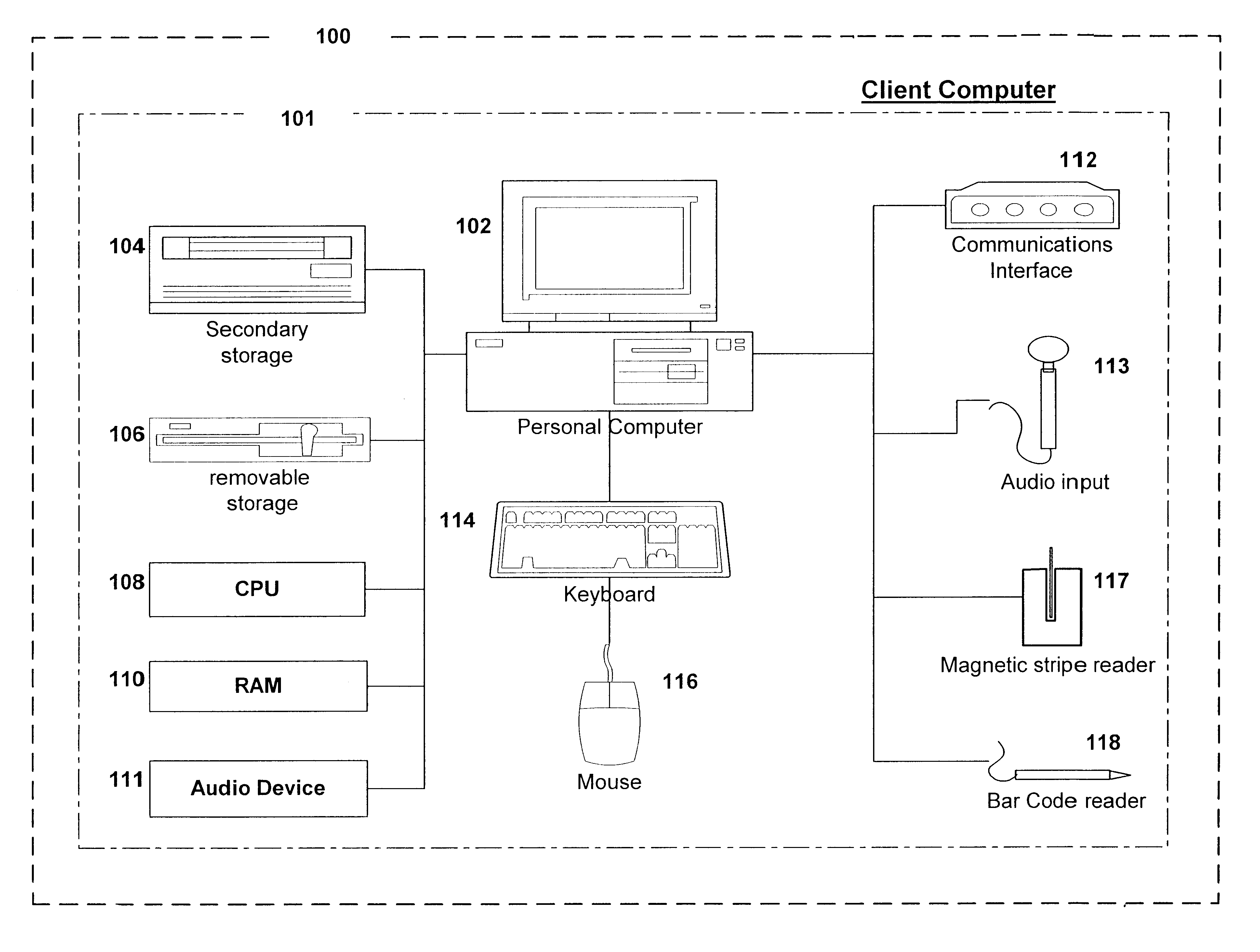
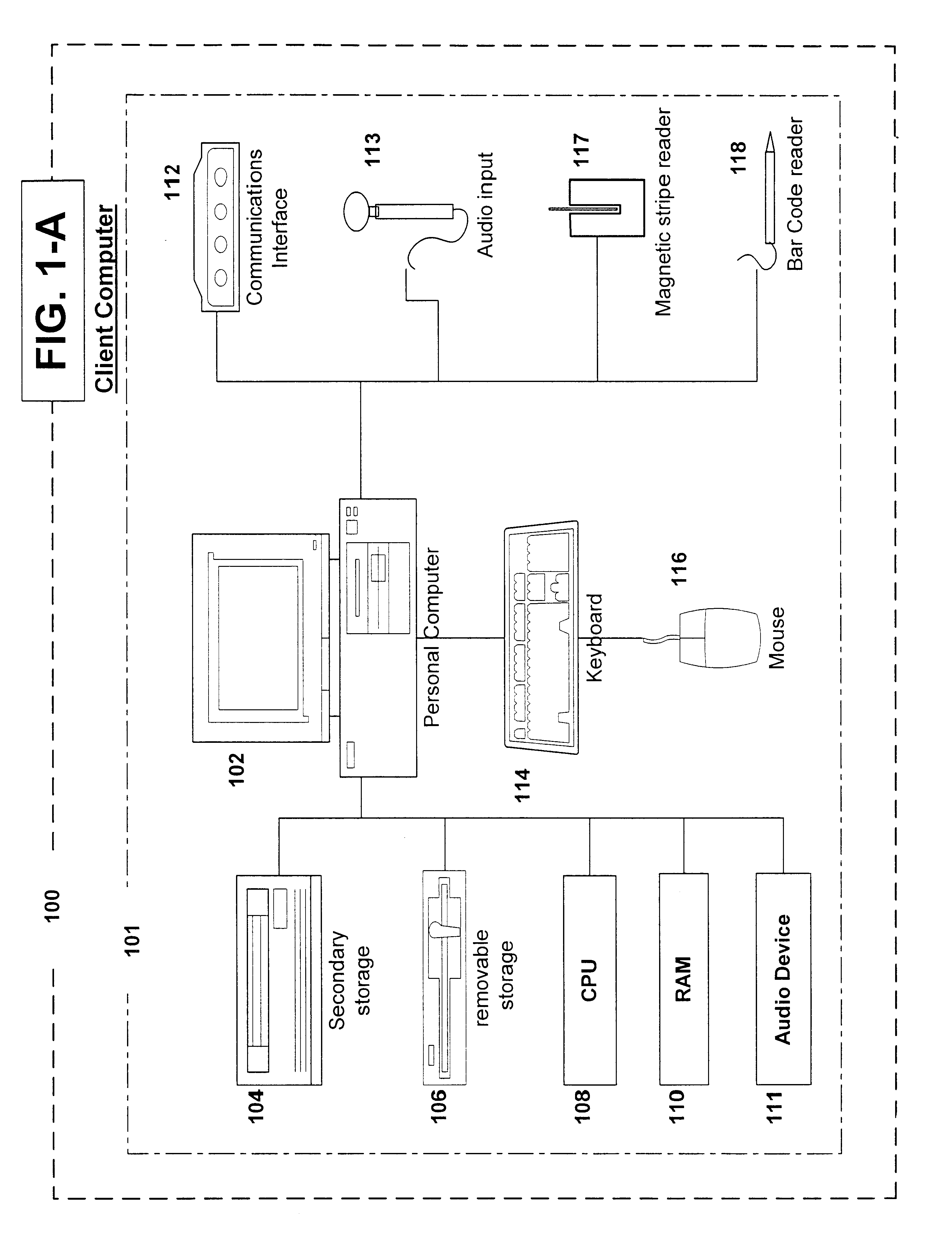
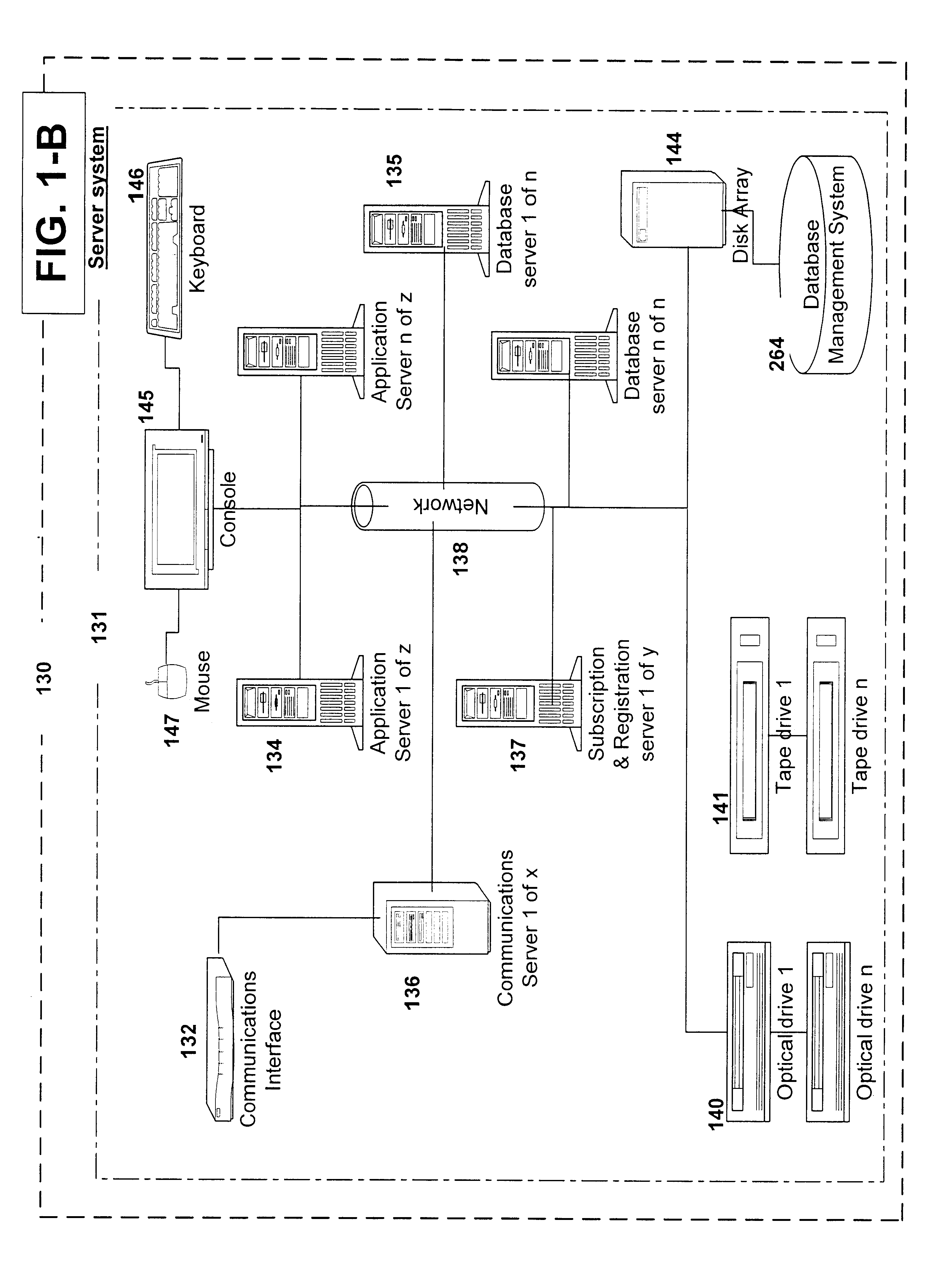
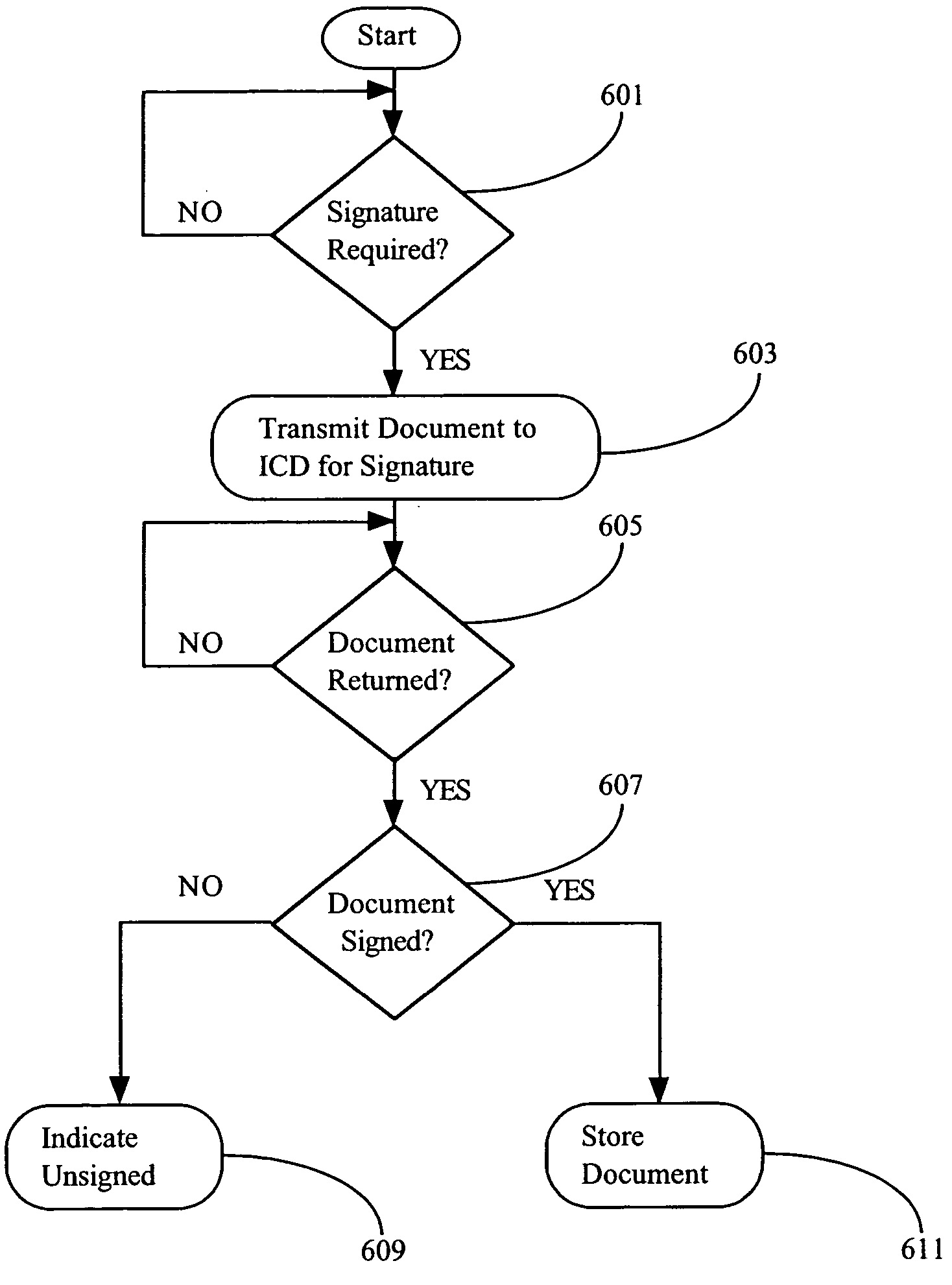
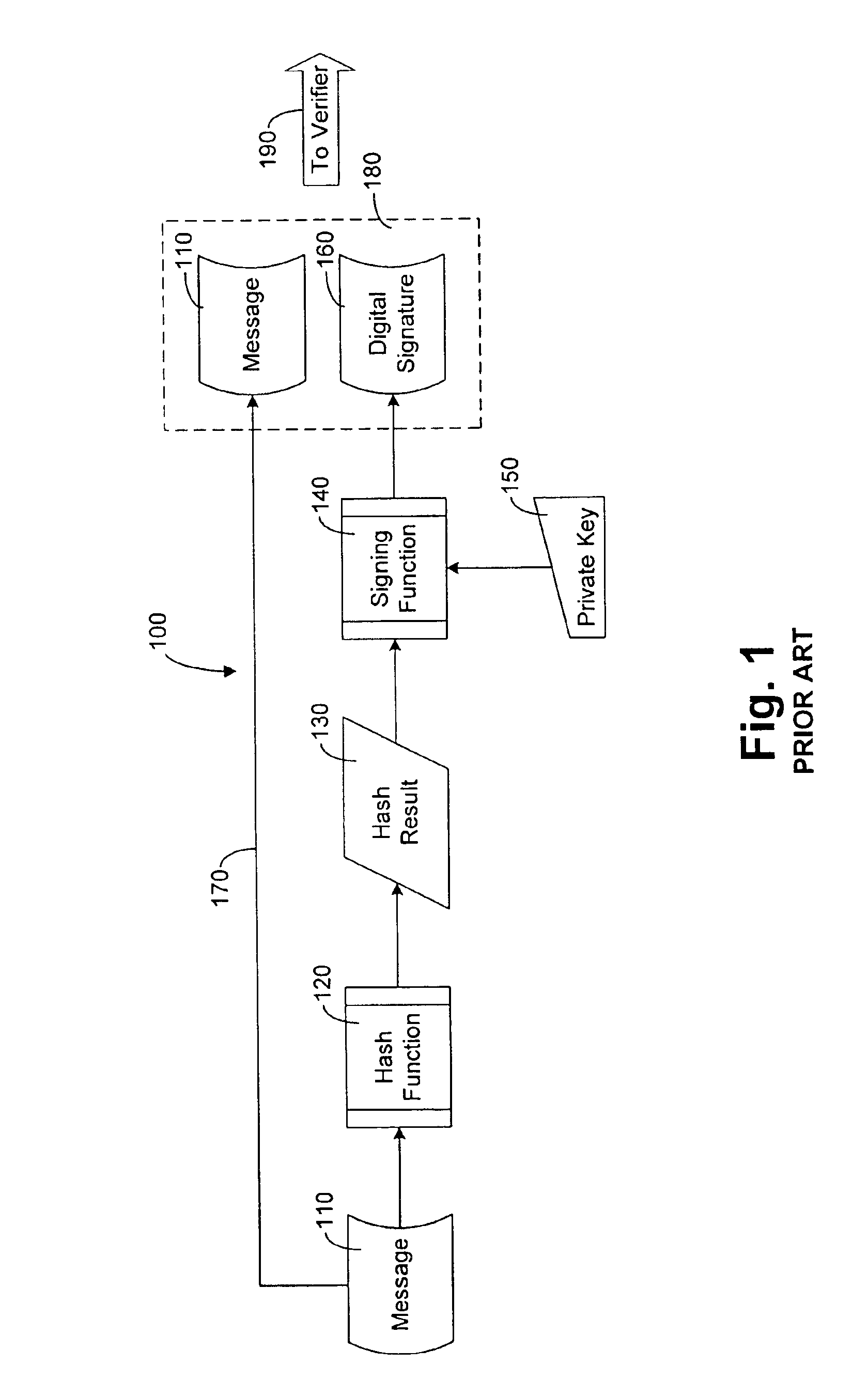
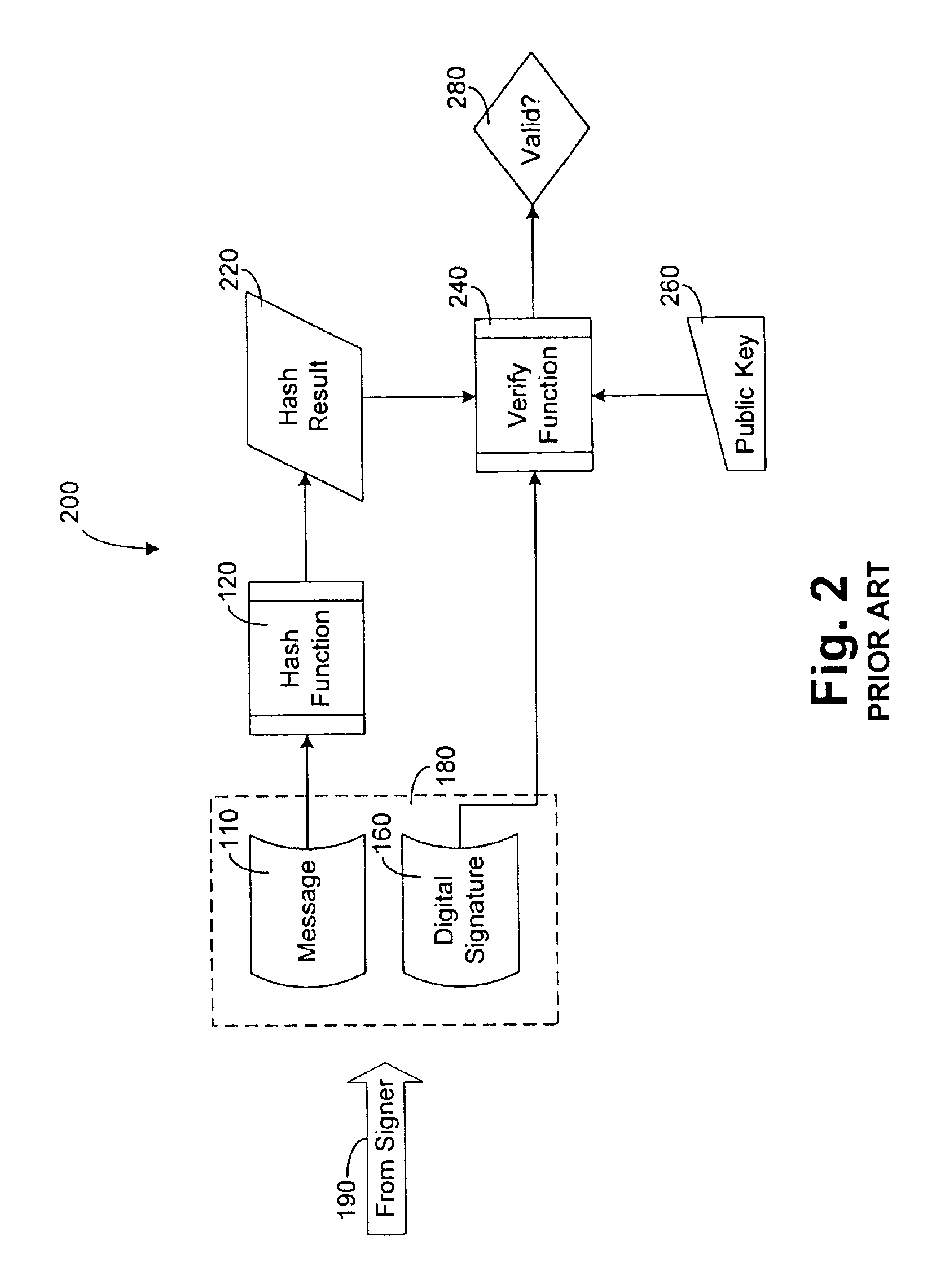
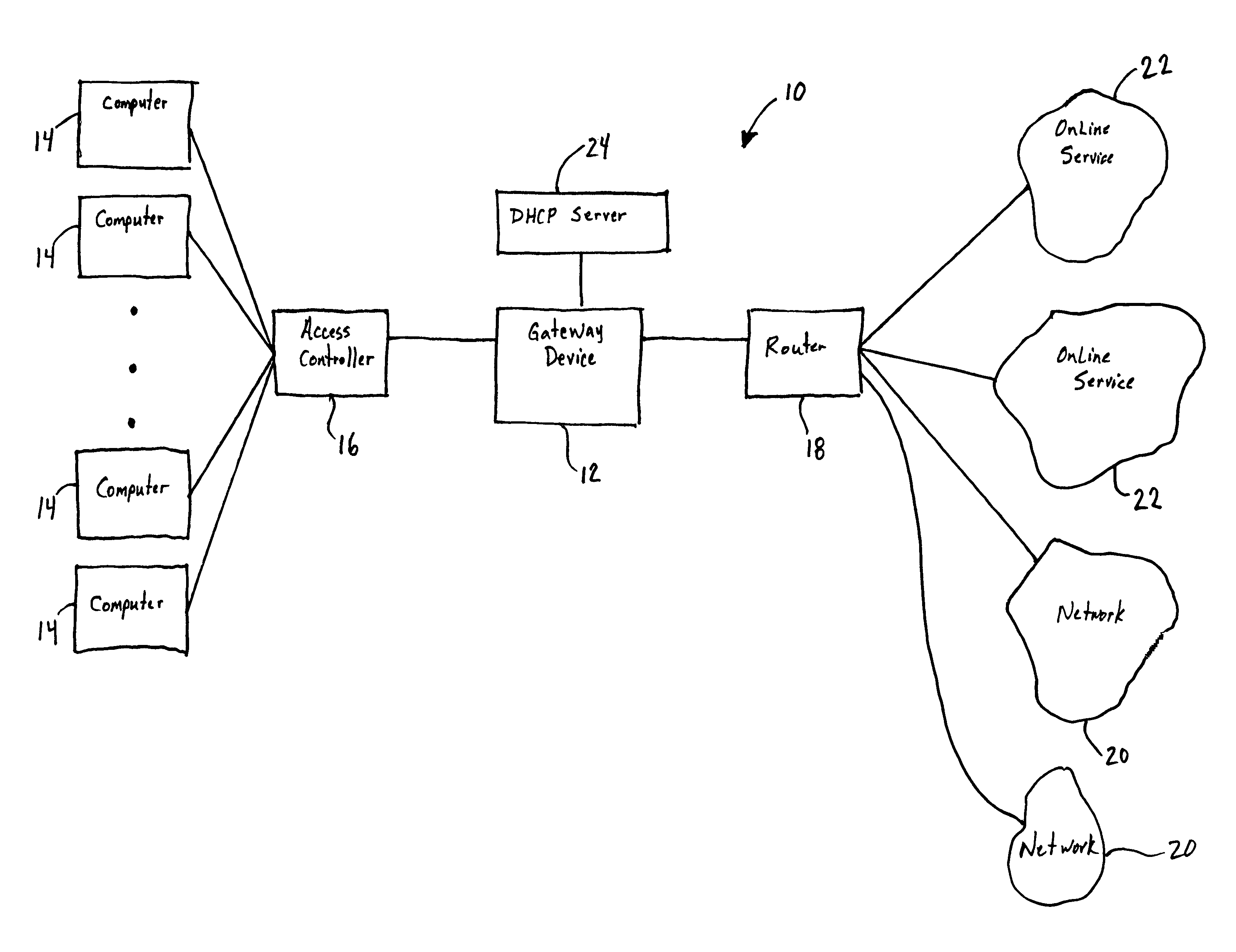
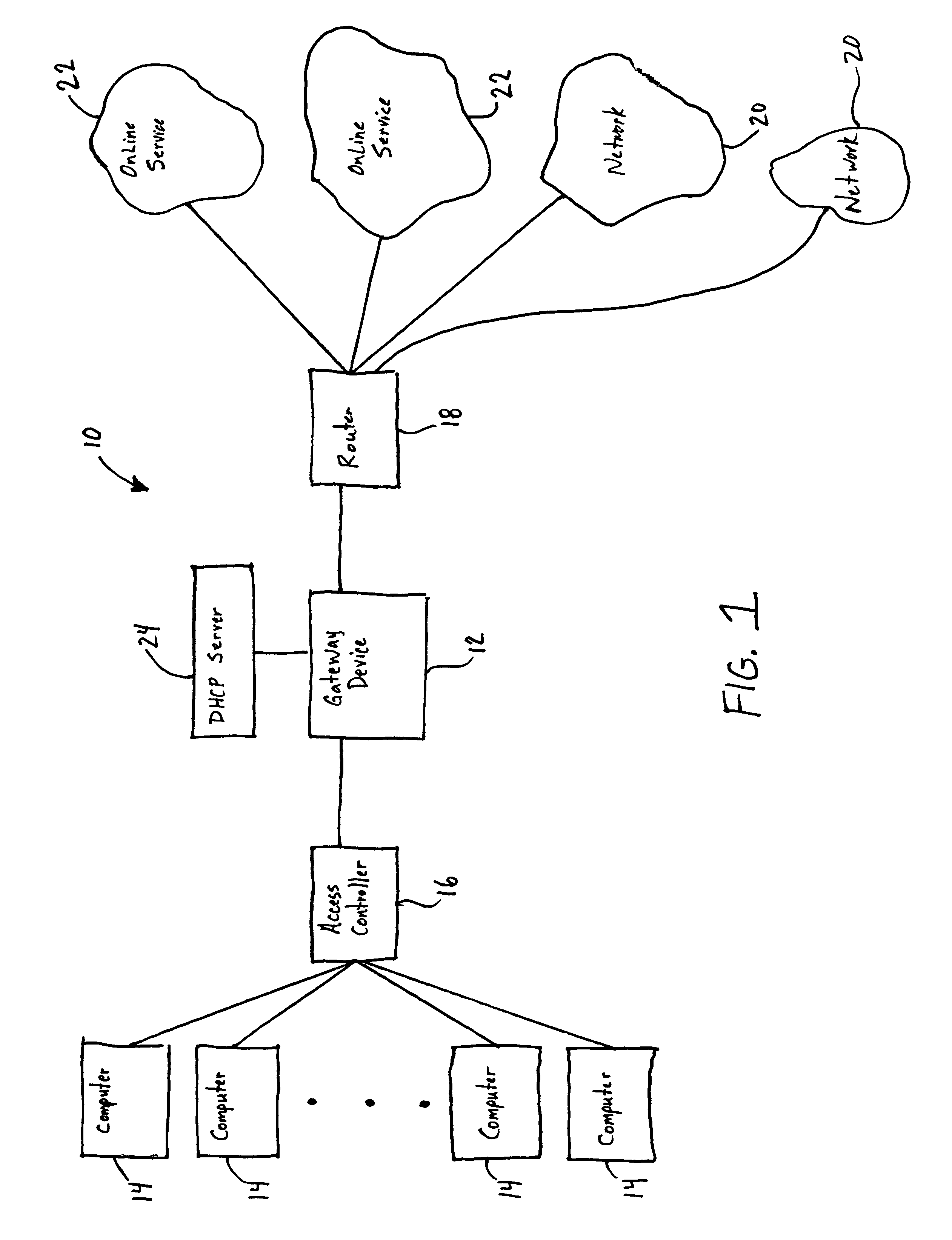
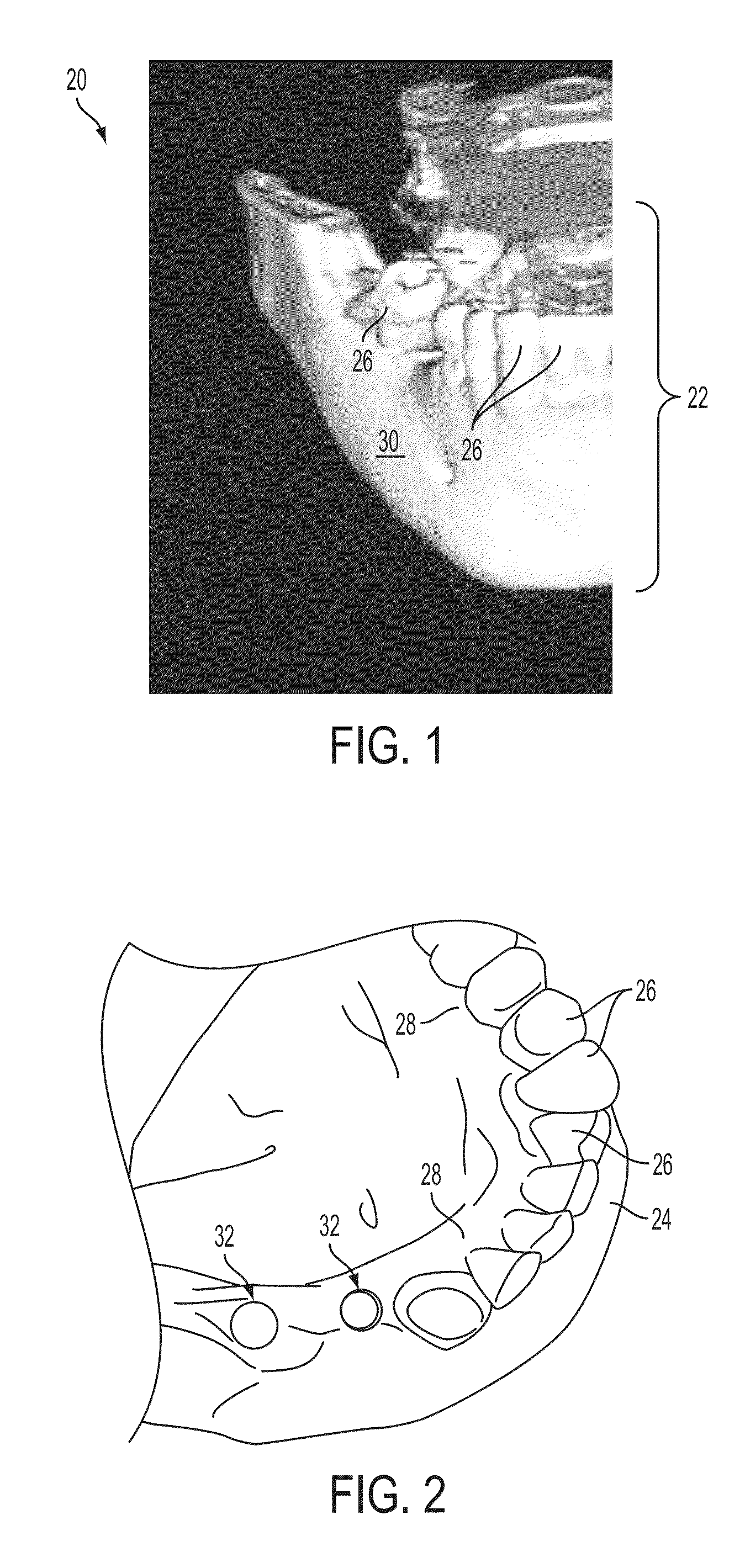
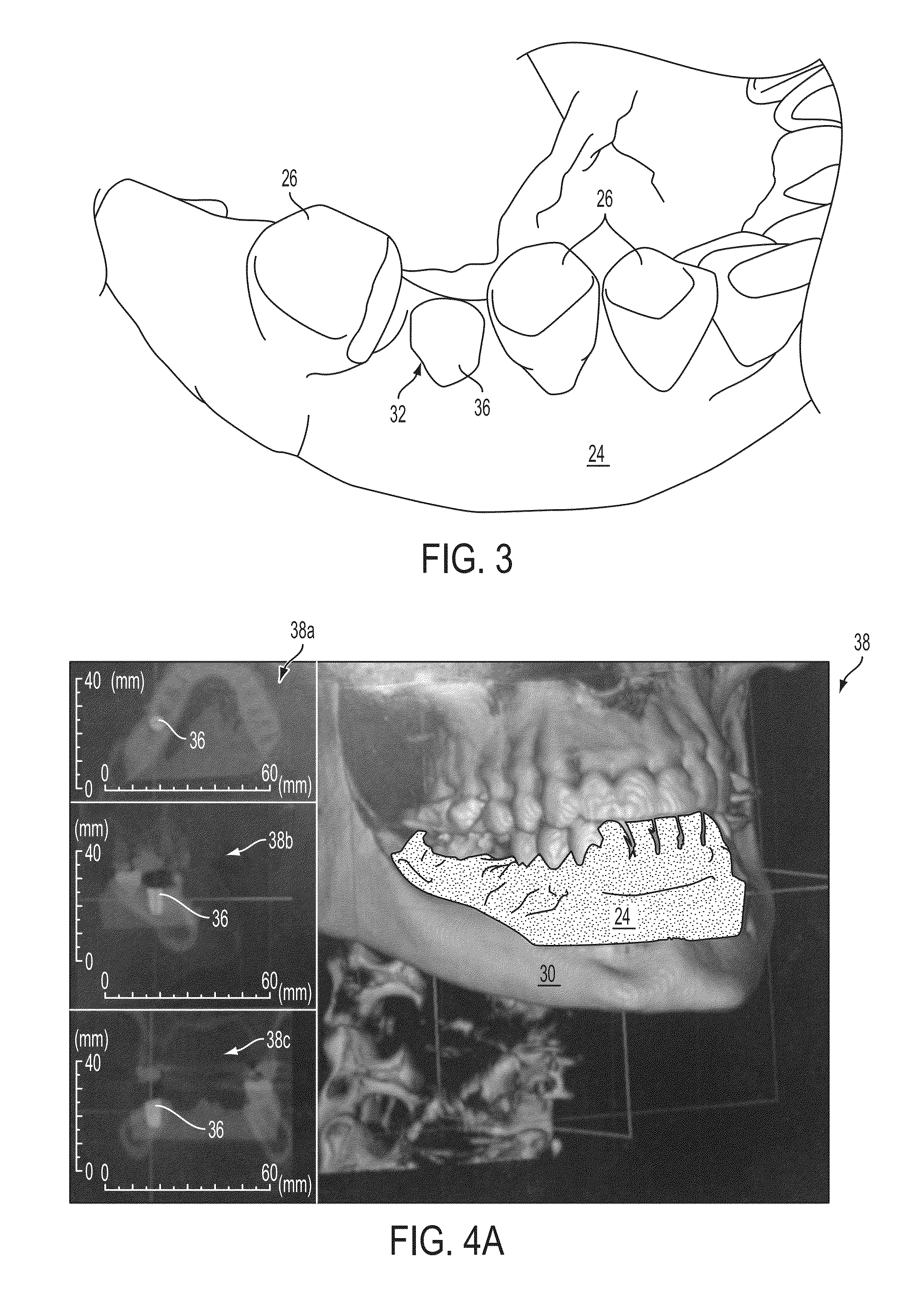
Patents
Literature
695 results about "Computer access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
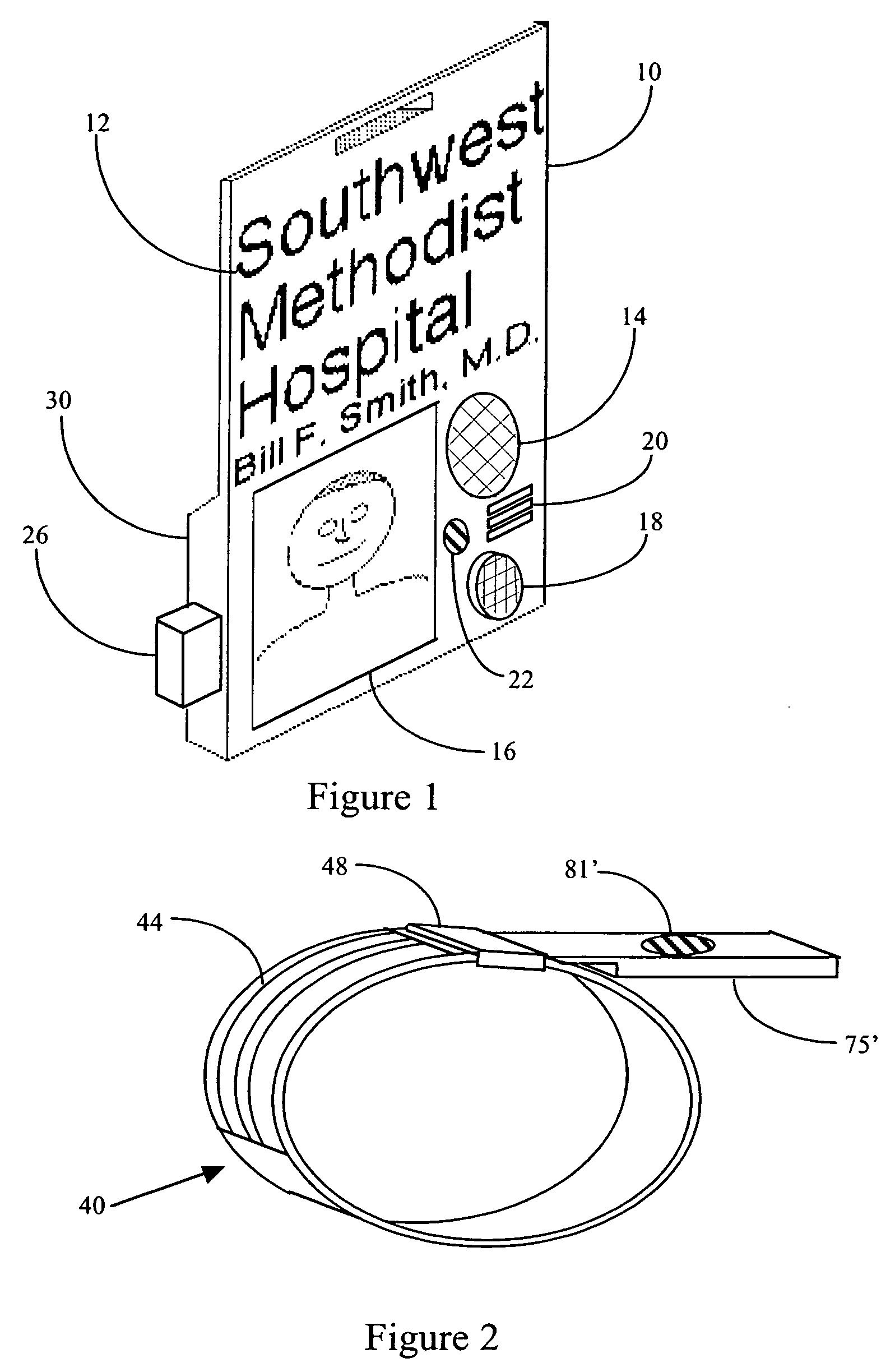
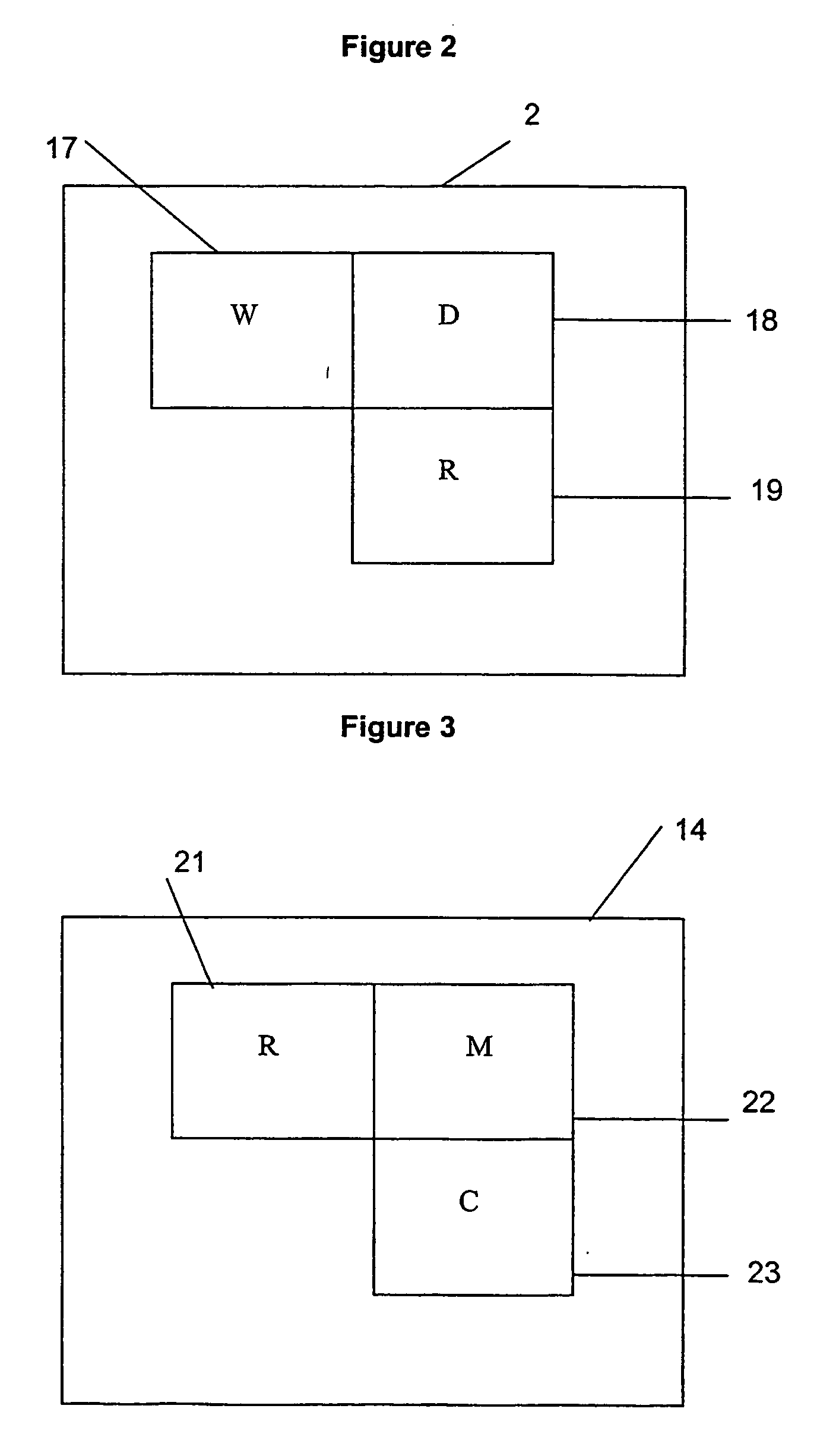
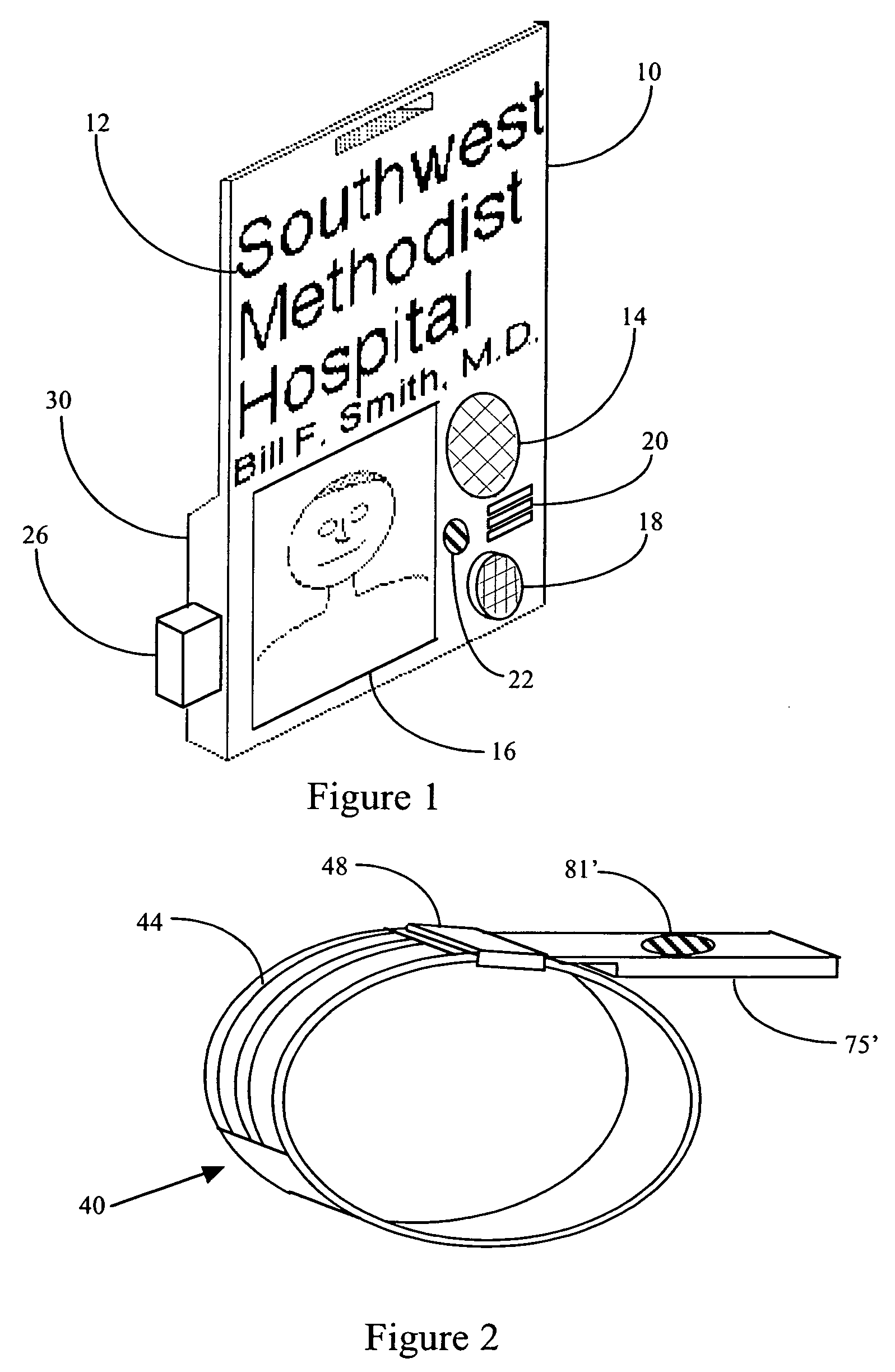
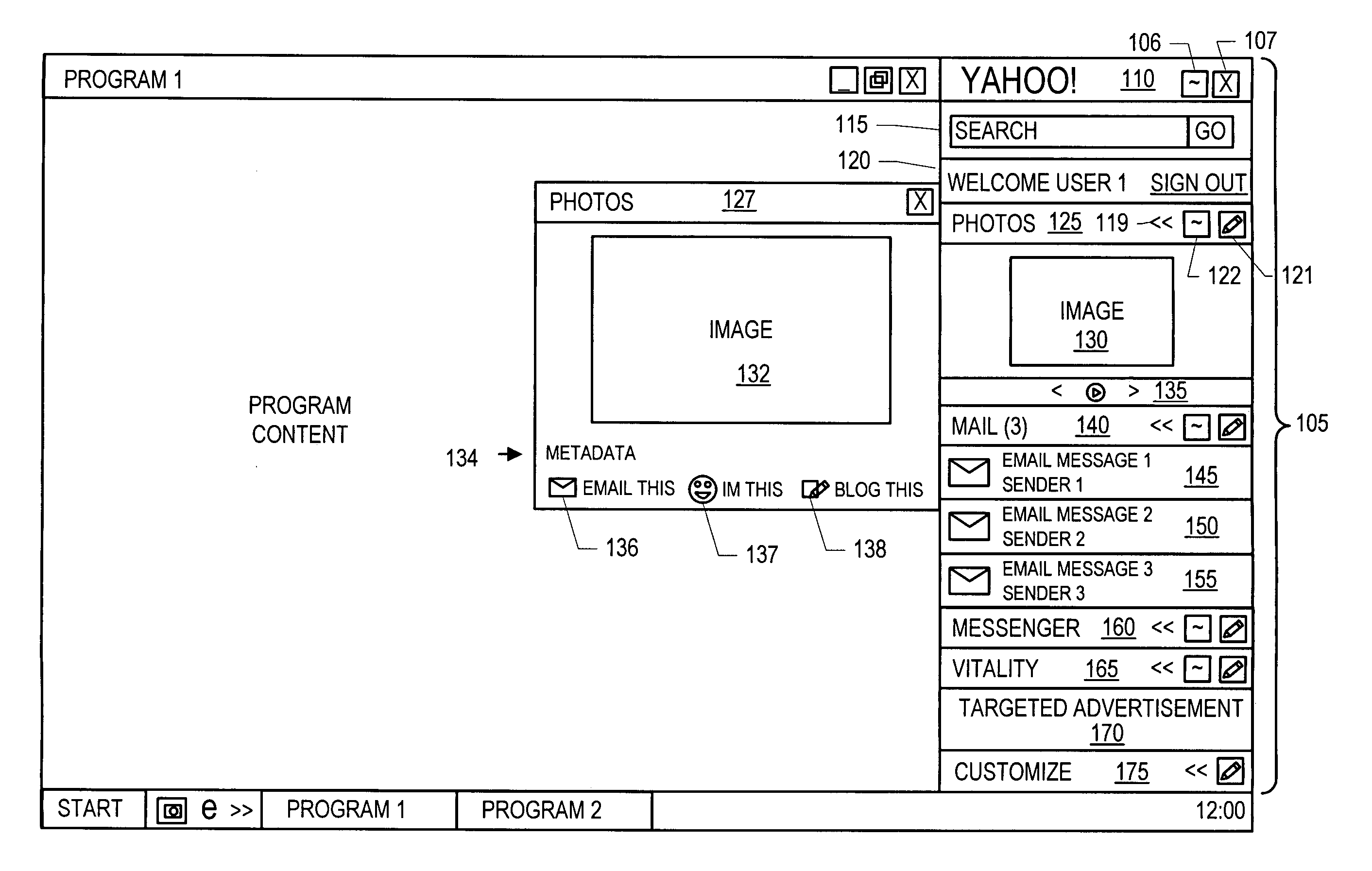
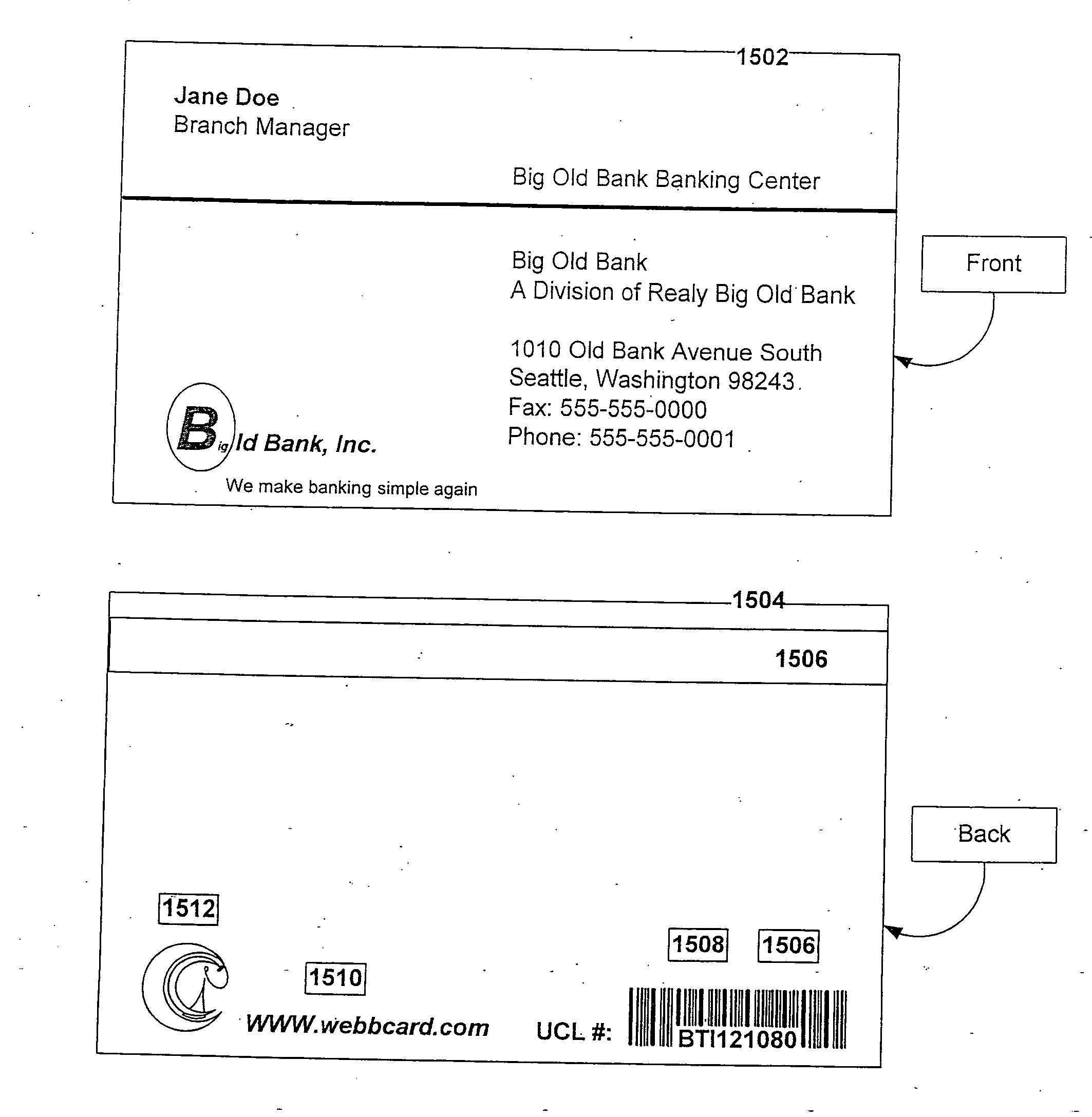
Business card and contact management system
InactiveUS6883000B1More cost-effectivelyMore accurateAdvertisementsOffice automationBusiness cardWeb browser
An Internet (or World-Wide-Web or other such public or private network) based business card and contact management system capable of conveying and managing advertising as well as traditional and other non-traditional business contact information. The invention is a system that: (1) accepts a Universal Contact Locator (UCL) as encoded on a business card in man and / or machine readable format and, when the Universal Contact Locator (UCL) is entered into a client program running on a client computer, (2) causes a web browser (or like program) and associated communications software to establish a communications session with a remote server computer which (3) accesses the stored contact and advertisement and news information of the card issuer associated with the Universal Contact Locator and (4) downloads the business contact and / or personal contact information and targeted advertisements and news items associated with the Universal Contact Locator to a client program running on a client computer which (5) loads the contact data into the Contact Management or Personal Information Management (PIM) system of the users choosing running on the users client computer and (6) stores the advertisements and news items downloaded from the server computer on the client computer's secondary storage device (i.e. hard disk) and (7) causes the advertisements and news items stored on the client computer's secondary storage device to be displayed to the user on a predetermined schedule in a portion of the client computer's output device (i.e. CRT or LCD panel).
Owner:MICROSOFT TECH LICENSING LLC
System and method to authenticate users to computer systems
InactiveUS20050091338A1Facilitates rapid secondary logLimited accessDigital data processing detailsDrug and medicationsTelecommunications linkTransceiver
A system utilizing a personal security device to provide access to a computer terminal where the personal security device includes circuitry and transceiver components for transmitting identification information and exchanging other digital information with a computer terminal and other compatible devices and the personal security device establishes a communication link with a computer terminal to allow a user to logon to the terminal so that when a user leaves the computer terminal, the communication link is terminated, causing the computer terminal to lock the keyboard, blank the monitor, and / or logoff the user if the communication link is not restored within a sufficient time period and also allowing the personal security device to facilitate subsequent computer access within a time range by providing time related access codes to the terminal that can be used to reestablish computer terminal access.
Owner:DLH TECH LLC
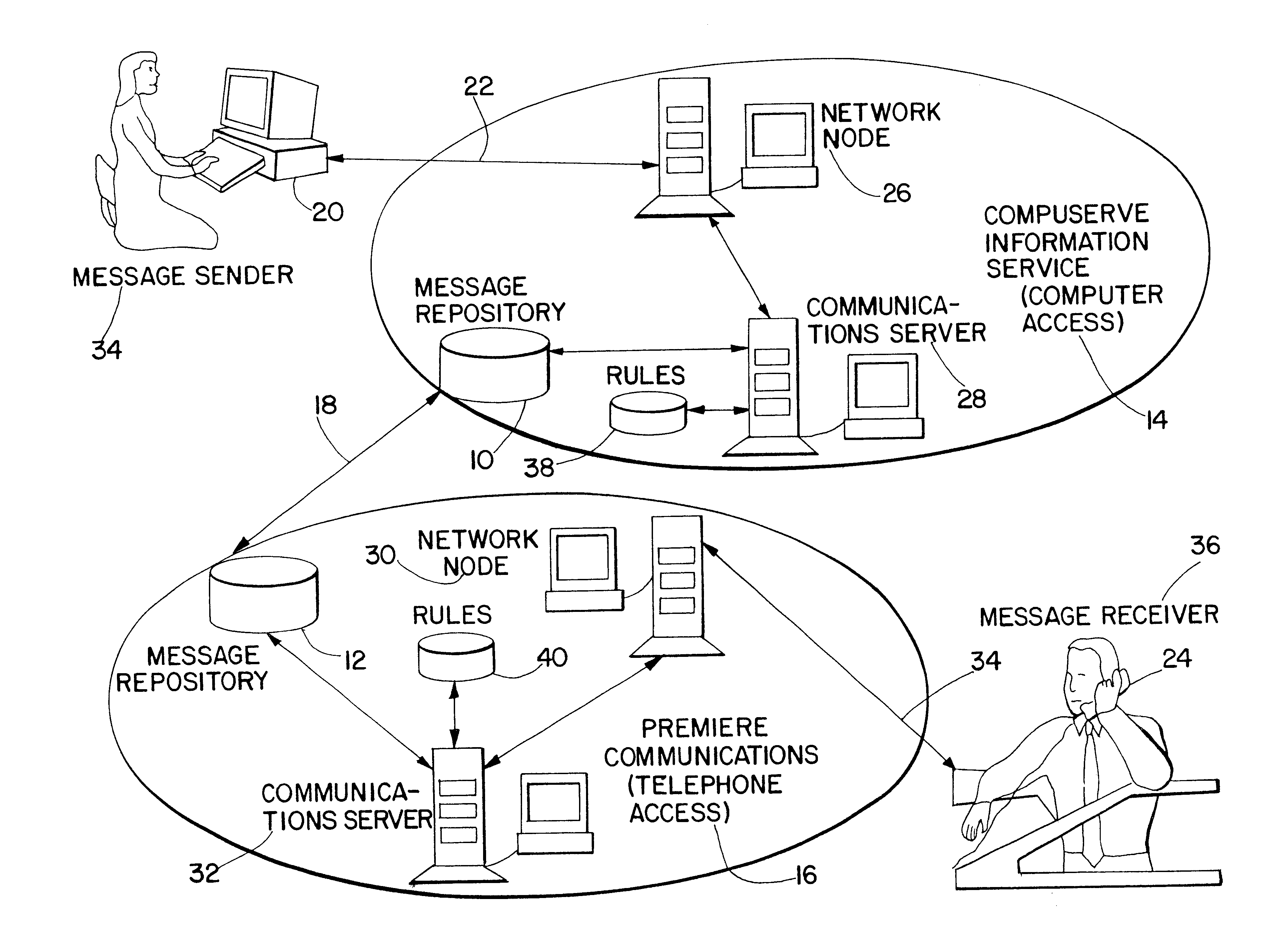
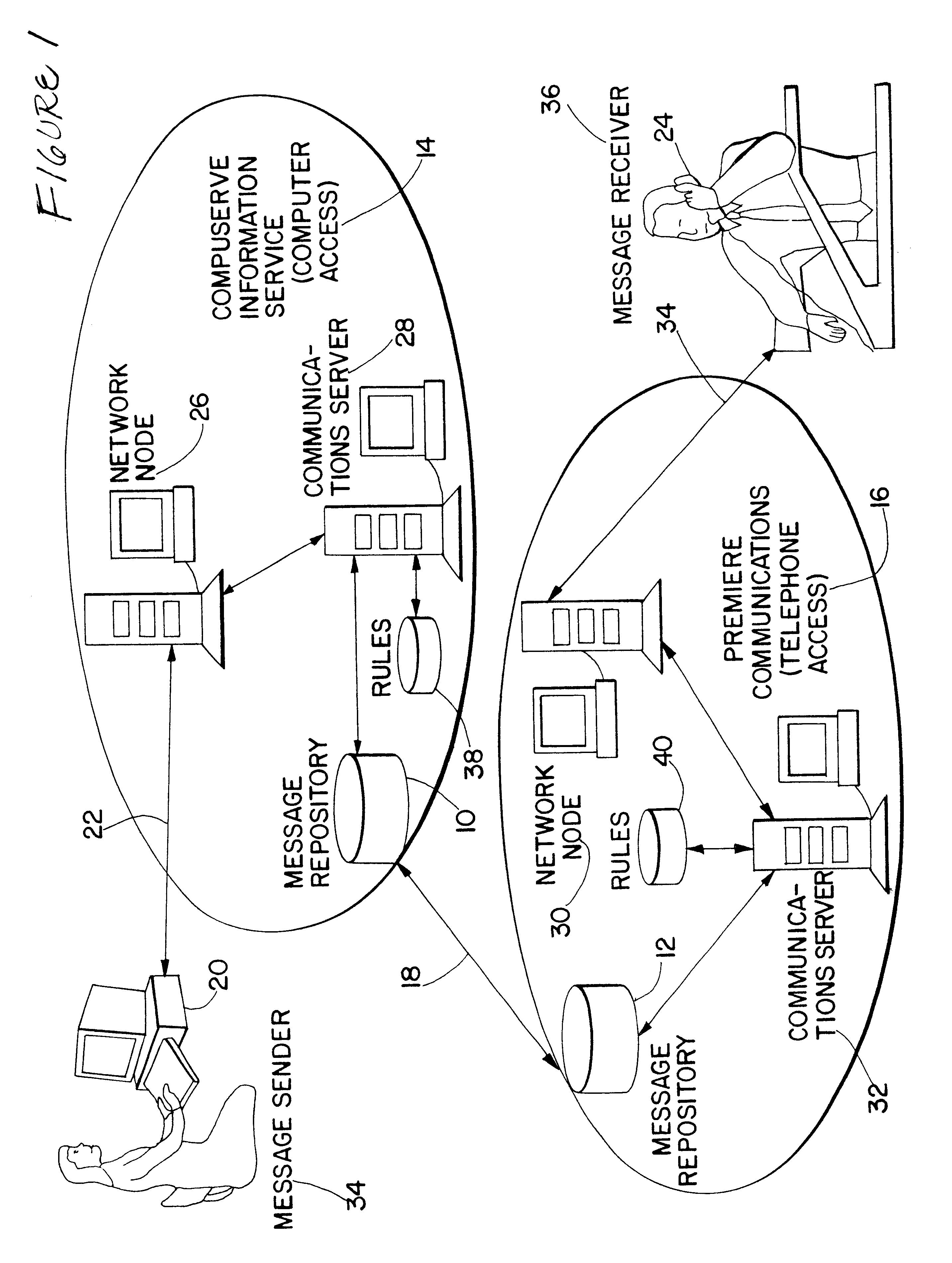
System for integrated electronic communications
InactiveUS6633630B1Special service for subscribersData switching networksModem deviceElectronic communication
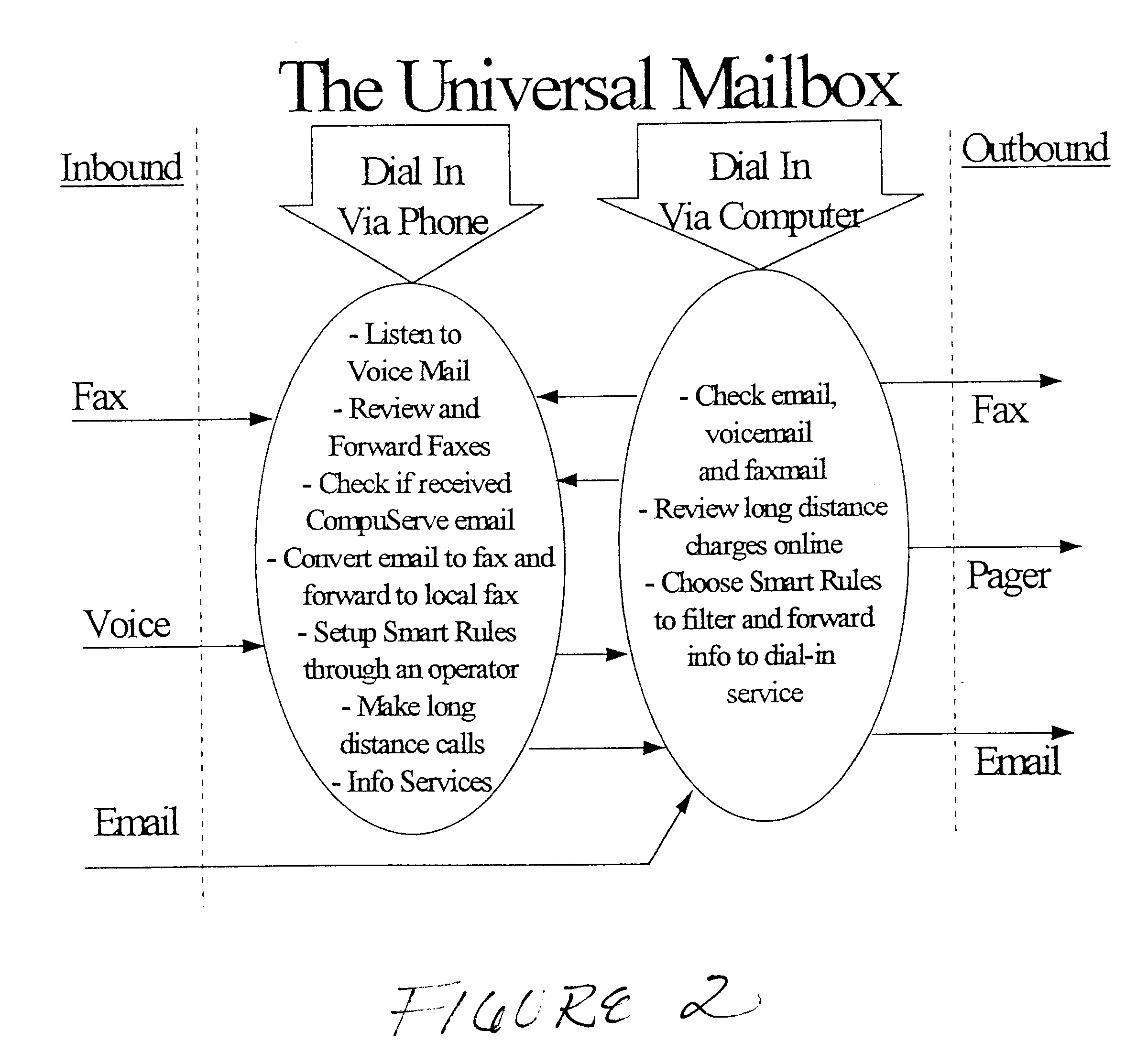
A system is disclosed for integrating electronic mail, voice mail, and fax mail in a universal mailbox. Message receivers may access their messages with a telephone or a computer regardless of the communication medium used by the message sender. Using a telephone, message receivers may playback voice mail, redirect fax mail, and "listen" to e-mail through a text-to-speech conversion process. Using a computer and modem, message receivers may playback voice mail, view fax mail, and read e-mail by accessing the universal mailbox via connection software. Message senders and receivers may choose from a variety of filter and forward options that allow them to manage their communications via the universal mailbox. Forwarding and conversion of messages is performed automatically. The options are used to define a set of rules to be applied to inbound and outbound messages so that messages are sent and received in accordance with the preferences of the senders and receivers.
Owner:CRANBERRY PROPERTIES
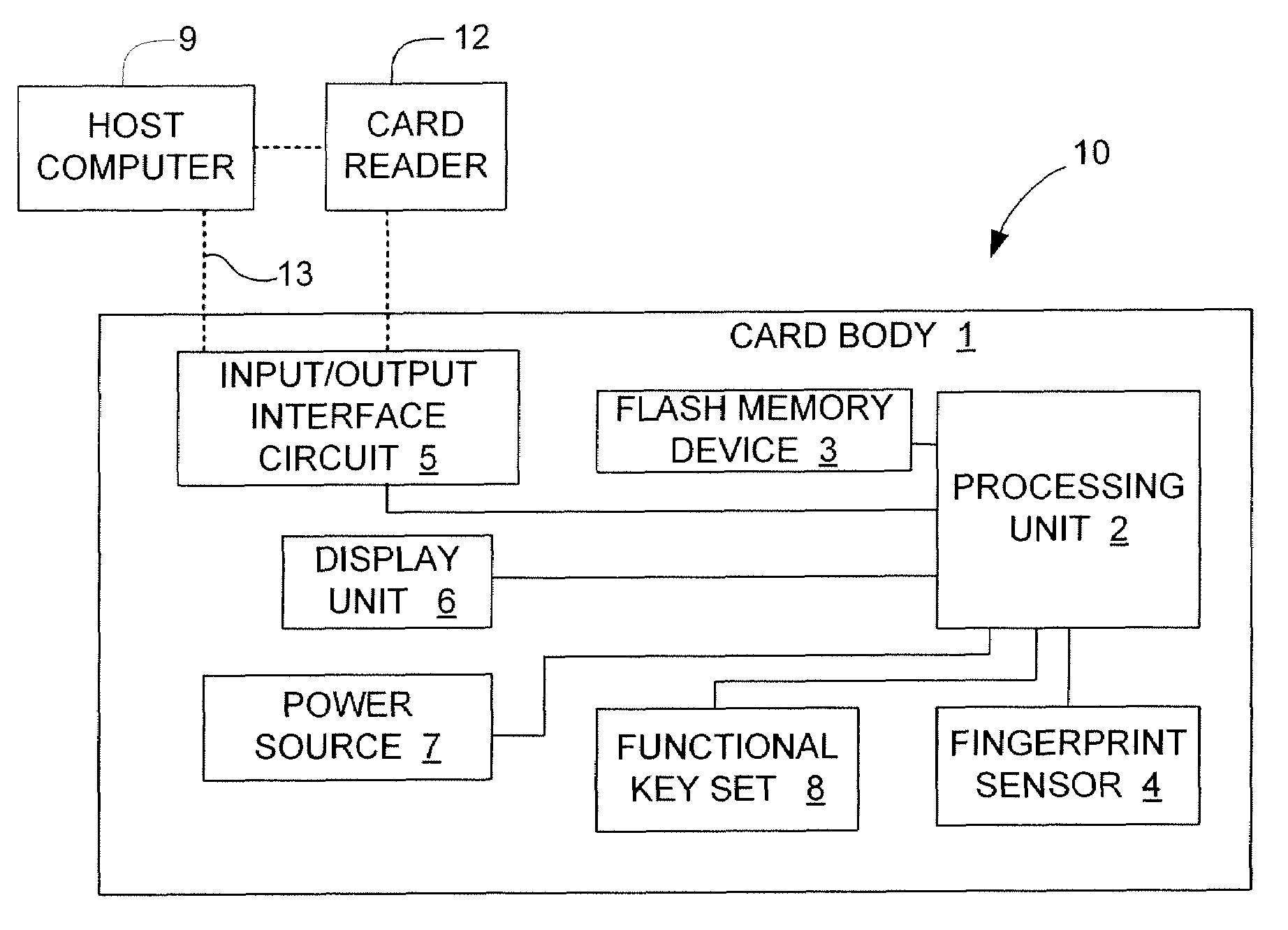
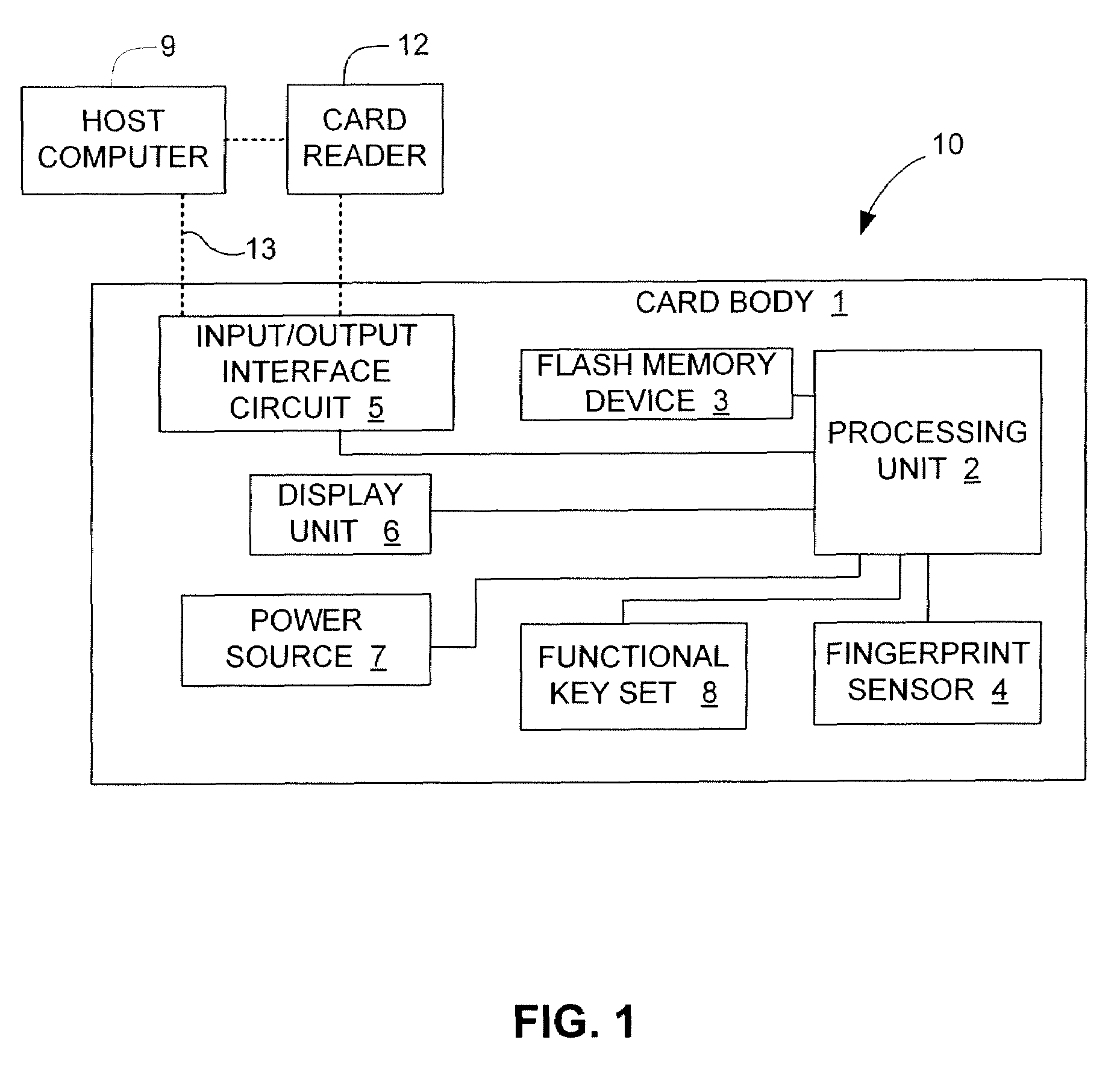
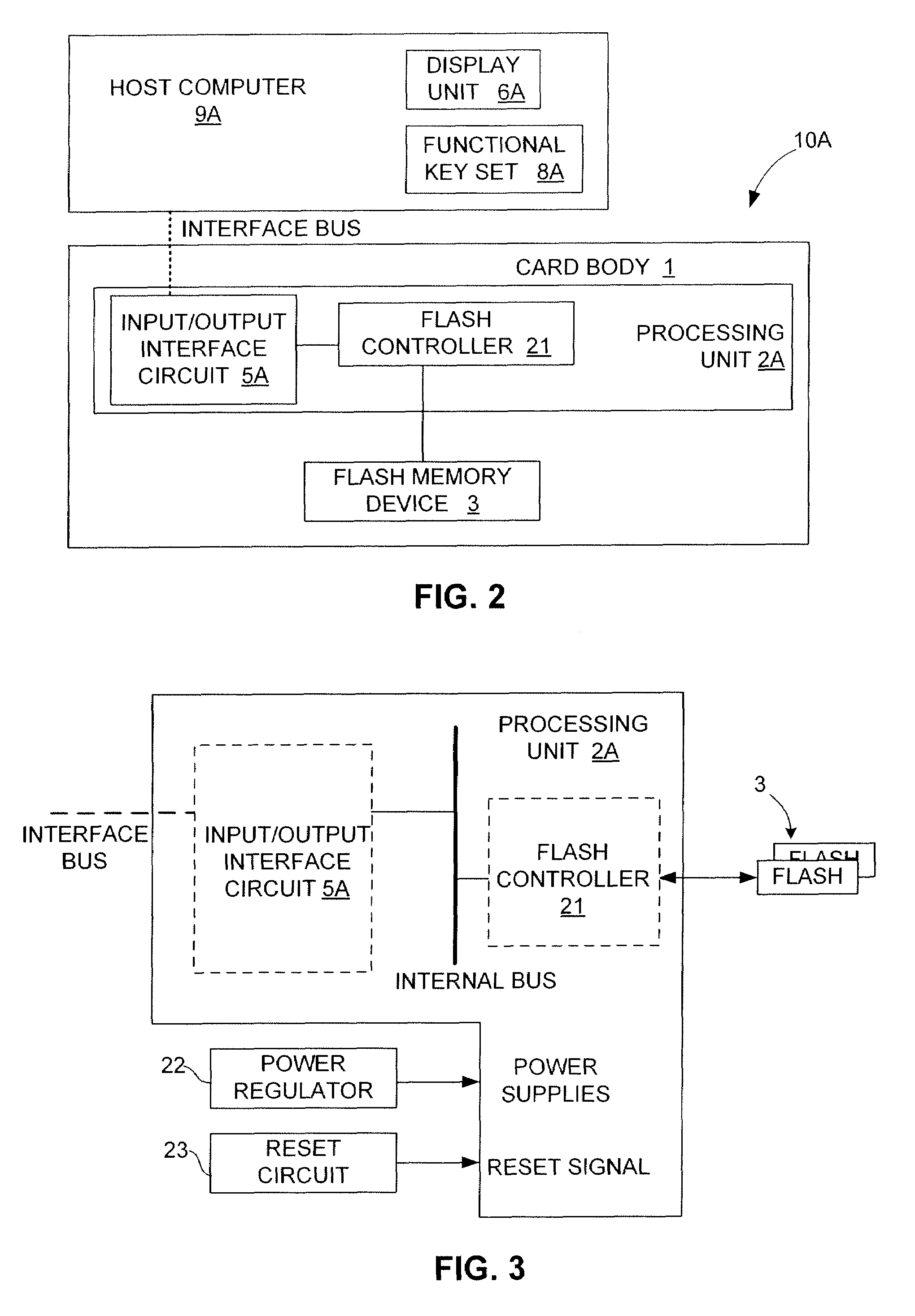
Managing bad blocks in various flash memory cells for electronic data flash card
InactiveUS20080082736A1Small sizeLow costMemory architecture accessing/allocationMemory systemsComputer accessFlash memory controller
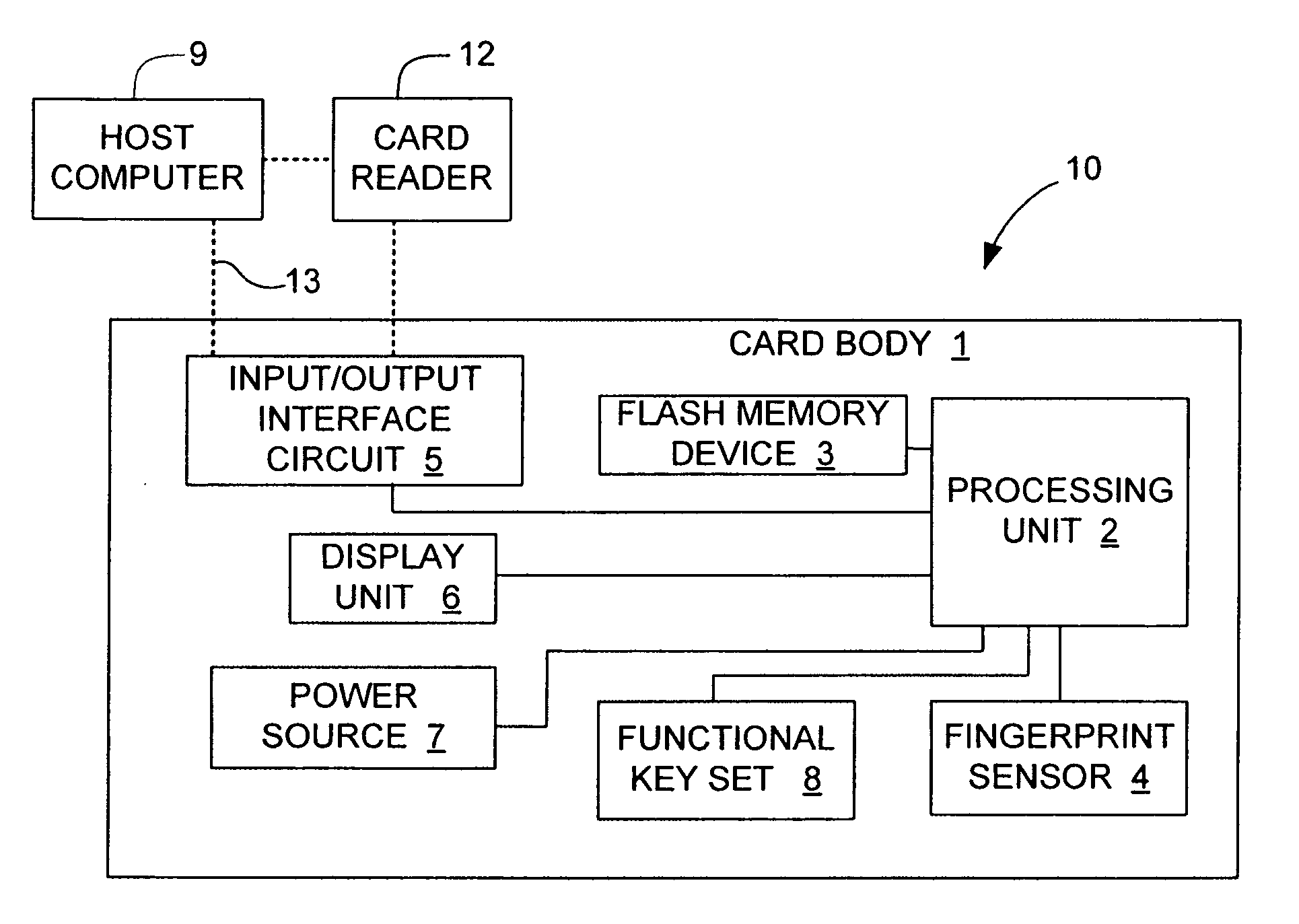
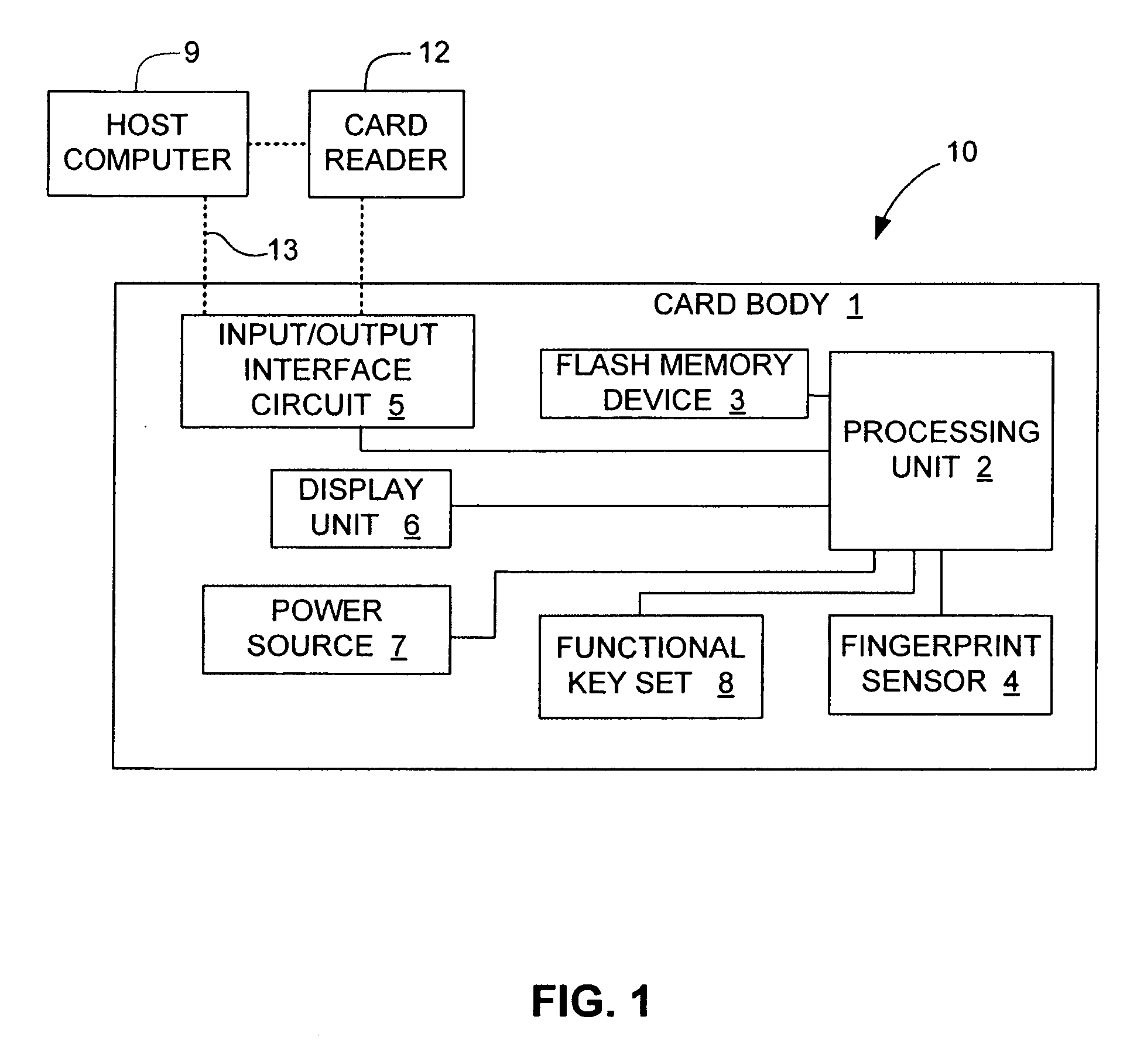
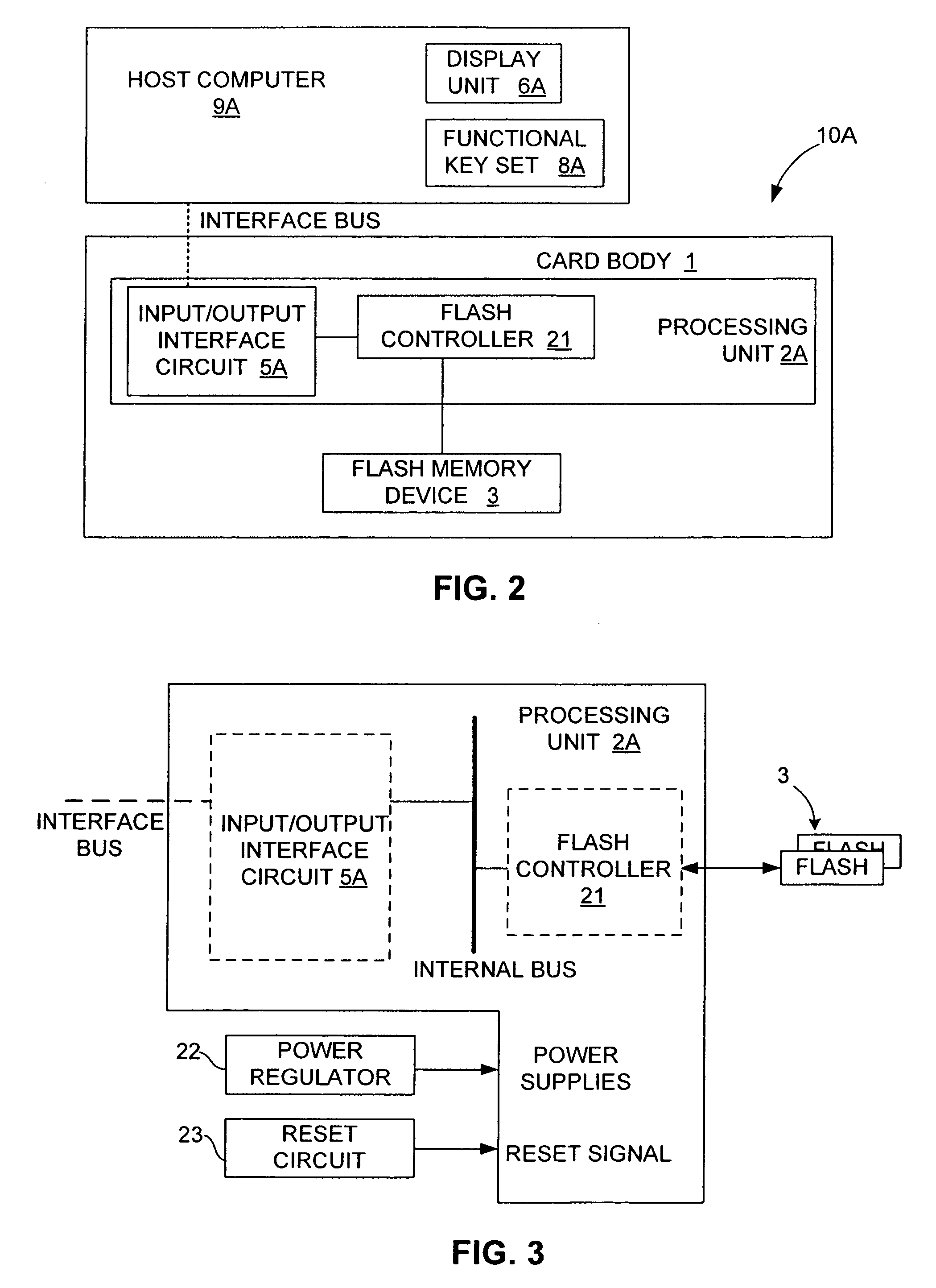
An electronic data flash card accessible by a host computer, includes a flash memory controller connected to a flash memory device, and an input-output interface circuit activated to establish a communication with the host. In an embodiment, the flash card uses a USB interface circuit for communication with the host. A flash memory controller includes an arbitrator for mapping logical addresses with physical block addresses, and for performing block management operations including: storing reassigned data to available blocks, relocating valid data in obsolete blocks to said available blocks and reassigning logical block addresses to physical block addresses of said available blocks, finding bad blocks of the flash memory device and replacing with reserve blocks, erasing obsolete blocks for recycling after relocating valid data to available blocks, and erase count wear leveling of blocks, etc. Furthermore, each flash memory device includes an internal buffer for accelerating the block management operations.
Owner:SUPER TALENT ELECTRONICS
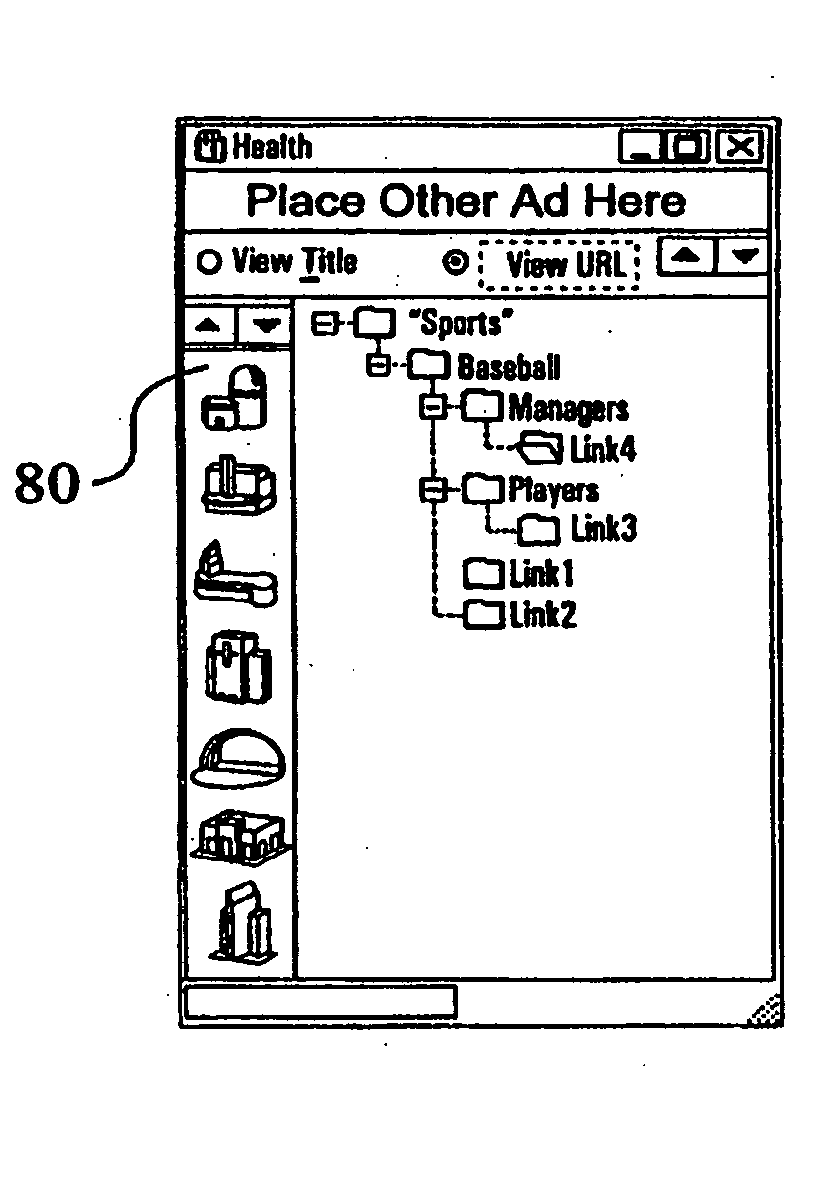
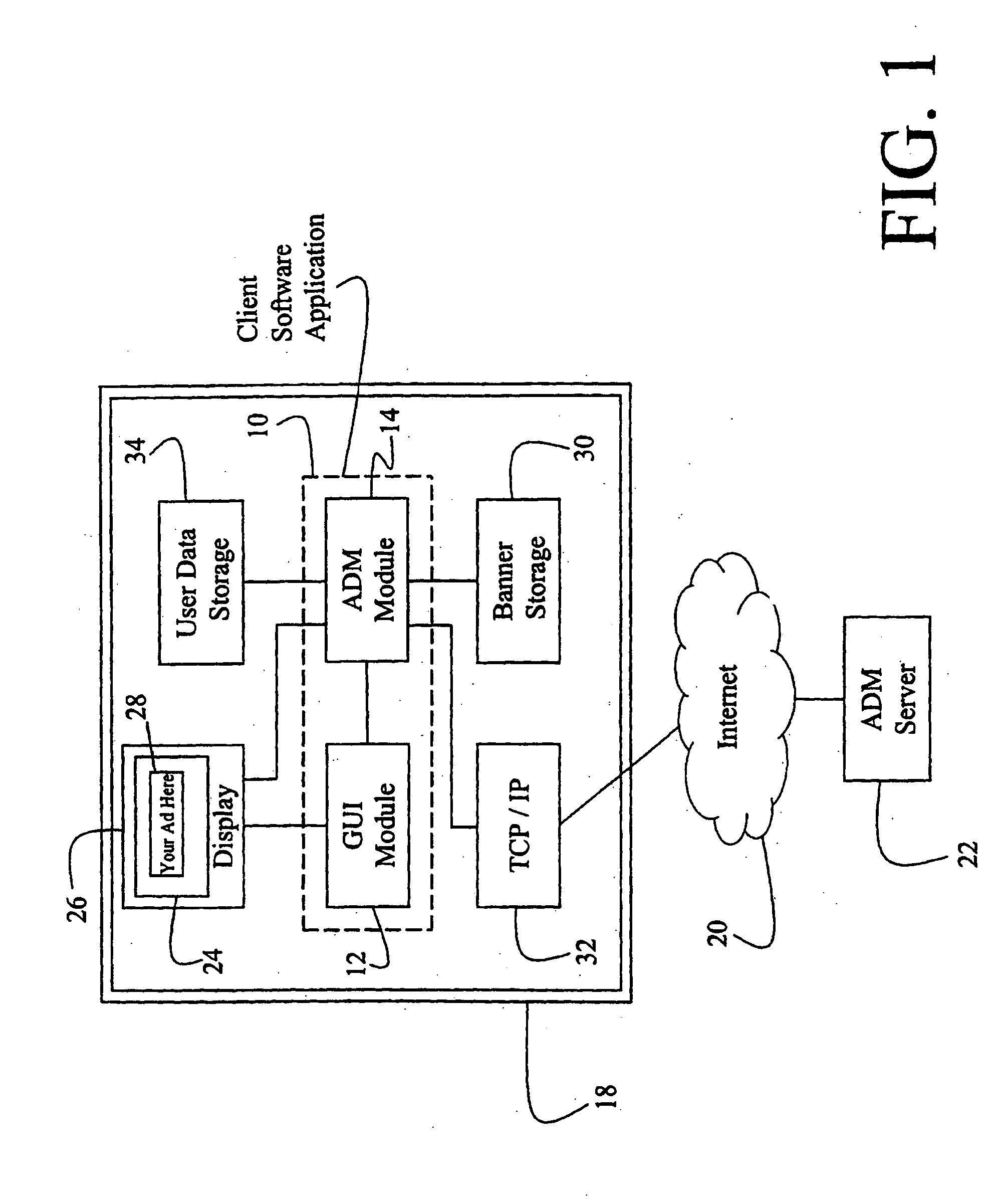
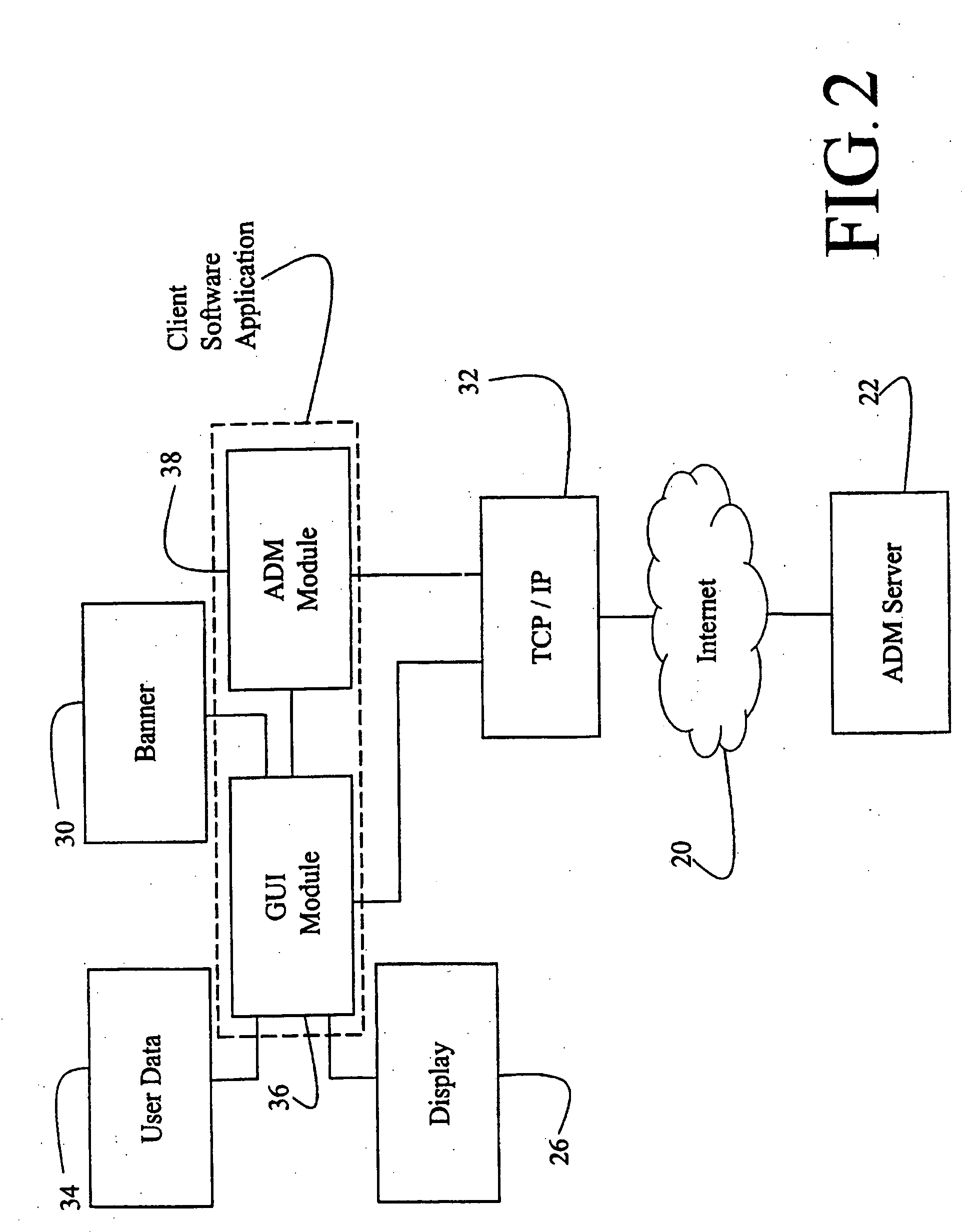
Computer interface method and apparatus with portable network organization system and targeted advertising
InactiveUS20050005242A1Permit targetingCathode-ray tube indicatorsProgram loading/initiatingPersonalizationSoftware distribution
A method and apparatus for providing an automatically upgradeable software application includes targeted advertising based upon demographics and user interaction with the computer. The software application includes a display region used for banner advertising that is downloaded over a network such as the Internet. The software application is accessible from a server via the network and demographic information on the user is acquired by the server and used for determining what advertising will be sent to the user. The software application further targets the advertisements in response to normal user interaction with the computer. Data associated with each advertisement is used by the software application in determining when a particular advertisement is to be displayed. This includes the specification of certain programs that the user may have so that, when the user runs the program (e.g., a spreadsheet program), a relevant advertisement will be displayed (e.g., an advertisement for a stock brokerage). This provides two-tiered, real-time targeting of advertising—both demographically and reactively. The software application includes programming that accesses the server to determine if one or more components of the application need upgrading. If so, the components can be downloaded and installed without further action by the user. A distribution tool is provided for software distribution and upgrading over the network. Also provided is a user profile that is accessible to any computer on the network. Furthermore, multiple users of the same computer can possess Internet web resources and files that are personalized, maintained and organized.
Owner:BETECH
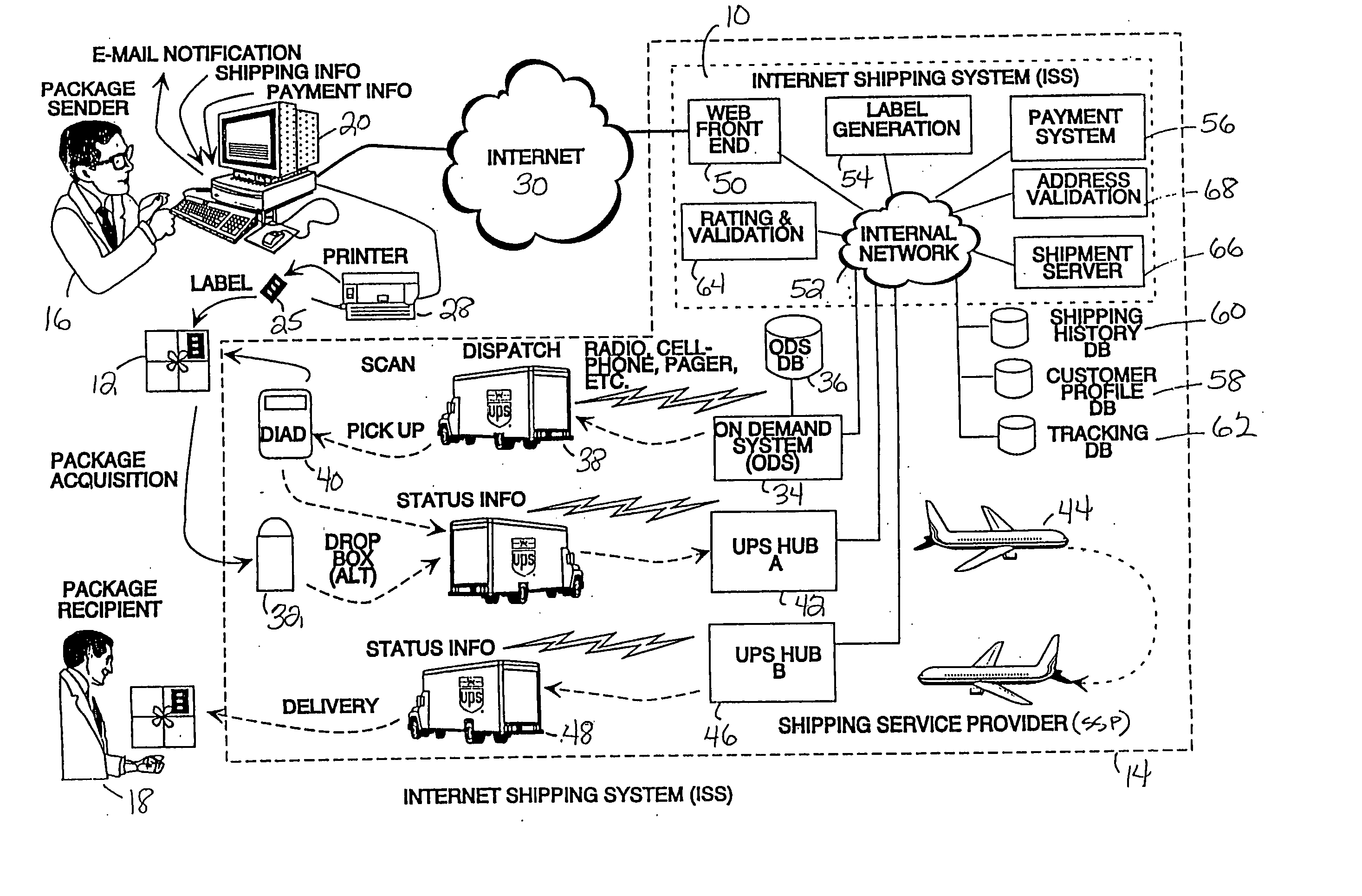
Internet package shipping systems and methods
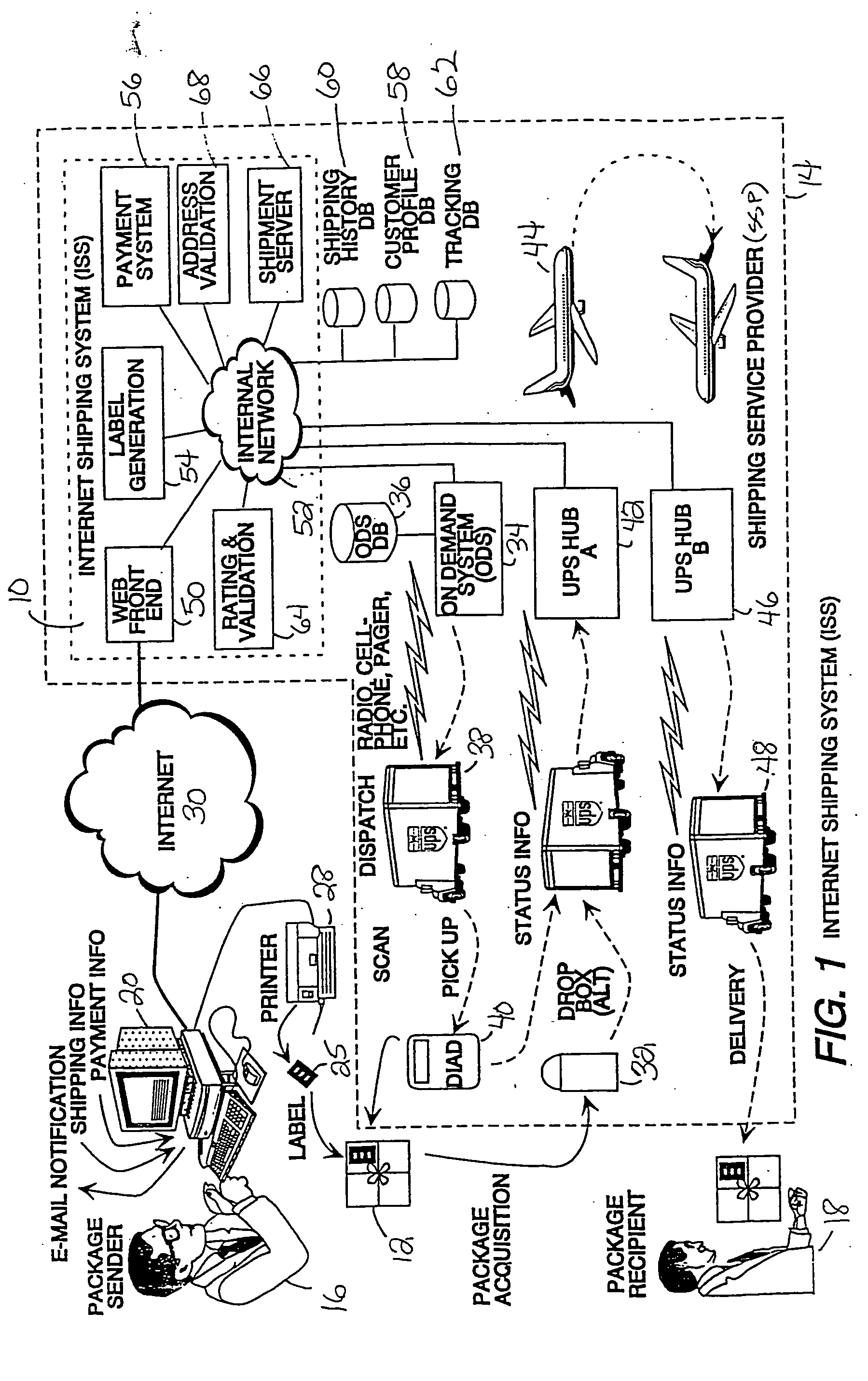
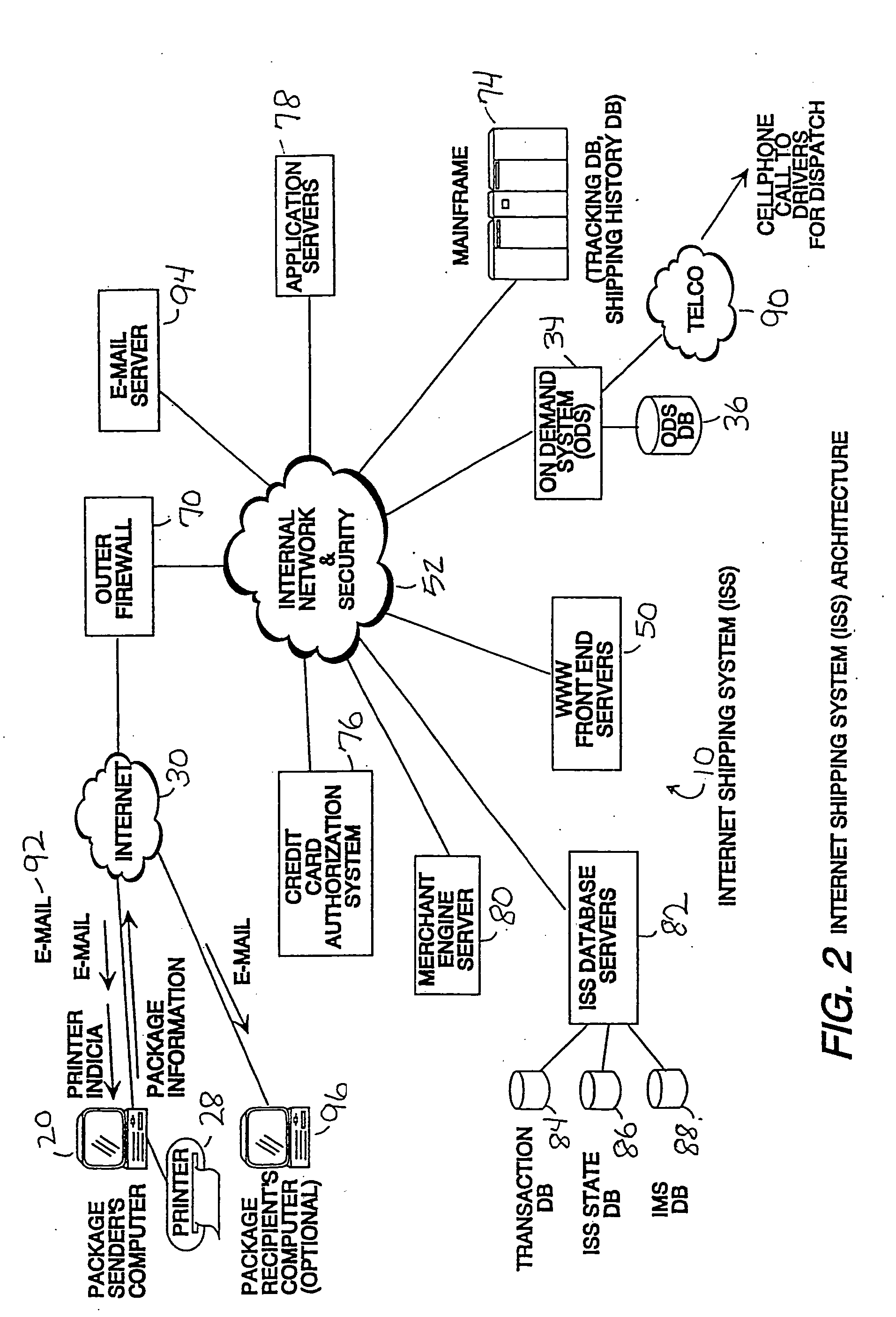
ActiveUS20050038758A1Convenience and securityFlexibility securityFranking apparatusStacking articlesPaymentInternet communication
A system and methods for shipping a package (12) from a package sender (16) to an intended recipient (18), utilizing Internet communications (30) to place shipping orders, request on demand package pickup, maintain and utilize prestored profile information, view shipping history, track orders, etc. A package sender (16) with an Internet-accessible computer (20) accesses an Internet site and associated shipping system (10) operated by a shipping service provider (14). The package sender (16) enters information required for shipping the package (12), including shipping options and methods for payment. The options and payment for the shipment transaction are validated. If the transaction is validated, printer indicia are communicated to the customer's computer (20), which is enabled to locally print a prepaid label (25) containing special machine-readable (876) as well as human-readable indicia (904). The shipping service provider (14) acquires the package by drop-off, standard pickup or on call pickup, scans the machine readable indicia, verifies other indicia of authenticity, and processes the package (12) in accordance with information encoded on the label.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
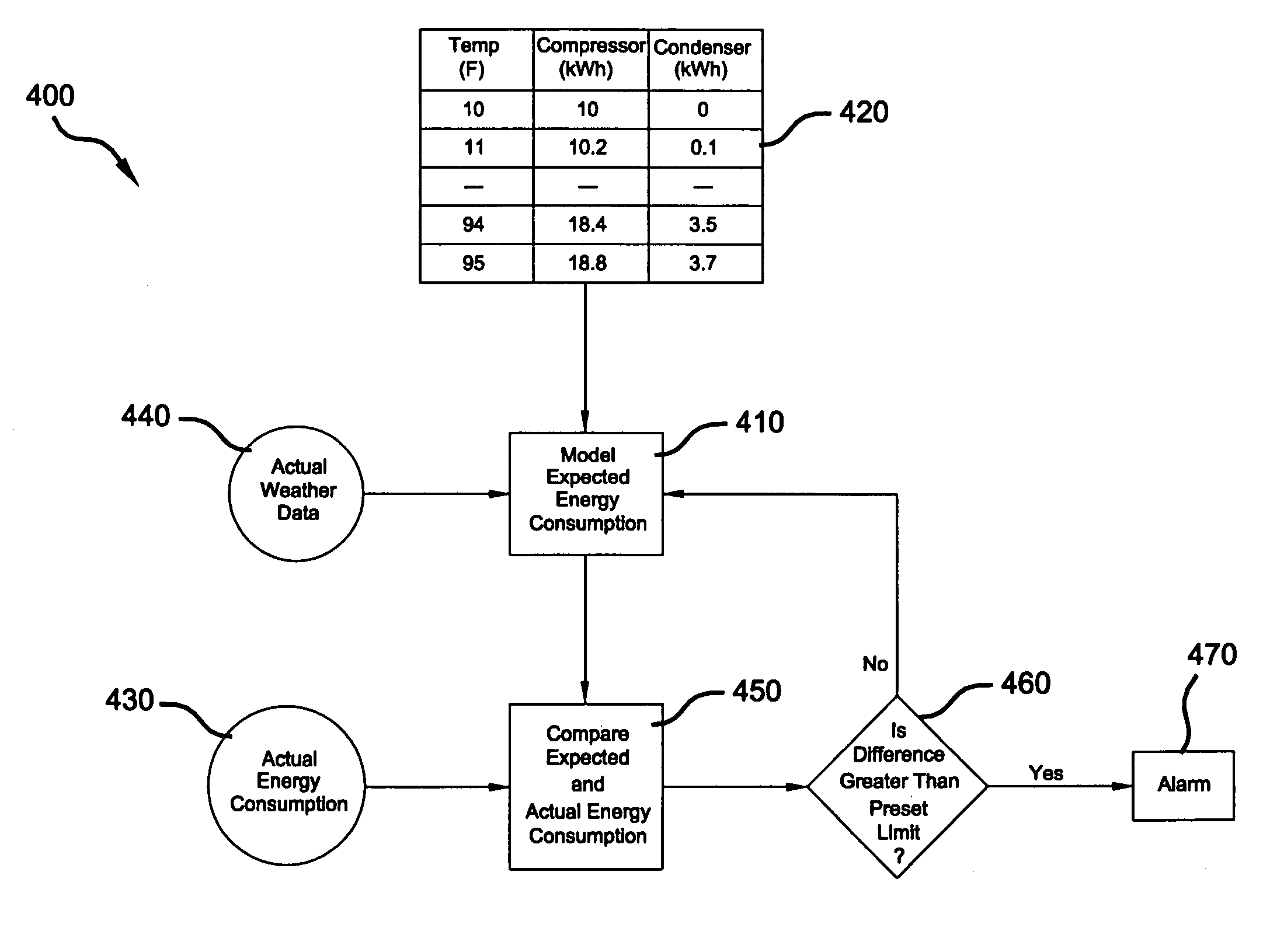
Model-based alarming
A system and method for managing energy consumption of a building system includes a source of actual energy consumption data, a source of actual weather data, and a database correlating discrete weather data values with expected energy consumption values for at least one component of the building system. A computer accesses the actual weather data, actual energy consumption data and database, wherein the computer compares the expected energy consumption values with actual energy consumption data and generates an output based on the comparison. The expected energy consumption values are generated for the discrete weather data values using an energy consumption model that functionally relates discrete weather data values and design information for the building system component.
Owner:EMERSON DIGITAL COLD CHAIN INC
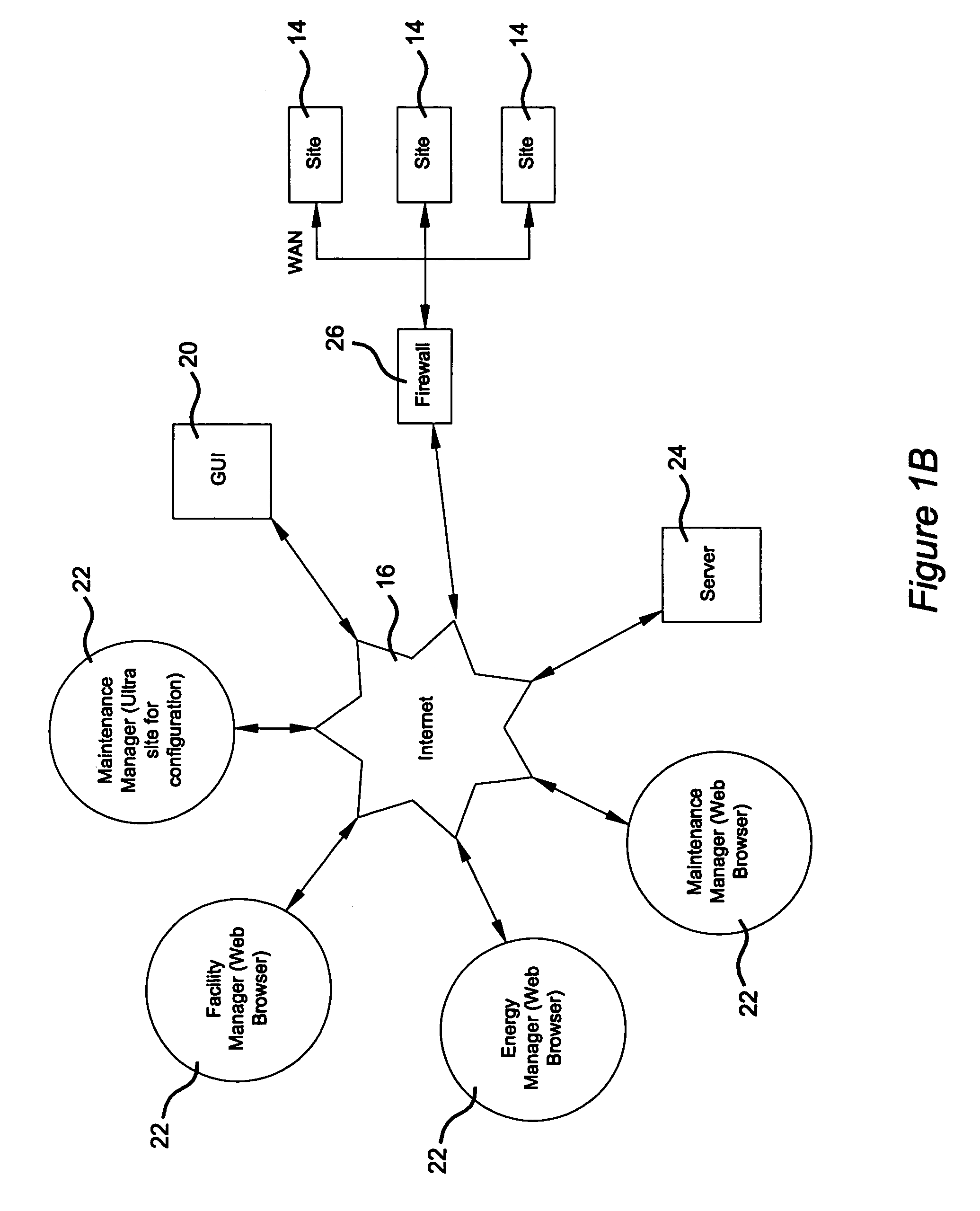
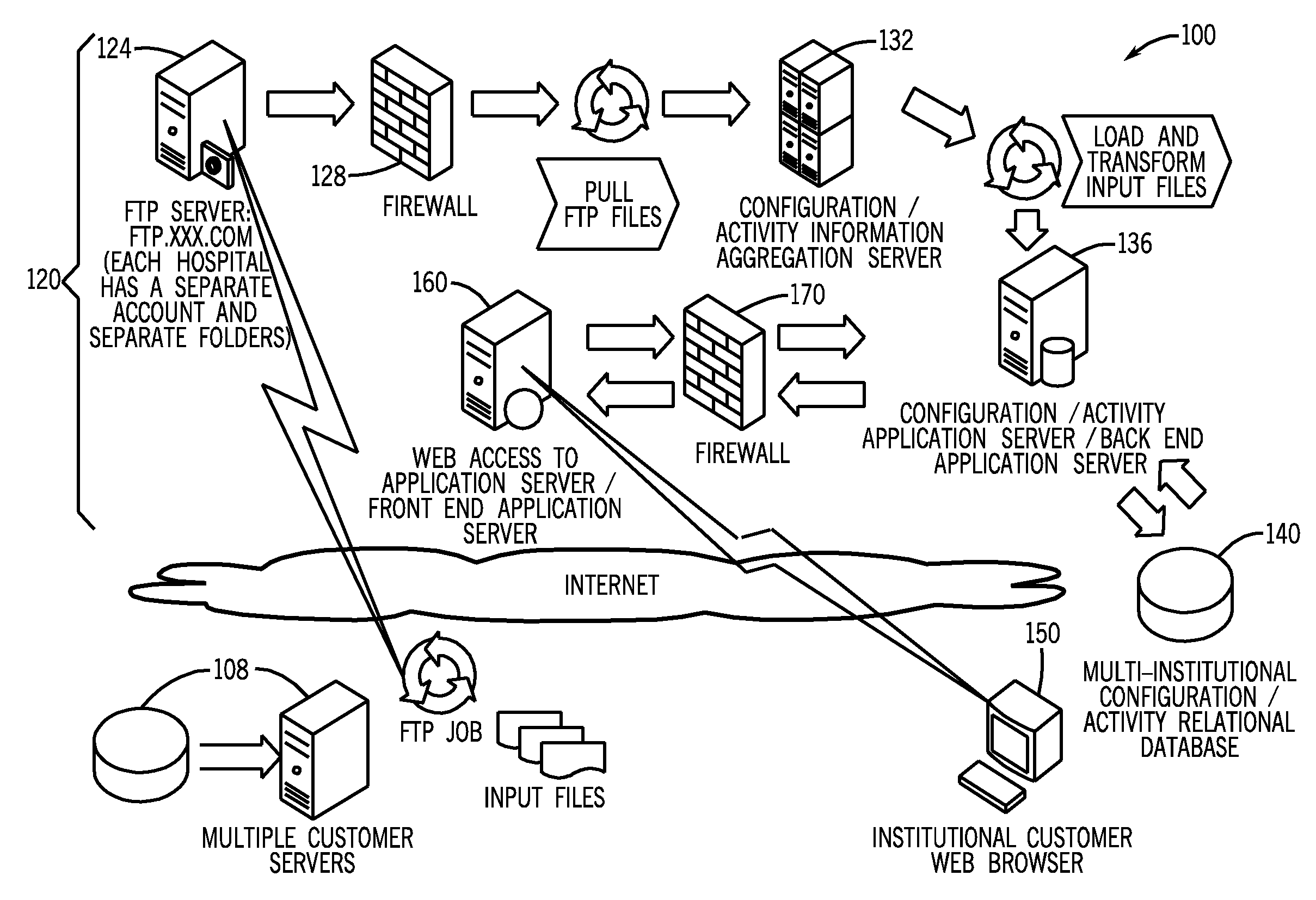
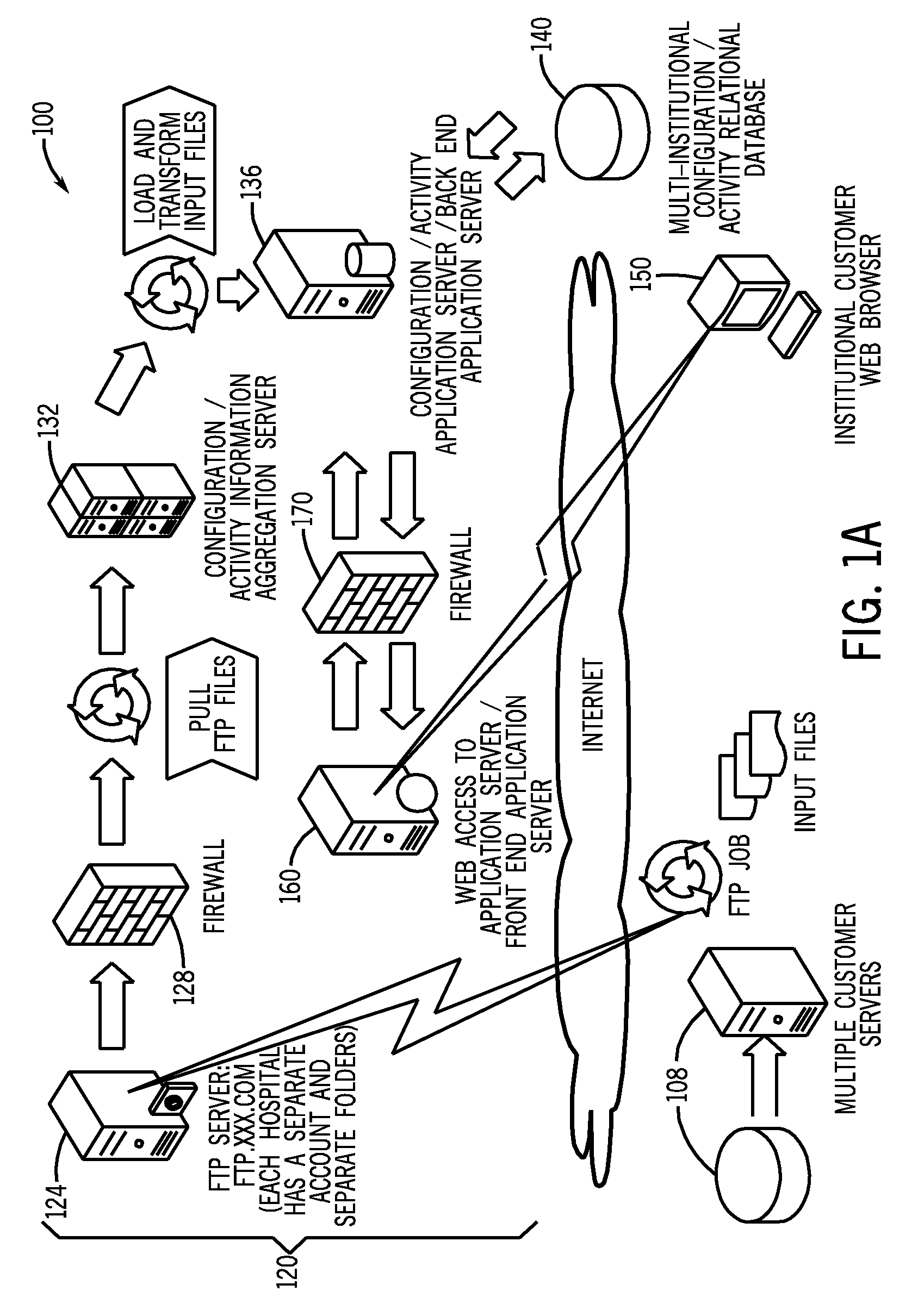
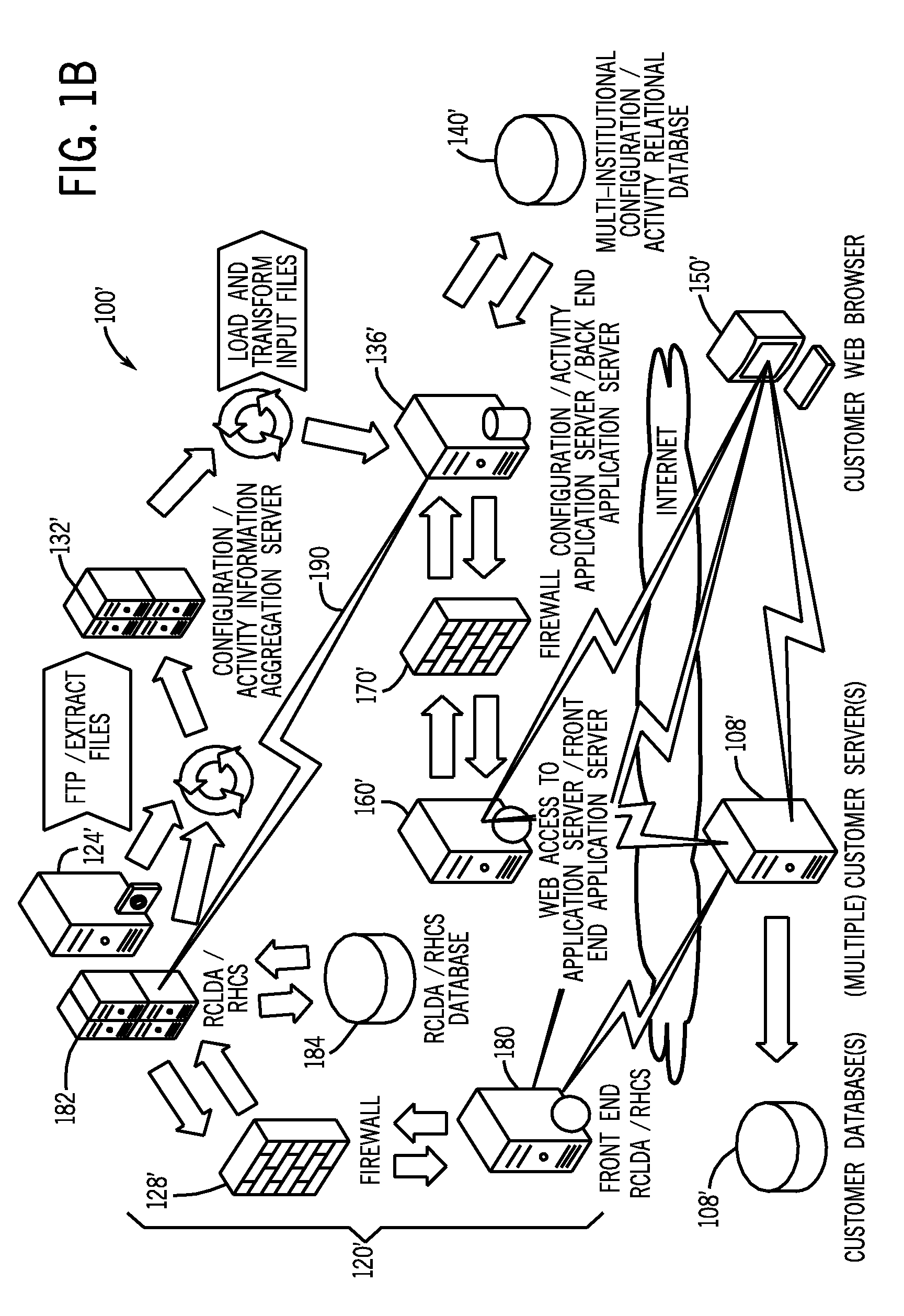
System and method for comparing and utilizing activity information and configuration information from multiple device management systems
InactiveUS20080091466A1Digital data information retrievalPatient personal data managementMedical equipmentPharmacy medicine
A method of aggregating and using medical device data from a plurality of remote institutions. The system and method electronically receives at a central computer system a plurality of established medical device data, each of the plurality of established medical device data being received from a respective medication delivery system, each of the respective medication delivery systems having a respective plurality of medical devices within the respective remote institution, such as medication delivery pumps, associated therewith and utilized therein. The system and method electronically combines and stores the plurality of established medical device data from each of the plurality of remote institutions within a memory, and electronically provides a remote client computer access to at least one of a central reporting application adapted for providing summary information to the remote client computer about the medical device data, and / or other applications.
Owner:ICU MEDICAL INC
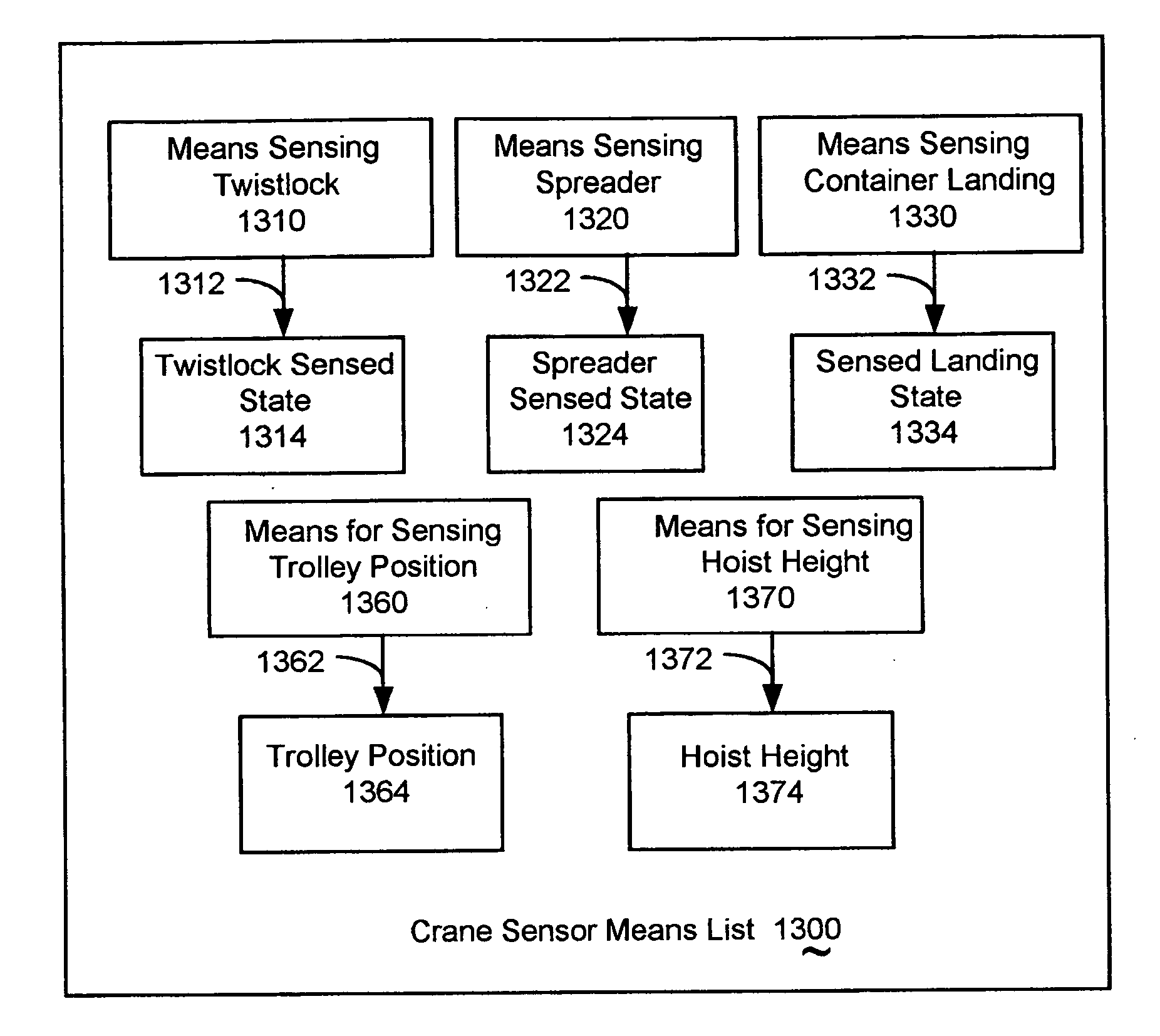
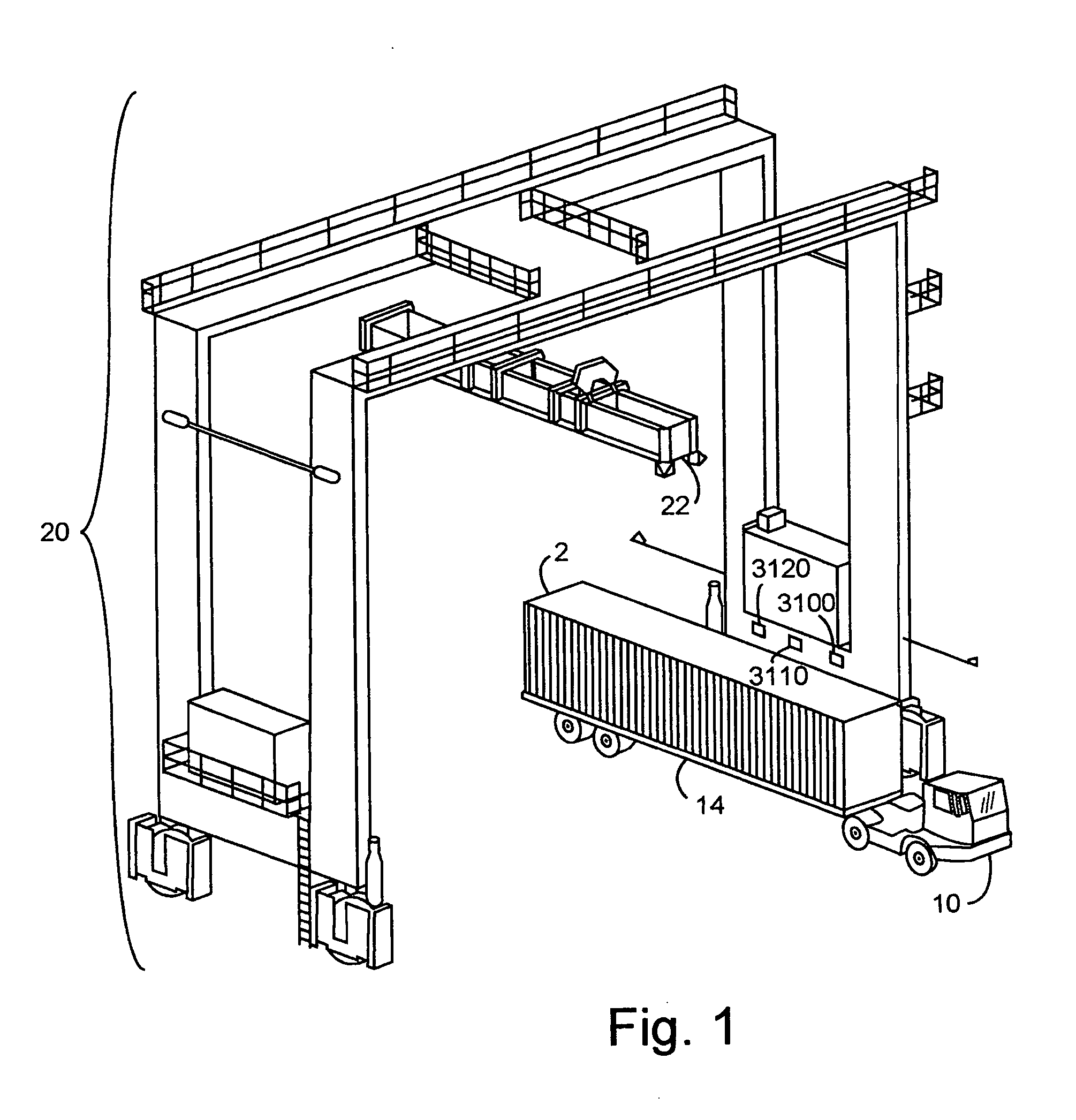
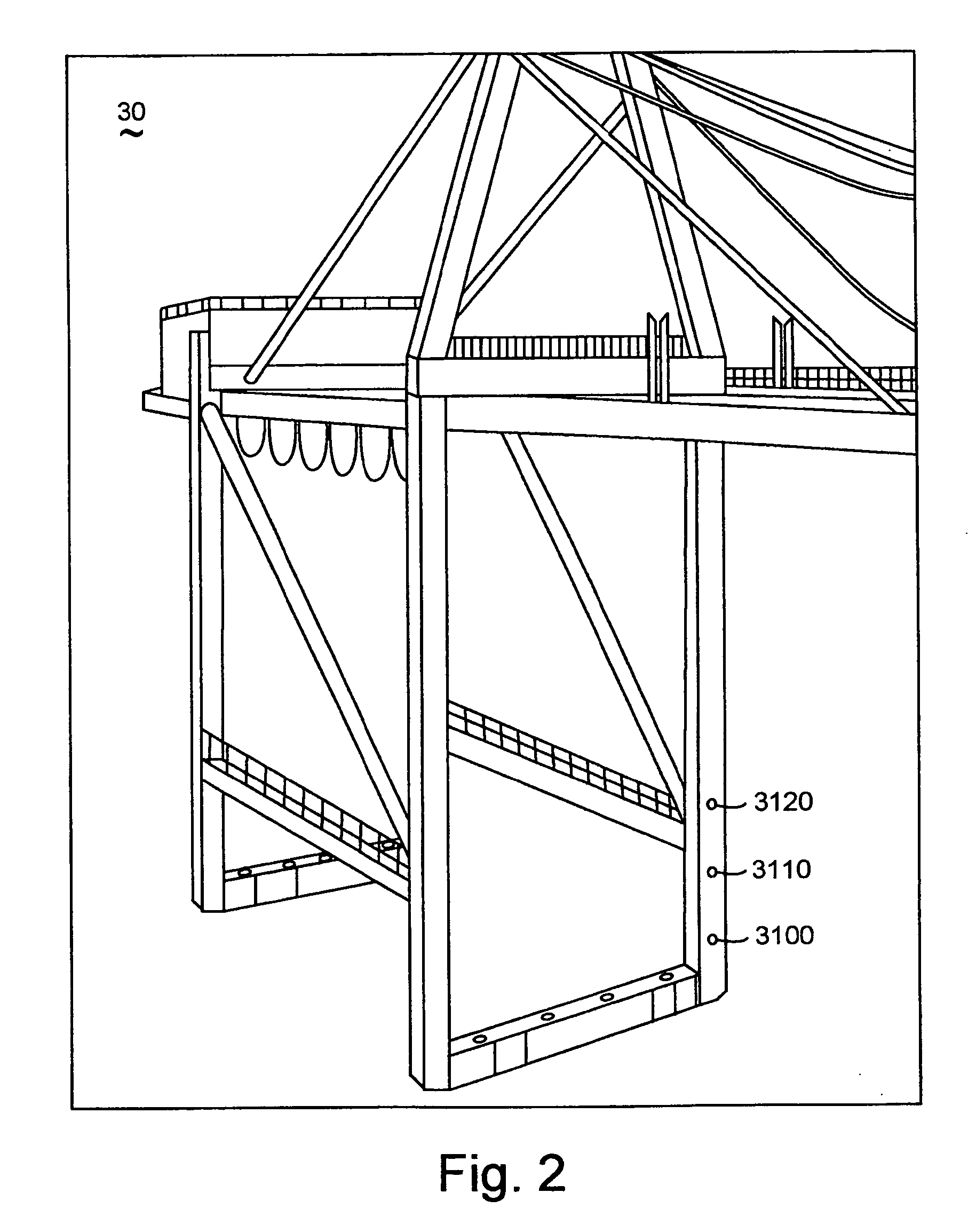
Method and apparatus for making status reporting devices for container handlers
ActiveUS20050256608A1Improve reliabilityDigital data processing detailsRoad vehicles traffic controlEngineeringComputer access
A mechanism and method for making status reporting devices for container handlers, including: providing a micro-controller module, and installing a program system into memory accessed by a computer directing the micro-controller module. The micro-controller module communicatively couples with means for wirelessly communicating and for sensing a state of the container handler. Means for wirelessly communicating may include means for wirelessly determining container handler location. The micro-controller module may be communicatively coupled to a separate means for determining location. An apparatus making the devices may include a second program system directing the invention's method through a second computer, which may control an assembly device in creating the micro-controller, coupled with the means for sensing and for wirelessly communicating.
Owner:HKI SYST & SERVICE
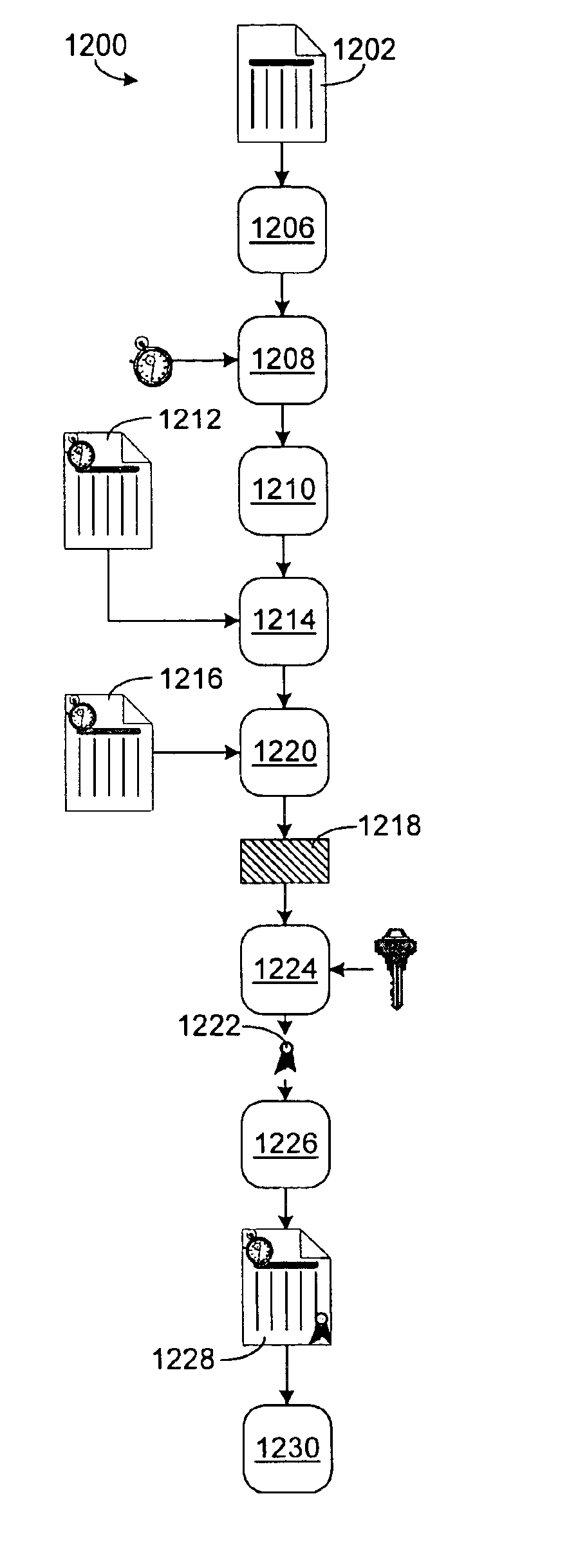
Method and system for determining and maintaining trust in digital data files with certifiable time
InactiveUS6895507B1Prevent fraudDigital data processing detailsUser identity/authority verificationDigital dataSignature file
A system and methods for proving dates of digital data files, which are accessed, created, modified, received, or transmitted by a computer includes a trusted time source in a tamperproof environment, a first subsystem for saving the file at a moment in time, a second subsystem for retrieving from the trusted time source a date and a time corresponding to the moment in time, a third subsystem for appending the date and the time retrieved from the trusted time source to the saved file, a fourth subsystem for signing the saved file with the date and the time retrieved from the trusted time source appended thereto, a fifth subsystem for hashing the signed file to produce a digest, a sixth subsystem for signing the digest with a key to produce a certificate, a seventh subsystem for appending the certificate to the saved file, and an eighth subsystem for saving the file with the certificate appended thereto. The trusted time source is a real time clock, which is not resettable, is independent of any system clock of the computer, and is installed locally relative to the computer.
Owner:TIME CERTAIN
Systems and methods for authorizing, authenticating and accounting users having transparent computer access to a network using a gateway device
InactiveUS8713641B1Avoid accessDigital data processing detailsMultiple digital computer combinationsComputer networkTransparent computing
A system and method for authorizing, authenticating and accounting users having transparent access to a destination network, wherein the users otherwise have access to a home network through home network settings resident on the user's computers, and wherein the users can access the destination network without altering the home network settings and without installing software on the user's computer. The system includes a gateway device for receiving a request from a user for access to the destination network, and means for identifying an attribute associated with the user based upon a packet received by the gateway device, wherein the packet is transmitted from the user's computer, and wherein the user's computer is configured for accessing the home network.
Owner:NOMADIX INC
System for reconfiguring and registering a new IP address for a computer to access a different network without user intervention
InactiveUS7007080B2Easy to useIncrease incomeMetering/charging/biilling arrangementsTelephonic communicationTraffic capacityRegistration status
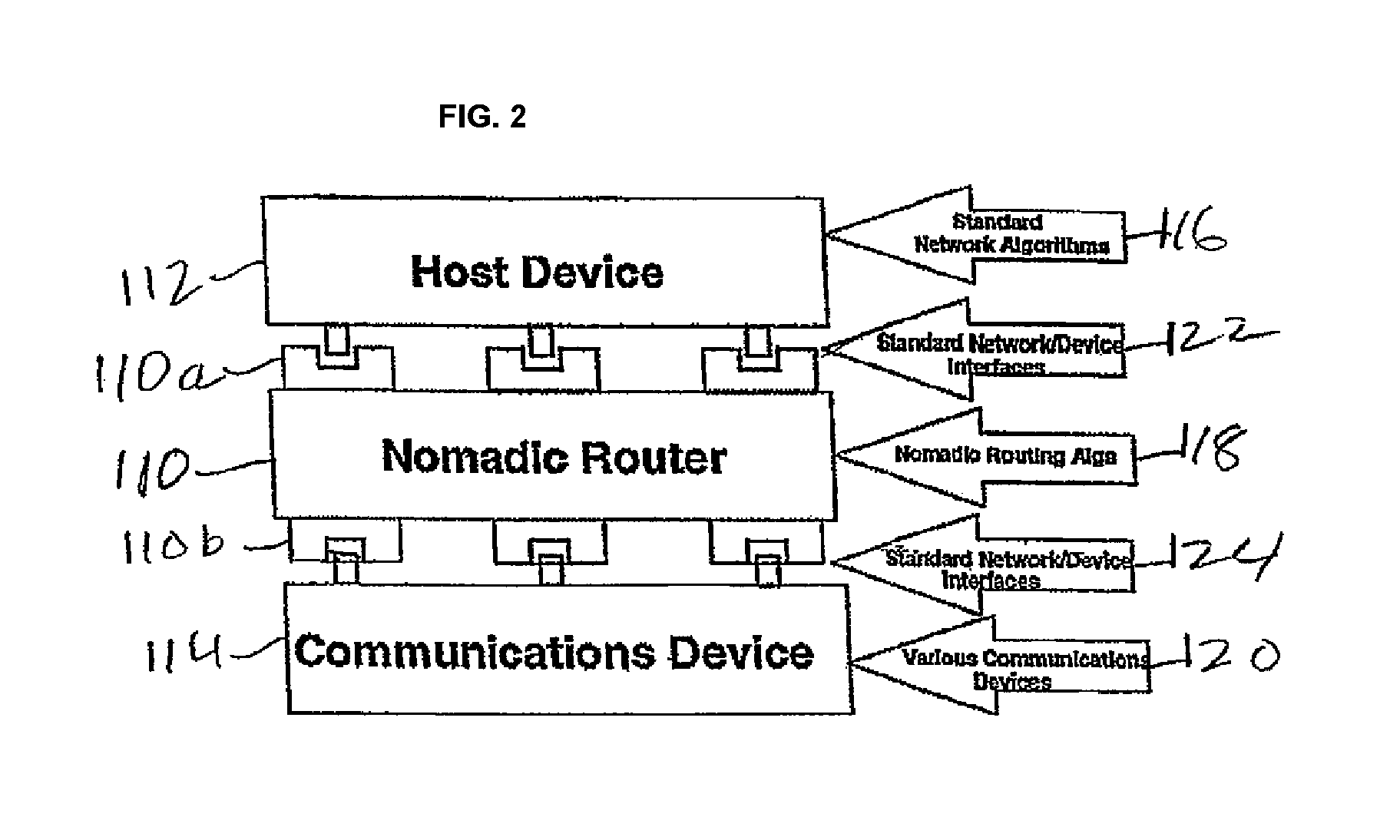
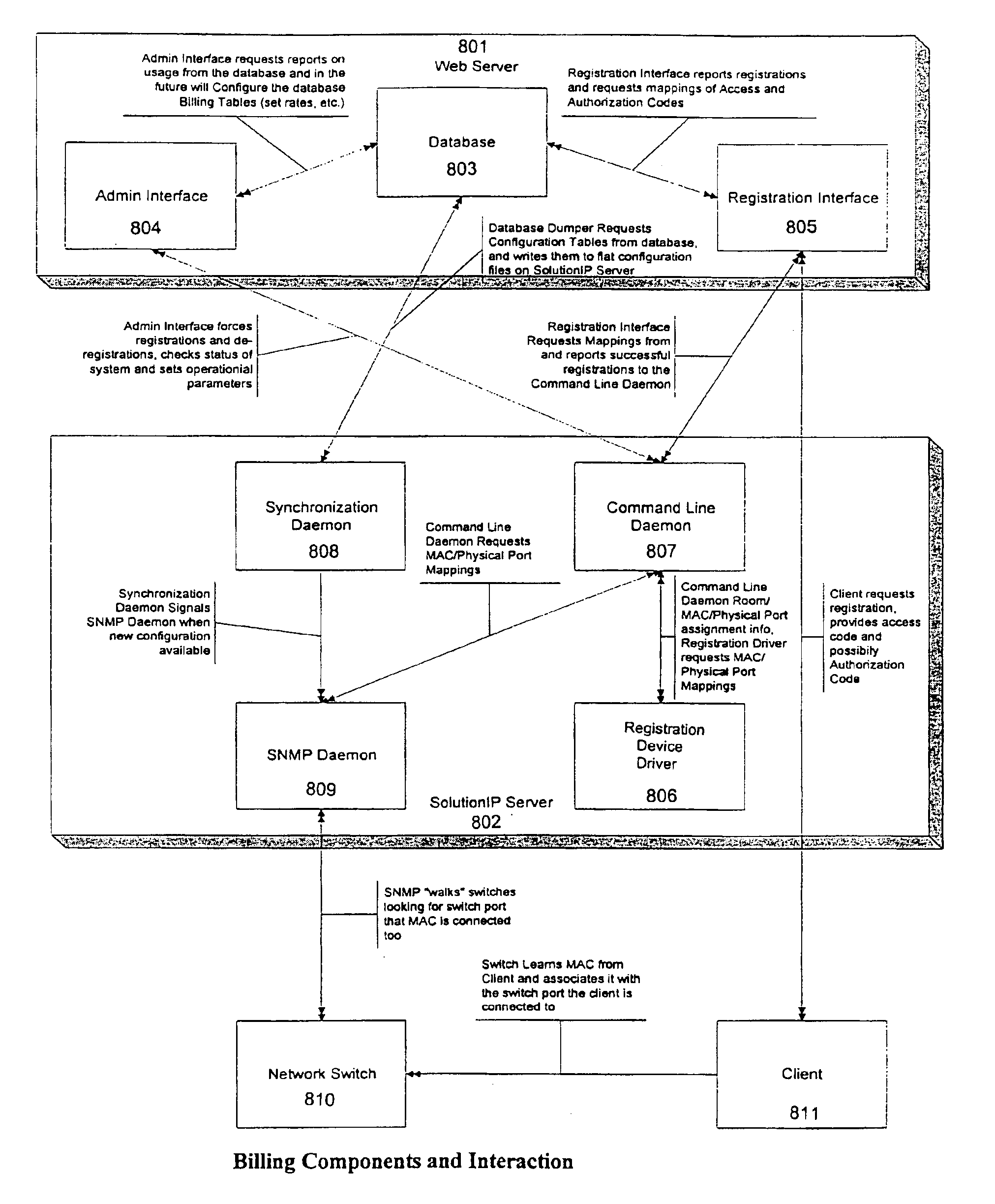
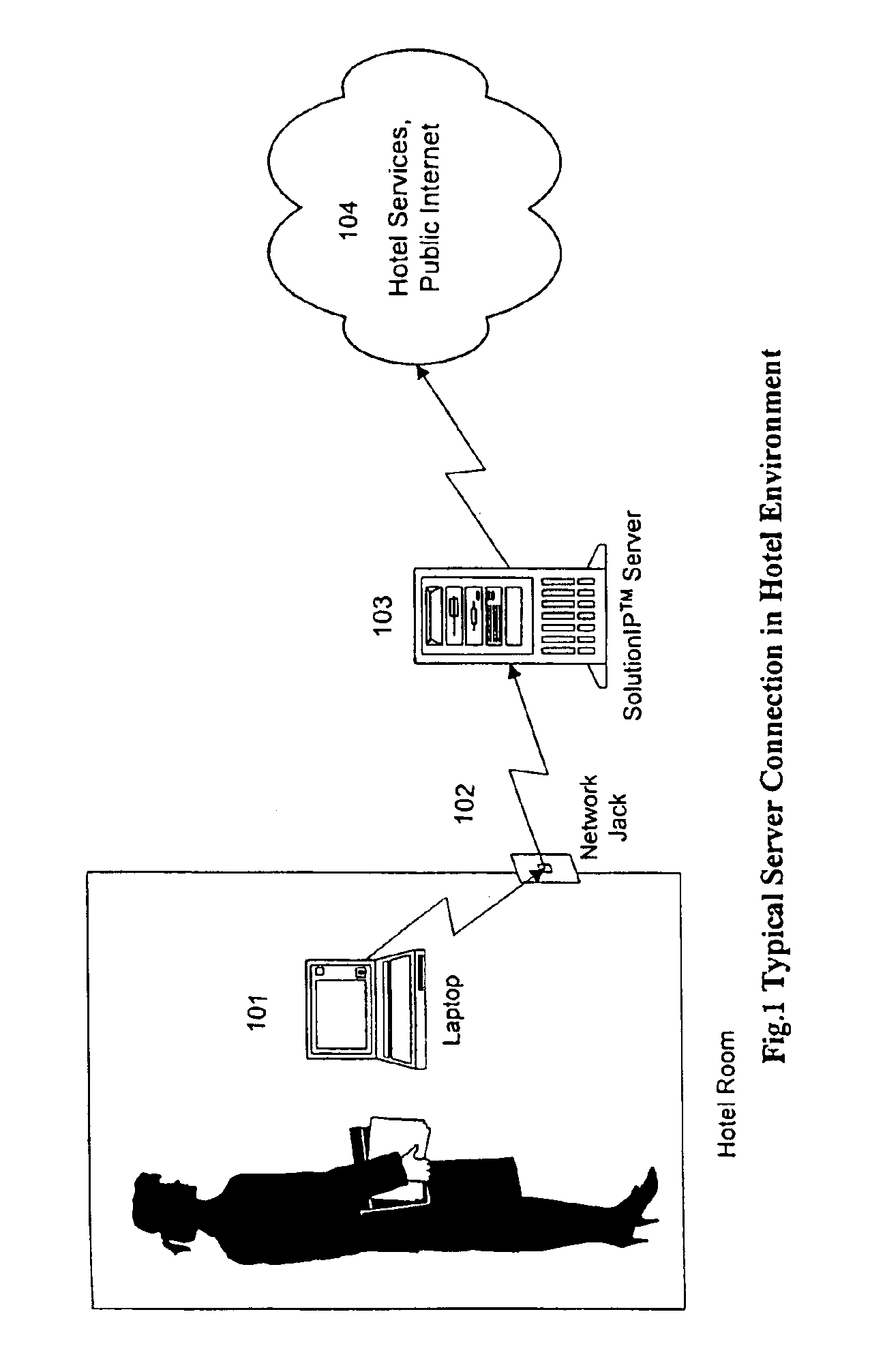
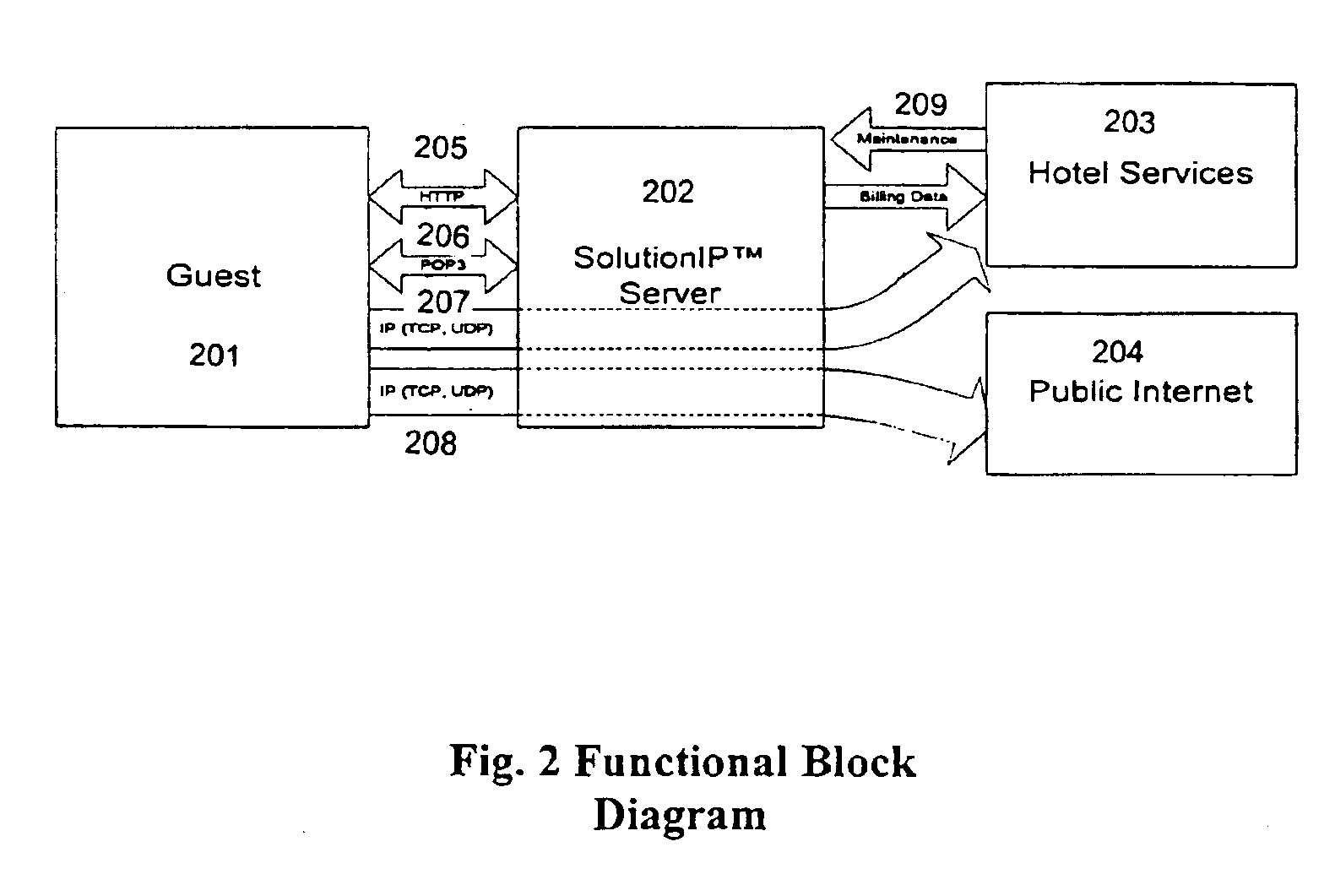
A server and method is provided that allows a computer configured for a different network to access a network without hardware or software configuration changes to the computer. The invention allows users to plug into the network and access not only the network that their computer is connected to but also to the Internet, the Worldwide Web and the individual's email. This is particularly useful to visitors to multiple unit buildings such as hotels. Not only can the service be provided by the server and method of the invention connected to and carried out on the network but it does not require manual configuration changes to the computer or new software or hardware for the computer. In situations where access is to be controlled this is done through a registration driver and module. Only registered guests have access to the network and the services and access it provides. The invention determines and assigns addressing information to properly direct traffic to and from the computer. The invention provides for the storage and maintenance of the addressing data. Registration status information and billing information is collected and maintained to determine access to and billing for services.
Owner:SOLUTIONINC LTD
Portable vital signs measurement instrument and method of use thereof
The invention is a portable vital signs measurement instrument, systems and methods that provide a variety of measurement capabilities, including blood pressure, temperature, pulse oximetry, and other indications of patient status. The instrument, systems and methods include the ability to communicate wirelessly, for example using Wi-Fi (IEEE 802.11B), with a server, so that information can be entered easily, securely and reliably into a medical database system accessible by way of the server. The systems and methods provide for the instrument to initiate a communication session by attempting to discover a server access point in its vicinity.
Owner:WELCH ALLYN INC
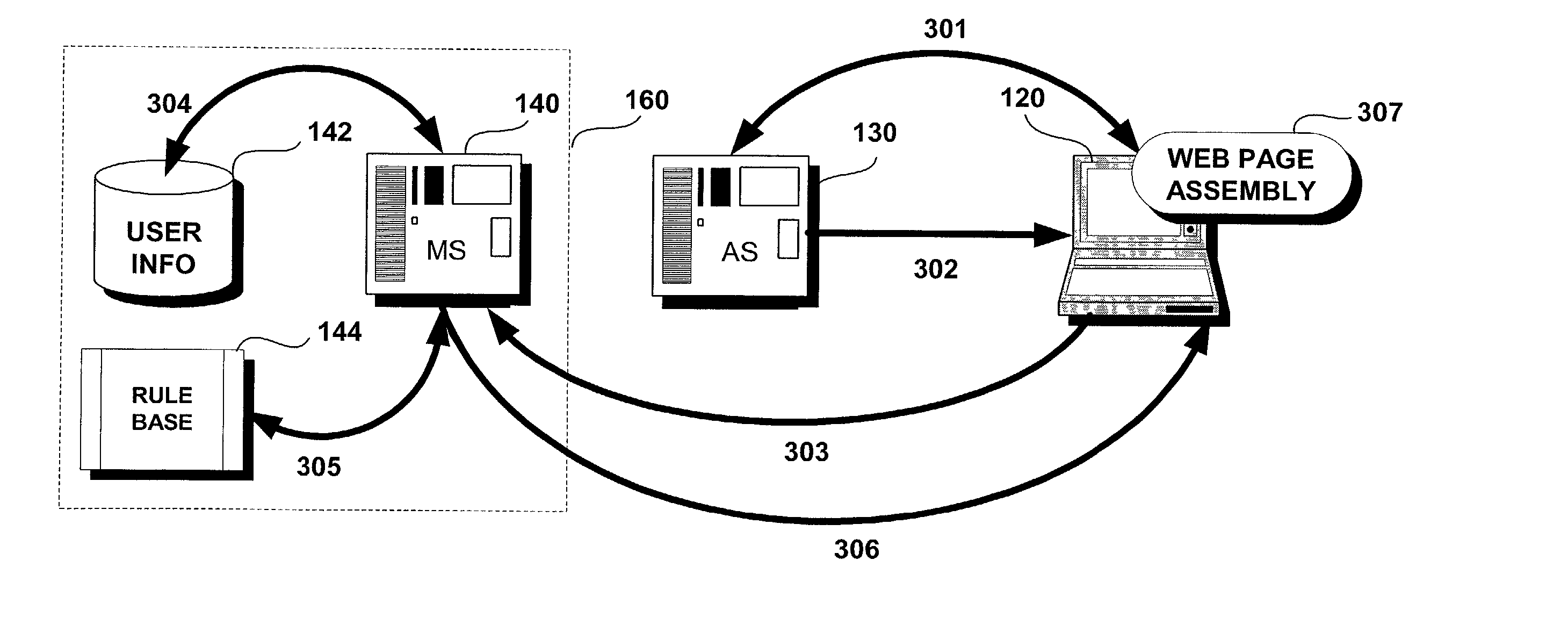
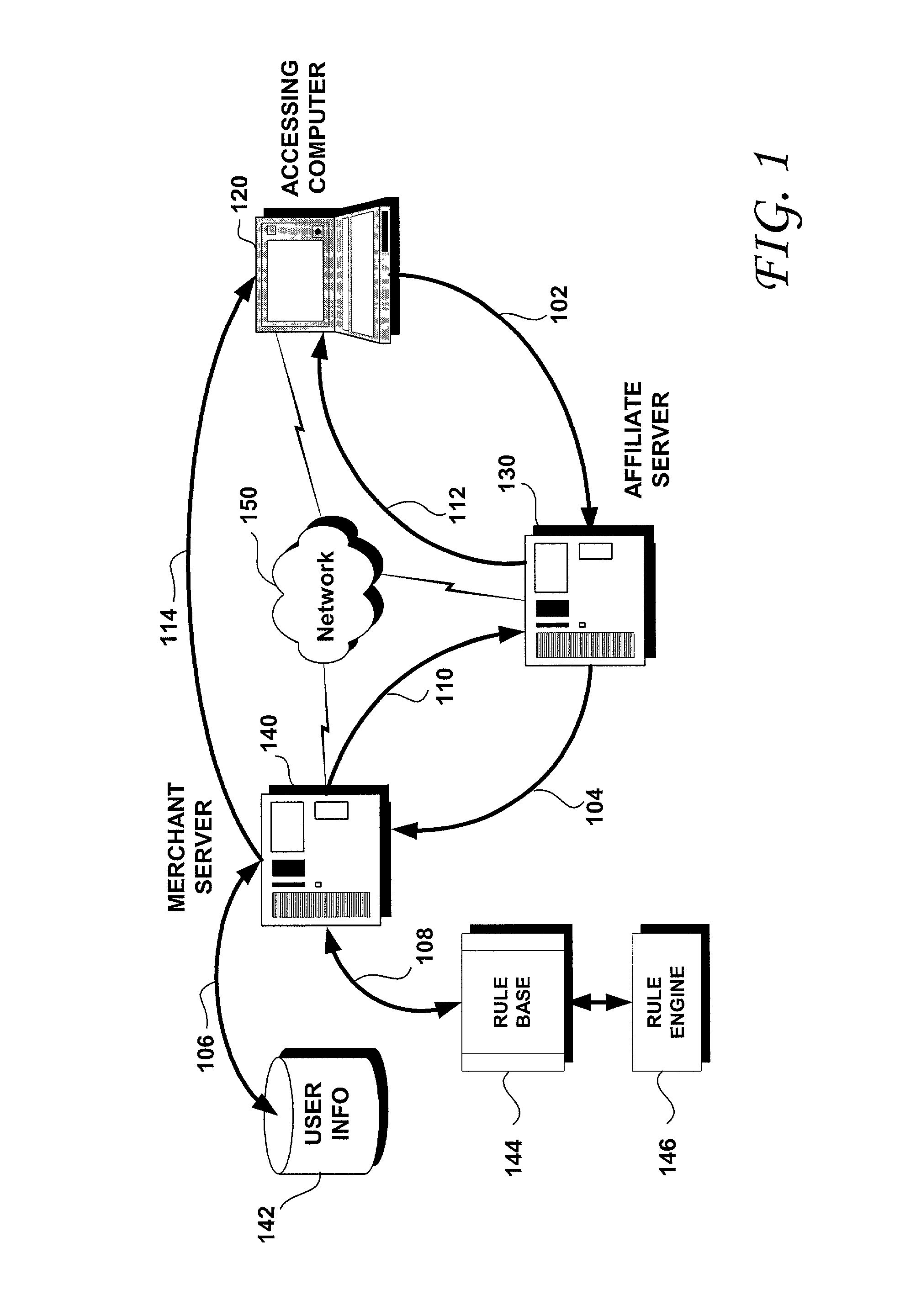
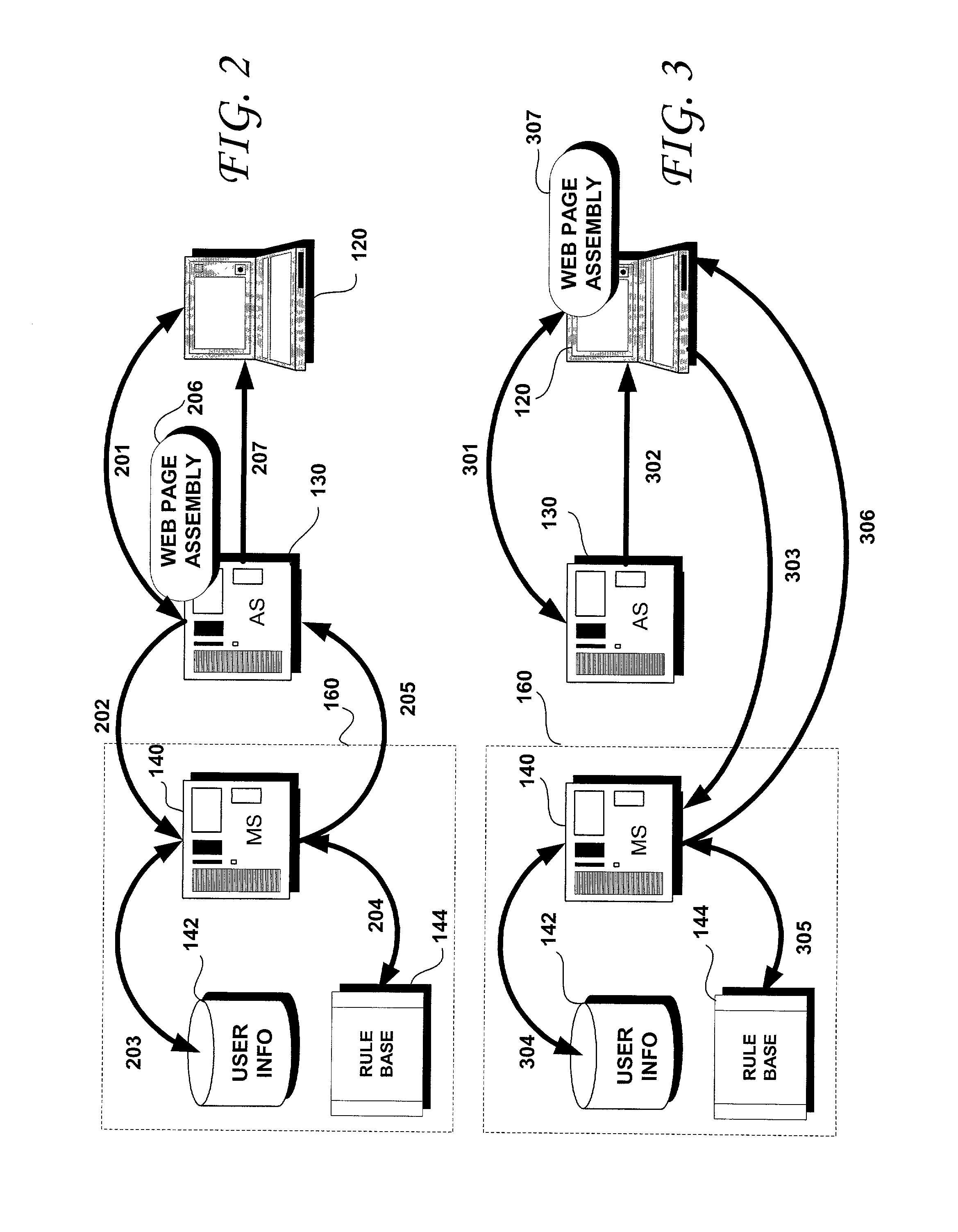
Methods and systems for rule-based distributed and personalized content delivery
ActiveUS20020069261A1Multiple digital computer combinationsWebsite content managementPersonalizationWeb site
Methods and systems are disclosed for delivering personalized content from a first server such as a merchant Web server to a computer accessing a second server such as an affiliate Web server. A system according to the present invention includes a merchant Web server and an affiliate Web server, the affiliate Web server being coupled to the merchant Web server over a computer network. A database of user information is accessible to the merchant Web server, as is a rule base that includes a plurality of configurable rules. User identification may be collected from the computer accessing a Web site controlled by the affiliate Web server and the collected user identification may be sent to the merchant Web server, along with a request for content. User information corresponding to the collected user identification may then be retrieved from the database. The user information obtained from the database may be applied to the plurality of rules and selected content may be returned to the affiliate Web server in response to the request for content. The returned content is selected based upon the result of the application of the user information to the plurality of rules.
Owner:ORACLE INT CORP
Collusion detection and control
InactiveUS20060189381A1Minimisation of any prejudiceApparatus for meter-controlled dispensingVideo gamesComputer accessPointing device
A system for detecting and controlling collusion in a game with a plurality of participating players The system (1) includes a gaming server (2) and a number of portals (3a, 3b) in the form of websites on the World Wide Web in the Internet. Each of the portal websites is an online casino website hosted on a corresponding casino web server (not shown). Each of the casino websites (3a, 3b) is accessible by one or more would-be poker players. Each player accesses the website using a computer with a display (5) and an associated pointing device (6). The system (1) includes an administration facility (13) which communicates with the gaming server (2) along a communication channel (12). There is also a collusion detection server (14) in communication with the game server (2) via communication channel (12).
Owner:CORK GROUP TRADING
System and method to authenticate users to computer systems
InactiveUS7941534B2Facilitates rapid secondary logLimited accessDigital data processing detailsDrug and medicationsTransceiverTelecommunications link
Owner:DLH TECH LLC
Network user database for a sidebar
InactiveUS20070157105A1TransmissionSpecial data processing applicationsService compositionInternet content
Sidebars group a plurality of Internet and other services in one easily accessible location on the desktop. In one embodiment, a user's sidebar preferences, such as, for example, the types of applications modules that populate their sidebar are stored by an Internet content provider on a network server. A user can access their personal sidebar preferences from any computer with an Internet connection. In addition, in one embodiment, application module information loaded into the application modules is also stored on a server, thus changes made in a sidebar are reflected in their “full service” counterpart applications.
Owner:EXCALIBUR IP LLC
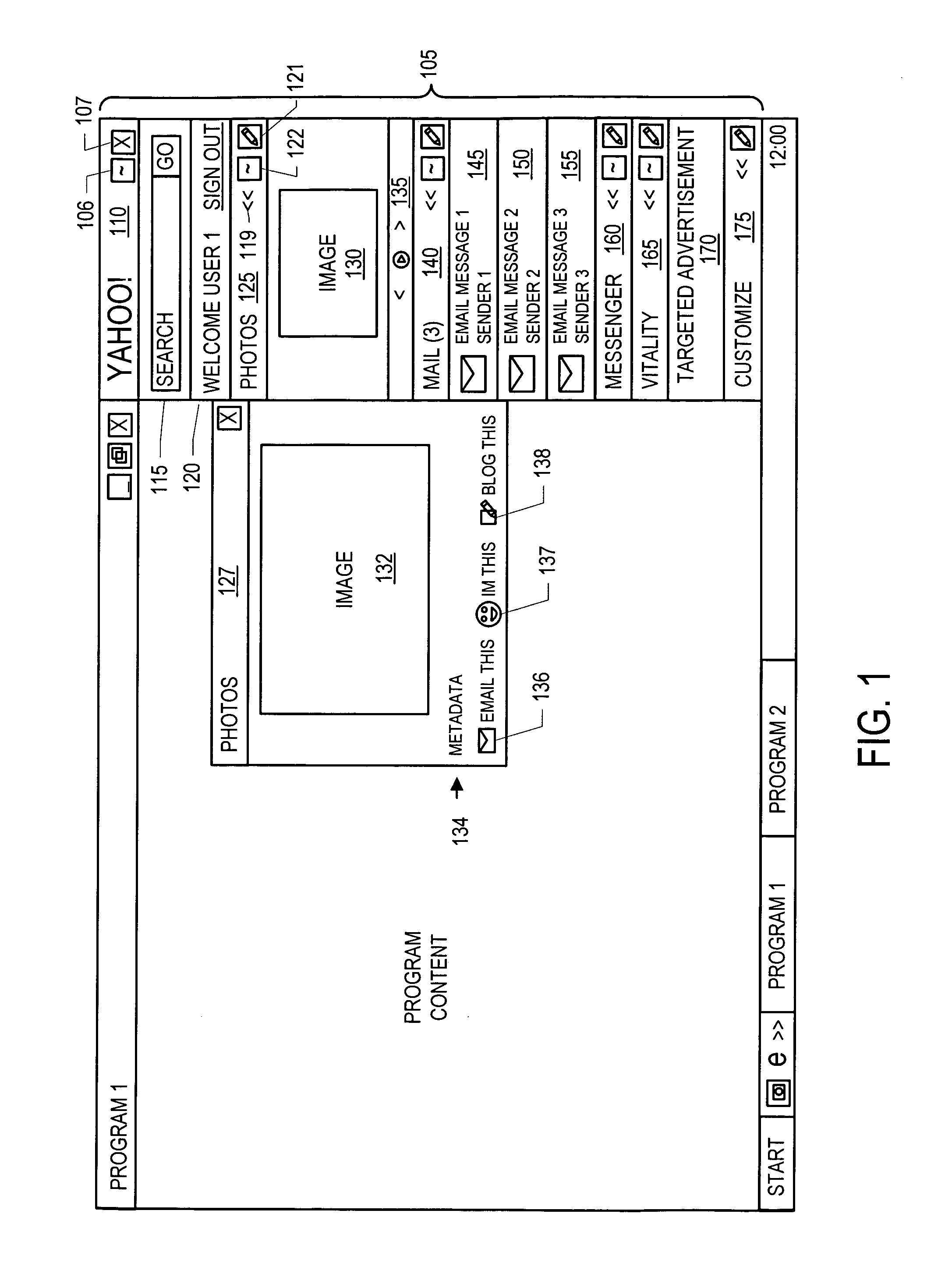
Business card and contact management system
InactiveUS20050251448A1More cost-effectivelyMore accurateAdvertisementsOffice automationWeb browserBusiness card
Owner:MICROSOFT TECH LICENSING LLC
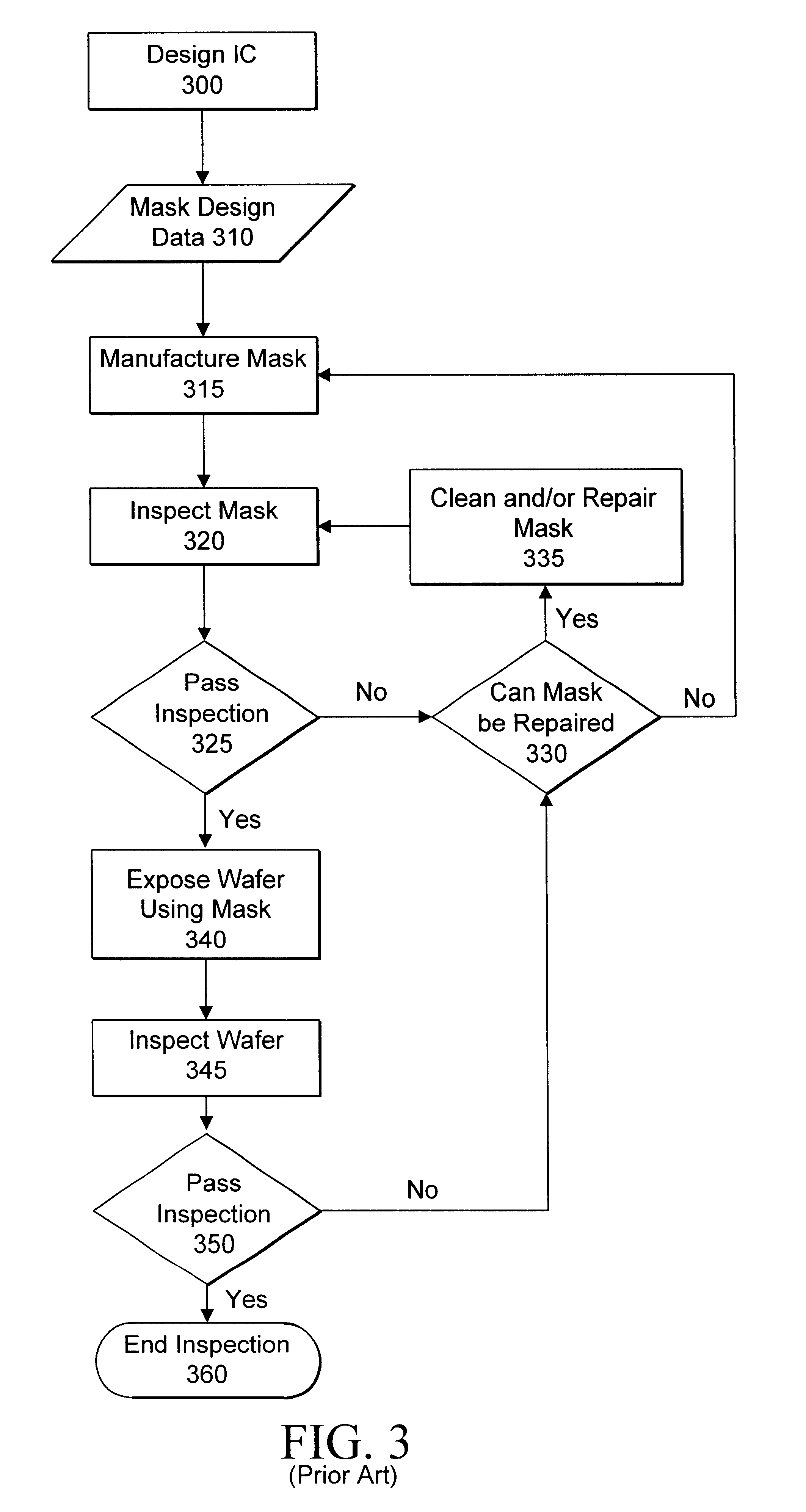
Method and apparatus for a network-based mask defect printability analysis system
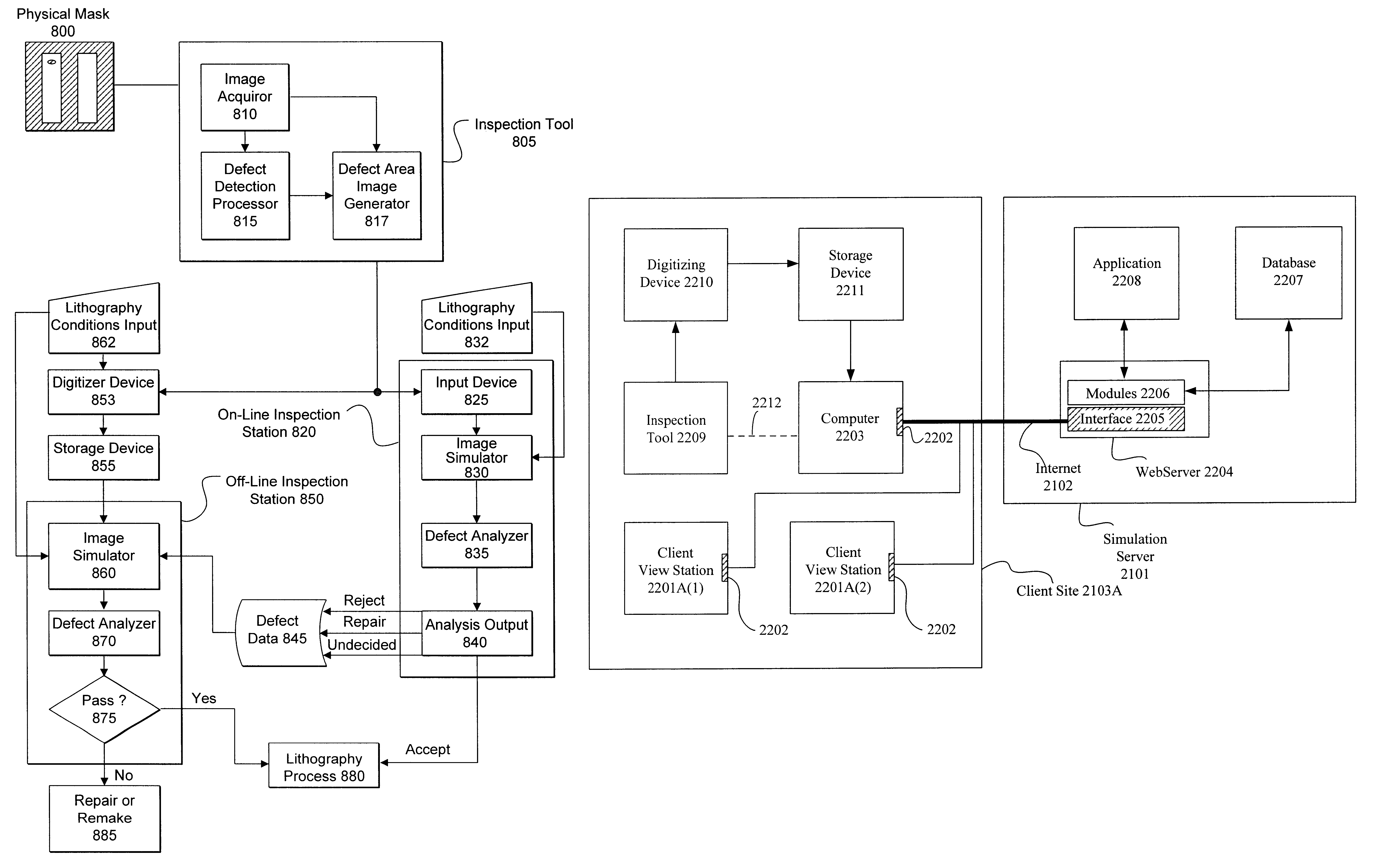
InactiveUS6578188B1Minimal additional costCode for implementing the network server is extremely robustImage enhancementNanotechThe InternetSimulation
A mask defect printability simulation server provides simulations, one-dimensional analysis, and reports to multiple clients over a wide area network, such as the Internet. This network-based simulation server allows a client to leverage a core of highly-trained engineers. Additionally, the network-based simulation server can be easily supported since only a single source for the tools associated with the simulation server is necessary for multiple clients. A client can access the simulation server using a standard personal computer having a browser, thereby eliminating the need for client to maintain an expensive database for the server. Finally, in the network-based simulation server, multiple users can view the same mask defect image and provide real-time comments to each other as simulation and analysis are performed on the defect image, thereby encouraging problem solving and decision-making dialogue among the users.
Owner:SYNOPSYS INC
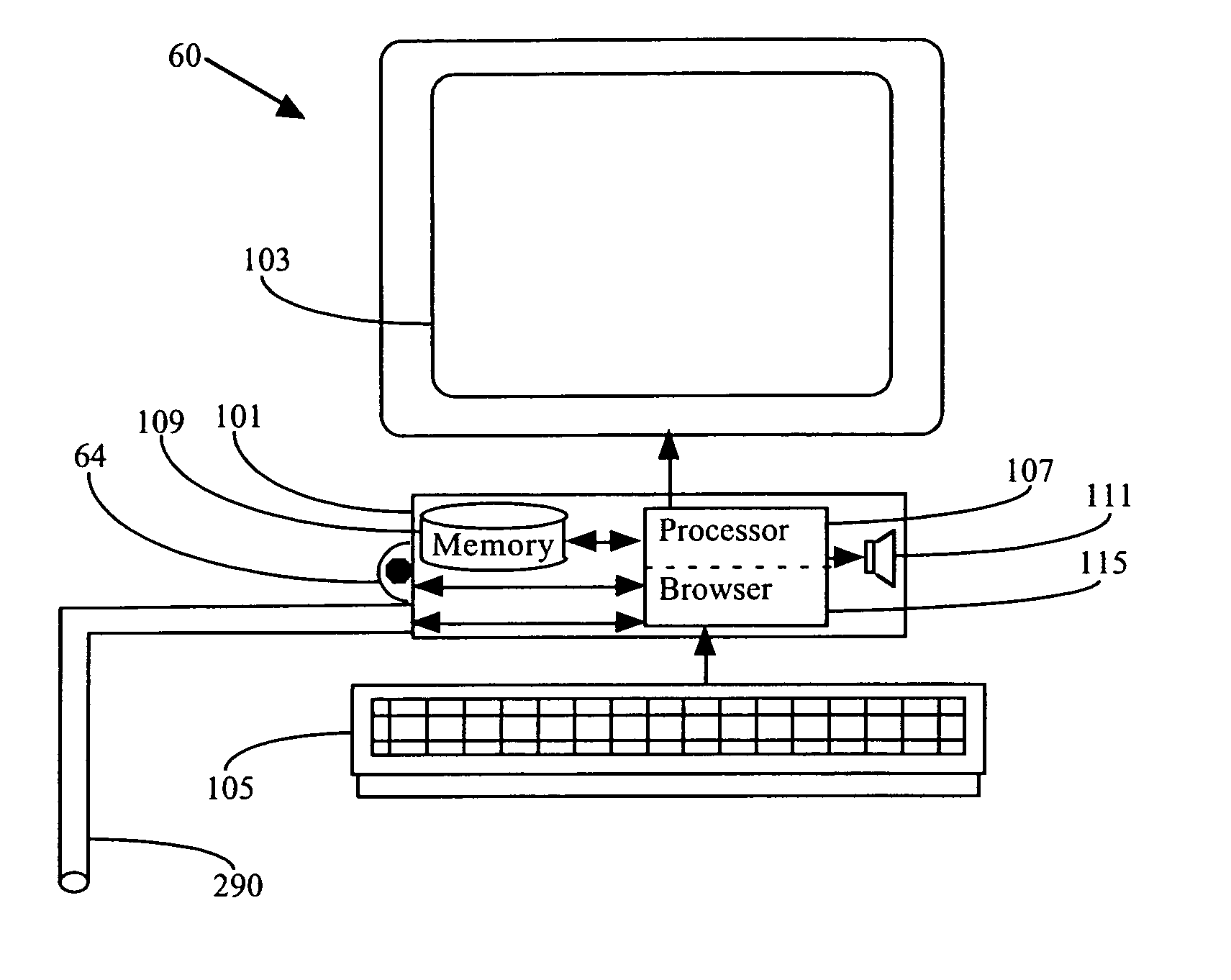
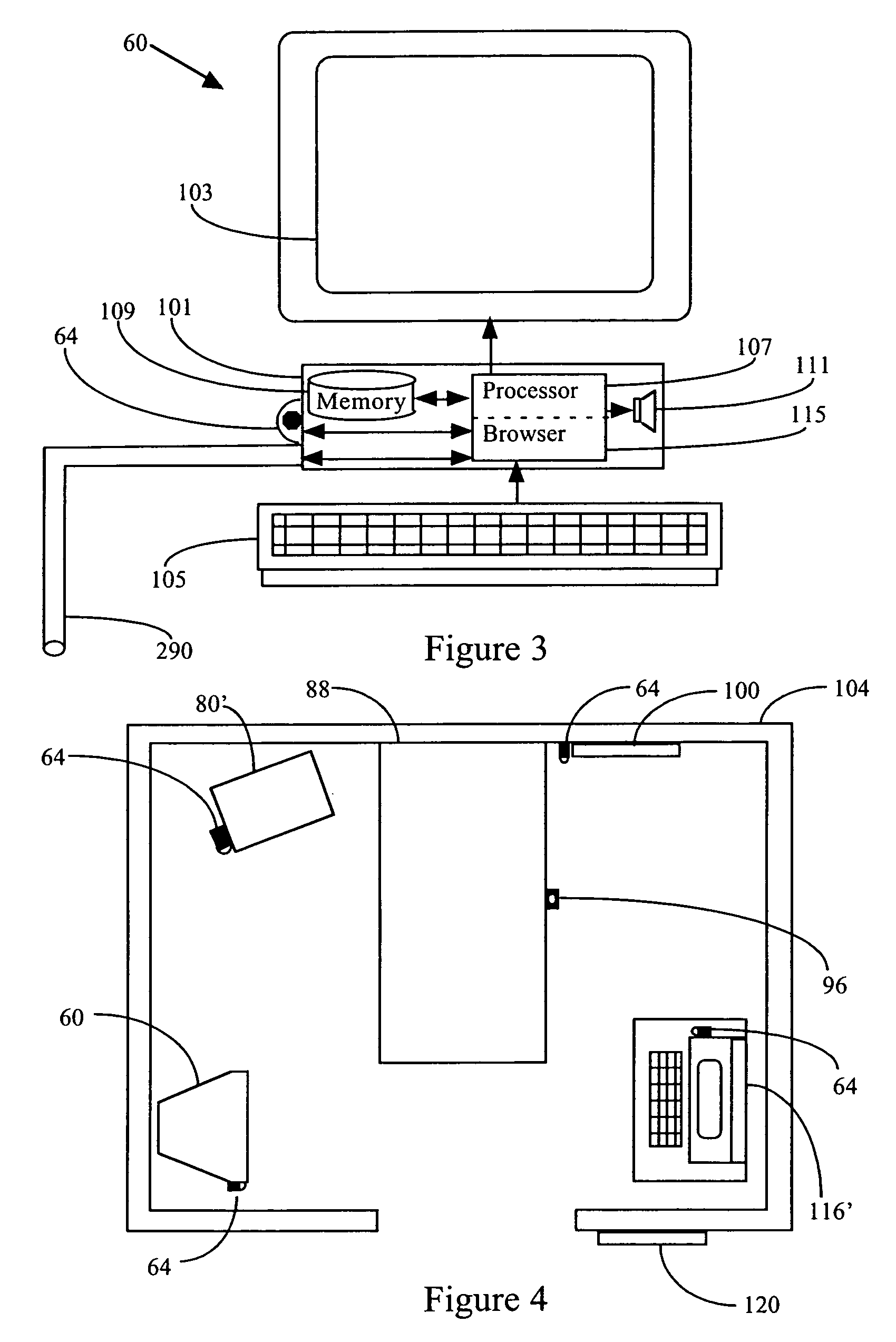
Data entry method and apparatus
InactiveUS6903723B1Shorten the timeReduce operator search timeInput/output for user-computer interactionCathode-ray tube indicatorsDisplay deviceEngineering
The apparatus and method of the invention relate to data entry and menu selection. Applications include: (a) data entry for ideographic languages, including Chinese, Japanese and Korean; (b) fast food ordering; (c) correction of documents generated by optical character recognition; and (d) computer access and speech synthesis by persons temporarily or permanently lacking normal motor capabilities. In a preferred embodiment, each option of a menu is associated respectively with a selectable region displayed adjacent an edge of a display, forming a perimeter menu and leaving a region in the center of the perimeter menu for the output of an application program. Selectable regions may be on the display, outside the display, or both. A menu option may be selected by clicking on the associated selectable region, by dwelling on it for a selection threshold period or by a cursor path toward the selectable region, or by a combination thereof. Remaining dwell time required to select a selectable region is preferably indicated by the brightness of the selectable region. Submenus of a perimeter menu may also be perimeter menus and the location of a submenu option may be foretold by the appearance of its parent menu option. Menu options may be ideographs sharing a sound, a structure or another characteristic. Ideographs, which may be homophones of one another, may be associated with colored indicating regions and selection of an ideograph may be made by speaking the name of the associated color.
Owner:FOREST DONALD K
Managing Bad Blocks In Flash Memory For Electronic Data Flash Card
InactiveUS20070283428A1Reduce search timeAvoid congestionDigital data processing detailsUser identity/authority verificationLogical block addressingComputer access
An electronic data flash card accessible by a host computer, includes a flash memory controller connected to a flash memory device, and an input-output interface circuit activated to establish a communication with the host. In an embodiment, the flash card uses a USB interface circuit for communication with the host. A flash memory controller includes an arbitrator for mapping logical addresses with physical block addresses, and for performing block management operations including: storing reassigned data to available blocks, relocating valid data in obsolete blocks to said available blocks and reassigning logical block addresses to physical block addresses of said available blocks, finding bad blocks of the flash memory device and replacing with reserve blocks, erasing obsolete blocks for recycling after relocating valid data to available blocks, and erase count wear leveling of blocks, etc. Furthermore, each flash memory device includes an internal buffer for accelerating the block management operations.
Owner:SUPER TALENT TECH CORP
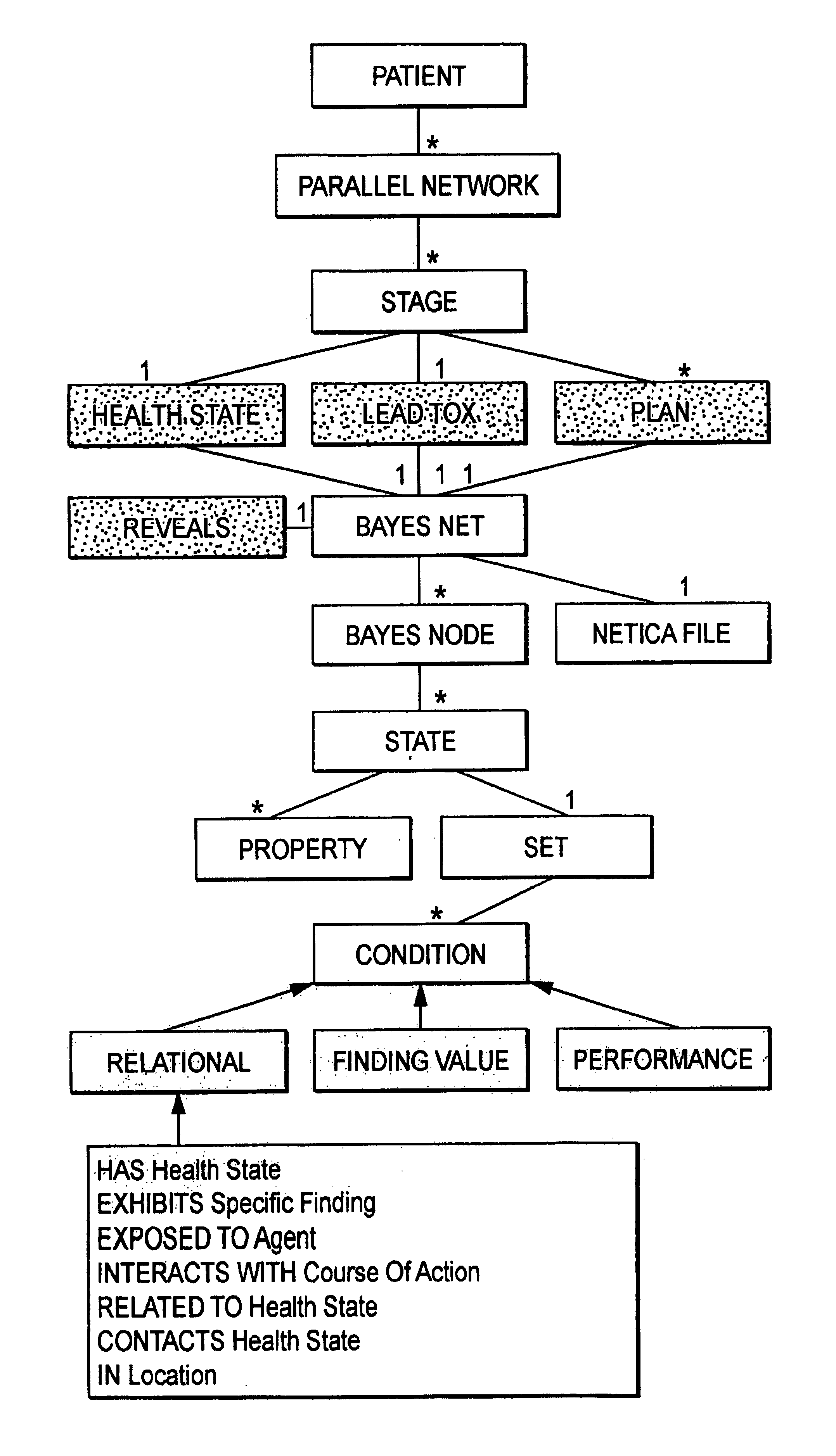
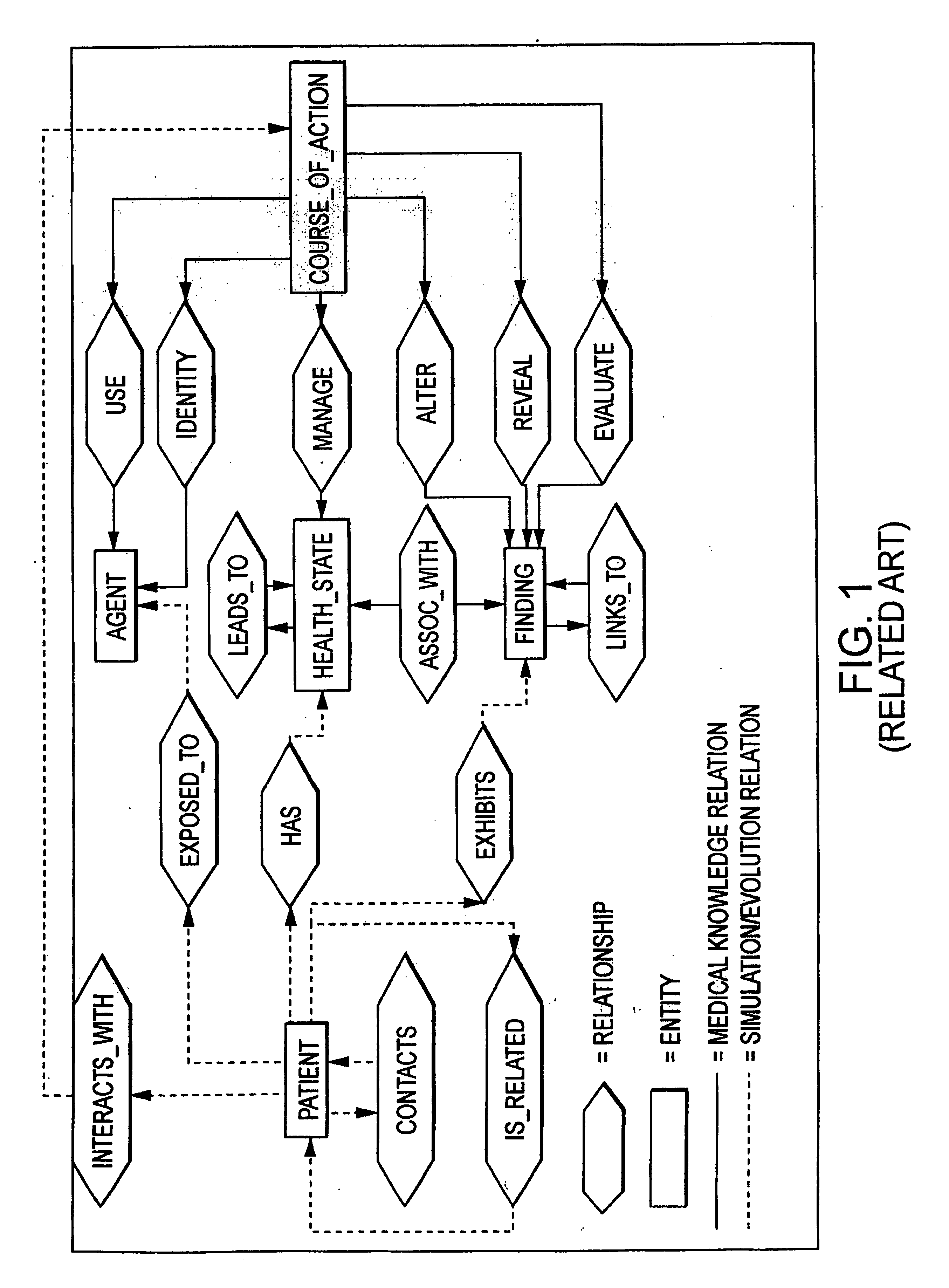
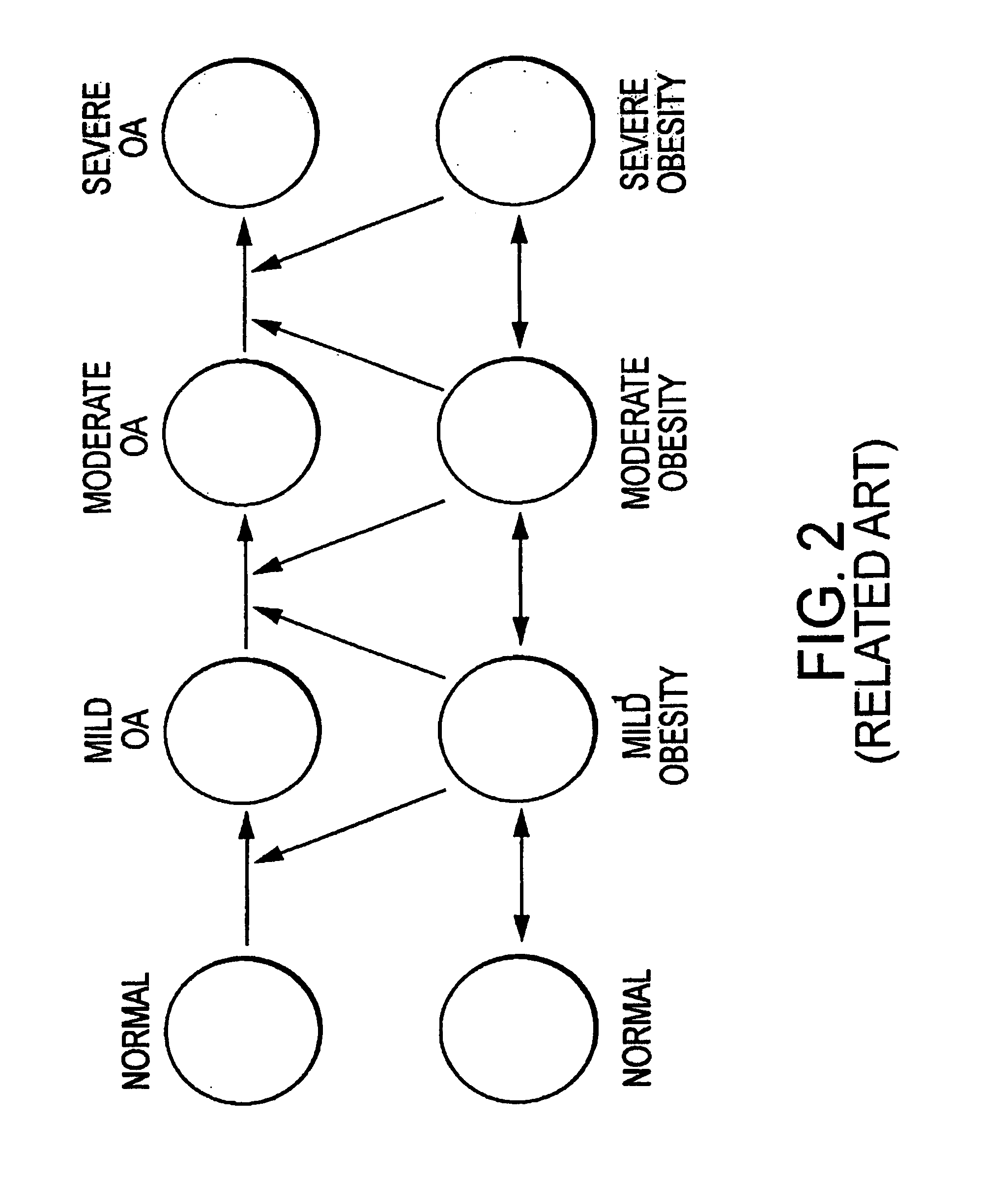
Computer architecture and process of patient generation, evolution, and simulation for computer based testing system using bayesian networks as a scripting language
InactiveUS7024399B2Economical and simpleReduce maintenance costsBiological neural network modelsComputer-assisted treatment prescription/deliveryScripting languageComputer access
A method and system for patient generation and evolution for a computer-based testing system and / or expert system. One or more belief networks, which describe parallel health state networks are accessed by a user or a computer. A knowledge base, at least in part, is scripted from the one or more belief networks by the computer. A model patient at least in part, is instantiated by the computer from the scripted knowledge base. Optionally, the model patient is evolved by the computer in accordance with the parallel health state networks and responsive to a received course of action.
Owner:AMERICAN BOARD OF FAMILY MEDICINE
End point control
ActiveUS20050144481A1Improved computing environmentDigital data processing detailsComputer security arrangementsControl systemComputer access
Systems and techniques are provided for controlling requests for resources from remote computers. A remote computer's ability to access a resource is determined based upon the computer's operating environment. The computer or computers responsible for controlling access to a resource will interrogate the remote computer to ascertain its operating environment. The computer or computers responsible for controlling access to a resource may, for example, download one or more interrogator agents onto the remote computer to determine its operating environment. Based upon the interrogation results, the computer or computers responsible for controlling access to a resource will control the remote computer's access to the requested resource.
Owner:AVENTAIL A WHOLLY OWNED SUBSIDIARY OF SONICWALL
System, computer product and method for interfacing with a private communication portal from a wireless device
InactiveUS6938076B2Data switching by path configurationMultiple digital computer combinationsPrivate communicationThe Internet
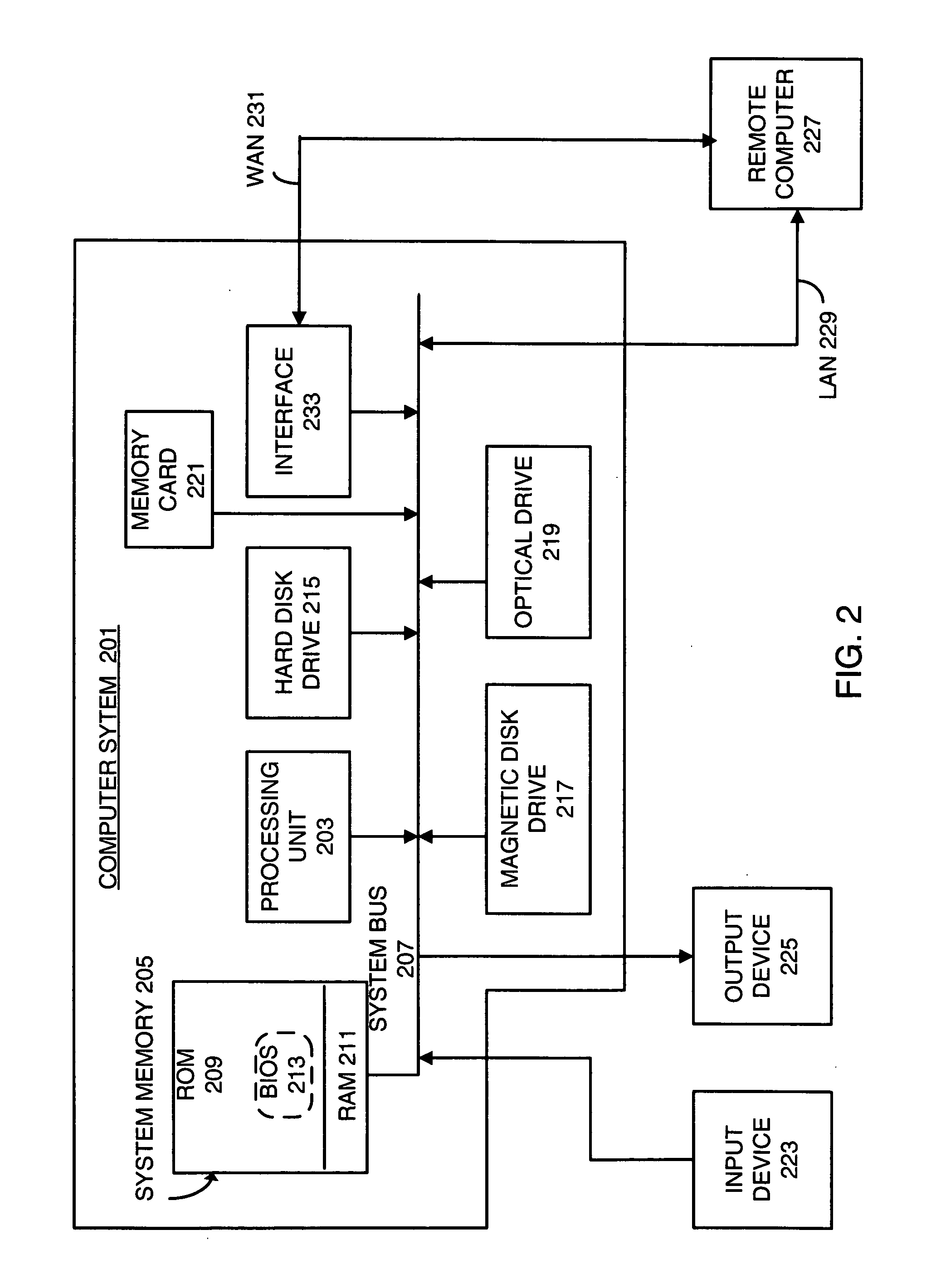
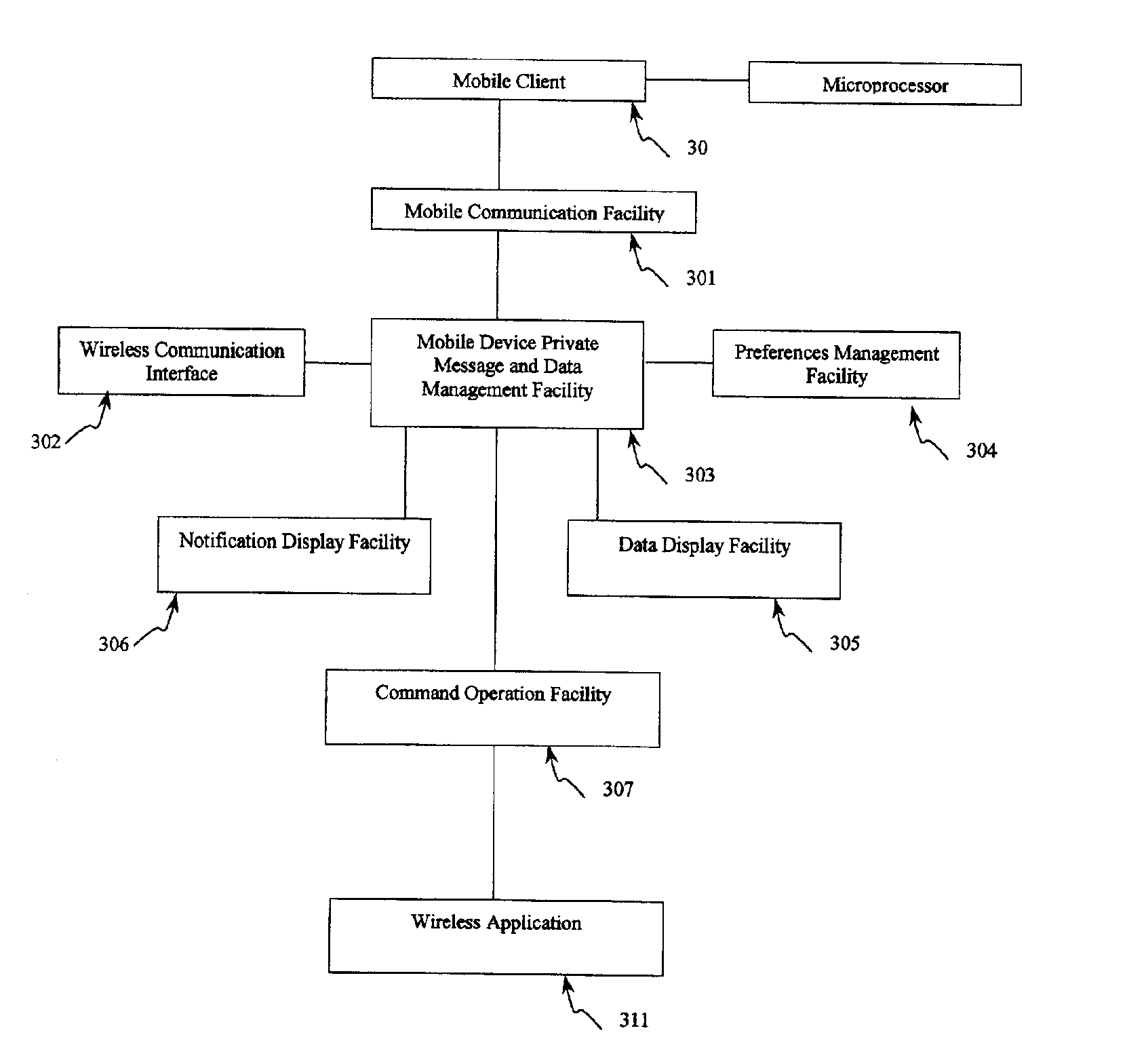
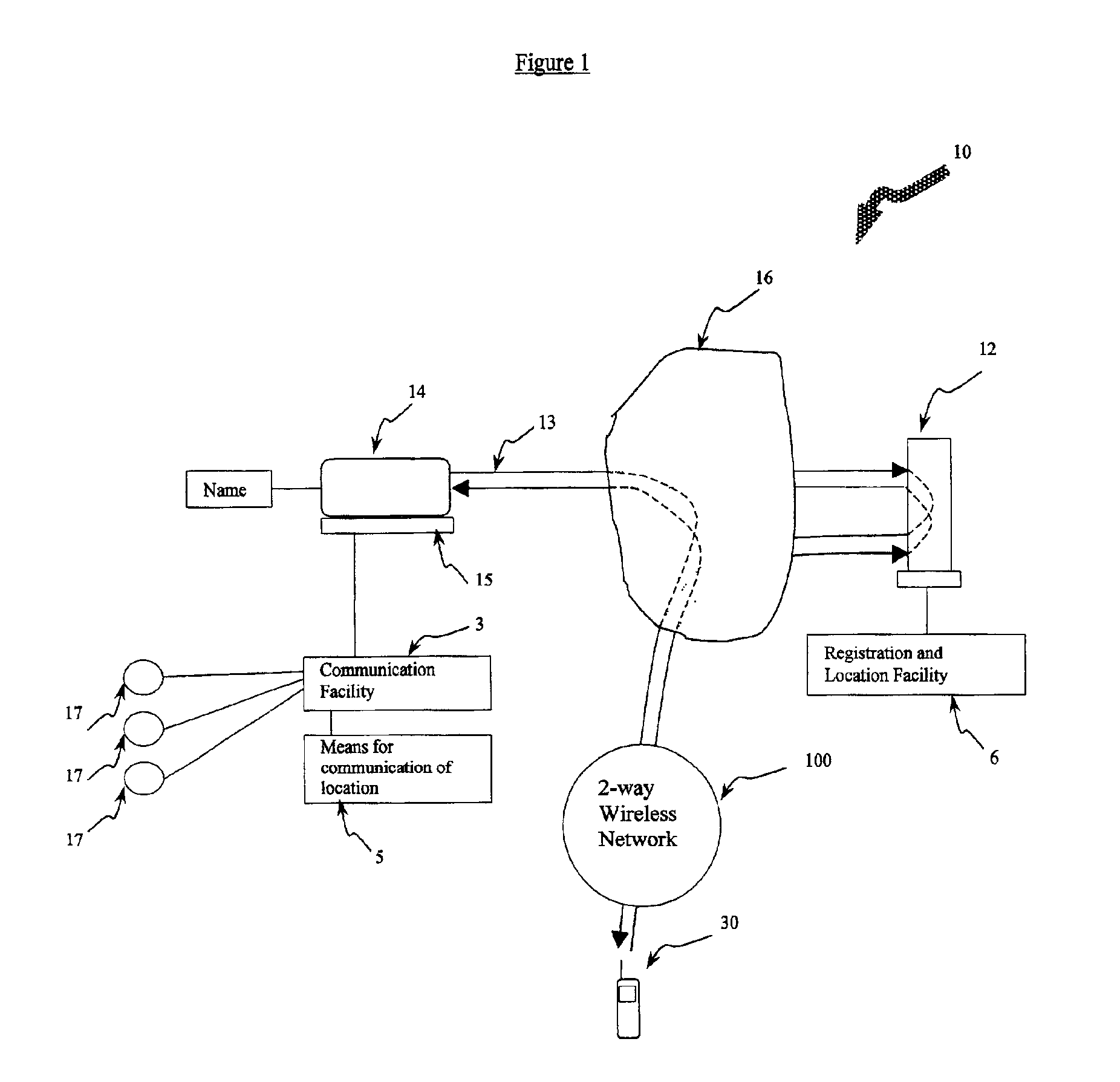
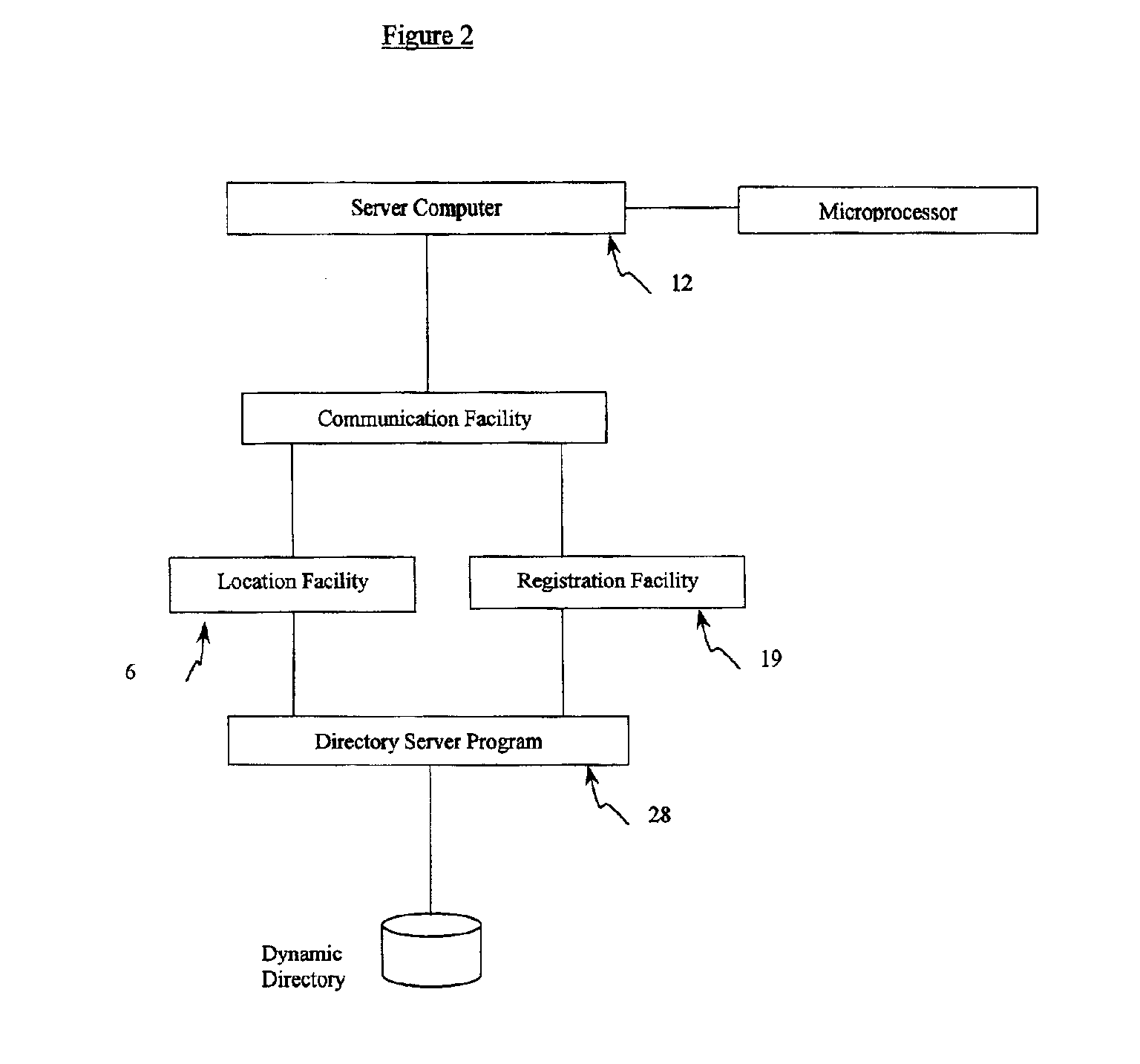
A system for providing provisioning and operation at a wireless device comprising a first computer comprising a communication facility adapted to communicate information to remote computers and the wireless device; a second computer comprising a locating facility for locating the first computer; and a wireless device comprising a microprocessor and a mobile communication facility; wherein the first computer, the second computer and the wireless device are connected to the Internet; wherein the locating facility is adapted to facilitate communication between the first computer and the wireless device; and wherein the first computer and the wireless device are adapted to permit a user of the wireless device to access information at the first computer from the wireless device.
Owner:01 COMMUNIQUE LAB INC
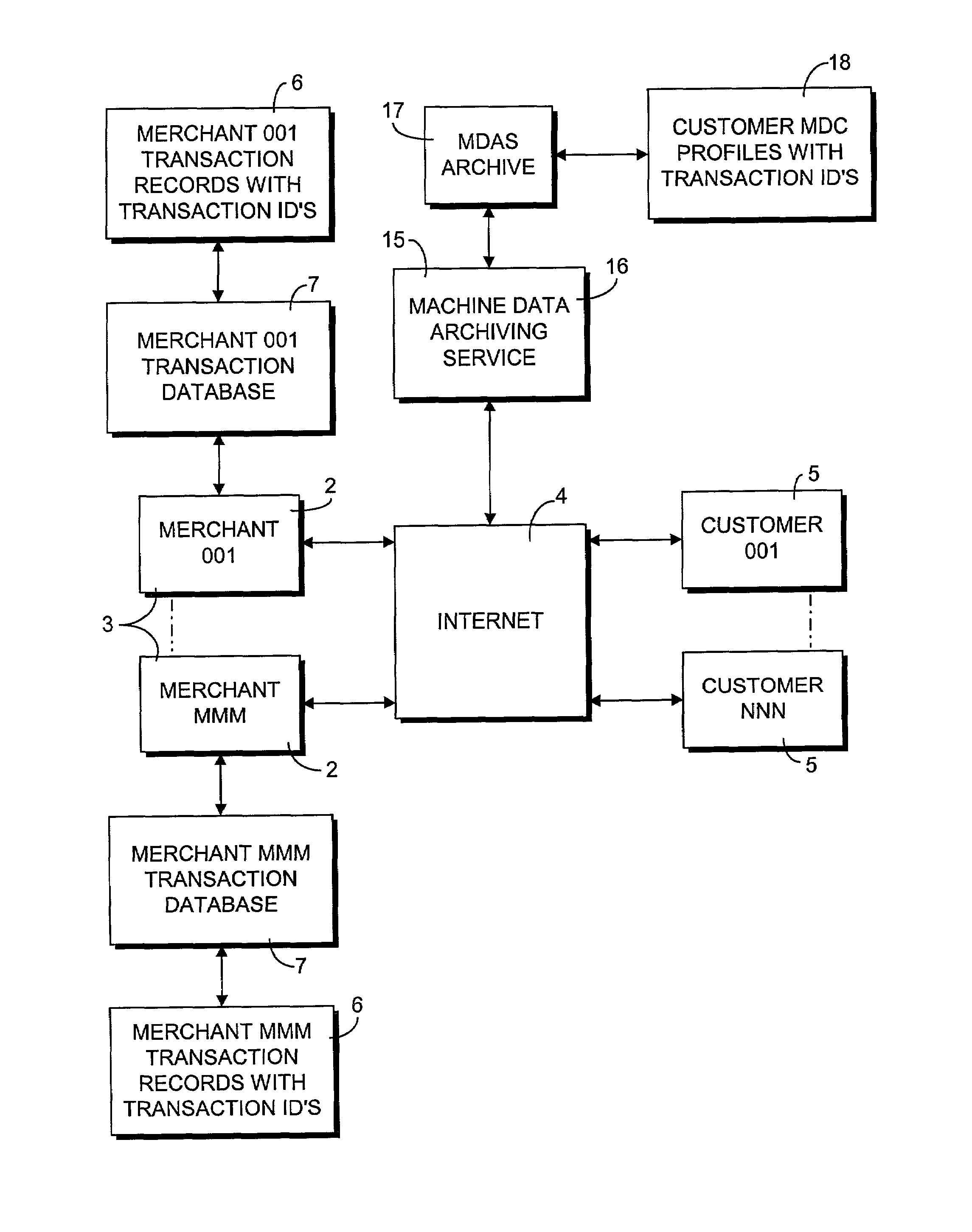
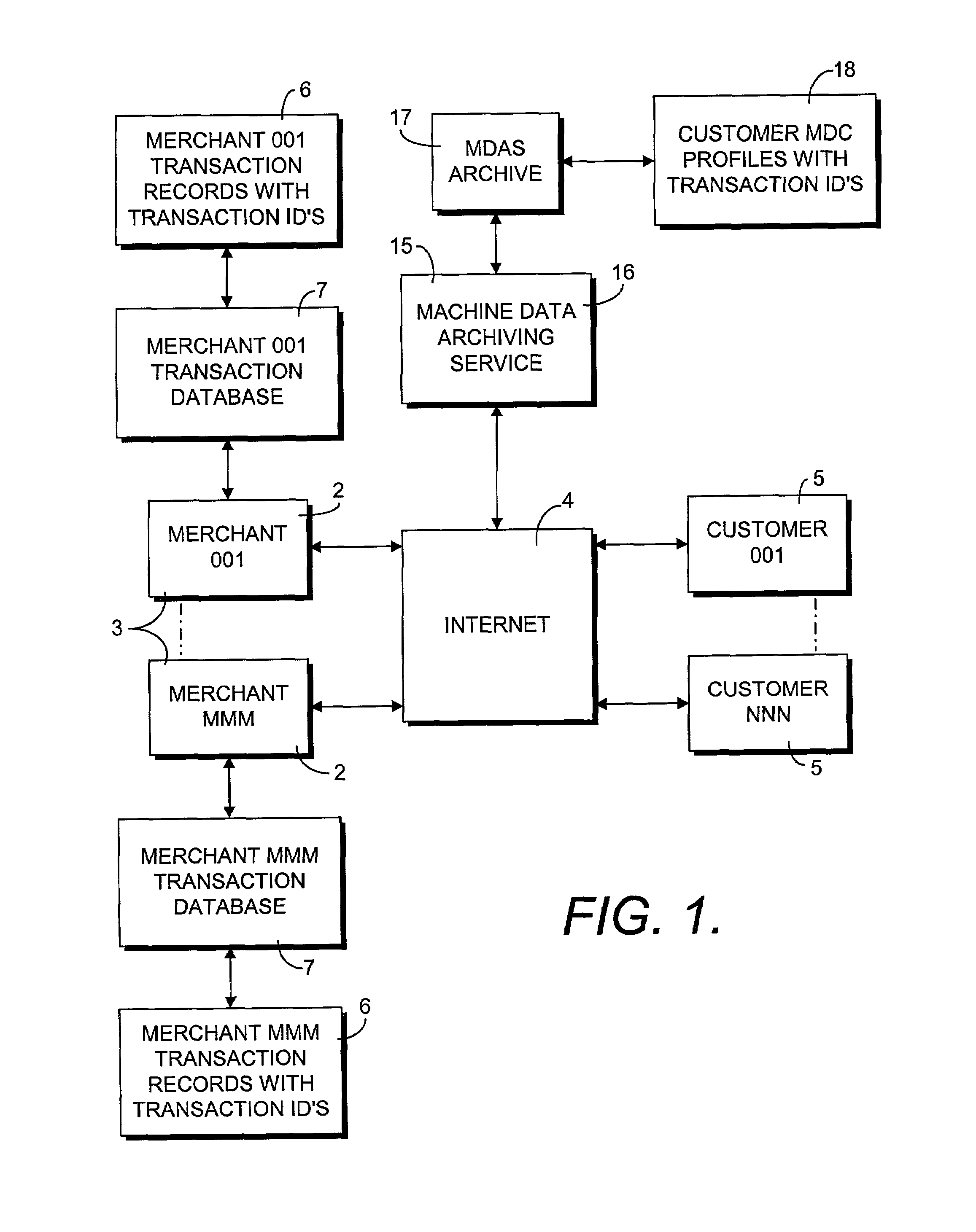
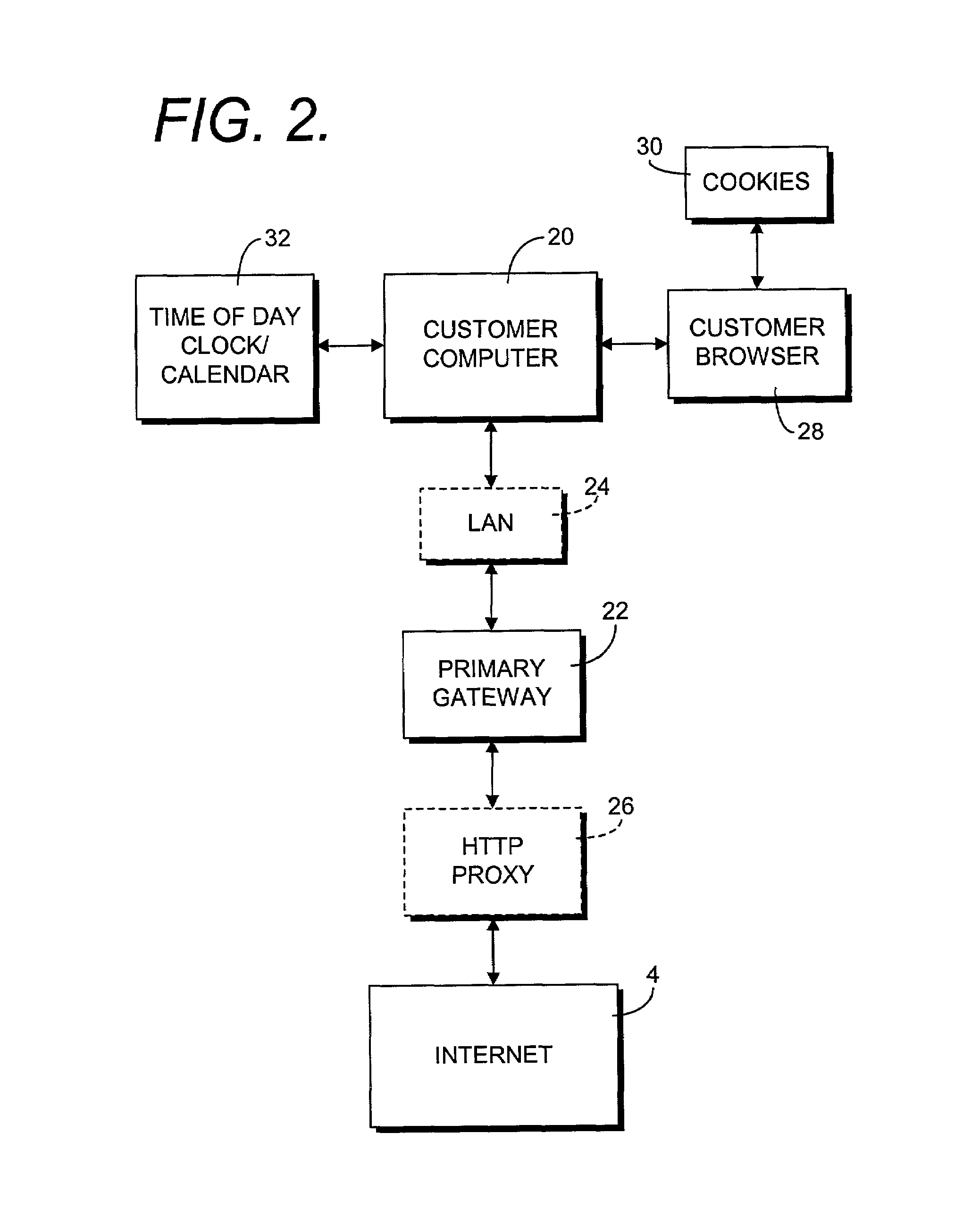
Online machine data collection and archiving process
InactiveUS7330871B2Narrow machine profileFinanceMultiple digital computer combinationsWeb siteIp address
An online machine data collection and archiving process generates a machine data profile of a customer computer accessing a transaction form of a merchant web site and links the machine data profile and a transaction record with customer identifying information using a unique transaction identification string. The process preferably captures parameters typically communicated as a part of web accesses, such as an IP address, an HTTP header, and cookie information. The process additionally causes the customer computer to process self-identification routines by processing coding within the merchant transaction form, the self-identification routines yielding further profile parameters. The process further includes a routine for bypassing an intervening proxy to the merchant web site to reveal the true IP address of the customer computer.
Owner:KOUNT
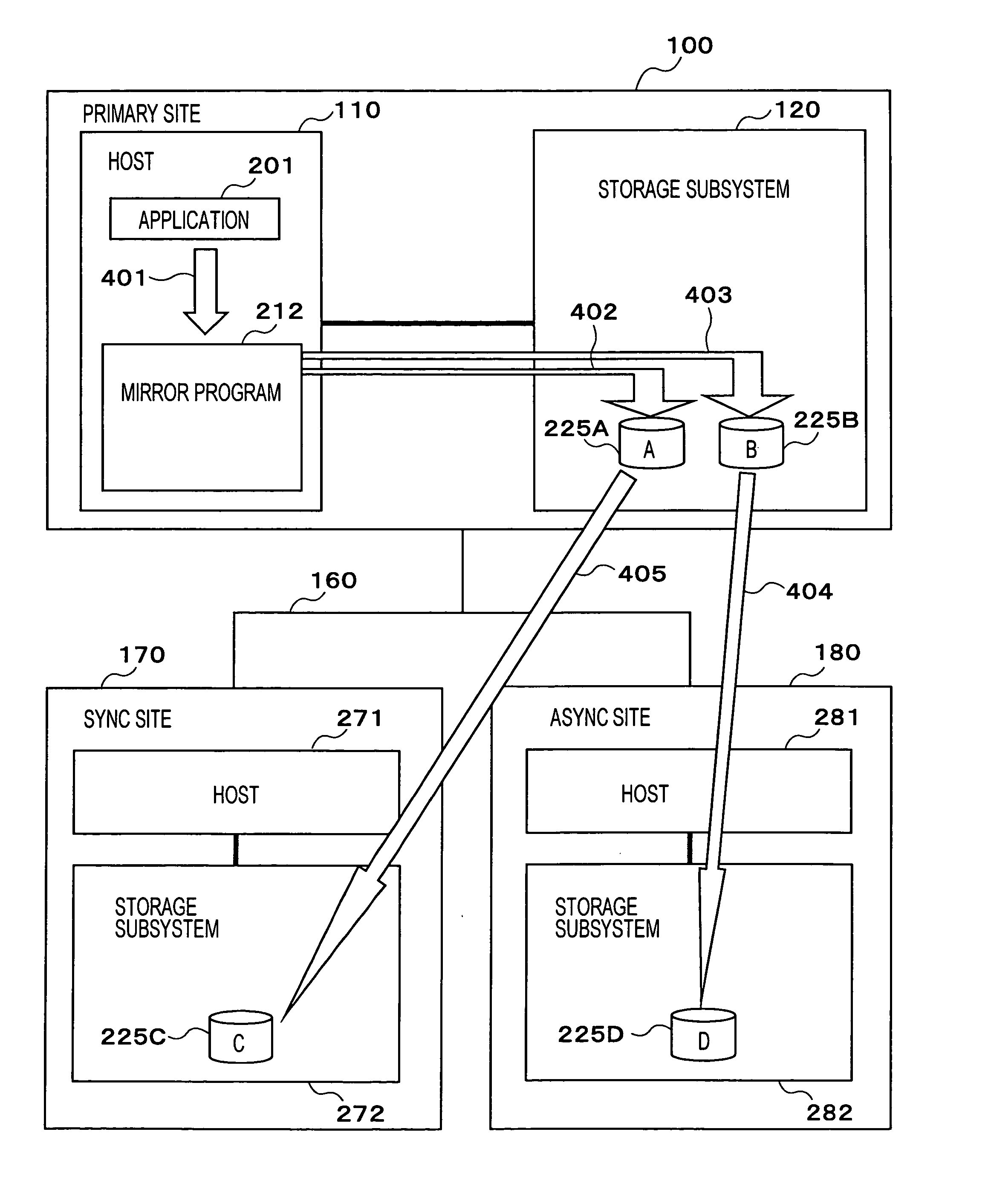
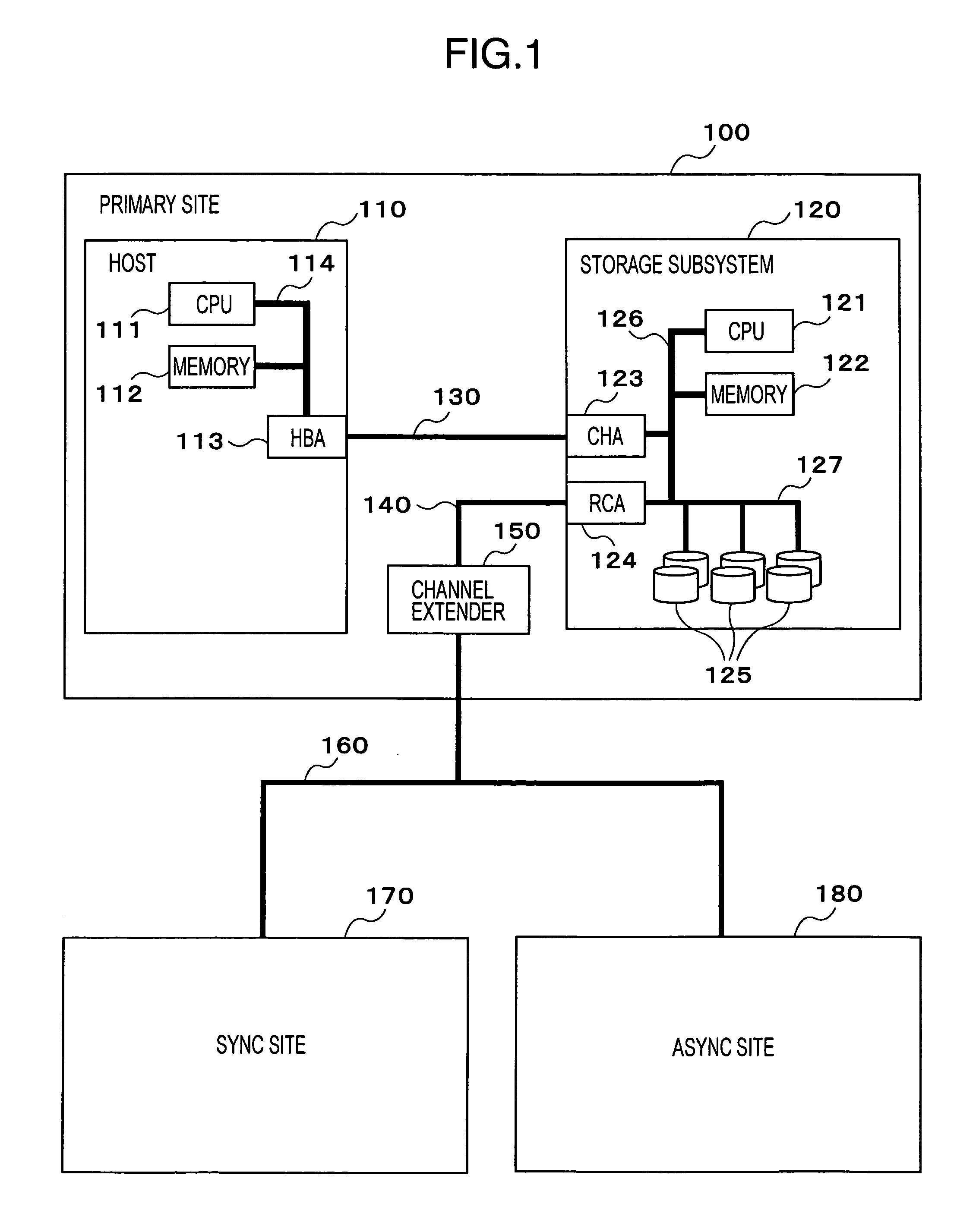
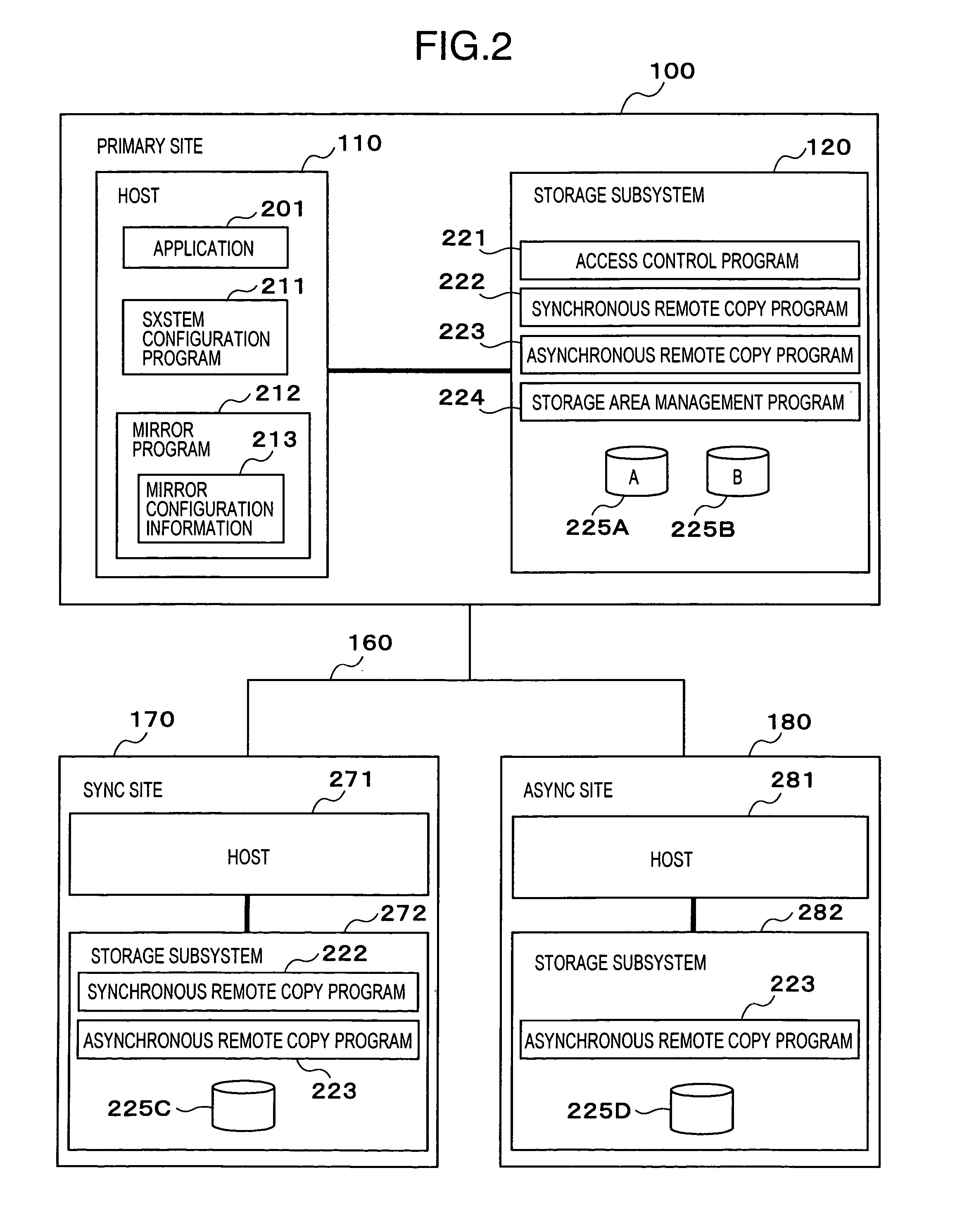
Multi-site remote-copy system
InactiveUS20050038968A1Reduce data volumeInput/output to record carriersData processing applicationsEngineeringComputer access
Two storage areas are created in a first storage subsystem, a synchronous remote copy is performed from a first storage area included in the first storage subsystem to a storage area included in a second storage subsystem, and an asynchronous remote copy is performed from a second storage area included in the first storage subsystem to a storage area included in a third storage subsystem. Besides, a computer accessing the first storage subsystem performs mirroring to both the storage areas included in the first storage subsystem.
Owner:HITACHI LTD
System and methods for providing network quarantine
InactiveUS20050131997A1Network resource is limitedMemory loss protectionDigital data processing detailsAccess networkSecure state
A system and method for ensuring that machines having invalid or corrupt states are restricted from accessing network resources are provided. A quarantine server located on a trusted machine in a network provides a bill of health to a quarantine agent located on a client computer that wishes to gain access to network resources administered by an organization. The quarantine agent requests bill of health from the quarantine server, and receives a manifest of checks that the client computer must perform. The quarantine agent then sends a status report on the checks back to the quarantine server. If the client computer is in a valid security state, the bill of health is issued to the client. If the client computer is in an invalid state, the client is directed to install the appropriate software / patches to achieve a valid state. When a client requests the use of network resources from a network administrator, the network administrator requests the client's bill of health. If the bill of health is valid, the client is admitted to the network. If the bill of health is invalid, or if the client does not have a quarantine agent, the client is placed in quarantine, in which the only network resources accessible to the client are those necessary to install the quarantine agent and requisite software / patches to achieve a valid state.
Owner:MICROSOFT TECH LICENSING LLC
System and method for identifying data streams associated with medical equipment
A system and method for uniquely identifying data streams associated with medical equipment are described. The system may be implemented in a variety of ways, including as a combination of a medical device, a data stream identifier, and a medical device identifier. The medical device generates a plurality of data streams. The data streams are uninterrupted transmissions of data from the medical device. The data streams include information regarding the operation of the medical device. The data stream identifier attaches a unique data tag to the data streams. The medical device identifier is configured to generate a medical device tag. The medical device tag includes information to uniquely identify the medical device and is accessible from an external computer. The data stream identifier and the medical device identifier are secured to the medical device.
Owner:BAXTER INT INC
Methods and systems for preemptive and predictive page caching for improved site navigation
InactiveUS20030088580A1Digital data information retrievalMultiple digital computer combinationsWeb siteRemote computer
A method for a first computer to request documents from a second computer includes steps of sending a first request for a first document to the second computer responsive to a first user action, receiving the first document sent by the second computer responsive to the first request; identifying all references to second documents in the received first document; independently of any user action, automatically sending a second request for at least one of the second documents referred to by the identified references; receiving the second document(s) requested by the second request and storing the received second document(s) in a storage that is local to the first computer, and responsive to a user request for one or more of the second documents, attempting first to service the user request from the local storage and sending a third request to the second computer for second document(s) only when the second document(s) is not stored in the local storage. A method of servicing a request for access to a Web site by a remote computer may include a receiving step to receive the request for access to the Web site; a first sending step to send a first page of the accessed Web site to the remote computer responsive to the request, and independently of any subsequent request for a second page of the Web site originating from the remote computer, preemptively carrying out a second sending step to send the remote computer at least one selected second page based upon a prediction of a subsequent request by the remote computer and / or a history of second pages previously accessed by the remote computer.
Owner:ORACLE INT CORP
Image-overlay medical evaluation devices and techniques
InactiveUS20130172731A1Easy to makePromote lowerImpression capsAdditive manufacturing apparatusDisplay deviceComputer access
A system and methods are provided for evaluating the position of surgical implants or openings formed in anatomical tissue during medical procedures, in which an initial 3-dimensional image of the anatomical tissue is combinable with one or more subsequent 3-dimensional images of the same or correlating tissue, and without the use of ionizing radiation on a patient for at least the subsequent images. The system includes a software program, a computer with display, a radiographic image scanning device, and a non-radiographic image scanning device. The computer accesses a medical patient information database and a medical implant database for images used by the software program. A pre-operative image is combined with subsequent images to facilitate evaluation of the proposed placement of a surgical implant or opening relative to tissues of the patient anatomy. Methods of evaluating the accuracy of surgical guides and of fabricating surgical guides are also disclosed.
Owner:GOLE PHILIP D
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com