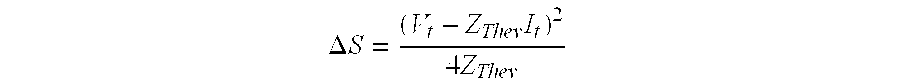Patents
Literature
930 results about "System protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
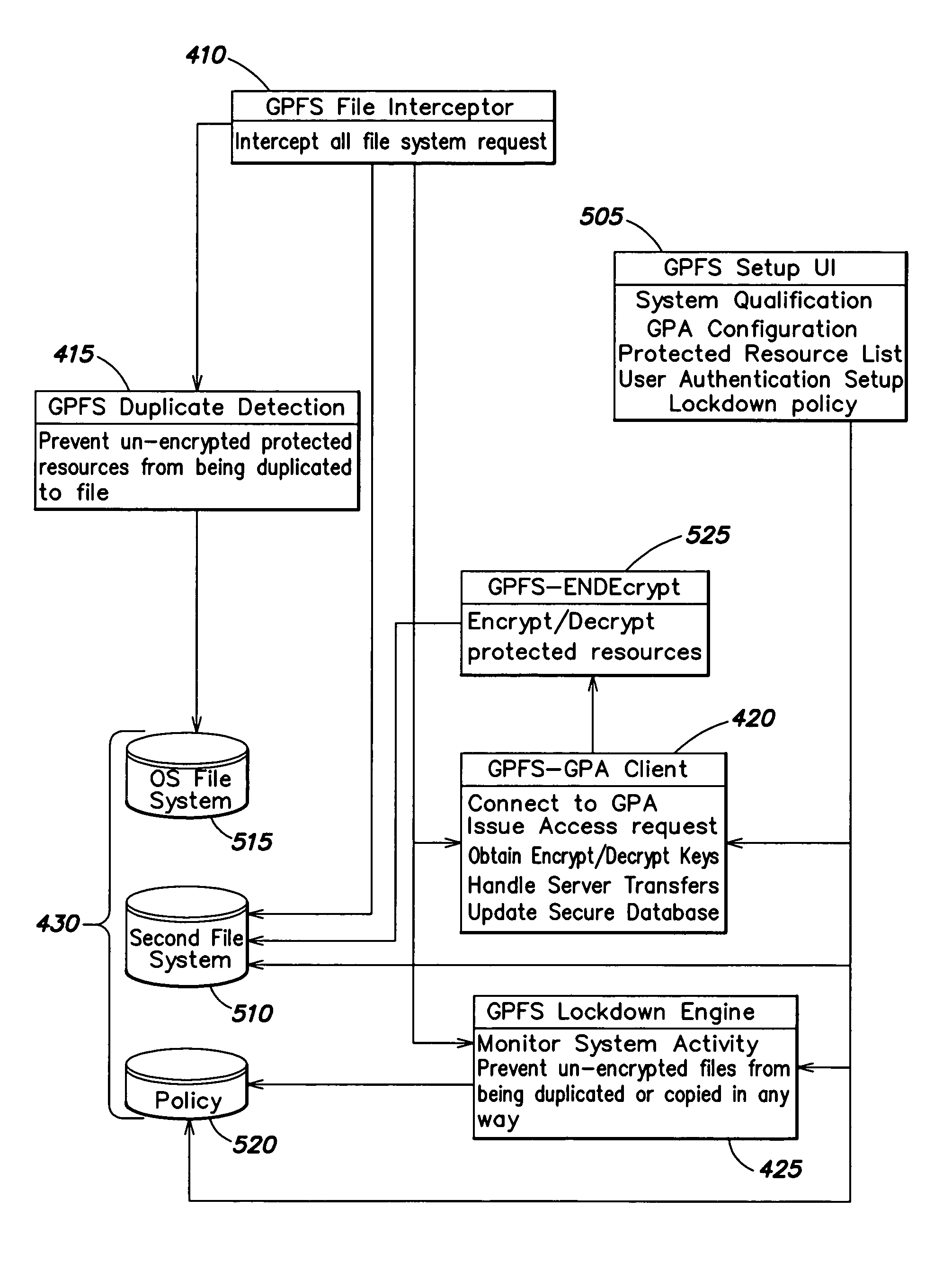
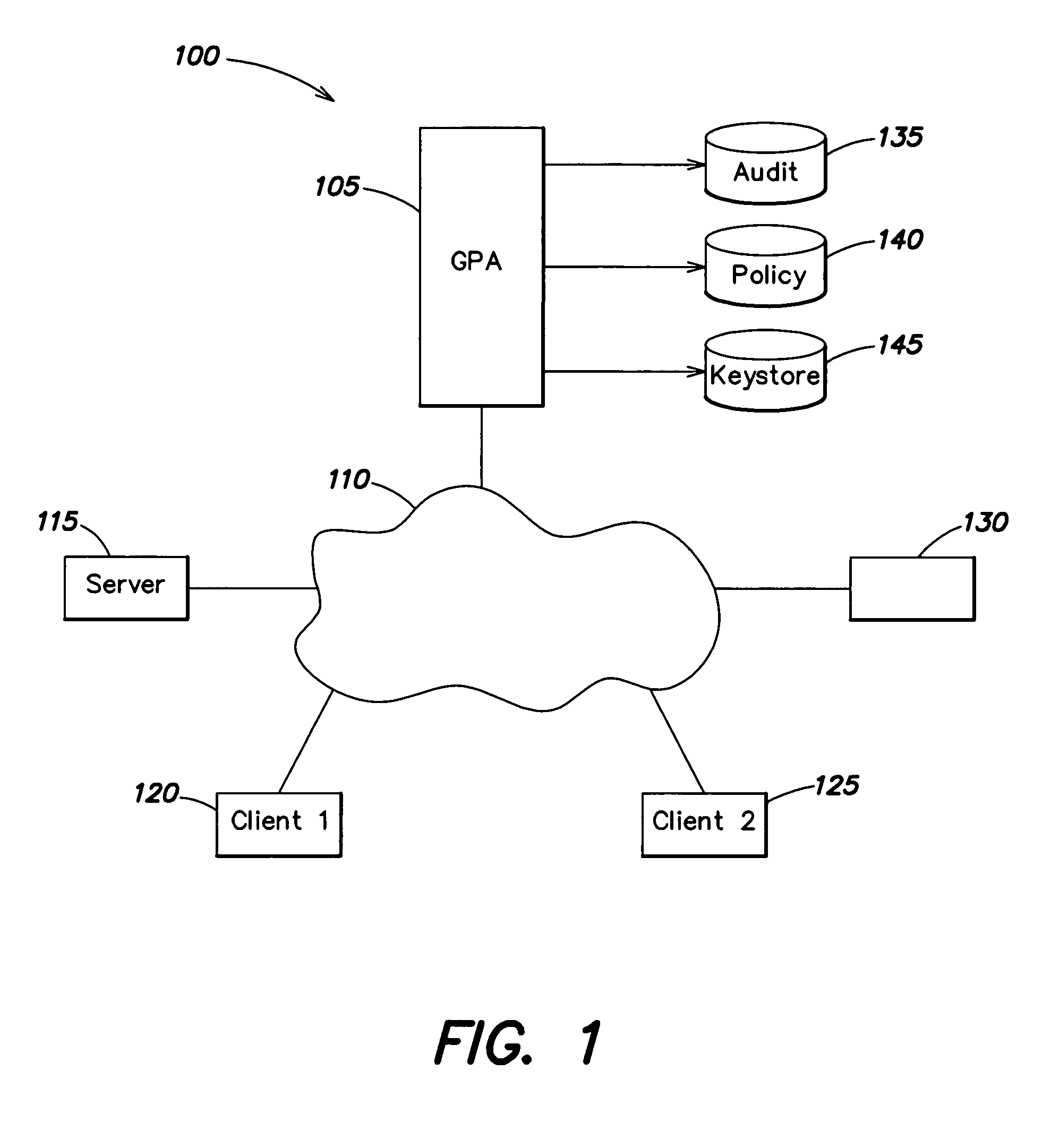
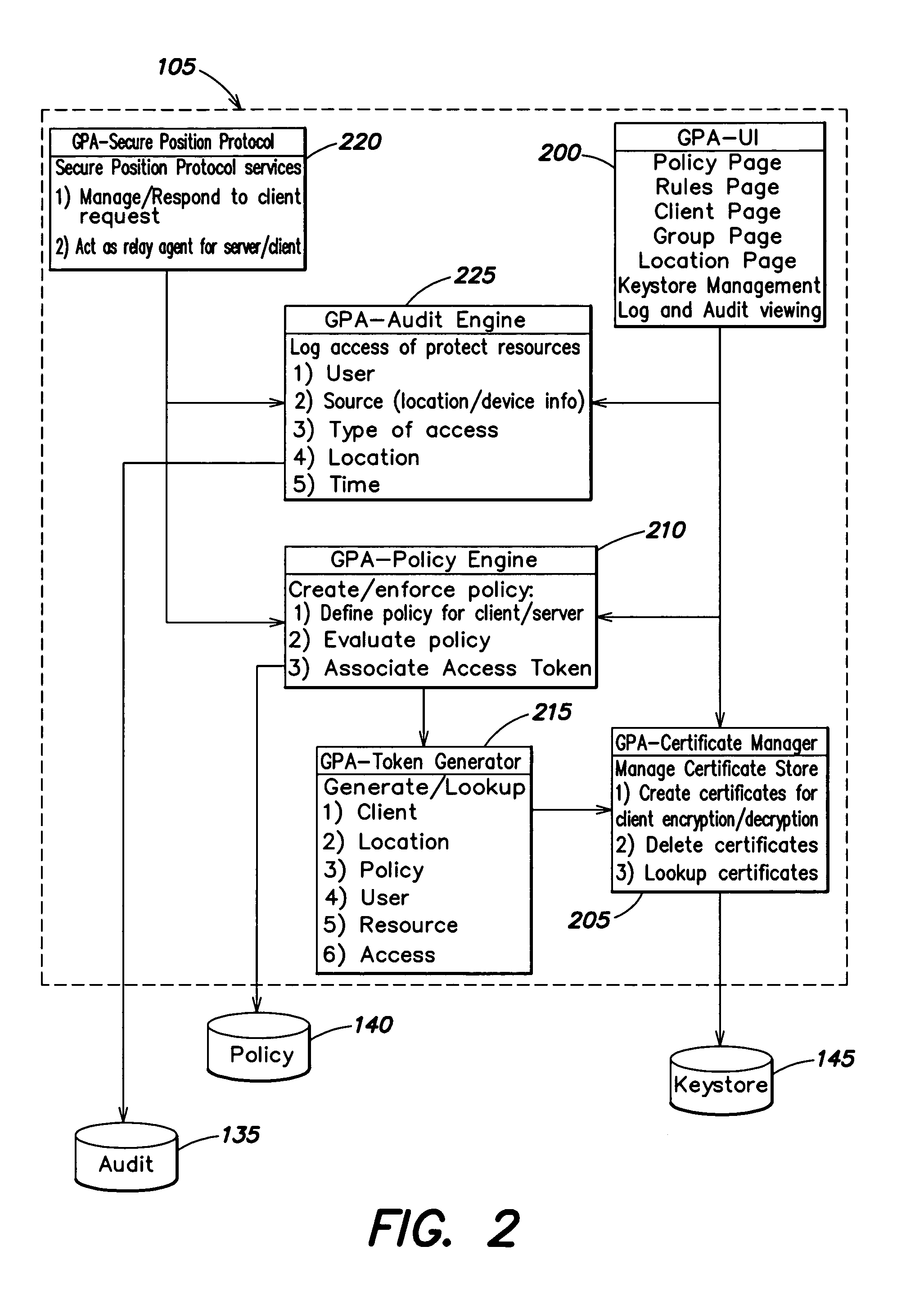
Method and apparatus for securing documents using a position dependent file system
ActiveUS8312064B1Provide securityEasy to manageUnauthorized memory use protectionHardware monitoringInternet privacyFile system
Access to information or a document is secured by a central global positioning authority that evaluates access requests in accordance with predefined policies. One component of an access request includes location information regarding at least one of the requesting entity and location of the requested resource. Access is either allowed or denied as a function of at least the requesting entity, position information and the applicable policy or policies. An encryption / decryption scheme is implemented where the encryption key is a function of the resource's position.
Owner:GEN DIGITAL INC
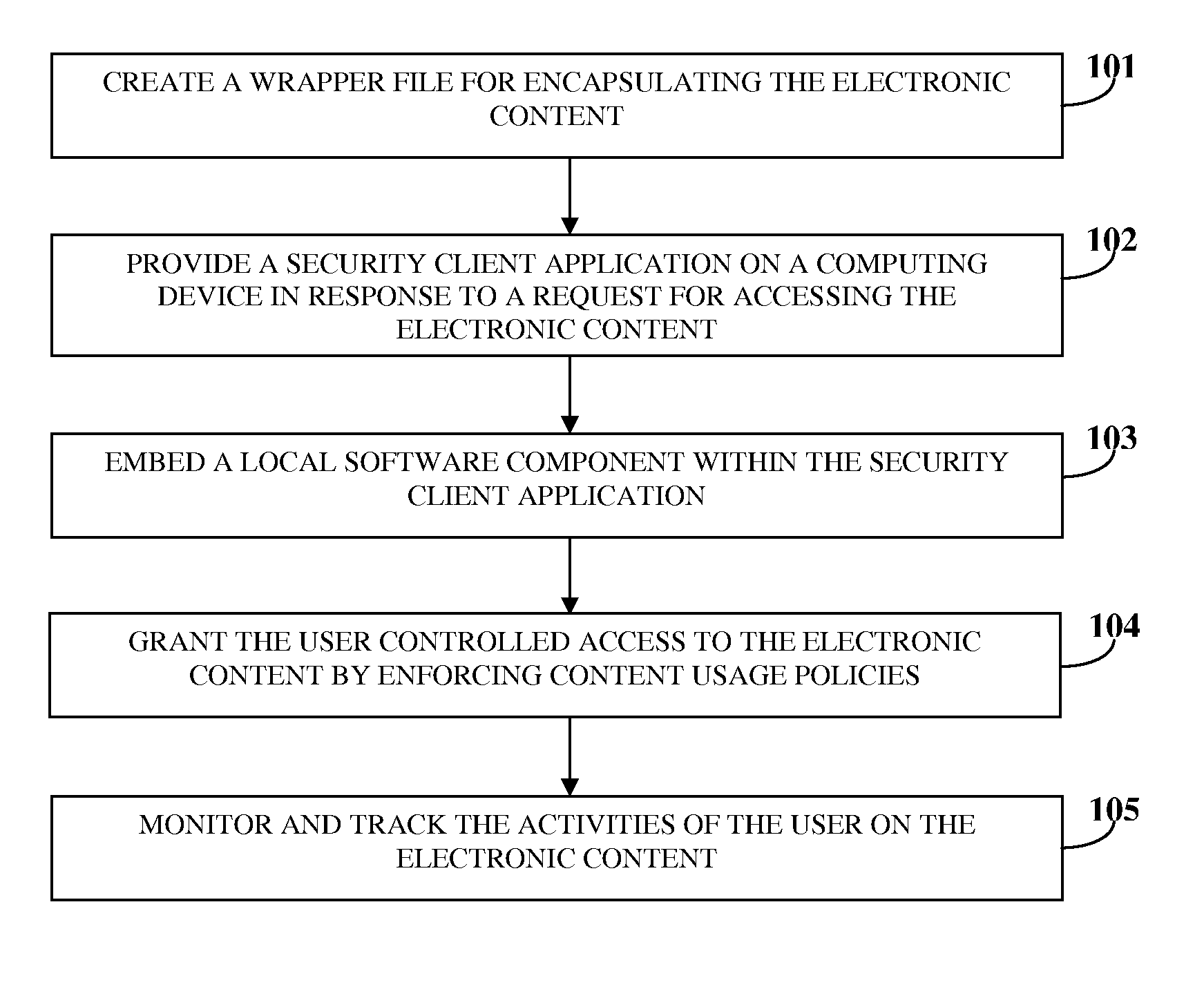
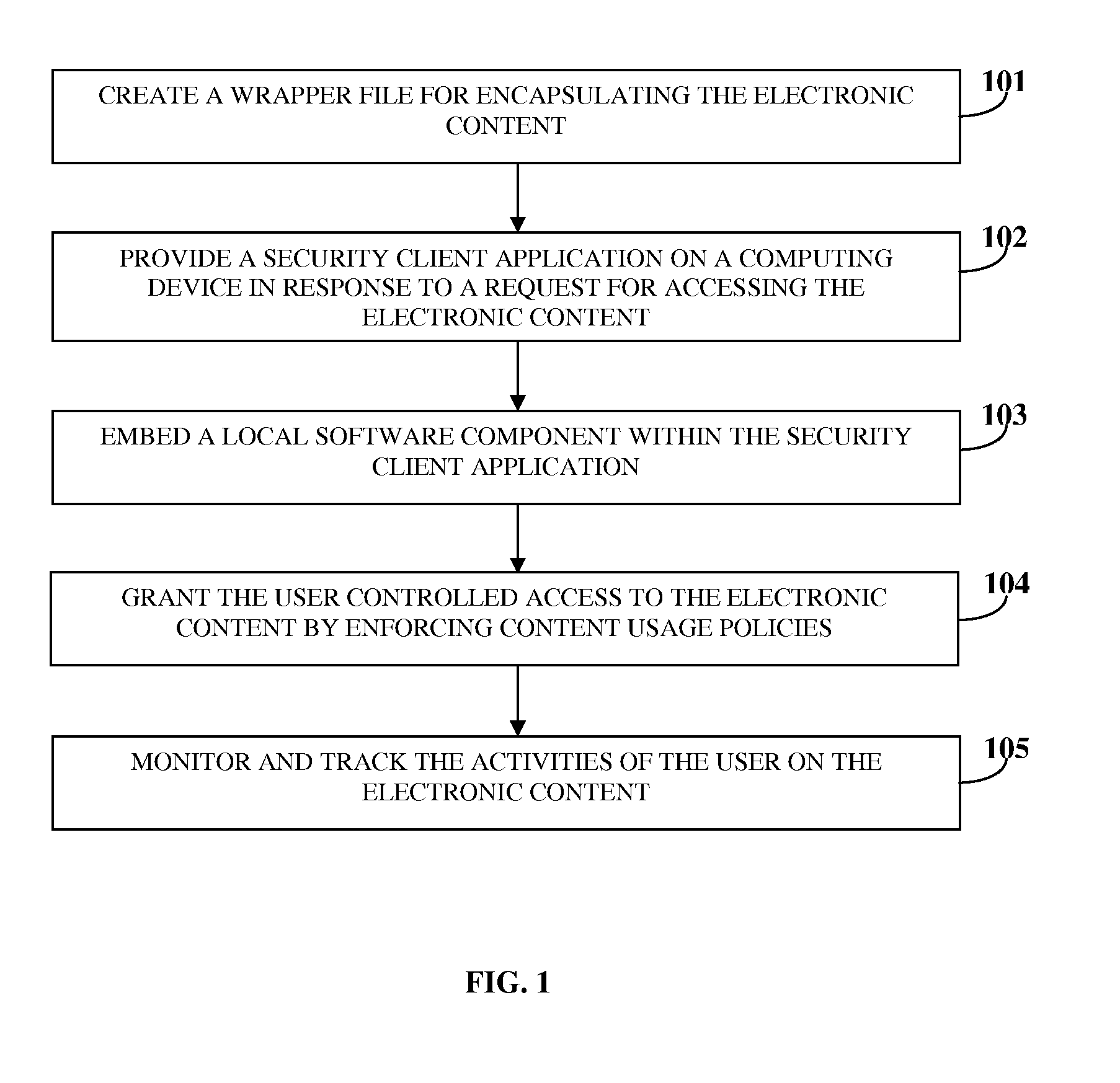
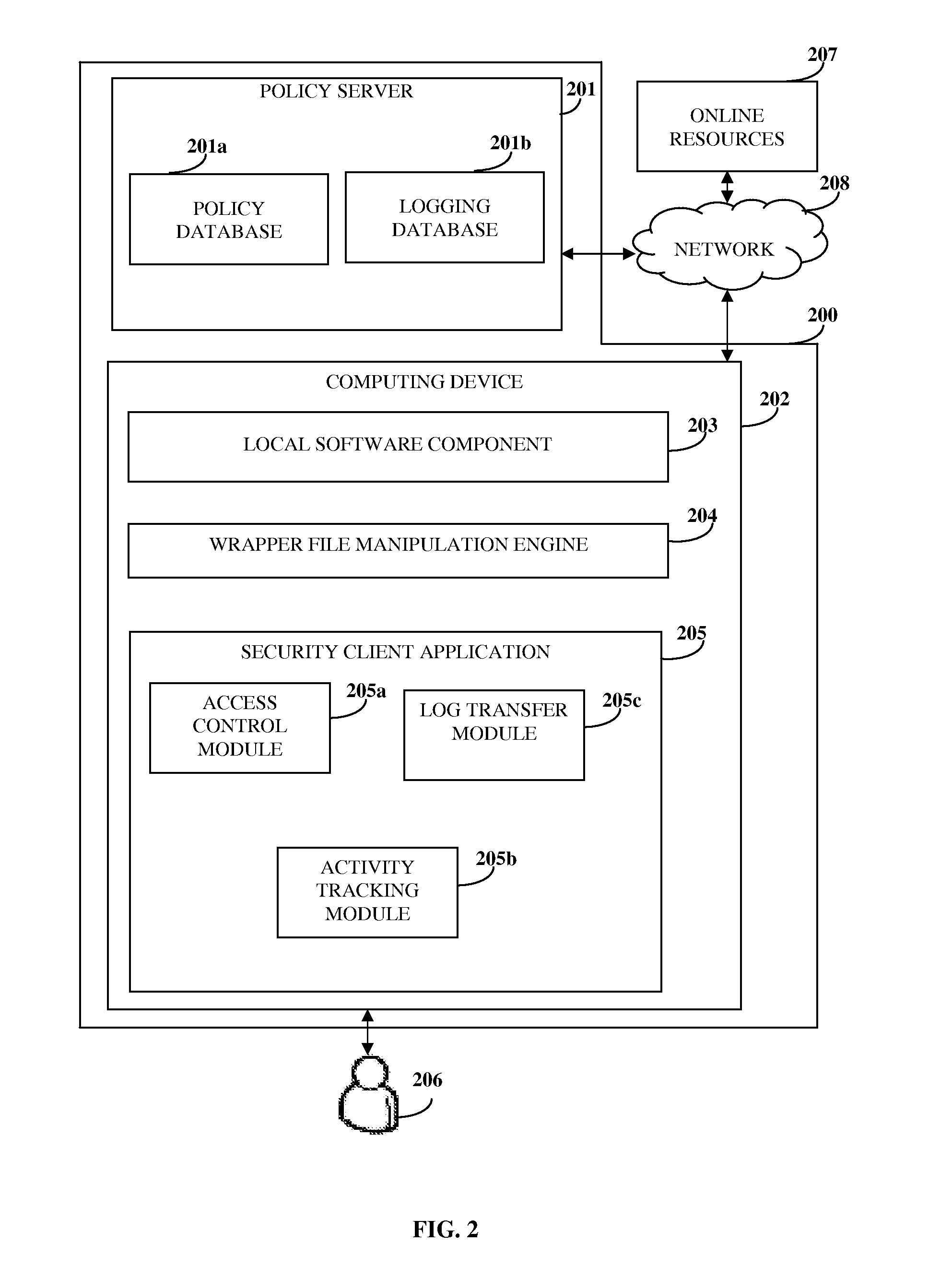
System To Secure Electronic Content, Enforce Usage Policies And Provide Configurable Functionalities
ActiveUS20100146269A1Avoid misuseDigital data processing detailsAnalogue secracy/subscription systemsClient-sideSystem protection
A computer implemented method and system for managing electronic content security and access within a networked environment are provided. A proprietary wrapper file is created for encapsulating the electronic content upon transferring the electronic content to the computing device of a user. The proprietary wrapper file is configured for enforcing content usage policies on the electronic content and for performing configurable functionalities. A security client application is provided on the computing device in response to a request for accessing the electronic content. A local software component employed for accessing the electronic content is embedded within the security client application. The user is granted controlled access to the electronic content by enforcing the content usage policies through the wrapper file. The activities of the user on the electronic content are monitored and tracked by the security client application to ensure compliance of the activities with the enforced content usage policies.
Owner:PAWAA SOFTWARE PVT +1
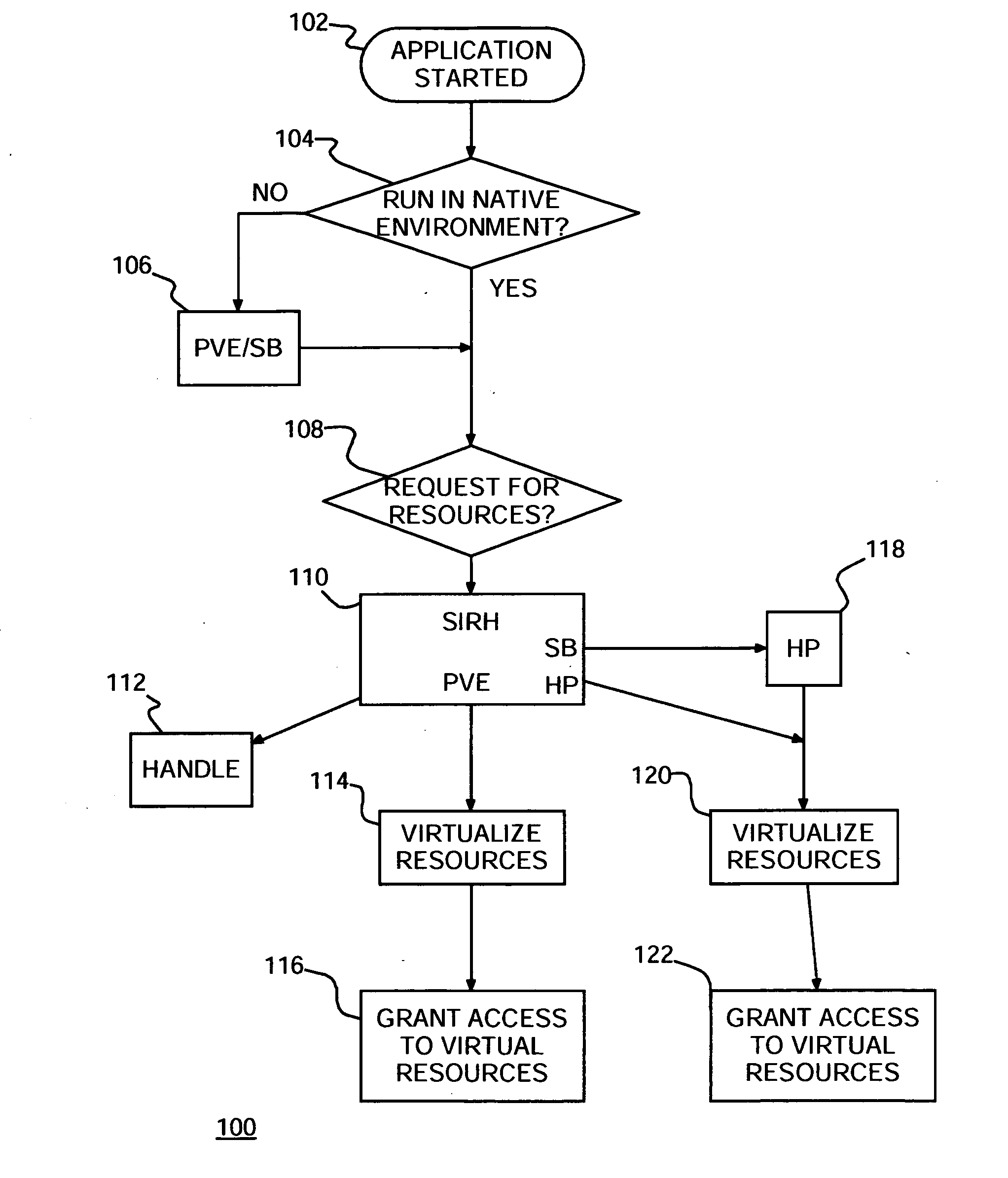
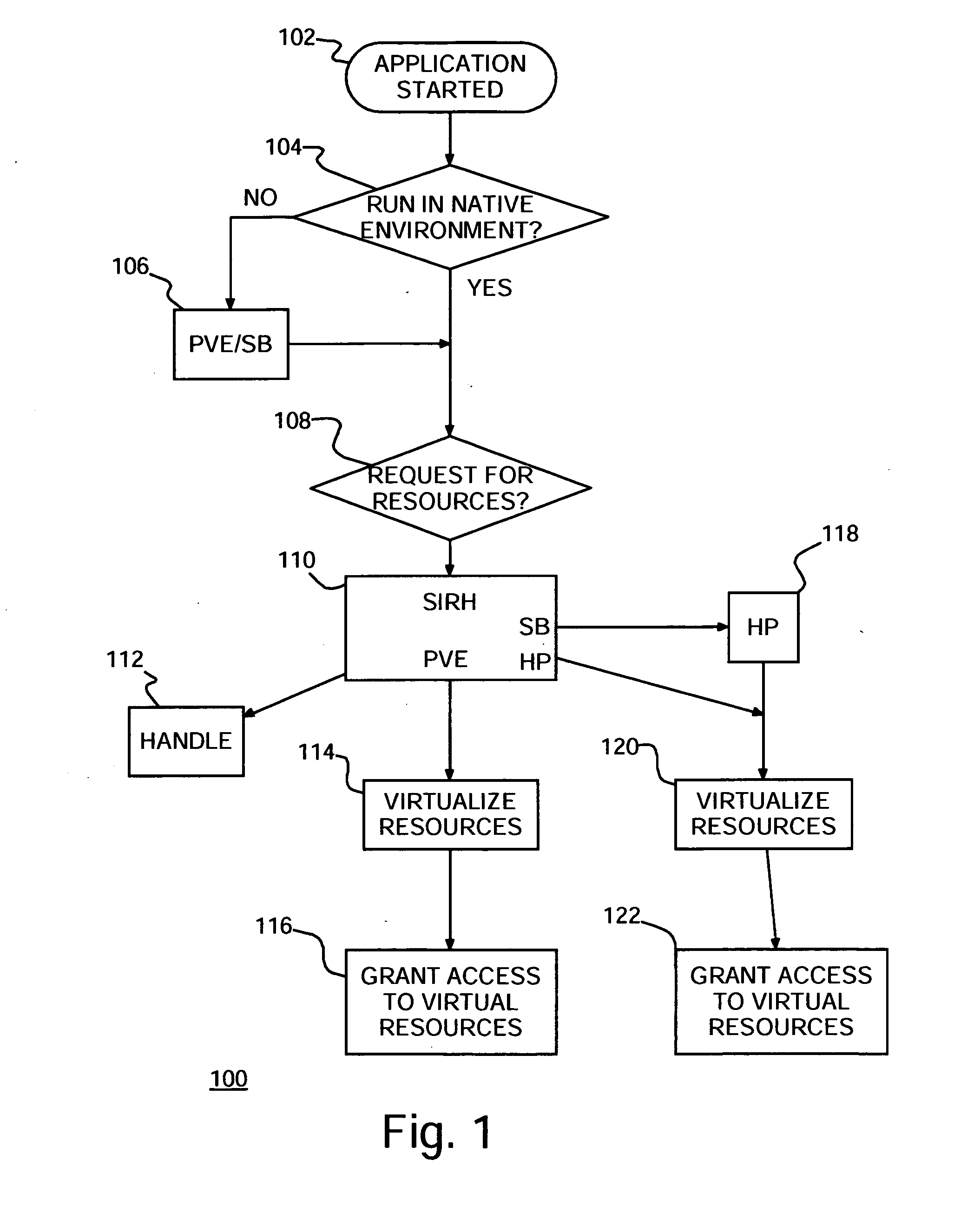
Intrusion detection system
InactiveUS20060161982A1Minimize wasted resourceMemory loss protectionError detection/correctionVirtualizationPersonalization
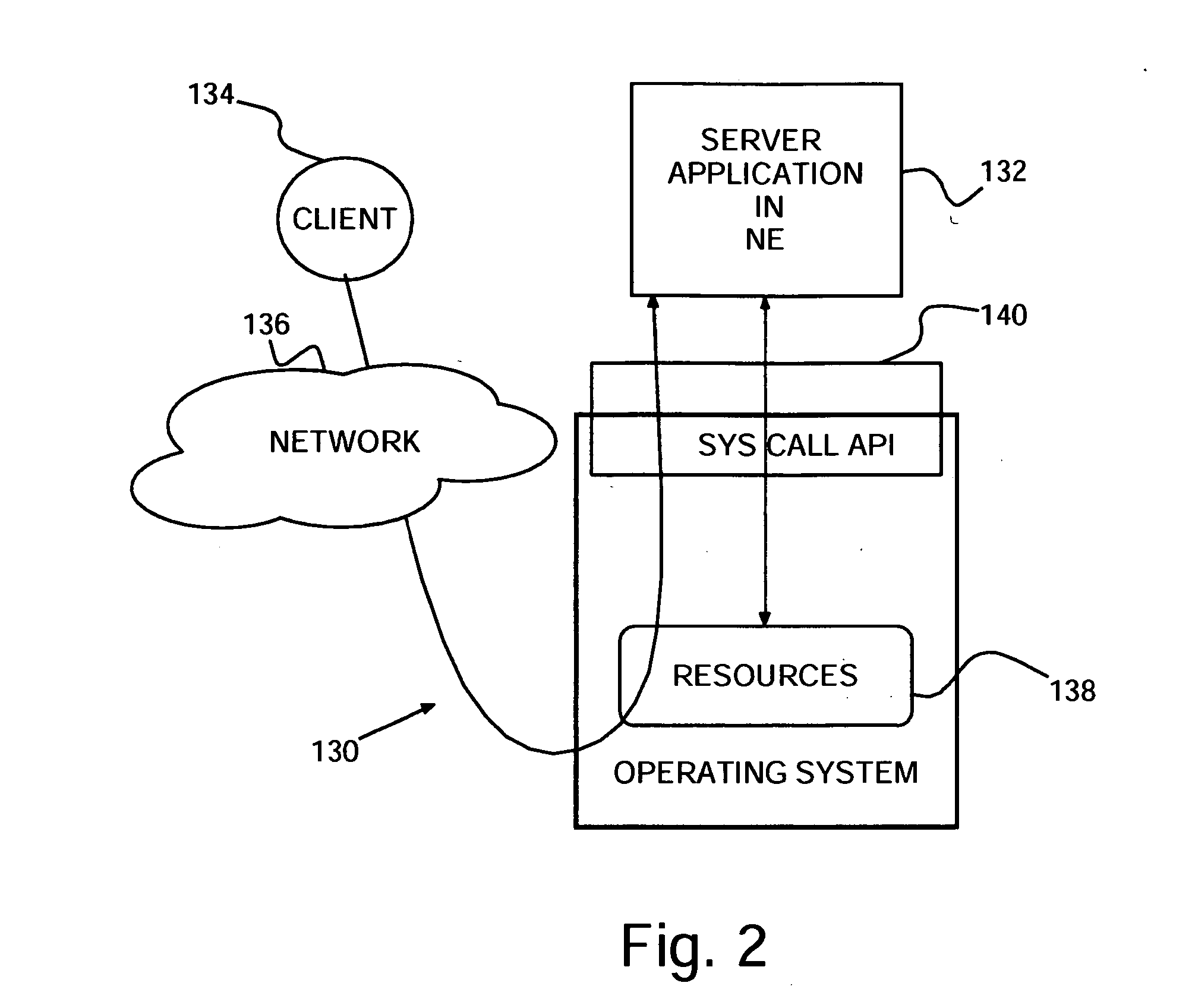
An intrusion detection system (IDS), method of protecting computers against intrusions and program product therefor. The IDS determines which applications are to run in native environment (NE) and places the remaining applications in a sandbox. Some of the applications in sandboxes may be placed in a personalized virtual environment (PVE) in the sandbox. Upon detecting an attempted attack, a dynamic honeypot may be started for an application in a sandbox and not in a PVE. A virtualized copy of system resources may be created for each application in a sandbox and provided to the corresponding application in the respective sandbox.
Owner:IBM CORP
System protection map
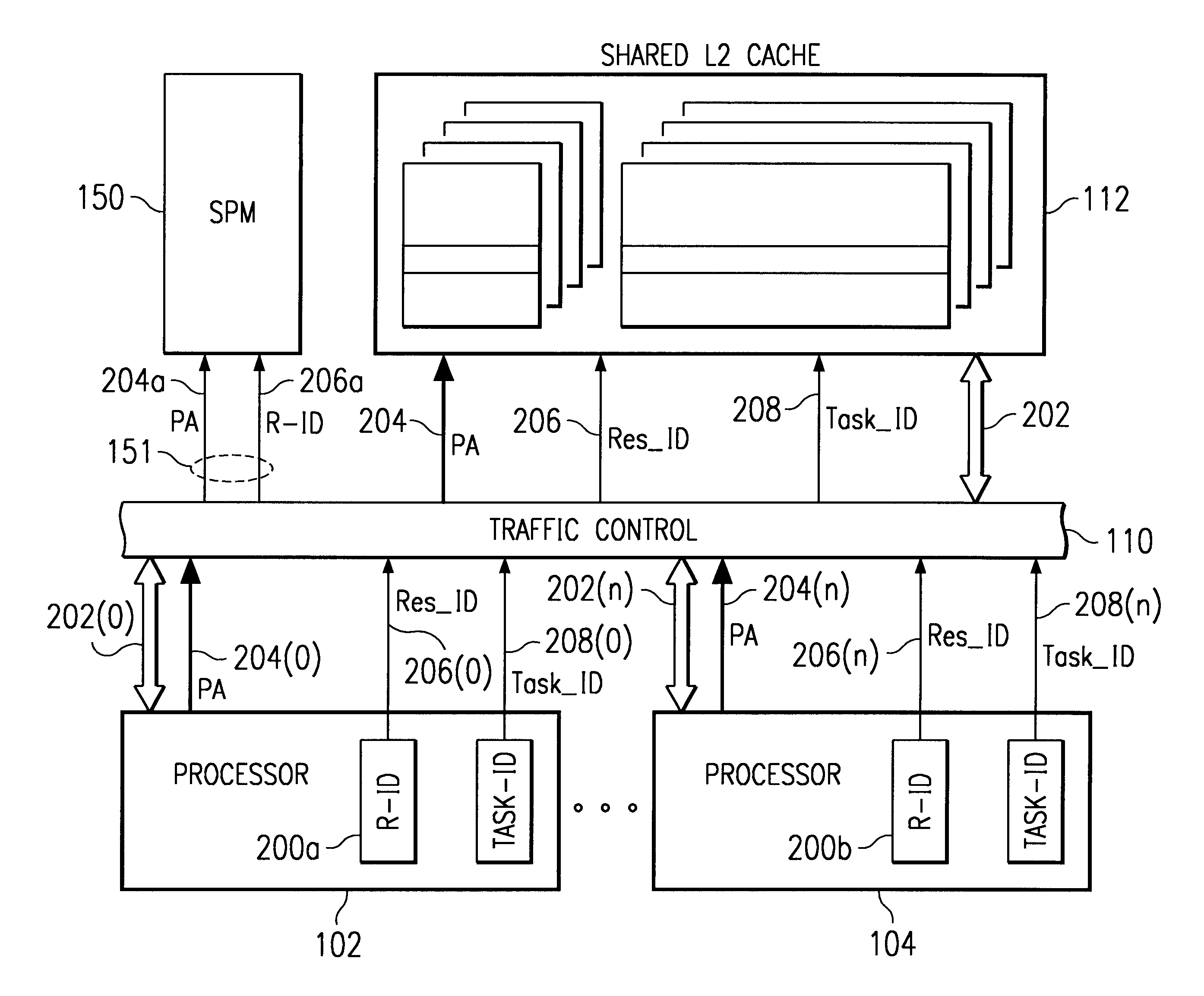
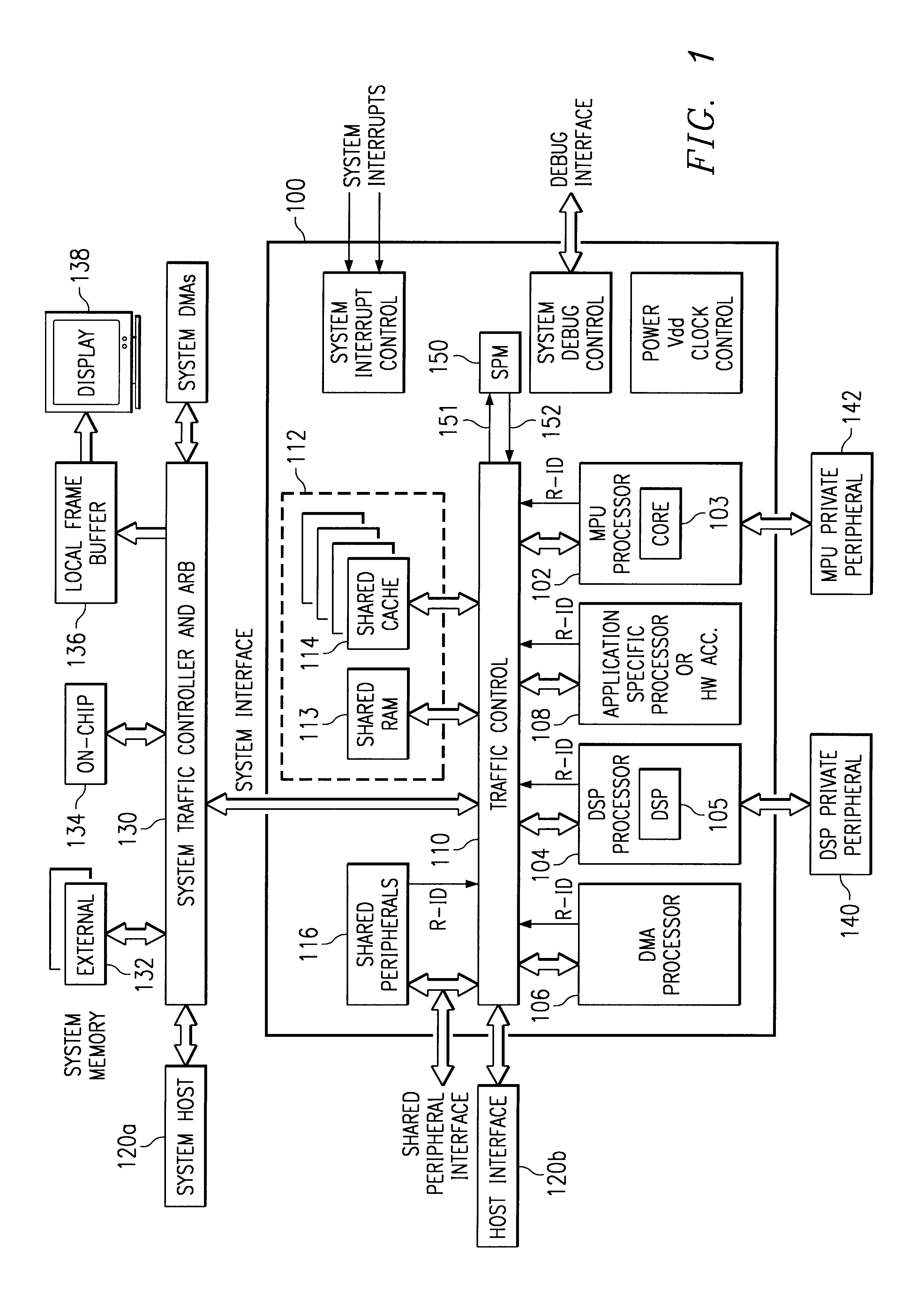
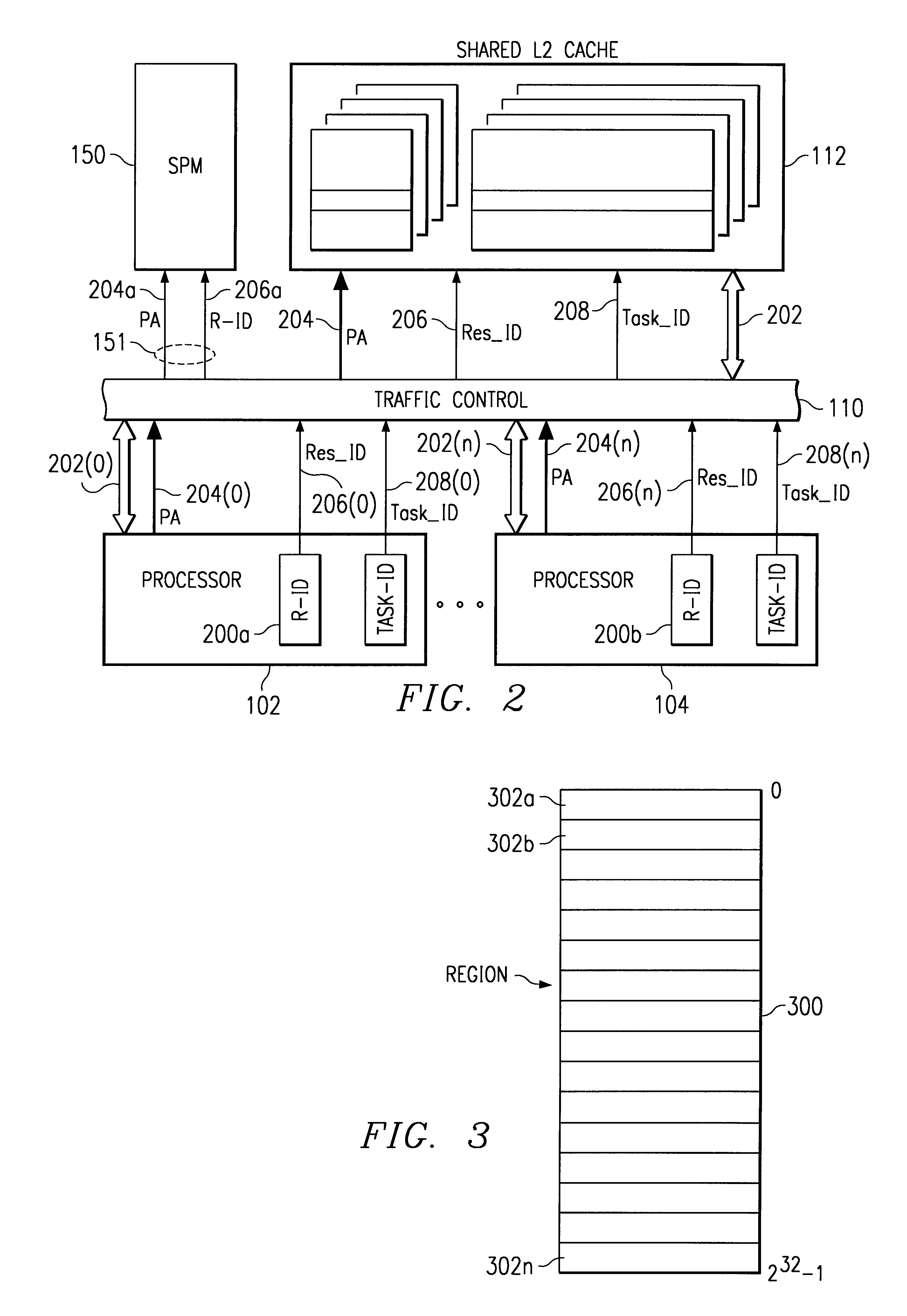
InactiveUS6775750B2Protection is in progressAvoid accessMemory adressing/allocation/relocationUnauthorized memory use protectionOperational systemSystem protection
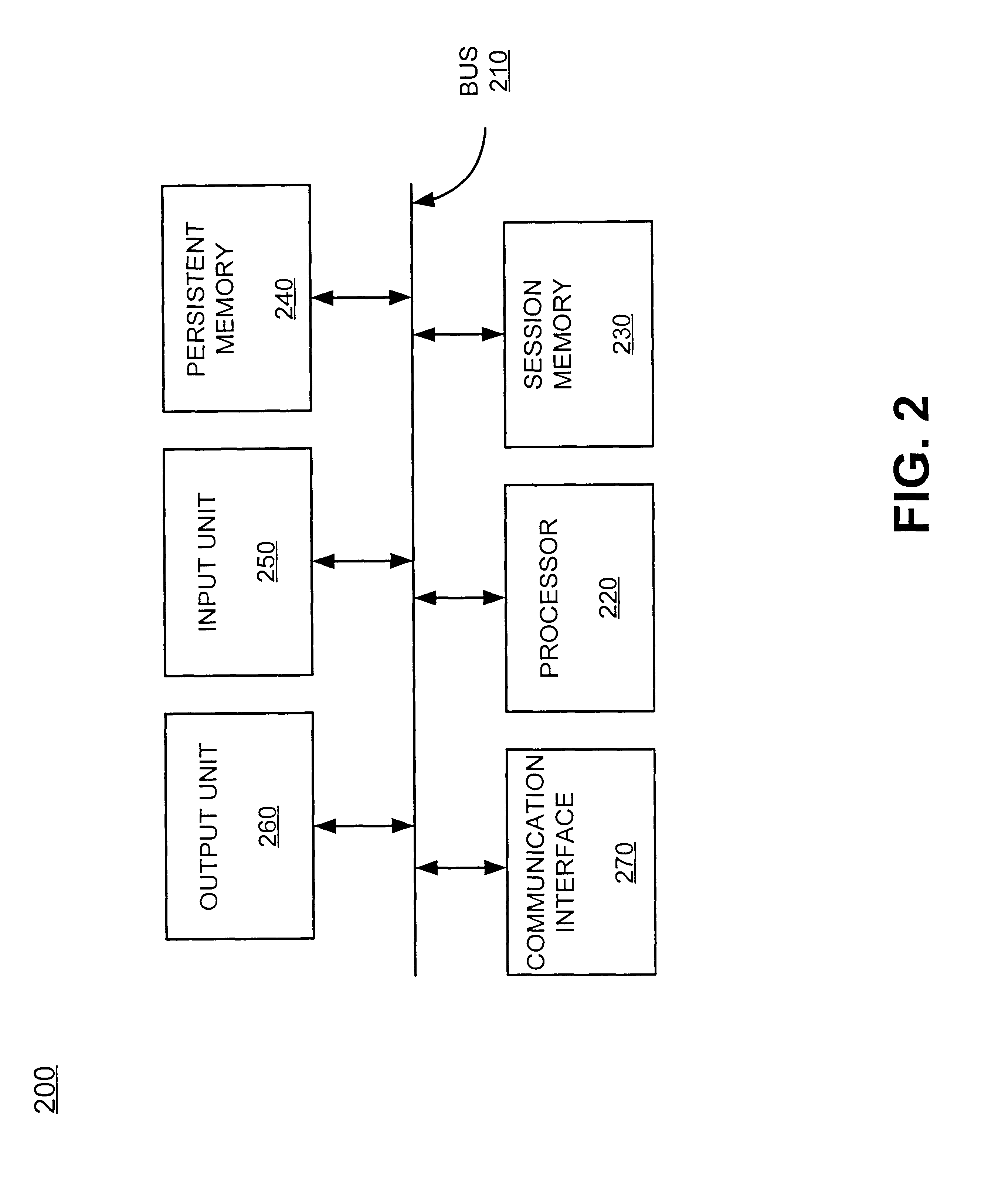
A method and apparatus is provided for operating a digital system having several processors (102, 104) and peripheral devices (106, 116) connected to a shared memory subsystem (112). Two or more of the processors execute separate operating systems. In order to control access to shared resources, a set of address space regions within an address space of the memory subsystem is defined within system protection map (SPM) (150). Resource access rights are assigned to at least a portion of the set of regions to indicate which initiator resource is allowed to access each region. Using the address provided with the access request, the region being accessed by a memory access request is identified by the SPM. During each access request, the SPM identifies the source of the request using a resource identification value (R-ID) provided with each access request and then a determination is made of whether the resource accessing the identified region has access rights for the identified region. Access to the identified region is allowed to an initiator resource only if the resource has access rights to the identified region, otherwise an error process is initiated (151).
Owner:TEXAS INSTR INC
Method and apparatus for protecting translated code in a virtual machine
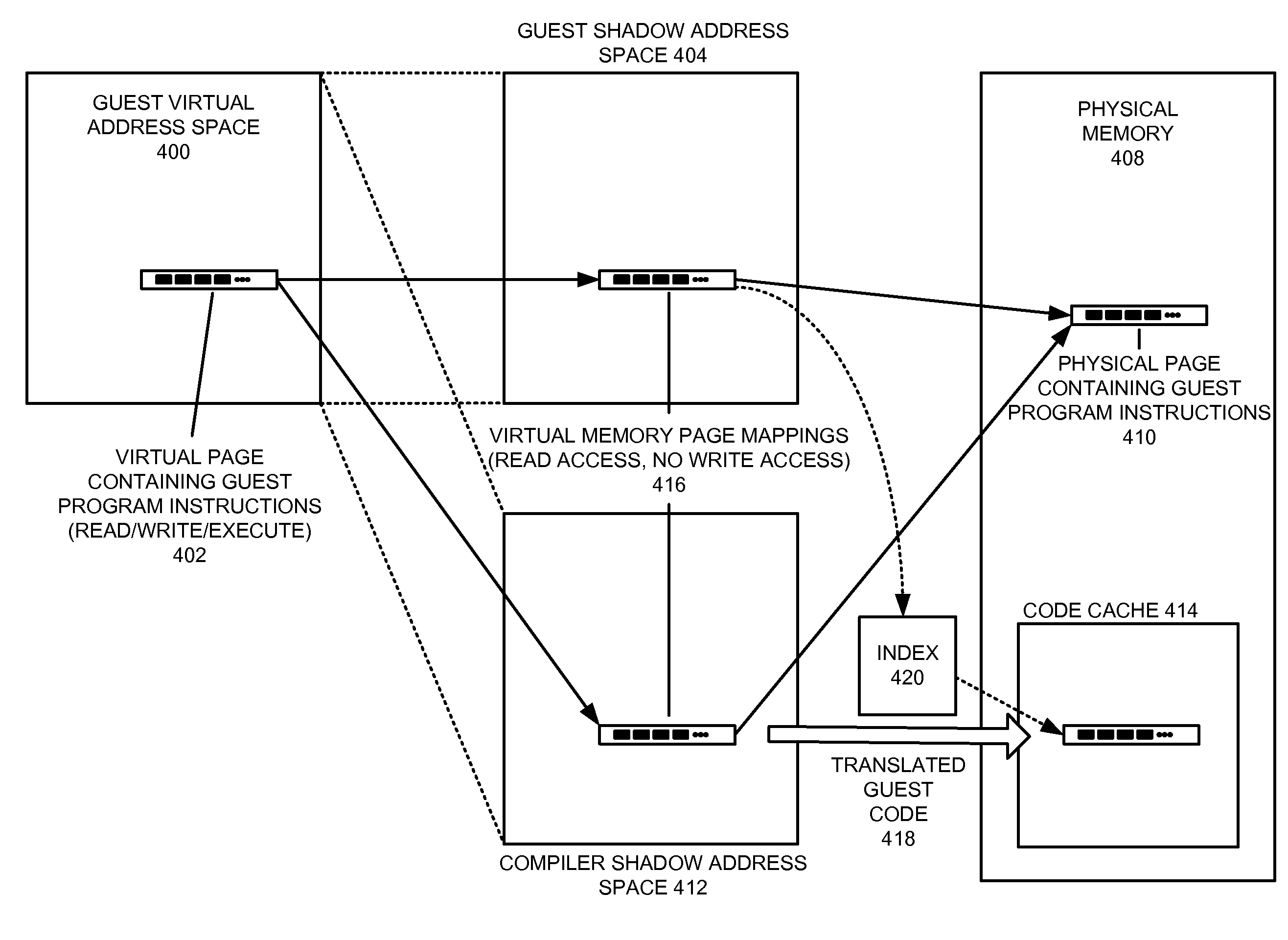
ActiveUS8799879B2Reduced overhead and checkSoftware simulation/interpretation/emulationMemory systemsDynamic compilationVirtual memory
One embodiment provides a system that protects translated guest program code in a virtual machine that supports self-modifying program code. While executing a guest program in the virtual machine, the system uses a guest shadow page table associated with the guest program and the virtual machine to map a virtual memory page for the guest program to a physical memory page on the host computing device. The system then uses a dynamic compiler to translate guest program code in the virtual memory page into translated guest program code (e.g., native program instructions for the computing device). During compilation, the dynamic compiler stores in a compiler shadow page table and the guest shadow page table information that tracks whether the guest program code in the virtual memory page has been translated. The compiler subsequently uses the information stored in the guest shadow page table to detect attempts to modify the contents of the virtual memory page. Upon detecting such an attempt, the system invalidates the translated guest program code associated with the virtual memory page.
Owner:SUN MICROSYSTEMS INC
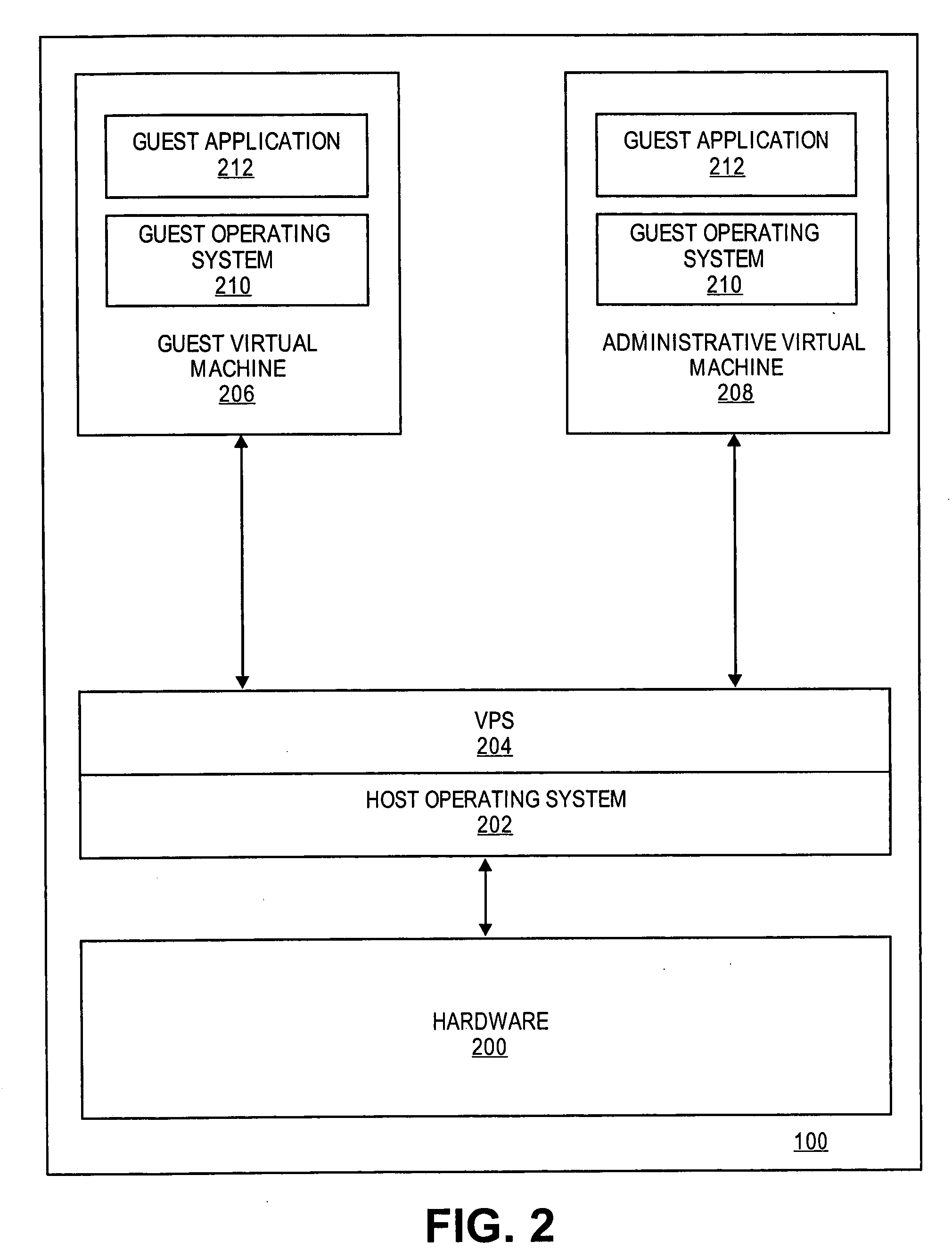
Computer system protection based on virtualization
ActiveUS20070005919A1Prevent write accessUnauthorized memory use protectionPlatform integrity maintainanceVirtualizationOperational system
Embodiments of the present invention provide a virtualization protection system (VPS) that leverages virtual machine monitor (VMM) technology. In some embodiments, a computer system contains a host operating system and one or more virtual machines that run on “guest” operating systems. The VPS makes certain areas of memory of the computer system read-only, making it essentially impossible for the virtual machines or other component to compromise the system.
Owner:RED HAT
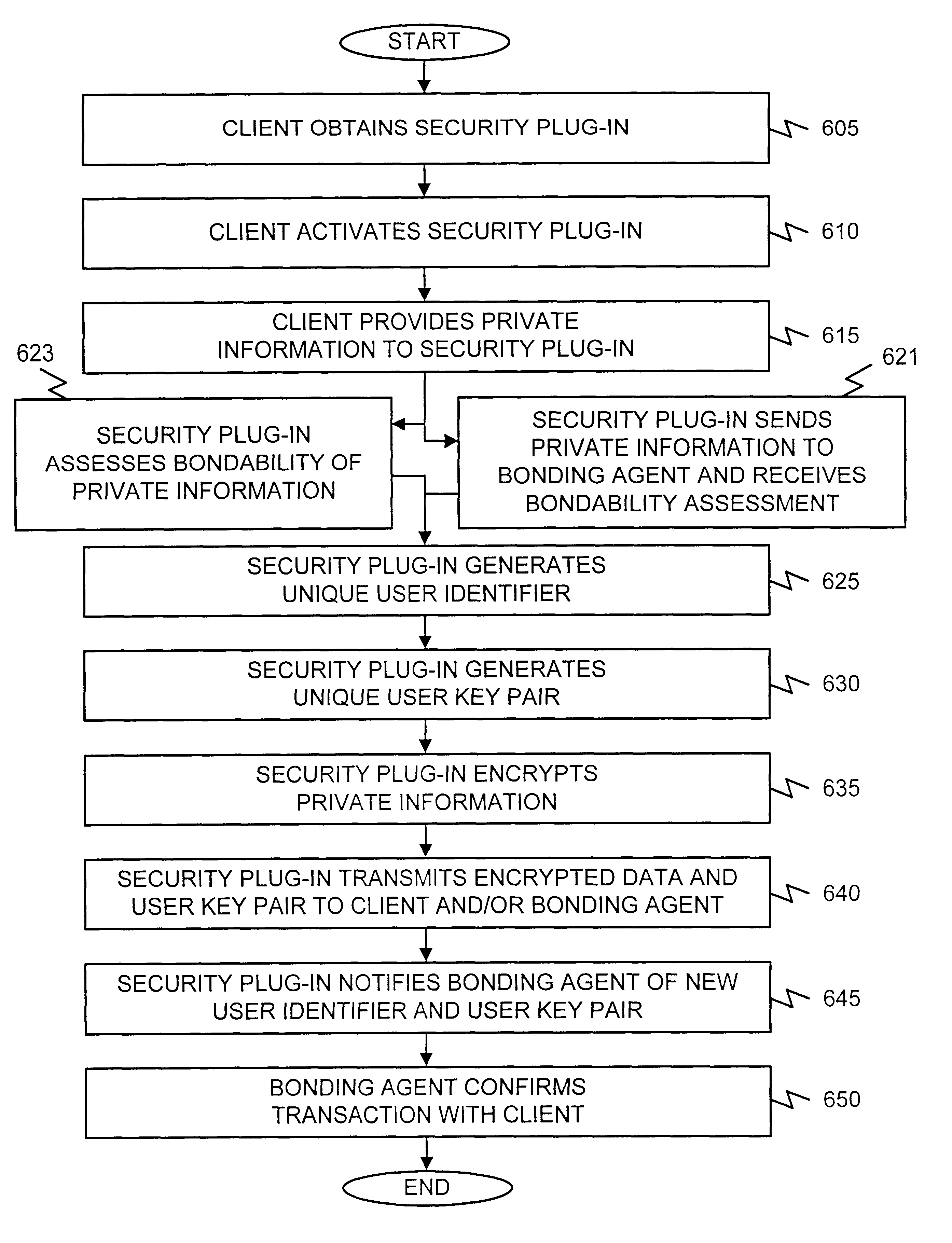
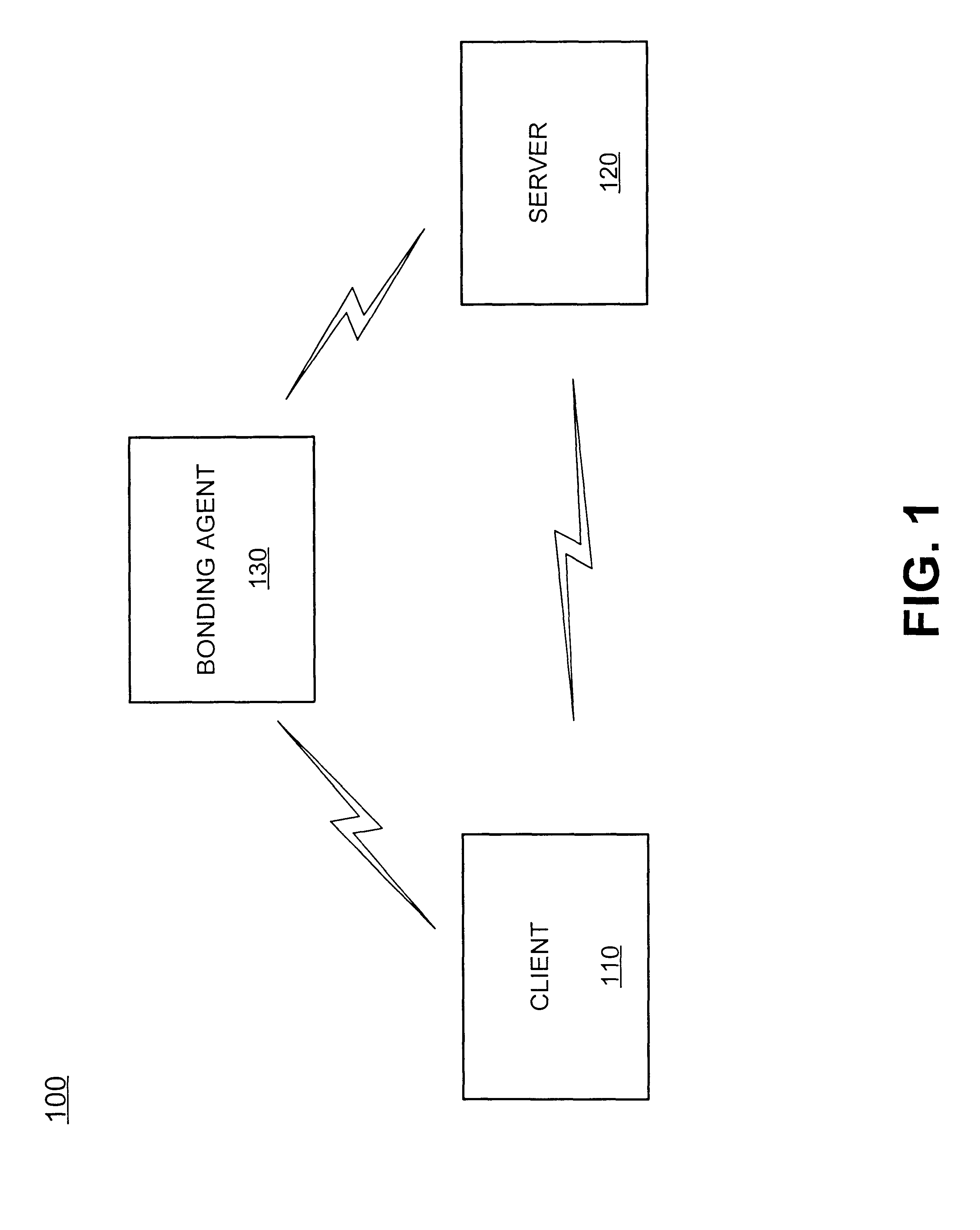
Systems and methods for protecting private information
InactiveUS6269349B1User identity/authority verificationPayment architectureSystem protectionClient-side
A system protects private information provided in an exchange between a client and a server. The system receives the private information from the client and determines whether it is of a type to which a bond may be assigned. The bond provides an indemnity to the client for misuse of the private information. The system then assigns a bond to the private information, if it is determined to be of the type to which a bond may be assigned, and provides the private information to the server under bond.
Owner:LF CAPITAL PARTNERS LLC +1
Railway hopper car discharge gate
A railroad hopper car discharge gate is assembled from unitary stacked frames that provide unimpeded flow of lading during discharge. A low-wear glide system minimizes friction between the gate panels and other components of the apparatus, and an improved sealing system protects lading from contaminants such as rain, dust and insect infestation and provides enhanced vacuum sealing for greater efficiency during vacuum discharge.
Owner:AERO TRANSPORTATION PRODS
Mobile hard disk drive free fall detection and protection
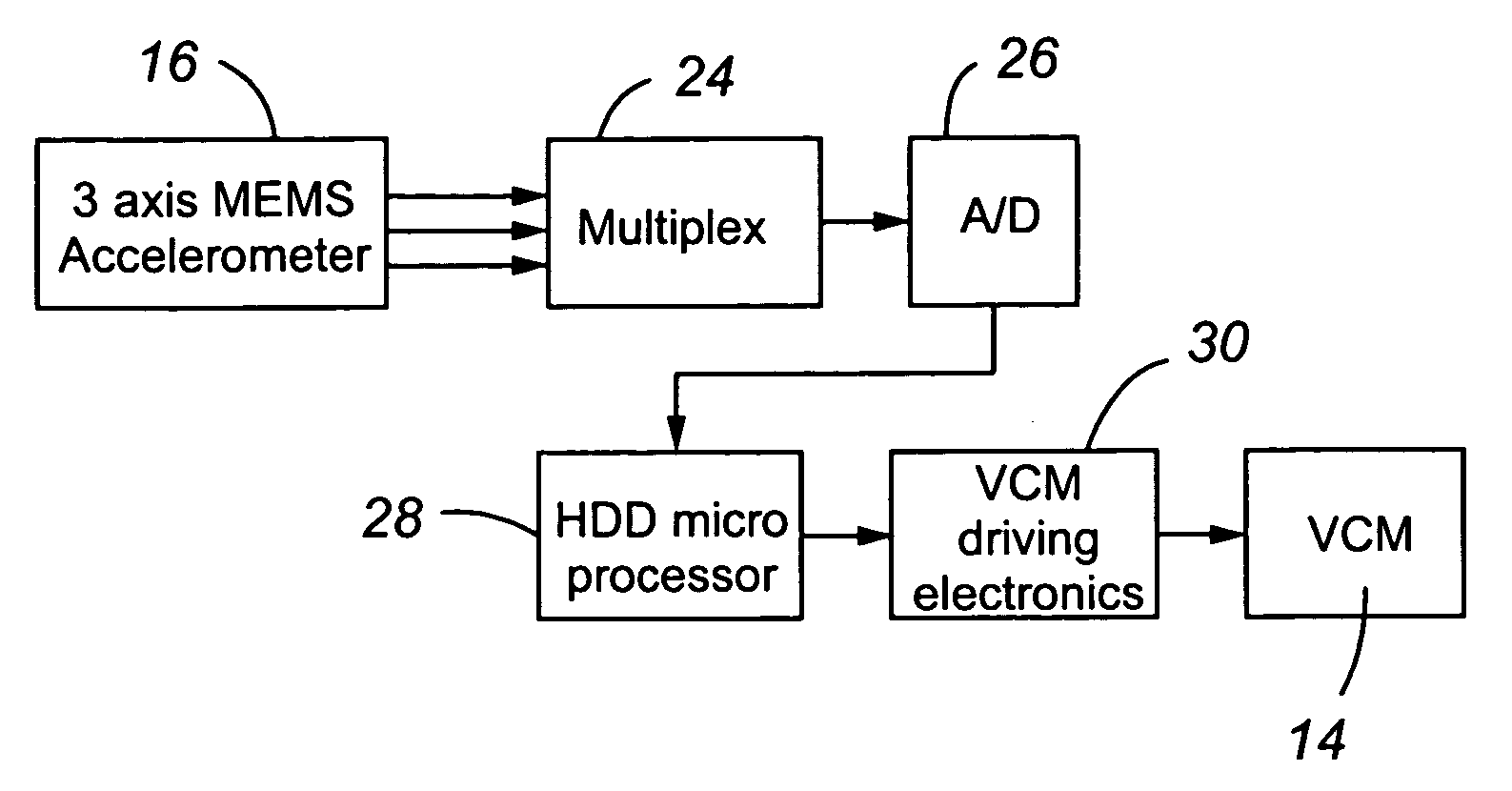
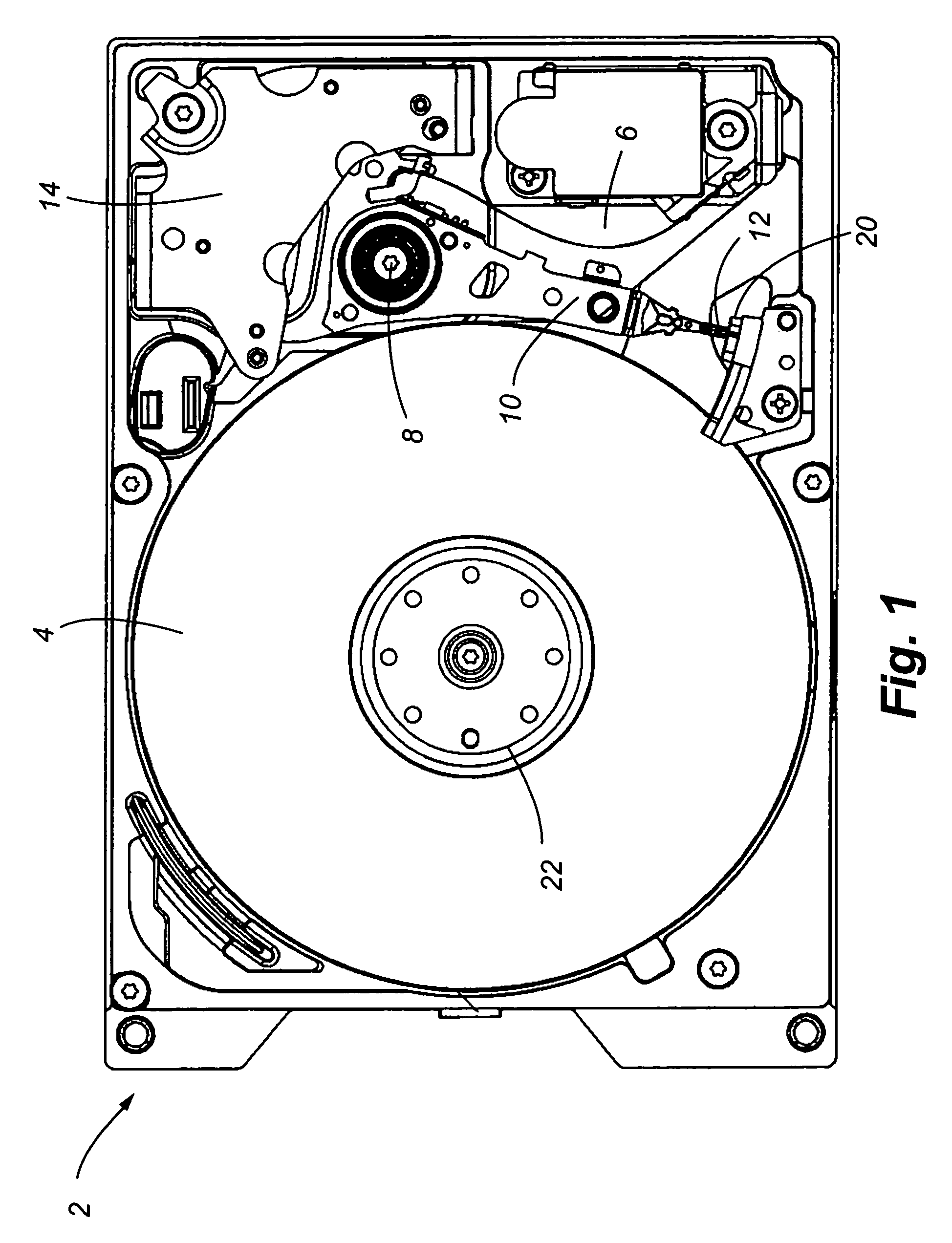
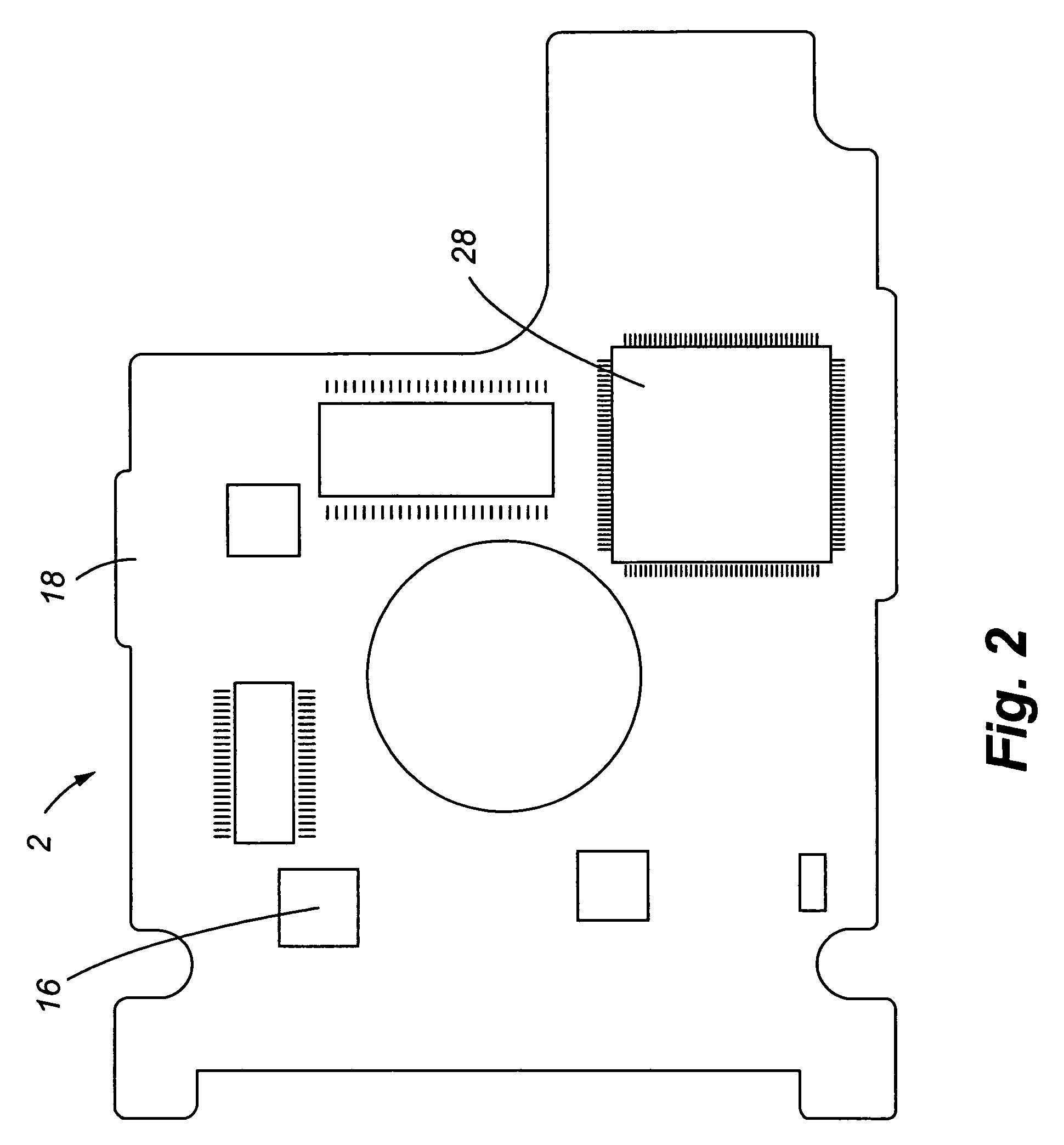
ActiveUS7369345B1Reliable and quicker and precise to measureReliable, quicker and more precise way to measure free fallDisposition/mounting of recording headsDriving/moving recording headsFree fallingHard disc drive
A system provided for protecting a disk drive from impact damages. More specifically, a disk drive is provided that includes an accelerometer interconnected to a printed circuit board that detects free fall of the disk drive. In addition, the velocity of spinning disks of the disk drive is also monitored to assess changes in velocity thereof that may indicate the presence of a tumbling condition. Furthermore, the change in acceleration measured by the accelerometer is monitored to prevent false indications of free fall due to common vibrations. Thus an enhanced system is provided that protects disk drives from the effect of free falls under a wide variety of conditions and allowing for drops from shorter distances to be identified.
Owner:SEAGATE TECH LLC +1
Method and a system for establishing mechanical and multiple-fluid couplings between a tool and a tool-carrier frame
InactiveUS6899509B1Actuation can be preventedReduce riskMechanical machines/dredgersLifting devicesFluid couplingClassical mechanics
The invention concerns a system wherein the tool-bearing frame (1) and the tool (2) are each equipped with a multiple fluidic connection box, for example hydraulic provided with complementary male-female connecting members: each of said boxes is provided with a mobile and retractable protective cover, which normally covers the connecting members contained in said box. Said covers are arranged such that, in a first phase, the proper positioning of the tool-bearing-frame opposite the tool automatically causes the covers to retract, directly matching the fluidic connection members of the two boxes, so as to enable subsequently, in the second and third phases, the mechanical followed by the fluidic connection of the tool-bearing frame and the tool. The system protects the connecting members from the outside environment, while enabling easy and secure connection of the tool with the tool-bearing frame, without any risk of deterioration of the fluidic connectors.
Owner:MAILLEUX
Health and safety system for a table saw
InactiveUS20100307307A1Reduces long-term riskEasy accessMetal sawing accessoriesGuide fencesInjury causeCollection system
An improved health and safety system for a table saw includes one or more of: a blade guard that protects the operator from the saw blade, and contains and collects sawdust; a proximity detector and emergency saw motor braking means for use in connection with such blade guard; an anti-kickback device for use in connection with such blade guard, a rip fence adapter for use in connection with such a blade guard, and hoses and fittings to connect the dust containment and collection system of said blade guard to a shop dust collection blower or vacuum system. The system protects the saw operator from potential traumatic injury to a hand, and from ingesting potentially carcinogenic sawdust.
Owner:BUTLER DAVID J
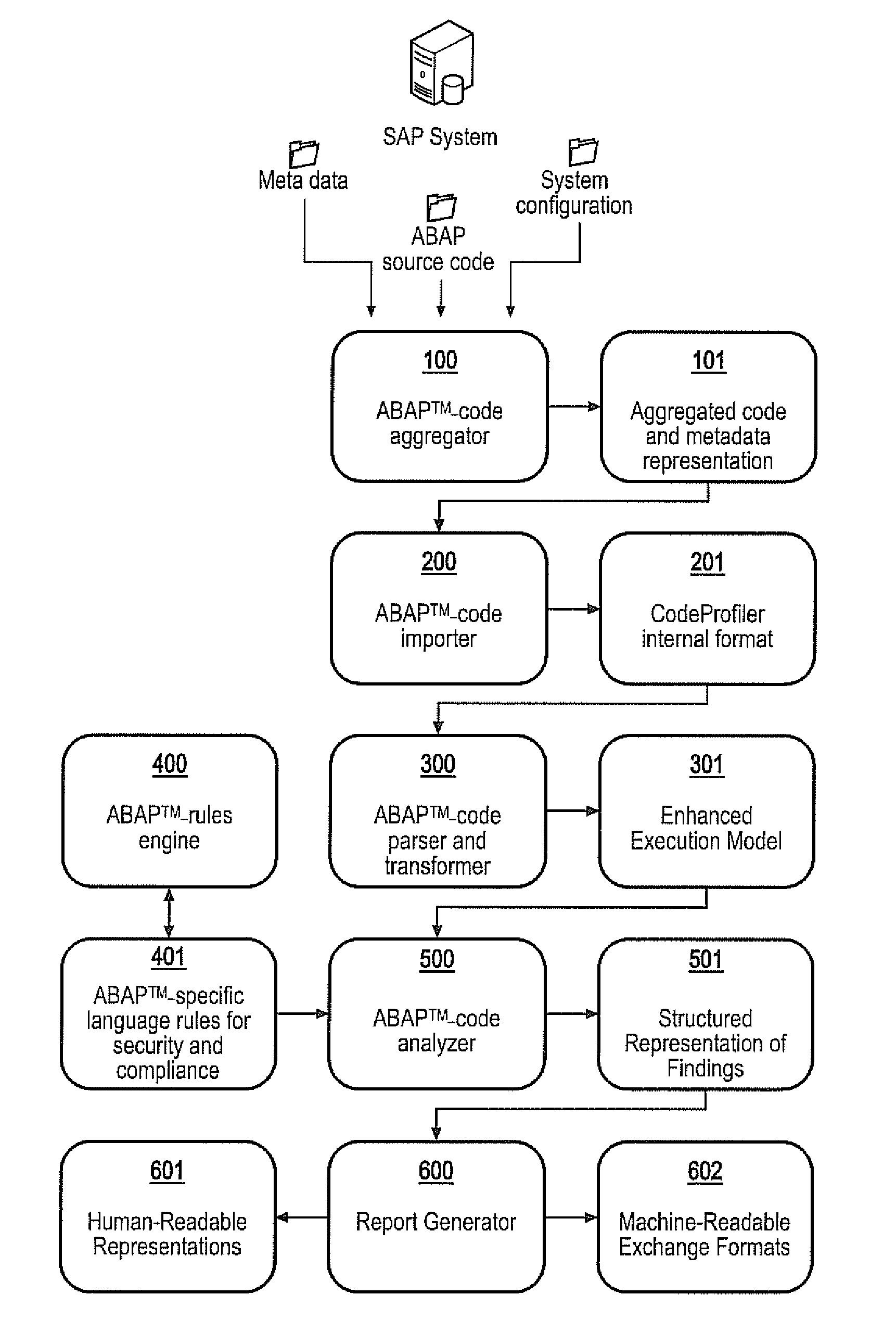
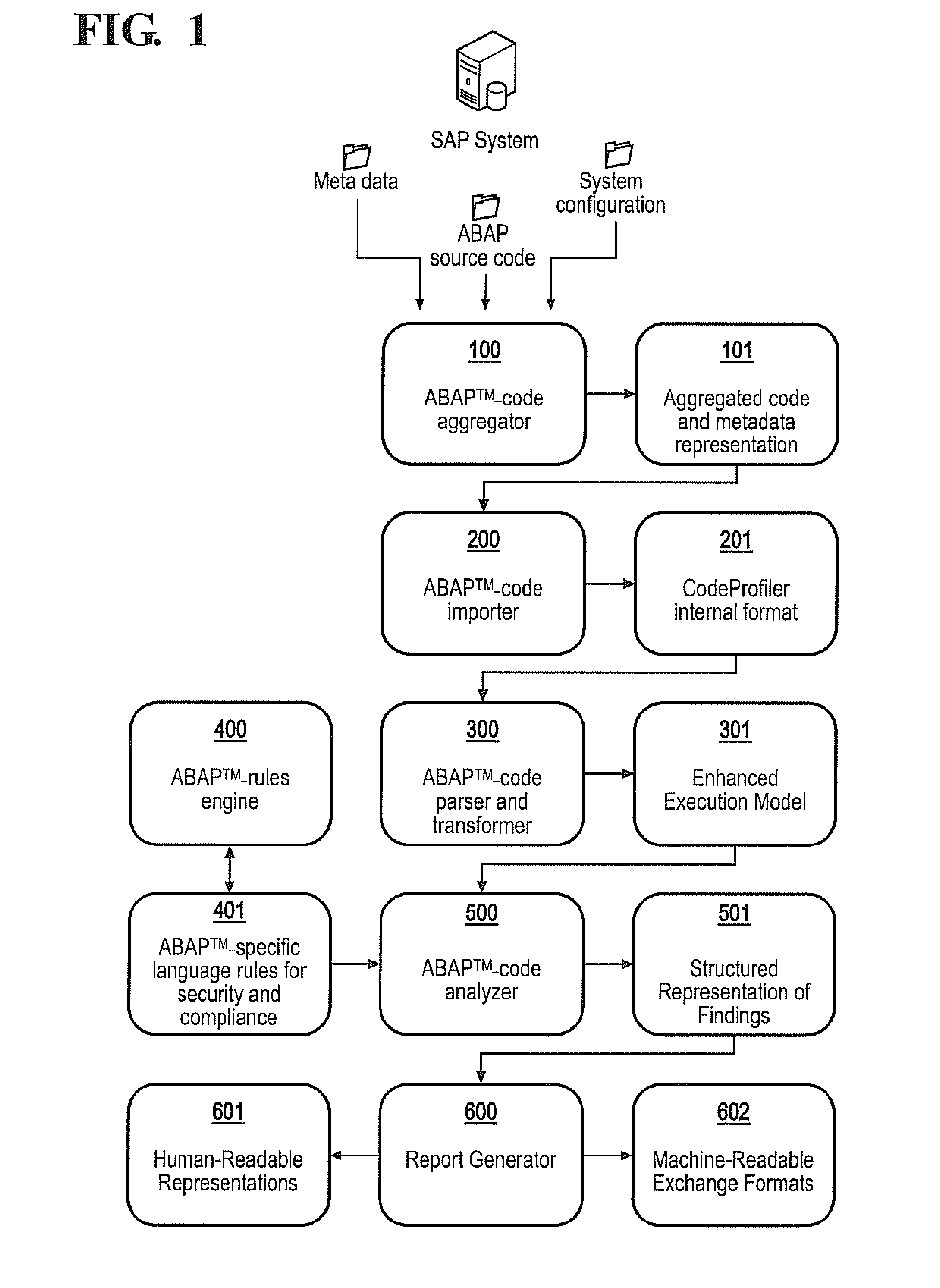
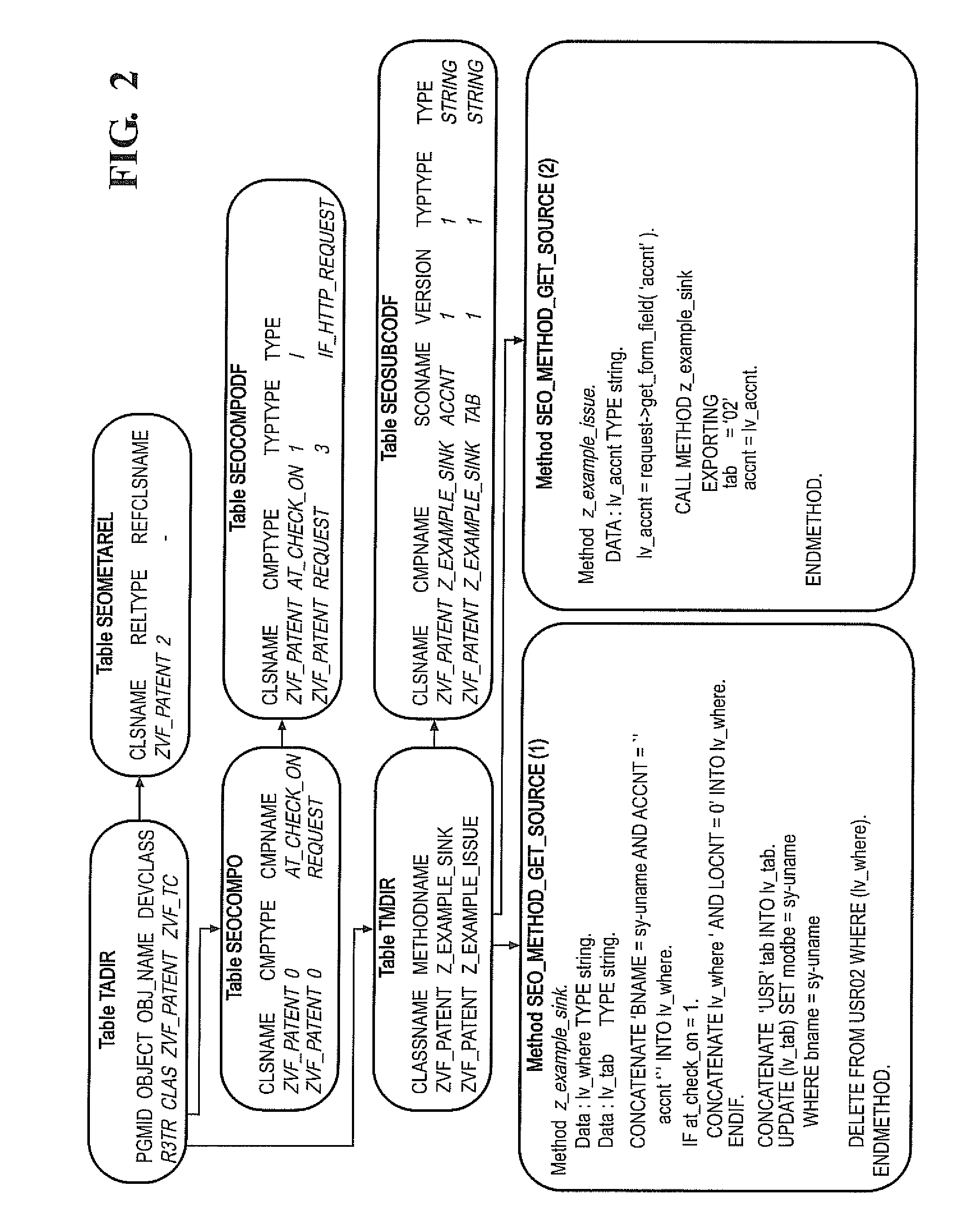
APPARATUS AND METHOD FOR DETECTING, PRIORITIZING AND FIXING SECURITY DEFECTS AND COMPLIANCE VIOLATIONS IN SAP® ABAPtm CODE
A static code analysis (SCA) tool, apparatus and method detects, prioritizes and fixes security defects and compliance violations in SAP® ABAP™ code. The code, meta information and computer system configuration settings are transformed into an interchangeable format, and parsed into an execution model. A rules engine is applied to the execution model to identify security and compliance violations. The rules engine may include information about critical database tables and critical SAP standard functions, and the step of applying the rules engine to the execution model may include the calculation of specific business risks or whether a technical defect has a business-relevant impact. In particular, an asset flow analysis may be used to determine whether critical business data is no longer protected by the computer system. Such critical business data may include credit or debit card numbers, financial data or personal data.
Owner:VIRTUAL FORGE
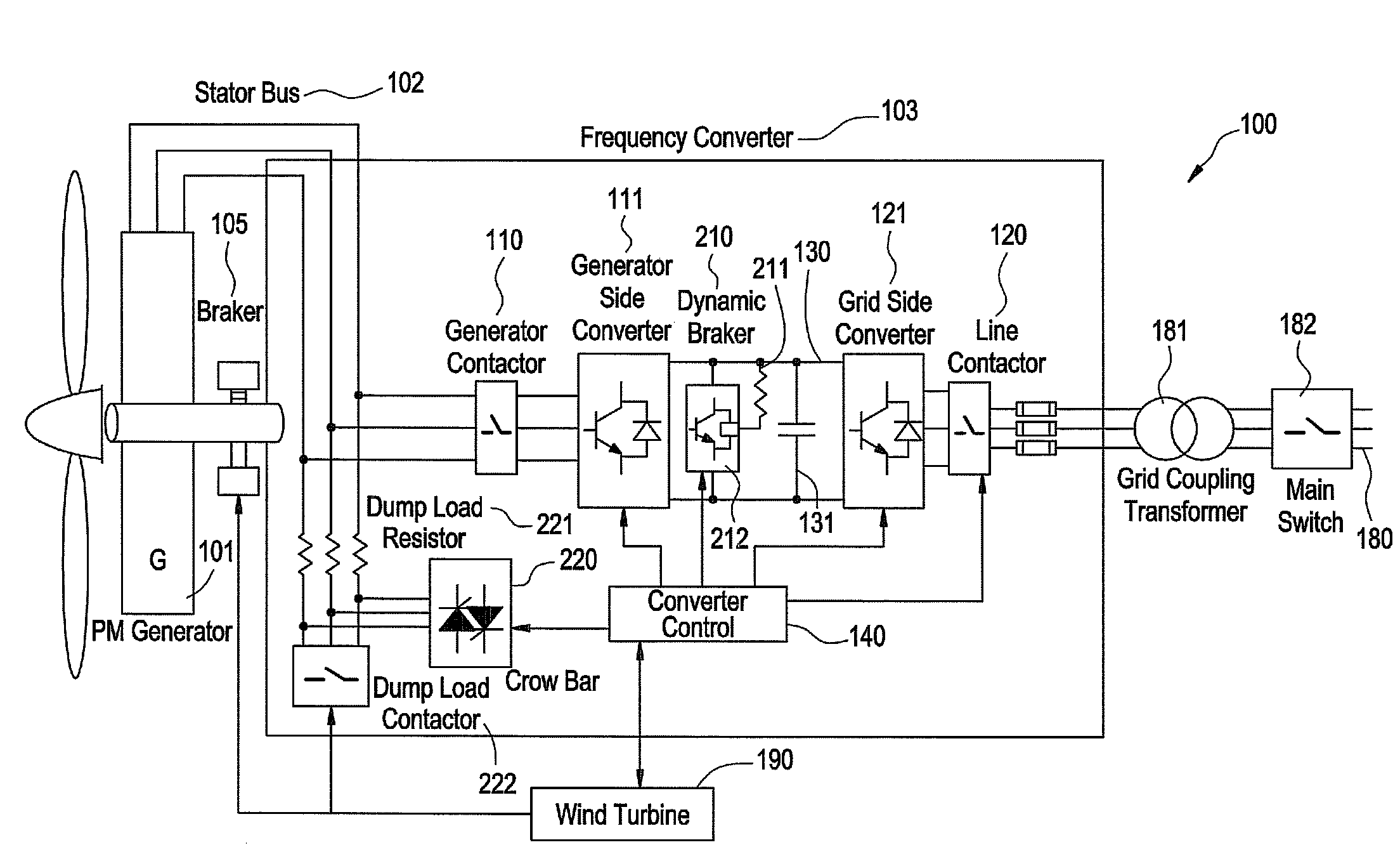
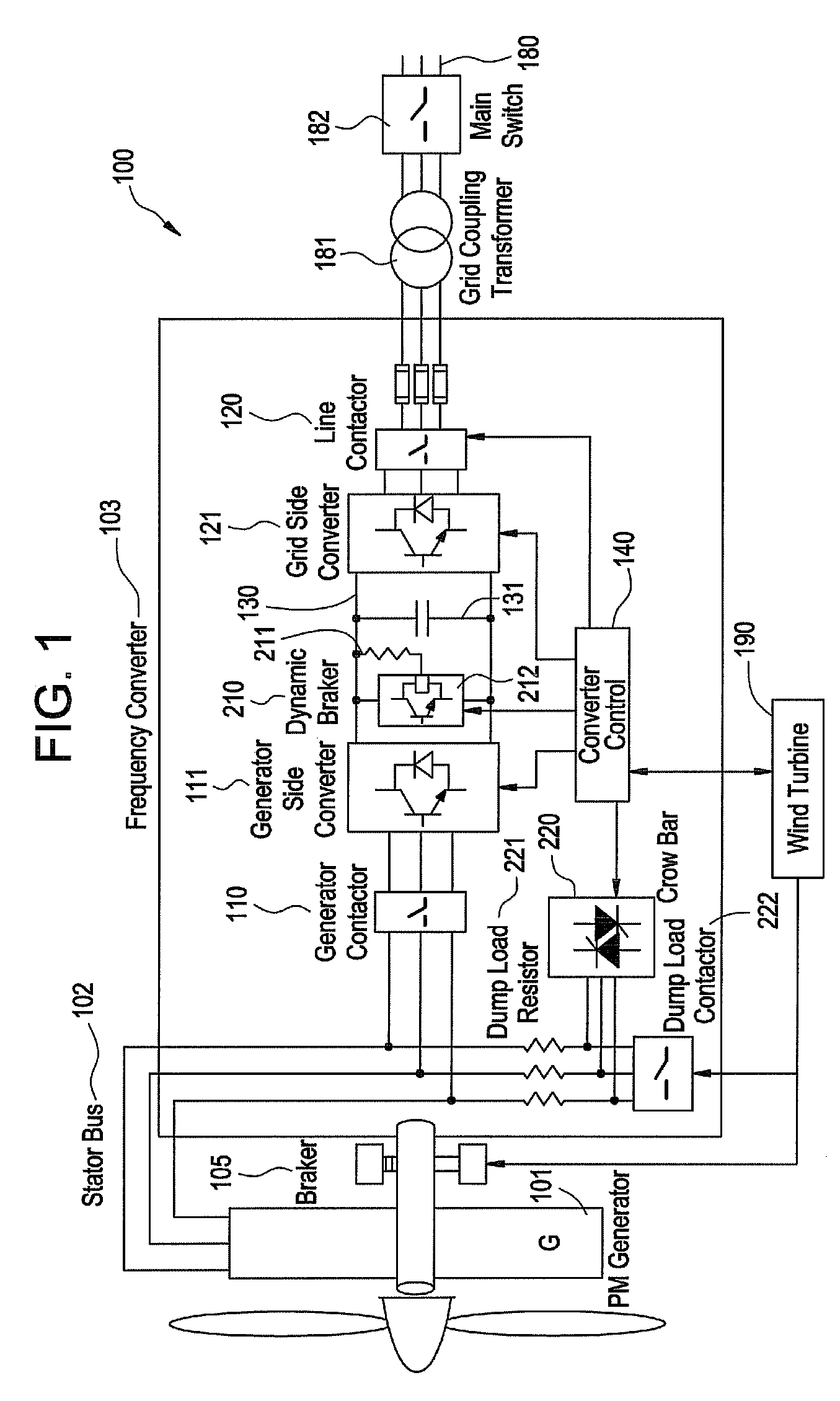
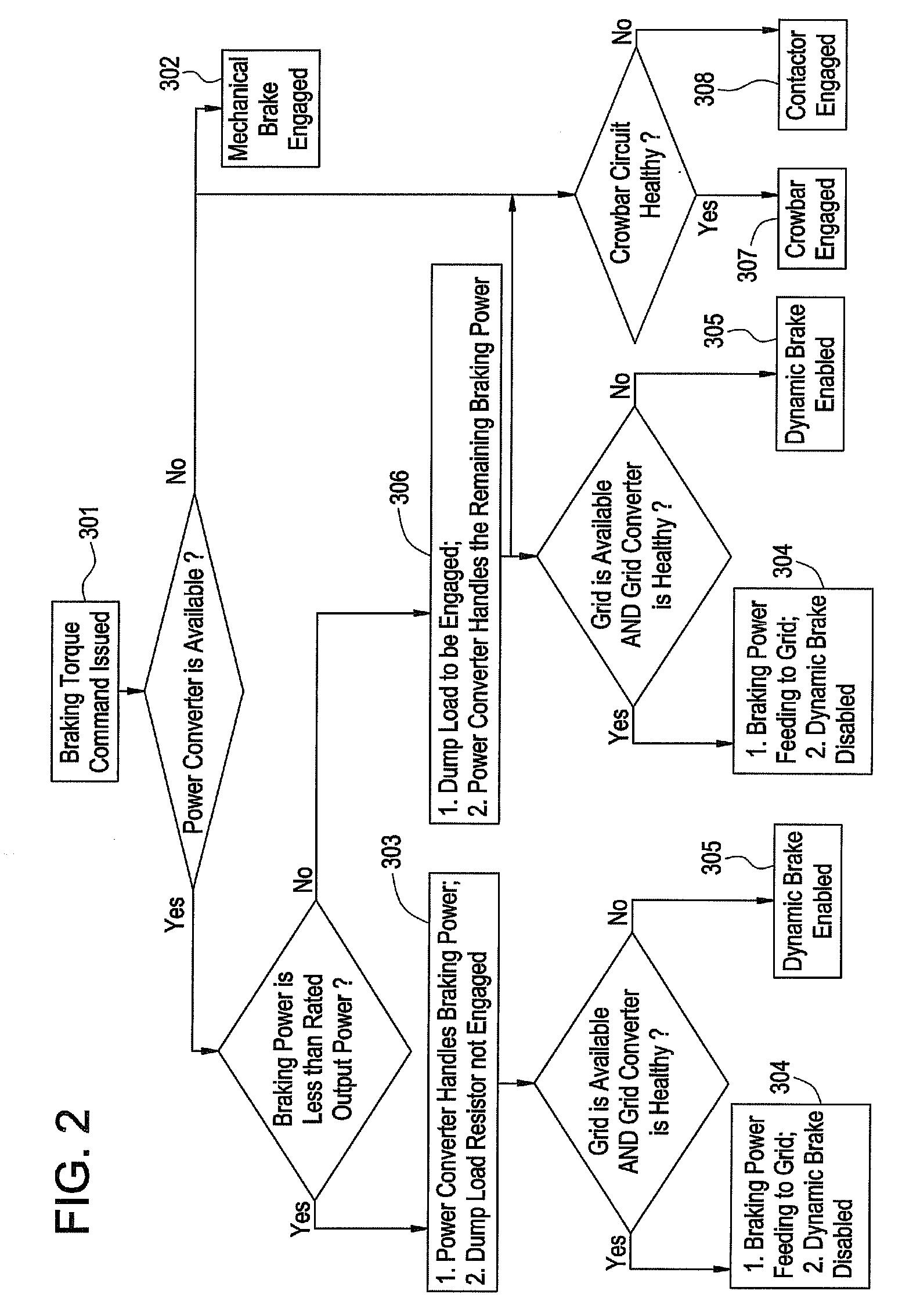
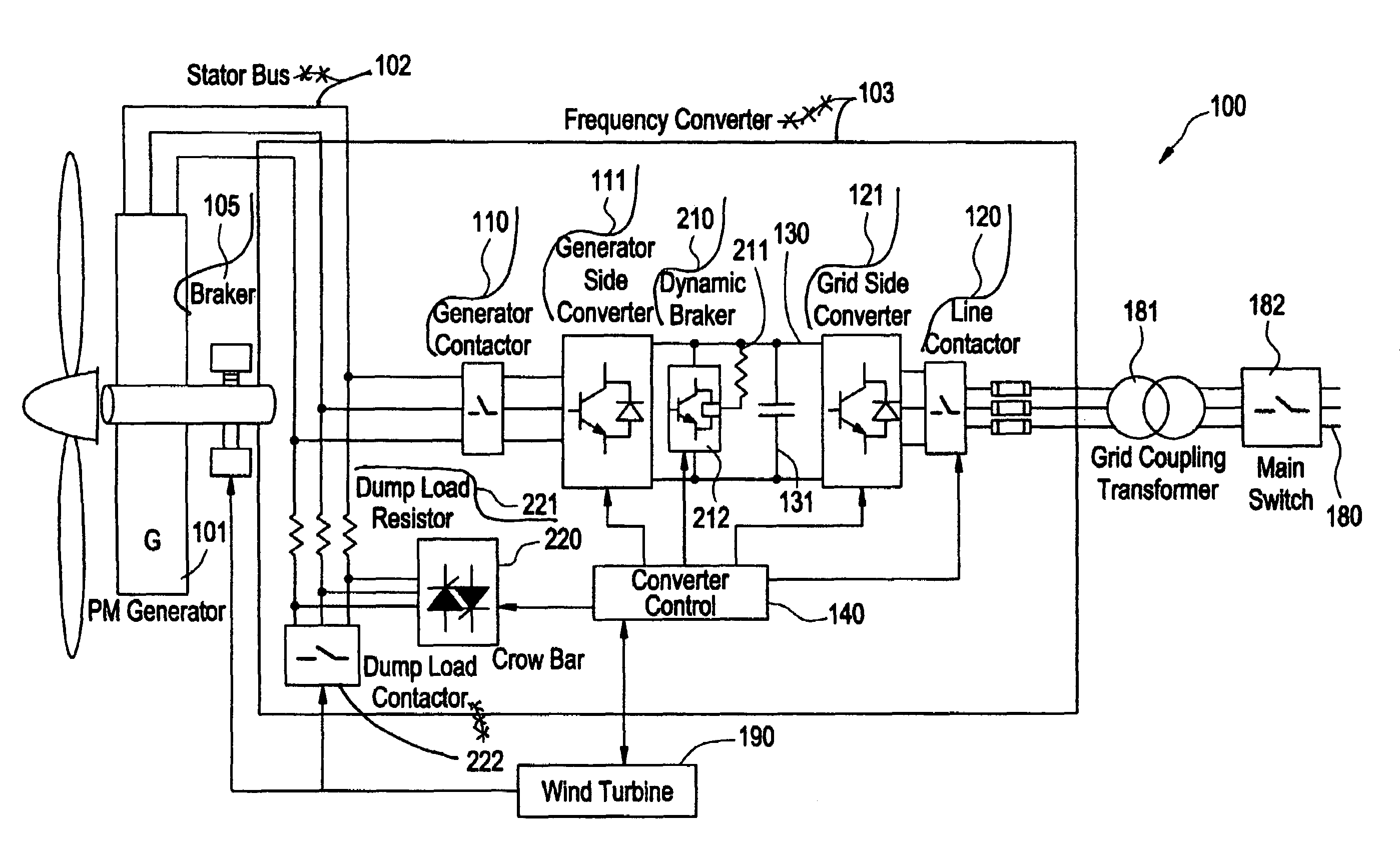
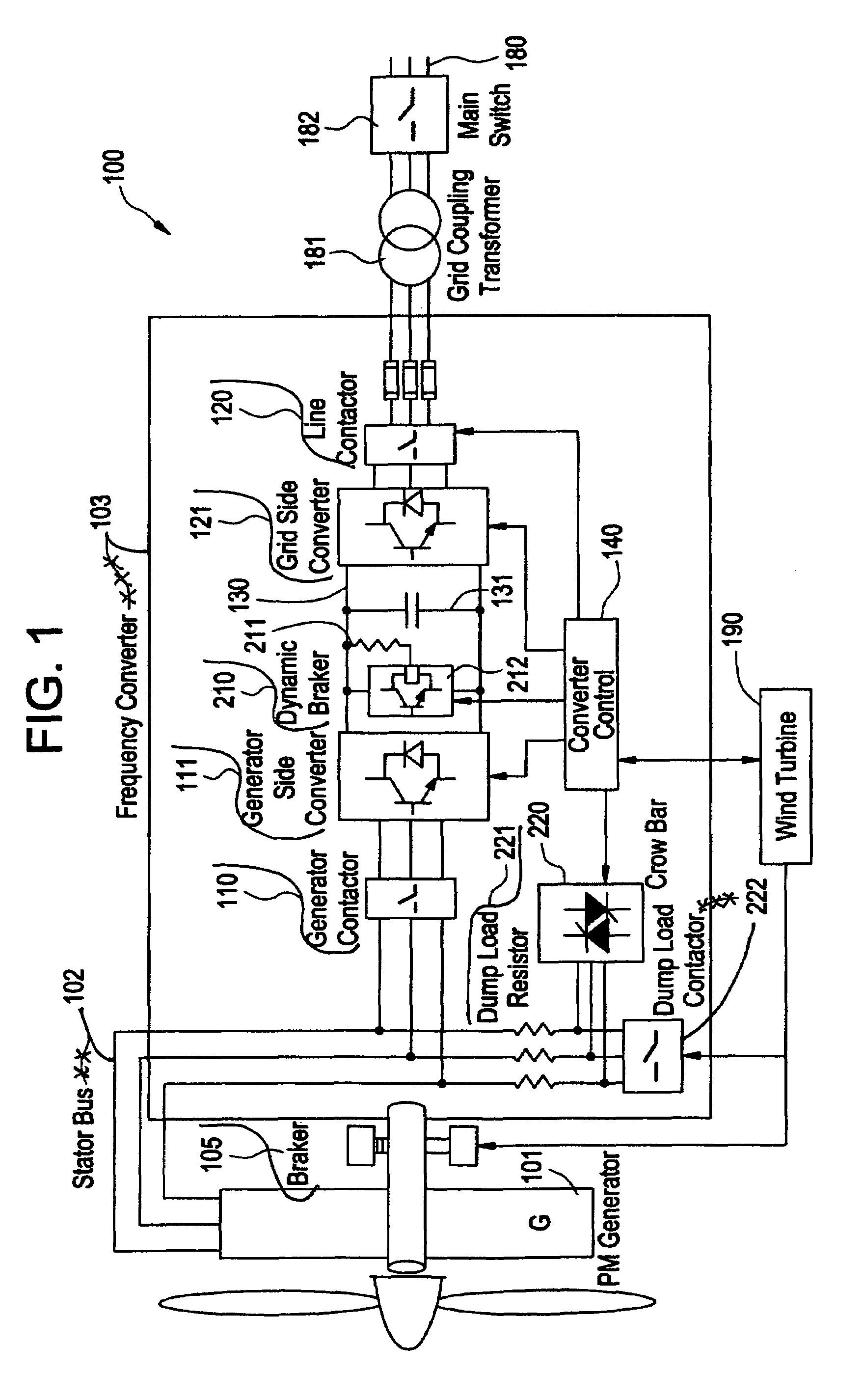
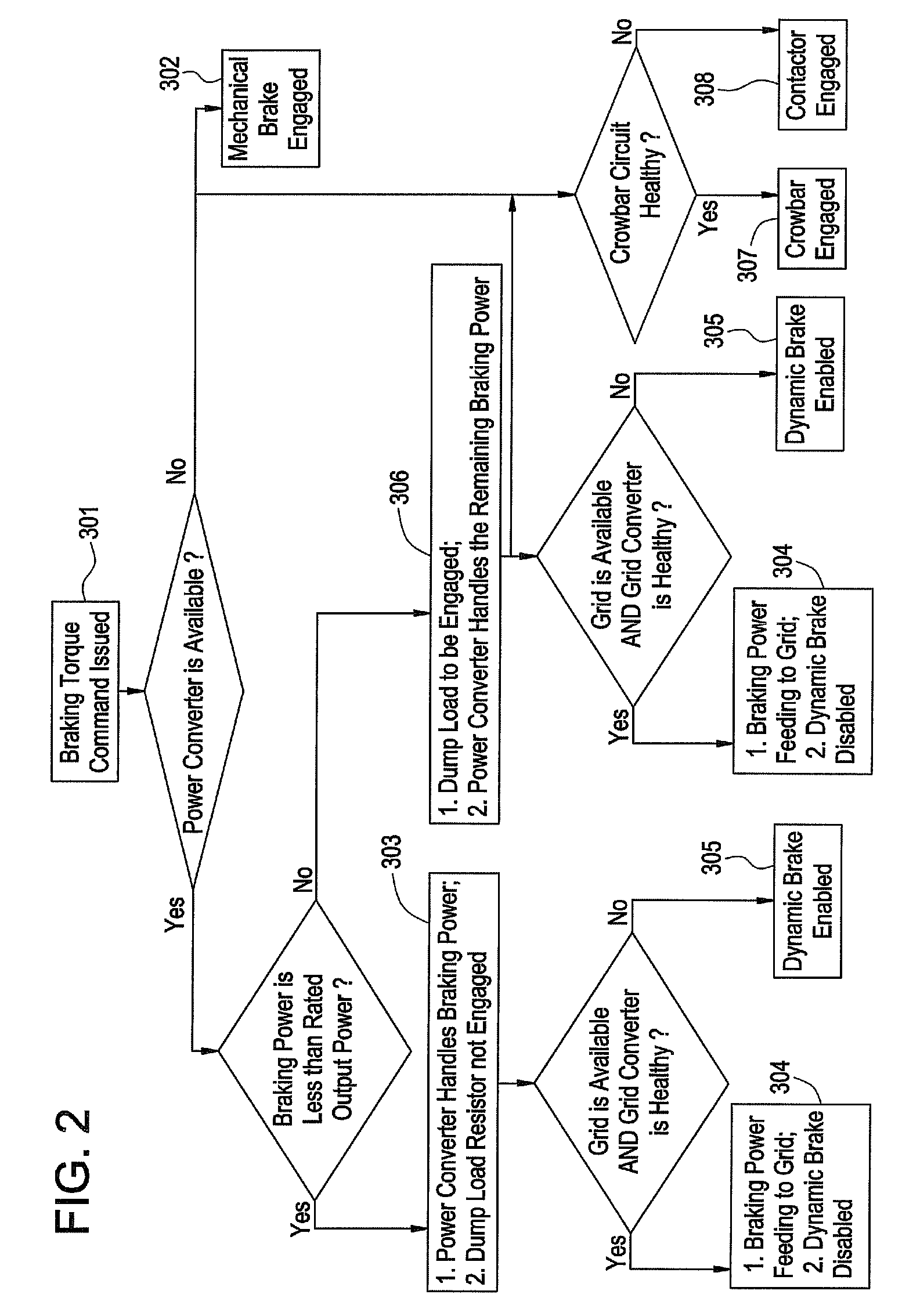
Redundant electrical brake and protection system for electric generators
ActiveUS20070279815A1Consume energySynchronous motors startersWind motor controlElectricityEngineering
An apparatus for electric braking and system protection for an electric generator includes a dynamic brake and a crowbar circuit designed for cooperation with power converters to dump power upon command. The dynamic brake includes at least one resistor and the crowbar circuit includes another at least one resistor for dissipating power from the electric generator. Methods for use of the electric braking and system protection calls for shunting the power to at least one of the dynamic brake, the crowbar circuit and the generator side power converter.
Owner:GENERAL ELECTRIC CO
Method and apparatus for downhole artificial lift system protection
A fluid conditioning system designed to be installed between the well perforation and the intake of a pump used to effect artificial lift is used to filter and chemically treat production fluids. The fluid conditioning system is an apparatus that provides scale inhibitors and / or other chemical treatments into the production stream. In some embodiments, the fluid conditioning system may be a part of the production stream filter wherein the filtering material is comprised of a porous medium that contains and supports the treatment chemical. In other embodiments, the chemical treatment may be accomplished by the gradual dissolution of a solid phase chemical. The treating chemical may be recharged or replenished by various downhole reservoirs or feeding means. In yet other embodiments, the treating chemical may be replenished from the surface by means of a capillary tube. In certain other embodiments, the apparatus may be retrievable from the surface thereby permitting recharge or replenishment of the chemical in the apparatus on an as-needed basis. The filtration apparatus may incorporate a by-pass valve that allows fluid to by-pass the filter as sand or other particulate matter fills up or blocks the filter.
Owner:OILFIELD EQUIP DEVMENT CENT
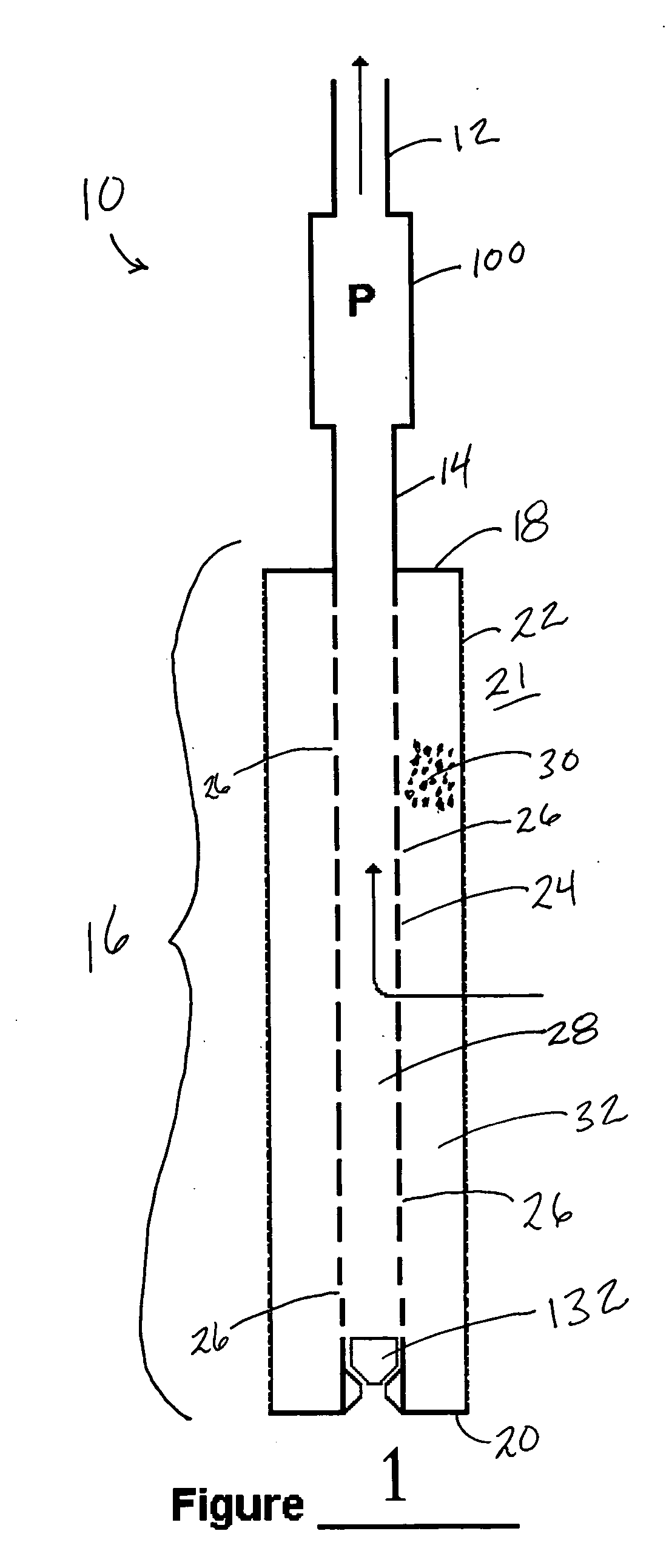
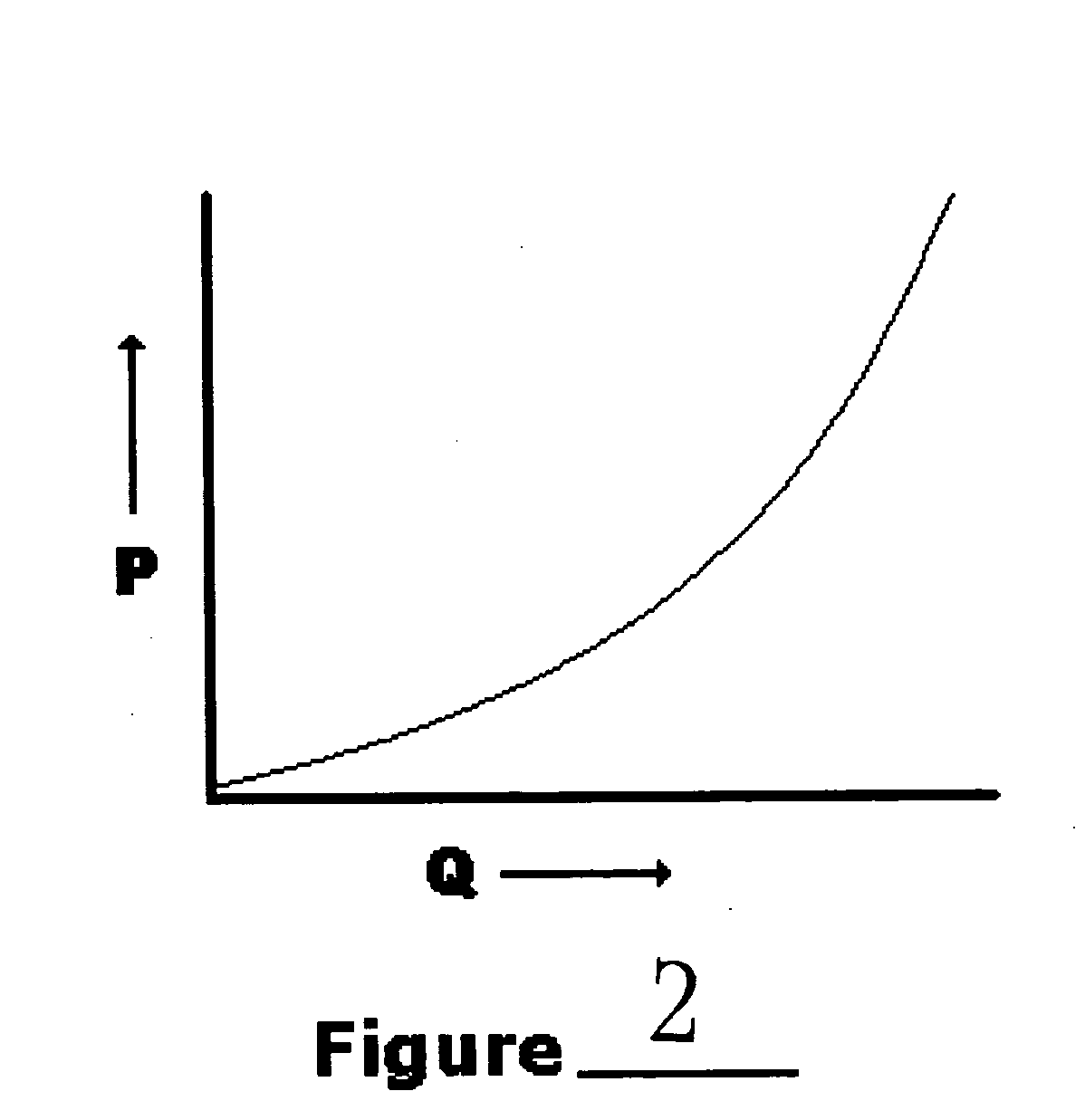
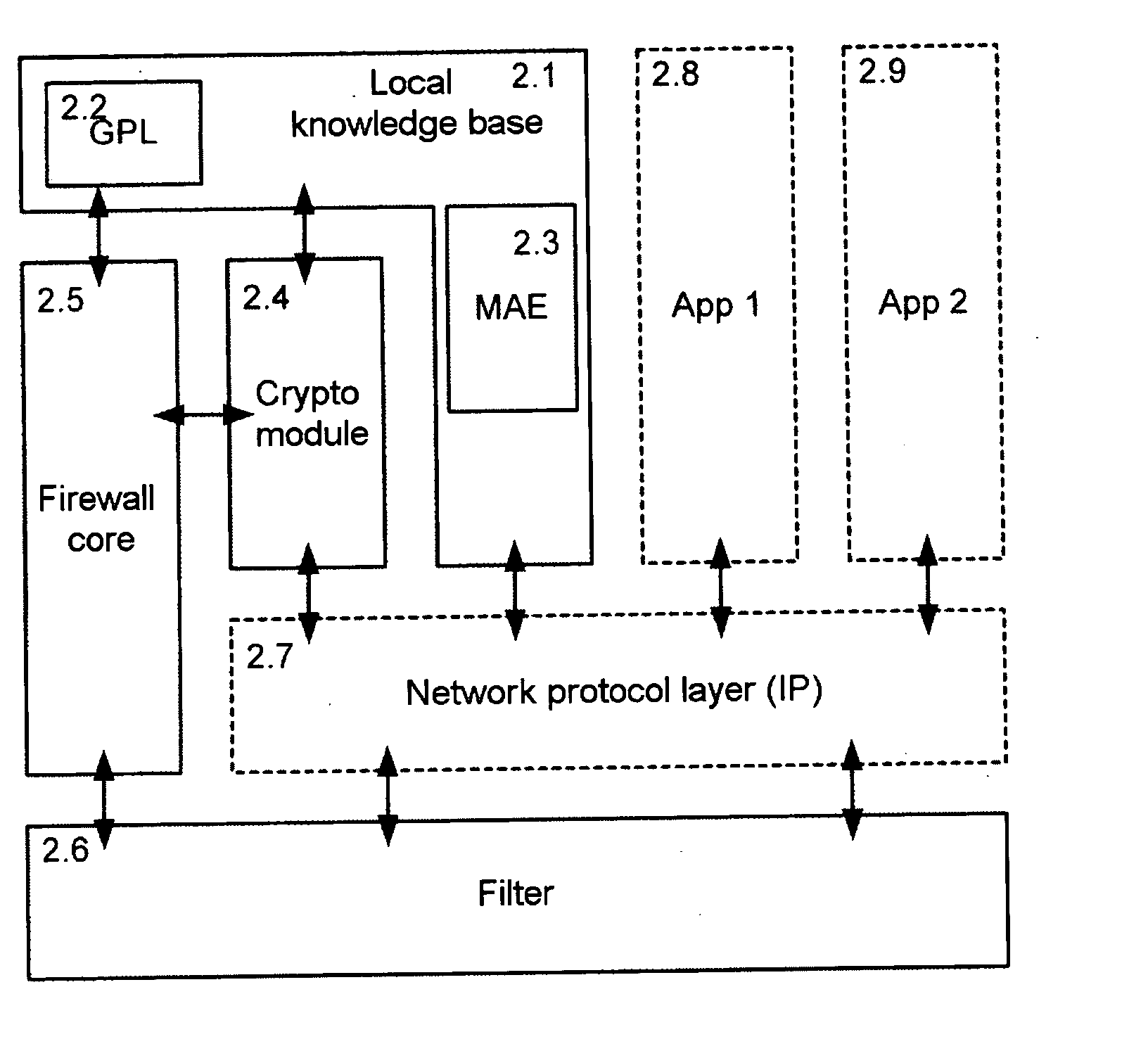
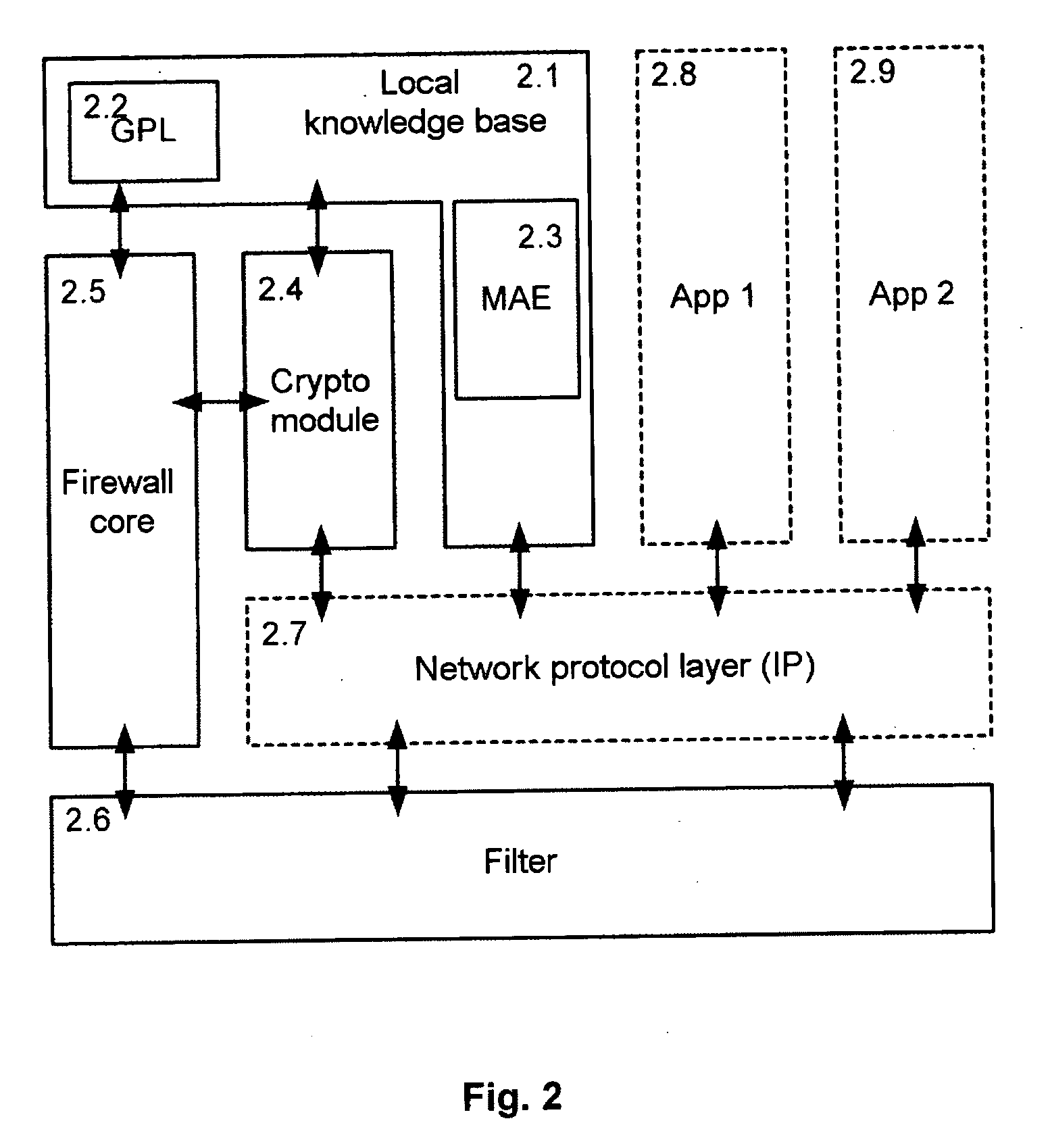
Firewall system protecting a community of appliances, appliance participating in the system and method of updating the firewall rules within the system
InactiveUS20060010491A1Data taking preventionDigital data processing detailsSystem protectionDistributed computing
The invention relates to the protection by firewall of a domestic community of interconnectable appliances. The invention allows distributed and totally decentralized management of the firewall policy, implemented at the level of each appliance, which is consistent and adapts dynamically to the changes occurring within the domestic network. We shall speak of ubiquitous firewalls.
Owner:INTERDIGITAL CE PATENT HLDG
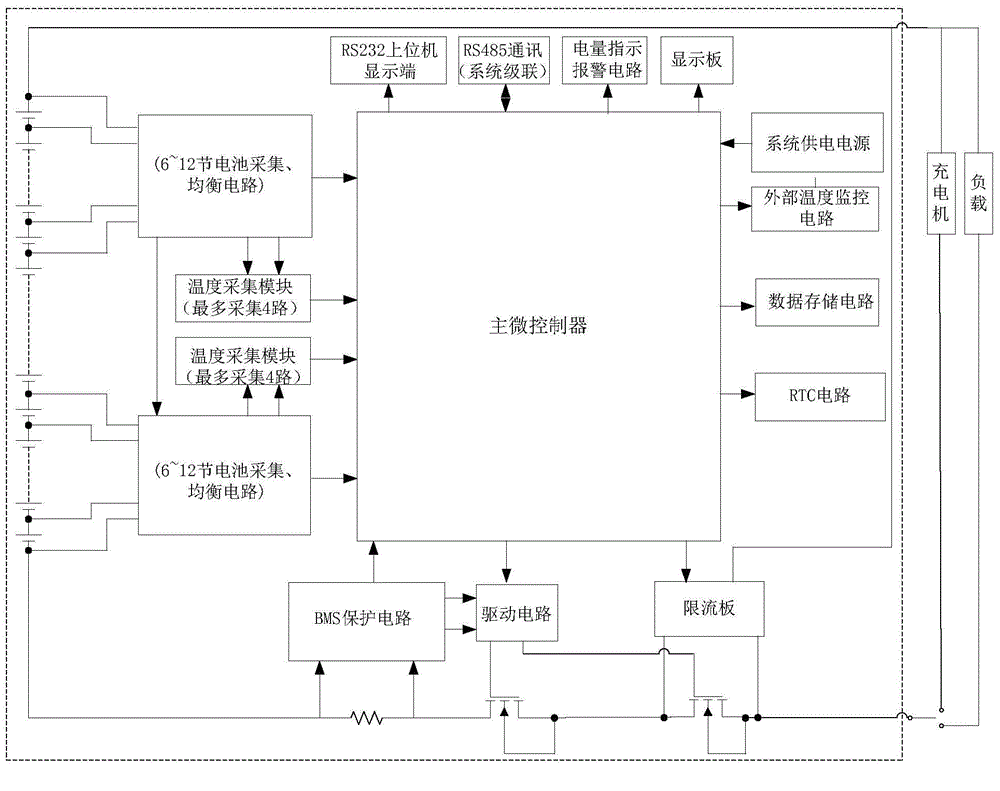
Cell management system
InactiveCN104868546AEnsure safetyStatus real-time monitoringBatteries circuit arrangementsSecondary cellsCurrent cellCell system
The invention discloses a cell management system. The system is formed by a mainboard, a current limiting board and a display panel. The mainboard is a technology core of the system. The mainboard completes monitoring of a voltage of a single cell and a temperature and equalization management, monitors the total voltage and the current, manages charging, discharging and a cell running state, estimates a battery-pack charged state and carries out system protection and fault diagnosis alarm. The current limiting board limits a charging current of a charger. The mainboard controls on and off of the current limiting board through a switching value. The display panel completes a state information display function of the battery pack. The mainboard and the display panel are communicated by using serial port communication. Through the display panel, a current cell management system state can be known in real time. The system possesses a cascade function. Communication connection is performed on a plurality of systems through an RS485 interface. Through using an RS485 bus, a transmission rate is increased; electromagnetic interference is effectively reduced and information transmission accuracy is guaranteed. The mainboard can send cell system information to an upper computer and the information can be displayed through the upper computer.
Owner:SHENYANG ZHONGKE E WAY ELECTRONICS TECH CO LTD
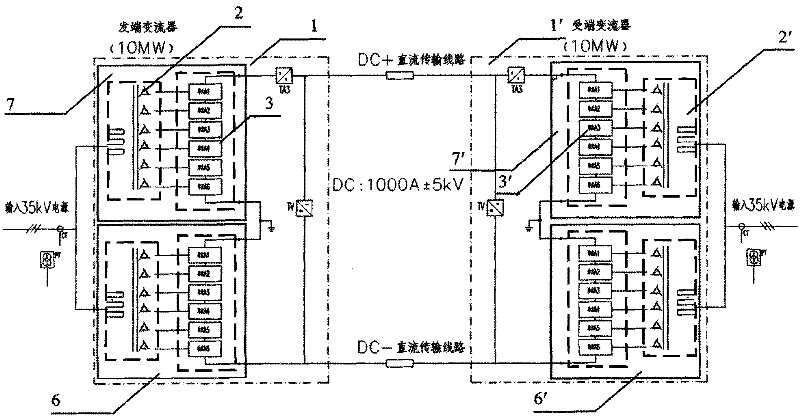
Protection method of DC electricity transmission high-voltage convertor station
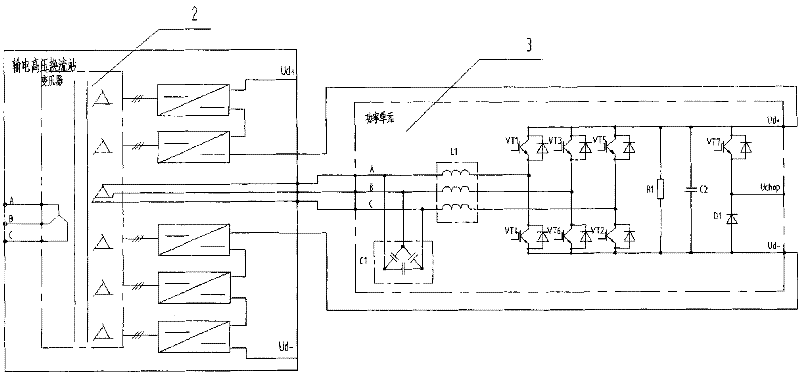
InactiveCN101752873AImprove protectionReduce shockElectric power transfer ac networkEmergency protective circuit arrangementsThree levelElectricity
The invention relates to a protection method of a DC electricity transmission high-voltage convertor station, which is used for protection of the DC electricity transmission high-voltage convertor station in the field of electricity transmission and transformation and divides the defects existing in a high-voltage convertor station into three levels of a convertor station system level, a convertor device level and a unit convertor level to design. When a DC electricity transmission system generates the defects, the system sorts and transfers the defects by a defect library, grades the defects according to different defect sorts, carries out corresponding processing and carries out corresponding alarm and action. The protection method can carry out grading comprehensive protection for the high-voltage convertor station. When the defects occur, the system can rapidly query the types of the defects and then carry out corresponding judgment and action for the defects according to the system protection levels, so the protection method reliably and effectively protects the DC electricity transmission system and can minimize the shock impact of the transient disturbance of the high-voltage convertor station on the DC electricity transmission system.
Owner:ZHUZHOU NAT ENG RES CENT OF CONVERTERS
System level testing for substation automation systems
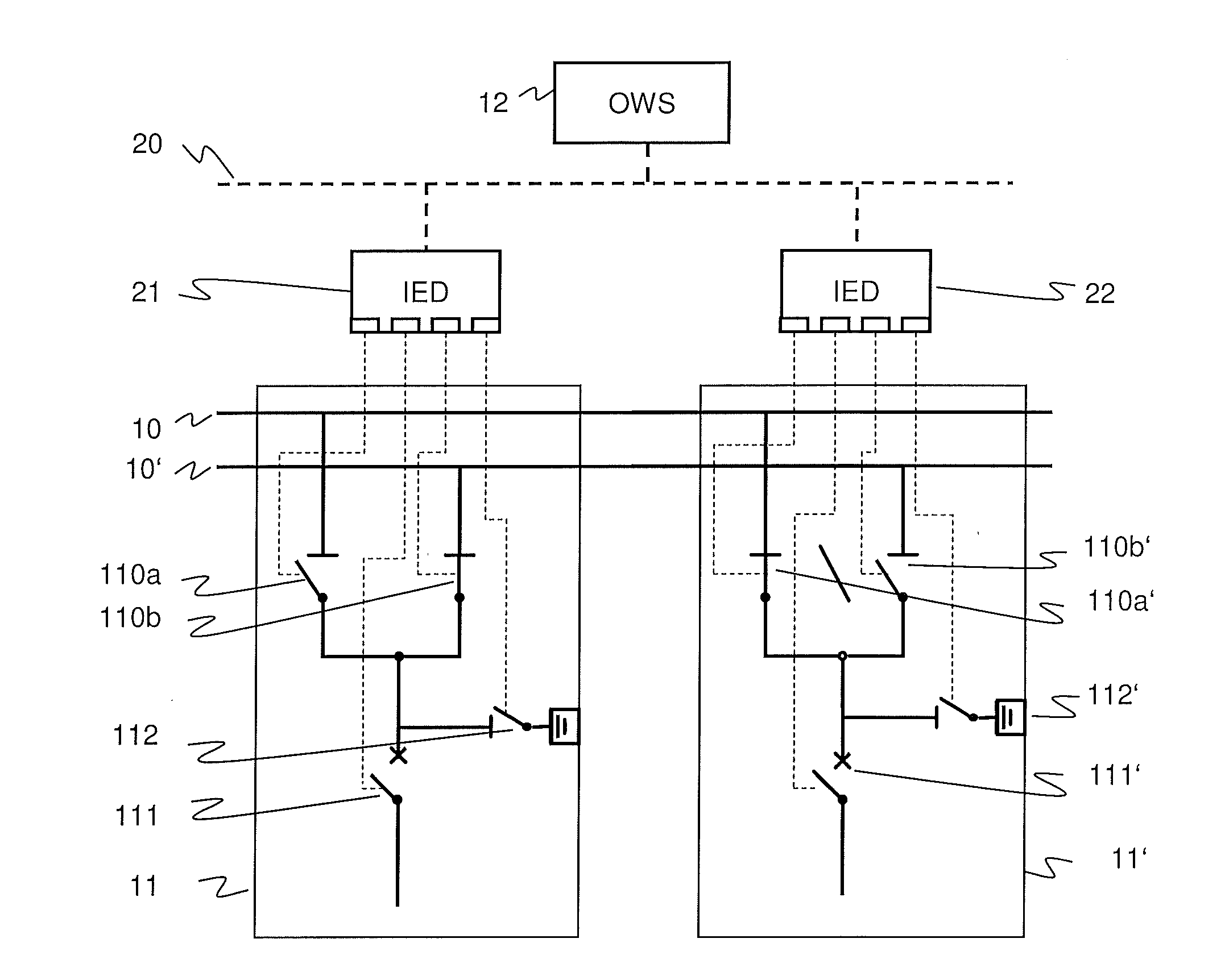
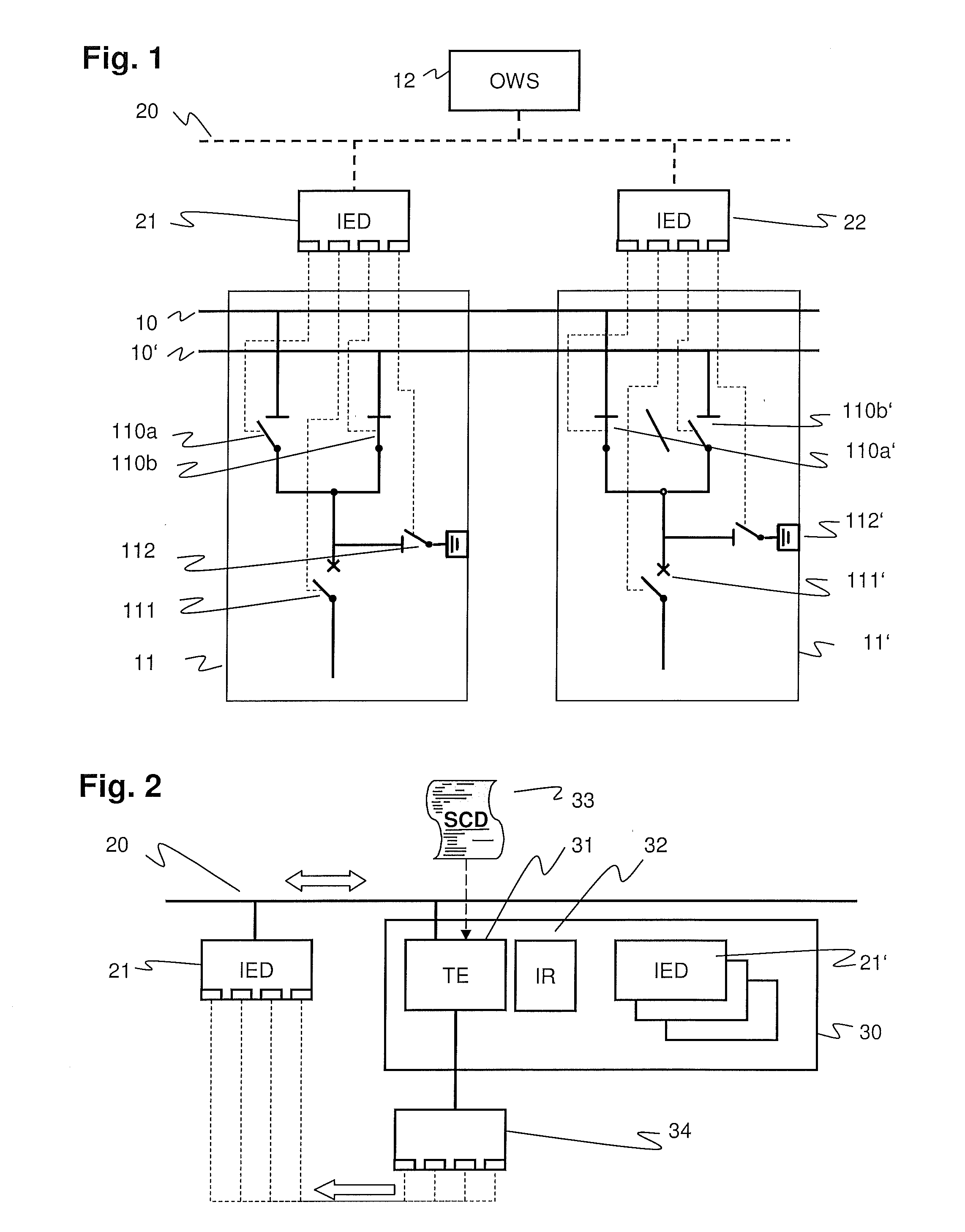
ActiveUS20100204948A1Resistance/reactance/impedenceError detection/correctionTime informationSystem testing
Protection, measurement and control IEDs in a substation compute if switches they control may be operated safely, according to interlocking rules or physical principles as well as the dynamic topology of the substation. The IEDs have access to the substation electrical topology, to real-time information generated by other IEDs, and to the rules for interlocking. A standardized Substation Configuration Description (SCD) of the substation for which a Substation Automation system is intended, and a standardized description of the implemented device functions or capabilities of an individual IED are utilized. The substation topology is available from SCD file, real time information about the position of switches and line voltage / current can be obtained via an appropriate protocol, and the interlocking rules are available in script form. These features apply both to simulated and real devices, and increase system testing possibilities by supporting an efficient configuration of a simulation.
Owner:HITACHI ENERGY SWITZERLAND AG
Method and device for assessing the stability of an electric power transmission network
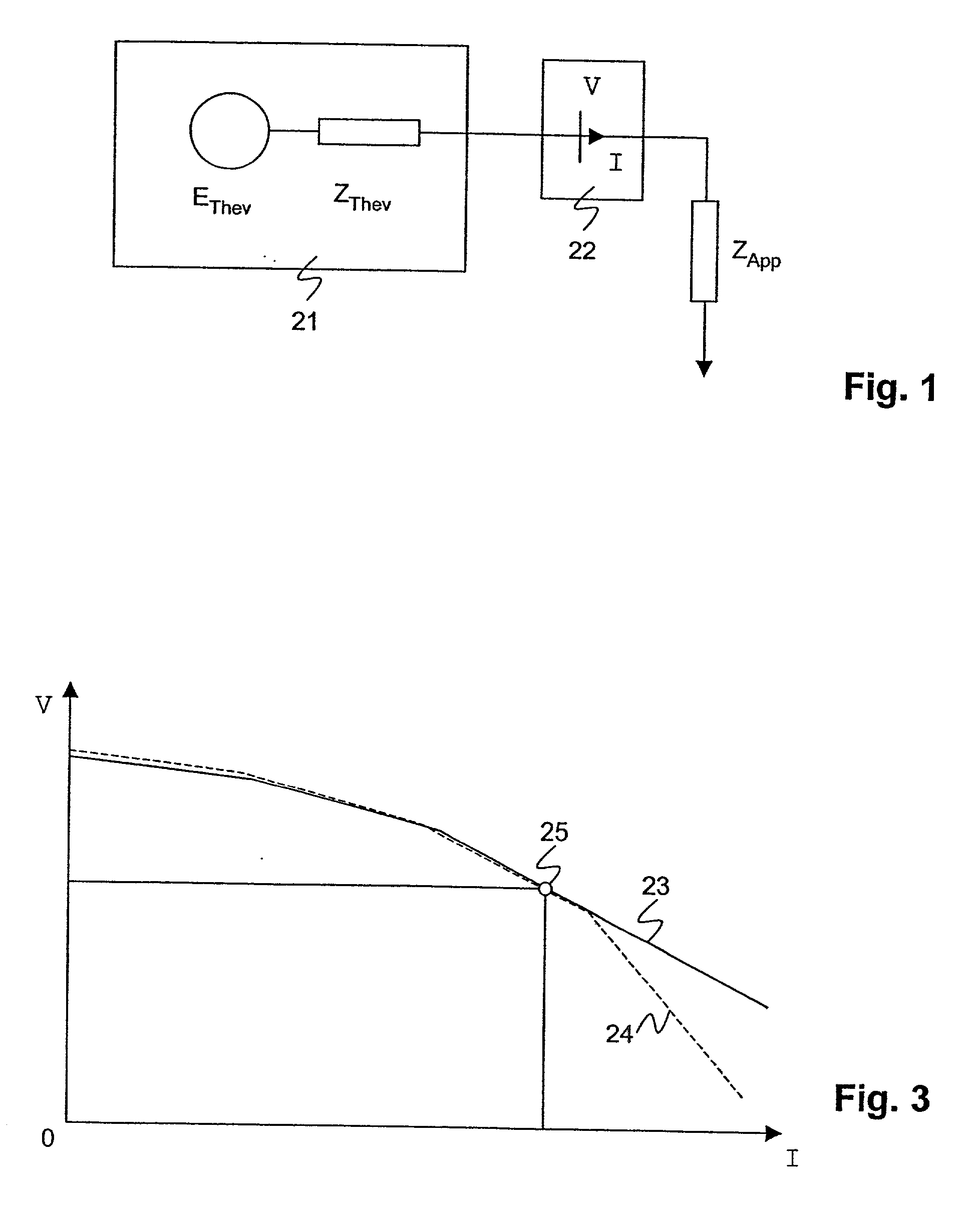
InactiveUS6754597B2Aggravating the condition of the network even furtherLimit its operationMechanical power/torque controlData processing applicationsElectric power transmissionTime information
Owner:ABB POWER GRIDS SWITZERLAND AG
Motor vehicle battery disconnect circuit having electronic disconnects
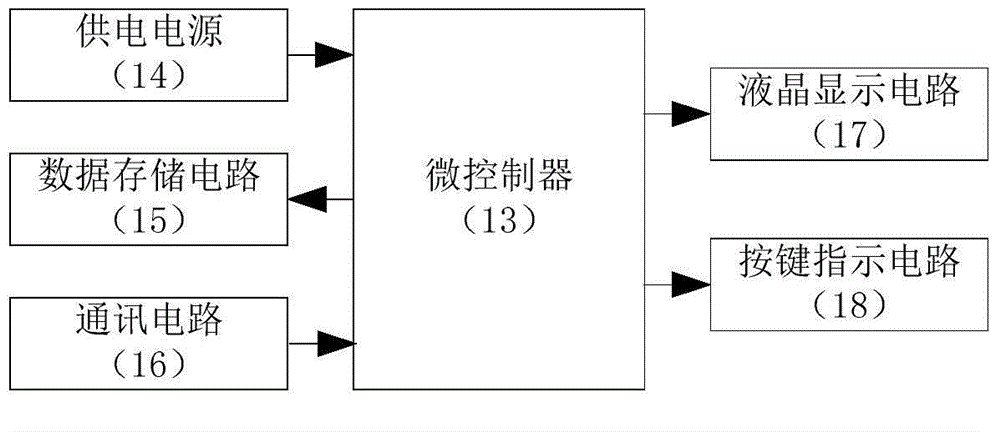
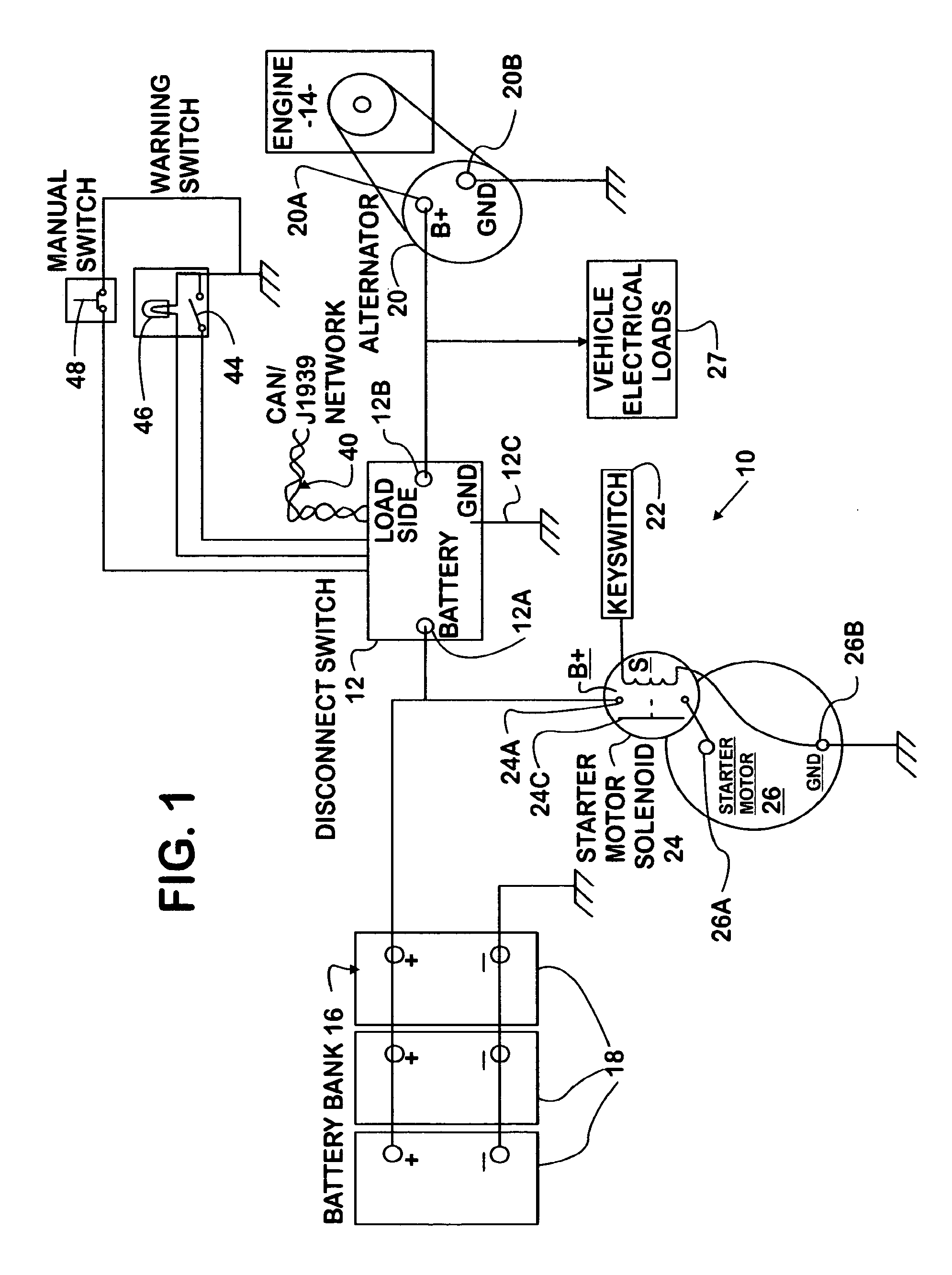
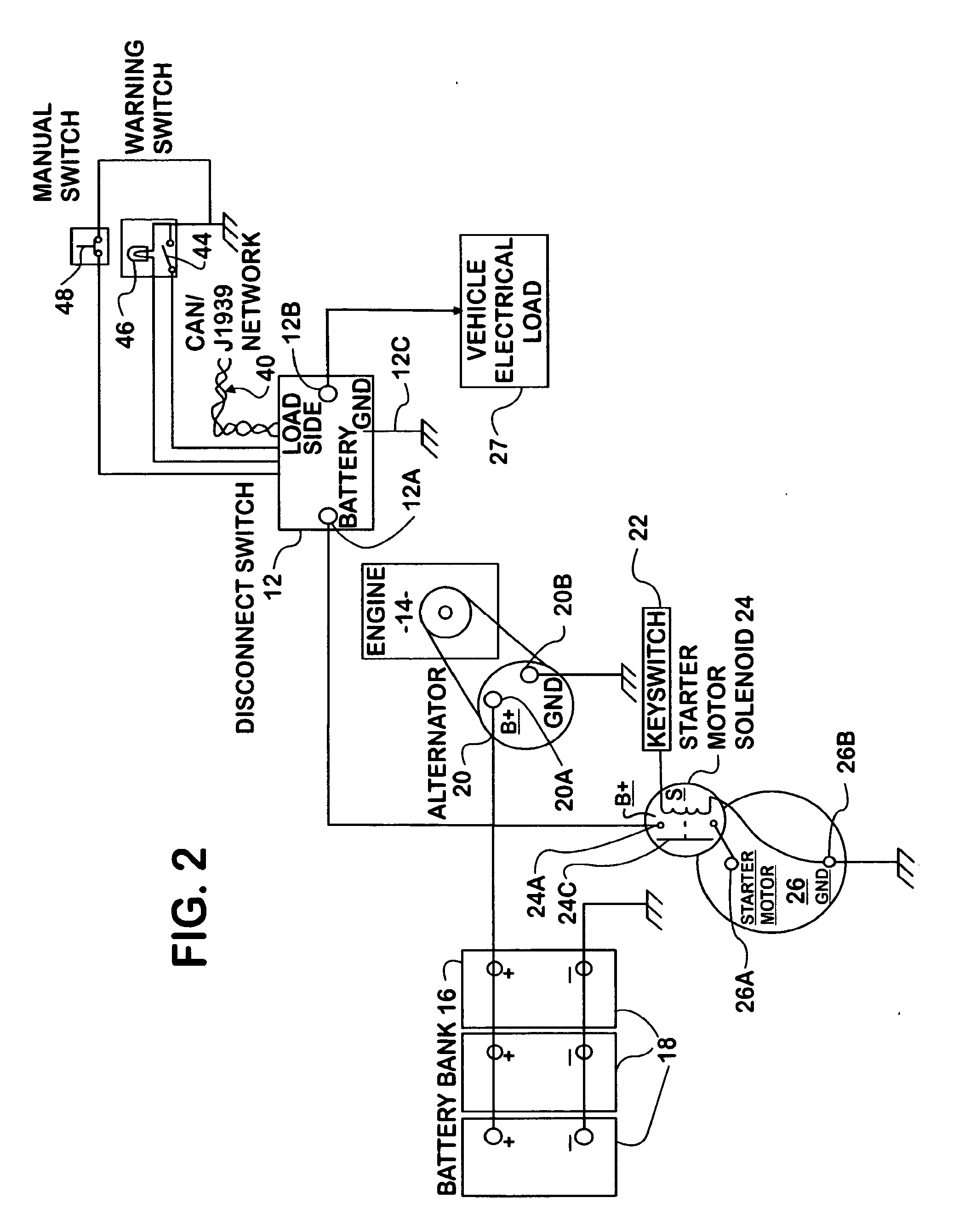
InactiveUS20080079389A1Add featureLower resistanceAnalogue computers for vehiclesSafety arrangmentsLoad circuitMicrocontroller
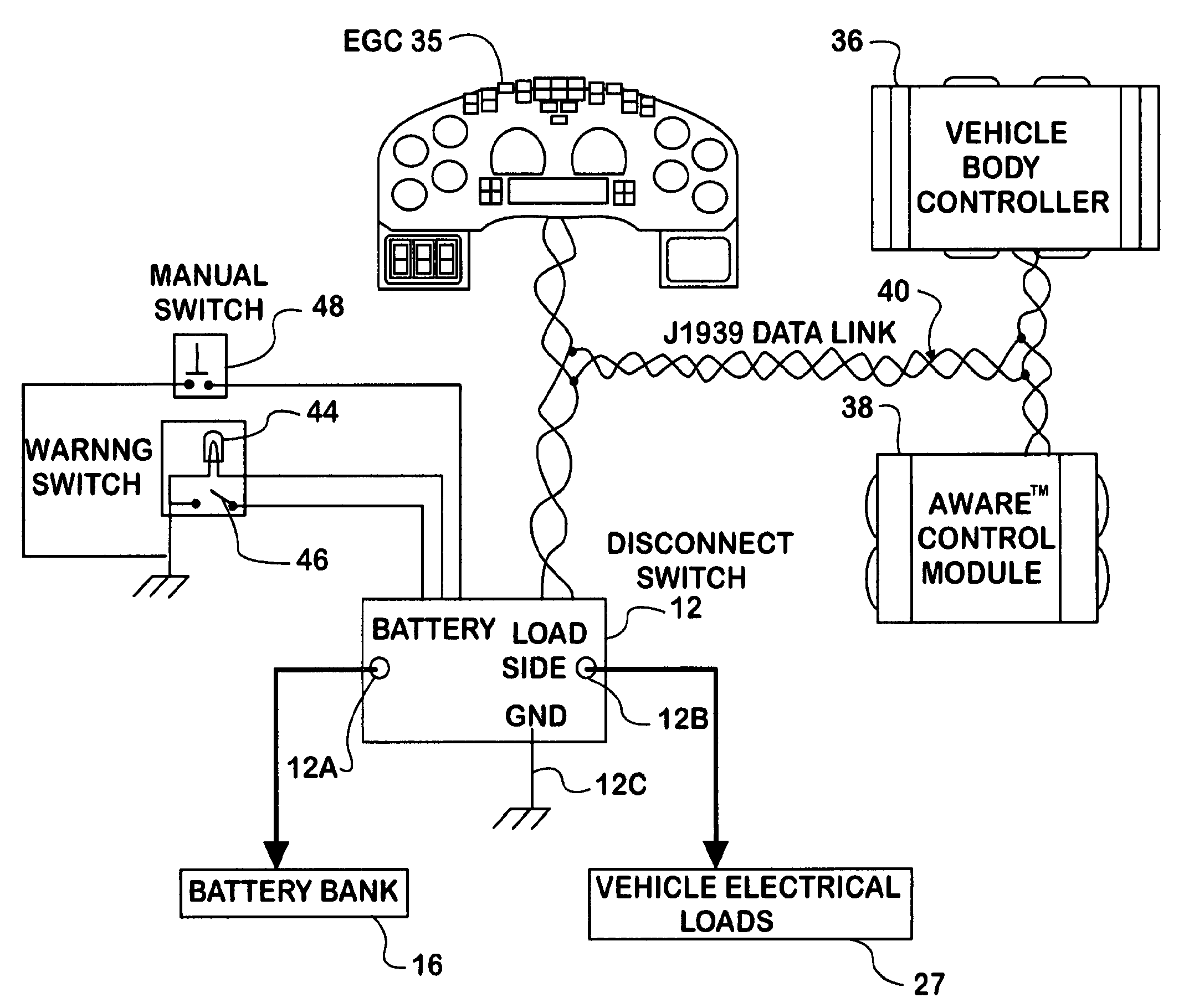
An electronic disconnect switch module (12) in a motor vehicle has one or more pairs of high-current, high-side solid state switch devices (30A, 30B, 32A, and 32B). The source terminal of one device of each pair is connected to vehicle load circuits (27), the source terminal of the other device of each pair is connected to the vehicle battery bank (16), and the drain terminals of the devices of each pair are connected in common. The module also has a microcontroller (34) that interfaces the switch devices with the vehicle electrical system. Four feature groups are provided: Vehicle Electrical System Protection, Battery Charge Control, Battery Disconnect, and Battery Monitoring.
Owner:INT TRUCK INTPROP LLC
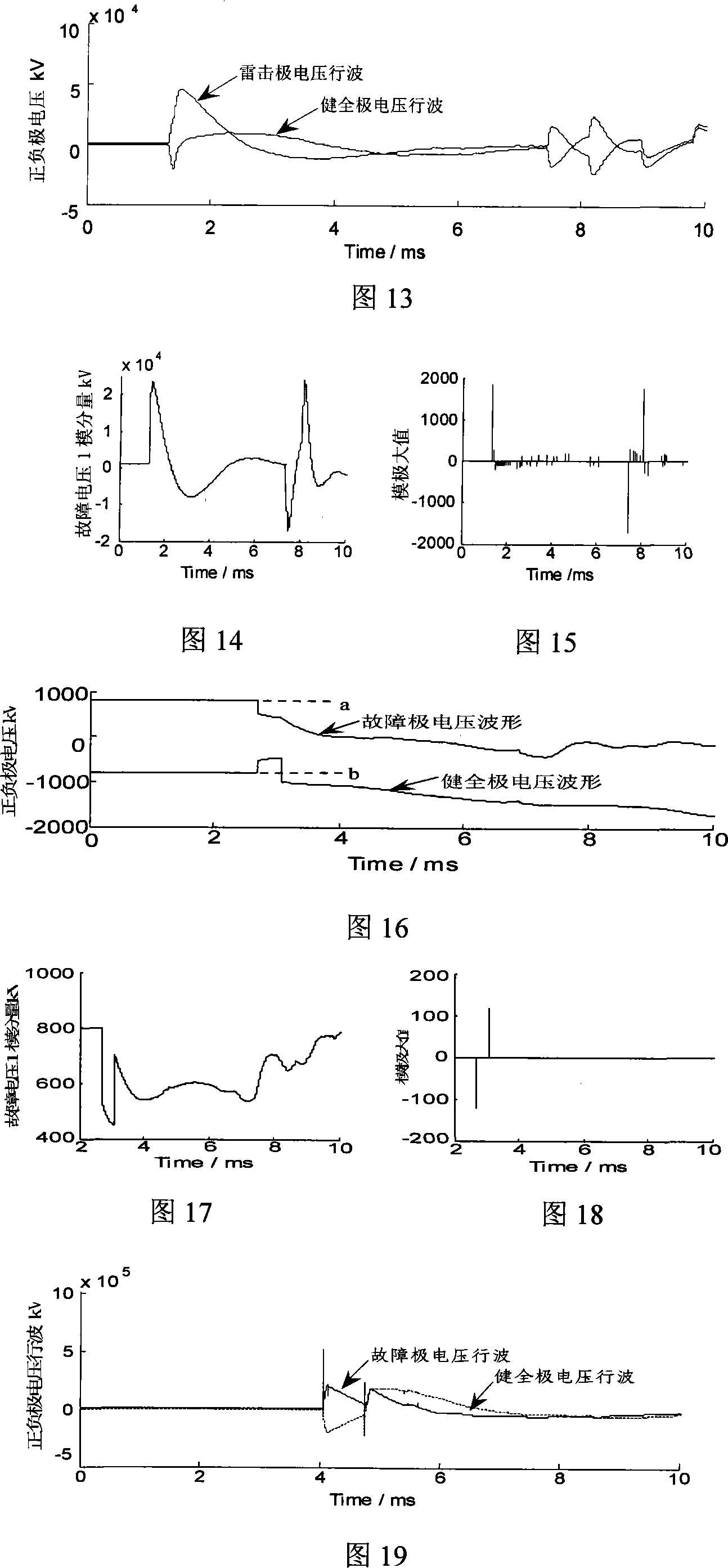
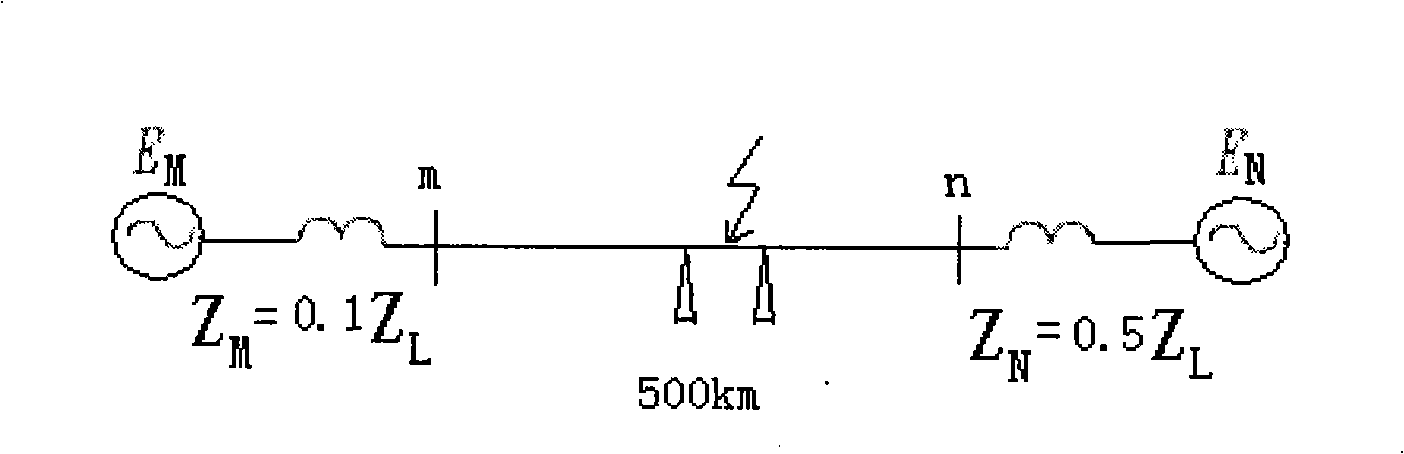
Thunder failure recognition method for row wave protection of DC power transmission line
InactiveCN101242098AQuick identificationEmergency protective circuit arrangementsLightning strikeShort circuit fault
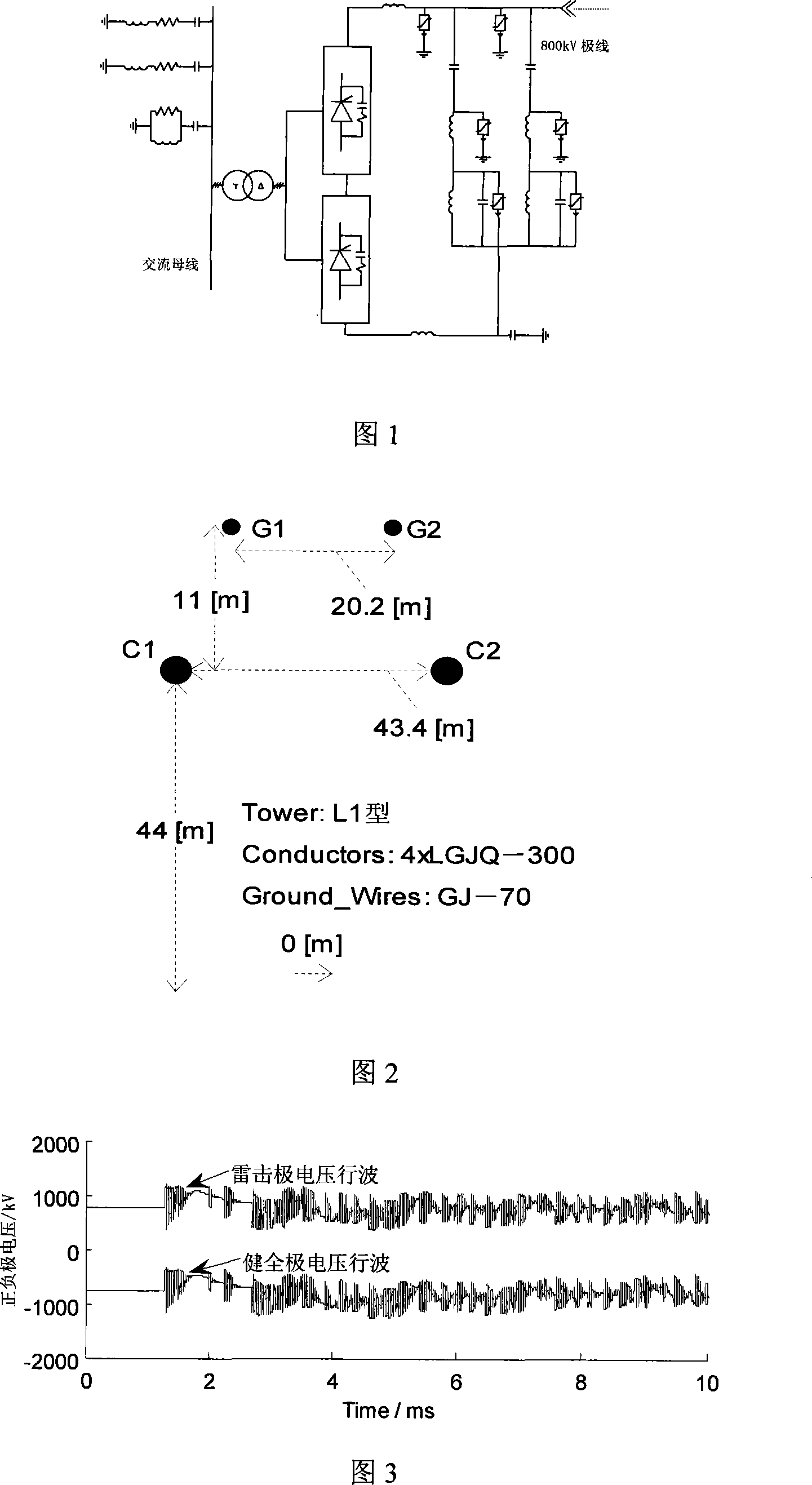
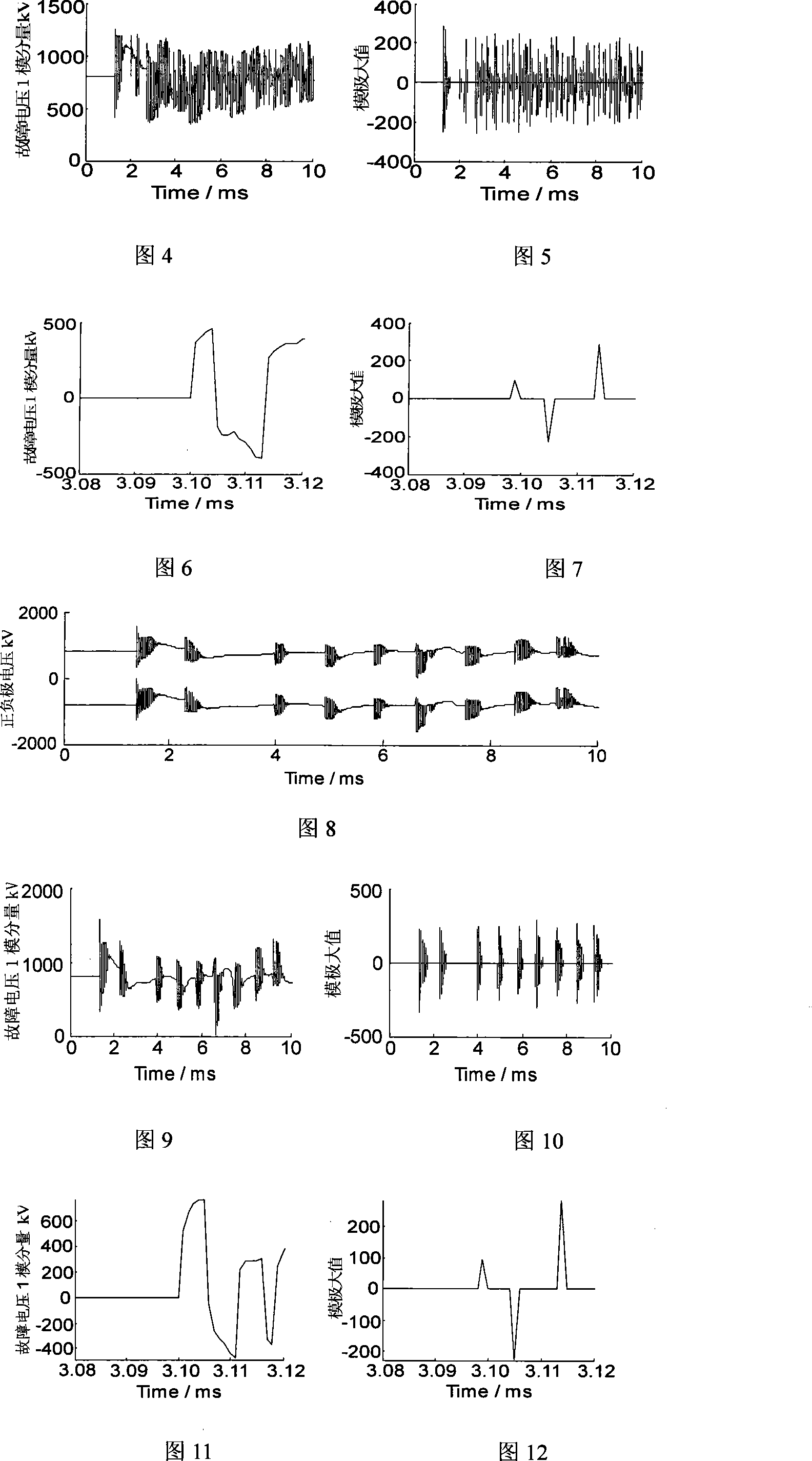
The invention relates to a lightning striking fault identifying method of a direct current power transmitting line traveling wave protection. According to the characteristic difference of voltage traveling wave shape between the formed faults and unformed faults, two-pole voltage traveling wave weight and origin direct current weight are used to identify changing trend of the wave shape; ratio of a initial traveling wave mode maximum value and the second mode maximum value is used for representing saltation that the wave shape is cut; combining the two characteristics to achieve the identification of the voltage traveling wave while not causing the faults by lightning pole tower, lightning striking lightning line, lightning striking line shift central distance and the voltage traveling wave of non-lightning short circuit fault by the lightning pole tower, lightning striking line shift central distance. The interference and identification of the two lightning weaves are combined to improve the identifying reliability. A large number of emulations represent that this method is reliable and effective. The physical conception of this invention is intuitionistic and clear and has a rapid action function. The invention does not be influenced by the fault type and transition resistance and it is easy to achieve and suitable for apllying to direct current system protecting device.
Owner:KUNMING UNIV OF SCI & TECH
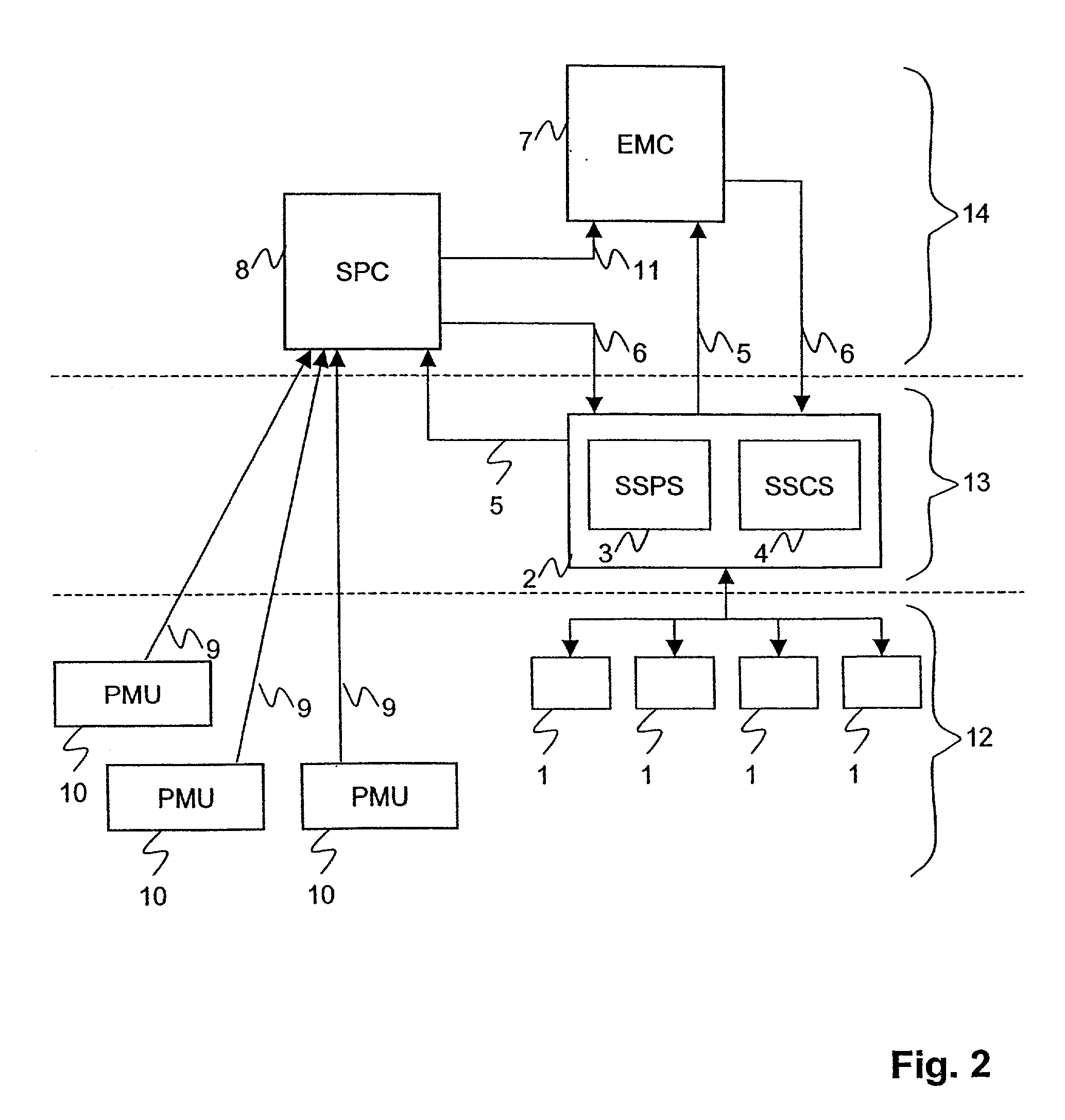
Method and device for assessing the stability of an electric power transmission network
InactiveUS20010021896A1Aggravating the condition of the network even furtherLimit its operationLevel controlPower measurement by current/voltageElectric power transmissionTime information
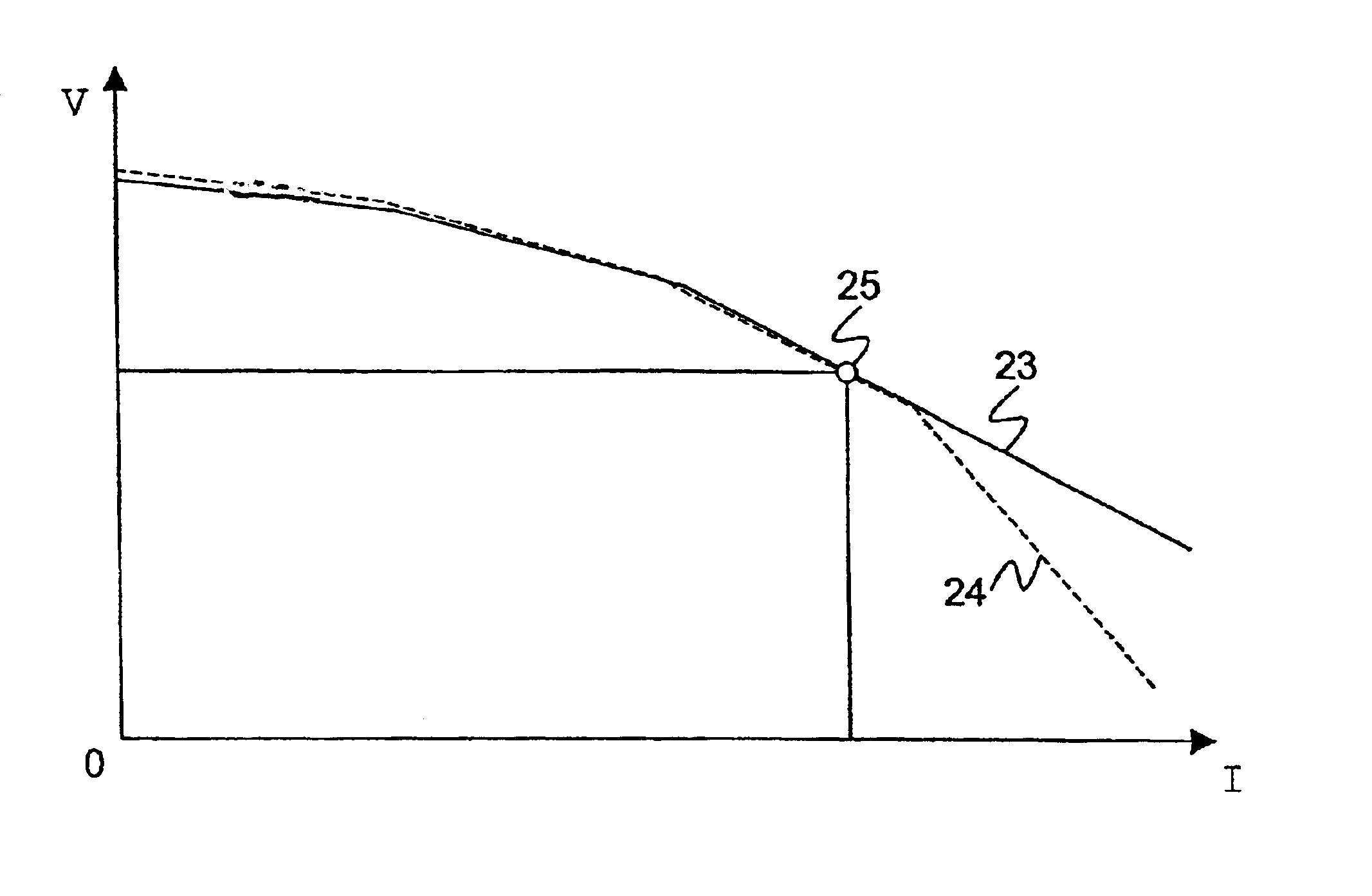
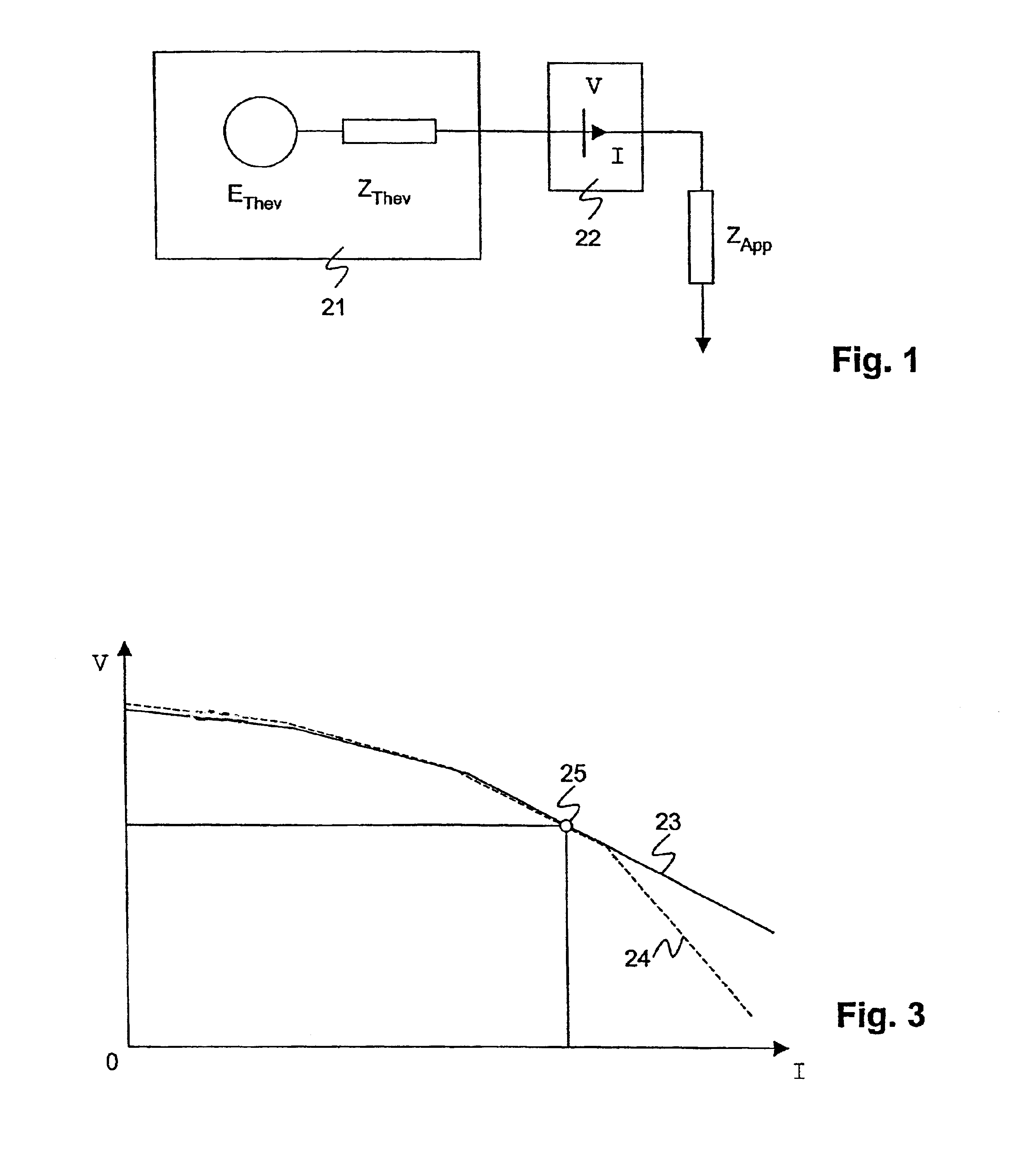
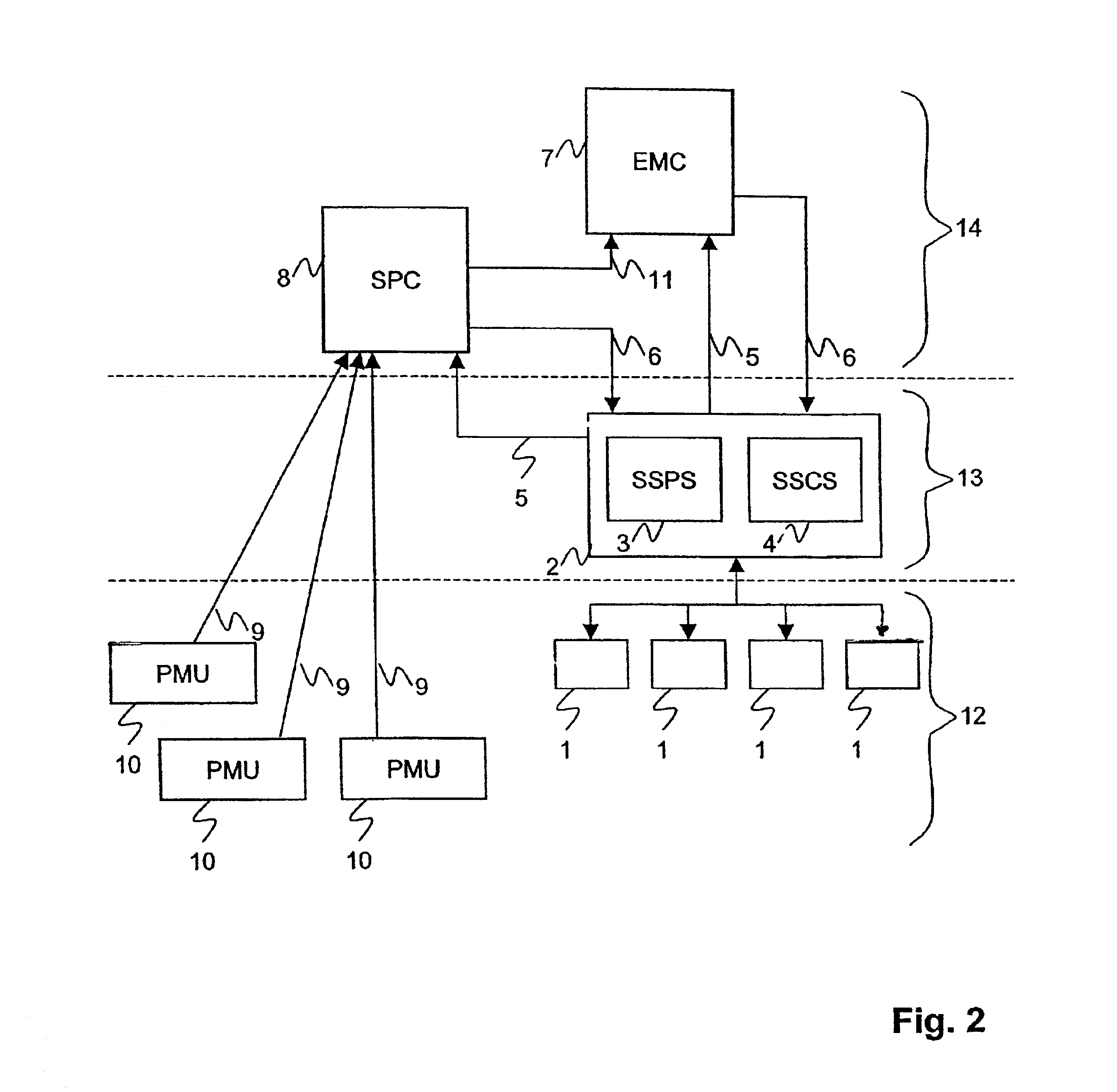
The inventive method assesses the stability of an electric power transmission network, where said network comprises a plurality of substations, buses and lines, and a system protection center (8). It comprises the steps of 1. measuring phasor data (9) for voltages and currents at a plurality of locations of the network, 2. transmitting said phasor data (9) to said system protection center (8), 3. transmitting information (5) regarding the state of switches of at least one substation to the system protection center (8), and 4. the system protection center (8) determining at least one stability margin value of the transmission network. In this way, detailed real-time information about the state of the network is collected at a system level of the network, allowing a corresponding global analysis of the information. In a preferred embodiment of the invention, the system protection center determines one or more control commands (6), based on the phasor data (9) and on the state of switches. The control commands (5) are transmitted to at least one substation and executed there.
Owner:ABB POWER GRIDS SWITZERLAND AG
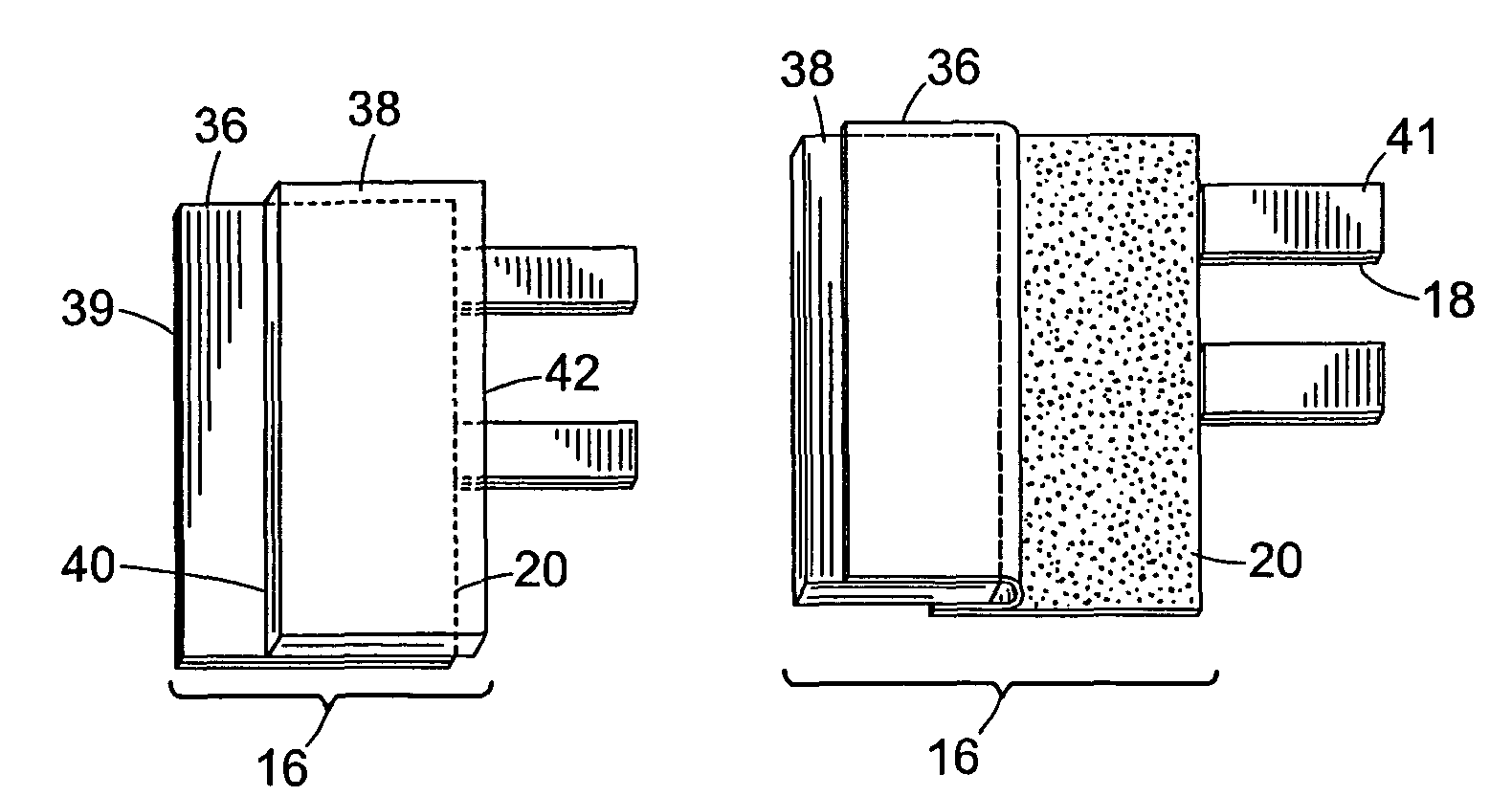
Device for laceration or incision closure
InactiveUS7354446B2Improve comfortEasy to processSurgical veterinaryWound clampsSystem protectionBiomedical engineering
Disclosed is a two-component device for closing a laceration or incision. The device includes a first component comprising a first adhesive-backed anchoring member and one or more first connecting members extending from one edge thereof in a first direction. The first adhesive-backed anchoring member is protected by a two-stage release liner system which includes: 1) a release liner with a bottom surface covering the adhesive-backed surface of the first anchoring member; and 2) a semi-rigid tab attached to a portion of the top surface of the release liner. The semi-rigid tab includes a first and a second edge. The first edge is oriented generally parallel to the wound edge of the first anchoring member and attached to the release liner at a position intermediate in the release liner between the portion of the release liner protecting the wound edge and the portion of the release liner protecting the edge of the first anchoring member generally opposite the wound edge. The second edge extends unattached beyond the wound edge. The device also includes a second component with substantially similar structural features as those described for the first component. Also provided is a means for attaching the one or more first connecting members to the second anchoring member and means for attaching the one or more second connecting members to the first anchoring member. The attachment of the connecting members to the anchoring members forms attached and bridging portions of the one or more connecting members. The attached portions are attached to an anchoring member, and the bridging portions span the over-laceration area between the first and second anchoring members. Also disclosed is a two-stage release liner system which is not associated with a specific device. Methods of use are also disclosed.
Owner:CLOZEX MEDICAL LLC
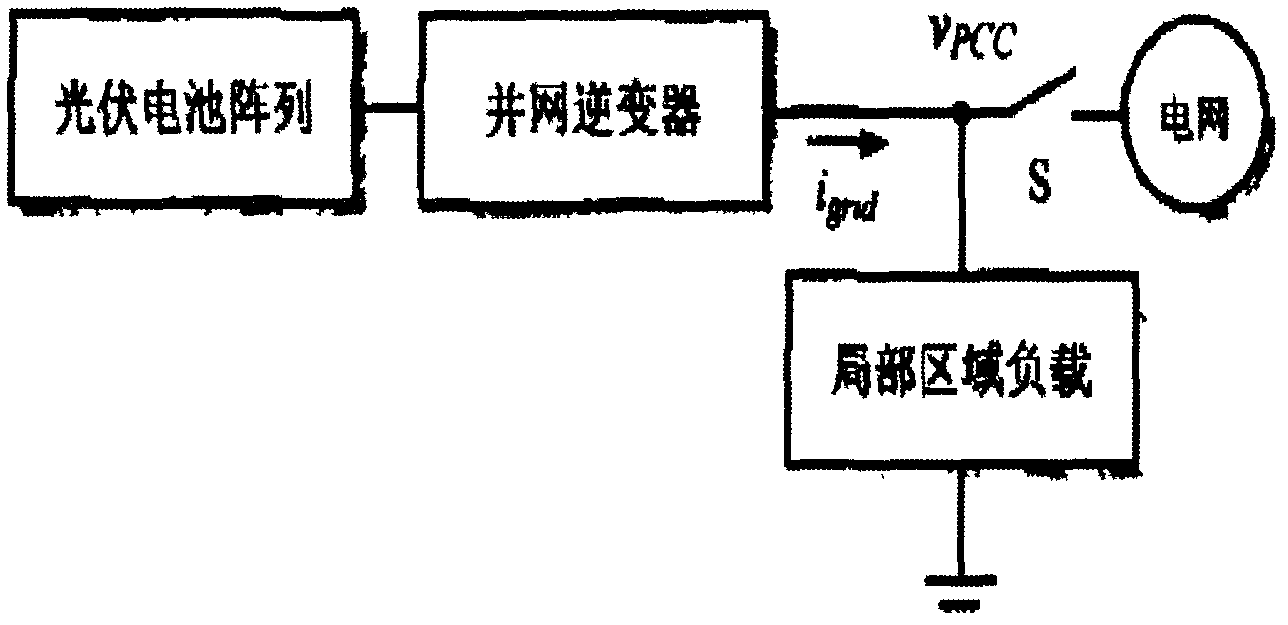
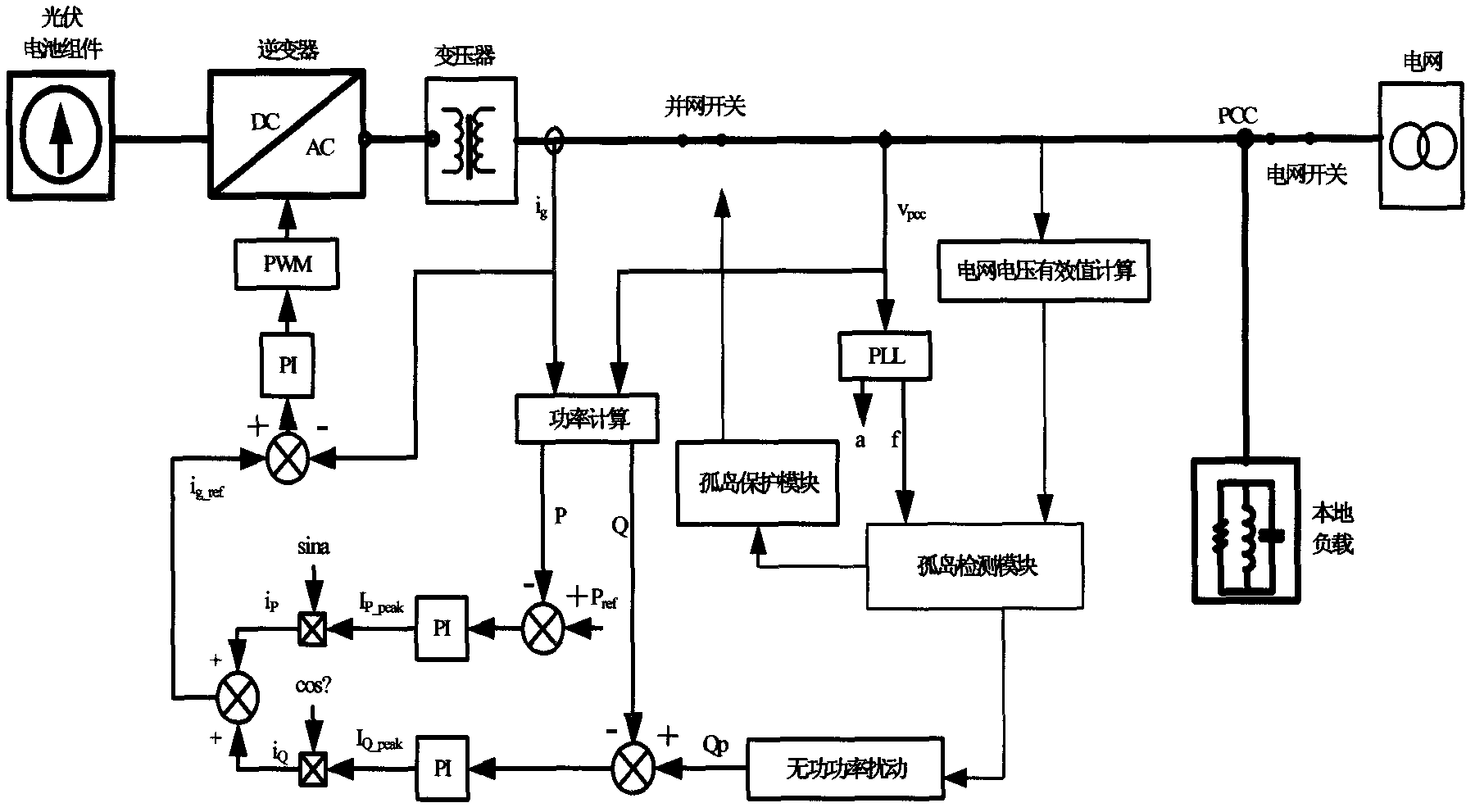
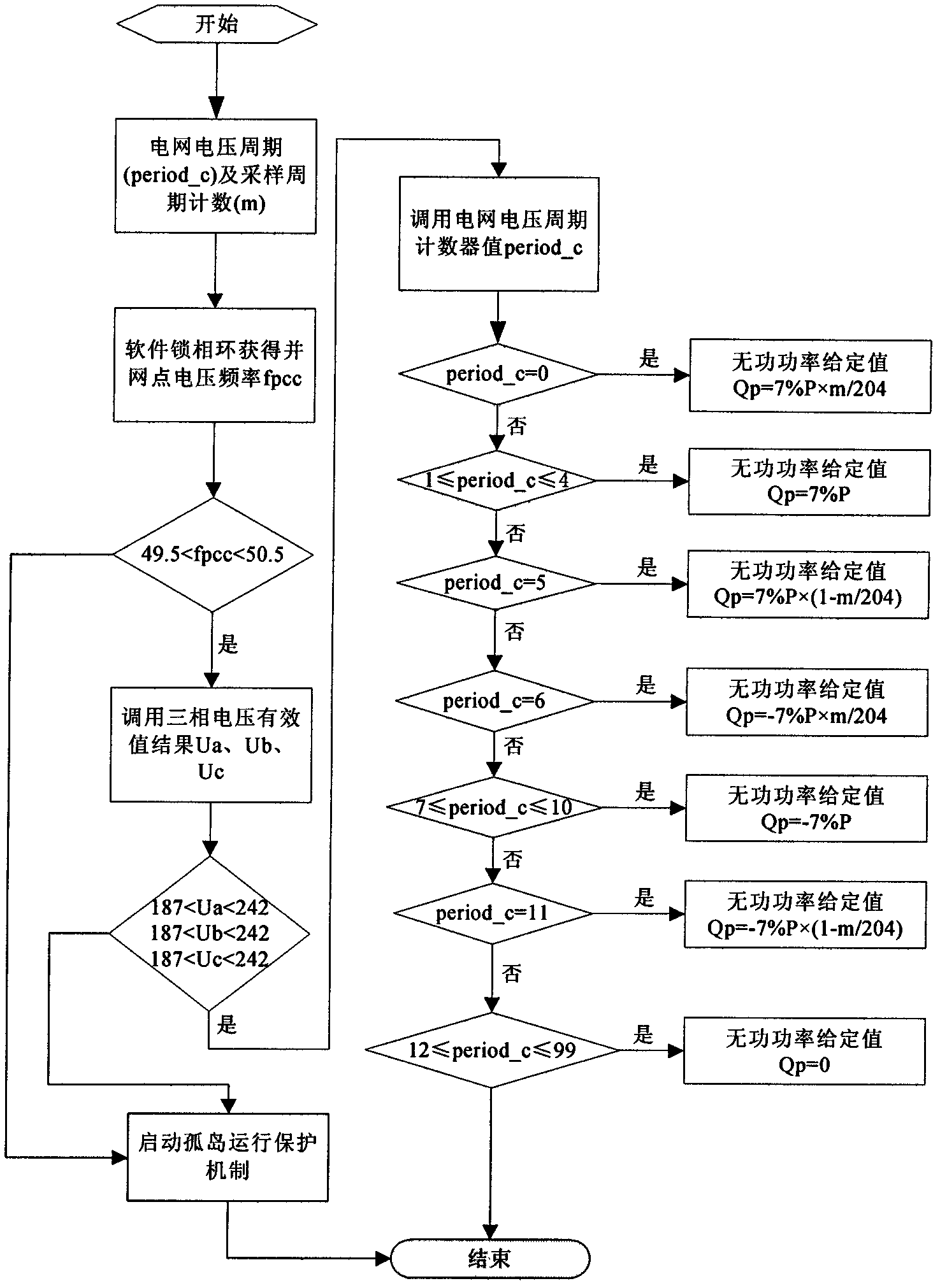
Reactive-power-disturbance-based grid-connected island detection method for photovoltaic system
InactiveCN102208817ADetection speedReduce distractionsCurrent/voltage measurementSingle network parallel feeding arrangementsVoltage amplitudeControl system
The invention discloses a reactive-power-disturbance-based island detection method for a photovoltaic grid-connected power generation system. The method is characterized by comprising the following steps of: detecting the voltage amplitude and frequency of a grid connection point in real time by using the system, judging whether the voltage amplitude and frequency of the grid connection point reach system protection threshold values or not, and if the voltage amplitude and frequency of the grid connection point reach the system protection threshold values, enabling an anti-island protection signal; and if the voltage amplitude and frequency of the grid connection point do not reach the system protection threshold values, controlling an inversion output signal of the system by using bilateral intermittent periodical reactive power disturbance to realize the change of the output voltage amplitude and frequency of the system, and detecting the change of the output voltage amplitude and frequency of the system in real time, wherein a bilateral intermittent period comprises a reactive power output time period and an intermittent time period, reactive power disturbance values of each time period take the voltage period of a power grid voltage and the sampling period of the system as regulation variables, and the reactive power disturbance realizes the change of the output voltage amplitude and frequency of the system by the inversion control of a reactive power ring. By the method, the rapid and accurate power-grid island running detection of the photovoltaic system can be realized, and the disturbance to the power-grid system can be reduced.
Owner:36TH RES INST OF CETC
Multi-inverter module paralleling frequency conversion device for transmission system and control policy
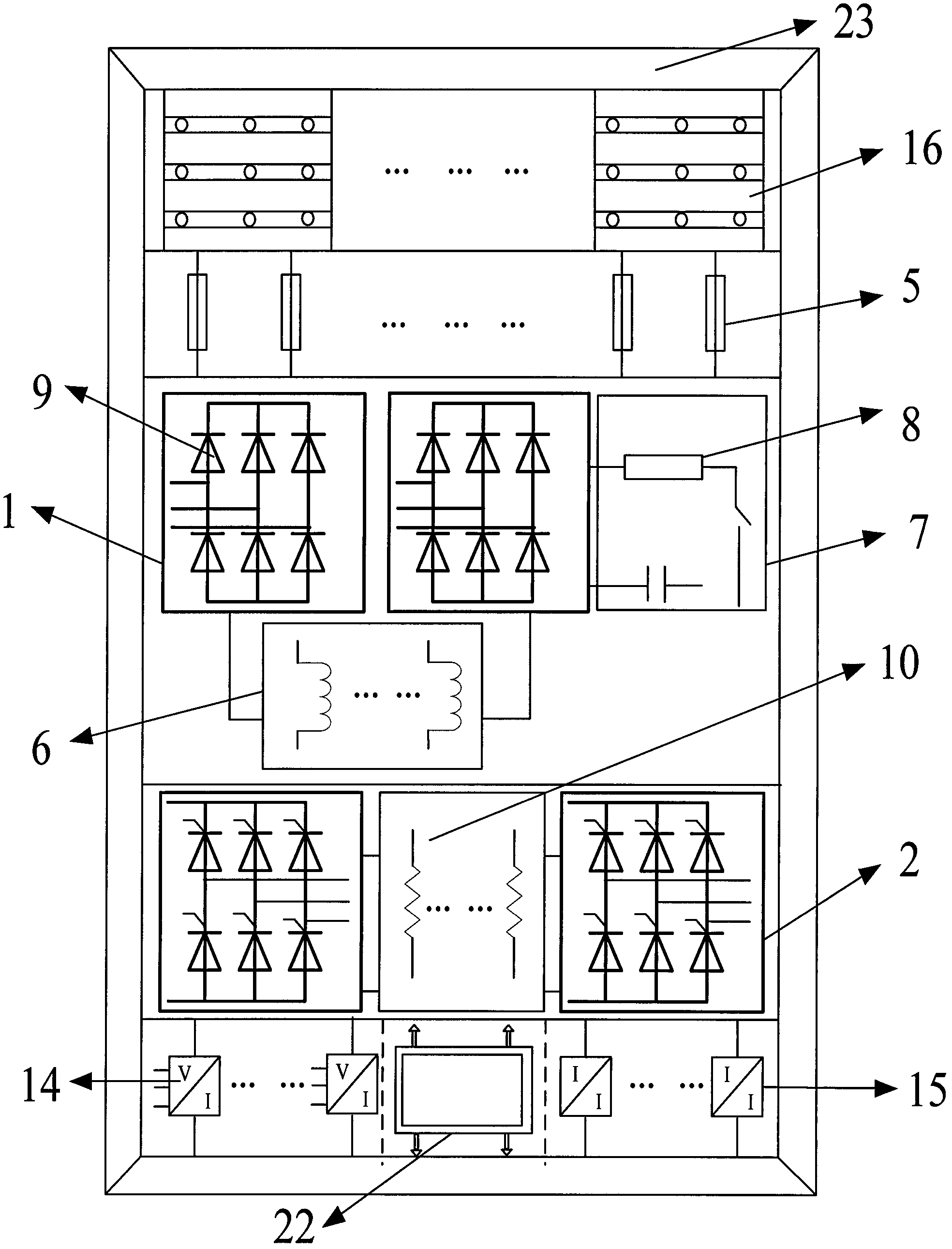
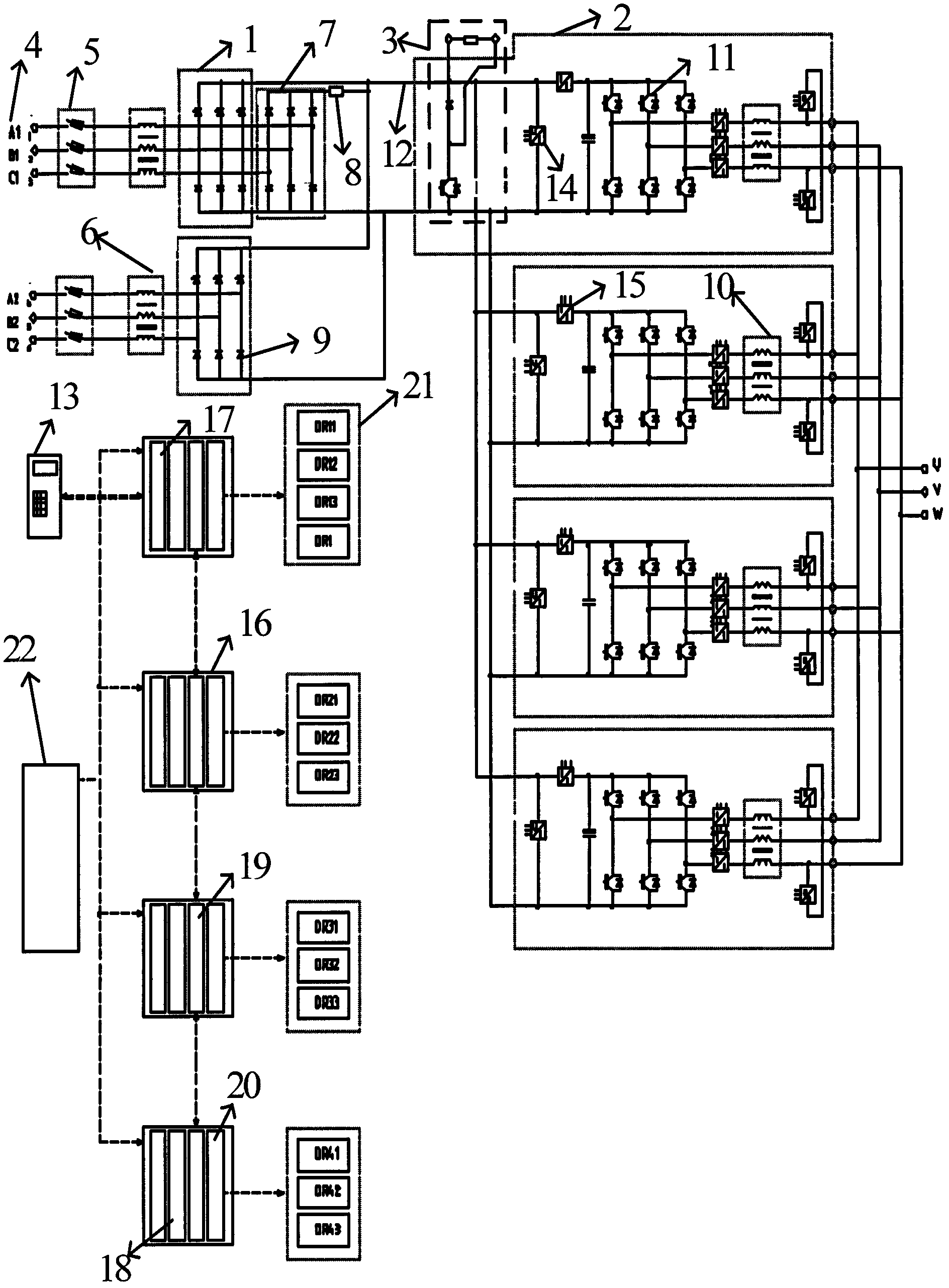
InactiveCN102355195AAdapt to the needs of speed controlImprove power factorElectronic commutation motor controlAC motor controlPower factorEngineering
The invention relates to a multi-inverter module paralleling frequency conversion device for a transmission system and a control policy. The device comprises a rectifier, inverters, a braking device, a cooling system, a protection device, an interface and the like, and is characterized in that an inverter paralleling structure realizes a relatively high power factor; through the parallel connection of multiple rectifying modules and the parallel connection of multiple inversion units, the output capacity of the inverters is increased, and the input / output harmonic waves are reduced; a control box drives a motor to operate by controlling the work of a frequency converter; and a fuse group and control power supply perform fault protection on the system and provide power to each part. In the control policy, a motor driving mode that master and slave modules perform hierarchical control is adopted; as the master control module synchronizes the slave control module, the problem of difficult same-frequency and same-phase output of multiple inverters in the case of motor load is solved; by monitoring the current of each inversion module (multiple inversion modules) and dynamically adjusting the output of each inversion module, the key technology of realizing homogeneous flow of the outputs of multiple paralleling inversion modules is broken through, and an inverter paralleling frequency conversion and speed regulation control method with relatively high static and dynamic performance is realized; and high power of the frequency conversion device with multiple paralleling inversion modules for the transmission system is realized.
Owner:乔鸣忠 +2
Simulation system and simulation method for high voltage AC and DC power transmission training
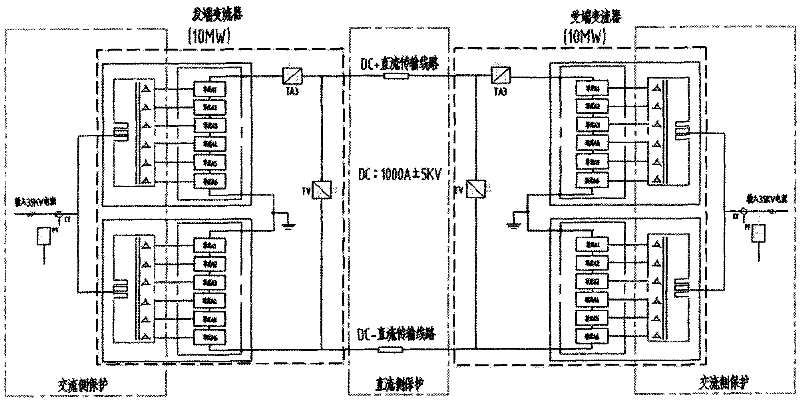
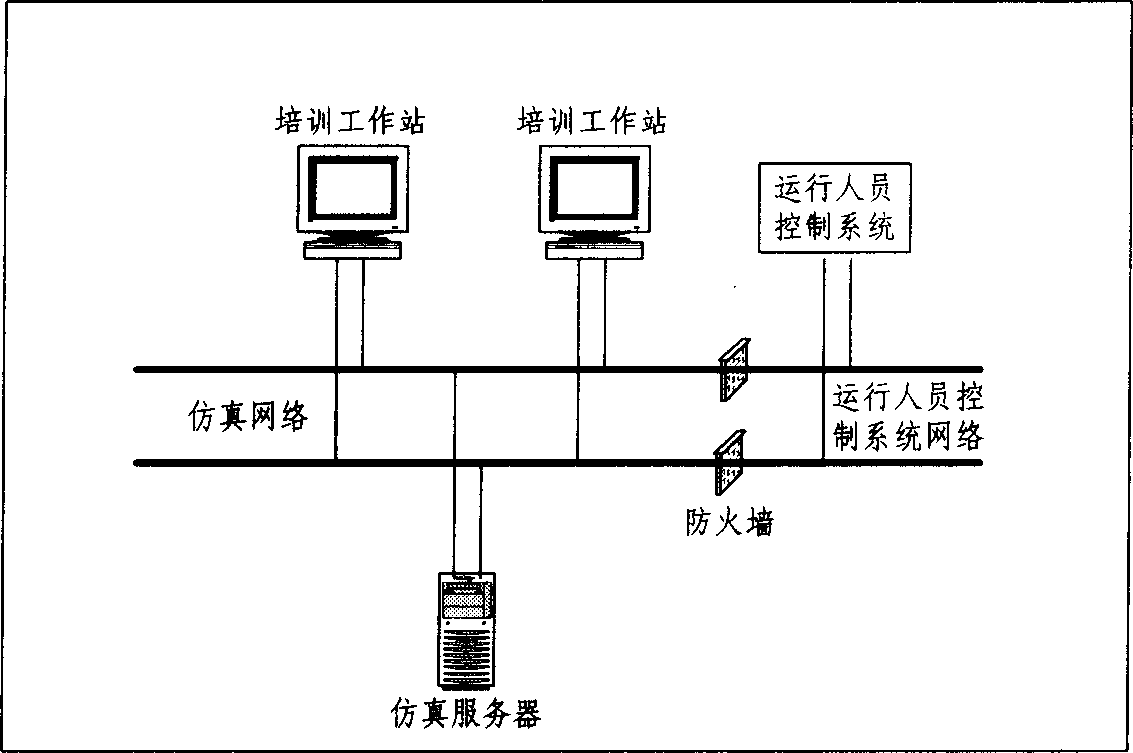
InactiveCN1881202APowerful simulation configurationEasy to set upData switching networksSpecial data processing applicationsInformation processingWorkstation
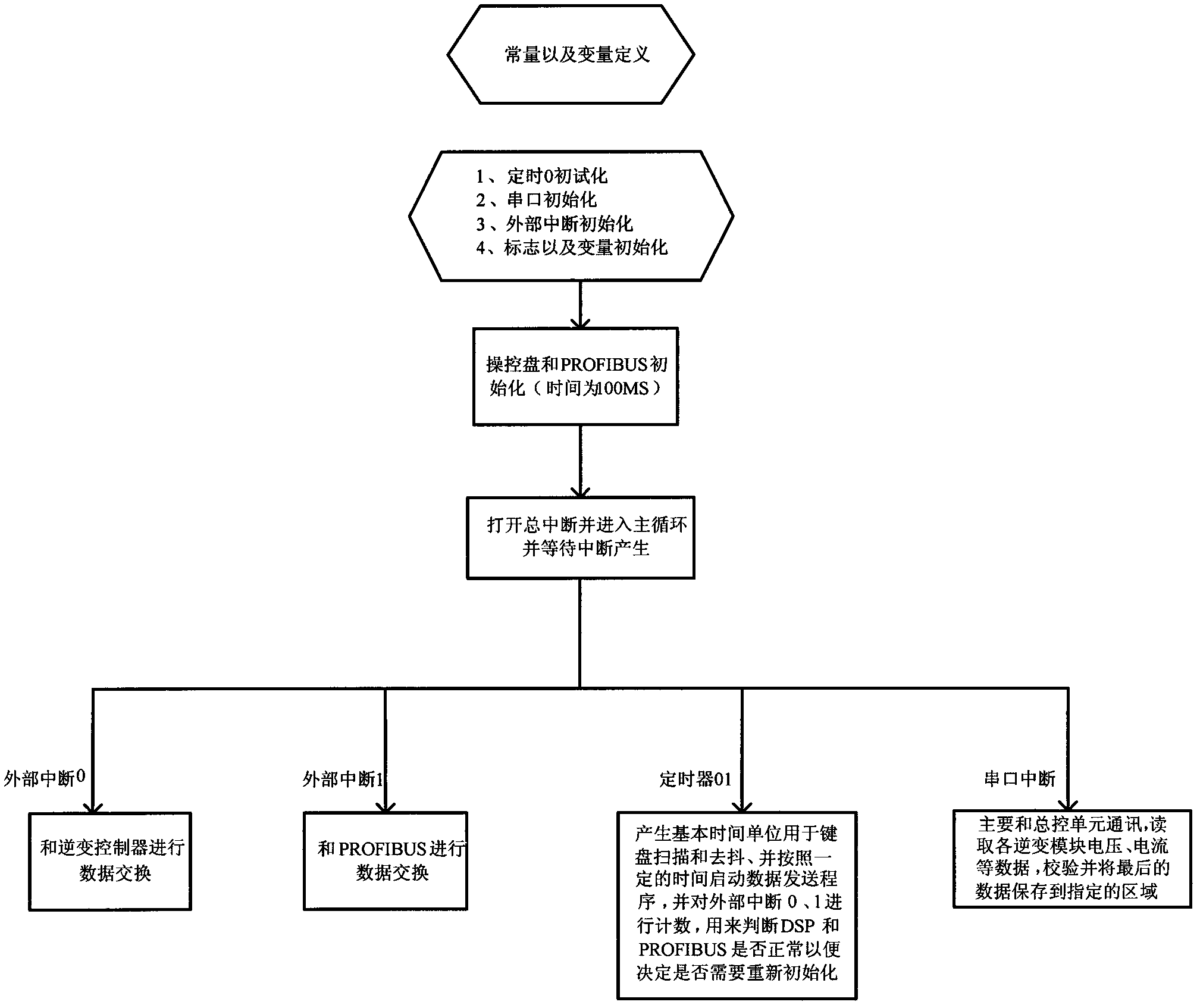
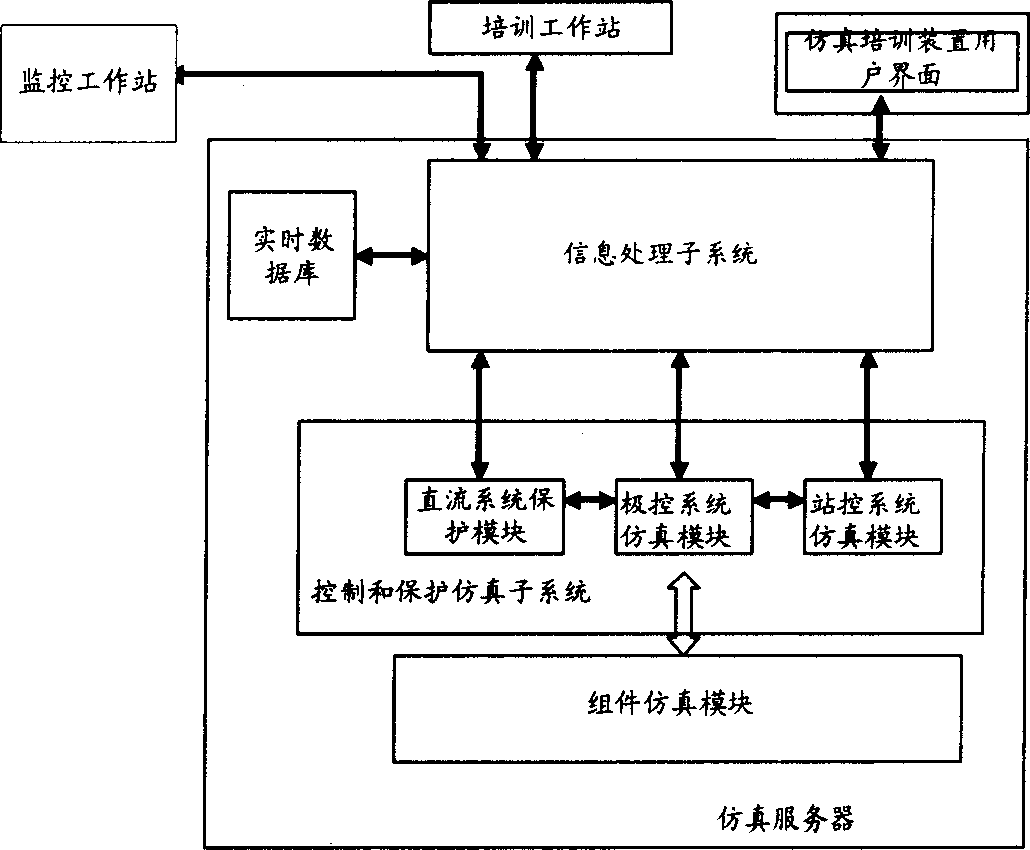
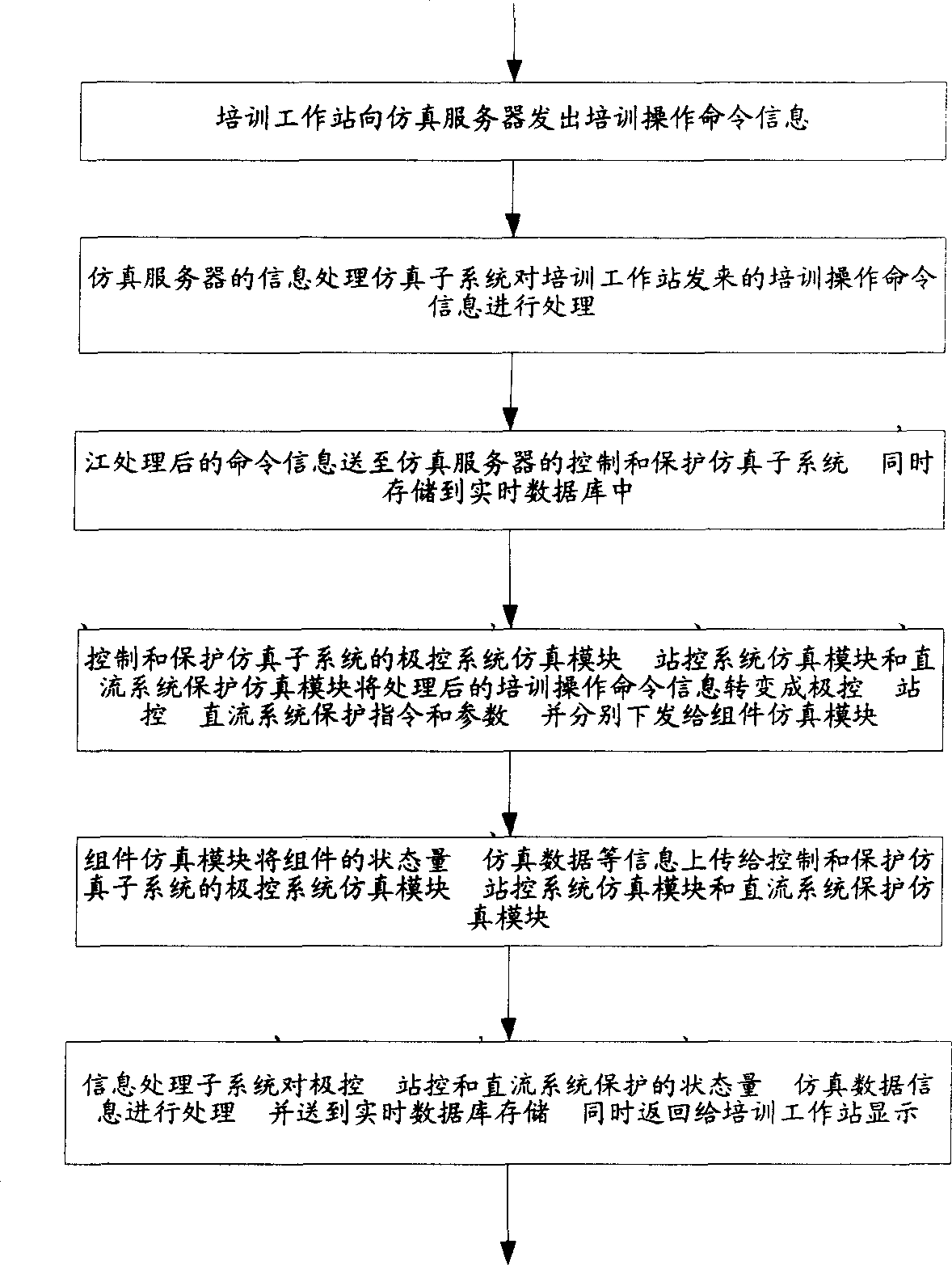
The invention relates to a high-voltage alternative direct current transmission training simulate system, wherein the simulate server comprises a simulate module, a control protective simulate subsystem, a real-time database, an information processing subsystem, and at least one train working station; the working station sends the train operation command to the simulate server; the information processing simulate subsystem processes the train operation command and sends it to the control protective simulate subsystem to be stored in the real-time database; the pole control and station control of control and protective simulate subsystem and the direct-current protective simulate module transform the treated train operation command into the relative command and parameters to be sent to the element simulate module; the element simulate module transmits the state value and the simulate data of element to the pole control, station control and the direct current protective simulate module; the information processing subsystem processes said state value, simulate data to be sent to the real-time database to be stored and feedback to the train working station to be displayed.
Owner:XUJI GRP +1
Alternating-current powerline thunderbolt shielding failure and counterattack recognition method
ActiveCN101290336AAccurate identificationReliable methodFault locationTransient stateAlternating current
The invention relates to a method for recognizing lighting shielding failure and counterattack of an AC transmission line. The different theories generated by the electromagnetic transient component of the lighting shielding failure and the counterattack of the high-voltage DC transmission line and different paths of transmission of the thunderbolt electromagnetic transient component on the circuit cause that the energy distribution of different frequency bands of the generated current transient state signals are different greatly. Therefore, in a travelling wave analysis and high-speed acquisition system at the protective installation position, the small wave analysis is adopted to extract the energy of the zero modulus current in different frequency bands. The shielding failure and the counterattack are differentiated according to the property of the energy distribution. A large amount of emulations show that the method is reliable and effective and can recognize accurately the shielding failure and the counterattack of the AC transmission line. The method has intuitive theory base and clear physical concepts, thereby being easy to implement, being widely applied to an AC system protective device, providing important data for the lightening protection design of the AC transmission line and providing reference for the operation and maintenance of the transmission line.
Owner:KUNMING UNIV OF SCI & TECH
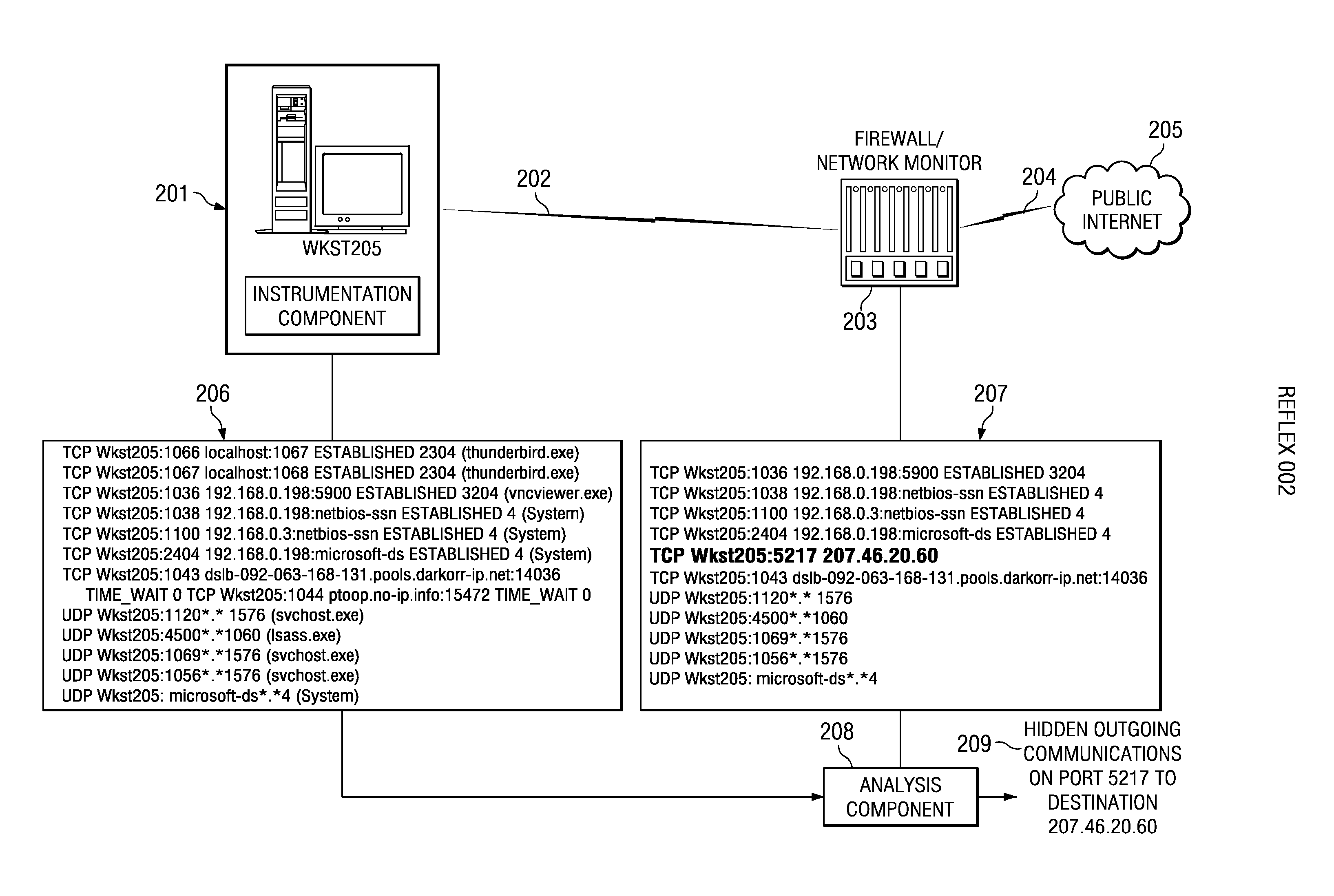
Detection of system compromise by per-process network modeling
InactiveUS20070169192A1Efficient and cost-effectiveMemory loss protectionError detection/correctionNetwork activityCommunications system
A computer system protection method monitors and evaluates per process network communications activity to determine whether the process has been compromised. In one embodiment, a network modeling scheme gathers data to build a model and then compares networking activities to the model as they occur. In an alternate embodiment, modeling is not required and the comparison is done of network data collected at one layer of a communication system to network-related data collected at another layer. As a result of a comparison and an indication of compromise, a given remedial action is taken.
Owner:STRATACLOUD
Travelling wave analysis recognition method for thunderbolt shielding failure and counterattack discrimination of direct current transmission line
ActiveCN101345415APhysical concepts are clear and intuitiveEasy to implementEmergency protective circuit arrangementsFault locationElectric power systemEngineering
The invention relates to a traveling wave analysis and recognition method for distinguishing lightning shielding failure from lightning counterattack of direct current transmission line. The lightning shielding failure of line is that lightning avoids the lightning shield line and directly strokes on the transmission line, while lightning counterattack of line is that lightning directly strokes on the lightning shield line or the tower. Because the earth resistance of tower exists, the potential on tower top suddenly increases and causes insulation flashover. The electromagnetic transient component generation mechanism of the high voltage direct current transmission line and the propagation path of lightning electromagnetic transient of the line in the lightning shielding failure are different from those in the lightning counterattack, the size and polarity of the initial surge voltage and the second surge voltage of the voltage transient signal exist significant difference. The traveling wave analysis and recognition method of the invention analyzes zero mode voltage using wavelet and distinguishes the lightning shielding failure and lightning counterattack failure according to the size and polarity of the initial surge voltage and the second surge voltage of the zero mode voltage in the traveling wave analysis and high-speed acquisition system of the protection zone. A lot of simulation results show that the method is reliable and effect. The physical concept of the invention is visible and clear, the method is easy to achieve and wide to use in the direct current system protector, also provides accurate initial data for researching lightning characteristics, analyzing lightning accident, discussing lightning protection countermeasure of transmission line and designing insulation coordination in the power system.
Owner:KUNMING UNIV OF SCI & TECH
Redundant electrical brake and protection system for electric generators
An apparatus for electric braking and system protection for an electric generator includes a dynamic brake and a crowbar circuit designed for cooperation with power converters to dump power upon command. The dynamic brake includes at least one resistor and the crowbar circuit includes another at least one resistor for dissipating power from the electric generator. Methods for use of the electric braking and system protection calls for shunting the power to at least one of the dynamic brake, the crowbar circuit and the generator side power converter.
Owner:GE INFRASTRUCTURE TECH INT LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com