Patents
Literature
871 results about "Access to information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
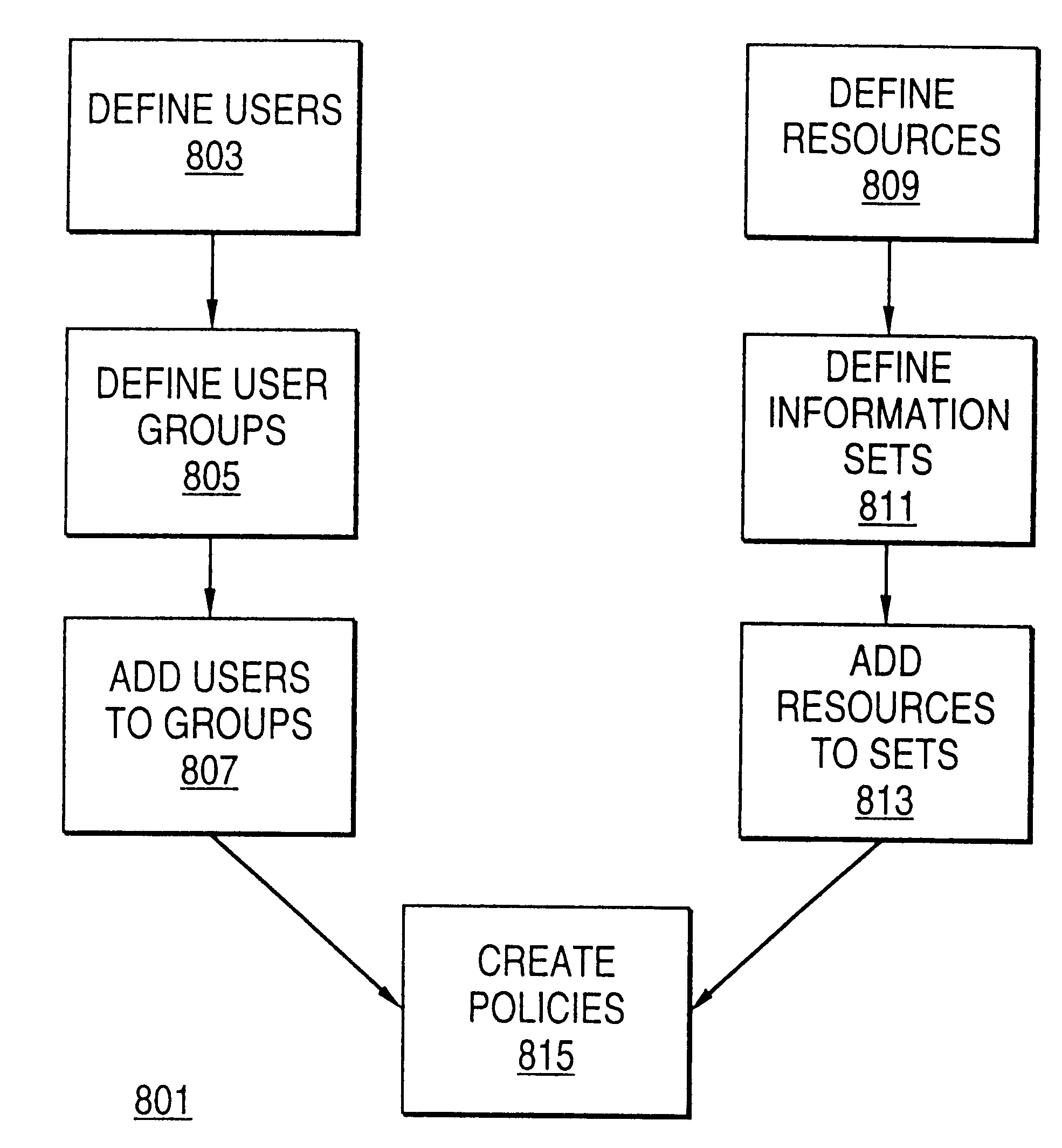
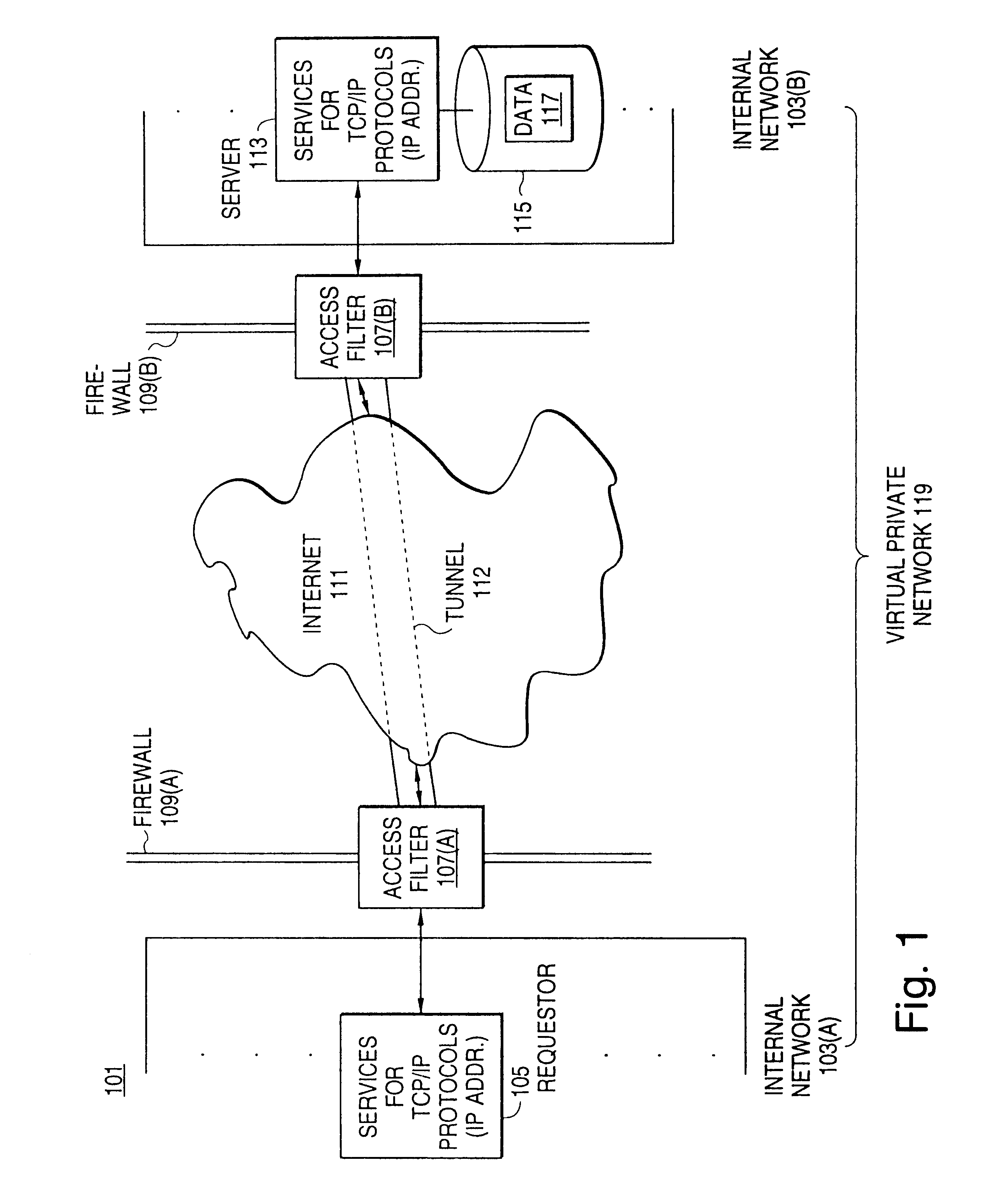
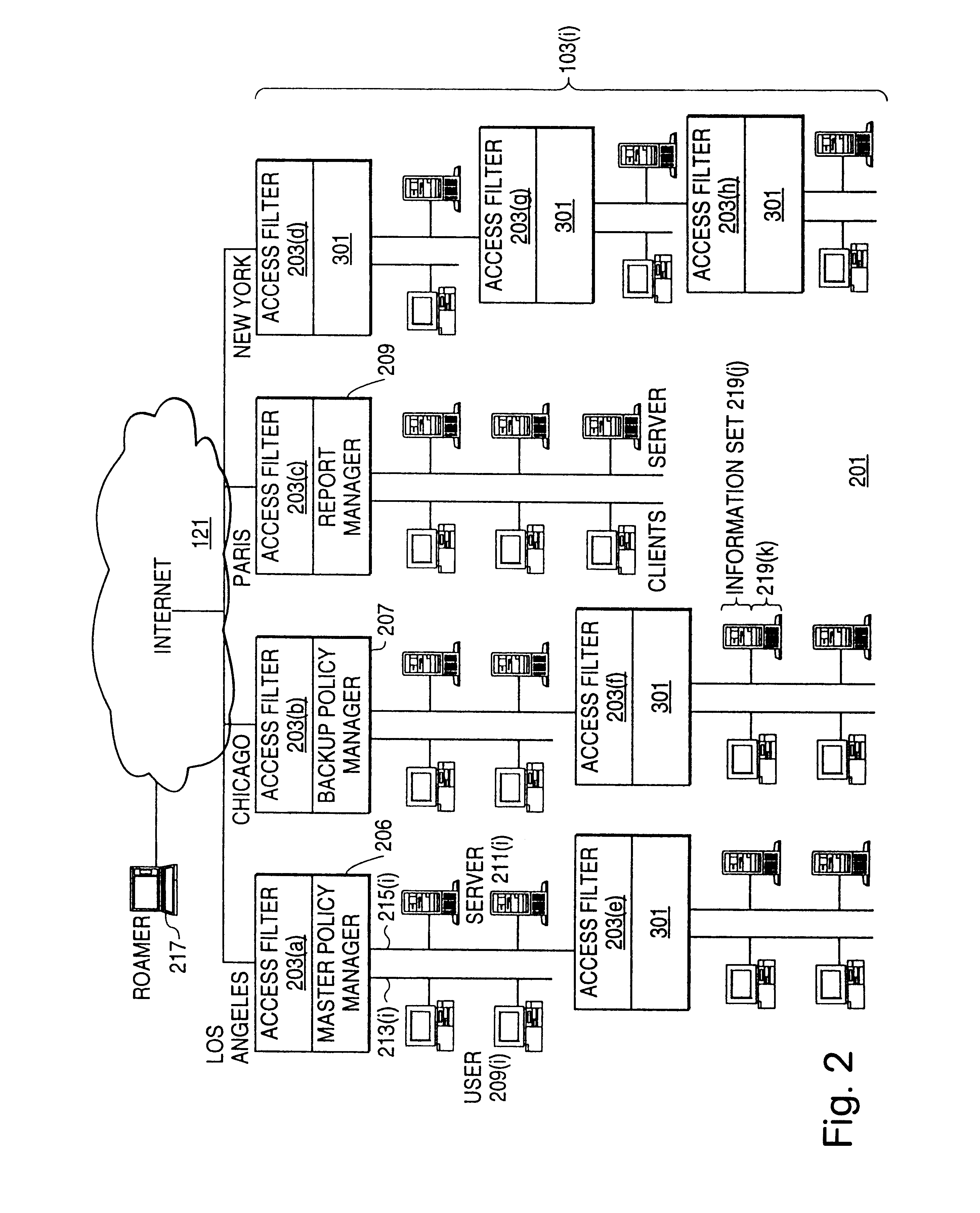
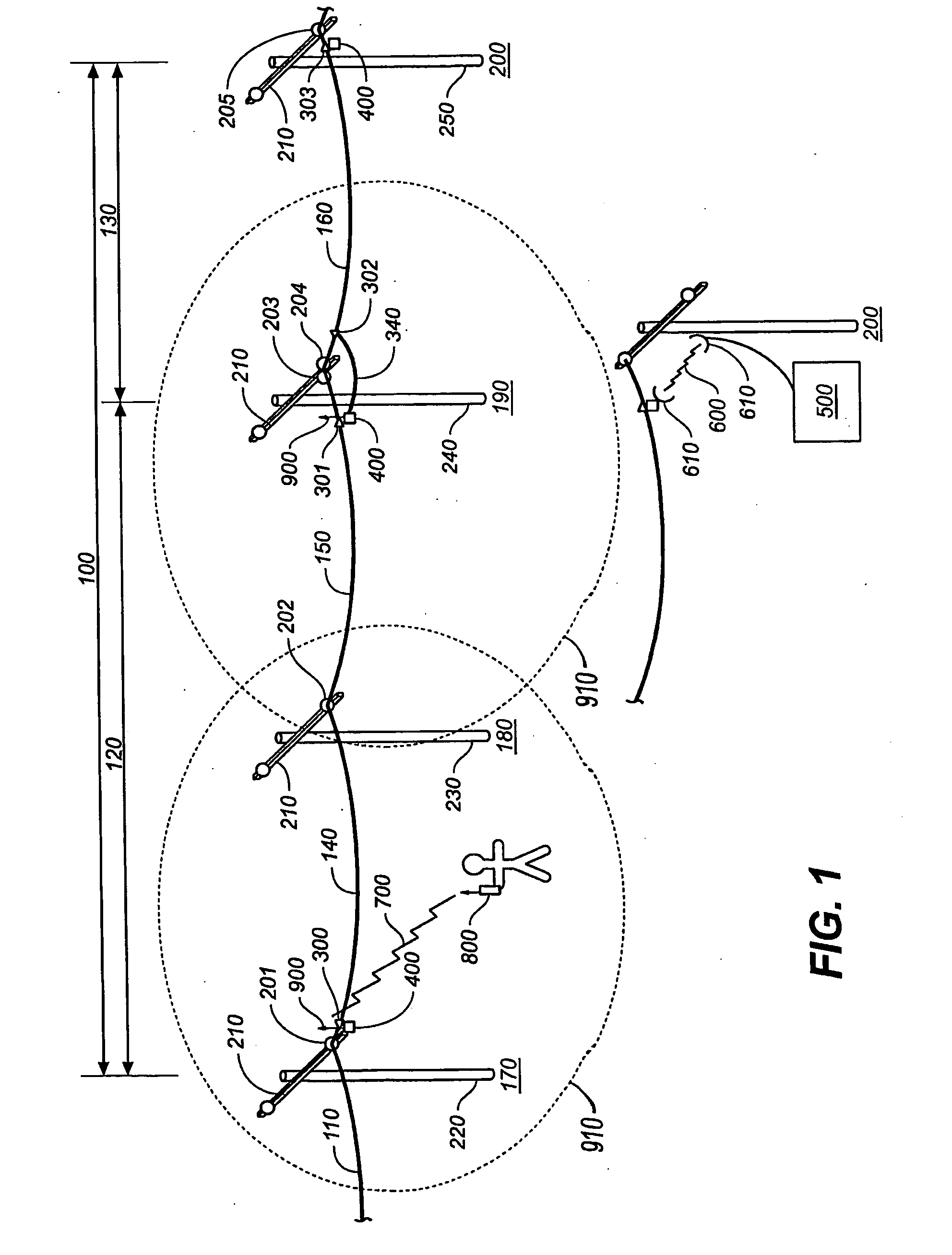
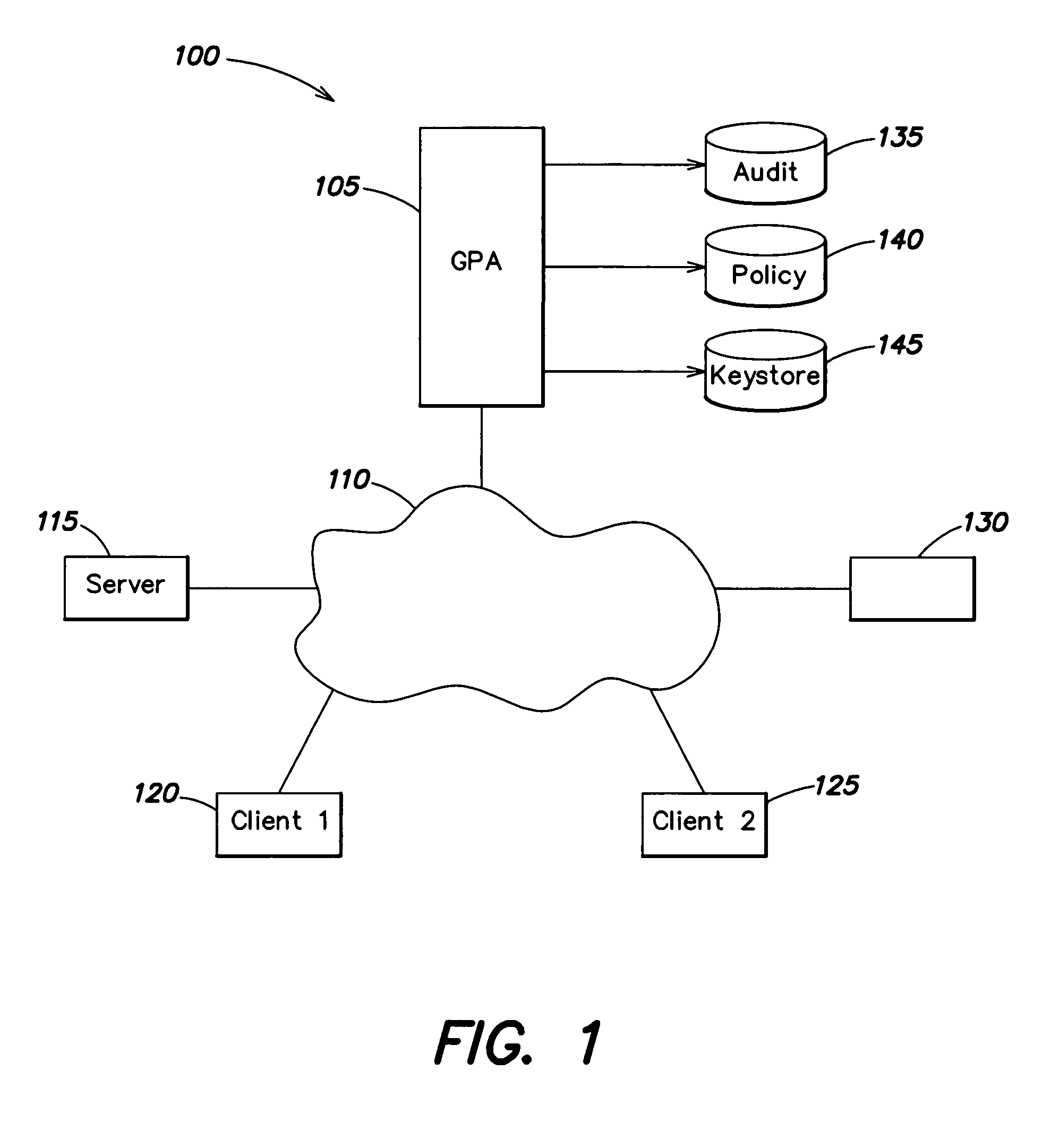
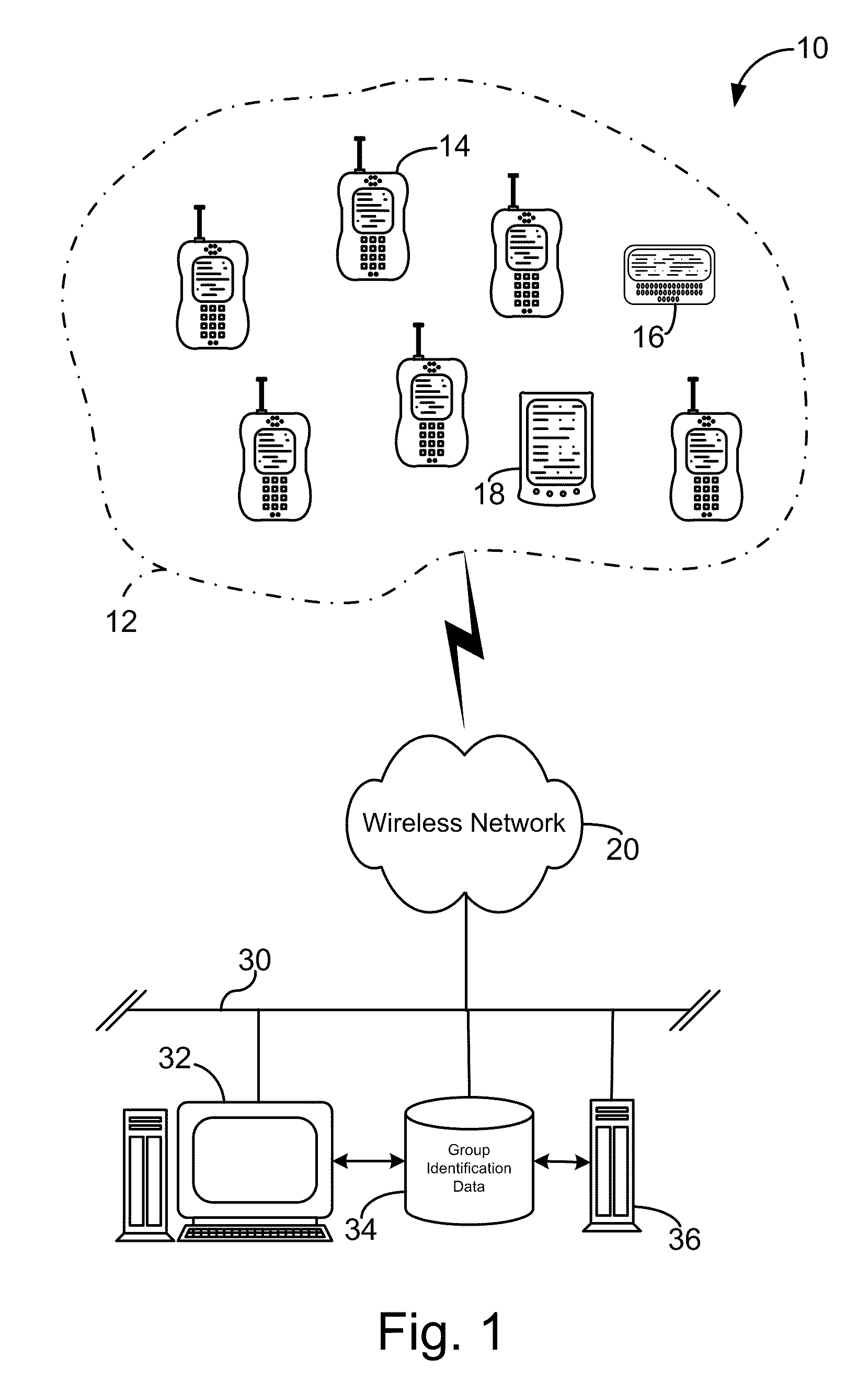
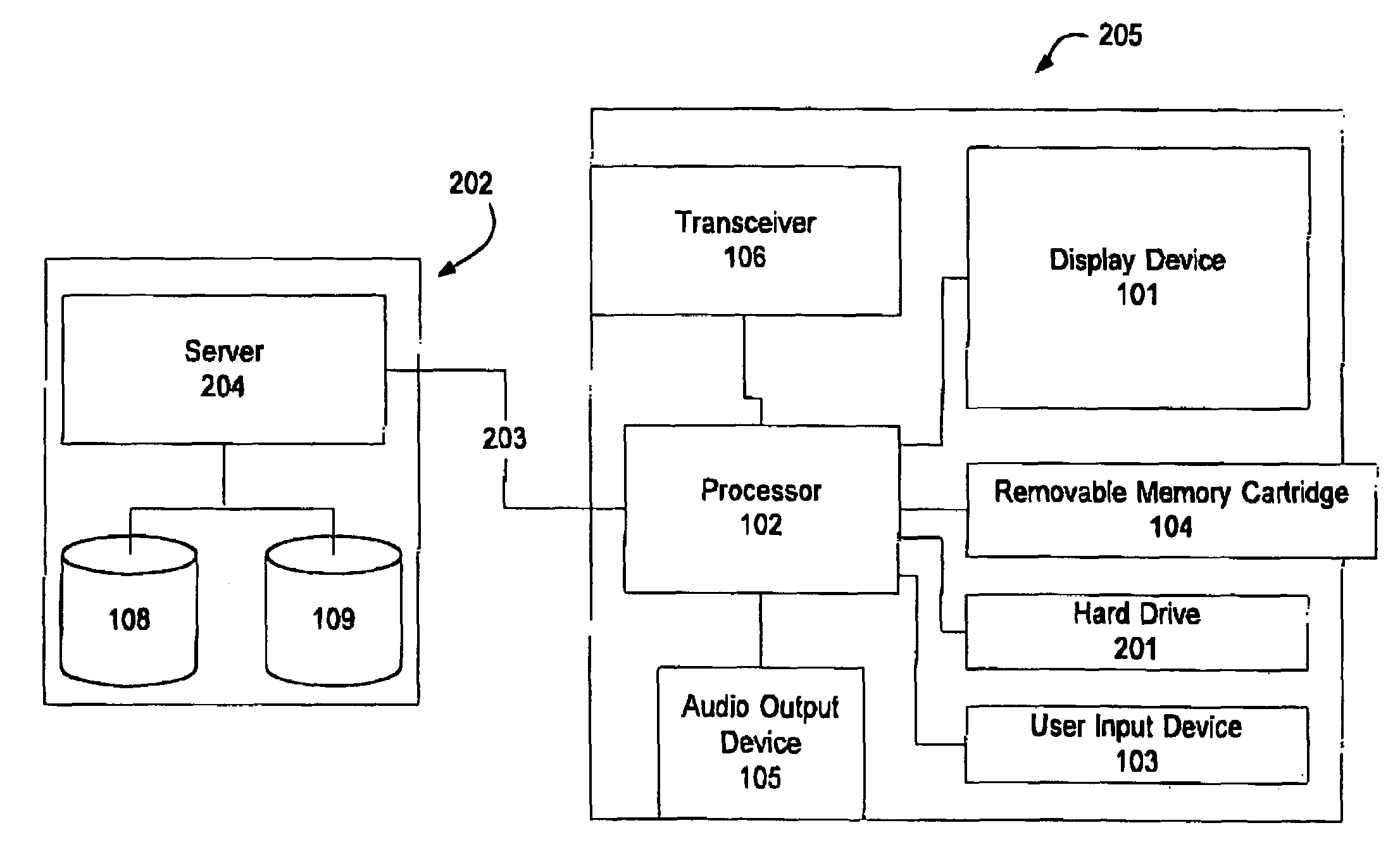
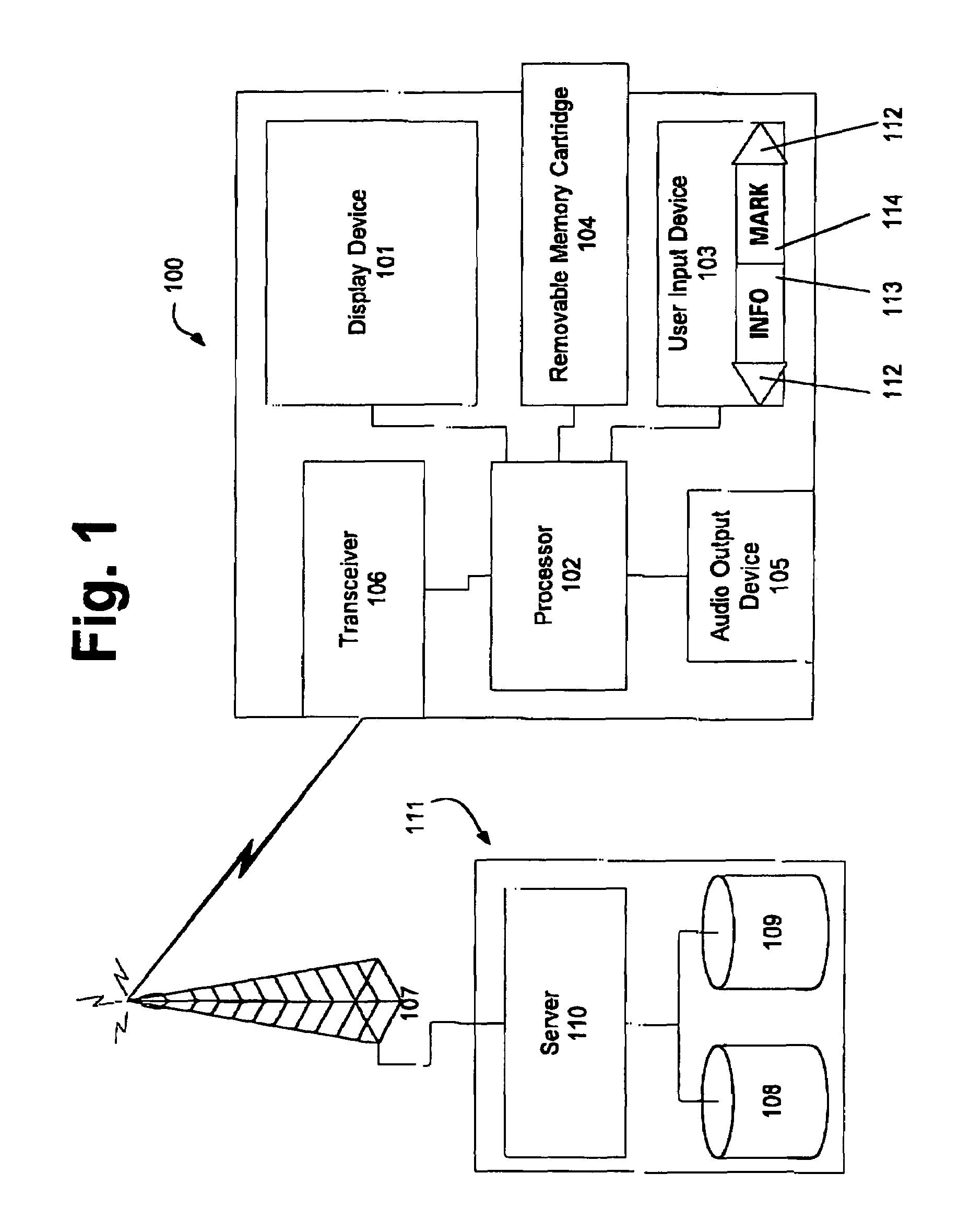
Distributed administration of access to information
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
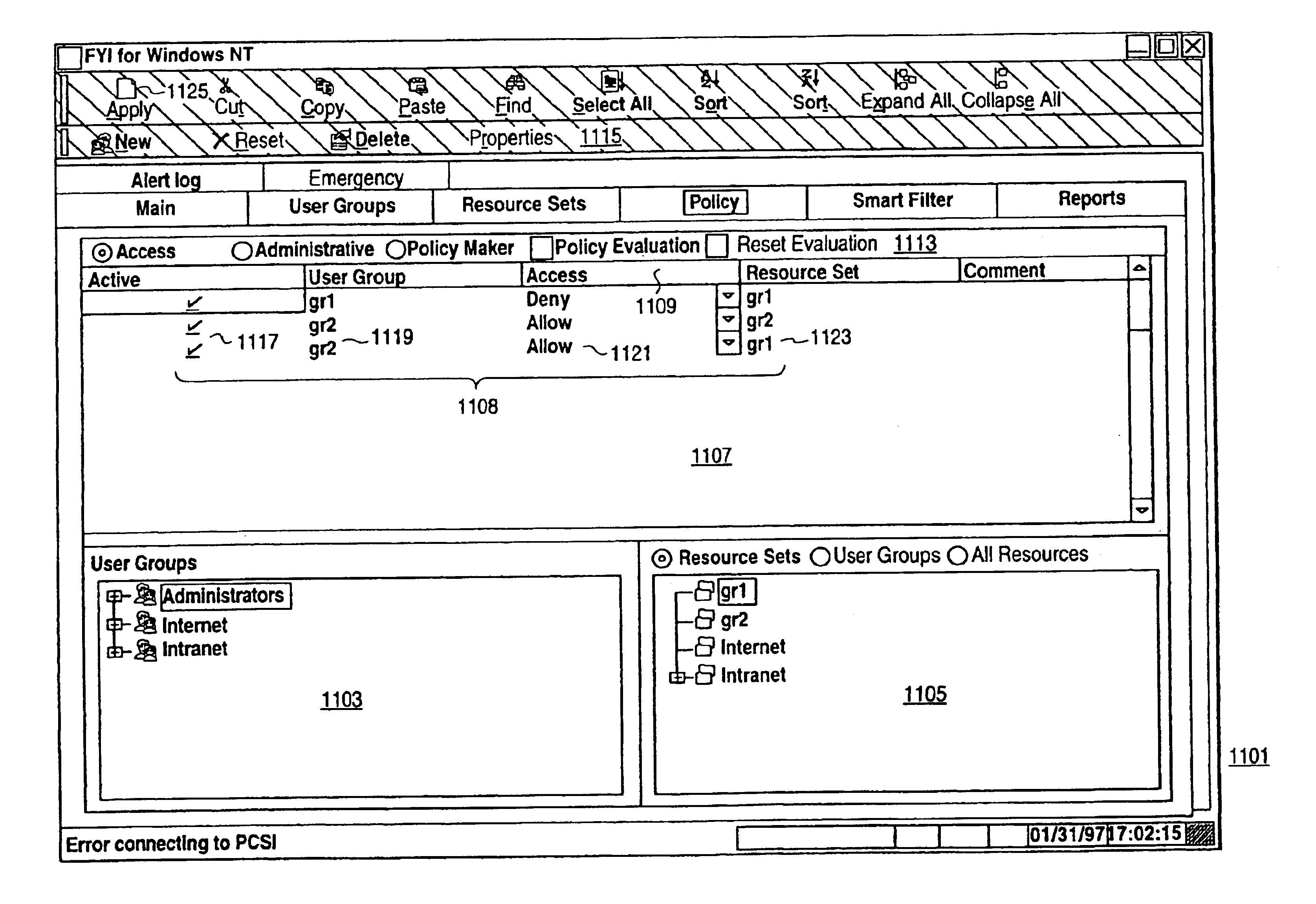
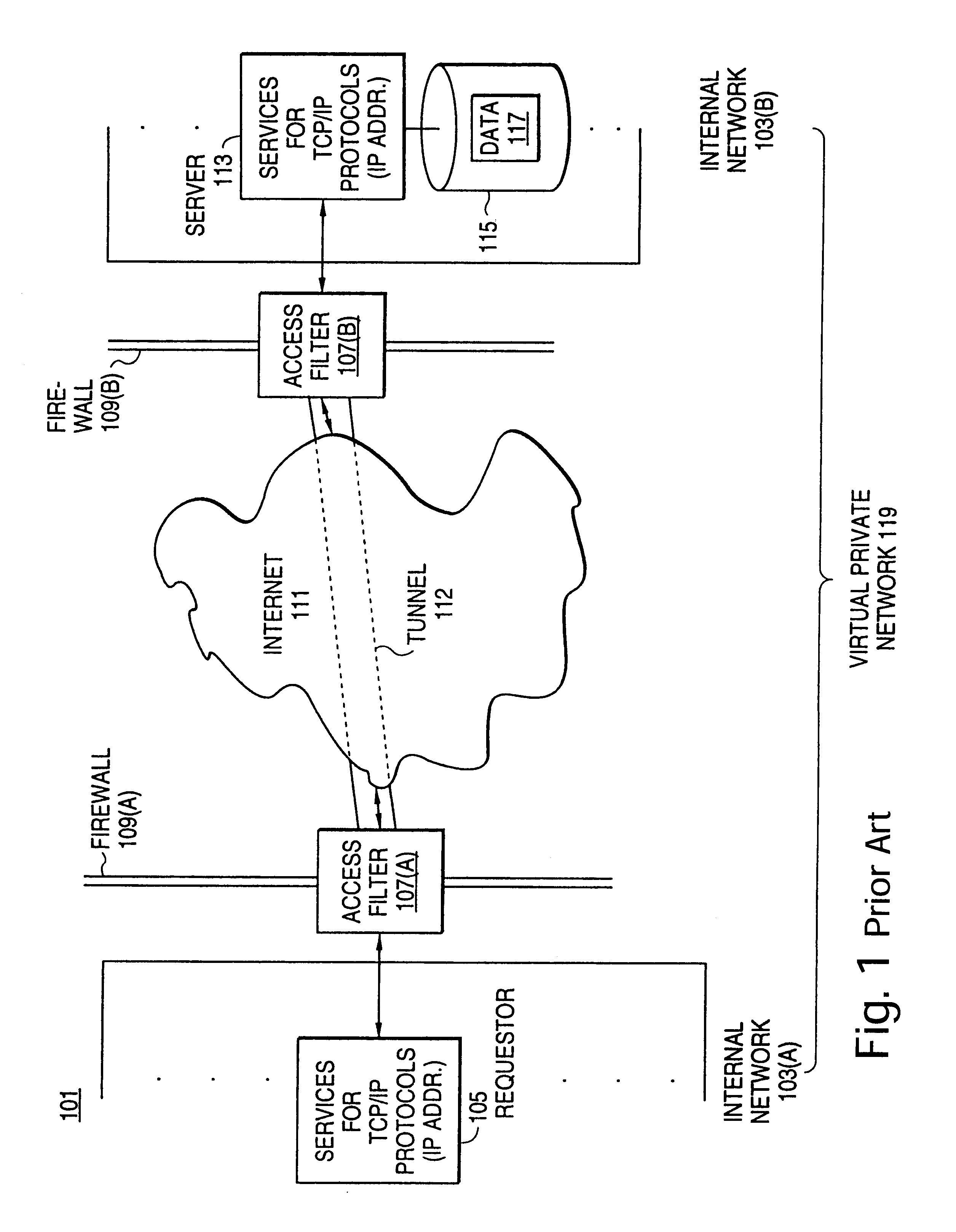
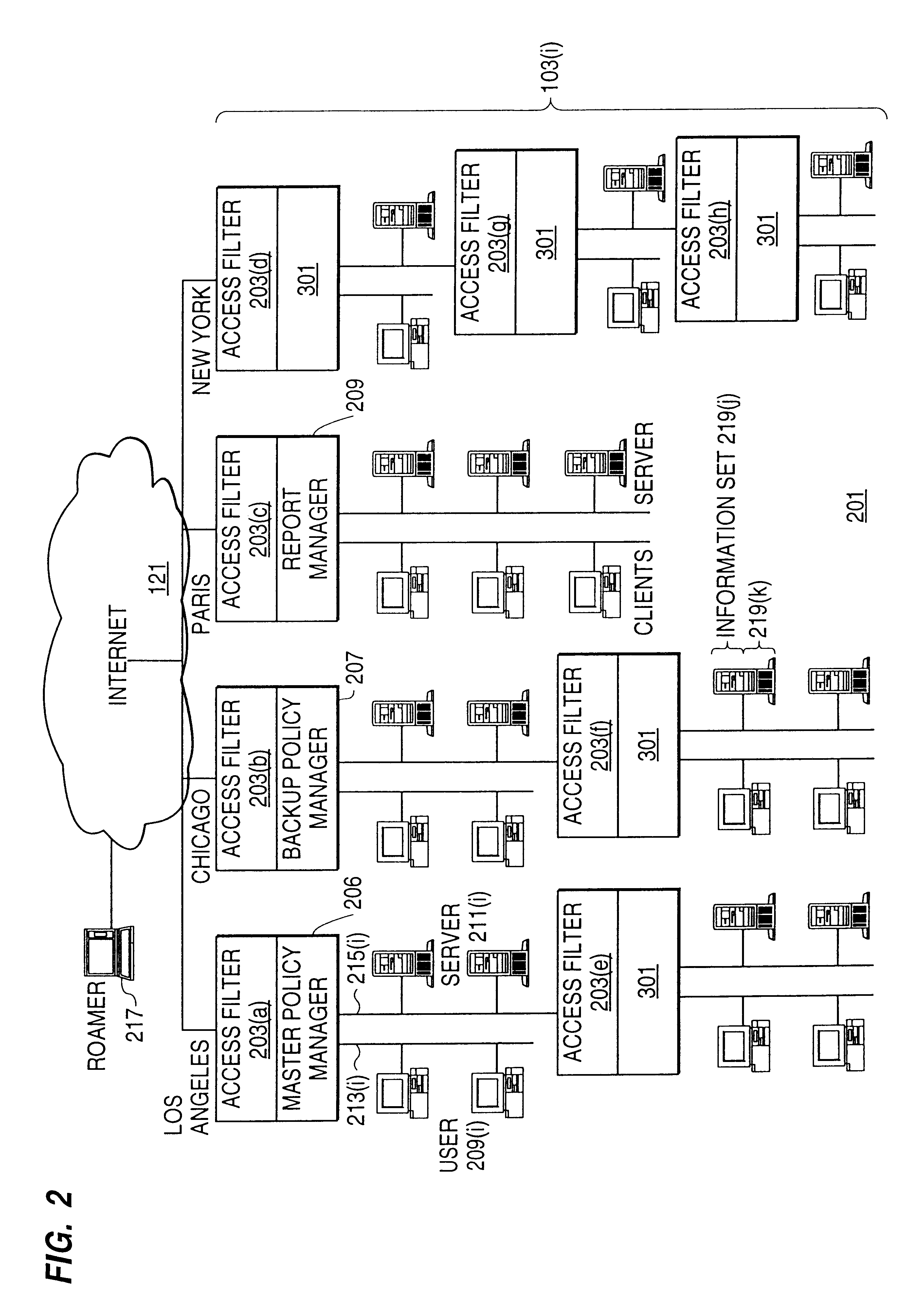
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Distributed antenna system using overhead power lines
InactiveUS20090079660A1Great contributionReadily apparentPower distribution line transmissionBroadcast transmission systemsTransport systemDistributed antenna system
A distributed antenna system having a transport portion including at least one overhead power line for transmitting system information along its length, and a distribution portion including at least one local access point disposed along the length of the power line for providing local access to information transported by the transport portion.
Owner:CORRIDOR SYST INC
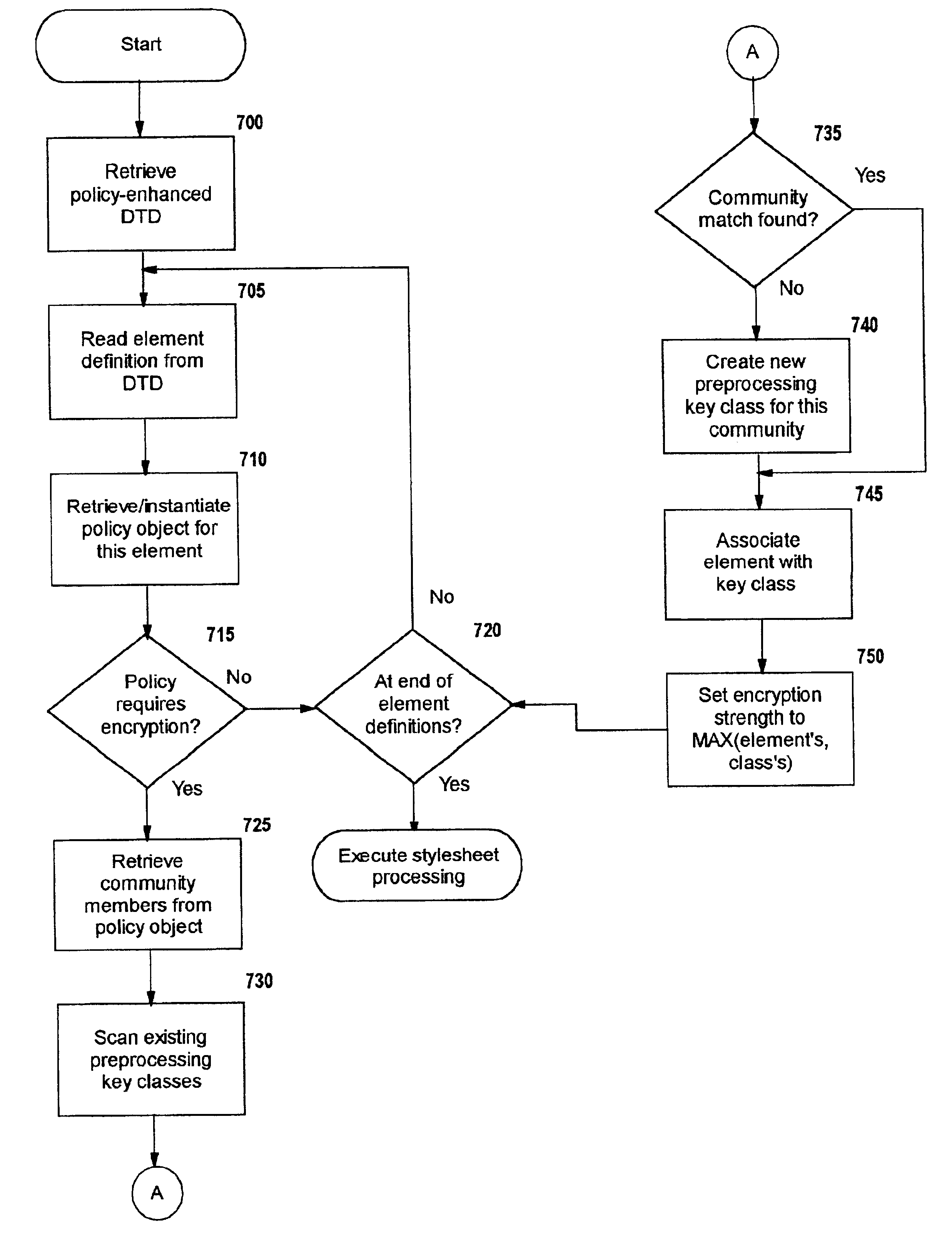
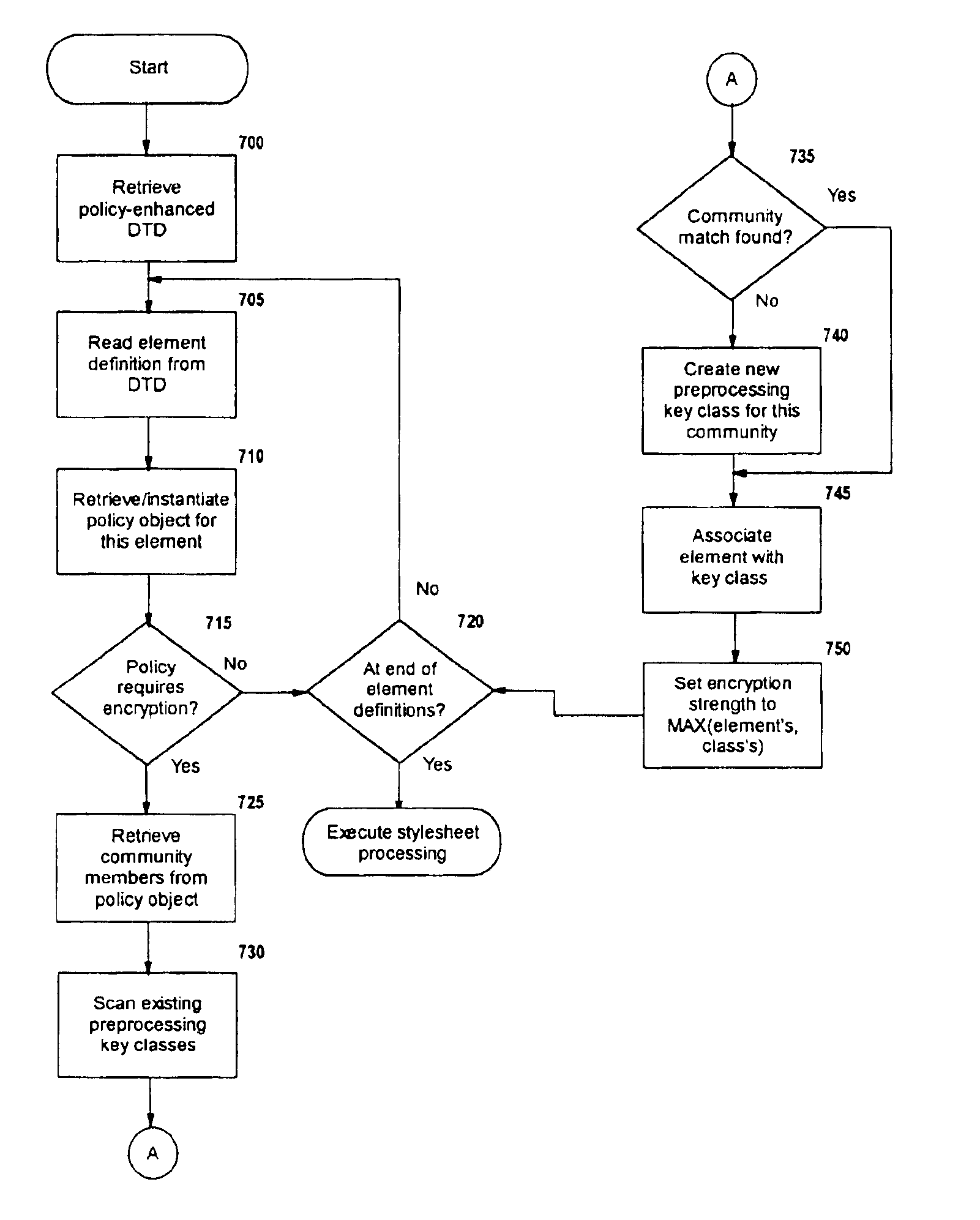
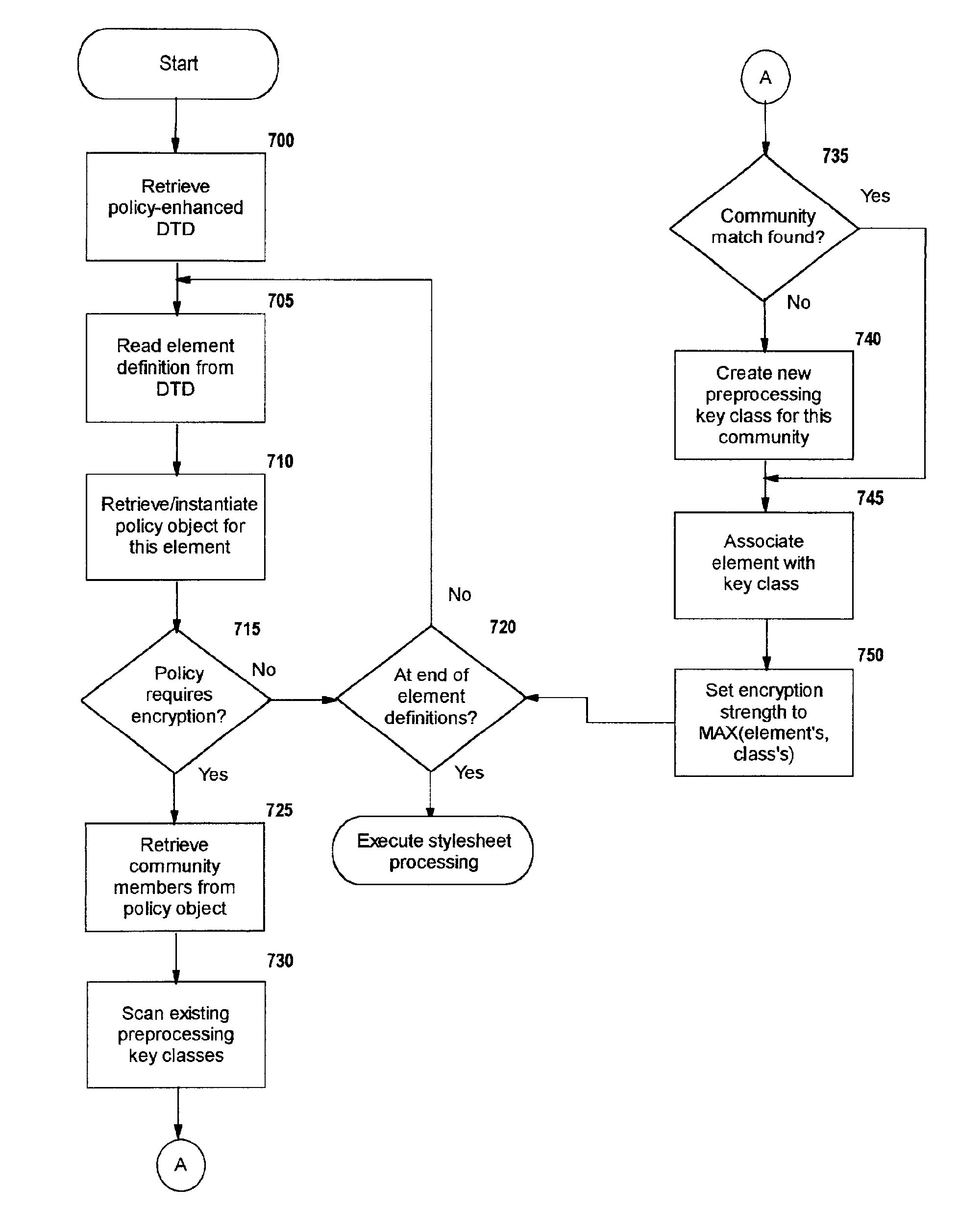
Selective data encryption using style sheet processing
InactiveUS6931532B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
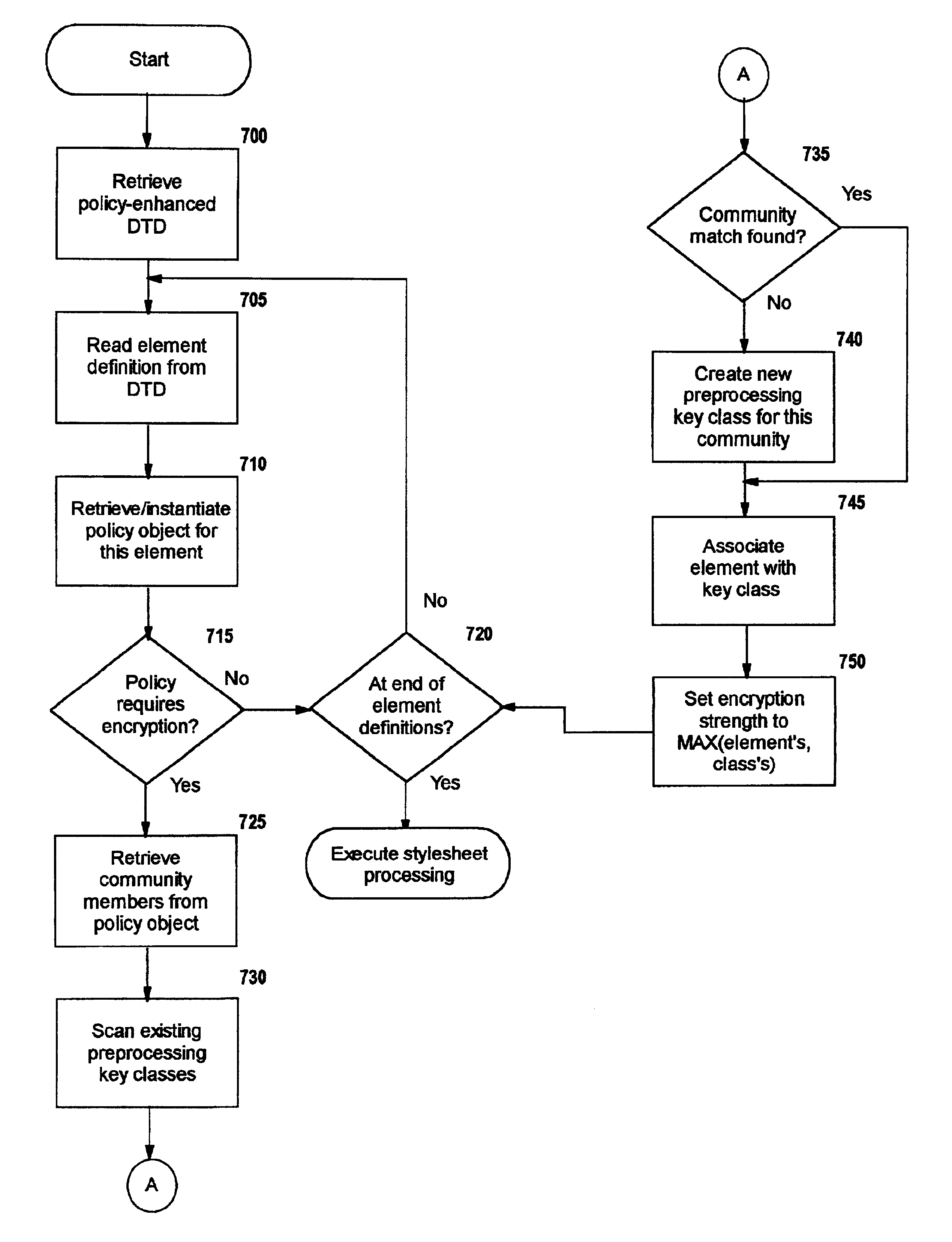
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
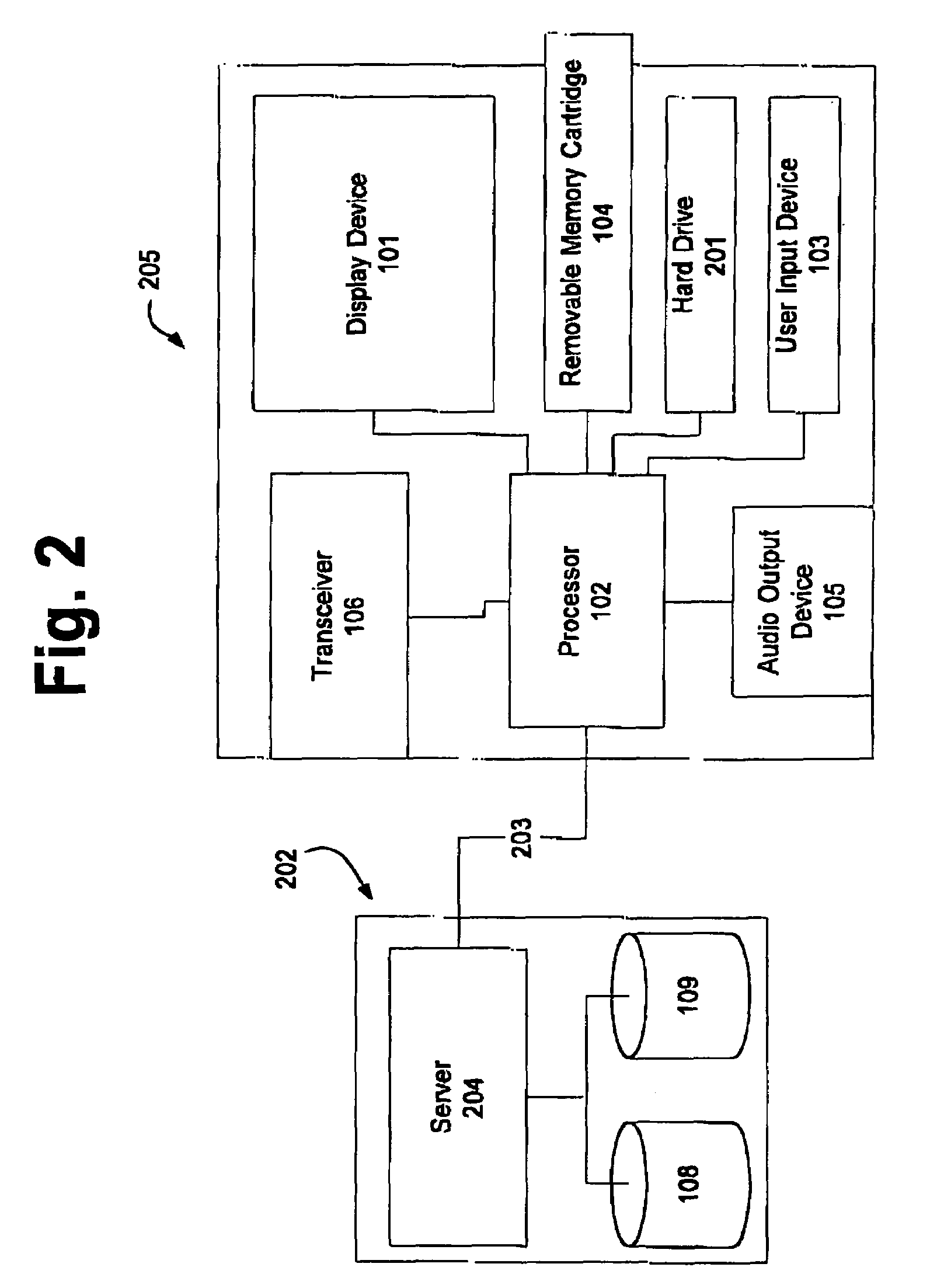
Distributed administration of access to information
InactiveUS6785728B1Cathode-ray tube indicatorsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Selective data encryption using style sheet processing for decryption by a client proxy
InactiveUS6978367B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureDocument preparation
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
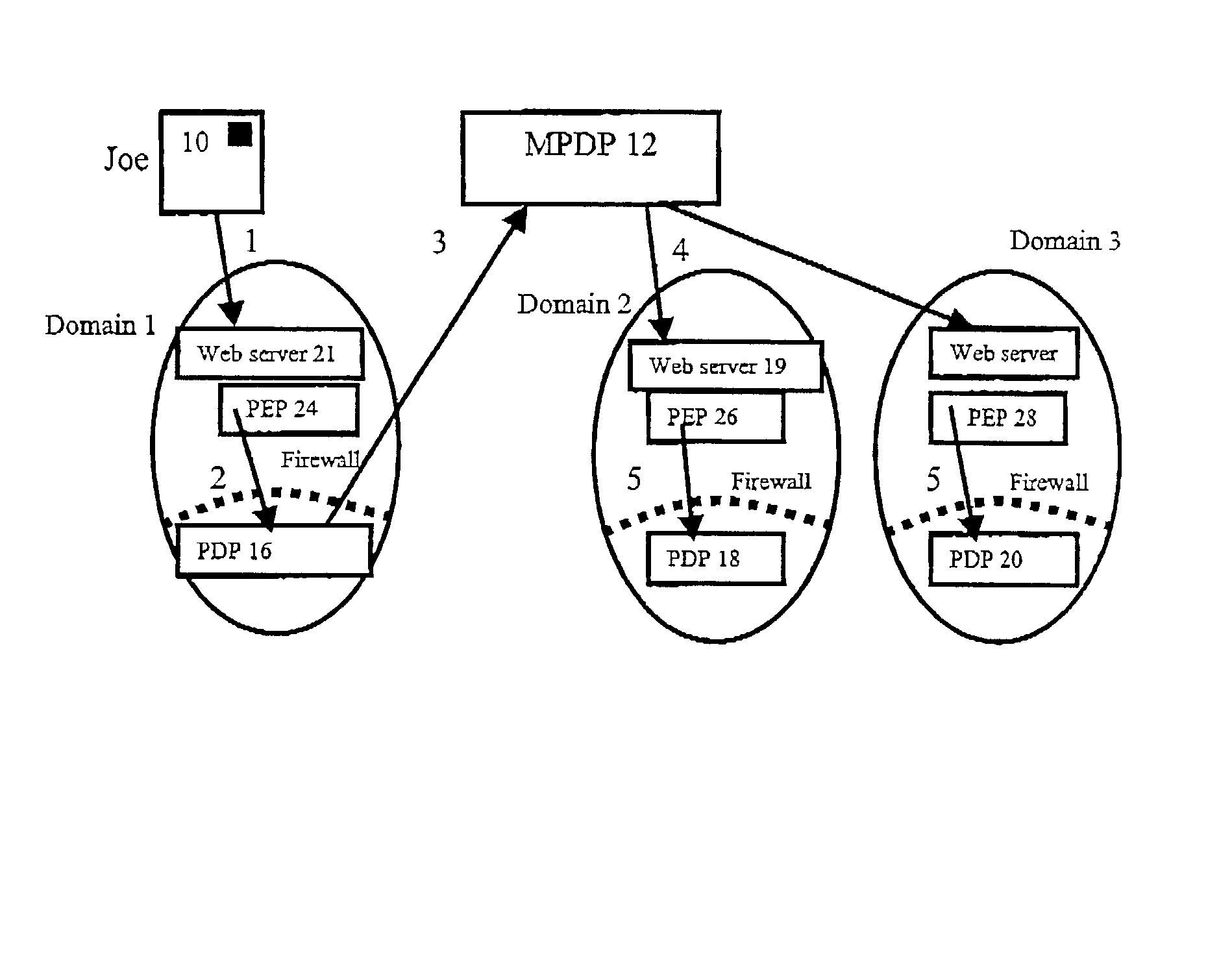
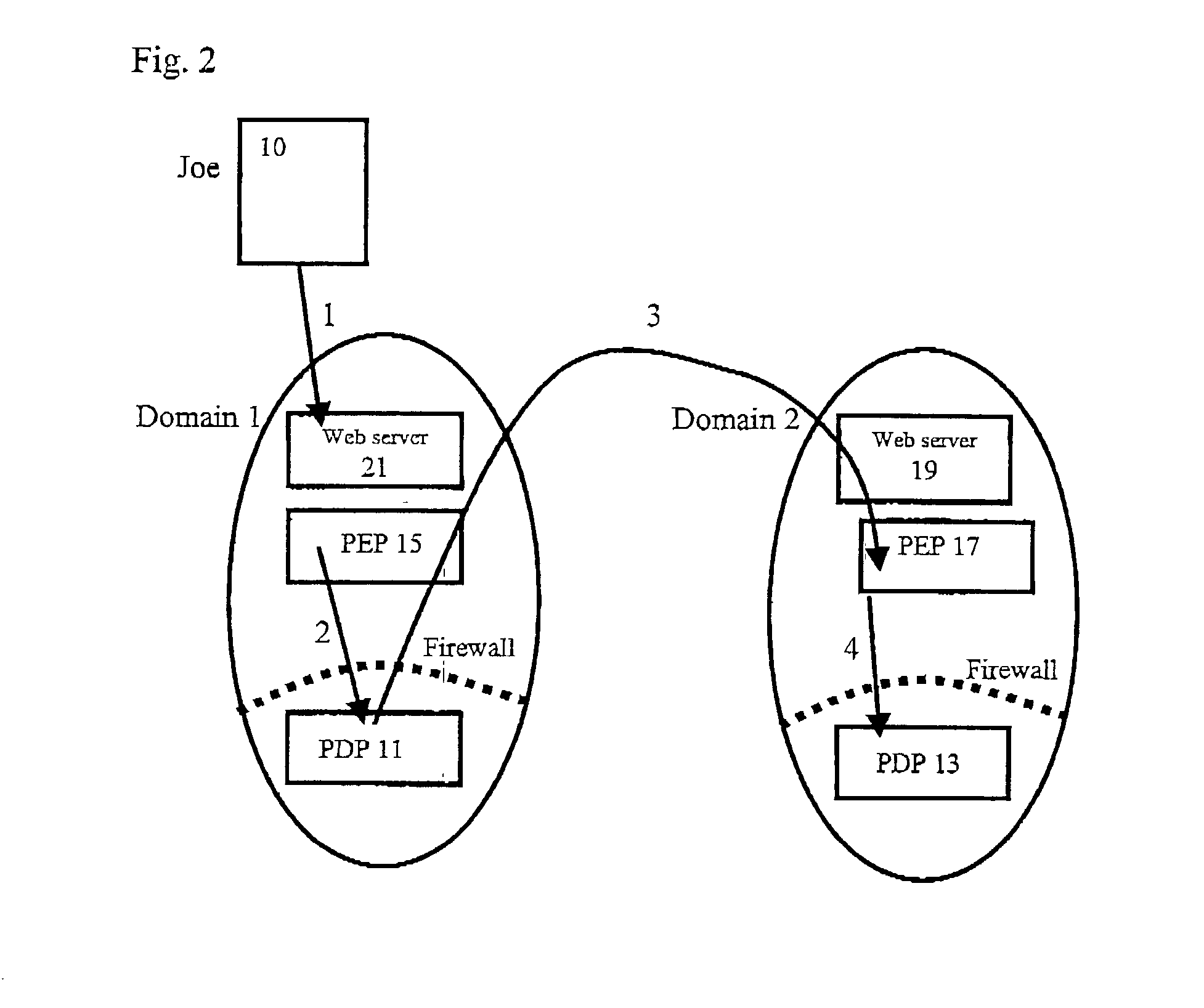
Multi-domain authorization and authentication
ActiveUS20030023880A1Special data processing applicationsSecuring communicationPolicy decisionAuthorization
A method of multi-domain authorisation / authentication on a computer network comprises: a user making a request to a policy enforcement point of a computer for access to information on the computer; providing a location address for a user's authorisation and / or authentication information, a policy decision point of the service on the computer network then verifying the authorisation / authentication information; and the user being given access by the PEP to the information or the service requested, if the request is accepted, wherein the user's authorisation / authentication and / or further information is located on a meta policy decision point (MPDP).
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
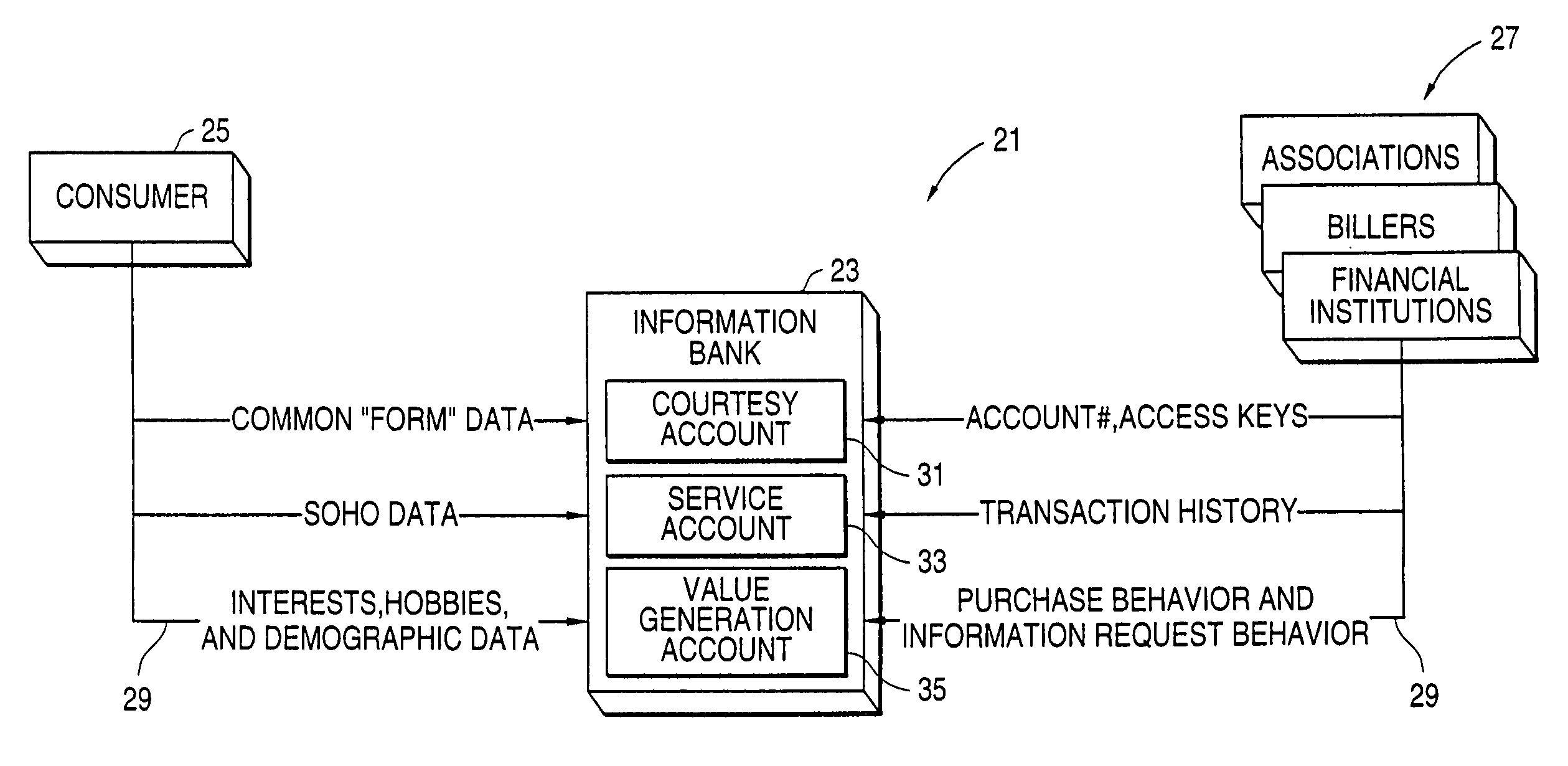
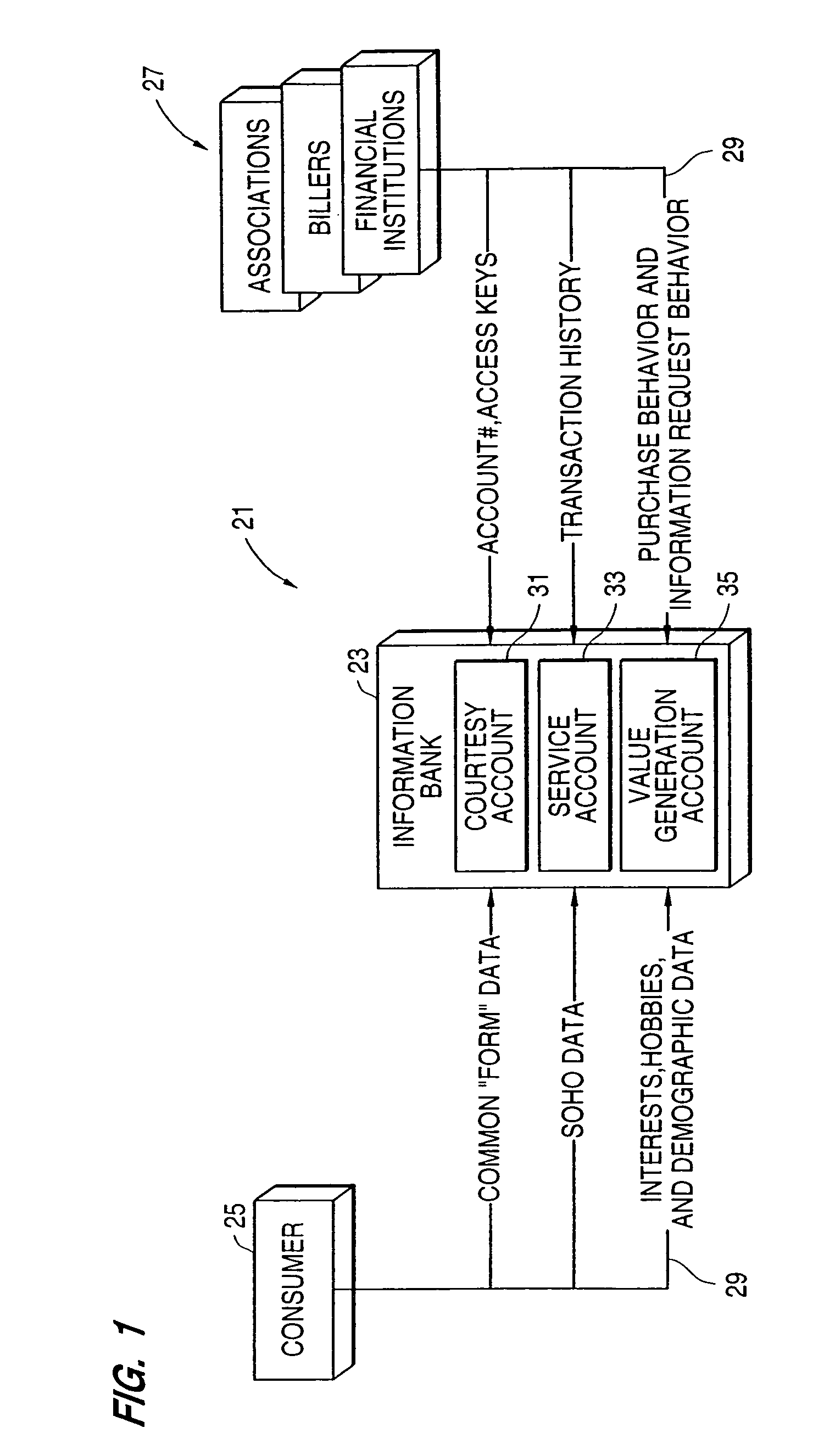
Method and system for anonymizing purchase data
InactiveUS7200578B2Easy accessEliminate needComplete banking machinesFinanceInternet privacyData storing
A system, in which information is the primary asset and in which investments may be made in information, includes multiple data stores for storing different types of a user's information. The safe, secure and properly authorized transfer of information while preserving individual privacy is provided. The system also provides for secure backup and storage, as well as for ubiquitous and nomadic access to information while maintaining the privacy of such information. A first data store includes static identification data about a user. A second data store includes moderately dynamic personal data about the user. A third data store includes dynamic demographic information data about the user. An electronic wallet can be used with the system to download selected portions of the data for use by the user. A method of use of the data includes using the data for billing out forms, providing services to the user and allowing merchants to selectively target users for sales while maintaining user anonymity.
Owner:CITICORP CREDIT SERVICES INC (USA)
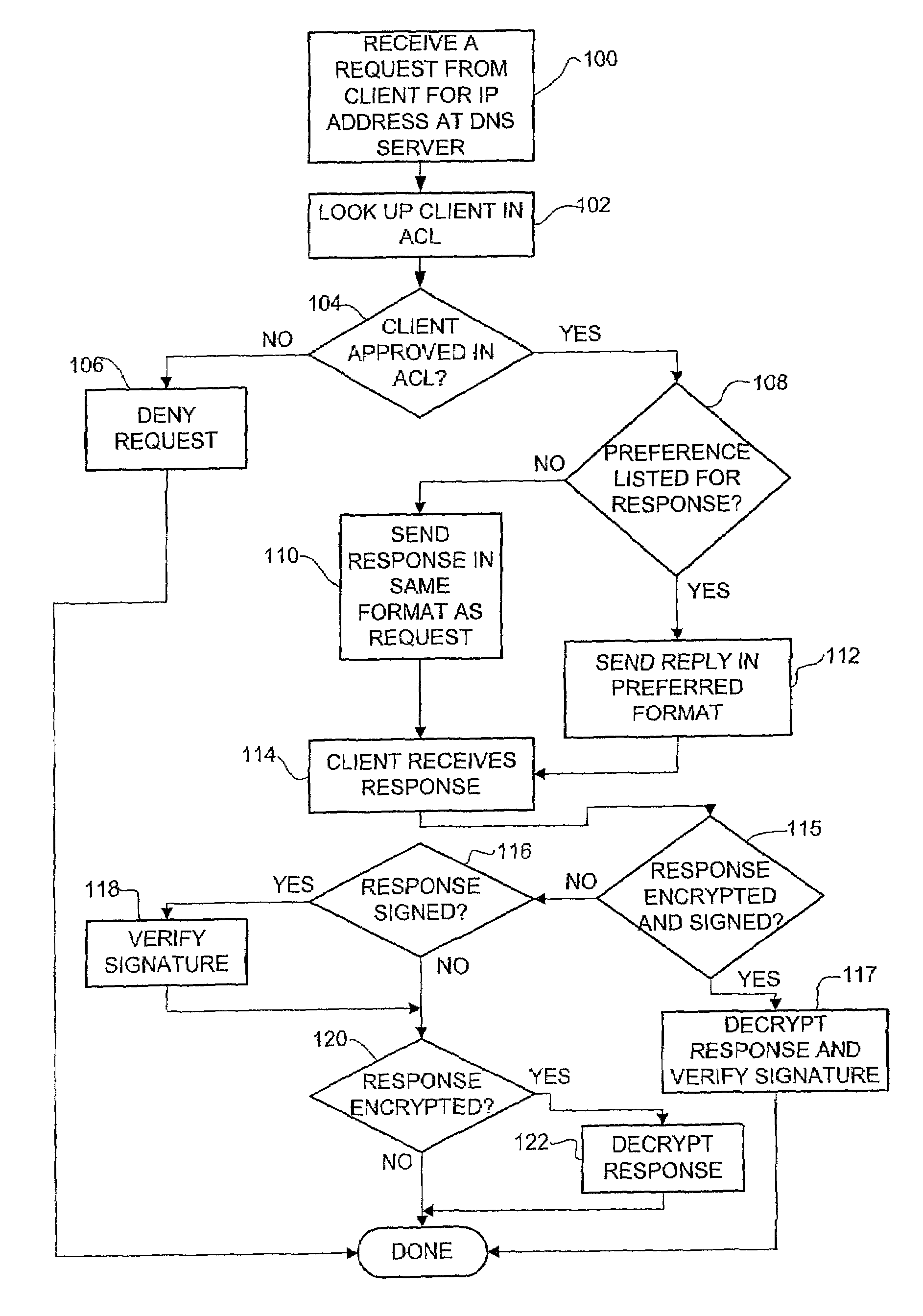
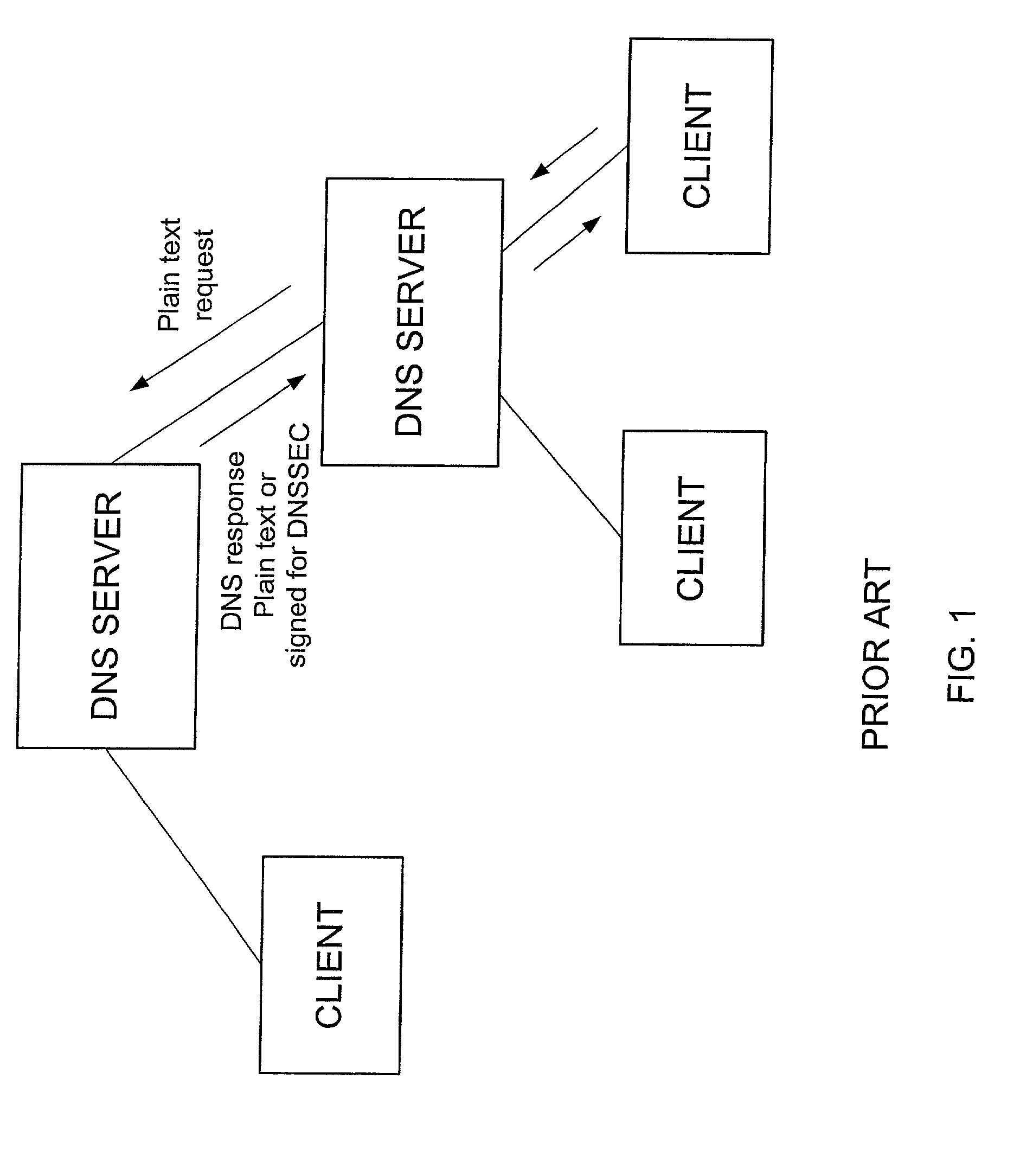
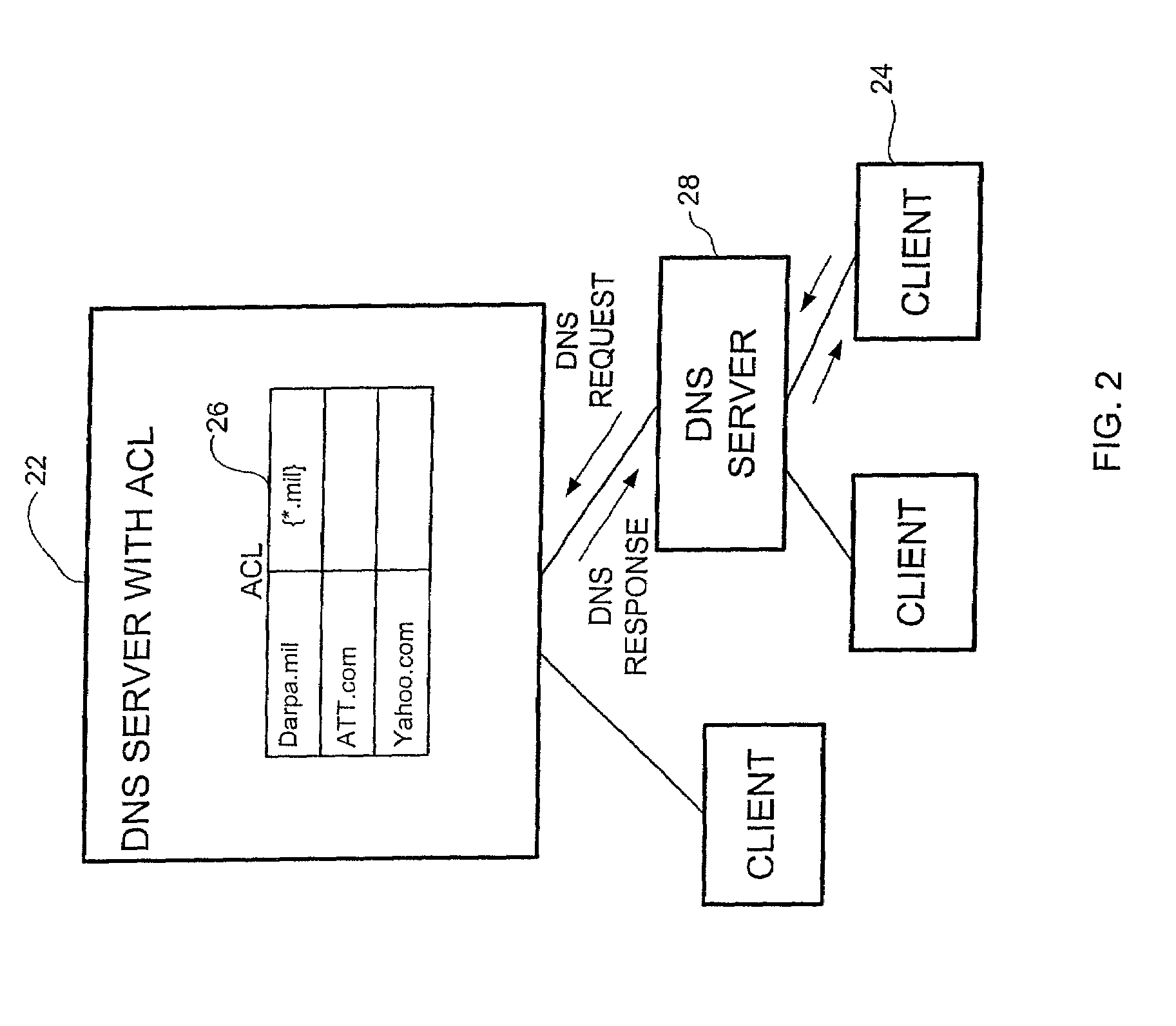
DNS server access control system and method
A method for controlling access to information from a DNS server having an access control list specifying clients approved to receive an IP address corresponding to a domain name of a target host is disclosed. The method includes receiving a request from a client for an IP address of a domain name at the DNS server and looking up the domain name in an access control list. The client is sent a reply containing the IP address of the domain name if the client is authorized in the access control list to receive the IP address. If the client is not authorized to receive the IP address, the request is denied.
Owner:MCAFEE LLC
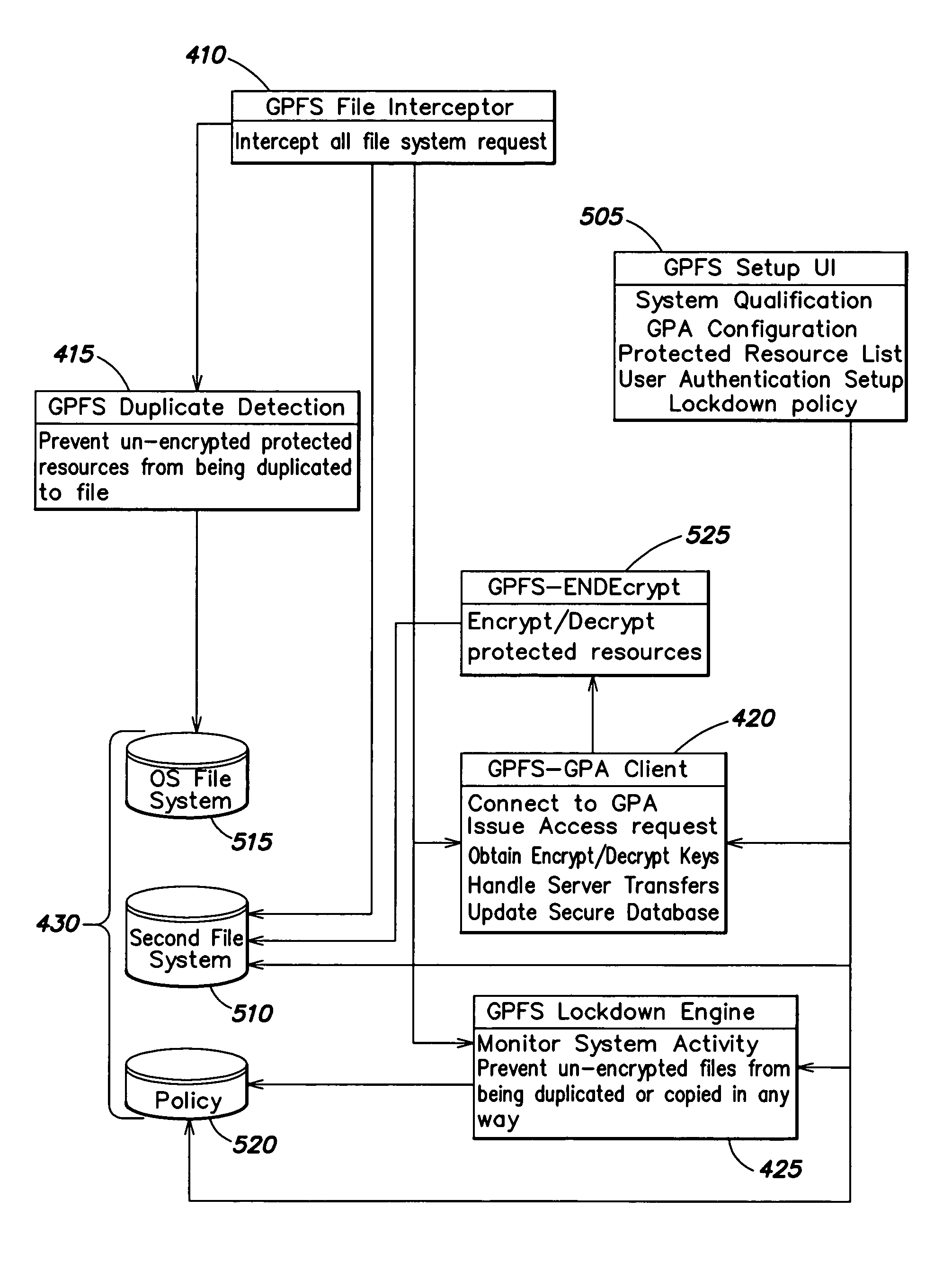
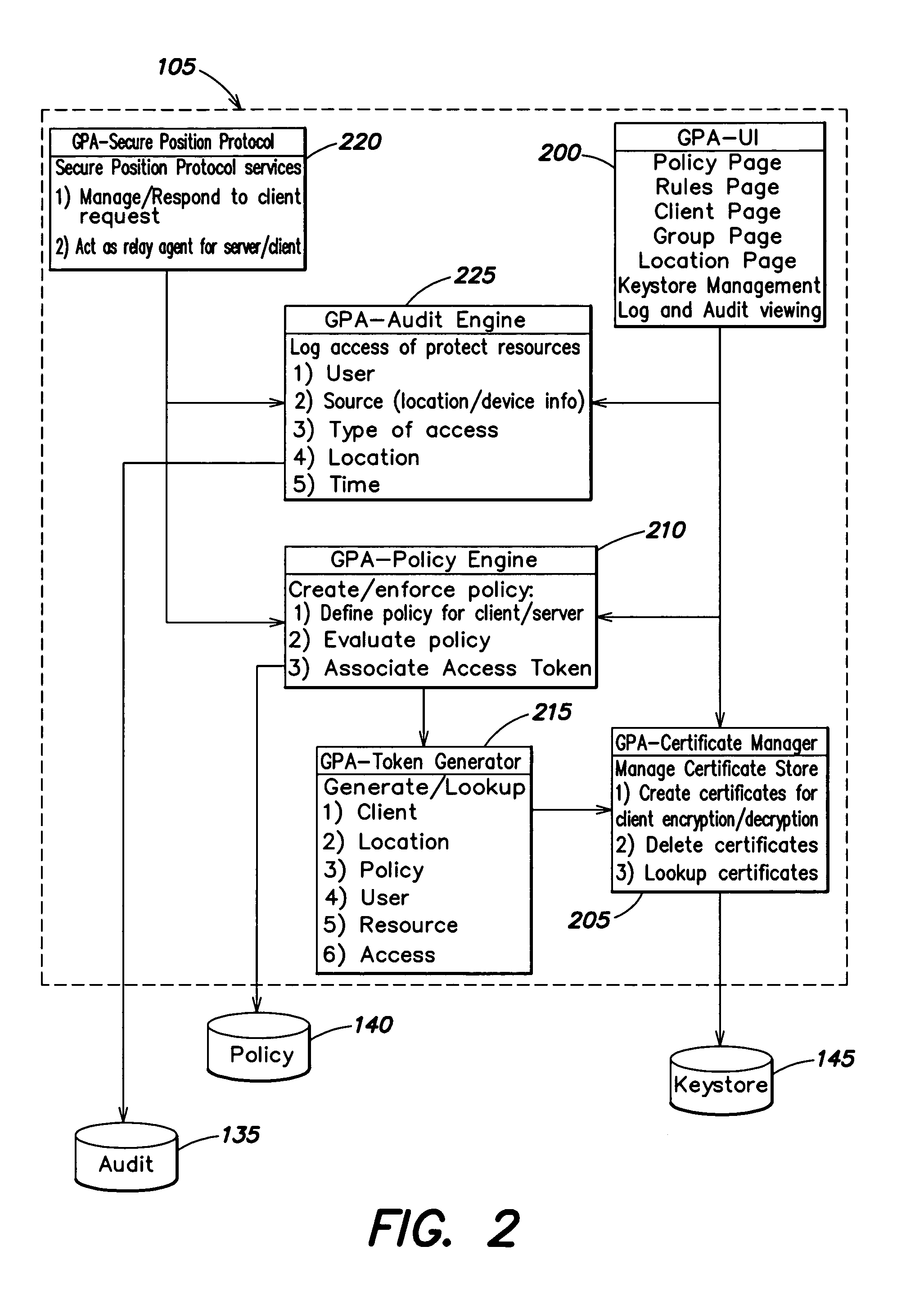
Method and apparatus for securing documents using a position dependent file system
ActiveUS8312064B1Provide securityEasy to manageUnauthorized memory use protectionHardware monitoringInternet privacyFile system
Access to information or a document is secured by a central global positioning authority that evaluates access requests in accordance with predefined policies. One component of an access request includes location information regarding at least one of the requesting entity and location of the requested resource. Access is either allowed or denied as a function of at least the requesting entity, position information and the applicable policy or policies. An encryption / decryption scheme is implemented where the encryption key is a function of the resource's position.
Owner:GEN DIGITAL INC
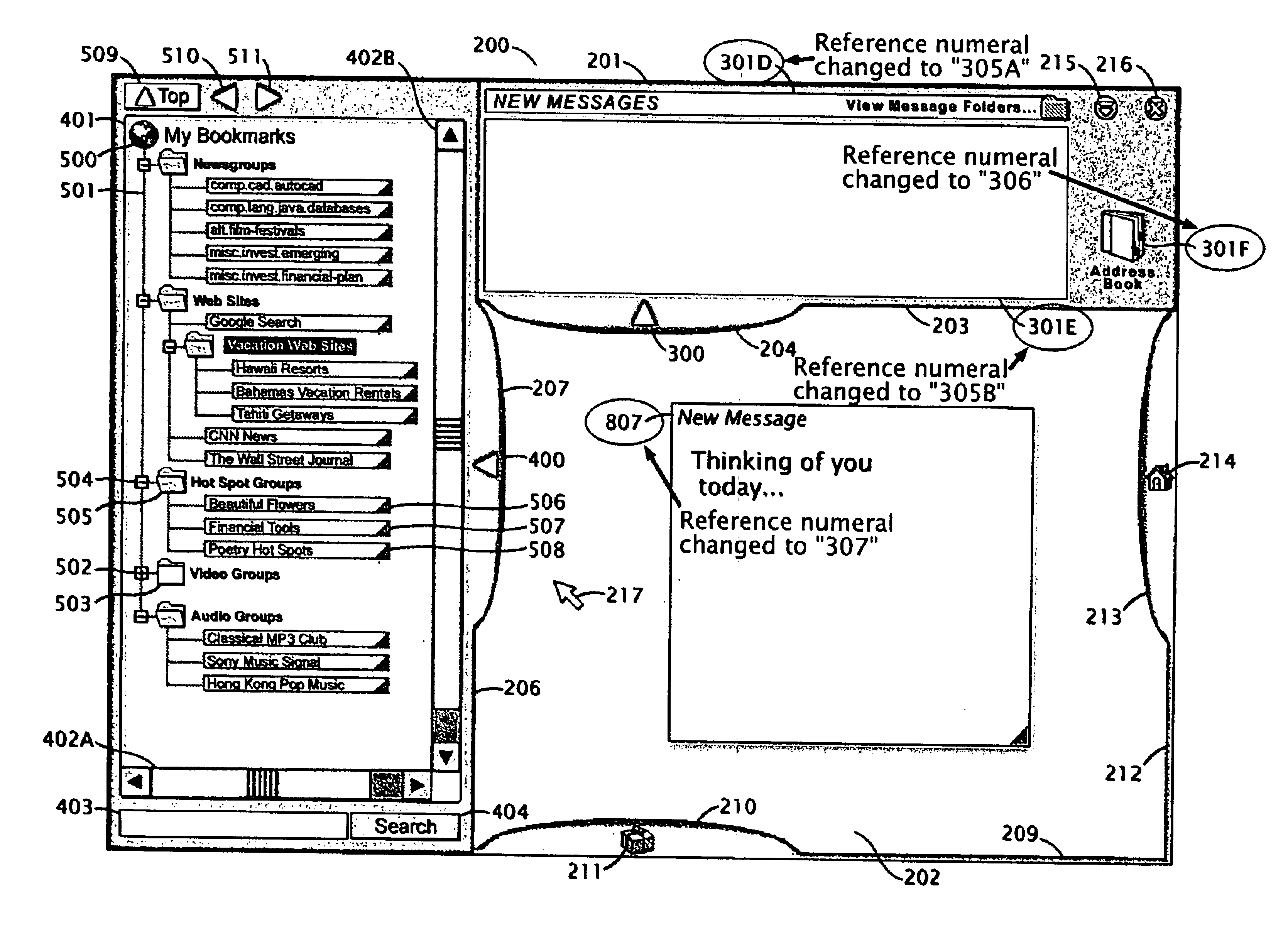
Method and apparatus for accessing information, computer programs and electronic communications across multiple computing devices using a graphical user interface
InactiveUS6850255B2Efficient accessEnsure effective implementationCathode-ray tube indicatorsInput/output processes for data processingDisplay deviceNavigation system
A GUI containing a panel along each of its edges is produced within a computer's display. Each of the four panels are always visible and accessible within the GUI and contain items that display or reference network-based information, communication, navigational systems, computer programs, and other items. These items have been assigned to the panels based upon a hierarchal containment system which, in the preferred embodiment of the invention, uses the categories “people, places, things, and home” as its first logical grouping of the various items and services a user would seek to utilize within the GUI. This organizational system, and its associated visual representation within the panels, enables the GUI to be displayed and operated within multiple computer devices, even though the designs of those devices may include a wide range of display and control systems. This consistency across various computing devices enables a user to quickly apply knowledge gained from having used the GUI on another computing device. Furthermore, the items presented within the GUI, as well as the GUI's configuration, are stored in, and retrieved from, a networked “server” computer thereby enabling a user to produce and access their familiar GUI workspace and items using a variety of networked computer devices. The GUI therefore may be accessed within multiple computing devices and provide access to information, computer programs, and electronic communications.
Owner:MUSCHETTO JAMES EDWARD
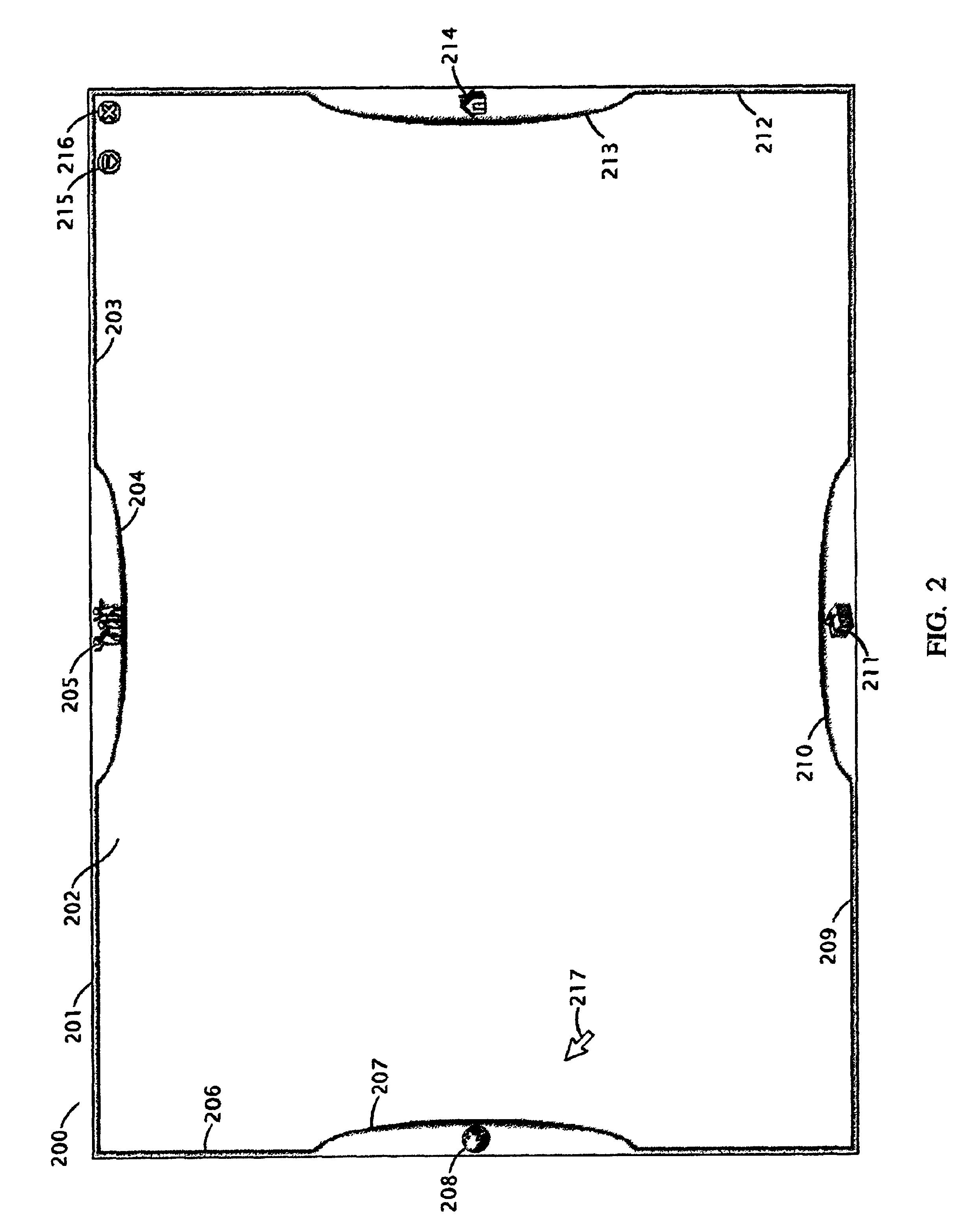
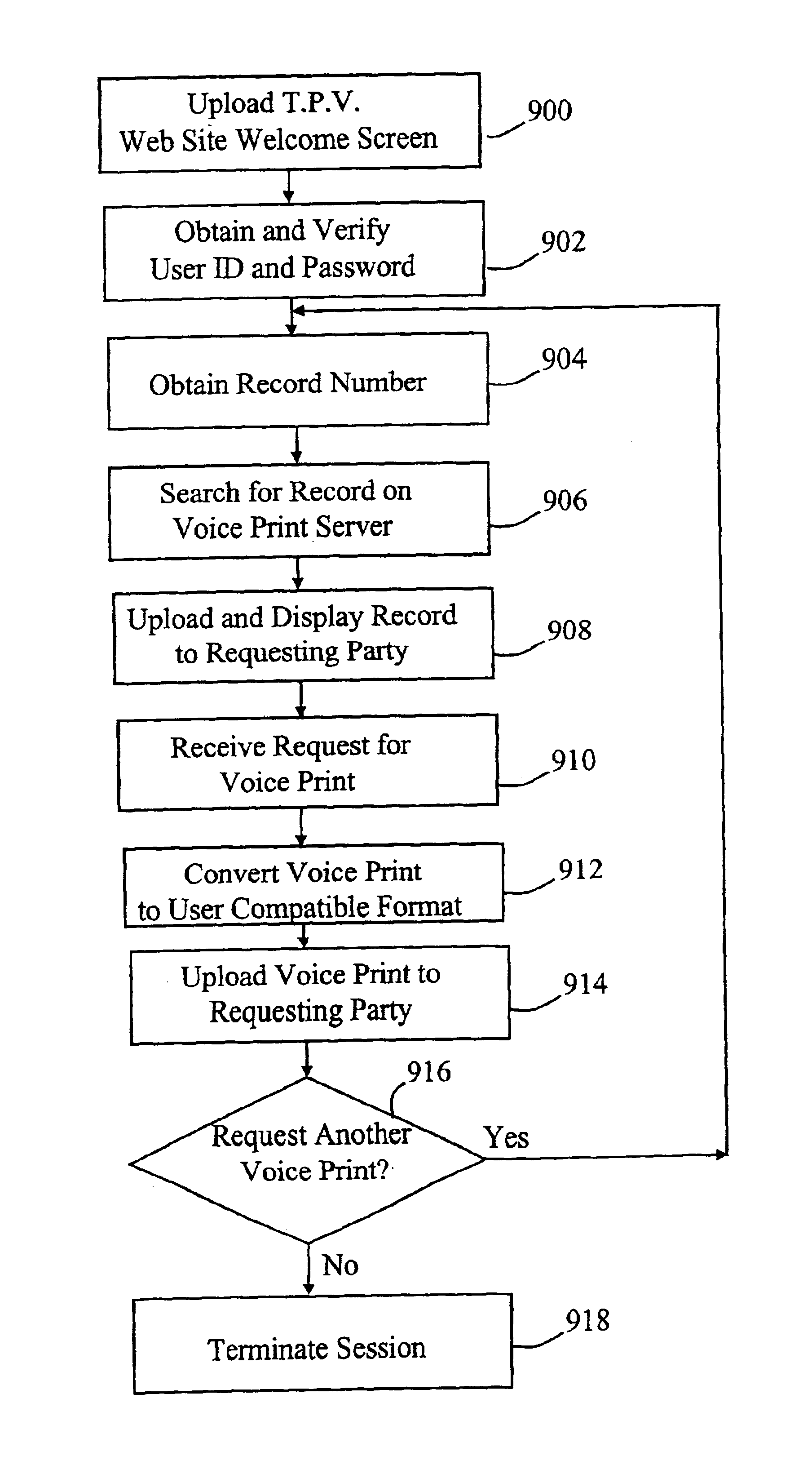
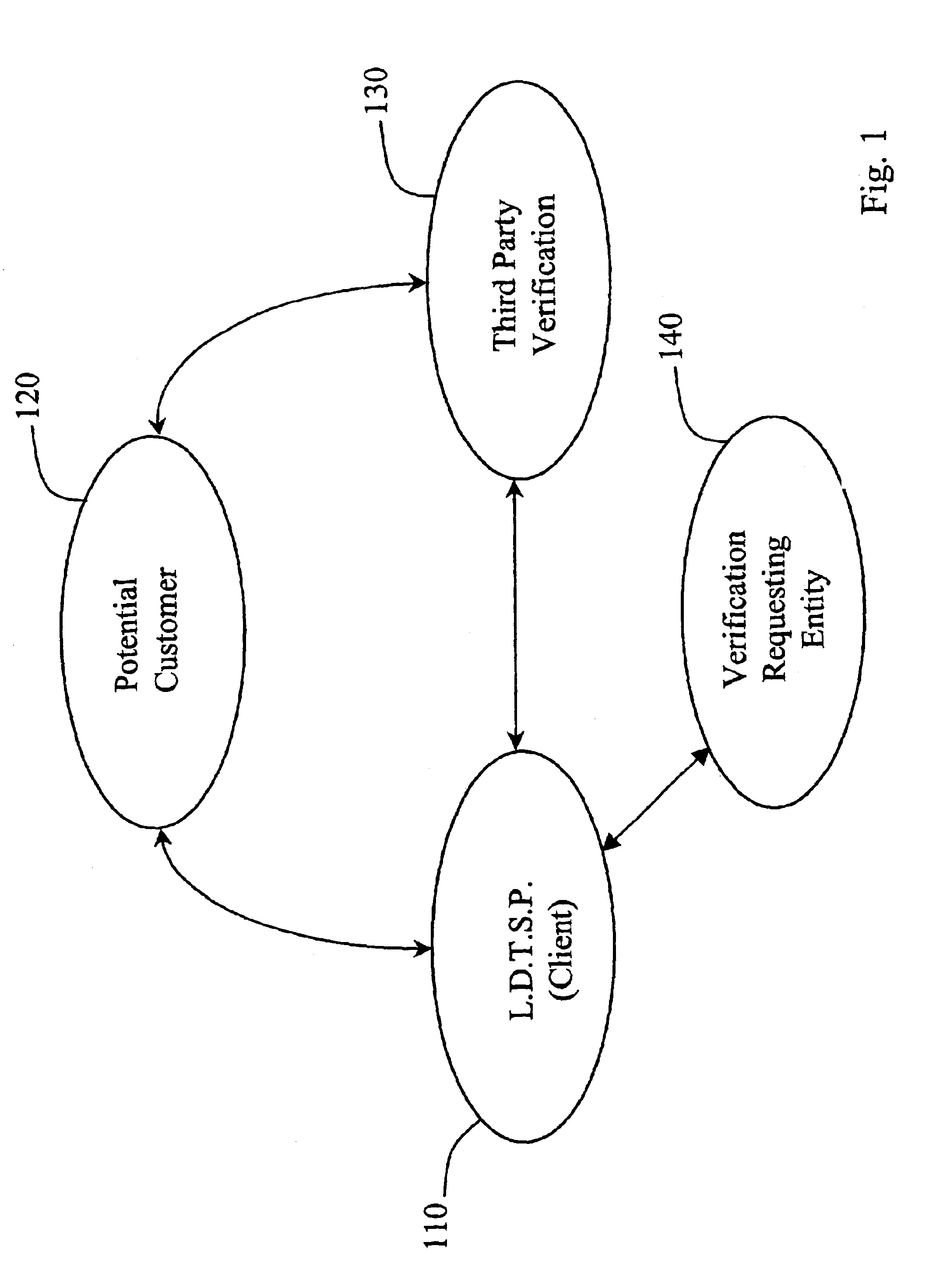
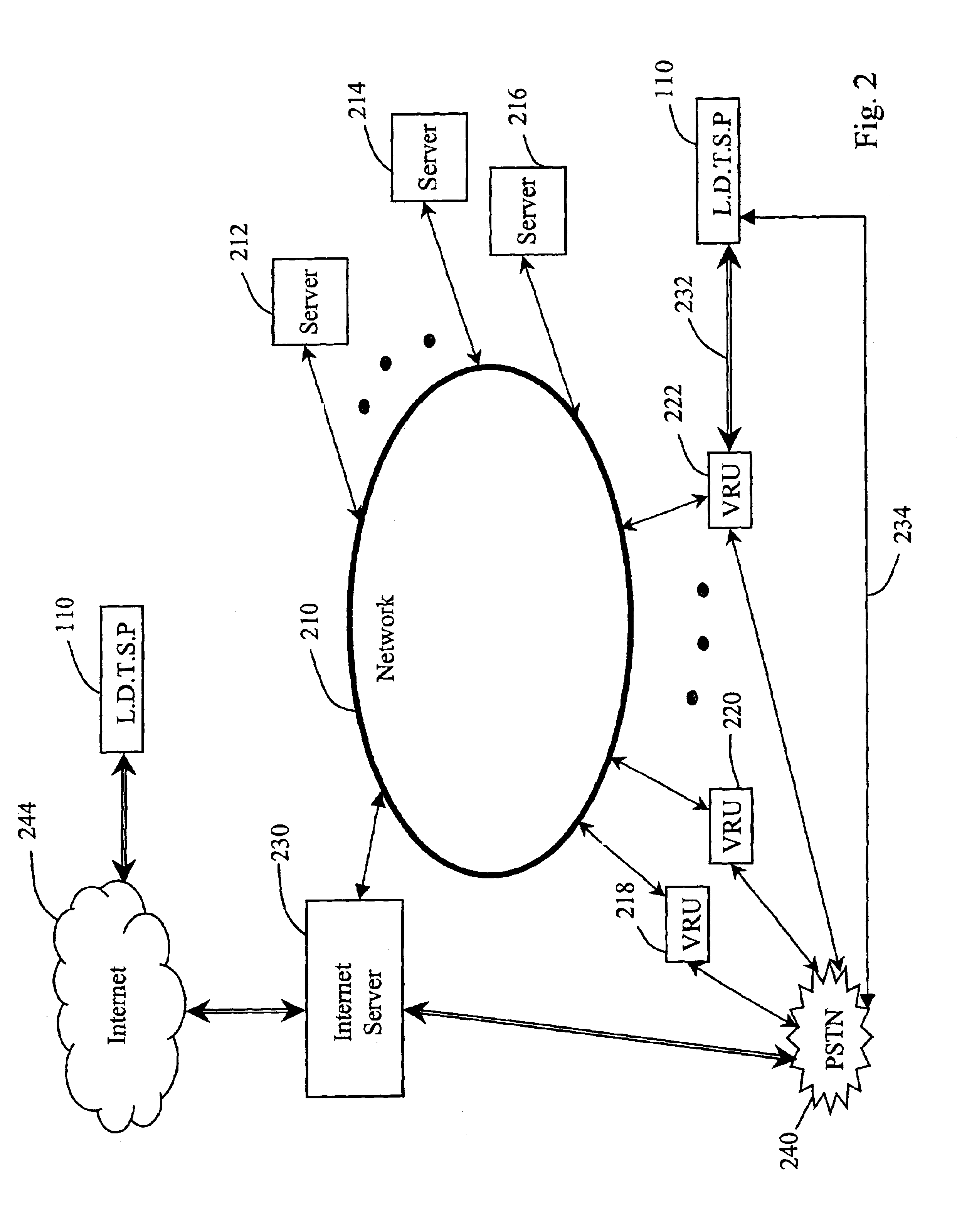
Automated third party verification system
A verification system for obtaining, storing and providing access to information regarding a commitment or position of an individual or entity is provided. In one embodiment the verification system comprises an interactive voice response system or computer program interface capable of obtaining and recording information regarding any of a number of commitments from an individual or entity, such as a commitment to change long distance telephone service providers. The verification system comprises a voice response unit configured to query pertinent information from an individual and record the responses to the queries in a digital format. Upon completion of a successful session, the voice response unit forwards the recorded responses confirming consent, to a storage device, such as a computer server. As desired, the recorded responses can be retrieved from the server by telephone or computer for verification of the consent, commitment, or position of the individual or entity.
Owner:RED HAT
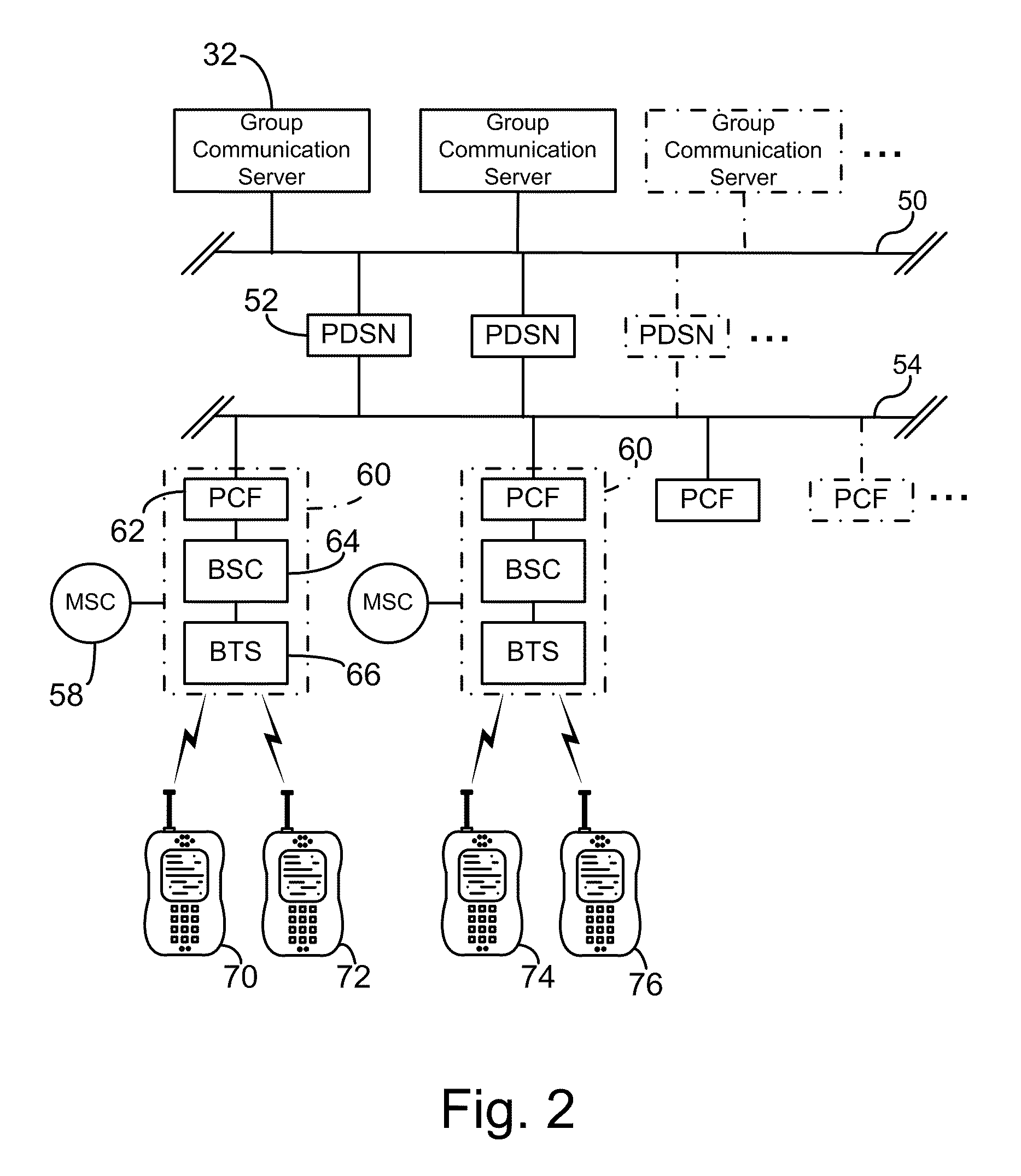
Communication system architecture and operating methodology providing a virtual neighborhood network
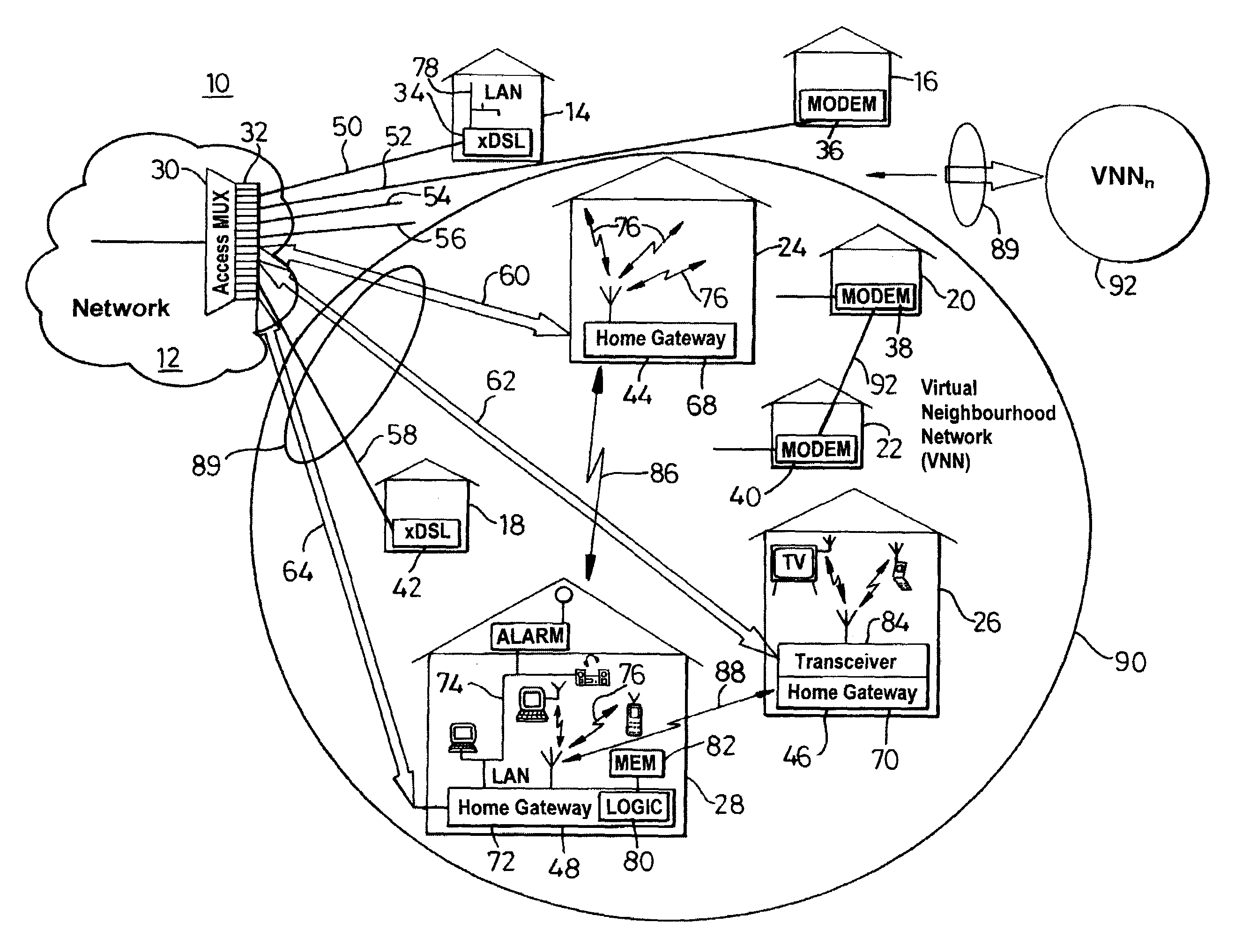
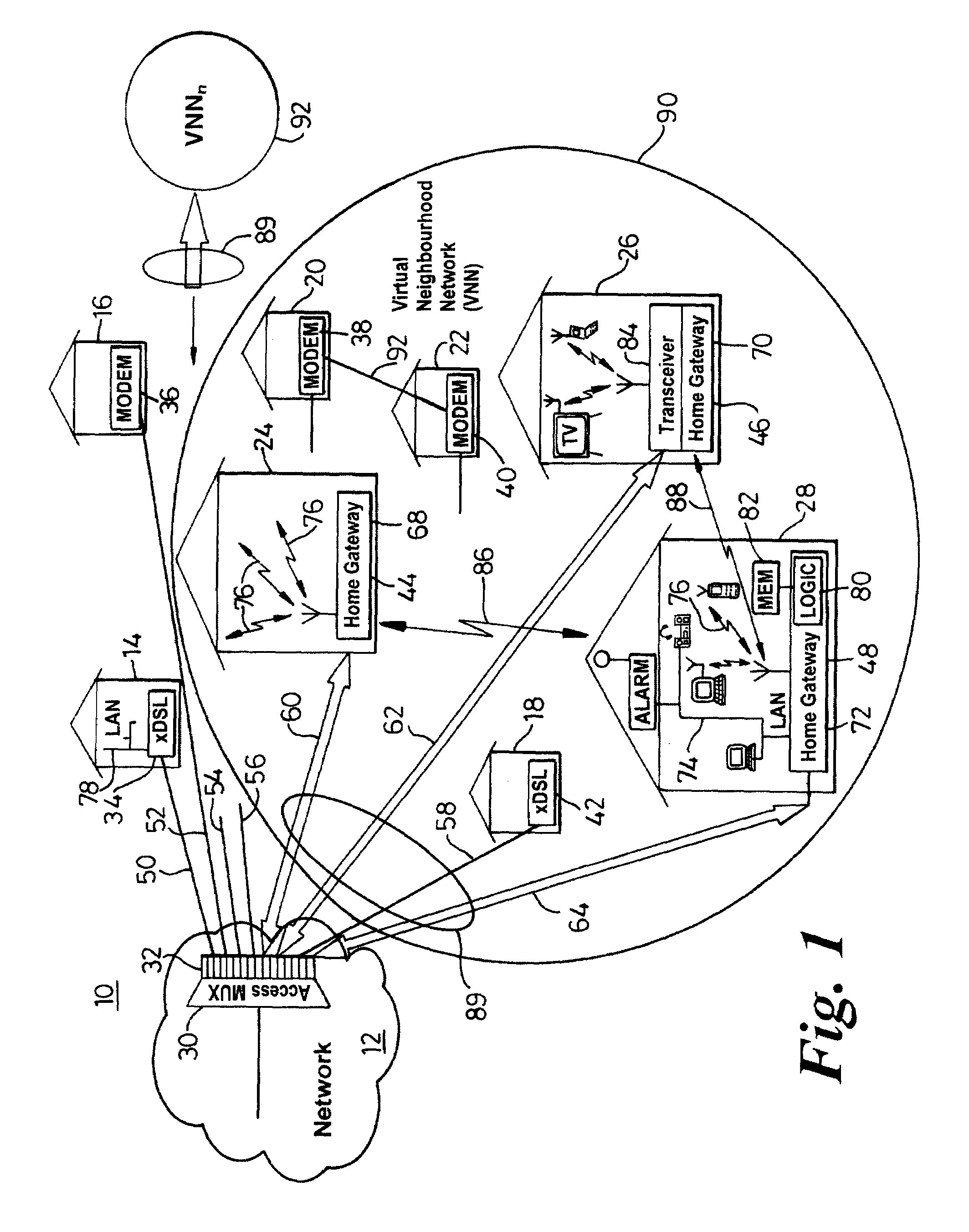
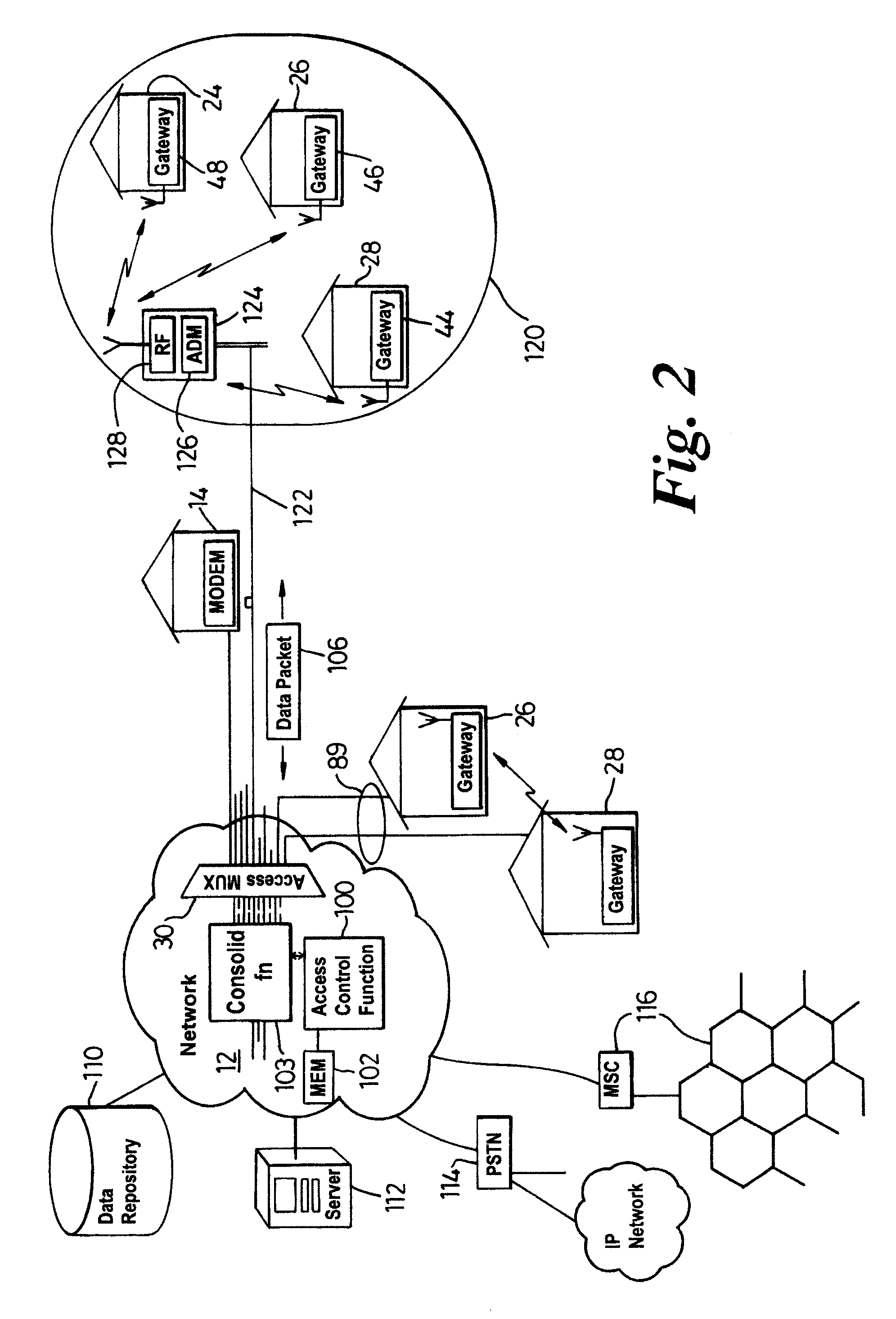
InactiveUS7142503B1Overcome bandwidth limitationIncreased peak bandwidth capacityError preventionFrequency-division multiplex detailsEnd-to-end encryptionTransceiver
A communication system (10) supports the provision of a plurality of dedicated communication resources (50–64), such as copper drops, RF links and optical fibers, to dedicated home-gateway devices (44–48) or distribution points (124). The communication resources (50–64) support broadband interconnection (104) between the dedicated home-gateway devices (44–48) or distribution points (124) and an access multiplexor (30) in a network (12). Each gateway device (44–48) or distribution point (124) generally includes a local RF transceiver (84) and associated control logic (80–82) that allows local communication (86) between gateway devices (44–48) and hence statistically multiplexed access (60–64, 89) to multiple communication resources, thereby providing increased bandwidth in uplink and / or downlink directions. With the control logic (80) operable to provide a routing and prioritisation / arbitration function, each gateway (44–48) is able to selectively engage use of supplemental, non-reserved communication resources usually associated with a dedicated ono-to-one connection between the access network (12) and at least one secondary gateway. Physical layer access to information routed via a secondary gateway within a virtual neighborhood network (90–92) comprising several gateways is restricted through an end-to-end encryption algorithm between an originating gateway and, at least, the access multilpexor (30).
Owner:RPX CLEARINGHOUSE
Apparatus and method for user-based control of television content
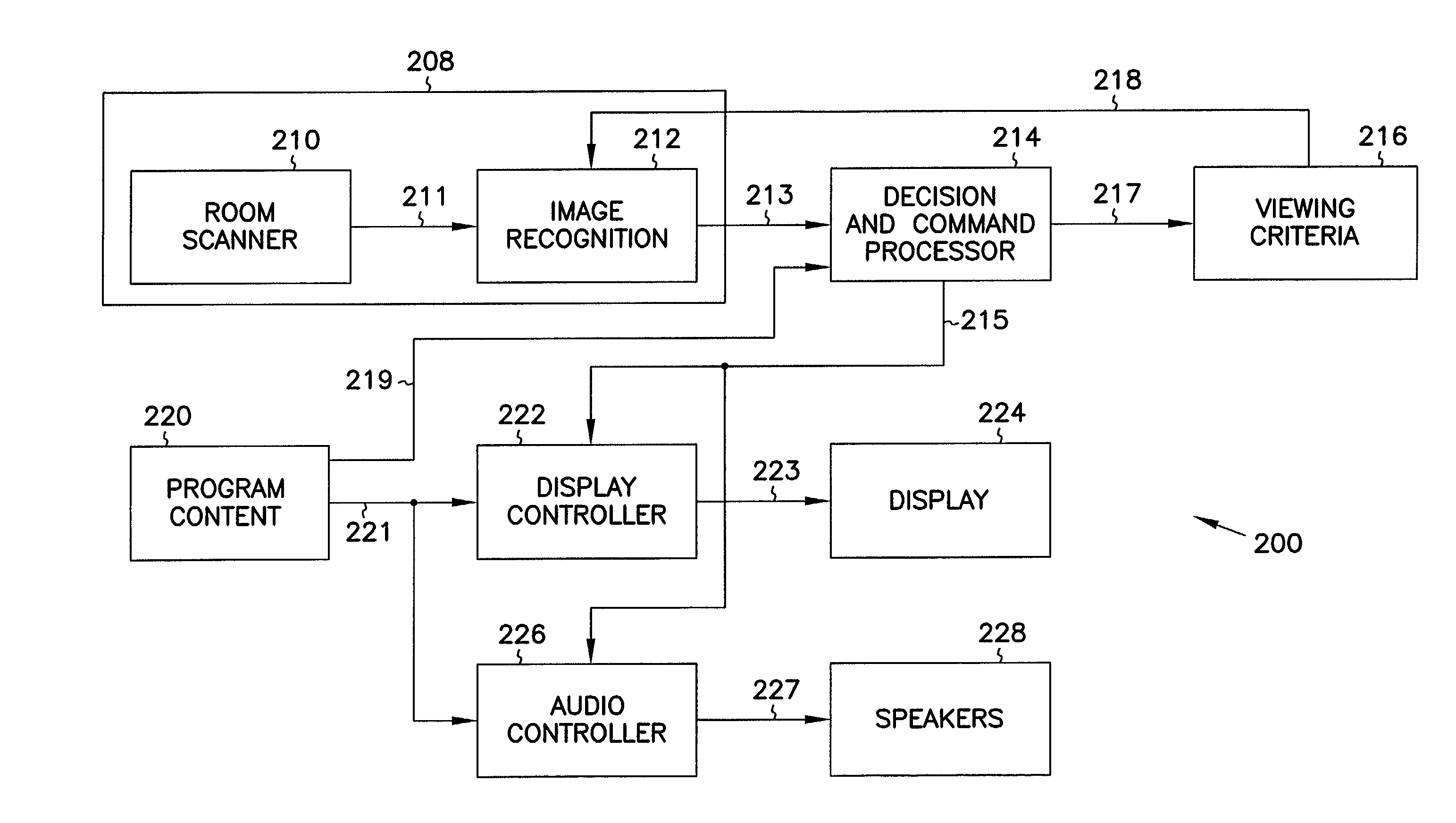
InactiveUS7134130B1Analogue secracy/subscription systemsBroadcast components for monitoring/identification/recognitionDisplay deviceHuman–computer interaction
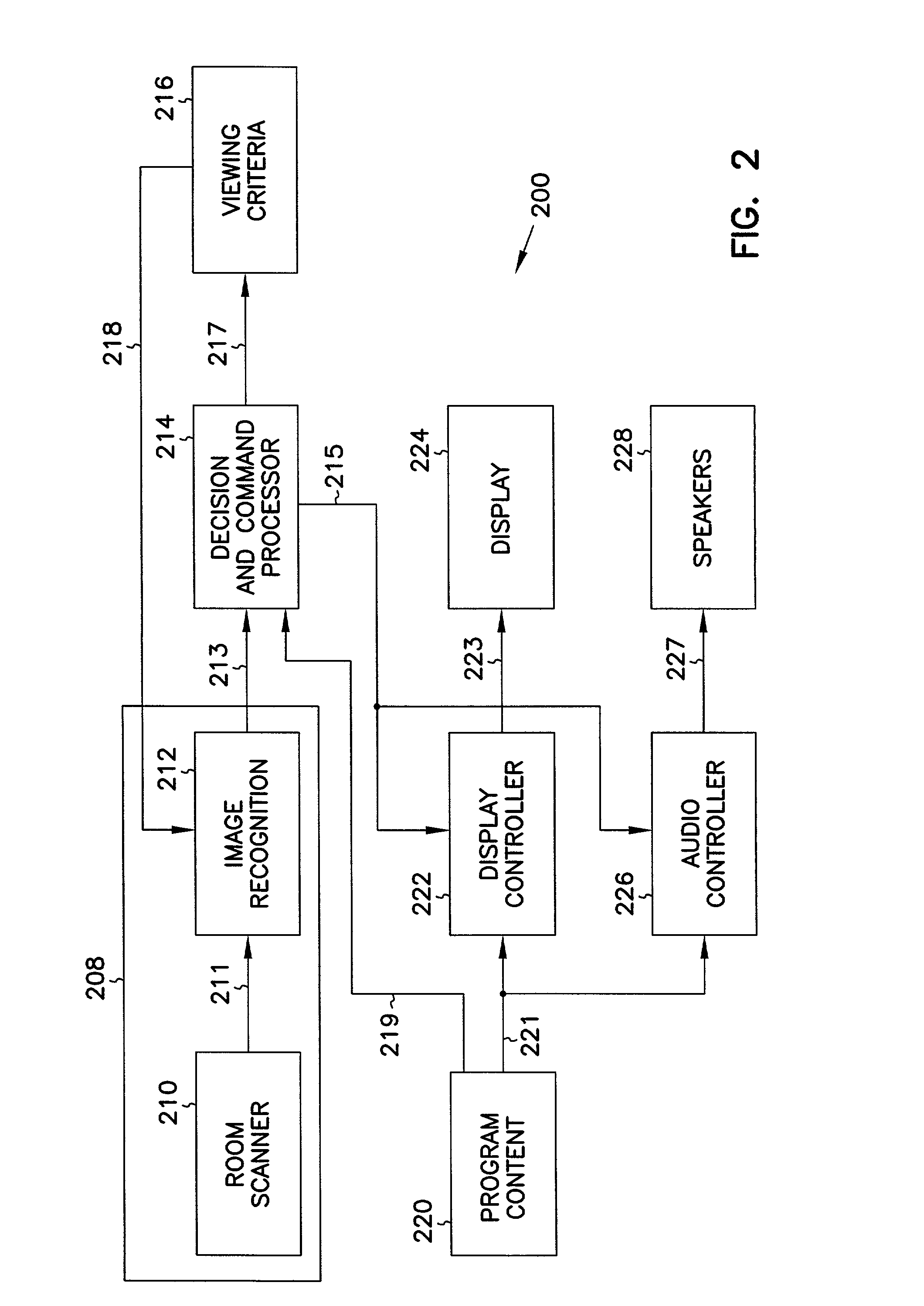
An apparatus and method for controlling access to information based on content of the information and user identity. The apparatus includes a video display that displays the information to be viewable by one or more users. A user-recognition input device determines that an additional user is newly present in a given area having access to the display. A blocking device coupled to the user-recognition input device selectively blocks display of the information based on whether the additional user is newly present. In one embodiment, the user-recognition input device includes a video input device, and a feature recognition device operable to distinguish between two or more users based on one or more video features of the users. In another embodiment, the user-recognition input device includes an audio input device, and an audio feature recognition device operable to distinguish when an additional user arrives. In yet another embodiment, the user-recognition input device includes a movement-detection device operable to distinguish when an additional user arrives.
Owner:GATEWAY
System and method for providing global information on risks and related hedging strategies
InactiveUS20050144114A1Increase productivityIncrease valueFinanceSpecial data processing applicationsAnalytic modelManagement tool
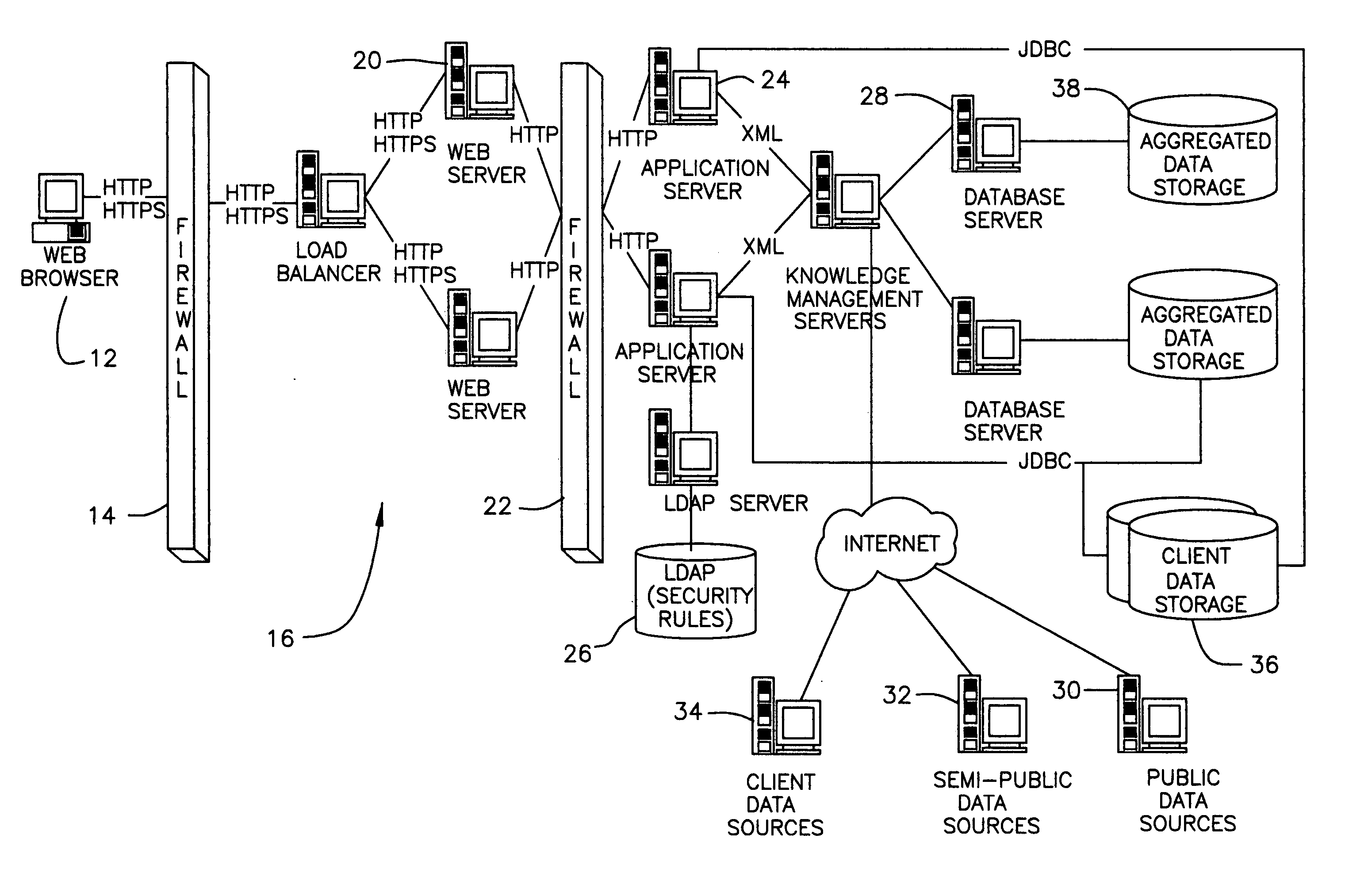
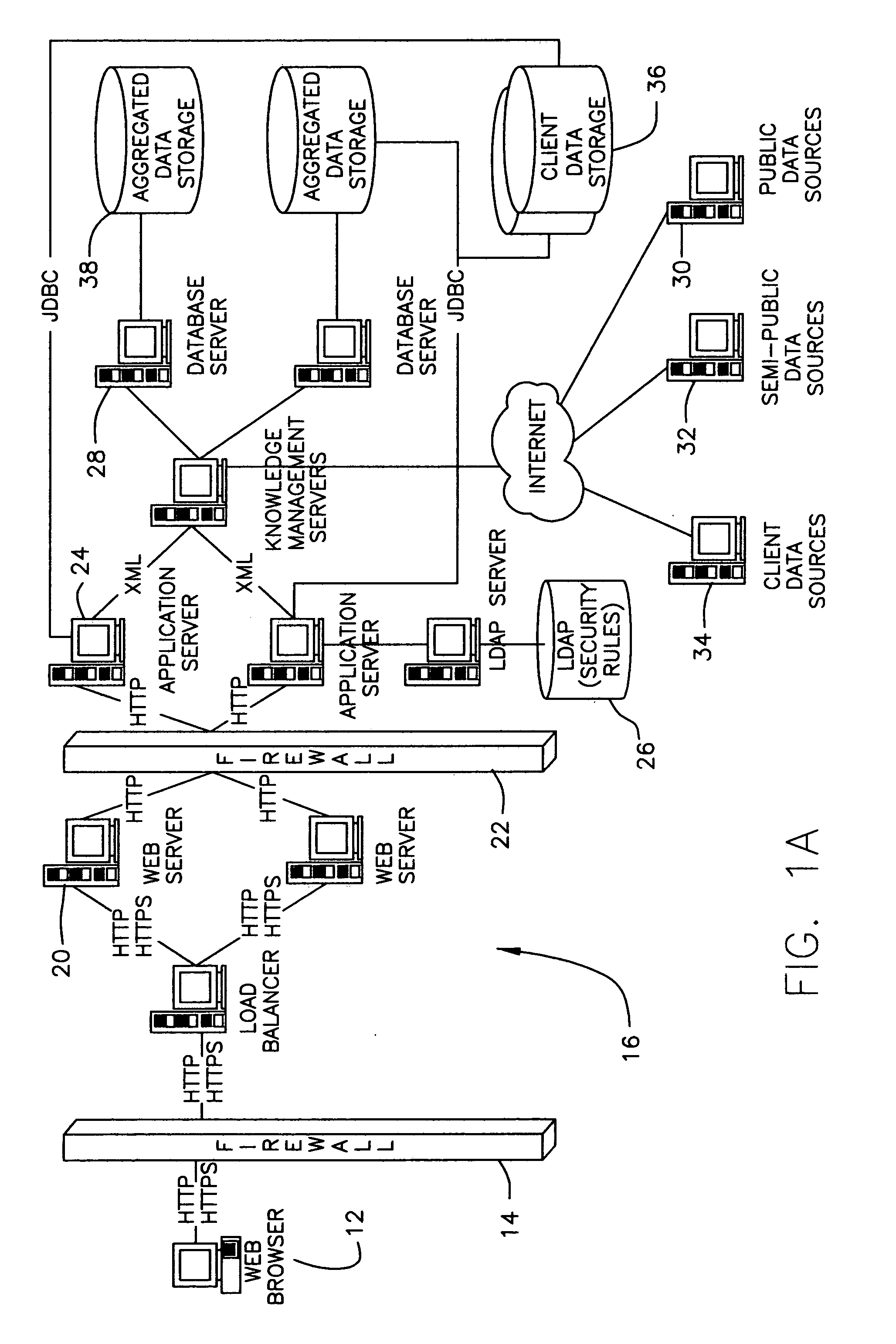
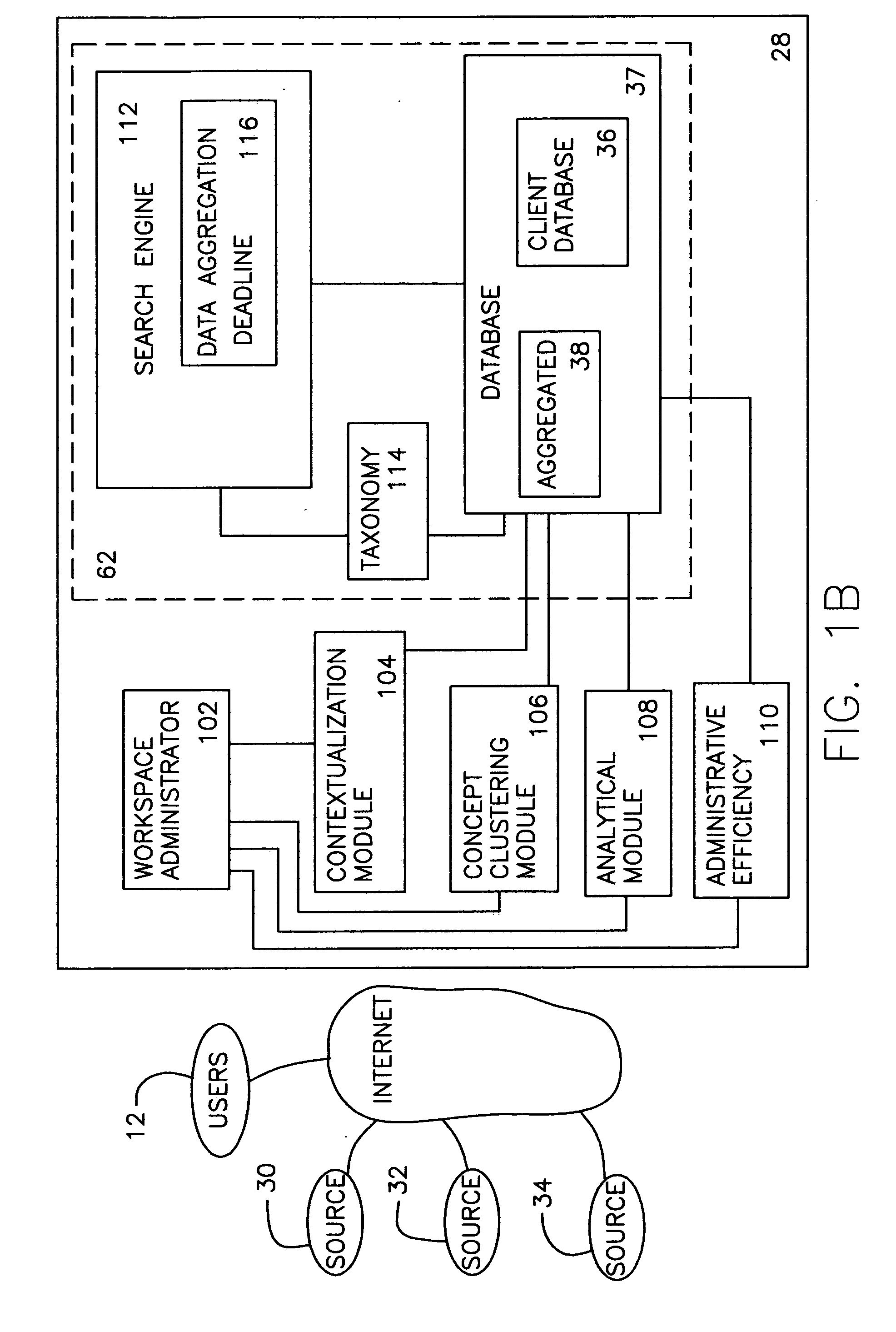
The present invention provides a system and method for information and data aggregation and analysis which provides risk managers, benefits managers, brokers, insurers and other insurance professional to have access to information resources, knowledge management tools, and powerful analytical models needed to increase their value and productivity. In accordance with one embodiment of the invention, the system and method provided is designed for information and data aggregation that allows for the compilation of data for mining and categorization by a knowledge management system, which stores all retrieved information in accordance with categories provided by a categorization engine referred to as a Taxonomy module. A contextualization module is configured to retrieve relevant information, based on various factors, including the user's profile, and the user's particular task. The system dynamically provides relevant information as the user interacts and conducts various tasks. The stored information is analyzed by a concept clustering module, so that various concepts relating to a particular topic can be uncovered and stored. In accordance with another embodiment of the invention, the system provides for various analytical tools that allow users to carry on with highly complex analysis of insurance related topics. The range of available analytical tool dynamically varies based on the user's needs and research topics. In accordance with yet another embodiment of the invention, the system provides for a unique interactive workspace that combines the features explained above in a logical manner. To this end, the system interface provides for various job templates, so as to enable the user's to carry various projects by a template driven task assignments. As the user navigates through the workspace, the range of available information to the user changes, based on the user's profile and navigation pattern.
Owner:ADVISEN
Management of and access to information and other material via the world wide web in an LDAP environment
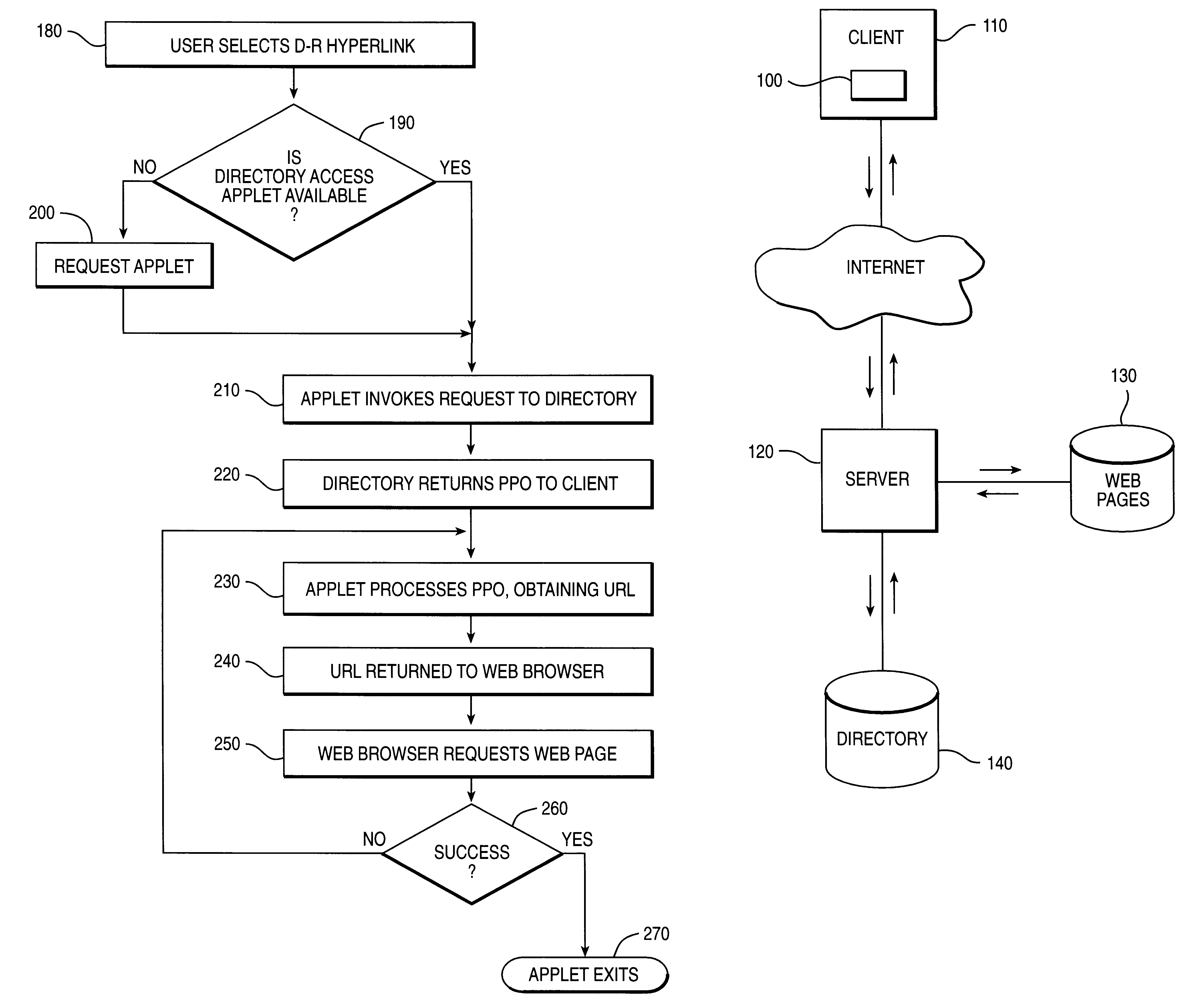
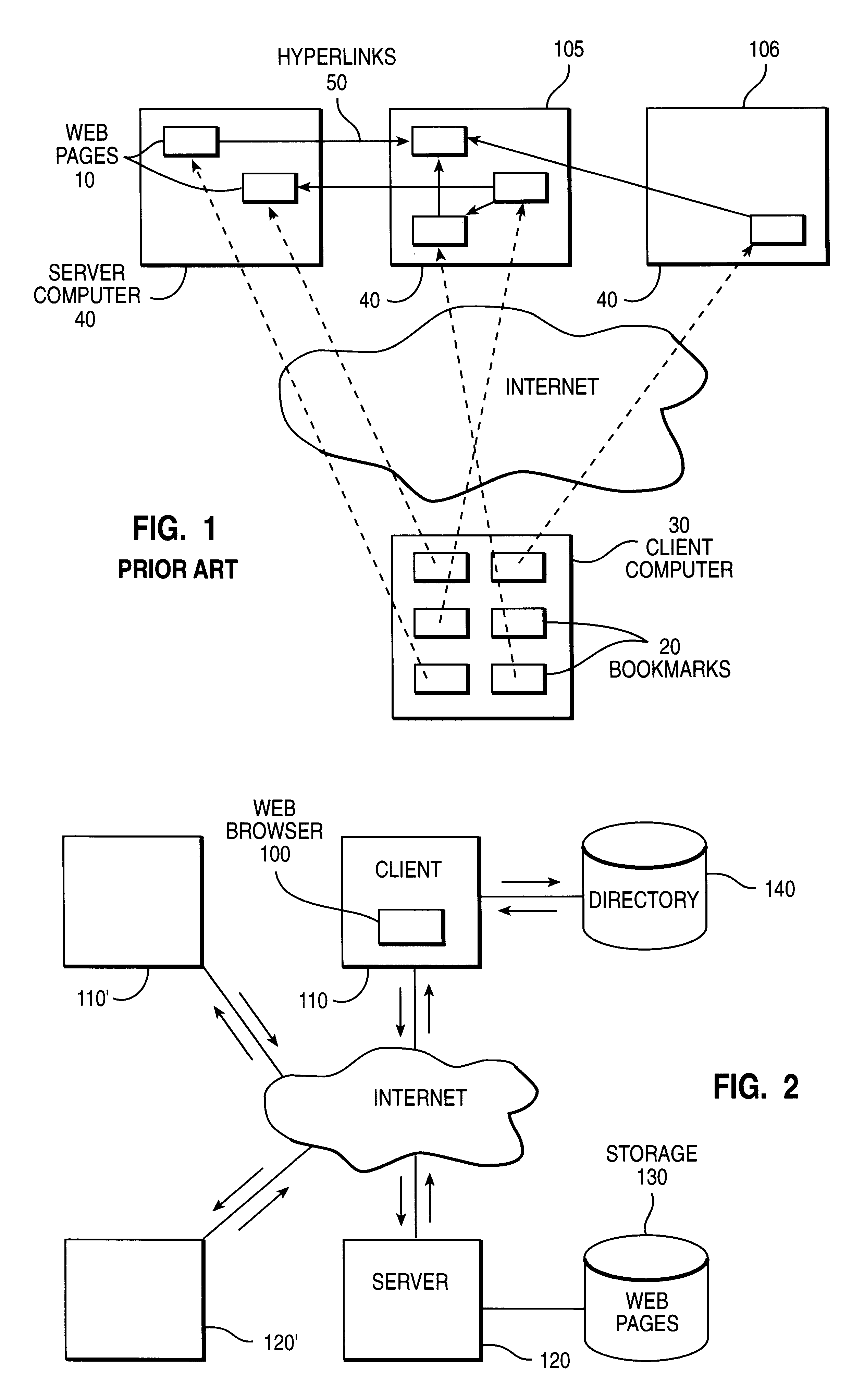
InactiveUS6209036B1Data processing applicationsMultiple digital computer combinationsHyperlinkService improvement
Provided is a method and apparatus for improved access to material via the World Wide Web Internet service. Web page URLs are stored as attribute-values of directory objects and Web page hyperlinks to those directory objects are provided together with access logic responsive to the hyperlinks for retrieving the URLs for use by a client. This indirect access to Web pages via hyperlinks to directories has significant advantages for Web page organization and facilitates more flexible methods of Web page access than the known use of hyperlinks which include URLs pointing directly to the target Web pages.
Owner:IBM CORP
System and method for providing dynamic user information in an interactive display
InactiveUS20080120569A1Quick and convenient and consistentCathode-ray tube indicatorsInput/output processes for data processingDisplay deviceInteractive displays
The present invention is directed to a method and system for use in a computing environment to present and provide access to information that a user cares about. A scheme is provided for presenting frequently used controls and information in tiles within a sidebar. Tiles are hosted individually or in groups, within a sidebar, for interaction by a user. Tiles can be added or removed from the sidebar automatically or by user request. The present invention is further directed to a method for providing a scaleable and useable preview of tiles within a sidebar. Further still, the present invention is directed to maintaining an overflow area of icons for tiles that would not fit within the sidebar. The sidebar has content that dynamically adjusts in response to the addition, expansion, squishing or removal of tiles. Even Further, a user can customize the sidebar of the present invention.
Owner:MICROSOFT TECH LICENSING LLC
Efficient large-scale access control for internet/intranet information systems
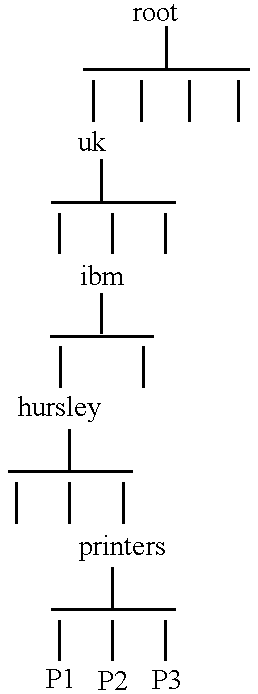
InactiveUS6219667B1Data processing applicationsDigital data processing detailsDecompositionInformation object
An efficient method and apparatus for regulating access to information objects stored in a database in which there are a large number of users and access groups. The invention uses a representation of a hierarchical access group structure in terms of intervals over a set of integers and a decomposition scheme that reduces any group structure to ones that have interval representation. This representation allows the problem for checking access rights to be reduced to an interval containment problem. An interval tree, a popular data structure in computational geometry, may be implemented to efficiently execute the access-right checking method.
Owner:IBM CORP
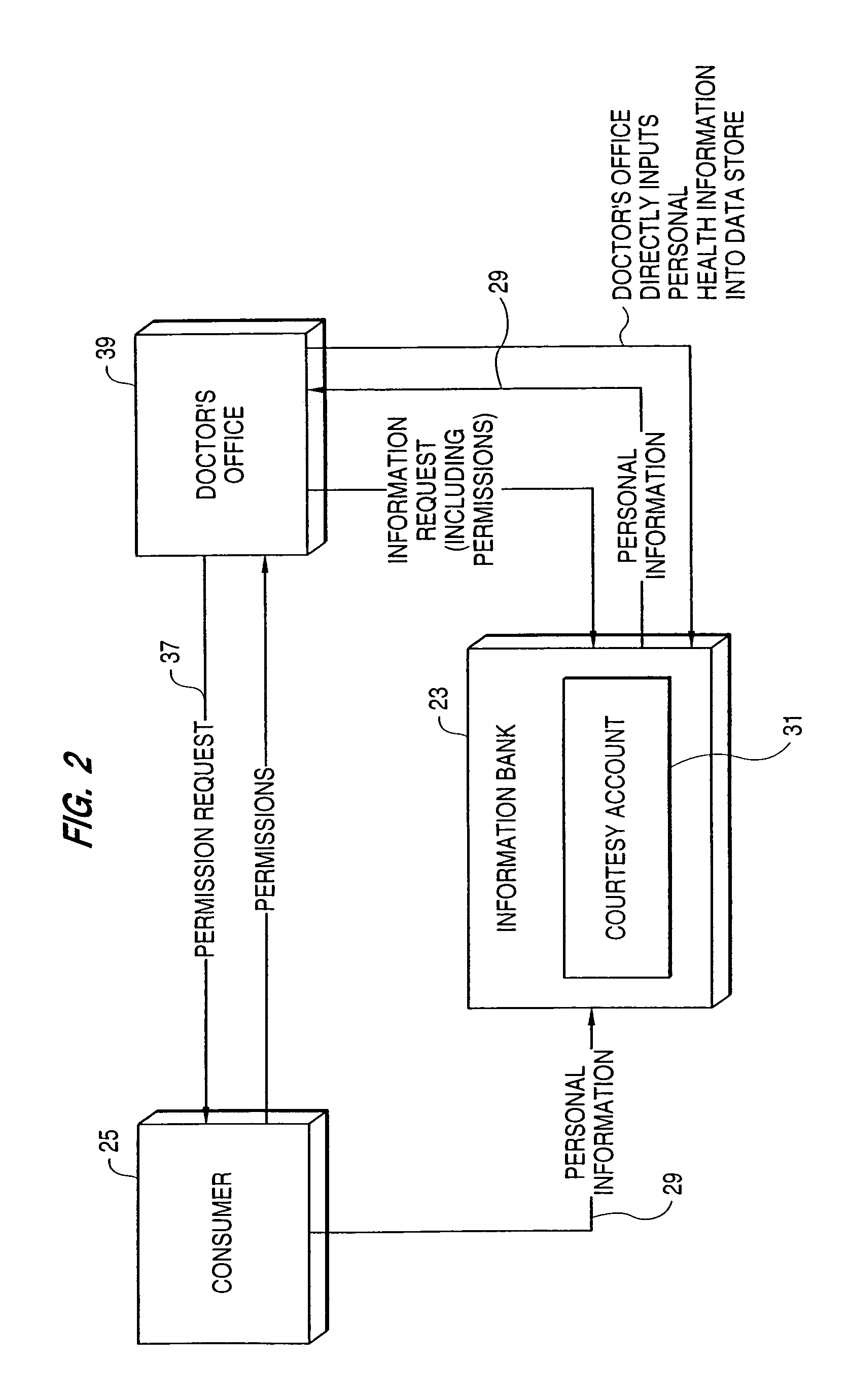
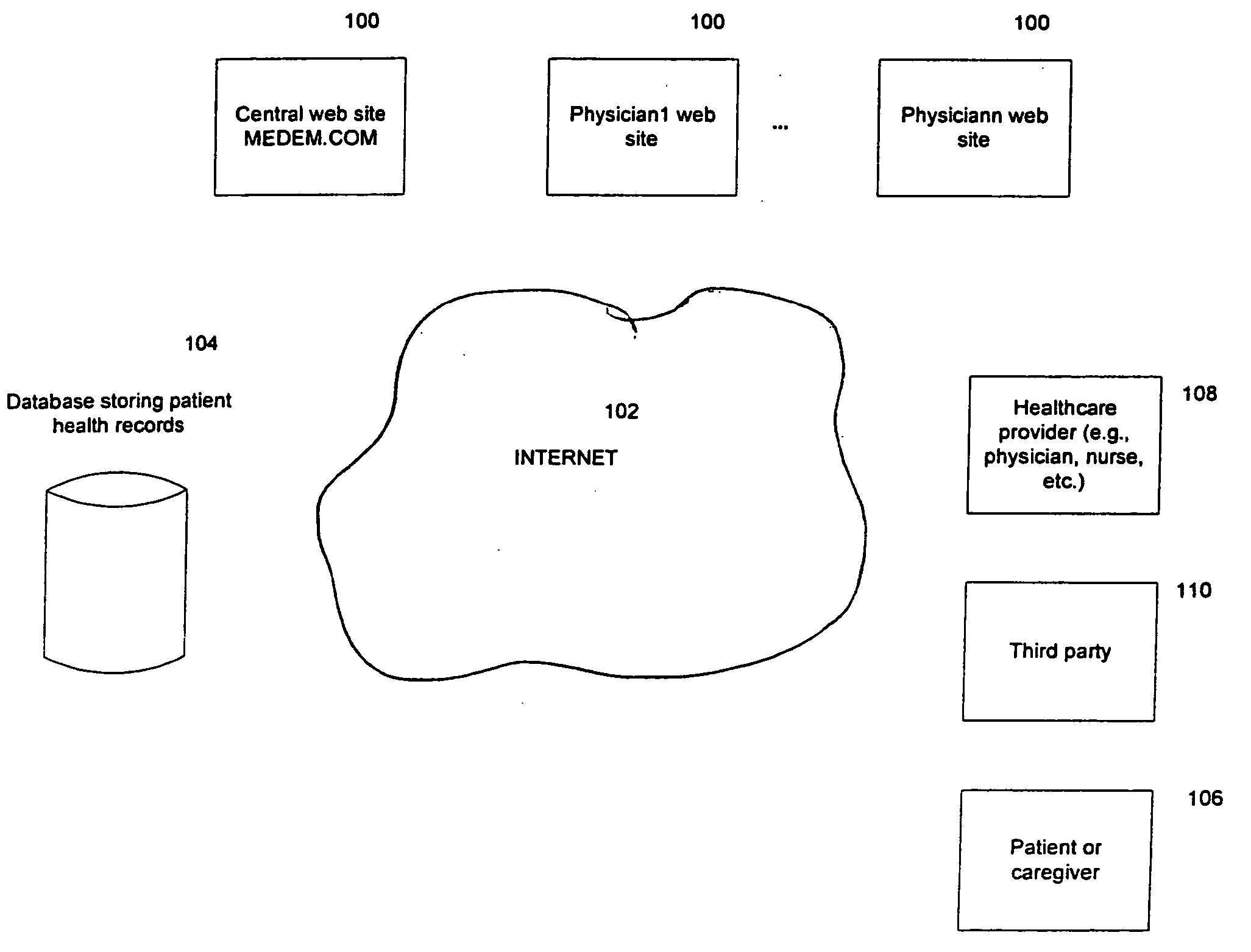
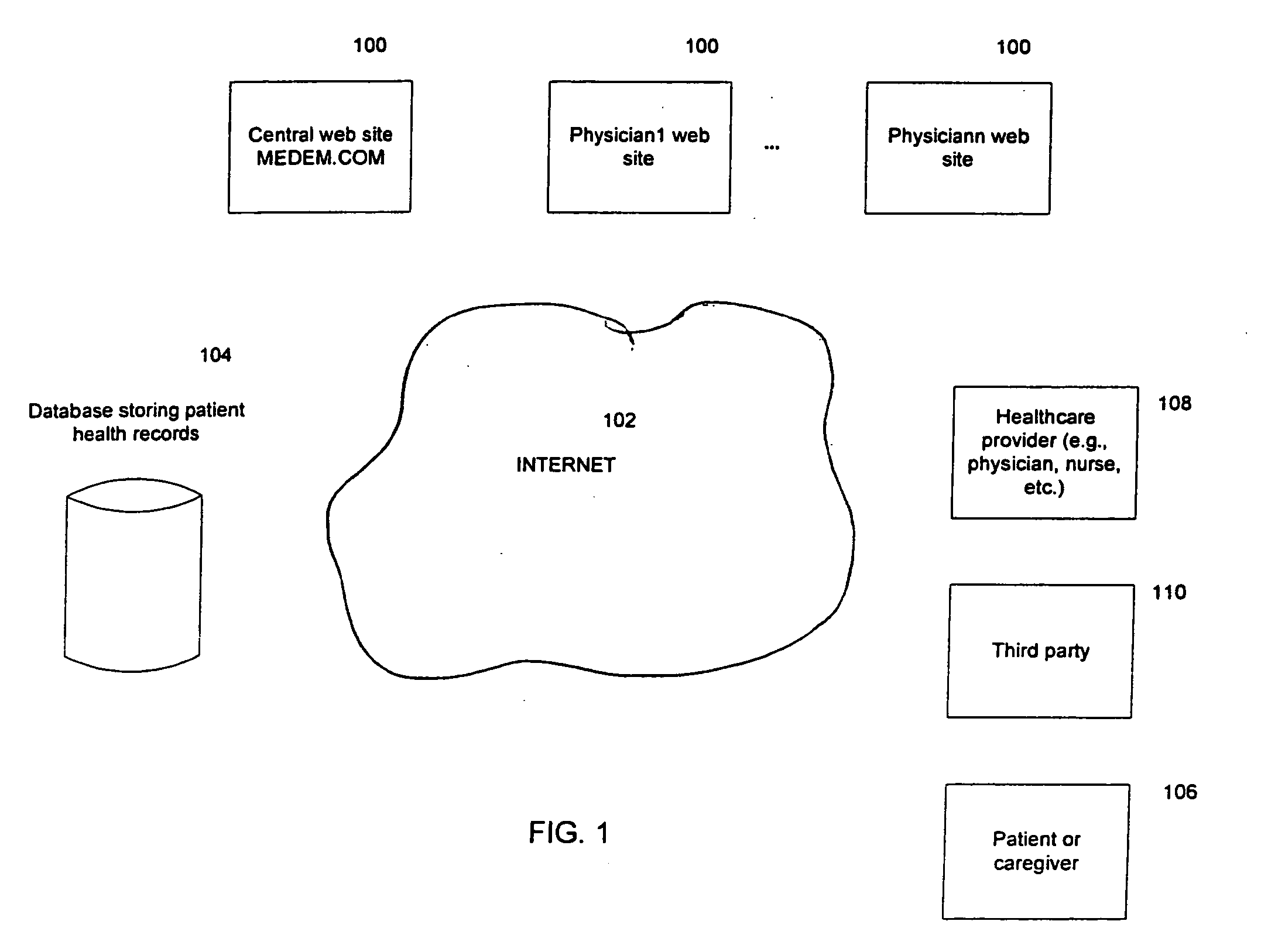
Electronic personal health record system
Methods and apparatus for providing access to information associated with a patient are disclosed. Information associated with a patient may be stored electronically, enabling the information from an electronic health record (e.g., electronic personal health record controlled by a patient) or a portion thereof to be provided to an entity such as a healthcare provider. Patient records may be maintained and controlled by multiple entities, such as the healthcare providers, patients, payors, or other third parties. Information from these records may be transferred among these entities, thereby enabling updates to such records to be performed. These updates may occur automatically or upon acceptance by the receiving entity (e.g., patient or healthcare provider).
Owner:INTUIT INC
Selective data encryption using style sheet processing for decryption by a key recovery agent
InactiveUS6941459B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:PHONENICIA INNOVATIONS LLC SUBSIDIARY OF PENDRELL TECH
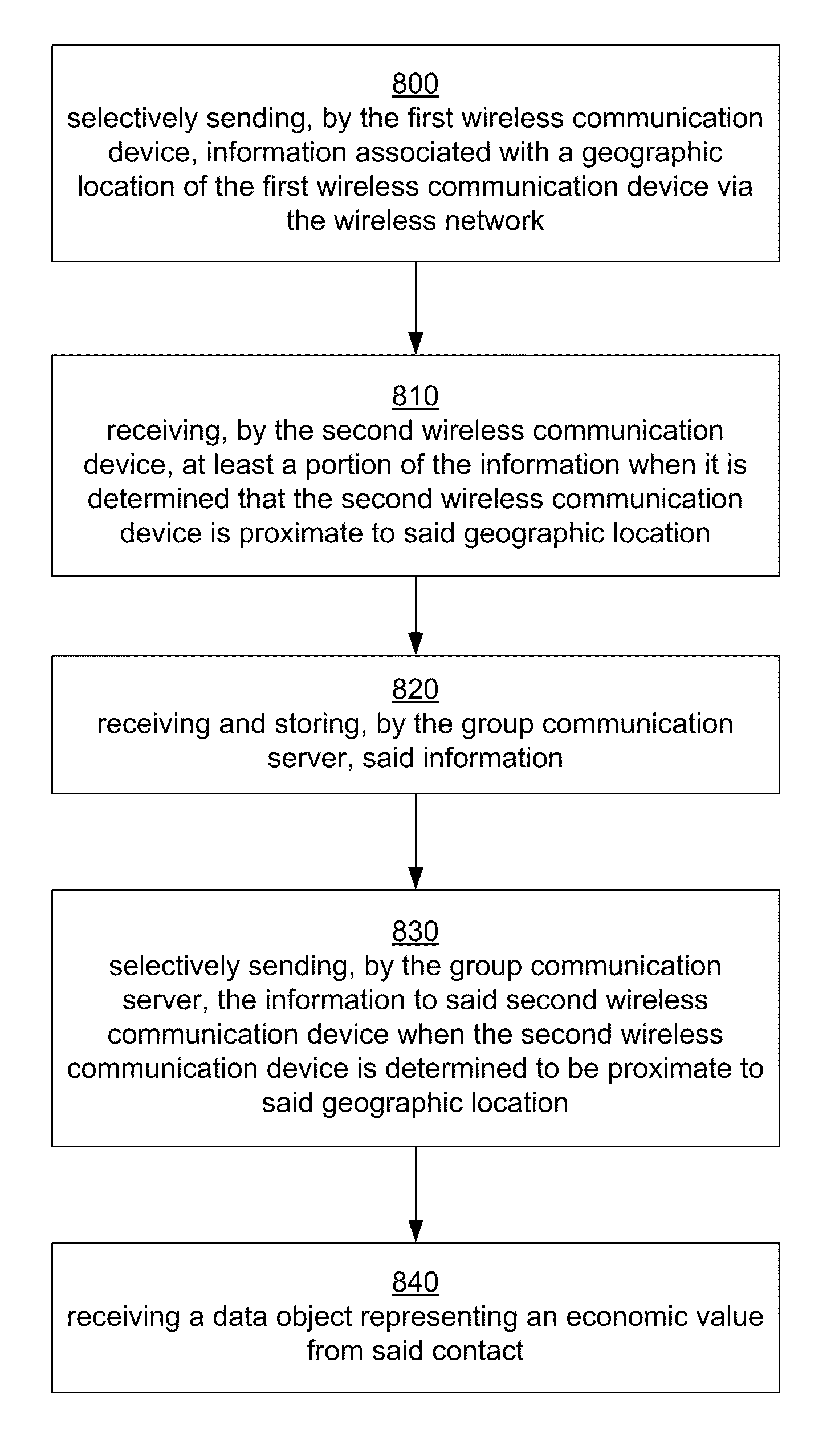
System for multimedia tagging by a mobile user
ActiveUS8447324B2Easy to share informationDigital data information retrievalInformation formatTelecommunicationsGeolocation
A system, method, and wireless communication device that provide a mobile user with selective access to information based on a predefined trigger such as a user's vicinity. In an embodiment, selected information from a first wireless communication device of a communication group may be associated with a geographic location and stored. A portion of the information may be selectively transmitted to a second wireless communication device of the communication group when the second wireless communication device is determined to be proximate to the geographic location associated with the information. In one embodiment, the second wireless communication device may receive the information automatically based on trigger settings.
Owner:QUALCOMM INC
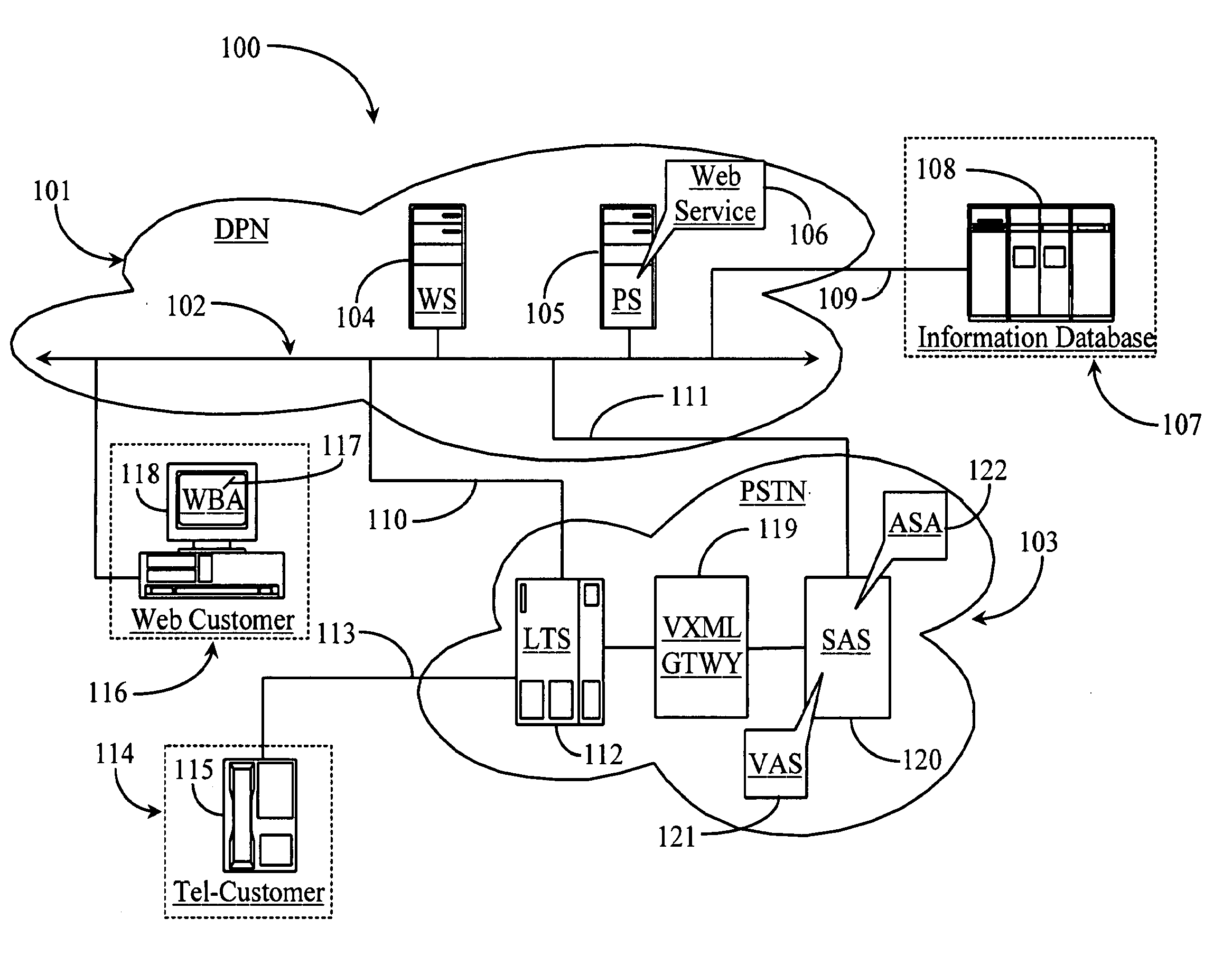
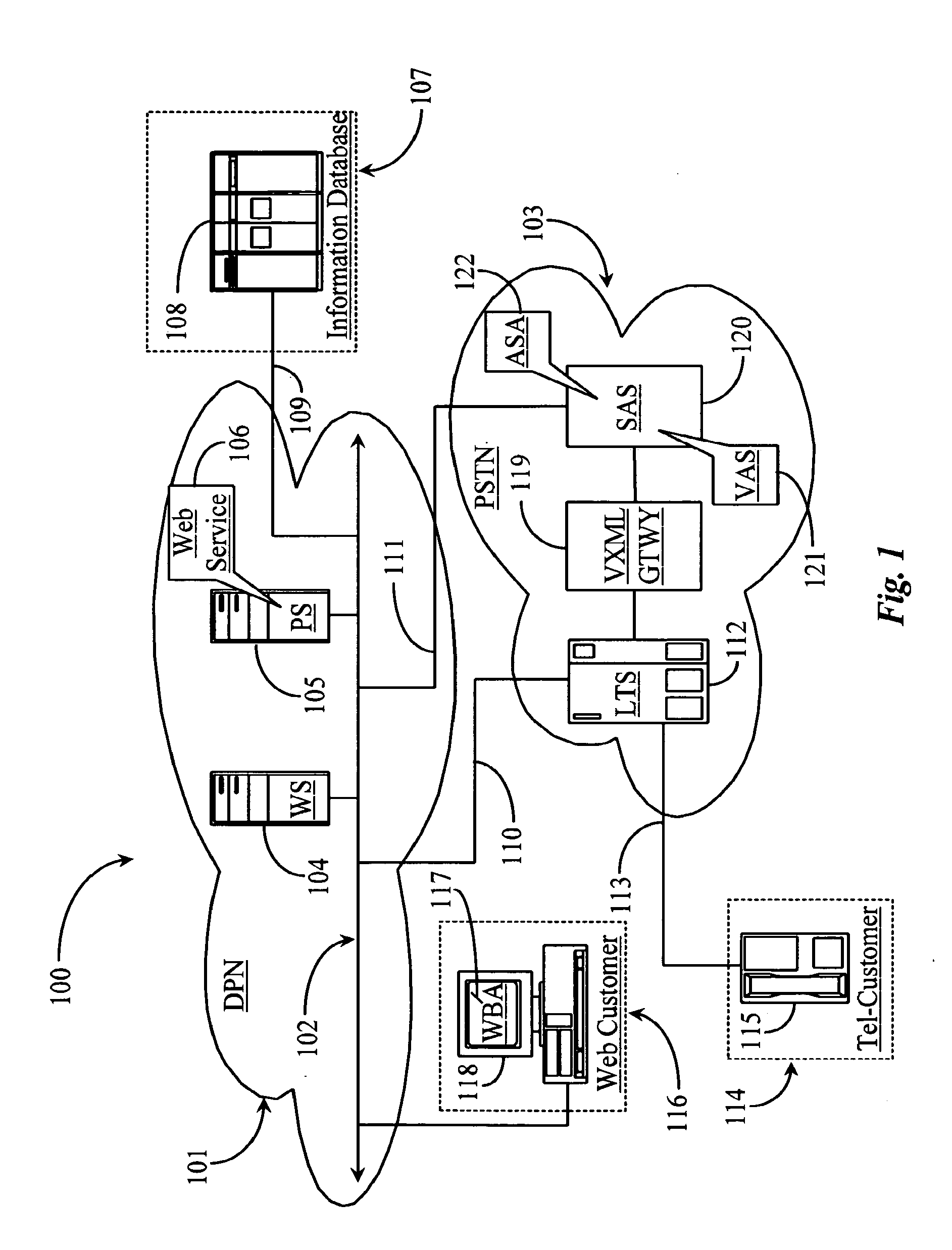
System and methods for dynamic integration of a voice application with one or more Web services
A system is provided for leveraging a Web service to provide access to information for telephone users. The system includes a first network service node for hosting the Web service, an information database accessible from the service node, a voice terminal connected to the first service node, and a service adaptor for integrating a voice application executable from the voice terminal to the Web service. In a preferred aspect, the service adaptor subscribes to data published by the Web service and creates code and functional modules based on that data and uses the created components to facilitate creation of a voice application or to update an existing voice application to provide access to and leverage of the Web service to telephone callers.
Owner:APPTERA
Selective data encryption using style sheet processing for decryption by a group clerk
InactiveUS6961849B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g., an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Method and system for interactive digital radio broadcasting and music distribution
InactiveUS6990312B1Easy to buySpecific information broadcast systemsBroadcast transmission systemsRelevant informationDigital radio
Owner:SONY CORP +1
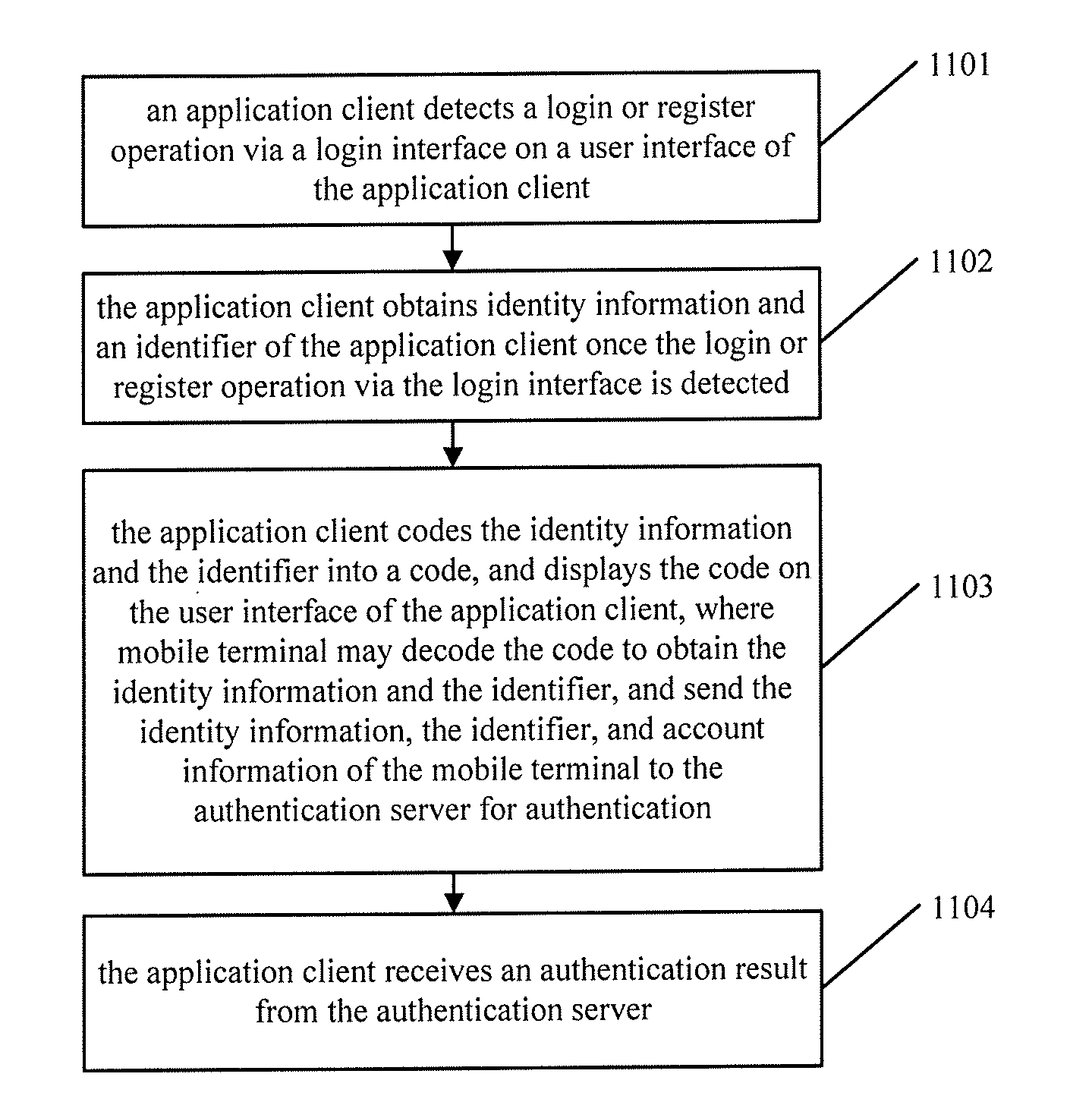
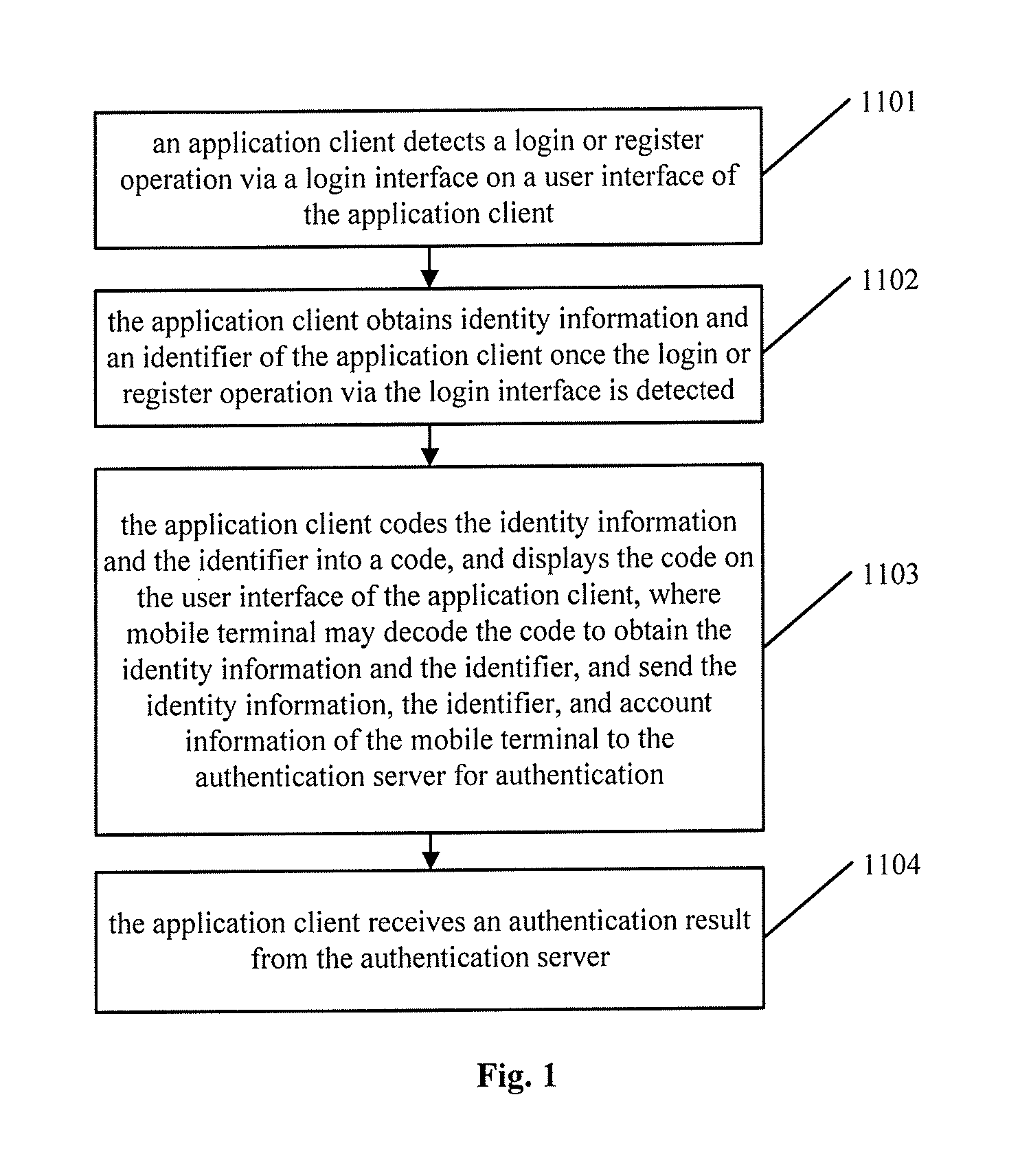
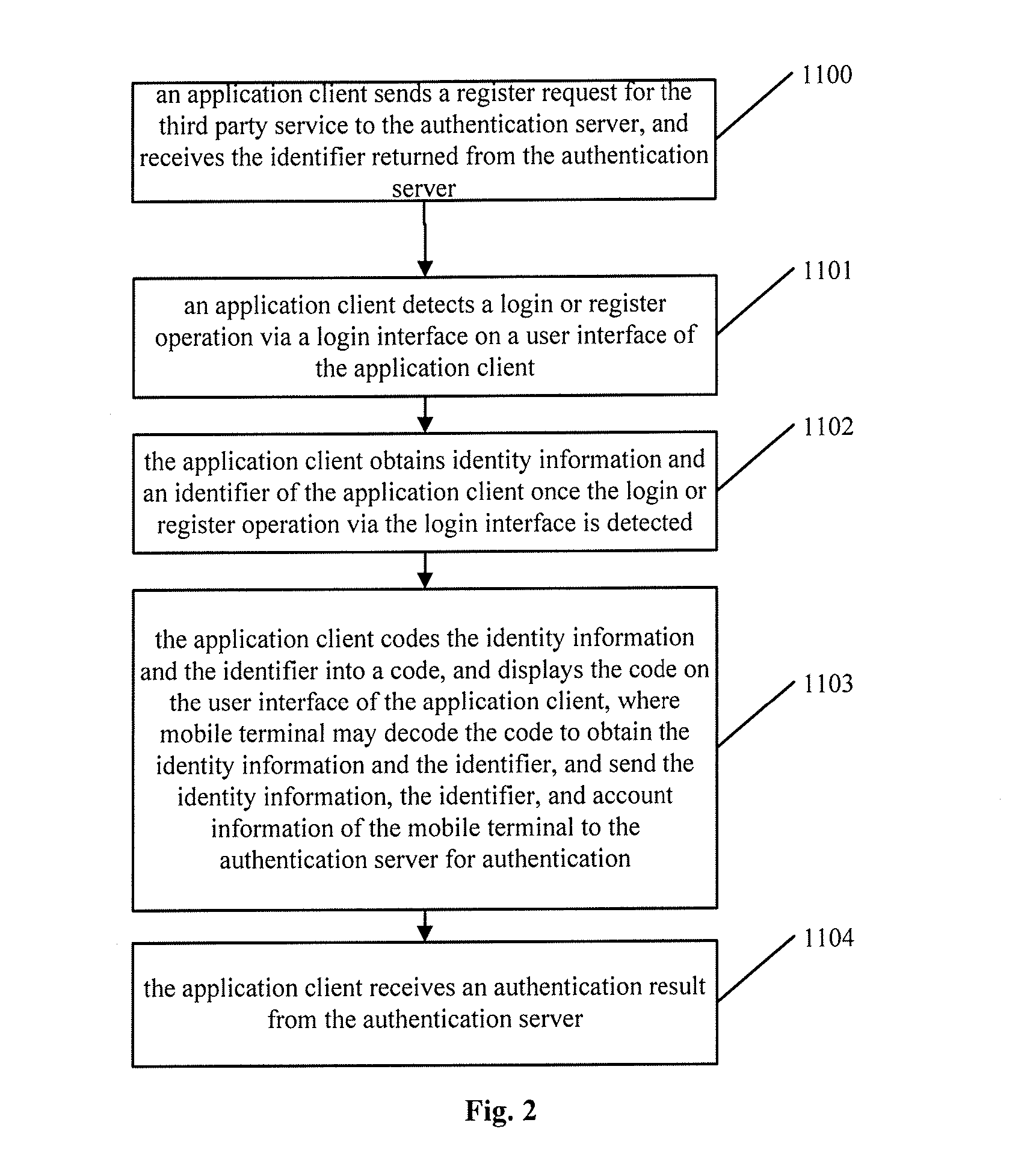
Method, client and system of identity authentication
ActiveUS20140289508A1Easy to operateOperation is inconvenientDigital data processing detailsMultiple digital computer combinationsThird partyComputer terminal
A method, client device and system of identity authentication are provided. The method may include detecting a login or registration operation, to a server, via a login interface on a user interface of an application client. In response, identity information and an identifier of the application client may be determined The identity information and the identifier may be encoded into a code displayed on the application client. A mobile terminal may obtain and decode the code to obtain the encapsulated identity information and the identifier. The mobile terminal may also have access to information about an account registered with the authentication server in advance. The mobile terminal may send the identity information, the identifier, and account information to the authentication server for authentication. The application client may then receive an authentication result from the authentication server enabling the user to access the third party service.
Owner:TENCENT TECH (SHENZHEN) CO LTD
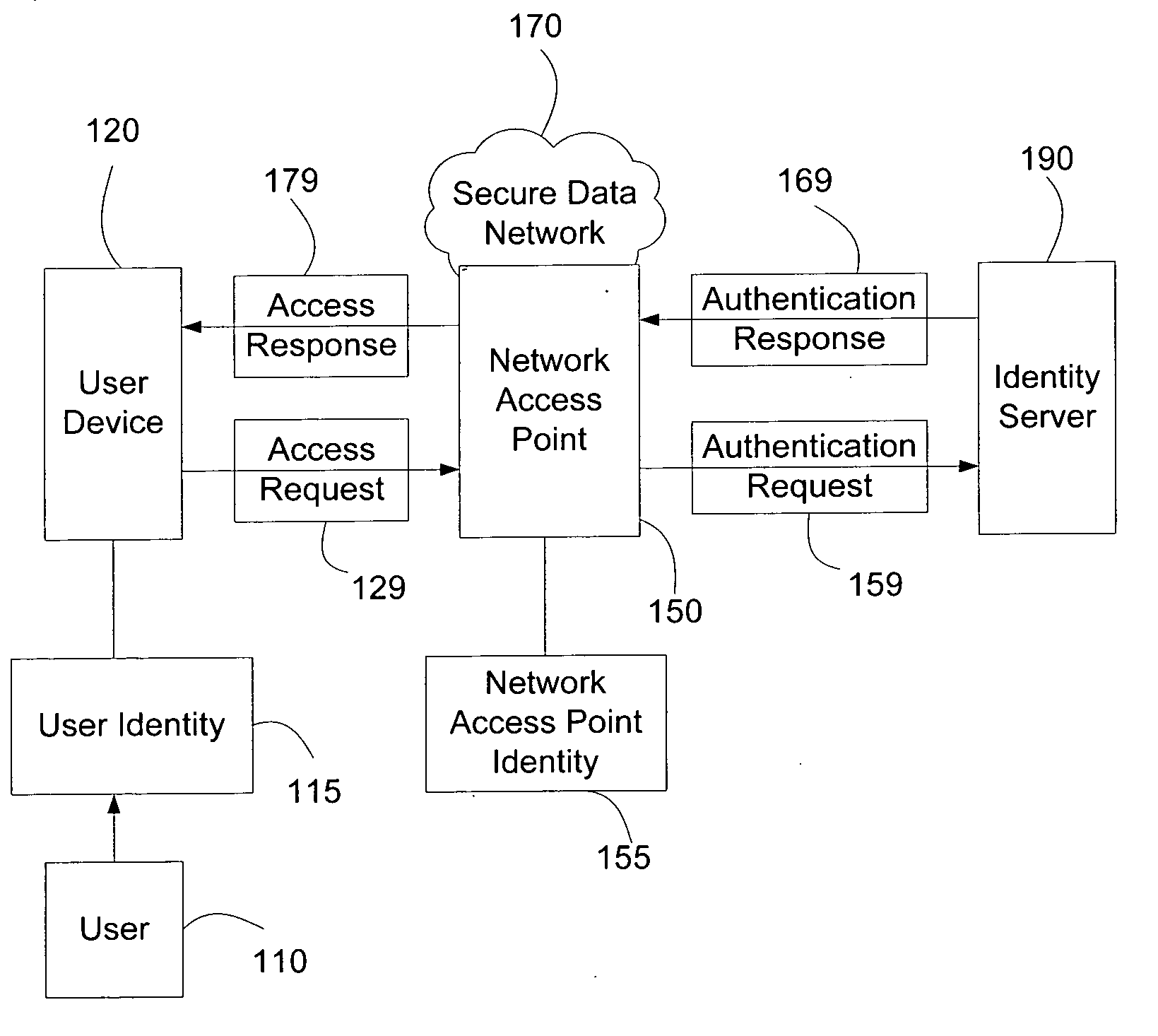
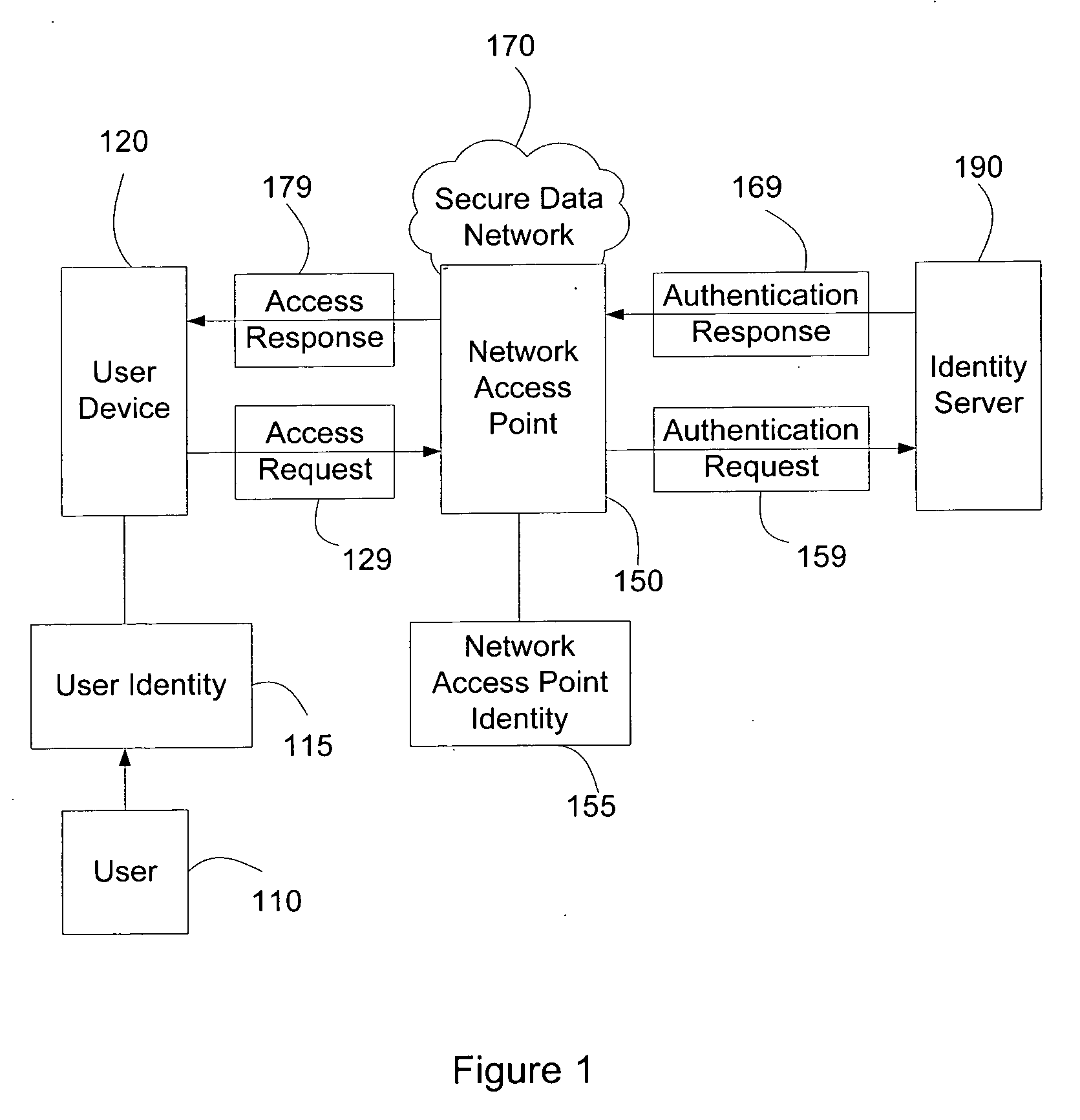
Systems and methods for user access authentication based on network access point
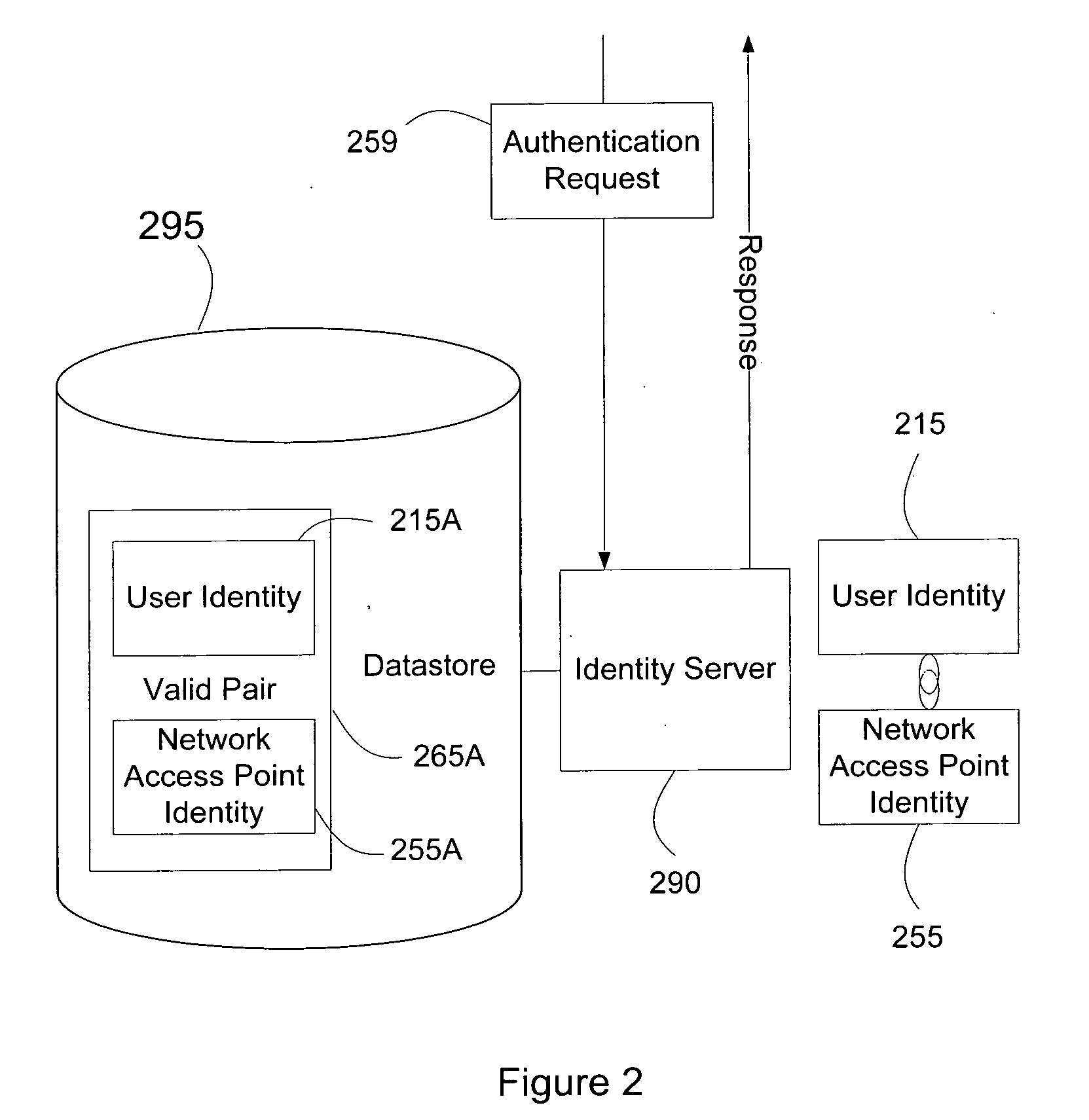
ActiveUS20070271598A1Random number generatorsUser identity/authority verificationTime informationAuthentication system
Systems and methods of authenticating user access based on an access point to a secure data network include a secure data network having a plurality of a network access points serving as entry points for a user to access the secure data network using a user device. The user is associated with a user identity, each network access point with a network access point identity. The user uses a user device to send an access request, requesting access to the secure data network, to the network access point, which then sends an authentication request to an identity server. The identity server processes the authentication request, by validating the combination of the user identity and the network access point identity, and responds with an authentication response, granting or denying access, as communicated to the user device via an access response. The secure data network may comprise an application level secure data network, in which the user uses the user device to request access to a network application. Furthermore, the identity server may validate the combined user identity and network access point identity data in conjunction with time information, access allowance data, and / or traffic volume data.
Owner:A10 NETWORKS
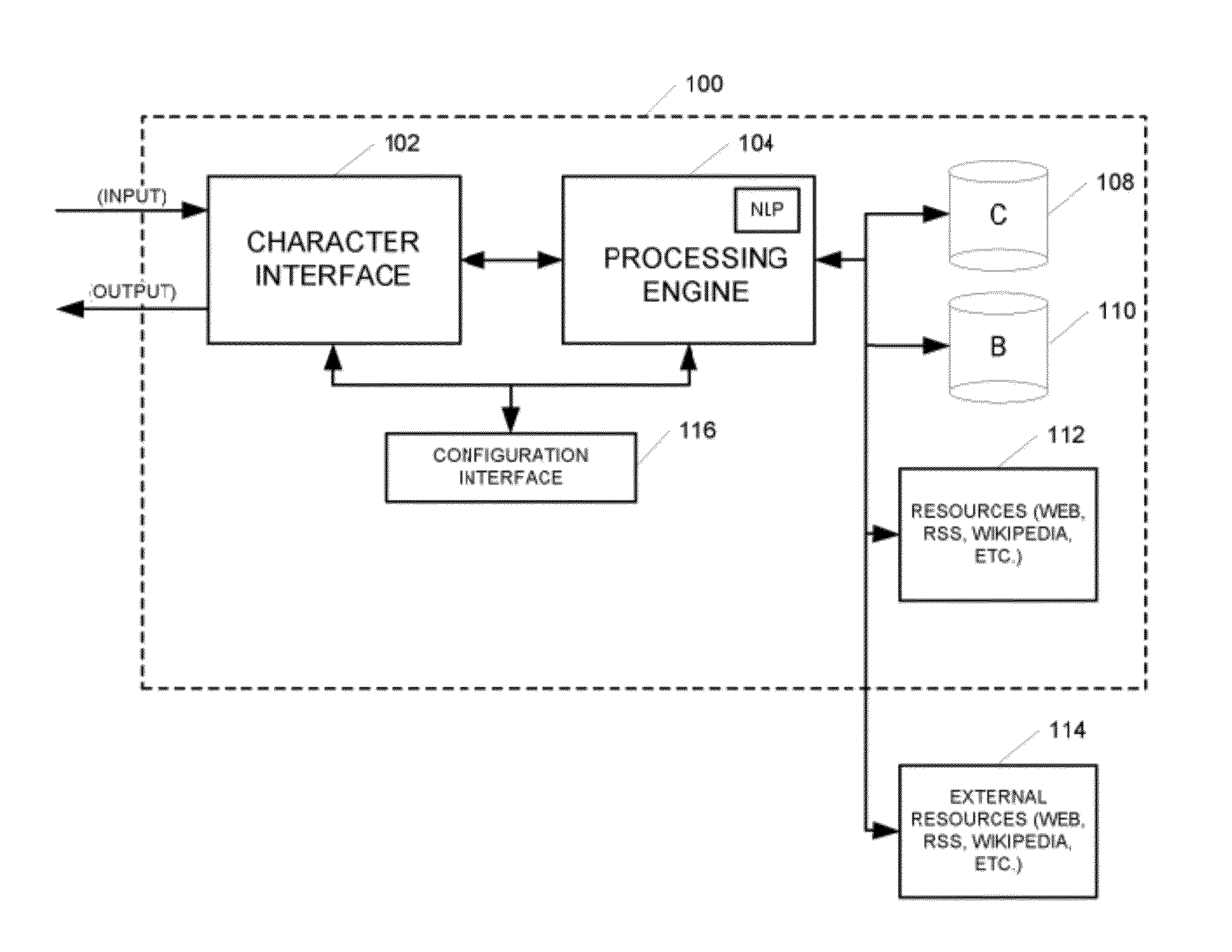
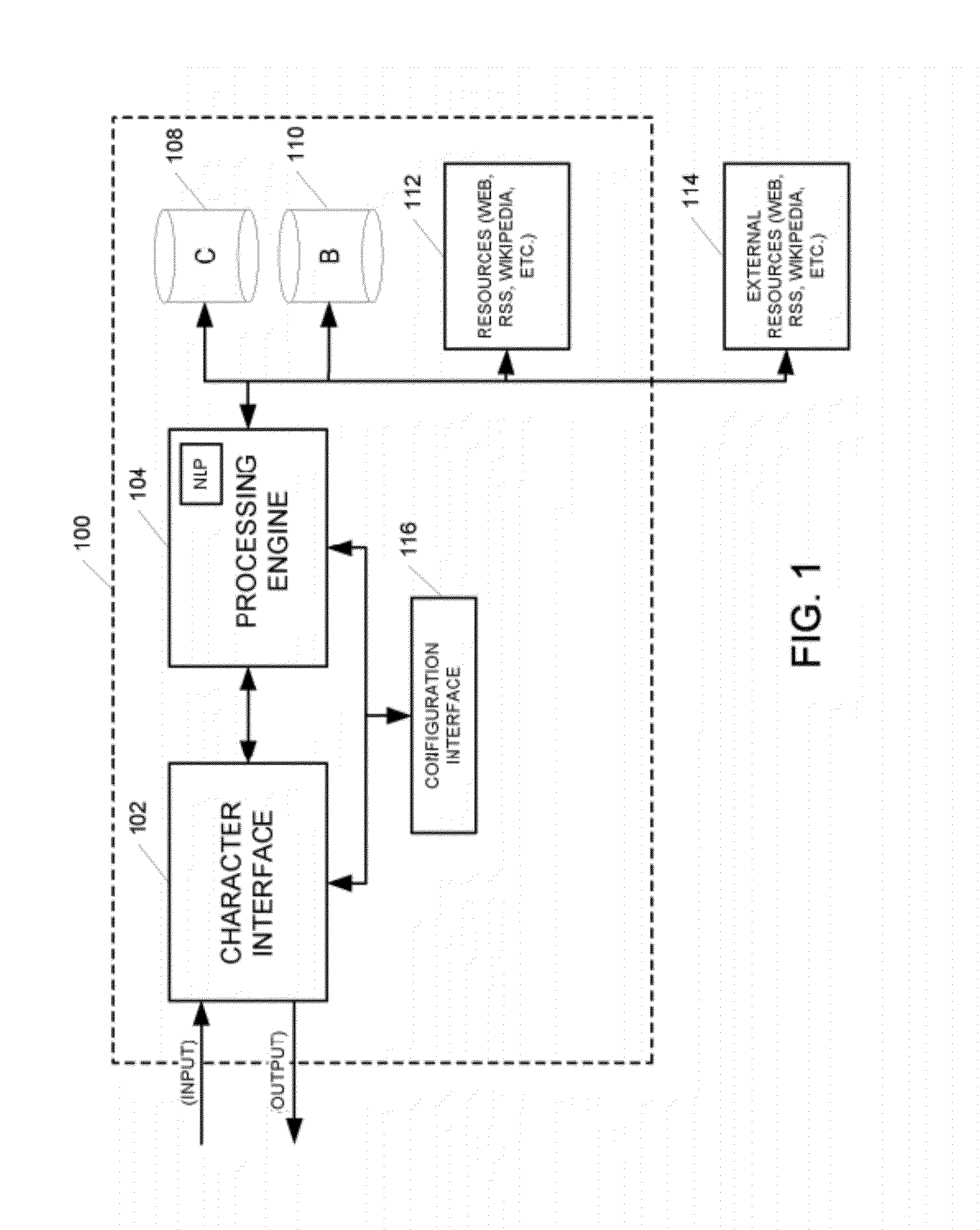
Systems and methods for generating and implementing an interactive man-machine web interface based on natural language processing and avatar virtual agent based character
An interactive virtual agent (avatar) system includes a plurality of databases configured to store at least one of client specific information and non-client specific information, internal resources configured to provide access to information sources, the character interface configured to receive information from a user, and respond to the user with information based on the received information, a processing engine coupled with the client knowledge database, the basic knowledge database, the internal resources, and the character interface.
Owner:INTELIWISE Z O O
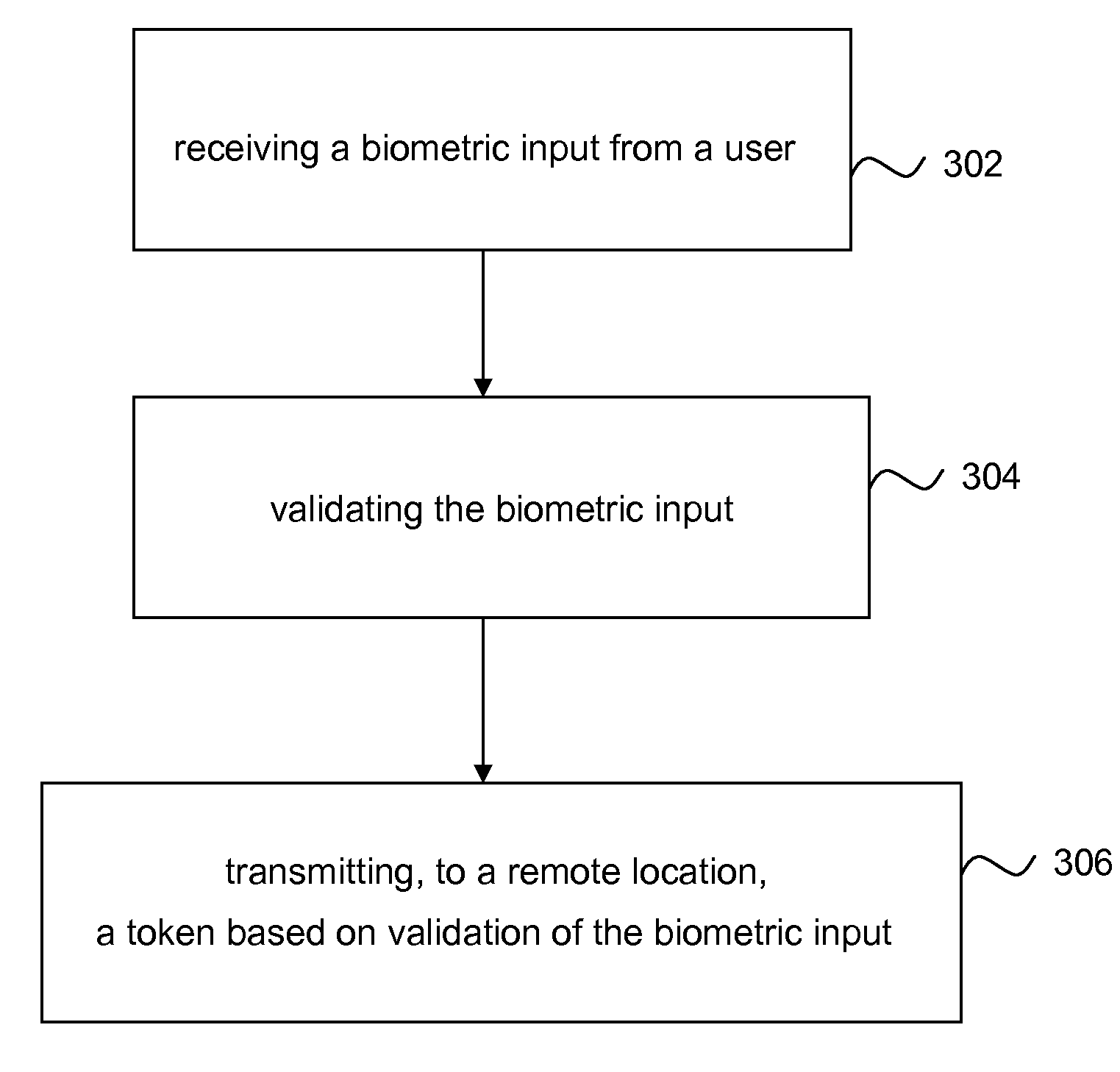
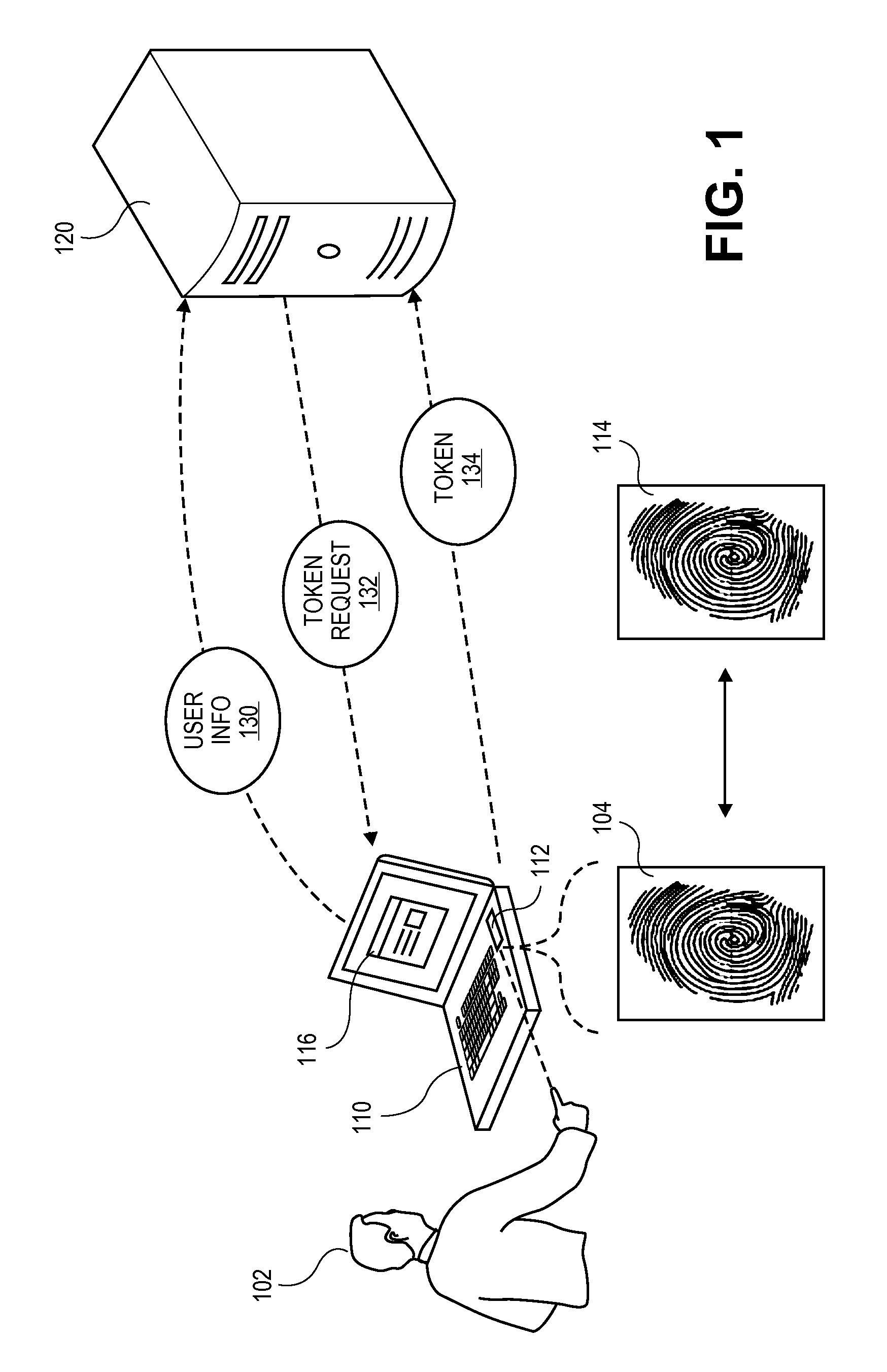
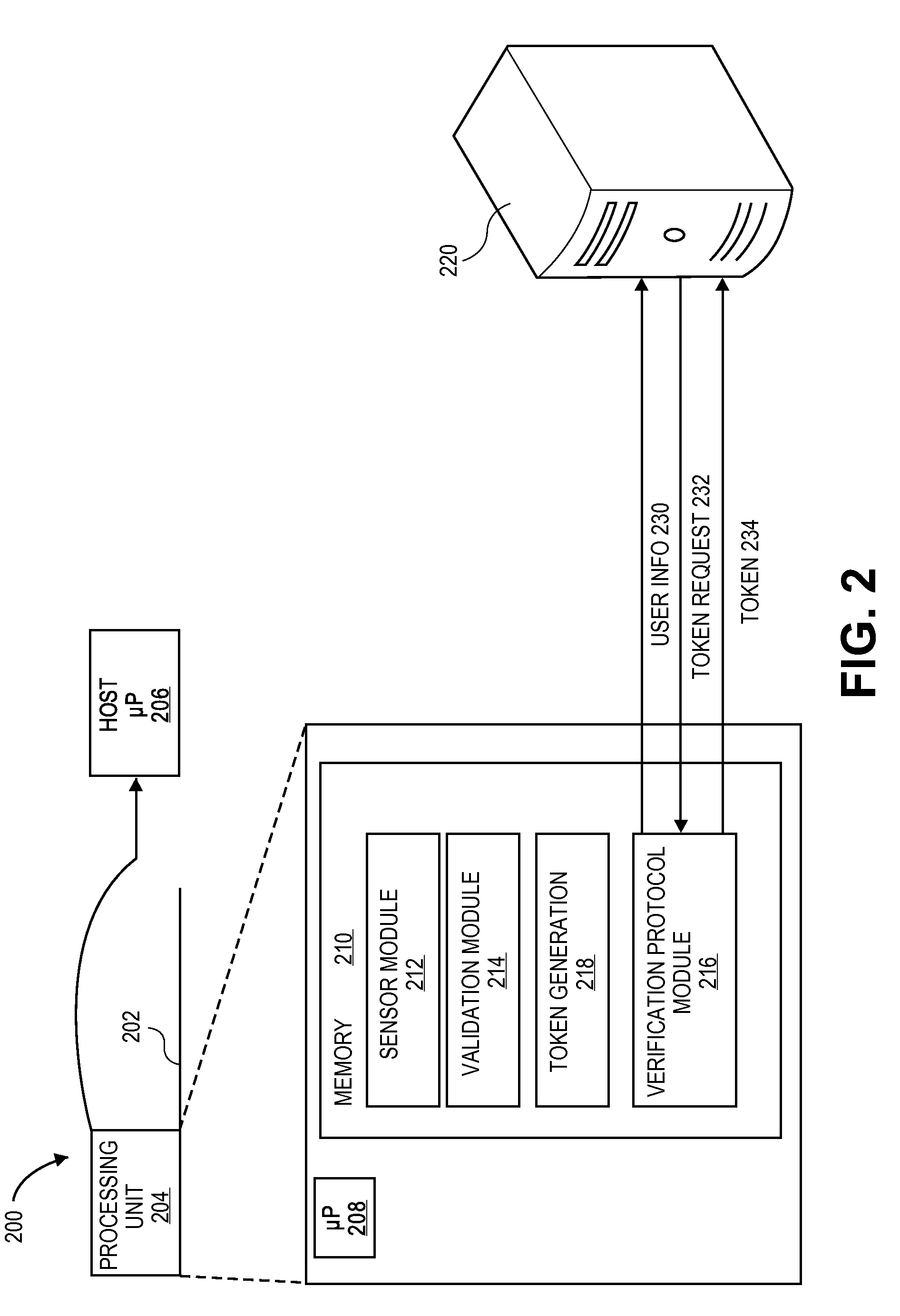
Fingerprint Sensor Device and System with Verification Token and Methods of Using
InactiveUS20100083000A1Electric signal transmission systemsDigital data processing detailsValidation methodsSecure authentication
A method and system of verification is provided for sensing a fingerprint. The present invention offers a secure authentication method and system based on a user's fingerprint data to grant the access to information at a remote location. A biometric input corresponding to the fingerprint is provided by a user and the biometric input is than validated. Based on the validation, a token is transmitted to a remote location. The method and system can be further enhanced by additional security comprising receiving a request based on the authentication of the user information and transmitting, to a second remote location, a token based on the biometric input in response to the request.
Owner:SYNAPTICS INC
Integrated method and apparatus for capture, storage, and retrieval of information
InactiveUS20050091186A1Simple wayDigital data processing detailsWeb data navigationGraphicsRelevant information
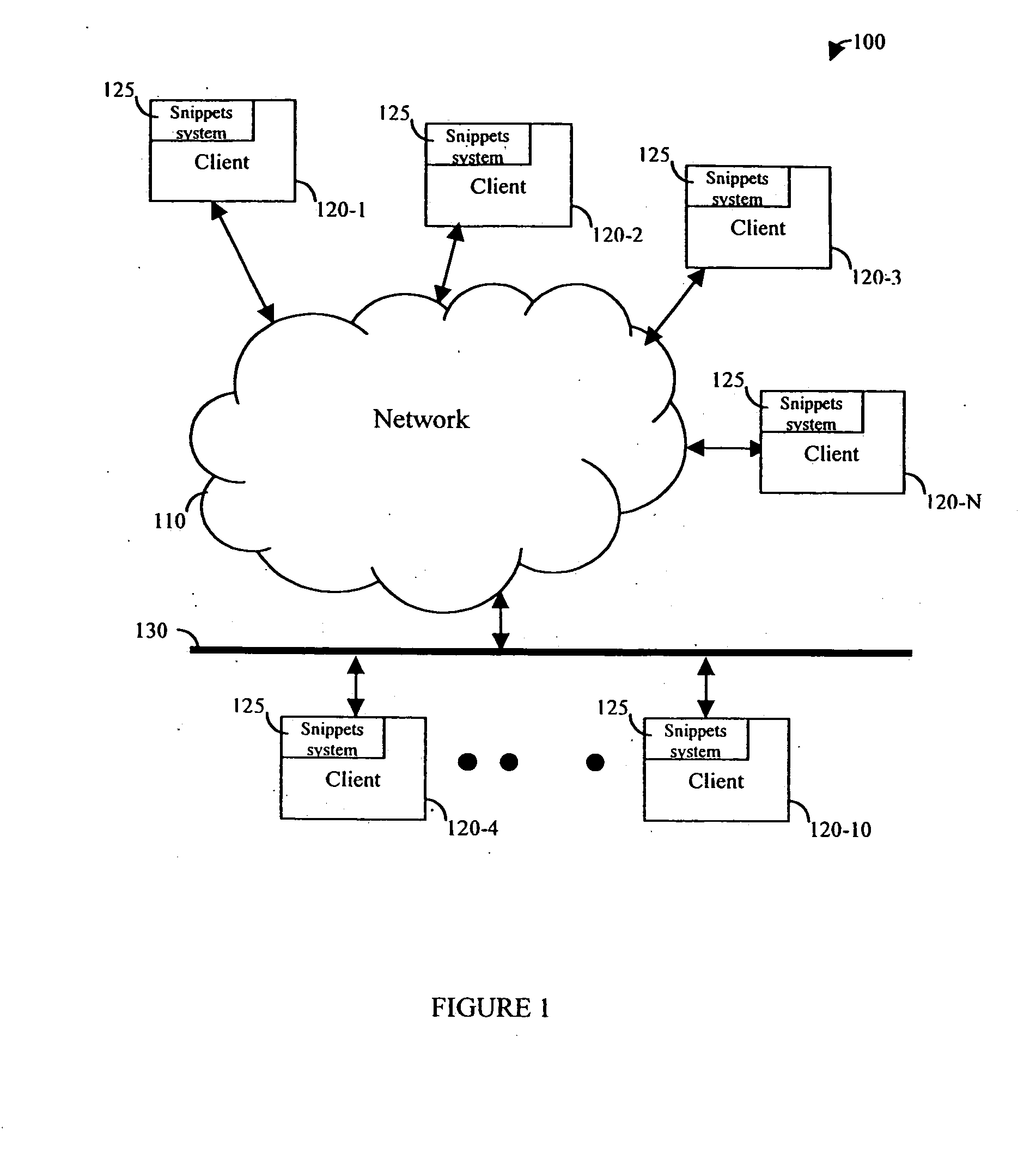
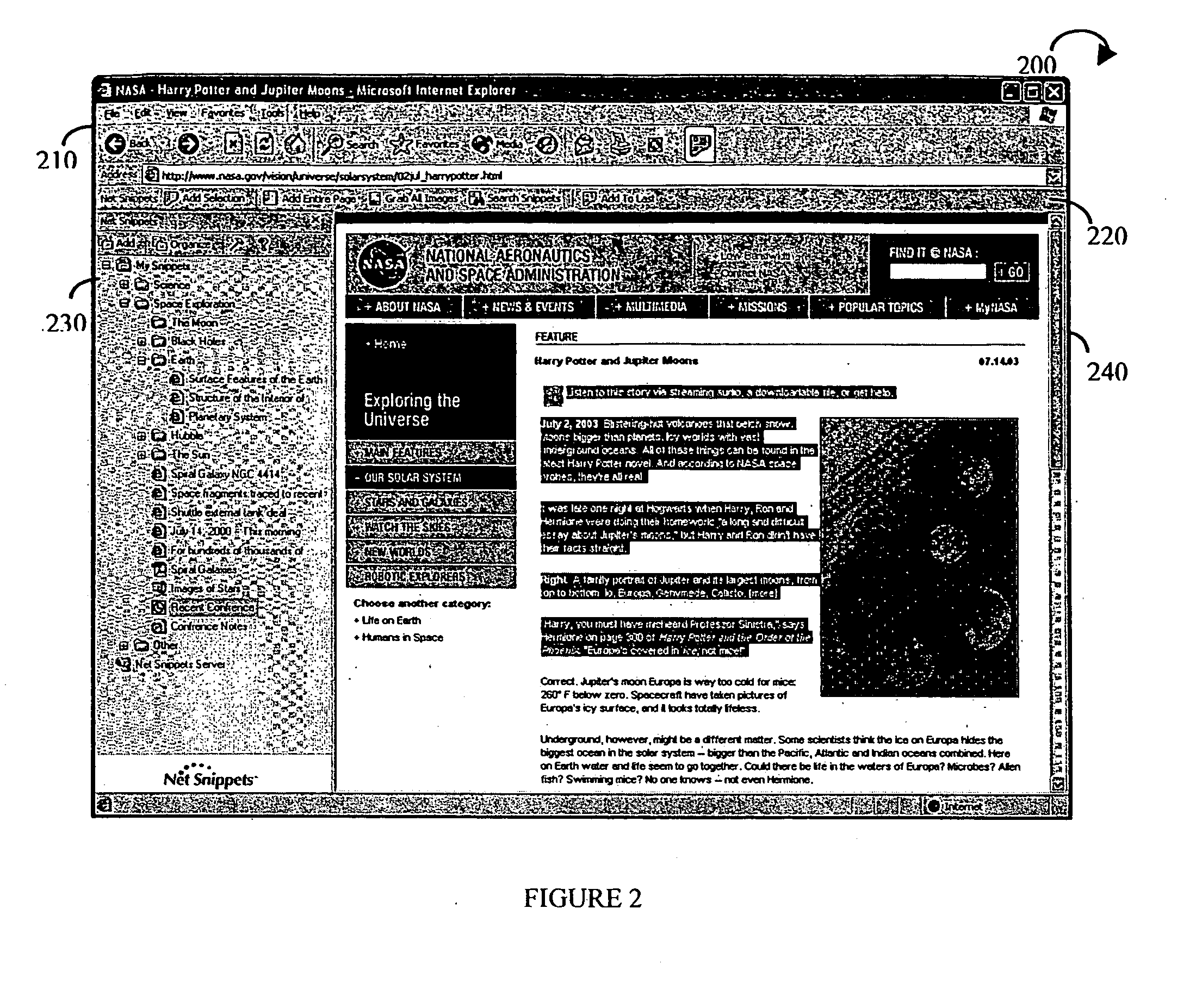
An integrated method and apparatus is provided for capturing, storing, organizing, and sharing pertinent information from a plurality of sources in a simple and effective manner. The invention allows for the local capture of pertinent information from files, Web pages, Web files, e-mail items, and the like, as well as portions thereof. The pertinent information may be captured in any granularity that is selected by a user. The invention also provides a graphical user interface (GUI) for a consistent handling and viewing of all information. The integrated method and apparatus can operate in conjunction with a software browser, such as Microsoft's Internet Explorer, Netscape's Navigator, or any other commercial or custom-designed browser that allows access to information.
Owner:NET SNIPPETS
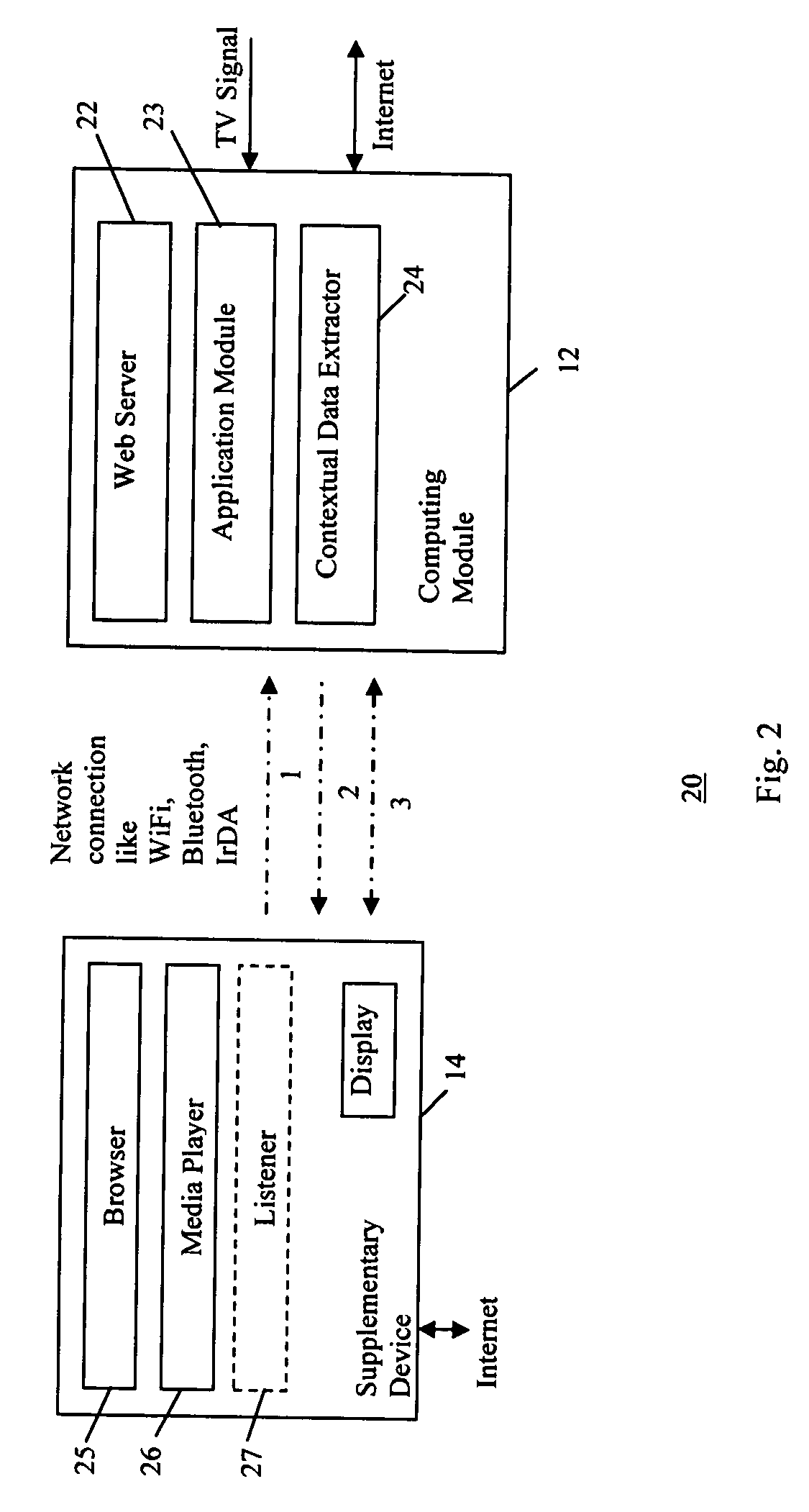
Method and system for providing information using a supplementary device
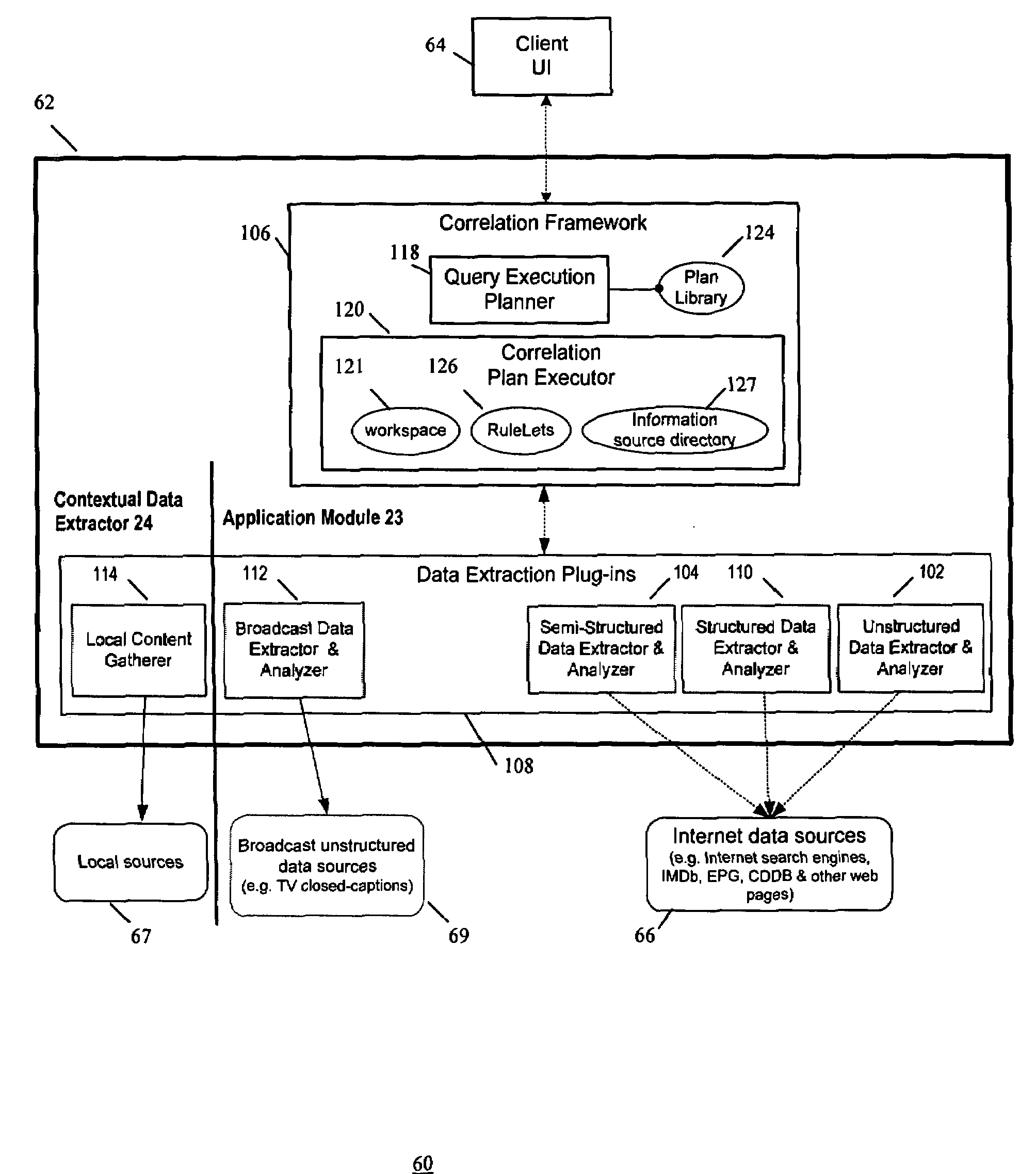
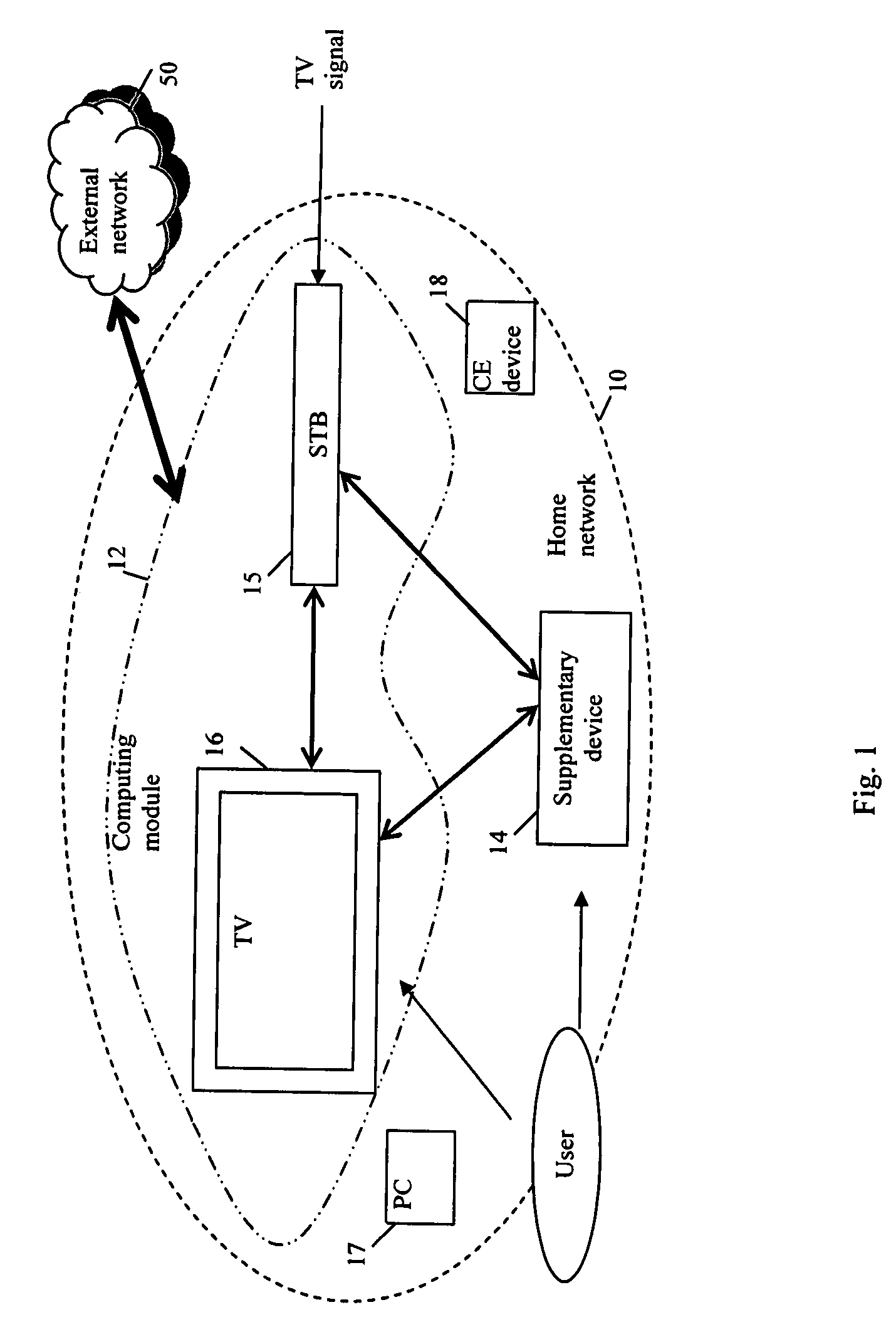
InactiveUS20080208839A1Digital data processing detailsSpecial data processing applicationsSystem monitoringAccess to information
A method and system for providing access to information via a supplementary device is provided. User access to primary information via a primary device is monitored. Key information related to the primary content is obtained by extracting and analyzing metadata sources for the primary information. Then, supplementary information related to the primary information is obtained based on the key information. The supplementary information is provided for user access via the supplementary device.
Owner:SAMSUNG ELECTRONICS CO LTD
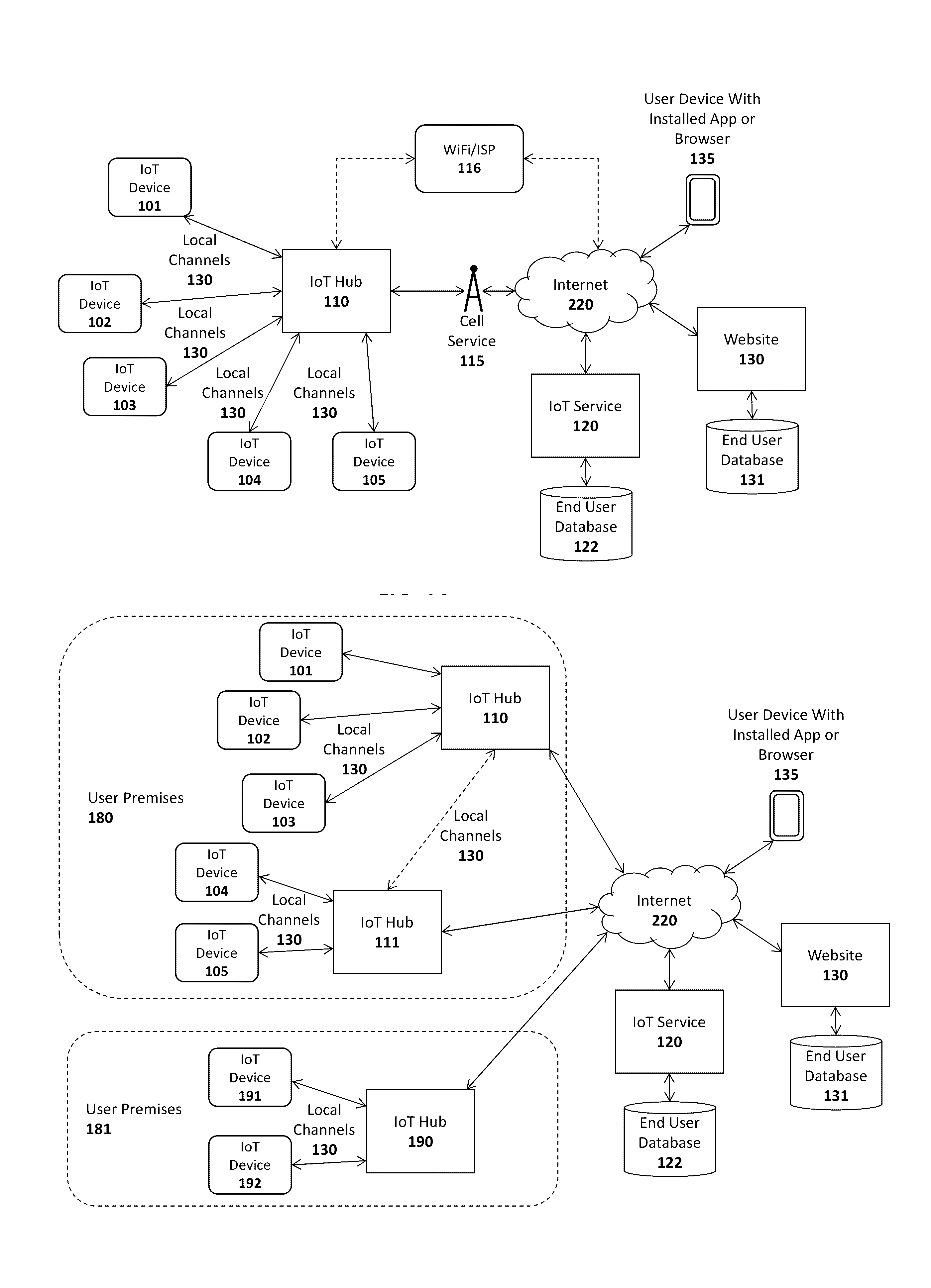
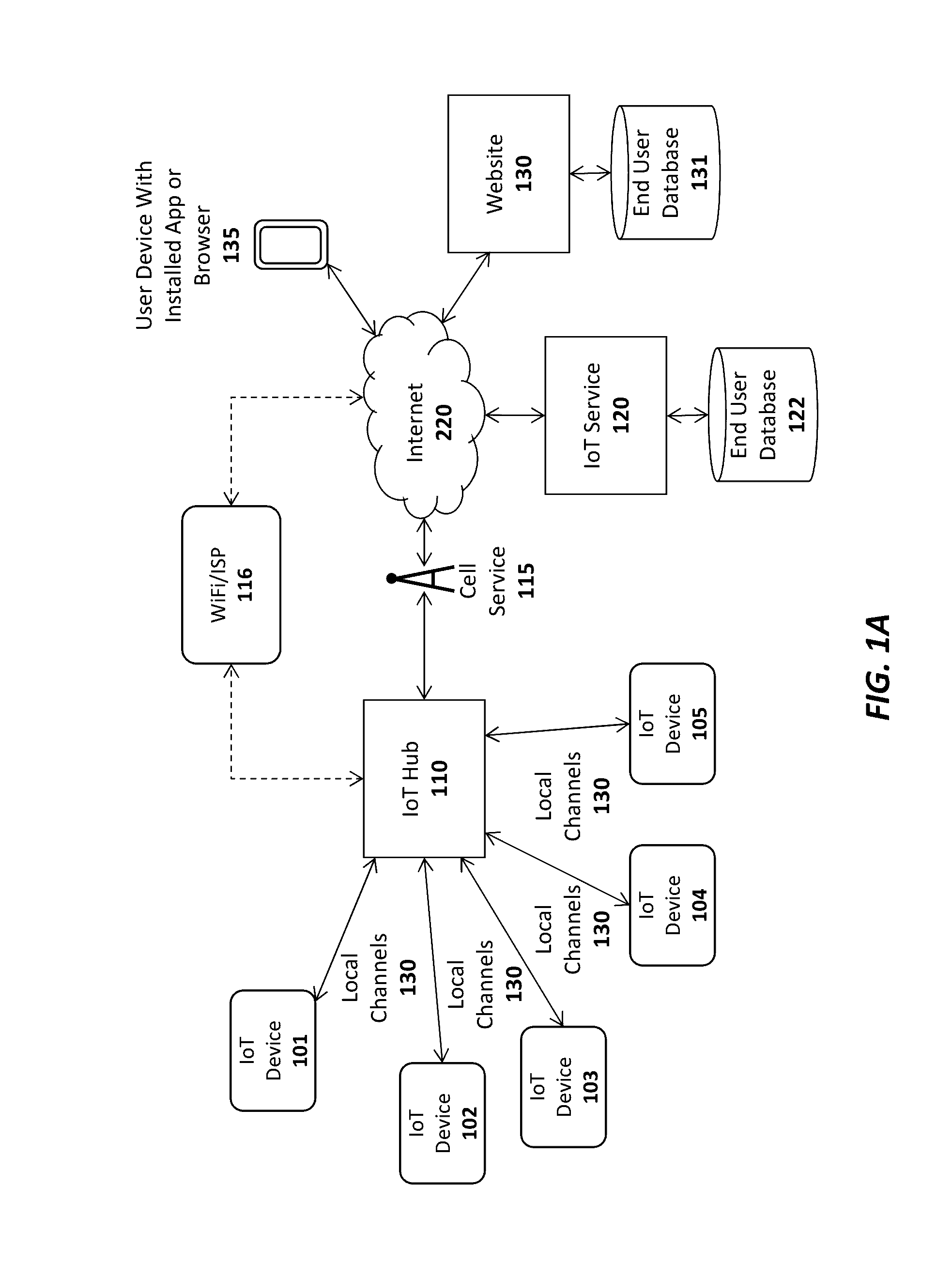
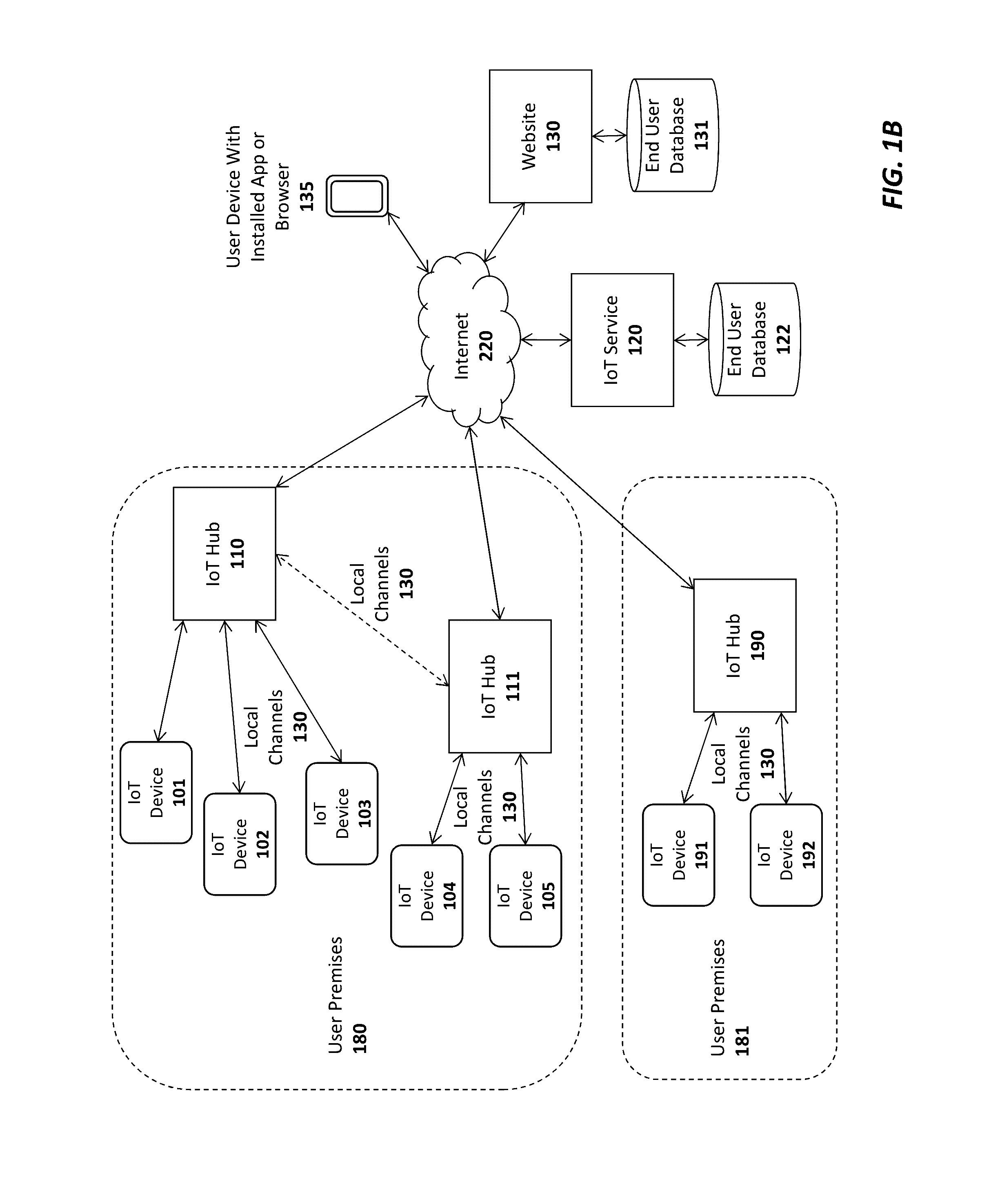
System and method for virtual internet of things (IOT) devices and hubs
A system and method are described for virtualizing Internet of Things (IoT) devices and hubs. For example, one embodiment of a system comprises: a primary Internet of Things (IoT) cloud service to register IoT devices owned by users who have subscribed with the primary IoT cloud service; IoT device management logic on the primary IoT cloud service to provide access to data generated by the primary IoT devices and to control the IoT devices responsive to user input; the IoT device management logic to establish a communication channel with an external IoT cloud service responsive to a user registering one or more external IoT devices controlled by the external IoT cloud service; and wherein upon the external IoT cloud service providing the IoT device management logic with access to the one or more external IoT devices, the IoT device management logic to generate virtual representations of the one or more external IoT devices to allow user access to information generated by the external IoT devices and to allow the user to control the external IoT devices through the virtual representations.
Owner:AFERO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com