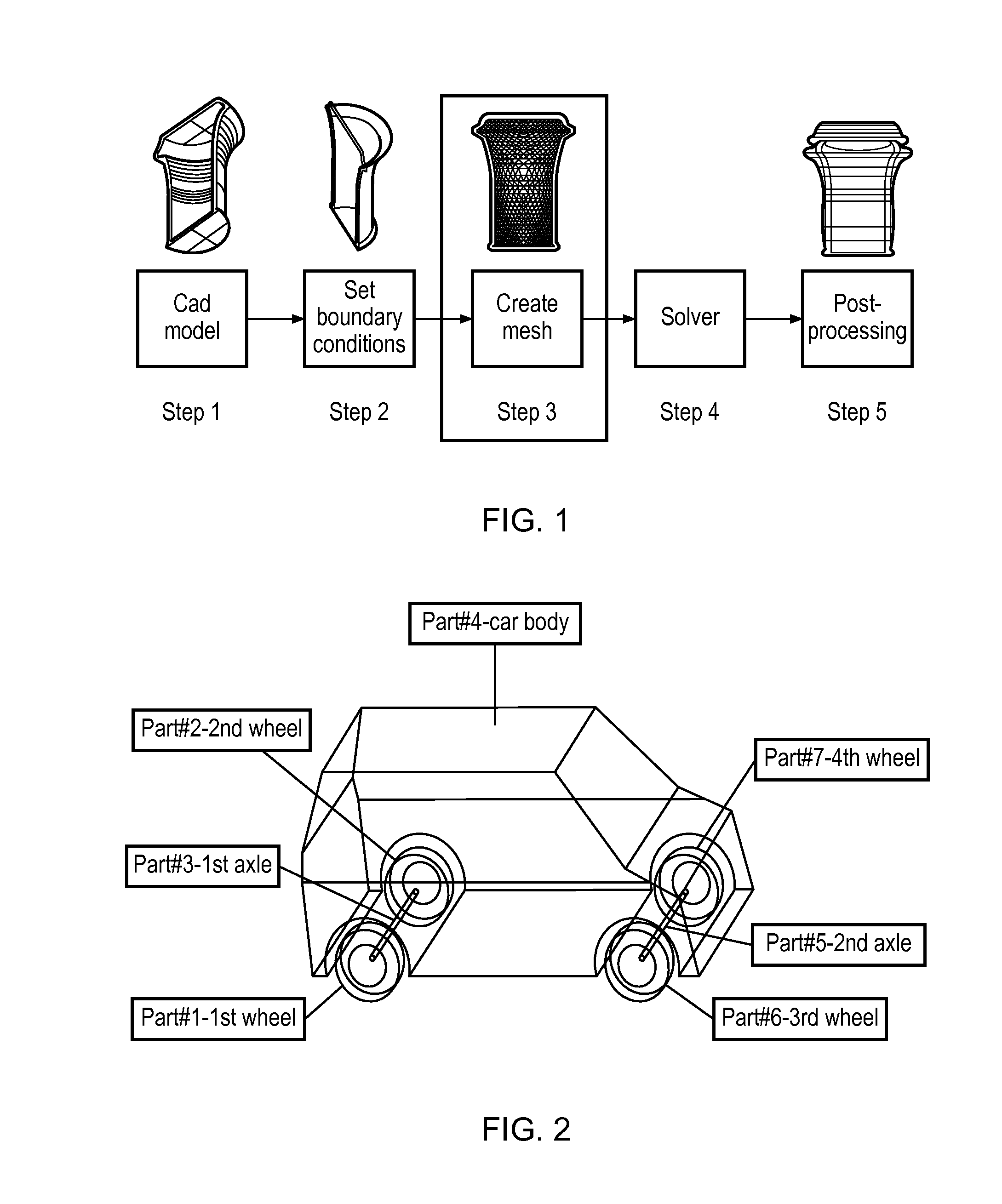
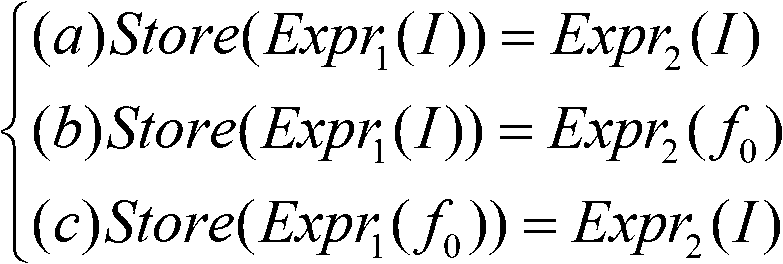Patents
Literature
767 results about "Assembly" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
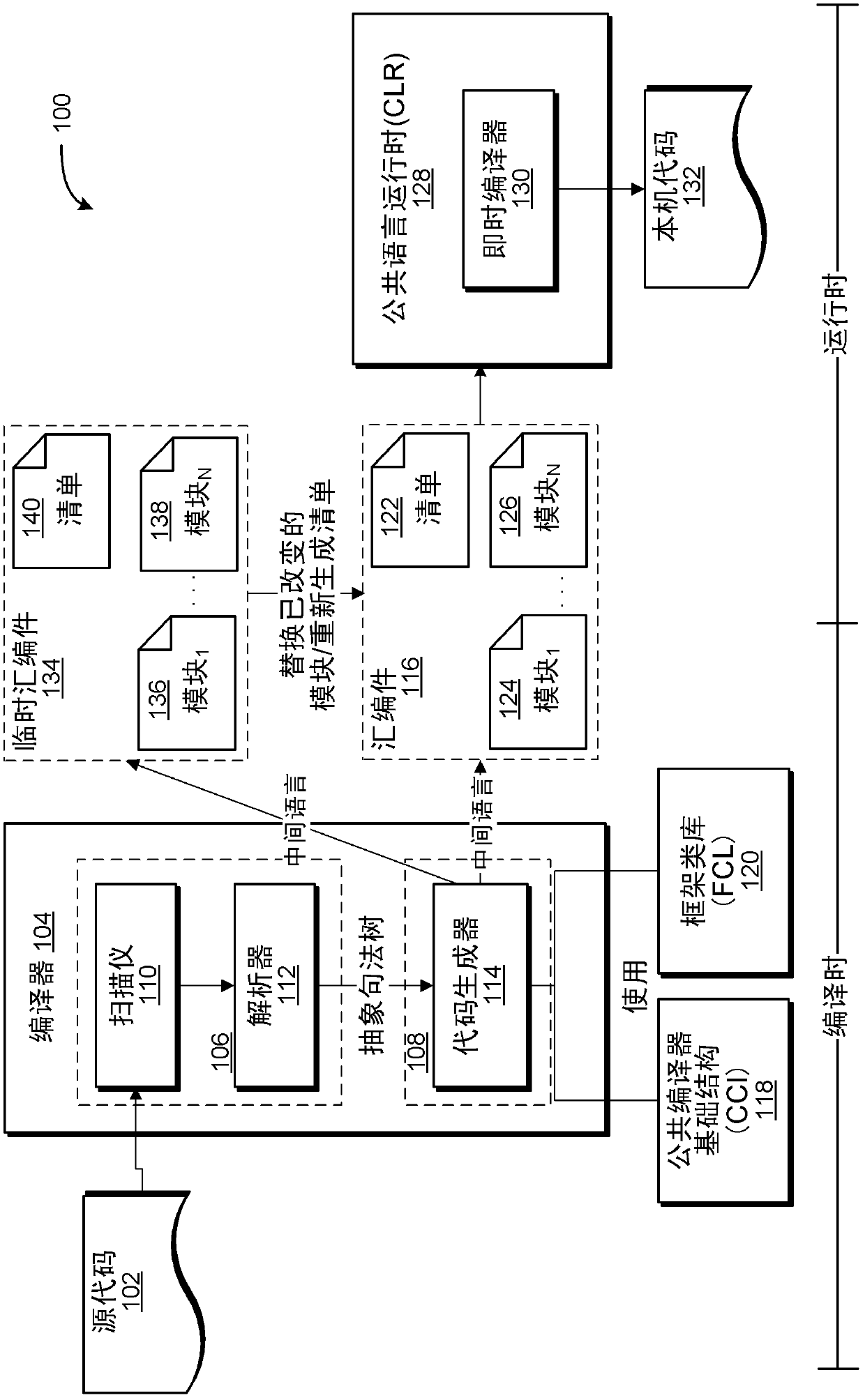
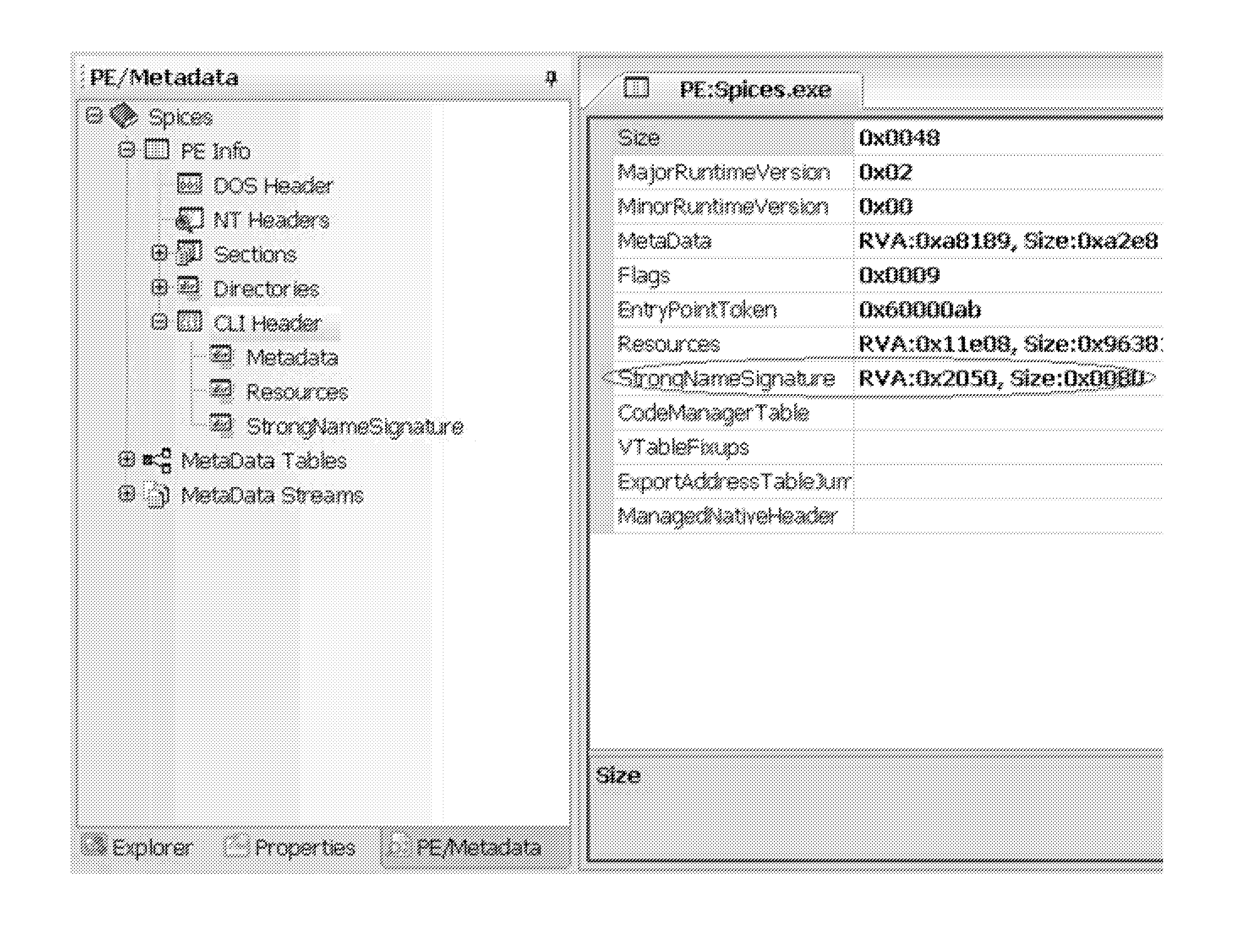
In computer programming an assembly is a runtime unit consisting of types and other resources. All types in an assembly have the same version number. Often, one assembly has only one namespace and is used by one program. But it can span over several namespaces. Also, one namespace can spread over several assemblies. In large designs, an assembly may consist of multiple files that are held together by a manifest (i.e. a table of contents).
System and method for securing sensitive data
ActiveUS20140344943A1Digital data processing detailsUser identity/authority verificationSoftware engineeringOperating system
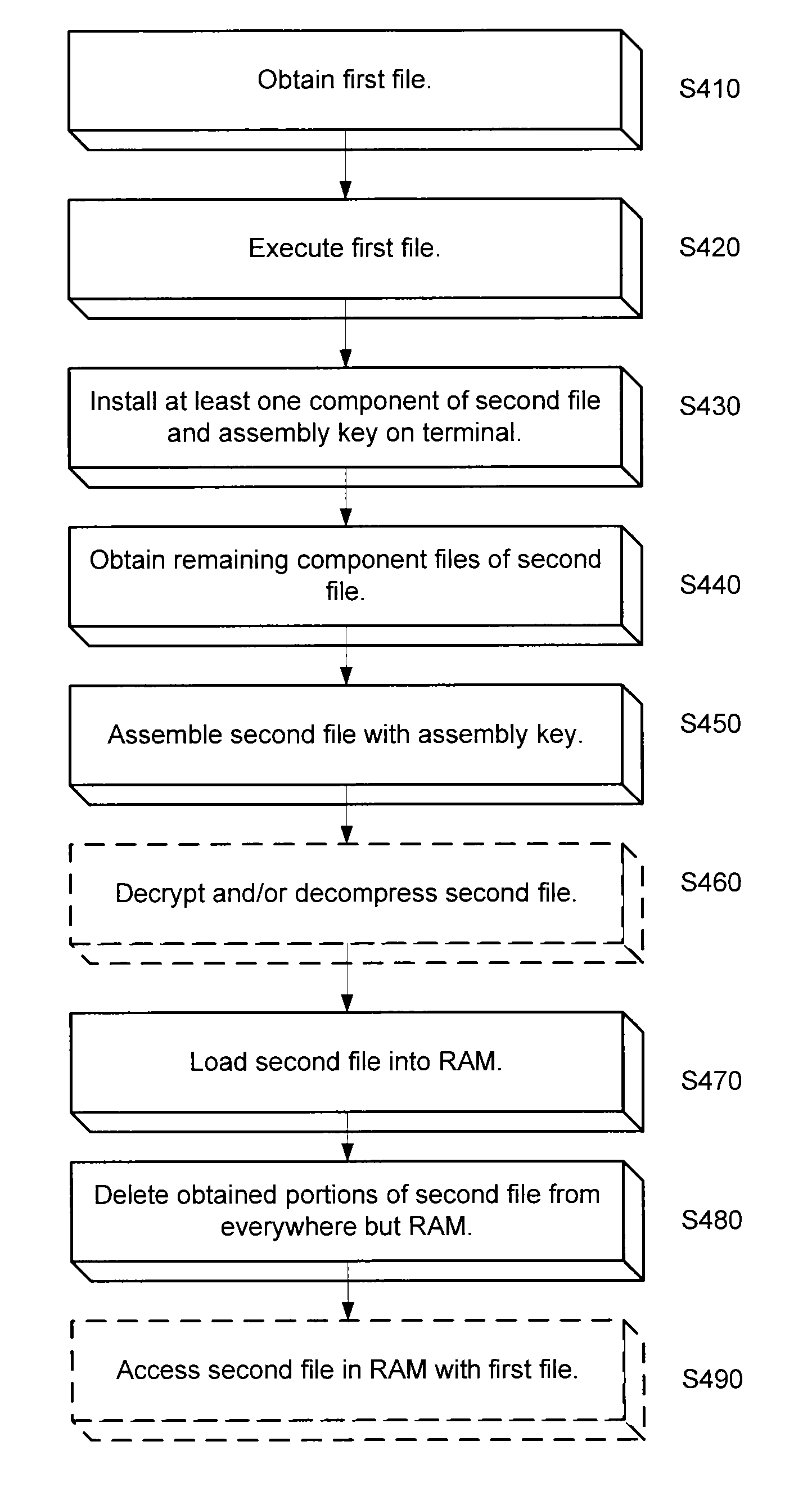
An approach is provided for securing data in a technical environment. In one embodiment, a processor obtains a first file, which when executed installs a first portion of a second file and an assembly key to assemble the second file. The processor executes this first file and then obtains the second portion of the second file. The processor assembles the second file using the first portion, the second portion, and the assembly key.
Owner:HAND HELD PRODS
Method for accessing relational databases of different types
InactiveCN101645074AReduce complexityExecution efficiency advantageSpecial data processing applicationsRound complexitySyntax
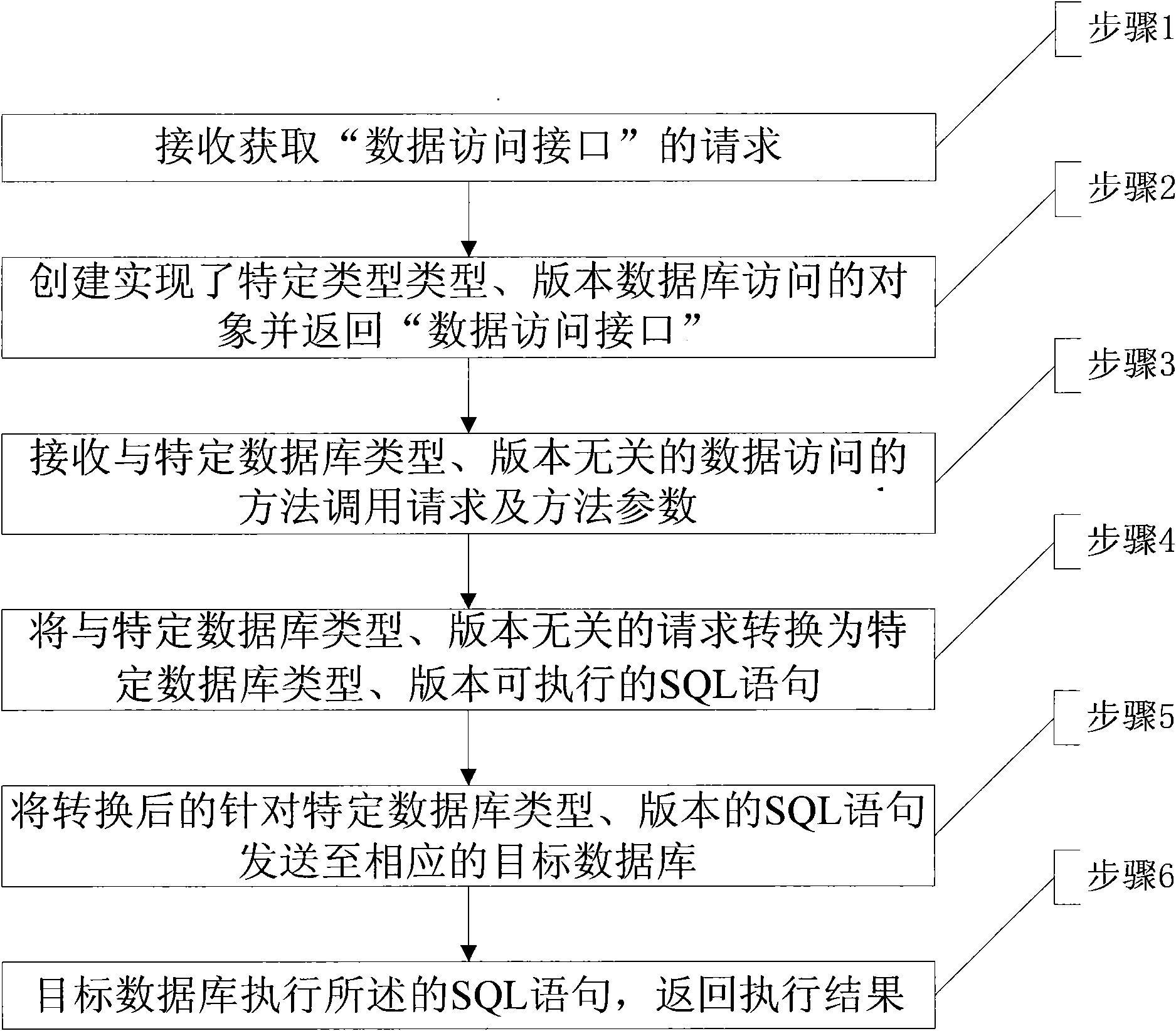
The invention relates to a method for accessing relational databases of different types, comprising the following steps: encapsulating aiming at difference by analyzing and identifying the differenceof the relational databases of different types and editions; externally providing a consistent programming access interface in an assembly way, uniformly transferring a standard and a writing form foran SQL statement syntax and various database functions and commands and shielding the difference caused by the relational databases of different types and editions; internally respectively and pointedly realizing the shielding of the difference according to the types and the editions of the databases, and when the difference of the types and the editions of the databases is shielded, using two methods, i.e. the programming access interface and the SQL statement syntax, to encapsulate the difference. The two methods can be used together, therefore not only the effect on shielding the difference of the types and the editions of the databases can be achieved but also the complexity of realizing programming can be lower; meanwhile, the invention is lighter and has obvious advantages on execution efficiency corresponding to a way of using a complete private SQL statement syntax to define, analyze and translate the SQL statement syntax.
Owner:INSPUR COMMON SOFTWARE
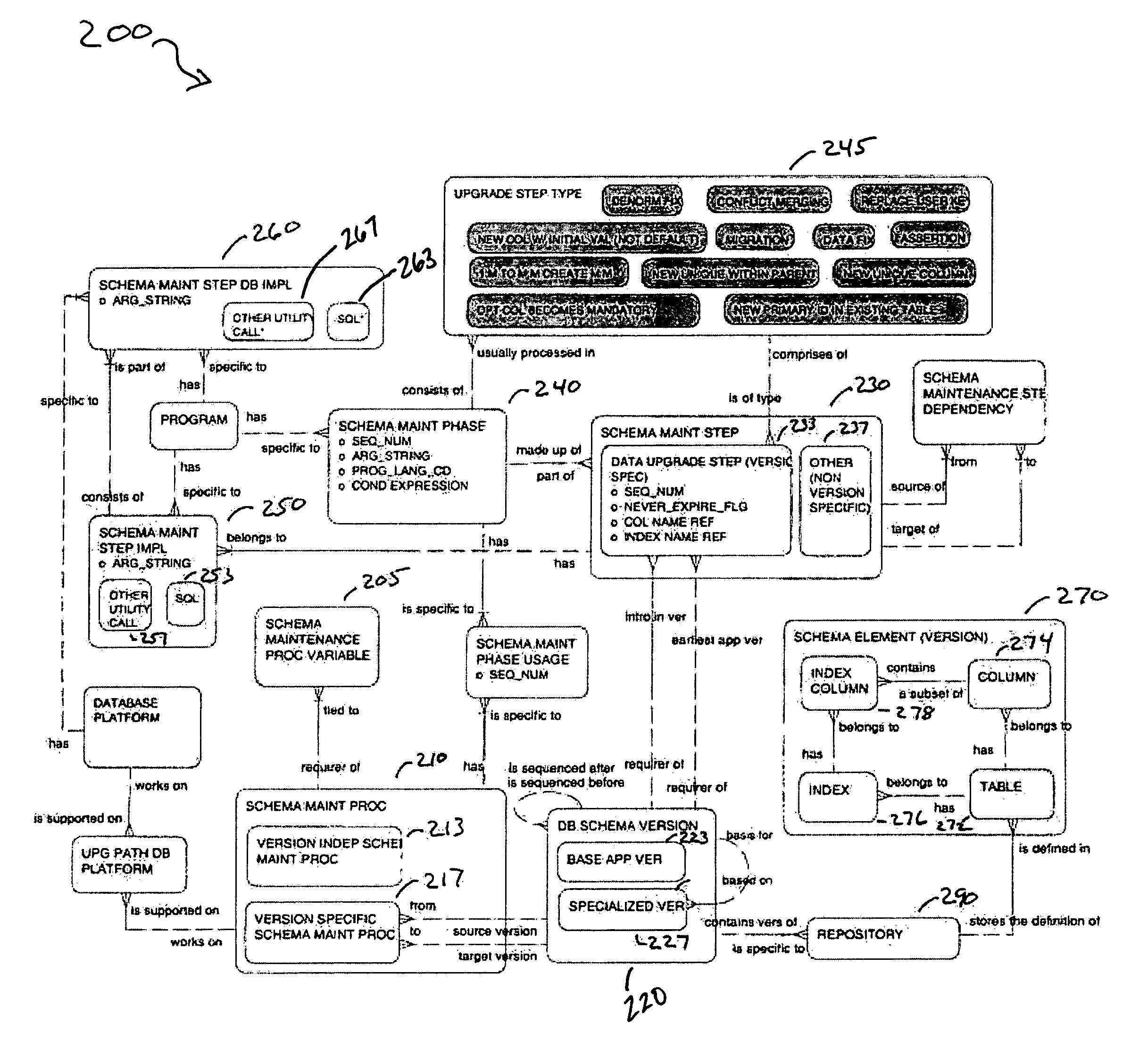
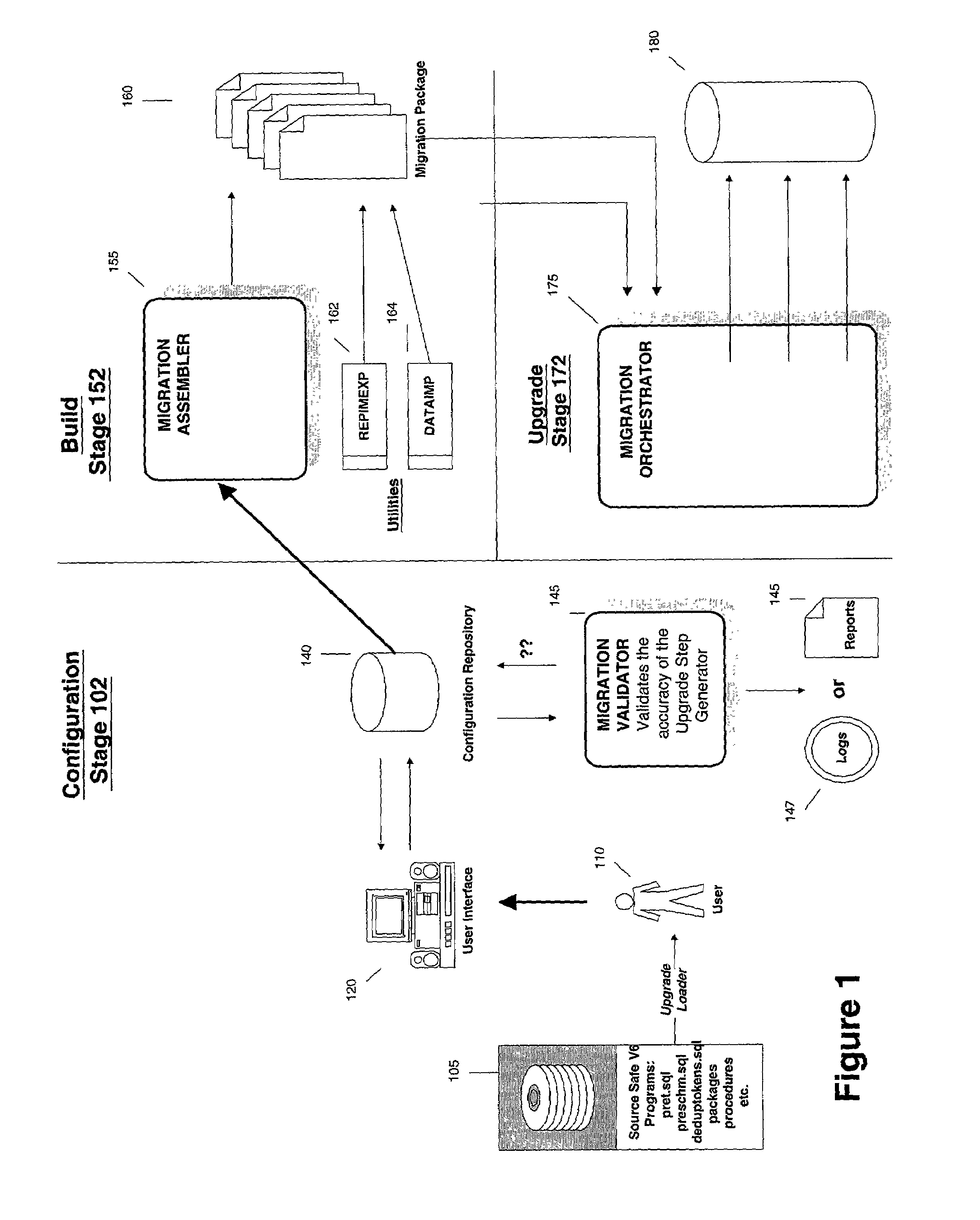
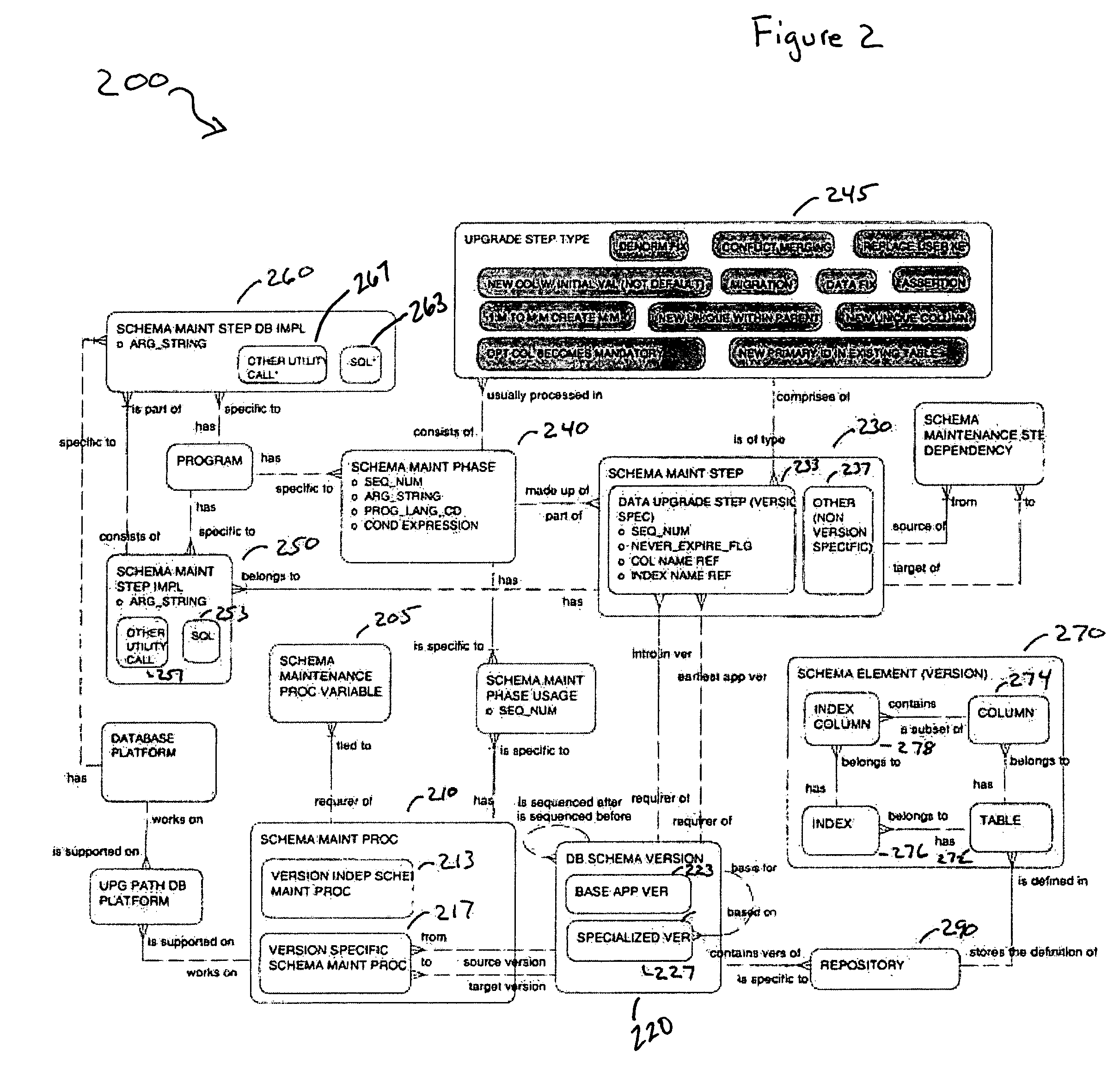
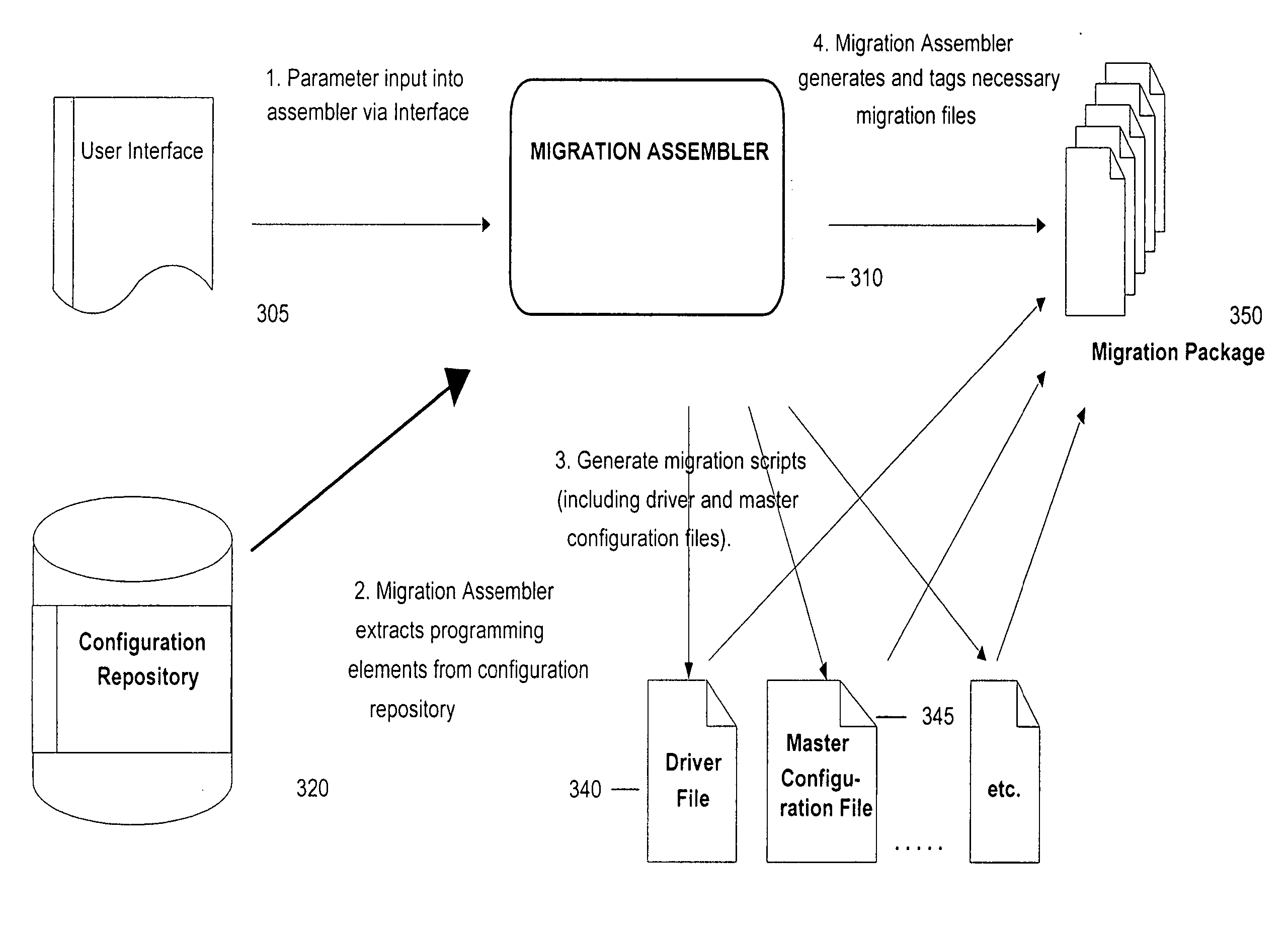
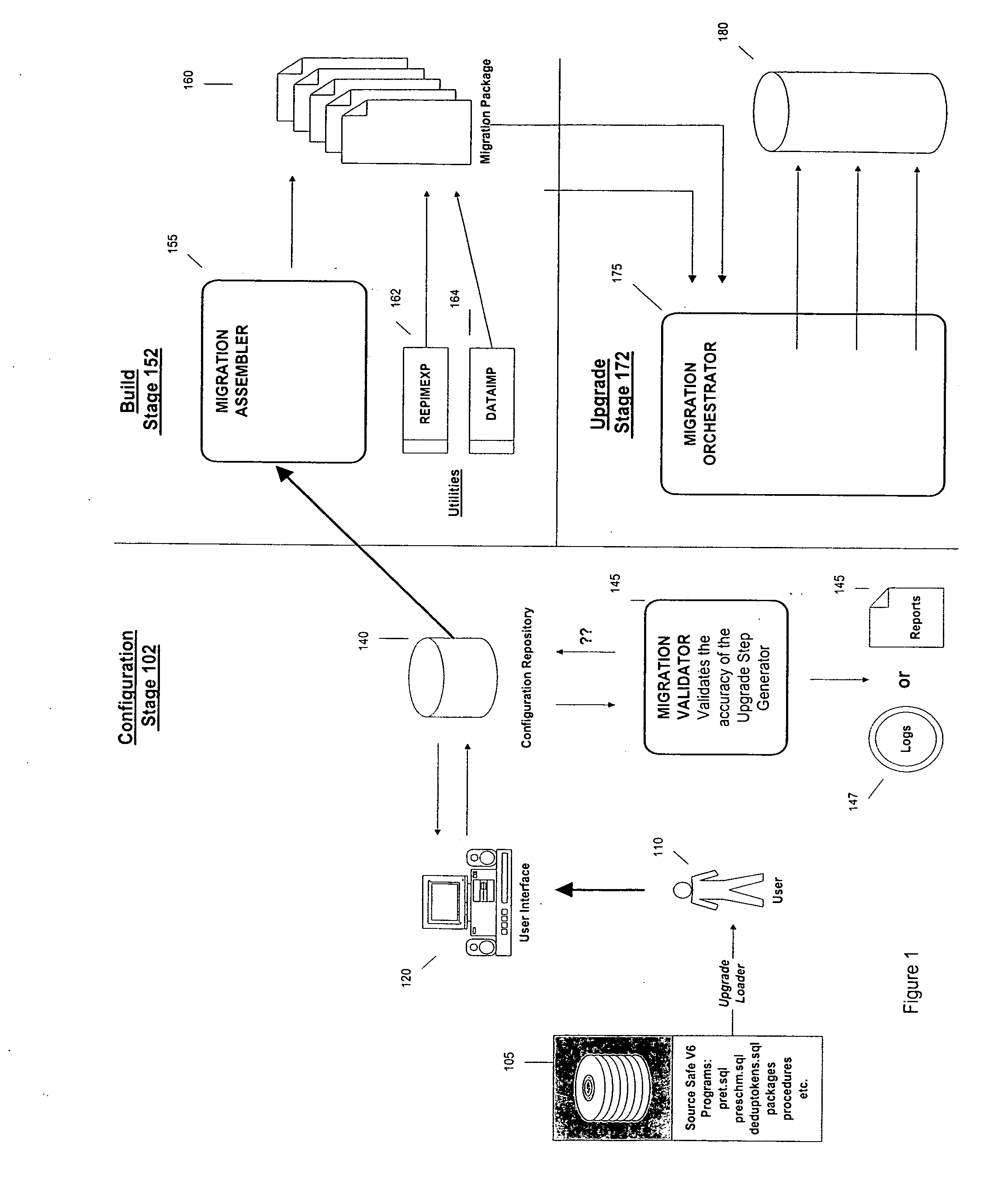
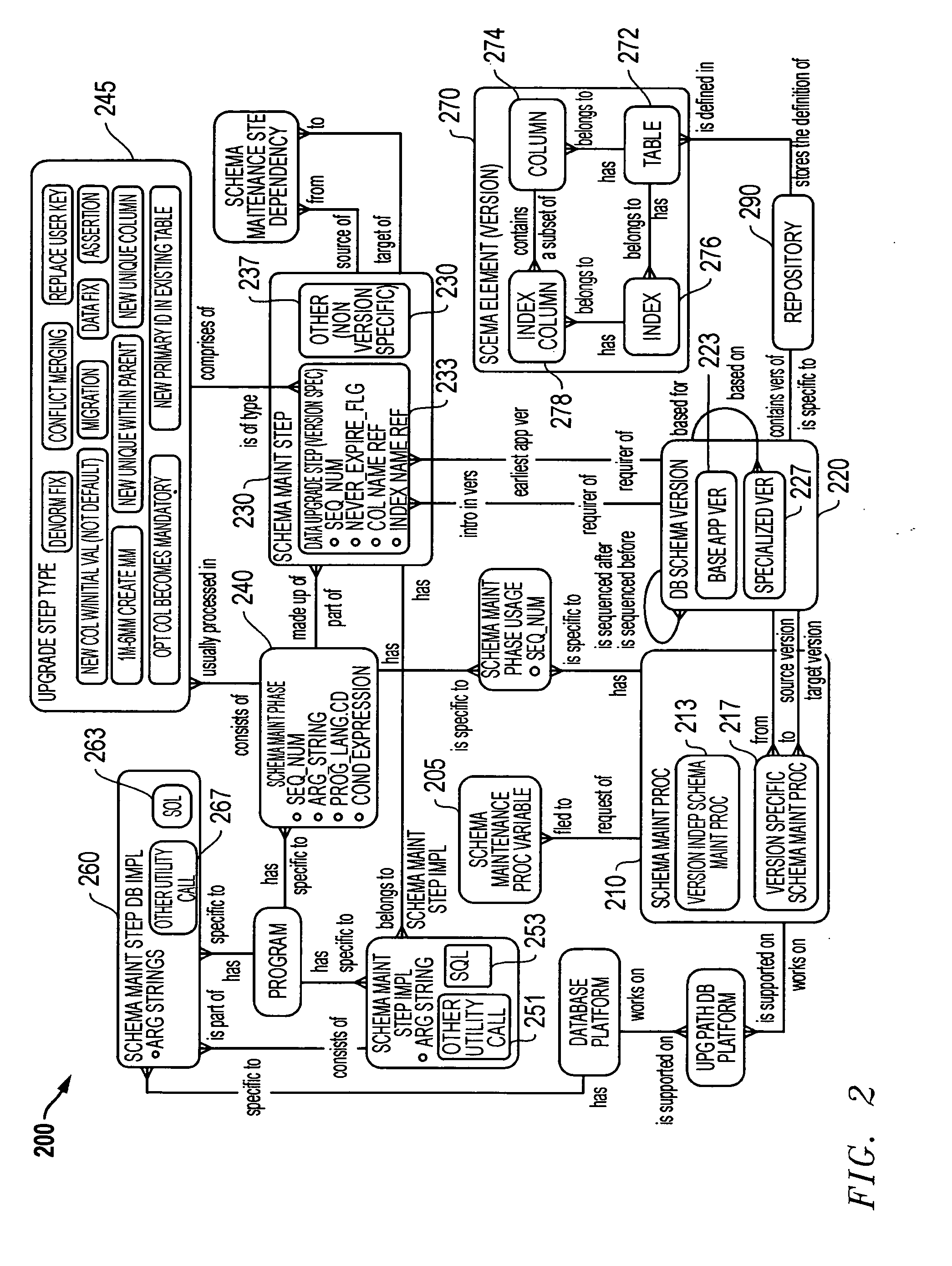
Infrastructure for the automation of the assembly of schema maintenance scripts
A method and apparatus to build a migration package. According to one embodiment of the invention, a plurality of programming elements are developed and stored in a configuration repository. The configuration repository also includes metadata used to describe each of the programming elements. Selected programming elements are placed in a set of one or more migration scripts to be stored in the migration package. The set of migration scripts may include a master configuration file and a driver file.
Owner:ORACLE INT CORP
Infrastructure for the automation of the assembly of schema maintenance scripts
A method and apparatus to build a migration package. According to one embodiment of the invention, a plurality of programming elements are developed and stored in a configuration repository. The configuration repository also includes metadata used to describe each of the programming elements. Selected programming elements are placed in a set of one or more migration scripts to be stored in the migration package. The set of migration scripts may include a master configuration file and a driver file.
Owner:SIEBEL SYST INC
Mapper compiler
ActiveUS20050132282A1Enhance run-time performanceImprove performanceNatural language data processingSpecial data processing applicationsAuto-linkingXSLT
Mapping between a source object and a destination or target object uses techniques and functoids that provide an auto-linking feature in which mappings are automatically provided based solely on source and target field names, or, ignoring field names, field locations within hierarchy. Functoids provide support for callout to programming artifacts, such as custom programming logic embedded in .NET assemblies or custom XSLT, and table-looping to generate and map data into a target document even though that data did not exist in the map input.
Owner:MICROSOFT TECH LICENSING LLC
Detection method for software vulnerability
InactiveCN102385550AGuaranteed validityEfficient detectionSoftware testing/debuggingCode tableInformation security
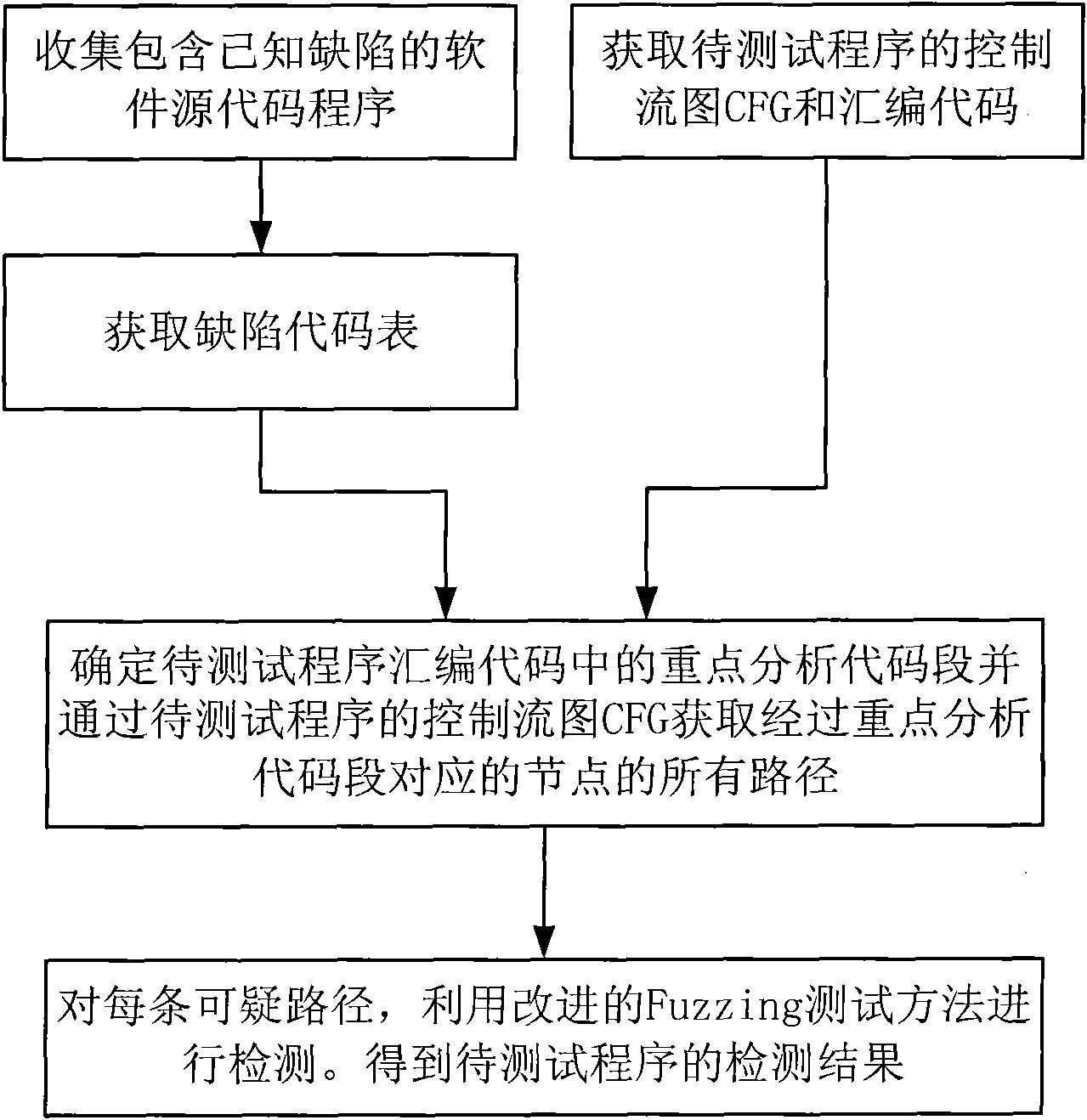
The invention relates to a detection method for software vulnerability, and belongs to the technical field of information security. The detection method comprises the following specific steps of: (1) collecting a software source code program containing known vulnerability; (2) obtaining a vulnerability code table; (3) obtaining a control flow graph CFG and an assembly code of the program to be tested; (4) determining key analysis code segments in the assembly code of the program to be tested and obtaining all paths of passing through nodes corresponding to the key analysis code segments through the control flow graph CFG of the program to be tested; and (5) for each suspicious path, an improved Fuzzing test method is used for detection to obtain the test results of the program to be tested. In the invention, when a fitness function is determined, the dependence on the source code of the tested program is eliminated, and the availability of information is kept; and the redundant information in an abstract syntax tree is eliminated and the integrity of useful information is kept, therefore, the practicality is better, and the efficiency is higher.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method of automatically generating layering exploded view
ActiveCN104598683AAchieving an integrated processSpecial data processing applicationsSequence planningComputer Aided Design
The invention provides a method of automatically generating a layering exploded view. The method comprises the following steps of obtaining a three-dimensional CAD (Computer Aided Design) assembly drawing; extracting constrained relationships among parts of an assembly body in the three-dimensional CAD assembly drawing to obtain a contact-connection matrix and an extension interference matrix; planning a layering assembly sequence; automatically generating the layering exploded view. According to the method, an automatic exploded view generating technology and assembly modeling, assembly sequence planning and simulation technologies are combined for research, the extension interference matrix and a generation method of the extension interference matrix are provided, and the integrated flow of the assembly planning is realized on the basis of a multi-rule screening ASP (Assembly Sequence Planning) algorithm and an automatic exploded view generation method based on the ASP. According to the invention, each link of the assembly planning is remolded by layering, the advantages of the layering used for processing the complicated product exploded view generation process are analyzed, and according to the assembly relationship matrix, the assembly relationship matrix generation, a sub assembly body planning, the ASP algorithm and the layering exploded view generation flow sequences, the procedures are carried out in sequence.
Owner:NORTHEASTERN UNIV
Decoupled parallel meshing in computer aided design
InactiveUS20140039847A1Easy to assembleImprove good performanceGeometric CADProgram initiation/switchingComputer Aided DesignComputer science
In a meshing method for use in a computer-aided design (CAD) or computer-aided engineering (CAE) system, in which one or more serial meshing units are used to carry out a decoupled parallel meshing process in respect of all parts of a CAD assembly model, input parameters for the meshing process automatically, for each part to be processed, are set using live runtime information about the meshing process for the part concerned, such as information about the outcome of previous attempts to carry out the meshing process of the part.
Owner:FUJITSU LTD
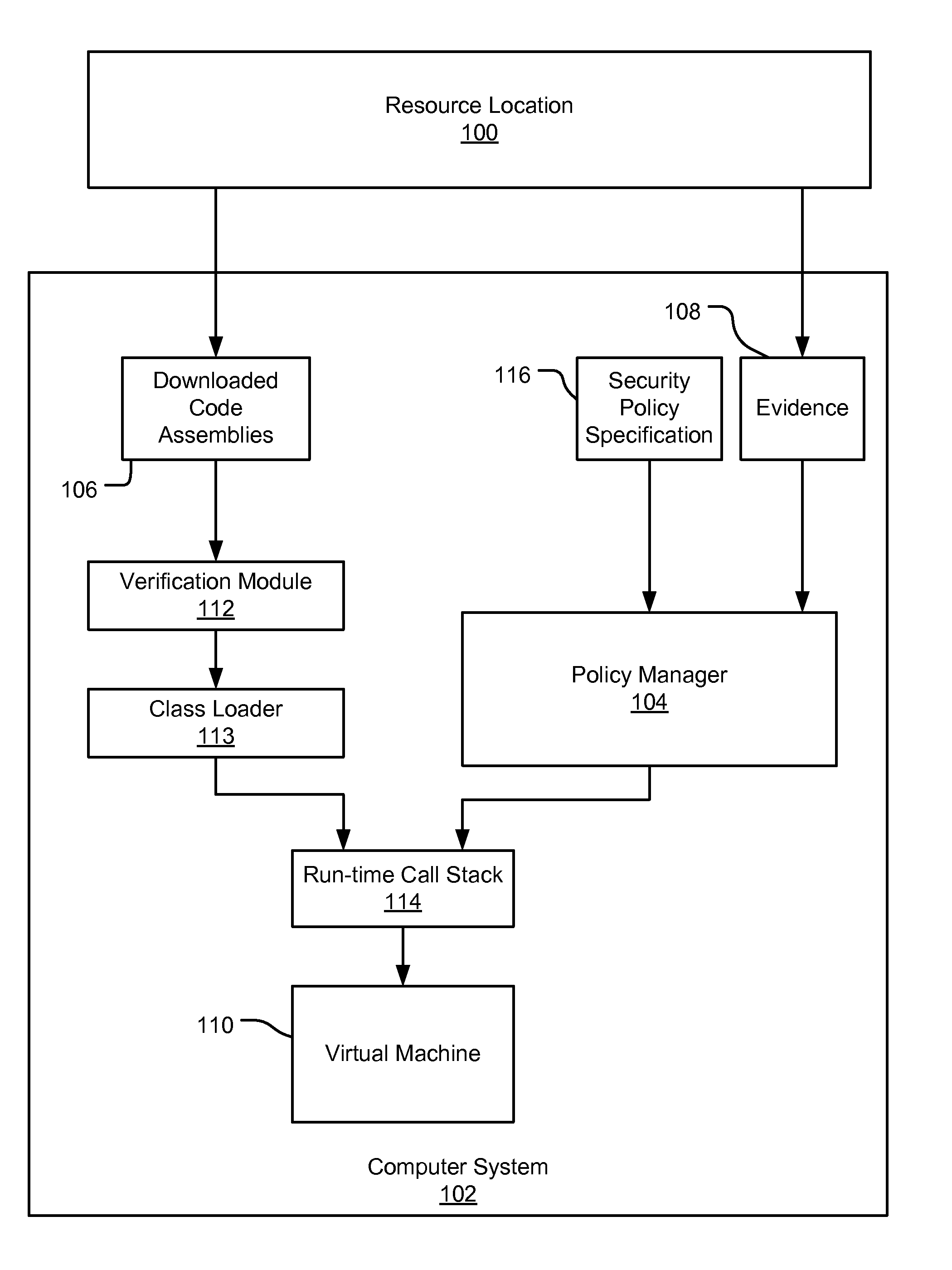
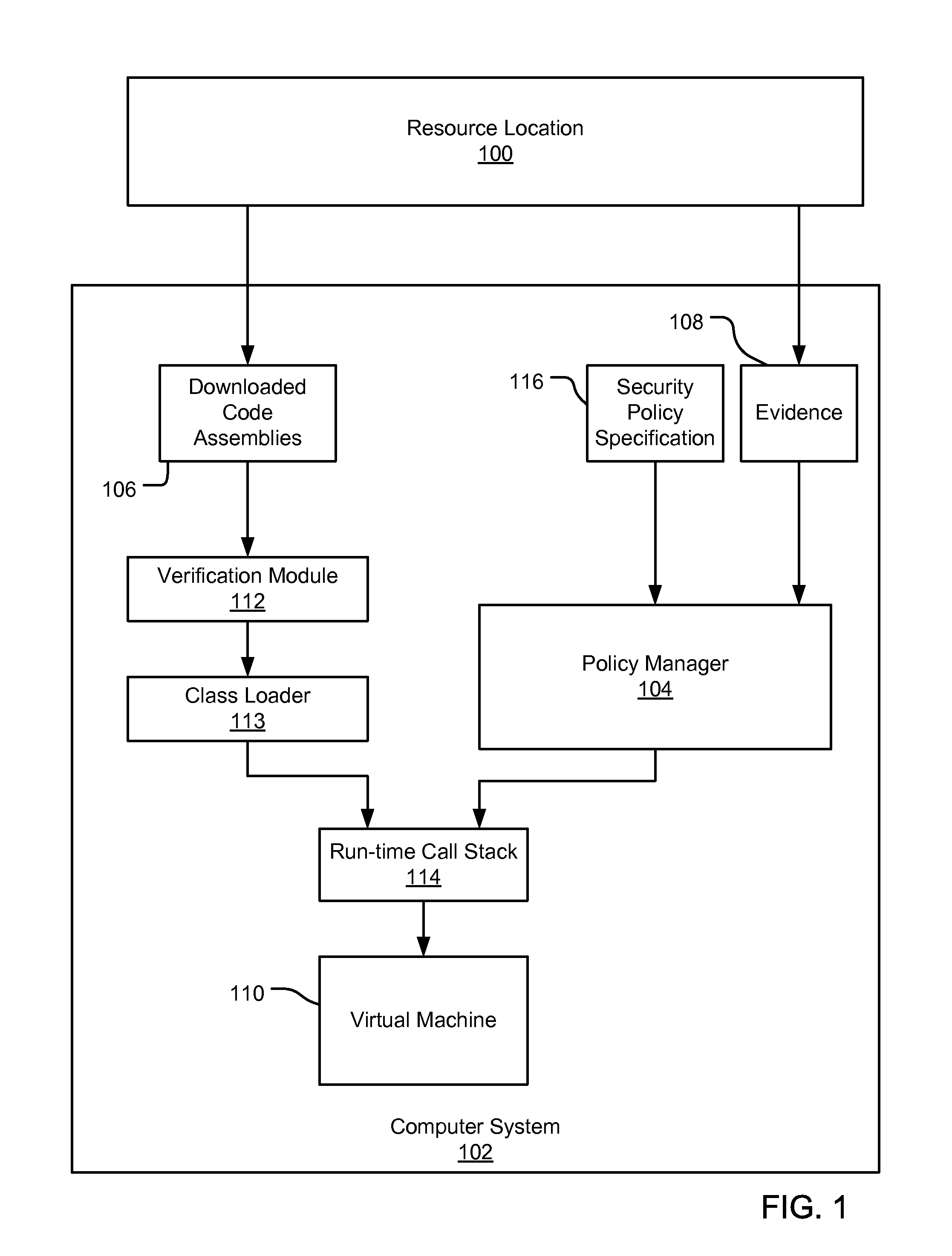
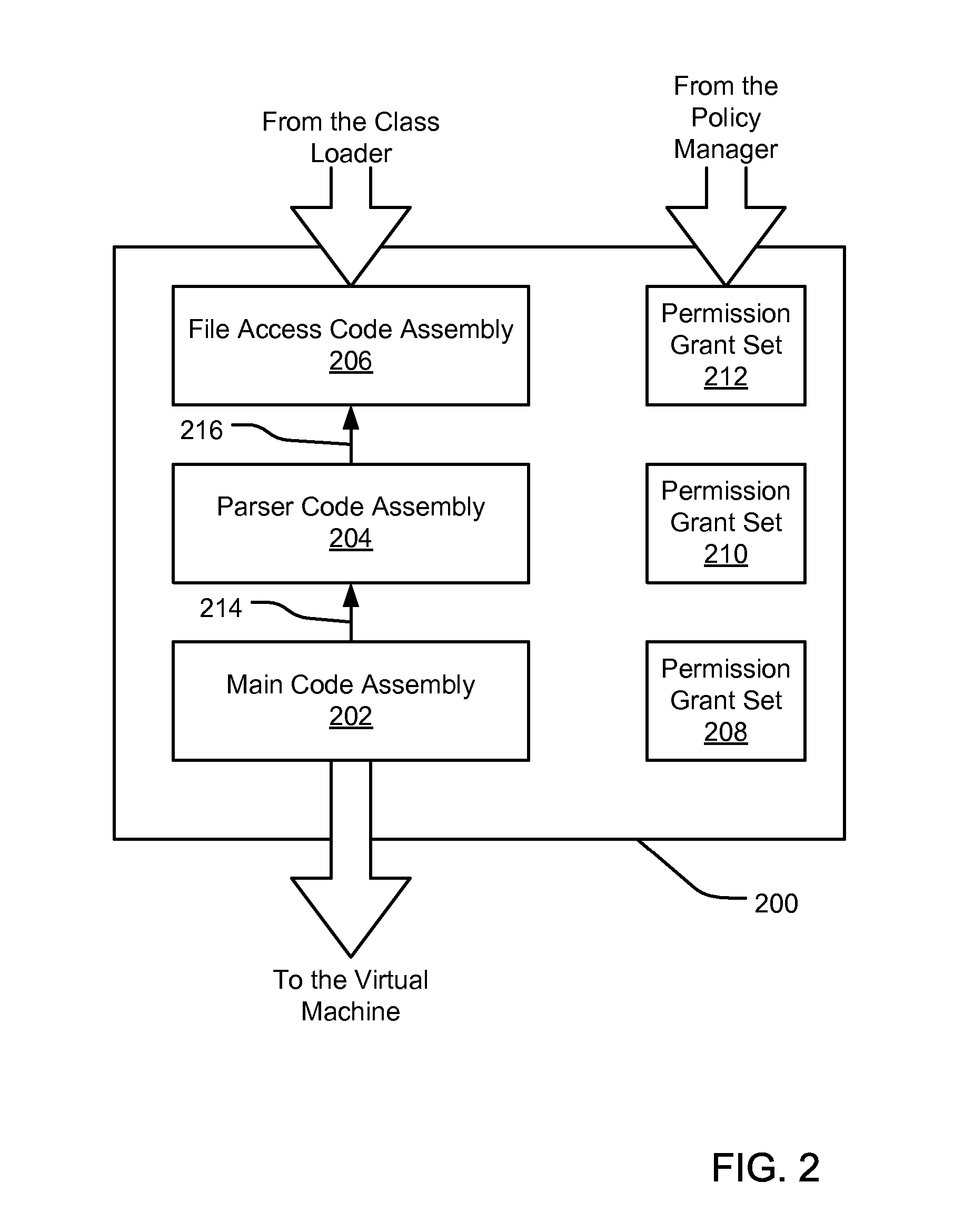
Partial grant set evaluation from partial evidence in an evidence-based security policy manager
InactiveUS20070192839A1Digital data processing detailsUser identity/authority verificationCall stackEngineering
An evidence-based policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager executes in a computer system (e.g., a Web client or server) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. The policy manager may determine a subset of the permission grant set based on a subset of the received code assembly's evidence, in order to expedite processing of the code assembly. When the evidence subset does not yield the desired permission subset, the policy manager may then perform an evaluation of all evidence received.
Owner:MICROSOFT TECH LICENSING LLC
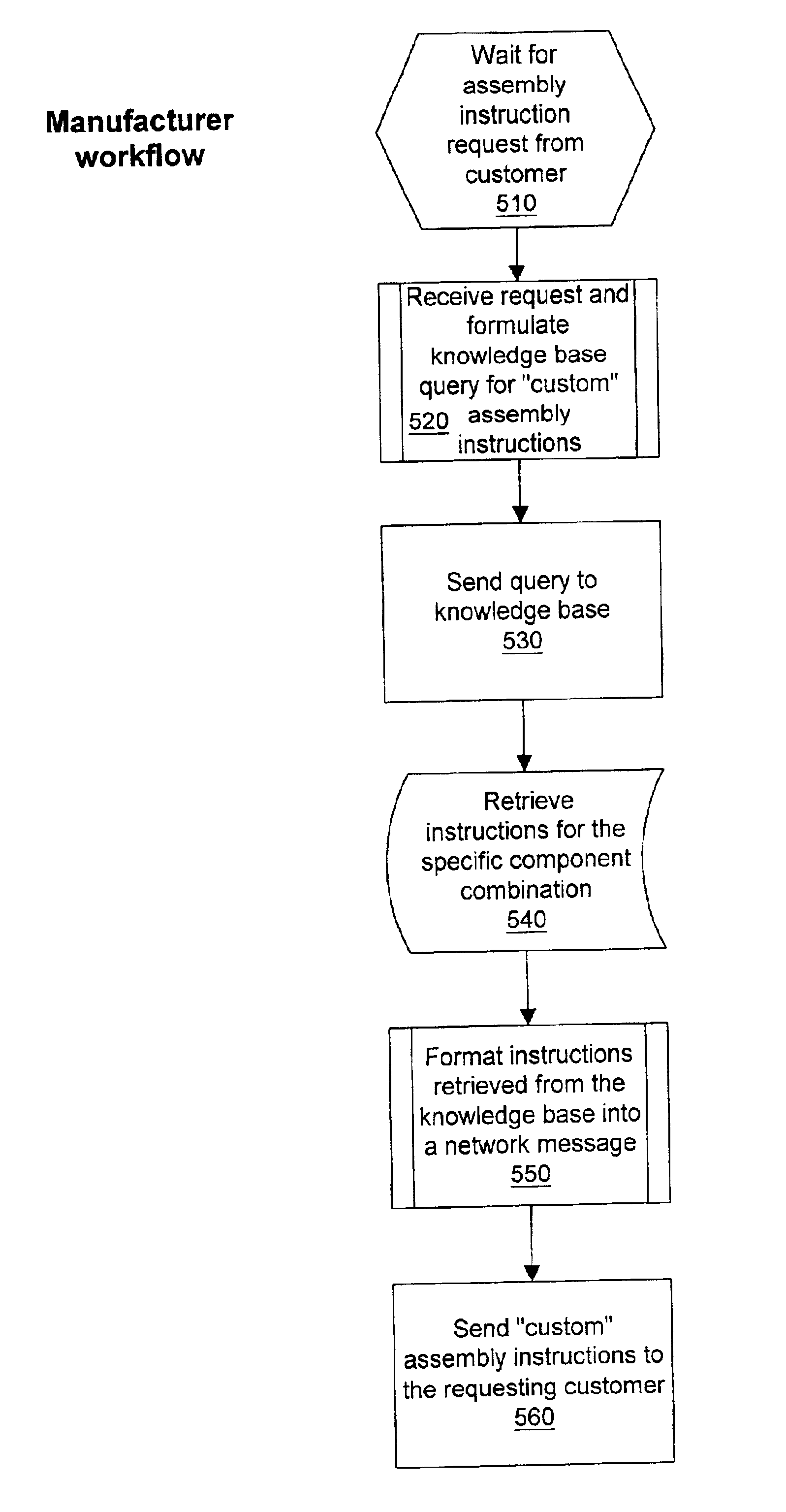
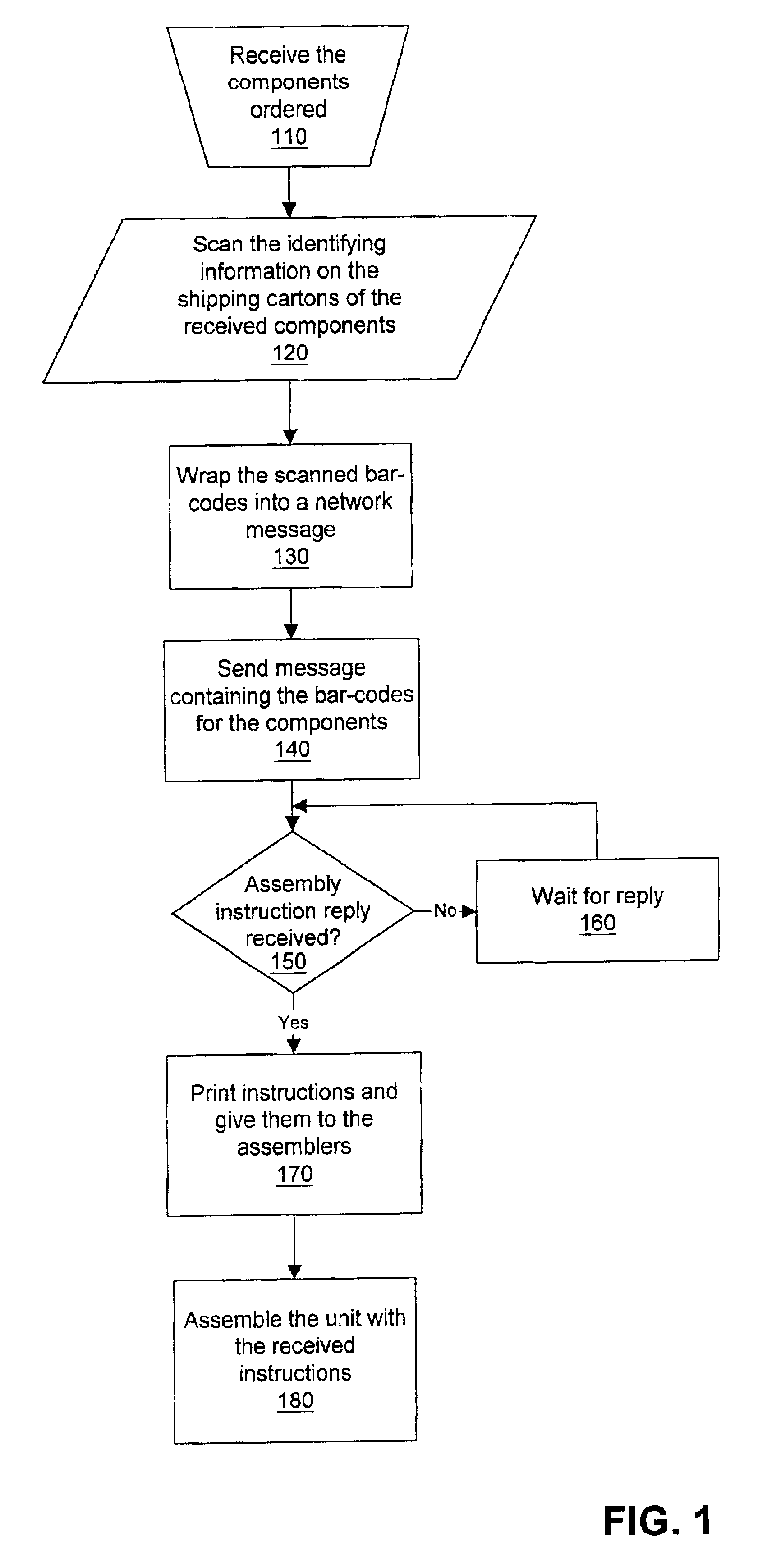
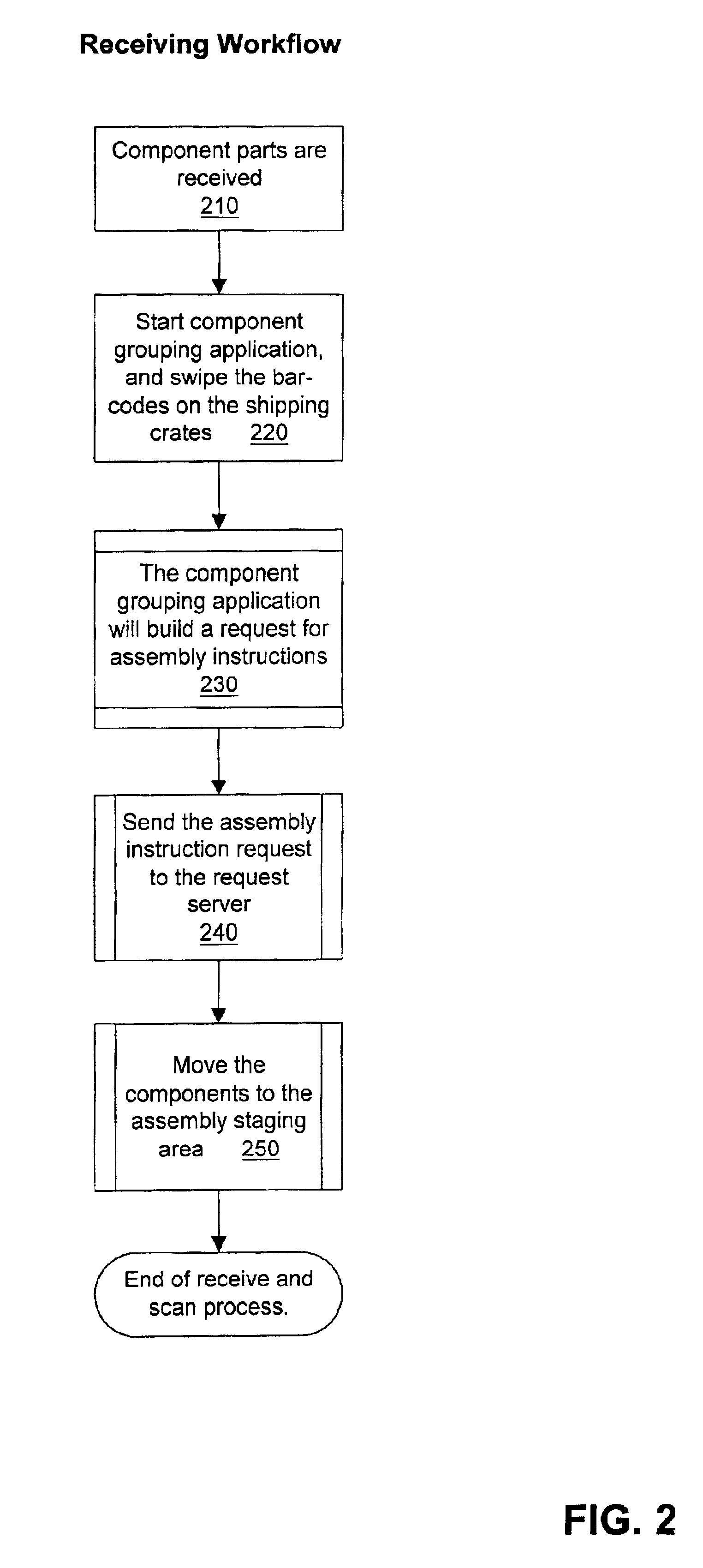
Method to use the internet for the assembly of parts
A method that comprises: 1) sending to a manufacturer a customer request for assembly instructions for a grouping of components; and 2) presenting to assemblers a set of assembly instructions which are customized and specific to the grouping of components.
Owner:HEWLETT PACKARD DEV CO LP
Code static detection method
ActiveCN104965788AEnable cross-language analysisRealize analysisSoftware testing/debuggingArray data structureSource code
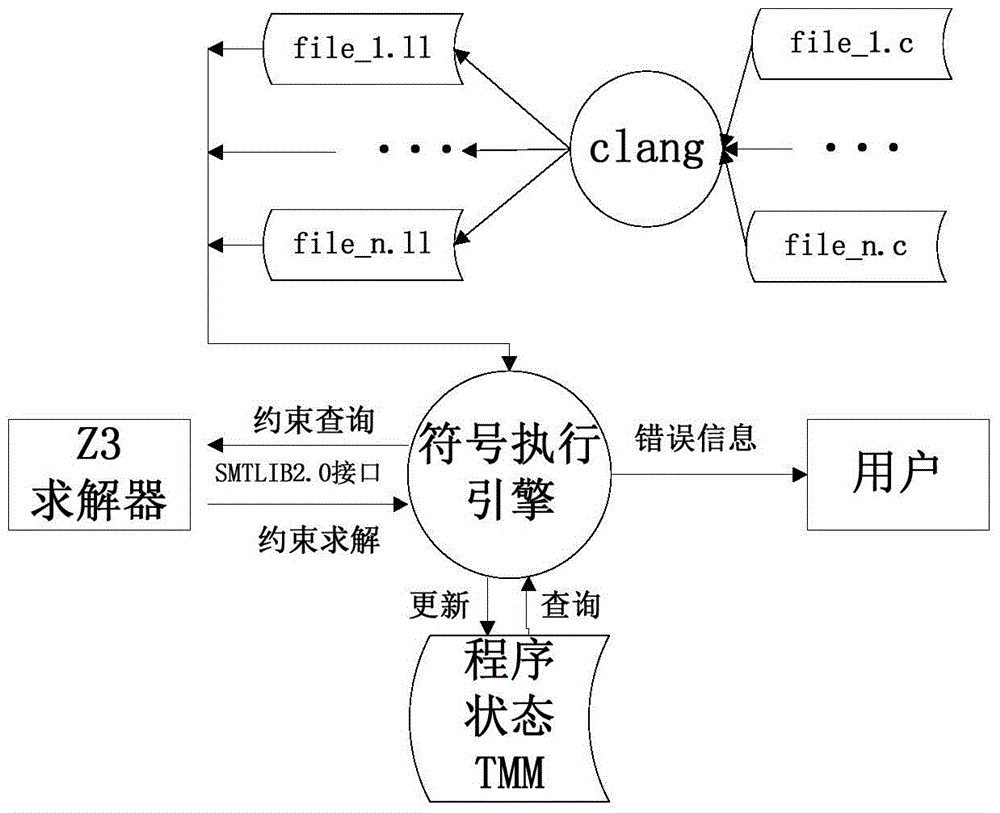
The invention discloses a code static detection method, particularly relates to an LLVM IR (low level virtual machine intermediate representation) based symbol execution algorithm in the technical field of utilization of initial values of variable symbols of given programs, and solves the problems of single supported language and incapability of better processing pointers and aliases for a static detection method in the prior art and the problems in detecting potential program bugs and the like. The method comprises the steps of: (1) obtaining a source code, and preprocessing and converting the source code into an LLVM assembly program; (2) simulating interpretive execution of the LLVM assembly program obtained by conversion by applying the symbol execution algorithm, and recording the symbol value of each variable in different paths and the constraint conditions of each path; and (3) according to the recorded symbol value of each variable in different paths and constraint conditions of each path, calling an SMT (satisfiability modulo theories) solver Z3 to check whether the symbol value of the variable meets the path constraint and the bug constraint, and judging whether the program has potential bugs. The method is applied to array bound overflow, division by zero and null pointer dereference.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Generation method of dynamic binary code test case
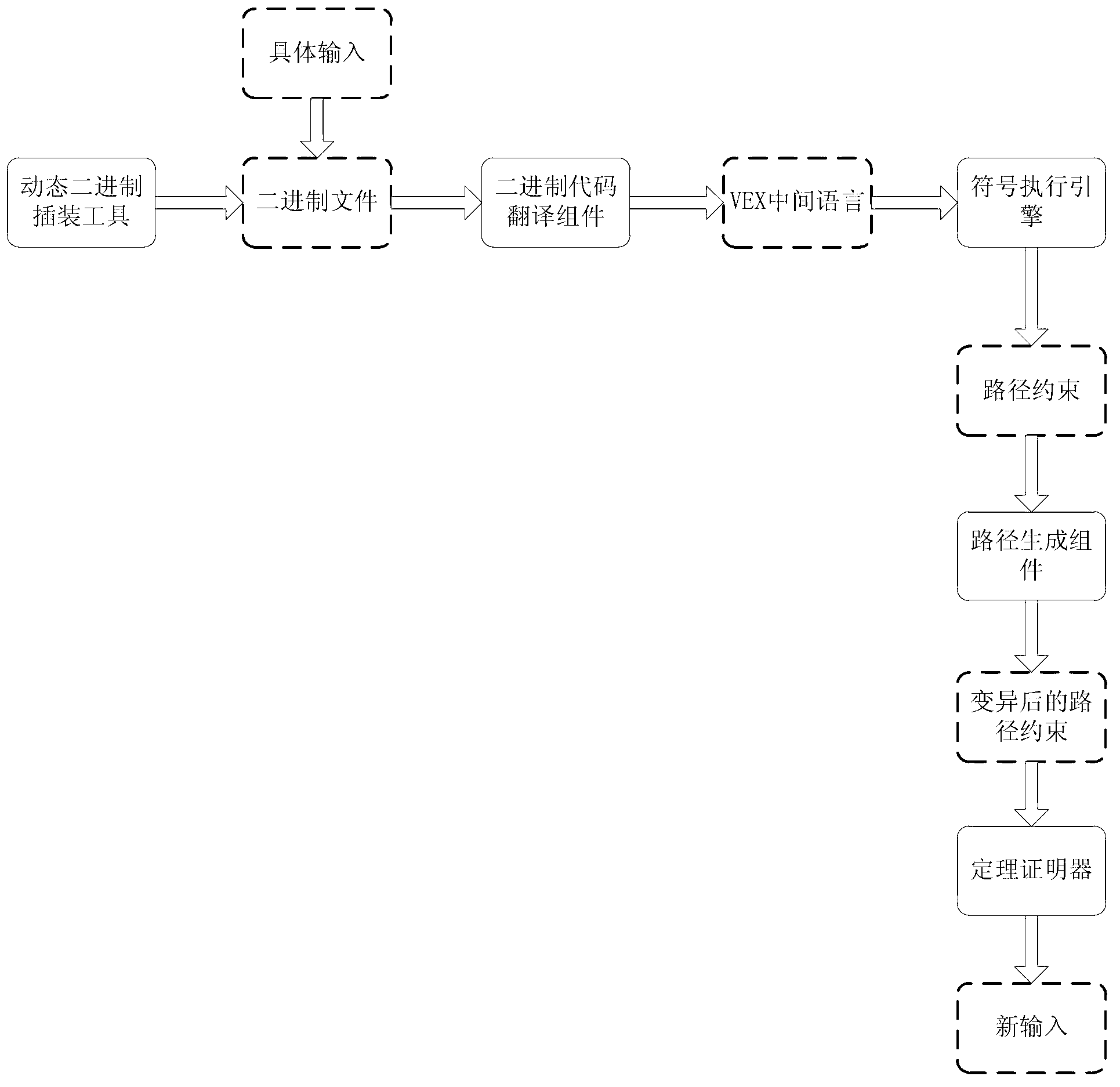
InactiveCN102799529AImprove path coverageSoftware testing/debuggingAlgorithmTheoretical computer science
The invention discloses a generation method of a dynamic binary code test case. The generation method comprises the following steps: a dynamic binary insertion tool is achieved to collect the context information including a register, a memory, a thread, system invoking, base loading and the like in the execution process of the binary code, transmitting such information into a binary code translation assembly, converting the information into an intermediate language, carrying out symbol execution on the intermediate language, disseminating symbol input, and collecting a path constraint depending on the input. And then, inputting the path constraint into a path generation assembly, providing a new in-step branch-path mutation algorithm and a strategy, generating new path constraints as much as possible after each symbol execution, using a theorem prover to solve the new path constraint, obtaining the new input satisfying the path constraint, transmitting the new input to the binary code to carry out specific execution for one time, obtaining new path constraints from the new execution in continuously circular manner, generating new inputs, and improving the cover ratio of the binary code.
Owner:BEIHANG UNIV
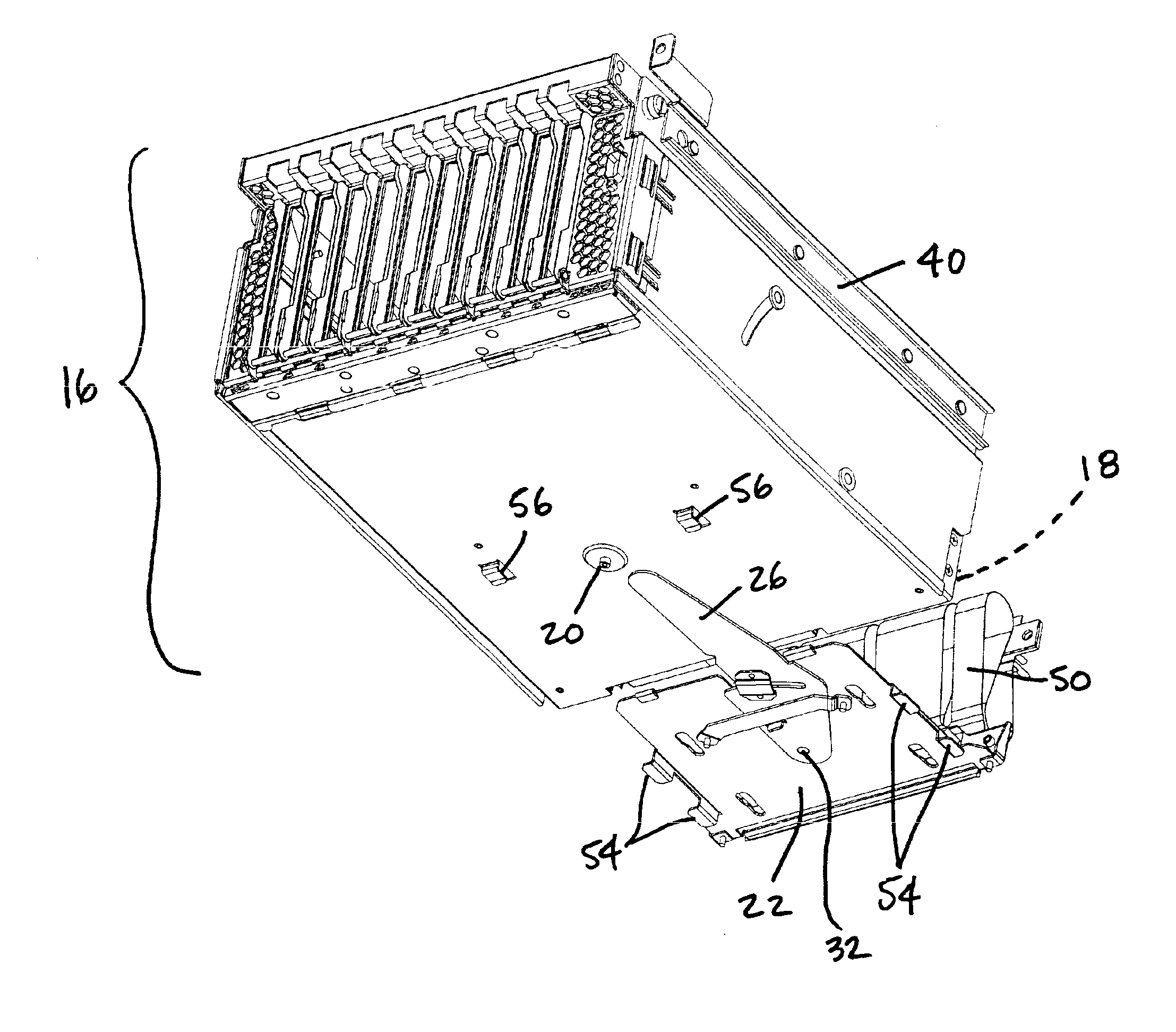
Modular computer system and mounting assembly therefor
InactiveUS6891728B1Engagement/disengagement of coupling partsDigital processing power distributionComputerized systemEmbedded system
A computer system is provided having a chassis at least partially defining an interior and an access opening. The interior of the chassis accommodates a connector that is oriented for connection along an insertion axis. The computer system also includes a subassembly configured for insertion into and removal from the interior of the chassis through the access opening along the insertion axis. The subassembly has a subassembly connector oriented for connection with the connector in the chassis along the insertion axis. The computer system also includes a mounting assembly configured for engaging the subassembly at least partially within the interior of the chassis and for connecting the connector in the chassis to the subassembly connector.
Owner:UNISYS CORP
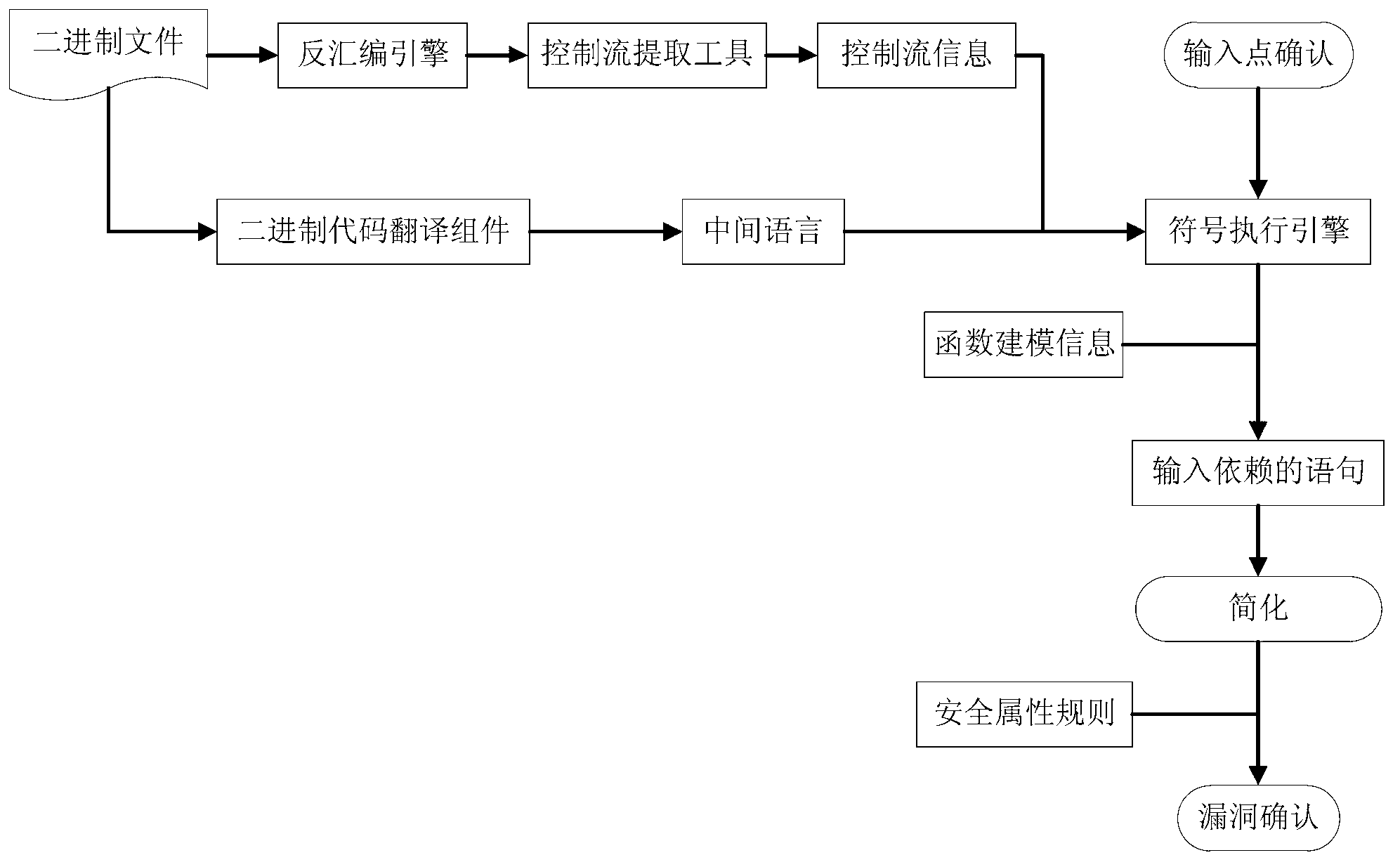
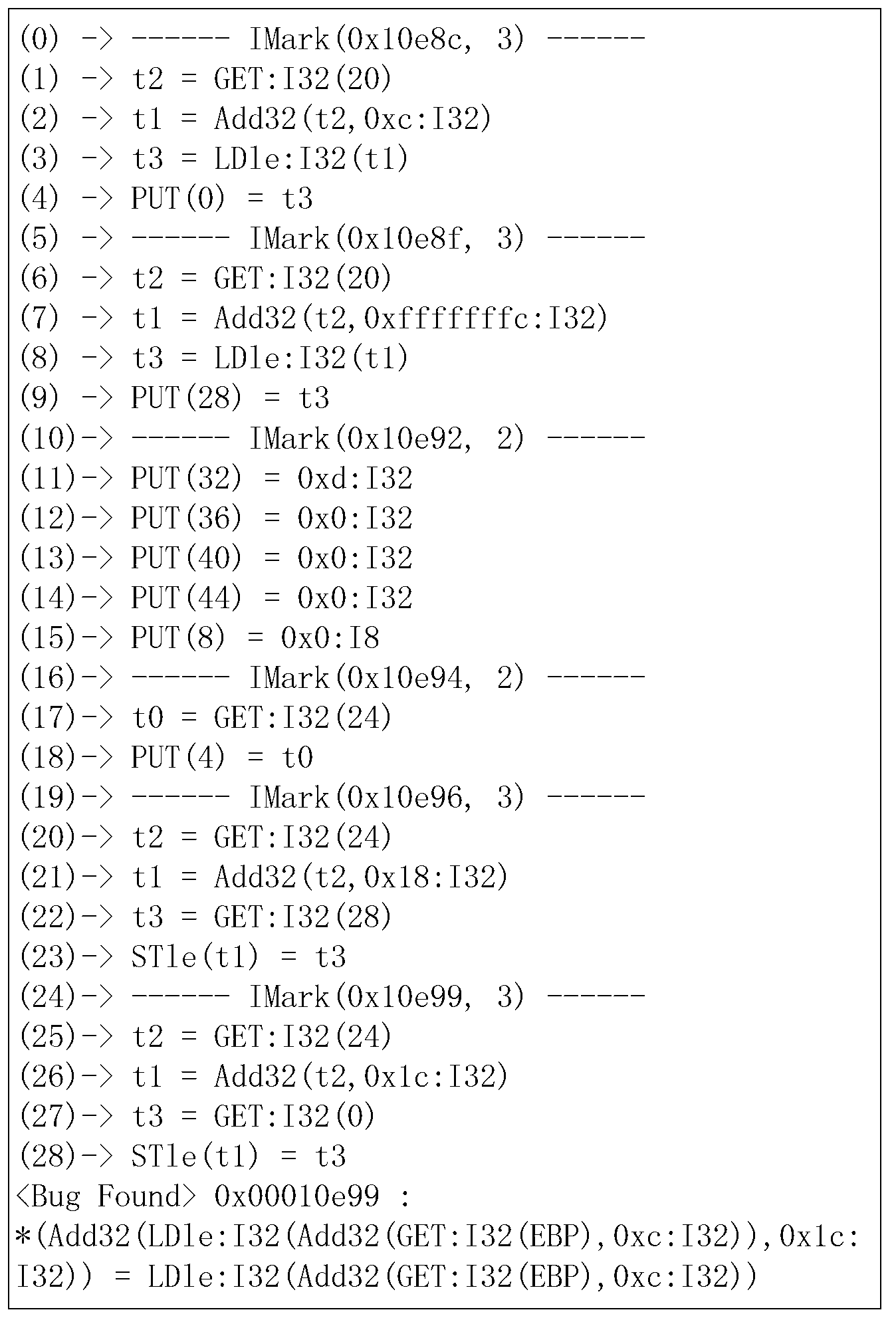
Method for binary code vulnerability discovery on basis of simple symbolic execution
The invention discloses a method for binary code vulnerability discovery on the basis of simple symbolic execution. The method comprises five steps that: firstly, binary codes are translated into an intermediate language with a static single assignment through a binary code translation component; and then, a disassembling engine is used to disassemble the binary codes, the control flow information of the binary codes is extracted, static symbolic execution is carried out in the intermediate language on the basis of the control flow information, an entrance point needs to be determined during the symbolic execution process, an input vector is converted into a symbol, and a called function is modeled. After the symbolic execution process is completed, the statement assembly of the intermediate language which depends on the input vector can be obtained, the statements of an assembly are simplified, and a vulnerability discovery confirmation report is generated after security attribute rules are used to confirm.
Owner:BEIHANG UNIV
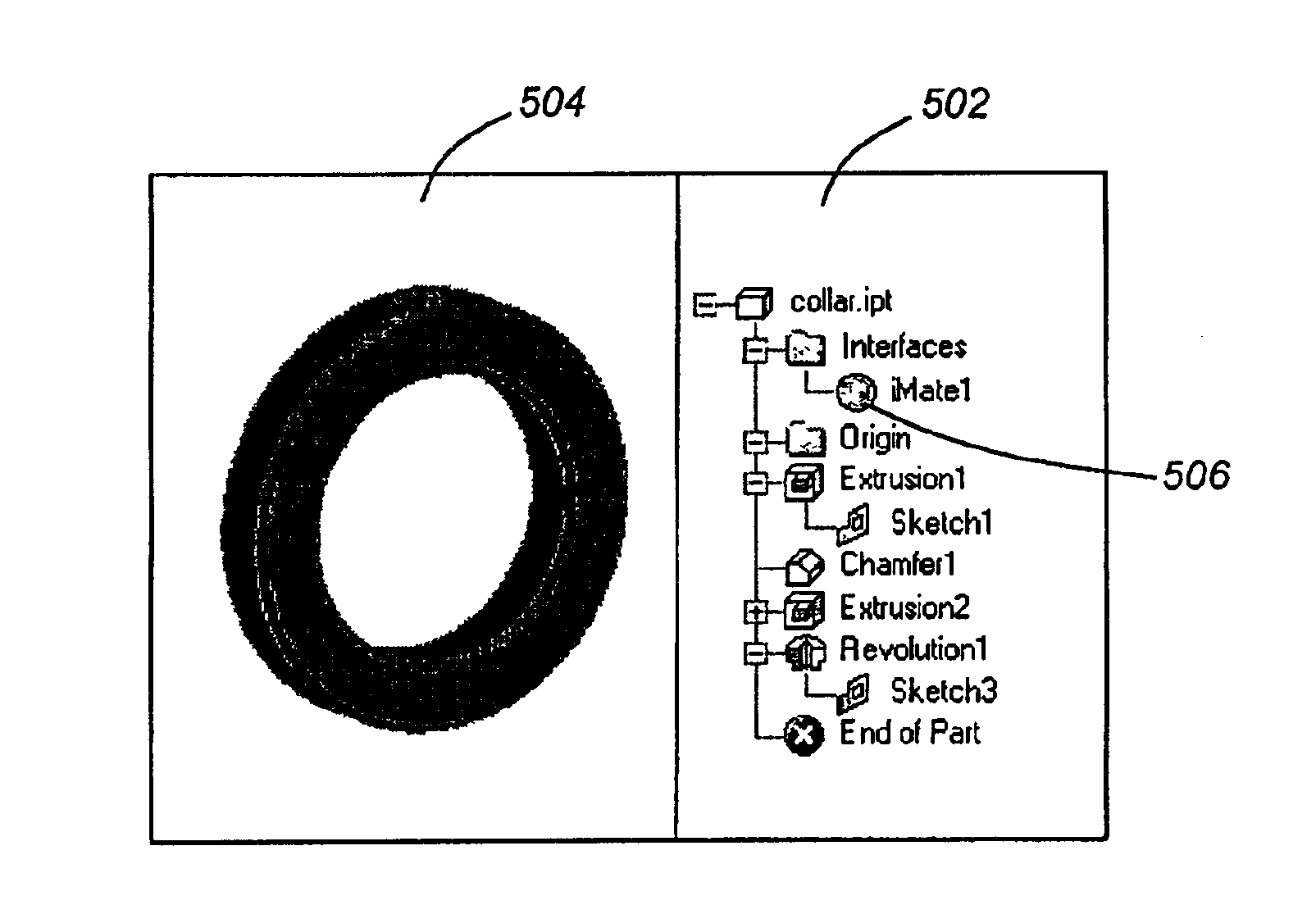
Intelligent constraint definitions for assembly part mating
InactiveUS6907573B2Adjustment of settingData processing applicationsConstraint-based CADGraphicsMating
One or more embodiments of the invention provide a method, apparatus, and article of manufacture for defining mating properties of a graphical component in a computer-implemented drawing program. An option to create a first constraint interface for a first geometric characteristic of a first component is initiated. In response to the initiation, a dialog window for specifying settings for the first constraint interface regardless of whether a second constraint interface is currently displayed is displayed. The settings define mating properties for how the first geometric characteristic of the first component mates with the second constraint interface. Once specified, the first constraint interface of the first geometric characteristic is persisted with the first component.
Owner:AUTODESK INC
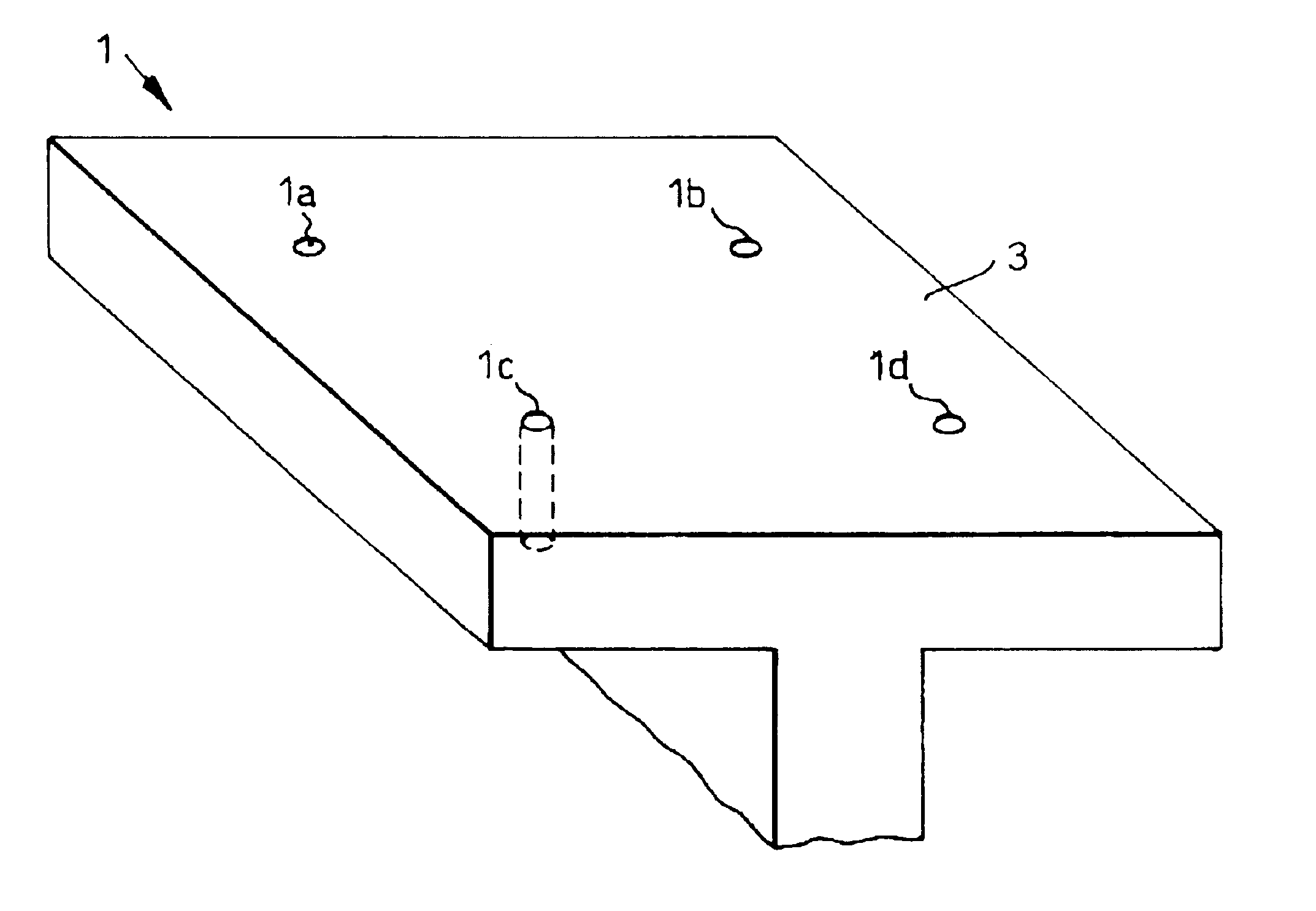
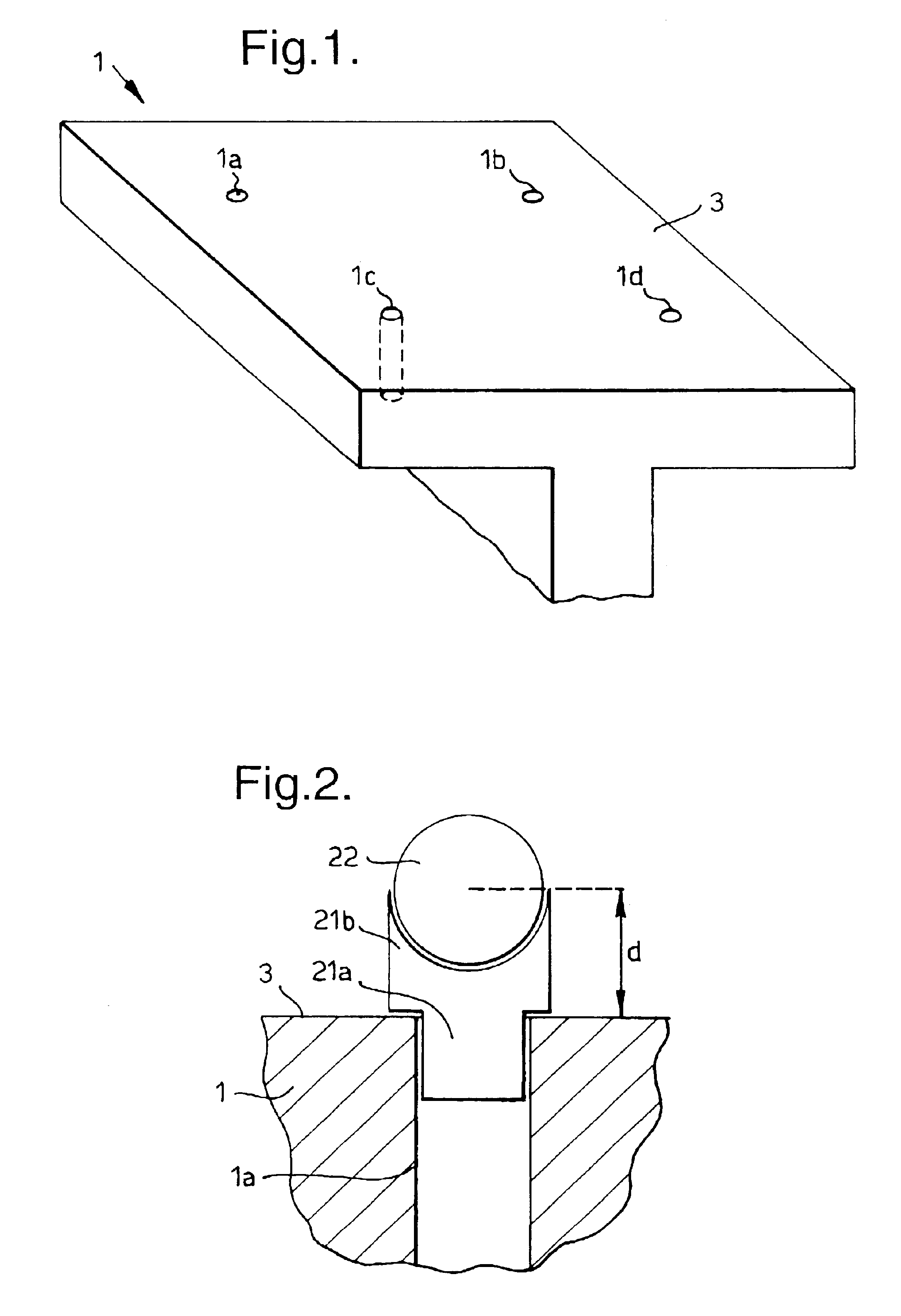
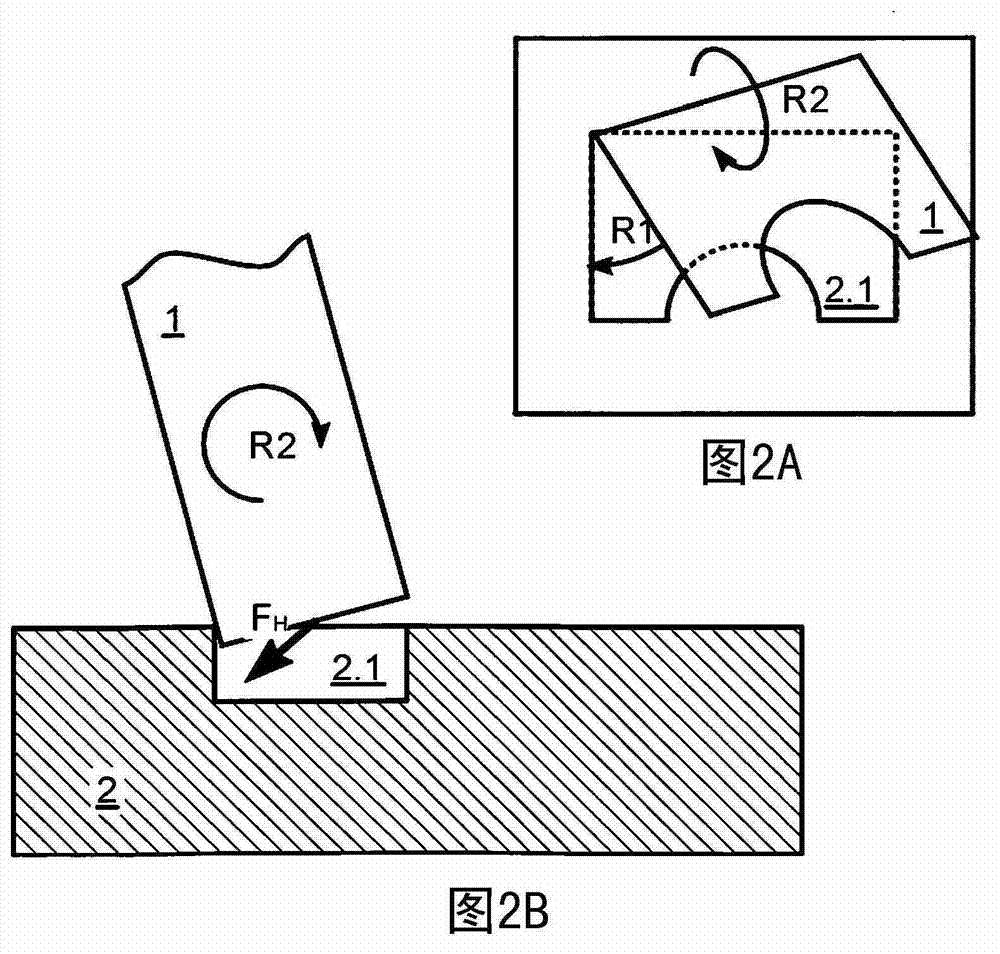
Assembly method
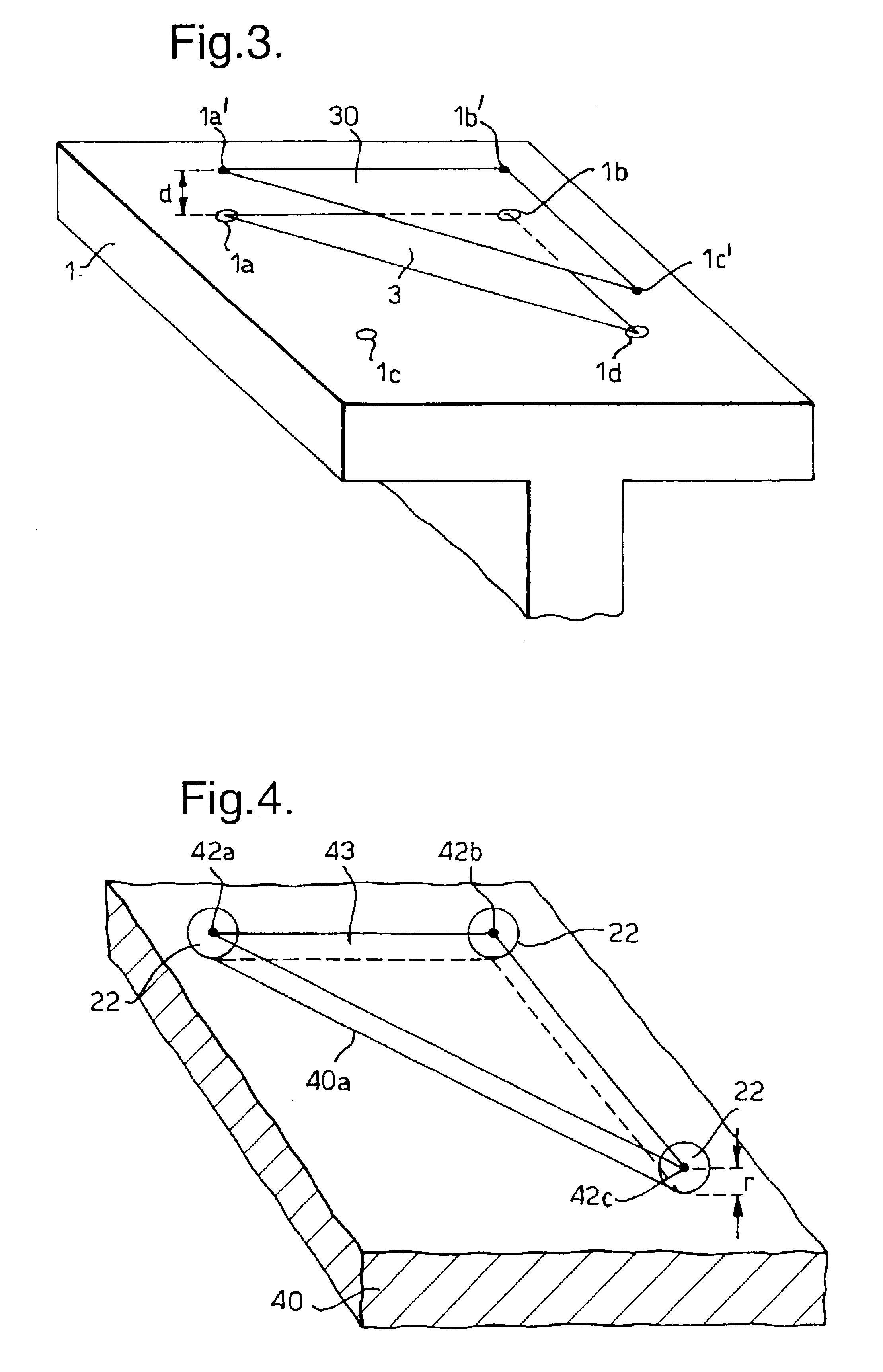
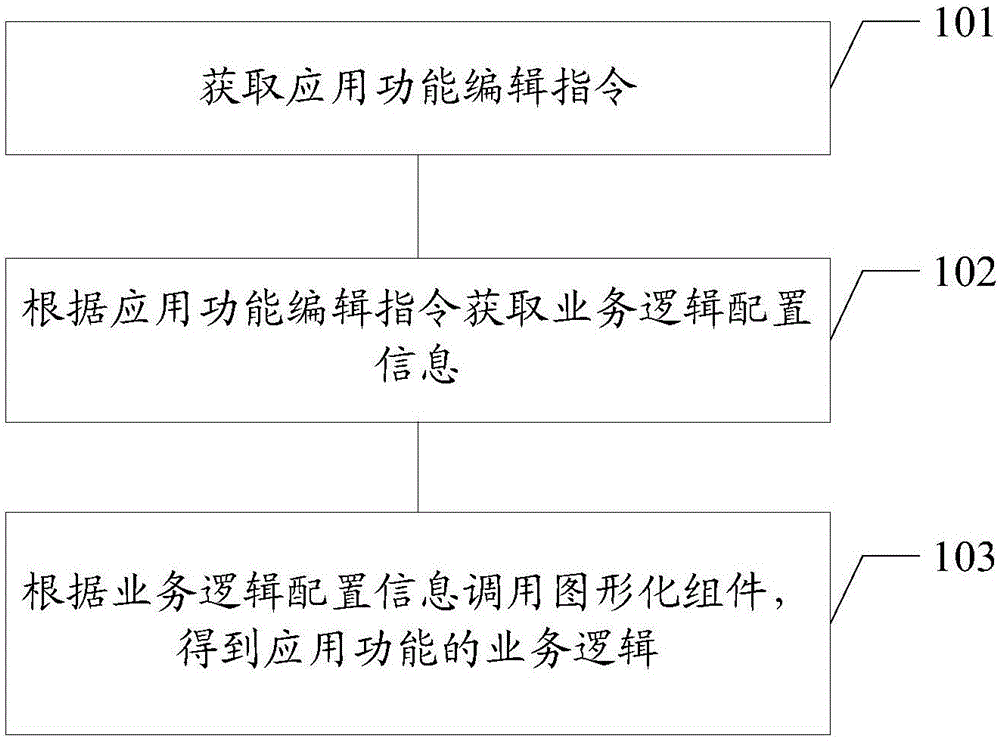
InactiveUS6892160B2Accurate identificationEfficient methodDrilling/boring measurement devicesDigital computer detailsEngineeringAssembly line
A method of locating an assembly point (P) on a first part (40), at which assembly point the first part is to be joined to a second part (1), the method comprising the steps of: determining an assembly location (1a, 1b, 1c, 1d) in respect of the second part; measuring a portion (42a, 42b, 42c) of a surface (43) of the first part, the surface being spaced away from the second part, so as to define the position and orientation of the surface; and, calculating the assembly point on the surface of the first part, where the surface of the first part is intersected by a vector (N) passing between the determined assembly location and the surface of the first part.
Owner:BAE SYSTEMS PLC
Service logic configuration method and configuration system of application software
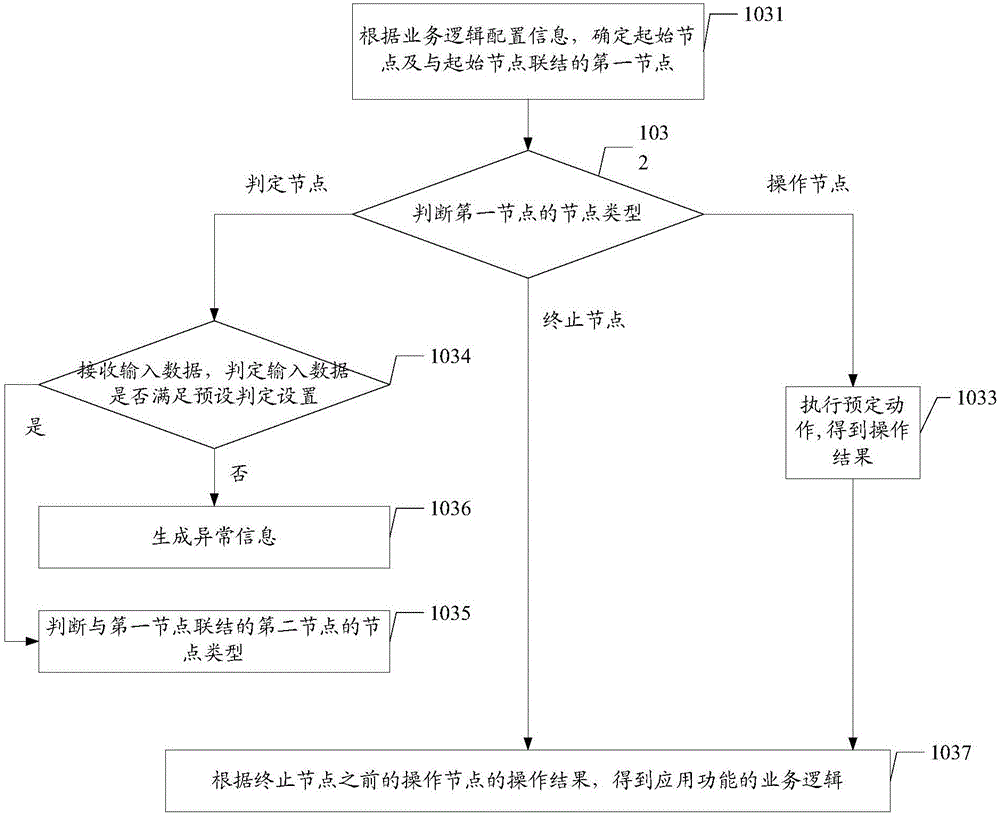
InactiveCN106775617AImprove development efficiencyReduce workloadVersion controlModel driven codeGraphicsSoftware engineering
Embodiments of the invention disclose a service logic configuration method and configuration system of application software, which are used for calling a configured graphical assembly by virtue of service logic configuration information, so that a service logic of an application function is obtained, the complexity for developing the application software is alleviated, and the development efficiency of the application software is improved. The method comprises the following steps: acquiring an application function editing instruction, wherein the application function editing instruction is used for realizing an application function of the application software; acquiring the service logic configuration information according to the application function edit instruction; and calling the graphic assembly according to the service logic configuration information to obtain the service logic of the application function, wherein the graphic assembly is a pre-encapsulated program code.
Owner:深圳市中润四方信息技术有限公司
Method and apparatus for protecting application security based on virtual machine
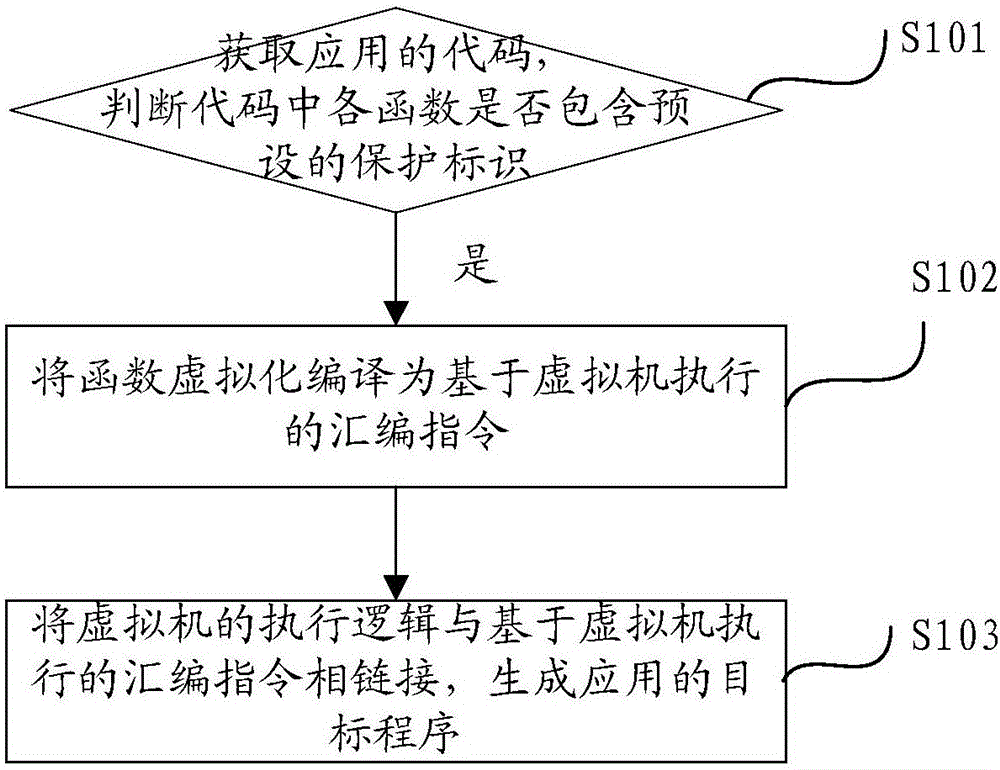
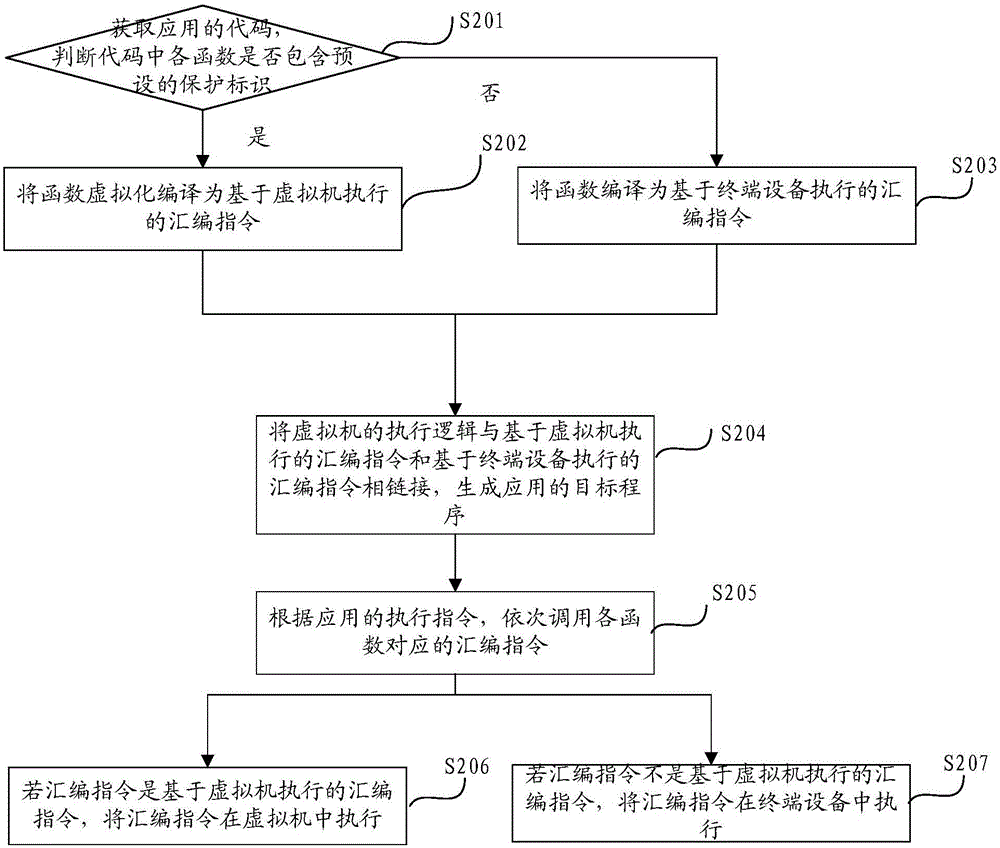
InactiveCN106599627AProtection securityIrreversibleProgram/content distribution protectionSoftware simulation/interpretation/emulationVirtualizationApplication security
The invention discloses a method and apparatus for protecting application security based on a virtual machine. The method comprises the following steps: obtaining a code of an application, and judging whether each function in the code contains a preset protection identifier; if the function contains the preset protection identifier, compiling the function into an assembly instruction that is executed on the basis of the virtual machine; and linking execution logic of the virtual machine with the assembly instruction that is executed on the basis of the virtual machine to generate a target program of the application. In the scheme, the code in the function containing the preset protection identifier is virtually compiled through an operation environment of the assembly instruction corresponding to the application self-defined by the virtual machine, the entire virtual compilation process is irreversible and cannot be restored, therefore even if decompilation is performed on the virtualized assembly instruction, the obtained code is not the original code of the application, and thus the security of the code of the application is protected.
Owner:JIANGSU PAYEGIS TECH CO LTD
Method for debugging binary application program based on dynamic inverse compiling technique
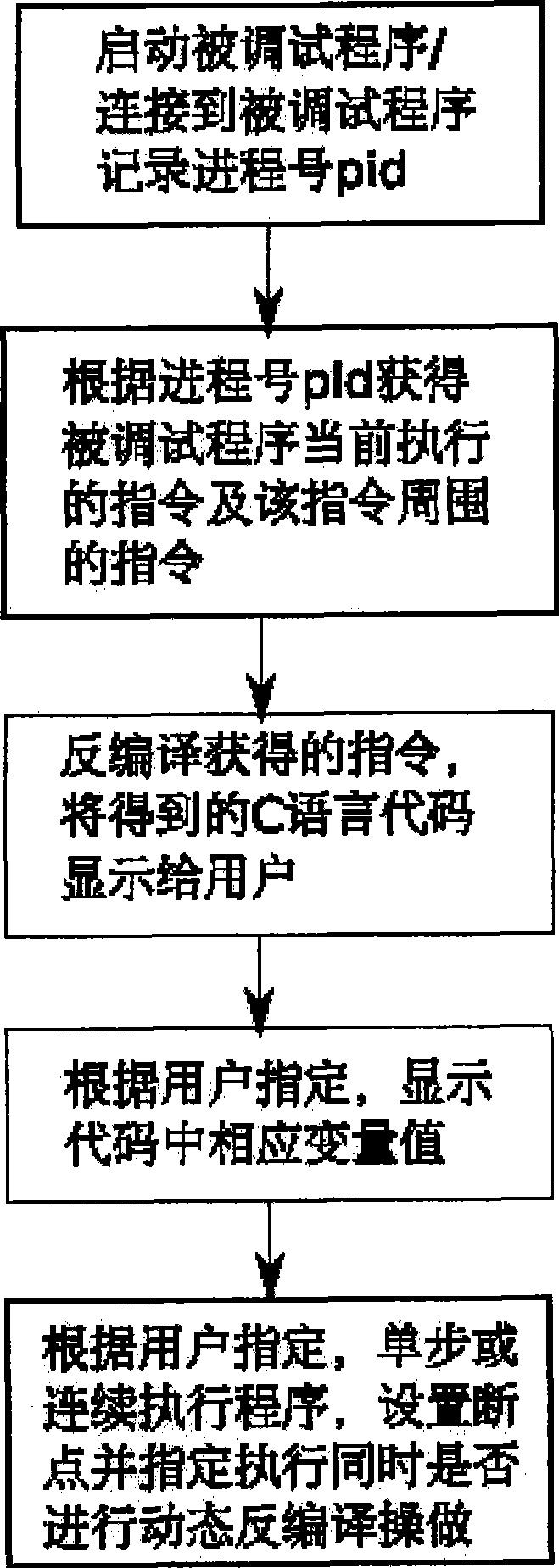
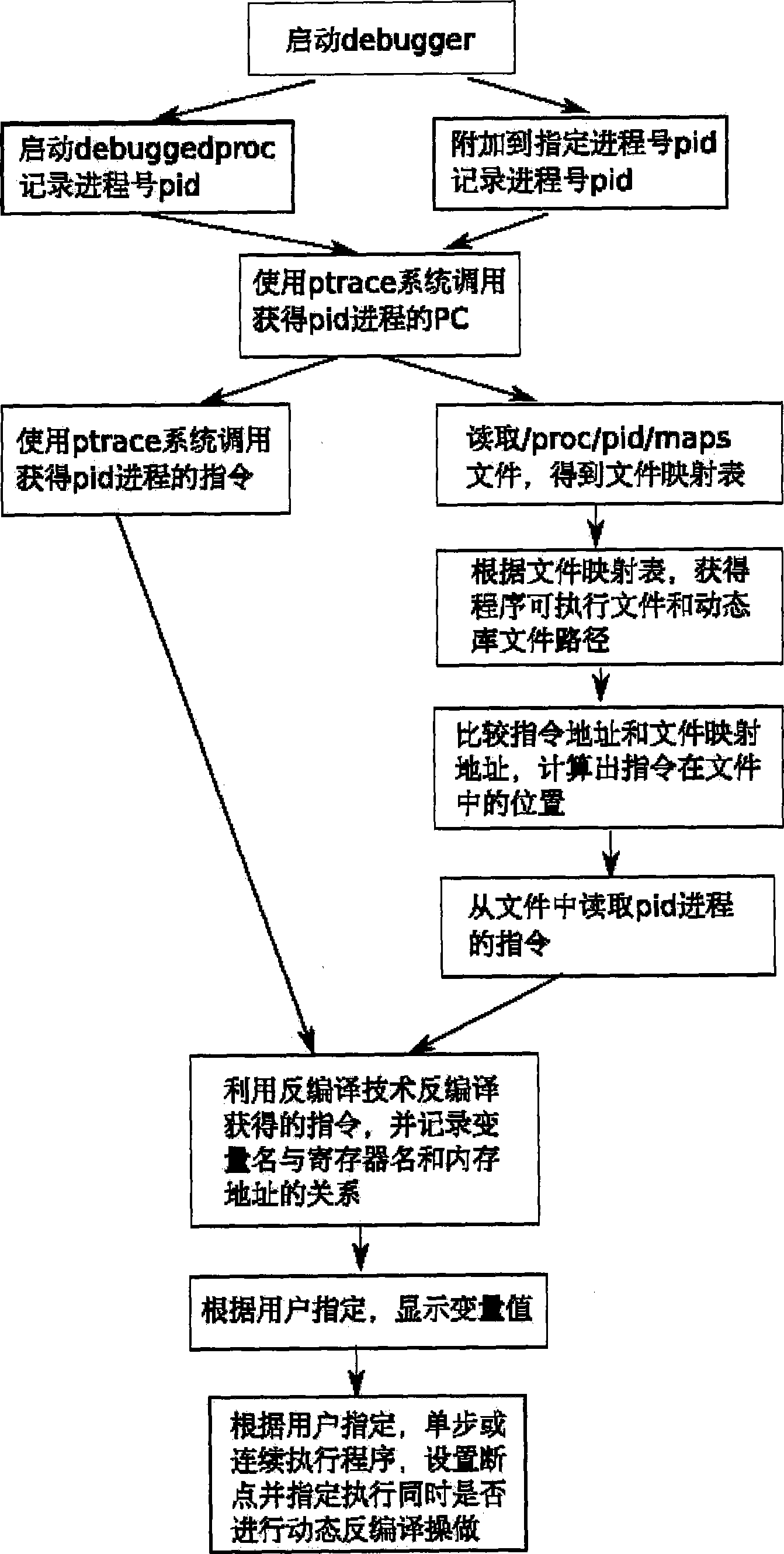
ActiveCN101414278AImprove efficiencyEasy to callSoftware testing/debuggingProgram controlApplication softwareDebugger
The invention relates to a debug method of a binary application program based on a dynamic decompiling technology. Debug staff starts the application program by a debugger or assigns a process number of a process to be debugged, if the debugged program is started by the debugger, the debugger records a process number of a sub-process; when the program is executed to a breakpoint, an operating system suspends the debugged program, and the debugger obtains a command; an instruction of the debugged program is obtained by a system call or application programming interface (API) which is provided by the operating system, the instruction is decompiled by the dynamic decompiling technology, and the obtained C language code is displayed to the debug staff. The debug method has the advantages of being capable of facilitating the debug staff to debug the binary application program without reading complicated assembly codes, and effectively enhancing efficiency of debugging programs.
Owner:INSIGMA TECHNOLOGY CO LTD
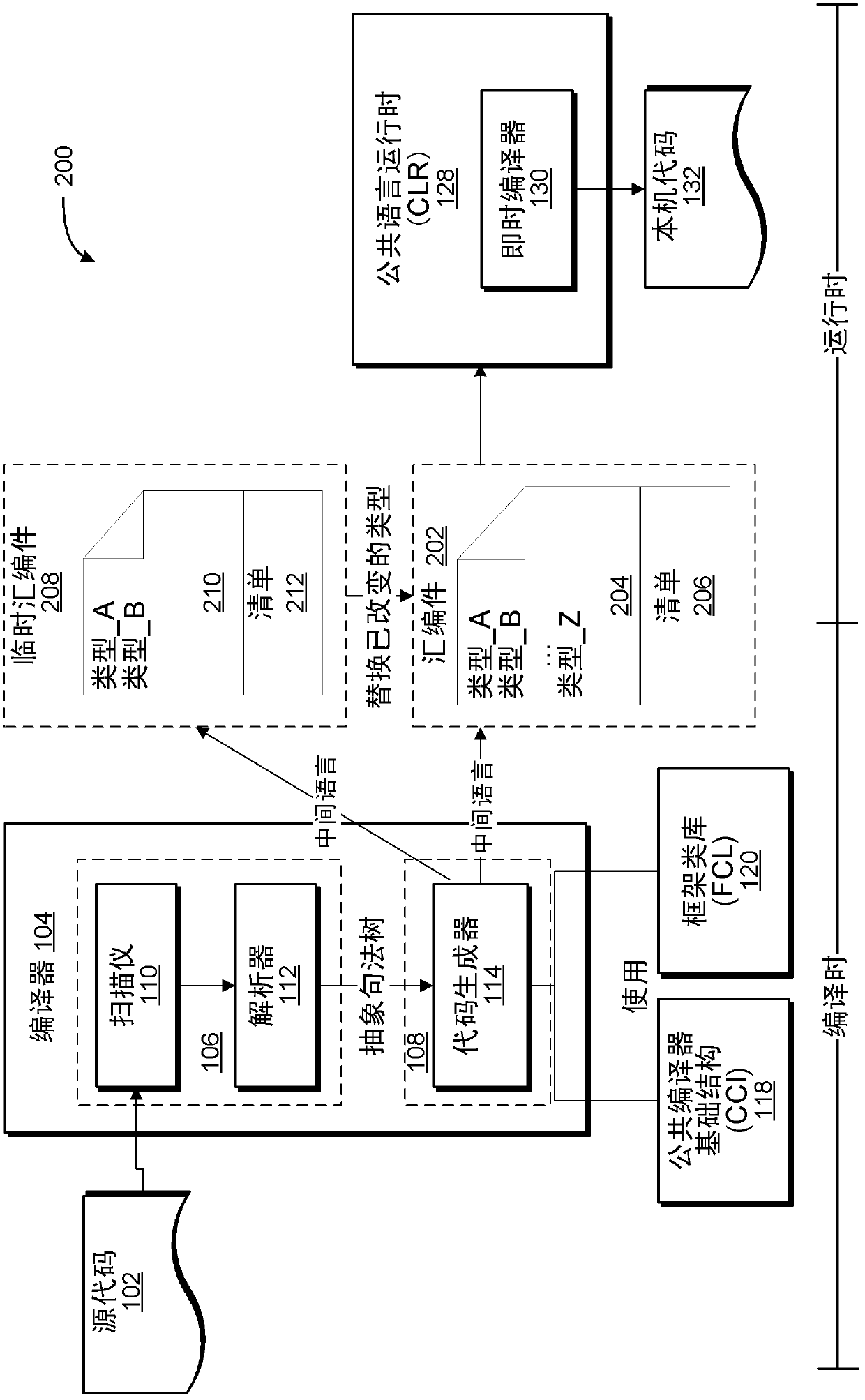
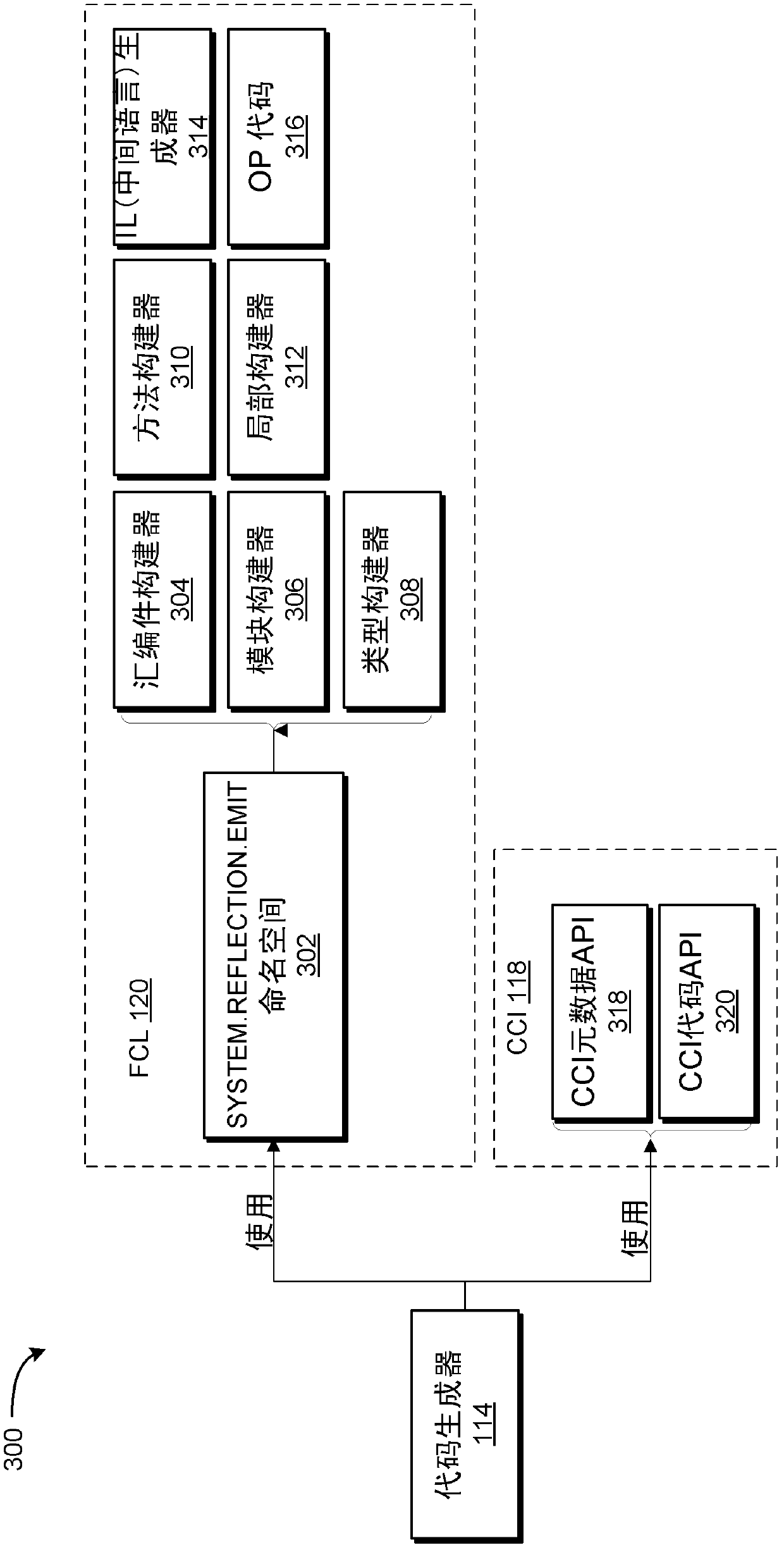
Incremental generation of managed assemblies
Concepts and technologies are described herein for incremental generation of managed assemblies. In accordance with some of the concepts and technologies disclosed herein, a compiler incrementally generates a managed assembly thereby facilitating a rapid application development environment in which changes to the assembly require recompilation of only a changed portion of the assembly instead of recompilation of the entire assembly.
Owner:MICROSOFT TECH LICENSING LLC
System and method for a functional extensibility framework
ActiveUS7590980B1Speed up the processSoftware engineeringMultiprogramming arrangementsExtensibilityProcess module
There is disclosed a framework which utilizes contemporaneous assembly of processing modules, strong typing, and integrated caching to assemble processing elements from different sources robustly and minimize system failures as software modules are upgraded.
Owner:NETCRACKER TECH SOLUTIONS
Intelligent development platform for database application system
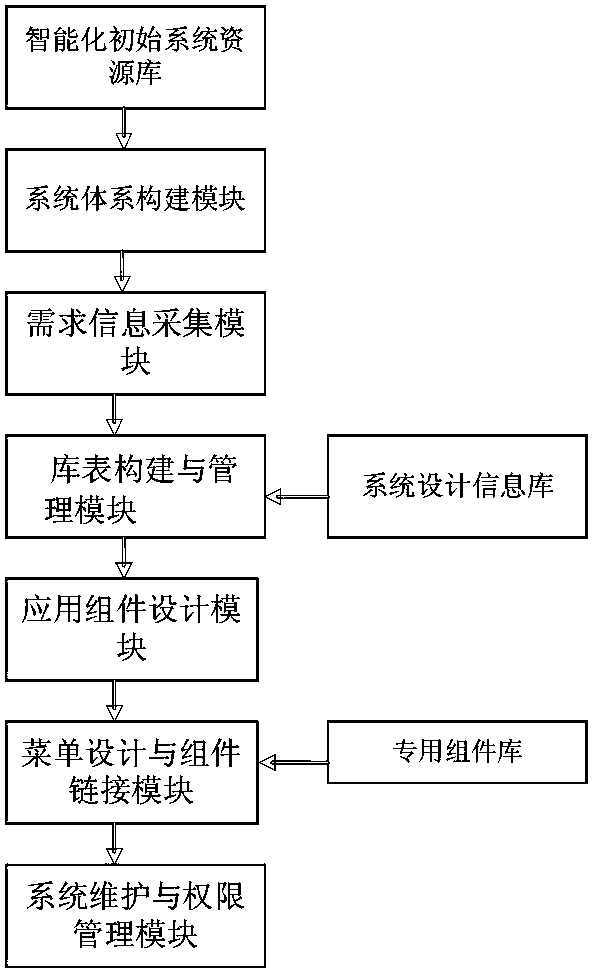
ActiveCN103425778AReal-time maintenance or expansion of application system functionsRealize management innovationSpecial data processing applicationsSpecific program execution arrangementsOperating instructionSystems design
The invention discloses an intelligent development platform for a database application system. The intelligent development platform comprises an intelligent development platform support resource base, a special assembly base, a system design information base, a system building module, a demand information collection module, a base table building and management module, an application assembly design module, a menu design and assembly link module and a system maintenance and authority management module. When the platform is used for developing the database system, any programming is not needed, only the interface configuration is needed through information with various functions, the operation enters the corresponding configuration interface according to the sequence given by the platform, the design information is configured through being guided by operation instructions and cases, the platform can select the proper solving technology according to the information, a database and an application system required by users can be automatically built, and the functions of the application system can be maintained or expanded in time. The intelligent development platform has the advantages that the development difficulty of the database application system can be greatly reduced, the development efficiency is improved, bugs generated during the program development are avoided, and the management innovation in the application can be realized.
Owner:STATE GRID CORP OF CHINA +1
Application software realization method and device as well as computer equipment
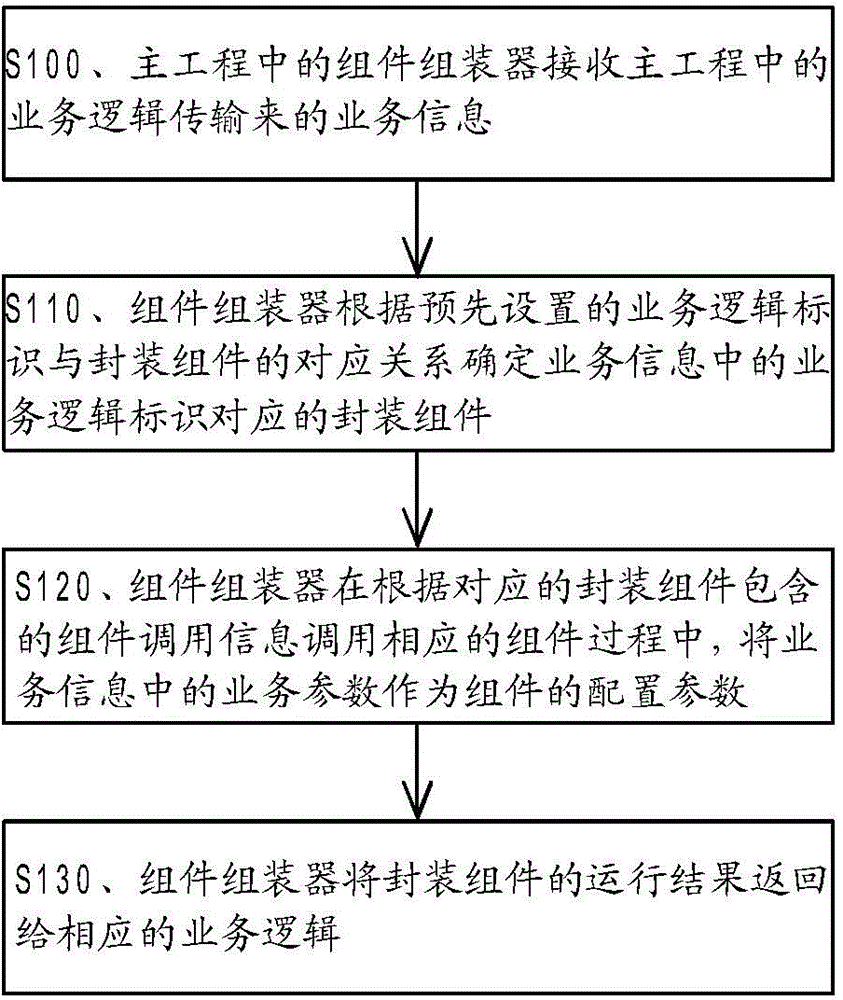
ActiveCN104572091AImprove scalabilitySpeed up refactoringSpecific program execution arrangementsSoftware engineeringApplication software
The invention provides an application software realization method and device as well as computer equipment, wherein the method comprises the following steps that an assembly assembler in main engineering receives service information transmitted from service logics in the main engineering; an encapsulation assembly corresponding to a service logic identification in the service information is determined by the assembly assembler according to the corresponding relationship of the preset service logic identification and the encapsulation assembly; in the process that the assembly assembler calls the corresponding assembly according to assembly calling information contained in the corresponding encapsulation assembly, service parameters in the service information are used as configuration parameters of the assembly, and the assembly belongs to sub engineering; the assembly assembler returns an operation result to the corresponding service logic. When the technical scheme provided by the invention is adopted, application software has the characteristics that the expansion is easy, the reconstitution is easy, the debugging is easy, the compilation speed is higher, and the like; the quality of the application software is finally improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
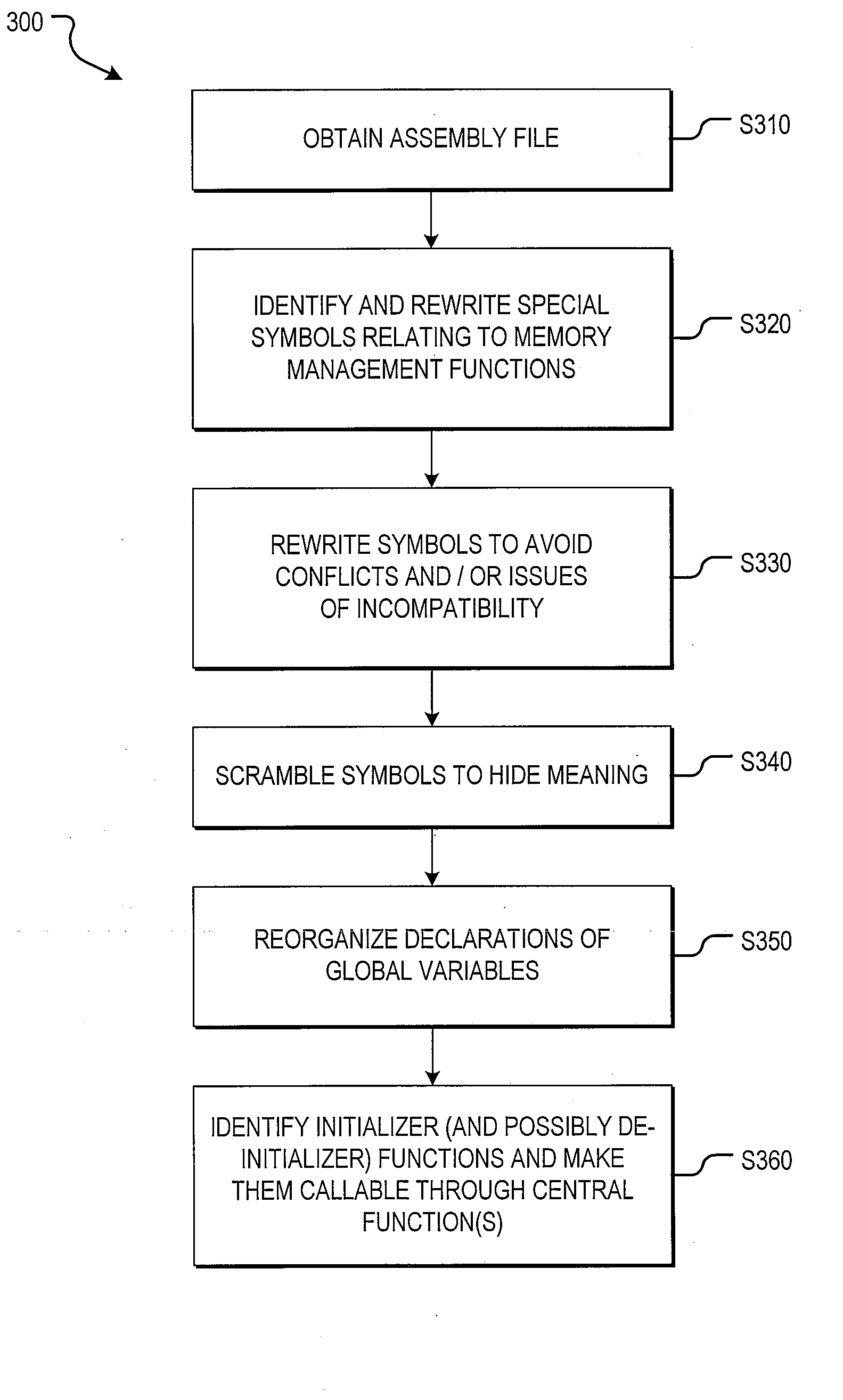
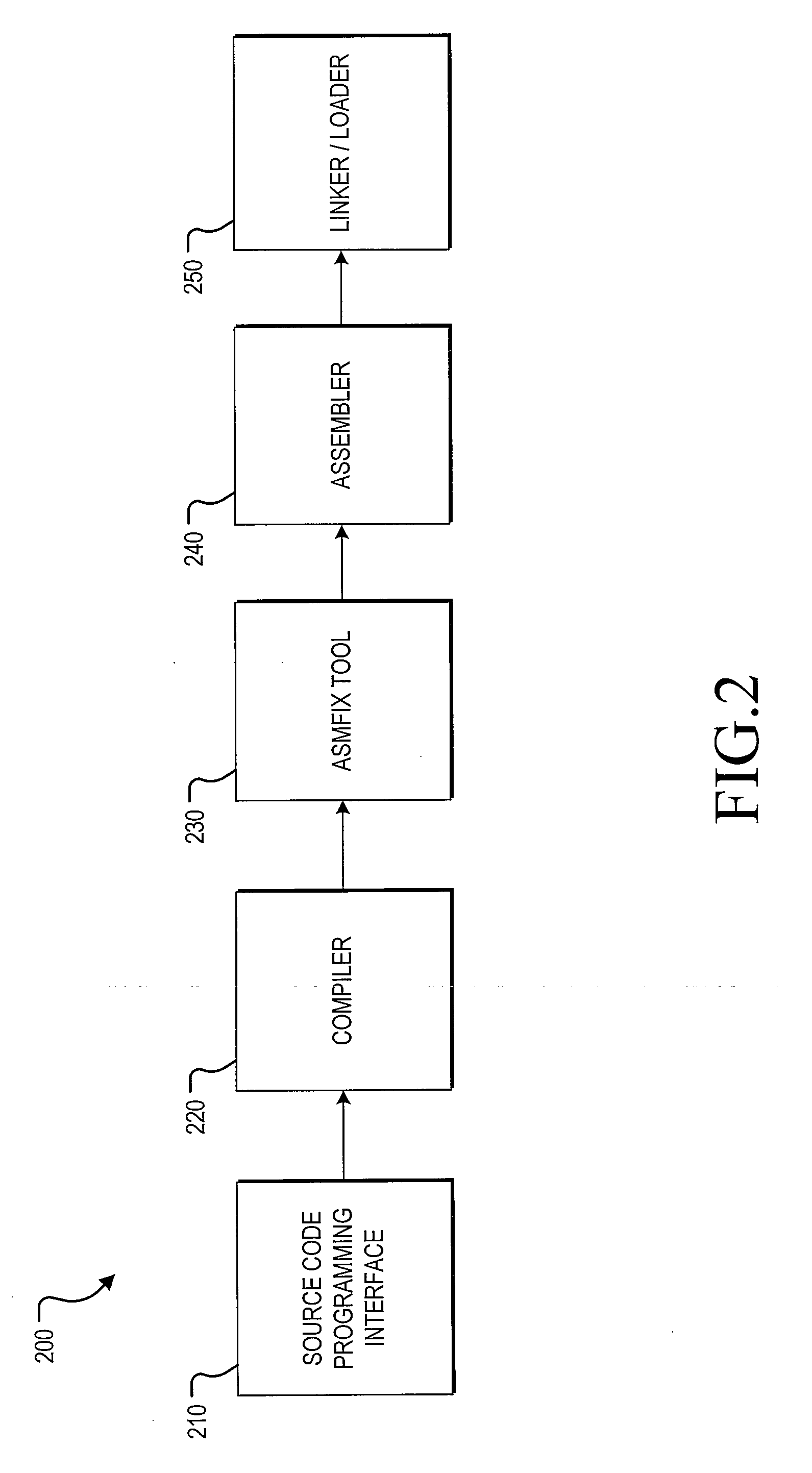
Method for modifying the assembly output of a compiler
The present invention performs manipulations on the assembly file level. As a compiler outputs an assembly file, the assembly file may be inspected and modified before it is sent to the assembler. One or more of the following modifications may be made to the assembly file: rewrite certain symbols, scramble program symbols, reorganize declarations of global variables so that their layout and default values are known prior to linking, and identify initializer and de-initializer functions in order to make them callable through central initialization and de-initialization functions, respectively.
Owner:OPERA SOFTVEAR AS
Method and apparatus for enhancing comprehension of code time complexity and flow
ActiveUS20110191760A1Simple taskEliminate errorsTime indicationSynchronous motors for clocksRound complexityTheoretical computer science
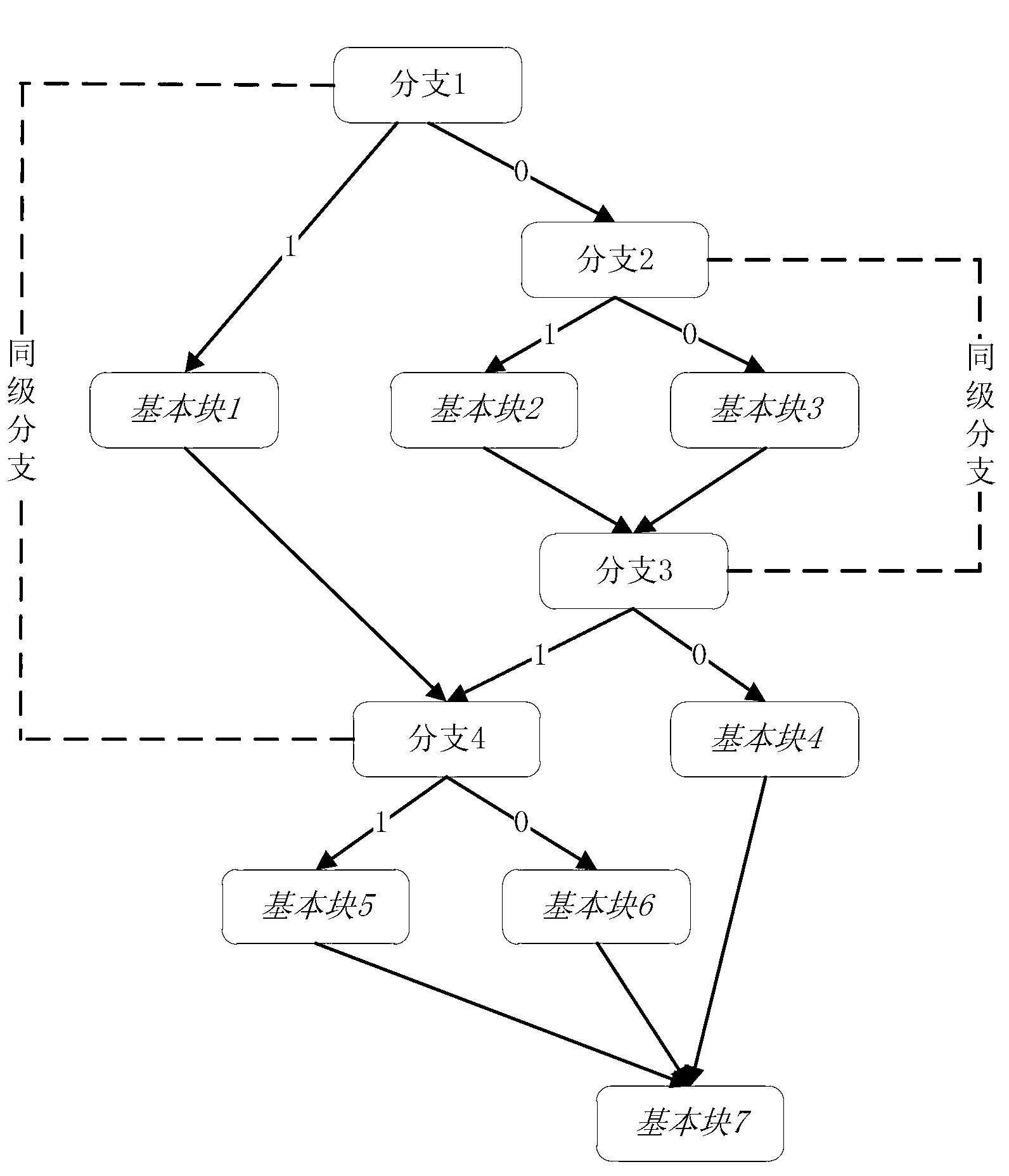
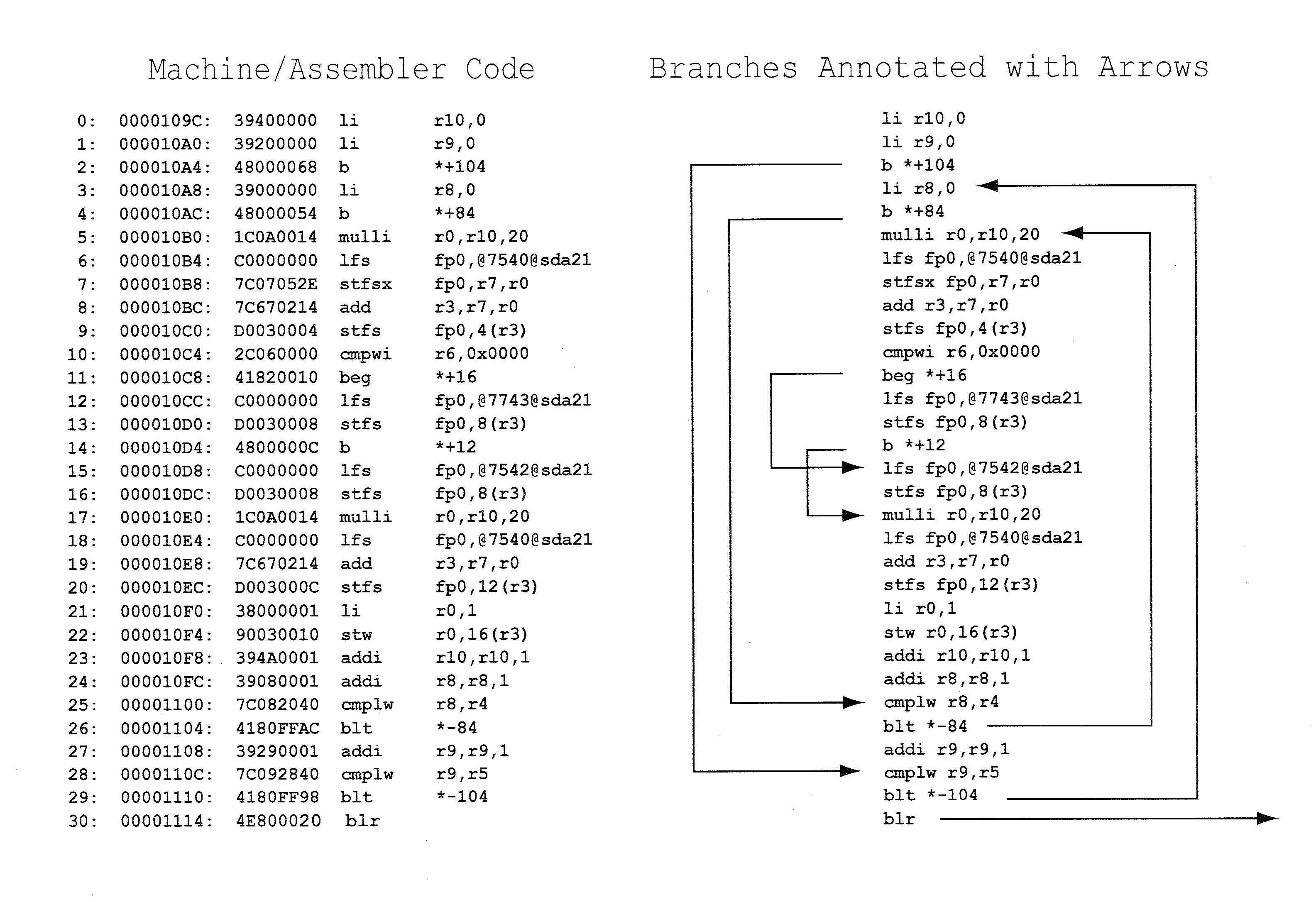
A method and apparatus that utilizes techniques for formatting assembly and / or machine code, including using arrows, indentations and textual symbols, so that a programmer who reads the code has an enhanced understanding of the program flow. Different methods of assessing computing time complexity (e.g., the up branch method and the strongly connected subgraph method) have strengths and weaknesses but benefit from being used together.
Owner:NINTENDO CO LTD
Process module library and programming environment for programming a manipulator process
ActiveCN102821917AUnleash your full potentialFast programmingProgramme controlProgramme-controlled manipulatorGraphicsProcess module
A process module library according to the invention for programming a manipulator process, in particular an assembly process, comprises a plurality of parametrisable process modules (''search()'',''peg_in_hole()'',''gear()'',''screw()'') for carrying out a sub-process which in particular is common to different manipulator processes. Each of the process modules comprises a plurality of basic commands of a common set of basic commands for carrying out a basic operation, in particular an atomic or molecular operation, and a process module can be linked, in particular mathematically, to a further process module and / or a basic command. During programming, a manipulator can be controlled by means of a functional module of a graphic programming environment (100).
Owner:库卡实验仪器有限公司
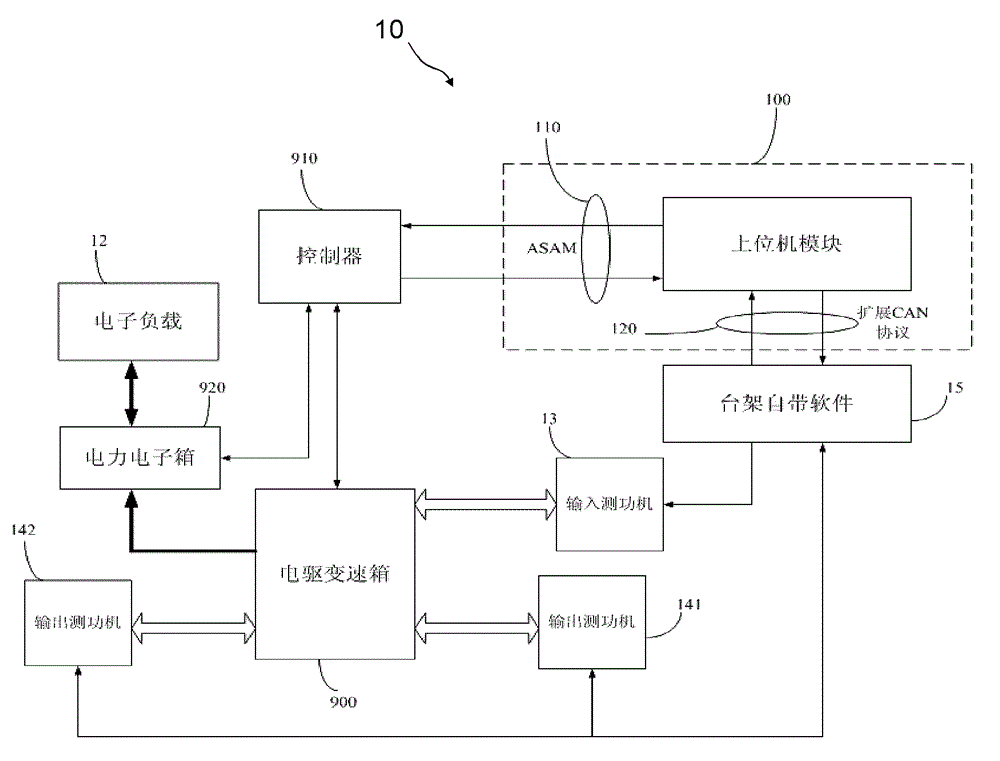
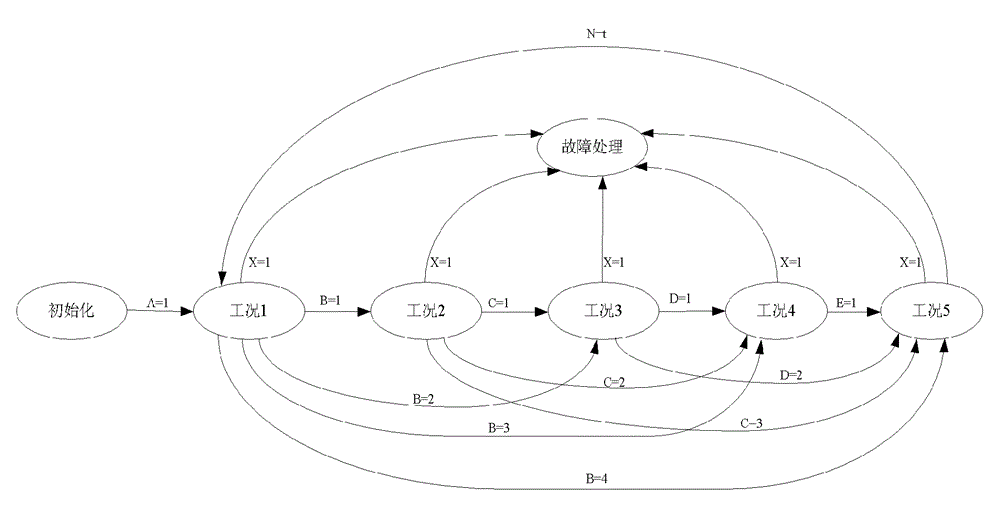
Testing system of power assembly
InactiveCN104422593AEasy to controlIncrease opennessVehicle testingMachine gearing/transmission testingSystem testingControl engineering
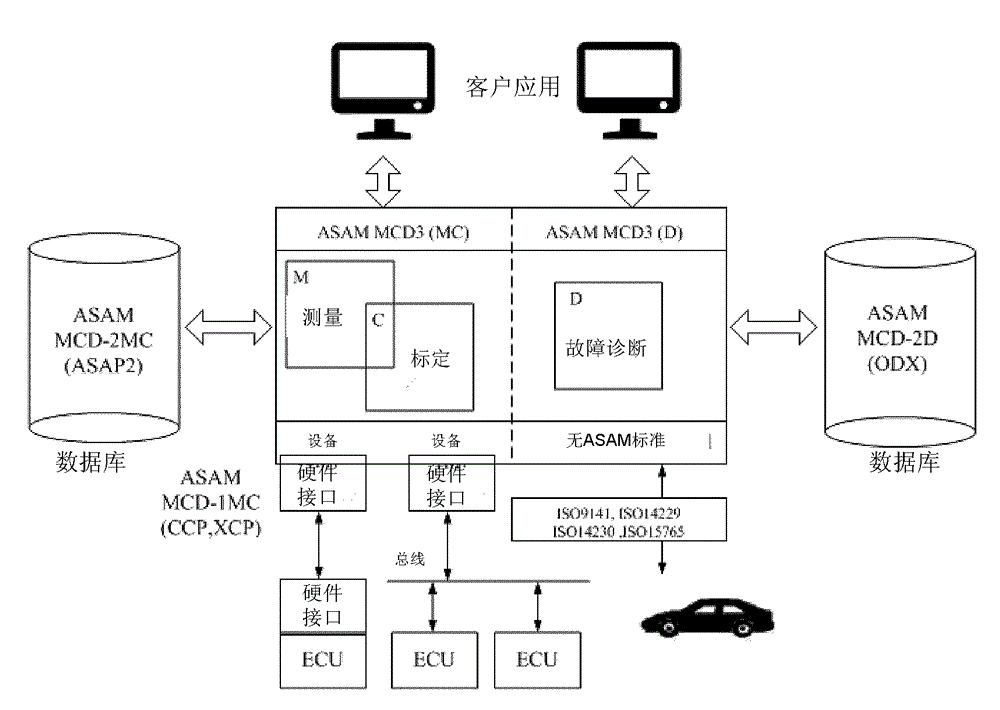
The invention provides a testing system of a power assembly, and belongs to the technical field of testing of power systems. The testing system at least comprises a power testing machine, a first control module, an upper computer module and an extension control protocol developing module, wherein the first control module is used for correspondingly controlling the power testing machine, the upper computer module is configured to define different working conditions according to a state machine architecture so as to continuously switch between different working conditions, and perform communication with a power assembly controller in any state according to a ASAM-MCD (association for standardization of automation and measuring systems - measurement, calibration and diagnosis) communication protocol, the extension control protocol developing module is used for developing an extension control protocol between the upper computer module and the first control module, and the remote communication is performed between the first control module and a second control module which is integrated into the upper computer module according to the extension control protocol, so as to control the power testing machine on the basis of the second control module. The testing system has the advantages that the compatibility and the extendibility are good, the continuous switching between different working conditions is easy, the cost is low, and the testing period is short.
Owner:SAIC MOTOR
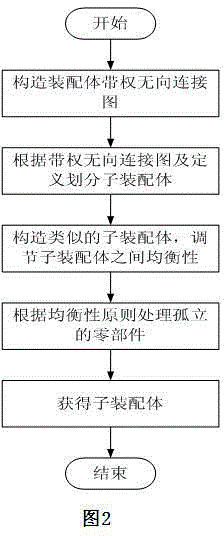
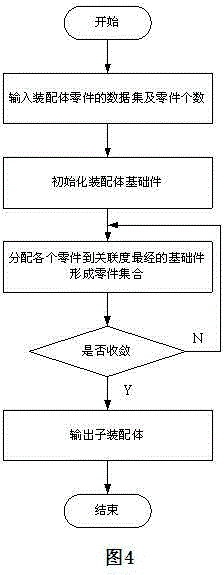
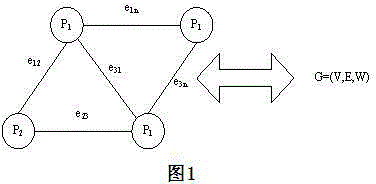
Recognition method for subassembly in assembly sequence planning
InactiveCN104573194AReduce planning timeReduce the difficulty of assemblySpecial data processing applicationsSequence planningAlgorithm
The invention discloses a recognition method for a subassembly in assembly sequence planning. The recognition method comprises the steps of building a weighted non-vector connection diagram through a relationship between assemblies, and then determining basic parts; judging the subassembly according to the definition and the association degree of parts; finally, realizing a subassembly recognition algorithm through designing and compiling under a Matlab (matrix laboratory) environment. According to the recognition method disclosed by the invention, an algorithm instance verifies that a great significance in realizing assembly sequence optimization and shortening assembly sequence planning time is obtained by applying the subassembly recognition to the assembly sequence planning, an assembly sequence is simplified, and the assembly difficulty and the assembly cost are reduced.
Owner:XIAN TECHNOLOGICAL UNIV
System and method for tamper-proofing executable binary assemblies
InactiveUS8200983B1Eliminate disadvantagesDigital data processing detailsUnauthorized memory use protectionTamper resistanceHash function
A method, system and computer program product for tamper-proofing an executable assembly, including identifying assembly-time constants in source code; encrypting the assembly-time constants during the assembly process using public key cryptography; and signing the executable assembly using a digital signature. The executable assembly, at run-time, decrypts the assembly-time constants using the digital signature. A hashing function, a compression function or a one-way cryptographic block function is used to encrypt the assembly-time constants. Different keys or the same keys can be used to launch the assembly and to encrypt the assembly-time variables. The assembly-time constants are placed into a heap prior to the encrypting step. The assembly-time constants include strings and databases.
Owner:VICTOR Y VICTOROV
Detection method and device for homogenization application
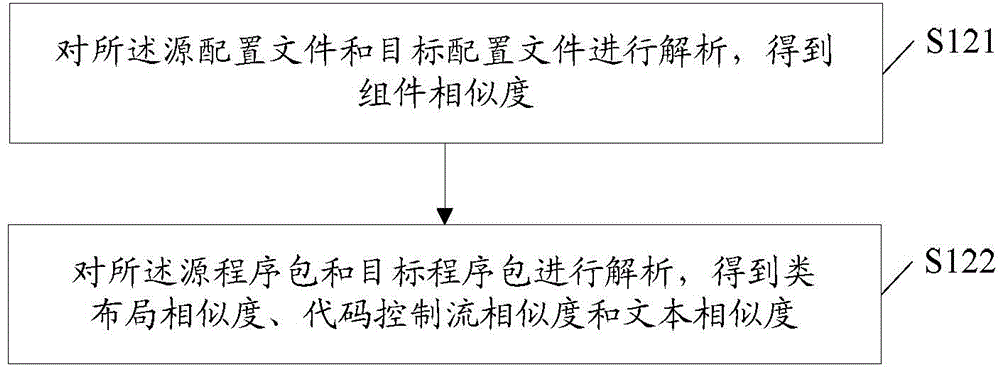
InactiveCN105550540AThe similarity is accurately determinedSure exactly sureProgram/content distribution protectionControl flowAlgorithm
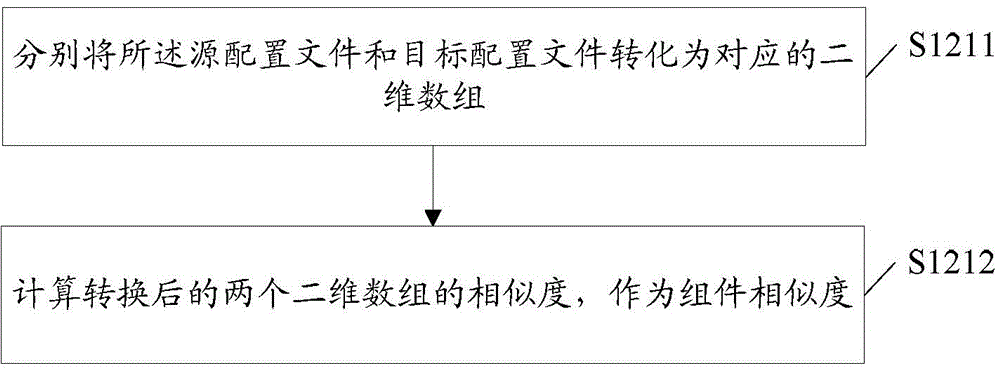
The embodiment of the invention discloses a detection method and a detection device for homogenization application. The detection method comprises the steps of respectively performing code decompilation processing on a source application and a target application, thus obtaining source application information and target application information; analyzing the source application information and target application information to obtain assembly similarity, class layout similarity, code control flow similarity and text similarity; and determining the similarity between the source application and target application according to the assembly similarity, class layout similarity, code control flow similarity and text similarity.
Owner:CHINA MOBILE GROUP JIANGSU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com