Virtual currency transaction validation method based on block chain multi-factor cross-validation
A cross-validation and virtual currency technology, which is applied in the field of information security, can solve the problems of receiver B's loss and invalid records not being confirmed, and achieve the effect of avoiding loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The specific method of the present invention will be described in detail below in conjunction with the accompanying drawings.
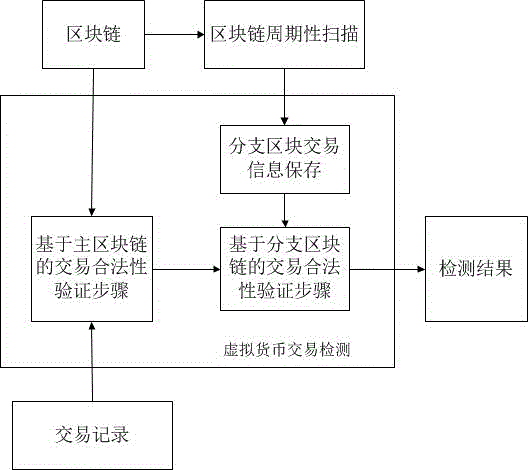
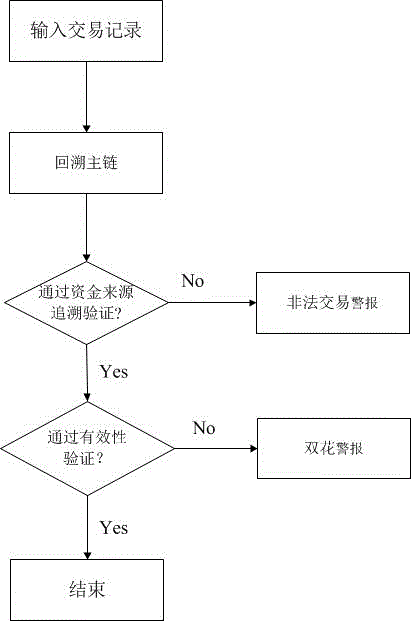
[0028] figure 2 It is the workflow of the present invention.
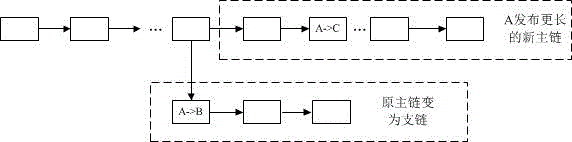
[0029] figure 2 It is the working process of the present invention. First, the miner node periodically scans the block chain to find the newly generated branch blocks since the last scanning cycle; then reads the transaction information in the branch blocks, including the transaction source account number, transaction target account number, transaction amount, transaction time, transaction confirmation; insert the transaction information in the branch block into the hash list array; Factor cross-validation, including transaction legitimacy verification based on the main block chain and transaction legitimacy verification based on branch blocks; if the transaction record fails to pass the transaction legitimacy verification of the main block chain, the transaction record will be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com