Patents
Literature
33results about How to "Improve immutability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
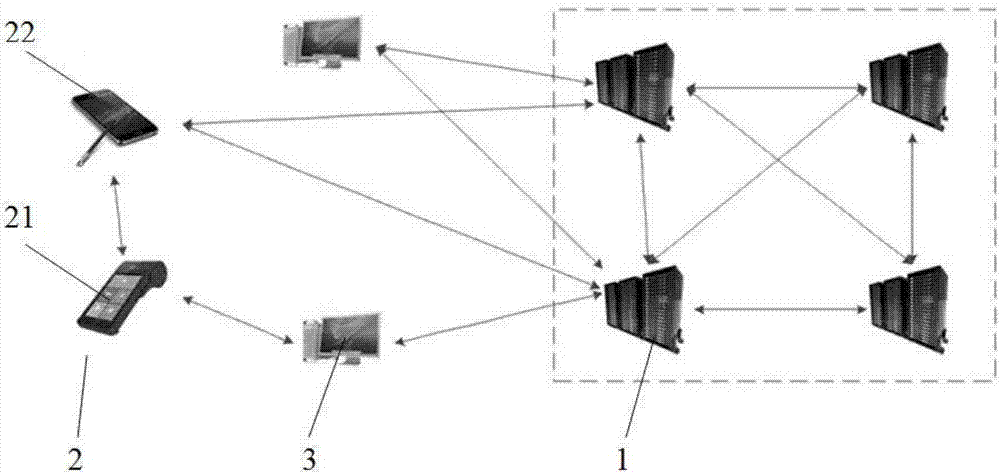
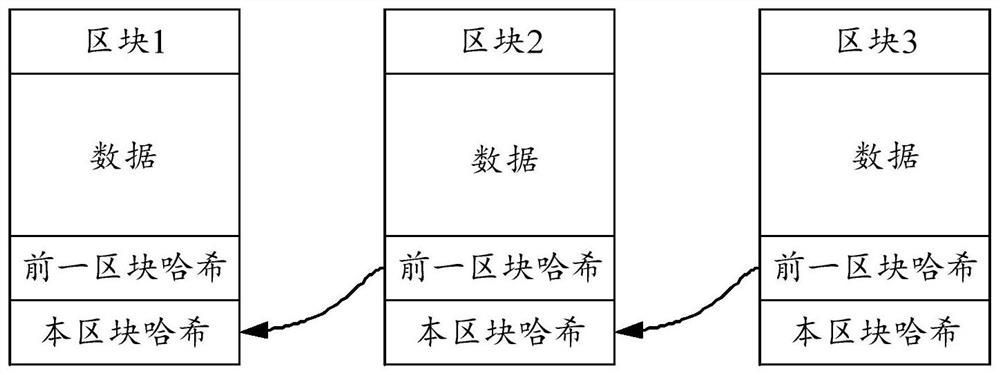
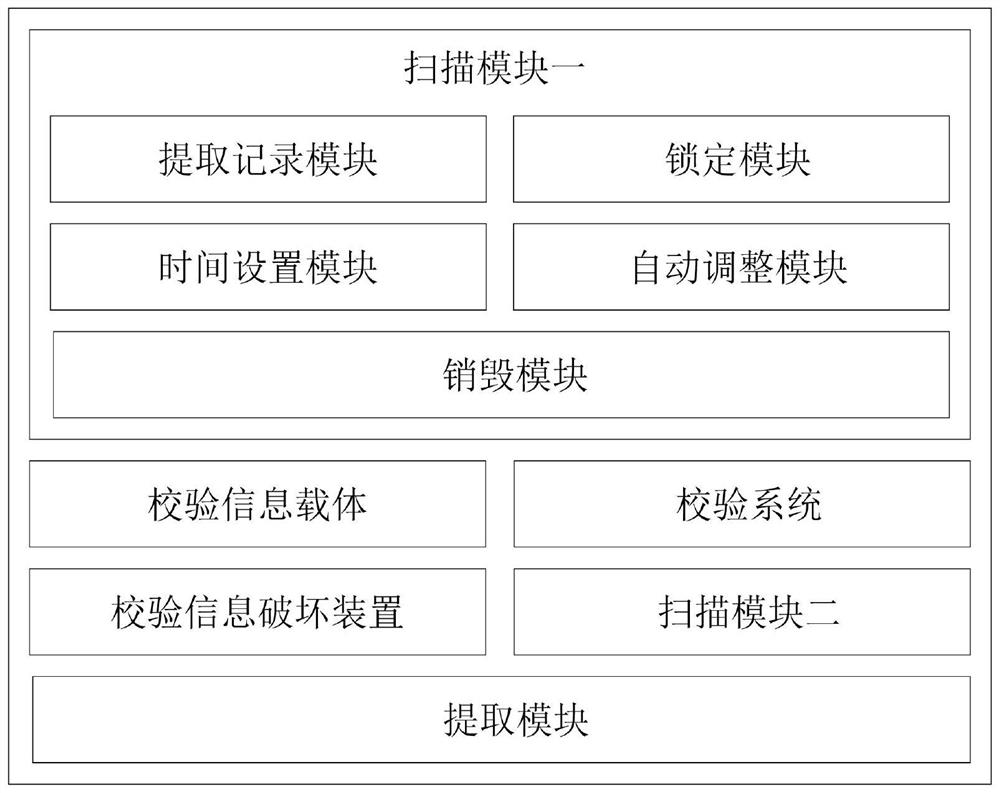
Lightweight terminal block chain system
InactiveCN107317672AIncrease credibilityImprove immutabilityFinanceEncryption apparatus with shift registers/memoriesTransaction dataTerminal equipment
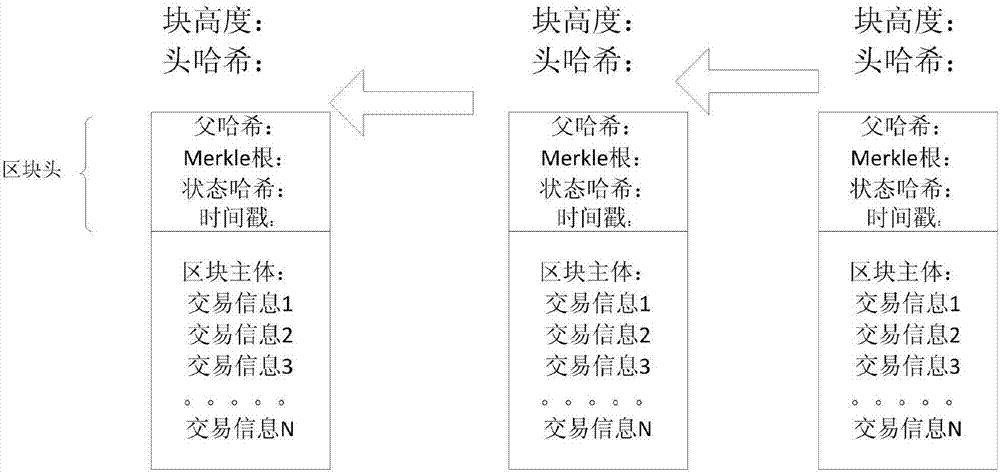
The invention provides a lightweight terminal block chain system. The system comprises a plurality of nodes, wherein the nodes comprise a core node and lightweight nodes; the core node is used for participating in block chain consensus, keeping accounts and generating a new block, and the block comprises a block head and a block main body; the lightweight node stores the block head and participates in node discovery, transaction broadcast and transaction validity verification. By adoption of the lightweight terminal block chain system, when a lightweight terminal device accesses the network, the lightweight terminal device participates in the transaction verification, transaction broadcast, block check and other functions of the block chain system, so that the transaction data in the block chain network back up more transaction information that cannot be tampered on more devices, thereby fully utilizing the idle resources of a part of terminal devices, and enhancing the reliability and the non-tampering property of the block chain system. Meanwhile, the system fully considers the limited storage, calculation and network resources of the terminal devices, so that the terminal devices join in the block chain system by the lightweight nodes, that is, maintain the normal operation of the block chain system by very small resource costs.
Owner:GUANGDONG YOUMAI INFORMATION COMM TECH
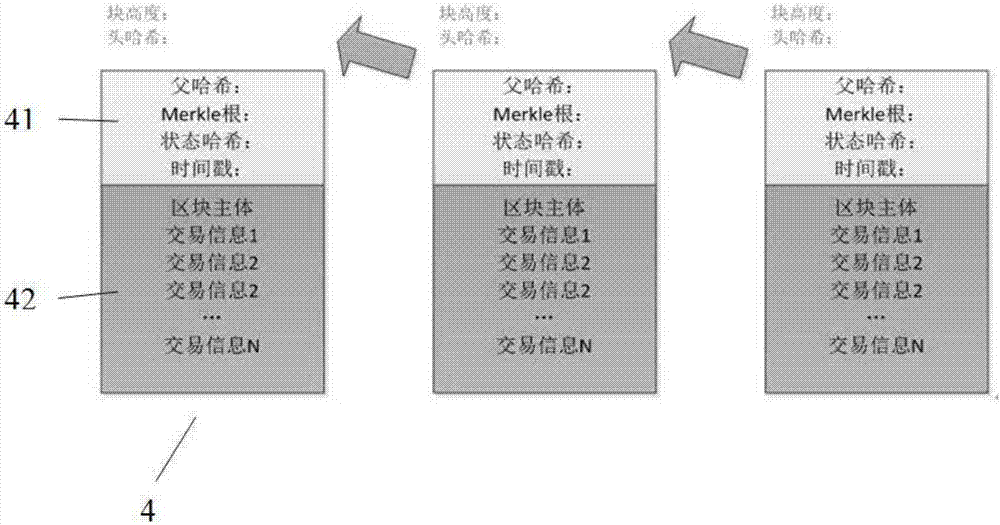
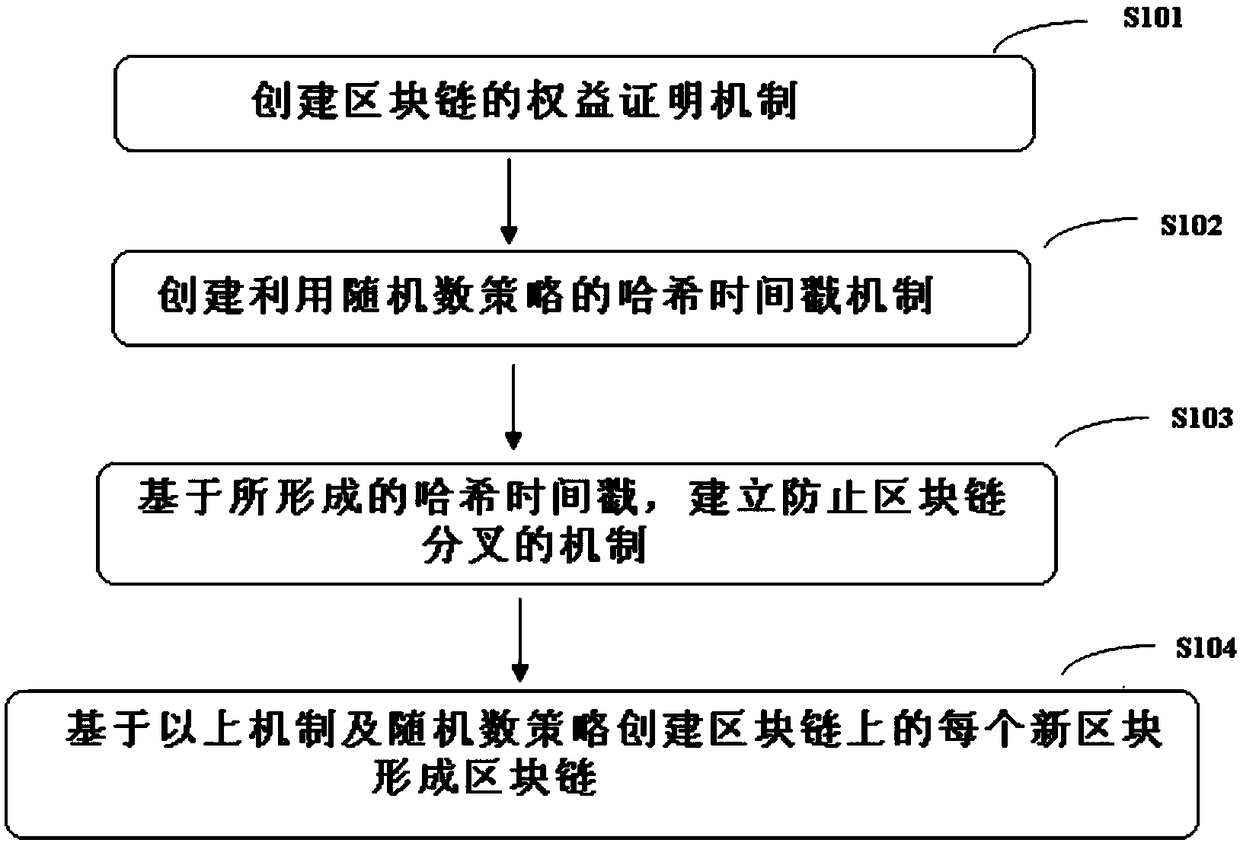
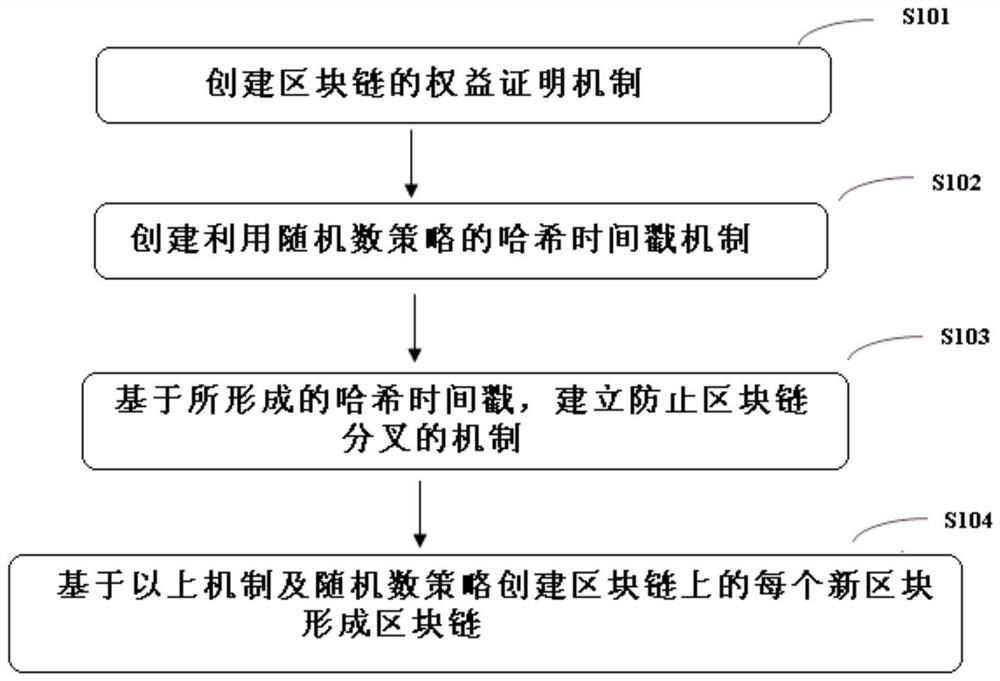
Method, device and readable storage medium for creating block chain
ActiveCN109039648AImprove transaction securityImprove immutabilityFinanceUser identity/authority verificationTimestampProof-of-stake
The invention discloses a method for creating a block chain, a device and a readable storage medium. The methods include: creating rights and interests proof mechanism of block chain; creating a hashtimestamp mechanism using random number policy; based on the formed hash timestamp, establishing a mechanism for preventing block chain bifurcation ; based on the above mechanism and random number strategy, creating each new block on the block chain to form a block chain. The adoption of that technical scheme, Competition among the parties entitled to create new blocks does not control random numbers, so that you cannot gain building-block-first privileges, improving the security and non-tampering of block chain transactions, rights and interests are proportional to the driving force of systemsecurity, based on hash-based timestamp, the person who has the right to keep account eliminates bifurcation with the maximum possibility is decided, punishment mechanism for the creators of historical blocks who do not obey the rules and do not participate in the maintenance of several blocks is established, a fair, stable and efficient block chain trading environment is created, the trust modelis optimized, and a good mechanism is provided to control the chain growth rate.
Owner:CROSBIL LTD
Coherent information processing method based on blockchain, and terminal
InactiveCN107197036AEnhancing trustworthiness and immutabilityIncrease credibilityUser identity/authority verificationBlockchainCoherent information
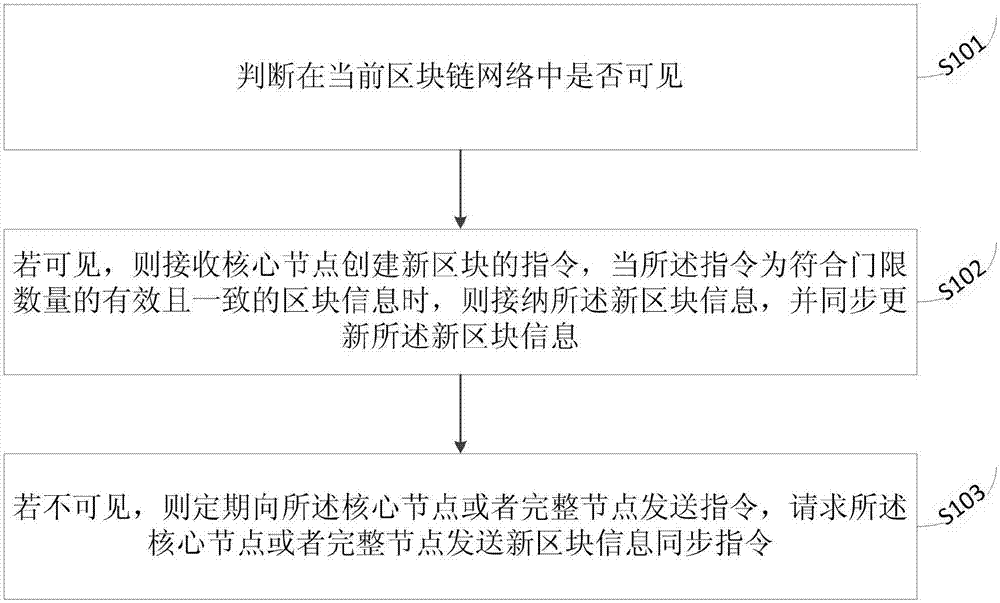
The invention discloses a coherent information processing method based on a blockchain, and a terminal. The method comprises the following steps: judging whether the terminal is visible in a current blockchain network or not; if the terminal is visible in the current blockchain network, receiving a command of a core node for creating a new block, and receiving and synchronously updating new block information when the command is effective and coherent block information complying with a threshold number; and if the terminal is not visible in the current blockchain network, sending commands to the core node or a complete node at regular times to request the core node or the complete node to send new block information synchronization commands. The method disclosed by the invention has the advantage that the problem in the prior art that a blockchain system cannot utilize a huge number of terminal resources to achieve higher credibility and reliability is solved.
Owner:GUANGDONG YOUMAI INFORMATION COMM TECH
Blockchain-based violation event processing method, system, device, and storage medium
PendingCN110427432ARealize automatic collectionIncrease credibilityData processing applicationsRoad vehicles traffic controlTamper resistanceEvent data
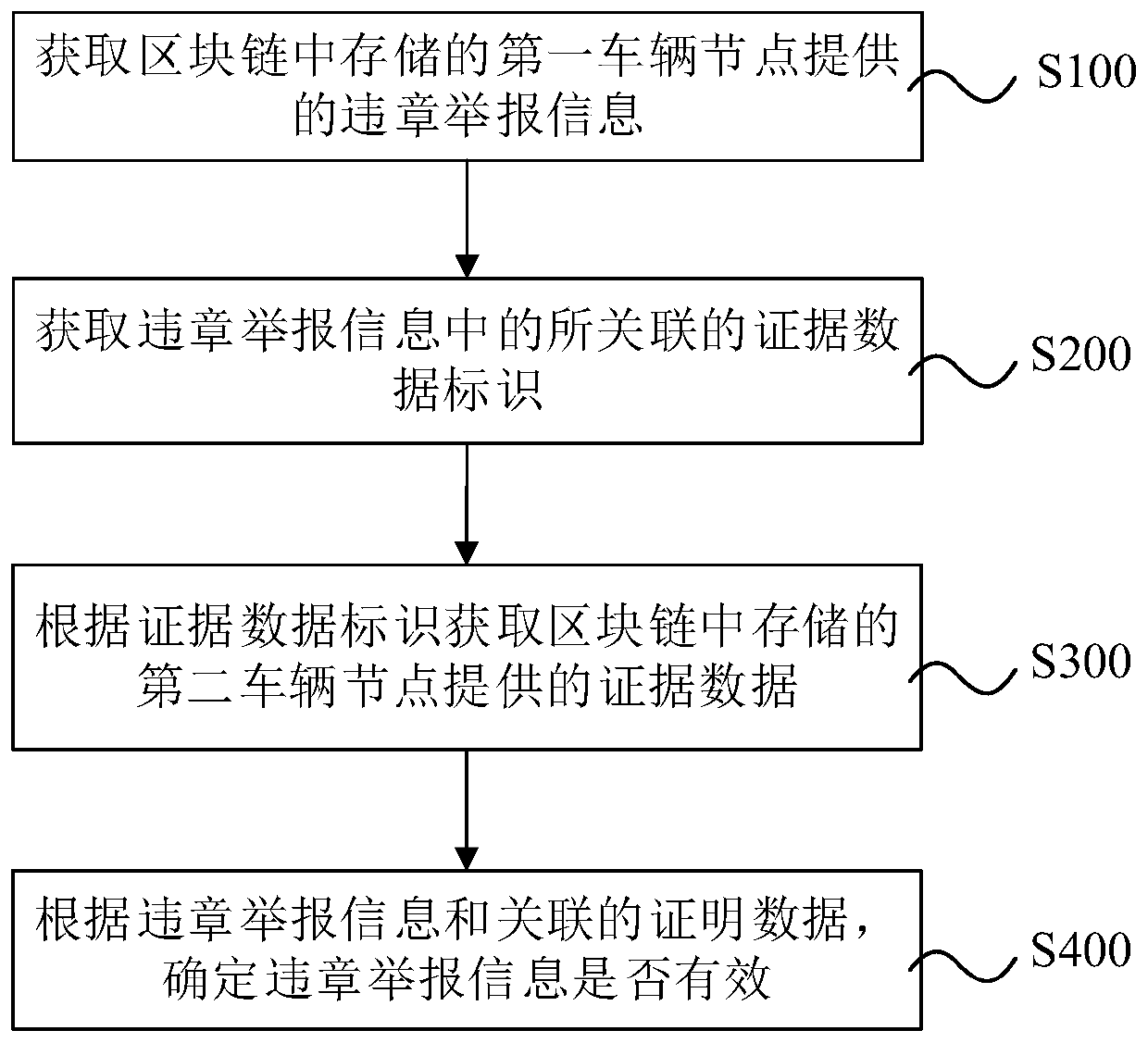
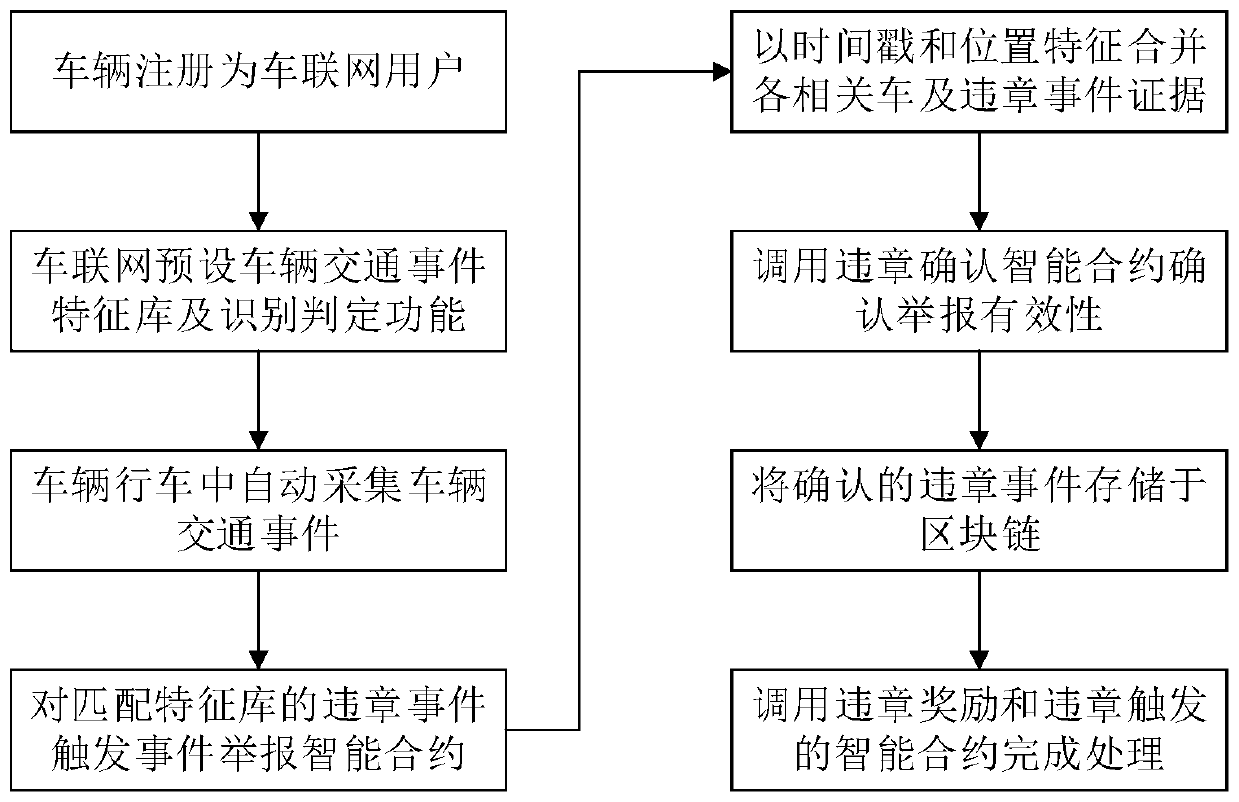
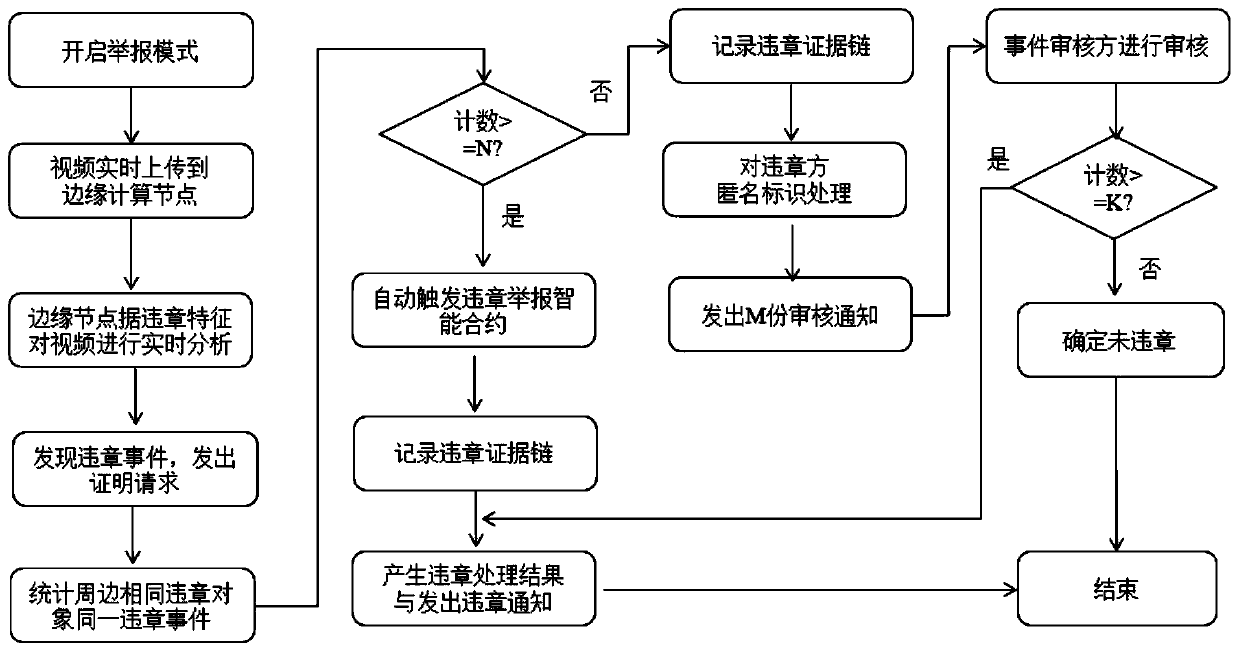
The invention provides a blockchain-based violation event processing method, a system, a device and a storage medium. The method comprises the steps of obtaining violation report information providedby a first vehicle node and stored in a blockchain; obtaining an associated evidence data identifier in the violation report information; obtaining evidence data provided by a second vehicle node andstored in the blockchain according to the evidence data identifier; and determining whether the violation reporting information is valid or not according to the violation reporting information and theassociated certification data. According to the method, violation event data are automatically collected through each vehicle node in the blockchain, credible violation judgment is completed based onthe smart contract, and credibility and tamper resistance of violation judgment are improved based on record information of a plurality of associated blockchain nodes.
Owner:INVENTECSHANGHAI TECH +2
Copyright trading method and system based on block chain technology
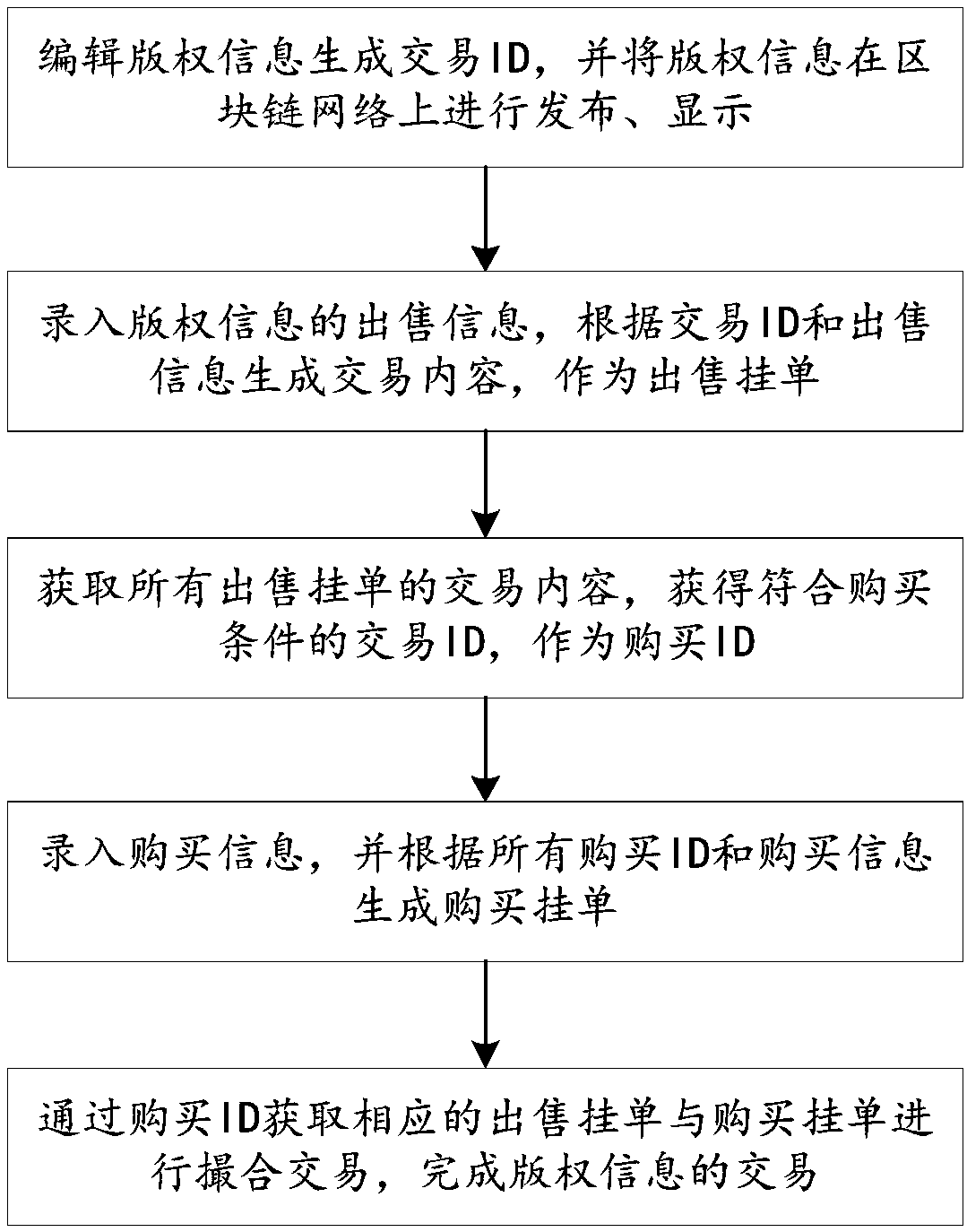
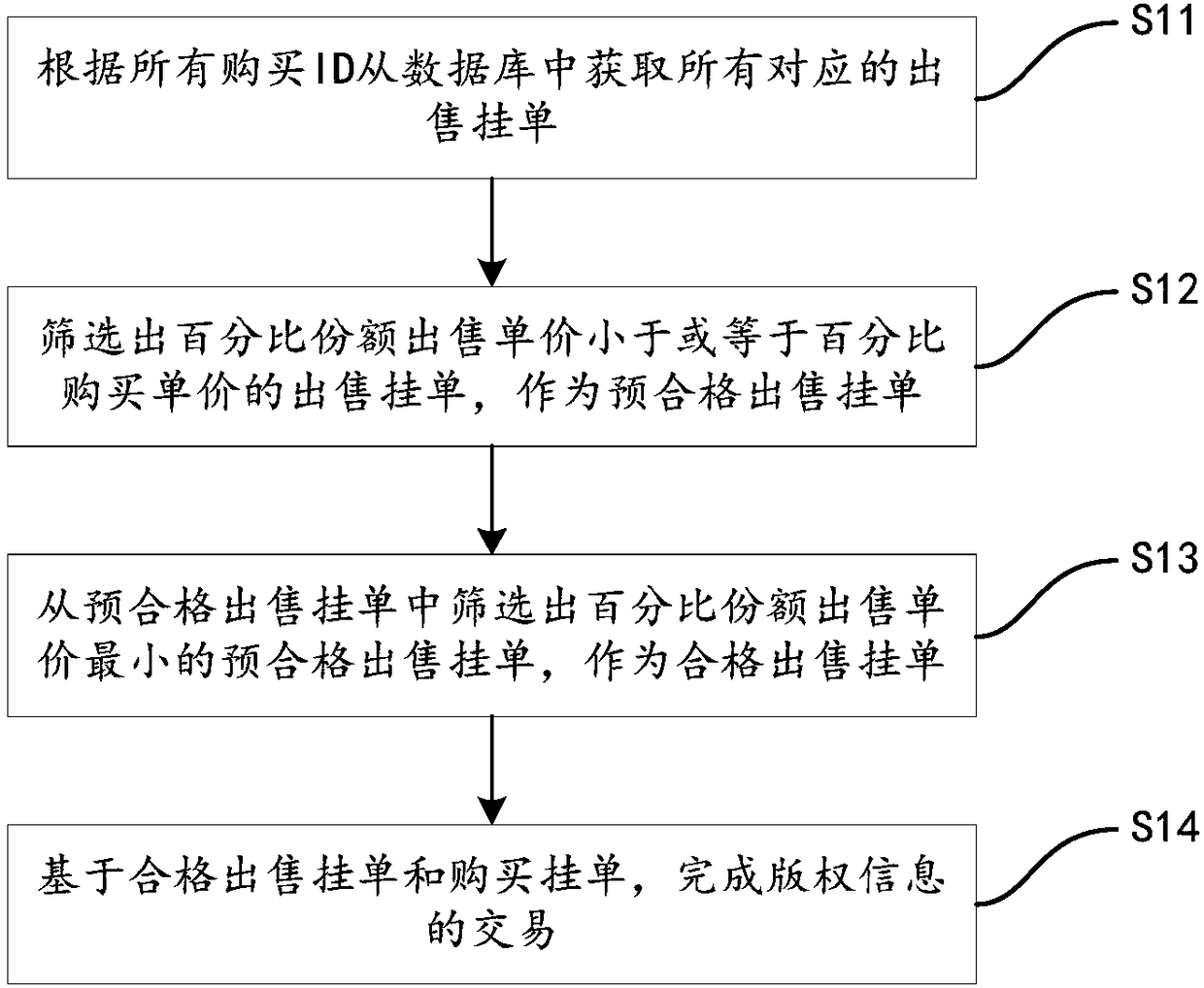
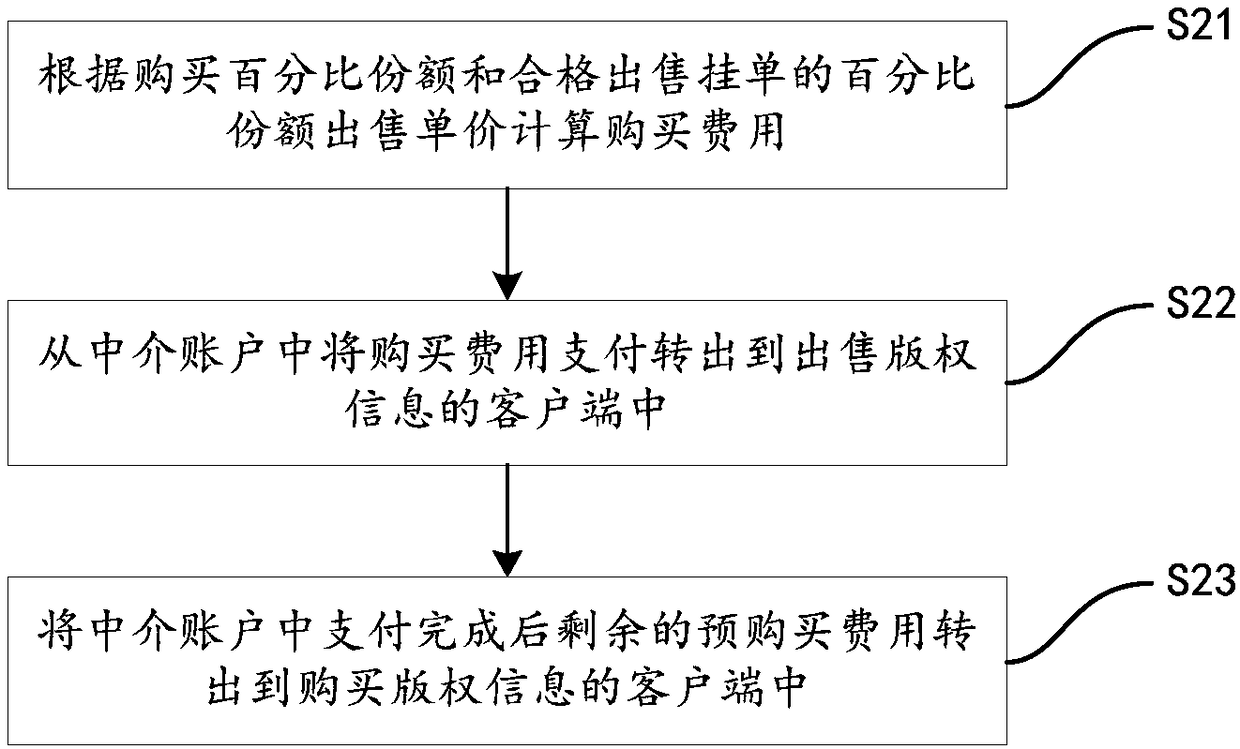
ActiveCN108537627AProtection of rights and interestsImprove securityFinanceBuying/selling/leasing transactionsPurchasingComputer science
The invention relates to a copyright trading method and system based on a block chain technology. The copyright trading method comprises steps: copyright information is edited to generate a trading ID; sales information is inputted, and a trading content is generated according to the trading ID and the sales information; the trading content is acquired and displayed; according to all trading contents, a trading ID which meets a purchasing condition is acquired as a purchasing ID; according to all purchasing IDs and the purchasing information, a purchasing entry order is generated; a corresponding sales entry order and the purchasing entry order are subjected to married deal, and trading of the copyright information is completed. In the embodiment of the invention, the trading process is recorded through the block chain technology, the safety and the non tampering of the trading itself are improved; through enabling the sales side and the purchasing side to be subjected to married deal,the purchasing side can purchase a proper copyright with the most favorable condition, the characteristics of openness and transparency of the block chain make supervision more fair and impartial, decentration of the block chain enables trading to be more direct, quicker and lower in cost, and the rights and the interests of a copyright owner are ensured.
Owner:朱志文
Medical information sharing authentication method based on block chain
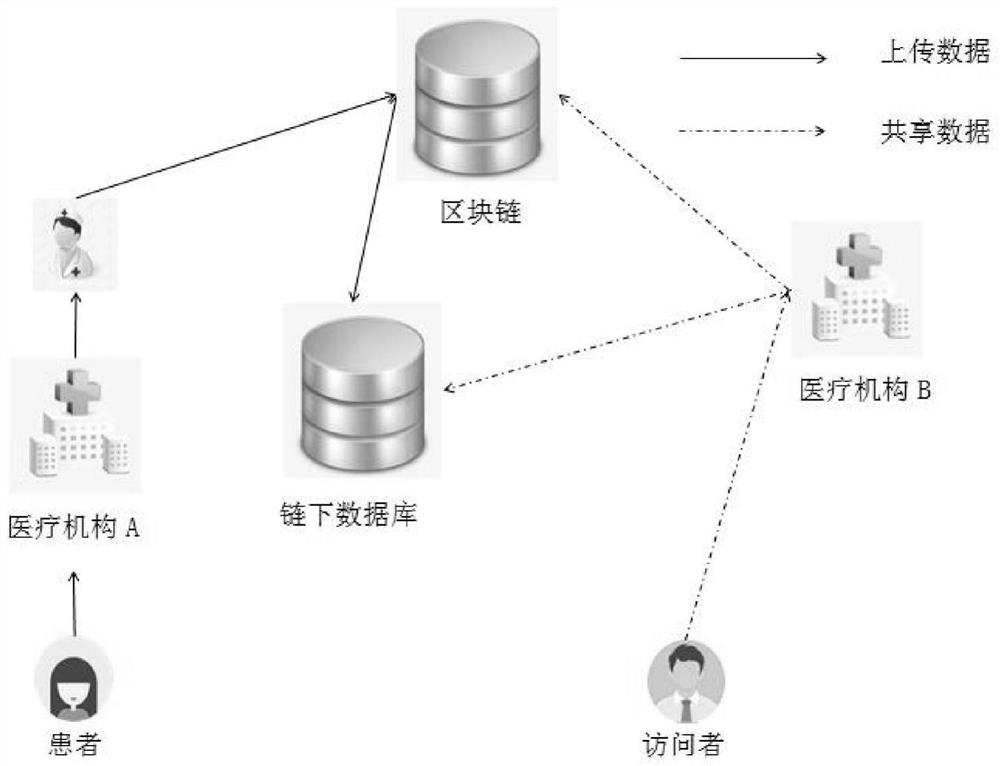
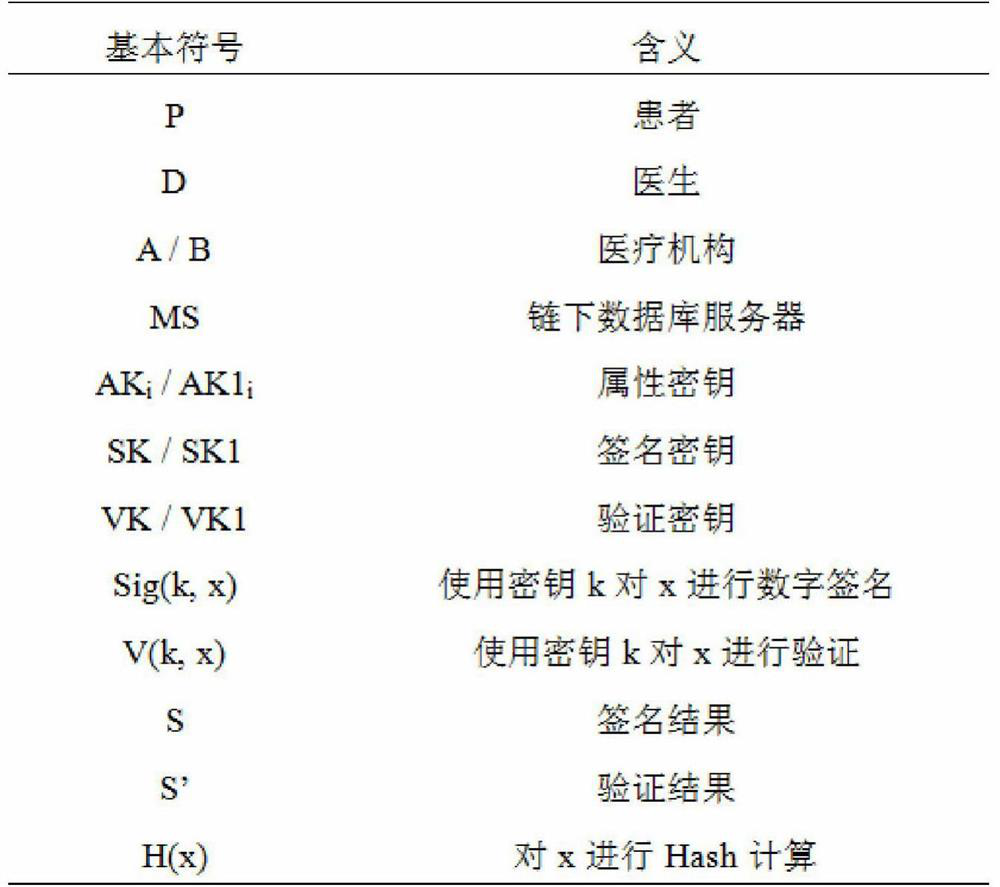
ActiveCN111863165AReduce storage burdenReduce maintenance costsEncryption apparatus with shift registers/memoriesUser identity/authority verificationMedical recordPatient diagnosis
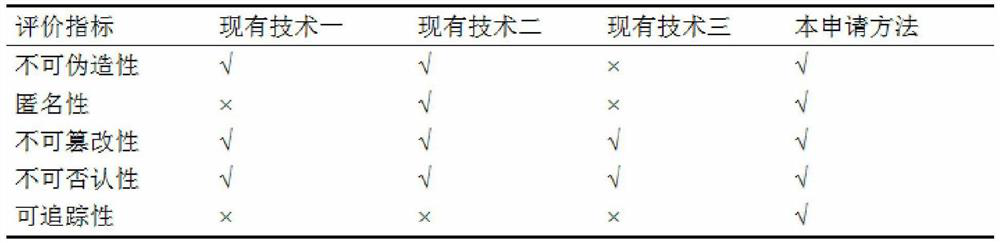
The invention discloses a medical information sharing authentication method based on a block chain, and relates to the technical field of the block chain. The method comprises the following steps: a doctor diagnoses a patient and stores a whole-course diagnosis result in a system provided by a medical institution, the doctor cannot create an electronic medical record, only the medical institutioncan create the electronic medical record and store an electronic medical record signature in an off-chain database, and then the storage address signature of the electronic medical record in the off-chain database is broadcasted to a block chain; visitors for the block chain and the off-chain database are only medical institutions; a doctor submits an application to a medical institution where thedoctor is located, the medical institution accesses the data on the block chain to obtain the address of the patient electronic medical record in the off-chain database, accesses detailed data of thepatient electronic medical record in the off-chain database, and finally sends the detailed data to a legal doctor through an internal system of the medical institution. The method has the advantagesof no forgery, anonymity, no tampering, no repudiation, traceability and the like.
Owner:SHIJIAZHUANG TIEDAO UNIV
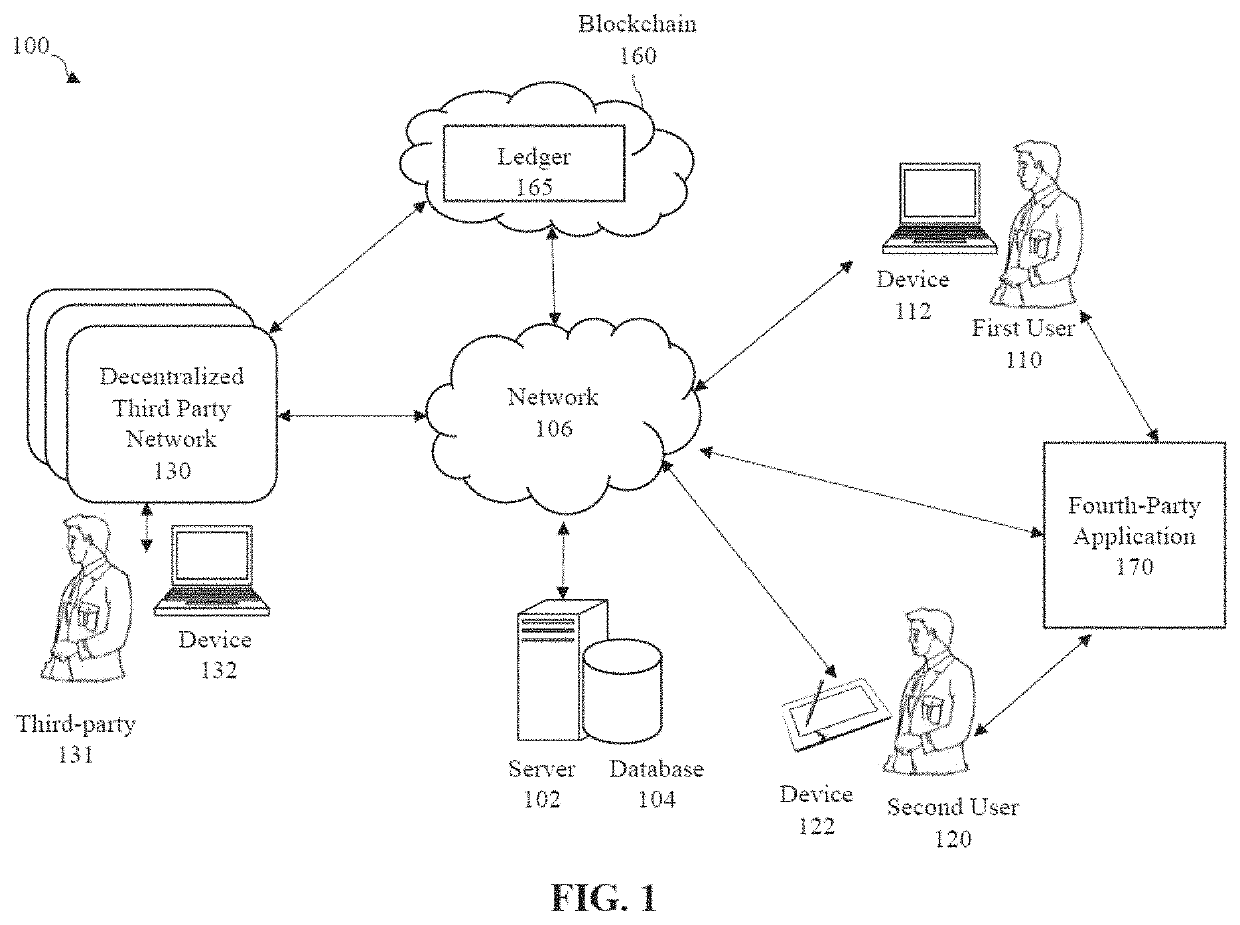
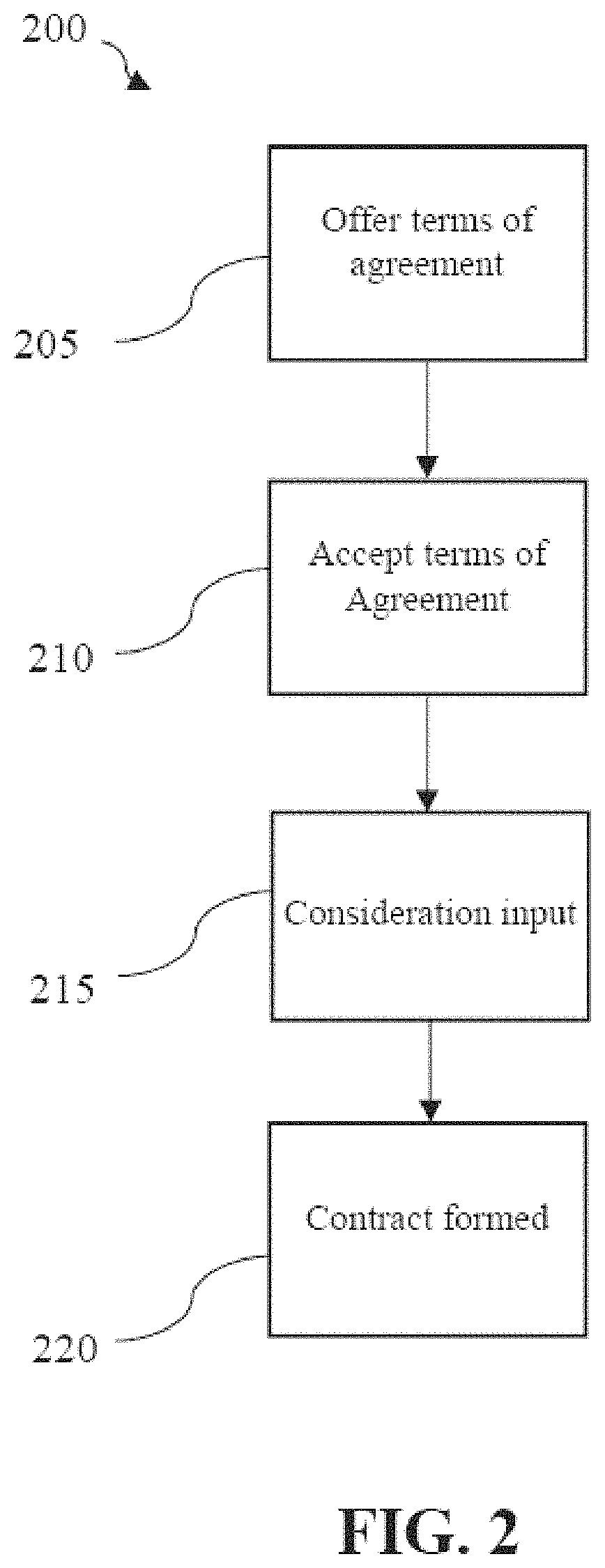
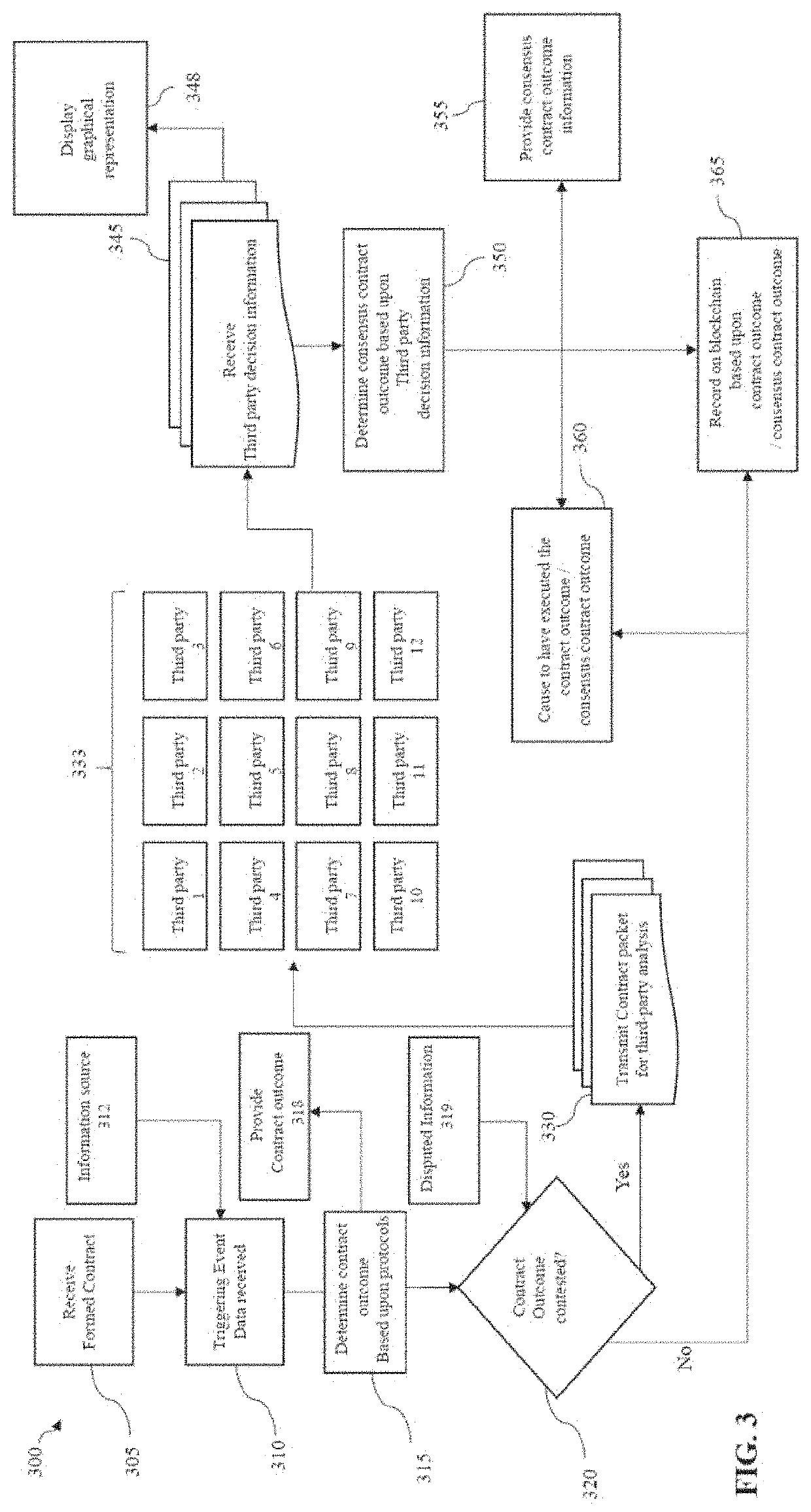
Systems and methods for storing contract information on multiple blockchain ledgers
ActiveUS20200151842A1Improve immutabilityFacilitates distributed trustFinanceApparatus for meter-controlled dispensingInternet privacyEngineering
A system and method for resolving contract disputes utilitizes one or more computing devices to receive a dispute resolution request, invite other parties to submit a response to the dispute resolution request, and submit the dispute to a plurality of delegates based on the type of dispute and the qualifications of the delegates. The delegates provide dispute resolution decisions, and a consensus algorithm is applied to the decisions to arrive at a consensus contract outcome. A record of the consensus contract outcome, including the disputed contract and the nature of the dispute are recorded on a permissioned blockchain and also optionally recorded on an external blockchain distributed ledger.
Owner:ASTRA ENTERPRISE LTD
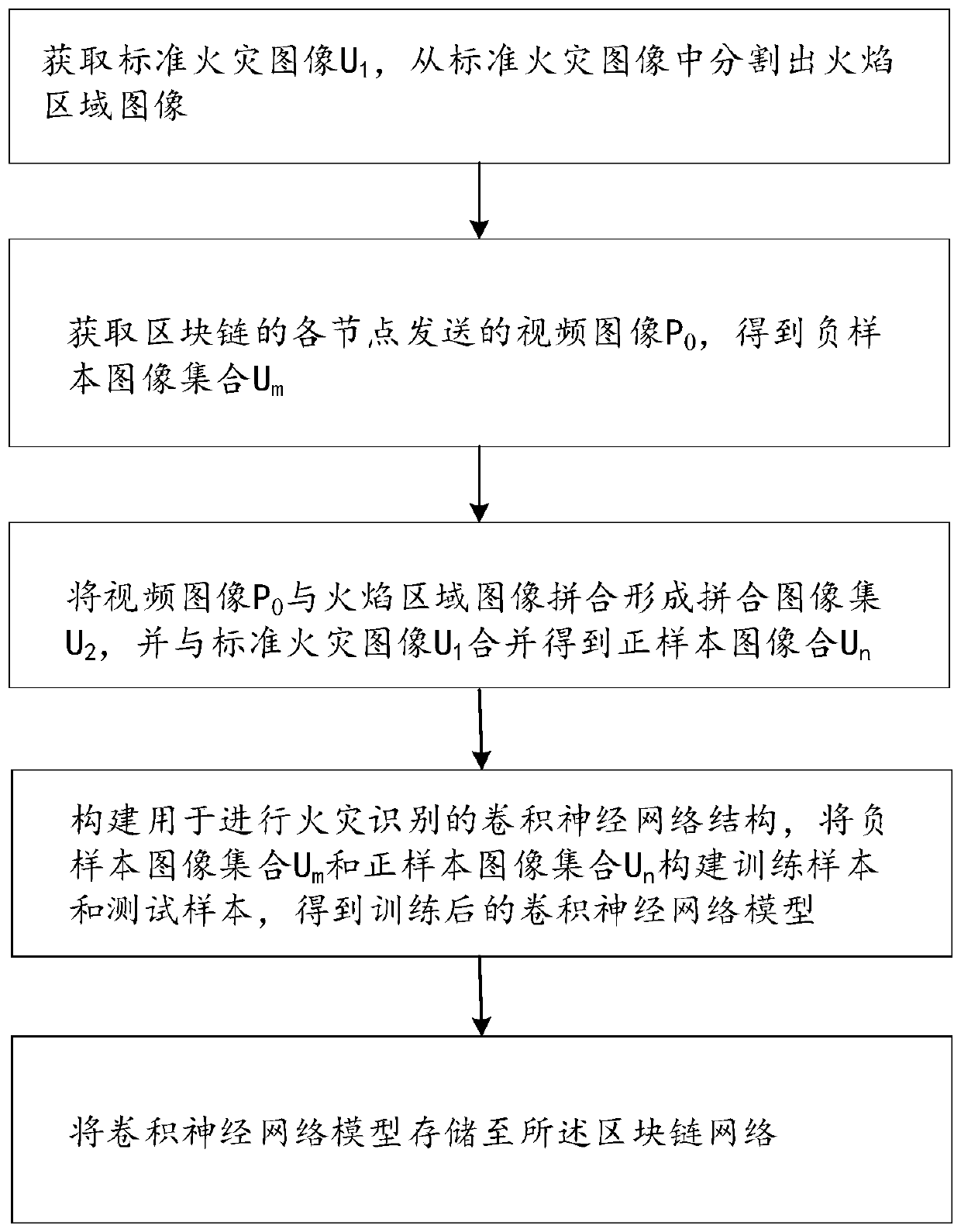
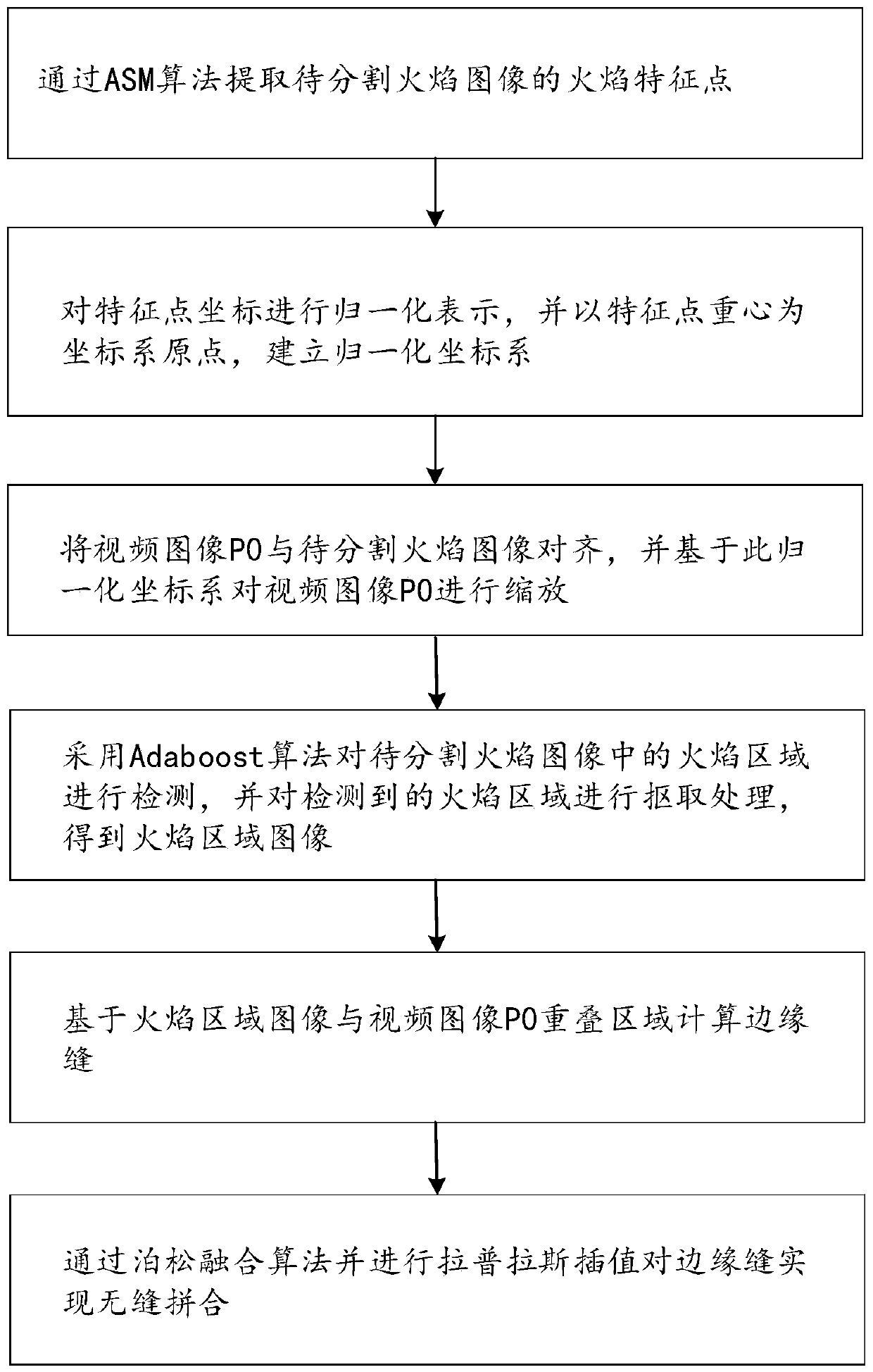
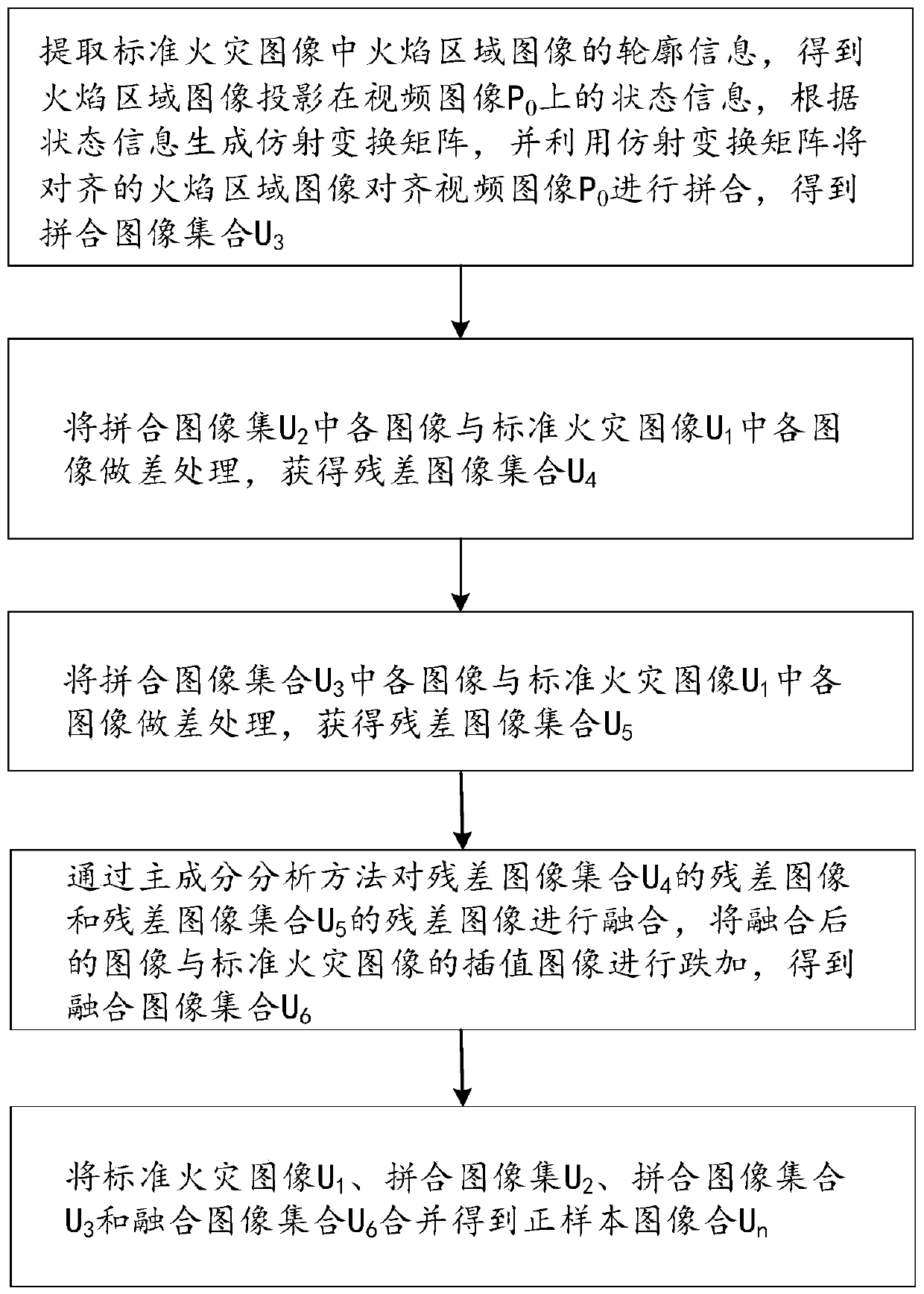
Fire identification method and system based on block chain
ActiveCN111553298AImprove accuracyImprove stabilityCharacter and pattern recognitionNeural architecturesChain networkBlockchain
The invention provides a fire identification method and system based on a block chain. The method comprises the steps of obtaining a standard fire image U1, and segmenting a flame region image from the standard fire image, obtaining a video image P0 sent by each node of the block chain to obtain a negative sample image set Um, splicing the video image P0 and the flame region image to form a spliced image set U2, and combining the spliced image set U2 with a standard fire image U1 to obtain a positive sample image Un, constructing a convolutional neural network structure for fire identification, and constructing a training sample and a test sample by using the negative sample image set Um and the positive sample image set Un, and storing the convolutional neural network model to the block chain network. According to the method, the defects of information islands of traditional fire recognition are overcome through the block chain network, sharing of the training data and the convolutional neural network model is achieved, the convolutional neural network model has very high stability and robustness, and the accuracy of fire recognition is improved.
Owner:ANHUI ZHONGCHENG INTELLIGENT TECH
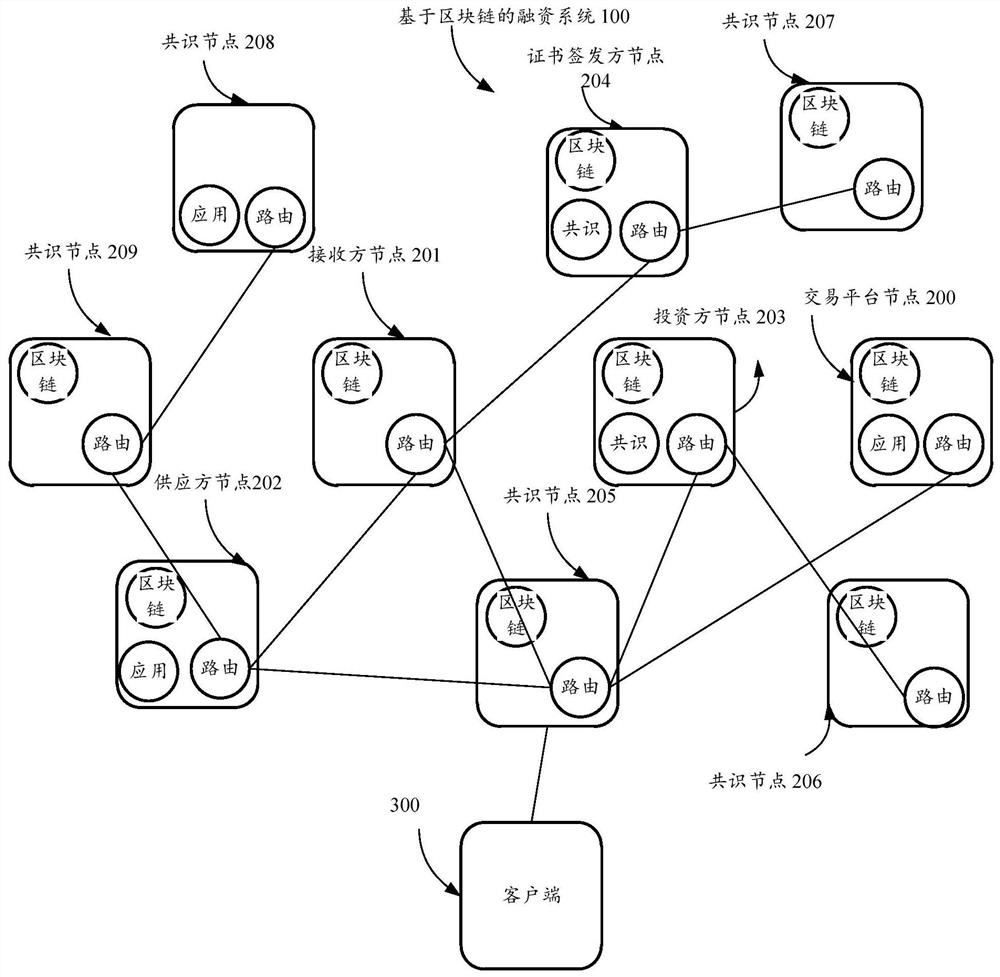
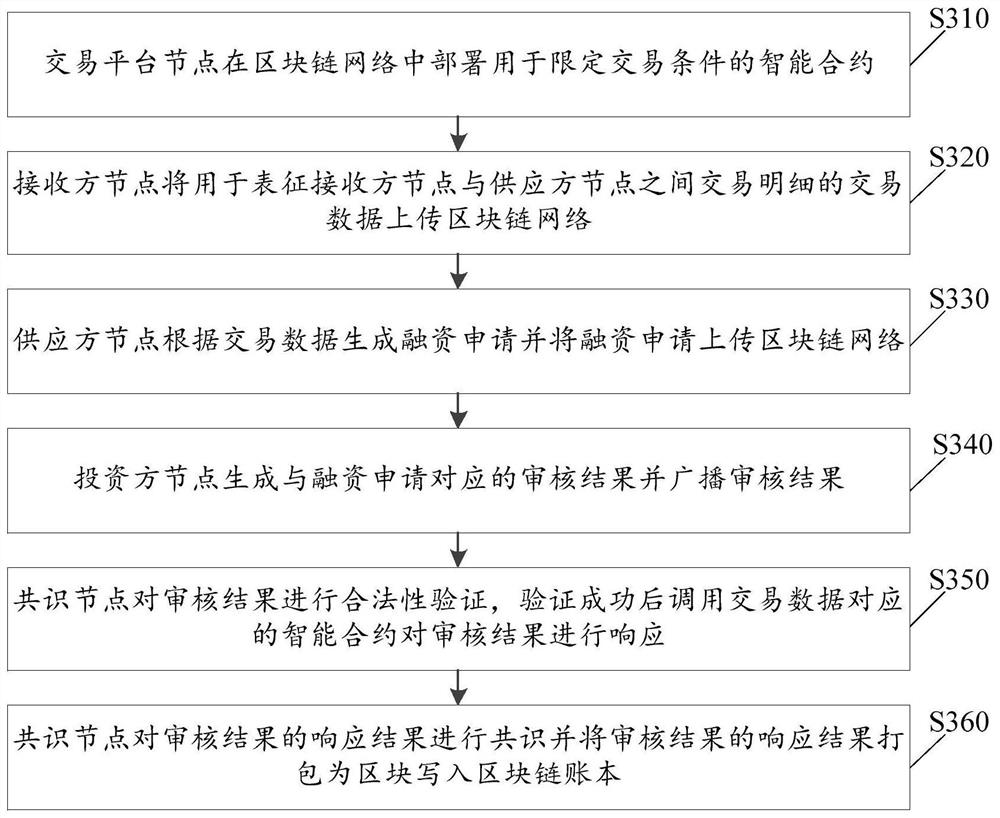
Financing method and system based on block chain and computer readable storage medium
PendingCN113706313AImprove accuracyAchieve traceabilityFinanceDigital data protectionChain networkDistributed computing
The invention provides a financing method based on a block chain, a financing system based on the block chain and a computer readable storage medium, and relates to the technical field of block chains. The method comprises the steps that a transaction platform node deploys an intelligent contract used for limiting transaction conditions in a block chain network; the receiver node uploads transaction data used for representing transaction details between the receiver node and the supplier node to the block chain network; the supplier node generates and uploads a financing application according to the transaction data and uploads the financing application to the block chain network; the investor node generates and broadcasts an audit result corresponding to the financing application; the consensus node performs legality verification on the auditing result, and calls an intelligent contract corresponding to the transaction data to respond to the auditing result after the verification succeeds, and consensuses nodes consensus response results of the audit results, packages response results of the financing application into blocks and writes the blocks into a block chain account book. According to the invention, each participant can efficiently and accurately complete the financing process under the restriction of the smart contract.
Owner:TENCENT TECH (SHENZHEN) CO LTD
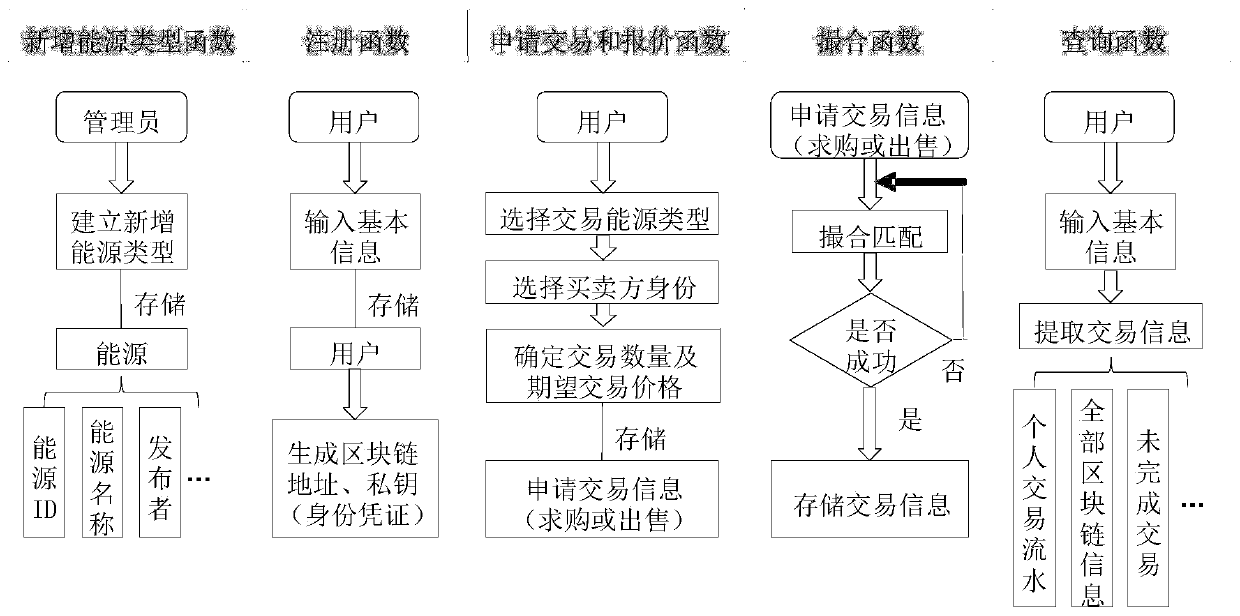
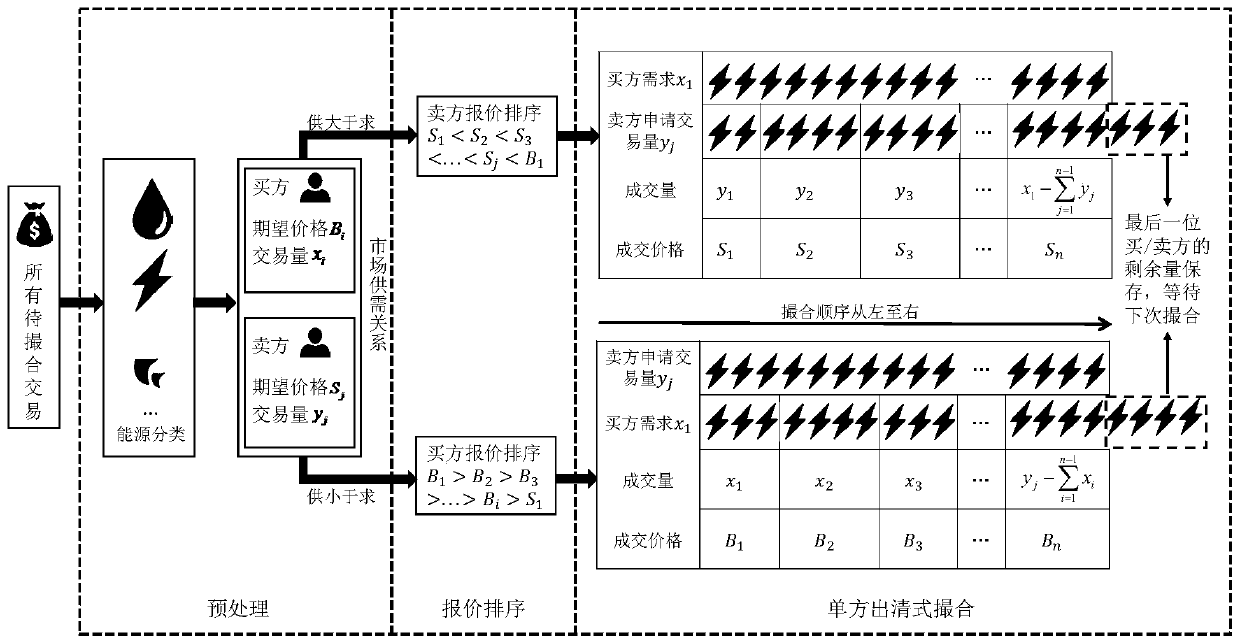
Multi-energy distributed transaction and intelligent contract design method based on Ethereum private chain
PendingCN111429276AFix security issuesRealize mutual transactionMarket predictionsFinanceEffective solutionFinancial transaction
The invention relates to a multi-energy distributed transaction and intelligent contract design method based on an Ethereum private chain, and the method comprises the following steps: 1), setting aninitial node of an intelligent contract as an administrator node, and setting other nodes as user nodes; 2) distinguishing system functions and account authorities of administrator nodes and user nodes, wherein only the administrator nodes can add and delete tradable energy types in the block chain through an energy switch function; and 3) enabling the user to realize simultaneous transaction of multiple energy sources, and enabling the intelligent contract to perform matchmaking transaction on information published by the user according to market supply and demand conditions. According to theinvention, the problems of insufficient centralization and security assurance and the like of the current energy transaction system can be effectively solved, and meanwhile, an effective solution isprovided for the problem that the development of the current block chain technology in the field of multi-energy transaction is limited.
Owner:XI AN JIAOTONG UNIV +2
Agricultural product tracing method based on block chain
PendingCN111861505AImprove securityImprove immutabilityCommerceManufacturing computing systemsData informationProduct traceability
The invention discloses an agricultural product tracing method based on a block chain, and relates to the technical field of block chains. The method comprises the following steps: a user accesses a traceability system and submits a product anti-counterfeiting code; a web server in the traceability system positions a user node corresponding to the anti-counterfeiting code according to the anti-counterfeiting code; the user node positions a block storage node of the corresponding data chain according to the related hash value; a step of positioning to a database address according to the data block information; a step of returning the data information, the abstract, the information abstract stored in the data block and the abstract of the related data block; a step of analyzing the data information, and comparing whether the abstract stored in the database is the same as the abstract of the related information on the blockchain or not; a step of querying whether the related data block abstract is the same as the related information abstract on the anchoring chain or not; and a step of returning the final result to the query user. According to the method, the credibility and transparency of the traceability information can be improved, agricultural product traceability data sharing is realized, and the supervision cost is reduced.
Owner:SHIJIAZHUANG TIEDAO UNIV
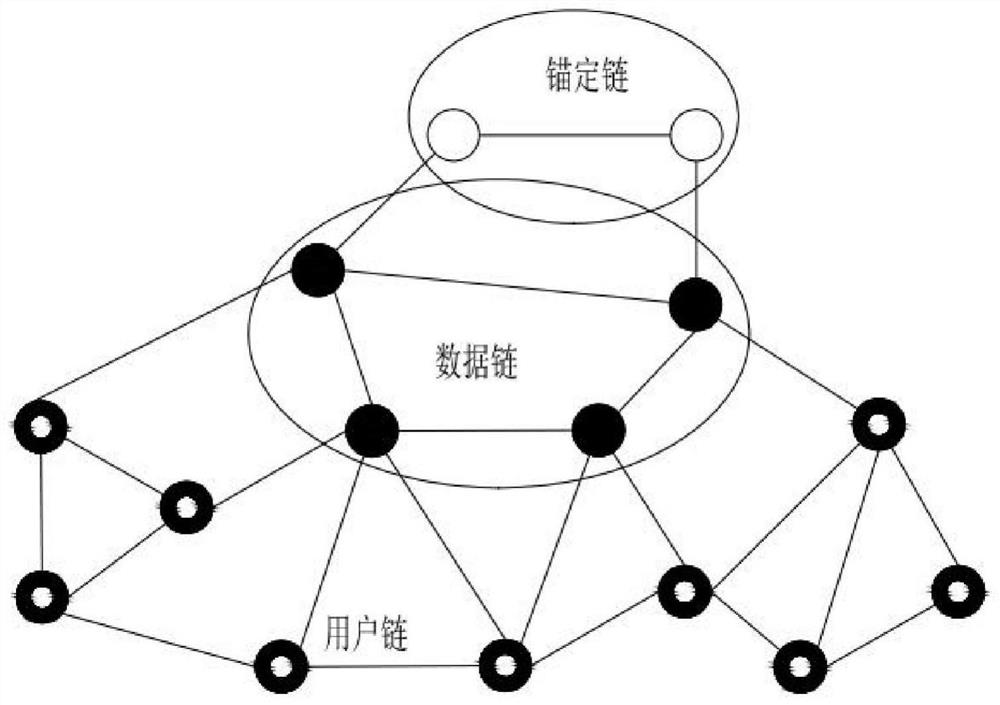
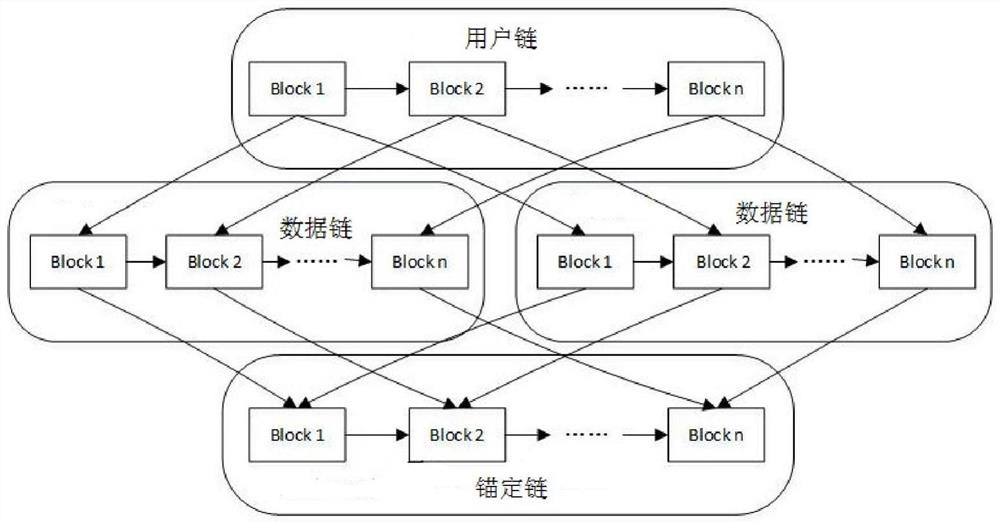
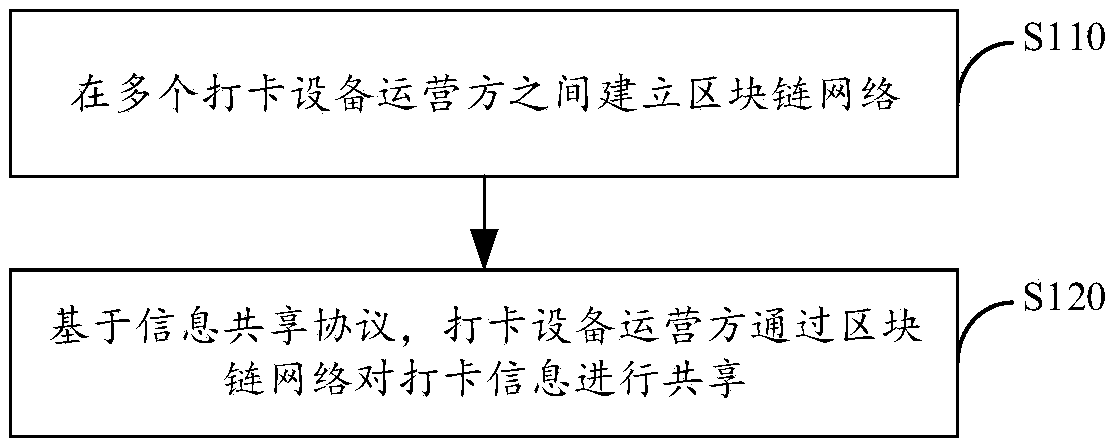
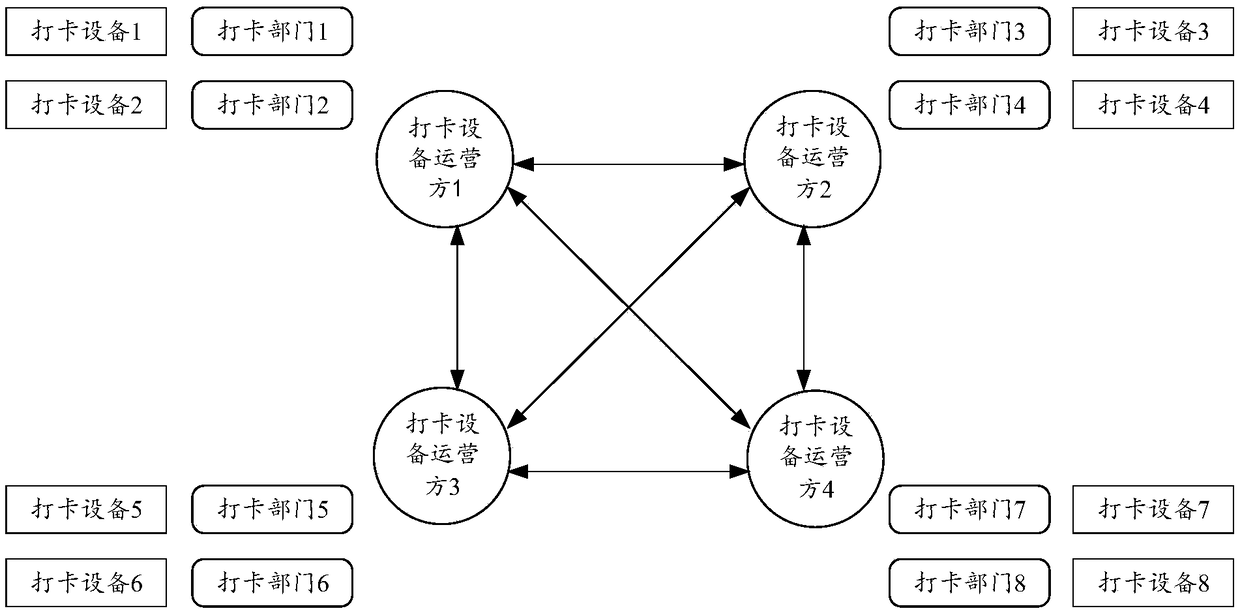
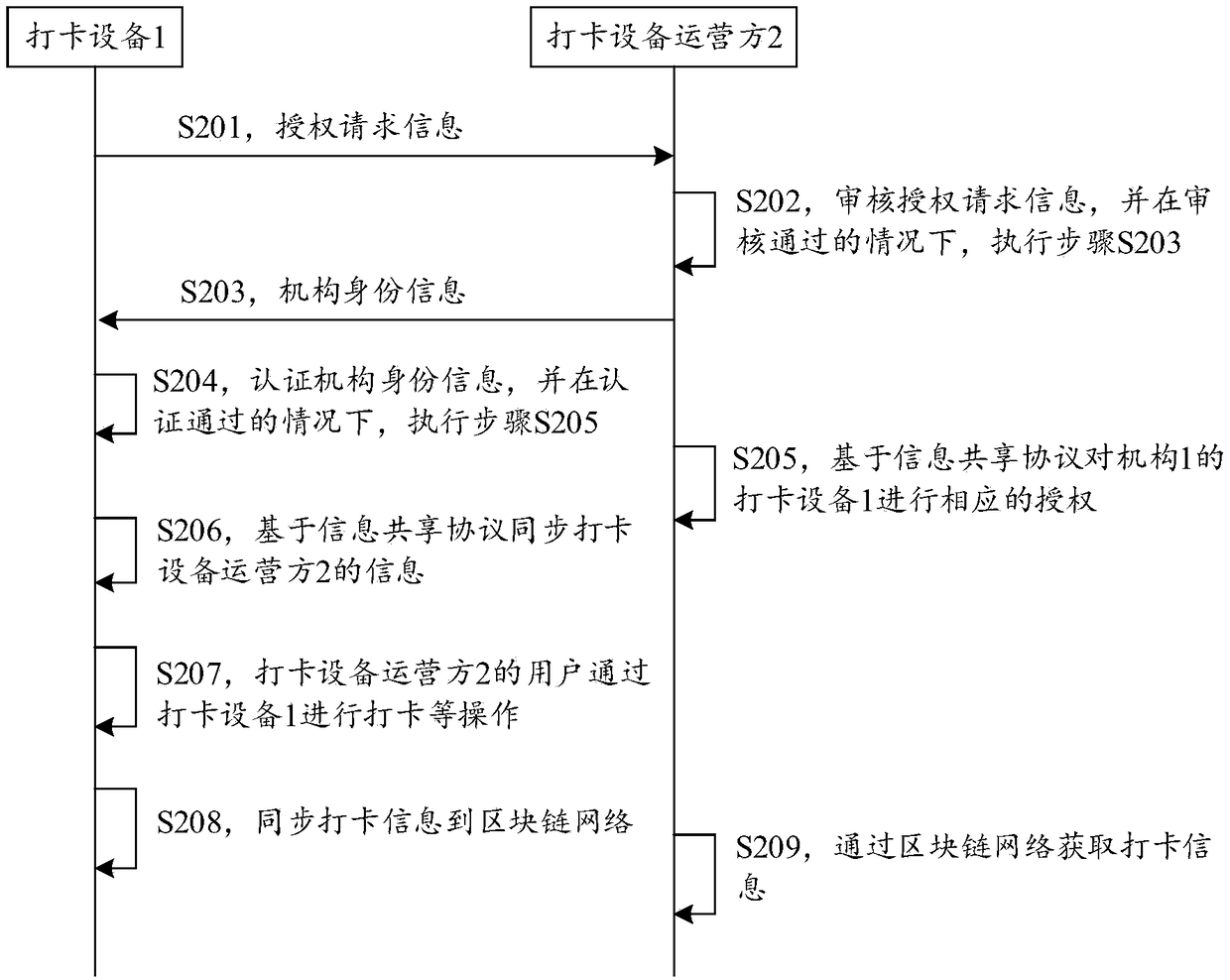
Block chain-based clock punching information sharing method and system
InactiveCN108833579AImprove accuracyImprove immutabilityTransmissionEquipment OperatorInformation sharing
The invention provides a block chain-based clock punching information sharing method and system, which relate to the technical field of block chains. The method comprises steps: a block chain networkis built among multiple clock punching equipment operators; and based on an information sharing protocol, the clock punching equipment operators share the clock punching information through the blockchain network. Through adopting the block chain technology, the clock punching information accuracy and the irreversibility can be improved, and the safe information authorized sharing mode between different organizations can be improved.
Owner:北京阿尔山金融科技有限公司
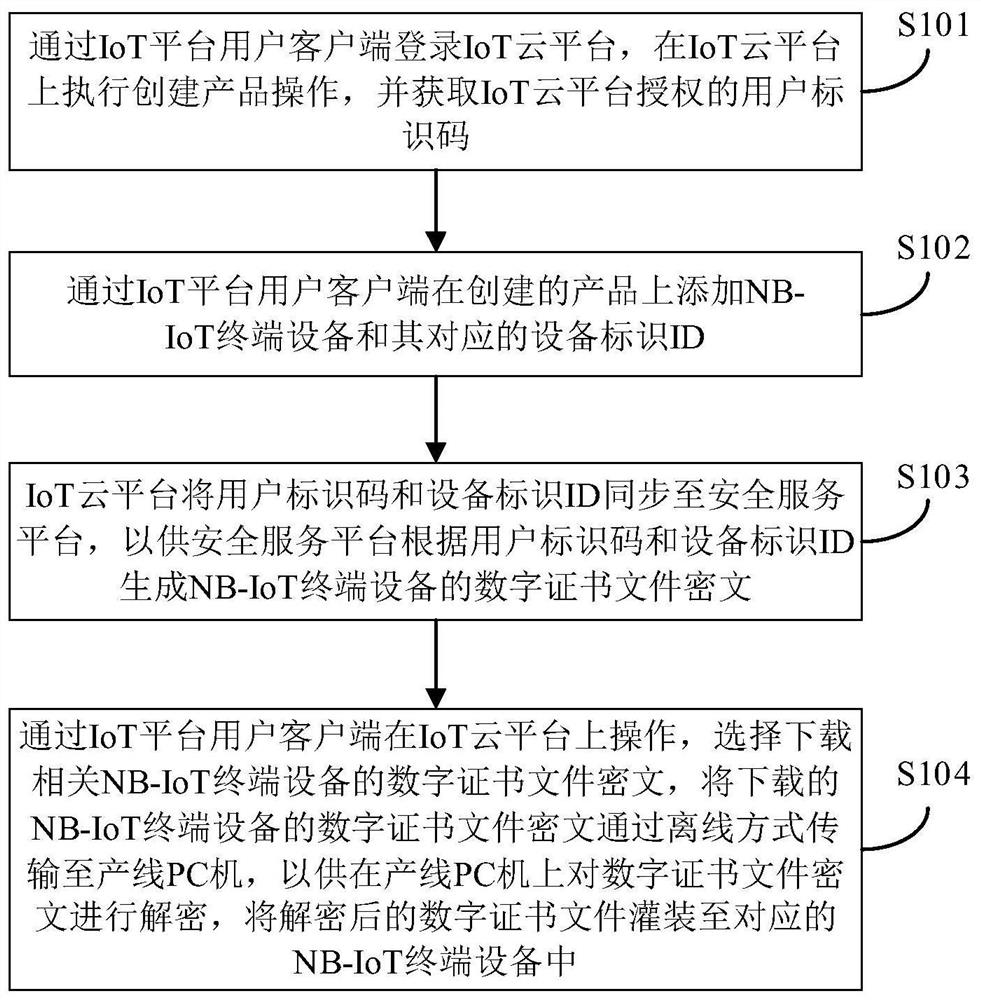
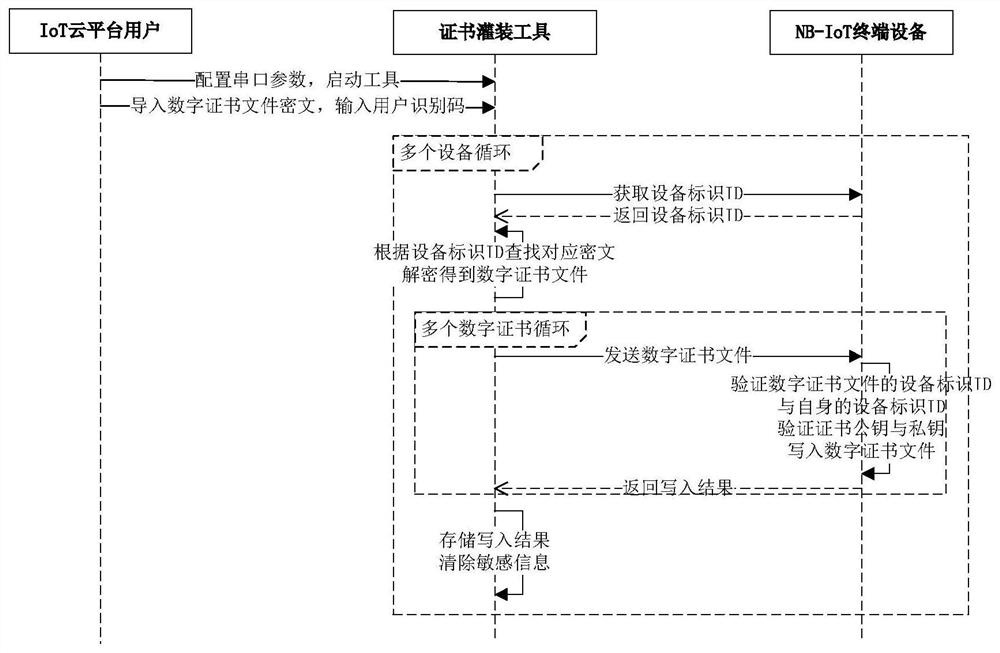
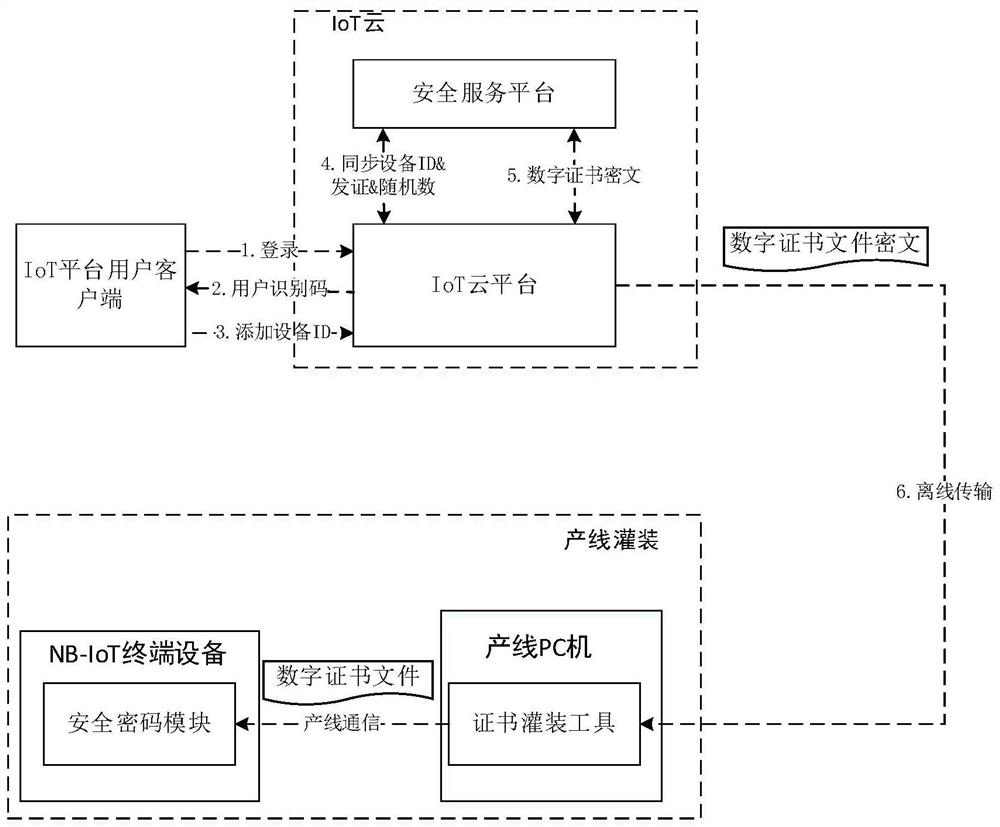
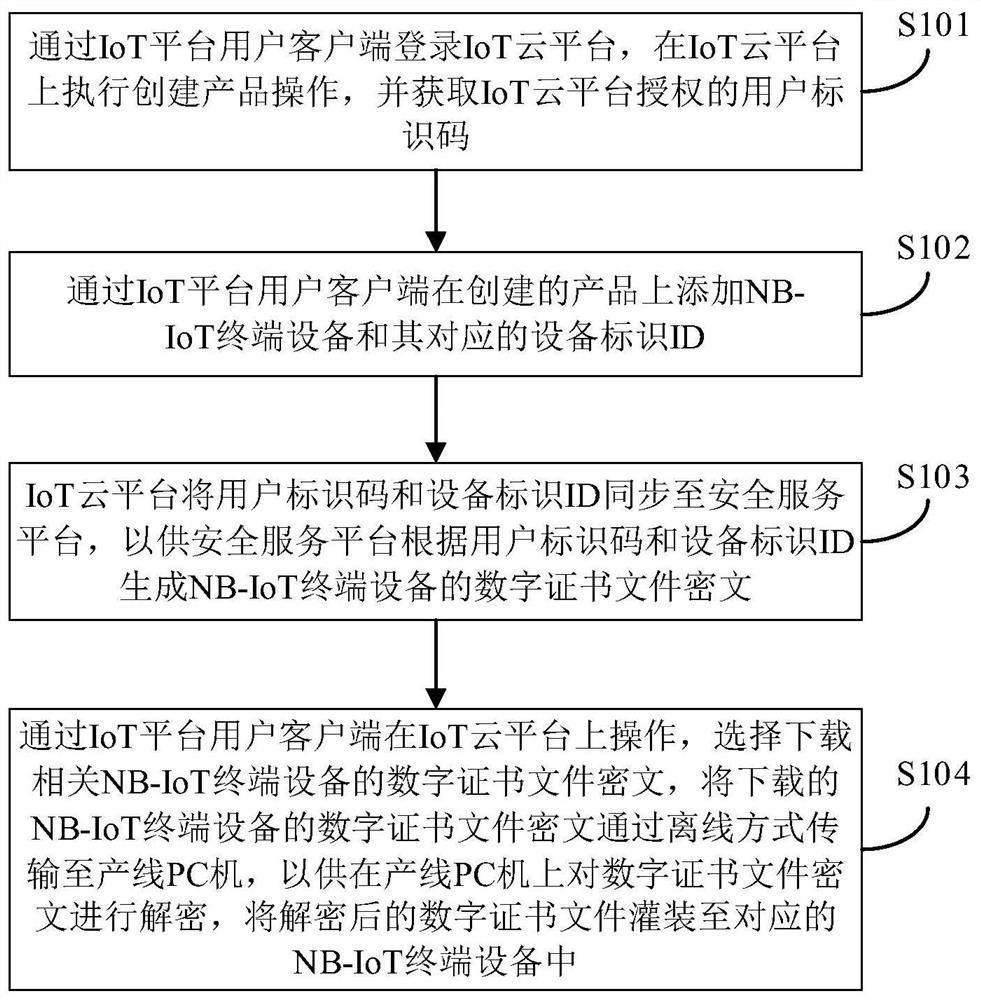
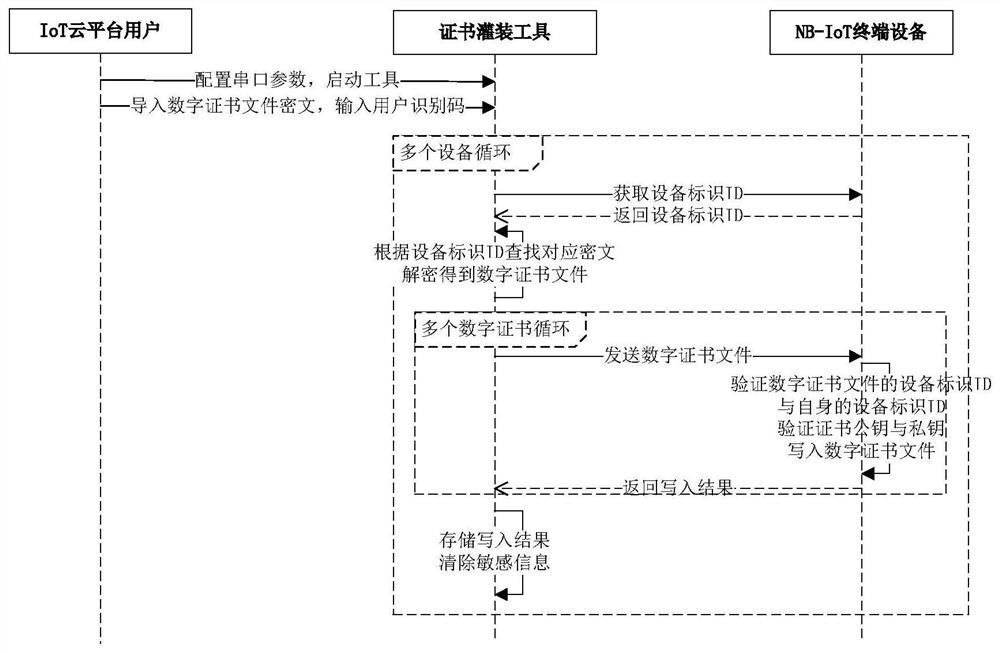
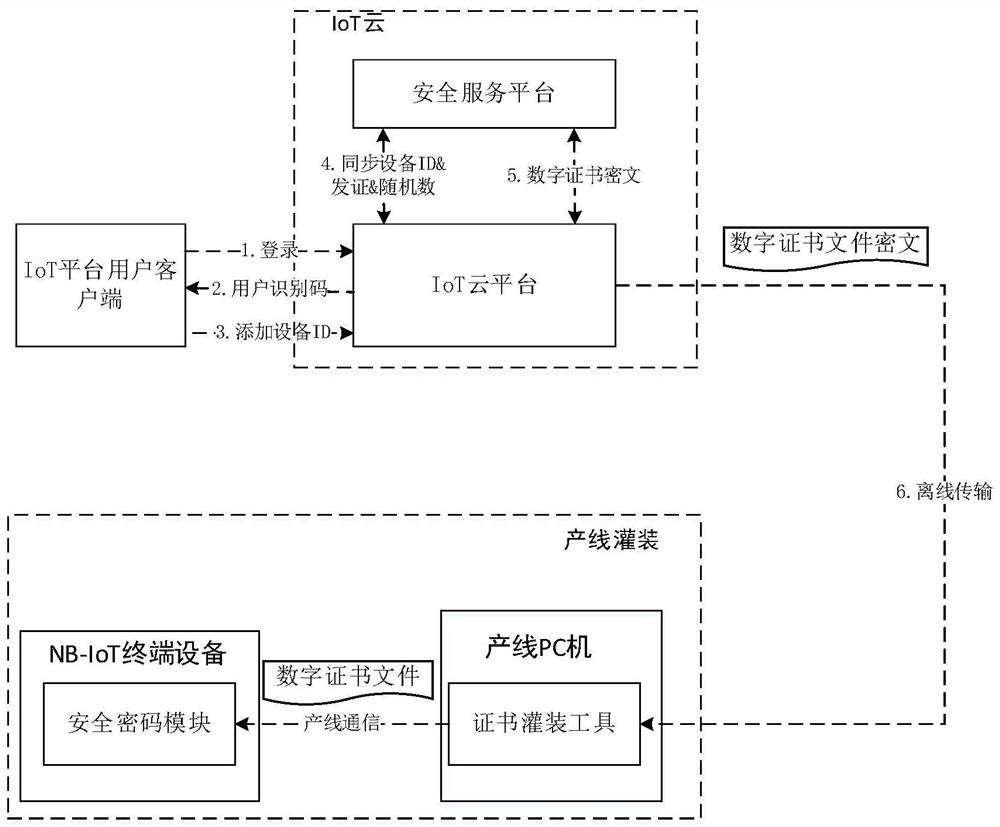
Digital certificate offline secure distribution method and system for NB-IoT terminal equipment
ActiveCN112422289AImprove confidentialityImprove integrityKey distribution for secure communicationUser identity/authority verificationCiphertextDistribution method
The invention provides a digital certificate offline secure distribution method and system for NB-IoT terminal equipment. The method comprises the following steps: logging in an IoT cloud platform through an IoT platform user client, executing a product creation operation on the IoT cloud platform, and obtaining a user identification code authorized by the IoT cloud platform; adding nB-IoT terminal equipment and an equipment identifier ID corresponding to the NBIoT terminal equipment to a created product by the IoT platform user client; enabling the IoT cloud platform to synchronize the user identification code and the equipment identifier ID to a security service platform, so that the security service platform generates a digital certificate file ciphertext of the NB-IoT terminal equipment according to the user identification code and the equipment identifier ID; a user client of an IoT platform operates on the IoT cloud platform, selects to download a digital certificate file ciphertext of related NBIoT terminal equipment, and transmits the downloaded digital certificate file ciphertext of the NB-IoT terminal equipment to a production line PC (Personal Computer) in an off-line manner, so that the digital certificate file ciphertext is decrypted on the production line PC. The decrypted digital certificate file is filled into the corresponding NB-IoT terminal equipment.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Internet of Things communication method and device
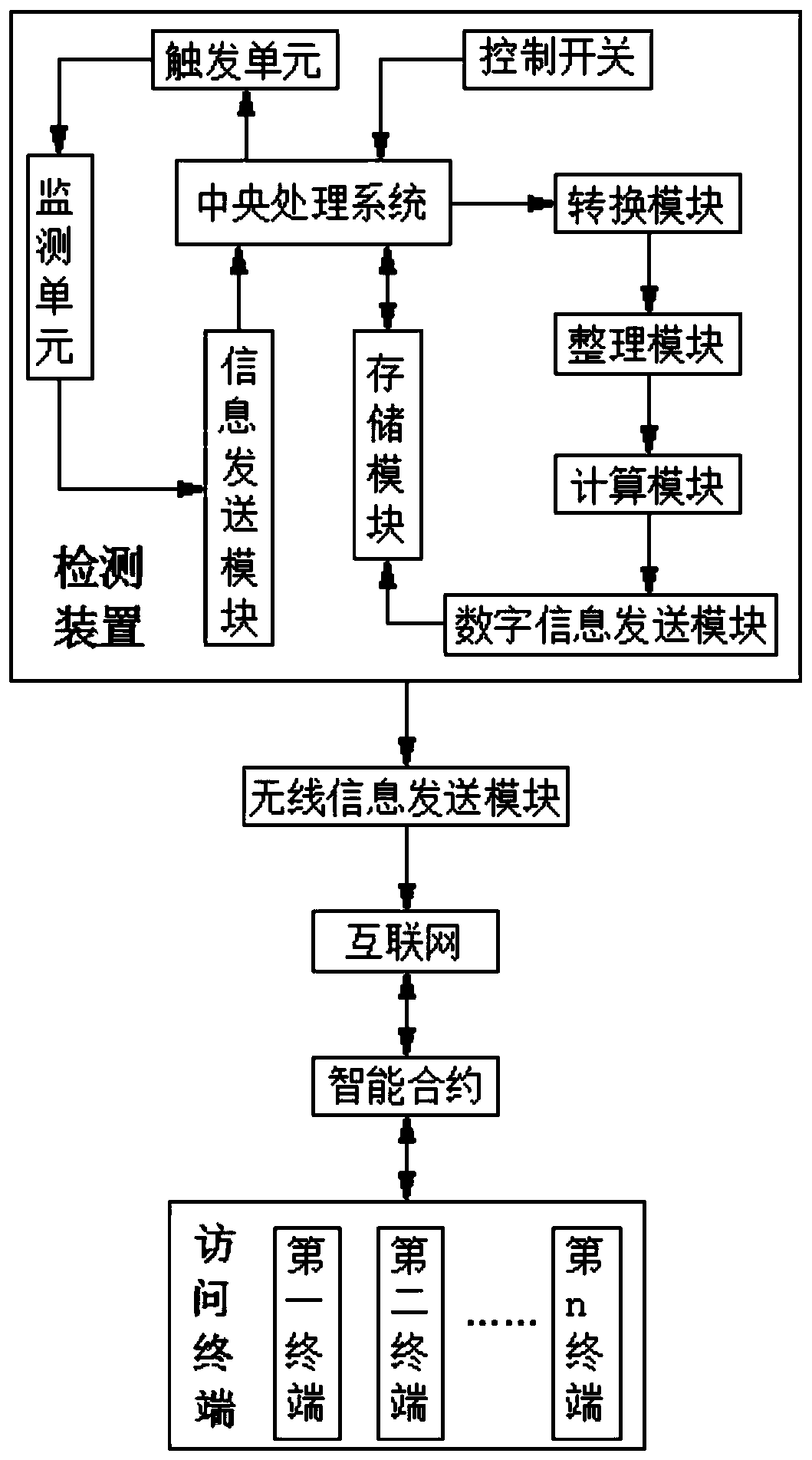
InactiveCN111542013AImprove securityImprove immutabilityParticular environment based servicesTransmissionTelecommunicationsThe Internet
The invention discloses an Internet of Things communication method. The method comprises a data uploading stage and a data consulting stage. The invention discloses an Internet of Things communicationdevice. The Internet of Things communication device includes a detection device and is characterized in that the output end of the detection device is electrically connected with the input end of a wireless information sending module through a wire, and the output end of the wireless signal sending module is connected with the input end of the Internet in a wireless mode, the Internet is in bidirectional connection with the intelligent contract in a wireless mode, and the intelligent contract is in bidirectional connection with the access terminal in a wireless mode. According to the Internetof Things communication method and device, a visitor can access the information in the Internet through any intelligent terminal, the visitor can consult the information anytime and anywhere, the useis more convenient, the visitor has no right to carry out any change, transfer and other operations on each piece of information, the system can also automatically record access records, and the security and tamper resistance of the information are improved.
Owner:广州上仕船务有限公司
Decentralized access control method and system based on transaction
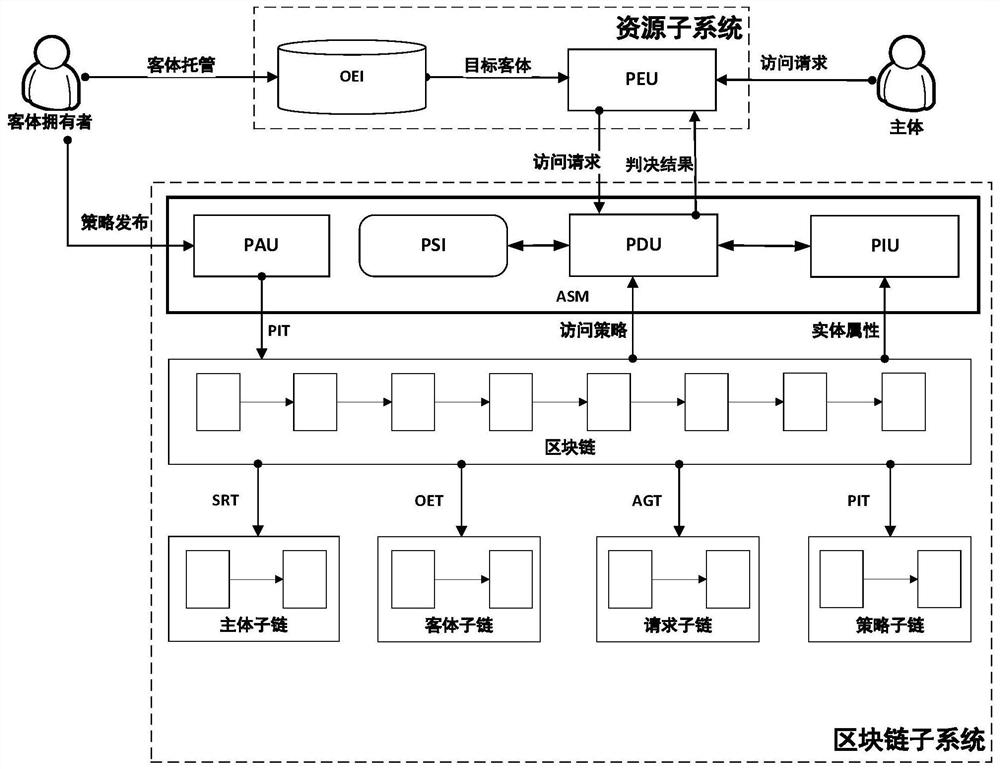
ActiveCN112350863AHigh transparencyImprove complianceFinancePayment protocolsPasswordNetworked system
The invention discloses a decentralized access control method and system based on transaction. The system is composed of nodes responsible for different functions on a decentralized network. An authorization service module for constructing the nodes comprises a strategy judgment unit, a strategy management unit, a script interpreter and a strategy information unit. The transaction is used as a propagation medium and an evidence for access control in the decentralized network system, the transaction types comprise a subject registration transaction, an object hosting transaction, a strategy release transaction and an access authorization transaction, the transaction types are used for recording related entity attributes and operations executed by nodes, and the integrity and authenticity ofthe transaction are guaranteed by adopting a scripted password authentication technology. The access control system based on transaction circulation provided by the invention covers a resource hosting process, a main body registration process, a strategy release process and an access authorization process in access control, and can realize authorization management based on a dynamic access strategy without a trusted party.
Owner:UNIV OF SCI & TECH BEIJING
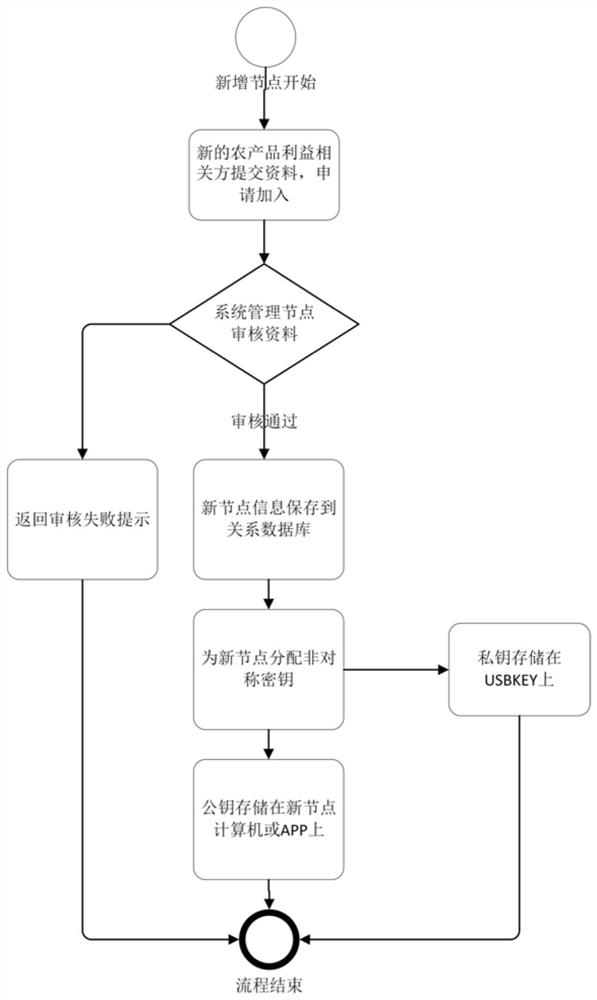
Large agricultural product traceability management system based on block chain technology
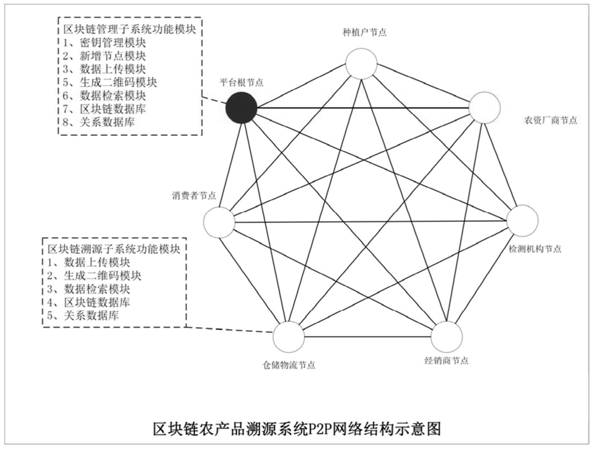
PendingCN112464253AStrong scalabilityImprove usabilityDatabase distribution/replicationRelational databasesBlockchainSource data
The invention discloses an agricultural product traceability management system based on a block chain technology. The agricultural product traceability management system comprises a management node, an agricultural product benefit related party node and a block chain management and block chain traceability subsystem. The management node is a platform root node, and the agricultural product benefitrelated party node is a collaborator and is responsible for uploading related process tracing data; the management node is in point-to-point connection with each agricultural product benefit relatedparty node through a P2P network. The block chain management subsystem is deployed on a management node server and is used for key management, node addition, data uploading and data retrieval; the block chain traceability subsystem is used for uploading data, generating a two-dimensional code and retrieving the data; the secret key management adopts an asymmetric secret key management system and is used for generating a pair of secret key public key and private key for the newly added node, and the public key is used for encrypting data and verifying signatures; and the private key is used fordecrypting the data and the personal signature. According to the agricultural product traceability management system, data cannot be tampered, the system is complete and real, and the trust problem of agricultural product traceability can be solved.
Owner:云南天质弘耕科技有限公司
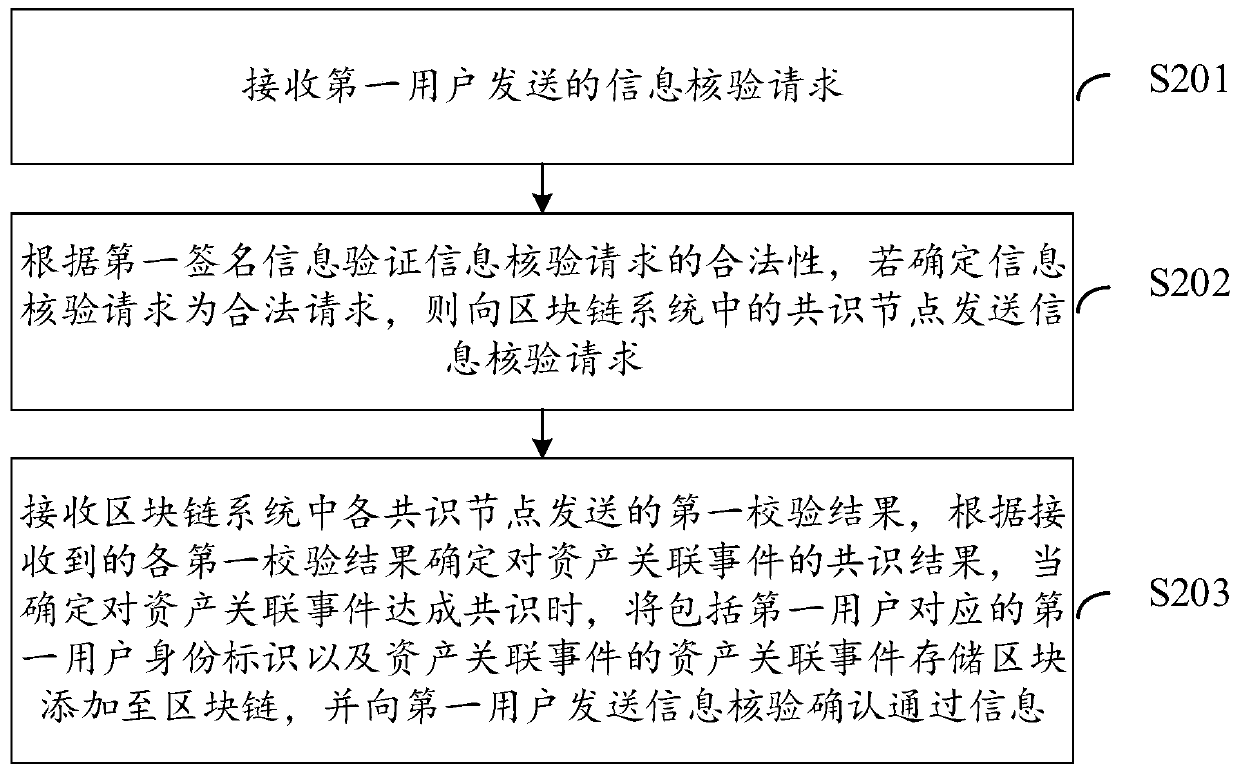
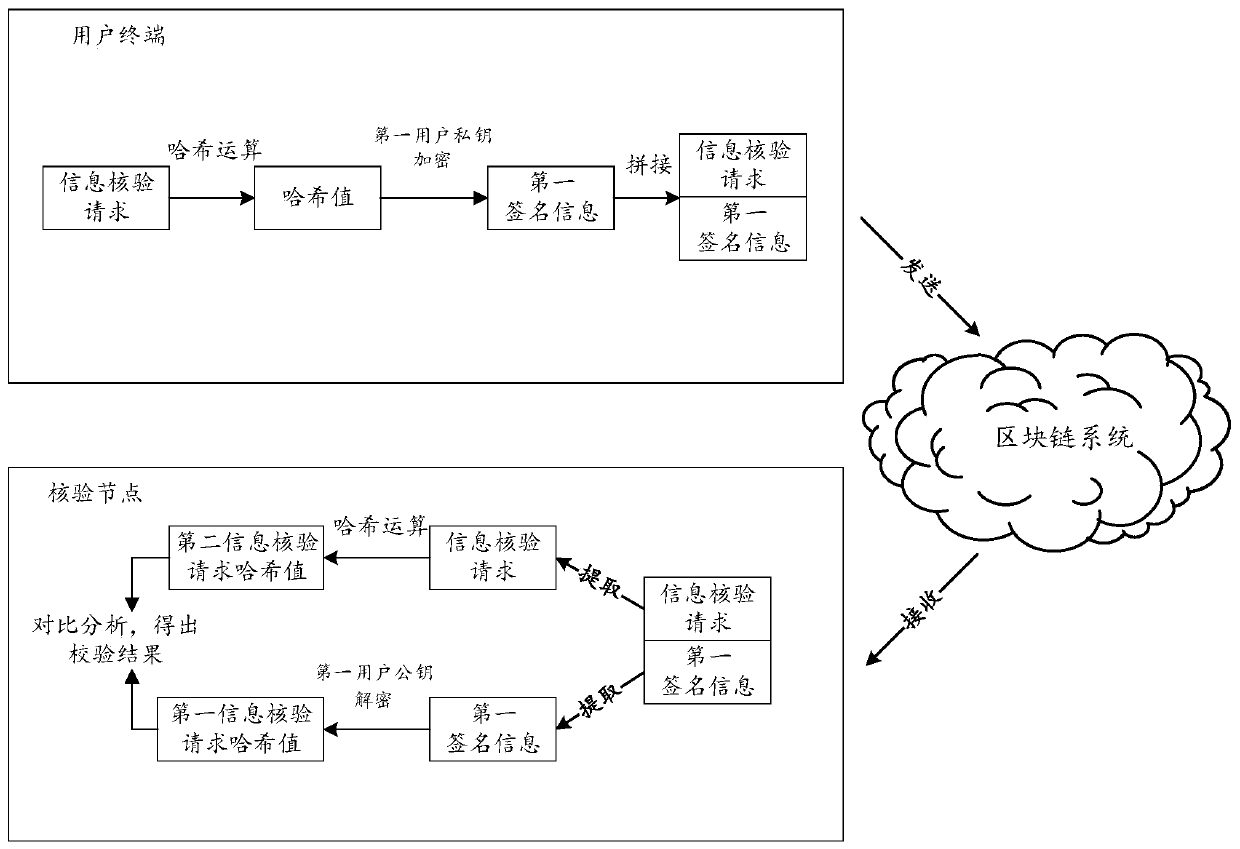
Data processing method and device based on block chain
PendingCN111324666AIncrease authenticityImprove immutabilityDatabase distribution/replicationDigital data protectionEngineeringComputer science
The embodiment of the invention discloses a data processing method and device based on a block chain. The method comprises the steps that an information verification request sent by a first user is received, and if it is determined that the information verification request is a legal request, the information verification request is sent to consensus nodes in a block chain system, so that the consensus nodes determine a first verification result of an asset association event according to the information verification request. Receiving a first verification result sent by each consensus node, determining a consensus result of the asset association event according to each received first verification result, and when it is determined that the asset association event reaches a consensus, addingan asset association event storage block comprising a first user identity identifier corresponding to the first user and the asset association event to the block chain, and sending information verification confirmation pass information to the first user. By adopting the embodiment of the invention, the authenticity and the tamper resistance of the user information can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Distributed ledger-based methods and systems for certificate authentication
PendingUS20220294647A1Improve availabilityImprove immutabilityUser identity/authority verificationFinancial transactionDatabase
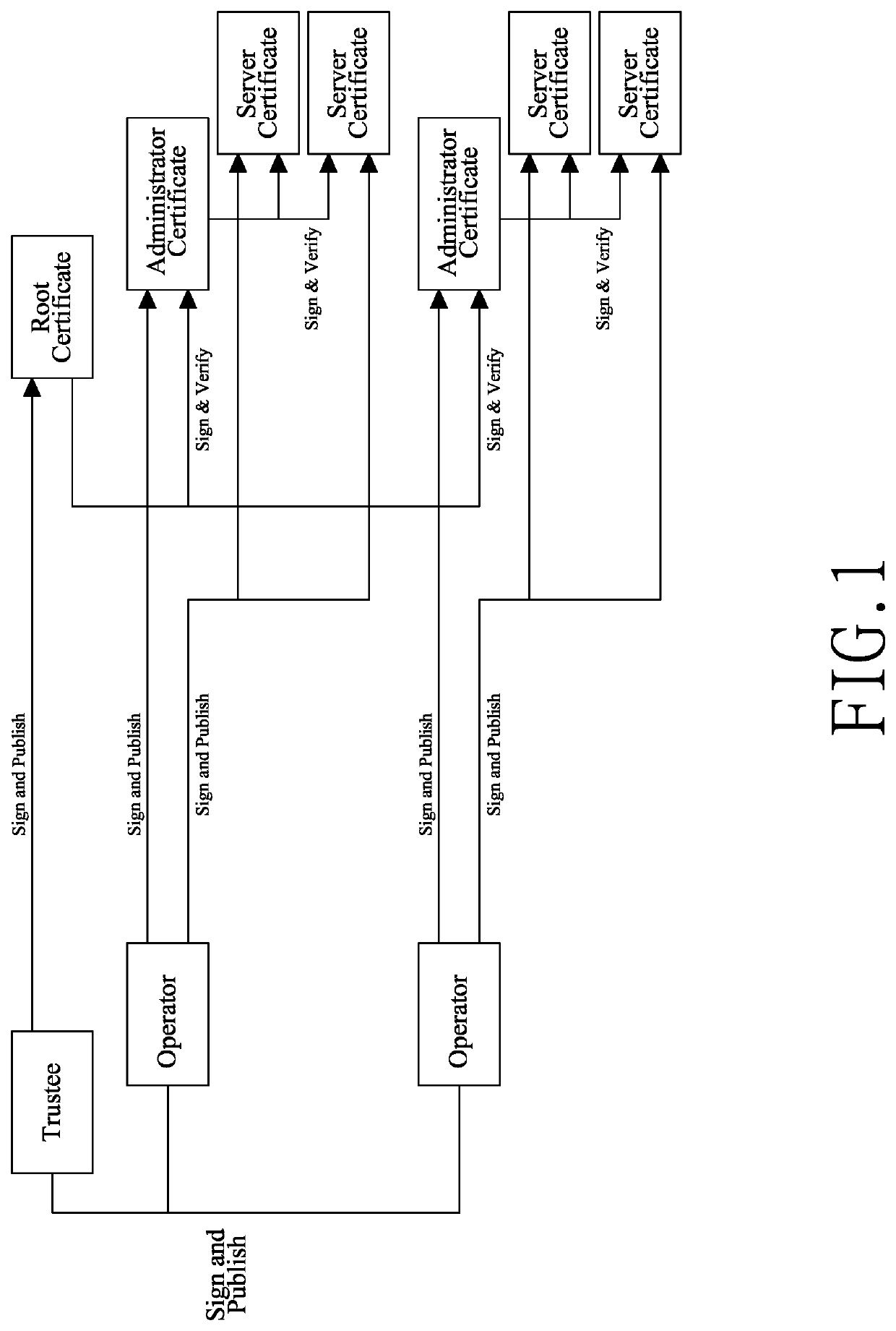
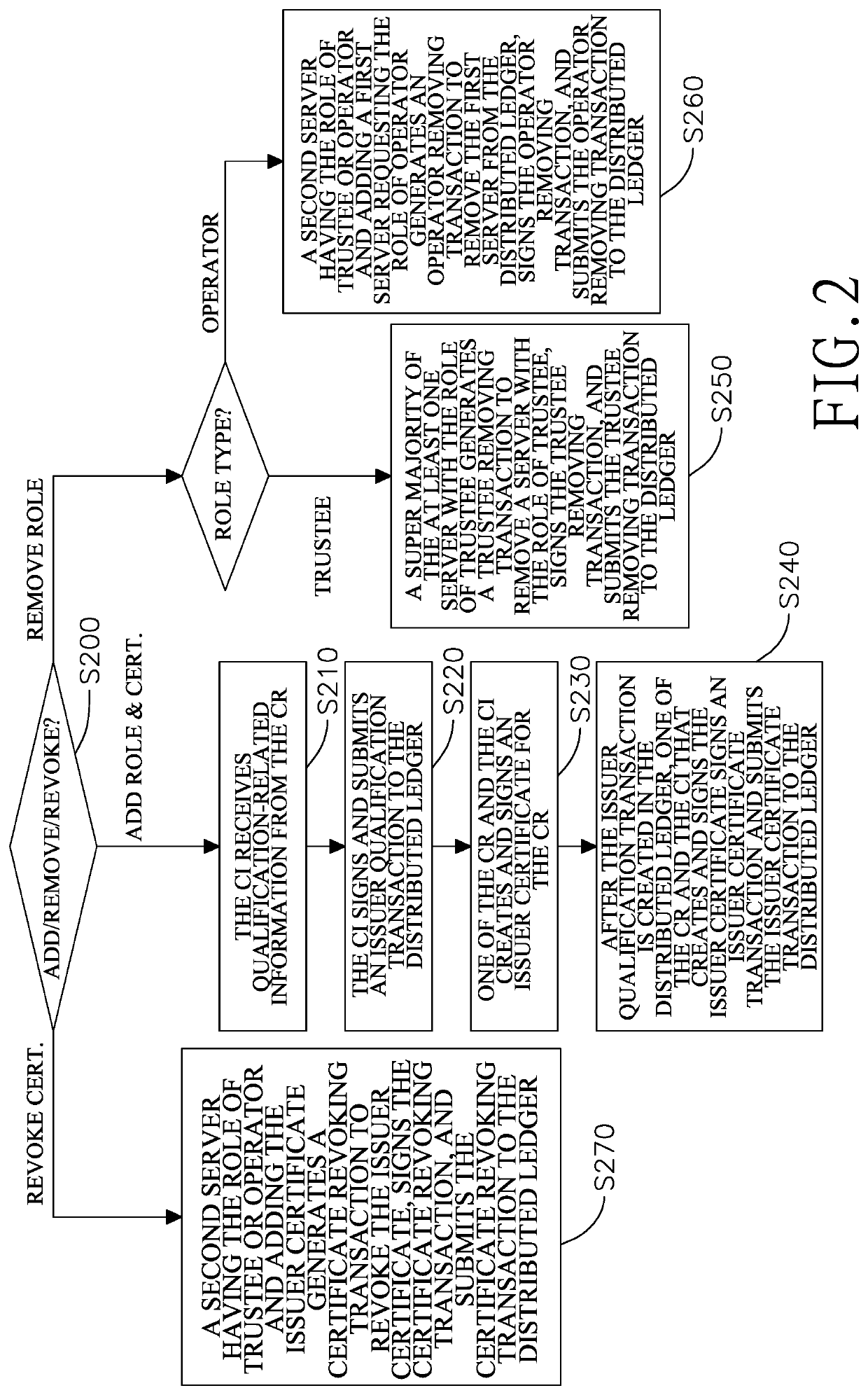
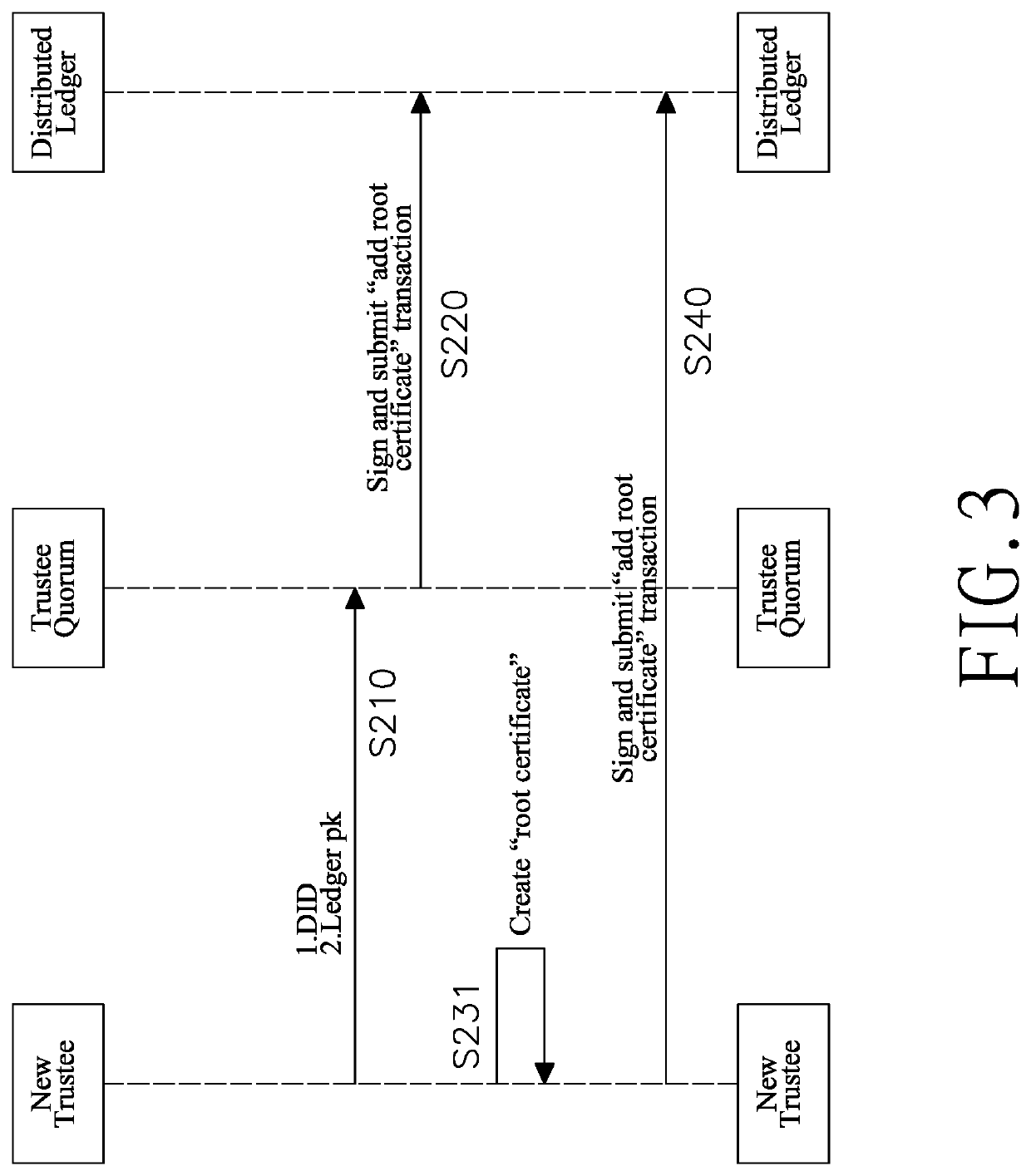
Disclosed are methods and systems for publishing transactions for adding and removing roles and certificates to and from a distributed ledger and for authenticating certificates of two connected servers. The roles specify what server with the roles can publish what types of transactions for certificates and roles. When a role is requested, two transactions for adding the role and an issuer certificate are published to the distributed ledge. When a certificate of a server without any role is requested, only a transaction for adding the certificate is published to the distributed ledger. All the transactions are published through operation among a certificate-requesting server, a certificate-issuing server, and a distributed ledger network maintaining the distributed ledger. Two connected servers can verify authenticity of their counterpart's identities with the certificate retrieved from the distributed ledger and having the benefits of certificate immutability and availability of the distributed ledger technology.
Owner:TBCASOFT INC
Encryption and decryption method based on RSA algorithm
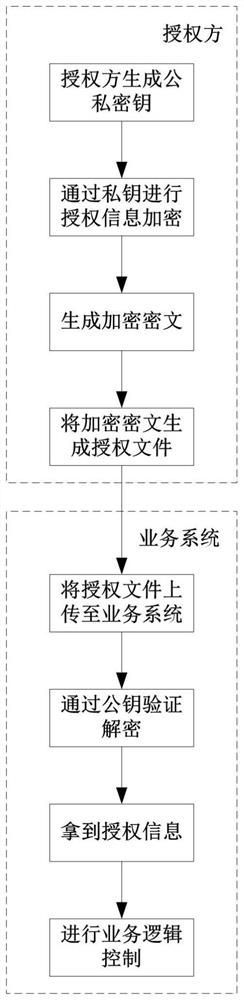
PendingCN114844640AGuaranteed source uniquenessEnsure safetyPublic key for secure communicationUser identity/authority verificationAlgorithmCiphertext
The invention provides an encryption and decryption method based on an RSA algorithm, and the method comprises the steps: 1, enabling an authorization party to generate a public key and a private key, enabling the authorization party to store the private key, and enabling the public key to be placed in a business system; 2, the authorization party encrypts the authorization information through a private key; 3, generating an authorization file from the encrypted ciphertext; 4, uploading the authorization file to a service system; 5, verifying and decrypting the authorization file through a public key in the service system; step 6, obtaining authorization information in the authorization file; and step 7, performing service logic control according to the authorization information. According to the invention, an asymmetric encryption mode is adopted, the security and non-tampering property of the authorization file are improved, the risk of secret leakage is reduced through a public and private key mode, and the requirements of security and uniqueness of the authorization file are met.
Owner:山东华软金盾软件股份有限公司
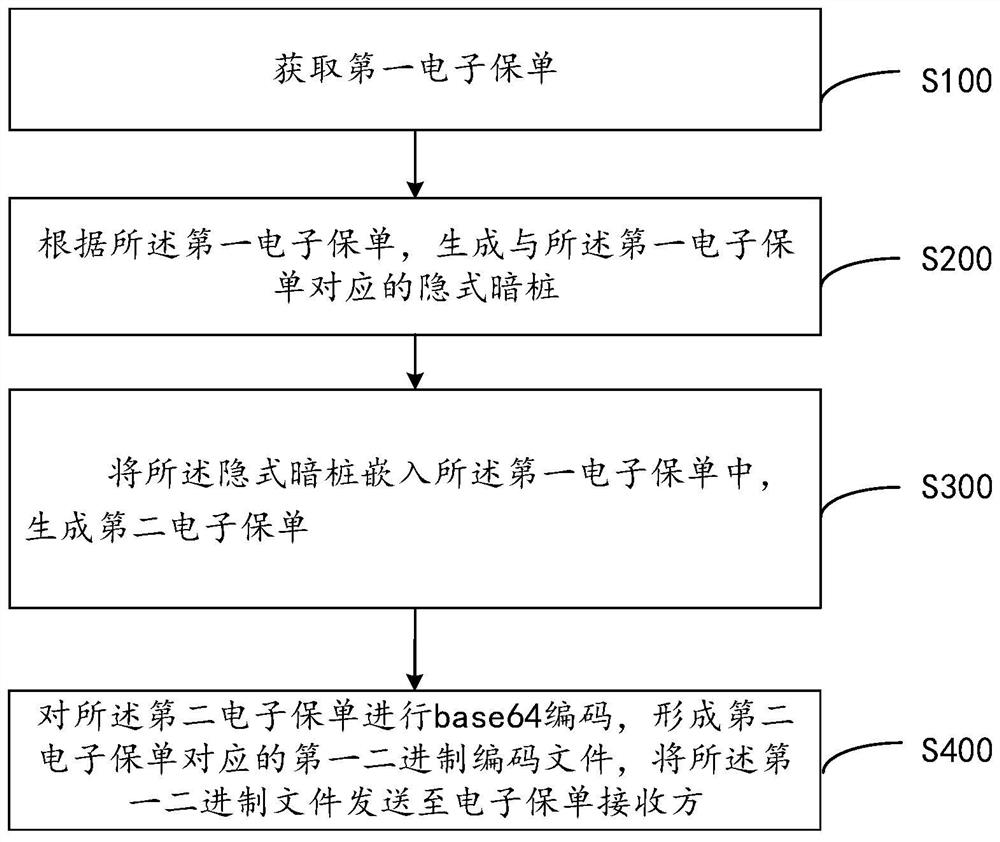
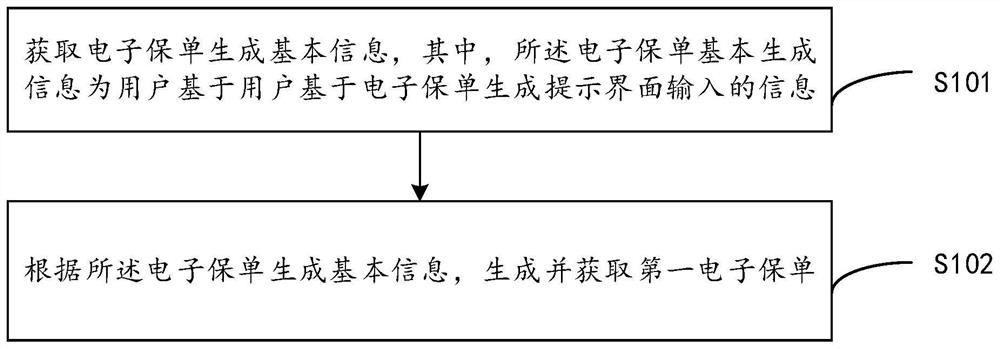
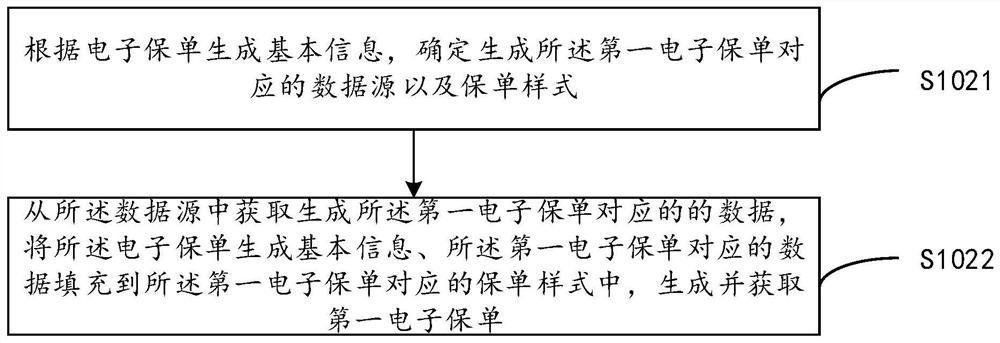
Electronic insurance policy information security management and control method and system
PendingCN112016900AImprove immutabilityAchieve traceabilityFinanceDigital data protectionTamper resistanceInformation security management
The invention provides an electronic insurance policy information security management and control method. The method comprises the steps of obtaining a first electronic insurance policy; generating animplicit hidden pile corresponding to the first electronic insurance policy according to the first electronic insurance policy; embedding the implicit hidden pile into the first electronic insurancepolicy to generate a second electronic insurance policy; and performing base64 coding on the second electronic insurance policy to form a first binary coded file corresponding to the second electronicinsurance policy, and sending the first binary file to an electronic insurance policy receiver. According to the electronic insurance policy information security management and control method provided by the invention, the tamper resistance of the electronic insurance policy is improved, when the electronic insurance policy leaks, the source can be traced rapidly through the binary coded file, and the supervision risk caused by the leakage of the electronic insurance policy information is reduced.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
A digital certificate offline security distribution method and system of NB-IoT terminal device
ActiveCN112422289BImprove confidentialityImprove integrityKey distribution for secure communicationUser identity/authority verificationCiphertextDistribution method
The present invention provides a method and system for offline secure distribution of digital certificates of NB-IoT terminal equipment. The method includes: logging in to the IoT cloud platform through the IoT platform user client, performing the operation of creating a product on the IoT cloud platform, and obtaining a user identification code authorized by the IoT cloud platform; adding NB‑ to the created product through the IoT platform user client The IoT terminal device and its corresponding device ID; the IoT cloud platform will synchronize the user ID and device ID to the security service platform, so that the security service platform can generate a digital certificate for the NB‑IoT terminal device based on the user ID and device ID File ciphertext; operate on the IoT cloud platform through the IoT platform user client, choose to download the ciphertext of the digital certificate file of the relevant NB‑IoT terminal device, and transmit the ciphertext of the downloaded digital certificate file of the NB‑IoT terminal device offline To the production line PC, for decrypting the ciphertext of the digital certificate file on the production line PC, and filling the decrypted digital certificate file into the corresponding NB-IoT terminal device.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
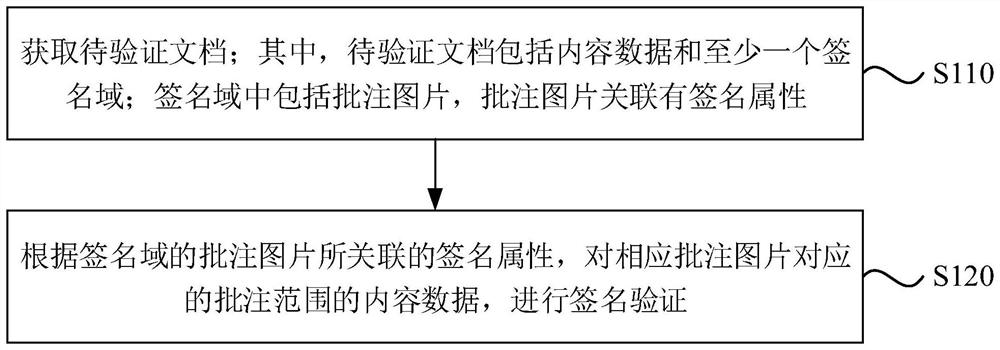
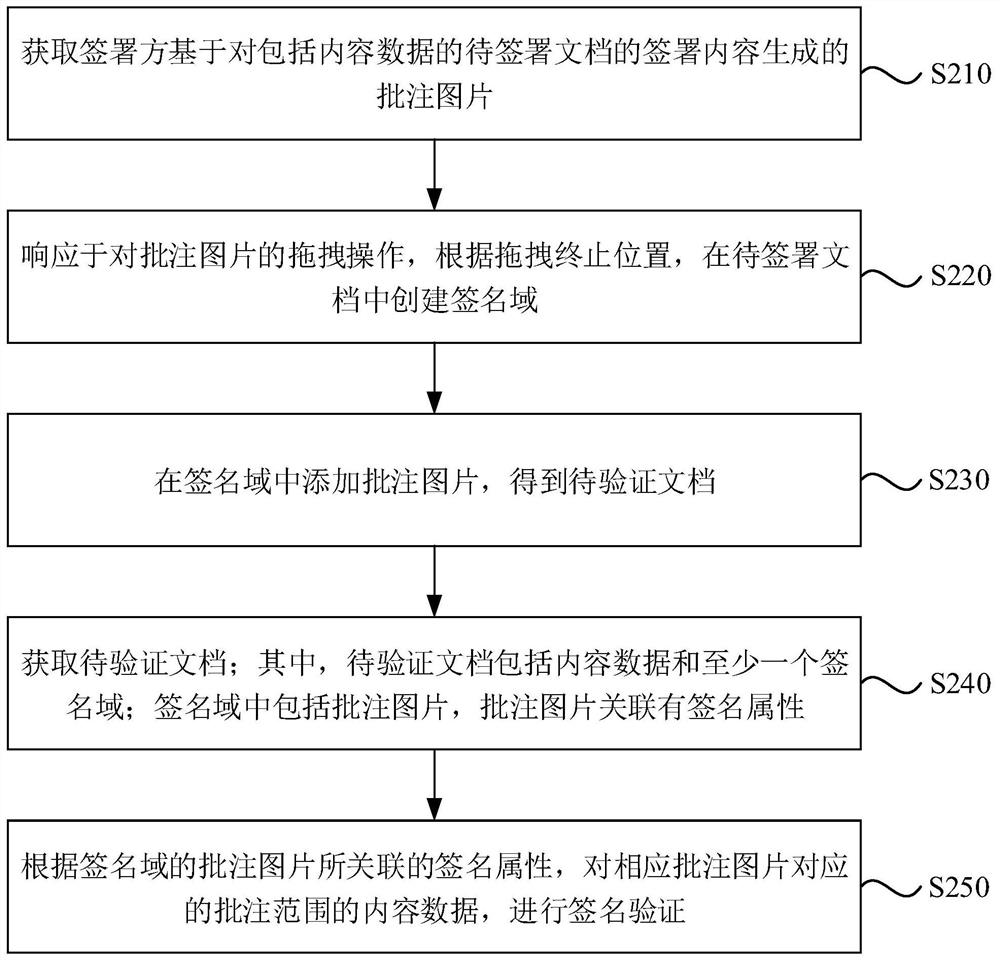
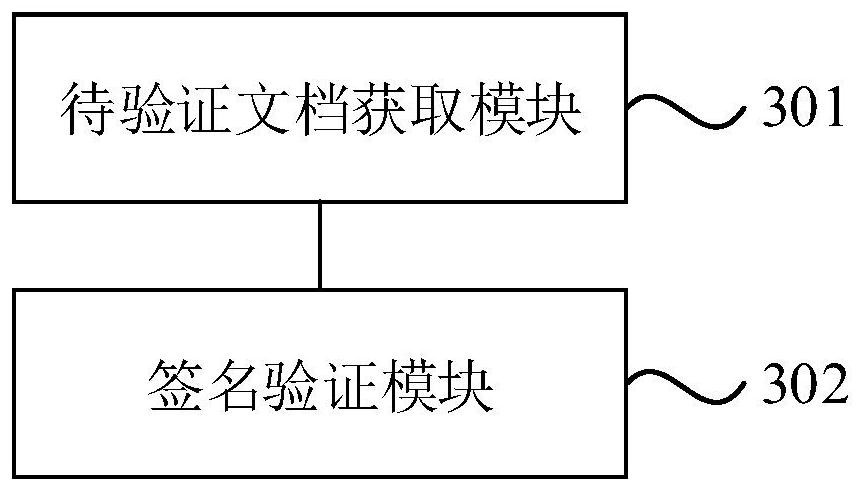
Electronic document verification method and device and electronic equipment
PendingCN114297731AIncrease authenticityImprove immutabilityCharacter and pattern recognitionDigital data protectionElectronic documentEngineering
The embodiment of the invention discloses an electronic document verification method and device and electronic equipment. The method comprises the following steps: acquiring a to-be-verified document; wherein the to-be-verified document comprises content data and at least one signature domain; the signature domain comprises an annotation picture, and the annotation picture is associated with a signature attribute; and according to the signature attribute associated with the annotation picture of the signature domain, carrying out signature verification on the content data of the corresponding annotation range of the corresponding annotation picture. According to the embodiment of the invention, the signature verification accuracy of the to-be-signed document is improved.
Owner:北京吉大正元信息技术有限公司 +1
A blockchain creation method, device and readable storage medium
ActiveCN109039648BImprove transaction securityImprove immutabilityFinanceUser identity/authority verificationTimestampProof-of-stake
The invention discloses a block chain creation method, equipment and readable storage medium. The method includes: creating a block chain equity proof mechanism; creating a hash time stamp mechanism using a random number strategy; establishing a mechanism to prevent block chain forks based on the formed hash time stamp; based on the above mechanism and the random number strategy Every new block on the blockchain is created, forming a blockchain. With this technical solution, parties with the right to create new blocks cannot control the random number in competition, so they cannot obtain the priority authority for building blocks, improve the security of blockchain transactions and cannot be tampered with, and the rights and interests are proportional to the driving force of system protection. Based on hash Timestamp, when determining who has the right to bookkeeping, the greatest possible guarantee to eliminate forks, establish a punishment mechanism for historical block creators who did not abide by the rules and did not participate in the maintenance of several blocks, creating a fair, stable and efficient block Chain transaction environment, while optimizing the trust model, providing a good mechanism to control the growth rate of the chain.
Owner:CROSBIL LTD
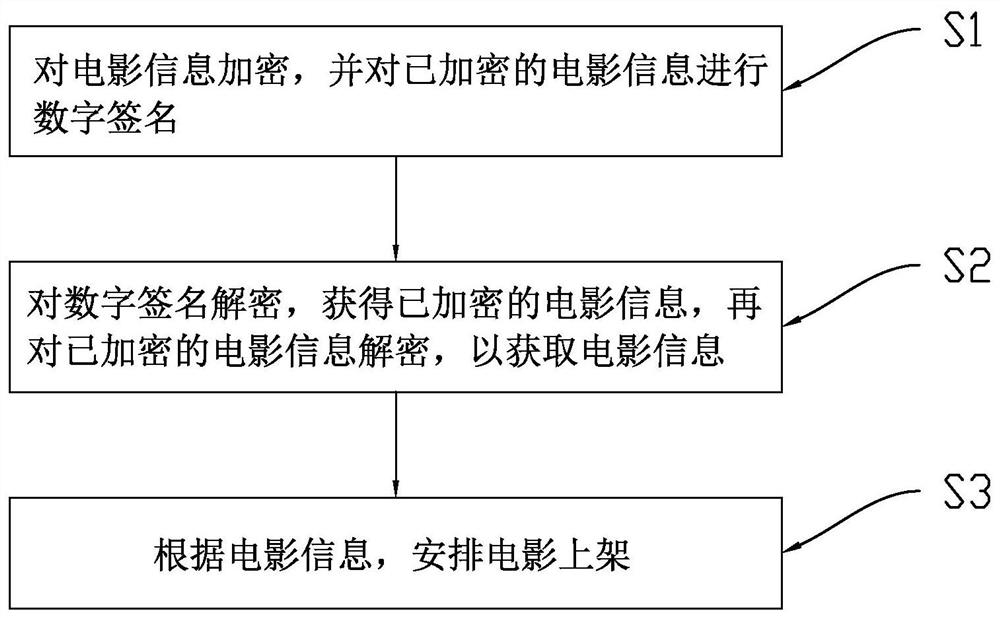
Movie key distribution management method, device, computer equipment and storage medium
ActiveCN112733089BImprove securityImprove immutabilityDigital data protectionProgram/content distribution protectionDigital signatureEngineering
The present invention relates to a movie key distribution management method, device, computer equipment and storage medium; wherein, the method includes: encrypting movie information, and digitally signing the encrypted movie information; decrypting the digital signature to obtain the encrypted movie information, and then decrypt the encrypted movie information to obtain movie information; according to the movie information, arrange movies to be put on the shelves. The present invention greatly enhances the security, non-forgeability and non-tampering of data, and also reduces the errors caused by human operation, and reduces the possibility of digital hard disk being leaked or cracked after copying during transportation. It also greatly reduces transportation costs.
Owner:深圳市龙影天下信息系统有限公司
Method for extracting equipment fingerprint information in wired network card signal
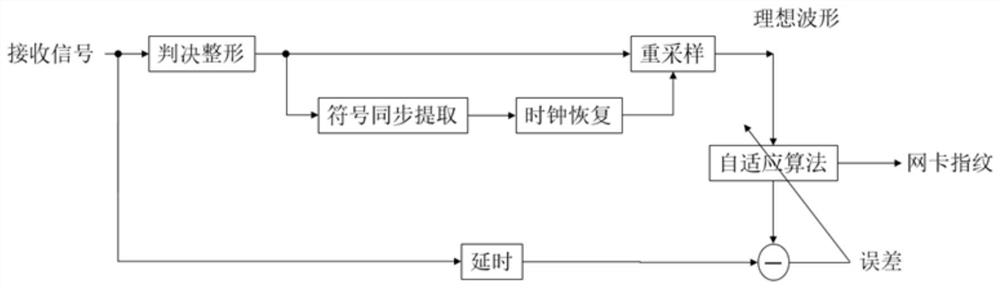
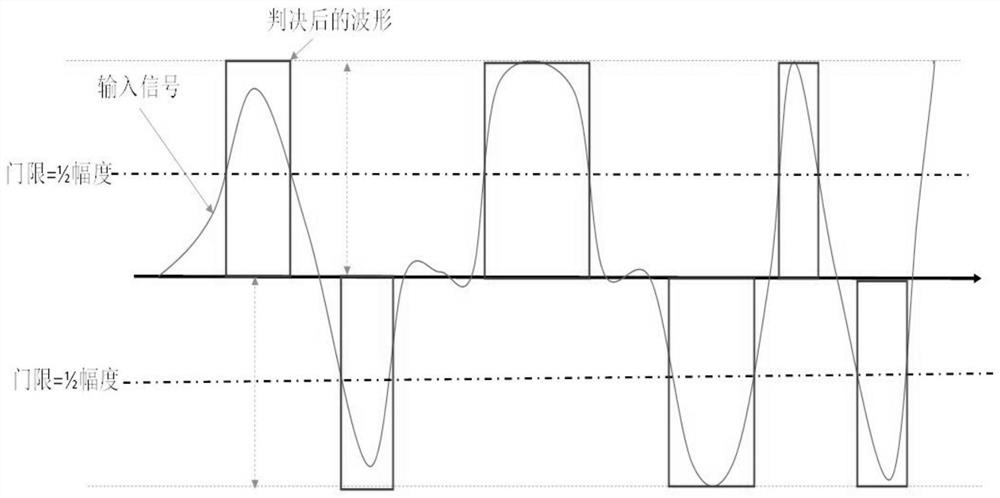
ActiveCN113158157AHigh reliability and immutabilityImprove securityDigital data protectionDigital data authenticationAdaptive filterLeast mean square error
The invention discloses a method for extracting equipment fingerprint information in a wired network card signal, which comprises the following steps of: performing normalization processing and judgment on an input signal to obtain a judgment signal; performing rising edge and falling edge clock extraction on the judgment signal, and synchronizing a local clock to obtain a synchronous clock; sampling the judgment signal by using a synchronous clock to obtain an ideal waveform synchronous with a local clock; using the ideal waveform signal as the filtering input of the adaptive filter and processing, so that the ideal signal approximates the received signal with the minimum mean square error after filtering, wherein the adaptive filter parameter at the moment is the equipment fingerprint of the network card; and extracting fingerprints from the input signals in a plurality of time periods to obtain stable fingerprints of the network card equipment. According to the invention, the device fingerprint information in the wired network card can be extracted, and the device fingerprint with both stability and identifiability is obtained, so that the identity authentication and authentication of the terminal device are realized, and the security of network access is realized.
Owner:SOUTHEAST UNIV +1
Microgrid power big data transaction management system applying blockchain and artificial intelligence
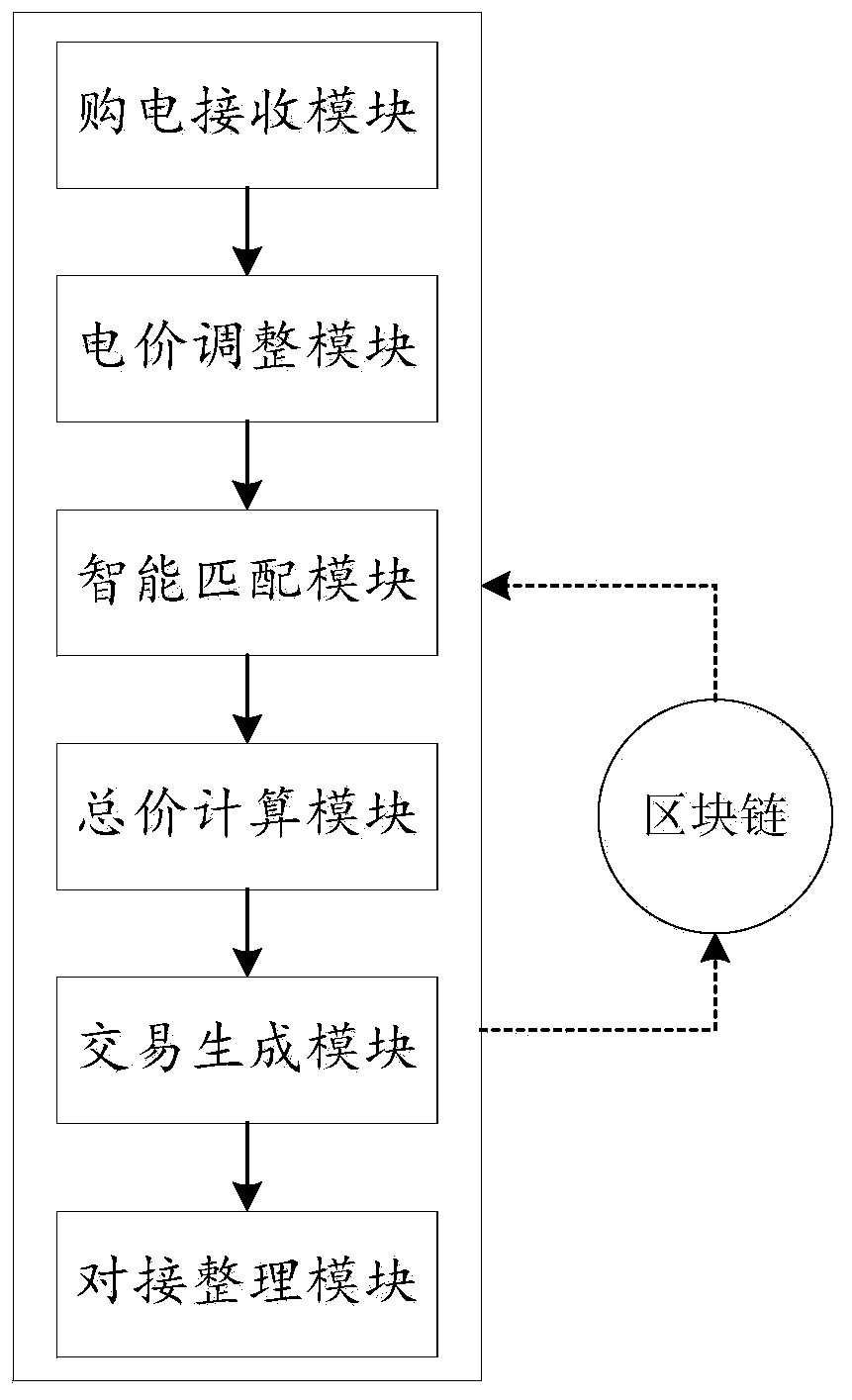
ActiveCN111507766AAccurate and fast transactionsOccupies less system resourcesMarket predictionsFinancePower gridSystems engineering
The invention discloses a microgrid power big data transaction management system applying a blockchain and artificial intelligence. The method comprises the following steps that an electricity purchasing receiving module organizes an electricity purchasing unit price of which transaction is completed according to previous electricity consumption data records of an electricity consumption side, andrecords the electric quantity required to be purchased at the power utilization side; an electricity price adjusting module uses the average value of the electricity purchasing unit prices which havecompleted the transaction as an initial electricity price and compares the total electricity generation amount of all the current electricity generation sides with the total electricity quantity which needs to be purchased by all the electricity utilization sides, and the intelligent matching module screens the electricity generation sides which can meet the electricity quantity which needs to bepurchased by the electricity utilization sides and selects the appropriate electricity generation sides for matching; according to the invention, on the basis of artificial intelligence, the blockchain technology is combined at the same time, so the intelligence and decentralization of the transaction management system and the non-tampering performance of data are enhanced.
Owner:SIPING POWER SUPPLY COMPANY OF STATE GRID JILINSHENG ELECTRIC POWER SUPPLY
A blockchain-based electronic signing device and method
ActiveCN108197891BImprove securityImprove immutabilityDigital data authenticationOffice automationElectronic contractsInternet privacy
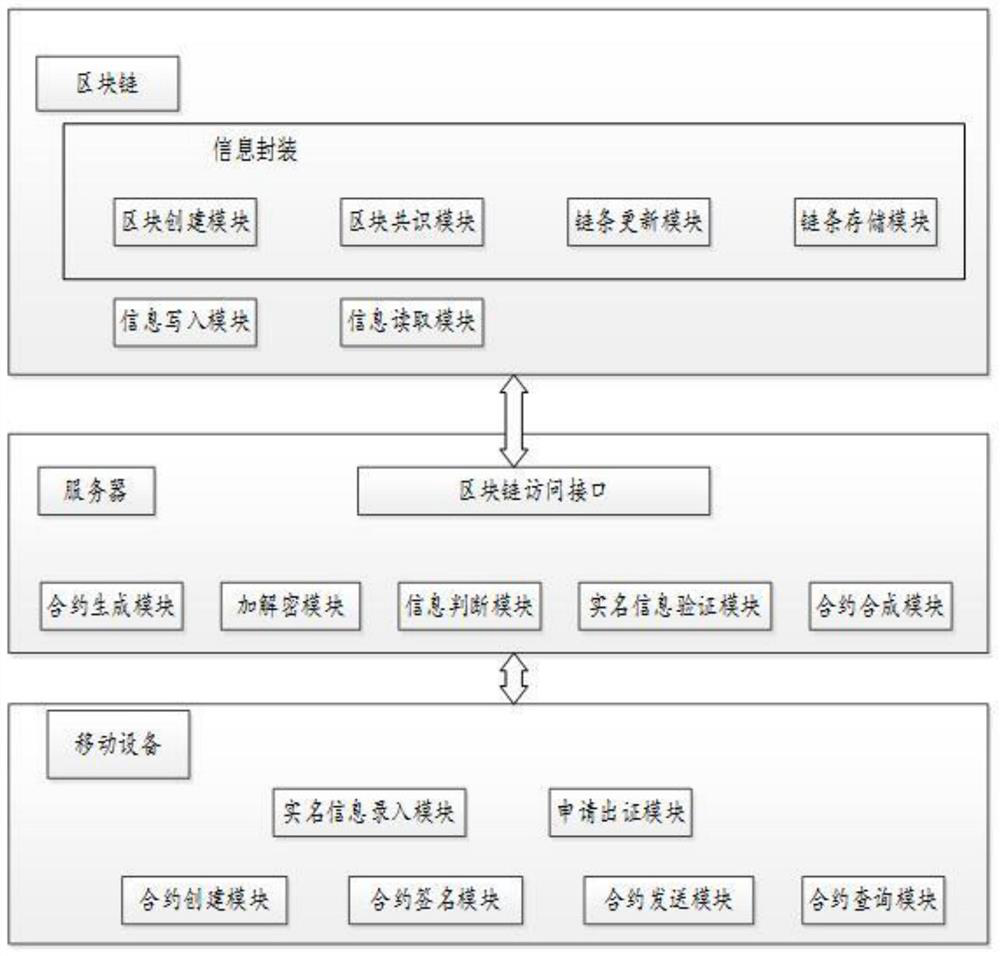
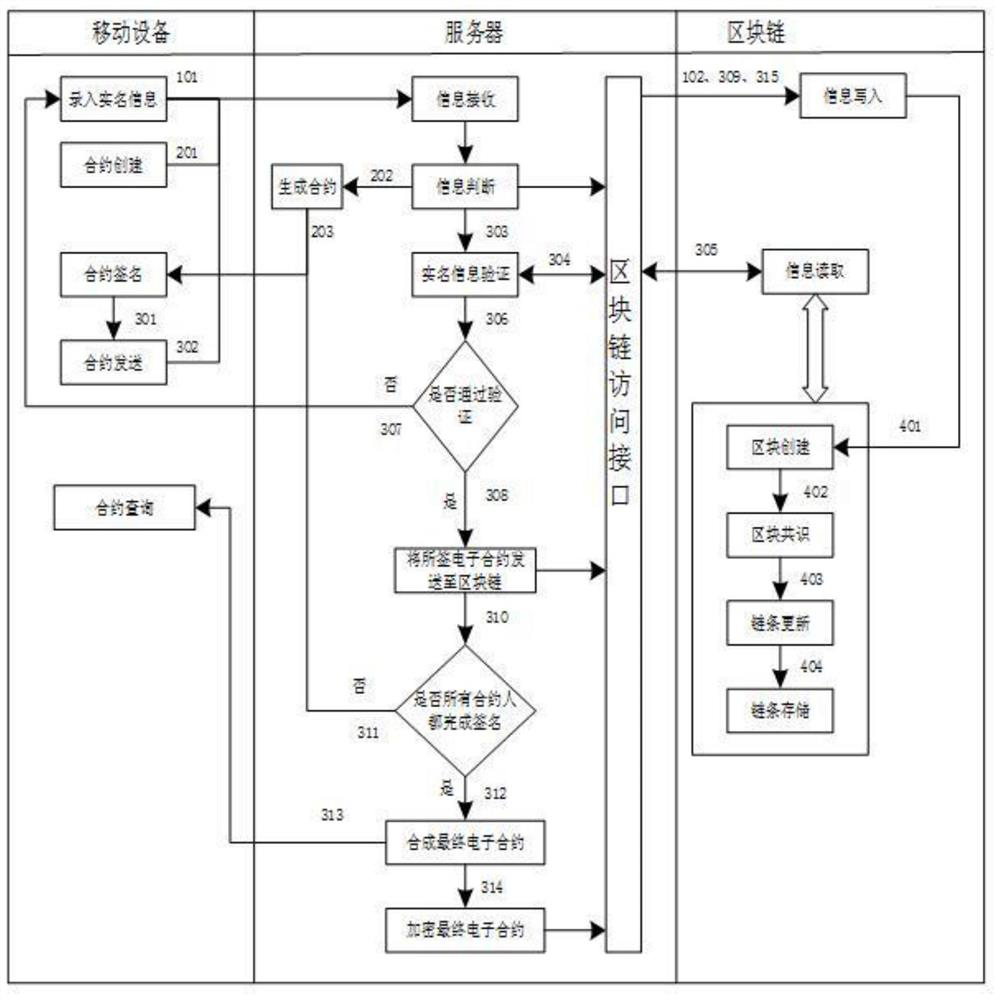
A block chain-based electronic signing device and method proposed by the present invention relate to the technical field of electronic contract signing, including mobile devices, servers and block chain networks. Mobile devices are used to provide users with real-name information entry, electronic contract signing, etc. service; the server is a server controlled by an authoritative certification institution, which is used to receive and process service requests sent on mobile devices in real time; the blockchain is composed of m authoritative certification institution nodes, and a single authoritative certification institution The data received by the nodes is packaged to form a block consensus and stored in all nodes of the entire network. The invention can not only make the signed contract authentic, reliable and non-tamperable, but also issue valid certification documents through the authoritative certification organization in time in the case of user breach of contract, so that the signed electronic contract becomes credible. judicial evidence.
Owner:法信公证云(厦门)科技有限公司
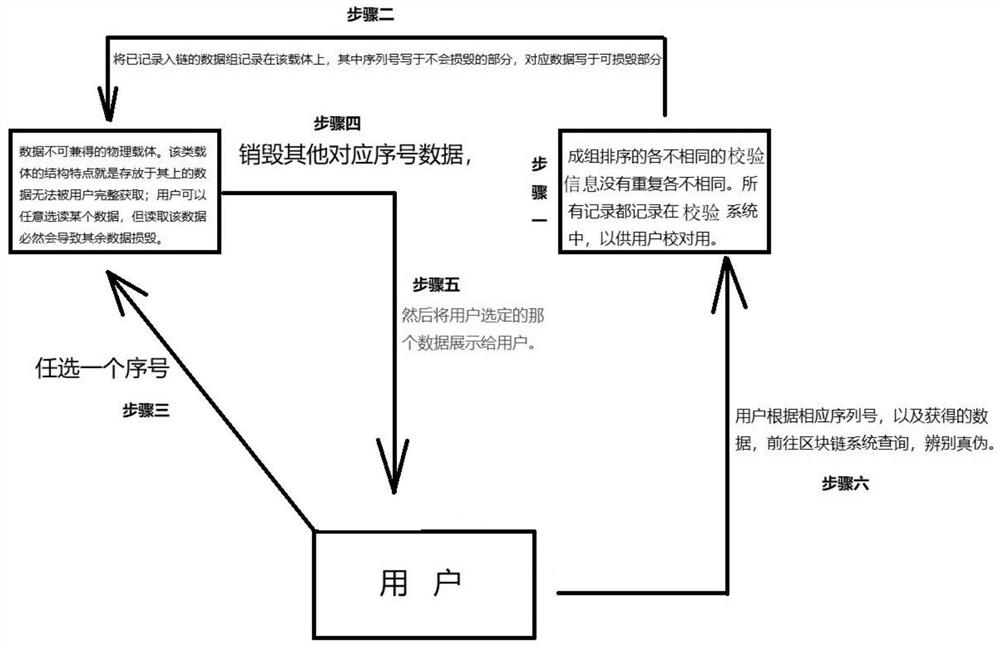
Data protection method and system with anti-theft function
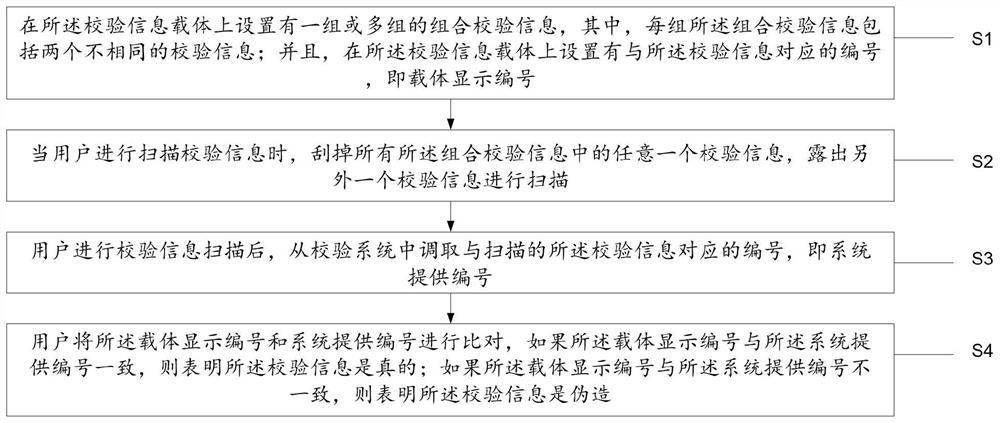
PendingCN113420337APrevent theftIncrease randomnessDigital data protectionCommerceVerification systemSerial code
The invention provides a data protection method and system with an anti-theft function. The method comprises the following steps: setting one or more groups of combined verification information on a verification information carrier, and when a user scans the verification information, scraping any one piece of verification information in all the combined verification information, and exposing the other piece of verification information for scanning; after a user scans verification information, calling a serial number corresponding to the scanned verification information from a verification system, that is, the system provides the serial number; enabling the user to compare the carrier display number with the system providing number, and if the carrier display number is consistent with the system providing number, indicating that the verification information is true; and if the carrier display number is inconsistent with the number provided by the system, indicating that the verification information is forged. The system comprises modules corresponding to the steps of the method.
Owner:庄定善
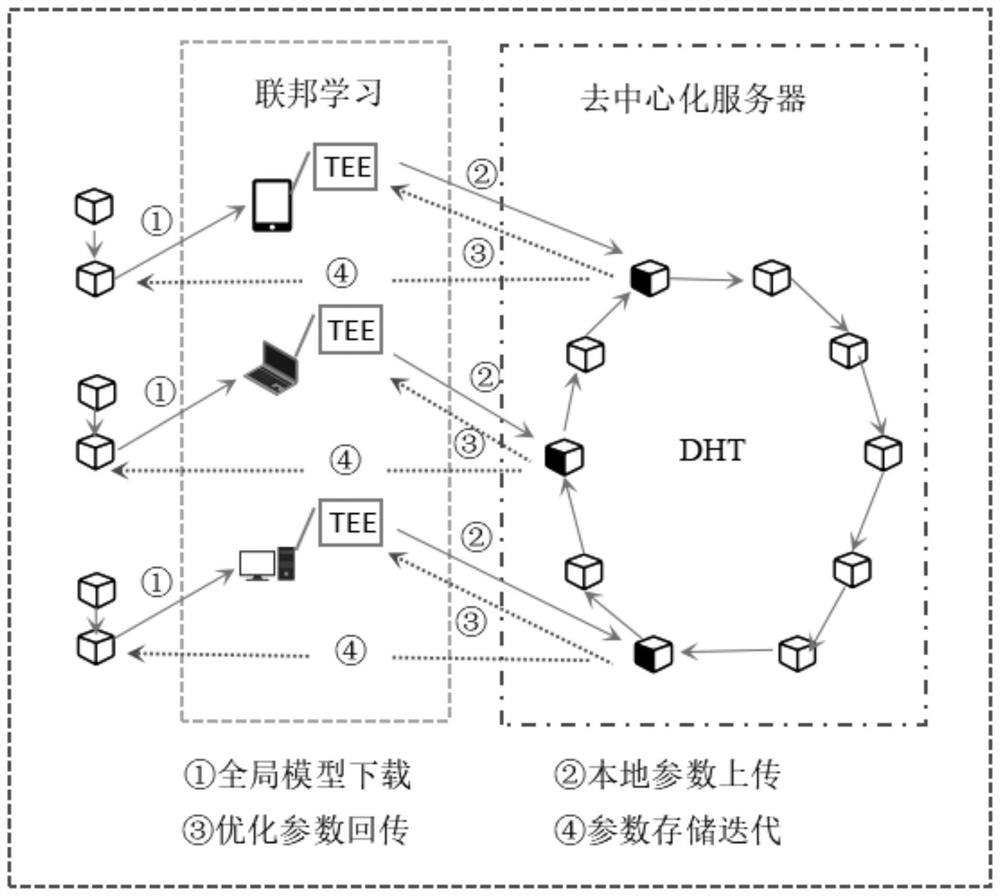
Data privacy protection method and device in data fusion process and storage medium
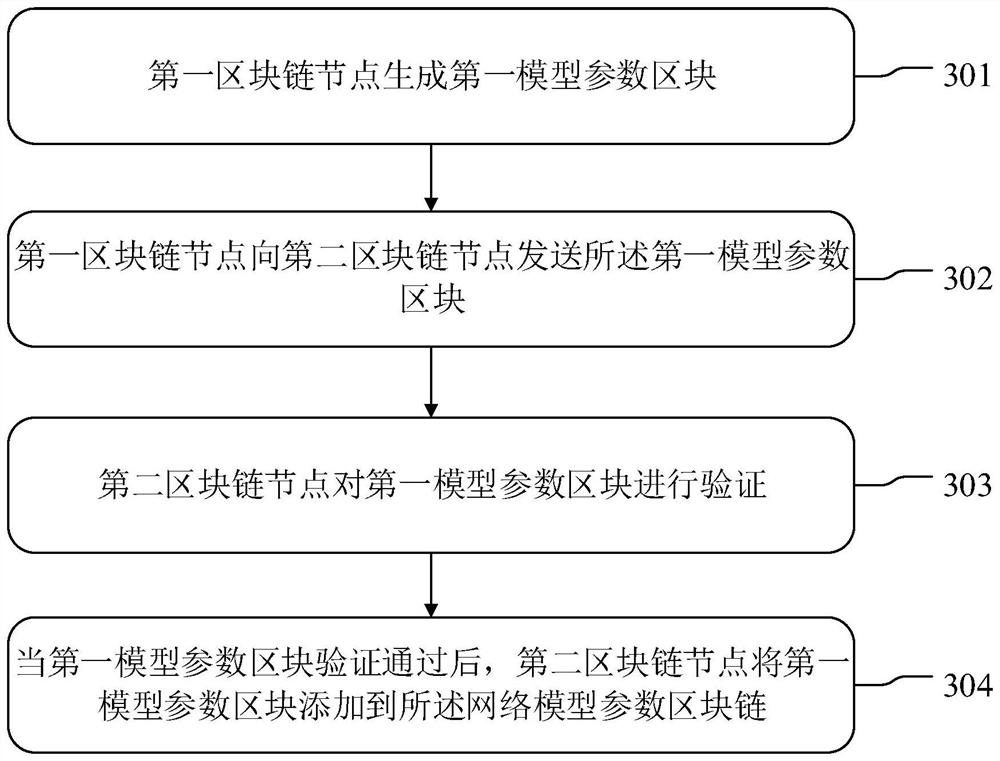
PendingCN114785494AImprove immutabilityAchieving verifiabilityKey distribution for secure communicationUser identity/authority verificationData privacy protectionComputation process
The invention discloses a data privacy protection method and device in a data fusion process and a storage medium, and the method comprises the steps that a first block chain node generates a first model parameter block, and the first model parameter block comprises a local model updating parameter of a preset network model at the first block chain node; the first block chain node sends the first model parameter block to a second block chain node; the second block chain node verifies the first model parameter block; and after the verification of the first model parameter block is passed, the second block chain node adds the first model parameter block to the network model parameter block chain. According to the method and the device, federal learning and a block chain technology are fused, so that the non-tampering property and the verifiability of a federal learning result are increased, the trust problem of a participant on a calculation process and a result is solved, the acceptance cost of a terminal is reduced, the security of data storage is ensured, and the data privacy is effectively ensured in a data fusion process.
Owner:CHINA ACADEMY OF INFORMATION & COMM
Document data security verification method based on block chain
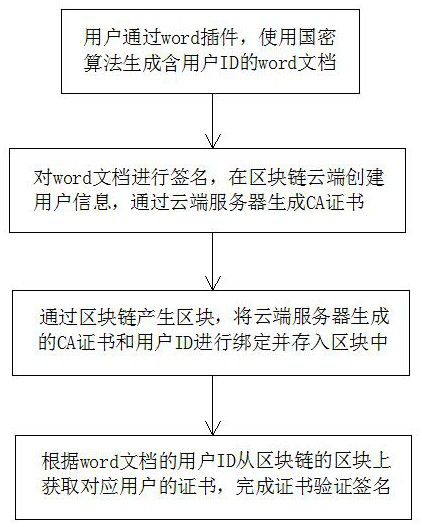
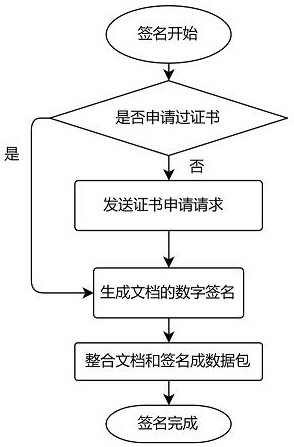
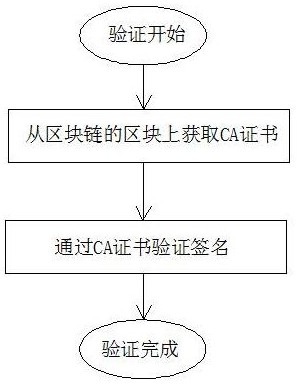
PendingCN114679311AGuaranteed accuracyEasy to operateKey distribution for secure communicationUser identity/authority verificationDigital documentUser information
The invention discloses a document data security verification method based on a block chain, which belongs to the technical field of document processing, and is characterized by comprising the following steps: a, a user generates a word document containing a user ID (Identity) by using a national cryptographic algorithm through a word plug-in, and the national cryptographic algorithm comprises an SM2 algorithm and an SM3 algorithm; b, signing the word document, creating user information at a block chain cloud, and generating a CA certificate through a cloud server; c, generating a block through the block chain, binding the CA certificate generated by the cloud server with the user ID, and storing the CA certificate and the user ID in the block; and d, obtaining the certificate of the corresponding user from the block of the block chain according to the user ID of the word document, and completing certificate verification signature. The system has a distributed characteristic, each user can independently sign and verify the electronic document, the precision of a verification result is guaranteed, the electronic document can be written locally, and the operation is more convenient and humanized.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com