Survivable security features for image replacement documents
a security feature and document technology, applied in the field of document protection methods and products, can solve the problems of security images contained on conventional commercial paper, such as original checks, not being able to survive scanning process, and originating banks not being able to as effectively verify if,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] One embodiment of the invention, which has particular benefits for the banking industry, features a cost effective security feature in the form of a latent (covert) security image that can survive the imaging process on the check processing technology currently in use. The survivable security image enables originating banks to assure the authenticity of the new electronic checks under the standards adopted for the Check Clearing Act for the 21st Century of 2004, referred to as “Check 21” standards. The invention can also be practiced under the industry standards published by the Accredited Standards Committee X9, Incorporated. Significantly, no expensive software or hardware is necessary to utilize the advance.
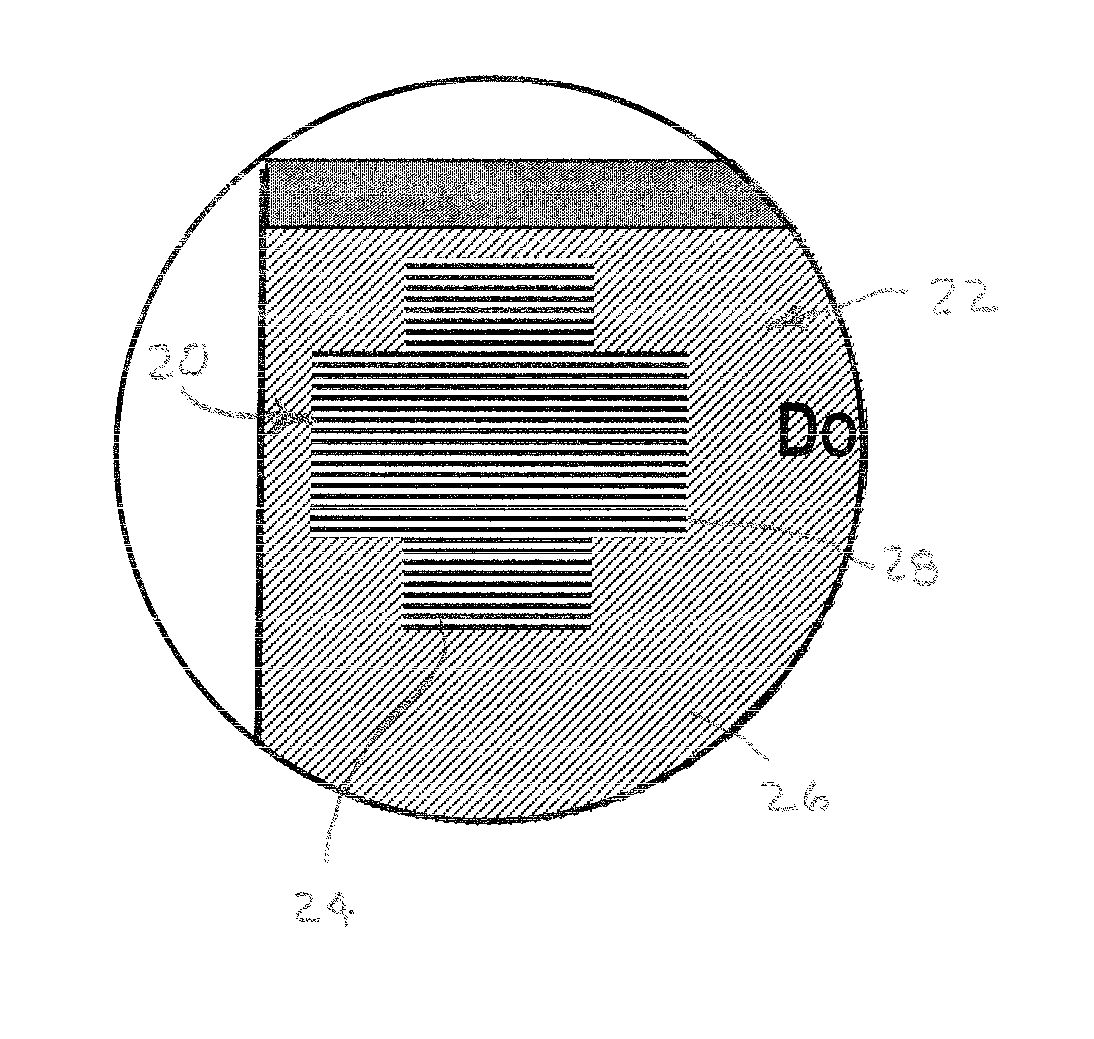
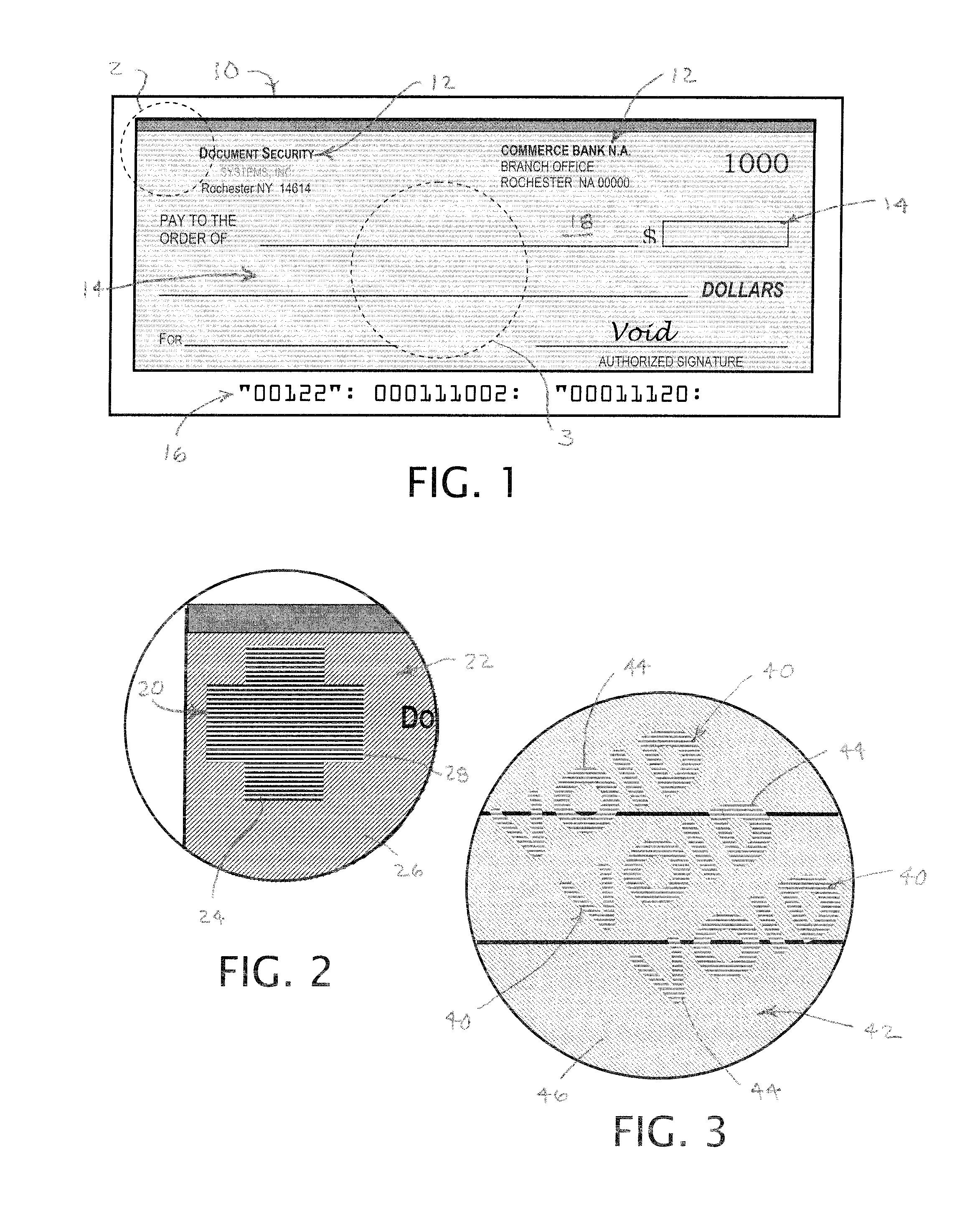
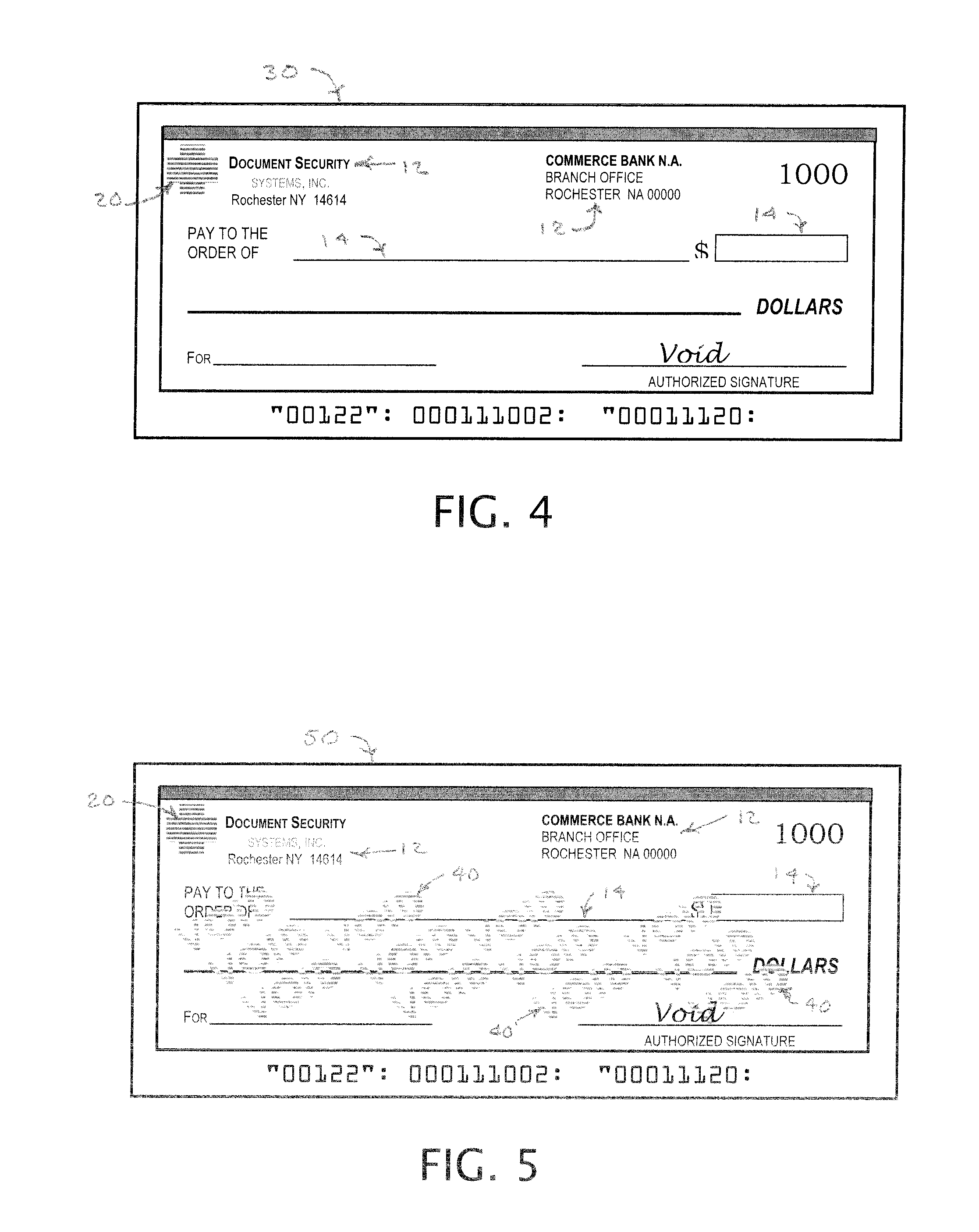
[0048] Referring to the drawings for more details of the embodiment, an original printed document in the form of a bank check 10 is shown in FIG. 1 having a number of preprinted areas 12, containing information about the payor and the payor bank, along with designated ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com