Patents
Literature
4979 results about "Verification system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
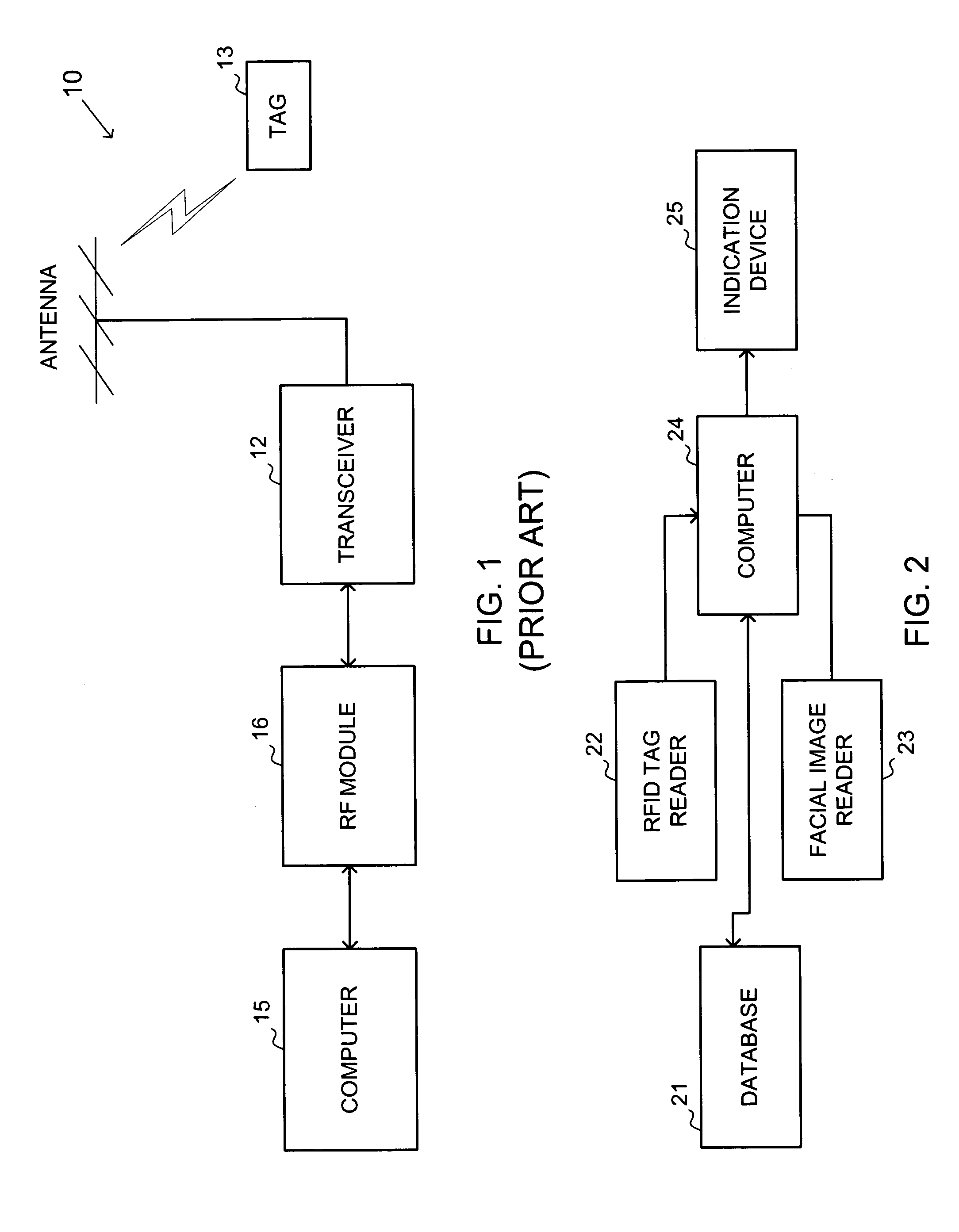
System Verification. System Verification is a set of actions used to check the correctness of any element, such as a system element, a system, a document, a service, a task, a requirement, etc.
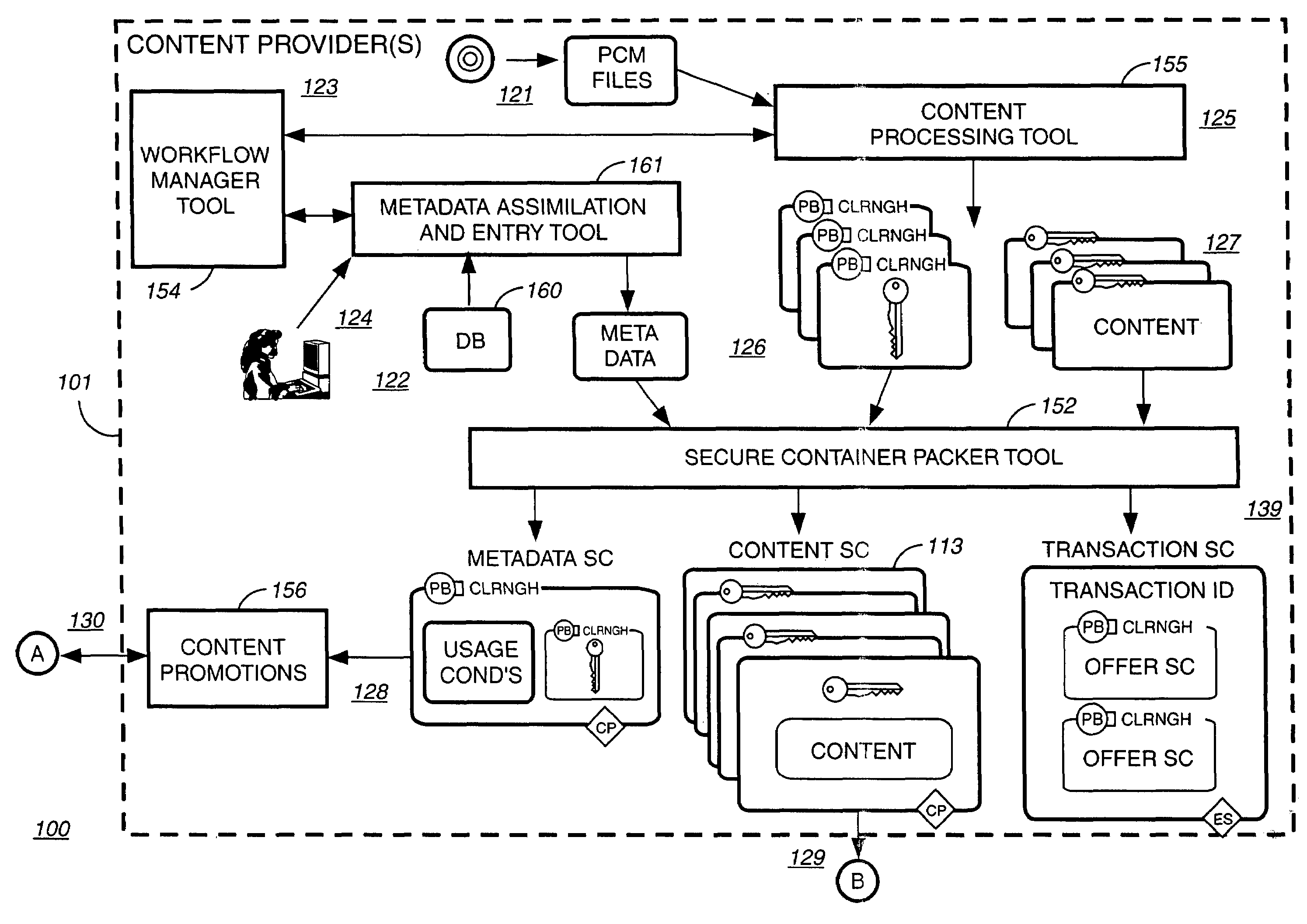
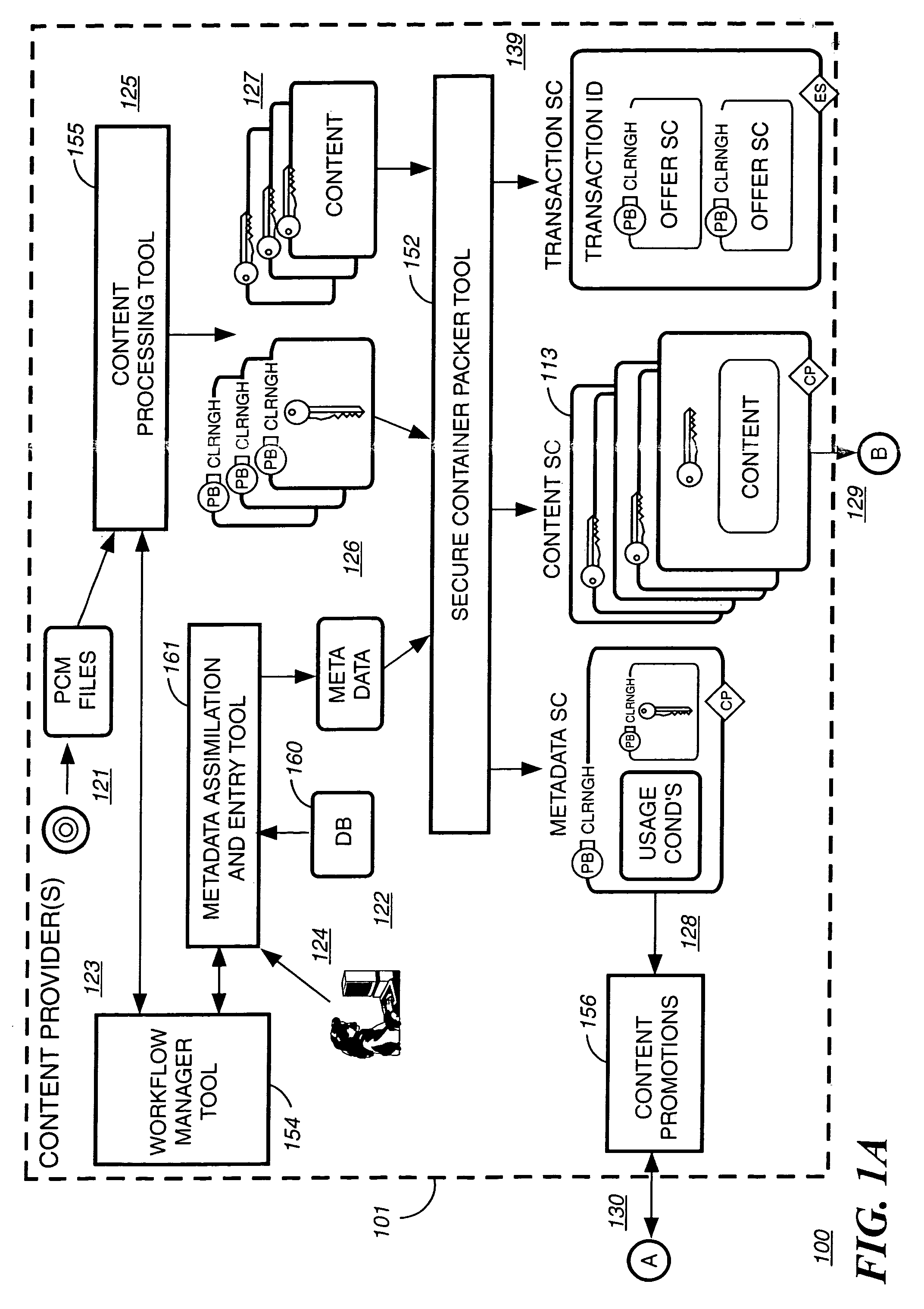
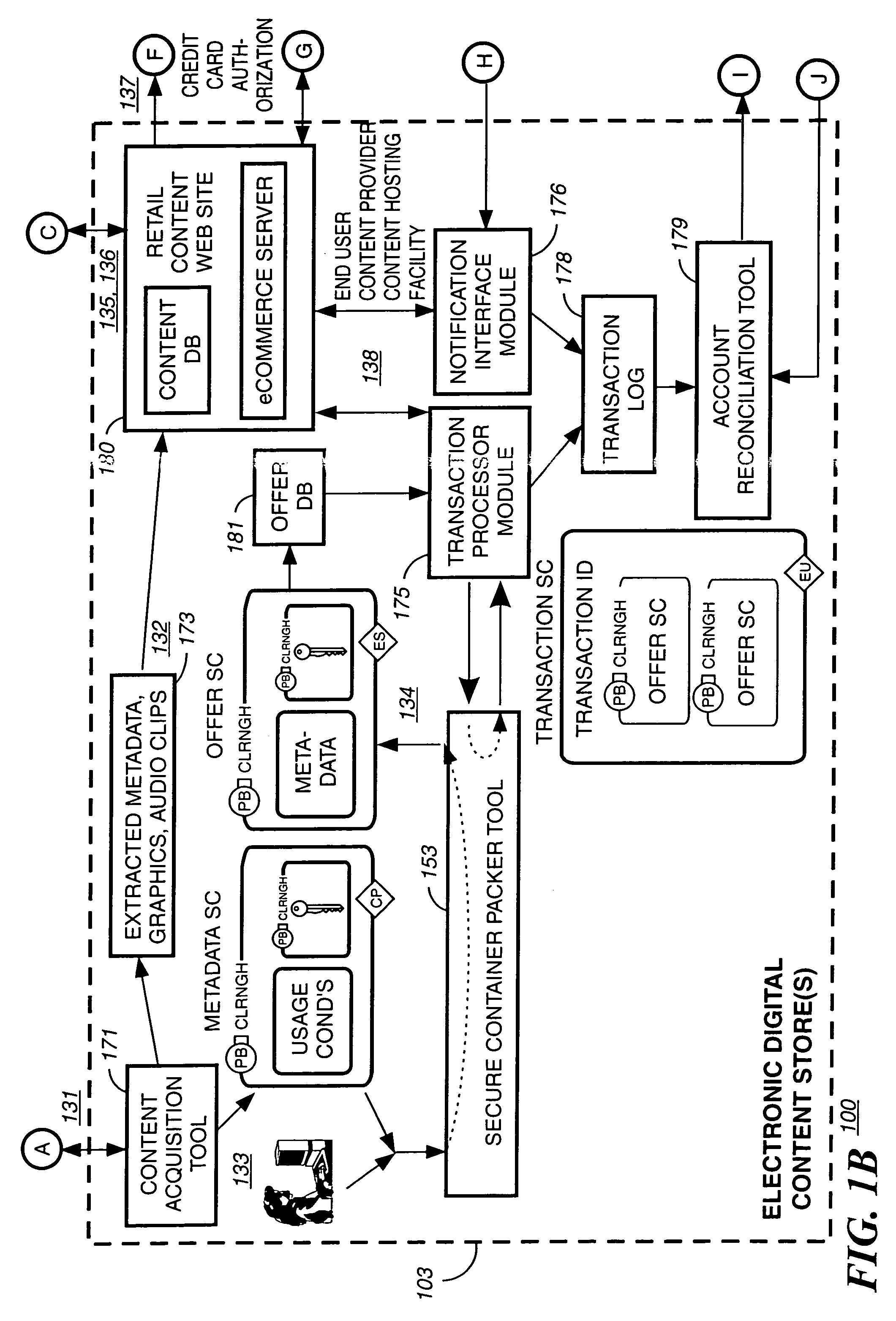
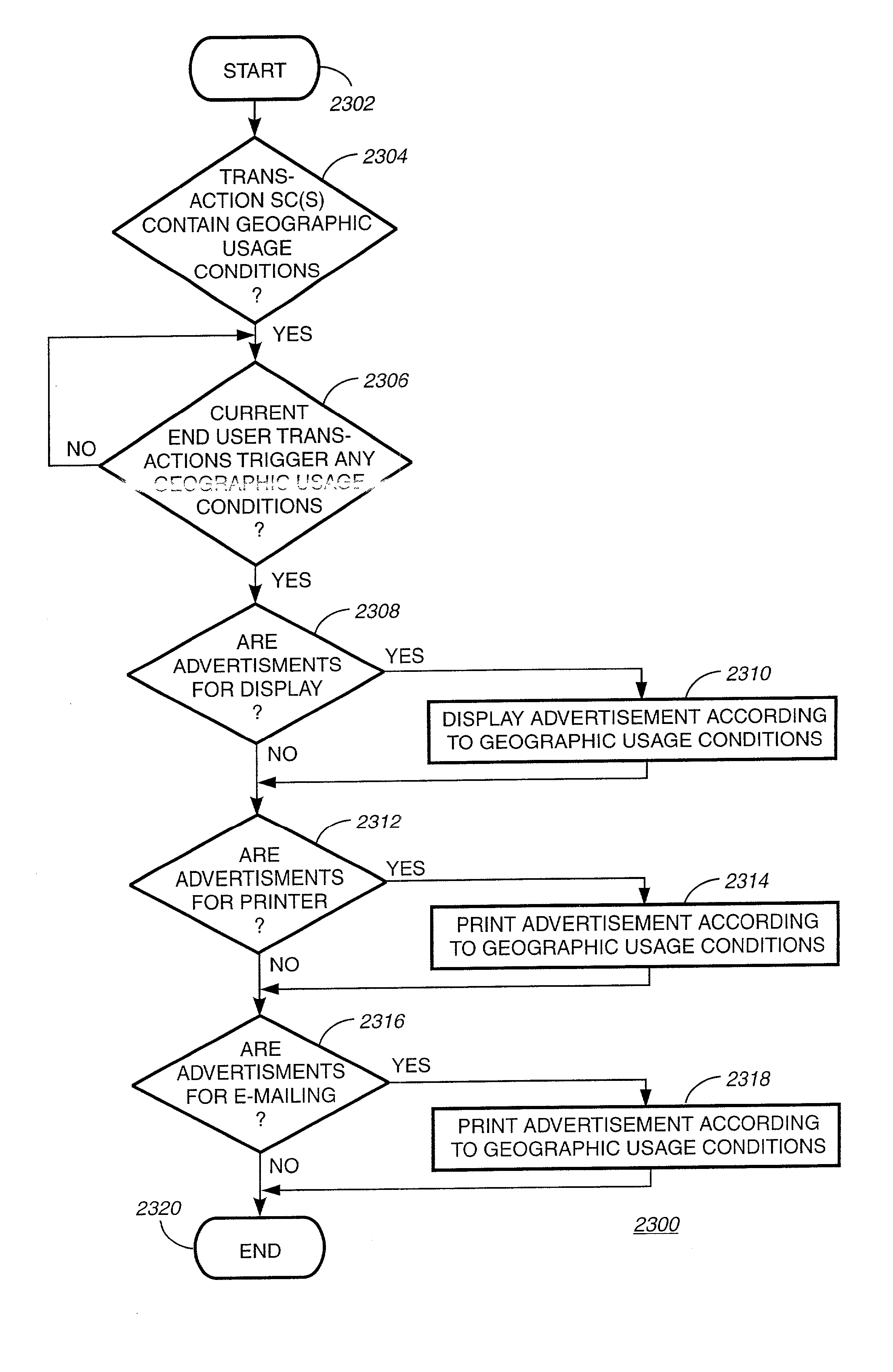
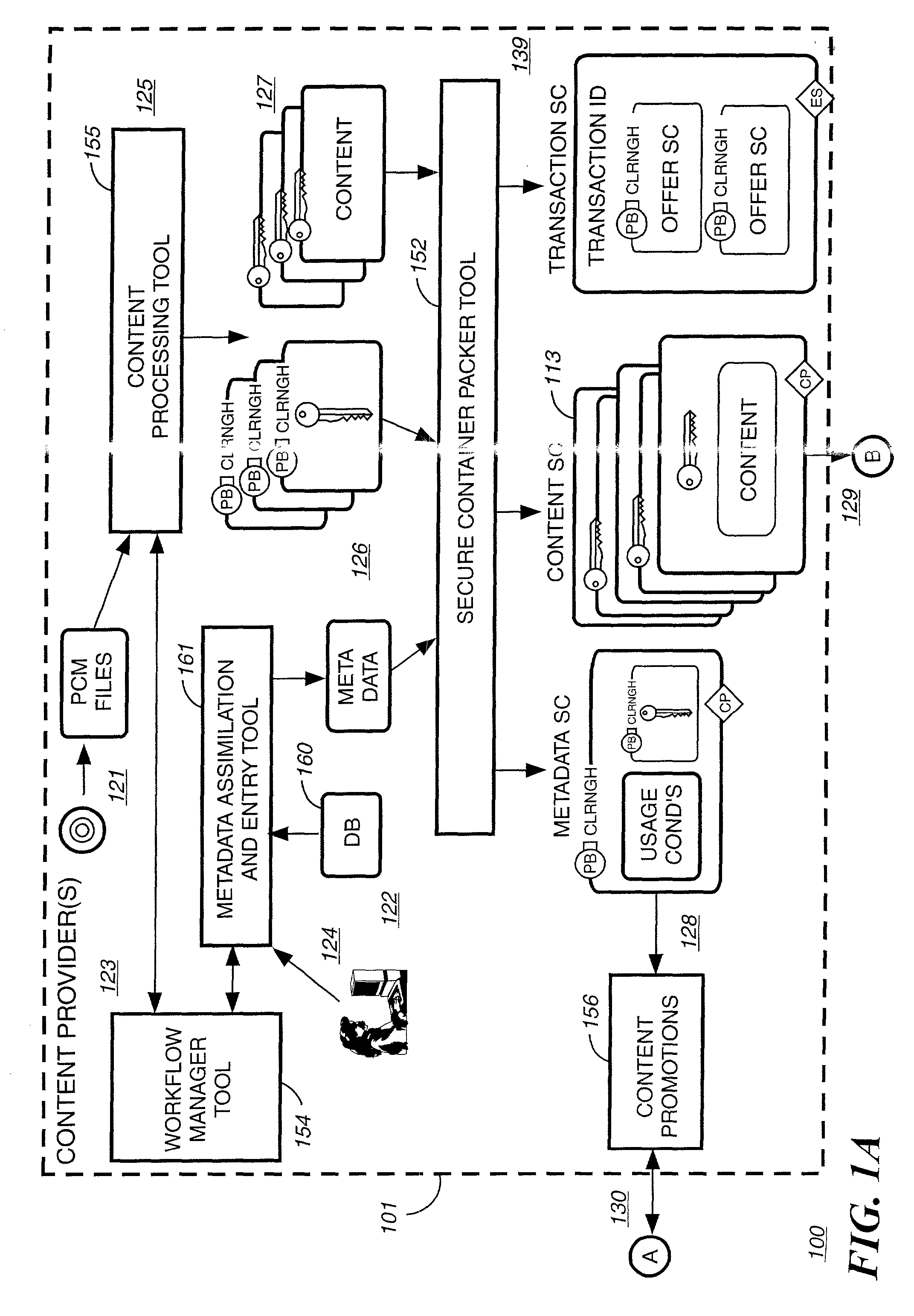
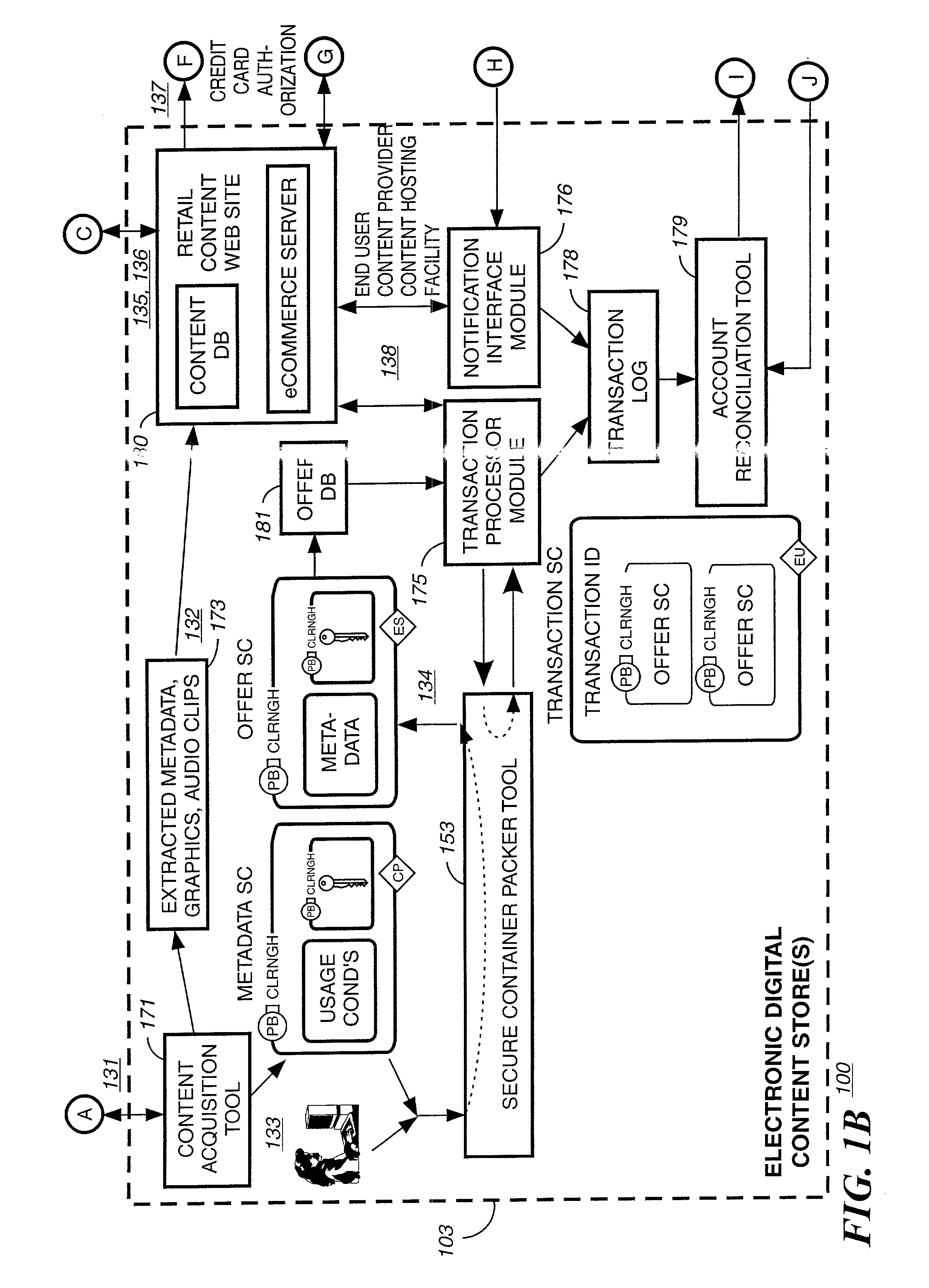
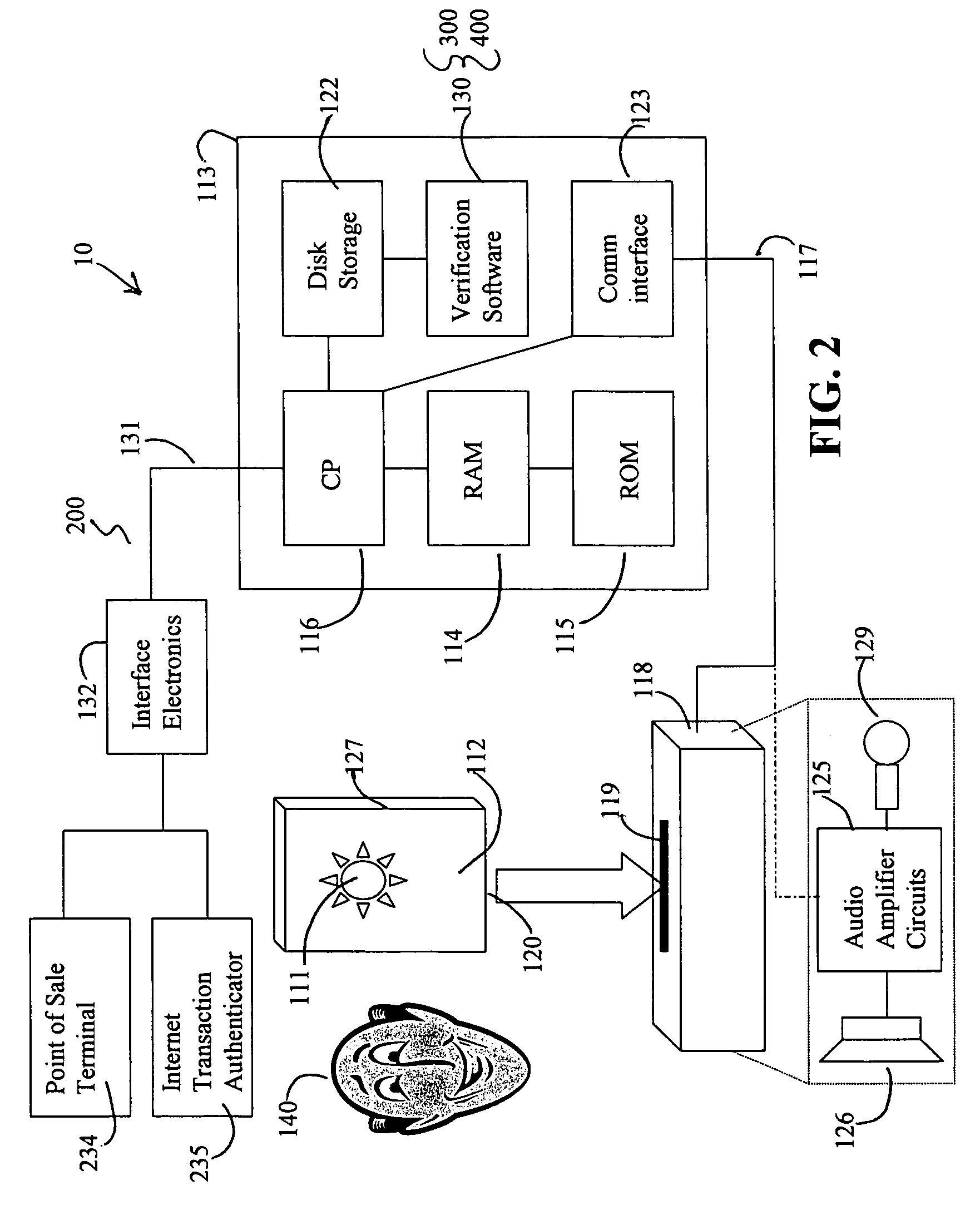
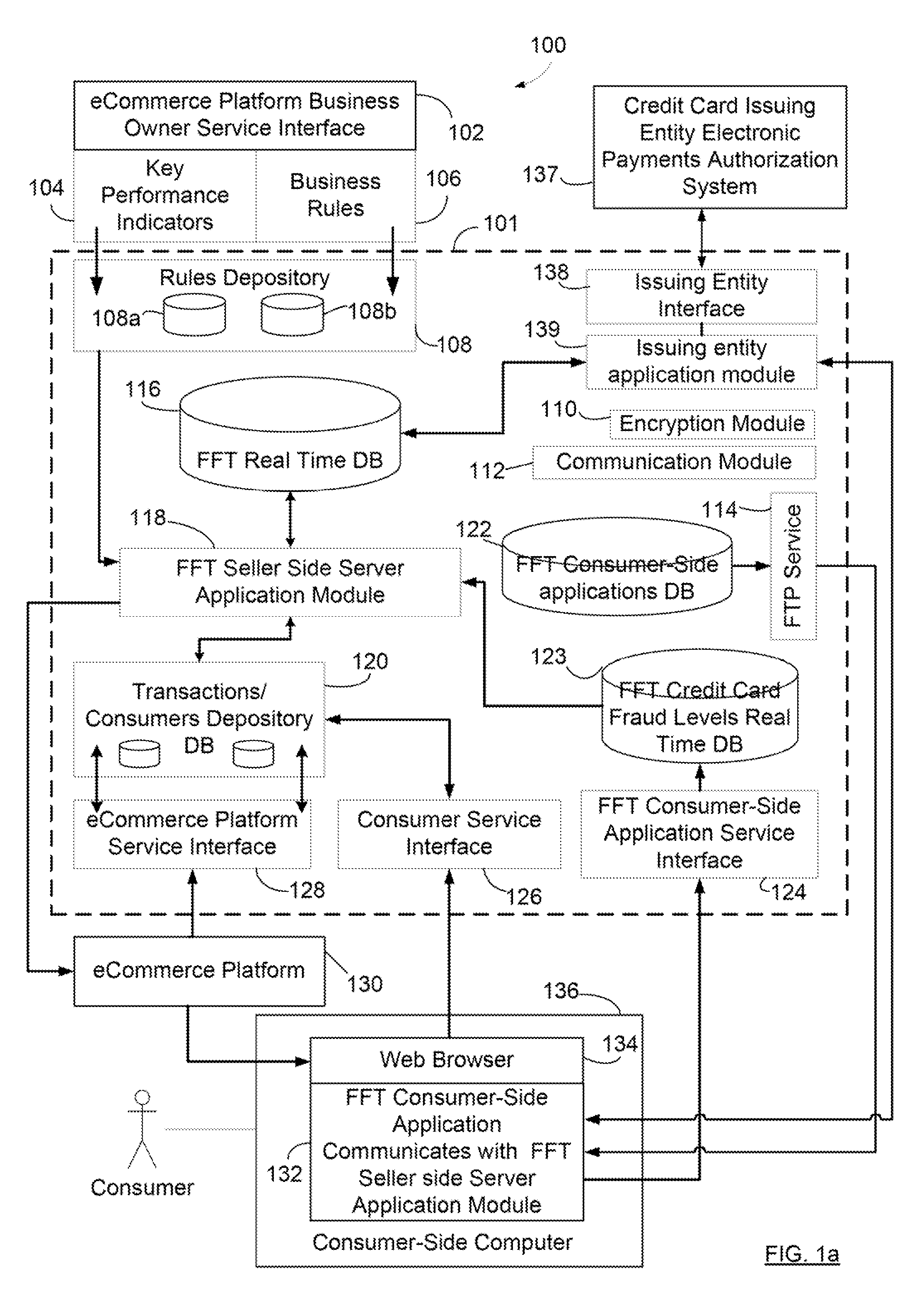
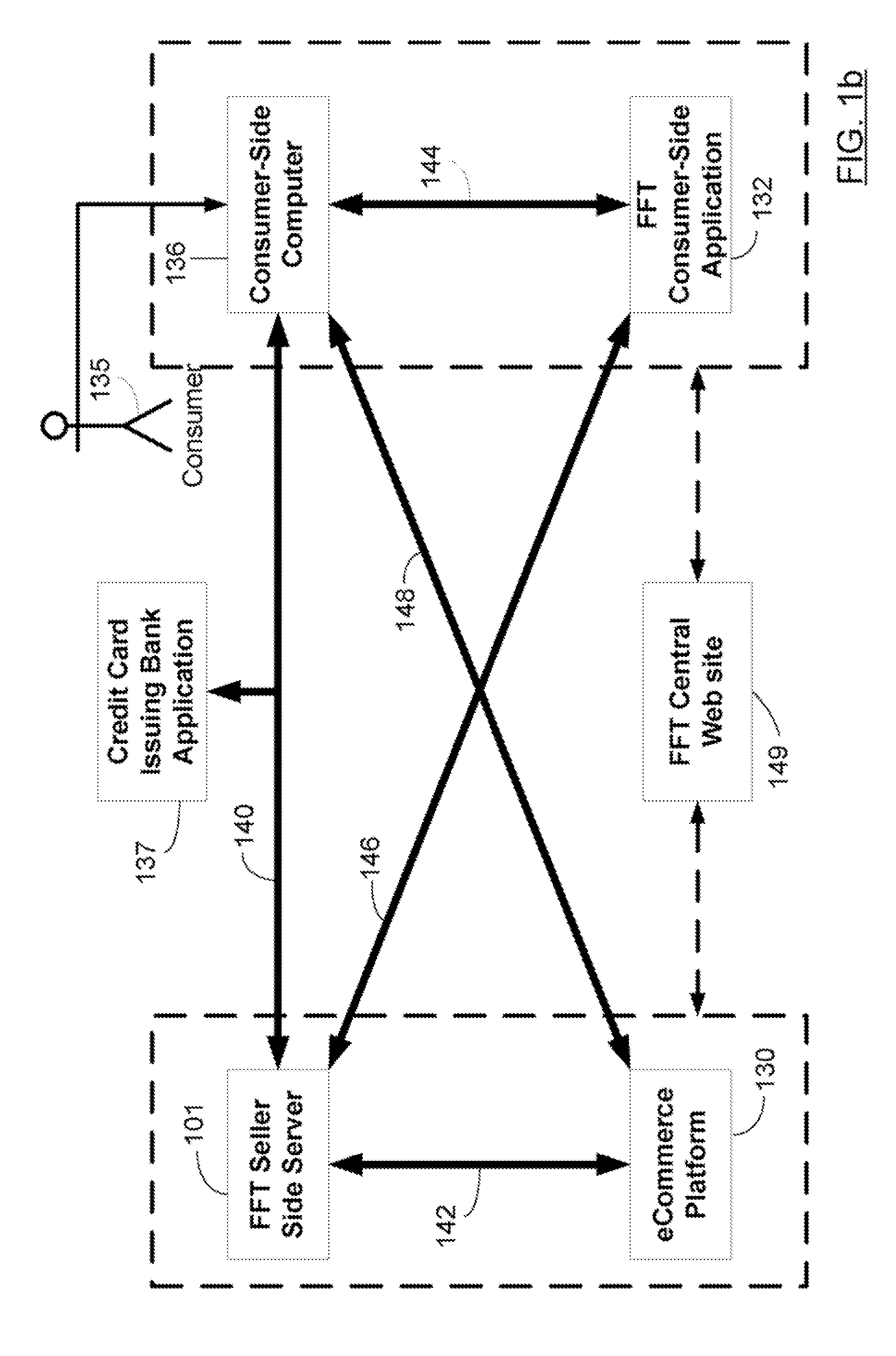
Method and system for delivering encrypted content with associated geographical-based advertisements
A method, a system and computer readable medium at an electronic digital content store, such as a web site, for associating advertisement with digital content. The geographic location of the end user device receiving the encrypted digital content is determined using an address verification system. Advertisement is selected to be associated with the delivery of encrypted digital content if the address verification system returns an address in a predetermined geographic region. The address verification system includes the IP address of the end user device, the country codes found in the trace routes to the IP address, and the billing address.
Owner:LEVEL 3 COMM LLC
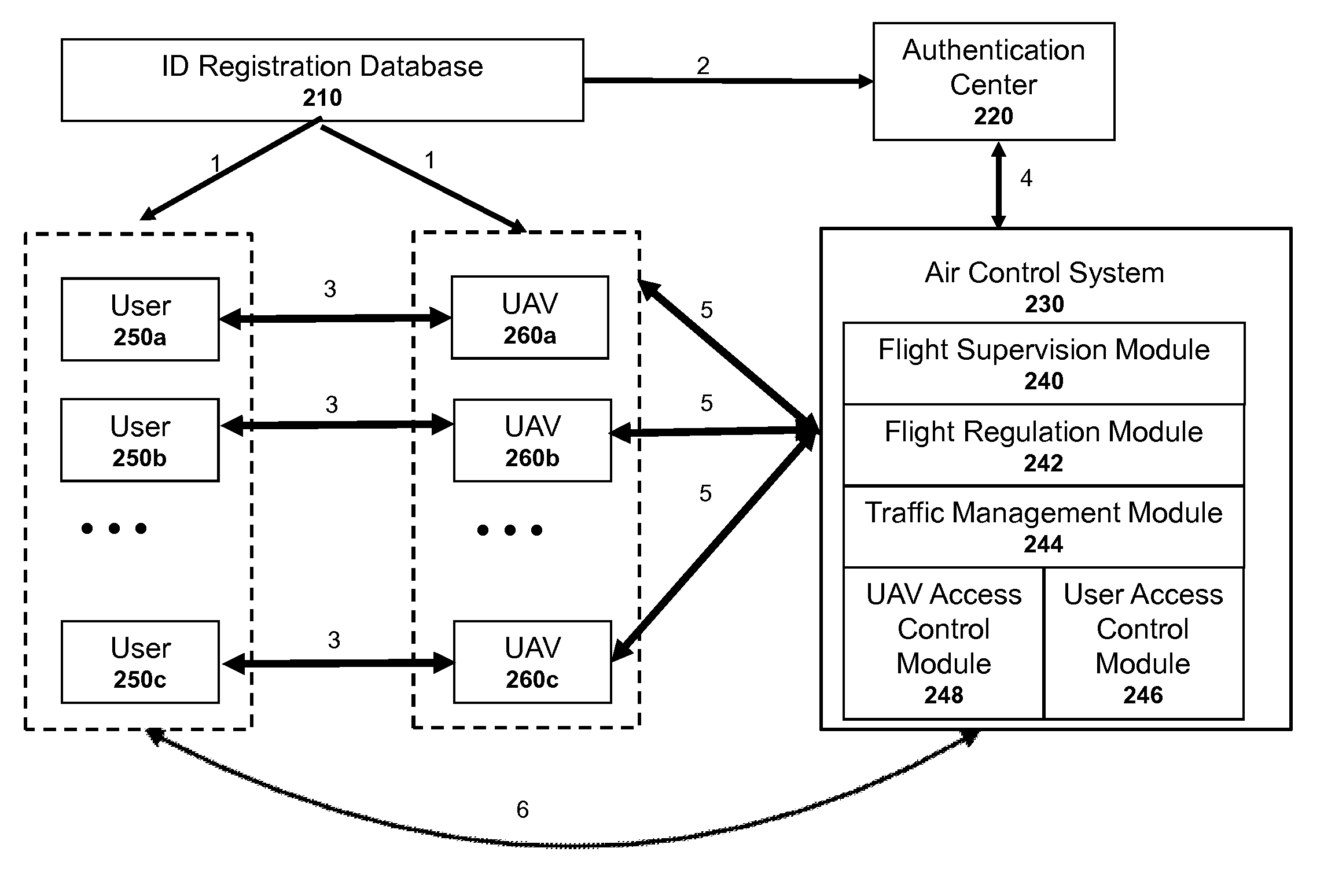
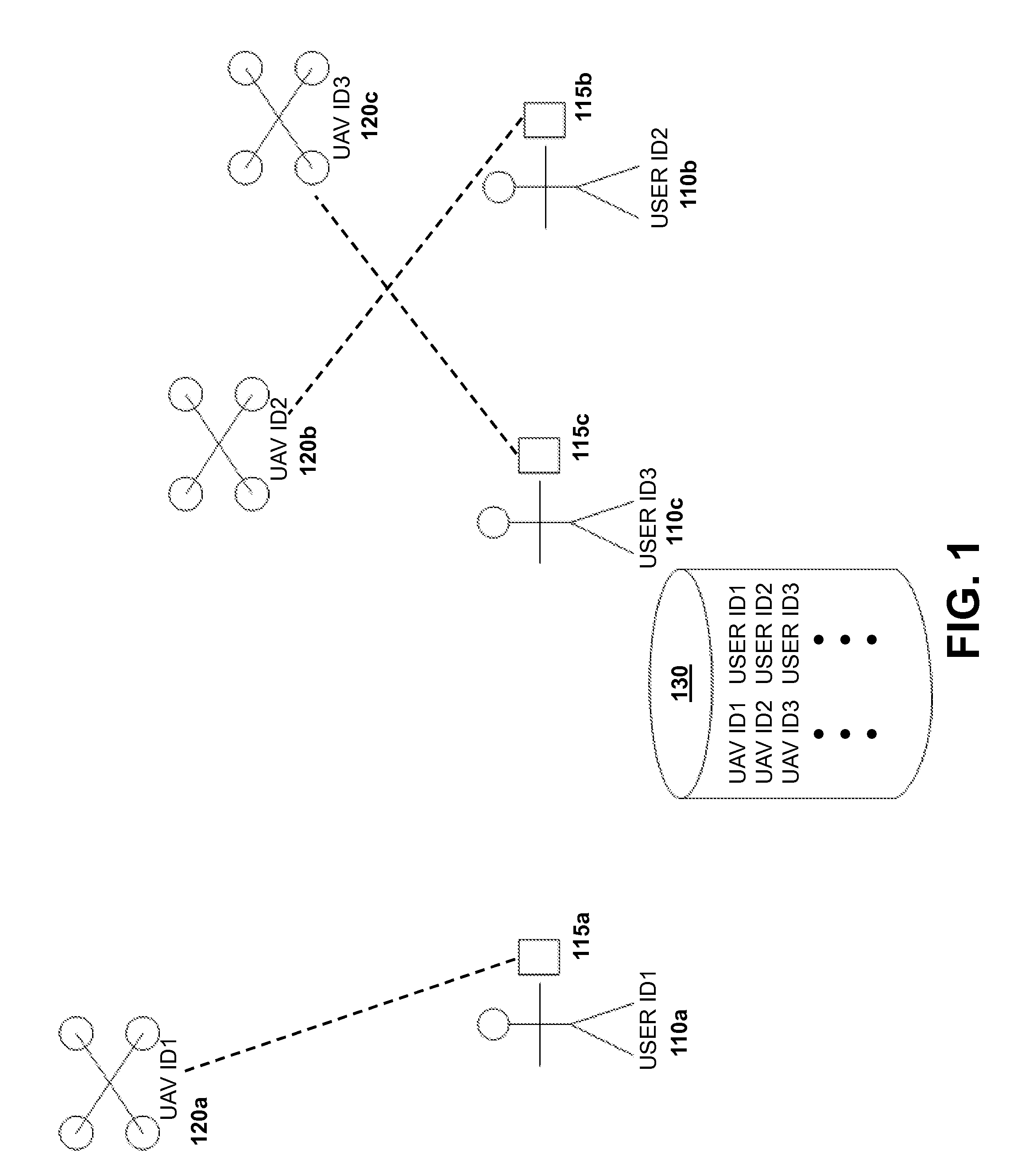
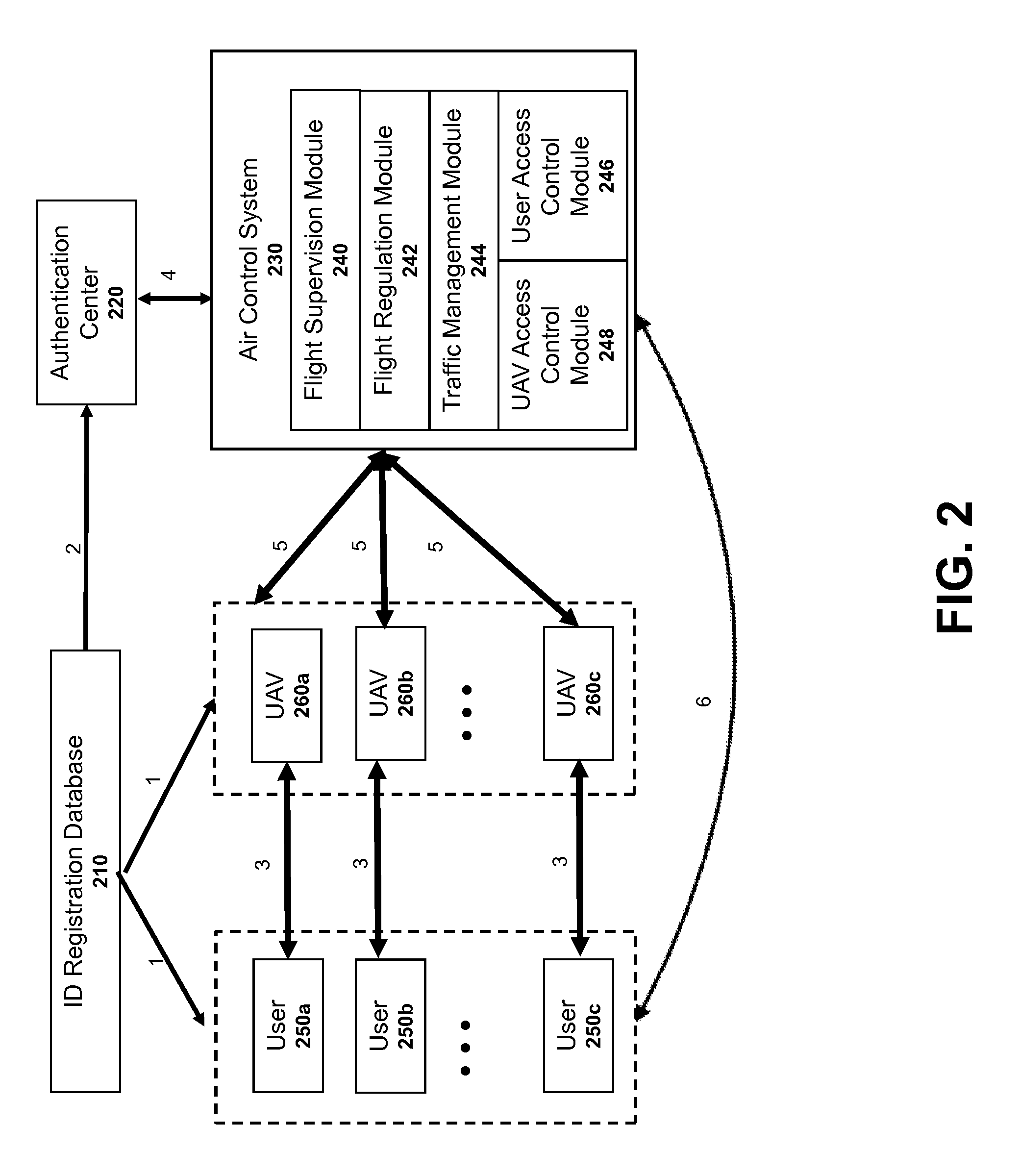
Authentication systems and methods for generating flight regulations
ActiveUS9412278B1Improve flight safetyRemote controlled aircraftDigital data authenticationAuthentication systemComputer science
Systems and methods for UAV safety are provided. An authentication system may be used to confirm UAV and / or user identity and provide secured communications between users and UAVs. The UAVs may operate in accordance with a set of flight regulations. The set of flight regulations may be associated with a geo-fencing device in the vicinity of the UAV.
Owner:SZ DJI TECH CO LTD
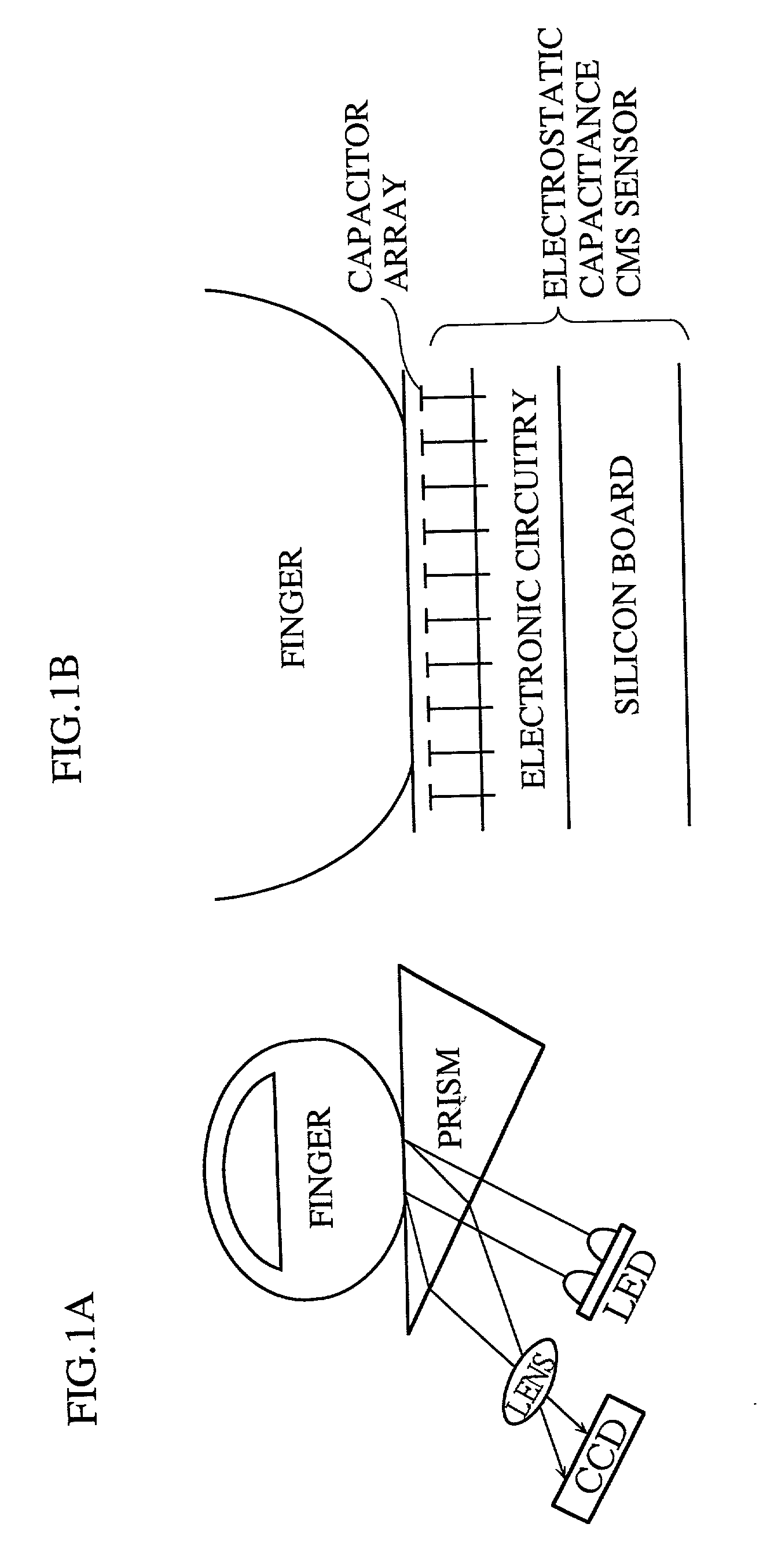
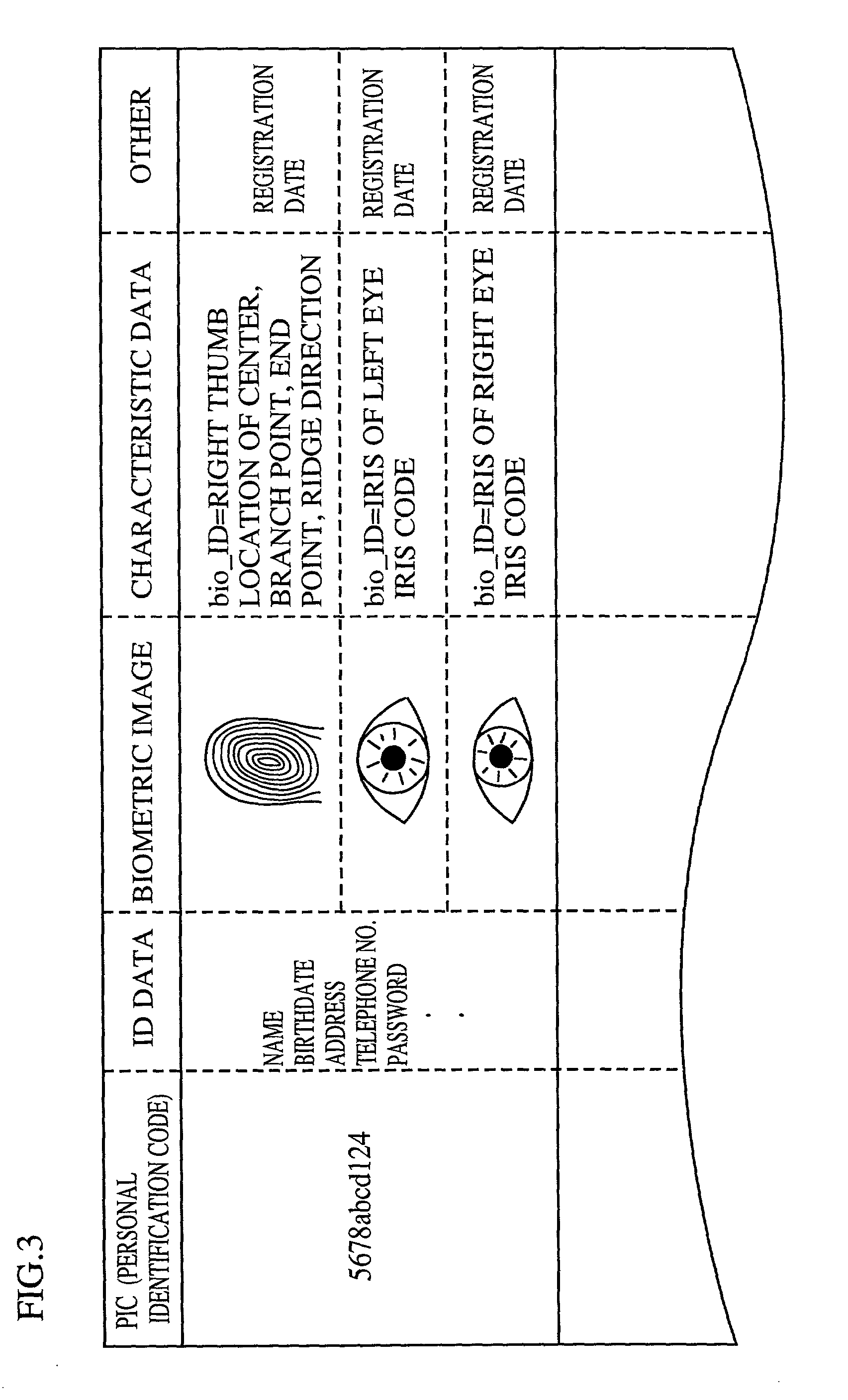
Apparatus for identity verification, a system for identity verification, a card for identity verification and a method for identity verification, based on identification by biometrics
InactiveUS20010026632A1Improve reliabilityLow costImage analysisUser identity/authority verificationCommunication interfaceImaging processing
An identity verification system is used to identify persons with high accuracy, while avoiding direct contact with the device to prevent any negative psychological reaction from a user. The system includes: a camera unit and an image processing unit for obtaining object images of body parts (such as fingerprints and irides) by scanning, without physical contact; an image display unit for displaying layered images of the body part as scanned and a guide showing the body part in an optimal position; a control unit for extracting biometric characteristic data from object images and sending the data to a verification server after encrypting by an encryption unit; and a communications interface unit.
Owner:PANASONIC CORP
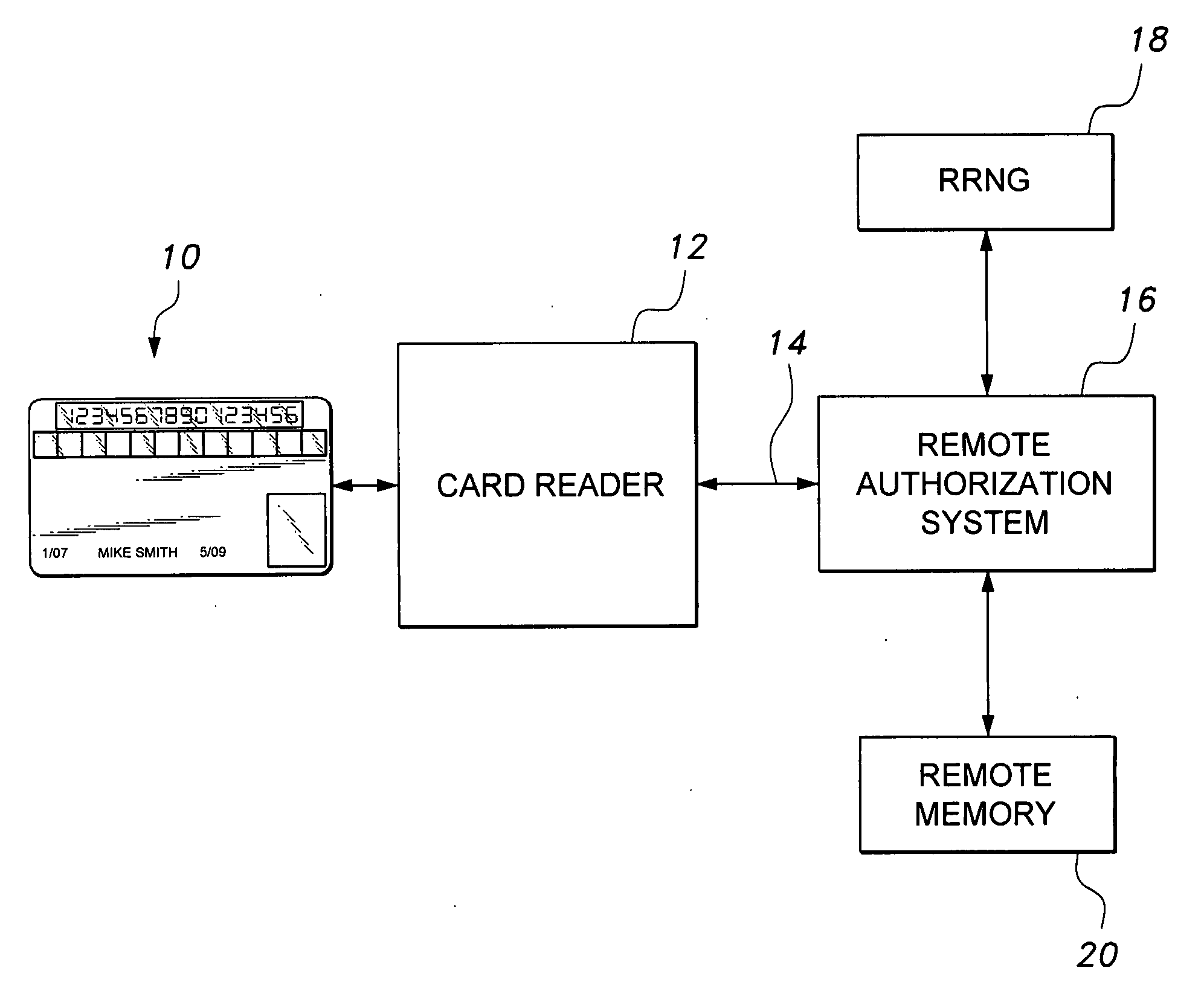
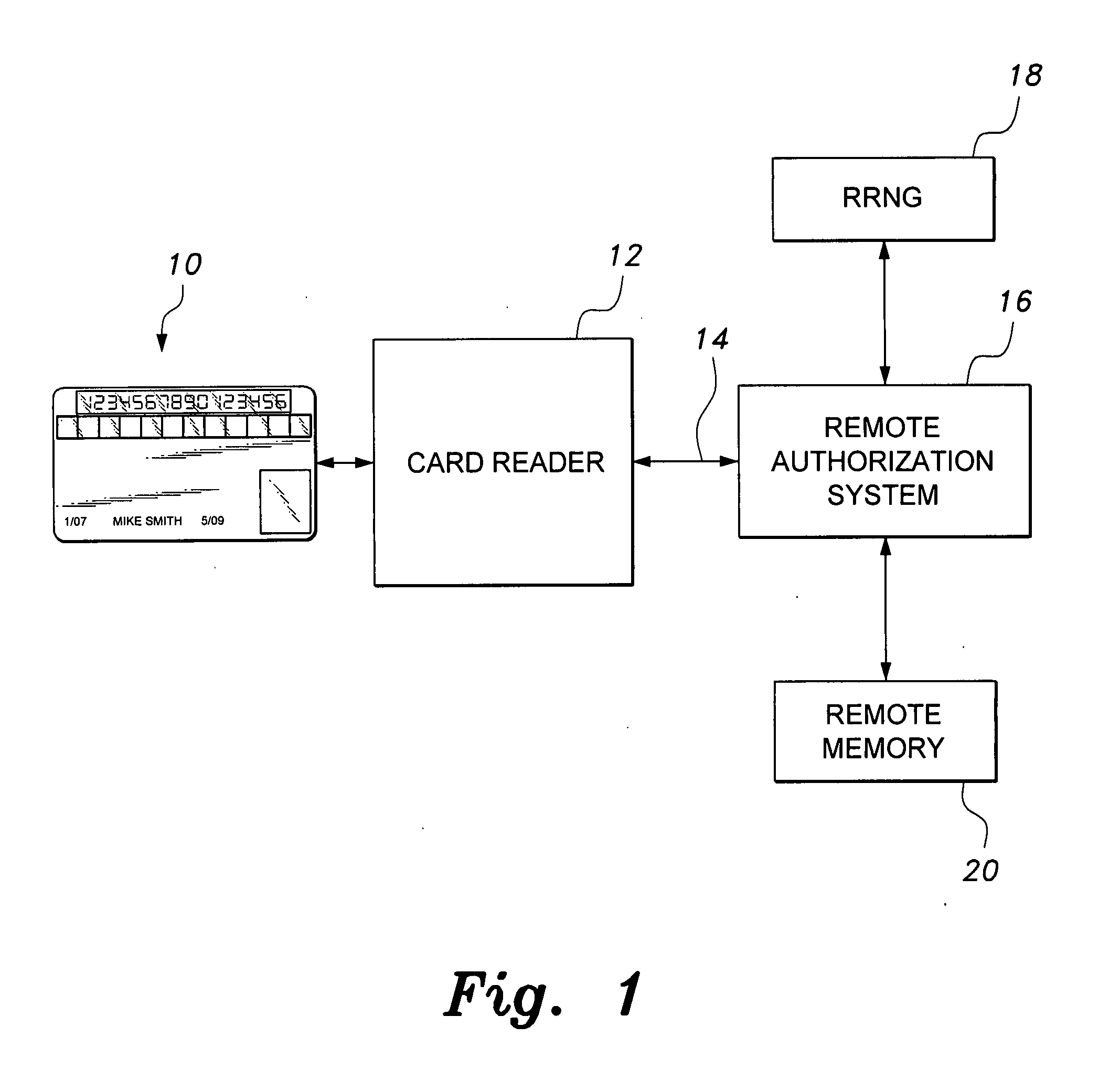
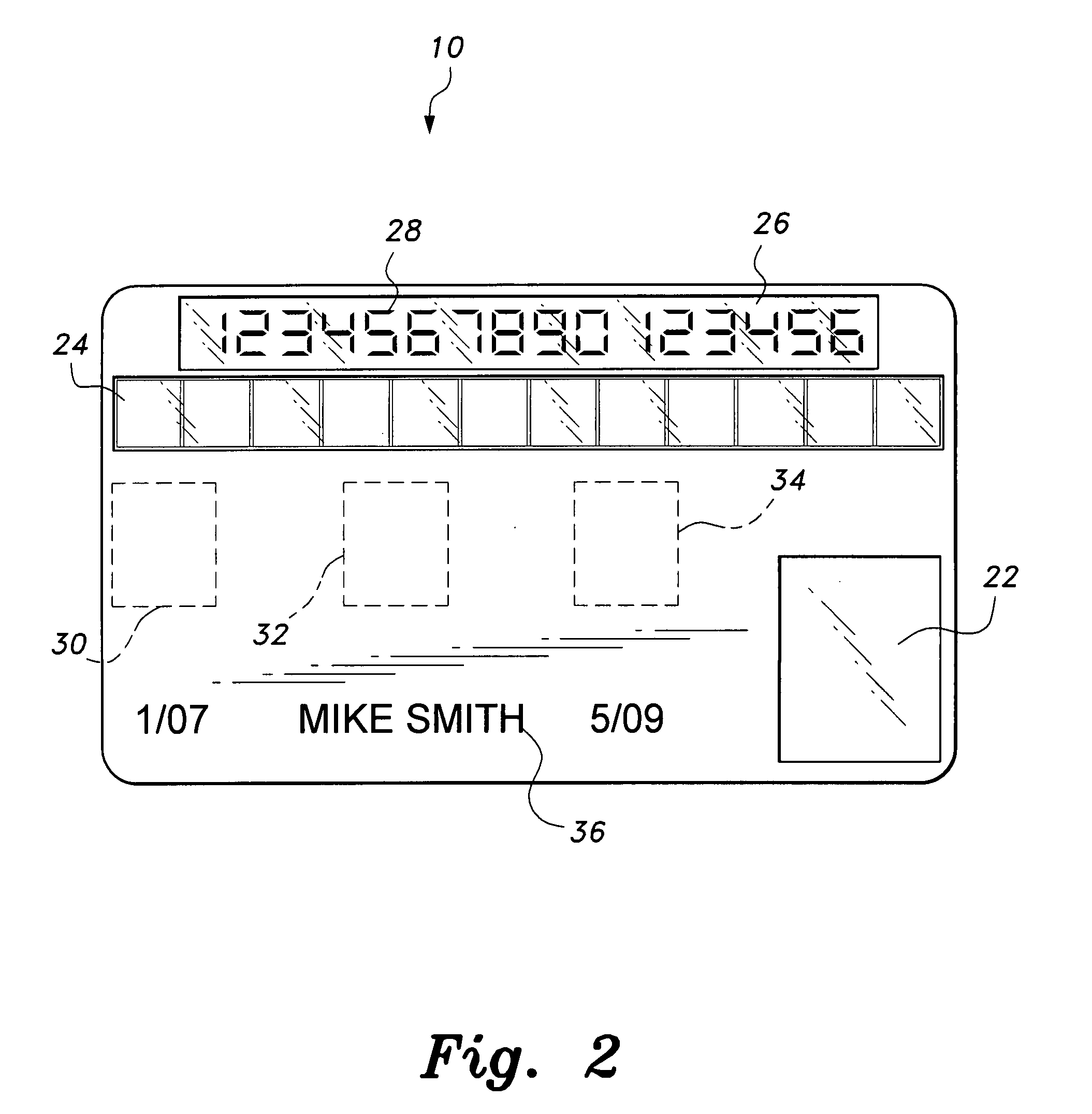
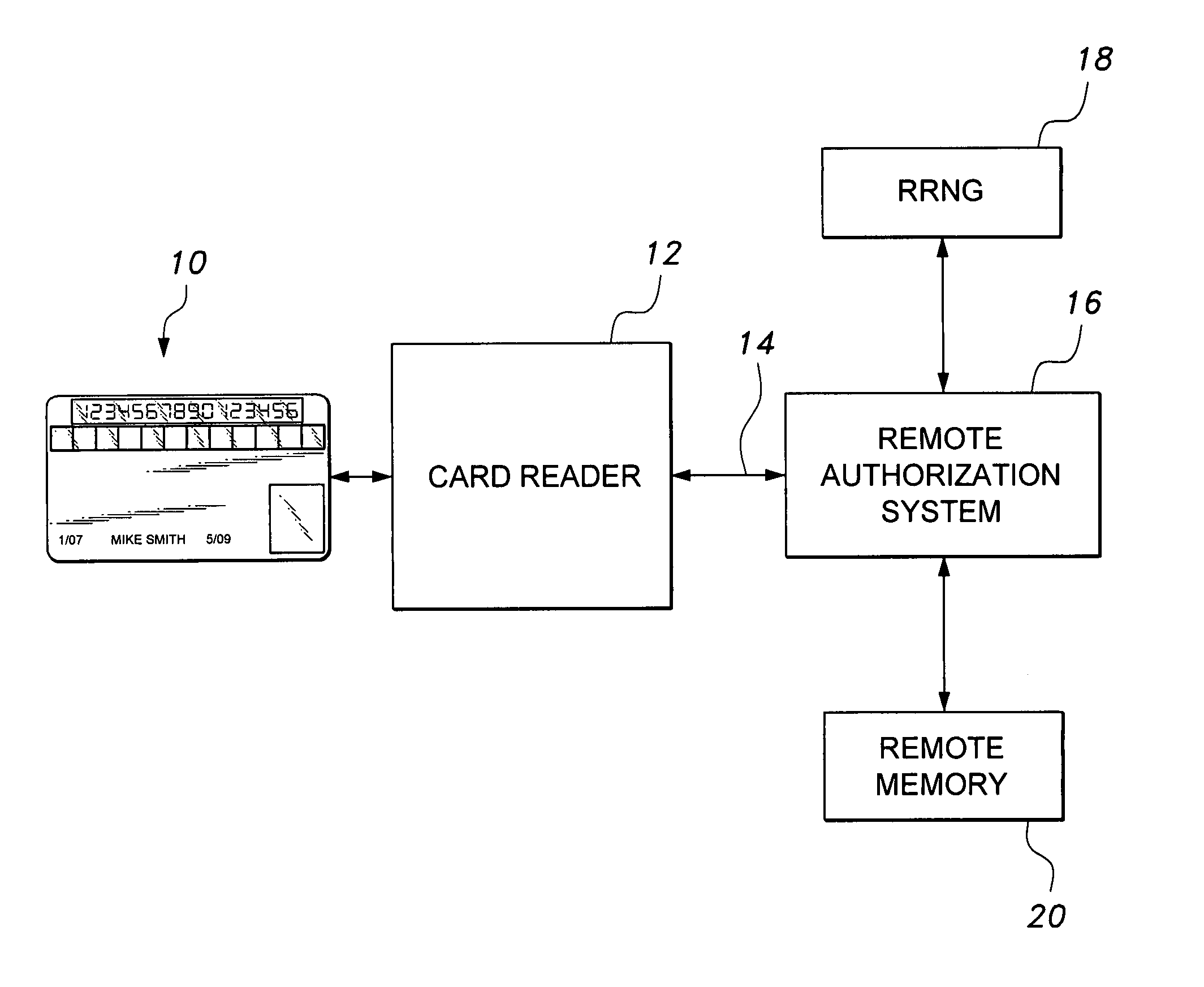
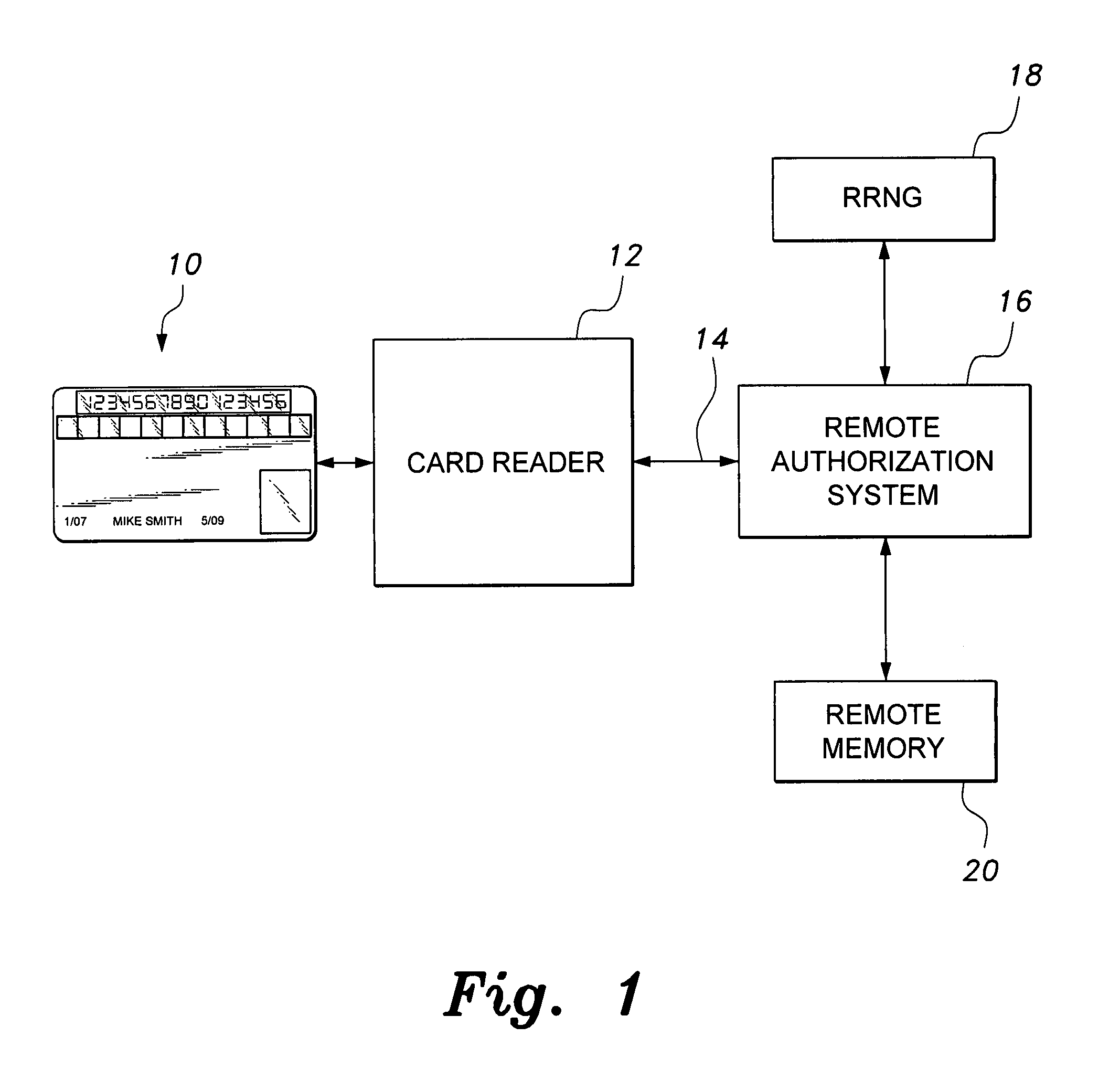
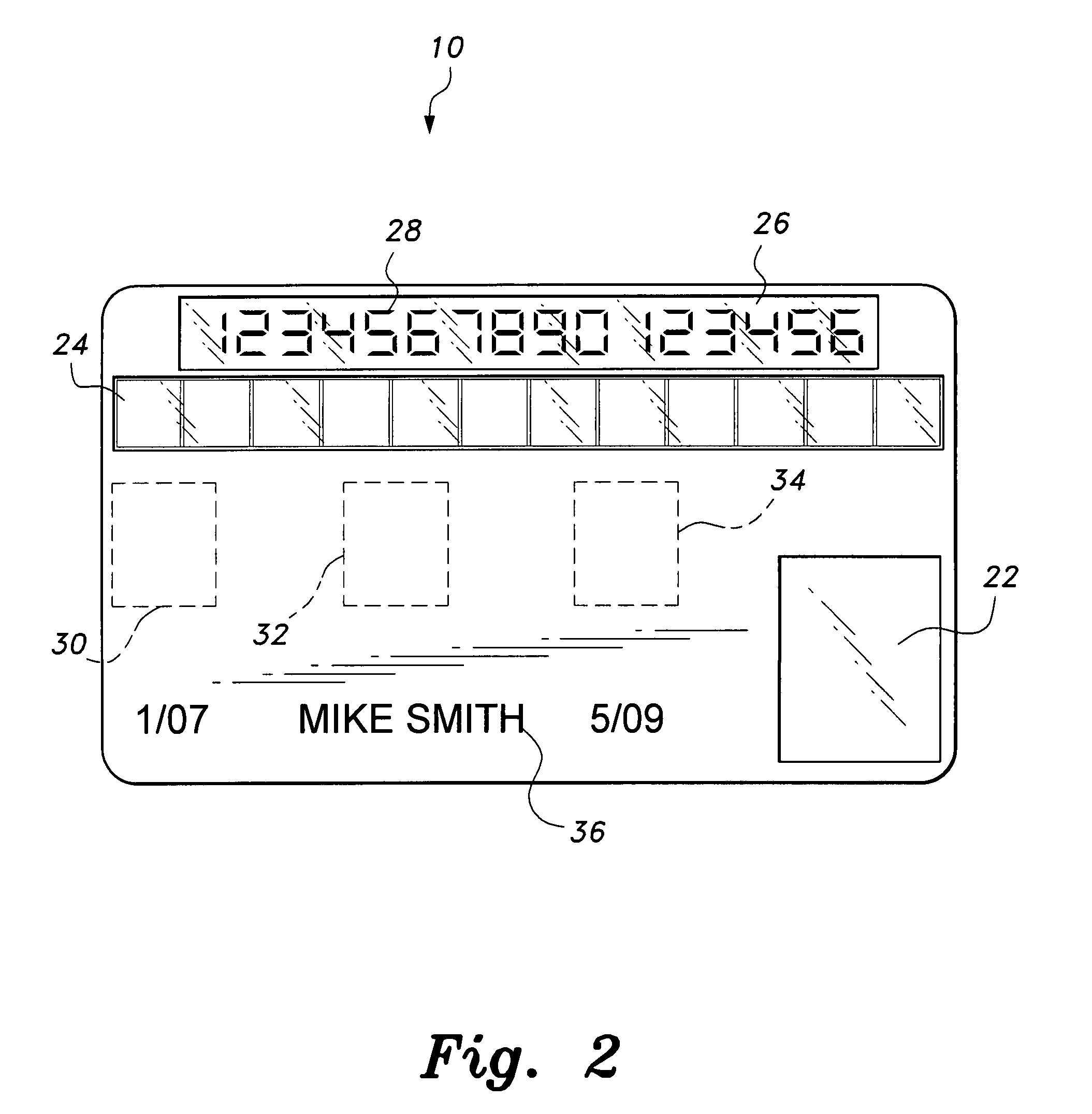
Smart card with random temporary account number generation
The smart card with random temporary account number generation provides an authenticating system coupled with an access or transaction card, such as a credit card. The card includes first and second memory storage media, with the first memory medium containing a plurality of temporary account or authentication numbers. The card also has a biometric sensor, such as a fingerprint scanner, and the second memory stores the biometric parameters of the authorized user. A processor compares the biometric parameters with the measured biometric readings to enable the card. The processor has a random number generator, allowing for the randomized selection of one of the account numbers stored in the first memory, thus providing a temporary account number for the transaction. A remote site includes an identical random number generator and set of account numbers, allowing the temporary account number to be verified and then discarded, following the transaction.
Owner:HEWTON ALFRED
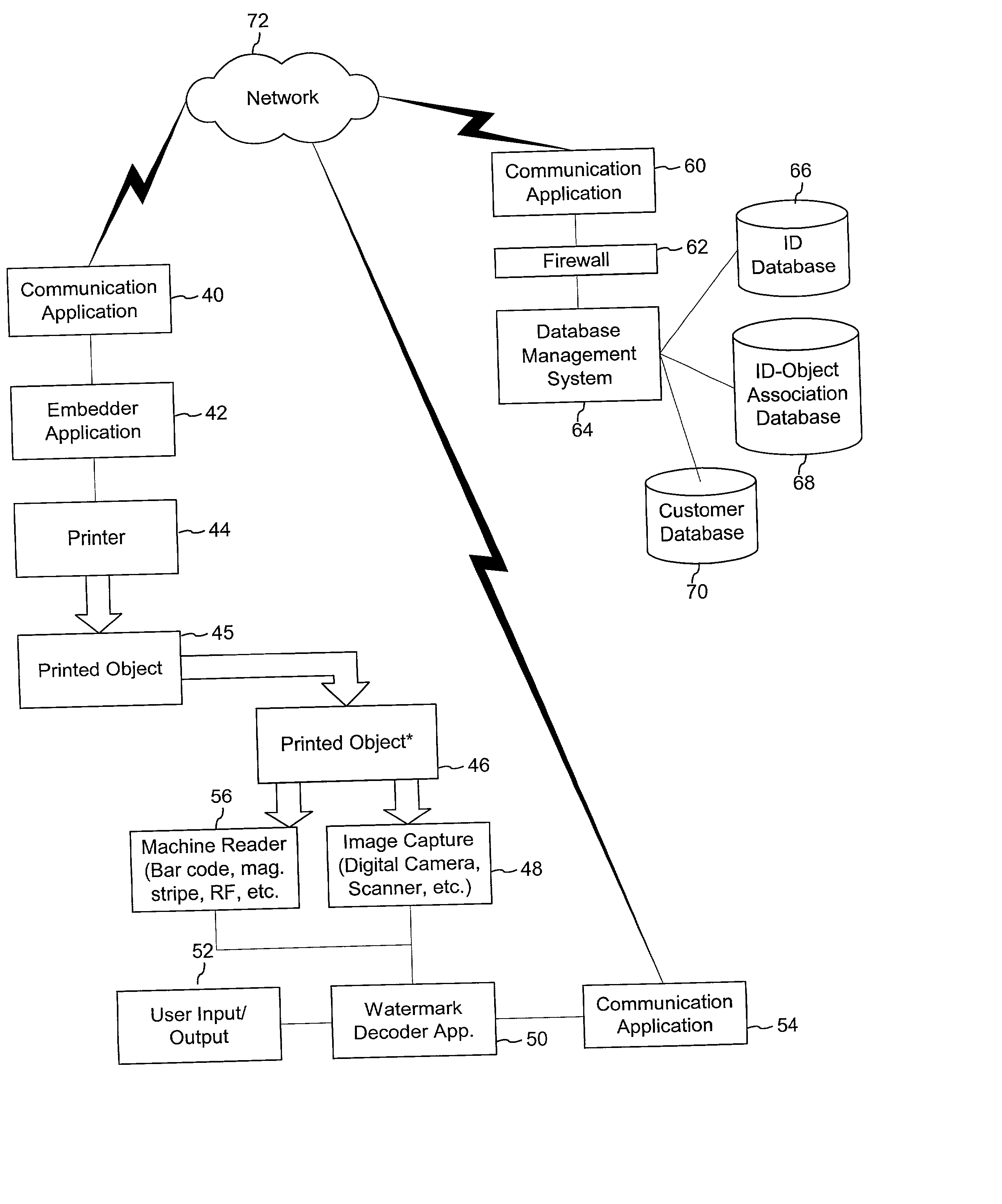
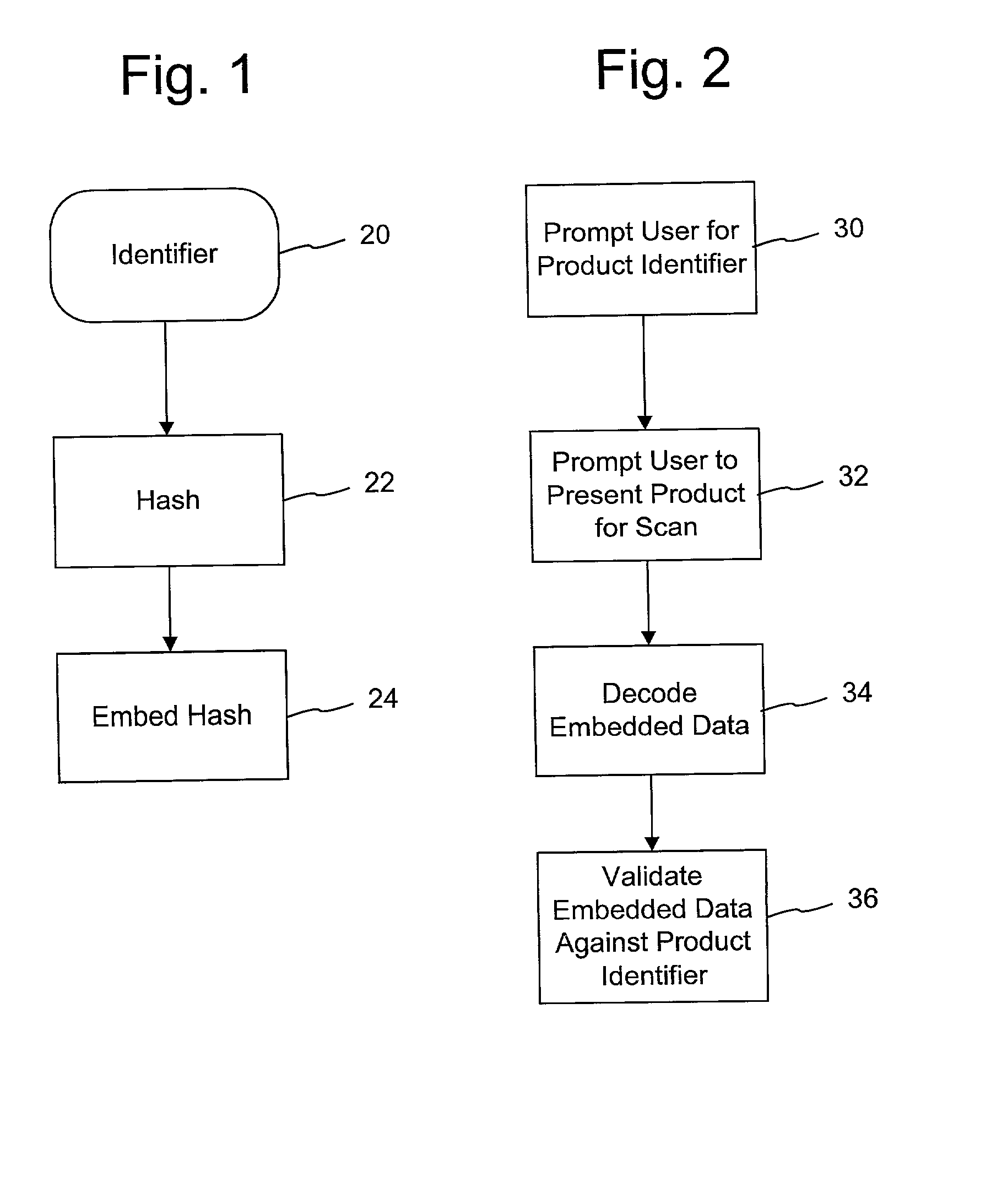
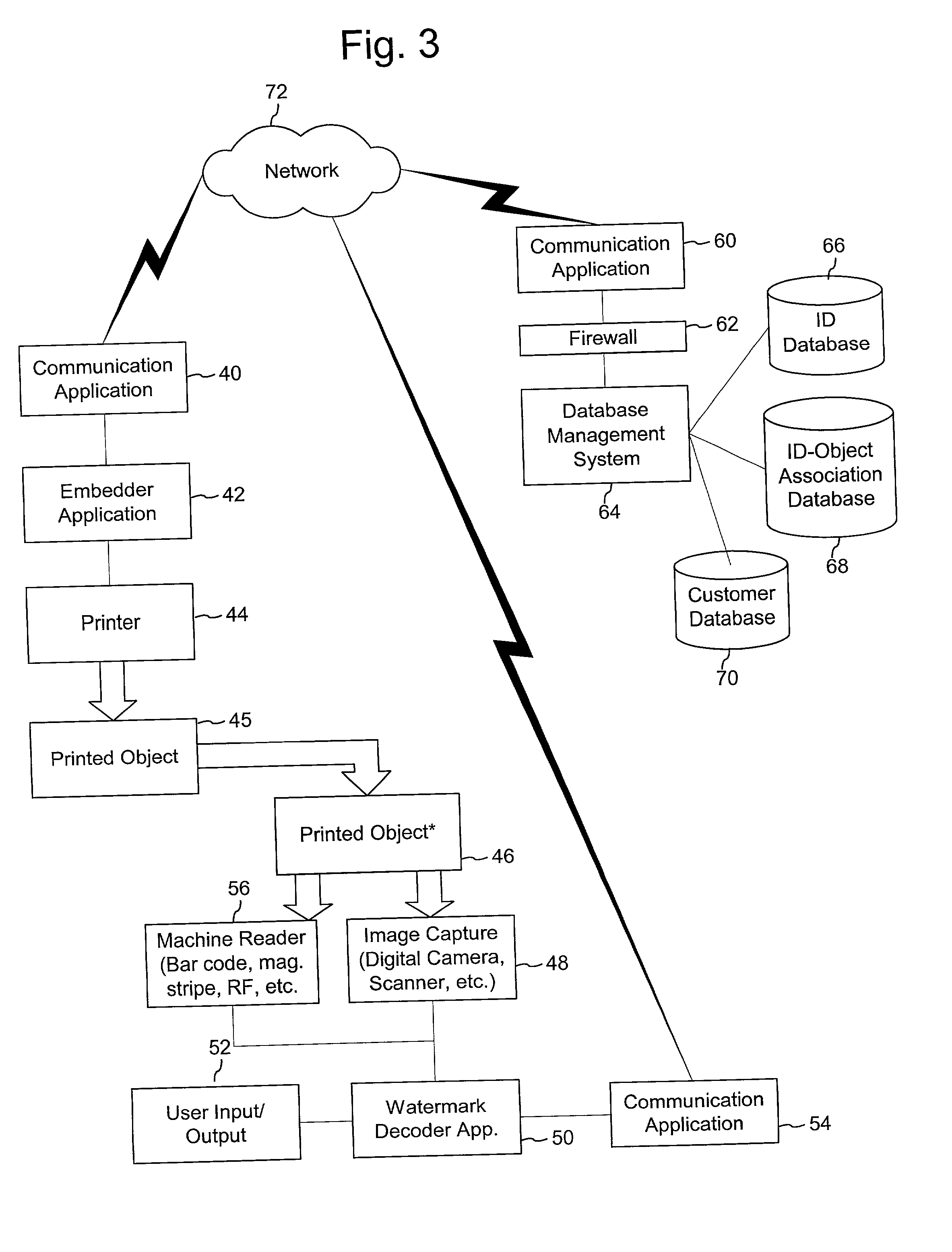
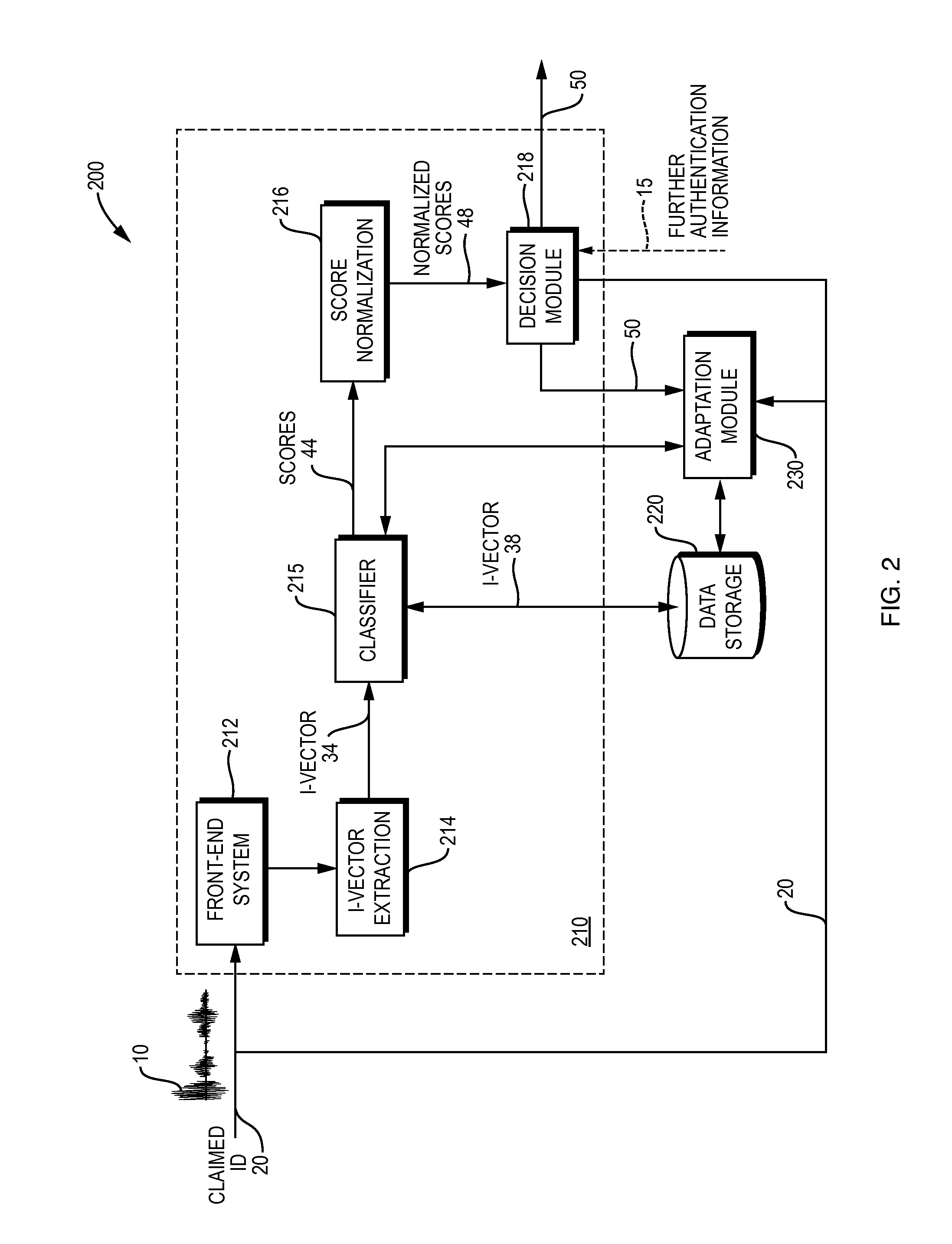
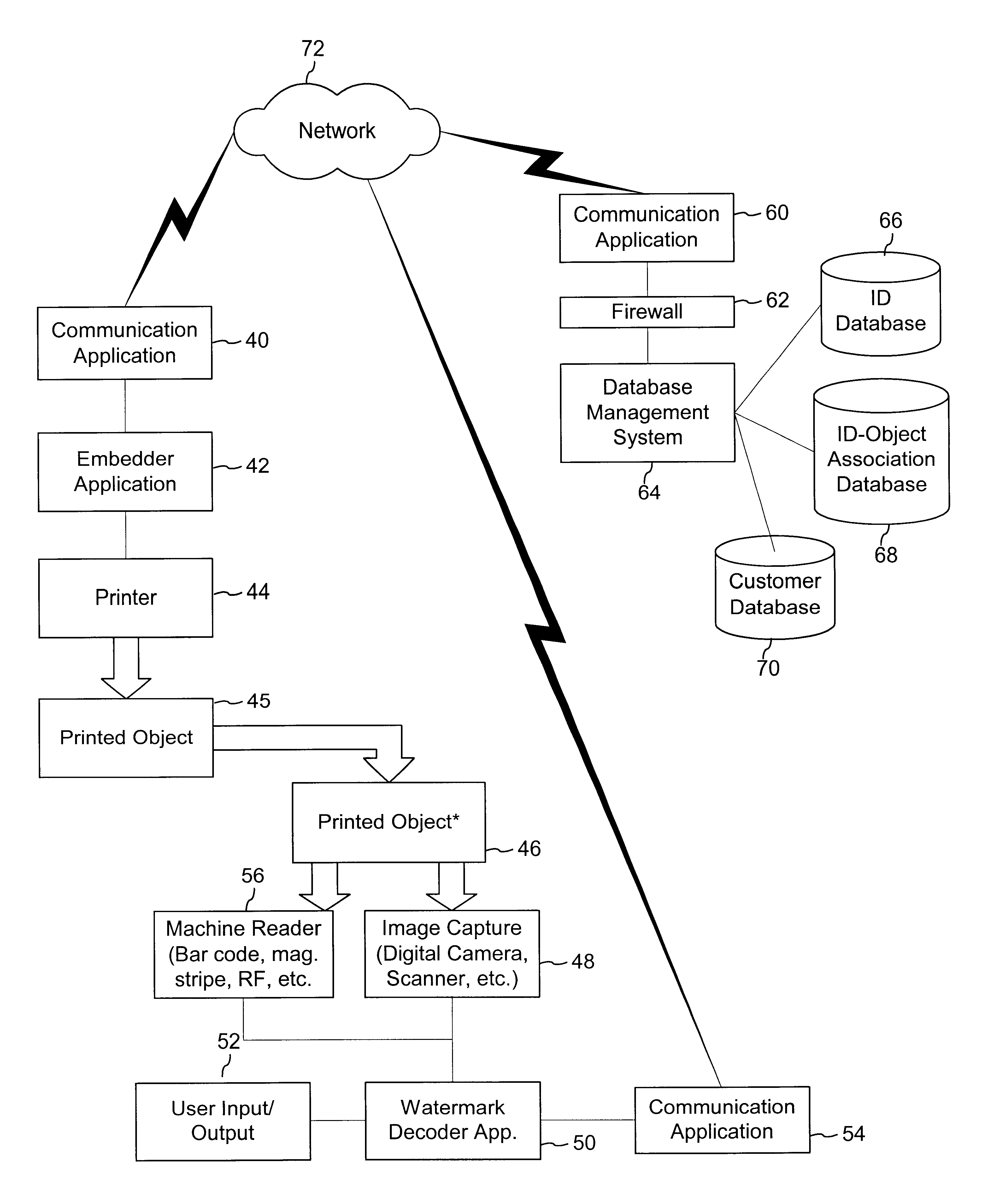
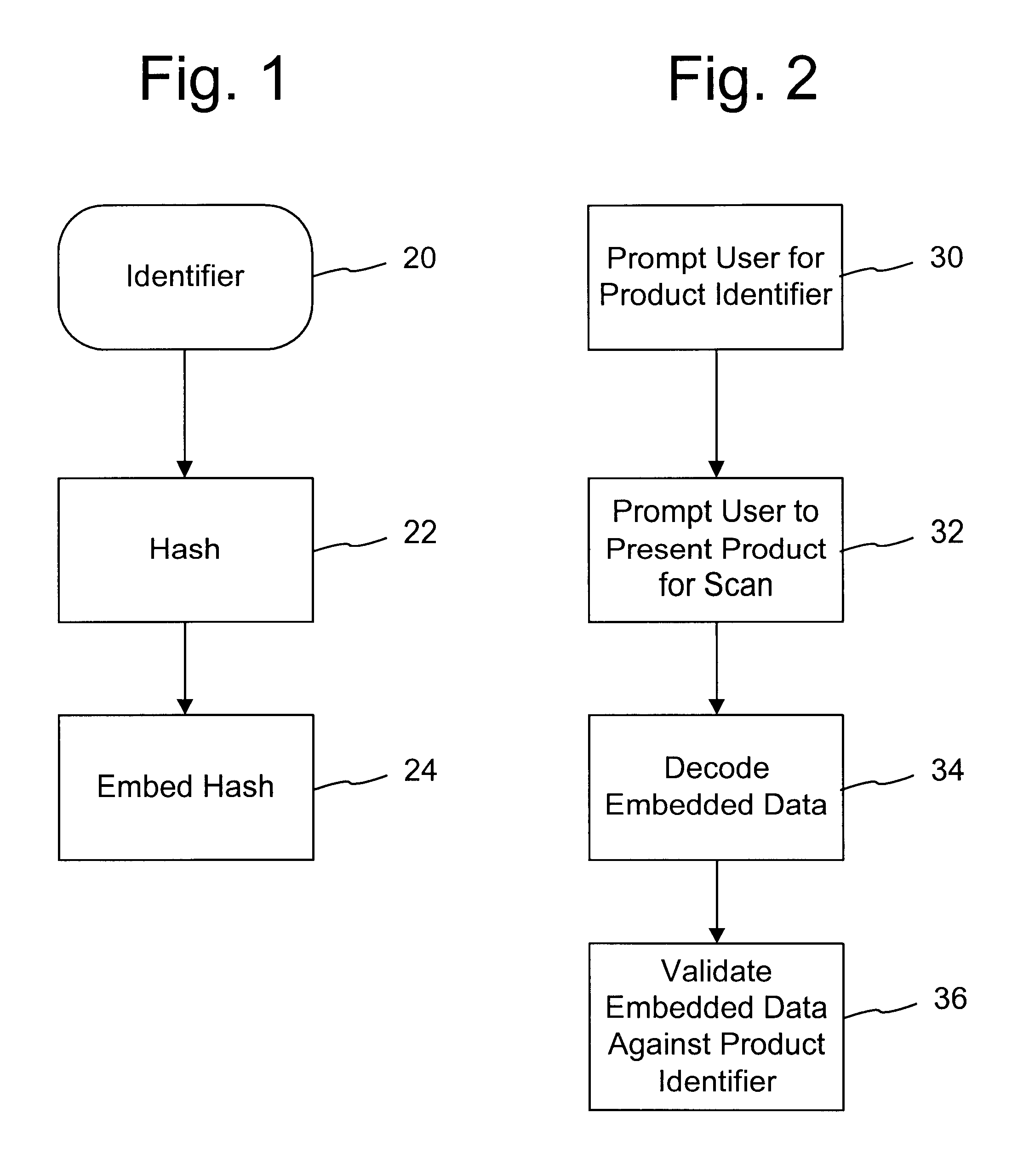
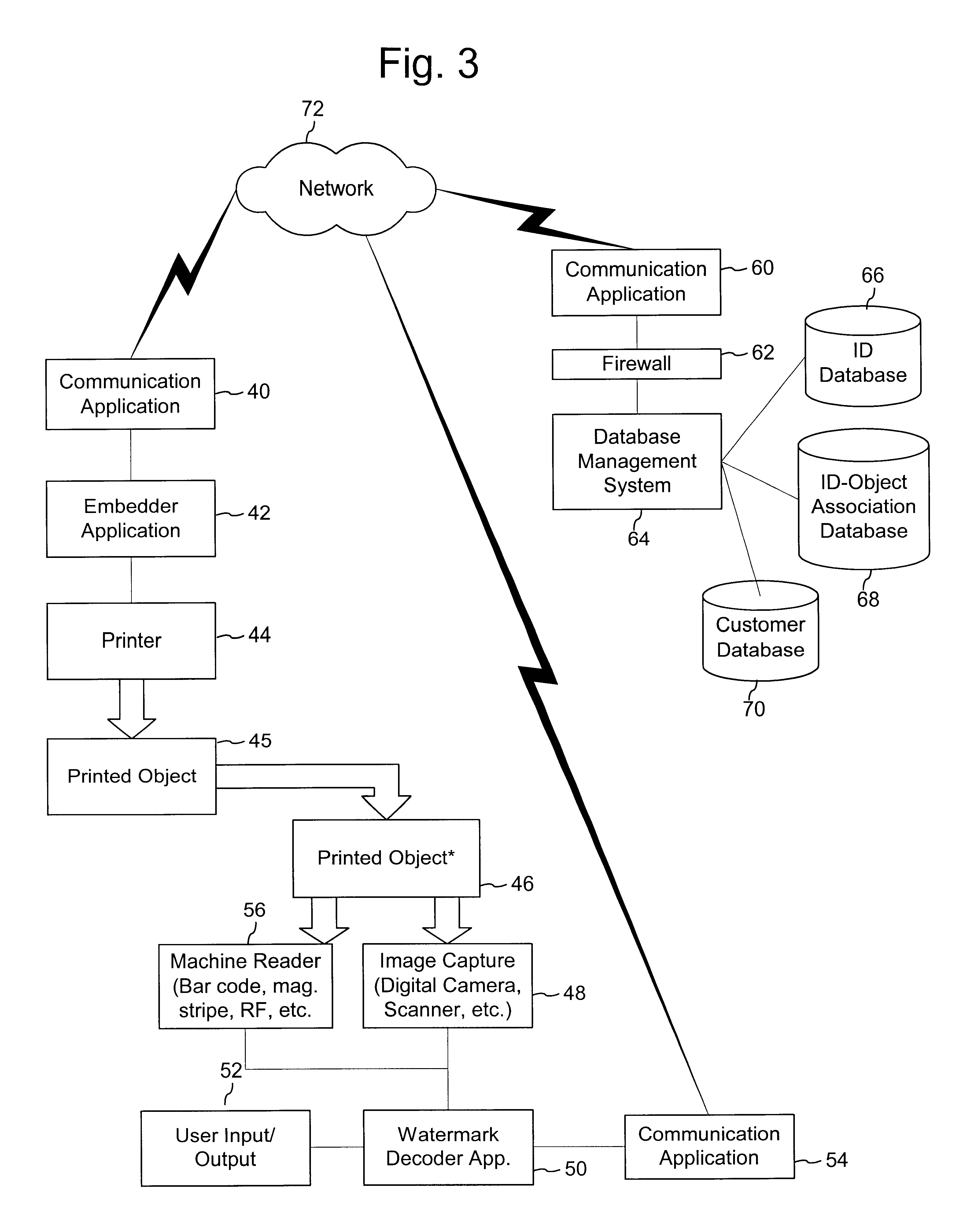
Authentication watermarks for printed objects and related applications
InactiveUS20020012445A1Correct Geometric DistortionMore dataOther printing matterPaper-money testing devicesRelevant informationCopy detection
The disclosure describes systems for creating and authenticating printed objects using authentication and copy detection watermarks. For example, one verification system includes a watermark decoder and a verification module. The watermark decoder detects a copy detection watermark in a printed object to determine whether the printed object has been reproduced. The verification module processes a message decoded from an authentication watermark on the printed object to authenticate the printed object or bearer of the printed object. The authentication and copy detection watermarks may be implemented as the same or different watermarks. For example, the copy detection watermark may be a fragile watermark that carries the message and that degrades in response to a reproduction operation, such as photocopying or scanning and then reprinting the object. Alternatively, the authentication and copy detection watermarks may be separate watermarks embedded in an image that is printed on the object. The authentication watermark, in some applications, includes an identifier that links the object to a database entry with related information about the object. This related information can be used to check the bearer of the object by comparing it with attributes of the bearer (such as a user ID or photo) or the validity of the object by comparing it with attributes that are visible or machine readable on the object.
Owner:INTUIT INC
Method and system for delivering encrypted content with associated geographical-based advertisements
A method, a system and computer readable medium at an electronic digital content store, such as a web site, for associating advertisement with digital content. The geographic location of the end user device receiving the encrypted digital content is determined using an address verification system. Advertisement is selected to be associated with the delivery of encrypted digital content if the address verification system returns an address in a predetermined geographic region. The address verification system includes the IP address of the end user device, the country codes found in the trace routes to the IP address, and the billing address.
Owner:LEVEL 3 COMM LLC
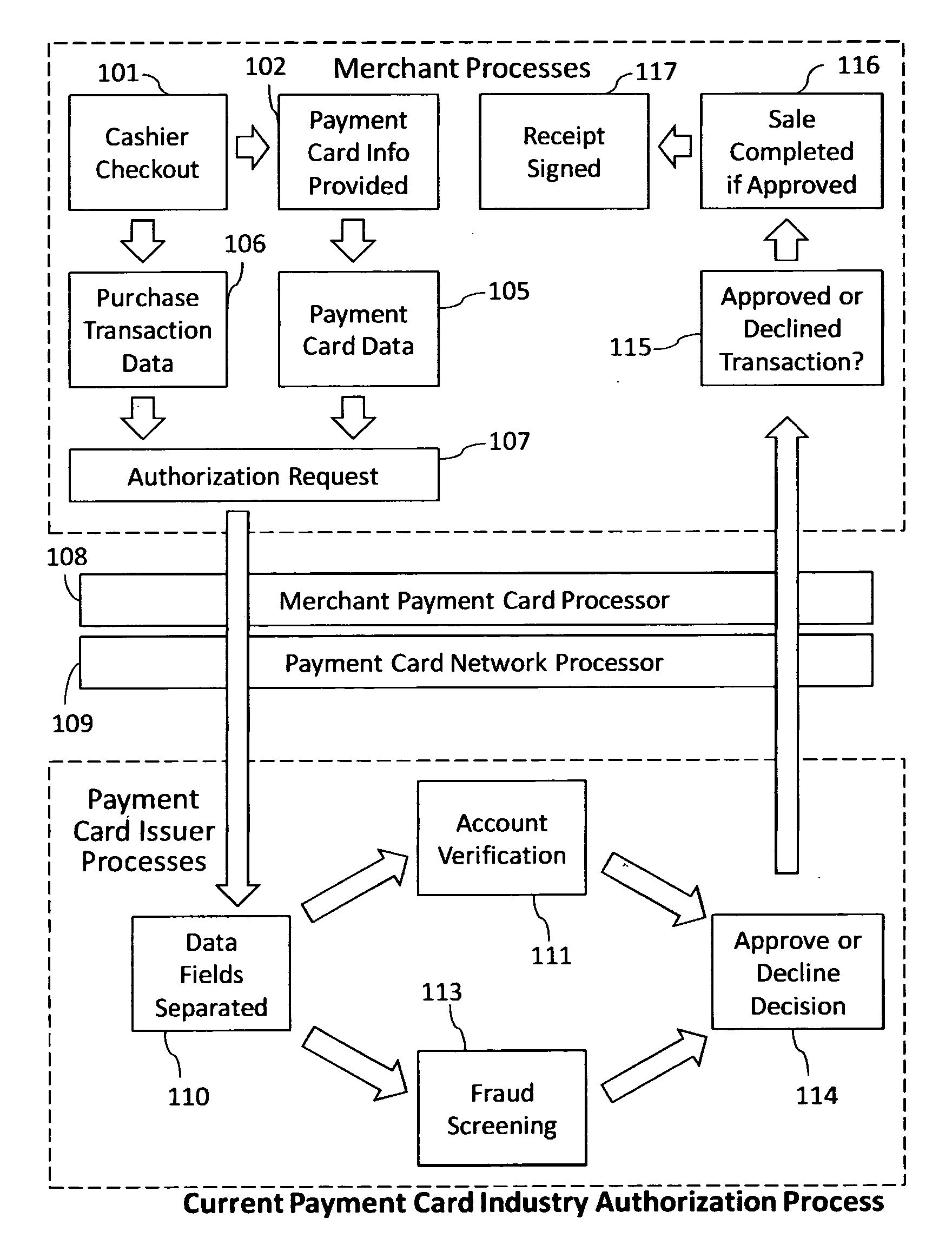
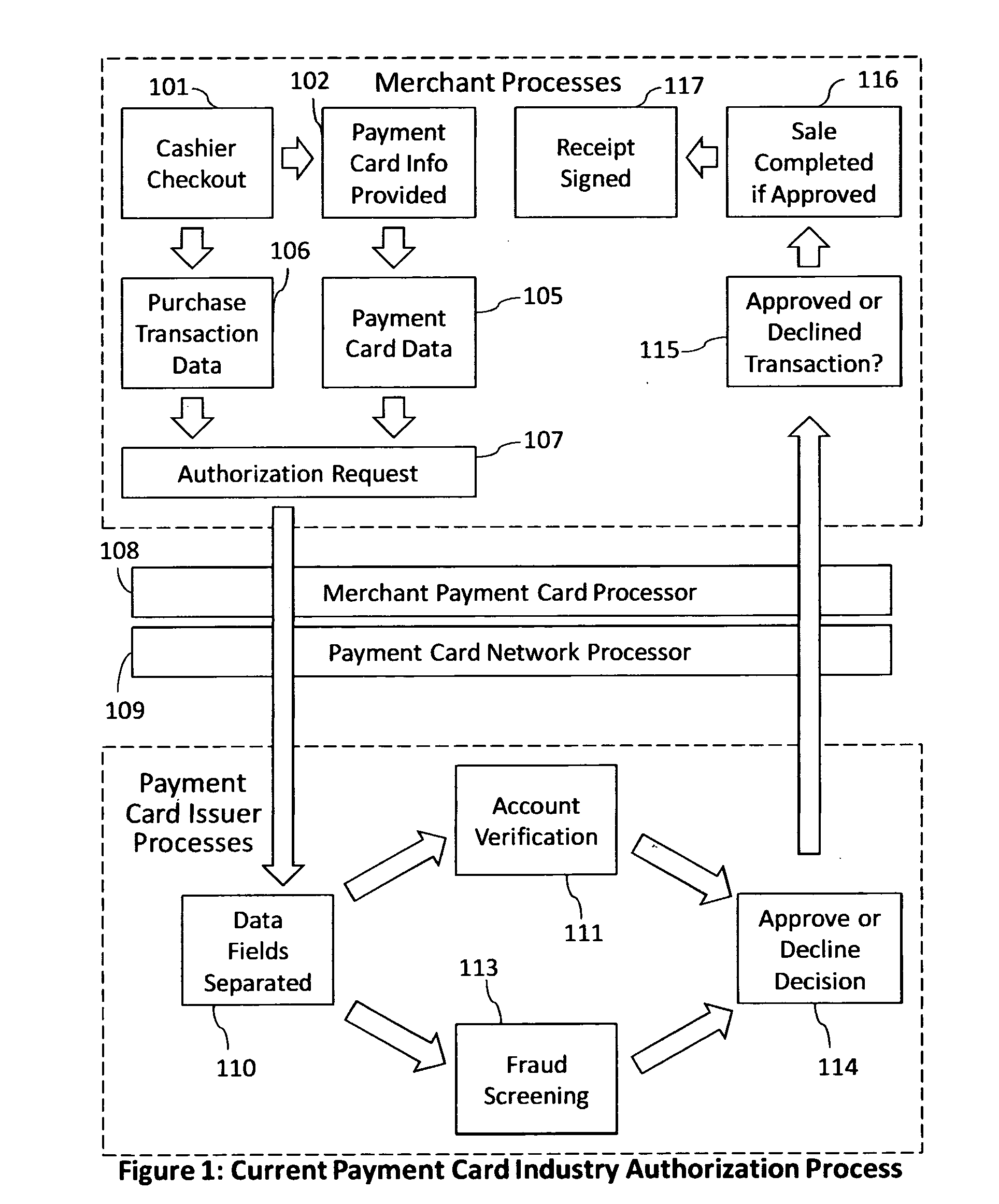
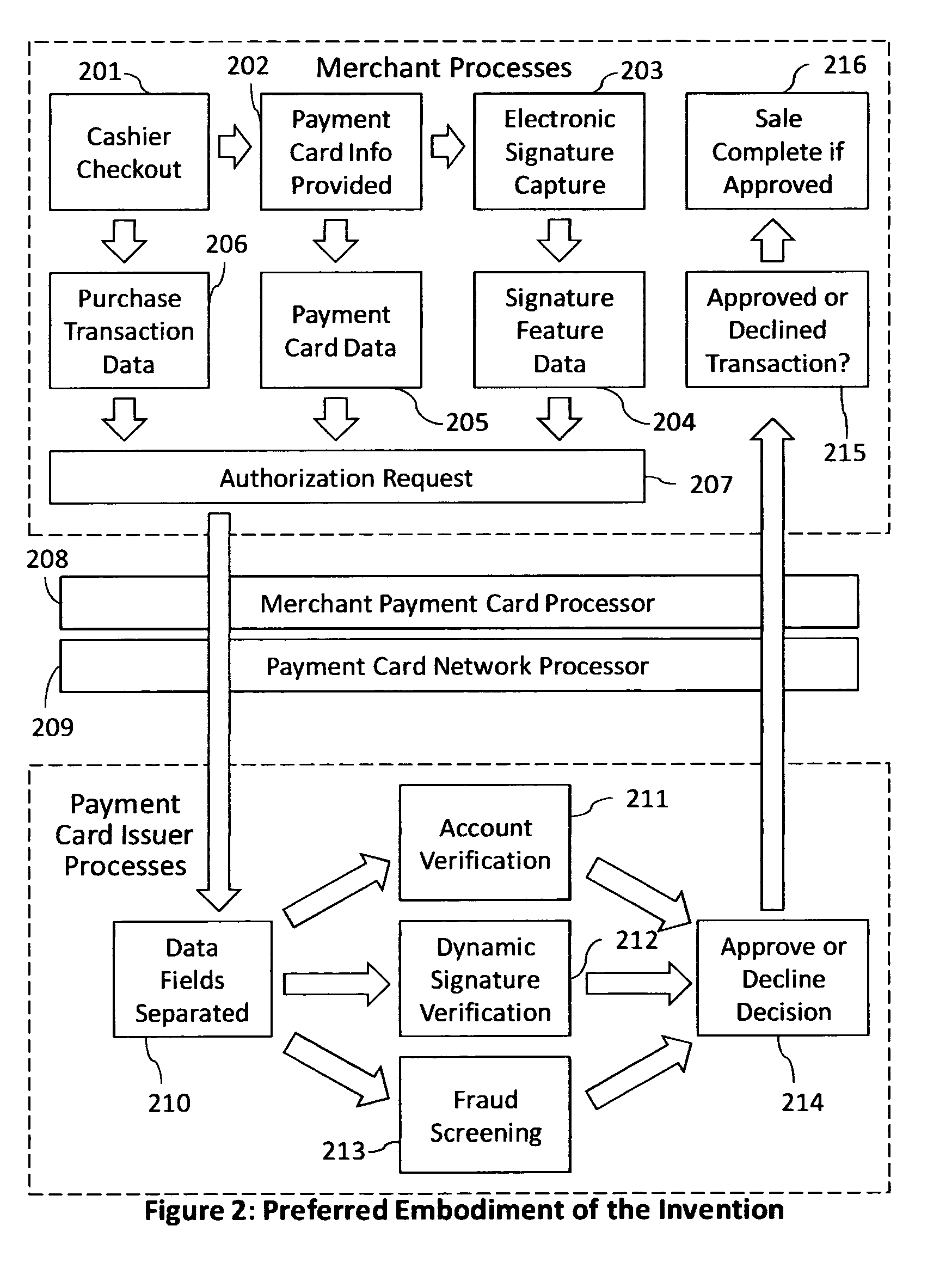
Reduction of transaction fraud through the use of automatic centralized signature/sign verification combined with credit and fraud scoring during real-time payment card authorization processes
InactiveUS20110238510A1Reduce payment card industry fraud lossReduce the amount of dataFinanceCharacter and pattern recognitionDigital signatureIdentity theft
A dynamic signature / sign biometric verification system for detecting and preventing fraudulent transactions is described. The system comprises remote digital signature / sign input devices, a means to extract spatial and temporal features from the signature, a means to transmit the signature / sign features along with customer identifier information to a centralized signature / sign verification authority, a means for combining signature / sign feature verification with other forms of fraud detection technology, and a means for transmitting the results of a signature / sign verification back to the remote location where the signature / sign was captured. The system was primarily developed for use in payment card industries (e.g. credit cards, debit cards) but has applicability to other centralized signature / sign verification applications such as Automated Teller Machine authorizations and other identity theft detection and monitoring services.
Owner:BIOCRYPT ACCESS LLC
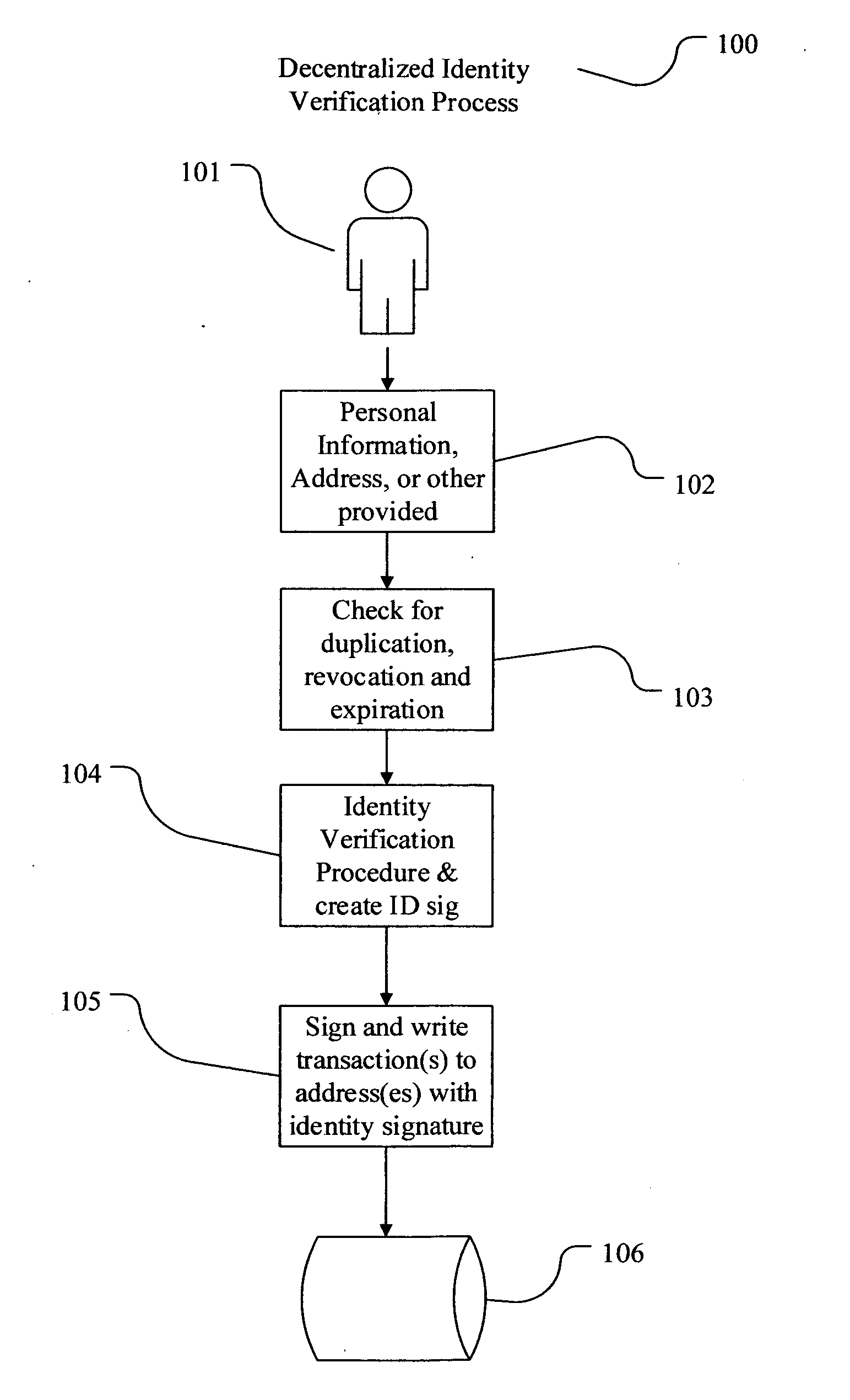
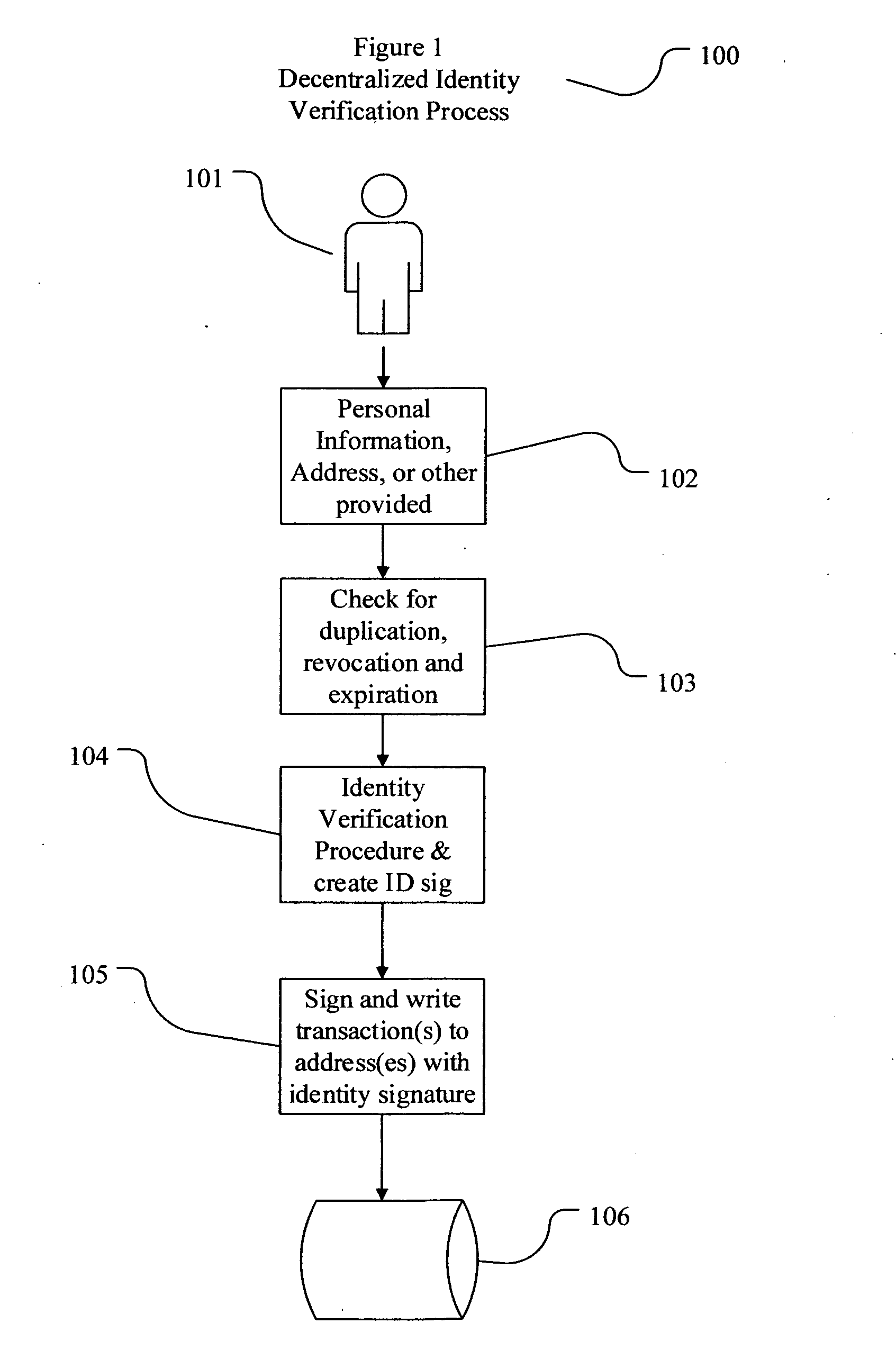
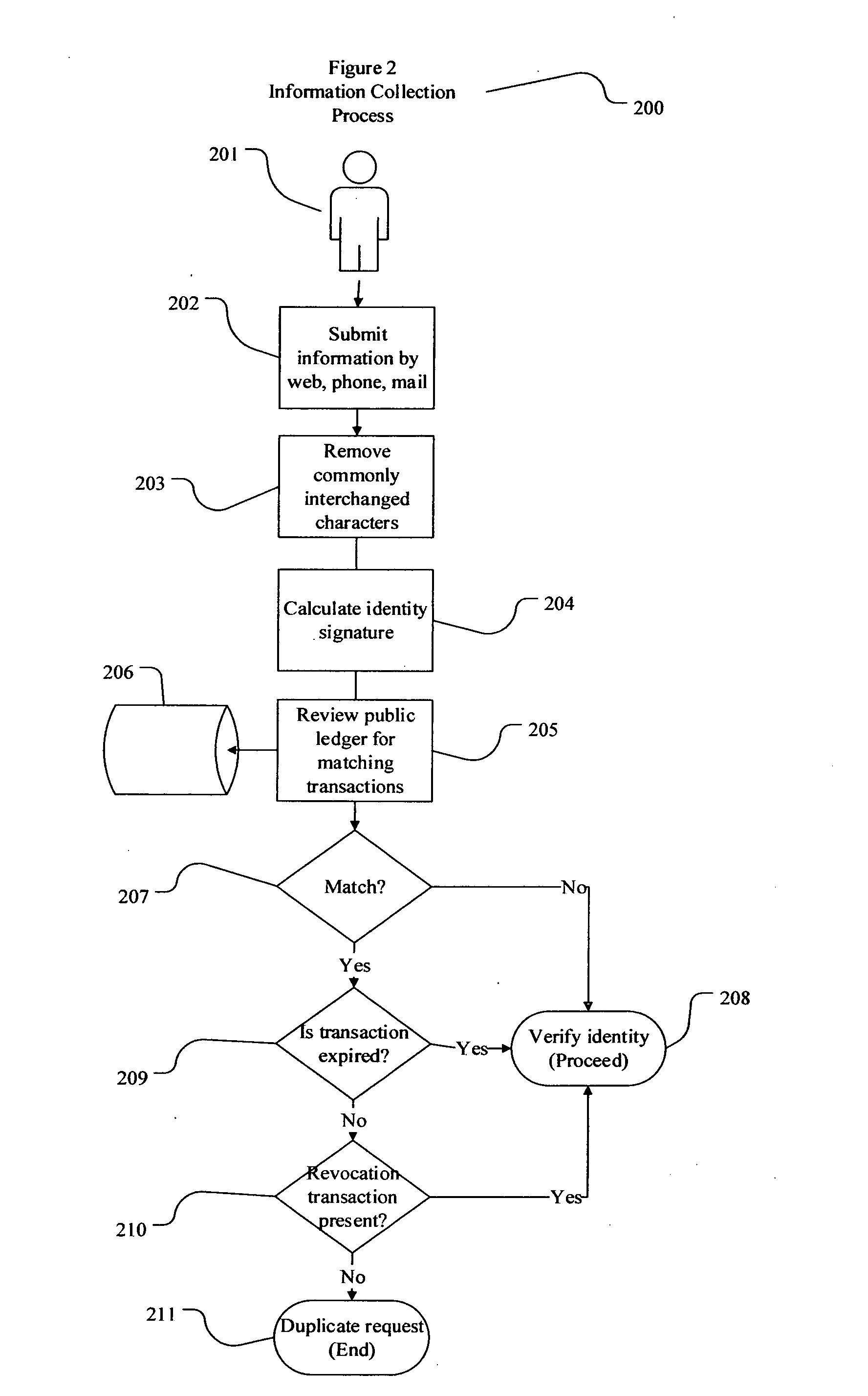
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
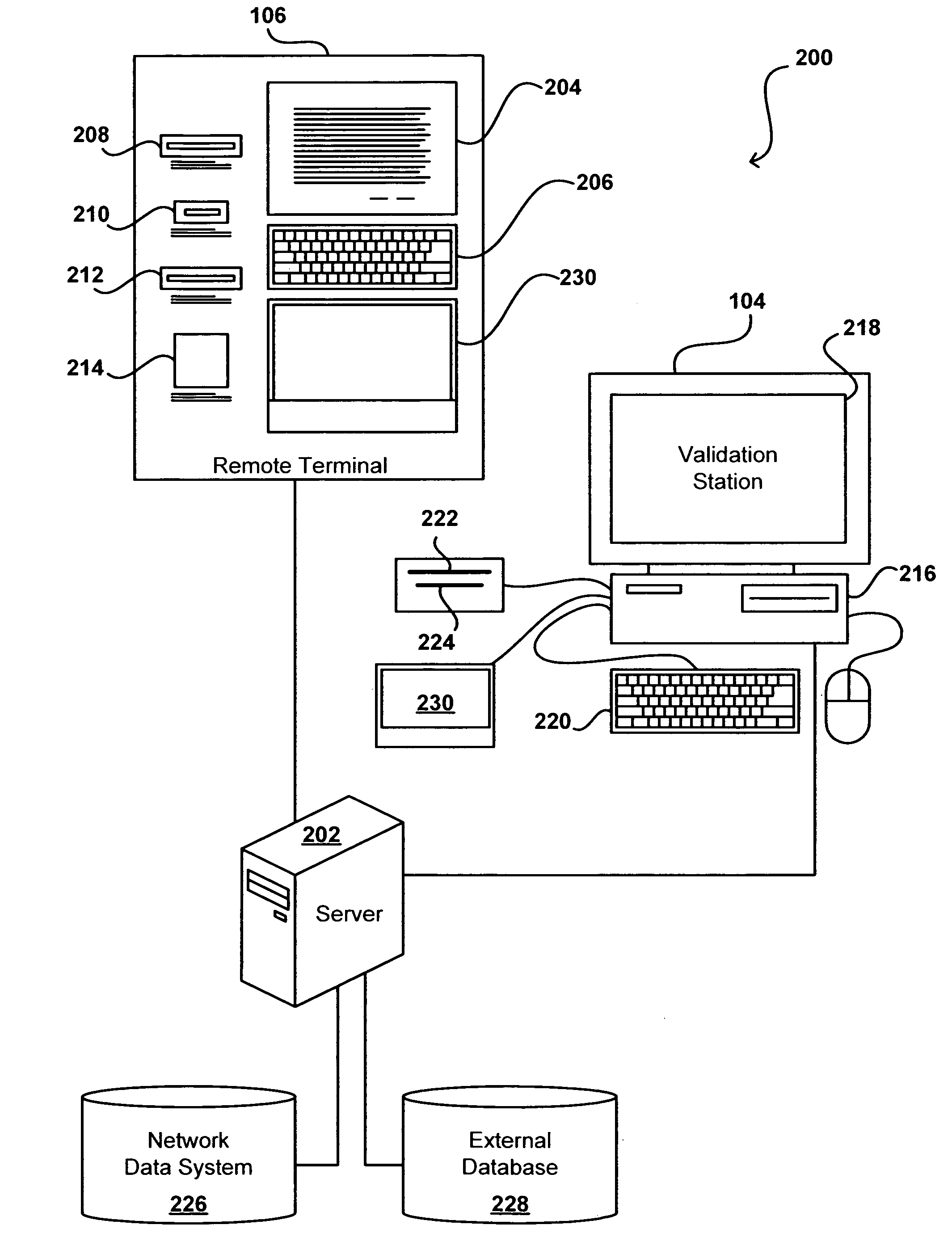
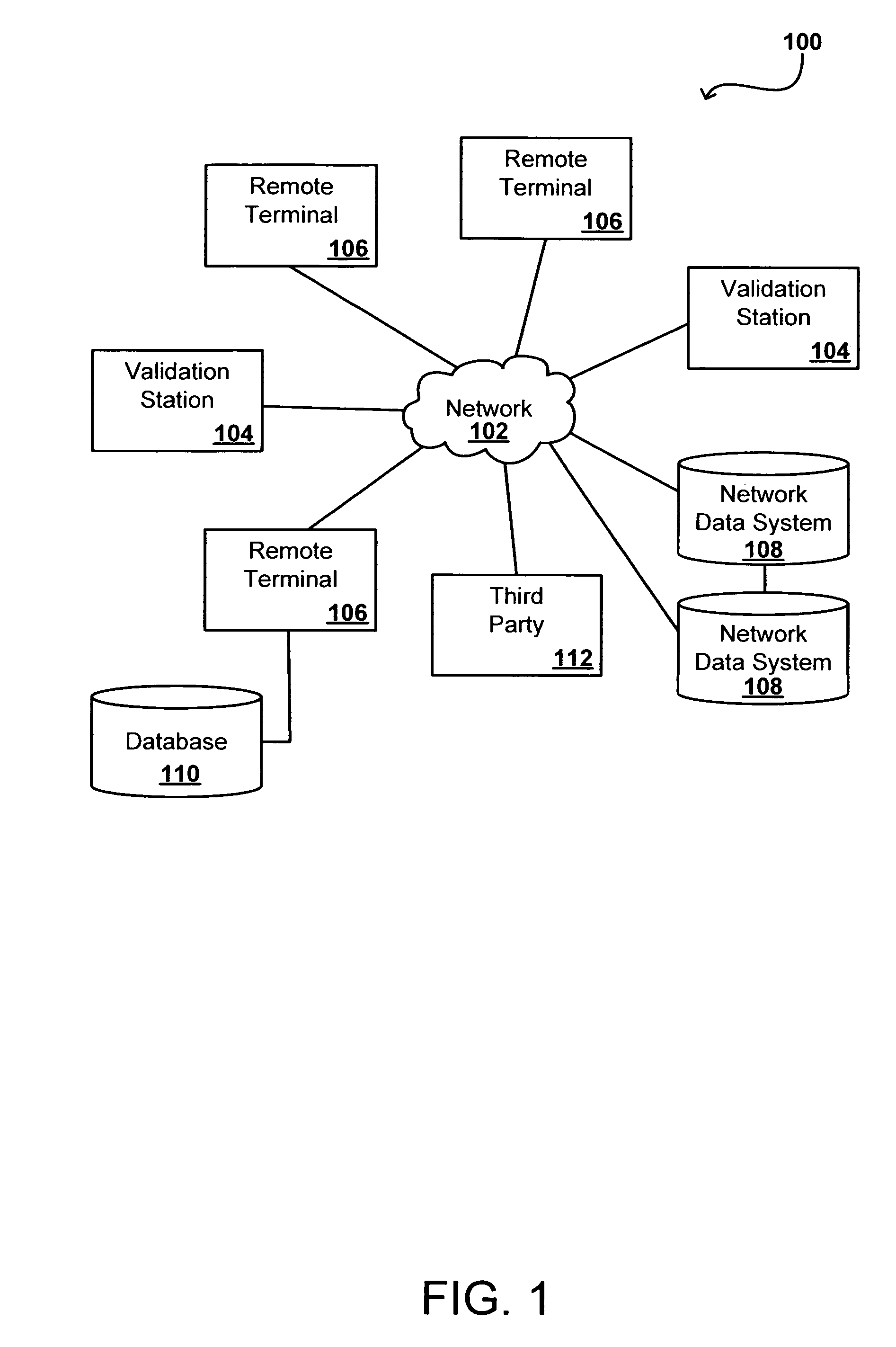
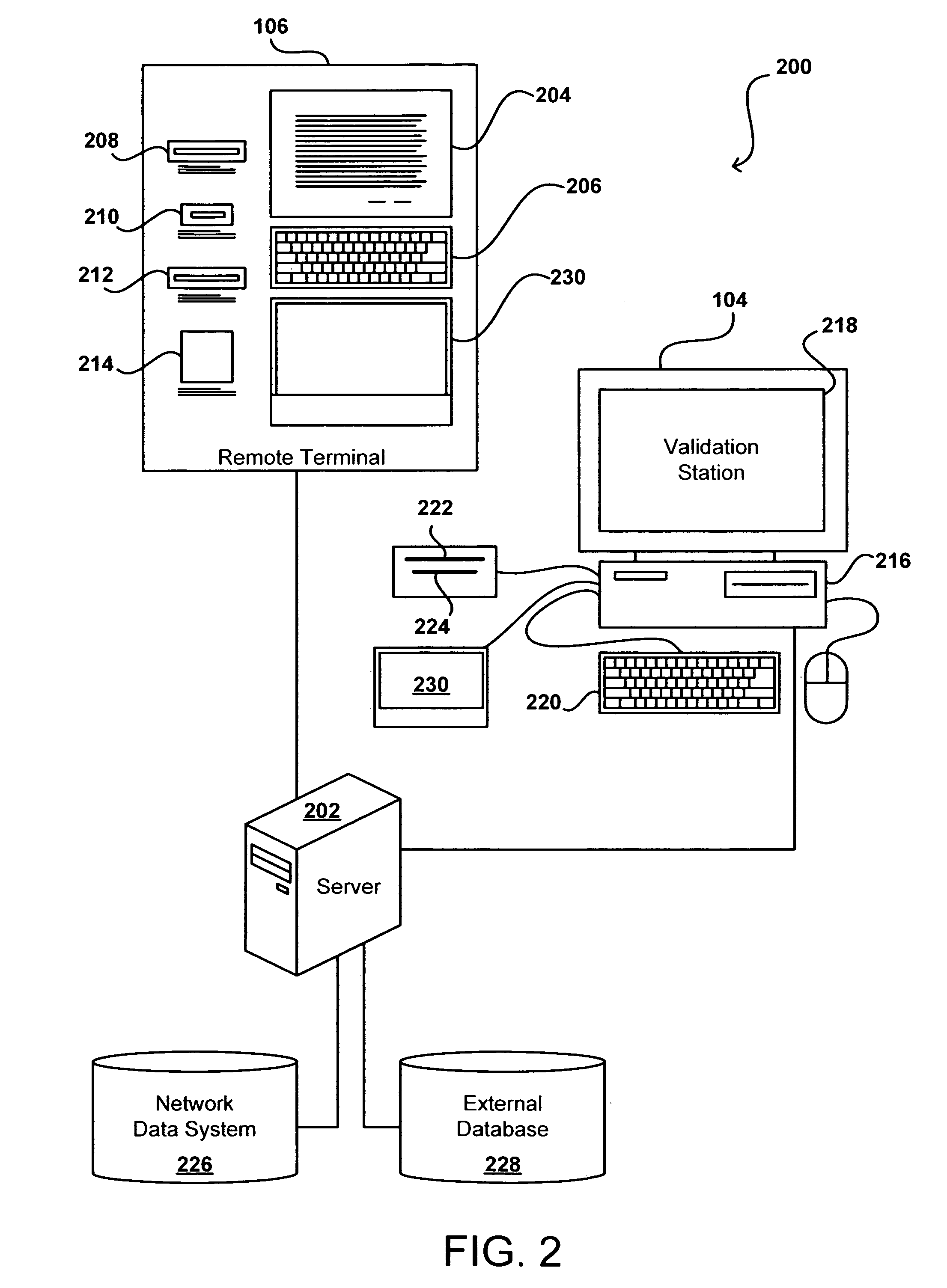
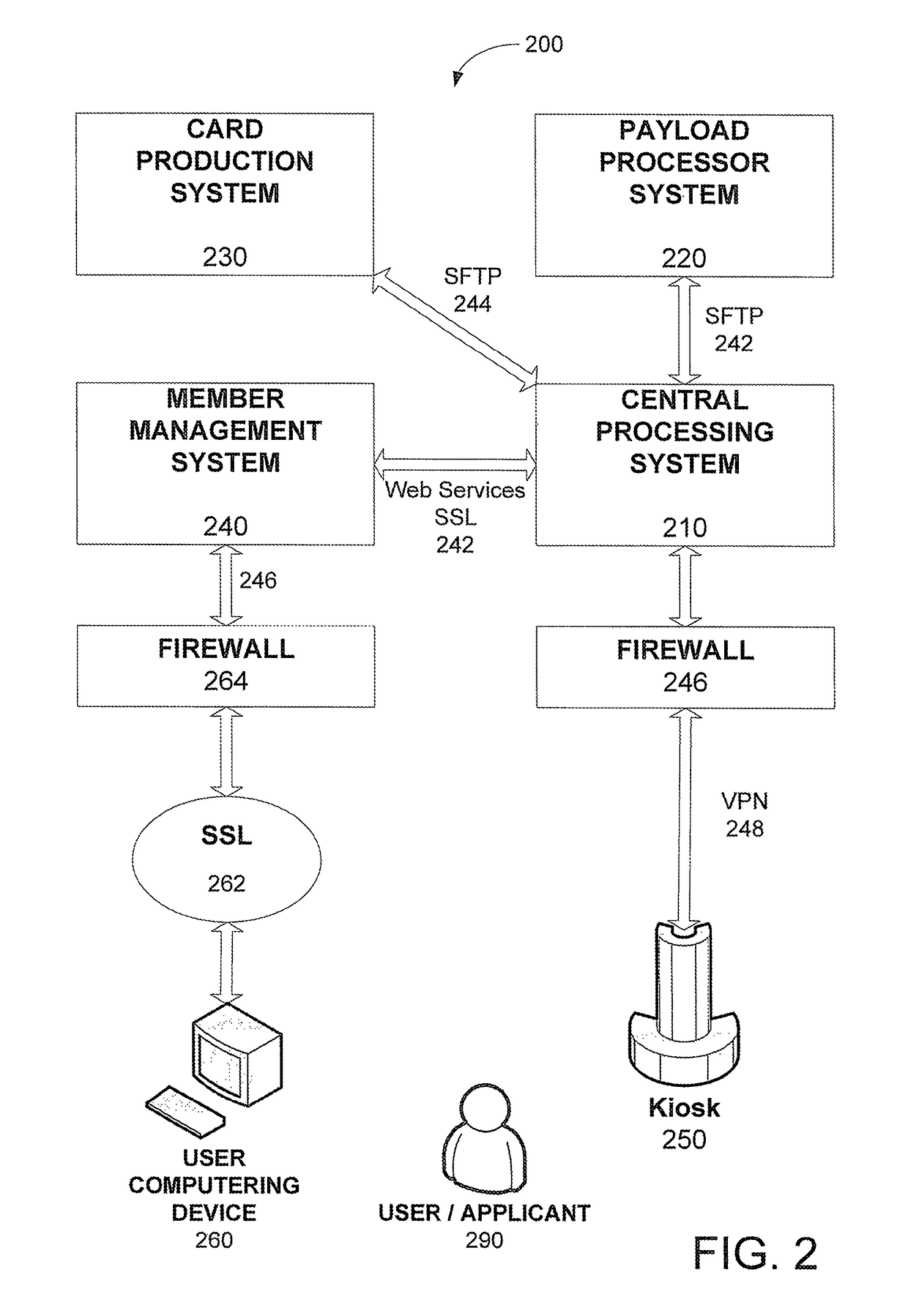
Remote validation system useful for financial transactions
A financial services and transaction network including multiple networked validation stations and remote terminals allows users to access a number of financial services and transactions. A user visiting a remote terminal indicates a desired service or transaction. The user provides any currency or funding information needed for the selected service, after which the remote terminal issues the user a transaction voucher. The user can take this transaction voucher to any of the validation stations in order to authenticate the user's identity and activate the voucher. Once the voucher is activated, the user or a recipient of the voucher can present the voucher at any remote terminal to receive funding or otherwise complete the transaction or service, subject to recipient authentication. The user provides necessary information using the remote terminal or validation station, or supplies the information using the voucher, which is collected upon performance of the requested service or transaction.
Owner:CUCINOTTA ROBERT
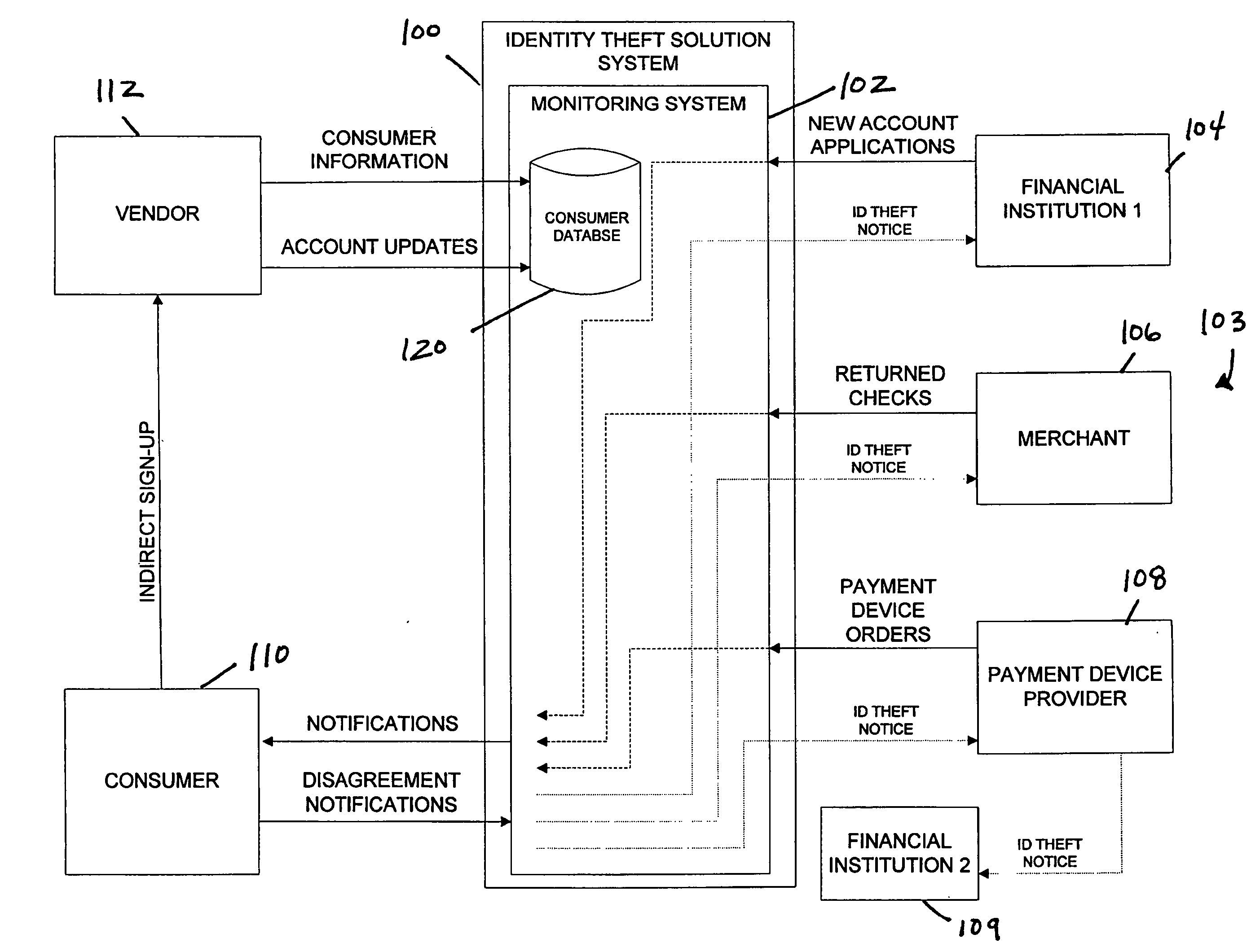
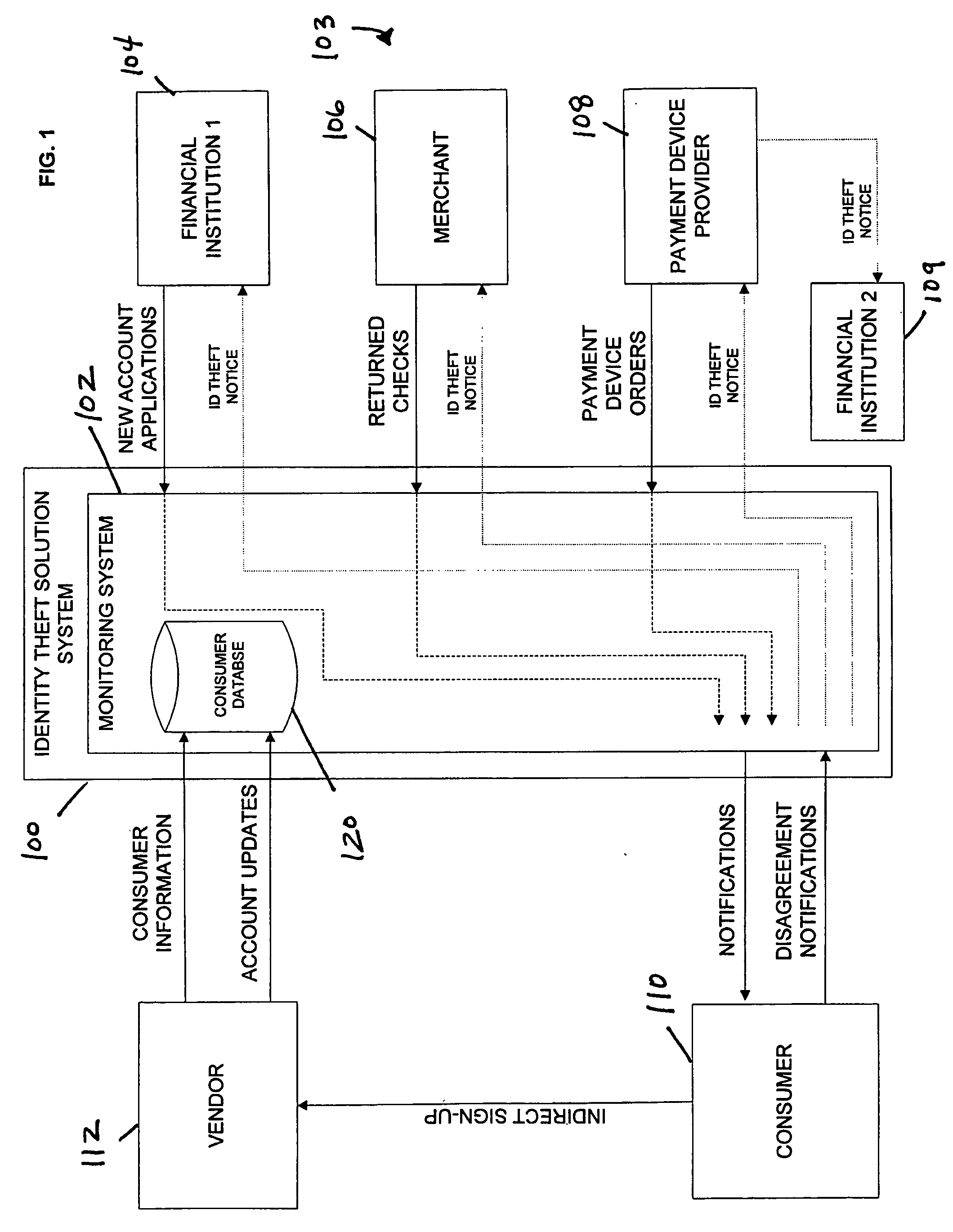
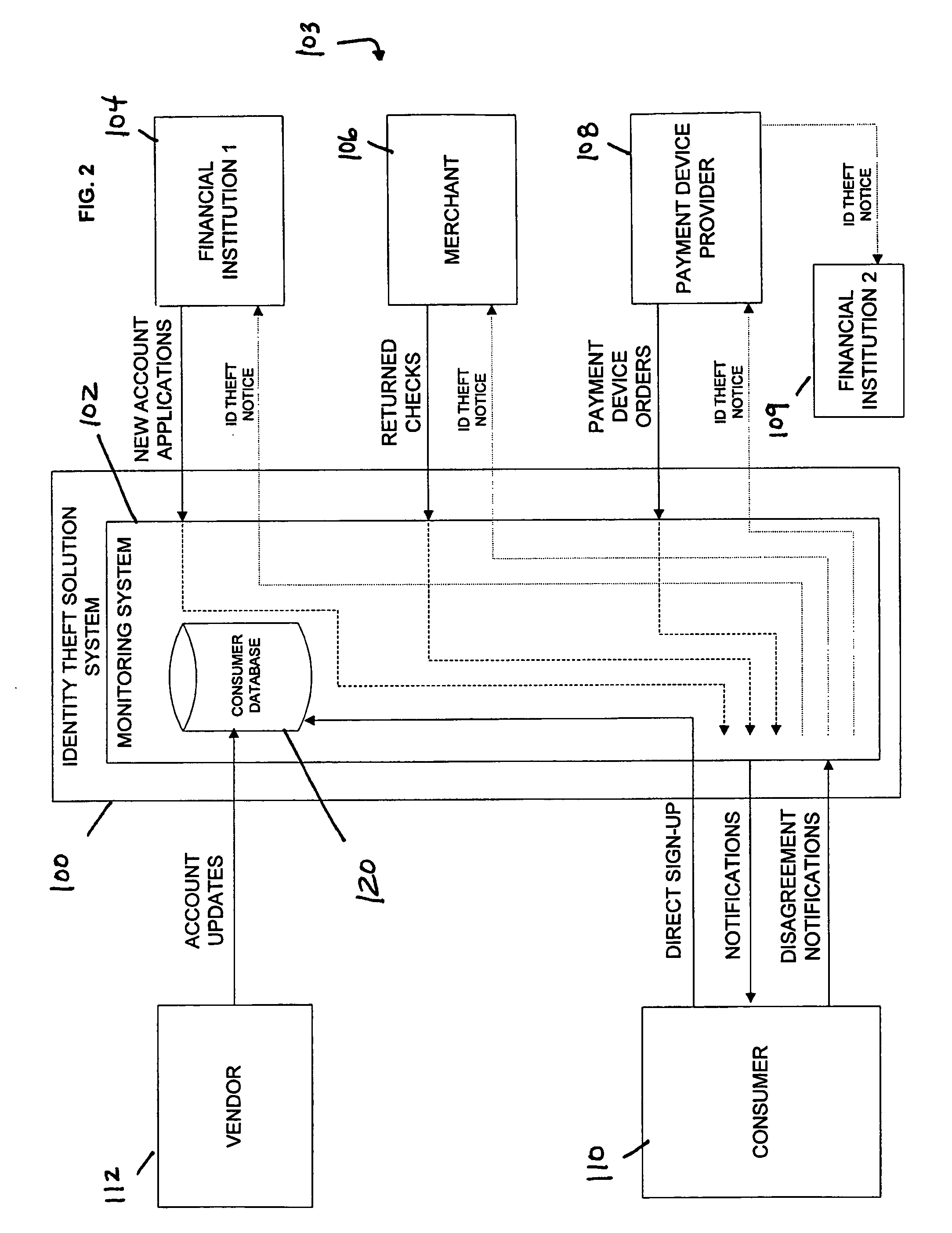
Identity theft monitoring and prevention
InactiveUS20060271457A1Prevent and limit potential financialPrevent and limit and reputation lossFinanceSecret communicationIdentity theftSystem configuration
Systems and methods of monitoring financial information of a consumer for fraudulent activity. One system can include an identity verification system configured to verify an identity of a consumer. The system can include a new account identity theft detection system configured to determine a first score for a new account application submitted by the consumer, the first score indicating likelihood that the new account application is fraudulent, and an address analyzer configured to determine a second score for an address modification submitted by the consumer, the second score indicating likelihood that the address modification is fraudulent.
Owner:EFUNDS CORP
System and method for user enrollment in a secure biometric verification system
ActiveUS9721078B2User identity/authority verificationDigital data authenticationBiometric dataVerification system
Owner:ALCLEAR LLC
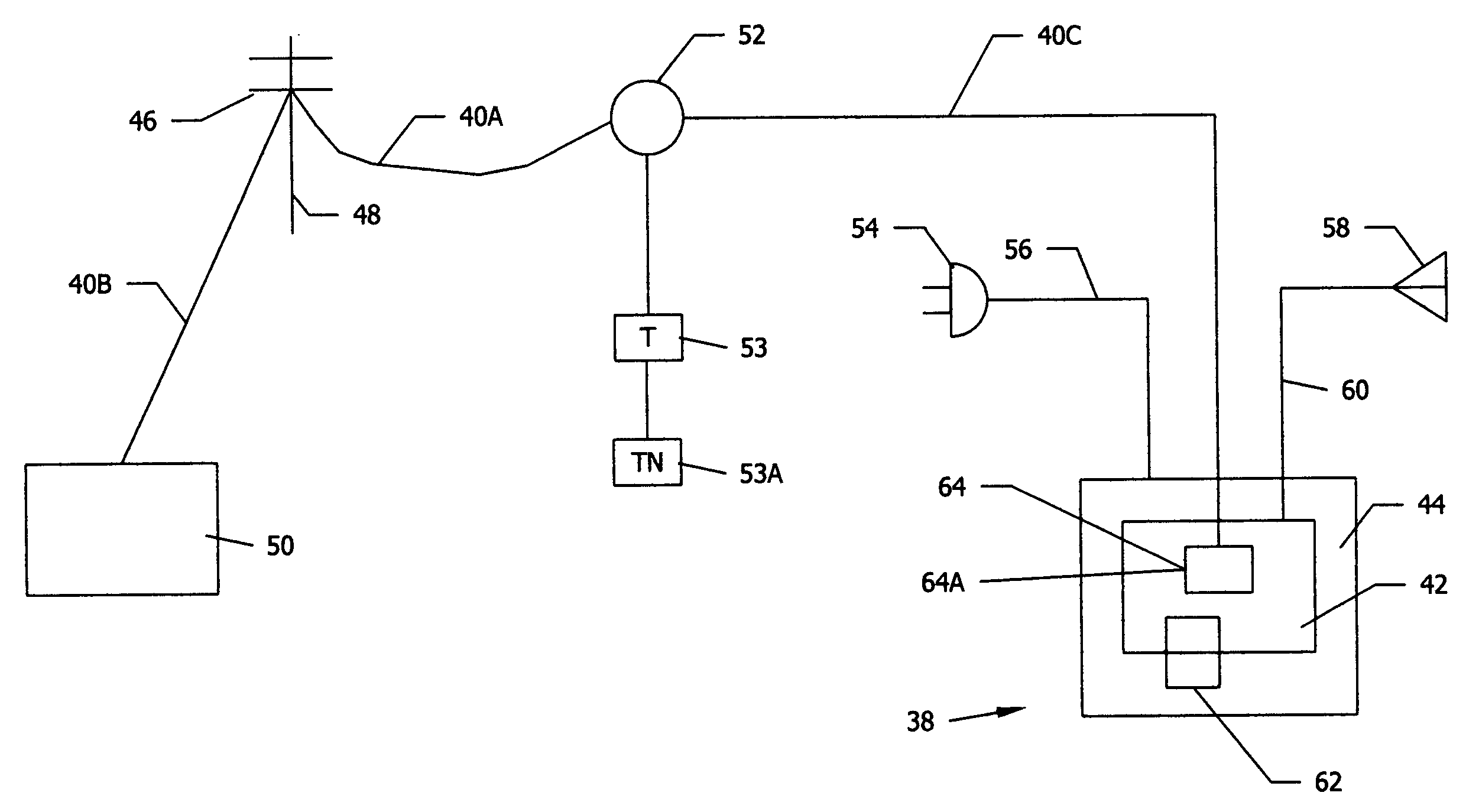
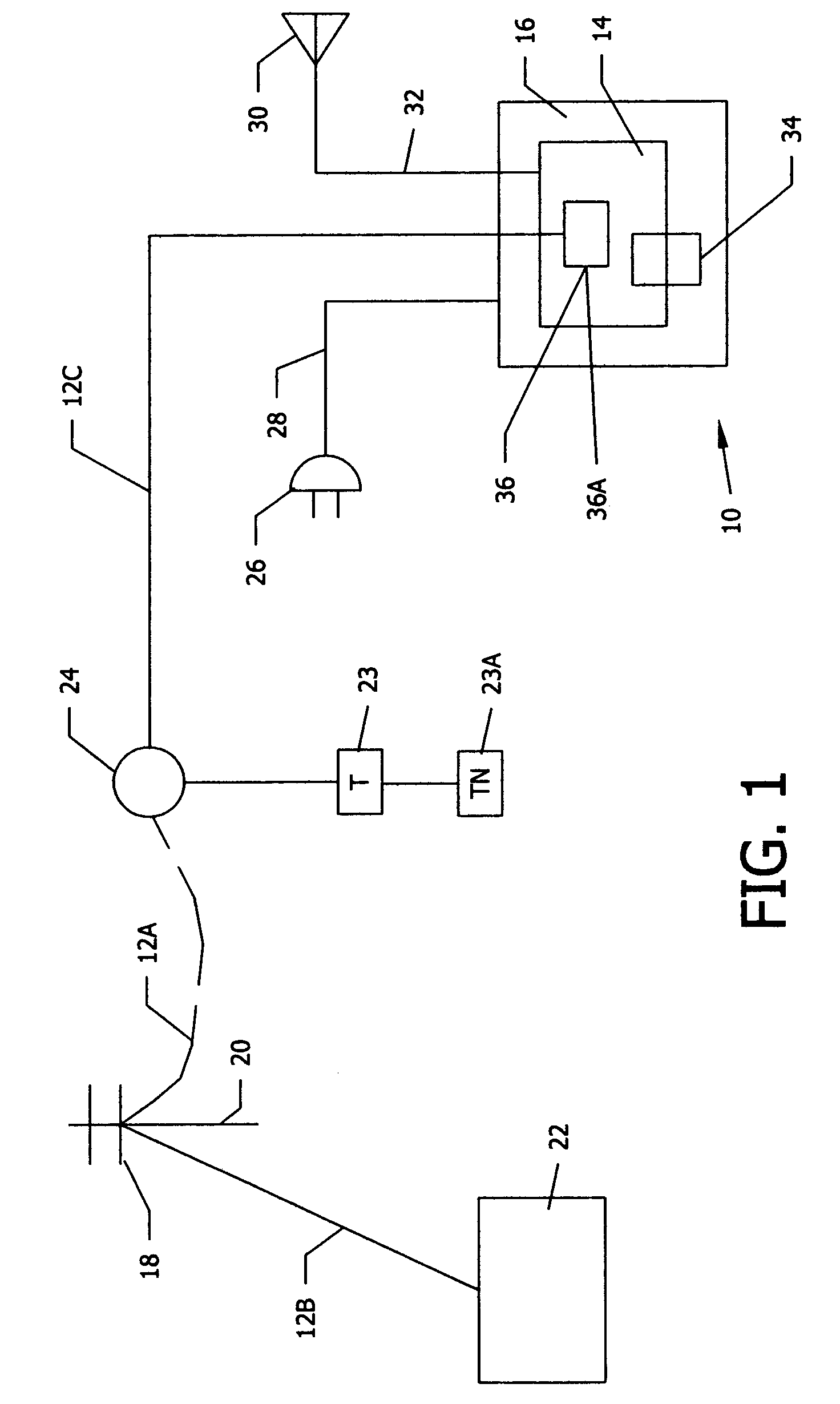
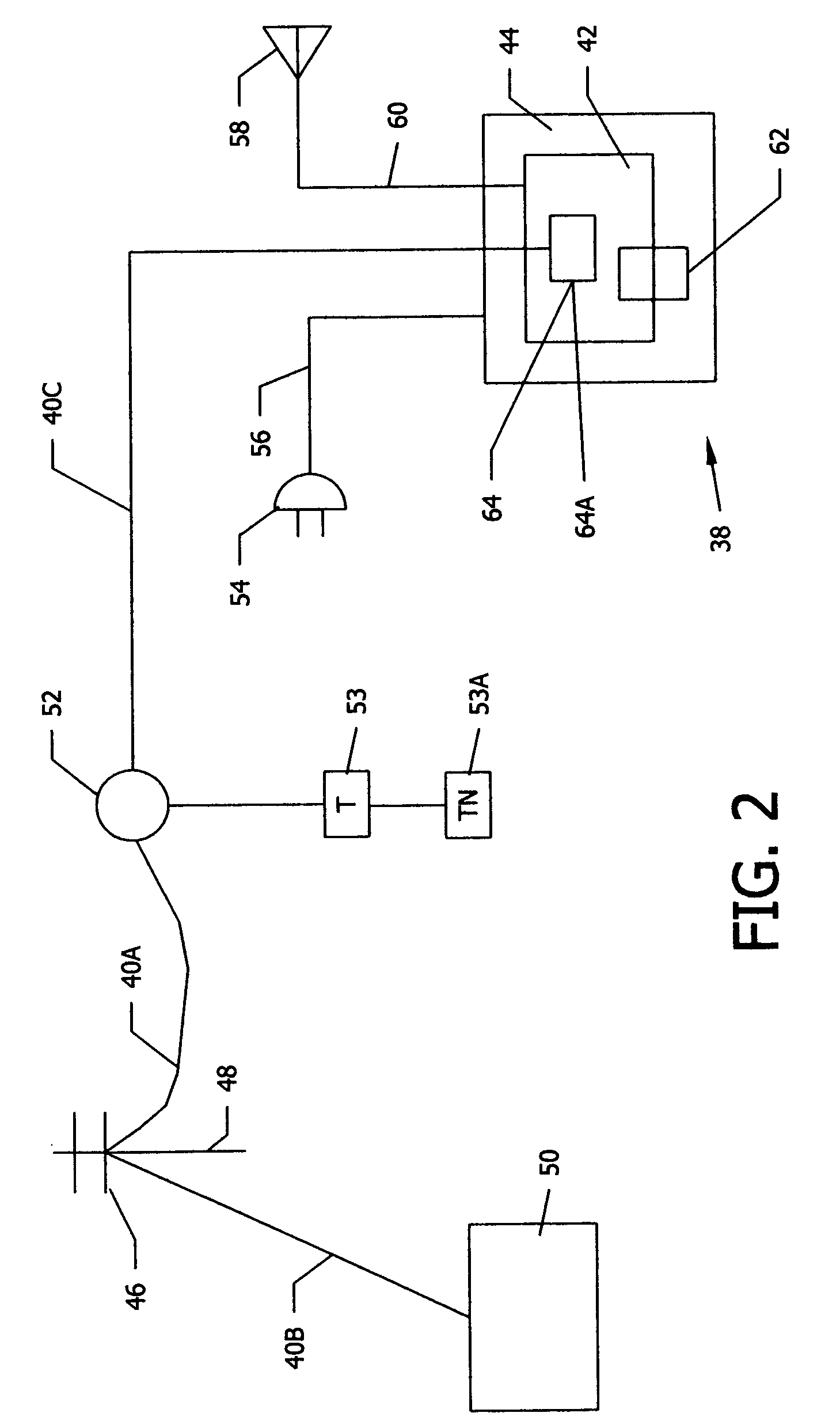
Satellite TV security system
InactiveUS20050198673A1Transmission becomes disabledGHz frequency transmissionAnalogue secracy/subscription systemsIntegrated receiver/decoderOperability
A satellite TV security system including a TV satellite operated by a satellite TV provider directed to a television set of a satellite TV subscriber that defends the satellite TV provider from illegal reception of TV signals from a TV satellite. An addressable integrated receiver / decoder (IRD) positioned in the TV set top box has an assigned identification number and a smart card positioned in the IRD has an assigned identification number. A security module is provided that is integrated with the IRD. Upon command of the satellite TV provider or automatically, the security module makes a periodic verification of a match of the two identification numbers. Lack of verification of a match triggers a signal from the security module to the IRD to stop transmitting TV signals to the subscriber television. As an alternative verification, the security module initiates periodic verifications of the operability of the telephone line connection between the satellite TV provider and the IRD of the subscriber. Lack of verification of the operability of the telephone line triggers a signal from the security module to the IRD to stop transmitting TV signals to the subscriber TV. The two systems of verification can be operated independently or simultaneously. The subscriber telephone number can be added as an assigned identification number, so that a three-way verification of identification numbers by the security module is required for continued transmission of TV signals to the subscriber television.
Owner:KIT JOHN +2
System, Method, and Apparatus for Preventing Identity Fraud Associated With Payment and Identity Cards
InactiveUS20070291995A1Easy and efficient to manufactureDurable and reliable constructionCharacter and pattern recognitionInternal/peripheral component protectionIdentity fraudDriver's license
The system, method, and apparatus of the present invention, address the problem of identity theft associated with the use of payment cards such as credit and debit cards, as well as identity theft associated with the use of identity cards such as driver's licenses and social security cards. An apparatus including a biometric input component that authenticates a system user is disclosed herein. Upon authentication, a proxy account number and a time varying security code are generated and displayed on the apparatus. The dynamically generated number and security code are then used to validate the user's identity within the system. Furthermore, the system, method, and apparatus of the present invention can be used to consolidate into one instrument, several payment and identity instruments.
Owner:RIVERA PAUL G
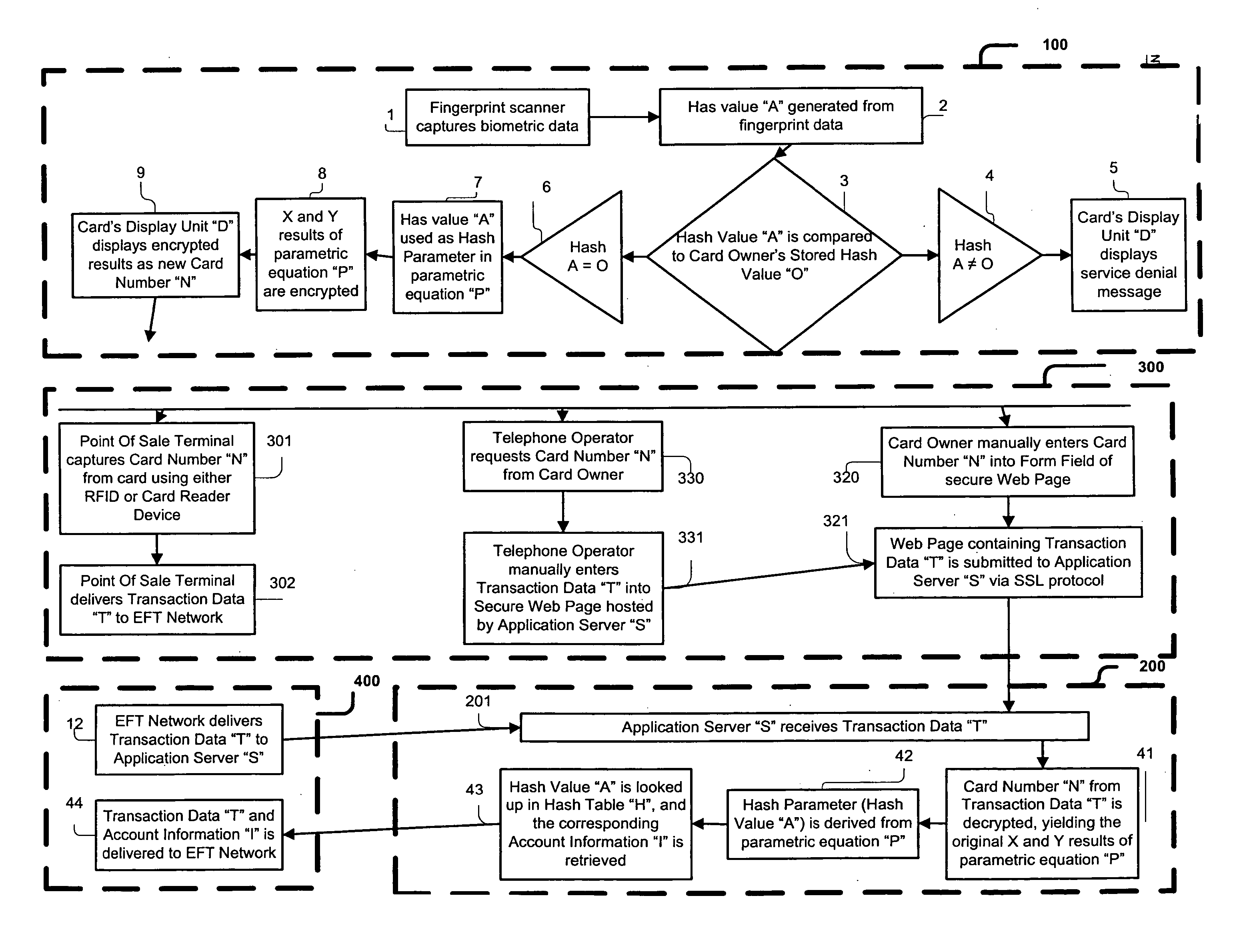
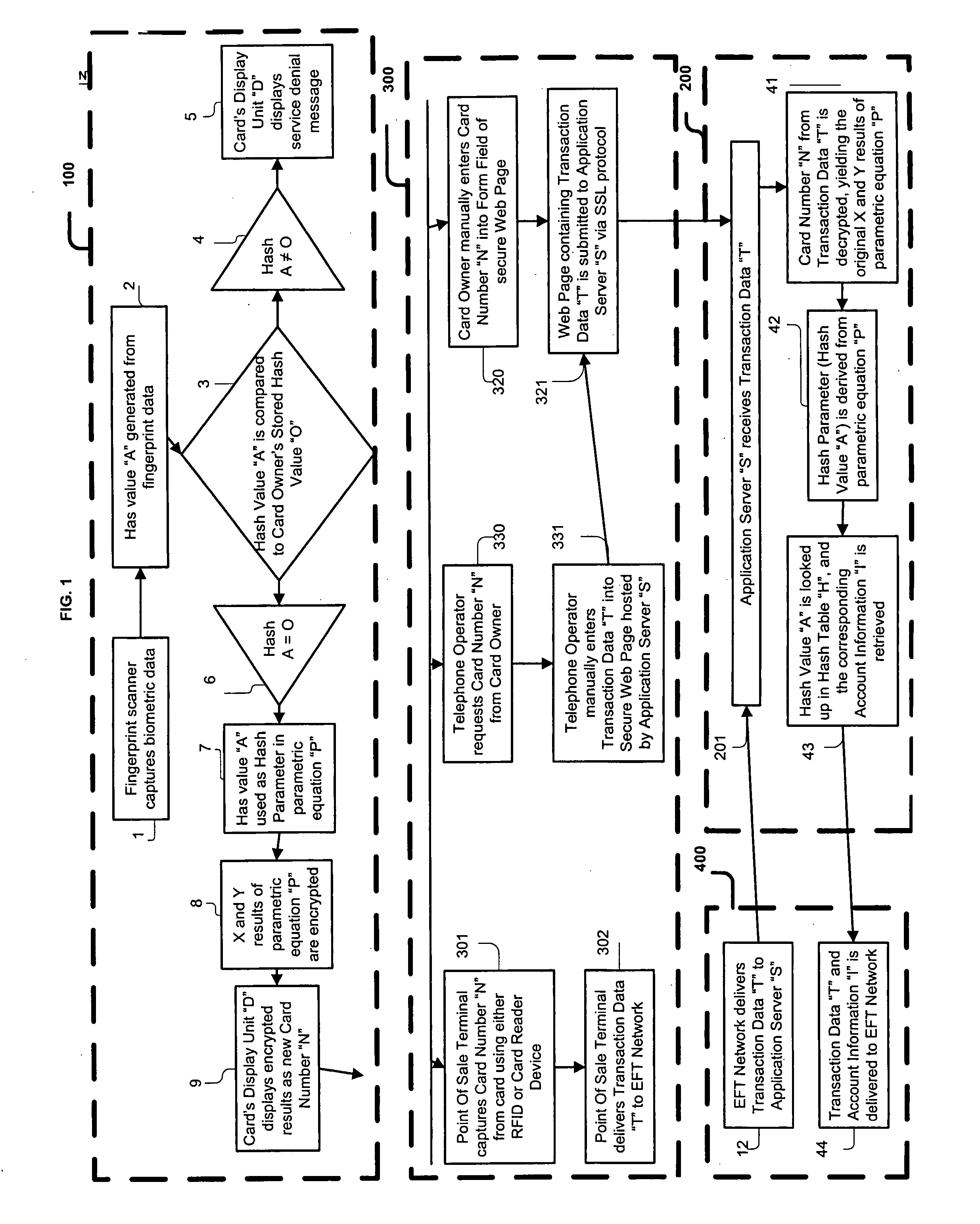
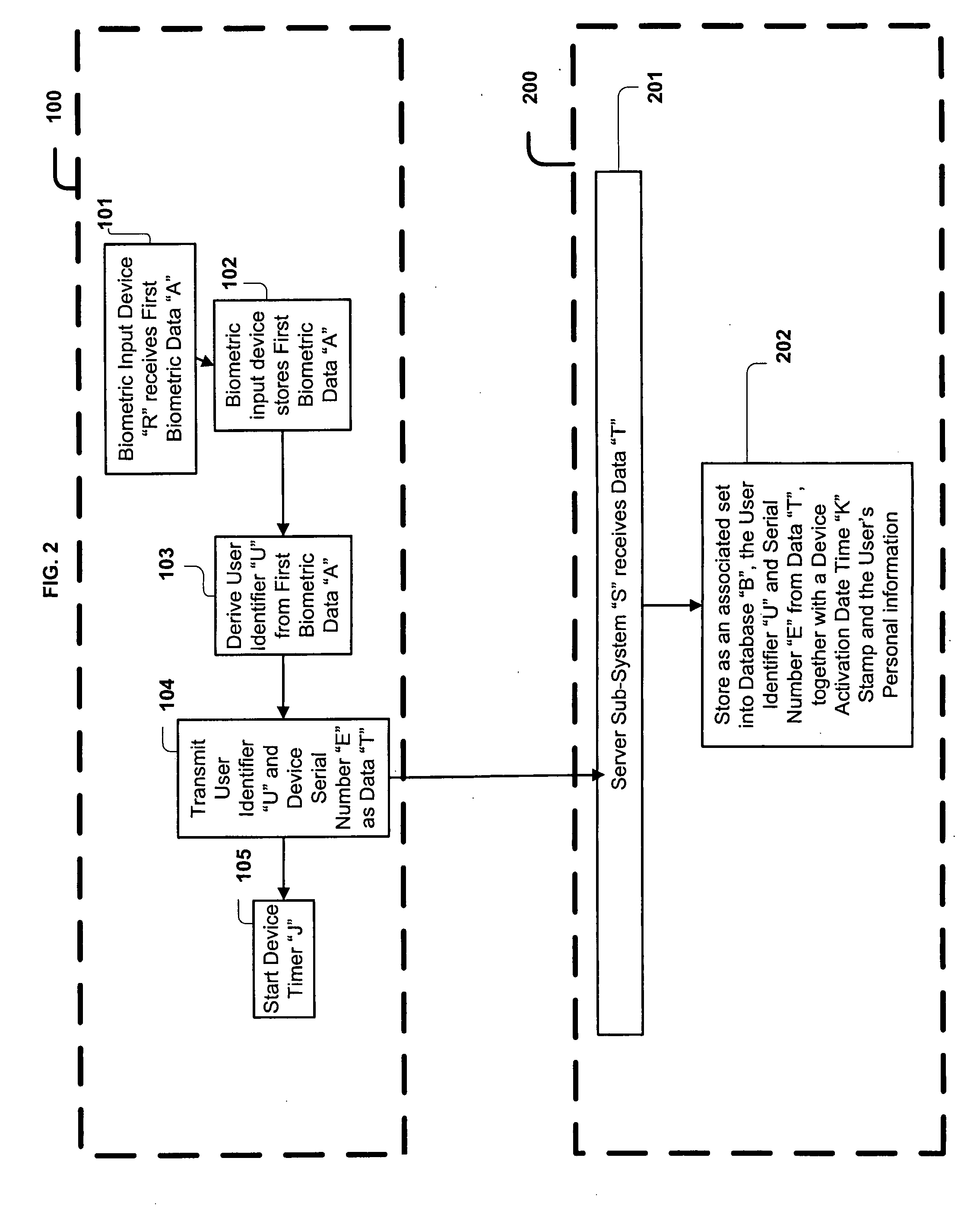
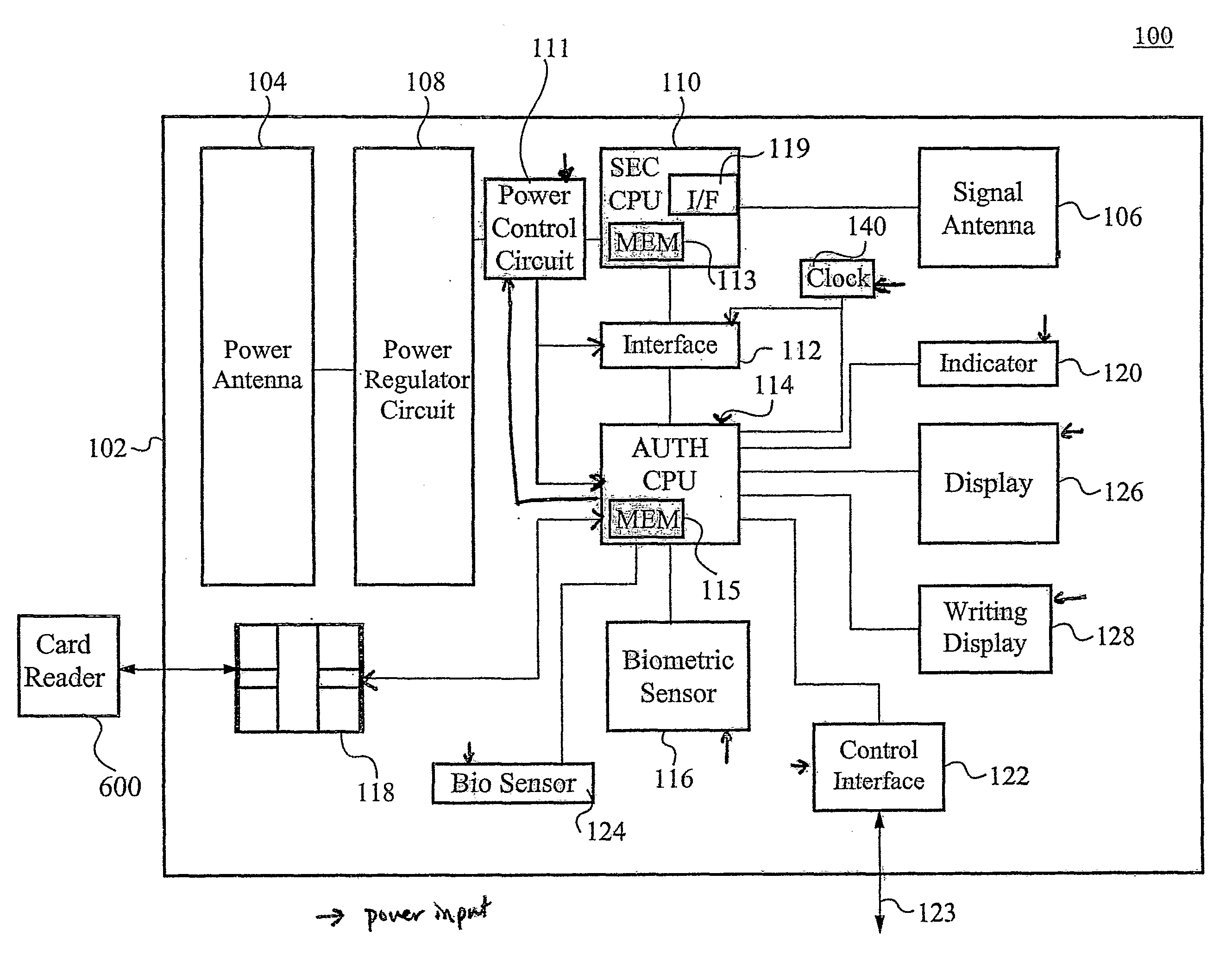
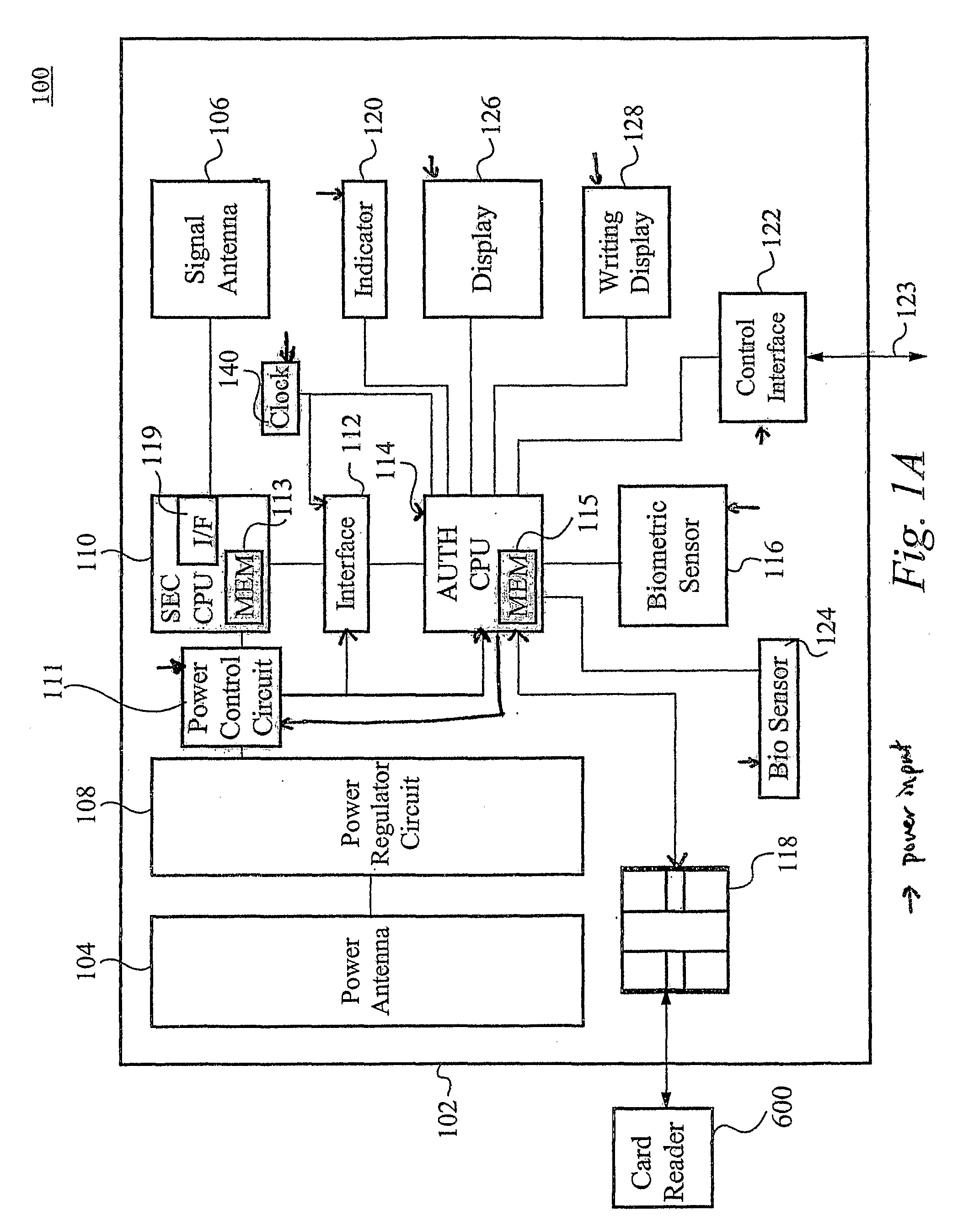
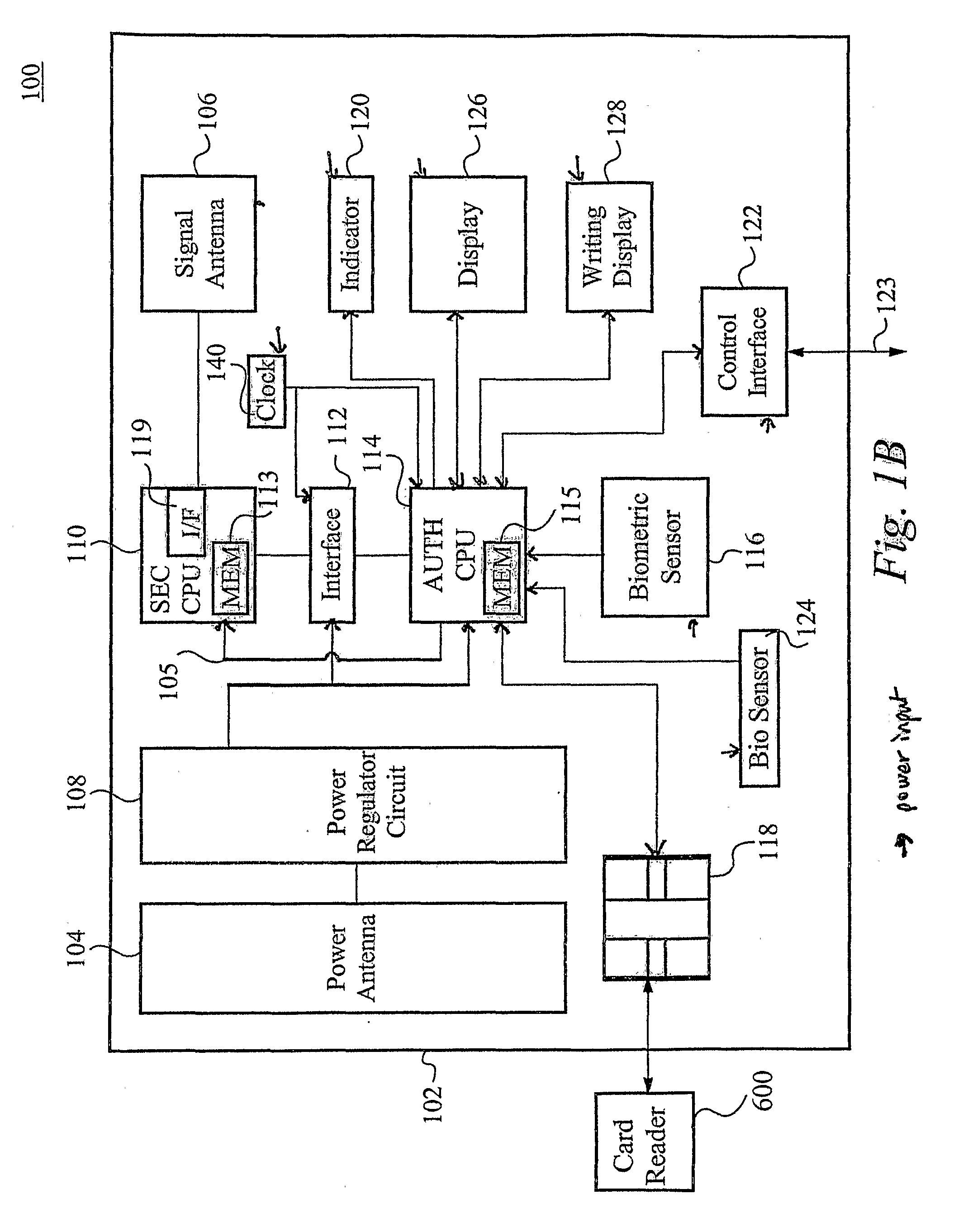
Biometric Identity Verification System and Method
A card authenticates a cardholder. The card includes a substrate, a sensor module, a wireless transceiver module, and a power circuit. The sensor module includes (a) a biometric sensor adapted to detect biometric information from a person's body, (b) a processor unit adapted to authenticate the person in response to the detected biometric information and generate an authentication signal representing an authentication result, and (c) a memory adapted to store biometric information of a specific individual associated with the card. The wireless transceiver module transmits signals received from the processor unit and receives a wirelessly-transmitted power signal. The power circuit generates at least one supply voltage from the received power signal and provides the supply voltage to the sensor module. An electronic passport is embedded with the card, and a terminal module is used for wirelessly transmitting power to and receiving signals from the electronic passport.
Owner:IVI HLDG
Facial image verification utilizing smart-card with integrated video camera
InactiveUS7039221B1Prevent fraudProvide securityAcutation objectsCharacter and pattern recognitionDocking stationPrincipal component analysis
A biometric facial image verification system capable of recognizing human users which includes a smart-card having stored thereon encoded first human facial images, a video camera and video digitizer embedded within said smart-card for acquiring data representative of a second human facial image. A computer-based device with a docking station capable of receiving said smart-card and software resident within said computer-based device for facial recognition, which includes Principal Component Analysis, Neural Networks, or another equivalent algorithm for comparing said first human facial images with said second human facial image and producing an output signal therefrom for use in verifying the identity of said human users. The apparatus can further include software for fingerprint and speech recognition. In addition, said smart-card is capable of acquiring and storing information pertaining to each of said human users such as would be required for use in a high-security environment or preventing fraud in point of sale and Internet-based financial transactions.
Owner:DONALD R STARKWEATHER
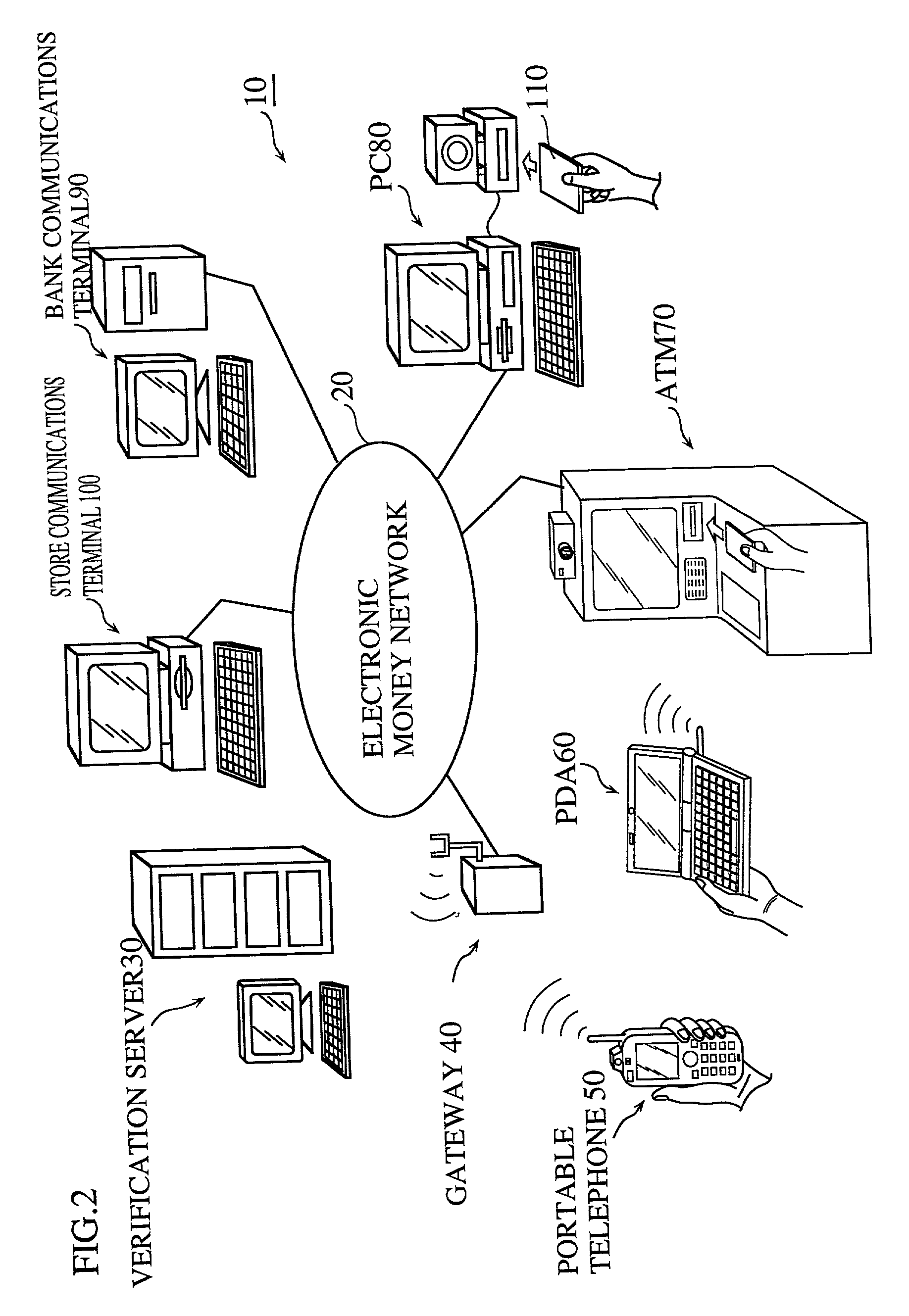
Method for determining internet users geographic region
InactiveUS6859791B1Digital data processing detailsRecord information storageCredit cardGeographic regions
A method at a clearing house to verify the geographic region of an end user device for receiving encrypted digital content. In one embodiment the geographic region is a country. The method comprising three sub-methods. In the first sub-method the address is verified by determining the credit card clearing address of the end user using an address verification system. In the second sub-method the address is verified by determining the IP address of the end user device requesting delivery of the encrypted digital content. And in the third sub-method the address is verified by checking that the IP address of the end user device requesting delivery of the encrypted digital content is the identical IP address of the end user device requesting a license to use the encrypted digital content. Depending on predetermined system settings, one or more of the above combination of the three sub-methods is then checked, before authorizing the decrypting of the encrypted digital content includes decrypting the encrypted digital content if the address verification system returns an address in a predetermined geographic region and the IP address of the end user device is in a predetermined geographic region.
Owner:LEVEL 3 COMM LLC
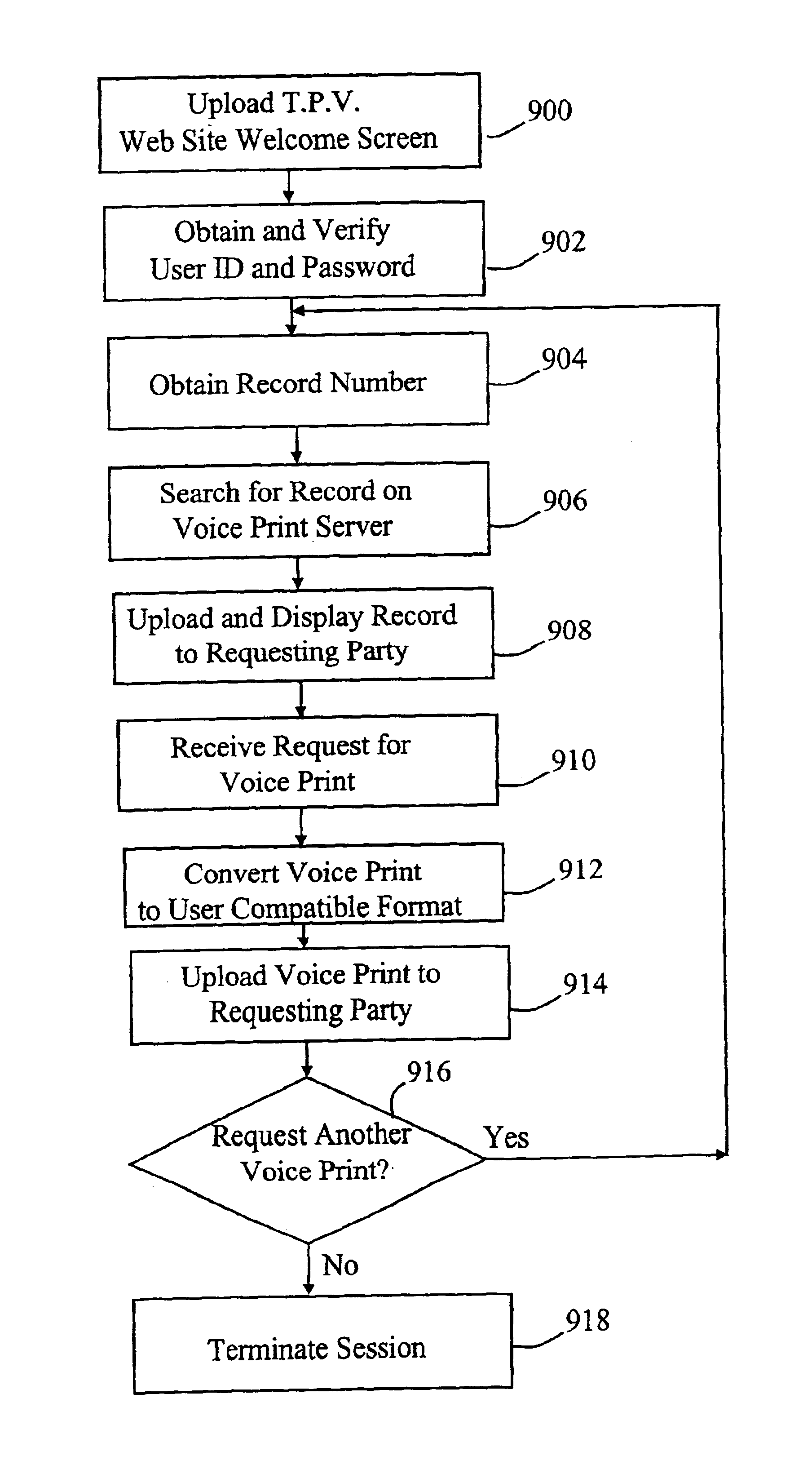
Automated third party verification system
A verification system for obtaining, storing and providing access to information regarding a commitment or position of an individual or entity is provided. In one embodiment the verification system comprises an interactive voice response system or computer program interface capable of obtaining and recording information regarding any of a number of commitments from an individual or entity, such as a commitment to change long distance telephone service providers. The verification system comprises a voice response unit configured to query pertinent information from an individual and record the responses to the queries in a digital format. Upon completion of a successful session, the voice response unit forwards the recorded responses confirming consent, to a storage device, such as a computer server. As desired, the recorded responses can be retrieved from the server by telephone or computer for verification of the consent, commitment, or position of the individual or entity.
Owner:RED HAT
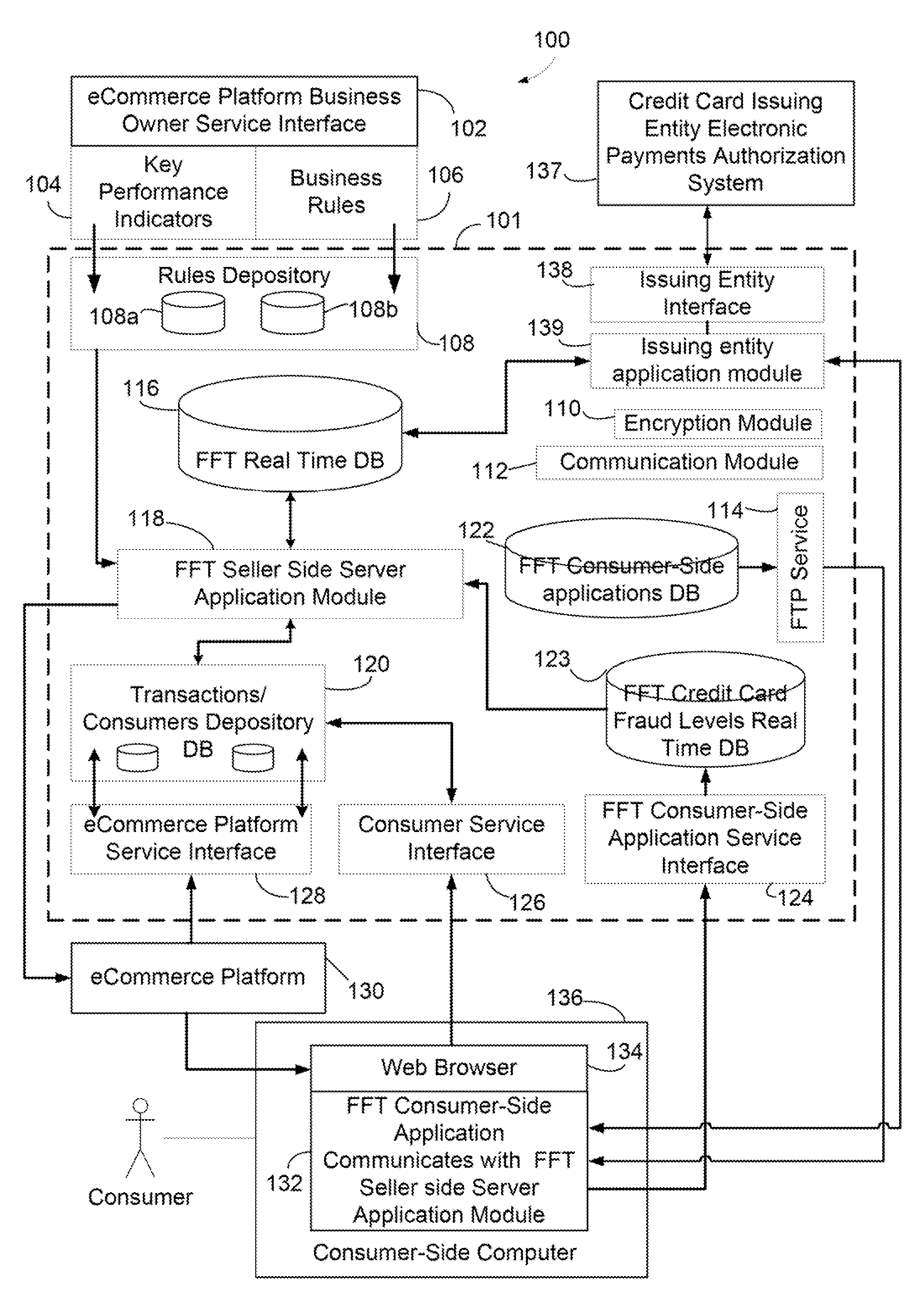
Systems and Methods for Automatic and Transparent Client Authentication and Online Transaction Verification
Systems and methods are described for providing fraud deterrents, detection and prevention during e-commerce, e-transactions, digital rights management and access control. Fraud deterrent levels may be automatically selected by a requesting transaction approval entity server (and can be related to level of risk, or security, related to fraud) or may be selected by a consumer. These deterrent levels can determine the manner in which the transaction occurs as well as the types of information that must be provided and validated for successful approval of the transaction. The client can associate their credit card with a specific device, an e-identity, such as an instant messaging identity, and the e-identity is contacted as a part of finalizing a payment transaction so that a client response of ‘approve’ or ‘reject’ can be obtained. The anti-fraud technology also provides for management and storage of historical transaction information. Entity-to-client communication occurs according to merchant permission parameters which are defined by the client and which enable messages sent by the entity to be automatically allowed, rejected, and managed in other ways as well.
Owner:JOHN MICHAEL SASHA
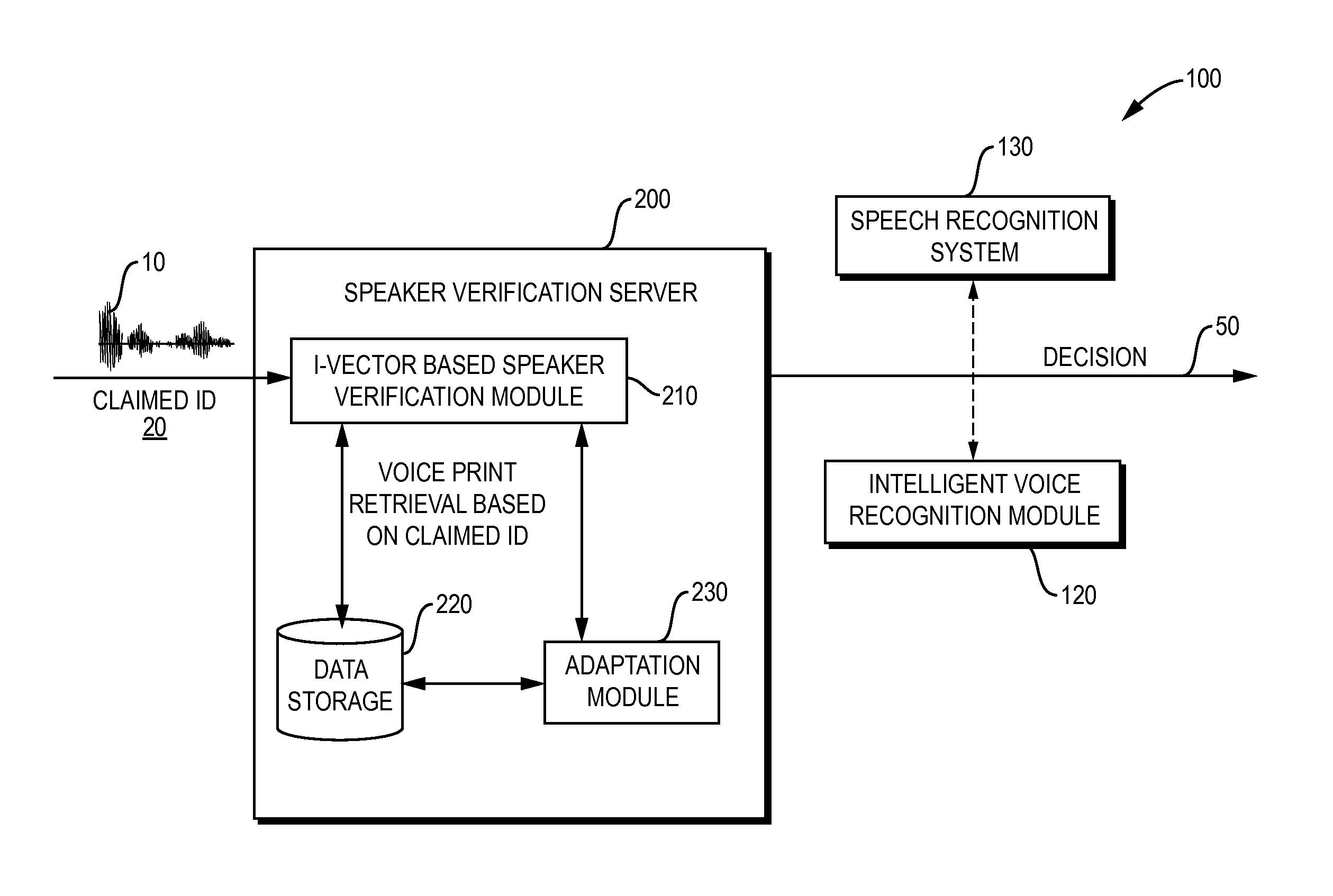
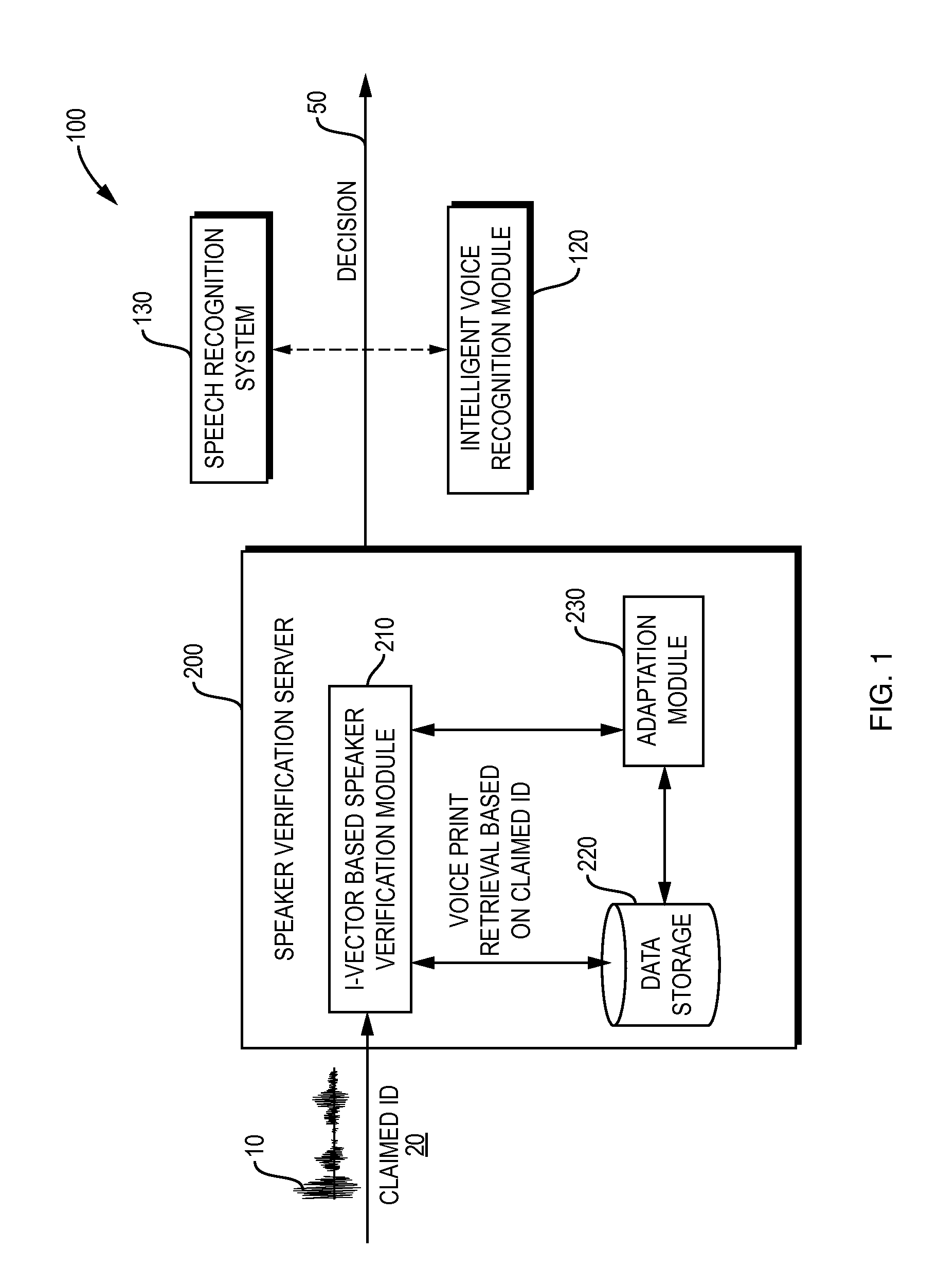
Method and Apparatus for Automated Speaker Parameters Adaptation in a Deployed Speaker Verification System
Typical speaker verification systems usually employ speakers' audio data collected during an enrollment phase when users enroll with the system and provide respective voice samples. Due to technical, business, or other constraints, the enrollment data may not be large enough or rich enough to encompass different inter-speaker and intra-speaker variations. According to at least one embodiment, a method and apparatus employing classifier adaptation based on field data in a deployed voice-based interactive system comprise: collecting representations of voice characteristics, in association with corresponding speakers, the representations being generated by the deployed voice-based interactive system; updating parameters of the classifier, used in speaker recognition, based on the representations collected; and employing the classifier, with the corresponding parameters updated, in performing speaker recognition.
Owner:NUANCE COMM INC
Authentication watermarks for printed objects and related applications
InactiveUS6823075B2More dataCompact formOther printing matterPaper-money testing devicesRelevant informationCopy detection
Owner:INTUIT INC
Smart card with random temporary account number generation
Owner:HEWTON ALFRED
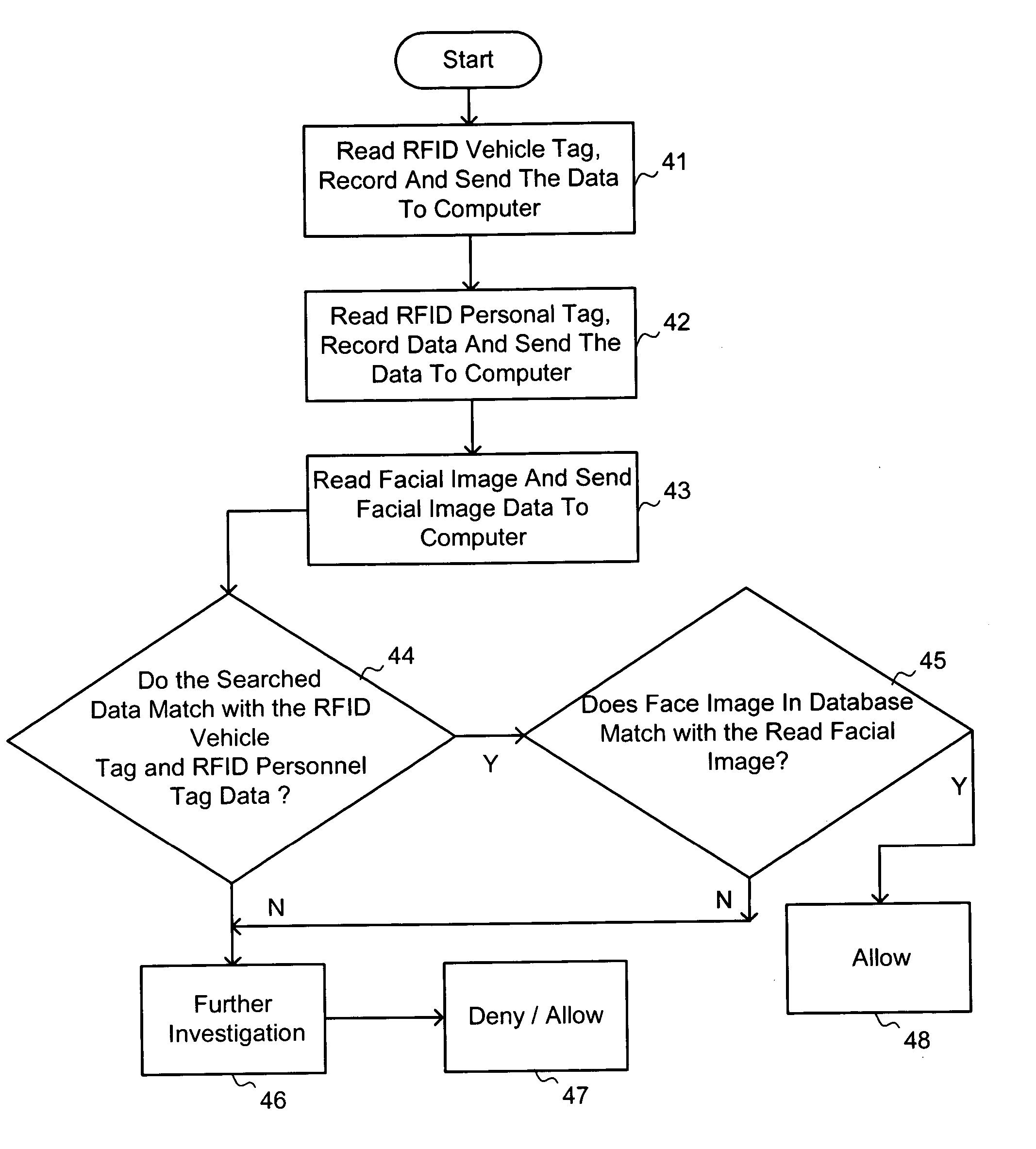
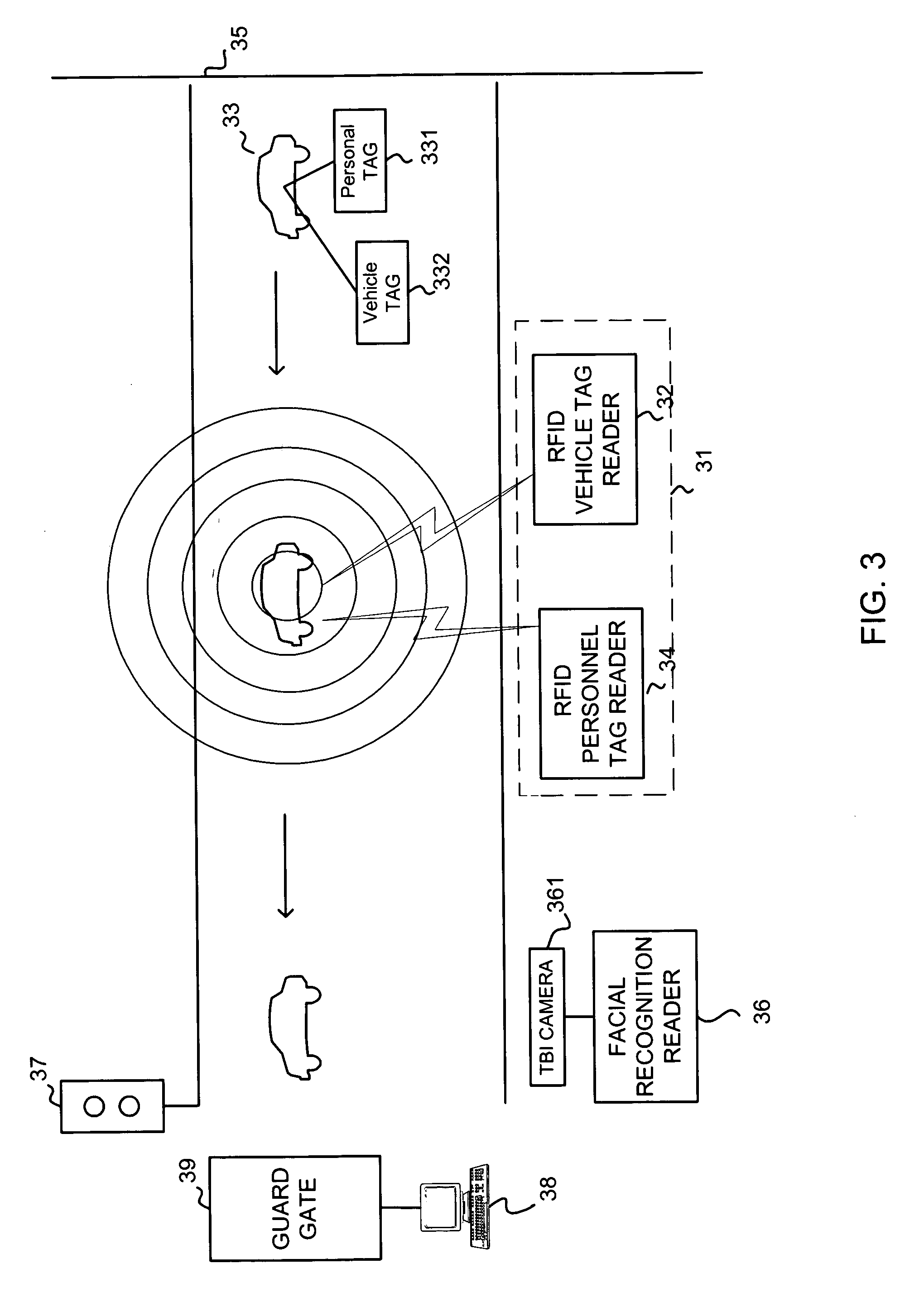
System and method for dynamic stand-off biometric verification
InactiveUS20050055582A1Fast and secureFast and secure verificationElectric signal transmission systemsImage analysisDriver/operatorFace verification
A system for providing stand-off biometric verification of a driver of a vehicle at a control gate while the vehicle is moving, including an RFID vehicle tag reader, an RFID personal tag reader and a facial detection and recognition (verification) system. The RFID vehicle tag reader scans and reads data from an RFID vehicle tag of the vehicle that is trying to pass through the gate. The RFID personal tag reader reads data from an RFID personal tag carried by personnel who are driving in the vehicle. The facial detection and verification system scans and reads facial images for the driver. All the data and facial images detected by the reader are sent to a computer for further processing (final face verification).
Owner:HONEYWELL INT INC
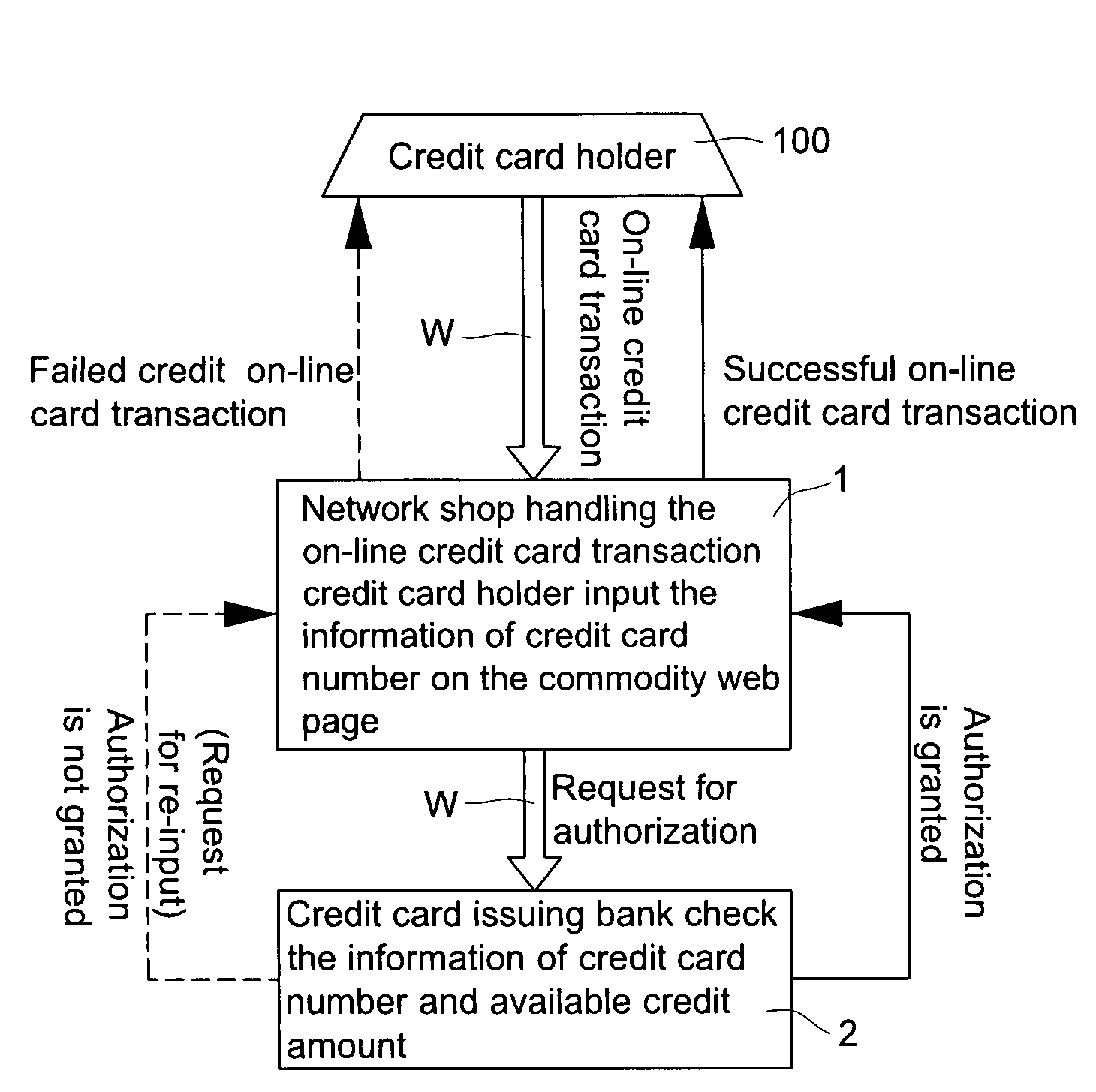
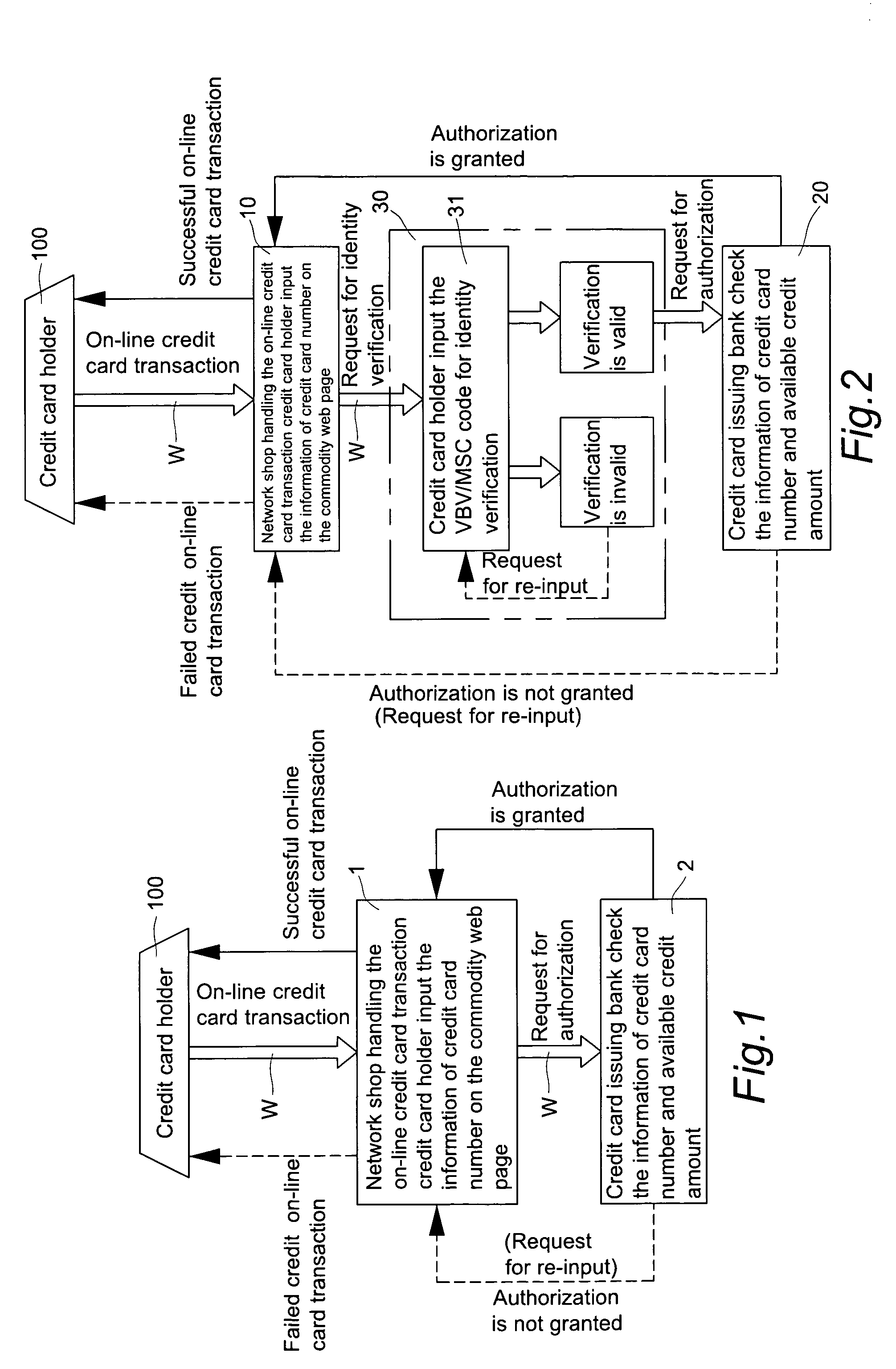
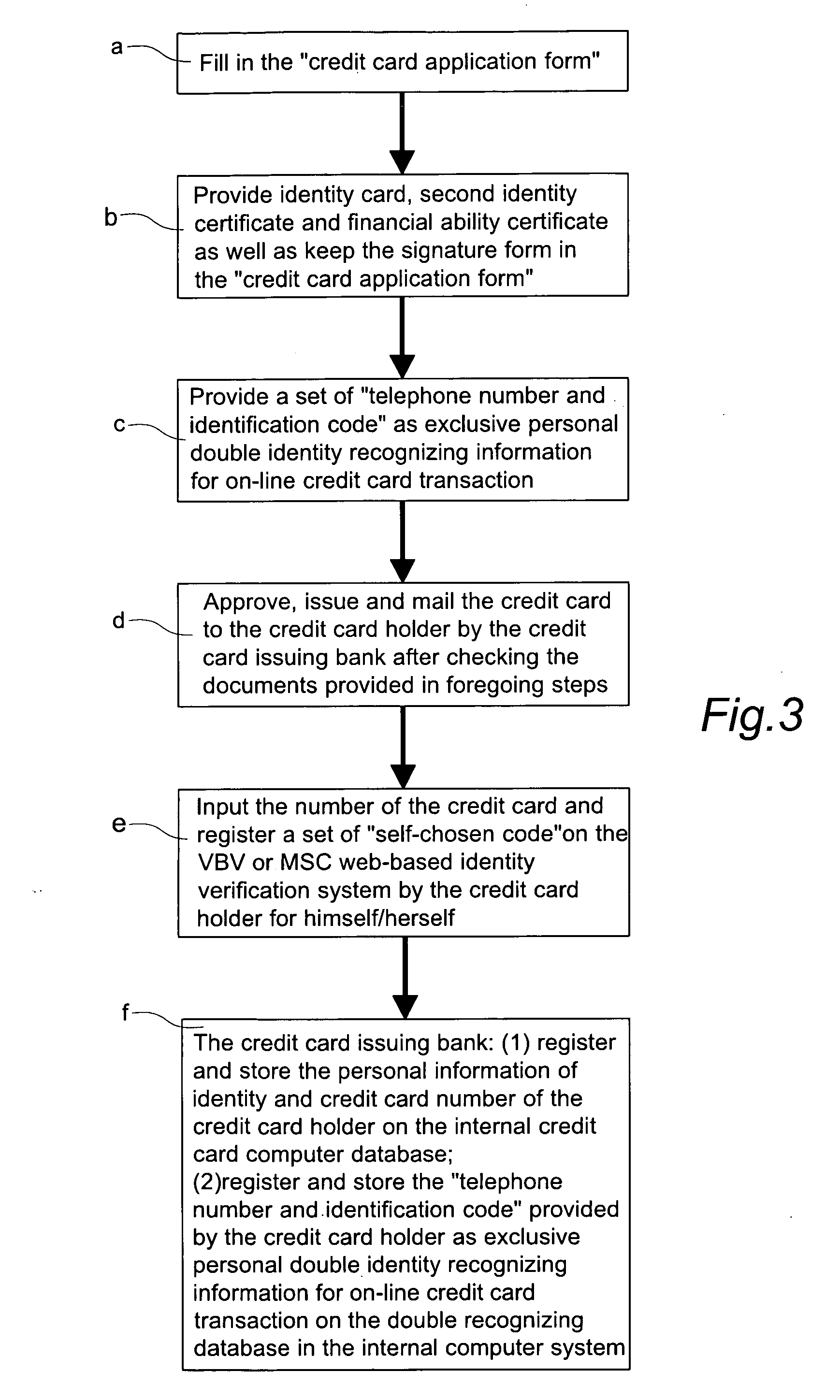
Double recognizing method by means of telephone number and identification code for online credit card transactions over the internet
The present invention relates to a “double recognizing method by means of telephone number and identification code for online credit card transactions over the internet,” in which the credit card holder not only registers a “self-chosen code” by himself / herself for VBV (Verified By VISA) or MSC (MasterCard SecureCode) network identity verification but also registers another set of “telephone number and identification code” by himself / herself for serving as an exclusive personal double identity recognizing information for online credit card transactions. The credit card issuing bank registers and stores the set of “telephone number and identification code” on a double recognizing database after checking truth of the related identity certificate provided by the credit card holder. When the credit card issuing bank handles the online credit card transaction of the credit card holder over the network, the credit card issuing bank not only proceeds the check on the “self-chosen code” used in the original VBV or MSC verification system but also performs the double check on the “telephone number and identification code” used in the telecommunications transceiving processor platform of the internal credit card double recognizing computer system, for example by sending out a short message to the credit card holder for requesting him / her to immediately reply by another short message to his / her “telephone number and identification code.”
Owner:LIN CHUNG YU
Identity verification system with self-authenticating card
InactiveUS20050212657A1Easy to compareImprove accuracyElectric signal transmission systemsDigital data processing detailsData matchingCard reader
An identity verification system that includes a self-authenticating identity card and a card reader. The self-authenticating card has a programmable microchip with data pertaining to the authorized card bearer, including data for a stored biometric feature, such as a fingerprint, a retinal scan, a voice print, a DNA sequence, etc. The card also includes a biometric sensor that senses an applied biometric feature and a data lock that releases data upon determinination of a match between the stored and the applied biometric features. In order to self-authenticate the card, the card bearer must provide the applied biometric feature. For example, the card bearer applies a finger tip to the sensor, if the applied biometric feature is a fingerprint. If the data match, the data lock transmits data stored on the card to the card reader for processing.
Owner:SIMON RUDY
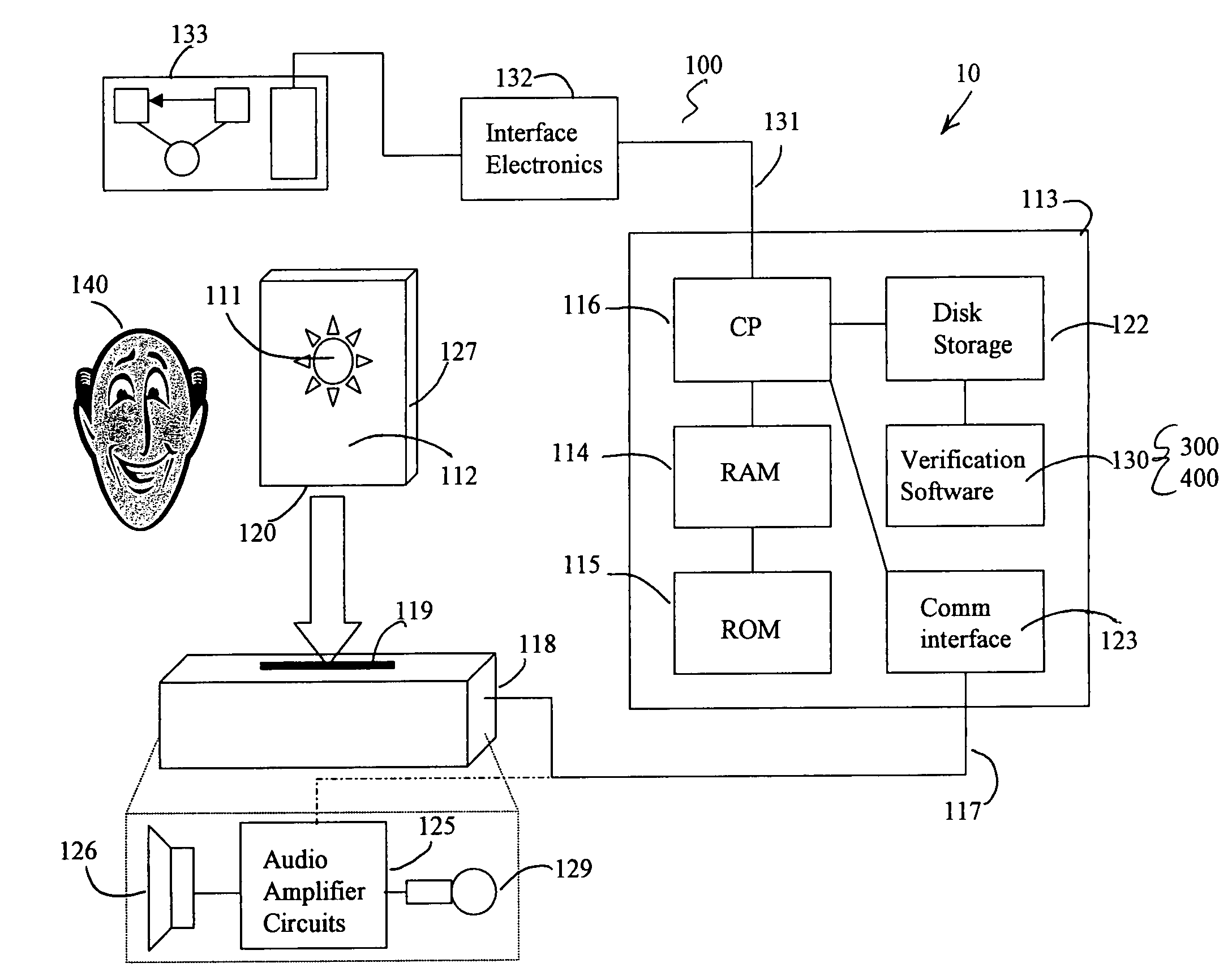
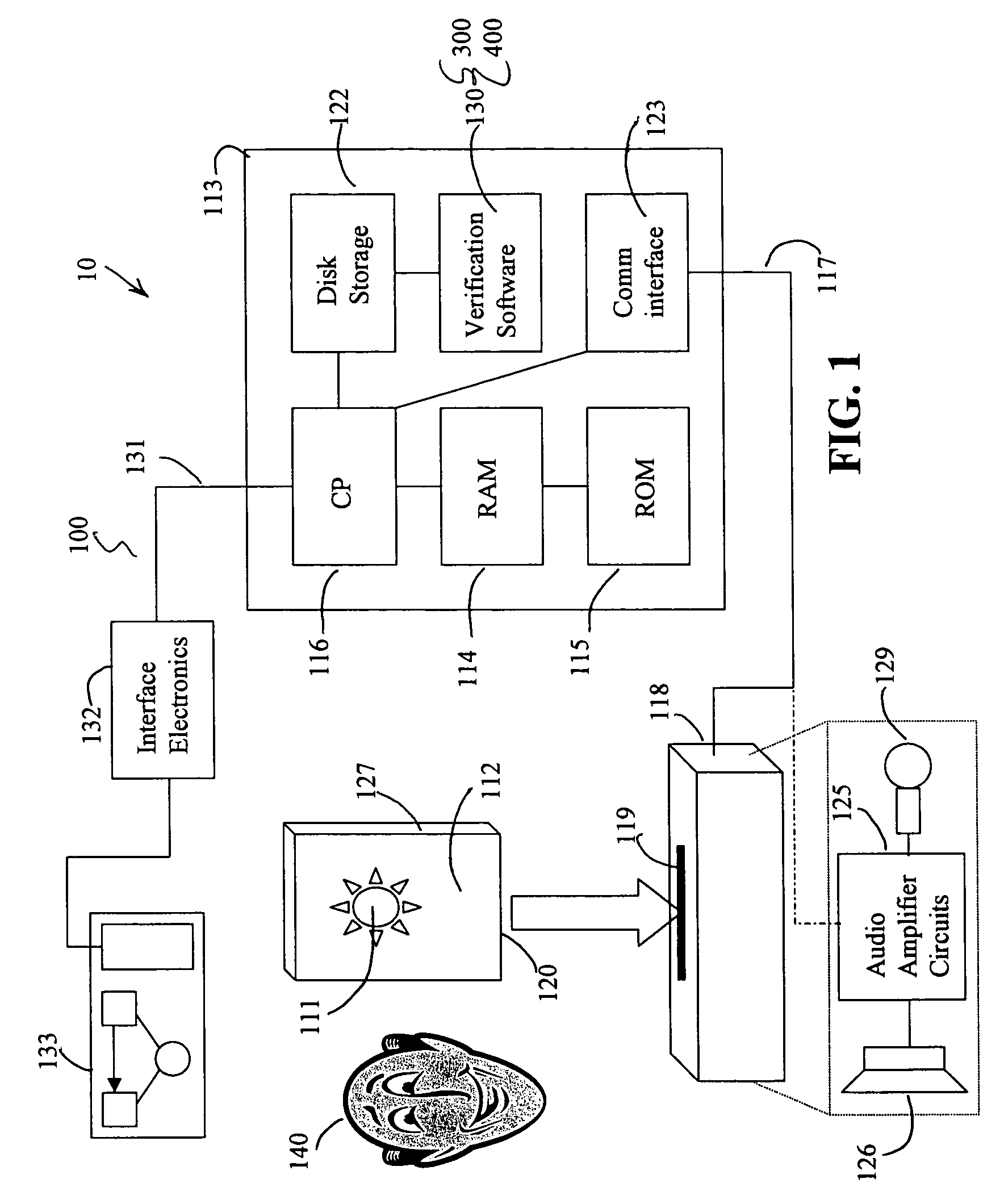
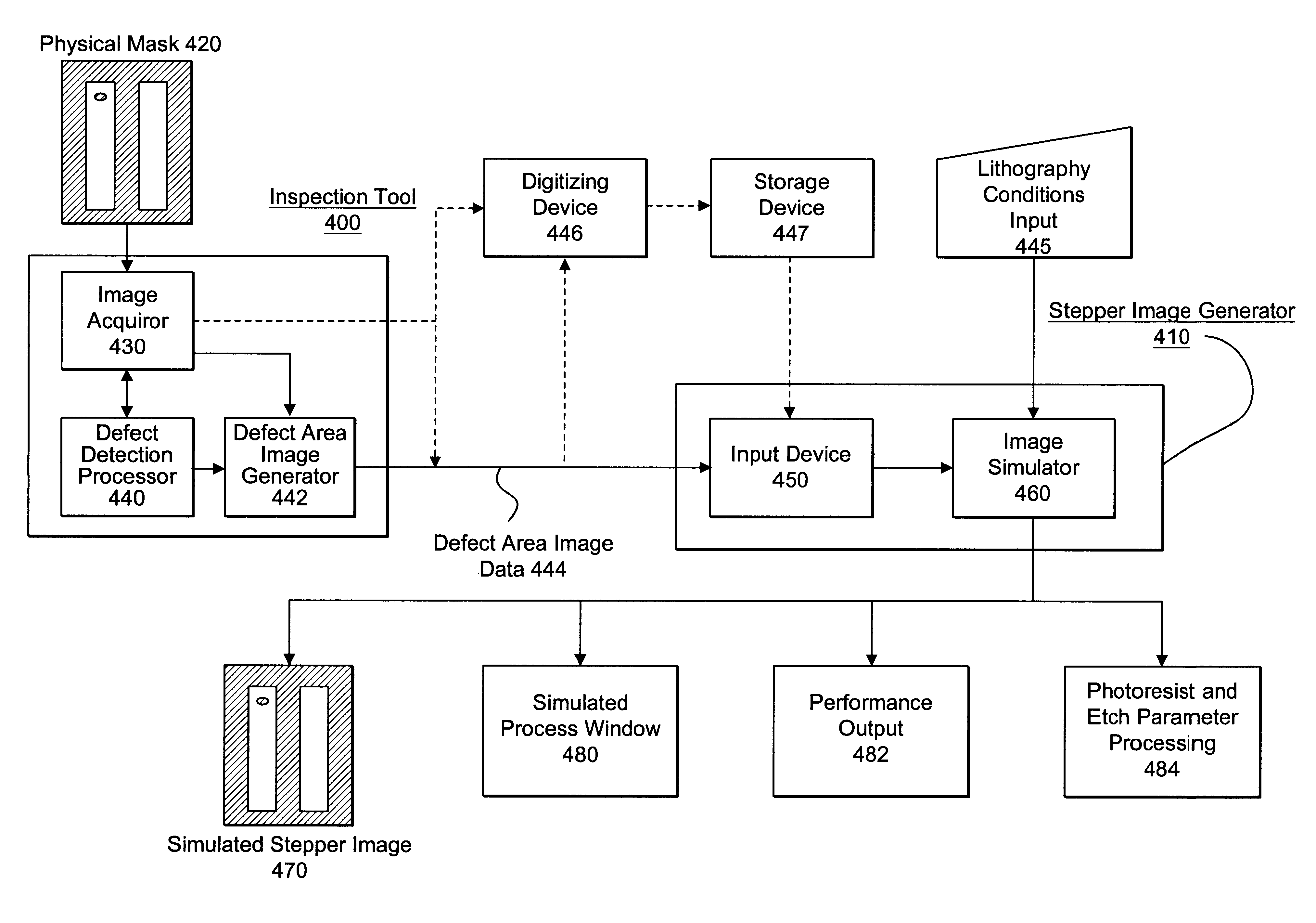
Visual inspection and verification system
A method and apparatus for inspecting a photolithography mask for defects is provided. The inspection method comprises providing a defect area image to an image simulator wherein the defect area image is an image of a portion of a photolithography mask, and providing a set of lithography parameters as a second input to the image simulator. The defect area image may be provided by an inspection tool which scans the photolithography mask for defects using a high resolution microscope and captures images of areas of the mask around identified potential defects. The image simulator generates a first simulated image in response to the defect area image and the set of lithography parameters. The first simulated image is a simulation of an image which would be printed on a wafer if the wafer were to be exposed to an illumination source directed through the portion of the mask. The method may also include providing a second simulated image which is a simulation of the wafer print of the portion of the design mask which corresponds to the portion represented by the defect area image. The method also provides for the comparison of the first and second simulated images in order to determine the printability of any identified potential defects on the photolithography mask. A method of determining the process window effect of any identified potential defects is also provided for.
Owner:SYNOPSYS INC
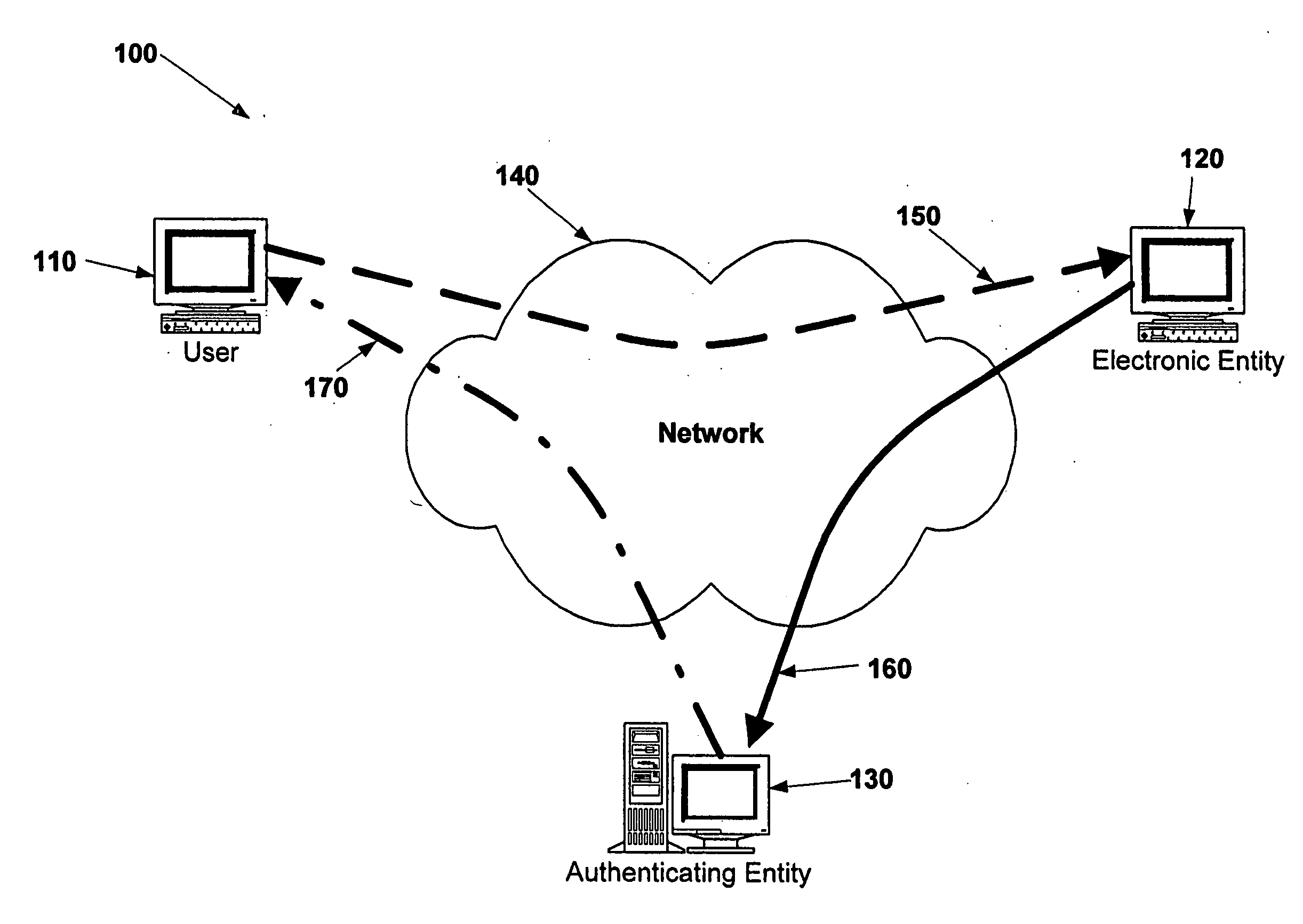
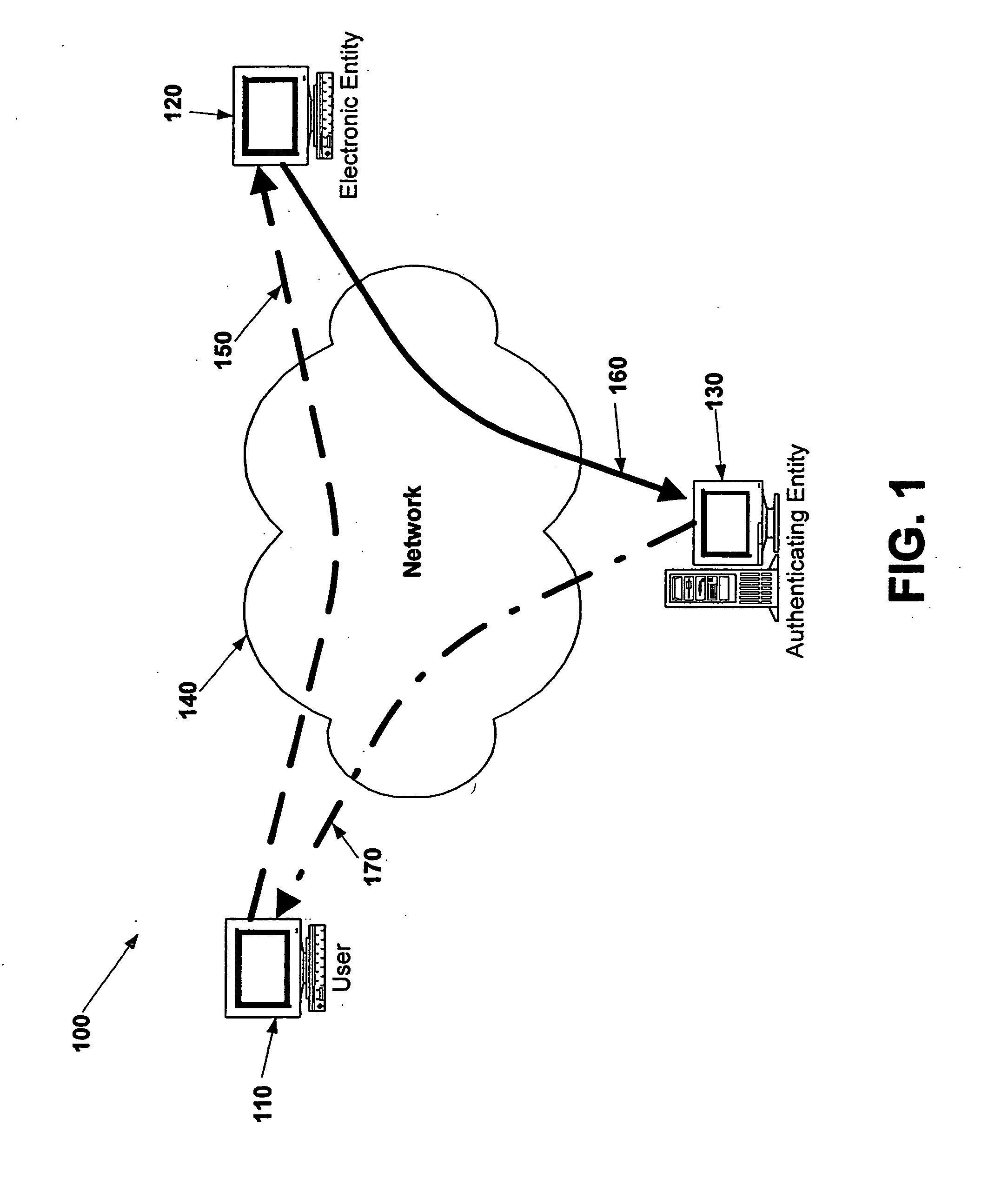
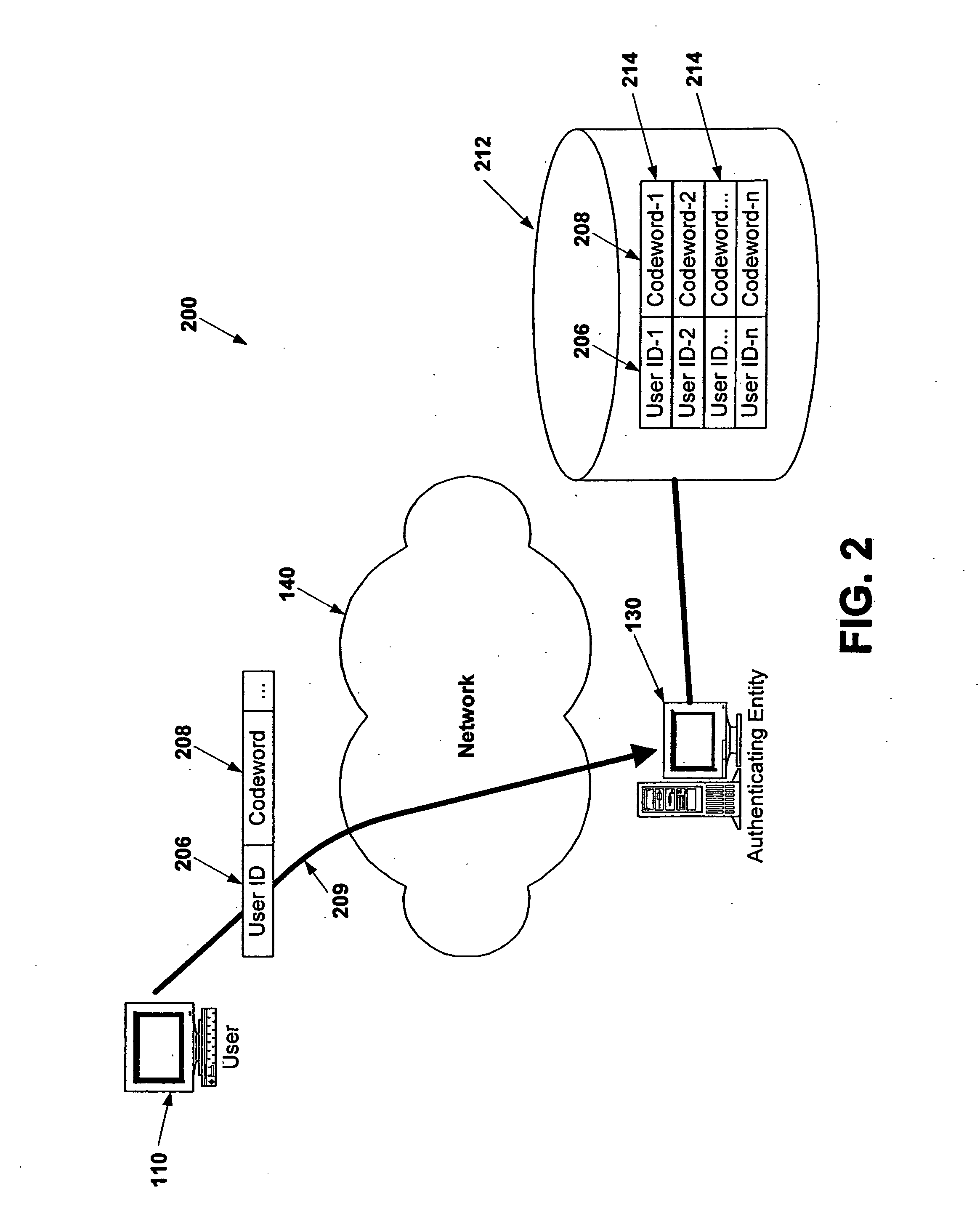
Electronic verification systems
ActiveUS20060200855A1Verify authenticityPrevent account hijacking and frustrate fraudulent electronic transactionsDigital data processing detailsUser identity/authority verificationObject basedThe Internet
A verification system which can be used over electronic networks, such as the Internet, to help prevent phishing, electronic identity theft, and similar illicit activities, by verifying the authenticity of electronic entities (for example, websites). Users and electronic entities register with an authenticating entity. The authenticating entity shares an encryption method with registered electronic entities and establishes a secret code for each registered electronic entity. The secret code is combined with other information and encrypted before being transmitted over the network to ensure that the secret code cannot be compromised. Also disclosed are systems for virtual token devices, which provided object-based authentication without a physical device. Also disclosed are dynamic media credentials, which display nearly-unique behavior, previously specified and known to a user, to assist in verifying the authenticity of the presenter.
Owner:SYCCURE INC
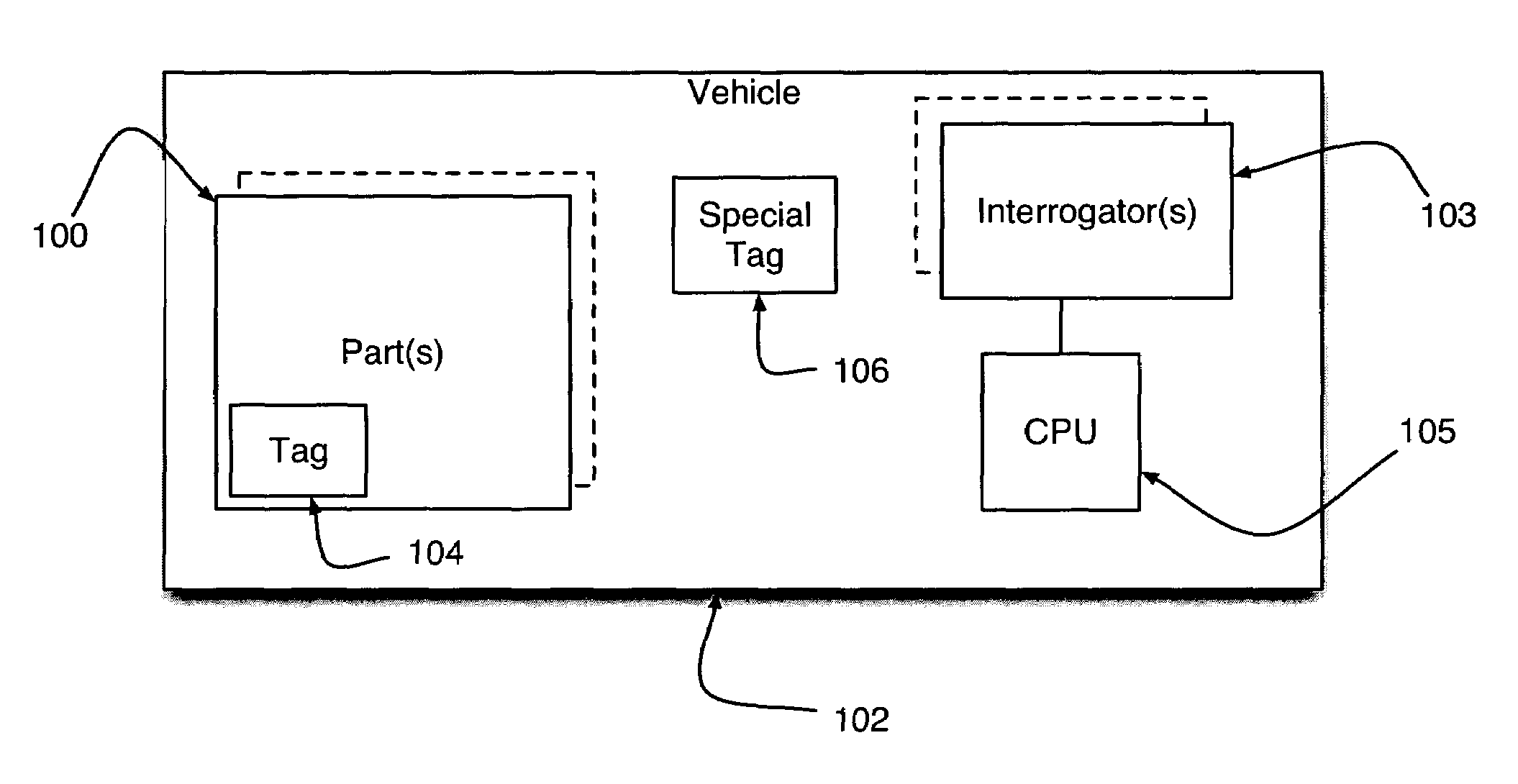
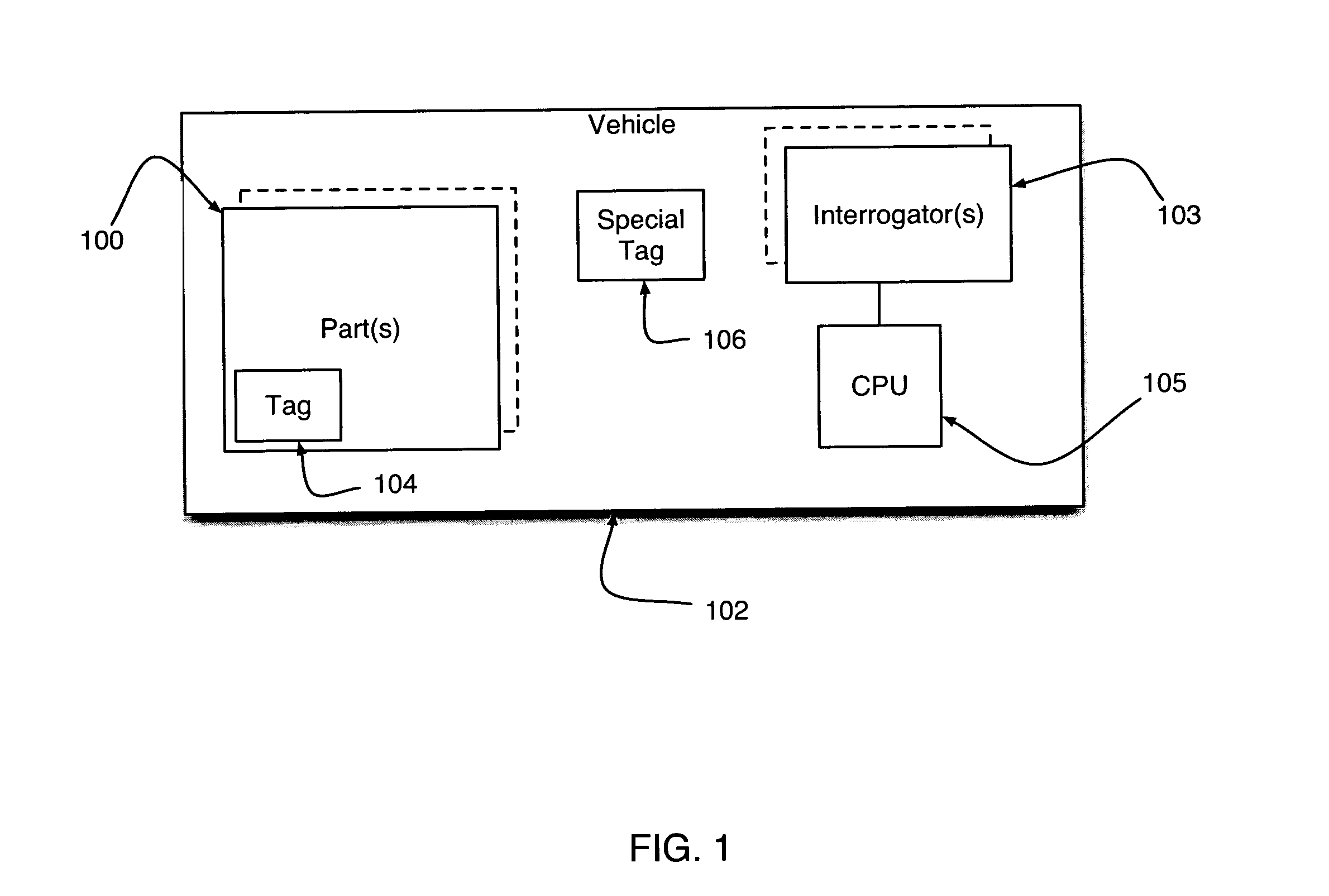
Radio frequency identification parts verification system and method for using same
InactiveUS7042346B2Registering/indicating working of vehiclesDigital data processing detailsRadio frequency signalEngineering
A system and method for collecting data relating to the parts of a vehicle and using such data to determine if the vehicle can be operated. The system entails the deployment of a plurality of radio frequency identification tags on or within various parts of the vehicle that are capable of issuing radio frequency signals containing data related to each corresponding part. A radio frequency transceiver capable of interfacing with and receiving data stored within each tag operates in conjunction with a central processor unit capable of analyzing the data from each tag and determining whether the vehicle needs parts to be replaced or can be operated with its existing set of parts.
Owner:GBP SOFTWARE
Integrated verification system
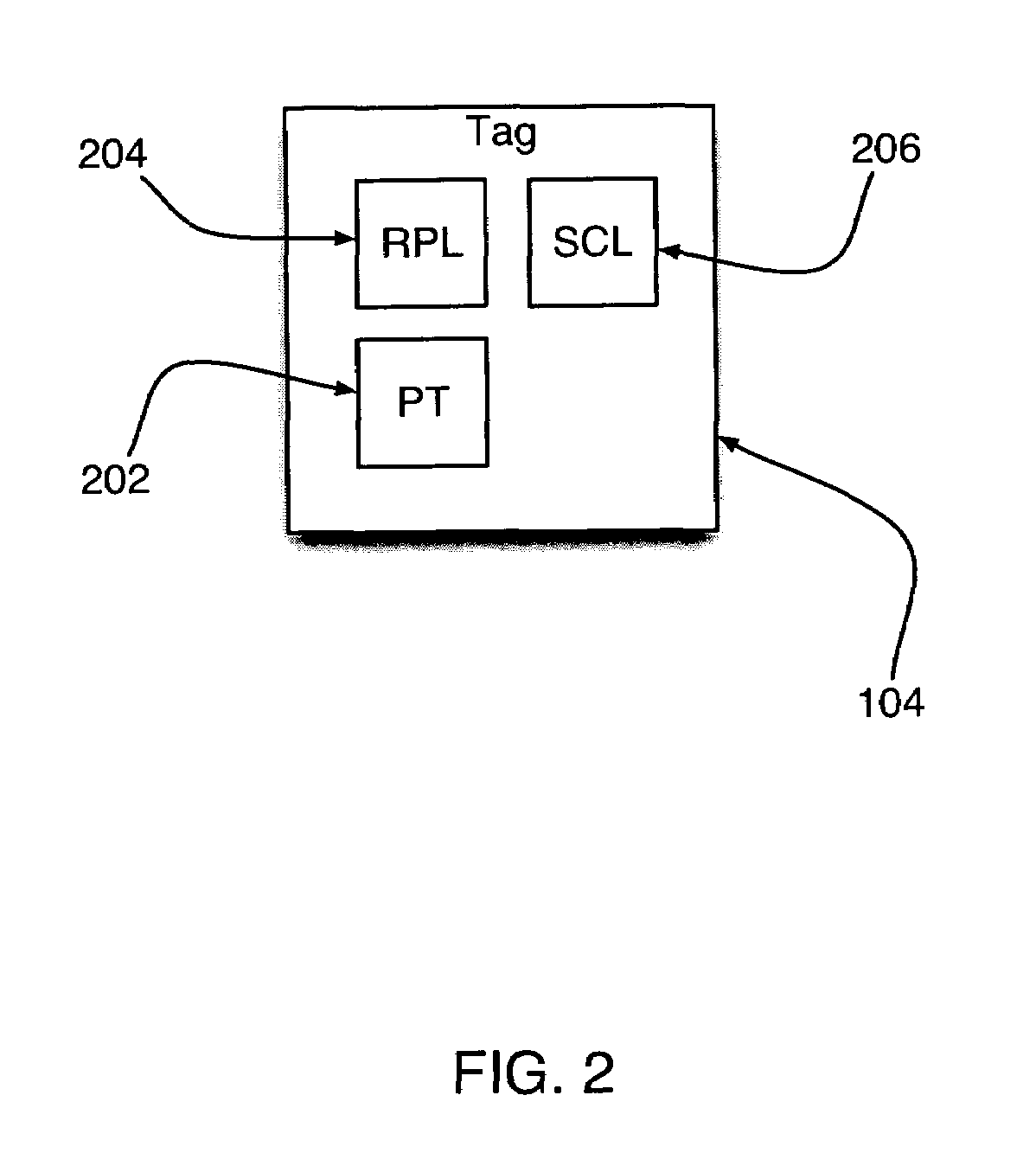
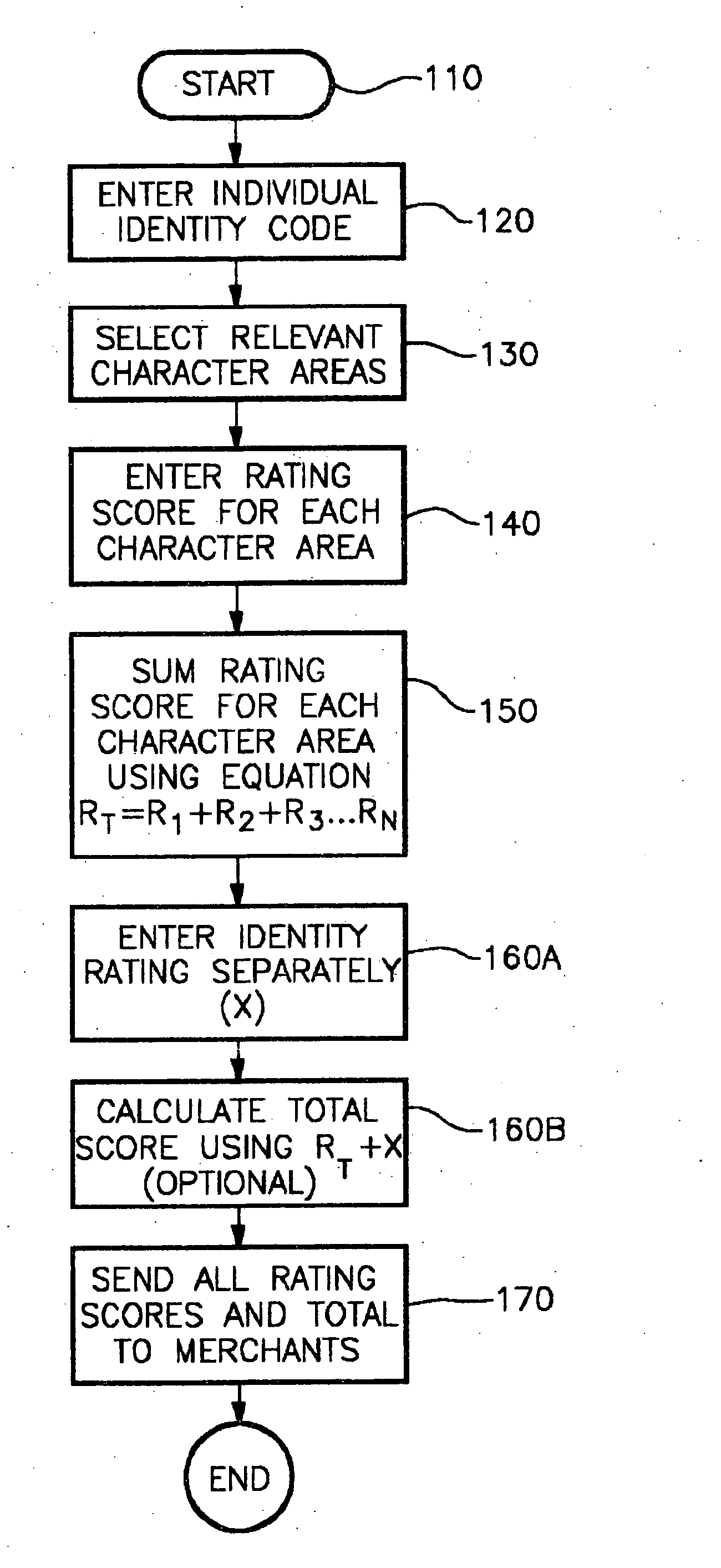
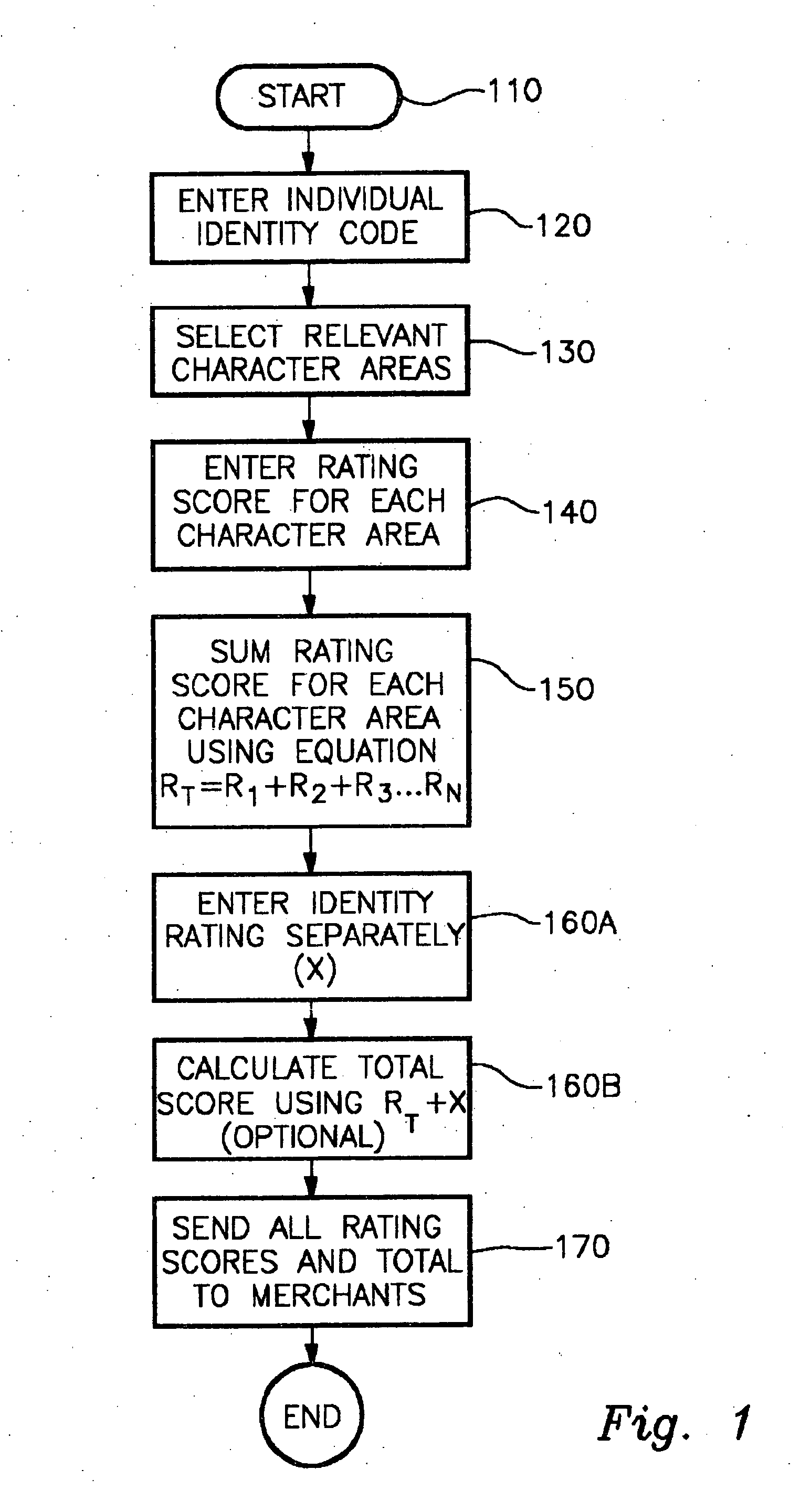
InactiveUS20050027983A1Avoid lostHigh identity scoreUser identity/authority verificationDigital data authenticationDigital signatureVerification system
The subject invention comprises a process and means for an integrated and standardized verification rating of individuals seeking credit or access, or for sending a digital signature for access purposes including means comprising of a scaled rating for an individual's identity, along with potential other individual attributes that will be rated in order to apprise a merchant or other entity of the authenticity of the individual seeking credit or permit access to an entity or sending a digital signature.
Owner:KLAWON KEVIN T
Identity verification system
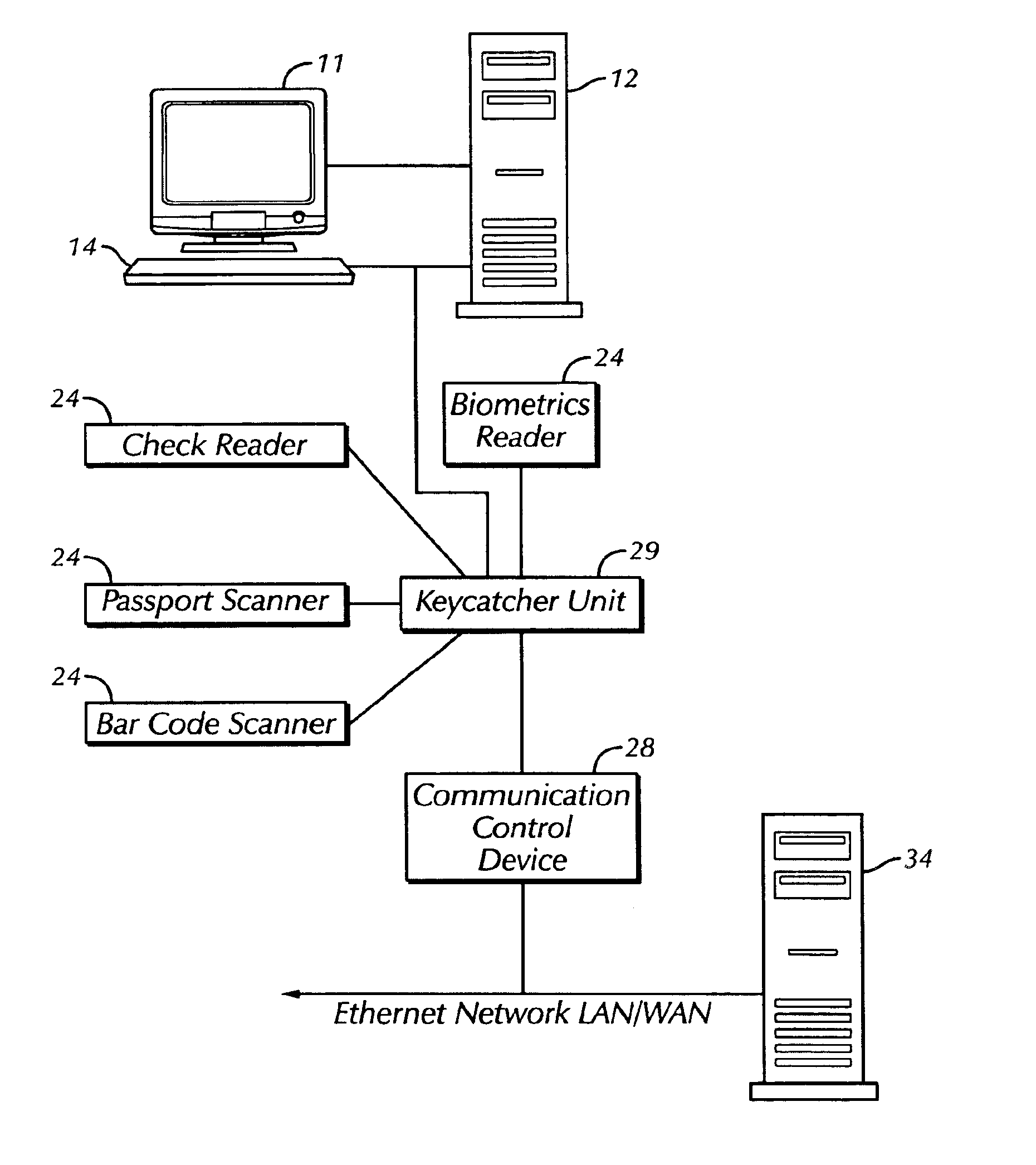
The present invention is a security system that utilizes an identity verification system having a biometrics component, such as but not limited to a face, fingerprint, or iris recognition system. The system connects a biometric data entry device such as a standard analogue or digital camera to a communication control device which captures, compresses and digitizes the biometric data as well as converts data from data input devices and sends the compressed and digitized biometric data along with the data from a data input device to a central processing unit for processing by a biometric recognition system and comparison to stored biometric data.
Owner:BIOCOM
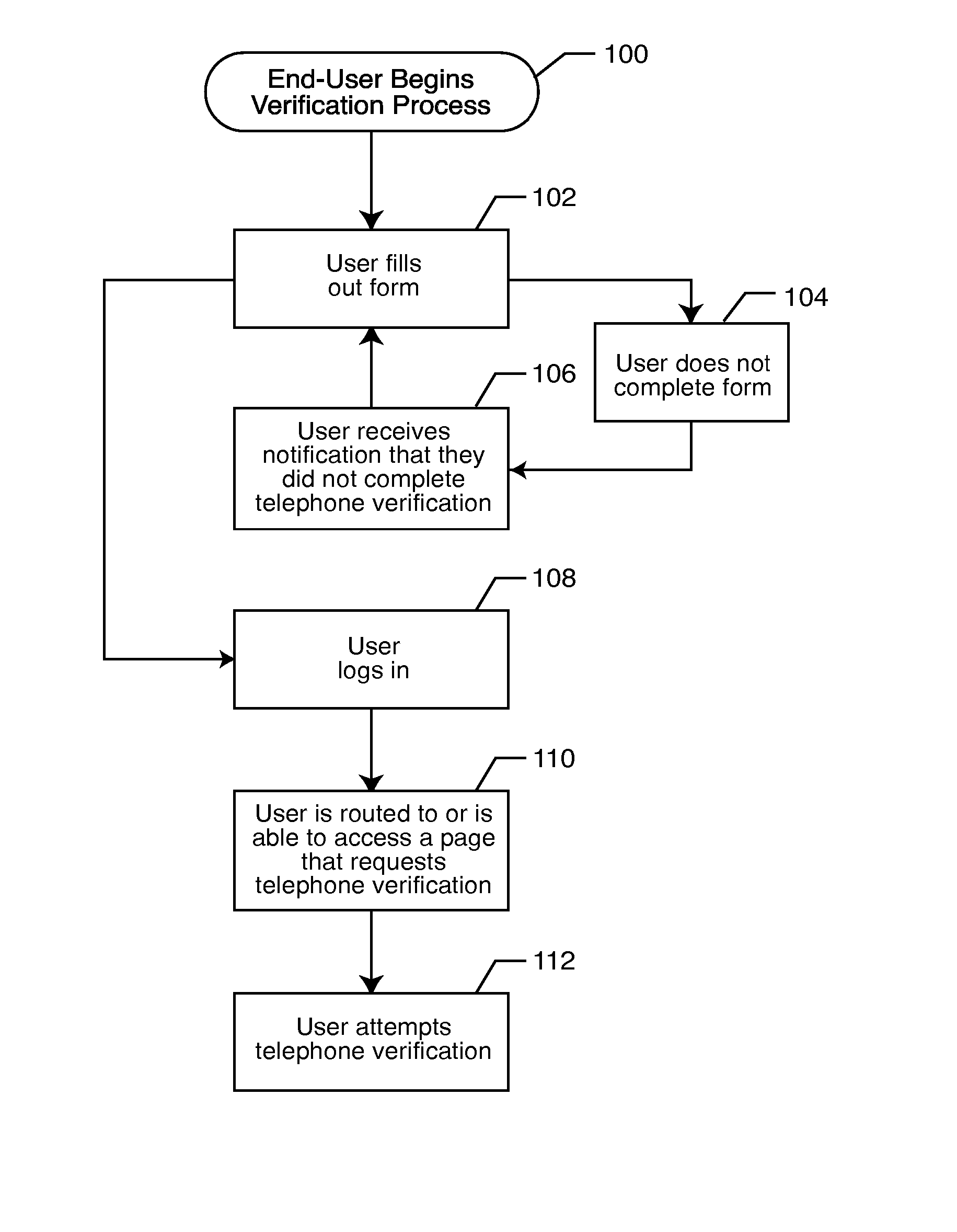
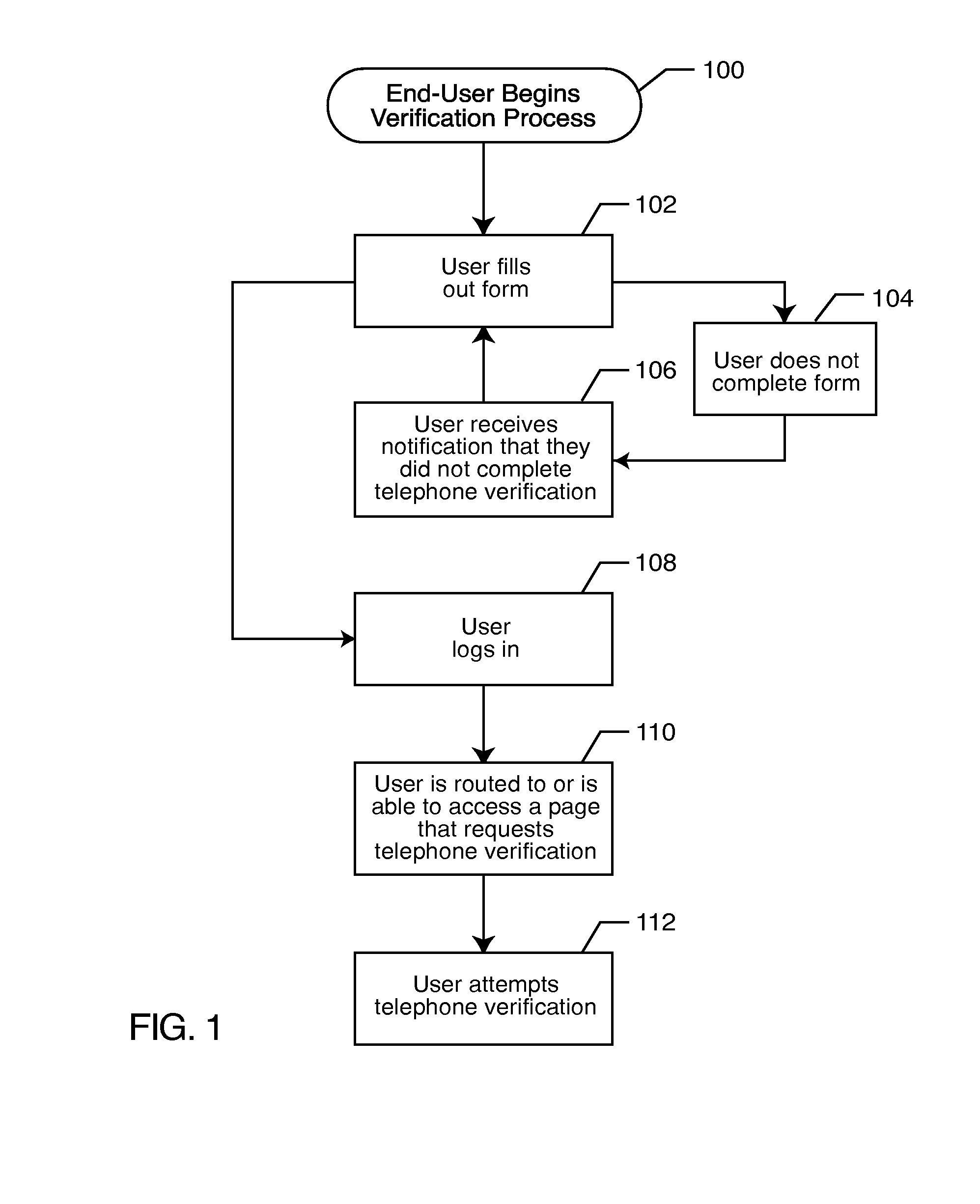
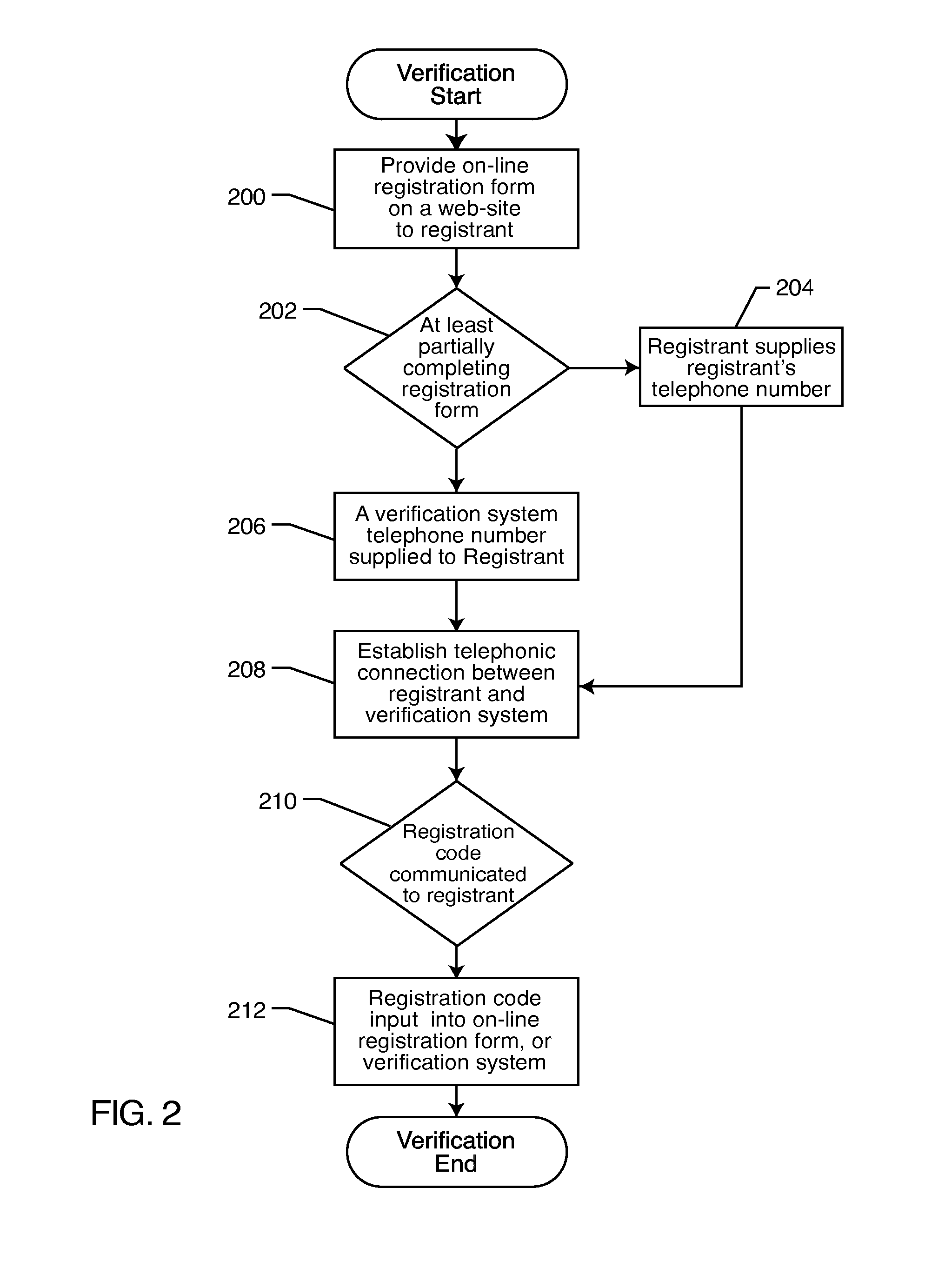
Registration, verification and notification system
ActiveUS20080010687A1Digital data processing detailsUser identity/authority verificationVerification systemNotification system
A registrant provides at least one registrant electronic contact, such as a telephone number, during a registration process. The registrant's information may be compared to a database of such information. The registrant is verified by establishing a connection with the registrant via the registrant contact. The verification code is communicated to the registrant, which is input into an on-line form or a telephone verification system. Notification events are established, and the registrant is notified of the occurrence of a previously established notification event by establishing a connection with the registrant via the registrant contact.
Owner:TELESIGN CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com