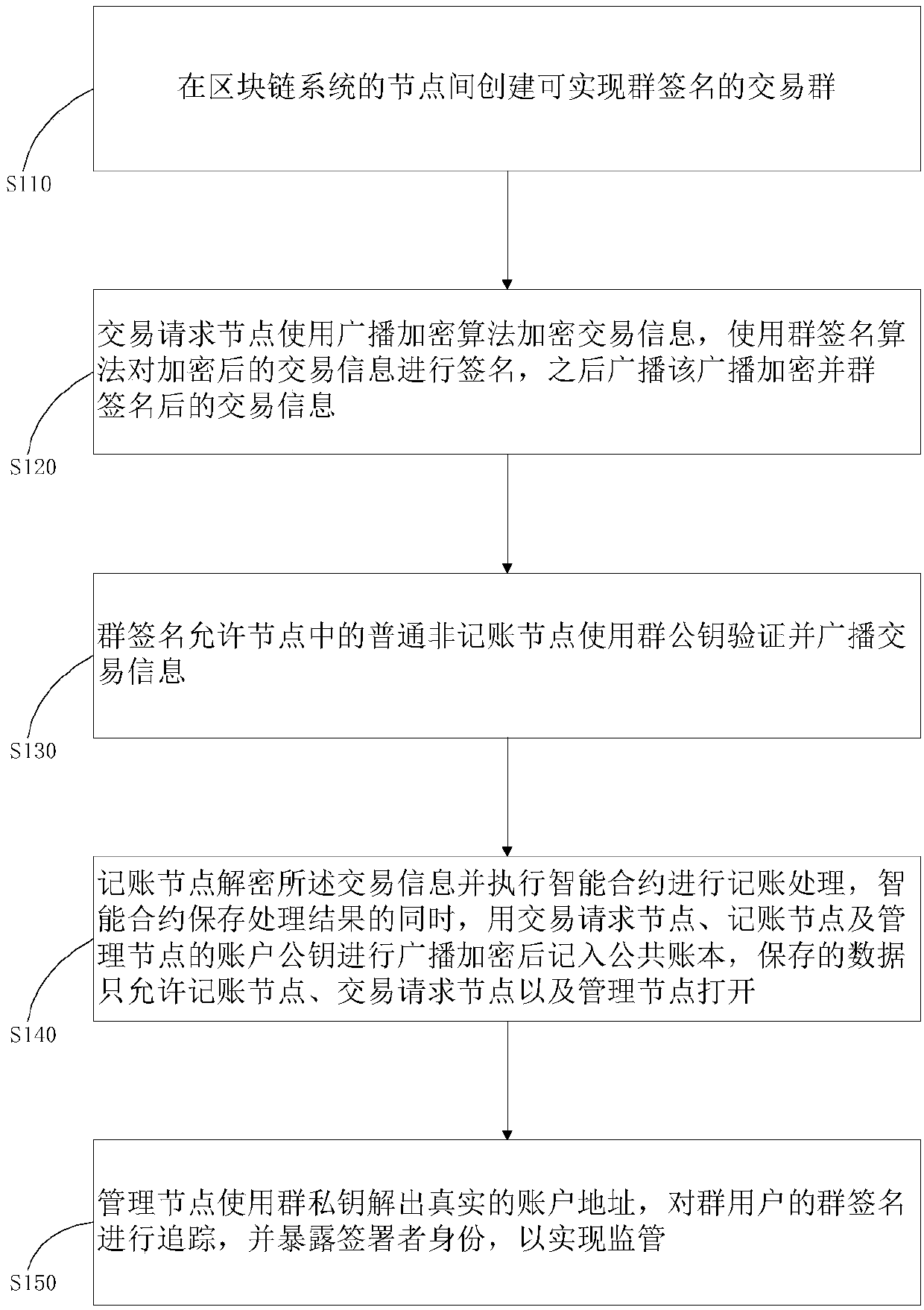
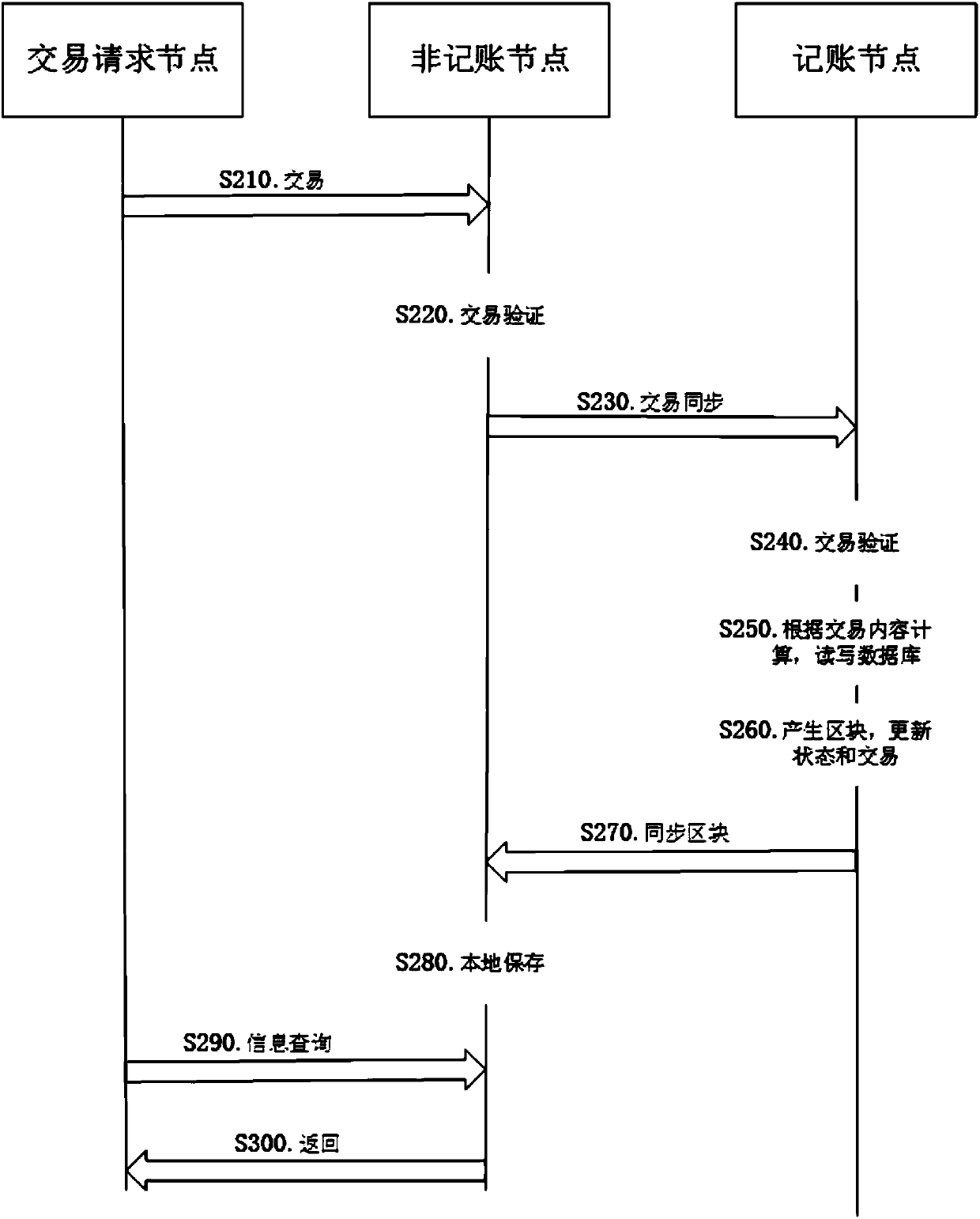
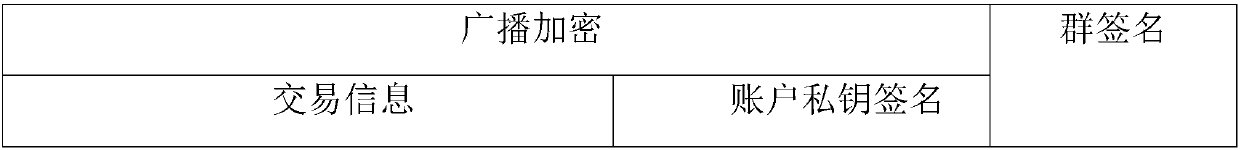
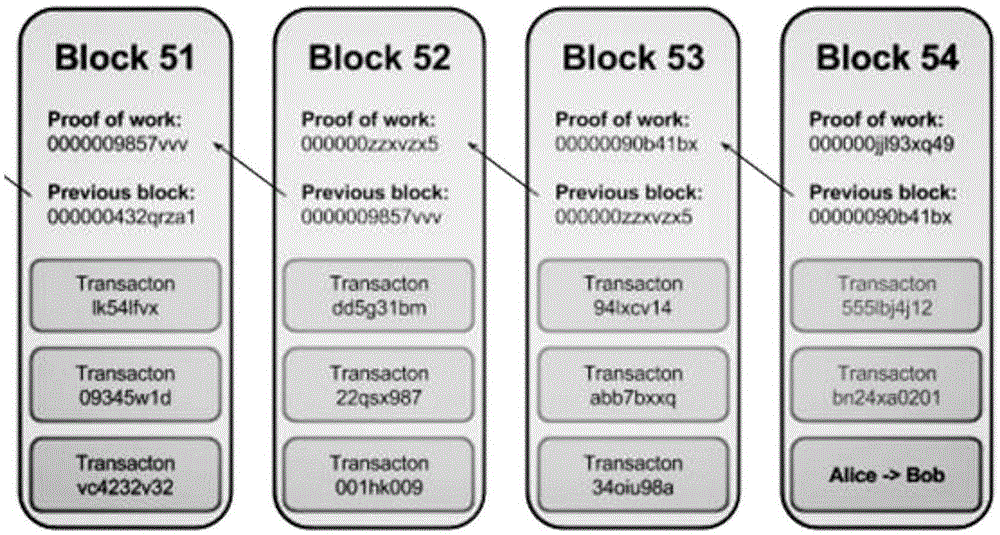
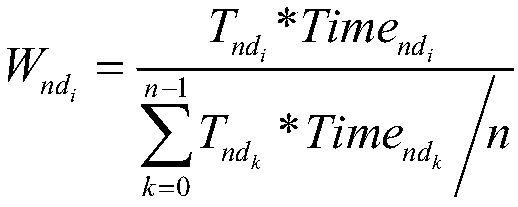Patents
Literature
1064 results about "Chain system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
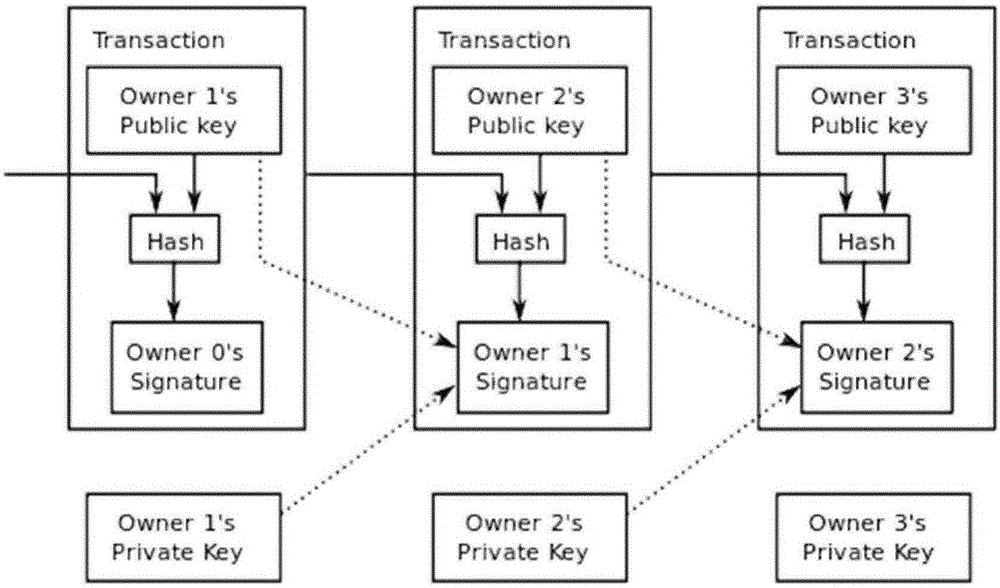
Chain System. The Chain System is a feature where a player's stats are boosted if specific players are present in the match. The system also serves to expand the character's relationship with other characters.
Method and system for privacy protection of block chain transaction
ActiveCN107911216ARealize regulationSupport reviewKey distribution for secure communicationFinancePublic accountPrivacy protection
The invention provides a method and system for privacy protection of block chain transaction. The method comprises: a transaction group is established between nodes of a block chain system, a user establishes an account at a node, and the node generates public and private key information of the account and then joining of a group is carried out; a transaction request node encrypts transaction information by using a broadcast encryption algorithm, carries out group signature processing on the encrypted transaction information, and then broadcasts the transaction information after broadcast encryption and group signature processing; a common non-account-recording node verifies the transaction information and then broadcasts the transaction information, an account-recording node decrypts thetransaction information and performs an intelligent contract to carry out account recording, broadcast encryption is carried out and then the information is recorded into a public account book, wherein the stored data are only allowed to be opened by the account-recording node, the transaction request node and an administration node. With the broadcast encryption algorithm and group signature technology, a privacy protection problem in the block chain system is solved and the traceability of the transaction is ensured.
Owner:JUZIX TECH SHENZHEN CO LTD +1
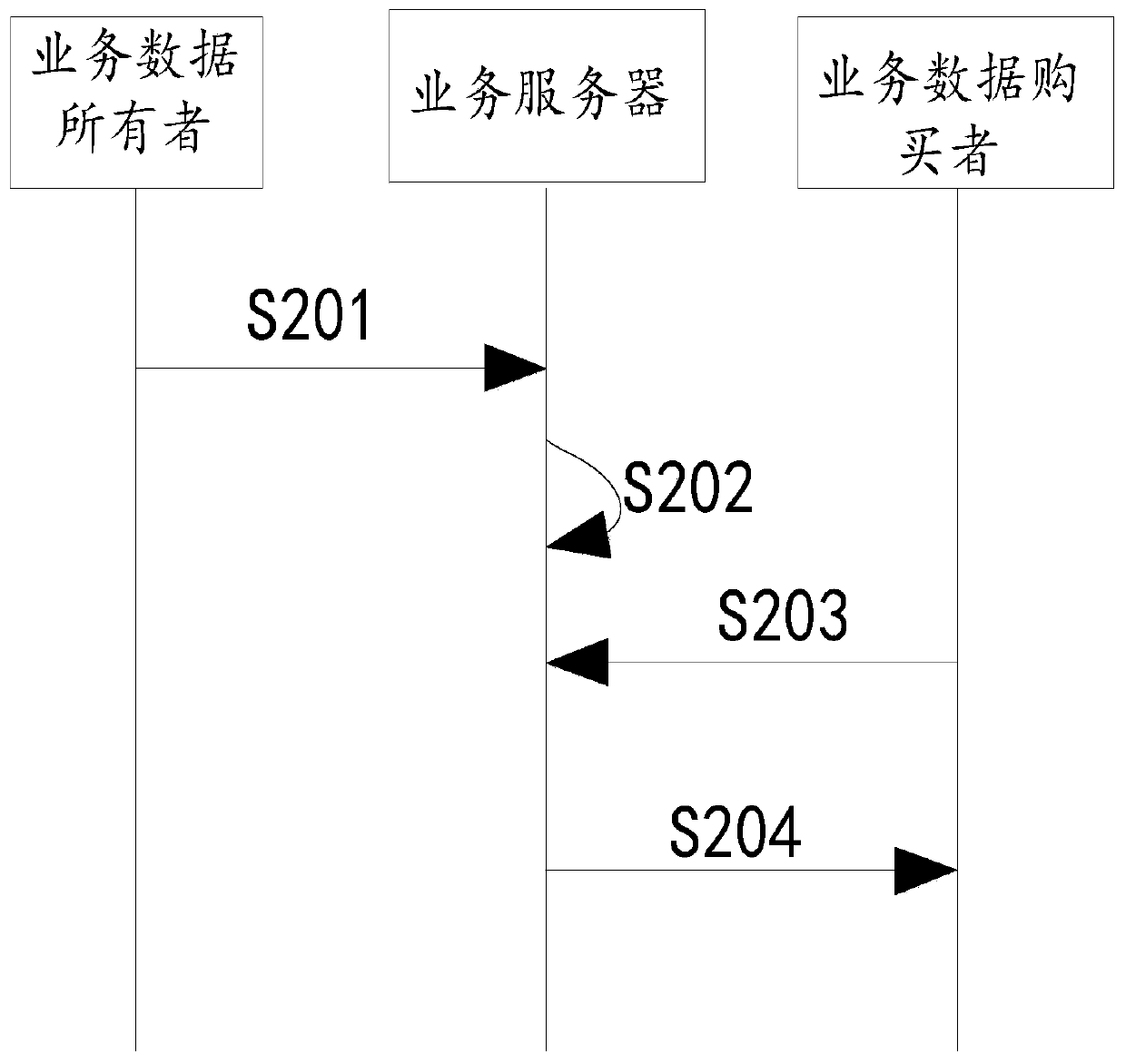
Block chain-based credit investigation data sharing and trading system
InactiveCN106651346APerfect risk control levelSolve imperfectionsPayment protocolsBuying/selling/leasing transactionsRisk ControlData provider
The invention relates to a block chain-based credit investigation data sharing and trading system. The credit investigation data sharing and trading system comprises at least two P2P network nodes; each network node comprises an underlying block chain system and a credit investigation data sharing platform running in the underlying block chain system; and the credit investigation data sharing platform comprises a data sharing module, a data query trading module, a member management module and a block chain adaption layer. According to the credit investigation data sharing and trading system, a trusted credit investigation data sharing and trading platform is established by using a block chain technology; and special data sharing mechanism, data query mechanism and data trading mechanism are used, so that credit investigation data owners and credit investigation data demanders can be attracted to perform use, credit investigation data providers can perform data trading under the condition that data is protected, and credit investigation data queriers can obtain the credit investigation data to improve risk control levels of themselves.
Owner:上海凯岸信息科技有限公司
Method, System and Program Product for Tracking and Securing Transactions of Authenticated Items over Block Chain Systems.
InactiveUS20160217436A1Tracking chainRead-only accessPayment circuitsProtocol authorisationDigital currencyTransaction data
A method, system and program product comprise accessing a system having a digital currency infrastructure. At least three user addresses are created. Rules for filtering acceptable transactions on the system are prepared in form of recursion base and recursion steps. Items are initiated on the system according to the defined rules. The assets transaction data is transferred to the system wherein the system links asset data and the parties to the transaction according to the said rules.
Owner:BRAMA DROR SAMUEL
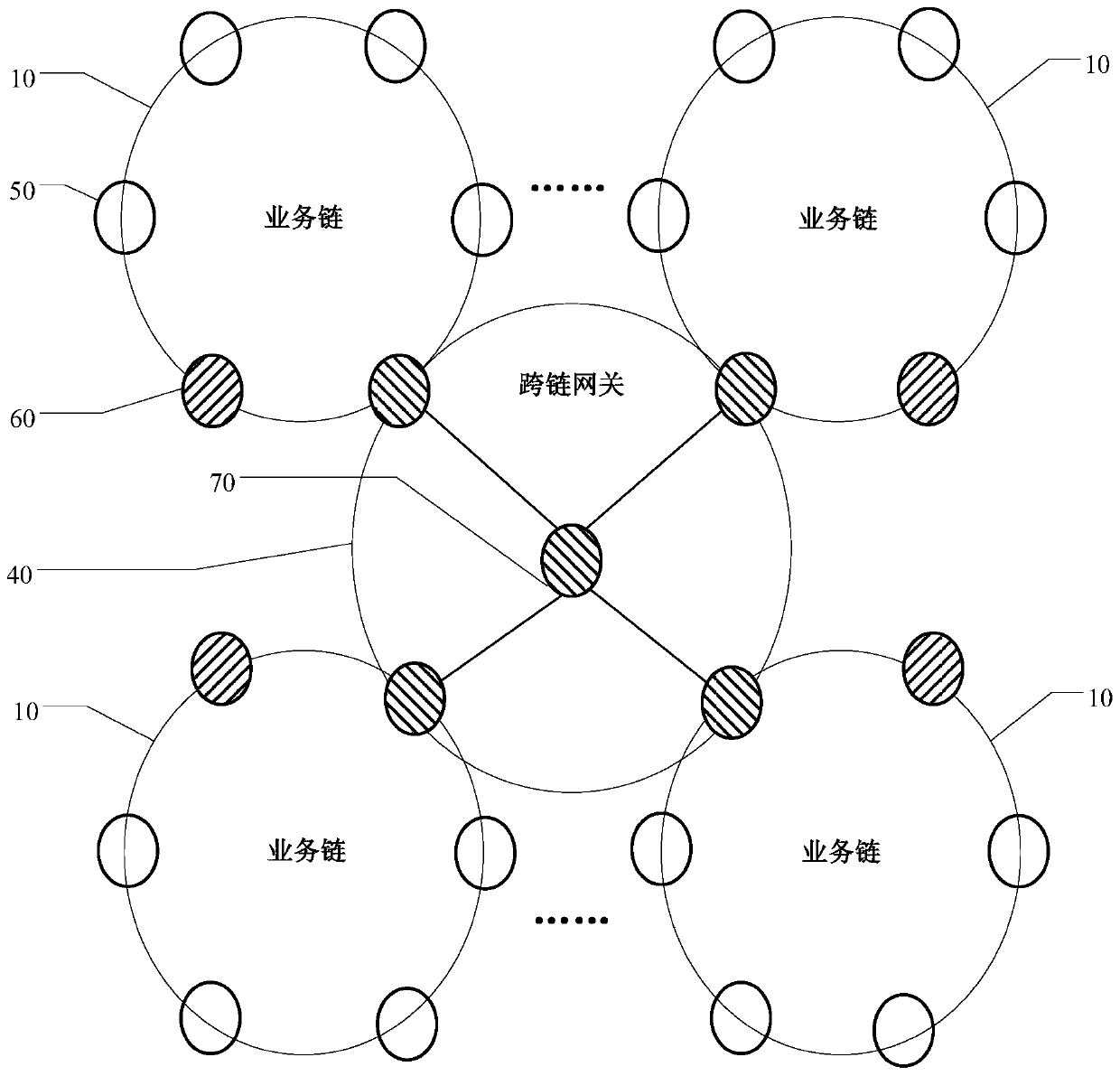
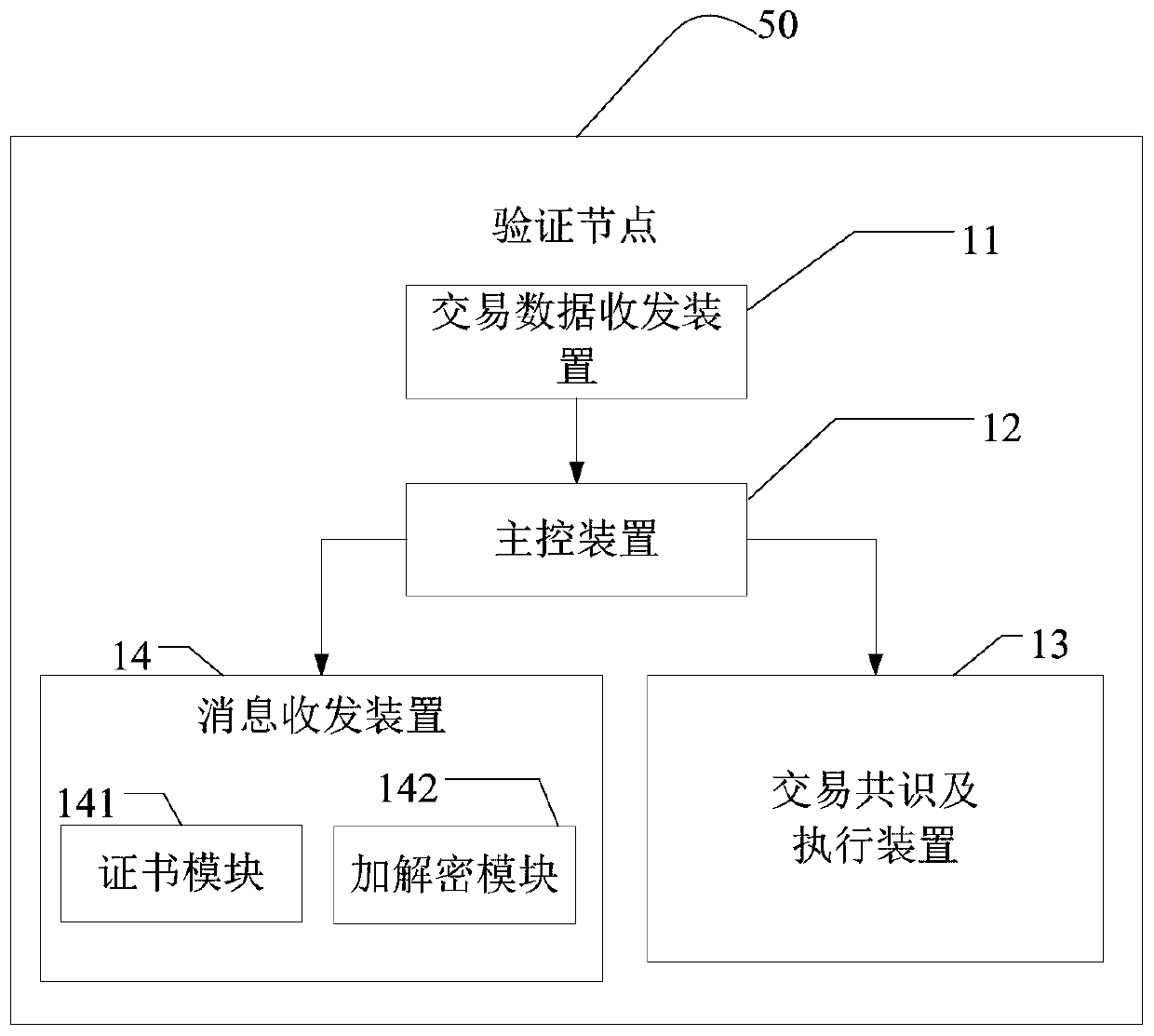
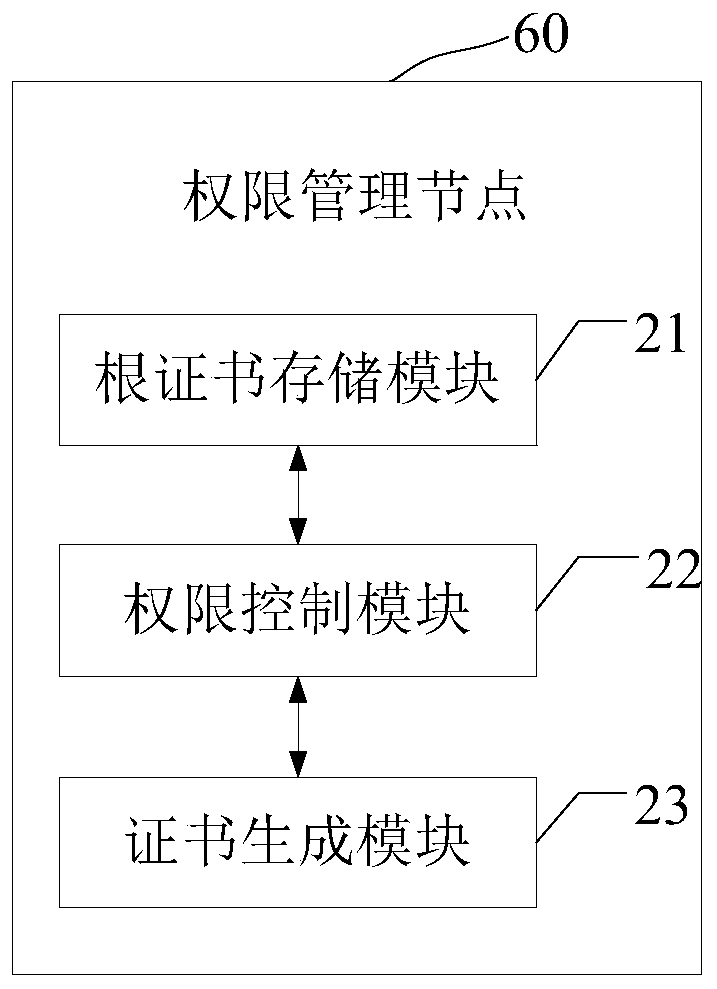
Blockchain-based cross-chain interconnection method, device and system
ActiveCN110266655AReach fusionSolve information silosFinanceUser identity/authority verificationInformation processingError processing
The invention provides a blockchain-based cross-chain interconnection method, a blockchain-based cross-chain interconnection system, computer equipment and a computer readable storage medium, and relates to the technical field of information processing. The system comprises a cross-chain gateway node and a plurality of service chains, each service chain comprises an authority management node, a gateway node and a plurality of verification nodes, and the gateway node in the plurality of service chains and the cross-chain gateway node form a cross-chain gateway; and the cross-chain gateway is used for realizing message format standardization and a cross-chain conversion protocol among the plurality of service chains so as to promote adaptation and forwarding of cross-chain messages, support error processing of request message timeout during cross-chain interconnection and finally realize mutual access and intercommunication of cross-chain data. Mutual access among the alliance chains of a plurality of different block chain technologies is achieved by introducing the bridging gateway chain, the problem of information island among a plurality of block chain systems is solved, and application and popularization of the block chain technology can be accelerated.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
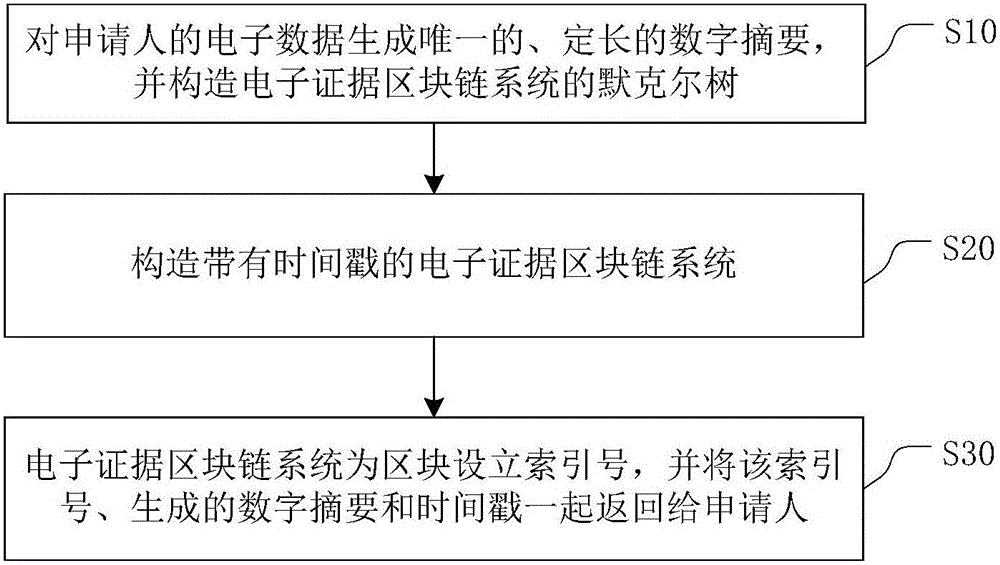
Method and system for constructing electronic evidence
ActiveCN105790954AReduce identification costsImprove objectivityUser identity/authority verificationTimestampChain system
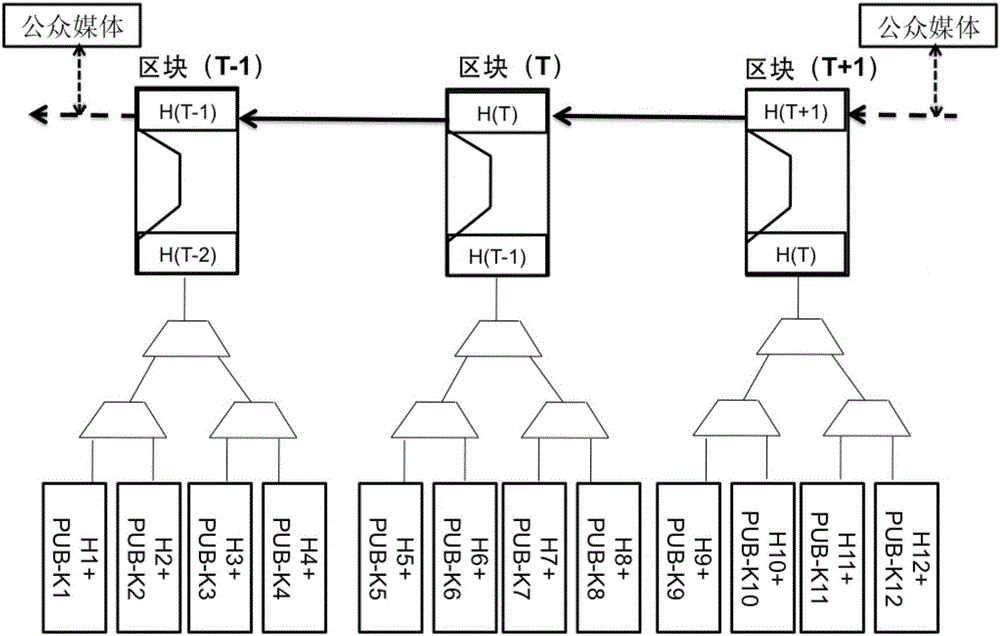
The invention relates to a method for constructing an electronic evidence. The method specifically comprises the following steps: generating a unique length-fixed digital abstract for electronic data of an applicant, and constructing a Merkle tree of an electronic evidence block chain system; constructing the electronic evidence block chain system with a timestamp; and setting an index number for a block by the electronic evidence block chain system, and returning the index number, the generated digital abstract and the timestamp to the applicant together. According to the method and the system disclosed by the invention, all participating parties can construct jointly, maintain jointly and supervise jointly, thereby meeting the right to know and the supervision right of each party; the identification cost of the electronic evidence is reduced, the identification efficiency is improved, and the objectivity and the reliability of the electronic evidence are enhanced.
Owner:BUBI BEIJING NETWORK TECH CO LTD
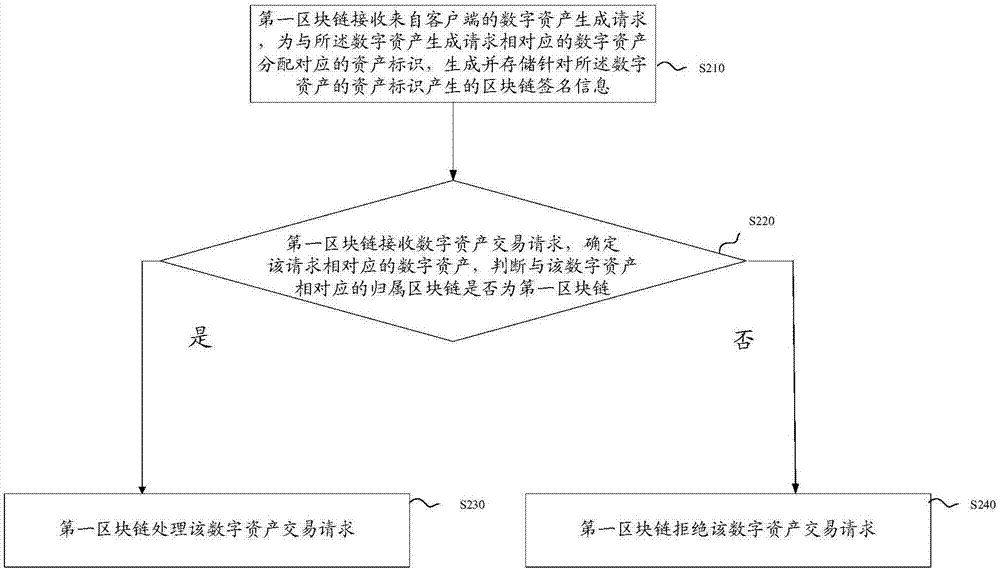
Block chain system-based digital asset transaction method and block chain system
InactiveCN107392608AAchieve concurrencyImprove securityPayment protocolsSecuring communicationFinancial transactionTree shaped
The invention discloses a block chain system-based digital asset transaction method and a block chain system. The block chain system is a tree-shaped distributed block chain system including a plurality of levels of block chains. The method comprises the following steps that: a first block chain receives a digital asset transaction request from a client, and determines digital assets corresponding to the digital asset transaction request; whether an attribution block chain corresponding to the digital assets is a first block chain is judged; if the attribution block chain corresponding to the digital assets is the first block chain, the first block chain processes the digital asset transaction request; and if the attribution block chain corresponding to the digital assets is not the first block chain, the first block chain rejects the digital asset transaction request, wherein the attribution block chain corresponding to the digital assets is a block chain that generates the digital assets. The method is especially suitable for the transactions of one-time one-use digital assets, wherein the digital assets can be only used once; and moreover, the method can also realize a cross-chain transactions between the digital assets, and the digital assets are corresponding to different attribution block chains before and after the cross-chain transactions are executed, and therefore, the security of the assets can be improved.
Owner:北京博晨技术有限公司
Block chain generation method, data verification method, nodes and system
ActiveCN107807951AReduce occupancyIncrease profitUser identity/authority verificationDigital data protectionData validationData set
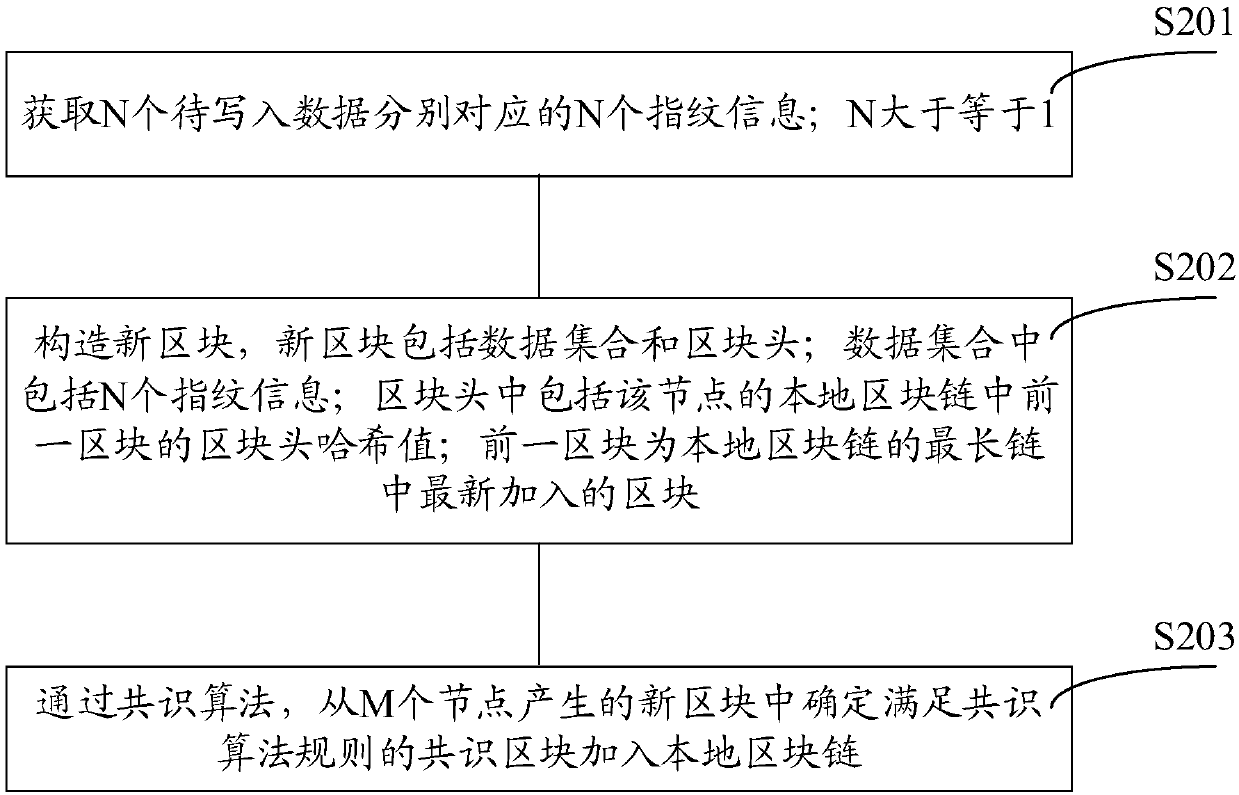
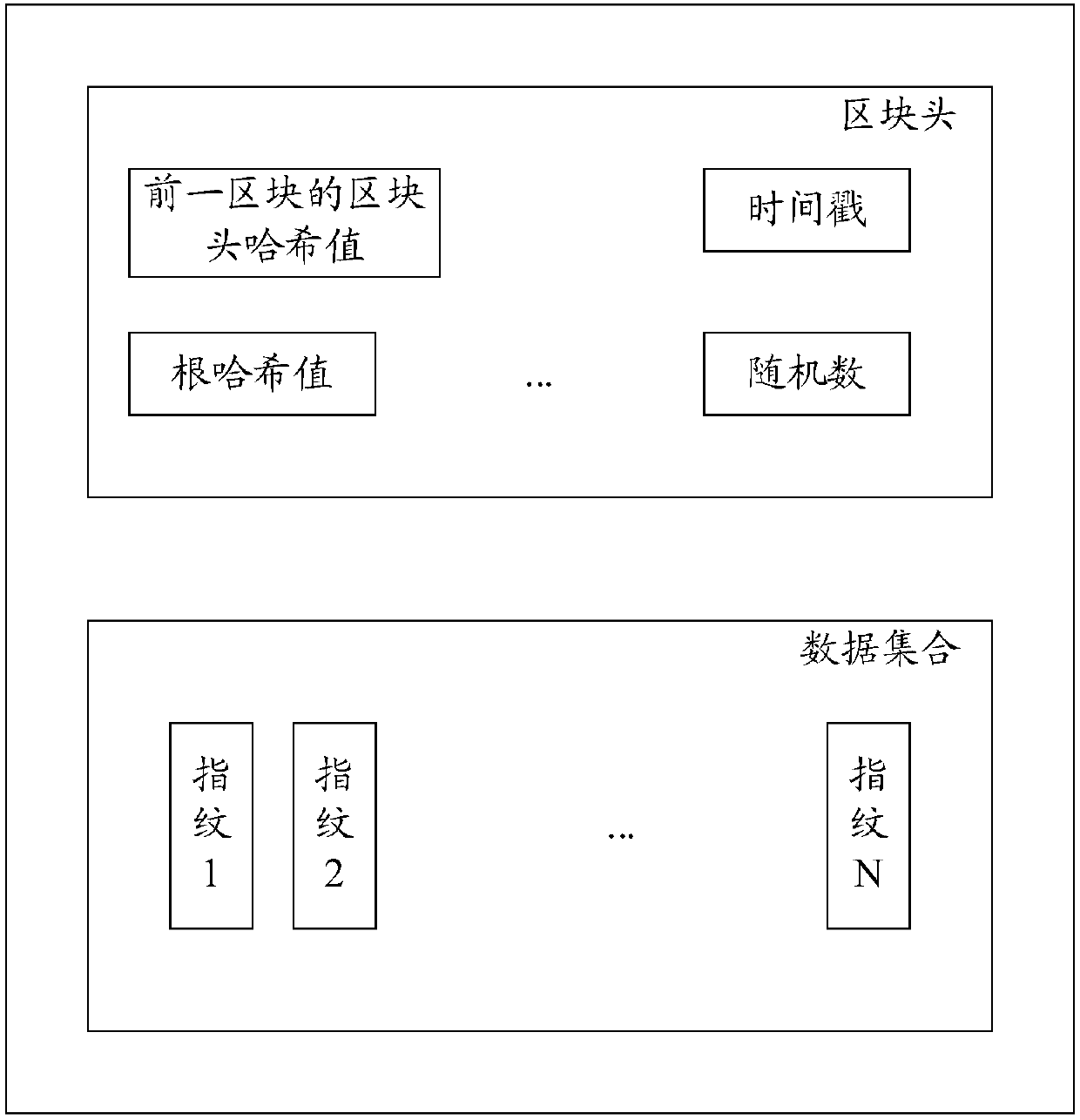
The invention discloses a block chain generation method, a data verification method, nodes and a system. The block chain generation method is used for increasing the utilization rate of a storage space and is applied to a block chain system containing M nodes. According to each of the M nodes, the block chain generation method comprises the steps that N pieces of fingerprint information corresponding to N pieces of to-be-written data are acquired, wherein N is greater than or equal to 1; a new block is constructed, wherein the new block comprises a data set and a block head; the data set comprises N pieces of fingerprint information; the block head comprises a Hash value of a block head of a previous block in a local block chain of the node, wherein the previous block is a newly added block in a longest chain of the local block chain; and through a consensus algorithm, a consensus block is determined from new blocks generated by M nodes and is added into the local block chain. In thisway, the storage space occupied by other information of non-to-be-written data in transaction information is saved, and therefore the utilization rate of the storage space and is increased.
Owner:UNION MOBILE PAY
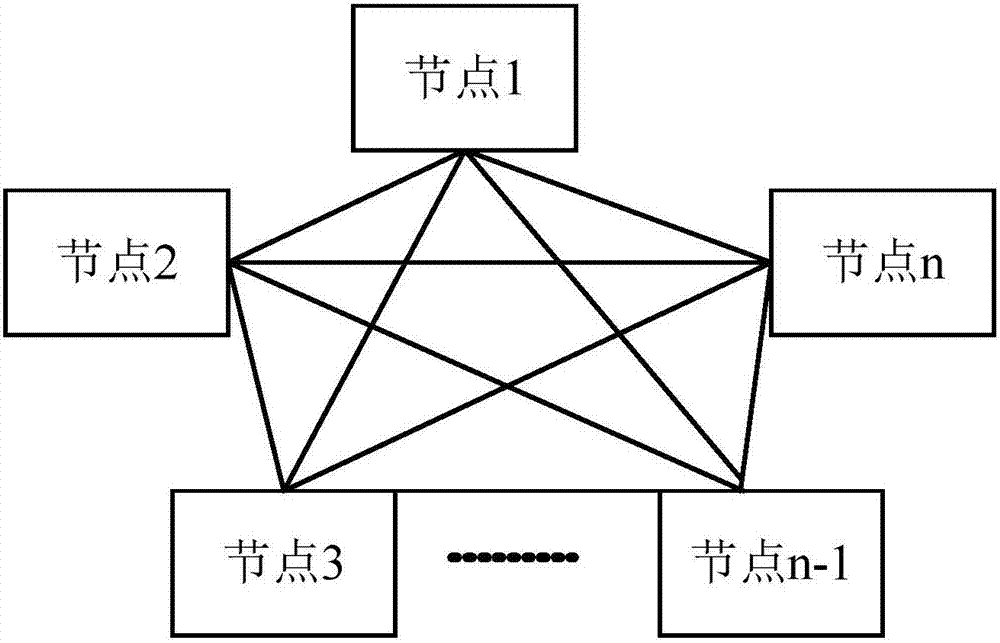
Block chain bottom consensus mechanism and block chain system based on block chain bottom consensus mechanism
InactiveCN107341660AReduce the concentration of computing powerNo centralization riskPayment protocolsPayment circuitsData synchronizationEqual probability
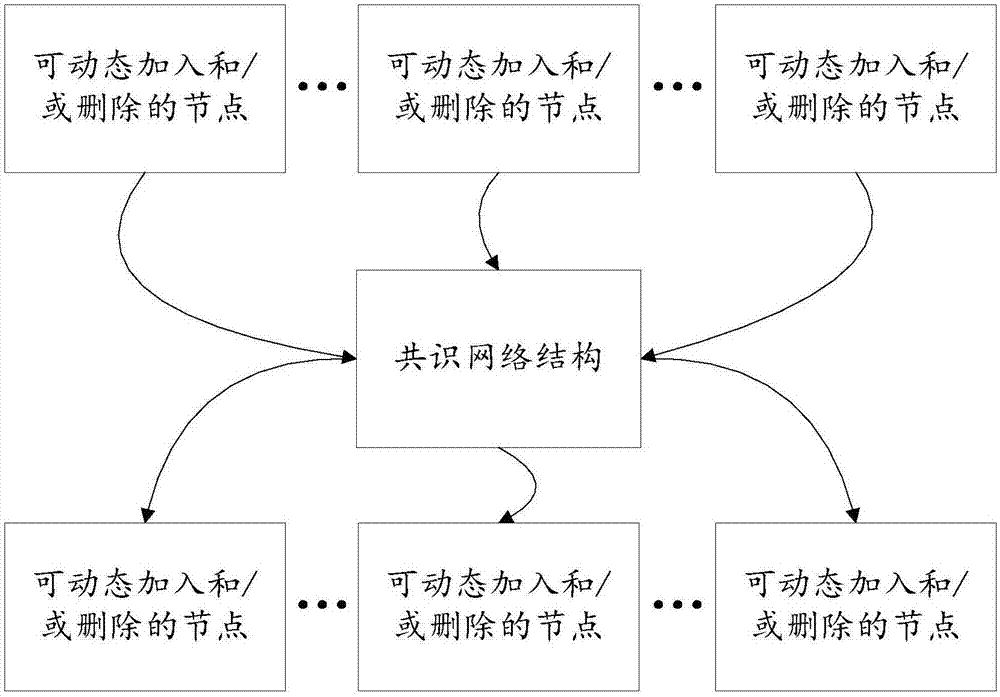
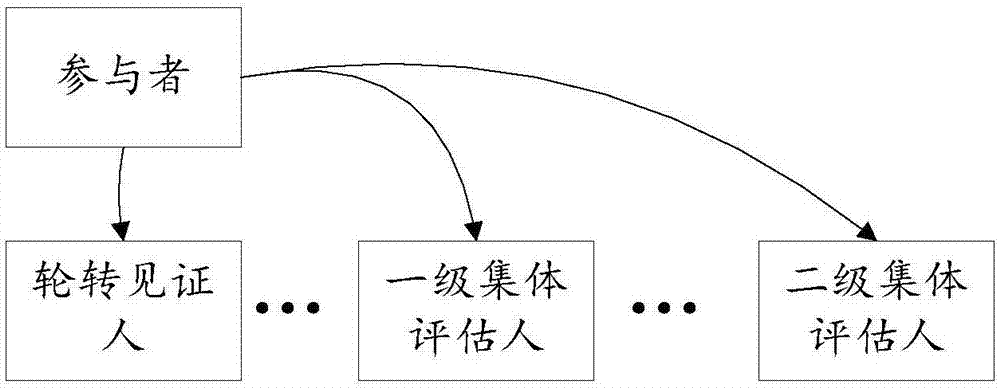
The invention discloses a block chain bottom consensus mechanism and a block chain system based on the consensus mechanism. The block chain bottom consensus mechanism comprises a consensus network structure, participants, a first protocol, a second protocol, and a third protocol; the consensus network structure is used for providing a carrier for transmitting and synchronizing data; the participants are used for participating in data storage and evaluation in the consensus network structure; the first protocol is used for voting for specific participants based on the rotate account sub-protocol and generating a new block when equal probability rotating; the second protocol is used for providing group voting or estimate for all participants holding tokens or digital shares based on the group estimate consensus sub-protocol and generating an extra new block; and the third protocol is used for connecting with each consensus mechanism network based on the gear consensus routing sub-protocol. According to the invention, the characteristics of the block chain data structure and the point to point network communication are combined to realize the secure, efficient, decentralized and application scenario flexible data synchronization consensus.
Owner:唐盛物联技术有限公司
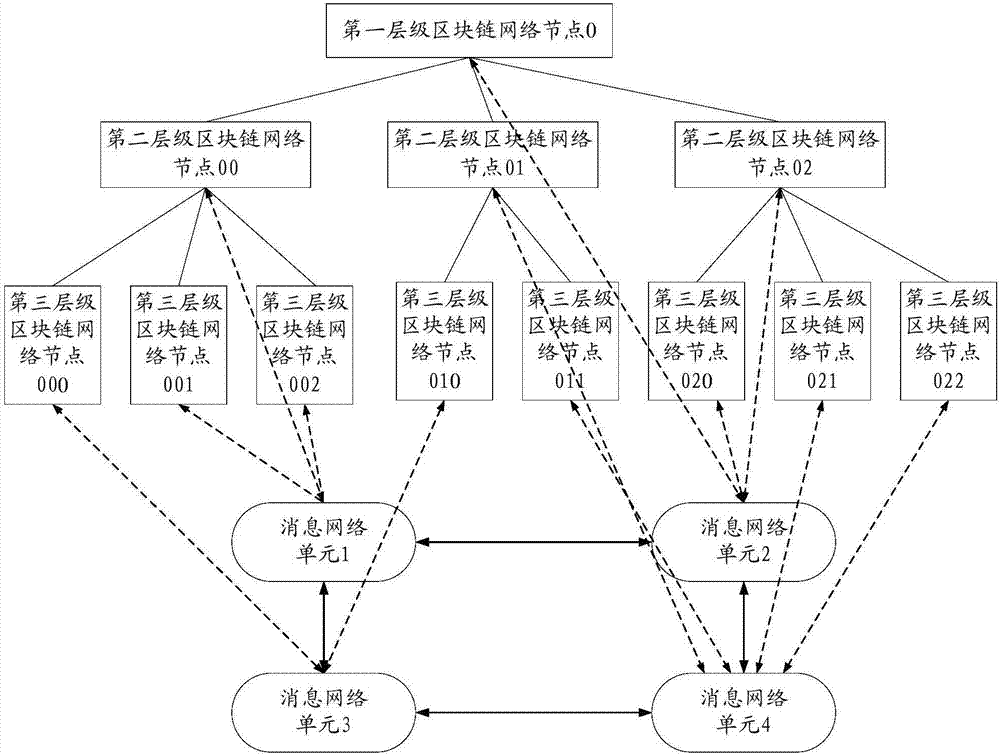
Network transaction method and apparatus based on block chain system
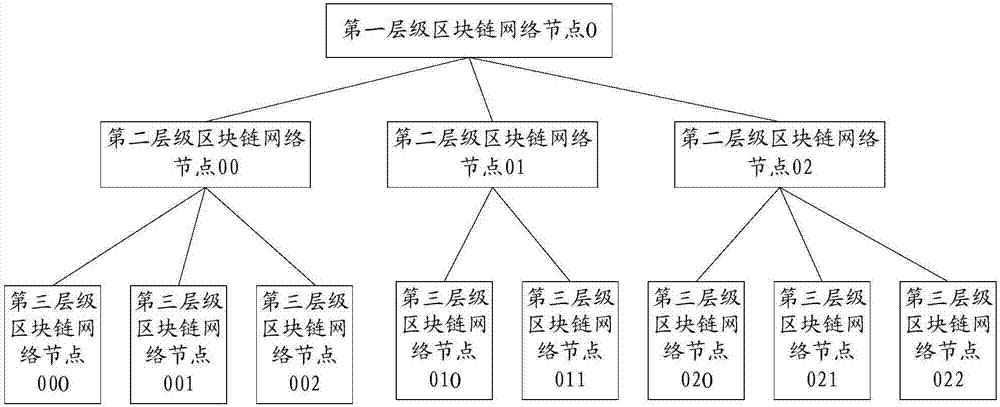
InactiveCN107239940AImprove transaction efficiencyEasy to operatePayment protocolsPayment circuitsFinancial transactionChain network
The invention discloses a network transaction method and apparatus based on a block chain system. The network transaction method and apparatus based on a block chain system are used for reducing time consuming of transaction and improving concurrency. The block chain system includes multiple levels of block chain network nodes; and the multiple levels of block chain network nodes at least include a first block chain network node of the first transaction party for network transaction, and a second block chain network node of the second transaction party for network transaction. The network transaction method based on a block chain system includes the steps: the first block chain network node generates transaction information corresponding to the network transaction; the transaction information is sent to the second block chain network node of the second transaction party for network transaction; the first block chain network node and the second block chain network node use a consensus algorithm to reach a consensus for the transaction information; and the first block chain network node and the second block chain network node synchronously keep accounts for the network transaction corresponding to the transaction information for which the first block chain network node and the second block chain network node reach a consensus.
Owner:北京博晨技术有限公司
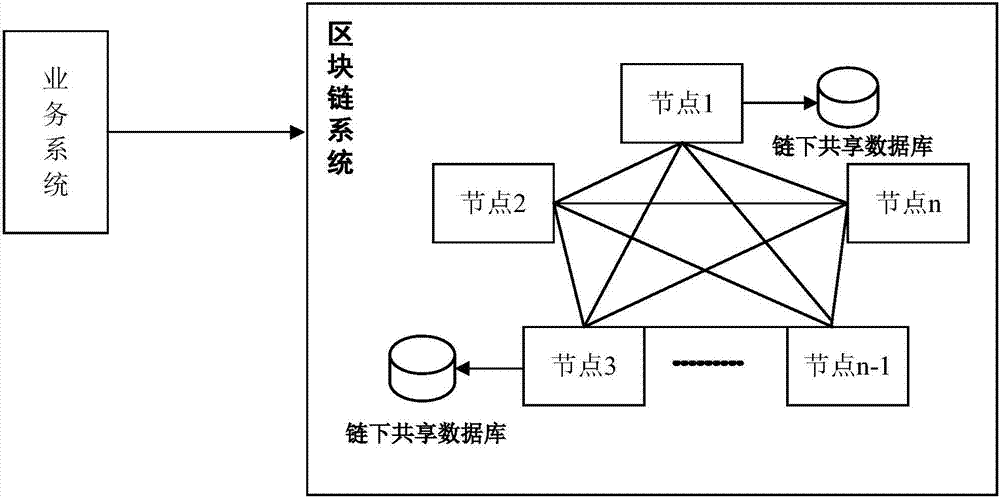
Service data chaining method and system based on block chain
The invention discloses a service data chaining method and a service data chaining system based on a block chain. The method is applied to a blockchain system, the system comprises at least one blockchain node, the method comprises the following steps: the blockchain node receives service structure data sent by a service server, and the service structure data comprises a service ID, a service association attribute, a service non-association attribute and a creator ID; the block chain node packages the service structure data into a first block; and after the block chain system verifies the first block successfully, the first block is linked. The process of the service data can be linked, the history of the service data corresponds through the ID of the service data in the block chain system, and the user can inquire the history information of the service.
Owner:BEIJING AIMORECE TECH CO LTD
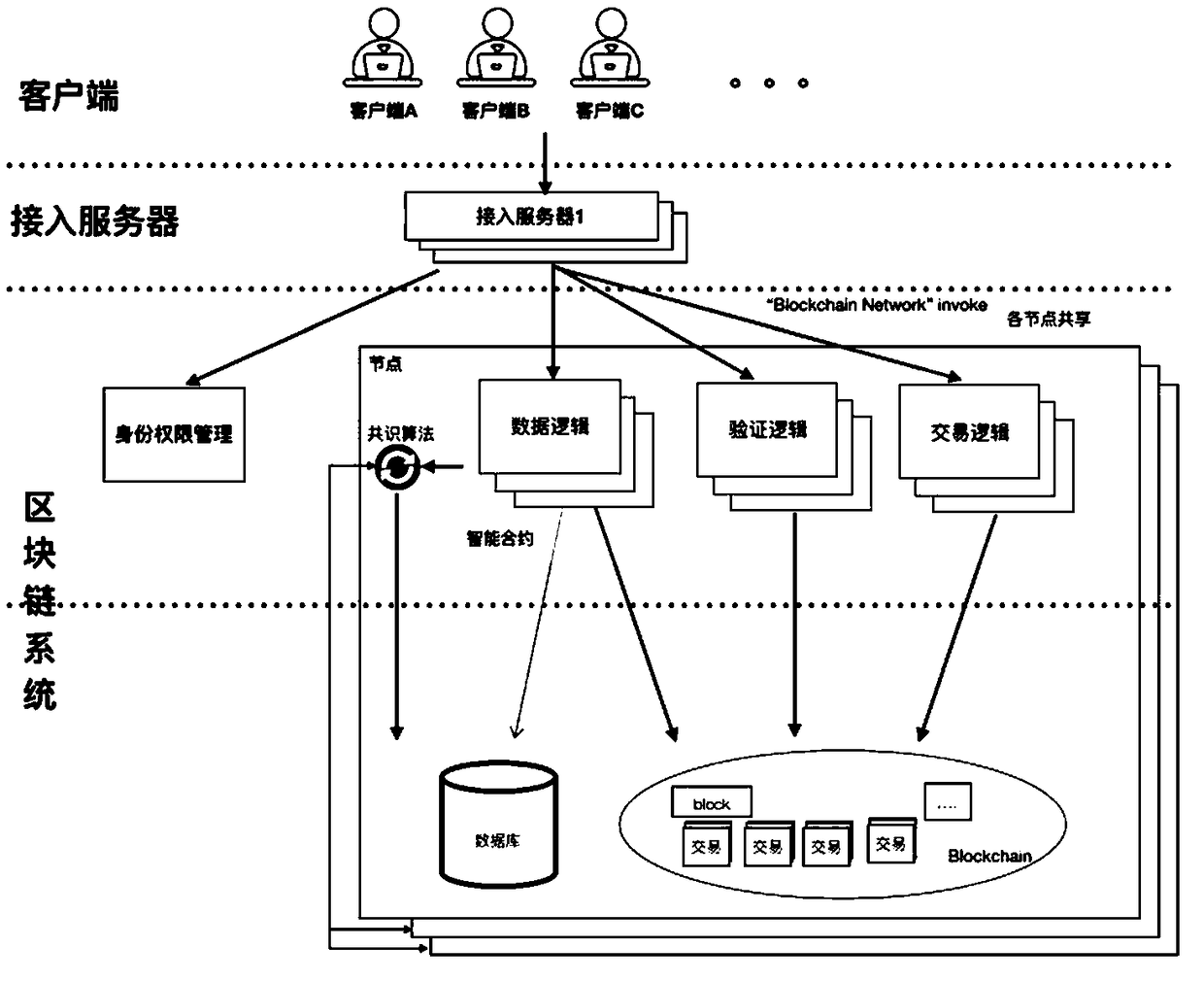
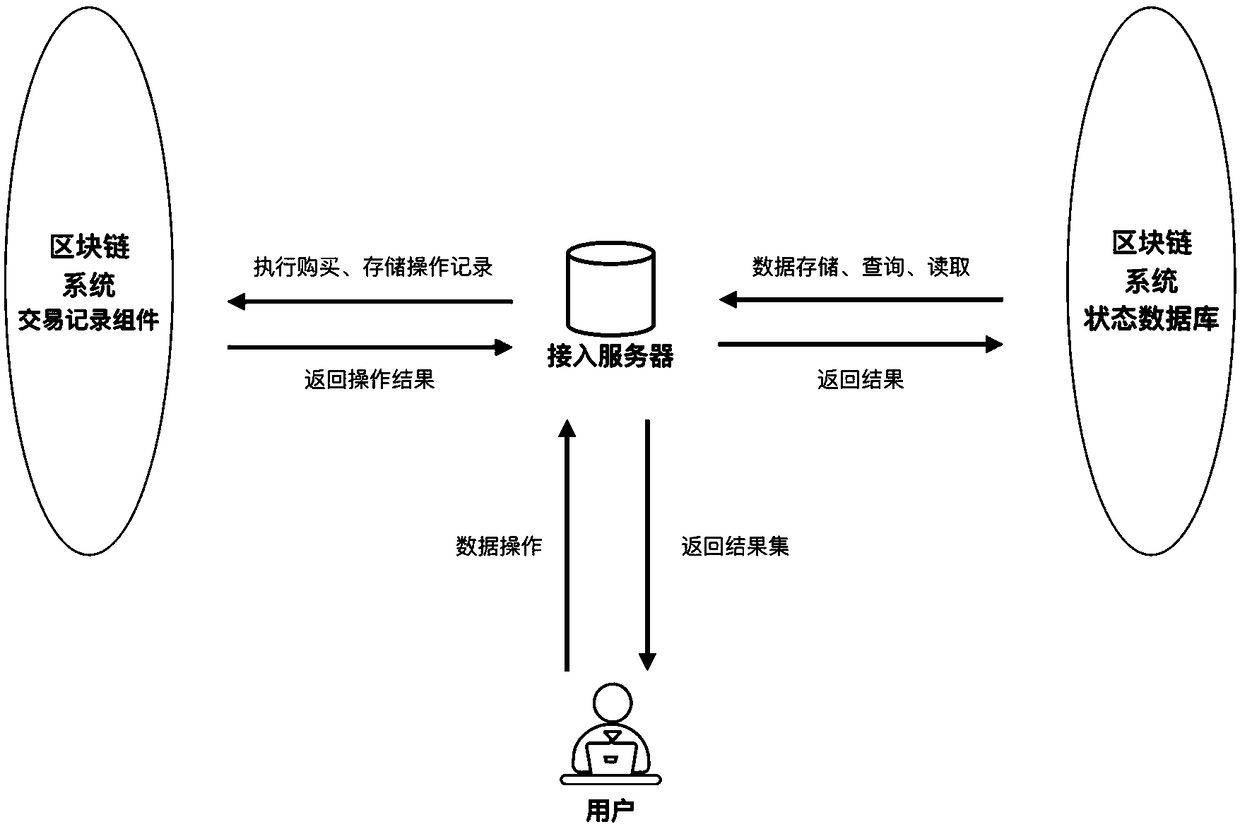
Block chain-based data sharing platform and implementation method thereof
InactiveCN109347941ADistrust hasTamper withEncryption apparatus with shift registers/memoriesUser identity/authority verificationTamper resistanceData operations
The invention provides a block chain-based data sharing platform and an implementation method thereof. The platform comprises multiple clients, one or more access servers and a block chain system; theclients are used for submitting registration applications, storing data instructions, querying the data instructions and using the data instructions; the access servers are used for receiving operation requests submitted by the clients, verifying identities of the clients and the operation requests, submitting the data operation requests to the block chain system and feeding results to the clients; and the block chain system is used for controlling storage and access of data, storing the data and storing citation and abstract information on the data, and access permissions are controlled by block chains and used as tamper-proof logs. According to the block chain-based data sharing platform and the implementation method thereof, the ownership and the right to use of the data are separated,a traceable path is provided for the ownership and usage of the data for audit, queries and transactions are asynchronously executed, and the data sharing efficiency and reliability are improved.
Owner:南京一目智能科技有限公司
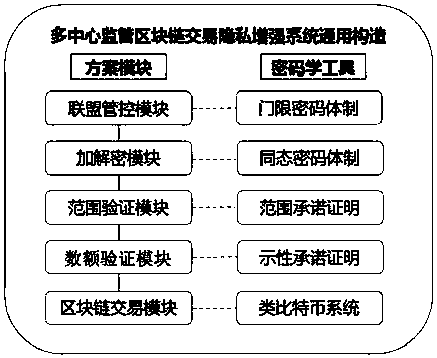
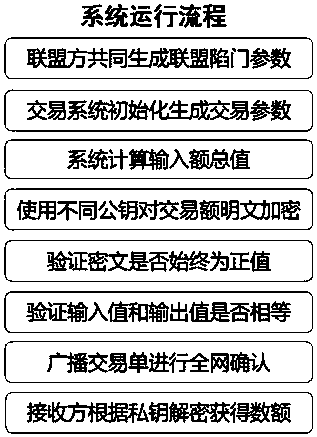
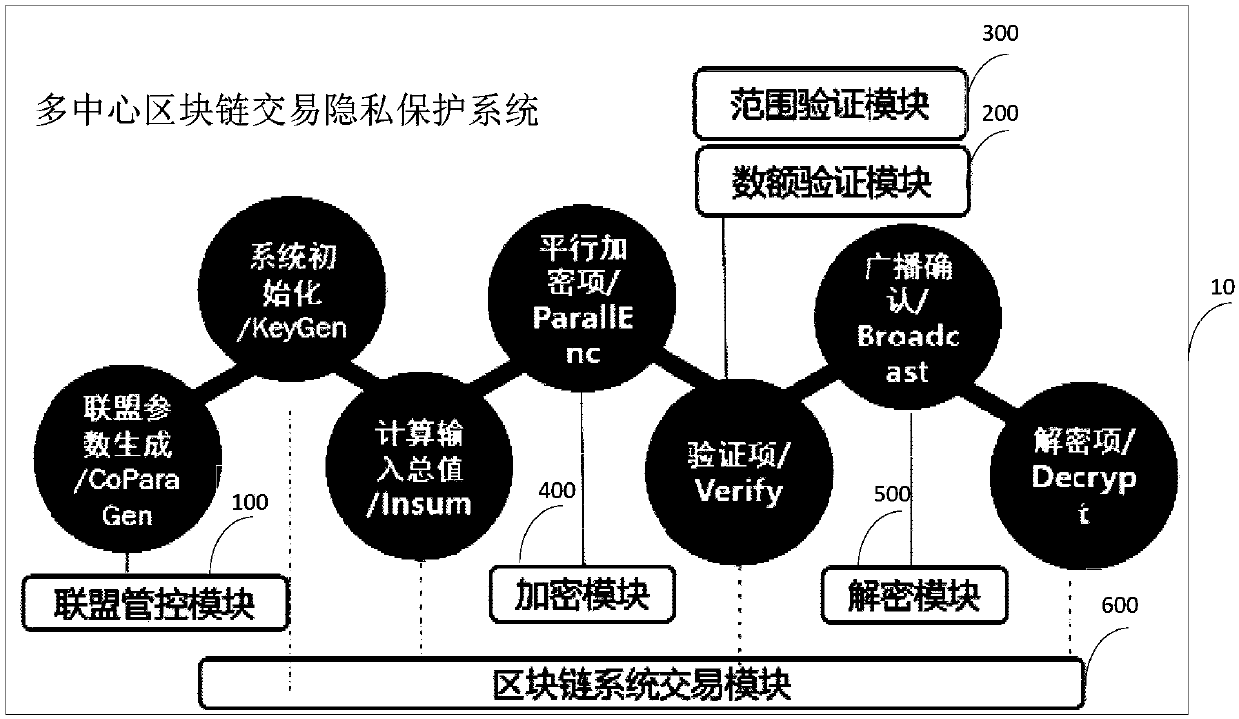
Multi-center block chain transaction privacy protection system and method
InactiveCN108021821ARealize privacy protectionEnhance the security of plaintext amountDigital data protectionCommunication with homomorphic encryptionDigital currencyCiphertext
The invention discloses a multi-center block chain transaction privacy protection system and method. The system comprises an alliance control module, an amount verification module, a range verification module, an encryption module, a decryption module and a block chain system transaction module, wherein the alliance control module is used for generating alliance parameters by multiple participants; the amount verification module is used for verifying that input and output of an encrypted ciphertext amount in a transaction are equal; the range verification module is used for verifying that theencrypted ciphertext amount in the transaction is in a specific interval and is constantly positive; the encryption module and the decryption module are used for carrying out homomorphic encryption and decryption on the amount in transmission and reception processes; and the block chain system transaction module is used for complete bitcoin-like digital currency transaction systems, and has a complete transaction process which comprises transmission, reception, broadcasting and block confirmation. The system is capable of enhancing general structures through block chain transaction privacies under a multi-center supervision mode, so as to realize privacy protection for trapdoor parameters under joint control of multiple parties and transaction metadata in transaction process, and effectively strengthen the safety of plaintext amounts in multi-center block chain system transaction process.
Owner:BEIHANG UNIV
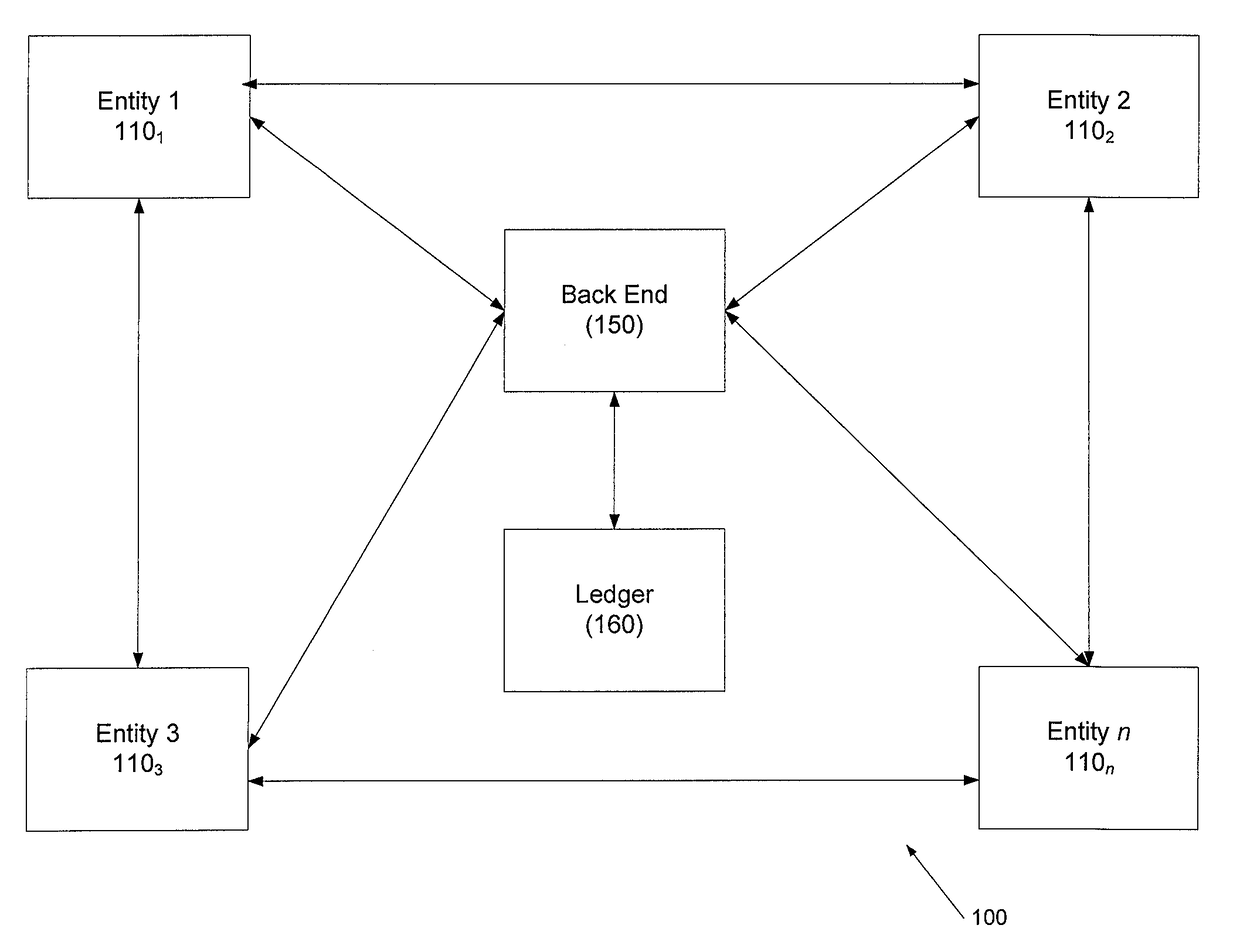
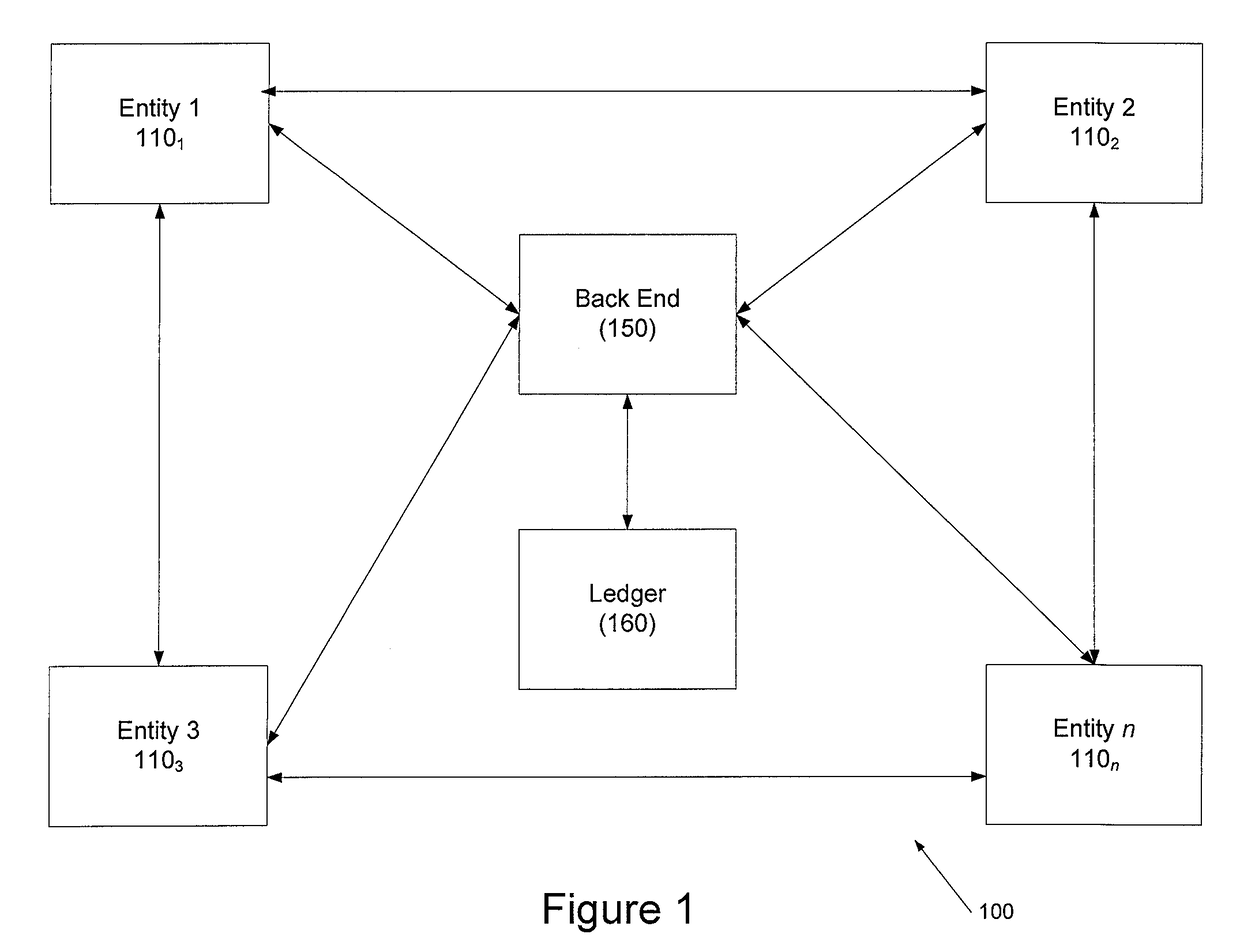
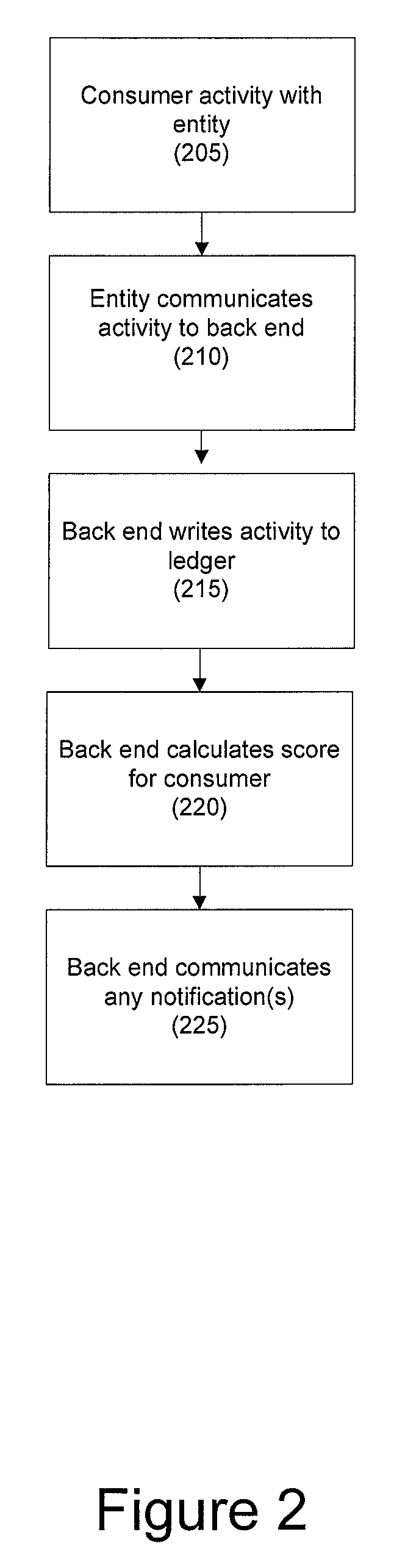
Systems and methods for enhanced organizational transparency using a credit chain
Systems and methods for enhanced organizational transparency using a linked activity chain in a ledger are disclosed. In one embodiment, a method may include (1) a back end for an organization comprising at least one computer processor receiving a first communication from a first entity comprising a first customer interaction with the first entity; (2) the back end writing the first communication to a ledger for the organization as a first block in a linked activity chain; (3) the back end receiving a second communication from a second entity comprising a second customer second activity with the second entity; (4) the back end writing the second communication to the ledger for the organization as a second block in the linked activity chain; (5) the back end calculating a summary score for the customer based on the blocks in the linked activity chain.
Owner:JPMORGAN CHASE BANK NA
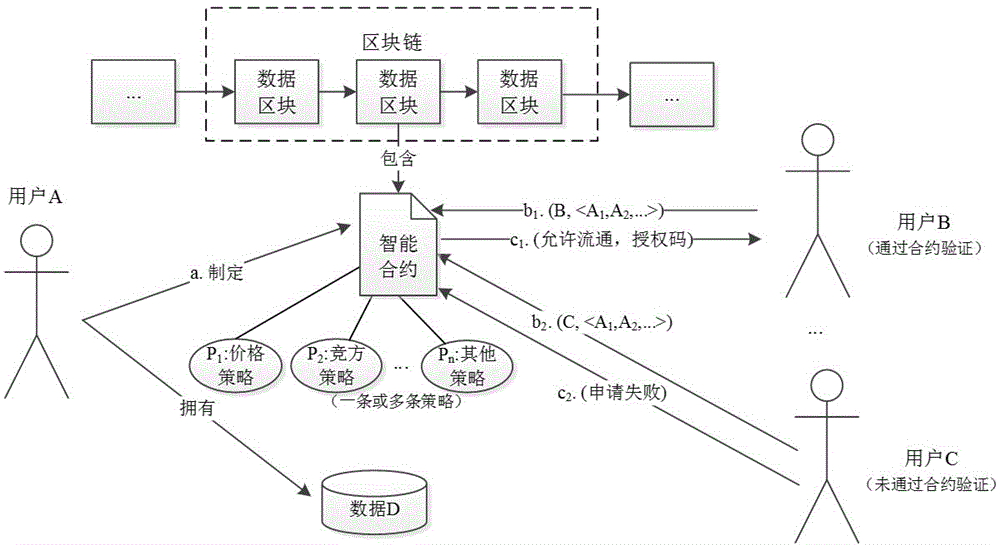
Block-chain-based data rights protection method
ActiveCN106600405ANot easy to tamper withNot easy to forgeFinanceDigital data authenticationThird partyStrategy execution
The invention belongs to the technical field of data security, and specifically relates to a block-chain-based data rights protection method. The steps of method are as follows: a user owning data formulates data circulation strategies according to data rights that need protection, compiles the circulation strategies into an intelligent contract, and deploys the intelligent contract on a block chain system; and before other users perform data circulation, the user serving as a data transferee needs to use identity information and related data circulation attributes to call the intelligent contract, and the intelligent contract automatically provides an approval result of a circulation application according to the established data circulation strategies: if circulation is allowed, a dynamic circulation authorization code is returned to the transferee user; otherwise application failure is returned. The block-chain-based data rights protection method provided by the invention is an application of a block chain system, removes dependence on a third-party authority organization in a data rights protection process, ensures that the data circulation strategies formulated by the data owner are not maliciously modified, and a strategy execution result is not manually manipulated, thereby providing a just, transparent and credible execution environment for data circulation processes of data transactions, data opening and sharing and the like.
Owner:FUDAN UNIV
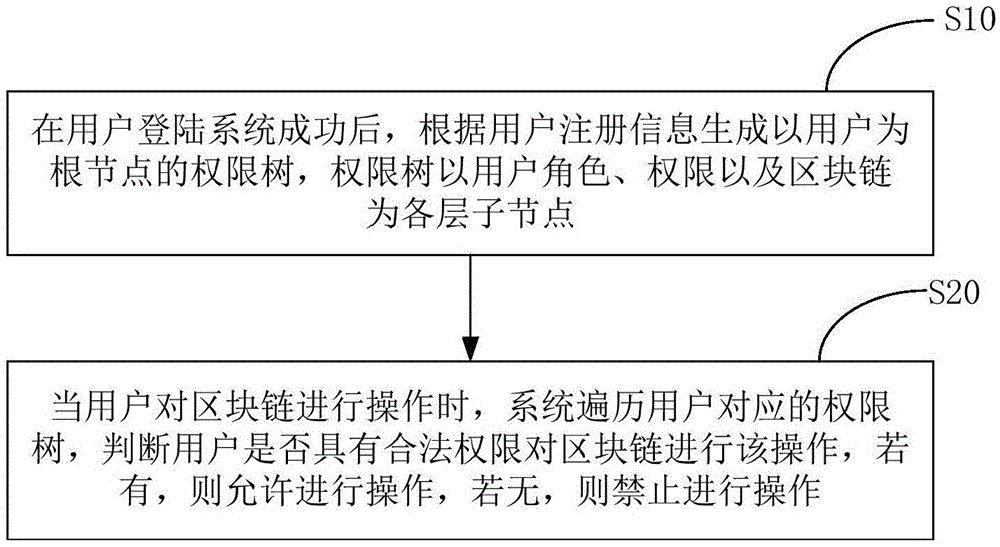
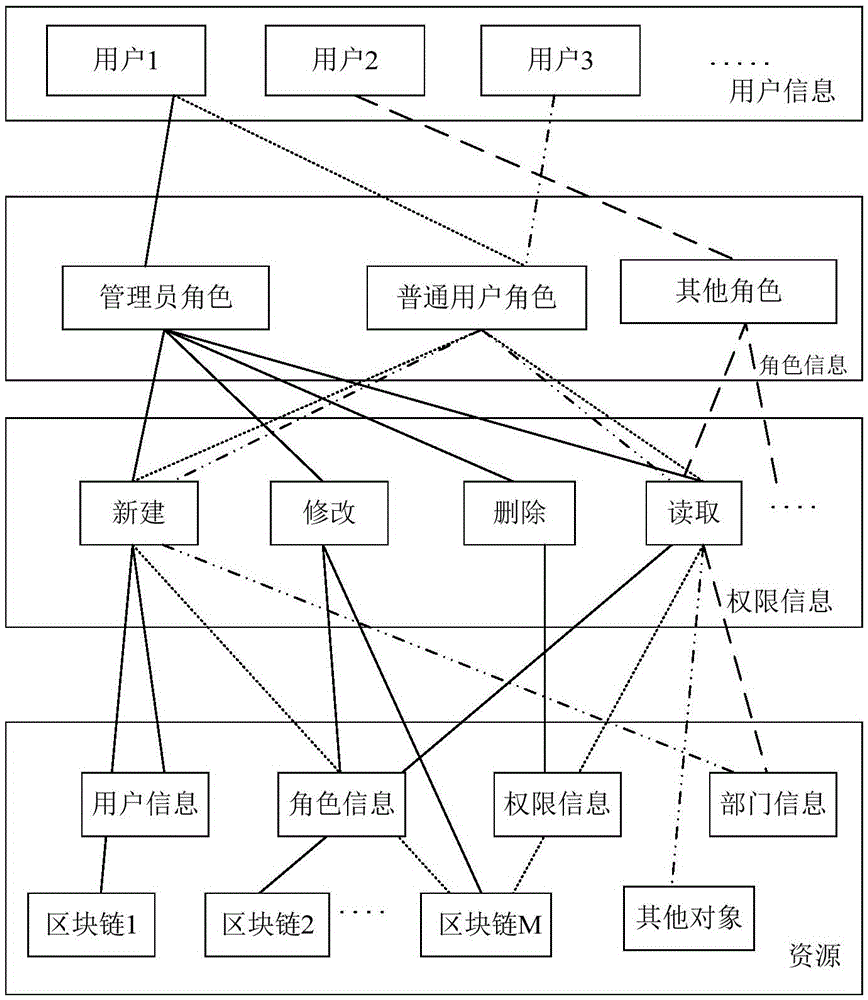
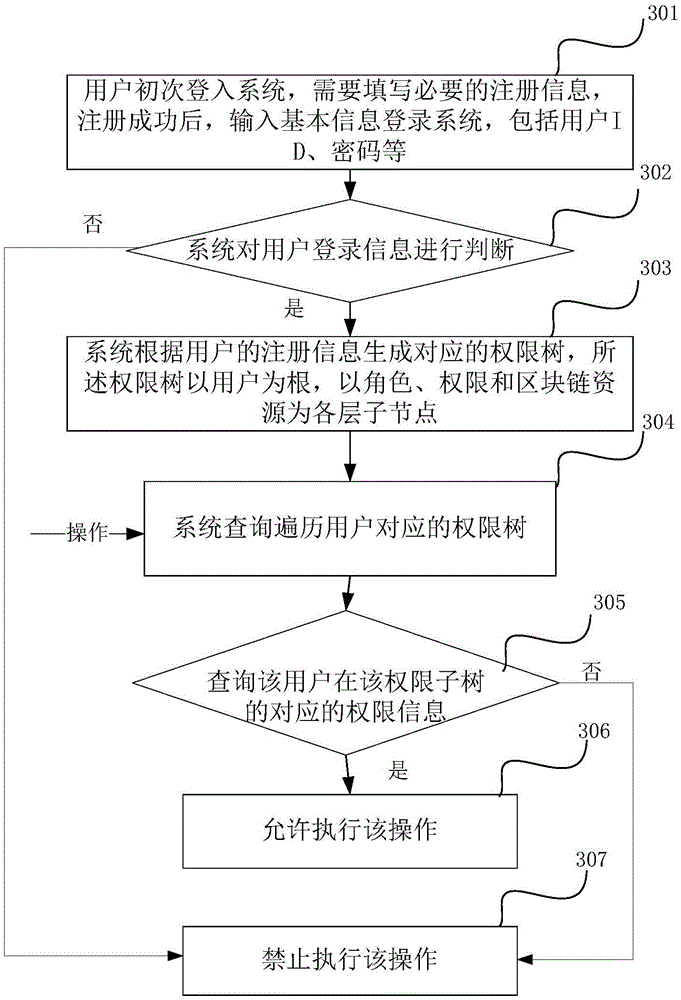
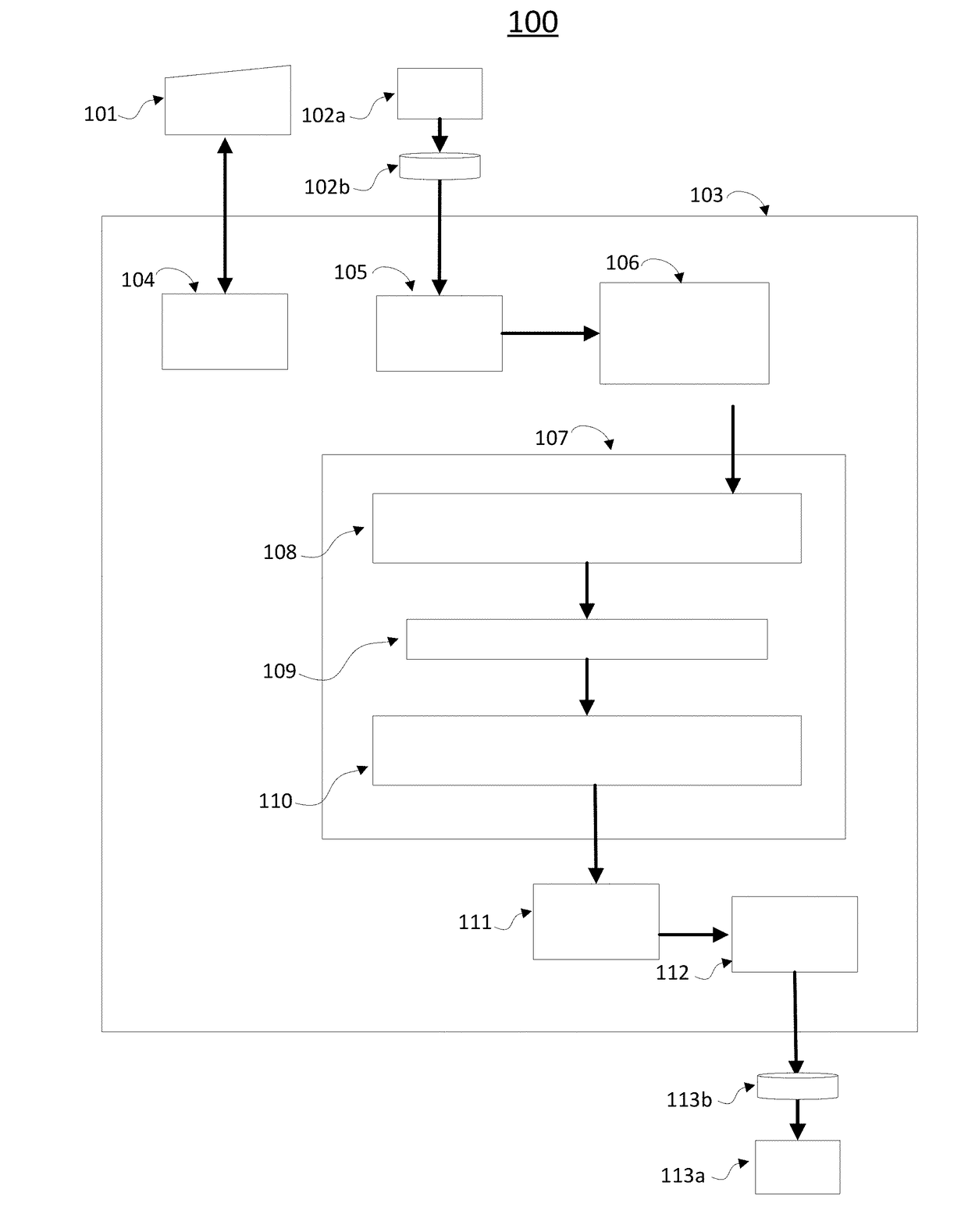
Authority management method and device for block chain system
ActiveCN105488431AReduce the number of layersQuick updateDigital data protectionResource consumptionRights management
The invention discloses an authority management method and device for a block chain system. The method comprises the following steps of generating an authority tree with a user as a root node according to user registration information after the user logs in to the system successfully, wherein the authority tree takes a user role, user permission and a block chain as a sub-node of each layer; and when the user carries out an operation on the block chain, informing a control module to traverse the authority tree corresponding to the user, judging whether the user has legal permission to carry out the operation on the block chain according to a traversing result of the control module, if yes, allowing the operation, and if no, forbidding the operation. According to the method and the device, the flexible authority control is carried out on the authority management by the authority tree, and furthermore, the authority tree has the characteristics of less number of layers and quick updating, so that the authority resource consumption can be reduced, and the efficiency for authority management is also guaranteed.
Owner:BUBI BEIJING NETWORK TECH CO LTD
Cryptographic asic including circuitry-encoded transformation function
ActiveUS20170206382A1Easy to decipherImprove noiseEncryption apparatus with shift registers/memoriesInternal/peripheral component protectionProof-of-work systemDigital rights management
A transform-enabled integrated circuit for use in cryptographic proof-of-work systems is provided. The transform-enabled integrated circuit includes a transformation block embedded among other circuitry components within the cryptographic datapath of the transform-enabled integrated circuit. The transformation block may be configured at a time subsequent to the manufacture of the integrated circuit to embody as circuitry any one of a plurality of mathematical transformation functions, thus enabling a user to systemically modify the results of cryptographic operations performed by the integrated circuit while retaining the high performance and efficiency characteristics of application-specific integrated circuits. Embodiments of the technology disclosed herein provides an hereto unachievable level of flexibility in the deployment of application-specific integrated circuits within proof-of-work verification systems, such as private block chain systems, public block chain systems, digital rights management, secure token and other cryptography-related fields.
Owner:BLOCKCHAIN ASICS LLC
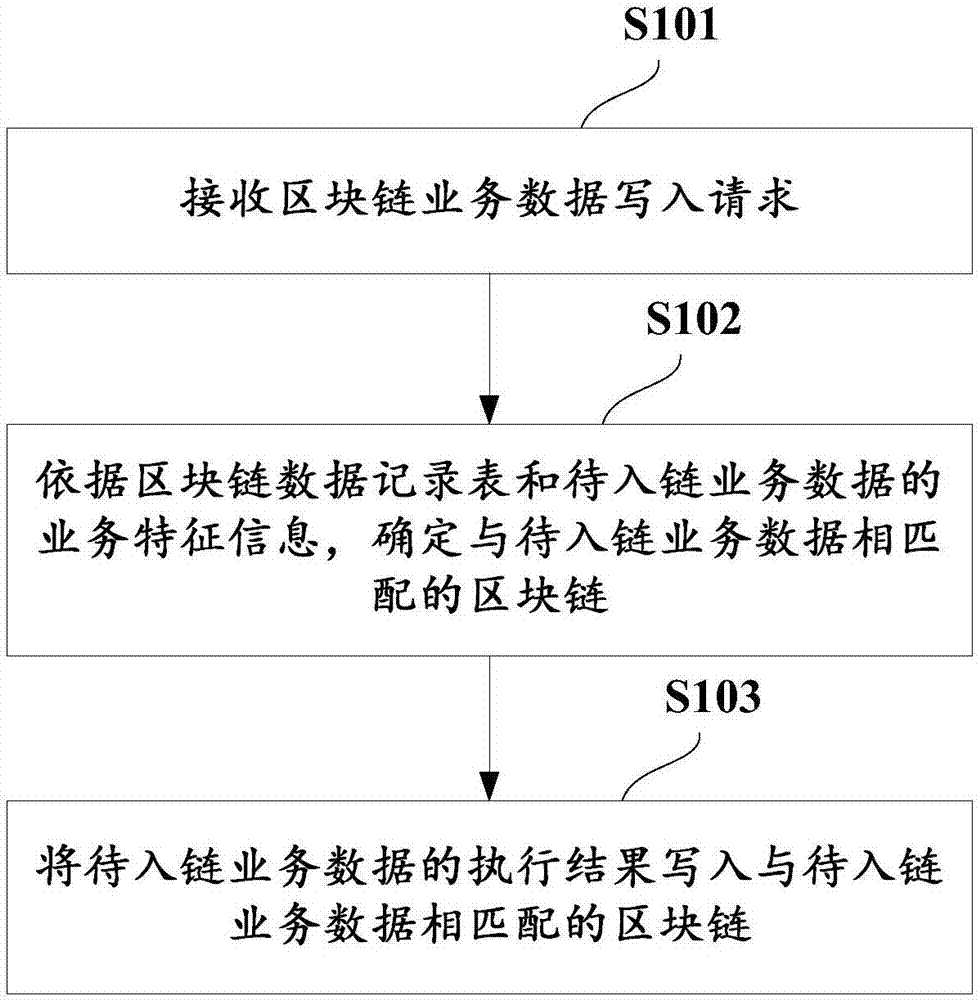
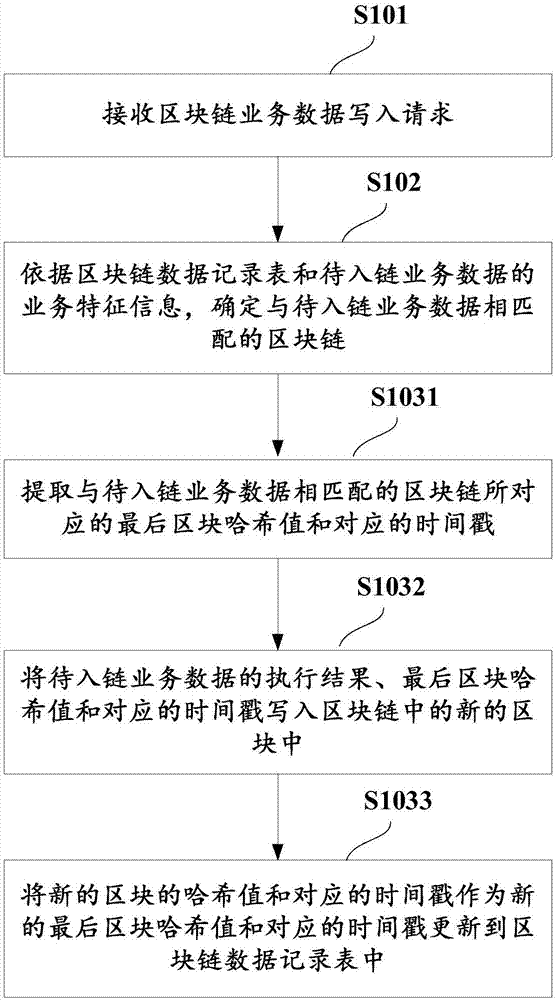
Method and device for writing business data in block chain system
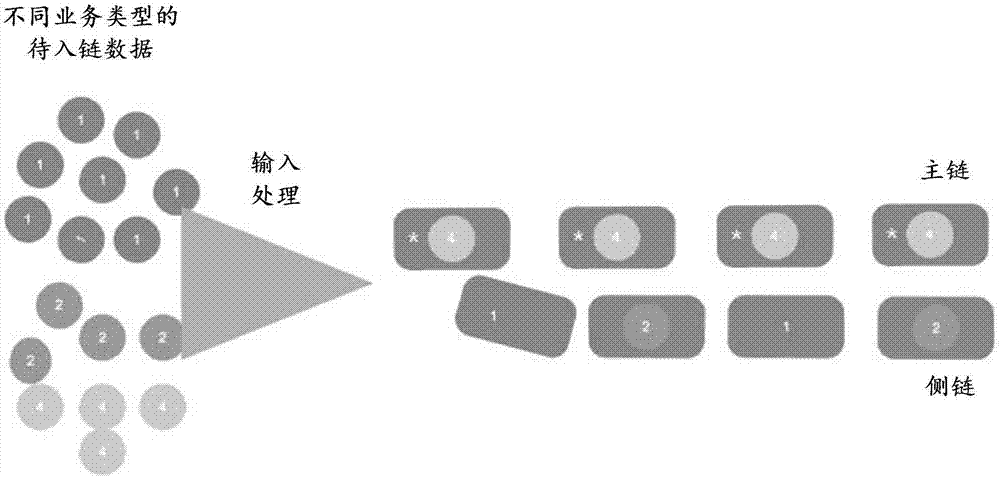
ActiveCN107368259AMeet processing needsInput/output to record carriersDatabase distribution/replicationBusiness dataChain system
The invention discloses a method for writing business data in a block chain system, and the block chain system comprises at least one block chain. The method comprises the following steps of: receiving a block chain business data writing request, wherein the block chain business data writing request comprises business feature information of to-be-chained business data; determining a block chain matched with the to-be-chained business data according to a block chain data record table and the business feature information of the to-be-chained business data, wherein business type identification information of the block chains is recorded in the block chain data record table, and the business type identification information is used for reflecting business feature information of chained business data in the block chains; and writing an execution result of the to-be-chained business data into the block chain matched with the to-be-chained business data. The invention furthermore discloses a corresponding device. By adoption of the method and the device, written block chains can be distinguished according to business types, so that processing requirements of different types of business data in the block chain system can be satisfied.
Owner:ADVANCED NEW TECH CO LTD
Method for dynamically adjusting block-chain consensus based on business trust degree
ActiveCN107169765ALower requirementEasy to useDigital data protectionProtocol authorisationBusiness dataData transmission
The invention discloses a method for dynamically adjusting a block-chain consensus based on a business trust degree. In a block chain system, nodes are divided into authentication nodes and consensus nodes; data are only transparently shared among the authentication nodes; and for weakly trusted or completely untrustworthy businesses, node sets for authentication and consensus participation are designated, so that the trust of the cooperation side can be obtained and privacy of the business data can be protected. Compared with the prior art, the method has the following beneficial effects: in the block chain system, the consensus is adjusted dynamically by combining the business trust, so that the block chain system can adapt to application scenes with different business trust; the whole-network popularization requirement of data transmission and storage can be reduced; the system can be trusted; cost minimization can be realized; and thus the block chain technology can be widely applied.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
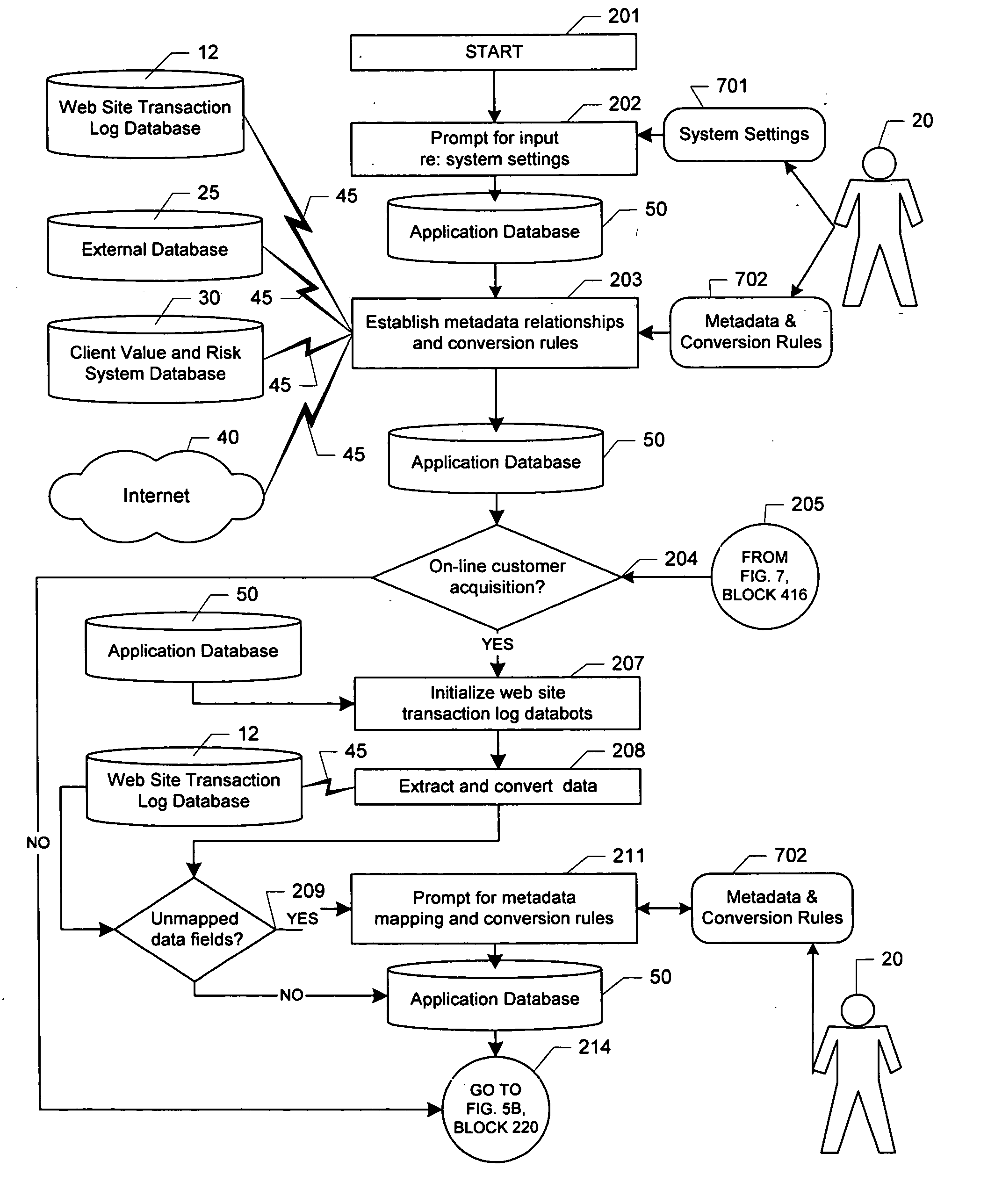
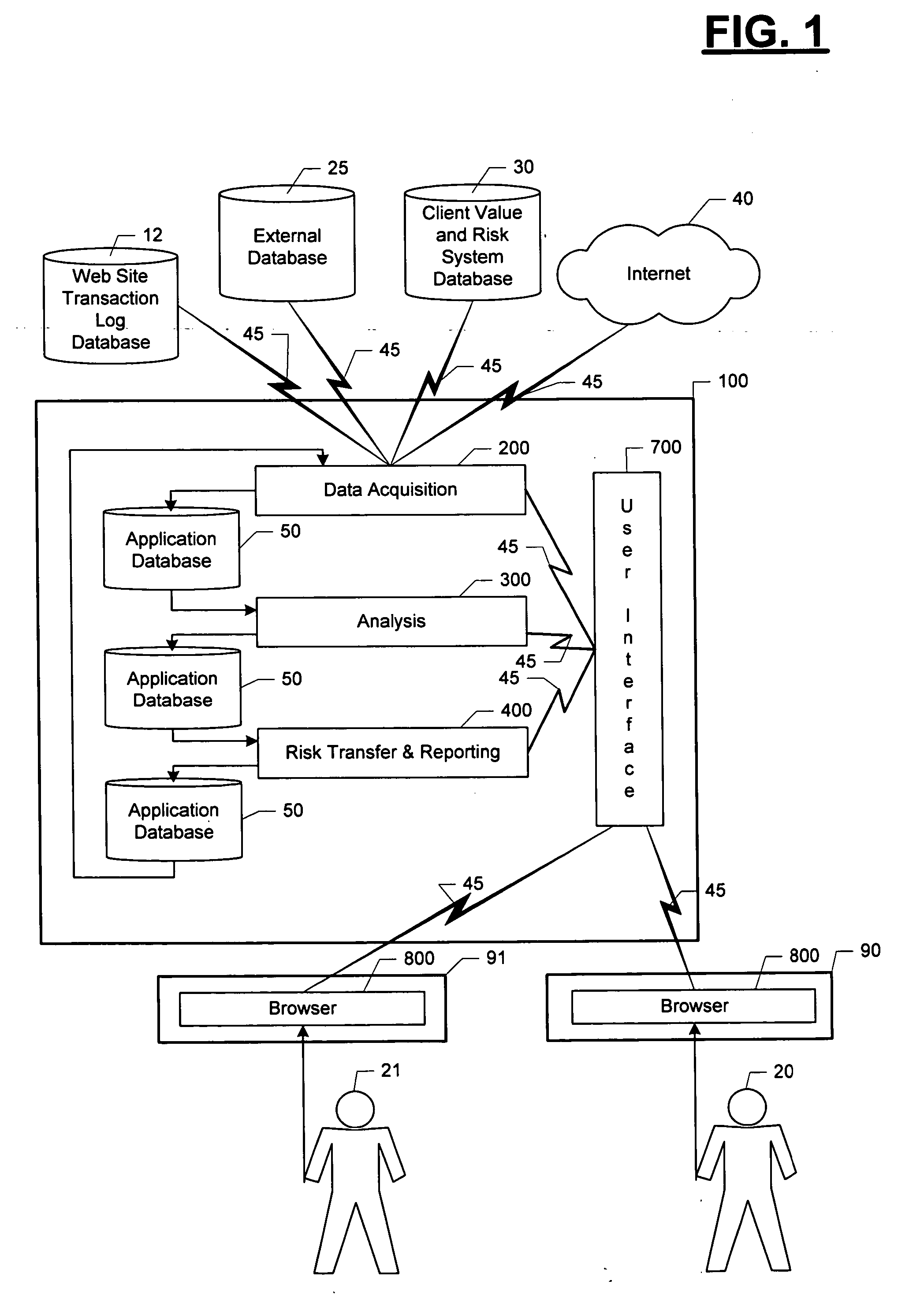
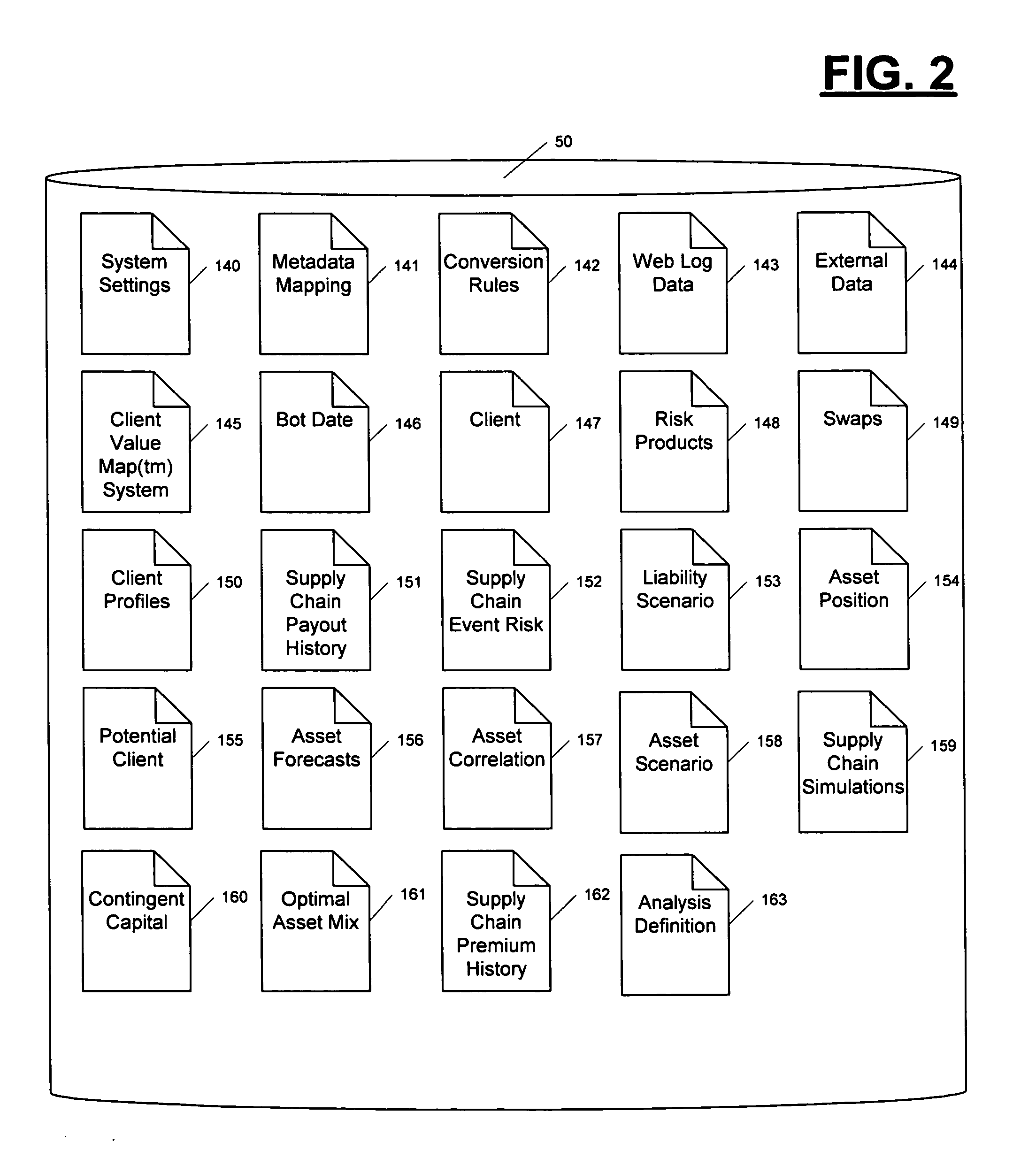
Risk transfer supply chain system
InactiveUS20050119919A1Overcome limitationsGreat ability to shape their risk profileFinanceSpecial data processing applicationsChain systemComputer science
An automated method and system (100) for supplying risk transfer products to a client company on a continual basis. After the client company provides a matrix of risk to the risk transfer supply chain, swaps and / or insurance products that provide the desired risk transfer are identified and priced. The information regarding the proposed risk transfer swaps and products is optionally reviewed by the user (20) and optionally accepted. If accepted, the transaction is completed in an automated fashion. Prices and contingent capital purchases are established as required to keep the operator of the risk transfer supply chain in compliance with regulatory reserve requirements.
Owner:EDER JEFFREY
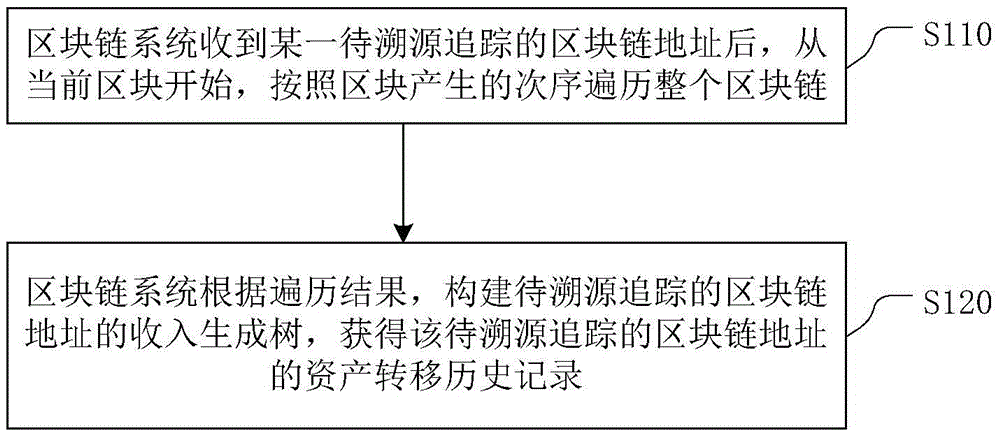
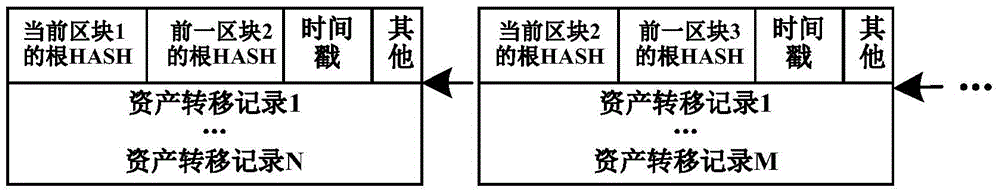
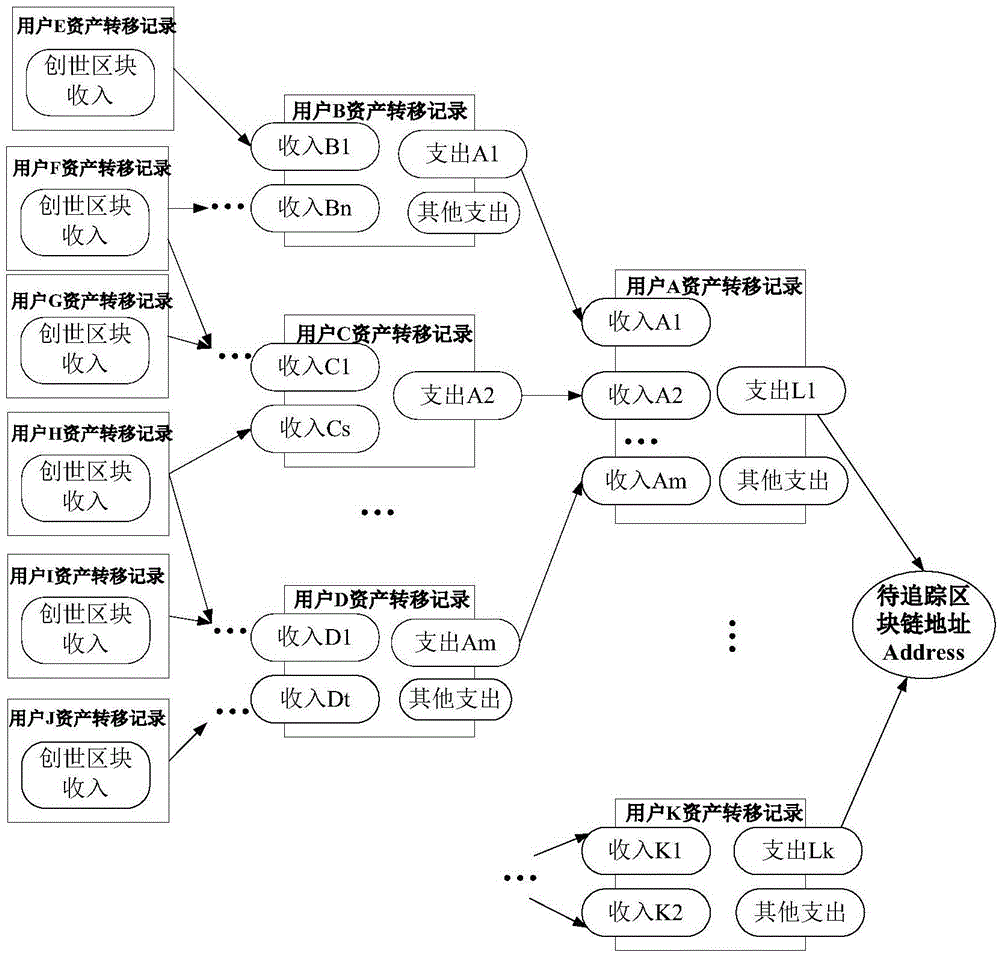
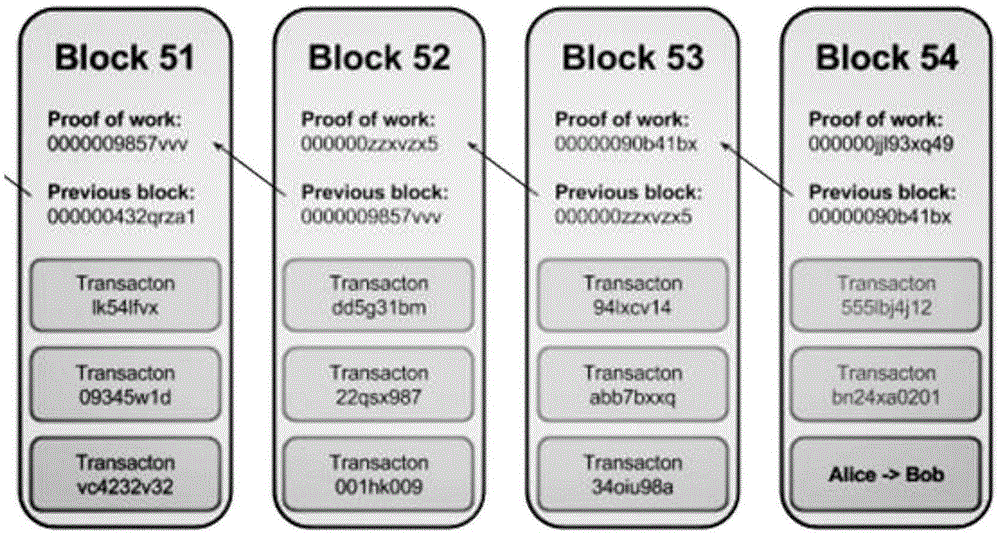
Block chain tracing method
The invention relates to a tracking method on internet, and provides a block chain tracing method. The method comprises the following steps: after receiving, by a block chain system, the address of a block chain to be traced, traversing the whole block chain by the block chain system according to the block generation sequence from the current block; and constructing, by the block chain system, an incoming generation tree and an outgoing generation tree of the address of the block chain to be traced according to the traversing result, so as to obtain an asset transformation history of the address of the block chain to be traced. The method is conducive to tracing the illegal using behaviors and illegal users of the block chain system so as to prevent the block chain system from becoming a tool utilized by the lawbreakers, so that basis is provided for the wider application of the block chain technology; and the method is mainly used for providing an audition function.
Owner:BUBI BEIJING NETWORK TECH CO LTD
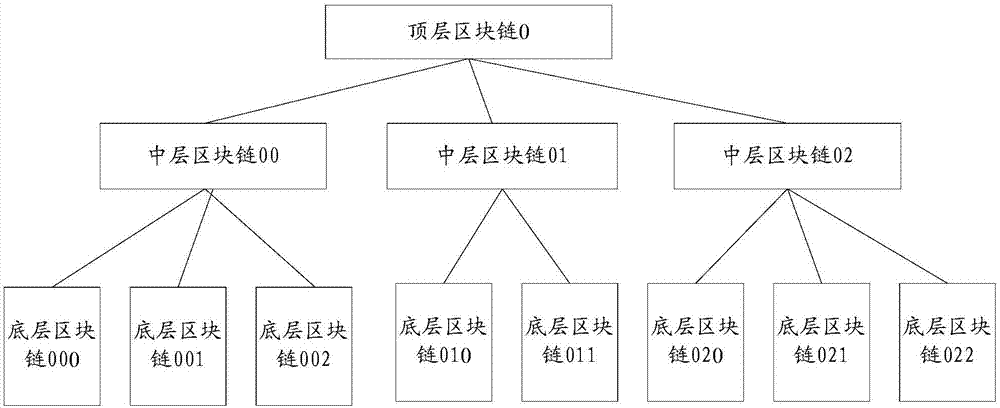
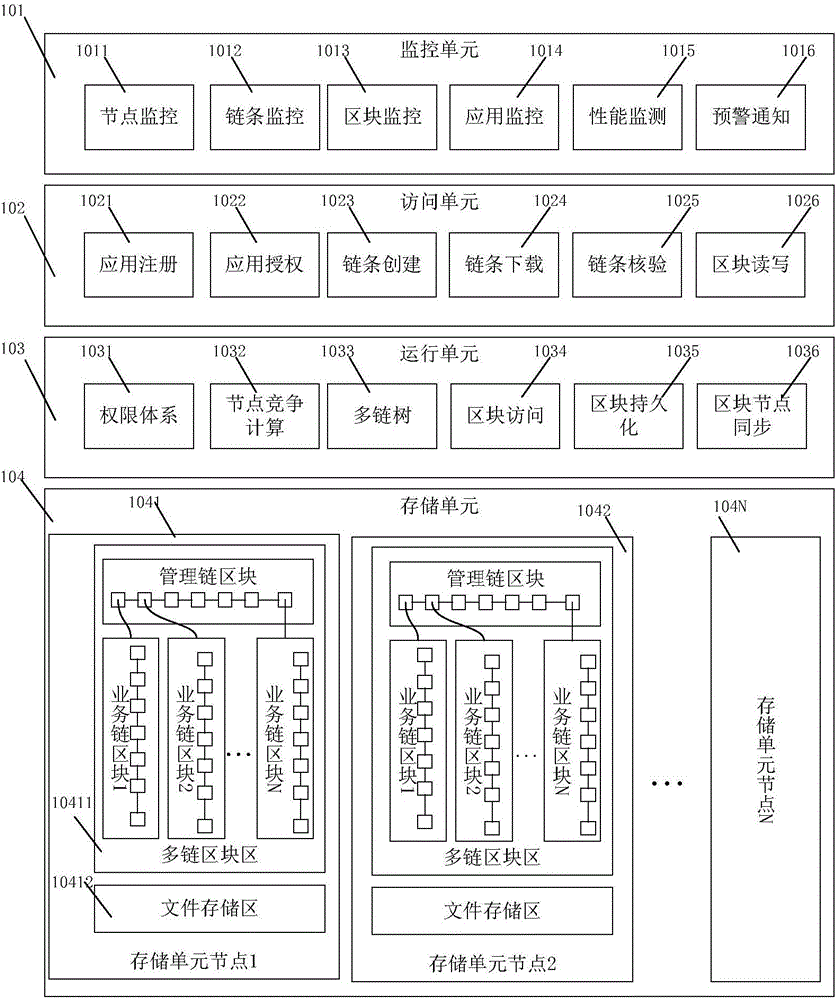
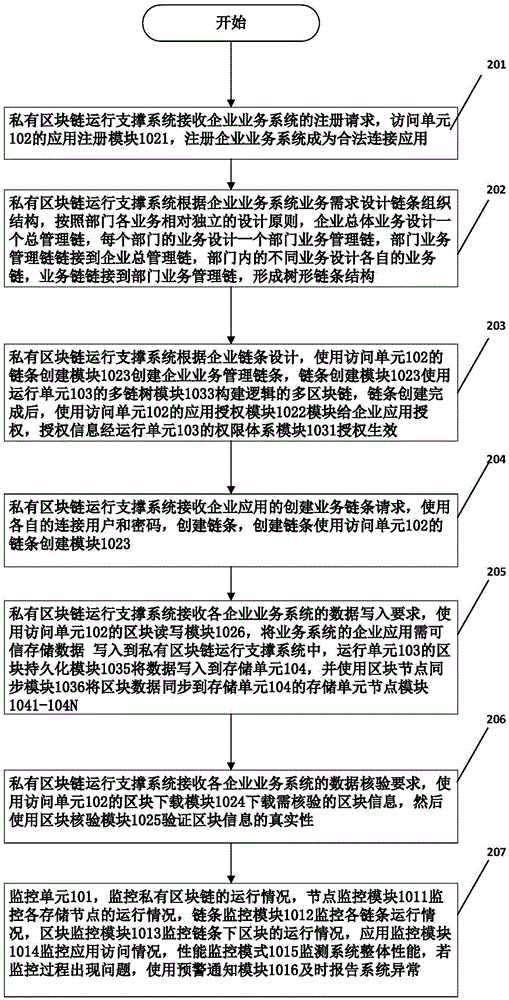
Private block chain operation support system that supports logical multi-chain, and working method thereof
ActiveCN106528775ARealize trusted managementLower barriers to useOffice automationStructured data retrievalData synchronizationStructure of Management Information
The invention discloses a private block chain operation support system that supports a logical multi-chain, and a working method thereof. The system comprises: a monitoring unit for monitoring the operating condition; an access unit for providing an external access channel; an operation unit for controlling the operation, coordinating the cooperative work among each storage unit node in a storage unit, and supporting automatic growth, data transaction, and data synchronization of each chain block; and the storage unit, which comprises a plurality of storage unit nodes, and is used for storage management of the block chain data on multiple storage unit nodes and for real-time synchronization of the block chain data among each storage unit node. Based on the existing common block chain system, the system constructs a private block chain operation support system that supports the logical multi-chain, the innovative transformation of the private block chain from the single-chain to the multi-chain is realized, the business key data management system of the tree structure is supported, monitoring and management on the block chain operation in a multi-chain mode are realized, and ease of use and the applicability of the private block chain are improved.
Owner:UNIV OF JINAN +1
System, method and article of manufacture for workflow management of a supply chain system
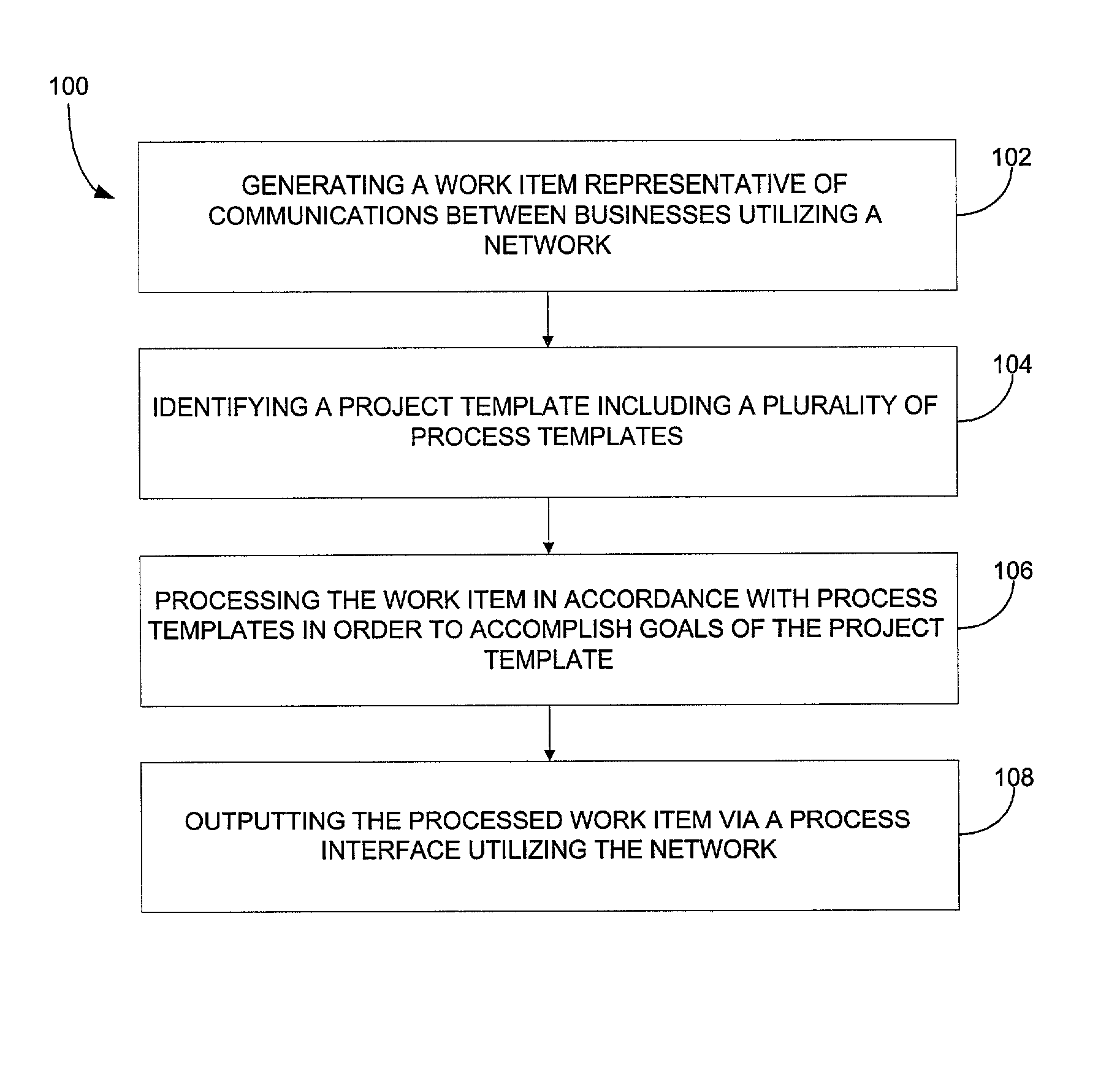
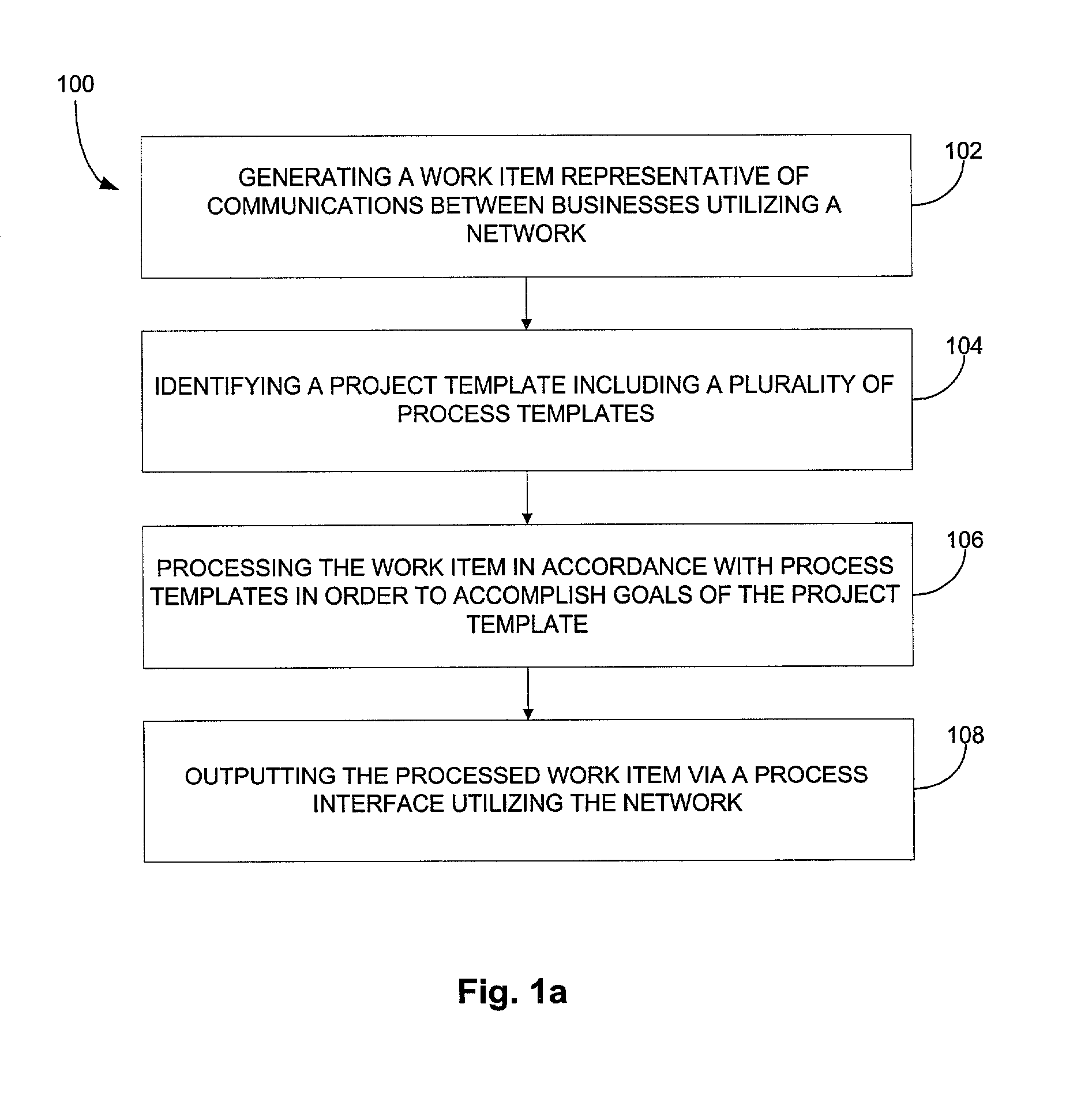
A system, method, and article of manufacture are provided for workflow management of a supply chain. During use, businesses are permitted to engage in activities utilizing a network. Such activities each include a plurality of steps. As the activities are being carried out, at least one document is updated for each activity upon completion of each of the steps. Further, services are executed to acquire information from users utilizing the network. Still yet, tasks are performed to populate the document with the information gathered by the execution of the services.
Owner:APPAREON
Credit-investigation data sharing and trading system based on block chain
InactiveCN106788987APerfect risk control levelSolve imperfectionsKey distribution for secure communicationFinanceRisk ControlData provider
The invention relates to a credit-investigation data sharing and trading system based on a block chain. The credit-investigation data sharing and trading system comprises at least two P2P network nodes; the network nodes include a bottom block chain system and a credit-investigation data sharing platform operating on the bottom block chain system; and the credit-investigation data sharing platform comprises a data sharing module, a data evaluating module, a data inquiring and trading module and a block chain adaptation layer. According to the credit-investigation data sharing and trading system disclosed by the invention, a credible credit-investigation data sharing and trading platform is constructed by using a block chain technology; a specific data sharing mechanism, data inquiring mechanism, data trading mechanism and data evaluating mechanism are used; therefore, a credit-investigation data owner and a credit-investigation data demander can be attracted to use; therefore, a credit-investigation data provider can realize data transaction in a condition that data is protected; a credit-investigation data inquirer can obtain credit-investigation data; and thus, the risk control level can be completed.
Owner:树读(上海)信息科技有限公司
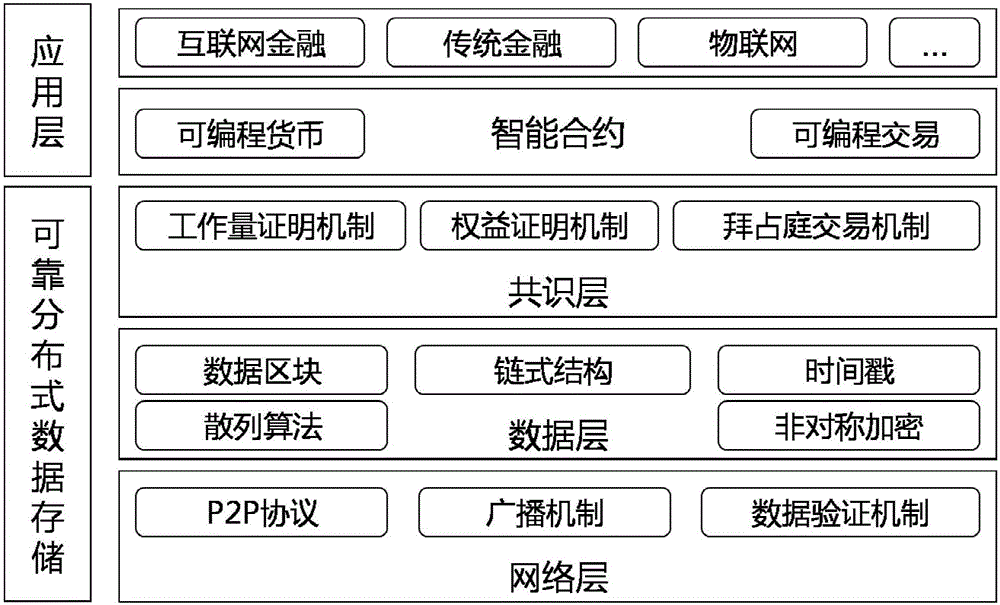
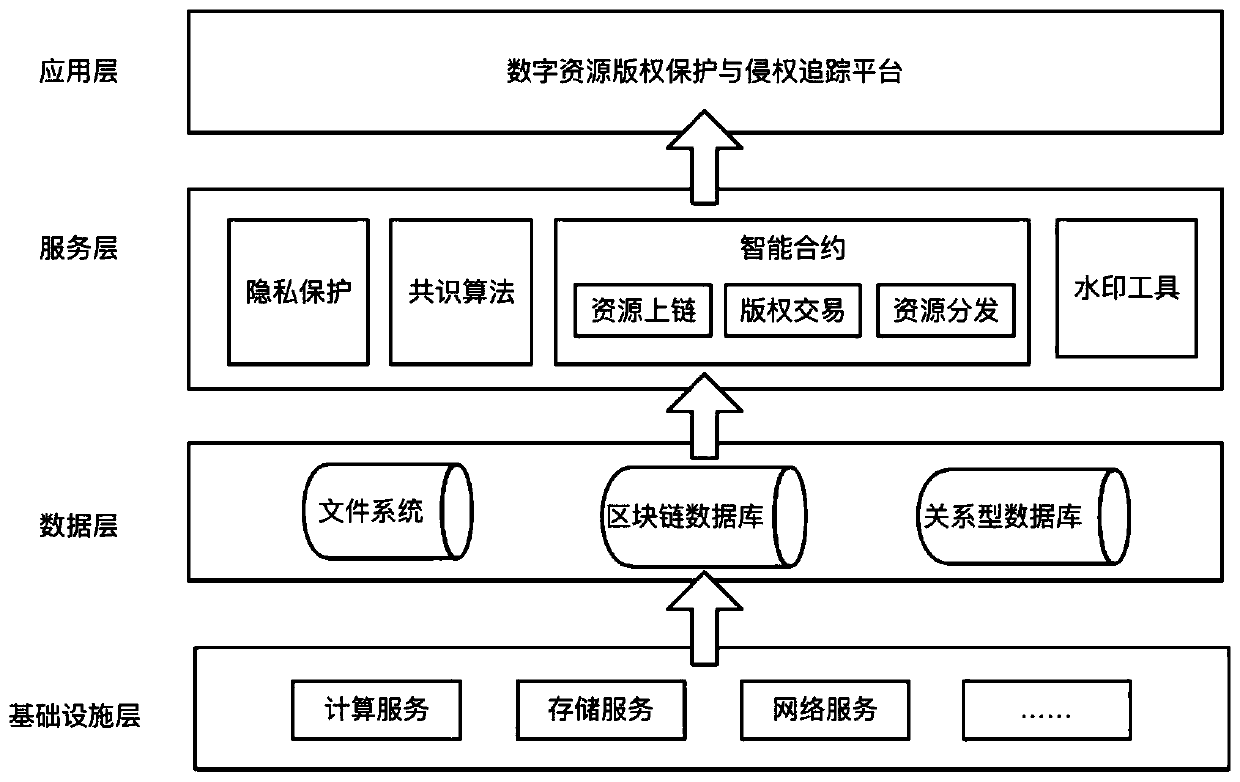
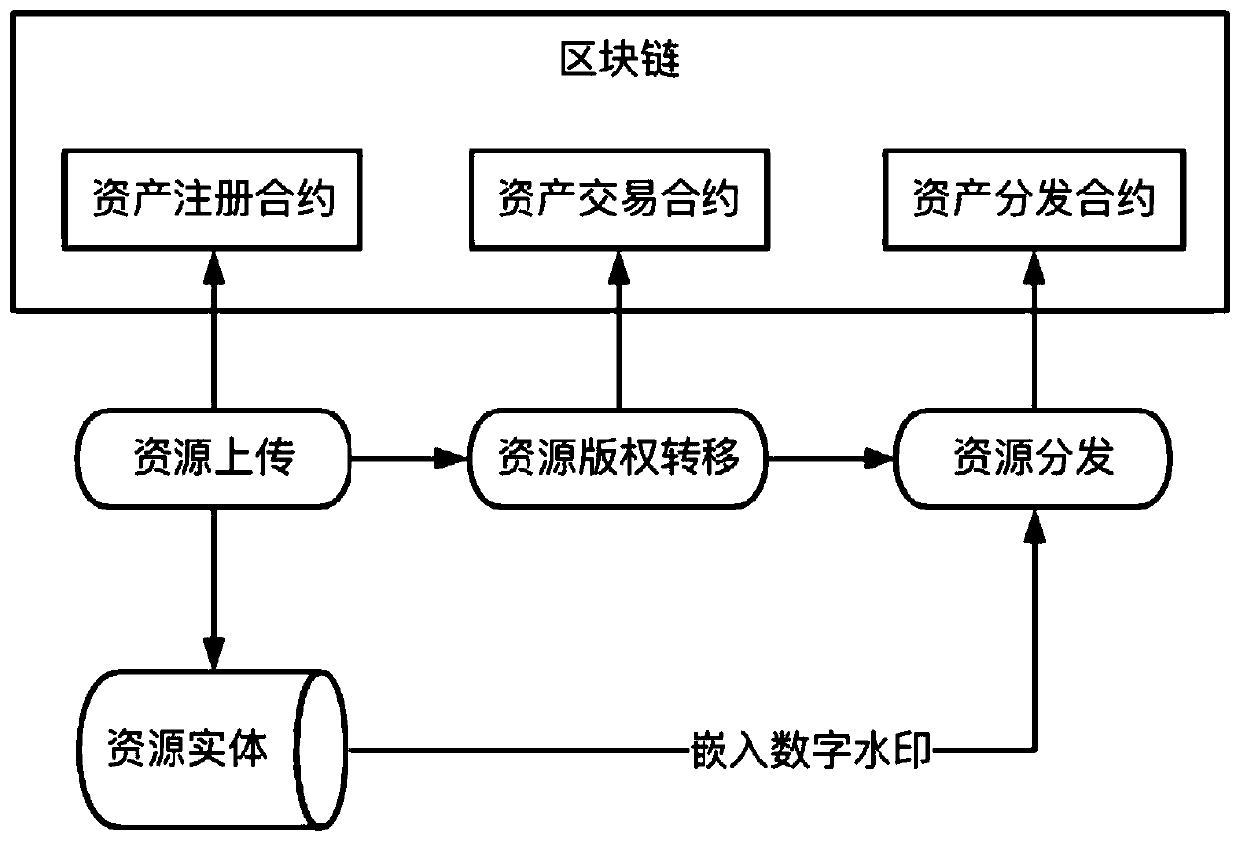
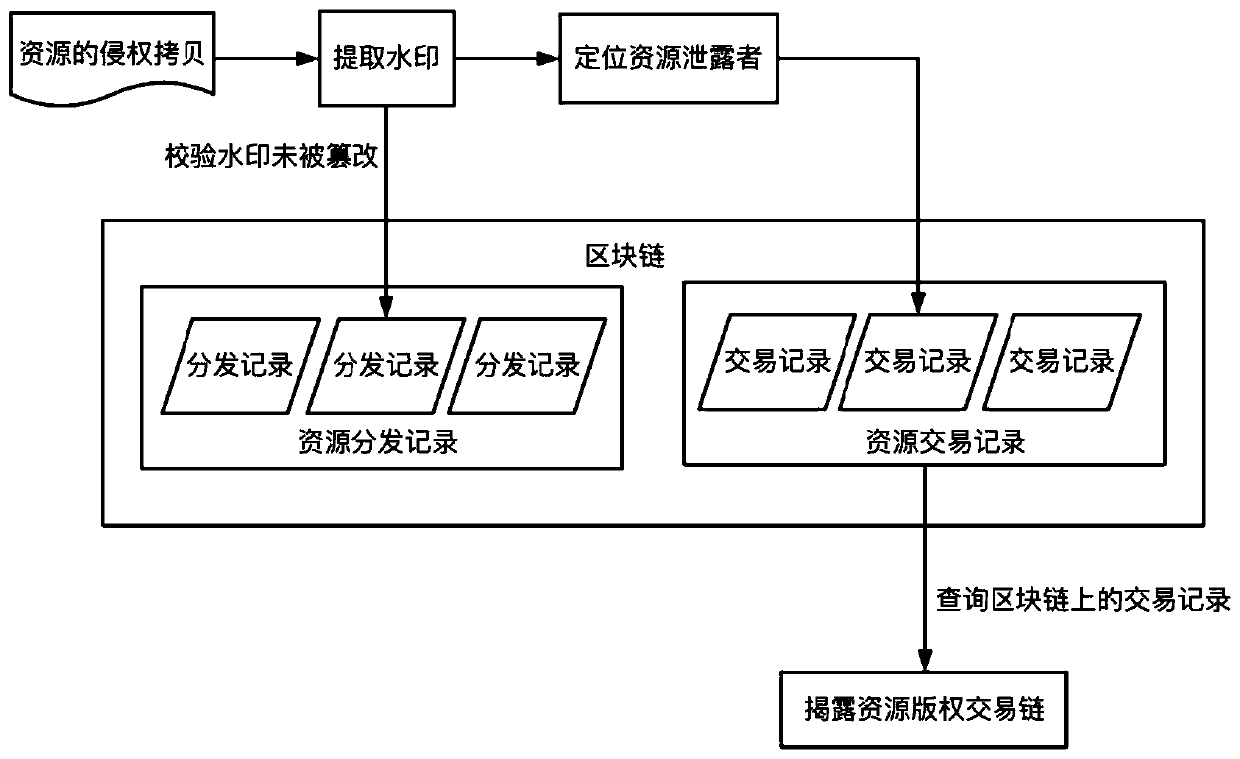
A digital resource infringement tracking method and system based on block chain digital watermarking
InactiveCN109711120ASolve pain pointsGuaranteed to be authenticFinanceDigital data protectionChronological timeChain system
The invention relates to the technical field of block chain application. The invention discloses a block chain digital watermark-based digital resource infringement tracking method and system, and themethod comprises the steps: packaging digital resource uploading, transaction and distribution information into a block, and recording the block in a block chain according to a time sequence, and comprises the steps: generating a block on the block chain when a user uploads digital resources, and recording copyright information; when the copyright of the digital resource is transferred, a block is generated on the block chain, and corresponding transaction information is recorded; when the digital resources are distributed, a block is generated on the block chain, corresponding distribution information is recorded, and a digital watermark is embedded into the digital resource entity; when infringement copying of digital resources occurs on the market, infringement tracking is carried outby combining the digital watermarks in the infringement copying of the digital resources with the transaction records of the digital resources on the block chain system. According to the method, the digital watermark is combined with the block chain, so that the digital watermark information can not be tampered with a chain, and infringement tracking information is guaranteed to be real and credible.
Owner:ZHEJIANG UNIV
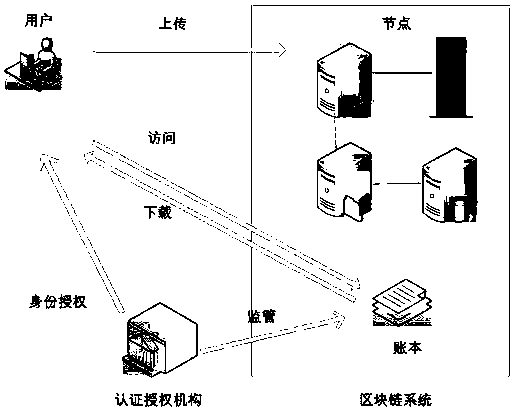
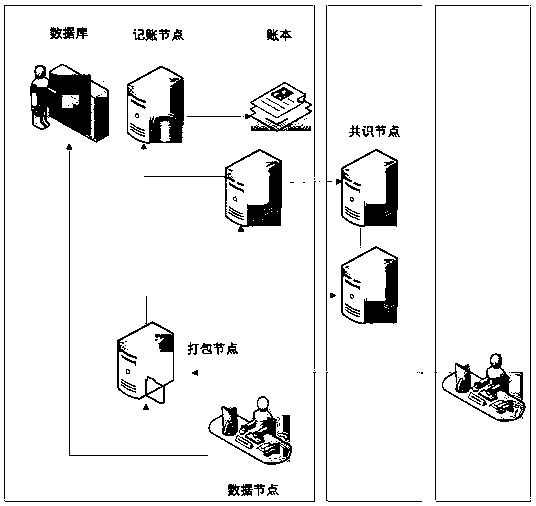
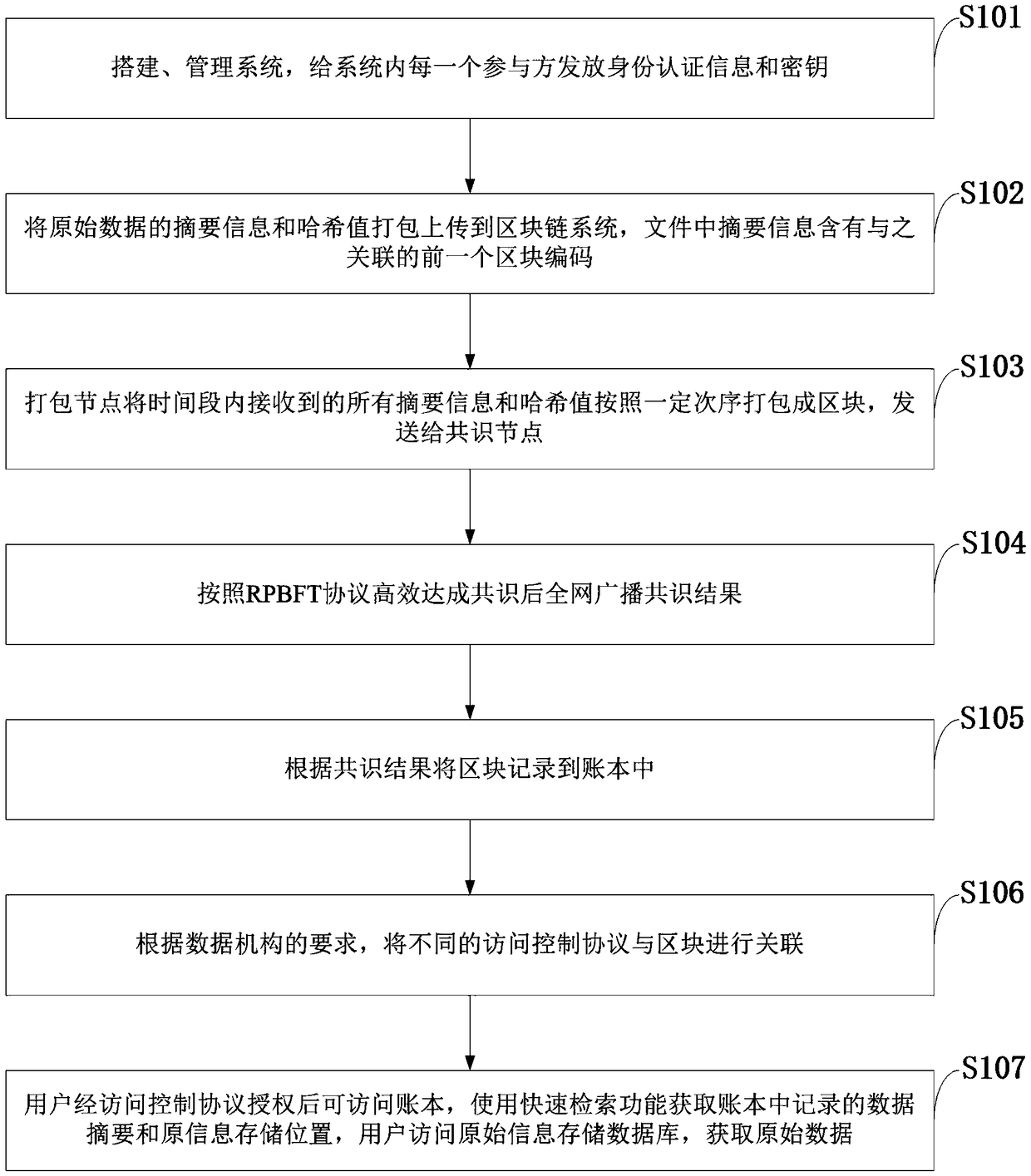
A data security protection and sharing method based on block chain, a system and an application thereof
ActiveCN109040012AImprove integrityRealize immutableEncryption apparatus with shift registers/memoriesUser identity/authority verificationInformation transmissionOriginal data
The invention belongs to the technical field of digital information transmission, and discloses a data security protection and sharing method based on block chain, a system and an application thereof.Each participant sends identity authentication information and a key. The summary information and hash value of the original data are packaged and uploaded to the block chain system. The packaging node packages all the summary information and hash values received in the time period into blocks according to a certain order and sends them to the consensus node. According to the RPBFT protocol, thewhole network broadcasts the consensus result after reaching the consensus efficiently; the block is recorded into the account book according to the consensus result; different access control protocols are associated with blocks. The user can access the account book after the authorization of the access control protocol, and obtain the data summary recorded in the account book and the original information storage location by using the quick retrieval function. The user accesses the original information storage database to obtain the original data. The invention can resist the tampering of themalicious node, realize the consensus efficiently, and remarkably improve the data retrieval efficiency.
Owner:XIDIAN UNIV
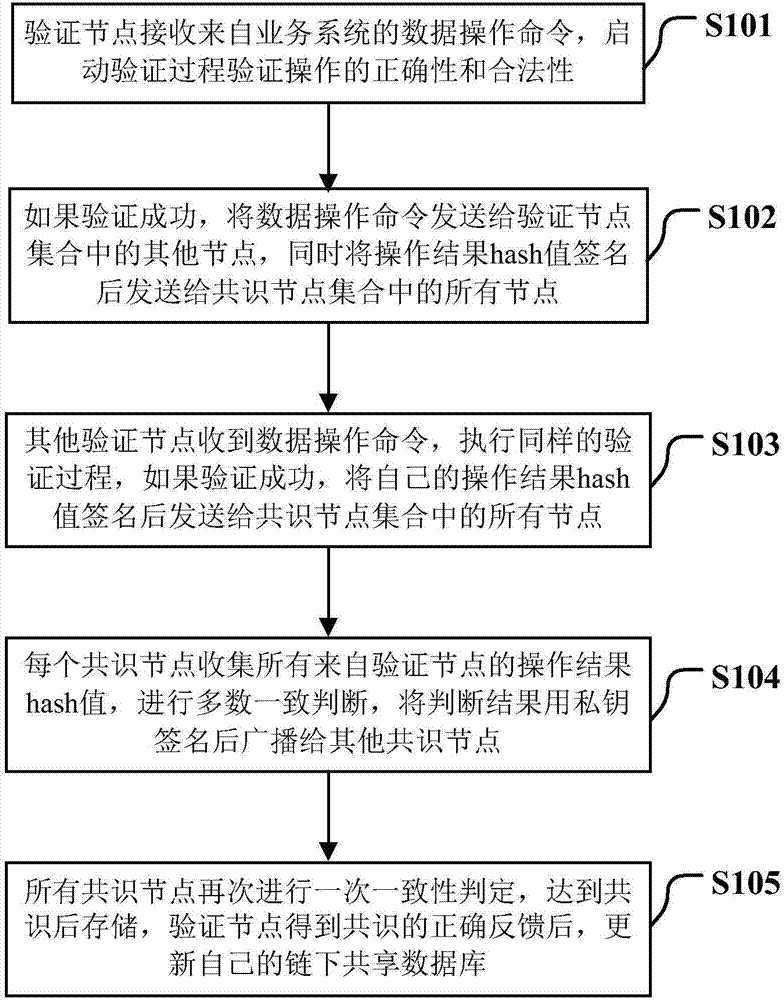
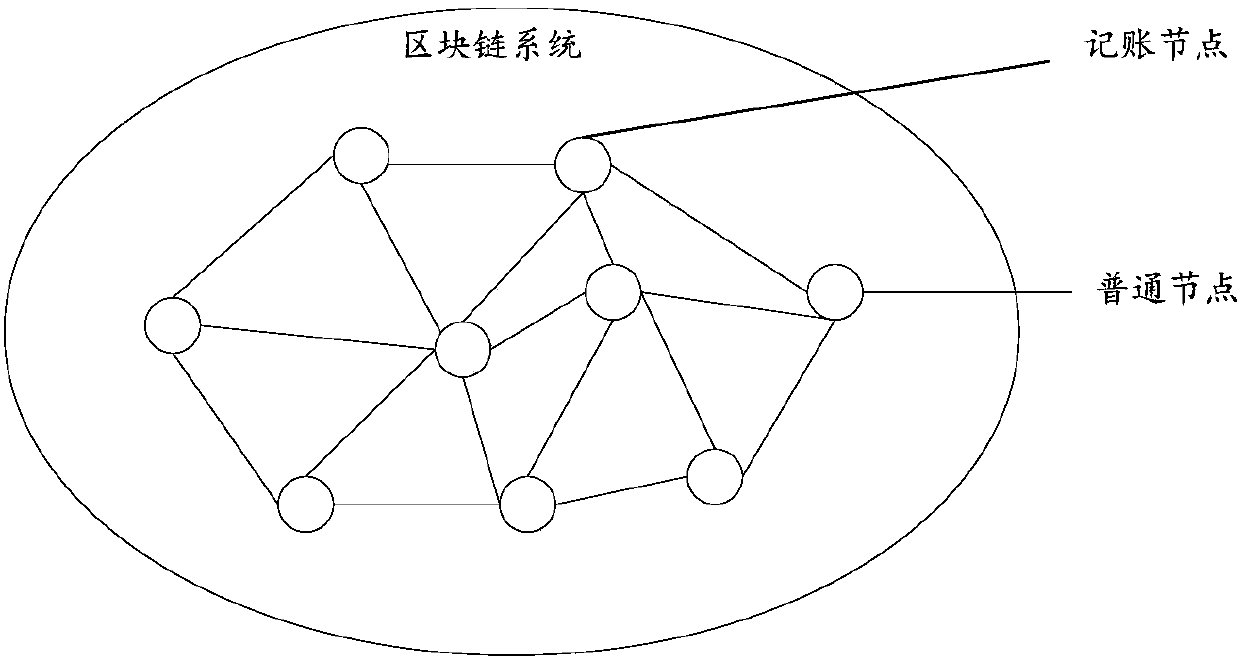
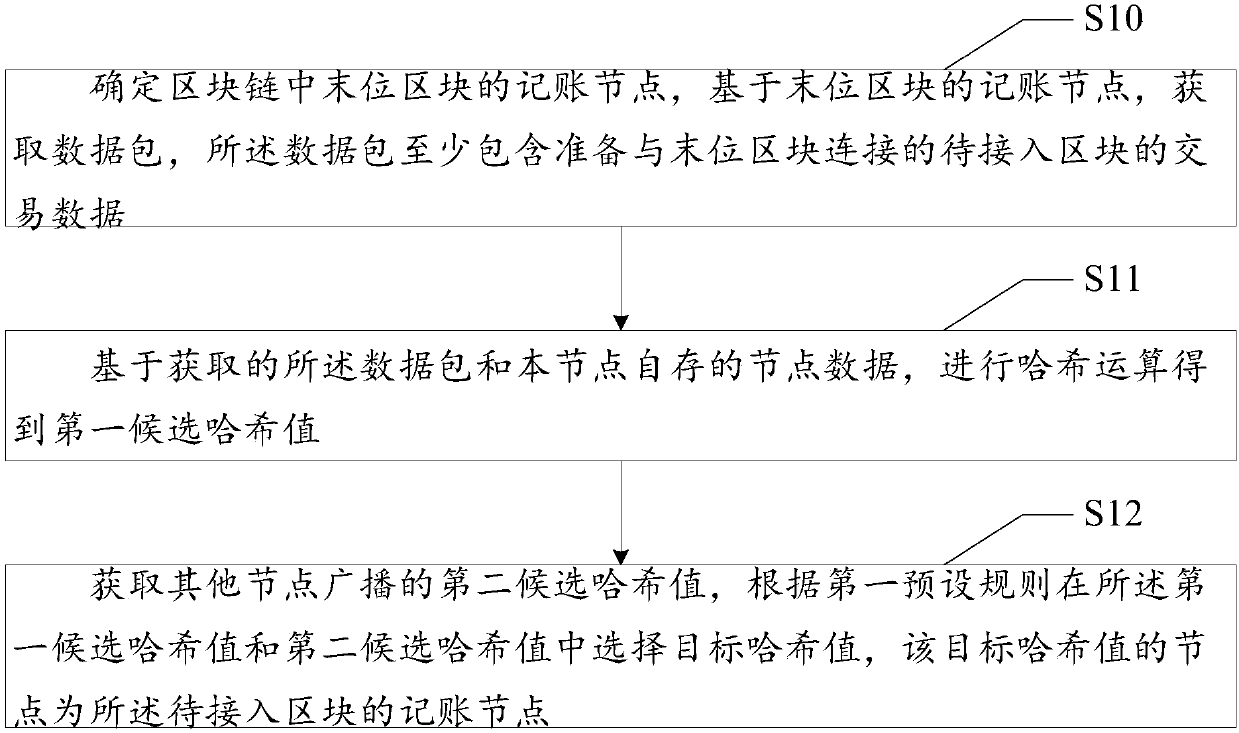
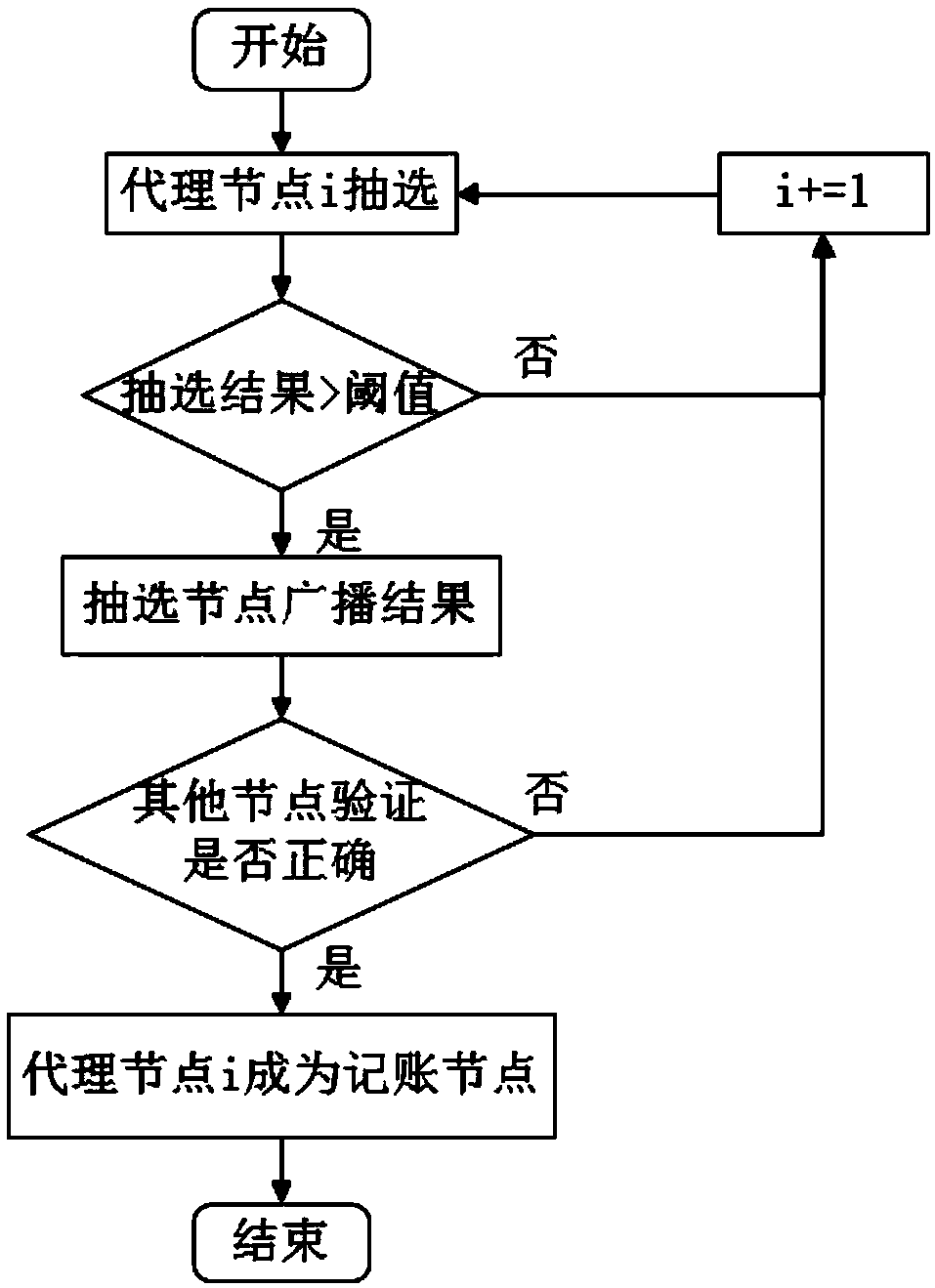
Consensus building method based on lottery mechanism, block chain system and storage medium
ActiveCN107566124ARule out evilCreated smoothlyEncryption apparatus with shift registers/memoriesUser identity/authority verificationNetwork packetTransaction data
The invention discloses a consensus building method based on a lottery mechanism, a block chain system and a storage medium. The method comprises the steps that an accounting node of a last block in ablock chain is determined, and a data packet is acquired on the basis of the accounting node of the last block, wherein the data packet at least comprises transaction data of a to-be-connected blockpreparing to be connected with the last block; Hash operation is conducted on the basis of the acquired data packet and node data saved in the node to obtain a first candidate Hash value; a second candidate Hash value broadcast by other nodes is acquired, and a target Hash value is selected from the first candidate Hash value and the second candidate Hash value according to a first preset rule, wherein the node of the target Hash value is the accounting node of the to-be-connected block. According to the consensus building method, it can be guaranteed that all nodes in the block chain competefor the accounting permission in complete equality, more people can be encouraged to participate in the block chain, and therefore the method is beneficial for application and popularization of the block chain.
Owner:SHENZHEN ECHIEV AUTONOMOUS DRIVING TECH CO LTD
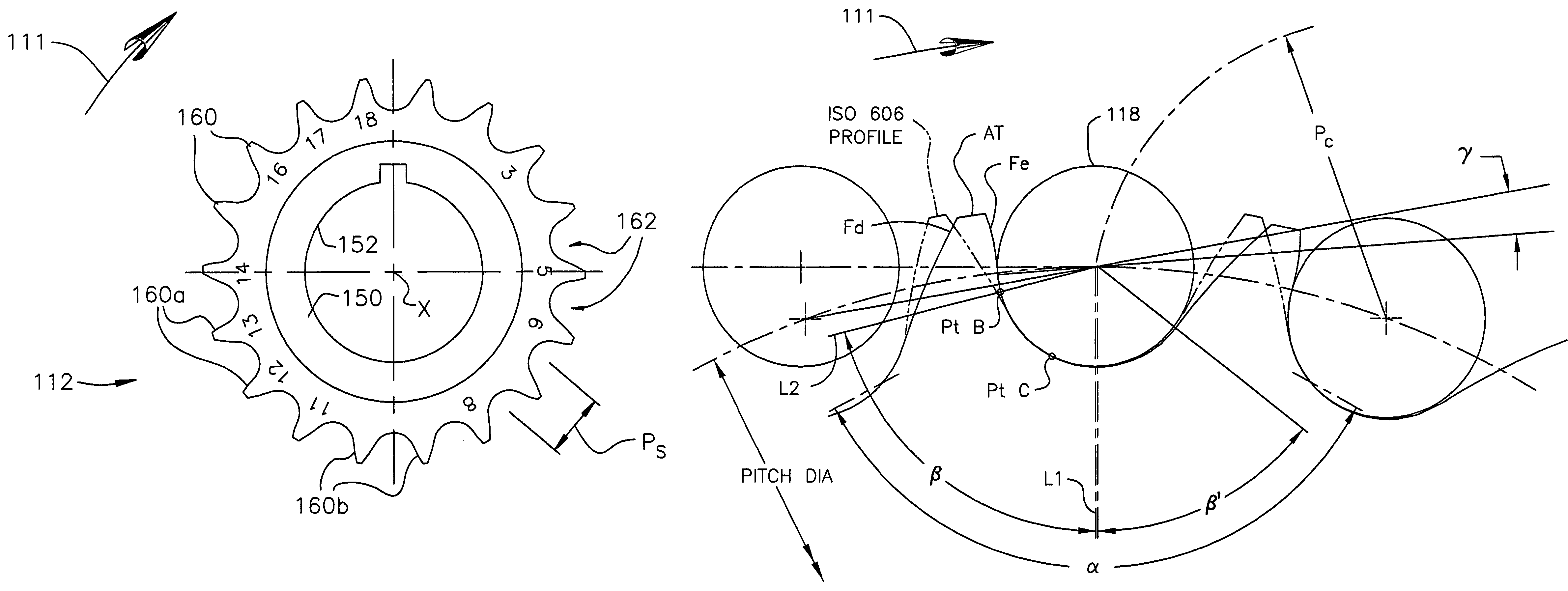
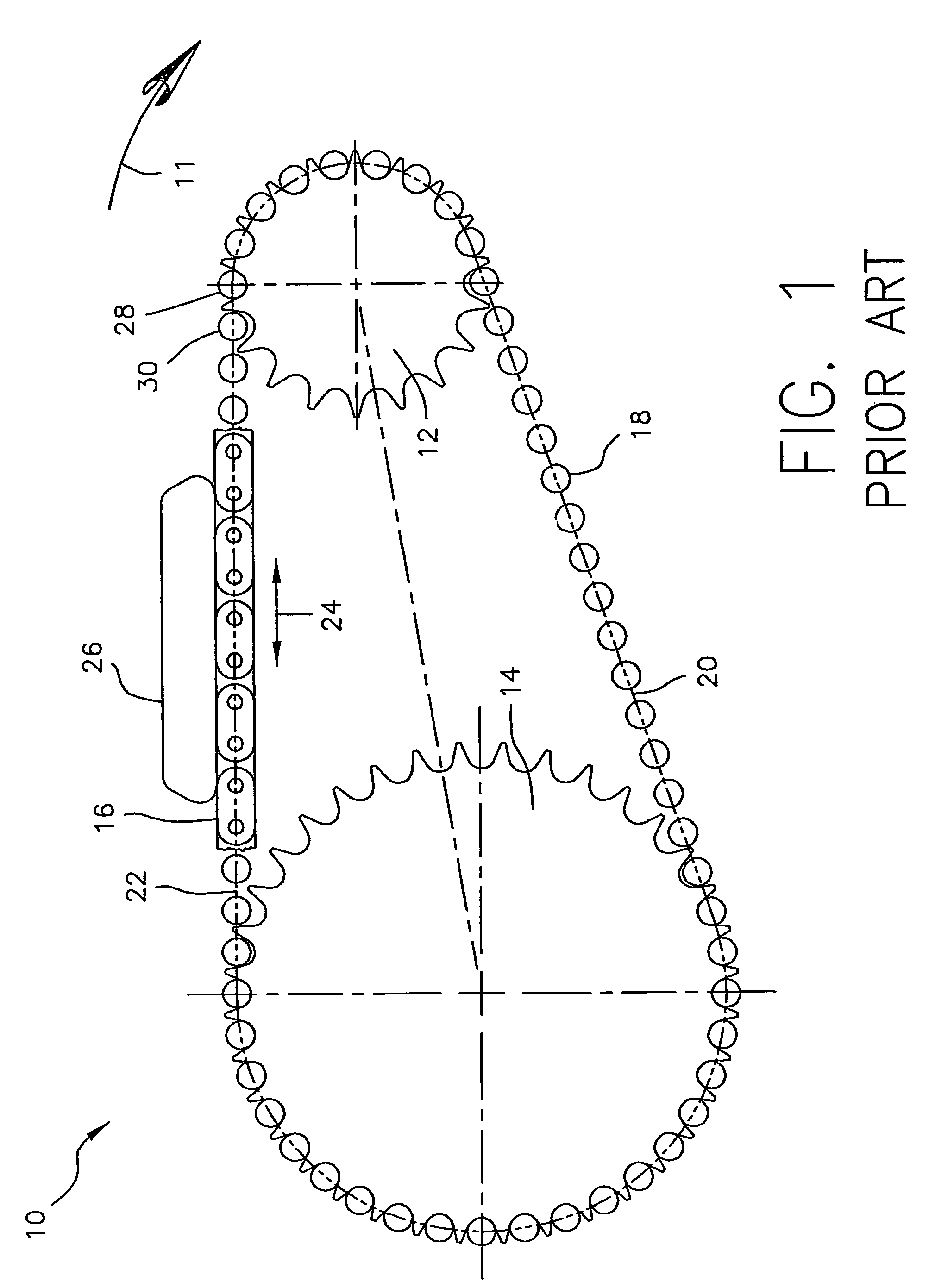
Random engagement roller chain sprocket and timing chain system including same
A sprocket and a roller chain drive system including same are disclosed. The sprocket is a random engagement sprocket comprising a first plurality of A-profile teeth formed with a first asymmetric profile and a second plurality of B-profile teeth formed with a second asymmetric profile. The A-profile teeth each define a first pressure angle and the B-profile teeth each define a second pressure angle that is at least 5 degrees greater than said first pressure angle so that a minimum separation Δ is defined. The sprocket is defined with added chordal pitch reduction of 0.2% up to 1% relative to the link pitch of the associated roller chain. The sprocket can be defined with root relief and / or can comprise resilient cushion rings. Initial roller contacts made with the A-profile and B-profile teeth are modulated owing to the pressure angle separation and added chordal pitch reduction.
Owner:HH CLOYES INC
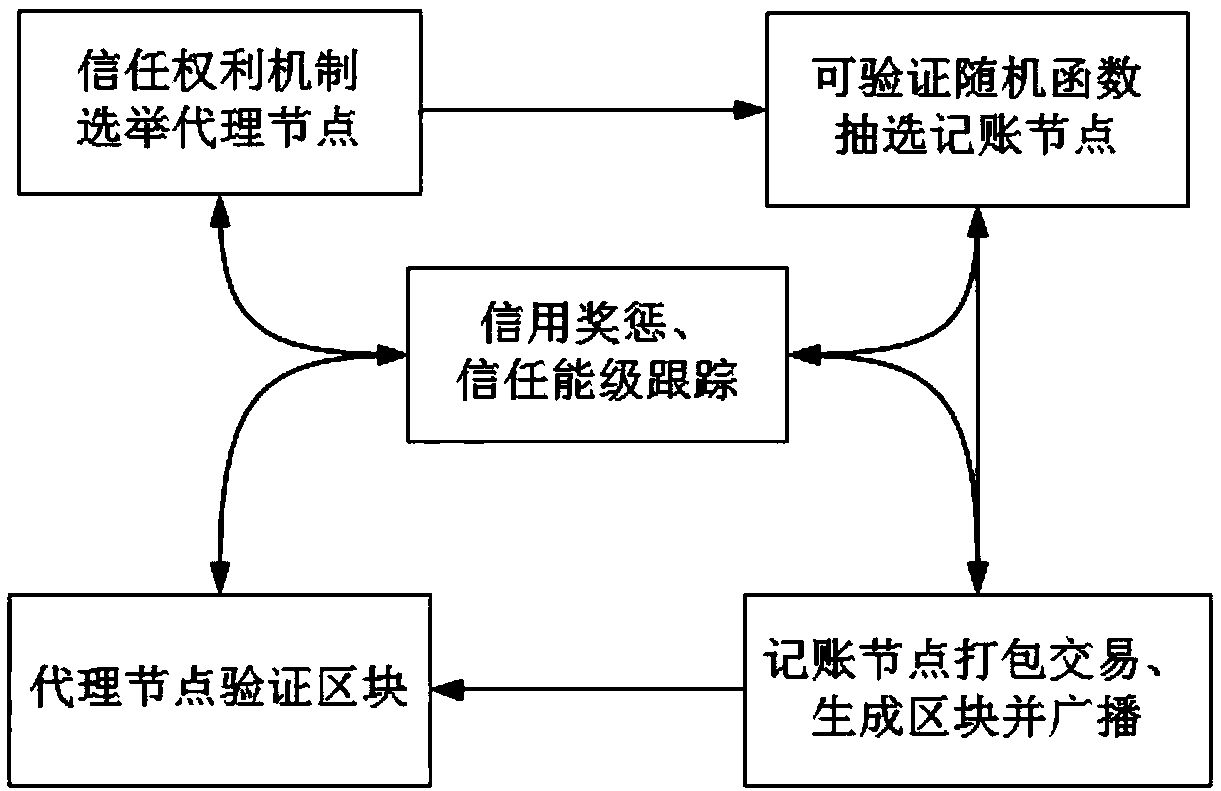
Block chain DPoS (Delegate Proof of Stake) consensus method based on trust mechanism
ActiveCN109639837ATimely exclusionIncrease engagementKey distribution for secure communicationPublic key for secure communicationChain networkProof-of-stake
The invention discloses a block chain DPoS (Delegate Proof of Stake) consensus method based on a trust mechanism. According to the method, concepts of trust degree and trust energy levels are importedfor nodes in a block chain system; the nodes with a trust energy level of error cannot participate in proxy node competitive election; proxy nodes are elected through utilization of a trust authoritymechanism; accounting nodes are extracted from the proxy nodes through adoption of a verifiable random function; and in a block chain network operation process, trust reward and penality are carriedout on node behaviors, and interruption and kickout policies employed for the accounting nodes of which trust energy level is reduced to the error energy level. According to the method, through tracking of the trust energy levels of the nodes and through trust reward and penality of the nodes, a probability that malicious nodes become the accounting nodes is reduced; participation active degree ofcommon nodes is improved; reliability of the whole consensus method is ensured; the trust degree is taken as a delegate proof of stake, so additional token money distribution is avoided.
Owner:SOUTHEAST UNIV
Lightweight terminal block chain system
InactiveCN107317672AIncrease credibilityImprove immutabilityFinanceEncryption apparatus with shift registers/memoriesTransaction dataTerminal equipment
The invention provides a lightweight terminal block chain system. The system comprises a plurality of nodes, wherein the nodes comprise a core node and lightweight nodes; the core node is used for participating in block chain consensus, keeping accounts and generating a new block, and the block comprises a block head and a block main body; the lightweight node stores the block head and participates in node discovery, transaction broadcast and transaction validity verification. By adoption of the lightweight terminal block chain system, when a lightweight terminal device accesses the network, the lightweight terminal device participates in the transaction verification, transaction broadcast, block check and other functions of the block chain system, so that the transaction data in the block chain network back up more transaction information that cannot be tampered on more devices, thereby fully utilizing the idle resources of a part of terminal devices, and enhancing the reliability and the non-tampering property of the block chain system. Meanwhile, the system fully considers the limited storage, calculation and network resources of the terminal devices, so that the terminal devices join in the block chain system by the lightweight nodes, that is, maintain the normal operation of the block chain system by very small resource costs.
Owner:GUANGDONG YOUMAI INFORMATION COMM TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com