Patents
Literature
592 results about "Application security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
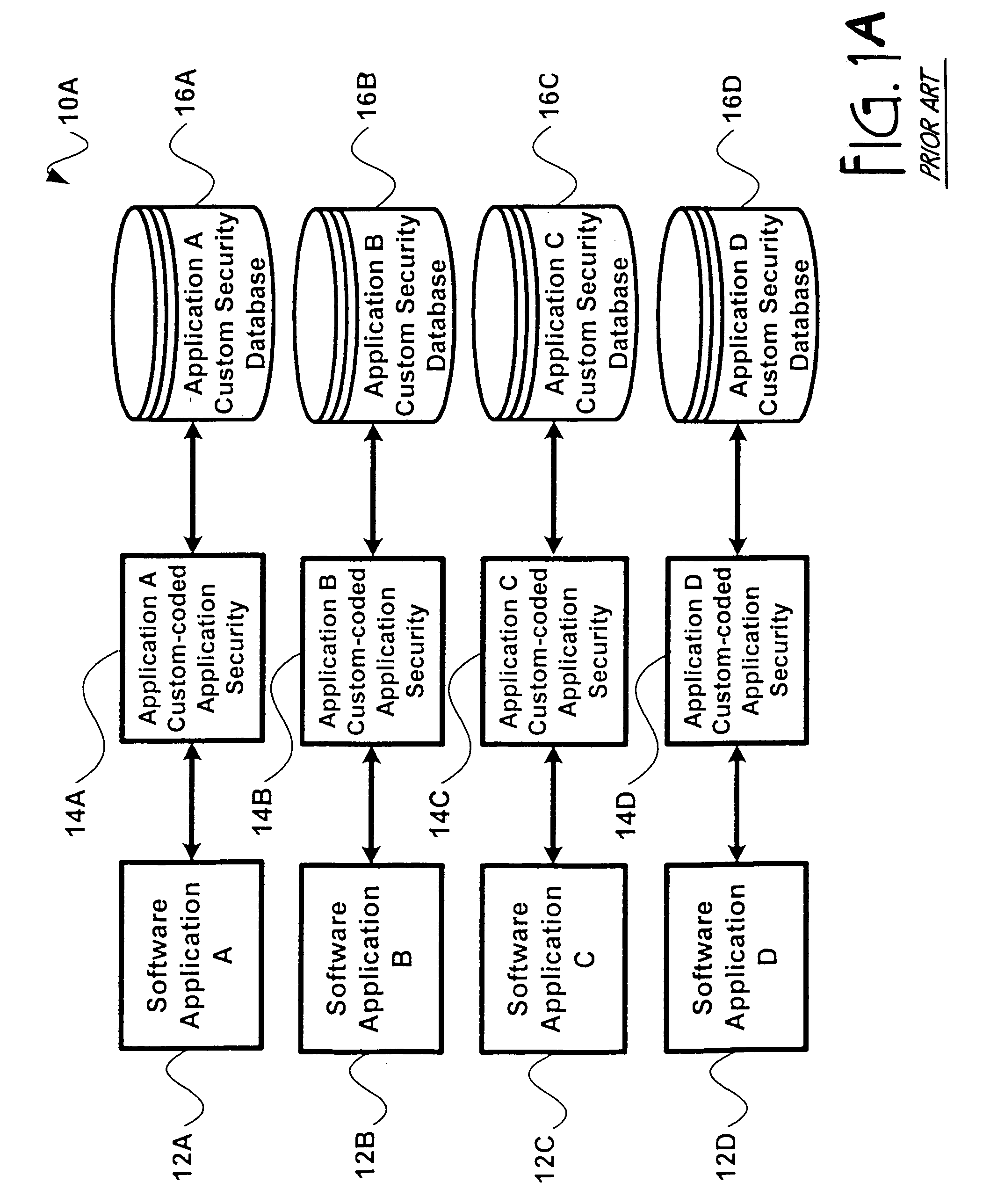
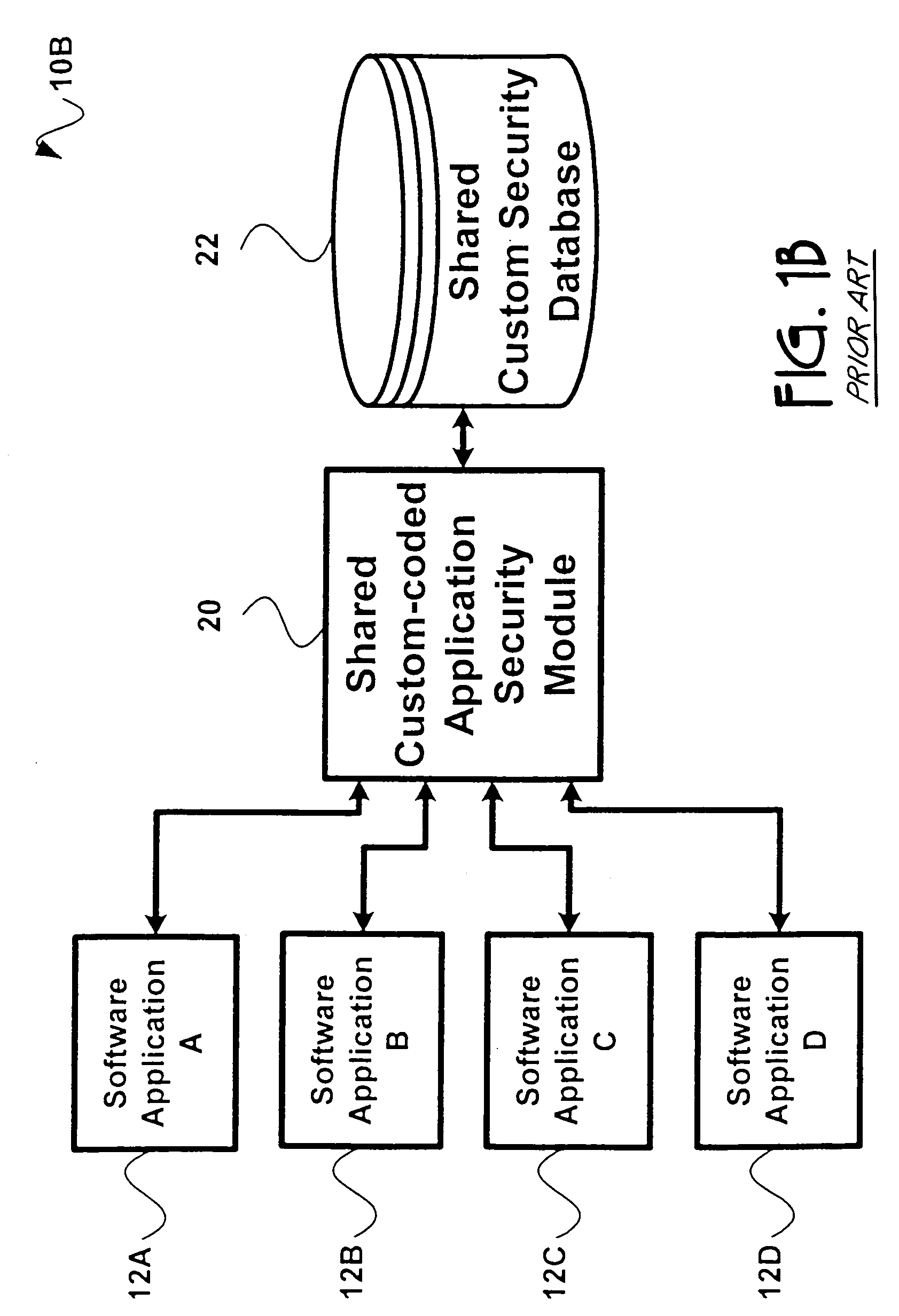
Application security encompasses measures taken to improve the security of an application often by finding, fixing and preventing security vulnerabilities. Different techniques are used to surface such security vulnerabilities at different stages of an applications lifecycle such as design, development, deployment, upgrade, maintenance.
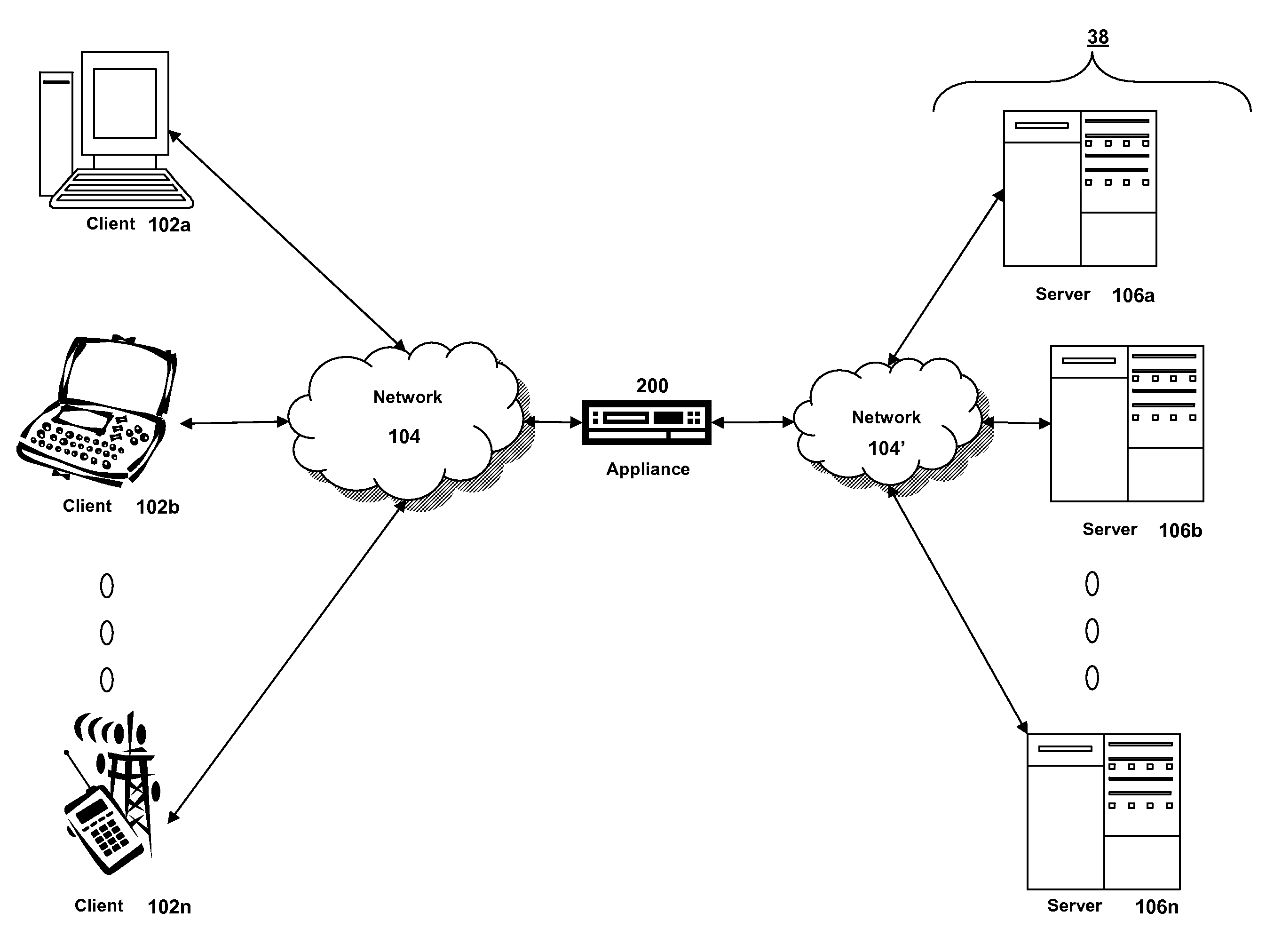
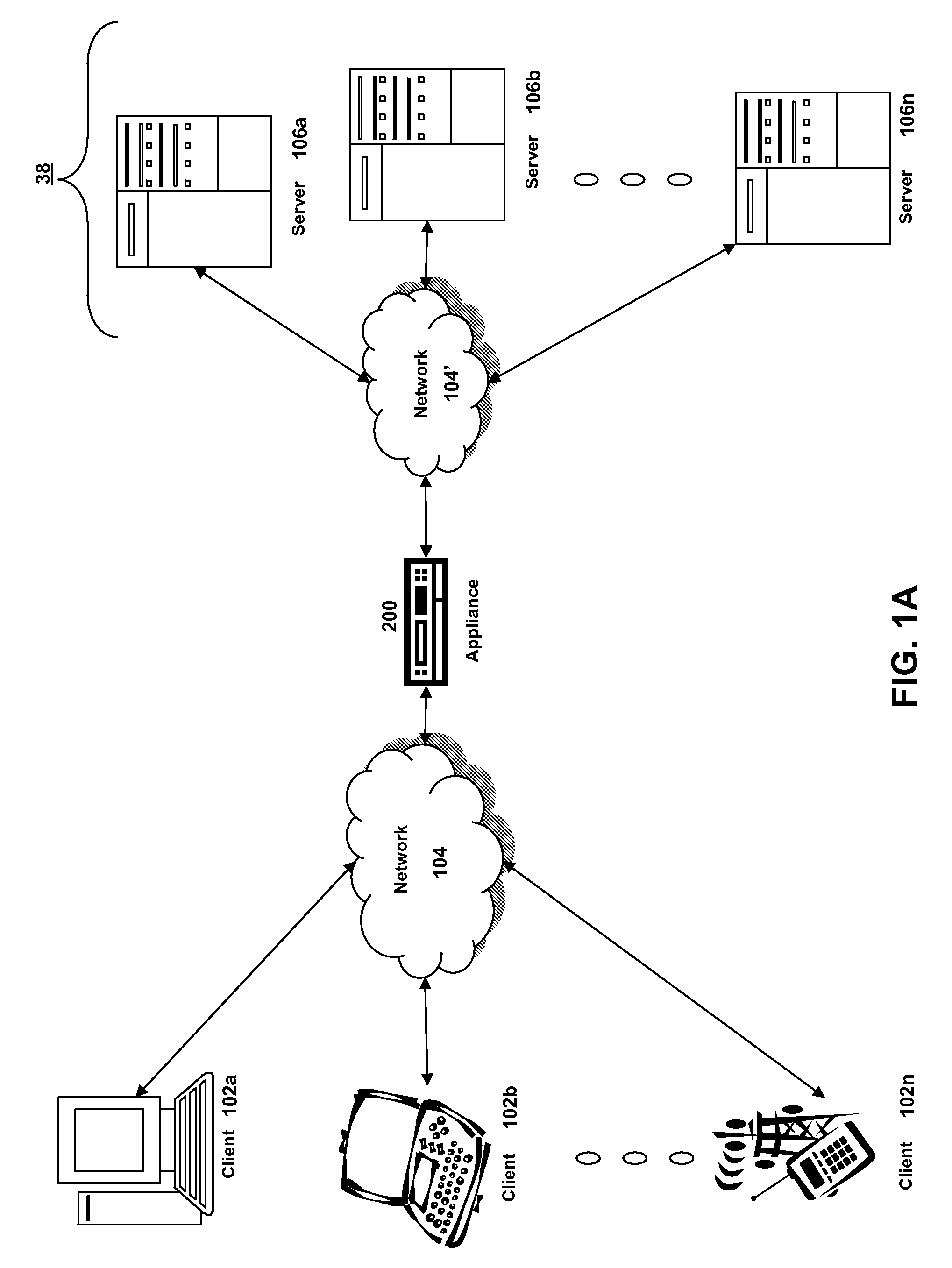
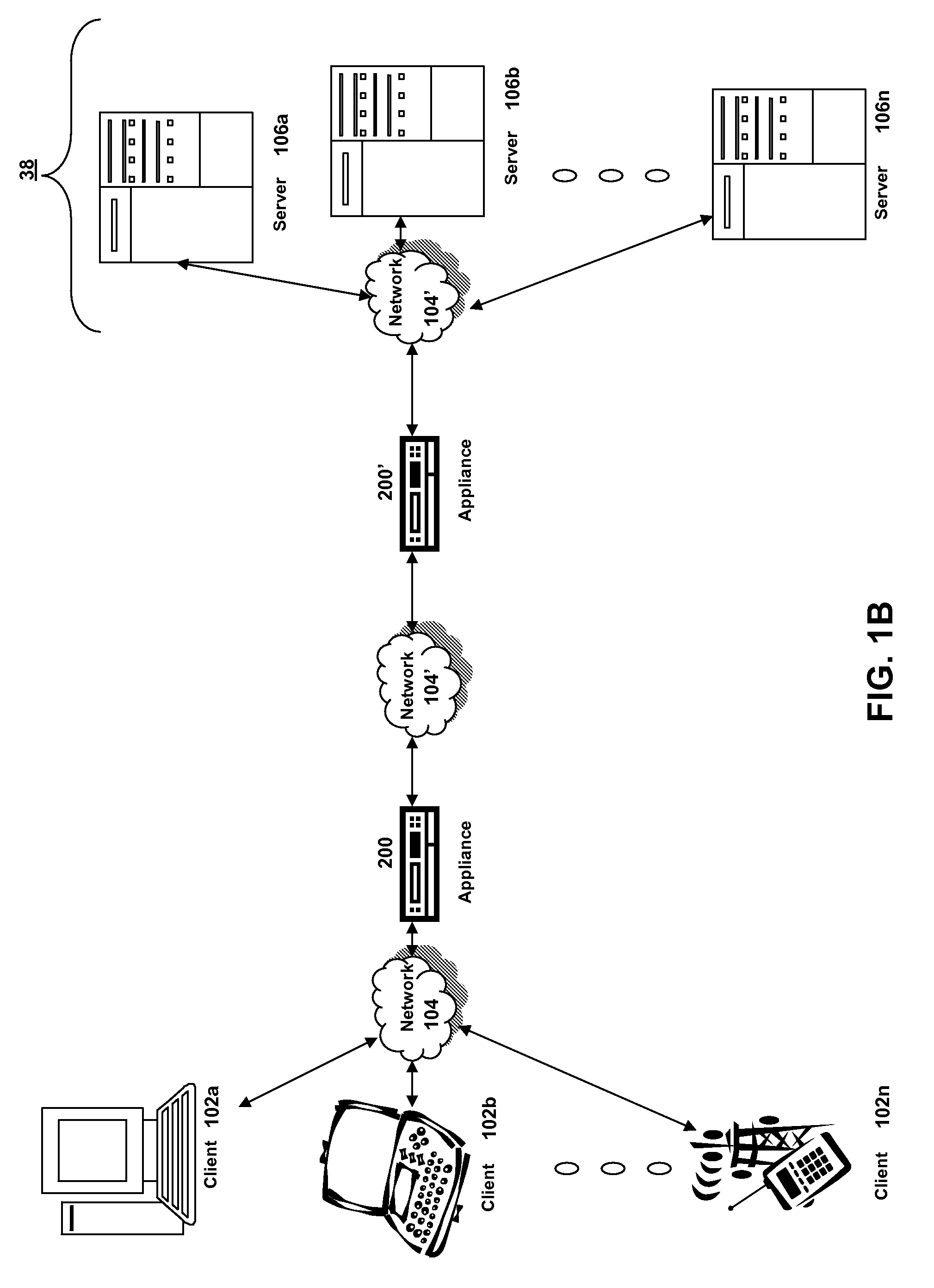
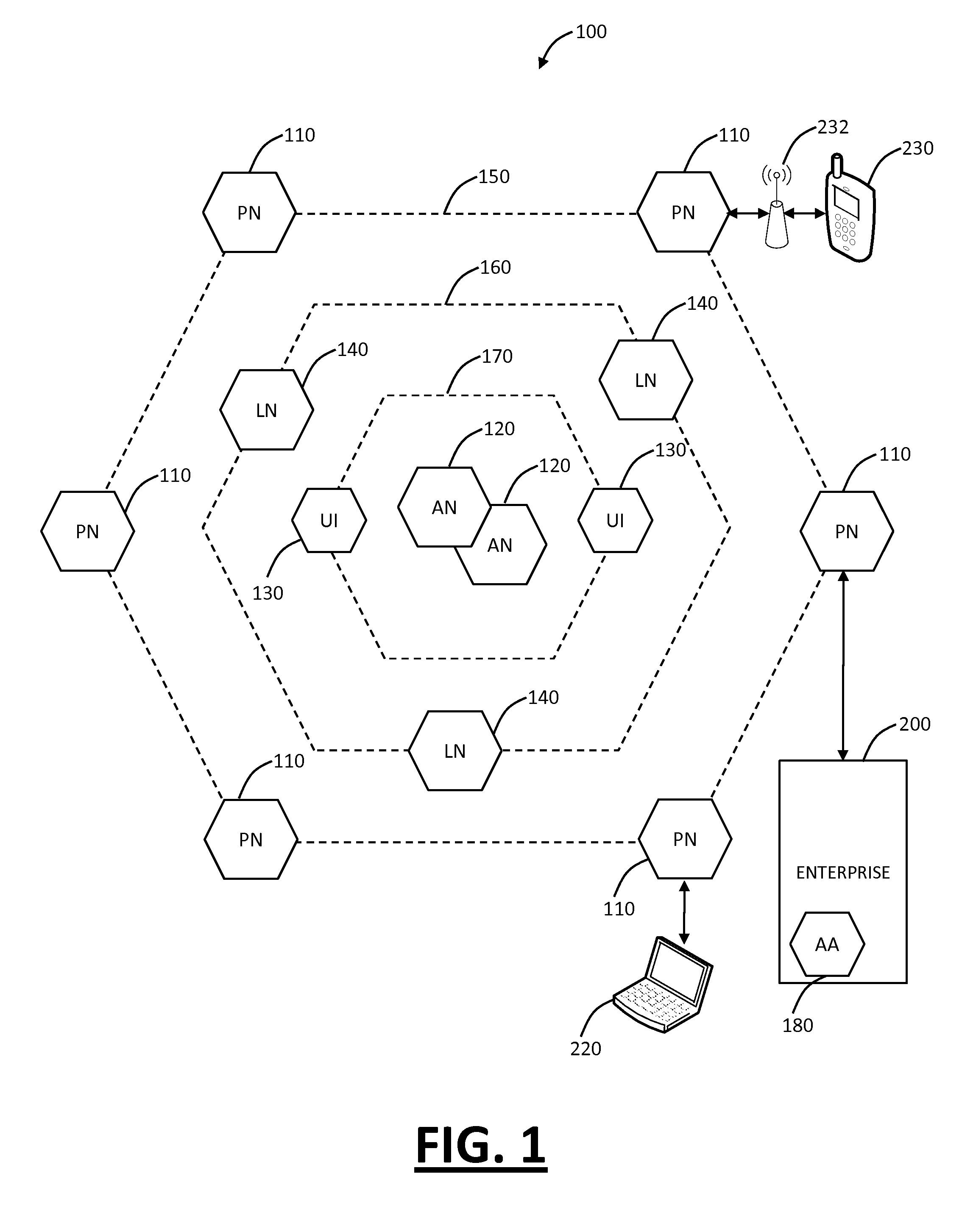
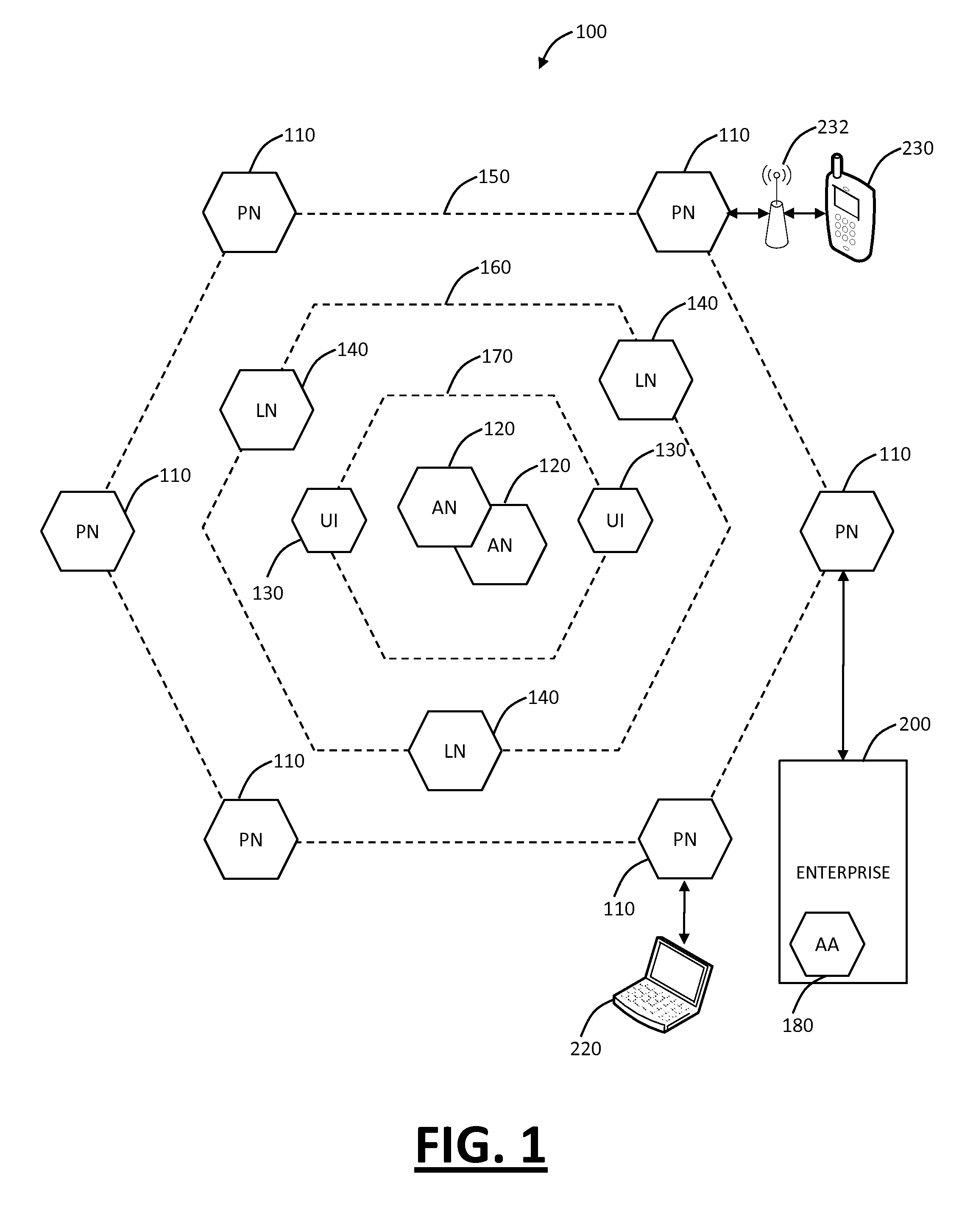
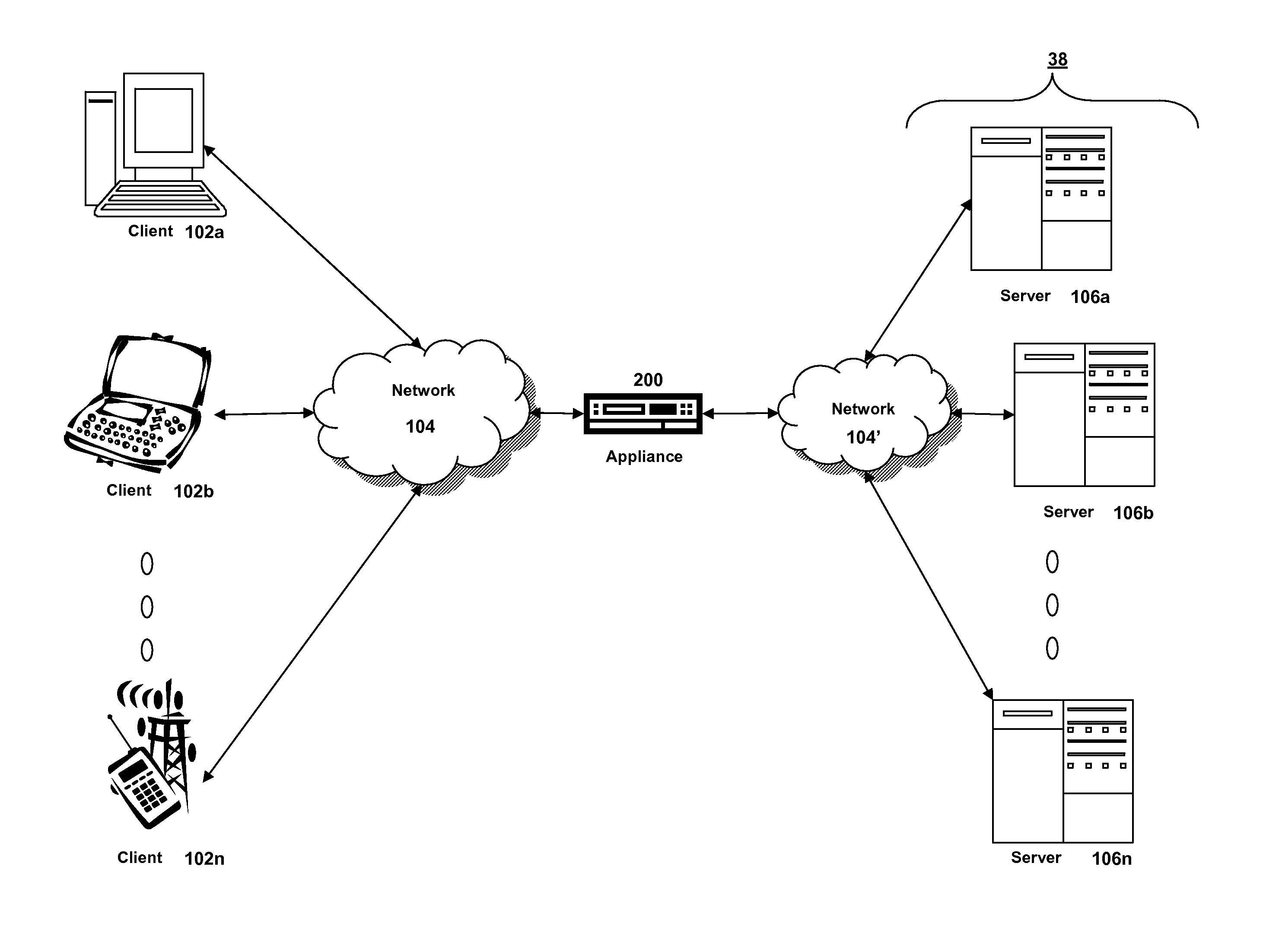
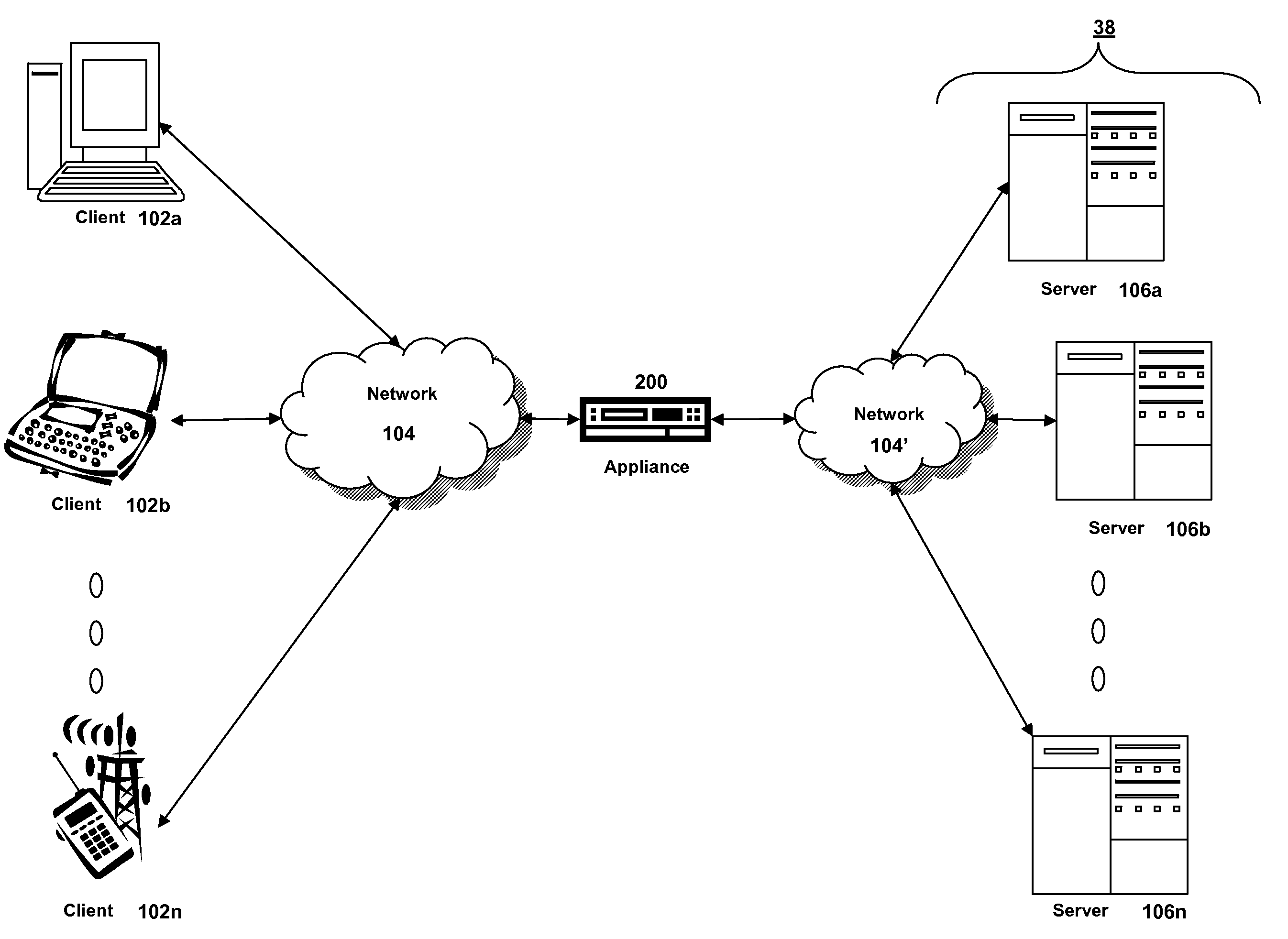
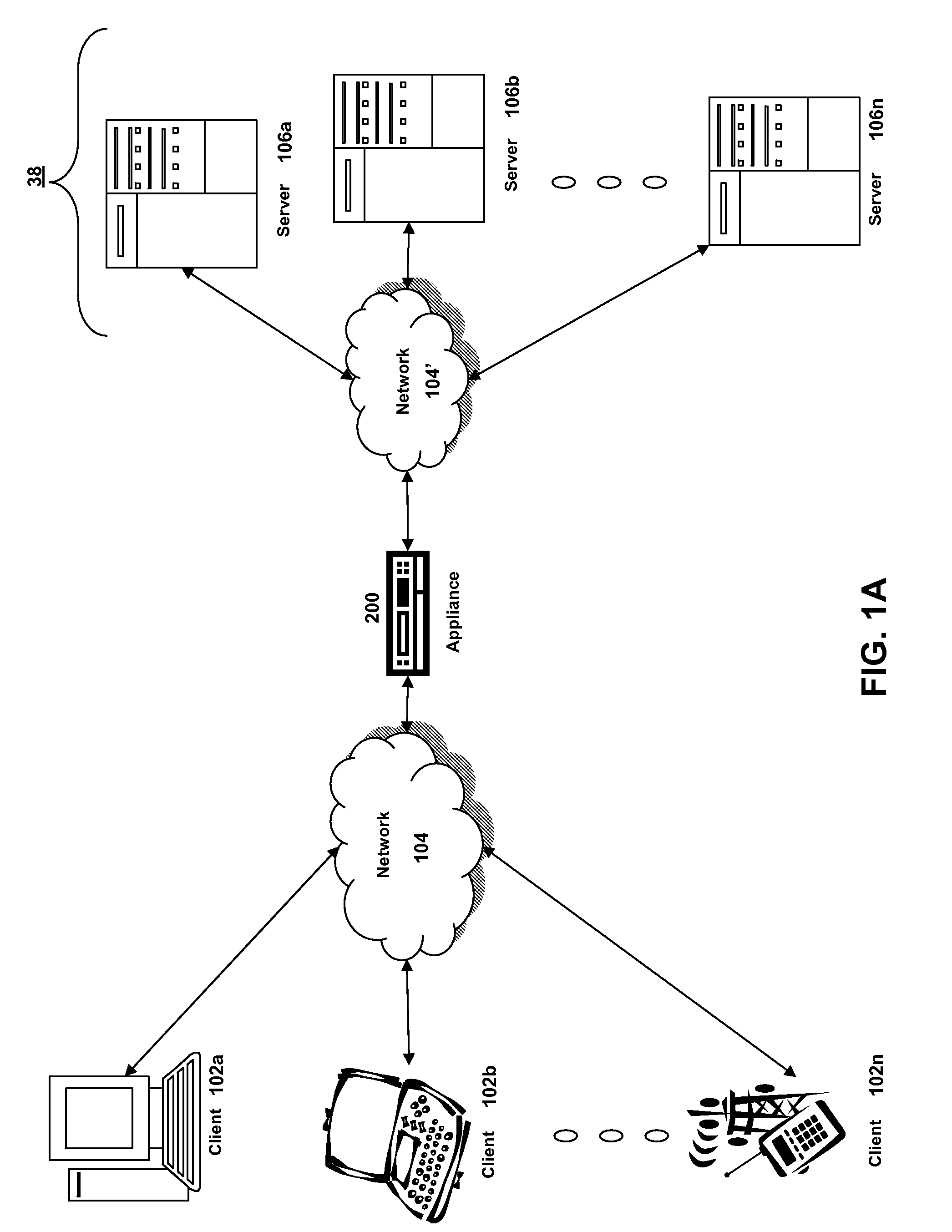
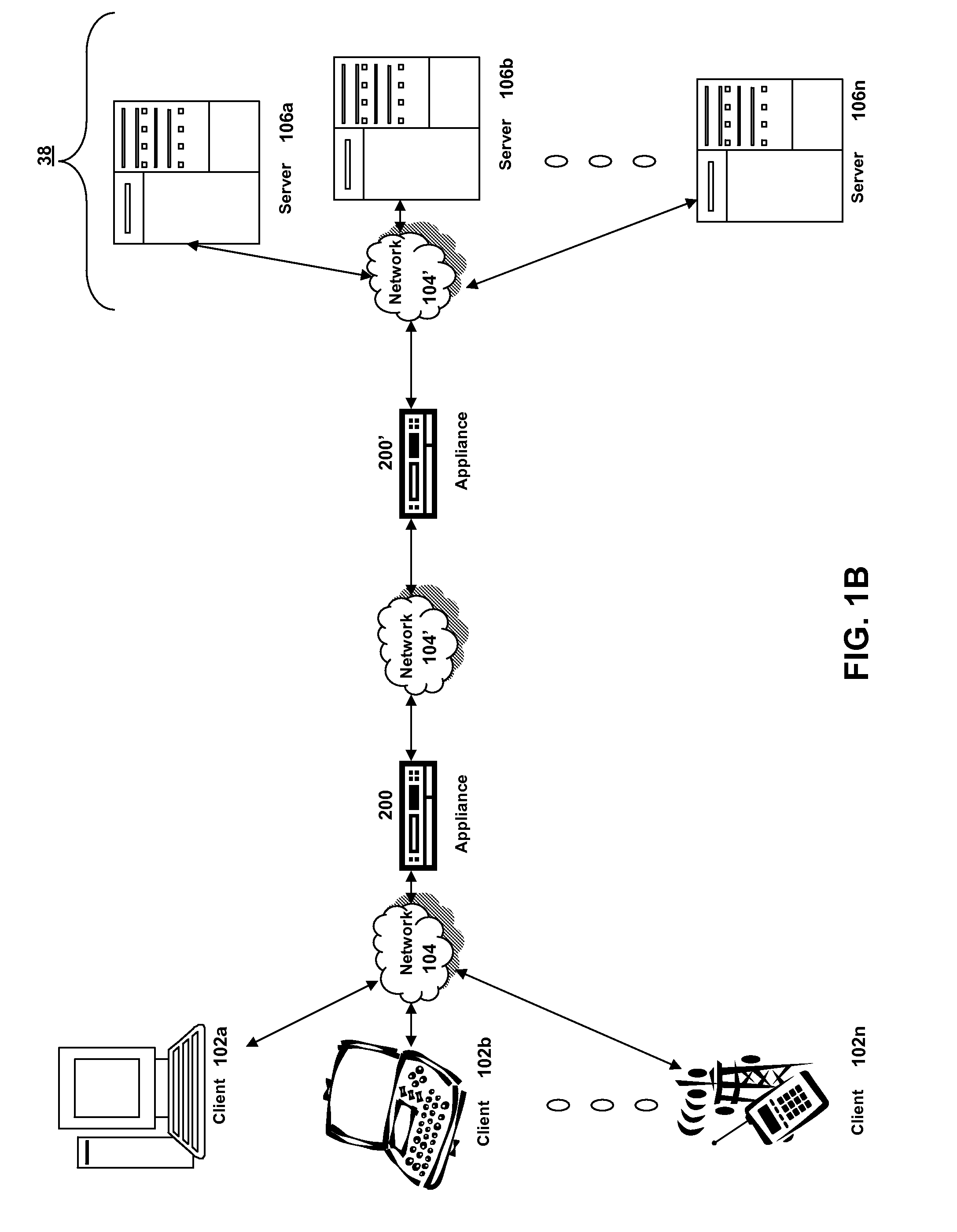
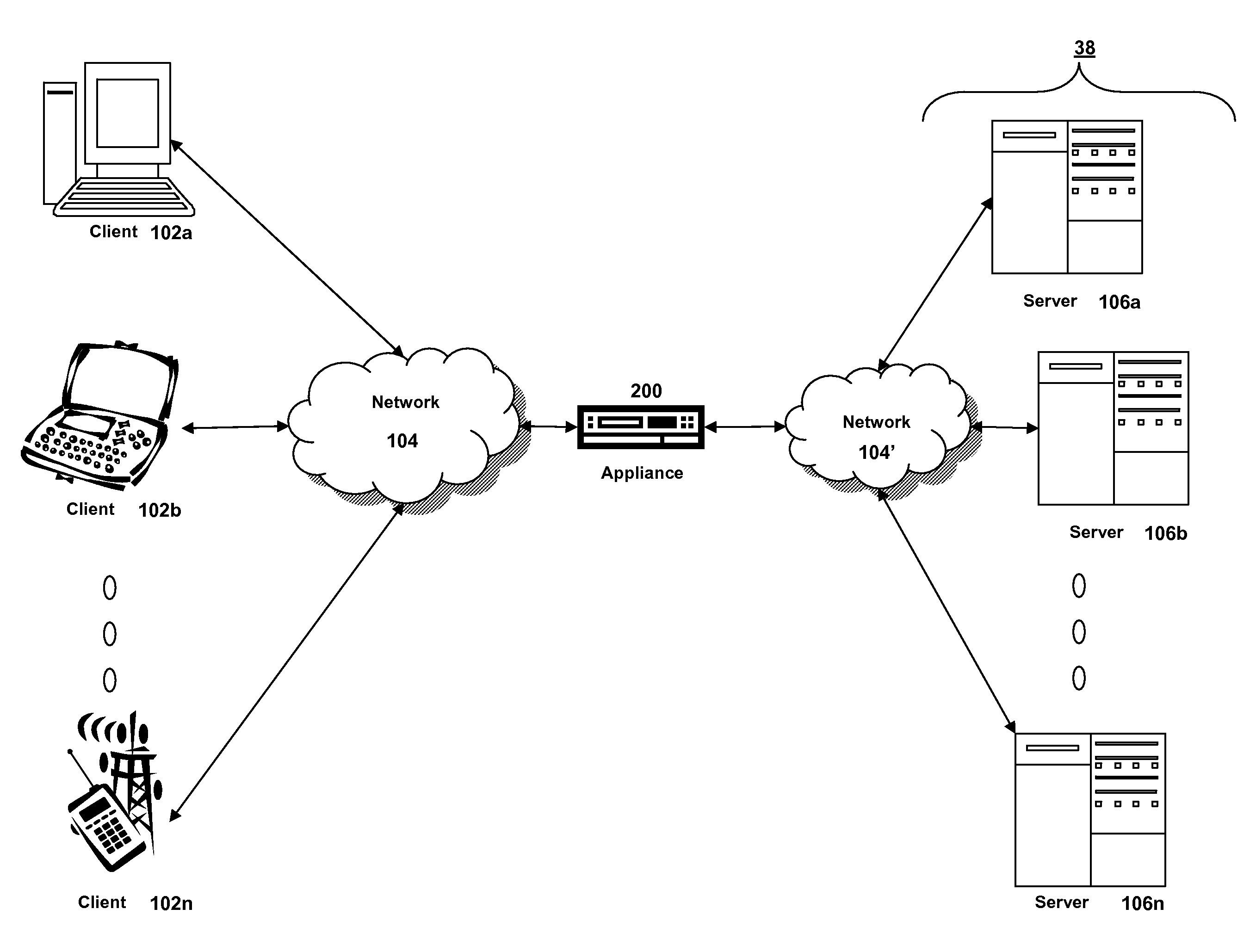
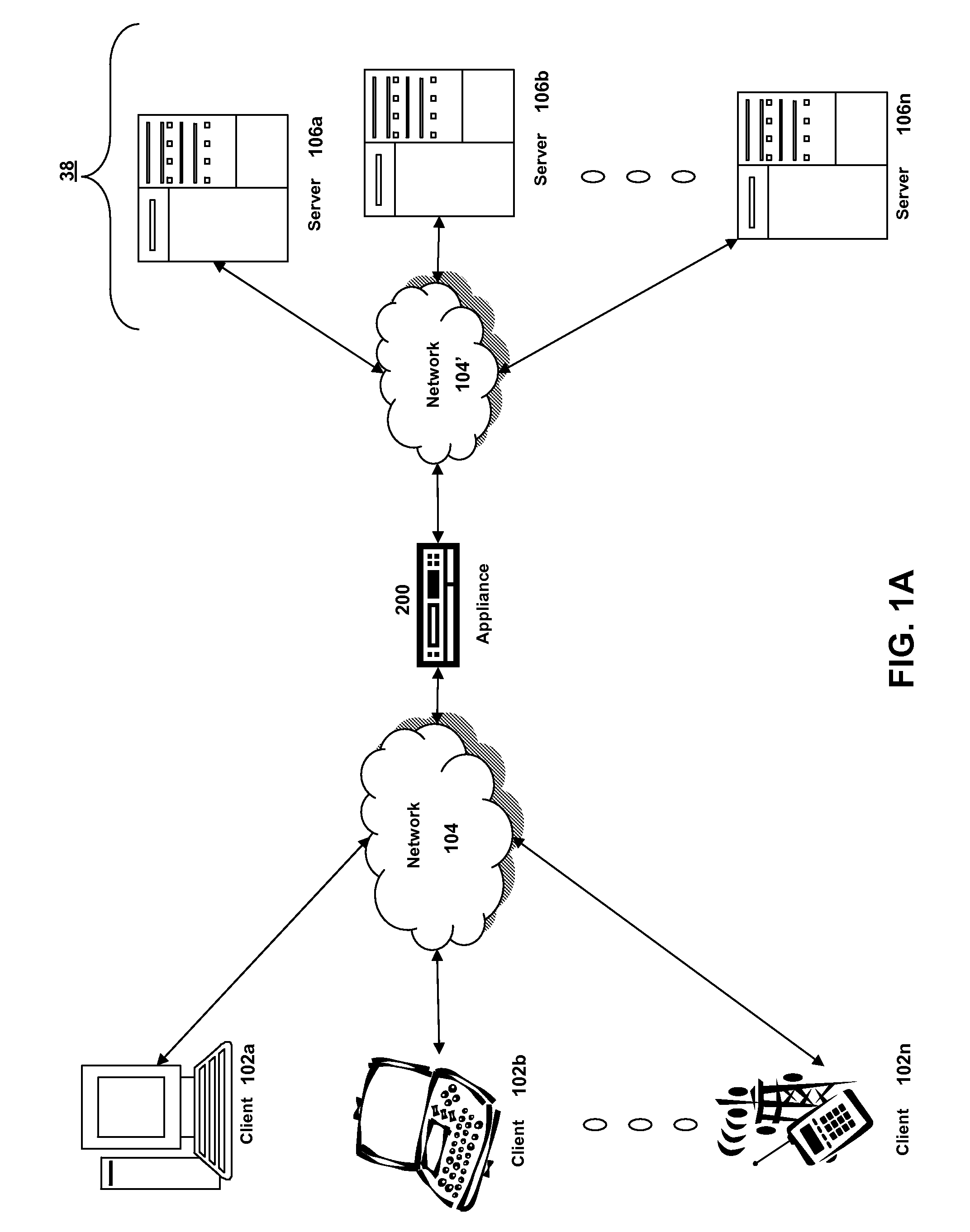
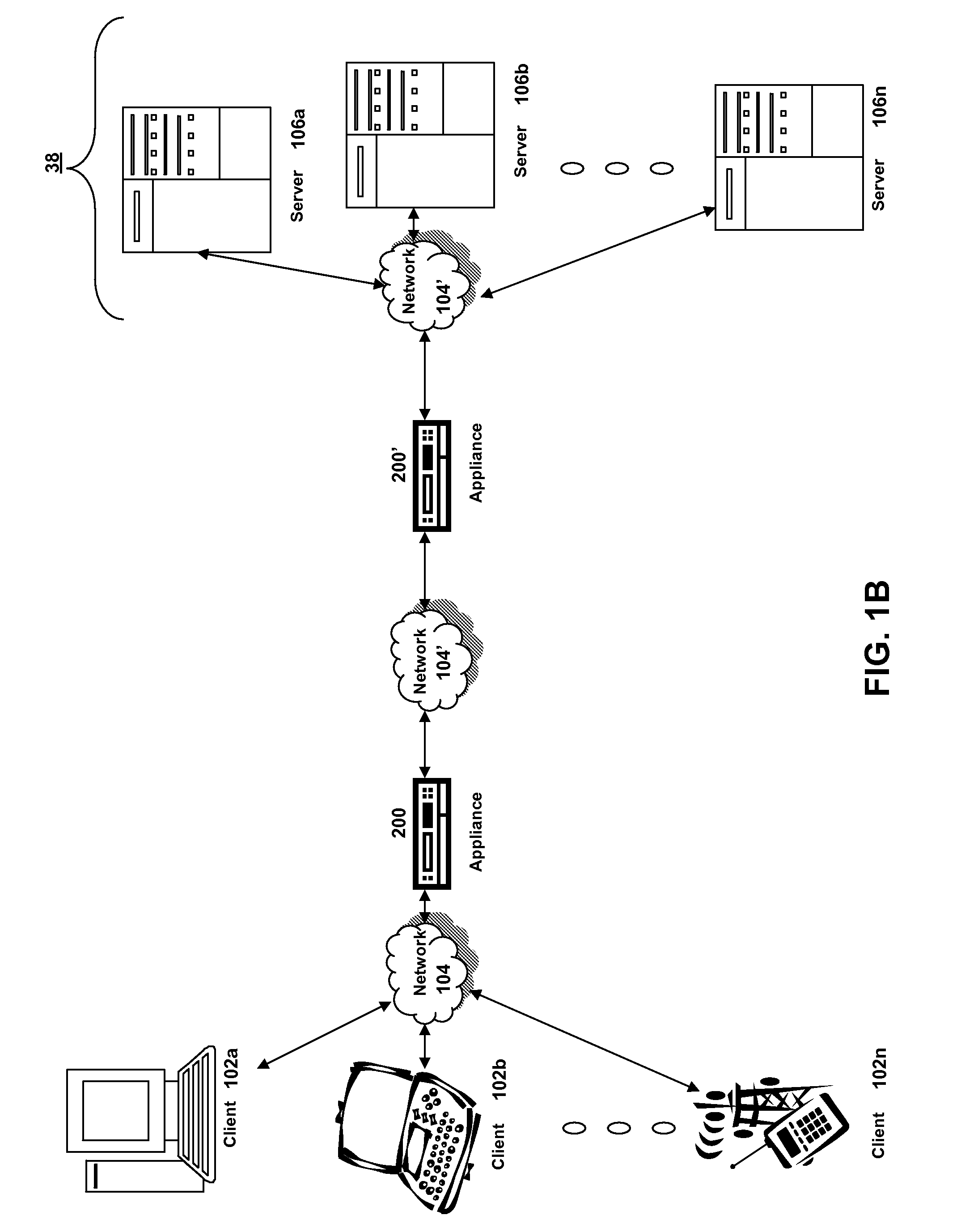
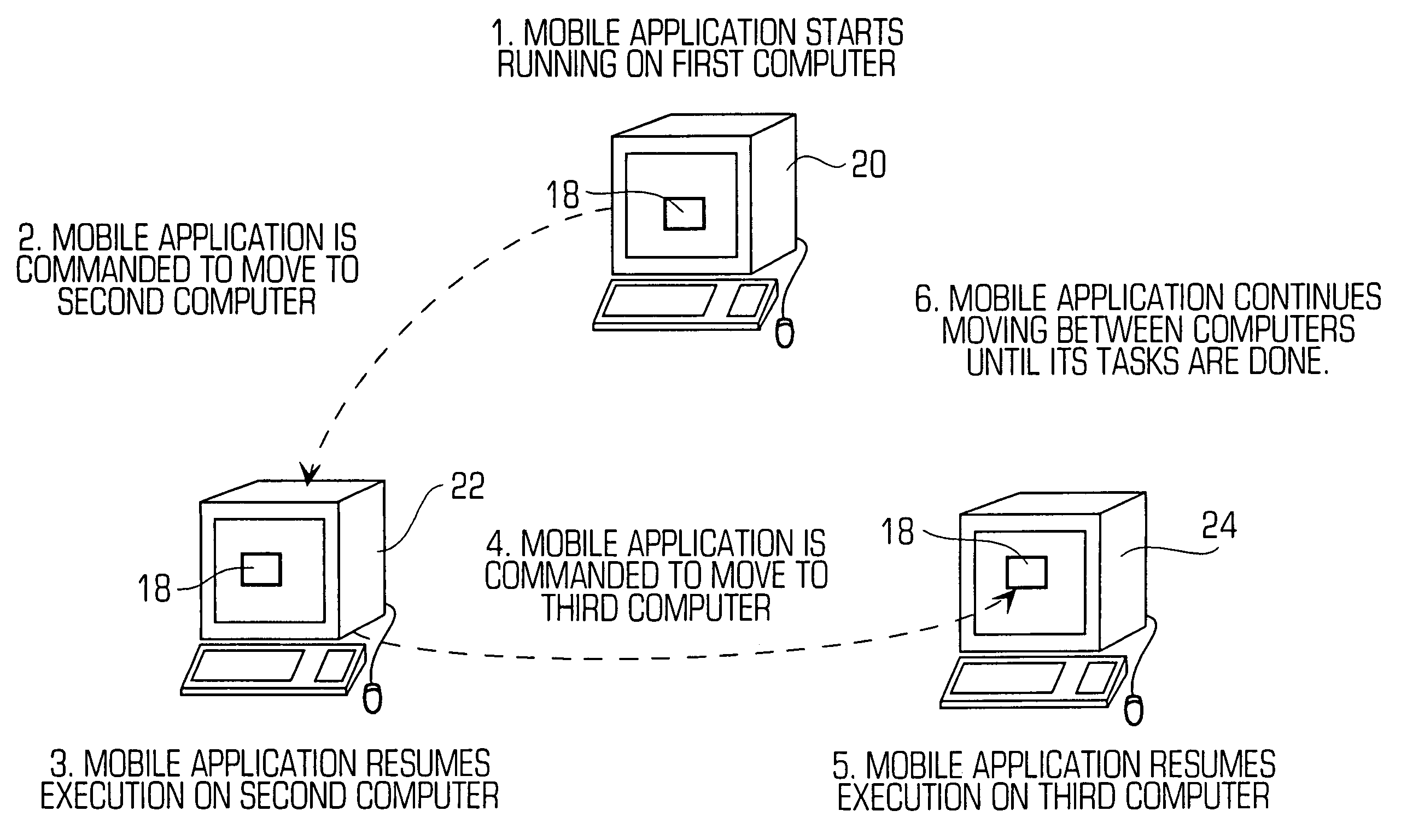
Systems and methods for providing stuctured policy expressions to represent unstructured data in a network appliance
ActiveUS20080225748A1Efficient configurationEfficient processingData switching by path configurationTraffic capacityData stream
Owner:CITRIX SYST INC
Systems and methods for mobile application security classification and enforcement
ActiveUS20110167474A1Avoid forwardingMemory loss protectionError detection/correctionUser deviceThe Internet
The present disclosure provides systems and methods for mobile application security classification and enforcement. In particular, the present invention includes a method, a mobile device, and a distributed security system (e.g., a “cloud”) that is utilized to enforce security on mobile devices communicatively coupled to external networks (i.e., the Internet). Advantageously, the present invention is platform independent allowing it to operate with any current or emerging mobile device. Specifically, preventing malicious applications from running on an end user's mobile device is challenging with potentially millions of applications and billions of user devices; the only effective way to enforce application security is through the network that applications use to communicate.
Owner:ZSCALER INC
Systems and methods for mobile application security classification and enforcement
The present disclosure provides systems and methods for mobile application security classification and enforcement. In particular, the present invention includes a method, a mobile device, and a distributed security system (e.g., a “cloud”) that is utilized to enforce security on mobile devices communicatively coupled to external networks (i.e., the Internet). Advantageously, the present invention is platform independent allowing it to operate with any current or emerging mobile device. Specifically, preventing malicious applications from running on an end user's mobile device is challenging with potentially millions of applications and billions of user devices; the only effective way to enforce application security is through the network that applications use to communicate.
Owner:ZSCALER INC
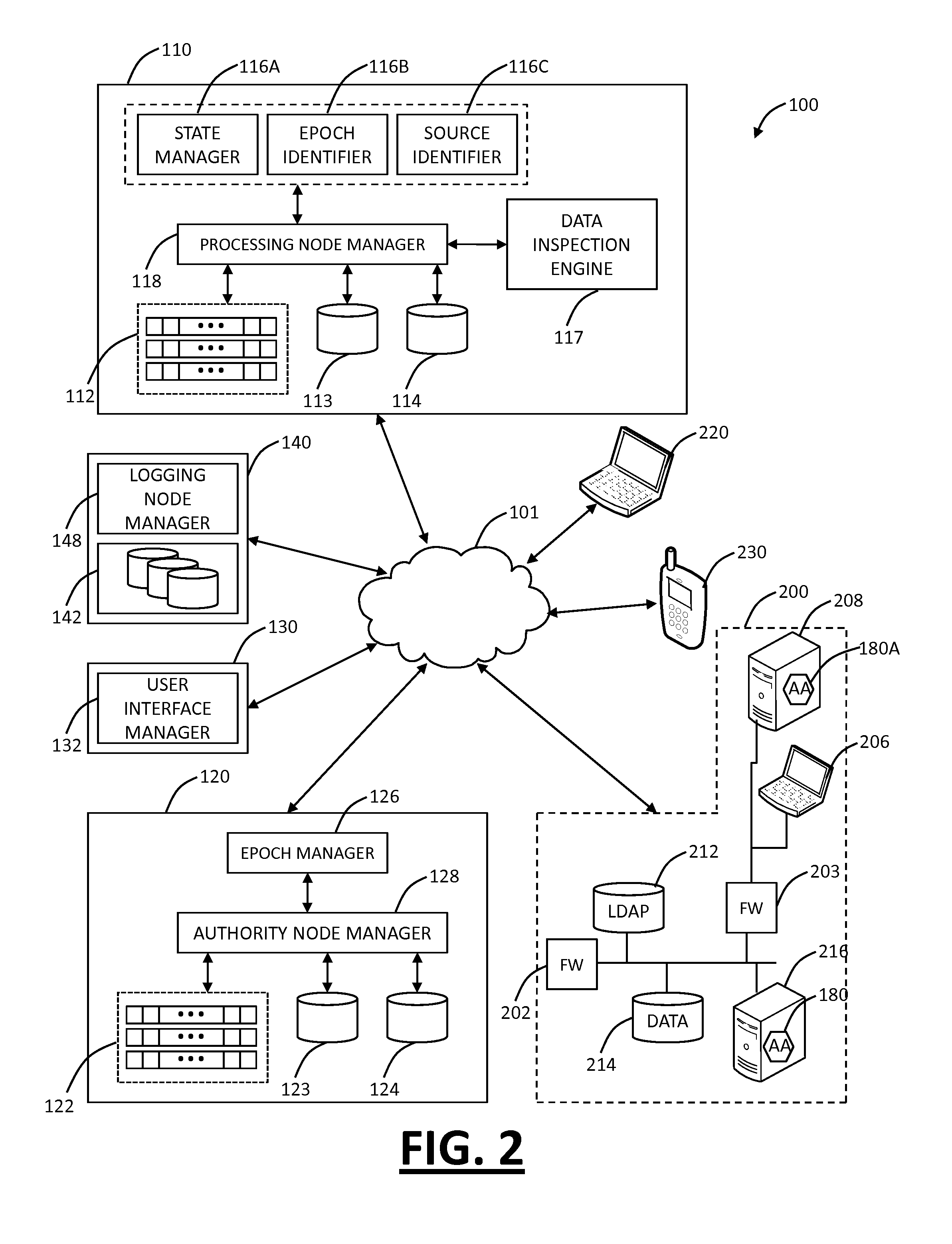
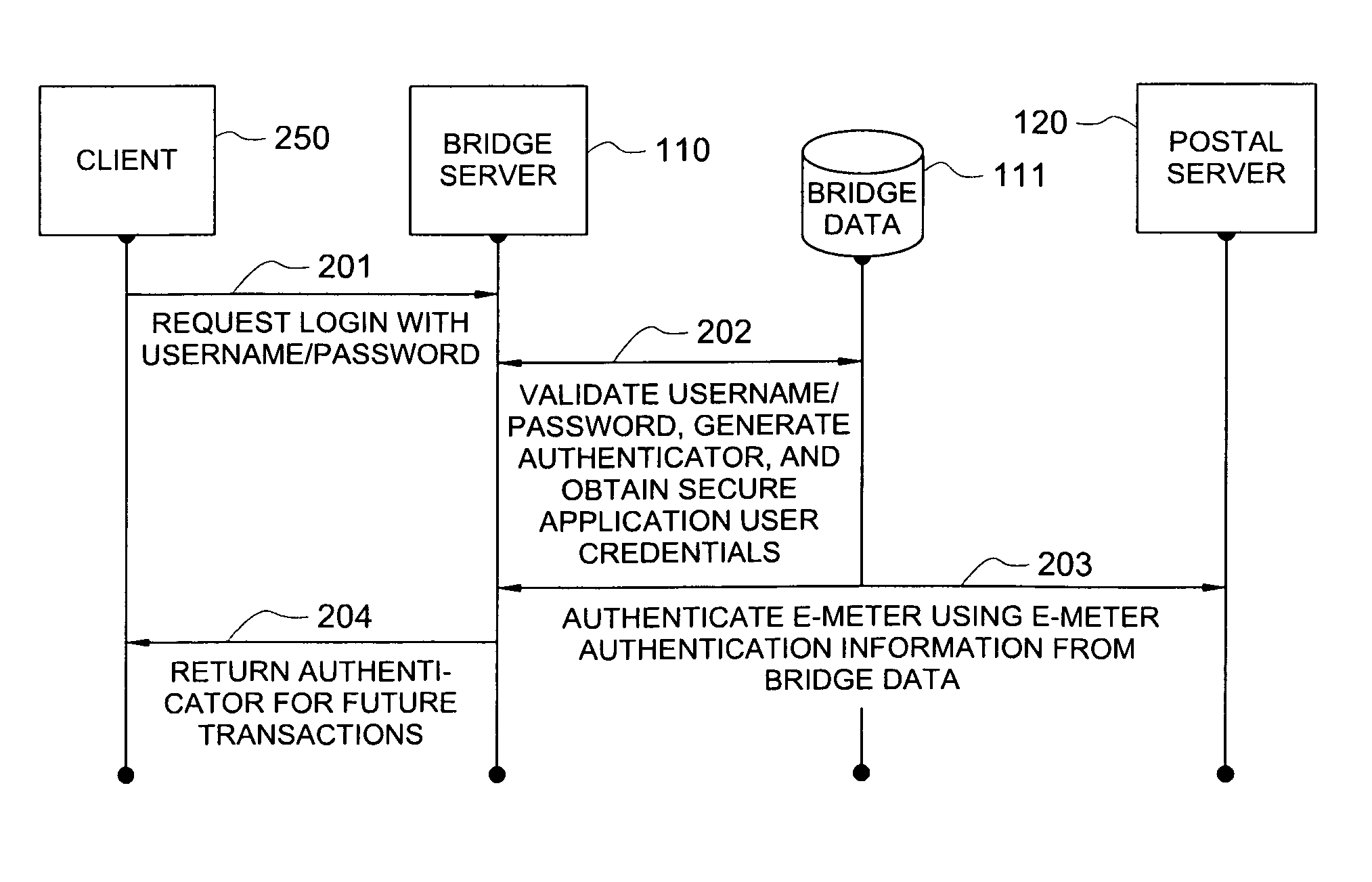
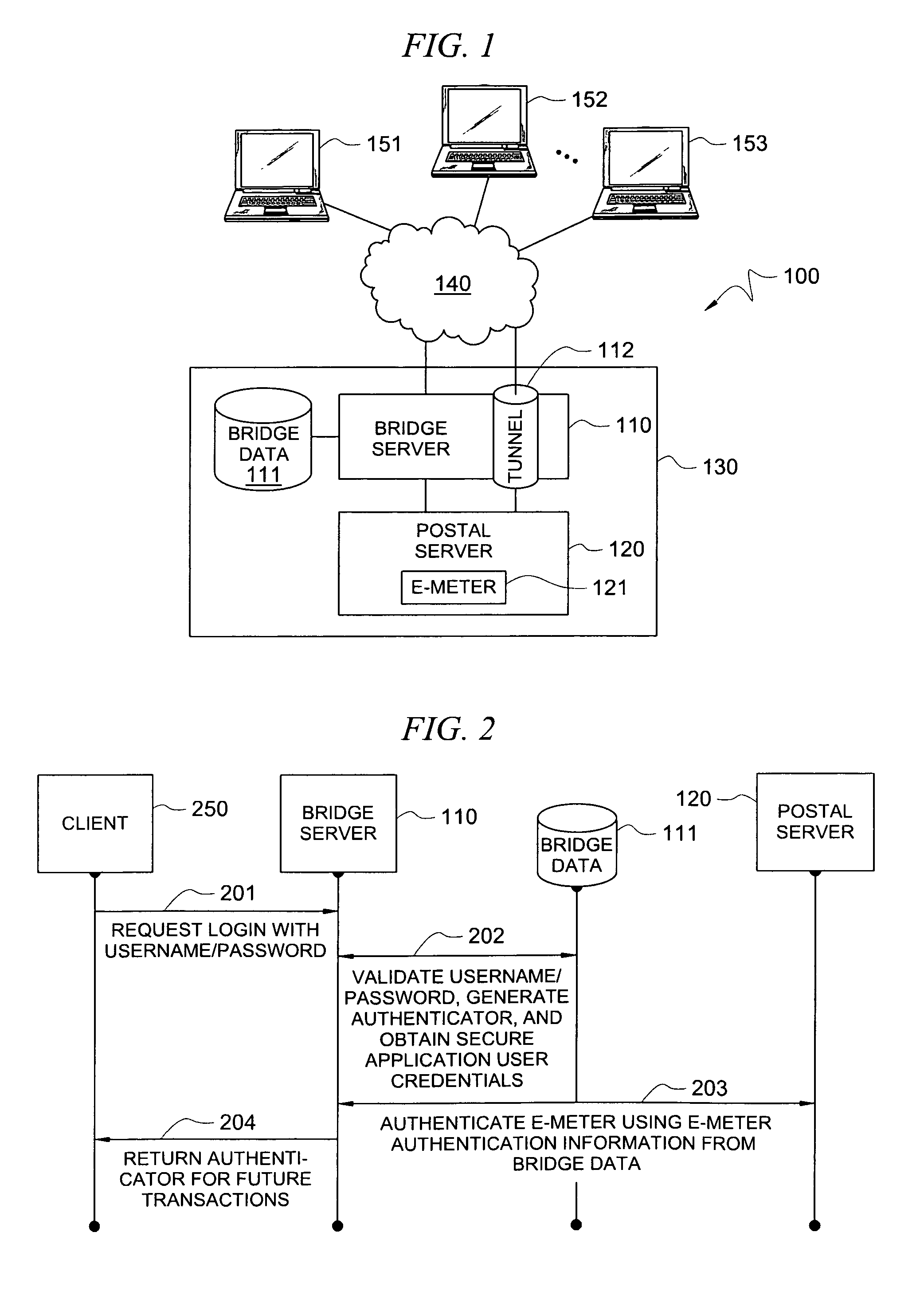
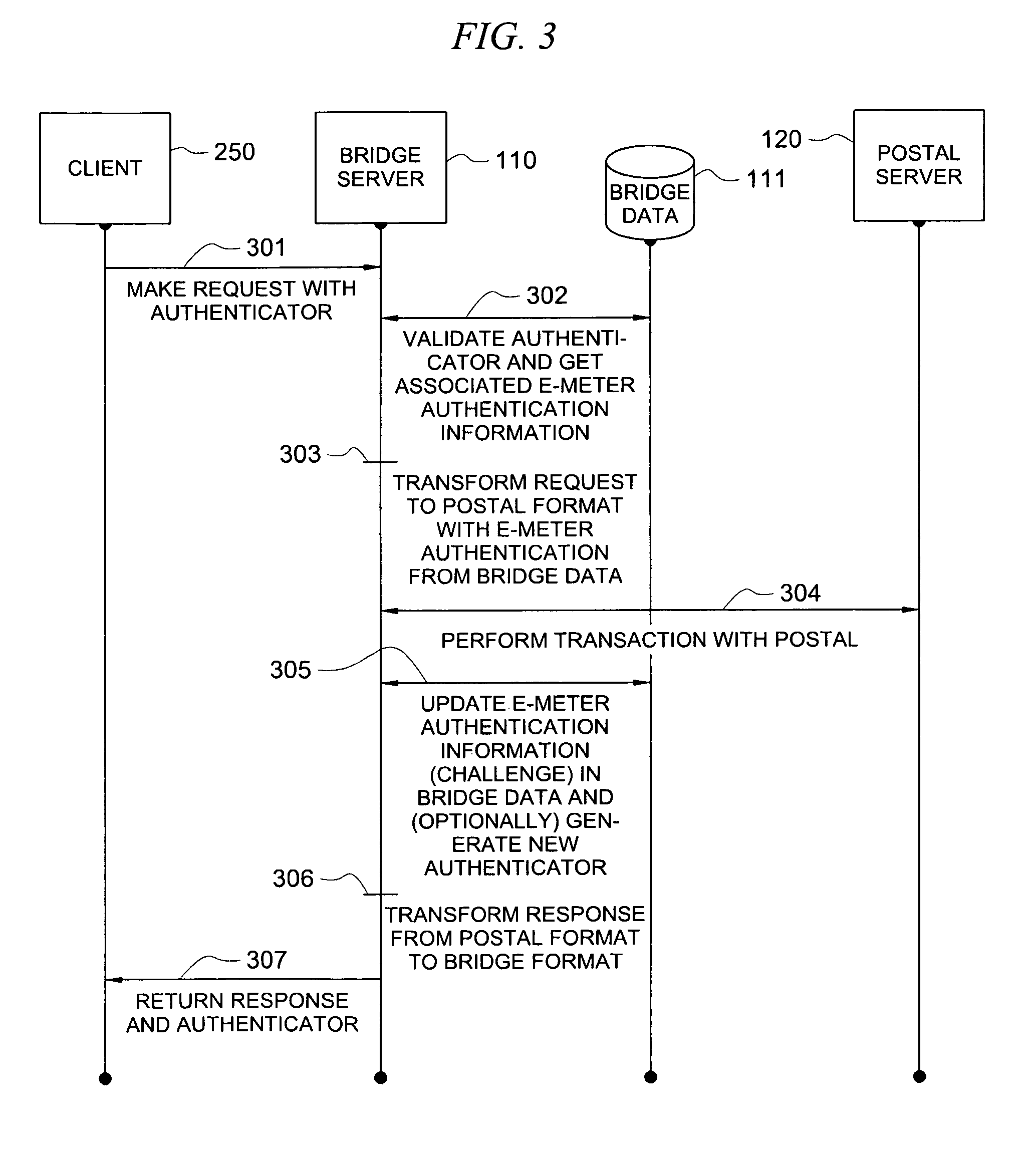
Secure application bridge server
ActiveUS8046823B1Easy to implementConvenient to accommodateDigital data processing detailsComputer security arrangementsApplication serverCryptographic protocol
Systems and methods are provided which implement a bridge server to provide user access to one or more secure applications. A bridge server of embodiments is disposed between a user and a secure application and invokes bridge server security protocols with respect to the user and secure application security protocols with respect to the secure application. In operation according to embodiments, client applications will link into a bridge server, the user will be authenticated by the bridge server, and a valid user will be correlated to an account of the secure application by the bridge server. Bridge servers of embodiments facilitate providing features with respect to secure application user access unavailable using the secure application security protocols.
Owner:AUCTANE INC
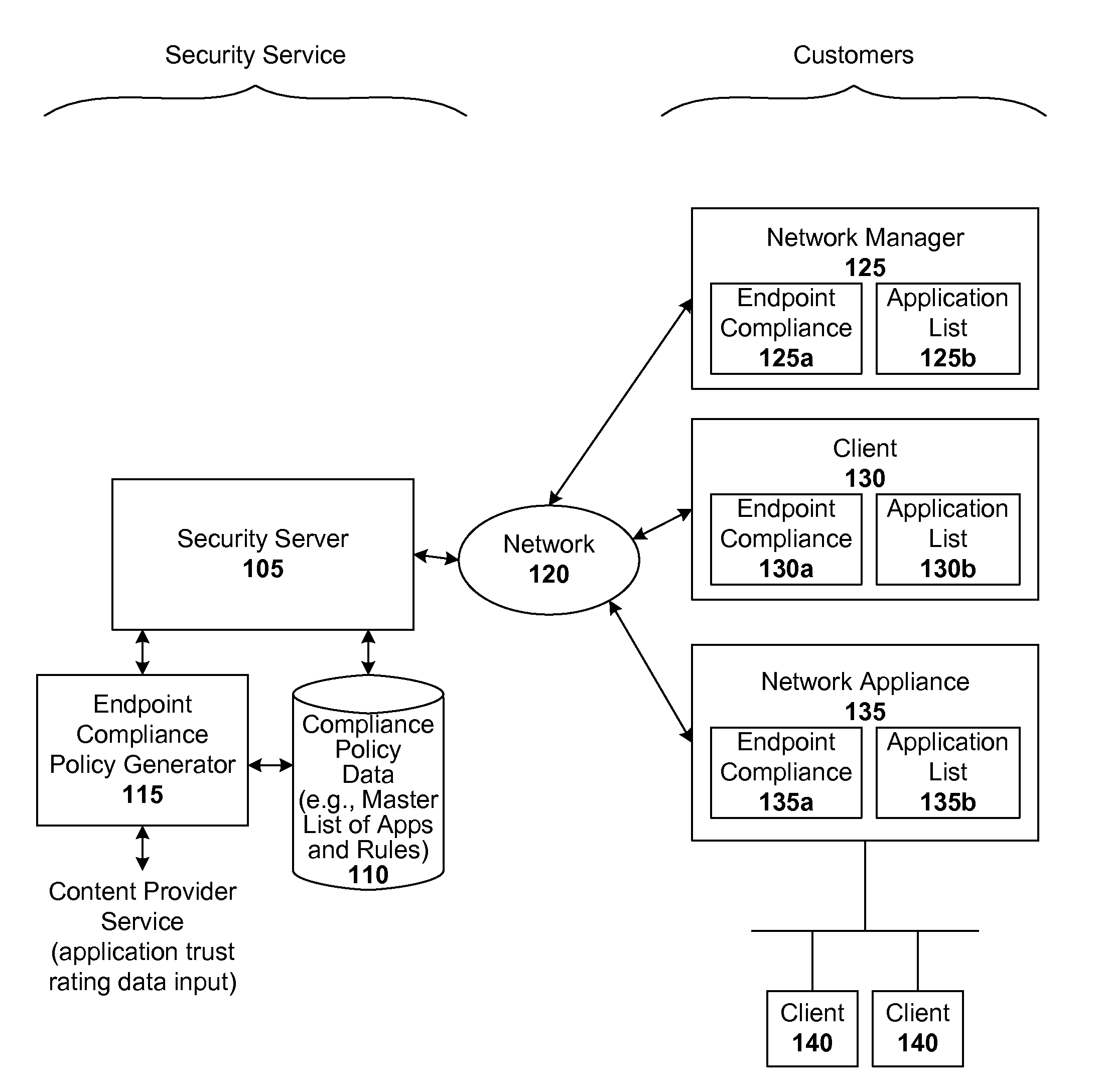
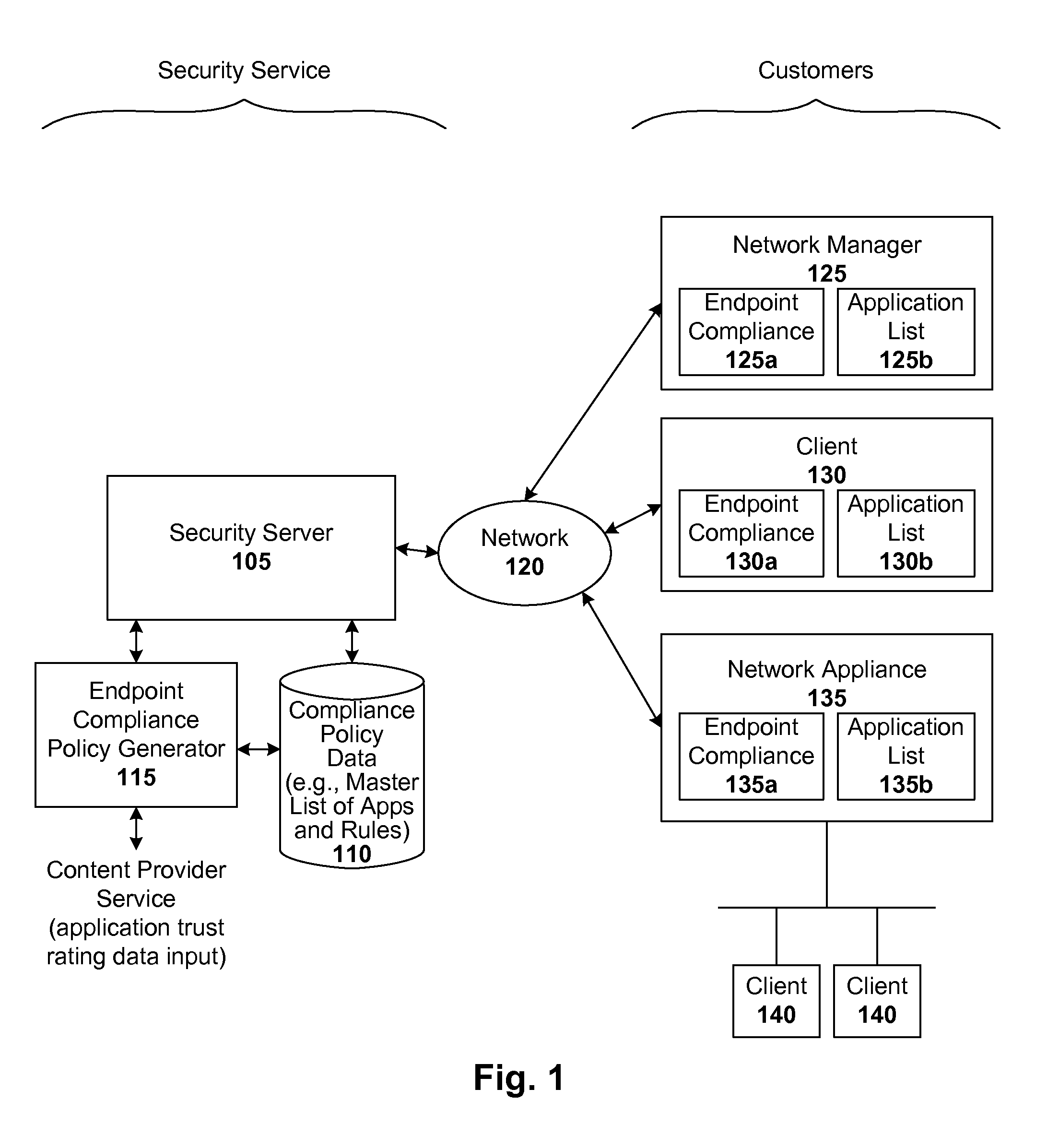
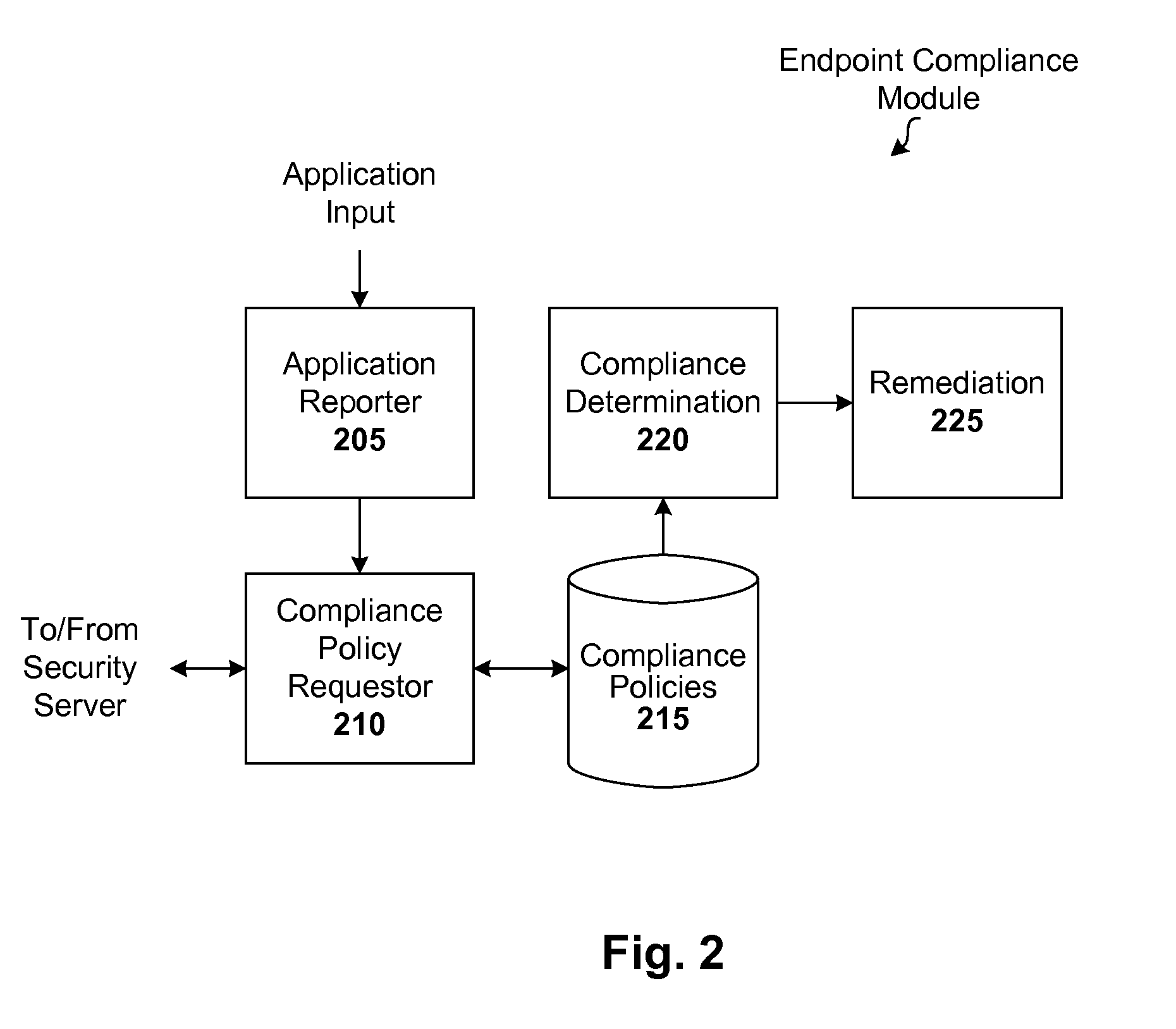
Endpoint management using trust rating data
ActiveUS8239915B1Digital data processing detailsComputer security arrangementsApplication softwareApplication security
Techniques are disclosed for implementing dynamic endpoint management. In accordance with one embodiment, whenever an endpoint joins a managed network for the first time, or rejoins that network, a local security module submits a list of applications (e.g., all or incremental) to a security server. The server validates the list and sends back a rule set (e.g., allow / block rules and / or required application security settings) for those applications. If the server has no information for a given application, it may further subscribe to content from a content provider or service. When the server is queried regarding an unknown application, the server sends a query to the service provider to obtain a trust rating for that unknown application. The trust rating can then be used to generate a rule set for the unknown application. Functionality can be shifted from server to client, and vice-versa if so desired.
Owner:CA TECH INC
Systems and methods for configuring policy bank invocations
ActiveUS20100095018A1Efficient configurationEfficient processingError preventionTransmission systemsTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Systems and methods for managing application security profiles
ActiveUS20080229381A1Efficient configurationEfficient processingMemory loss protectionError detection/correctionTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Systems and methods for configuring handling of undefined policy events
ActiveUS20080225753A1Efficient configurationEfficient processingDigital computer detailsData switching by path configurationTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Systems and methods for configuring flow control of policy expressions
ActiveUS20080225720A1Efficient configurationEfficient processingError preventionTransmission systemsTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
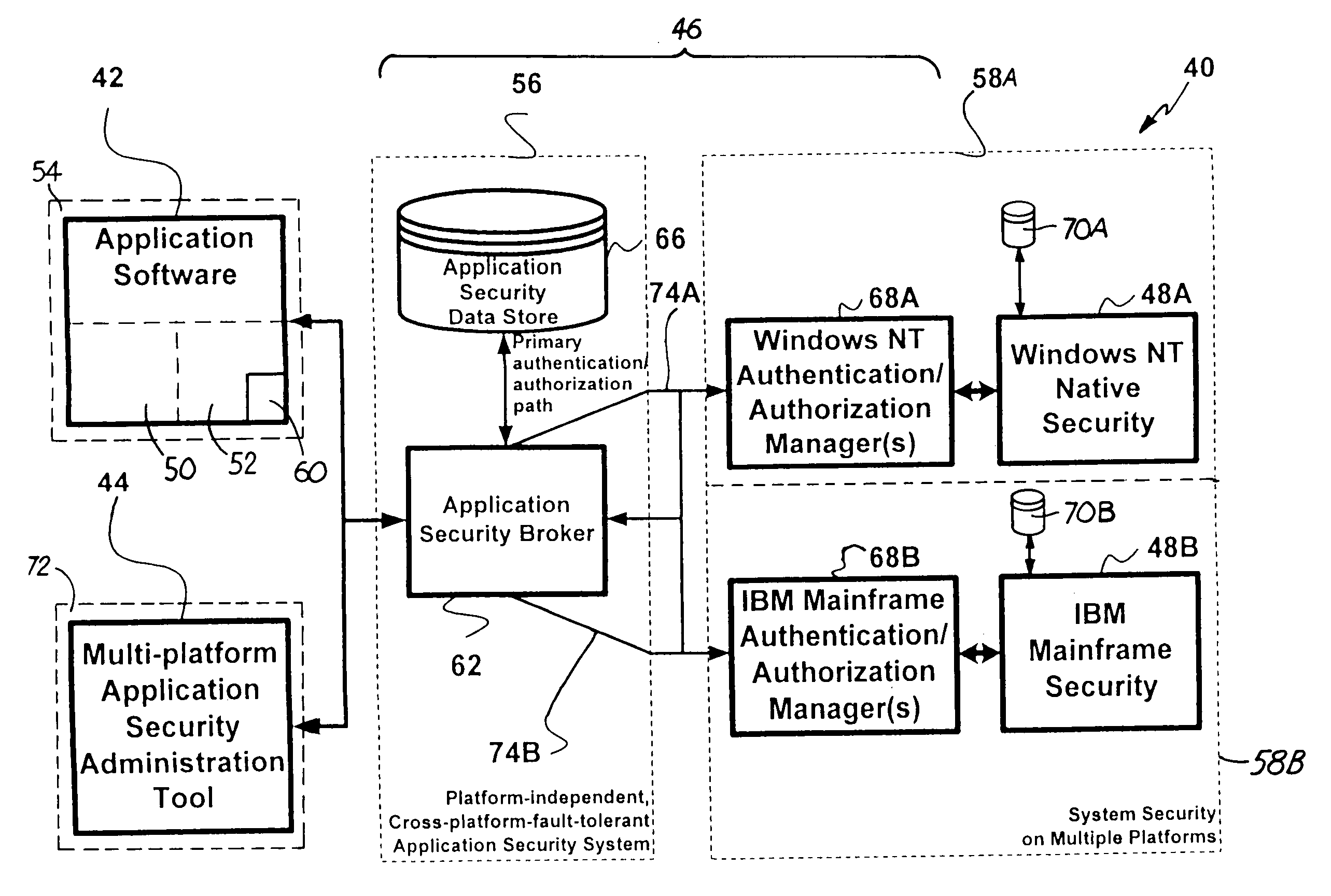
Computer security system
InactiveUS7131000B2Data processing applicationsDigital data processing detailsComputerized systemComputer security model
A computer system provides system-wide computer application security using role-based identifiers. The programmer identifies secured functions within a software application using a hierarchical identifier. The hierarchical identifiers are grouped together into privilege sets. The privilege sets and other hierarchical identifiers are grouped together into job functions, which are in turn grouped into larger subsets called user roles. These user roles are stored in a data store. User identifiers are created. Each user identifier is linked to one user role in the data store. A surrogate identifier is created to correspond to each user role and is stored in the data store. The surrogate identifiers are not disclosed to the users. A user is given permission to access secured functions within an application by retrieving a surrogate identifier from the data store, which shares the same user role as the user. Access rights are determined using the surrogate identifier to validate permissions on a security provider.
Owner:JOLLY SEVEN SERIES 70 OF ALLIED SECURITY TRUST I
Methods and systems for network-based management of application security
ActiveUS20070043943A1Digital data processing detailsUnauthorized memory use protectionComputer accessApplication security
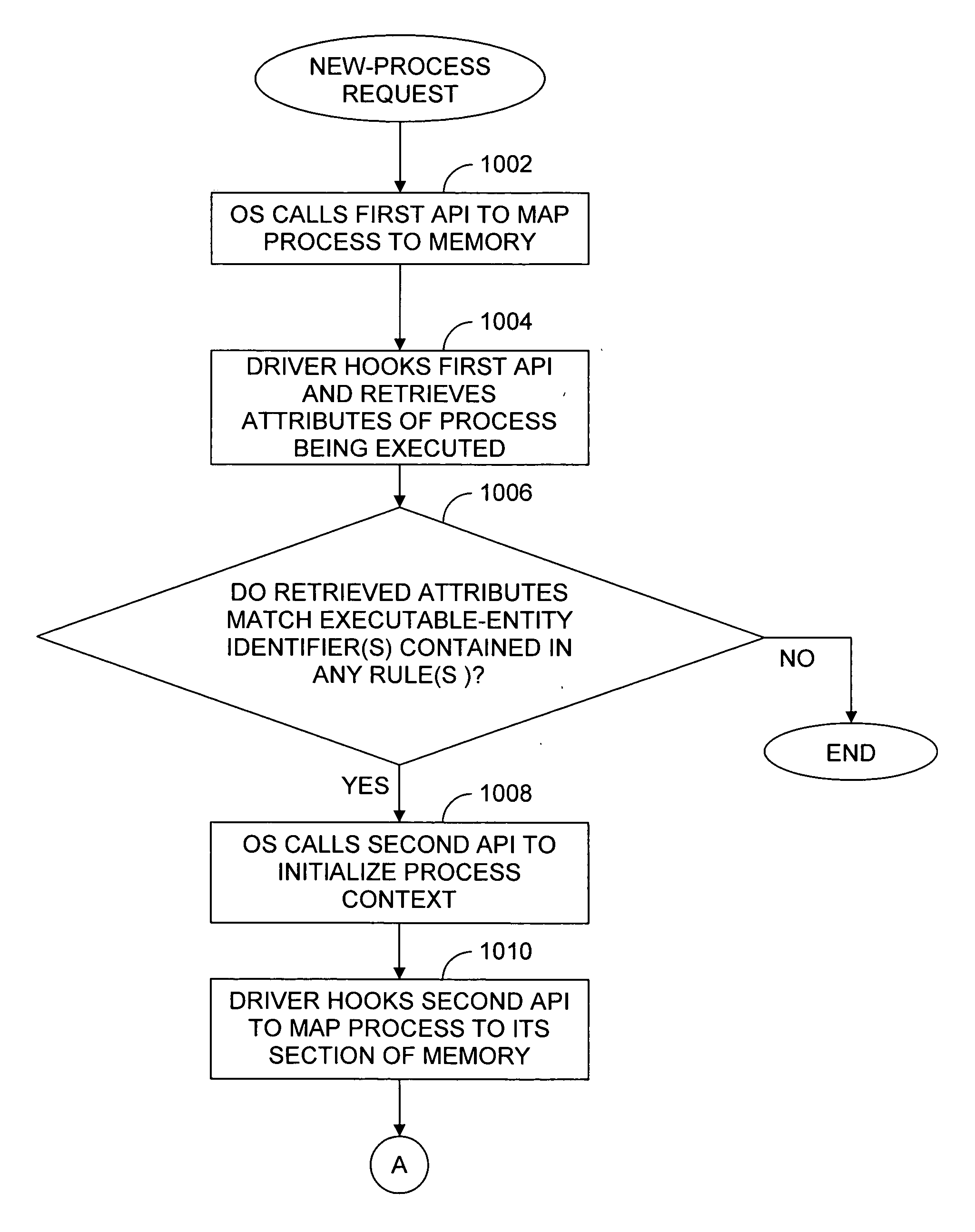
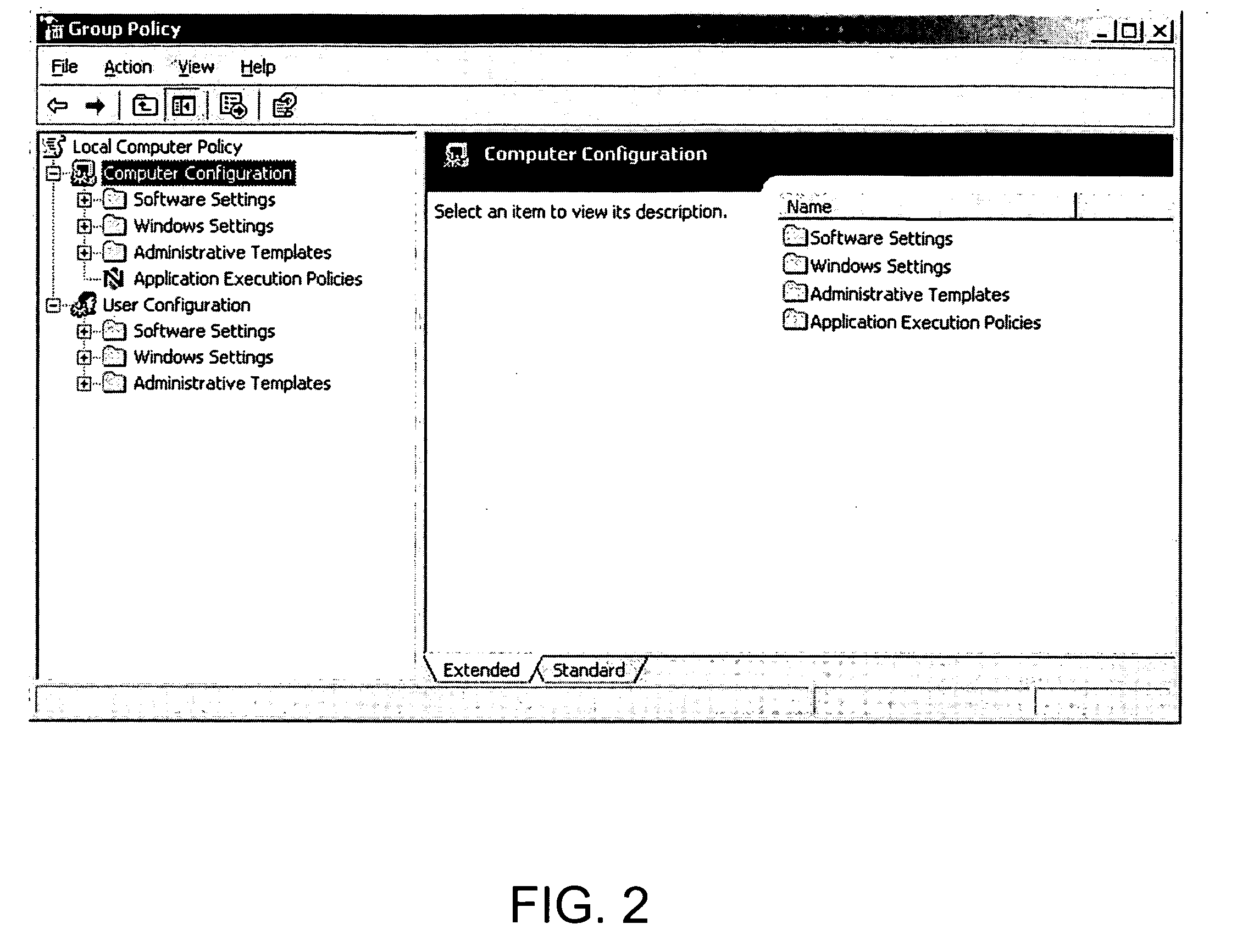
To control privileges and access to resources on a per-process basis, an administrator creates a rule that may be applied to modify a process's token. The rule includes an application-criterion set and changes to be made to the groups and / or privileges of a token. The rule is set as a policy within a group policy object (GPO), where a GPO is associated with one or more groups of computers. When a GPO containing a rule is applied to a computer, a driver installed on the computer accesses the rule(s) anytime a logged-on user executes a process. If the executed process satisfies the criterion set of a rule the changes contained within the rule are made to the process token, and the user has expanded and / or contracted access and / or privileges for only that process.
Owner:BEYONDTRUST SOFTWARE
Techniques for discovering and managing security of applications
Techniques for discovery and management of applications in a computing environment of an organization are disclosed. A security management system discovers use of applications within a computing environment to manage access to applications for minimizing security threats and risks in a computing environment of the organization. The security management system can obtain network data about network traffic to identify unique applications. The security management system can perform analysis and correlation, including use of one or more data sources, to determine information about an application. The system can compute a measure of security for an application (“an application risk score”) and a user (“a user risk score”). The score may be analyzed to determine a threat of security posed by the application based on use of the application. The security system can perform one or more instructions to configure access permitted by an application, whether access is denied or restricted.
Owner:ORACLE INT CORP
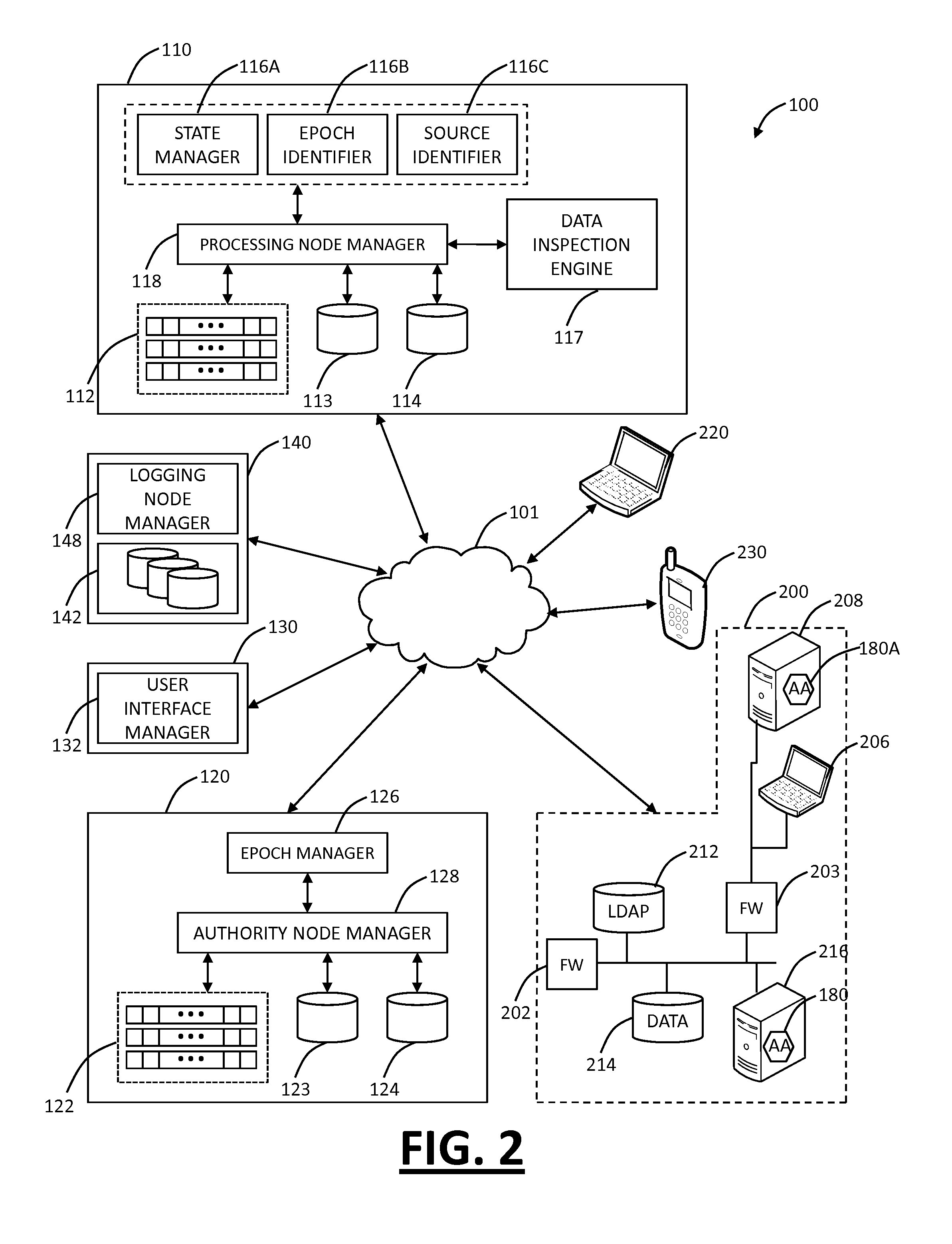
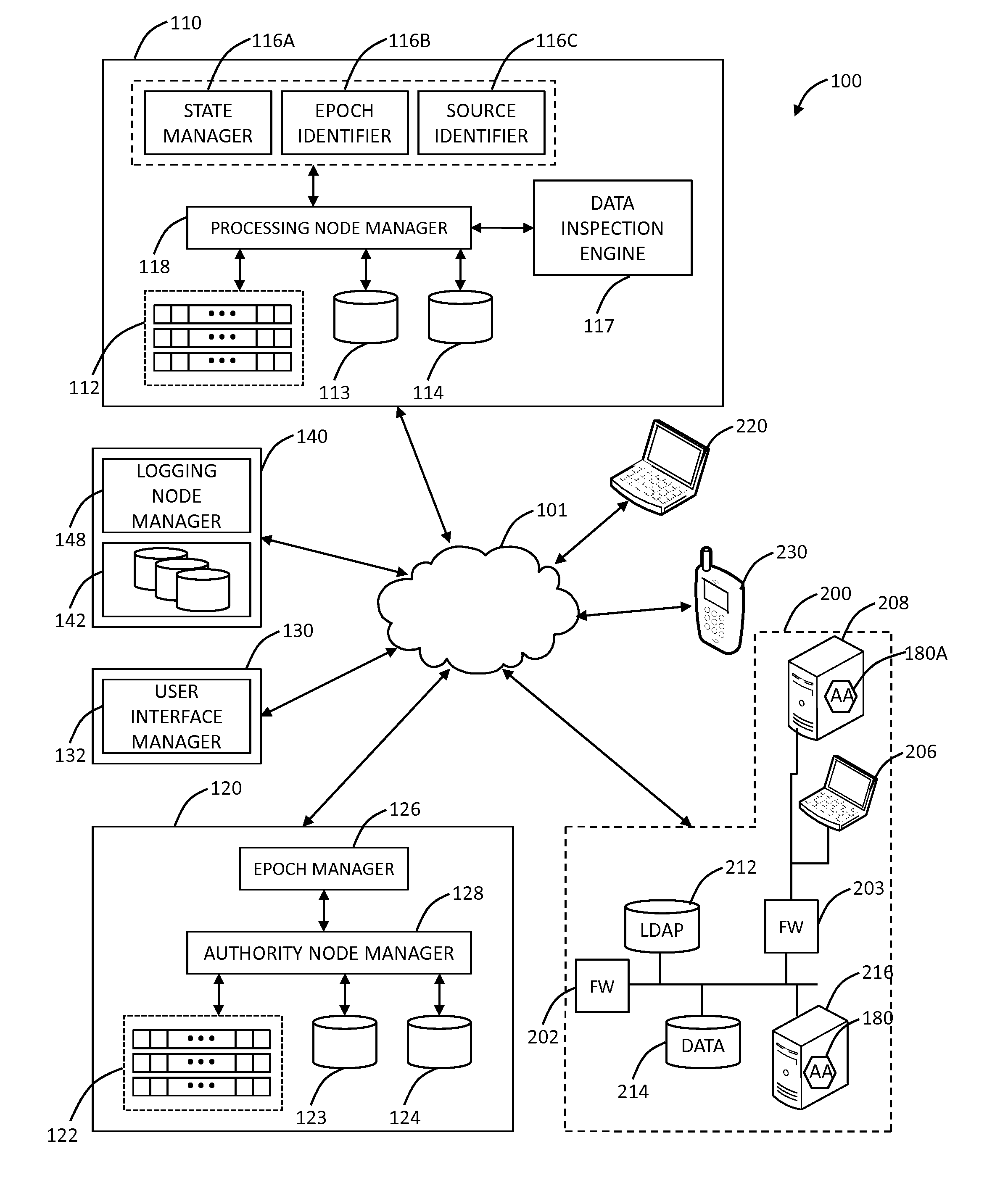
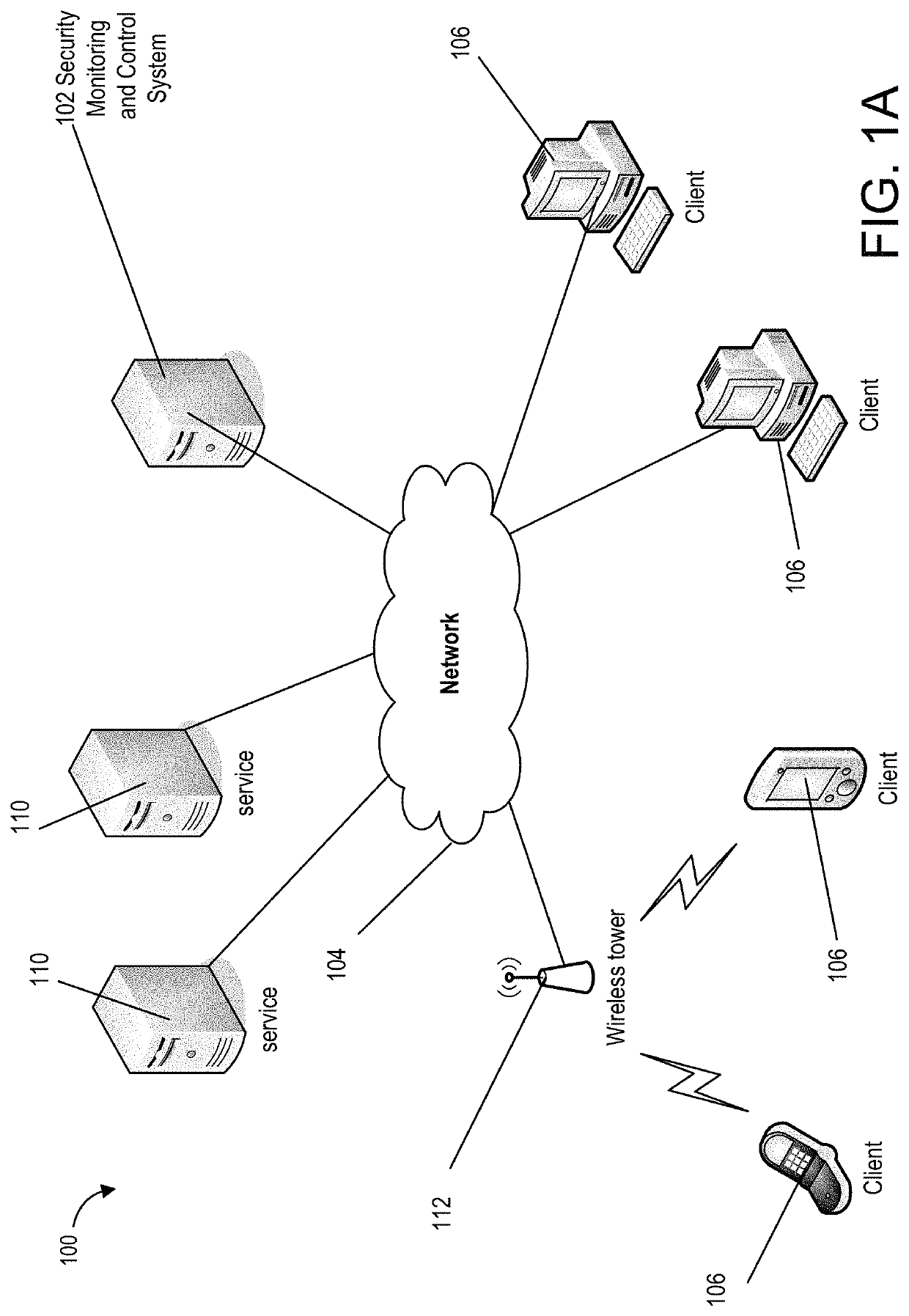
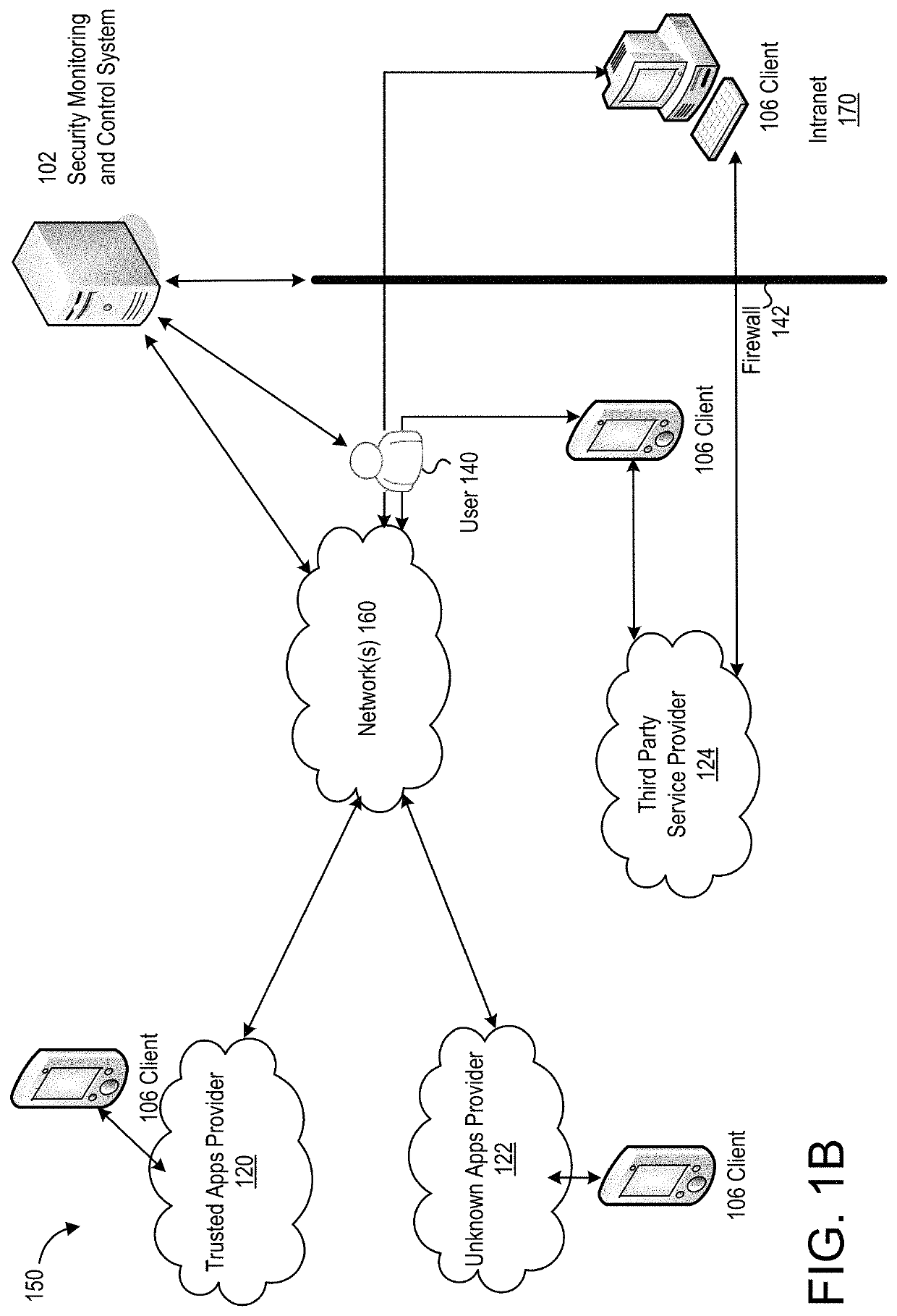
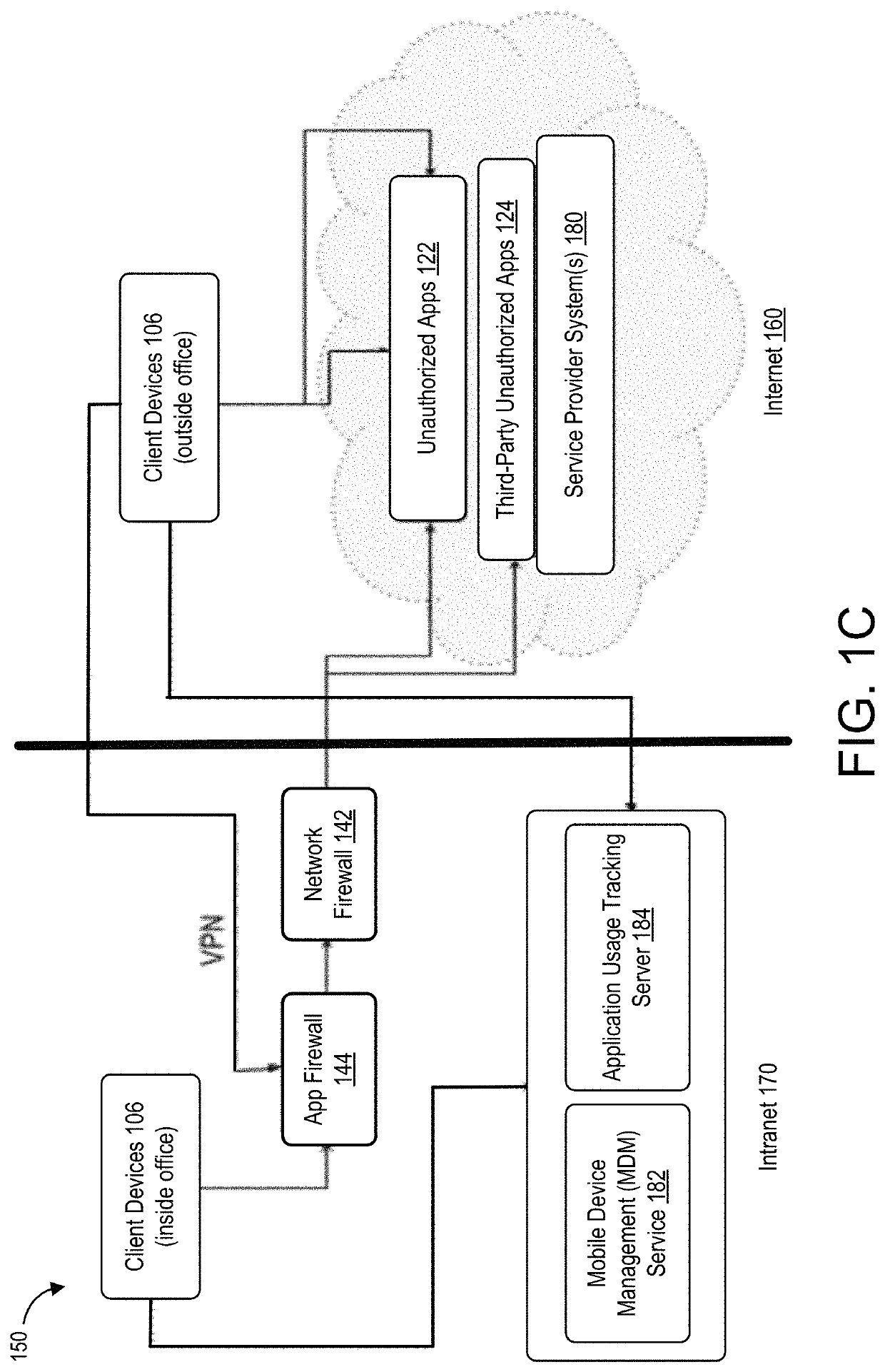
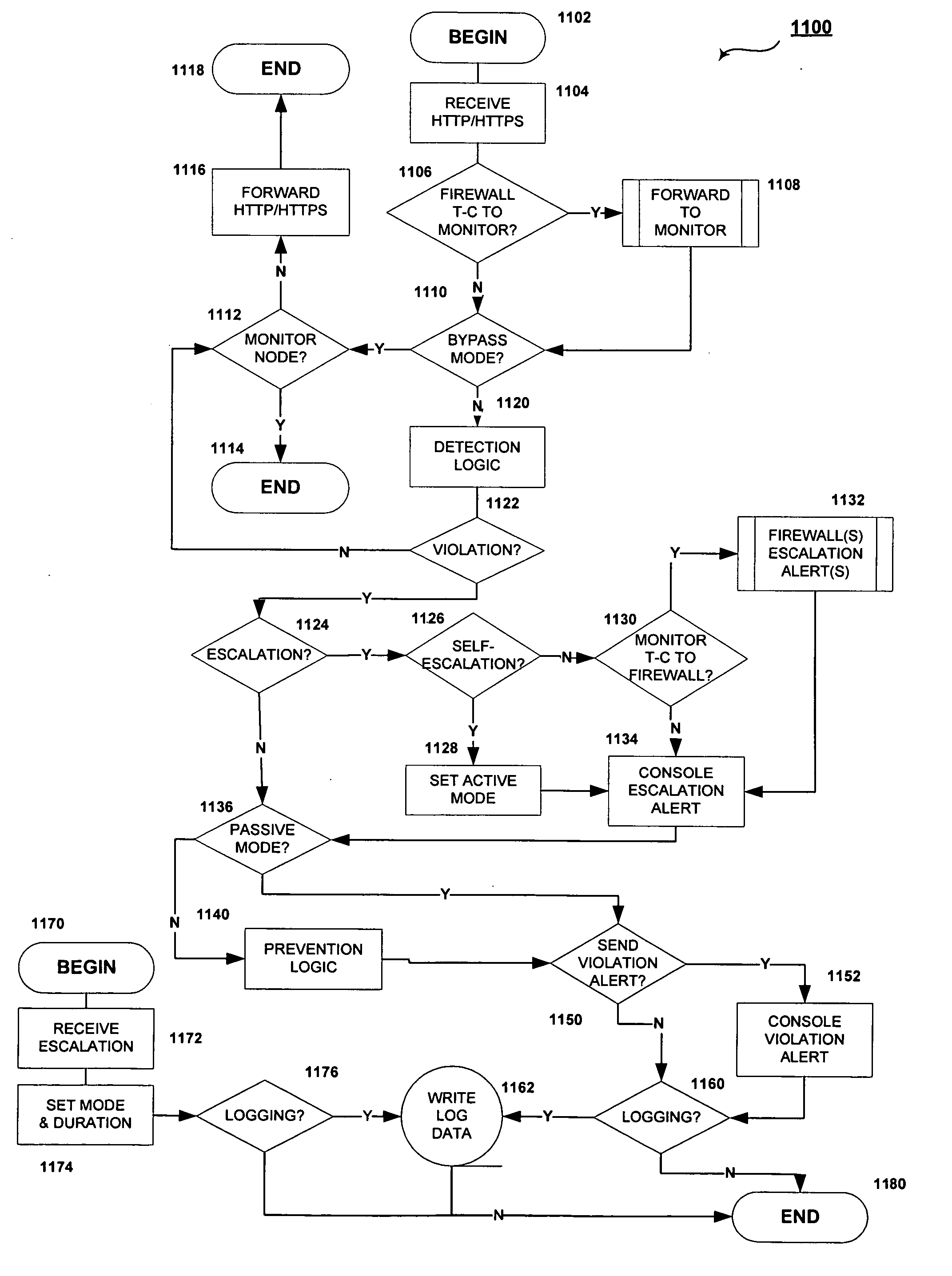
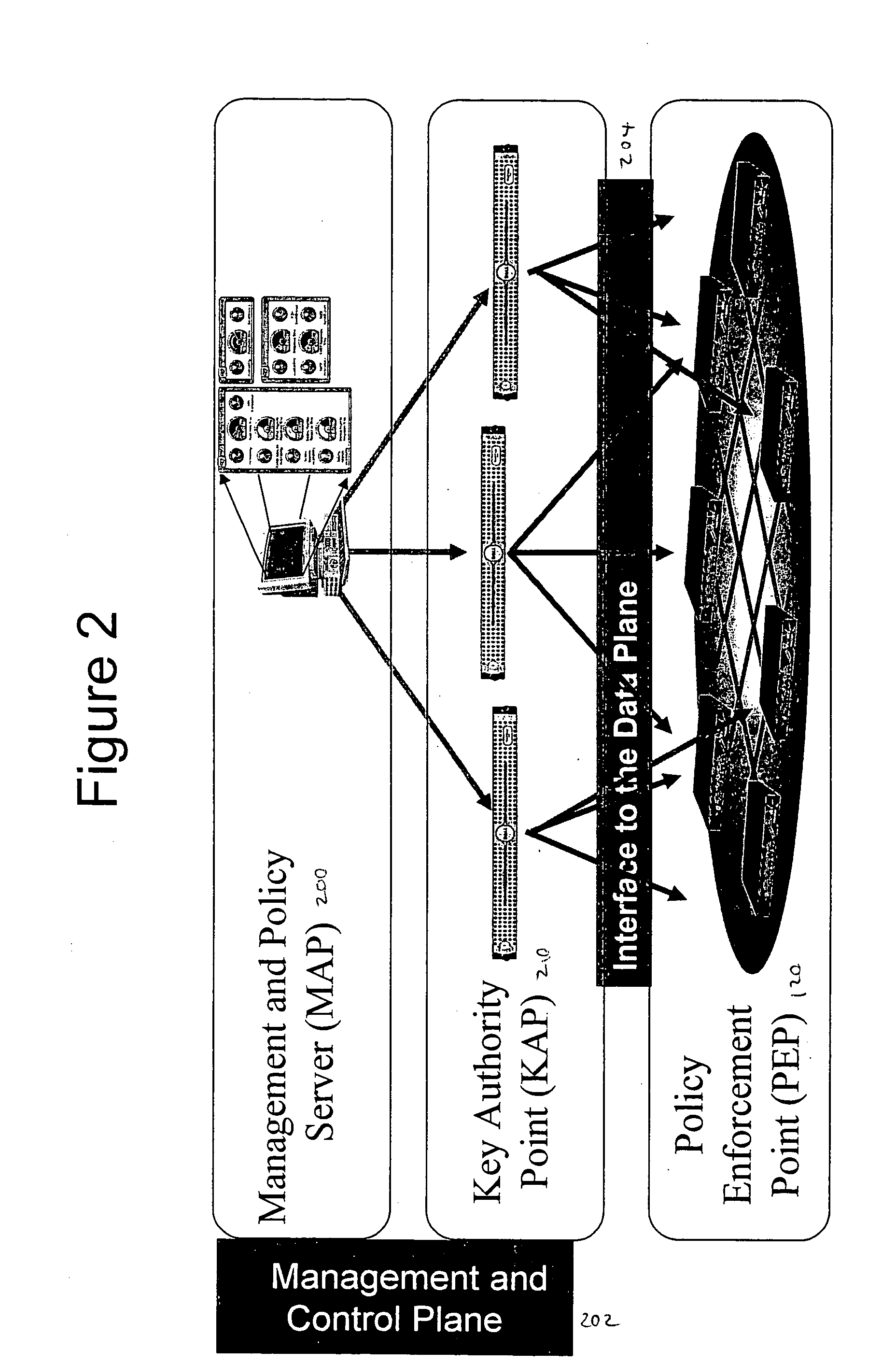
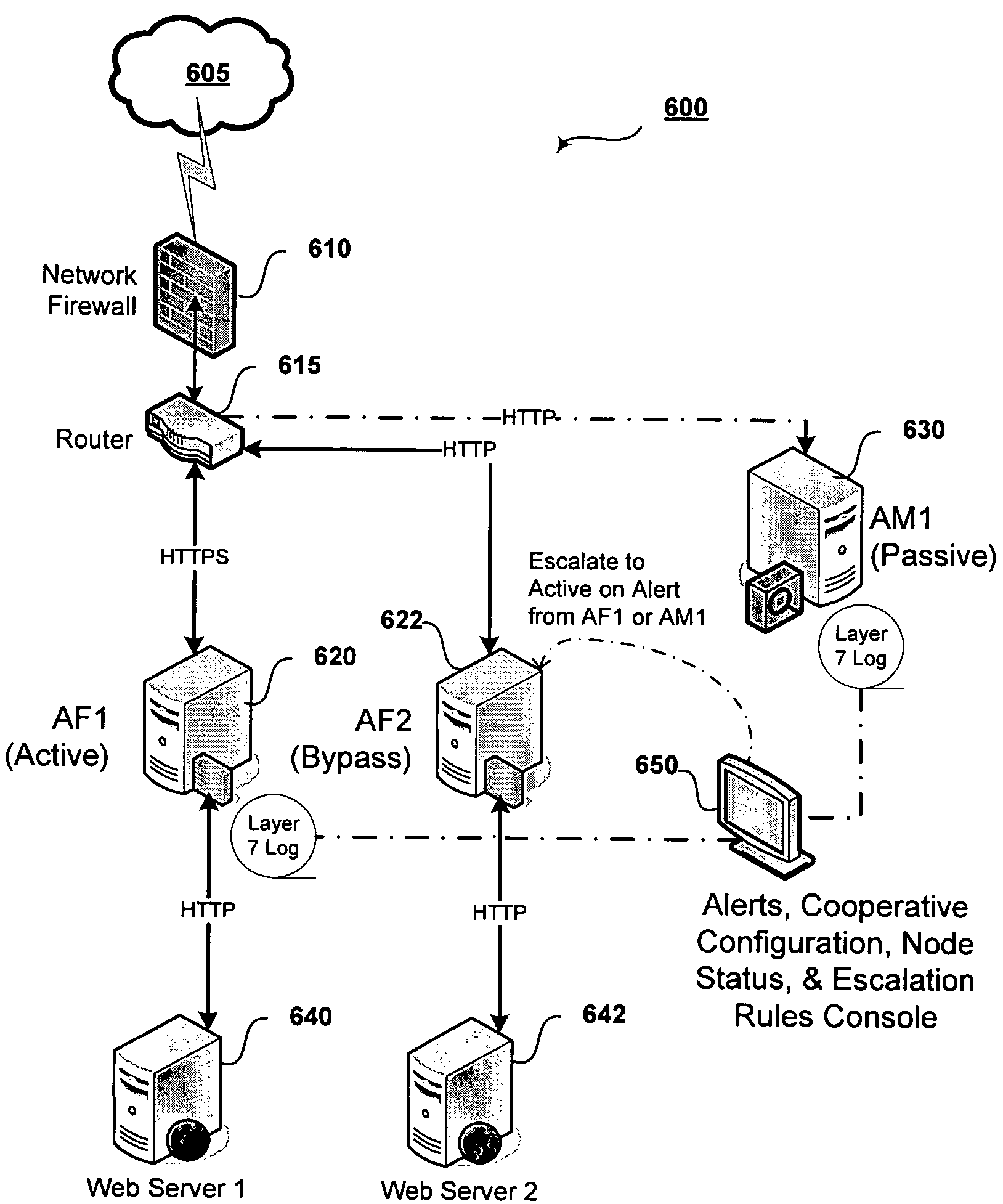
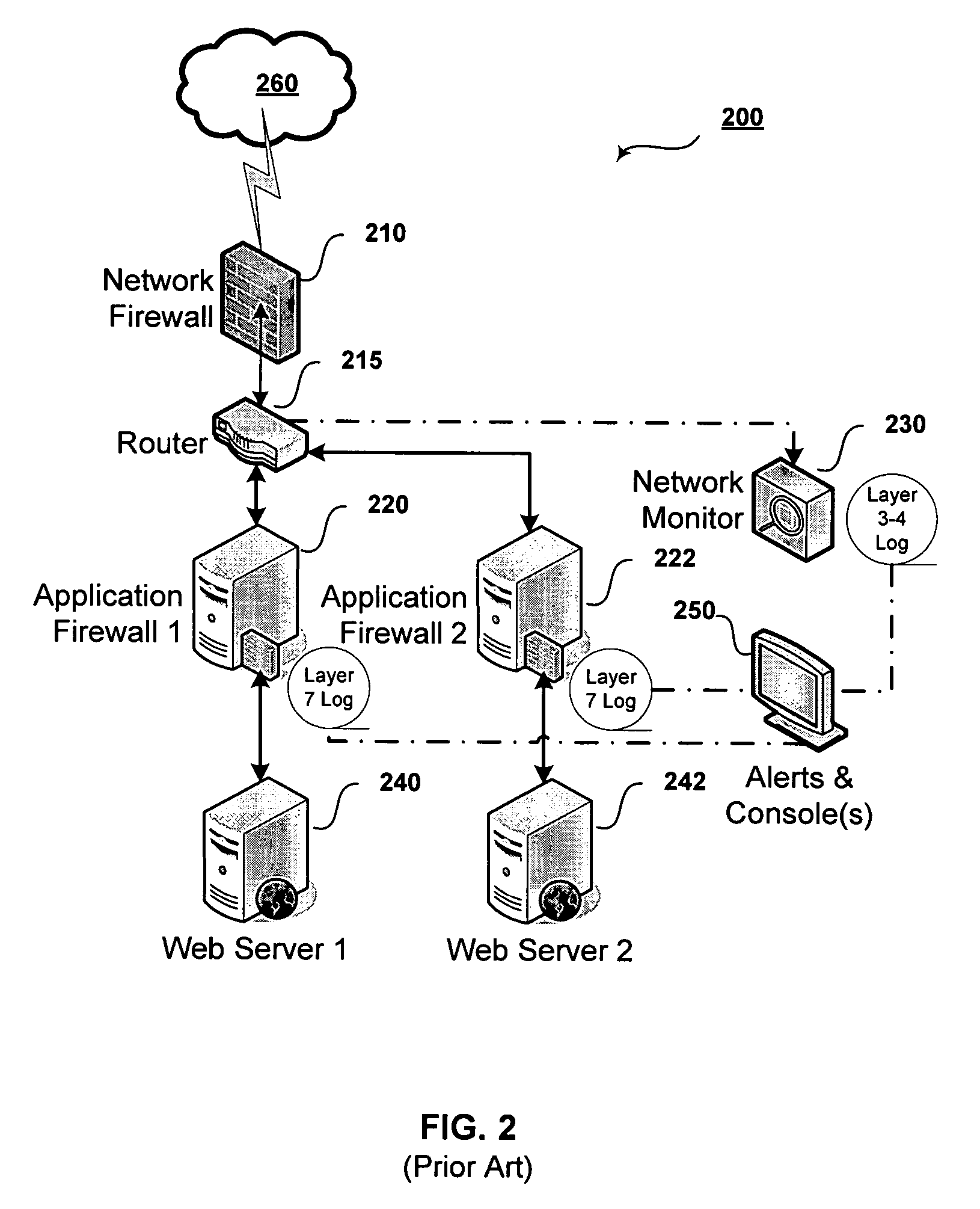
Cooperative processing and escalation in a multi-node application-layer security system and method
ActiveUS20060179296A1Digital data processing detailsMultiple digital computer combinationsDashboardOperation mode
A cooperative processing and escalation method and system for use in multi-node application-layer security management is disclosed. The method includes the steps of identifying individual application security nodes, grouping and configuring nodes for cooperative processing, assigning the default operational mode at each node, assignment of logging and alert event tasks at each node, and defining escalation and de-escalation rules and triggers at each node. Both loosely-coupled and tightly-coupled configurations, each with its cooperative processing model, are disclosed. The method includes provision for central console configuration and control, near real-time central console dashboard operations interface, alert notification, and operator override of operational modes and event tasks.
Owner:PROTEGRITY USA
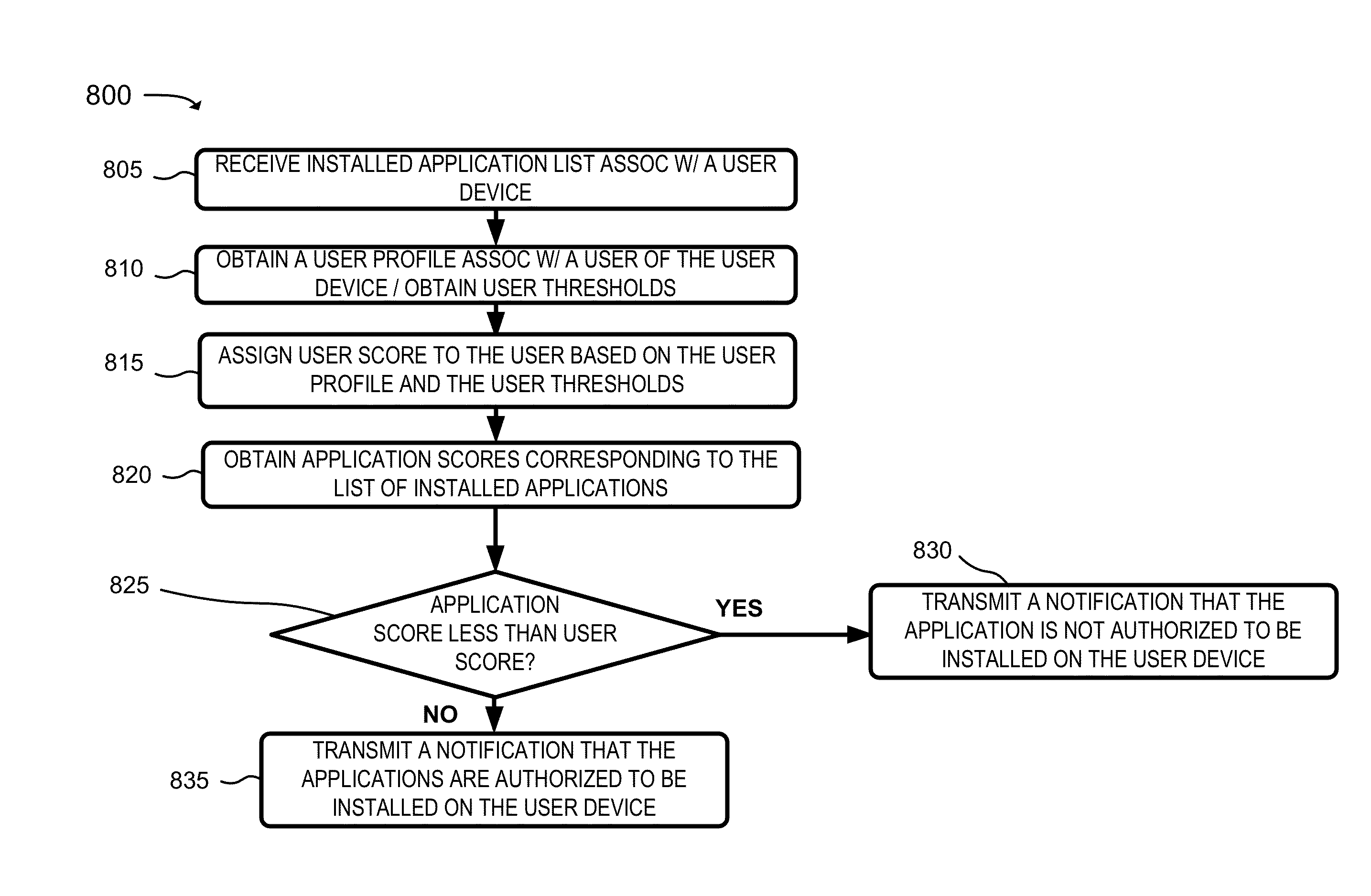
Mobile application security and management service
A system is configured to receive a list of applications installed on a user device; obtain application profiles that identify risk levels associated with the applications; obtain a user profile that identifies a job level, security risk level, or an access level to confidential information associated with the user of the user device; identify a highest risk level authorized for the user device based on whether the job level is greater than a first threshold, the security risk level is greater than a second threshold, or the access level is greater than a third threshold; determine whether any of the risk levels are greater than the highest risk level; and transmit a notification that one of the applications is to be removed from the user device when one of the risk levels, associated with the one of the applications, is greater than the highest risk level.
Owner:VERIZON PATENT & LICENSING INC
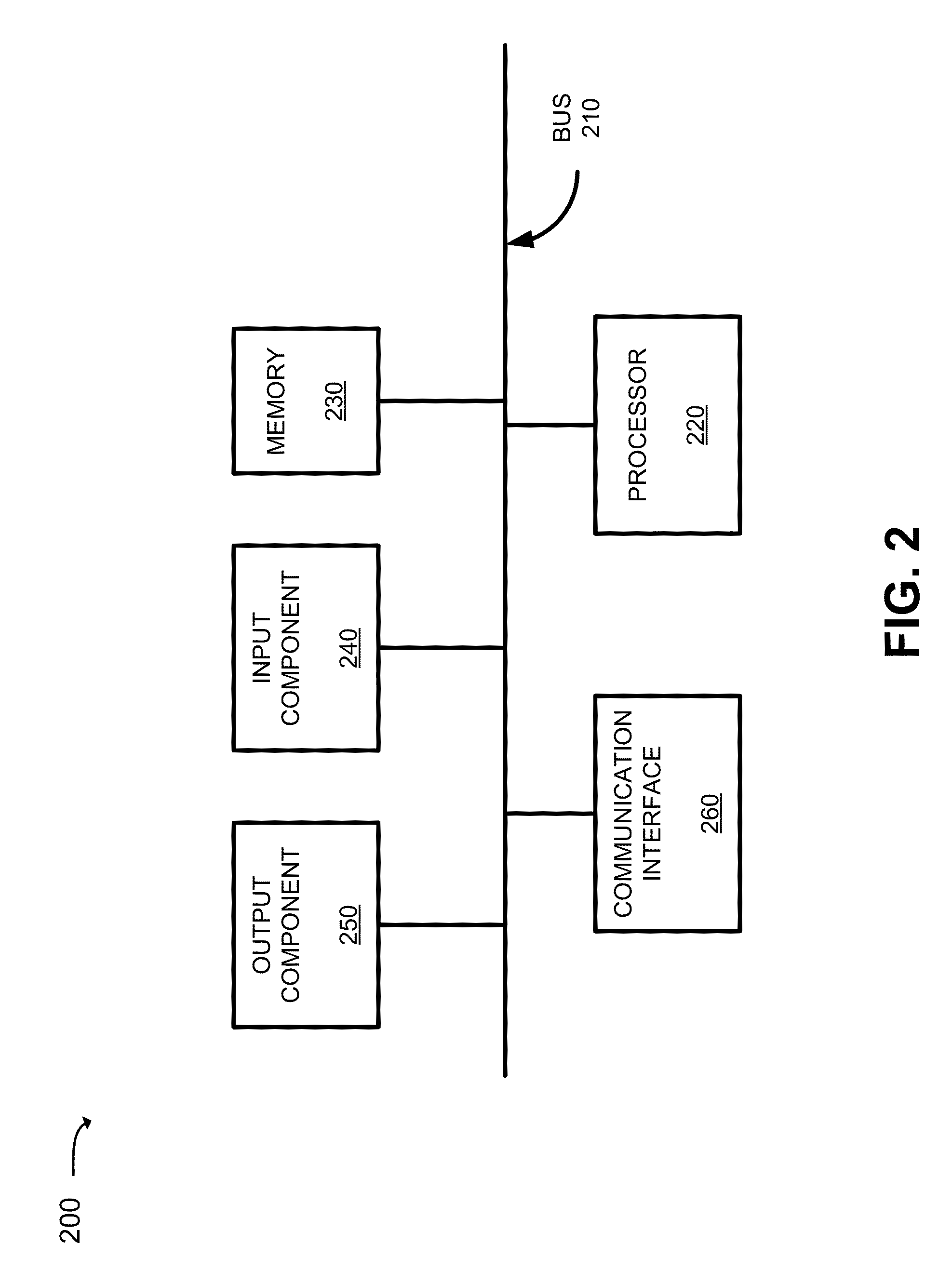
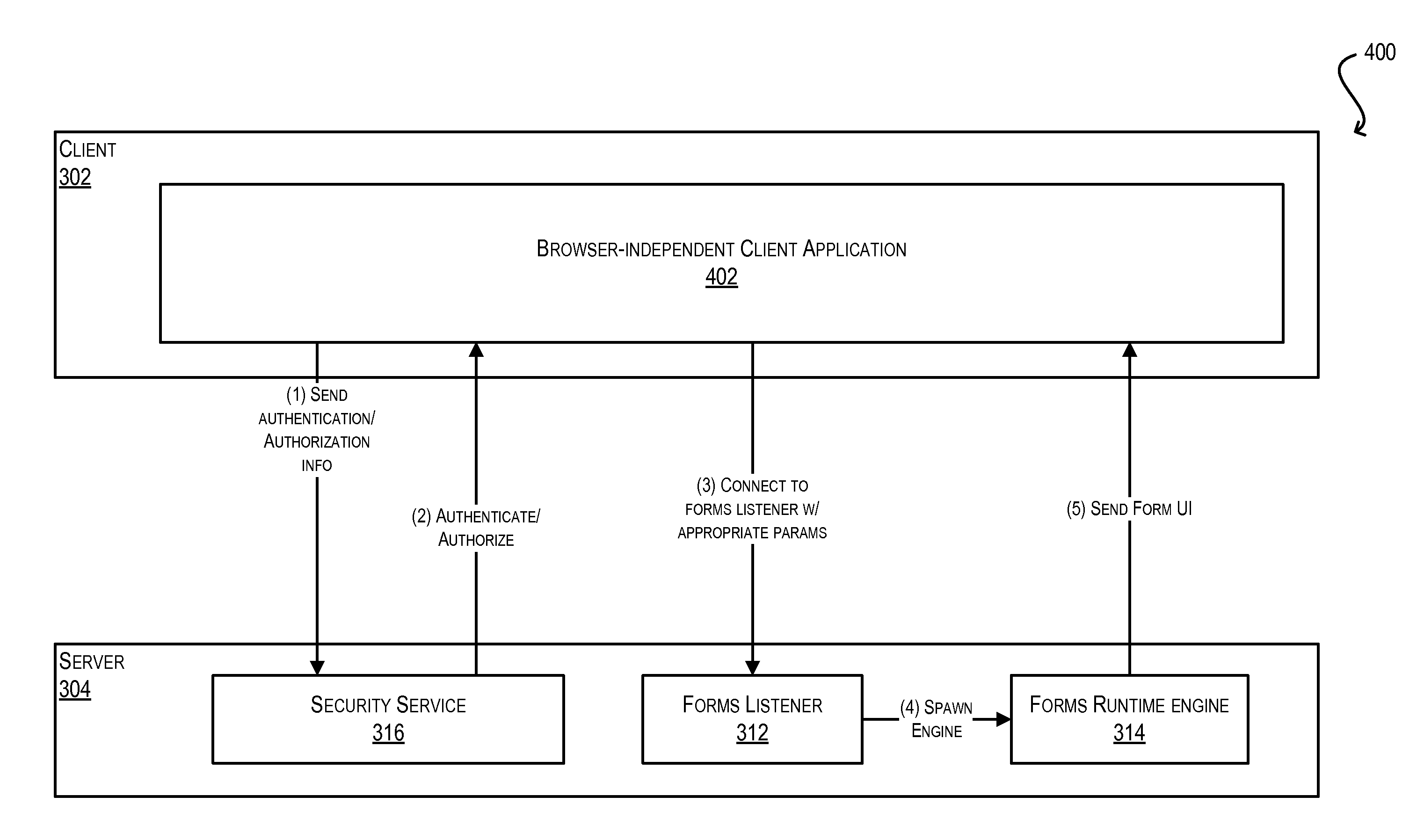
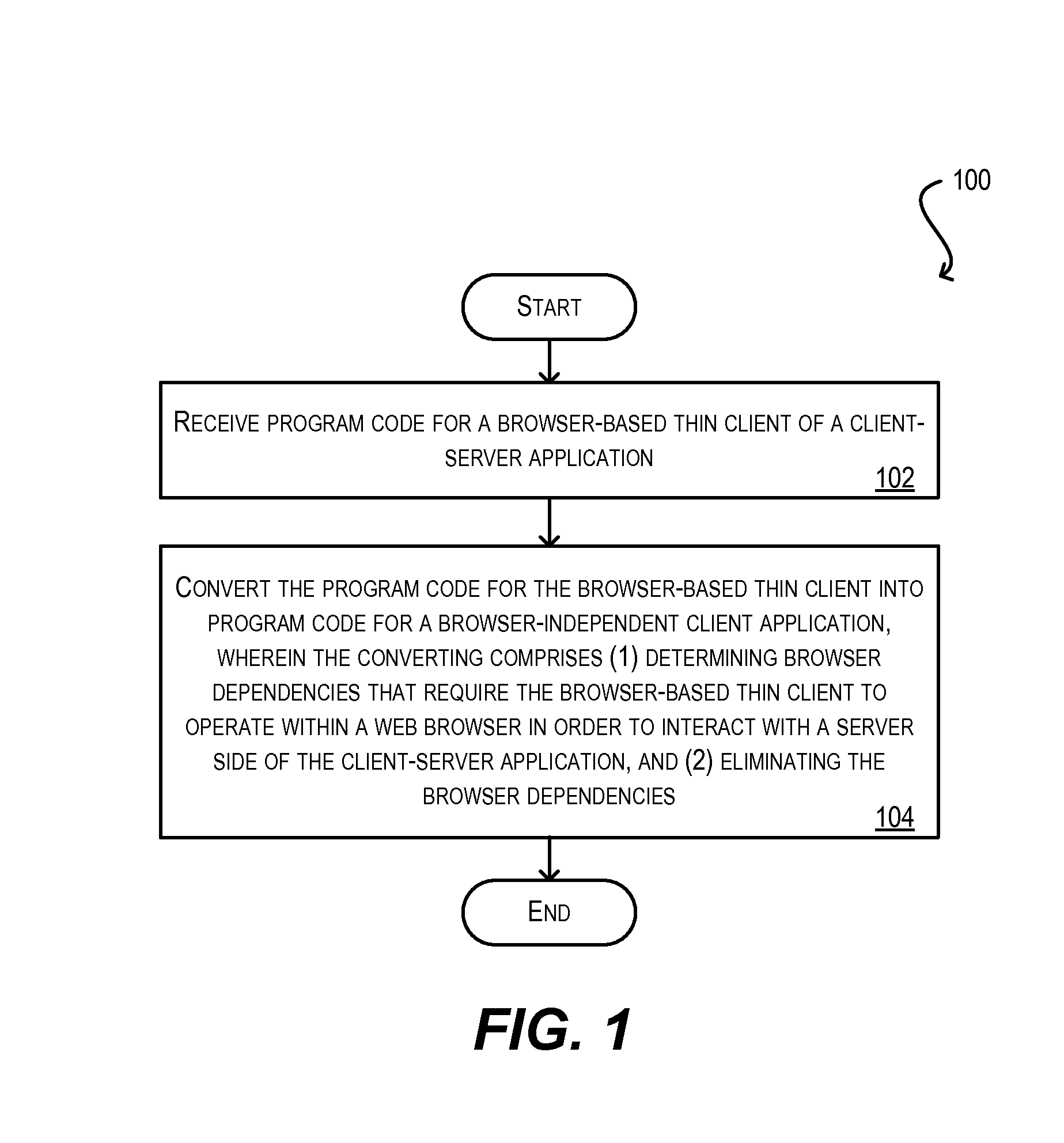
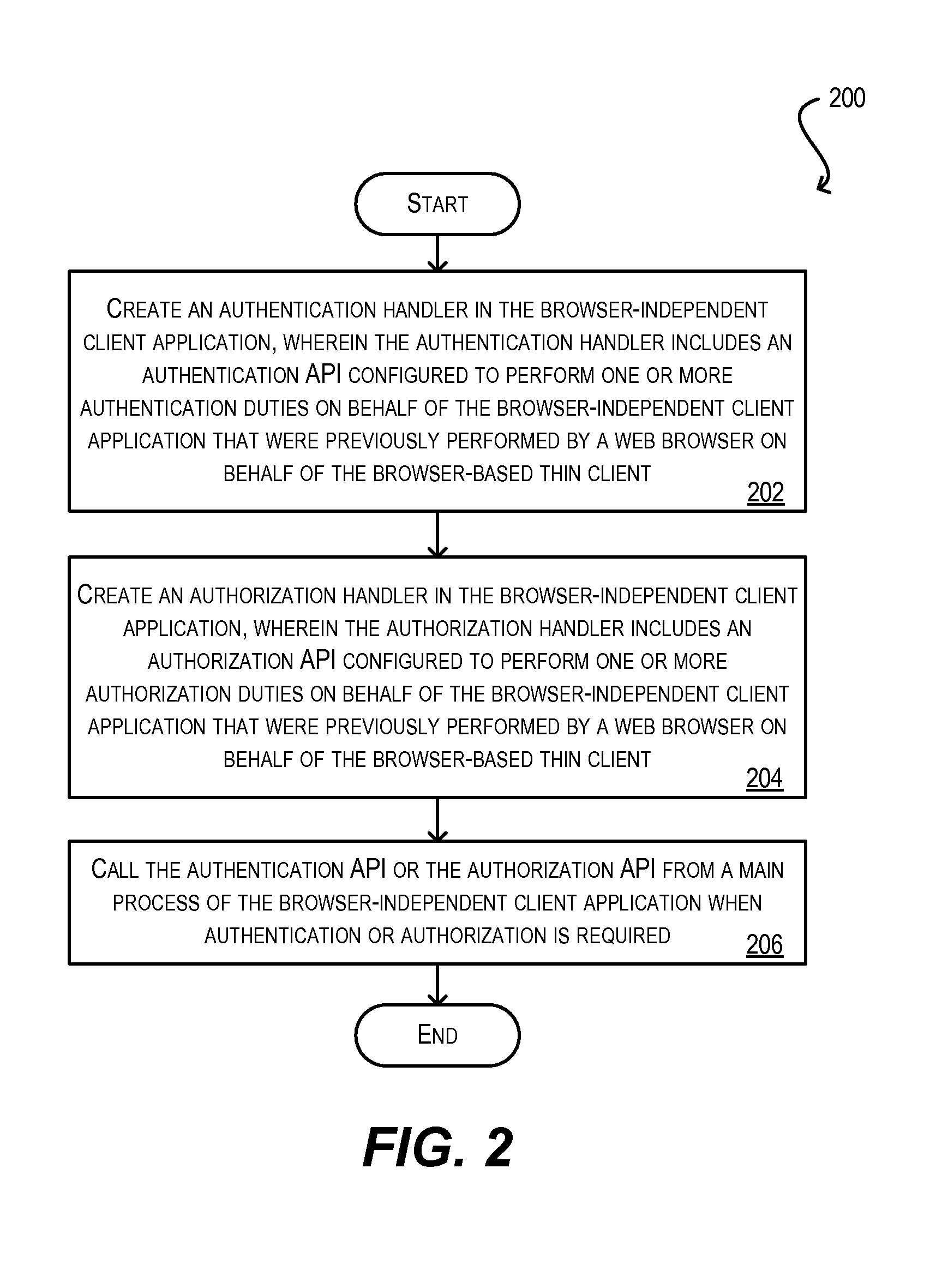
System and method for integration of browser-based thin client applications within desktop rich client architecture
ActiveUS20100057836A1Easy to reuseEliminating the one or more browser dependenciesSoftware maintainance/managementMultiple digital computer combinationsProgramming languageWeb browser
Techniques for facilitating the reuse of a browser-based thin client of a client-server application in a browser-independent context. These techniques may be used, for instance, to integrate the functionality of a browser-based thin client in a desktop-based, rich client infrastructure. In one set of embodiments, these techniques include determining one or more browser dependencies that require the thin client to operate within a web browser. For example, the thin client may depend on a web browser to handle application security, the loading / caching of client-side files, the receipt / passing of application parameters, and the like. These browser dependencies are then eliminated. As a result, the thin client can be subsequently reused without the presence of a web browser. In one set of embodiments, this process is performed by a conversion utility that automatically converts program code for the browser-based thin client into program code for a browser-independent client application.
Owner:ORACLE INT CORP
Systems and methods for configuring policy bank invocations
ActiveUS20080225722A1Efficient configurationEfficient processingMultiplex system selection arrangementsError preventionData packEngineering
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
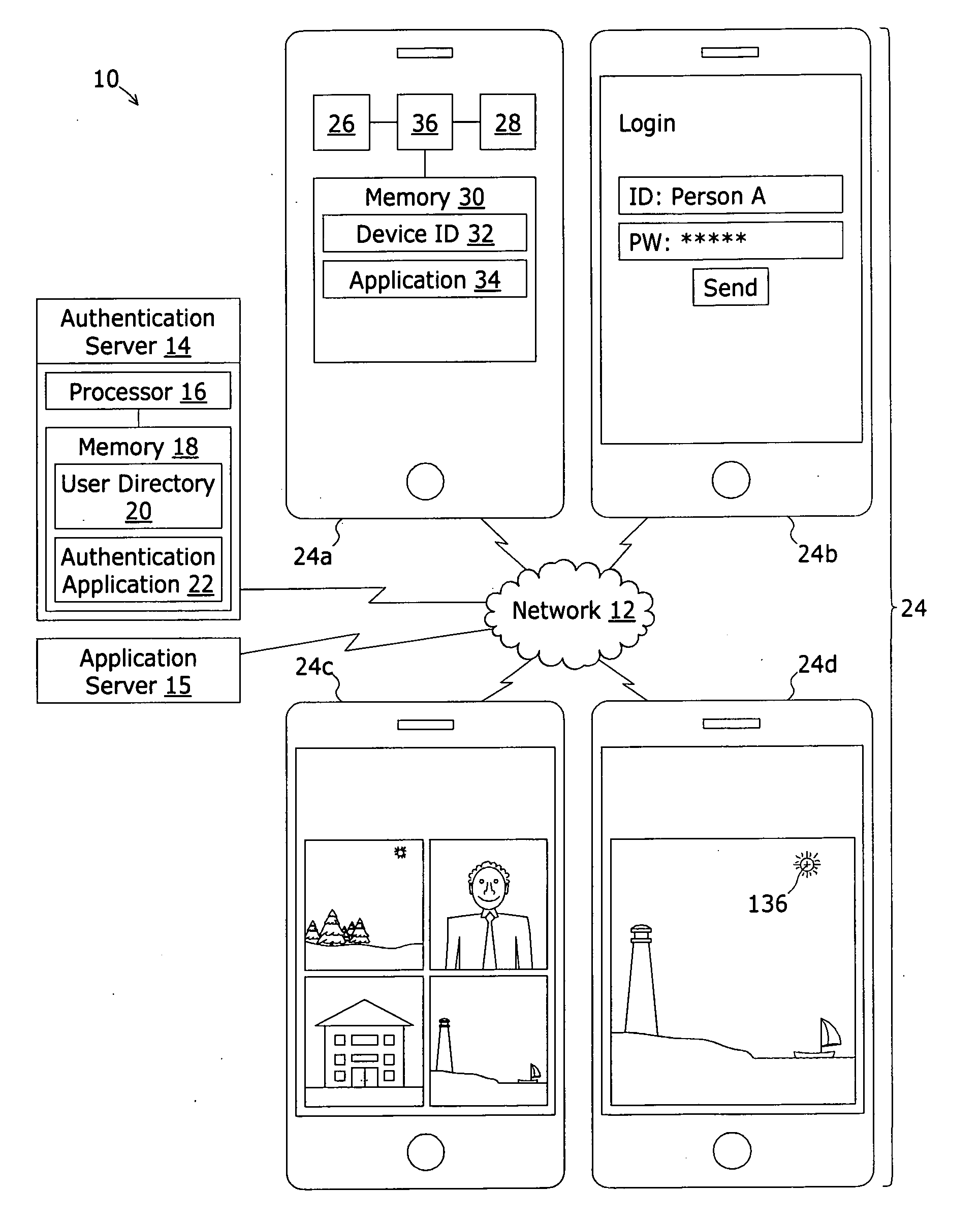
Mobile application security system and method
ActiveUS20130014248A1Digital data processing detailsUnauthorized memory use protectionInternet privacyApplication security
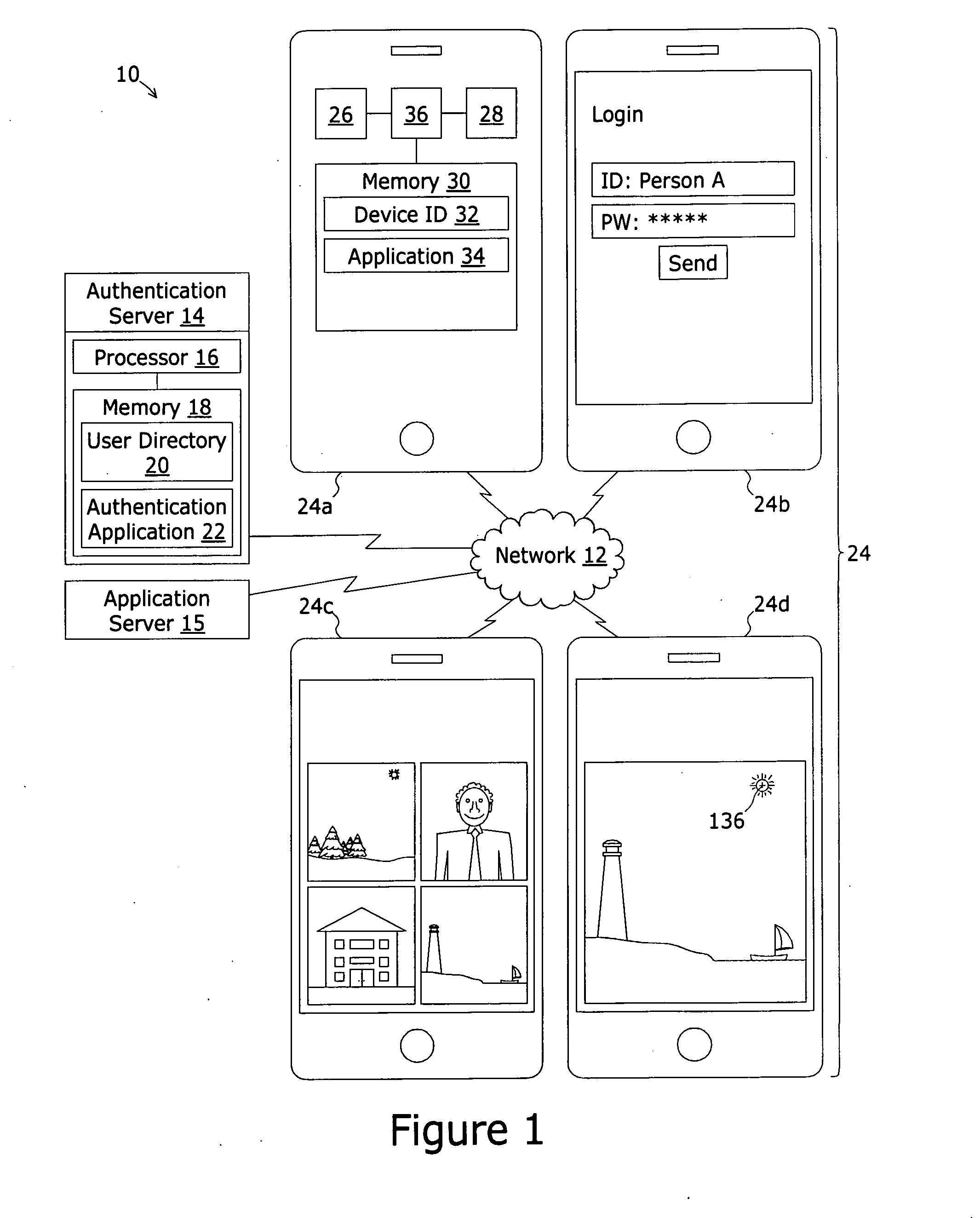
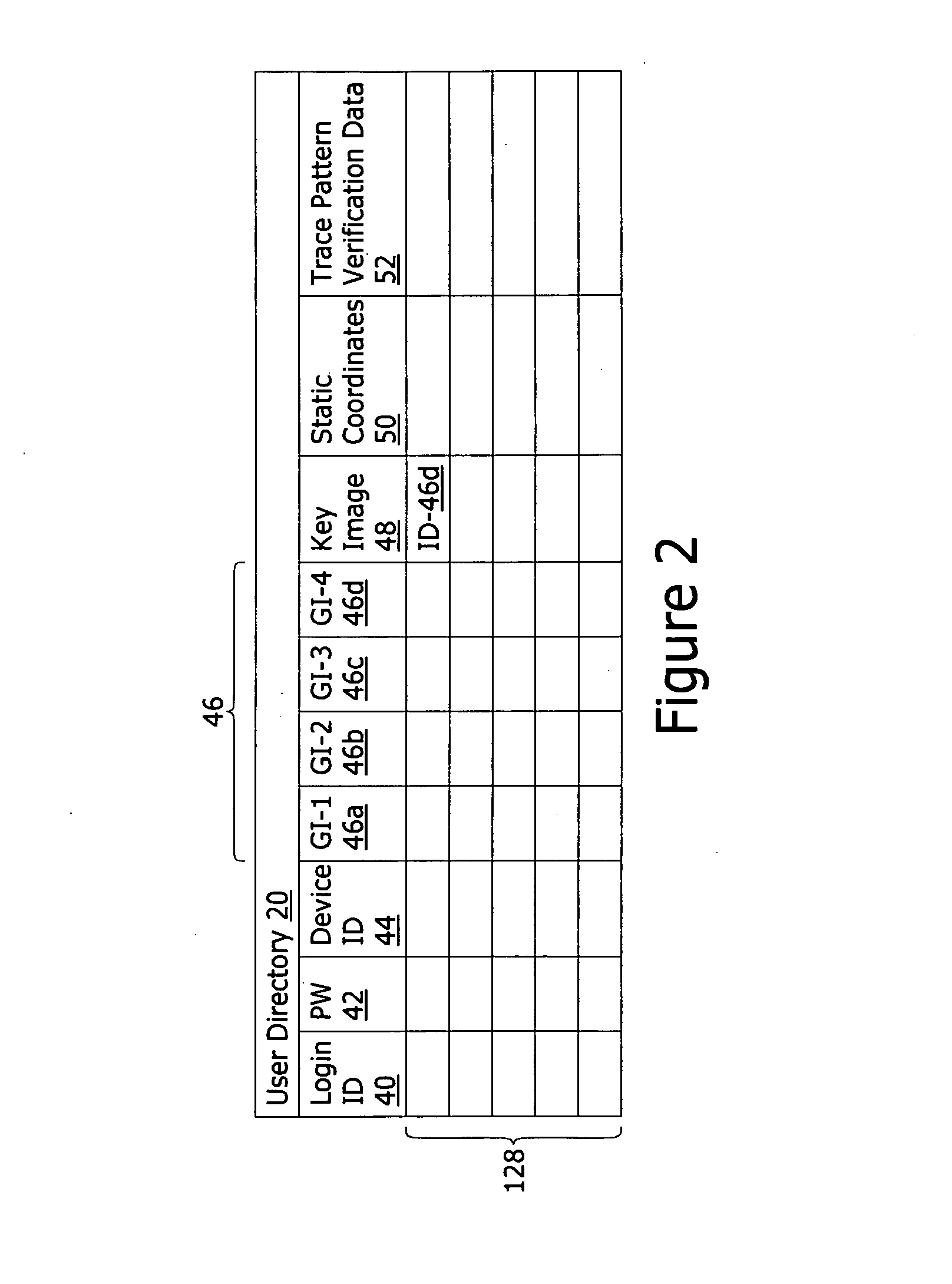
A system for authenticating the user of a computing device comprises an authorized user directory. Each record is uniquely associated with an authorized user and includes at least a computing device ID value that is a globally unique value assigned to the authorized user's computing device, a group of unique depictions such as photographs, an identification of a key depiction. Portions of each image form fiducials recognizable by the user. The record further includes trace pattern verification data representing continuous trace strokes between pairs of the fiducials within the key depiction. To authenticate, the group of images are displayed to the user. The user must first select the key image and secondly trace continuous trace strokes between the pairs of fiducials to match the trace pattern verification data.
Owner:BOTTOMLINE TECH
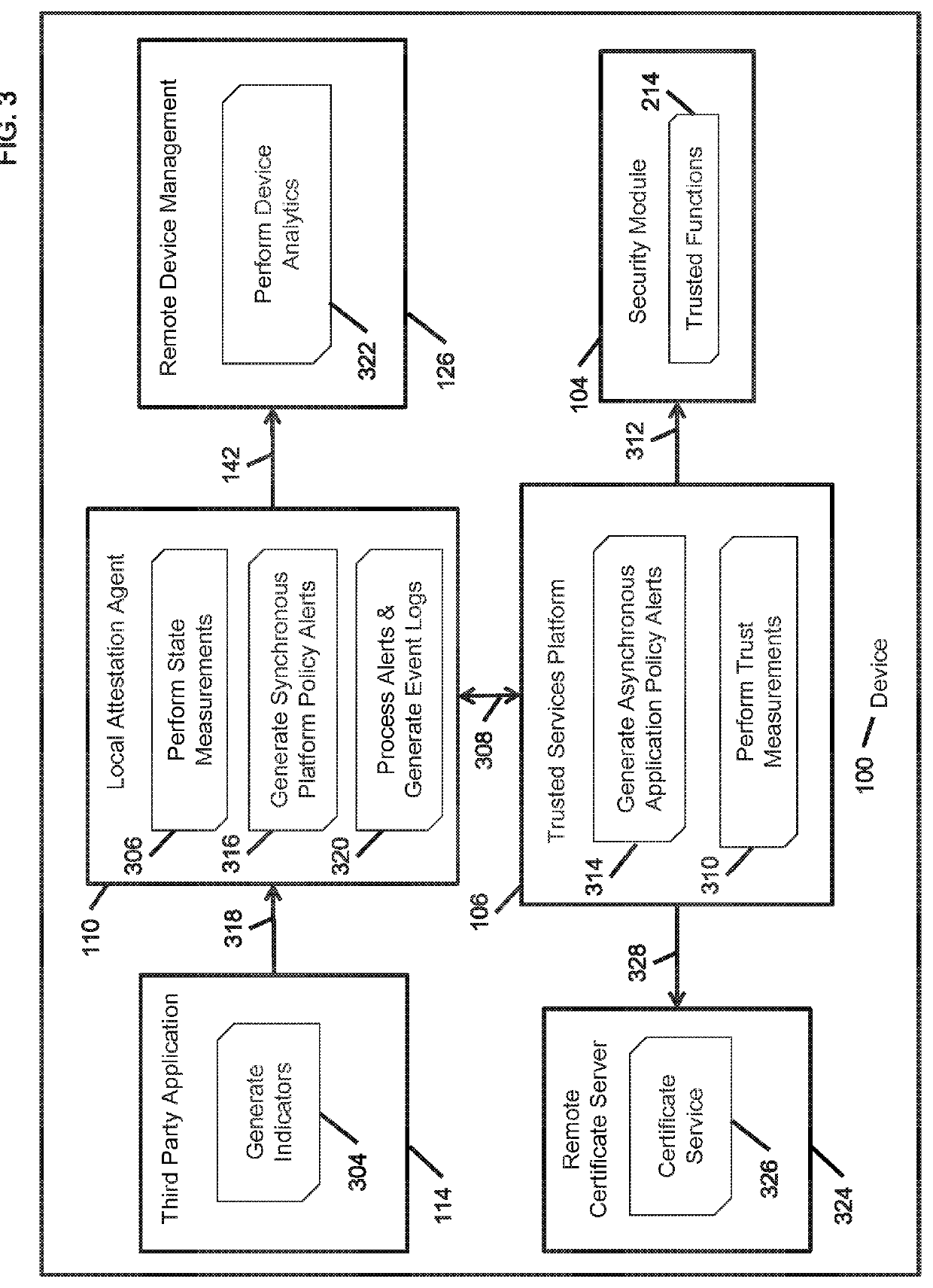
System and method for policy based adaptive application capability management and device attestation
ActiveUS20180109538A1Easy to controlTransmissionCapability managementApplication programming interface
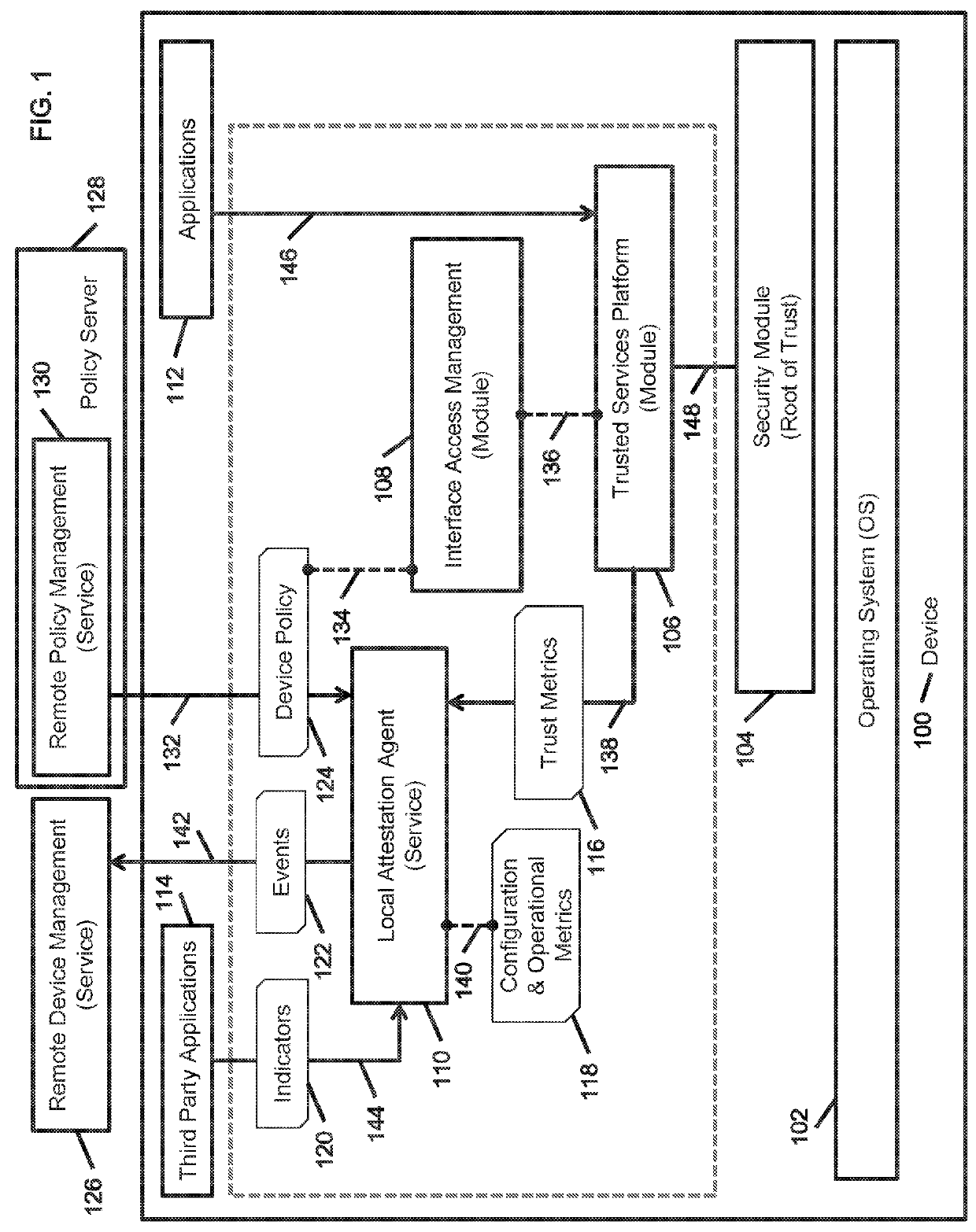
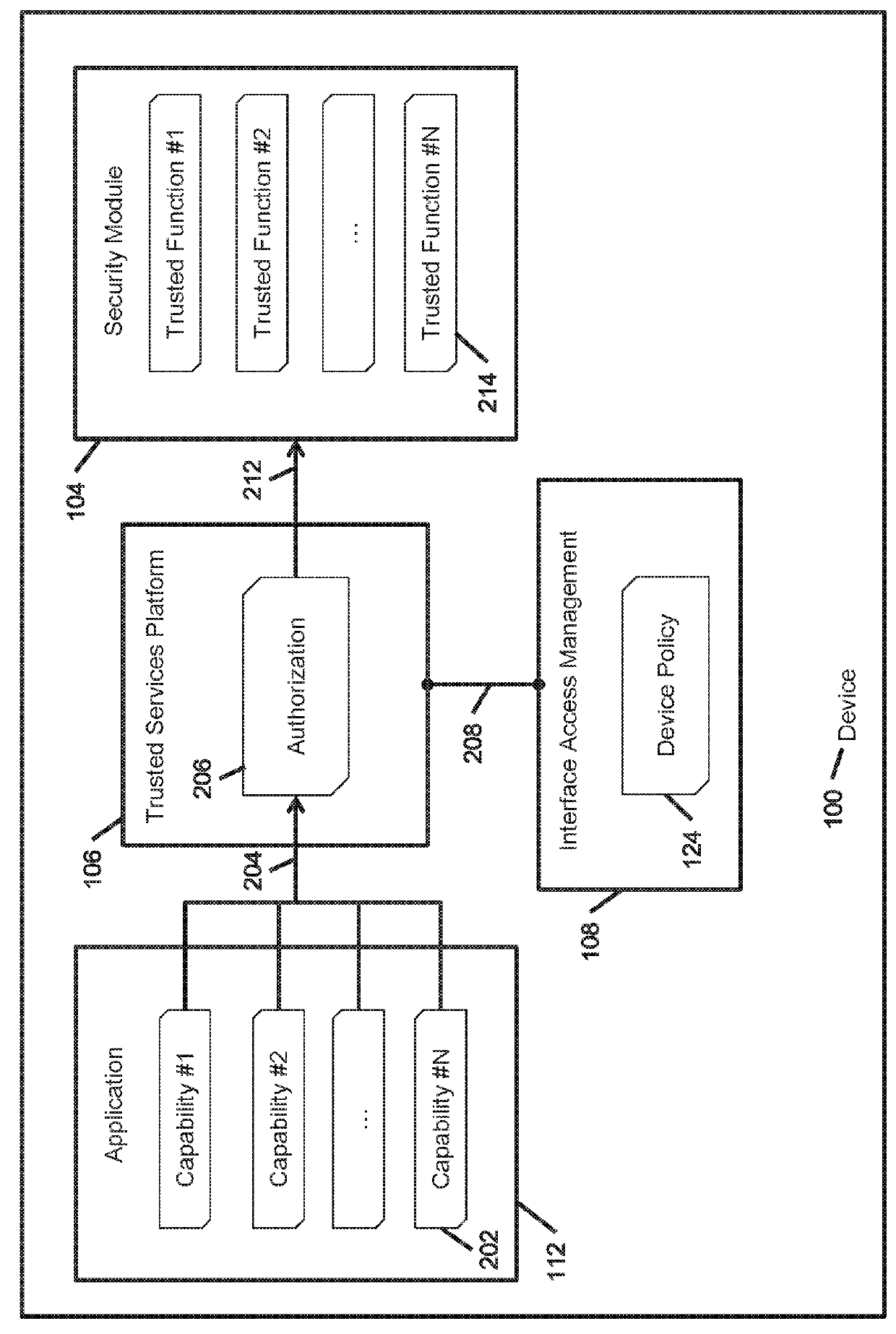
A method provides policy based adaptive application capability management and device attestation for dynamic control of remote device operations. The method includes instrumenting applications installed on a remote device to examine their runtime application programming interface (API) invocations to trusted functions abstracted by a trusted services platform anchored to an underlying firmware, software or hardware root of trust, and managing the application security operations based on the execution context and dynamic privilege controls to restrict their capabilities. The invention also provides a local attestation agent to perform state measurements for platform trust, configuration and operational metrics, and generates device policy based platform and application level alerts. These alerts allow operations technology (OT) administrators to dynamically control the operational capabilities of applications, to deal with discovered vulnerabilities and exploits, before requiring distribution of application software upgrades or patches onto a large number of distributed remote devices.
Owner:DIGICERT
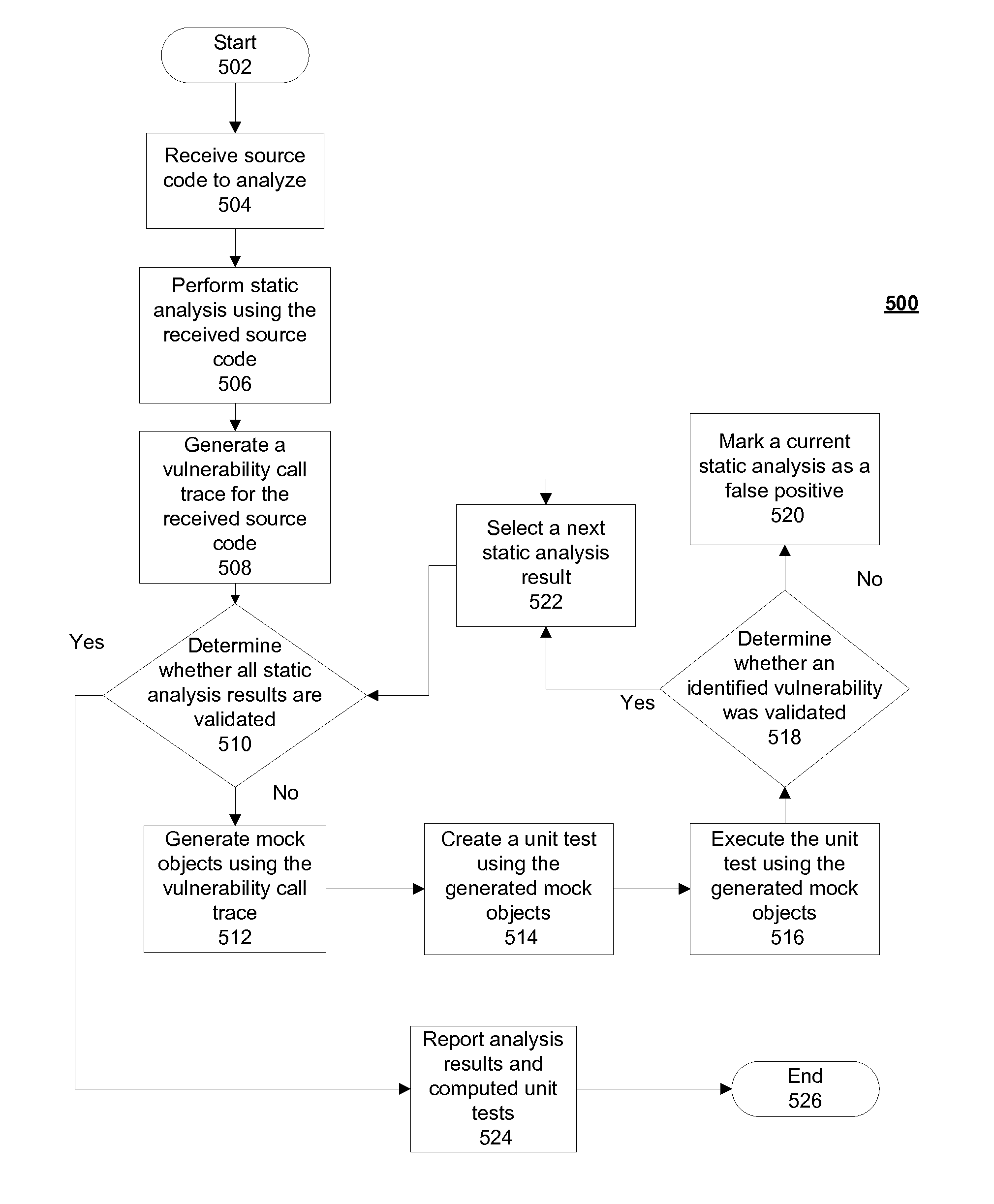
Verifying application security vulnerabilities
ActiveUS20130312102A1Memory loss protectionError detection/correctionStatic timing analysisApplication software
Verifying application security vulnerabilities includes receiving a source code to analyze, performing a static analysis using the received source code and generating a vulnerability call trace for the received source code. Responsive to a determination that all static analysis results are not validated, mock objects are generated using the vulnerability call trace and a unit test is created using the generated mock objects. The unit test is executed using the generated mock objects and responsive to a determination that an identified vulnerability was validated; a next static analysis result is selected. Responsive to a determination that all static analysis results are validated, results and computed unit tests are reported.
Owner:FINJAN BLUE INC
Application-to-application security in enterprise security services
ActiveUS7823192B1Provide securityDigital data processing detailsUser identity/authority verificationCharacter String Data TypeApplication software
The present system allows disparate secure applications to communicate directly with one another in a heterogeneous application environment by providing for the creation of tokens that can be passed between the applications without human intervention. Security information is passed between applications in the form of a token with a string data type. Since a string is a primitive data type, it can be recognized by a large number of applications and interfaces. The token has no header and therefore no application-specific header configuration, making it platform and technology independent. This eliminates the need for conversion of security information between different formats. The use of tokens also eliminates the need for an application to be authenticated and authorized every time it sends a message to another application. Instead of a permanent context or session, a context is created with every invocation from one application to another.
Owner:T MOBILE INNOVATIONS LLC
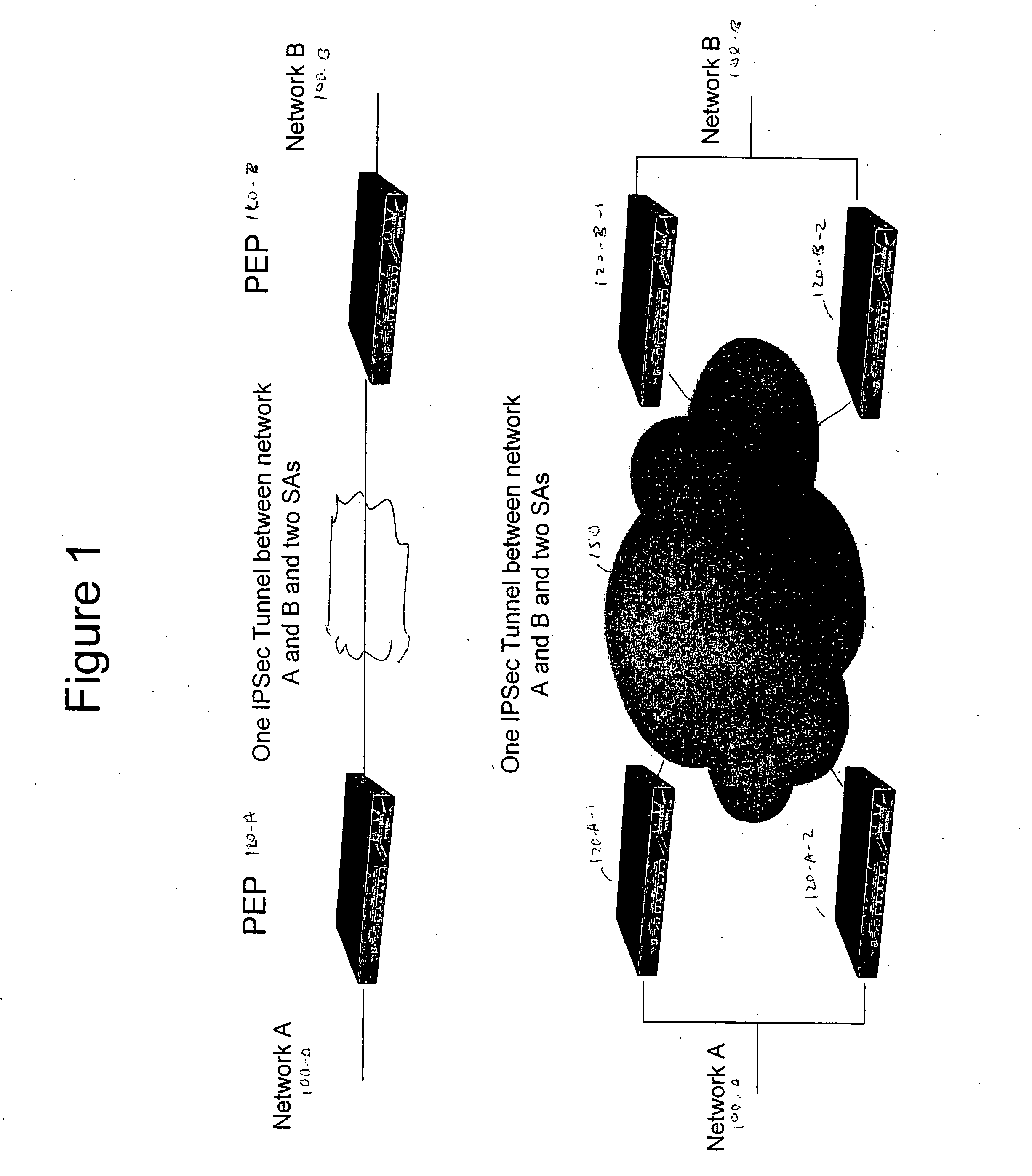
Deploying group VPNS and security groups over an end-to-end enterprise network
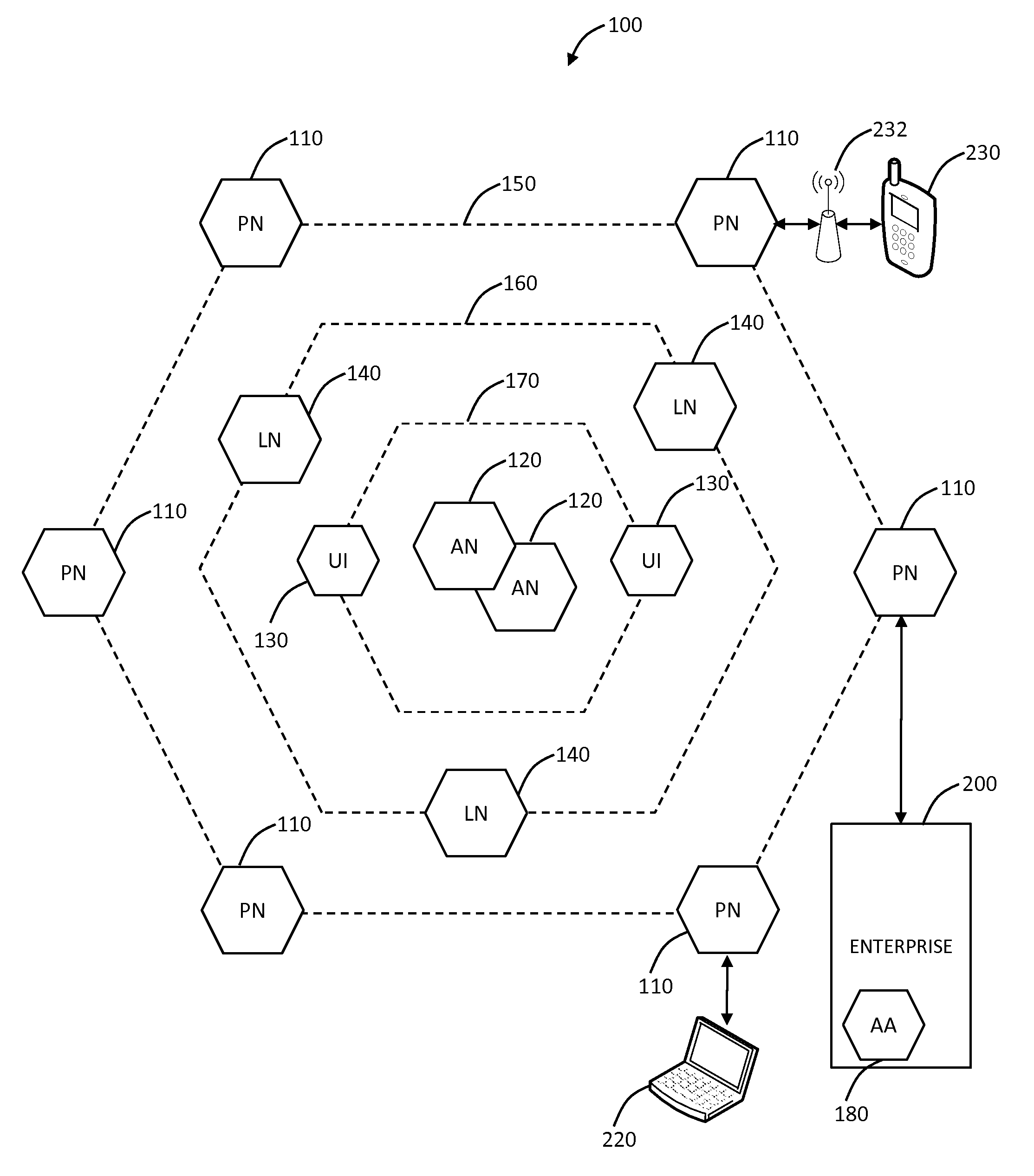
ActiveUS20080127327A1Key distribution for secure communicationDigital data processing detailsPrivate networkEndpoint security
Group Virtual Private Networks (Group VPNS) are provided for different types of machines in a data processing network. Security groups are defined by a security policy for each member. Security policies and encryption keys are deployed to members of a security group using an IPSec network infrastructure with authentication via VPN mechanisms. The group VPNs provide a trusted IP network that can leverage and co-exist with security access control technologies, such as endpoint security that controls client network access or application security that controls user access to enterprise applications.
Owner:CIPHEROPTICS
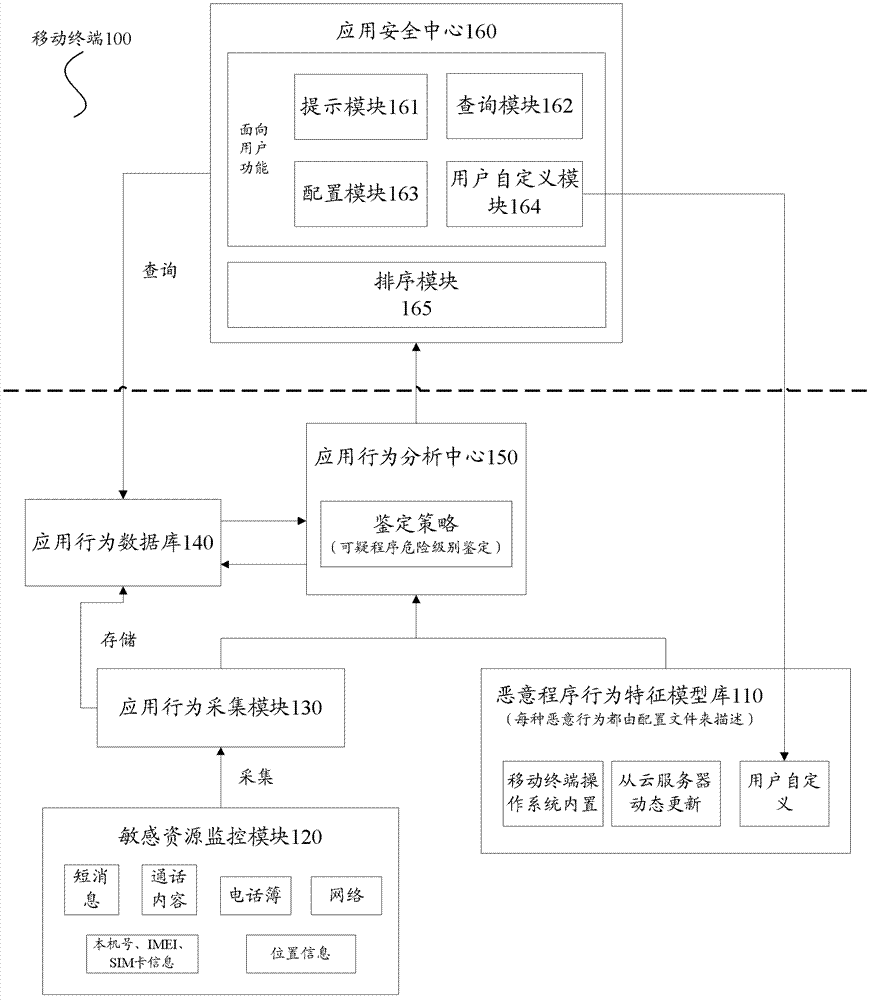
Mobile terminal, and system and method for suspicious behavior detection and judgment
ActiveCN103368904AExtensive range of securityData synchronizationSubstation equipmentTransmissionAnalysis centerComputer terminal
The invention provides a mobile terminal which comprises a malicious behavior feature model base used for storing malicious behavior models; a sensitive resource monitoring module used for monitoring access of an application program to sensitive resource; an application behavior acquisition module used for acquiring a corresponding sensitive behavior according to monitored behavior data; an application behavior database used for storing the sensitive behavior; an application behavior analysis center used for receiving the sensitive behavior, invoking the malicious behavior models in the malicious behavior feature model base and judging whether a behavior corresponding to the sensitive behavior is a malicious behavior; and an application security center used for querying the sensitive behavior, sorting application program accesses corresponding to the sensitive behavior in order of malicious degree and setting warning levels of the application program accesses. The invention further provides a suspicious behavior detection and judgment system and a suspicious behavior detection and judgment method. The mobile terminal, the suspicious behavior detection and judgment system and the suspicious behavior detection and judgment method of the invention have the advantage of being capable of providing safety guarantee for application programs and preventing and monitoring malicious behaviors.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Cooperative processing and escalation in a multi-node application-layer security system and method
ActiveUS7539857B2Digital data processing detailsUser identity/authority verificationDashboardOperation mode
A cooperative processing and escalation method and system for use in multi-node application-layer security management is disclosed. The method includes the steps of identifying individual application security nodes, grouping and configuring nodes for cooperative processing, assigning the default operational mode at each node, assignment of logging and alert event tasks at each node, and defining escalation and de-escalation rules and triggers at each node. Both loosely-coupled and tightly-coupled configurations, each with its cooperative processing model, are disclosed. The method includes provision for central console configuration and control, near real-time central console dashboard operations interface, alert notification, and operator override of operational modes and event tasks.
Owner:PROTEGRITY USA
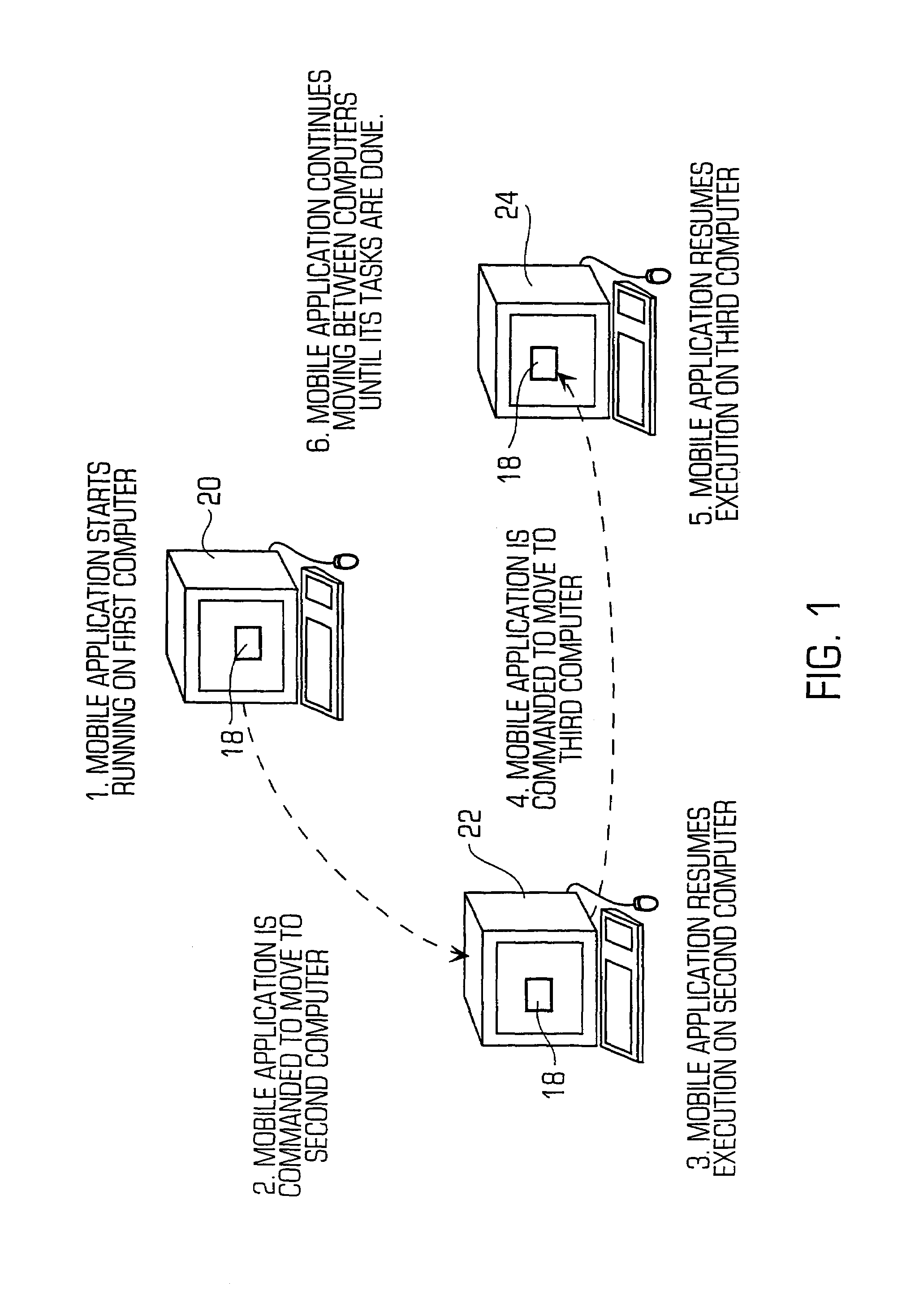
Mobile application peer-to-peer security system and method
InactiveUS7046995B2Improve security levelOvercome problemsUnauthorised/fraudulent call preventionEavesdropping prevention circuitsSecurity checkApplication software
Owner:ARAMIRA CORP
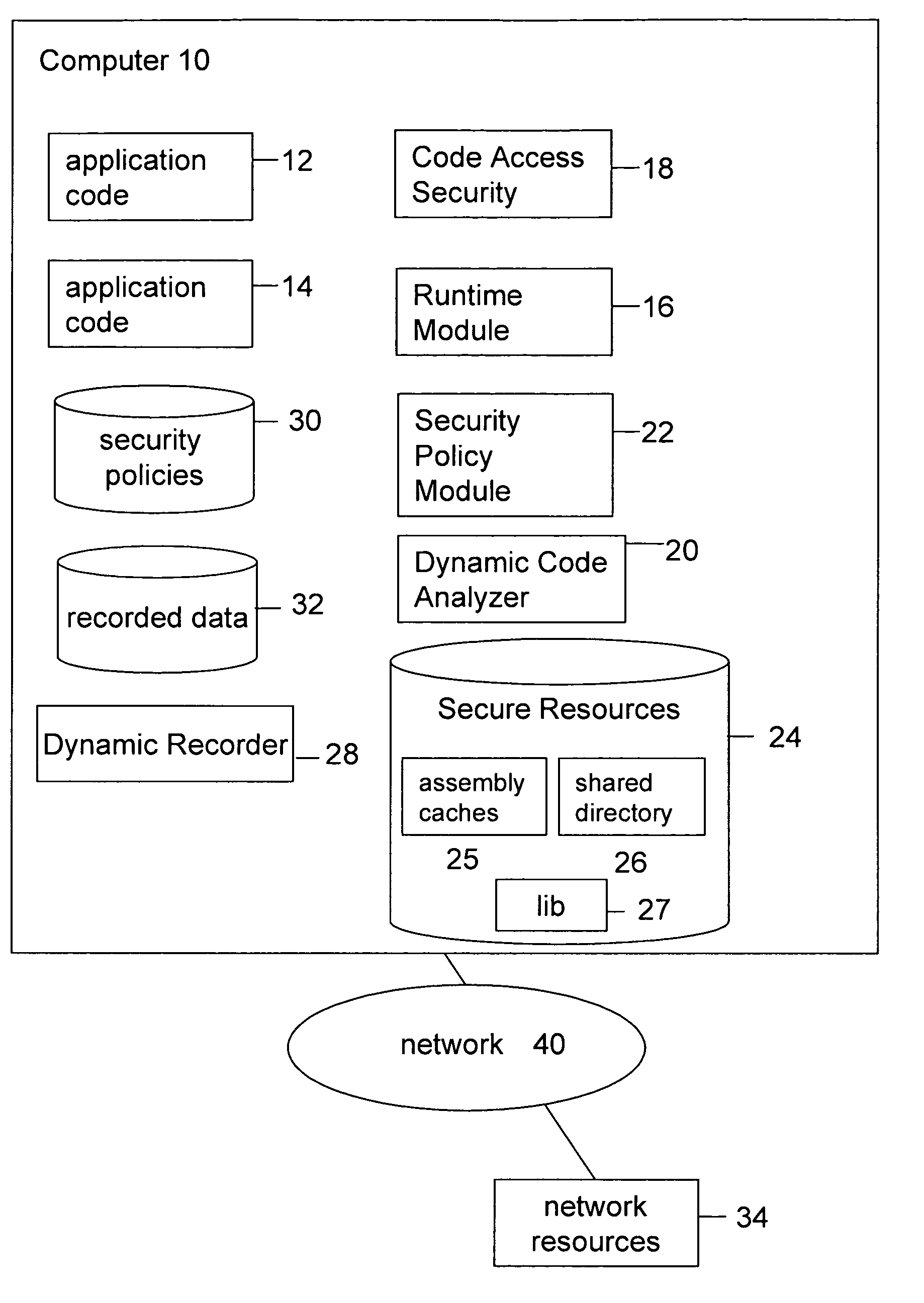
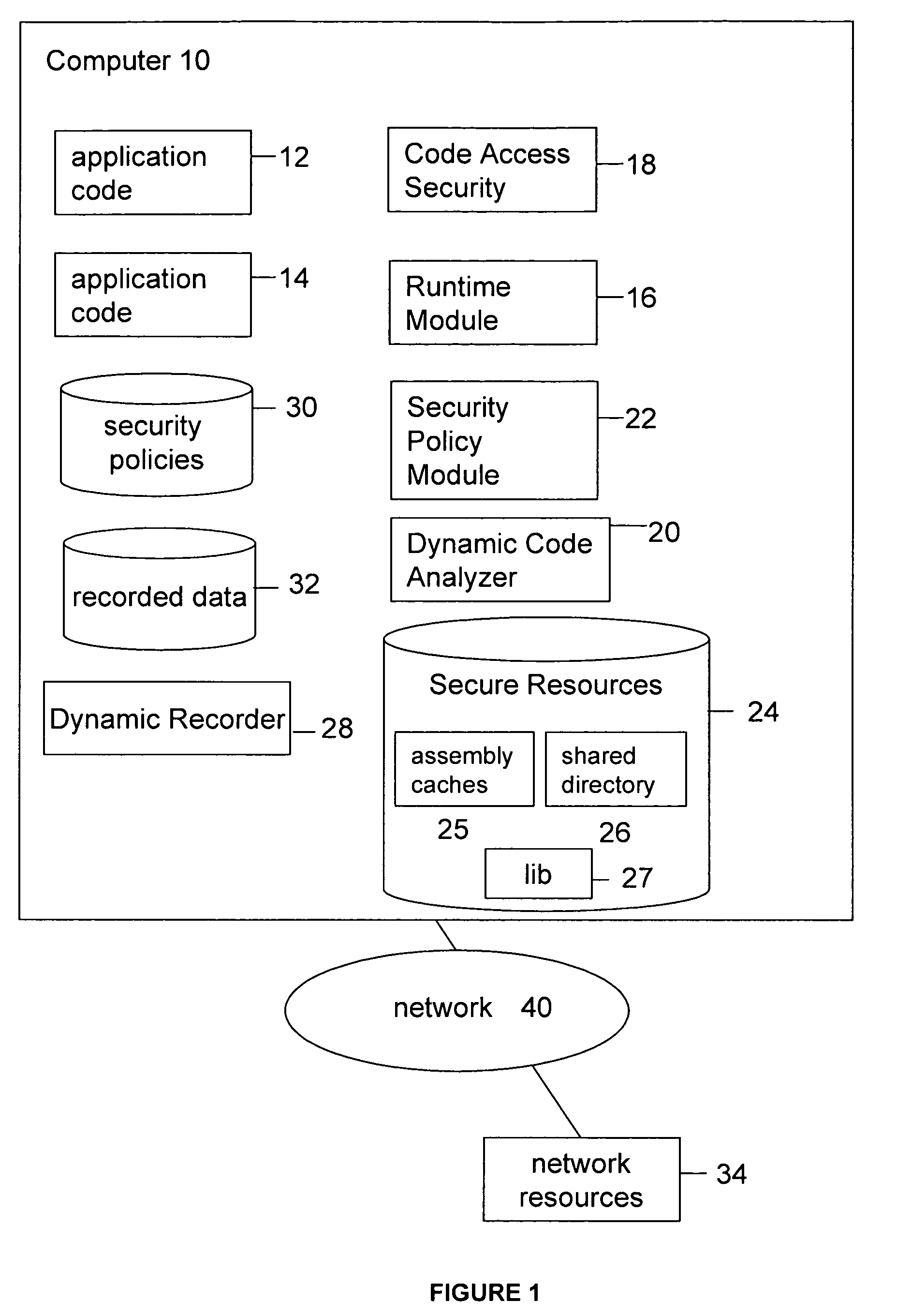
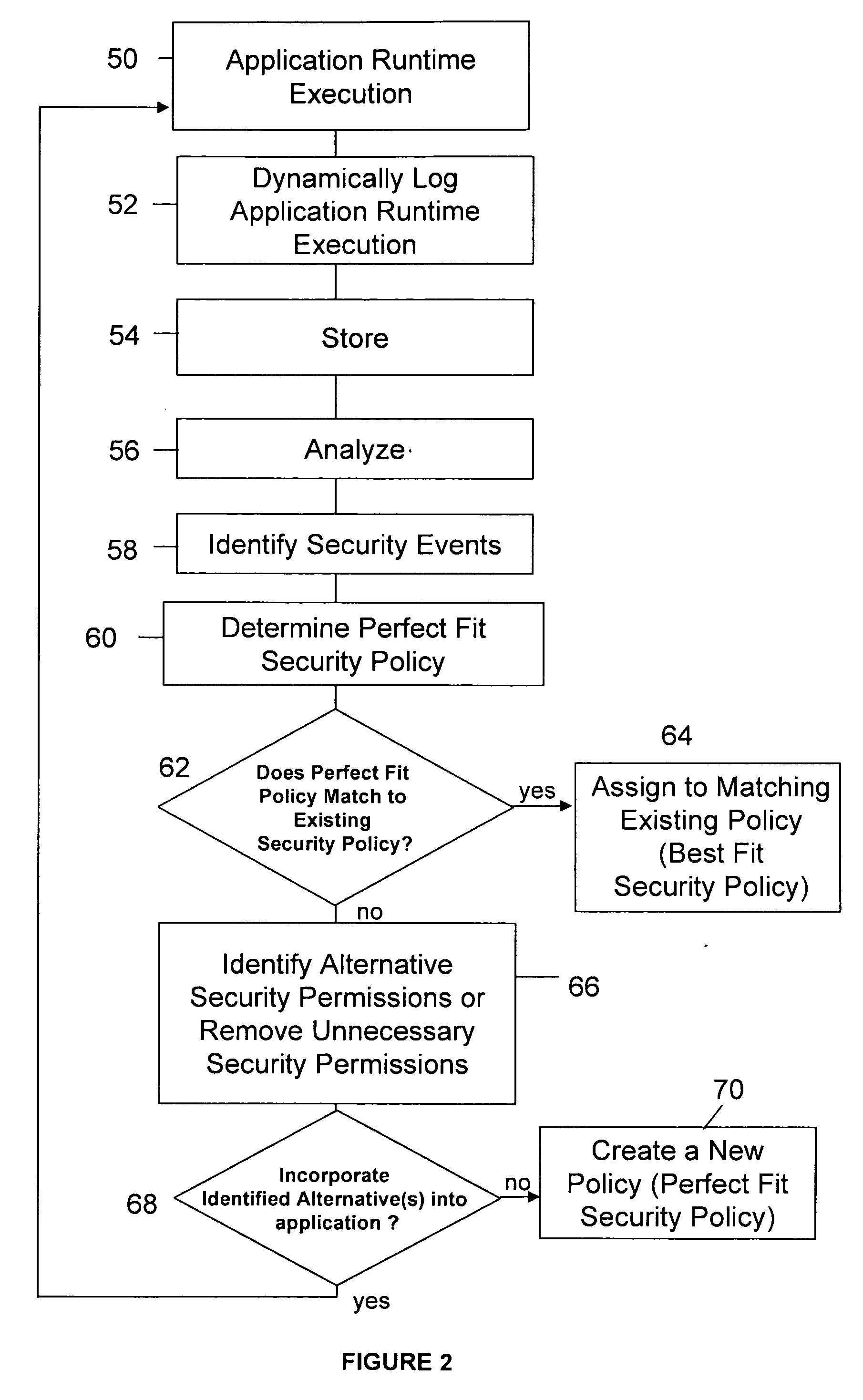
System and method for executing a permissions recorder analyzer
ActiveUS20070277222A1Avoid creatingAccurate and secure security policyMemory loss protectionError detection/correctionApplication softwareApplication security
System and method for accurately determining security policy for an application based on dynamic code analysis of application runtime execution(s). A dynamic recorder, dynamic code analyzer and security policy analyzer can evaluate and determine the security decisions and access to secure resources made during a security event within one or more executions of an application in order to identify an existing security policy that best matches an application's security needs. Security events may be analyzed to determine which security decisions and access to secure resources are necessary and which can be eliminated or replaced with alternative decisions or resources.
Owner:ORACLE INT CORP
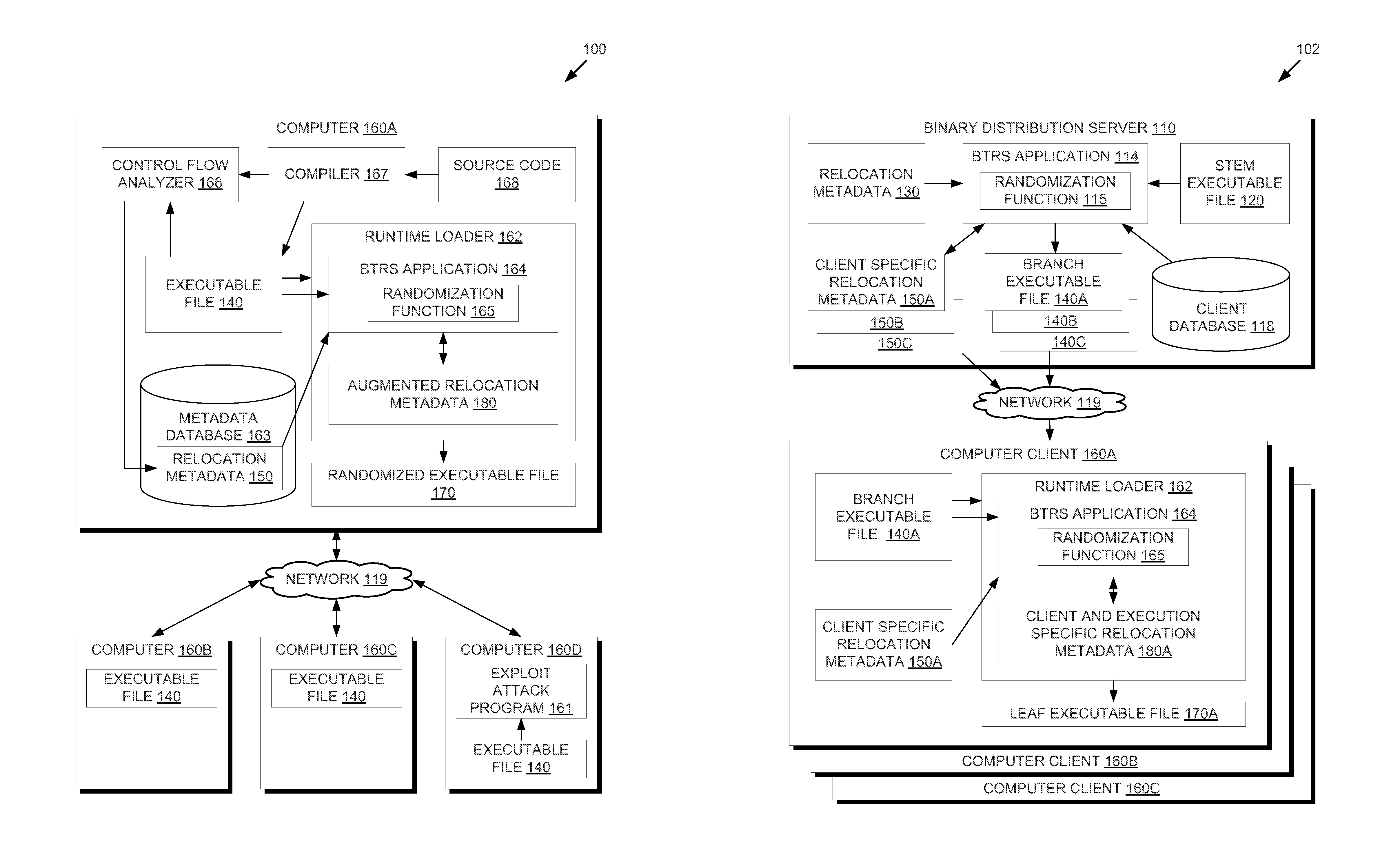
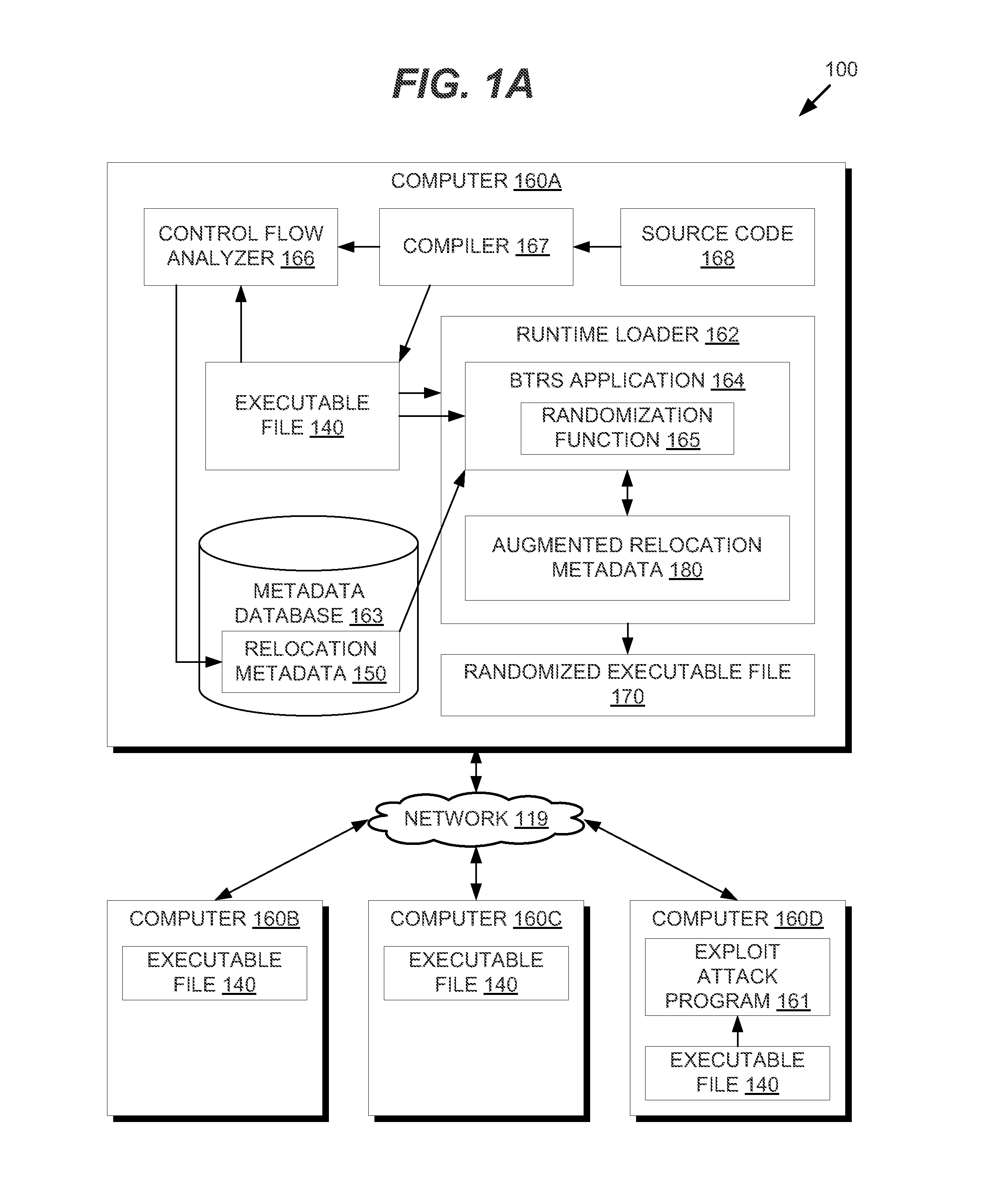
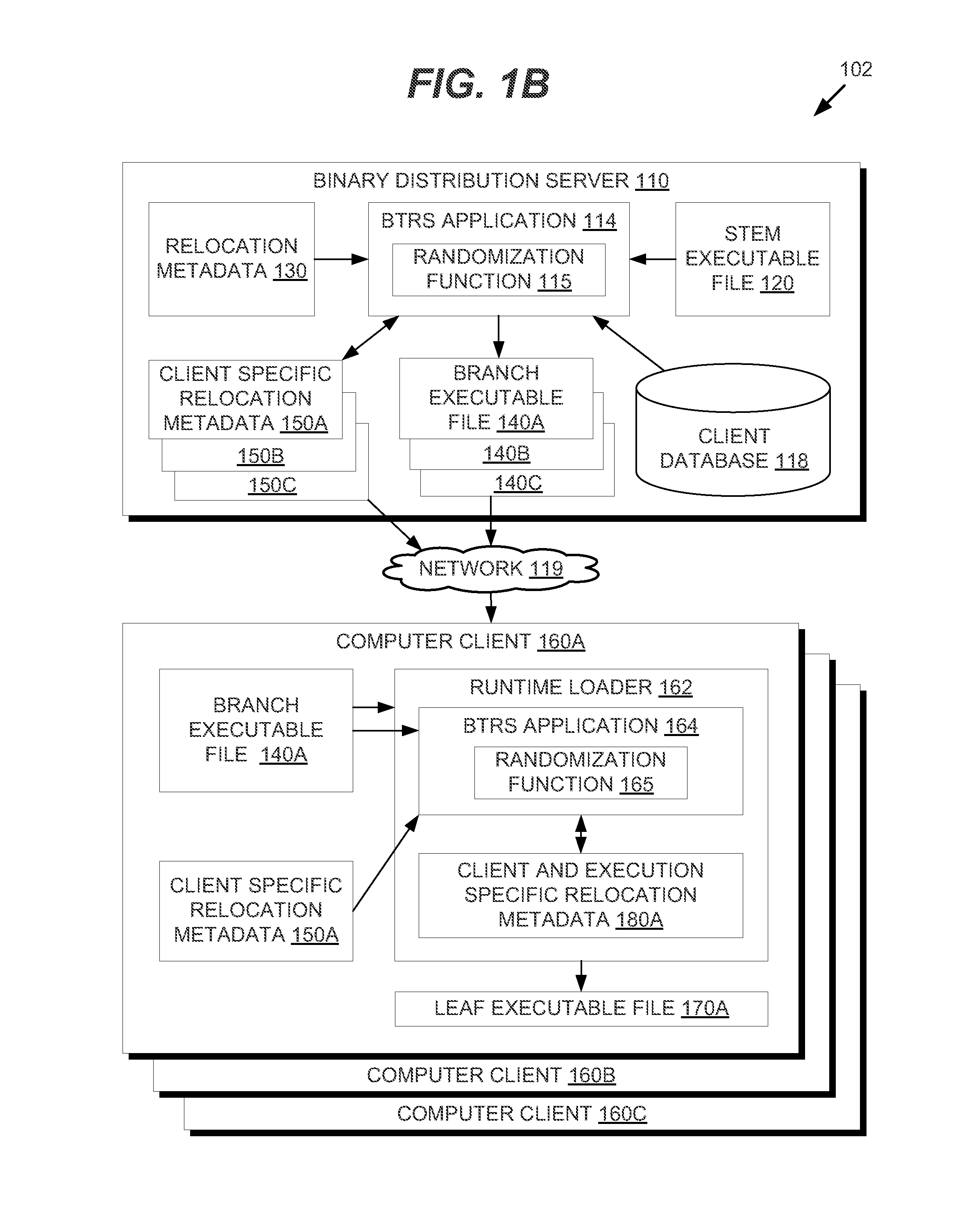
Binary Translation and Randomization System for Application Security
ActiveUS20150047049A1Digital data processing detailsAnalogue secracy/subscription systemsParallel computingExecution unit
In one embodiment, methods are described to provide a binary translation and randomization system. Relocation metadata is received, which comprises, for each of a plurality of execution units in an executable file, a mapping from the executable file into an address space range. For at least one of the plurality of execution units, the mapping is modified to replace instructions within the address space range with a relocated copy of the instructions at a randomly located address space range. An order of the plurality of execution units may thus be modified. An image is generated from the executable file using the relocation metadata, and an execution of the image is caused. The randomization may be carried out in two passes to provide executable files that are uniquely randomized for each computer and for each execution.
Owner:CISCO TECH INC
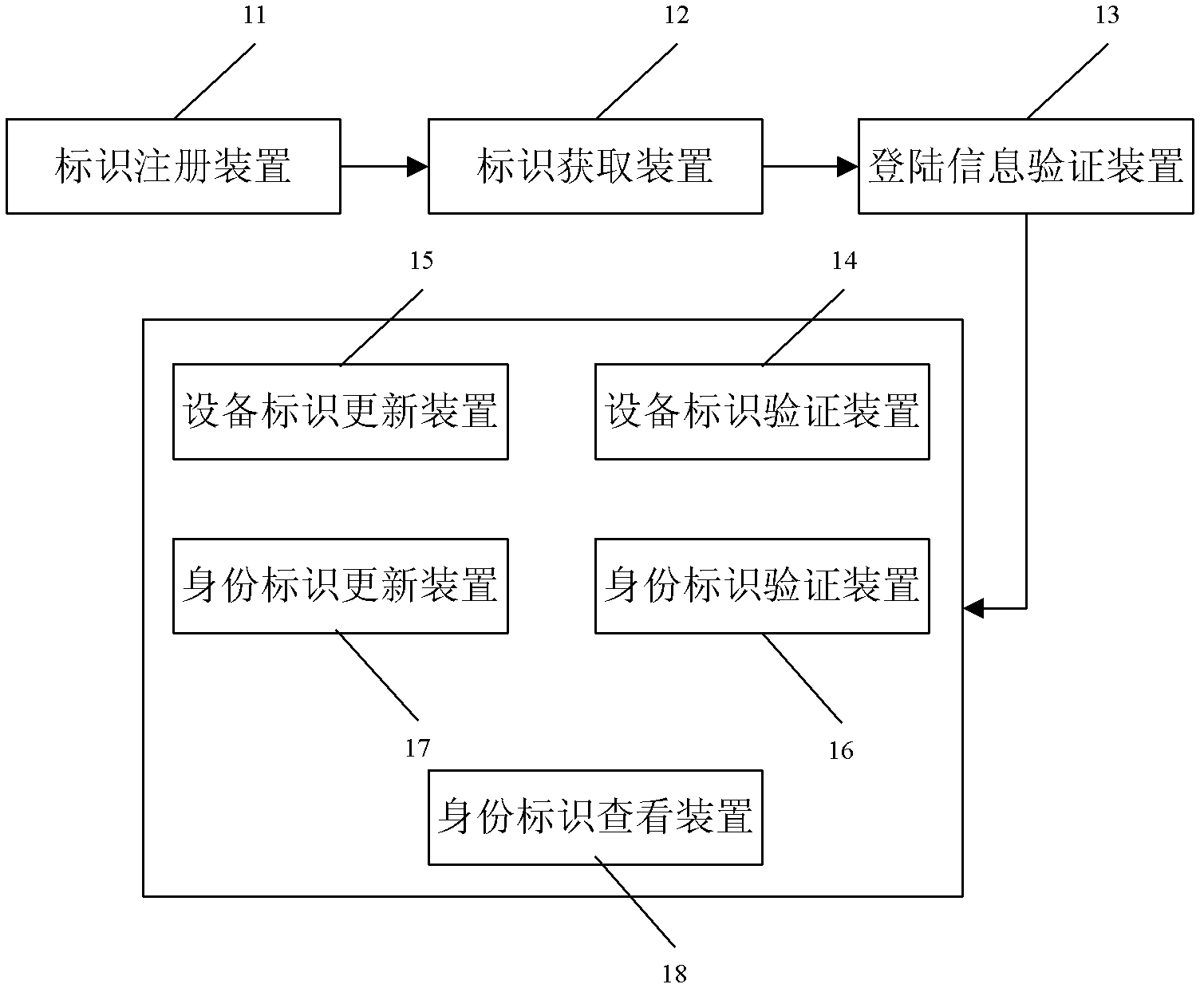
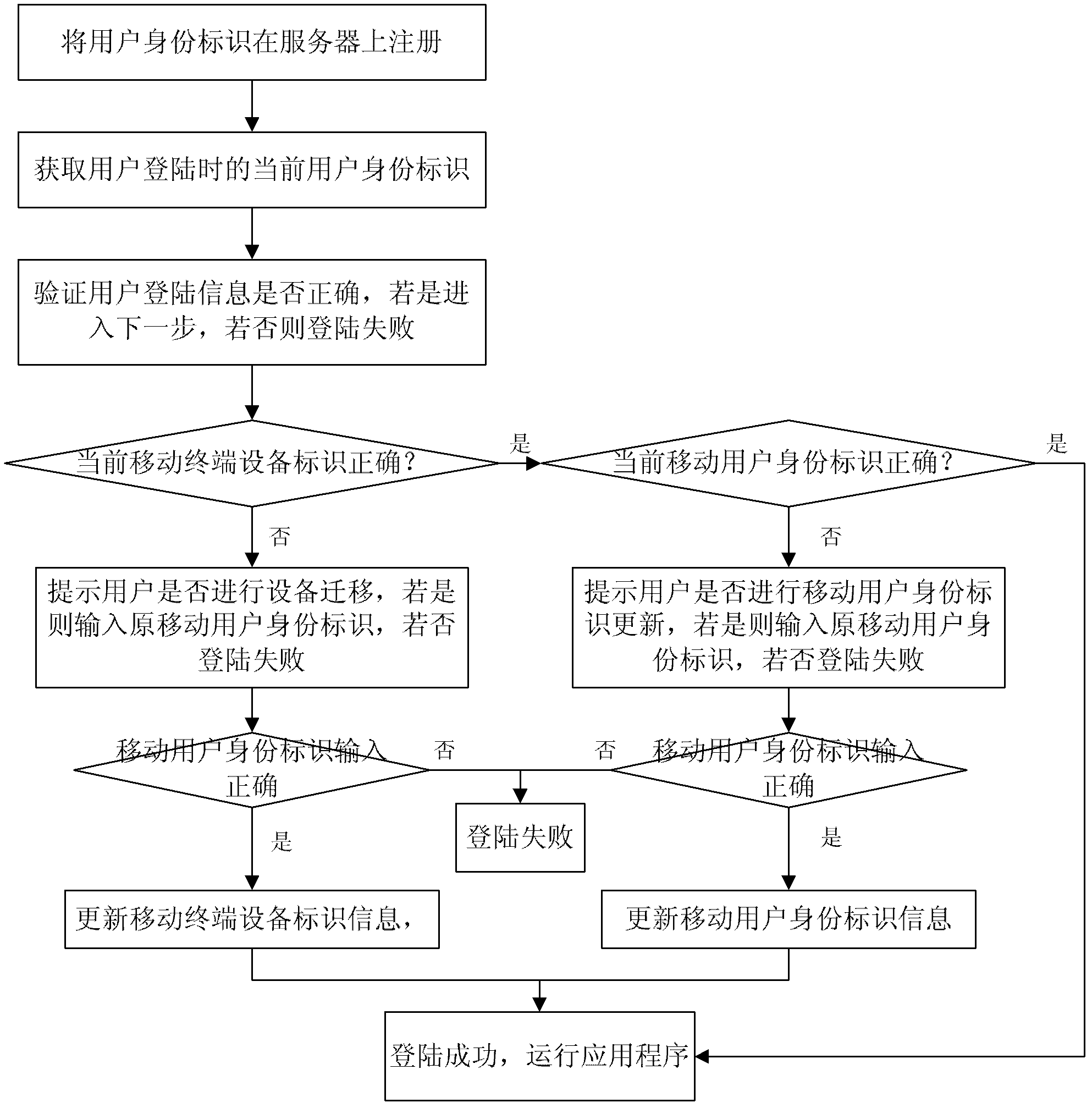
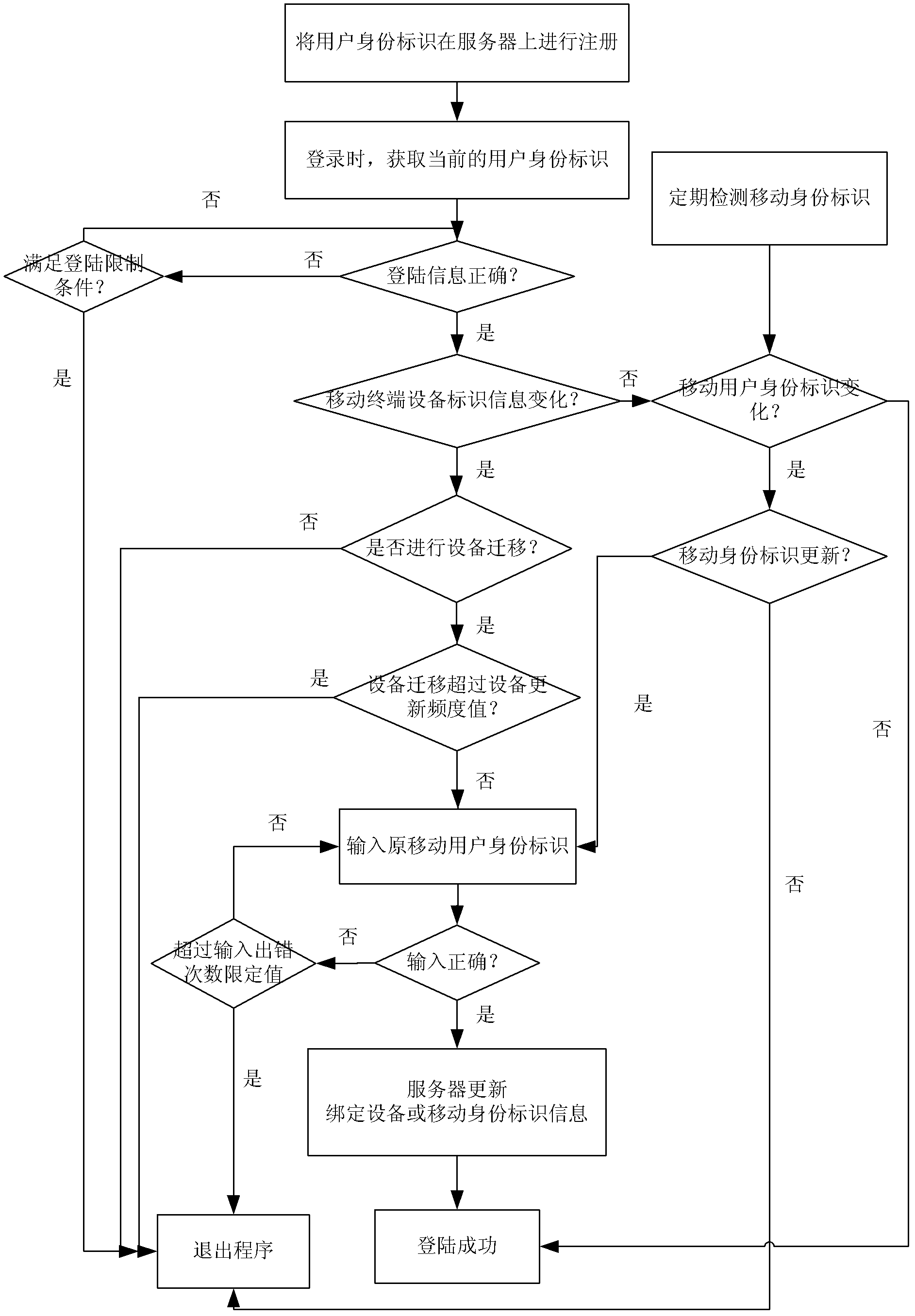
Security protection method and security protection system for mobile terminal application
ActiveCN103188668AImprove securityImprove convenienceSecurity arrangementTerminal equipmentApplication security
The invention discloses a security protection method and a security protection system for a mobile terminal application, and belongs to the field of terminal application security protection. The method comprises the steps that a mobile terminal equipment identity, a mobile subscriber identity and subscriber login information are sent to a server for registration during a registration course, and bound to form a subscriber identity; login information, the mobile terminal equipment identity and the mobile subscriber identity in the current subscriber identity are compared with the original subscriber identity in the server sequentially during a login course to determine information required to be updated; and updating is performed by authentication of the original mobile subscriber identity finally. According to the method and the system, a mobile terminal equipment information binding method is adopted, so that the security problems due to the fact that terminal equipment is updated, an SIM (Subscriber Identity Module) card number is replaced or the subscriber login information is stolen under the condition of single registration of a subscriber are solved, and the security and conveniences of the terminal application are improved.
Owner:方正国际软件(北京)有限公司
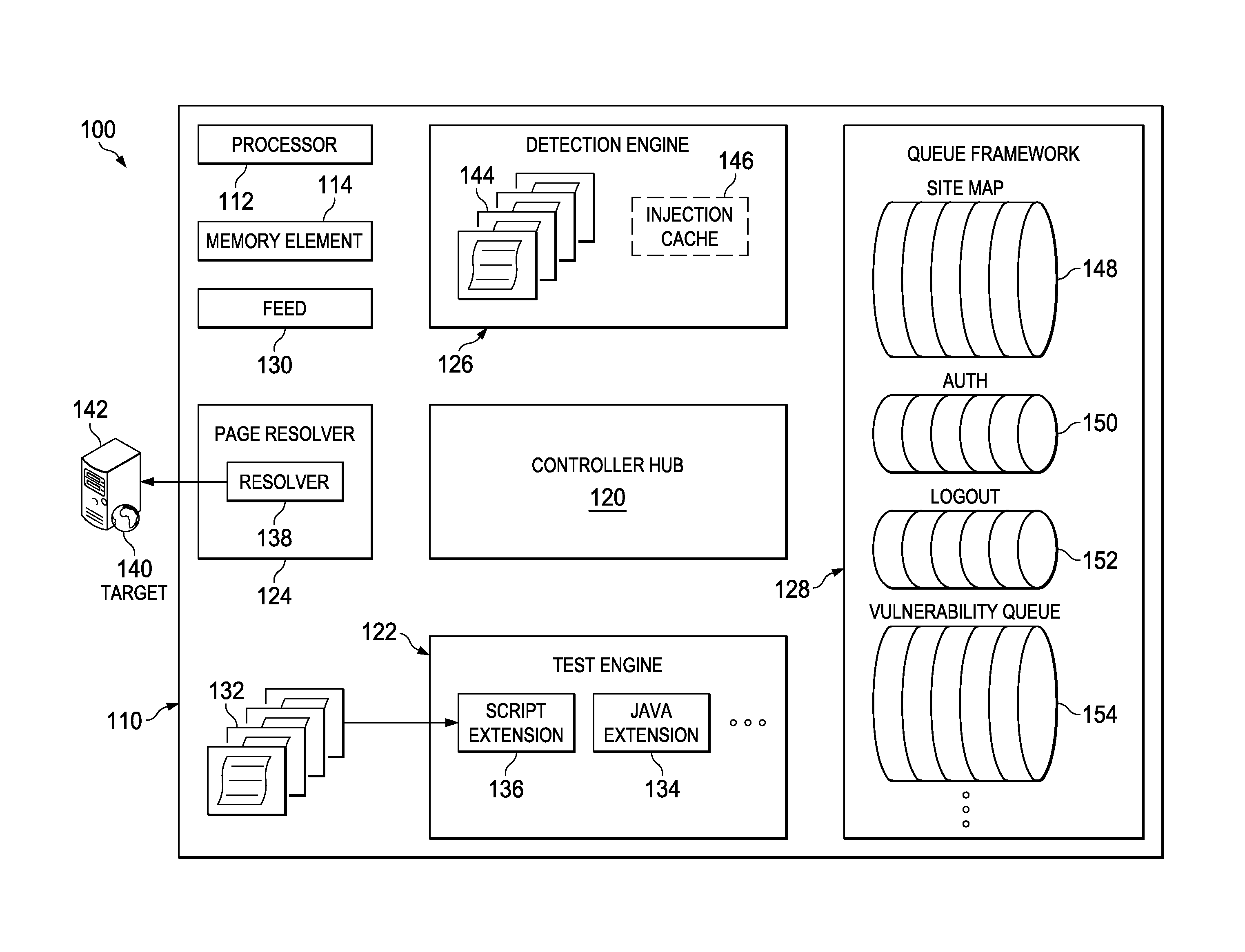
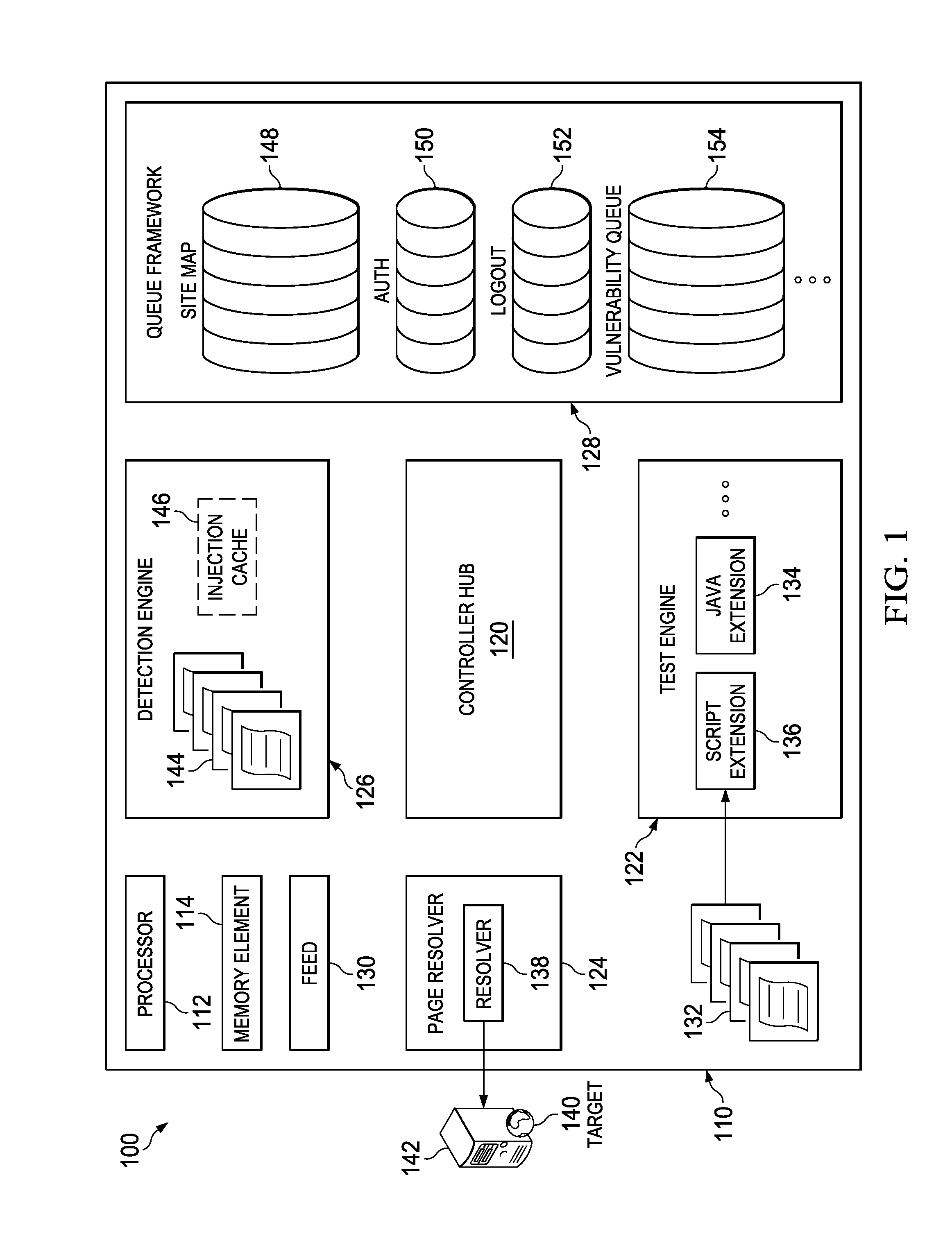
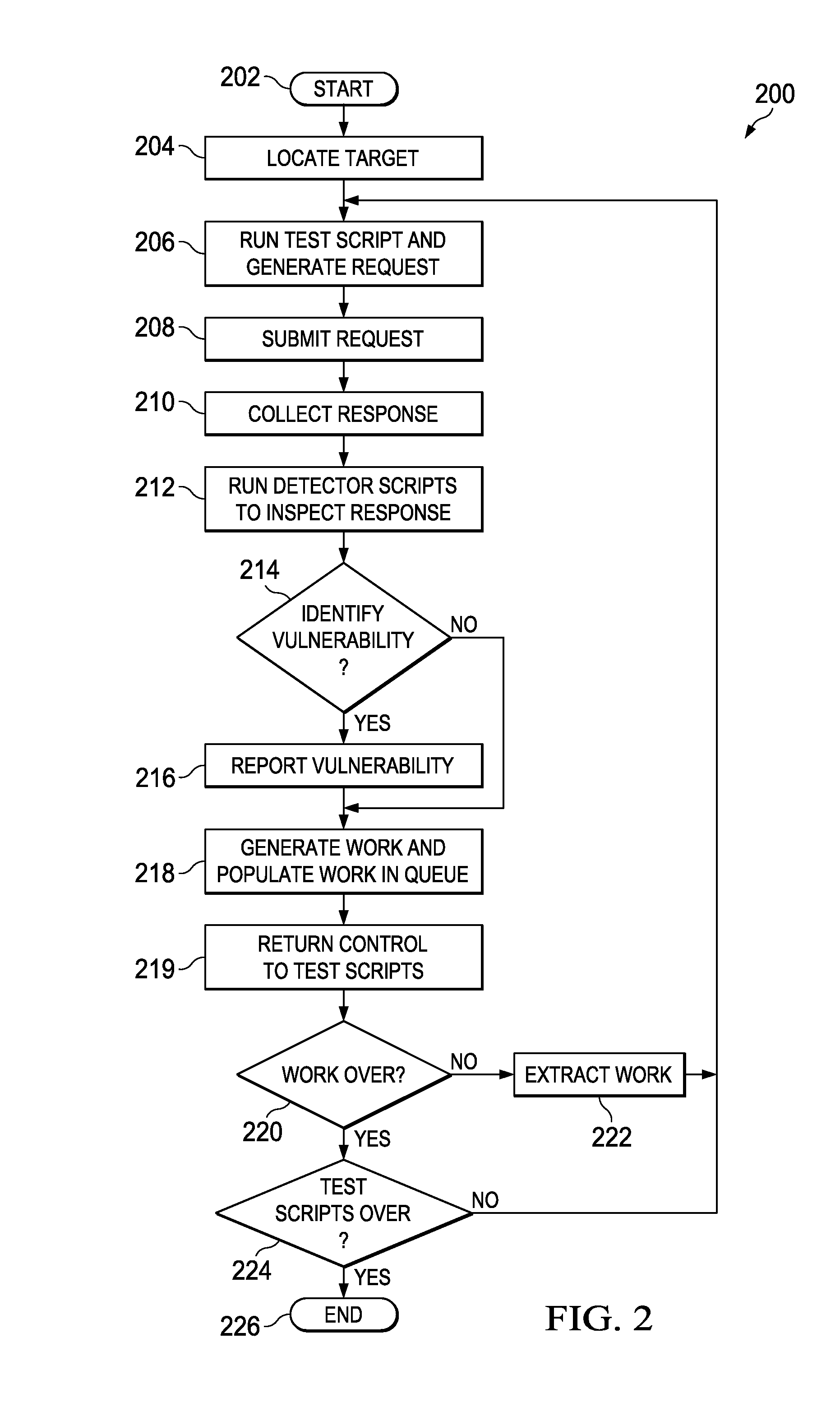
System and method for application security assessment
ActiveUS20130247204A1Memory loss protectionError detection/correctionTest scriptApplication security
A system and method in one embodiment includes modules for running a test script to generate a request to a target application, receiving a response from the target application, and running a detector script to inspect the response for a vulnerability. More specific embodiments include a target web site, populating a work in a queue, where the work corresponds to content in the response, and running a second test script or detector script to generate a follow-up request to the application if the vulnerability has been identified in the response. Other embodiments include extracting the work from the queue, and running a second test script corresponding to the extracted work. Other embodiments include storing an injection in an injection cache, de-registering the injection from the injection cache if it is identified in the response, and re-crawling the application, if the injection has not been de-registered from the injection cache.
Owner:MCAFEE LLC
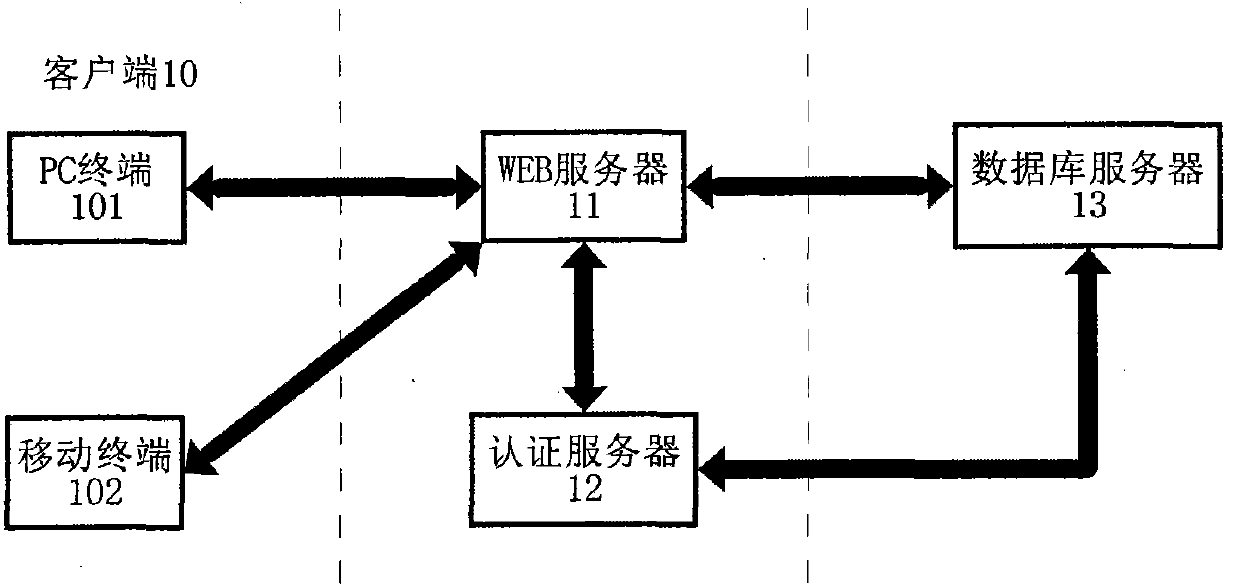
Method and system for improving SaaS application security
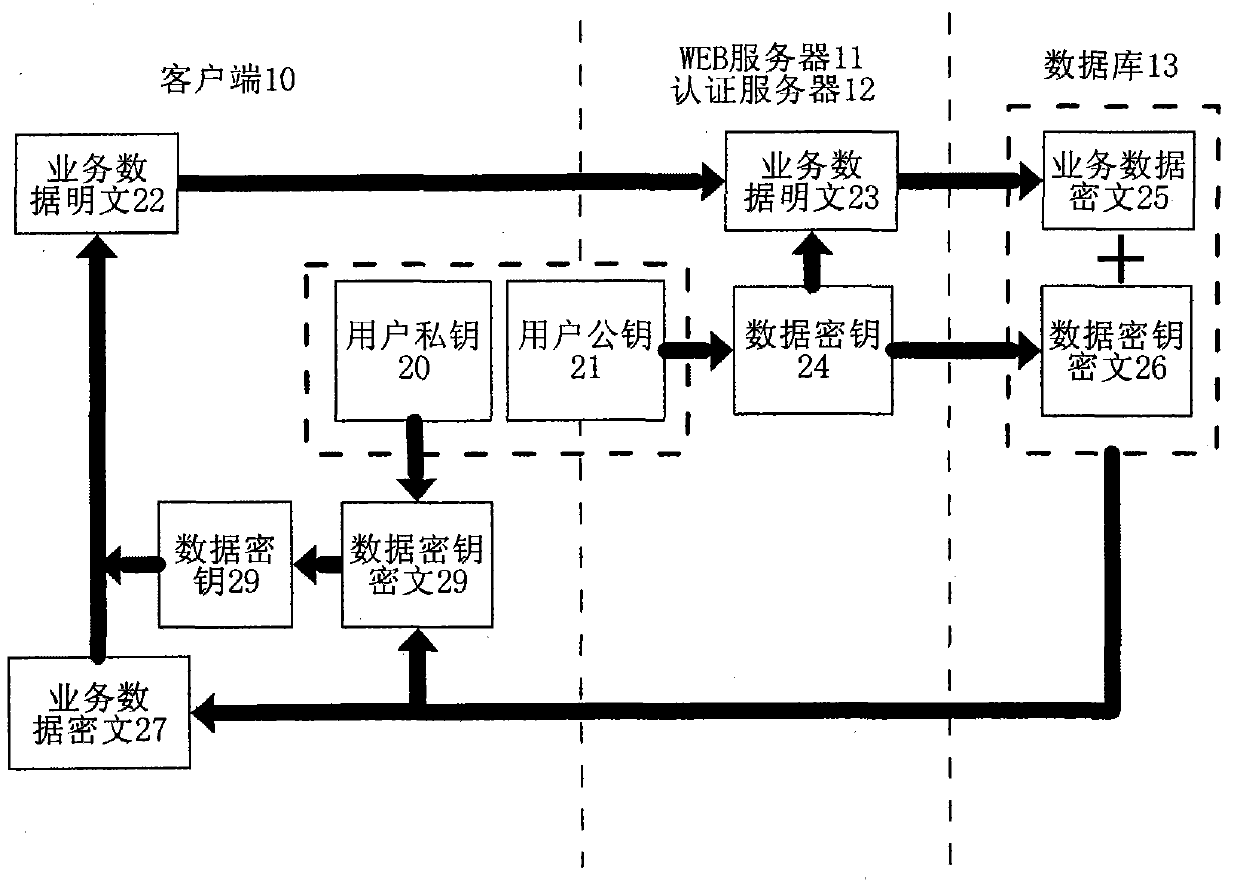
InactiveCN101771699AImprove securityPrevent leakageEncryption apparatus with shift registers/memoriesPublic key for secure communicationWeb serviceCiphertext
The invention provides a method and a system for improving SaaS application security. The encryption method includes that a public password belonging to the client is set up; a data password used for encrypting business data for the client is randomly generated when the business data of the client is saved; the data password is used as the password to encrypt the business data according to a symmetrical cryptographic algorithm; the business data are encrypted through the public password and according to an unsymmetrical cryptographic algorithm; the business data cryptograph and the data password cryptograph are saved in a server; the client gets the cryptograph saved in the server after successfully decrypting the challenge message of the server with the private password; the client decrypts the data password cryptograph with the private password and further decrypts the business data according to the symmetrical cryptographic algorithm. The system includes a WEB server, an authentication server and a database server which can transmit data each other. The invention effectively prevents the administrator from reveal and malicious use of the data password.
Owner:SOUTH CHINA UNIV OF TECH +1
Mobile application access control list security system
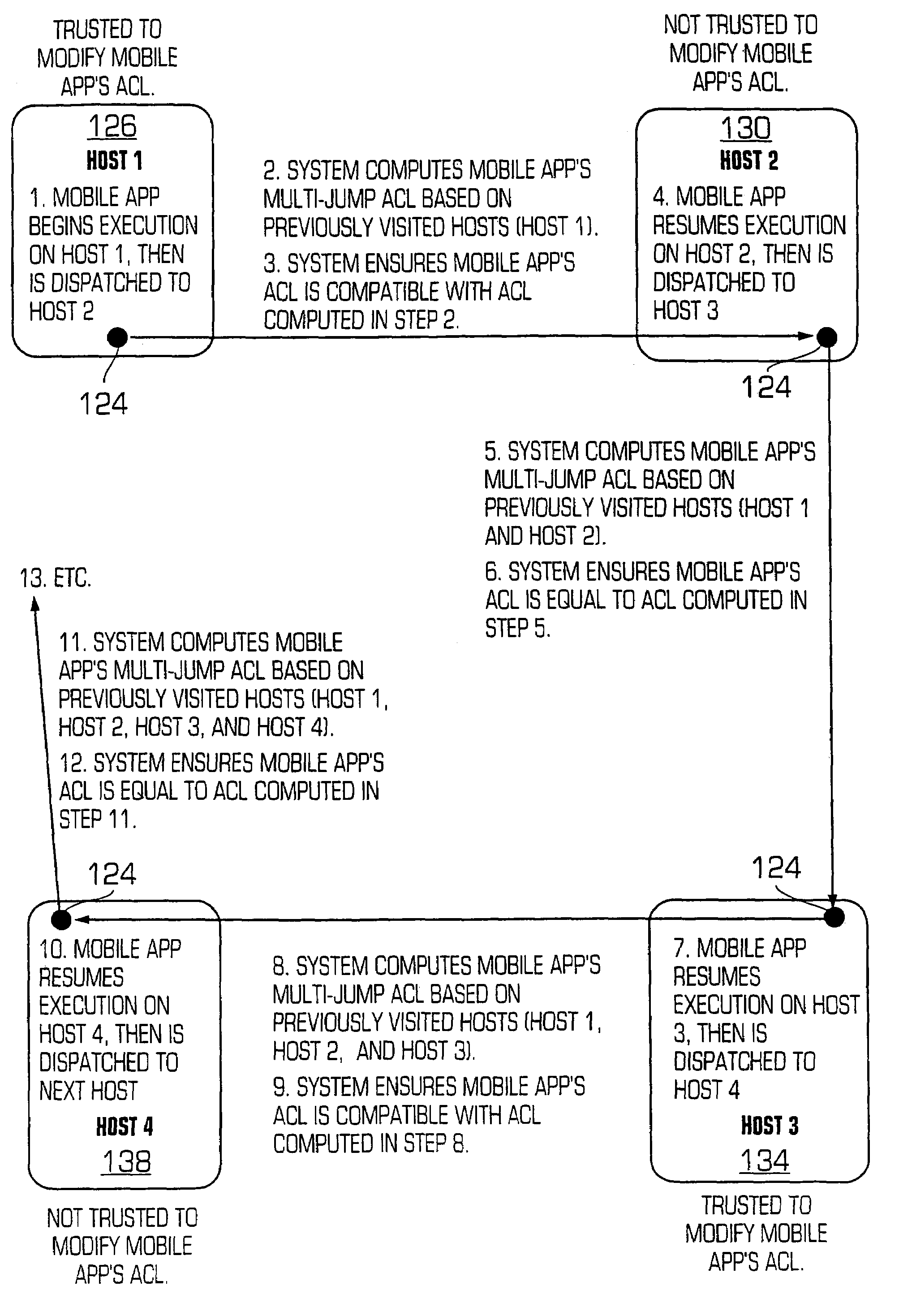
InactiveUS7065783B2Ensure safetyDigital data processing detailsUnauthorized memory use protectionComputer compatibilityApplication security
A mobile application security system and method, in the preferred embodiment, ensures the integrity of a mobile application's multi-jump access control list (ACL) by either (a) checking the compatibility of a mobile application's multi-jump ACL with a known accurate multi-jump ACL, or (b) overwriting a mobile application's multi-jump ACL with an ACL which is known to be accurate, depending on whether the host dispatching the mobile application is trusted or not trusted to modify a mobile application's multi-jump ACL, respectively.
Owner:ARAMIRA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com