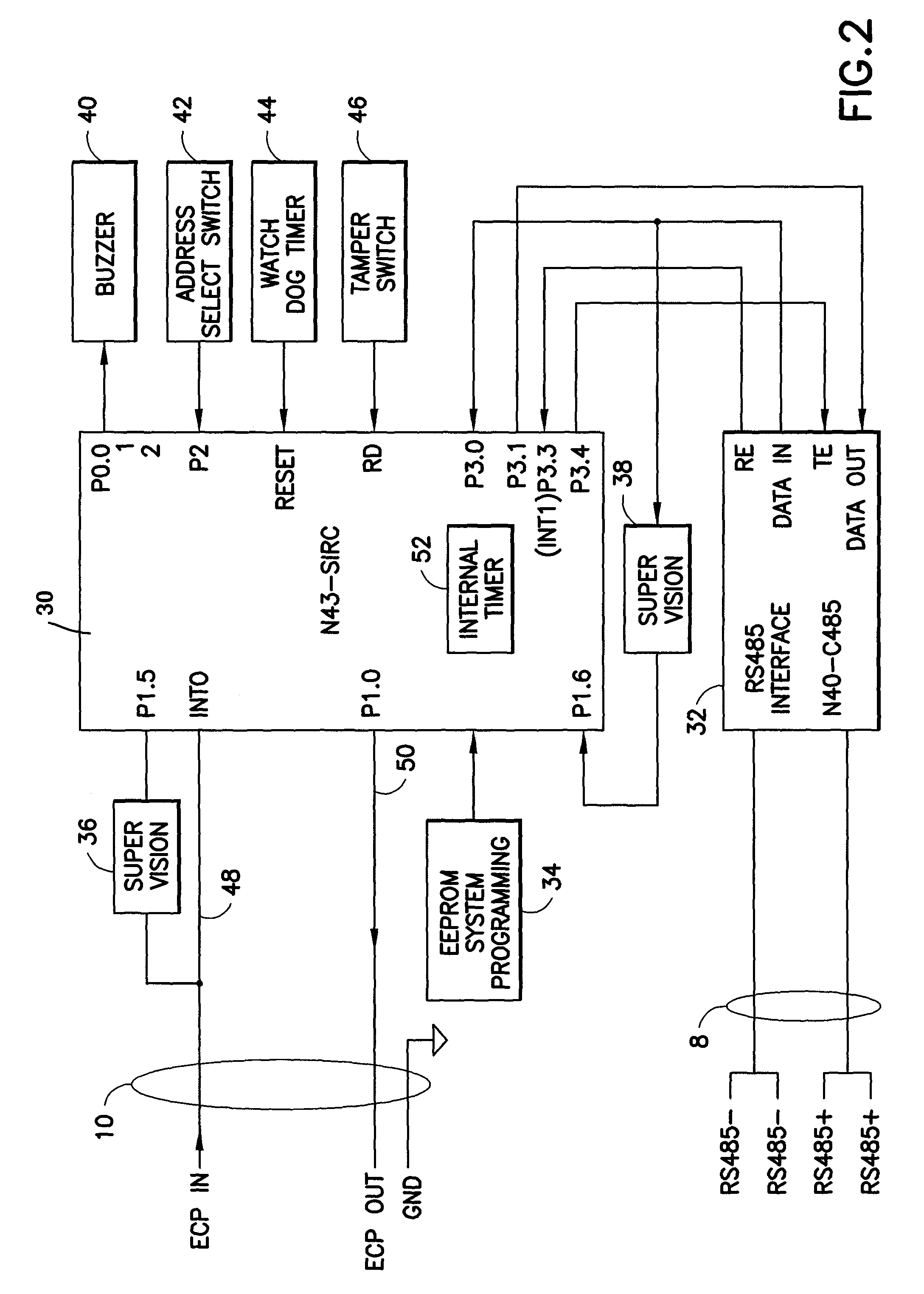
Conductive tamper switch for security devices
InactiveUS7388484B2Highly efficient and reliable in operationCost-effectively mountedInternal/peripheral component protectionRadio/inductive link selection arrangementsMonitoring siteFire alarm system
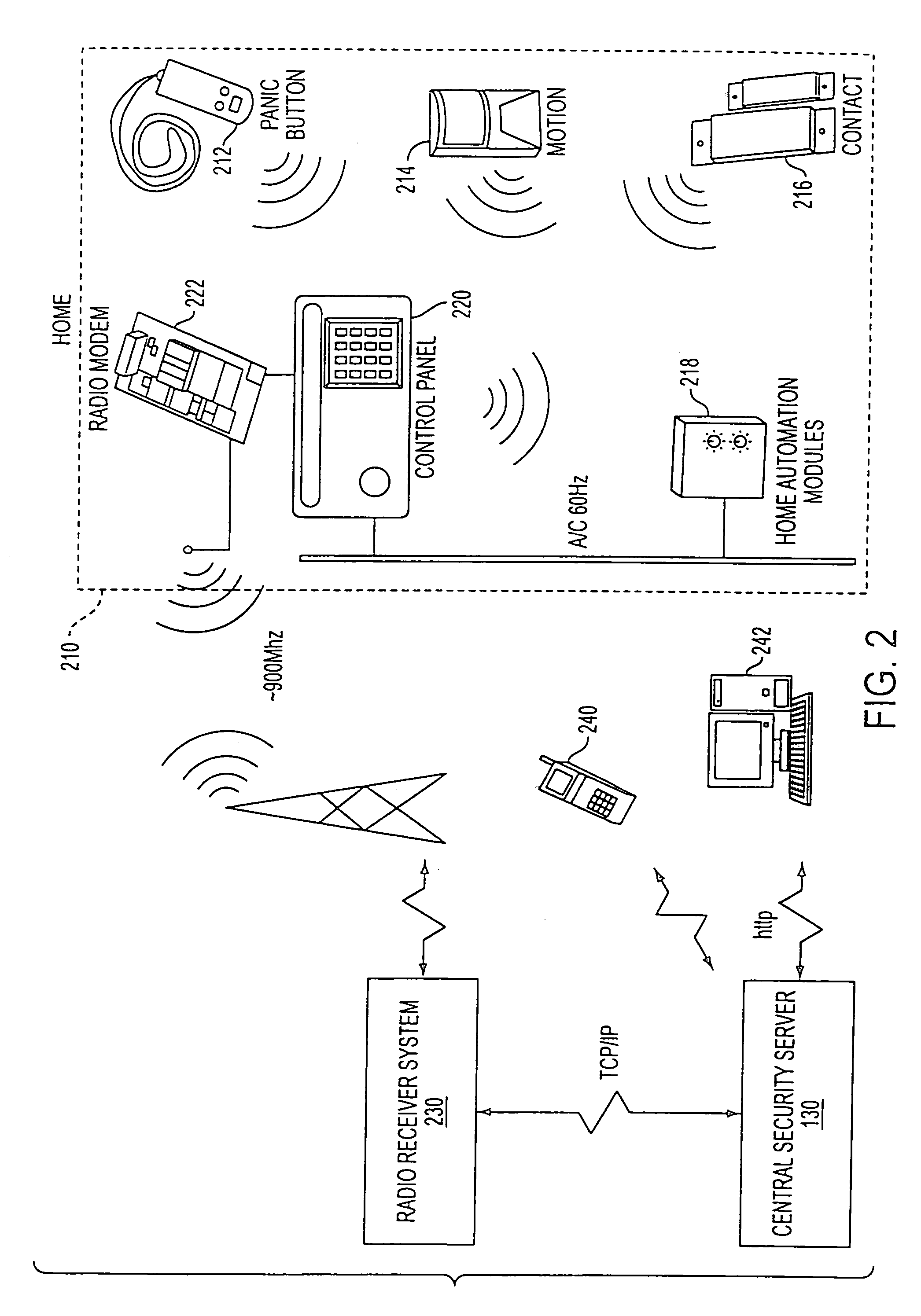
A tamper switch mechanism utilized in security interface devices such as keypad installations to render them tamper-resistant, wherein the devices are generally connected to burglar alarm and fire alarm systems. More particularly, provided is a conductive tamper switch which is installed in a security interface device, such as a keypad, which upon an unauthorized attempt to dislodge the device or keypad from a wall or surface on which it is mounted, will trigger an alarm or generate a warning signal at a monitoring site indicative that an effort at tampering with the device has been effected. Also disclosed is a method of providing the tamper switch mechanism in a security interface device, such as a keypad installation.
Owner:HONEYWELL INT INC
Flexible transparent touch sensing system for electronic devices
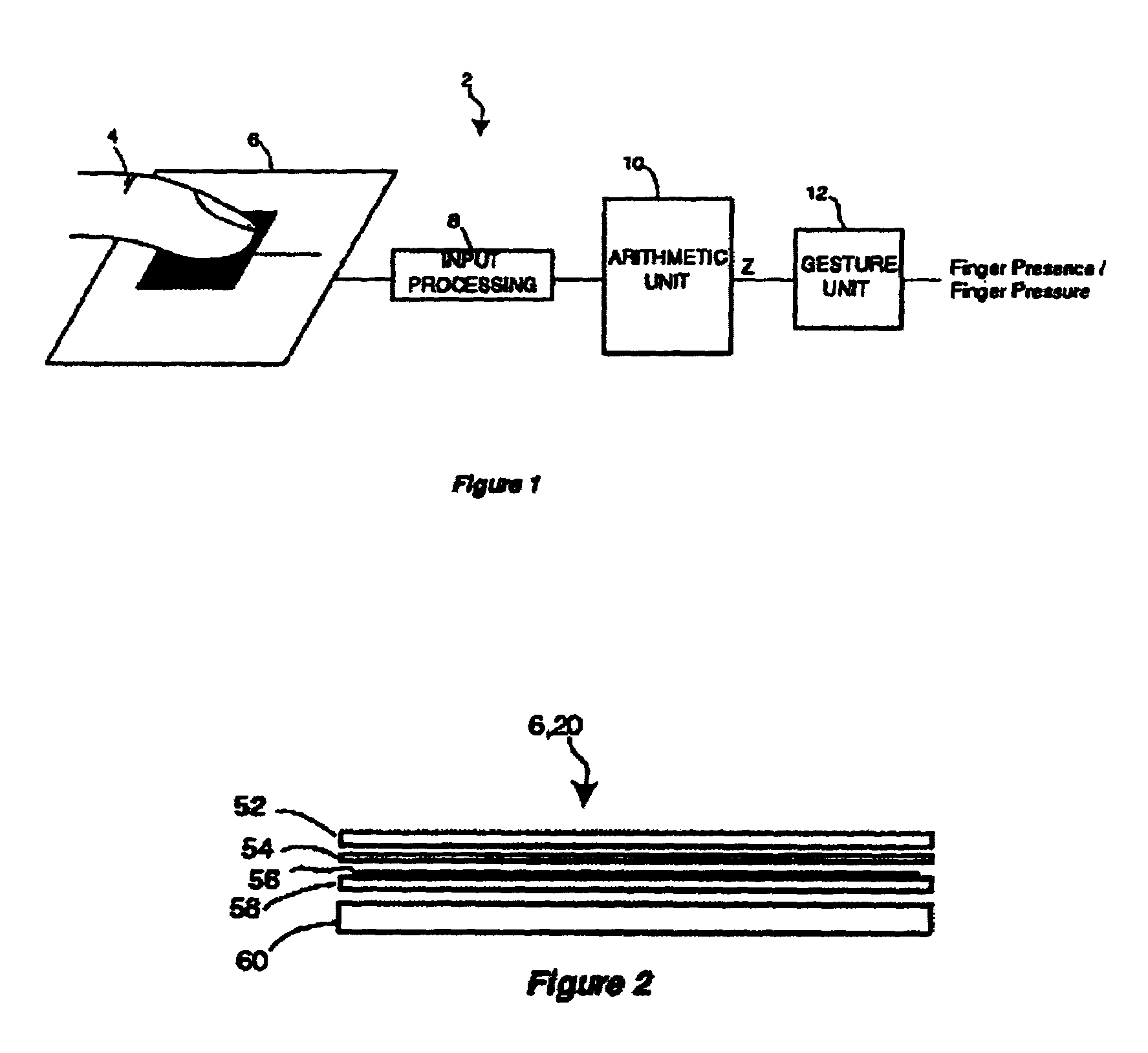
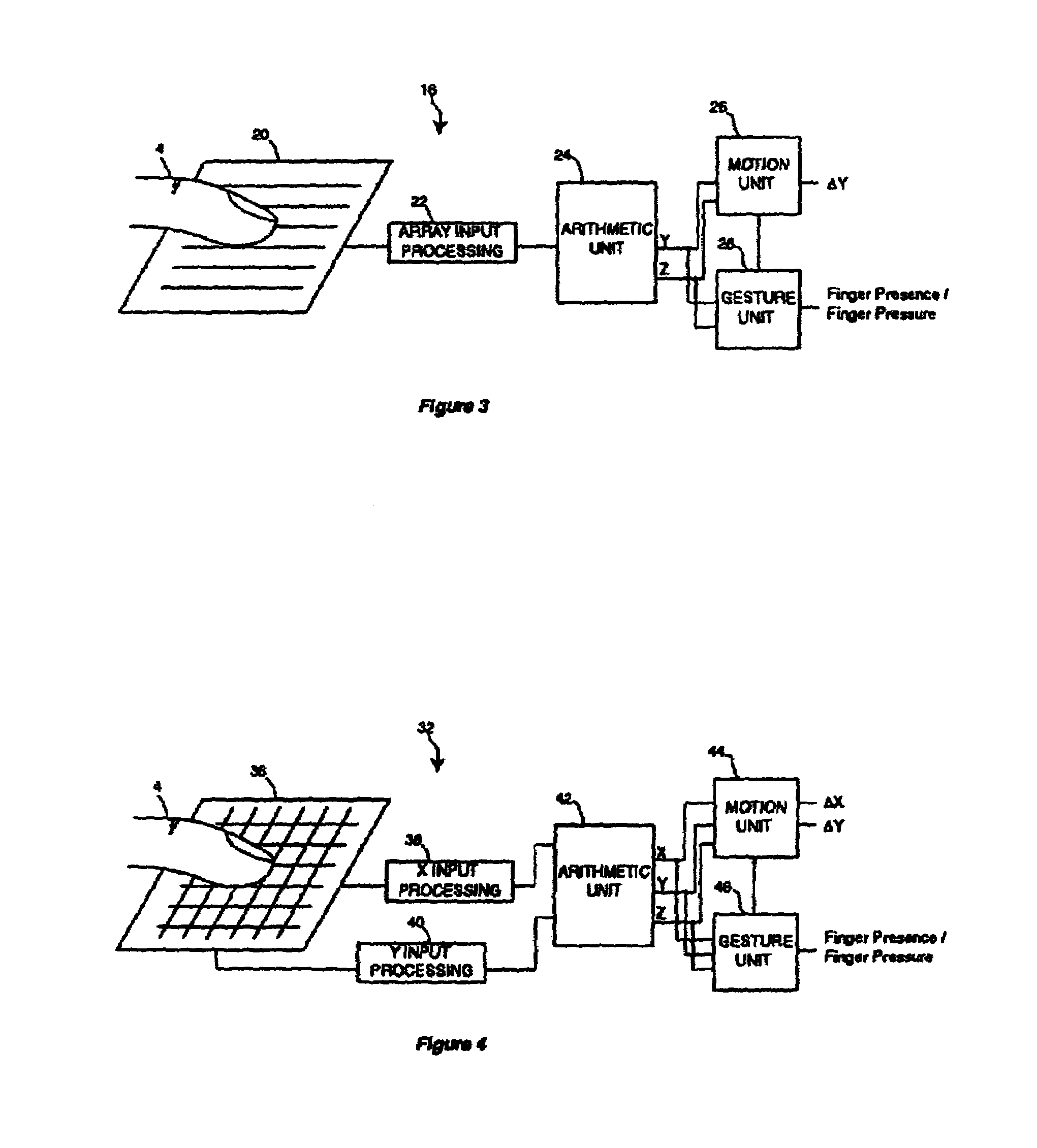
InactiveUS7030860B1Maximize transparencyAmount of overlapInput/output for user-computer interactionTransmission systemsDisplay deviceSensor observation
A transparent, capacitive sensing system particularly well suited for input to electronic devices is described. The sensing system can be used to emulate physical buttons or slider switches that are either displayed on an active display device or printed on an underlying surface. The capacitive sensor can further be used as an input device for a graphical user interface, especially if overlaid on top of an active display device like an LCD screen to sense finger position (X / Y position) and contact area (Z) over the display. In addition, the sensor can be made with flexible material for touch sensing on a three-dimensional surface. Because the sensor is substantially transparent, the underlying surface can be viewed through the sensor. This allows the underlying area to be used for alternative applications that may not necessarily be related to the sensing system. Examples include advertising, an additional user interface display, or apparatus such as a camera or a biometric security device.
Owner:SYNAPTICS INC
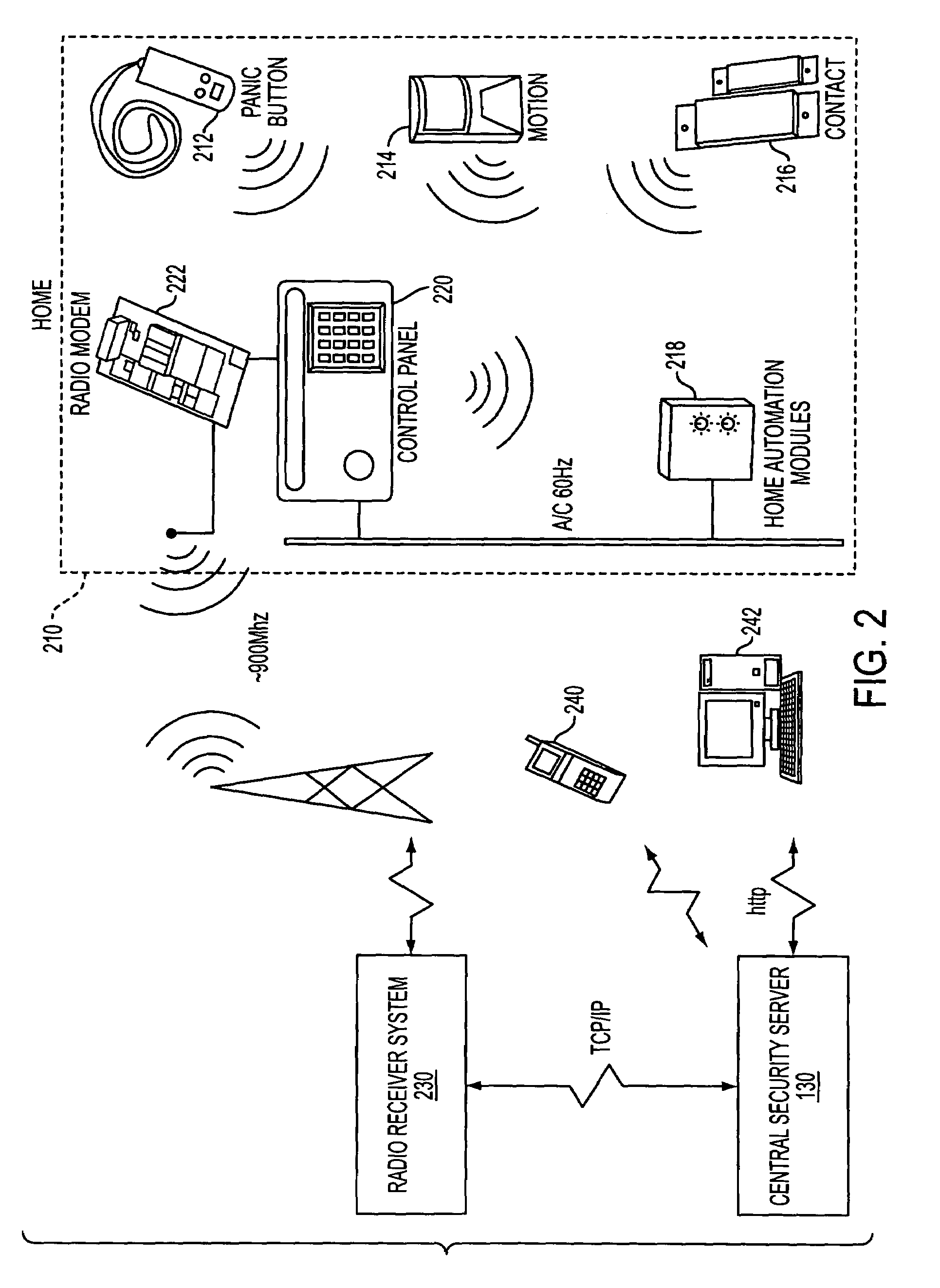
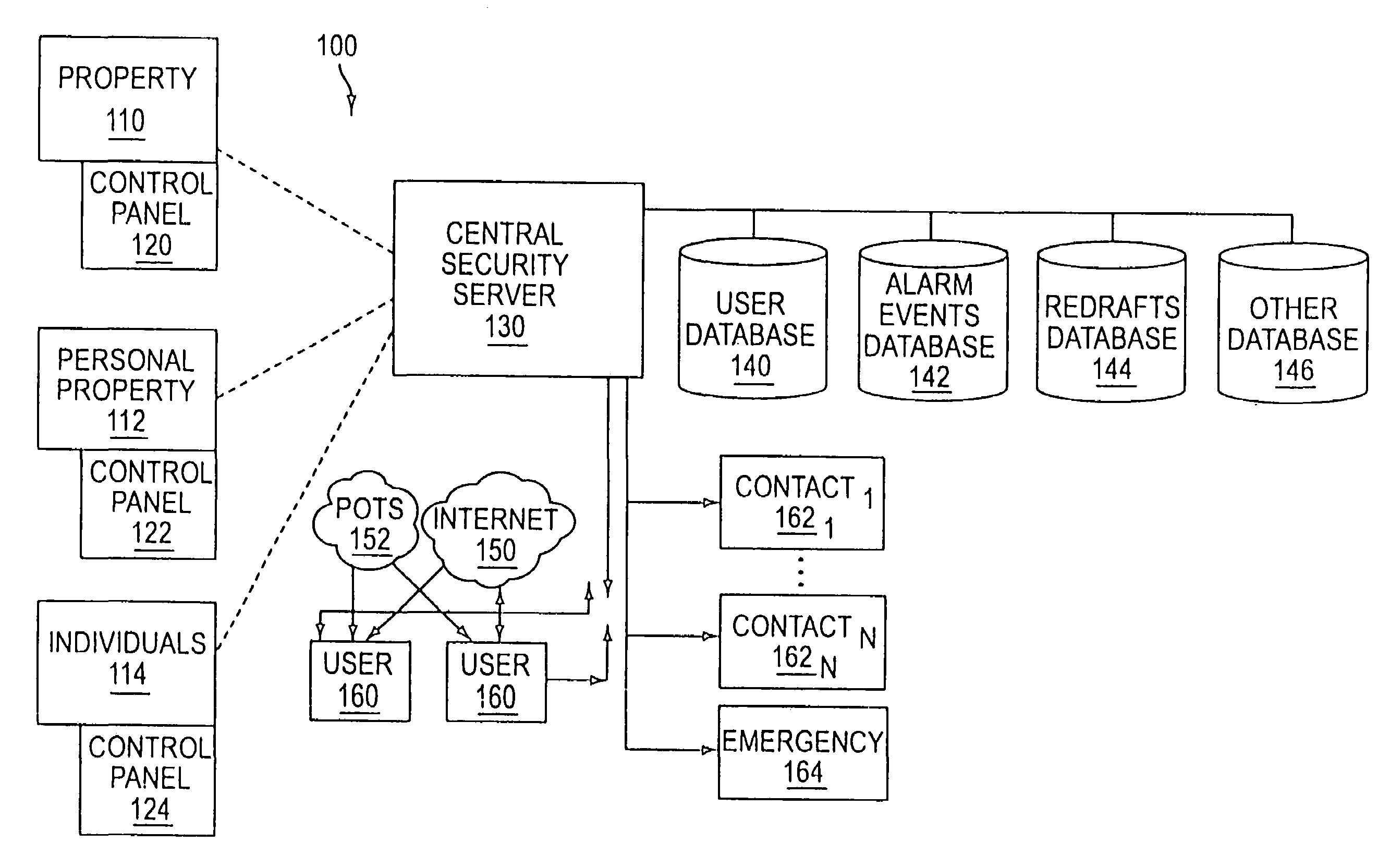
System and method for connecting security systems to a wireless device
InactiveUS7113090B1Electric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
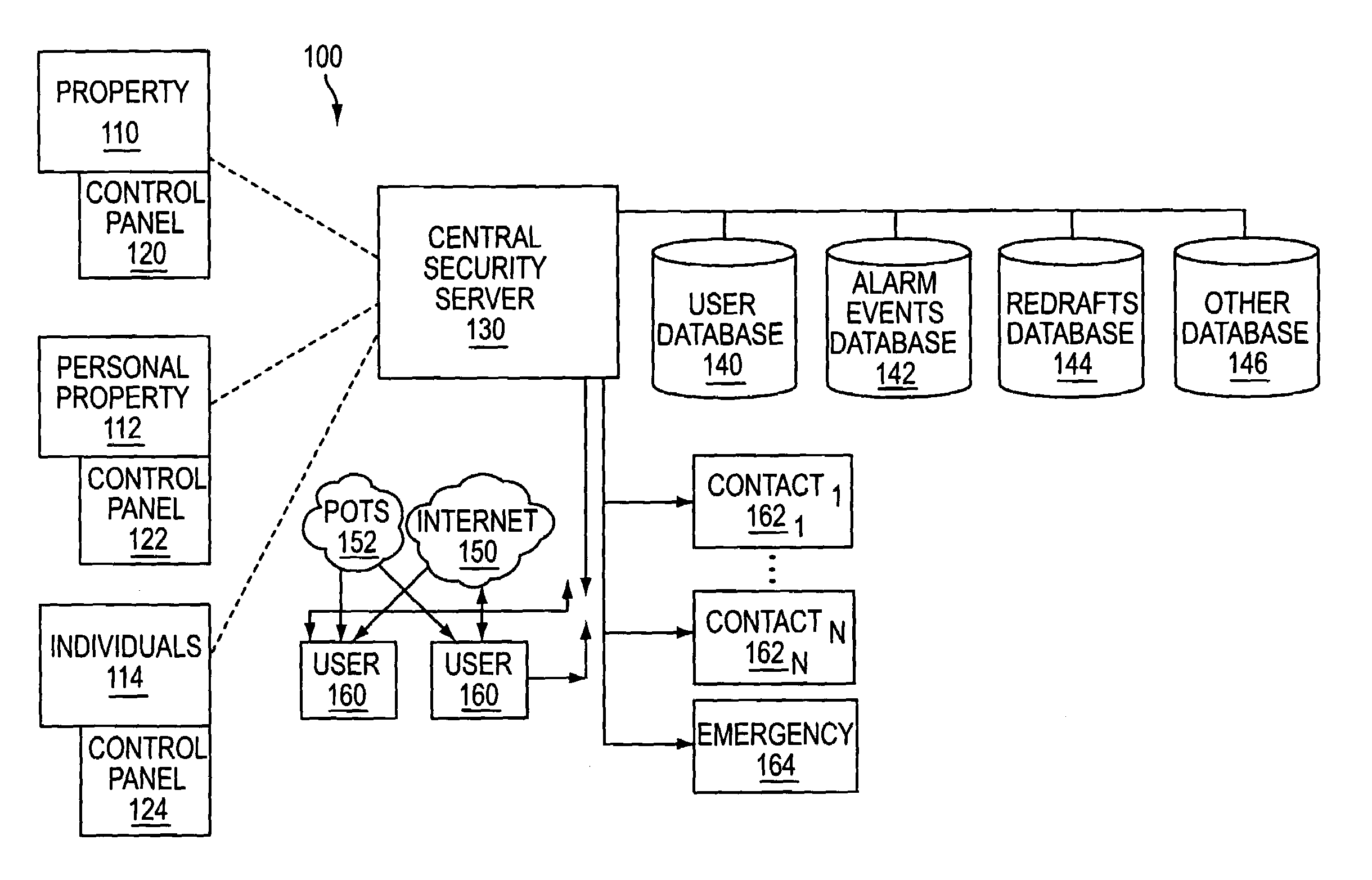
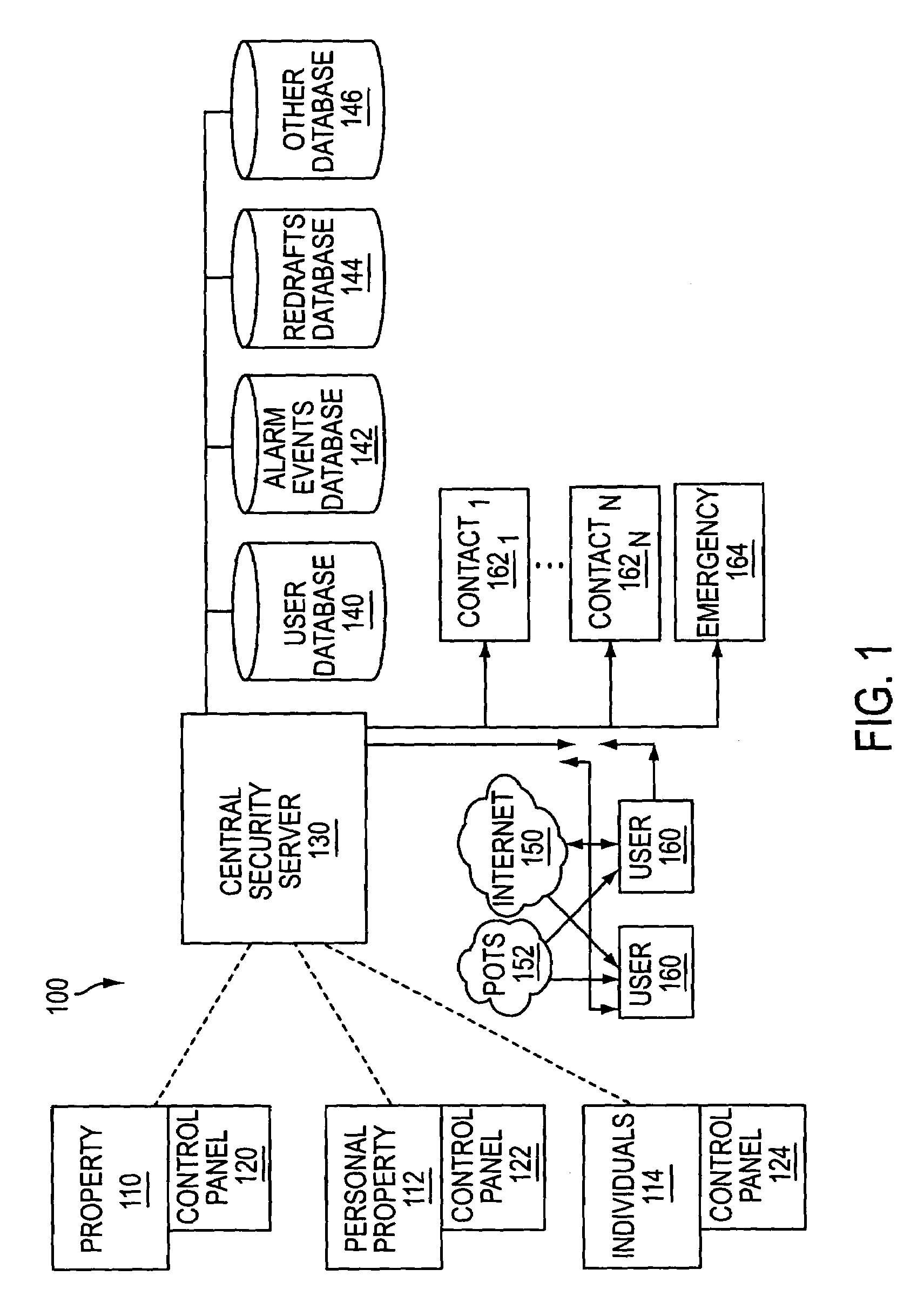
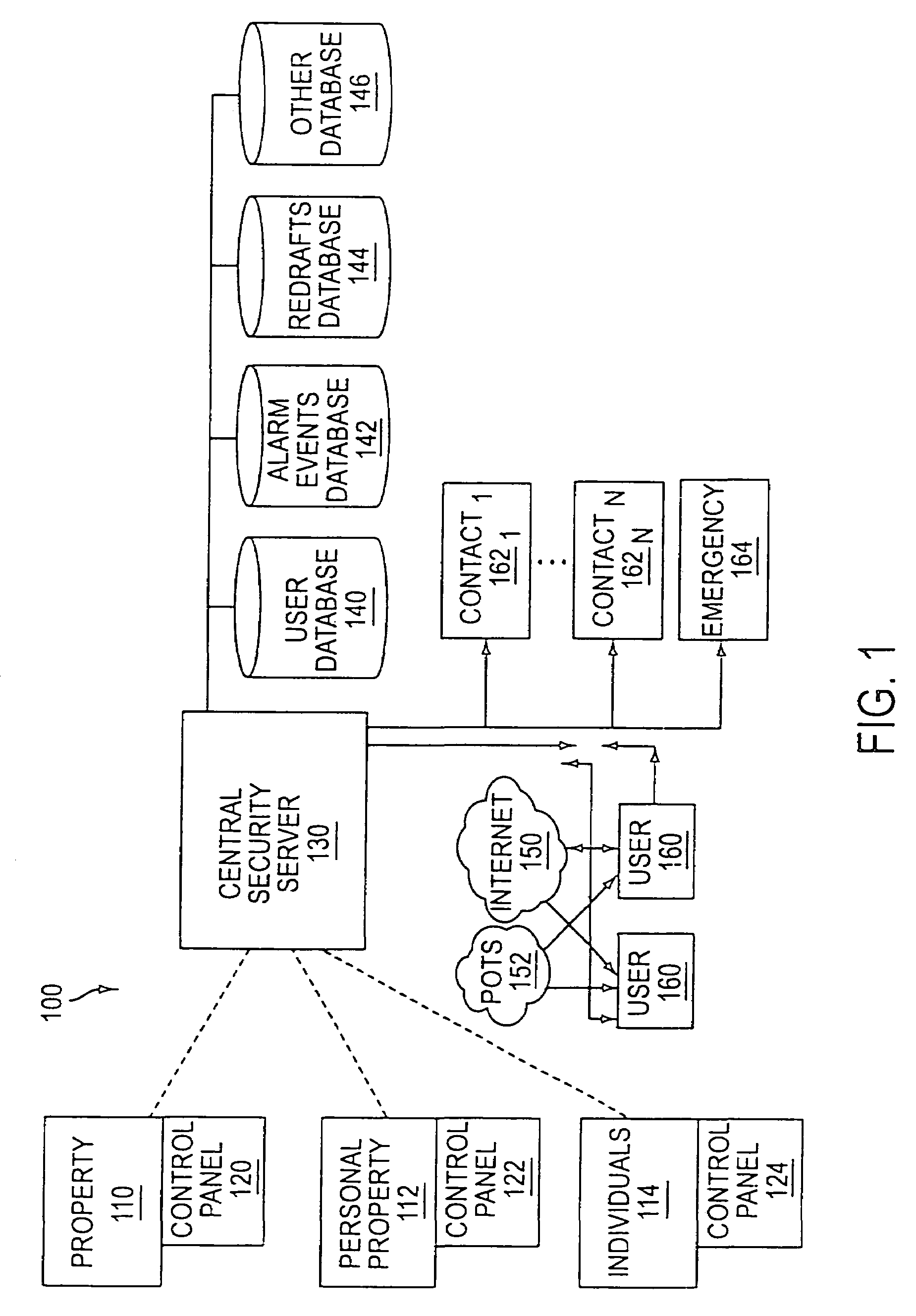
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
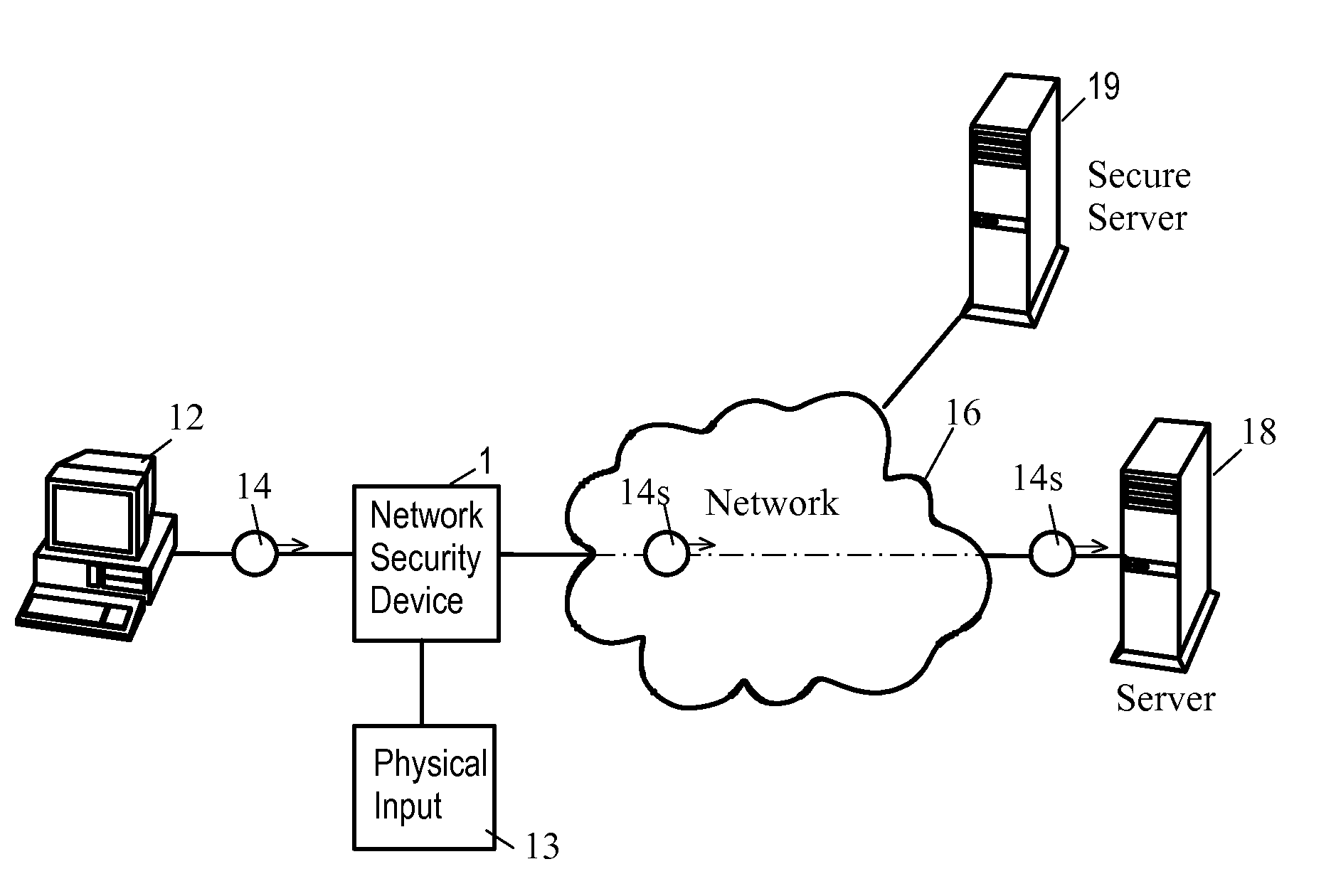
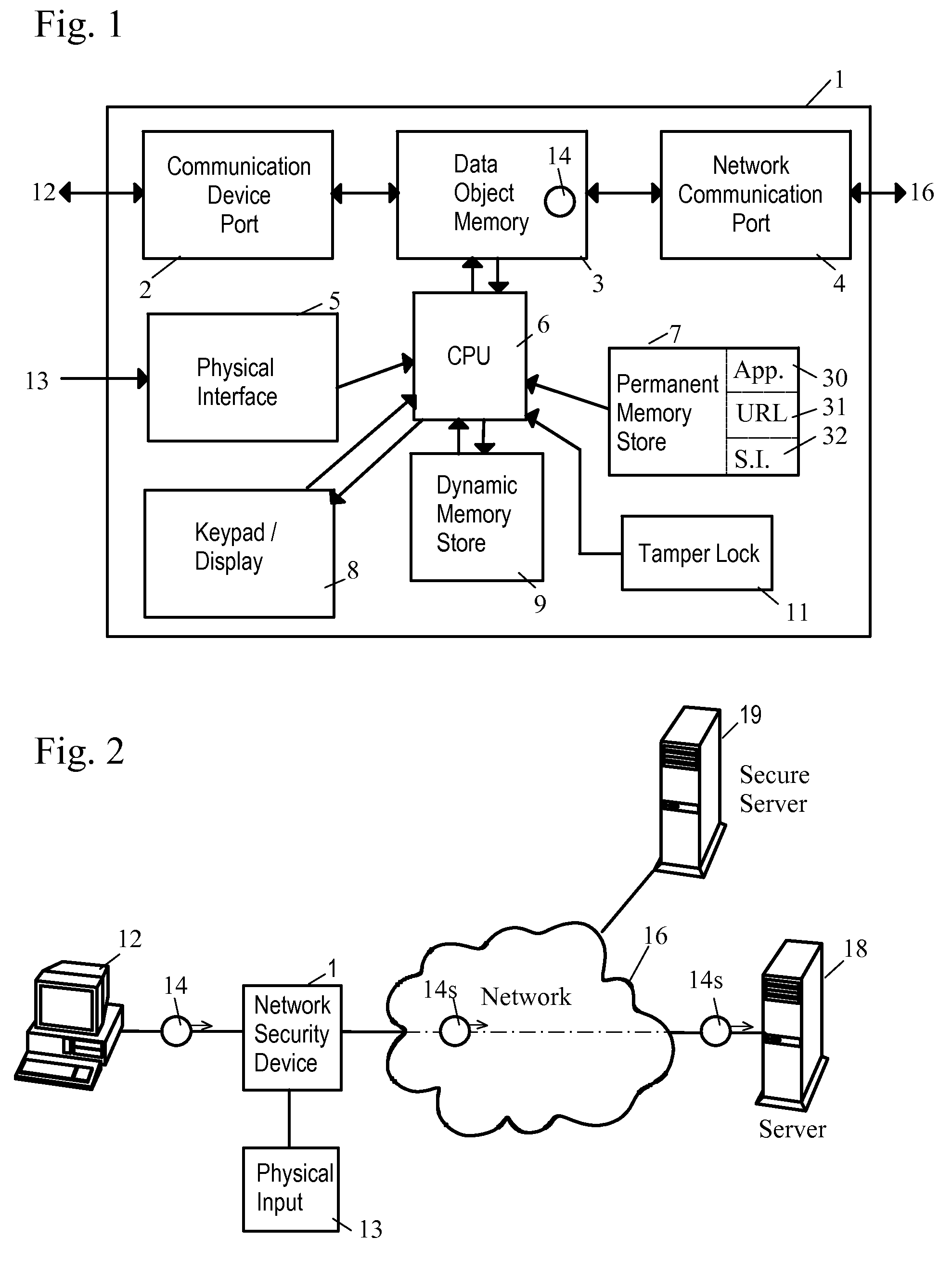
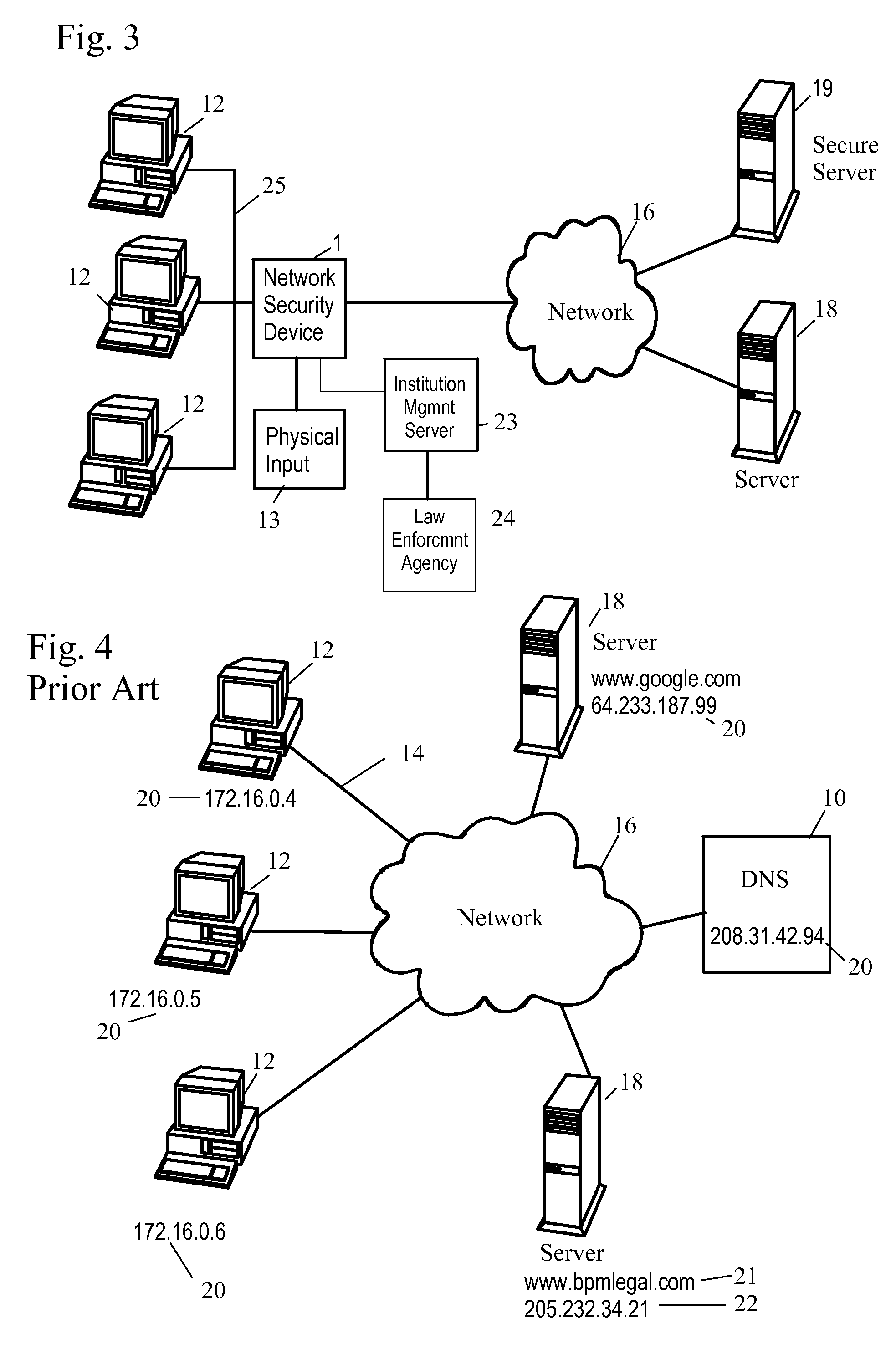
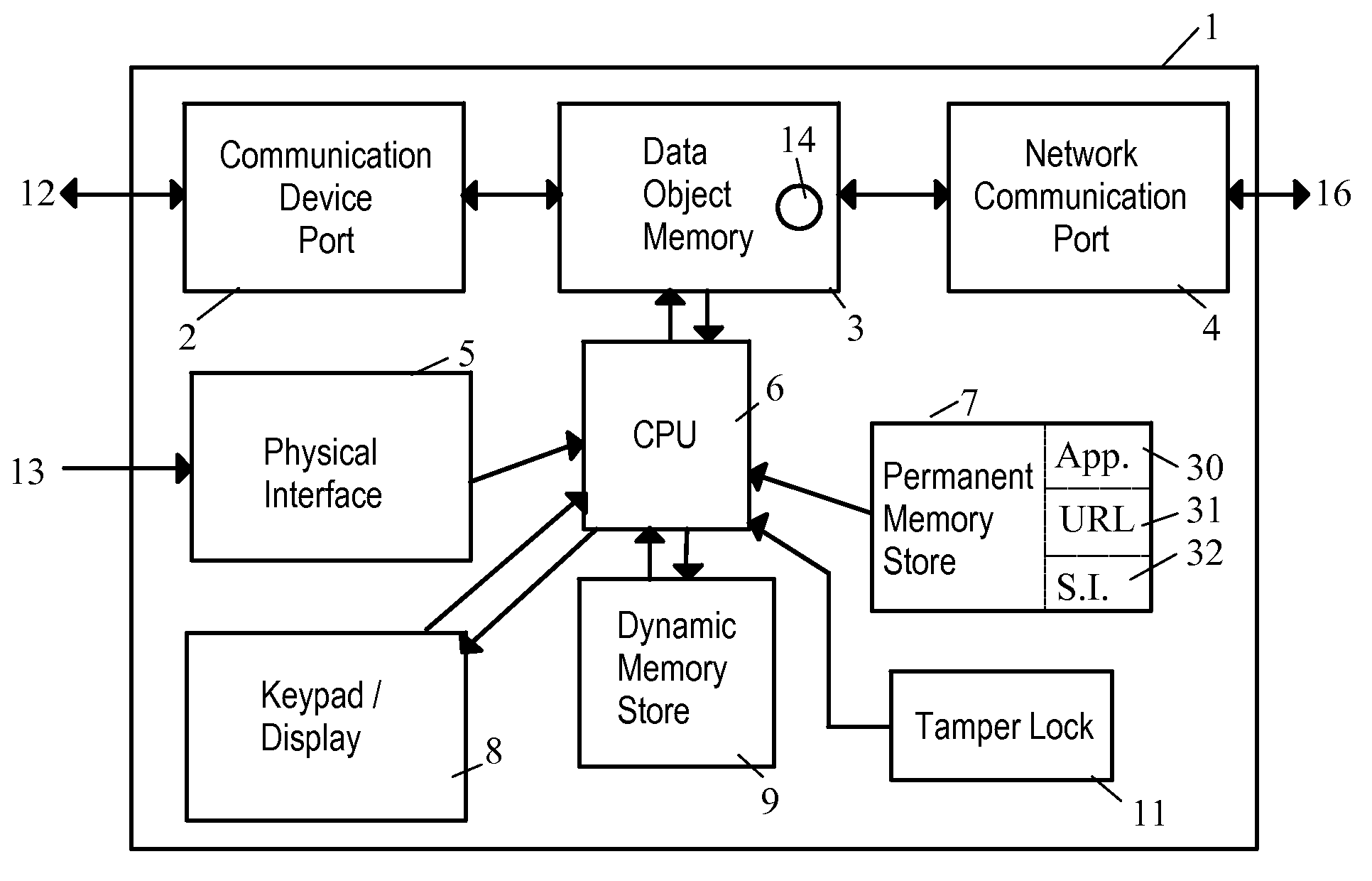
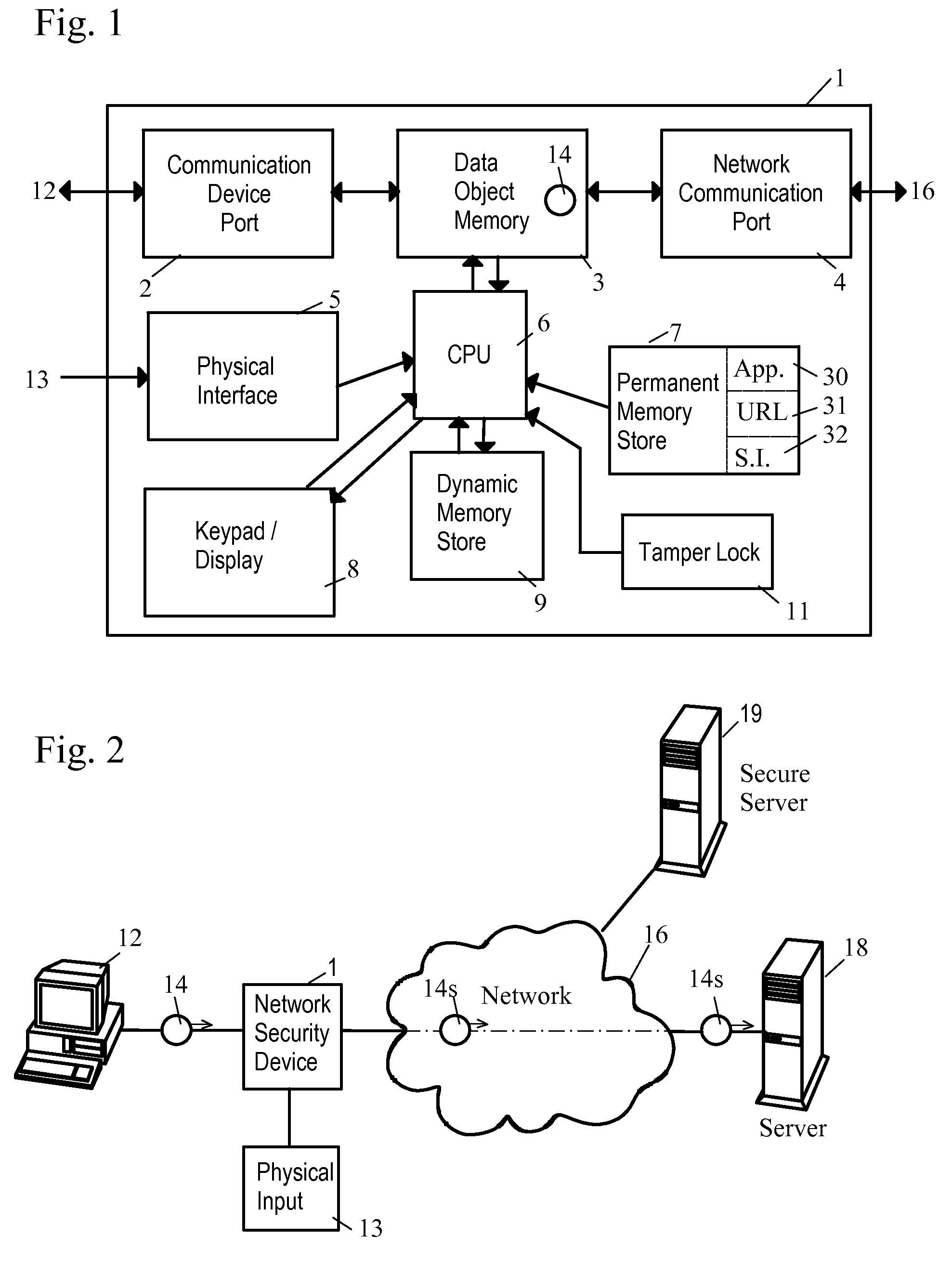
Network Security Device
ActiveUS20070261112A1Function providedFacilitate law enforcement effortDigital data processing detailsUser identity/authority verificationNetwork packetDatapath
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
Method and apparatus for regulating data flow between a communications device and a network
ActiveUS7890612B2Digital data processing detailsComputer security arrangementsTraffic capacityData stream
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
System and method for connecting security systems to a wireless device
InactiveUS6965313B1Not be preventElectric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
System and method to authenticate users to computer systems
InactiveUS20050091338A1Facilitates rapid secondary logLimited accessDigital data processing detailsDrug and medicationsTelecommunications linkTransceiver
A system utilizing a personal security device to provide access to a computer terminal where the personal security device includes circuitry and transceiver components for transmitting identification information and exchanging other digital information with a computer terminal and other compatible devices and the personal security device establishes a communication link with a computer terminal to allow a user to logon to the terminal so that when a user leaves the computer terminal, the communication link is terminated, causing the computer terminal to lock the keyboard, blank the monitor, and / or logoff the user if the communication link is not restored within a sufficient time period and also allowing the personal security device to facilitate subsequent computer access within a time range by providing time related access codes to the terminal that can be used to reestablish computer terminal access.
Owner:DLH TECH LLC
Detecting Malicious Network Content
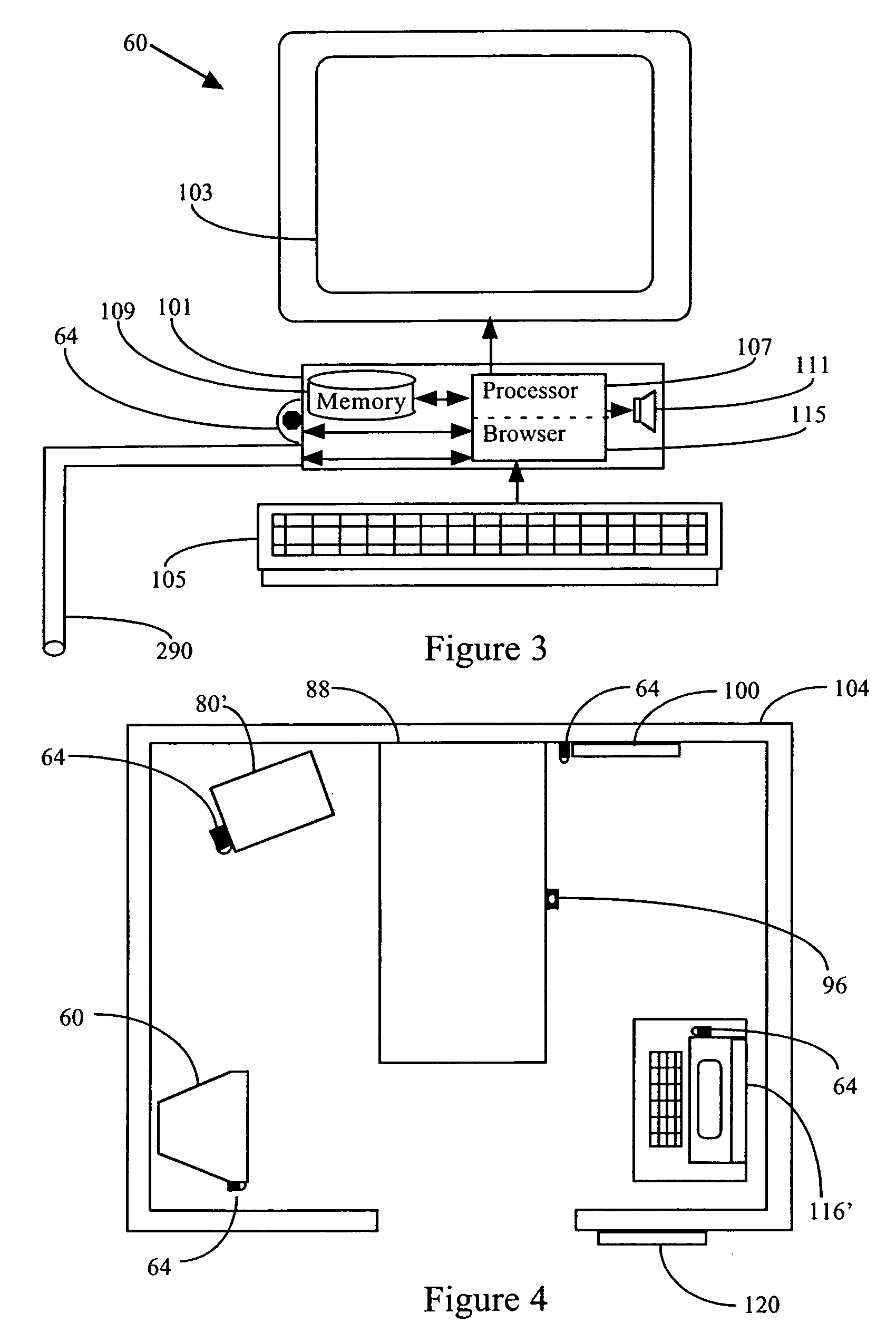
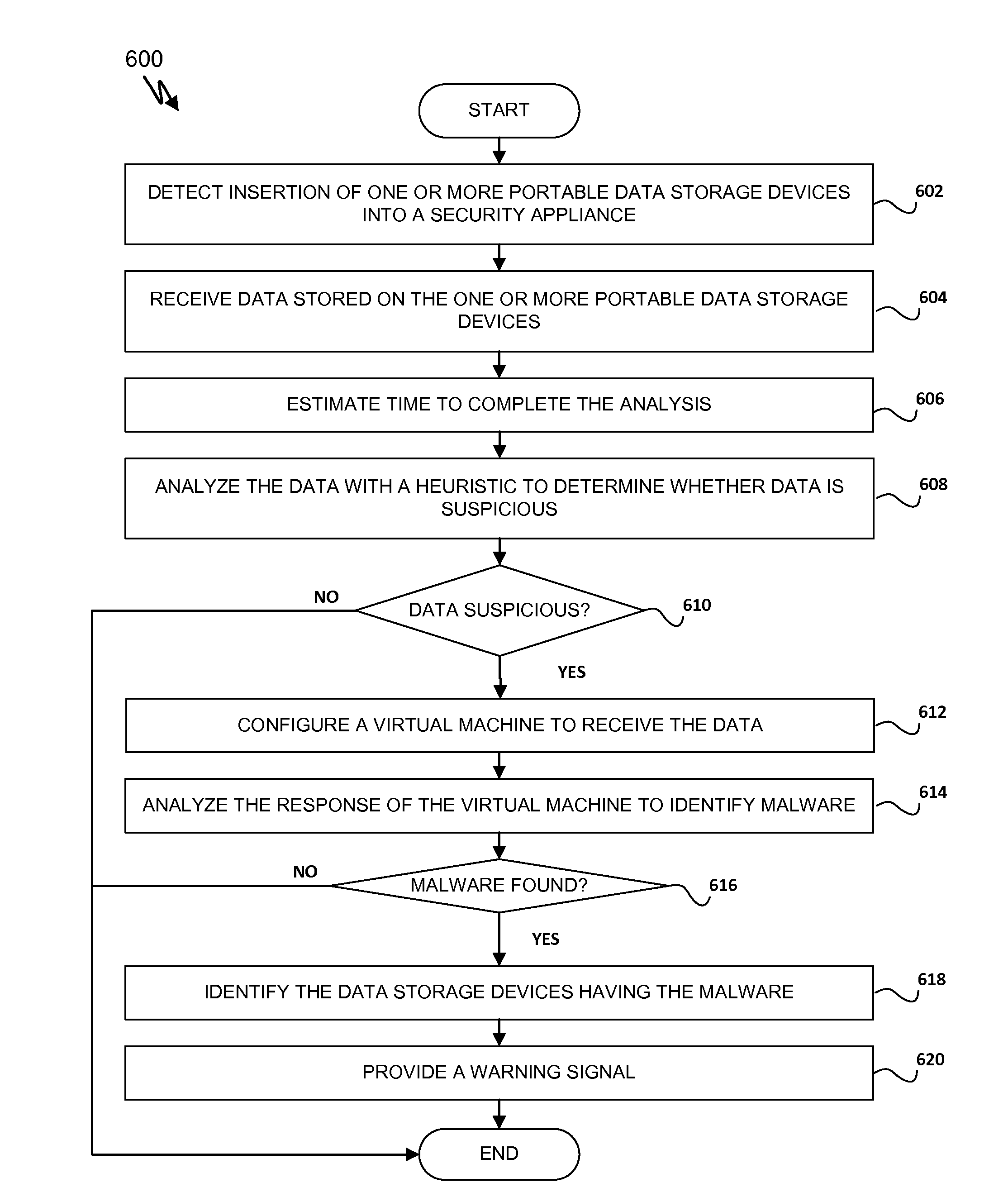
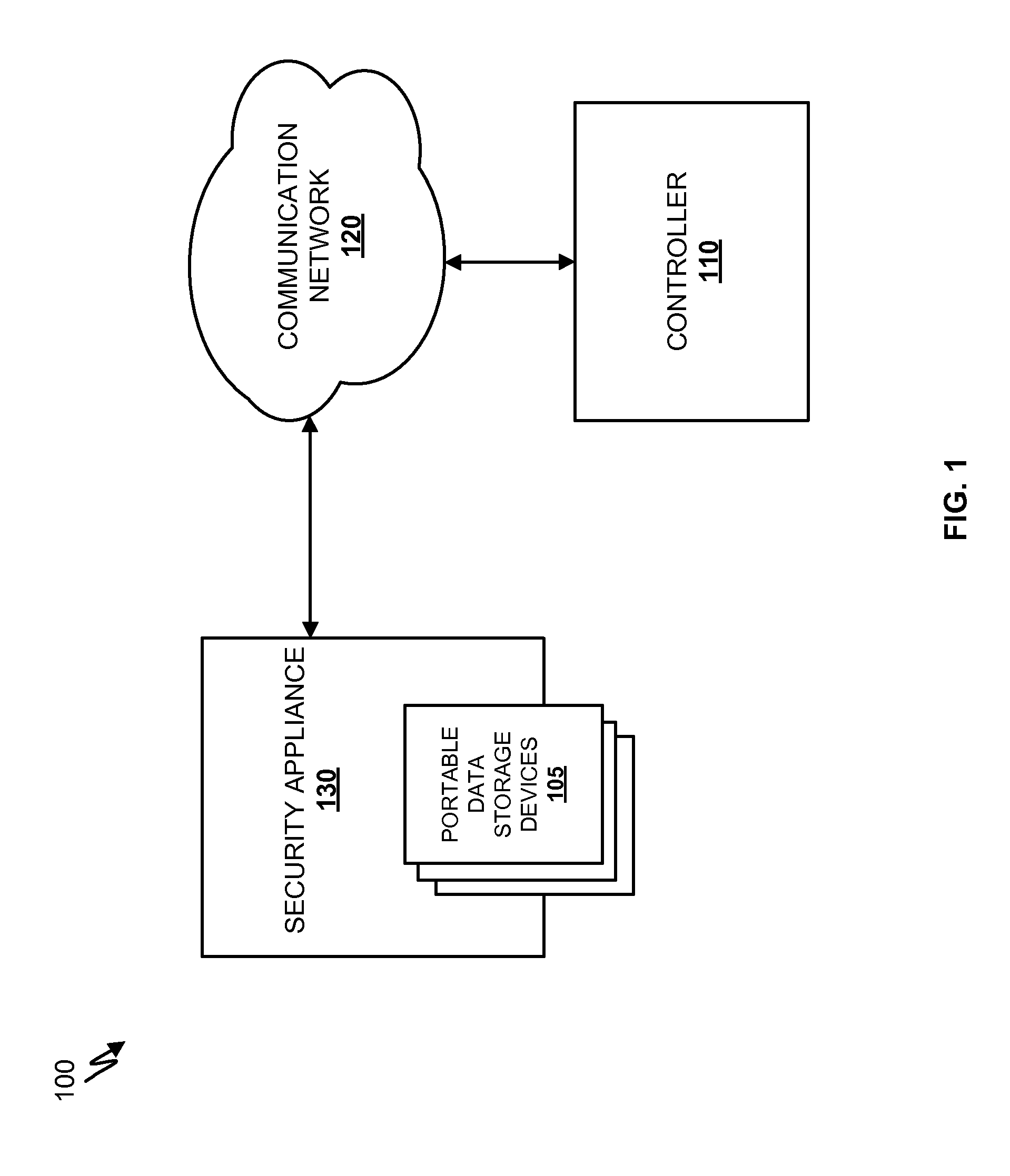
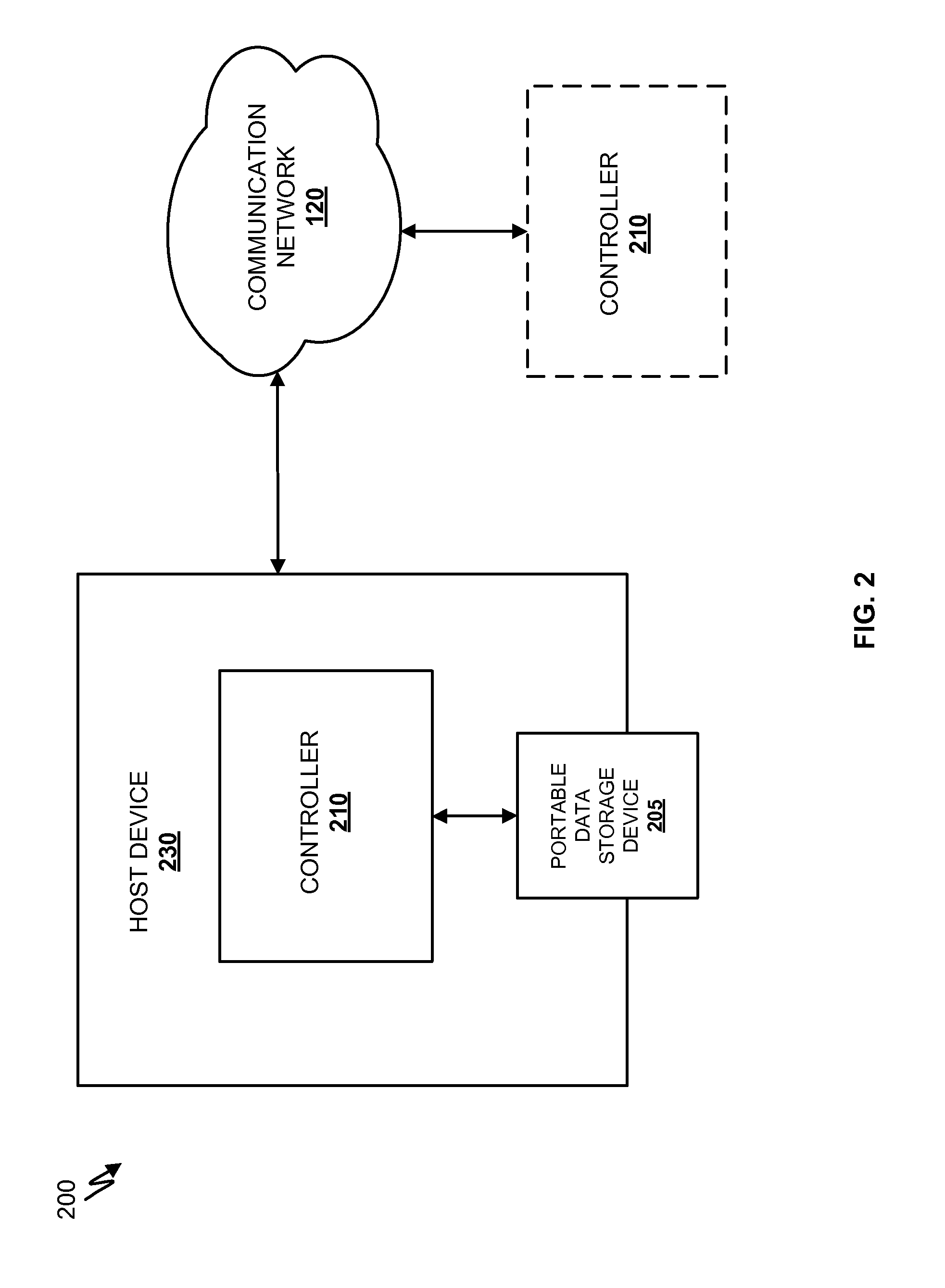
Systems and methods for detecting malicious content on portable data storage devices or remote network servers are provided. In an exemplary embodiment, a system comprises a quarantine module configured to detect one or more portable data storage devices upon insertion of the devices into a security appliance, wherein the security appliance is configured to receive the portable data storage devices, a controller configured to receive from the security appliance, via a communication network, data associated with the portable data storage devices, an analysis module configured to analyze the data to determine whether the data includes malware, and a security module to selectively identify, based on the determination, the one or more portable data storage devices storing the malware.
Owner:FIREEYE SECURITY HLDG US LLC
Method and apparatus for security policy management
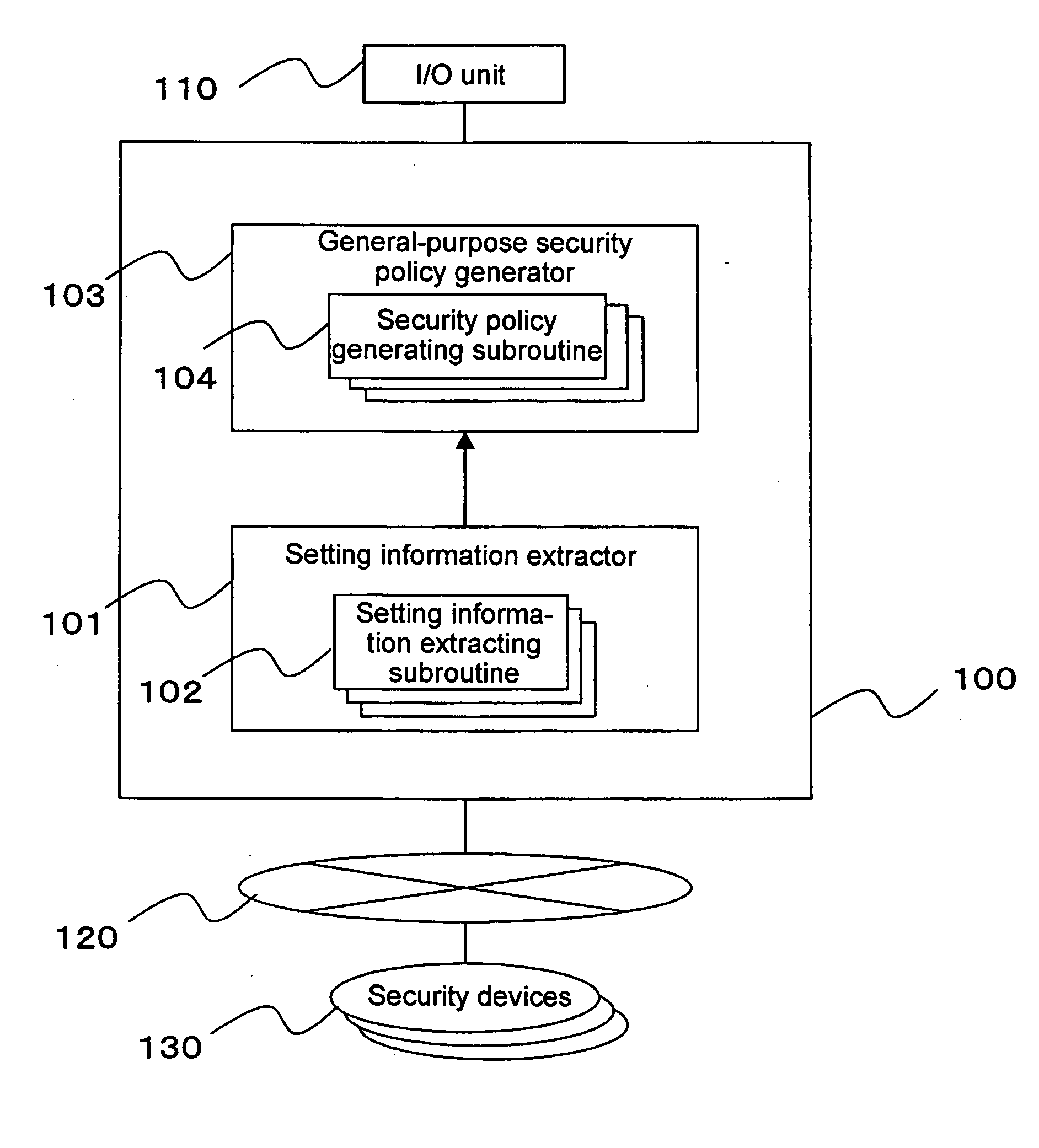
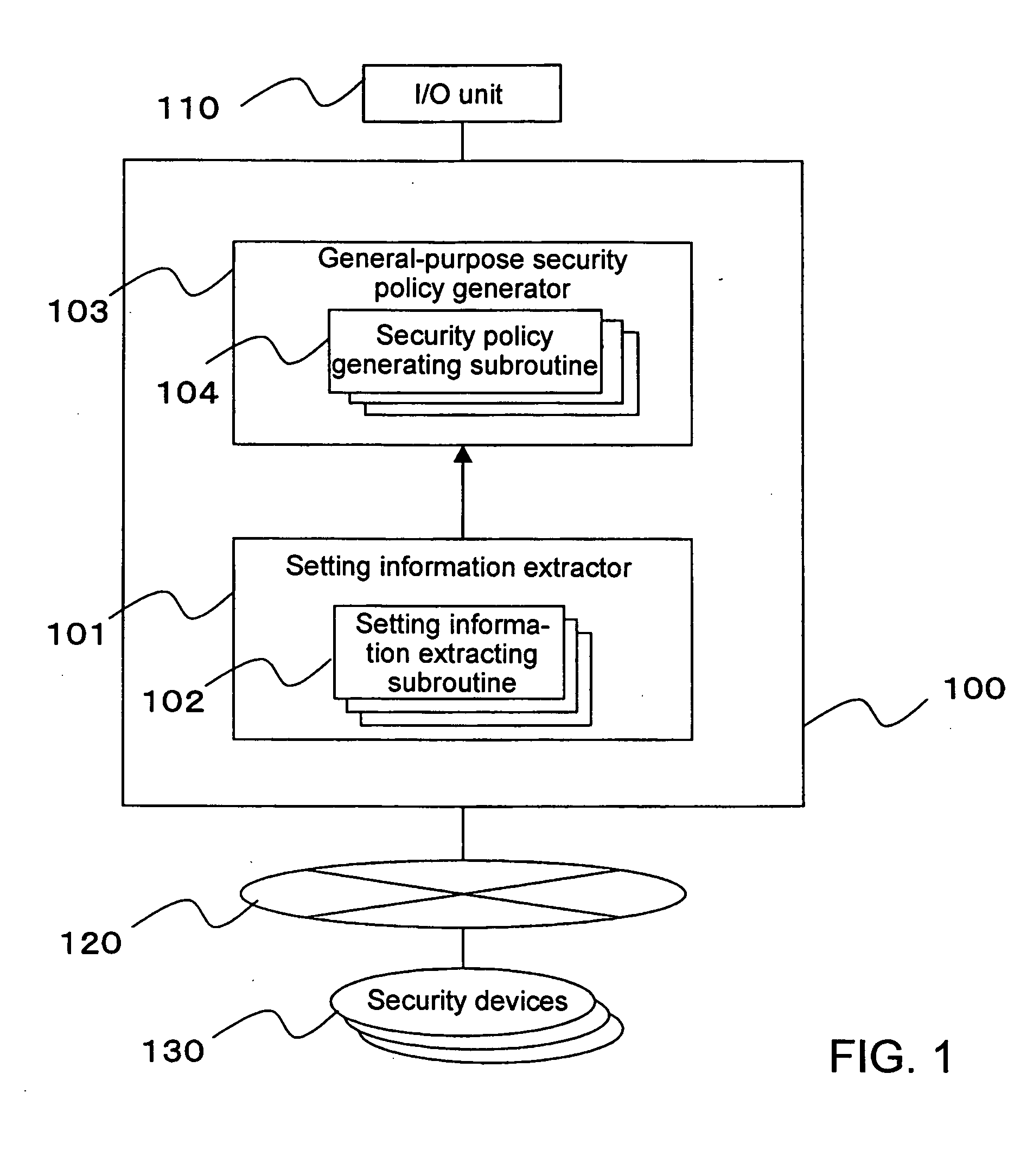
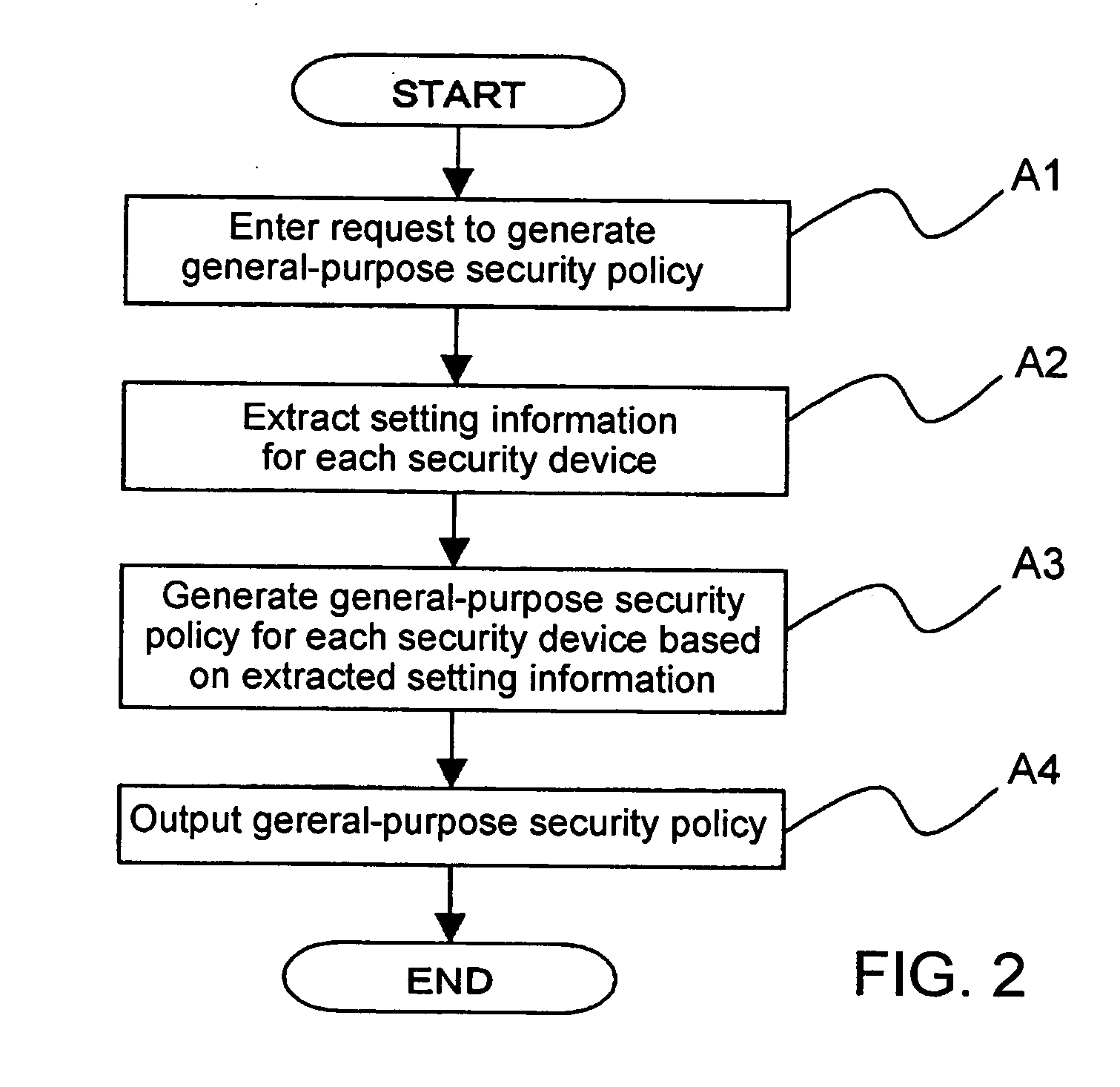
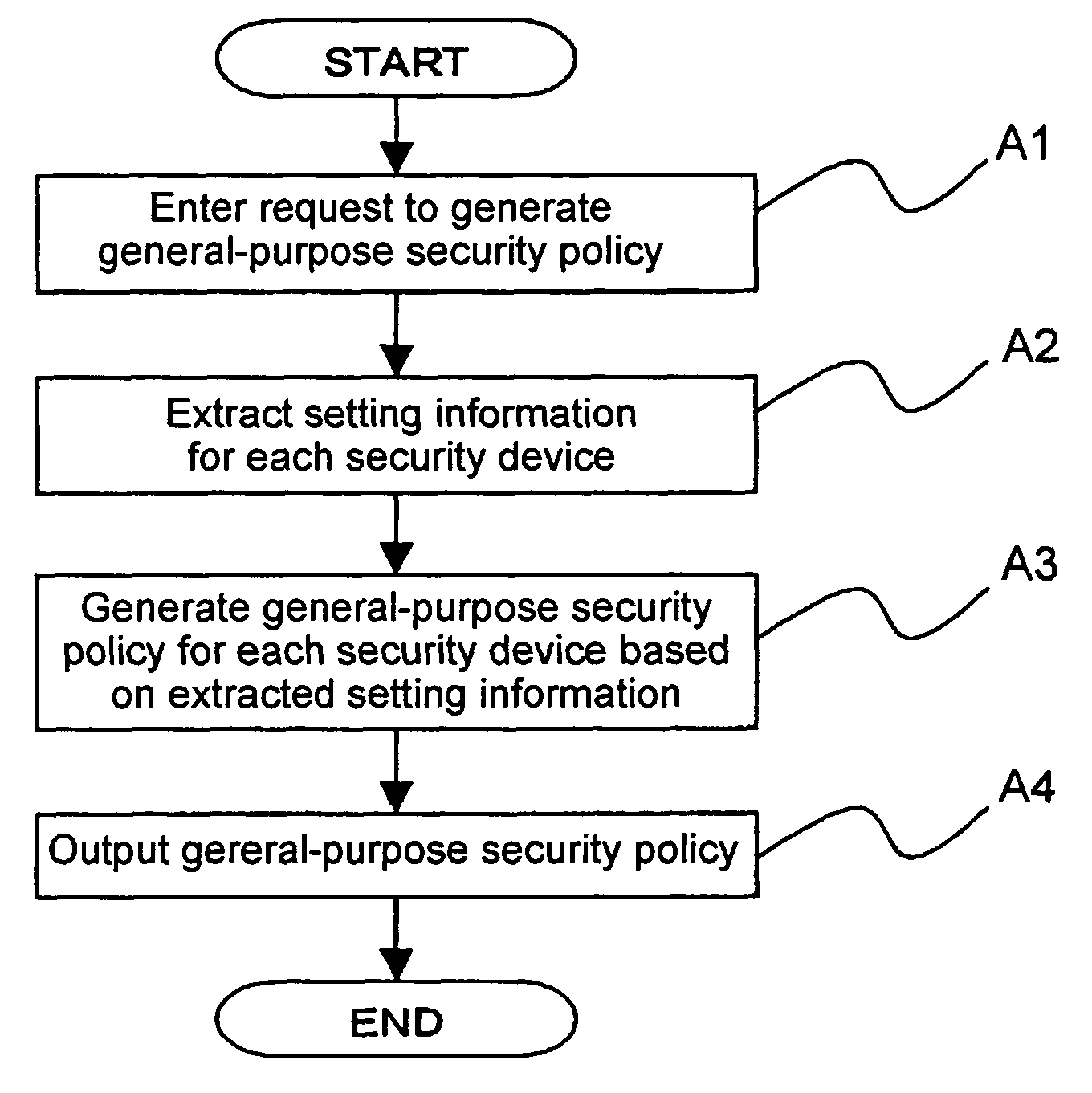
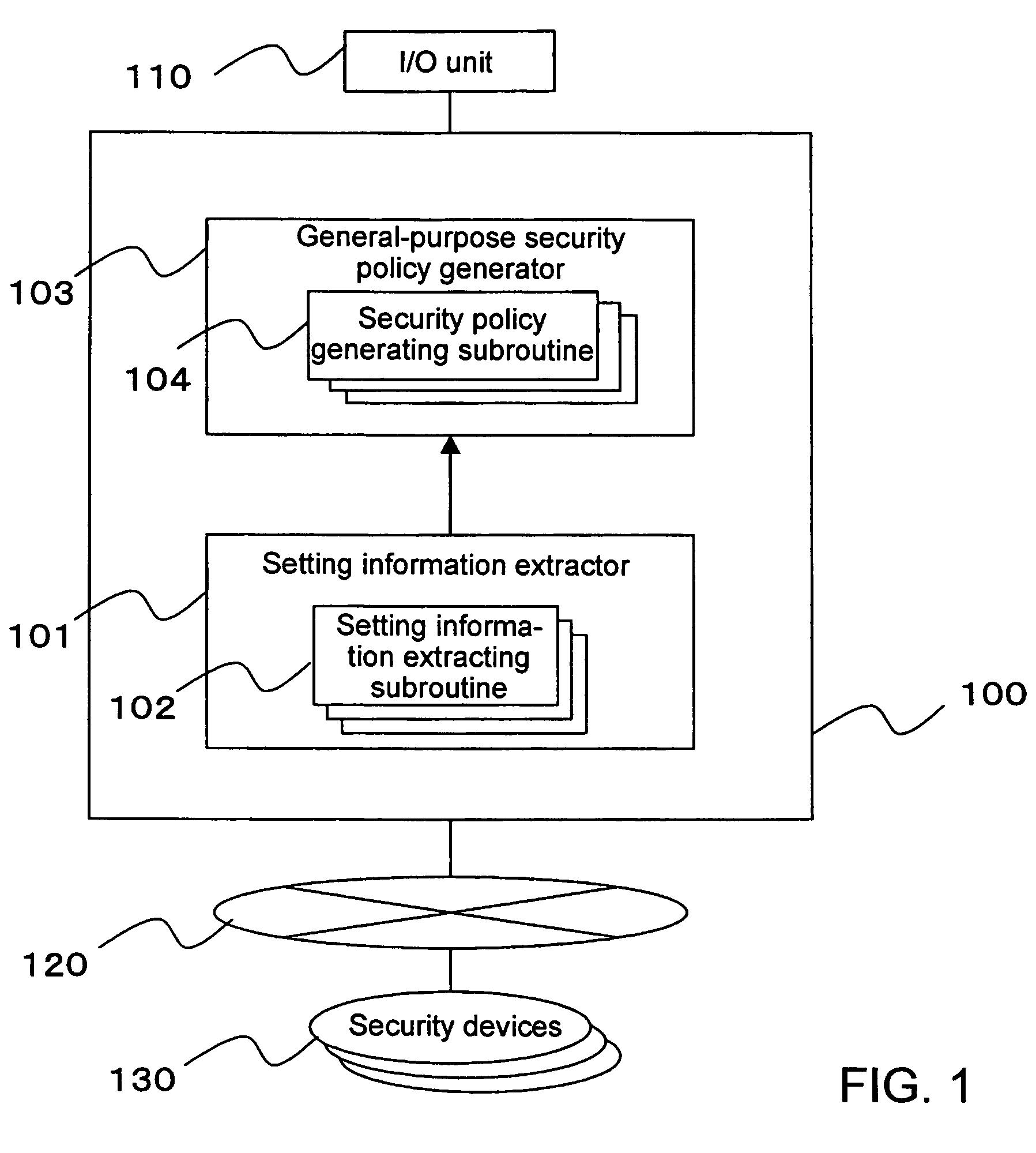
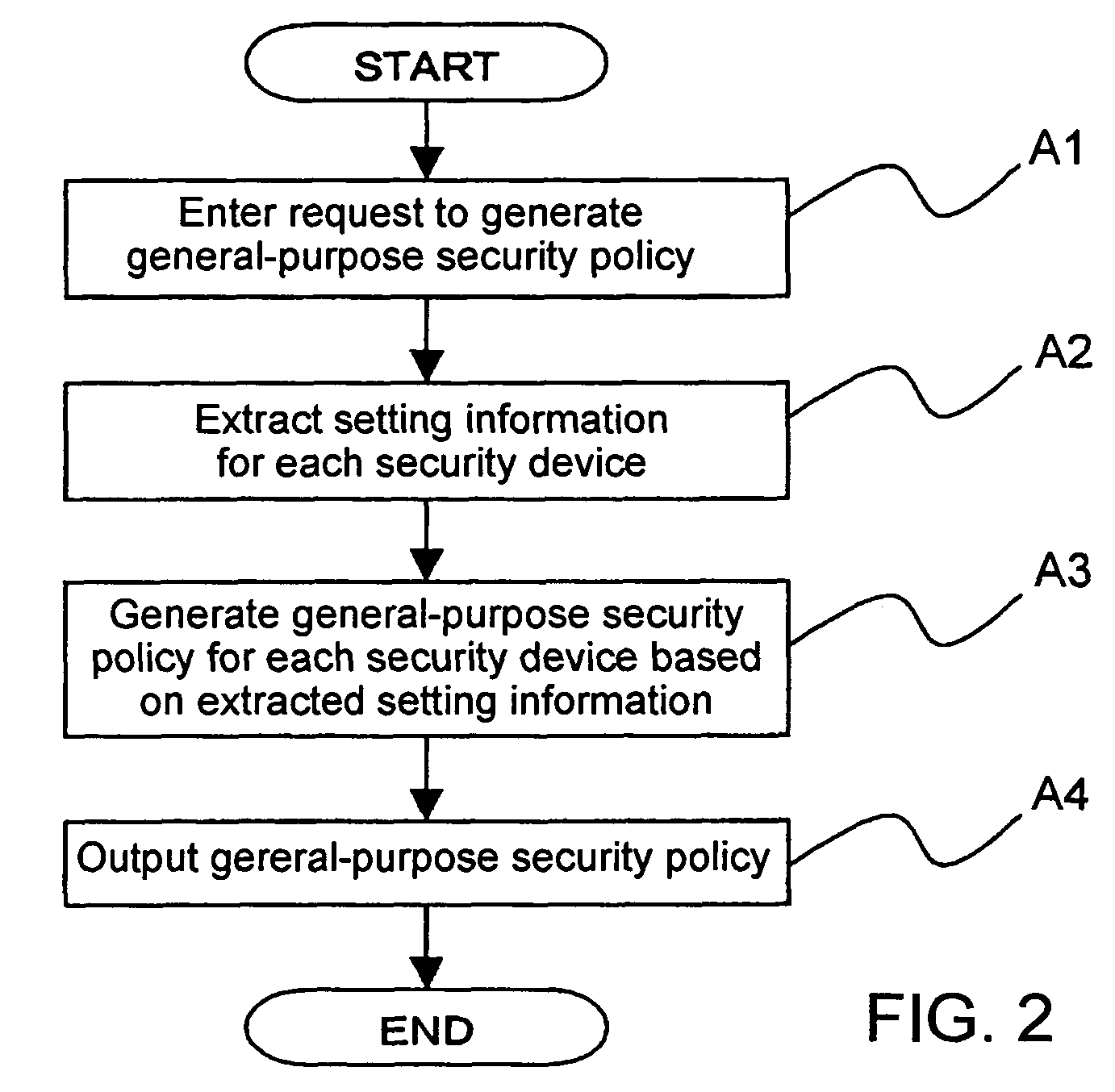
InactiveUS20050283823A1Reduce human interventionEasy to masterDigital data protectionResourcesGeneral purposeSecurity policy management
A security policy management system for deriving a security policy from setting details of security devices as components of an information system includes a setting information storage unit for storing setting information representing settings with regard to security functions of devices included in a network system to be managed, and a general-purpose security policy generator for generating a security policy including a description expressed in a format independent of descriptions depending on particular devices, based on the setting information stored in the setting information storage unit.
Owner:NEC CORP
Methods and apparatus for restricting access of a user using random partial biometrics
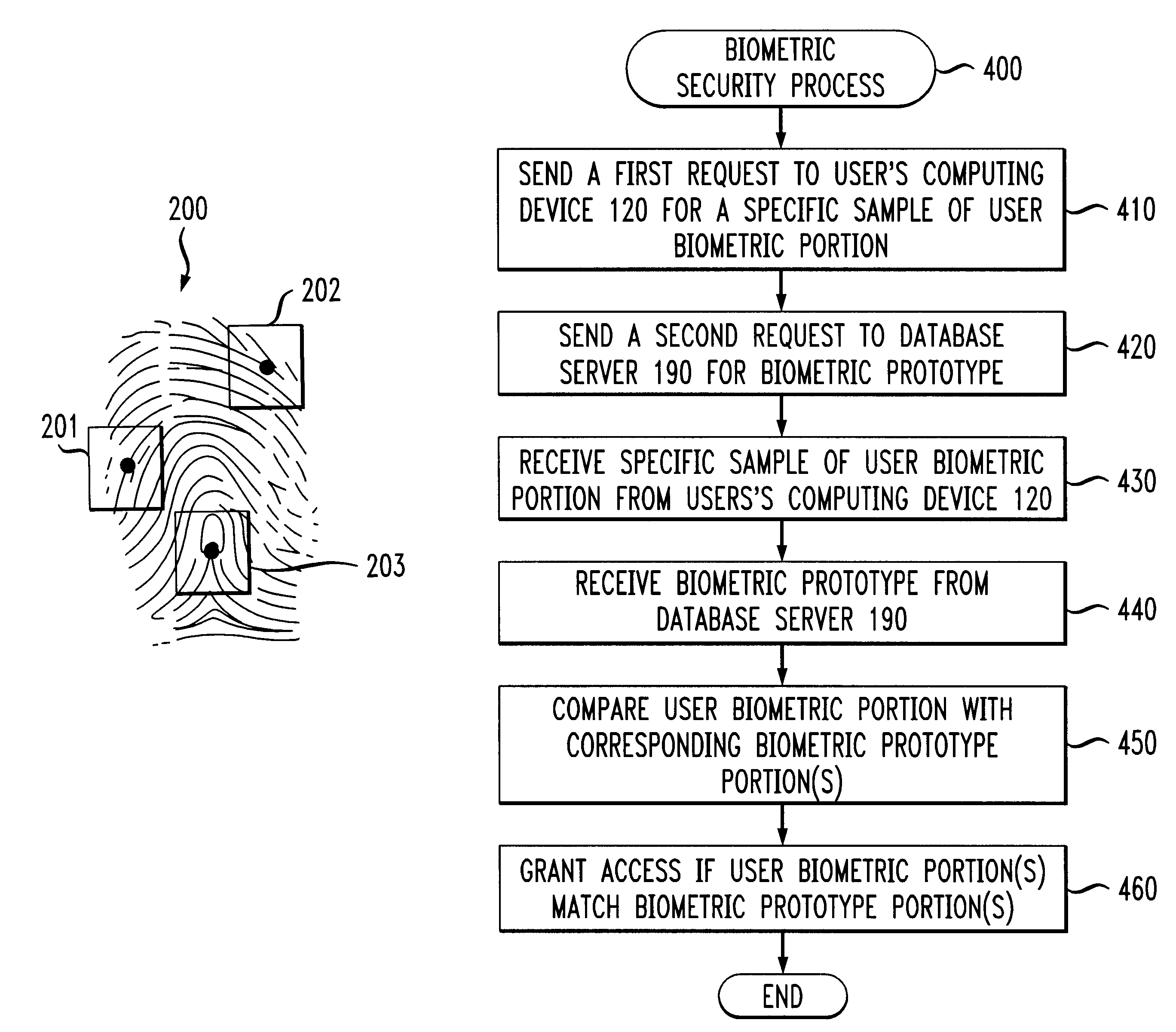
InactiveUS6735695B1Reduce riskDigital data processing detailsUser identity/authority verificationBiometric dataSecurity system
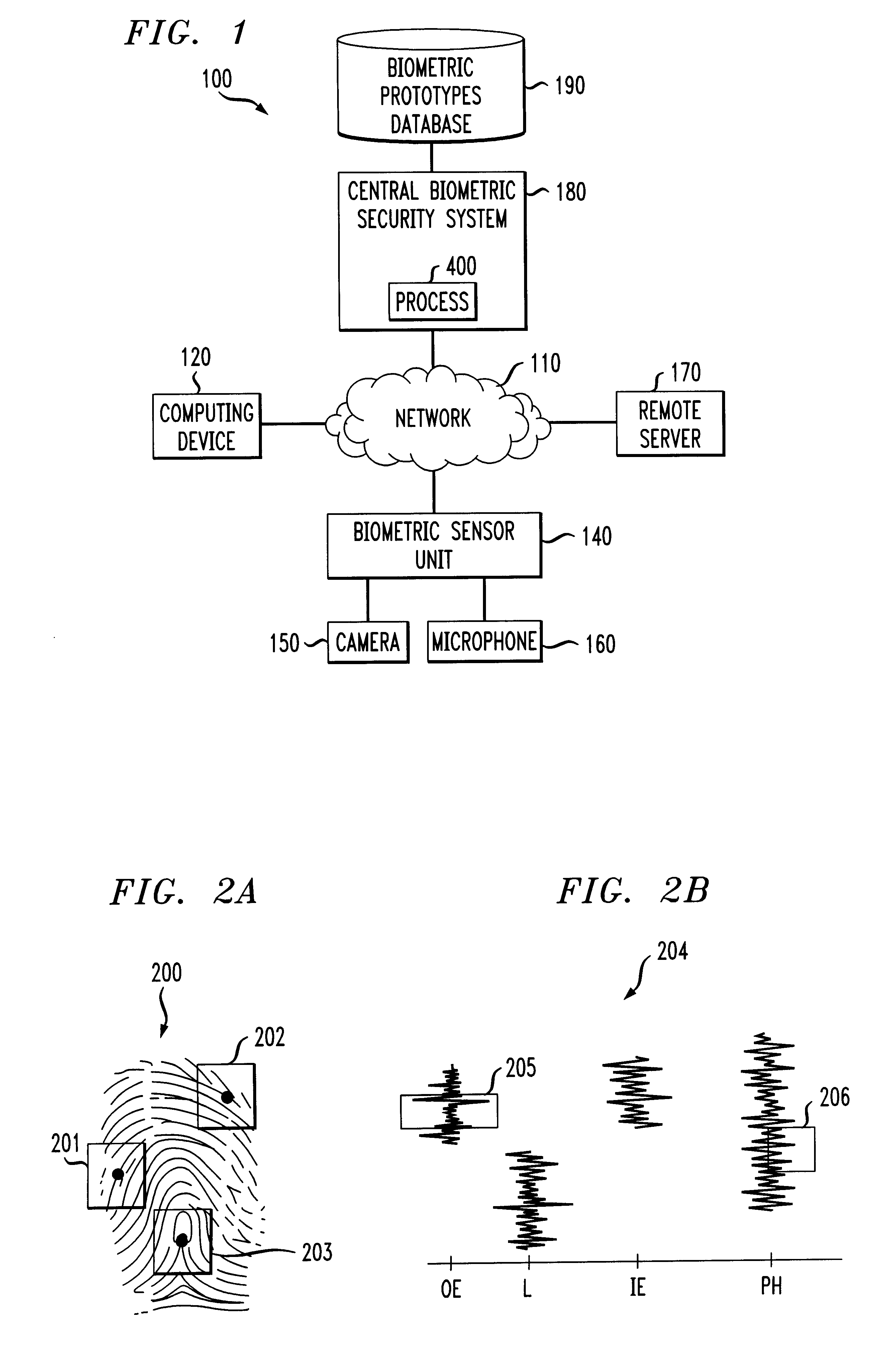
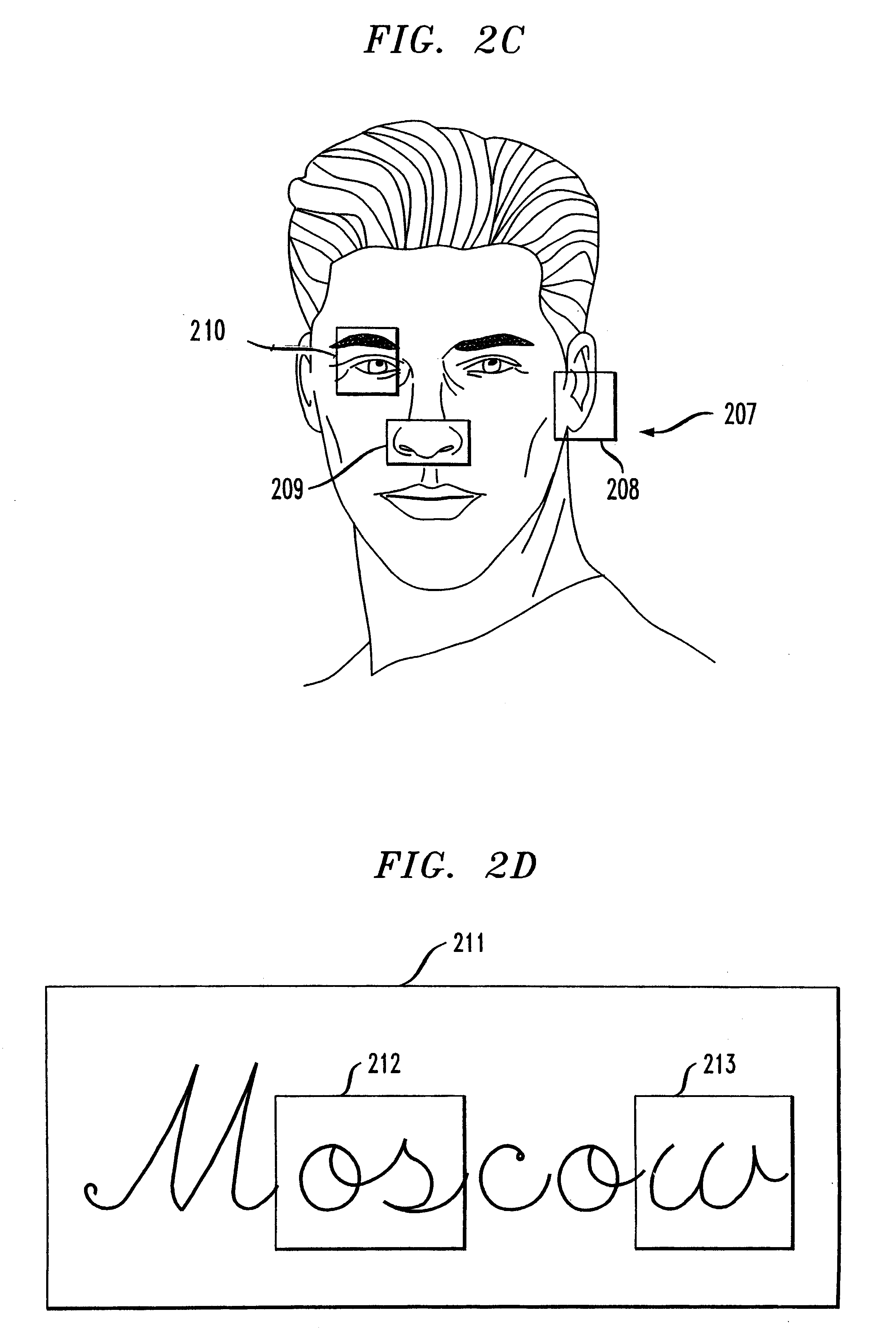
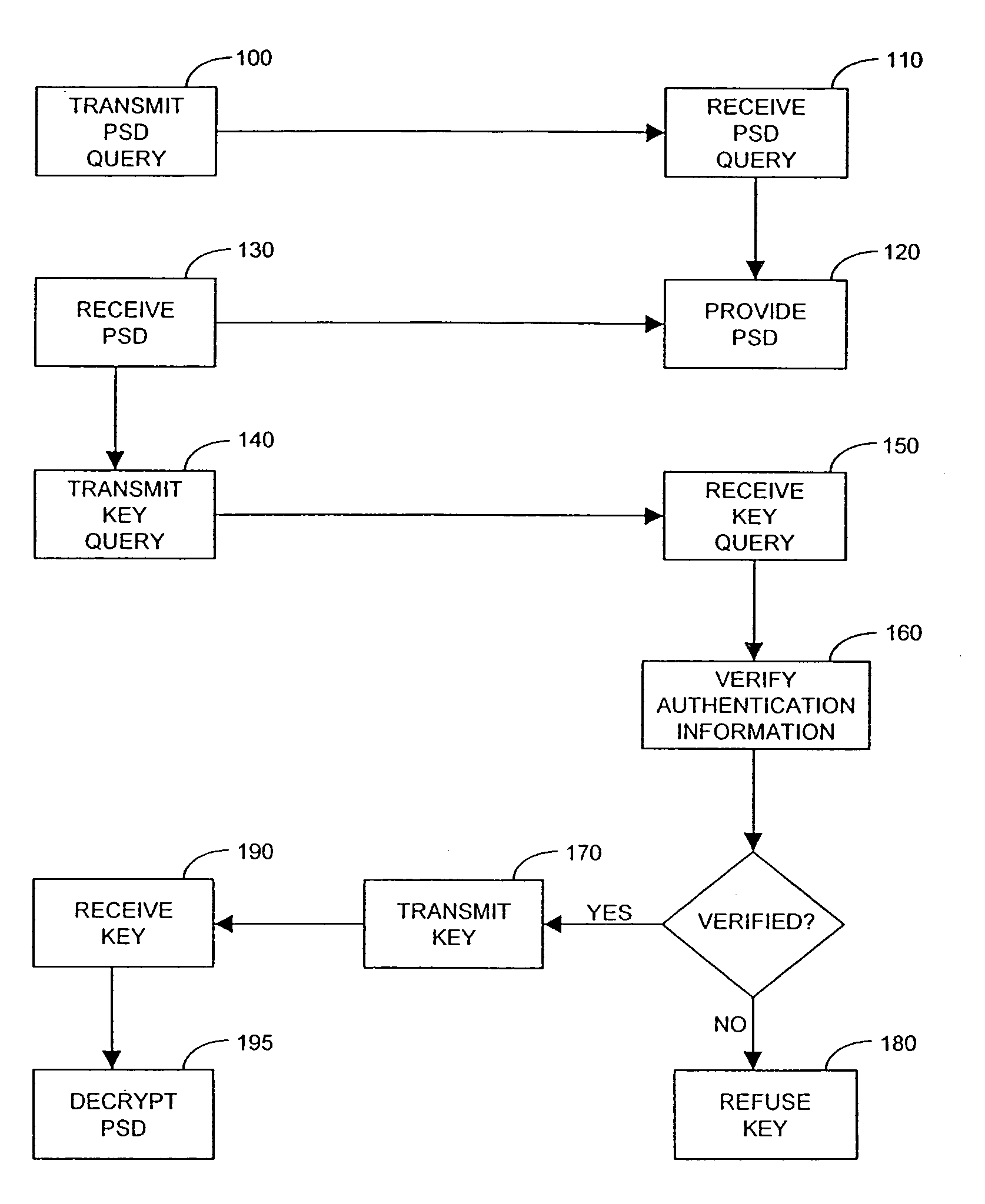
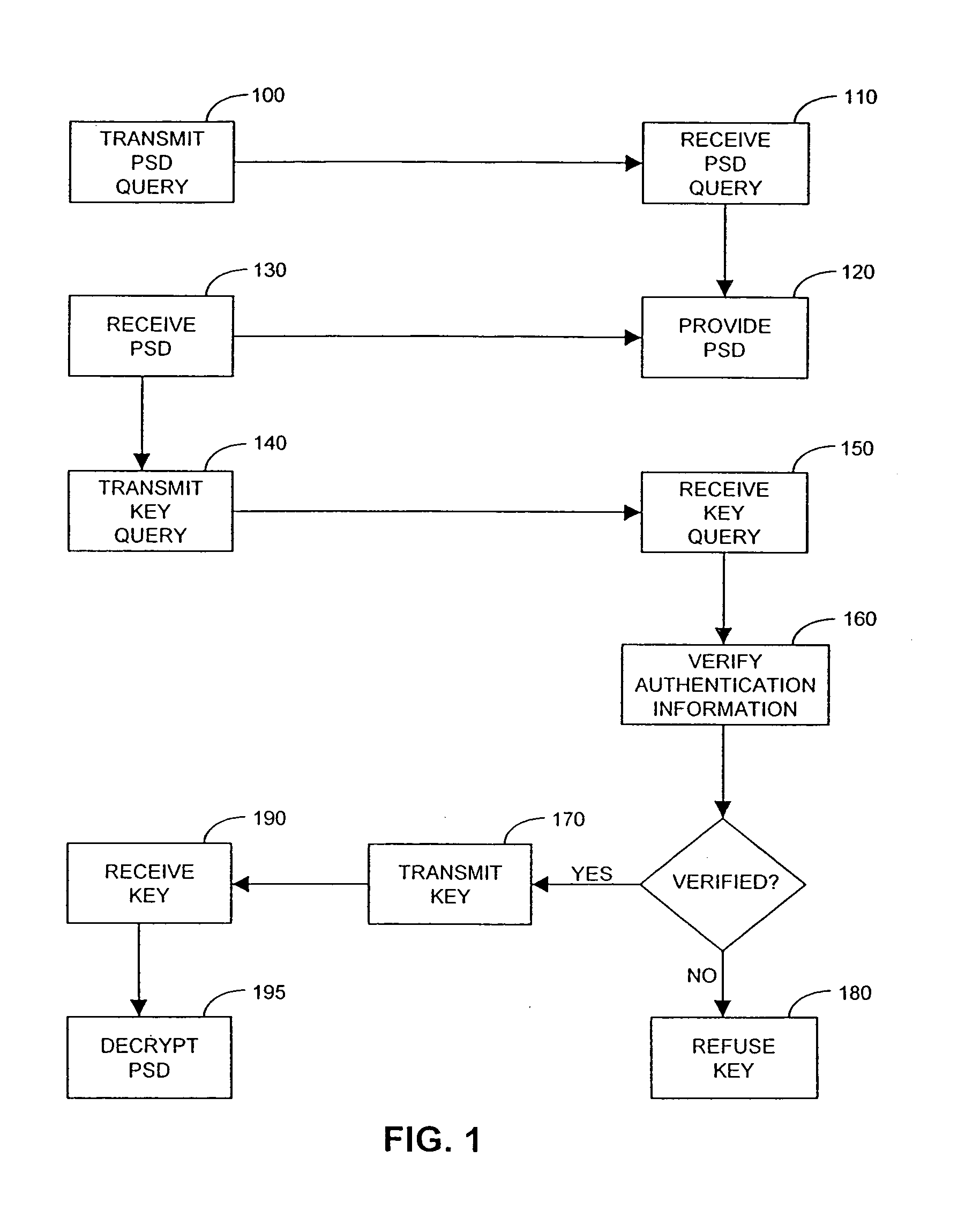
A biometrics security method and apparatus are disclosed that restrict the ability of a user to access a device or facility using a portion of biometric data to validate the user's identity. Upon a user request to access a secure device or facility, the central biometric security system initially sends a first request for a specific sample of a portion of the user's biometric information. The specific sample may be identified, for example, using a set of image coordinates. A second request is also sent to retrieve the biometric prototype from a database of registered users. The central biometric security system then compares the user biometrics portion with the corresponding biometrics prototype portions. The user receives access to the requested device if the user biometrics portion(s) matches the corresponding biometrics prototype portions. In one variation, the biometric security system transmits a security agent to the user's computing device upon a user request to access a remote device. The security agent serves to extract user biometric portions in accordance with the sampling request from the central biometric security system. In another variation, a local recognition is performed before a remote recognition to reduce the risk of a failed server side recognition due to a poor biometrics feature.
Owner:IBM CORP
System and methods for maintaining and distributing personal security devices
InactiveUS7111172B1Key distribution for secure communicationPublic key for secure communicationInternet privacyClient-side
This invention relates to methods and apparatus for securely accessing and providing information including the use of a personal security device on a client where the client is subject to compromise.
Owner:EMC IP HLDG CO LLC
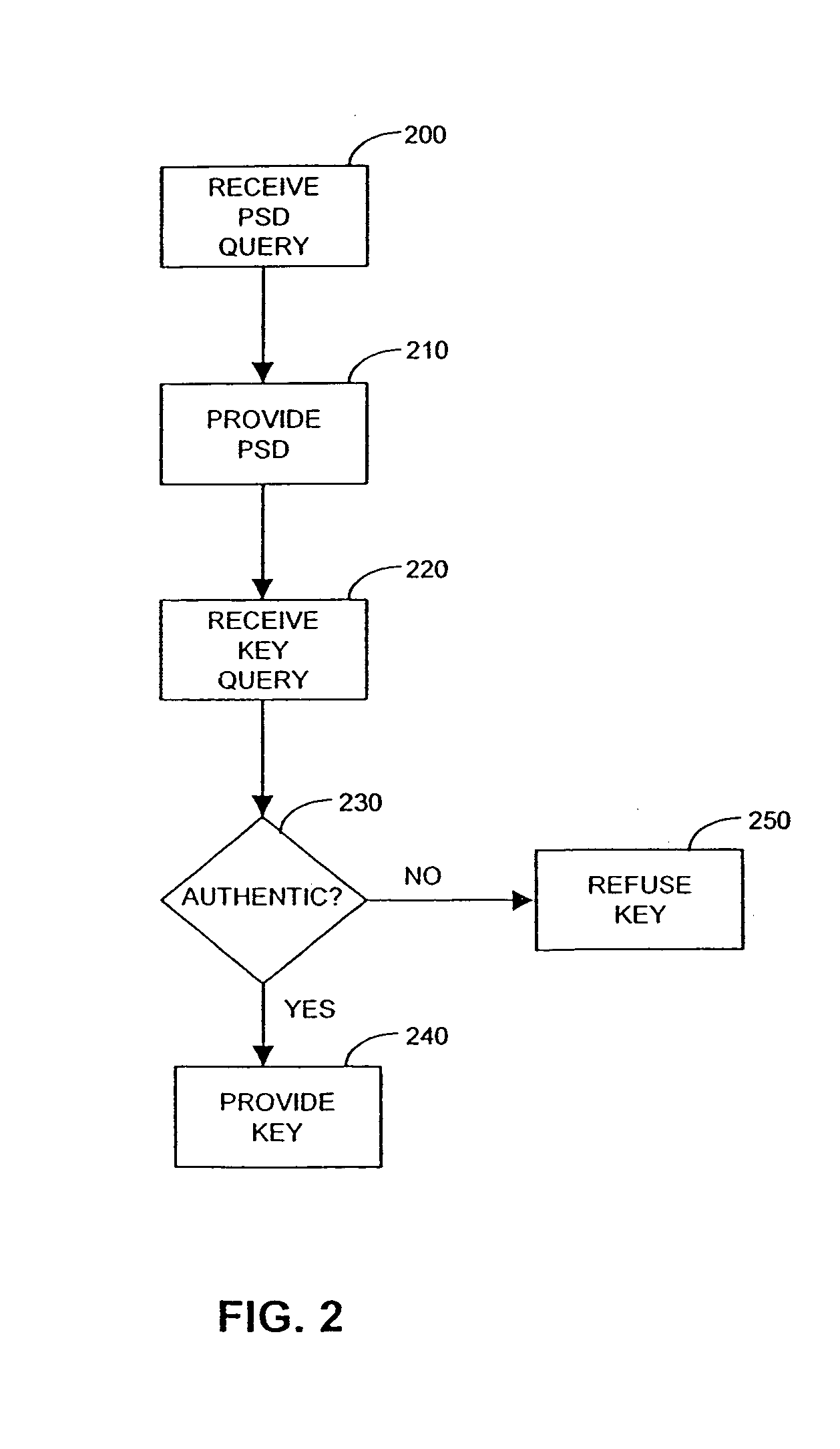
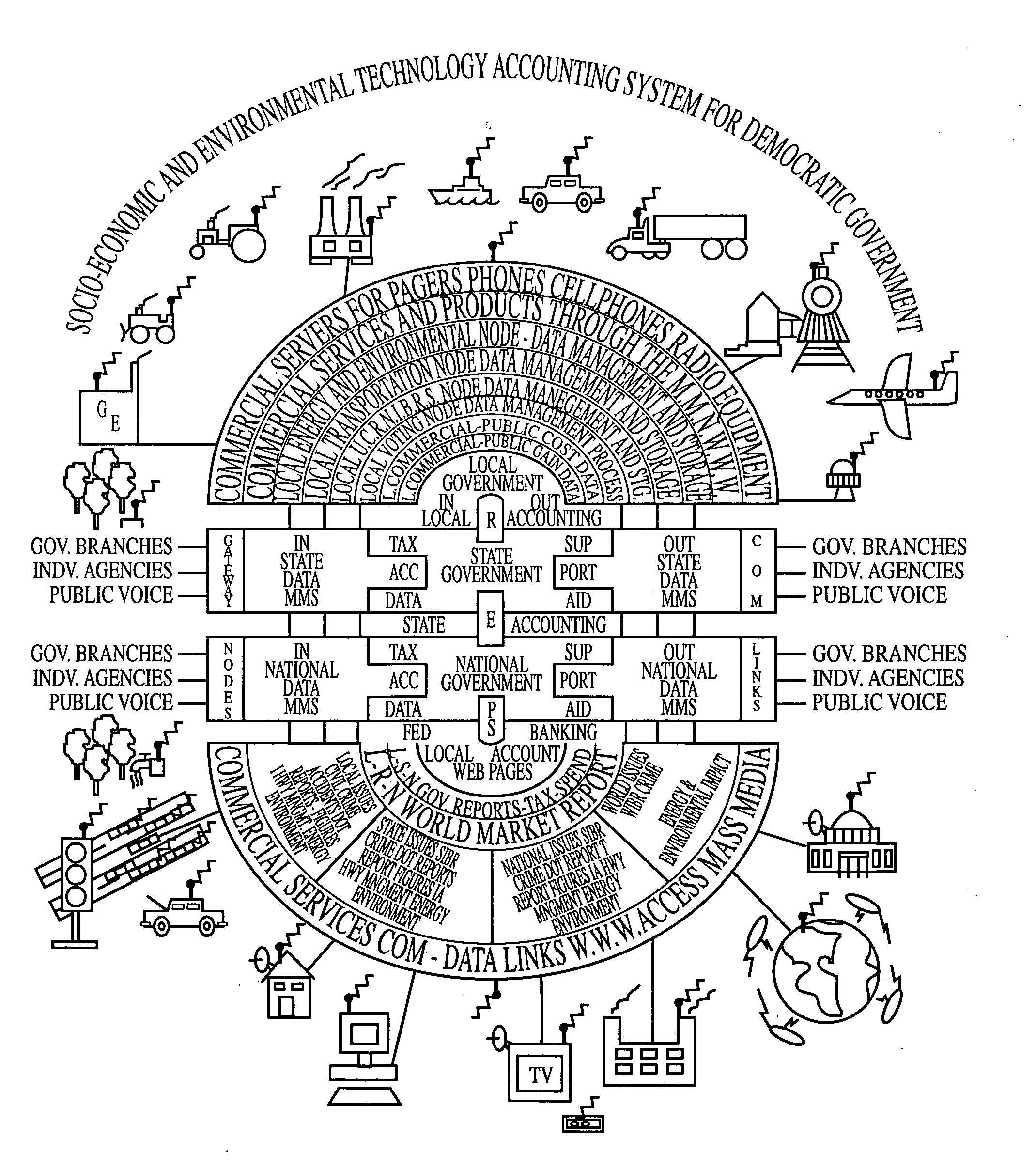
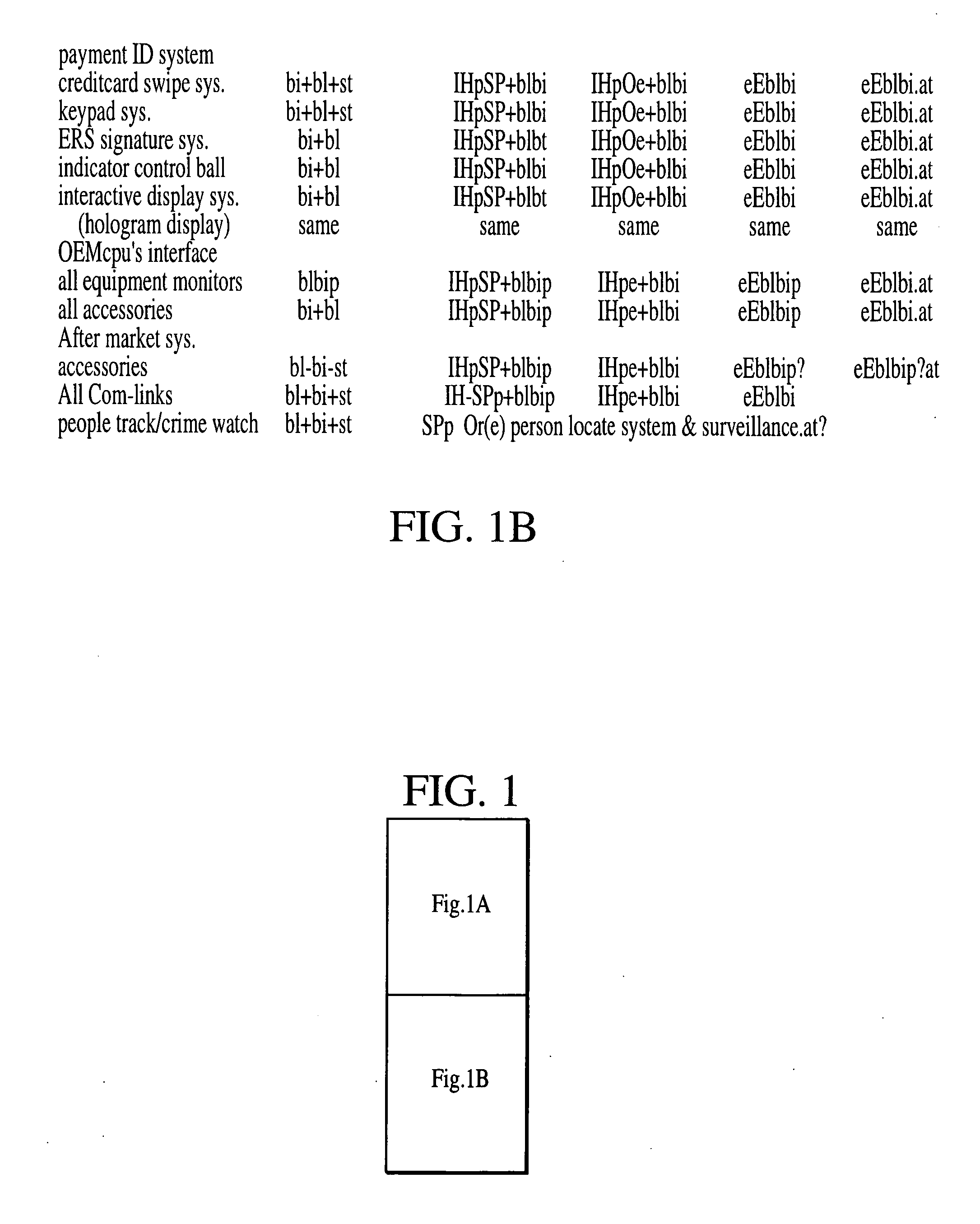
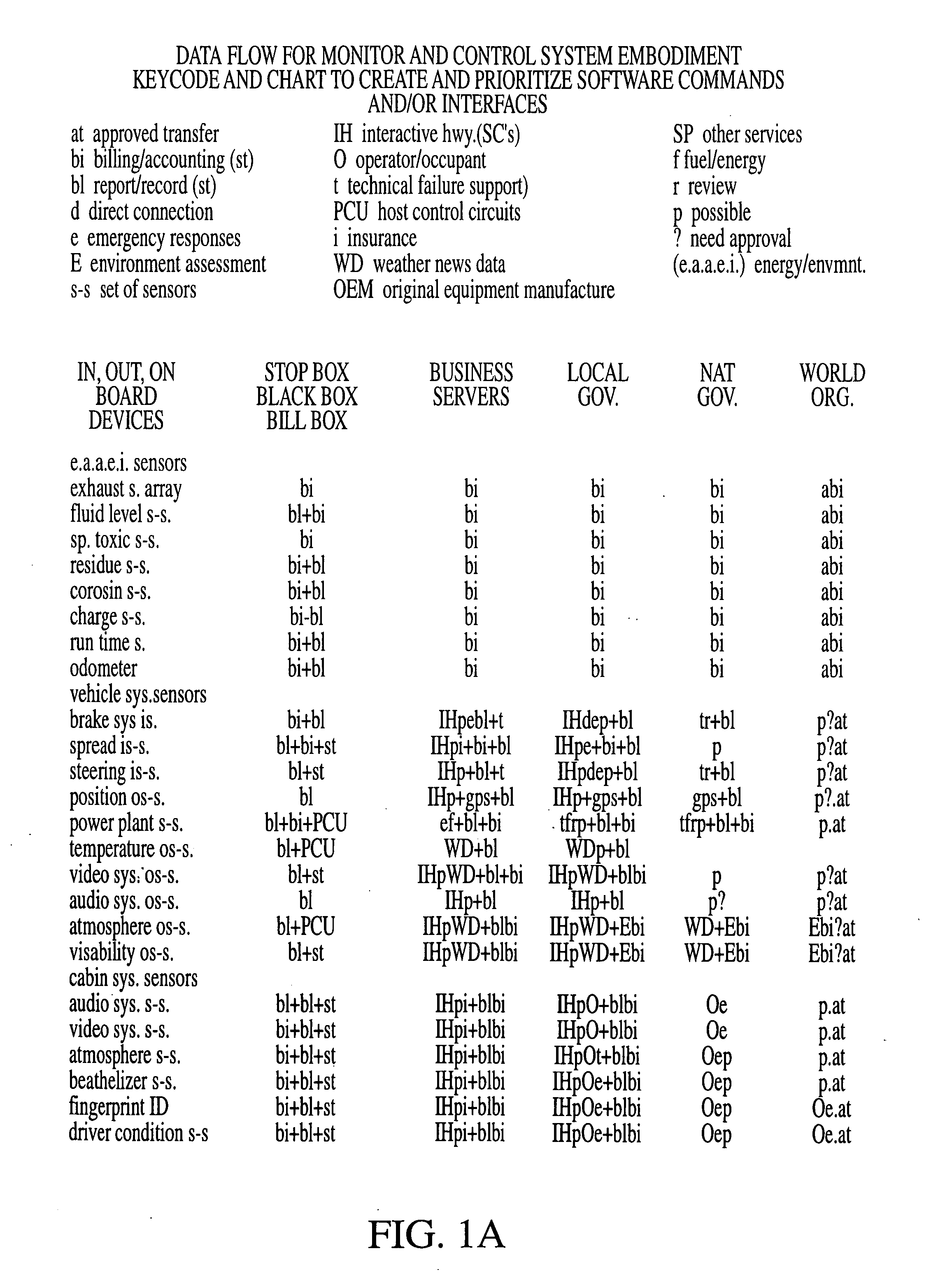
Automated accounting system that values, controls, records and bills the uses of equipment/vehicles for society
InactiveUS20060287783A1Fairly and accurately monitor and control the impact of equipment use on the world's environment andVehicle testingTelemetry/telecontrol selection arrangementsSecure communicationEnvironment effect
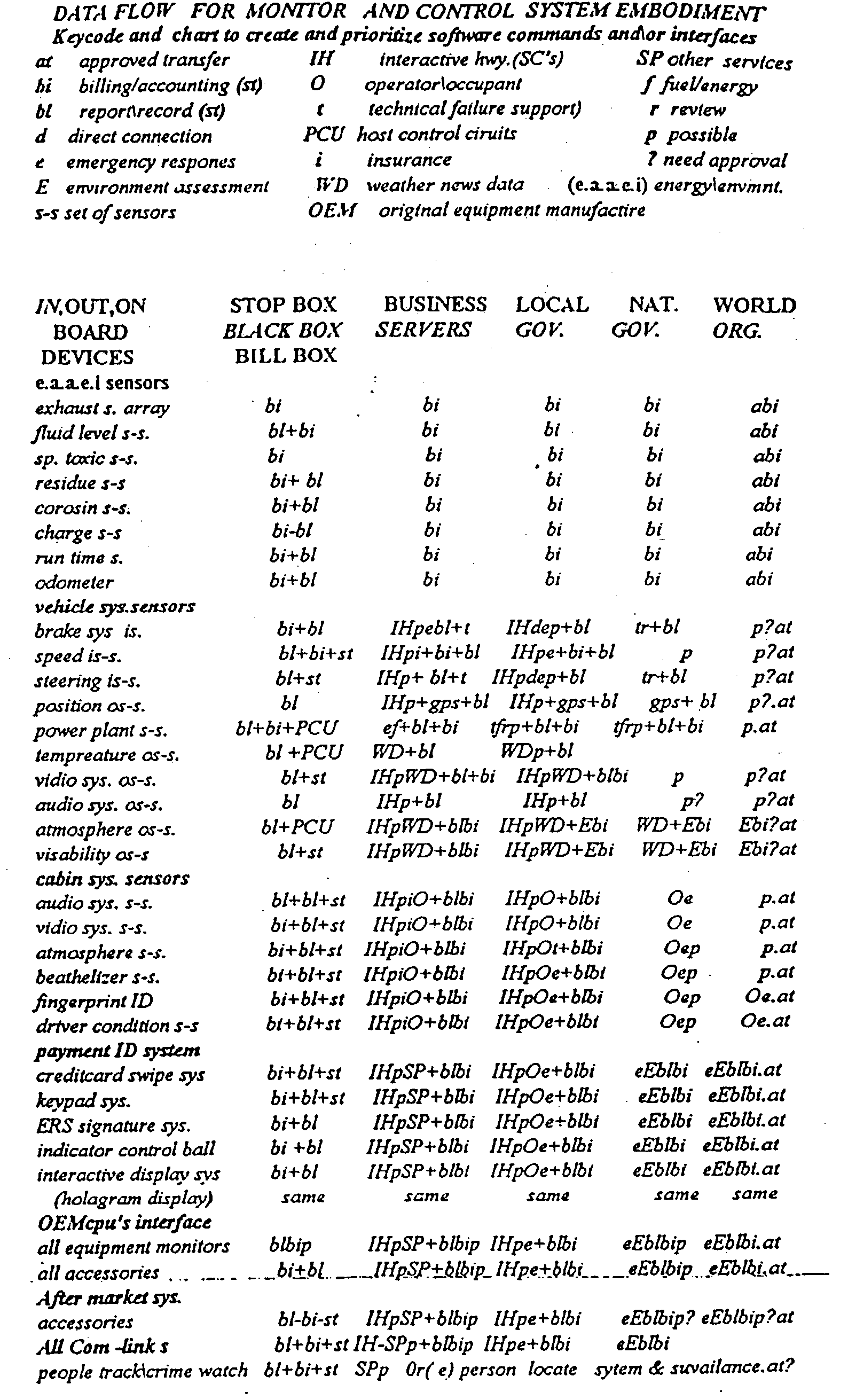
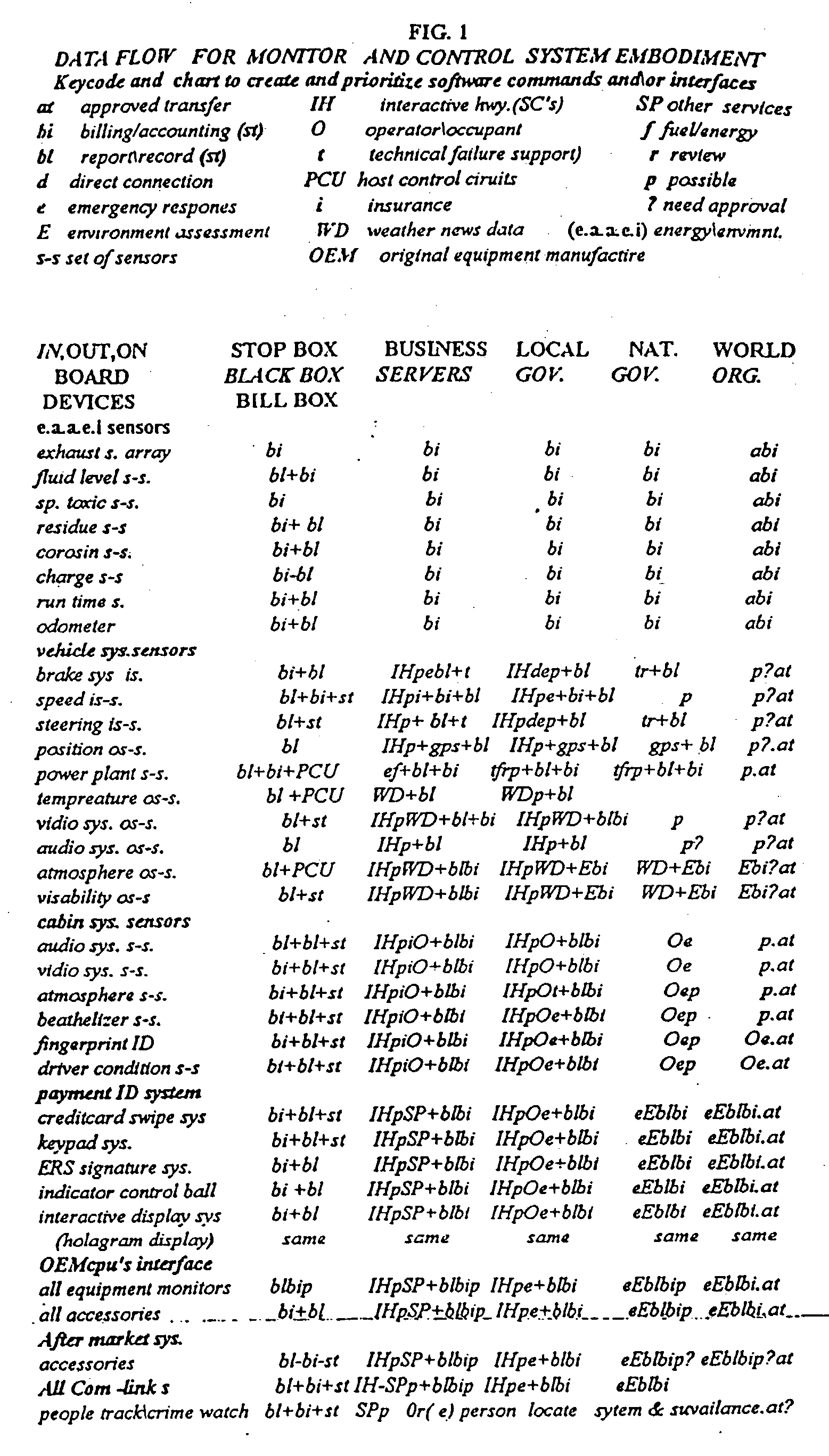
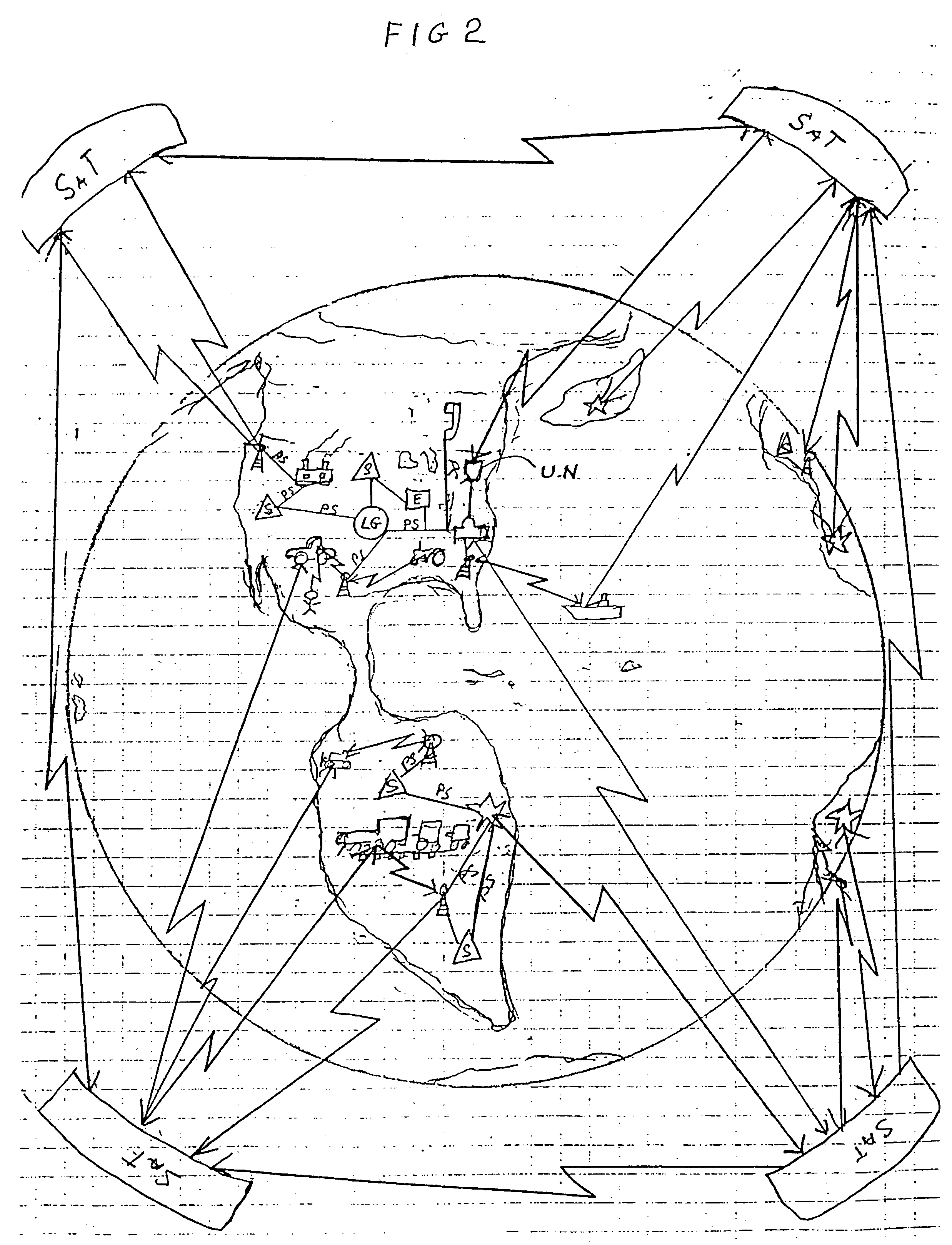
This invention addresses environmental social and commercial uses and includes a monitoring system which is a network of on, in, out and off-board devices working together with people through software and interfaces to provide services and make accountable humanity's machines and their actions through safe secure communication. Control devices are used to provide accountability for their socio-economic and environmental impact. Along with these systems networked together, additional devices and variations needed to complete these operations nationally and world wide are also provided. Unique ways interface a network of separate devices or IC circuits to create an interactive secure control system or center that can be remotely controlled. A control device for society to fairly and accurately monitor and control the impact of equipment use on the world environment, and a nation's infrastructure while developing commercial companies to fulfill these needs and services for the equipment and the people who own and operate them for today and into the future are also provided. A set of secure devices and systems are also included to analyze society and machine interaction.
Owner:KLINE & WALKER
Design of computer based risk and safety management system of complex production and multifunctional process facilities-application to fpso's
InactiveUS20120317058A1Strong robust attributeStrong robust attributesDigital computer detailsFuzzy logic based systemsProcess systemsNerve network
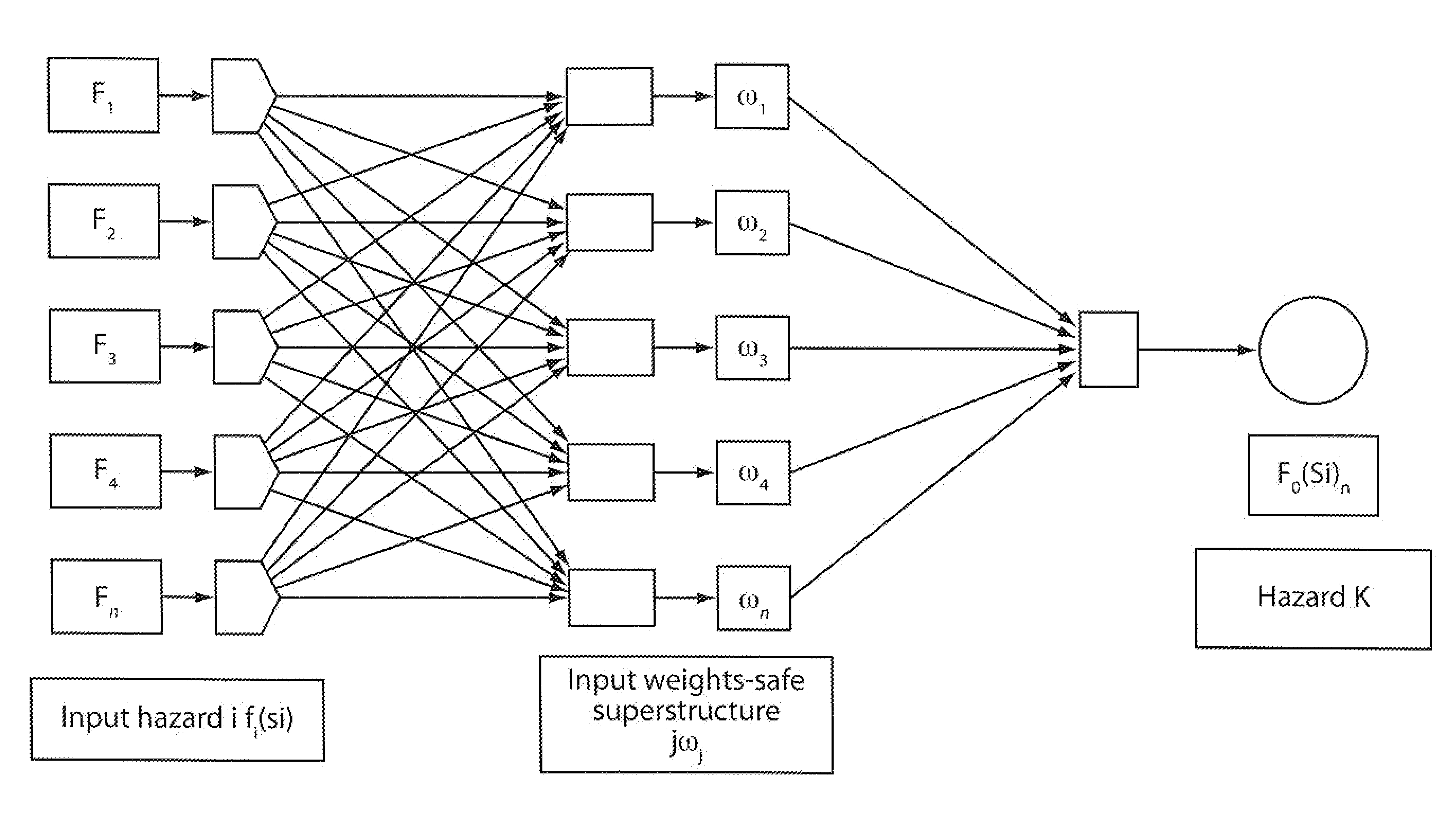
A method for predicting risk and designing safety management systems of complex production and process systems which has been applied to an FPSO System operating in deep waters. The methods for the design were derived from the inclusion of a weight index in a fuzzy class belief variable in the risk model to assign the relative numerical value or importance a safety device or system has contain a risk hazards within the barrier. The weights index distributes the relative importance of risk events in series or parallel in several interactive risk and safety device systems. The fault tree, the FMECA and the Bow Tie now contains weights in fizzy belief class for implementing safety management programs critical to the process systems. The techniques uses the results of neural networks derived from fuzzy belief systems of weight index to implement the safety design systems thereby limiting use of experienced procedures and benchmarks. The weight index incorporate Safety Factors sets SFri {0, 0.1, 0.2 . . . 1}, and Markov Chain Network to allow the possibility of evaluating the impact of different risks or reliability of multifunctional systems in transient state process. The application of this technique and results of simulation to typical FPSO / Riser systems has been discussed in this invention.
Owner:ABHULIMEN KINGSLEY E
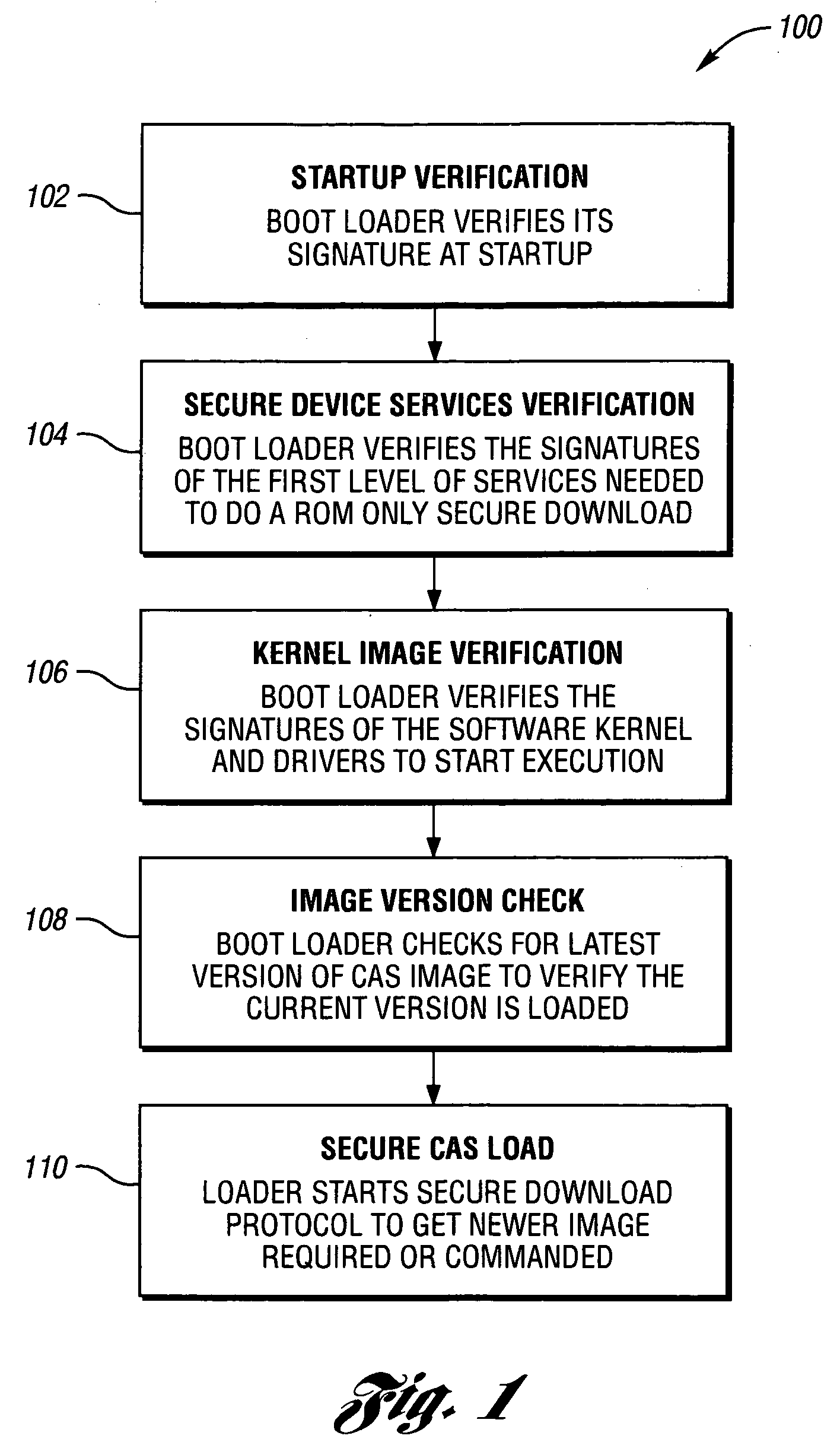
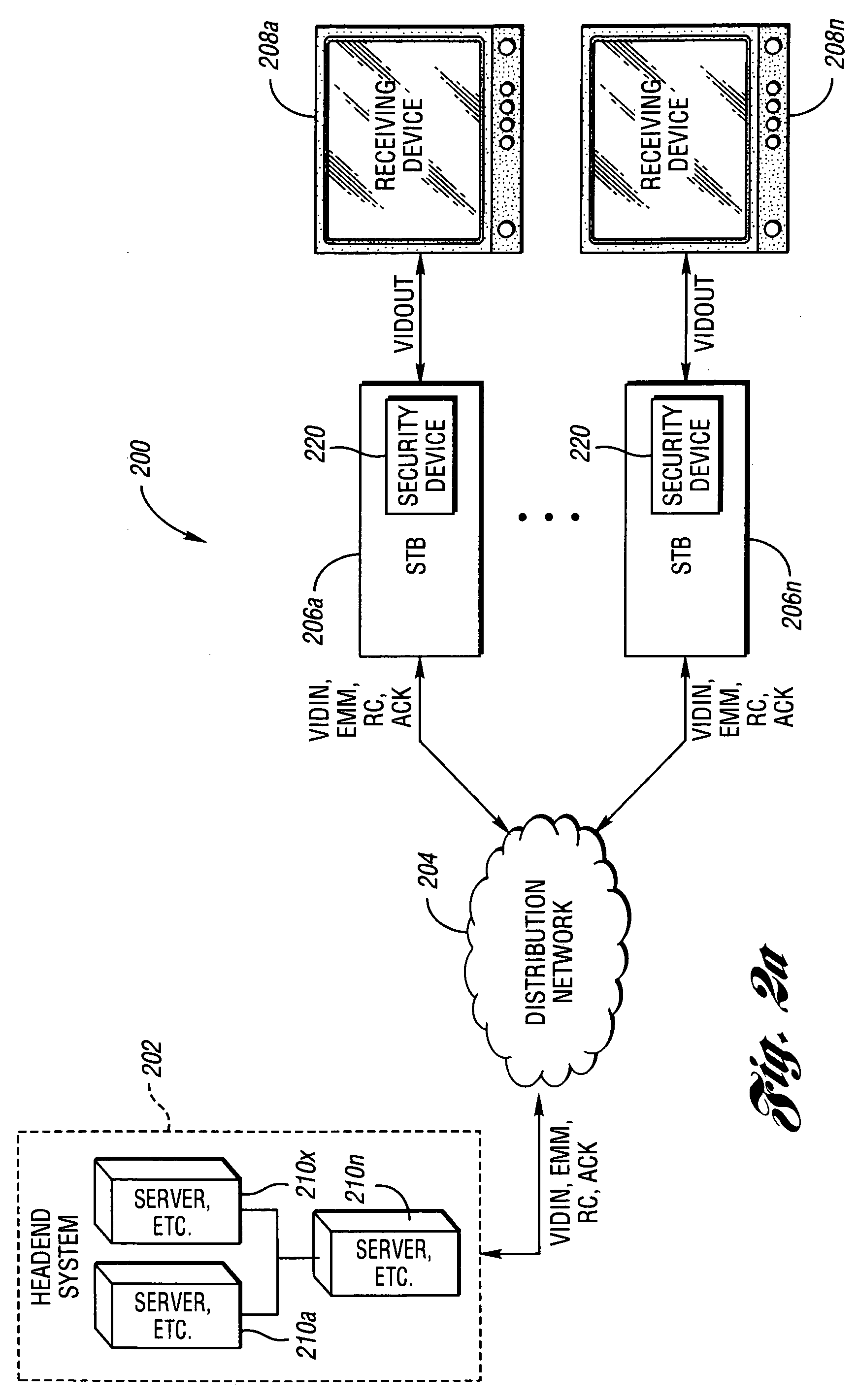
System and method for secure conditional access download and reconfiguration
ActiveUS20060137015A1Overcome deficienciesDigital data processing detailsUser identity/authority verificationSecurity softwareConditional access
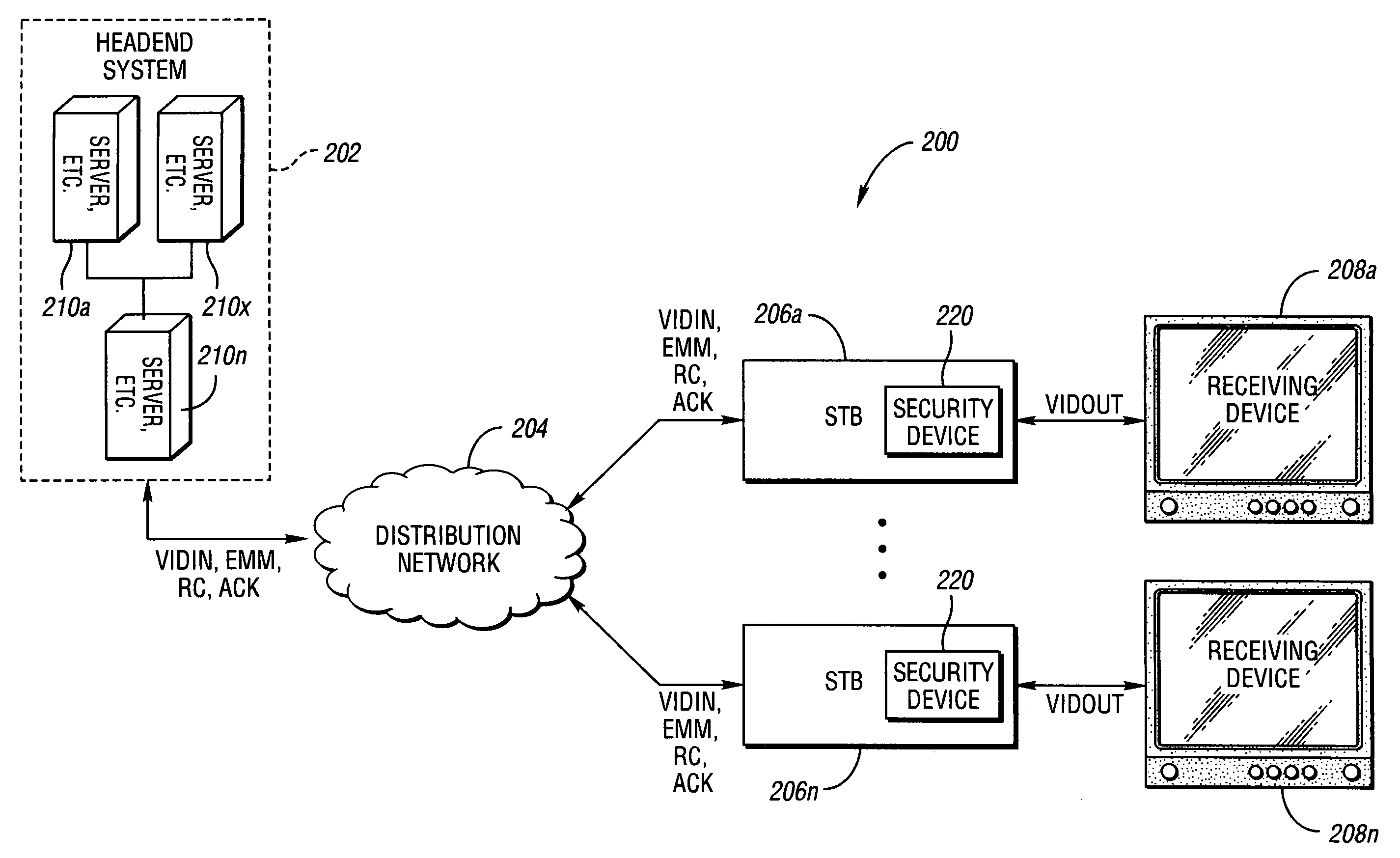
A method of securely downloading at least one of conditional access software (CAS), Digital Rights Management software (DRMS), Trusted Domain Software (TDS), and Gaming Security Software (GSS) includes presenting a specialized entitlement management message (EMM) to initiate the download to a receiver security device using a supervisory logon key (SLK) split to logon with a second split contained inside the receiver security device, presenting a receiver digitally signed random challenge from the receiver security device to a sender security server to establish authentication of the receiver security device to the sender security server, and signing and returning the receiver random challenge from the sender security server to the receiver security device with a sender random challenge to establish authentication of the sender security server to the receiver security device.
Owner:COMCAST CABLE COMM LLC
Solid state gimbal system
InactiveUS7459834B2Less powerHigh operating requirementsAdditive manufacturing apparatusPiezoelectric/electrostriction/magnetostriction machinesGuidance systemCommunications system
A non-mechanical gimbal system is presented. The gimbal system includes a gimbal housing, including hemispherical and annular caps, rotatable sphere, and at least two curvilinear actuators. The hemispherical cap is attached to the annular cap in a removable fashion so as to surround the rotatable sphere. The curvilinear actuators are disposed between the rotatable sphere and gimbal housing. Curvilinear actuators rotate the rotatable sphere, via shear induced motion, with respect to the interior surface of the gimbal housing. The present invention has immediate applicability within security devices, games, toys, weapons (including guidance systems and aiming), and communication systems.
Owner:QORTEK
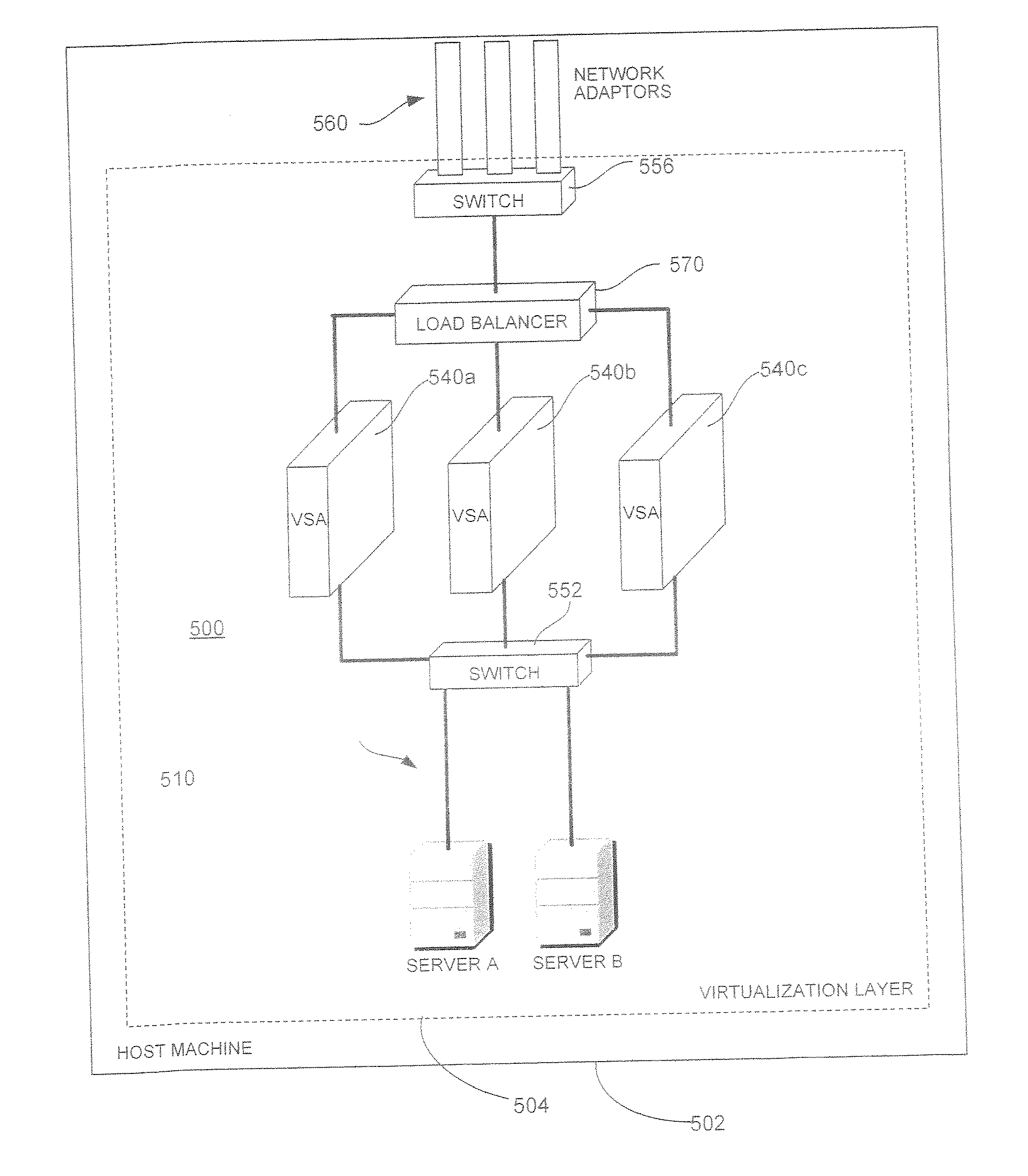
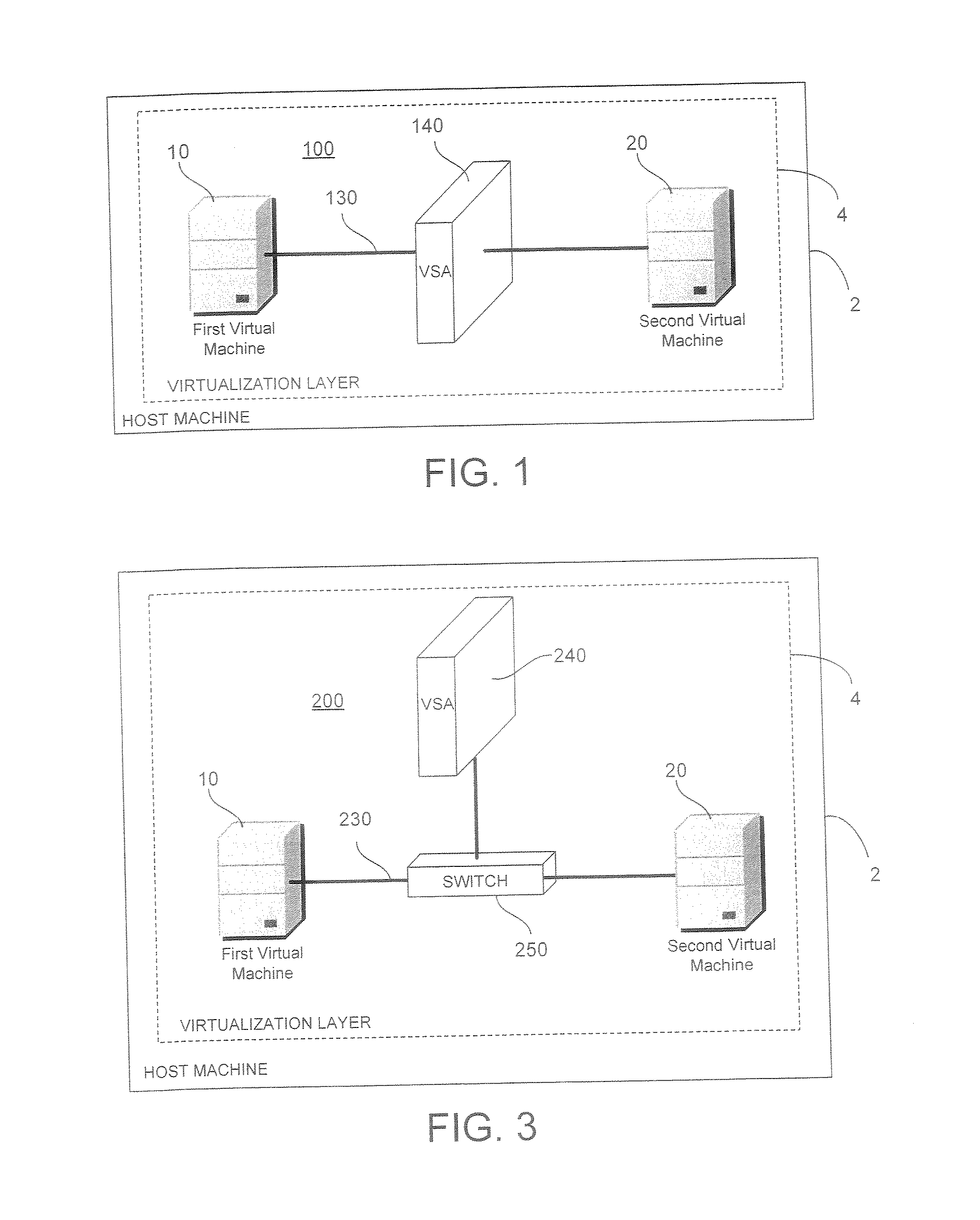
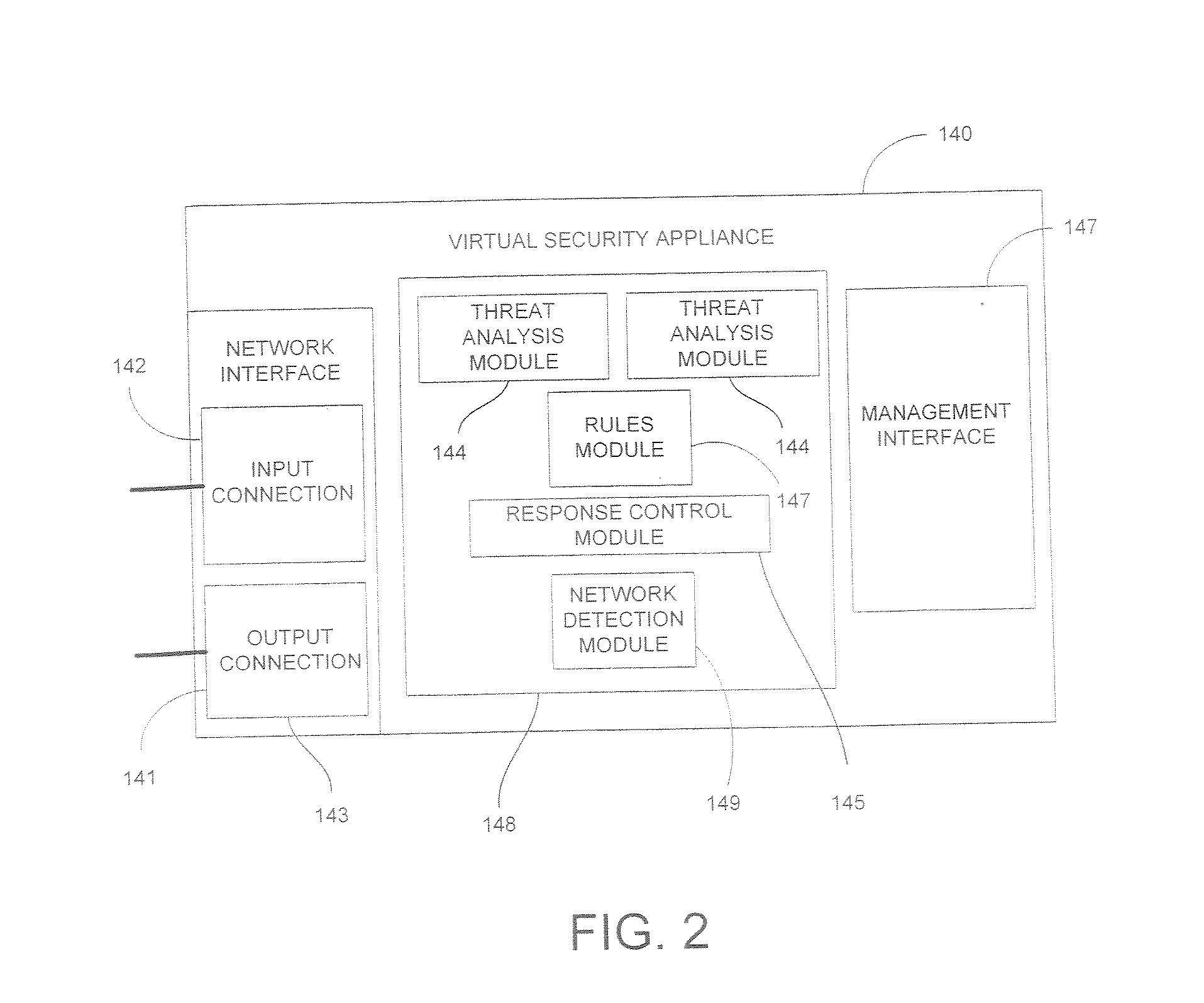
System and Method for Securing Information in a Virtual Computing Environment
InactiveUS20070266433A1Improve employee productivityIncrease the challengeMultiple digital computer combinationsPlatform integrity maintainanceVirtual computingHost machine
A virtual security appliance is provided for disposition in a virtual network having at least one other virtual network device, the virtual network residing on a host data processing machine. The virtual security appliance comprises an interface configured for receiving a data communication directed to the at least one other virtual network device and a security function module adapted for initiating a security function responsive to said data communication meeting predetermined criteria.
Owner:STRATACLOUD
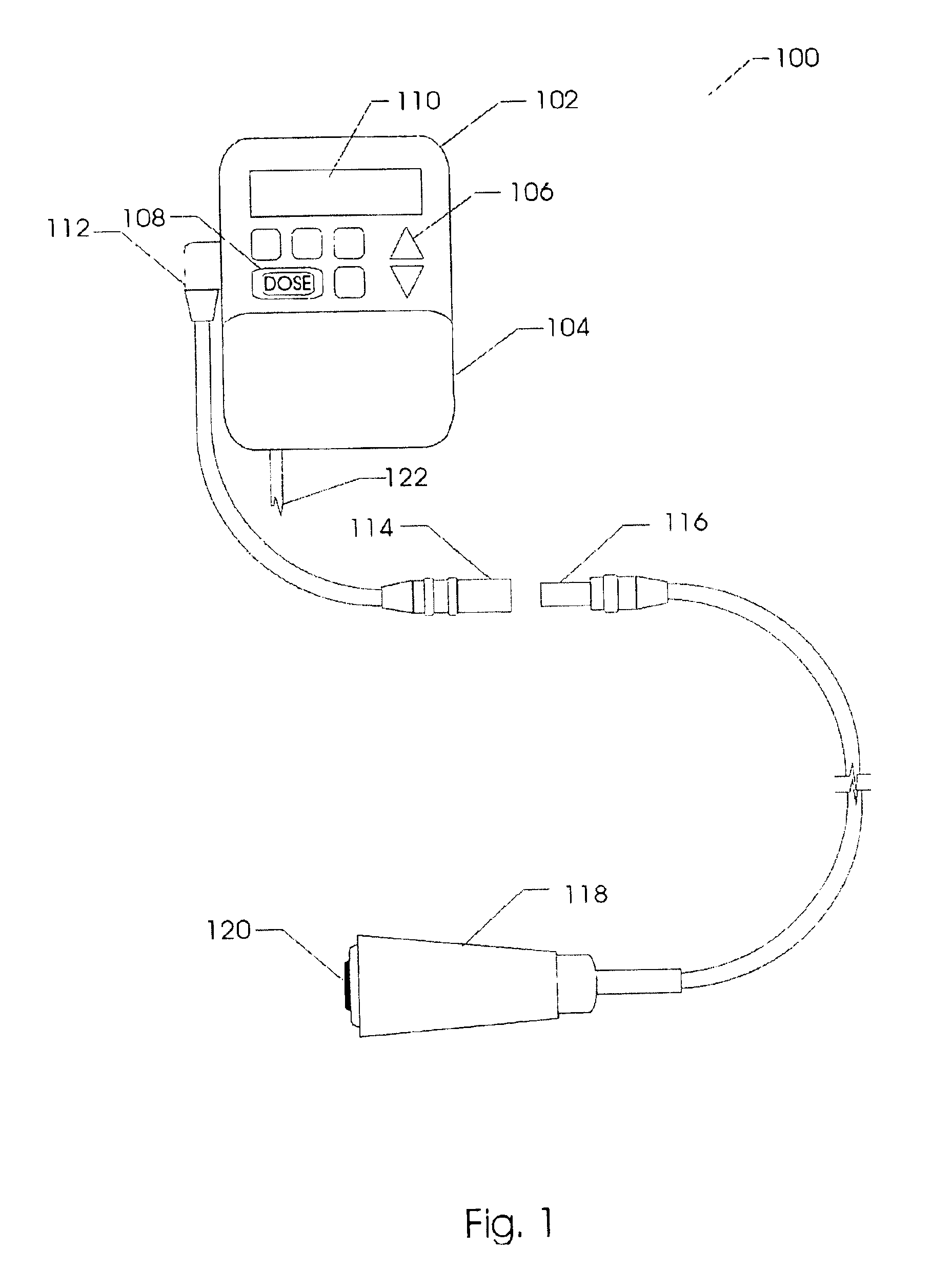
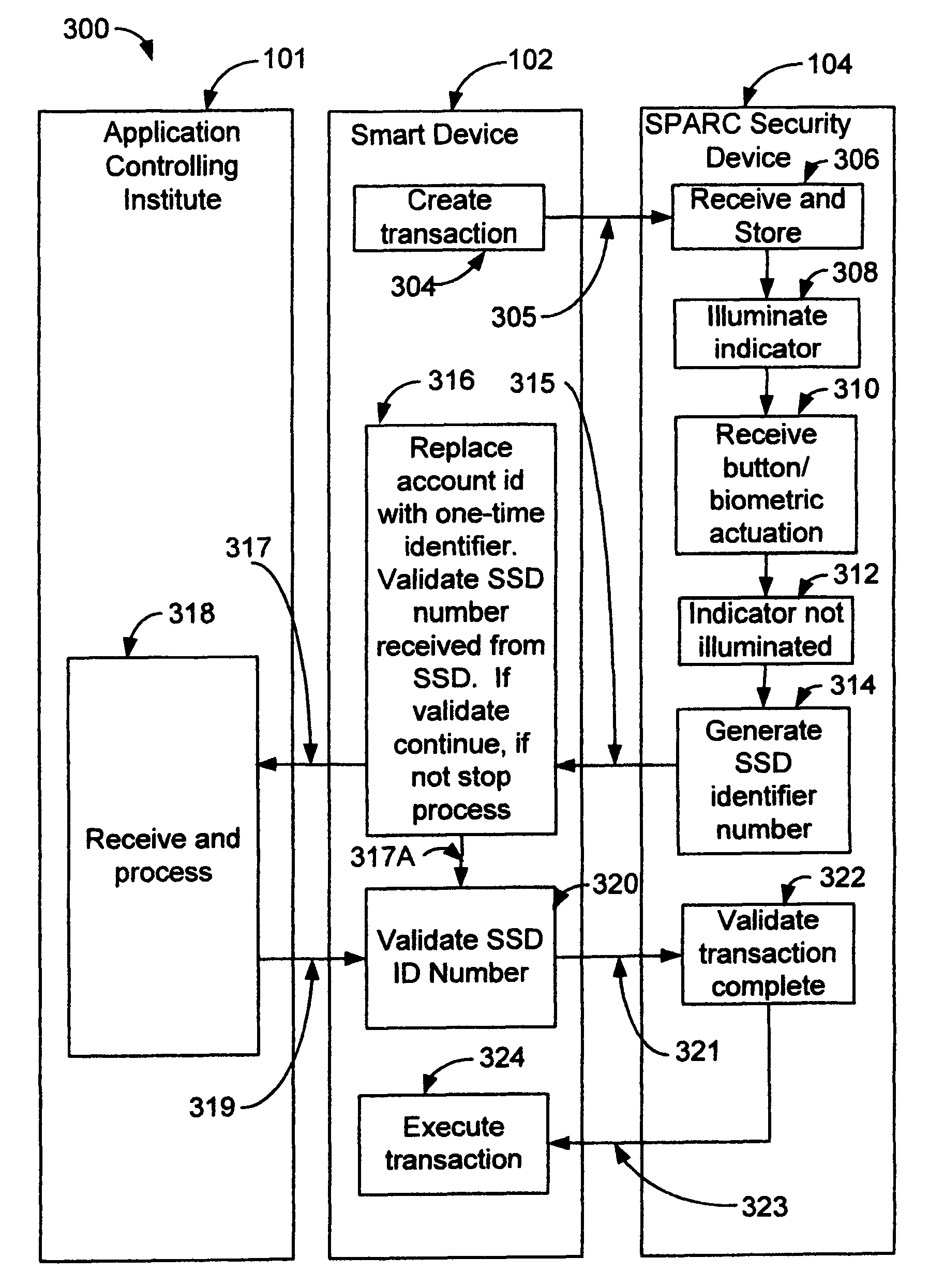
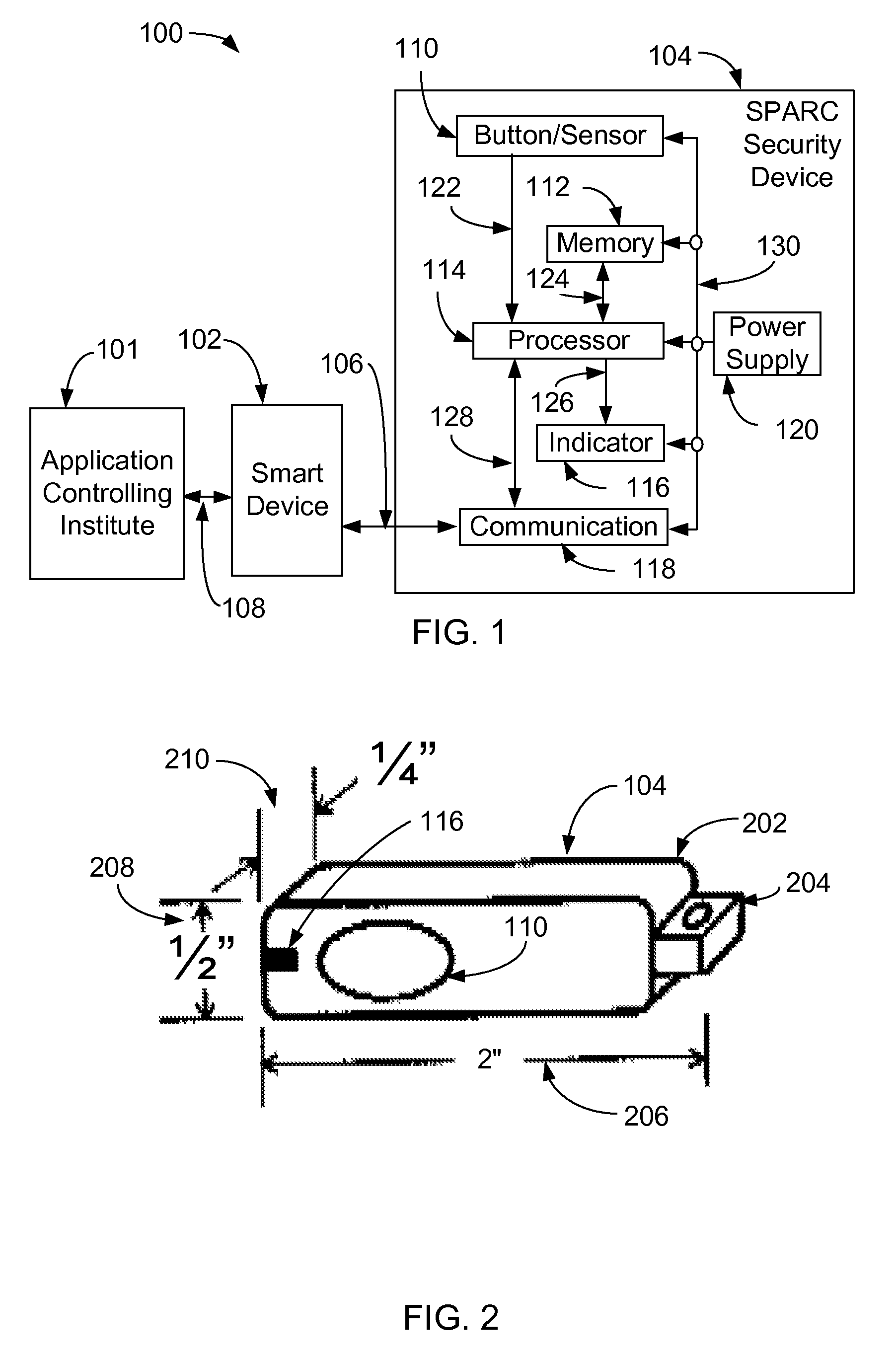
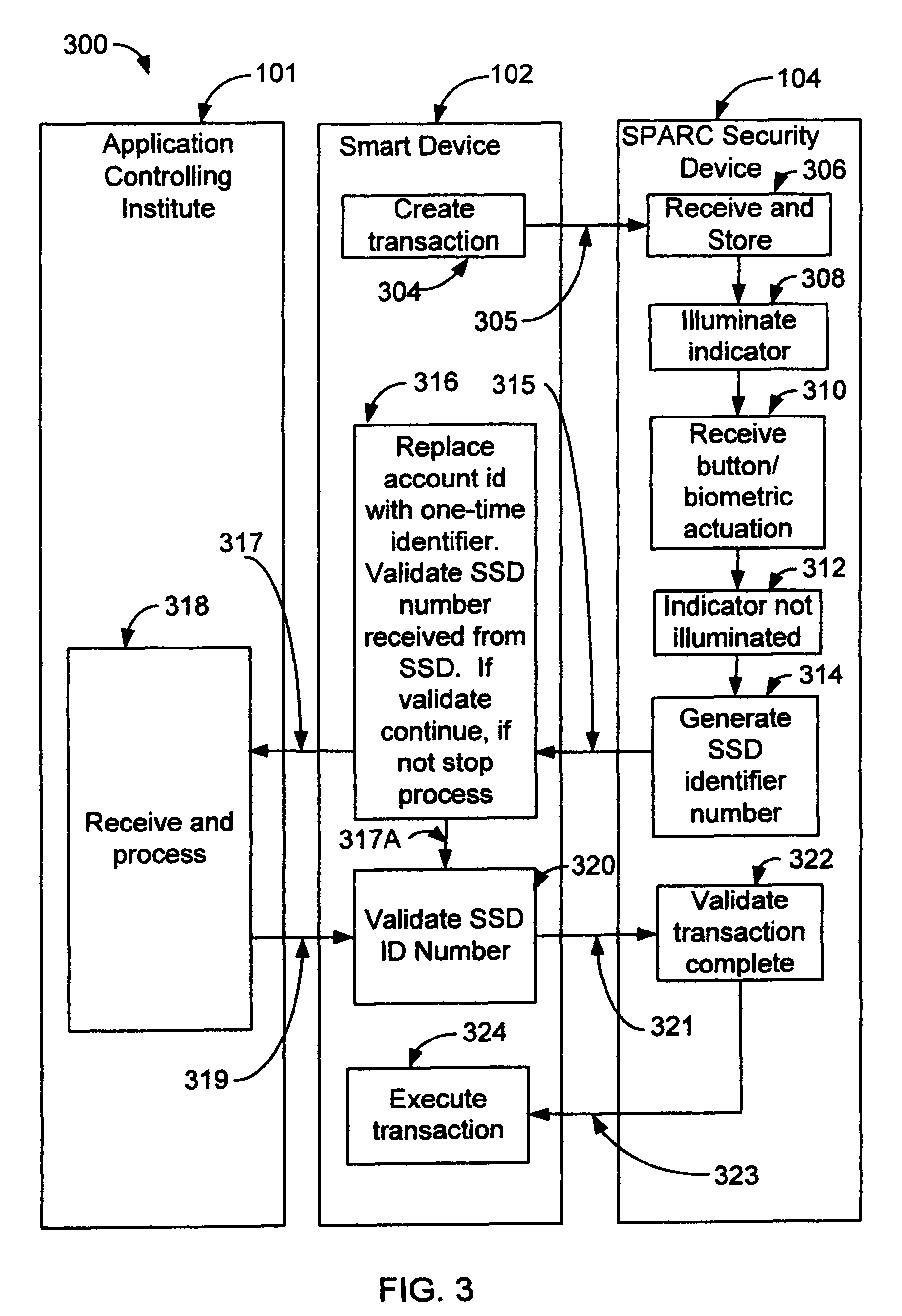
A Method, Device and System for Secure Transactions
InactiveUS20130081122A1Digital data processing detailsUser identity/authority verificationOperational safetyComputer security
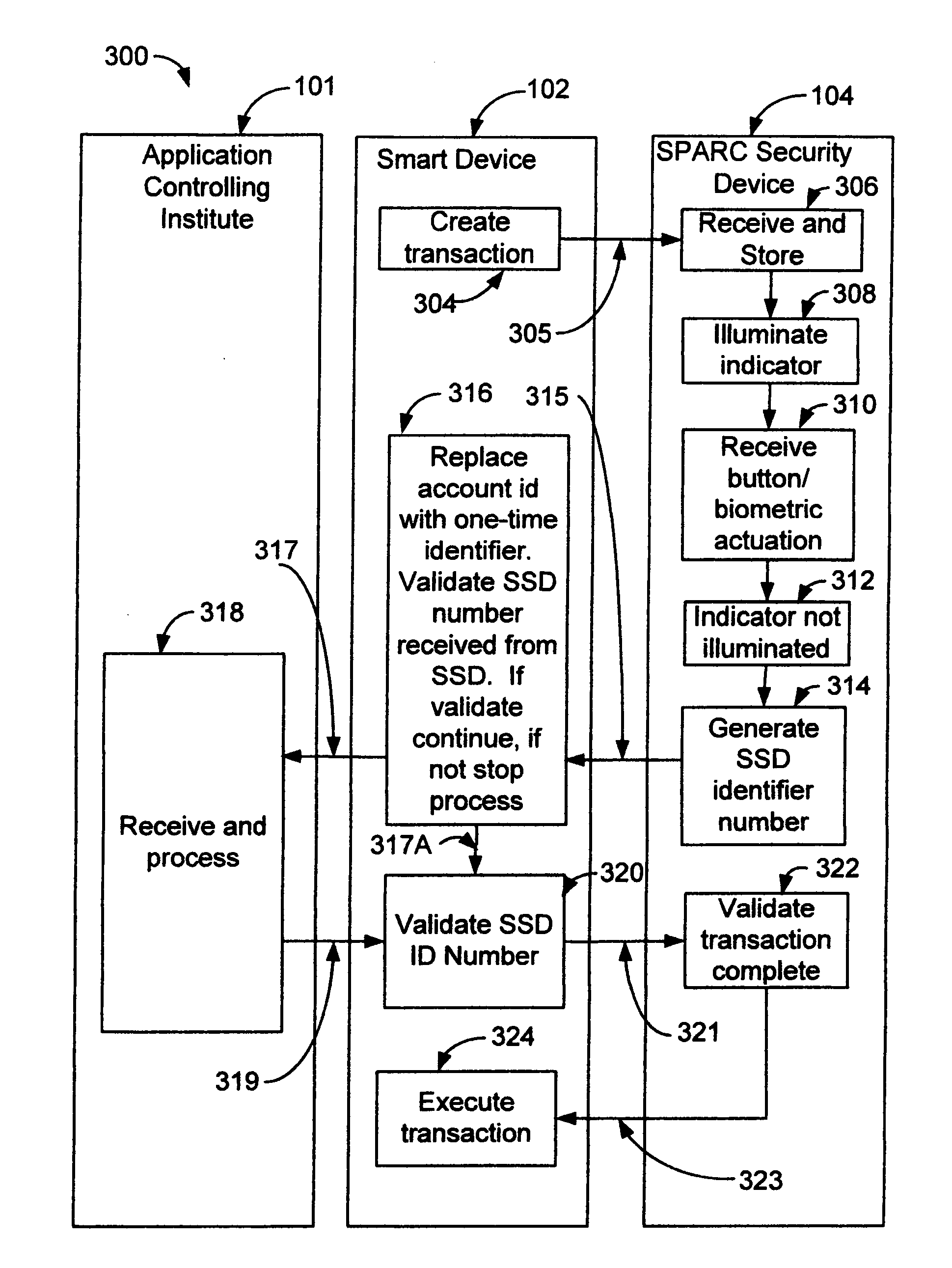
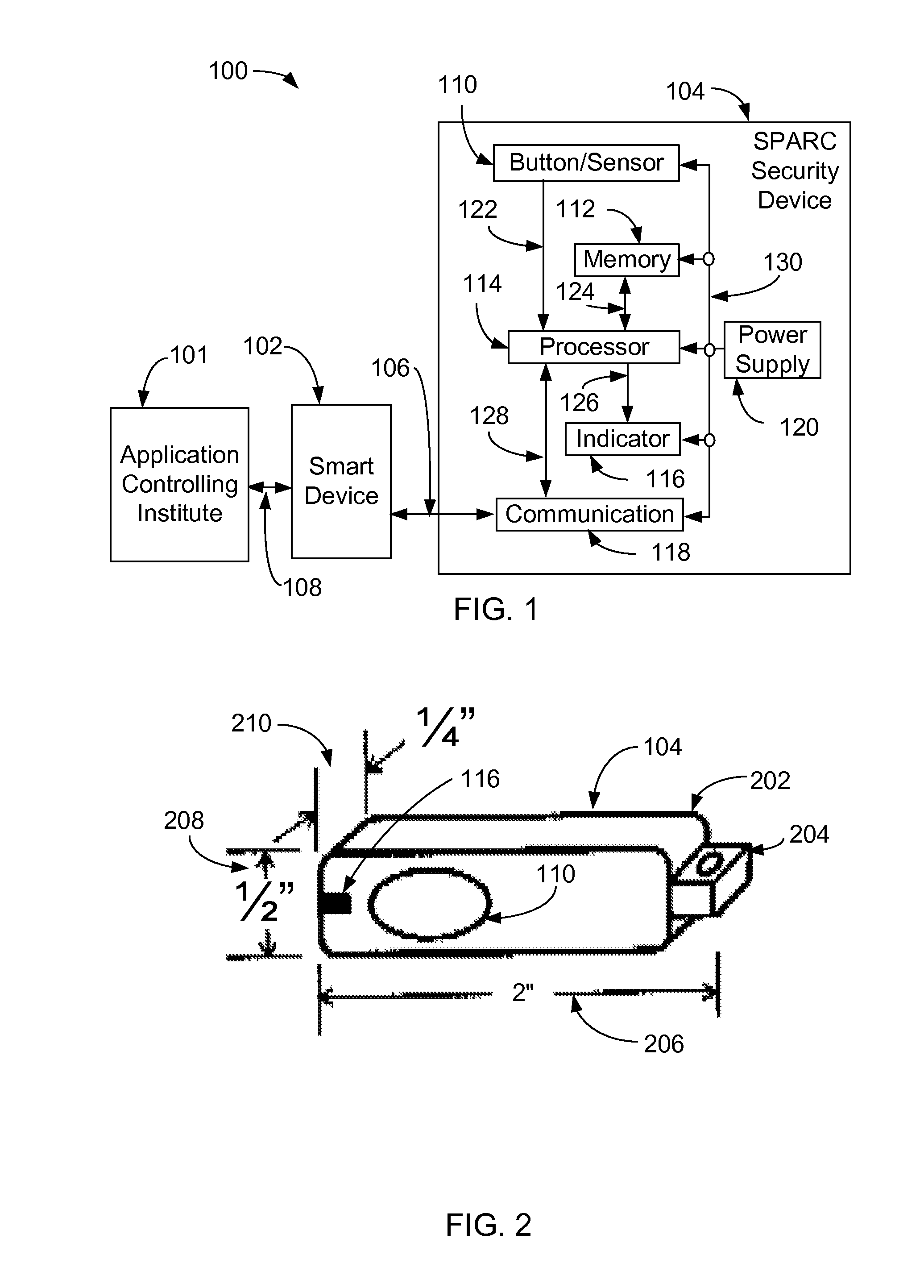
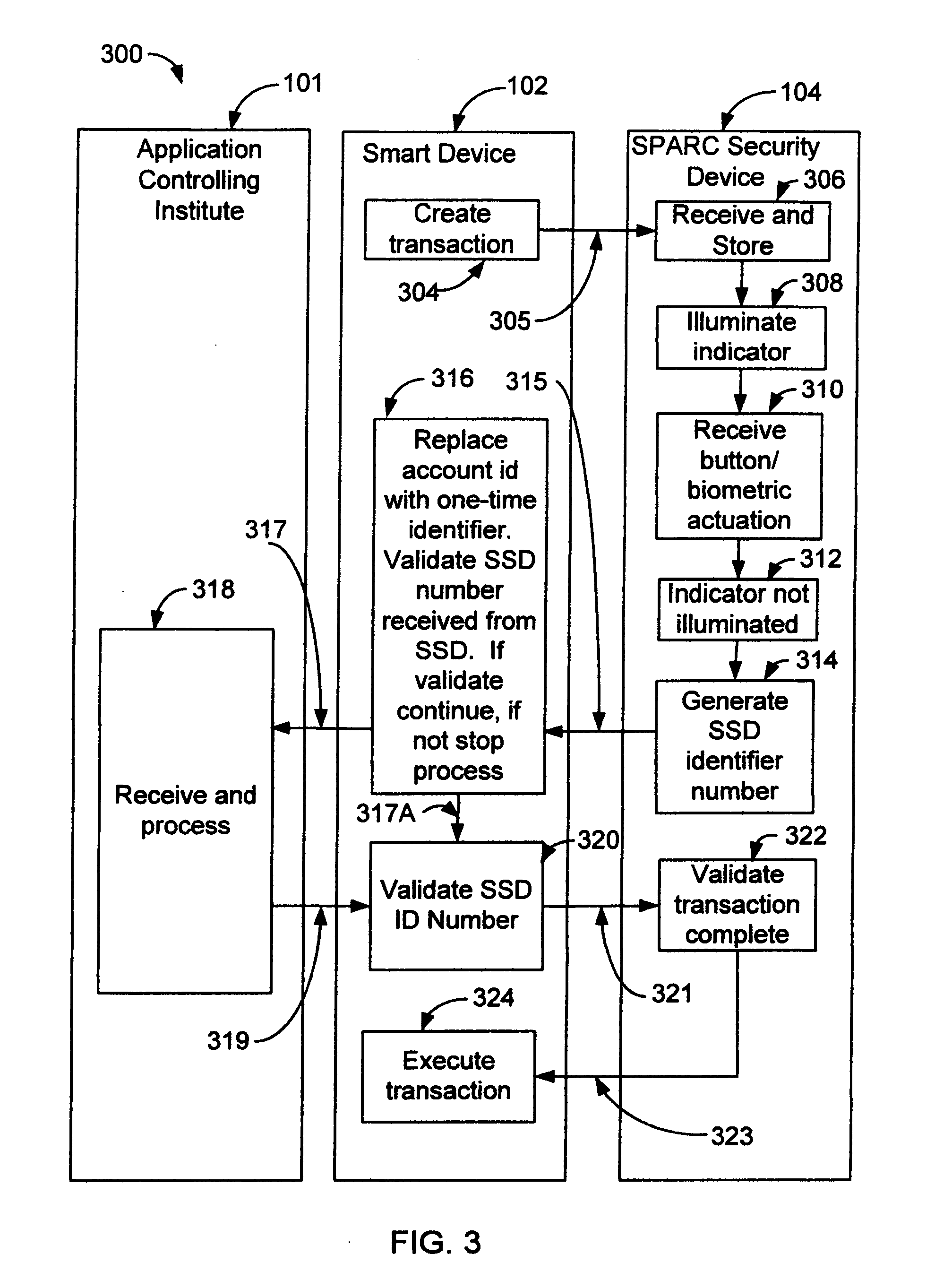
A method for operating a security device comprises receiving a request for a transaction from a programmable device executing an application obtained from an application controlling institute, and verifying a validity of the transaction. A user is alerted, in which the user indicates an acceptance of the request. A one-time identifier is generated. The one-time identifier comprises a security device identification, a transaction number, a date and a time. The one-time identifier is communicated to the programmable device, in which the application verifies a validity of the security device identification and instructs the programmable device to communicate the one-time identifier and transaction to the application controlling institute for processing. The application controlling institute verifies validity of the one-time identifier and processes the transaction, wherein said security device, application programmable device and application controlling institute securely processes the transaction.
Owner:SVIGALS JEROME +2
Medication security apparatus and method
Owner:HERRERA HECTOR J
Method, device and system for secure transactions
InactiveUS8453223B2Digital data processing detailsMultiple digital computer combinationsOperation safetyComputer security
A method for operating a security device comprises receiving a request for a transaction from a programmable device executing an application obtained from an application controlling institute, and verifying a validity of the transaction. A user is alerted, in which the user indicates an acceptance of the request. A one-time identifier is generated. The one-time identifier comprises a security device identification, a transaction number, a date and a time. The one-time identifier is communicated to the programmable device, in which the application verifies a validity of the security device identification and instructs the programmable device to communicate the one-time identifier and transaction to the application controlling institute for processing. The application controlling institute verifies validity of the one-time identifier and processes the transaction, wherein said security device, application programmable device and application controlling institute securely processes the transaction.
Owner:SVIGALS JEROME +2
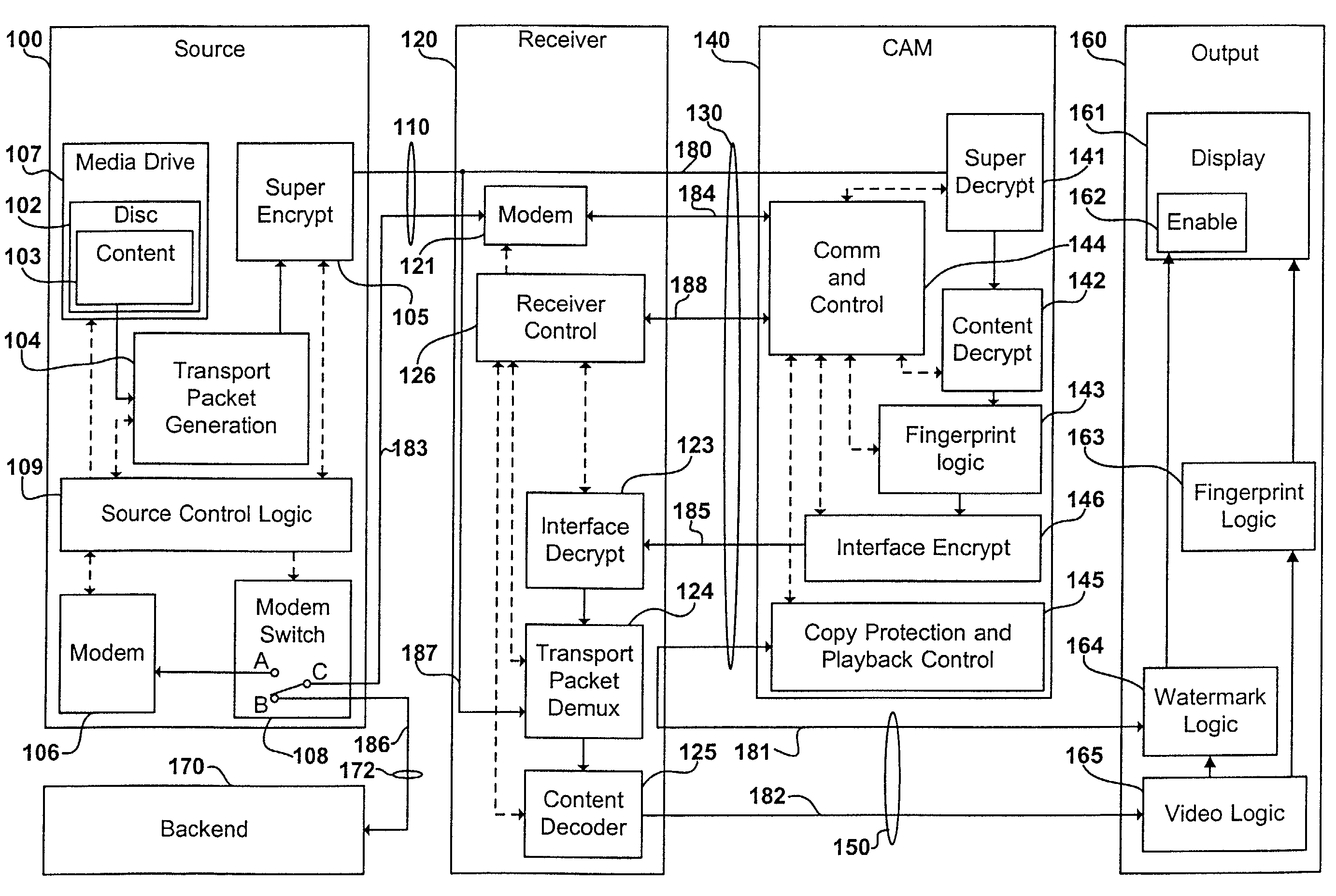
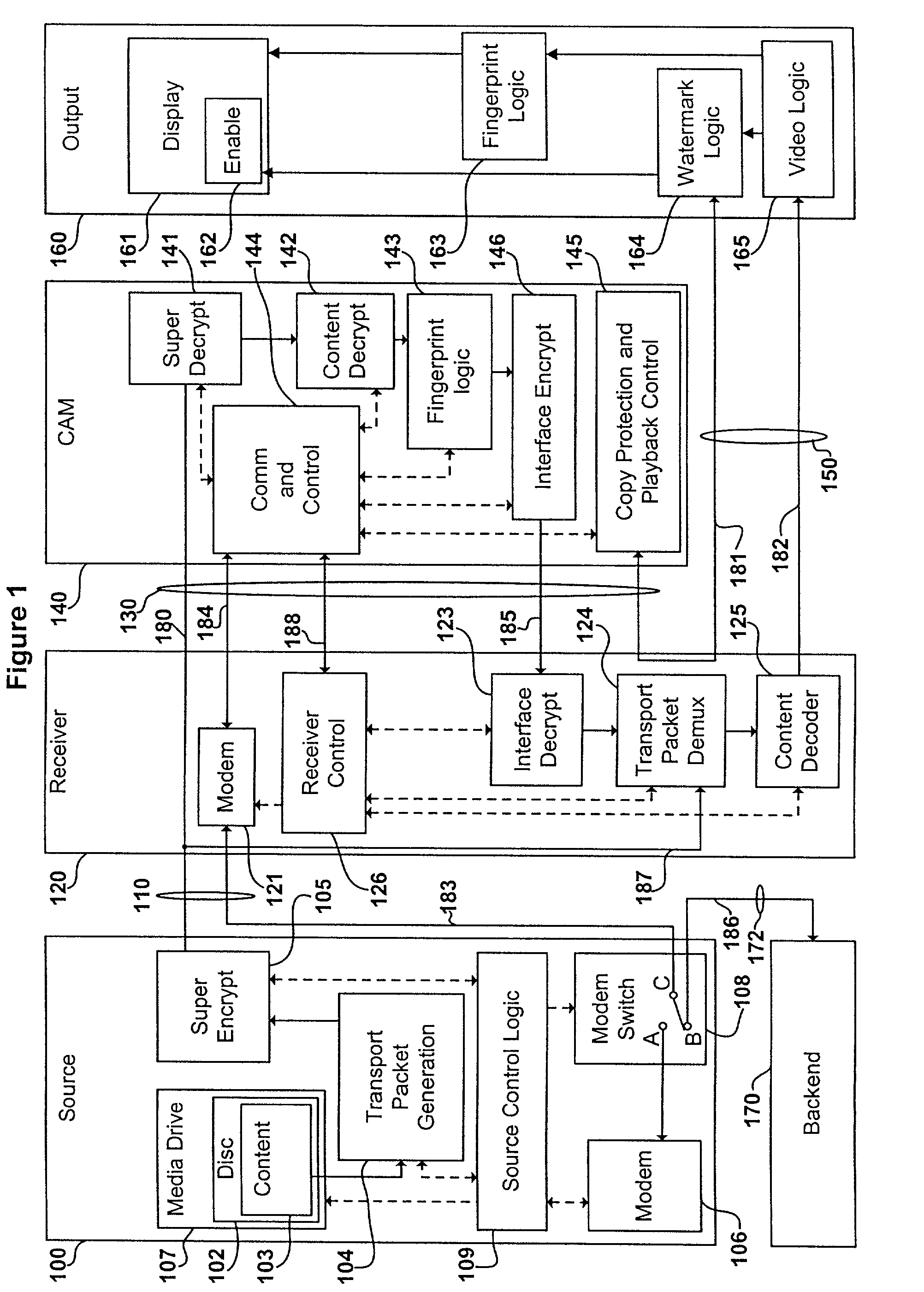
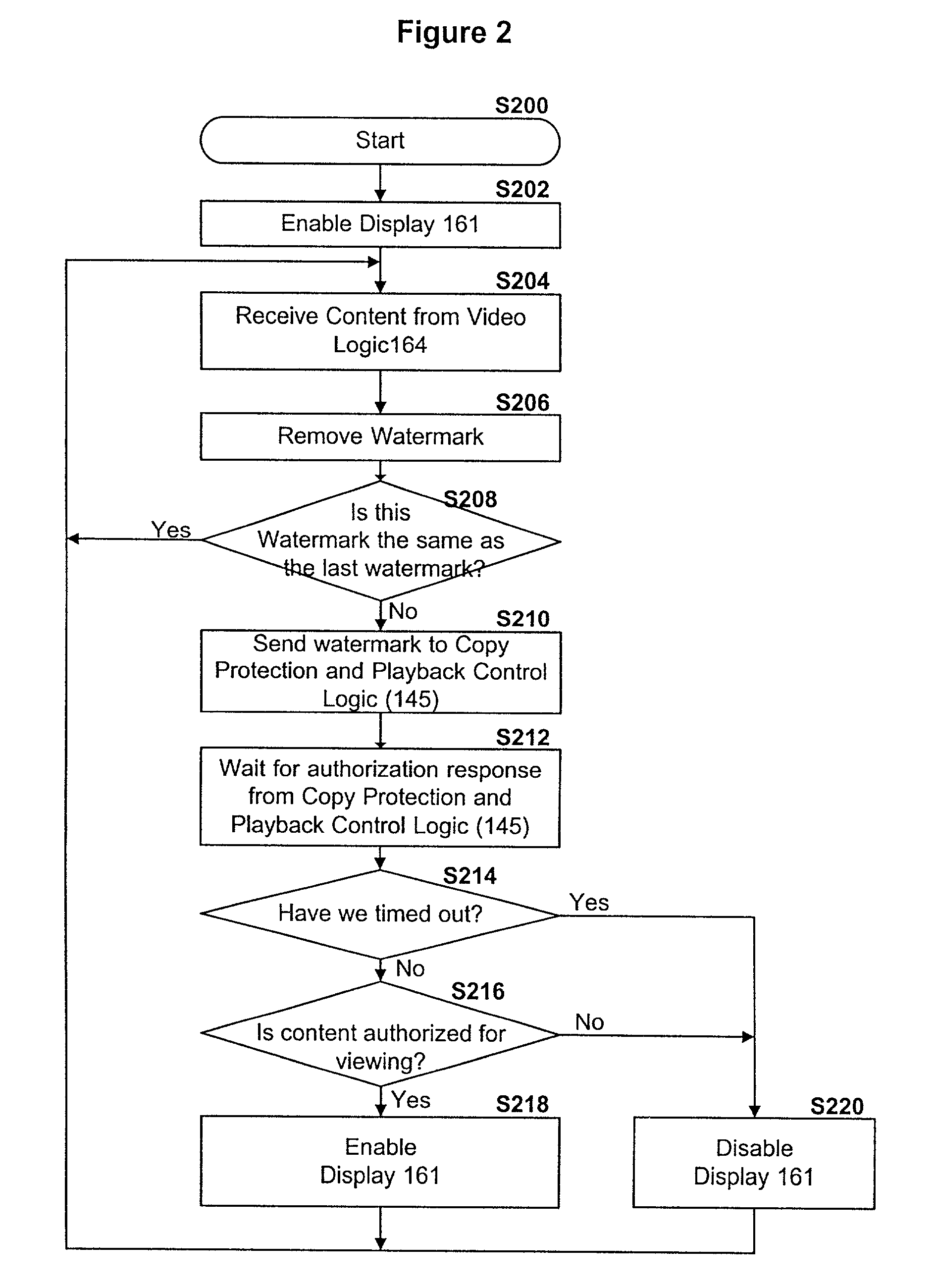
Digital content distribution system and method
InactiveUS7162642B2Prevent unauthorized accessObtaining unauthorized accessDigital data processing detailsUser identity/authority verificationContent distributionDigital content
A content distribution system and method which prevents unauthorized access to secured content such as movies and music. The apparatus includes a source, a receiver, an authorized security device such as a conditional access module (CAM) for decrypting authorized content, an output device for outputting content and a backend for managing accounts and system operations. One aspect of this invention provides a mechanism for providing secured content on a medium such as a DVD optical disc. These devices may verify that there is authorization to play the secured content, add watermarks to the secured content, convert the secured content to a displayable form and provide a means for preventing output of the secured content.
Owner:GOOGLE LLC
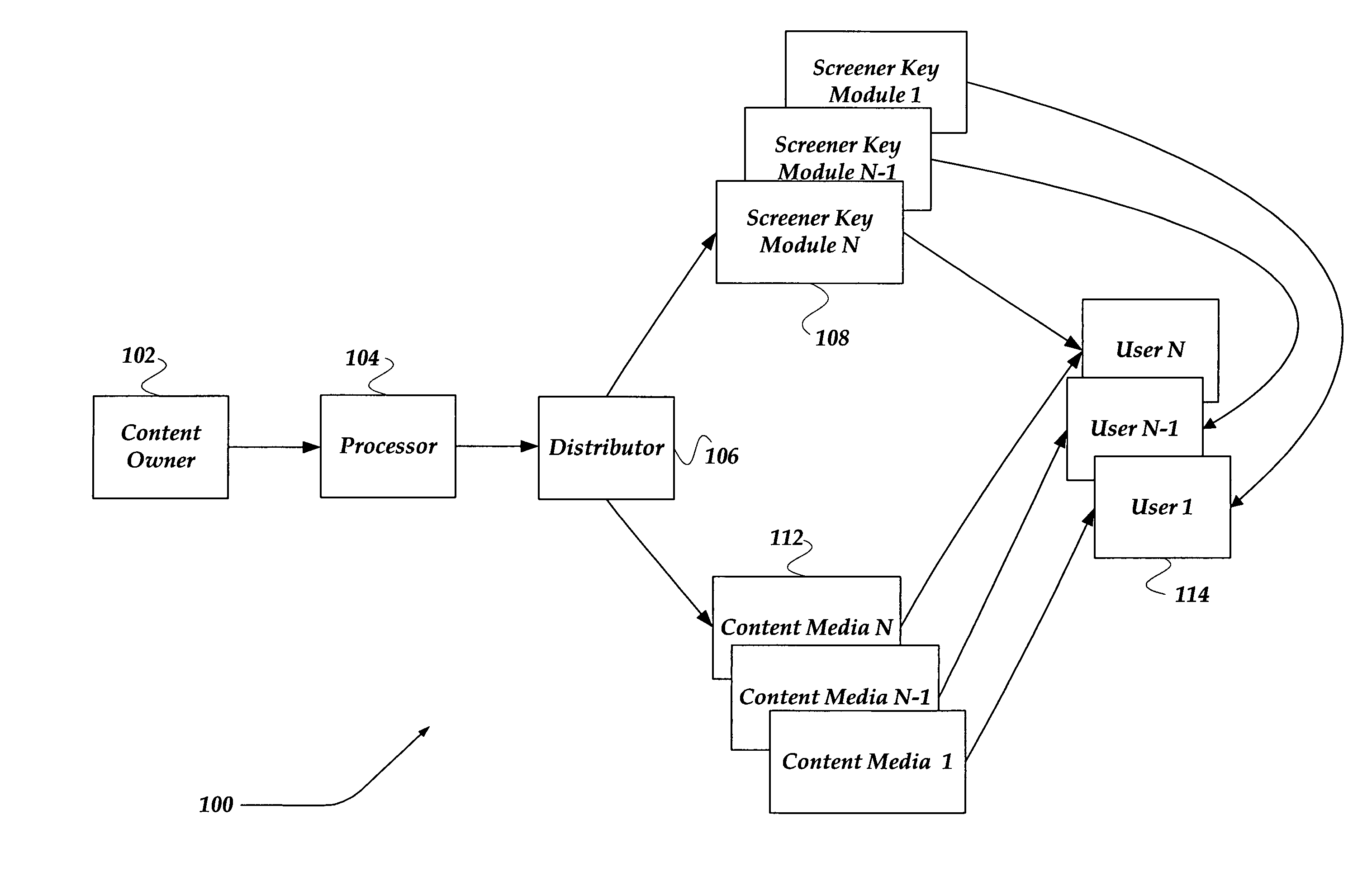
System, method, and apparatus for securely providing content viewable on a secure device
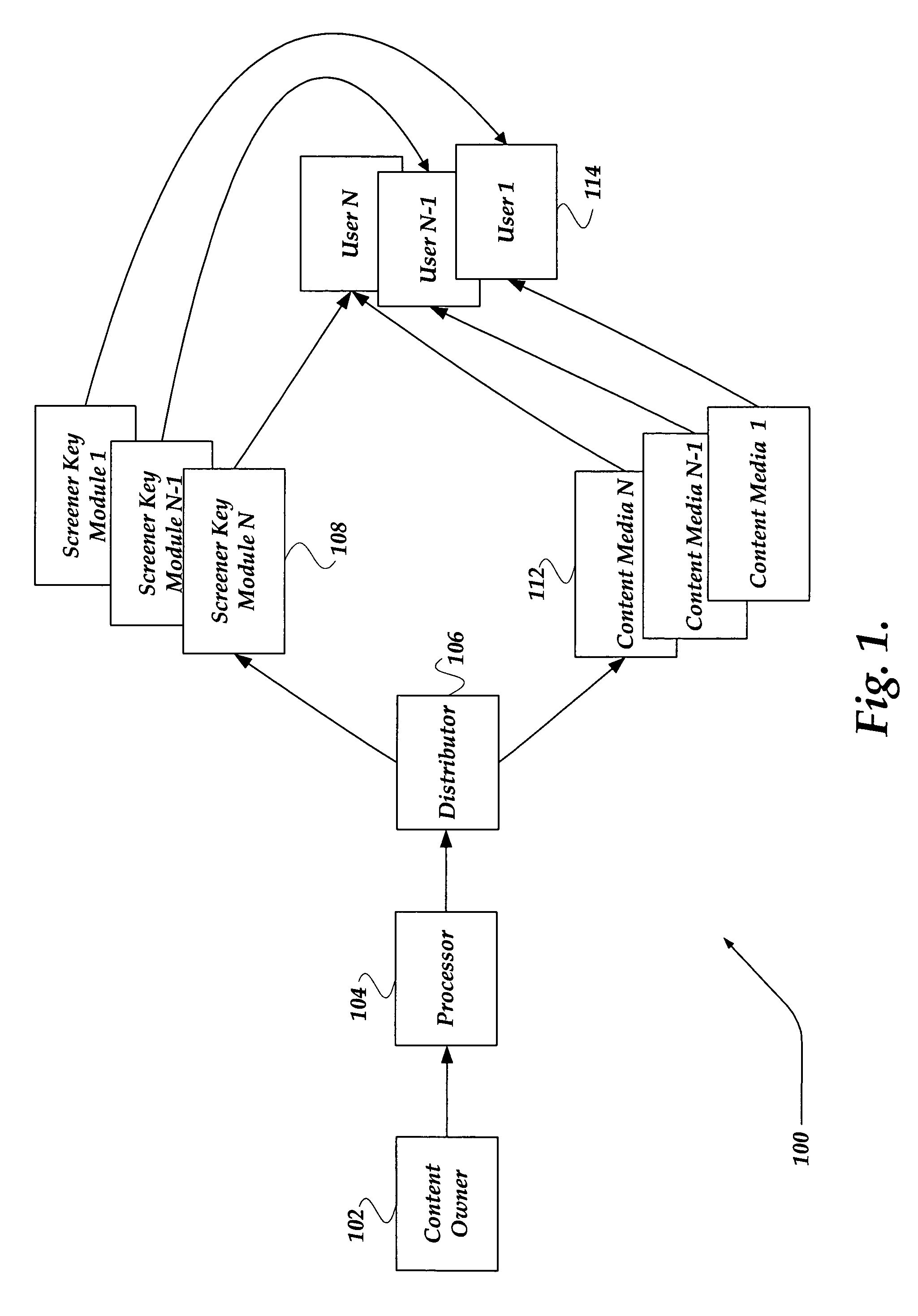
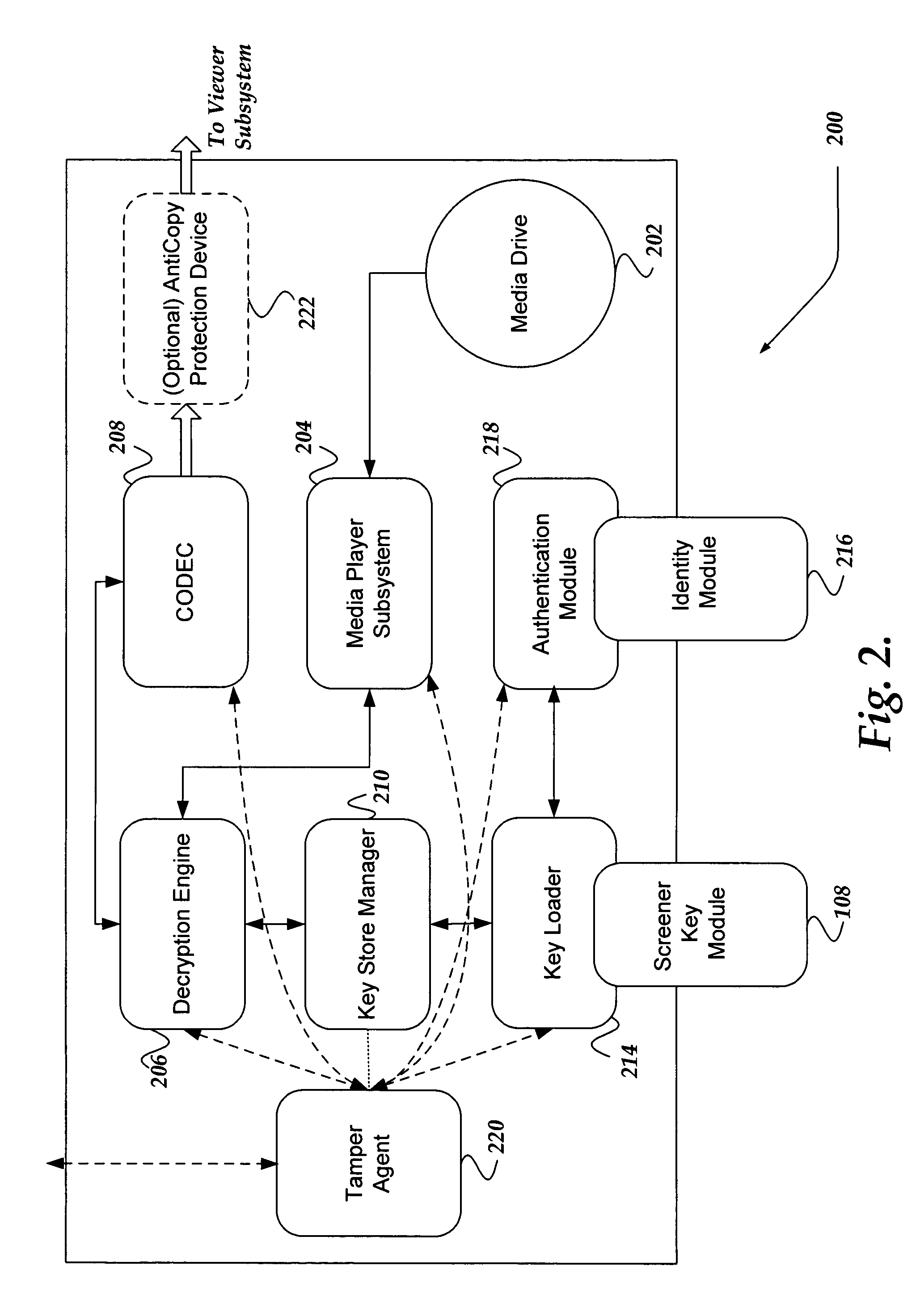
ActiveUS7007170B2Key distribution for secure communicationUser identity/authority verificationHigh definitionComputer security
A system, apparatus, and method are directed to providing and securely viewing secure content. In one embodiment, a secure player provides secure screening / previewing of secure content, such as a motion picture, by a member of an awards organization. A content key is employed to selectively encrypt at least a portion of a content stream. The content key is encrypted with a screener key. The encrypted content key is embedded into the secure content. The screener key is encrypted using public / private key pair that is bound to the secure player. The secure content may be distributed on a medium, such as a DVD, high definition DVD, and the like. The secure player is configured to receive the medium, screener key, and a screener identity. The screener identity and screener key are employed by the secure player to decrypt and enable secure viewing of the content.
Owner:GOOGLE LLC
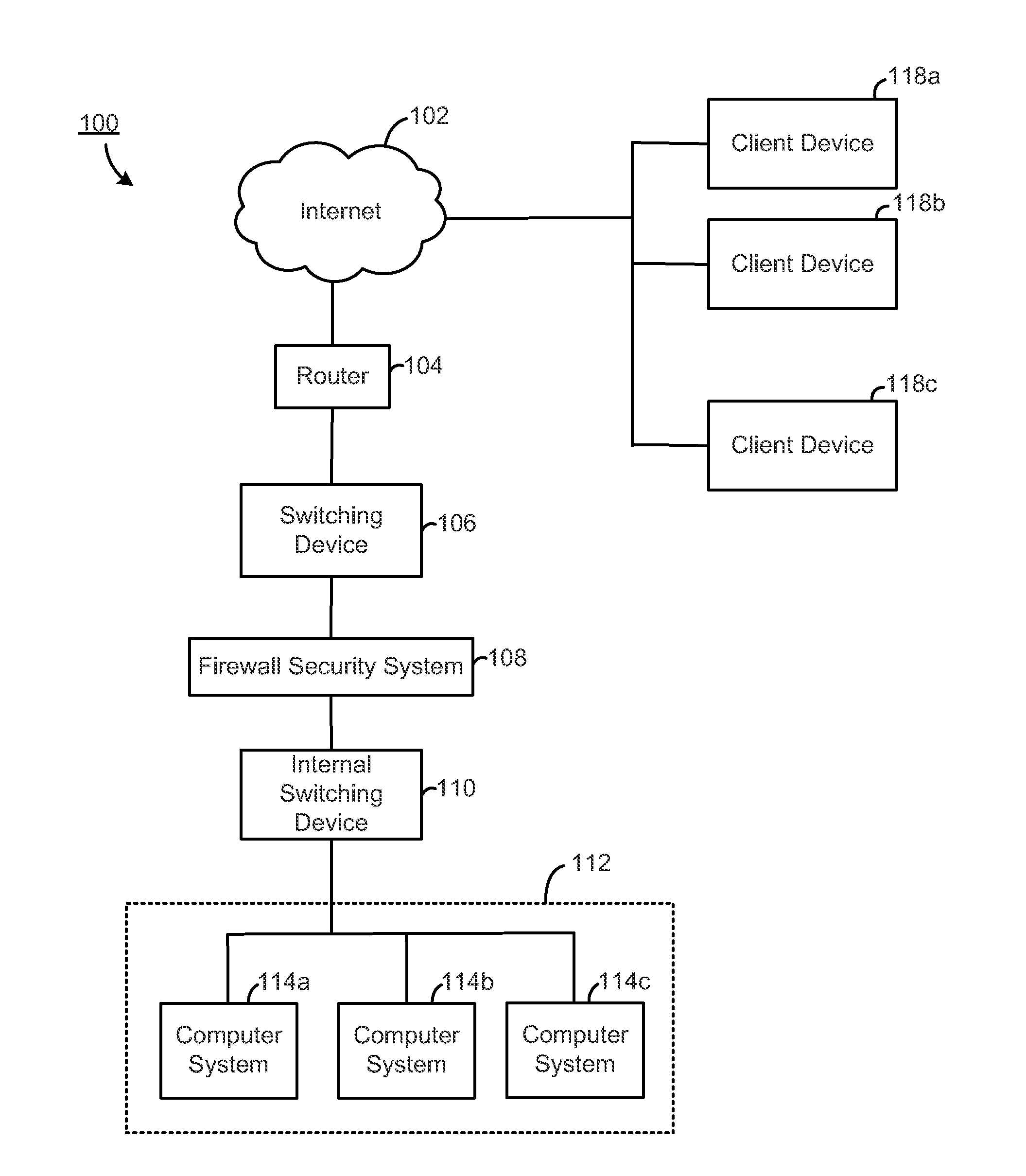
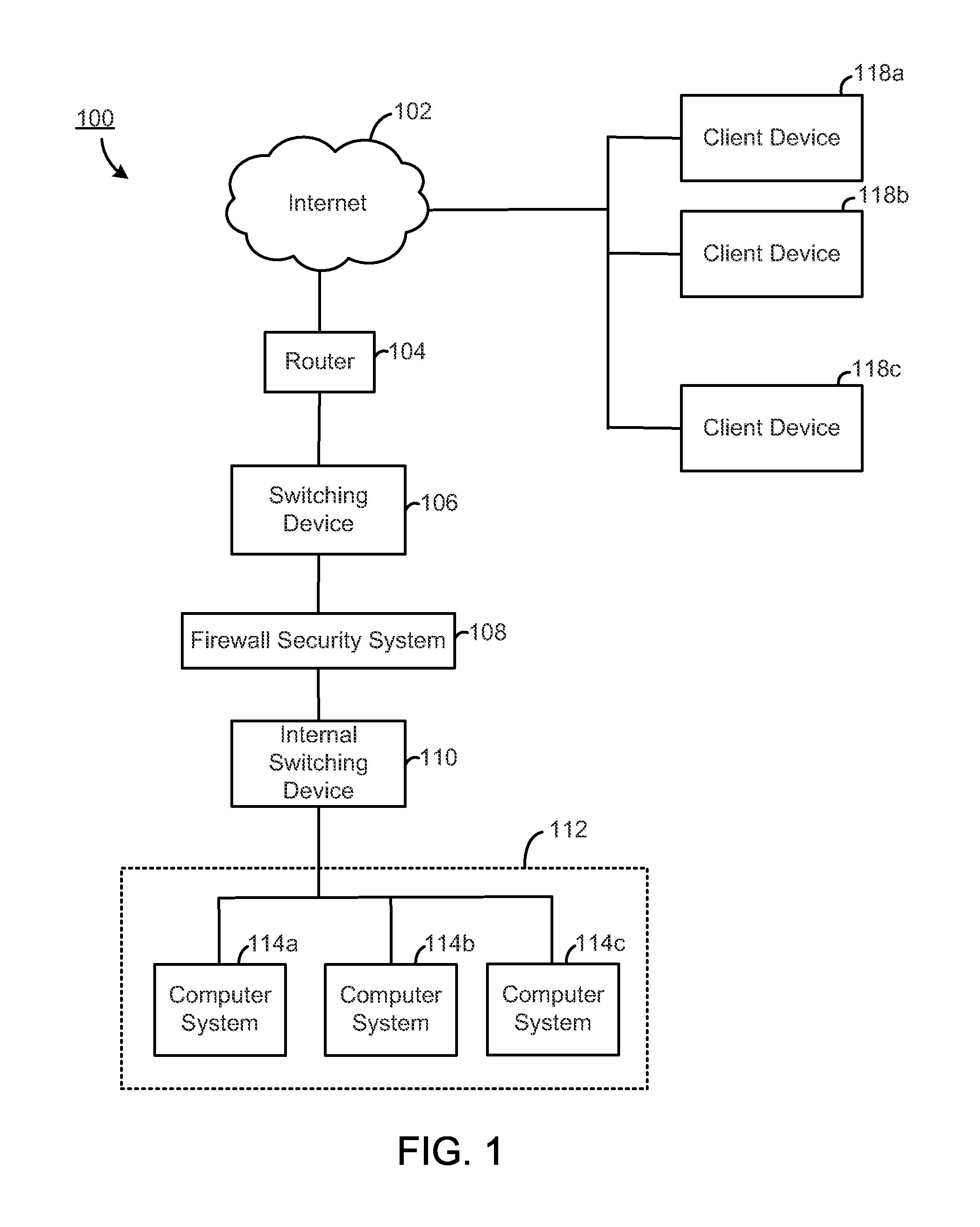
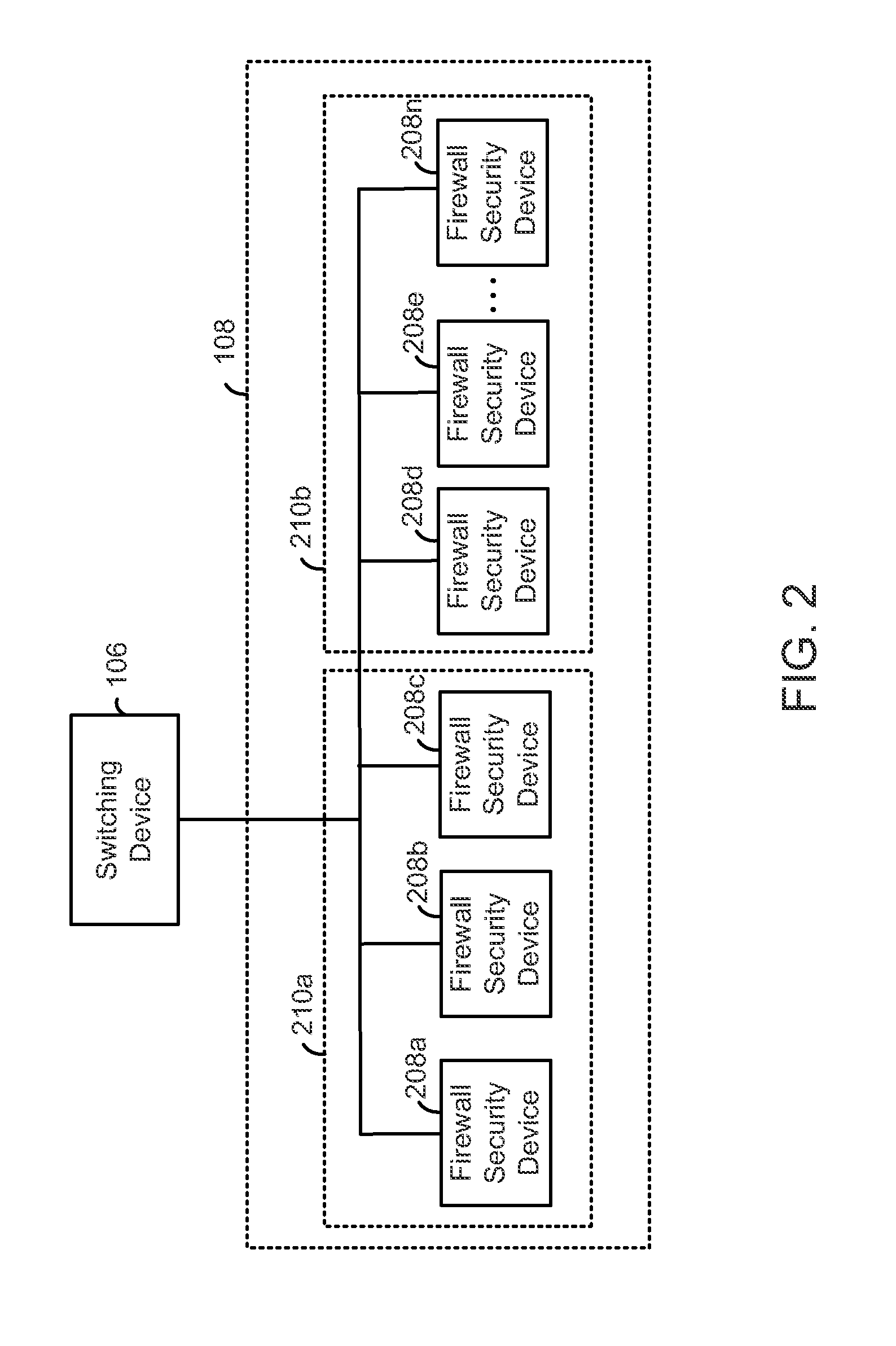
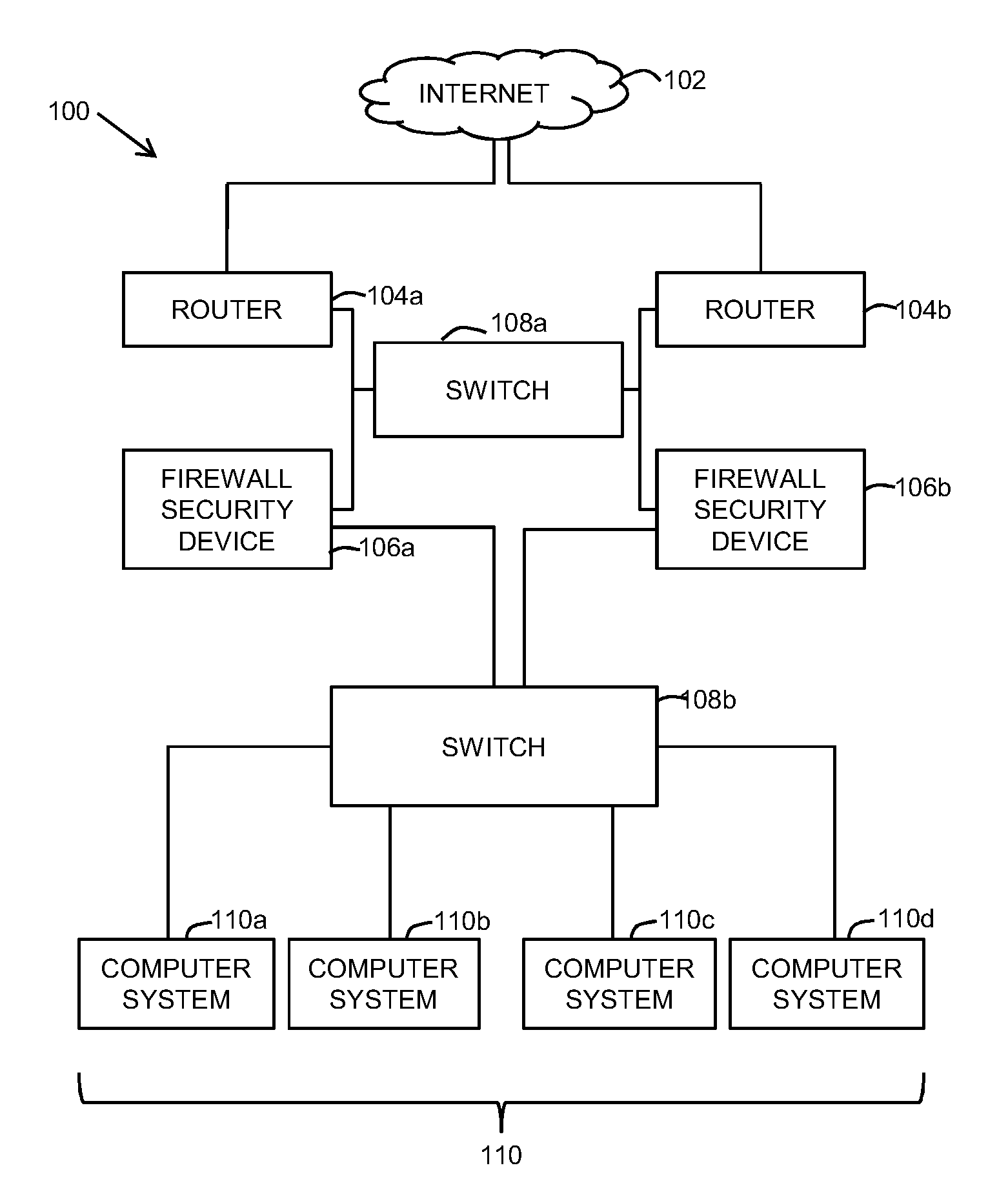
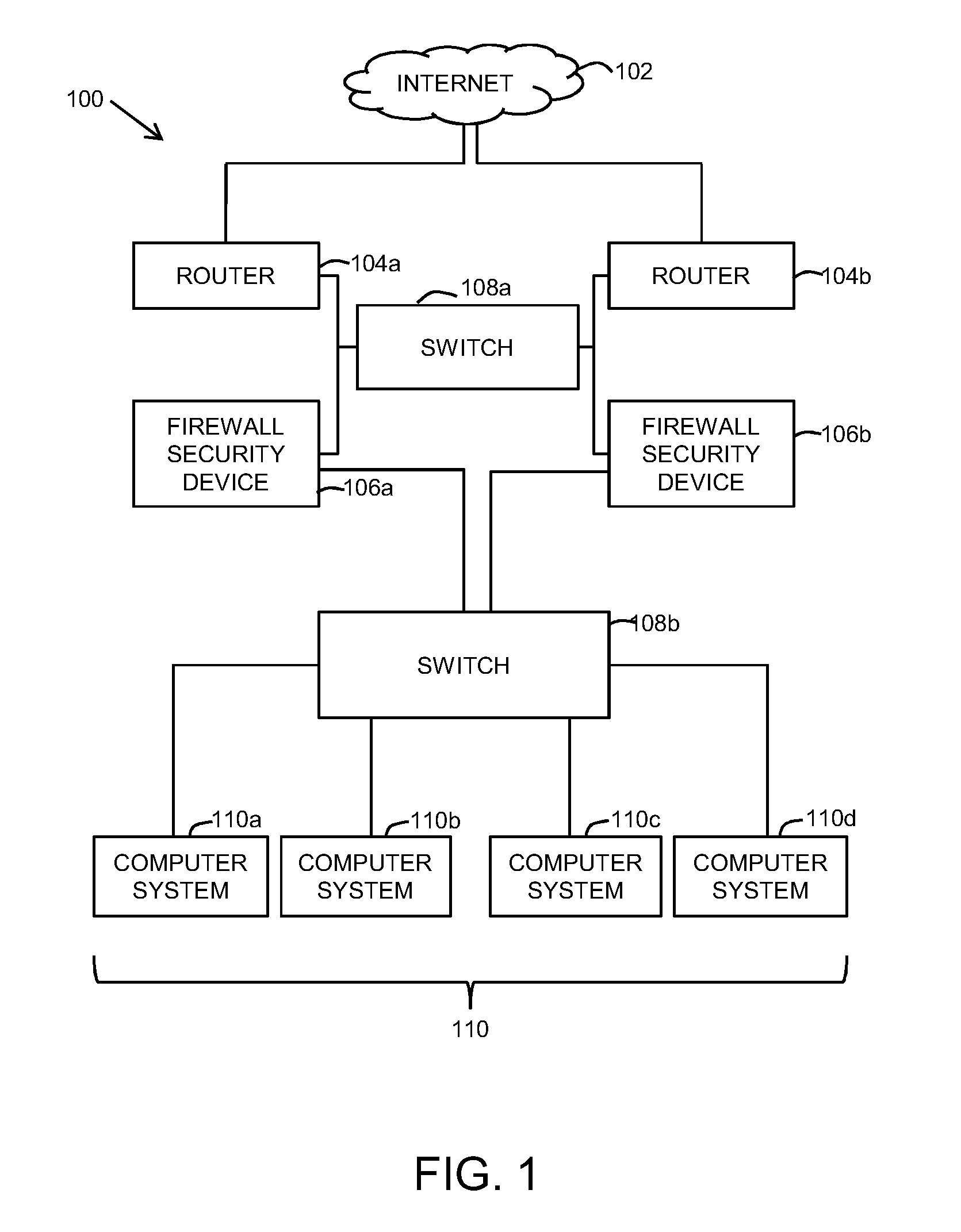
Load balancing among a cluster of firewall security devices
ActiveUS20140143854A1Improve reliabilityImprove performanceMultiple digital computer combinationsProgram controlLoad SheddingBalancing network
A method for balancing load among firewall security devices in a network is disclosed. Firewall security devices are arranged in multiple clusters. A switching device is configured with the firewall security devices by communicating control messages and heartbeat signals. Information regarding the configured firewall security devices is then included in a load balancing table. A load balancing function is configured for enabling the distribution of data traffic received by the switching device. A received data packet by the switching device is forwarded to one of the firewall security devices in a cluster based on the load balancing function, the load balancing table and the address contained in the data packet.
Owner:FORTINET
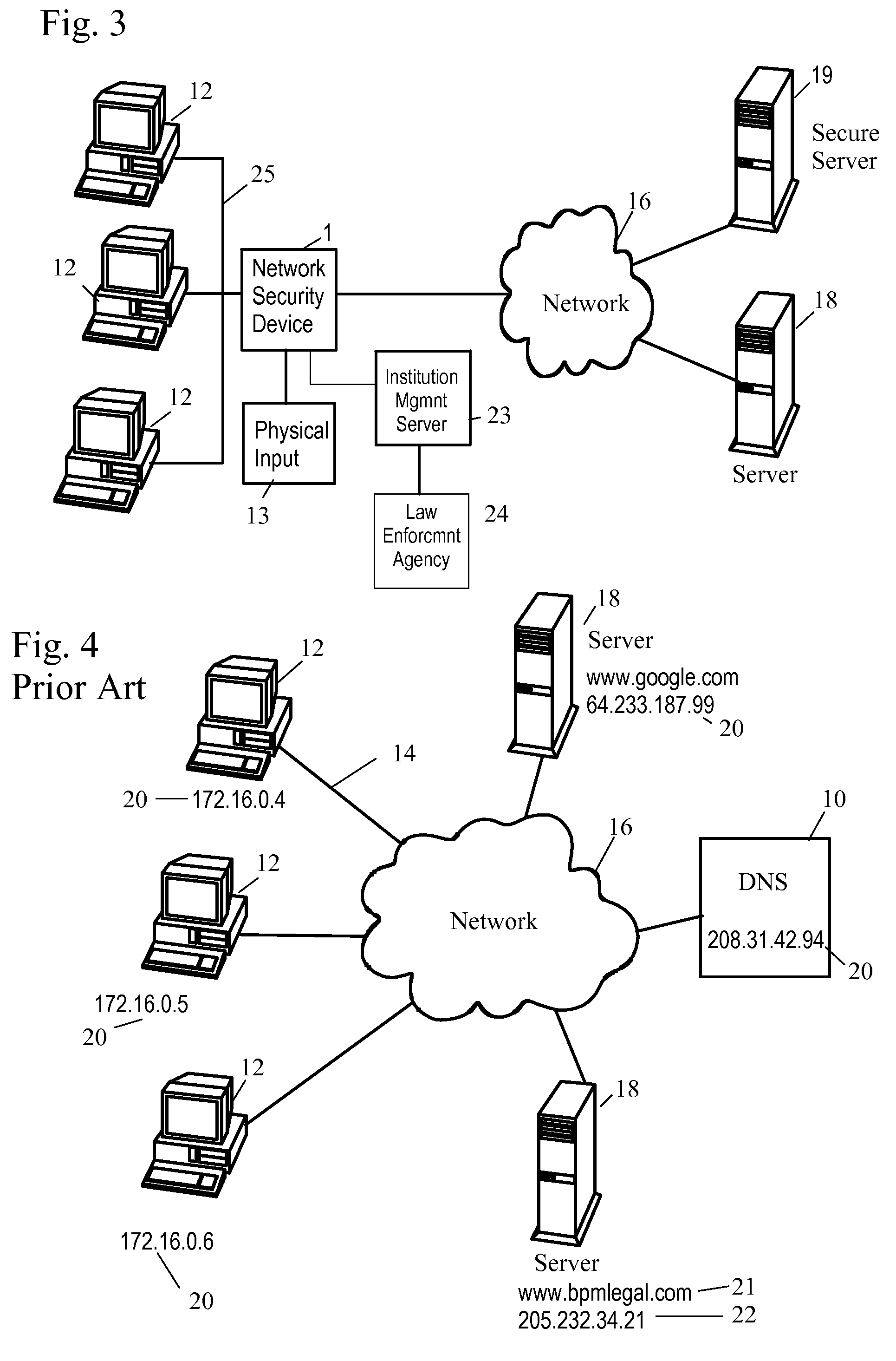
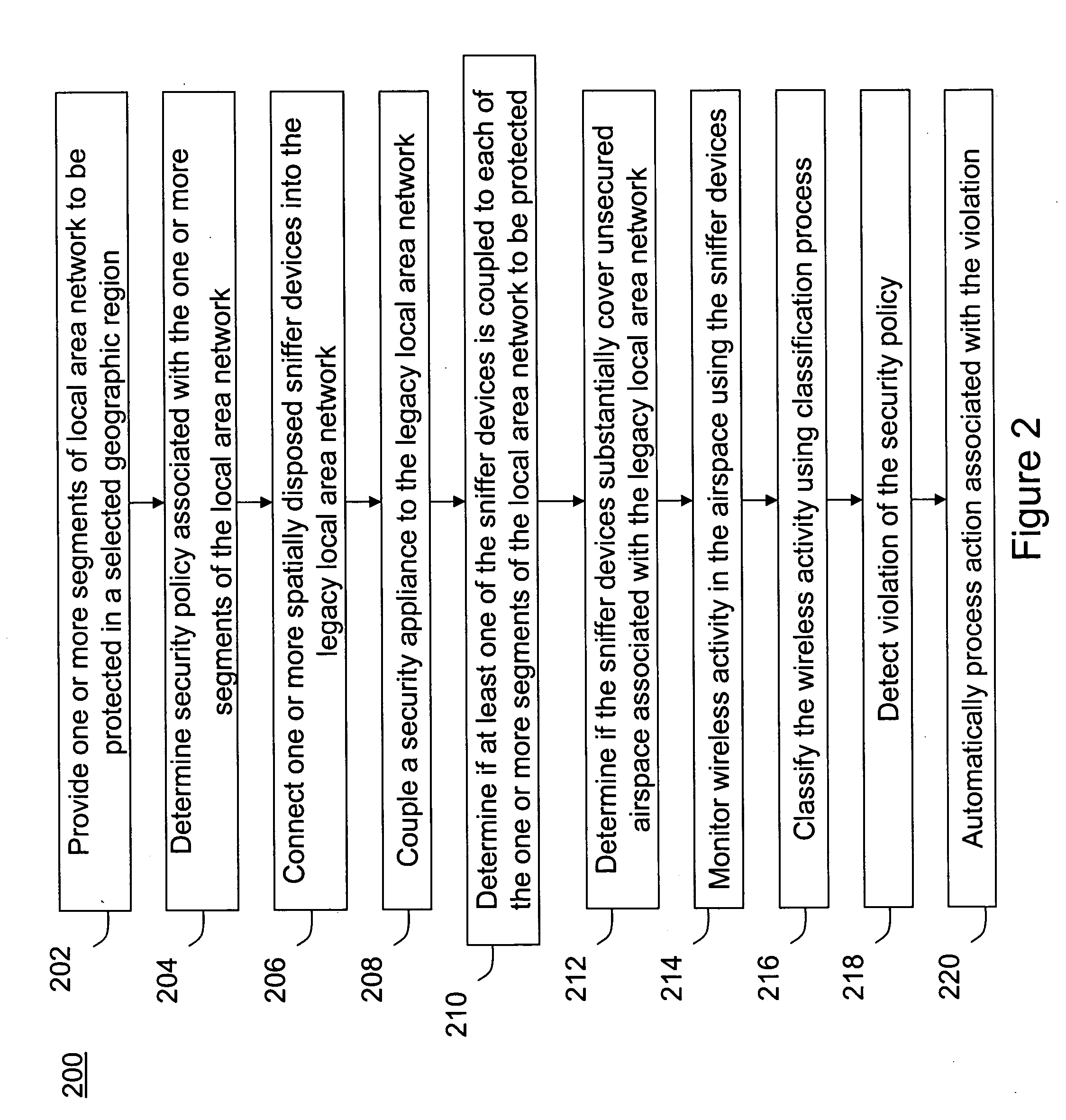
Method and system for monitoring a selected region of an airspace associated with local area networks of computing devices
ActiveUS20050128989A1Easy to usePrevent unauthorized wireless accessWave based measurement systemsData switching by path configurationBody area networkGeographic regions
A method for monitoring a selected region of an airspace associated with local area networks of computing devices is provided. The method includes providing one or more segments of a legacy local area network to be protected in a selected geographic region. The legacy local area network is characterized by an unsecured airspace within the selected geographic region. The method includes determining a security policy associated with the one or more segments of the legacy local area network. The security policy at least characterizes a type of wireless activity in the unsecured airspace to be permitted, denied, or ignored. Additionally, the method includes connecting one or more sniffer devices into the legacy local area network. The one or more sniffer devices are spatially disposed within the selected geographic region to cause at least a portion of the unsecured airspace to be secured according to the security policy. Moreover, the method includes coupling a security appliance to the legacy local area network. The method also includes determining if at least one of the sniffer devices is coupled to each of the one or more segments of the legacy local area network to be protected and determining if the one or more sniffer devices substantially covers the portion of the unsecured airspace to be secured. The method additionally includes monitoring wireless activity in the airspace using the one or more sniffer devices, and automatically classifying, using a classification process, a portion of information associated with the monitoring of the wireless activity to at least determine if the wireless activity communicates to at least one of the one or more segments to be protected. Further, the method includes detecting a violation of the security policy based upon at least the classifying of the portion of the information from the monitoring of the wireless activity, and automatically processing an action associated with the violation in accordance to the security policy for the one or more segments in the legacy local area network to be protected.
Owner:ARISTA NETWORKS
Automated accounting system that values, controls, records and bills the uses of equipment/vehicles for society
InactiveUS20030221118A1Reduce present day election useImprove economyData processing applicationsAnti-theft devicesEnvironmental resource managementSafety control
This invention addresses environmental social and commercial uses and includes a monitoring system which is a network of on, in, out and off-board devices working together with people through software and interfaces to provide services and make accountable humanity's machines and their actions through safe secure communication. Control devices are used to provide accountability for their socio-economic and environmental impact. Along with these systems networked together, additional devices and variations needed to complete these operations nationally and world wide are also provided. Unique ways interface a network of separate devices or IC circuits to create an interactive secure control system or center that can be remotely controlled. A control device for society to fairly and accurately monitor and control the impact of equipment use on the world environment, and a nation's infrastructure while developing commercial companies to fulfill these needs and services for the equipment and the people who own and operate them for today and into the future are also provided. A set of secure devices and systems are also included to analyze society and machine interaction.
Owner:KLINE & WALKER
Programmable security system and method for protecting merchandise
InactiveUS20110254661A1Reduce usageProgramme controlElectric signal transmission systemsComputer hardwareElectricity
A programmable security system and method for protecting an item of merchandise includes a programming station, a programmable key and a security system. The programming station generates a security code and communicates the security code to a memory of the programmable key. The programmable key initially communicates the security code to a memory of the security device and subsequently operates the security device upon a matching of the security code in the memory of the security device with the security code in the memory of the programmable key. The programmable key may also transfer power via electrical contacts or inductive transfer from an internal battery to the security device to operate a lock mechanism. The security code may be communicated by wireless infrared (IR) systems, electrical contacts or inductive transfer. A timer inactivates the programmable key and / or the security device after a predetermine period of time. A counter inactivates the programmable key after a predetermined maximum number of activations.
Owner:INVUE SECURITY PROD INC
Load balancing in a network with session information
ActiveUS20120210416A1Load balancingComputer security arrangementsMultiple digital computer combinationsTraffic capacityDistributed computing
Methods and systems for balancing load among firewall security devices are provided. According to one embodiment, a switch maintains a session table the session entries of which represent established traffic sessions between a source and a destination and form an association between the traffic session and a particular firewall security device (FSD). Responsive to receiving a packet of a first traffic session on a first port, a determination is made whether there exists a matching session entry. Responsive to a negative determination, a load balancing function is performed to select an FSD with which to associate the first traffic session and a corresponding reverse second traffic session. After processing of the packet by the selected FSD and receipt of the packet at a second port, a session entry is installed within the session table for the second traffic session and which associates the selected FSD with the second traffic session.
Owner:FORTINET
Secure interprocess communications binding system and methods
InactiveUS20050182966A1Inhibit exchangeFlexible performanceDigital data processing detailsMultiple digital computer combinationsTrust relationshipInter-process communication
The secure trust relationship between communicating programs is established at any policy defined level down to individual program instances. Policy enforcement modules installed on host computer systems support qualified encrypted communications channels between discretely selected program instances. Program instances are qualified to establish communication channels, each defined by a unique session encryption key, based on an evaluation of security data including the individual process execution contexts, user authorizations, and access attributes of the program instances. A security appliance server performs the policy-based qualification based on a mutually interdependent evaluation of the security data for both the communications channel source and target program instances.
Owner:PHAM DUC +3
System and method for panel linking in a security system
InactiveUS7734906B2Low costLimited accessDigital data processing detailsTelephonic communicationEngineeringSecurity system
A security system comprising a plurality of security subsystems each of the security subsystems being discretely located, typically in separate buildings. The security subsystems are interconnected by a system communications bus to enable bi-directional communication between the security subsystems. Each of the security subsystems comprises a user interface, a control panel, a plurality of security devices, a local communications bus, and a panel linking gateway. The panel linking gateway allows data on the local communications bus of each security subsystem to be transmitted to and received from the system communications bus. The security system allows a keypad or other user interface from one security subsystem to access and control a second remote security subsystem.
Owner:ADEMCO INC
Systems and methods for digital asset security ecosystems
A digital asset security device, includes an asset capture unit configured to electronically capture a digital asset, a processor configured to digitally sign the captured asset, a memory configured to store a digitally signed asset from the processor, and a hashing module in communication the asset capture unit, the processor, and the memory, and configured to provide a cryptographic hash to one or more of the captured asset and the digitally signed asset.
Owner:CABLE TELEVISION LAB
Method and apparatus for security policy management
InactiveUS7882537B2Reduce human interventionEasy to masterDigital data protectionResourcesGeneral purposeSecurity policy management
A security policy management system for deriving a security policy from setting details of security devices as components of an information system includes a setting information storage unit for storing setting information representing settings with regard to security functions of devices included in a network system to be managed, and a general-purpose security policy generator for generating a security policy including a description expressed in a format independent of descriptions depending on particular devices, based on the setting information stored in the setting information storage unit.
Owner:NEC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com