Patents
Literature
602 results about "Resource location" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
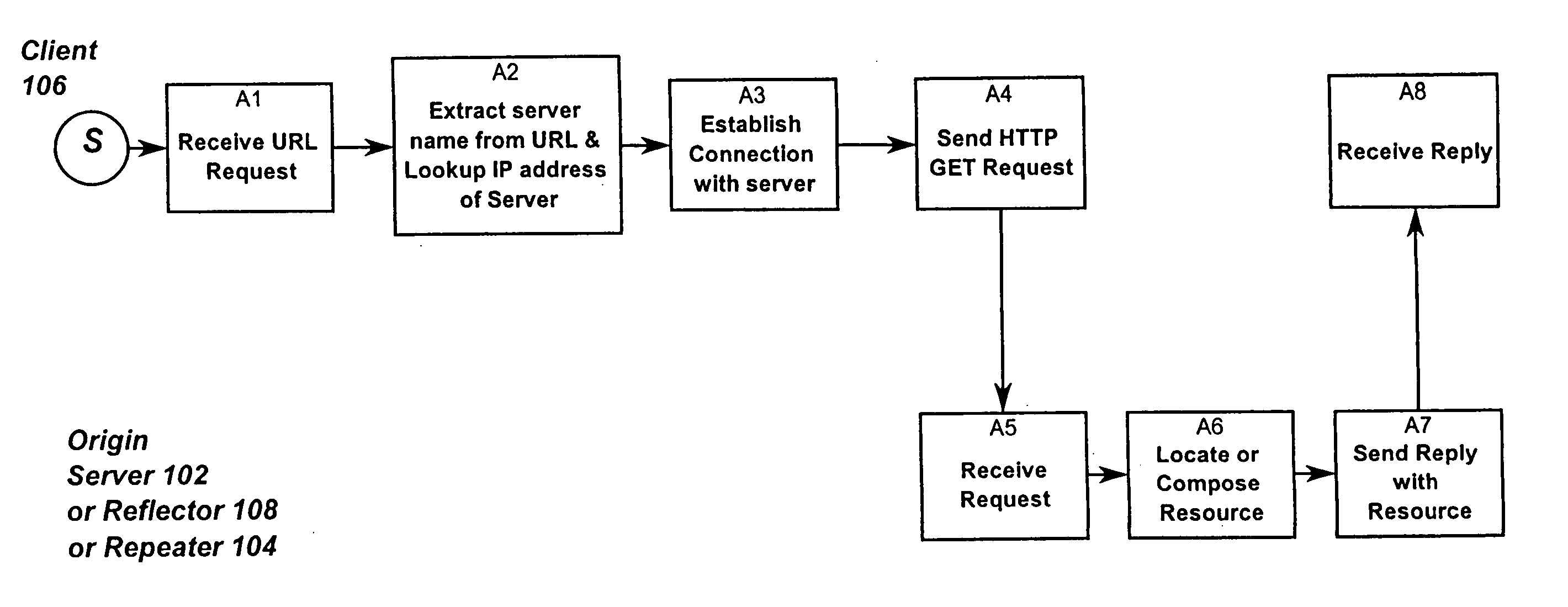
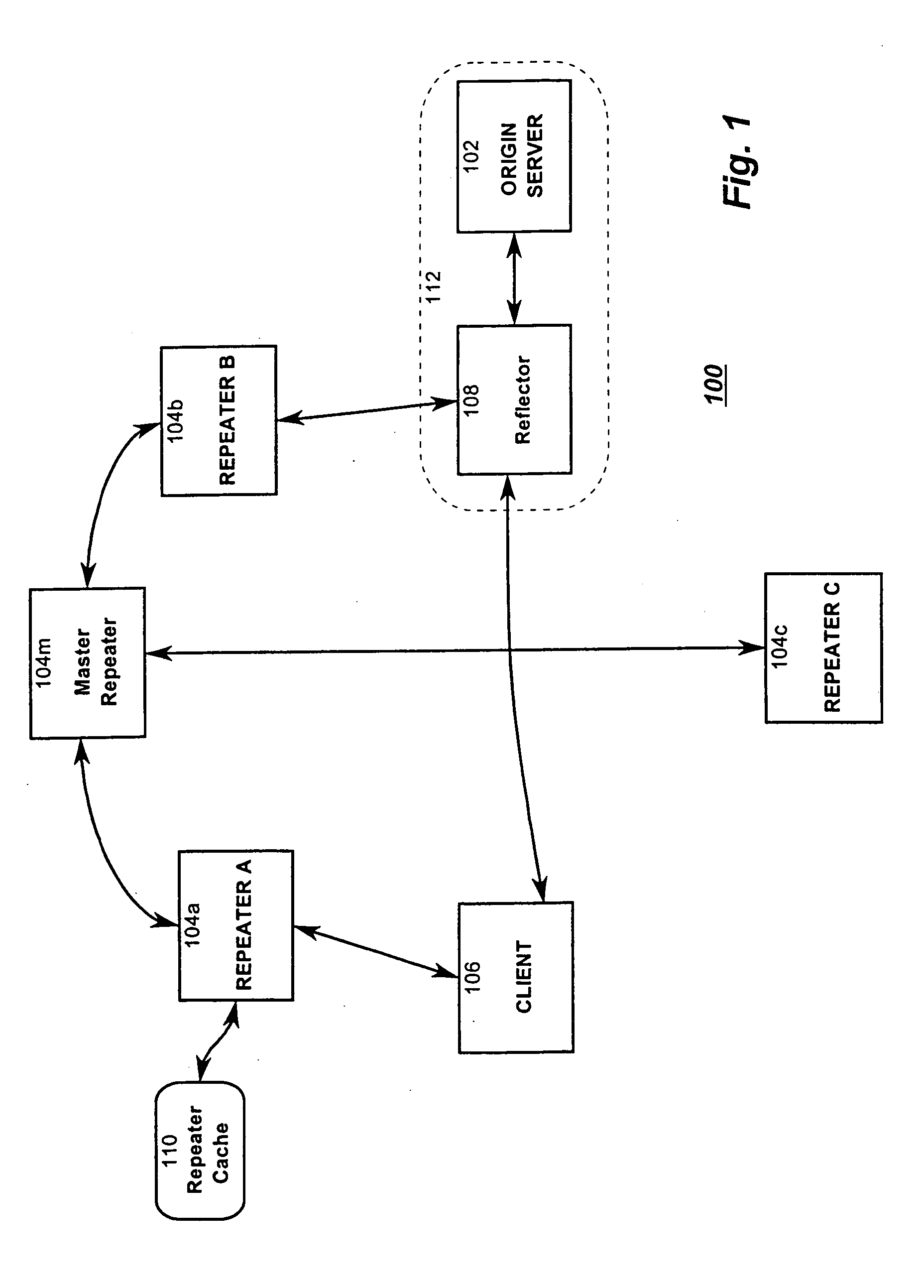
Optimized network resource location
InactiveUS20010056500A1Resource allocationMultiple digital computer combinationsEngineeringDistributed computing
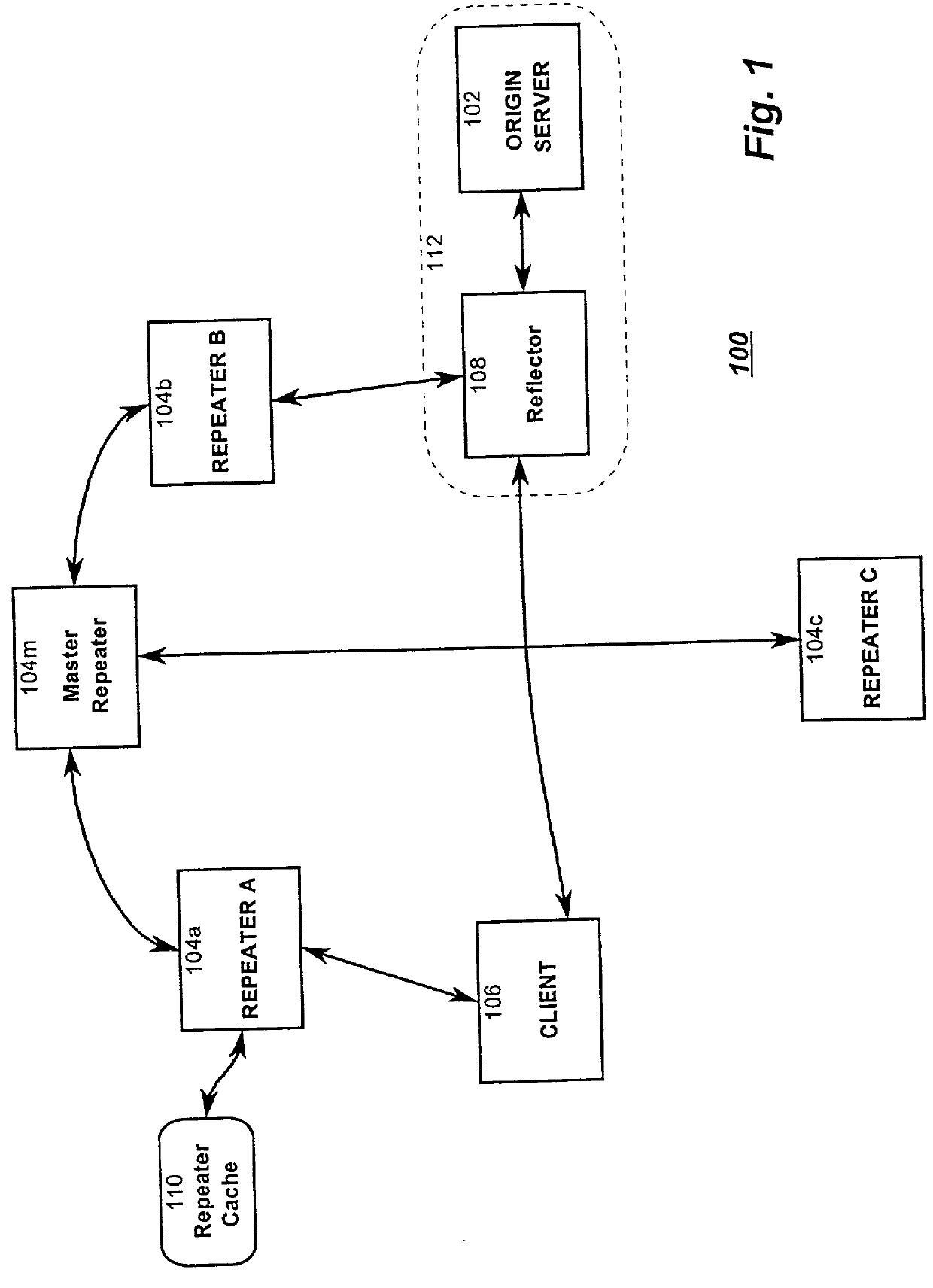
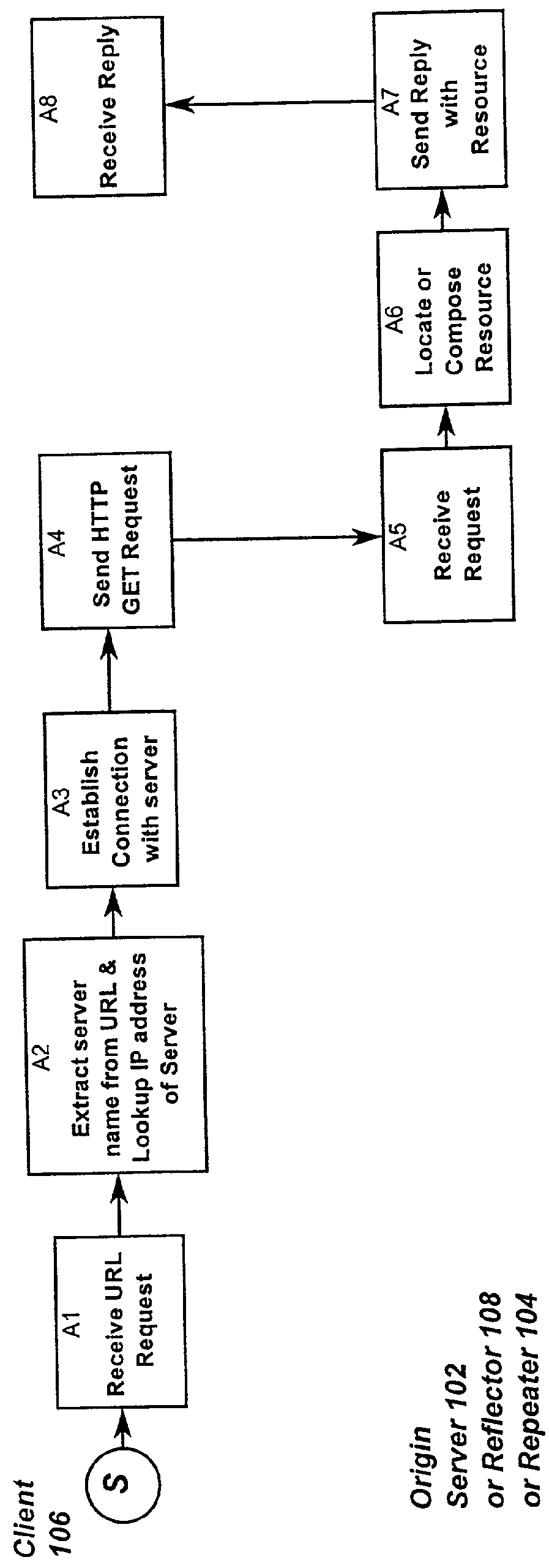
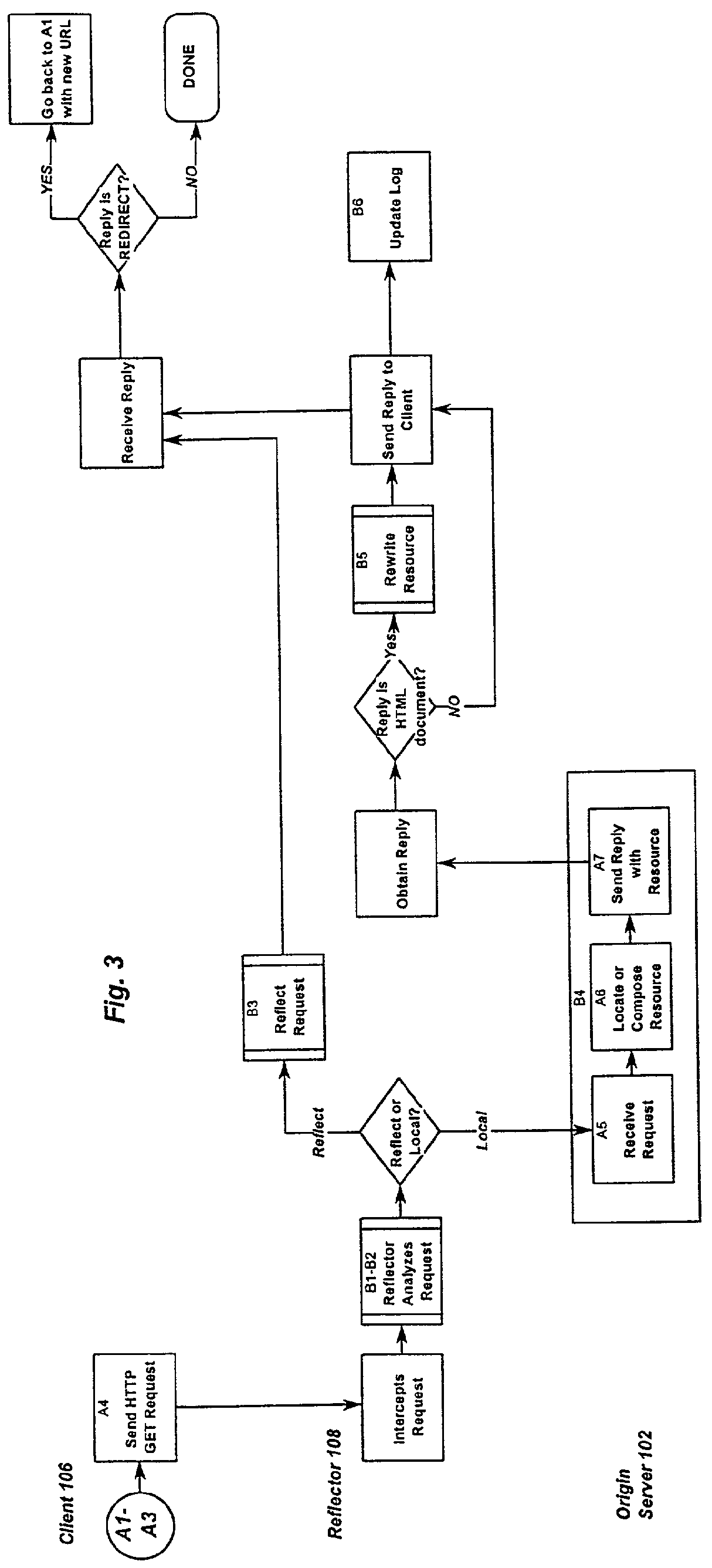
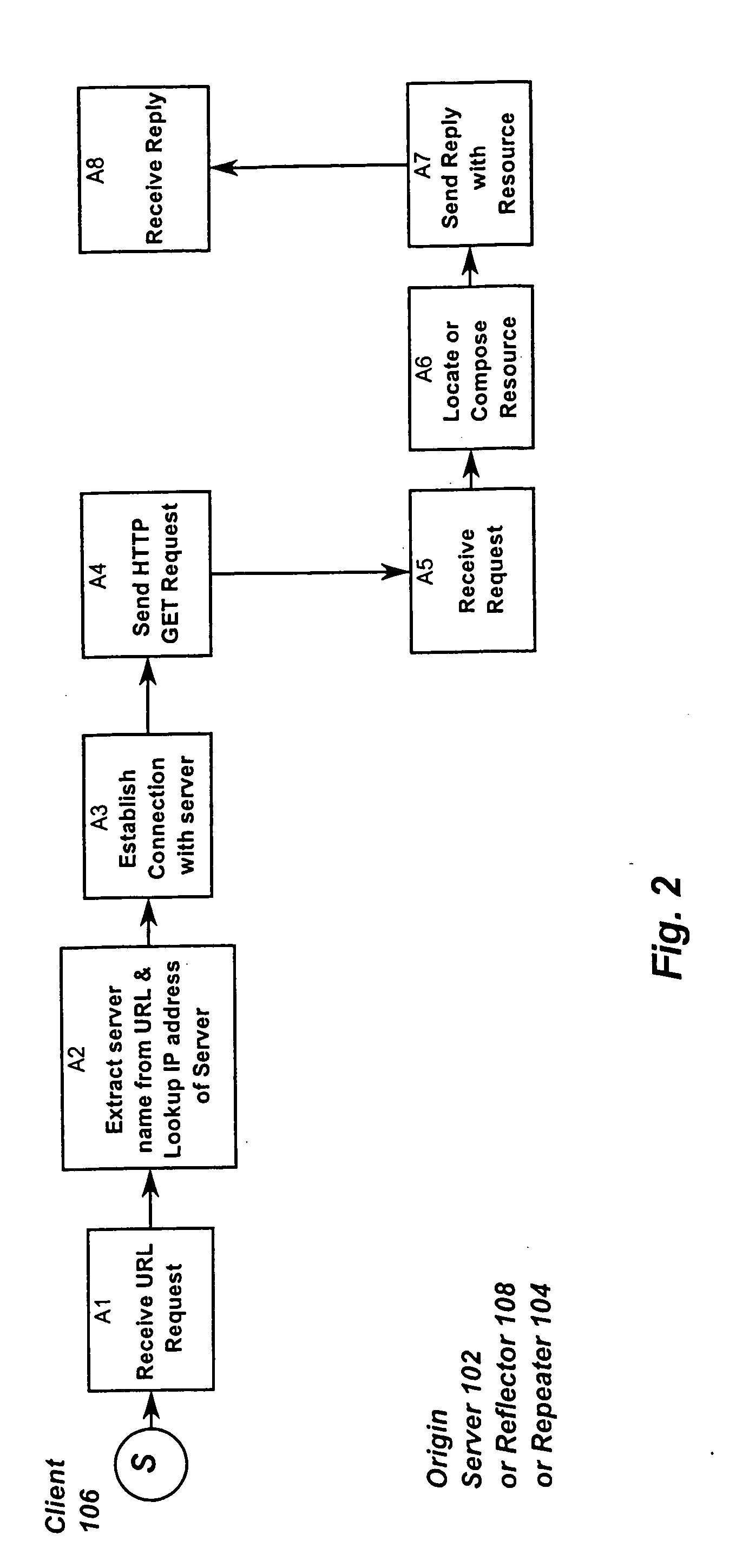
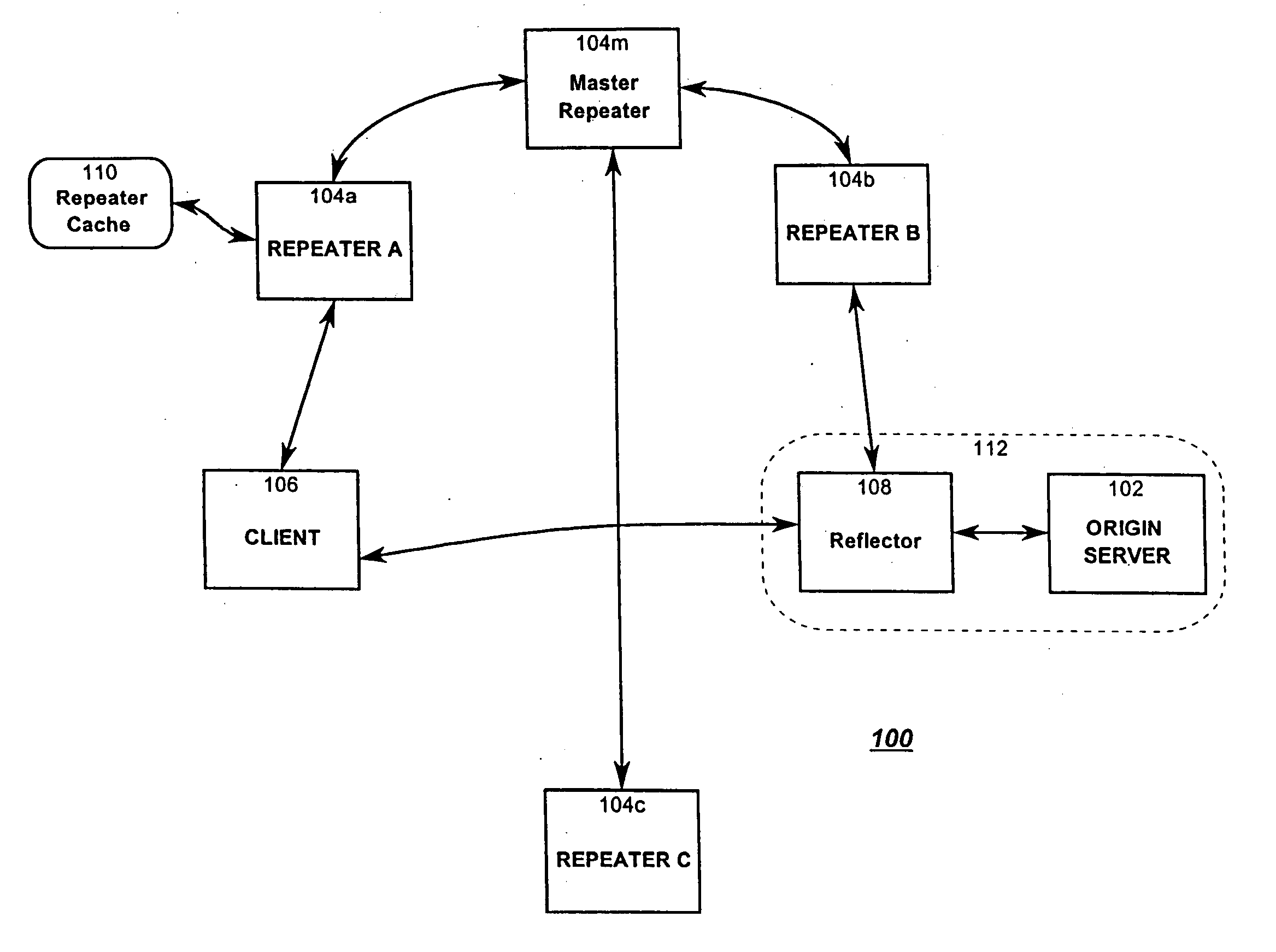
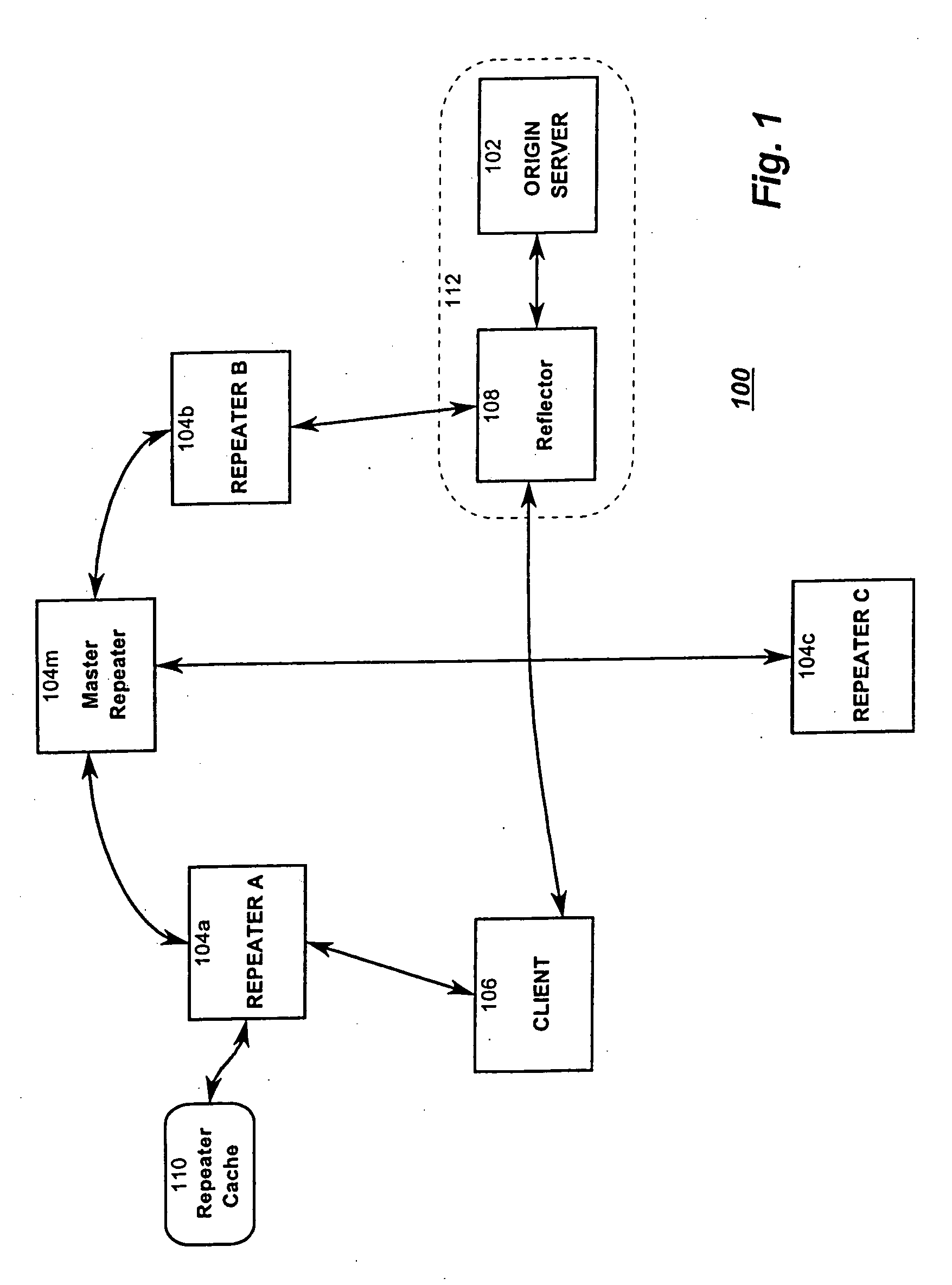
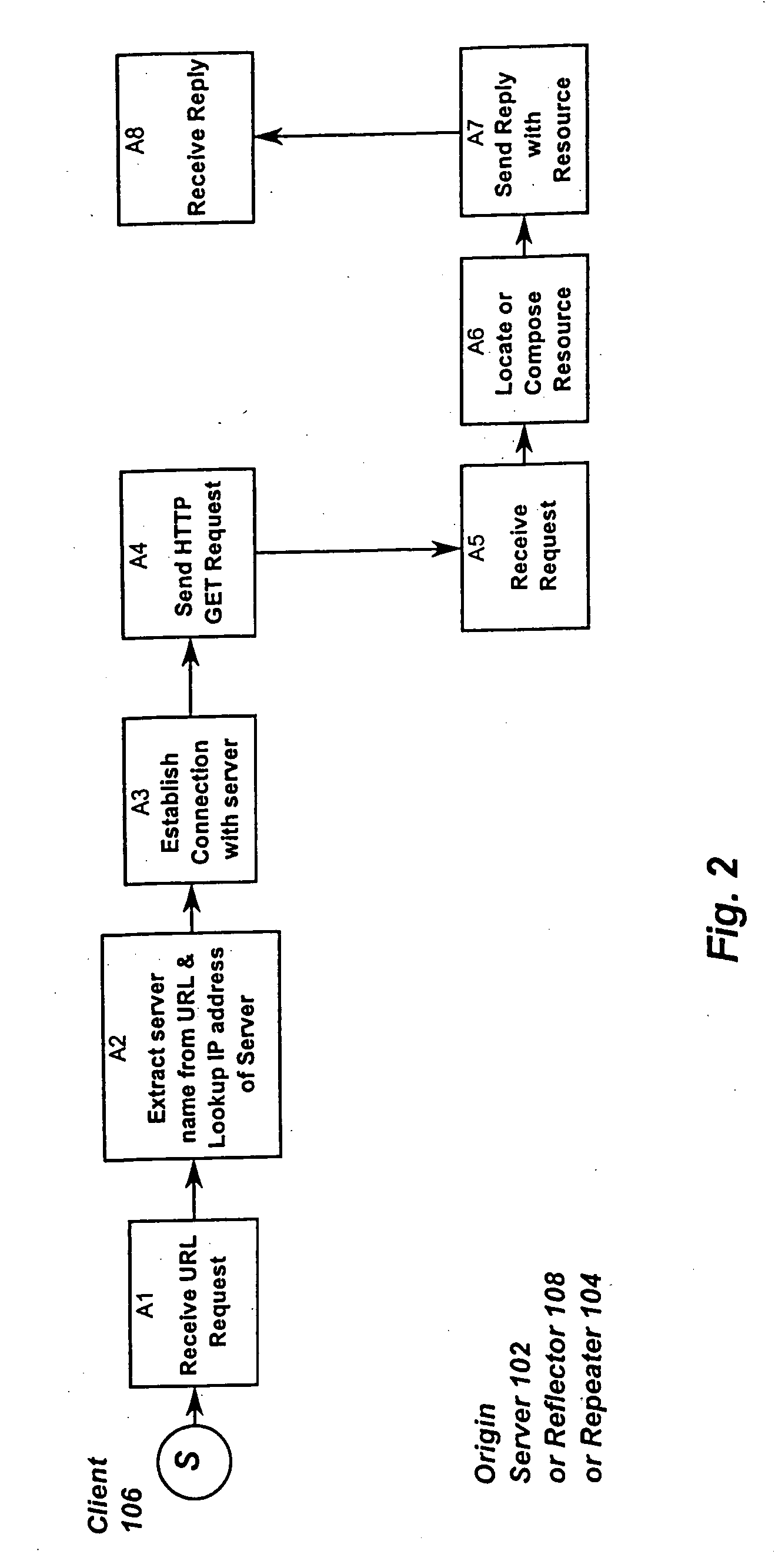
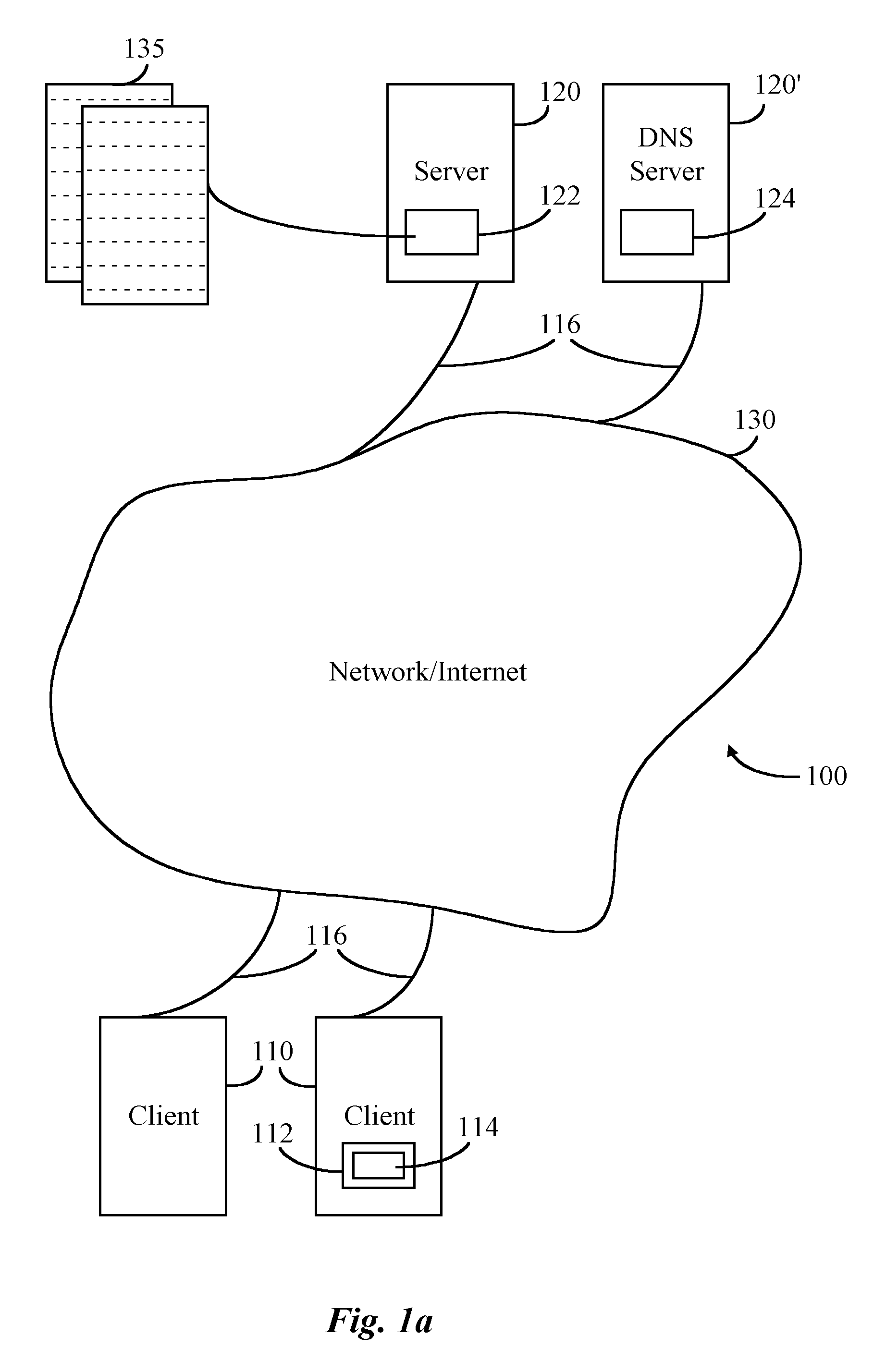
Resource requests made by clients of origin servers in a network are intercepted by reflector mechanisms and selectively reflected to other servers called repeaters. The reflectors select a best repeater from a set of possible repeaters and redirect the client to the selected best repeater. The client then makes the request of the selected best repeater. The resource is possibly rewritten to replace at least some of the resource identifiers contained therein with modified resource identifiers designating the repeater instead of the origin server.
Owner:DIGITAL ISLAND
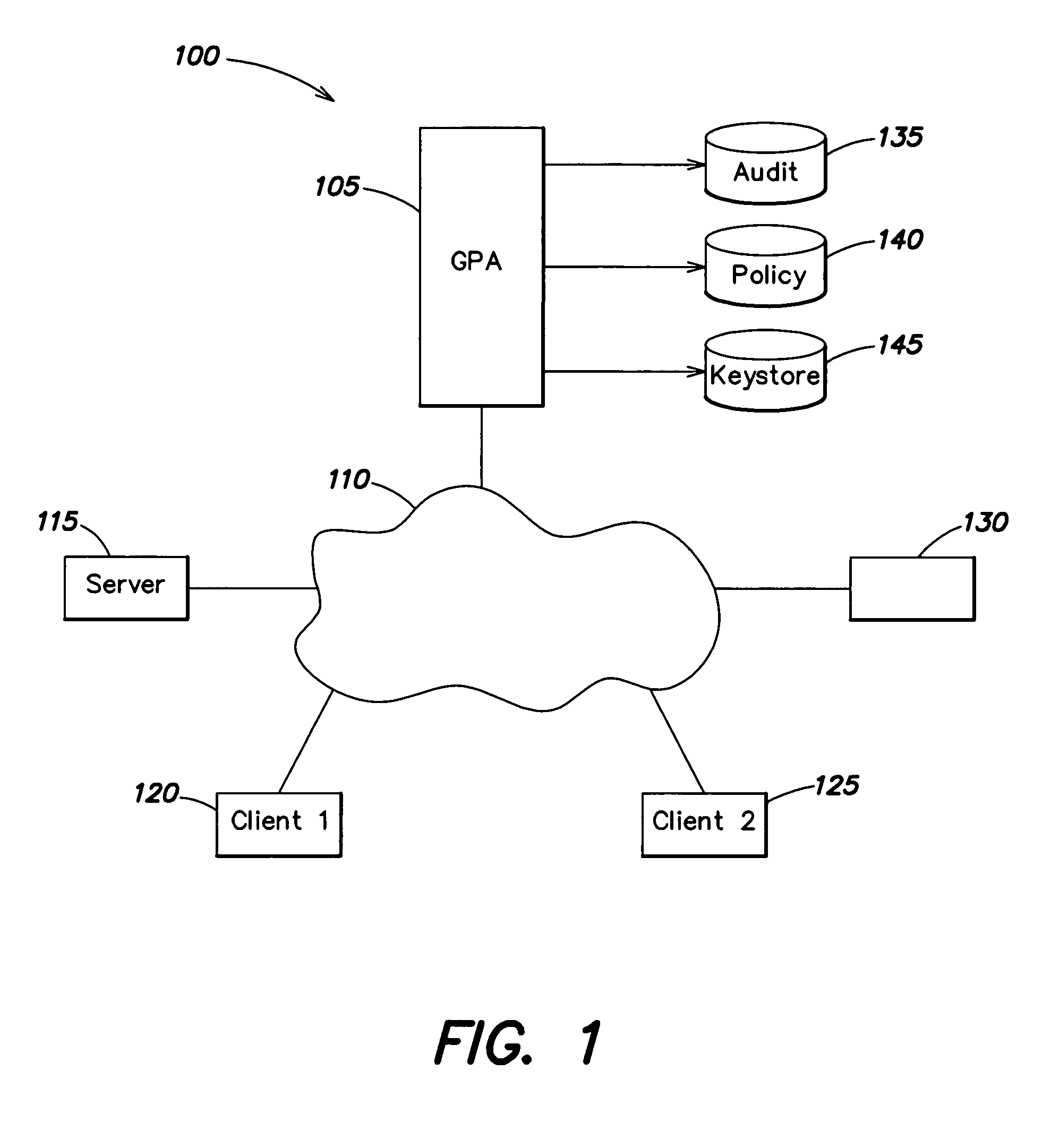
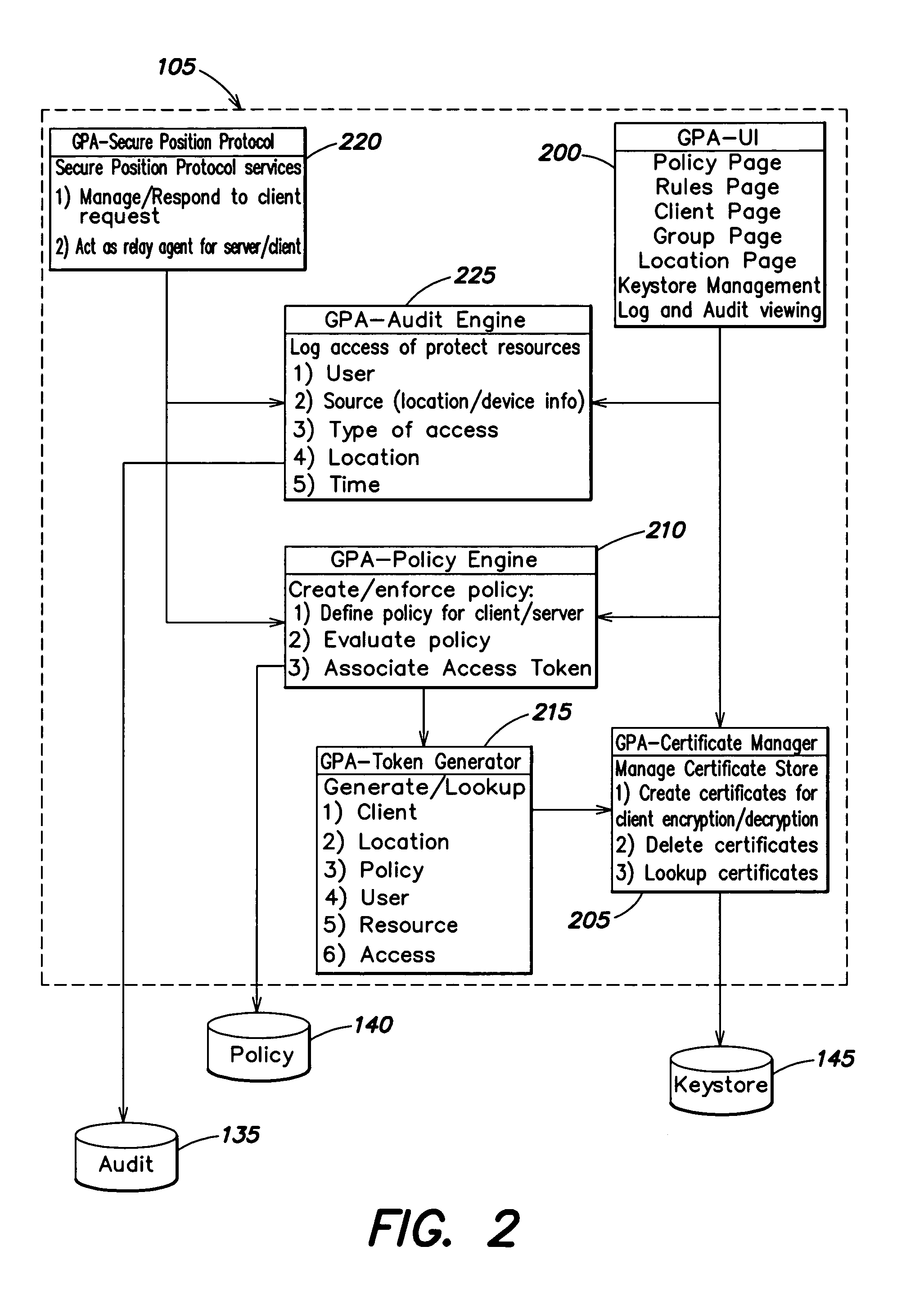
Method and apparatus for securing documents using a position dependent file system
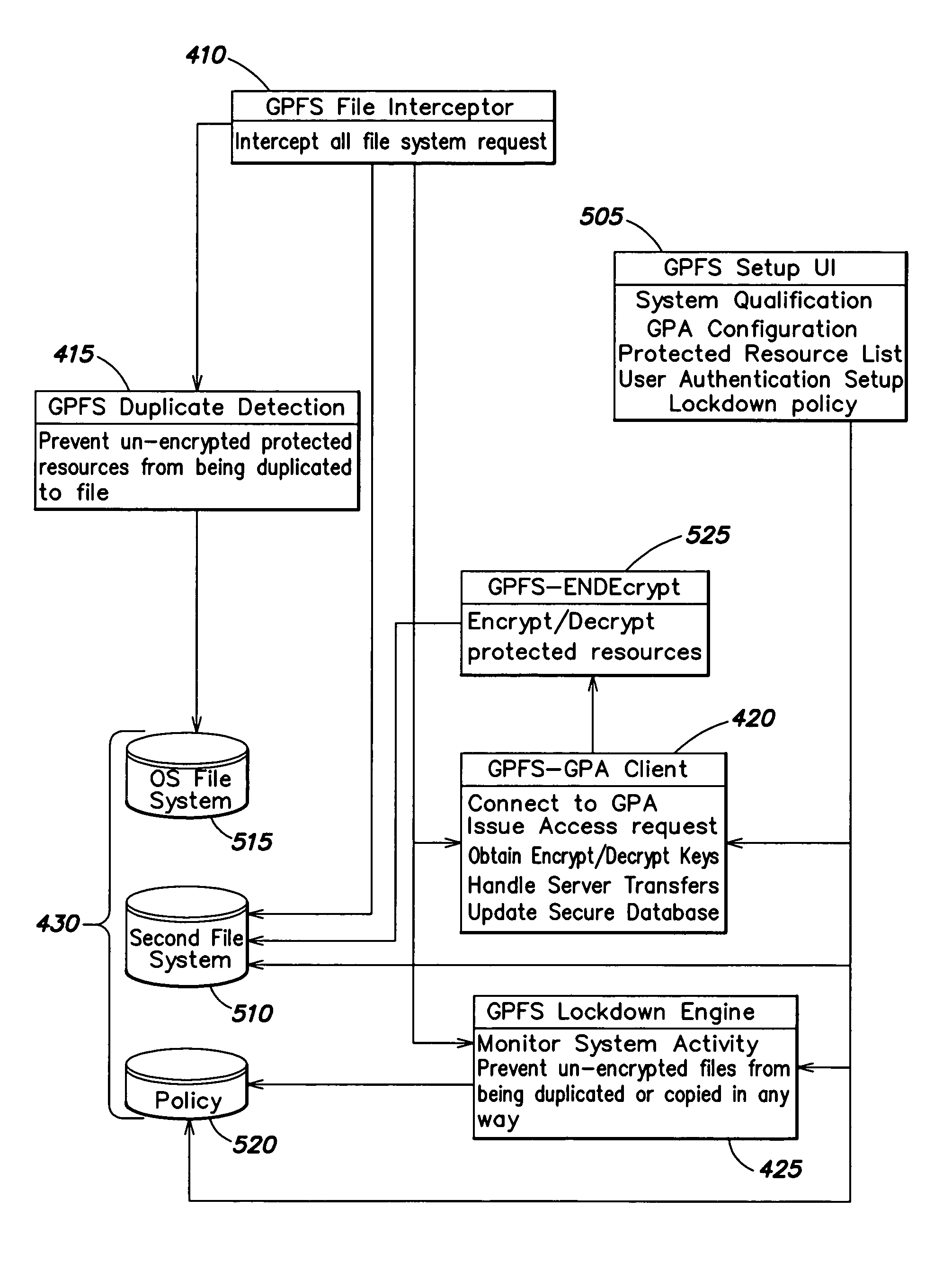
ActiveUS8312064B1Provide securityEasy to manageUnauthorized memory use protectionHardware monitoringInternet privacyFile system
Access to information or a document is secured by a central global positioning authority that evaluates access requests in accordance with predefined policies. One component of an access request includes location information regarding at least one of the requesting entity and location of the requested resource. Access is either allowed or denied as a function of at least the requesting entity, position information and the applicable policy or policies. An encryption / decryption scheme is implemented where the encryption key is a function of the resource's position.
Owner:GEN DIGITAL INC
Optimized network resource location
InactiveUS20050198334A1Resource allocationMultiple digital computer combinationsResource locationDistributed computing
Owner:DIGITAL ISLAND +1
Sitemap Access Method, Product, And Apparatus
InactiveUS20080005127A1Easy to understandSaving distribution costDigital computer detailsTransmissionAccess methodUser interface
When a network request such as a resource location request, search engine request, and WHOIS request to process input having a resource identifier is received a user interface can then be provided to perform a request to access and display at least one sitemap corresponding to said resource identifier while performing the network request.
Owner:MEC MANAGEMENT LLC
Optimized network resource location
Resource requests made by clients of origin servers in a network are intercepted by reflector mechanisms and selectively reflected to other servers called repeaters. The reflectors select a best repeater from a set of possible repeaters and redirect the client to the selected best repeater. The client then makes the request of the selected best repeater. The resource is possibly rewritten to replace at least some of the resource identifiers contained therein with modified resource identifiers designating the repeater instead of the origin server.
Owner:MOUNT SHASTA ACQUISITION +2
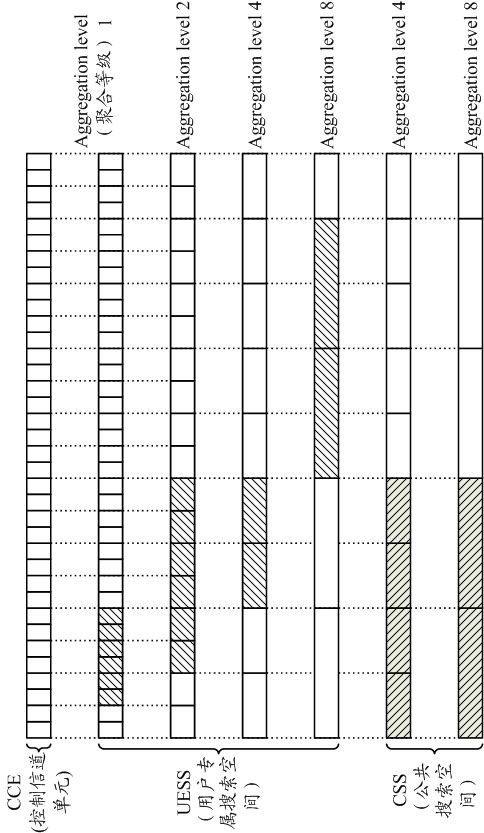
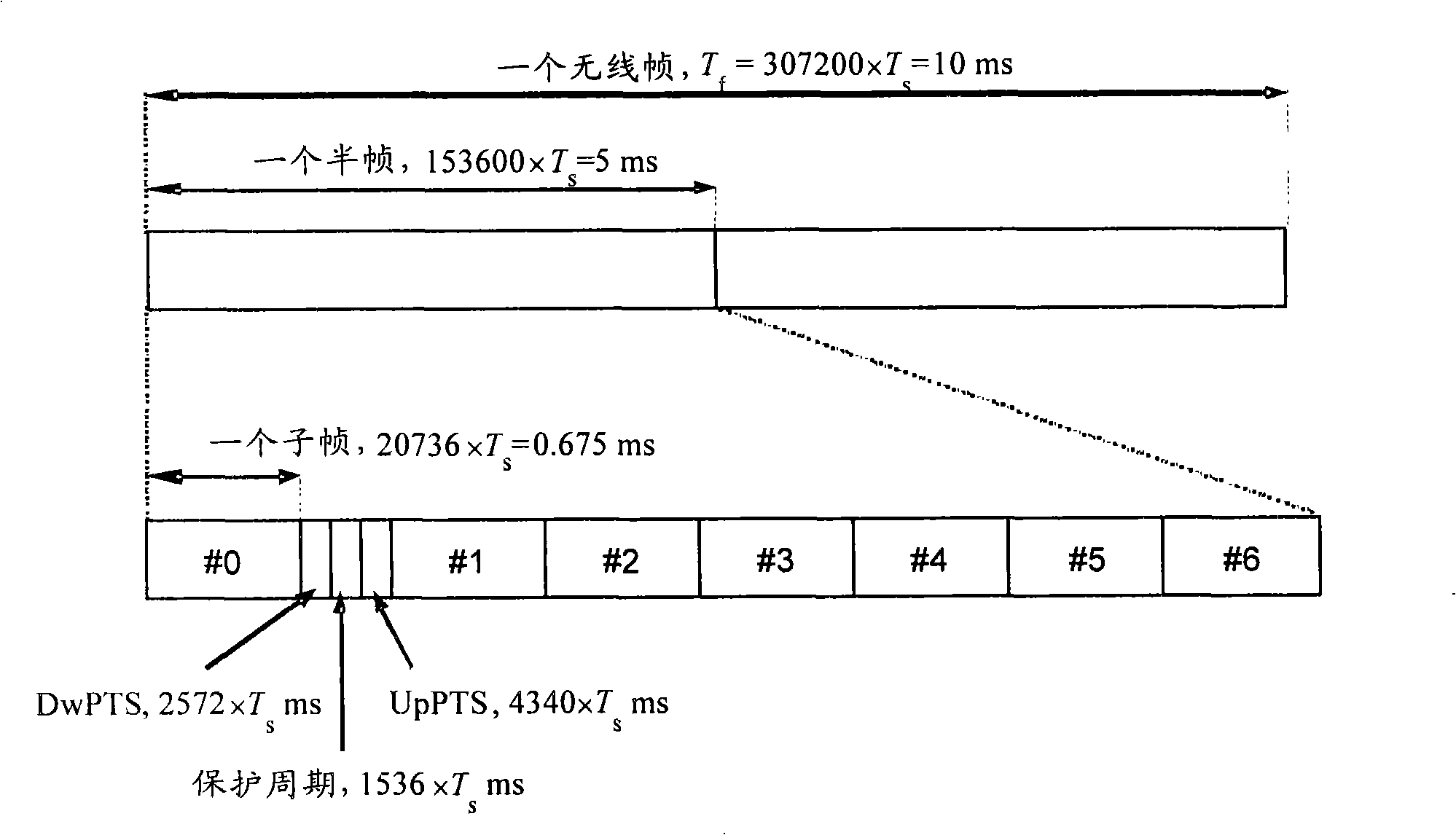
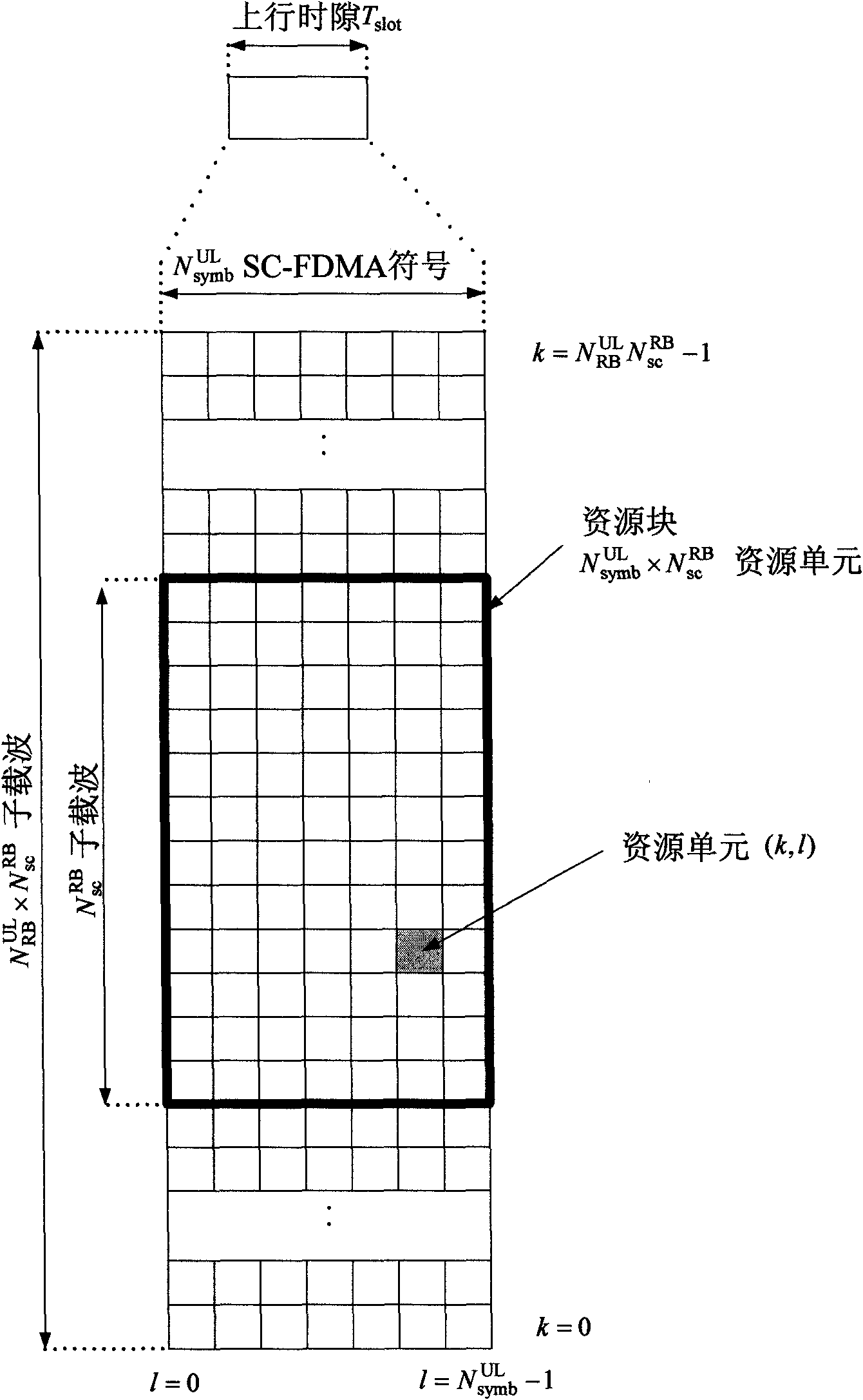
Method for receiving and transmitting information on physical downlink control channel and equipment thereof
InactiveCN102170703AImprove resource utilizationIncrease capacityWireless communicationControl channelUser equipment
The invention discloses a method for receiving and transmitting information on a physical downlink control channel and equipment thereof. The method comprises the following steps: the resource position of an enhanced physical downlink control channel cluster is indicated to user equipment by a base station; scheduling information is transmitted to the user equipment on the resource position of a physical downlink control channel cluster by the base station; the resource position of the enhanced physical downlink control channel cluster is determined by the user equipment according to the indication of the base station; and blind check carried out on the resource position of the enhanced physical downlink control channel cluster by the user equipment to receive the scheduling information transmitted by the base station to the user equipment. The invention can effectively provide the capacity of the physical downlink control channel, simultaneously, can effectively improve the utilization rate of the resource of the enhanced physical downlink control channel.
Owner:CHINA ACAD OF TELECOMM TECH
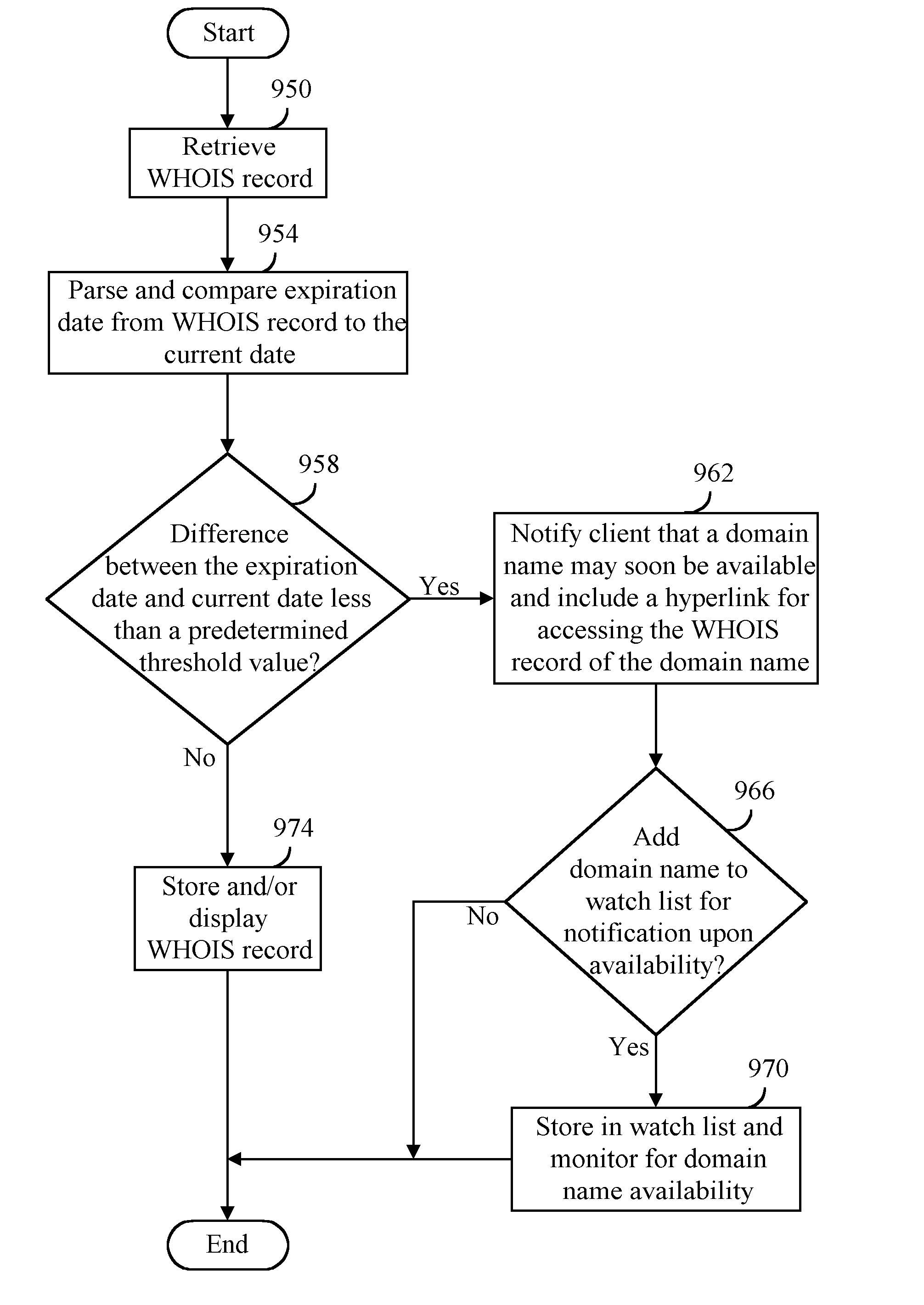
Method, product, and apparatus for enhancing resolution services, registration services, and search services
ActiveUS20080005342A1Minimize connection bandwidthMultiple digital computer combinationsTransmissionDomain nameWatch list
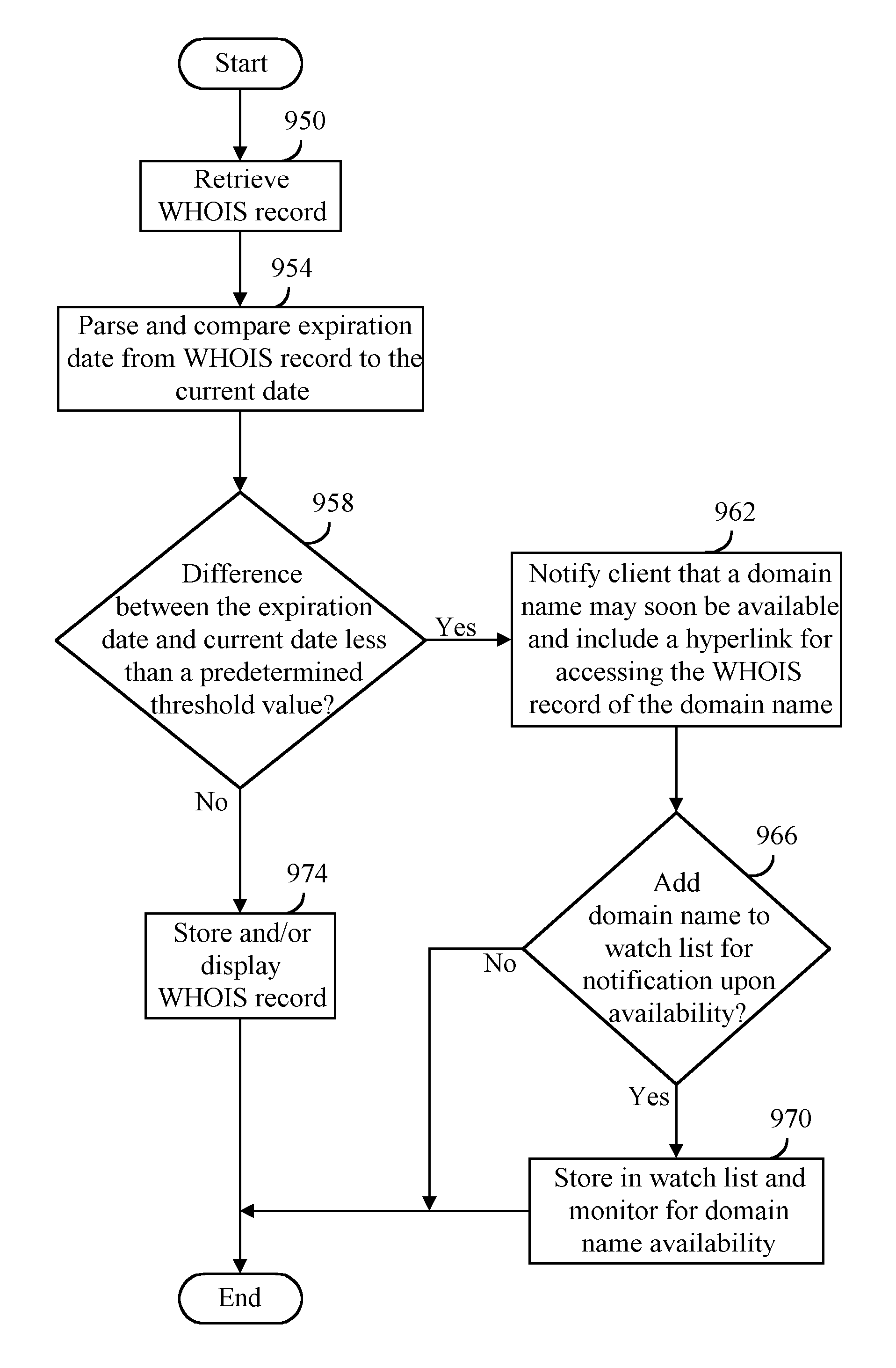
A WHOIS record of a domain name is retrieved at a first time, the WHOIS record including an expiry date of a second time, a time difference value can be calculated between the first time and the second time, and the time difference value provided to a user. Time difference value can be determined to satisfy at least one condition including a threshold value. An indication can be provided to the user that the at least one condition has been satisfied such as notifying the user of domain name expiration status, storing the domain name in a user expiration watch list, monitoring the domain name for expiration upon or after the second time, and attempting to register the domain name with a selected domain name registration provider after the second time or upon determining that either the domain name may soon be available for registration or available for registration. The WHOIS record can be retrieved in response to receiving or obtaining a request such as a resource location request, domain name resolution request, search engine request, WHOIS request, domain name availability request, and domain name registration request.
Owner:MEC MANAGEMENT LLC
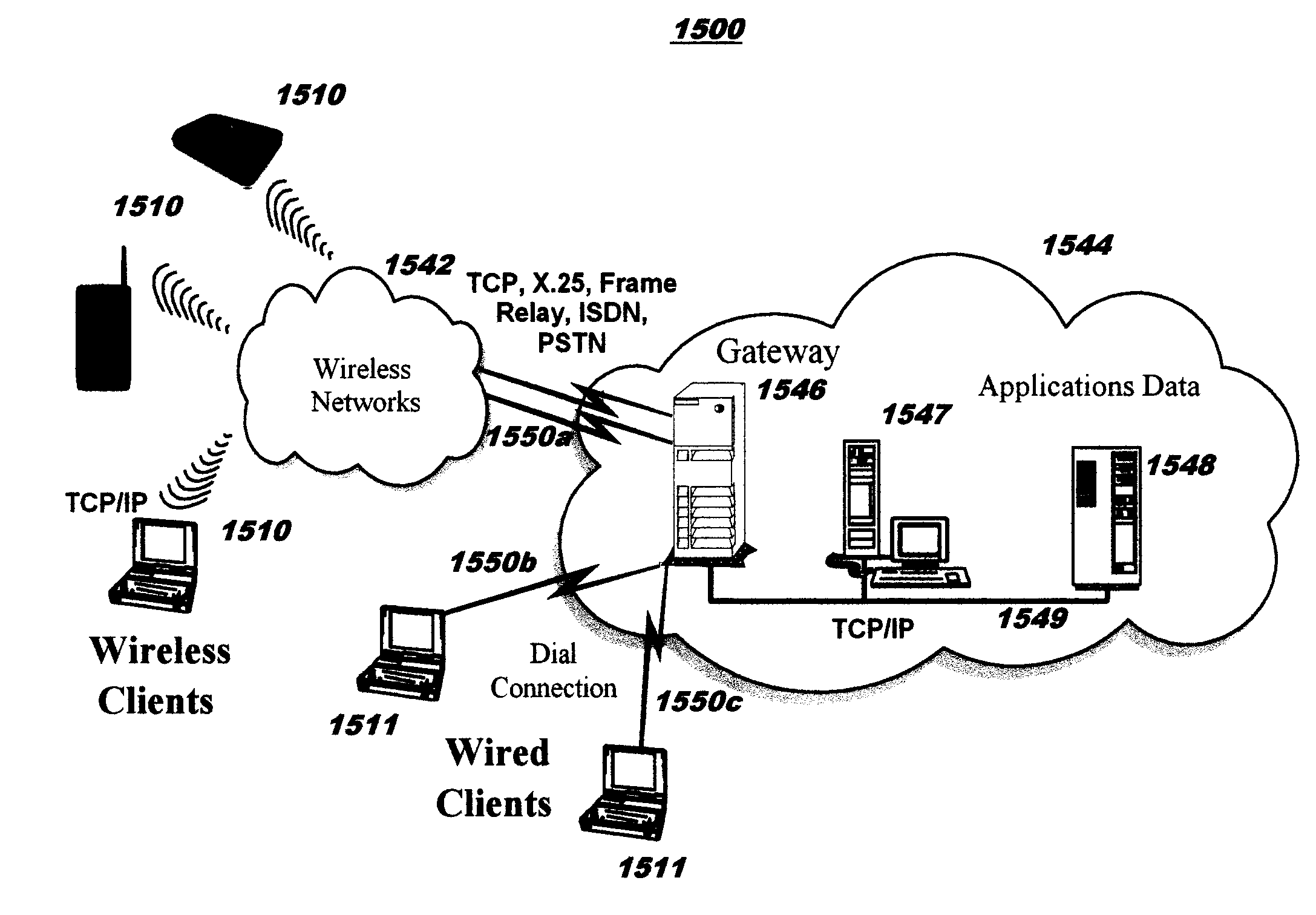
Apparatus and method of implementing fast internet real-time search technology (first)
An apparatus for and method of monitoring and retrieving identifiable statements and other information pertinent to one or more desired search terms or concepts. In a preferred embodiment, a fast Internet real-time search technology (FIRST) system provides a user interface for inputting and editing a list of desired search terms, and a list of resource locations to be monitored. A server causes the periodic access of each resource location listed to determine whether any information on a particular resource location has been added that is pertinent to the desired search terms since the previous visit to the location. Any added information is returned to the server for processing. An alert message can be generated and forwarded to an intended recipient to alert the recipient of the added information.
Owner:INFOLOCITY
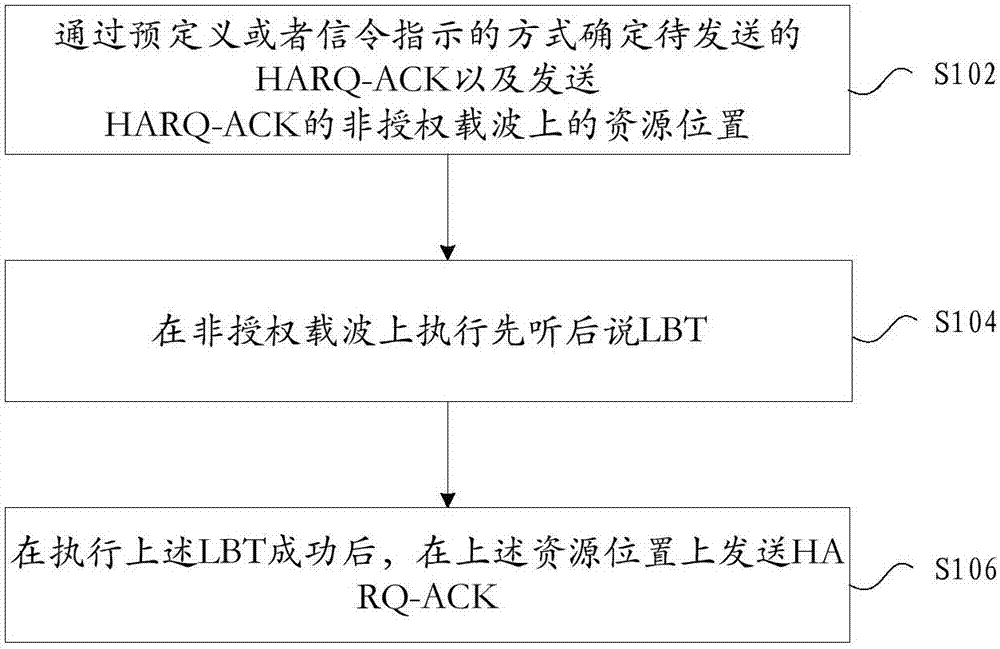
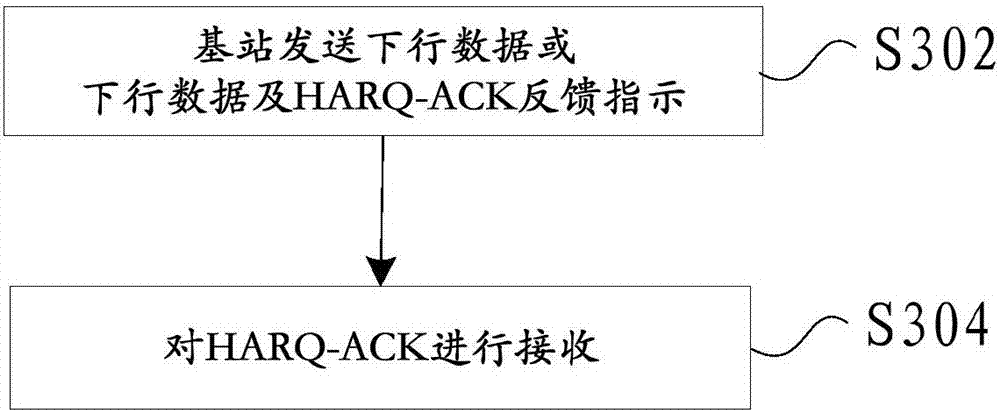
HARQ-ACK sending method and apparatus
ActiveCN107332646AIncrease probabilityIncrease flexibilityError prevention/detection by using return channelSignal allocationCarrier signalComputer science
The invention provides an HARQ-ACK sending method and apparatus. The method comprises the following steps: determining a to-be-sent HARQ-ACK and a resource position on an unauthorized carrier sending the HARQ-ACK in a predefined manner or a signaling indication manner; executing Listen Before Talk LBT on the unauthorized carrier; and after the LBT is successfully executed, sending the HARQ-ACK on the resource position. By adoption of the HARQ-ACK sending method and apparatus provided by the invention, the influence of a novel frame structure and LBT influence to the original timing relationship sending is solved, the HARQ-ACK sending probability and the feedback flexibility are improved, and the system performance is effectively improved.
Owner:ZTE CORP
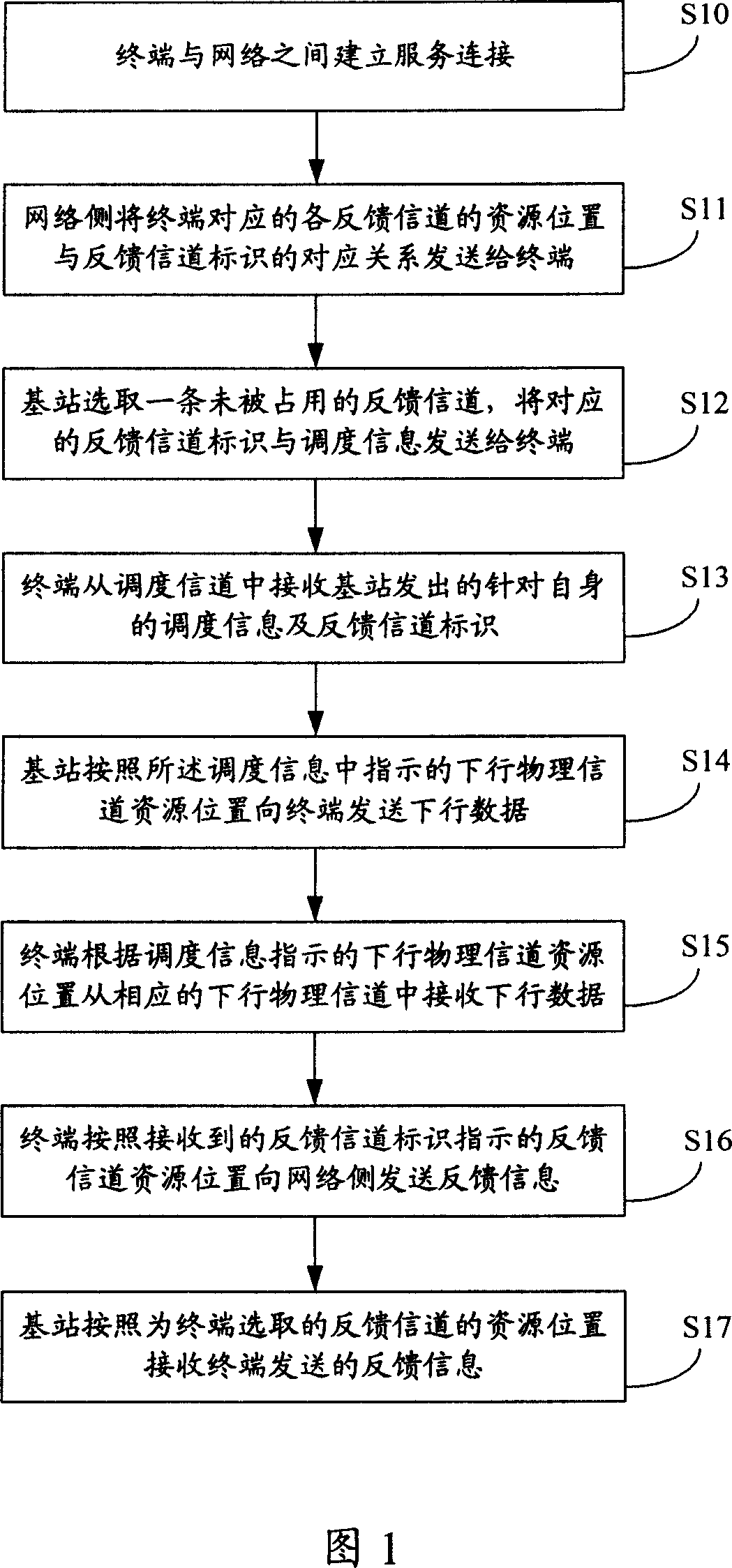
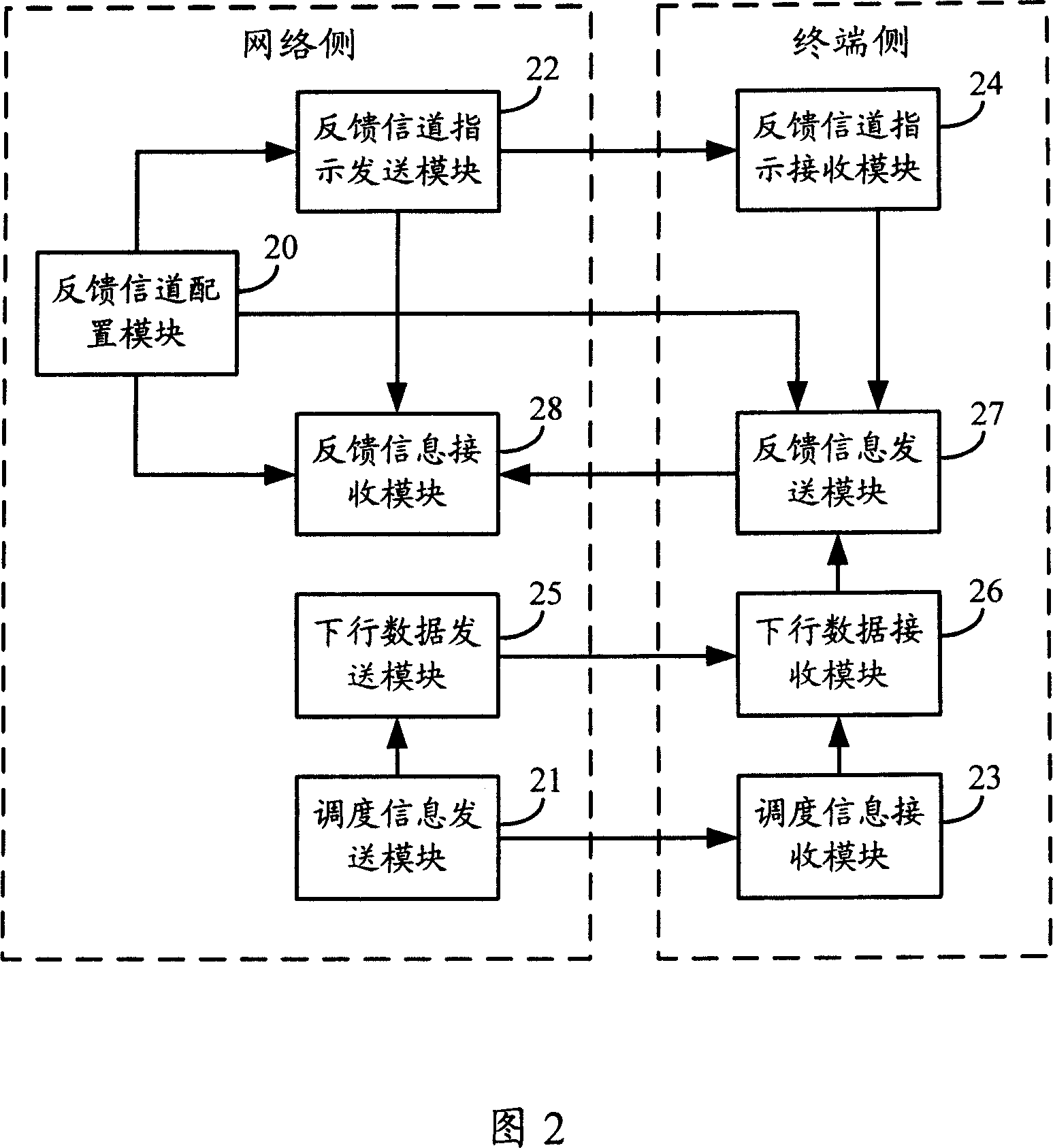
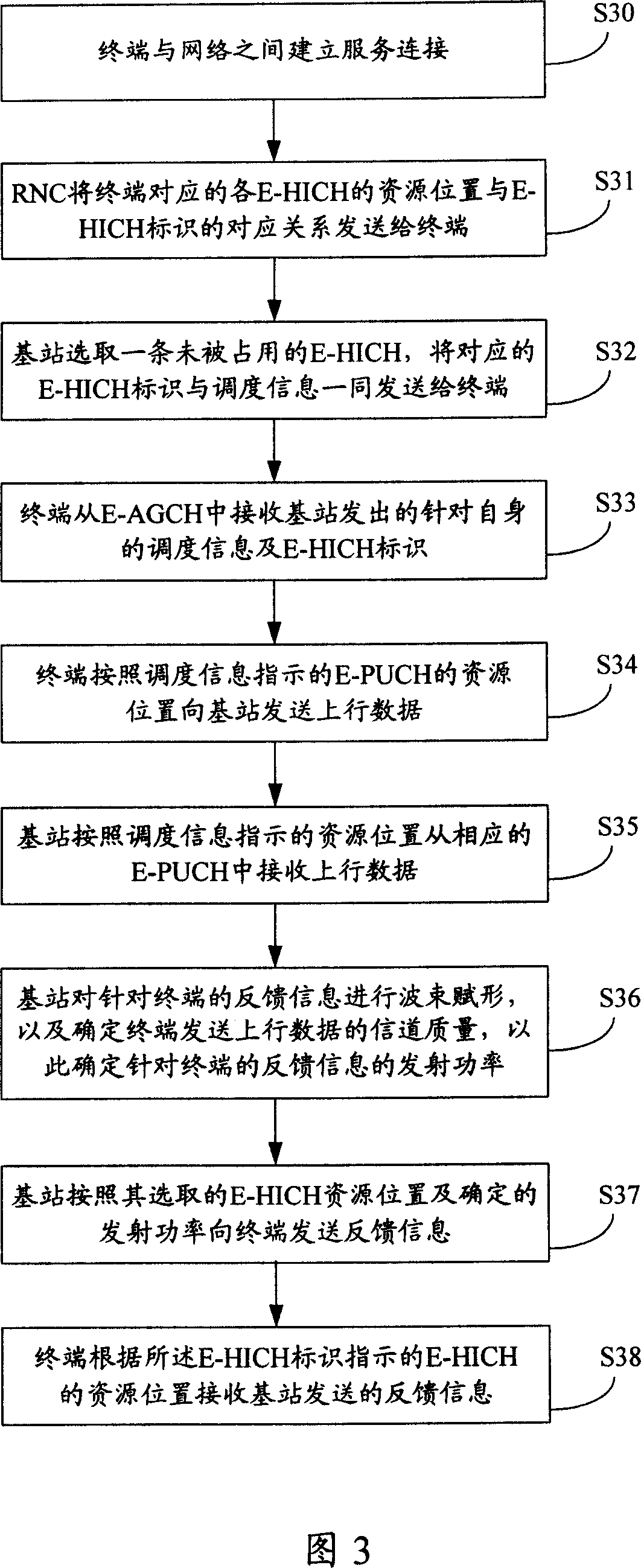
Feedback channel distribution indicating method and system
ActiveCN101114868ASolve conflictsReduce complexityRadio/inductive link selection arrangementsRadio transmission for post communicationResource locationBase station
The invention discloses an instructional method and system to allocate the feedback channels, which can facilitate a terminal to know the position of the resources occupied by the feedback channels allocated to the terminal through carrying the instructional information of the feedback channels allocated to the terminal in the dispatching channels, thereby solving the problem that in the down direction of the current LTE technique, when the base station dispatches a plurality of terminals by using the same dispatching channel at the same time, a plurality of terminals send the feedback information by using the same dispatching channel at the same time to the base station and the problem that in the current HSUPA technique, when the feedback information of a plurality of channels is transmitted by copying to a feedback channel, the complexity of realizing the base station and the terminal is high.
Owner:DATANG MOBILE COMM EQUIP CO LTD
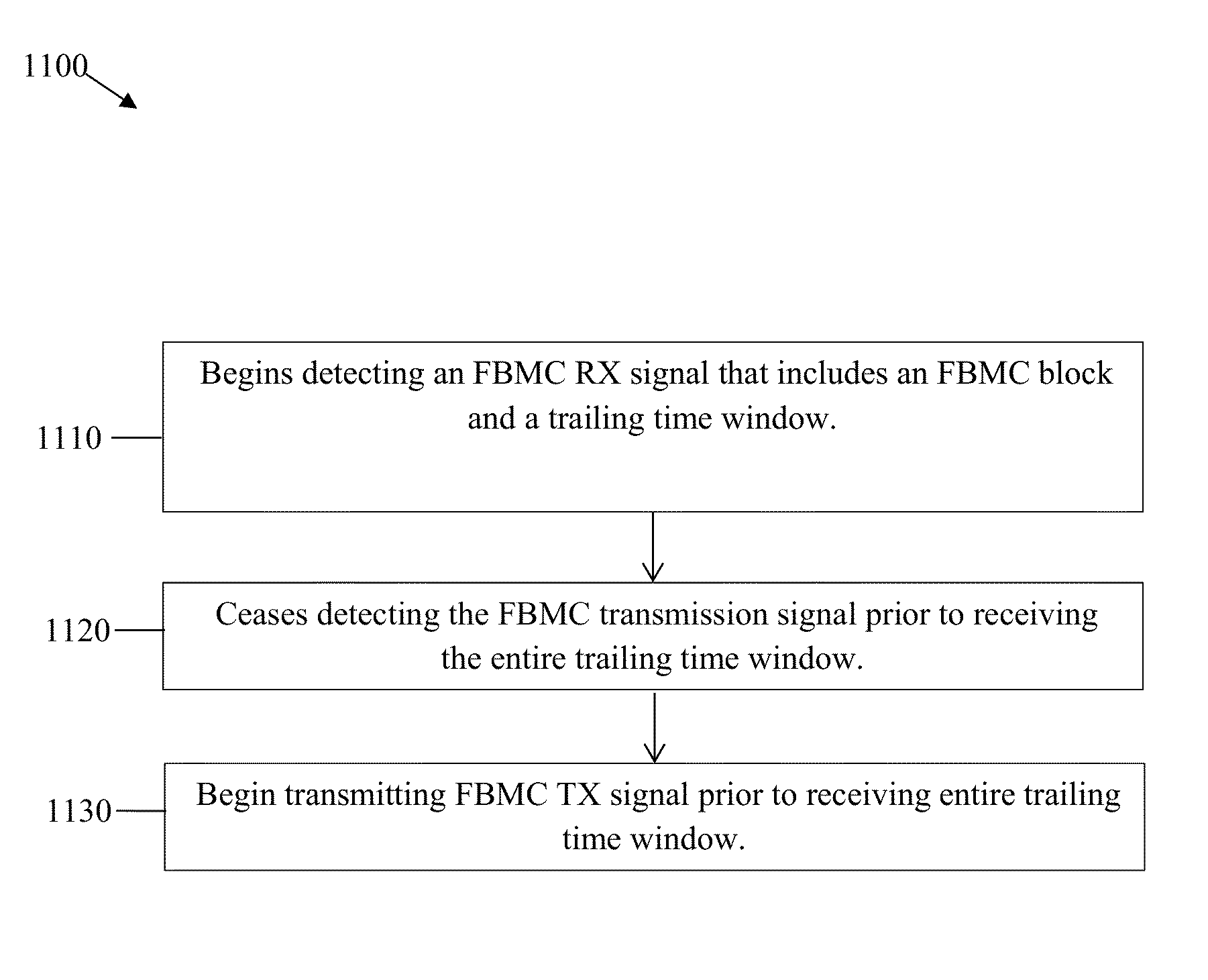
Frame Structure for Filter Bank Multi-Carrier (FBMC) Waveforms
ActiveUS20140233437A1Reduce overhead timeSynchronisation arrangementModulated-carrier systemsTime domainTelecommunications
A unified frame structure for filter bank multi-carrier (FBMC) and orthogonal frequency division multiplexed (OFDM) waveforms may allow FBMC and OFDM frames to be communicated over a common channel without significant inter-frame gaps. The unified frame structure may set an FBMC frame duration to an integer multiple of an OFDM frame element duration to enable alignment of FBMC frames and OFDM frames in the time domain. The unified frame structure may also map control channels in the FBMC and OFDM frames to common resource locations so that the respective control channels are aligned in the time and / or frequency domains. The unified frame structure may also share synchronization channels between FBMC and OFDM frames. Additionally, overhead in an FBMC time division duplexed (TDD) communications channel can be reduced by overlapping time windows appended to FBMC blocks.
Owner:HUAWEI TECH CO LTD
Sitemap access method, product, and apparatus
InactiveUS7565402B2Easy to understandSaving distribution costMultiple digital computer combinationsTransmissionAccess methodResource location
When a network request such as a resource location request, search engine request, and WHOIS request to process input having a resource identifier is received a user interface can then be provided to perform a request to access and display at least one sitemap corresponding to said resource identifier while performing the network request.
Owner:MEC MANAGEMENT LLC
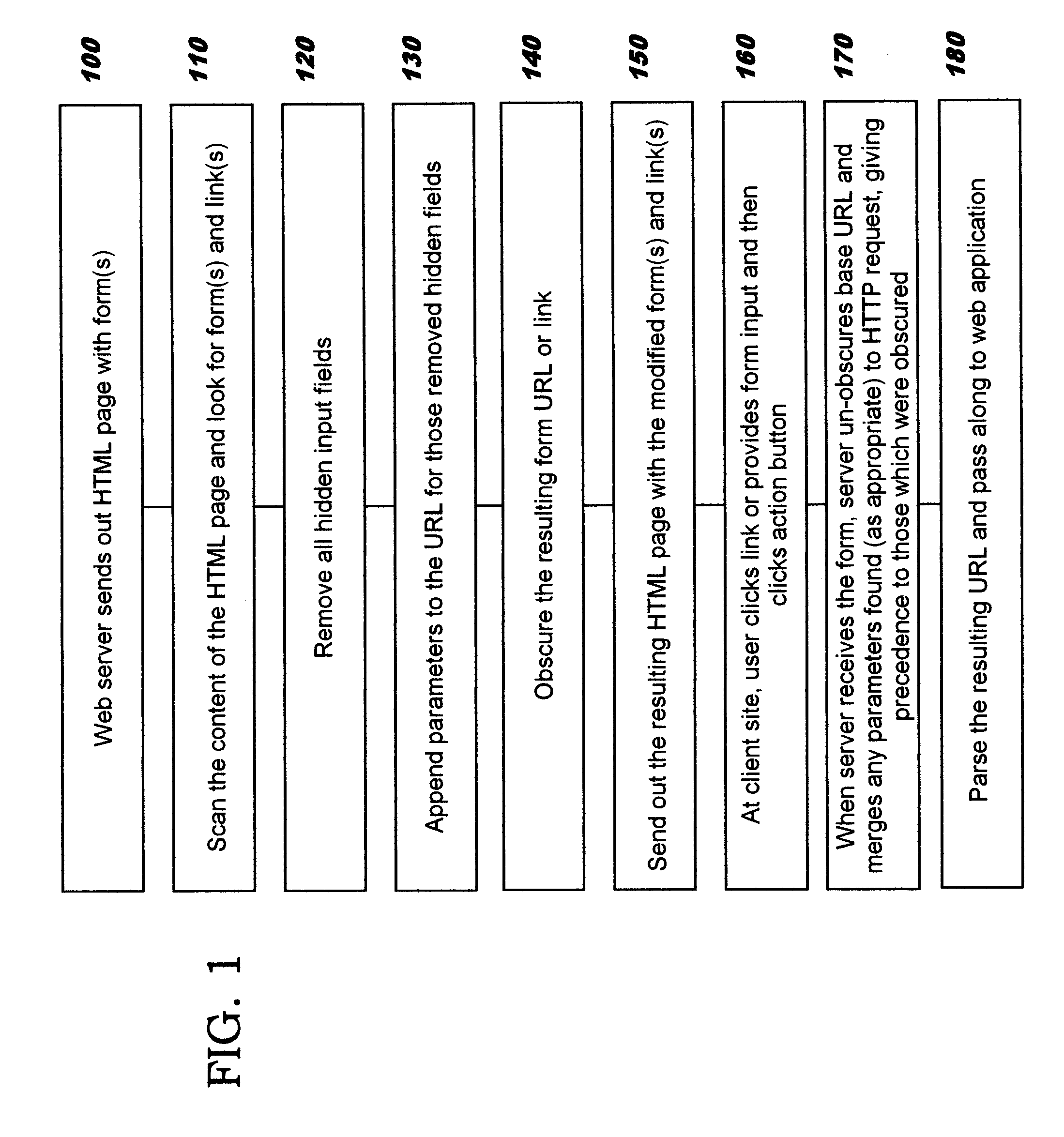
Obscuring form data through obfuscation
InactiveUS20110107077A1Digital data processing detailsAnalogue secracy/subscription systemsObfuscationUniform resource locator
Obscuring form data to be passed in forms that are sent in messages over a communications network. The form data to be obscured is removed from a form and inserted as a portion of a Uniform Resource Location (“URL”) string. The obscured form data may comprise hidden fields and / or links. An obfuscation is then applied to the portion of the URL string, thereby obscuring the information for sending on an outbound message. The original information is recovered from an inbound message which contains the obscured information by reversing the processing used for the obscuring. In one aspect, the obfuscation comprises encryption. In another aspect, the obfuscation comprises creating a tiny URL that replaces the portion of the URL string.
Owner:IBM CORP
Method, product, and apparatus for enhancing resolution services, registration services, and search services
InactiveUS8037168B2Minimize connection bandwidthError detection/correctionMultiple digital computer combinationsDomain nameWatch list
Owner:MEC MANAGEMENT LLC
Automated competitive bidding system and process
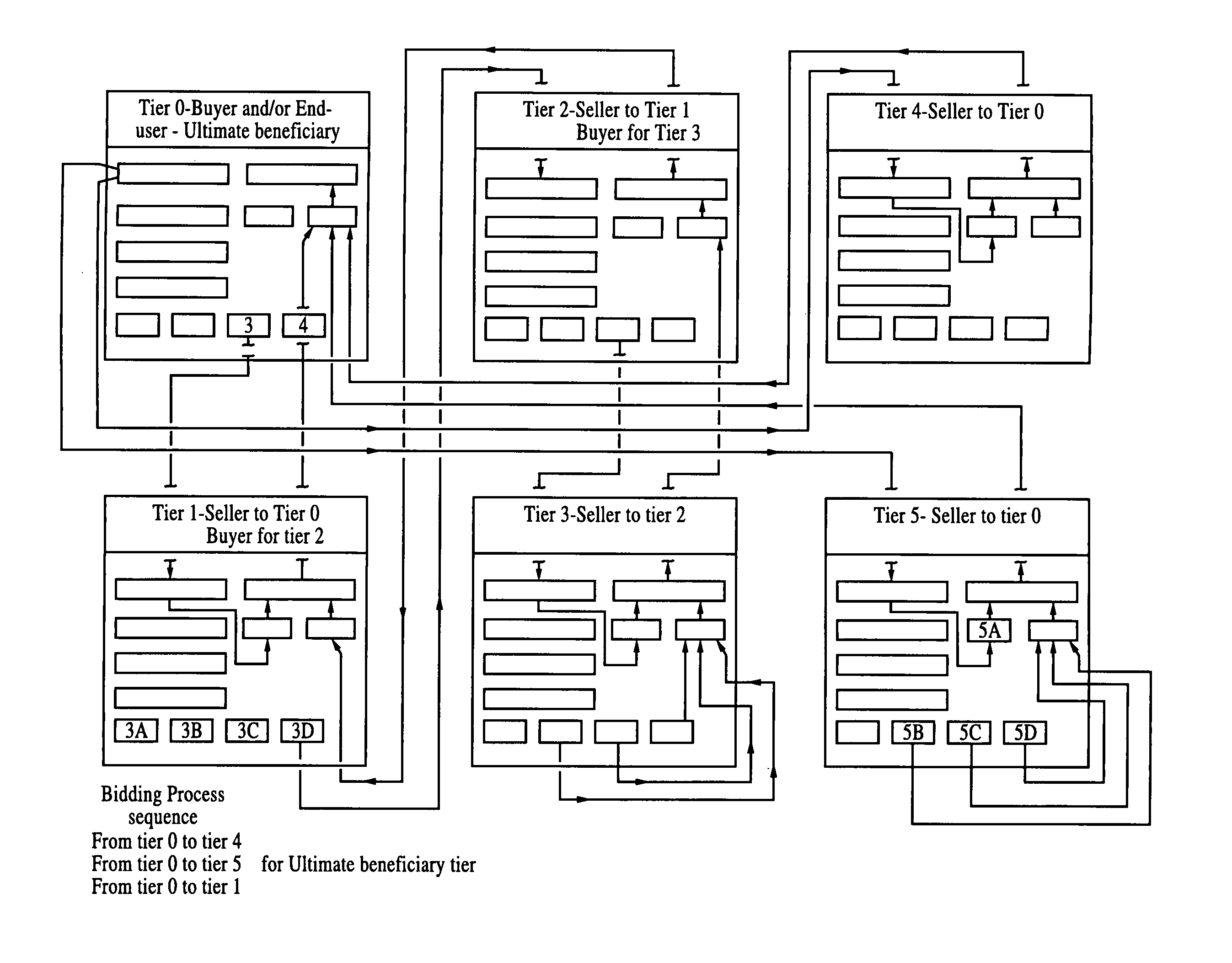
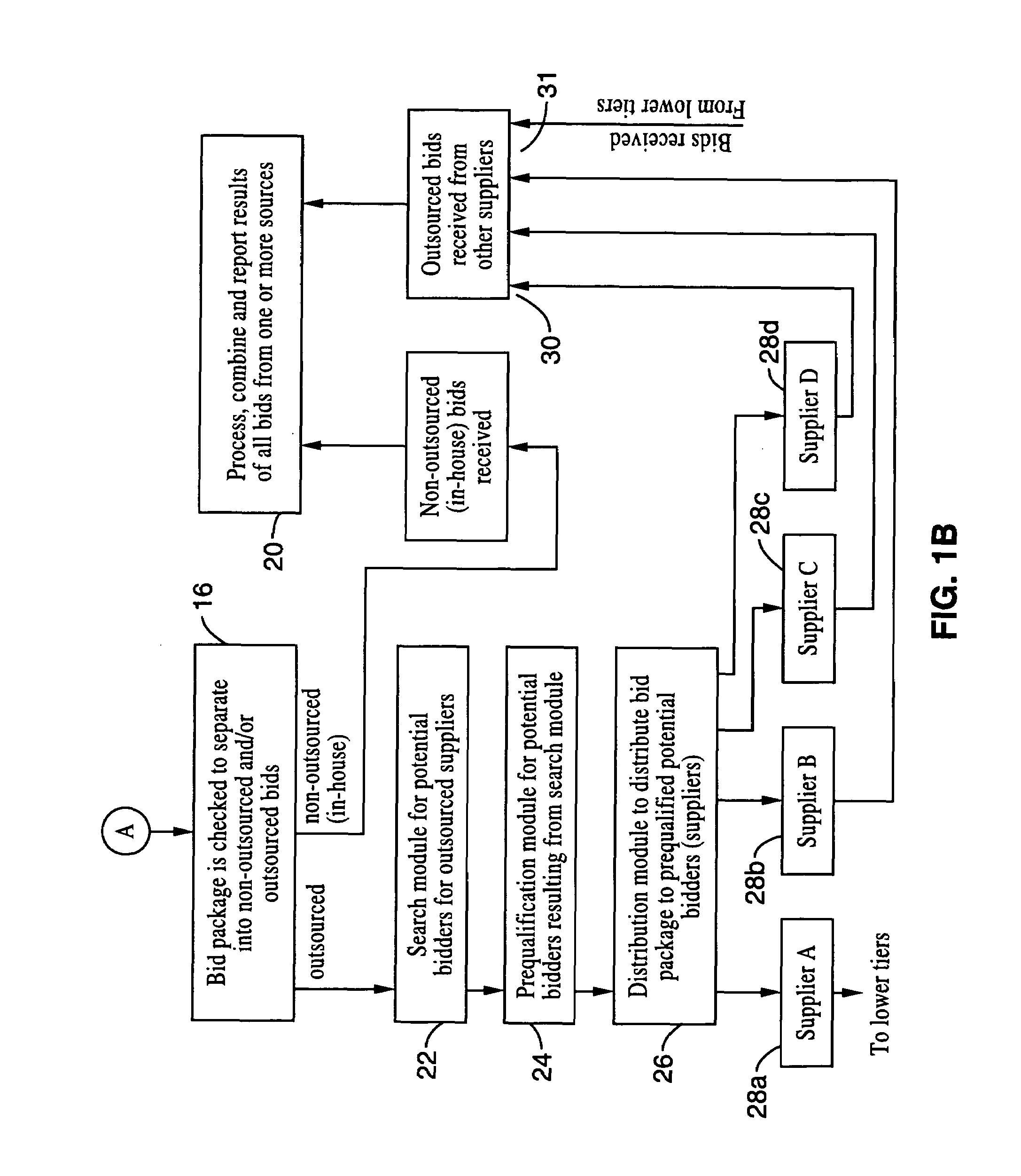
Utilizing the present invention, a buyer for products, services or both would prepare a bid package. The bid package would contain information necessary to complete the project the buyer would desire. At the buyer's option, the bid package is parceled into modules. The modules are prepared as discrete and stand-alone biddable items. A search for suppliers for each module is made from multiple sources based on the modules and directed by the buyer's specifications for the product or service. The system of the present invention packages, processes, connects, procures, bids and reports the competitive bidding cycle for buyers and makes the necessary connection with interested prequalified sellers in a given industry or market. The system receives, compiles, processes and reports the results. The system of the present invention includes a consortium of horizontal and vertical portals, gateways and universal resource locations that encompass trade, industry and market communities.
Owner:KHALIDI TARIQ
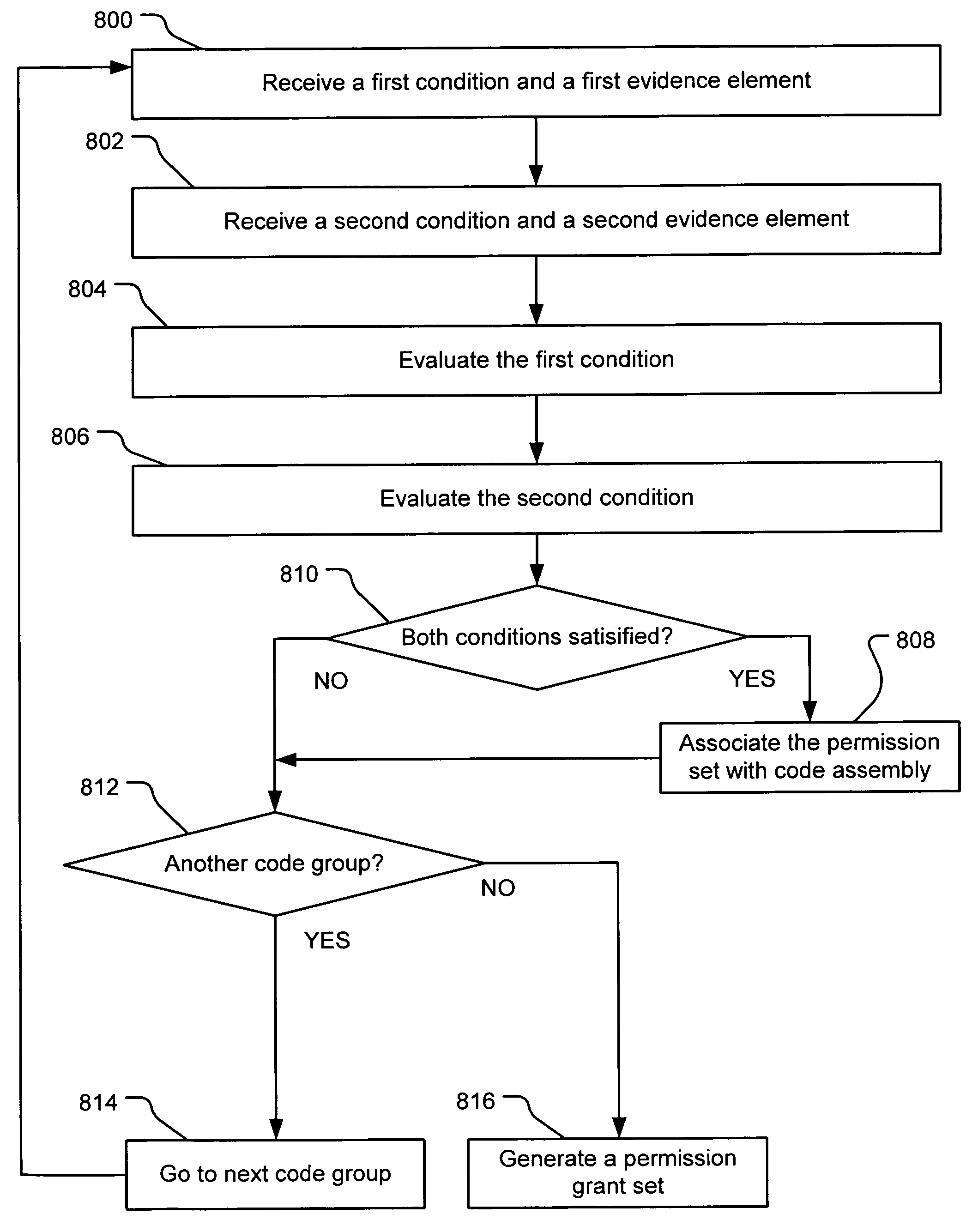
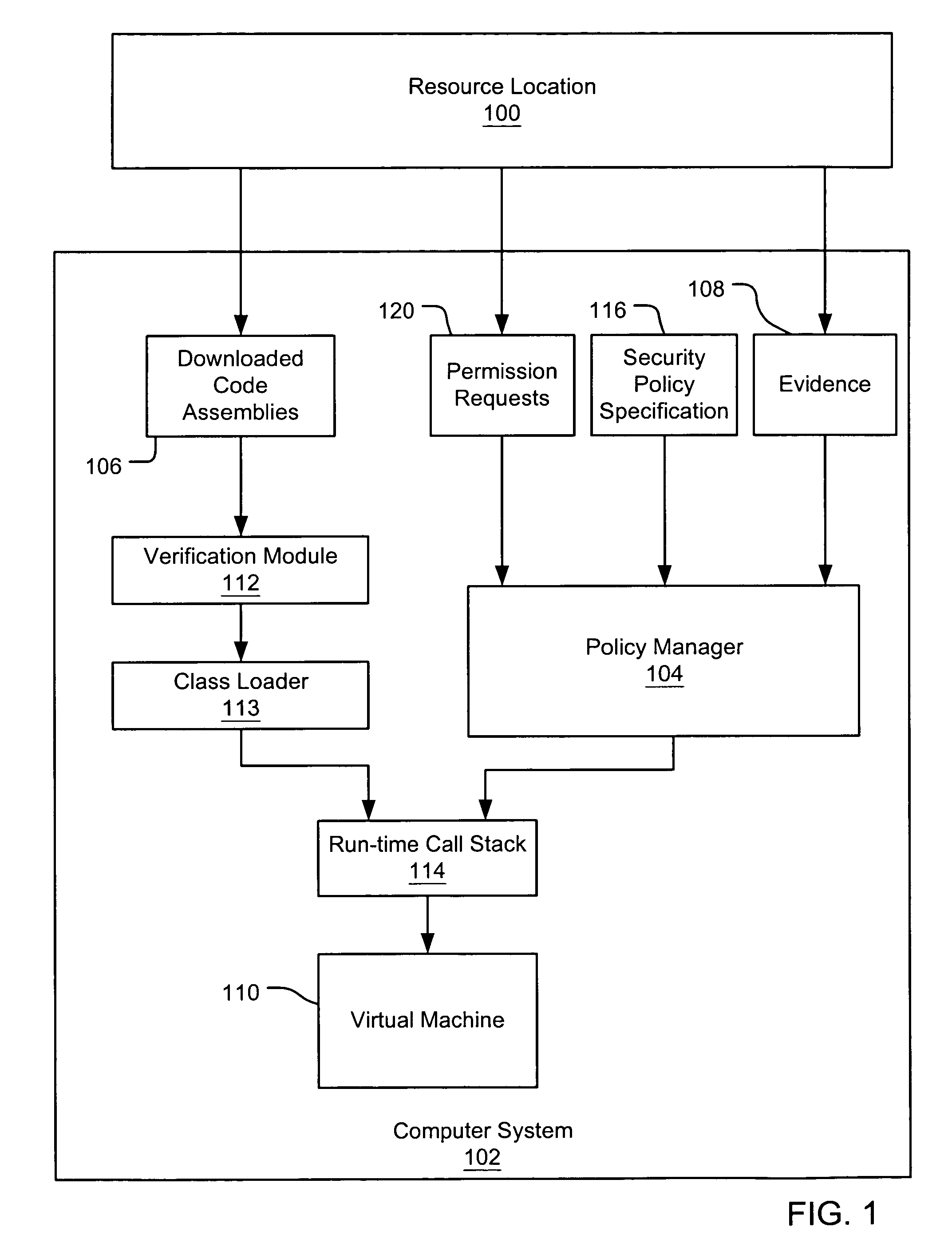
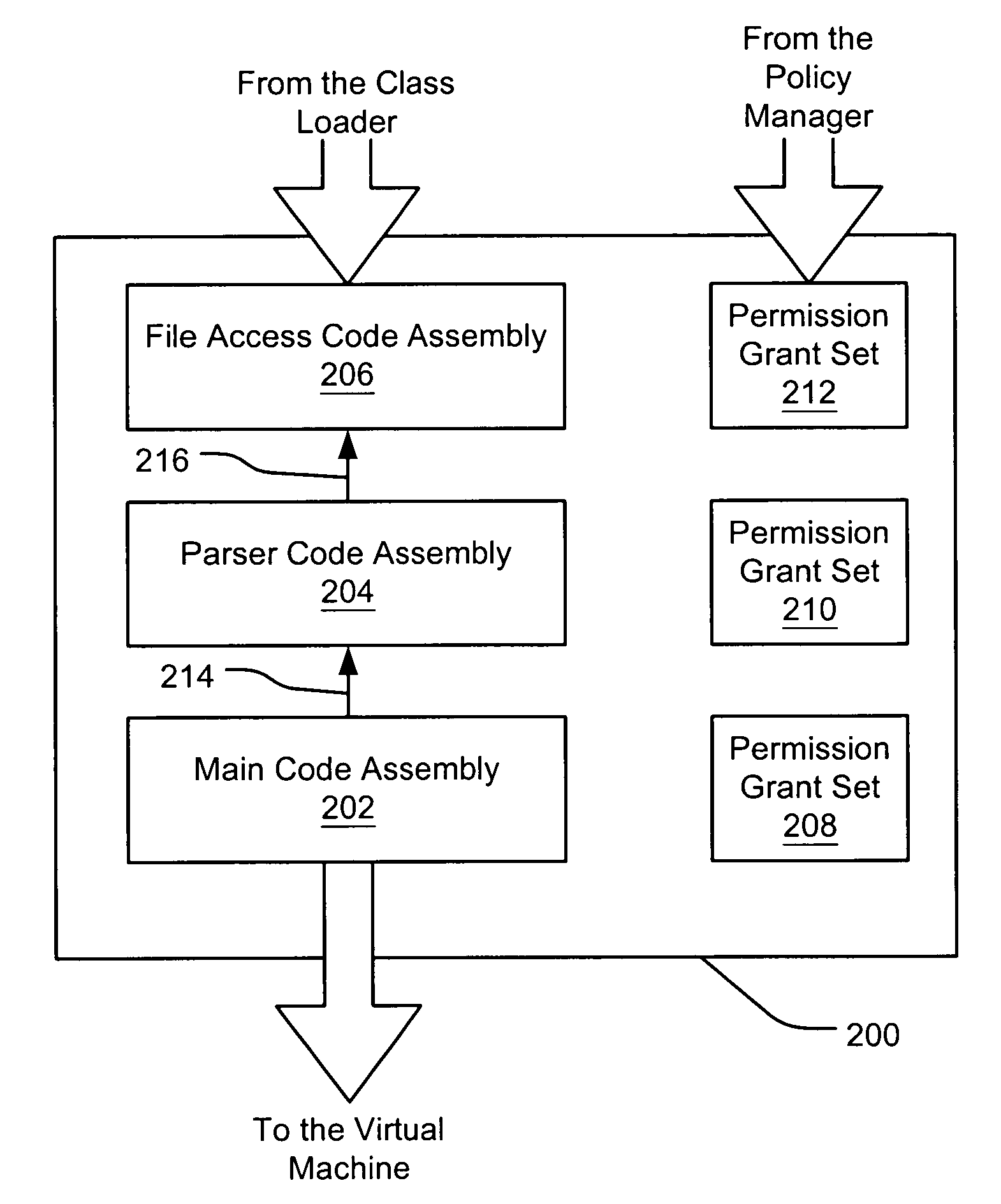
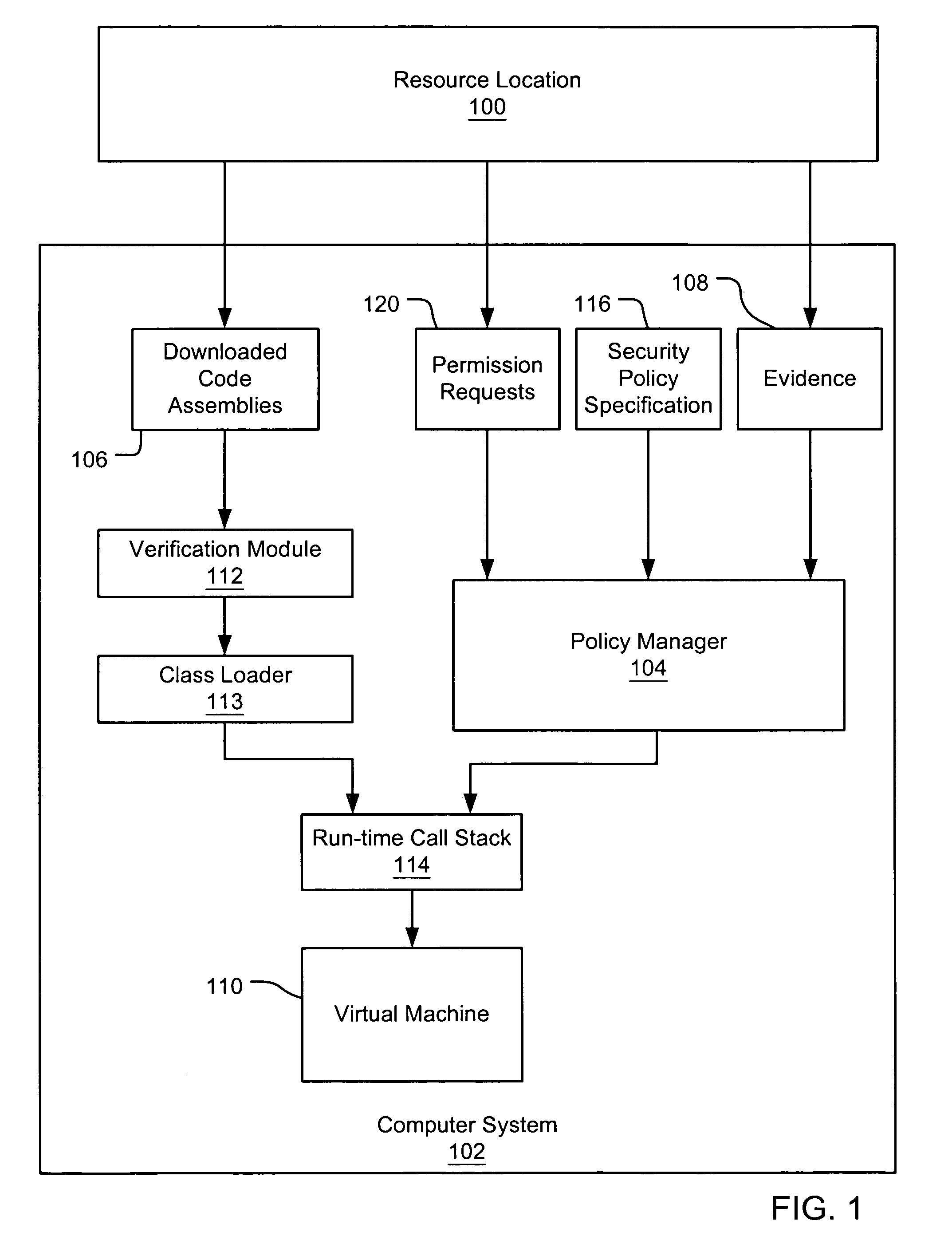
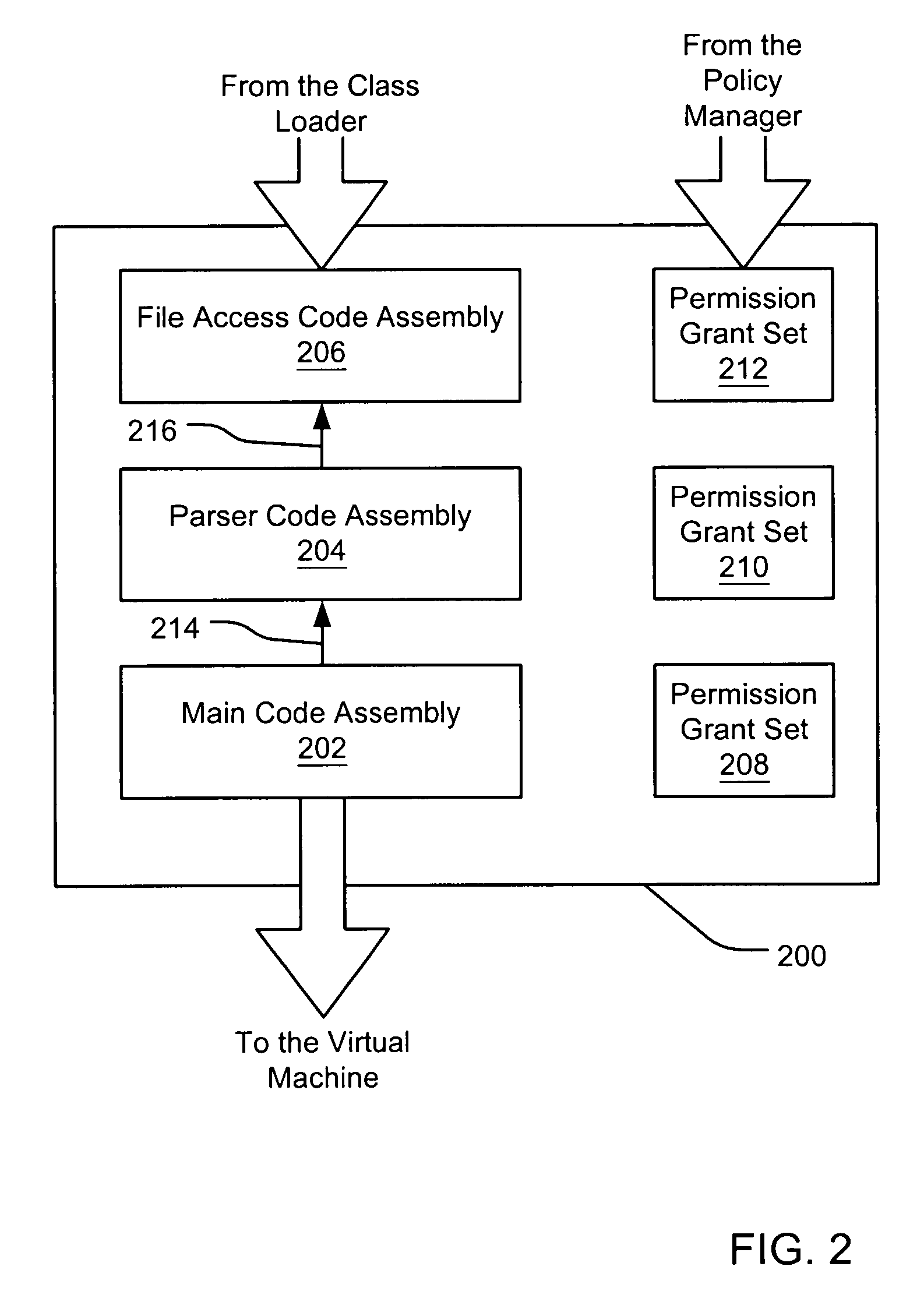
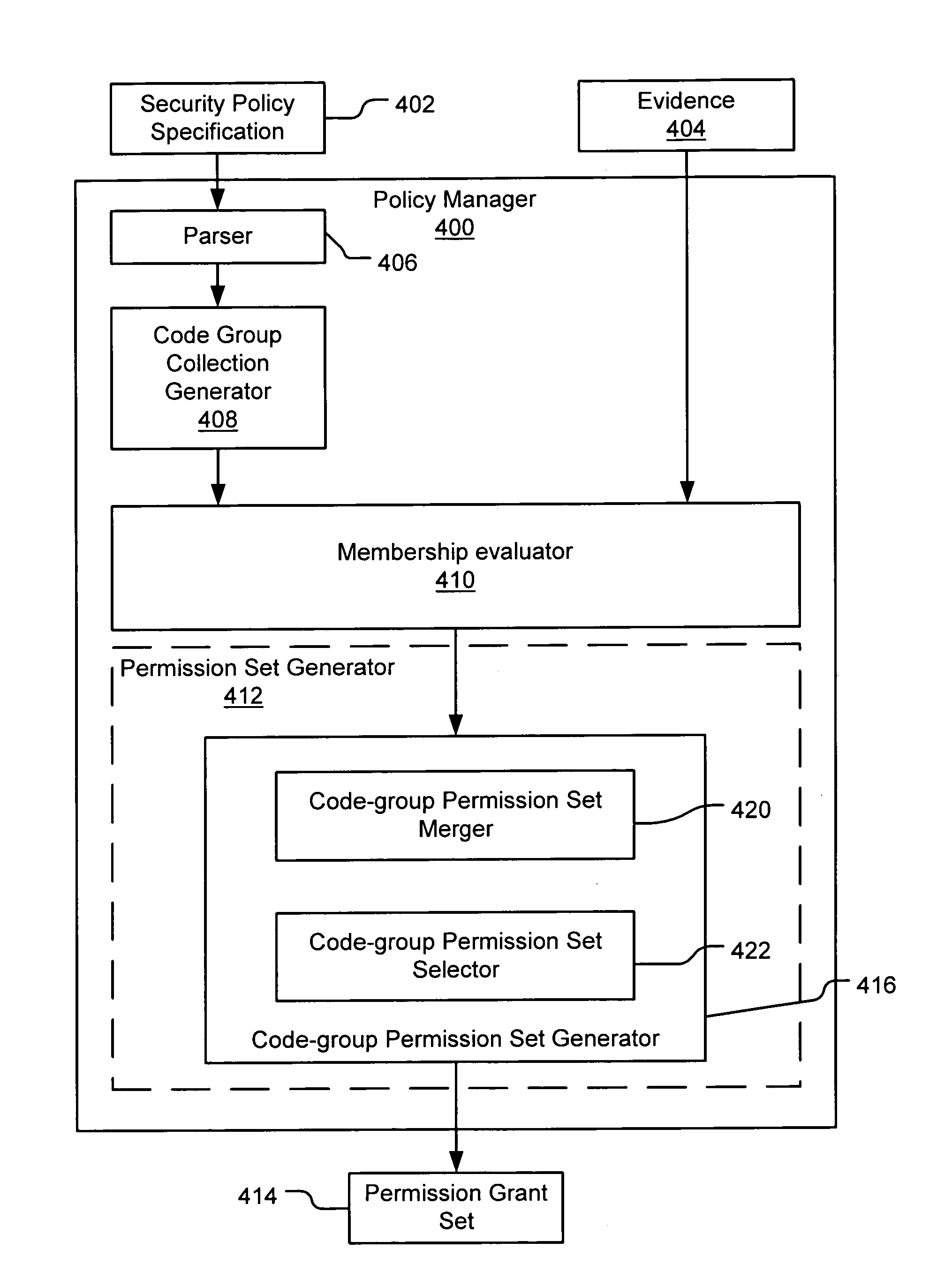
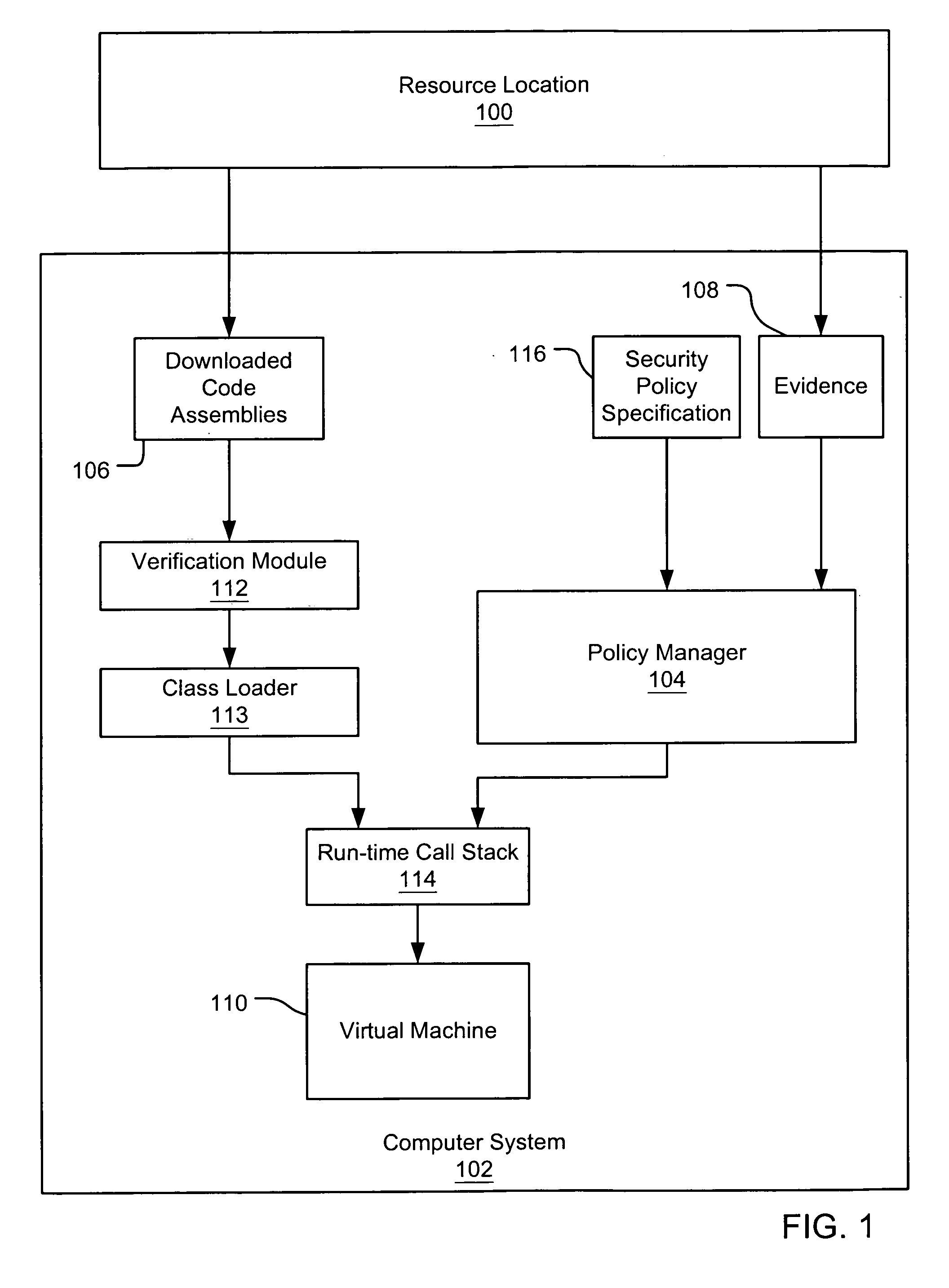
Evaluating initially untrusted evidence in an evidence-based security policy manager
InactiveUS7131143B1Digital data processing detailsAnalogue secracy/subscription systemsCall stackTrust level
An evidence-based policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager executes in a computer system (e.g., a Web client or server) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. Both code assemblies and evidence may be received from a local origin or from a remote resource location via a network (e.g., the Internet). Evidence having different levels of trust may be evaluated in combination so that a permission grant set is associated only with trusted code assemblies. The policy manager may comprise execution modules for parsing a security policy specification, generating one or more code hierarchies, evaluating membership of the received code assembly in one or more code groups, and generating a permission grant set based upon this membership evaluation.
Owner:MICROSOFT TECH LICENSING LLC
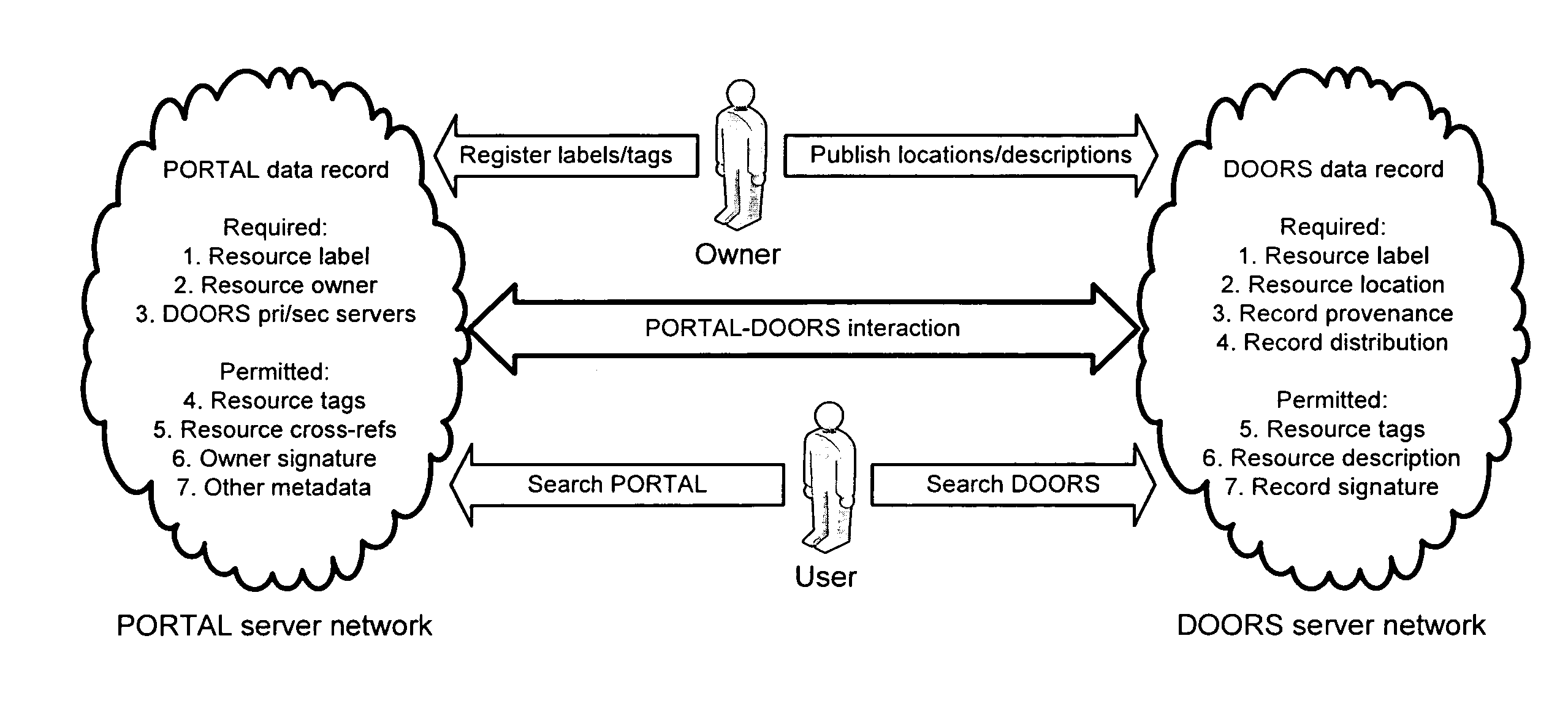
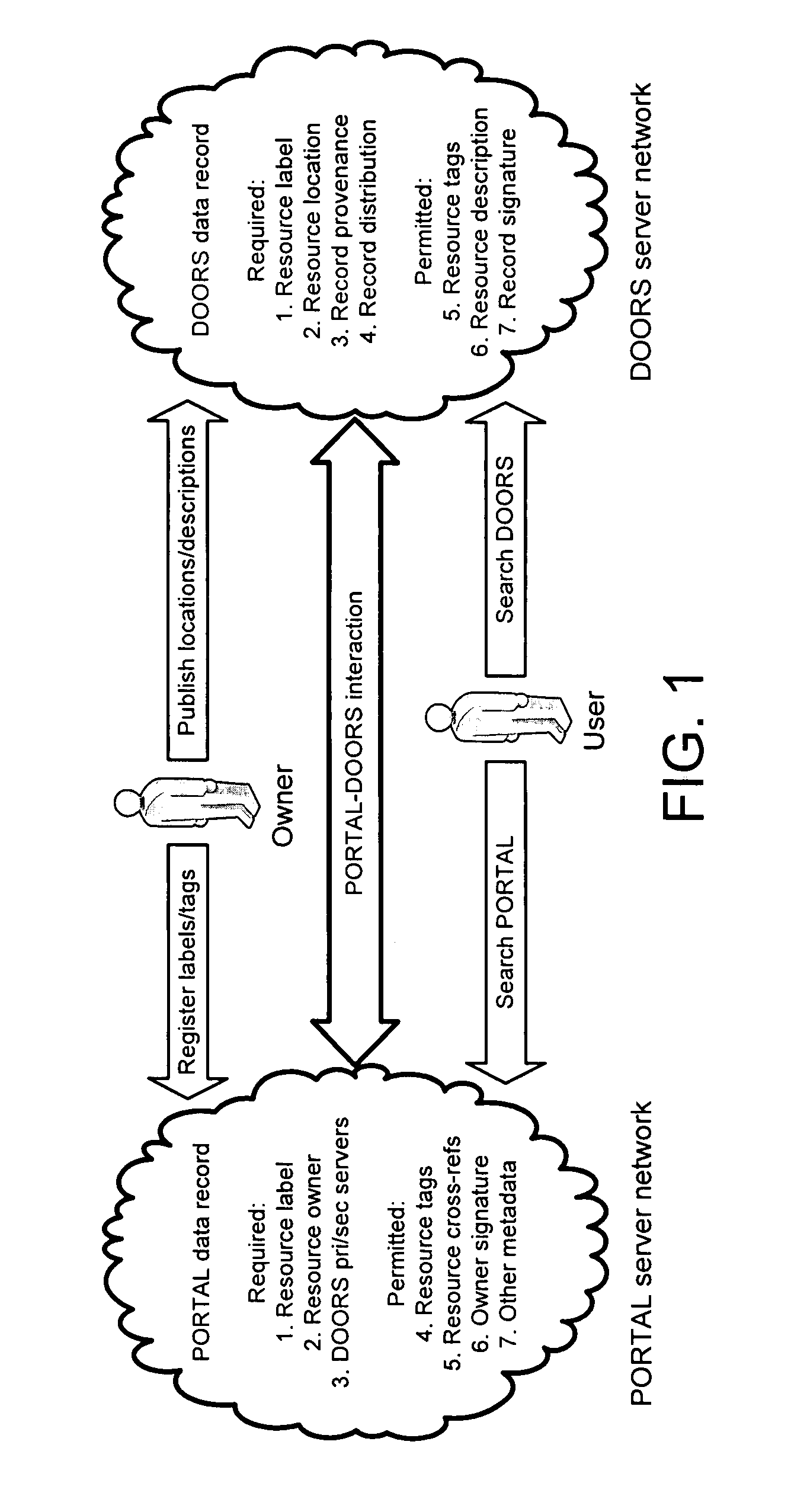
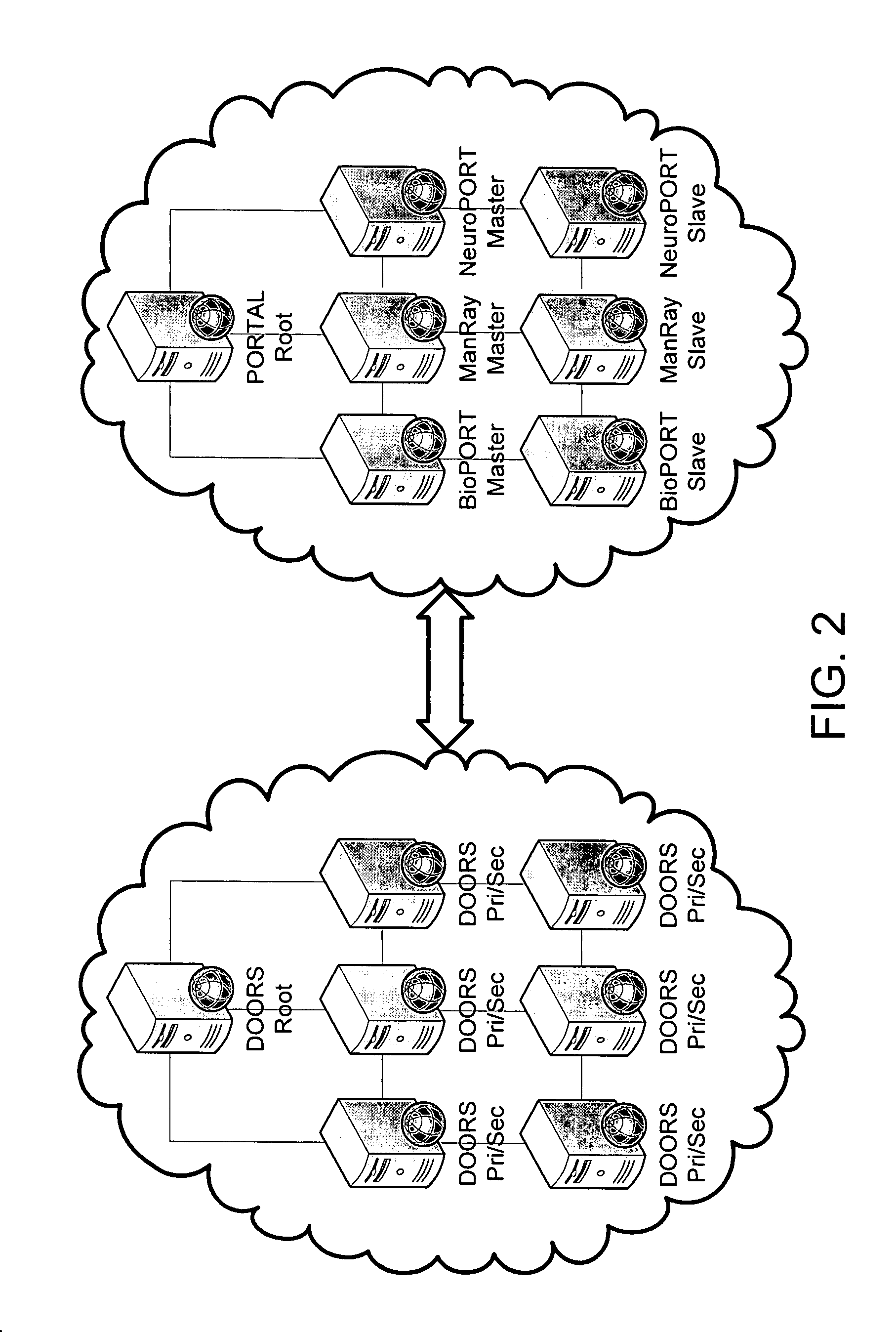
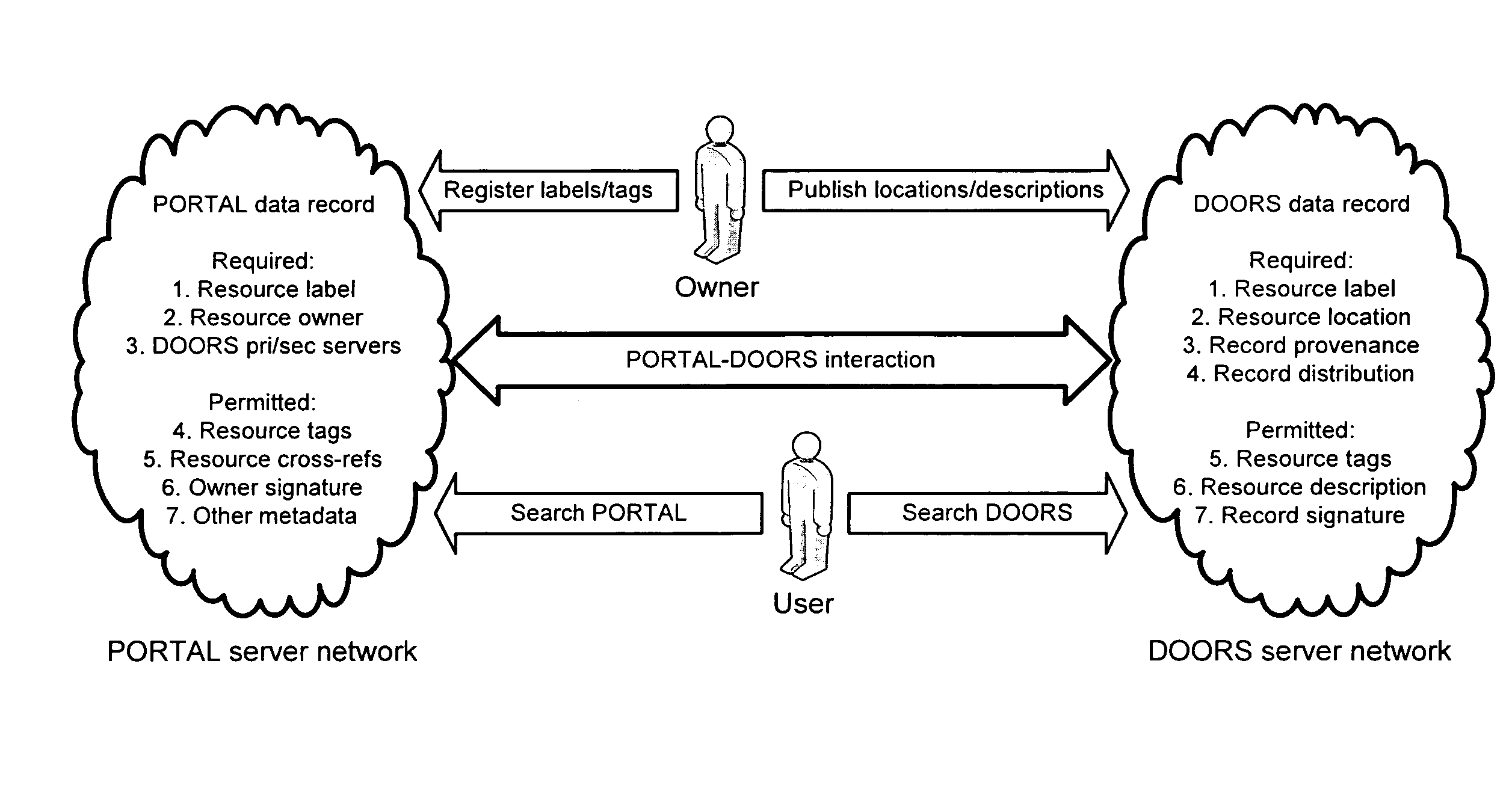
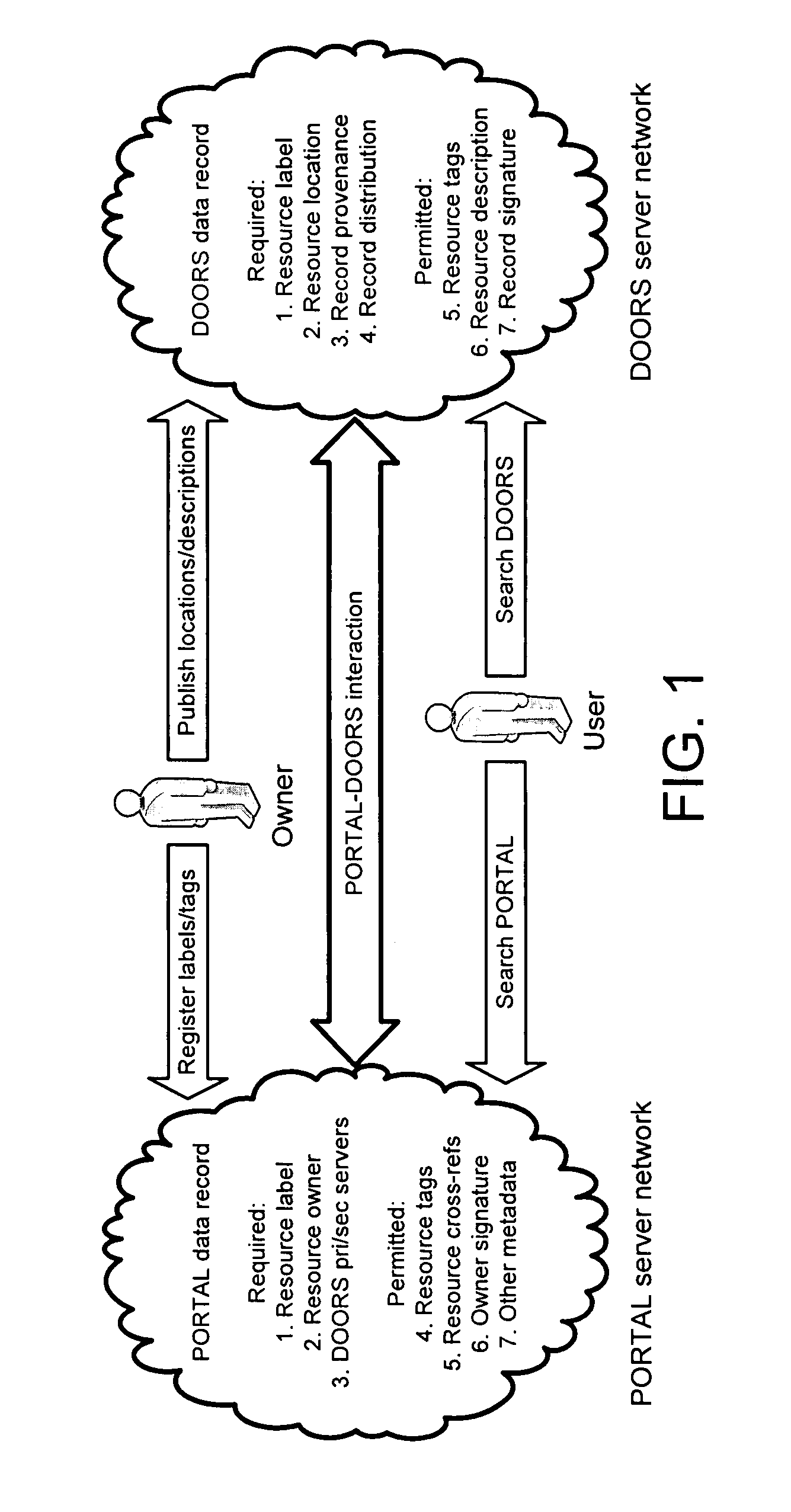
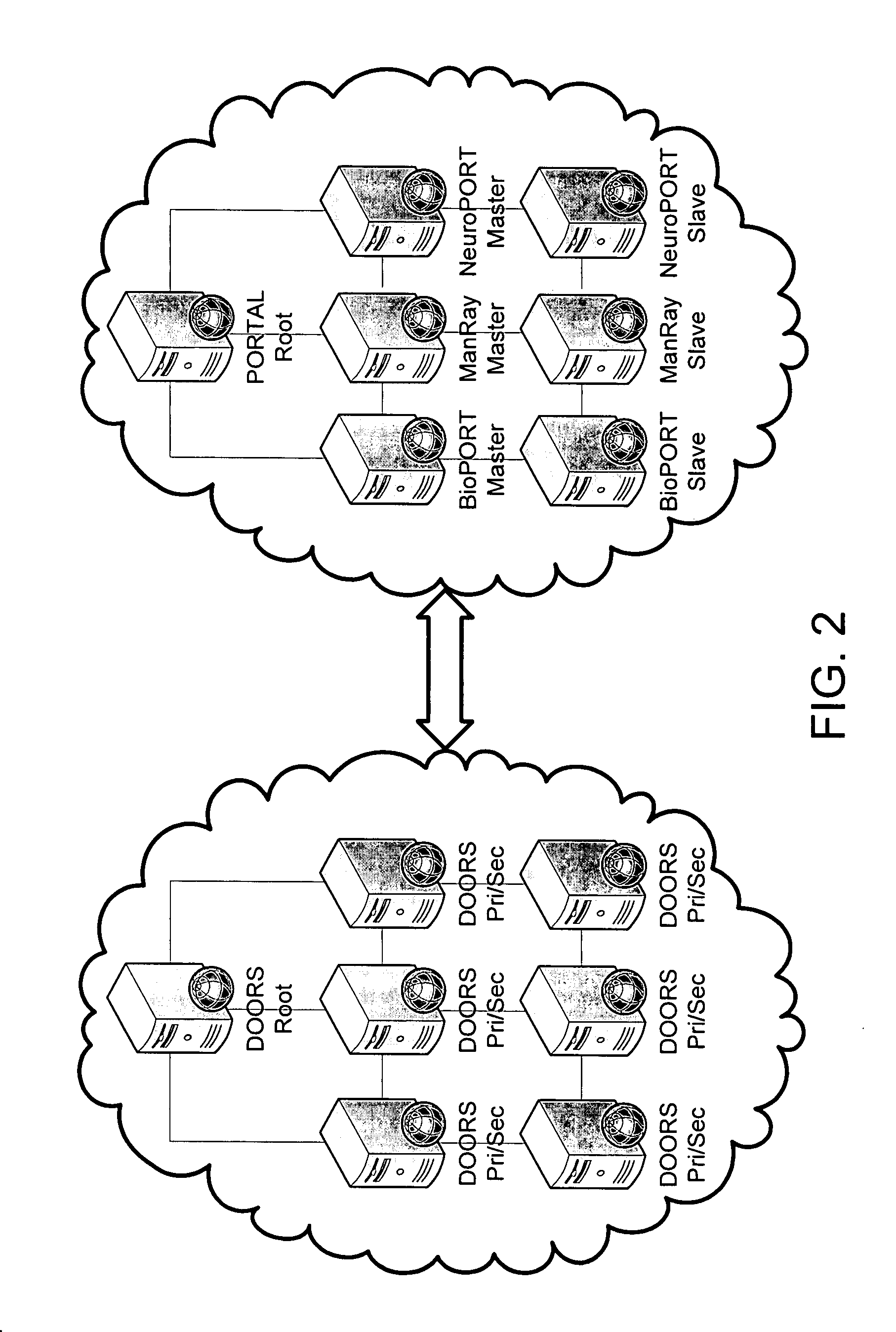
Portals and doors for the semantic web and grid
A Domain Ontology Oriented Resource System (DOORS) and a Problem Oriented Registry of Tags And Labels (PORTAL) are infrastructure systems for resource metadata within a paradigm serving as a bridge between the original web and the semantic web. IRIS registers domain names while DNS publishes domain addresses with mapping of names to addresses for the original web. Analogously, PORTAL registers resource labels and tags while DOORS publishes resource locations and descriptions with mapping of labels to locations for the semantic web. They provide an analogous resource label system, semantic search applications, and the benefits of collaborative semantic networks. Advertising is supported in several ways. Businesses purchase the right to display their products or services in association with searches. Also, content providers accept placement of advertising. Ads are then selected for display based on the content displayed utilizing the invention to match service providers with advertisers.
Owner:BRAIN HEALTH ALLIANCE INC
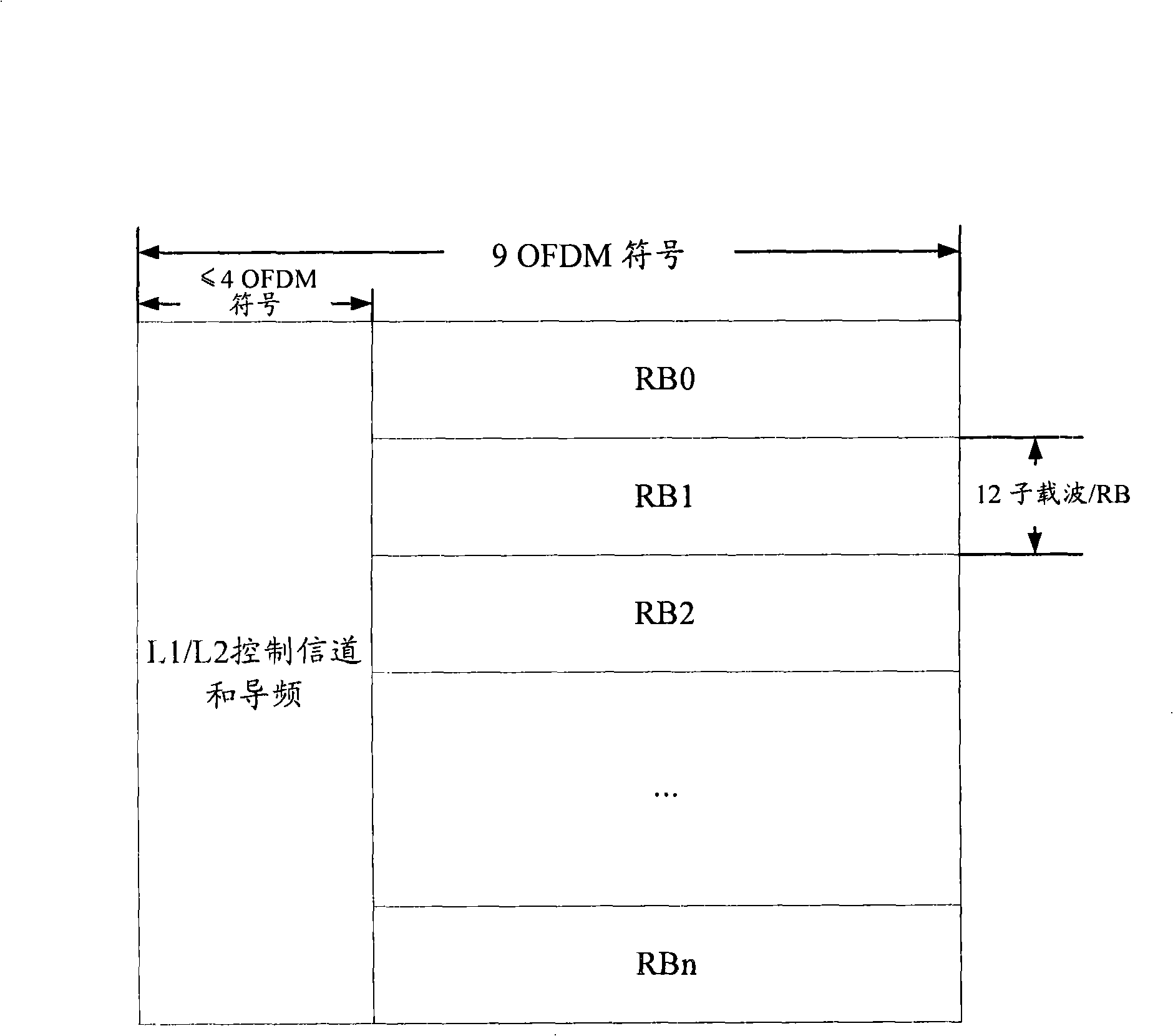
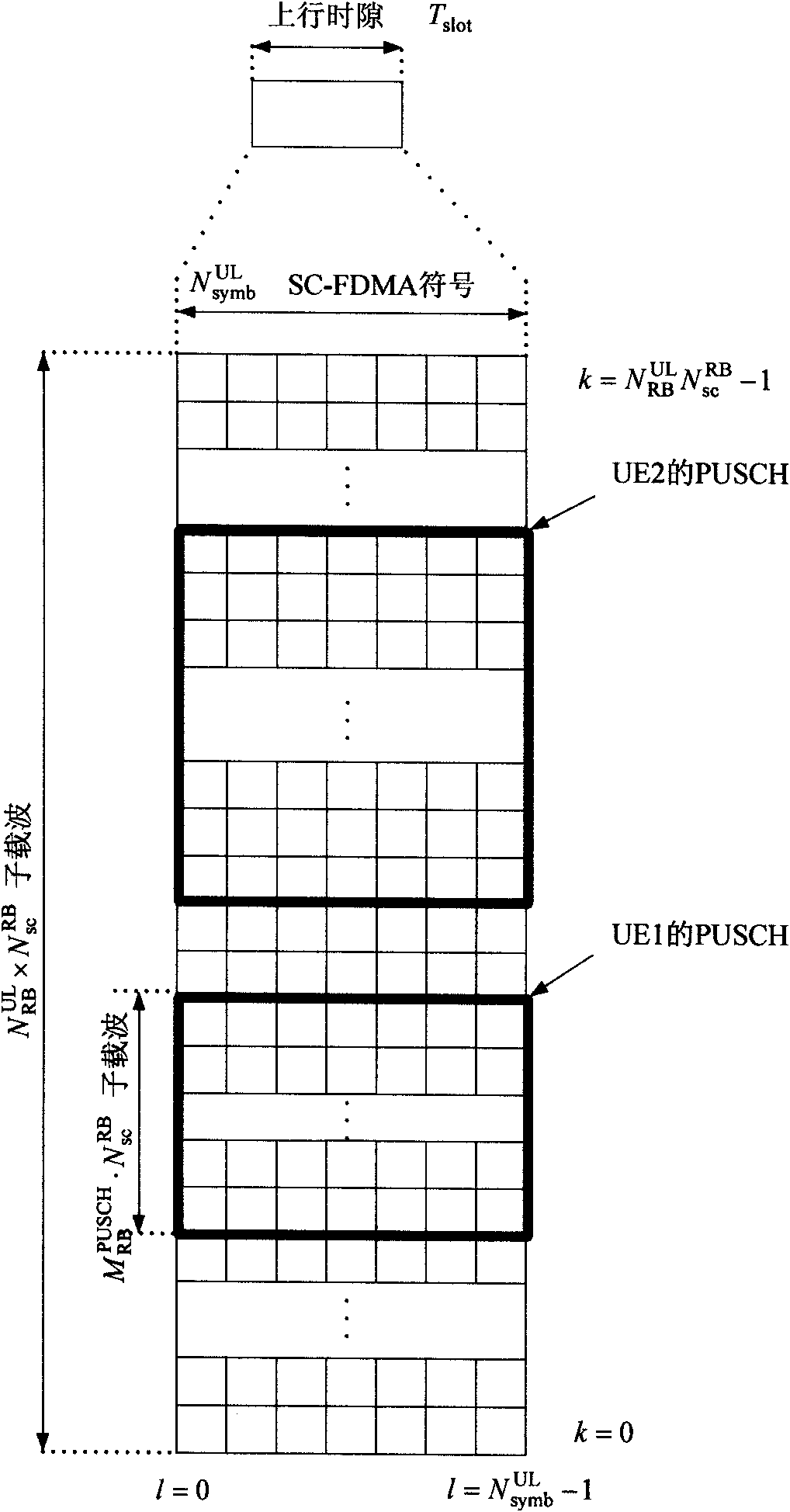
Indication method for scheduling authorization resource in LTE TDD system
InactiveCN101296508AReduce overheadMeet the requirements of frequency selective transmissionData switching by path configurationRadio/inductive link selection arrangementsResource blockAuthorization
The invention discloses an instruction method for scheduling authorized resources in an LTE TDD system, which comprises the steps as follows: wireless resource scheduling is started by a base station; a resource block range and a sub-frame bitmap are adopted as an authorized resource position instruction by the base station to generate scheduling authorized information containing the authorized resource position instruction which is transmitted to a terminal; the scheduling authorized information is received by the terminal and the authorized resource position instruction is extracted from the information by the terminal; data are received and transmitted by the terminal according to the authorized resource position instruction. Therefore, the authorized resource position is scheduled with the instruction of uplink and / or downlink by the using of the resource block range and the sub-frame bitmap of the invention, thereby not only obtaining lower expenditure for authorized instructive signaling, but also meeting the requirement of the system to the selective transmission of frequency.
Owner:ZTE CORP
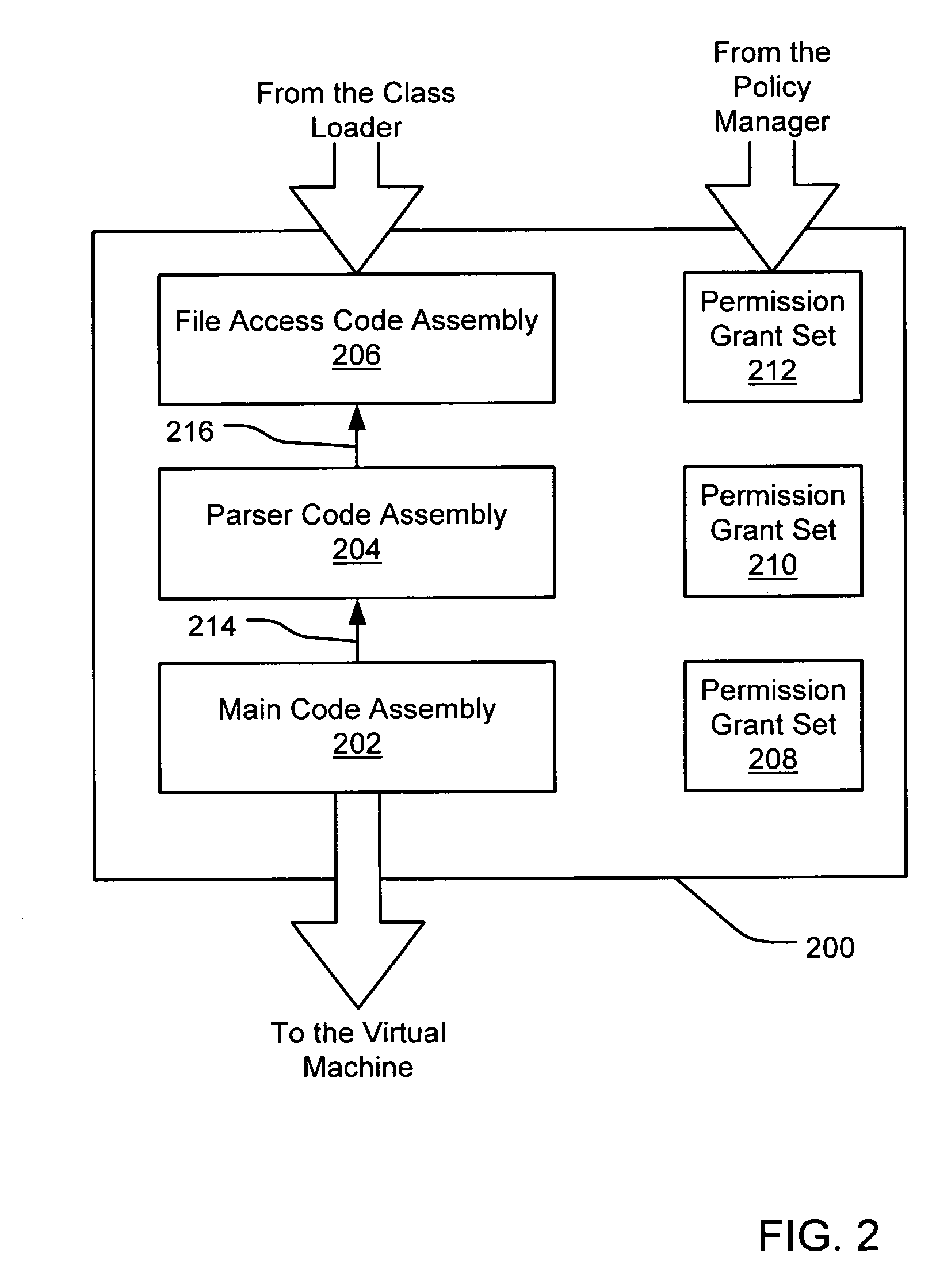
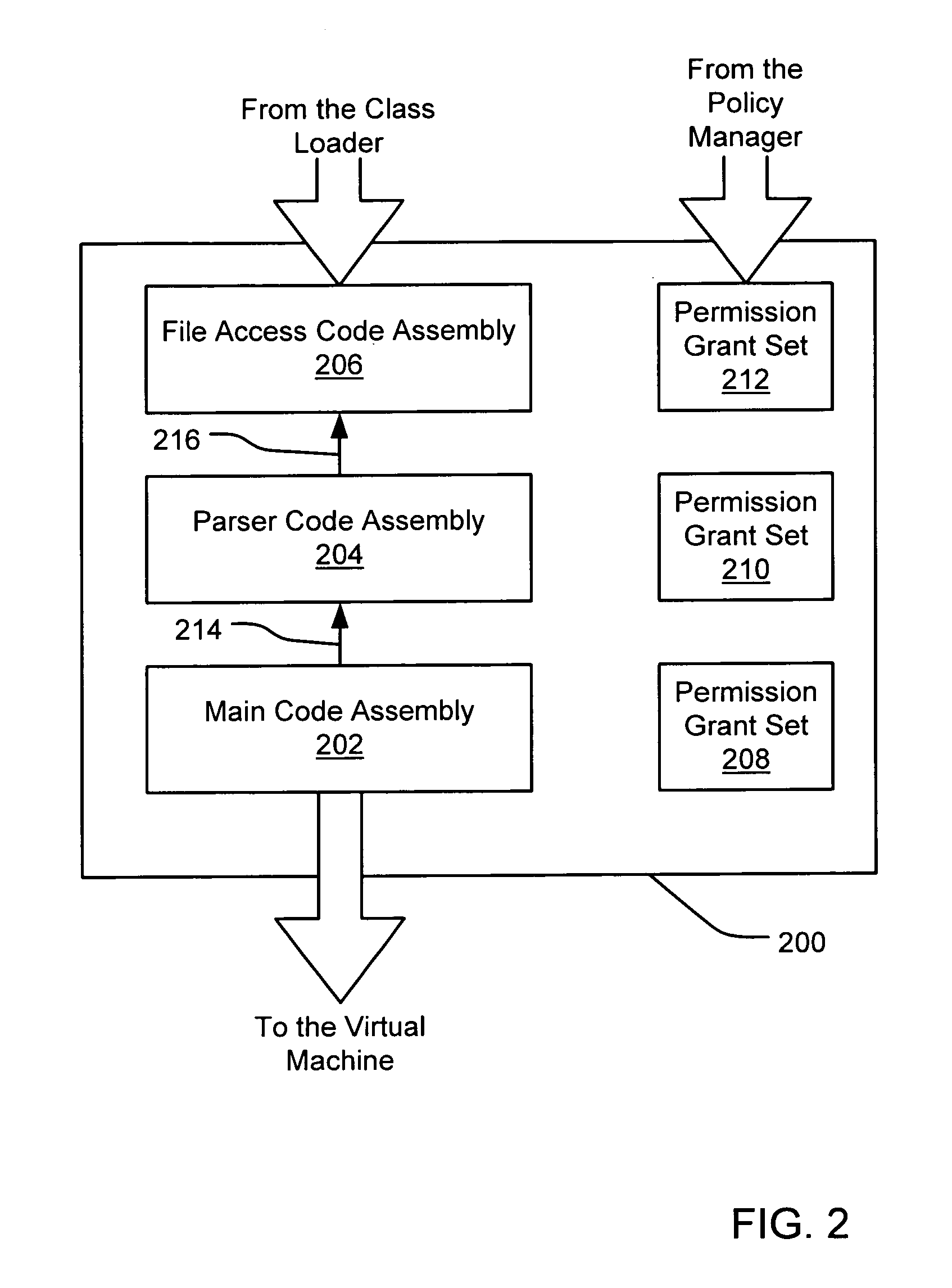
Filtering a permission set using permission requests associated with a code assembly
InactiveUS6981281B1Avoid contactPrevent inadvertent accessDigital data processing detailsUser identity/authority verificationCall stackComputerized system
A security policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager can execute in a computer system (e.g., a Web client) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. A permission request set may also be received in association with the code assembly. The permission request set may include a minimum request set, specifying permissions required by the code assembly to run properly. The permission request set may also include an optional request set, specifying permissions requested by the code assembly to provide an alternative level of functionality. In addition, the permission request set may include a refuse request set, specifying permissions that are not to be granted to the code assembly. The permission requests are used to filter a permission set to generate a permission grant set.
Owner:MICROSOFT TECH LICENSING LLC
PORTALS and DOORS for the Semantic Web and Grid
A Domain Ontology Oriented Resource System (DOORS) and a Problem Oriented Registry of Tags And Labels (PORTAL) are infrastructure systems for resource metadata within a paradigm serving as a bridge between the original web and the semantic web. IRIS registers domain names while DNS publishes domain addresses with mapping of names to addresses for the original web. Analogously, PORTAL registers resource labels and tags while DOORS publishes resource locations and descriptions with mapping of labels to locations for the semantic web. They provide an analogous resource label system, semantic search applications, and the benefits of collaborative semantic networks. Advertising is supported in several ways. Businesses purchase the right to display their products or services in association with searches. Also, content providers accept placement of advertising. Ads are then selected for display based on the content displayed utilizing the invention to match service providers with advertisers.
Owner:BRAIN HEALTH ALLIANCE INC
Method for indicating wireless channel resource allocation, base station, decoding method and terminal
InactiveCN102036387AReduce overheadReduce signalingWireless communicationDecoding methodsResource block
The invention discloses a method for indicating wireless channel resource allocation, a base station, a decoding method and a terminal, which can indicate resource positions and save signaling and are used for solving the problem that how to guarantee channel resource indication and signaling overhead in discontinuous resource allocation. The method comprises that: the base station enumerates the number and positions of resource block groups (RBG) possibly contained by each cluster in advance according to the system bandwidth, cluster number and the sizes of the RBG, and identifies each kind of combination of number and positions with unique state flag information; the base station and the terminal agree on the RBG number and positions indicated by each piece of state flag information; and in the process that the base station allocates resources to the terminal, the base station forms a state flag information group by the state flag information corresponding to each cluster of resources and sends the state flag information group to the terminal after determining each cluster of resources to be allocated to the terminal, namely RBG number and positions in each cluster.
Owner:王勇刚
Evidence-based security policy manager
InactiveUS7051366B1Increase flexibilityAddressing slow performanceDigital data processing detailsUser identity/authority verificationCall stackThe Internet
An evidence-based policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager executes in a computer system (e.g., a Web client or server) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. Both code assemblies and evidence may be received from a local origin or from a remote resource location via a network (e.g., the Internet). The policy manager may comprise execution modules for parsing a security policy specification, generating a one or more code hierarchies, evaluating membership of the received code assembly in one or more code groups, and generating a permission grant set based upon this membership evaluation.
Owner:MICROSOFT TECH LICENSING LLC
Application access method in a plurality of application service platform systems
The invention discloses an application access method in a plurality of application service platform systems. The application access method comprises the following steps: in one application service platform system, a proxy server receives a client-side request message, determines a corresponding application, creates an application context, adds the application context to the client-side request message and then distributes the client-side request message to an application server in which the corresponding application is located; after receiving the client-side request message sent by the proxy server, the application server delivers the client-side request message to the corresponding application for processing the message; the corresponding application processes the client-side request message and performs data resource location according to the application context so as to obtain the processing result; the application server returns the processing result to a client side through the proxy server; and a gateway performs cross-system access to the application among the application service platform systems. By adopting the application access method, the development difficulty of the application platform systems can be reduced, the deployment flexibility can be improved, and the deployment difficulty can be lowered.
Owner:BEIJING FEINNO COMM TECH
Relay method, relay system and relay device
InactiveCN101188816AImprove relay reliabilityRadio/inductive link selection arrangementsRadio transmission for post communicationComputer scienceResource location
The invention relates to a relay transfer method which comprises the following steps: a base station sends a first relay information element to a relay station, and the resource location belonging to the relay station is indicated; the relay station receives a service data, and the received service data which is required to be relayed is relayed and transferred through a relay area according to the indication of the base station. The invention also provides a relay mode switch method, a relay sensing method, a relay system, and a relay device. The relay station of the invention can perform the relay transfer of the service data through the relay area according to the indication of the base station, and adjust the transfer frequency, and the relay reliability can be improved. In addition, the relay station of the invention can switch the current relay mode according to the indication of the base station. The relay station of the invention also can sense the peripheral wireless environment, inform the base station when the self coverage area is judged to be interfered, and adjust the sending frequency to adapt the change of the wireless environment.
Owner:HUAWEI TECH CO LTD
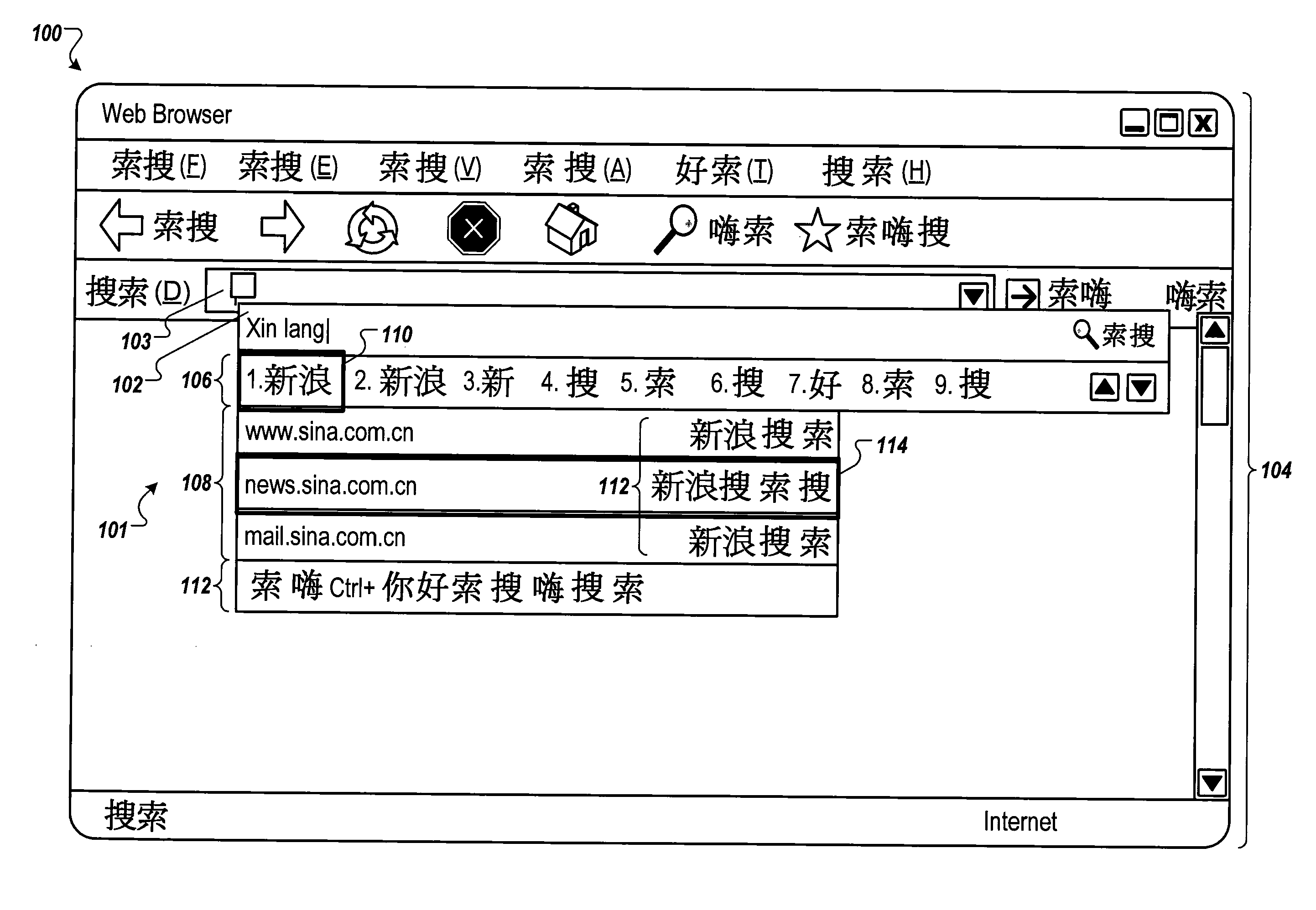
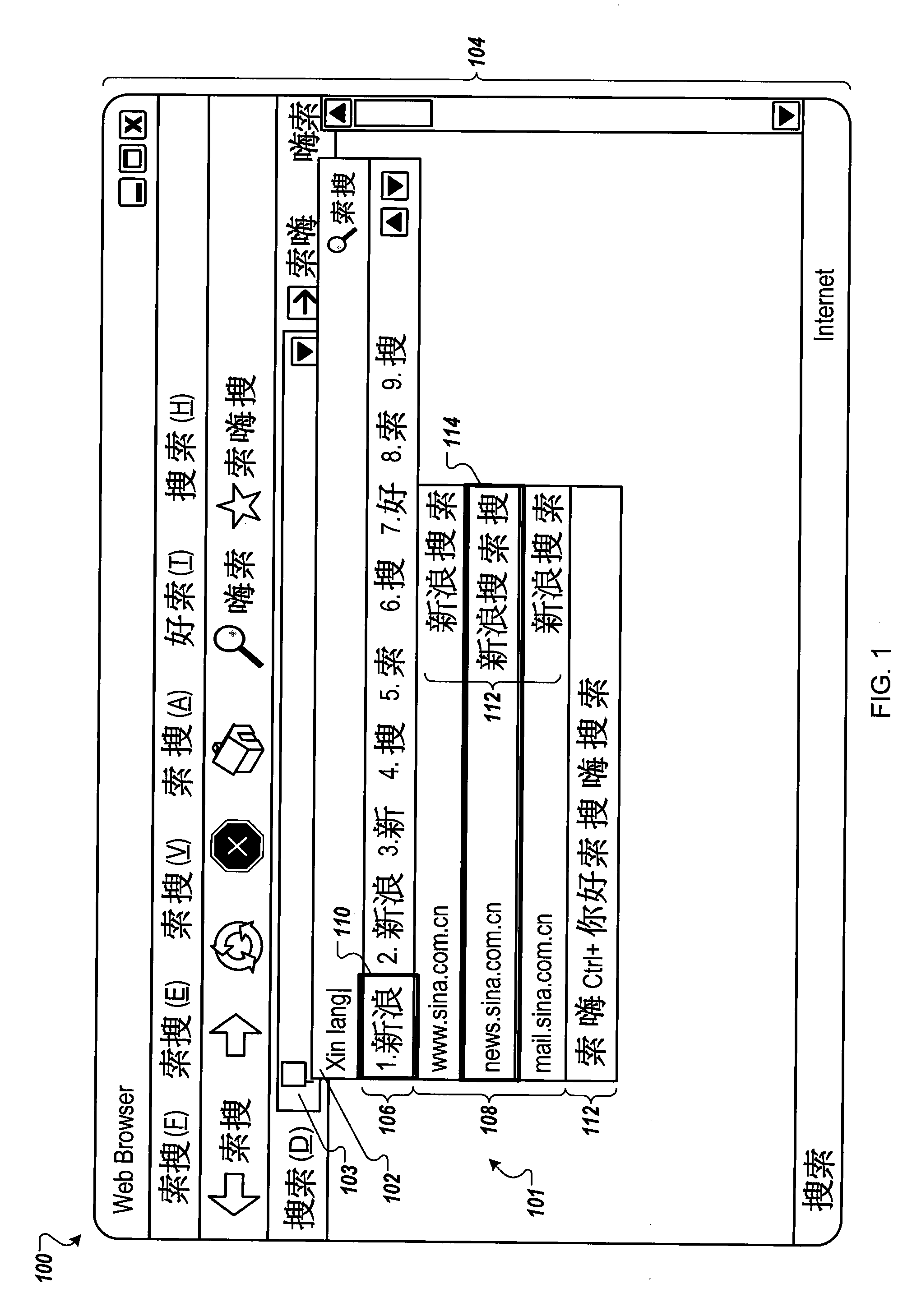
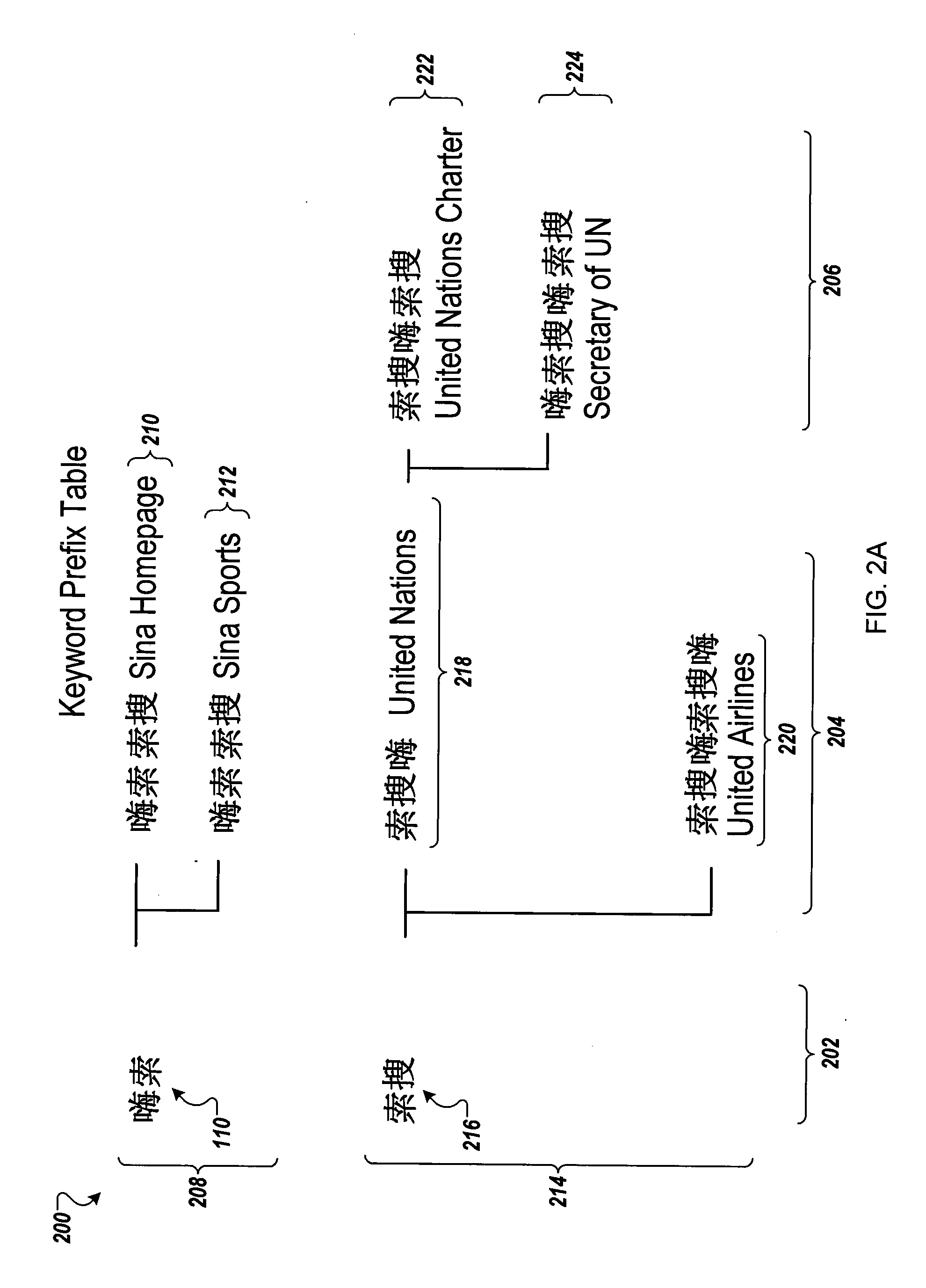
Resource locator suggestions from input character sequence
ActiveUS20100005086A1Natural language data processingSpecial data processing applicationsWorld Wide WebResource location
Methods, systems, and apparatus, including computer program products, in which an input method editor receives Roman character inputs, identifies keywords for candidate sets of a non-Roman character, and identifies an associated resource location. Upon identifying an associated resource location, associating the resource location with the candidate set of non-Roman characters.
Owner:GOOGLE LLC
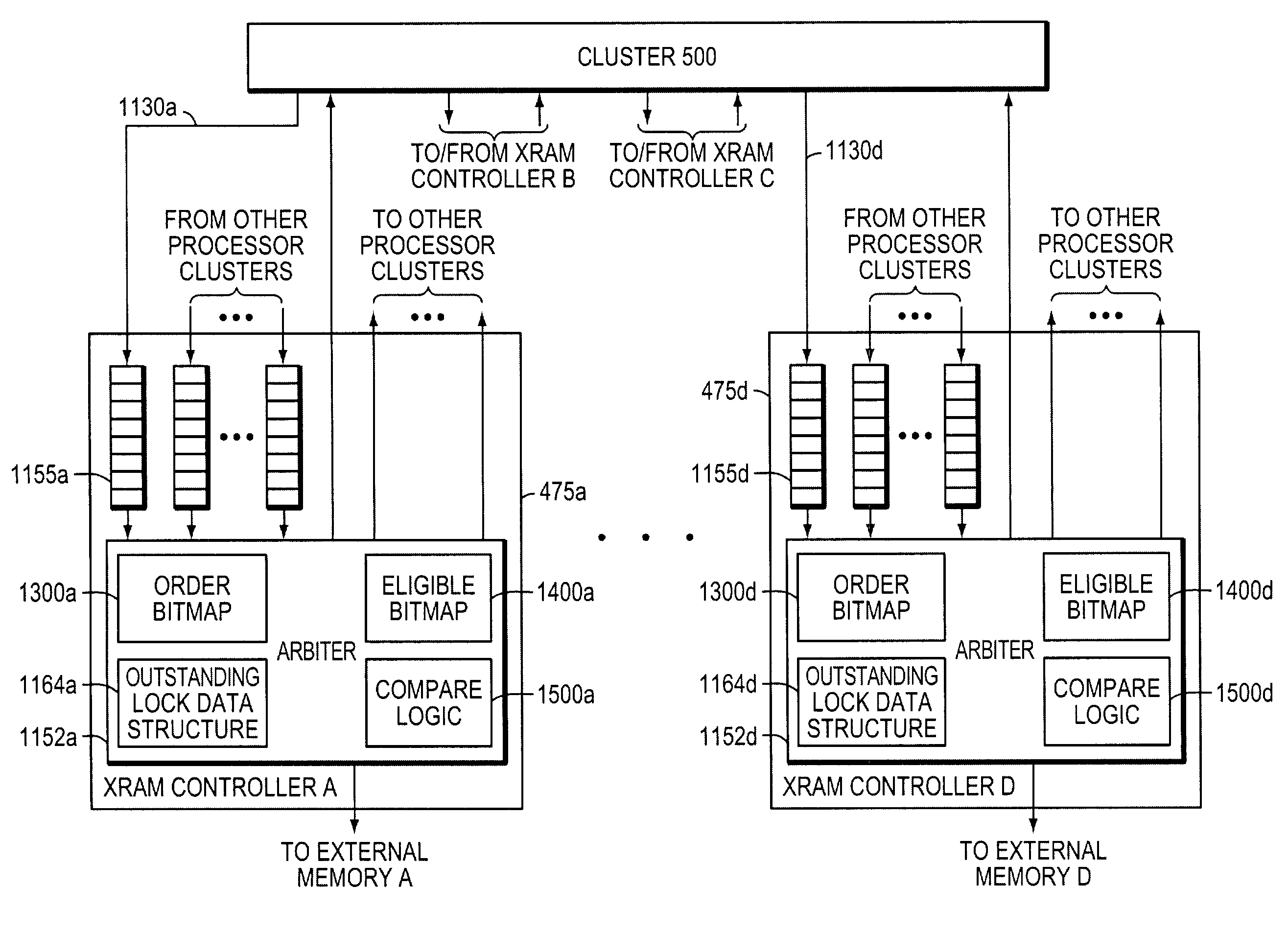
Zero overhead resource locks with attributes
A technique efficiently accesses locks associated with resources in a computer system. A processor accesses (e.g., acquires or releases) a lock by specifying and issuing a request to a resource controller, the request containing attribute and resource location information associated with the lock. In response, the resource controller applies the information contained in the request to an outstanding lock data structure to determine if the request should be blocked, blocked as a pending writer, allowed or an error condition. If the request is blocked, it remains blocked until the outstanding lock blocking the request is released. If the request is allowed, operations associated with the request are performed.
Owner:CISCO TECH INC
Indication method for scheduling authorization resource in long-term developing TDD system
ActiveCN101330372AReduce overheadMeet the requirements of frequency selective transmissionDuplex signal operationTime-division multiplexing usageResource blockAuthorization
The invention provides an indication method of dispatching authorized resources in a time division duplex system of long term evolution. A base station generates and sends dispatch and authorization information containing the position indication of authorized resource to a terminal. The indication method is characterized in that the position indication of authorized resource comprises resource block range and sub-frame information; and the sub-frame information comprises a sub-frame position or the initial position and the duration of the sub-frame; the total bit length of the sub-frame information is the same as the bit length of the duration in the long term evolution frequency division duplex system authorized resource position indication. The indication method utilizes a RB initial position, a RB final position and the sub-frame information to indicate the uplink or the downlink position of the dispatched and authorized resource, thereby acquiring lower authorization indication signaling overhead, enabling the authorization indication signaling forms of two systems of LET TDD and LTE FDD to be consistent, and meeting the requirement of the system for frequency selective transmission.
Owner:ZTE CORP
Processing method and device of downlink data
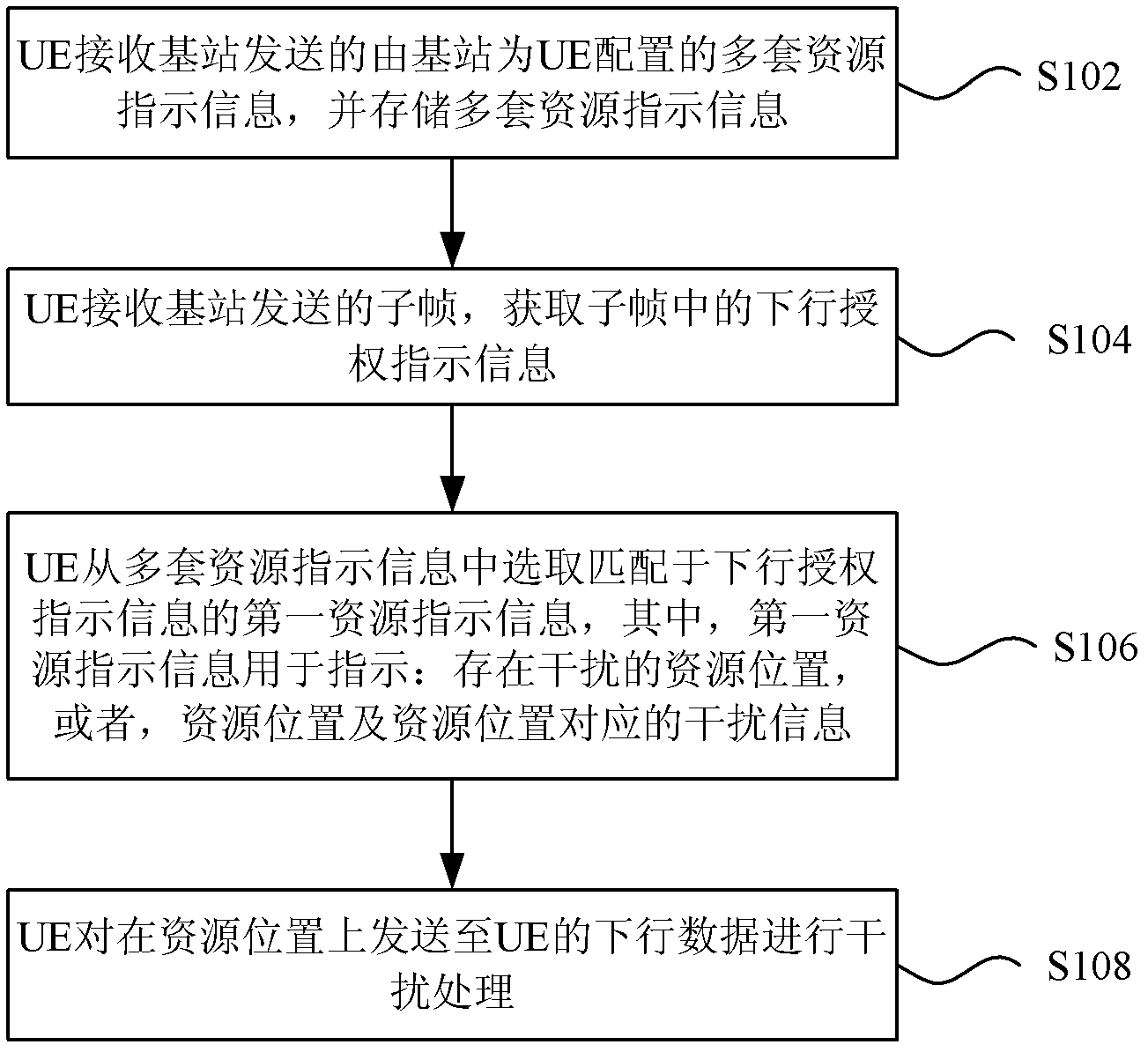
ActiveCN103220802AAvoid interferenceReduce wasteSite diversityCriteria allocationConducted InterferenceAuthorization
The invention discloses a processing method and a device of downlink data, wherein the method includes the steps of receiving through user equipment (UE) a plurality of sets of resource indication information which is configurated for the UE by a base station and is sent through a high-rise signal, and storing the plurality of sets of resource indication information; receiving through the UE a subframe which is sent by the base station, obtaining downlink authorization indication information in the subframe; selecting resource indication information which is matched with the downlink authorization indication information from the plurality of sets of resource indication information through the UE, wherein the resource indication information is used for indicating a resource position where interference exists or a resource position and corresponding interference information of the resource position; and conducting interference treatment through the UE on downlink data which are sent to the UE. According to the processing method and the device of the downlink data, cooperation transmission (including: joint sending, joint scheduling, joint beam shaping and dynamic node selection) among different nodes for the same UE is achieved. Therefore, the effect of reducing resource waste and the effect of avoiding interference for data demodulation caused by a control domain or pilot frequency are achieved.
Owner:ZTE CORP
Method for sending synchronization signals
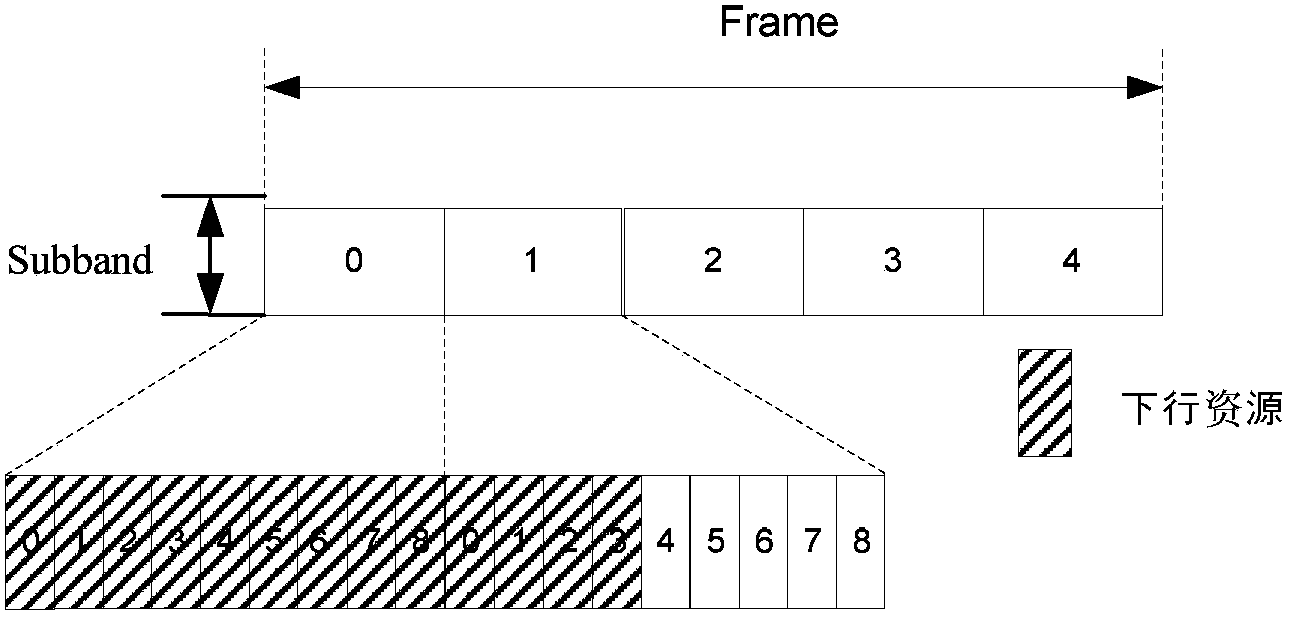
InactiveCN103428143ALower peak-to-average ratioMulti-frequency code systemsTransmission path multiple useTime domainResource location
The invention provides a method for sending synchronization signals. The method includes the steps that the synchronization signals of each sub-band are generated corresponding to each sub-band according to the ID of a cell and the serial number of a corresponding absolute sub-band of each sub-band, wherein the synchronization signals generated by the different sub-bands are mutually different; all points of the synchronization signals of each sub-band are mapped to the time-frequency resource positions of the synchronization signals of each sub-band where the pointes are located for transmitting, wherein time-frequency resources of the synchronization signals comprise all downlink resources on the whole sub-bands in a synchronization frame. By the application of the method for sending the synchronization signals, the peak-to-average ratio of time-domain signals can be reduced.
Owner:POTEVIO INFORMATION TECH
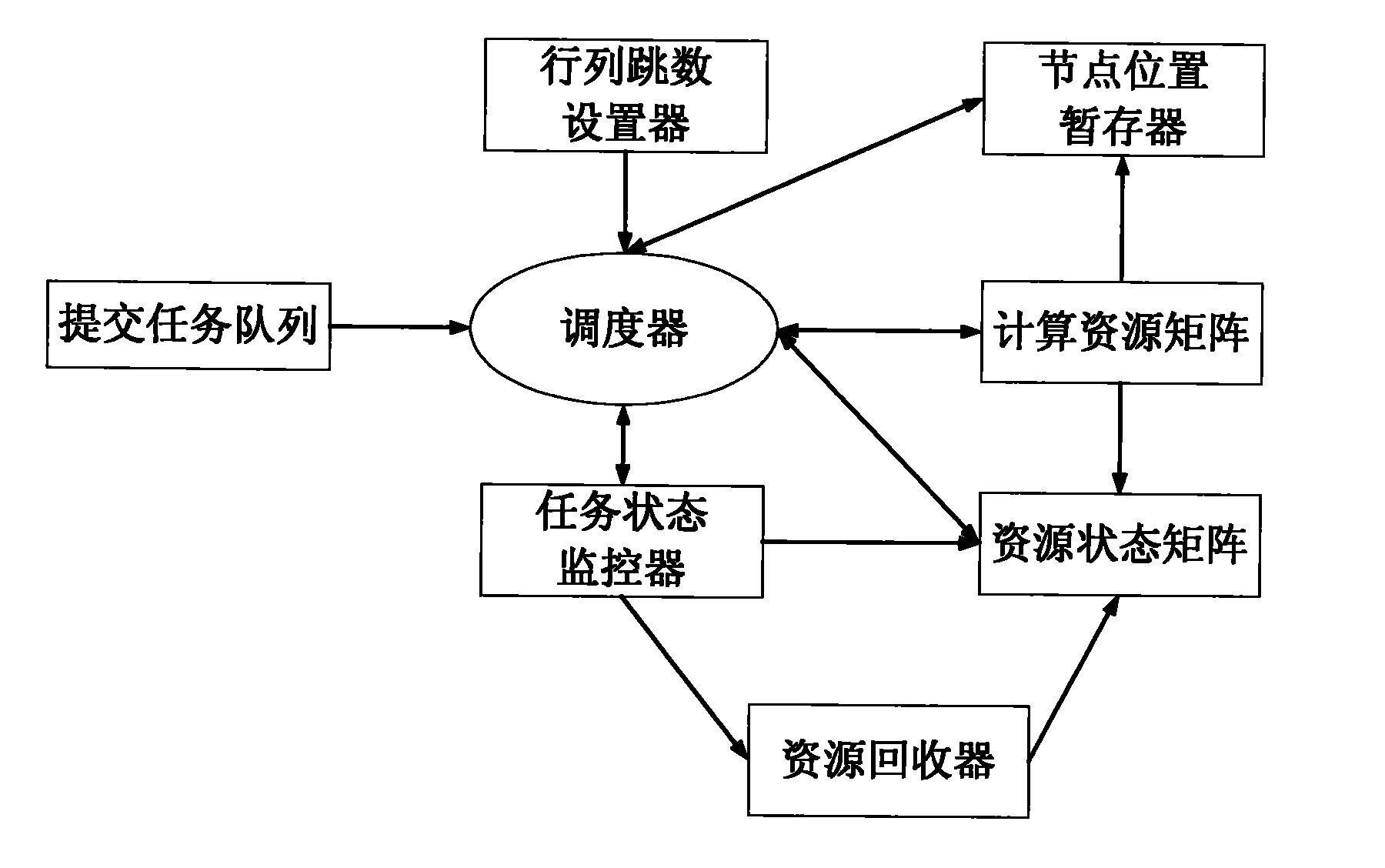
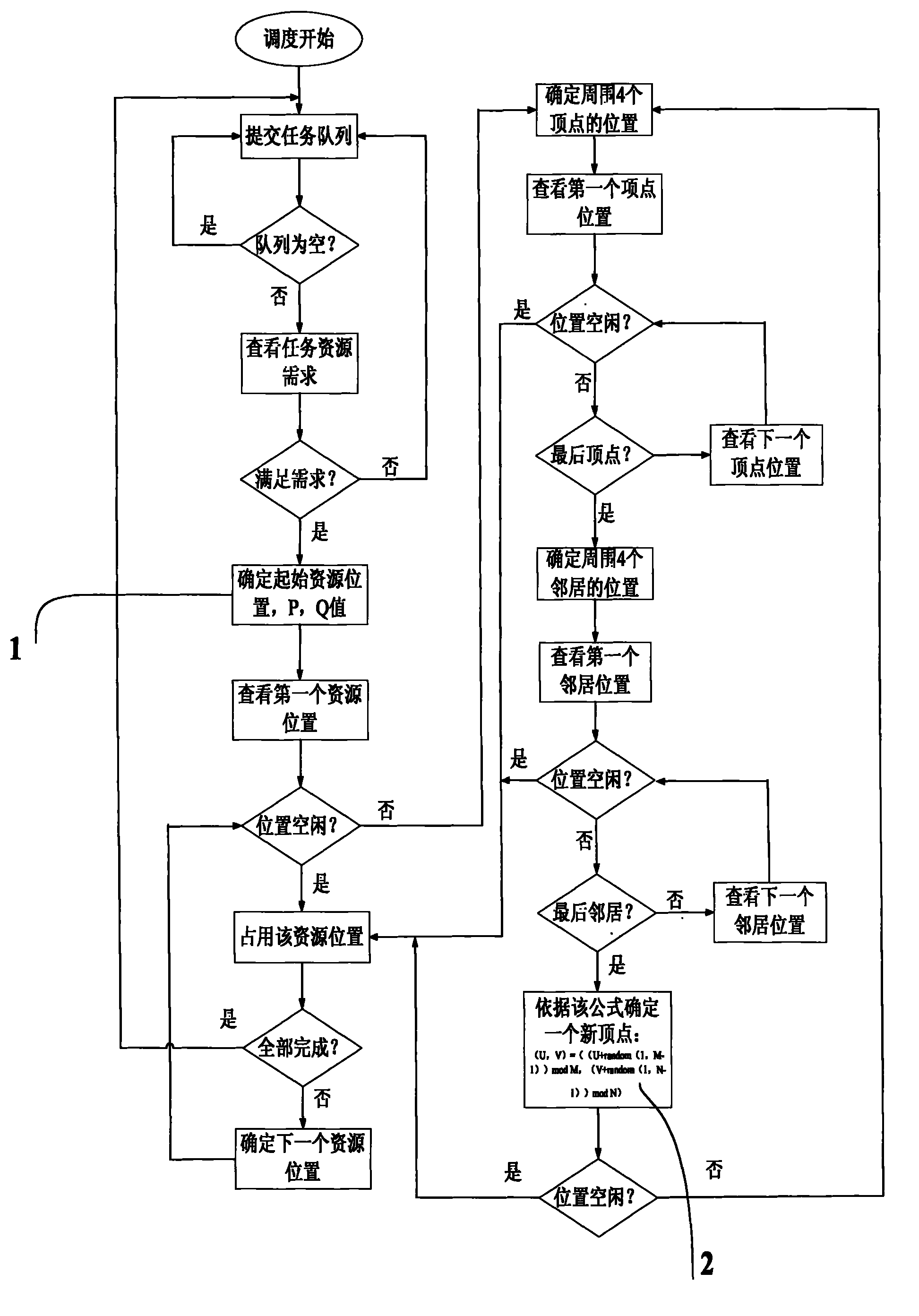
Cluster task resource allocation method for multi-core processor
InactiveCN101916209AAdequate heat dissipationReduced thermal effectsResource allocationDigital data processing detailsCluster systemsAllocation algorithm
The invention relates to a cluster task resource allocation method for a multi-core processor. In the method, CPU resource nodes are used as basic allocation units for task allocation according to operation tasks submitted by receiving users to a cluster, and a task resource allocator is formed. The task resource allocator maps resources on the cluster to an M*N matrix AR. When idle resource positions are searched for the tasks, in the method, the tasks are uniformly dispersed and required resources are allocated to the nodes, so that the resource node positions occupied by all tasks are spaced. The method avoids the problem that tasks are excessively concentrated in one certain area, a large amount of heat energy is concentrated in the area as time goes by, the temperature of a local chip is too high, and the normal operating efficiency of a computer is influenced in the traditional task allocation algorithm. The task scheduling algorithm adopted by the method is an online real-time task scheduling algorithm and has good application prospects in the operation and task management of a multi-core processor cluster system.
Owner:EAST CHINA JIAOTONG UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com