Patents
Literature
101 results about "Hash list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a hash list is typically a list of hashes of the data blocks in a file or set of files. Lists of hashes are used for many different purposes, such as fast table lookup (hash tables) and distributed databases (distributed hash tables).
Implementation method for multi-field rule matching
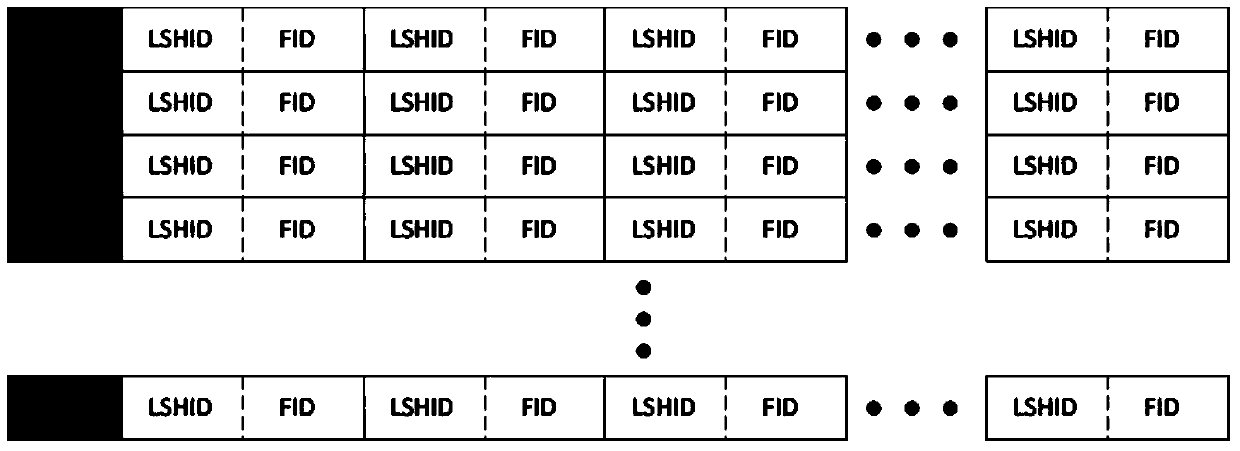
ActiveCN104468381AImprove query real-time response speedSolve the problem of finding the best ruleData switching networksData compressionData stream
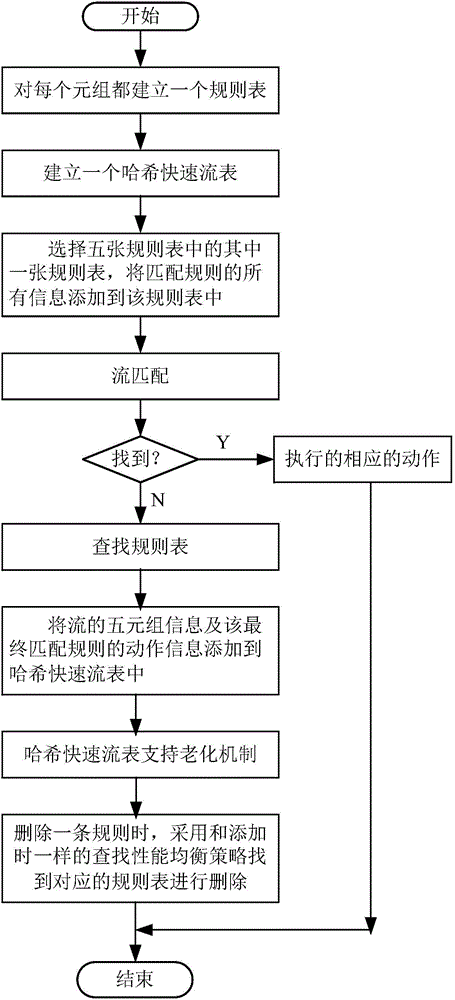
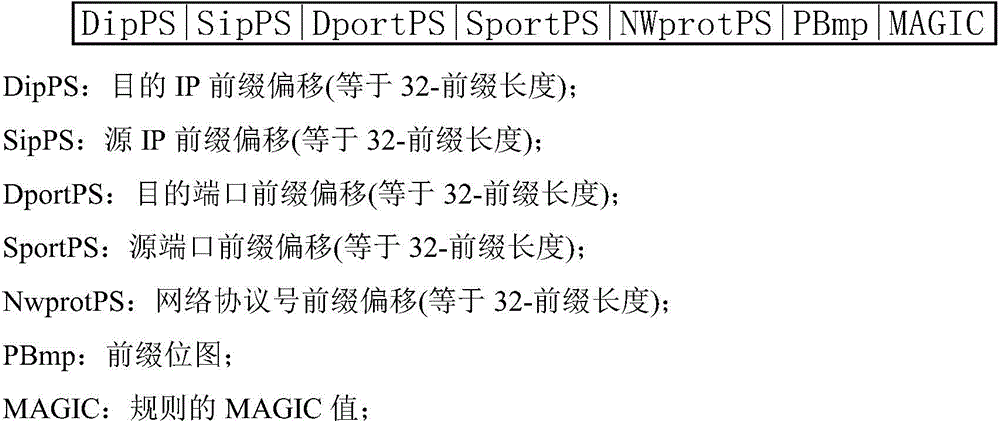
The invention discloses an implementation method for multi-field rule matching, and relates to the technical field of high-speed stream classification. The implementation method comprises the steps that firstly, a rule list is established for each tuple according to quintuple definition of IP message data streams, then a Hash rapid stream list is established, and all information matched with rules is added in the rule lists; secondly, IP message data stream matching is conducted, corresponding actions are executed if matched data streams are found, otherwise the rule lists are searched, and mask matching inquiries are conducted. According to the implementation method, the mode that a prefix extension Trie tree high in inquiring speed is improved, part of memory space is sacrificed, and data compression and the Hash list are combined is adopted, and thus under the premise that the inquiring speed is ensured, memory explosion caused by a large-capacity rule base can be avoided.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
Dynamically configurable reverse DNLC lookup
ActiveUS7822927B1Memory architecture accessing/allocationMemory adressing/allocation/relocationHash listOperating system
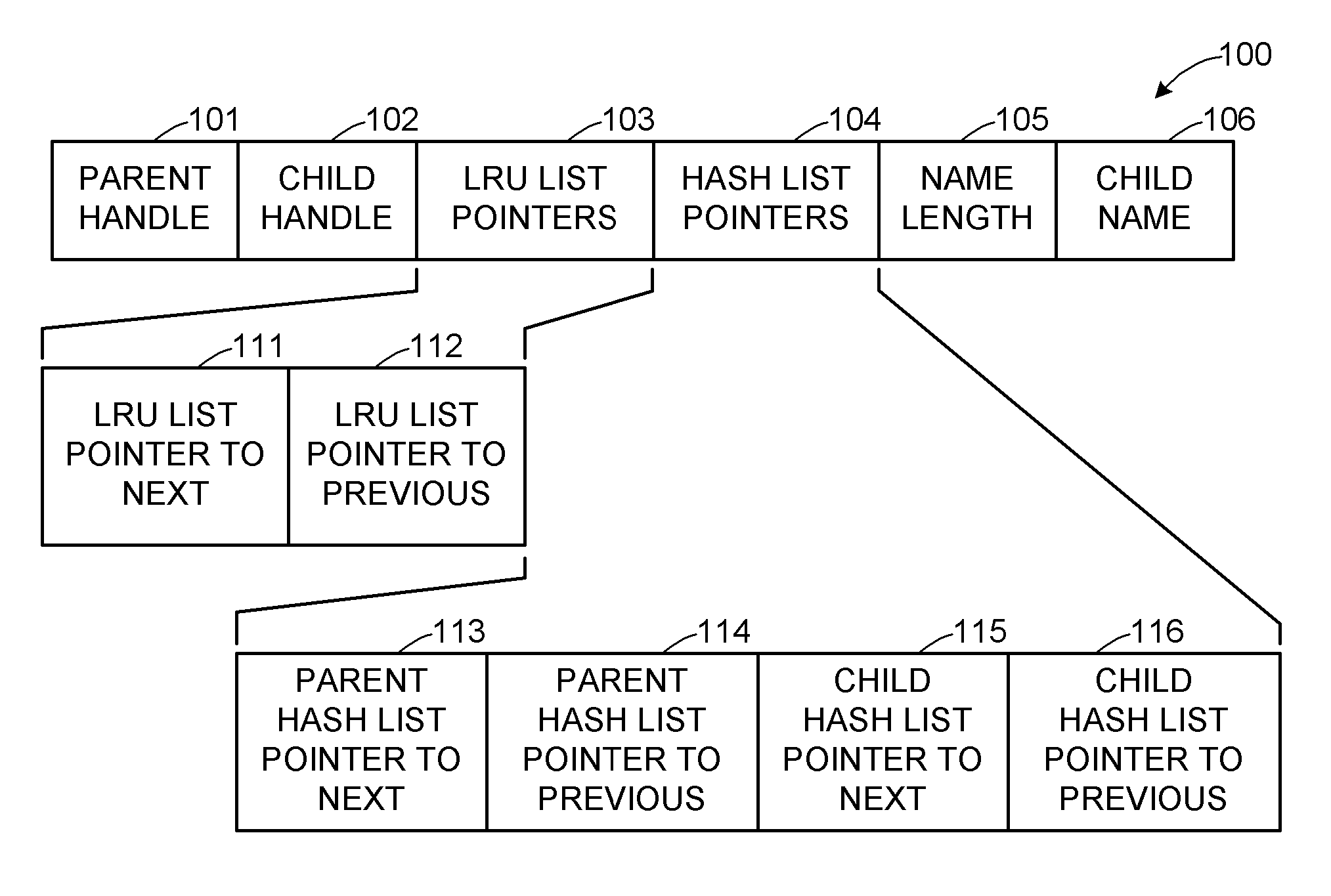
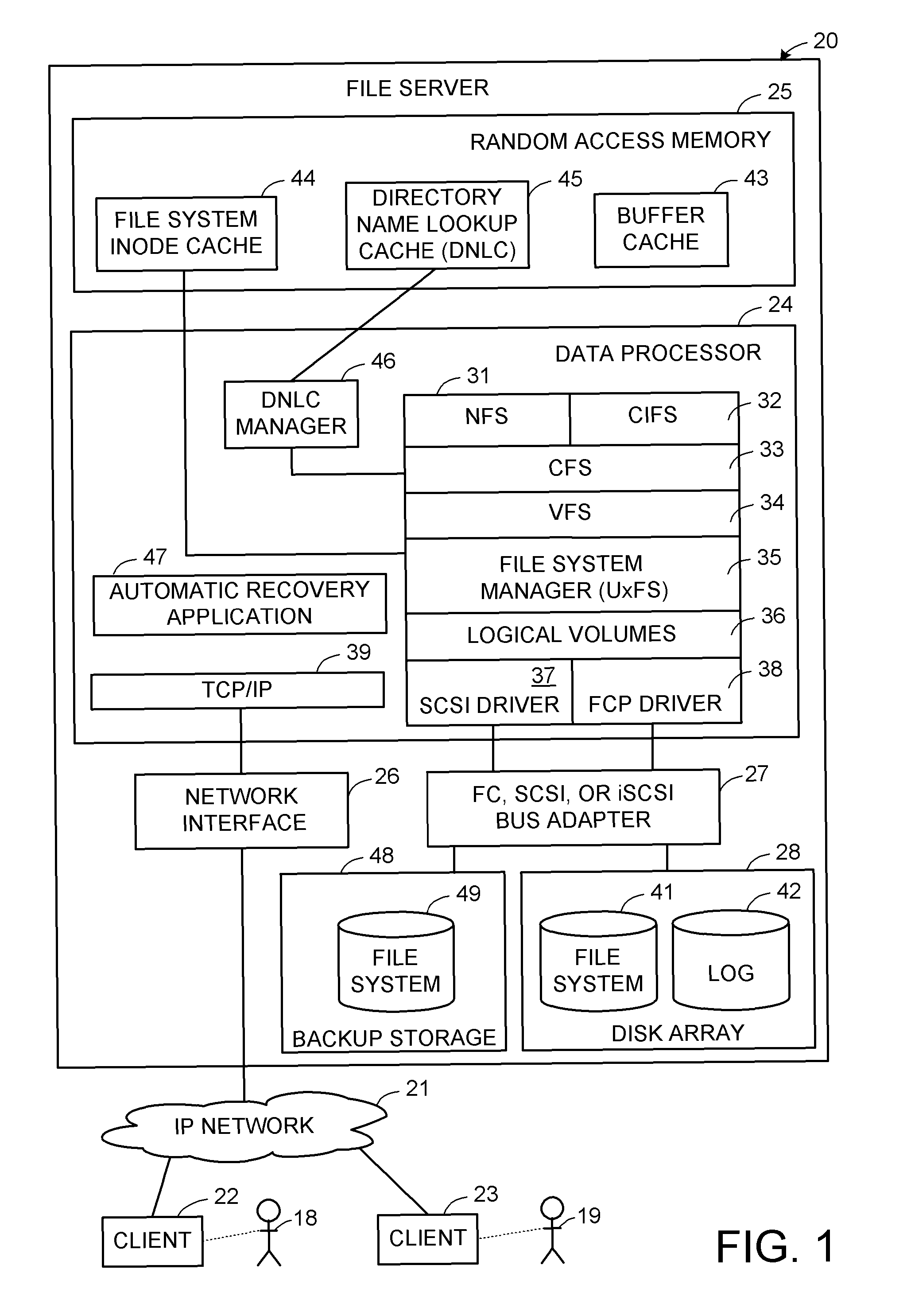
A directory name lookup cache (DNLC) provides a hashed forward mapping for finding the “child handle” associated with a “parent handle” and a “child name.” To provide an efficient reverse lookup capability, a second set of links is added to each cache entry for a “child hash list” indexed by a hashing of the child handle. For dynamically enabling and disabling the reverse mapping, when a new cache entry is added to its parent hash list, if the reverse mapping is enabled, then the new cache entry is also added to its child hash list; otherwise, the new cache entry is marked to indicate that it is not in any child hash list. To save memory, the parent hash lists and the child hash lists may share hash buckets.
Owner:EMC IP HLDG CO LLC
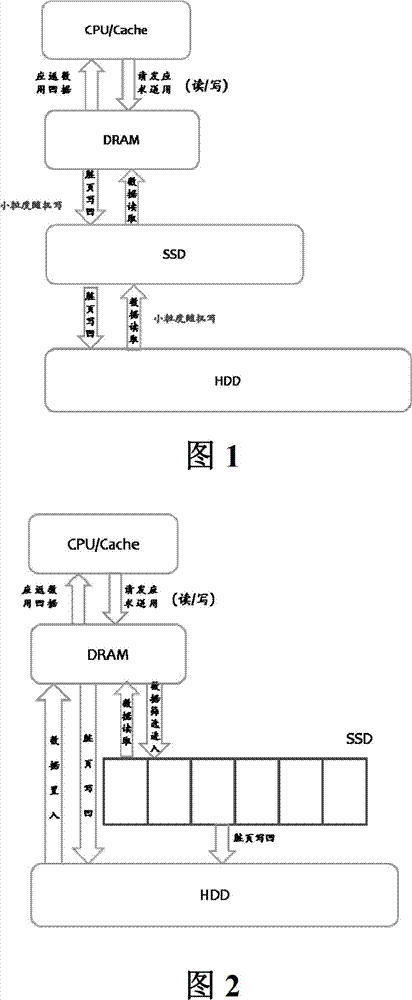
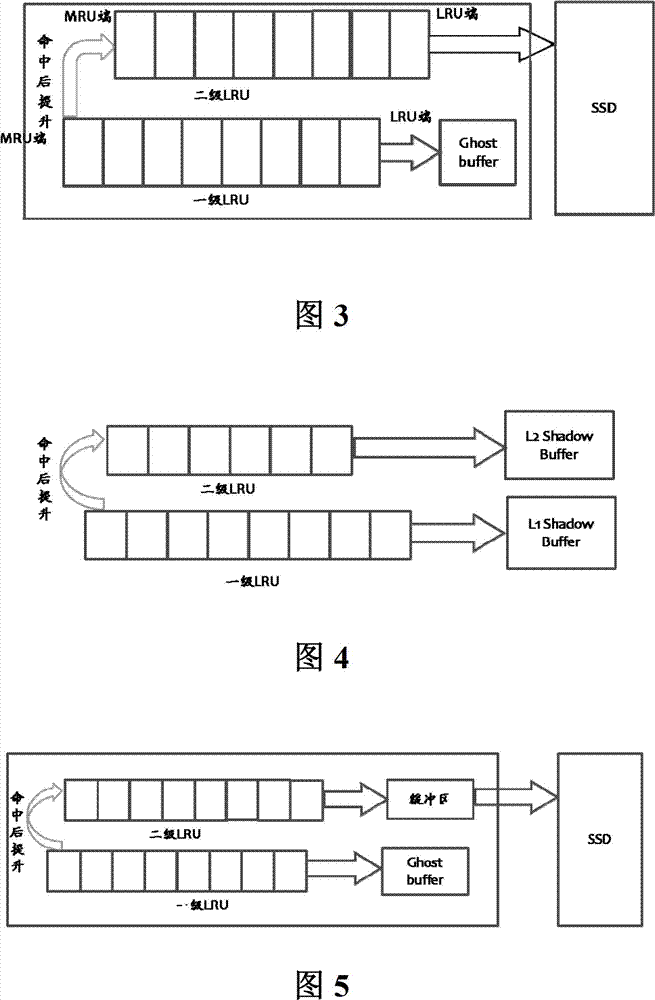
SSD-based (Solid State Disk) cache management method and system
ActiveCN102760101AReduce cache pollutionReduce write operationsMemory adressing/allocation/relocationWhole bodyGranularity
The invention discloses an SSD-based (Solid State Disk) cache management method and system. The SSD-based cache management method comprises the following steps: step 1, sending a read-write request, checking whether a cached DRAM (Dynamic Random Access Memory) hits data, searching a hash list, judging whether the data is existent, reading the data from the cached DRAM and returning the request if the data is existent, and reading data to the cached DRAM from a HDD (Hard Disk Drive) and carrying out step 2 if the data is nonexistent in the cached DRAM; step 2, carrying out data screening by using a two-level LRU (least recently used) linked list and a Ghost buffer, and identifying data heat; and step 3, carrying out self-adaptive change calculation on the length of the two-level LRU linked list, acquiring the granularity of a page cluster when the second-level LRU linked list of the cached DRAM is full, taking C pages behind the second-level LRU end as a whole body to replace the cached DRAM, and writing the C pages into an SSD in a large granularity, wherein the page cluster size is C pages, and C is an integral multiple of Block page number in the SSD.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI +1
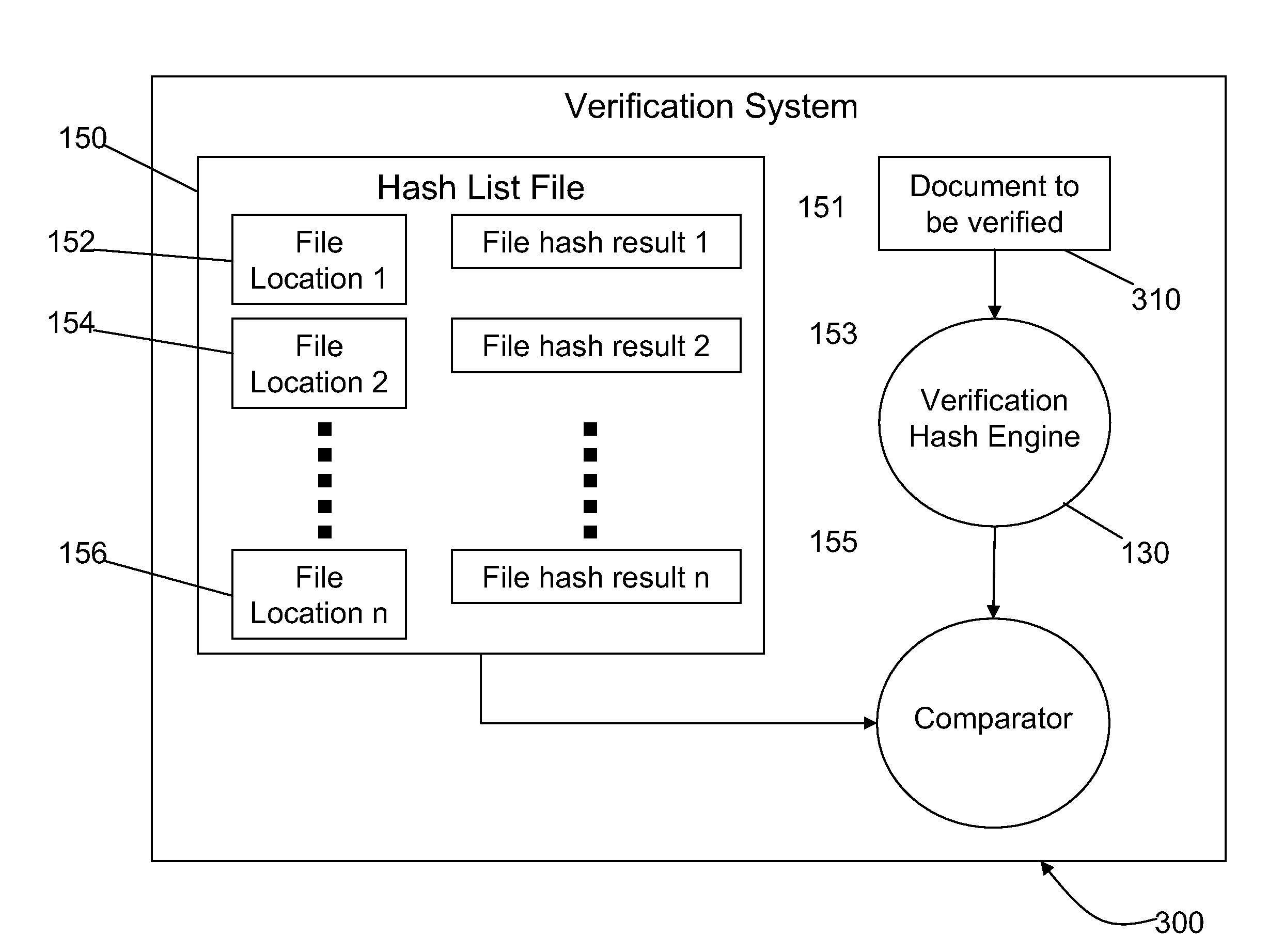
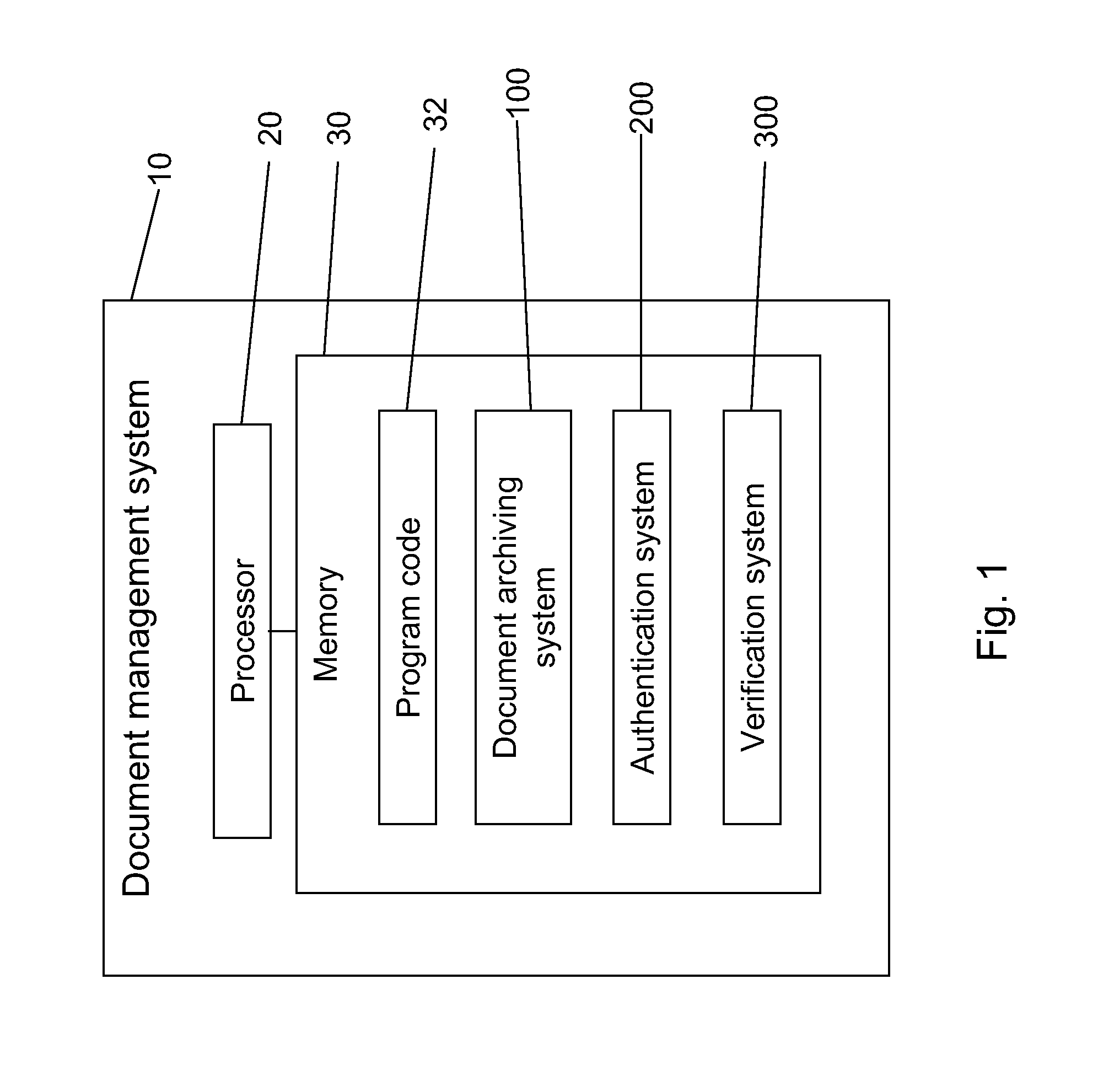
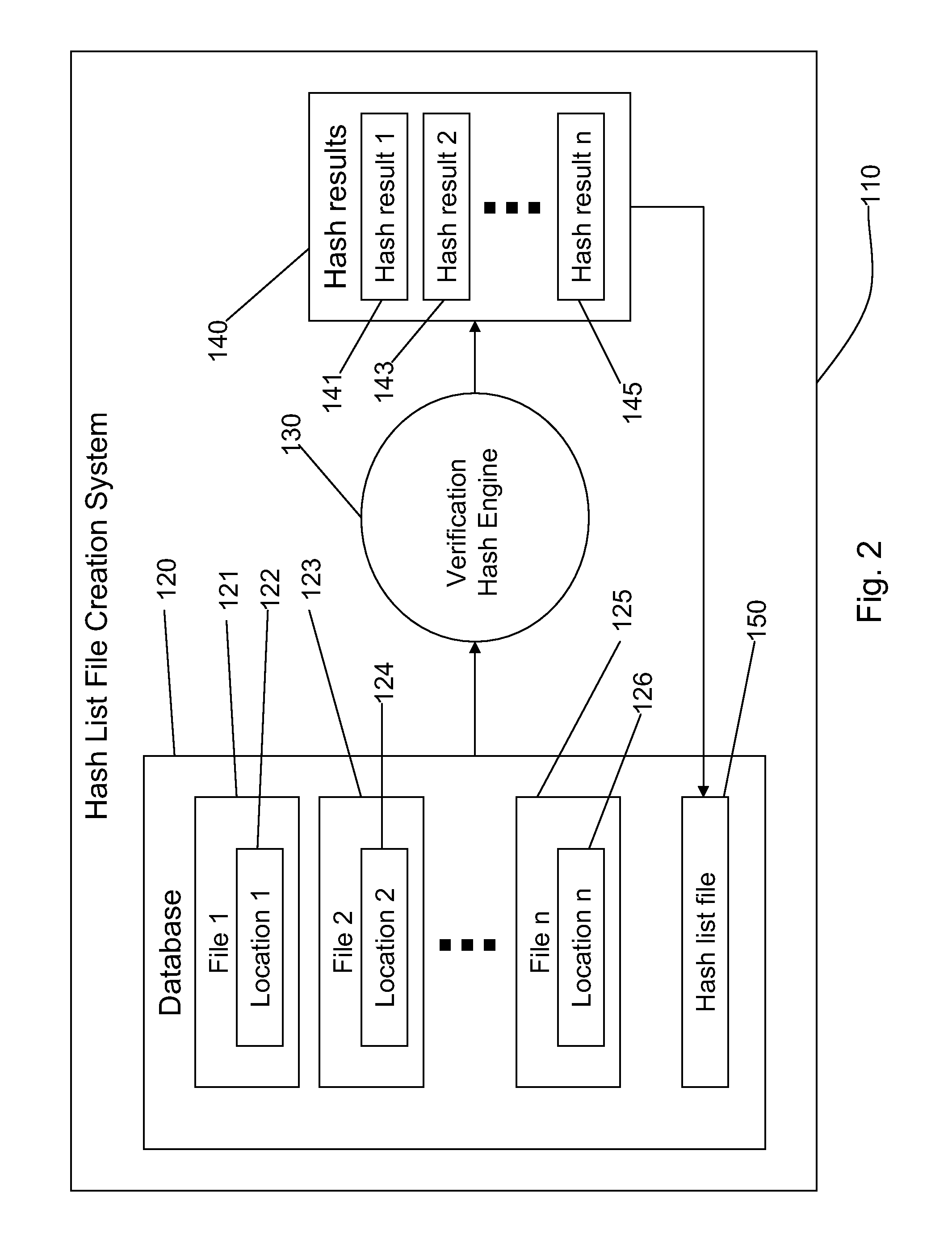
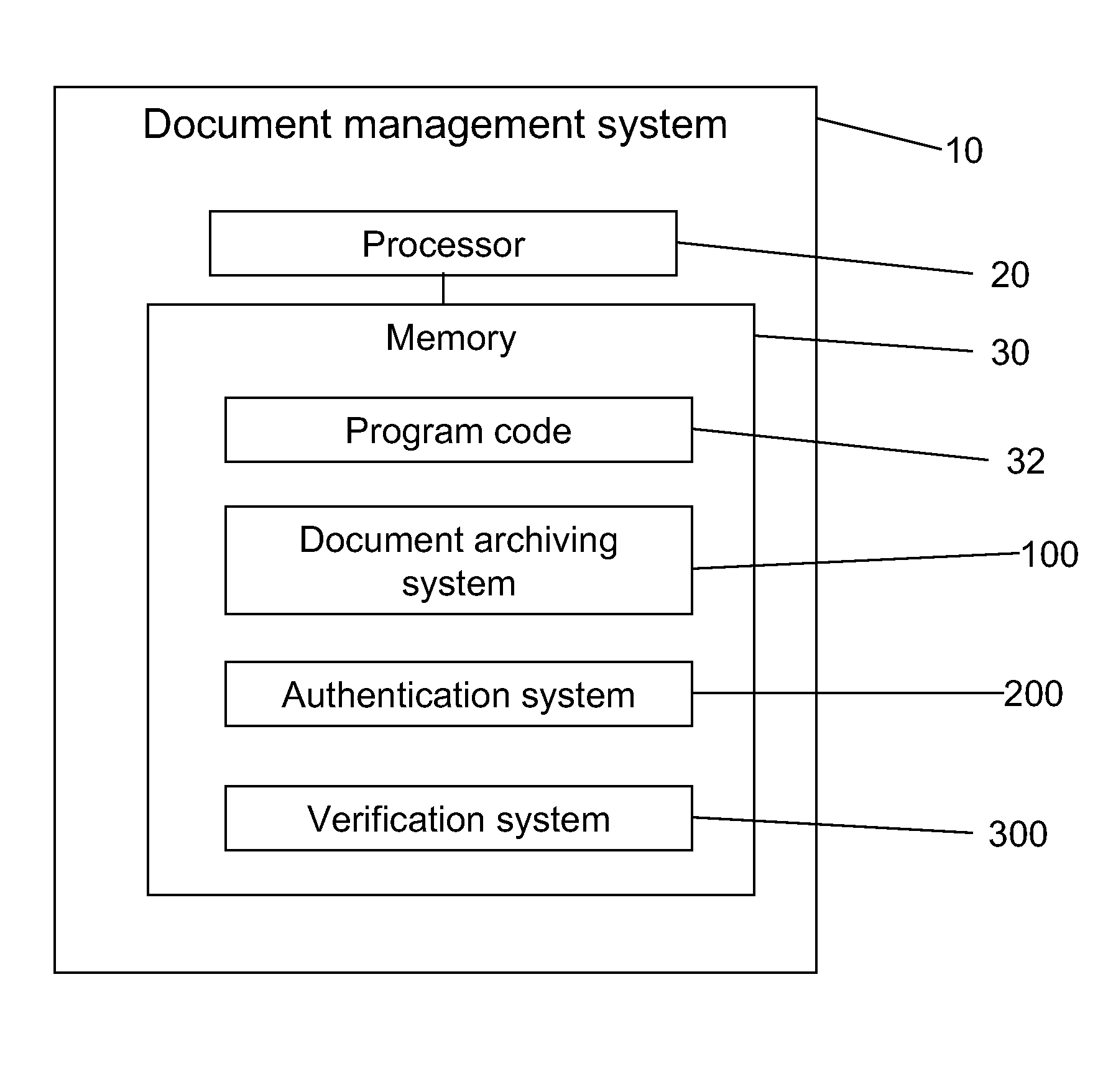
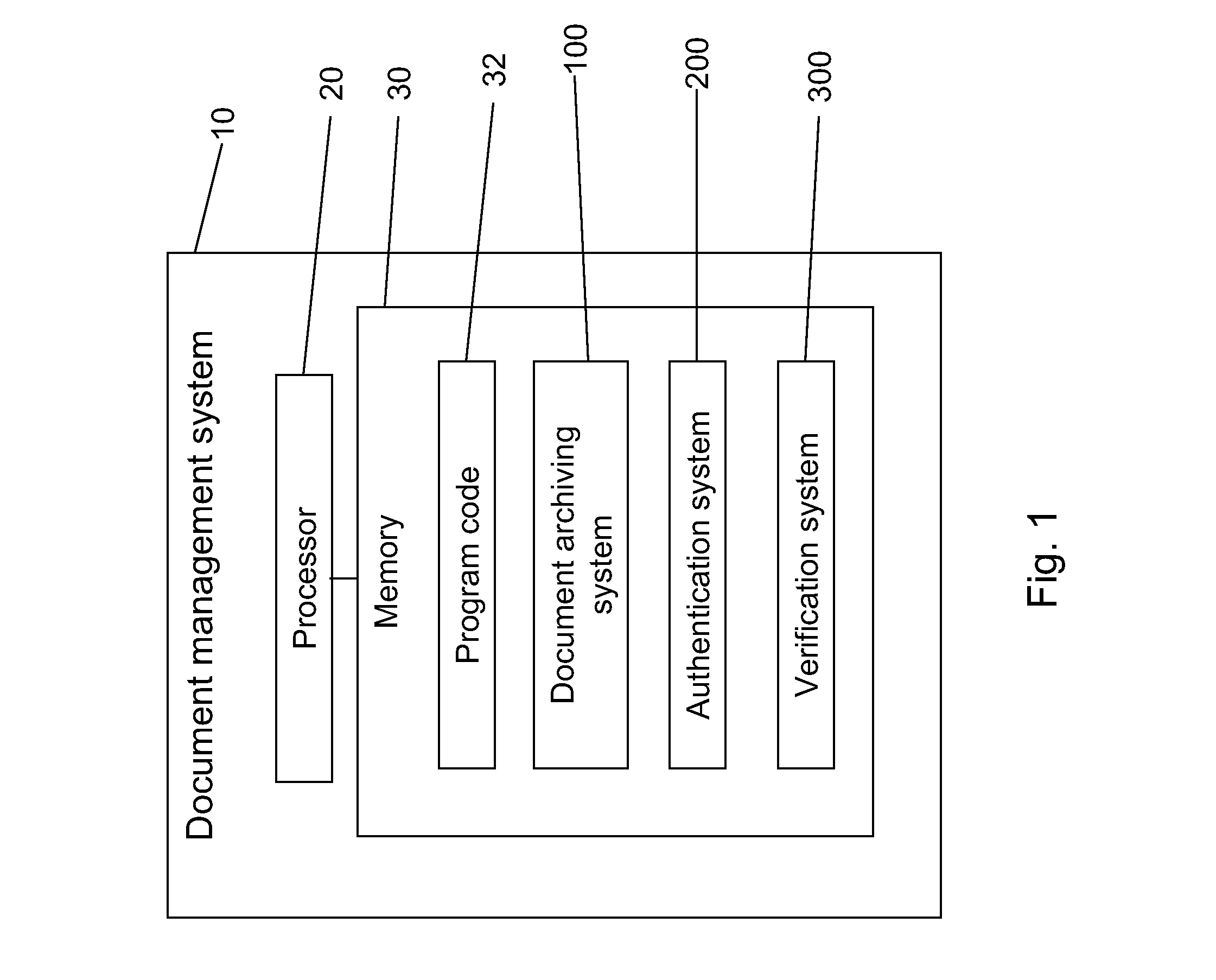
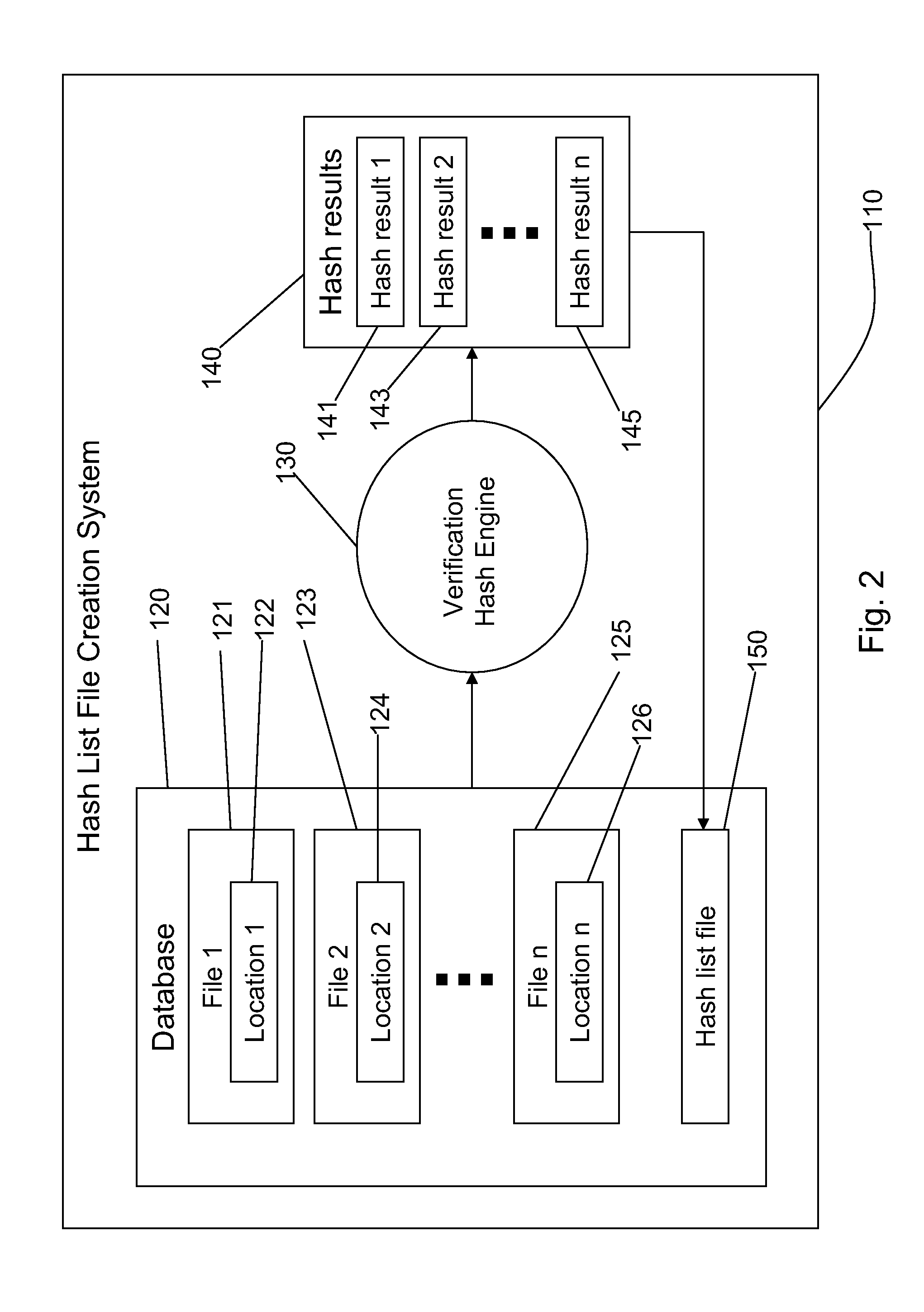
Document management with verifiable time-of-archive capability
ActiveUS20080141365A1Random number generatorsUnauthorized memory use protectionElectronic documentThird party
A document archiving and retrieval system enables third parties to verify that an electronic document had been archived on a particular date and time. For each document to be archived, a hash function generates a digital fingerprint of the document, and inserts it into a hash list file, together with an indicator of the location of the file in the archive. The hash list file is the submitted to an electronic time stamping authority to obtain a corresponding digital time stamp. Upon request, authentication of the hash list file with the digital time stamp, and verification that the current hash of the file matches that in the hash list file proves that the document was archived on the date indicated by the digital time stamp, and had not subsequently been altered.
Owner:AVAGO TECH INT SALES PTE LTD
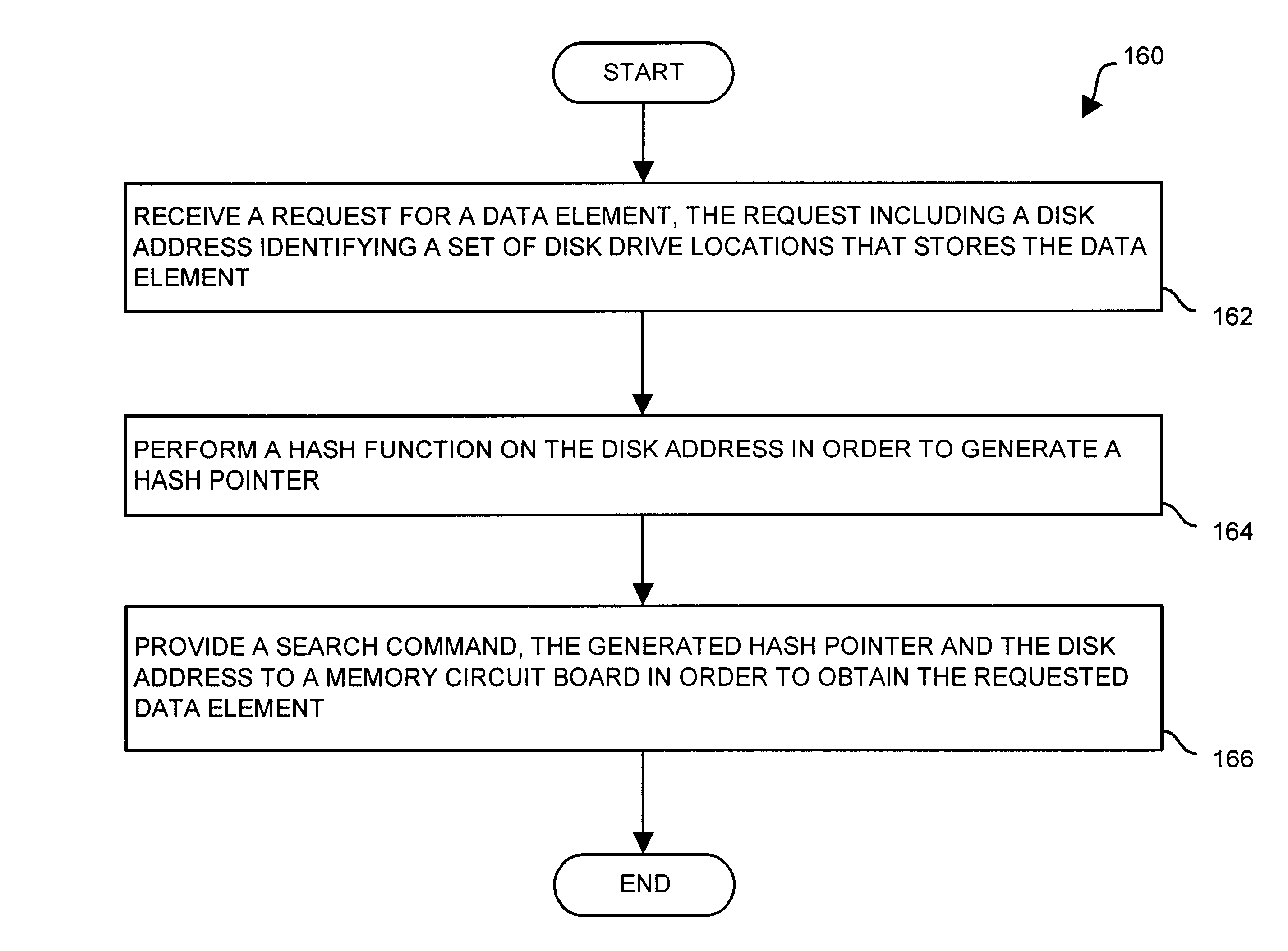
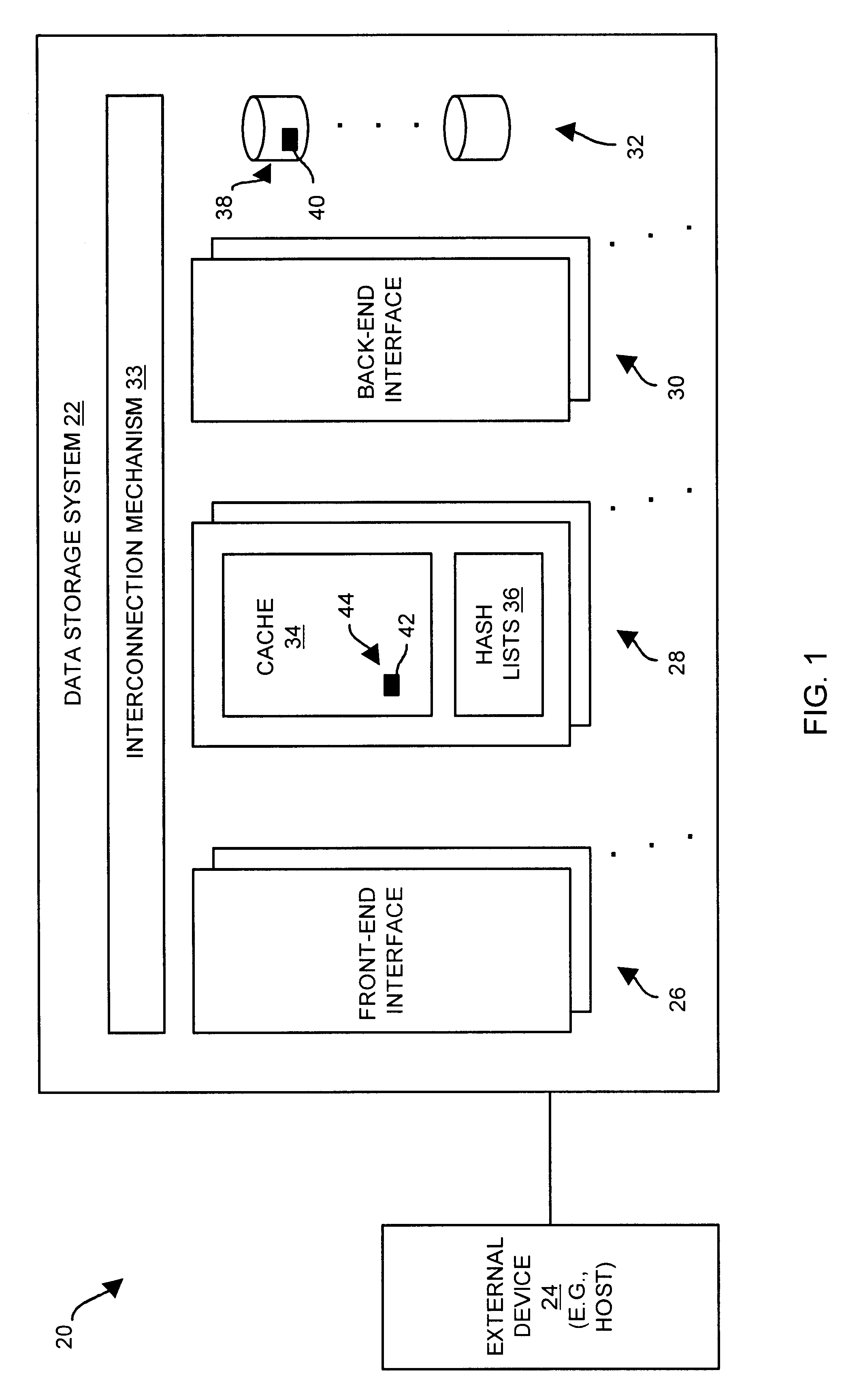
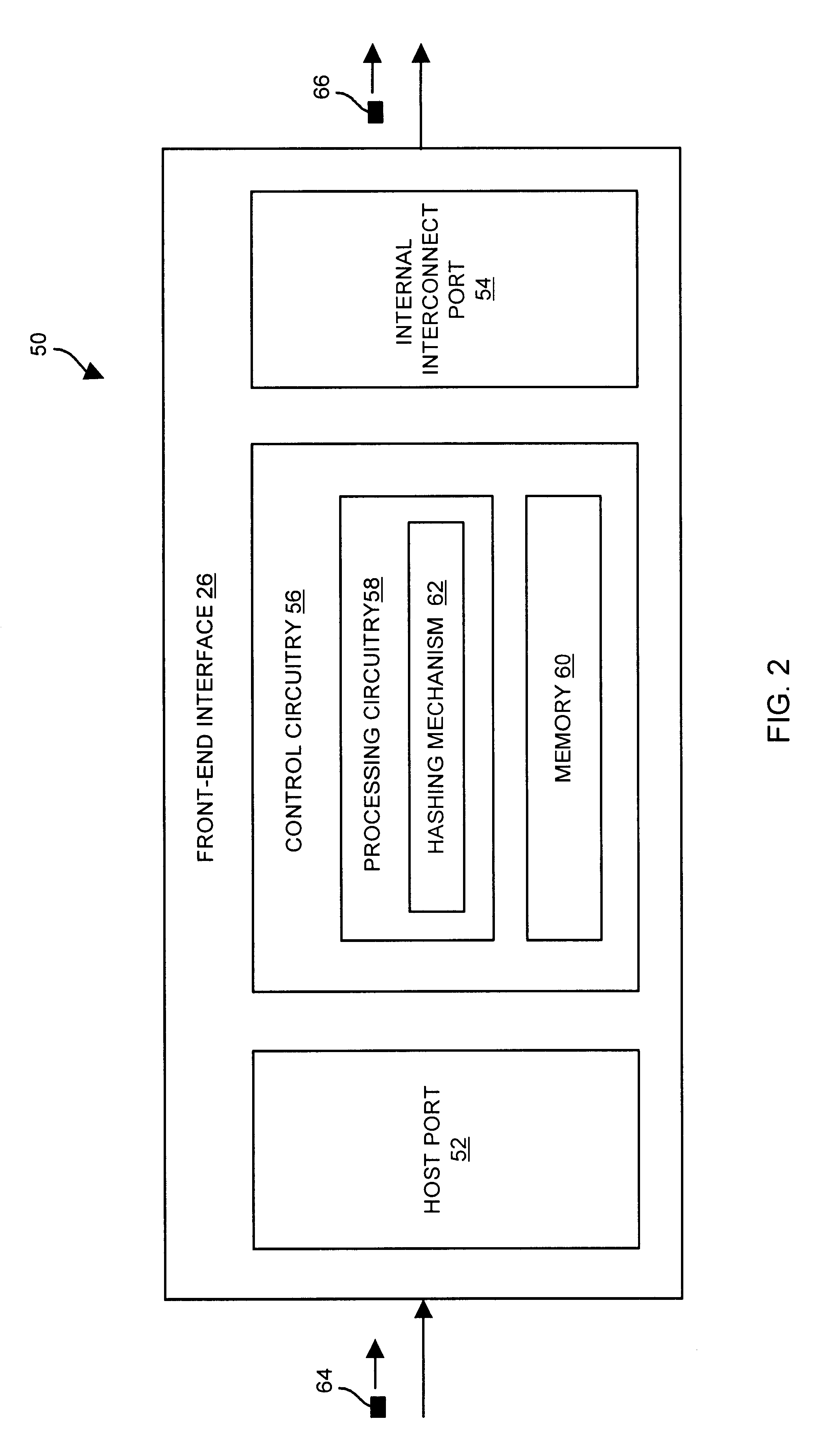
Methods and apparatus for accessing data elements using improved hashing techniques
ActiveUS7234021B1Improve performanceReduce trafficMemory architecture accessing/allocationMemory adressing/allocation/relocationHash functionMemory circuits
A data storage system has disk drives, memory circuit boards to store a set of hash lists and a cache, and a front-end interface. The front-end interface is configured to receive a data element request including a disk address identifying a set of disk drive locations that stores the data element; perform a hash function on the disk address in order to generate a hash pointer; and provide a search command, the disk address and the generated hash pointer to the memory circuit boards. The memory circuit boards are configured to receive the search command, the disk address, and the hash pointer from the front-end interface; search the set of hash lists based on the hash pointer and the disk address; and provide an indication to the front-end interface indicating whether the set of hash lists includes an entry indicating that the data element resides in cache.
Owner:EMC IP HLDG CO LLC
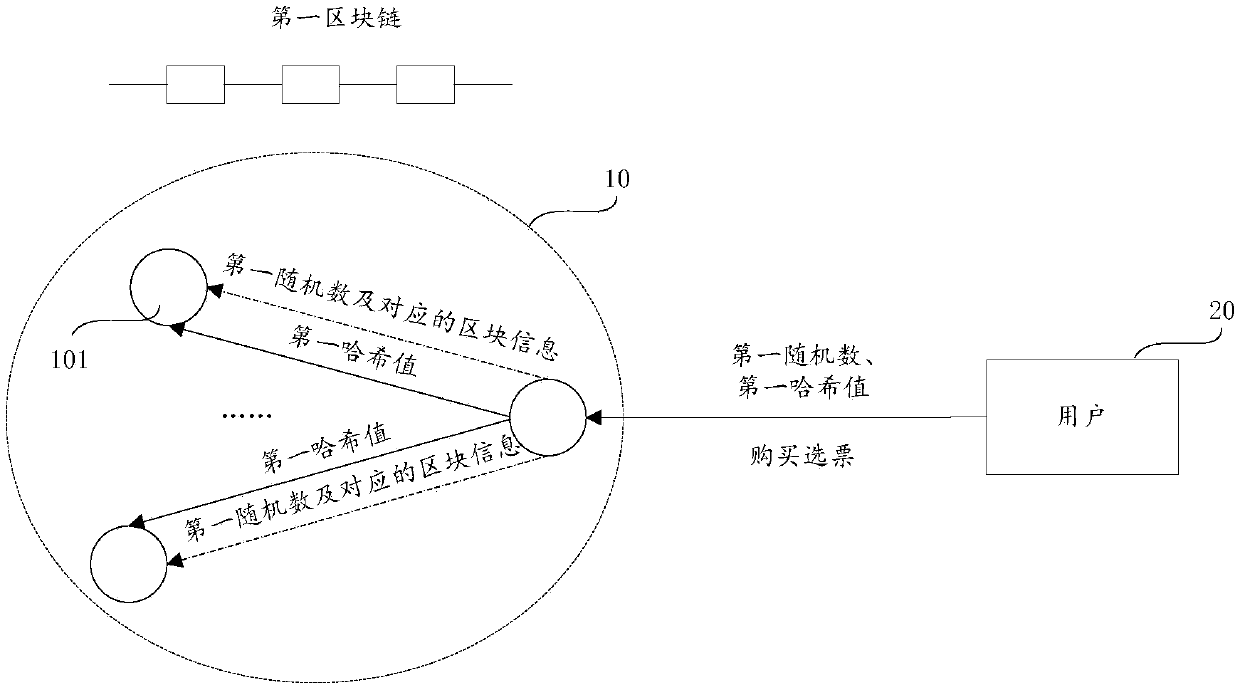
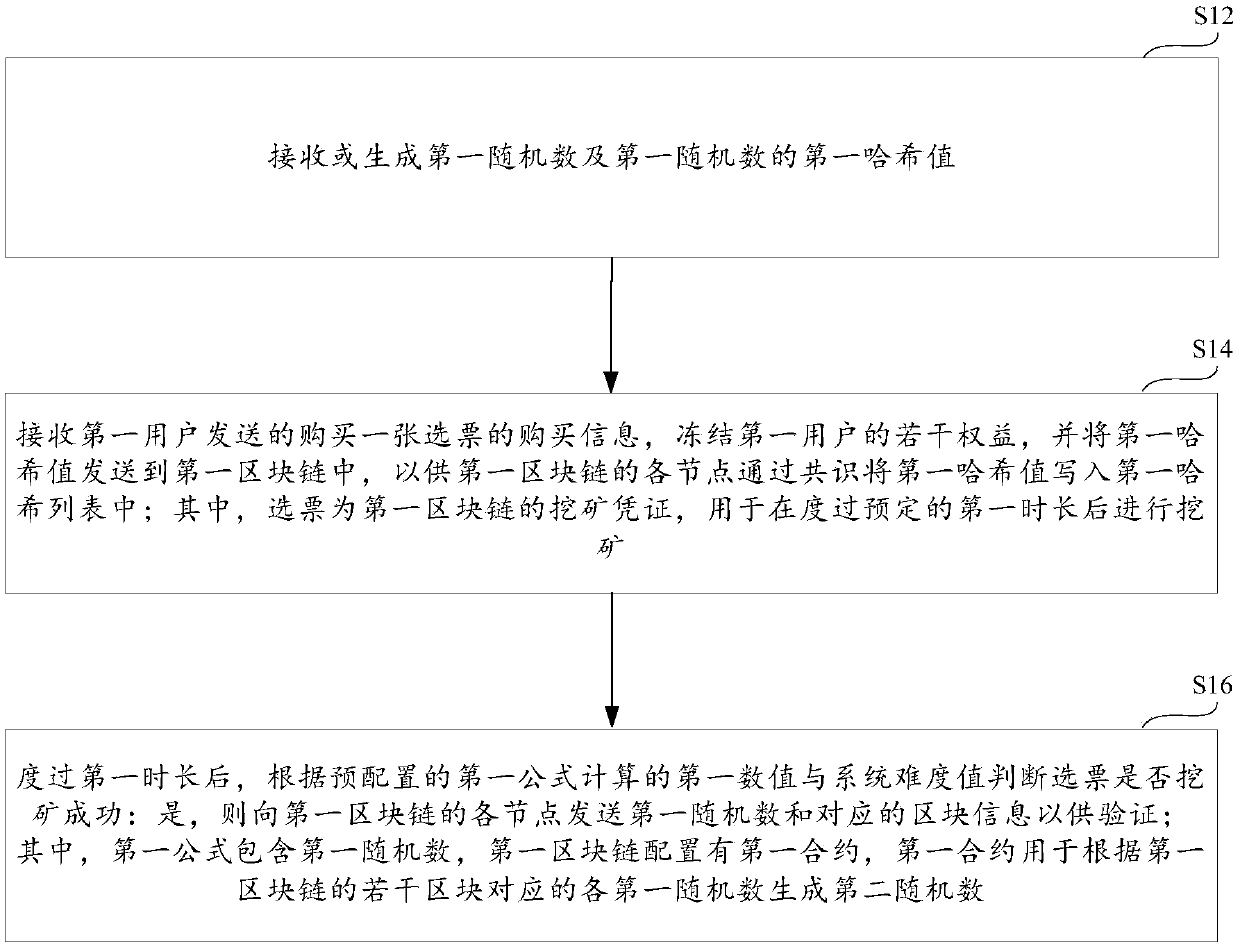
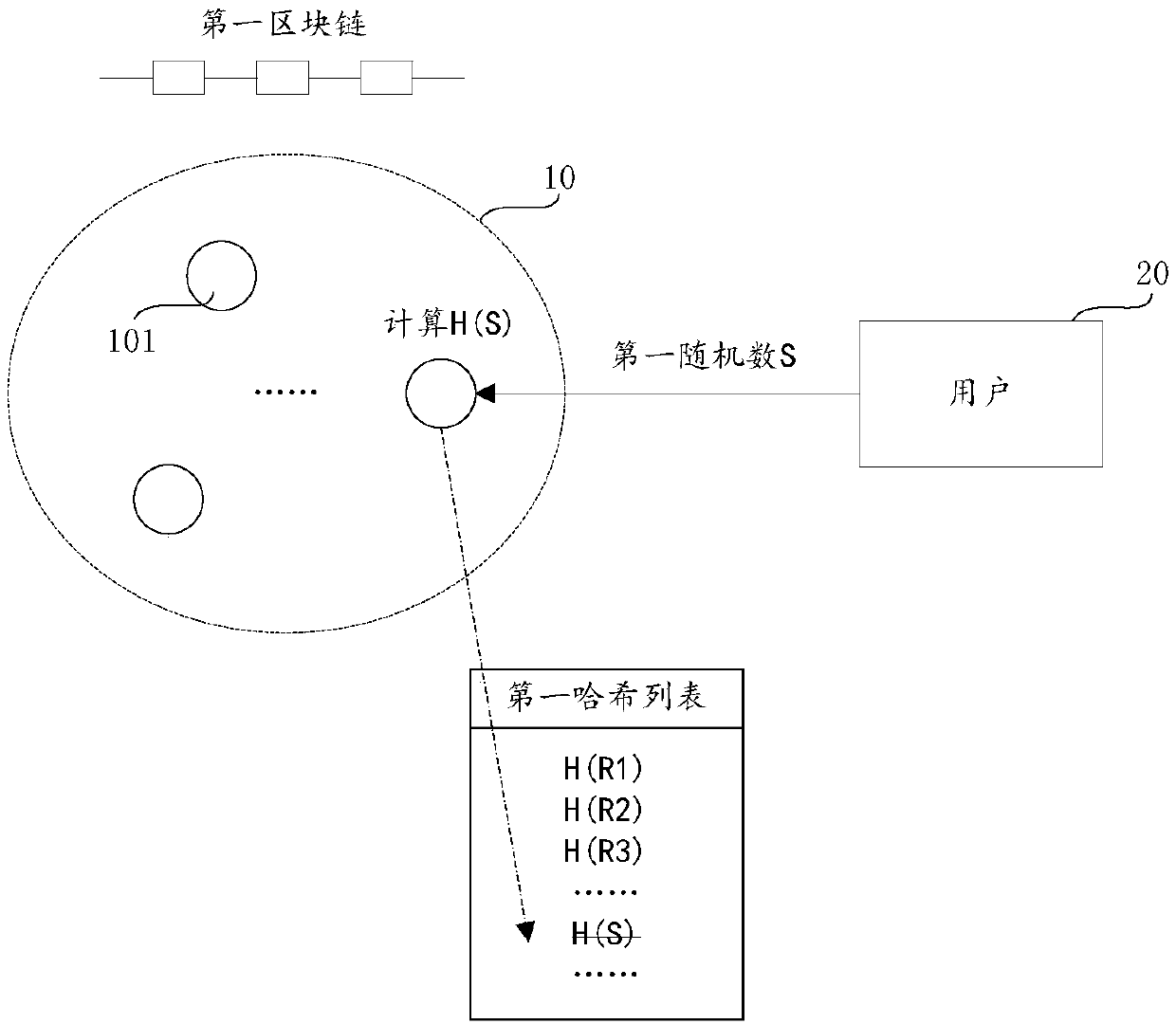
Random number generation method, anti-cheating block chain system, device and storage medium
ActiveCN109558112AIncrease punishmentImprove experienceRandom number generatorsFinanceVoucherChain system
The invention provides a random number generation method, an anti-cheating block chain system, a device and a storage medium. The method comprises the following steps of receiving or generating a first random number and a first hash value of the first random number; receiving purchase information of purchasing one vote sent by the first user, freezing a plurality of rights and interests of the first user, and sending the first hash value to the first block chain, so that each node of the first block chain writes the first hash value into the first hash list through consensus, wherein the votesare mining vouchers of the first block chain and are used for mining after a preset first duration is passed; and judging whether the vote is mined successfully or not according to a first numericalvalue calculated by a pre-configured first formula and a system difficulty value after the first duration: if yes, sending a first random number and corresponding block information to each node of thefirst block chain for verification. According to the invention, the completely random number which cannot be controlled by a user is obtained, and the mode of generating the random number is optimized.
Owner:HANGZHOU FUZAMEI TECH CO LTD
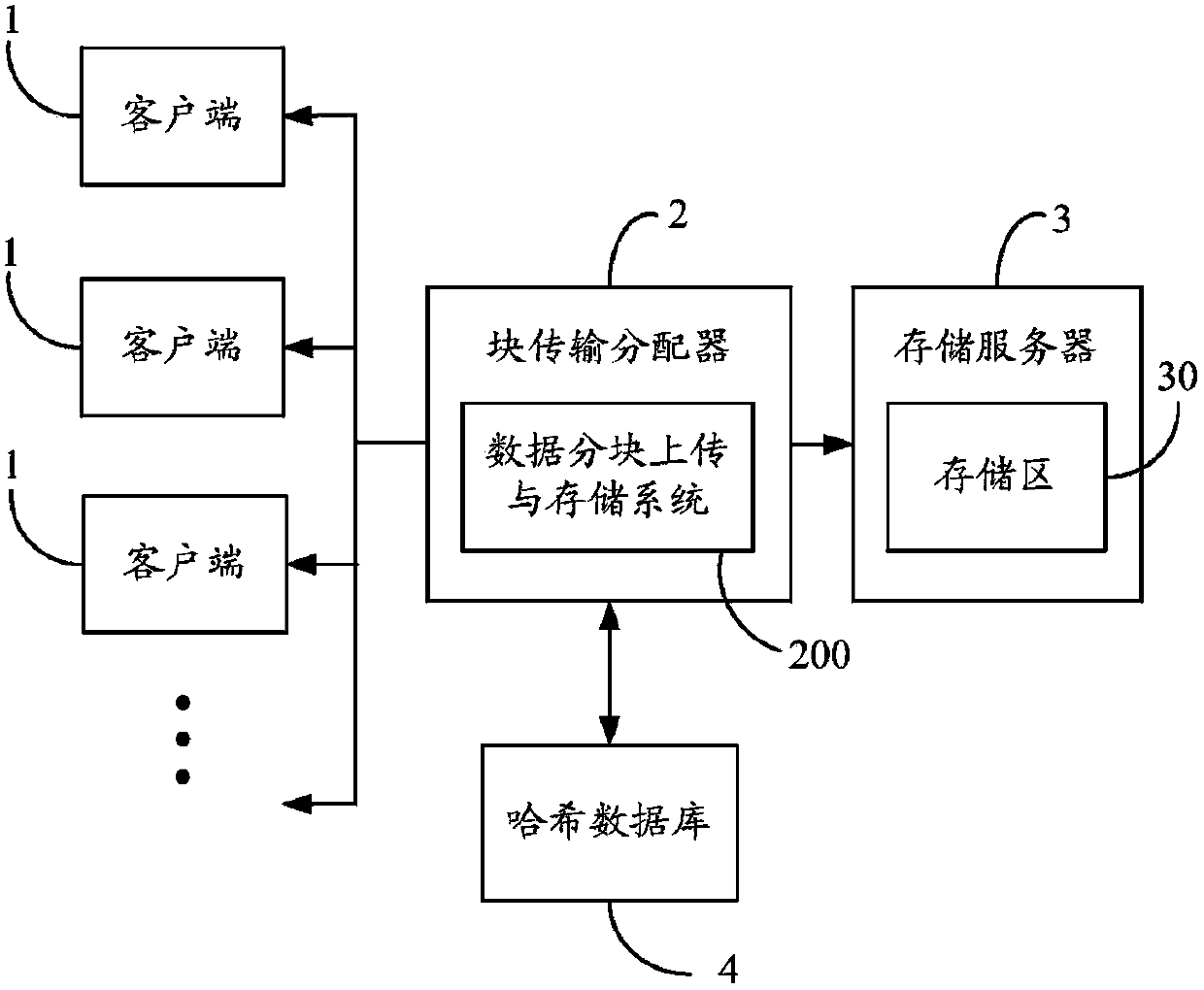
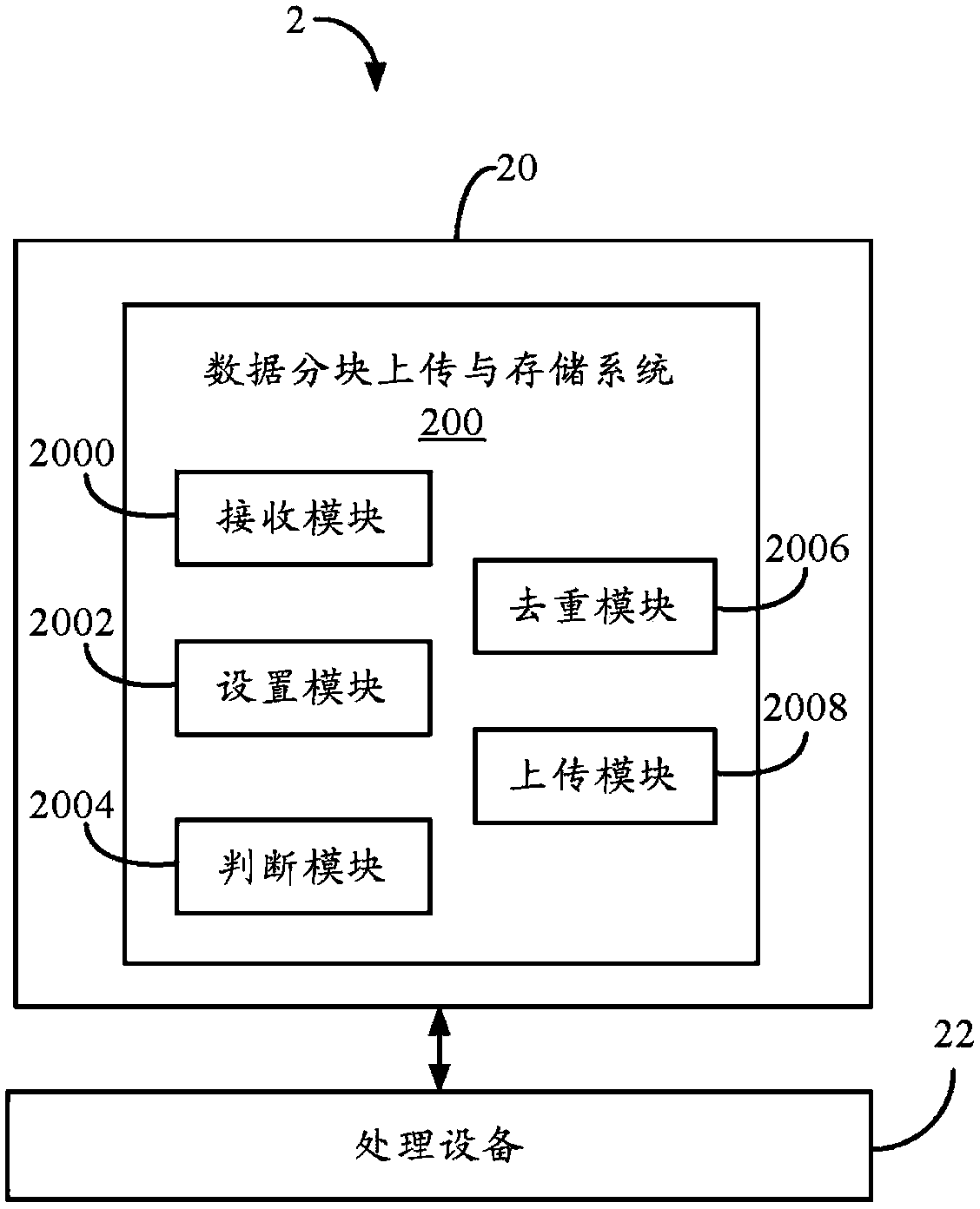
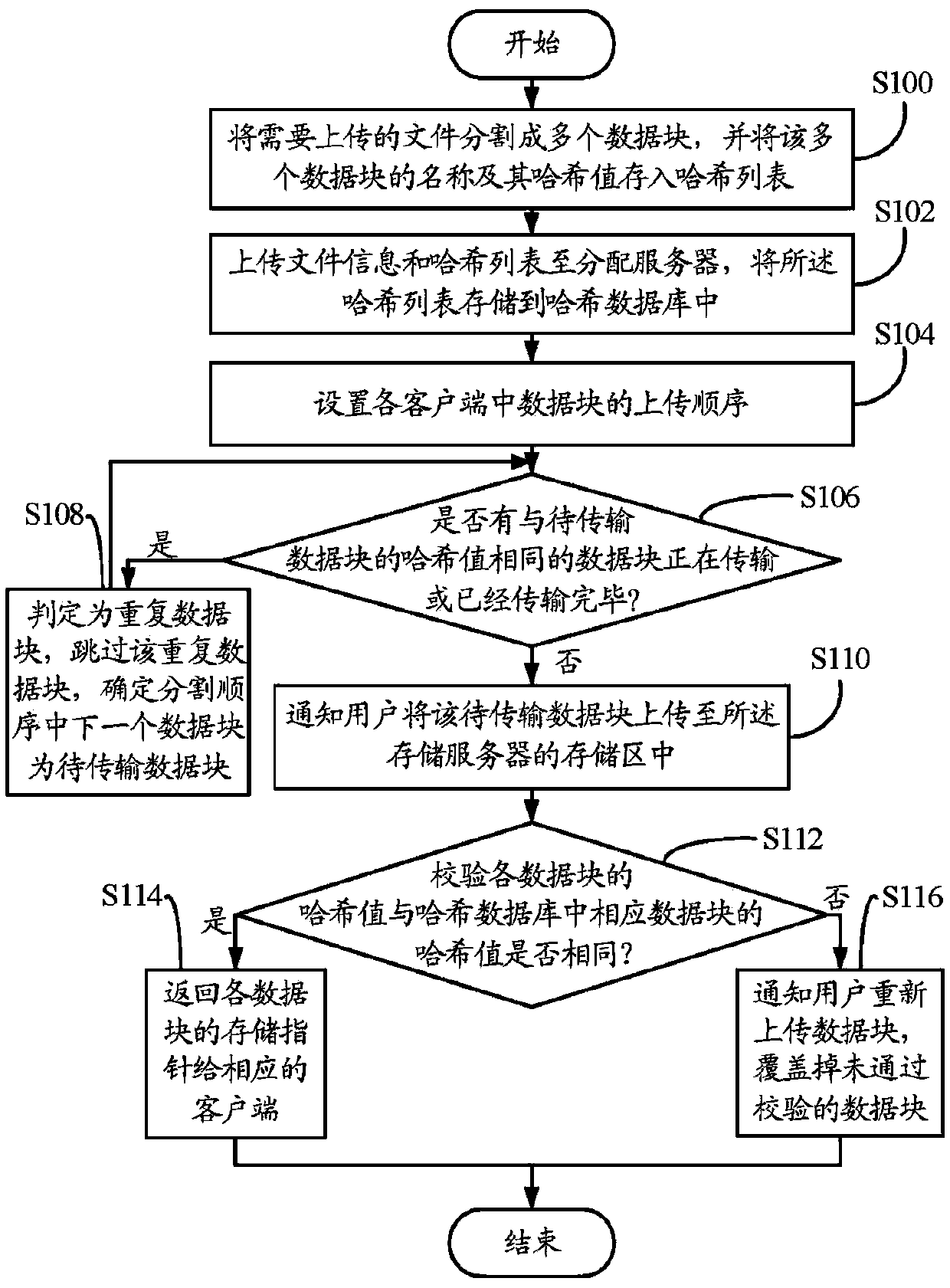
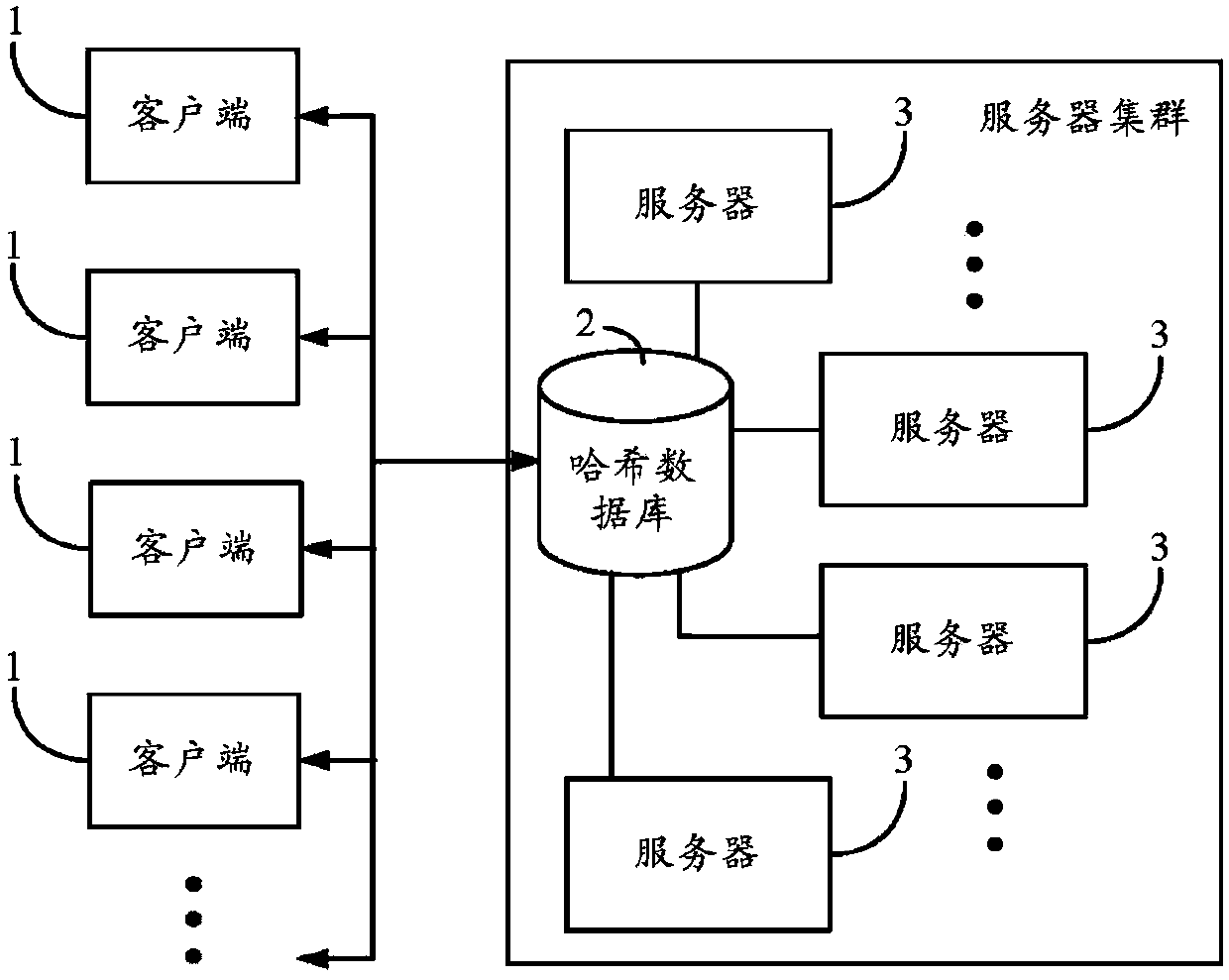
Data block uploading and storing system and method
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
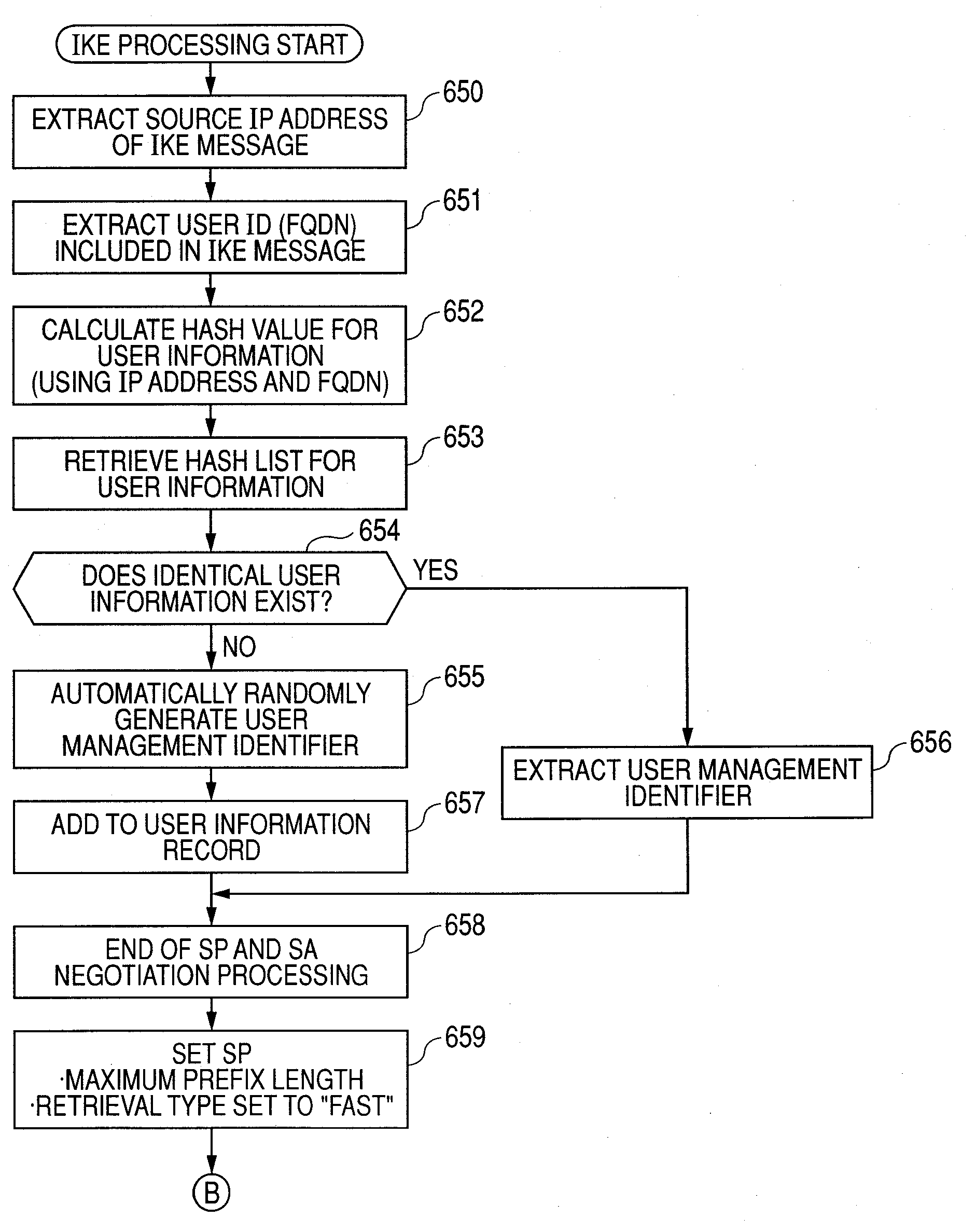
IPSec PROCESSING DEVICE, NETWORK SYSTEM, AND IPSec PROCESSING PROGRAM
InactiveUS20080052756A1Quick searchImprove retrieval speedDigital data processing detailsSpecial data processing applicationsNetworked systemIPsec
Security policy databases capable of being fast retrieved while securing sequentiality. An IPSec processing device of the present invention performs communications by encrypting IP packets exchanged between a first IP network and a second IP network. The IPSec processing device includes a security policy database that stores security policies. The security policy database includes first, second, and third security policy databases. The first and third security policy databases include a linear list structure, and the second security policy database includes a hash list structure. The IPSec processing device, when performing at least one of transmission and reception of the IP packet, retrieves a security policy in the order of the first, second, and third security policy databases.
Owner:HITACHI LTD
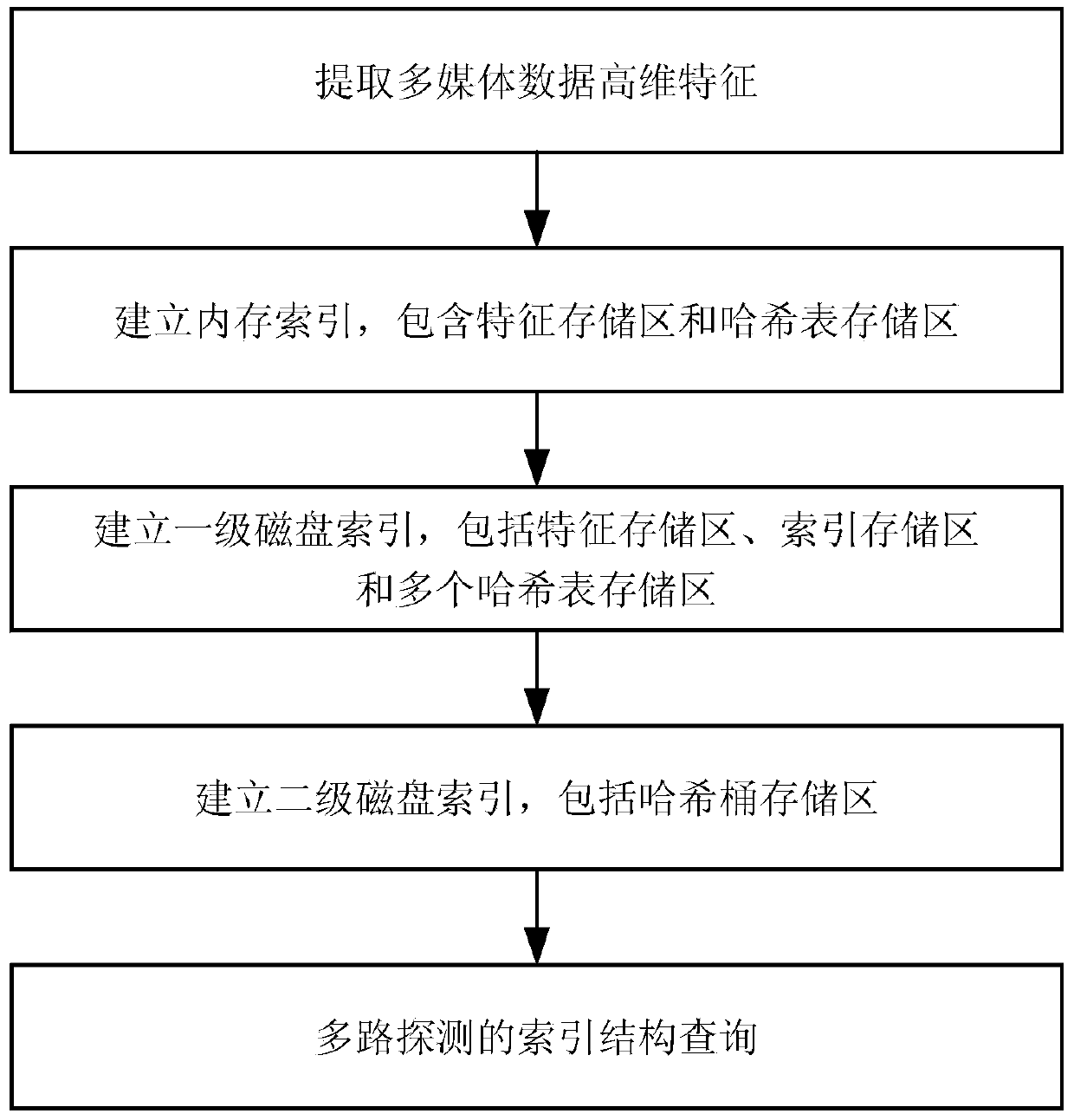
Locality-sensitive-hashing-based high-dimensional indexing method for large-scale multimedia data
ActiveCN104199827AReduce the number of exchangesQuick indexMultimedia data indexingSpecial data processing applicationsData ingestionHigh dimensional
The invention relates to a locality-sensitive-hashing-based high-dimensional indexing method for large-scale multimedia data. The method includes the following steps of extracting high-dimensional features of the multimedia data at the offline indexing stage; establishing an internal storage index, storing the multimedia high-dimensional features in a feature storage area, calculating the locality sensitive hashing vectors of the high-dimensional features, and storing feature numbers and the locality sensitive hashing vectors corresponding to the features in a hashing list storage area, wherein the internal storage index comprises the feature storage area and the hashing list storage area; establishing a first-stage disk index, wherein the first-stage disk index comprises a feature storage area, an index storage area and a plurality of hashing list storage areas; establishing a second-stage disk index, wherein the second-stage disk index comprises a hashing barrel storage area; repeatedly executing the steps mentioned above till all multimedia input is indexed. At the online query stage, features of the multimedia data used for queries are extracted, the queries are conducted on the basis of the established indexes, and similar query results are returned. By means of the method, the scheduling performance of internal storage and disks is improved, and the indexing speed and the retrieving speed of the multimedia data are increased.
Owner:PEKING UNIV
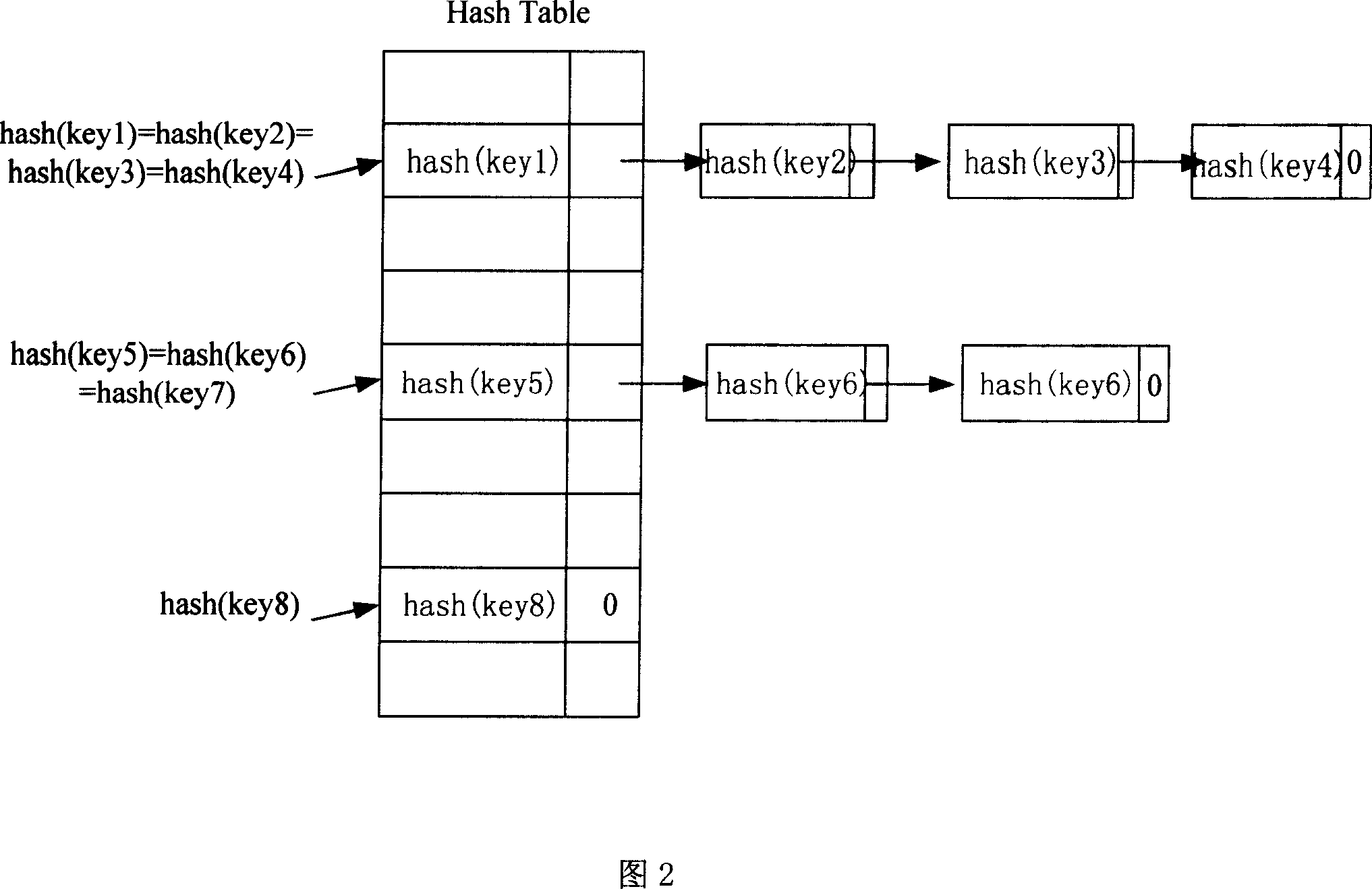
Method and device for solving Hash collision
InactiveCN1929451ASolve conflictsRealize wire-speed forwardingDigital data information retrievalData switching networksAlgorithmData information
This invention provides one method and device to solve Hash collision in network communication field, wherein the method comprises the following steps: processing Hash computation on memory data information; finding relative list items according to computation results; then storing the information computation results into list and setting index list in Hash list. This invention provides one device to solve Hash collision composed of Hash computation module, judgment module, address requirement module and information memory module and index set module.
Owner:BEIJING HUAWEI DIGITAL TECH
Method for large scale multimedia cut-in net gate
This invention puts forward a method for accessing gate by large scale media including: A starting the gate linked with a control server in a network state test technology to enable the server to identify all gates capable of providing services timely to get current load of the gates and generate a 'usable gate list', B When a user logs on to system by the control server, if will automatically select gate with the least load at its 'acc gate' from the list and informs the gate to serve the user, C. the gate system sets up a 'connector' objects, all objects are registered in a Hash list with deliver addresses as the key, D The gate system finds out the 'connector' according to the information of each deliverer information for transferring message.
Owner:BEIHANG UNIV
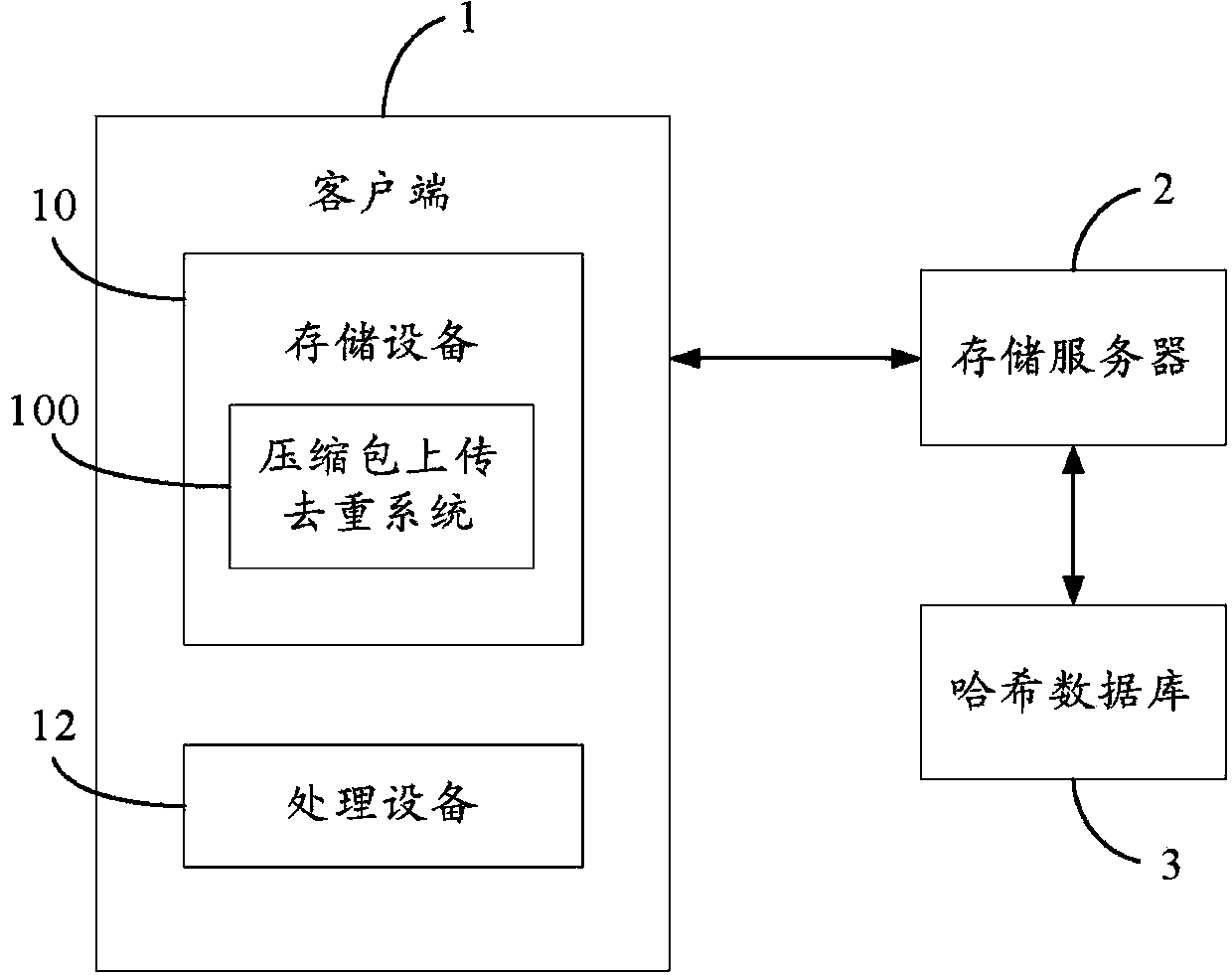
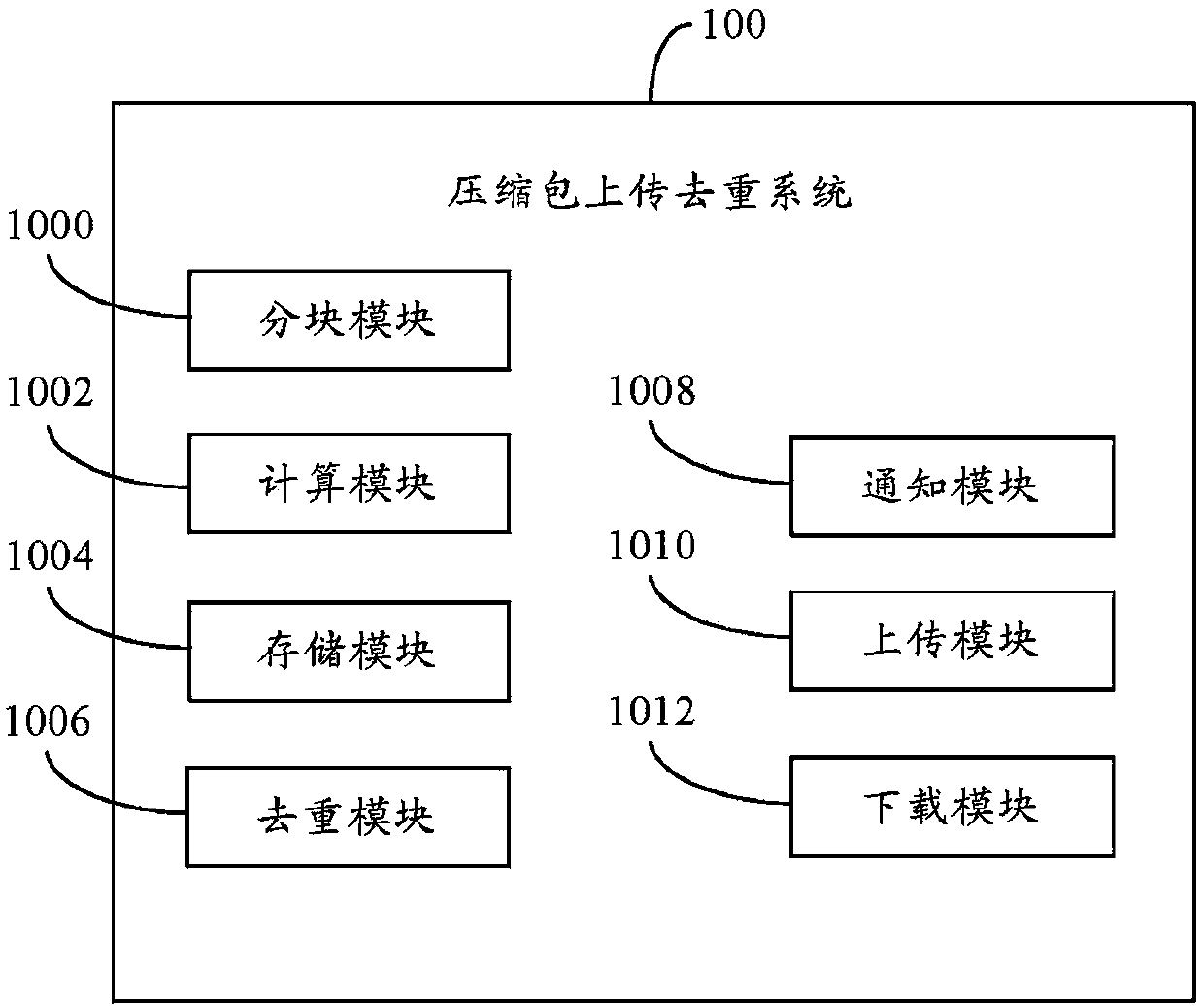
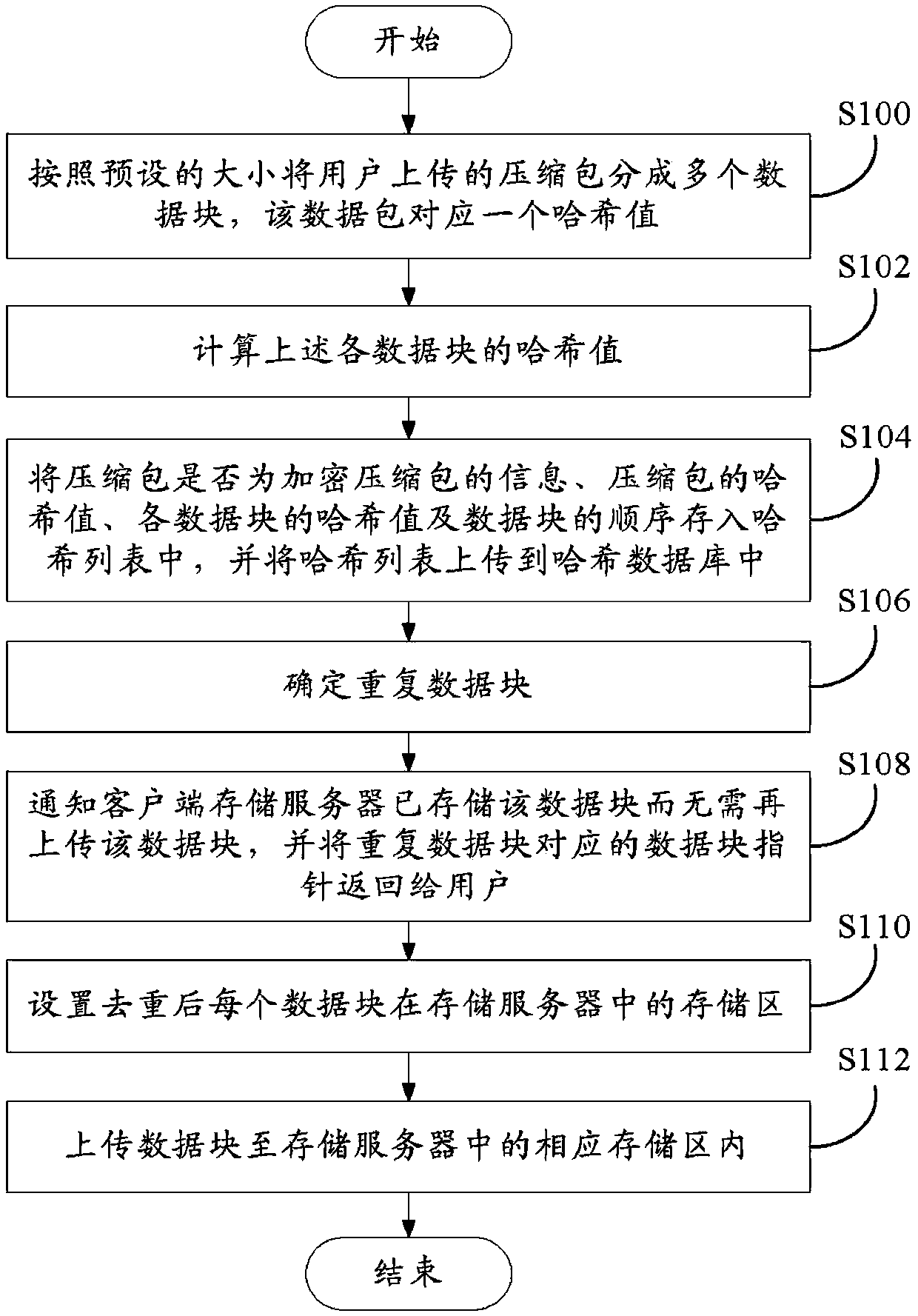
Compression packet uploading and duplication-removing system and method
Provided is a compression packet uploading and duplication-removing method which comprises that: a compression packet uploaded by a user is divided into multiple data blocks; Hash values of all the data blocks are calculated; information of whether the compression packet is the encrypted compression packet, the Hash value of the compression packet, the Hash values of all the data blocks and sequences of the data blocks are stored in one Hash table and then uploaded to a Hash database; when the Hash values in the Hash database are identical with the Hash values of the stored data blocks in a storage server, the data blocks corresponding to the Hash values in the Hash database are confirmed to be duplicated data blocks; corresponding client terminals are notified not to upload the data blocks and corresponding data block pointers of the duplicated data blocks are returned to users, and each data block is corresponding to one data block pointer according the position of the corresponding storage area; the storage area of each data block in the storage server after duplication removal is arranged; and the data blocks are uploaded to the corresponding storage areas in the storage server. The invention also provides a compression packet uploading and duplication-removing system. Storage space can be saved by utilizing the compression packet uploading and duplication-removing method.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Routing calculation method based on opened shortest route priority routing protocol
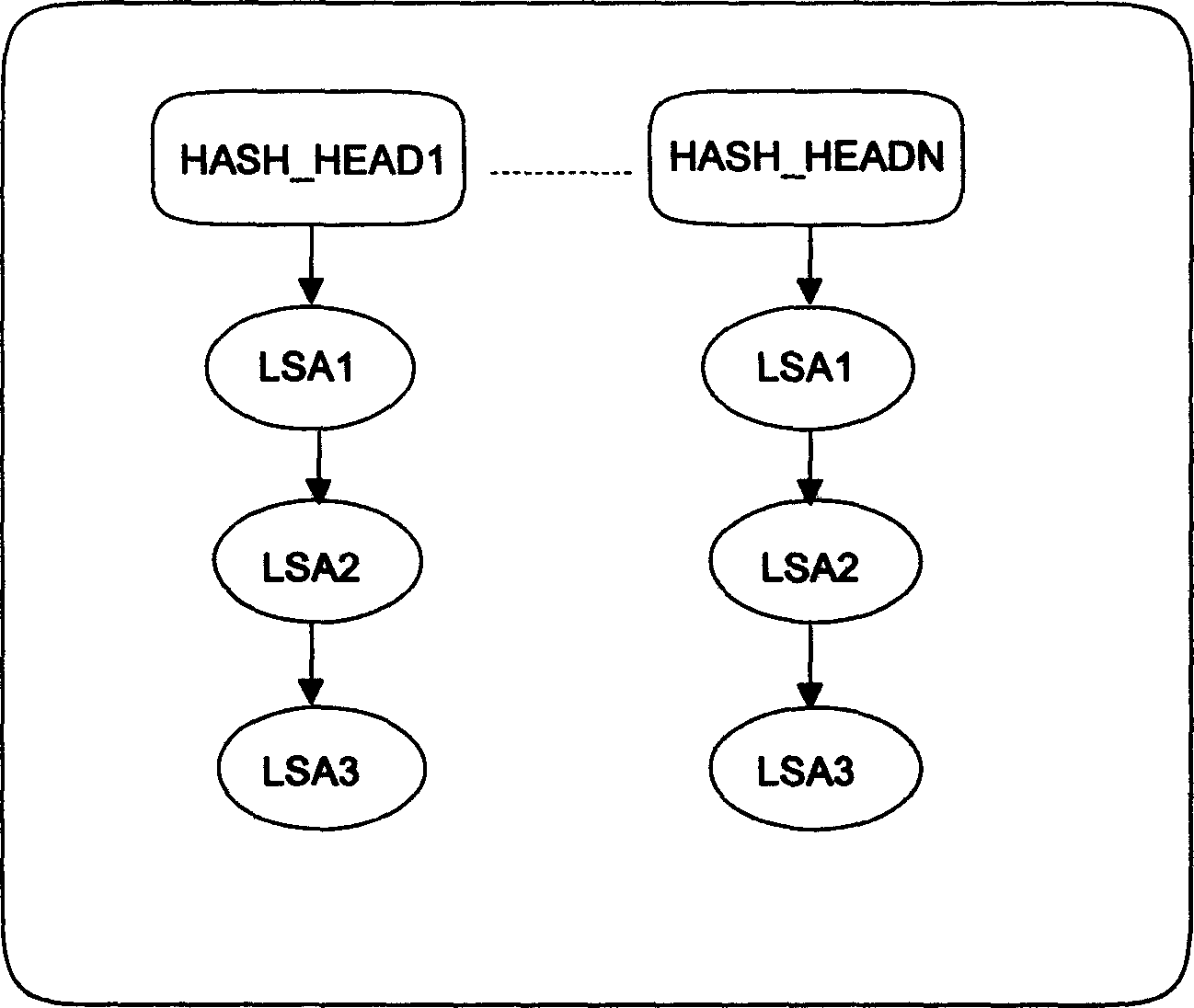
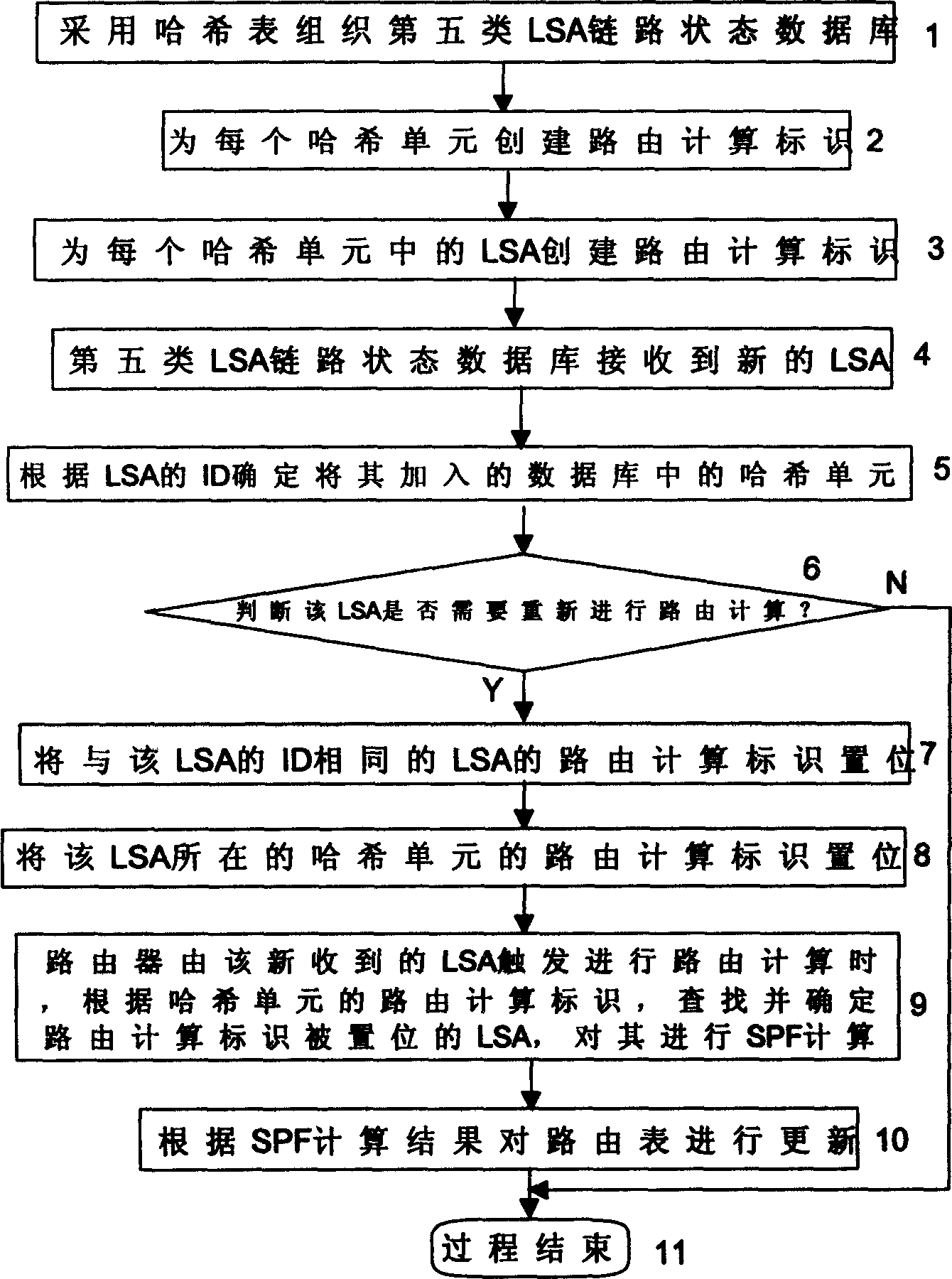
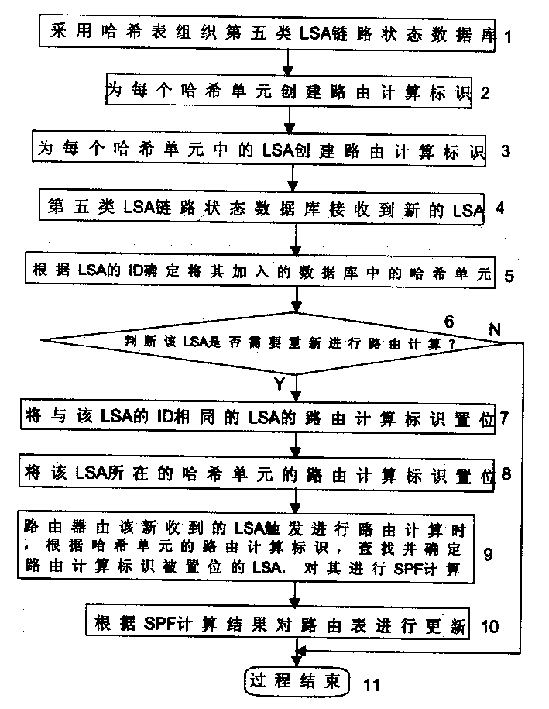
InactiveCN1469587AReduce time spentPrevent momentary interruptionData switching by path configurationSelection arrangementsOpen Shortest Path FirstHash list
The routing calculation method based on the shortest opened route priority routing protocol includes organizing with Hash list class-V LSA link state library, which has its Hash units and LSAs with routing calculating mark; adding newly accepted LSA into corresponding Hash unit and setting separately the said unit and the LSA routing calculating mark the same as the LSA destination address in this unit; then calculating the routing of LSA set by the routing calculating mark; and finally updating the routing list based on the calculation result. Adopting partial routing calculation method, the present invention can decrease the processor occupying time and raise the outing calculating efficiency. To the network nodes operating OSPF protocol, the said method can avoid instantaneous service break, instantaneous no response of router and other equipment, etc.
Owner:HUAWEI TECH CO LTD
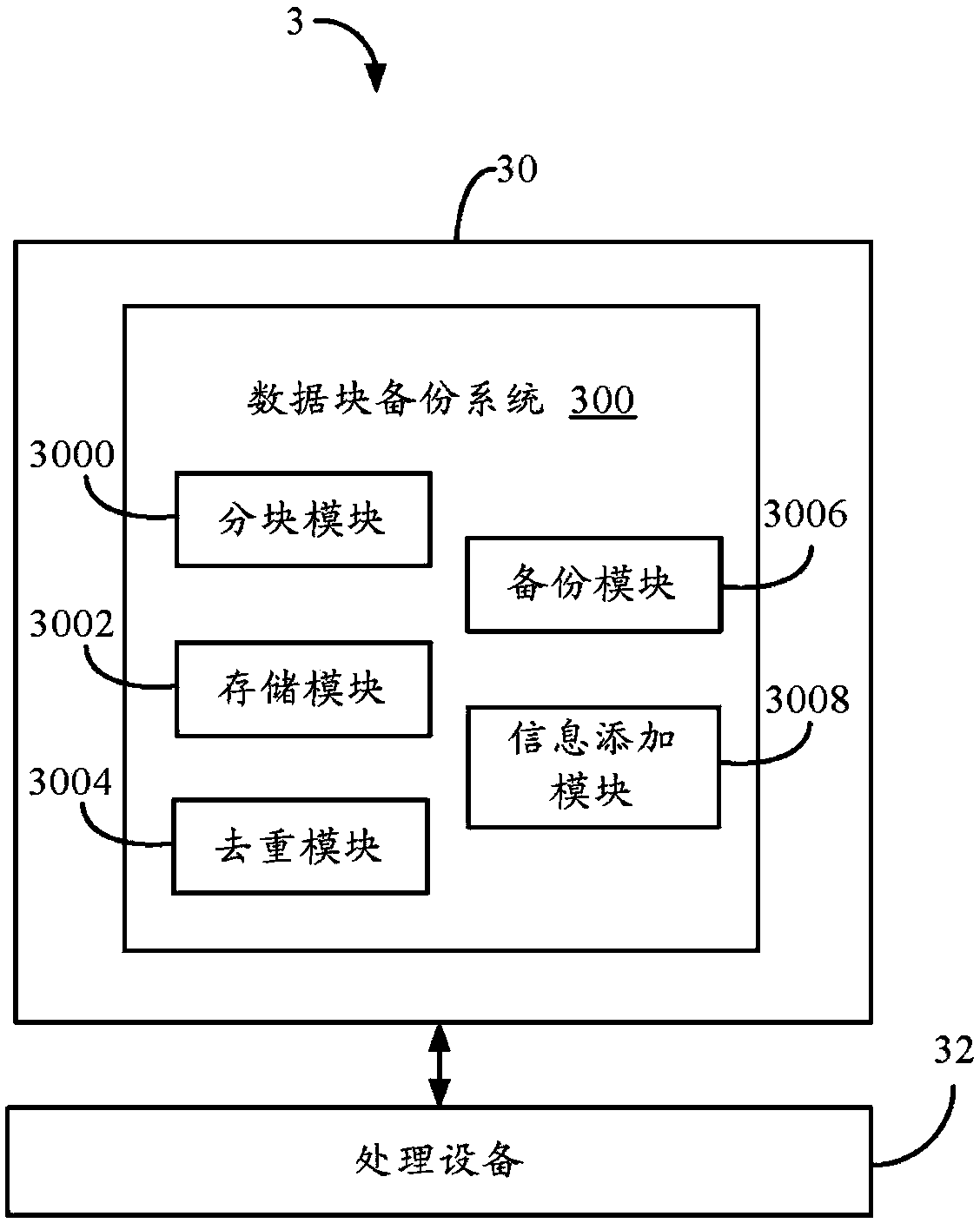
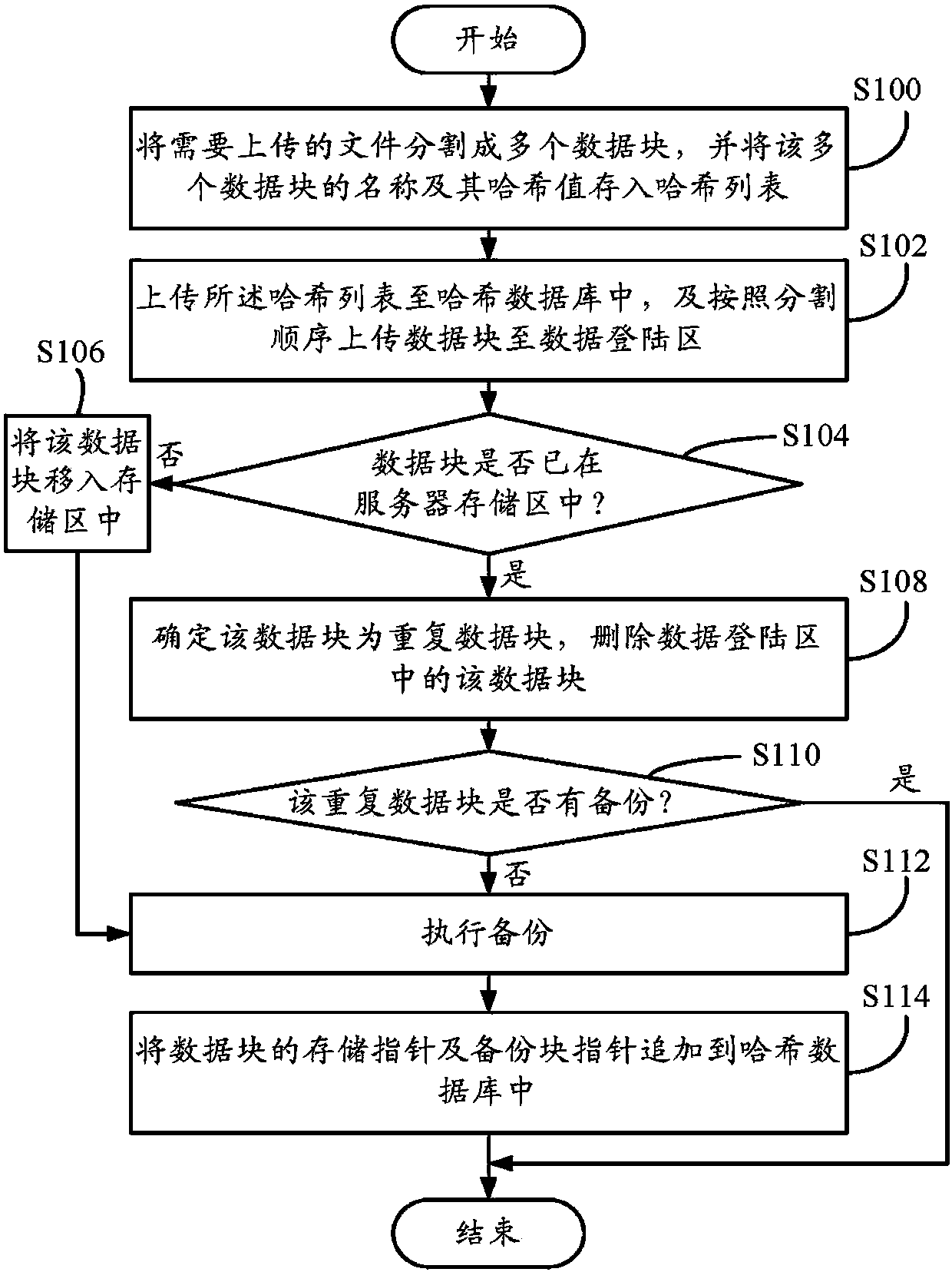
Data block backup system and method
InactiveCN103873503AAvoid incompleteIncomplete keepFile system administrationTransmissionHash listHash table
Provided is a data block backup method which comprises that: a Hash table storing names of file data blocks and Hash values of all the data blocks is uploaded to a Hash database, and the data blocks are uploaded to a data login area of a server according to the segmentation sequence of the data blocks; repetition of uploading of all the data blocks is judged according to the sequence in which the data blocks enter into the data login area, when the judgment result is that the data blocks are in a storage area of the server, the data blocks are confirmed to be duplicated data blocks, and the data blocks in the data login area are deleted; when the duplicated data blocks have no backup, the duplicated data blocks are stored in a backup area of the server; and storage pointers of the data blocks and the pointers of backup blocks are additionally stored in the Hash database. The invention also provides a data block backup system. The situation that files cannot be used due to damage, tampering or loss of the data blocks which are cited for multiple times can be avoided by utilizing the method.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
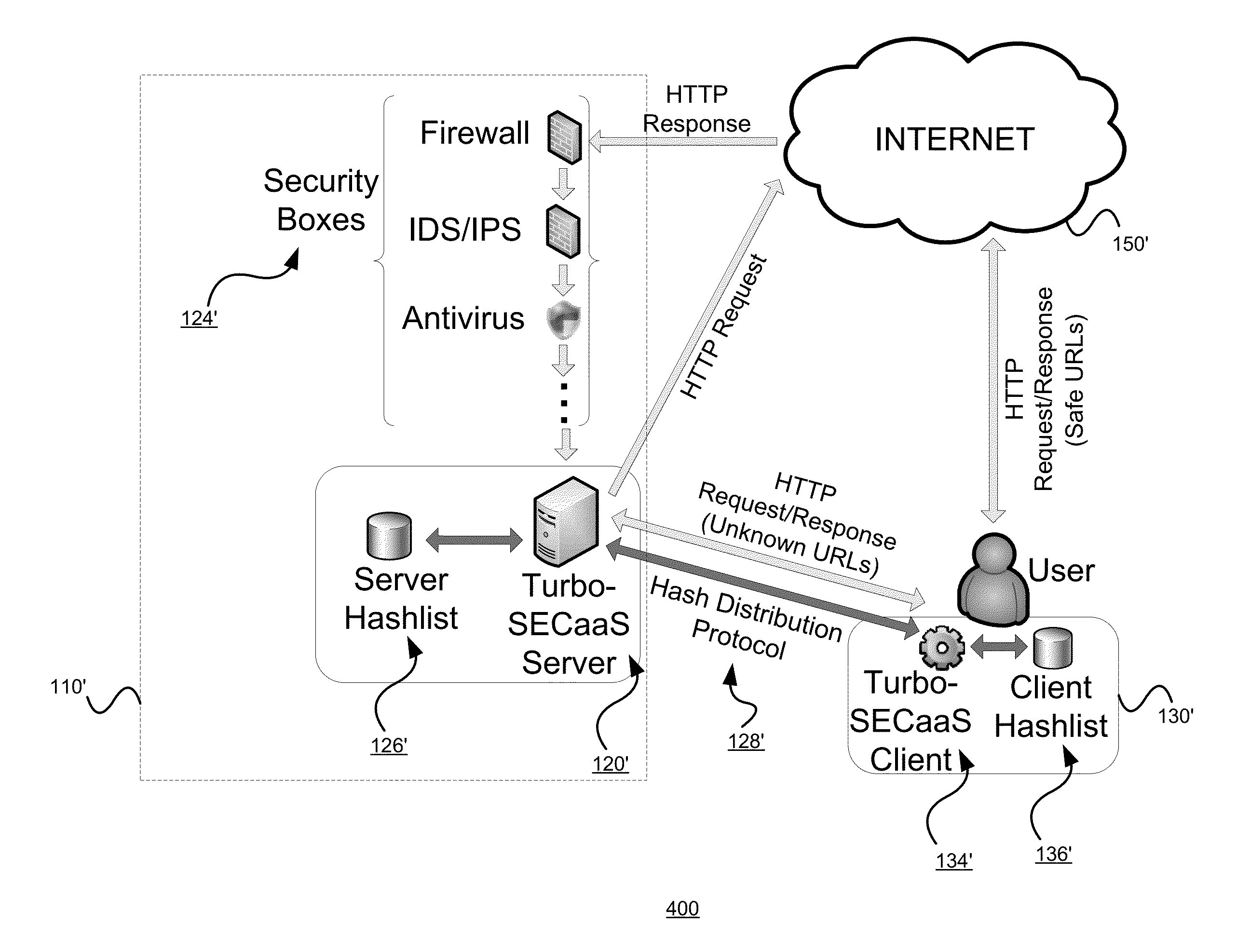
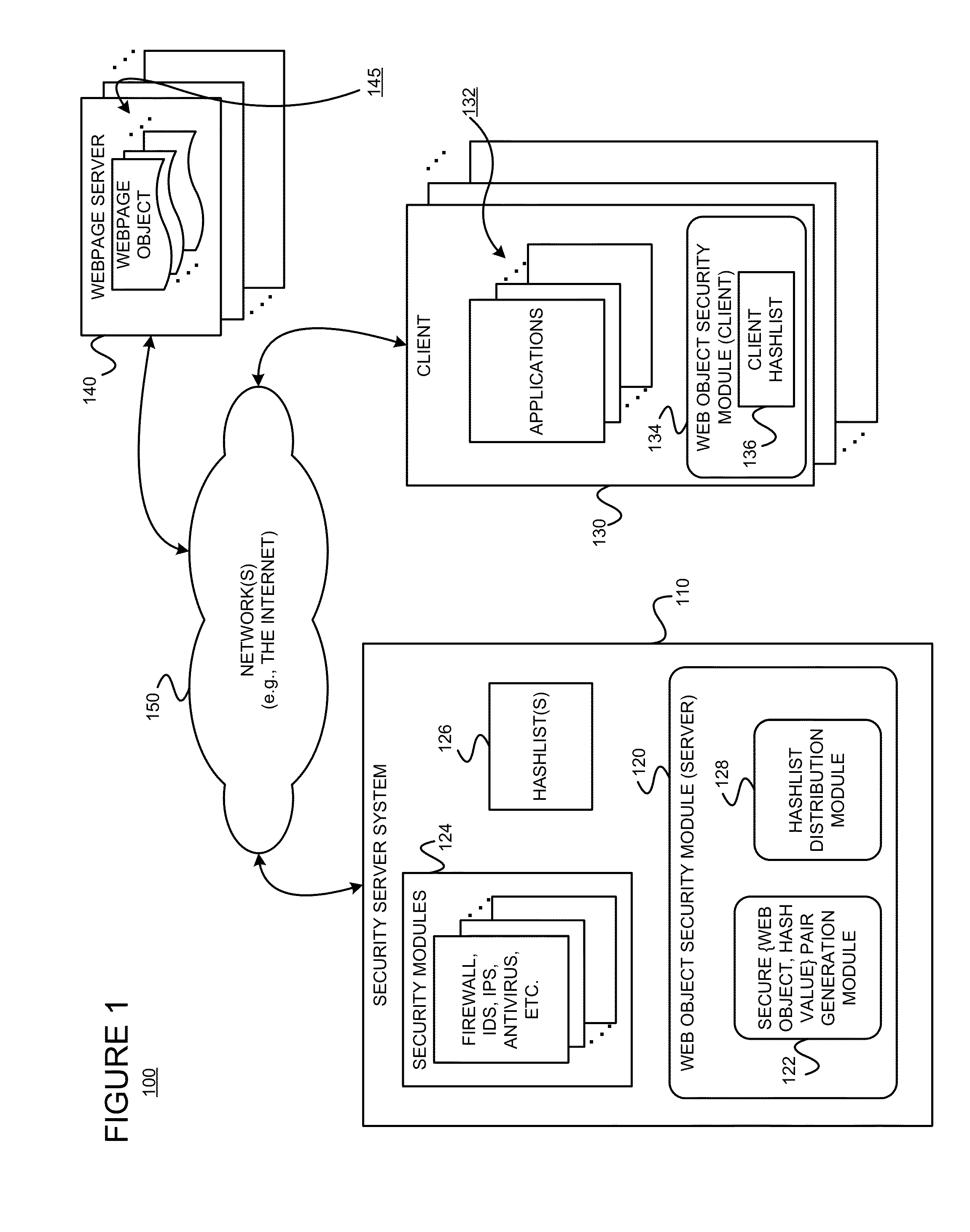
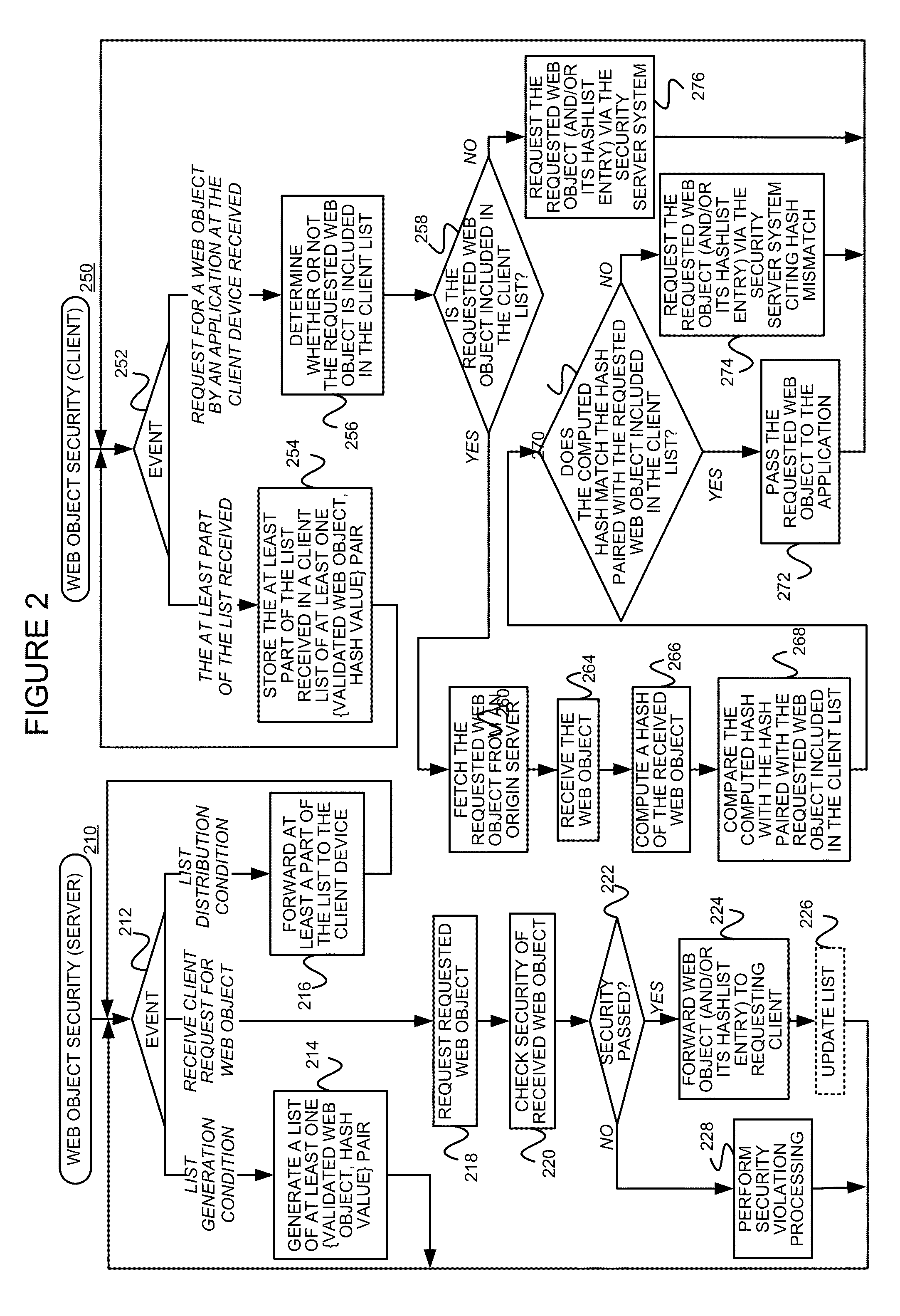
Providing a fast, remote security service using hashlists of approved web objects
ActiveUS20140173729A1Error minimizationMemory loss protectionError detection/correctionEngineeringHash list
A security system and service, which improves the performance of SECaaS services, is described. A security server system tracks the content that has successfully passed through its security modules and distributes this information to the end user client devices as hashlist information. The remote client devices can then safely bypass the cloud for a significant fraction of Web object requests by using information on a locally stored hashlist to validate Web objects.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
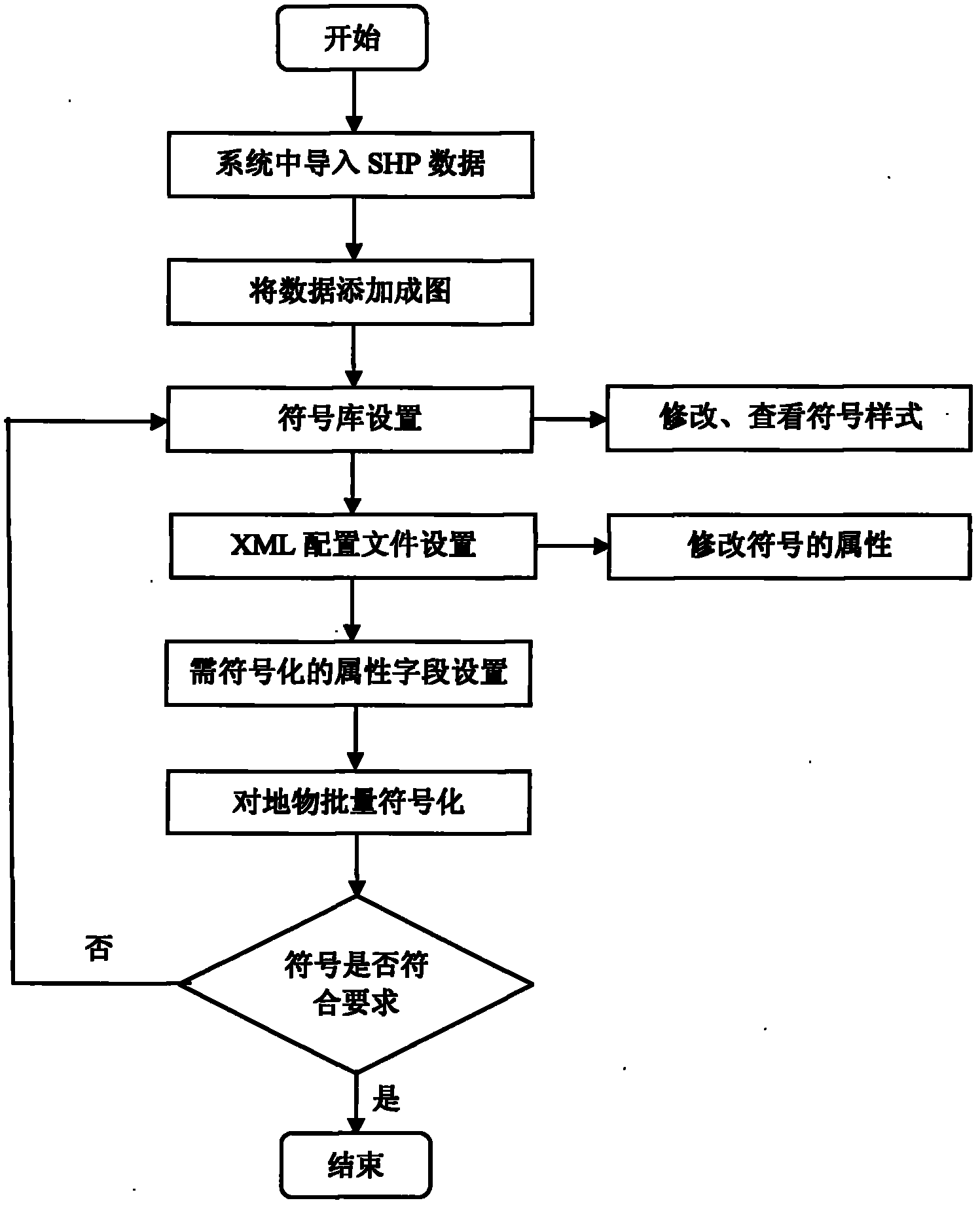
Method for quickly mapping by batch symbolization
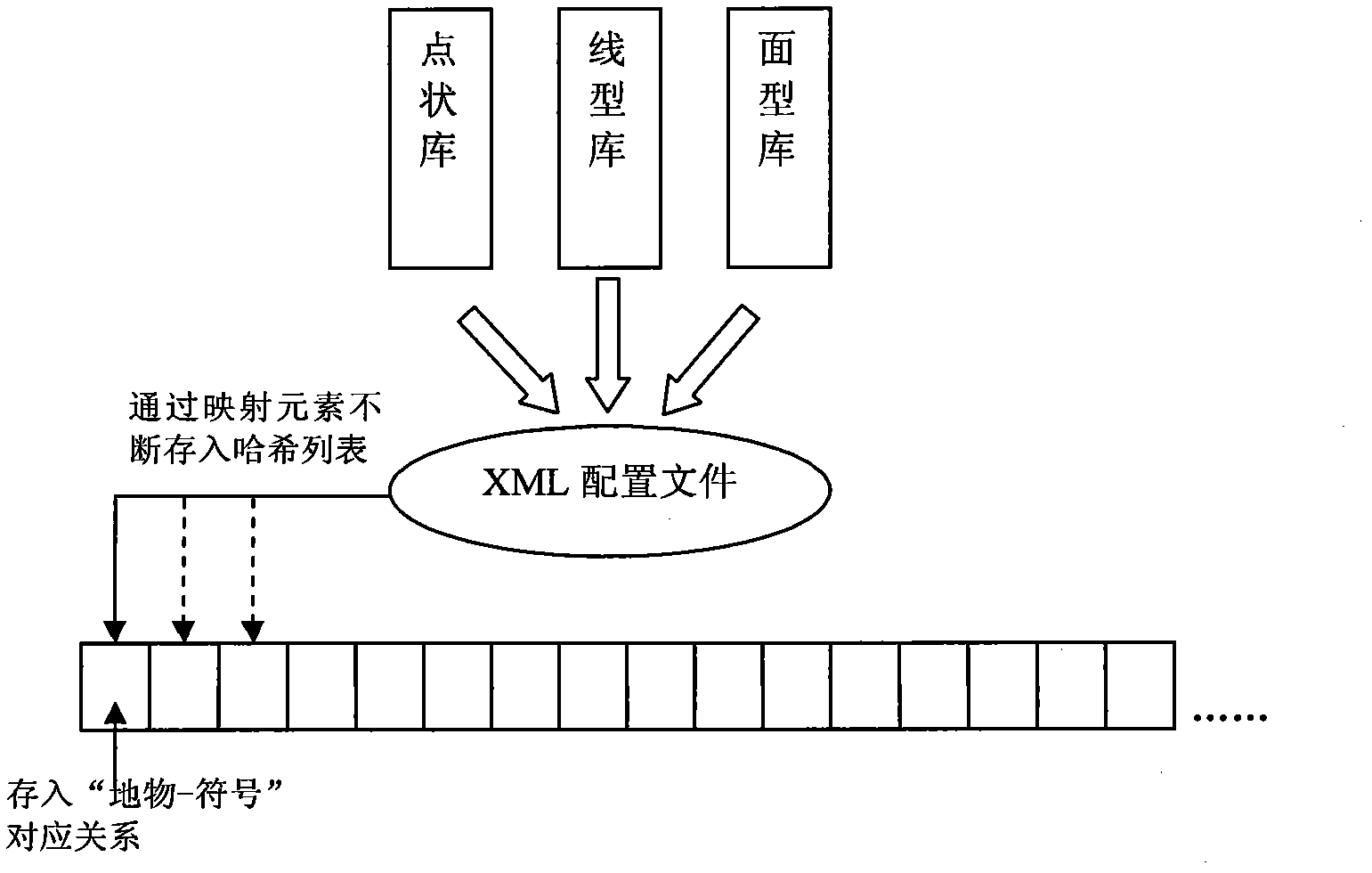
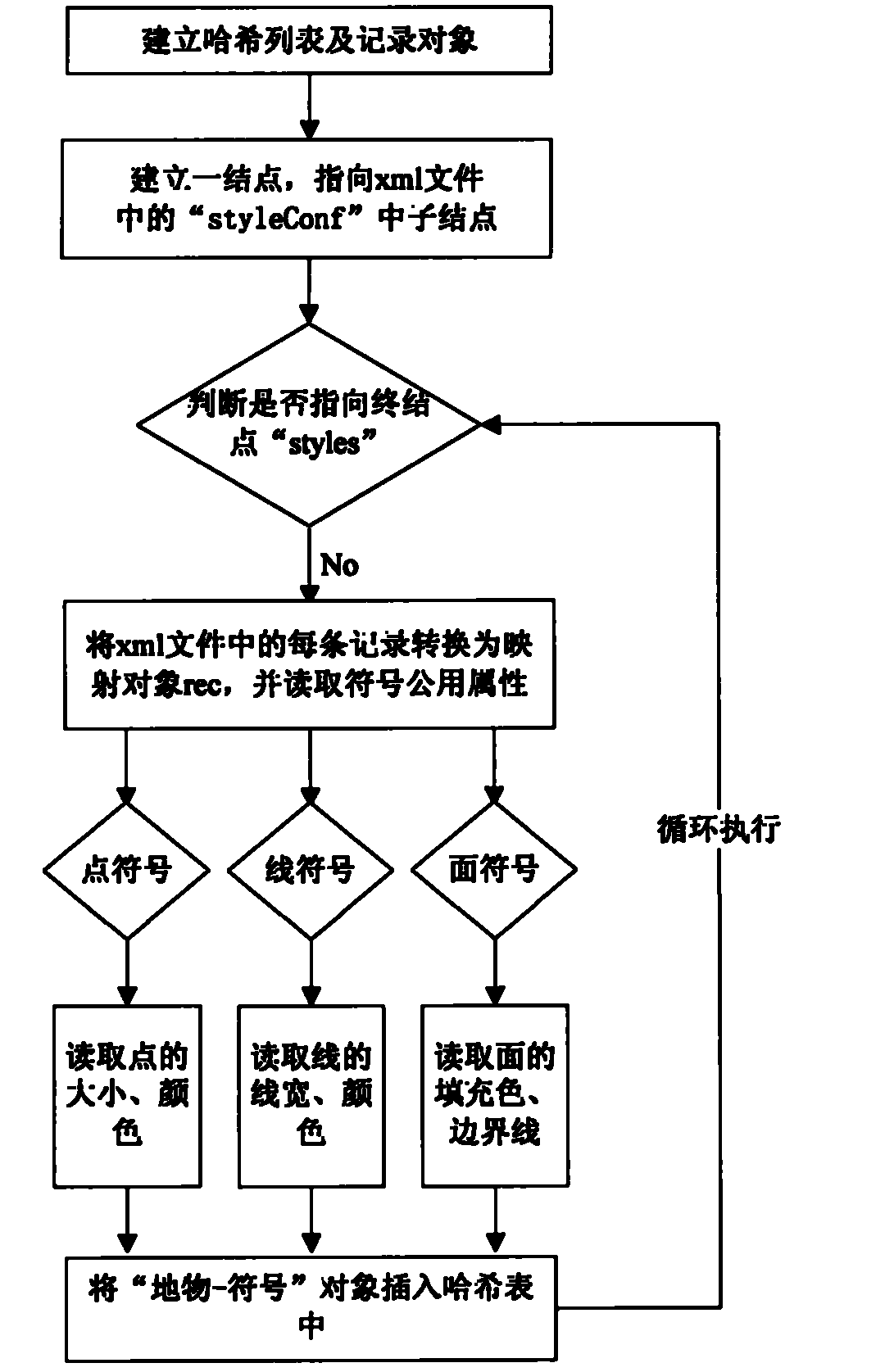
The invention discloses a method for quickly mapping by batch symbolization. The method based on a super map symbol library comprises the following steps of: (1) importing topographic map SHP data which are obtained by field measurement, and adding the data to a map; (2) configuring the symbol library; (3) setting an extensive makeup language (XML) configuration file to obtain a ground object-symbol configuration relationship; (4) storing the ground object-symbol configuration relationship into a hash list; (5) obtaining a data layer of the map, and according to ground class attributes of ground objects and the ground object-symbol configuration relationship, calling symbols from the symbol library to perform symbolization; and (6) checking whether the ground object without the symbol exists in the data layer, if so, reconfiguring the symbol library, if the required symbol is absent, adding the symbol into the library and resetting the XML file. The invention discloses the method for mapping by the batch symbolization; and due to the adoption of the method, the graphic drawing and editing speed of topographic maps are increased, the graphic quality is improved, and the batch calling and the quick and accurate drawing of topographic map symbols are realized.
Owner:SOUTHEAST UNIV
Quick Mass Data Manipulation Method Based on Two-Dimension Hash
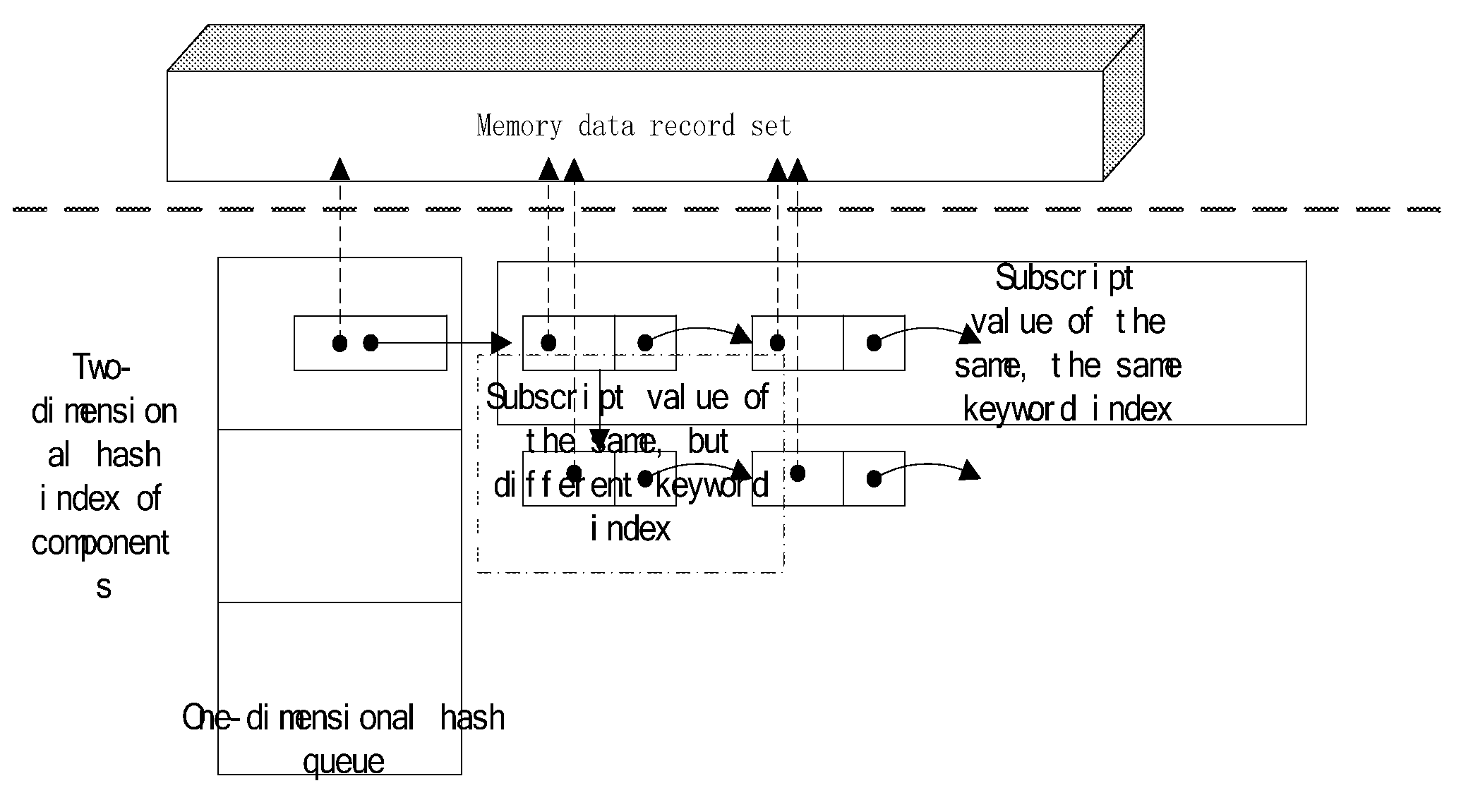
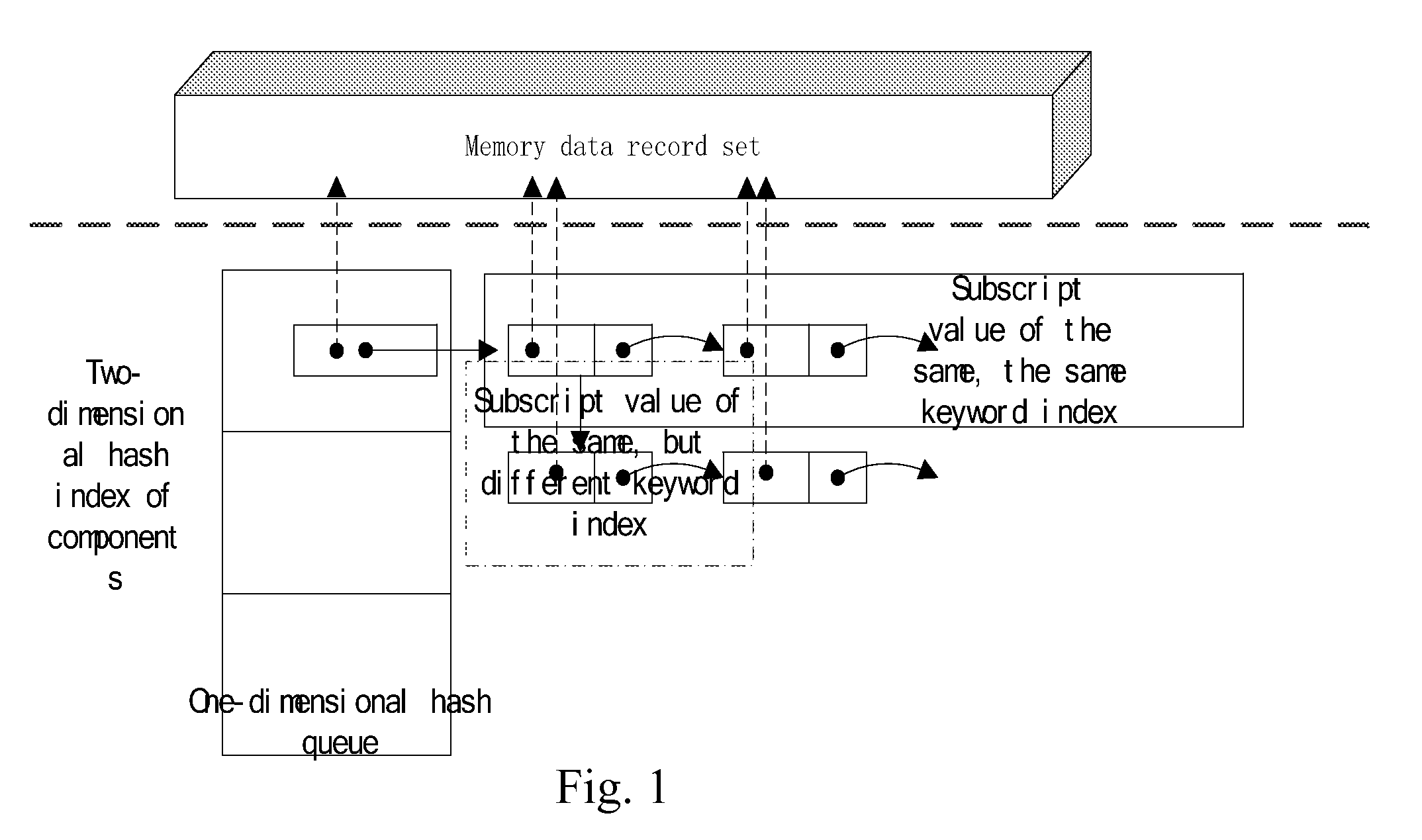
InactiveUS20100179954A1Data efficientSatisfies technological requestMultiple keys/algorithms usageDigital data processing detailsComputerized systemHash list
For the massive data of physical memory on the computer system, data indexing can be created base on the two-dimensional hash indexing algorithm, using specific mapping relationship conversion between the index keyword and index sequence address under hash algorithm, which realize the fast addressing while introducing two-dimensional hash list to solve the ‘confliction’ problem of mapping relations in hash queue, which caused by the same keyword index or hash algorithm.
Owner:LINKAGE TECH GROUP
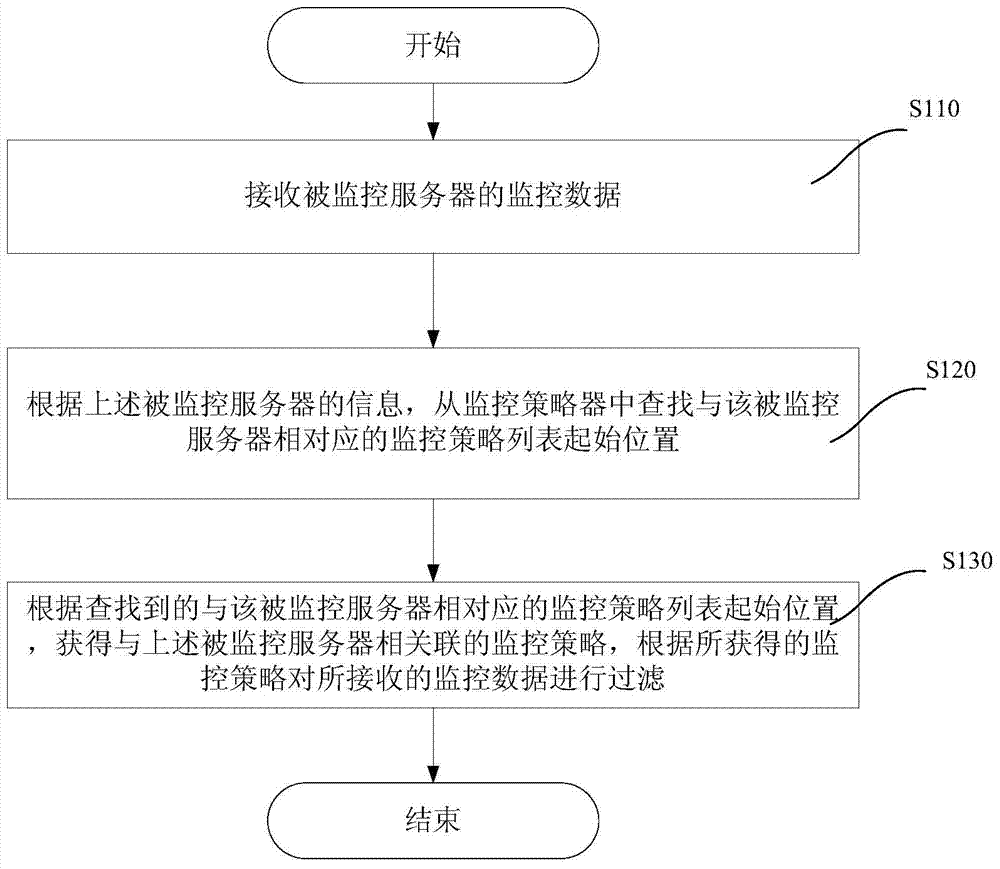
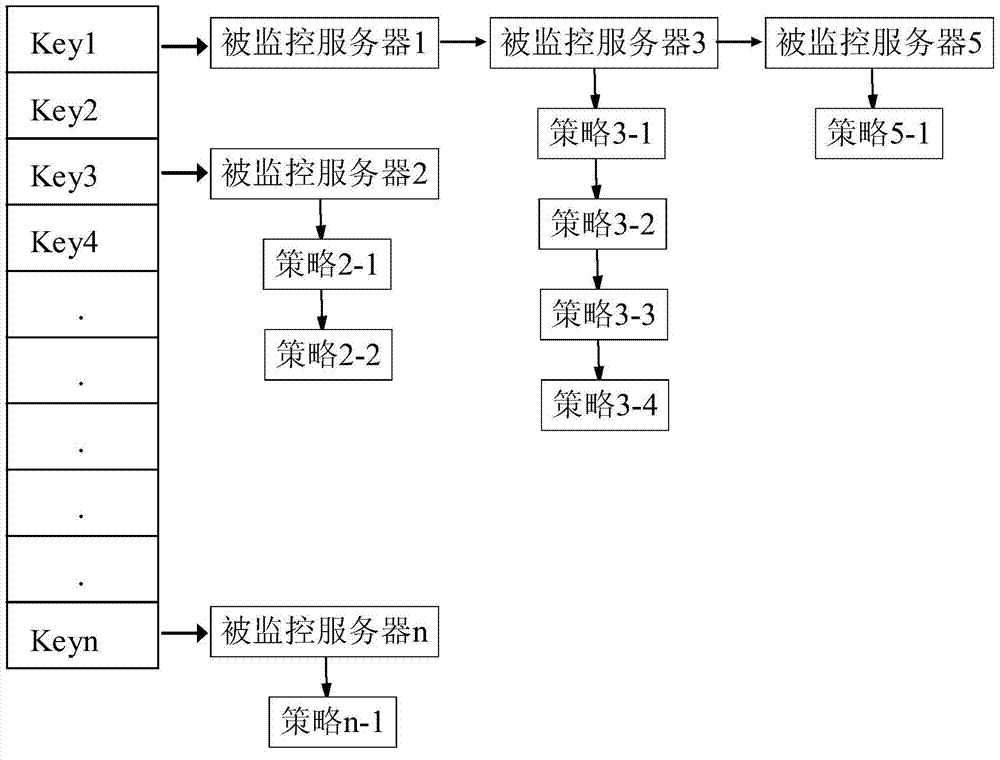
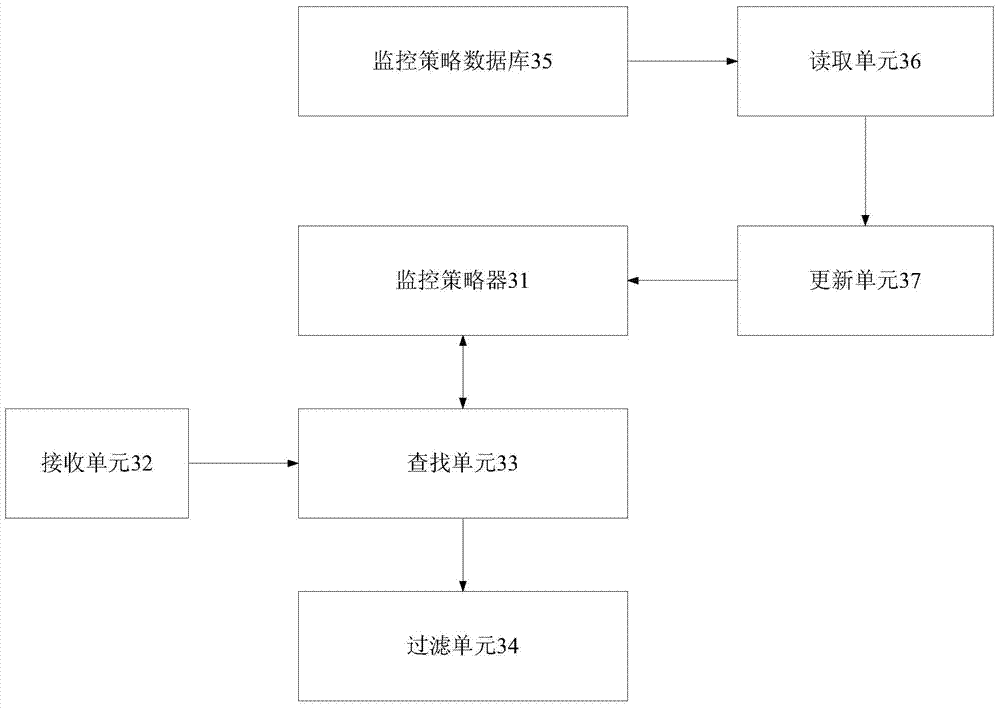
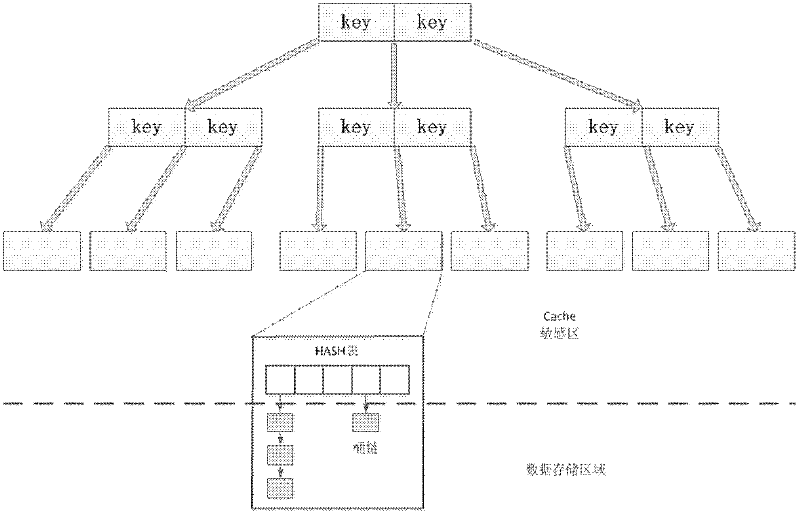
Method and device for filtering monitoring data
ActiveCN103490937AImprove update efficiencyCan't solveData switching networksHash listMonitoring data
The invention relates to a method and a device for filtering monitoring data. The method comprises the following steps: receiving monitoring data of a monitored server; searching the initial position of a monitoring policy list corresponding to the monitored server from a monitoring policy manager according to the information of the monitored server, wherein the monitoring policy manger comprises a hash list, each unit in the hash list comprises a hash value which is calculated according to the information of each server and a link of a monitoring policy list initial position corresponding to a server with the hash value, and each monitoring policy list initial position has a link of each monitoring policy related to a corresponding server; acquiring a monitoring policy related to the monitored server according to the searched monitoring policy list initial position corresponding to the monitored server, and filtering the received monitoring data according to the monitoring policy. Therefore, the technical problem that a monitoring policy in the prior art cannot be searched and updated quickly can be solved.
Owner:BEIJING QIHOO TECH CO LTD
Incremental data cleaning method based on memory mapping
InactiveCN102495834AFind quicklyRaise deleteSpecial data processing applicationsIncremental maintenanceData source
The invention discloses an incremental data cleaning method based on memory mapping. Data of a data source to be cleaned are loaded into a memory, and a memory MDB (meta database)-tree is built by the aid of a HASH list; quick data inquiry is completed by the aid of a top-down strategy, and operations of data insertion, deletion and the like are completed on the basis; views in the memory mapping are standardized into AUSPJ (aggregation, union, selection, projection and join) sections and D (differential) sections, and incremental maintenance of nodes is realized by the aid of relational algebraic operation; and finally data cleaning operation is realized by the aid of a result collection merging algorithmic method. The incremental data cleaning method can be widely applied to industries and fields with high data quantities and data quality requirements, such as education, telecommunication, governments and the like.
Owner:UESTC COMSYS INFORMATION
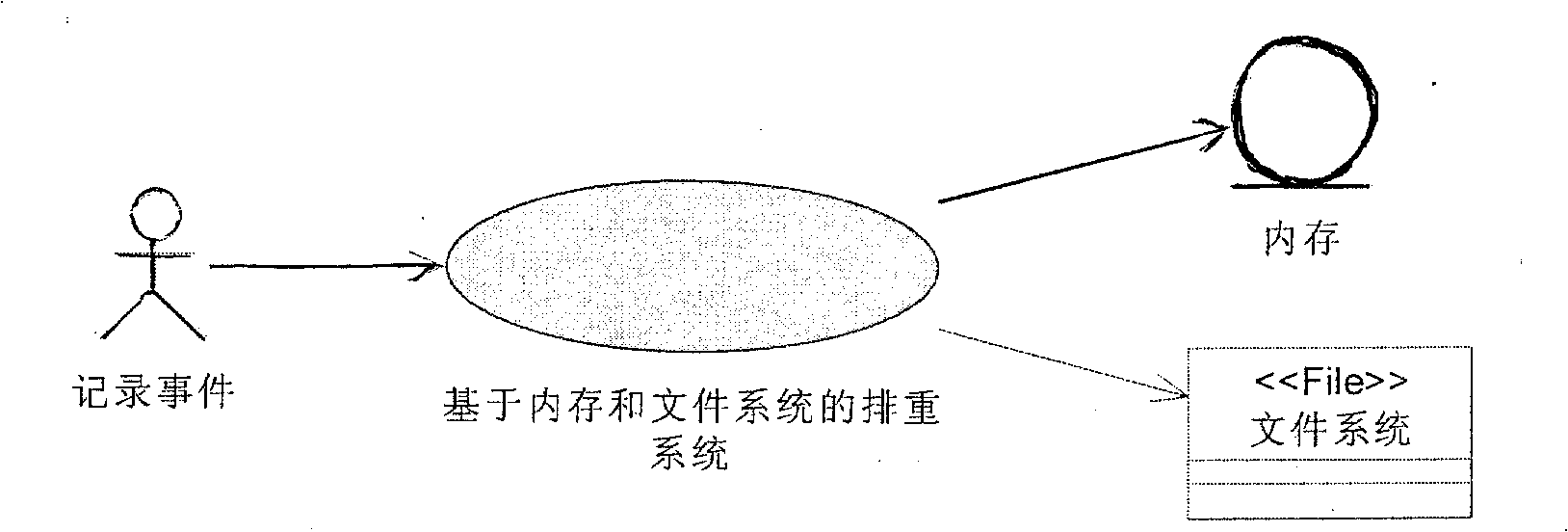
Internal memory and file system mixing rearrangement method based on HASH algorithm
InactiveCN101493835ASolve efficiency problemsSolve functionAccounting/billing servicesSpecial data processing applicationsInternal memoryFile system
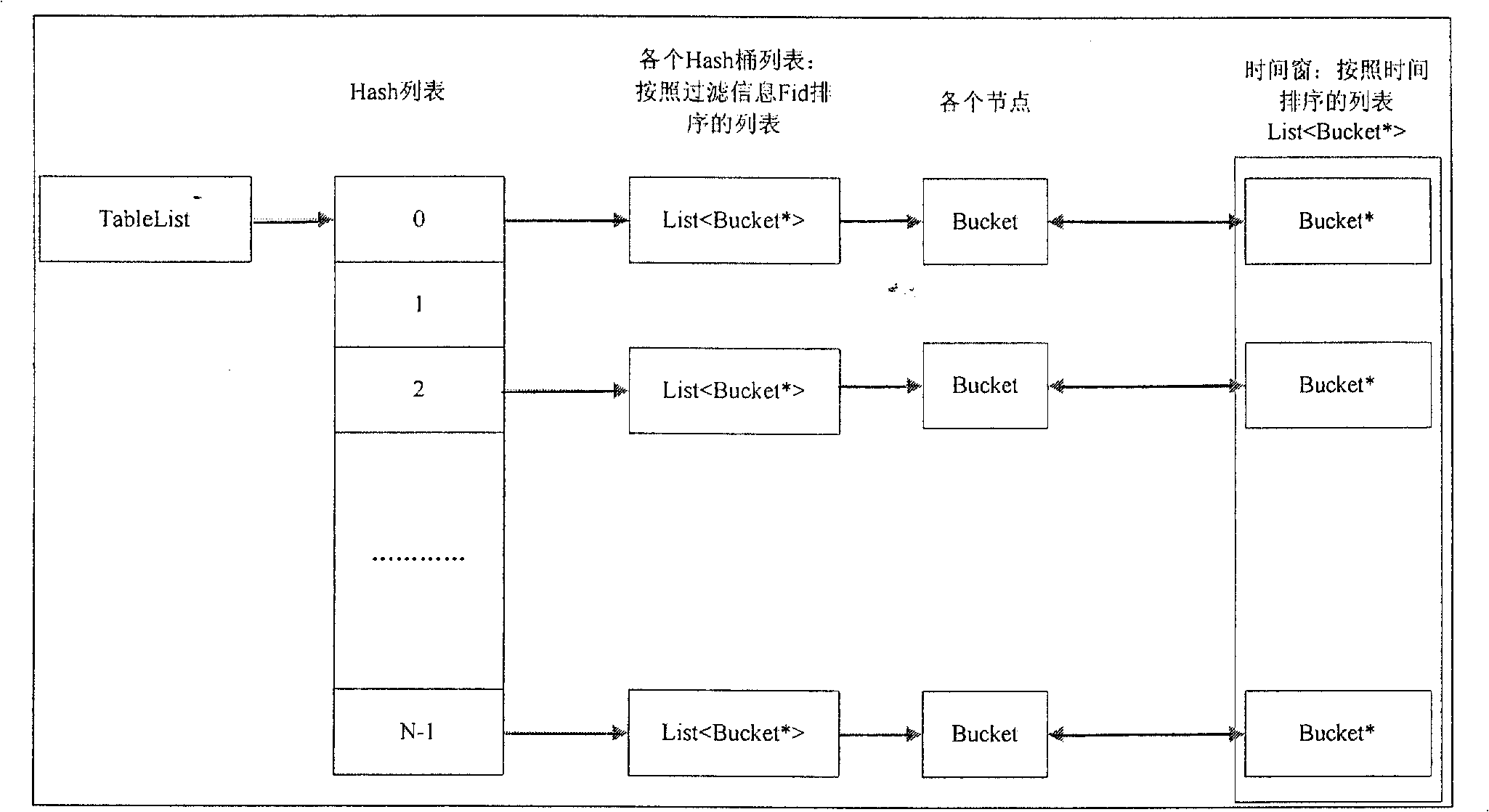
The invention relates to an implement method based on mixed tautology removal of an HASH algorithm memory and a file system, which adopts the combination of the tautology removal of the memory and the tautology removal of the file system so as to achieve a win-win result of data storage use space and processing efficiency. The implement method has the procedure that tautology removal information in a certain period of time is loaded into the memory and the tautology removal of the memory is adopted, and beyond the time the tautology removal of the document is adopted. The implement method mainly has the following steps: step 1. tautology removal configuration information (record format information, tautology removal types) is loaded into the memory; step 2. the tautology removal information in a certain period of time (configurable) is loaded into a private memory; step 3. the tautology removal of memory is performed, i.e., the tautology is removed according to the filtering information in the memory; and step 4. tautology removal of a file is performed, the tautology is removed according to the historical filtering information in the file. The storage structure of the information of the tautology removal in the memory has two characteristics of HASH lists and time window.
Owner:LINKAGE SYST INTEGRATION
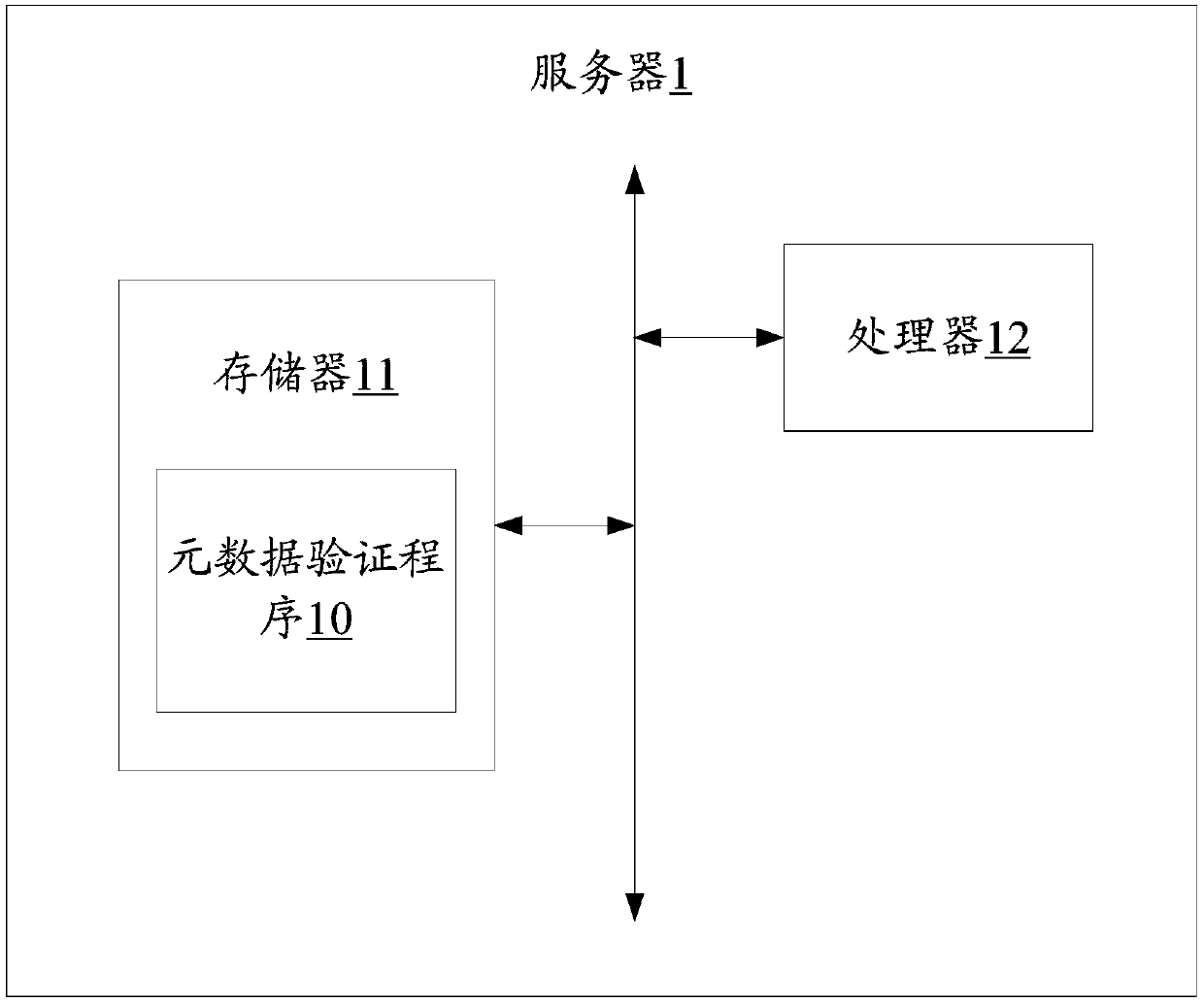
Metadata verification method, system server and computer readable storage medium
PendingCN109657499AImprove securityPrevent tamperingDigital data protectionFile access structuresHash listComputer science
The invention discloses a metadata verification method and system, a server and a computer readable storage medium. The method comprises the following steps: a server receives metadata of a file uploaded by a user side; wherein the metadata comprises a traceable node hash list in a Merkel tree constructed by a plurality of data blocks of the file; Then, the server calculates a root hash value of the Merkel tree according to the traceable node hash list, finally, the server judges whether the root hash value is the same as the hash value of the file, and if yes, it is determined that metadata verification is passed, and metadata is stored. Compared with the prior art, the method and the device have the advantage that the metadata writing safety is improved.
Owner:SHENZHEN THUNDER NETWORK TECH +1
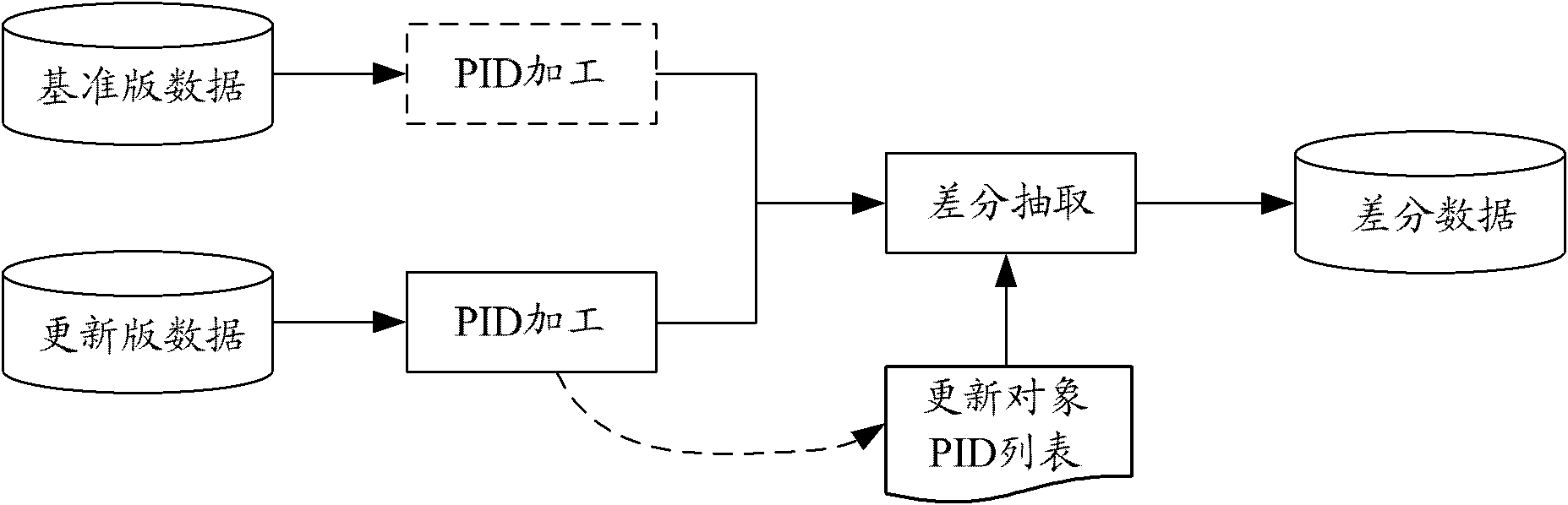
Difference data generation method and generation device for electronic navigation map
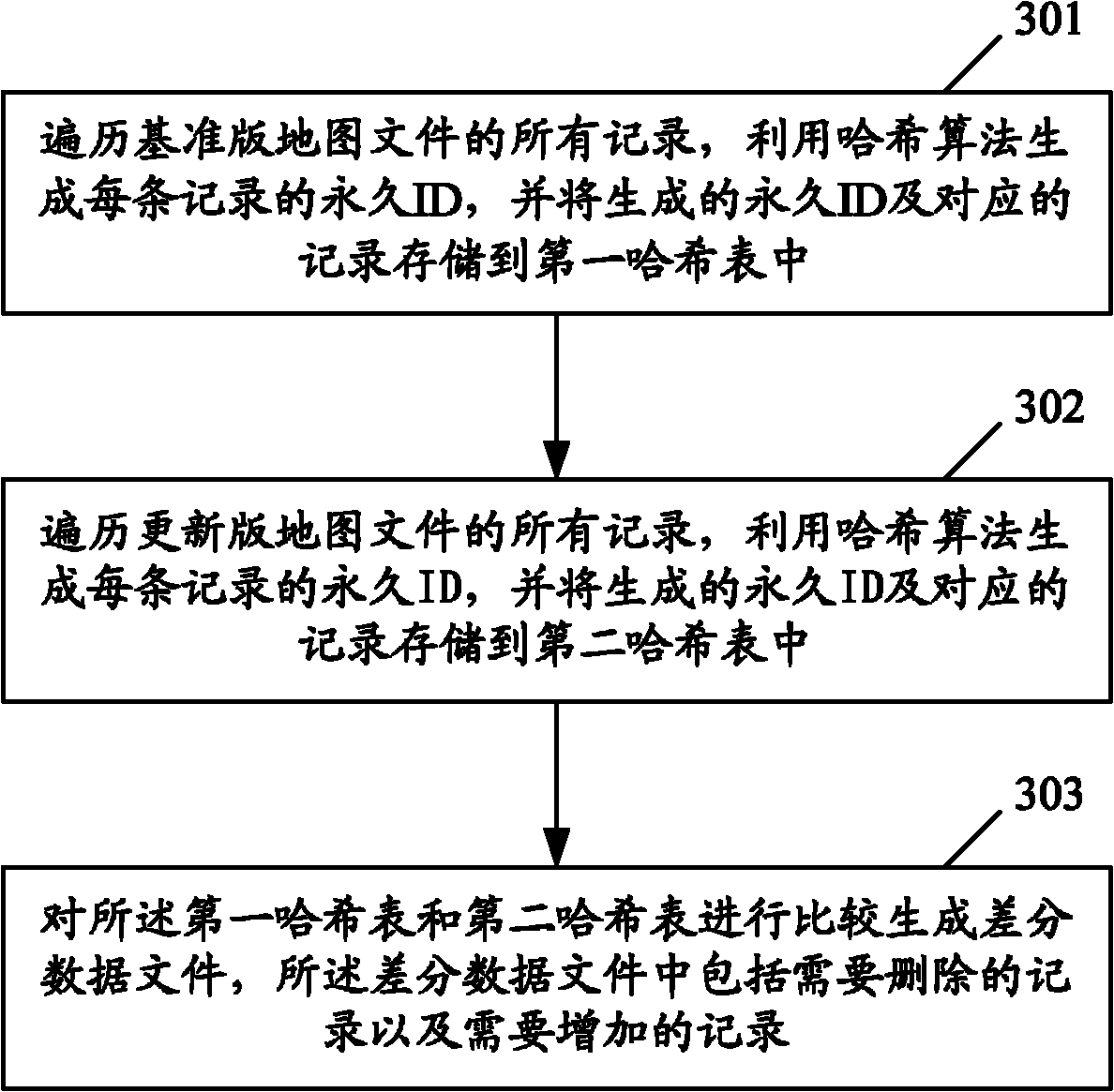
ActiveCN102607576AShorten the update cycleInstruments for road network navigationMaps/plans/chartsData fileHash list
The invention provides a difference data generation method and a difference data generation device for an electronic navigation map. The method comprises the following steps: traversing all records of a standard-version map, utilizing a Hash algorithm to generate a permanent ID for each record, and storing the generated permanent ID and the corresponding record in a first Hash list; traversing all records of an updated-version map, utilizing the Hash algorithm to generate a permanent ID for each record, and storing the generated permanent ID and the corresponding record in a second Hash list; and comparing the first Hash list and the second Hash list to generate a difference data file including records needing to be deleted and records to be added. According to the difference data generation method and the difference data generation device, the difference data of the electronic navigation map can be extracted without adding the permanent IDs for the records during data production.
Owner:NAVINFO
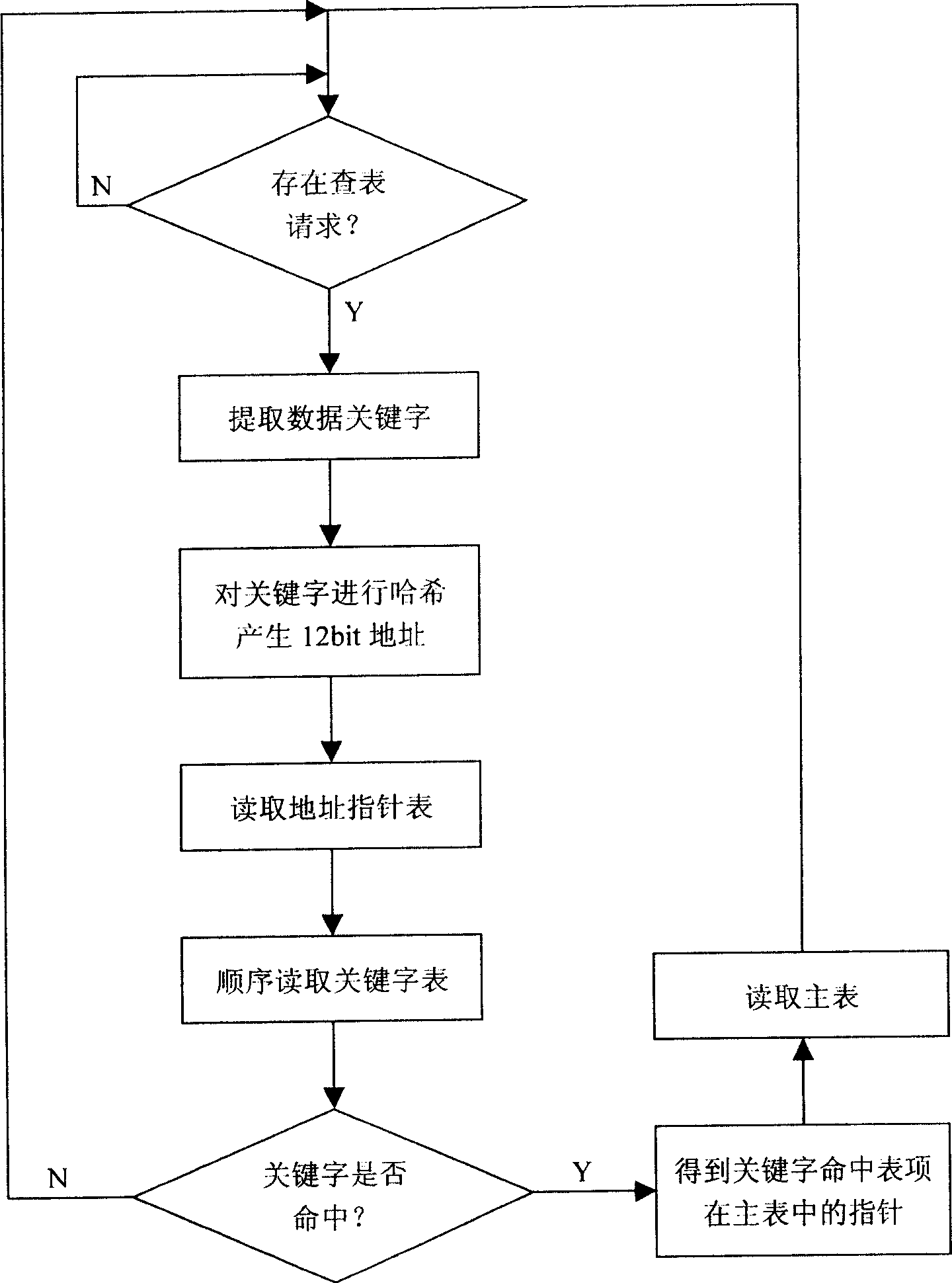
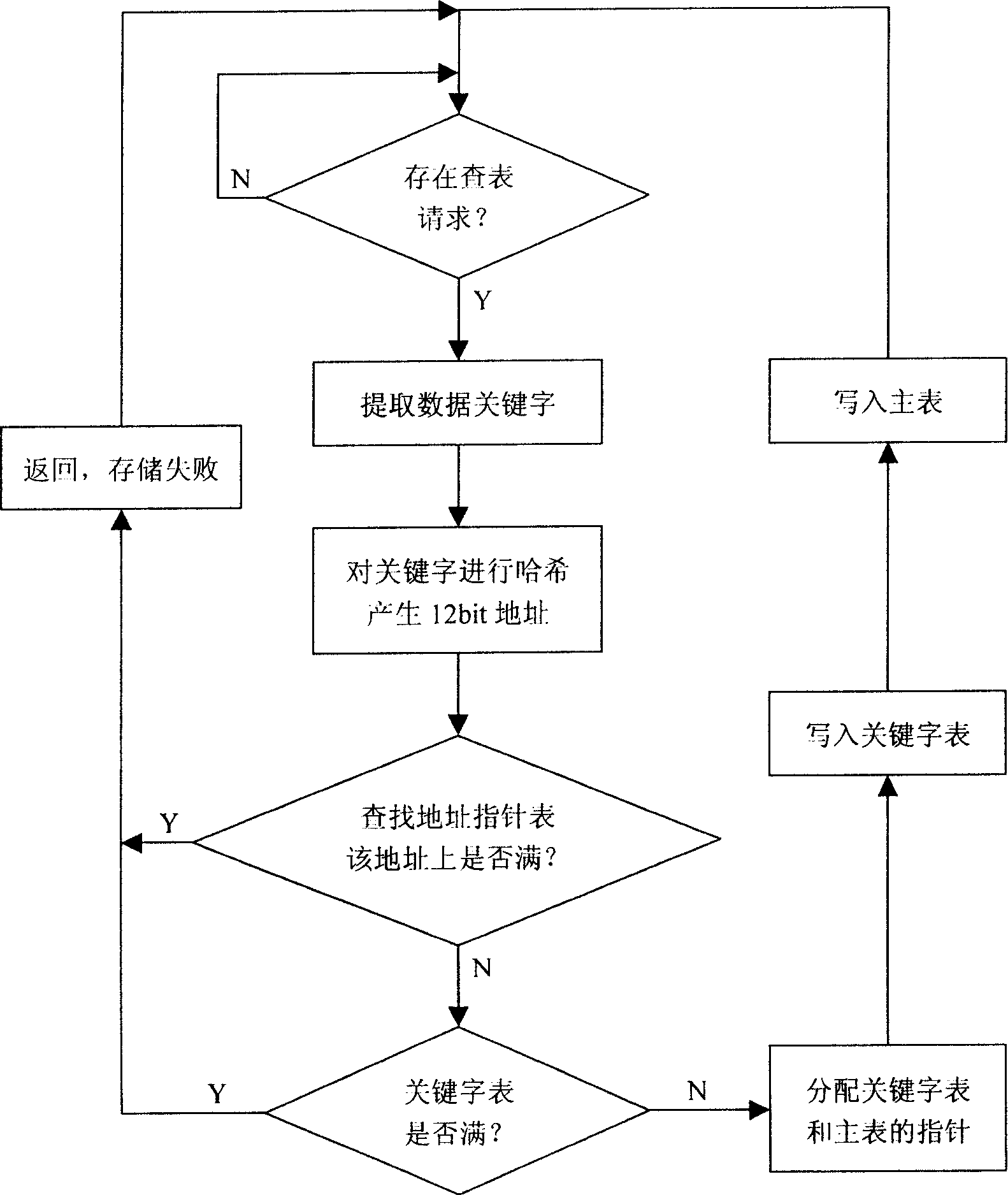
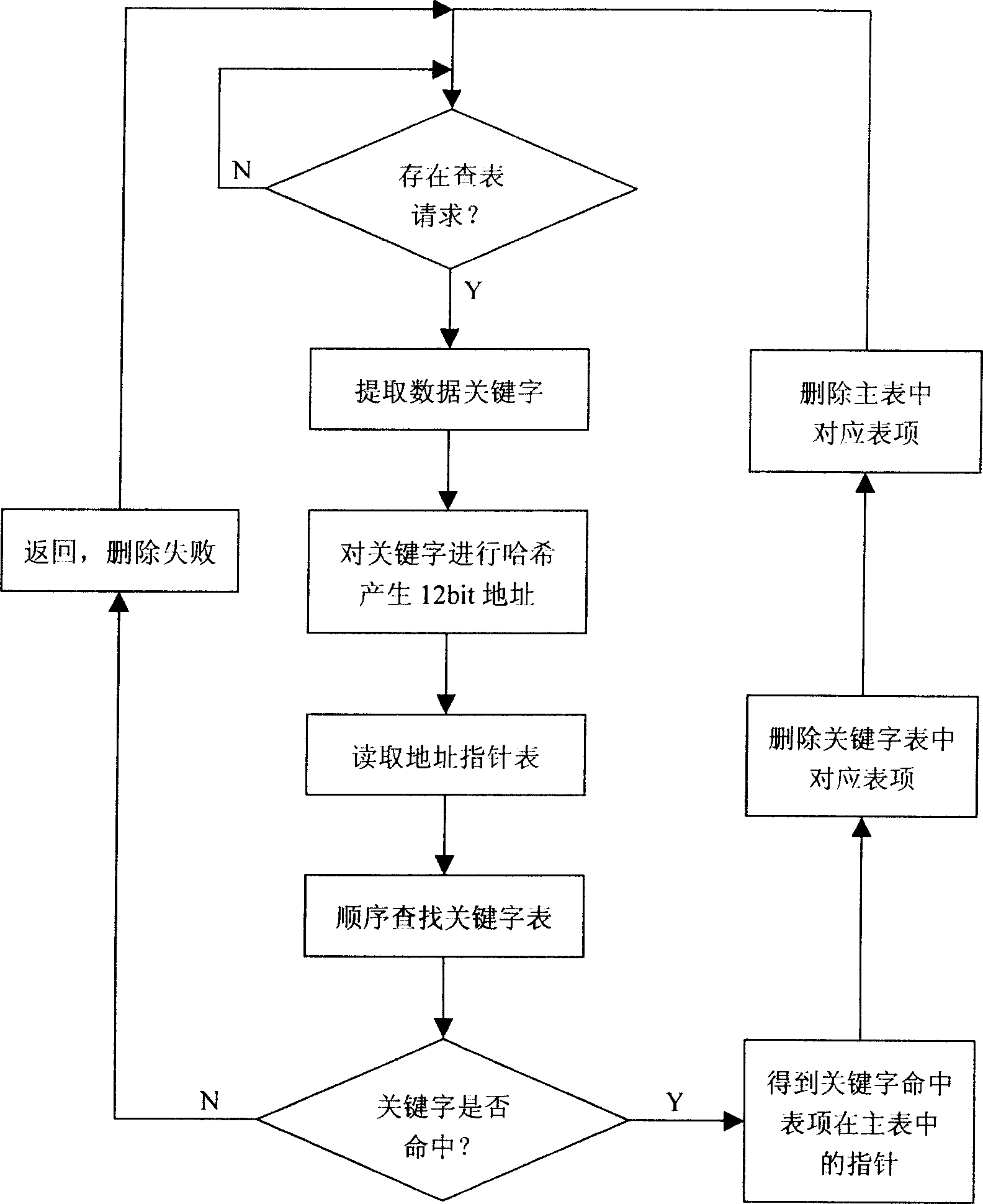
Look-up method of hash table
InactiveCN1912870AImprove utilization efficiencyBalance resourcesSpecial data processing applicationsWord listUsability
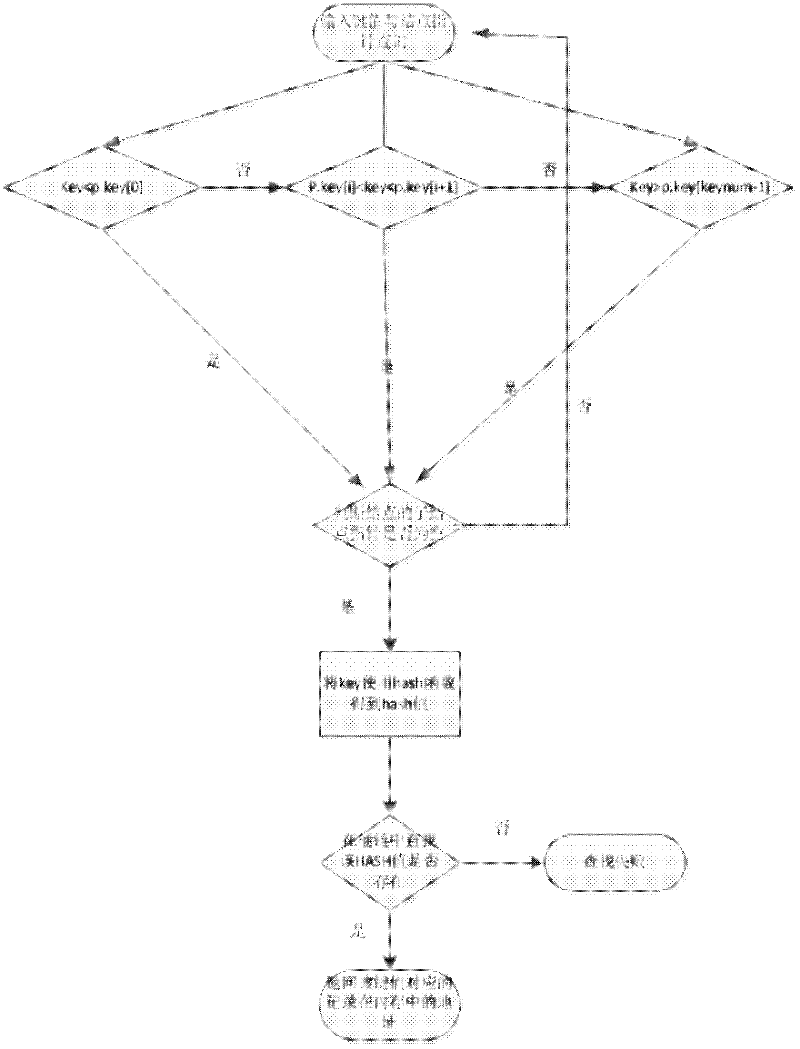
This invention relates to a data process method and provides a method for looking up Hash list including: a, picking up data key words to Hash an address of bit p, b, reading out different addresses of 2n list items in the Hash drum at the address place in the address pointer list, c, reading the key word list based on the addresses to judge if it hits the target. Advantages: providing more and deeper Hash drums so as to greatly increase the usability of Hash table and supporting parallel or serial lookup.
Owner:四川南山之桥微电子有限公司
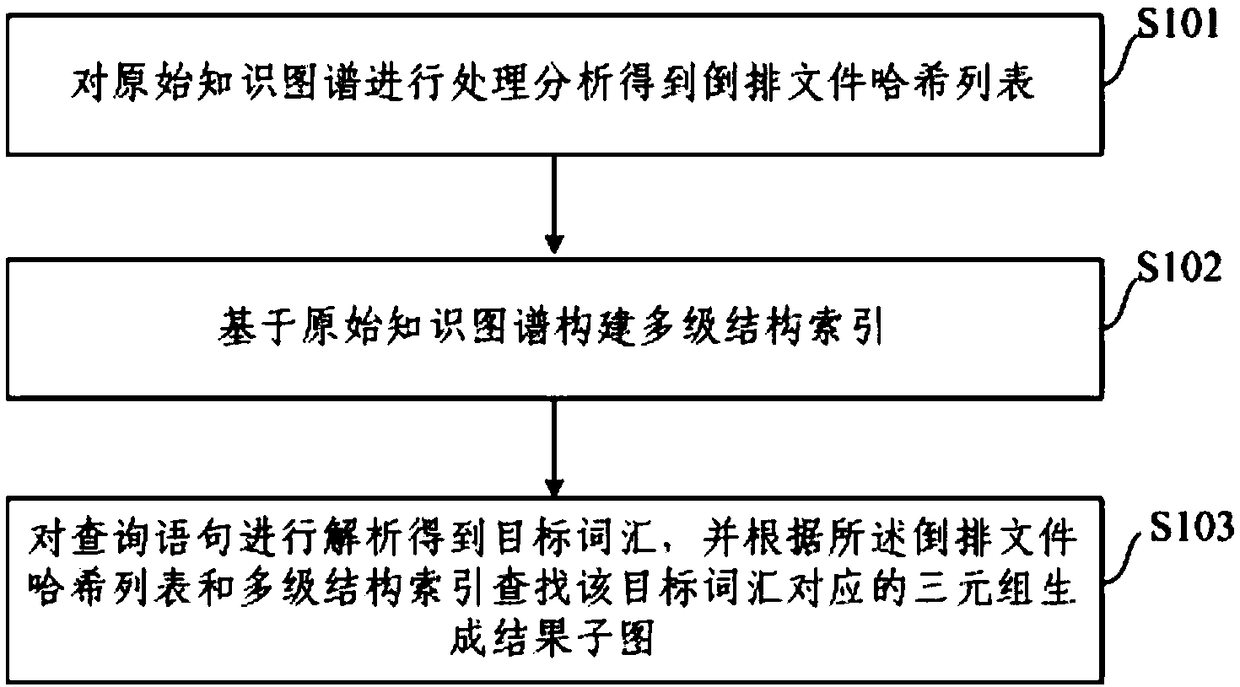
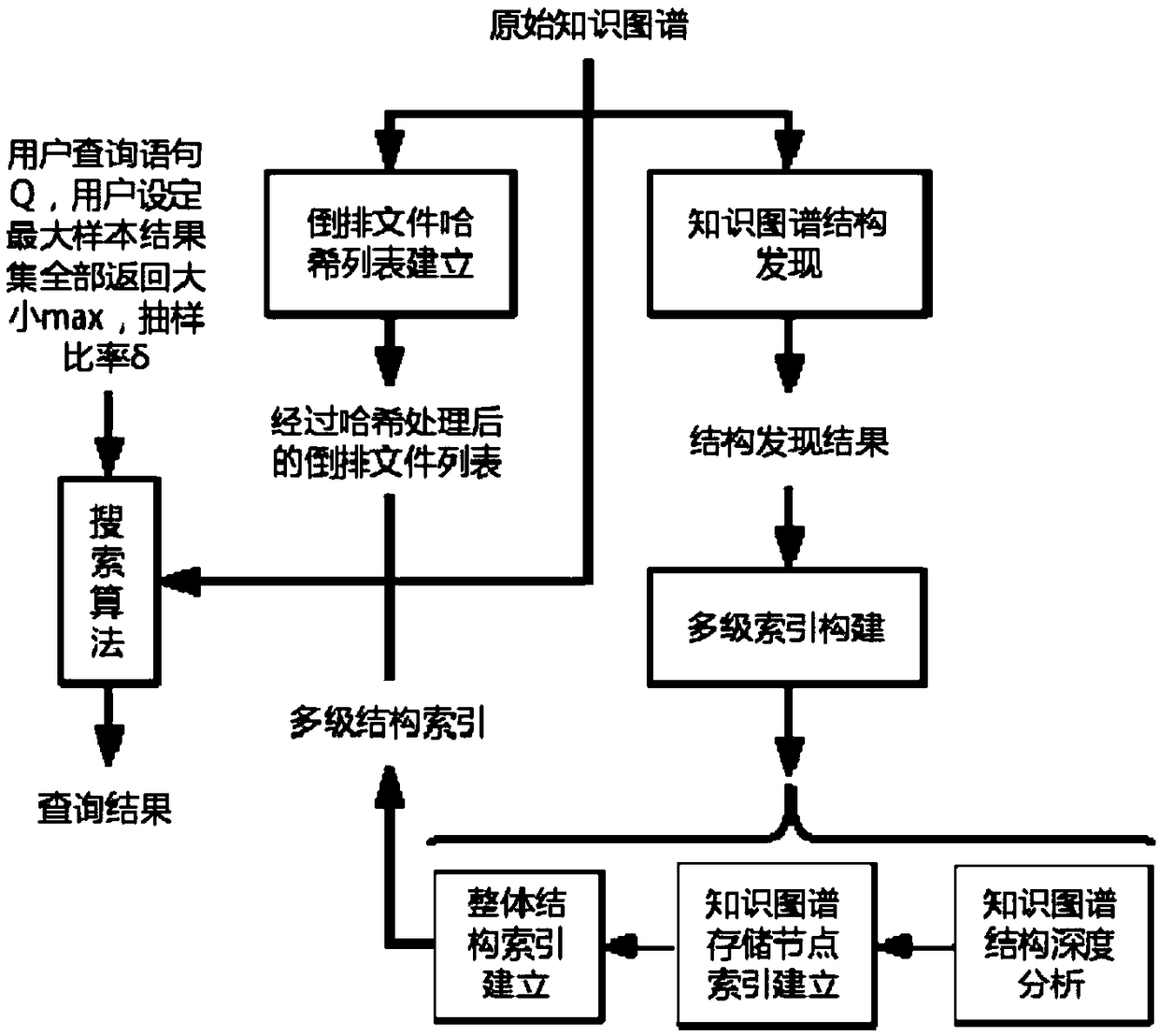
Real-time query method and system for large-scale knowledge map under memory constraint
ActiveCN109033314AImprove data processing capabilitiesReduce query timeNatural language data processingSpecial data processing applicationsLevel structureResult set
The invention relates to the technical field of data processing, and provides a real-time inquiry method and system of a large-scale knowledge map under the condition of limited memory. The method comprises the following steps: processing and analyzing the original knowledge map to obtain an inverted file hash list; constructing a multilevel structure index based on an original knowledge map; obtaining a target vocabulary by parsing the query sentence, and generating the result sub-graph by searching for the triple corresponding to the target vocabulary according to the inverted file hash listand the multi-level structure index. The invention greatly improves the knowledge map query ability of a single computer, and can provide a result set which meets both the user time requirement and the user precision requirement under the condition that the memory is extremely limited.
Owner:HARBIN INST OF TECH
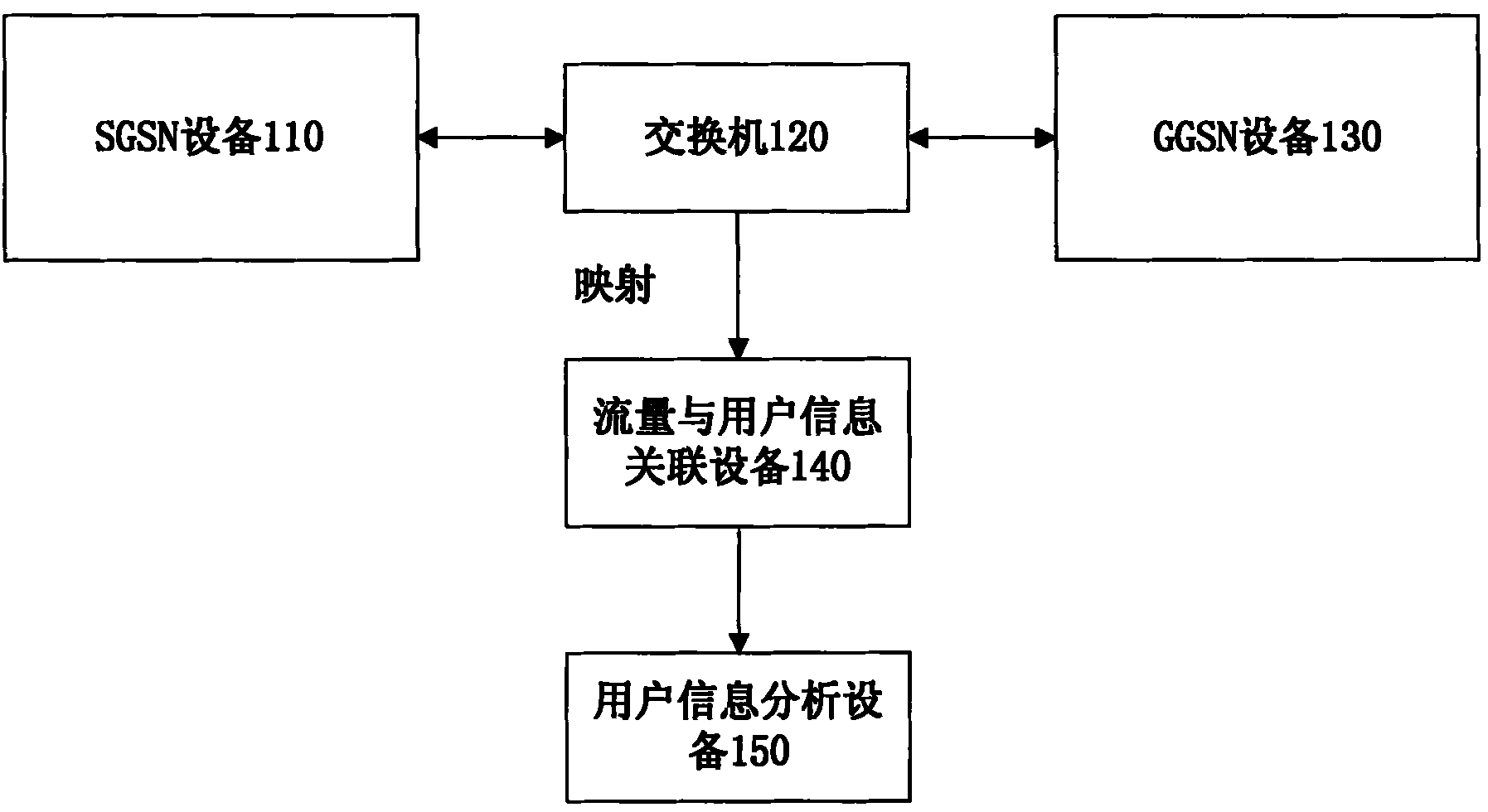
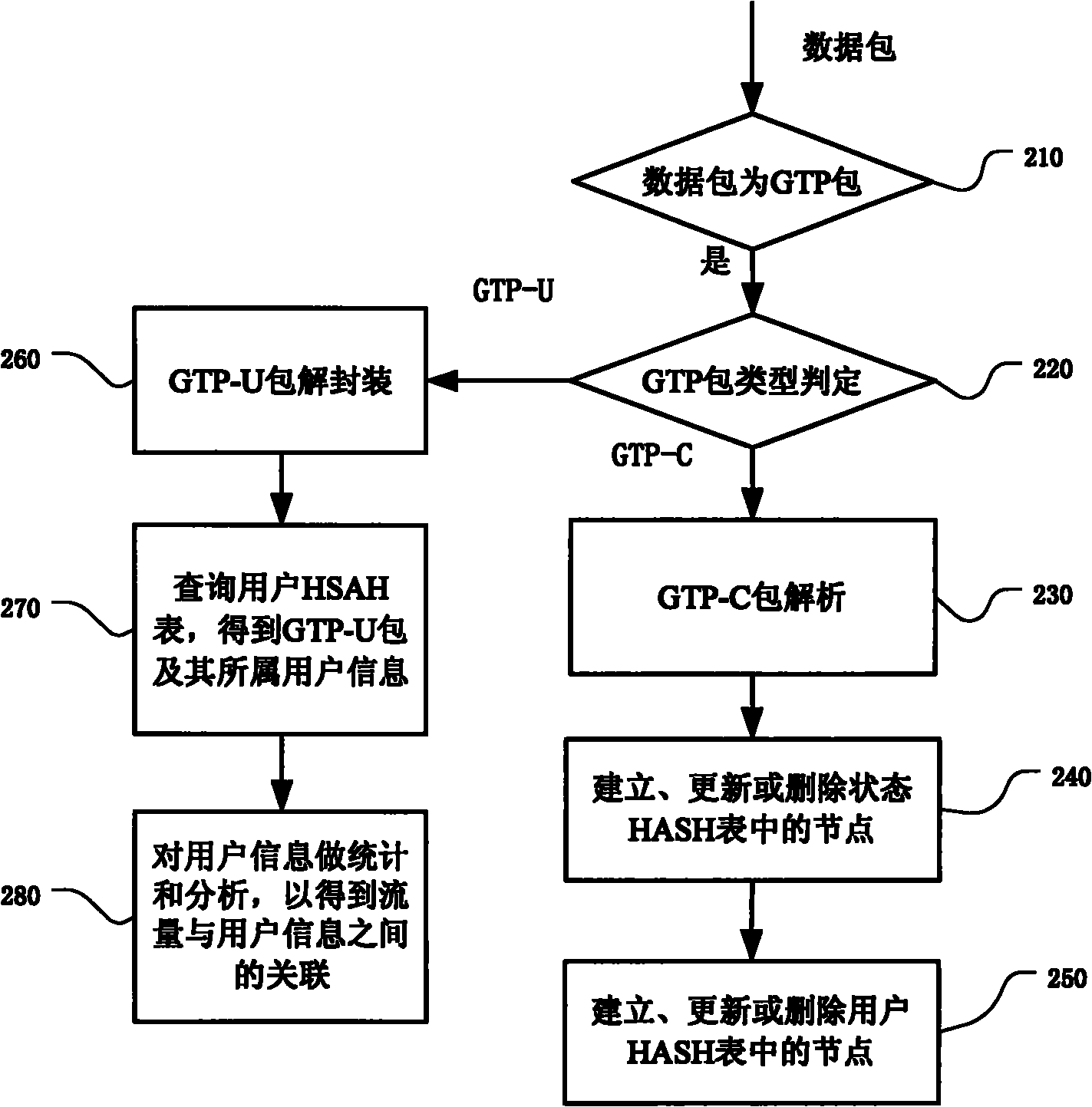
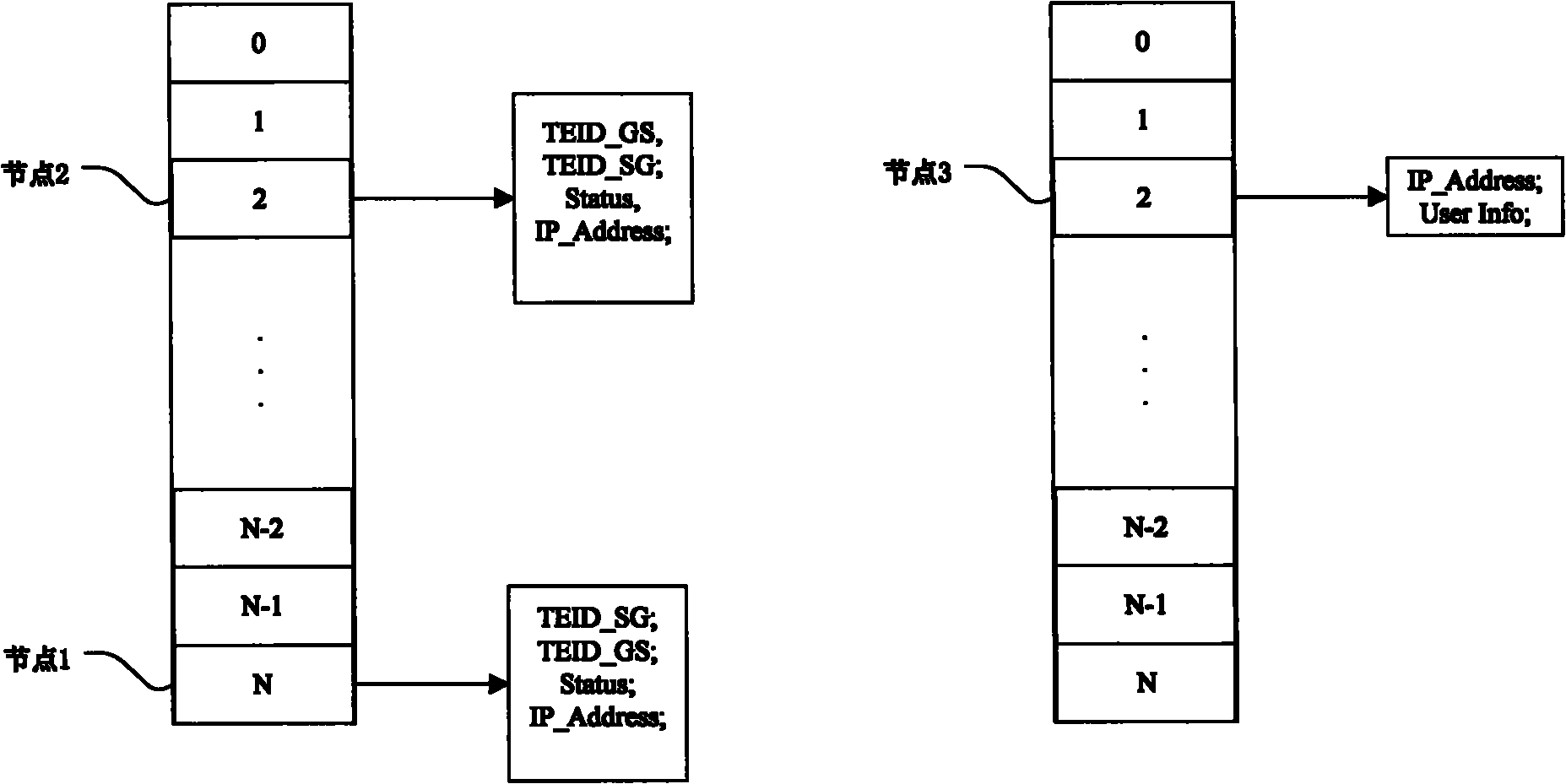
Method and system for correlating flow and user information in general packet radio service (GRPS) network
ActiveCN101969654AAccurate and convenient accessSolve the problem of not being able to directly obtain user-related informationWireless communicationTraffic capacityGeneral Packet Radio Service
The invention relates to a method and a system for correlating flow and user information in a GRPS network. The method comprises the following steps of: firstly, receiving a data packet of a control type and analyzing the data packet; secondly, adding one or more of the analyzed tunnel number, state, mobile phone internet protocol (IP) address and user information into nodes of a state HASH list;thirdly, adding the mobile phone IP address and user information of the nodes in the state HASH list into the node of a user HASH list; fourthly, receiving a data packet of a data type and unpacking the data packet to obtain the mobile phone IP address of a user to which the data packet belongs; and finally, searching for the user HASH list by using the mobile phone IP address as a keyword to obtain the information of the user to which the data packet belongs so as to correlate the flow and the user information. The method and the system can be applied to the system which is required to acquire the correlation of the network flow and the user.
Owner:BEIJINGNETENTSEC
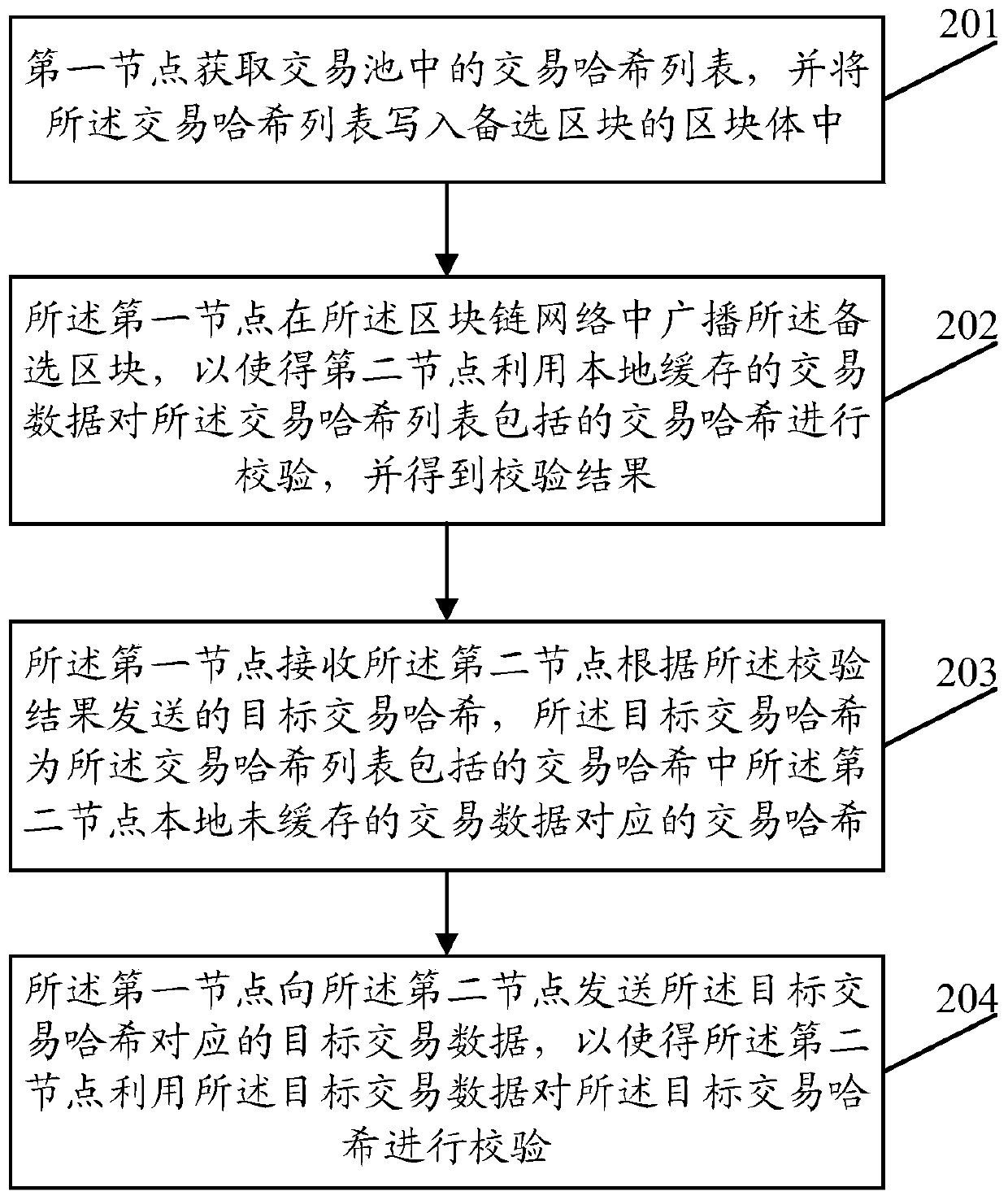
Data processing method and device, node equipment and computer storage medium
PendingCN111130801AAchieve compressionReduce consumptionUser identity/authority verificationTransaction dataPool
The embodiment of the invention provides a data processing method and device, node equipment and a computer storage medium. The method comprises the following steps: a first node acquires a transaction hash list in a transaction pool, writes the transaction hash list into the block body of the alternative block, and broadcasts the alternative block in a block chain network, so that a second node of the block chain network uses locally cached transaction data to verify a transaction hash included in the transaction hash list and obtains a verification result, the first node receives a target transaction hash sent by the second node according to the verification result, wherein the target transaction hash is a transaction hash corresponding to transaction data which is not cached locally bya consensus node in the transaction hash included in the transaction hash list; therefore, the first node can send the target transaction data corresponding to the target transaction hash to the second node, so that the second node verifies the target transaction hash by using the target transaction data, the network resource consumption can be reduced, and the consensus efficiency and the servicethroughput are improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for distinguishing RTP/RTCP flow capacity
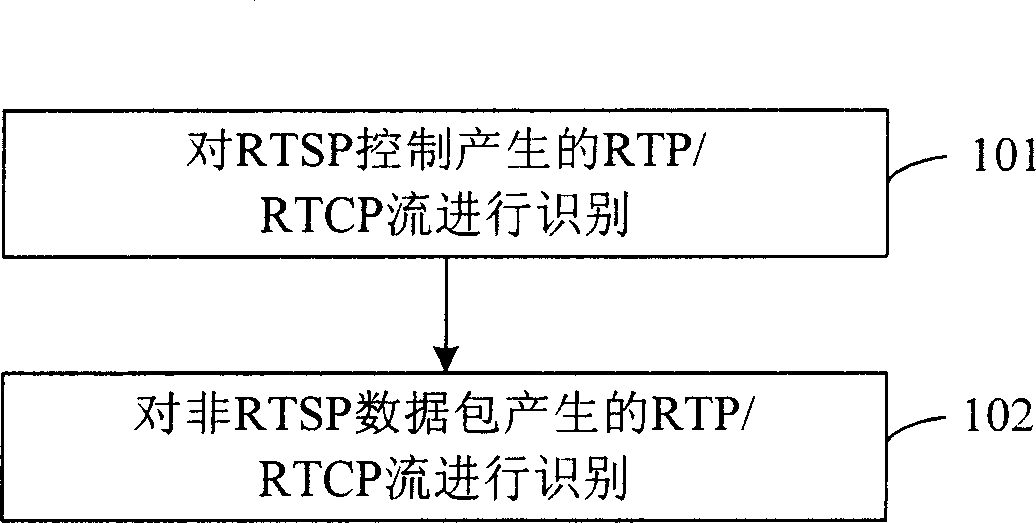
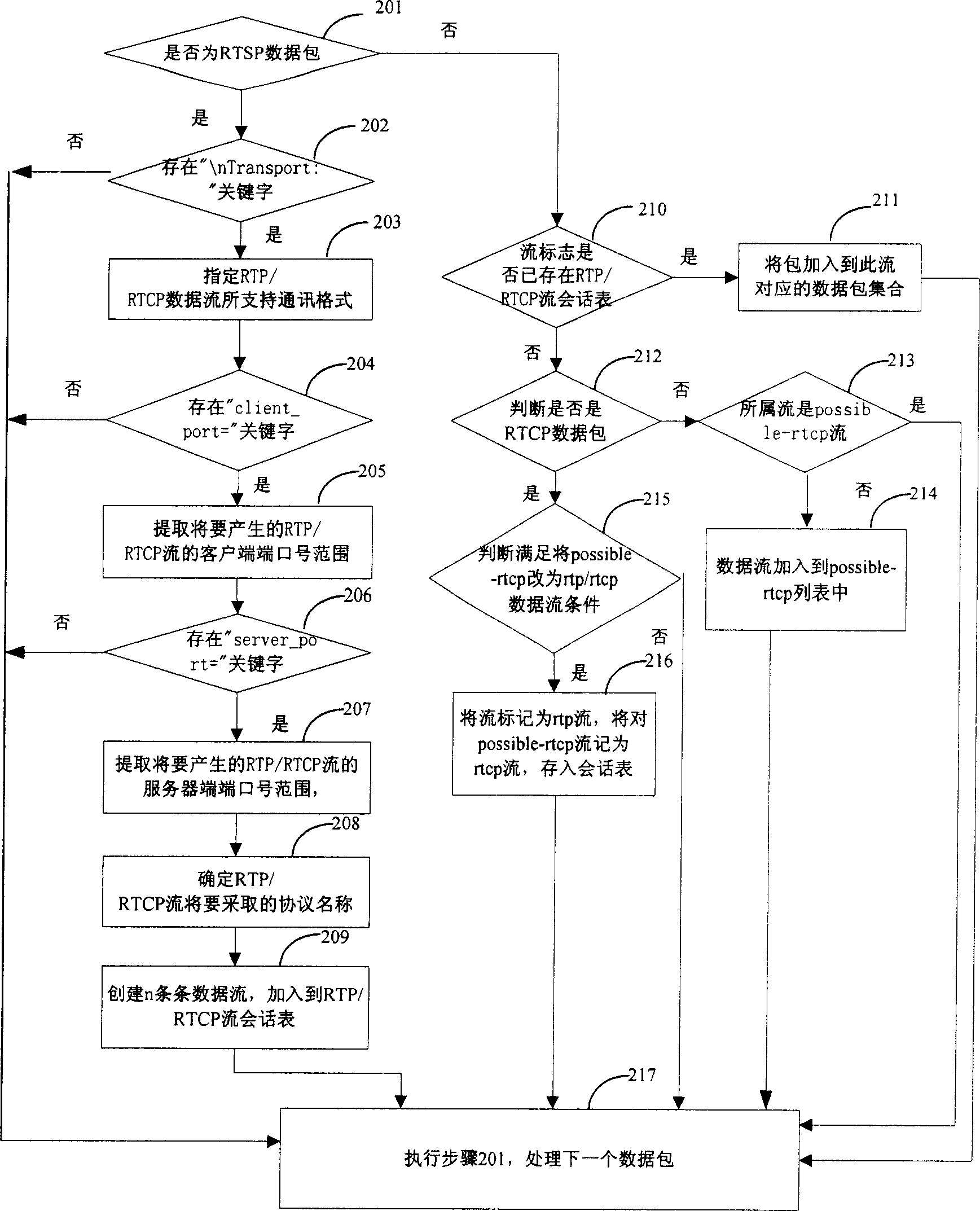
InactiveCN1909489ASimple processImprove scalabilityData switching networksSpecial data processing applicationsTraffic capacityNetwork packet
The invention relates to a method for recognizing RTP / RTCP flux, based on the protocol character and correlation operation, wherein said method comprises: A, recognizing the RTP / RTCP stream generated by RTSP control; B, recognizing the RTP / RTCP stream generated by non-RTSP data pack. For RTCP pack, the invention can only analyze the port information and one byte at fixed position of load that the second byte, to obtain the result, with low consumption; for RTP pack, only recognizing based on the IP and the port number and the maintained RTCP stream information; since the number of RTCP and RTP streams are only relative to the parallel RTP / RTCP conversation number of chain, but not relative to the band width capacity of chain, it has low consumption, and better expanding property. And it uses Hash list to reduce the consumptions on search, refresh and delete of RTP / RTCP stream; and it has low error report rate and leakage rate, since the application clients use random port.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
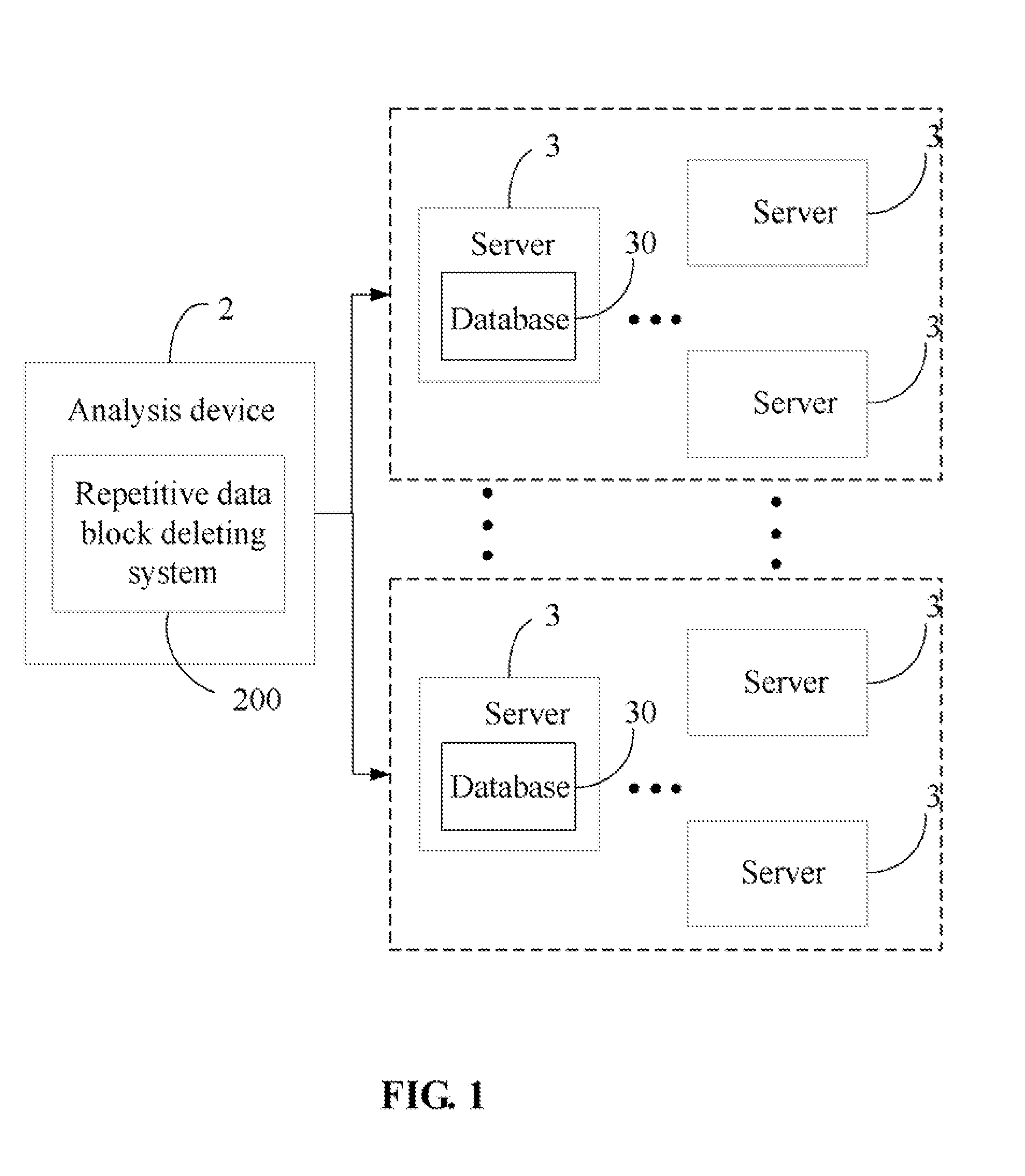
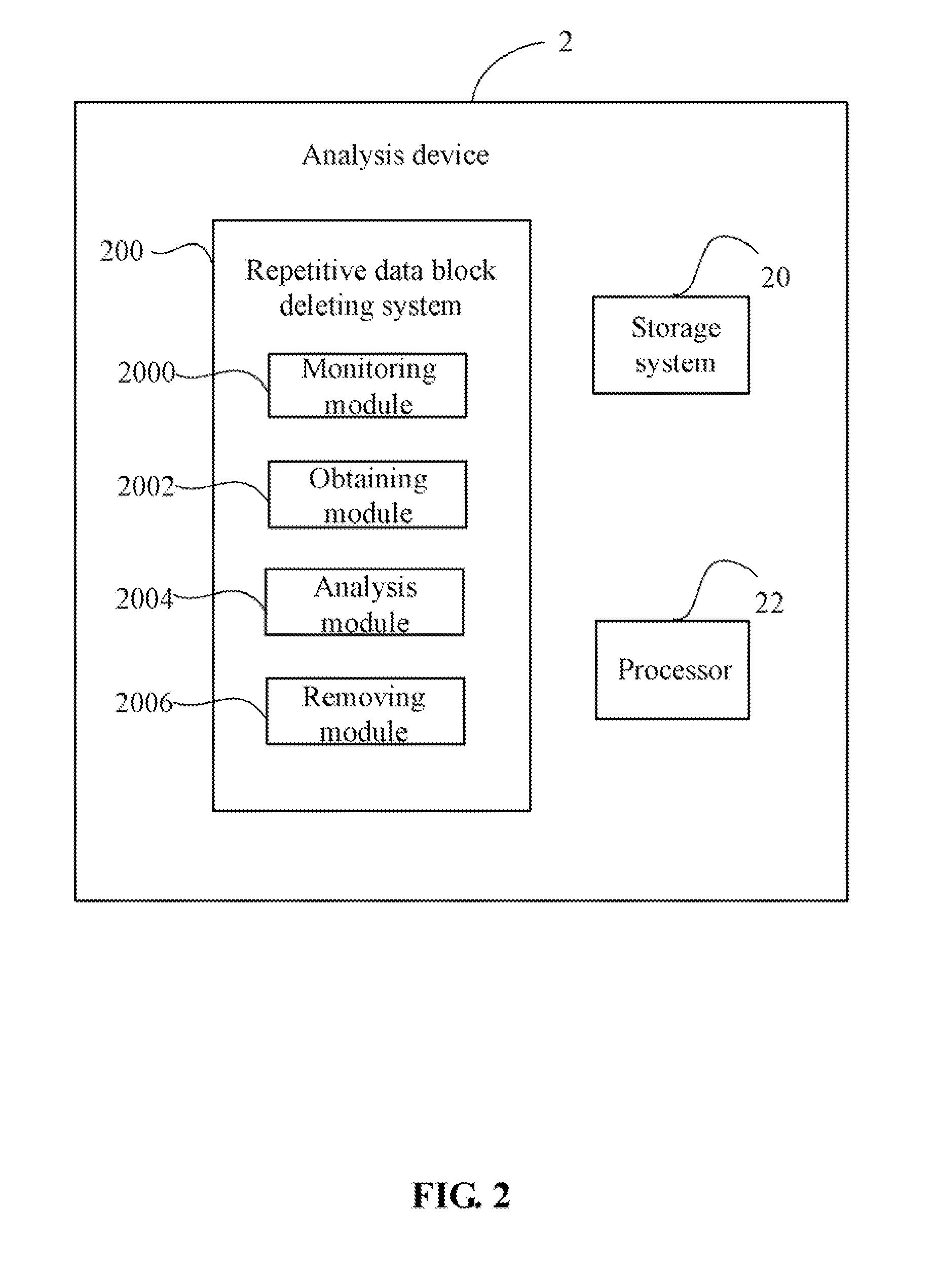
Repetitive data block deleting system and method
InactiveUS20140164339A1Input/output to record carriersDigital data processing detailsHash listOperating system
Owner:SHENZHEN AIRDRAWING TECH SERVICE CO LTD
Document management with verifiable time-of-archive capability
ActiveUS8892532B2Digital data processing detailsUnauthorized memory use protectionThird partyElectronic document
A document archiving and retrieval system enables third parties to verify that an electronic document had been archived on a particular date and time. For each document to be archived, a hash function generates a digital fingerprint of the document, and inserts it into a hash list file, together with an indicator of the location of the file in the archive. The hash list file is submitted to an electronic time stamping authority to obtain a corresponding digital time stamp. Upon request, authentication of the hash list file with the digital time stamp, and verification that the current hash of the file matches that in the hash list file proves that the document was archived on the date indicated by the digital time stamp, and had not subsequently been altered.
Owner:AVAGO TECH INT SALES PTE LTD
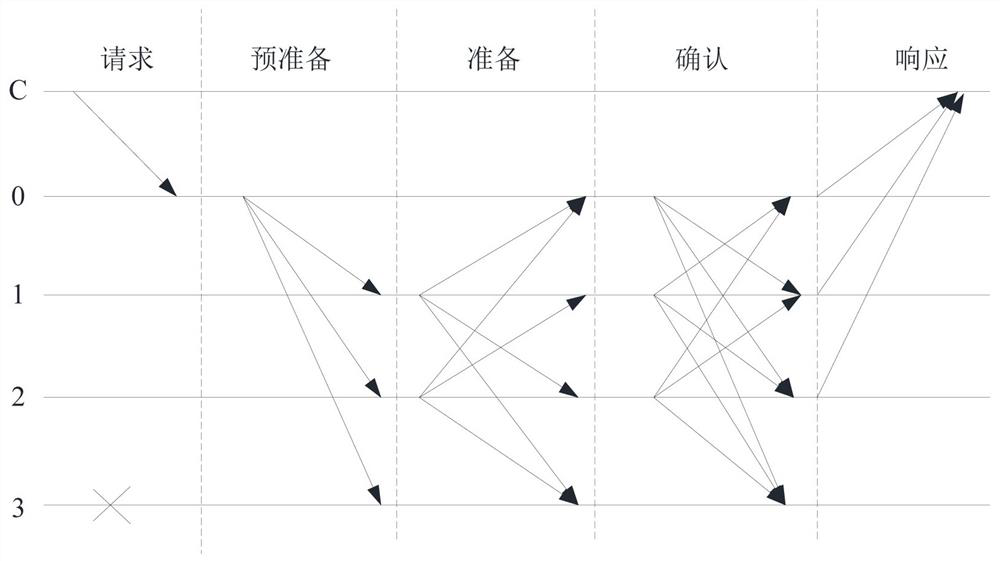
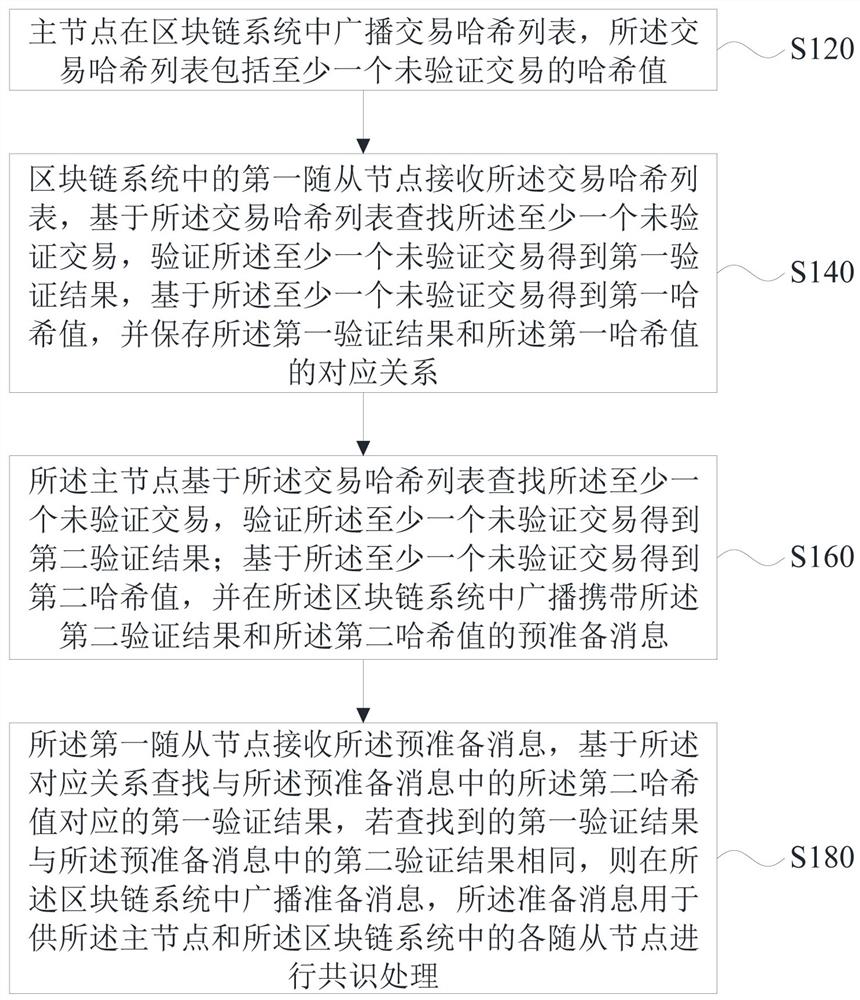
Consensus method and device and block chain system
ActiveCN113541968ASpeed up the consensus processImprove consensus efficiencyFinanceUser identity/authority verificationEngineeringFinancial transaction
The embodiment of the invention provides a consensus method and device and a block chain system. A master node directly broadcasts a transaction hash list comprising a hash value of at least one unverified transaction in the system, so that the slave node and the master node synchronously verify the at least one unverified transaction, and the slave node stores a first verification result obtained by verification and a first hash value of the at least one unverified transaction. And the master node carries an obtained second verification result and a second hash value of at least one unverified transaction in a preparation message after verification is completed, and broadcasts the preparation message, so that the slave node searches the first verification result based on the second hash value, and broadcasts the preparation message when the second verification result is the same as the searched first verification result, to enter a subsequent consensus stage to complete consensus processing. Thus, the master node and the slave node can synchronously verify the transaction needing to be linked in the consensus of this round, the consensus process is accelerated, and the consensus efficiency is improved.
Owner:CHINA ACADEMY OF INFORMATION & COMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com