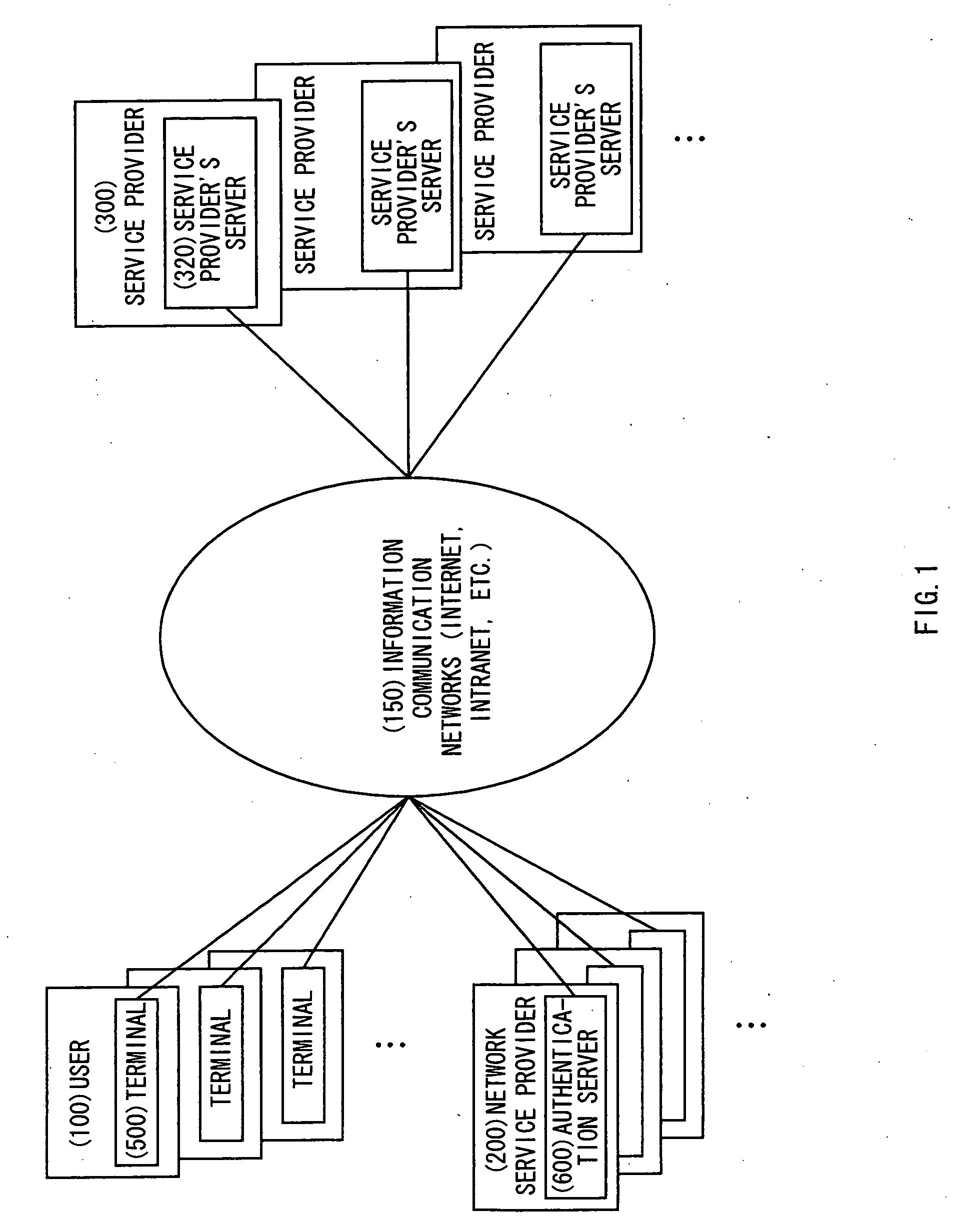
Patents
Literature
4680 results about "Validation methods" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method Validation. Method validation is the process used to confirm that the analytical procedure employed for a specific test is suitable for its intended use. Results from method validation can be used to judge the quality, reliability and consistency of analytical results; it is an integral part of any good analytical practice.
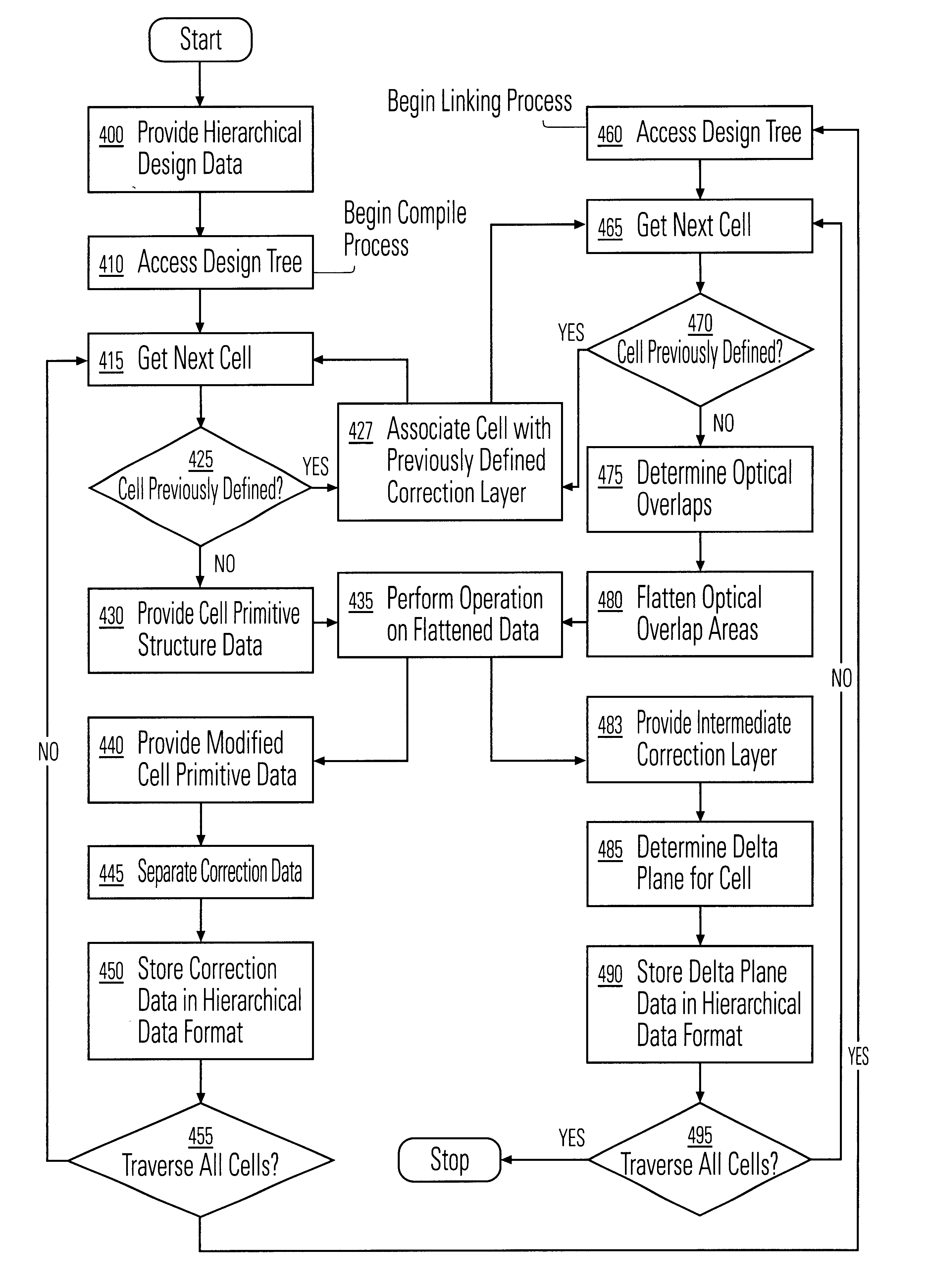
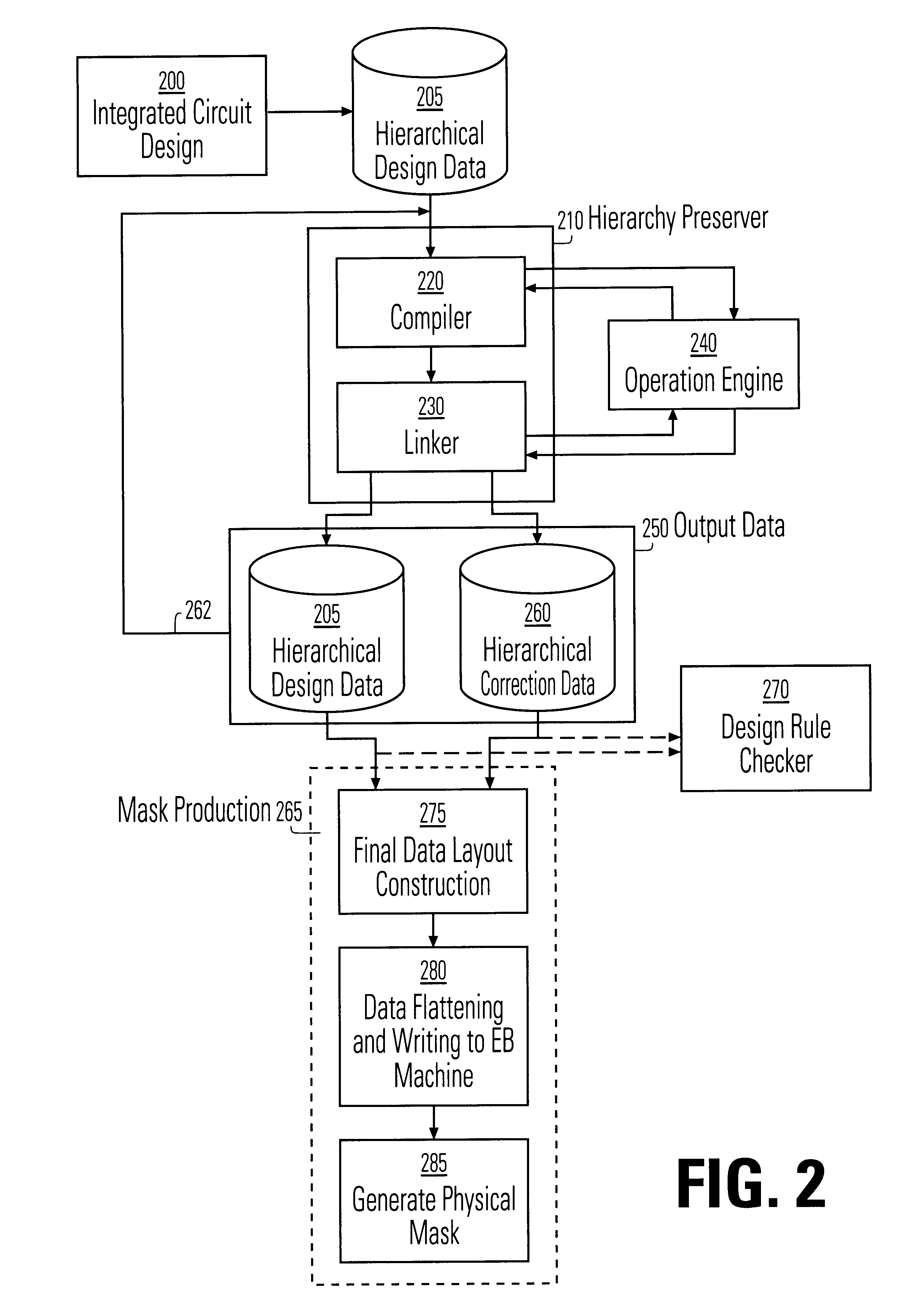
Data hierarchy layout correction and verification method and apparatus
InactiveUS6370679B1Computation using non-denominational number representationOriginals for photomechanical treatmentComputer architectureValidation methods
A method and apparatus for the correction of integrated circuit layouts for optical proximity effects which maintains the original true hierarchy of the original layout is provided. Also provided is a method and apparatus for the design rule checking of layouts which have been corrected for optical proximity effects. The OPC correction method comprises providing a hierarchically described integrated circuit layout as a first input, and a particular set of OPC correction criteria as a second input. The integrated circuit layout is then analyzed to identify features of the layout which meet the provided OPC correction criteria. After the areas on the mask which need correction have been identified, optical proximity correction data is generated in response to the particular set of correction criteria. Finally, a first program data is generated which stores the generated optical proximity correction data in a hierarchical structure that corresponds to the hierarchical structure of the integrated circuit layout. As the output correction data is maintained in true hierarchical format, layouts which are OPC corrected according to this method are able to be processed through conventional design rule checkers with no altering of the data.
Owner:SYNOPSYS INC
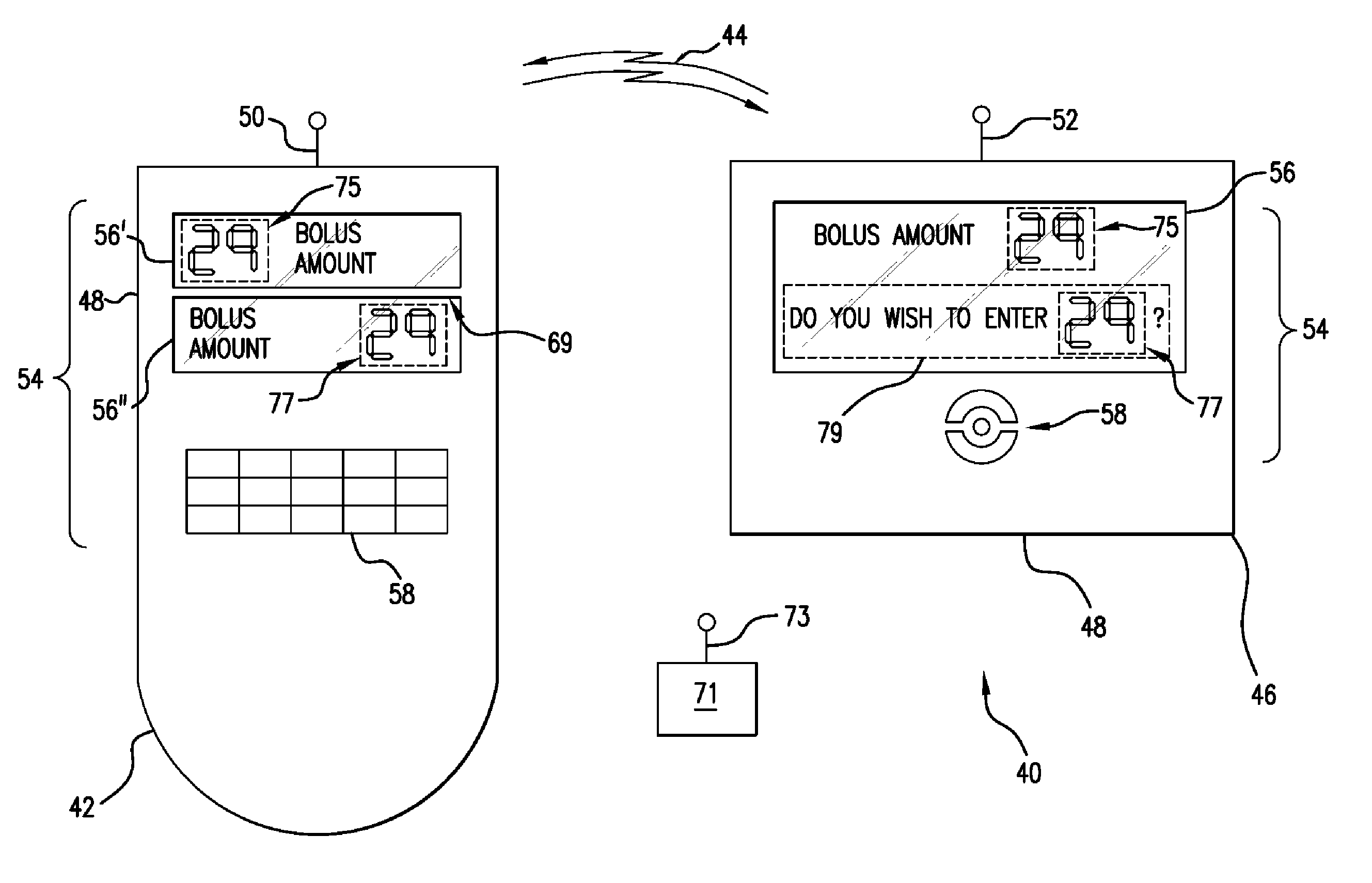
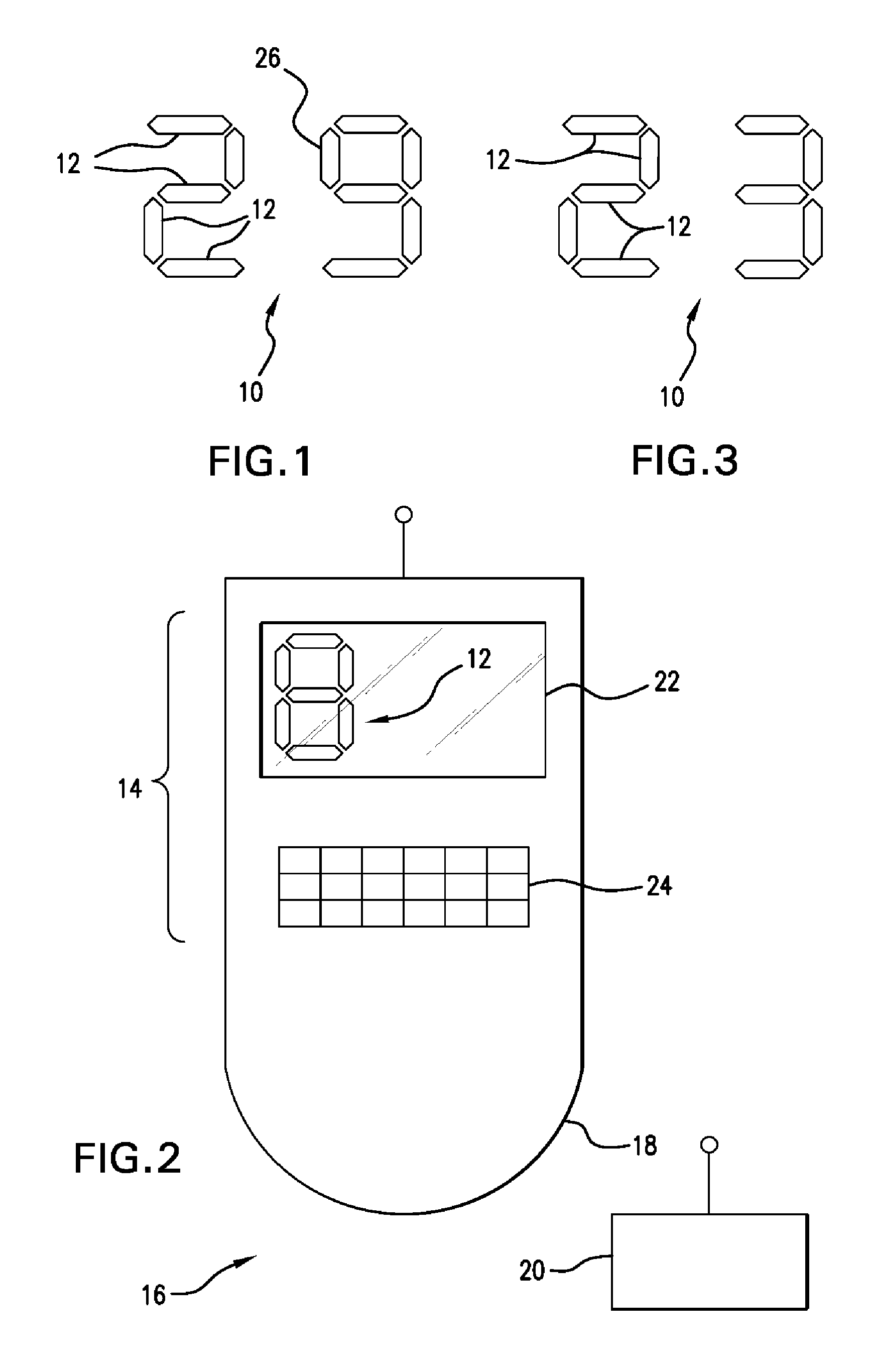
Method For Visual Output Verification
InactiveUS20050182366A1BiocideHydroxy compound active ingredientsValidation methodsHuman–computer interaction
A verification method including the steps of displaying a visual output in a first region of a user interface and displaying at least a portion of said visual output in at least a second region of said user interface, said at least a second region being different than said first region, wherein said first and said at least a second region are disposed on a single surface of a device.
Owner:INSULET CORP
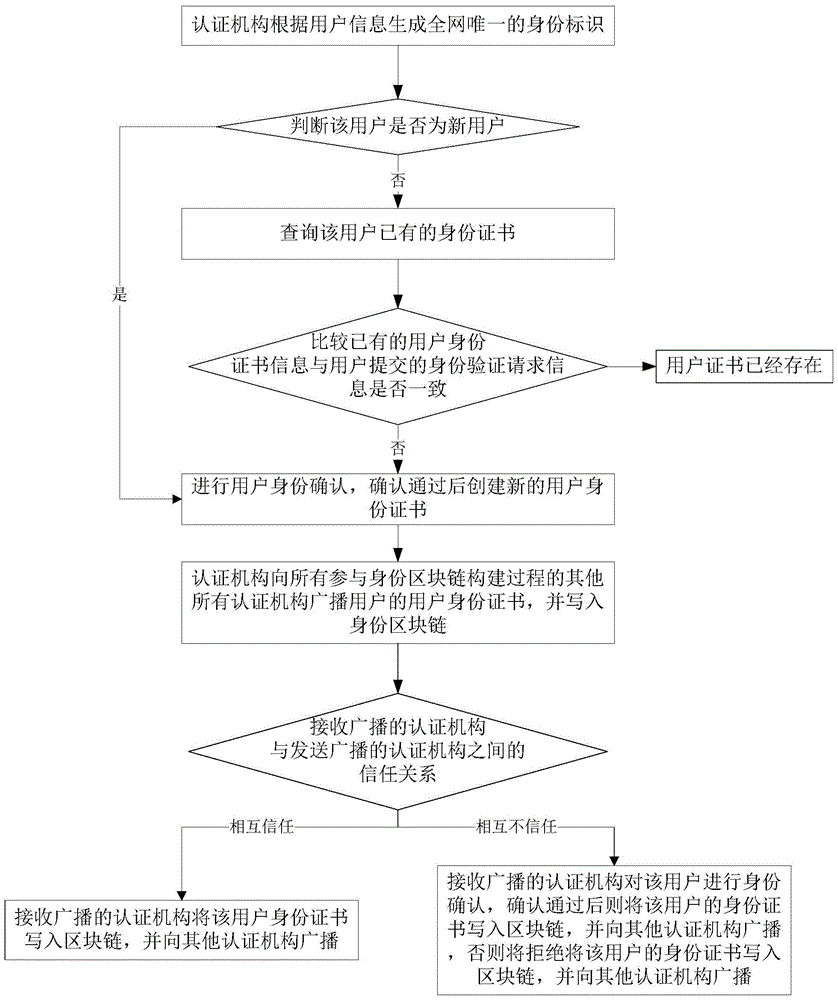
Block chain identity construction and verification method
ActiveCN105701372AImprove authentication efficiencyDoes not affect accuracyDigital data authenticationValidation methodsThe Internet
The present invention relates to identity construction and verification on the Internet, and provides a block chain identity construction and verification method. The method comprises the following steps: a certificate authority constructs a user identity block chain according to an identity verification request submitted by a user; and the certificate authority performs user identity verification processing by means of the identity block chain. According to the method provided by the present invention, user identity information is written into the block chain, and multiple certificate authorities jointly complete confirmation and storage of the identity information by means of an agreement mechanism, and then the user can conveniently perform identity verification by using the block chain. The method is not only capable of improving efficiency of user identity verification, but also will not affect accuracy of the user identity information due to the problem of an individual certificate authority, thereby greatly improving security of an identity verification process.
Owner:BUBI BEIJING NETWORK TECH CO LTD +1
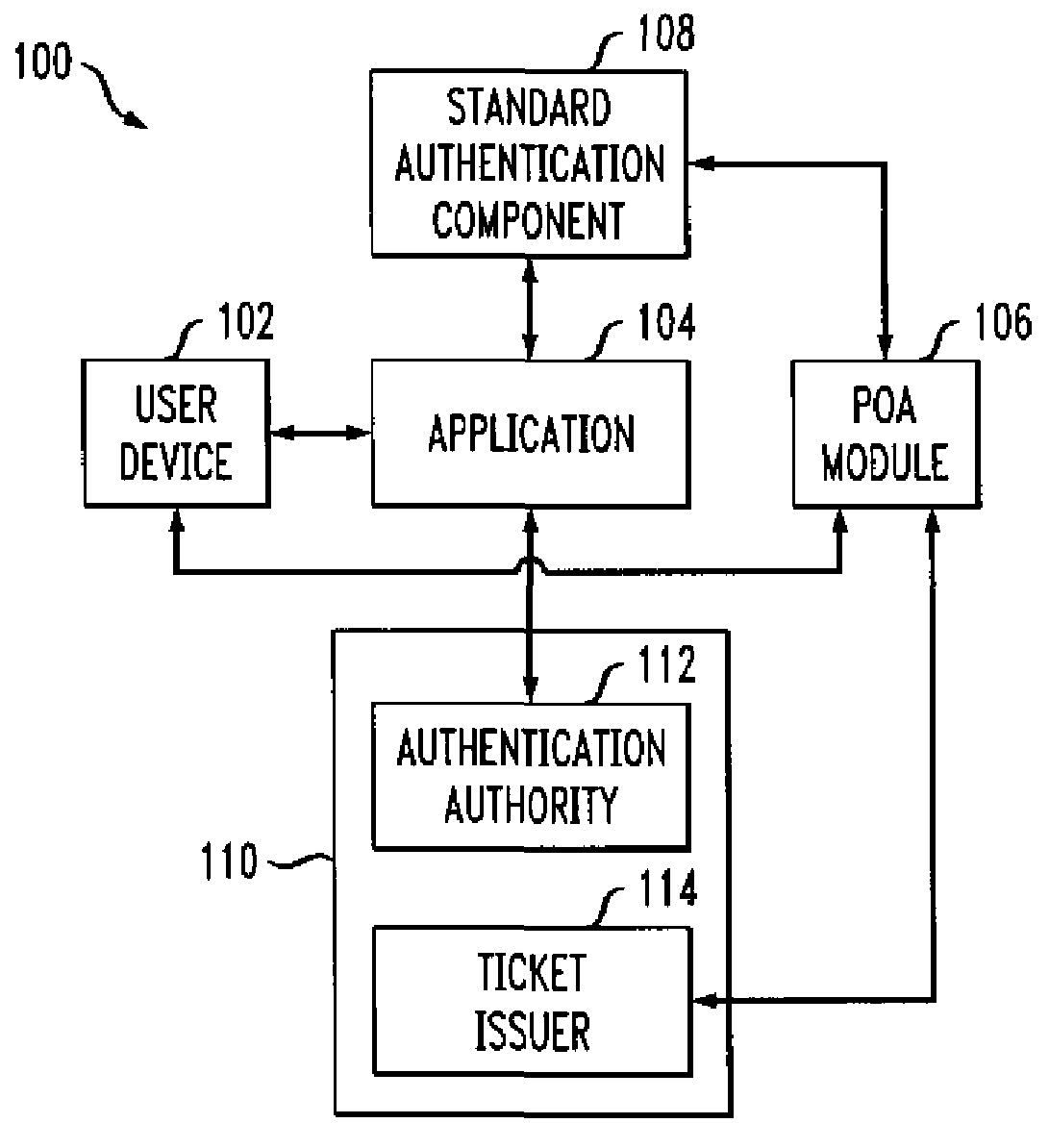
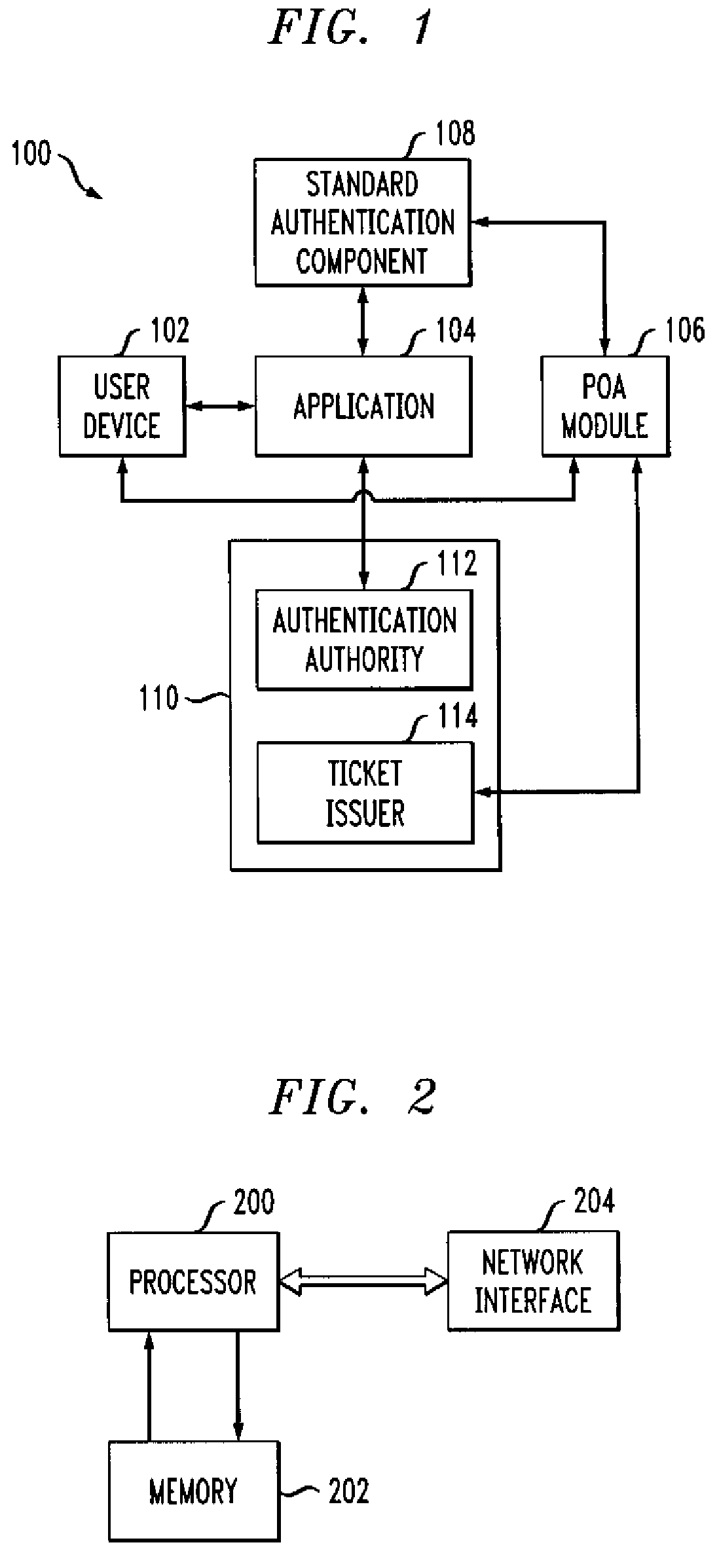
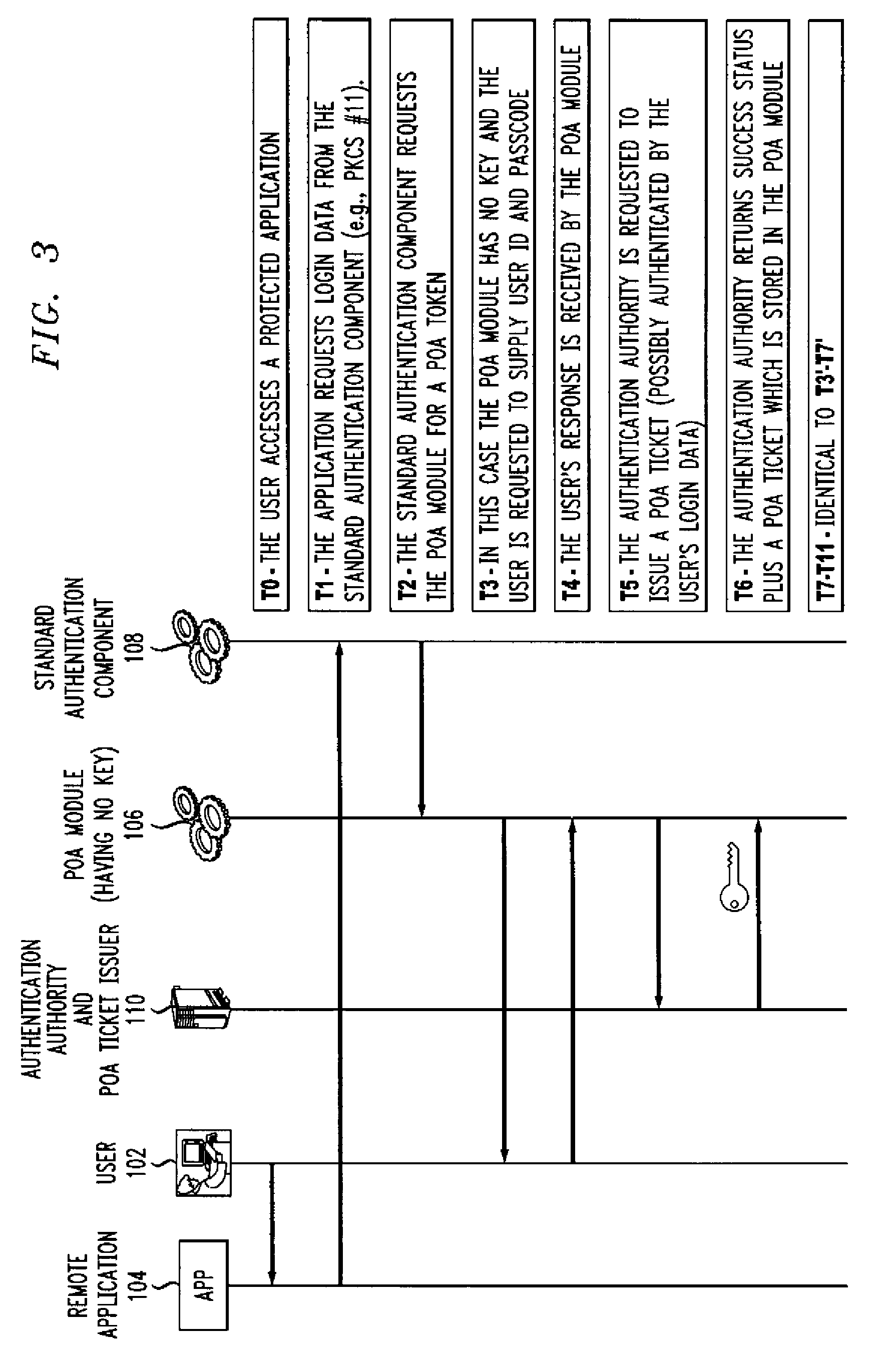
Authentication method and apparatus utilizing proof-of-authentication module
ActiveUS7562221B2Unauthorised/fraudulent call preventionDigital data processing detailsComputer hardwareValidation methods
A single sign-on technique allows multiple accesses to one or more applications or other resources using a proof-of-authentication module operating in conjunction with a standard authentication component. The application or other resource issues an authentication information request to the standard authentication component responsive to an access request from the user. The application or other resource receives, responsive to the authentication information request, a proof-of-authentication value from the standard authentication component, and authenticates the user based on the proof-of-authentication value. The standard authentication component interacts with the proof-of-authentication module to obtain the proof-of-authentication value. The proof-of-authentication module is configured to generate multiple proof-of-authentication values for authentication of respective access requests of the user.
Owner:EMC IP HLDG CO LLC
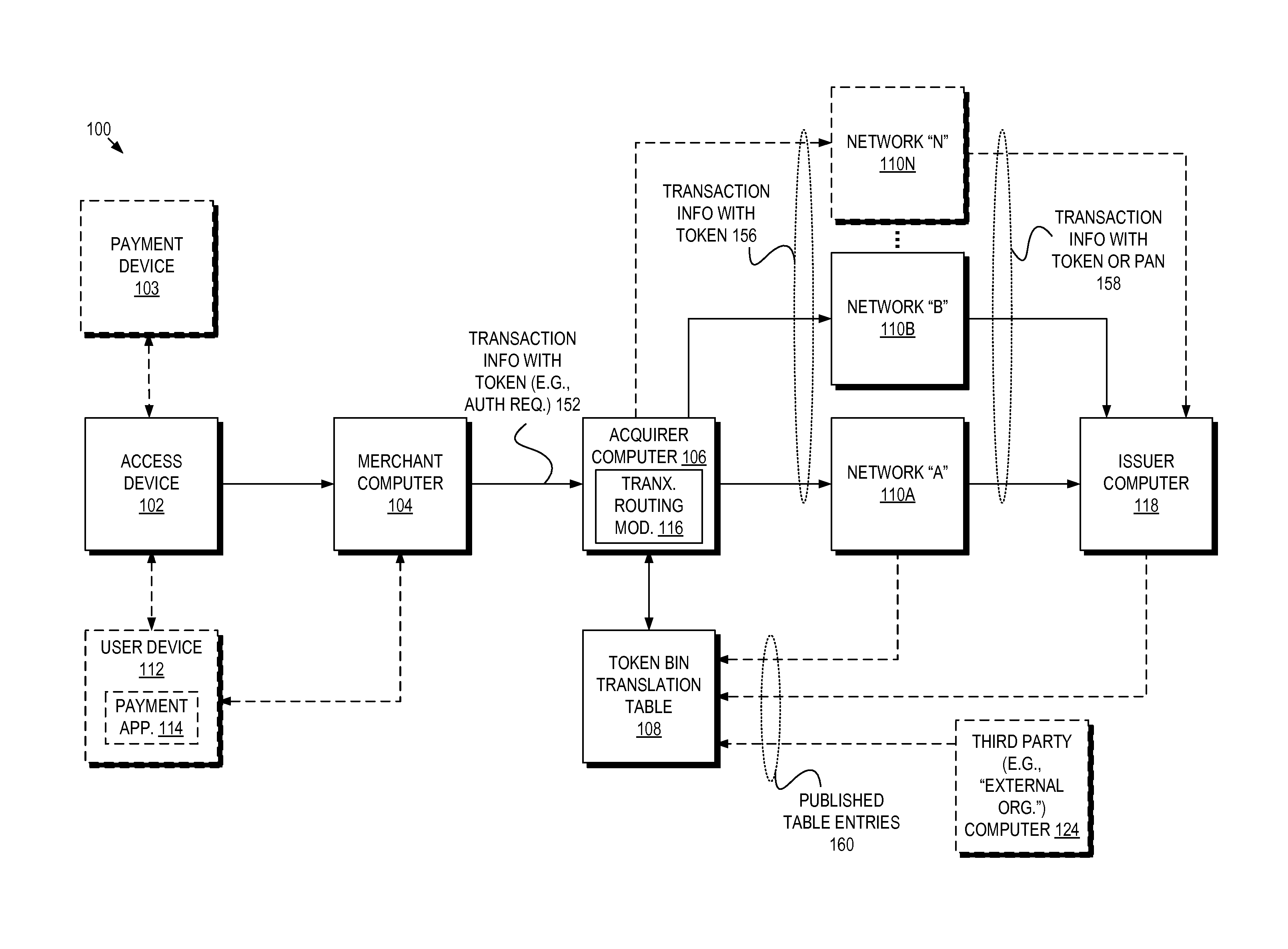
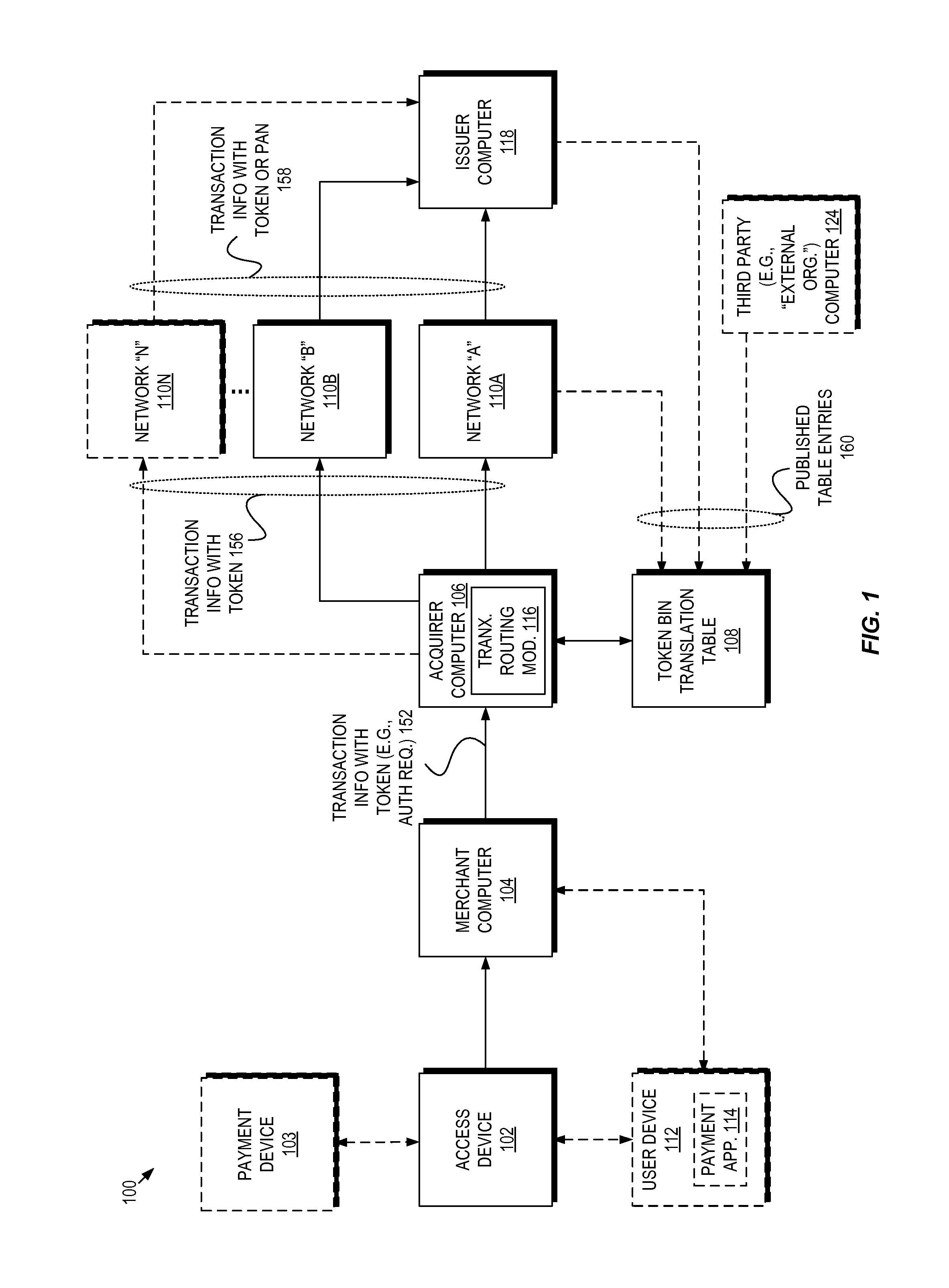
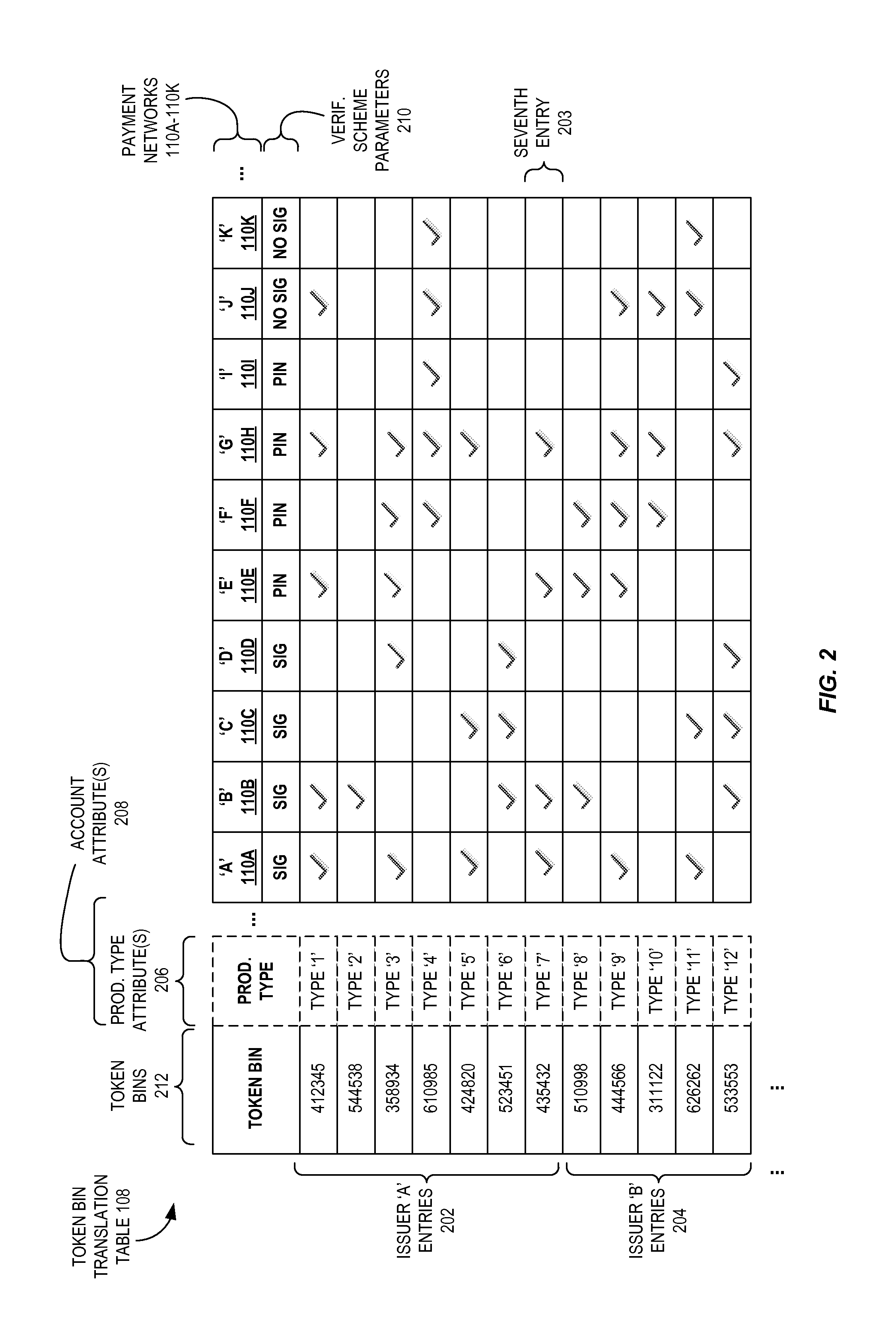
Multi-network token bin routing with defined verification parameters
Techniques described herein relate to using tokenization with BIN table routing by configuring a computer system, such as an acquirer computer, to utilize a token BIN translation table to determine which payment processing network(s) are eligible to route a transaction based upon a utilized token. In an embodiment, each token BIN translation table entry associates a token BIN with one or more payment processing networks that are eligible to route transactions. An acquirer computer, upon receiving a token for a transaction, thus may flexibly route the transaction to an eligible network from the set of payment processing networks identified by the entry corresponding to the token's BIN value. The entry may further identify verification methods for the eligible payment processing networks, and may identify product type attributes of the account associated with the token, either of which may be used in determining which payment processing network to select.
Owner:VISA INT SERVICE ASSOC
Object tracking system with automated system control and user identification
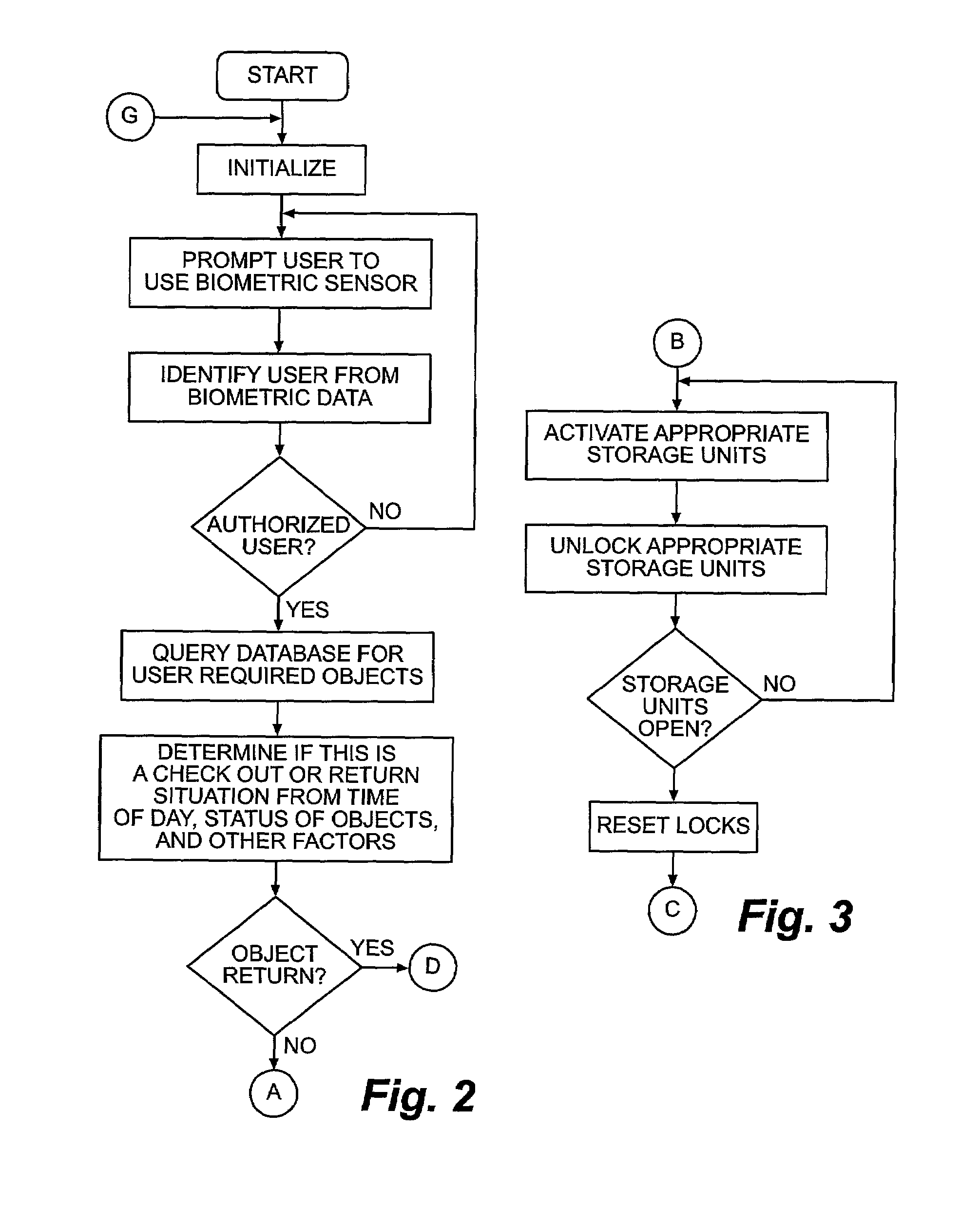
ActiveUS7336174B1Reduce significantly and eliminate completely levelReduces user interactionElectric/electromagnetic visible signallingWork tools storagePattern recognitionAutomatic control
An enhanced object tracking system for tracking and controlling access to a plurality of objects such as keys is disclosed. The object tracking system implements many improvements including automated user identification using biometric data extracted from the user with a minimum of user interaction, tracking of objects both inside and outside their storage units, the locking of objects within slots of their storage unit to guard against illicit removal and return of keys and to insure random slot rotation, image and visual based inventory verification methodologies, and tracking of objects during times when they are checked out of the system. The result is an intelligent object tracking system with automated control functions and high reliability.
Owner:KEY CONTROL HLDG
Opt-in directory of verified individual profiles
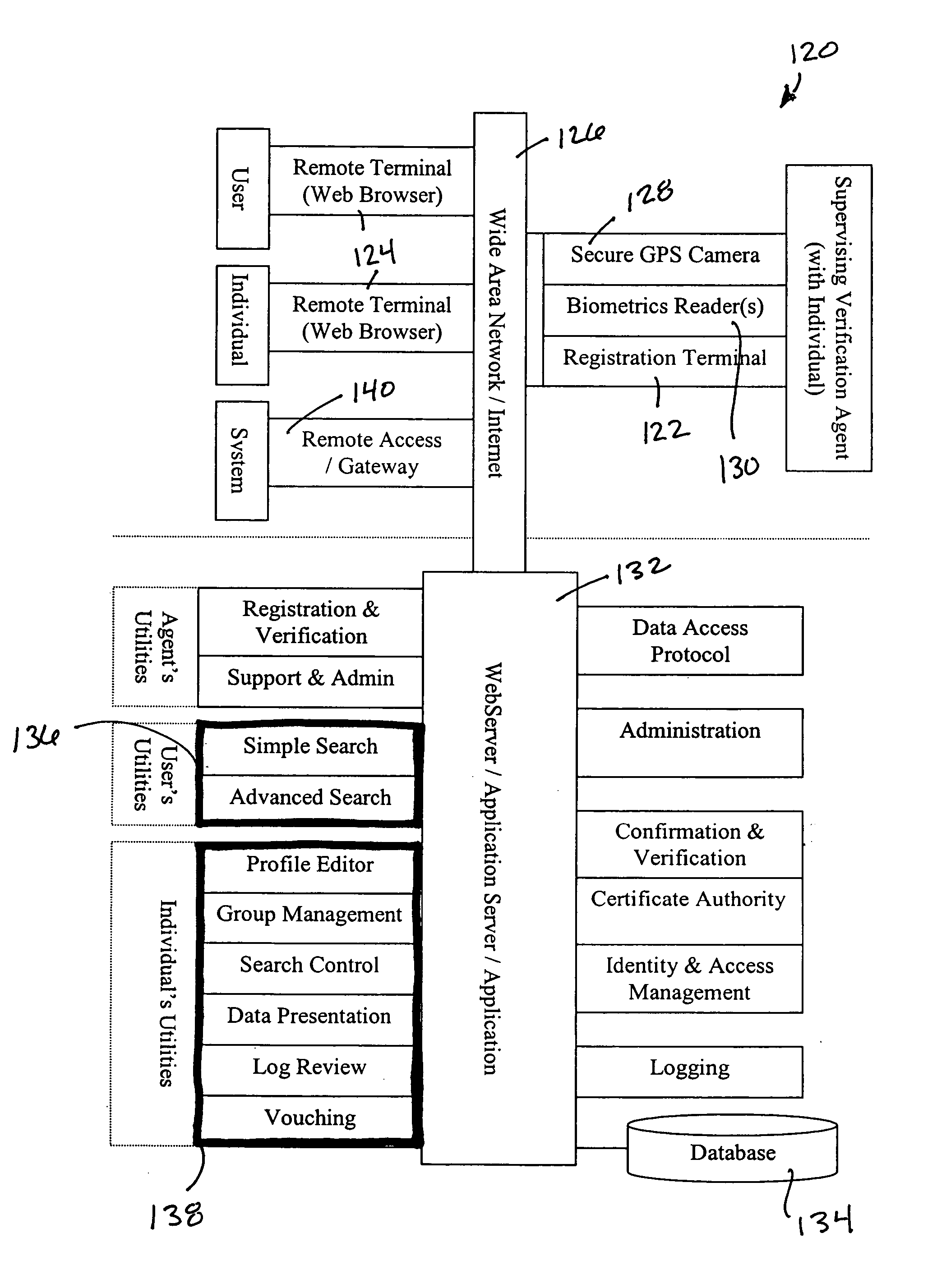
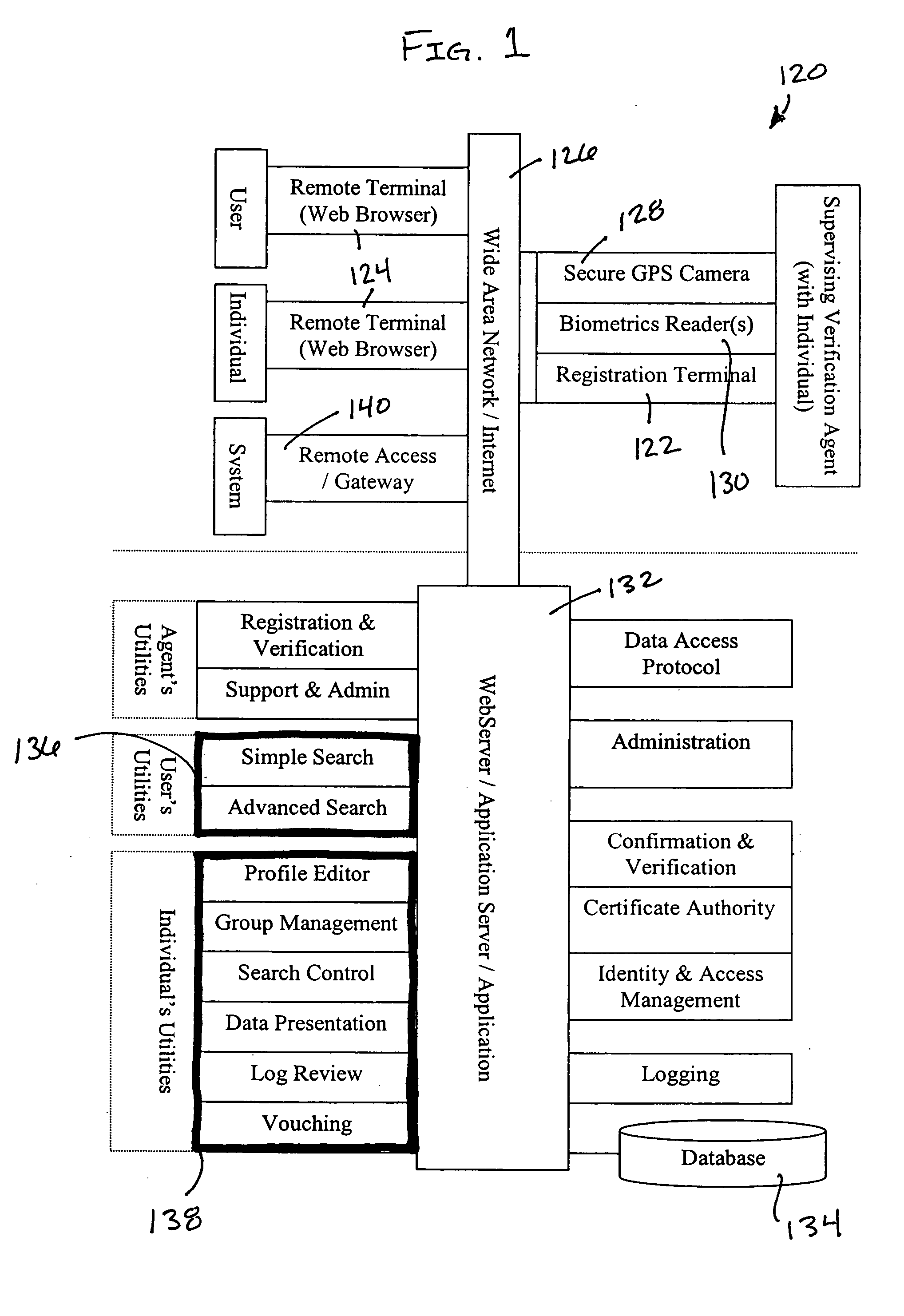
InactiveUS20060047725A1ConfidenceRestricted in mannerComputer security arrangementsSpecial data processing applicationsValidation methodsPersonal details
The present invention provides a system and method for generating and accessing a verified individual profile on a computer network comprising a registration terminal for entering data into a plurality of profile fields in a profile for an individual, wherein the data in at least one profile field is verified by an agent using a verification method, and a profile database for storing the profile. The opt-in directory system also comprises a search utility for allowing a user to search the profile database for the profile via the network and a configuration utility for allowing the individual to edit and configure the profile via the network.
Owner:OMNIBRANCH WIRELESS SOLUTIONS
Validation method and system for use in securing nomadic electronic transactions
ActiveUS20110246780A1Improve securityKey distribution for secure communicationFinanceData setValidation methods
A method involving a communication device, which comprises sending a request to a communication device; receiving a response from the communication device over a local communication path; deriving a received data set from said response; determining at least one data set that had been previously transmitted to the communication device over a wireless portion of a second communication path different from the local communication path; and validating the response based on the received data set and the at least one previously transmitted data set.
Owner:BCE
Fingerprint Sensor Device and System with Verification Token and Methods of Using
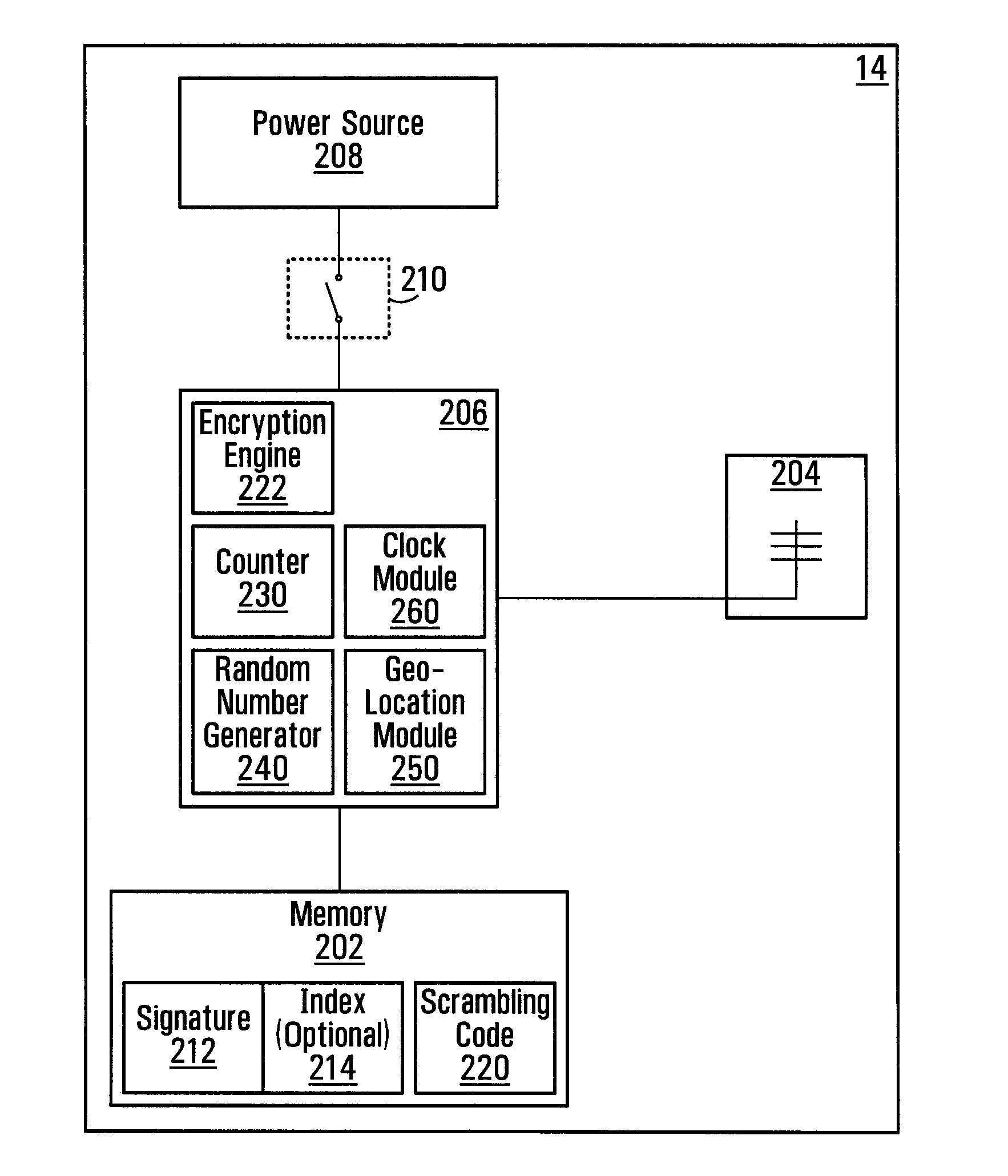
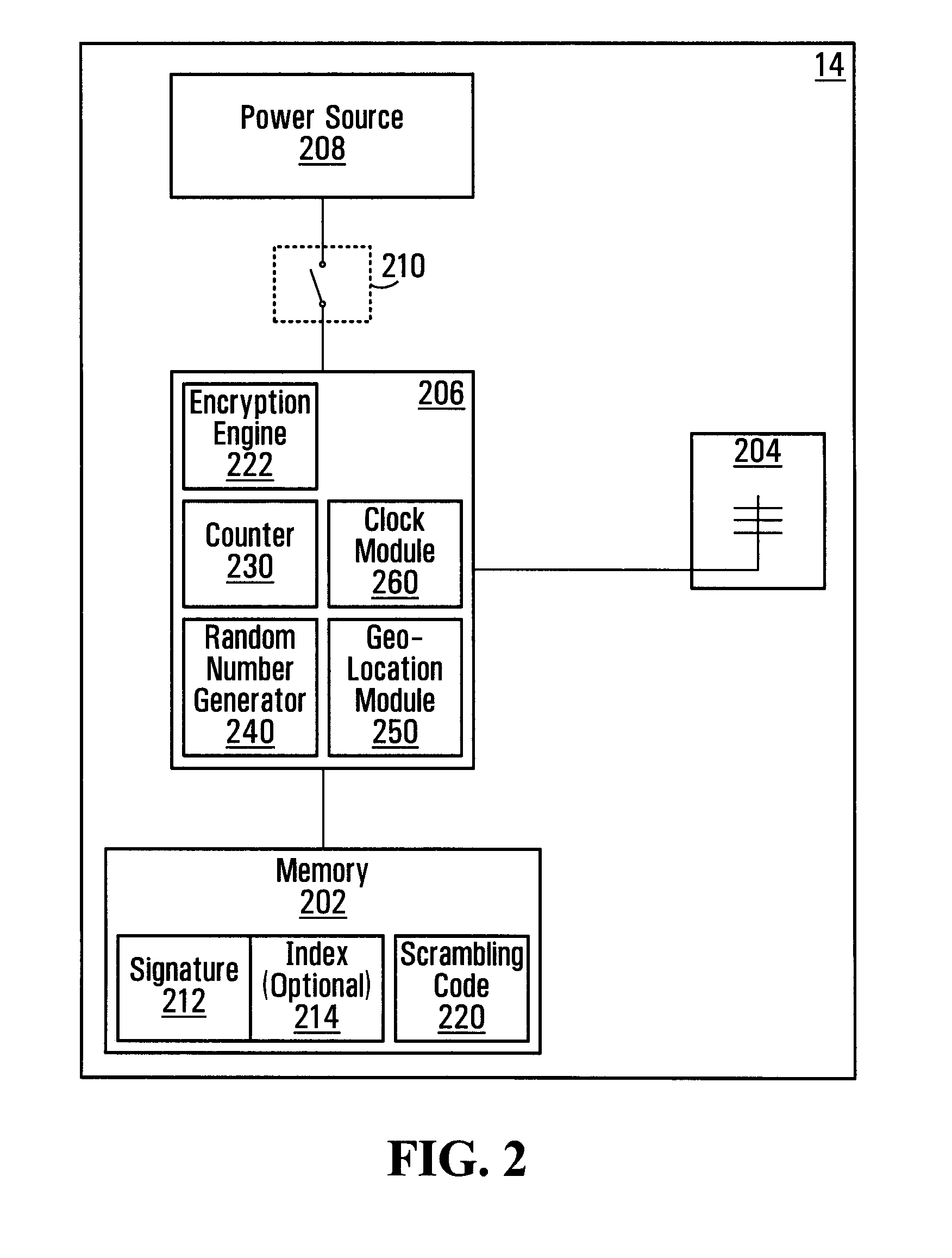
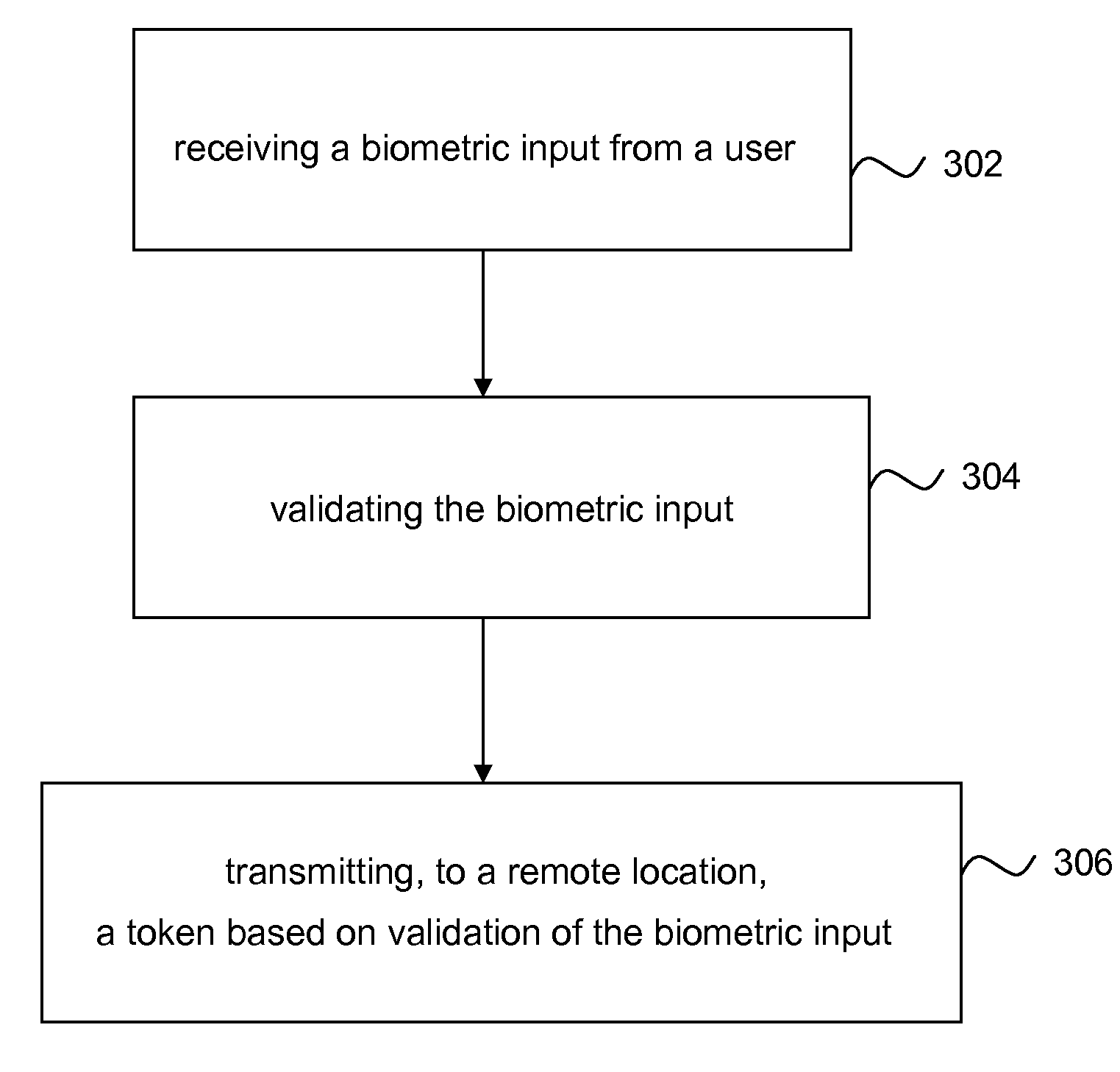
InactiveUS20100083000A1Electric signal transmission systemsDigital data processing detailsValidation methodsSecure authentication
A method and system of verification is provided for sensing a fingerprint. The present invention offers a secure authentication method and system based on a user's fingerprint data to grant the access to information at a remote location. A biometric input corresponding to the fingerprint is provided by a user and the biometric input is than validated. Based on the validation, a token is transmitted to a remote location. The method and system can be further enhanced by additional security comprising receiving a request based on the authentication of the user information and transmitting, to a second remote location, a token based on the biometric input in response to the request.
Owner:SYNAPTICS INC
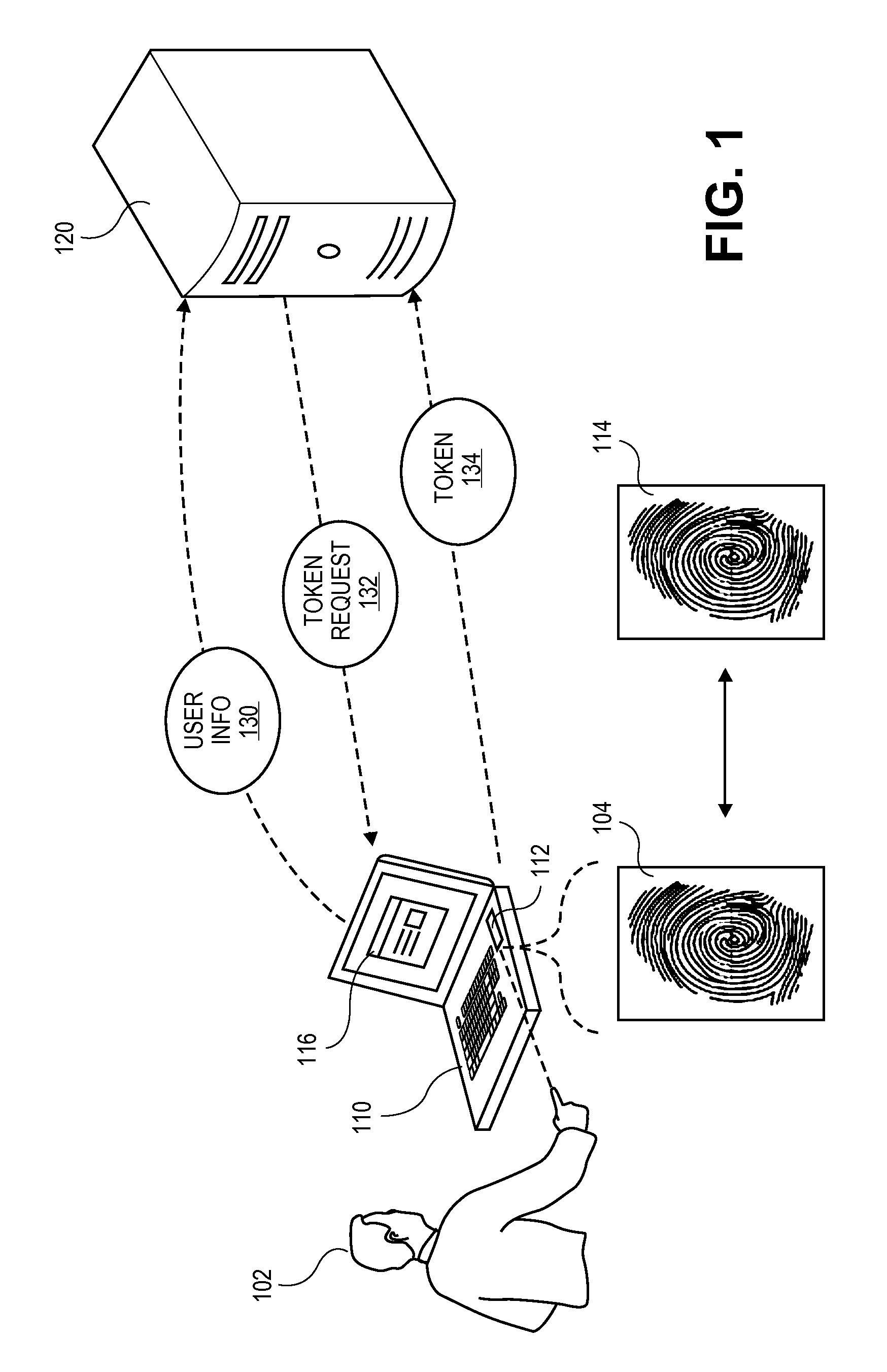
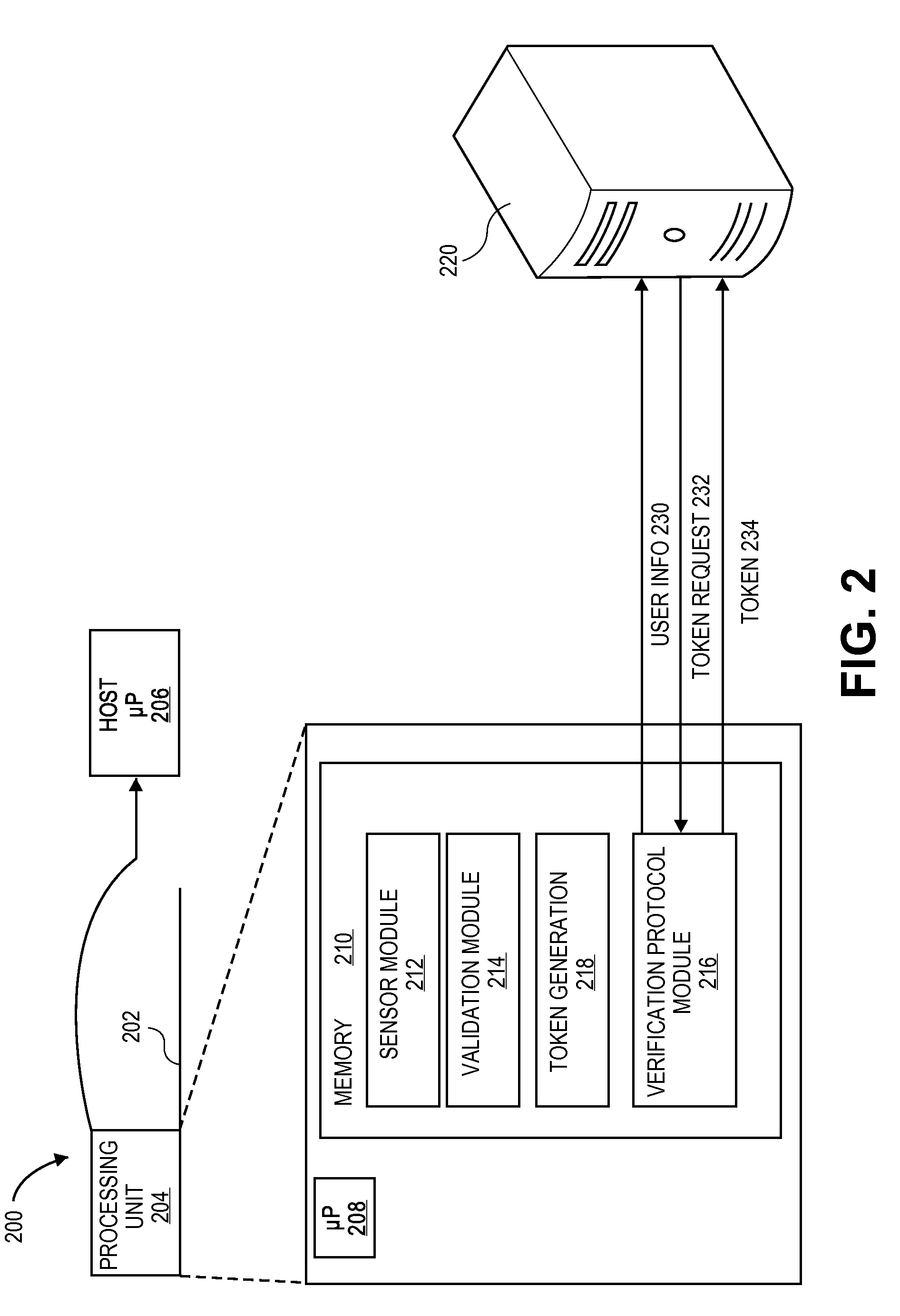
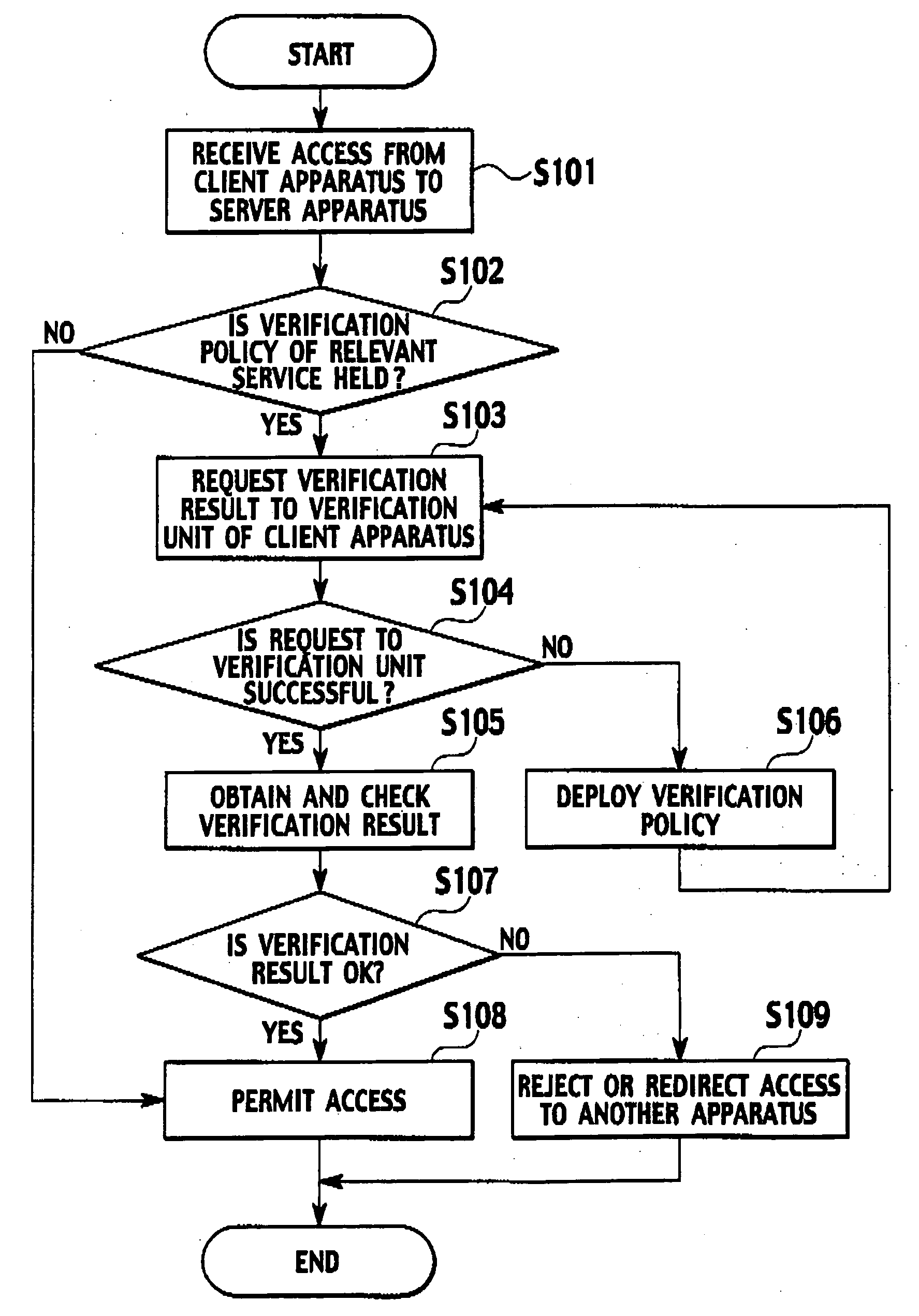
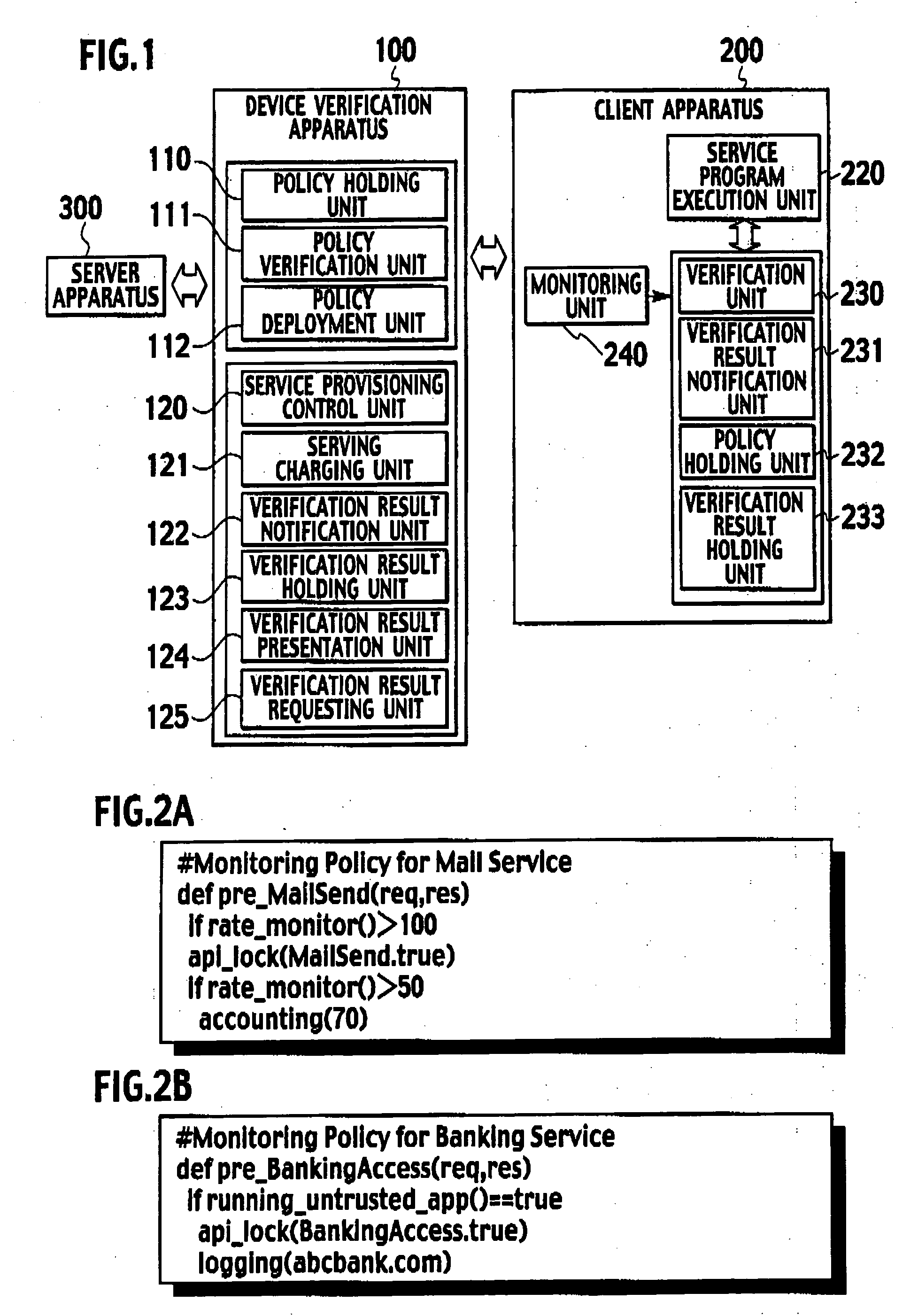
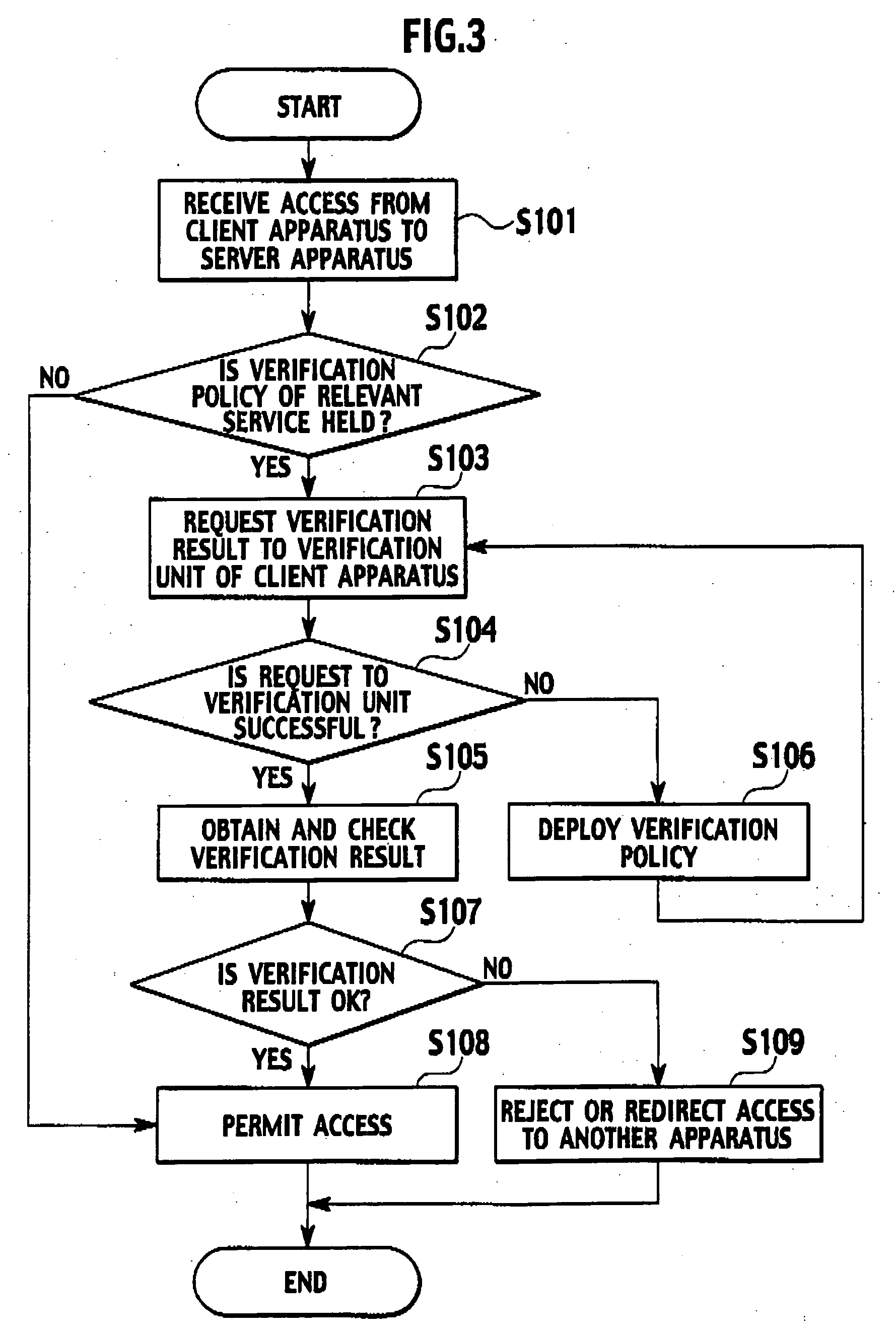
Client apparatus, device verification apparatus, and verification method
InactiveUS20060190987A1Digital data protectionDigital data authenticationValidation methodsClient-side
A client apparatus for utilizing services by executing service programs includes a policy holding unit, a verification unit, a verification result holding unit, and a verification result notification unit. The policy holding unit holds a service-specific verification policy pre-checked by a device verification apparatus. The verification unit verifies an operation and configuration of the client apparatus itself by using the verification policy when the service program is executed. The verification result notification unit notifies the verification result to the device verification apparatus, which requests the verification result.
Owner:NTT DOCOMO INC
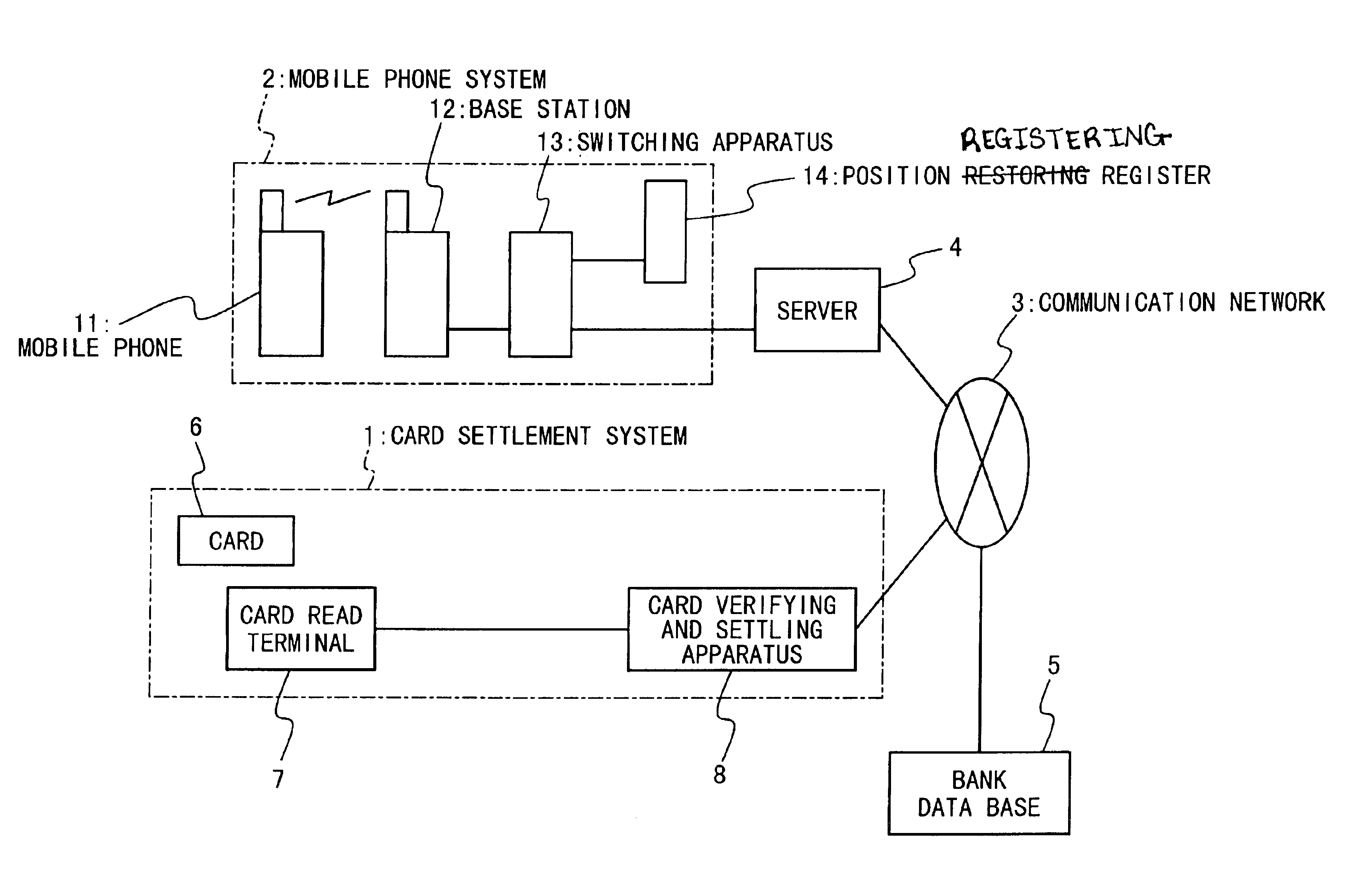
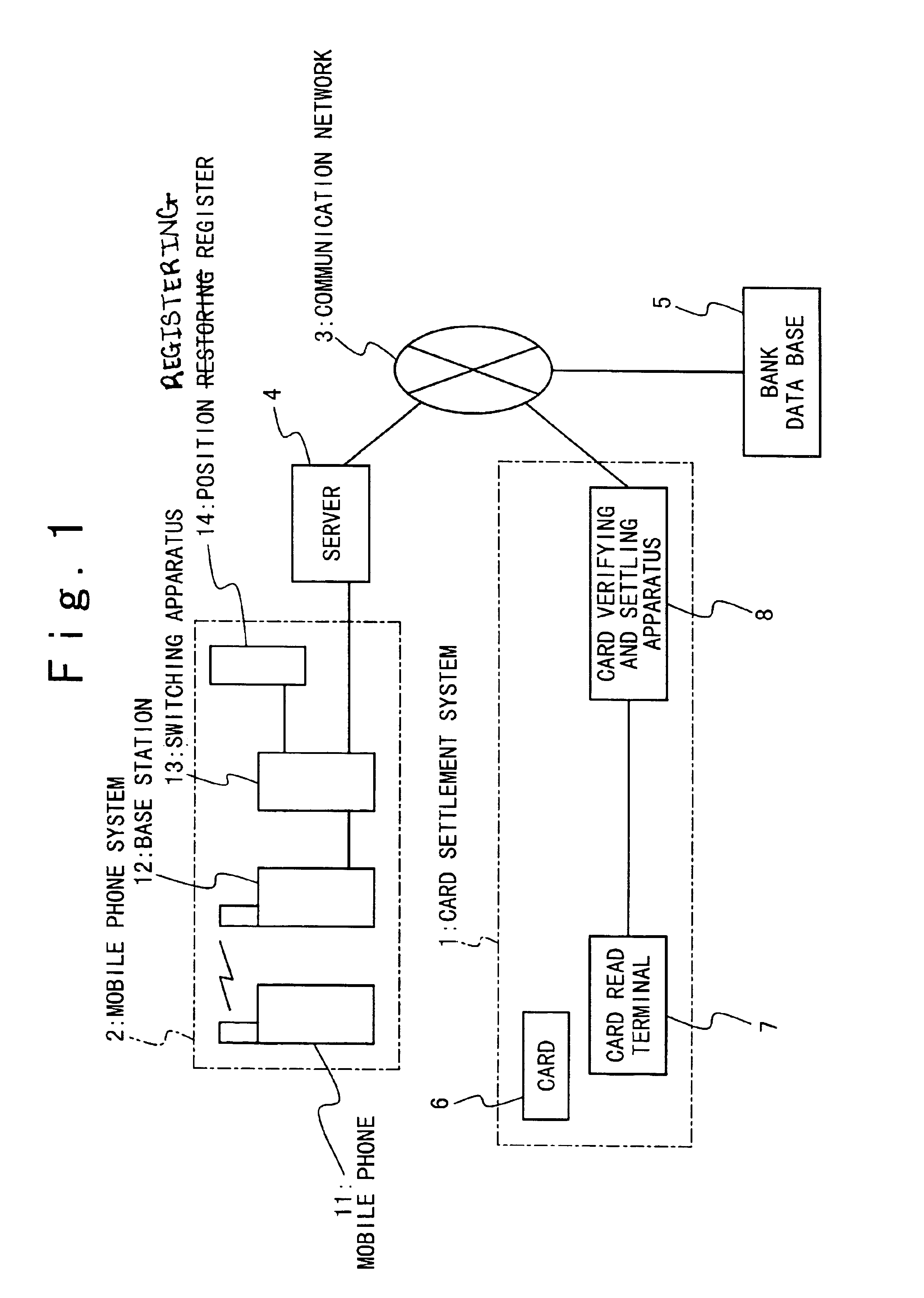
Card verification system and card verification method
InactiveUS6896182B2Reduce usageControl areaOther printing matterFinanceComputer hardwareValidation methods
A card verification system in which a card identification code is registered. A read unit reads the card identification code from the card. A verification apparatus verifies the card only when an existing place of the read unit belongs to an area corresponding to the card identification code. The card is a card used for settlement, and is used when the card identification code is read by the read unit. The use place of the card is coincident with the existing place of the read unit. By adding the use place of the card to a verification condition of the card, unjust use of the card can be prevented.
Owner:LENOVO INNOVATIONS LTD HONG KONG
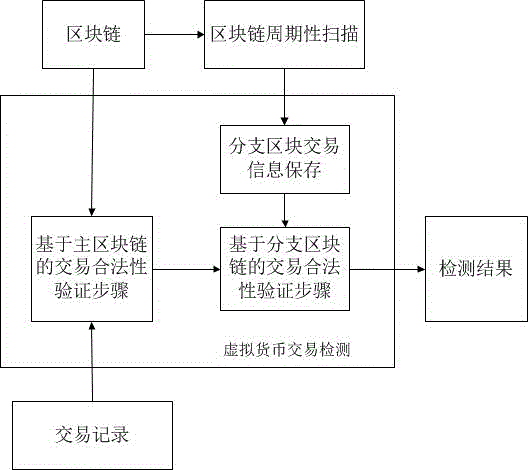
Virtual currency transaction validation method based on block chain multi-factor cross-validation
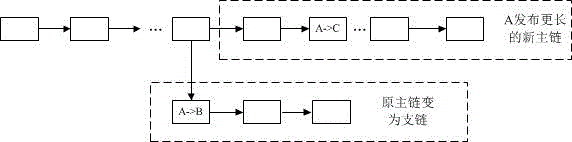
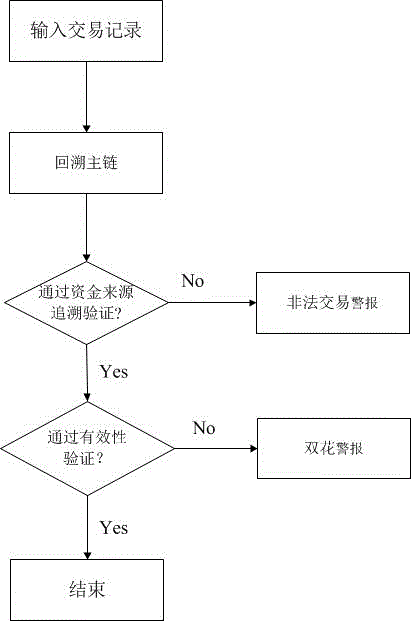
The invention provides a virtual currency transaction validation method based on block chain multi-factor cross-validation to solve the double-spending problem that virtual currency based on block chains are liable to 51% attacks and thus generates transactions. The method queries and backups a history block chain branch periodically, organizes confirmed transaction information into a hash chain list array which is easy for querying, and avoids branch transaction information losses induced by block chain evolution. During a virtual currency transaction, the method not only checks payer information, recipient information, a fund source, a currency transaction amount and the like recorded in a current main block chain, but also queries a backup branch block chain to check whether the current transaction and a history transaction on the branch block chain have the same fund source. If any transaction does not pass the check, a miner gives an alarm over the whole network about the transaction, so that the method can avoid the double-spending problem induced by illegal transactions.
Owner:SICHUAN UNIV
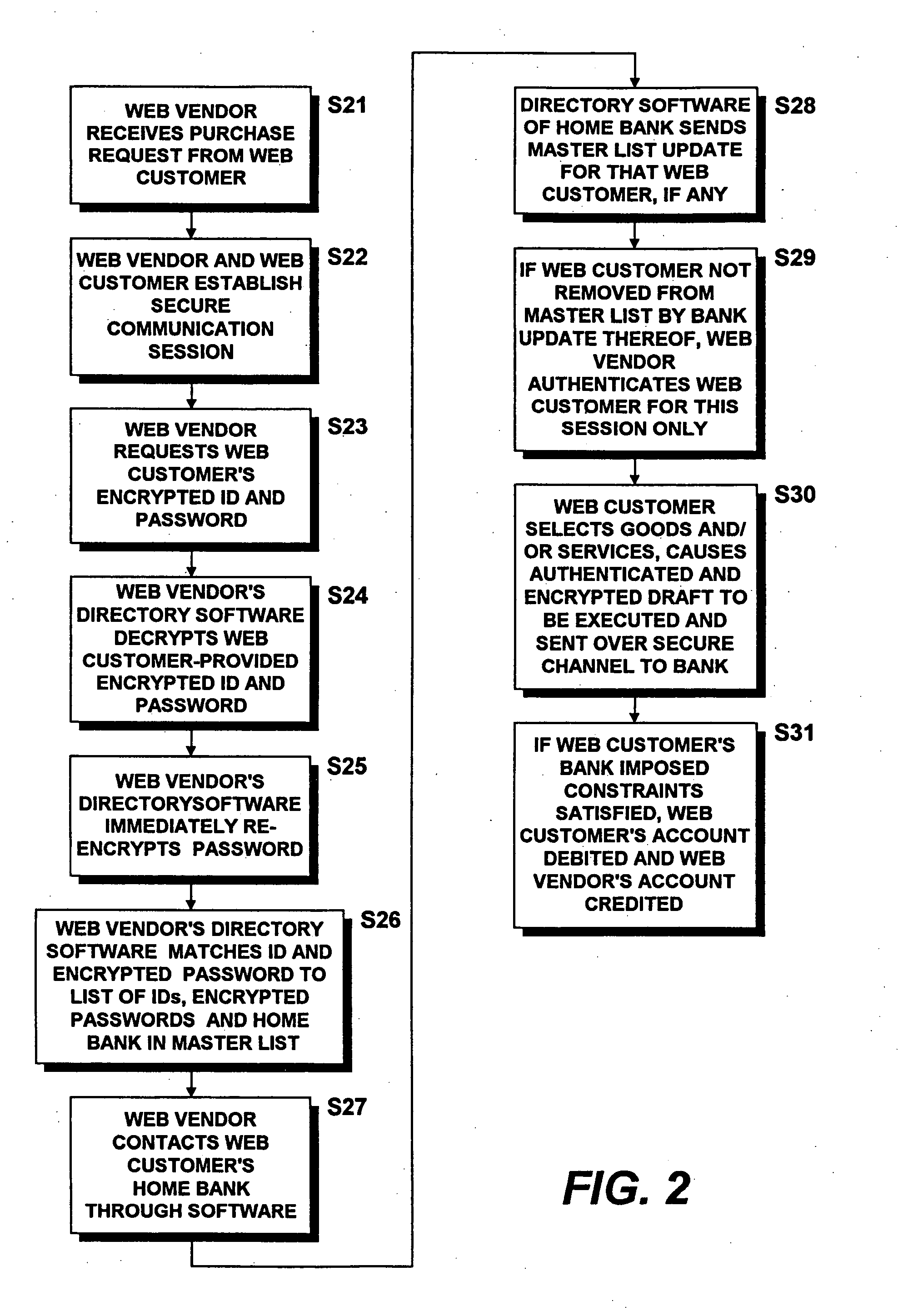
Methods and systems for single sign-on authentication in a multi-vendor e-commerce environment and directory-authenticated bank drafts
InactiveUS20050222963A1Ensure safety and integrityStimulate interestComputer security arrangementsPayment architectureData setBiometric data
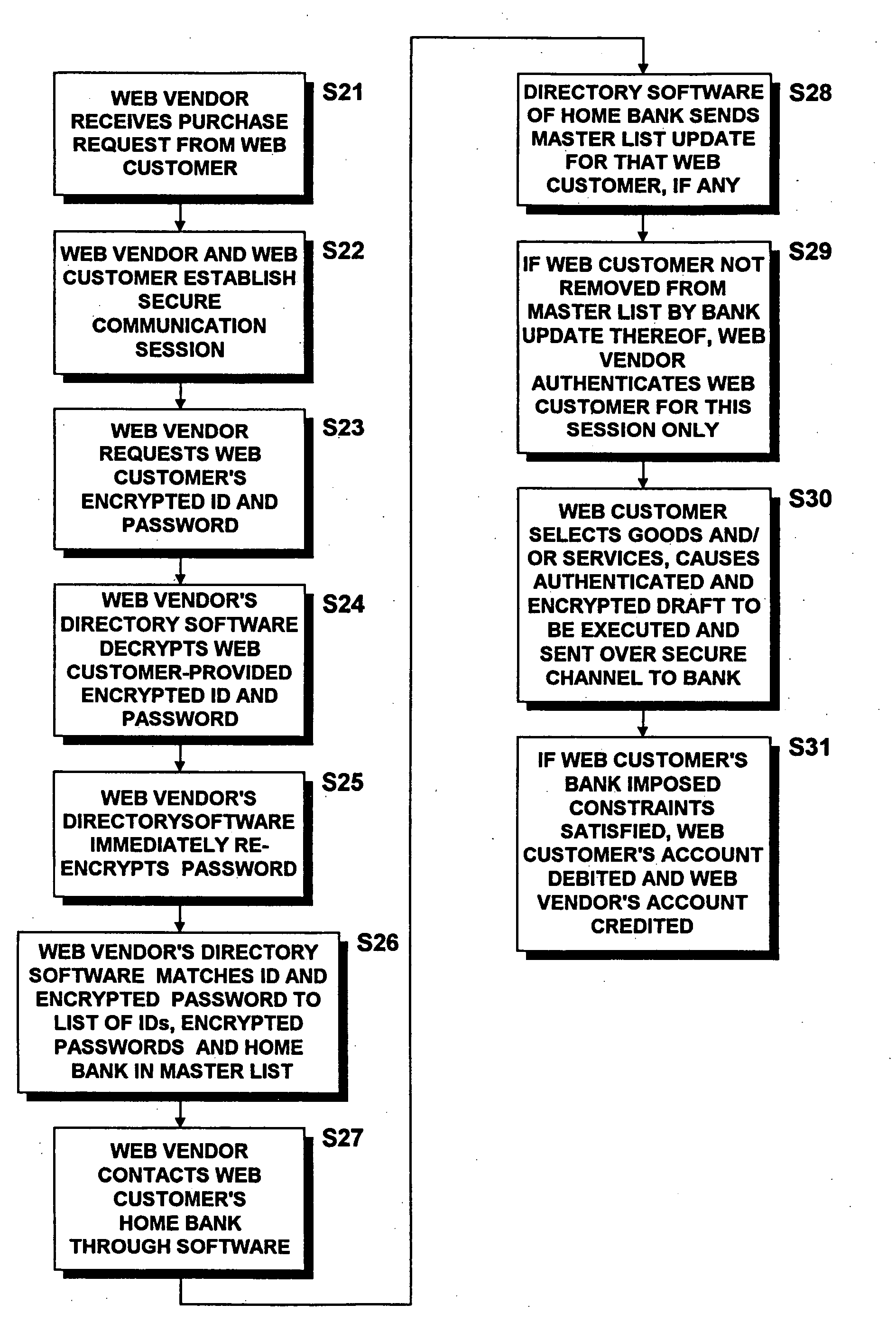
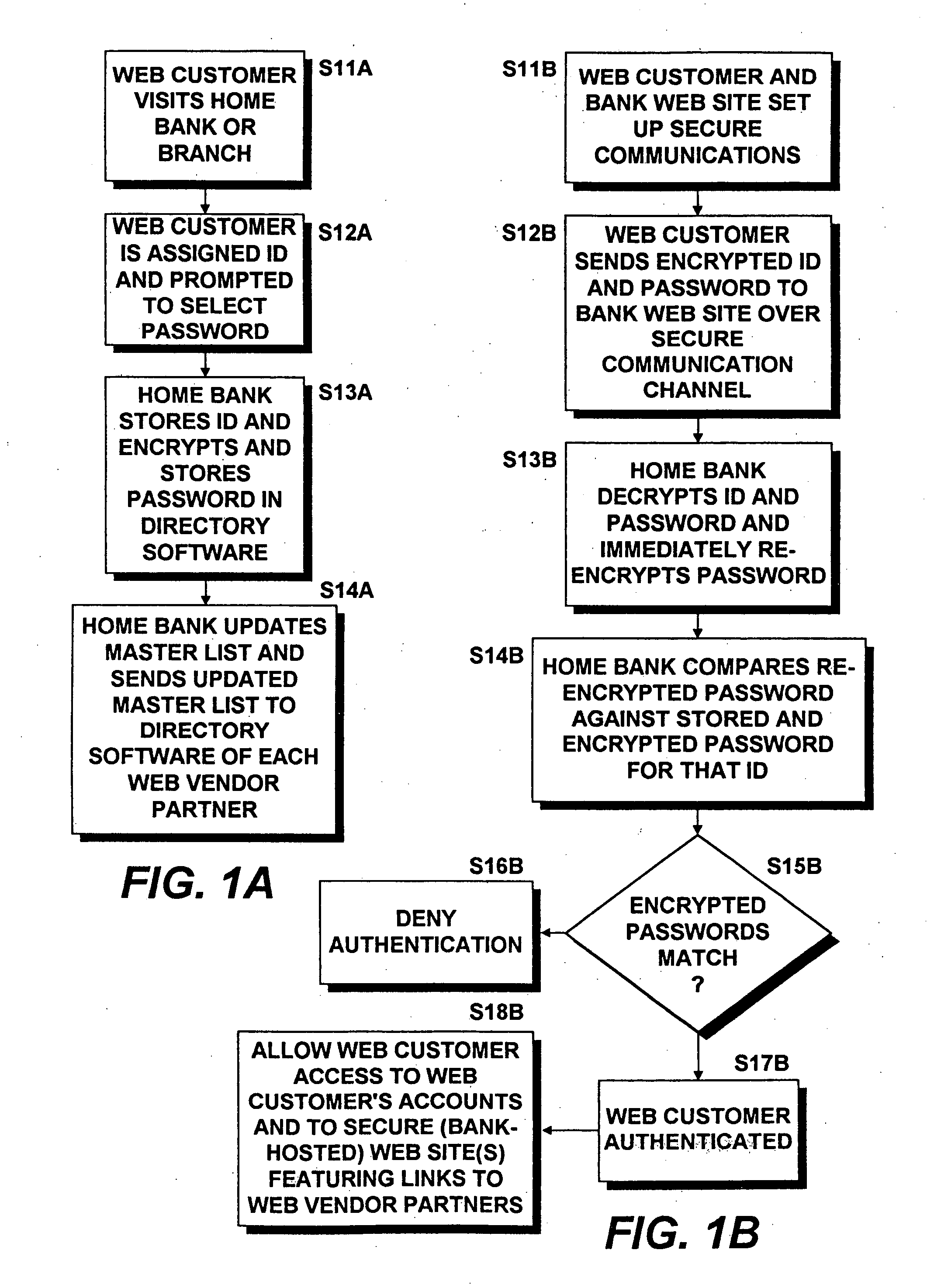
A computer-implemented draft authentication method for use in e-commerce includes the steps of establishing partner relationships between a financial institution and a plurality of World Wide Web (Web) vendors and storing, for each of a plurality of Web customers, at least one piece of unique identifying information linked to the Web customer's financial information. Web customers executing drafts or causing drafts to be executed by the Web vendors and presented to the financial institution are authenticated by immediately encrypting at least a portion of an identification data set provided by the Web customer over the network and by successfully matching the immediately encrypted identification data set with the stored piece(s) of encrypted identifying information. The Web customer's financial information is then retrieved only by the financial institution and constraints are established based on the retrieved information. The financial institution then honors drafts presented by the Web vendors with whom the drawee has a partner relationship only when the Web customer is successfully authenticated and the constraints are satisfied. Only the identification information (such as biometric data and / or ID and password pairs) of each of the Web customers is securely replicated from the financial institution to each of the Web vendors. LDAP-compatible Directory software may be utilized as the means of storing, processing and replicating the Web customer's identification information to each of the Web vendors. The financial institution warrants the security of the system and controls the replication and content of the Directories at each of the Web vendor sites.
Owner:ORACLE INT CORP
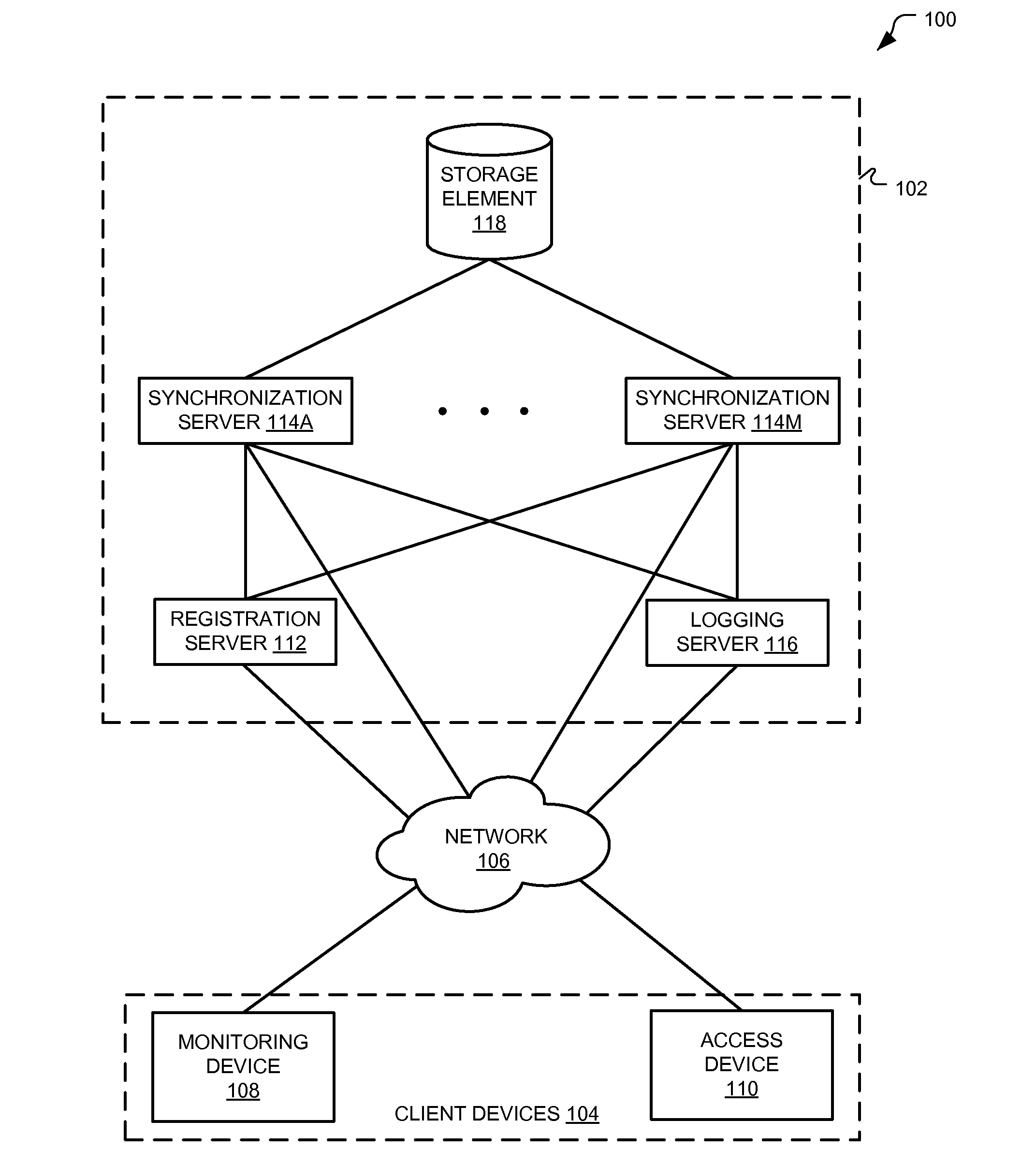
Multi-Tiered Authentication Methods For Facilitating Communications Amongst Smart Home Devices and Cloud-Based Servers
ActiveUS20140089671A1Digital data processing detailsMultiple digital computer combinationsLimited accessValidation methods
Apparatus, systems, methods, and related computer program products for synchronizing distributed states amongst a plurality of entities and authenticating devices to access information and / or services provided by a remote server. Synchronization techniques include client devices and remote servers storing buckets of information. The client device sends a subscription request to the remote serve identifying a bucket of information and, when that bucket changes, the remote server sends the change to the client device. Authentication techniques include client devices including unique default credentials that, when presented to a remote server, provide limited access to the server. The client device may obtain assigned credentials that, when presented to the remote server, provide less limited access to the server.
Owner:GOOGLE LLC
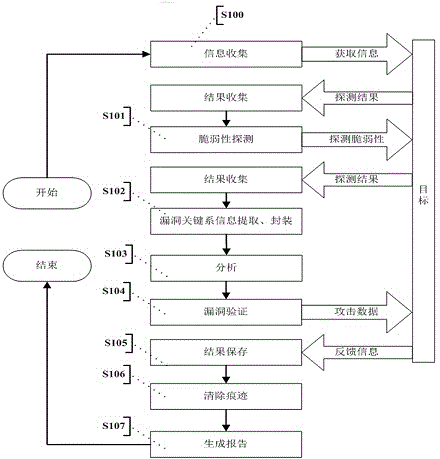
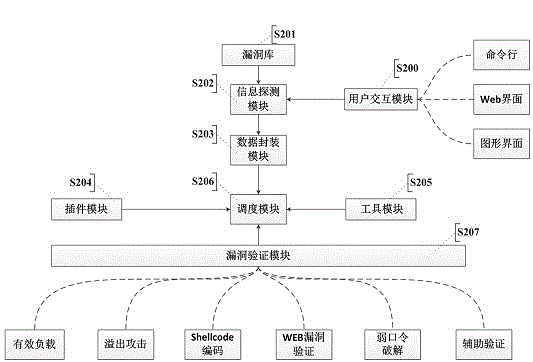
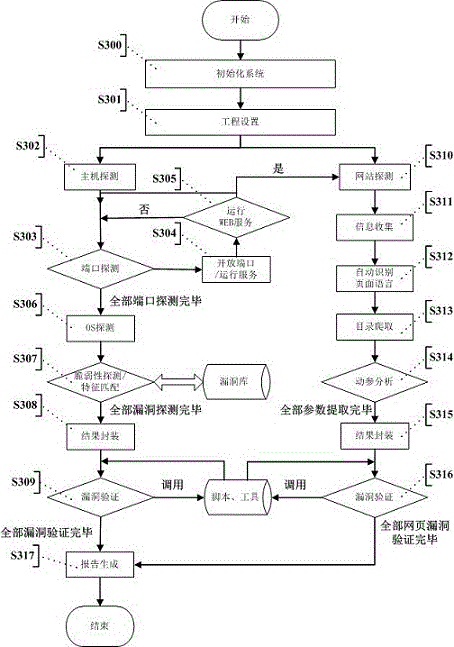
Automatic vulnerability validation method
InactiveCN104363236AAutomated verificationUnderstand the dangers of vulnerabilitiesPlatform integrity maintainanceTransmissionValidation methodsModularity
The invention provides an automatic vulnerability validation method. The method comprises the steps that firstly, validation information is collected, wherein an active detection way is adopted for carrying out information detection, topological detection, vulnerability detection and website directory structure detection on a target; secondly, the validation information is packaged, wherein suspicious vulnerability key information in vulnerability detection results is extracted, uniform-interface modularized packaging is carried out on the data; thirdly, a validation strategy is searched for, wherein according to the suspicious vulnerability identity and variety information, an appropriate attack script template and a vulnerability utilizing tool are selected; vulnerability validation is carried out, wherein scripts are called to be loaded into the packaged vulnerability information to carry out validation attack, and an utilization voucher is obtained and stored; fifthly, validation traces are removed, wherein validation attack traces are removed, sessions are recycled; finally, a scanning report is generated. The automatic vulnerability validation method solves the problem that an existing vulnerability scanning system is high in false alarm rate and cannot carry out effective validation, is automatic and procedural, can automatically recognize and validate vulnerabilities, lowers the requirement for the ability of non-professional staff and improves the vulnerability validation efficiency.
Owner:XIAN UNIV OF POSTS & TELECOMM +1
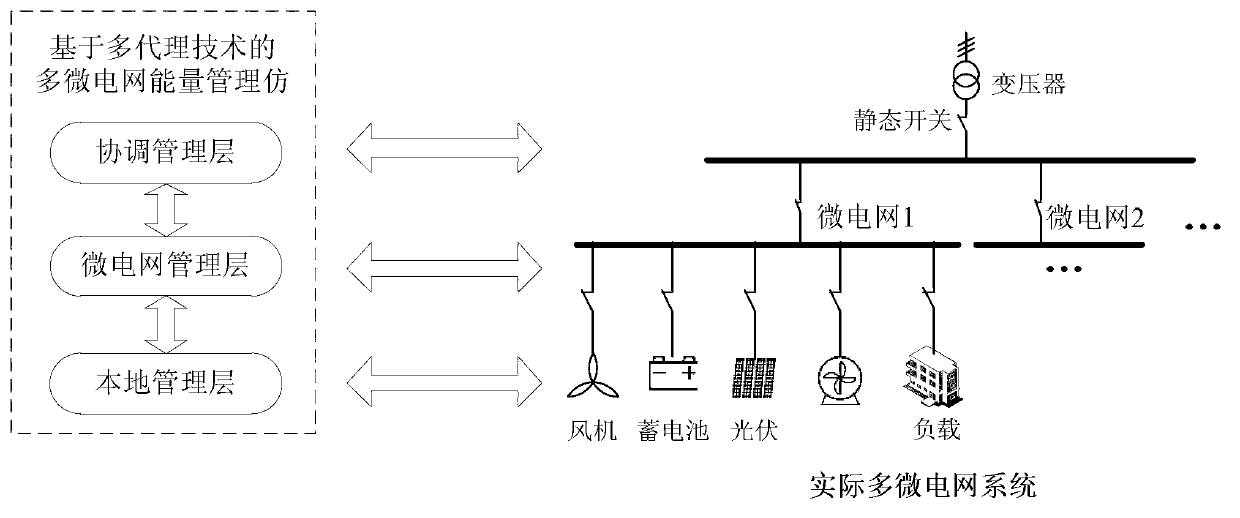
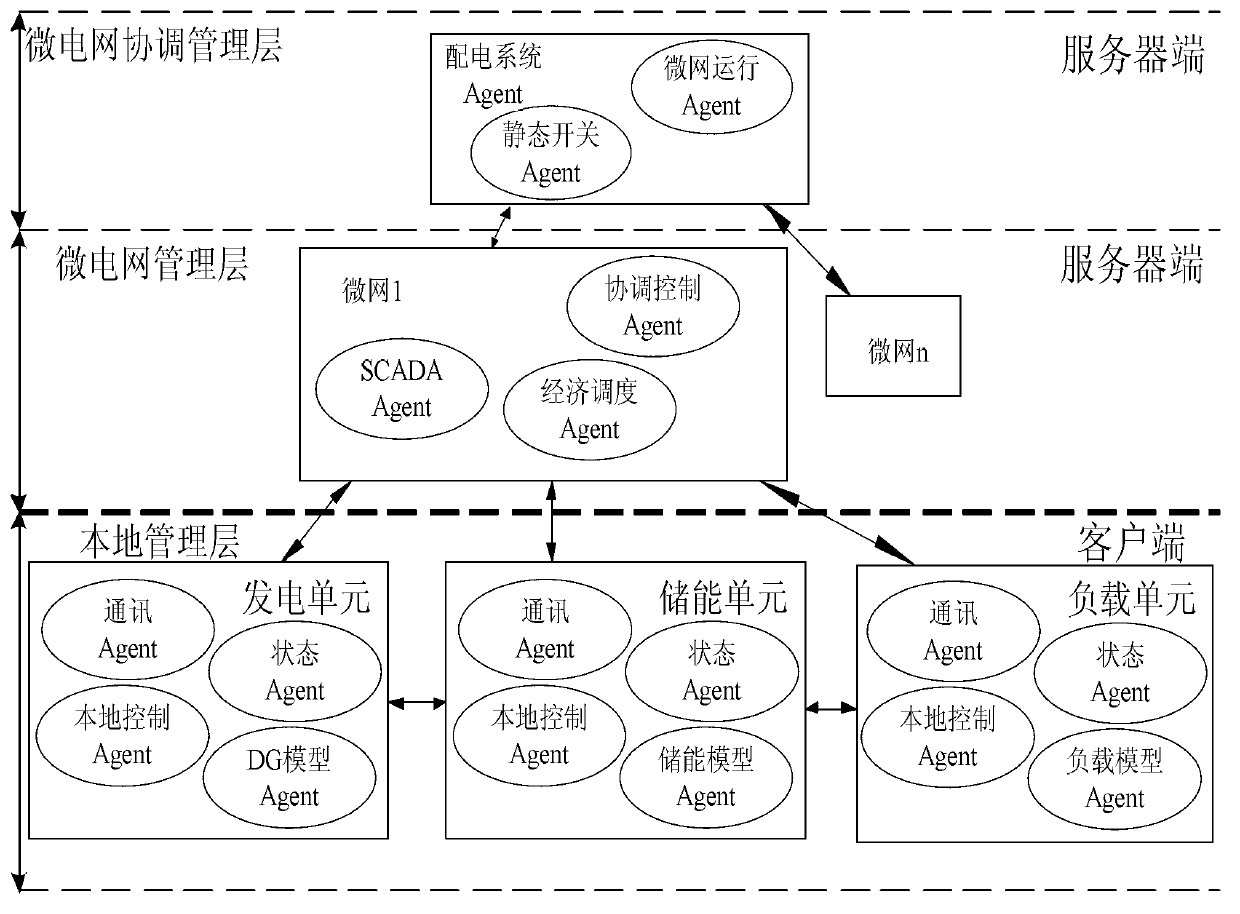
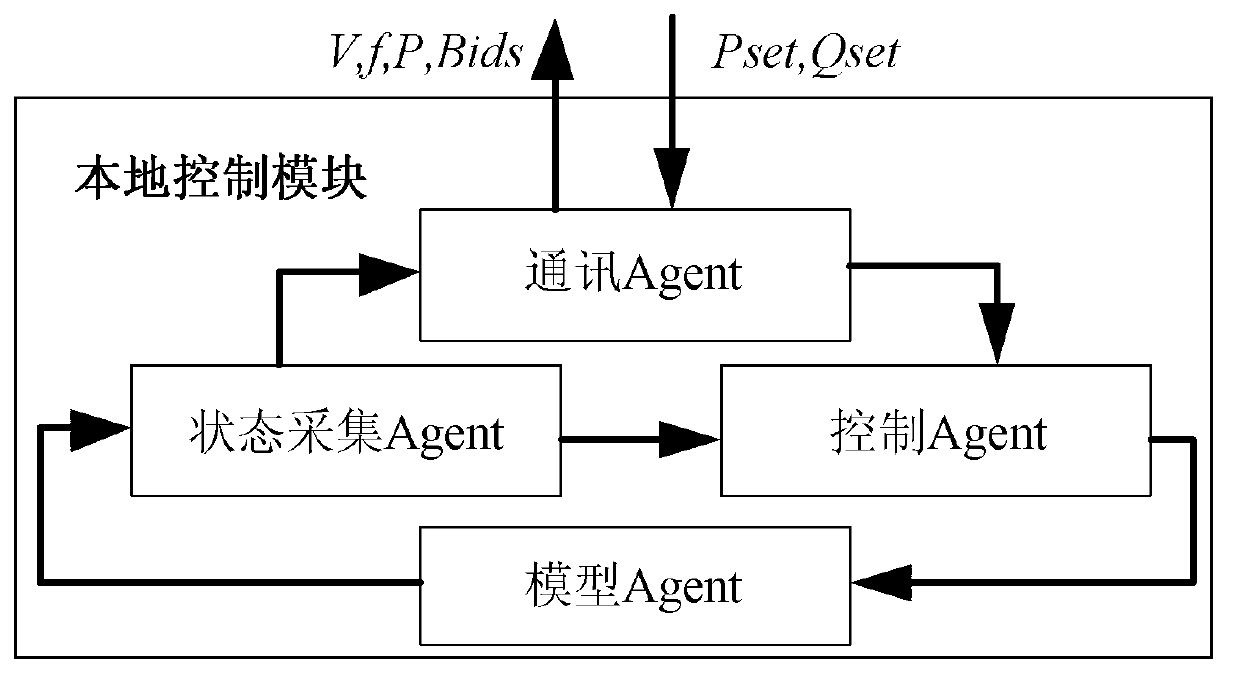
MAS-based (multi-agent system) multi-microgrid energy management system simulation method
ActiveCN103001225ADistributed energy control is efficientFlexibleAc networks with different sources same frequencyControl layerMicrogrid
The invention relates to an MAS-based (multi-agent system) multi-microgrid energy management system simulation method. The method is characterized in that a multi-microgrid energy management system is divided into a local management layer, a microgrid management layer and a microgrid coordinated management layer in different levels; various energy management functions of the different layers are used to establish a multi-microgrid energy management system model by different types of agents, and agent communication protocol is designed for coordination and convention of the agents. The agents in different control layers of the local management layer, the microgrid management layer and the coordinated management layer are integrated by a client-server architecture, and accordingly an MAT-based (multi-agent technology-based) multi-microgrid energy management system simulation platform is formed. The method is provided to verify different microgrid control strategies and scheduling plans.
Owner:HEFEI UNIV OF TECH
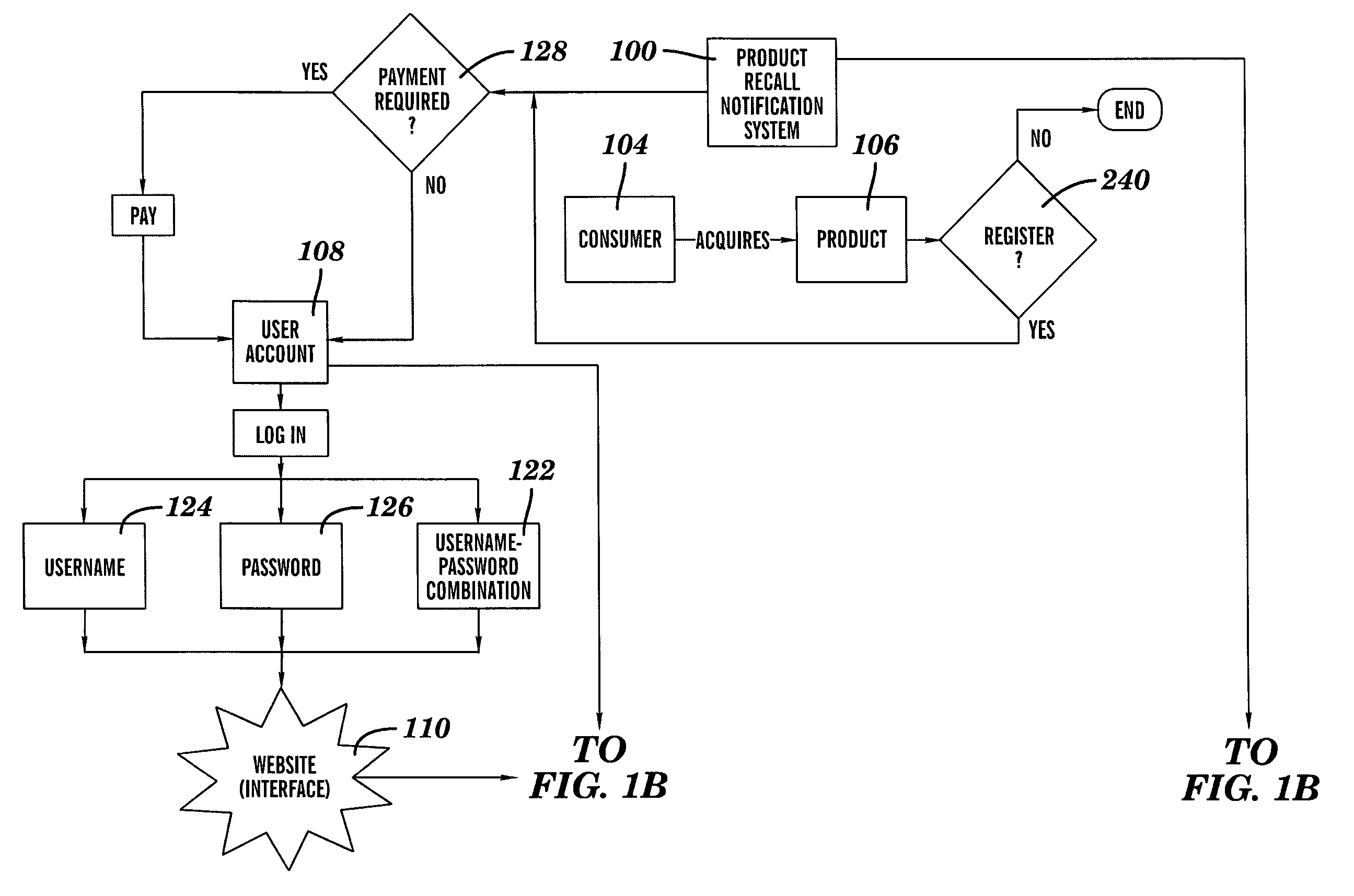
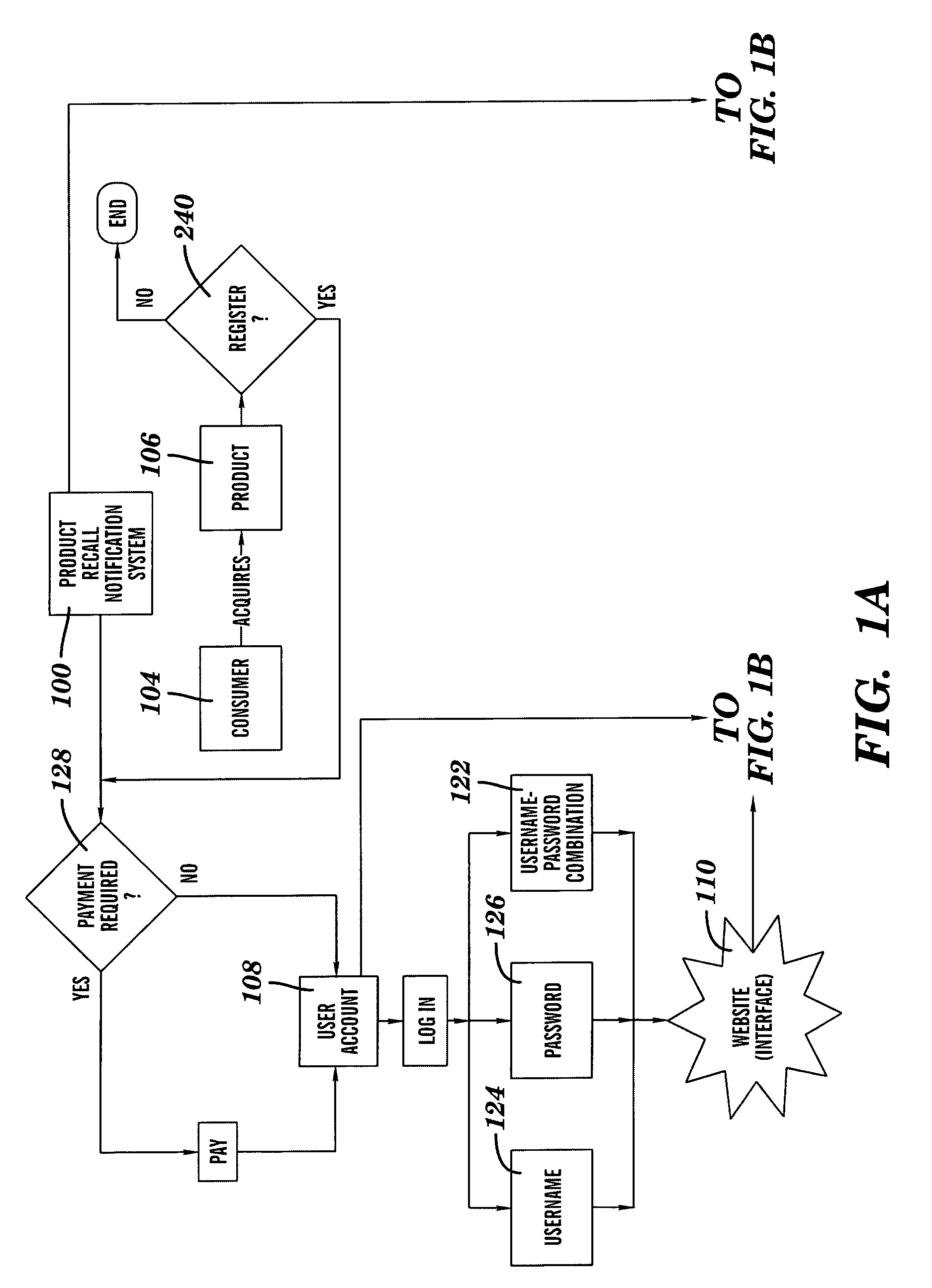
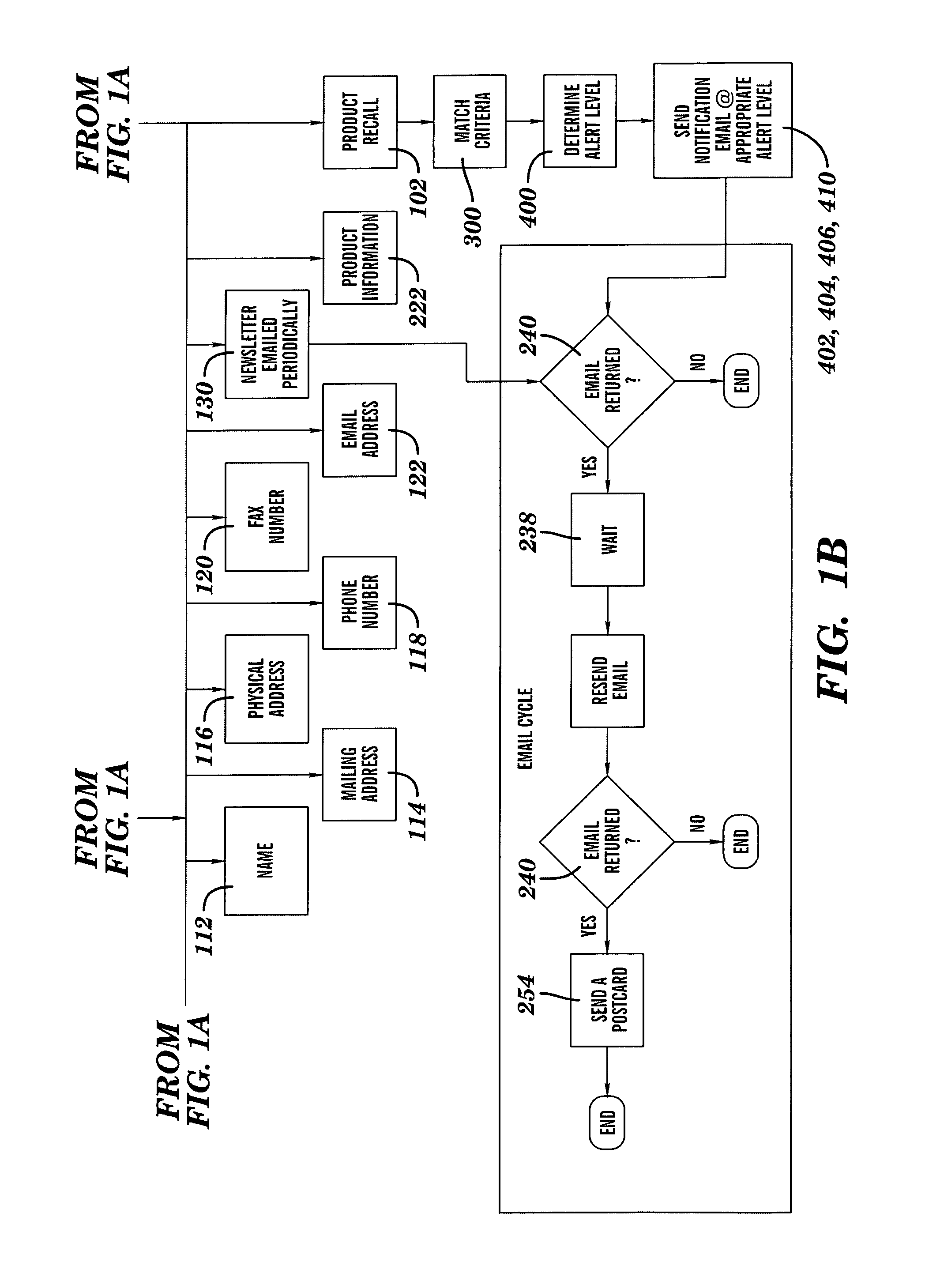
System and Method of Selectively Notifying Consumers of Product Recalls
Described herein is a system and method of using the system for notifying consumers regarding product recall comprising: assignment of a unique user account to a newly registered consumer by an internet-based product recall notification system, the user account comprising a database wherein all products registered by that consumer are listed and a web interface whereon the products the consumer has listed as owned are listed with product recall alert-level status shown, and the unique user account requiring a logon verification method that is selected from the group consisting of username-and-password match, username match, and password match; the product recall notification system collecting consumer contact information; the product recall notification system collecting product information from the consumer about one or more products that the consumer has acquired; the product recall notification system sending regular periodic email to the registered consumers; the product recall notification system responding to email returned undeliverable; the product recall notification system receiving information about a product recall; the product recall notification system comparing the information received about the product recall to the consumer's data; the product recall notification system generating an email alert at a level determined by the match between the consumer's registered product and a recalled product to the consumer notifying the consumer about the recall of the registered product; and the product recall notification system generating a flashing screen alert at a level determined by the match between the consumer's registered product and a previously recalled product when the consumer enters information about a product that has previously been recalled.
Owner:JOHNSON SCOTT KEVIN +1
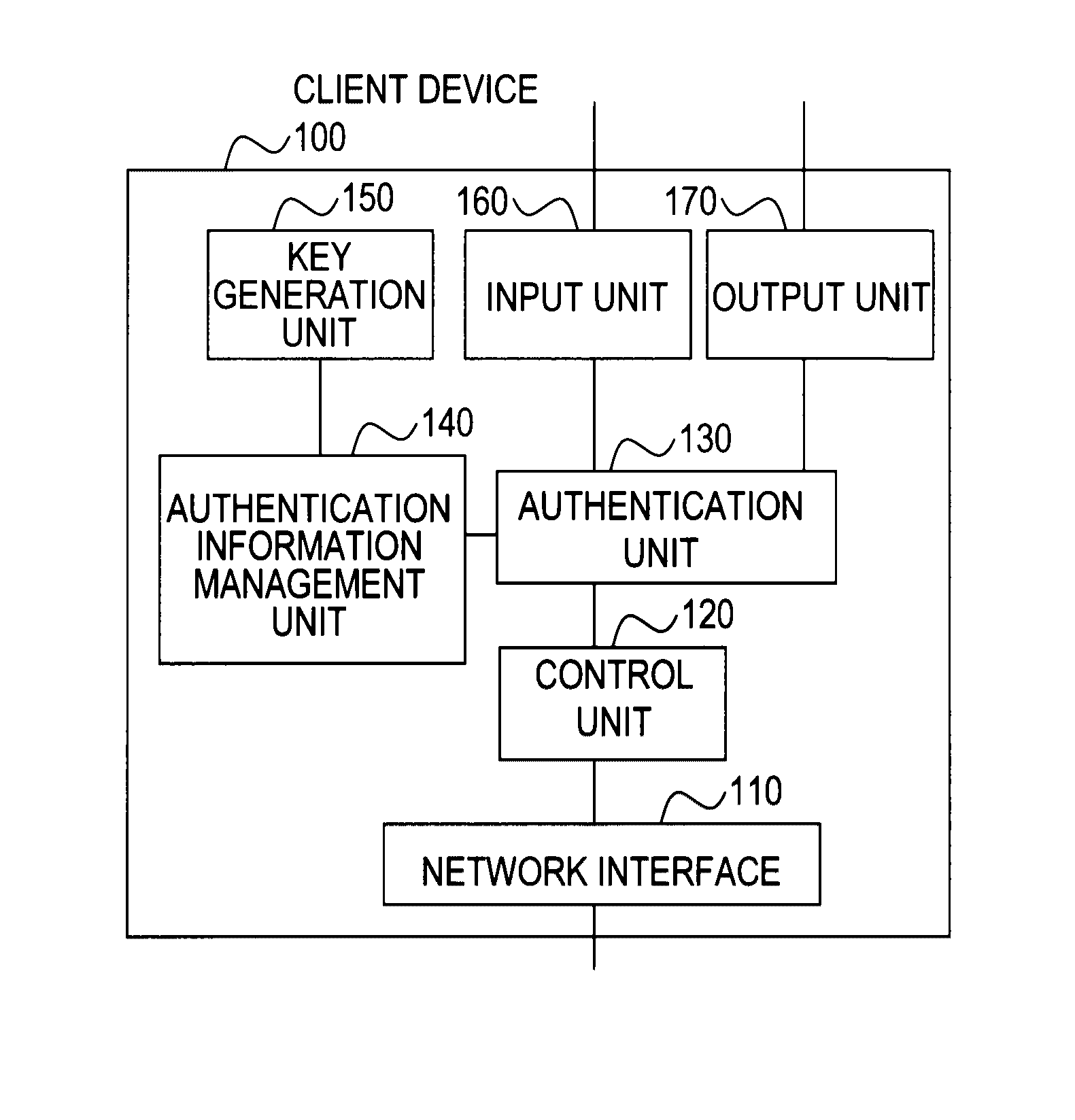
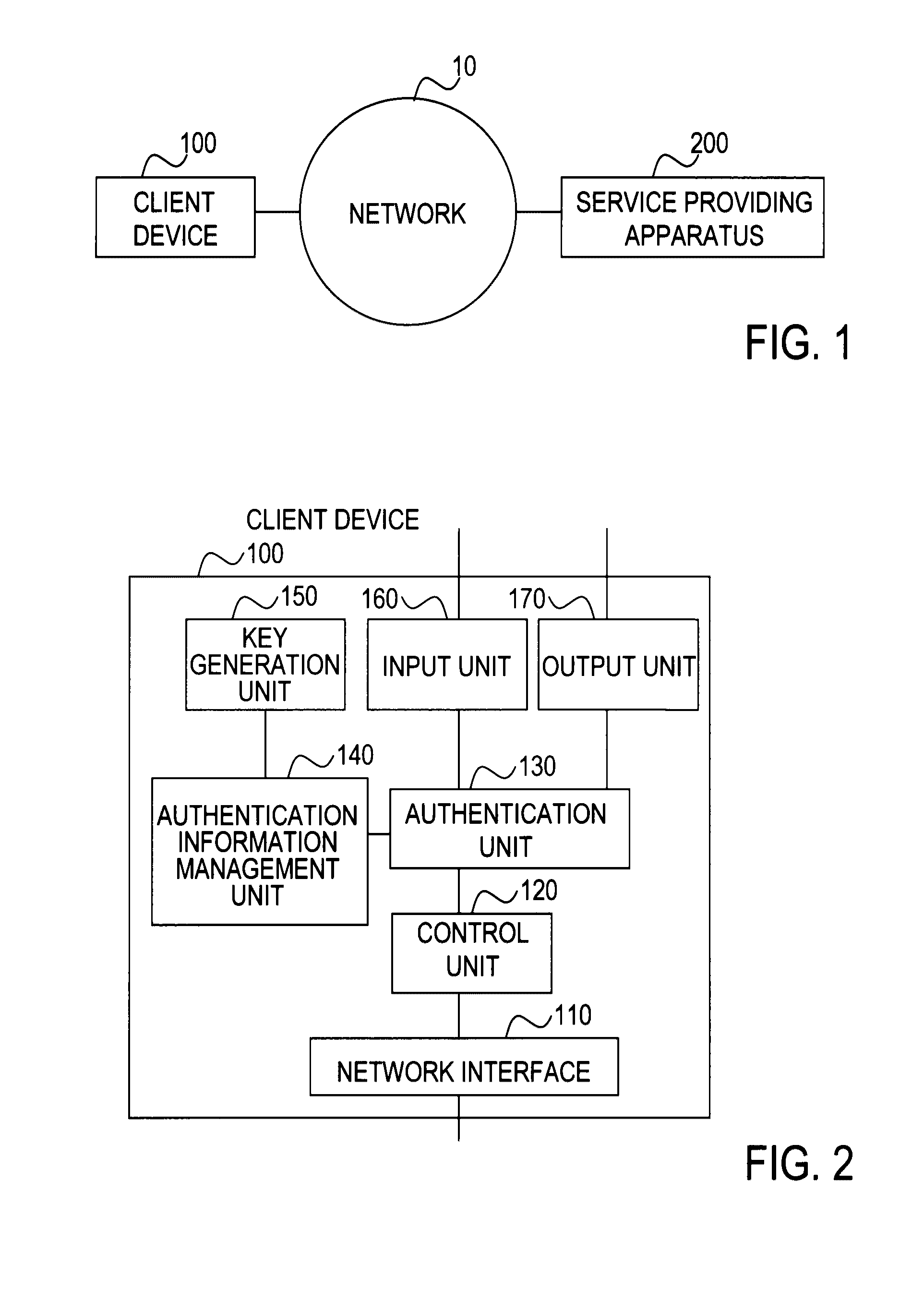
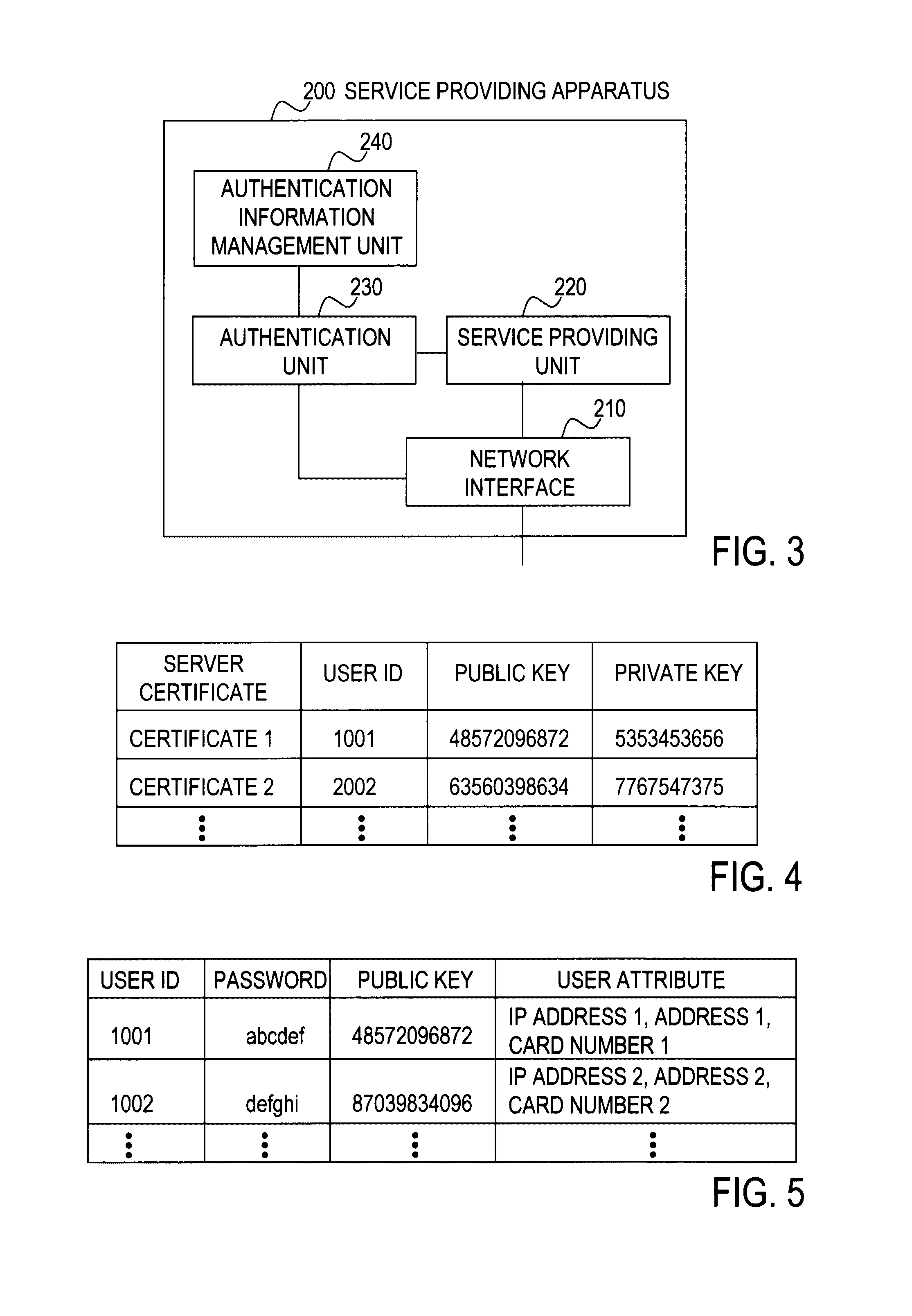
Client device, key device, service providing apparatus, user authentication system, user authentication method, program, and recording medium
ActiveUS20100088519A1Easy to switchEasy to replaceEncryption apparatus with shift registers/memoriesUser identity/authority verificationPublic key authenticationValidation methods
In a user authentication system according to the present invention, at user registration, a client device obtains a signature for a user ID, a password, and a public key by using a private key corresponding to the public key, and sends user information that includes the signature and the above-described information items to a service providing apparatus. The service providing apparatus verifies the signature by using the public key and stores the user information by which the password and the public key are associated with each other. When a request for a service is made, the client device allows authentication processing by sending to the service providing apparatus an authentication response that includes the user ID together with password authentication information, a signature for a challenge sent from the service providing apparatus, or a signature for the password and the challenge, irrespective of whether the authentication method for the service is password authentication, public key authentication, or public-key-and-password combination authentication.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
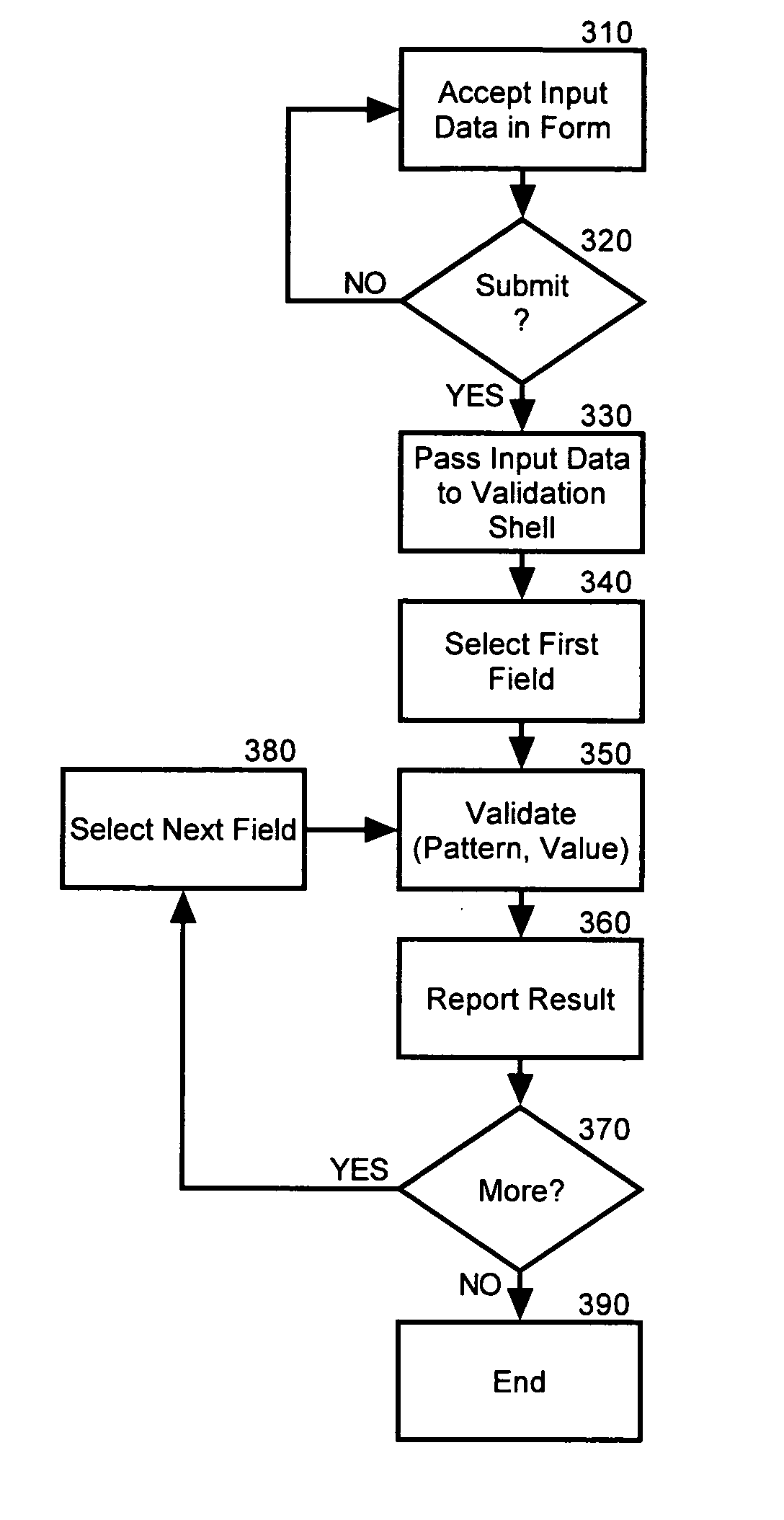
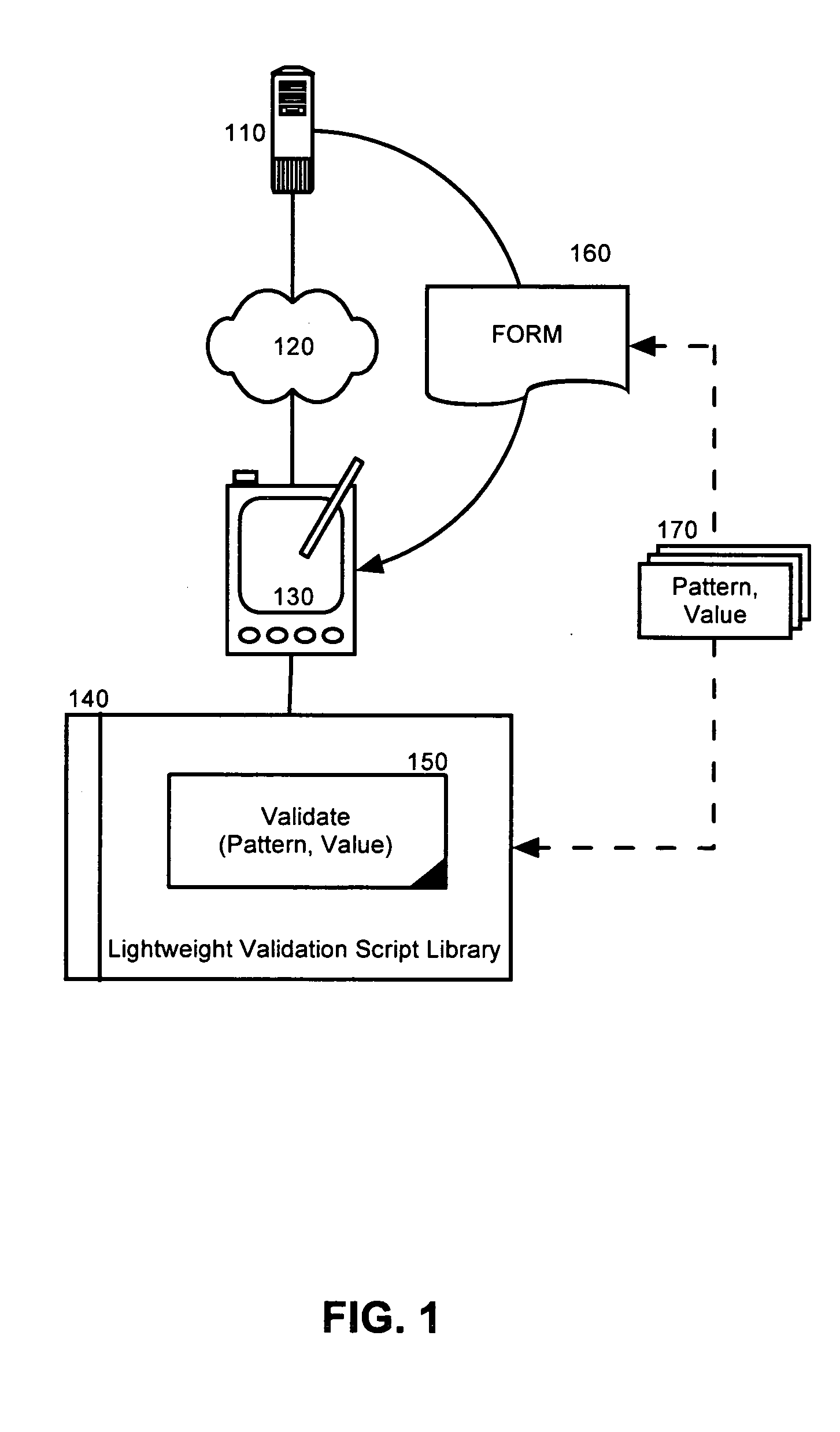
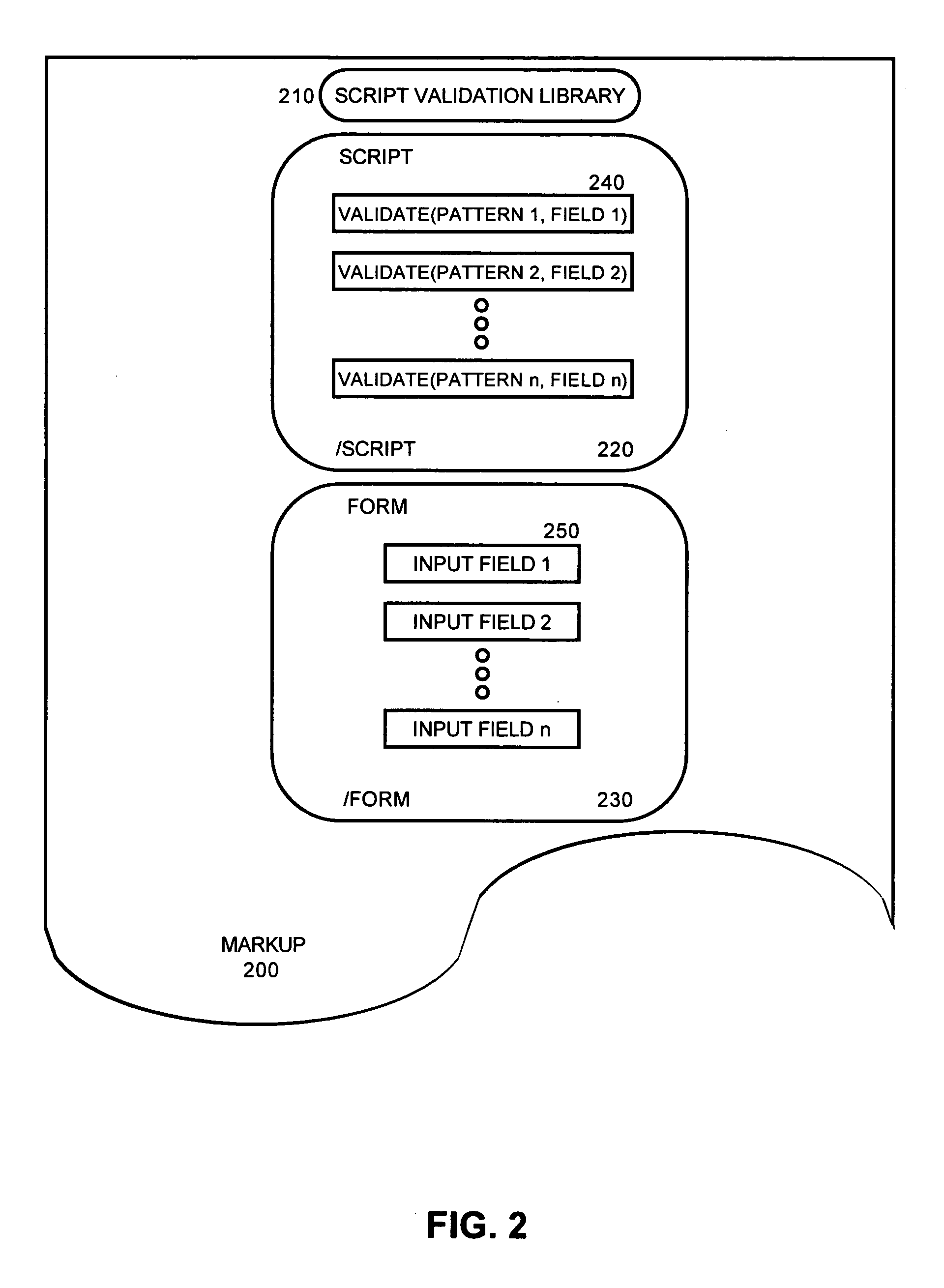
Lightweight form pattern validation
ActiveUS20050108624A1Make up for deficienciesNatural language data processingSpecial data processing applicationsValidation methodsAdditional values
A pattern validation method can include retrieving a value for a form based input field from a form defined in markup rendered in a content browser. The retrieved value along with a validation pattern for the form based input field can be passed to a validation process disposed within a lightweight validation library coupled to the rendered markup. Subsequently, the retrieved value can be validated in the content browser according to the validation pattern. Notably, each step of retrieving, passing and validating can be repeated for at least one additional value for at least one additional form based input field disposed in the markup rendered in the content browser. In this regard, the retrieving, passing, and validating steps can be performed in a validation shell function disposed in the markup rendered in the content browser.
Owner:TAASERA LICENSING LLC
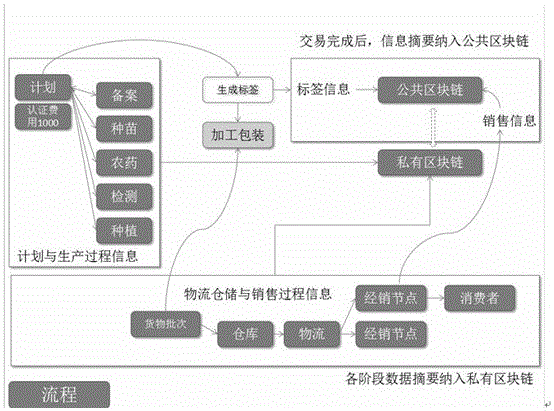
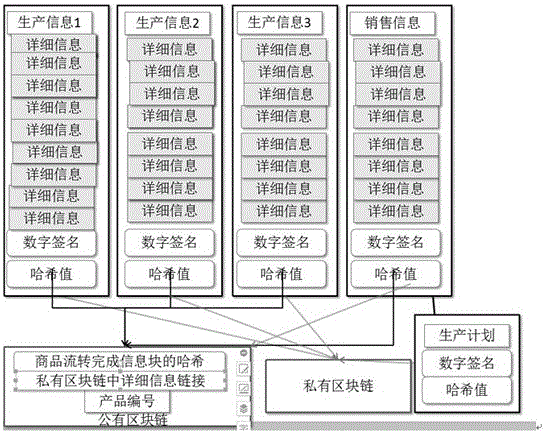
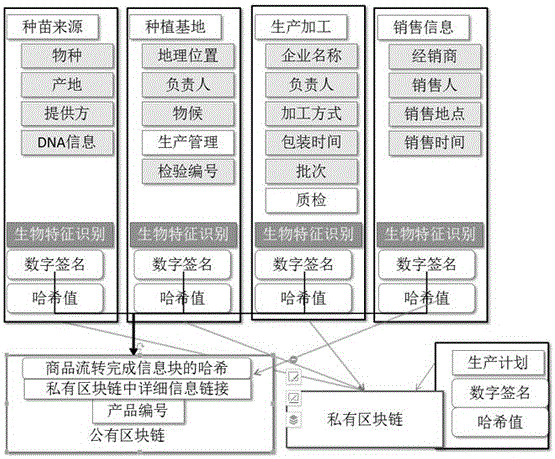
Product traceability verification method based on block chain technique
The invention discloses a product traceability verification method based on a block chain technique, which comprises a traceability step and a verification step. The traceability step comprises the following sub steps: 1) plan and production process information data are used for building blocks, and the blocks are stored in a private block chain; 2) three pieces of basic information are used for building verifiable label information; and 3) a distribution node adds the product consumption information and the label information to a public block chain. The verification step comprises the following sub steps: a, a product label is acquired; b, the product label is queried in the public block chain; and according to related records for the product label and the public block chain, the authenticity and the uniqueness of the product are determined. By adopting the method of the invention, the authenticity and the reliability of the traceability information can be ensured, technical problems that products are copied and over distributed and a responsibility person can not be bound can be solved, and besides, high-efficiency operation and the control cost of the traceability system can be ensured.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Automated employment information exchange and method for employment compatibility verification
InactiveUS20110055098A1High probability of successHigh probability of satisfactionInstrumentsSystems managementValidation methods
A computer implemented system is provided to manage the exchange of information about people seeking employment with suitable job opportunities through the use of linguistic technologies. The system is particularly useful for job hiring environments which require an exchange between companies looking to hire employees and individuals seeking employment. The system manages a database of job candidates who have been interviewed and answers have been recorded. The system converts the candidate's answers into a personal linguistic profile and then analyzes the linguistic profile to reveal the candidates unique talents and skills to find the most suitable job opportunities.
Owner:STEWART JEFFREY A
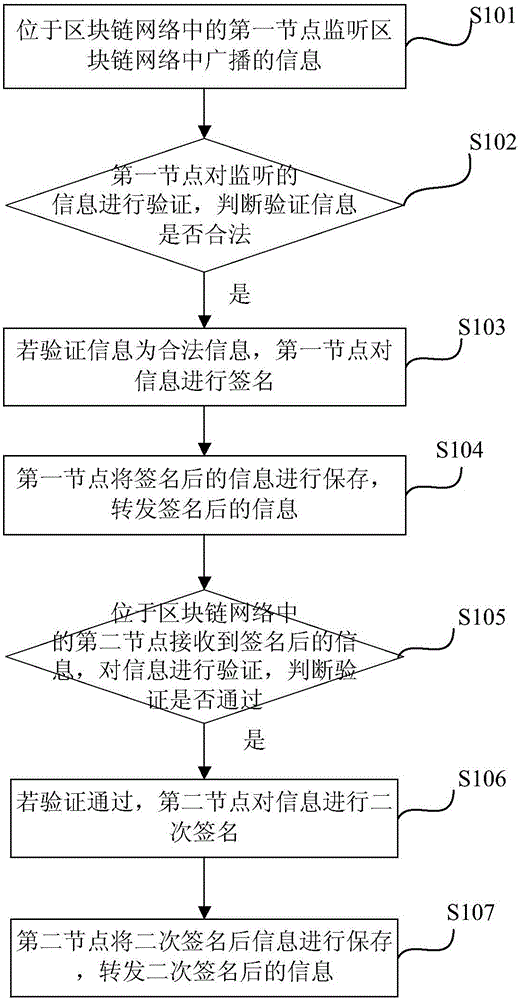
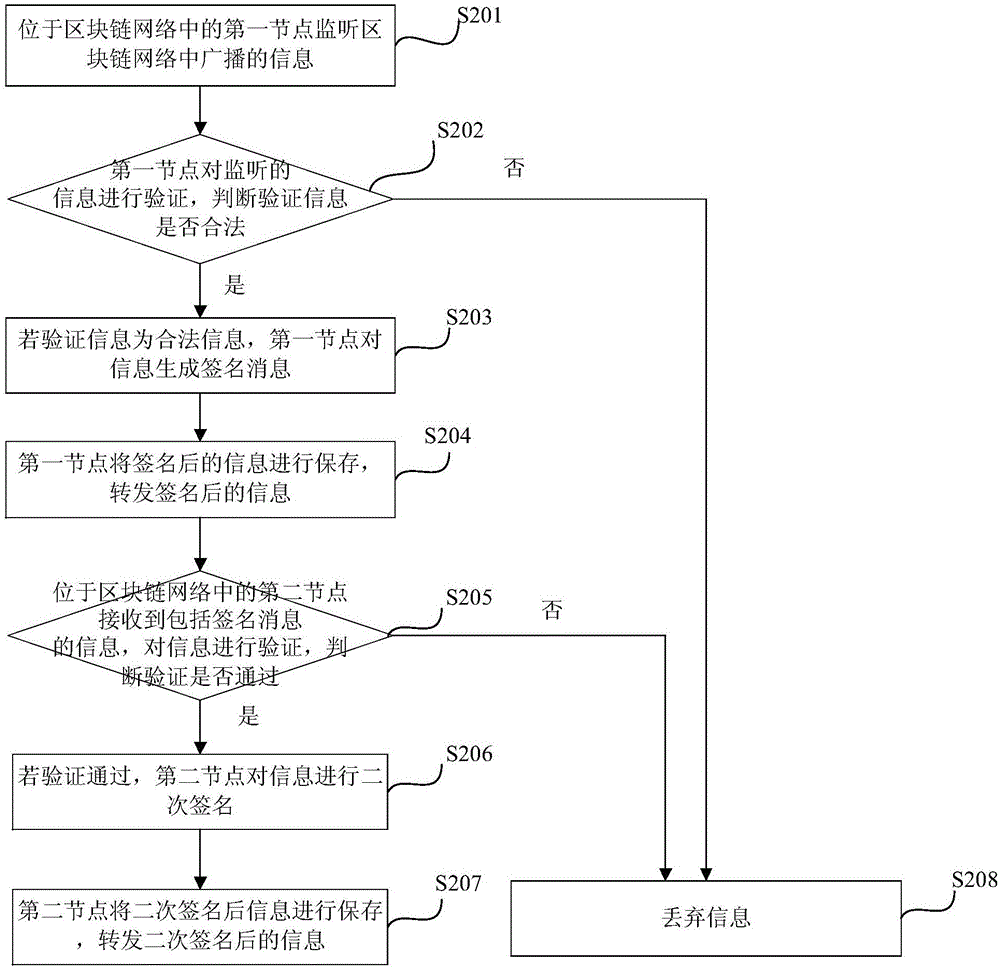
Verification method for information in block chain network and verification system thereof
ActiveCN106385319AFast forwardImprove forwarding speedUser identity/authority verificationValidation methodsChain network
The invention discloses a verification method for information in a block chain network and a verification system thereof. The method comprises the steps that a first node in the block chain network monitors information broadcasted in the block chain network; the first node verifies the monitored information, and the first node signs the information if the verified information is legal information; the first node saves the signed information and forwards the signed information; a second node in the block chain network receives the signed information and verifies the information; the second node secondarily signs the information if verification is passed; and the second node saves the secondarily signed information and forwards the secondarily signed information. With application of the scheme, the workload of node information verification can be reduced and forwarding speed of the information can be accelerated so that the information is enabled to be more quickly forwarded.
Owner:JIANGSU PAYEGIS TECH CO LTD +1
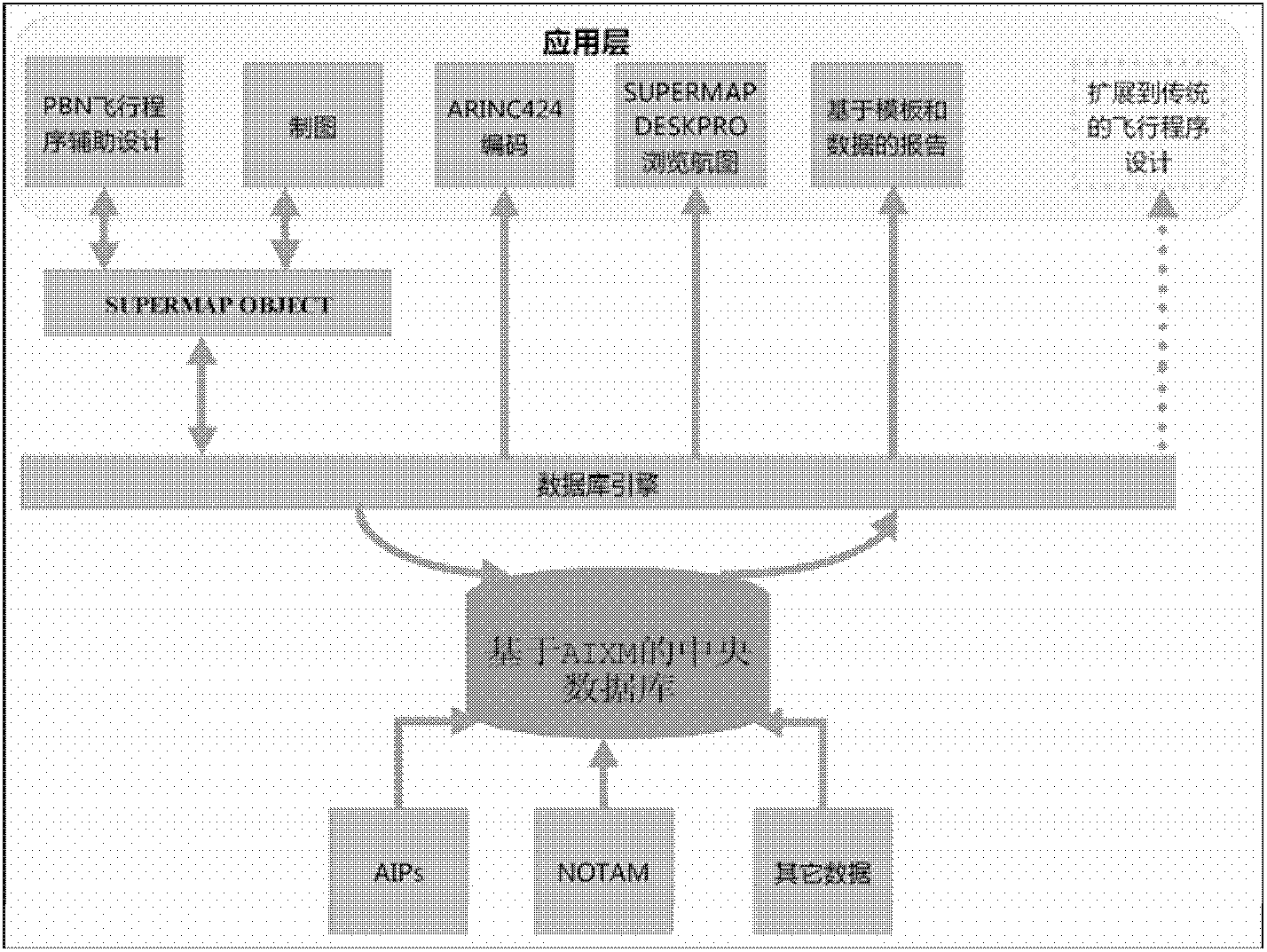
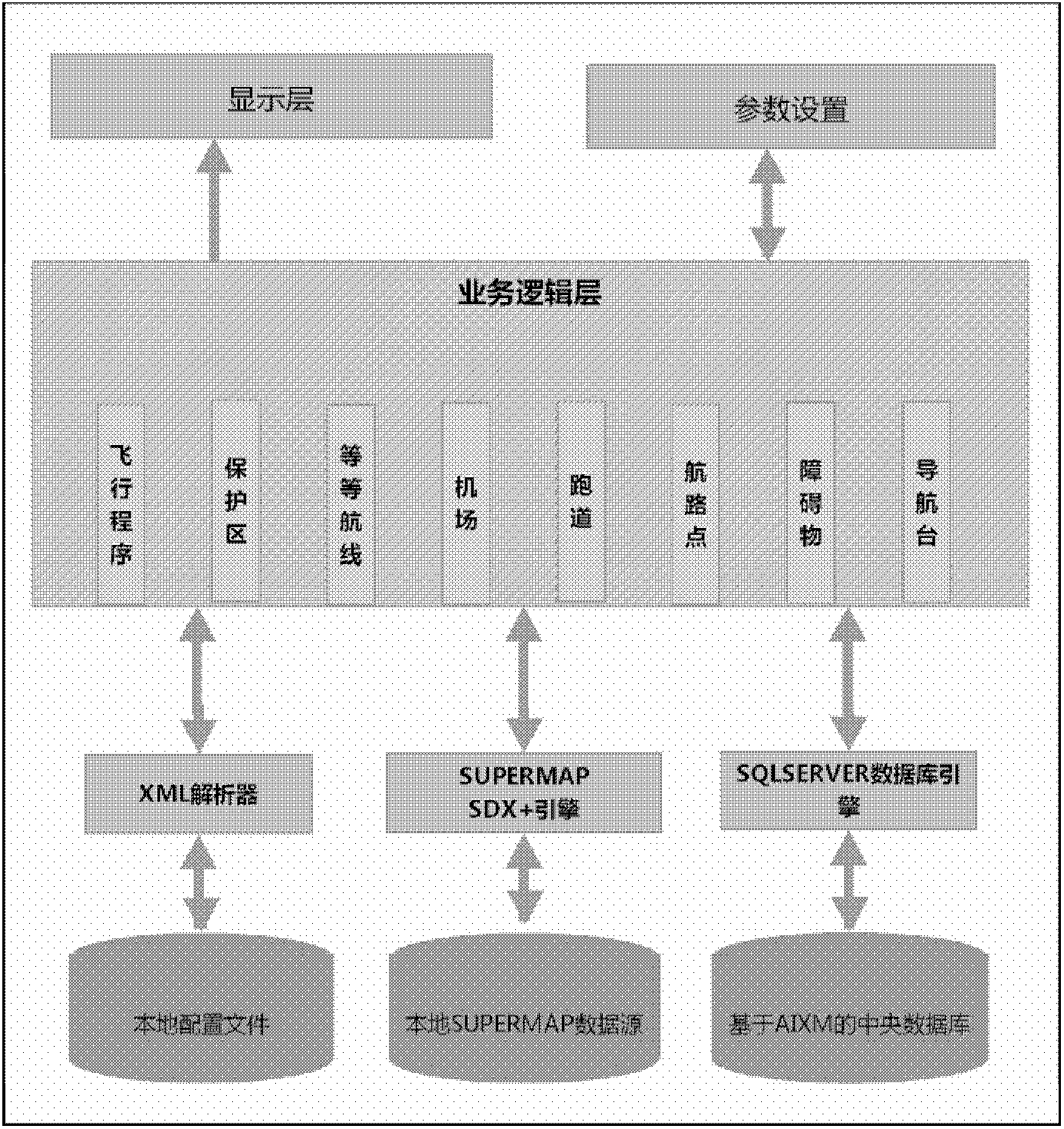
Flight program design system for performance-based navigation, verification platform and verification method
InactiveCN102867073ARealize automatic designQuick buildSpecial data processing applicationsAviationValidation methods
The invention discloses a flight program design system for performance-based navigation (PBN), a verification platform and a verification method, belonging to the field of aerial navigation. The program design system is based on an AIXM (Aeronautical Information Exchange Model) core database; a program protection region can be automatically drawn, an obstacle is evaluated, and a chart is generated; and thus, functions such as seamless connection and the like of the PBN program protection region and the conventional flight program protection region can be realized. According to the system, the chart can be automatically generated according to data finished by the flight program design, customized edition and modification can also be realized according to requirement, and program design and publishing are finished at one time. By using the flight program design system, the verification platform and the verification method, the PBN program can be directly added in a navigation database of the verification platform, and the navigation database can be edited and modified in a verification process. In addition, a visual scene database is increased; the defects and the disadvantages of the program design can be directly discovered according to geomorphology in a visual scene when the PBN flight program is verified; and the program is further modified perfectly.
Owner:CHINA ACAD OF CIVIL AVIATION SCI & TECH
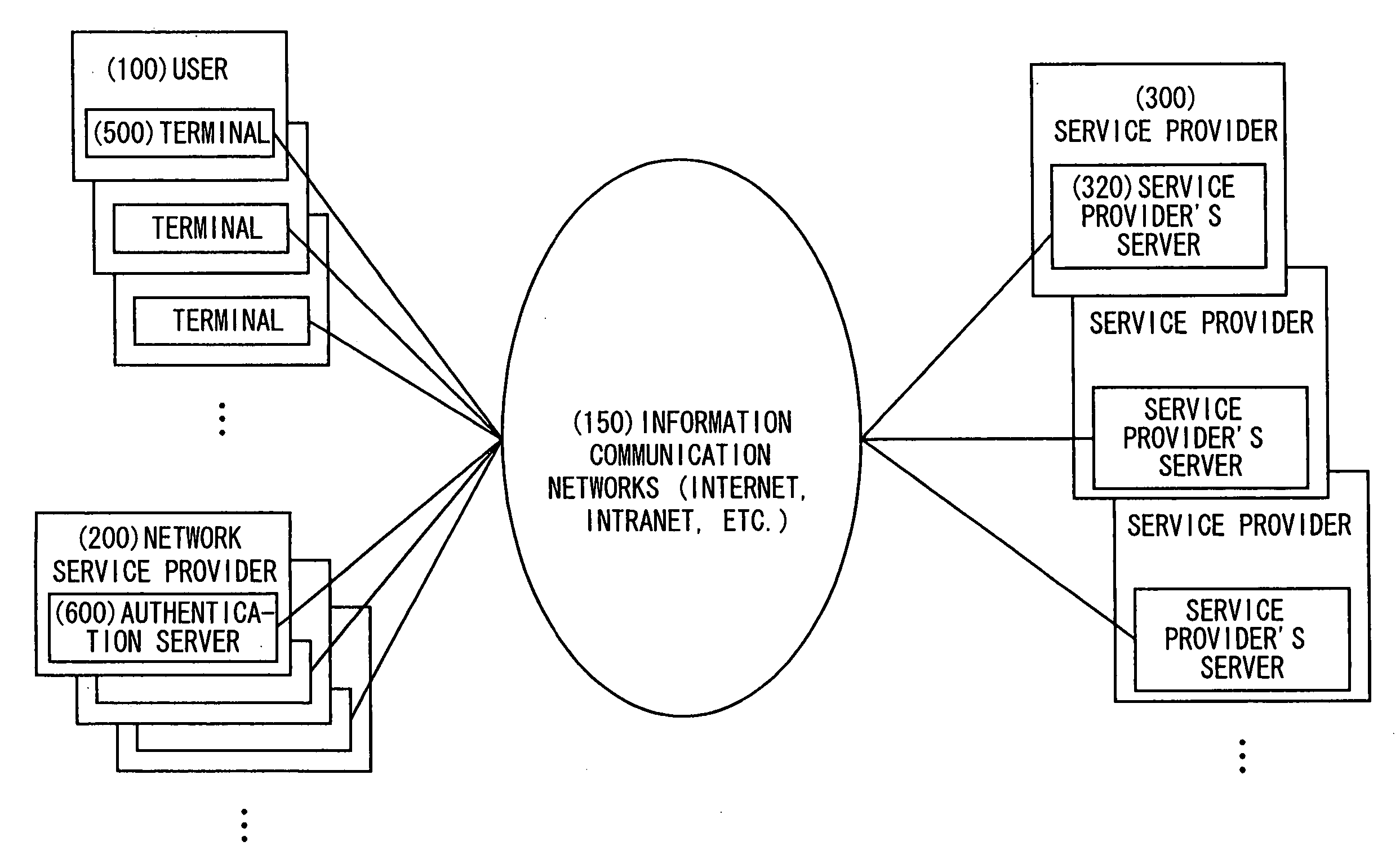
Authentication method, authentication system, and authentication server
InactiveUS20070044146A1Low costReduce buildRandom number generatorsUser identity/authority verificationService provisionValidation methods
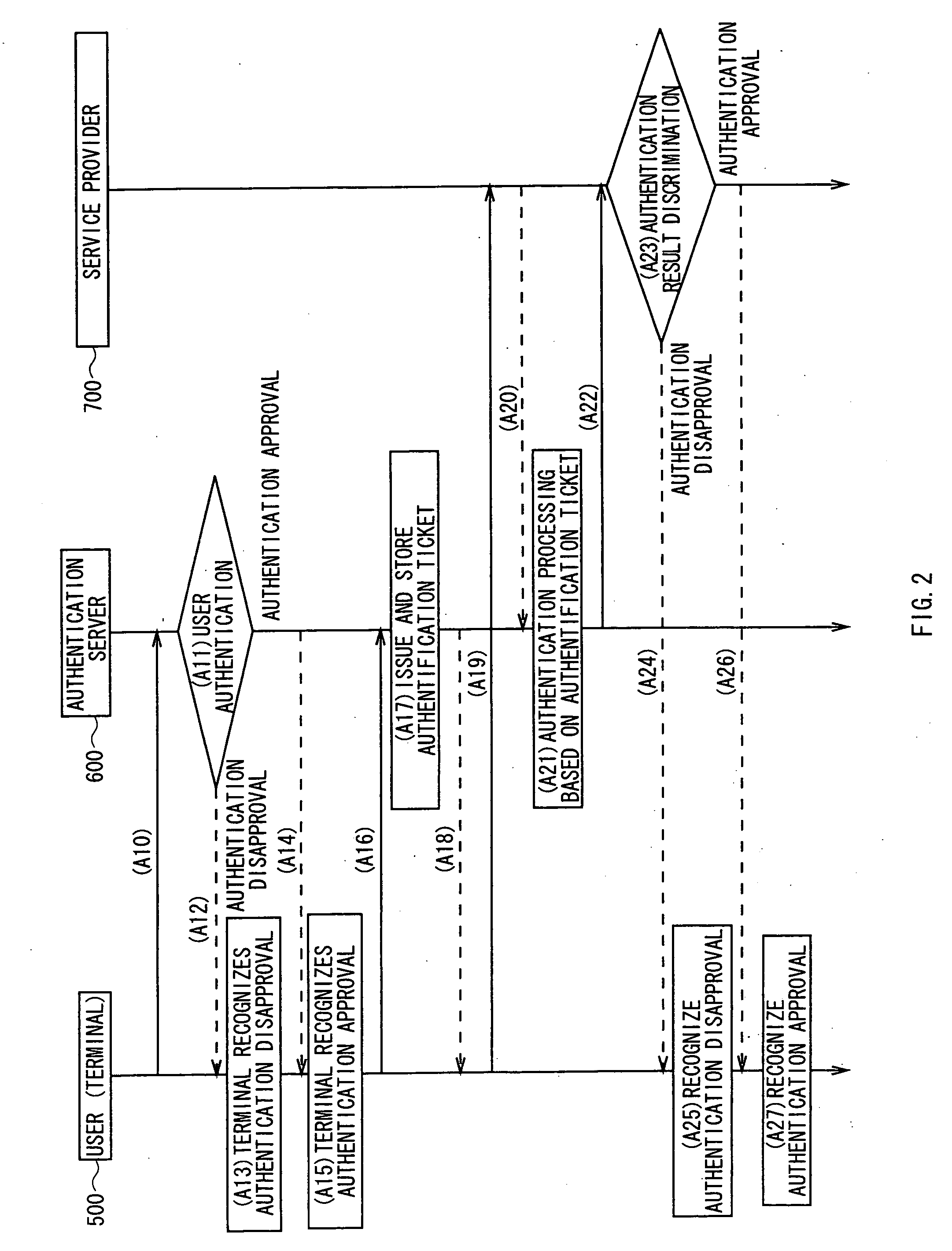
A user authentication processing is performed and an authentication session ID is returned to a terminal 500 (A14). An authentication server 600 issues and stores an authentication ticket (A17). The authentication ticket and authentication session are returned to the terminal 500 (A18). A user 100 transmits a request of service provision and the authentication ticket to a service provider's server 700, and the service provider's server 700 transmits the authentication ticket to the authentication server 600 (A20). The authentication server 600 performs an authentication processing of the authentication ticket (A21), and the authentication result is notified (A22). In the case of the authentication approval, a service session ID is issued together with the notification of authorization (A23). When receiving the notification of the authentication approval, the terminal 500 performs an establishment processing of the session using the received service session ID, and stores the service session ID (A27).
Owner:SONY CORP
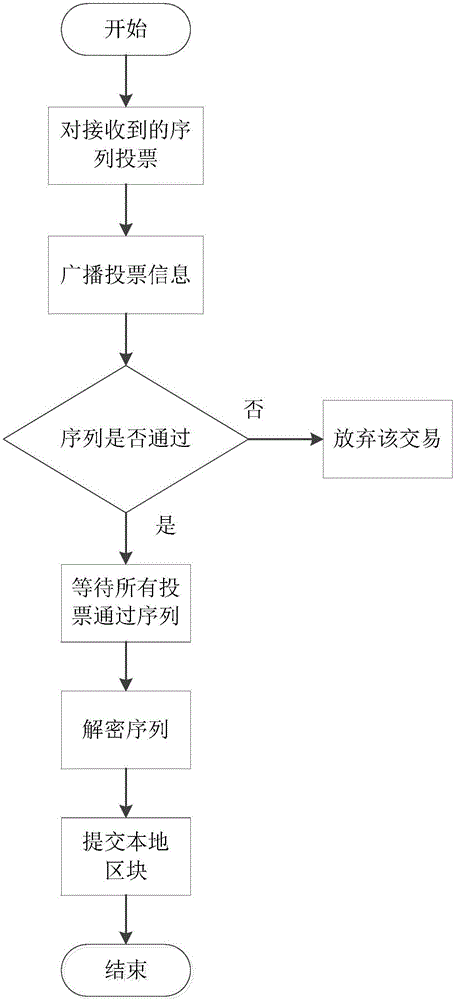
Node consensus verification method under league chain network through asynchronous mode
InactiveCN106529951AImprove throughputImprove network throughputFinanceElectronic credentialsValidation methodsChain network
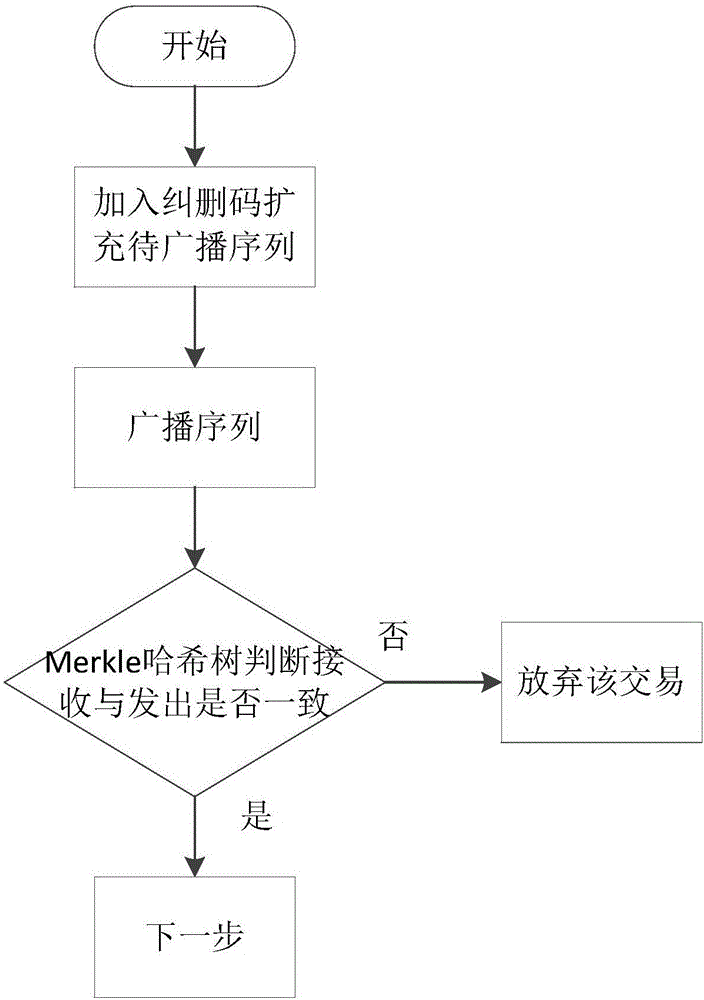
The invention discloses a node consensus verification method under a league chain network through an asynchronous mode. Each node takes a transaction request from the head of a buffer queue to act as a transaction sequence to be submitted and then encrypts the sequence by using threshold encryption; each node broadcasts the encrypted transaction sequence, ensures the integrity of the transmitted message by using an erasure code and ensures message consistency of different nodes by using a Merkle tree; and all the nodes vote the transaction sequences by using the binary Byzantine consensus agreement to reach a consensus, each node waits for local receiving all the voted transaction sequences and then decrypts the transaction sequences by using threshold decryption so as to finally obtain the decrypted transaction information to act as the transaction request written in blocks within the period. The method is completely decentralized, the system has no timeout mechanism and the broadcast message completely depends on the network bandwidth so that the method has higher network throughput when a large number of nodes exist in the network in comparison with the conventional synchronization Byzantine fault tolerance consensus method.
Owner:HANGZHOU YUNXIANG NETWORK TECH
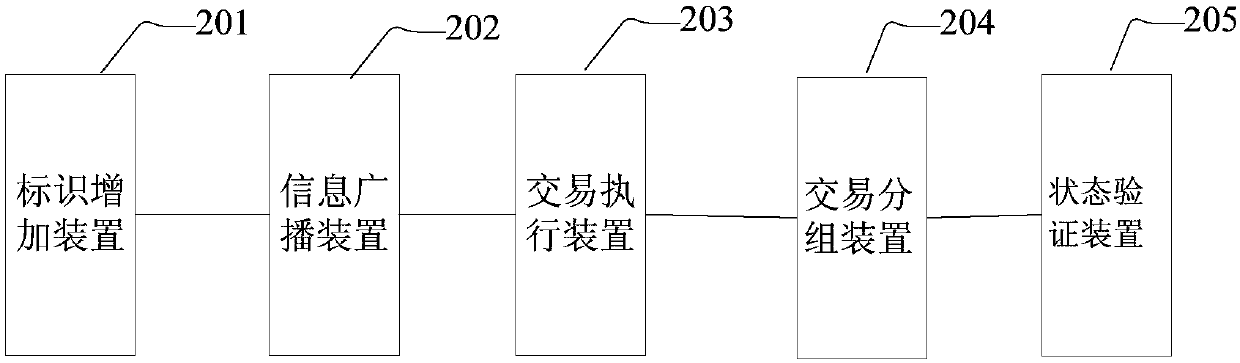
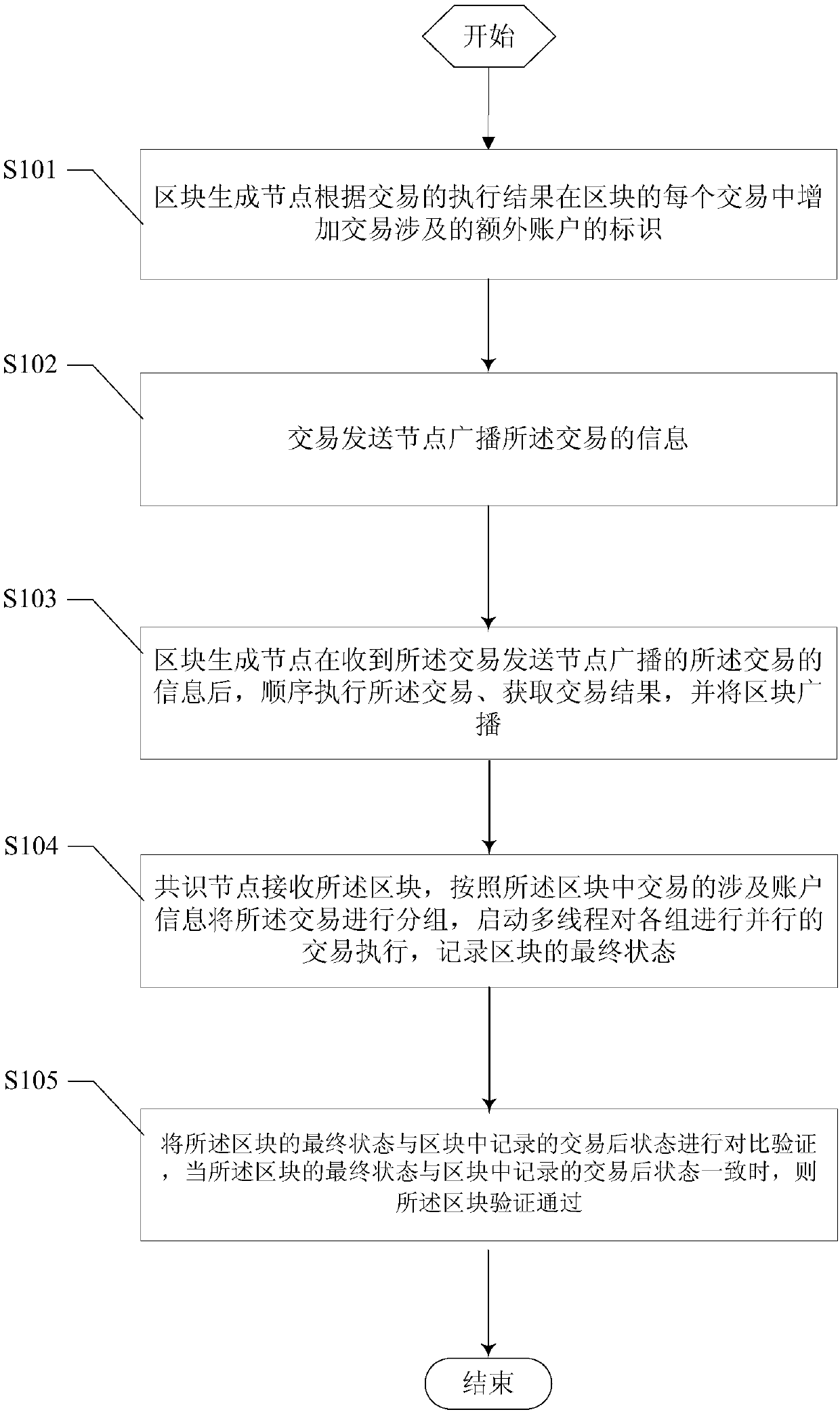
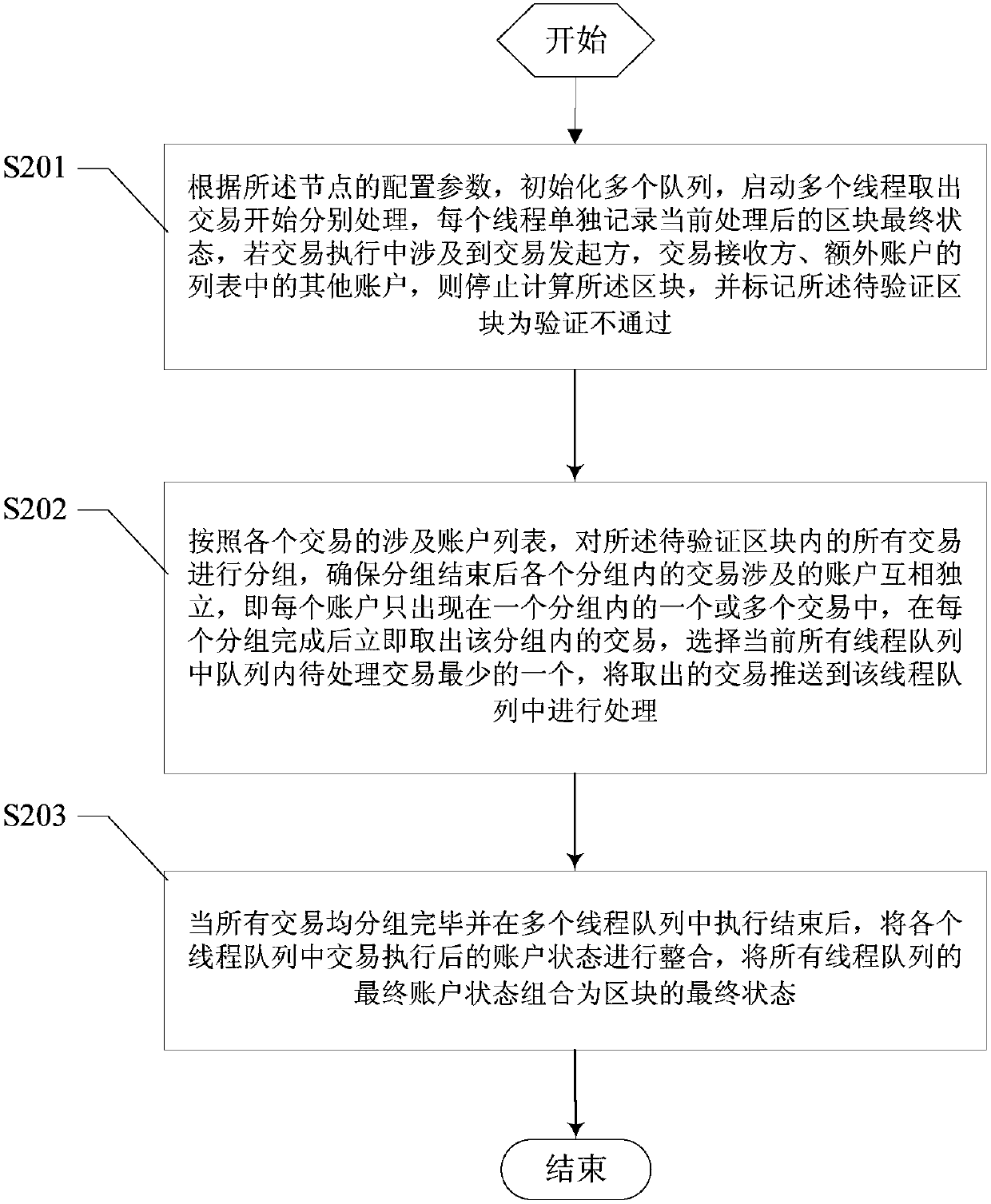
Transaction grouping-based block chain verification method and system
InactiveCN107678865AImprove performanceEnhanced authenticationProgram initiation/switchingInterprogram communicationValidation methodsFinancial transaction
The invention provides a transaction grouping-based block chain verification method and system, a computer device and a computer readable storage medium, and relates to the technical field of data processing. The method comprises the steps that a block generation node adds identifiers of additional accounts involved by transactions into the transactions of a block according to executive results ofthe transactions; a transaction sending node broadcasts information of the transactions; the block generation node sequentially executes the transactions, obtains transaction results, and broadcaststhe block; a consensus node performs grouping on the transactions according to account information involved by the transactions in the block, starts multiple threads to perform parallel transaction execution on groups, and records a final state of the block; and when the final state of the block is consistent with an after-transaction state recorded in the block, block verification is passed. Theblock verification and synchronization speed is increased by expanding system hardware; and finally the overall performance of a block chain transaction network can be greatly improved.
Owner:BANK OF CHINA
Auto-recoverable and auto-certifiable cryptostem using zero-knowledge proofs for key escrow in general exponential ciphers
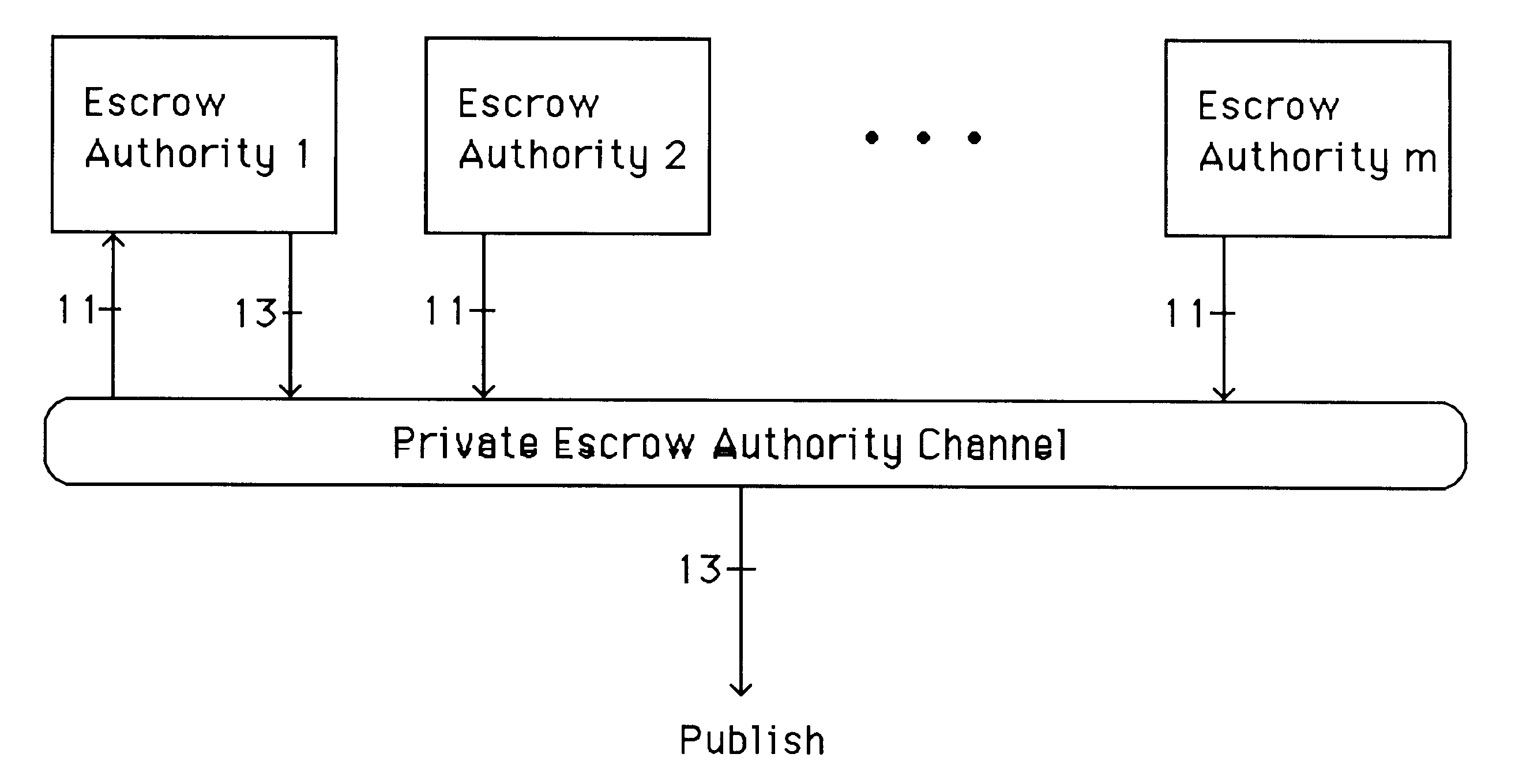
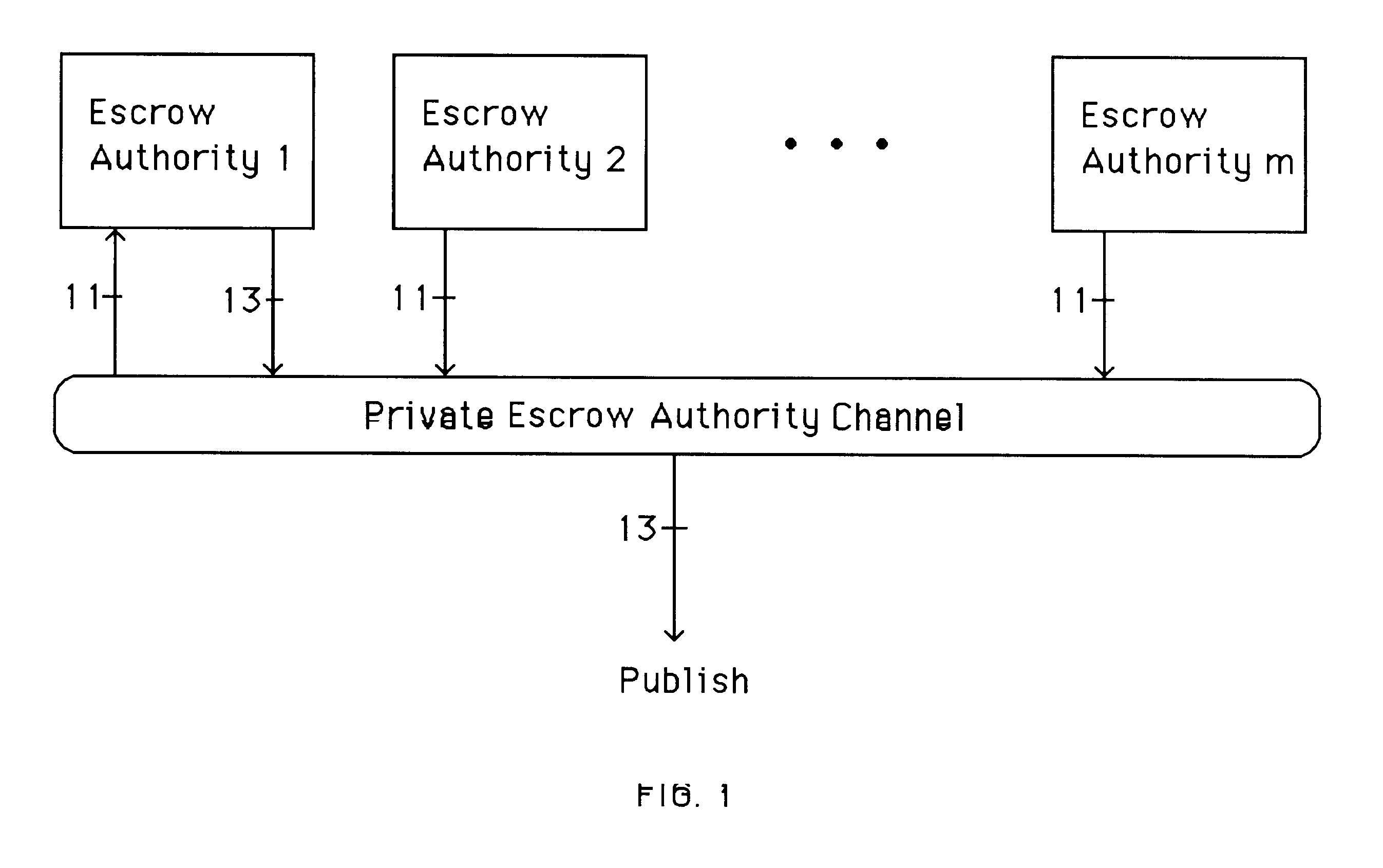
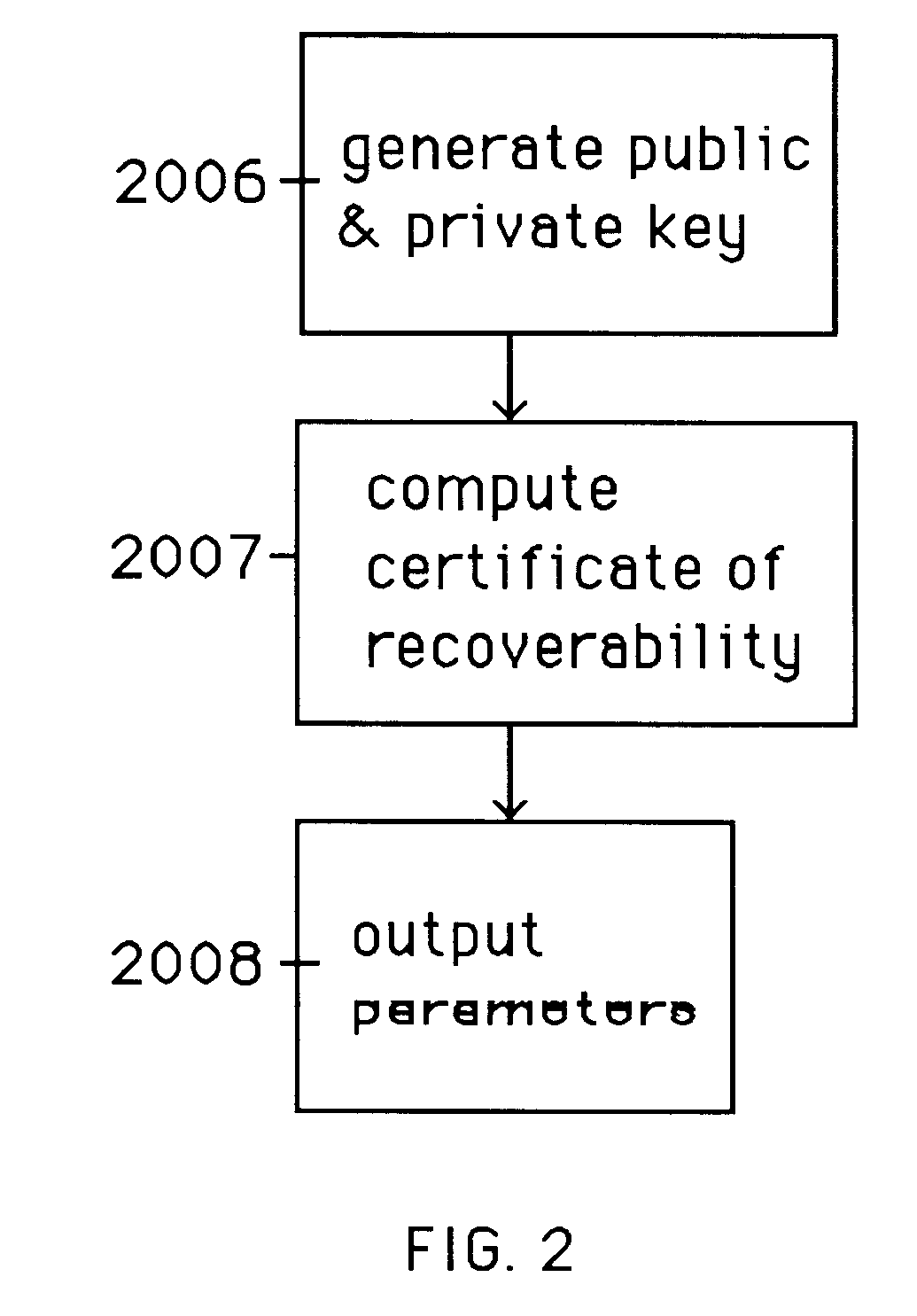
InactiveUS6282295B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityValidation methods
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The proof and verification method involves one party proving to a second party that a third party can gain access to an encrypted value. In addition, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or ElGamal cryptosystem. The system is applicable for lawenforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. The system security relies solely on the security of cipher systems involved whose security has been extensively studied in the past.
Owner:CRYPTOPEAK SECURITY LLC
Method for anti false verification based on identification technique in radio frequency, and anti false system
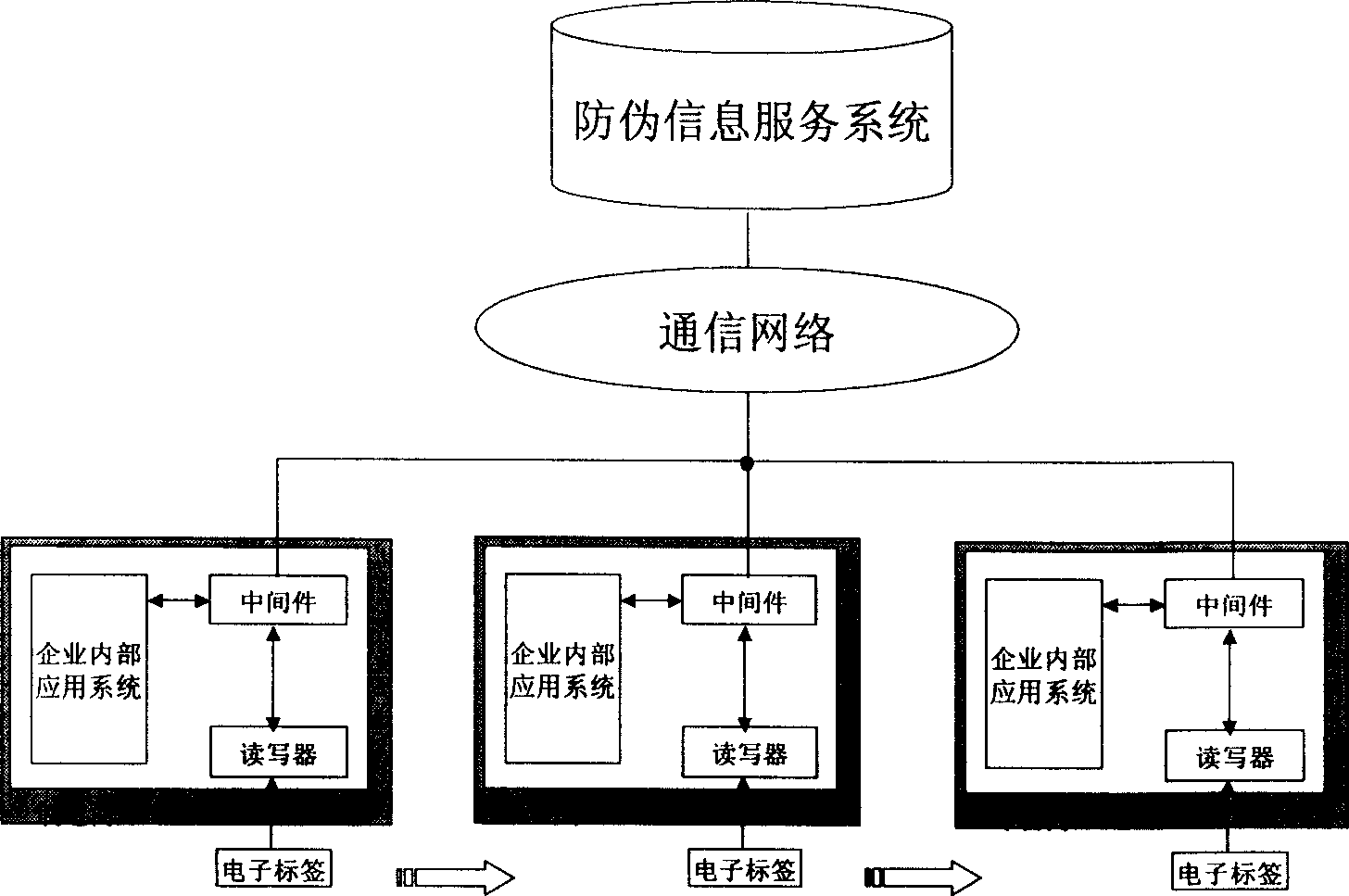
InactiveCN1728162AAdvantage Anti-counterfeitingSecurity advantageKey distribution for secure communicationData processing applicationsLogistics managementValidation methods
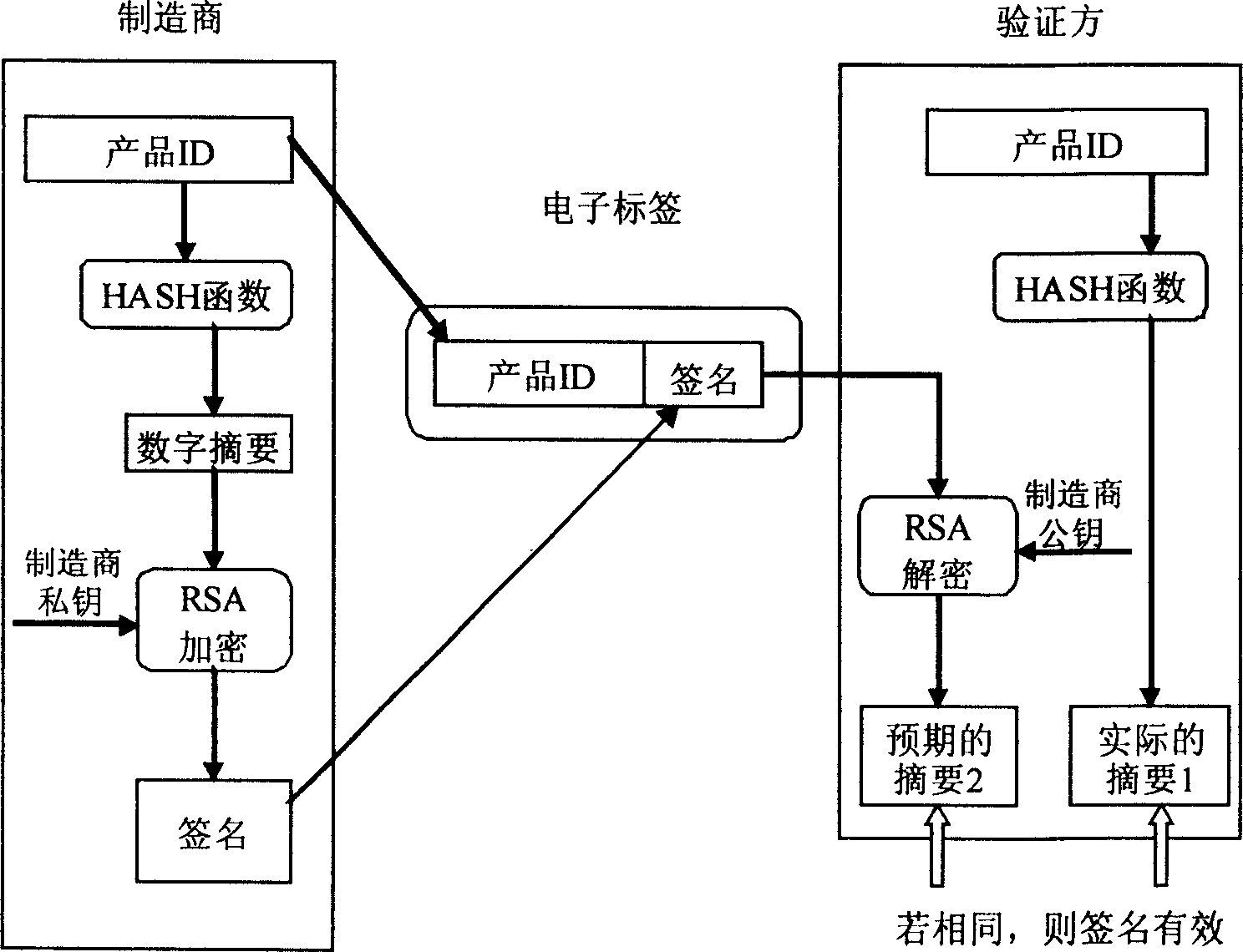
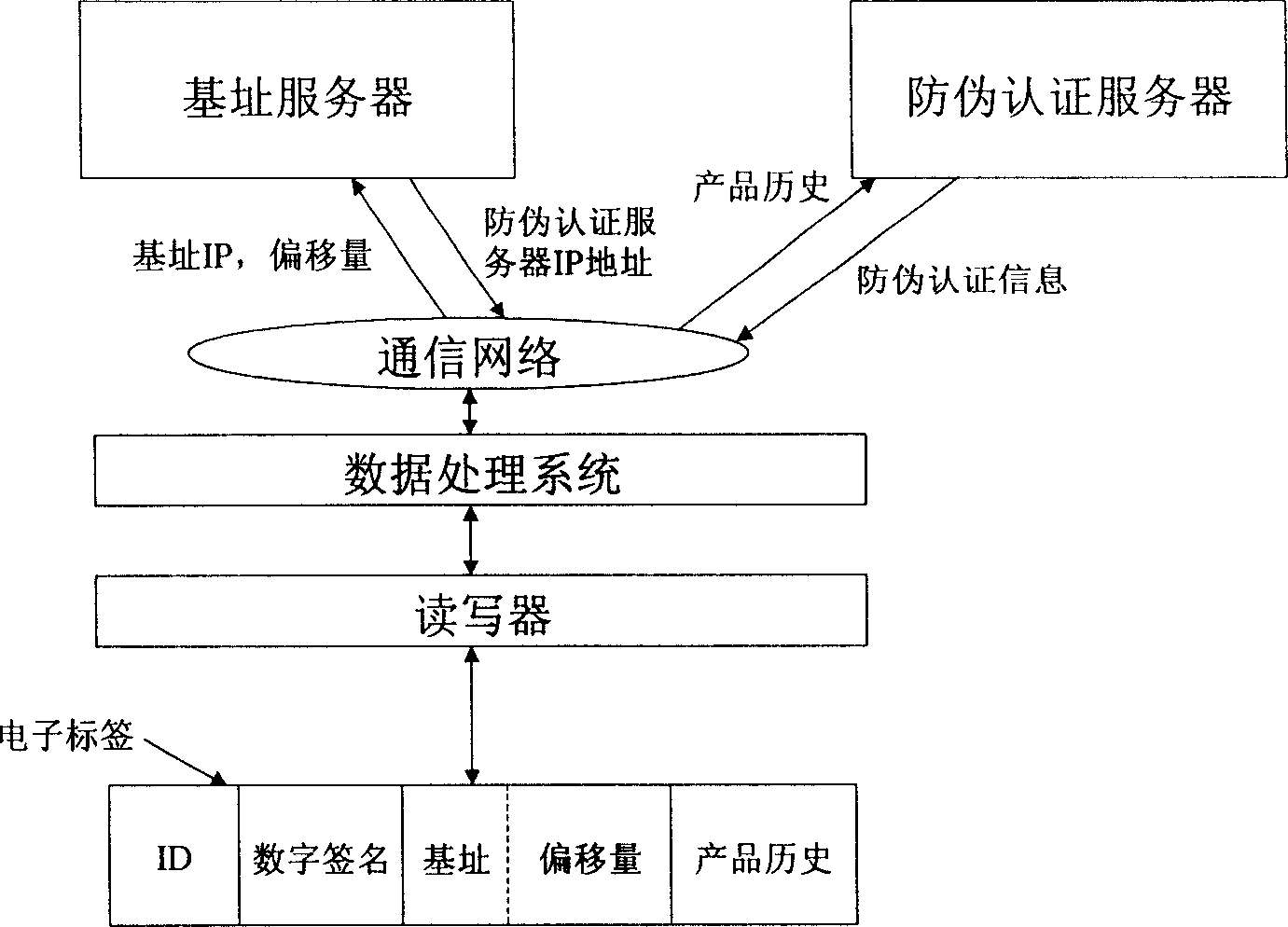
An antifalse system based on radio frequency technology comprises storage with electronic countermark of radio frequency identification, reader / writer and antifalse information service system. The said storage is divided to be four regions of basic information region, digital signature region for storing digital signature generated by ciphering with private key of manufacture, product history region for recording basic data of logistics tracking information, antifalse certifying server address indexing region for storing server address and address offset amount.
Owner:FUDAN UNIV
Method of safe and recoverable firmware update and device using the same
ActiveUS20100199078A1Maintain abilityMemory adressing/allocation/relocationDigital computer detailsValidation methodsEmbedded electronics
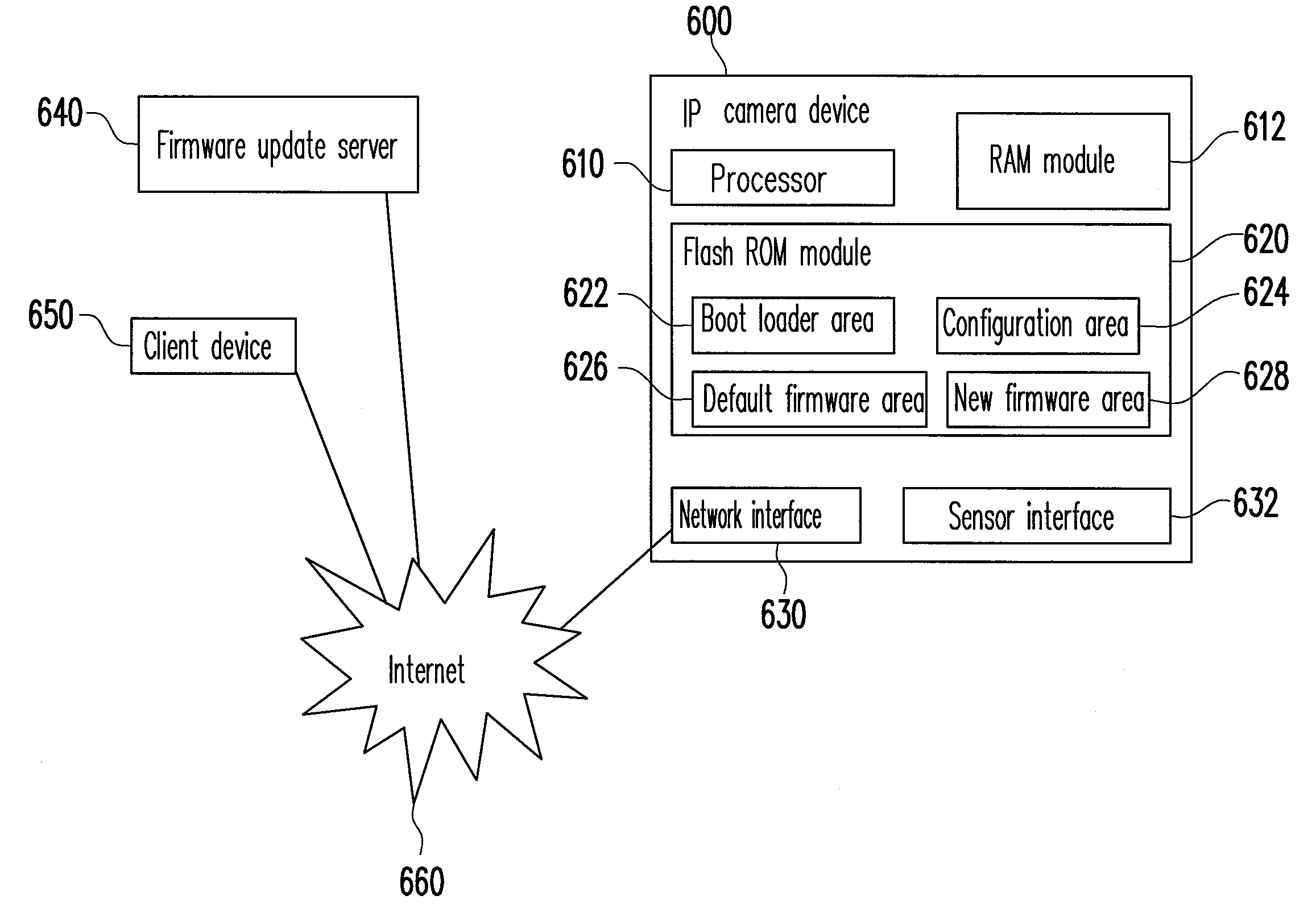
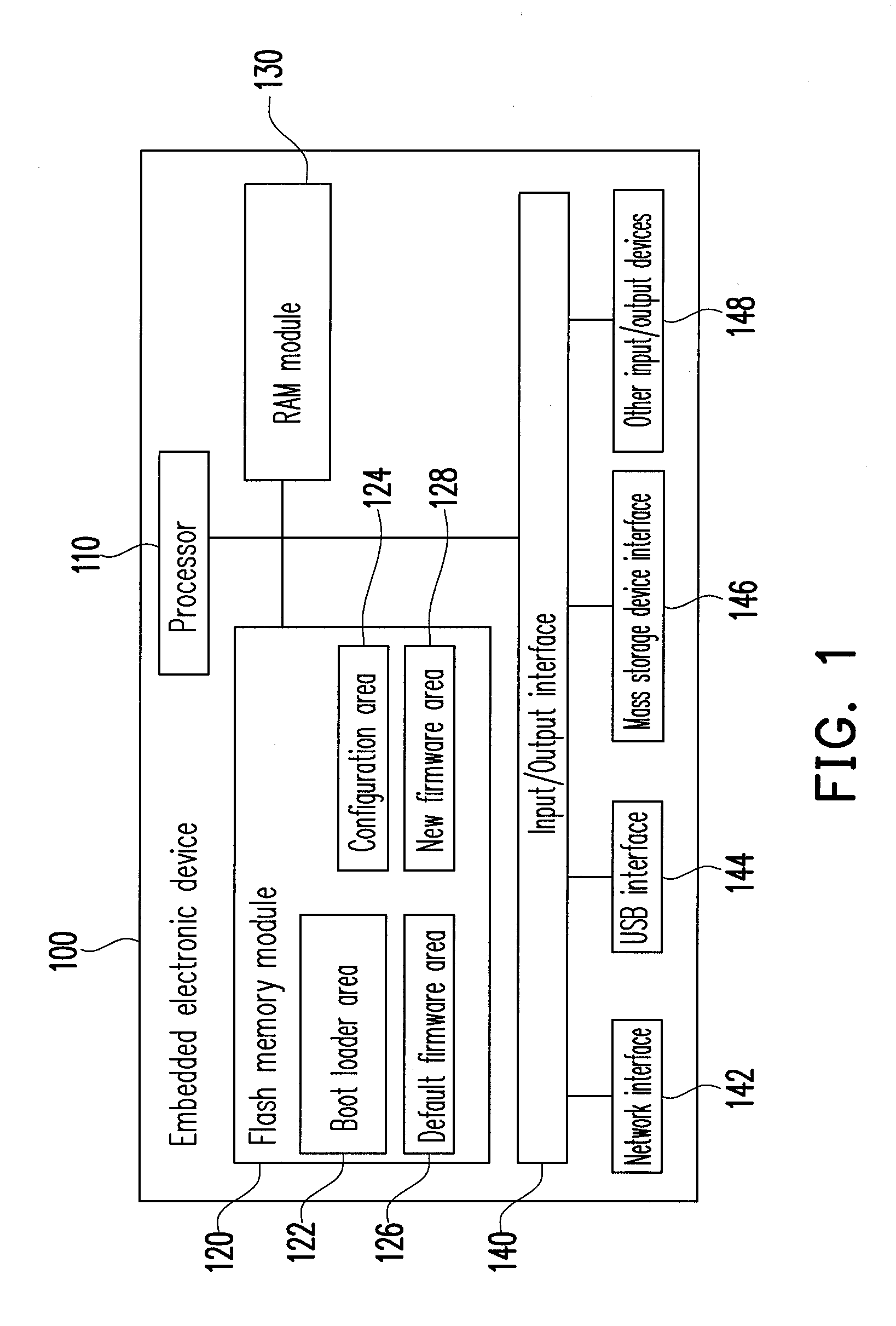
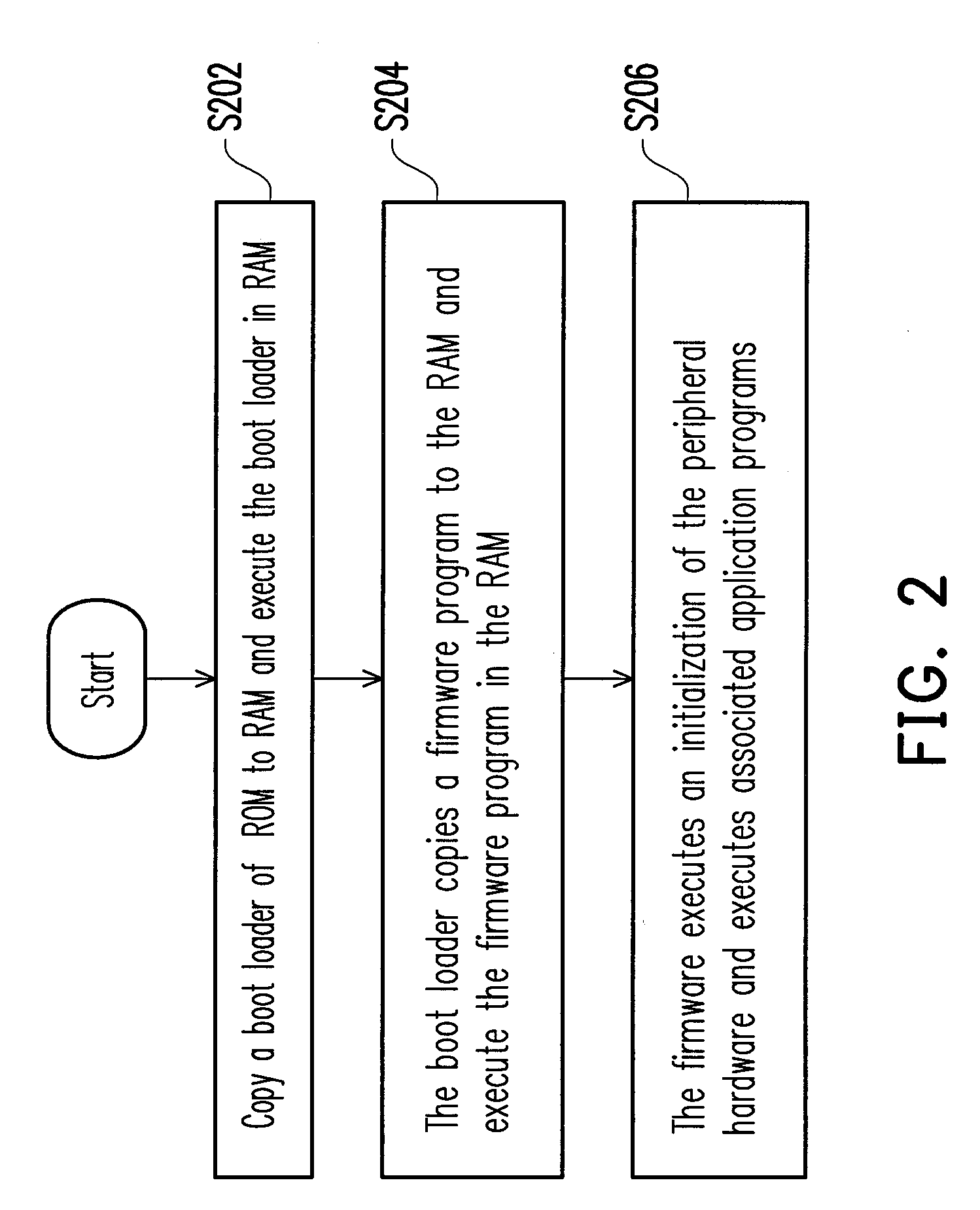
A safe and recoverable firmware update method which for a remote embedded electronic device and the device thereof. The method includes reading an update status in a flash memory, and determining the update status. If the update status is “DEFAULT”, a default firmware is executed. If the update status is not “DEFAULT”, the update status is further determined if it is “UPDATED”. If the update status is “UPDATED”, a configuration area is set as “BOOTING” and a new firmware is executed. If the update status is not “UPDATED”, the update status is determined if it is “RUNNEW”. If the update status is “RUNNEW”, a new firmware and an update validation method are executed. If the update validation method gets an update completion validation message, the update status is set as “RUNNEW”. If the update status is not “RUNNEW”, a default firmware is executed.
Owner:NOVATEK MICROELECTRONICS CORP
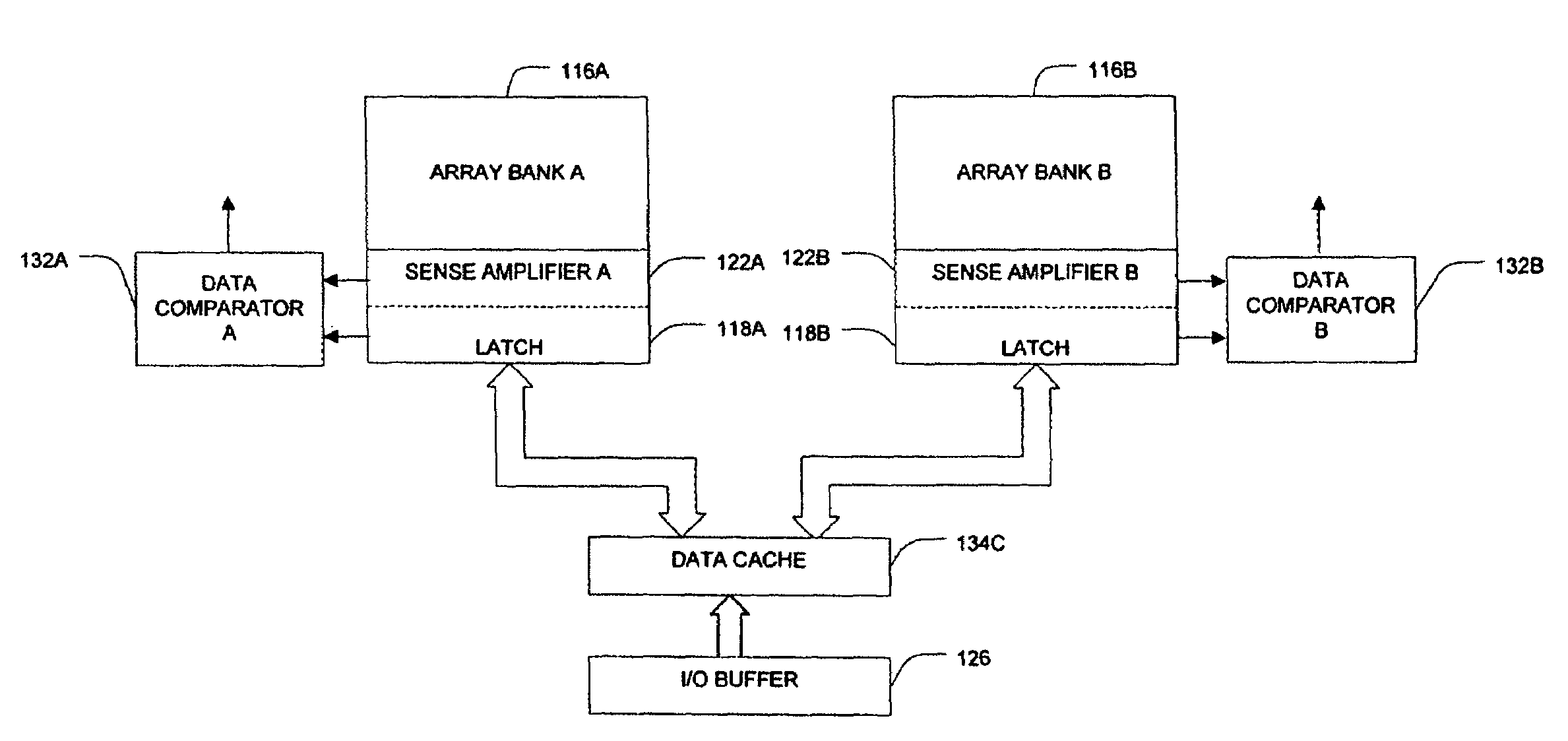
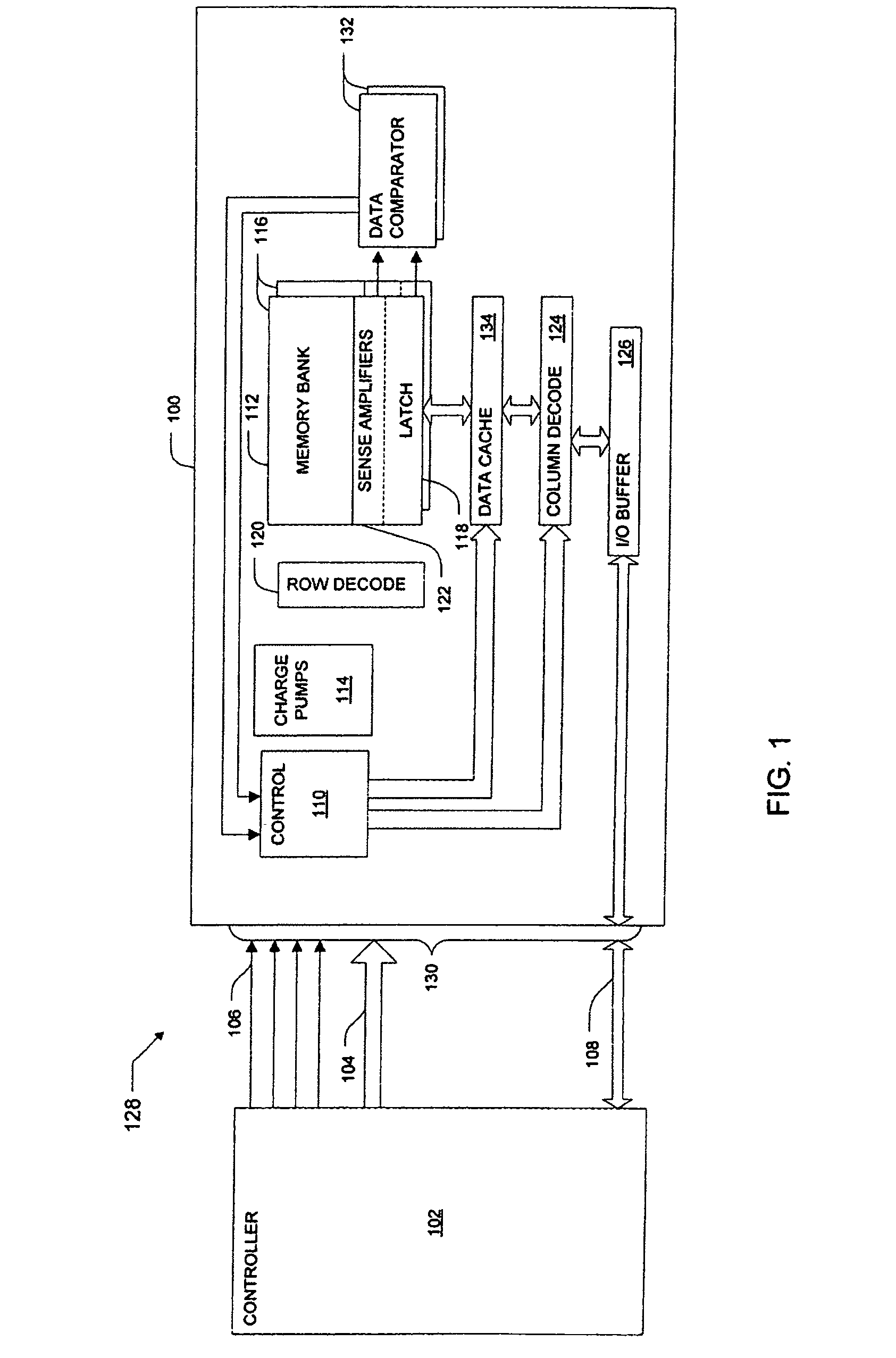
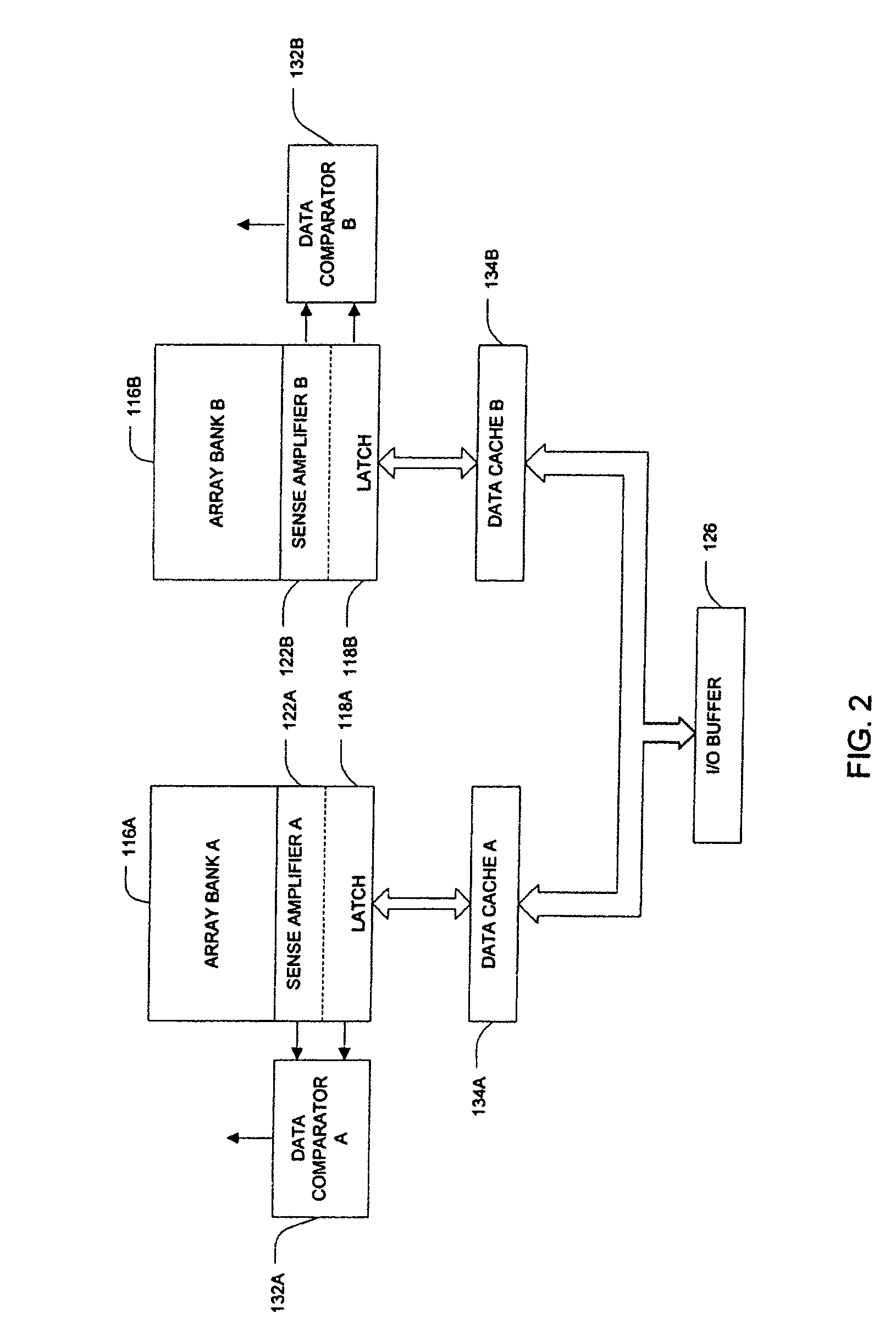
Interleaved memory program and verify method, device and system
Owner:ROUND ROCK RES LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com