Patents
Literature
255results about How to "Verify authenticity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
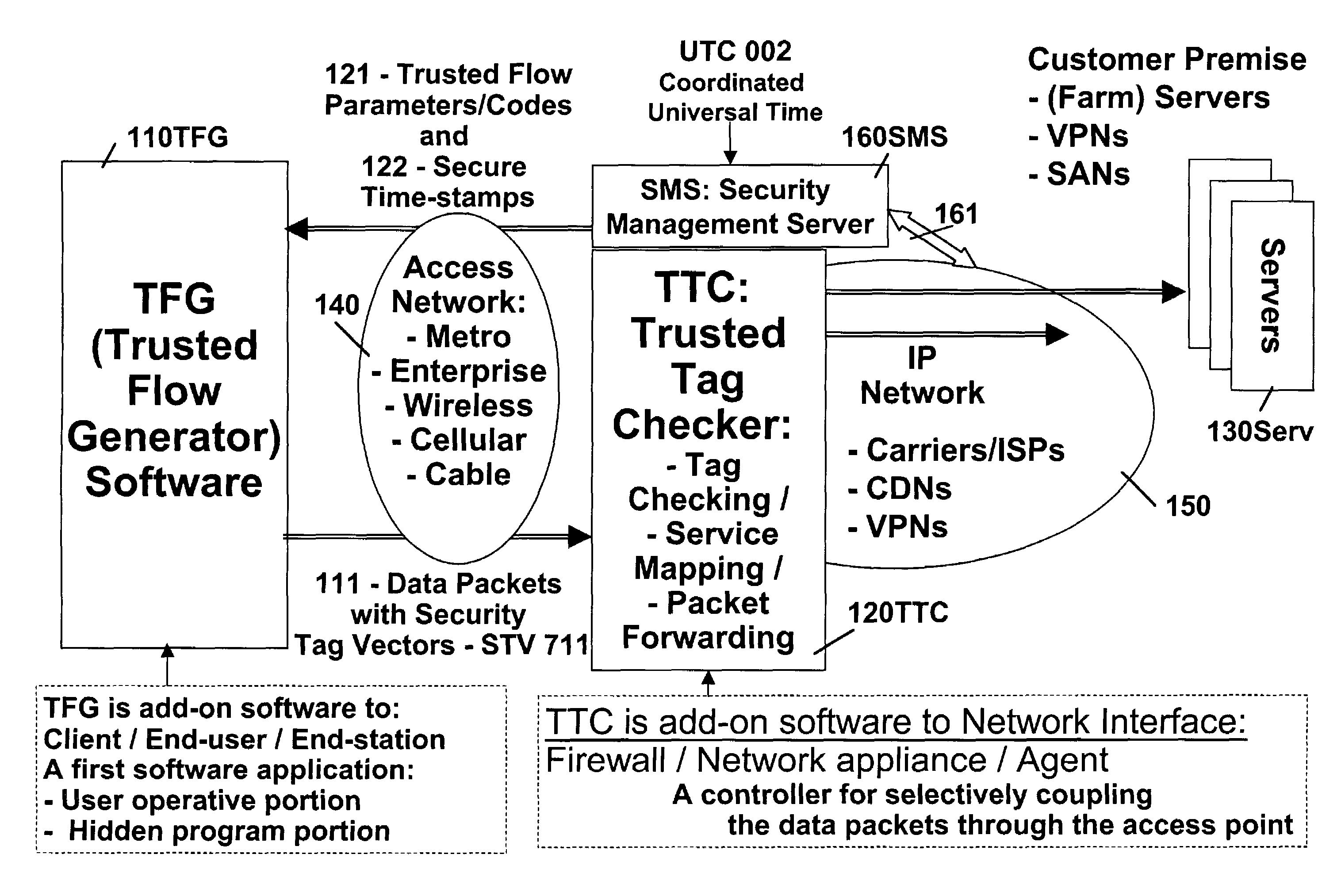
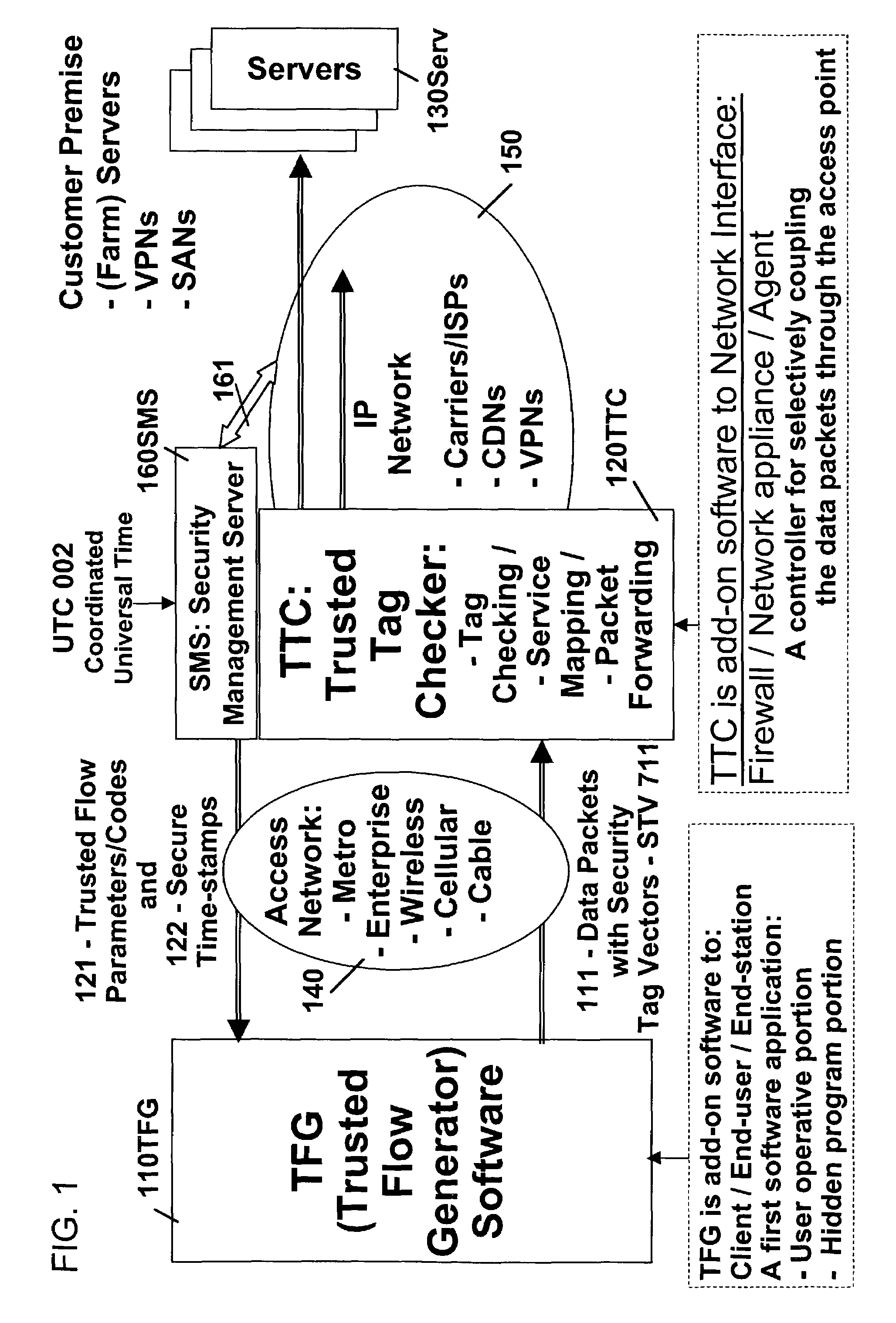
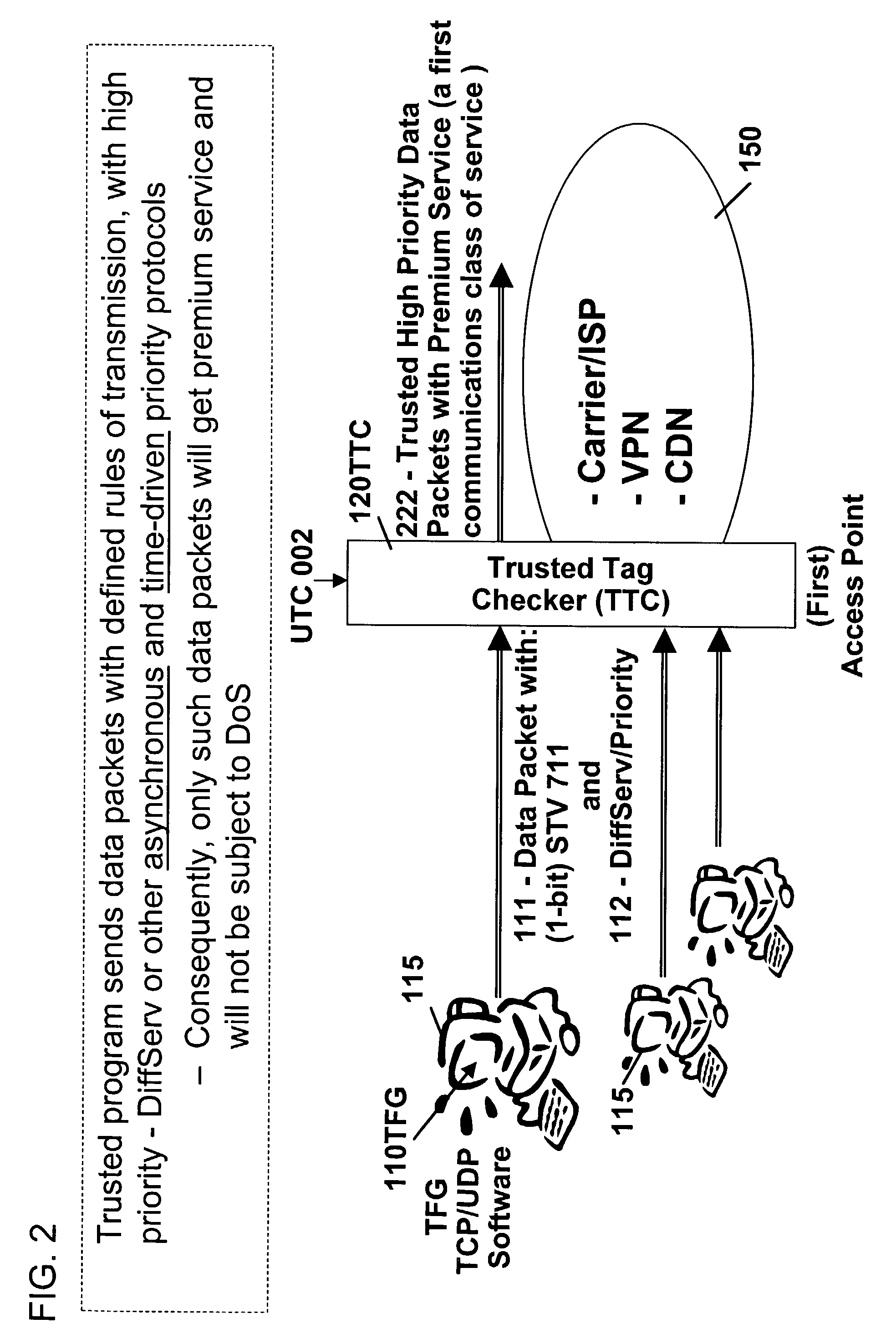
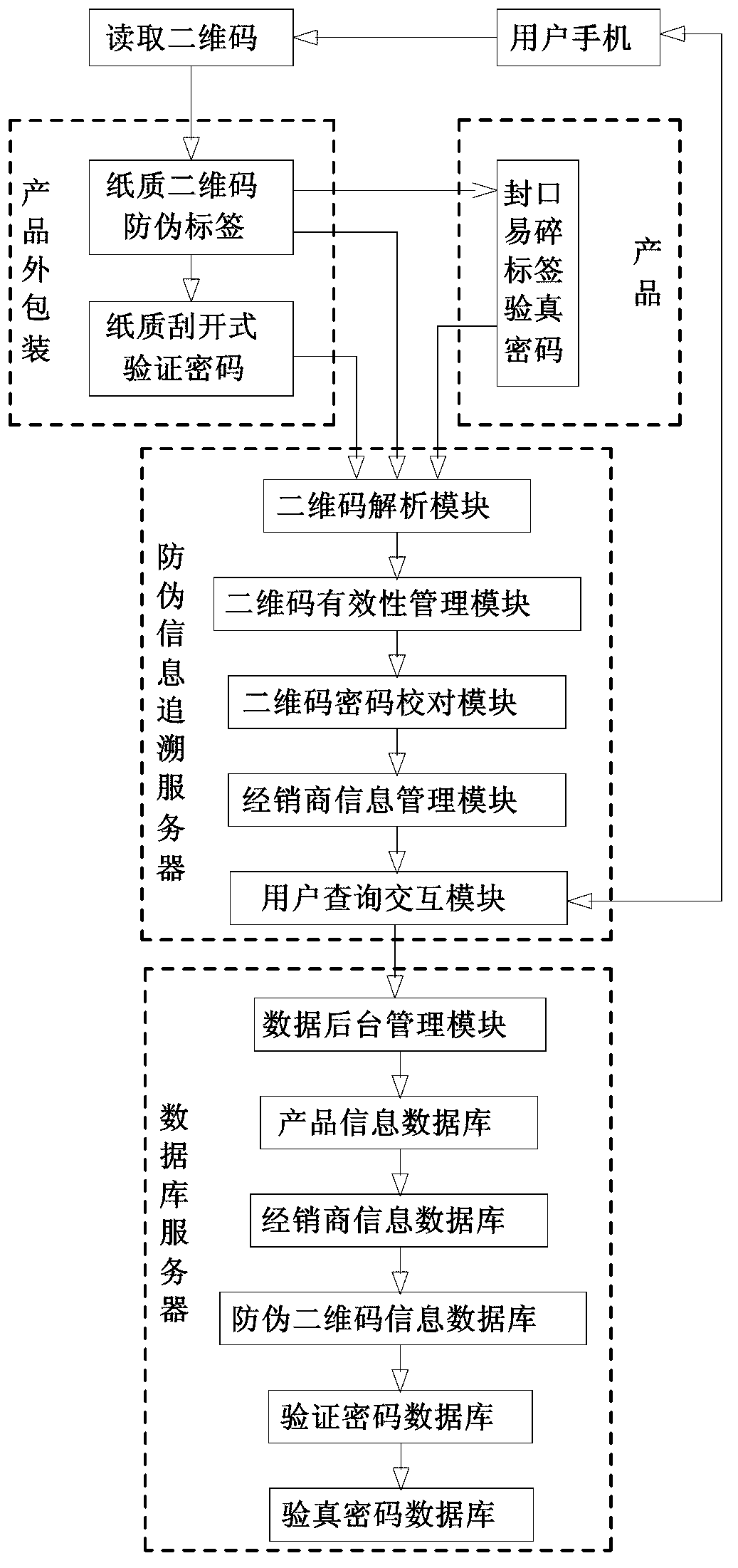
Trusted flow and operation control method
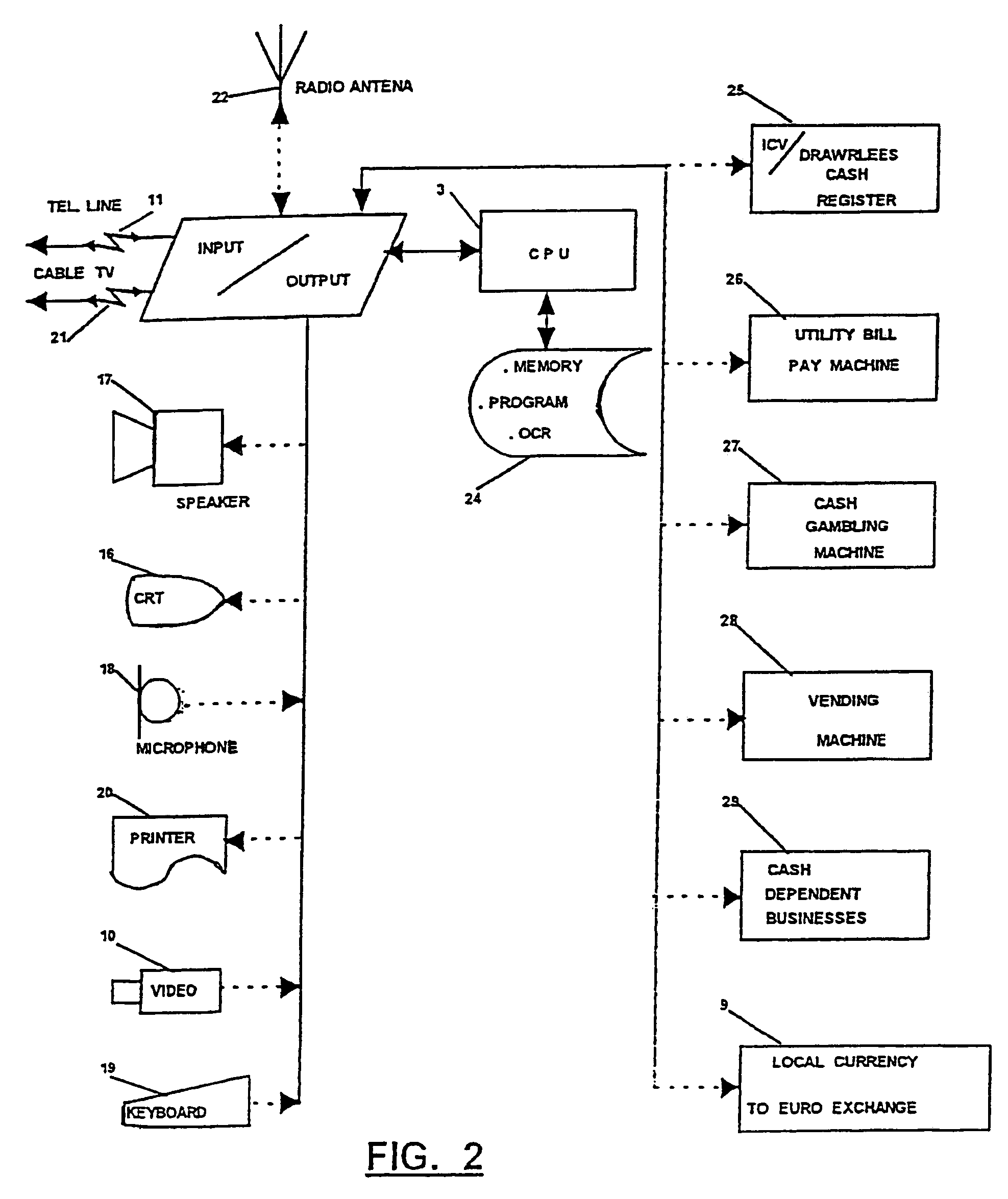
ActiveUS7343619B2Easy to implementFacilitates authentication and meteringData processing applicationsDigital data processing detailsNetwork packetComputer terminal
The objective of this invention is to ensure that programs that generate and send data packets are well behaved. This invention discloses a method and system that consist of an end station and a network interface, such that, the network interface is capable of determining the authenticity of the program used by the end station to generate and send data packets. The method is based on using a hidden program that was obfuscated within the program that is used to generate and send data packets from the end station. The hidden program is being updated dynamically and it includes the functionality for generating a pseudo random sequence of security signals. Only the network interface knows how the pseudo random sequence of security signals were generated, and therefore, the network interface is able to check the validity of the pseudo random sequence of security signals, and thereby, verify the authenticity of the programs used to generate and send data packets.
Owner:ATTESTWAVE LLC
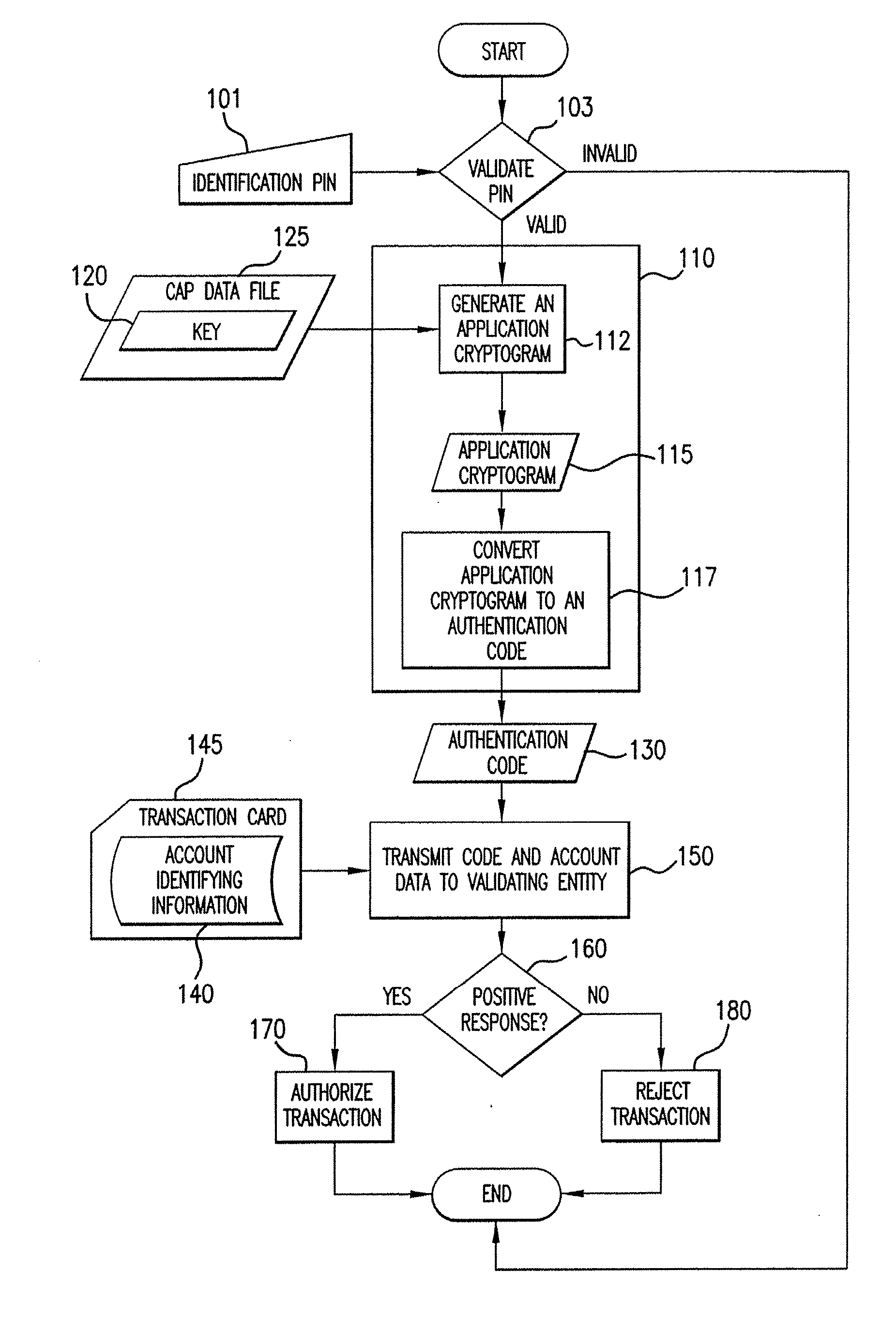
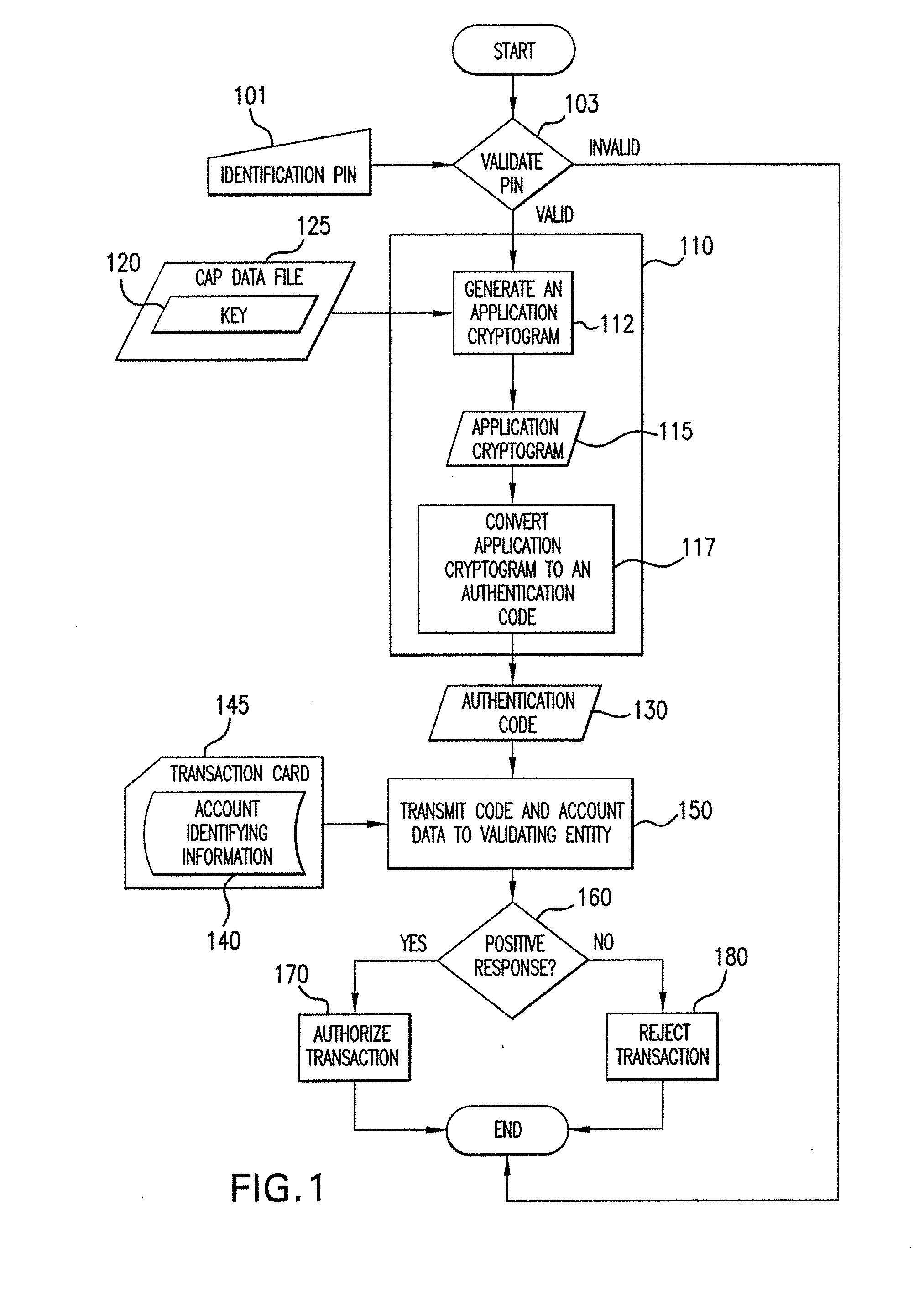
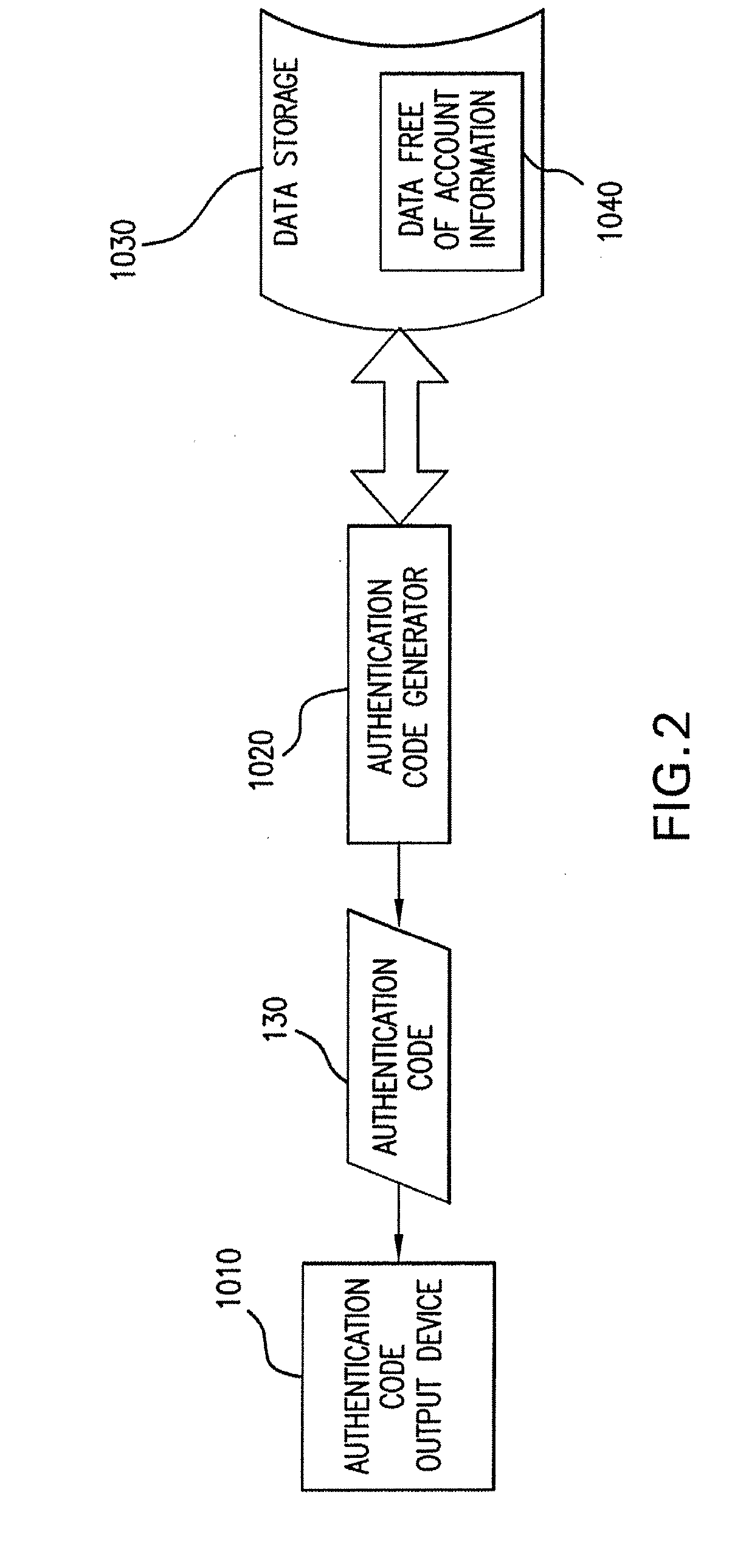
Method And System For Authorizing A Transaction Using A Dynamic Authorization Code
ActiveUS20080040285A1Verify authenticityDigital computer detailsDigital data authenticationMobile deviceAuthorization
A method and apparatus for conducting a secure transaction involving generation of a dynamic authentication code on a mobile device, based on secret data which does not identify an account. The authentication code and financial account identifying information are transmitted to a validating entity, which shares information about the secret data, to authorize the transaction.
Owner:MASTERCARD INT INC
Technologies and methods for security access
ActiveUS20140375422A1Verify authenticityWell formedProgramme controlElectric signal transmission systemsStart timeRemote computer
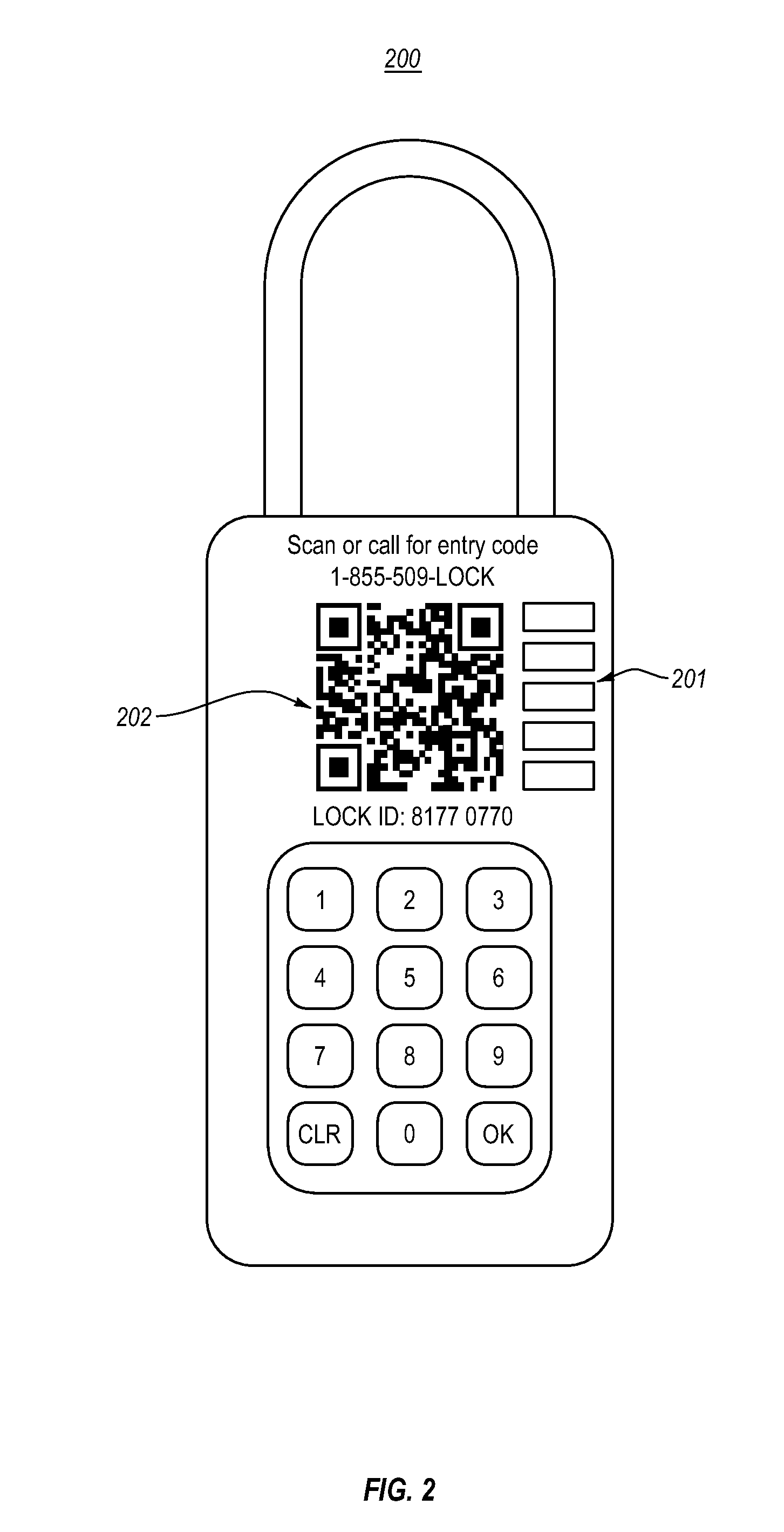
Embodiments herein are directed security access. Embodiments include an electronic lock that executes a time-based cryptographic algorithm to compute a time-based access code. The electronic lock compares the time-based access code with a received access code, and grants access to one or more lock features when the time-based access code matches the received access code. Embodiments also include providing an unlock code, including receiving a lock identifier and a user identifier. The lock identifier and the user identifier are sent to a remote computer system, and an access code for the lock is received from the remote computer system. Embodiments also include an electronic lock that receives and verifies an access code that includes a validity start time and a validity end time. When the current time is within the validity start time and the validity end time, the electronic lock grants access to one or more lock features.
Owner:BRIVO SYST LLC
Streaming Method and System for Processing Network Metadata
InactiveUS20140075557A1Easy to deployImprove system throughputMemory loss protectionError detection/correctionInternet trafficTemplate based
An improved method and system for processing network metadata is described. Network metadata may be processed by dynamically instantiated executable software modules which make policy-based decisions about the character of the network metadata and about presentation of the network metadata to consumers of the information carried by the network metadata. The network metadata may be type classified and each subclass within a type may be mapped to a definition by a unique fingerprint value. The fingerprint value may be used for matching the network metadata subclasses against relevant policies and transformation rules. For template-based network metadata such as NetFlow v9, an embodiment of the invention can constantly monitor network traffic for unknown templates, capture template definitions, and informs administrators about templates for which custom policies and conversion rules do not exist. Conversion modules can efficiently convert selected types and / or subclasses of network metadata into alternative metadata formats.
Owner:NETFLOW LOGIC
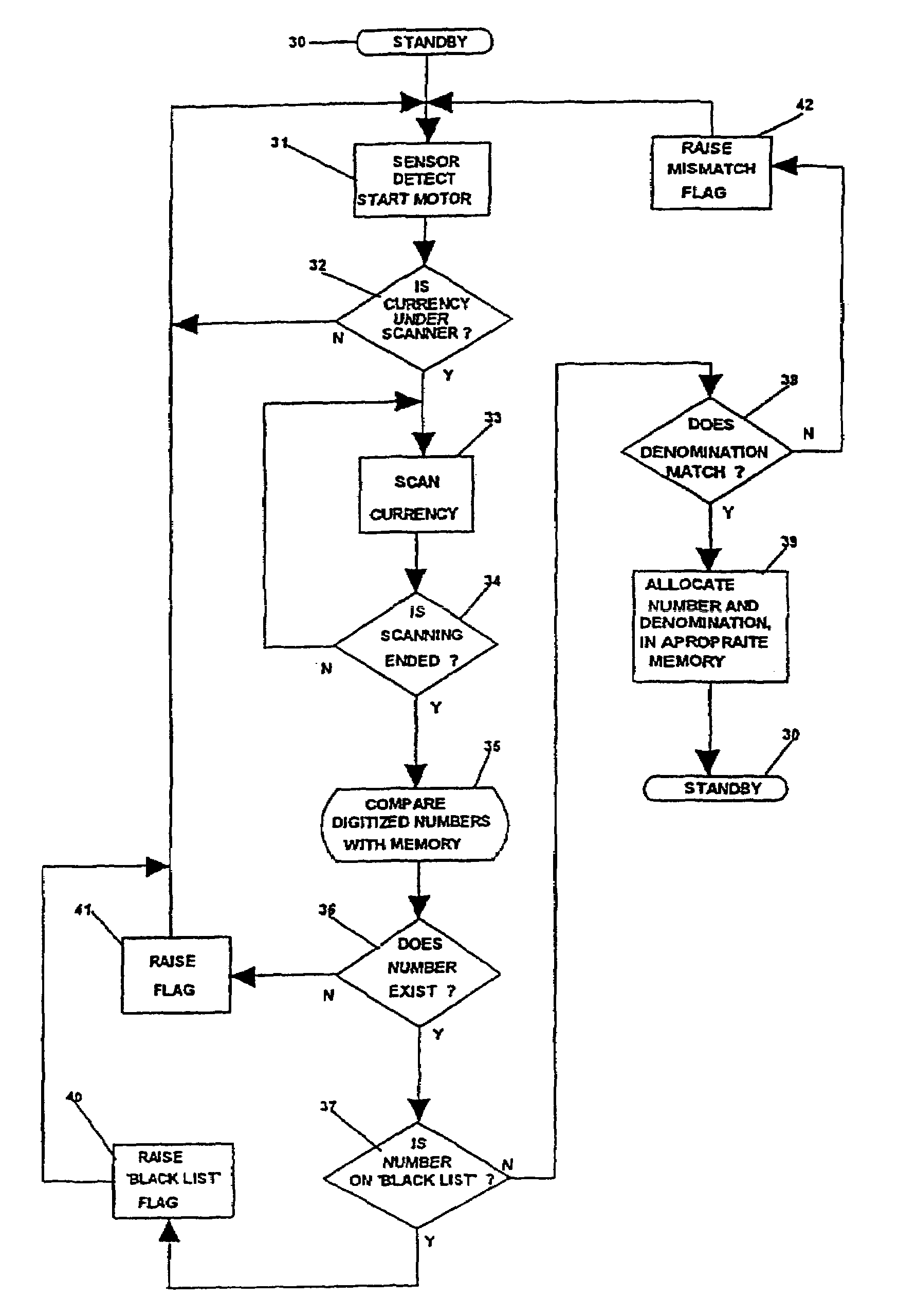
System and method for intelligent currency validation
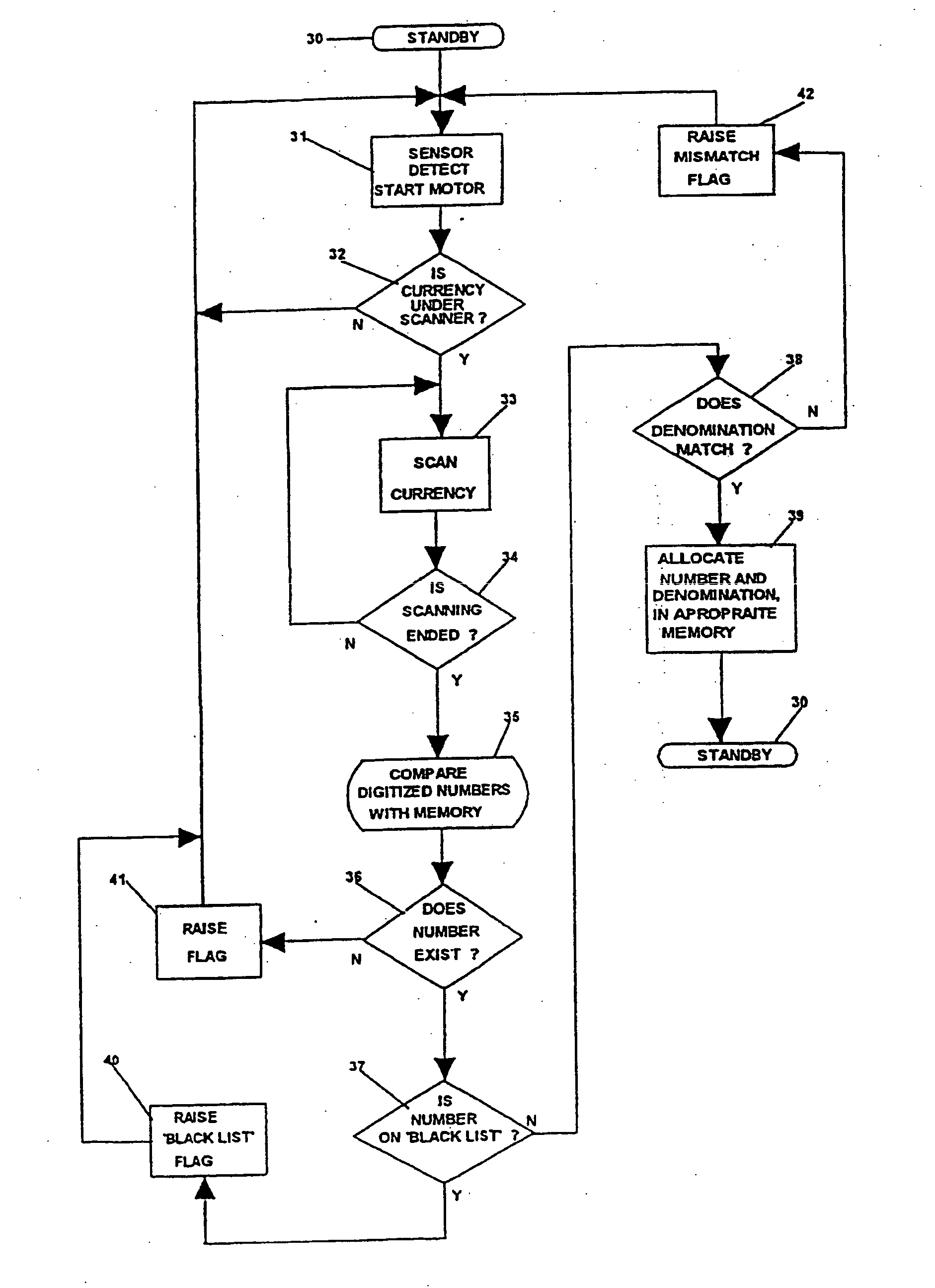
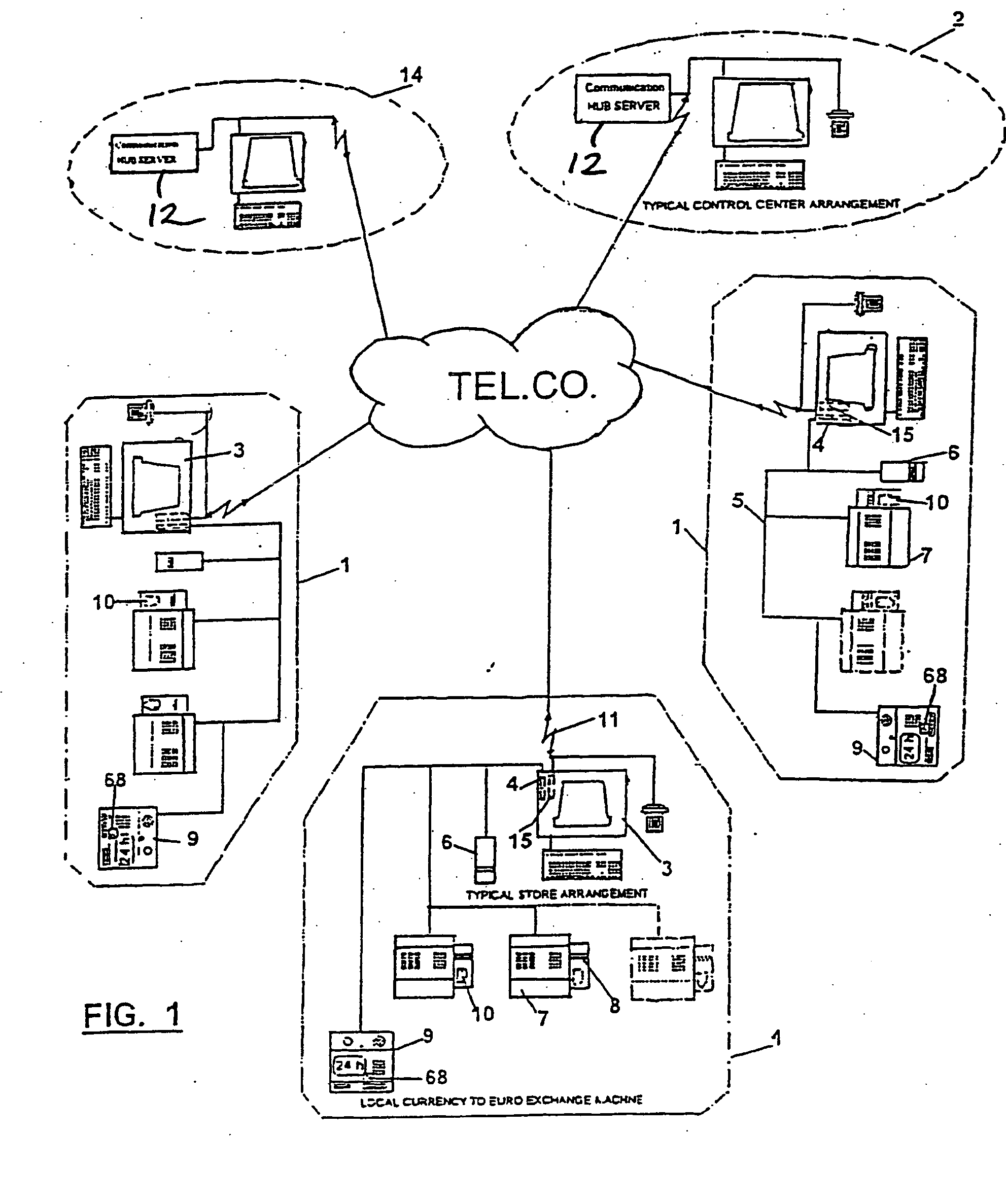
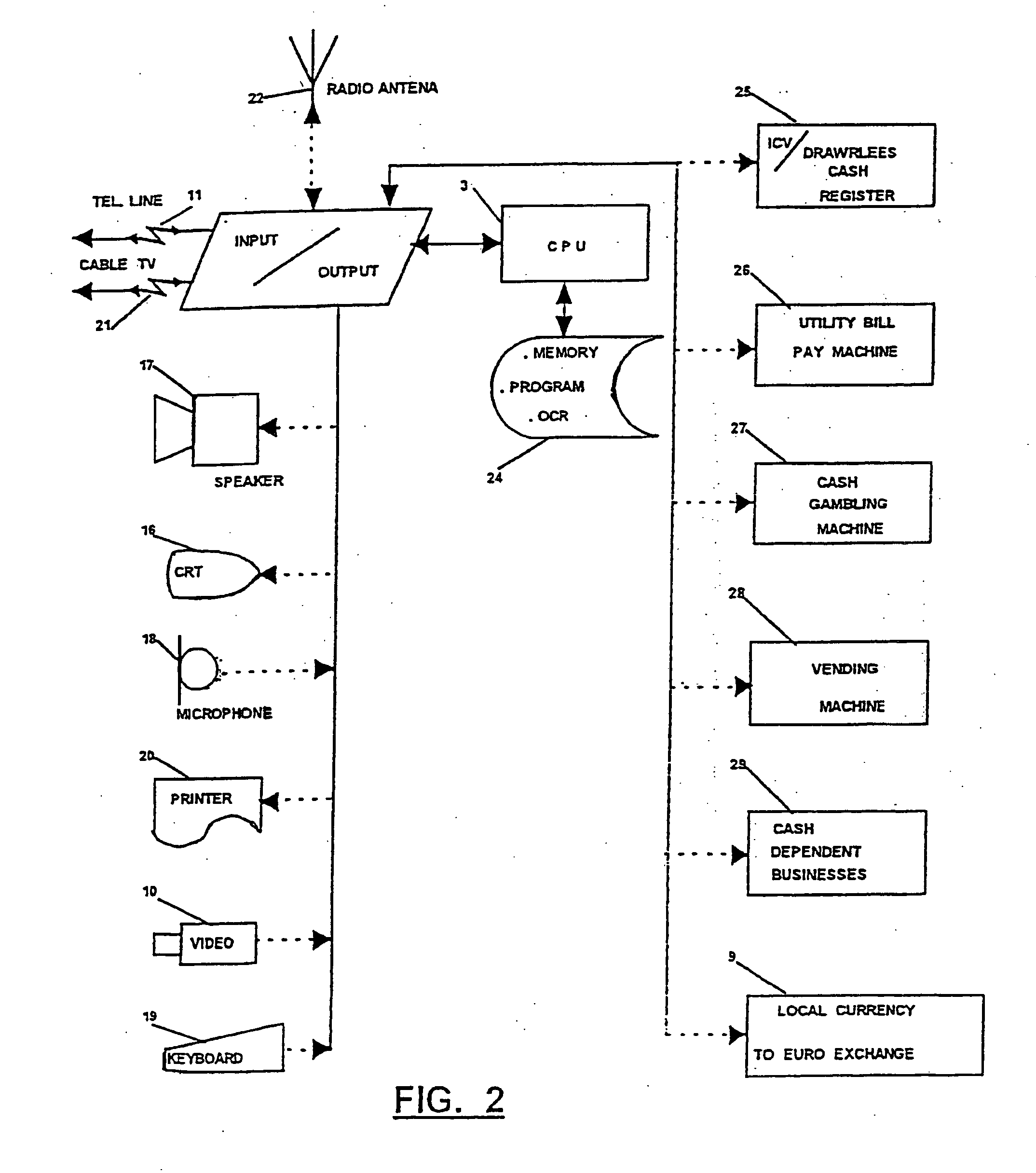
InactiveUS20070172106A1Reduce lossesVerify authenticityPaper-money testing devicesCoin/currency accepting devicesData miningOptical character recognition
Currency is validated by comparing identifying information extracted from the currency, such as a serial number associated with the currency, to identifying information in a list corresponding to invalid currency, such as counterfeit currency. If the extracted identifying information matches identifying information on the list, the currency is deemed invalid. A photograph or thumbprint image can be obtained by a person using the invalid currency to help in later identification of that individual. Optical character recognition techniques can be used to extract the identifying information.
Owner:ICVN INC +1
Tamper evident packaging
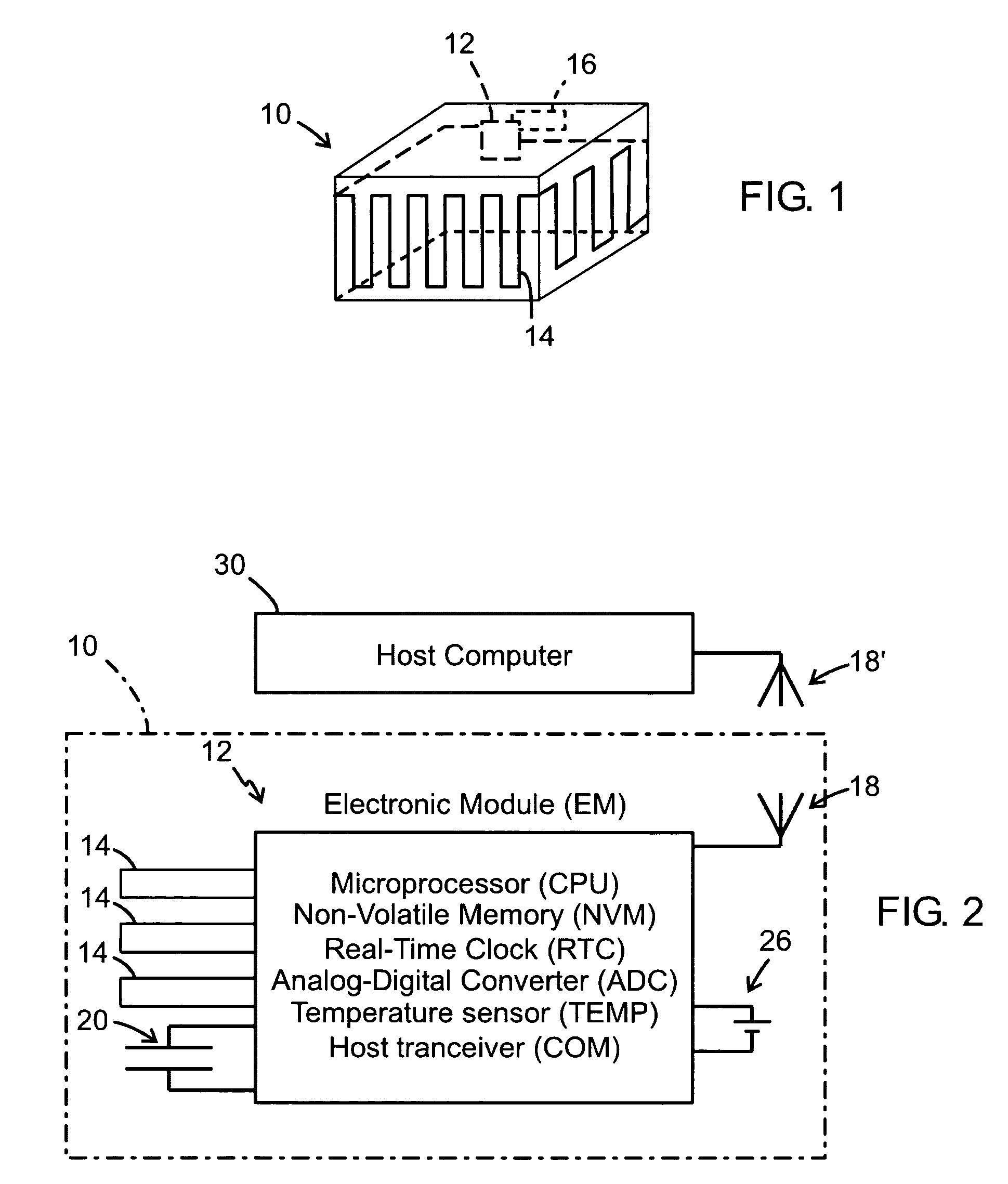
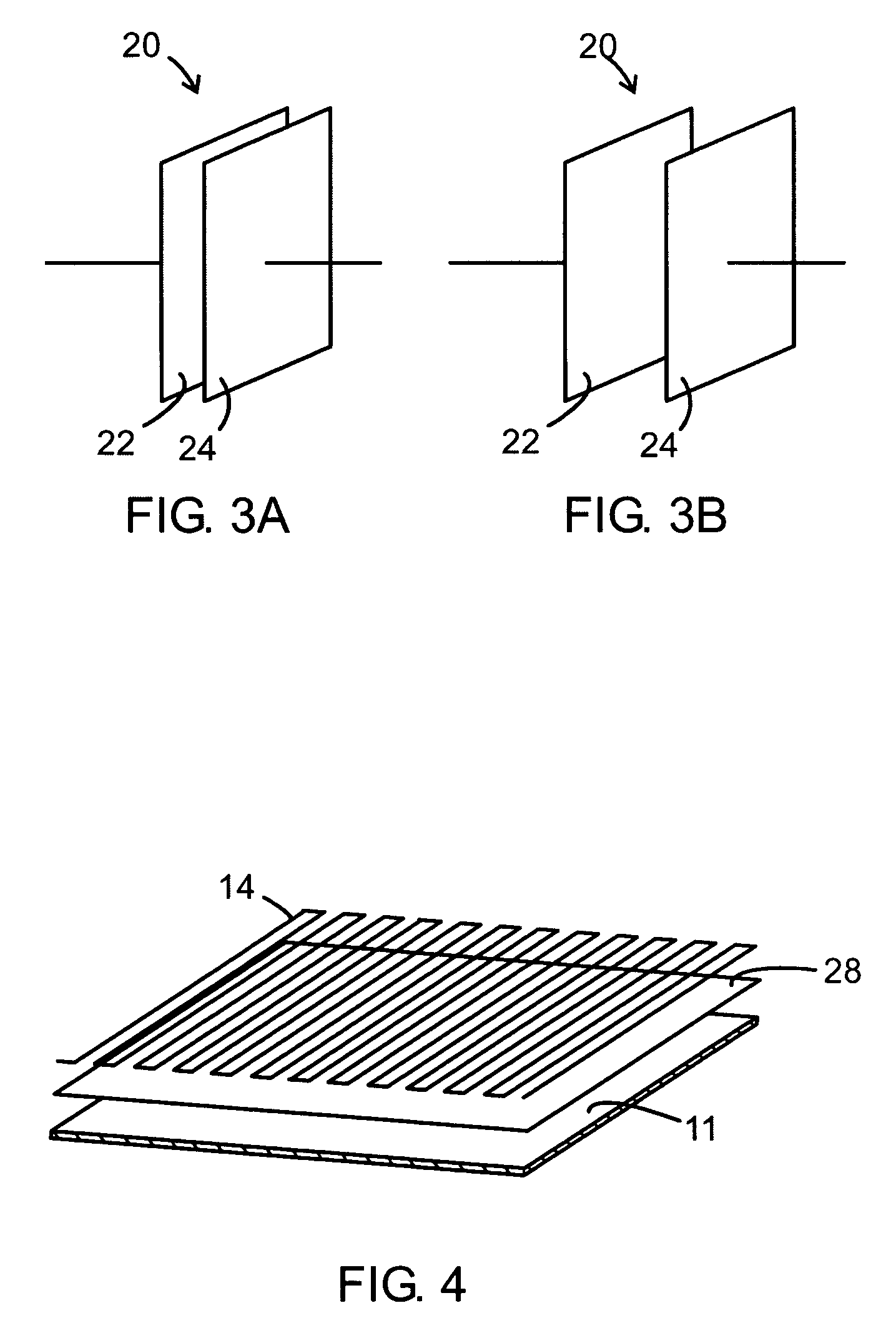
ActiveUS7170409B2Risk minimizationLess secureElectric/electromagnetic visible signallingPackagingLogistics managementTransceiver
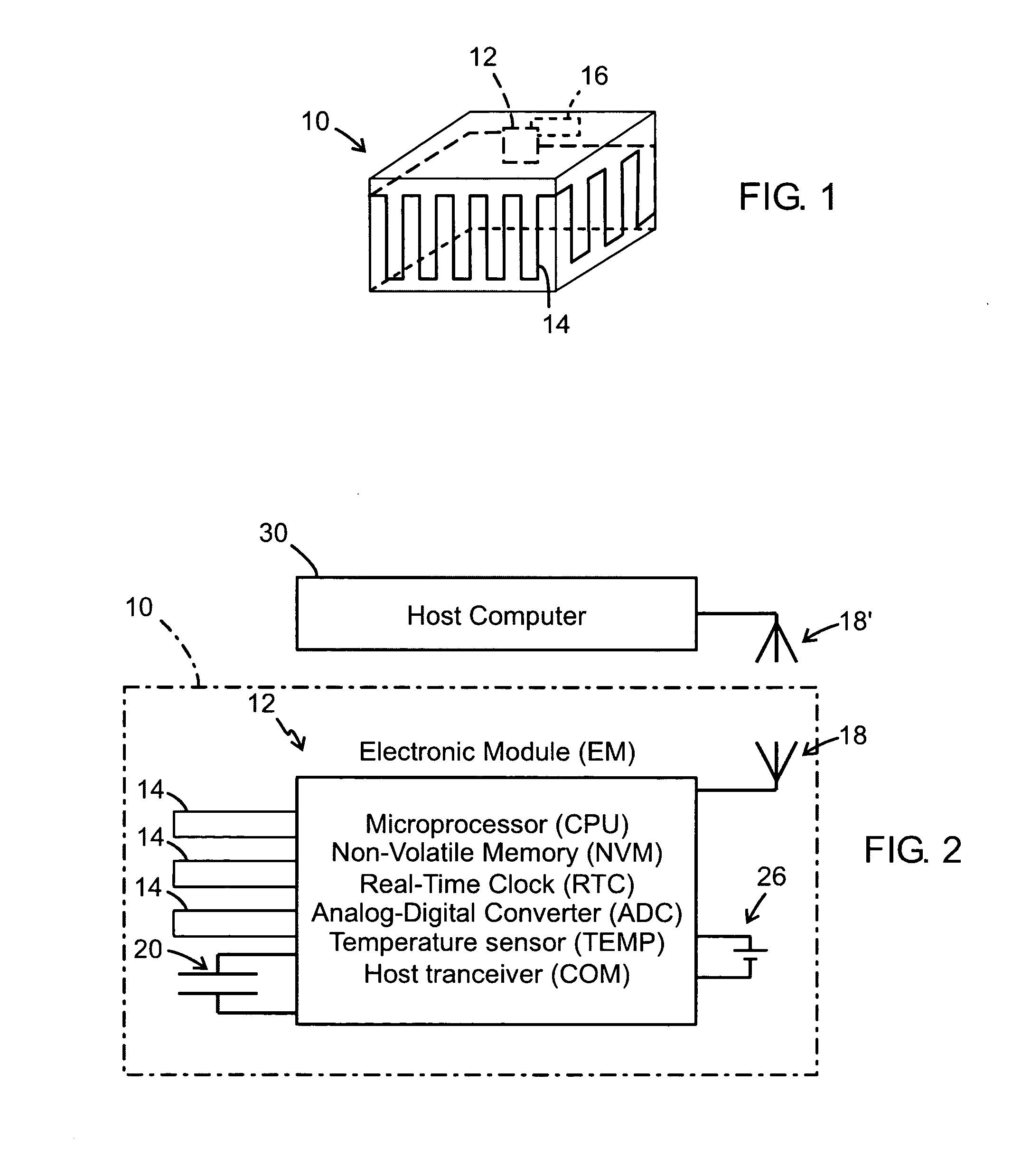
A packaging and a method for monitoring a packaging (10) of a disposable material in a chain of logistics. As an integral part of the packaging, the packaging has an electronic module (12) comprising electric energy supply means, data processing means, data storage nonvolatile memory means for storing information related to the packaging, time keeping means, and data transceiver means for transmitting and receiving said information in communication with a host computer (30). The electronic module also has sensor means (14, 20) for detecting a changed physical condition of the packaging and for signaling information representing said changed physical condition to the electronic module (12) to be stored in the memory means together with a notation of time from the time keeping means.
Owner:SONY CORP
Apparatus and methods for controlling the transmission of messages
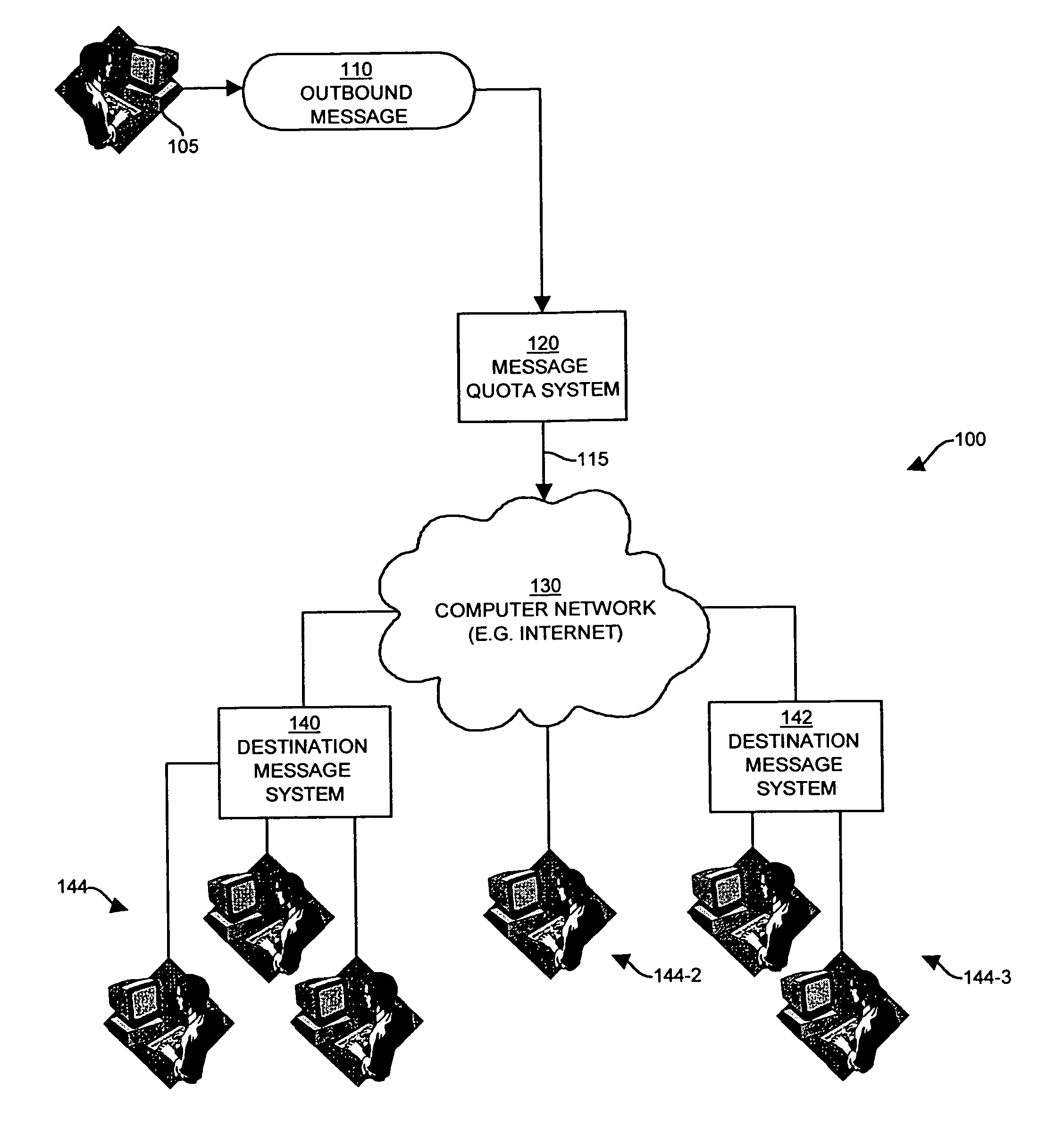
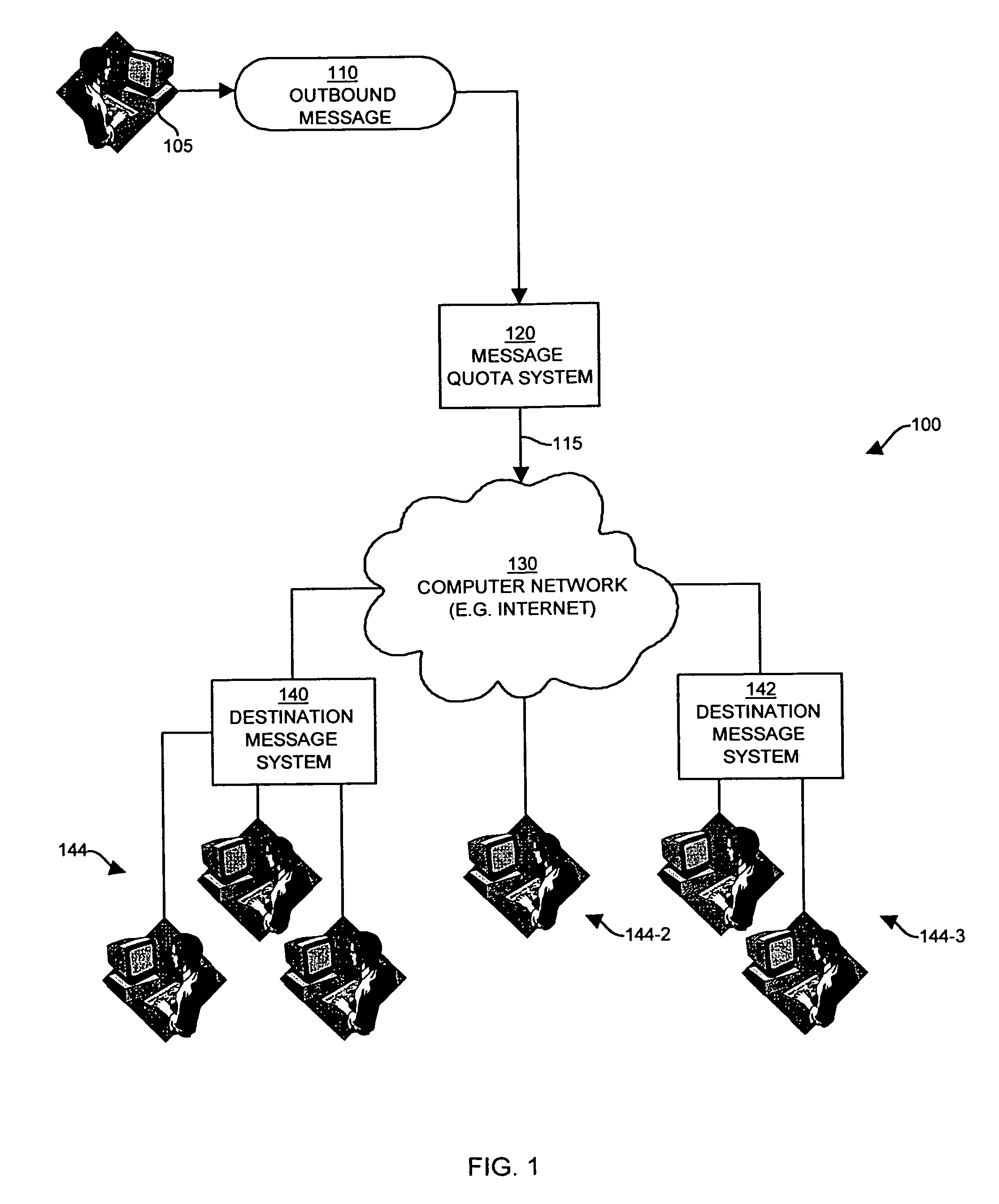
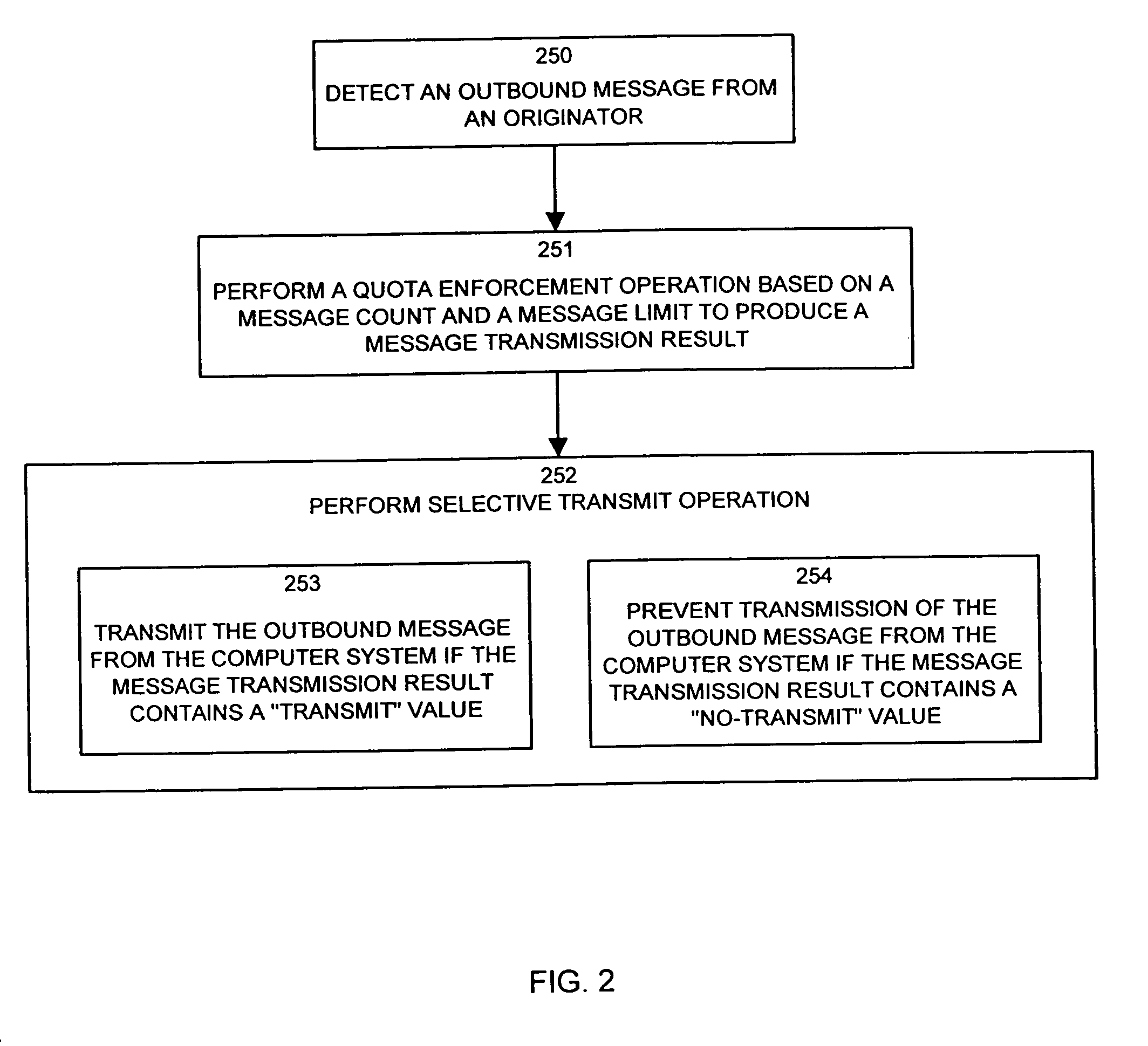
InactiveUS7672998B1Shorten the counting processVerify authenticityMultiple digital computer combinationsData switching networksComputer usersNetwork addressing
The invention provides systems, mechanisms and techniques for controlling transmission of outbound messages, such as e-mail or other types of messages, onto a computer network from an originator computer system. Connection equipment can authenticate and authorize the connection for the computer user and can capture and map originator network address information assigned to the originator computer system. A quota server can then determine if the message count exceeds the message limit for the originator identity associated with the outbound message Embodiments of the invention control message transmission from a sending or origination point prior to the messages being transmitted on the computer network, resources of a computer network are conserved and these embodiments prevent computer users from transmitting large amounts of outbound messages in excess of the message limits.
Owner:ZIPLINK
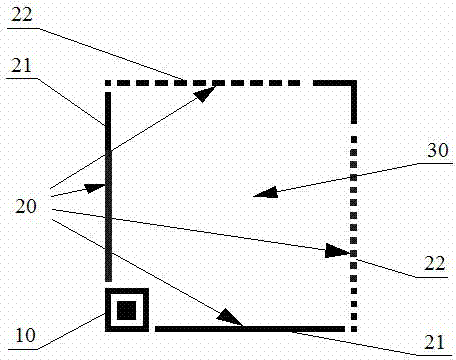
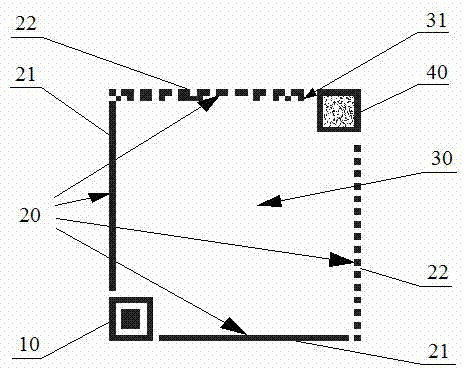
Construction verification method and device capable of verifying security two-dimensional code offline
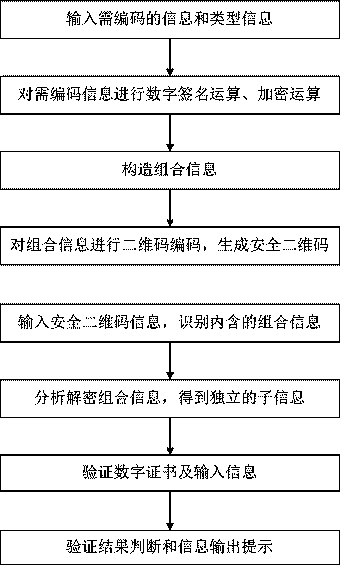
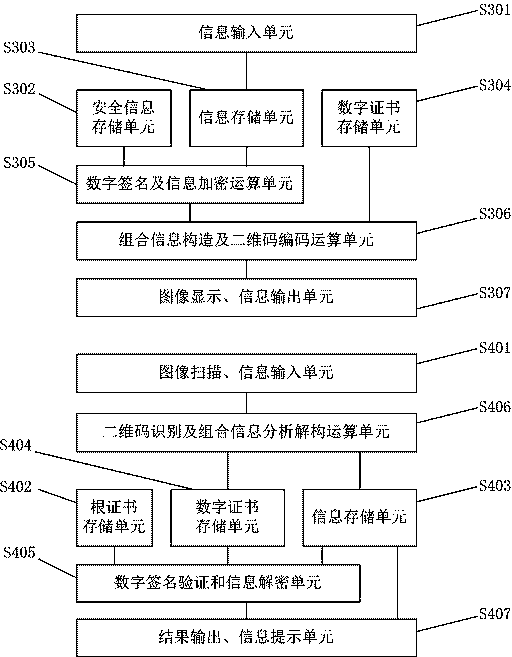
ActiveCN106452756AEasy to useCannot be tampered withKey distribution for secure communicationUser identity/authority verificationInformation analysisEffective time
Embodiments of the invention provide a construction verification method and device capable of verifying a security two-dimensional code offline. The method comprises the following steps of inputting information that needs coding and type information, carrying out digital signature operation and encryption operation on the input information according to an information release type, constructing combination information, and encoding to generate a security two-dimensional code which can be verified off-line according to a two-dimensional code coding rule; inputting the information of the security two-dimensional code and identifying included combination information and type information, analyzing and decoding the combination information to obtain independent sub-information according to the type information of the two-dimensional code, and verifying digital certificate effectiveness information, a digital signature of the input information and an effective time limit of the input information; and if all verifications pass, showing that the offline verification of the security two-dimensional code is correct and the coding information source of the security two-dimensional code is credible, otherwise showing that the information release source of the security two-dimensional code is incredible. The method and the device have the beneficial effects that the security two-dimensional code cannot be tampered, counterfeited and denied, the public or private information can be released, and the integrity of the information of the security two-dimensional code and the authenticity of the source can be verified offline without a network connection.
Owner:王栋
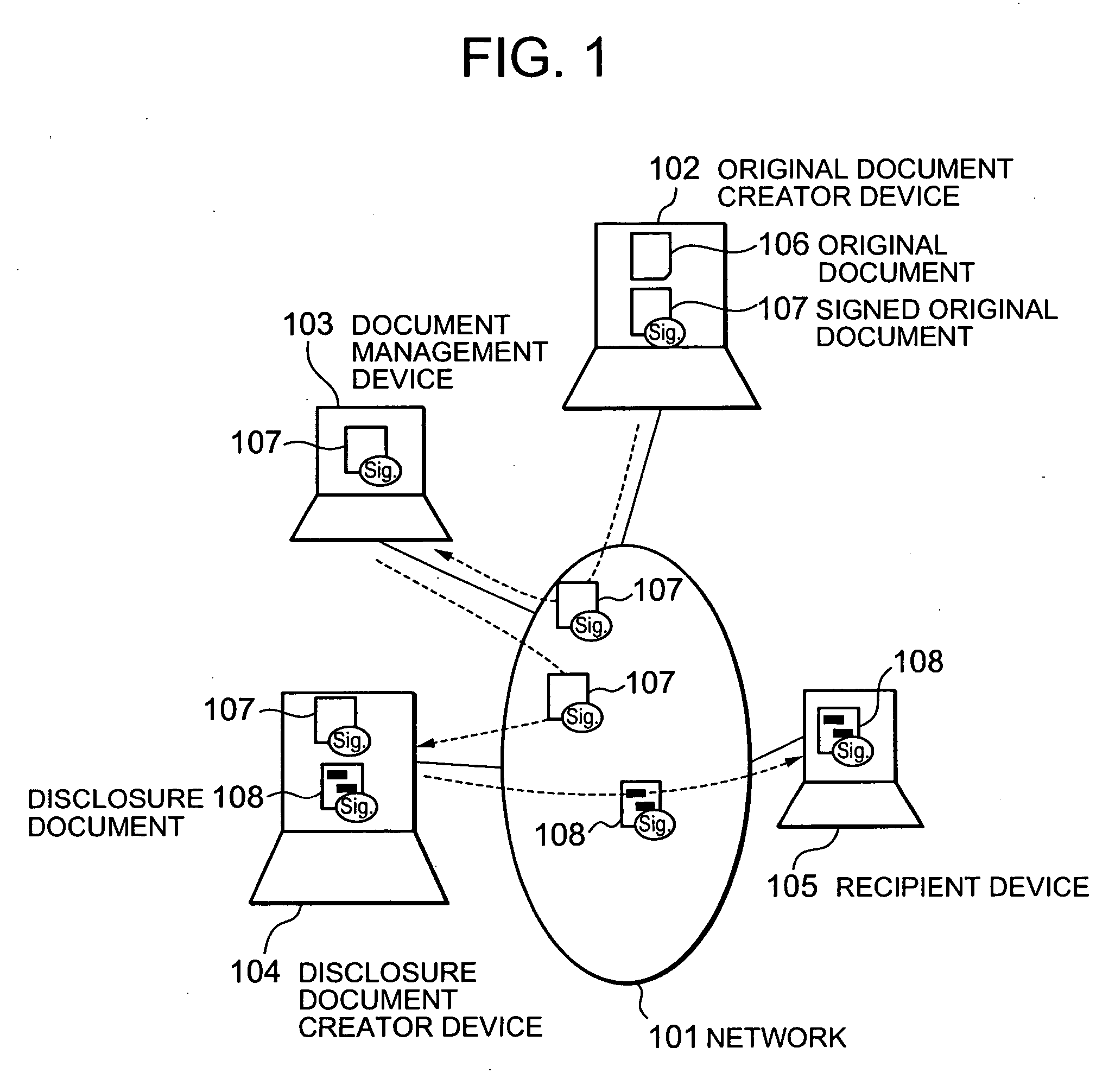
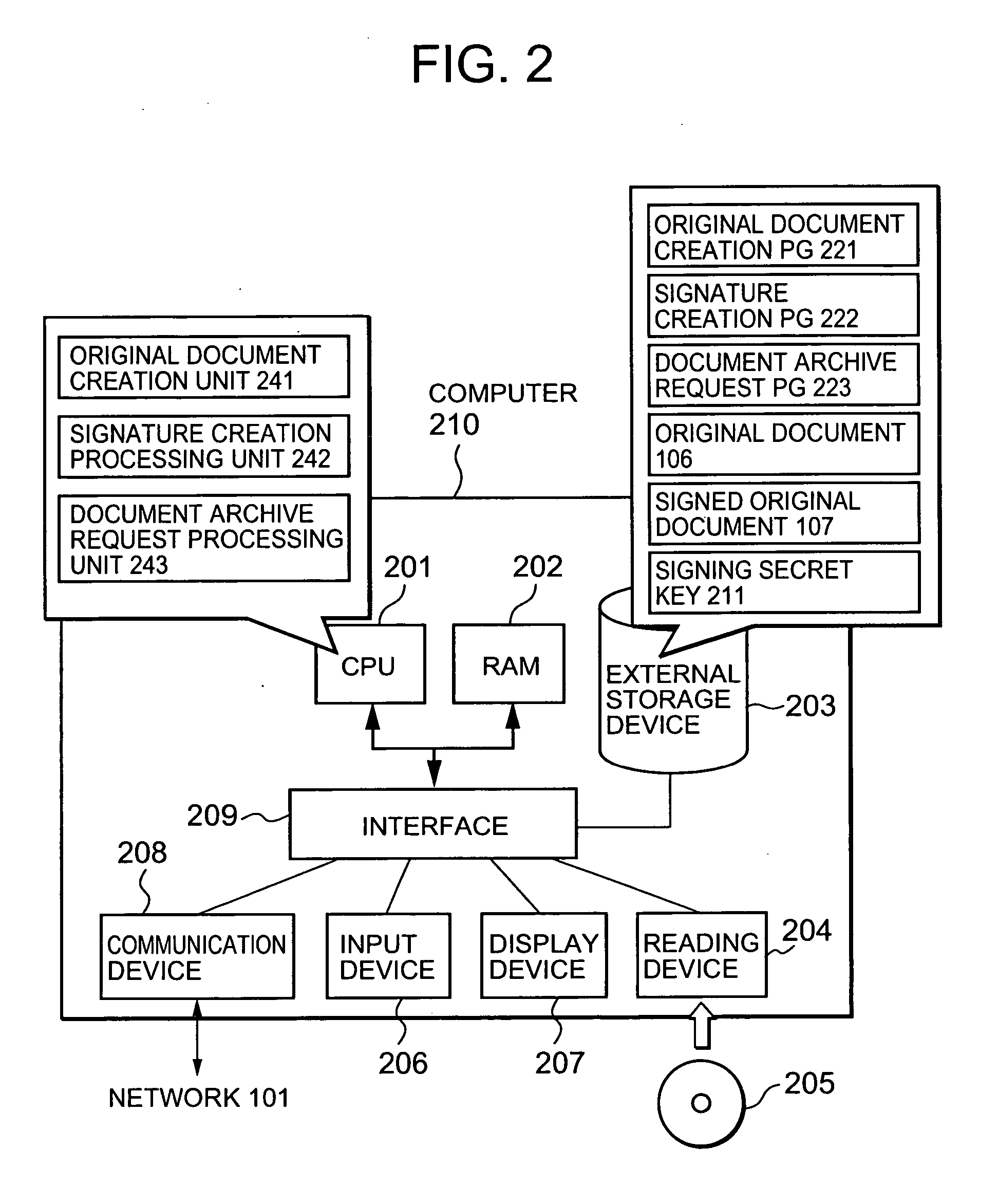
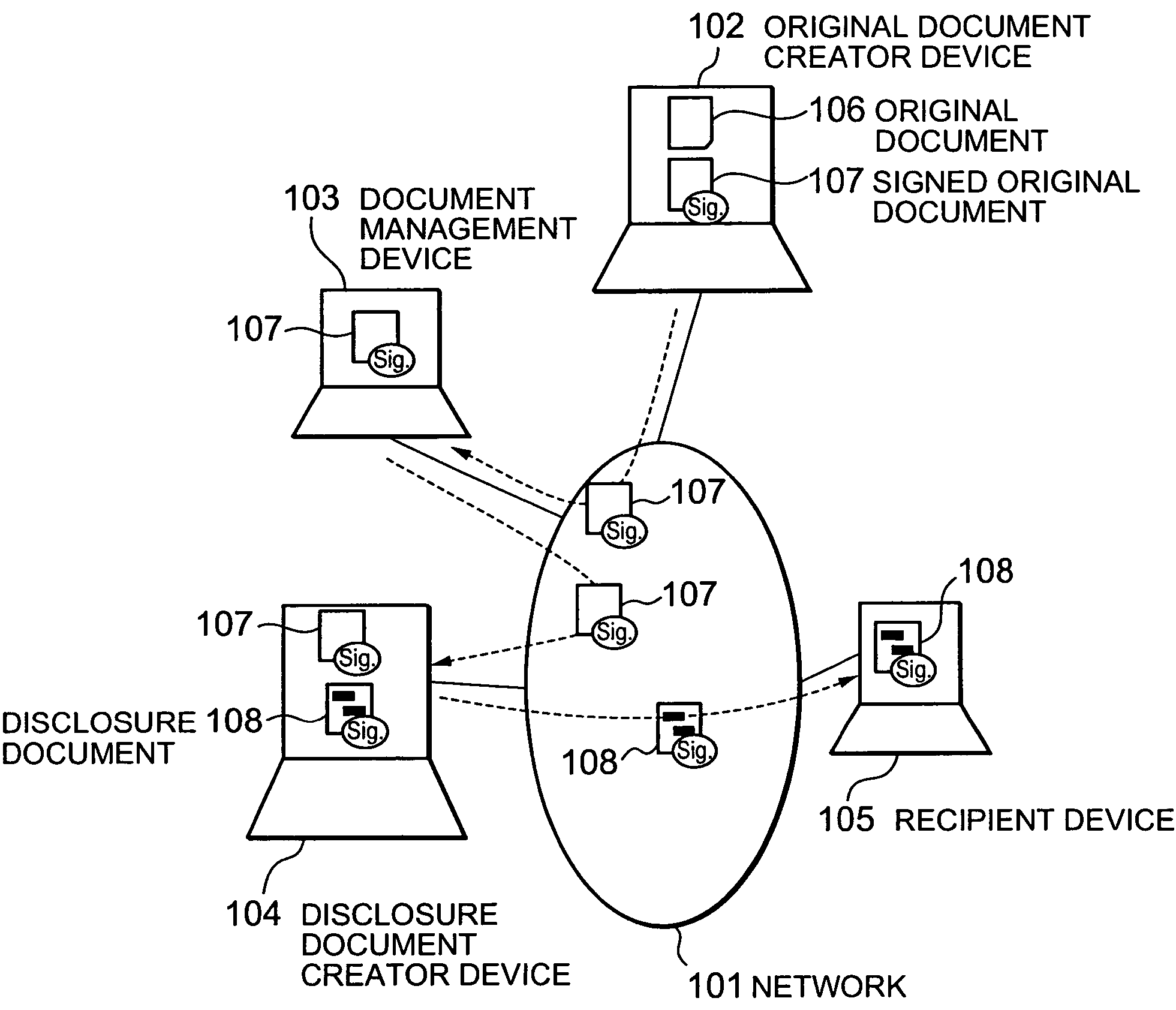
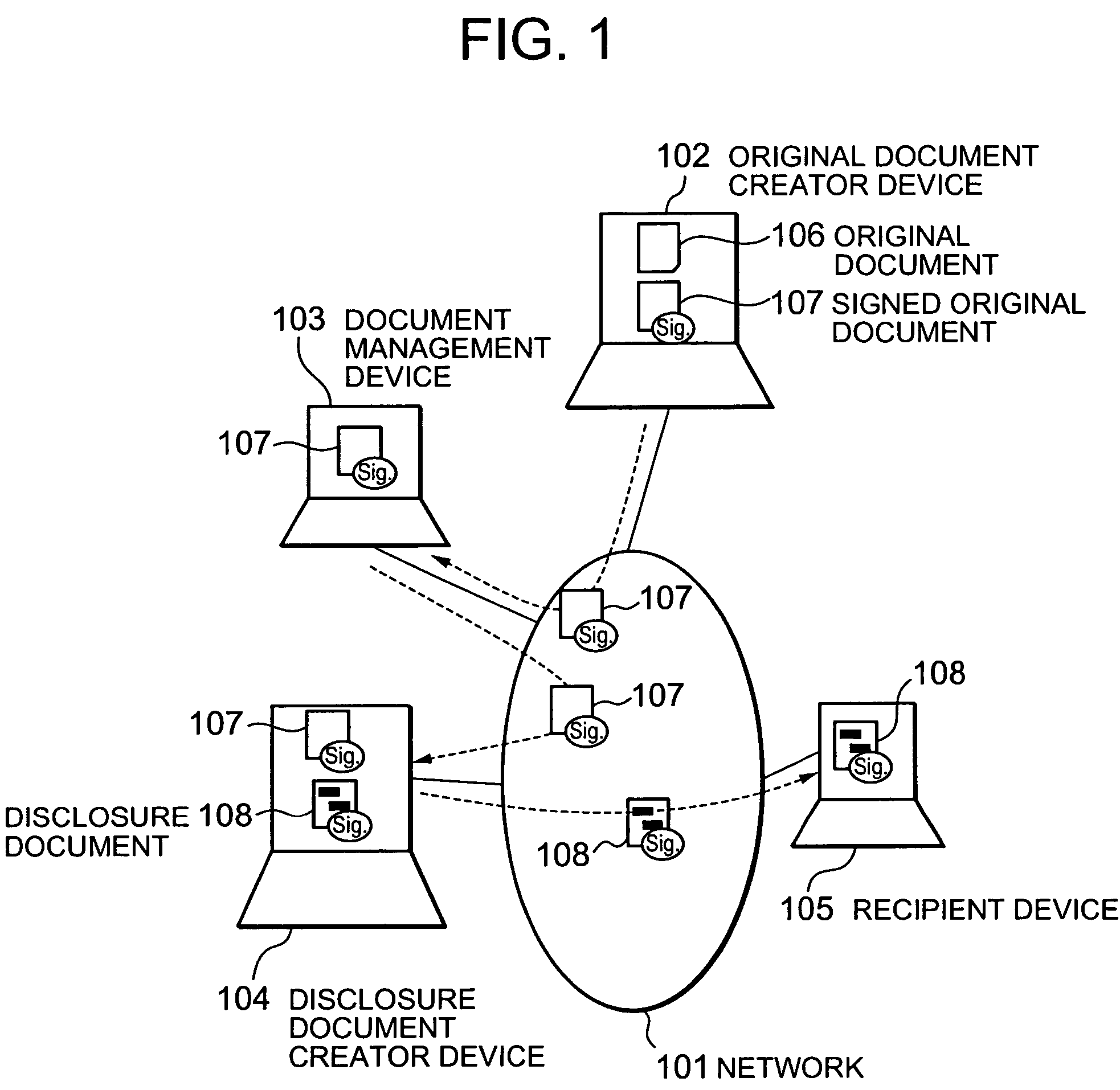
Electronic document authenticity assurance method and electronic document disclosure system
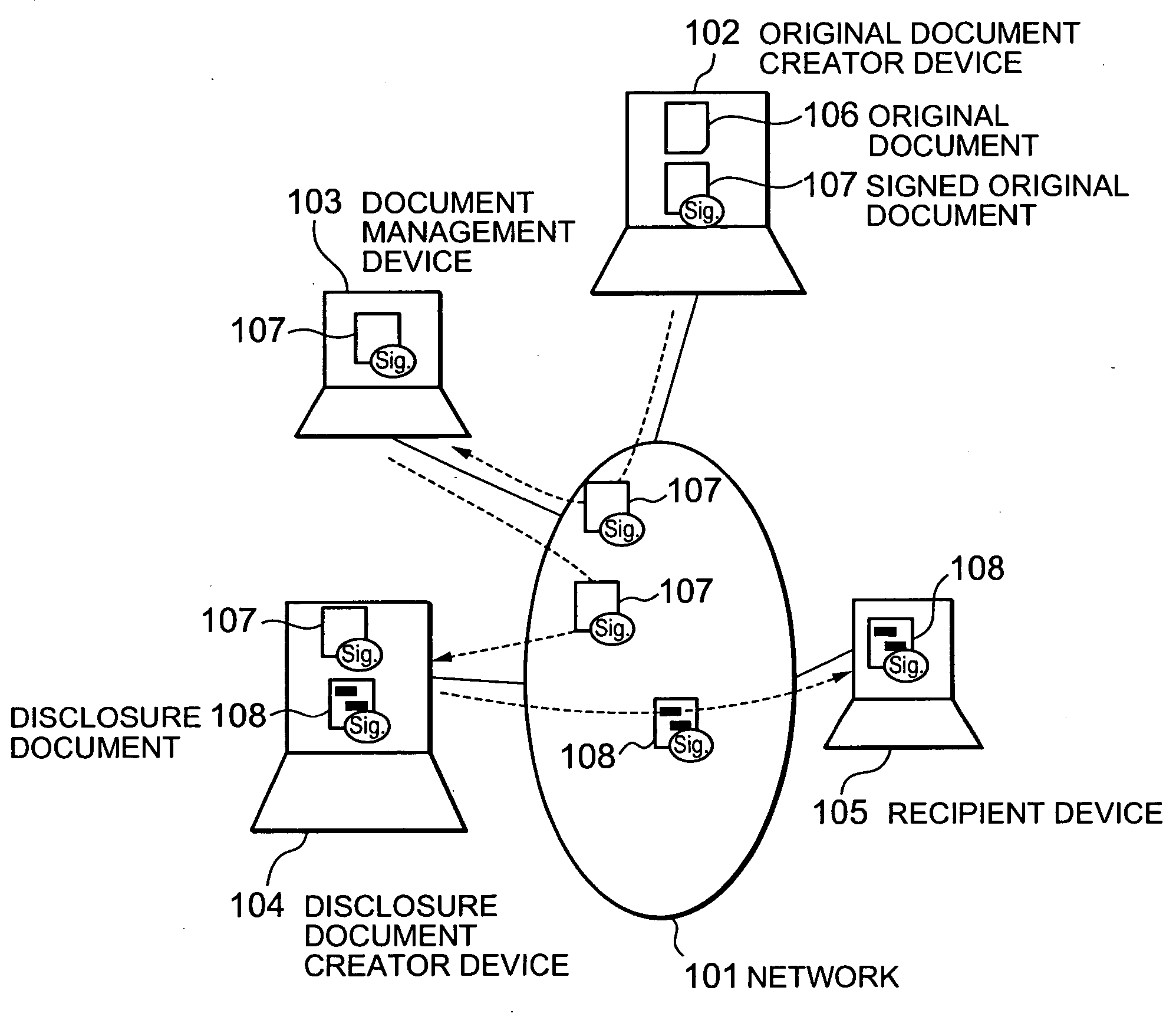
InactiveUS20050015600A1Verify authenticityUser identity/authority verificationUnauthorized memory use protectionPaper documentElectronic document
An electronic document authenticity assurance technique and an information disclosure system both of which can compatibly realize the assurance of the authenticity of disclosure documents and the deletion of information inappropriate for disclosure. An electronic document is divided into constituent elements and an electronic signature is affixed to an arbitrary subset of a set including all the constituent elements. Otherwise, an electronic signature is affixed to data obtained by binding each of the constituent elements to information specifying the relationship between a respective one of the constituent elements and the structure of the electronic document. Otherwise, the hash values of the respective constituent elements are calculated and an electronic signature is affixed to data obtained by binding the calculated hash values together. Otherwise, random numbers generated for the respective constituent elements are bound together, then the hash values of the respective random-numbered constituent elements are calculated, and then an electronic signature is affixed to data obtained by binding the calculated hash values together.
Owner:HITACHI LTD
System and method for intelligent currency validation
InactiveUS7454049B2Verify authenticityPaper-money testing devicesCoin/currency accepting devicesData miningOptical character recognition
Currency is validated by comparing identifying information extracted from the currency, such as a serial number associated with the currency, to identifying information in a list corresponding to invalid currency, such as counterfeit currency. If the extracted identifying information matches identifying information on the list, the currency is deemed invalid. A photograph or thumbprint image can be obtained by a person using the invalid currency to help in later identification of that individual. Optical character recognition techniques can be used to extract the identifying information.
Owner:ICVN INC +1
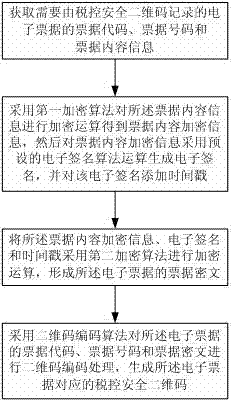
Tax-control safety two-dimensional code encoding and decoding processing method
InactiveCN103198344APromote exchangeEasy transferRecord carriers used with machinesSensing by electromagnetic radiationProgramming languageThe Internet
The invention discloses a tax-control safety two-dimensional code encoding and decoding processing method. By means of the method, a tax-control safety two-dimensional code generated through the method has a plurality of levels of tax-control safety protection, anti-counterfeiting and safety performance of the tax-control safety two-dimensional code is improved, electronic signature information carried by the code can serve as a tool carrying out off-line authenticity identification on the condition of separation from the internet, the problem that when electronic bill information is transmitted through the two-dimensional code in the prior art, the authenticity identification is limited by network conditions and time is solved, and tax-control safety of the tax-control safety two-dimensional code is effectively enhanced. The tax-control safety two-dimensional code decoding processing method not only can prevent illegal leakage of useful information in the tax-control safety two-dimensional code, but also can immediately identify authenticity of the electronic bill information contained in the tax-control safety two-dimensional code off-line on the condition that the internet is not relied on, and therefore the tax-control safety of the tax-control safety two-dimensional code during the decoding process is further improved.
Owner:CHONGQING FARSIGHT PRINTING +1
Communication apparatus for transmitting or receiving a signal including predetermind information
InactiveUS20130230173A1Improve securityVerify authenticityKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareSystems management
A storage stores a common key table containing a plurality of kinds of common keys usable for the communications with other communication apparatuses within the same system, its own identification information, and an update key associated with the identification information. The transmitter transmits the identification information to a system management apparatus for managing the common key table used in the system, the identification information on the communication apparatuses within the system, and the update key associated with the identification information. An acquiring unit acquires, from the system management apparatus that has received the identification information, a common key table for use in update (updating common key table) encrypted using the update key associated with the identification information. A decryption unit decrypts the encrypted updating common key table by use of the update key stored in the storage.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
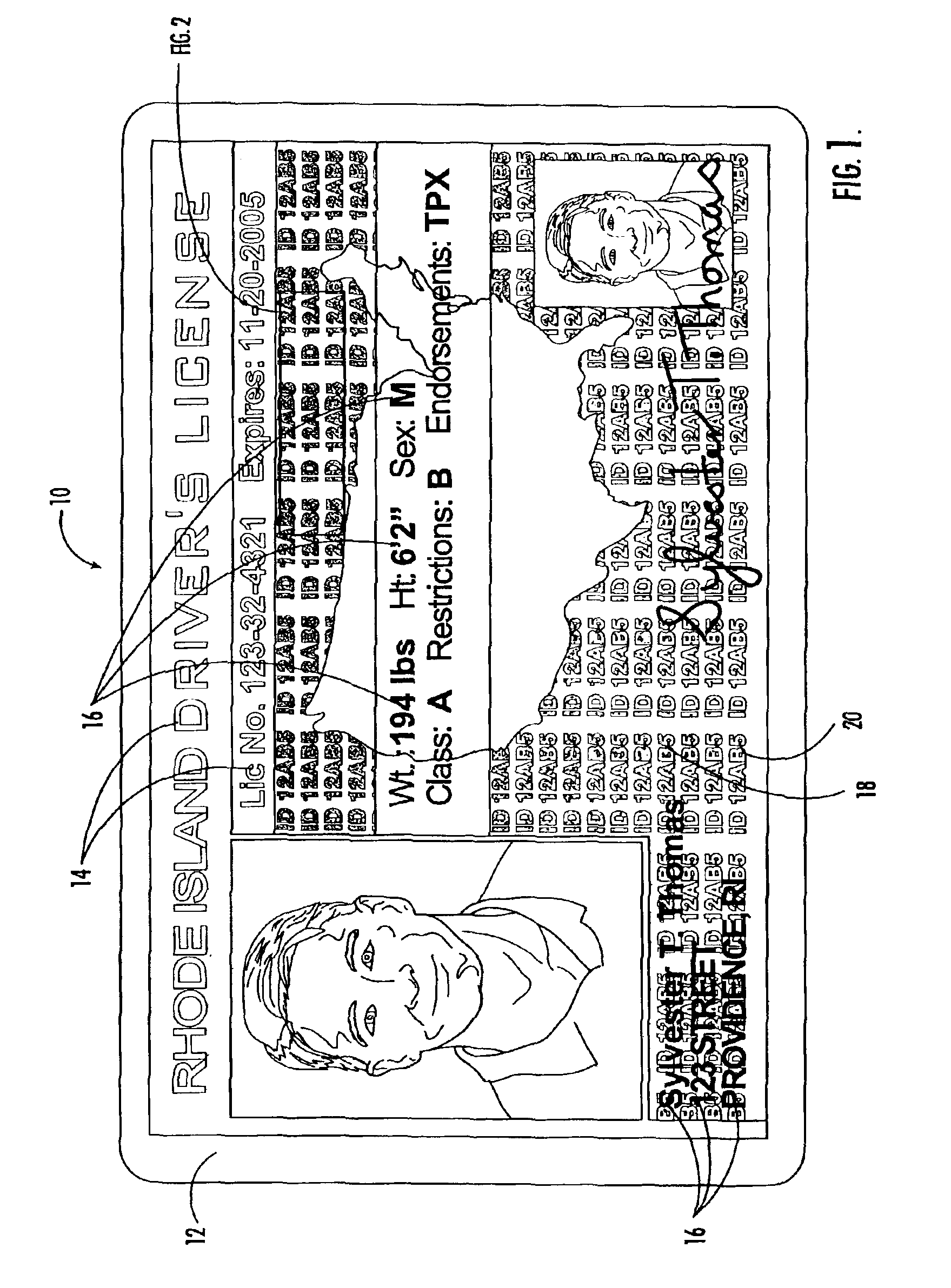
Printer driver log security verification for identification cards
InactiveUS6929413B2Reduce capacityQuality improvementOther printing matterCharacter and pattern recognitionCentral databaseSecurity validation
The present invention provides a counterfeit resistant ID card where a printed security feature is applied to the ID card at the issuance location at the time the card is issued. Specifically, the present invention provides for a process of producing an ID card having a unique imbedded security code that is generated and specifically matched to the particular ID card being printed and is applied at the time and place that the card is issued thereby providing a code by which the authenticity of the ID card can be cross verified. Verification is completed by comparing the code on the ID card to the date stamped log of all ID cards printed by the printer at the issuance location. Each entry in the log is encoded with a unique code number that corresponds to the specific print job and more importantly to the specific ID card printed. The present invention provides for the recording of this print log code into a central database to be maintained with the records corresponding to the particular ID card that was printed.
Owner:ZEBRA TECH CORP
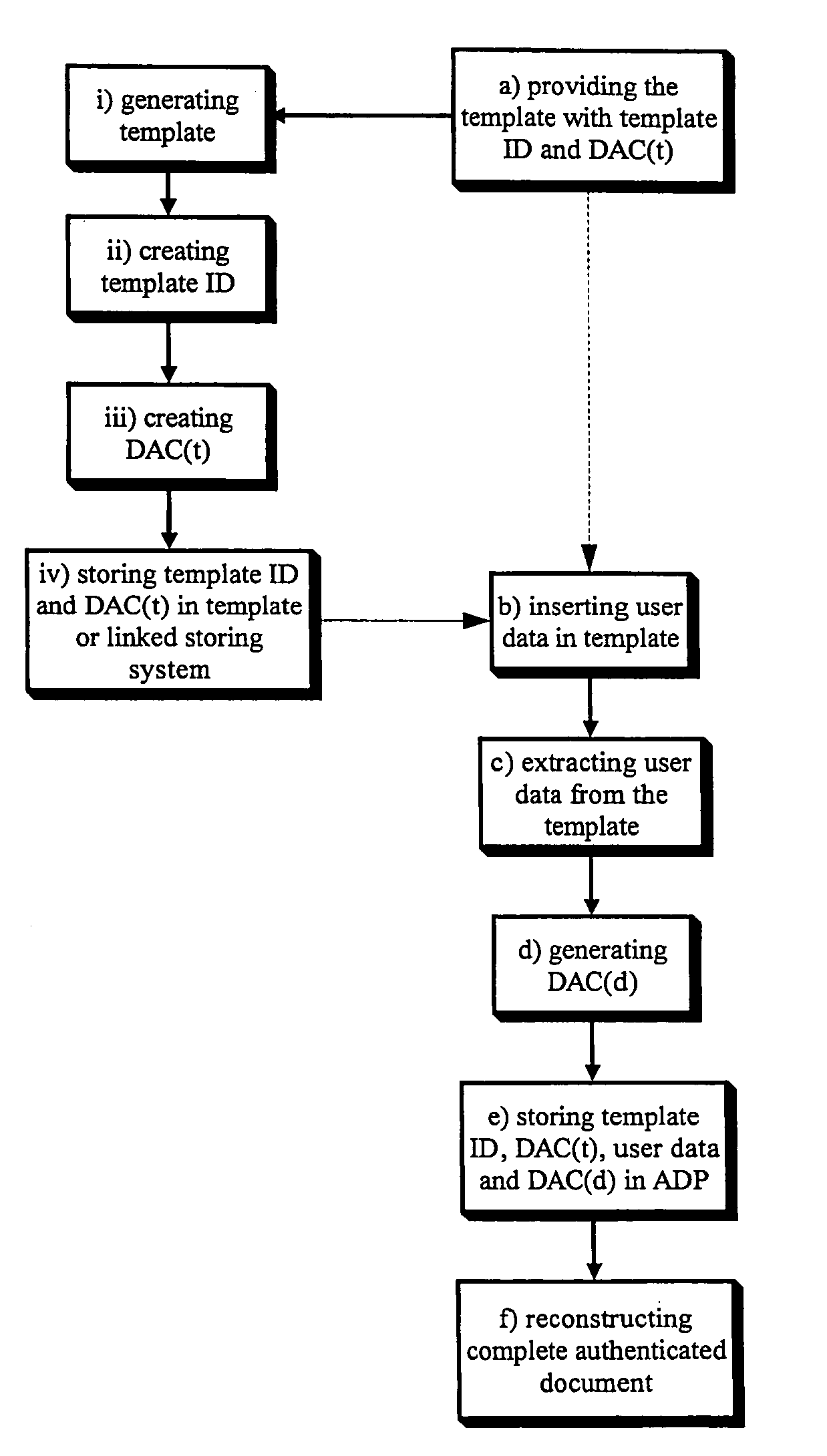
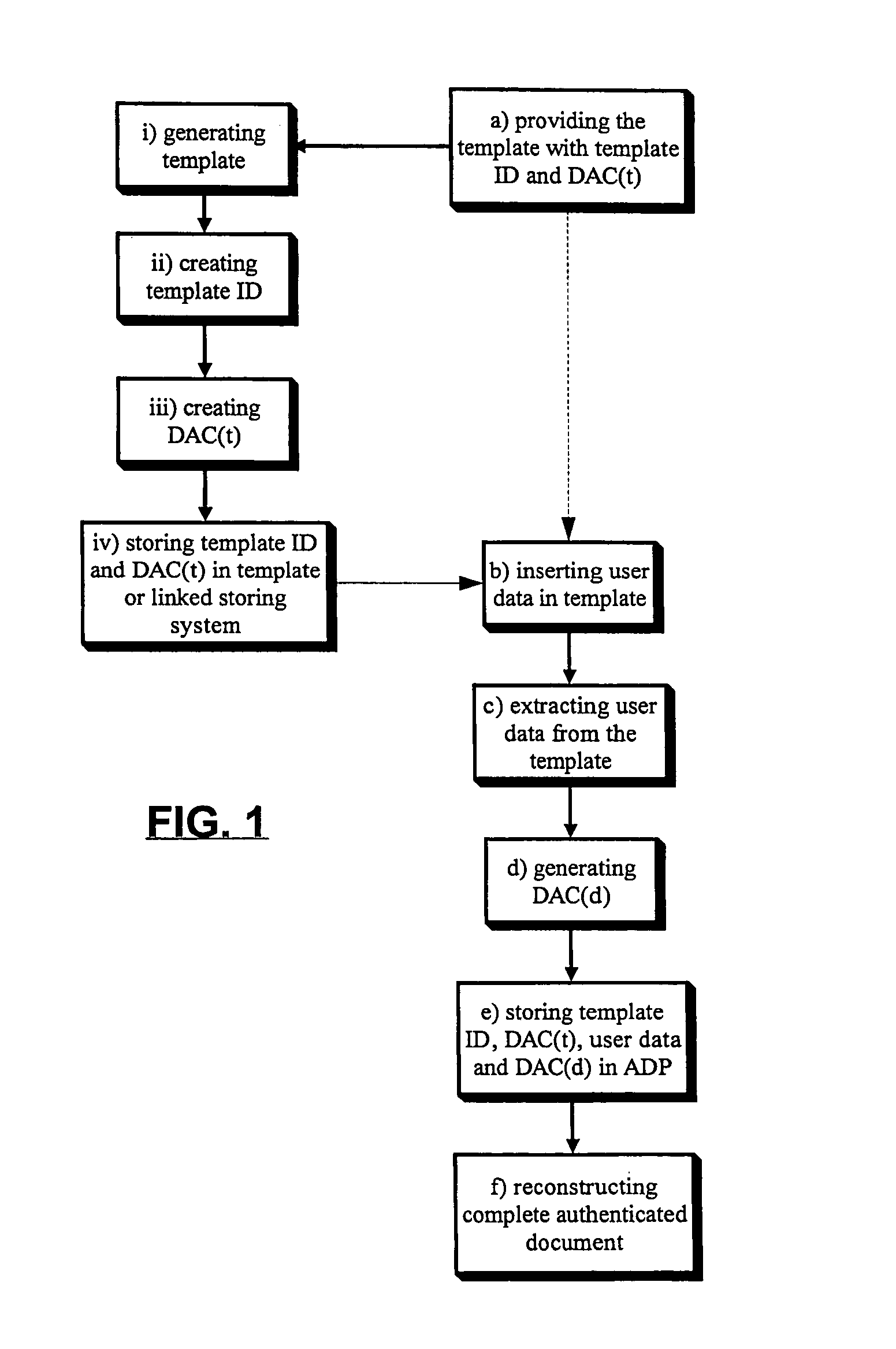
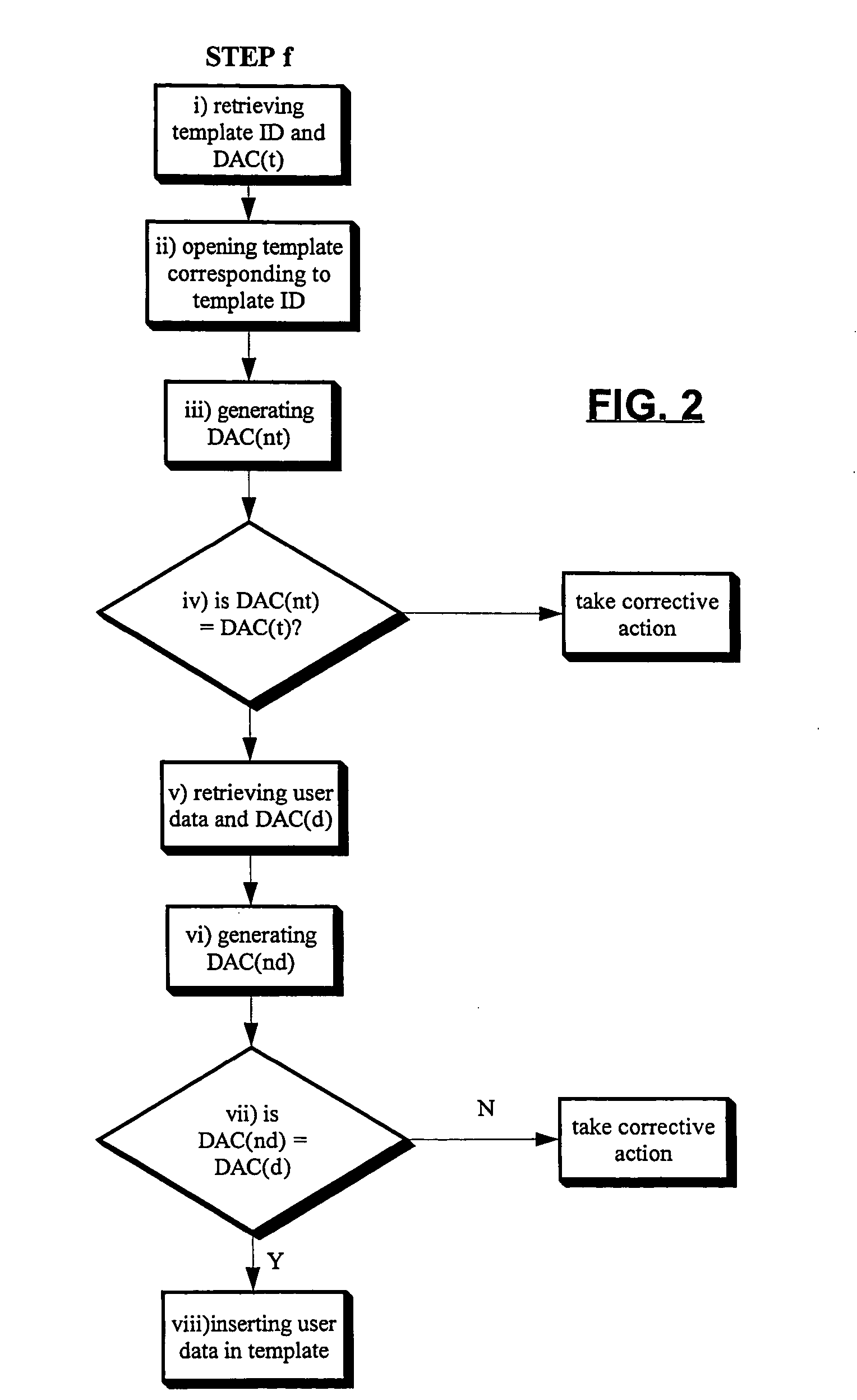
Method for the separate authentication of a template and user data
InactiveUS6931420B1Facilitate remote template approvalVerify authenticityData processing applicationsDigital data processing detailsComputer hardwareNetwork packet
A method for the separate authentication of a template and of data inserted therein. A template is provided with a template ID and a template Data Authentication Code (DAC(t)). User data is inserted in the template, and then extracted to be handled separately. A DAC(d) is generated on the user data by itself, and stored in an Approval Data packet with the template ID, DAC(t) and the user data. The complete document with the template and the user data can later be reconstructed. The method may be useful for many industries that rely on templates for collecting data.
Owner:SILANIS TECH
Electronic invoice security management service system based on cloud computing and cryptography
InactiveCN103870983AReduce application couplingIsolate dependenciesDigital data protectionBilling/invoicingInformatizationInvoice
The invention relates to the technical field of electronic invoice service management, in particular to an electronic invoice security management service system based on cloud computing and cryptography. The electronic invoice security management service system based on the cloud computing and the cryptography adopts technologies of the cloud computing, big data, anti-fake encryption, internet and mobile internet to ensure the correct generation, reliable storage, safety and uniqueness of electronic invoices, and provides convenient query authentication and other electronic invoice data services. The system can ensure the correct generation, reliable storage, query authentication, safety and uniqueness of electronic invoice information, realizes paperless, electronic, networked and automatic management of invoices, reduces the invoice cost and improves the informatization management level.
Owner:INSPUR QILU SOFTWARE IND
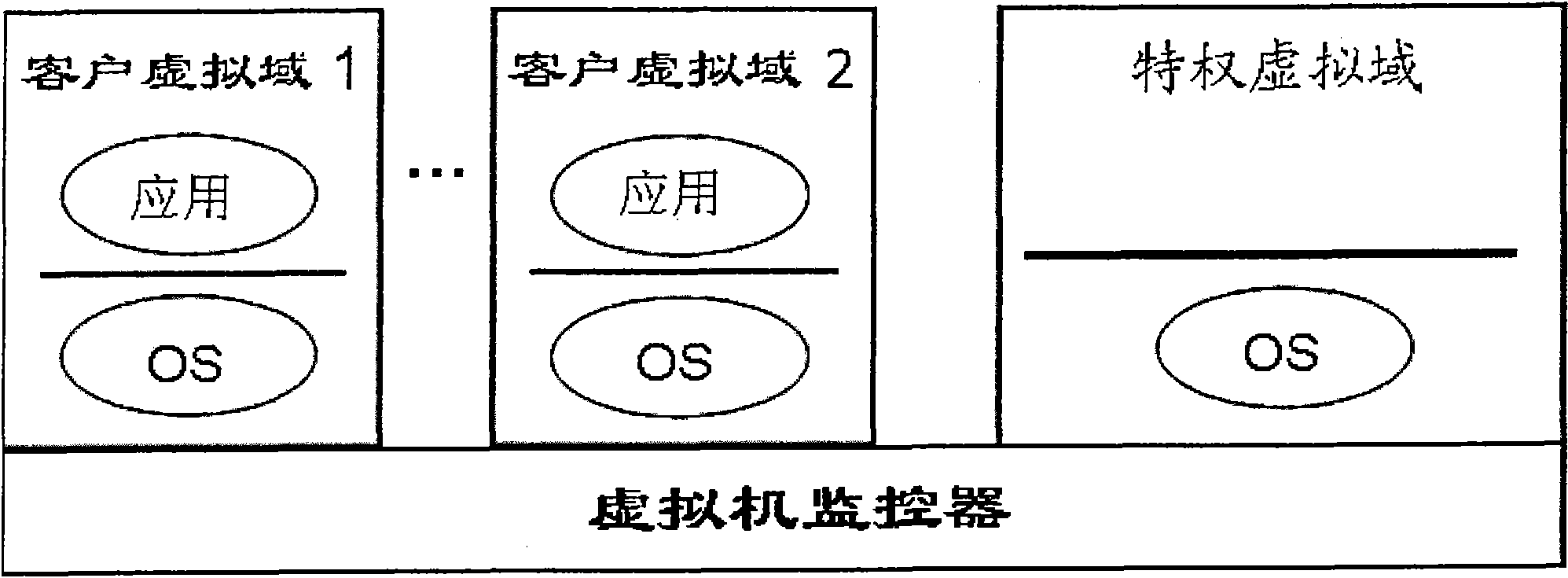
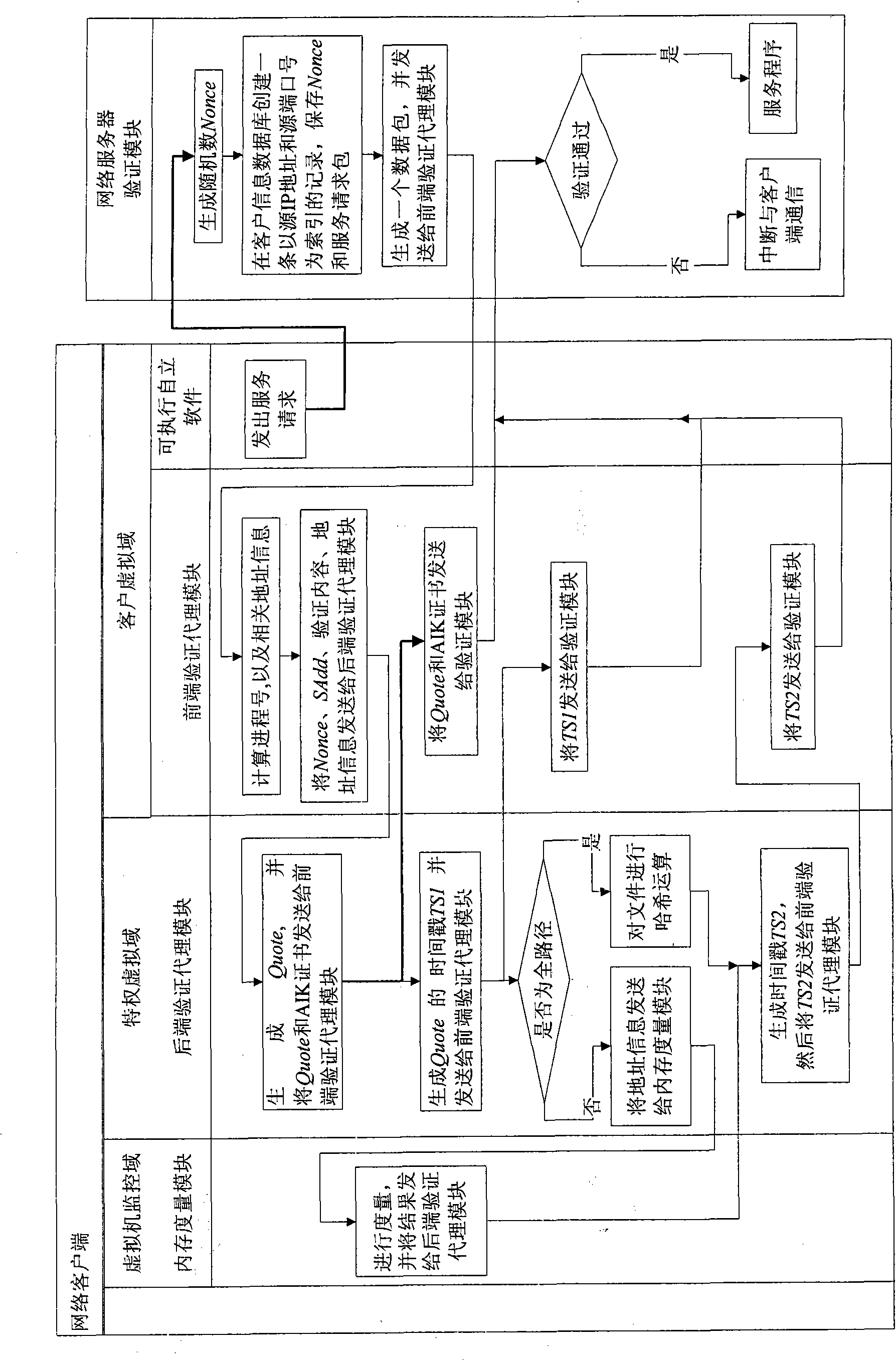
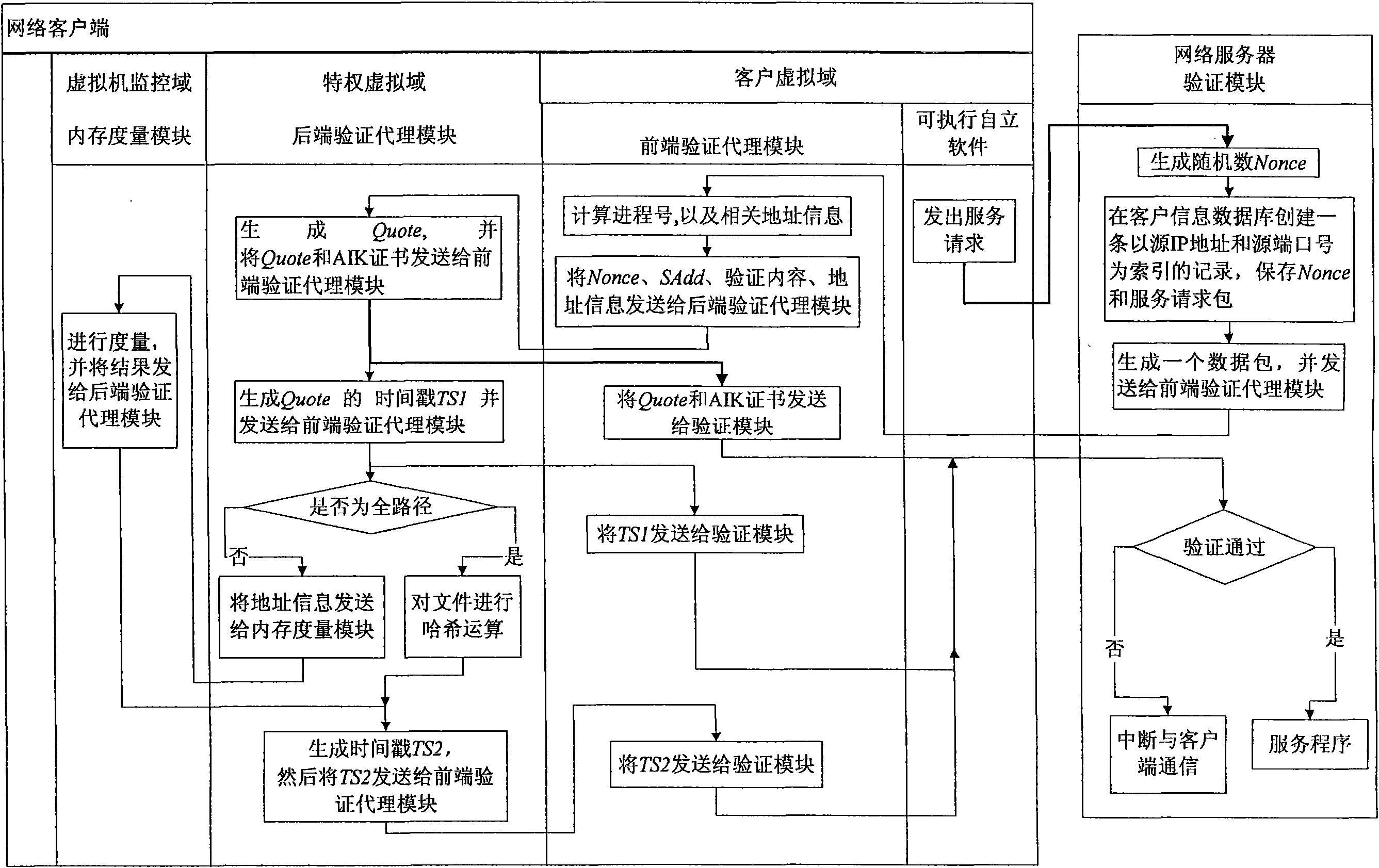
Method for remote dynamic verification on integrality of client software
The invention provides a method for remote dynamic verification on integrality of client software. In the method, a TCG (Trusted Computing Group) remote verification method, an Xen virtual machine security isolation property and a Trusted Platform Module (TPM) timestamp function are adopted to realize remote dynamic verification of a network server on self-contained executables of a network client untrusted client virtual domain. The network client is configured with a security chip TPM (Trusted Platform Module) and an Xen virtual machine system is also installed. A remote dynamic verification framework adopted by the method comprises three parts of an integrality measuring mechanism, a reporting mechanism and a verification mechanism, wherein the integrality measuring mechanism is completed by a back-end verification agent module installed in a network client privileged virtual domain and a memory measuring module installed in a network client virtual machine monitor; the reporting mechanism is completed by a front-end verification agent module installed in the network client virtual domain; and the verification mechanism is completed by a verification module installed d in the network server.
Owner:BEIJING JIAOTONG UNIV
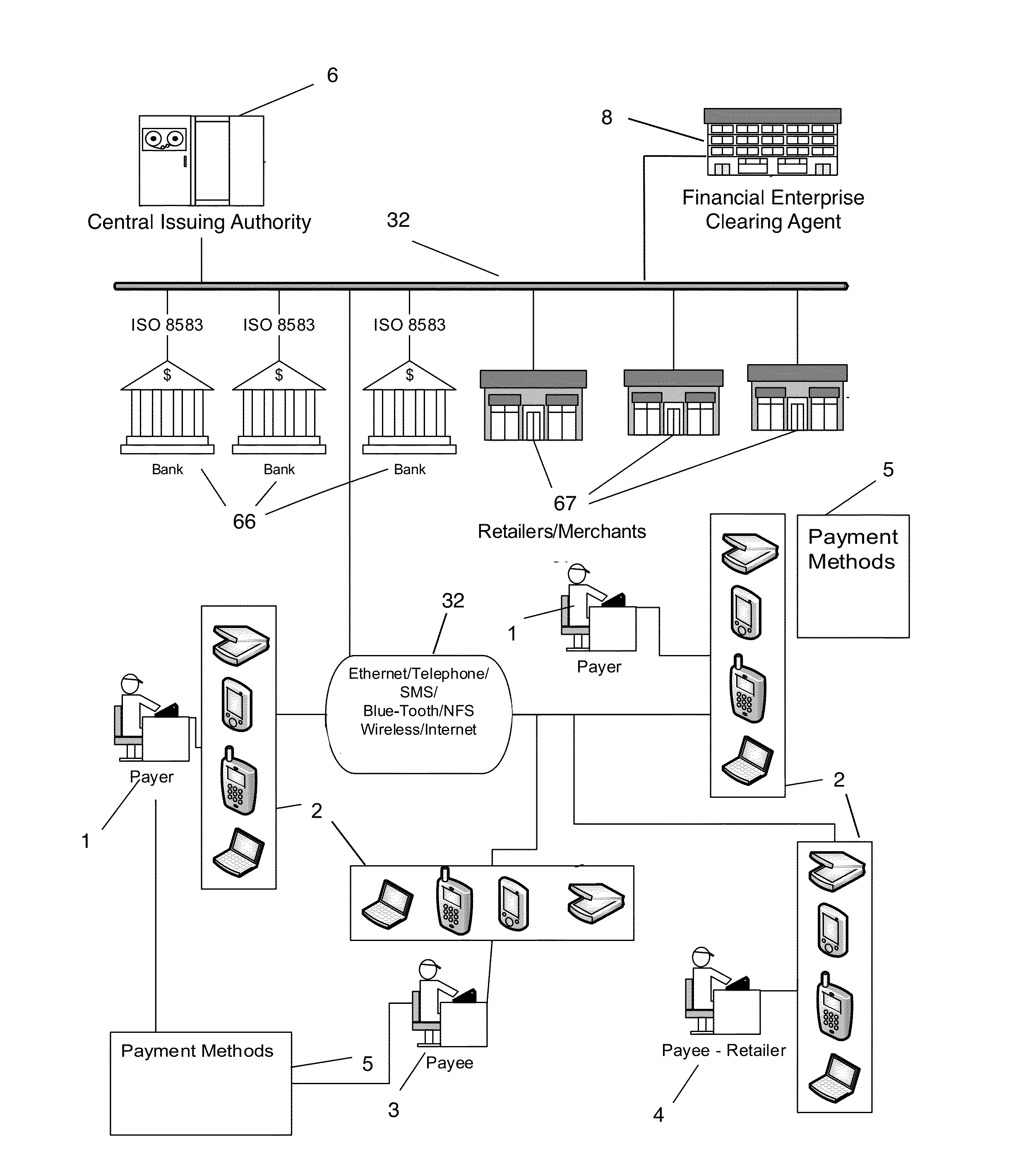
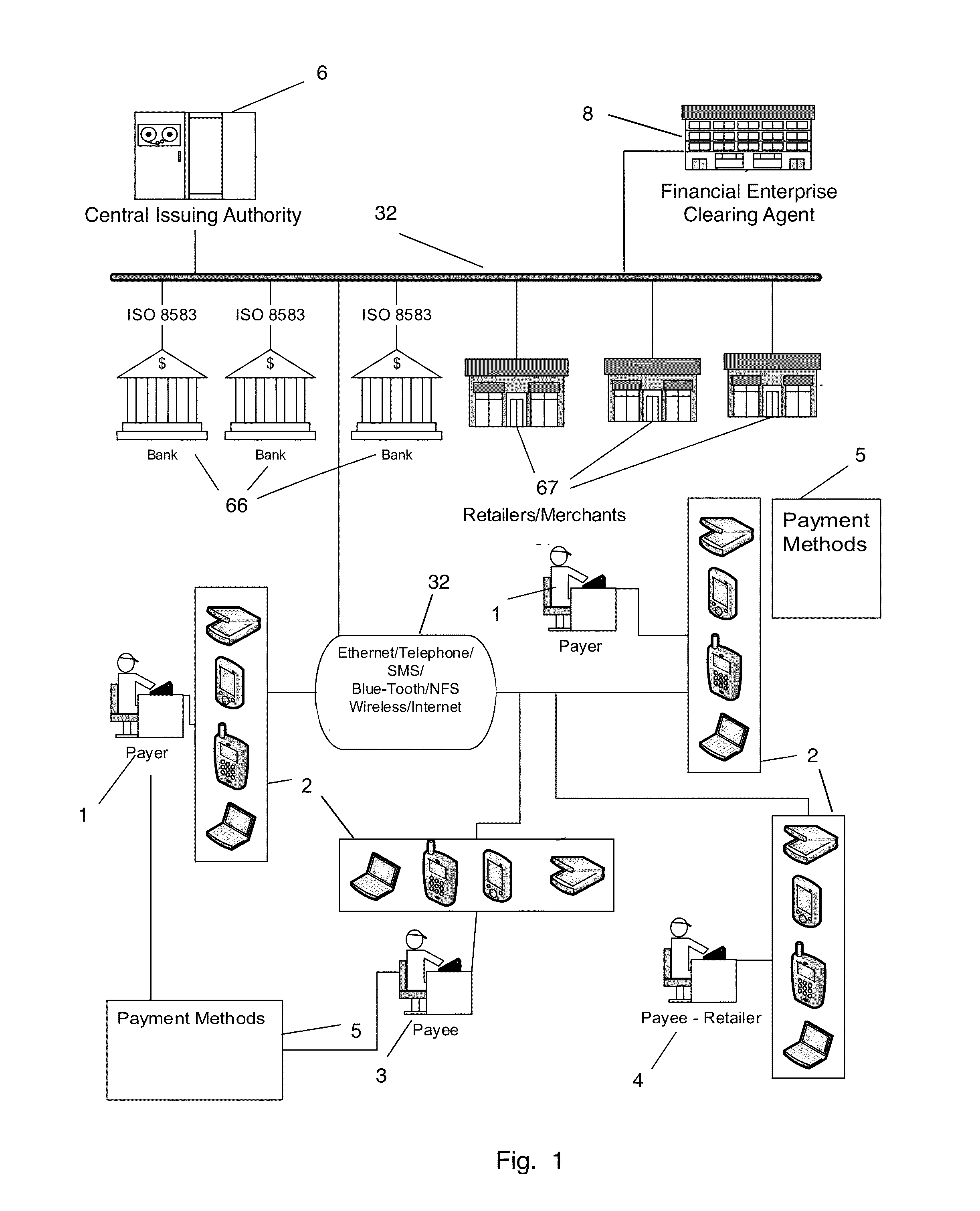
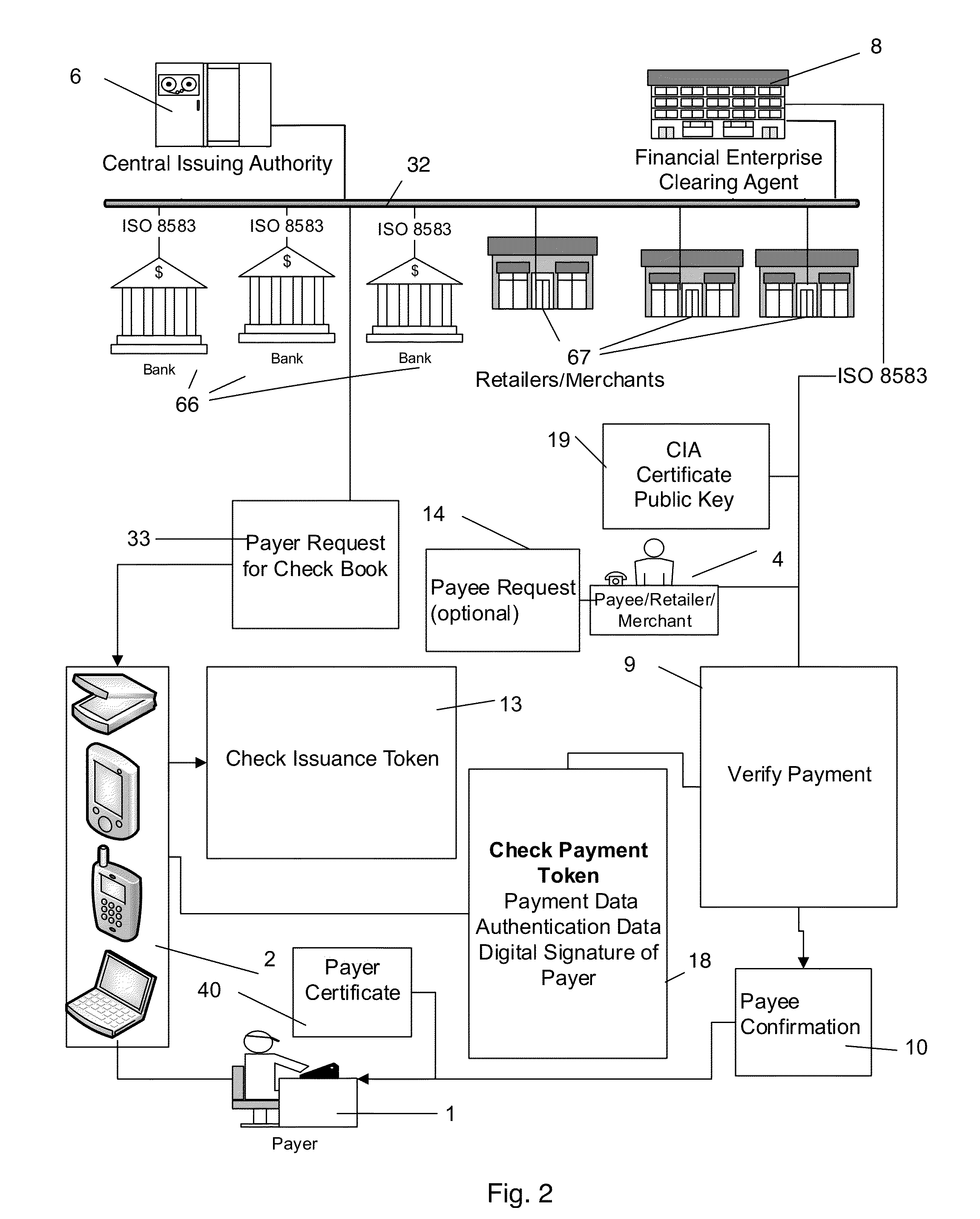
Electronic payment and authentication system
InactiveUS20150120536A1Enhance wireless paymentBetter user identificationFinancePayment protocolsChequeAuthentication system
The invention relates to electronic currency transactions, facilitated by electronic equivalents of checks and credit / debit cards. The electronic equivalents are encrypted tokens, which are data units suitable for storage in and transfer between participants' data storage devices. The invention provides an electronic payment system having Check- and Card-Issuing Authorities that are coupled to a token-generating server. Electronic checks and credit / debit cards, backed by correspondent Check- and Card-Issuing Authorities, are generated and issued to subscribing customers as issuance tokens. A plurality of token-generating devices are used by participants to generate payment tokens authorized by the issuance tokens, and to perform electronic check and card transactions by exchanging tokens with other participants and participating Financial Institutions. The invention provides methods for authentication and verification of the token data, for maintaining the integrity of the system, and for detecting and preventing counterfeiting and tampering within the system.
Owner:TALKER ALBERT
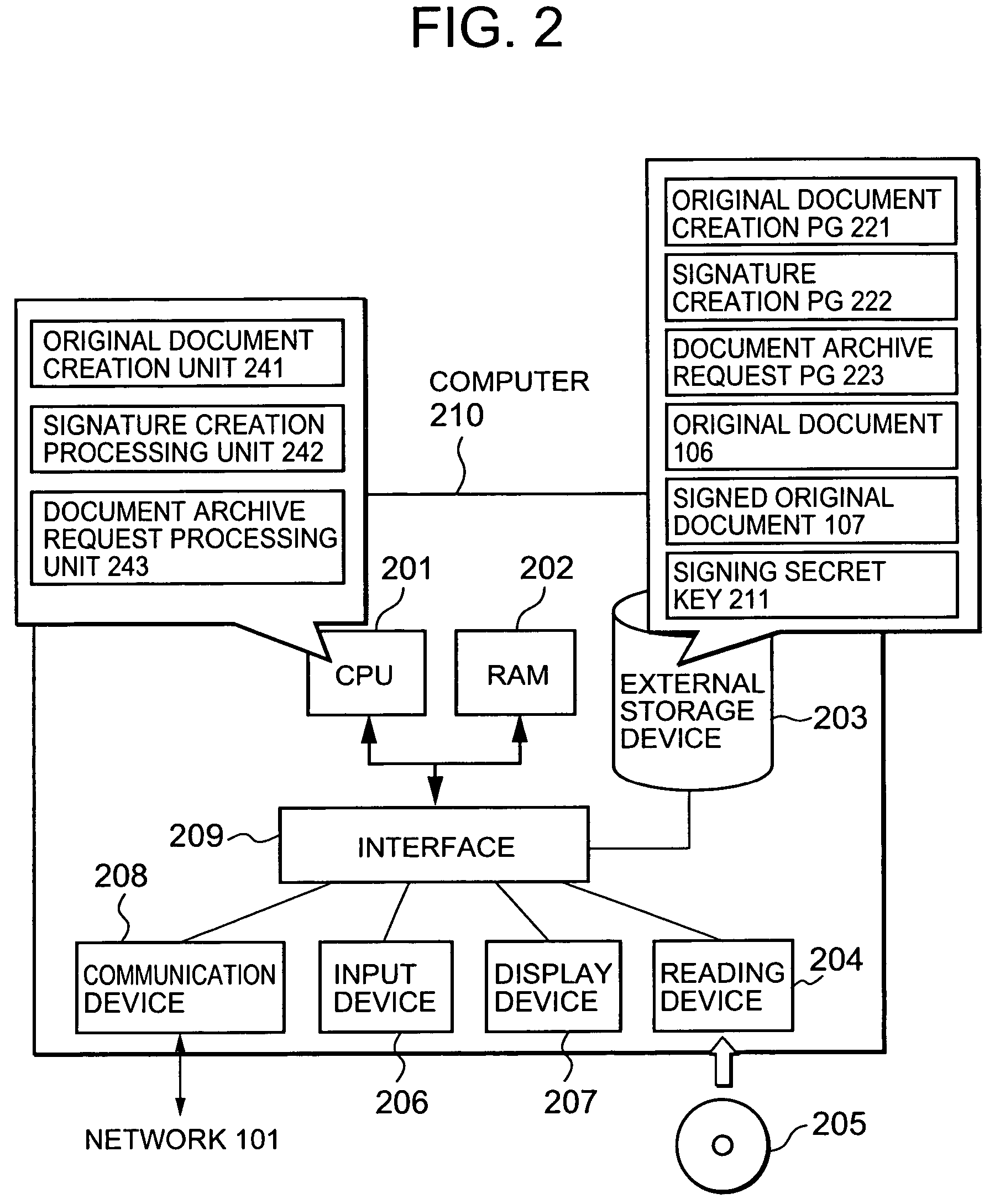
Method and system for signing and authenticating electronic documents via a signature authority which may act in concert with software controlled by the signer
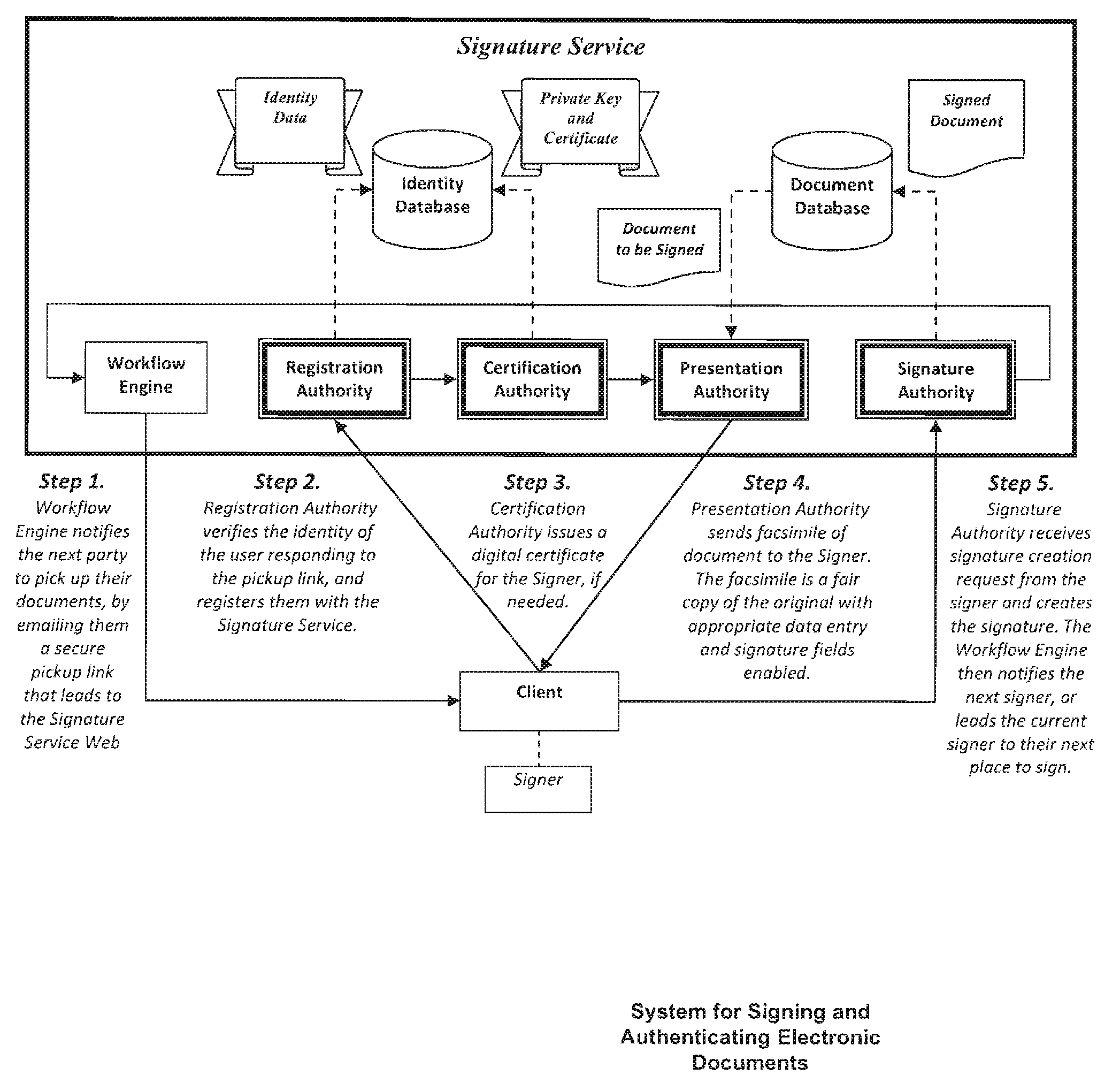
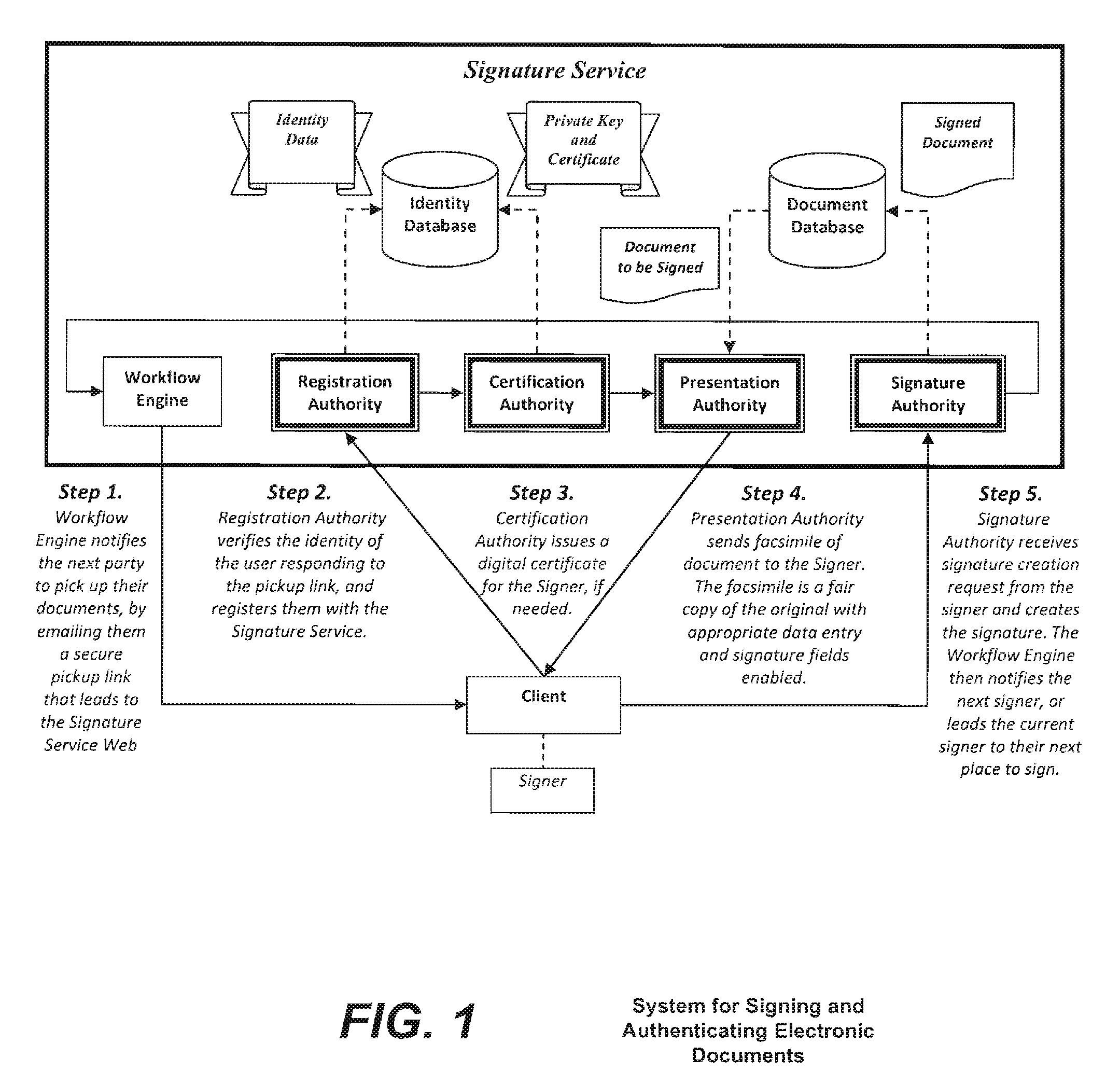
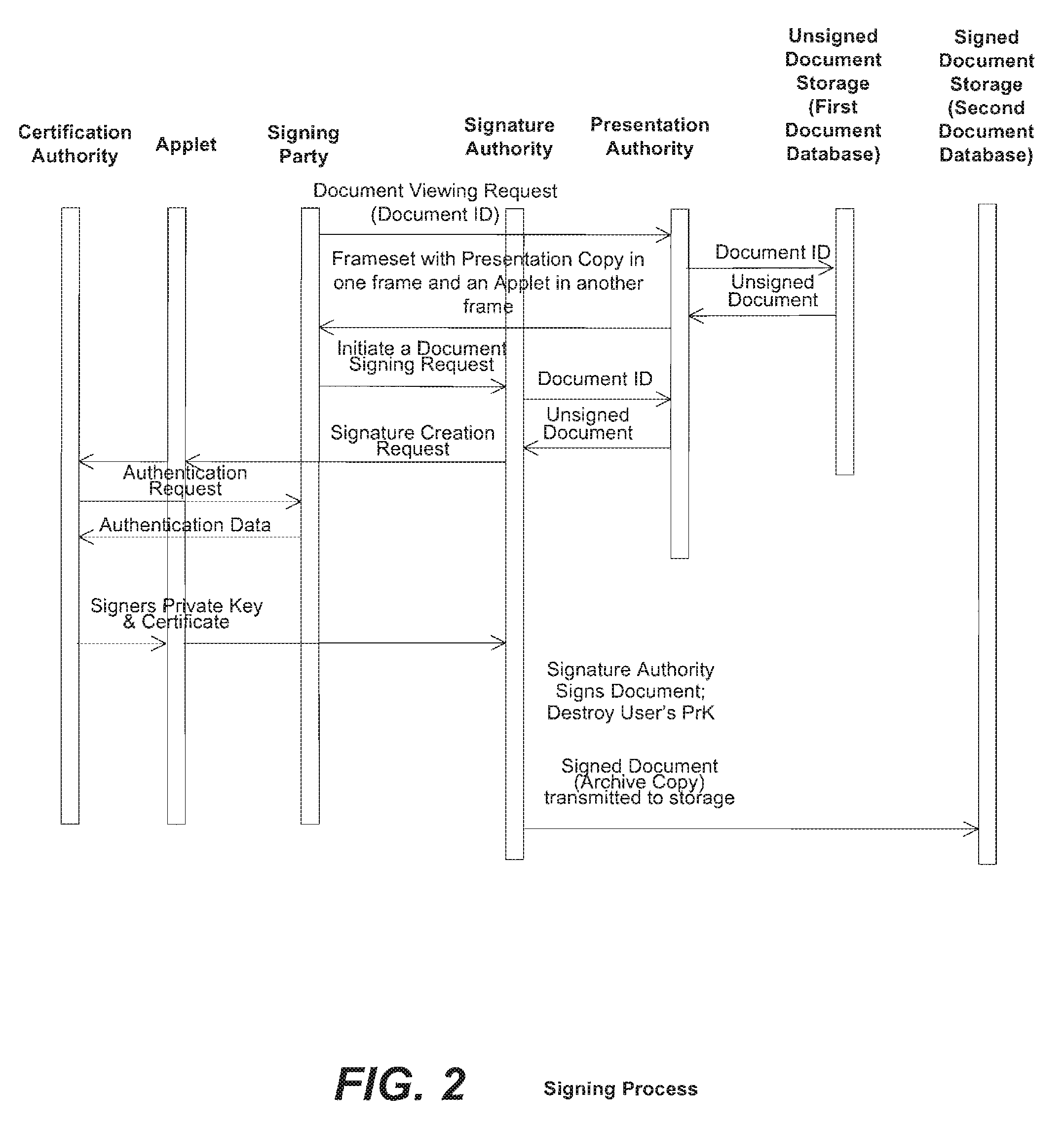
ActiveUS20100313032A1Verify authenticityUser identity/authority verificationElectronic documentComputer cluster
A system and method for signing and authenticating electronic documents using public key cryptography applied by one or more server computer clusters operated in a trustworthy manner, which may act in cooperation with trusted components controlled and operated by the signer. The system employs a presentation authority for presenting an unsigned copy of an electronic document to a signing party and a signature authority for controlling a process for affixing an electronic signature to the unsigned document to create a signed electronic document. The system provides an applet for a signing party's computer that communicates with the signature authority.
Owner:SIGNIX
Security pigments and the process of making thereof
InactiveUS20080274028A1Low costVerify authenticityMaterial nanotechnologyPigmenting treatmentRare earthPigment
Disclosed are methods for using color inconstancy pigments and / or dyes, such as rare earth doped color inconstancy pigments, in security applications including semi-overt and covert security application.
Owner:SUN CHEM CORP
Badge verification device
ActiveUS20060267773A1Verify authenticityResonant long antennasRadiating element housingsEngineeringElectrical and Electronics engineering
A badge, such as that used by police officers and other law enforcement officials, includes a badge body constructed and arranged to support one or more components of the badge, such as an officer's badge number, indicia indicating the organization with which the officer is affiliated, a pin or other arrangement by which to secure the badge to an object, and so on. The badge body may be made of metal, and an RFID device may be attached to the badge body. The RFID device may include a coil antenna and a processor in communication with the coil antenna arranged to function as an RFID transponder. At least one antenna-enhancing structure may be attached to the badge body and be adjacent the coil antenna so as to enhance an ability of the RFID device to communicate wirelessly with an RFID reader.
Owner:BLACKINTON V H
Survivable security features for image replacement documents
InactiveUS20070241554A1Verify authenticityEasy to distinguishOther printing matterPaper-money testing devicesComputer graphics (images)Paper document
A security image embedded in an original printed document survives a conversion process into an image replacement document in binary image form having a commercial equivalency with the original printed document. The security image is embedded in a background at an approximately common visual density with the background so that the security image is at least partially indistinguishable from the background to the naked eye. Print elements of the security image are arranged differently than the print elements of the background and both are further arranged so that that upon conversion into the image replacement document in binary image form, the security image survives and the background drops out.
Owner:DOCUMENT SECURITY SYST
Systems and methods for verifying the authenticity of a remote device
ActiveUS20090049297A1Easy to demonstrateEfficiently and securely interactUser identity/authority verificationSecurity arrangementComputer hardwareMedia server
Some embodiments of the invention are directed to, among other things, systems, computer readable media, methods and any other means for verifying the authenticity of a client device. In some embodiments, a token is issued by one or more remote media servers that allows the client device to download video, media or other data from one or more remote media servers.
Owner:APPLE INC
Method and system for automatically identifying voice recording equipment source
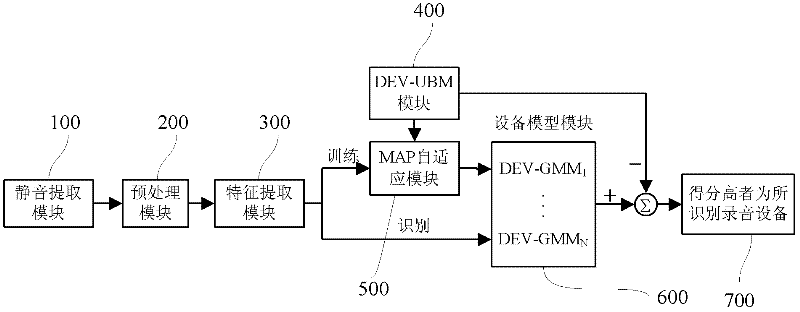
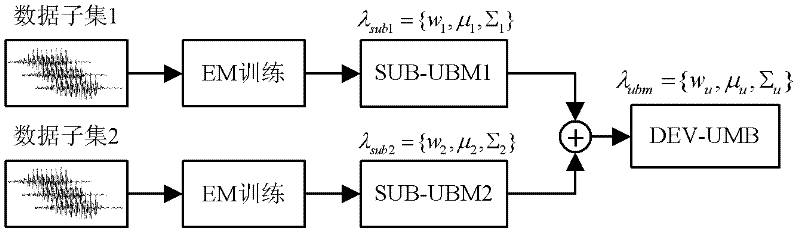
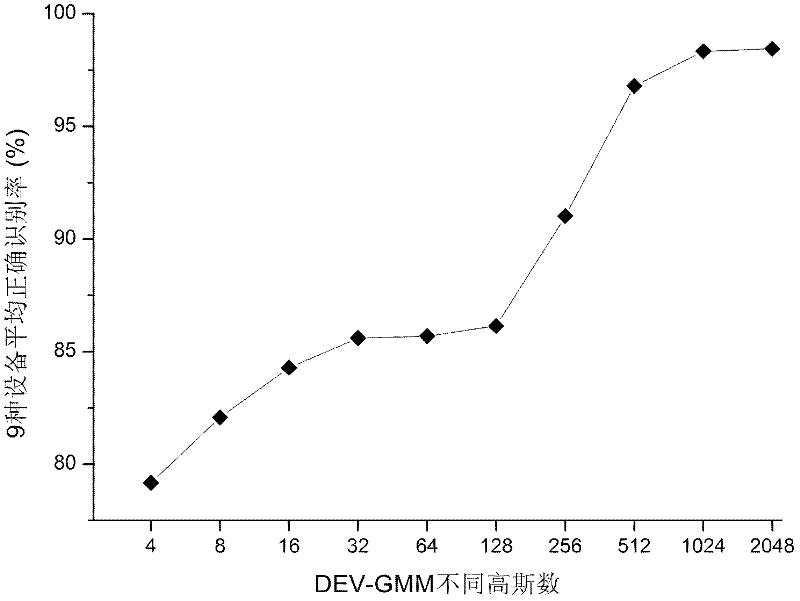
InactiveCN102394062AEfficient detectionReduce complexitySpeech recognitionComputation complexitySpeech sound
The invention relates to the technical fields of intelligent voice signal processing, mode identification and artificial intelligence, and in particular relates to a method and system for automatically identifying a voice recording equipment source. The method comprises the following steps of: a, extracting a characteristic of voice recording equipment from a voice signal; b, constructing a statistical model of the voice recording equipment by using a Gaussian mixture model-universal background model (GMM-UBM); and c, performing classification judgment by using a normalized likelihood as a final score. Different voice recording equipment can comprise different equipment noises; in the method and the system, the characteristics of the voice recording equipment are extracted by using silence fields and the statistical model of the voice recording equipment is constructed so as to perform the classification and identification on the equipment. By the technical scheme in the embodiment of the invention, the extracted characteristic dimension, the computing complexity and the error identification rate are low.
Owner:SOUTH CHINA UNIV OF TECH
Tamper evident packaging
ActiveUS20050011163A1Improve accuracyVerify authenticityElectric/electromagnetic visible signallingPackagingTransceiverLogistics management
A packaging and a method for monitoring a packaging (10) of a disposable material in a chain of logistics. As an integral part of the packaging, the packaging has an electronic module (12) comprising electric energy supply means, data processing means, data storage nonvolatile memory means for storing information related to the packaging, time keeping means, and data transceiver means for transmitting and receiving said information in communication with a host computer (30). The electronic module also has sensor means (14, 20) for detecting a changed physical condition of the packaging and for signaling information representing said changed physical condition to the electronic module (12) to be stored in the memory means together with a notation of time from the time keeping means.
Owner:SONY CORP
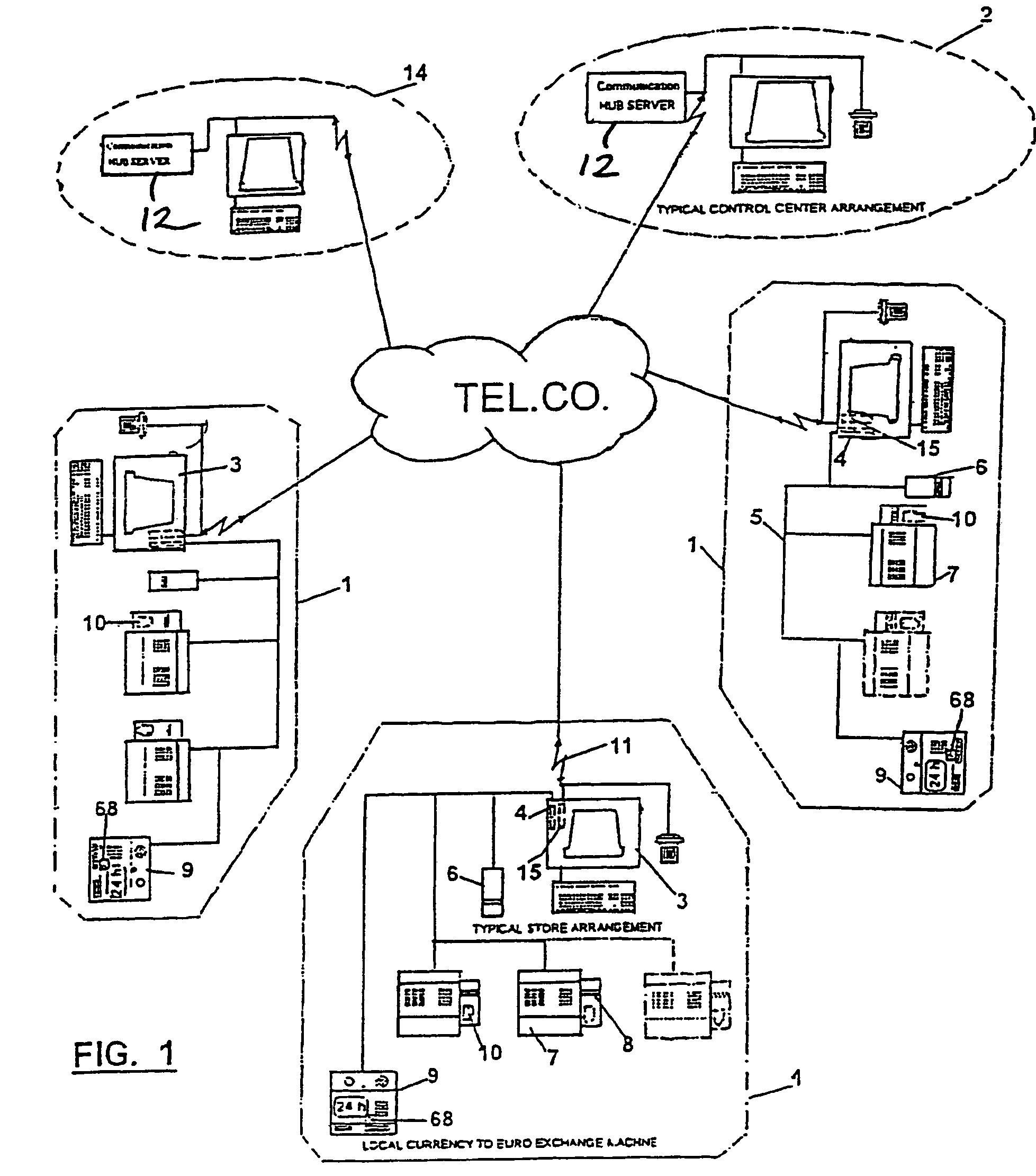
Method and apparatus for internet coupon fraud deterrence
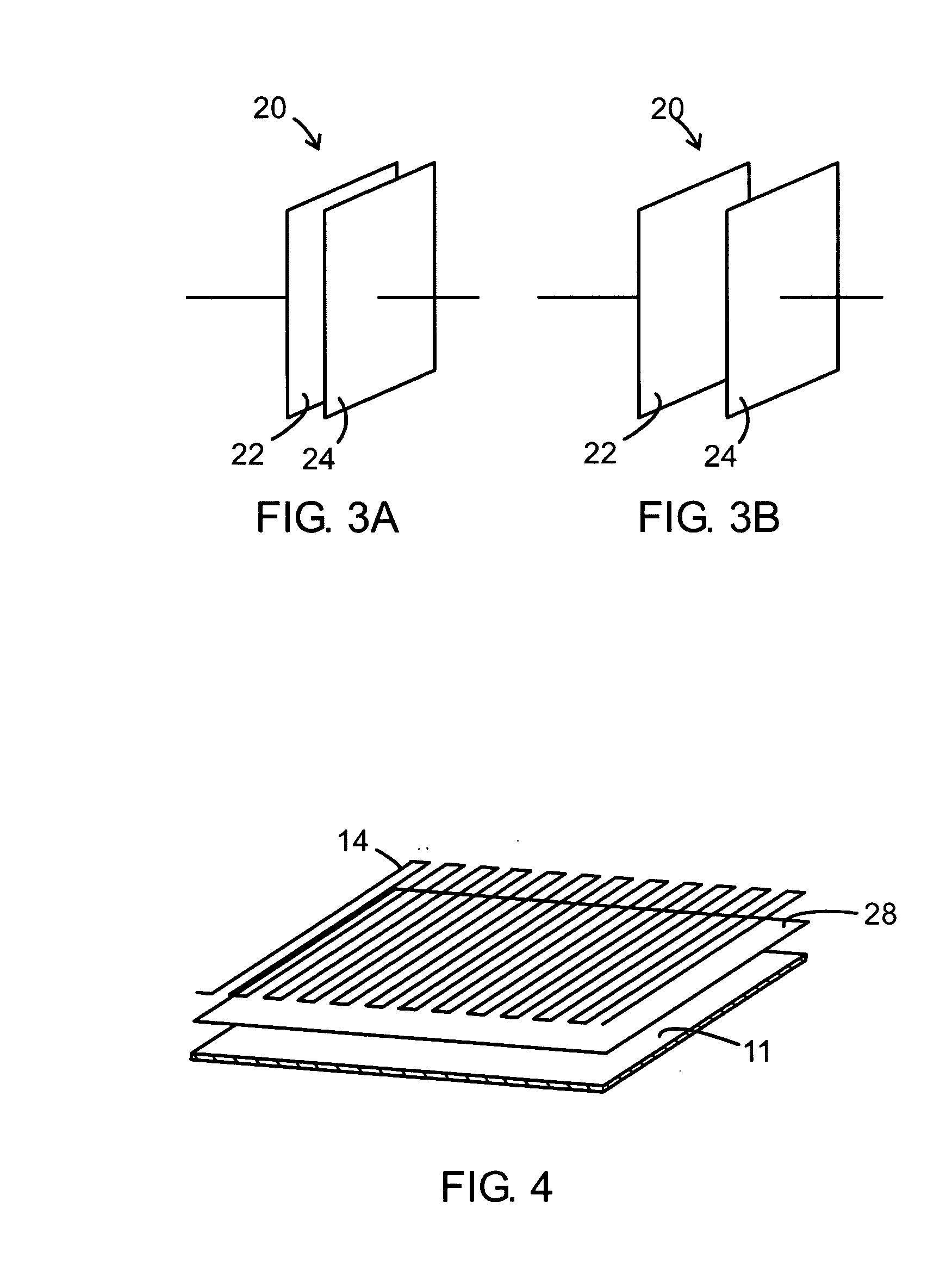
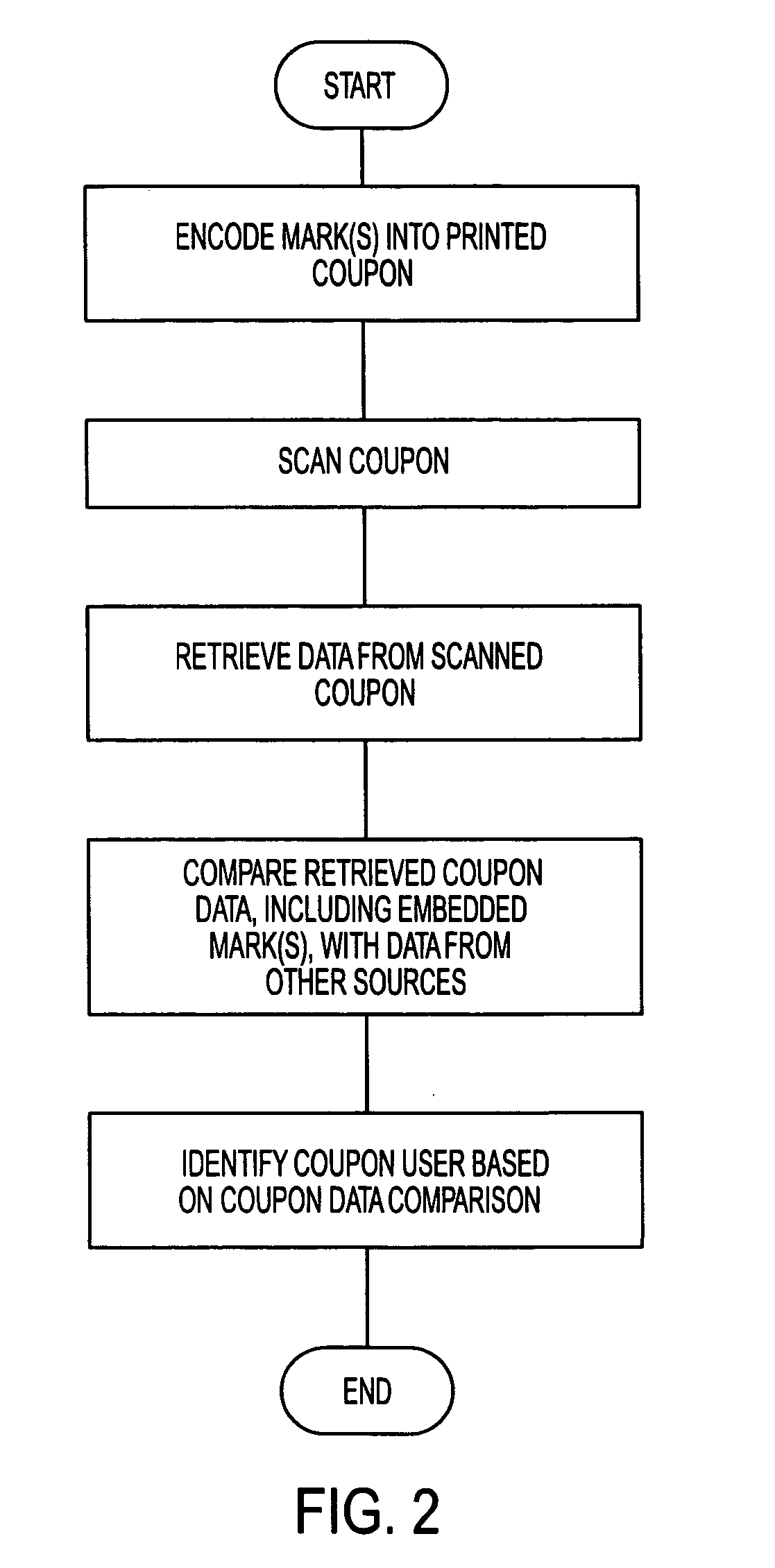
InactiveUS20060061088A1Verify authenticityImprove protectionOther printing matterPaper-money testing devicesInternet privacyThe Internet
Systems and methods that allow for anti-counterfeiting marks that carry user information and other data to be embedded into an original coupon design. The marks may be invisible, or visible but difficult to remove. At the receiving sides of the coupons, the embedded data are used to detect fraud and trace back the coupon users.
Owner:XEROX CORP
Method and computer system for ensuring authenticity of an electronic transaction
InactiveUS20090319797A1Easy to useReduce the risk of fraudKey distribution for secure communicationDigital data processing detailsComputerized systemSecurity level
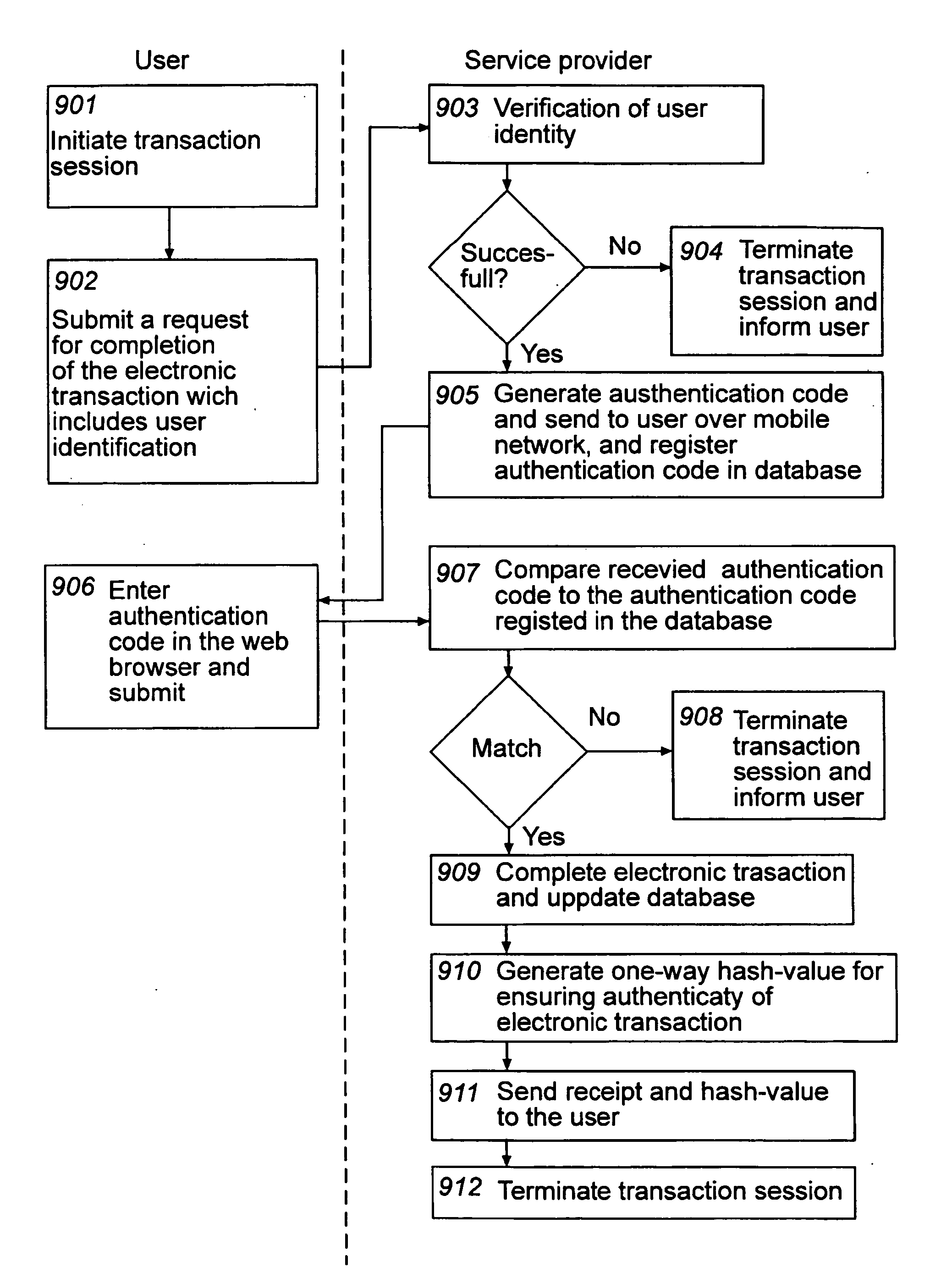
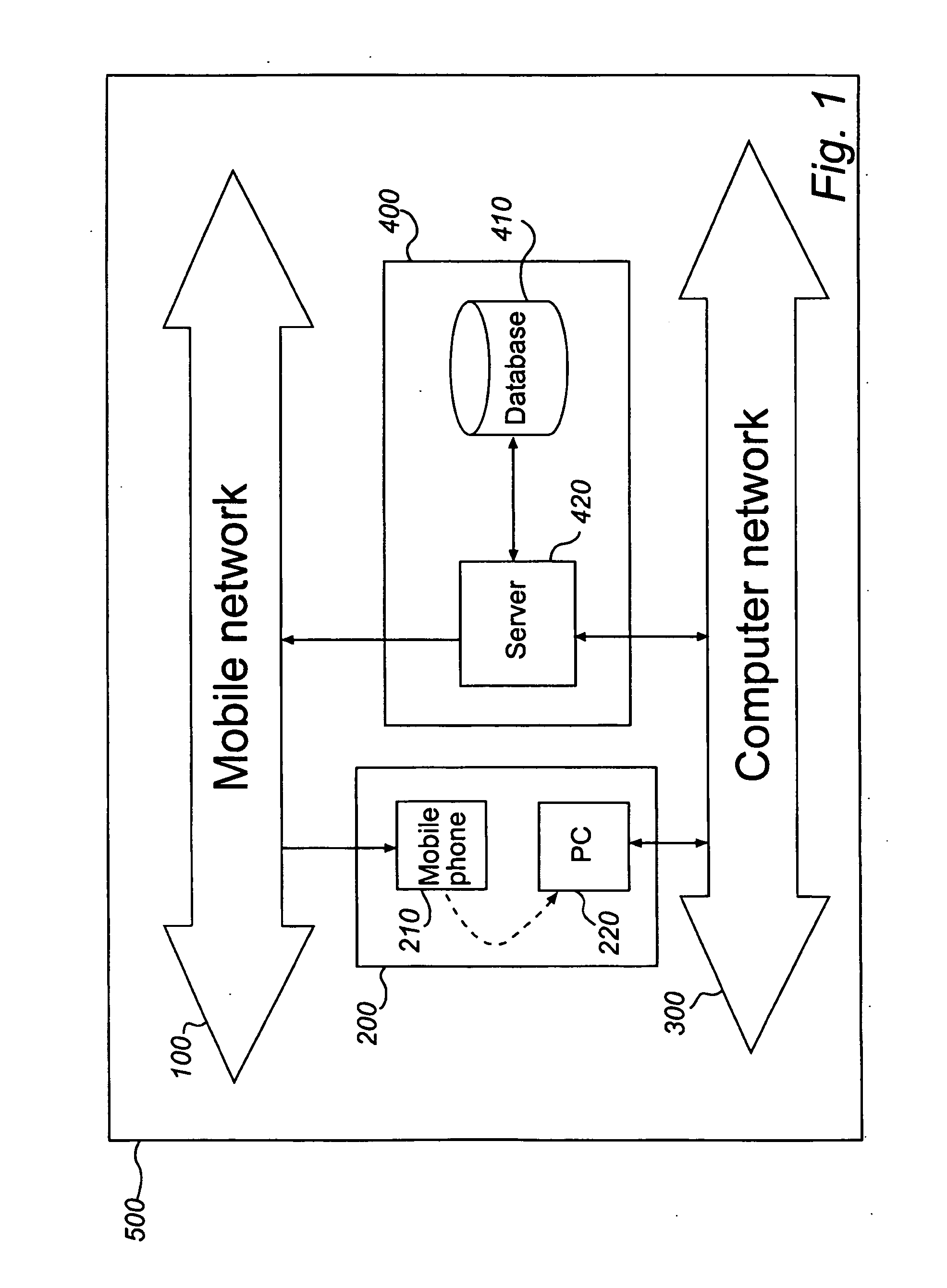
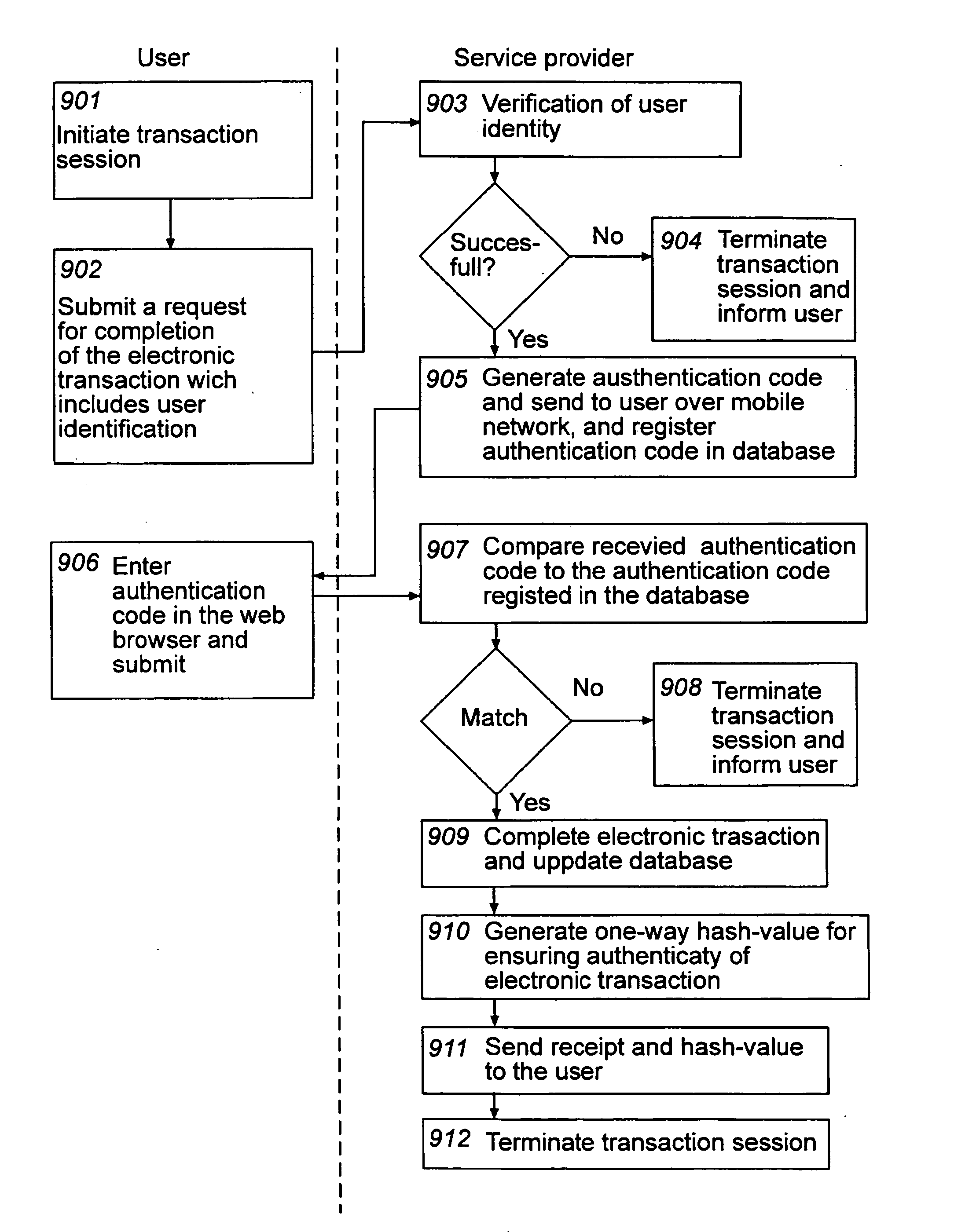
At least one embodiment of the present invention relates to a method for ensuring authenticity of an electronic transaction performed during a transaction session. The method includes receiving, over a first network, a request from a user for the completion of an electronic transaction; receiving, over the first network, an authentication code from the user which has been provided to the user over a second network separated from the first network, thereby authenticating the user, completing the electronic transaction; and storing information associated with the electronic transaction and the transaction session. The method further includes generating a one-way hash value based on information comprised in the electronic transaction and information associated with the transaction session, and providing the one-way hash value to the user, wherein the one-way hash value is usable for ensuring the authenticity of the electronic transaction. The procedure enables authentication, integrity, non-repudiation, and time stamping in a cost efficient way. An enhanced security level can be achieved as the network used for providing the authentication code to the user is separate from the network where the user returns the authentication code. At least one embodiment of the present invention also relates to a corresponding computer system adapted for ensuring the authenticity of an electronic transaction.
Owner:COMFACT AB
System and method for implementing internet trade guarantee payment and financing
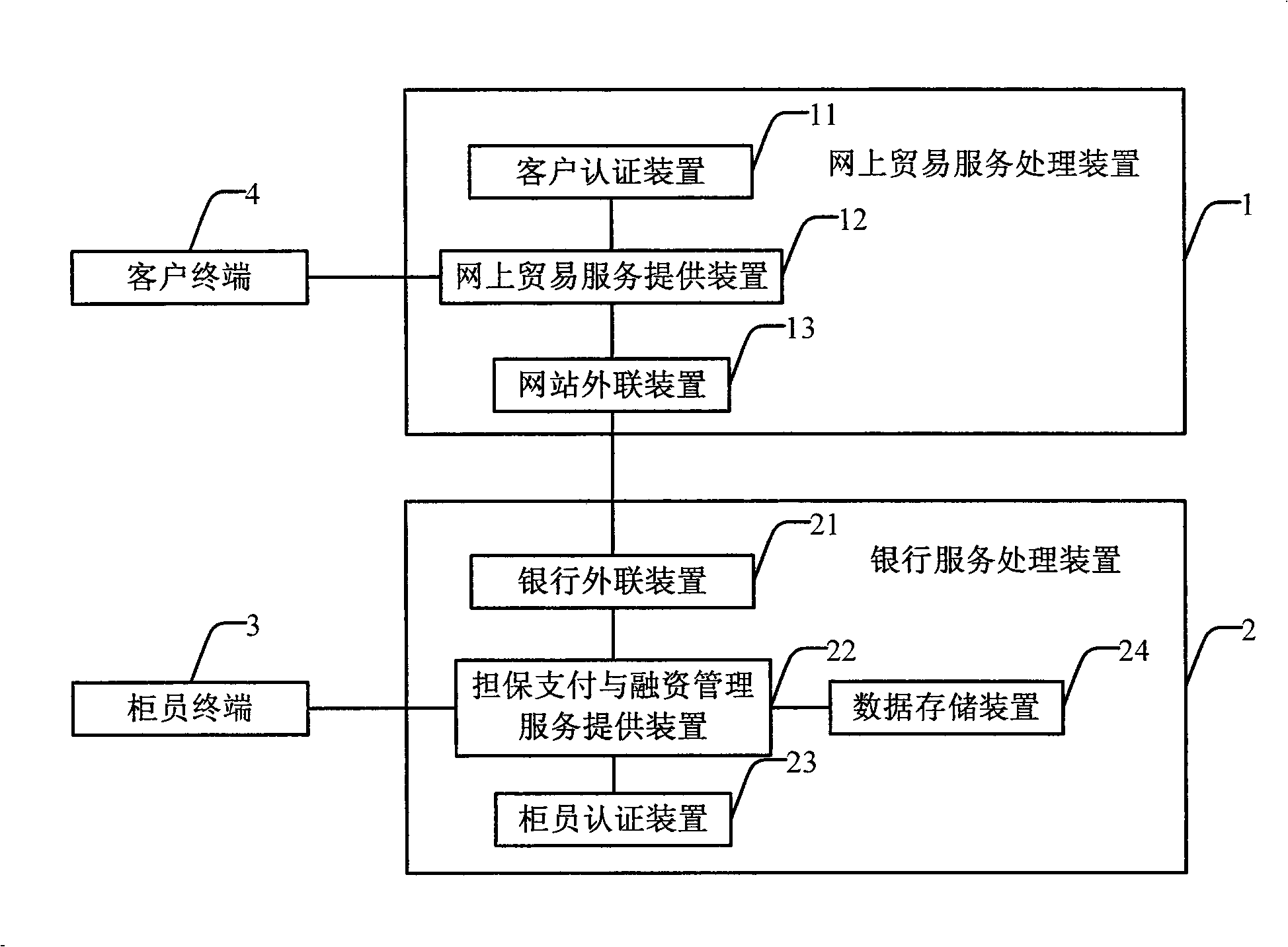
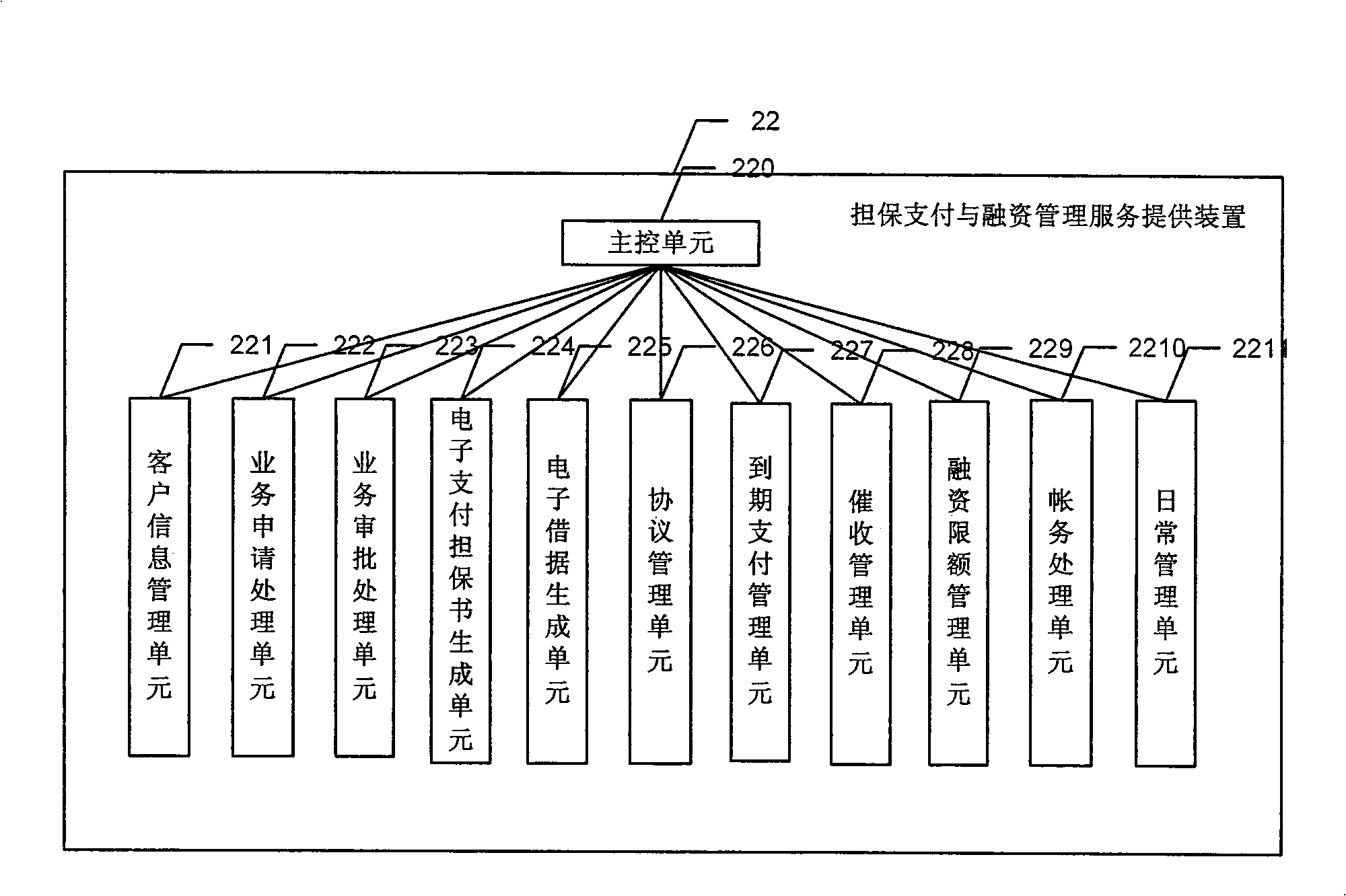
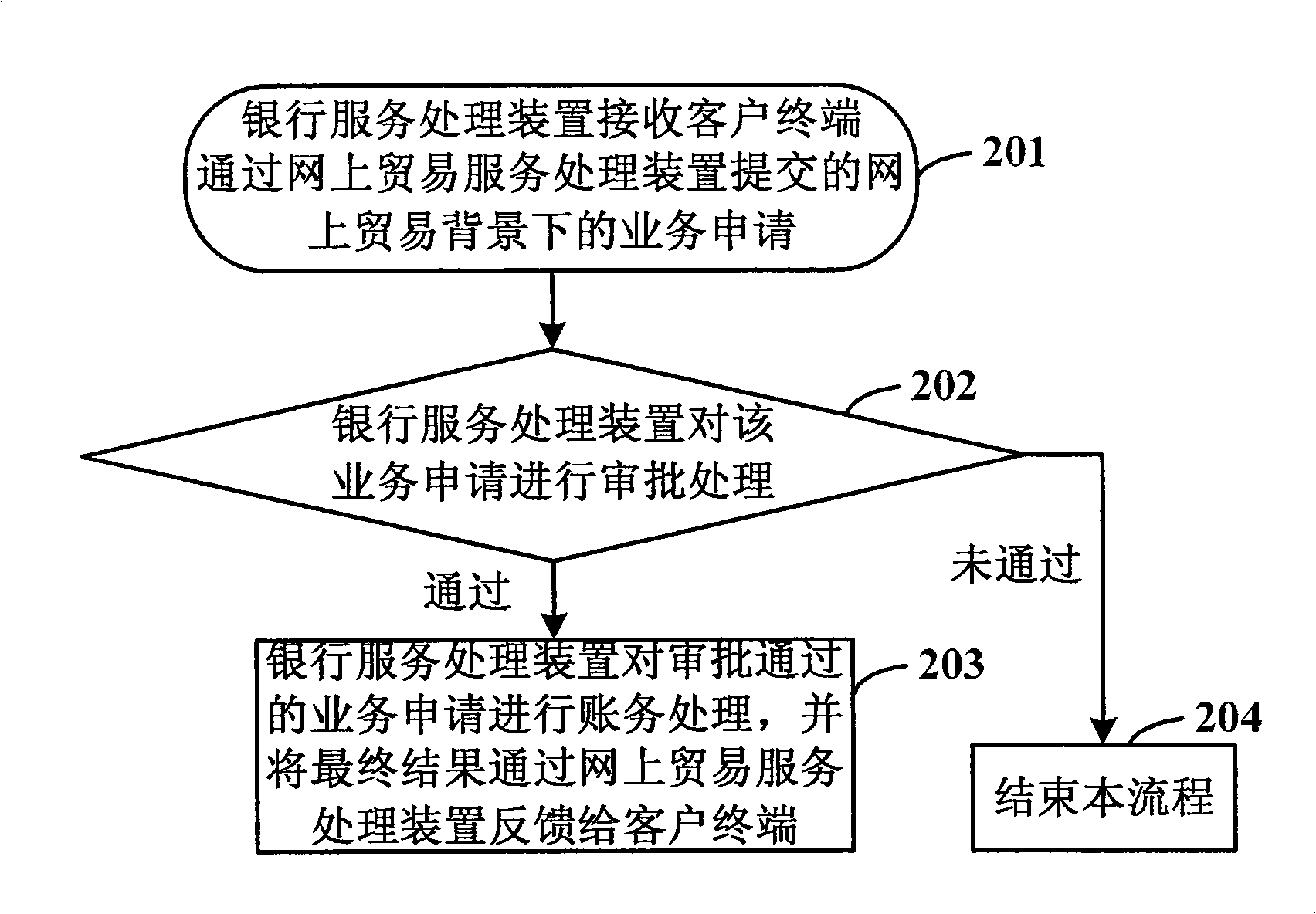
InactiveCN101354765AOvercoming the Defects of Issuing Letters of CreditEnabling fully electronic processingFinancePayment architecturePaymentBank teller
The invention discloses a system capable of realizing online trading guarantee payment and financing. The system comprises an online trading service processing device, a banking service processing device, a teller terminal and a client terminal, wherein the online trading service processing device is used for receiving the access requests from clients, carrying out the client identity authentication and processing the online trading transactions, and is responsible for communicating with a banking system; the banking service processing device is used for communicating with the online trading service processing device, receiving the business requests submitted by the client terminal through the online trading service processing device , receiving the access of the teller terminal, carrying out the authentication for the teller terminal, and realizing the inner business processing flow and accounting treatment of banks; the teller terminal is used for allowing bank tellers to log on the banking service processing device; the client terminal is used for allowing the clients to log on the trade service processing device . The invention discloses a method capable of realizing the online trading guarantee payment and financing. With the invention, the banking guarantee payment and financing can be transacted directly on line, and more convenient services are provided for the online trade.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Two-dimensional code dynamic anti-fake information intelligent tracing system based on network
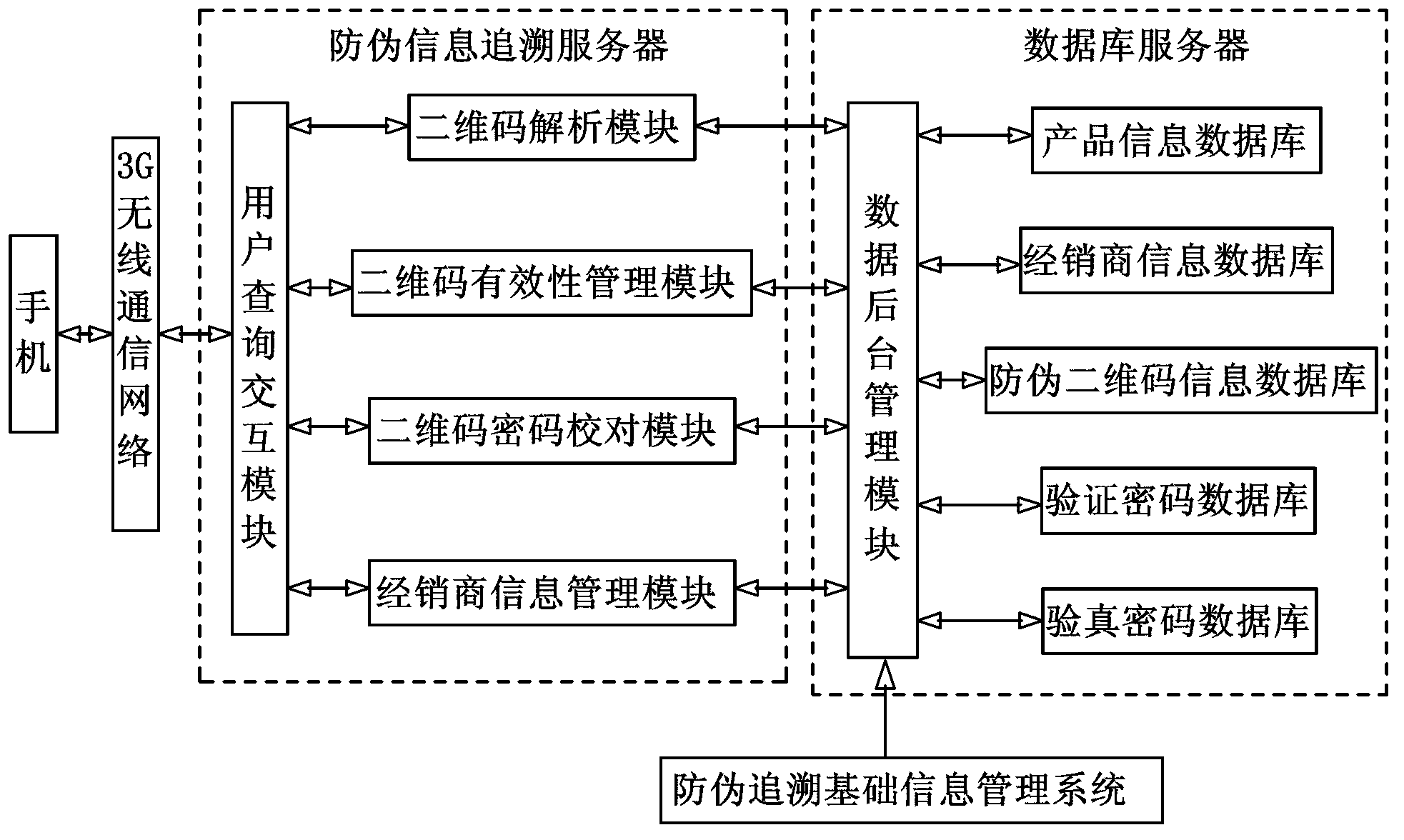
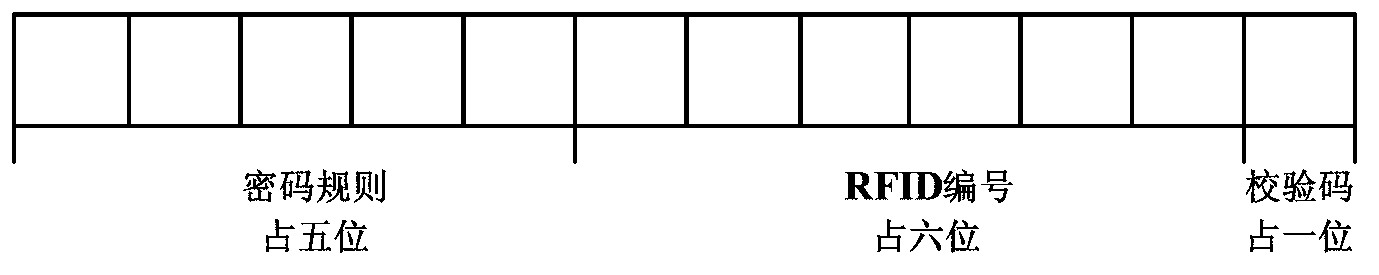
InactiveCN103295137AAvoid circulationPrevent cross-sellingCo-operative working arrangementsCommerceMonitoring systemNetwork management
A two-dimensional code dynamic anti-fake information intelligent tracing system based on a network comprises an anti-fake label, an identity identifying terminal, a communication network, an anti-fake information tracing system and an anti-fake tracing basic information management system. The identity identifying terminal is used for identifying the anti-fake label and sending anti-fake label information to the anti-fake information tracing system through the communication network. The anti-fake tracing basic information management system is connected with the anti-fake information tracing system and used for typing in anti-fake information. The anti-fake label comprises a two-dimensional code label. The identity identifying terminal comprises a two-dimensional code scanner and a network transmission device. The anti-fake tracing basic information management system comprises a two-dimensional code generating device and a two-dimensional code product information remote network management platform. According to the two-dimensional code dynamic anti-fake information intelligent tracing system based on the network, the condition of product distribution flow link execution can be effectively monitored, controlled and supervised, the authenticity of products can be verified reliably and an advanced technology guarantee and a monitoring system are offered to market supervision enhancement of supervising departments such as government quality testing departments, industry and commerce departments and food and drug security departments.
Owner:QINGDAO ODO ENVIRONMENTAL TECH CO LTD
Electronic document authenticity assurance method and electronic document disclosure system
InactiveUS7526645B2Verify authenticityUser identity/authority verificationUnauthorized memory use protectionElectronic documentDocument preparation
An electronic document authenticity assurance technique and an information disclosure system both of which can compatibly realize the assurance of the authenticity of disclosure documents and the deletion of information inappropriate for disclosure. An electronic document is divided into constituent elements and an electronic signature is affixed to an arbitrary subset of a set including all the constituent elements. Otherwise, an electronic signature is affixed to data obtained by binding each of the constituent elements to information specifying the relationship between a respective one of the constituent elements and the structure of the electronic document. Otherwise, the hash values of the respective constituent elements are calculated and an electronic signature is affixed to data obtained by binding the calculated hash values together. Otherwise, random numbers generated for the respective constituent elements are bound together, then the hash values of the respective random-numbered constituent elements are calculated, and then an electronic signature is affixed to data obtained by binding the calculated hash values together.
Owner:HITACHI LTD
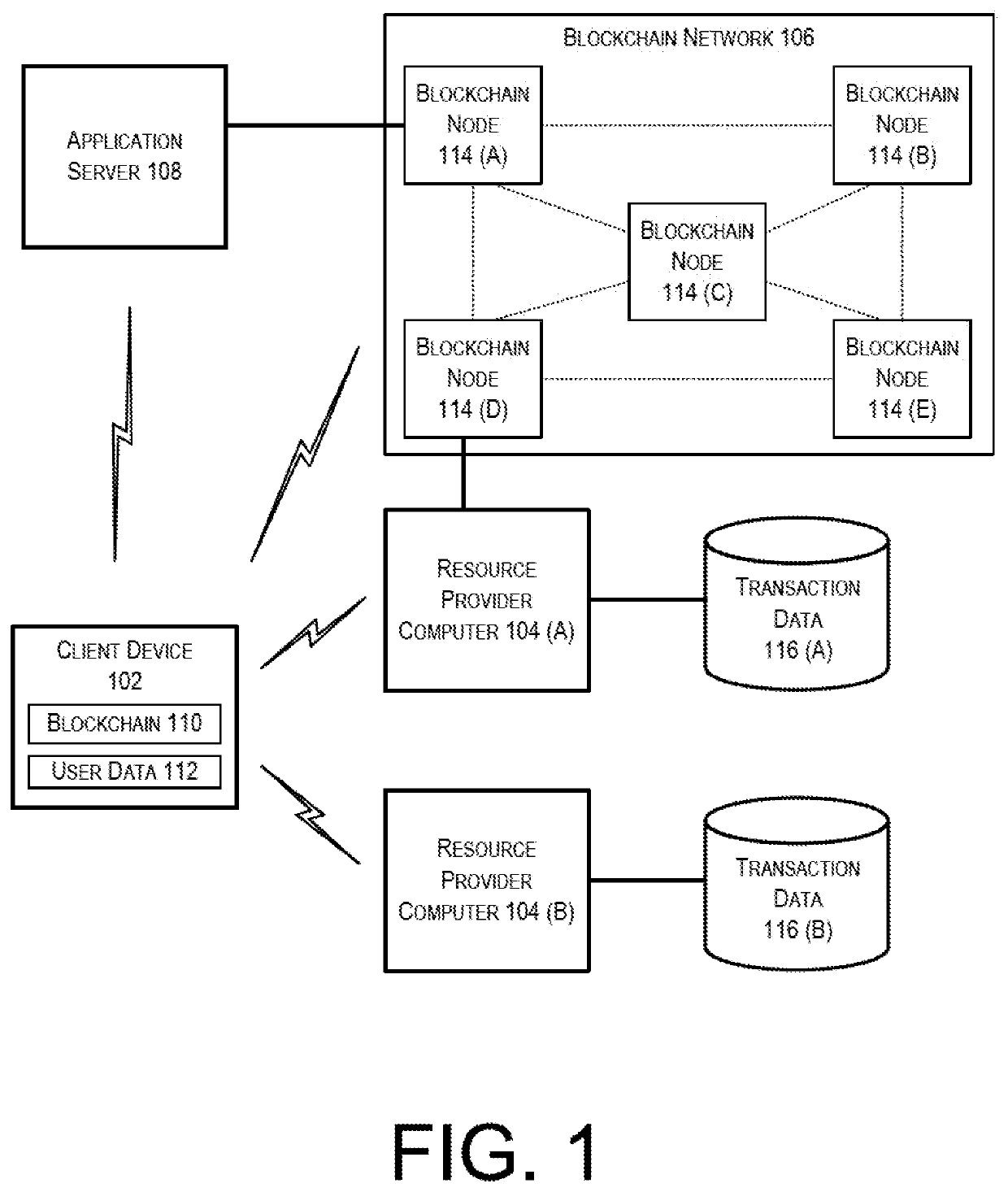
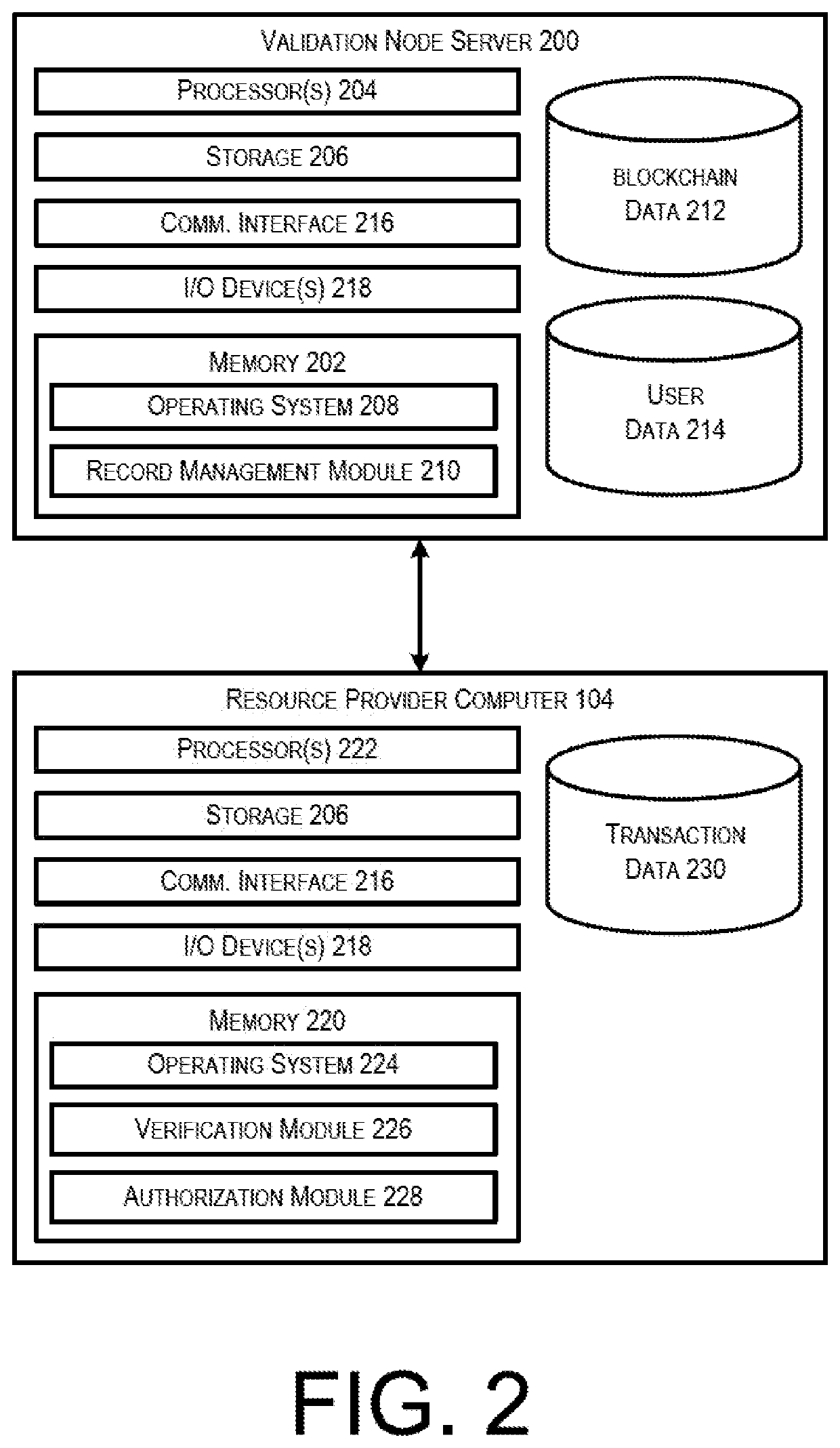
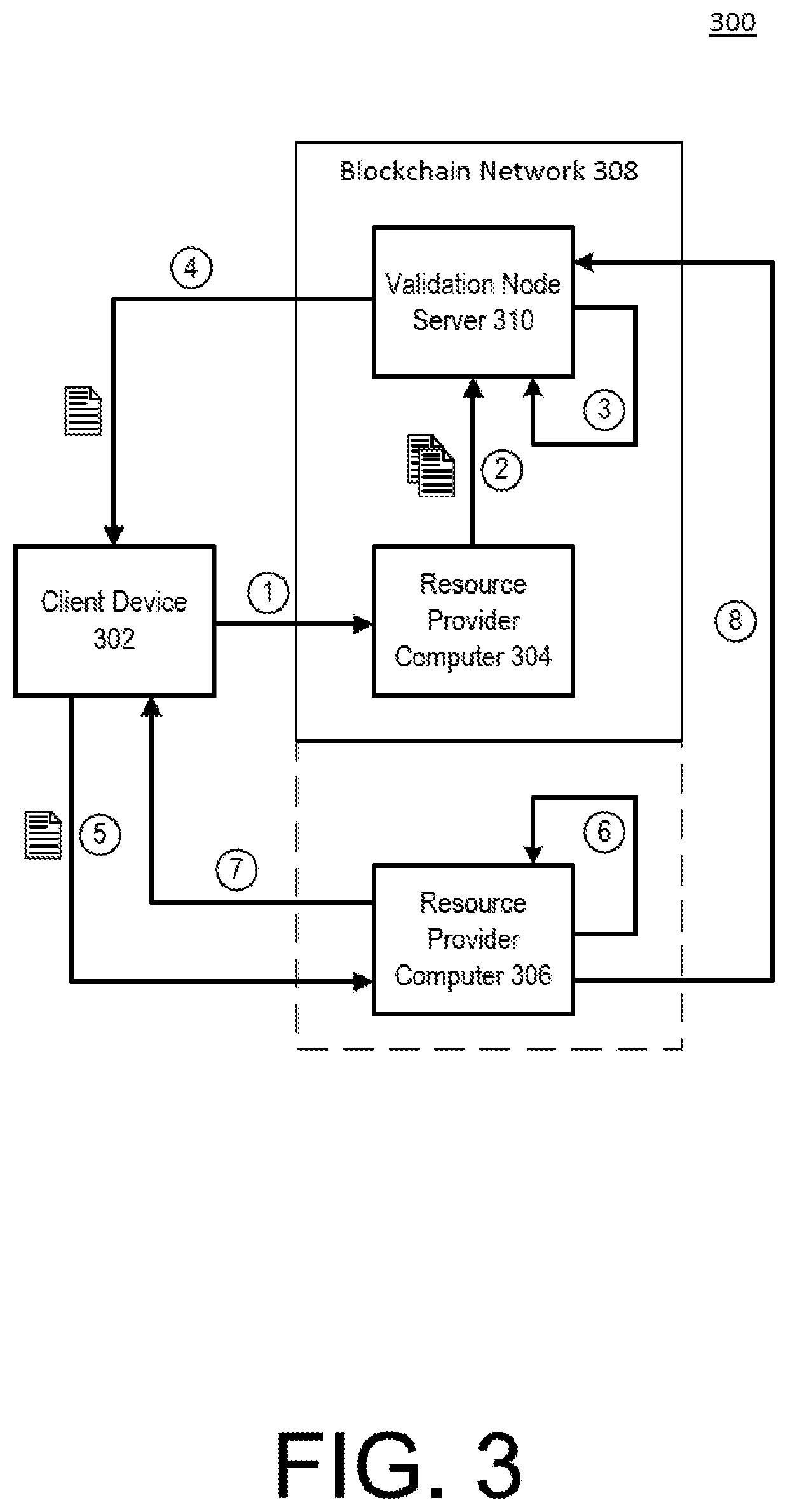
Blockchain architecture with record security
PendingUS20200250676A1Prevent unauthorized accessVerify authenticityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital signatureEngineering
Described herein is a system in which an electronic record is stored within a distributed environment. In this system, a validation node may receive a transaction record from an acceptance node. The validation node may verify that the acceptance node is authorized 5 to participate in a blockchain network, identify a user associated with the transaction record, and append the transaction record to an electronic record. The transaction record may be associated with a digital signature formed by hashing multiple data elements, and then encrypting the hashed data elements using a private encryption key.
Owner:VISA INT SERVICE ASSOC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com