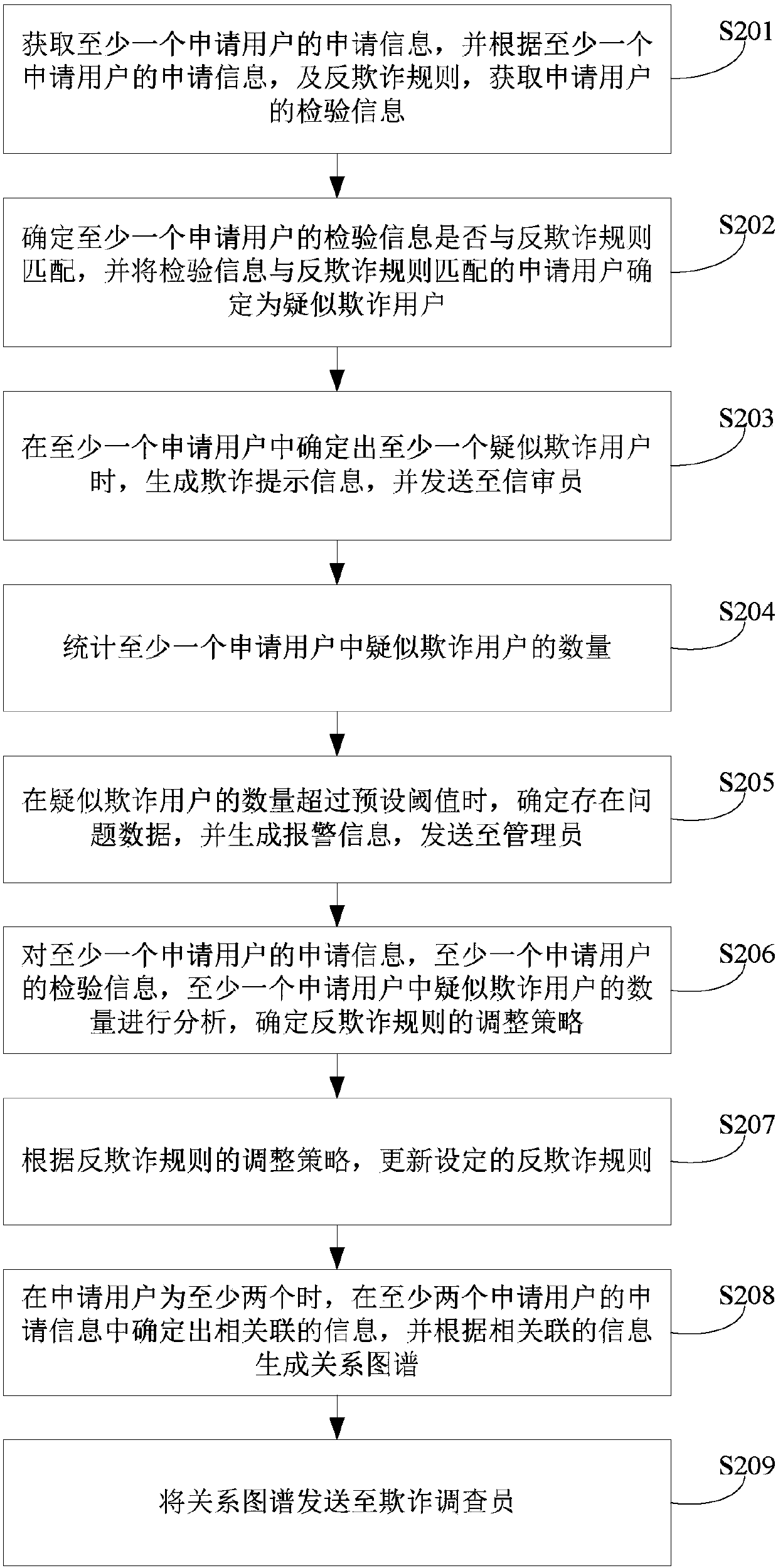
Patents
Literature
91results about How to "Reduce the risk of fraud" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
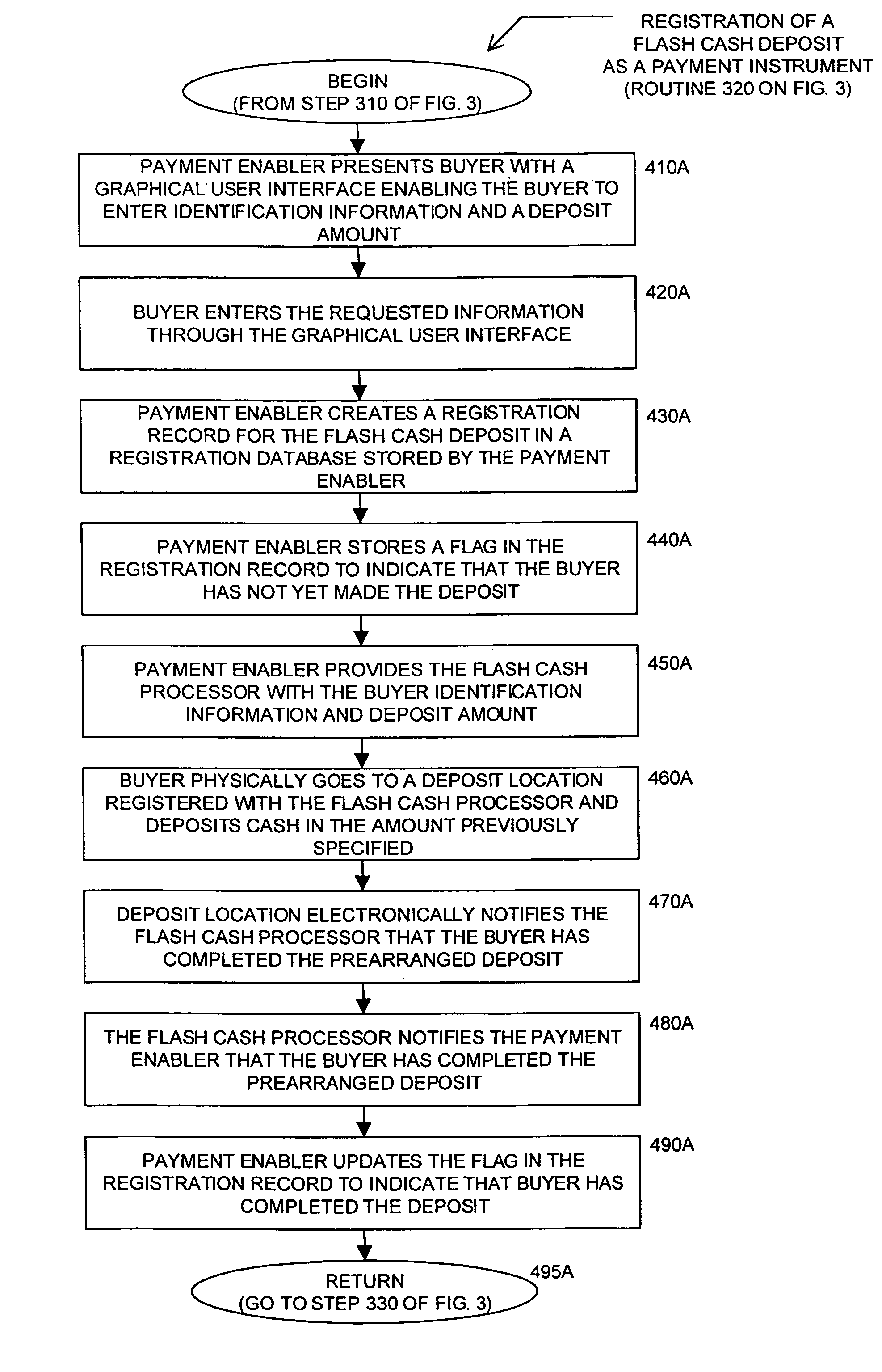
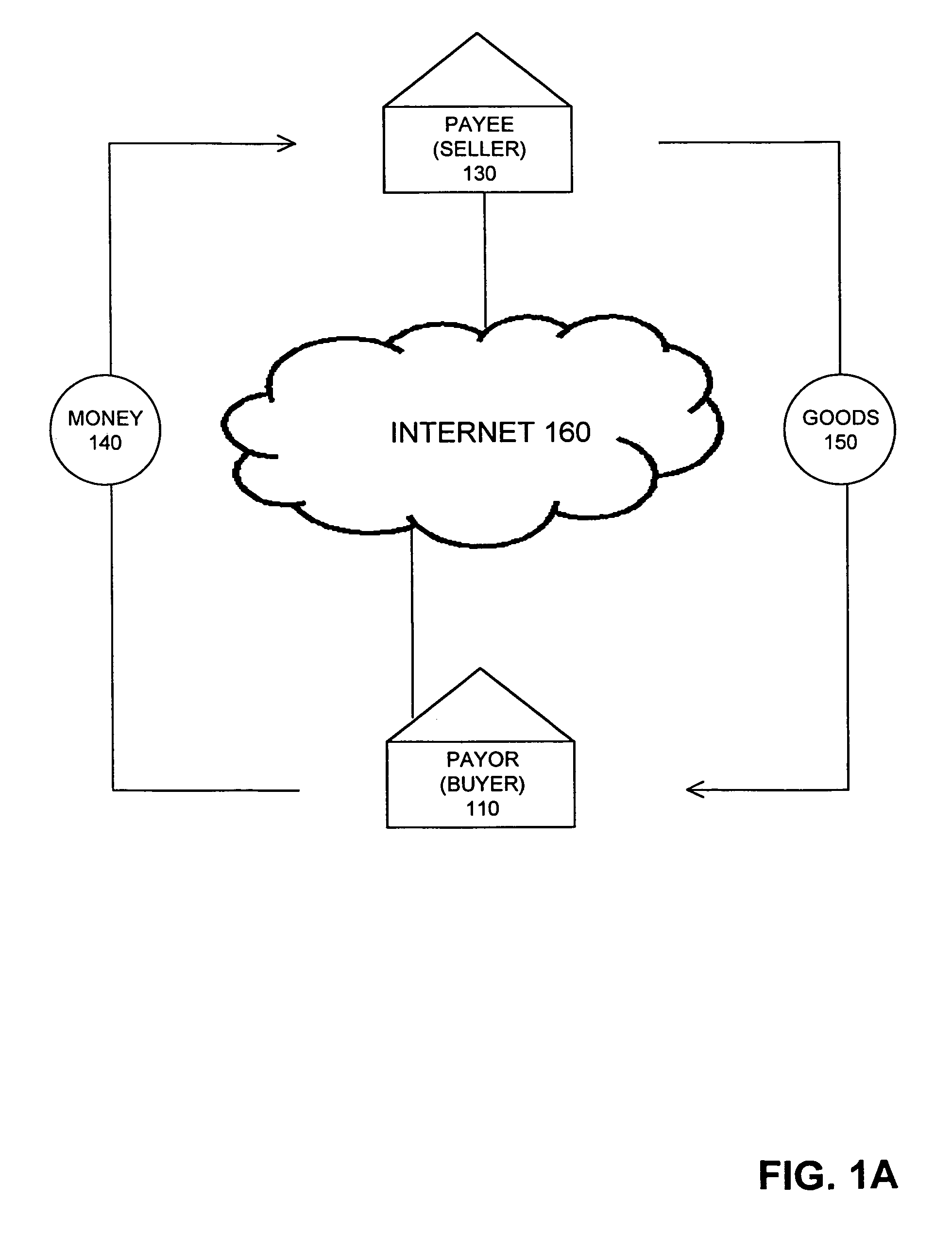
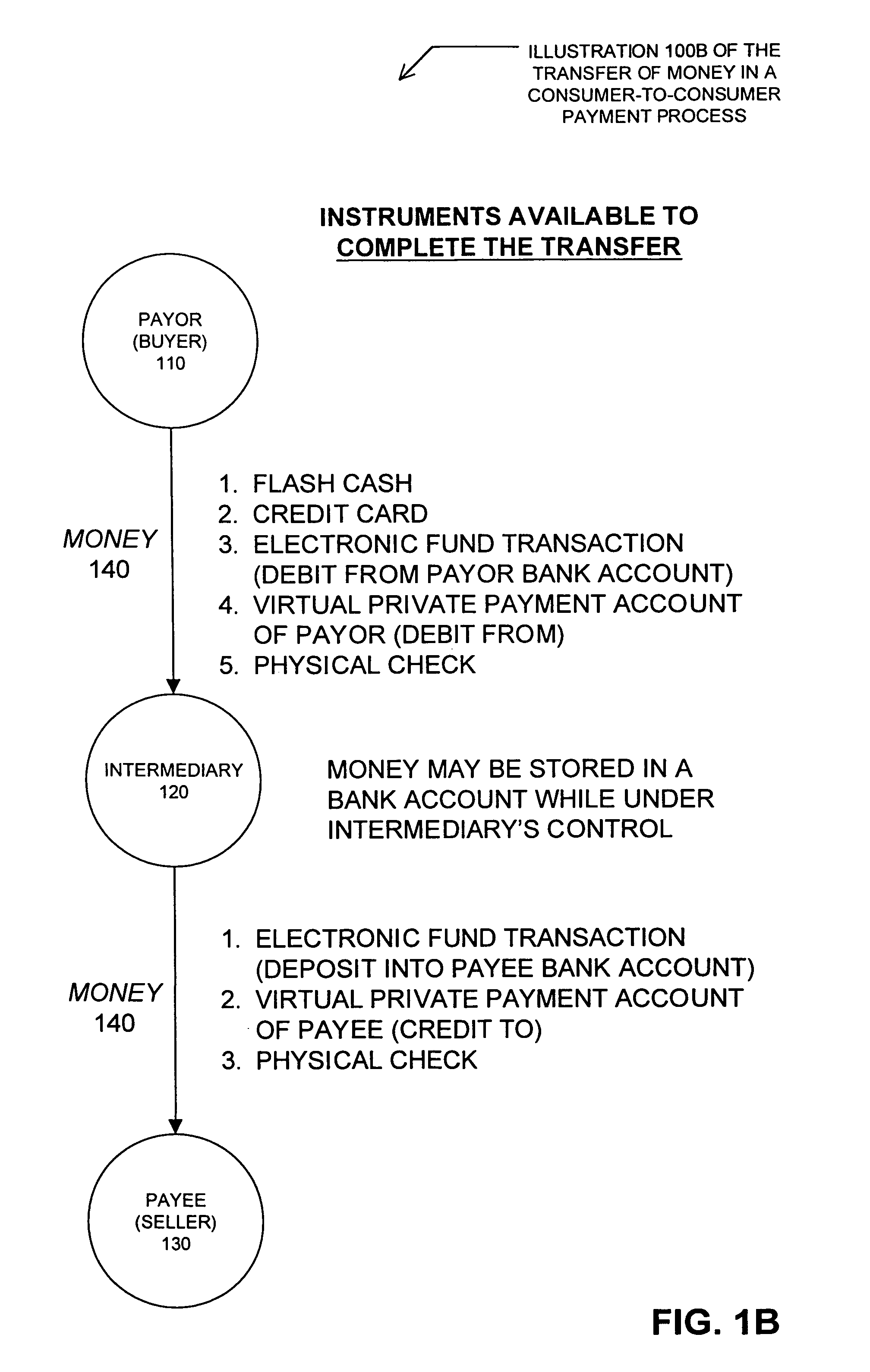
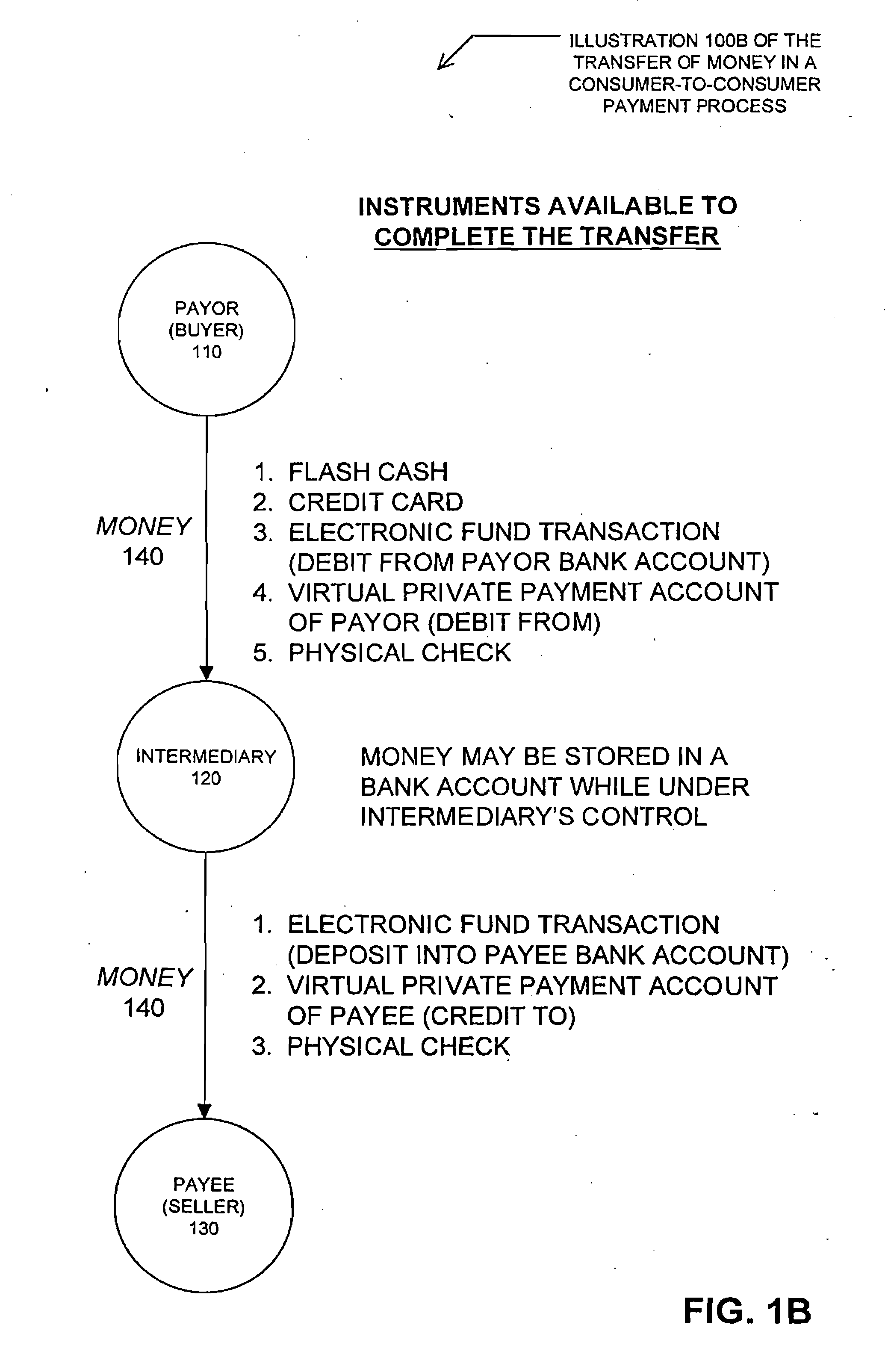
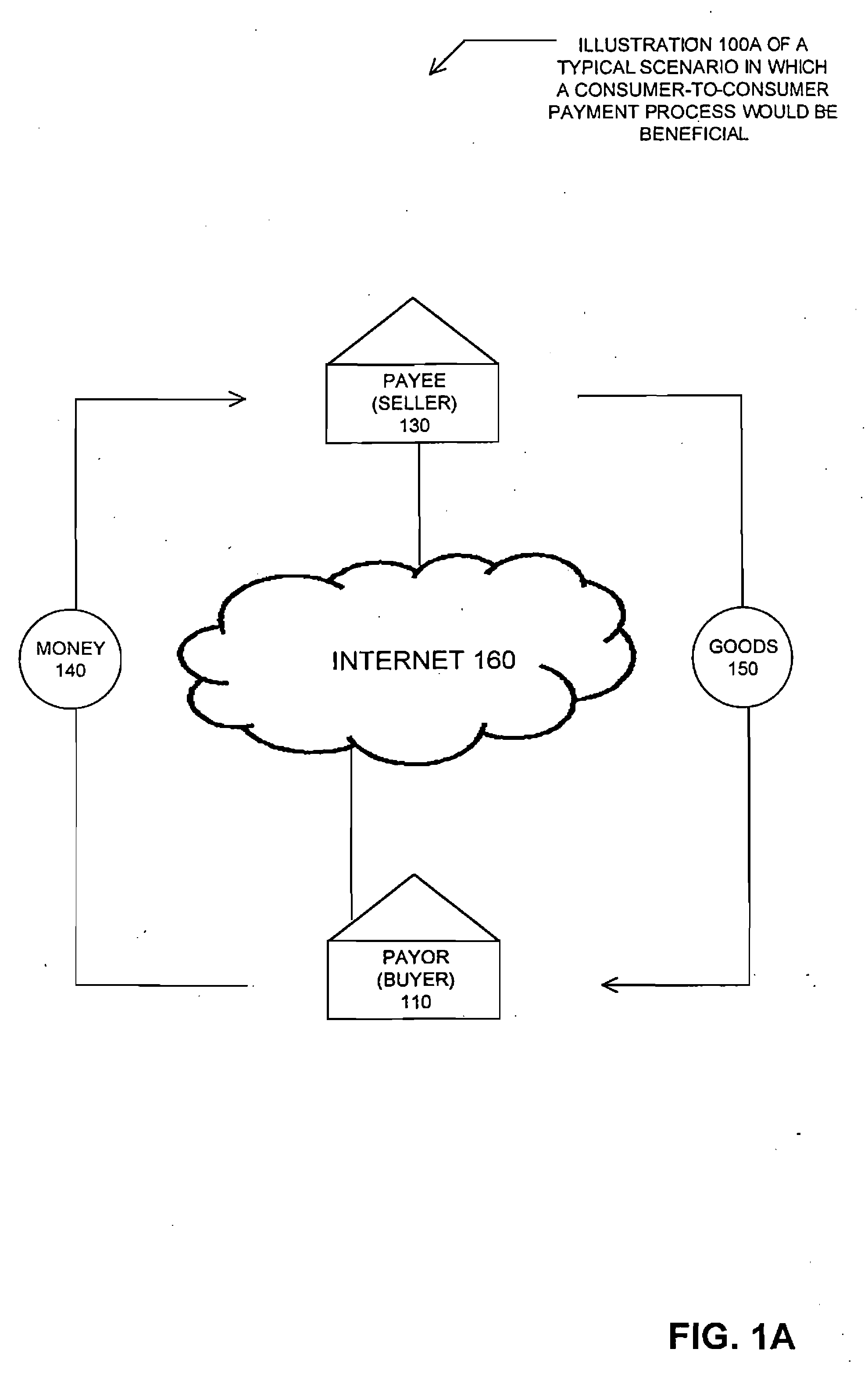
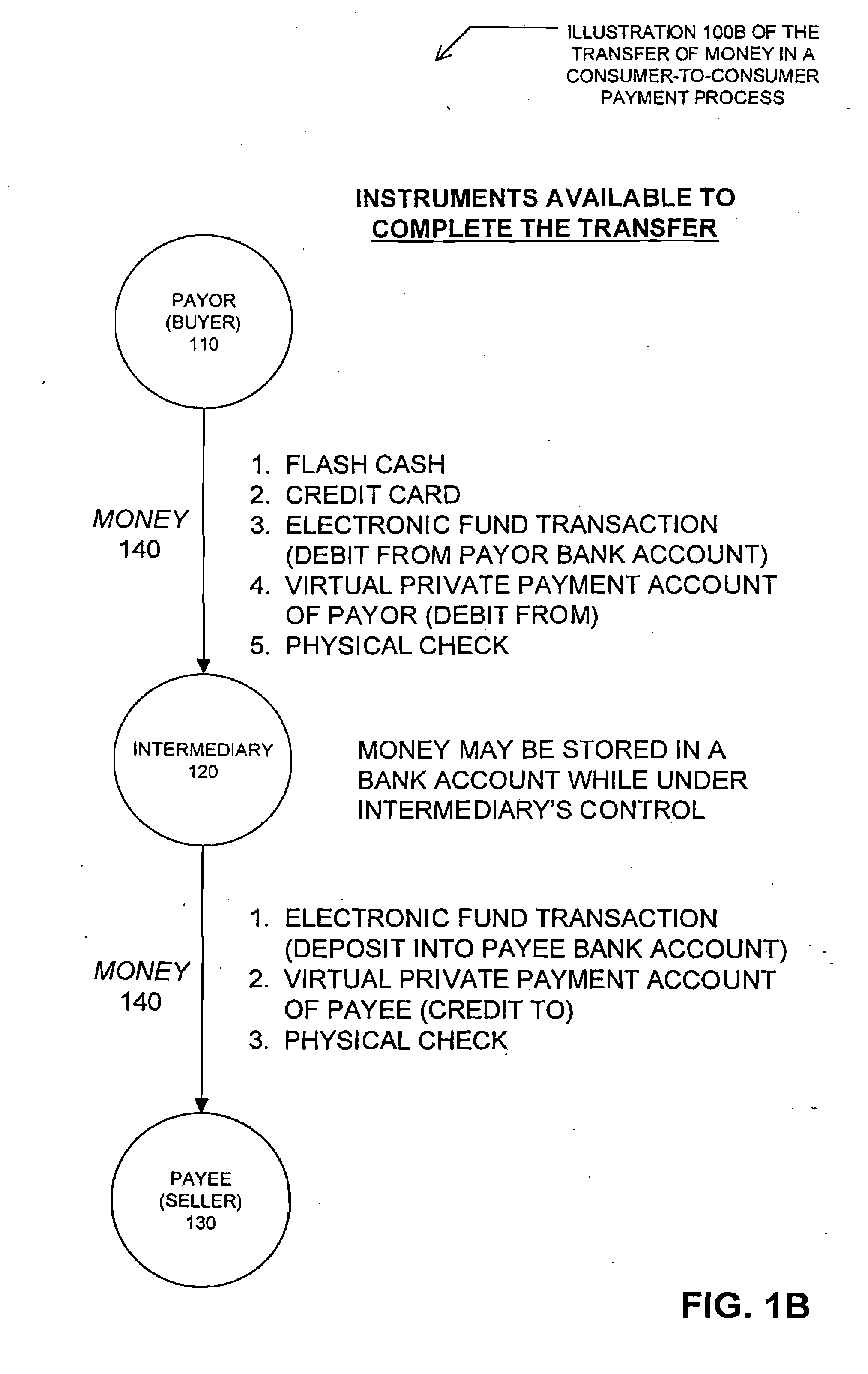
Method and system for facilitating financial transactions between consumers over the internet
InactiveUS7177836B1Reduce the risk of fraudFinanceBuying/selling/leasing transactionsPaymentThird party
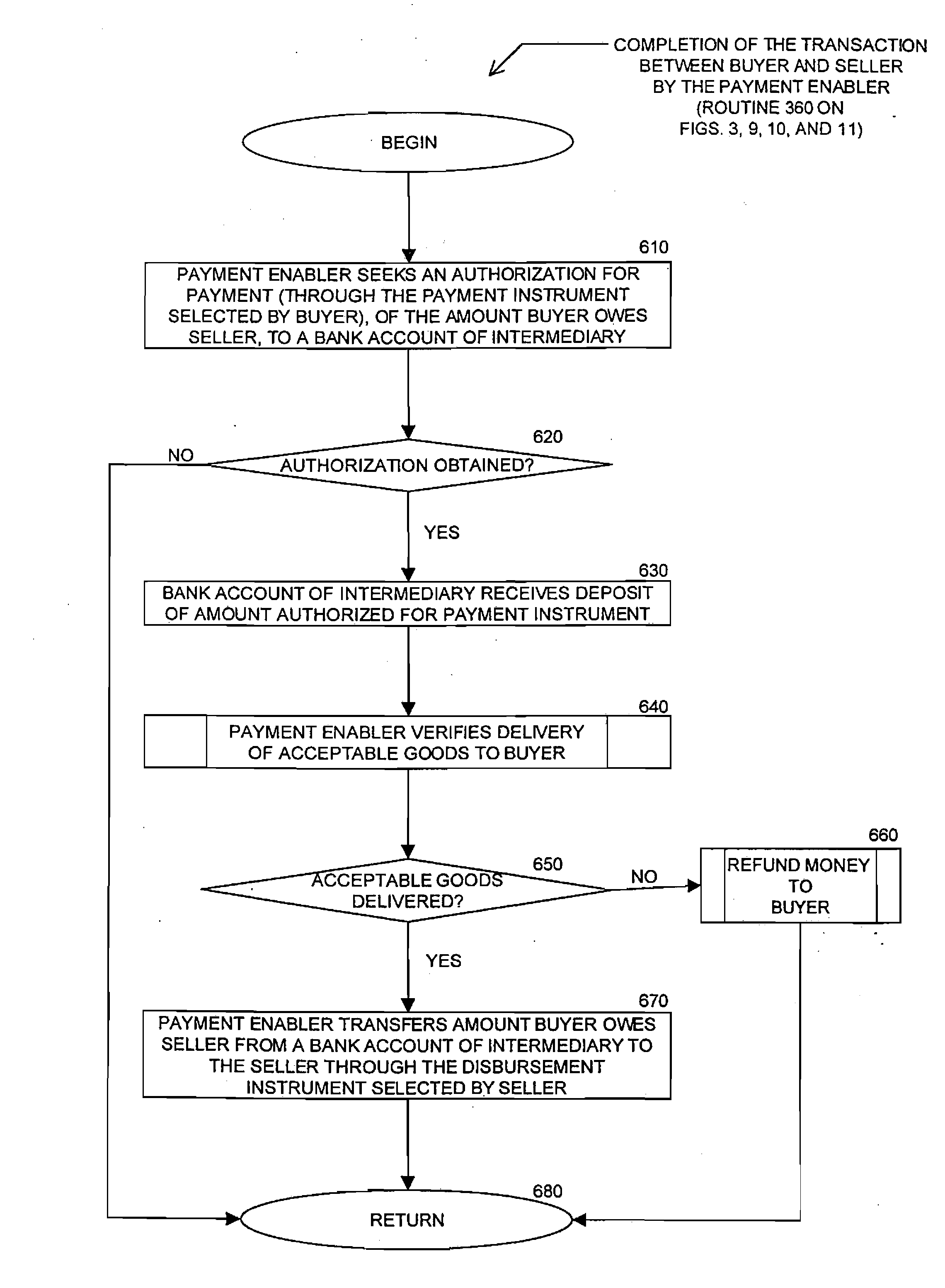
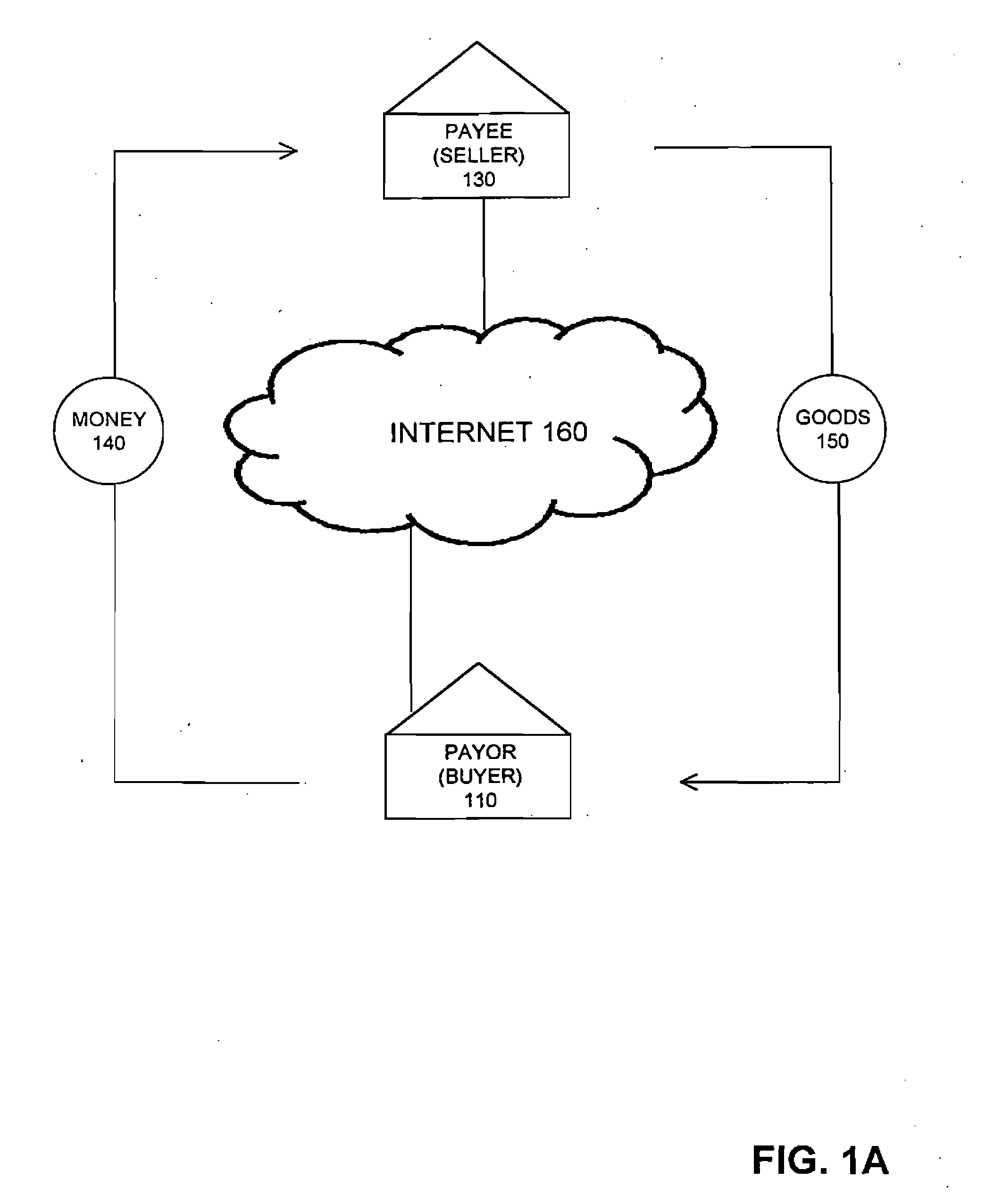
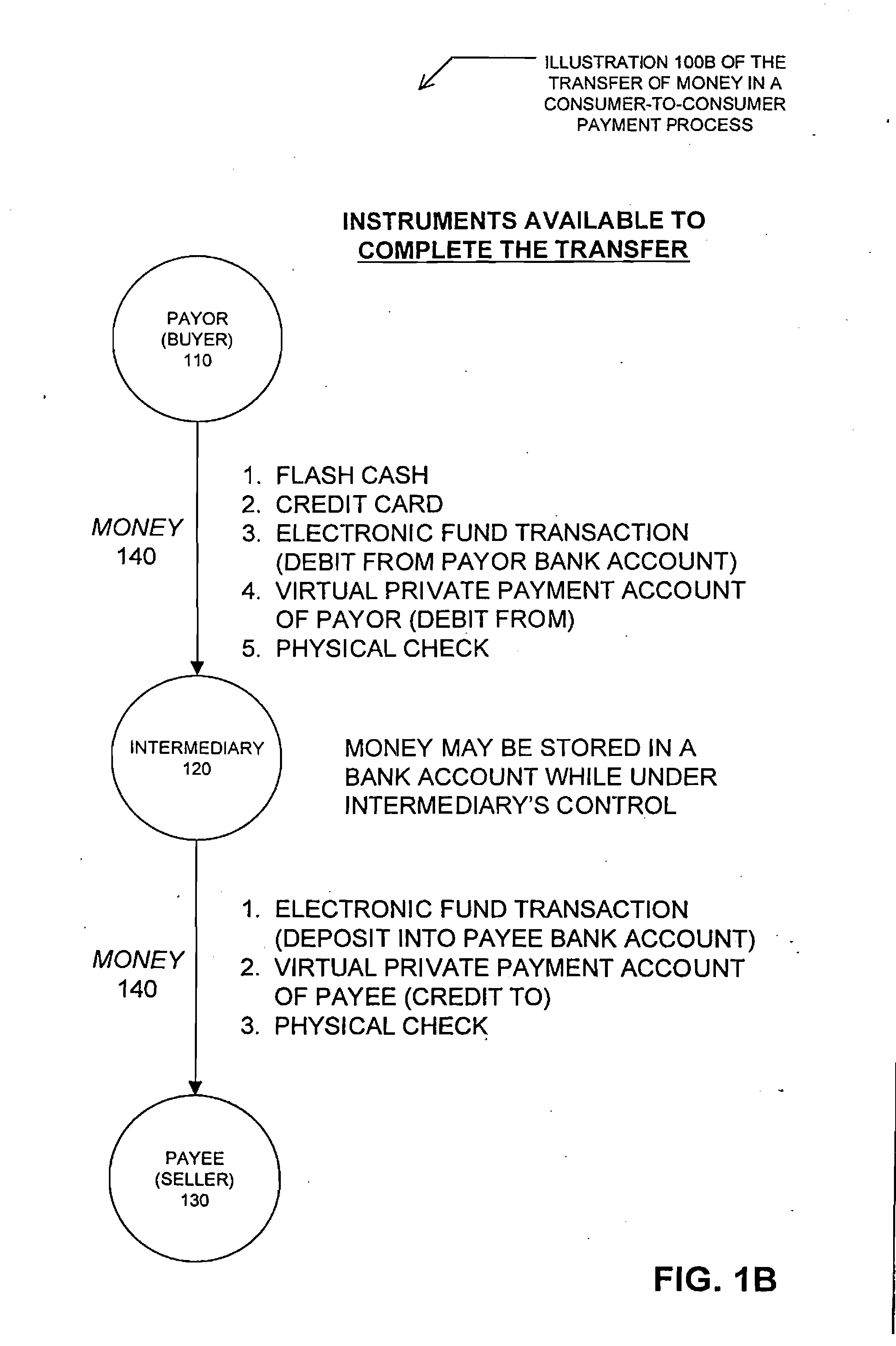
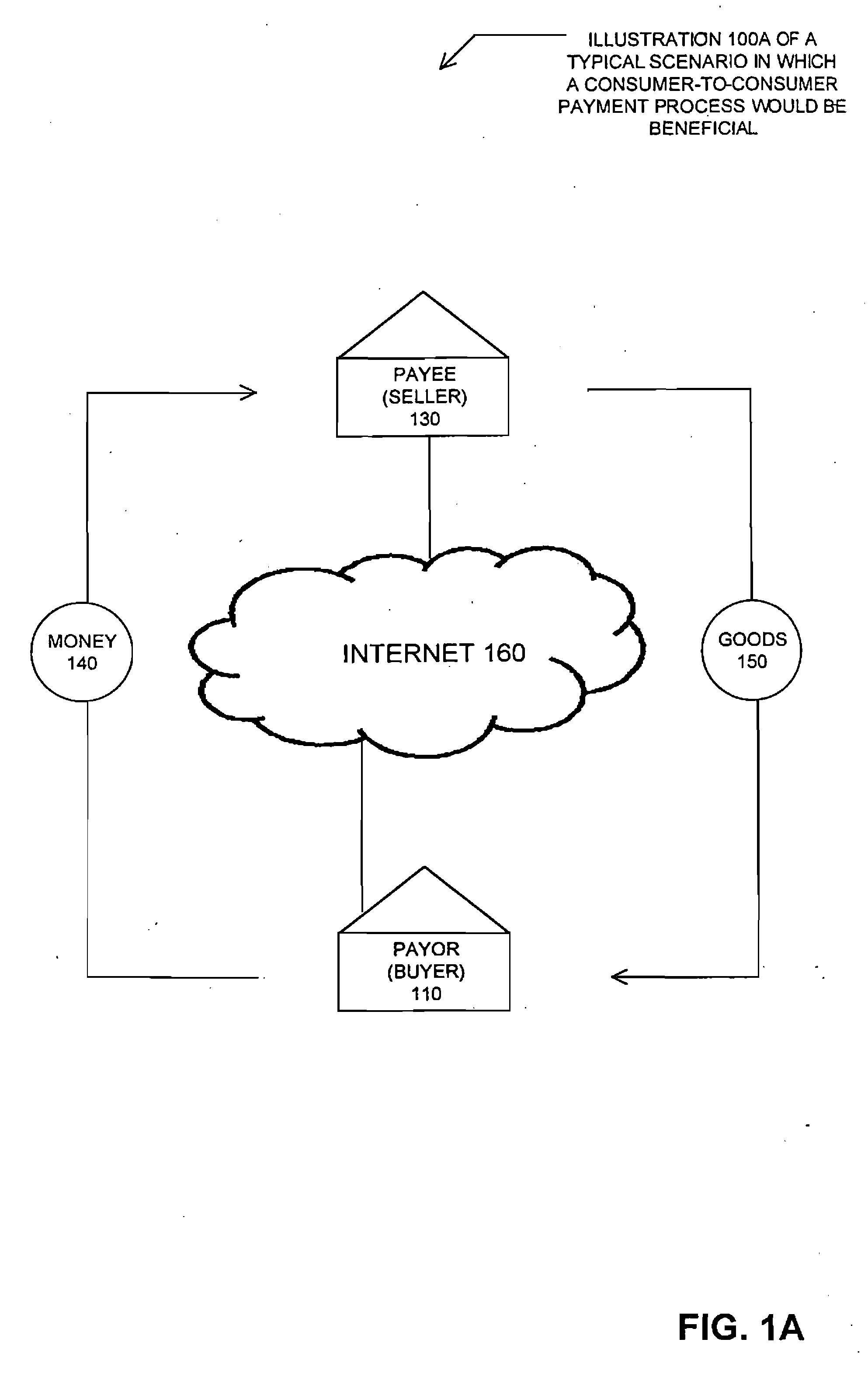
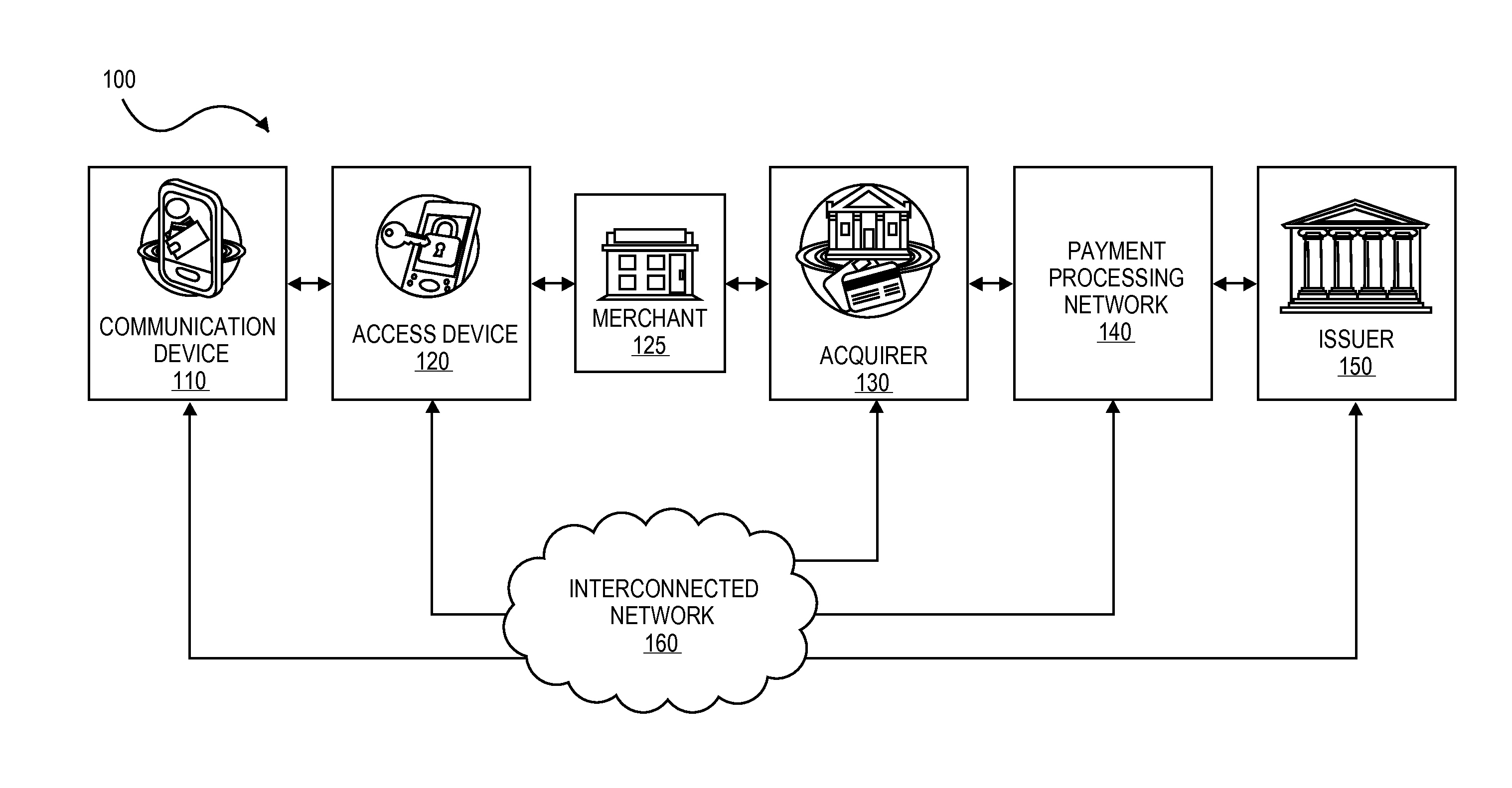
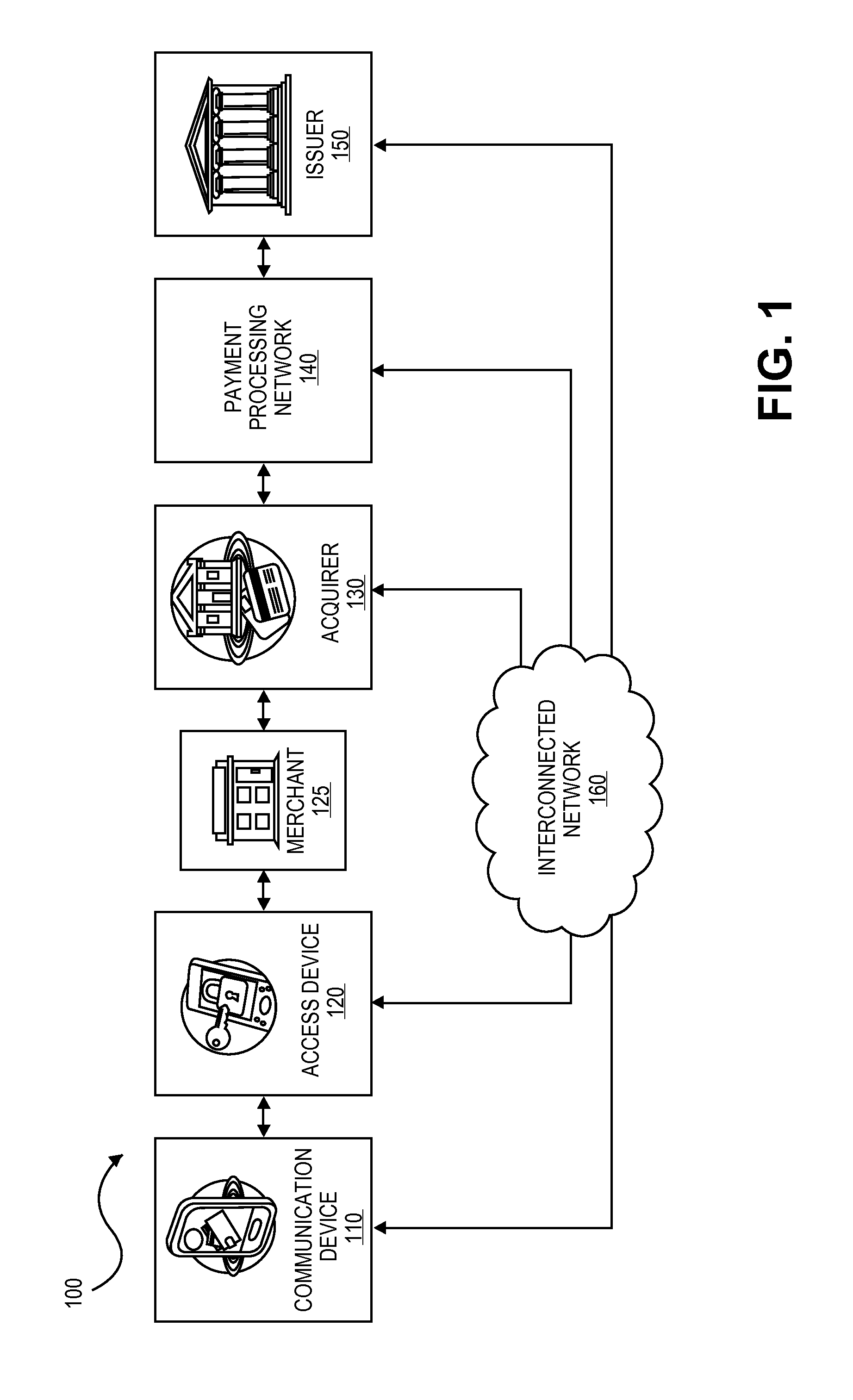
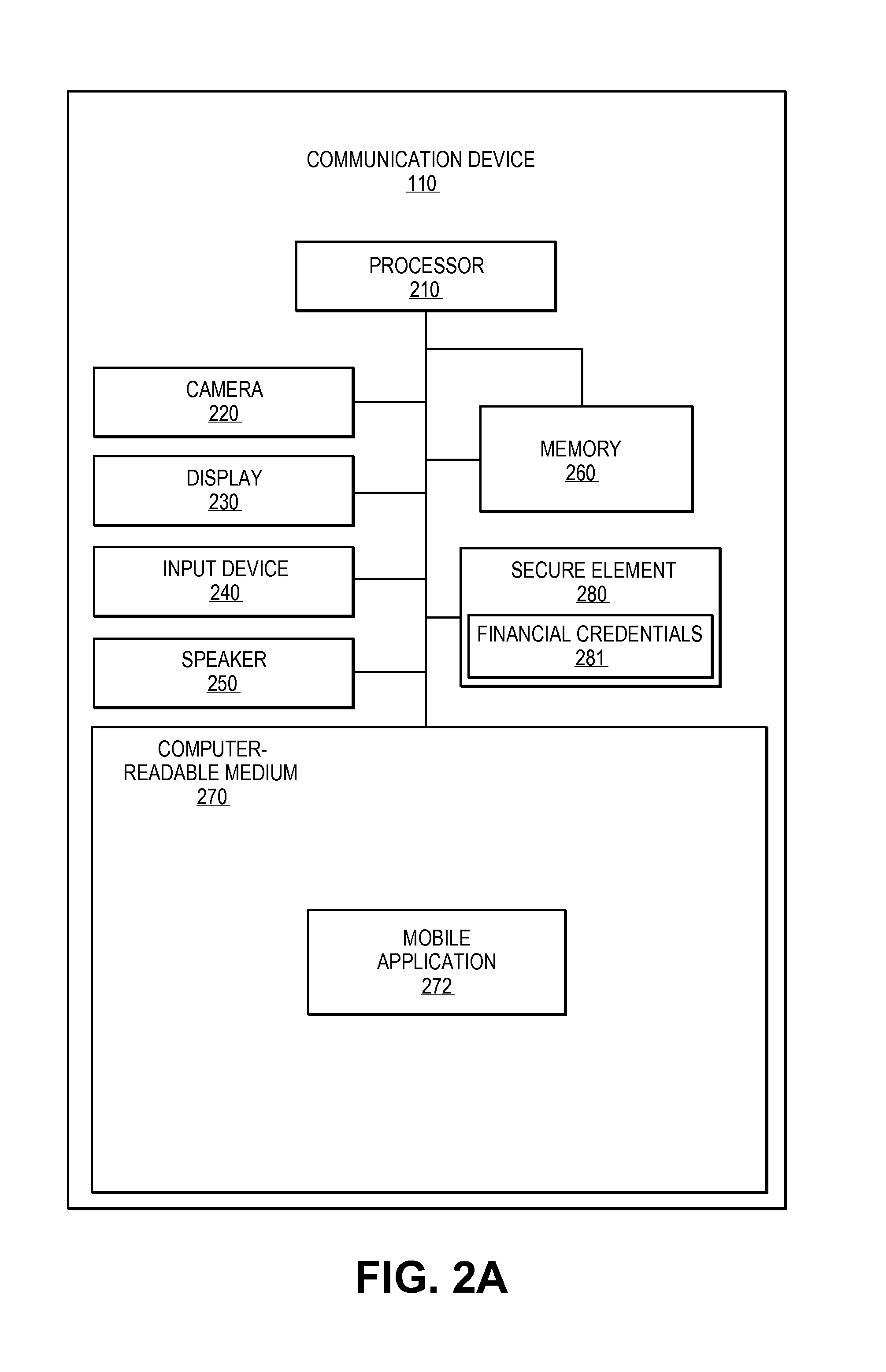
A method for enabling two individual consumers to complete a transaction that includes payment from one consumer (the payor, or buyer) to another consumer (the payee, or seller). An intermediary typically operates the service over a computer network of nodes, such as the Internet. The buyer has the convenience of paying through a variety of different payment instruments. Likewise, the seller has the convenience of receiving payment through a variety of different disbursement instruments. For a fee, the intermediary collects the payment from the buyer and pays the seller. Although the intermediary may receive payment from the buyer before the intermediary transfers the payment to the seller, the intermediary may choose to pay the seller before receiving payment from the buyer. In this case, the intermediary assumes the risk of nonpayment by the buyer. Alternatively, the intermediary may pay a third party that specializes in processing transactions for the payment instrument chosen by the buyer to assume the risk of nonpayment by the buyer. In this case, the intermediary receives a promise of payment from the third party before the intermediary pays the seller. Such a promise of payment from the third party is referred to as an authorization.
Owner:THE WESTERN UNION CO +1
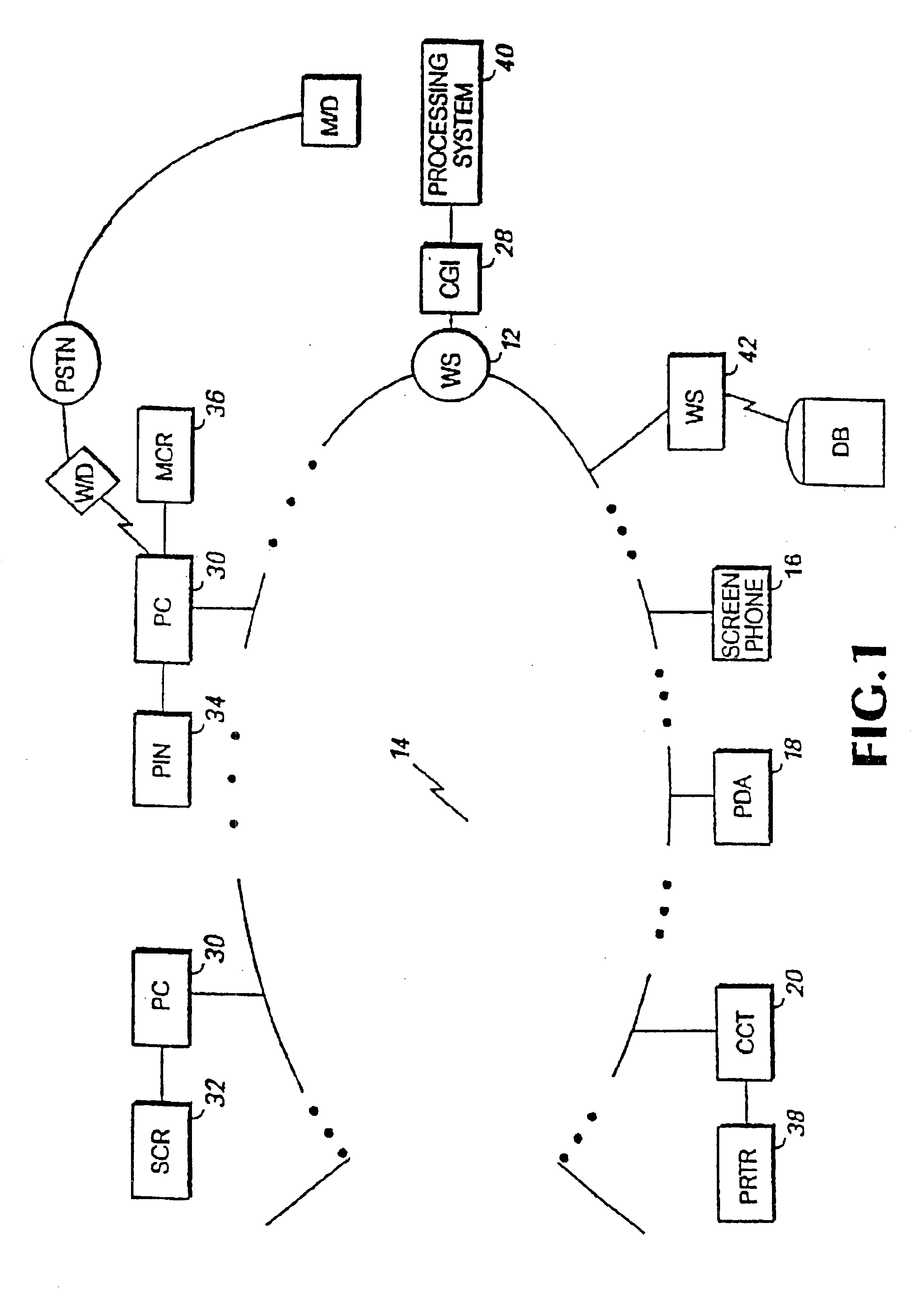
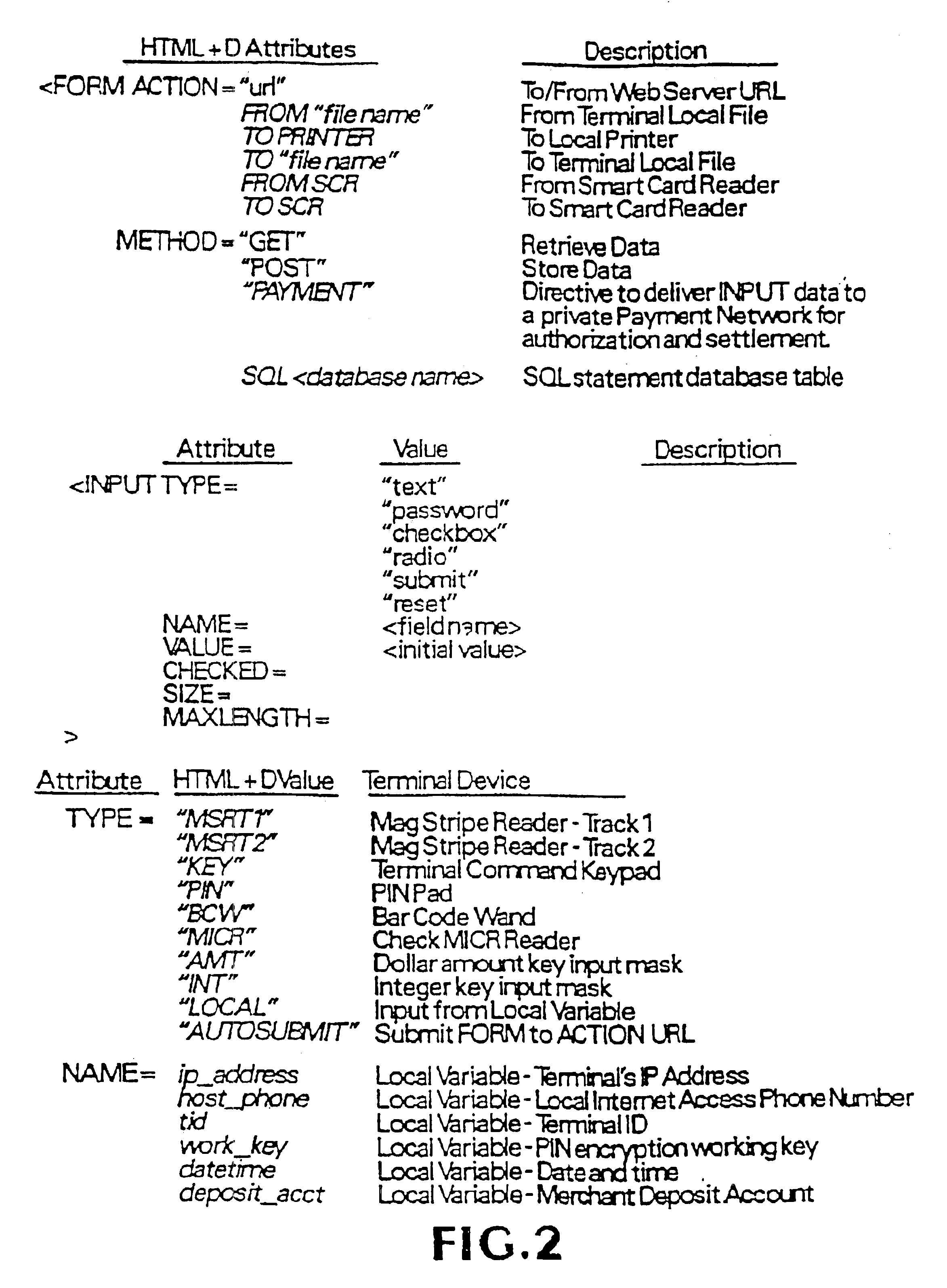
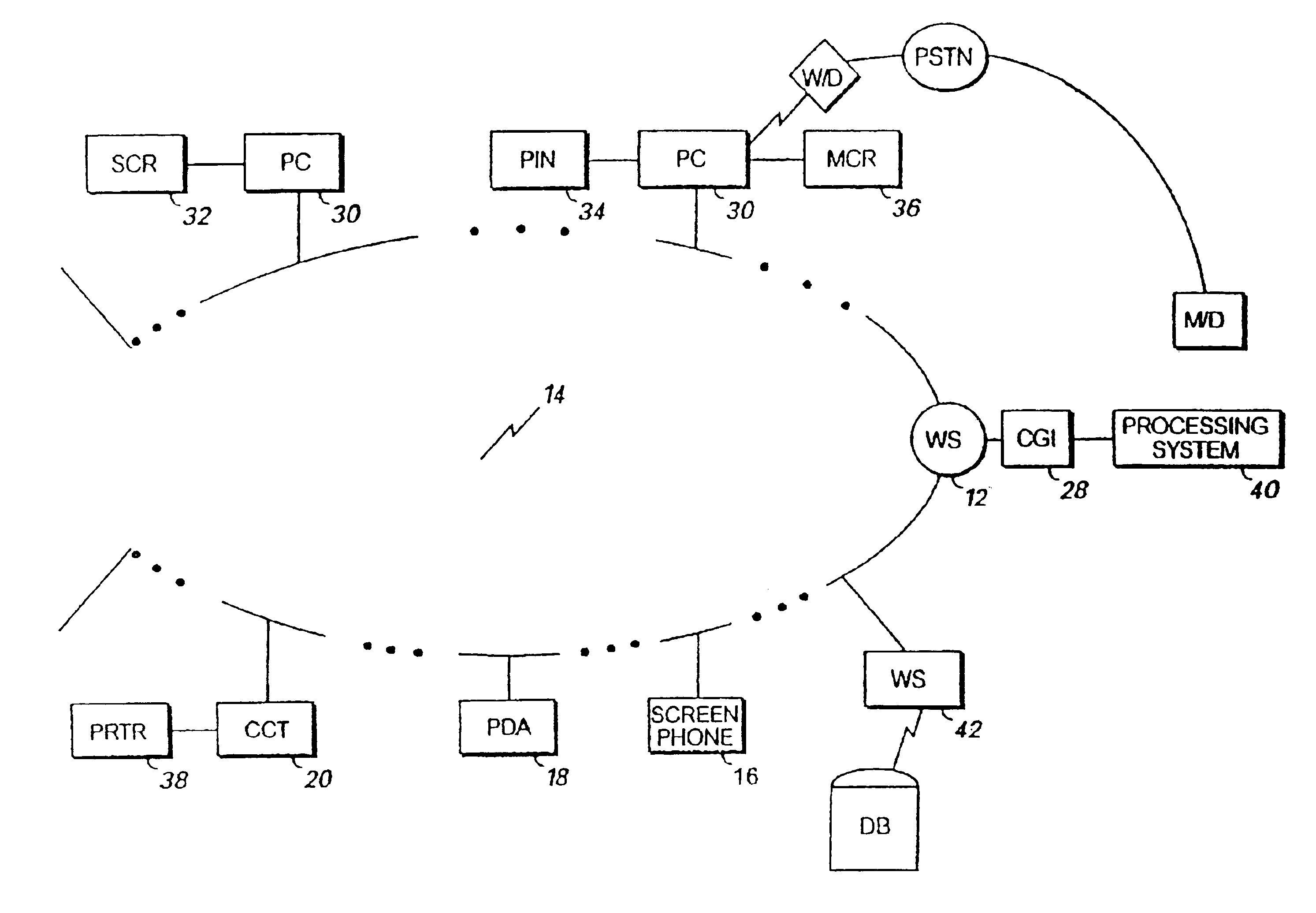
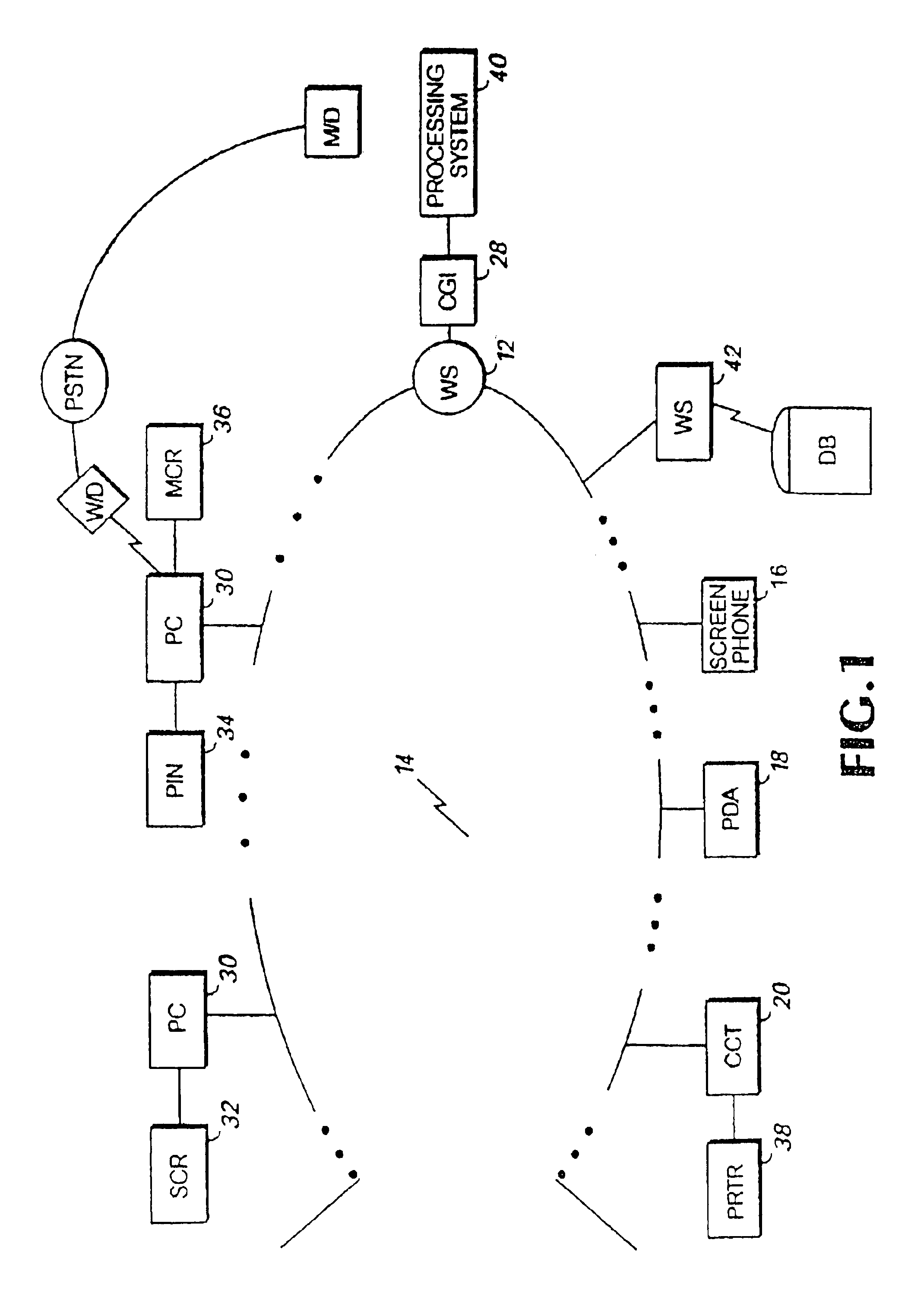
System and method for enabling transactions between a web server and an automated teller machine over the internet
InactiveUS6850996B2Reduce the risk of fraudInformation receivedDigital data processing detailsMultiple digital computer combinationsComputer networkComputer interpretation
An automated teller machine (ATM) implements financial transactions over the Internet. The ATM includes a computer and at least one non-standard I / O device coupled to the computer. The computer of the ATM interprets extended open network protocol statements to control the non-standard I / O device for purposes of implementing a financial transaction.
Owner:WI LAN TECH INC
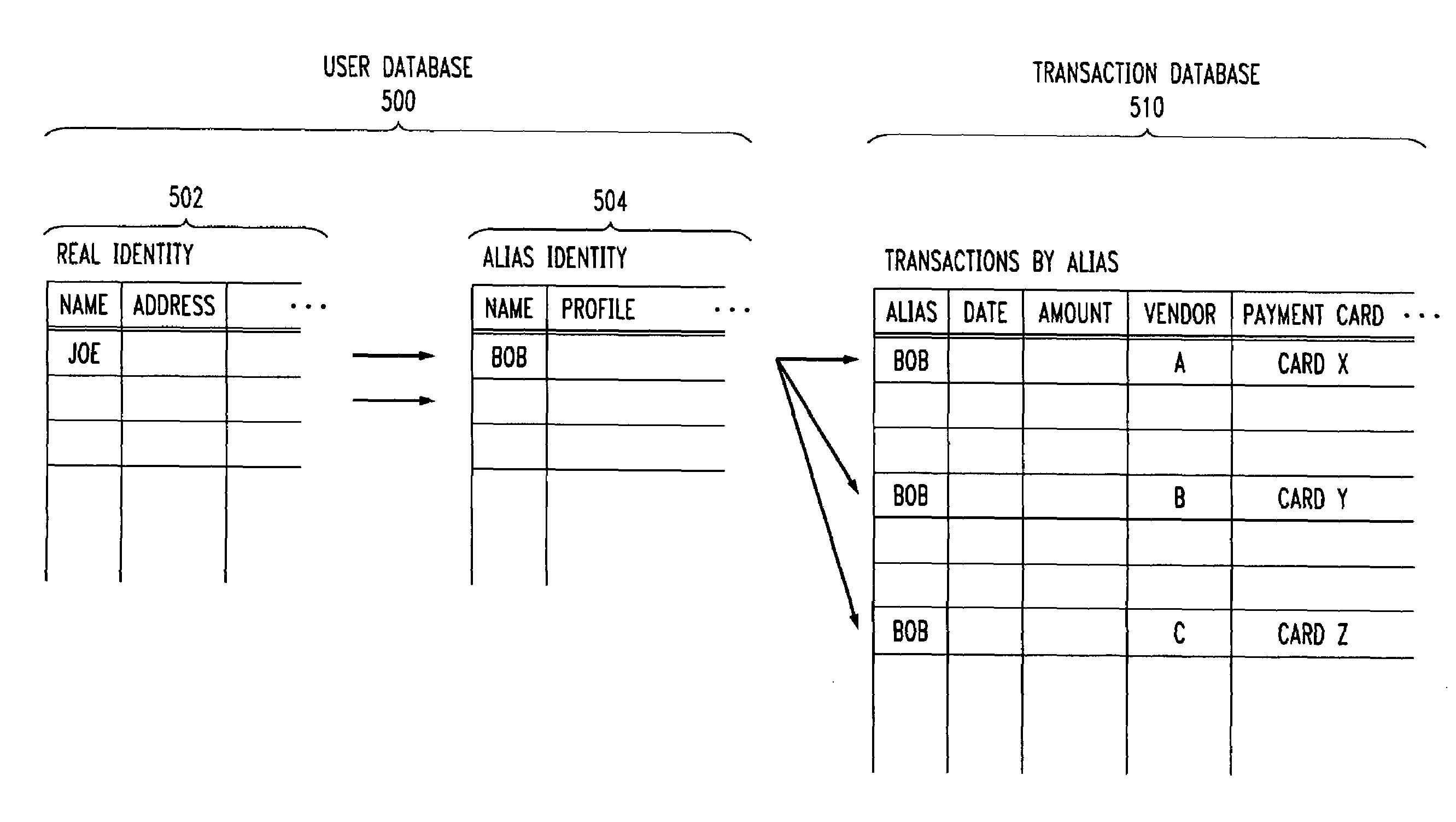
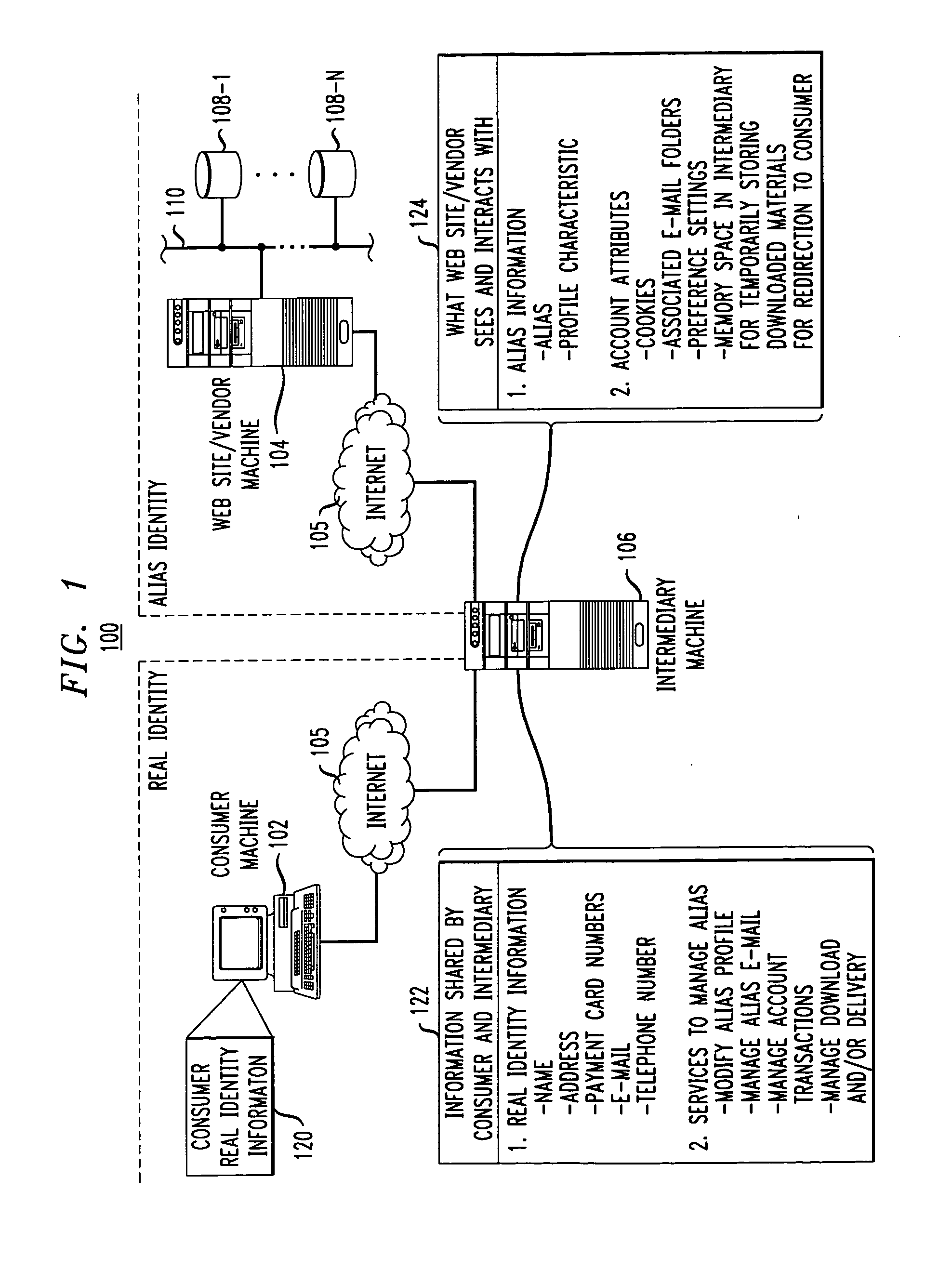
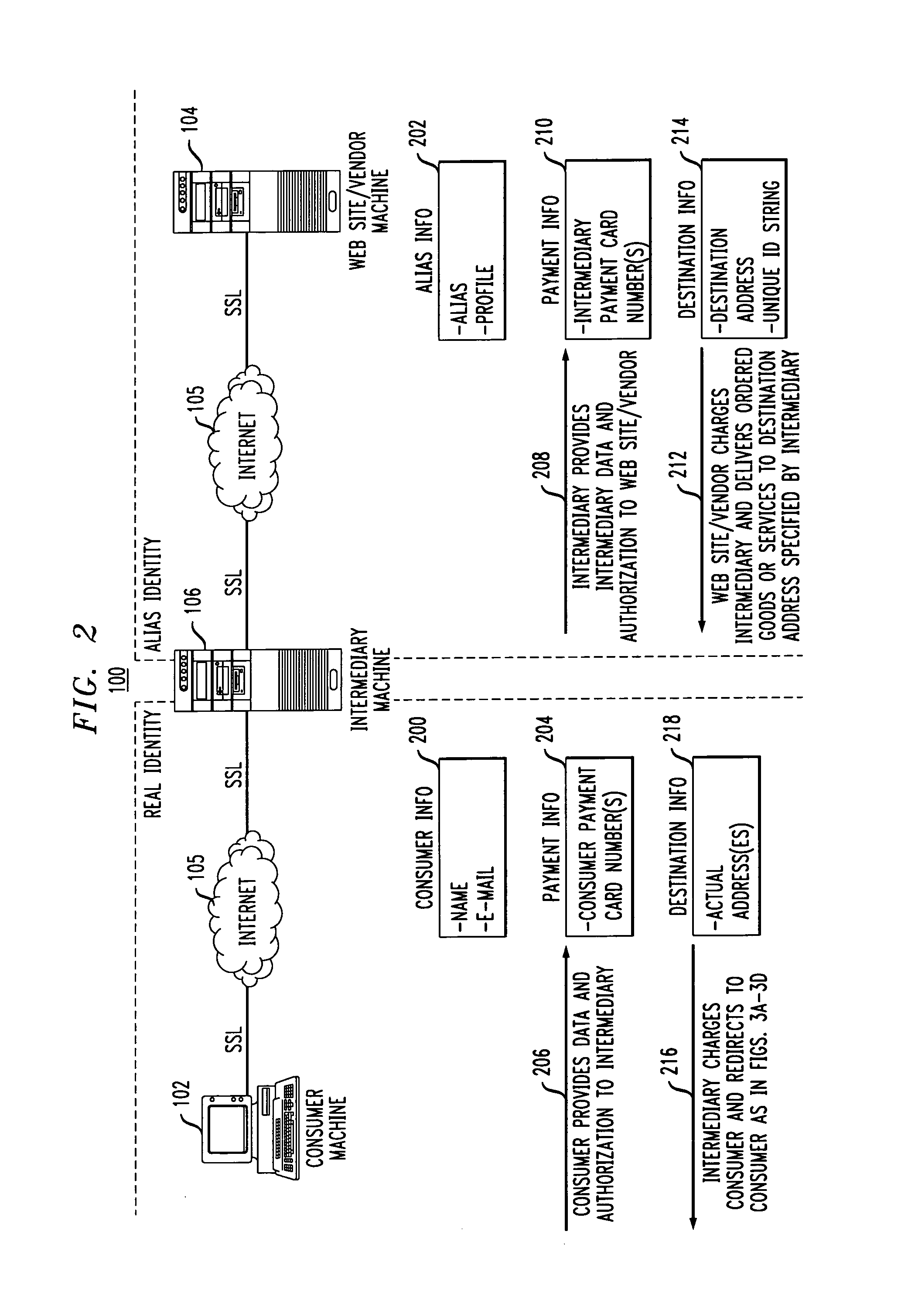
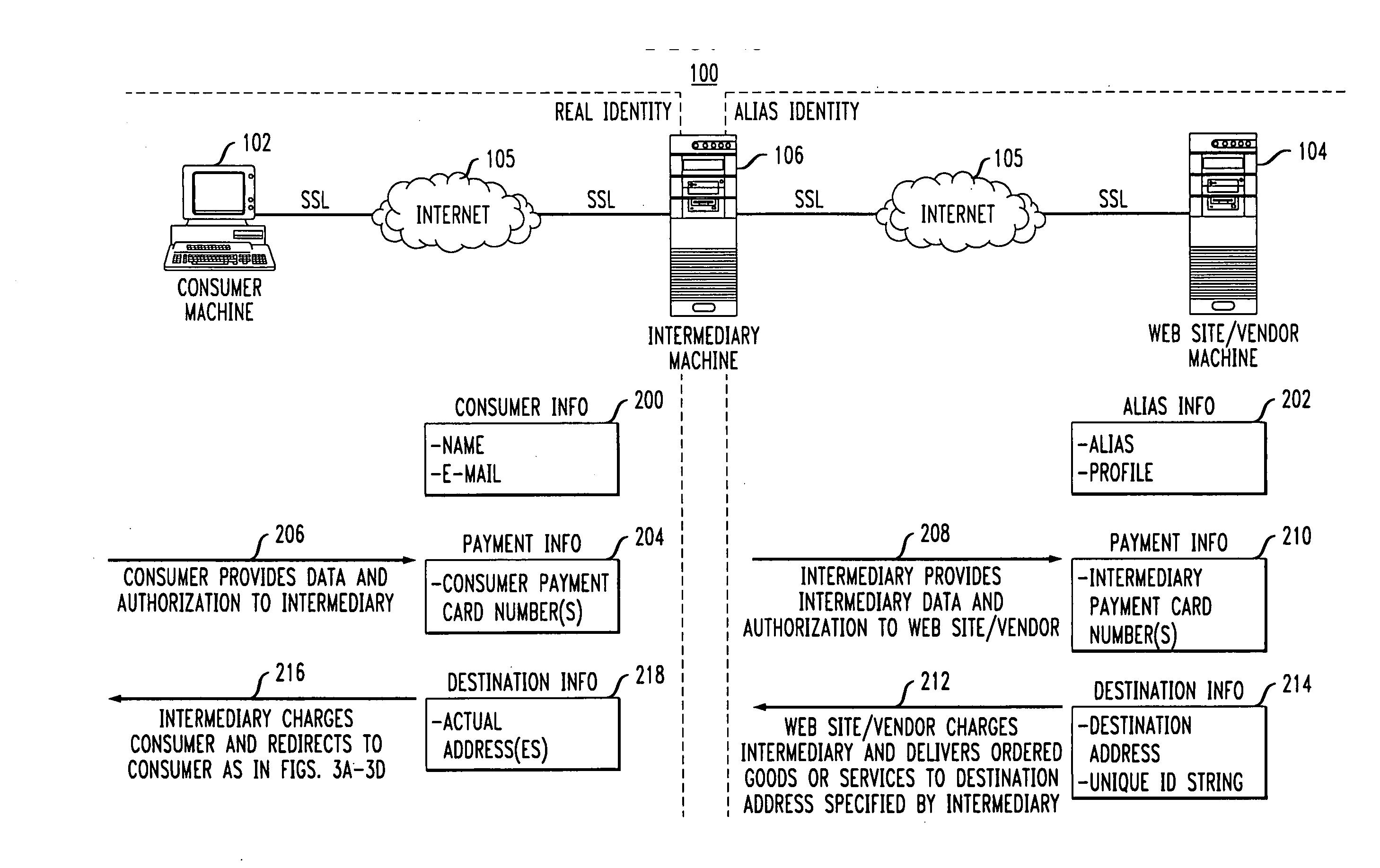
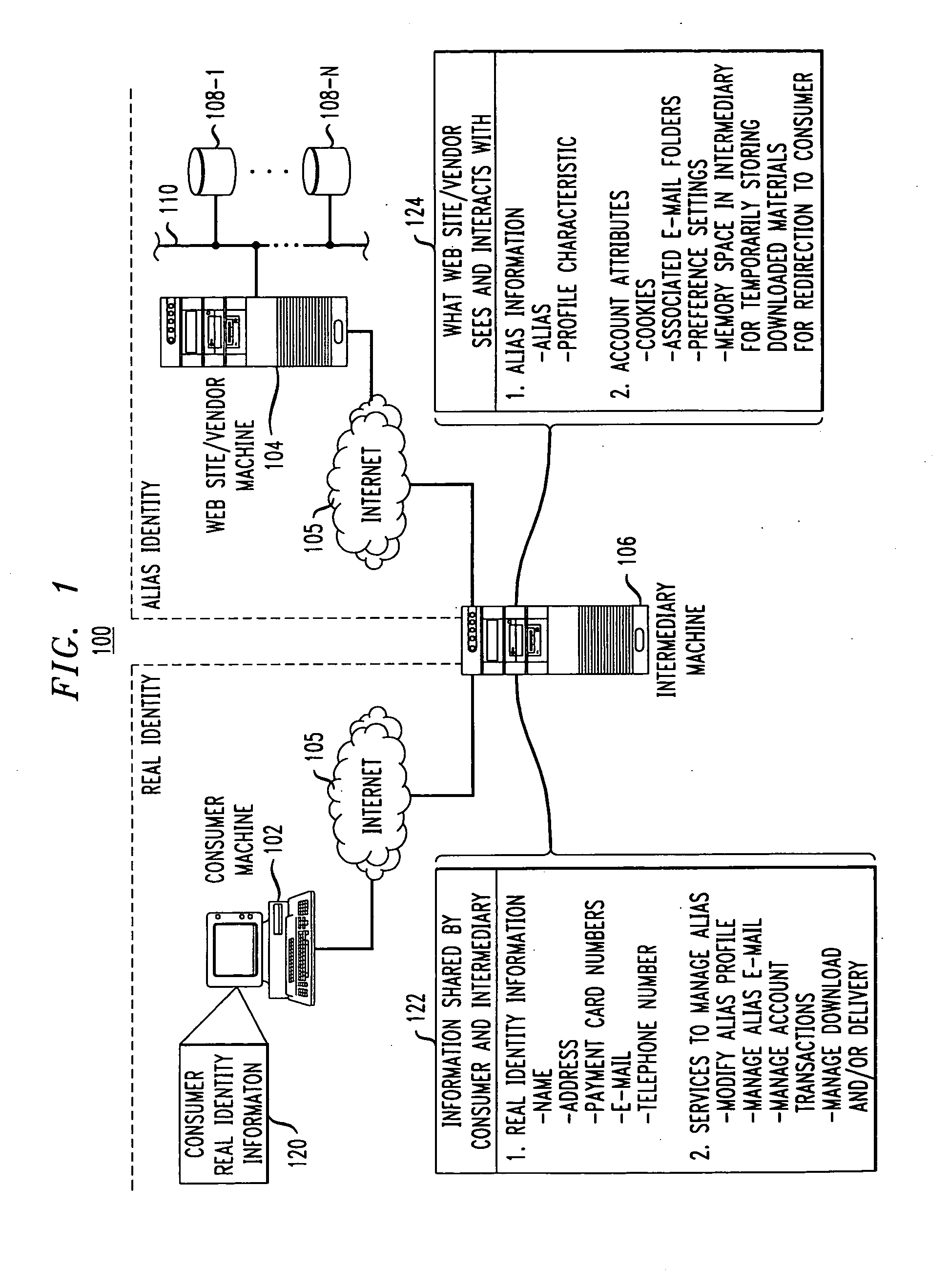
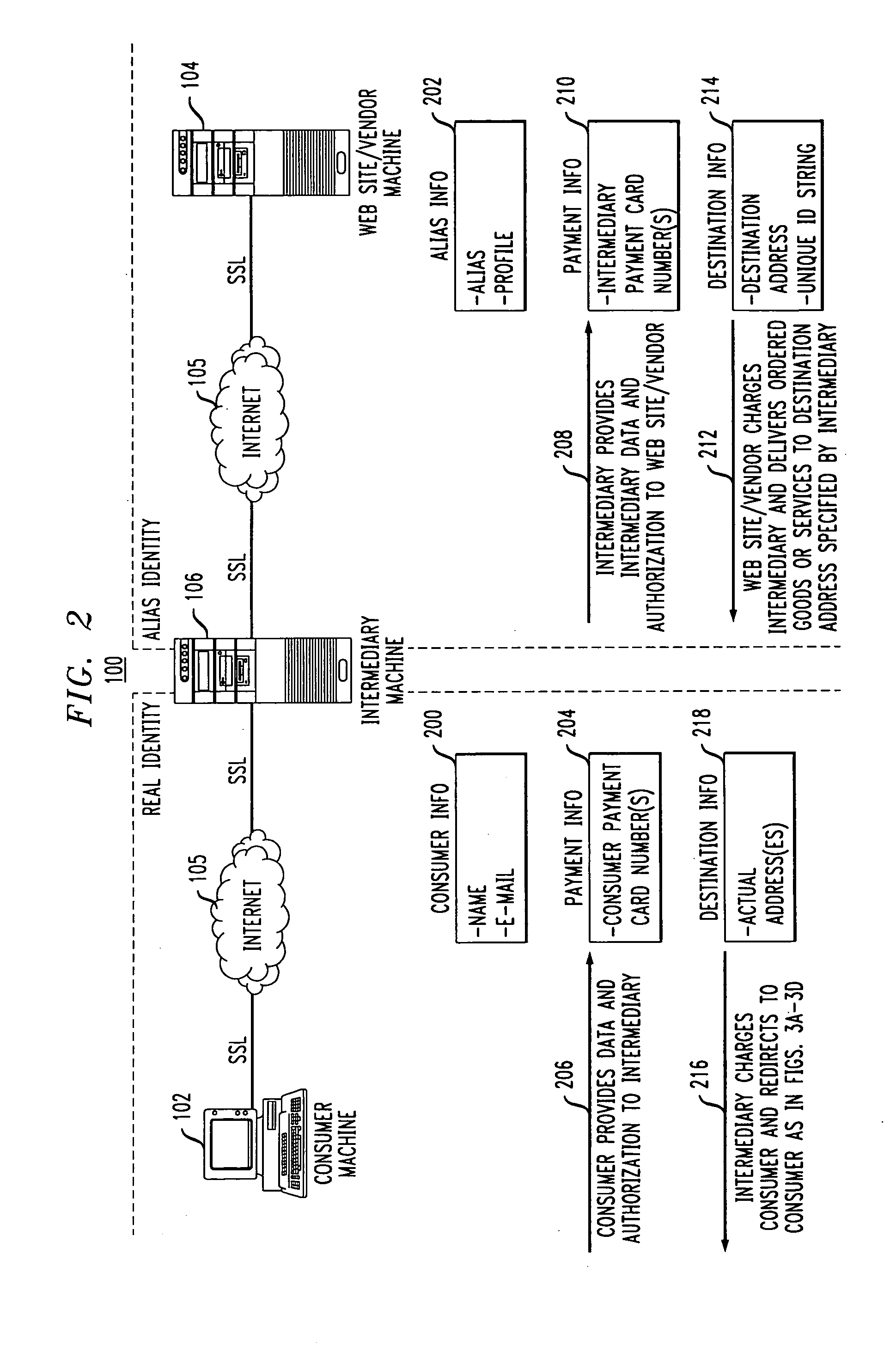
Methods and apparatus for providing user anonymity in online transactions
InactiveUS7203315B1Maintaining anonymityLimit fraud riskDigital data processing detailsMultiple digital computer combinationsWeb siteThird party
End-to-end user anonymity is provided in electronic commerce or other types of online transactions through the use of an intermediary. An intermediary machine, which may be implemented in the form of a set of servers or other type of computer system, receives communications from a consumer or other user, and generates and maintains an alias for that user. Connections between the user machine and any online vendor or other web site are implemented through the intermediary using the alias. When the user desires to make a purchase from a given online vendor, the intermediary may present the user with a number of options. For example, the user may be permitted to select a particular payment card number and real destination address as previously provided to the intermediary. The intermediary then communicates with the online vendor and supplies intermediary payment information, e.g., a payment card number associated with the intermediary rather than the user, along with appropriate authorizing information and an alias destination address, e.g., a third party physical shipping address for deliverable goods, an alias electronic address for downloadable material, etc. The online vendor charges the purchase to the intermediary, and redirects the delivery of the goods or services to the destination address provided by the intermediary. The intermediary charges the payment card number of the user, and arranges for the redirection of the delivery to the real user address. In this manner, the invention provides complete end-to-end anonymity for the user, even when the user desires to enter transactions involving purchase and receipt of deliverable goods and services.
Owner:PRIVACY LABS
Methods and a system for providing transaction related information
InactiveUS20100179907A1Reducing minimising exposureMinimize risk of fraudAccounting/billing servicesFinanceSystem usageMobile telephony
Methods and a system for providing a service enabling users to securely request and receive data representing details of a payment card using a mobile telephony device. The data representing details of a payment card can then be used to partake in a commercial transaction in which the user is not present at, or remotely located from, the point of transaction.
Owner:MONITISE GRP LTD
Open network system and method for I/O operations with non-standard I/O devices using an extended open network protocol
InactiveUS6907476B2Reduce the risk of fraudInformation receivedMultiple digital computer combinationsPayment architectureNetworking protocolApplication procedure
An open network system supports input / output (I / O) operations for non-standard I / O devices coupled to an open network. The system includes a server coupled to a plurality of I / O devices through an open network, at least some of the I / O devices being non-standard I / O devices. The non-standard I / O devices communicate with a client program that processes extended open network protocol statements. The extended open network protocol statements communicated between the server and the non-standard I / O devices are processed by the server and the client program to support I / O operations between the non-standard I / O devices and the server or application programs coupled to the server.
Owner:WI LAN TECH INC
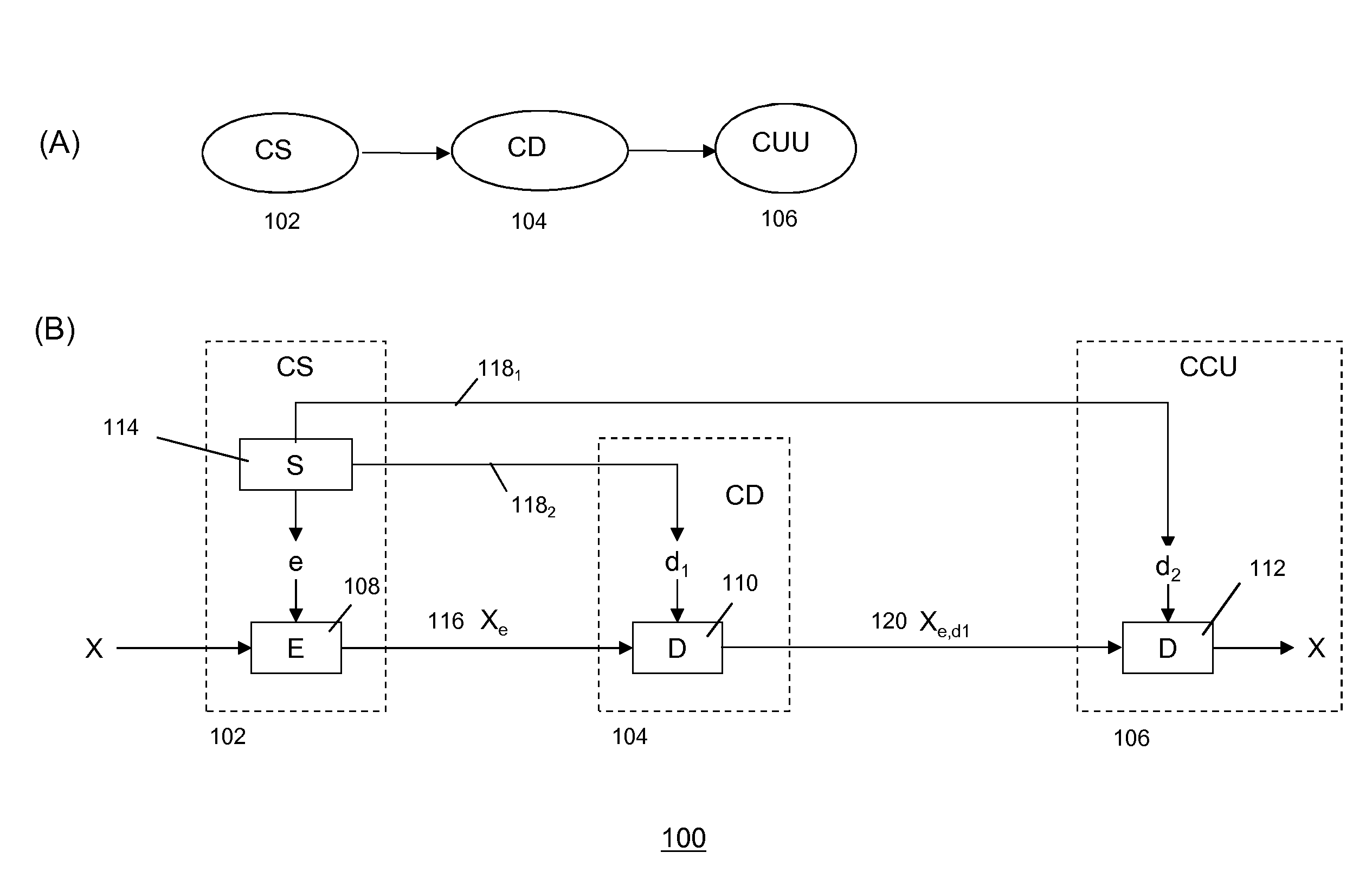
Secure Distribution of Content
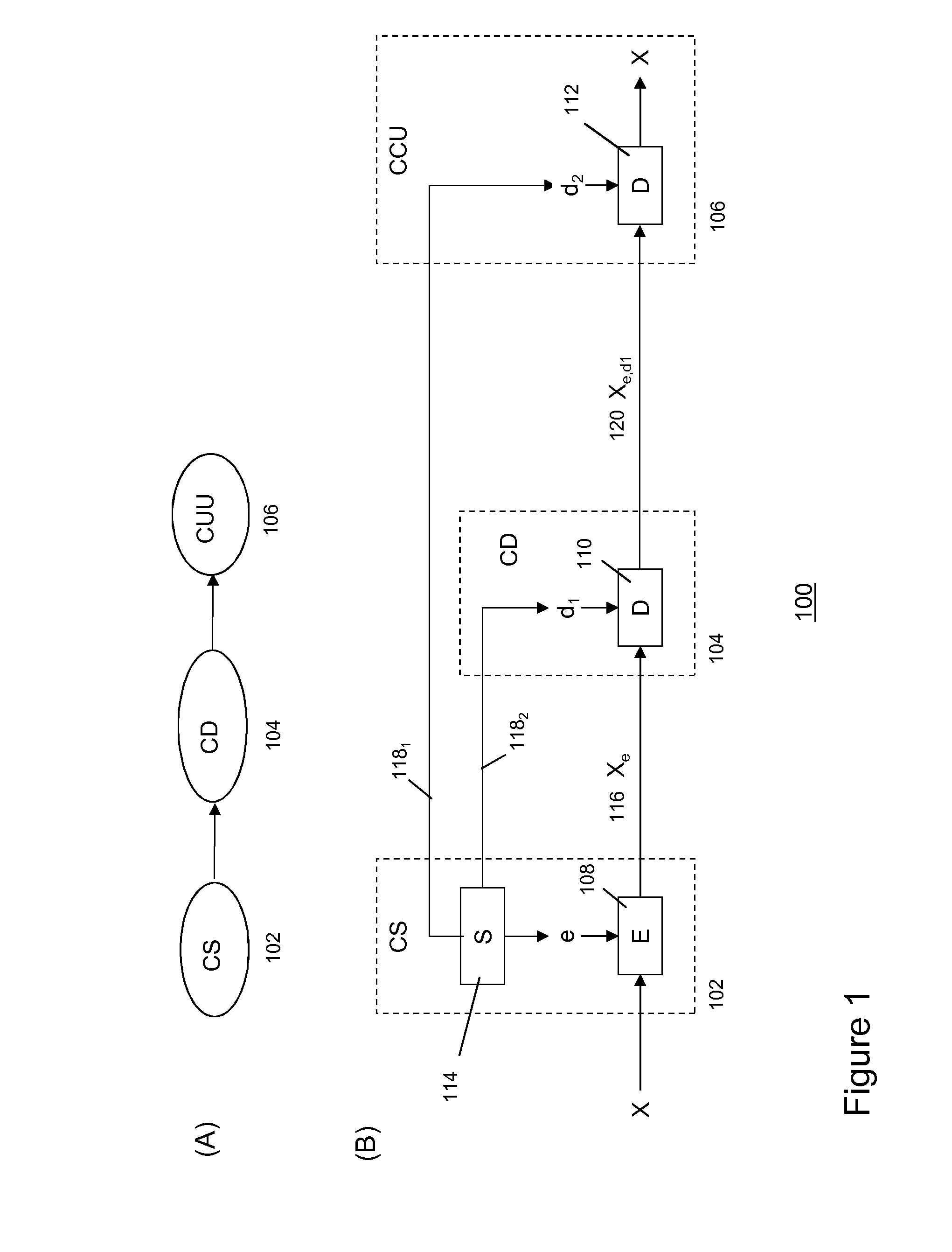
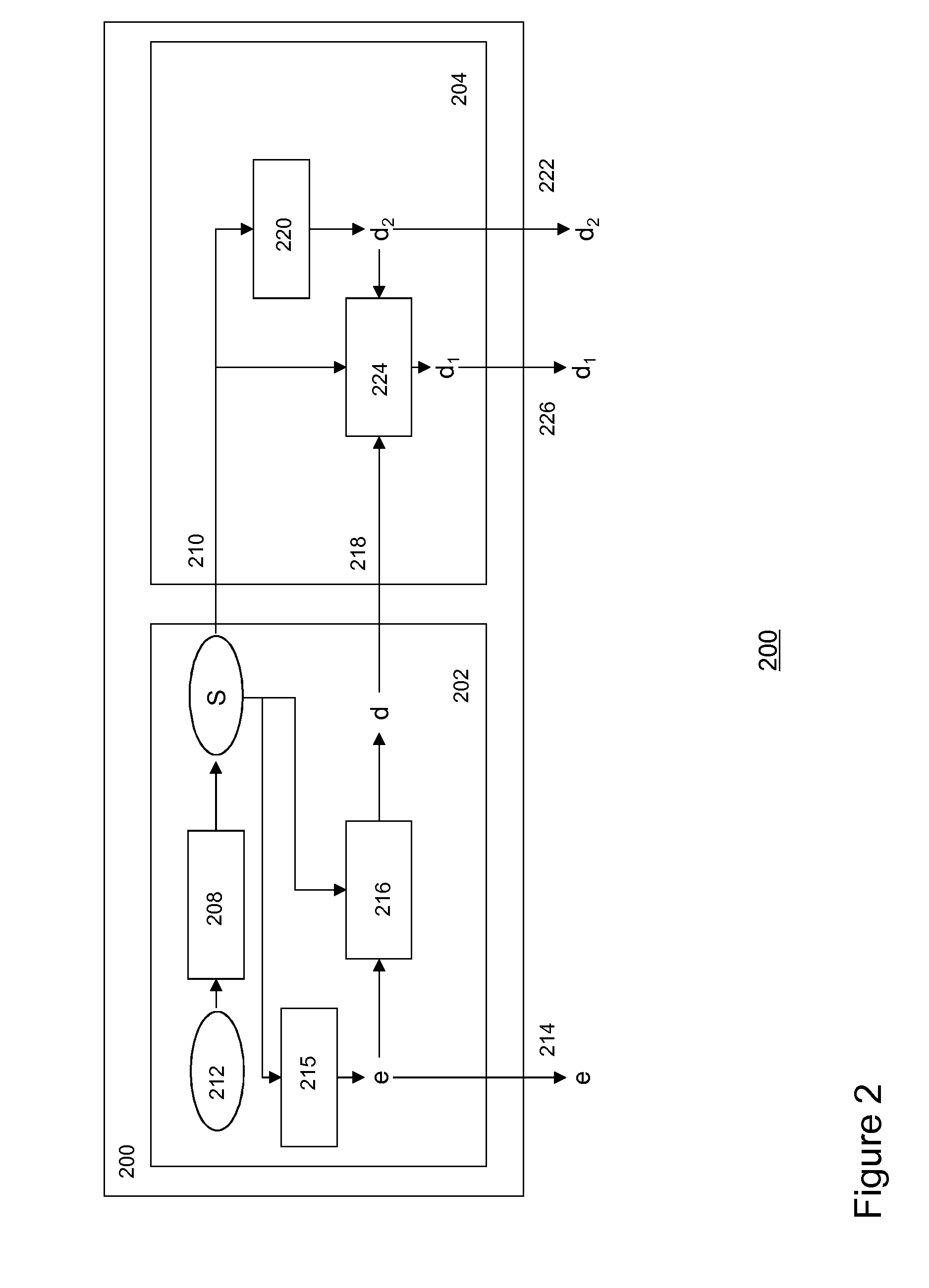
ActiveUS20140233740A1Reduce riskReduce the risk of fraudKey distribution for secure communicationData stream serial/continuous modificationCryptosystemKey generator
Methods and systems are described for secure delivery of a content item from at least a first content distribution network (CDN1) to at least one content receiving entity using a split-key cryptosystem comprising encryption and decryption algorithms E and D, a cipher algorithm for generating encryption and decryption keys e,d on the basis of secret information S and a split-key algorithm using secret information S for splitting e into i different split-encryption keys e1, e2, . . . , ei and / or for splitting d into k different split-decryption keys d1, d2, . . . , dk respectively, such that Ddk(Ddk-1( . . . (Dd2(Dd1(Eei(Eei-1( . . . (Ee2(Ee1(X)) . . . ))=Ddk(Ddk-1( . . . (Dd2(Dd1(Xe1, e2, . . . , e1))=X wherein i,k≧1 and i+k>2. The method may comprise: a content source providing said at least one CDN1 with at least one an encrypted content item Xe; a key generator associated with said content source comprising said cipher and split-key algorithm generating first split-key information and transmitting said first split-key information to said first CDN1, preferably to a first secure module associated with said CDN1; generating a partially decrypted content item on the basis of said encrypted content item Xe, said decryption algorithm D and said first split-key information; and, transmitting said partially decrypted content item to said content receiving entity.
Owner:ELTA SYST LTD +2
Methods and apparatus for providing user anonymity in online transactions
InactiveUS20060274896A1Avoid the needEliminate the problemDigital data processing detailsMultiple digital computer combinationsPaymentWeb site
End-to-end user anonymity is provided in electronic commerce or other types of online transactions through the use of an intermediary. An intermediary machine, which may be implemented in the form of a set of servers or other type of computer system, receives communications from a consumer or other user, and generates and maintains an alias for that user. Connections between the user machine and any online vendor or other web site are implemented through the intermediary using the alias. When the user desires to make a purchase from a given online vendor, the intermediary may present the user with a number of options. For example, the user may be permitted to select a particular payment card number and real destination address as previously provided to the intermediary. The intermediary then communicates with the online vendor and supplies intermediary payment information, e.g., a payment card number associated with the intermediary rather than the user, along with appropriate authorizing information and an alias destination address, e.g., a third party physical shipping address for deliverable goods, an alias electronic address for downloadable material, etc. The online vendor charges the purchase to the intermediary, and redirects the delivery of the goods or services to the destination address provided by the intermediary. The intermediary charges the payment card number of the user, and arranges for the redirection of the delivery to the real user address. In this manner, the invention provides complete end-to-end anonymity for the user, even when the user desires to enter transactions involving purchase and receipt of deliverable goods and services.
Owner:LIVESAY PAUL OWEN
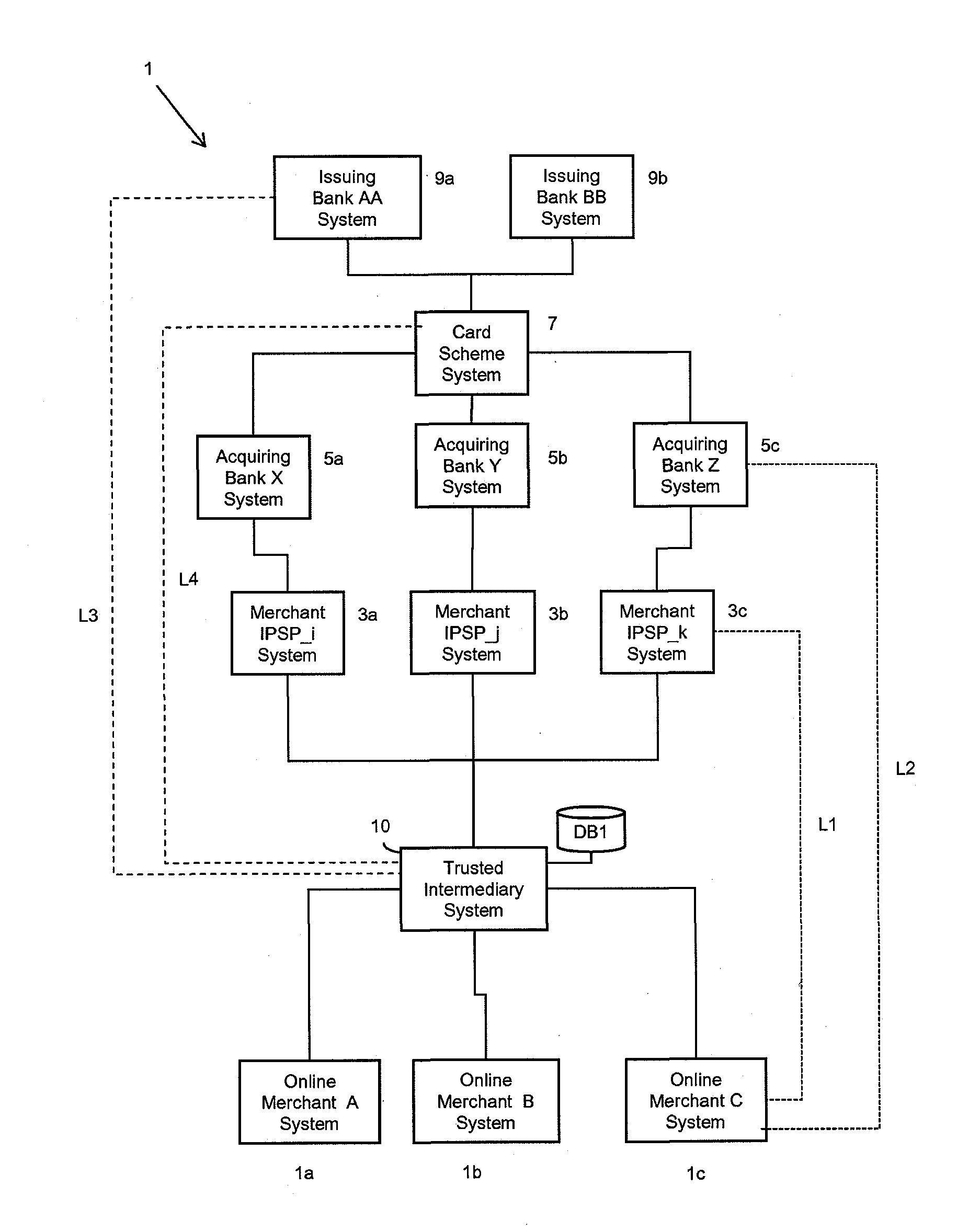
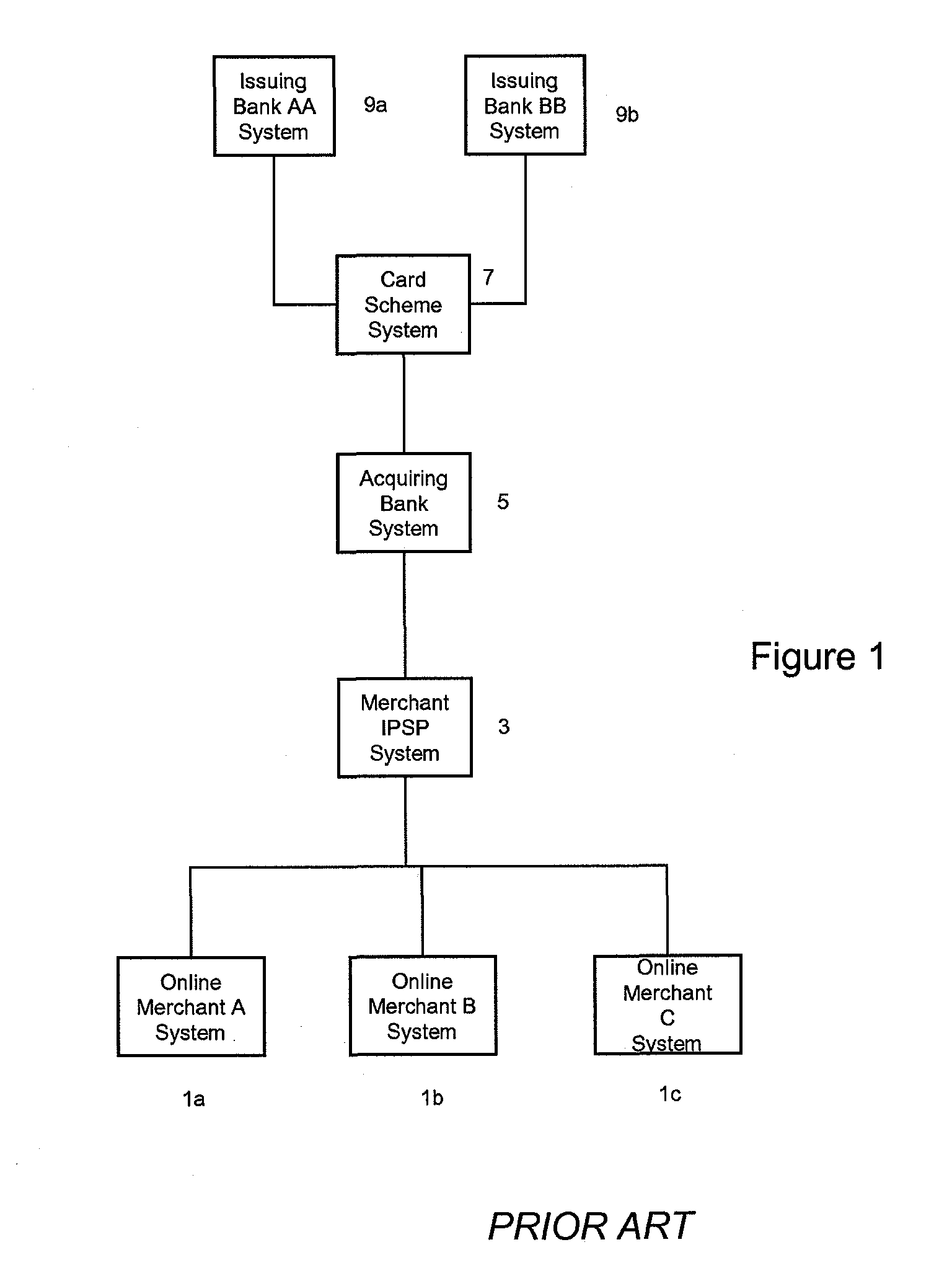
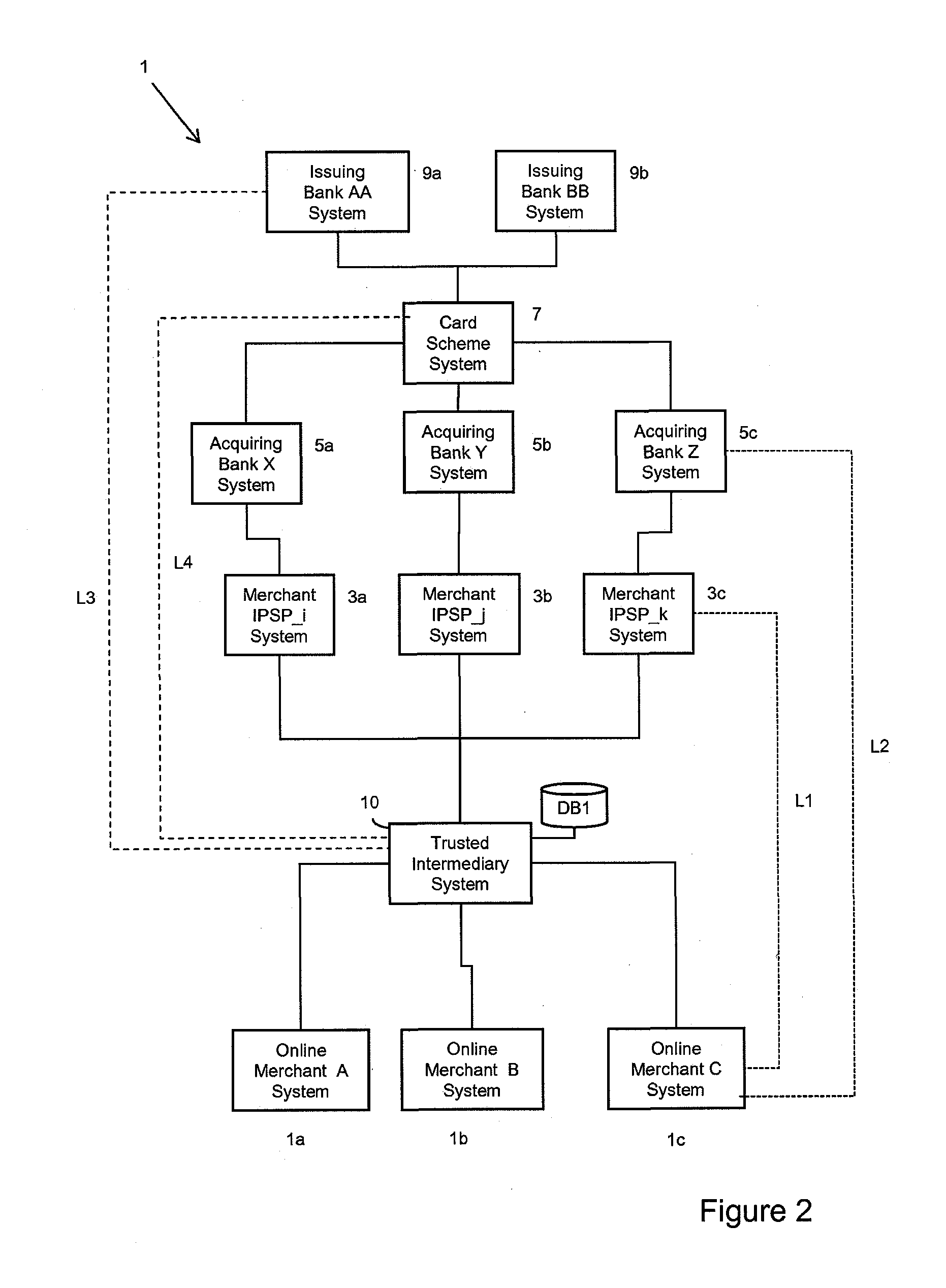
Payment system
ActiveUS20120030066A1Reduce the risk of fraudEffect transactions more quickly and convenientlyFinancePayment circuitsService provisionPayment transaction
Embodiments of the invention provide a method of processing payment authorization requests for payment transactions to be conducted via a data communications network on behalf of online merchants, the payment authorization requests are conducted as a result of orders by financial instrument holders via a plurality of different online merchant systems. Each of the online merchants has an online merchant identity. The method is conducted by a trusted central intermediary system which is arranged to transmit payment authorization requests to each of a plurality of different online merchant Internet Payment Service Provider (IPSP) systems. Each merchant IPSP system is arranged to transmit payment authorization requests to at least one of a plurality of acquiring bank payment processor systems, and each of said plurality of acquiring bank payment processor systems is responsible for processing payment authorizations for at least one of said acquiring banks. Embodiments of the invention enable a user to select a payment method on a per transaction basis, whilst removing the requirement for the user to provide payment details to individual online merchant systems or to their merchant IPSP systems. Thus, providing that online merchants, or their merchant IPSPs, subscribe to a service arranged to perform the method, users only have to submit their respective payment details, preferably only once, to a separate, trusted entity.
Owner:VISA EUROPE
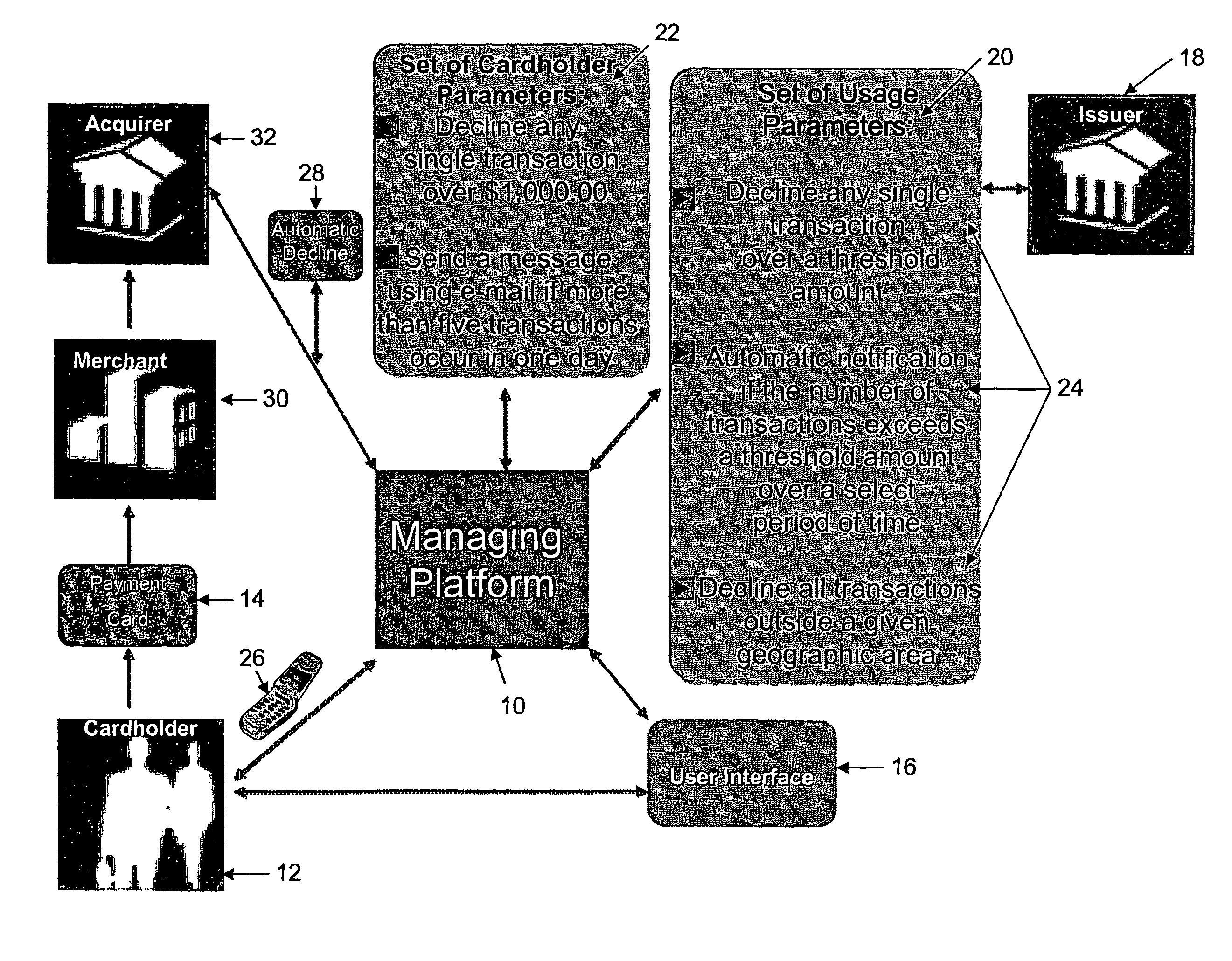
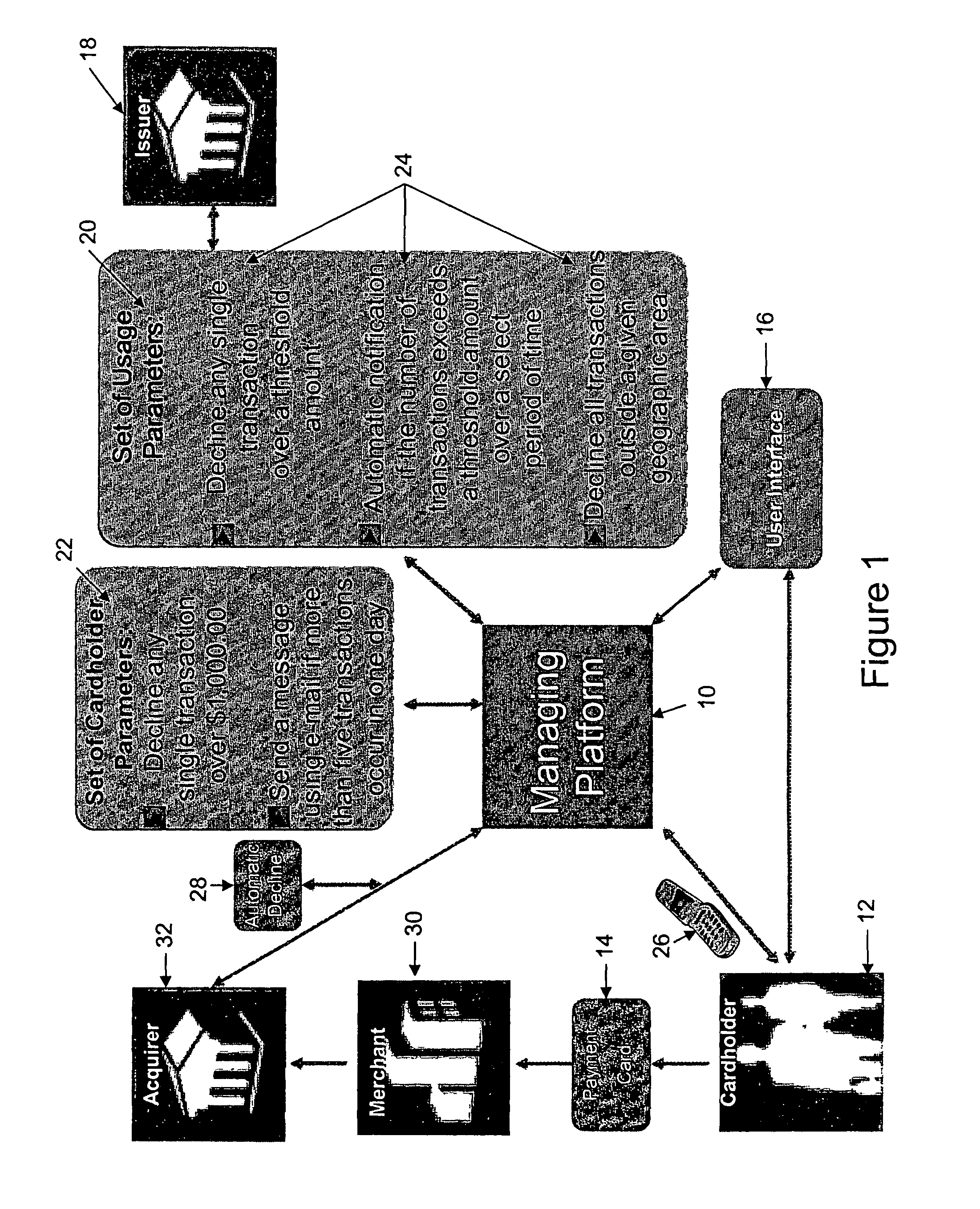
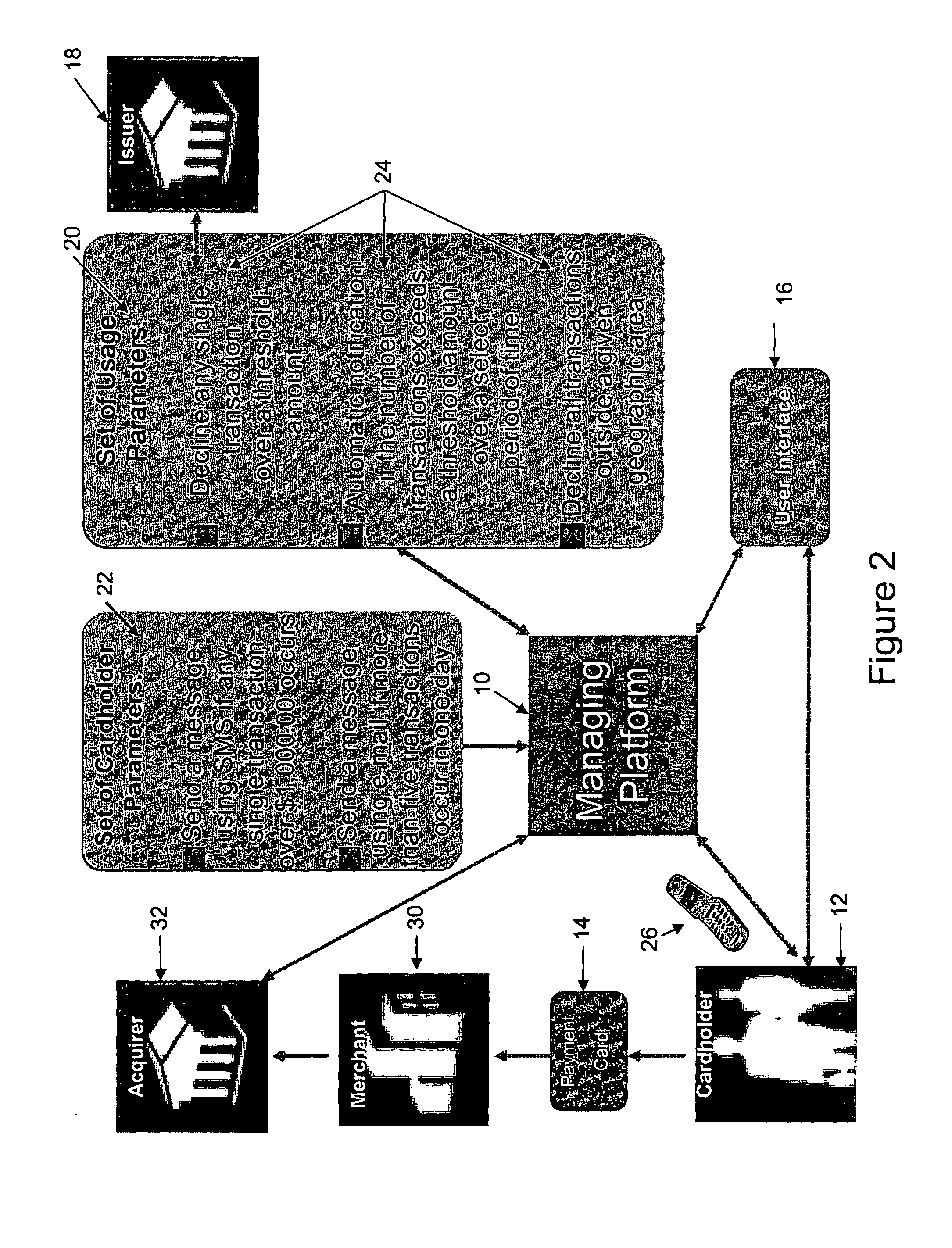
Method for a payment cardholder to control and manage the use of a payment card
InactiveUS20110202462A1Reduce the risk of fraudEasy to useFinanceProtocol authorisationFinancial transactionPayment order
A method for providing a payment cardholder with control over a payment card is provided herein, hi one respect, the method of the present invention uses a managing platform to configure a set of usage parameters for usage of the payment card. After that, the payment card is associated with the managing platform, and allows the payment cardholder to select one or more of the usage parameters. Based on the selected usage parameters, a set of cardholder parameters are associated with the payment card, and include defining rules for determining an acceptable transaction and an unacceptable transaction for the payment card. Then, the managing platform intercepts an authorization for each transaction of the payment card and identifies, based on the cardholder parameters, each of the transactions as being one of the acceptable transactions or the unacceptable transactions. Finally, a message notifies the payment cardholder of at least one of the unacceptable transactions.
Owner:MASTERCARD INT INC
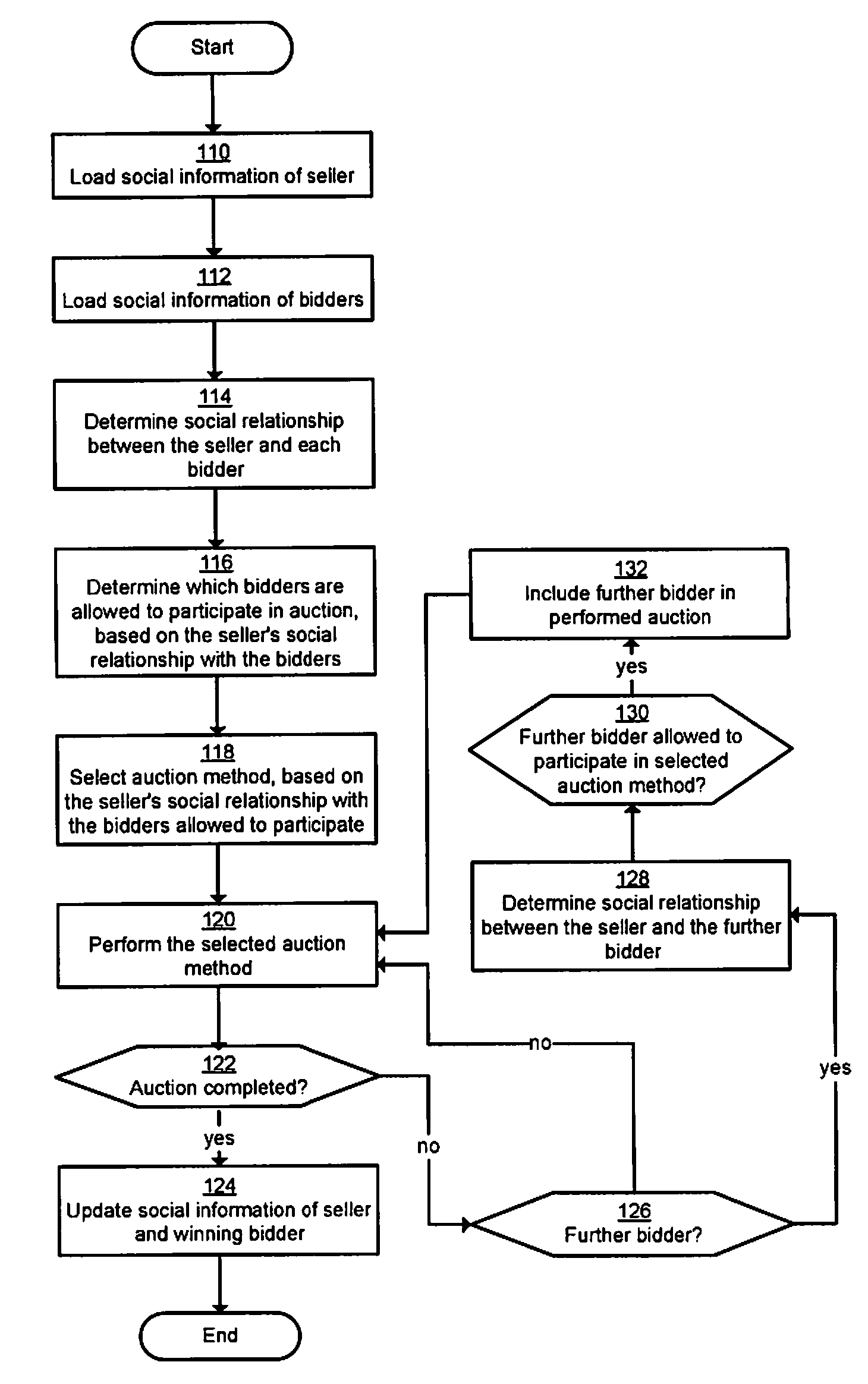
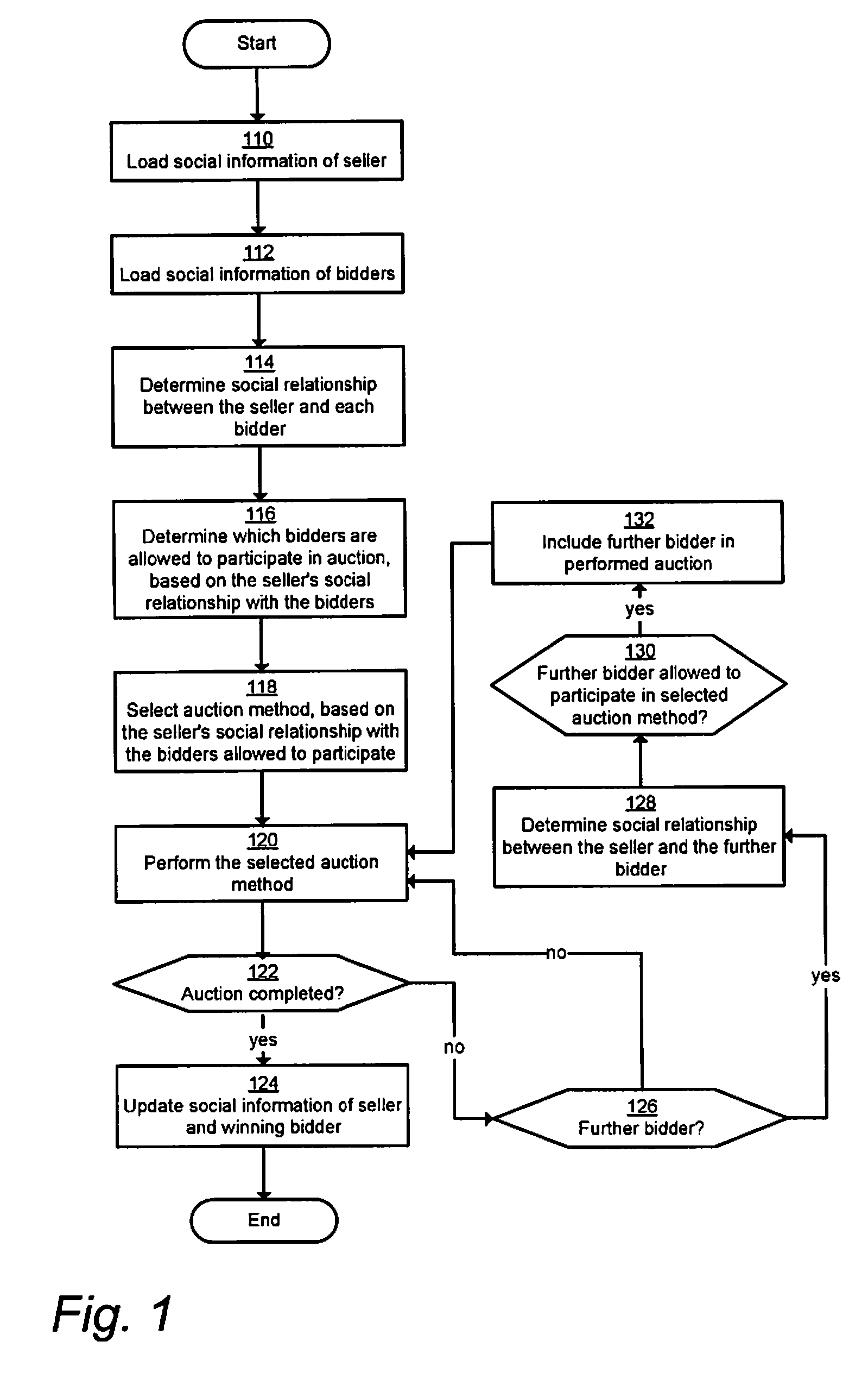
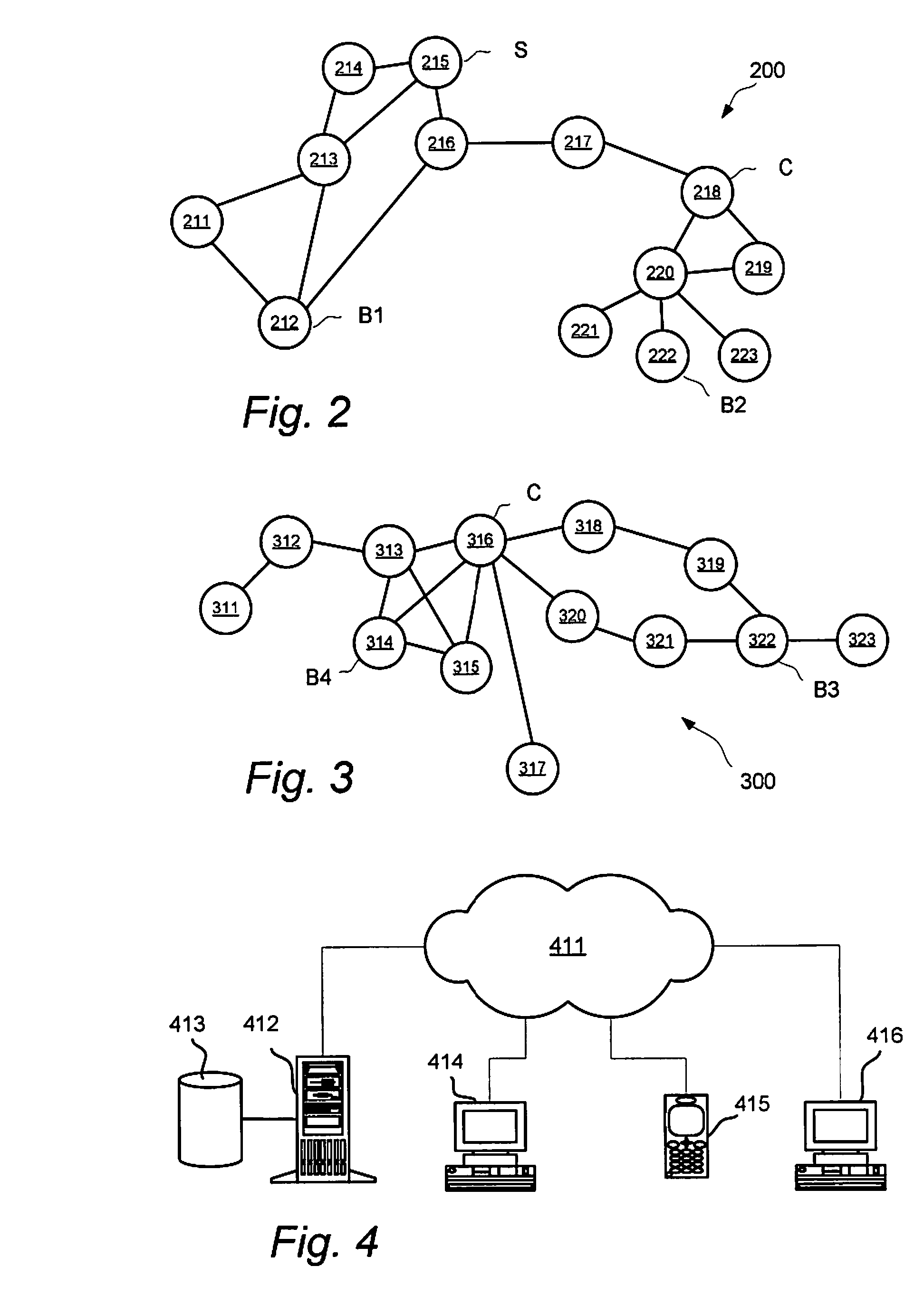
Trusted auctions
Embodiments for method and a system for an on online auction system involving a computer server is closed. Values representing a relationship between a seller and a plurality of bidders are determined based on social connections of the seller and social connections of the bidders. An auction method is selected based on the values representing a relationship between the seller and the bidders. The selected auction method is performed for the purpose of selling an item of the seller at a winning bid quoted by any of the bidders.
Owner:IDTP HLDG
Method for secure storage of sensitive data in a memory of an embedded microchip system, particularly a smart card, and embedded system implementing the method
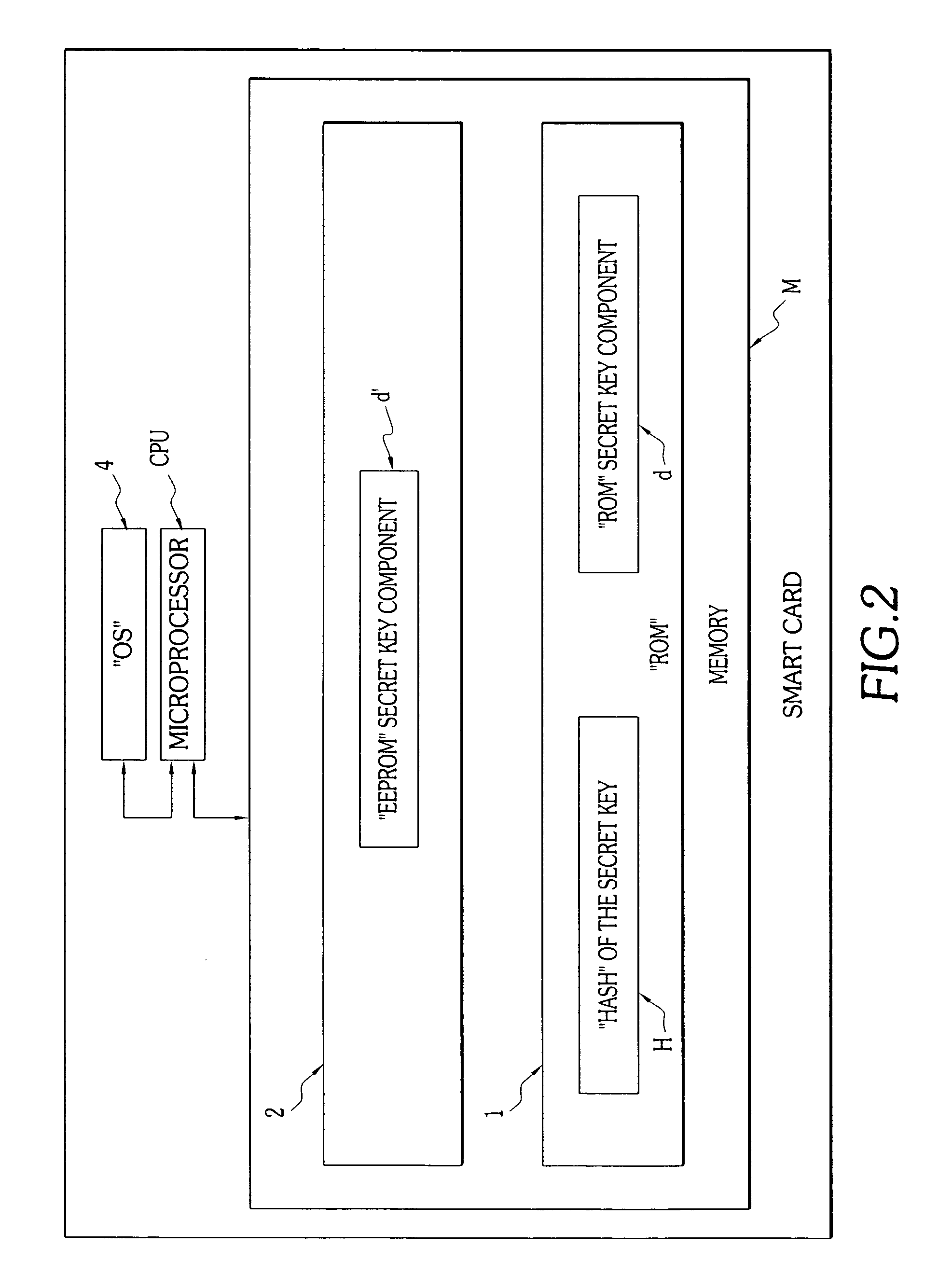
InactiveUS7260727B2Drawback can be obviatedReduce the risk of fraudDigital data processing detailsUnauthorized memory use protectionChecksumSmart card
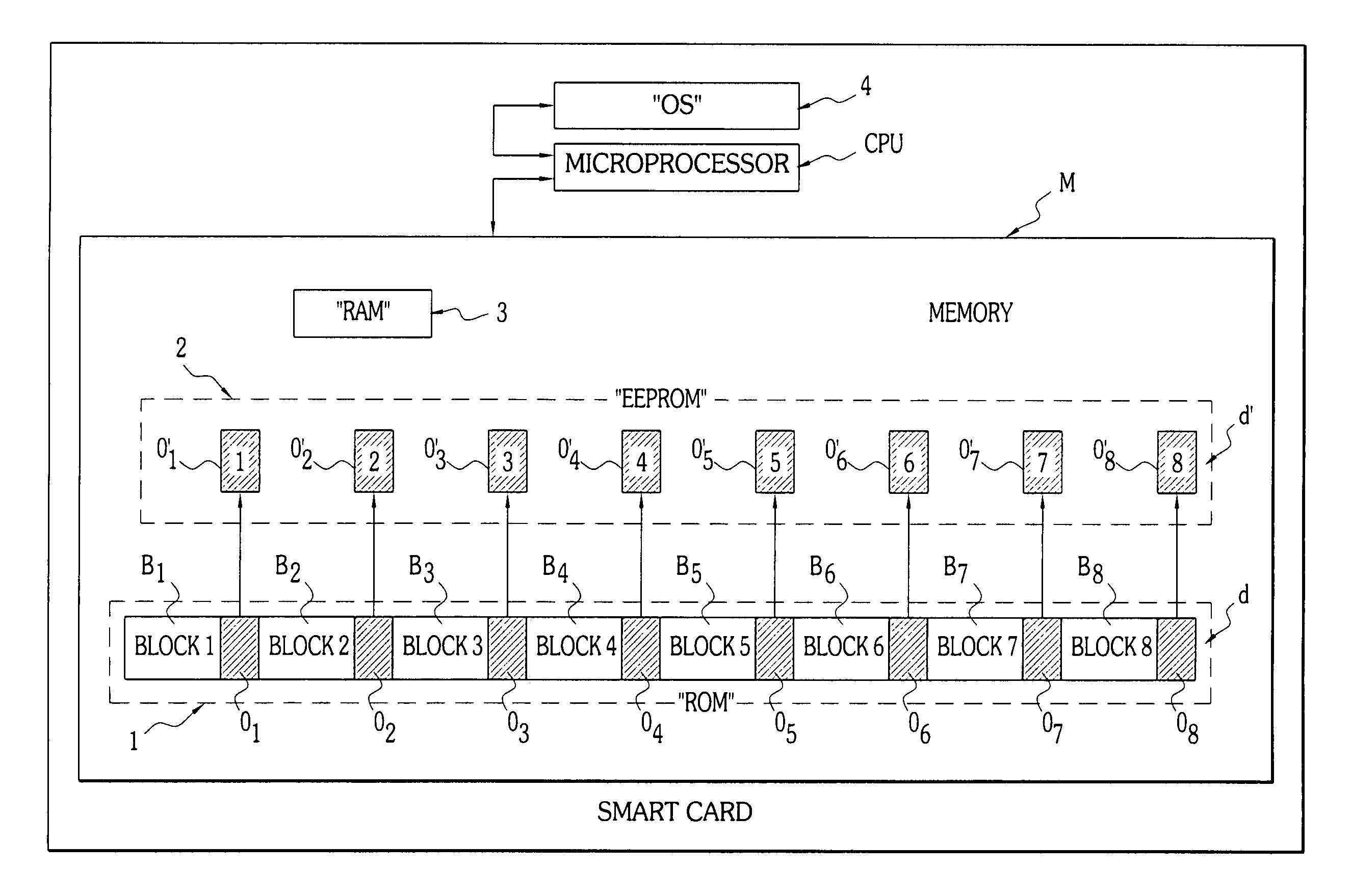
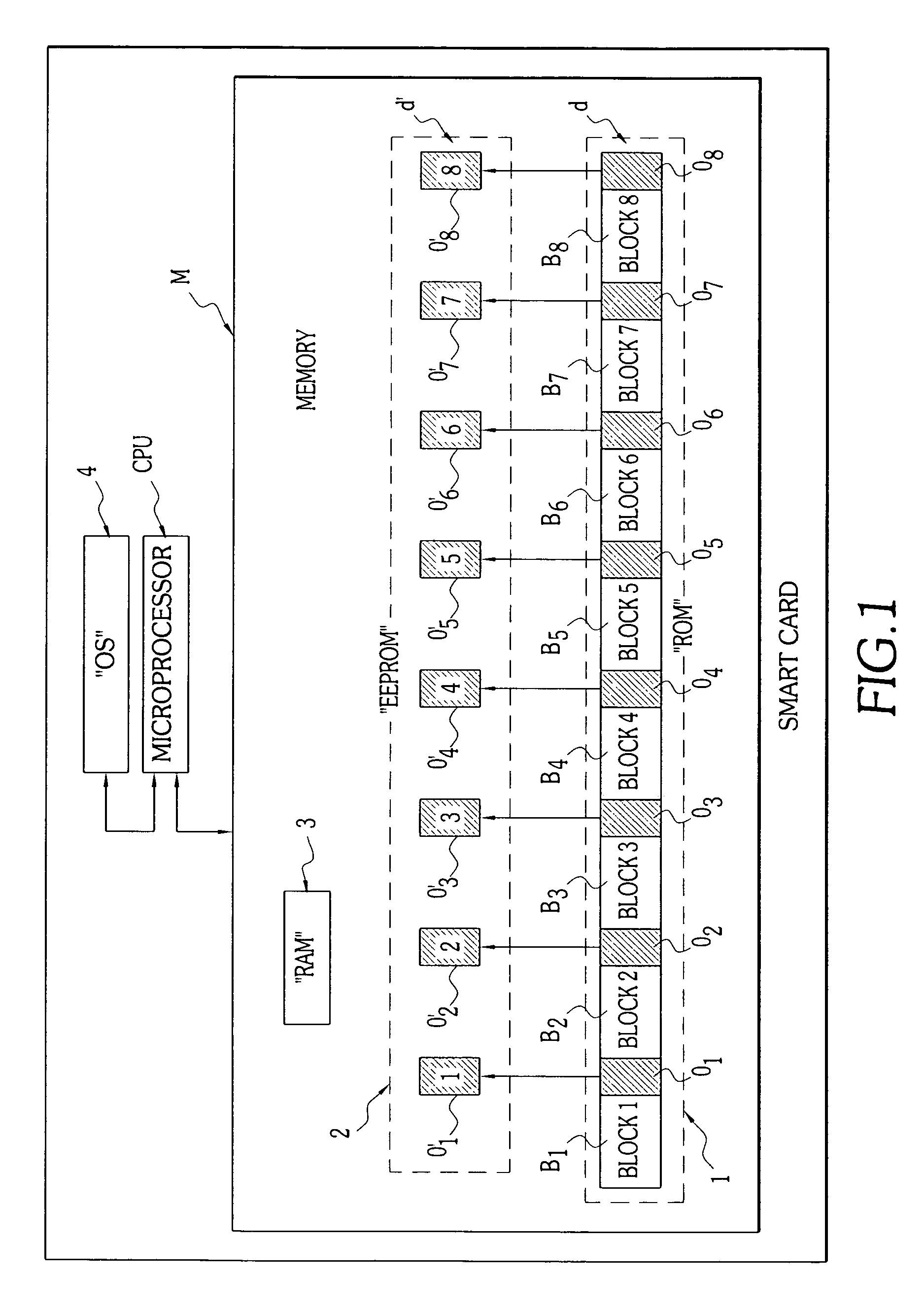
The invention concerns a method for secure storage of a piece of so-called sensitive data, for example an encryption key, in a memory (M) of an embedded microchip system, particularly a smart card (CP). The memory (M) comprises two physically distinct storage devices (1, 2), for example a permanent memory of the “ROM” type (1), and a second, re-programmable memory of the “EEPROM” type (2). The piece of sensitive data is divided into at least two parts (d, d′), in a given logical configuration, each of these parts being stored in one of the distinct storage devices (1, 2). An additional piece of verification data, a checksum or hash data, can also be stored in the first storage device (1), at the same time as the first sensitive data part (d).The invention also concerns an embedded microchip system, particularly a smart card (CP).
Owner:CP8 TECH SA
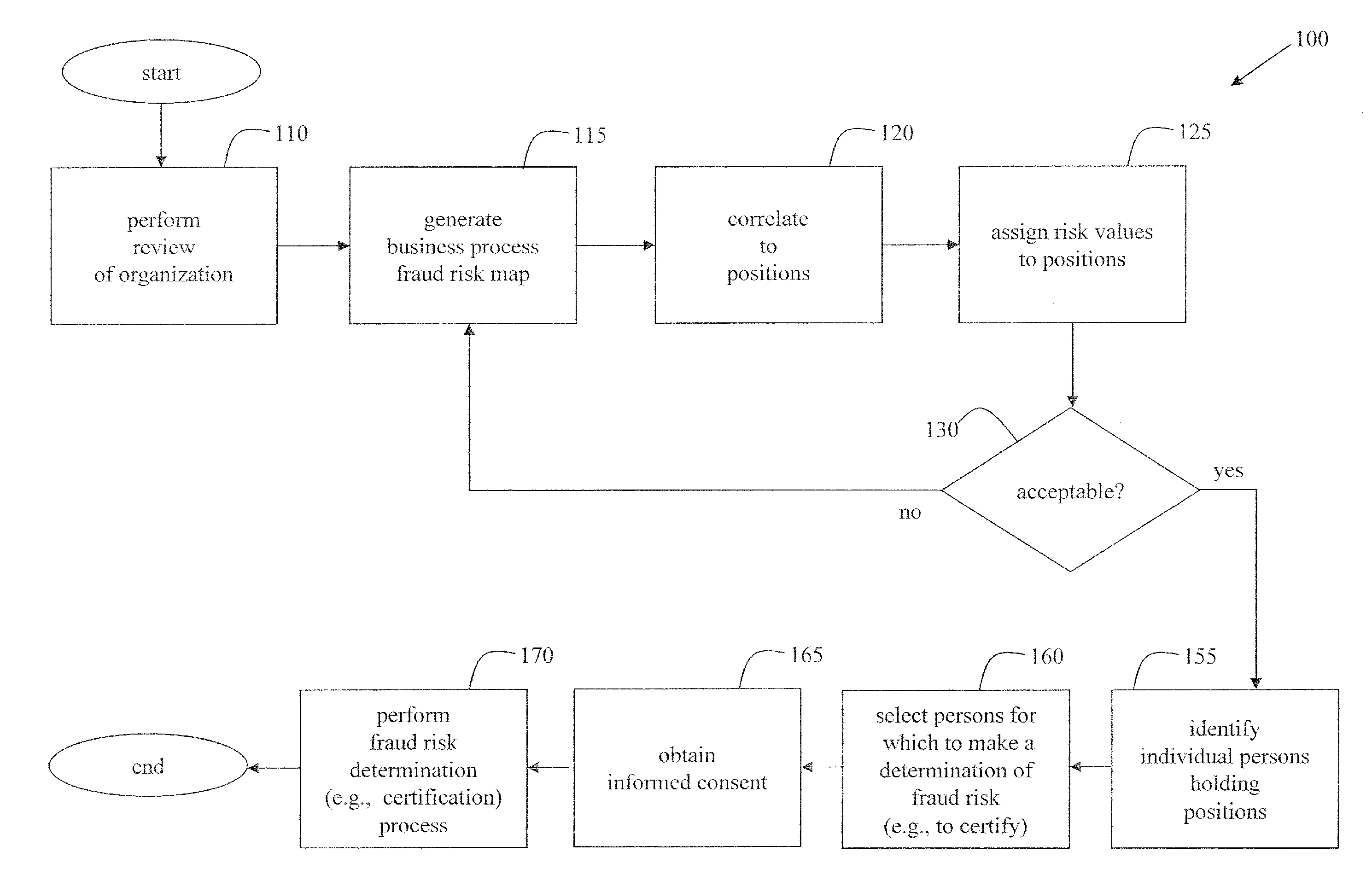
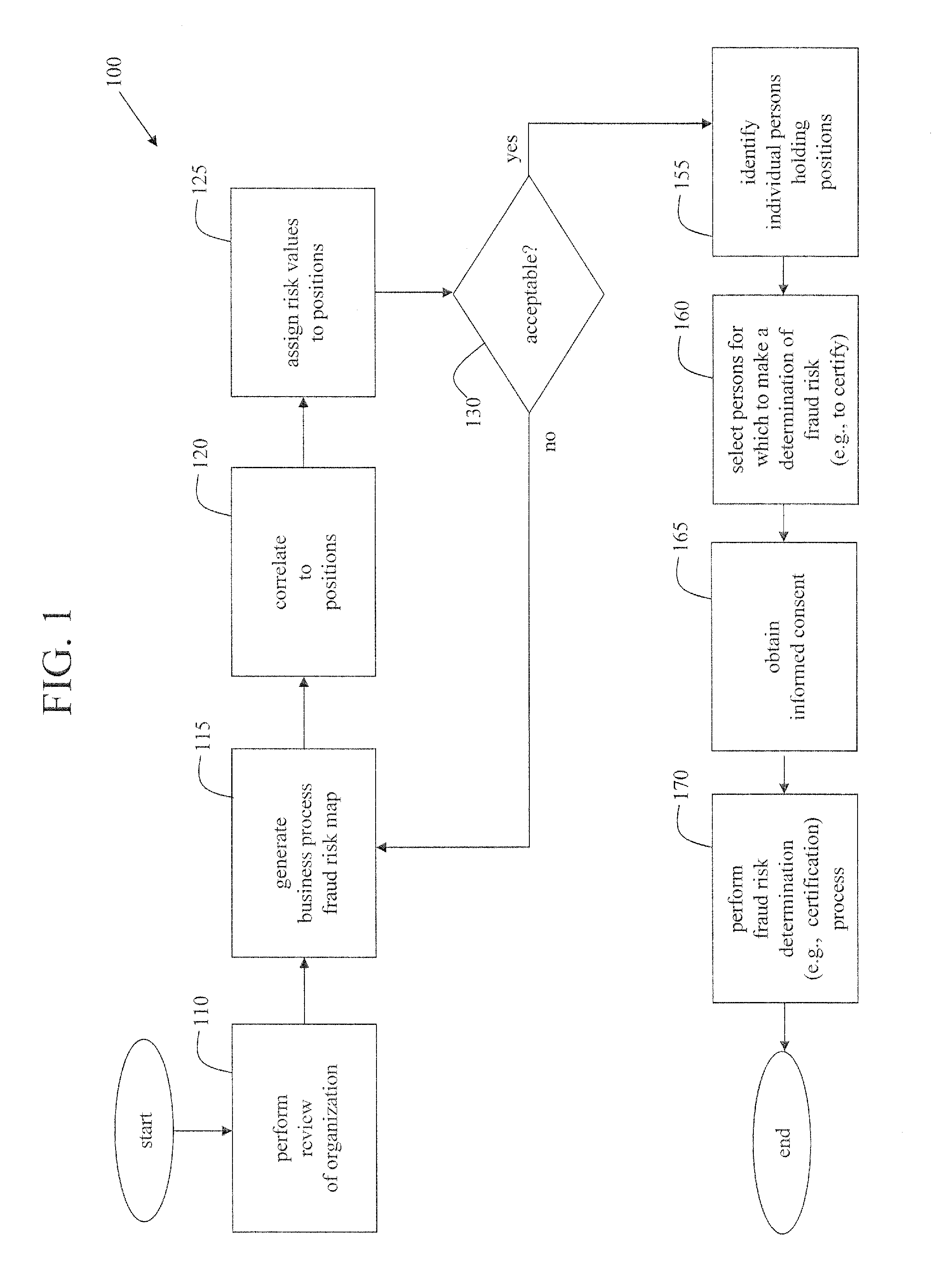
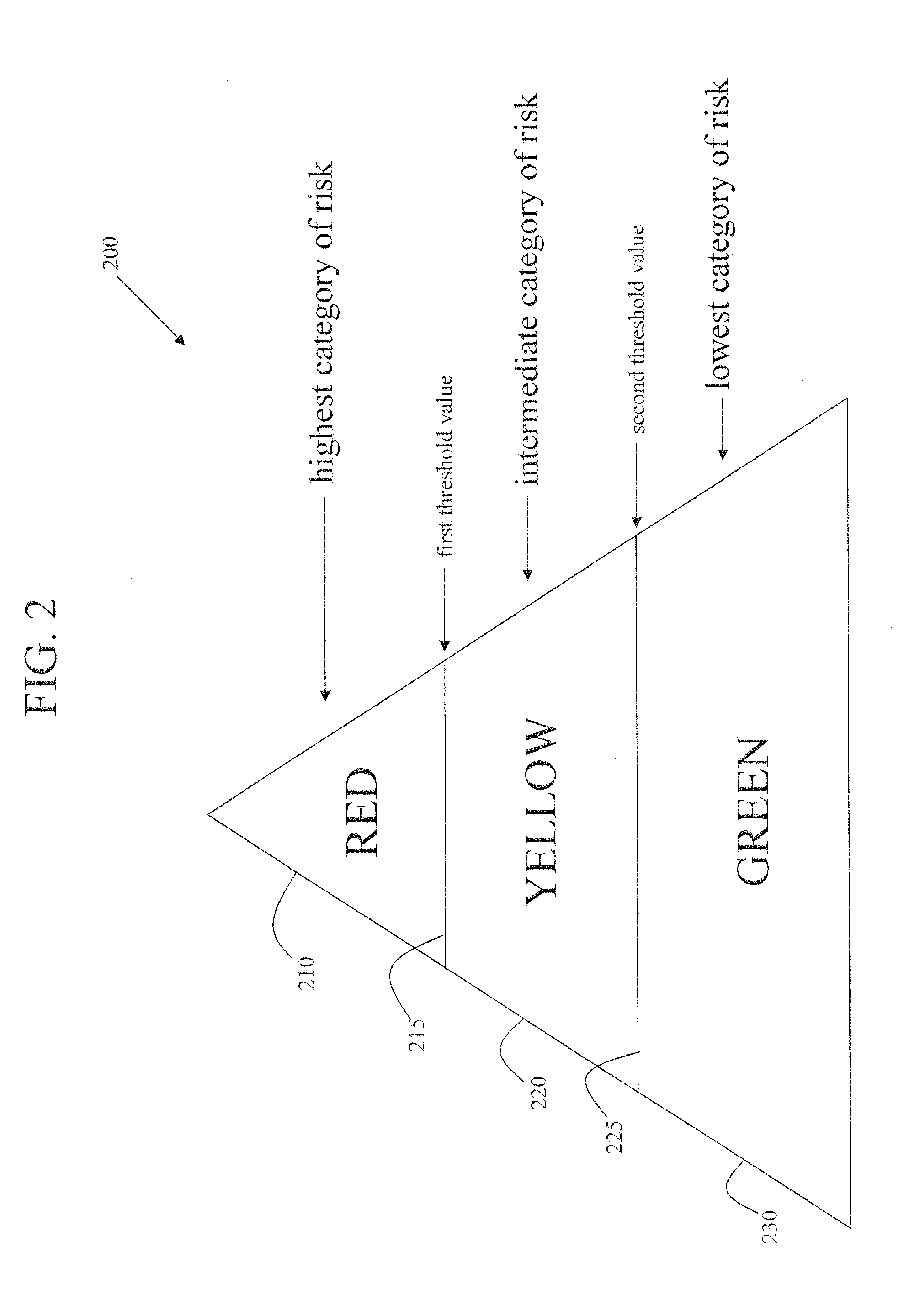
Methods of assessing fraud risk, and deterring, detecting, and mitigating fraud, within an organization
A method to assess risk of fraud within an organization is disclosed. A review of an organization's business processes with respect to risk is performed. A first business process fraud risk map is generated based on the review by generating and assigning first risk values to the business processes of the organization. The first business process fraud risk map is correlated to positions of responsibility within the organization and second risk values are generated and assigned to the correlated positions. Business processes may be adjusted in an attempt to reduce a number of positions deemed to be of relatively high risk. Individual persons holding positions subject to risk may be designated for going through a fraud risk determination (e.g., certification) process and subsequent monitoring process, all designed to reduce fraud risk by helping deter and / or detect and / or mitigate fraud.
Owner:CURRY EDITH L +3
Method and computer system for ensuring authenticity of an electronic transaction
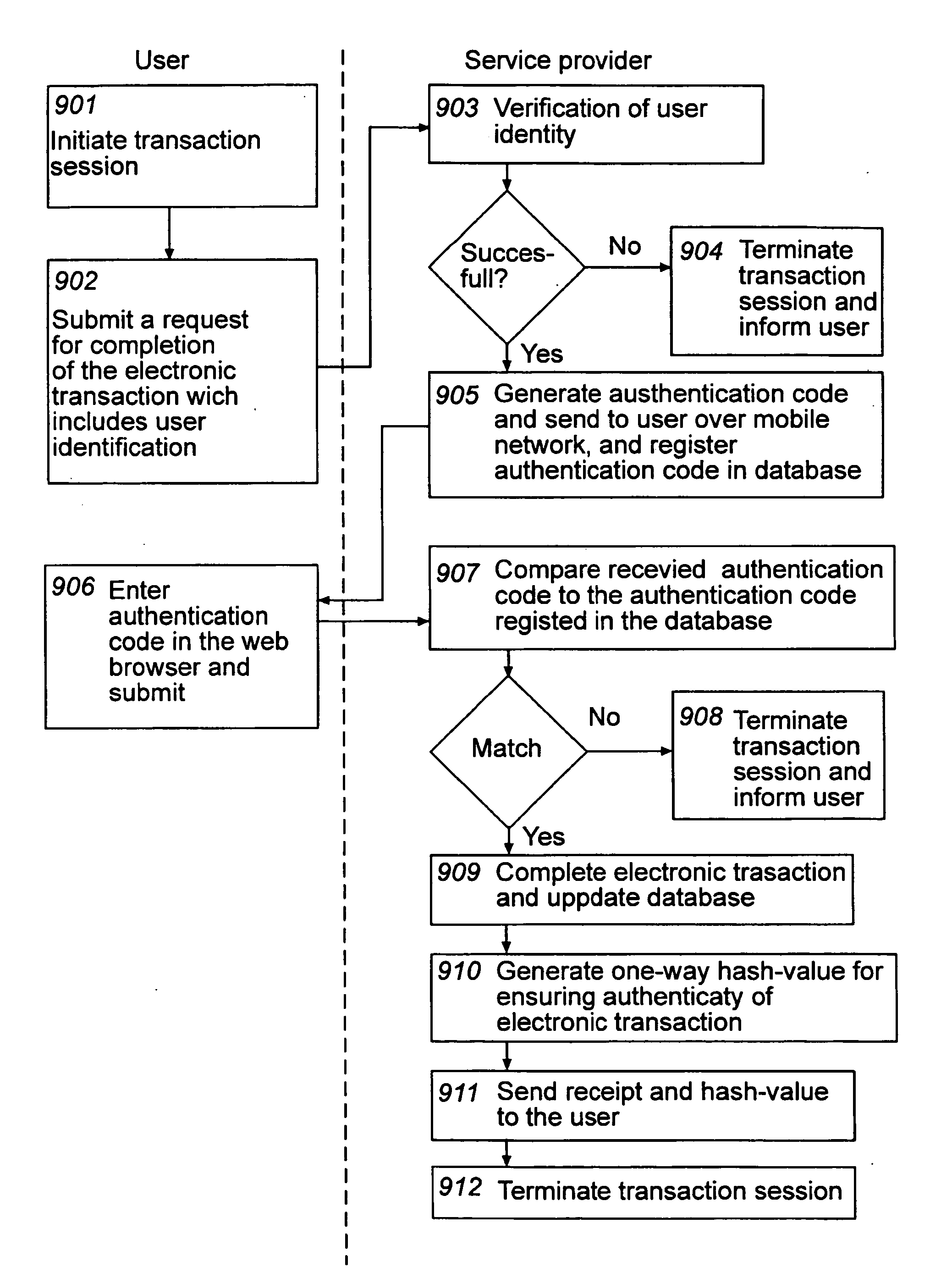
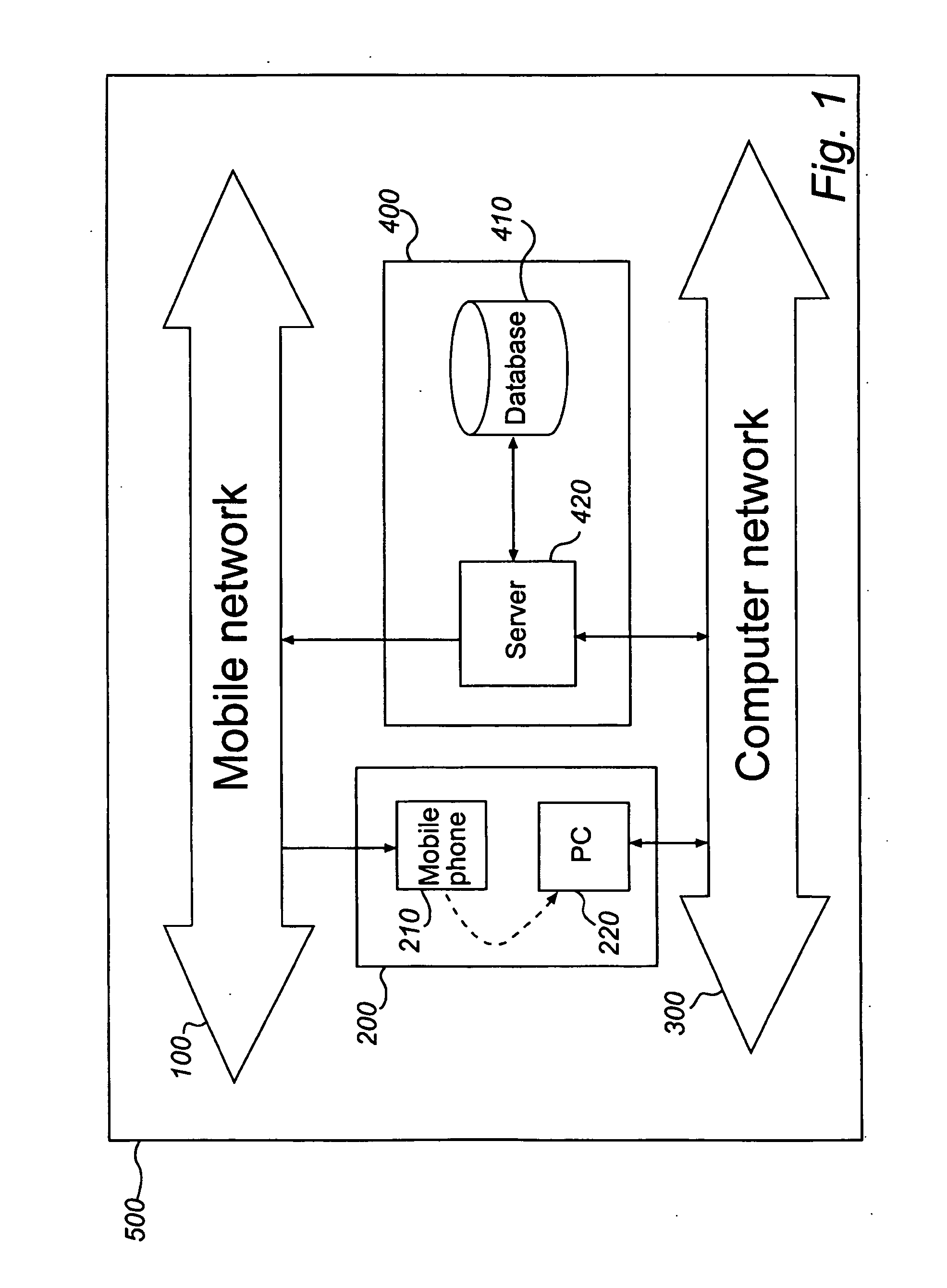
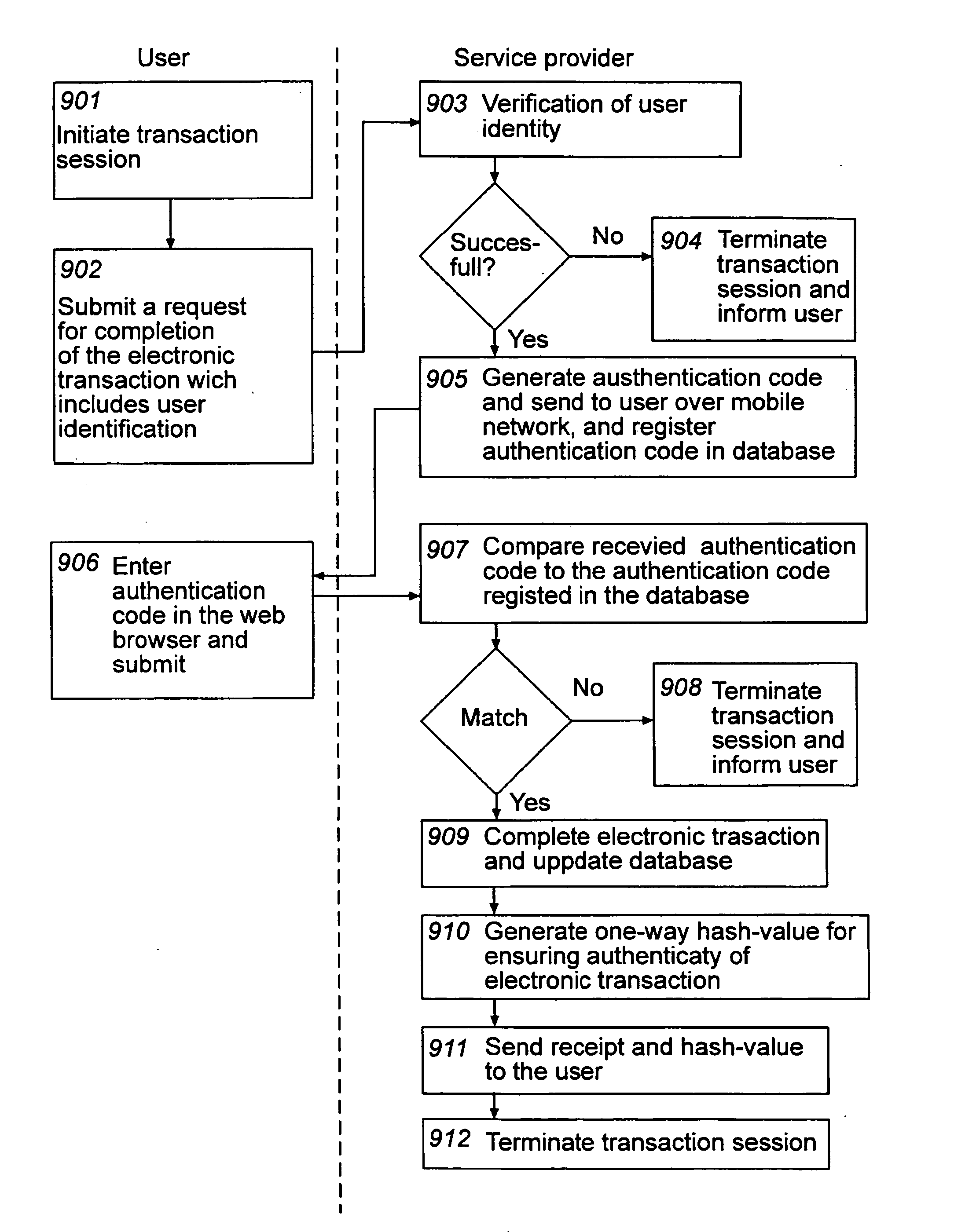
InactiveUS20090319797A1Easy to useReduce the risk of fraudKey distribution for secure communicationDigital data processing detailsComputerized systemSecurity level
At least one embodiment of the present invention relates to a method for ensuring authenticity of an electronic transaction performed during a transaction session. The method includes receiving, over a first network, a request from a user for the completion of an electronic transaction; receiving, over the first network, an authentication code from the user which has been provided to the user over a second network separated from the first network, thereby authenticating the user, completing the electronic transaction; and storing information associated with the electronic transaction and the transaction session. The method further includes generating a one-way hash value based on information comprised in the electronic transaction and information associated with the transaction session, and providing the one-way hash value to the user, wherein the one-way hash value is usable for ensuring the authenticity of the electronic transaction. The procedure enables authentication, integrity, non-repudiation, and time stamping in a cost efficient way. An enhanced security level can be achieved as the network used for providing the authentication code to the user is separate from the network where the user returns the authentication code. At least one embodiment of the present invention also relates to a corresponding computer system adapted for ensuring the authenticity of an electronic transaction.
Owner:COMFACT AB
Method and System For Facilitating Financial Transactions Over the Internet Using Registered Financial Instruments
InactiveUS20070143209A1Reduce the risk of fraudFinanceBuying/selling/leasing transactionsThird partyThe Internet
A method for enabling two individual consumers to complete a transaction that includes payment from one consumer (the payor, or buyer) to another consumer (the payee, or seller). An intermediary typically operates the service over a computer network of nodes, such as the Internet. The buyer has the convenience of paying through a variety of different payment instruments. Likewise, the seller has the convenience of receiving payment through a variety of different disbursement instruments. For a fee, the intermediary collects the payment from the buyer and pays the seller. Although the intermediary may receive payment from the buyer before the intermediary transfers the payment to the seller, the intermediary may choose to pay the seller before receiving payment from the buyer. In this case, the intermediary assumes the risk of nonpayment by the buyer. Alternatively, the intermediary may pay a third party that specializes in processing transactions for the payment instrument chosen by the buyer to assume the risk of nonpayment by the buyer. In this case, the intermediary receives a promise of payment from the third party before the intermediary pays the seller. Such a promise of payment from the third party is referred to as an authorization.
Owner:FIRST DATA CORP
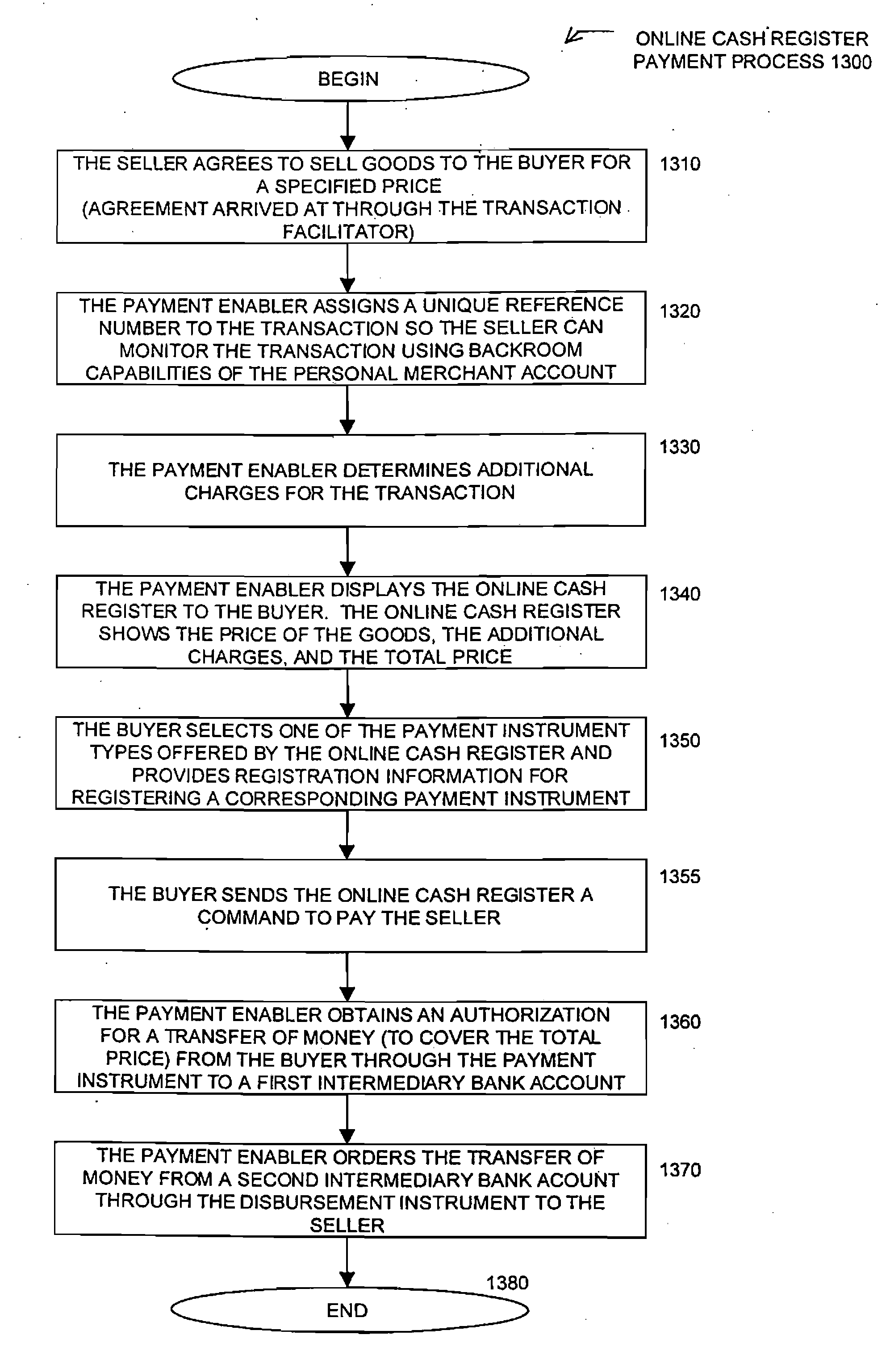
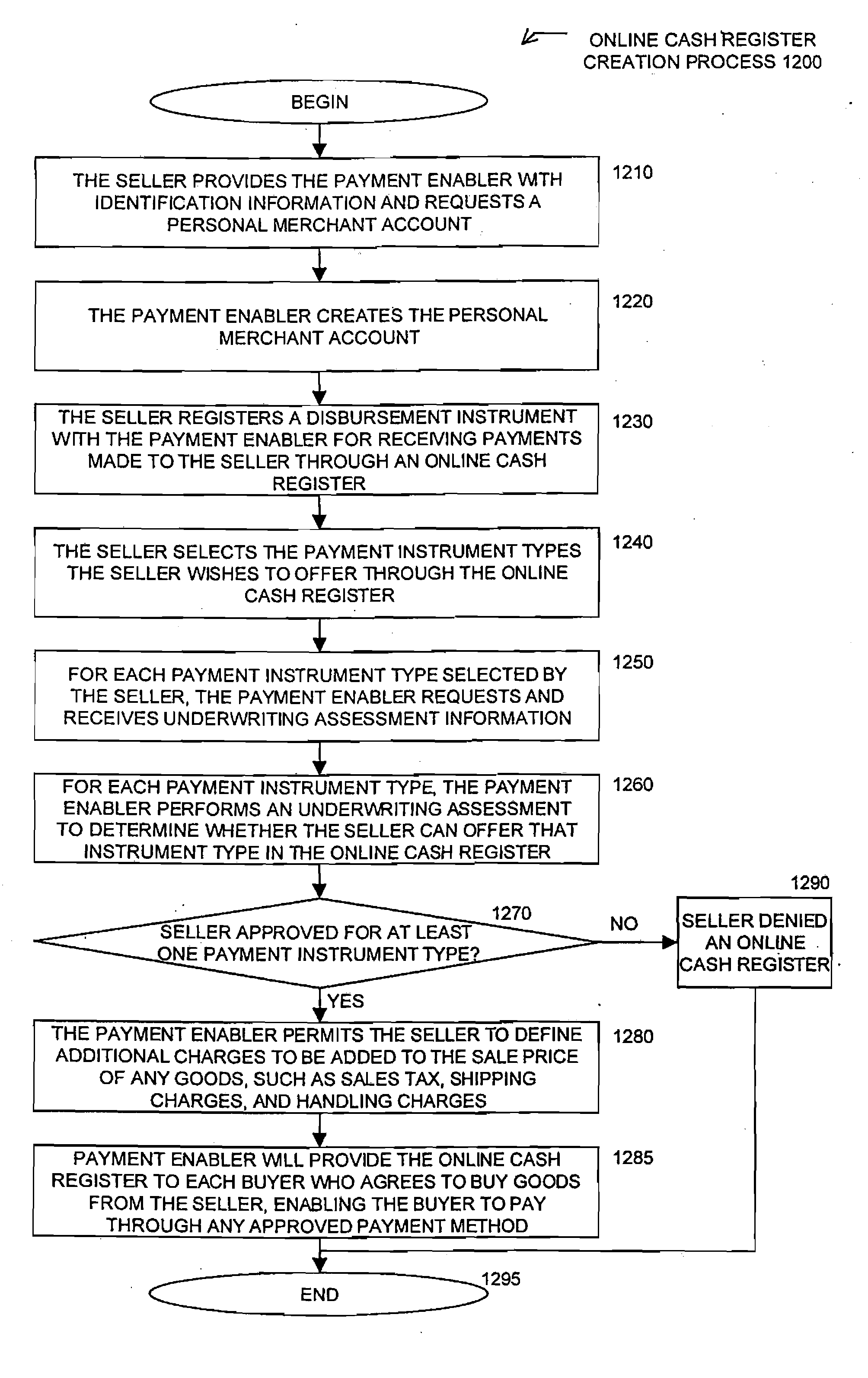
On-line cash register for use in providing a consumer-to-consumer payment service
InactiveUS20070136189A1Reduce the risk of fraudFinanceBuying/selling/leasing transactionsThird partyThe Internet
A method for enabling two individual consumers to complete a transaction that includes payment from one consumer (the payor, or buyer) to another consumer (the payee, or seller). An intermediary typically operates the service over a computer network of nodes, such as the Internet. The buyer has the convenience of paying through a variety of different payment instruments. Likewise, the seller has the convenience of receiving payment through a variety of different disbursement instruments. For a fee, the intermediary collects the payment from the buyer and pays the seller. Although the intermediary may receive payment from the buyer before the intermediary transfers the payment to the seller, the intermediary may choose to pay the seller before receiving payment from the buyer. In this case, the intermediary assumes the risk of nonpayment by the buyer. Alternatively, the intermediary may pay a third party that specializes in processing transactions for the payment instrument chosen by the buyer to assume the risk of nonpayment by the buyer. In this case, the intermediary receives a promise of payment from the third party before the intermediary pays the seller. Such a promise of payment from the third party is referred to as an authorization.
Owner:FIRST DATA
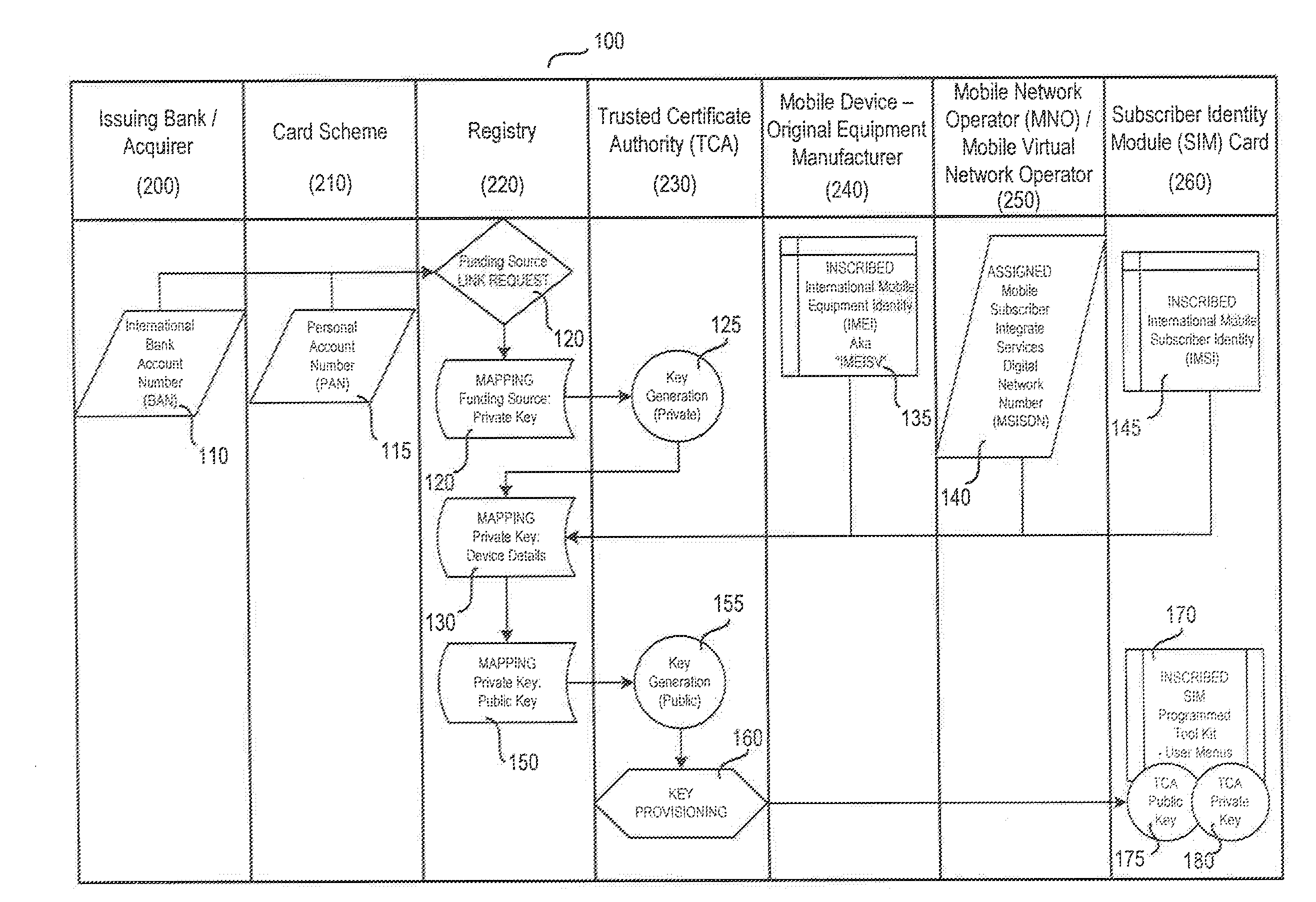
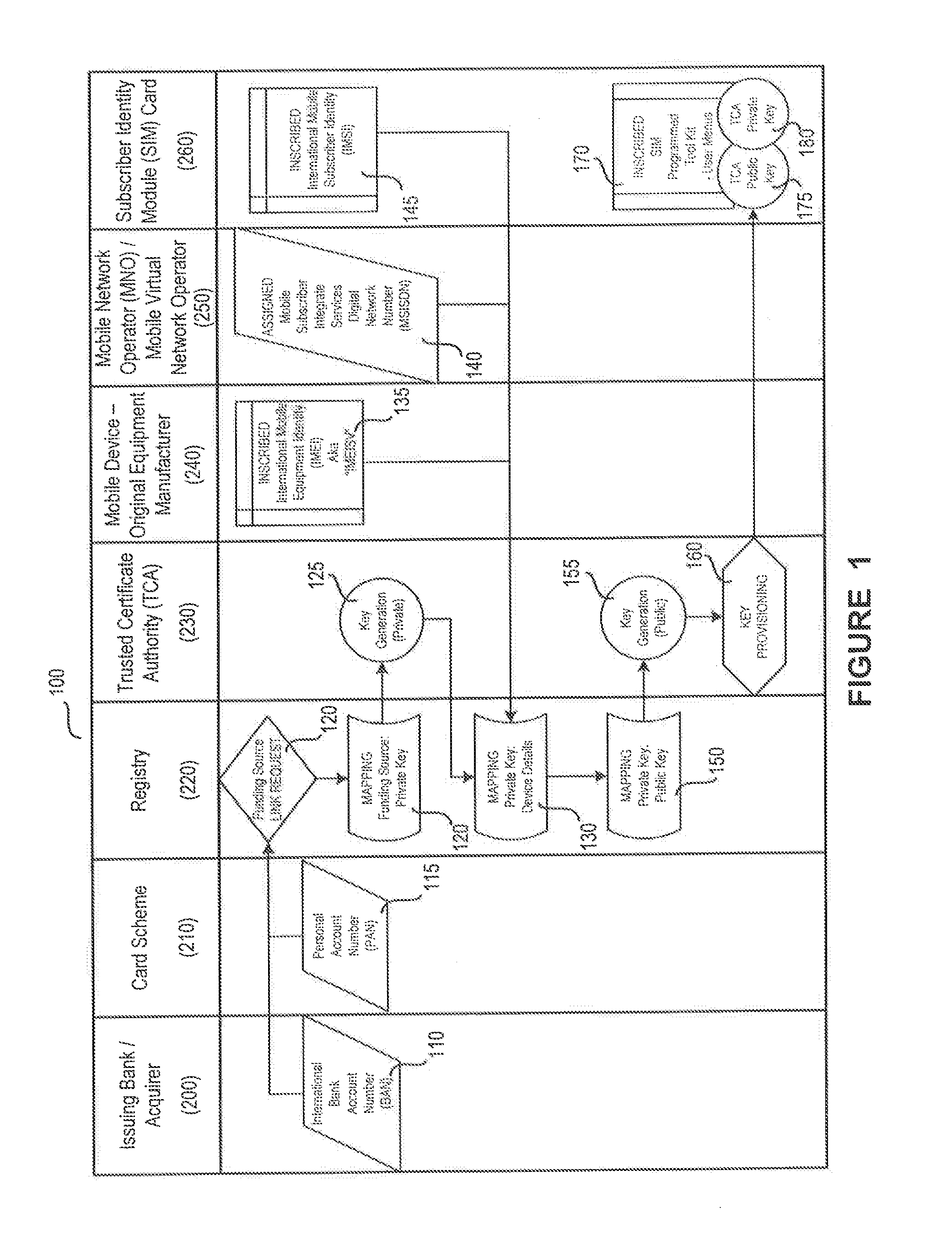
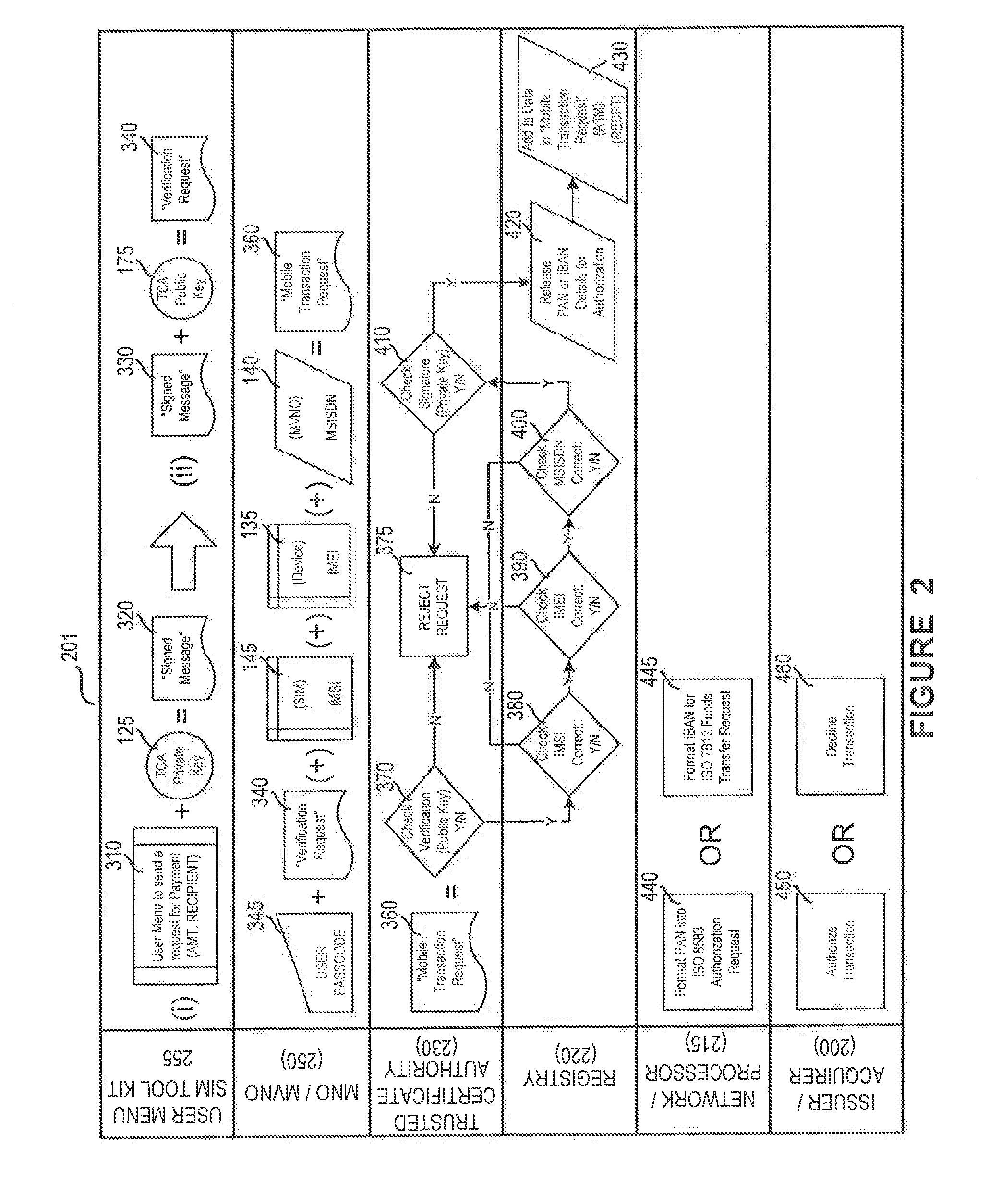
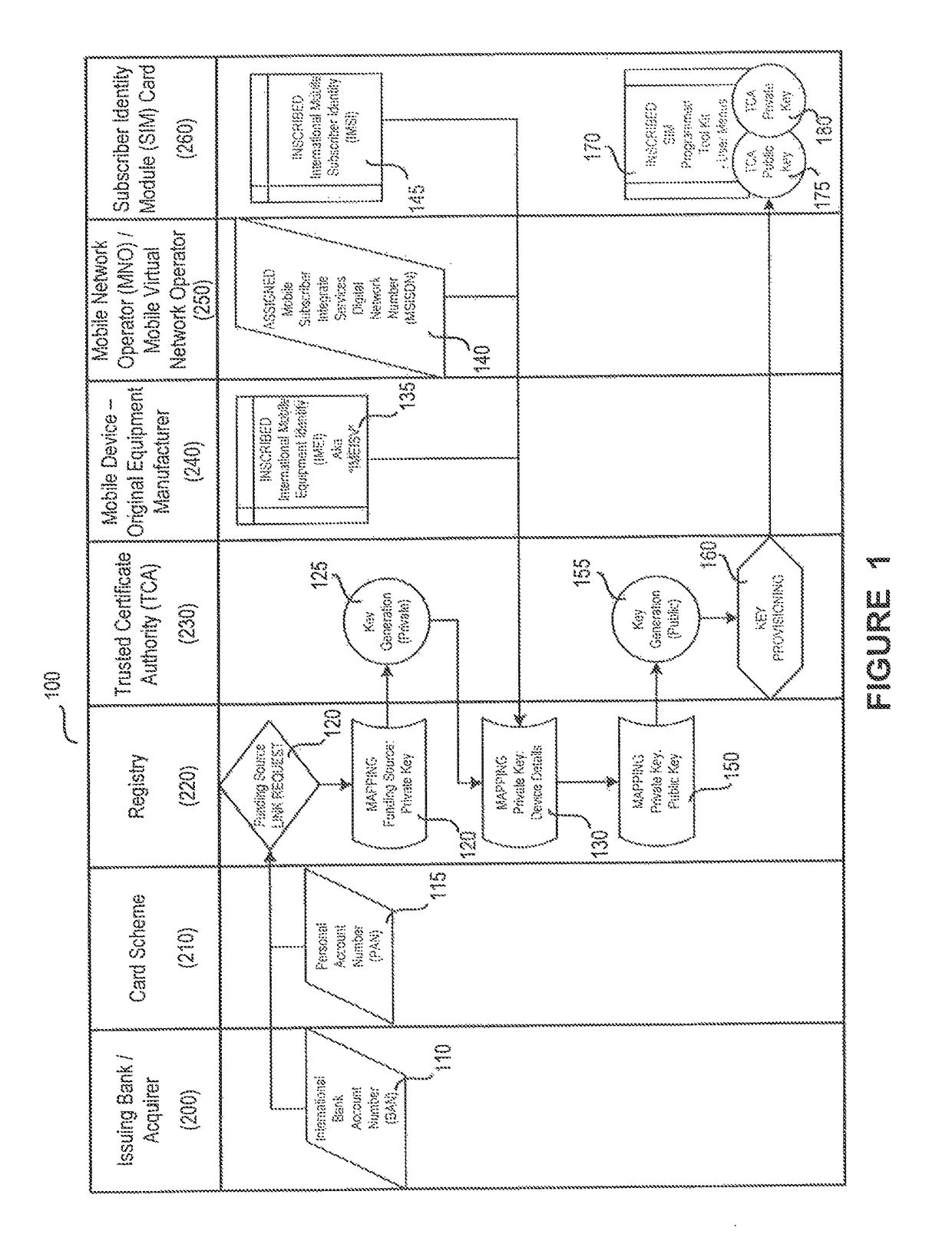
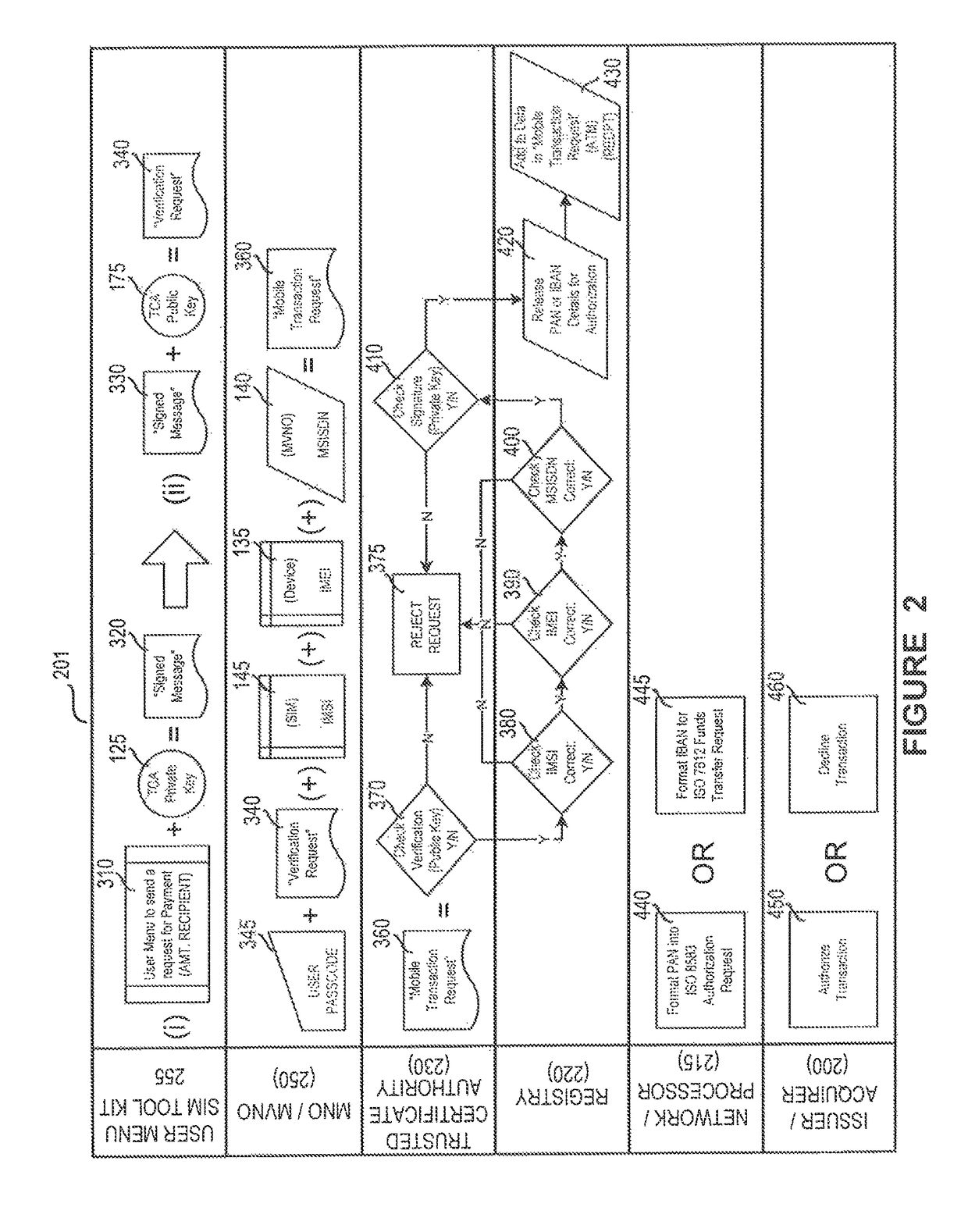
System and method for multi-factor mobile user authentication
ActiveUS20160080944A1Reduce the risk of fraudMake up for deficienciesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsUser authenticationMobile device
A system and method are disclosed herein leveraging financial networks standards with mobile device data and SIM card chip knowledge to authenticate a device. For instance, a party to a transaction may utilize these elements of information, not traditionally associated with wireless transactions, to achieve a lower probability of fraud and / or a higher confidence associated with the transaction.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
System and method for automatically enrollng an item in a virtual wallet
InactiveUS20150100486A1Reduce the risk of fraudProvide convenienceFinancePre-payment schemesPayment card
Systems and methods for enrolling one or more items into a virtual wallet are provided. A transaction message for a transaction is received. The transaction message includes information associated with the one or more items and a primary payment card associated with a user. The information associated with the one or more items is enrolled into the virtual wallet associated with a user. The virtual wallet includes information associated with a primary payment account associated with the user.
Owner:VISA INT SERVICE ASSOC
Method and system for facilitating payment of an online auction transaction
InactiveUS20070136192A1Reduce the risk of fraudComplete banking machinesFinanceThird partyThe Internet
A method for enabling two individual consumers to complete a transaction that includes payment from one consumer (the payor, or buyer) to another consumer (the payee, or seller). An intermediary typically operates the service over a computer network of nodes, such as the Internet. The buyer has the convenience of paying through a variety of different payment instruments. Likewise, the seller has the convenience of receiving payment through a variety of different disbursement instruments. For a fee, the intermediary collects the payment from the buyer and pays the seller. Although the intermediary may receive payment from the buyer before the intermediary transfers the payment to the seller, the intermediary may choose to pay the seller before receiving payment from the buyer. In this case, the intermediary assumes the risk of nonpayment by the buyer. Alternatively, the intermediary may pay a third party that specializes in processing transactions for the payment instrument chosen by the buyer to assume the risk of nonpayment by the buyer. In this case, the intermediary receives a promise of payment from the third party before the intermediary pays the seller. Such a promise of payment from the third party is referred to as an authorization.
Owner:FIRST DATA
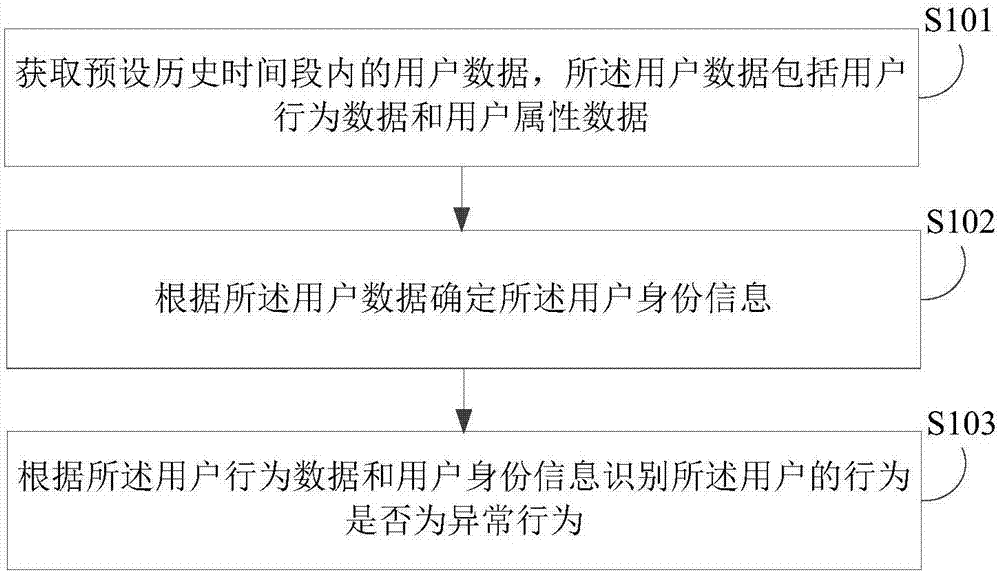
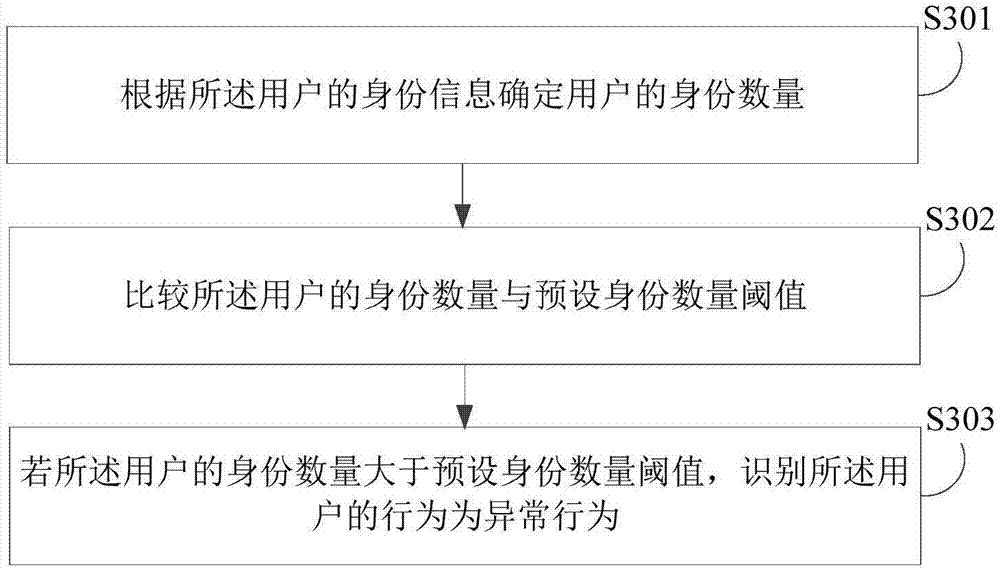
Abnormal behavior recognition method, device, electronic device and storage medium
PendingCN107958382AReduce the risk of fraudReduce economic lossMarketingInternet privacyRepeatability
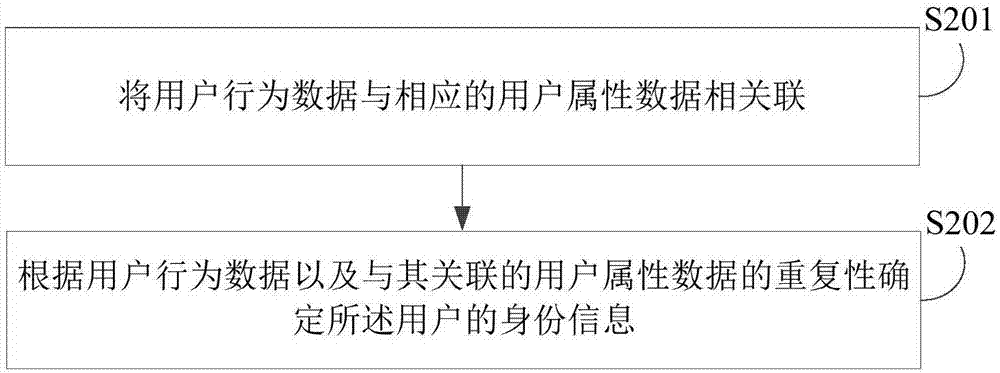
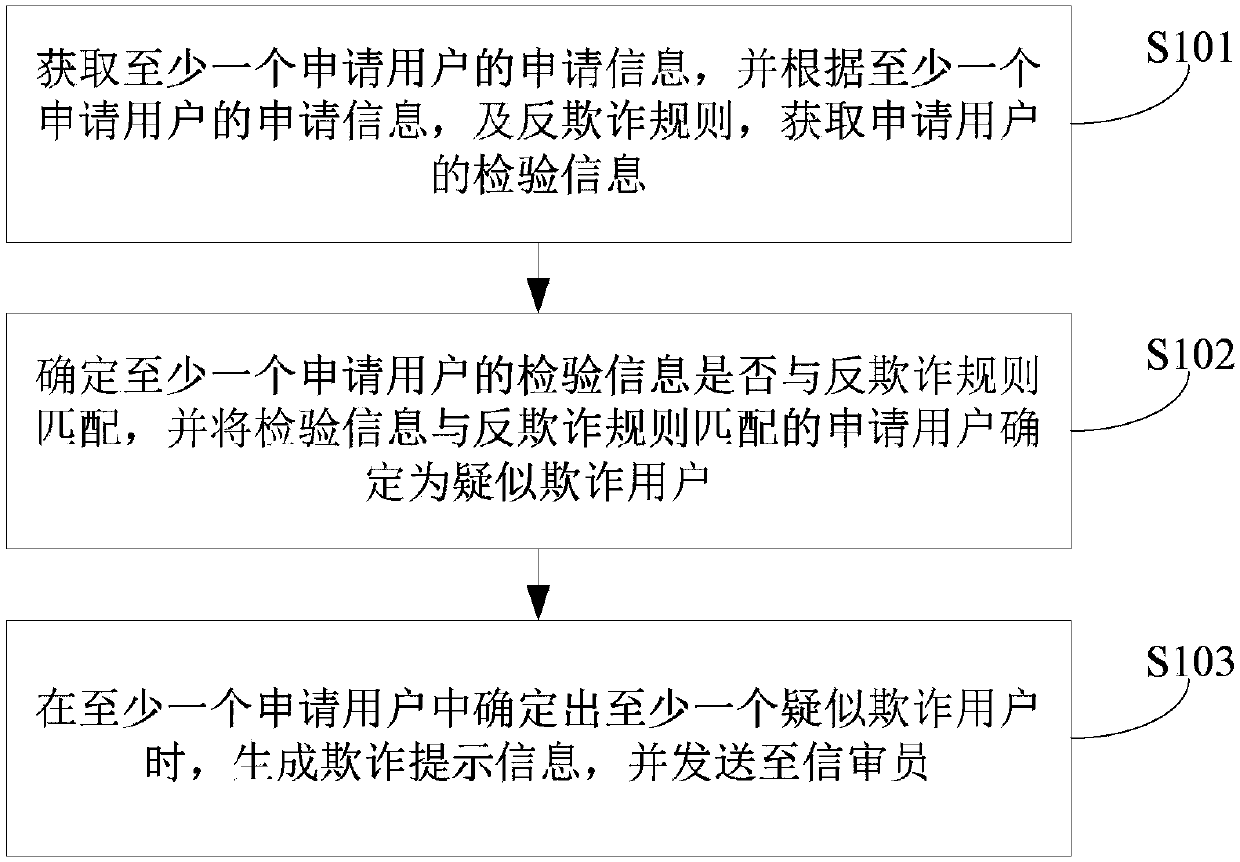
An embodiment of the invention discloses an abnormal behavior recognition method, device, electronic device and storage medium. The abnormal behavior recognition includes acquires user data in a preset history period, wherein the user data includes user behavior data and user attribute data; determining identity information of the user according to the user data; identifying whether the user behavior is an abnormal behavior or not according to the user behavior data and the identity information of the user, wherein user data based identification of user identity information includes correlating user behavior data with the user attribute data and determining the identity information of the user according to the repeatability of the user behavior data and the user attribute data correlated to the same. The method provided by the invention can reduce cheating risks of different parties as a whole effectively and reduce economic loss of a discount operation body.
Owner:BEIJING XIAODU INFORMATION TECH CO LTD
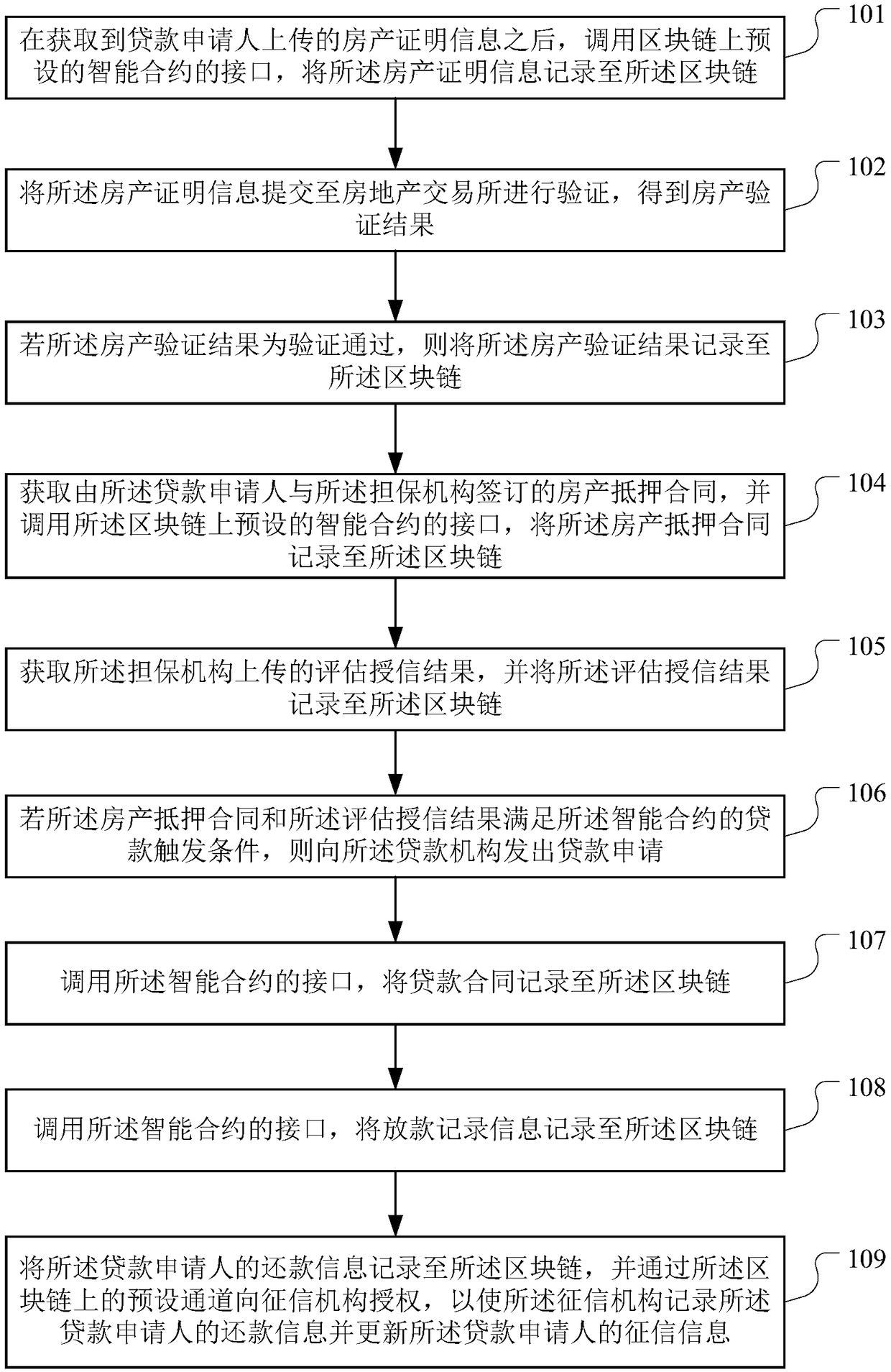
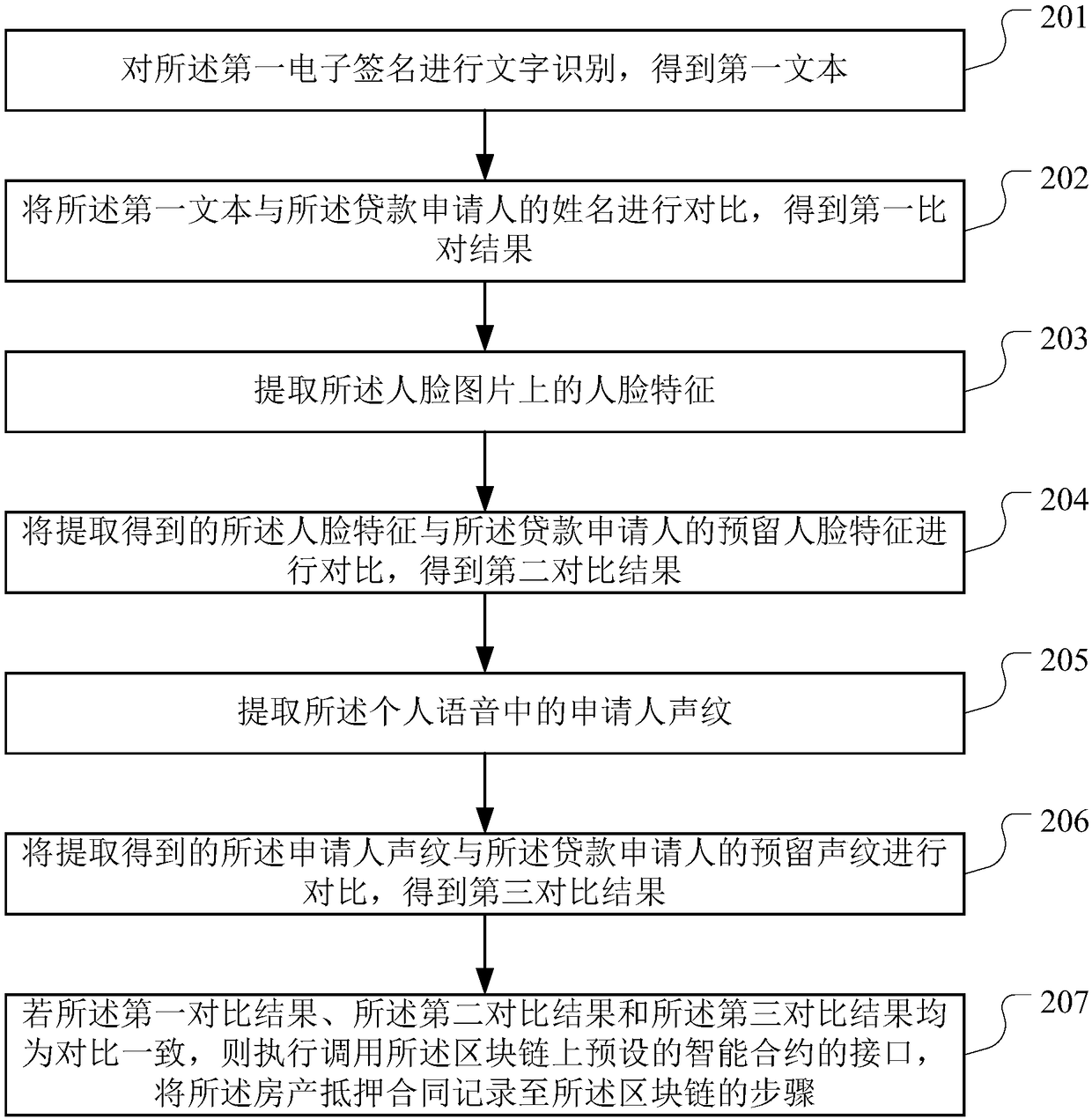
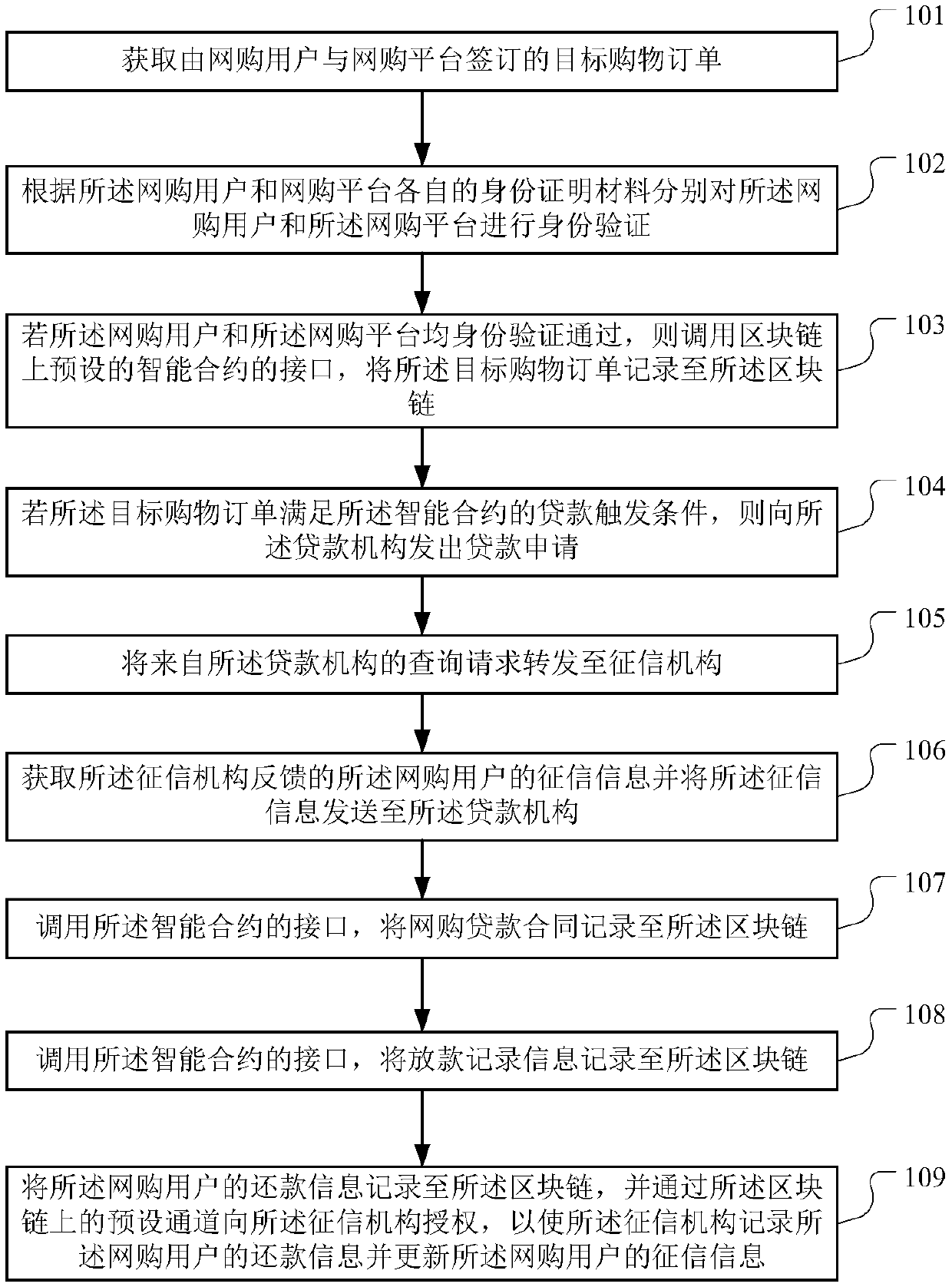
Loan data processing method, device and equipment based on block chain and storage medium
The invention discloses a loan data processing method, device and equipment based on a block chain and a storage medium, which are applied in the technical field of the block chain and are used for solving the problem of fraud risk existing in a real estate mortgage loan business. The method provided by the invention comprises the following steps of after obtaining the property certificate information, recording the property certificate information into the block chain; submitting the property certification information to the real estate exchange for verification, and obtaining the property certification results; if the verification is passed, recording the property verification result to the block chain; obtaining the mortgage contract and linking it up; obtaining and uploading the evaluation and credit granting results uploaded by the guarantee institution; if the loan triggering conditions are met, issuing a loan application to the lending institution; recording the loan contract, loan record information and repayment information to the block chain, and authorizing the credit information to the credit investigation organization through a preset channel on the block chain, so that the credit investigation organization records the repayment information of the loan applicant and updates the credit investigation information of the loan applicant.
Owner:PING AN TECH (SHENZHEN) CO LTD
Loan data processing method and device based on block chain, equipment and storage medium
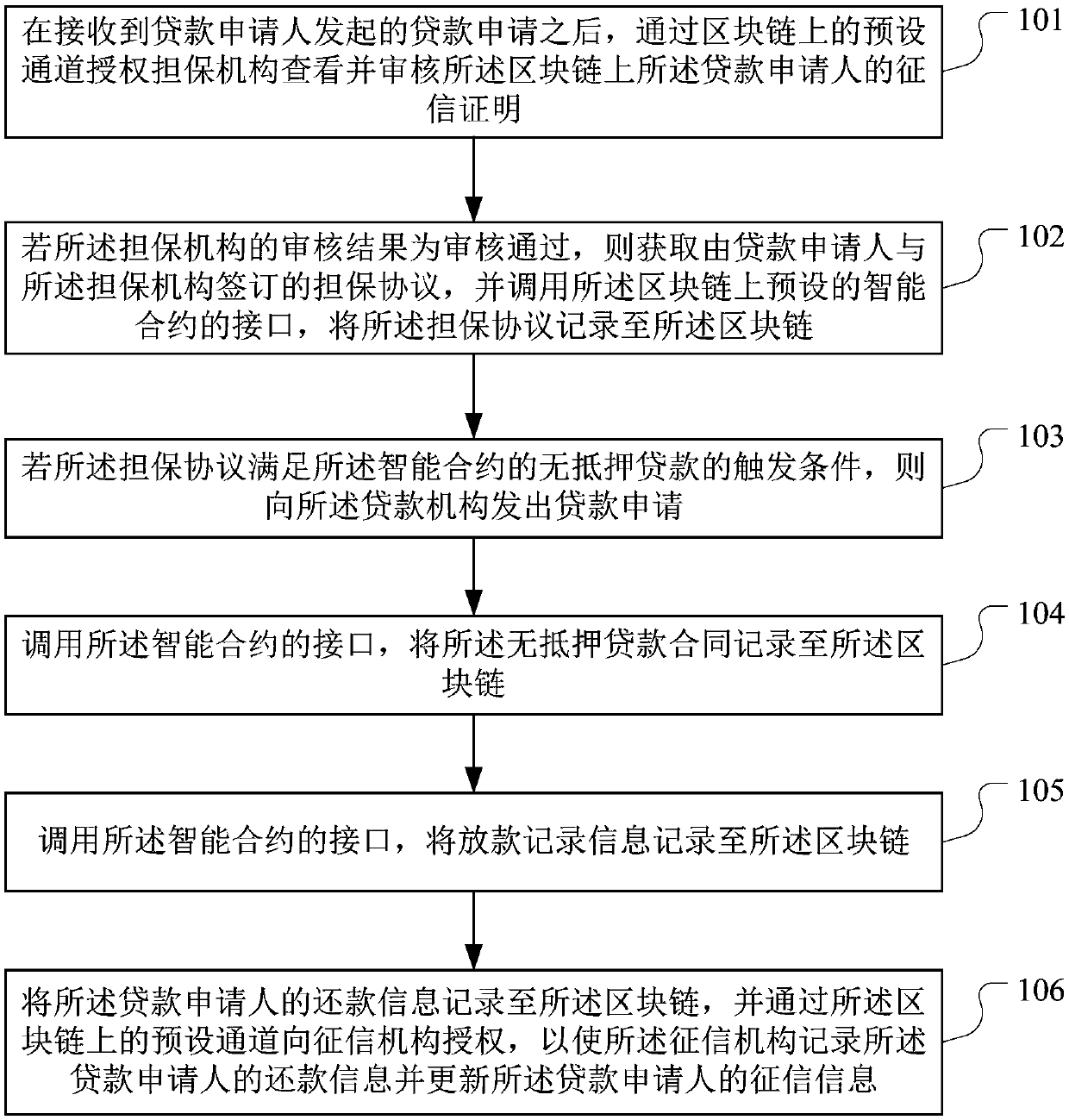
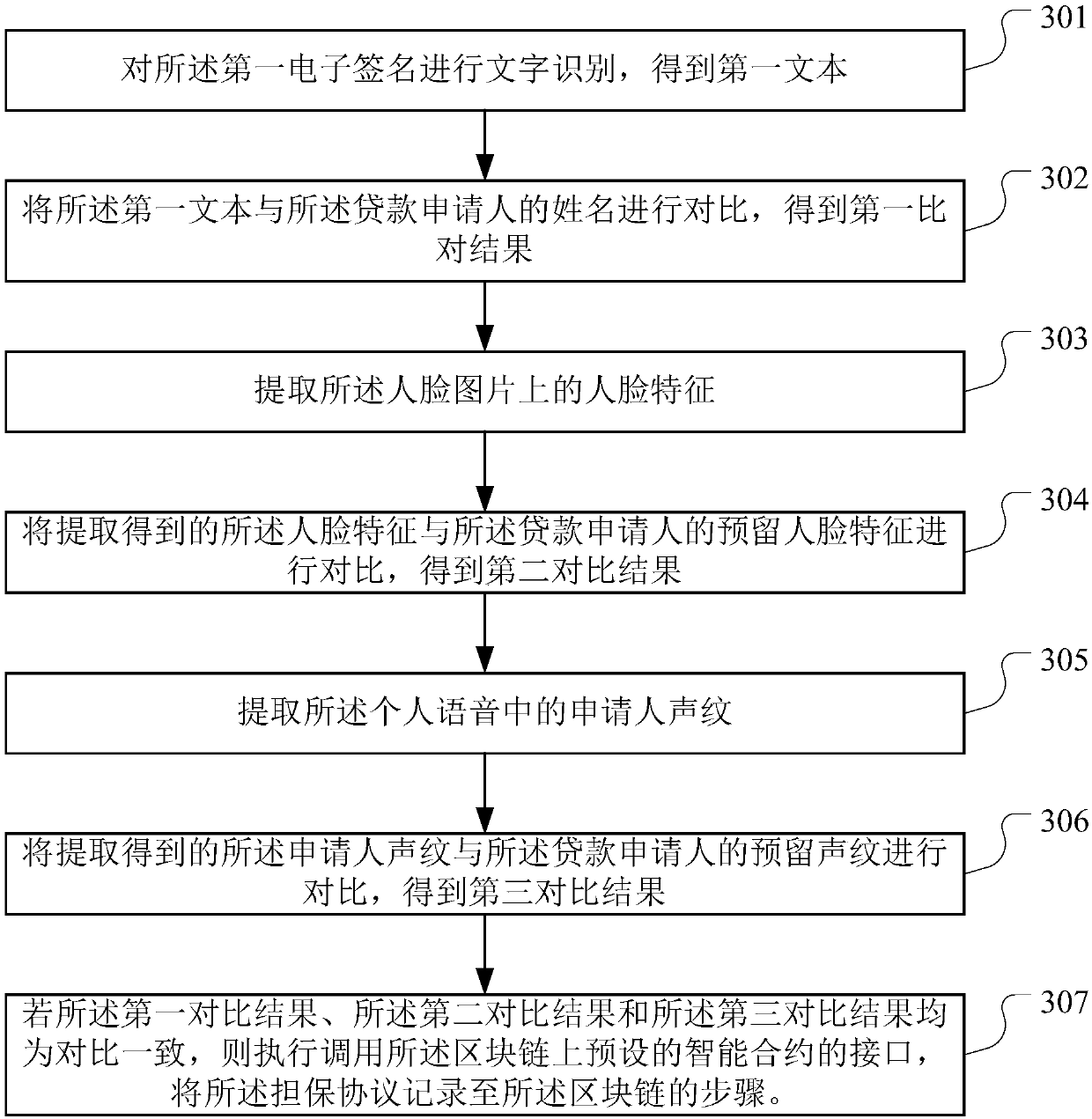
PendingCN109584043AIncrease authenticityReduce the risk of fraudFinanceOffice automationComputer scienceBlockchain
The invention discloses a loan data processing method and device based on a block chain, equipment and a storage medium, is applied to the technical field of block chains, and is used for solving theproblem that a mortgage-free loan service has a fraud risk. The method provided by the invention comprises the following steps: after receiving a loan application, authorizing a guarantee agency to check and audit a credit investigation certificate of a loan applicant on a block chain through a preset channel on the block chain; If the verification is passed, obtaining a guarantee protocol signedby a loan applicant and the guarantee mechanism, and recording the guarantee protocol to the block chain; If the guarantee protocol meets the trigger condition,sending a loan application to the loan agency; And recording the non-mortgage loan contract record, the loan record information and the repayment information to the block chain, and authorizing a credit investigation mechanism through a preset channel on the block chain, so that the credit investigation mechanism records the repayment information of the loan applicant and updates the credit investigation information of the loan applicant.
Owner:PING AN TECH (SHENZHEN) CO LTD
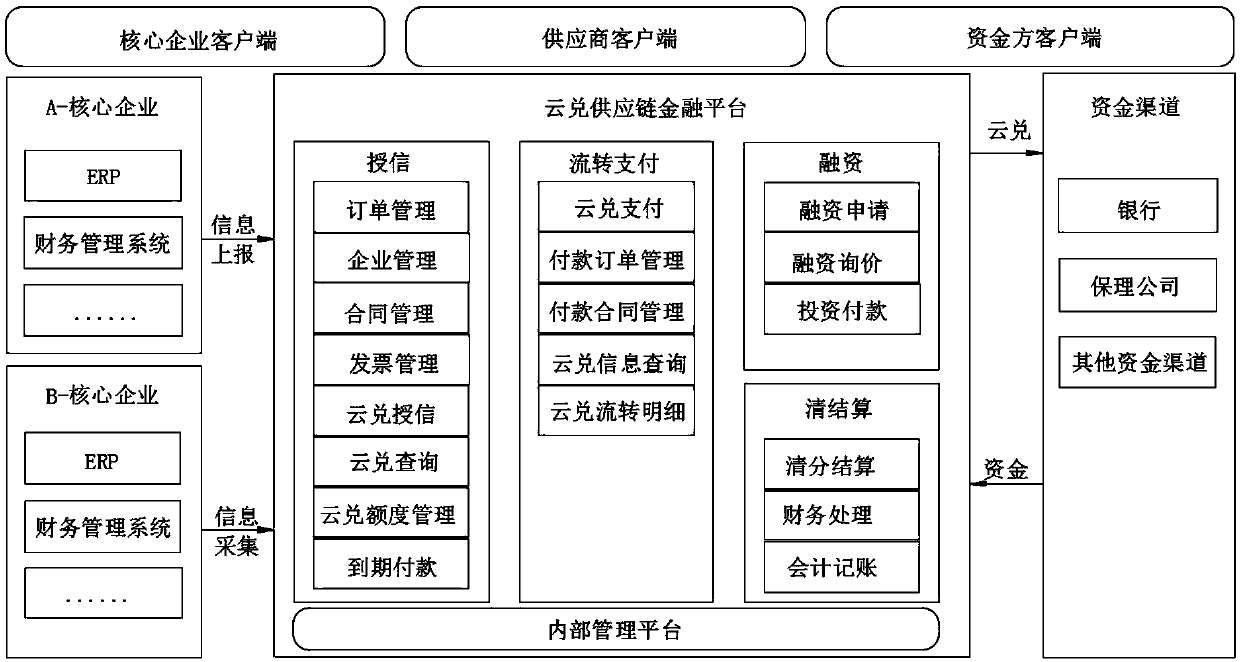
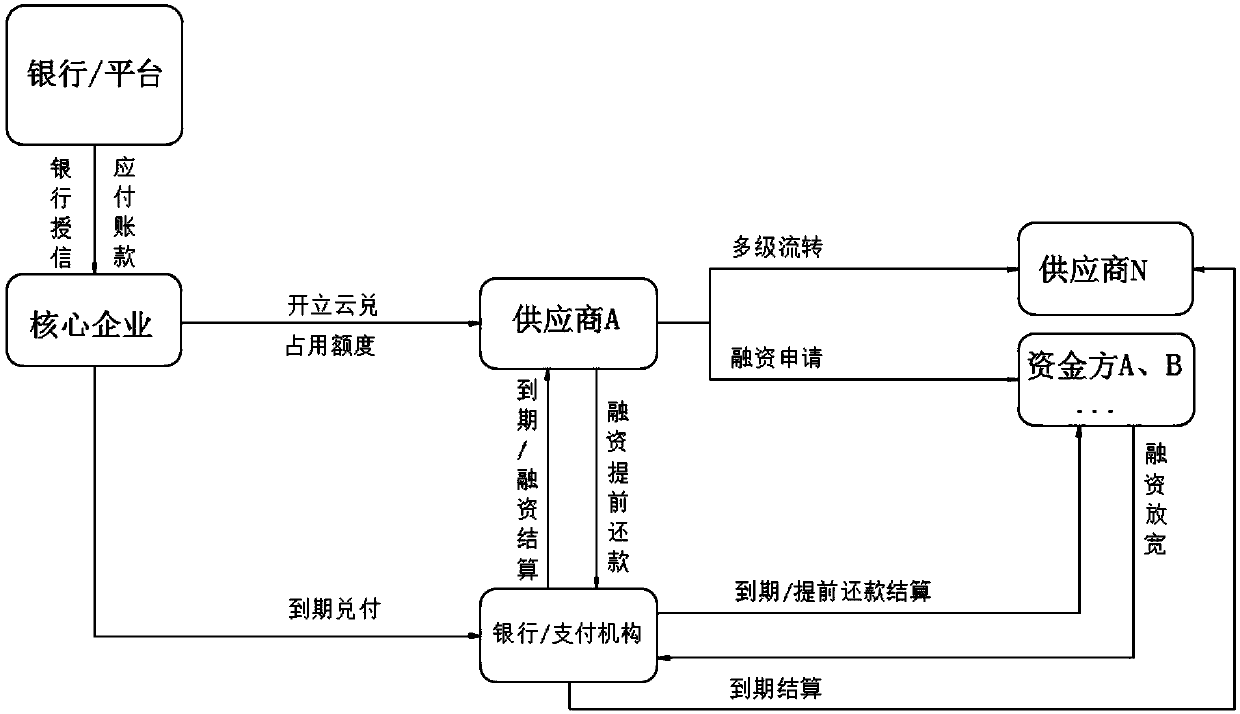
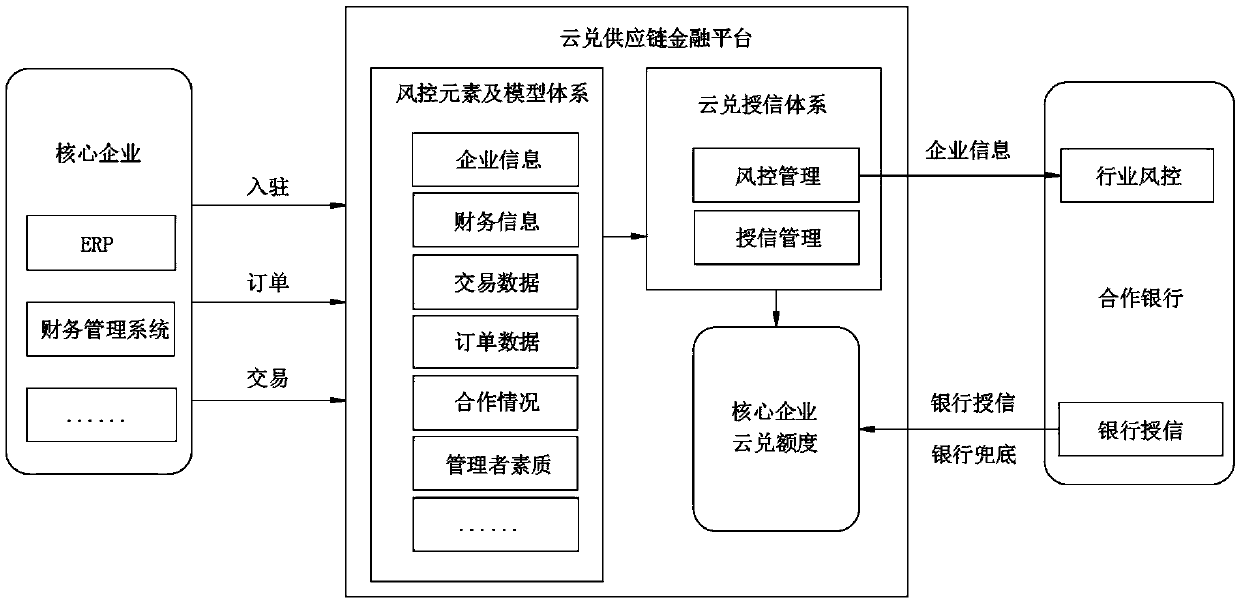
A supply chain financial software system and method
The invention discloses a supply chain financial software system and method, including a core enterprise client, a supplier client, a fund party client and an internal management platform,, the core enterprise client reports information to a background database of the internal management platform to obtain a cloud exchange credit line, the core enterprise sends the cloud exchange information in the credit line to the supplier client, and the supplier client sends the cloud exchange information to other enterprises for payment of goods. The invention discloses a supply chain financial softwaresystem and method. Firstly, separation of commodity exchange and currency exchange is realized; the requirements of a payment enterprise on operation funds are reduced; secondly, credit transfer of core enterprises is achieved, bank guarantee is achieved, the bad account risk of the seller is effectively reduced, online transfer and timely transfer of credit and related service information can beachieved, market demand information and financing party operation information can be accurately fed back, the financing risk is reduced, and a better use prospect is brought.
Owner:北京锐融天下科技股份有限公司
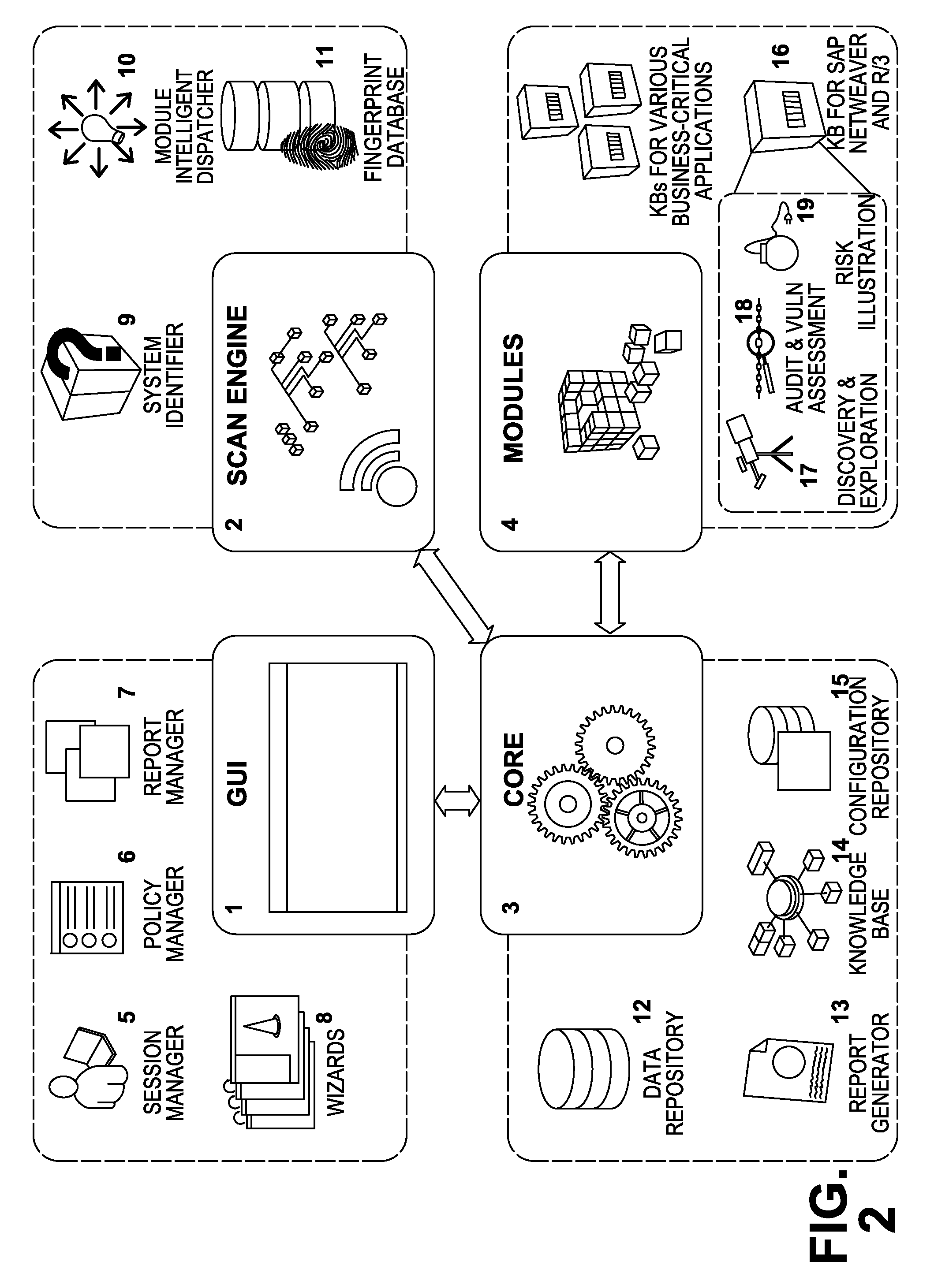
Automated security assessment of business-critical systems and applications
ActiveUS9009837B2Reduce the risk of fraudReduce audit costsWeb data indexingMemory loss protectionCritical systemApplication security
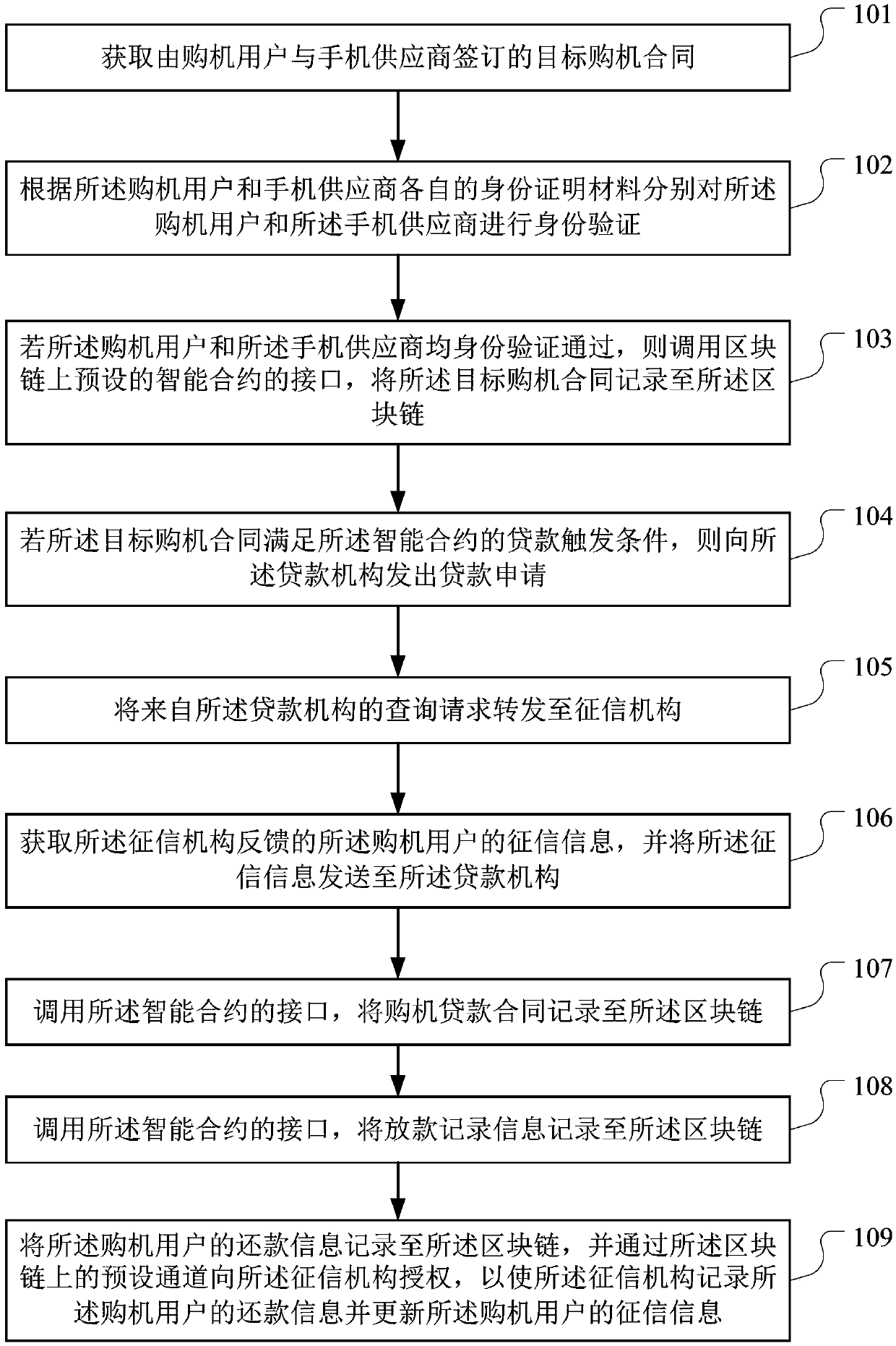
Systems and methods which provide a new application security assessment framework that allows auditing and testing systems to automatically perform security and compliance audits, detect technical security vulnerabilities, and illustrate the associated security risks affecting business-critical applications.
Owner:ONAPSIS
Block-chain-based data processing method, device and apparatus and storage medium
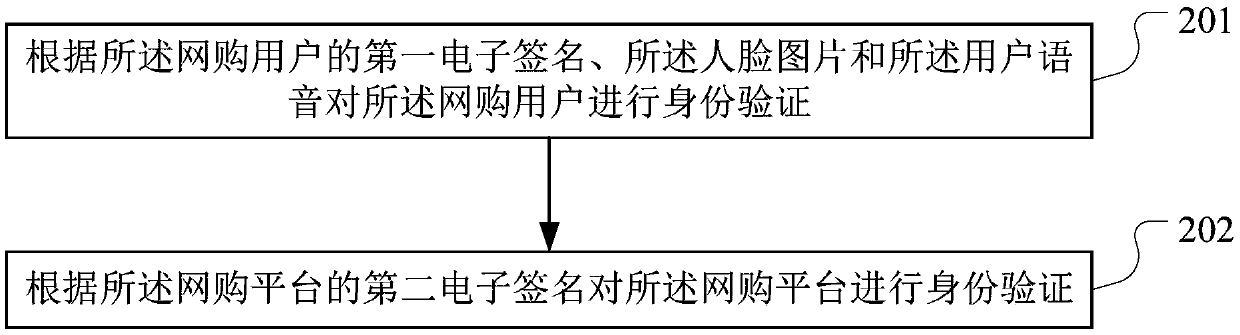
PendingCN109544156AIncrease authenticityReduce the risk of fraudFinancePayment protocolsData processingData science
The invention discloses a data processing method, a block-chain-baseddevice and apparatus and a storage medium, which are applied in the technical field of the block chain and are used for solving theproblem of fraud risk existing in online shopping loan business. The method provided by the invention comprises the following steps: obtaining a target purchase order signed by an online shopping user and an online shopping platform; performing identity verification on online shopping users and online shopping platform; If the verification is passed, the interface of the preset intelligent contract on the block chain is called, and the target purchase order is recorded to the block chain; If the loan triggering conditions are met, a loan application is issued to the lending institution; Forwarding the inquiry request to the credit reporting authority; Obtaining the credit information from the credit reporting institution and send it to the lending institution; recording the online purchase loan contract, loan record information and repayment information to the block chain, and authorizing the credit investigation organization through the preset channel on the block chain, so that thecredit investigation organization records the repayment information of the online purchase user and updates the credit investigation information of the online purchase user.
Owner:PING AN TECH (SHENZHEN) CO LTD
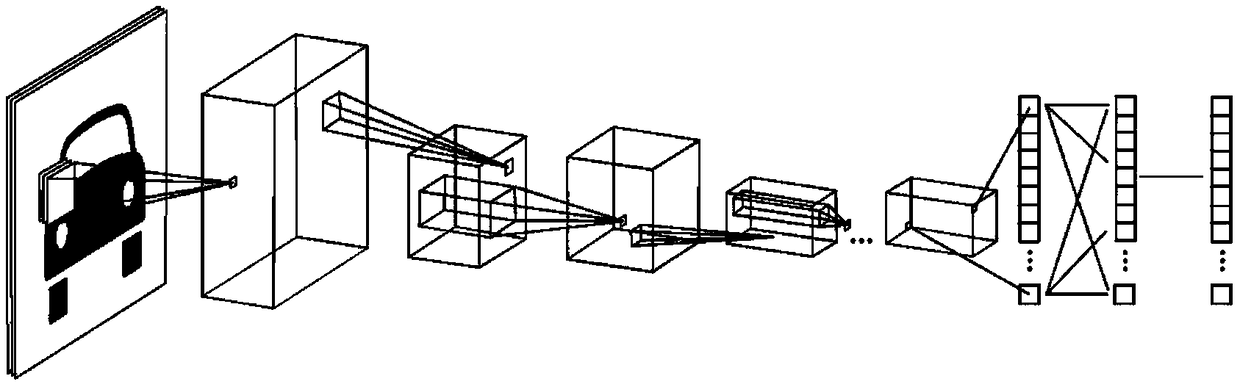
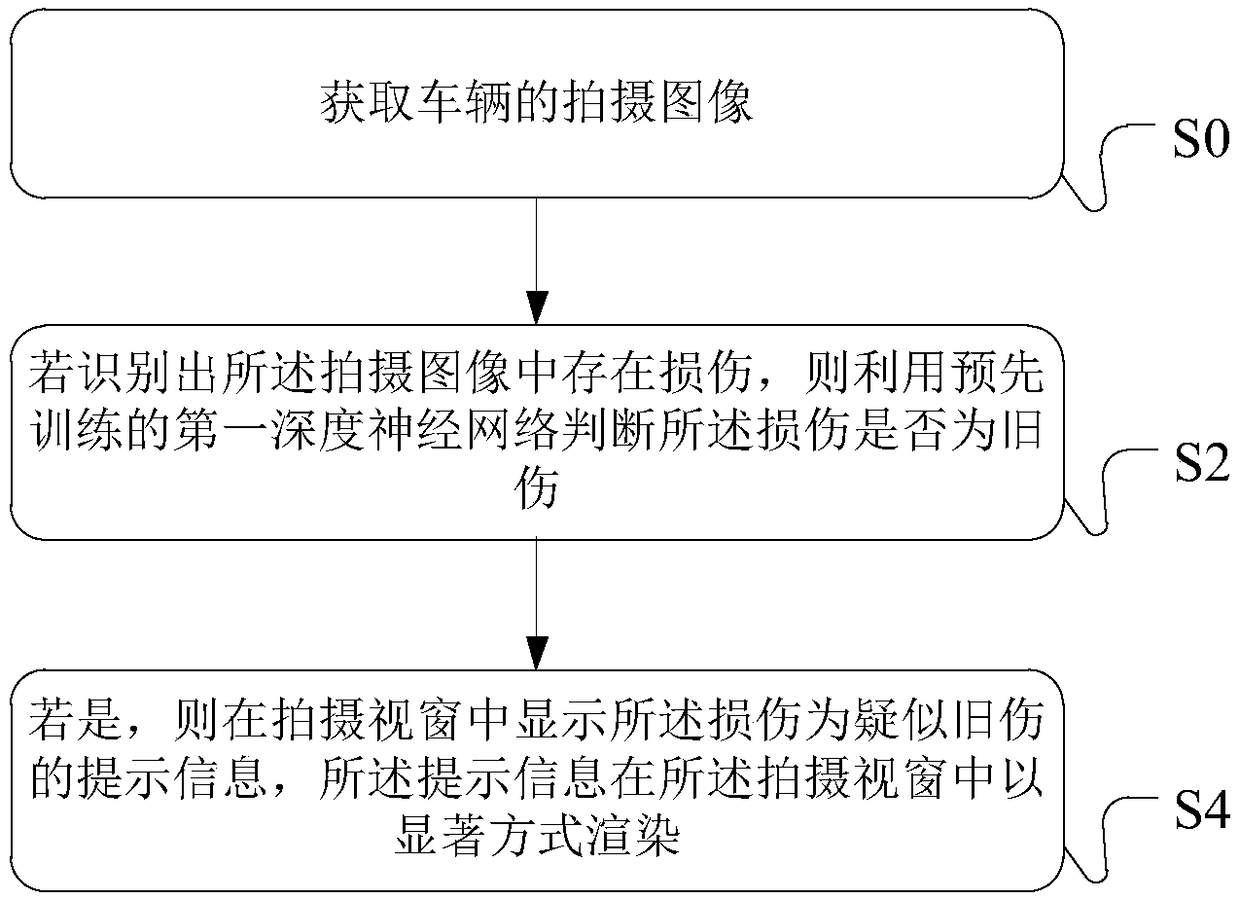
Processing method and processing equipment for vehicle damage identification, client and server
InactiveCN108647712AImprove reliabilityLower skill requirementsFinanceRegistering/indicating working of vehiclesTerminal equipmentComputer science
Embodiments of the invention disclose a processing method and processing equipment for vehicle damage identification, a client and a server. The processing method of the invention is characterized inthat: in one embodiment, whether a vehicle damage is an old damage can be identified automatically on terminal equipment, and whether the damage is the old damage is identified in real time when an image or video is shot without human intervention, thus requirements for skills of survey staff can be effectively reduced; at the same time, information of an identified suspected old damage can be automatically recorded and transmitted to a designated server system, such as an insurance company, in this way, even if the survey staff or malicious users delete images or videos of the old damage, theinformation that the damage has been identified to be an old damage can not be concealed, thus a fraud risk can be effectively reduced, reliability of damage identification can be improved, and reliability of a loss assessment result can be further improved.
Owner:ADVANCED NEW TECH CO LTD
System and method for multi-factor mobile user authentication
ActiveUS9681305B2Reduce the risk of fraudMake up for deficienciesUser identity/authority verificationSecurity arrangementUser authenticationMobile device
A system and method are disclosed herein leveraging financial networks standards with mobile device data and SIM card chip knowledge to authenticate a device. For instance, a party to a transaction may utilize these elements of information, not traditionally associated with wireless transactions, to achieve a lower probability of fraud and / or a higher confidence associated with the transaction.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Loan data processing method, device and equipment based on block chain and storage medium
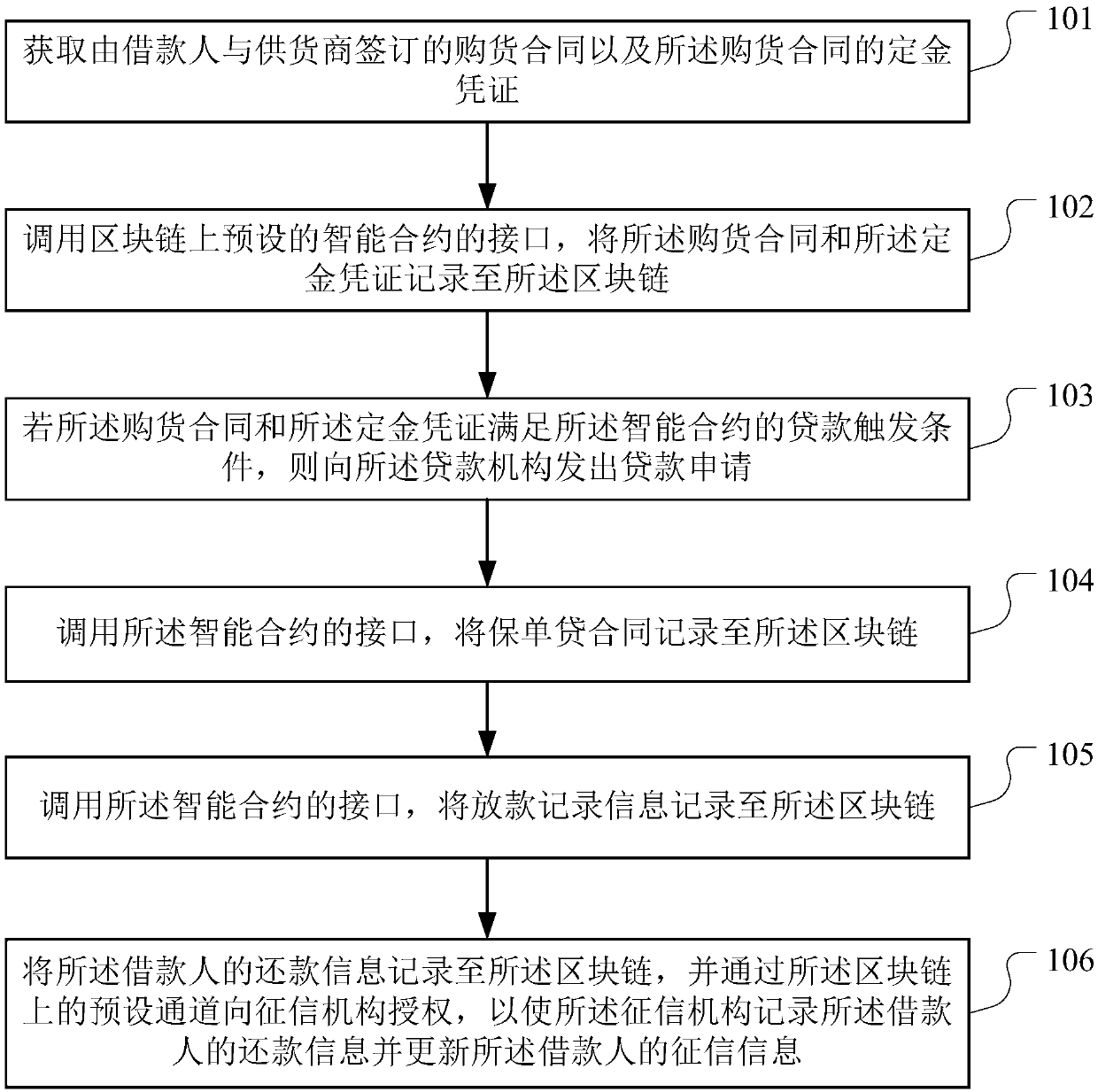
The invention discloses a loan data processing method, device and equipment based on a block chain and a storage medium, which are applied to the technical field of block chains, and are used for solving the problem that insurance policy pledge loan services have fraud risks. The method provided by the invention comprises the following steps of obtaining a purchase contract and a settlement voucher; calling an interface of a preset smart contract on a block chain, and recording the purchase contract and the deposit certificate to the block chain; recording the loan contract for insurance policy, the loaning record information, the repayment information to the block chain; authorizing a credit investigation mechanism through a preset channel on the block chain, wherein the preset channel comprises the supplier, the loan agency and the credit investigation mechanism, so that the credit investigation mechanism records the repayment information of the borrower and updates the credit investigation information of the borrower, the repayment information is generated every time the borrower repays according to the insurance policy loan contract, and the preset channel comprises the supplier, the loan agency and the credit investigation mechanism.
Owner:PING AN TECH (SHENZHEN) CO LTD
Block chain-based business data processing method, apparatus and device, and storage medium
PendingCN109584040AIncrease authenticityReduce the risk of fraudFinanceDigital data protectionComputer scienceMobile phone
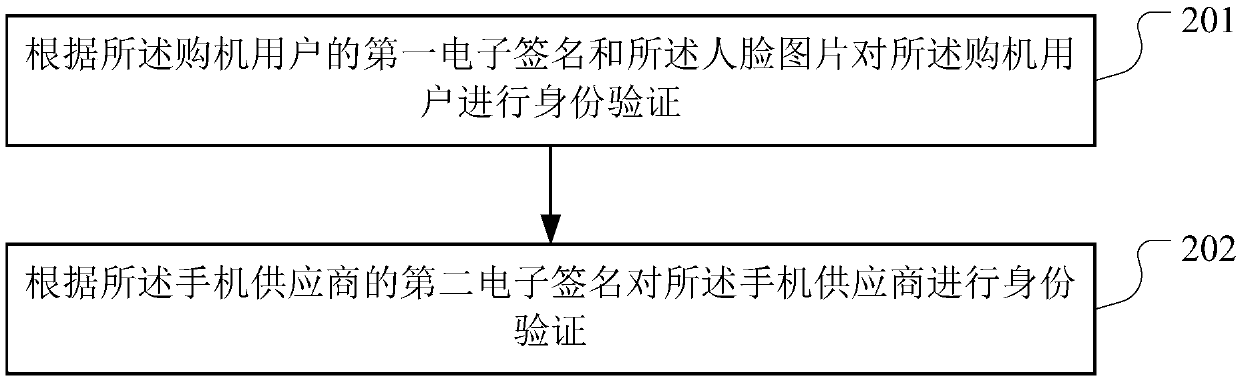
The invention discloses Block chain-based business data processing method, apparatus and device, and storage medium, is applied to the technical field of block chains, and is used for solving the problem that a machine purchase loan service has a fraud risk. The method provided by the invention comprises the following steps: obtaining a target machine purchase contract signed by a machine purchaseuser and a mobile phone supplier; Respectively carrying out identity verification on the machine purchase user and the mobile phone supplier according to respective identity verification materials ofthe machine purchase user and the mobile phone supplier; If the verification is passed, recording the target machine purchase contract to a block chain; If the loan triggering condition is met, sending a loan application to a loan institution; Forwarding the query request to a credit investigation mechanism; Obtaining credit investigation information fed back by the credit investigation mechanismand sending the credit investigation information to the loan mechanism; And recording the machine purchase loan contract, the loaning record information and the repayment information of the machine purchase user to the block chain, and authorizing the credit investigation mechanism through a preset channel on the block chain, so that the credit investigation mechanism records the repayment information of the machine purchase user and updates the credit investigation information of the machine purchase user.
Owner:PING AN TECH (SHENZHEN) CO LTD
Block-chain-based transaction data processing method, device, apparatus and storage medium
ActiveCN109544335AIncrease authenticityReduce the risk of fraudFinanceDigital data protectionTransaction dataVoucher
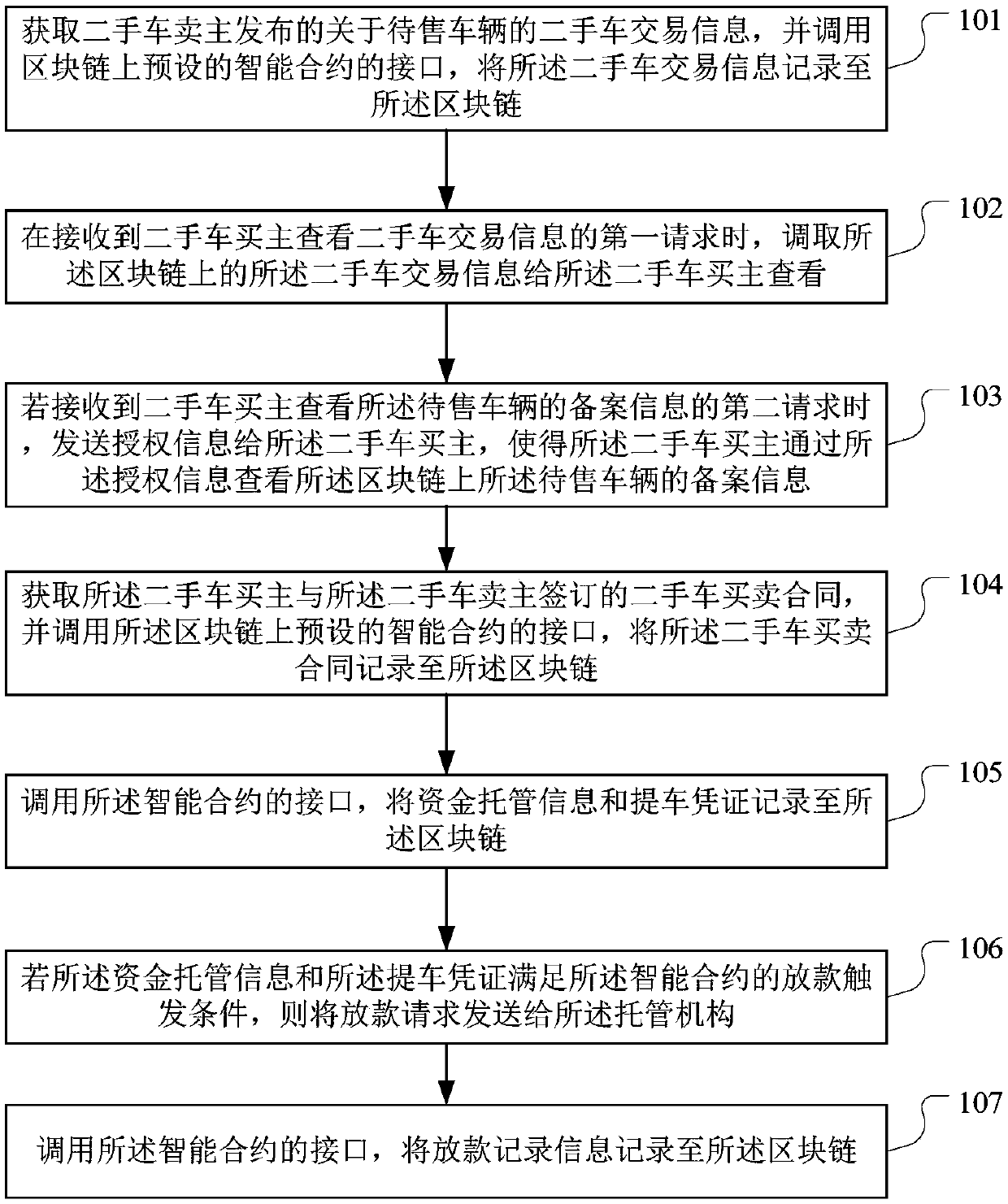
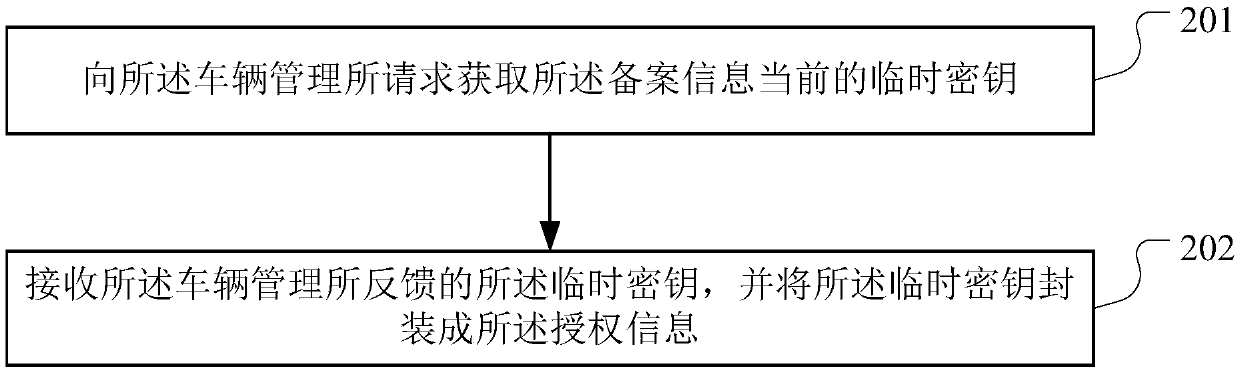
The invention discloses a block-chain-based transaction data processing method, device and apparatus and a storage medium, which are applied in the technical field of the block chain and are used forsolving the problem of fraud risk existing in a used car transaction. The method provided by the invention comprises the following steps: acquiring used car transaction information, and recording theused car transaction information to a block chain; upon receiving the first request to view the second-hand car transaction information, the second-hand car transaction information on the block chainis transferred to the second-hand car buyer for viewing. if the second request for viewing the filing information is received, the authorization information is sent to the second-hand car buyer, so that the second-hand car buyer can view the filing information of the vehicle to be sold on the block chain through the authorization information; obtaining the second-hand car sales contract and recording the second-hand car sales contract to the block chain; recording the fund custody information and vehicle lifting voucher to the block chain; if the fund custody information and the vehicle withdrawal voucher meet the loan triggering conditions, the loan request is sent to the custodian institution; recording the loan record information to the block chain.
Owner:PING AN TECH (SHENZHEN) CO LTD
Detection method and device of fraud user
InactiveCN107679046AReduce the risk of fraudDoes not affect experienceRelational databasesResourcesInternet privacy
Owner:SHANGHAI QIANLONG INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com