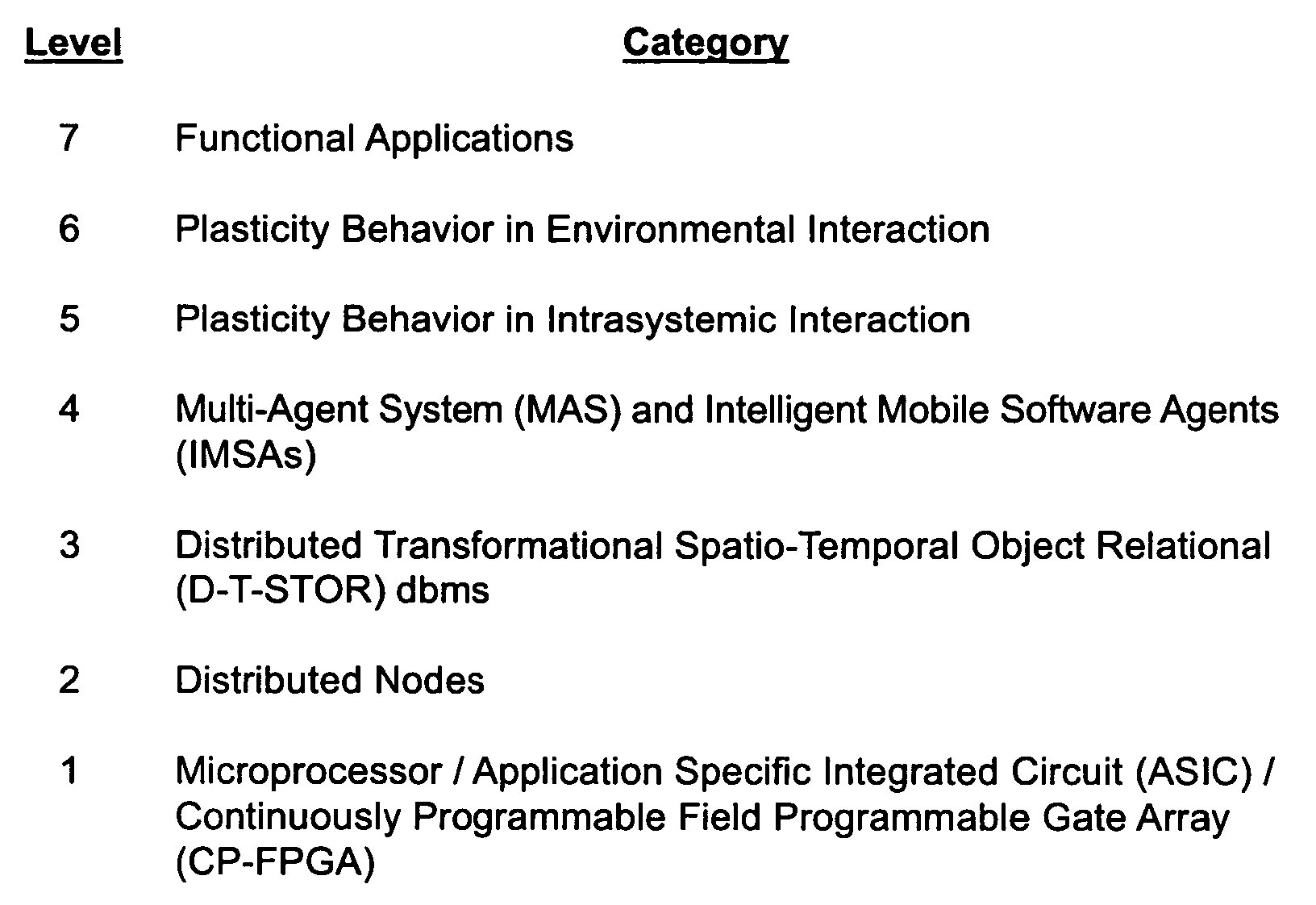
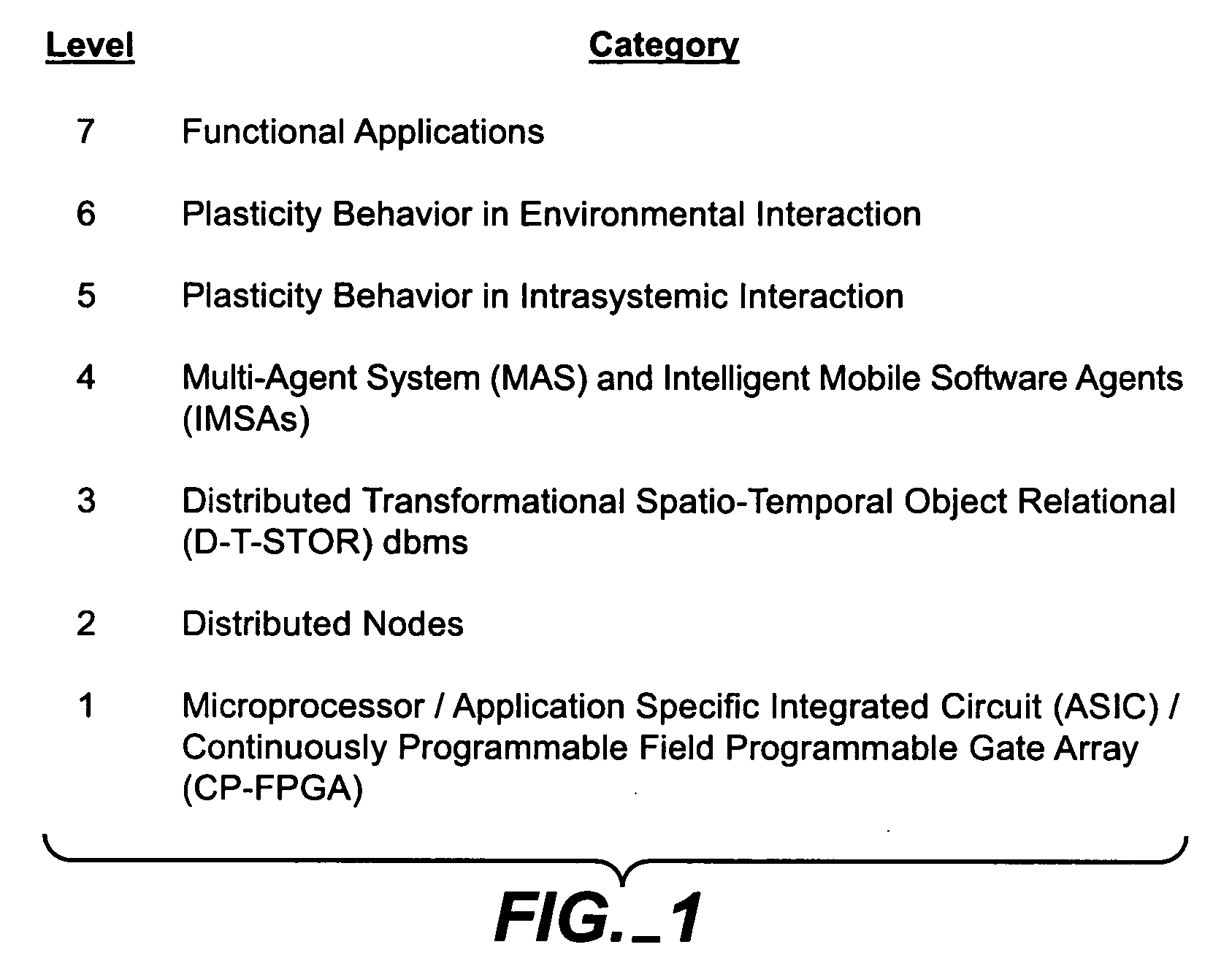
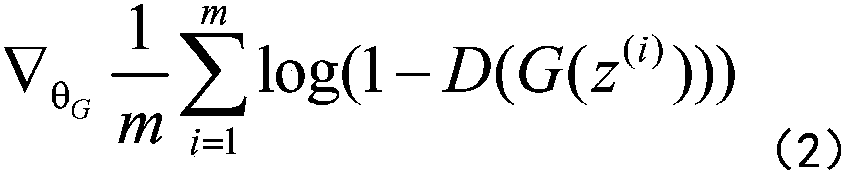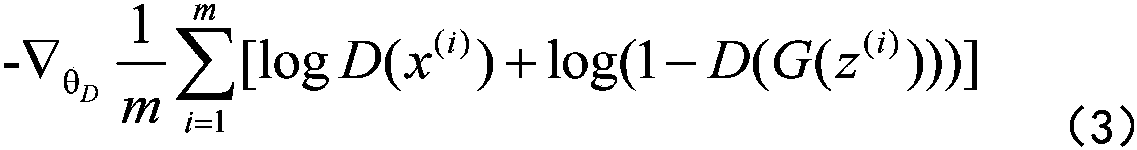Patents
Literature
2158 results about "Complex network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
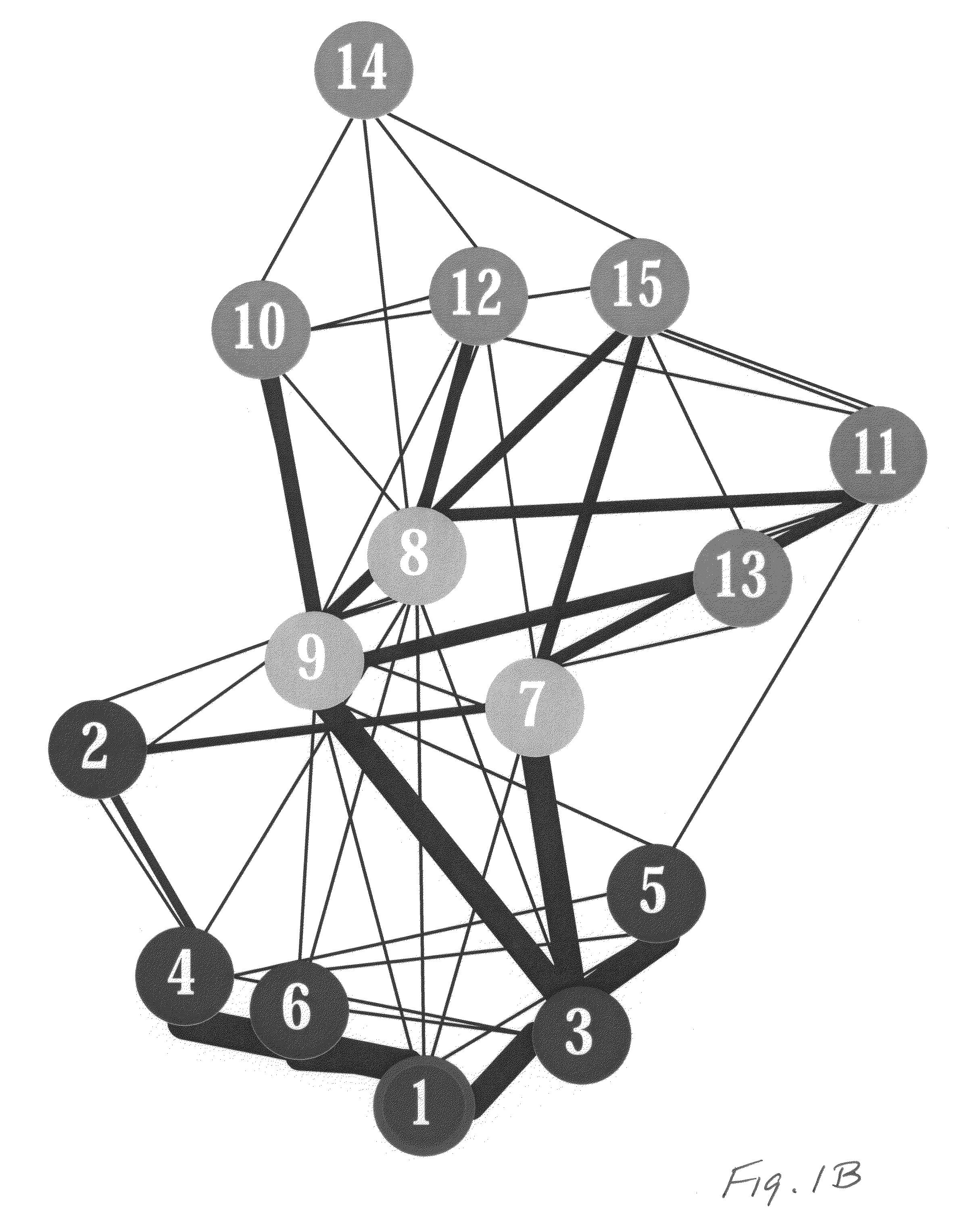
In the context of network theory, a complex network is a graph (network) with non-trivial topological features—features that do not occur in simple networks such as lattices or random graphs but often occur in graphs modelling of real systems. The study of complex networks is a young and active area of scientific research (since 2000) inspired largely by the empirical study of real-world networks such as computer networks, technological networks, brain networks and social networks.
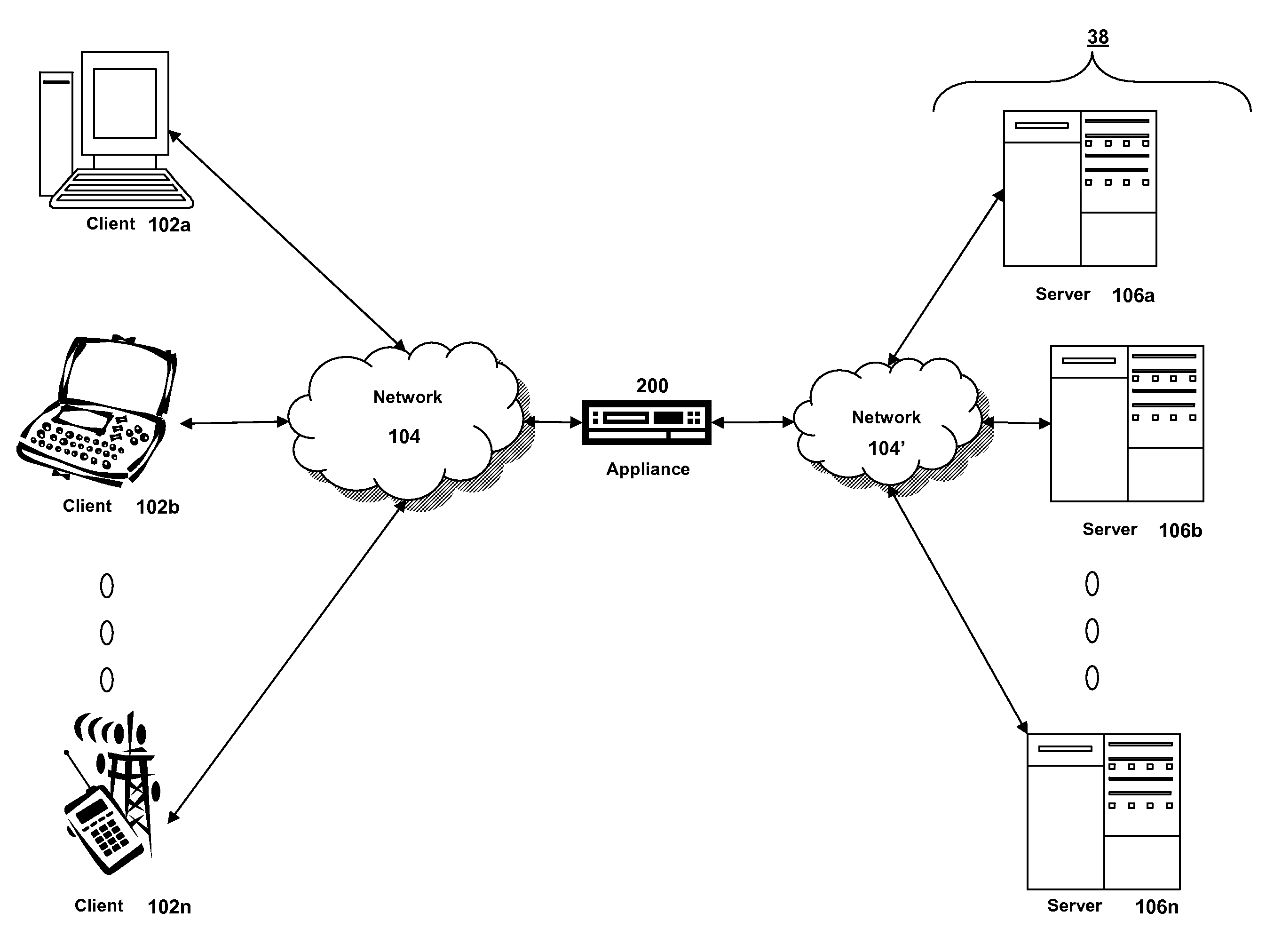
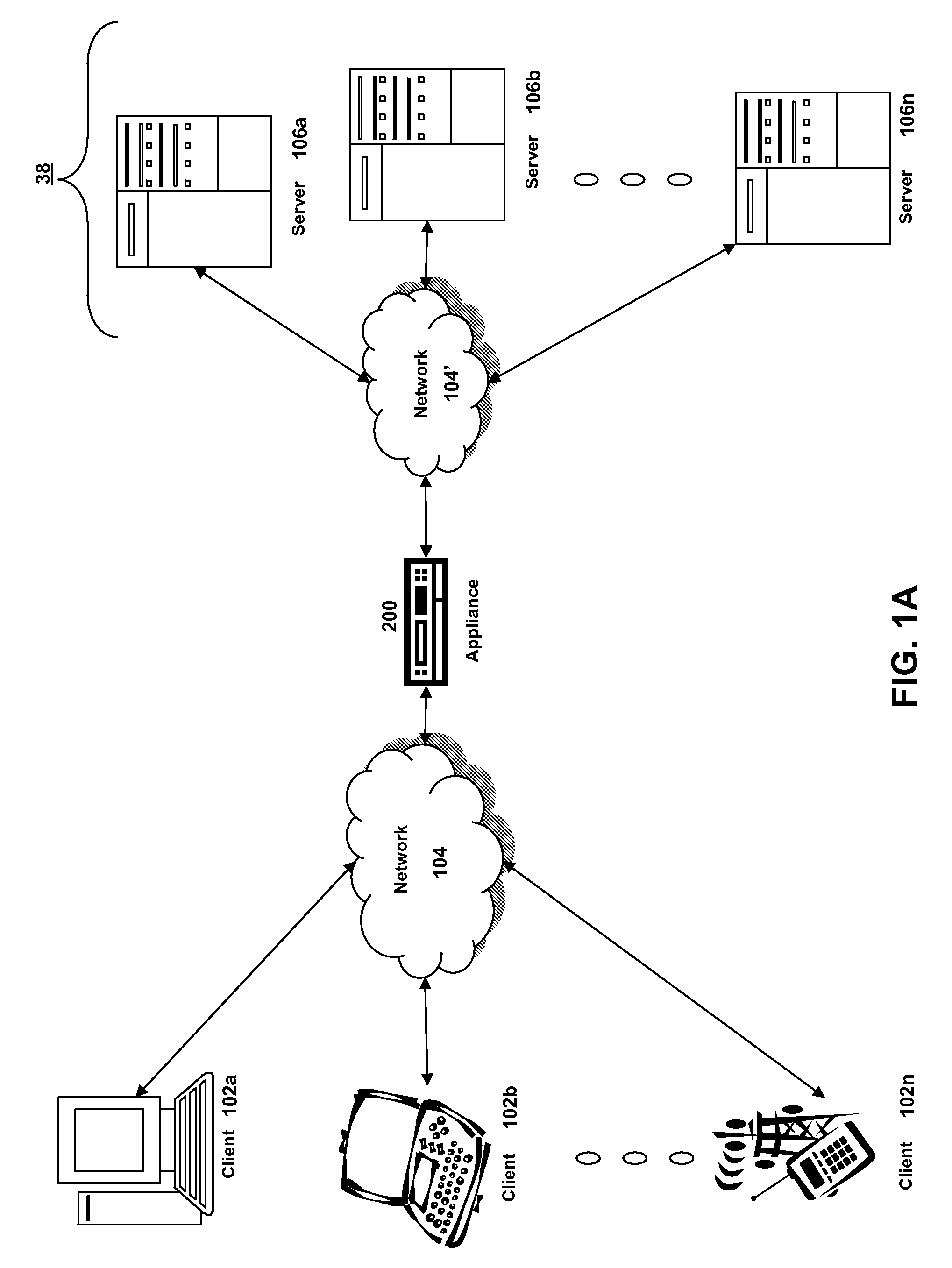
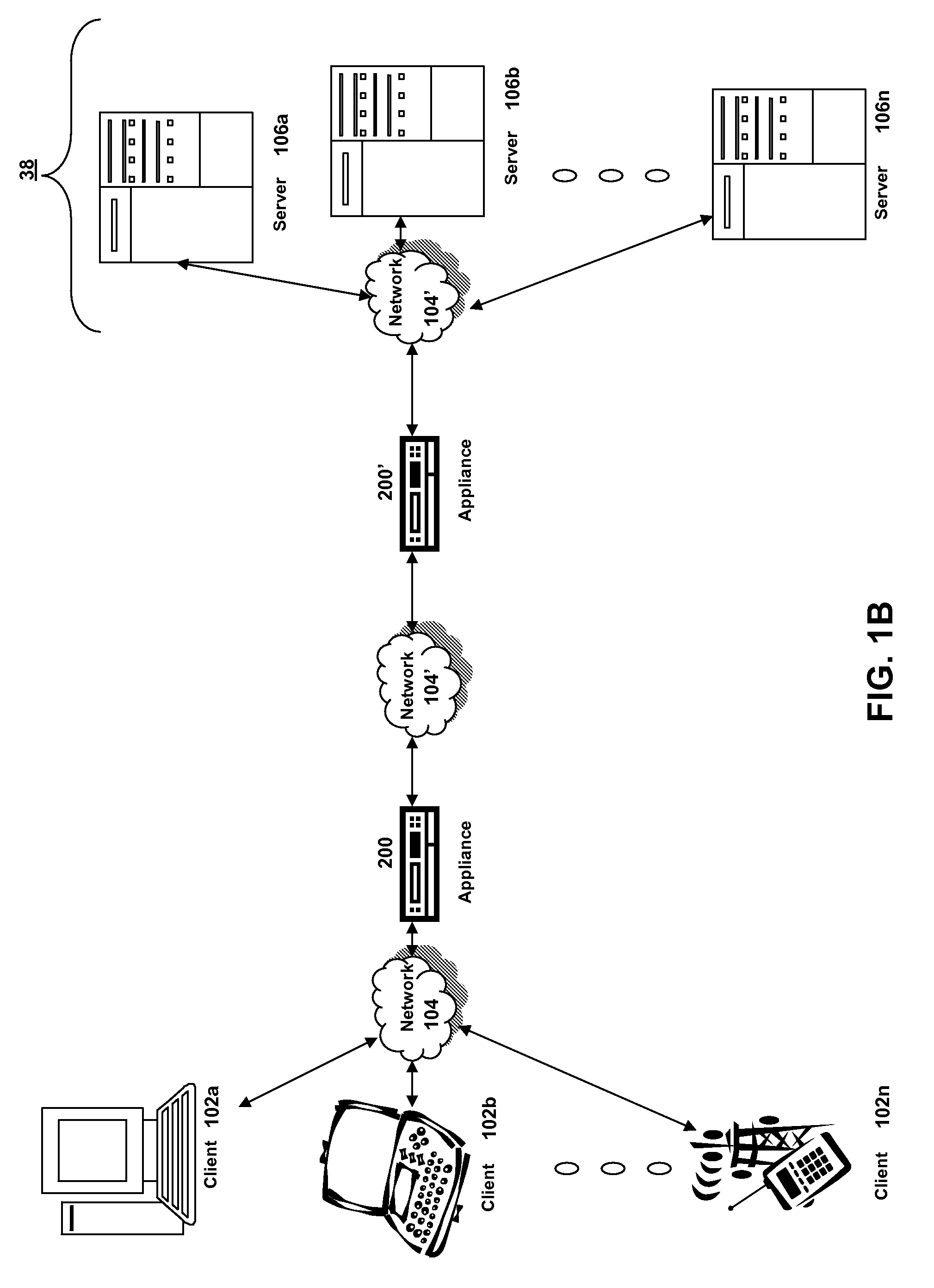
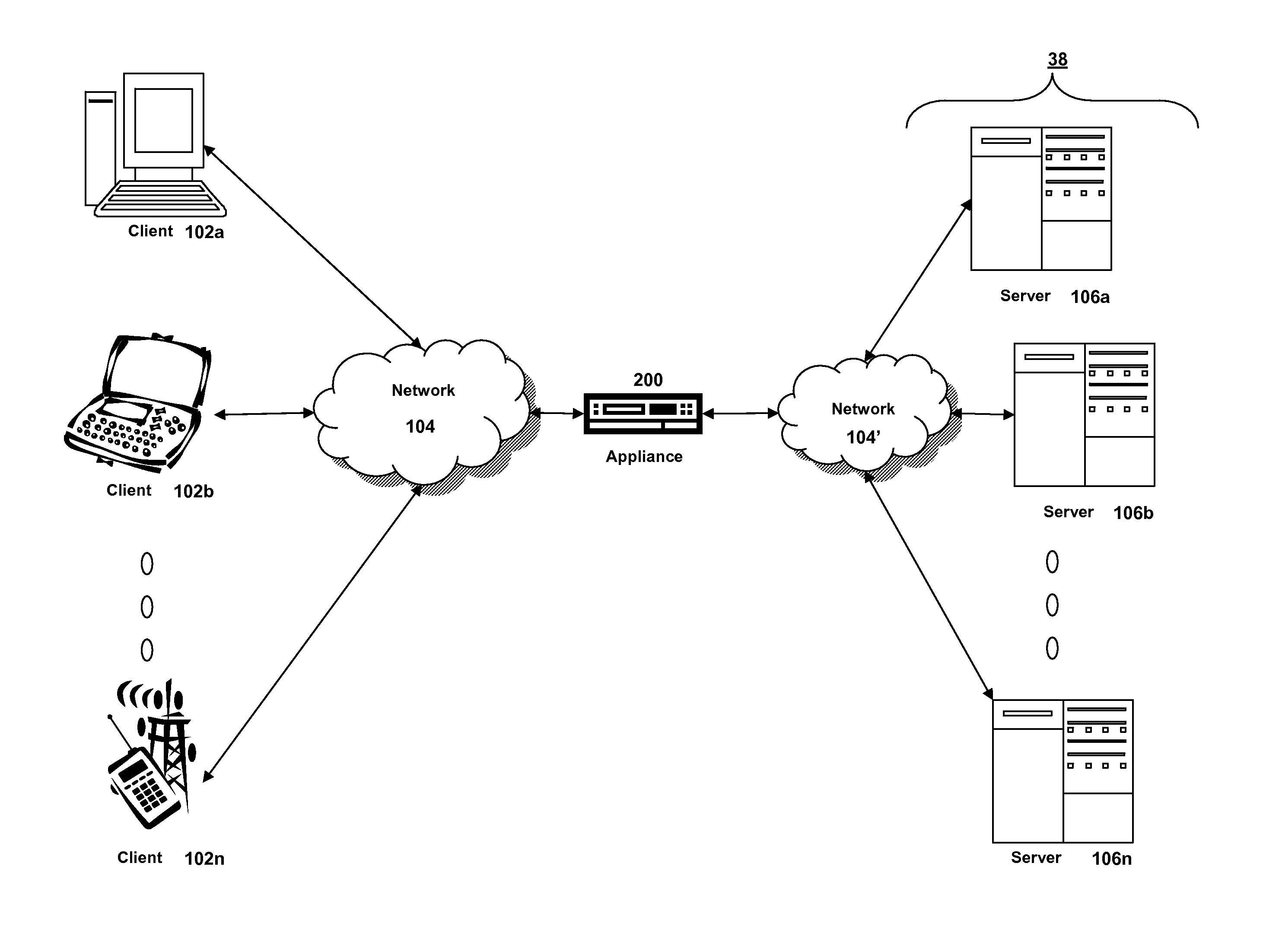
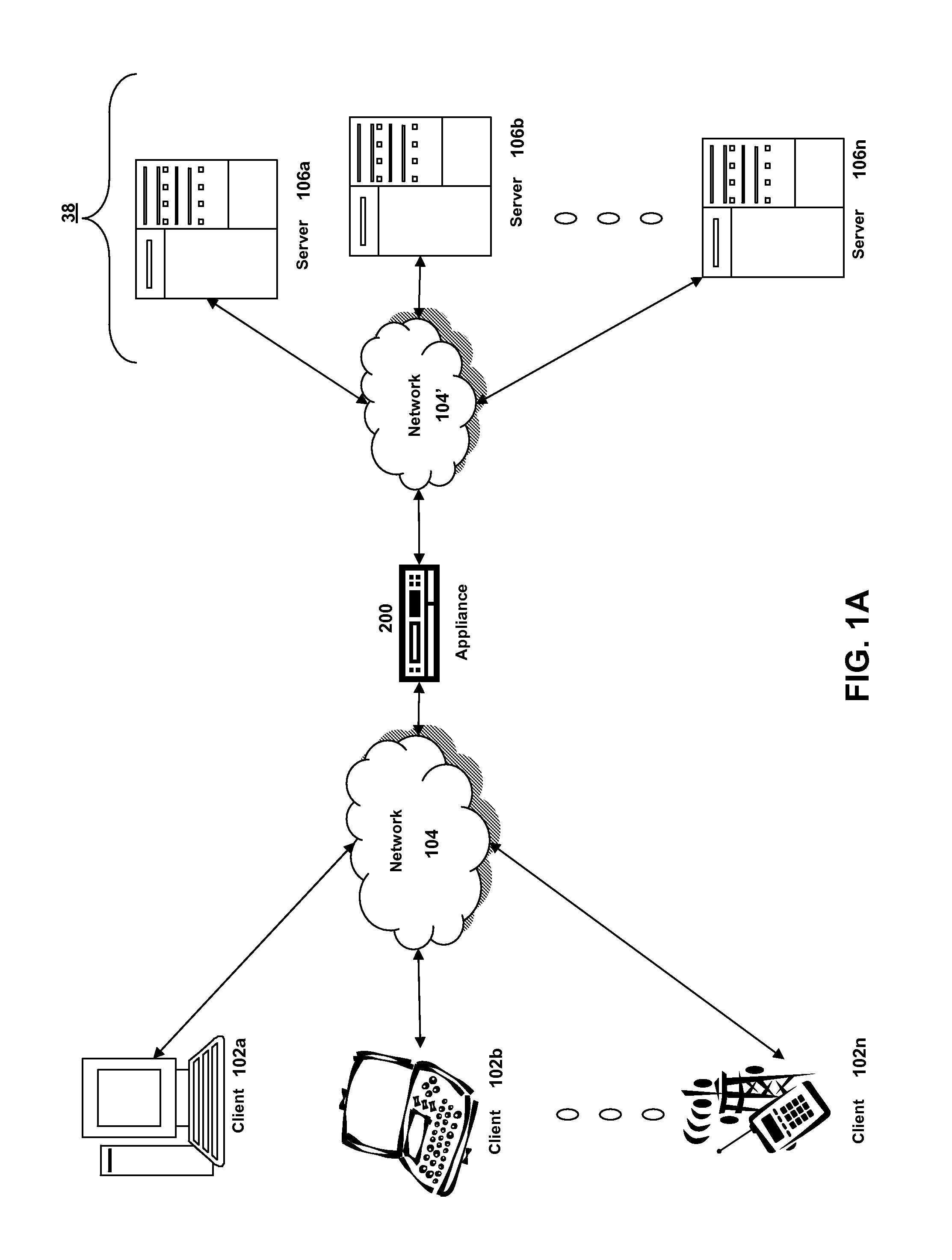
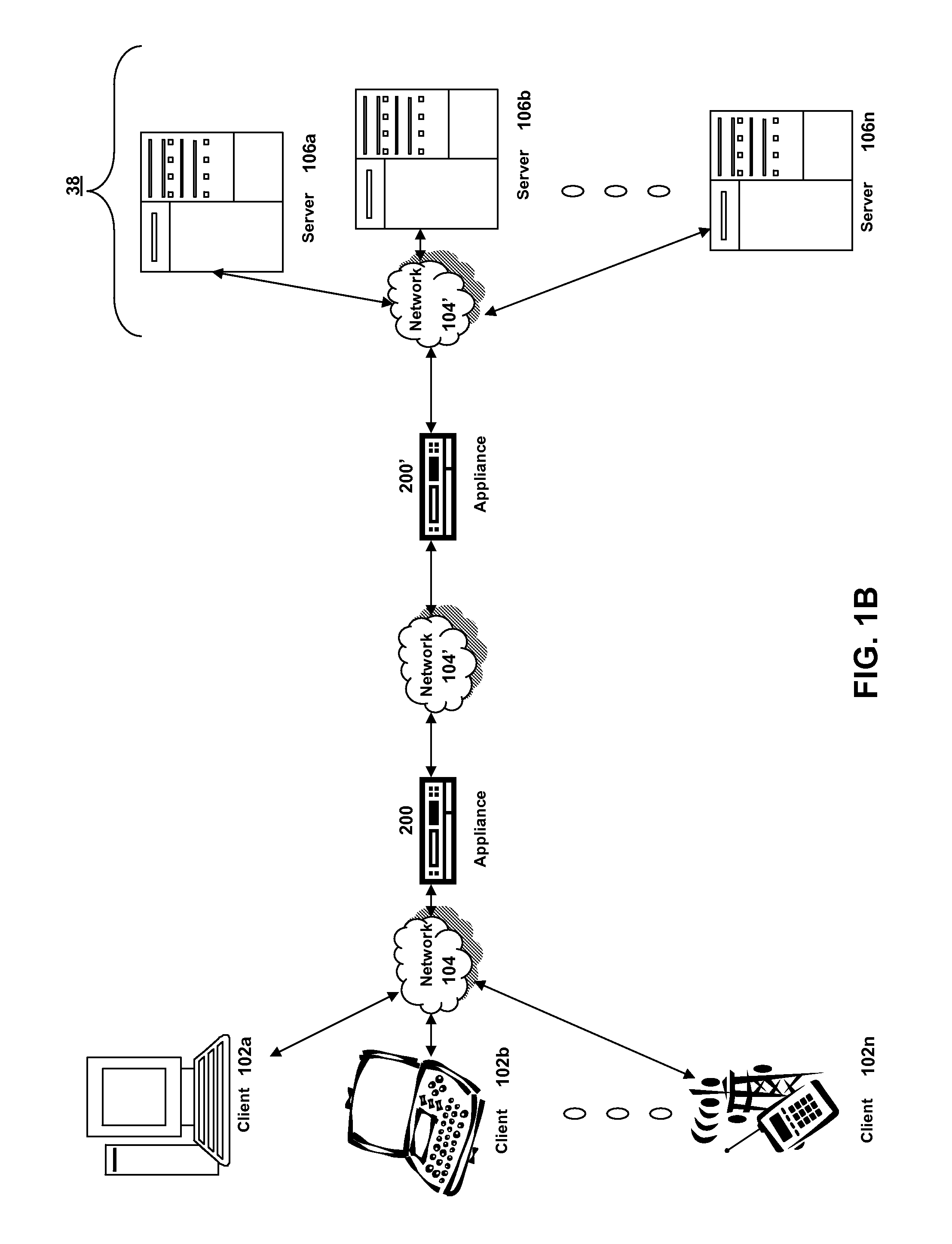
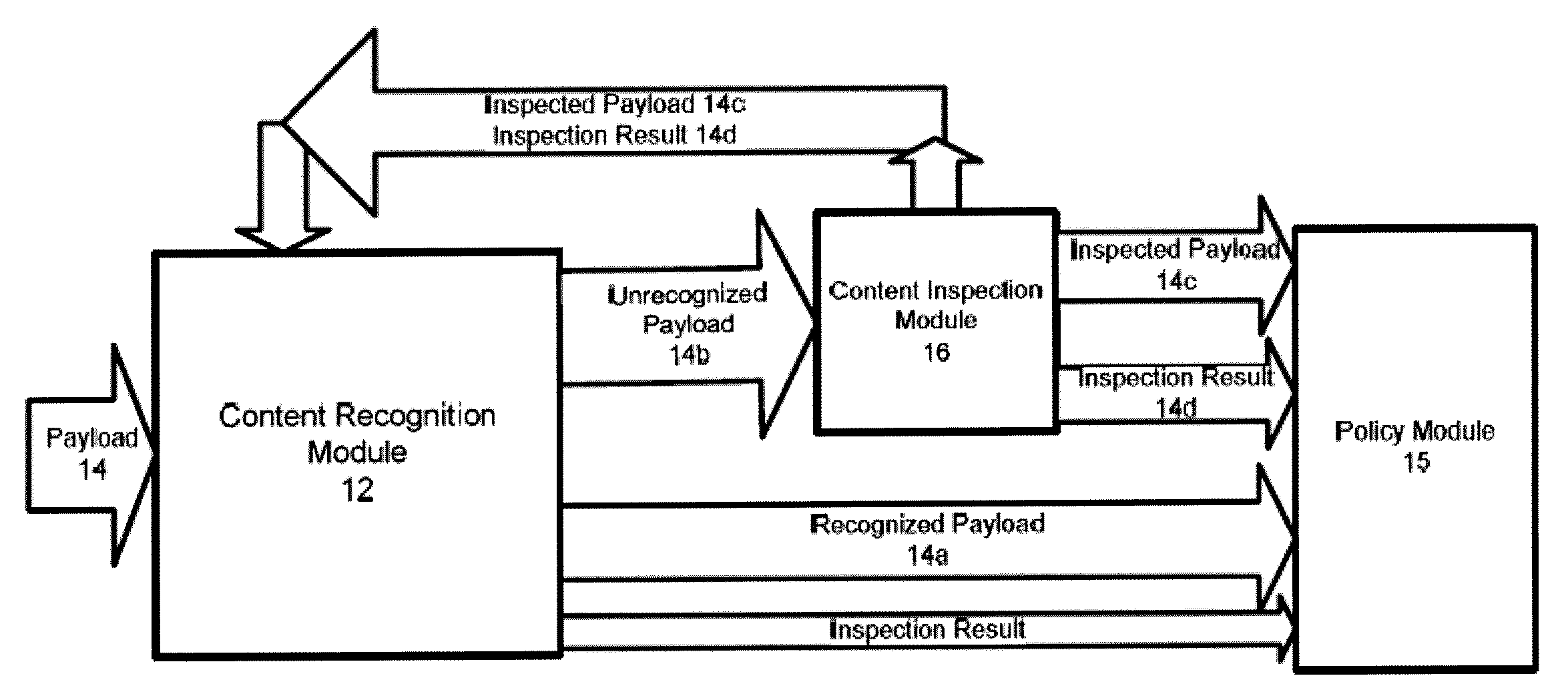
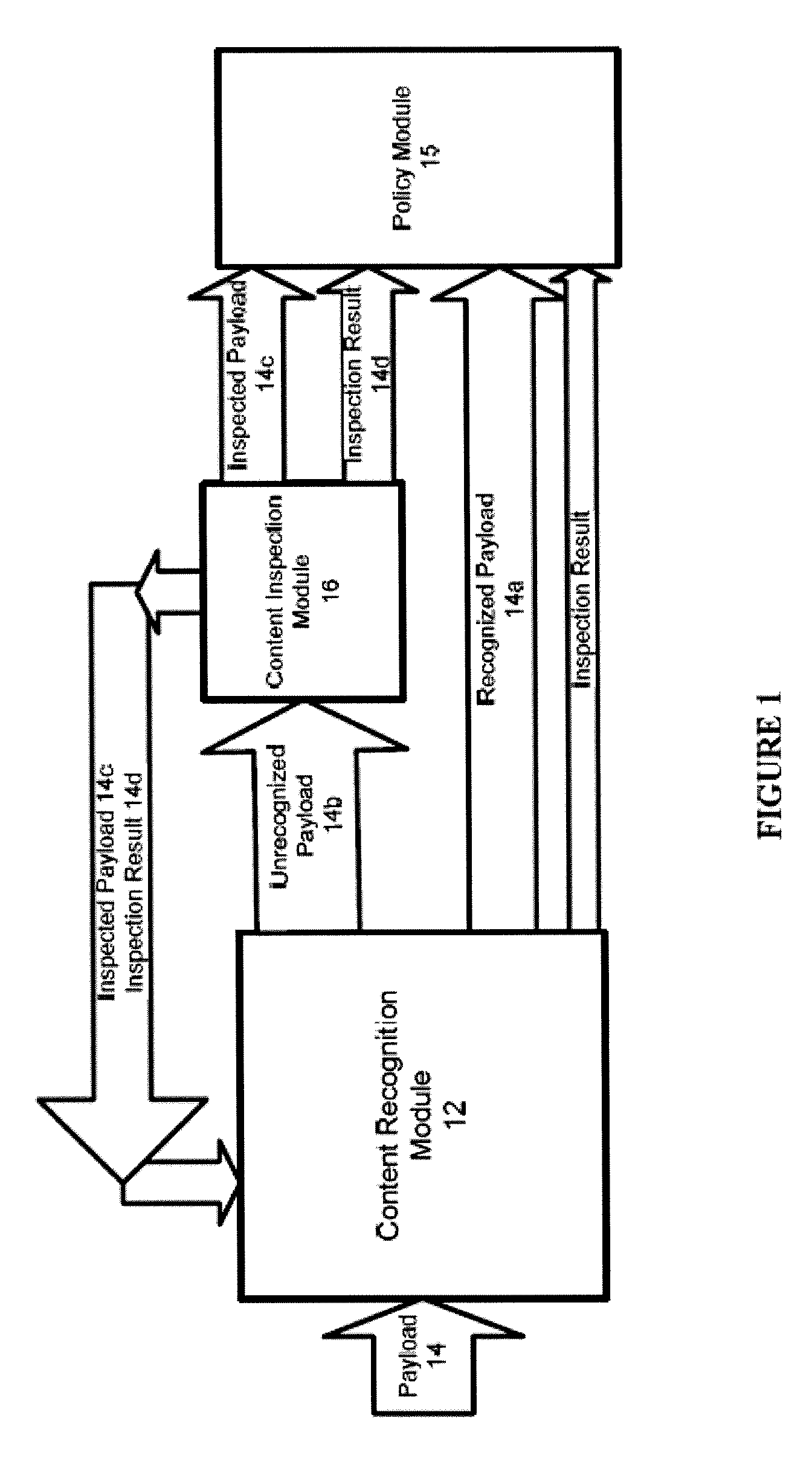
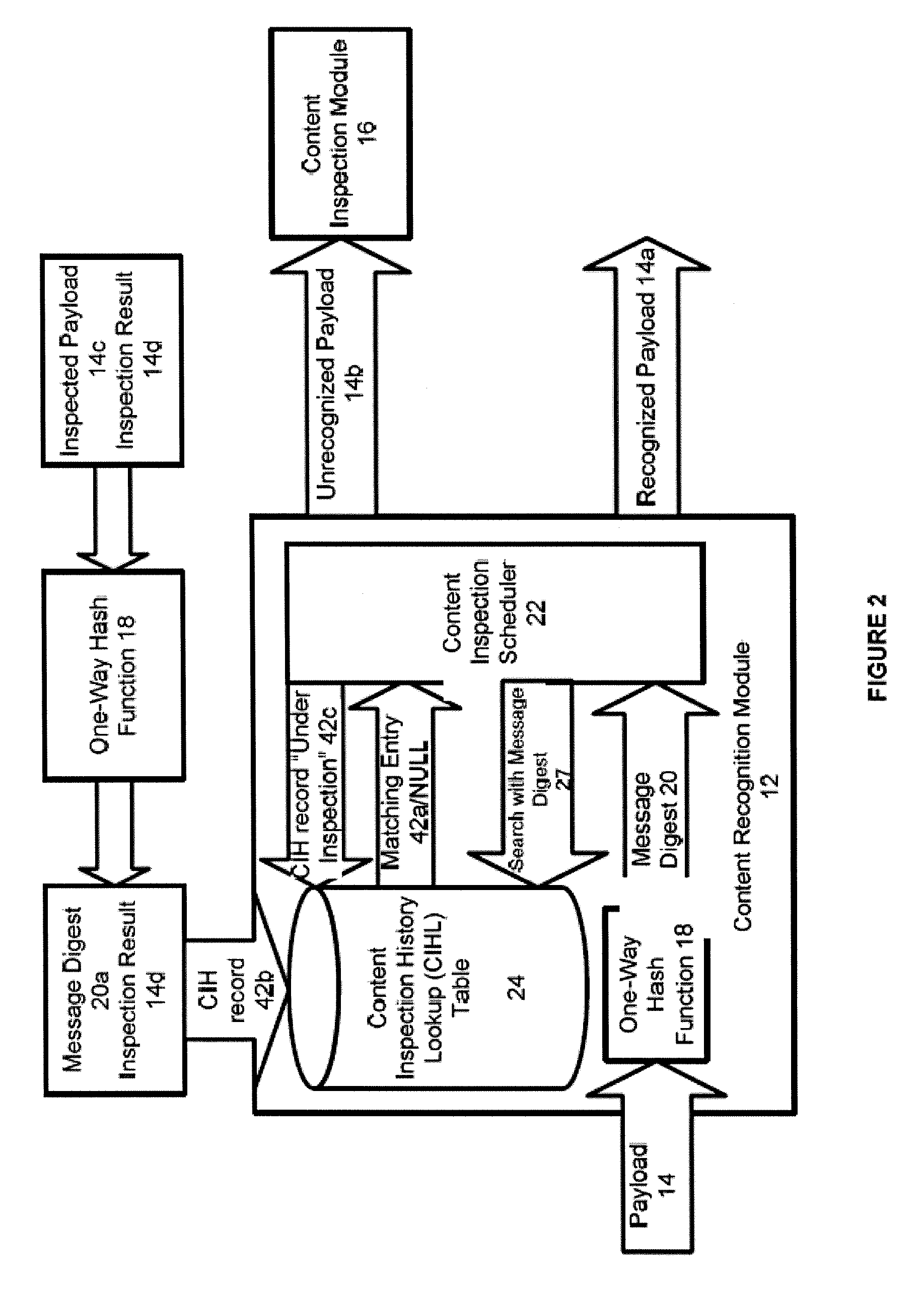
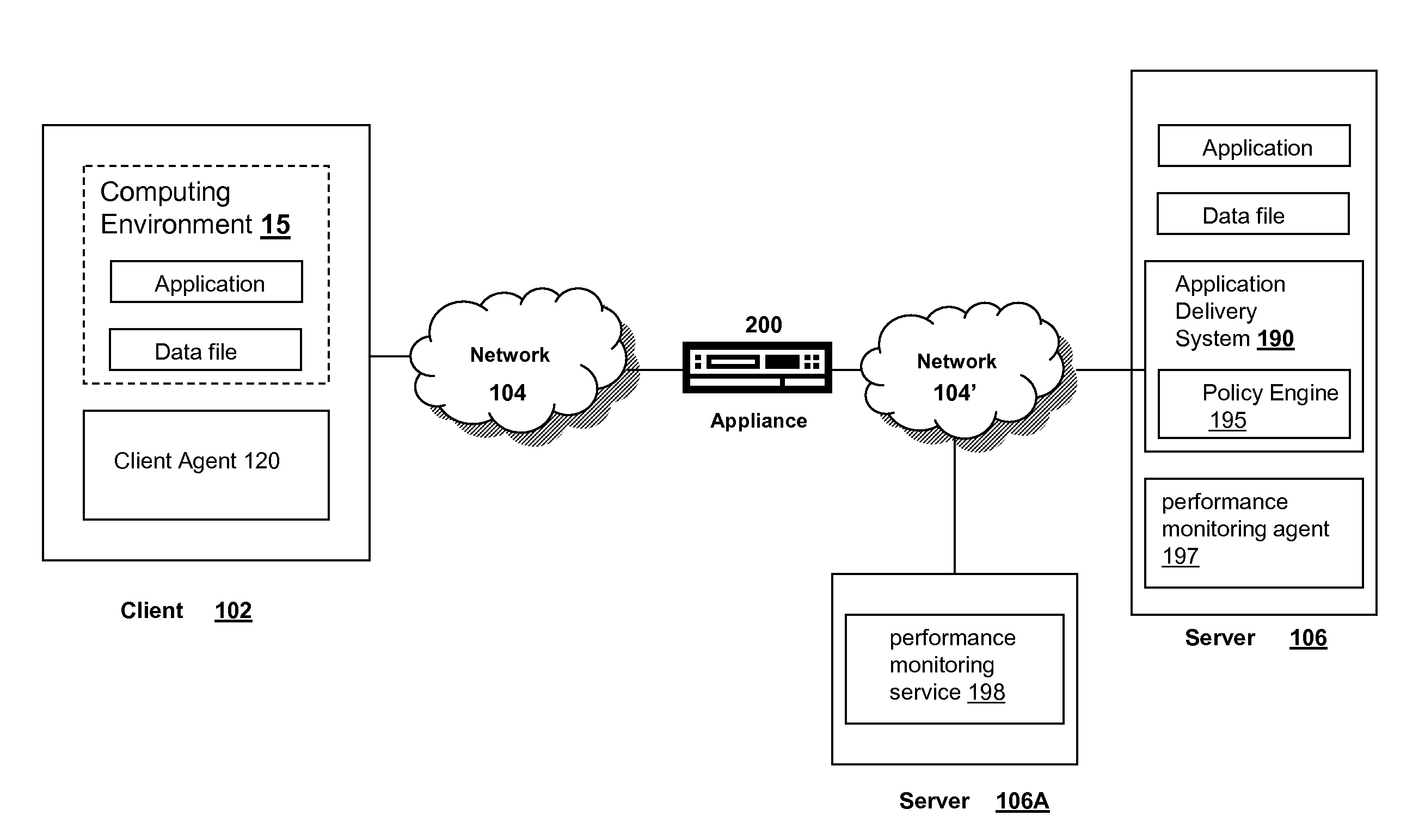
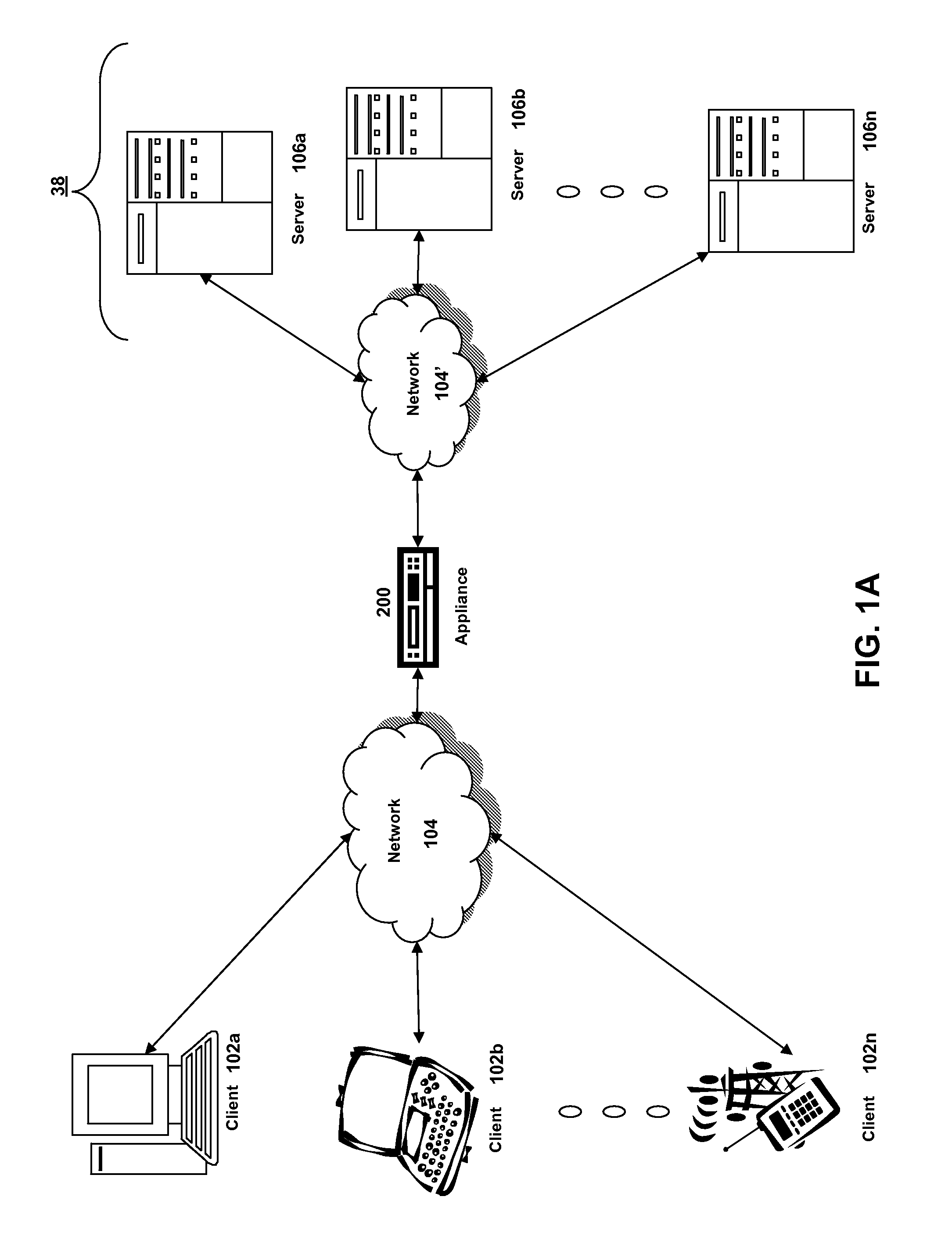
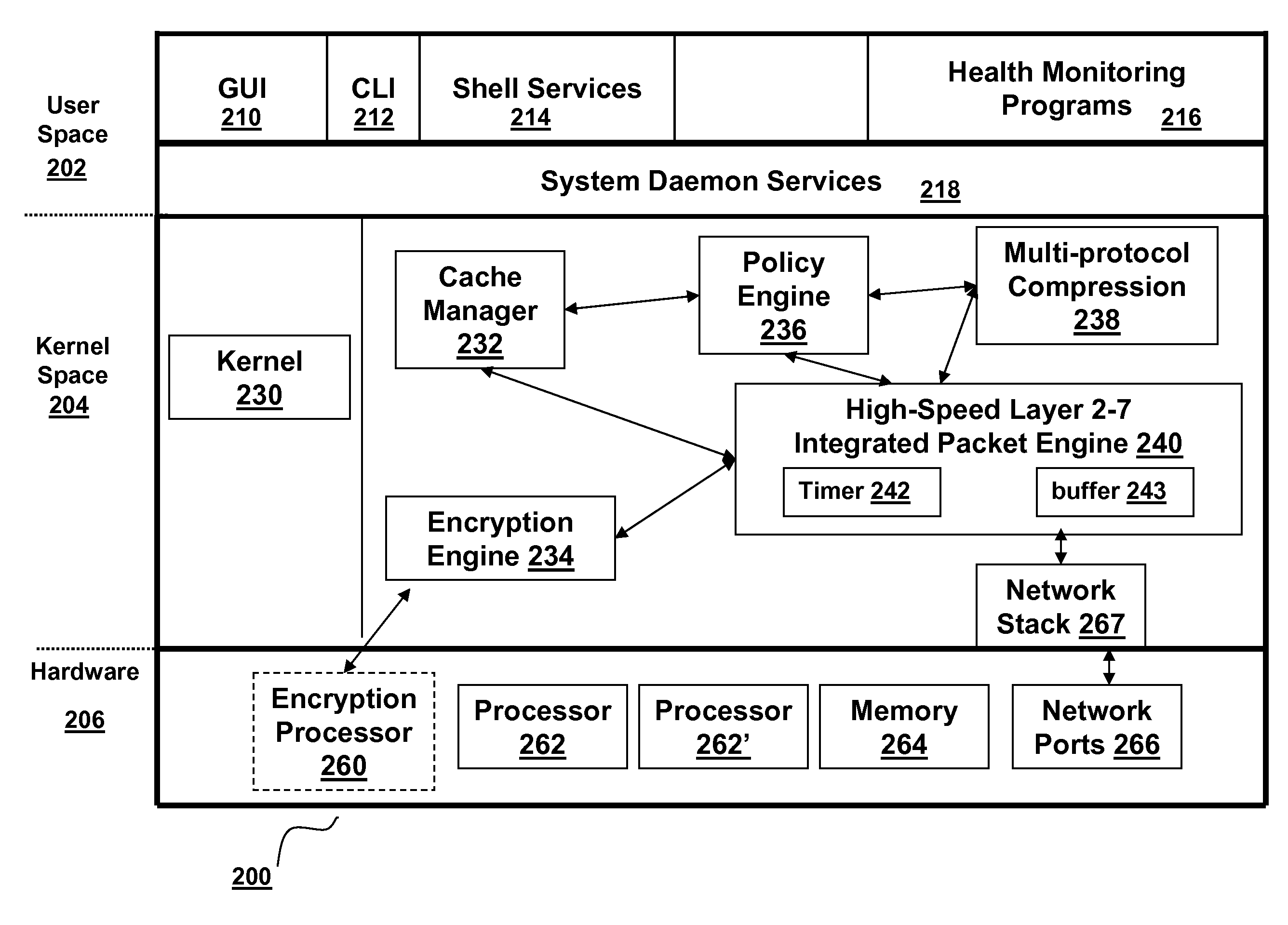
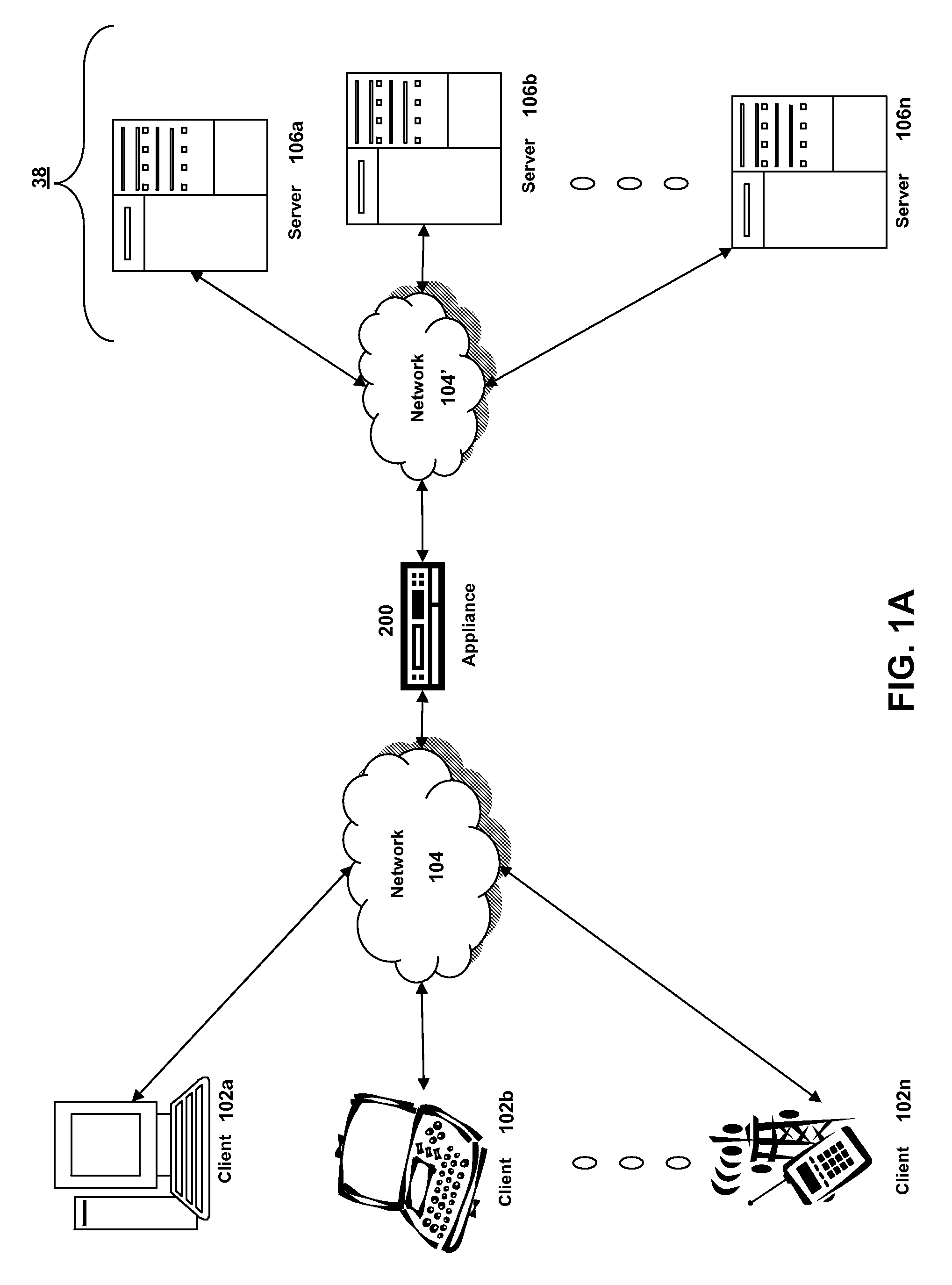
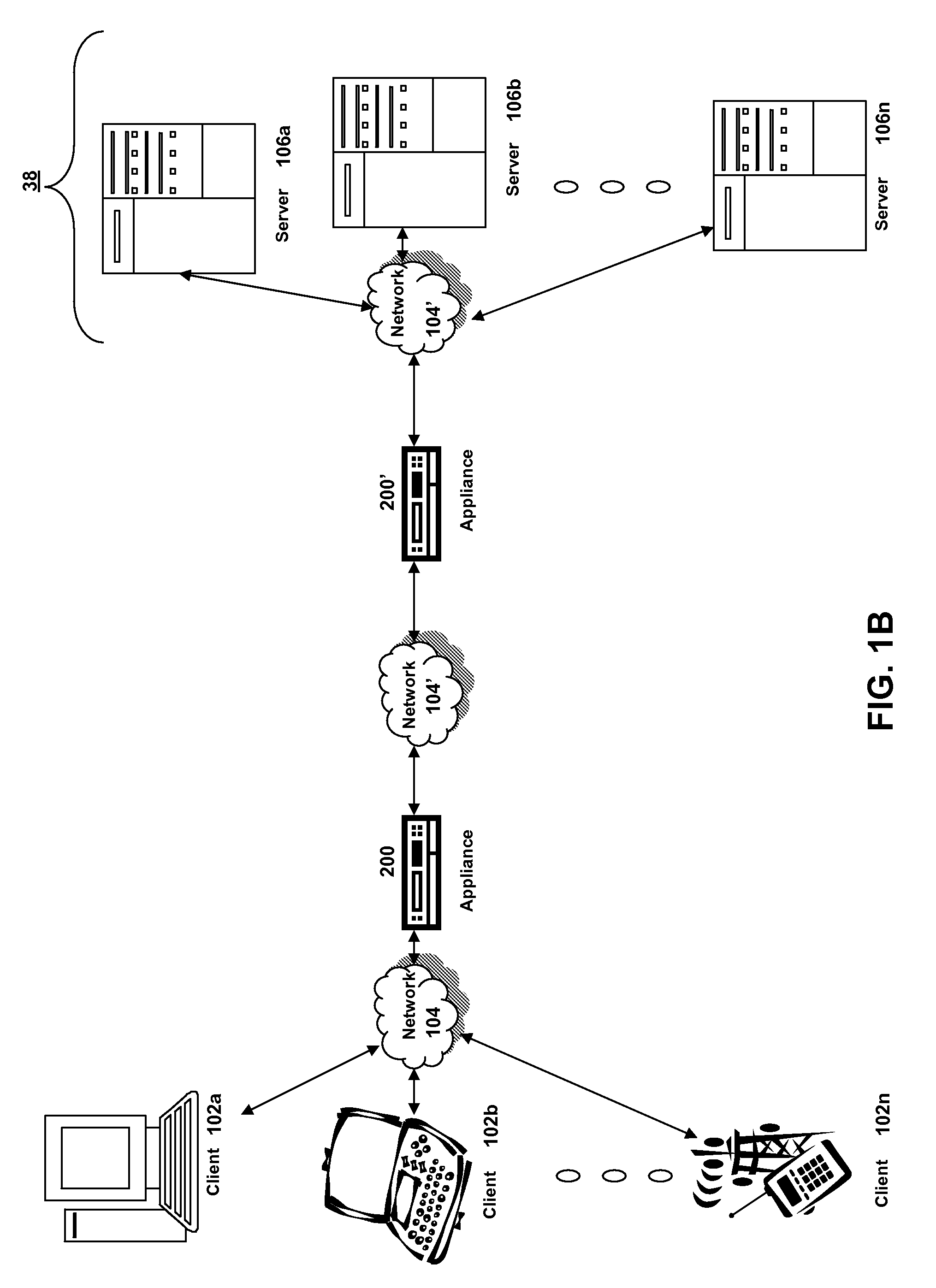
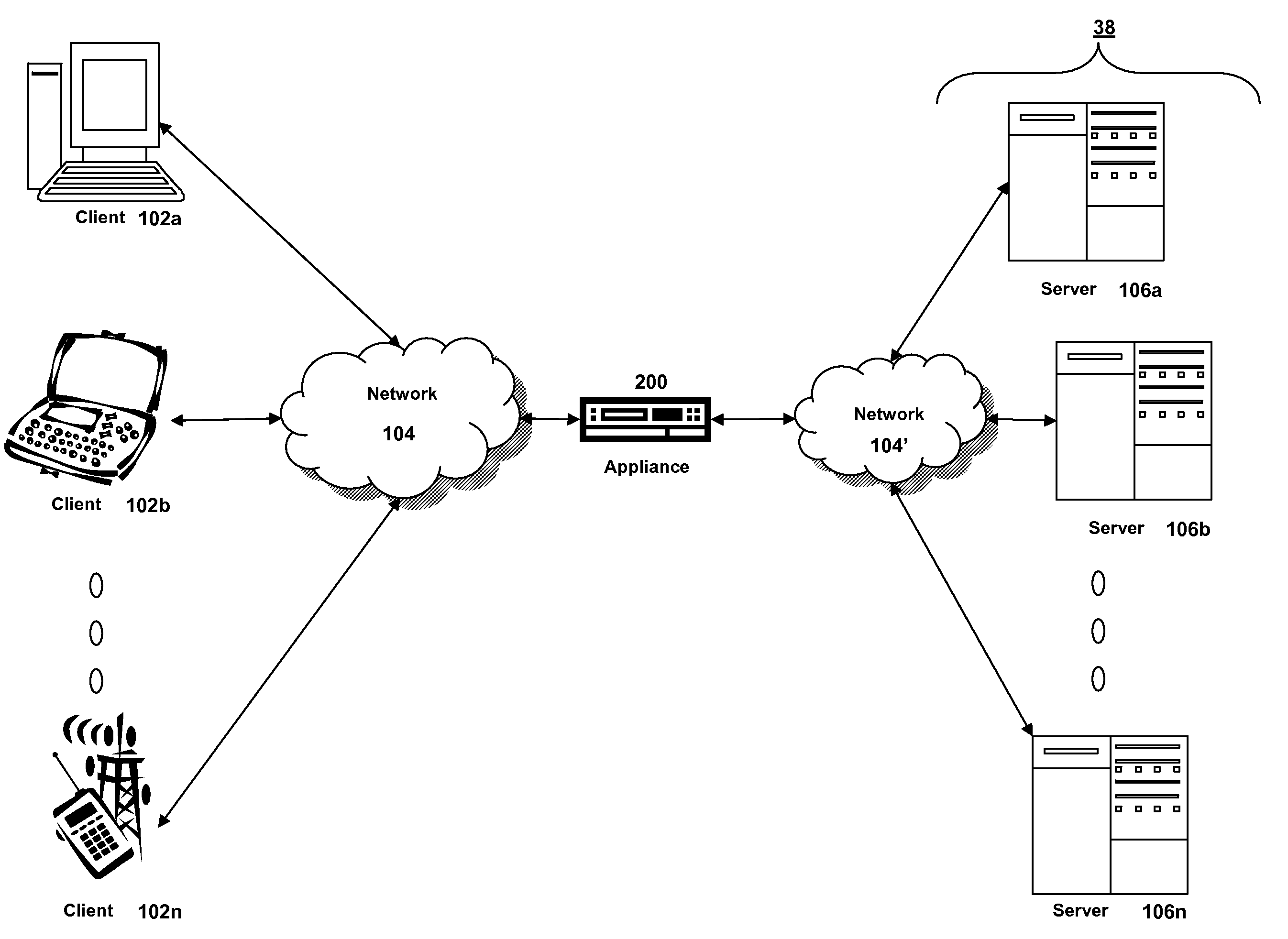
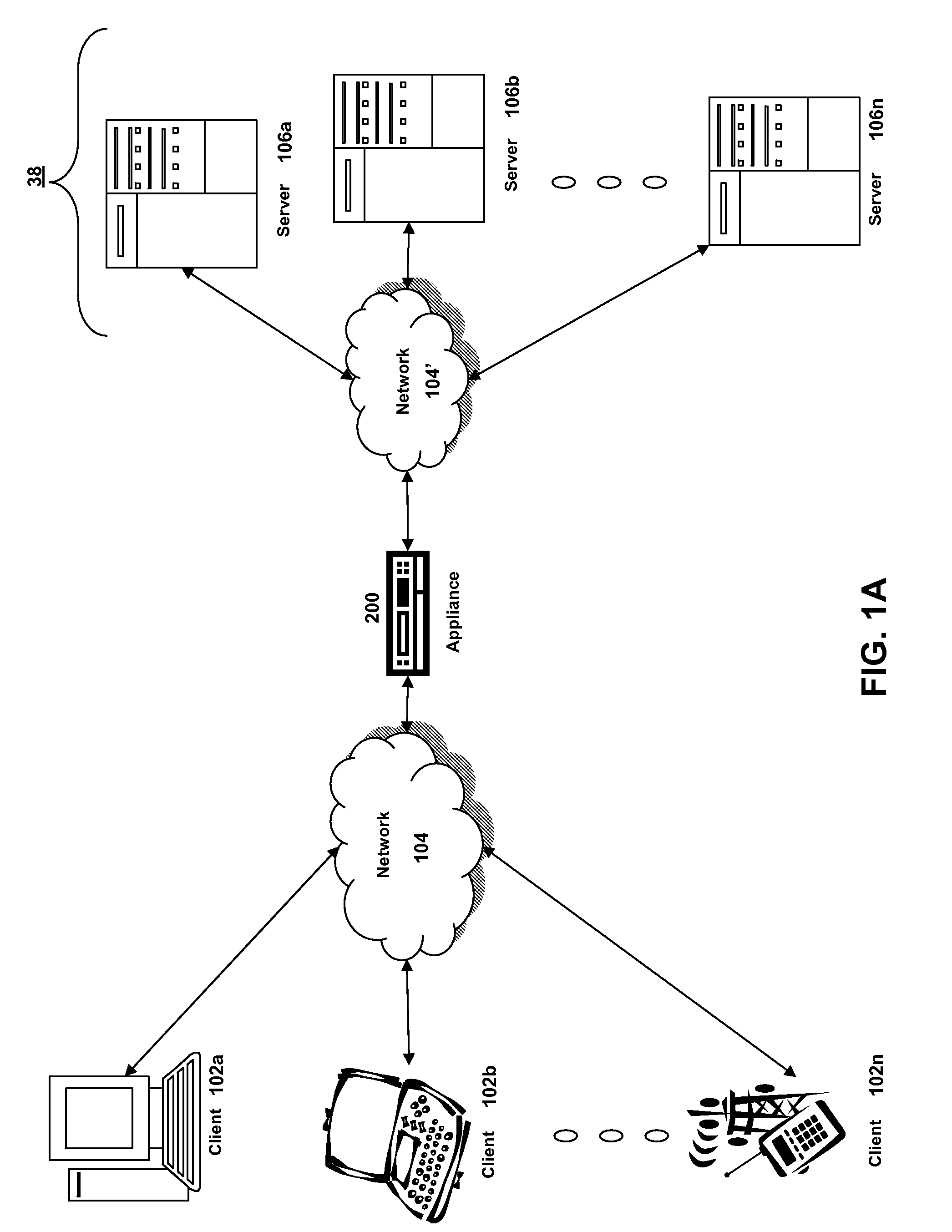
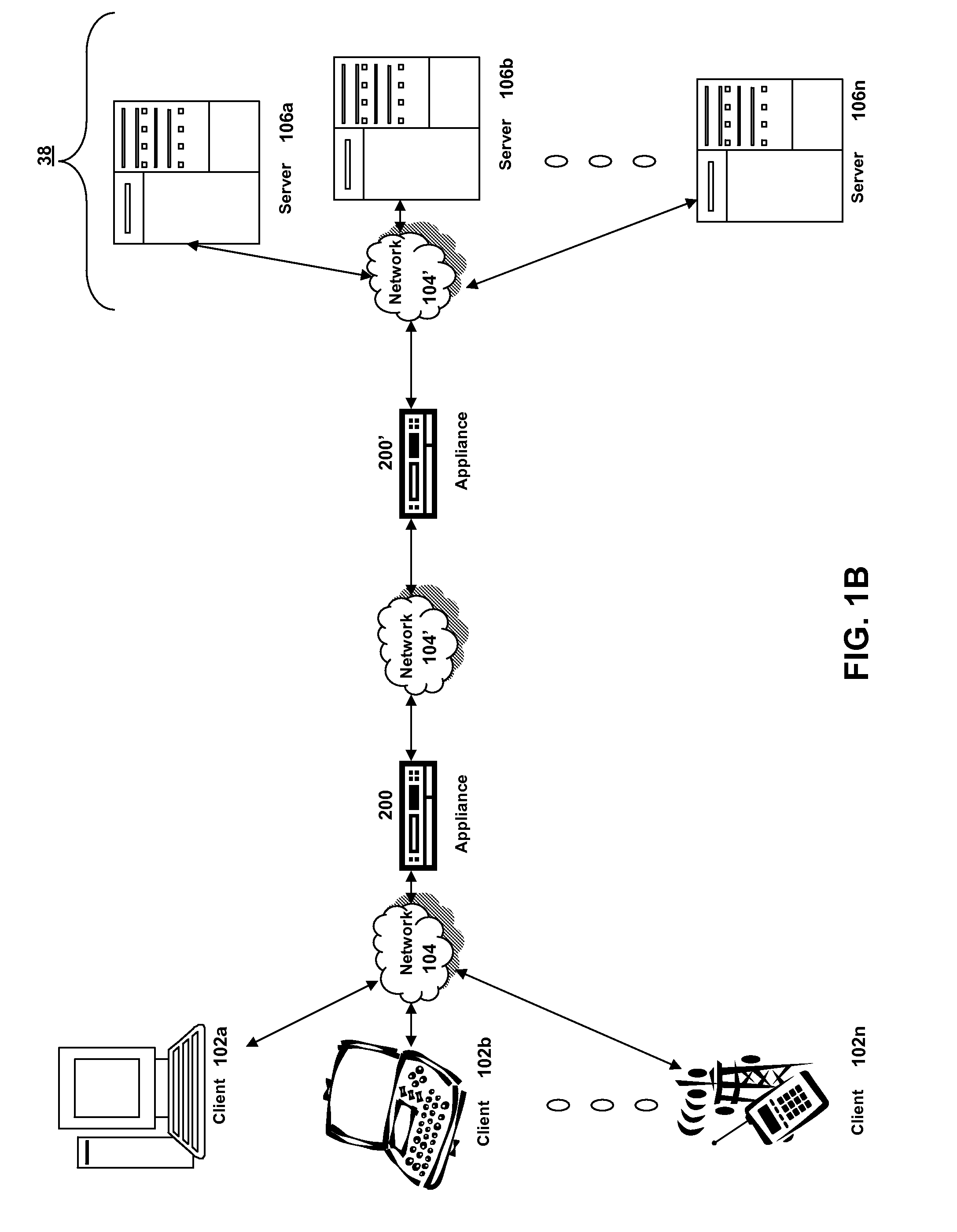
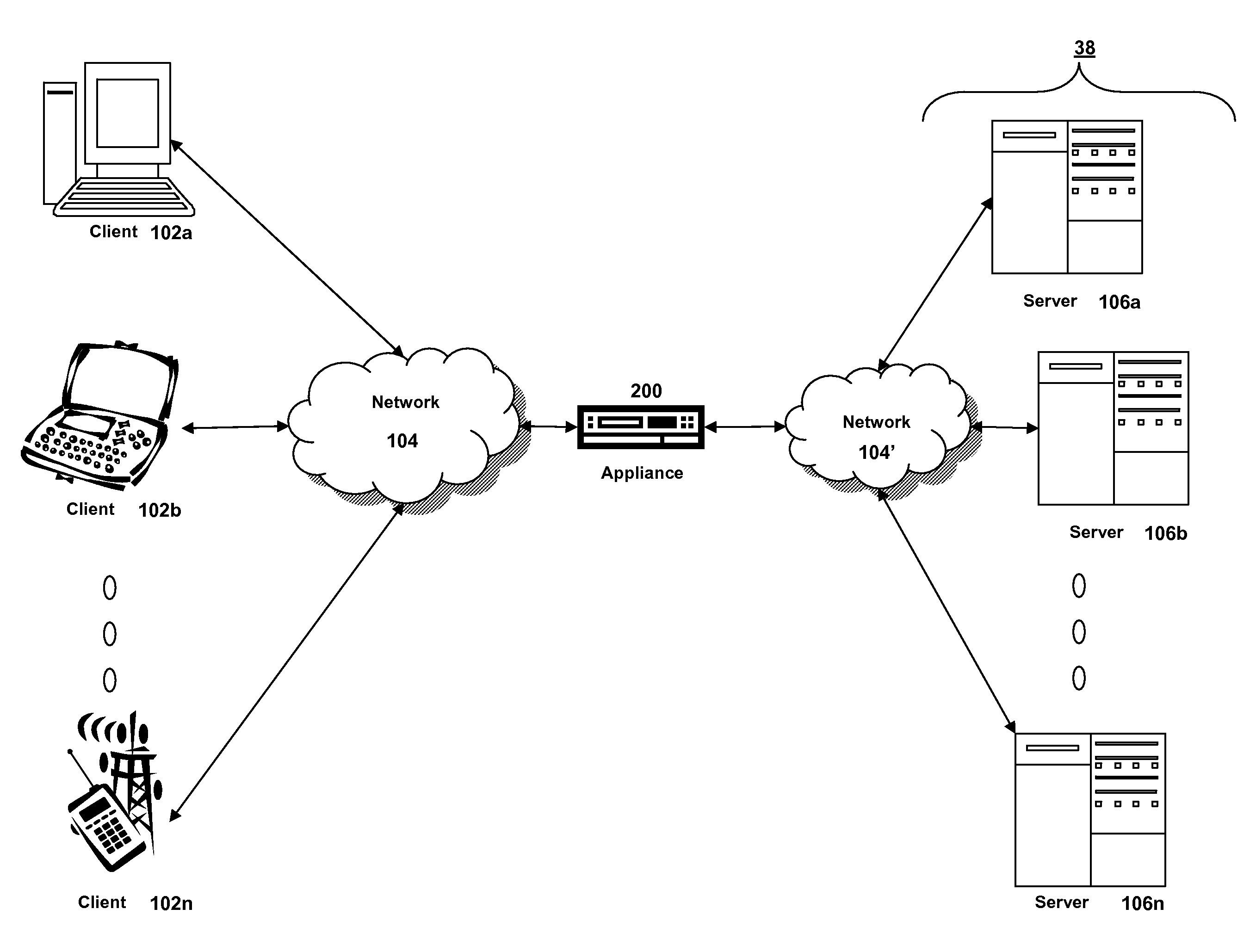
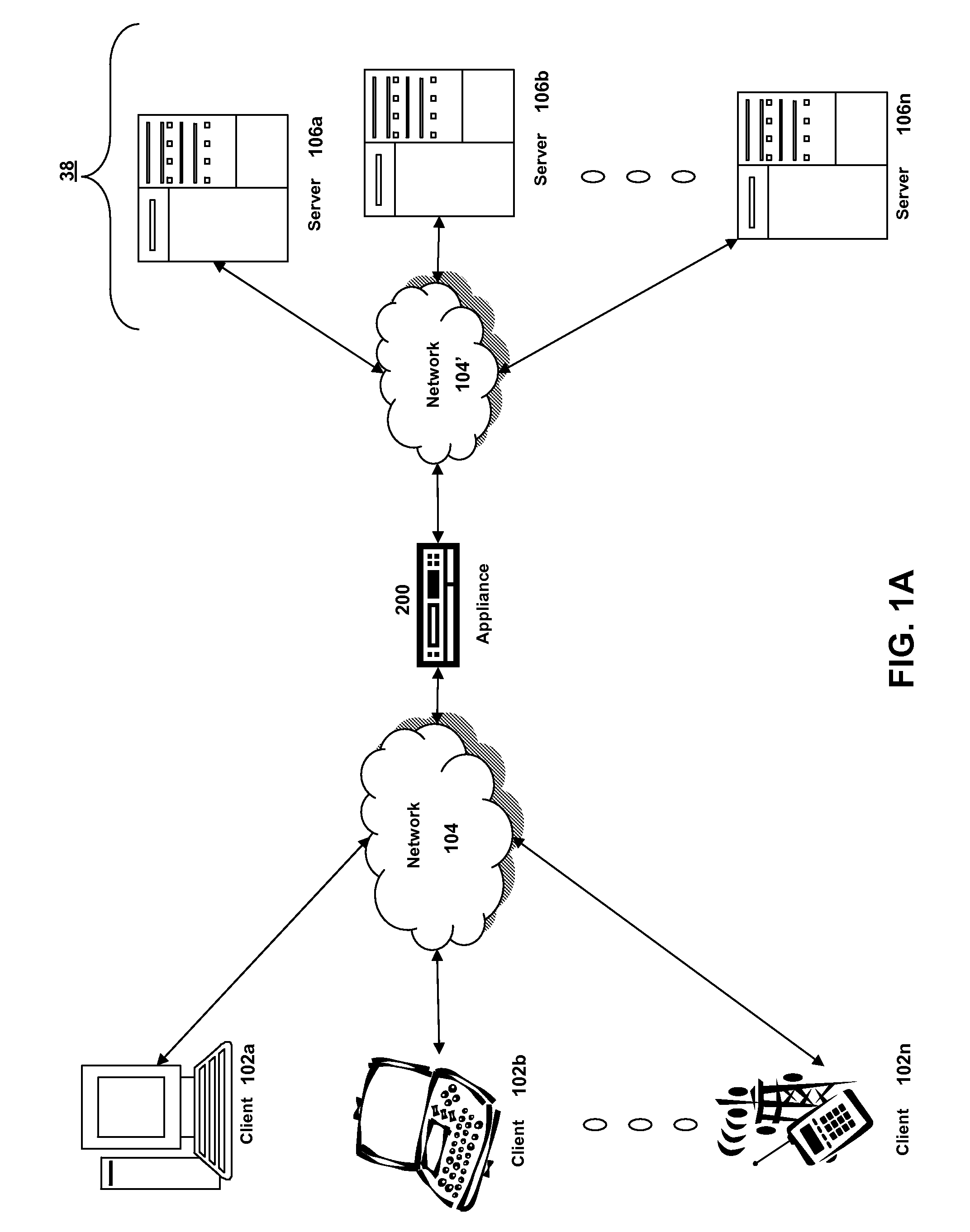
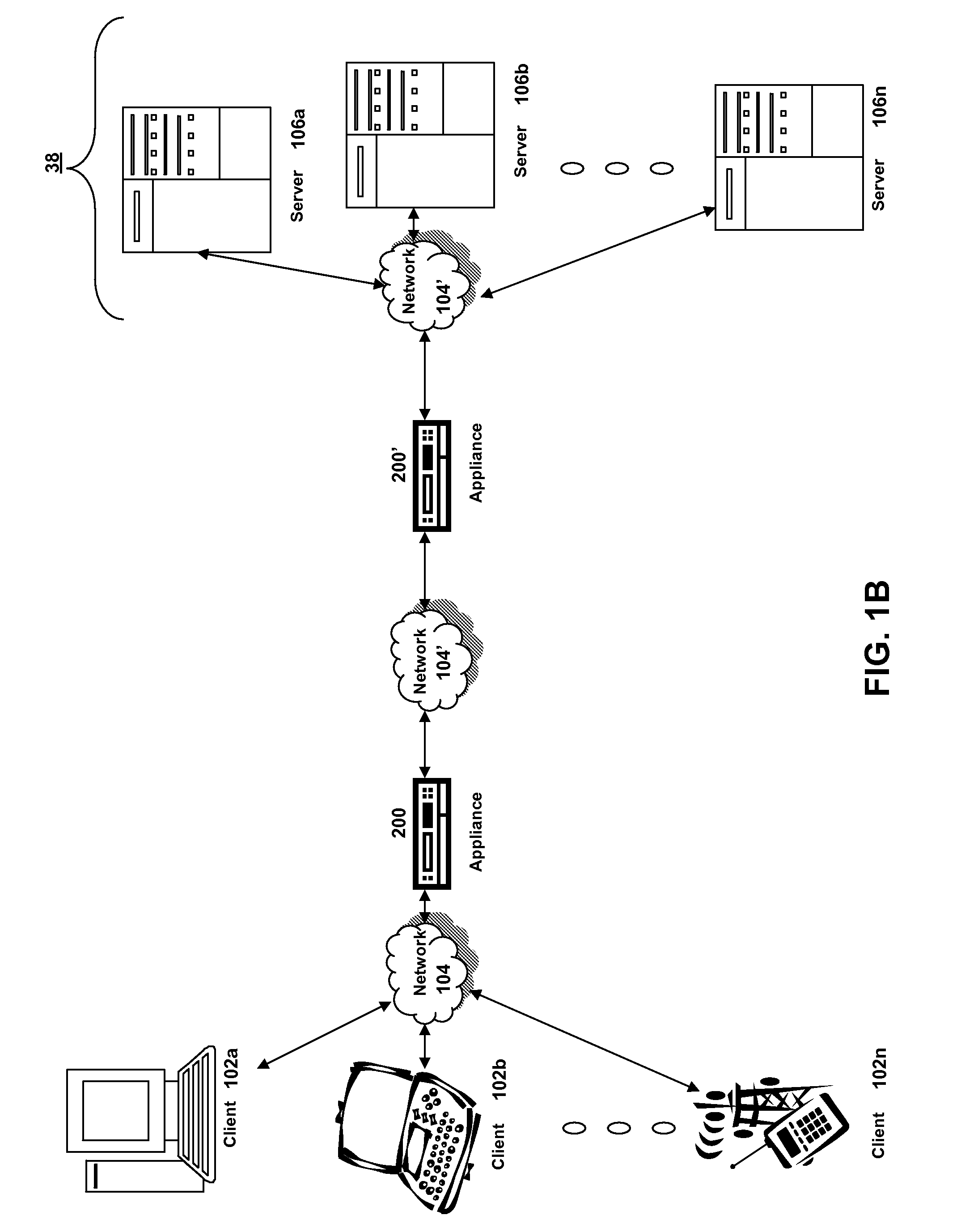
Systems and methods for providing stuctured policy expressions to represent unstructured data in a network appliance
ActiveUS20080225748A1Efficient configurationEfficient processingData switching by path configurationTraffic capacityData stream
Owner:CITRIX SYST INC
Method for inter-scene transitions
InactiveUS20060132482A1Television system detailsGeometric image transformationComputer graphics (images)Display device
A method and system for creating a transition between a first scene and a second scene on a computer system display, simulating motion. The method includes determining a transformation that maps the first scene into the second scene. Motion between the scenes is simulated by displaying transitional images that include a transitional scene based on a transitional object in the first scene and in the second scene. The rendering of the transitional object evolves according to specified transitional parameters as the transitional images are displayed. A viewer receives a sense of the connectedness of the scenes from the transitional images. Virtual tours of broad areas, such as cityscapes, can be created using inter-scene transitions among a complex network of pairs of scenes.
Owner:EVERYSCAPE
Method and apparatus for distributed community finding
ActiveUS7958120B2New informationData processing applicationsDigital data processing detailsGraphicsDiffusion
Methods and apparatus for a new approach to the problem of finding communities in complex networks relating to a social definition of communities and percolation are disclosed. Instead of partitioning the graph into separate subgraphs from top to bottom a local algorithm (communities of each vertex) allows overlapping of communities. The performance of an algorithm on synthetic, randomly-generated graphs and real-world networks is used to benchmark this method against others. An heuristic is provided to generate a list of communities for networks using a local community finding algorithm. Unlike diffusion based algorithms, The provided algorithm finds overlapping communities and provides a means to measure confidence in community structure. It features locality and low complexity for exploring the communities for a subset of network nodes, without the need for exploring the whole graph.
Owner:NETABEER +1
Systems and methods for configuring policy bank invocations
ActiveUS20100095018A1Efficient configurationEfficient processingError preventionTransmission systemsTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Systems And Methods For Improved Network Based Content Inspection
ActiveUS20070160062A1Efficient and effective inspectionRisk minimizationData switching by path configurationPlatform integrity maintainanceNetworking protocolKnowledge gain
The invention relates to network based content inspection (NBCI). More specifically, the invention provides systems and methods for improved NBCI in complex networks that are typical for enterprises and service providers. These networks are shared by large numbers of concurrent users who send and retrieve application content of various sizes via a variety of communication protocols. This invention improves the efficiency of the NBCI of an individual communication session by learning from the processing results of other communication sessions which may be carried via different network protocols. In addition, the invention provides methods that do not weaken the overall security for the network and that improve the stability of NBCI systems by minimizing the risk of system resource exhaustion if subjected to a burst of large payloads. The invention also improves perceived network stability by preventing the system resources from being “live-locked” by a few large content inspection tasks. Further still, the invention improves the cost-effectiveness of NBCI by allowing the optimization knowledge gained by one NBCI node be shared with other nodes.
Owner:WEDGE NETWORKS
Systems and methods for managing application security profiles
ActiveUS20080229381A1Efficient configurationEfficient processingMemory loss protectionError detection/correctionTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
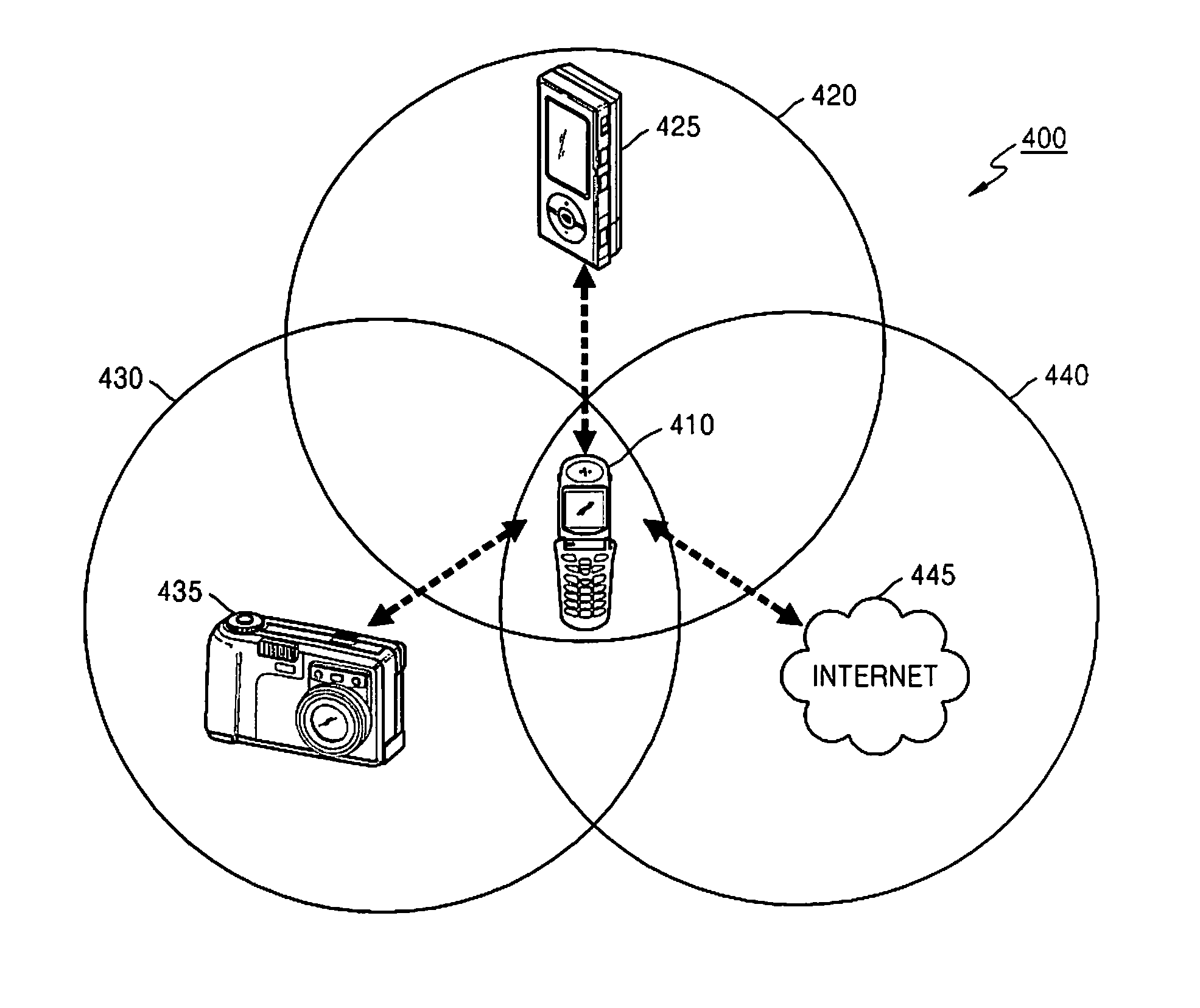
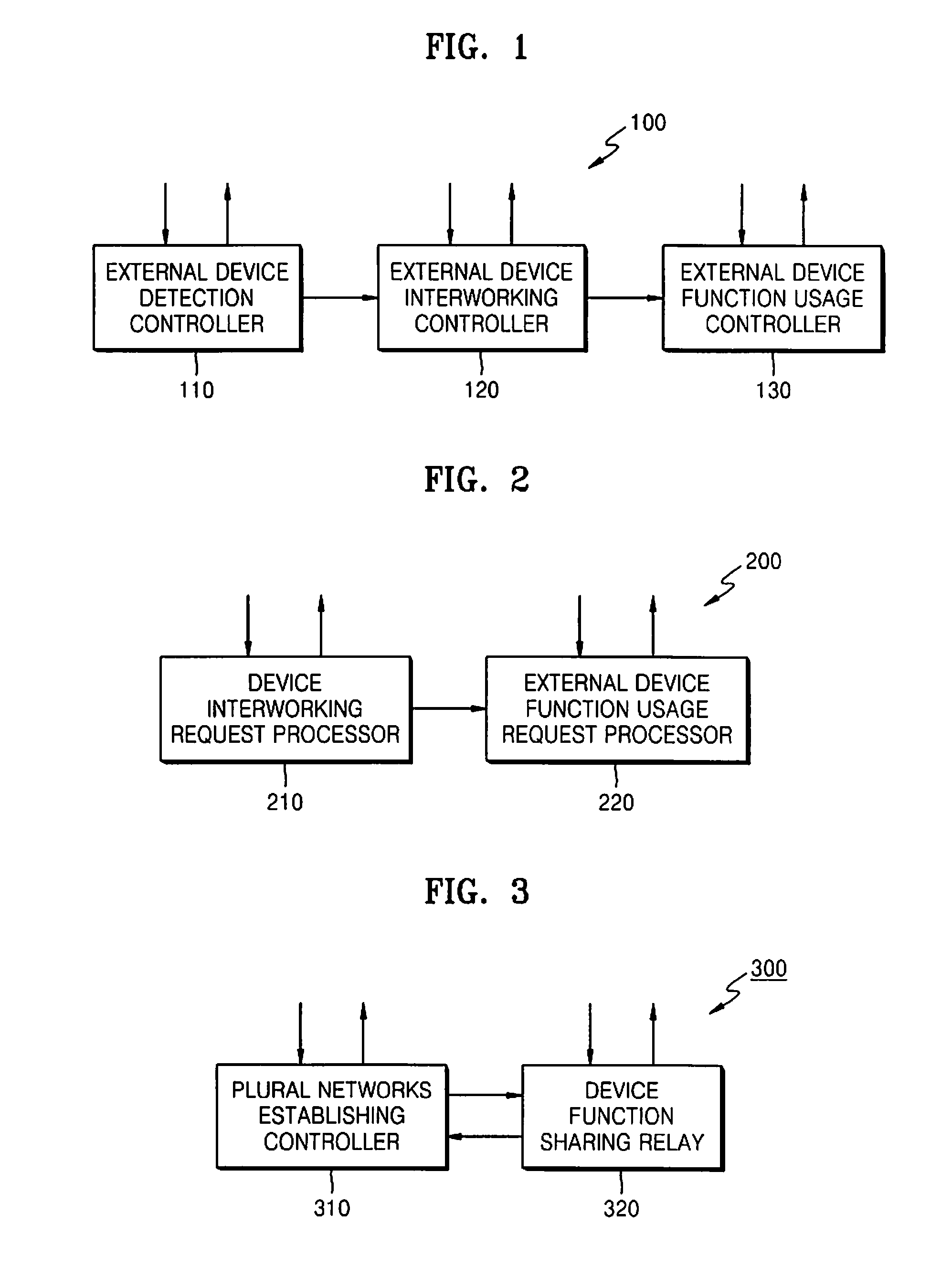
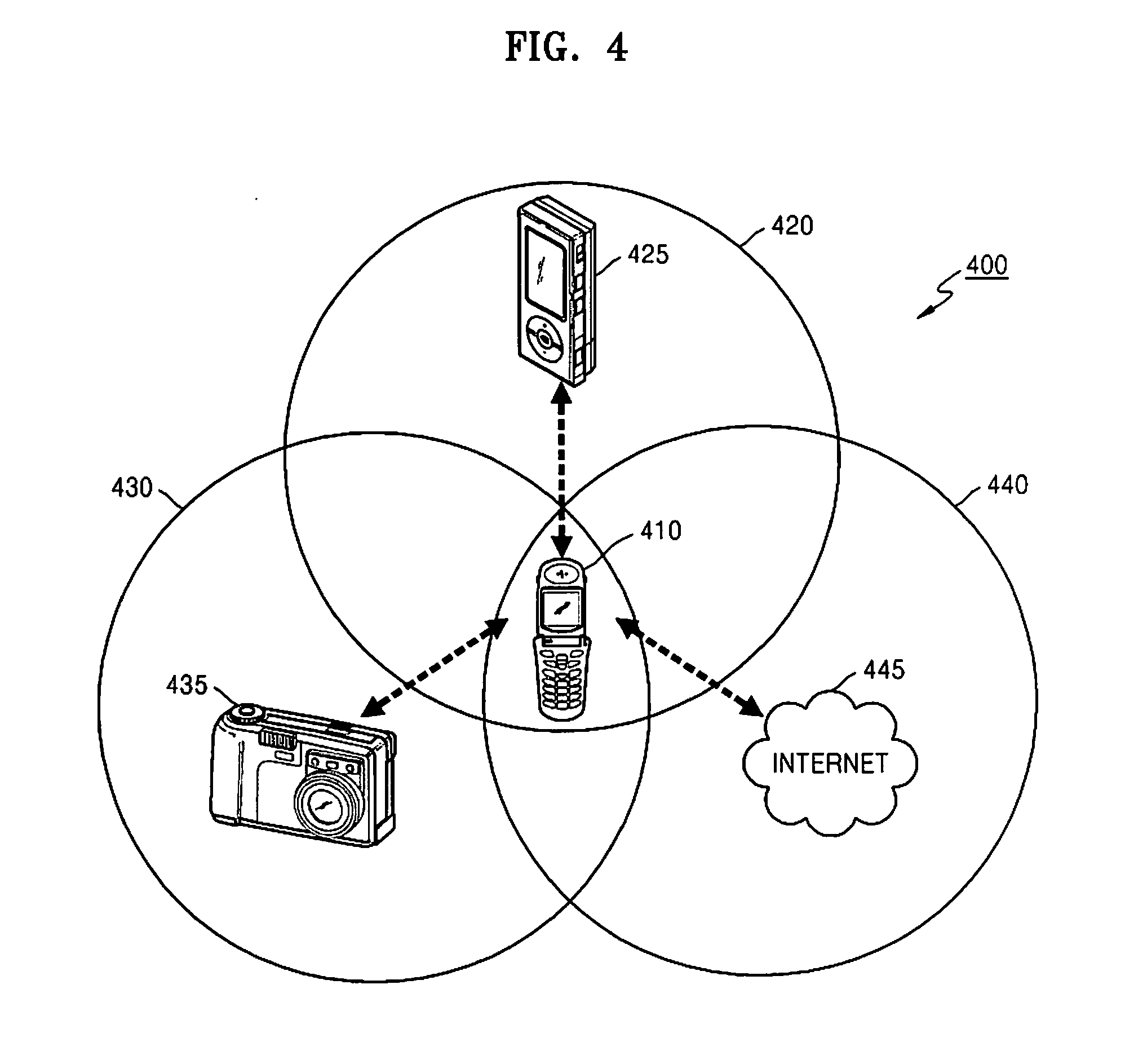
Method and apparatus for sharing function of external device through complex network
InactiveUS20110047266A1Telemetry/telecontrol selection arrangementsNetwork topologiesComputer hardwarePeripheral
Owner:SAMSUNG ELECTRONICS CO LTD
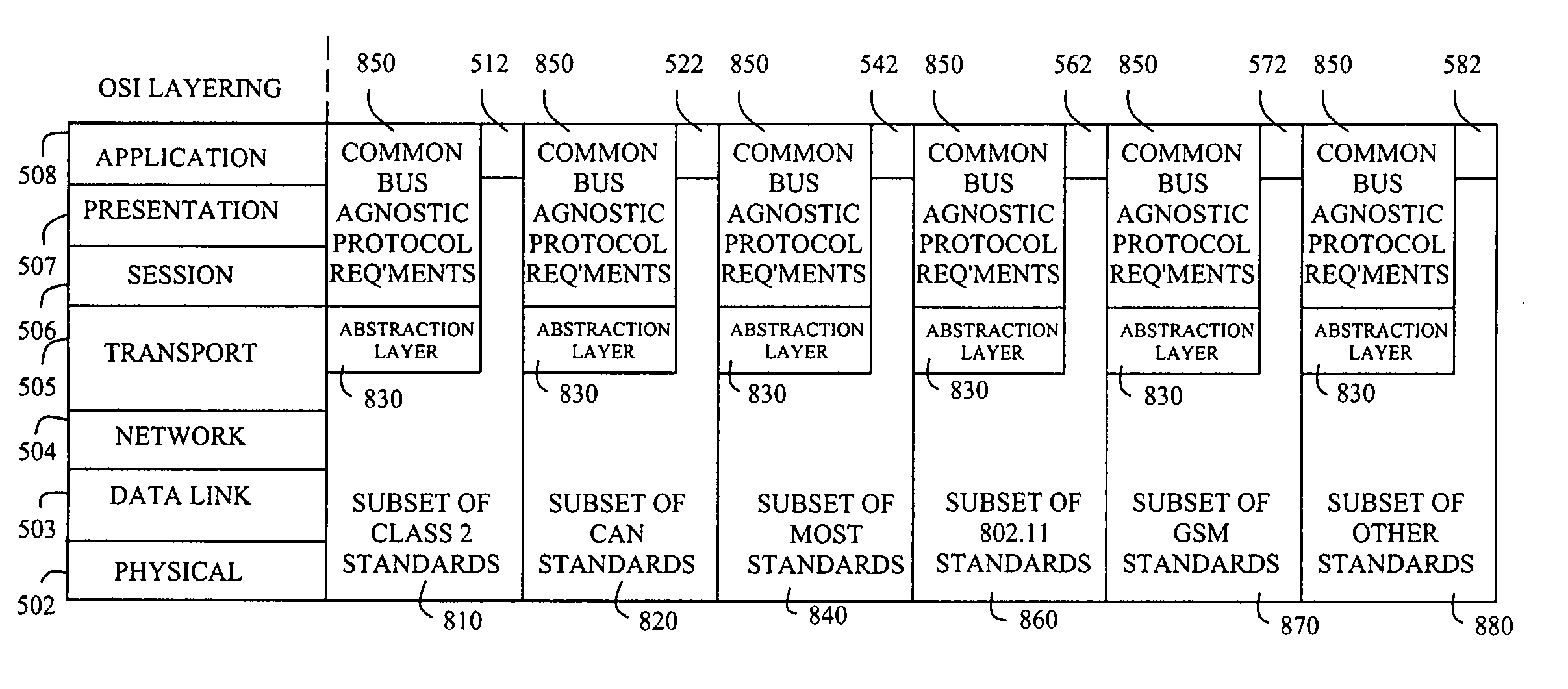
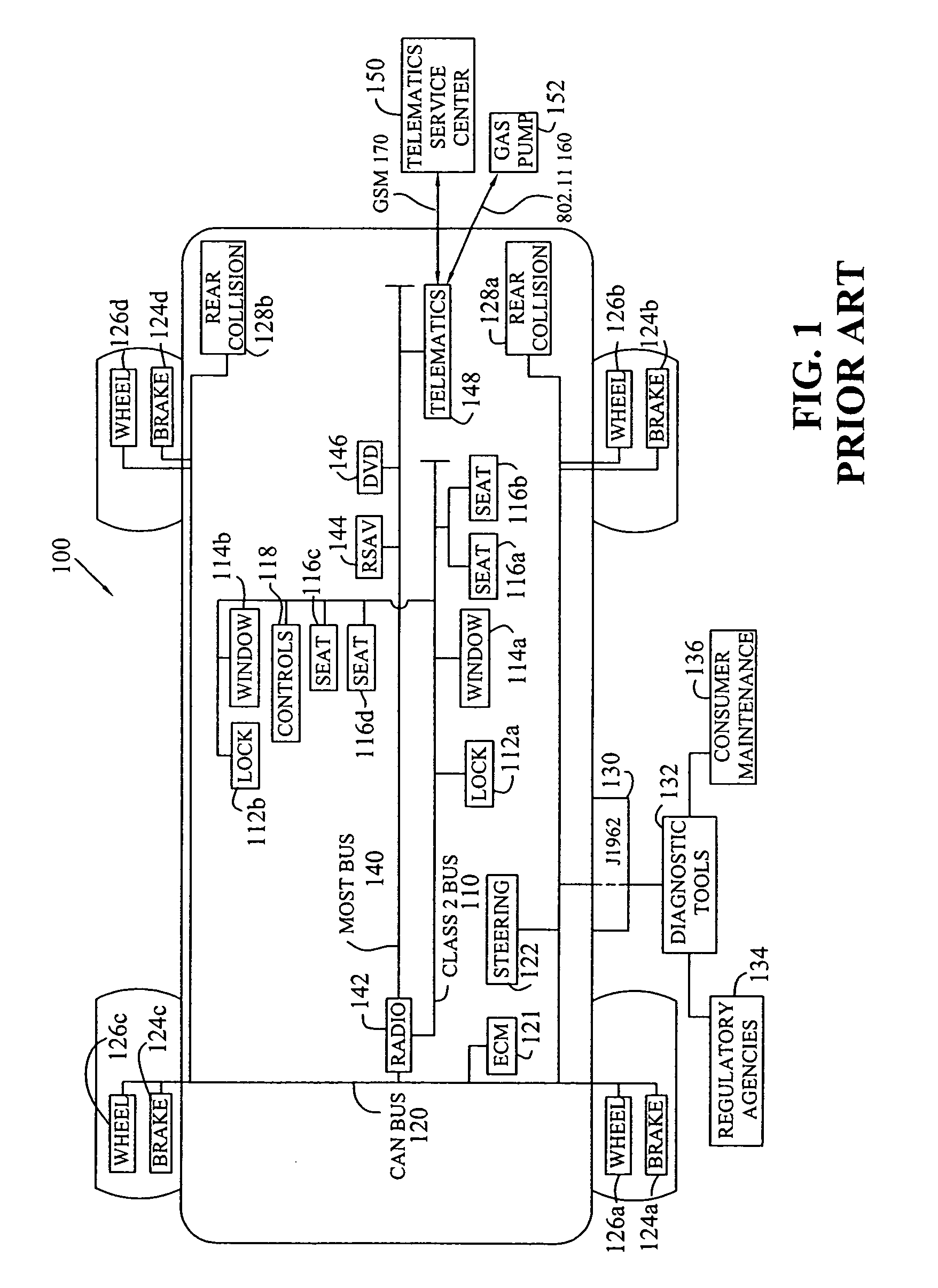
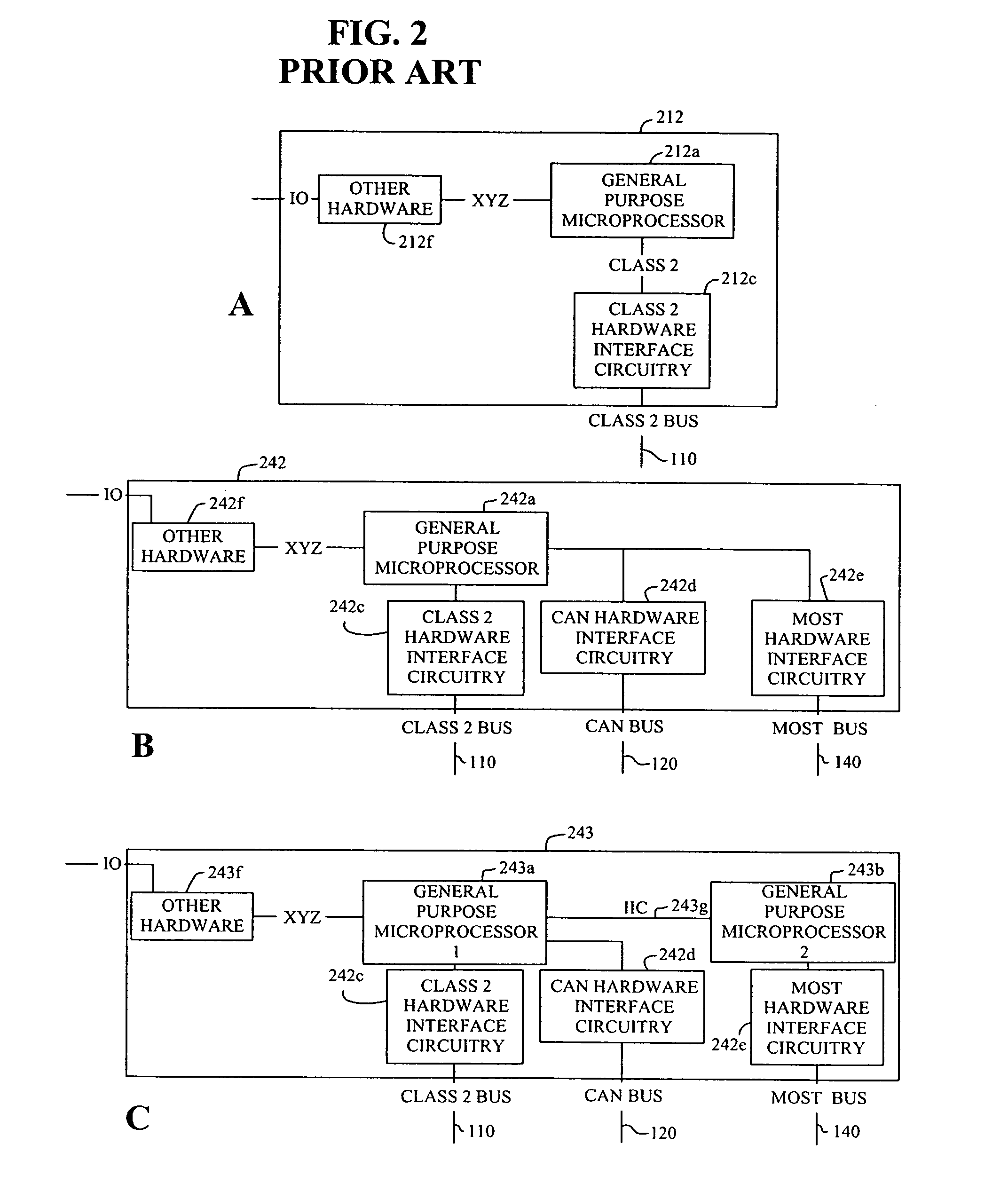
Method and protocol for diagnostics of arbitrarily complex networks of devices
InactiveUS20050251604A1Removal costPreserving abilityNetworks interconnectionNetwork connectionsAbstraction layerCommunications software
The present invention includes a network having a plurality of communication buses, at least two of the plurality of buses utilizing different communication bus protocols; a plurality of computer devices, at least one of the plurality of computer devices coupled to at least one of the plurality of communication buses and containing computer device software having an architecture including bus communication software for communicating with at least one of the plurality of communication buses; and an abstraction layer in communication with the bus communication software and capable of abstracting messages from the communication bus protocols, the plurality of computer devices including at least one gateway computer device coupled to multiple of the plurality of communication buses and containing computer device software having an architecture further including a gateway in communication with the abstraction layer and capable of routing the abstracted messages between computer devices coupled to the multiple communication buses to which the at least one gateway computer device is coupled.
Owner:APTIV TECH LTD
Dynamic adaptive distributed computer system
InactiveUS20050177593A1Most efficientOptimizes adaptive self-organizing operationDigital data processing detailsDigital computer detailsSearch analyticsComplex system
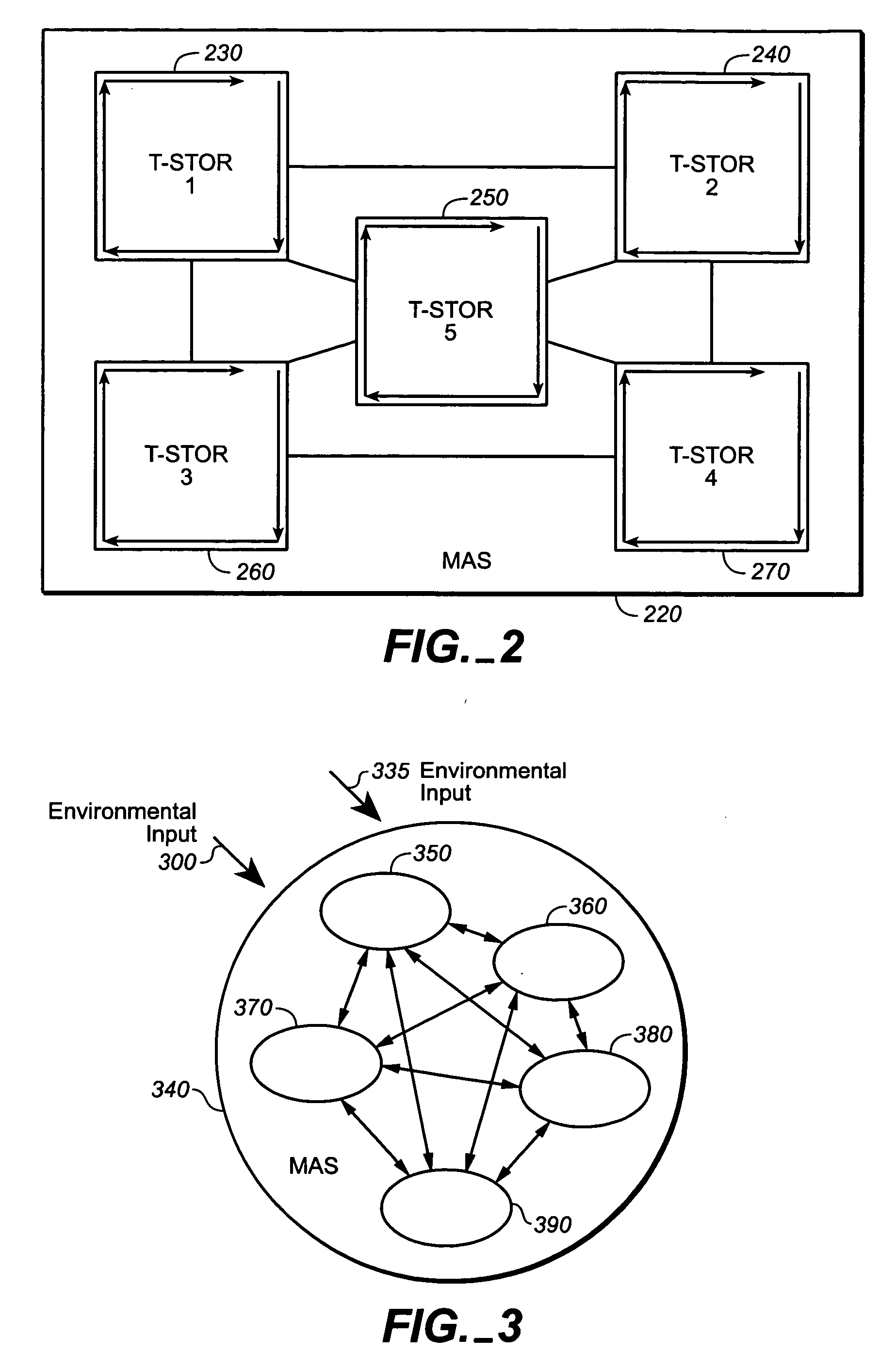
A system, methods and apparatus are described involving the self-organizing dynamics of networks of distributed computers. The system is comprised of complex networks of databases. The system presents a novel database architecture called the distributed transformational spatio-temporal object relational (T-STOR) database management system (dbms). Data is continuously input, analyzed, organized, reorganized and used for specific commercial and industrial applications. The system uses intelligent mobile software agents in a multi-agent system in order to learn, anticipate, and adapt and to perform numerous functions, including search, analysis, collaboration, negotiation, decision making and structural transformation. The system links together numerous complex systems involving distributed networks to present a novel model for dynamic adaptive computing systems, which includes plasticity of collective behavior and self-organizing behavior in intelligent system structures.
Owner:SOLOMON NEAL
Systems and methods for configuring handling of undefined policy events
ActiveUS20080225753A1Efficient configurationEfficient processingDigital computer detailsData switching by path configurationTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Systems and methods for configuring flow control of policy expressions
ActiveUS20080225720A1Efficient configurationEfficient processingError preventionTransmission systemsTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
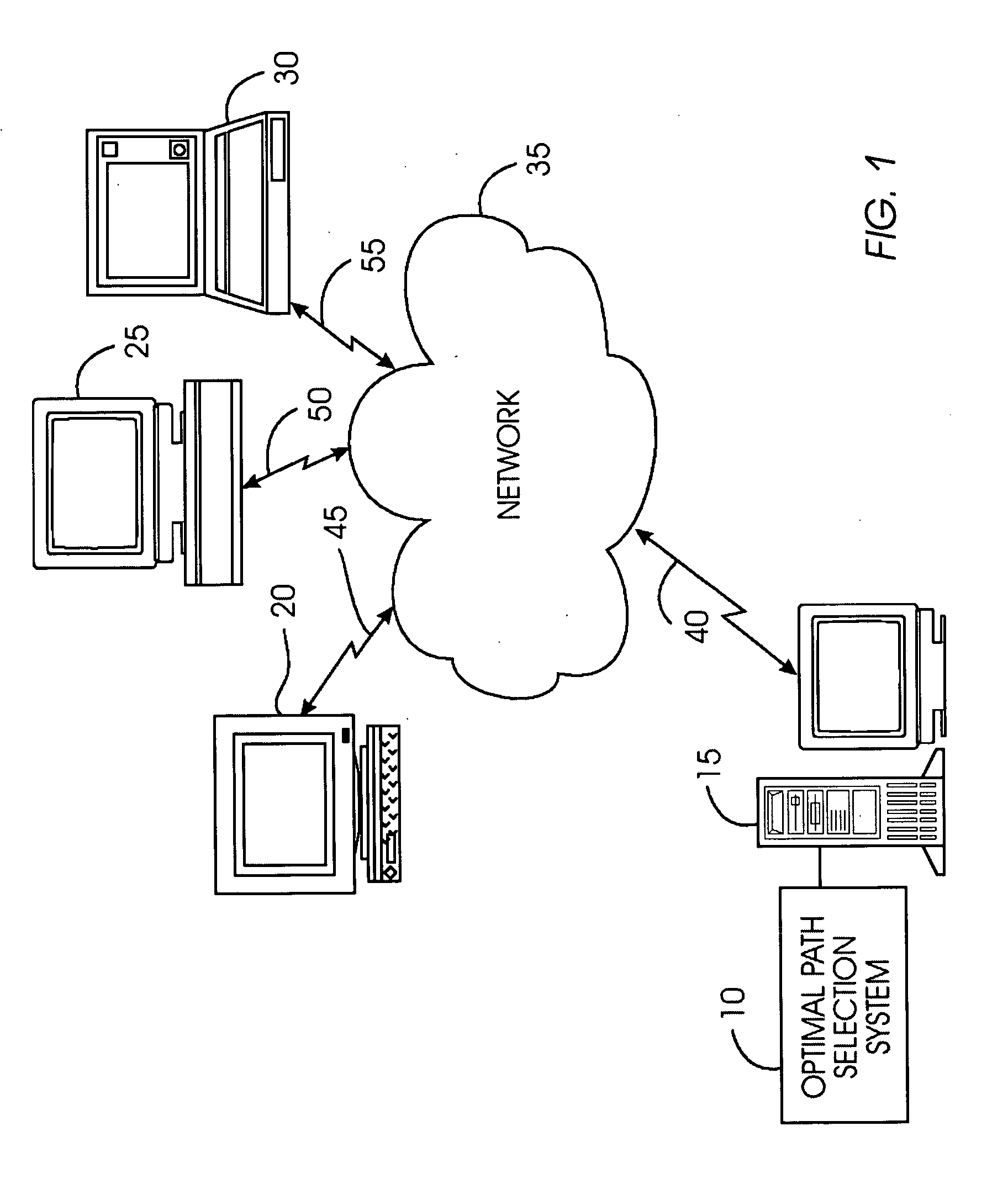
System, method, and service for finding an optimal collection of paths among a plurality of paths between two nodes in a complex network
InactiveUS20050243736A1Optimize locationHandy search resultsError preventionForecastingGraphicsAlgorithm
An optimal path selection system extracts a connection subgraph in real time from an undirected, edge-weighted graph such as a social network that best captures the connections between two nodes of the graph. The system models the undirected, edge-weighted graph as an electrical circuit and solves for a relationship between two nodes in the undirected edge-weighted graph based on electrical analogues in the electric graph model. The system optionally accelerates the computations to produce approximate, high-quality connection subgraphs in real time on very large (disk resident) graphs. The connection subgraph is constrained to the integer budget that comprises a first node, a second node and a collection of paths from the first node to the second node that maximizes a “goodness” function g(H). The goodness function g(H) is tailored to capture salient aspects of a relationship between the first node and the second node.
Owner:IBM CORP
Systems and methods for configuring policy bank invocations
ActiveUS20080225722A1Efficient configurationEfficient processingMultiplex system selection arrangementsError preventionData packEngineering
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
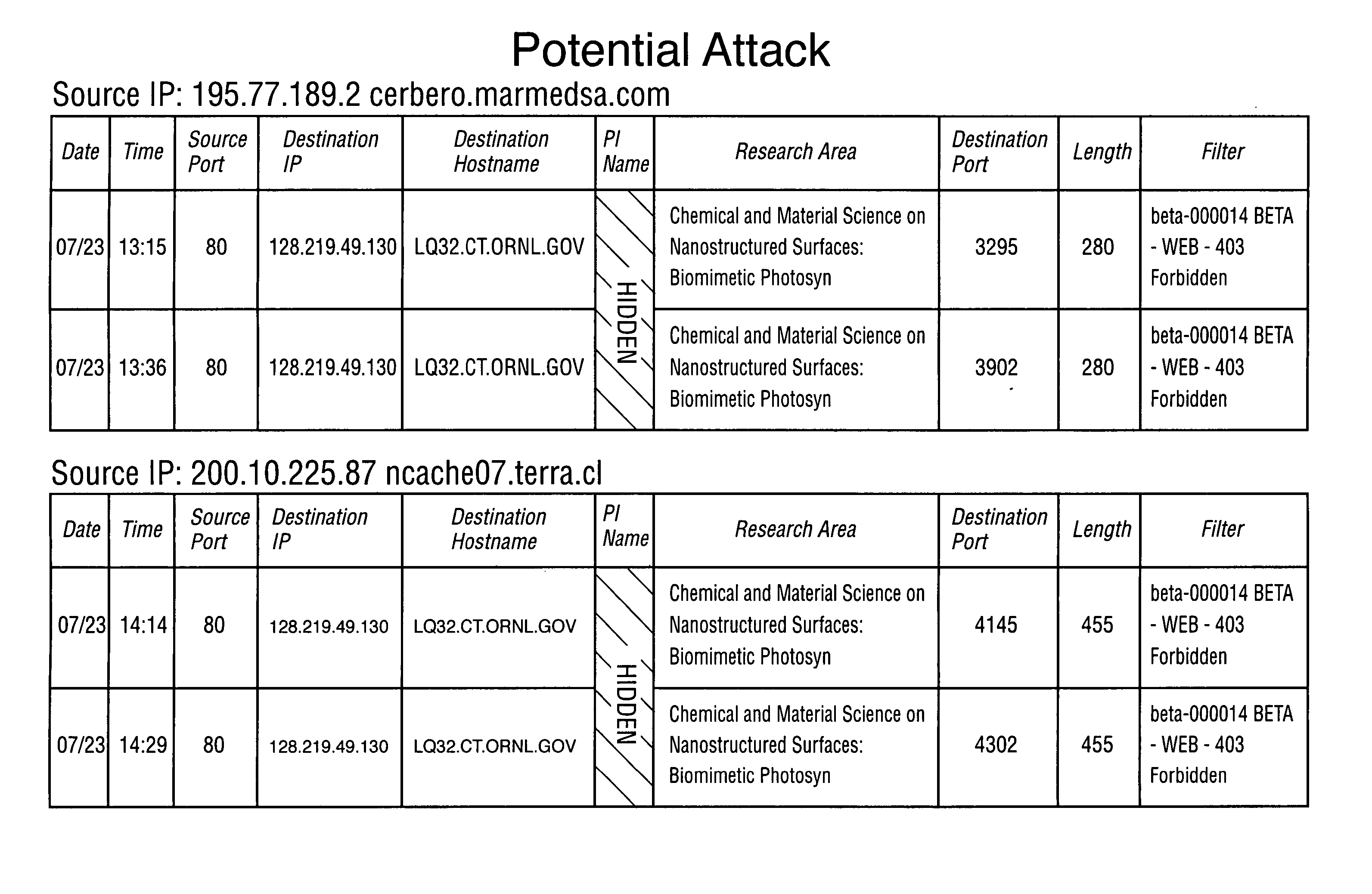
Method for detecting sophisticated cyber attacks
InactiveUS20060265748A1Memory loss protectionError detection/correctionCyber-attackInformation networks
Owner:UT BATTELLE LLC
Distributed knowledge data mining device and mining method used for complex network
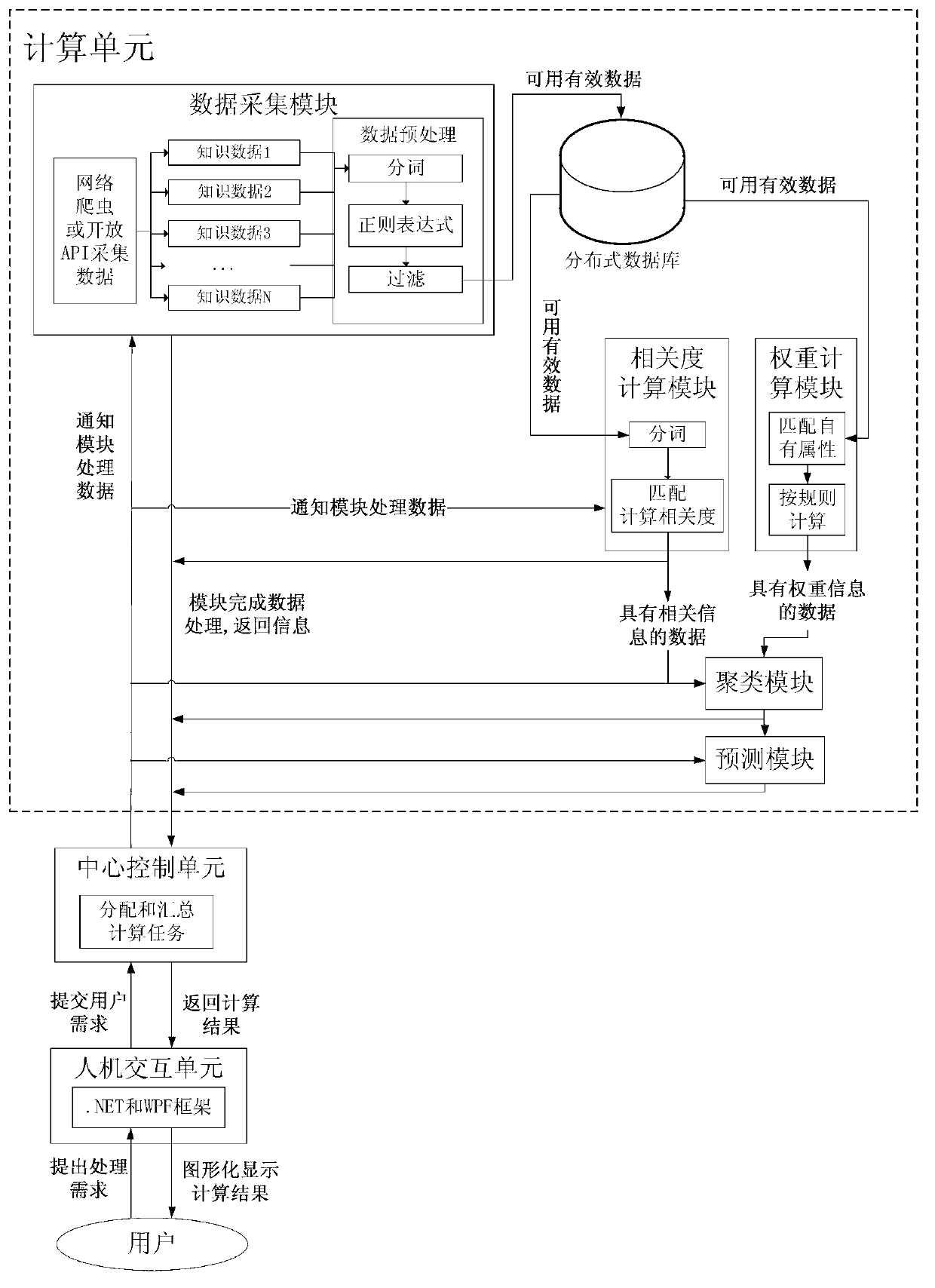
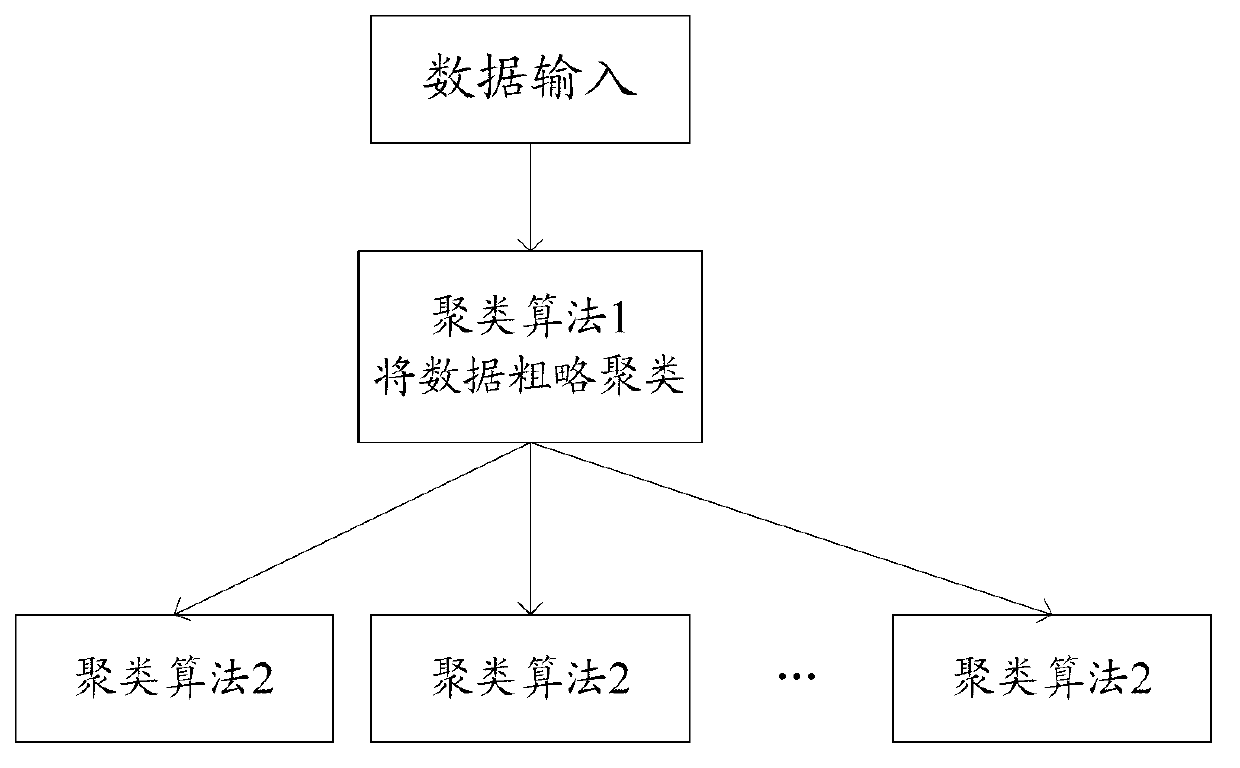
InactiveCN103136337AReduce time complexityThe result is accurateSpecial data processing applicationsCluster algorithmData dredging
The invention discloses a distributed knowledge data mining device and method used for a complex network. The distributed knowledge data mining device adopts a distributed computing platform which is composed of a control unit, a computing unit and a man-machine interaction unit, wherein the innovation key is to finish the calculated amount needed by a multifarious clustering algorithm in the data mining by different servers so as to improve the efficiency of the data mining. Aiming at different knowledge data, the degrees of relation and the weights of knowledge data also can be computed by applying different standards, so that a more credible result is obtained. A second-level clustering mode is adopted in the knowledge data mining process; the result of the first-level clustering is relatively rough, but the computing complexity is very low; and the computing complexity of the second-level clustering is relatively high, but the result is more precise. By combining the first-level clustering with the second-level clustering efficiently, the distributed knowledge data mining device improves the time complexity and clustering precision greatly in comparison with the traditional first-level clustering mode. According to the invention, as a visual and direct exhibition network structure and a dynamic evolutionary process are adopted, references are provided for the prediction in the fields of disciplinary development and hotspot research.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method, device and system for detecting interference
InactiveCN102595436AFlexible deploymentFlexible interferencePower managementReceivers monitoringDisparate systemComplex network
The embodiment of the invention discloses a method, a device and a system for detecting interference. Taking the implementation of the method embodiment as an example, the method comprises the following steps that: a measuring base station obtains a measuring reference mark of an interference base station, and the configuration information of the measuring reference mark; and the measuring base station detects a measuring reference mark receiving quality valve of the interference base station according to the configuration information. The embodiment of the invention provides the method and the system for the base station to detect the interference, provides long-term steady channel measurement result, and solves the problem of detecting and processing the interference of the downlink transmitting of the interference base station in common frequency, pilot frequency and disparate system on the uplink receiving of the measuring base station in the same system or disparate system on the neighboring frequency band under complex network condition, thus, the networks can be flexibly deployed and coexist with interference.
Owner:HUAWEI TECH CO LTD
Visualizing a complex network based on a set of objects of interest
A user interface of a device for displaying a representation of a network of objects wherein a plurality of selectable objects are rendered, and each of the plurality of selectable objects are rendered having a given positioning relative to each other of the plurality of selectable objects. One or more edges are rendered interconnecting the plurality of selectable objects within a first region of the user interface. A second region is rendered in response to one or more of the selectable objects of the first region being selected. Objects corresponding to the selected objects are depicted in the second region while maintaining the given relative positioning. A number of additional objects may be retrieved from a database that indicates objects that are adjoining the corresponding objects. The adjoining objects are positioned in the second region and are interconnected to the corresponding objects by one or more additional edges.
Owner:RIVERBED TECH LLC +1
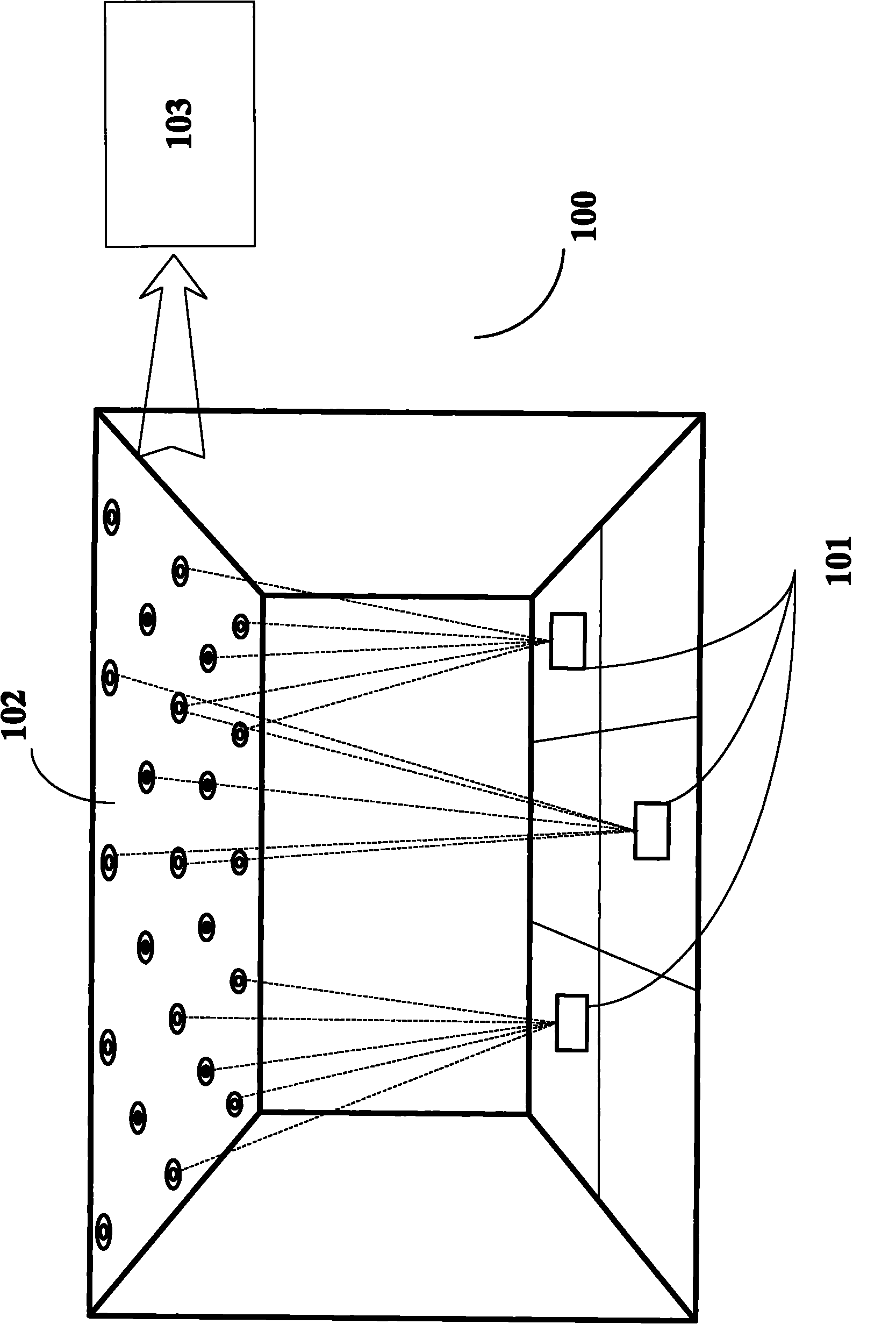
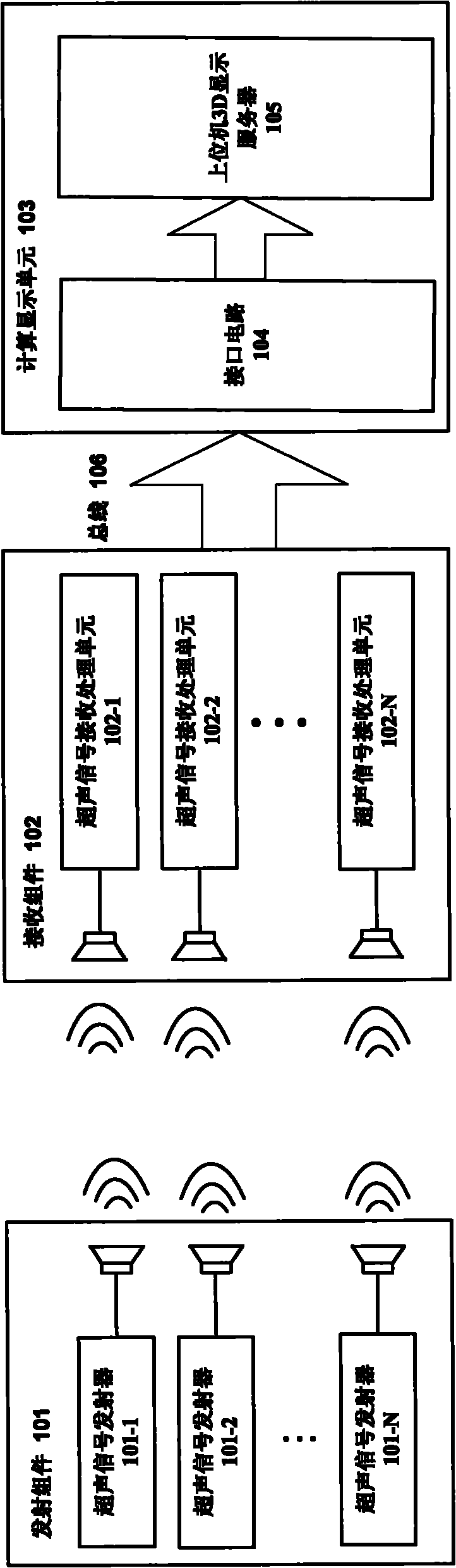
Large-scale multiple-object ultrasonic tracking and locating system and method
ActiveCN102033222AEnable indoor location trackingOvercoming intractable flawsPosition fixationSonificationEngineering
The invention provides a large-scale multiple-object ultrasonic tracking and locating system and method, relating to an indoor object tracking and locating system and method based on ultrasonic wave. The large-scale multiple-object ultrasonic tracking and locating system comprises an emitting assembly, a receiving assembly and a calculating display unit, wherein the emitting assembly comprises a plurality of ultrasonic signal emitters with different frequencies or different time slot features, and each emitter is installed on different objects and used for periodically emitting ultrasonic signals; the receiving assembly comprises a plurality of ultrasonic signal receiving and processing units for receiving and processing the ultrasonic signal emitted by the emitter; and the calculating display unit comprises a USB (Universal Serial Bus) and an upper computer three-dimensional display server. The invention realizes the tracking and the locating of large-scale multiple-object by schemesof spatial subdivision, time frequency combination, spatial handoff and the like. The locating system of the invention has the characteristics of large locating range, multiple tracking objects, no synchronous error, no need of complex network protocol, low power consumption, high stability and the like.
Owner:JILIN UNIV
Rapid networking method for power line carrier communication
ActiveCN104539315AImplement partial refactoringSmall local refactoring scopePower distribution line transmissionSelf-healingCommunications system
The invention provides a rapid networking method for power line carrier communication and specific implementation steps thereof, and aims to solve the problems of low networking efficiency, complex network structure and poor reliability in a power line carrier communication system. Compared with a conventional networking way, the rapid networking method provided by the invention has the advantages that a node association process is synchronously performed in the processes of completing hierarchical management and forming a system route, and a node association table is formed, so that the communication reliability of the system is ensured while the networking efficiency is increased. The local reconstruction range of a network is small; the efficiency is high; and the self-healing ability is high. The rapid networking method is suitable for data communication of a power line carrier communication system.
Owner:SHANGHAI ELECTRICAL APP RES INST +1
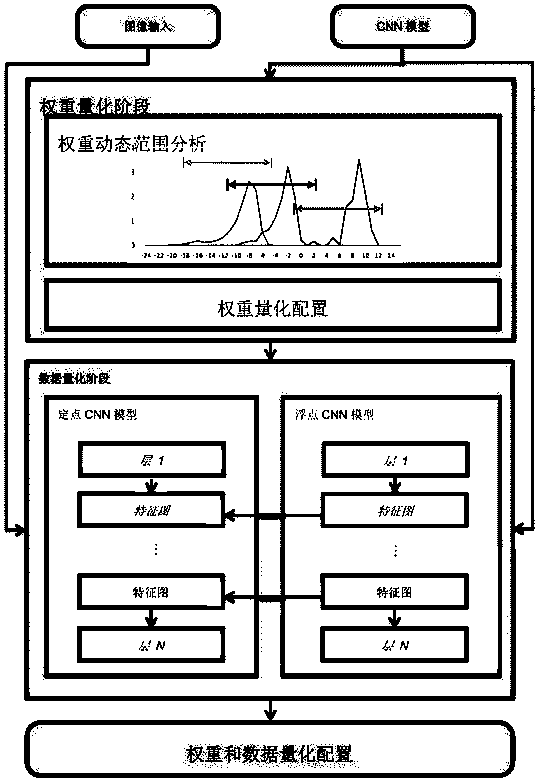
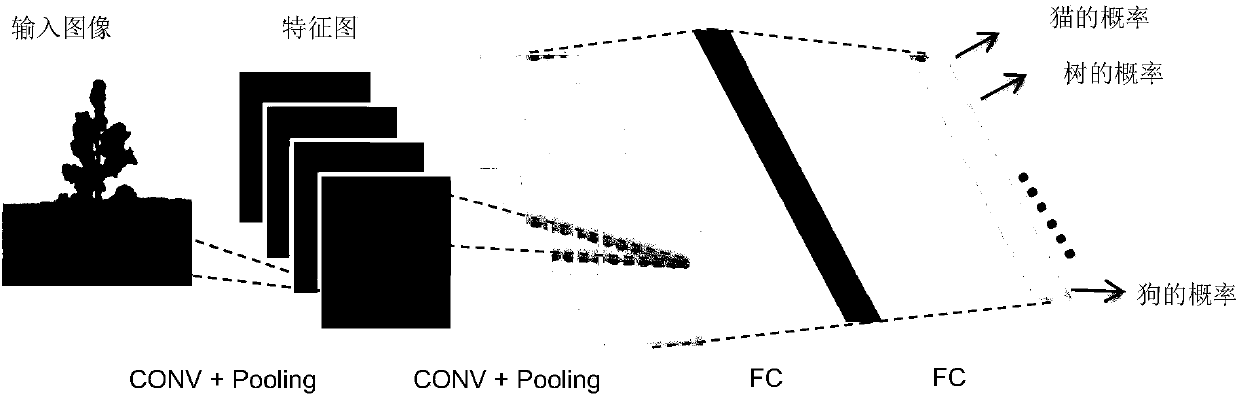
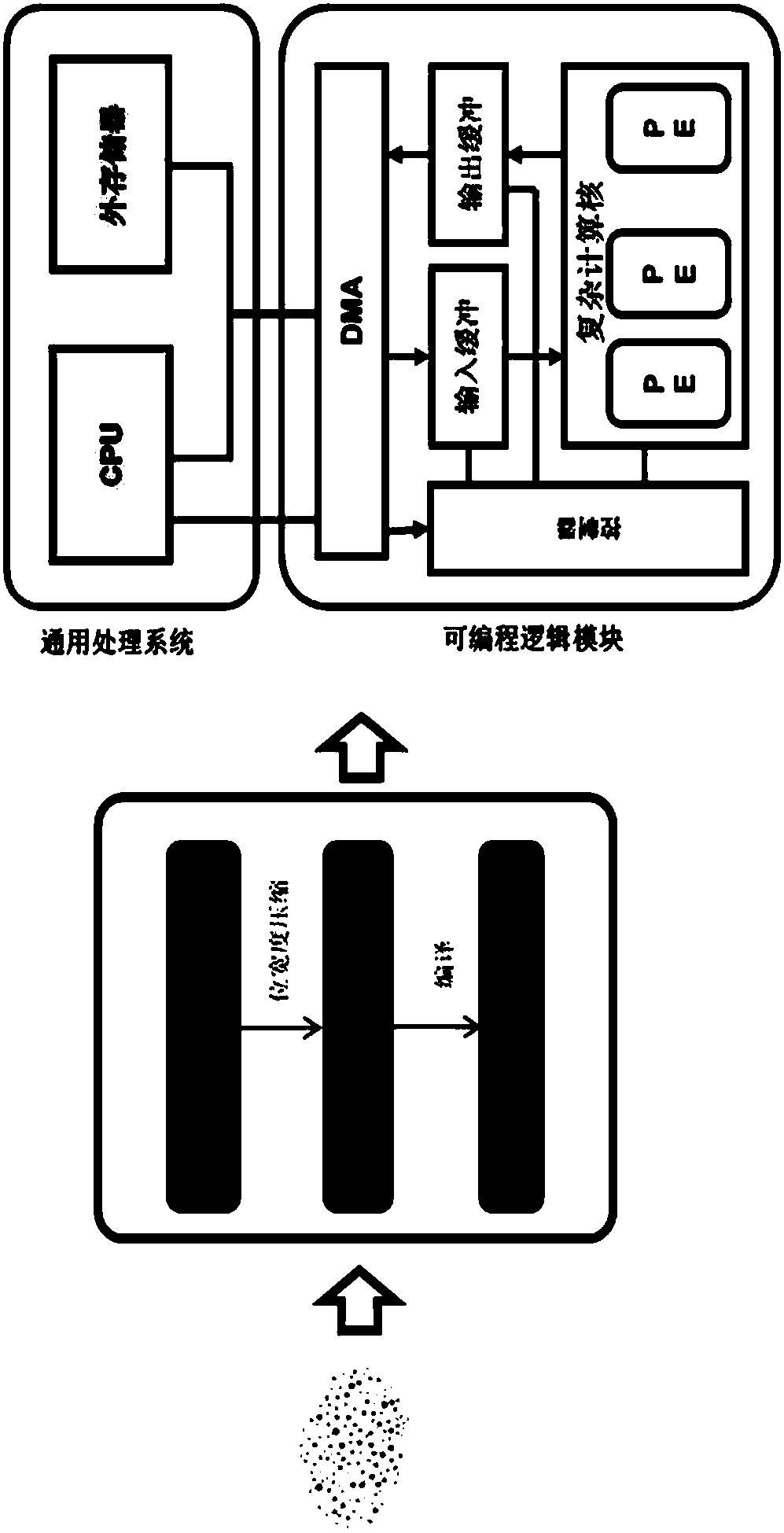
Layering quantization method and device for complex neural network
ActiveCN107688855ASolve fixed-point problemsCharacter and pattern recognitionNeural learning methodsBioinformaticsComplex network
The invention relates to an artificial neural network (ANN), for example, a convolutional neural network (CNN), in particular to how to achieve compression and acceleration of the ANN through fixed-point quantization of a complex neural network.
Owner:XILINX INC
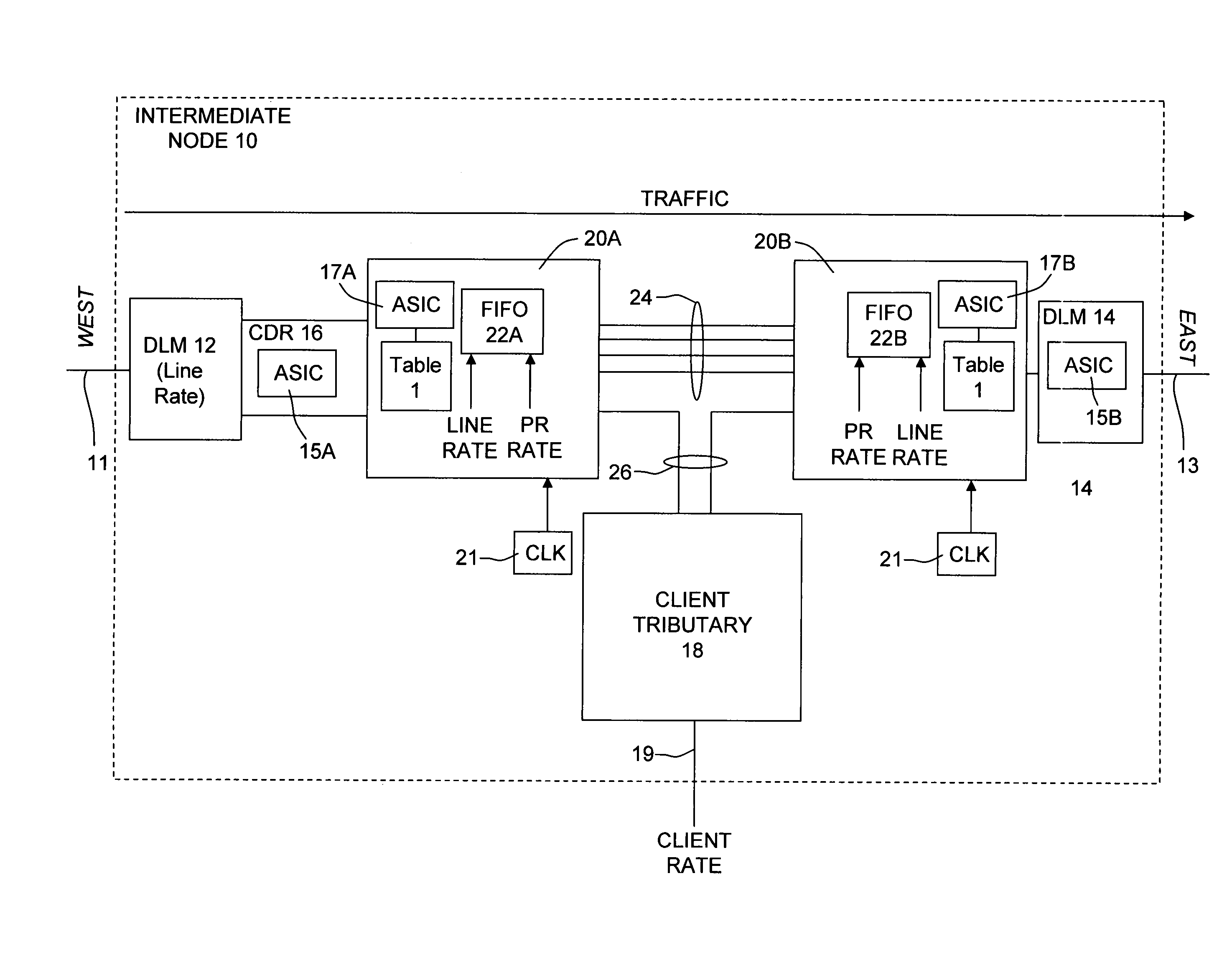
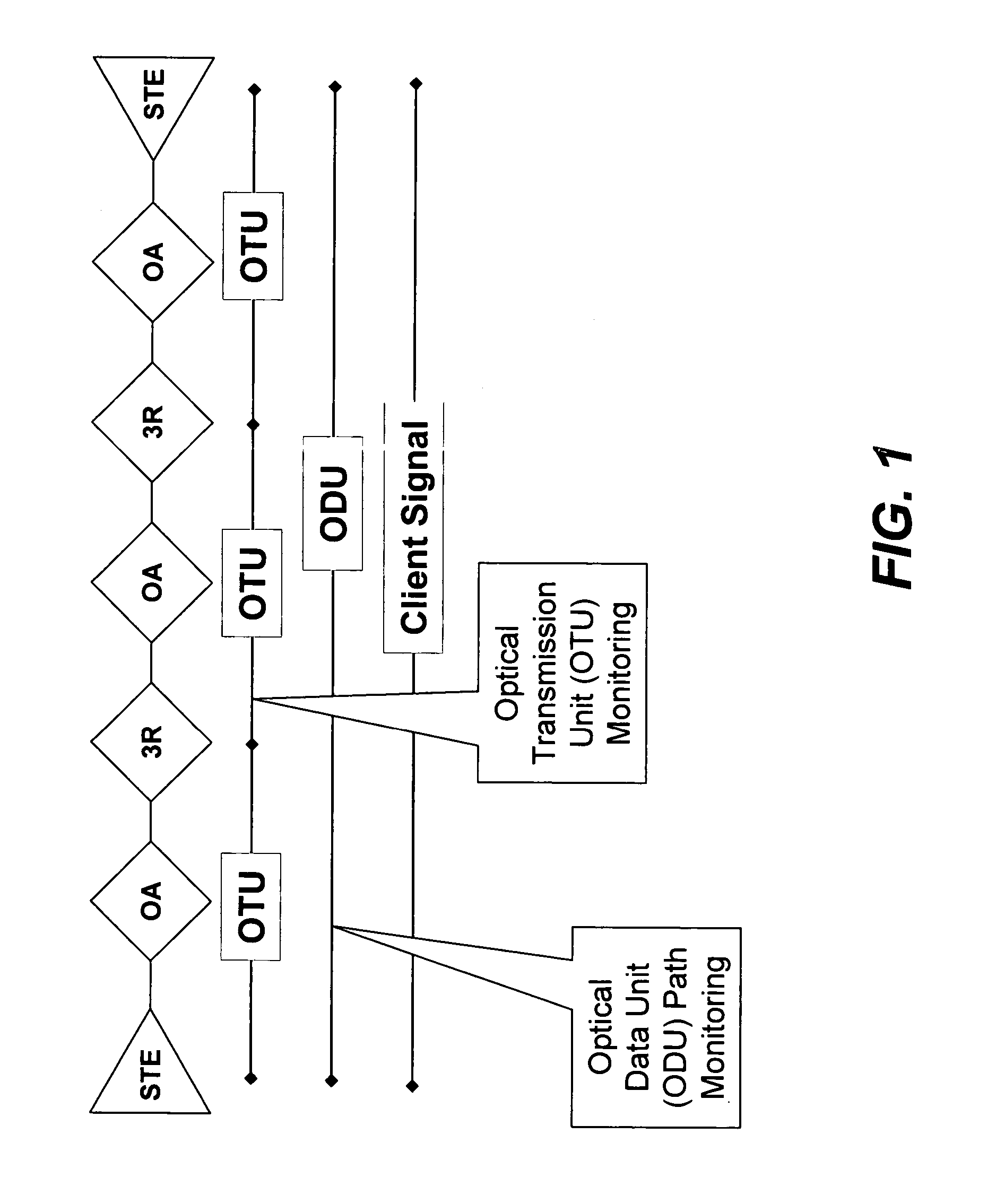
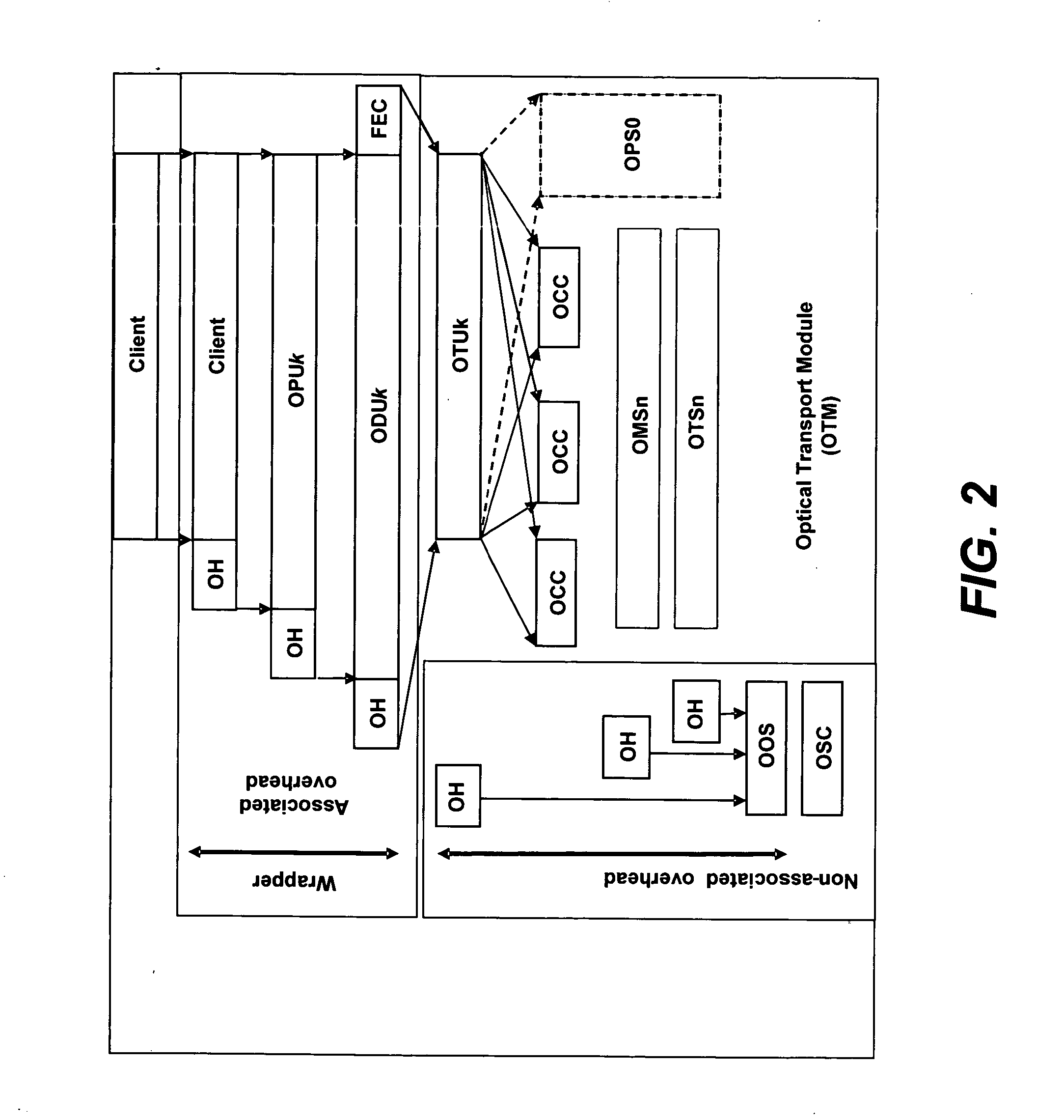
Optical transmission network with asynchronous mapping and demapping and digital wrapper frame for the same
ActiveUS7286487B2Reduce manufacturing costLow costError preventionFrequency-division multiplex detailsTransmission protocolLine rate
An optical transmission network is inherently asynchronous due to the utilization of a variable overhead ratio (V-OHR). The network architecture makes extensive use of OEO regeneration, i.e., deals with any electronic reconditioning to correct for transmission impairments, such as, for example, FEC encoding, decoding and re-encoding, signal reshaping, retiming as well as signal regeneration. The optical transmission network includes a plesiochronous clocking system with intermediate nodes designed to operate asynchronously with a single local frequency clock without complicated network synchronization schemes employing high cost clocking devices such as phase locked loop (PLL) control with crystal oscillators and other expensive system components. The asynchronous network operation provides for asynchronous remapping or remapping of any client signal utilizing any type of transmission protocol where the line side rate or frequency is always the same frequency for the payload signal and the local frequency at an intermediate node is set to a local reference clock in accordance with the payload type and its overhead ratio, i.e., the overhead ratio is varied to meet the desired difference between the line rate or frequency and the desired client signal payload rate or frequency for the particular client signal payload type.
Owner:INFINERA CORP
Deep learning-based method for building position prediction model by considering vehicle driving influence factors in internet-of-vehicles complex network
ActiveCN107609633AImprove forecast accuracyImprove stabilityRoad vehicles traffic controlCharacter and pattern recognitionSimulationThe Internet
Characteristics of criss-cross roads, non-uniform vehicle distribution and the like objectively exist in city roads, so that vehicle positions are easily changed to cause the problem of data transmission distortion of an internet-of-vehicles network layer, and the problem becomes a bottleneck hindering the development of internet-of-vehicles application services. An existing vehicle position prediction model is trained by generally utilizing historical track data of vehicles, so that consideration of complex vehicle states and real-time road condition information is lacking, and relationshipsbetween complex driving environments and vehicle driving behaviors and between the complex driving environments and vehicle position changes are mined insufficiently. For the problem, a deep learning-based method for building a position prediction model by considering vehicle driving influence factors in an internet-of-vehicles complex network comprehensively considers the vehicle driving influence factors such as vehicle body attributes, road information, driving environments and the like; in combination with a deep learning technology, the relationships between the vehicle driving influencefactors and the vehicle positions are mined; and the vehicle position prediction model is proposed, so that the purpose of improving vehicle position prediction accuracy is achieved, and assistance isprovided for improving the stability of route protocol design of the internet-of-vehicles network layer and effectively solving the data distortion problem.
Owner:TONGJI UNIV
Intrude detection method and device
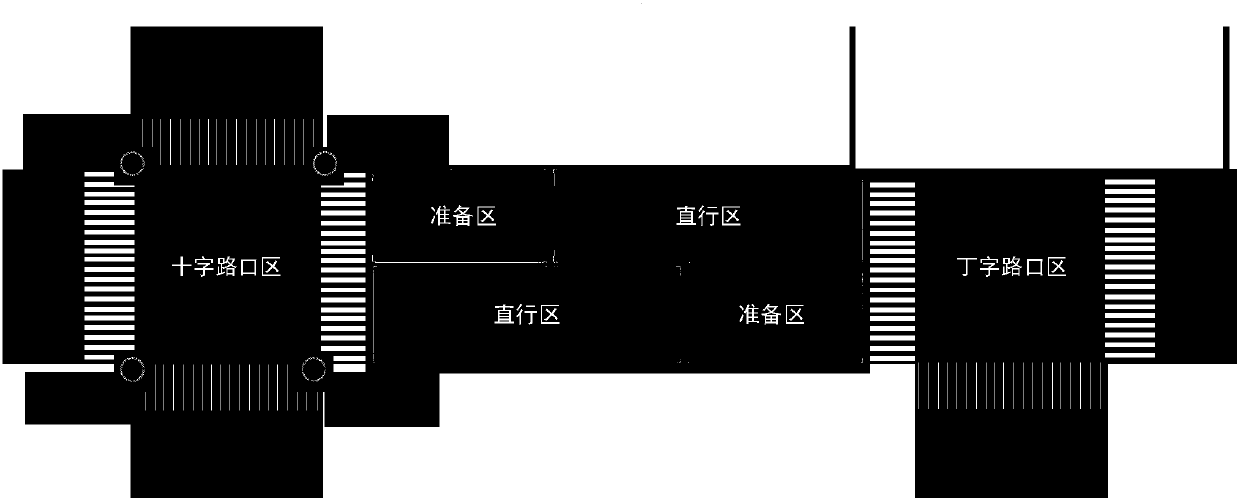
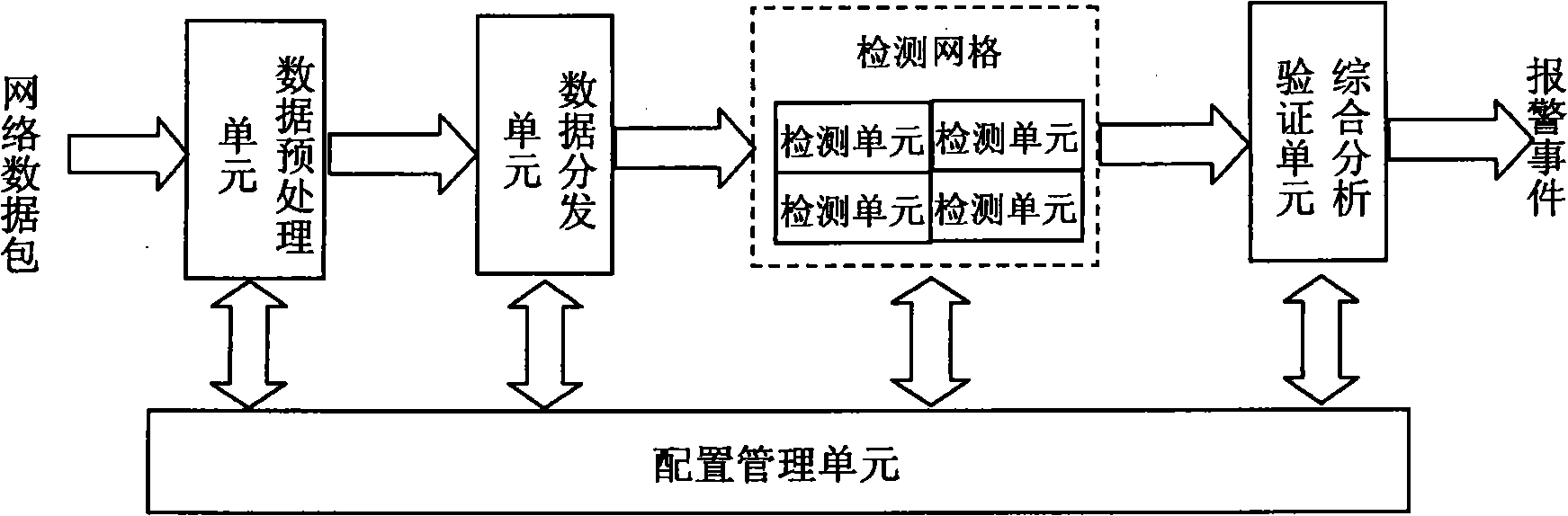
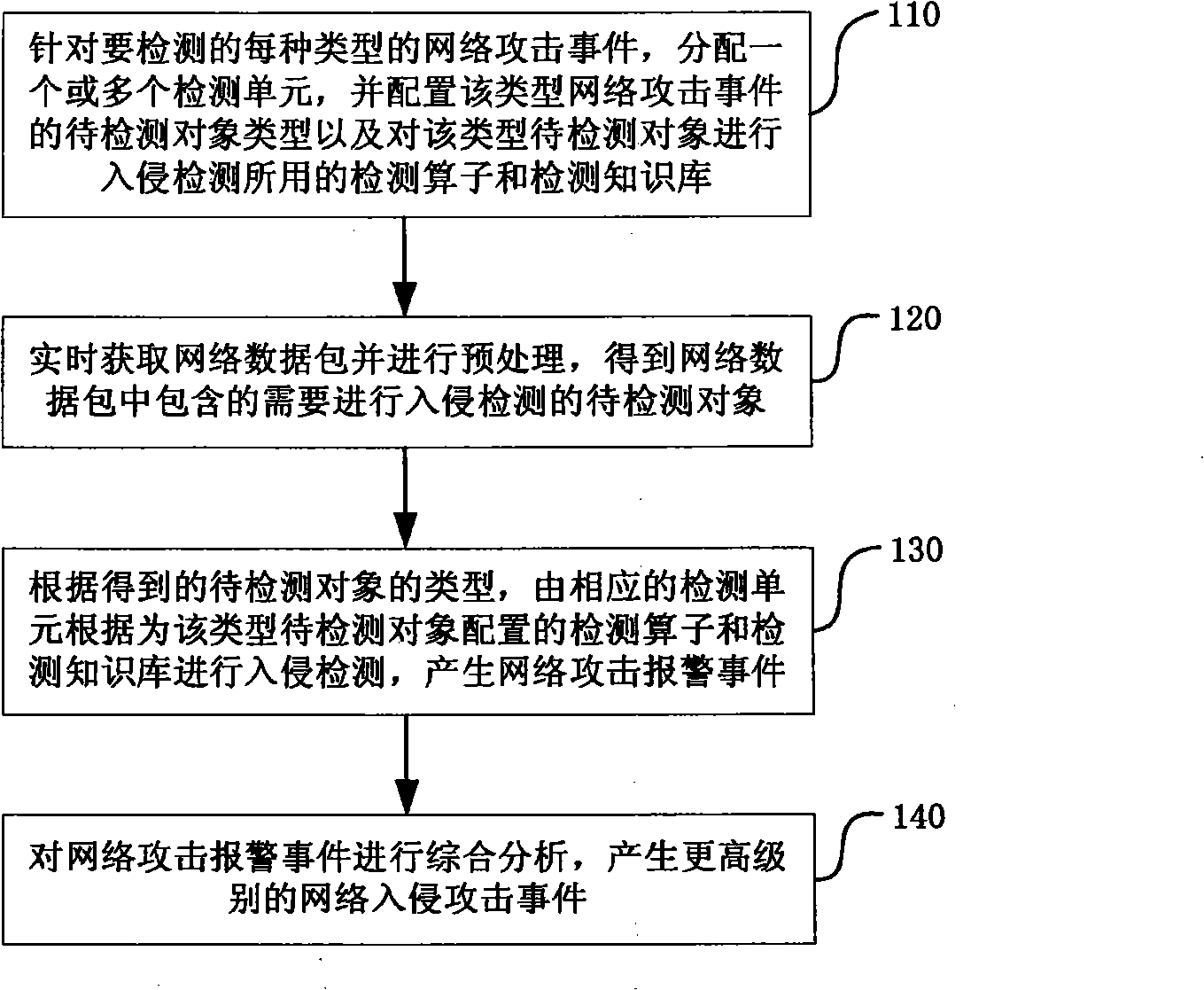
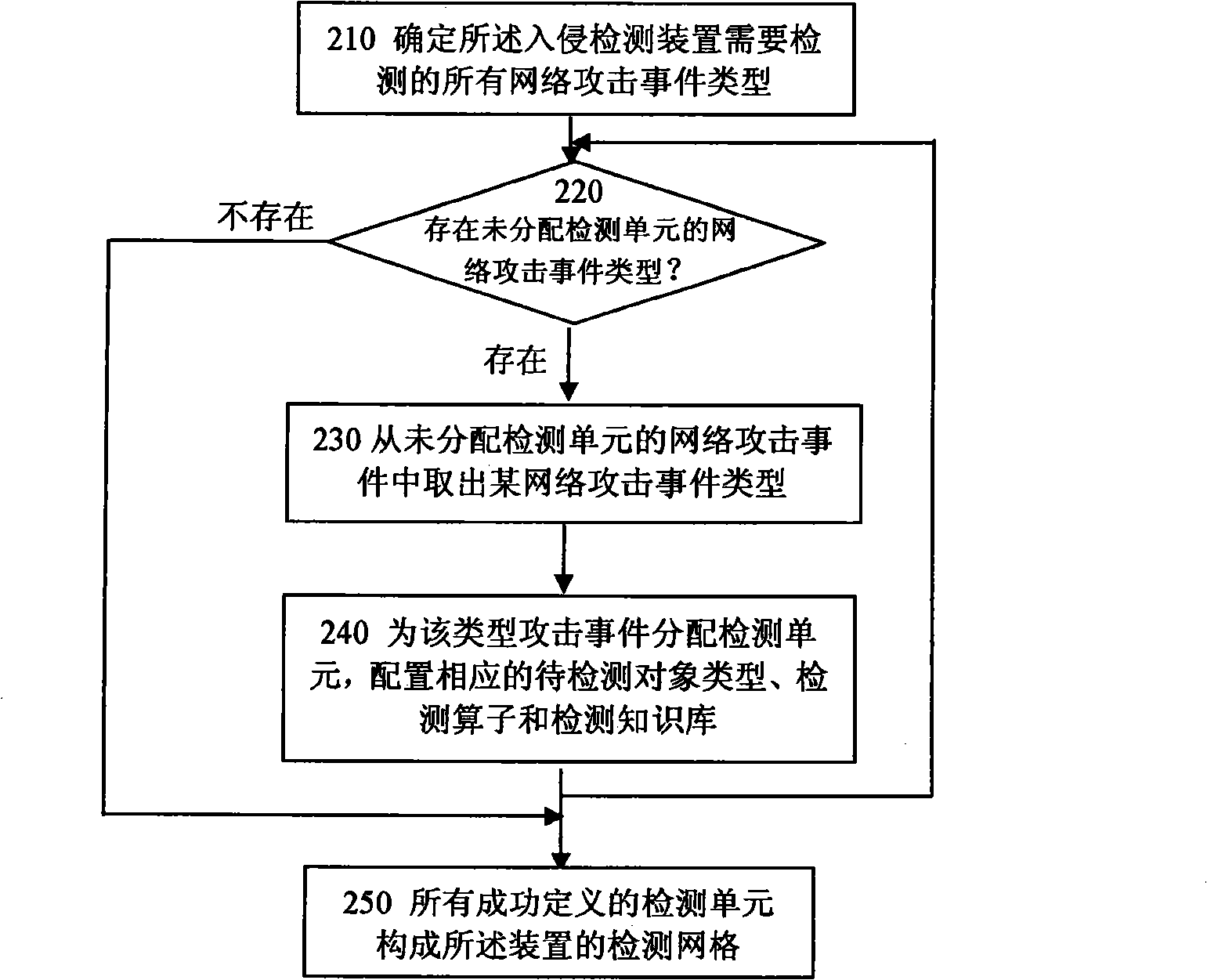
InactiveCN101350745AEasy to detectReduce maintenance and upgrade costsData switching networksNetwork packetNetwork data
The present invention relates to an intrusion detection method and a device thereof. The method distributes one or more than one detection units to various types of network attacks to be detected, and is provided with the type of the object to be detected in the network attack of the type, a detection operator and a detection knowledge base. When the intrusion is detected, the real-time network data packet which comprises the object to be detected is acquired; the corresponding detection unit detects the intrusion according to the configured detection operator and the detection knowledge base, so as to generate the occurrence of alarming the network attack. The intrusion detection device orderly comprises a data pre-processing unit, a data distribution unit, a detection network which comprises one or more than one detection units, and a configuration management which is used for managing the connection of the unit. The method supports the precise detection of various complex network attacks, and comprises the detection efficiency of the whole intrusion detection device.
Owner:BEIJING VENUS INFORMATION TECH +1
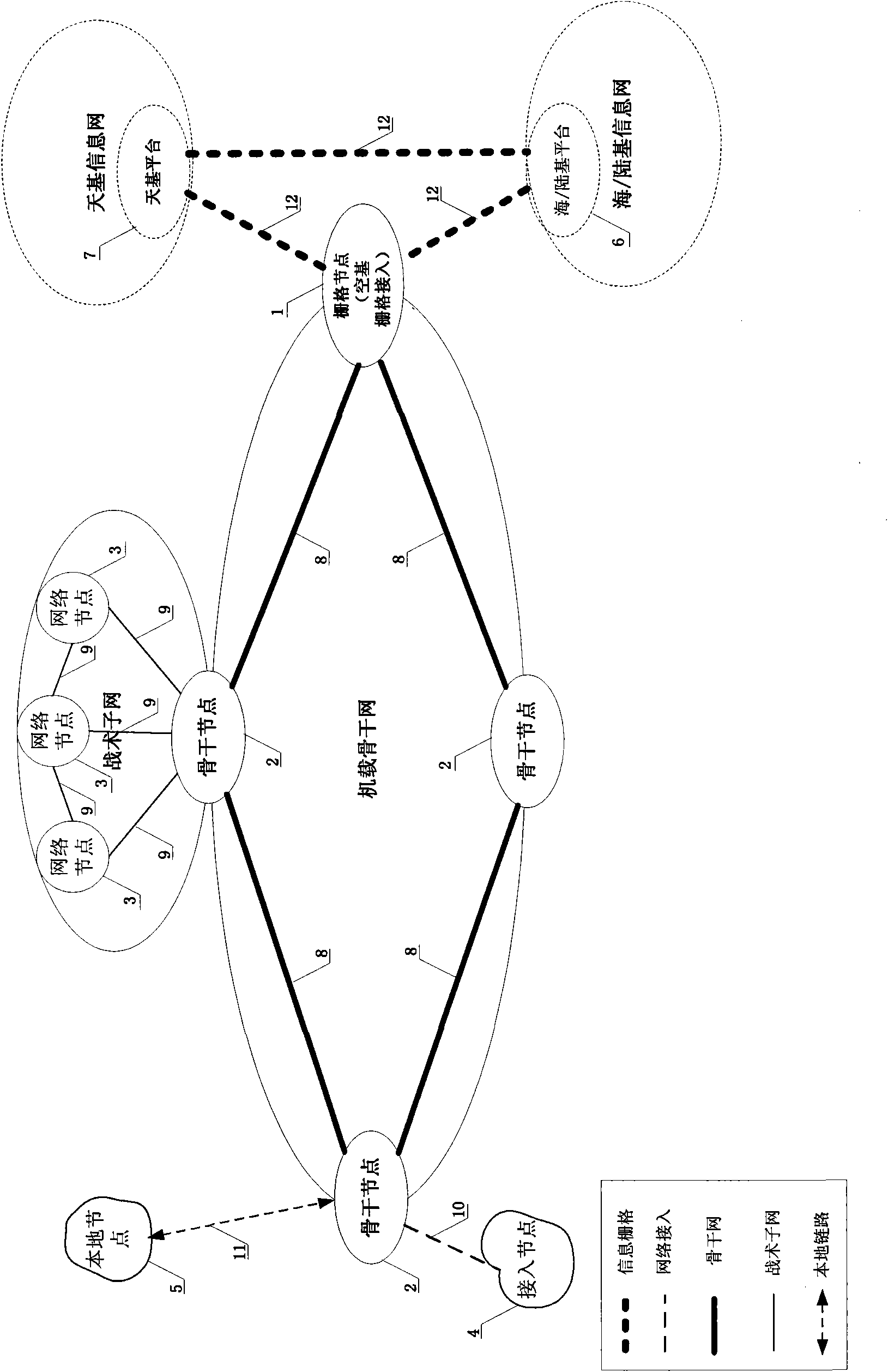
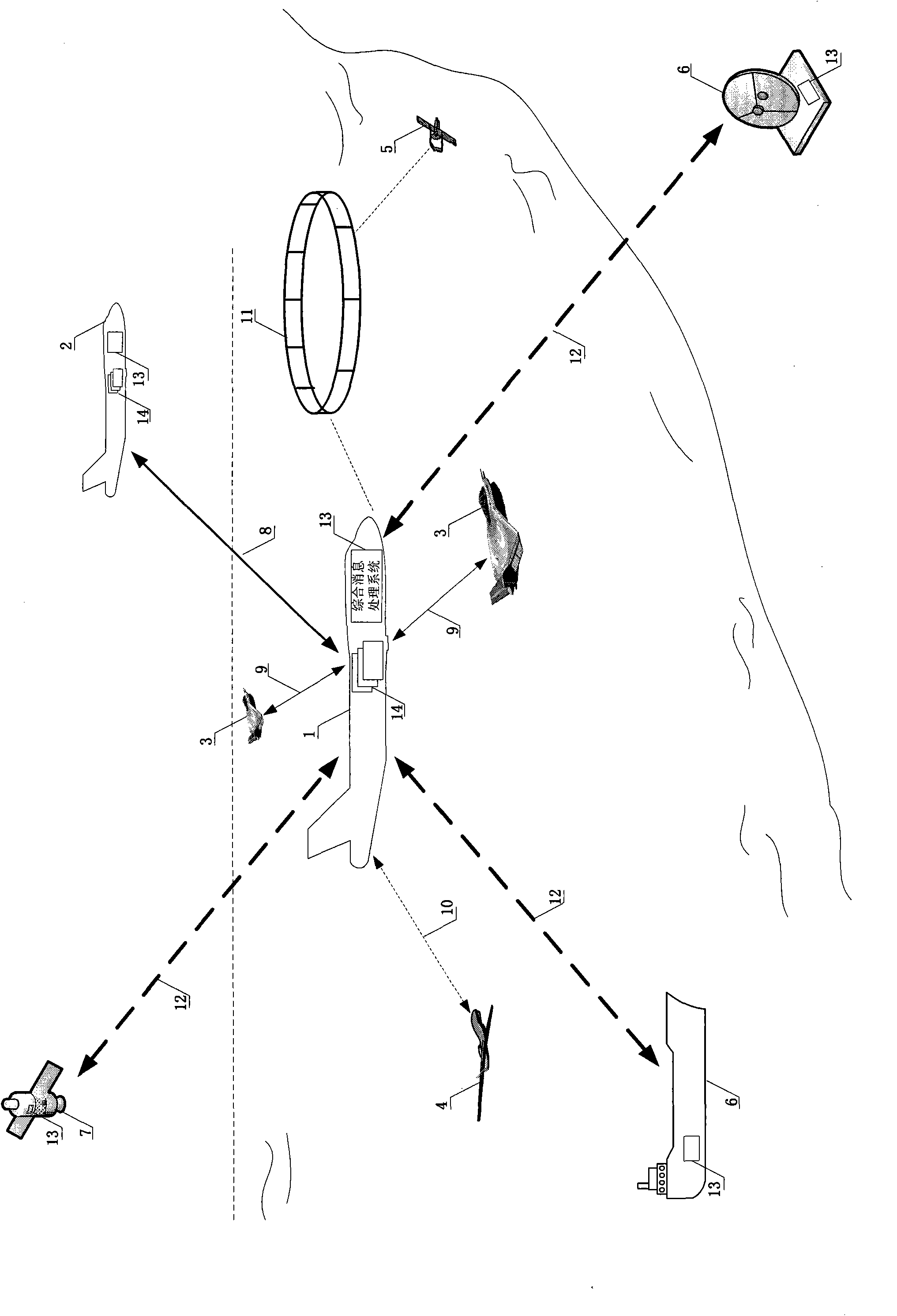
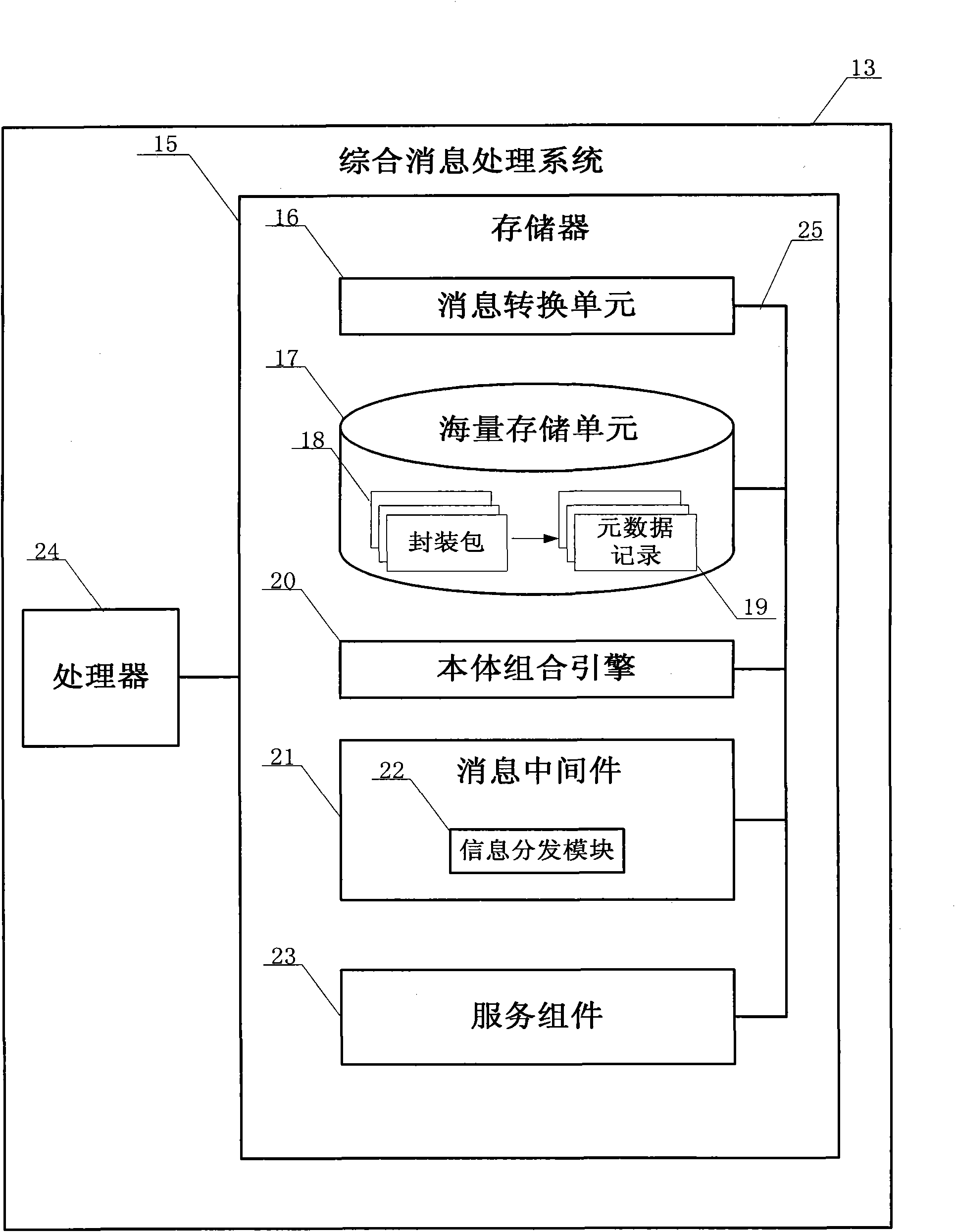
On-board network system and backbone node message processing method thereof
InactiveCN101964958AFlexible and Efficient AccessLess remodeling workNetwork topologiesMessaging/mailboxes/announcementsResource utilizationInformation access
The invention discloses an on-board network system and a backbone node message processing method thereof. In the system, a mixed layered network structure of combining a ratio Mesh backbone network and a heterogeneous access network is adopted, and the interconnection of various access networks is realized through an on-board backbone network, thereby the flexibility and the expandability of the system are improved. Meanwhile, a backbone node message processing method is adopted in the comprehensive message processing system of backbone network nodes. The method realizes the transformation of heterogeneous messages between a core network and an edge network, and a publishment / subscription mechanism based information distribution service is adopted, thereby the resource utilization ratio and the information access efficiency in complicated network environment are improved. The invention has military and civil values and particularly has wide application prospects in the fields of airborne command collaborative constellation of military integration information grids, civil aviation networked communication, navigation, monitoring, and the like.
Owner:BEIHANG UNIV
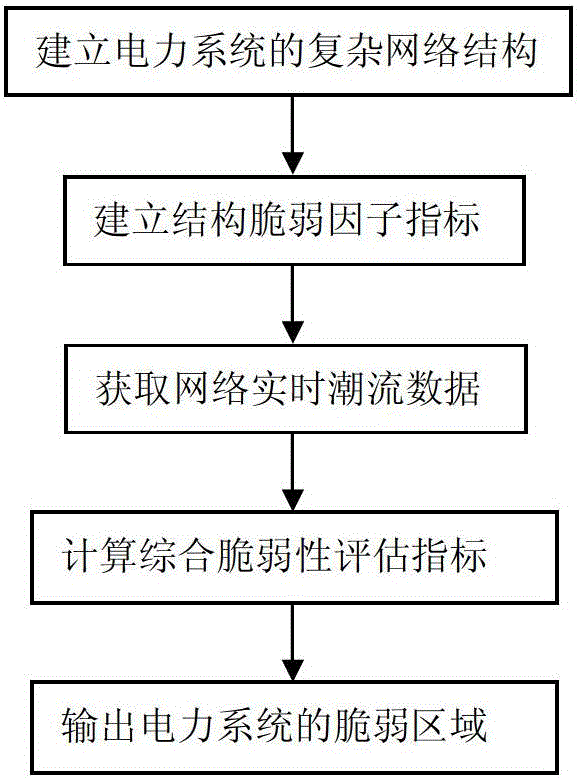
Electric power system vulnerability assessment method
InactiveCN104156769ACatastrophe preventionFully determinedData processing applicationsAc network circuit arrangementsStructural vulnerabilityEngineering
The invention discloses an electric power system vulnerability assessment method, and relates to the field of a power network safety analysis technology. The electric power system frangibility assessment method comprises the following steps: (1), establishing a complex network structure of an electric power system; (2), establishing a structure vulnerability factor indicator through electrical betweenness in the complex networks structure; (3), obtaining network real-time trend data through a static energy function method; (4), calculating a state vulnerability factor, and calculating to obtain an integrated vulnerability assessment indicator through combination with a structural vulnerability factor in step (2); and (5), outputting a vulnerable area of the electric power system. According to the invention, since the electric power system vulnerability assessment method analyzes vulnerable links which may exist in the electric power system from a global perspective, the vulnerable area in the operation of the electric power system can be comprehensively, accurately and effectively determined, the defects of a conventional single one-sided electric power system vulnerability assessment method and the like can be made up for, emphases are provided for prevention and control of safe operation of the electric power system, and collapse of the electric power system, caused by disturbance or accidents, is effectively prevented.
Owner:ELECTRIC POWER SCHEDULING CONTROL CENT OF GUIZHOU POWER GRID CO LTD +1
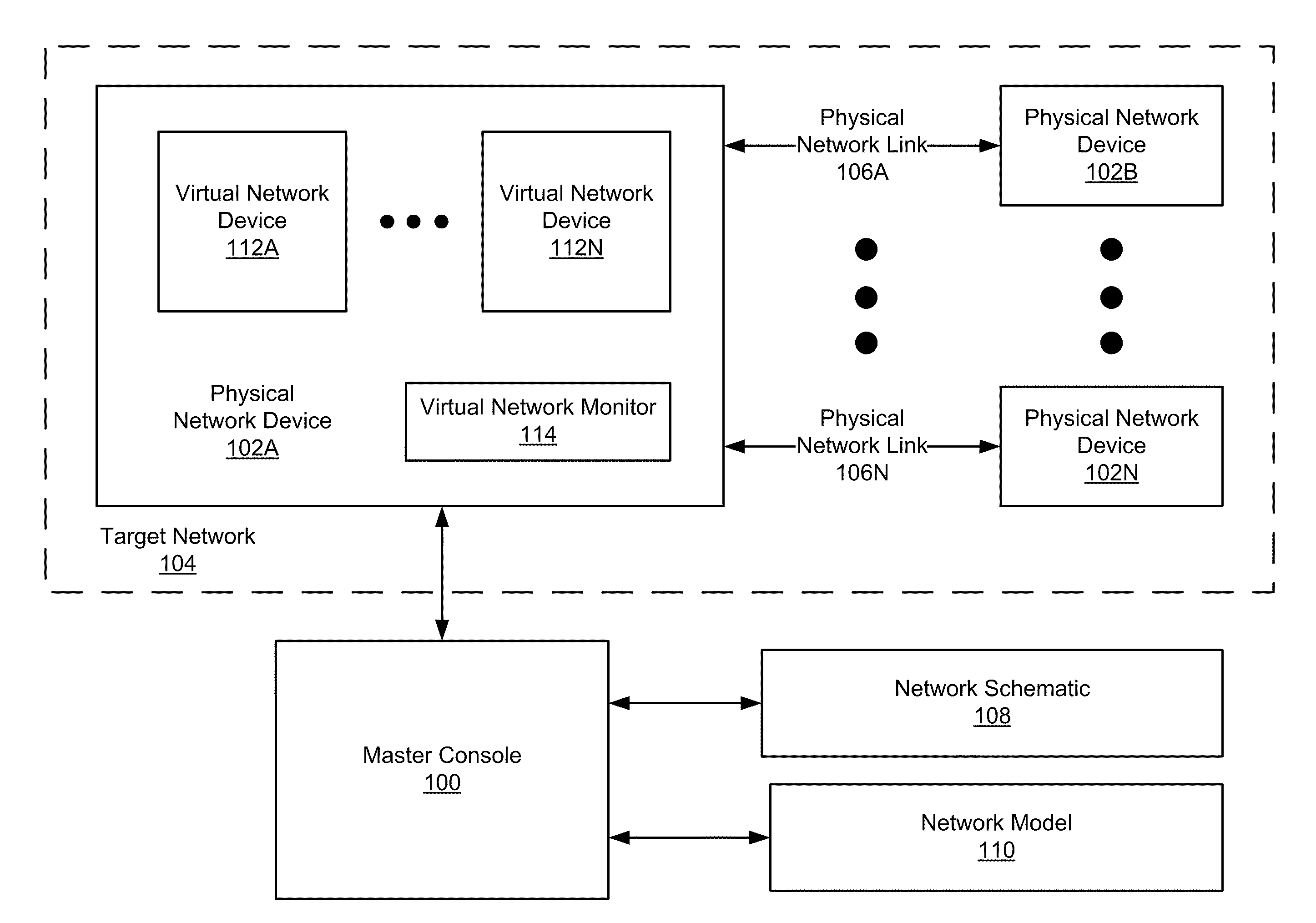
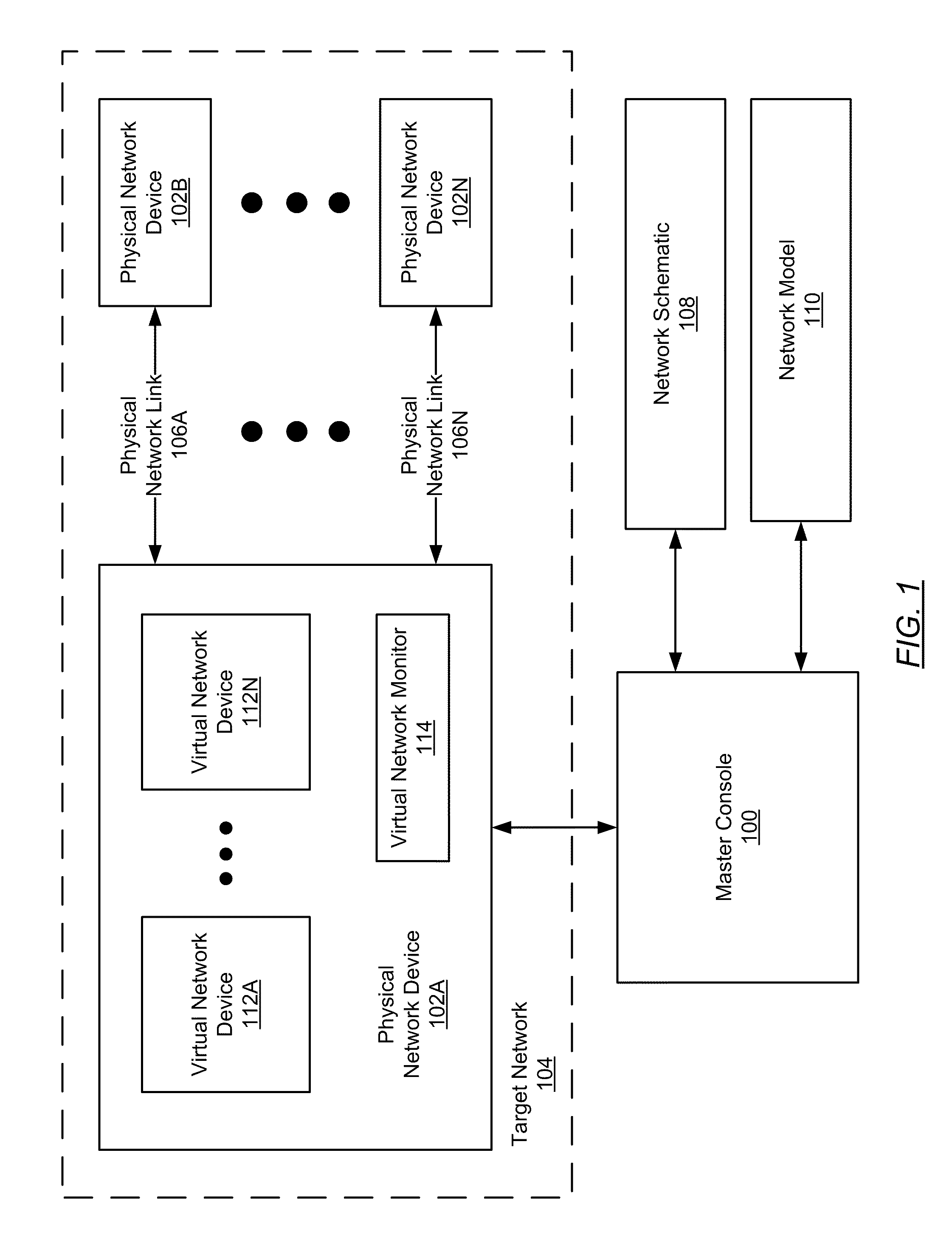
Virtualizing complex network topologies
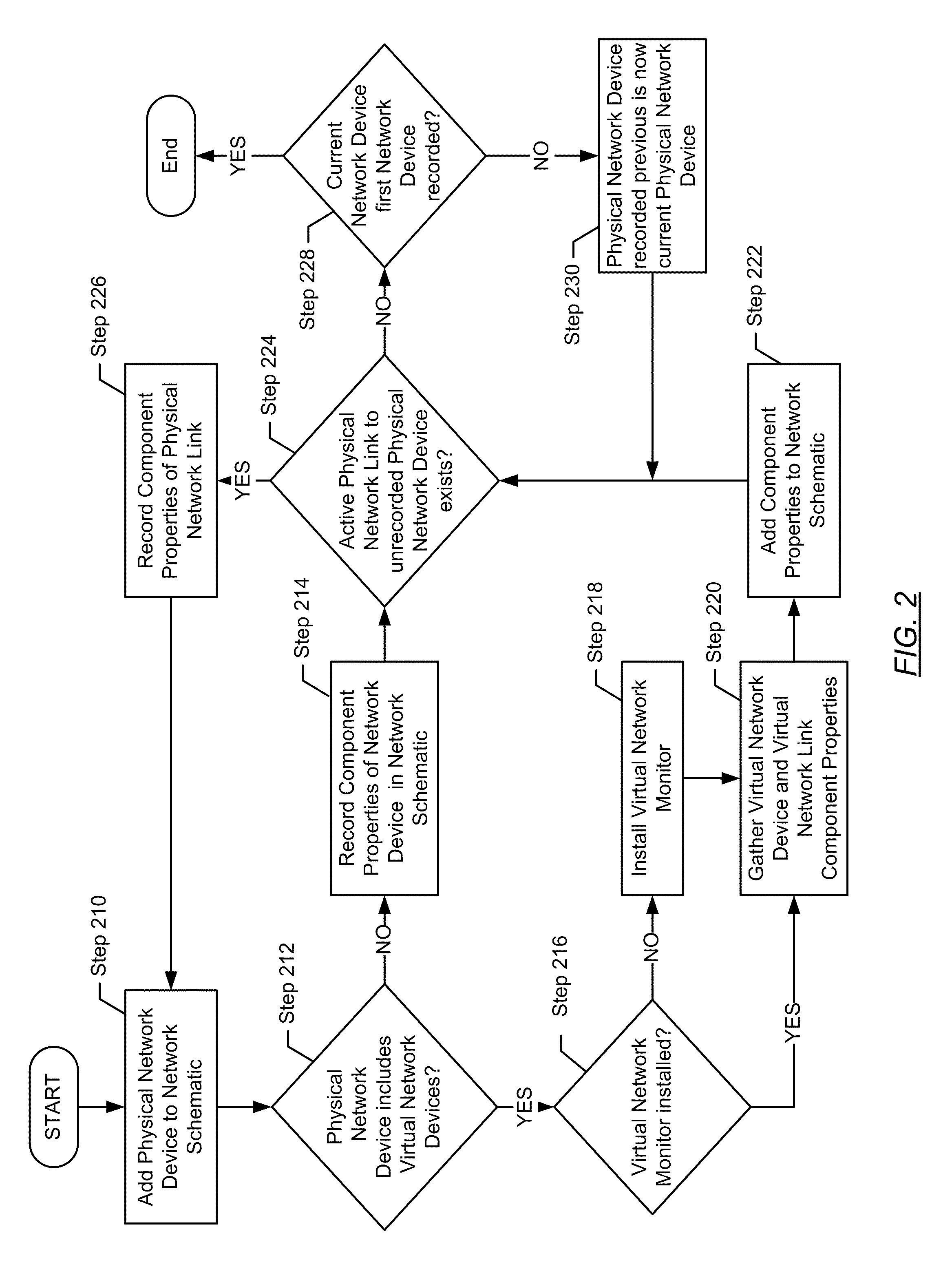
ActiveUS20110093251A1Geometric CADAnalogue computers for electric apparatusVirtualizationNetwork model
In general, the invention relates to a creating a network model on a host. The invention includes: gathering first component properties associated with a first physical network device on a target network; creating a first container using first component properties; determining that a second physical network device is operatively connected to the first physical network device via a physical network link; gathering second component properties associated with the physical network link; creating a first VNIC associated with the first container; determining that at least one virtual network device is executing on the second physical network device; gathering third component properties associated with the at least one virtual network device; creating a second container, wherein the second container is configured using the third component properties; and creating a second VNIC associated with the second container.
Owner:ORACLE INT CORP
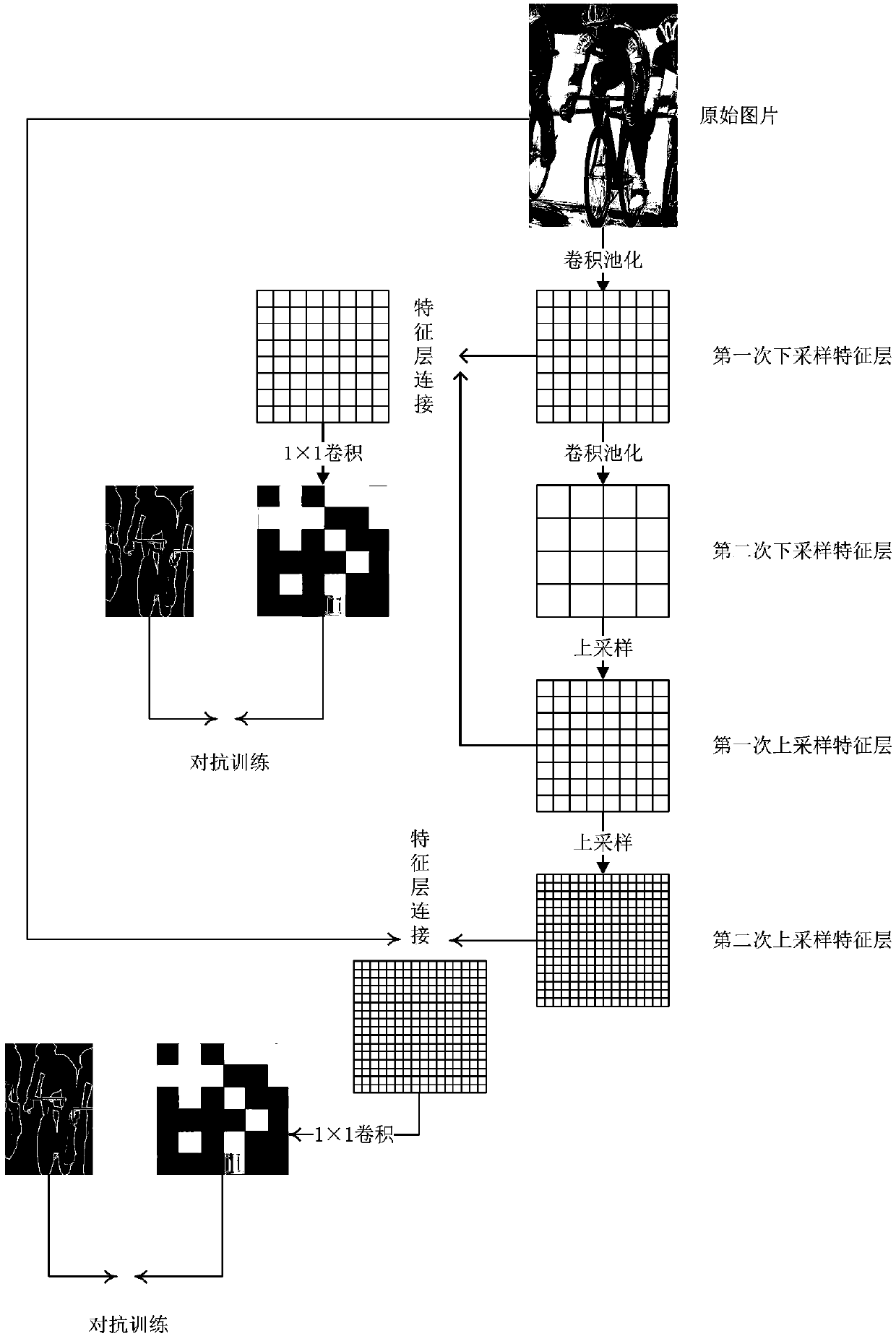
Image semantic segmentation method based on confrontation training
ActiveCN107767384AAvoid initialization parameter processRealize organic integrationImage analysisCharacter and pattern recognitionGeneral functionPattern recognition
The invention belongs to the technical field of computer vision, discloses an image semantic segmentation method based on confrontation training and is used for solving a problem that the existing semantic segmentation method cannot achieve meaningful fusion of global information and local information of images and cannot perform learning on high-order potential energy in the images. According tothe invention, a loss function of the whole network is defined based on a confrontation training network to serve as a confrontation network of a general function approximator, thereby not only beingcapable of learning how to combine different levels of information, but also being capable of forcing the generated network to learn information such as single points, paring and high-order potentialenergy in a segmented picture, achieving organic integration of local features and global features of the image and acquiring a segmentation image with the effect being more authentic; and meanwhile,the layer-by-layer training method avoids the complex network parameter initialization process, and enabling the whole network to use a method of random initialization.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
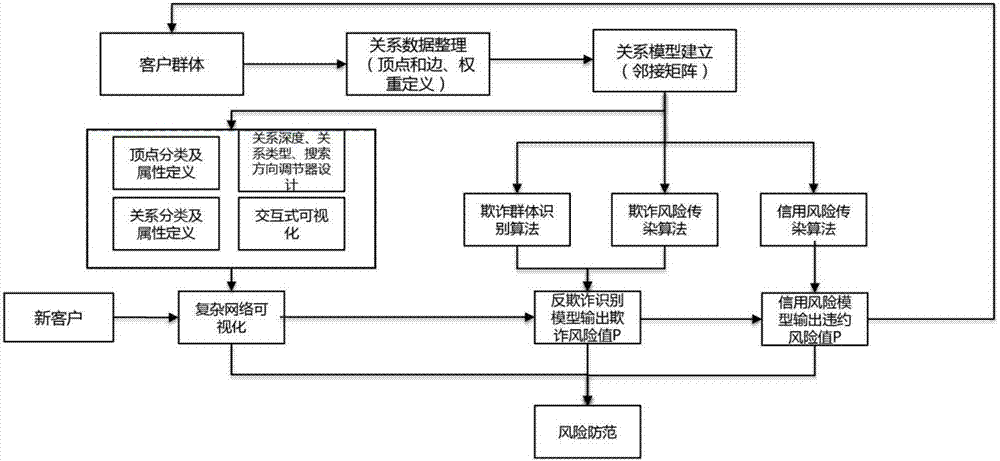
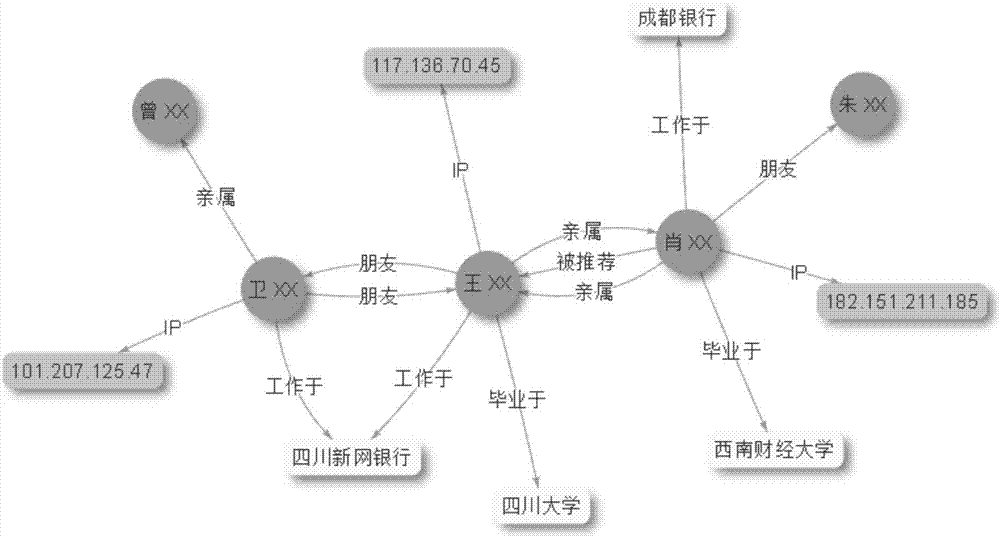
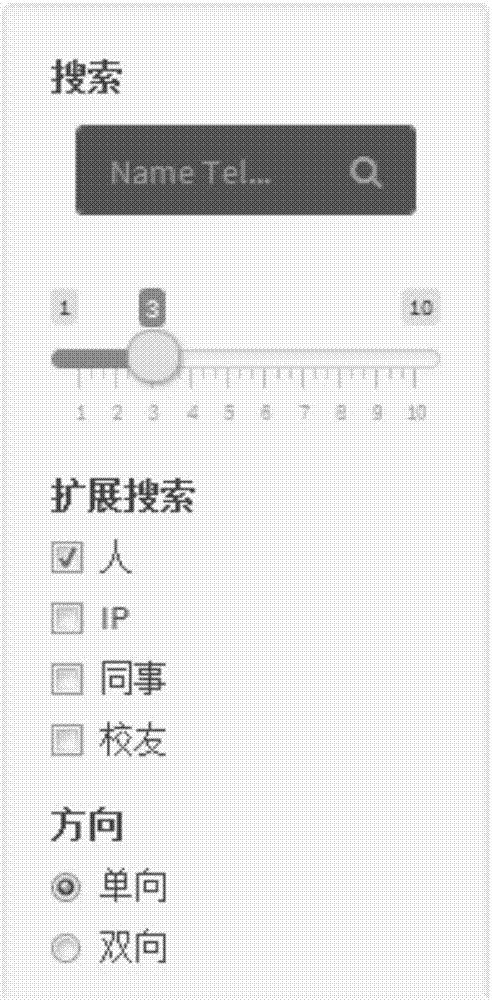
Anti-fraud and credit risk prediction method based on complex social network
The invention discloses an anti-fraud and credit risk prediction method based on complex social networks; aiming at complex social relations between people, the method can integrate the relative relations, friend relations and colleague relations so as to build a mathematics model, thus identifying and predicting client fraud risks and credit risks according to the complex social networks; the method can improve the fraud recognition rate and credit risk prediction accuracy, and can display the complex social networks in visualization, thus helping people to deeply understand and parse complex networks.
Owner:SICHUAN XW BANK CO LTD
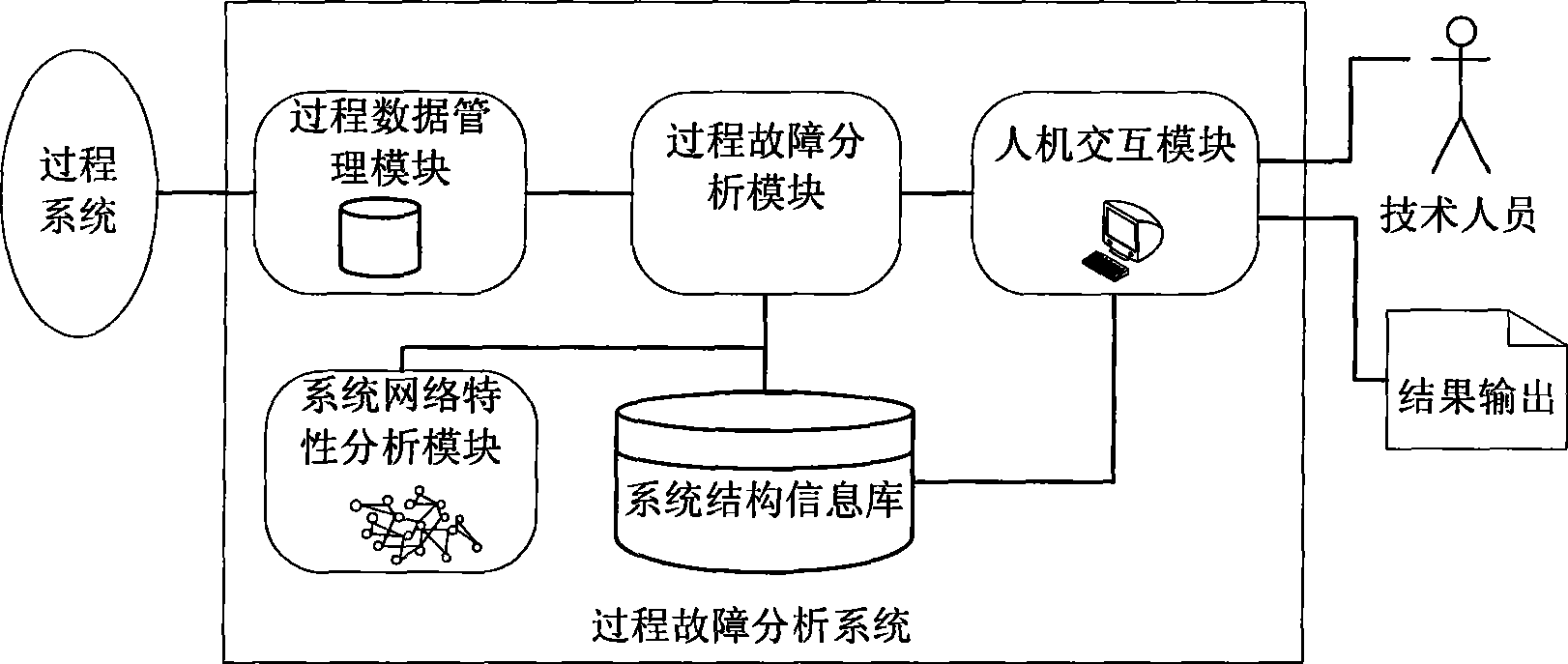
Process fault analysis device of process industry system and method therefor
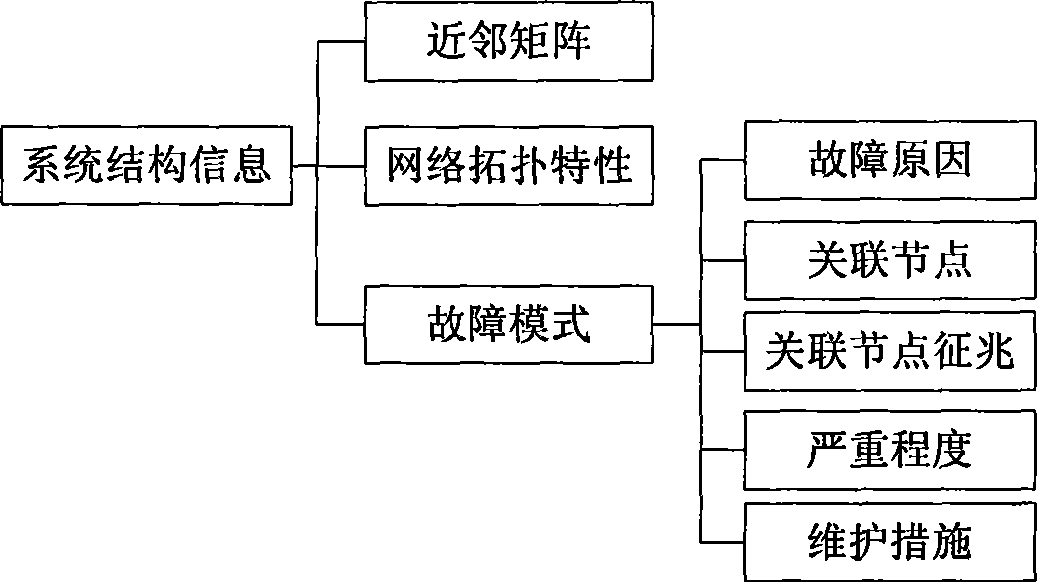
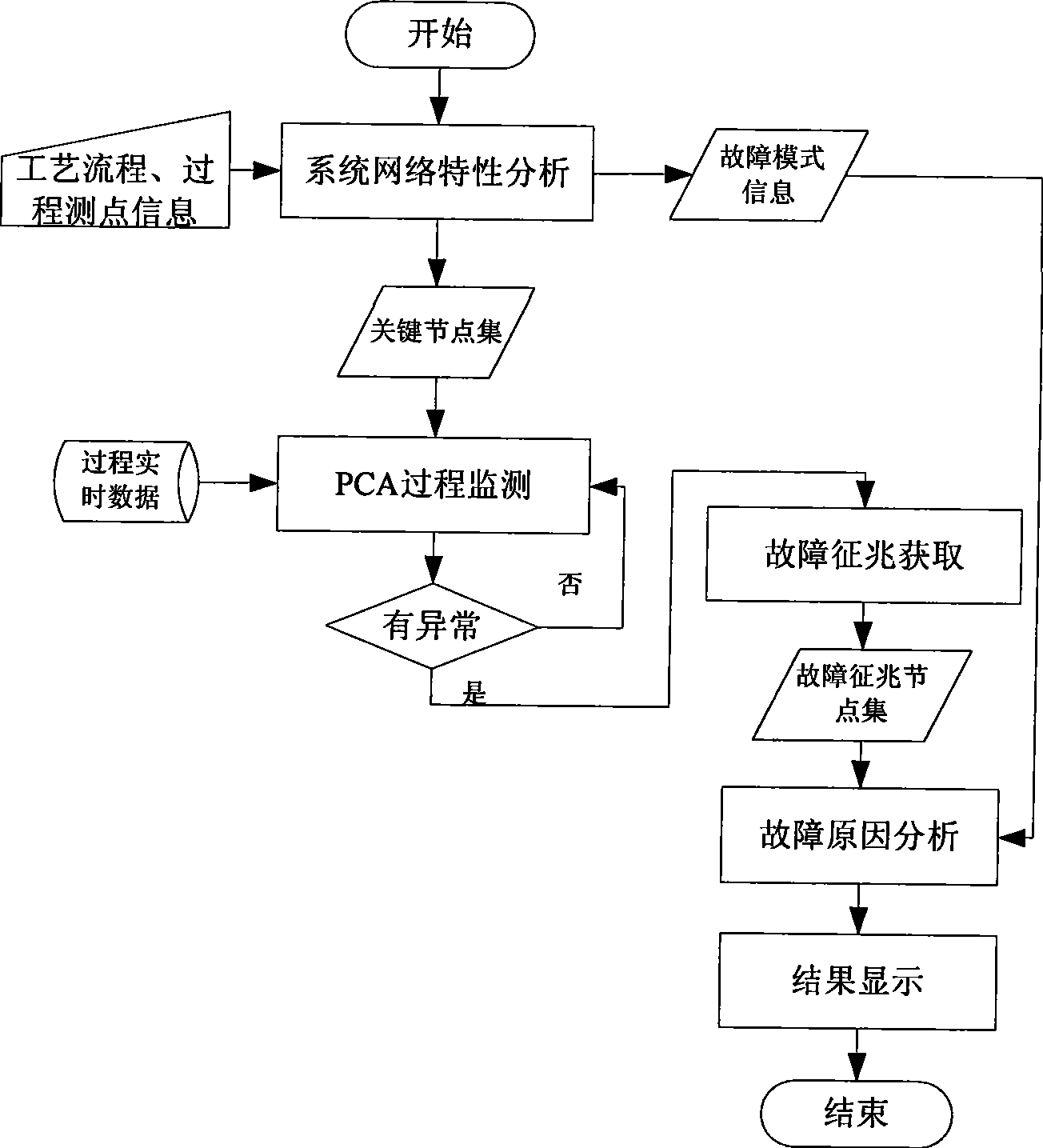
InactiveCN101446827AEasy to identifyEasy to separateTechnology managementTotal factory controlProcess systemsReal-time data
The invention relates to a process industry system fault analysis device based on complex network theories and a method therefor. The device comprises a system structure information base, a man-machine interaction module, a process data management module, a system network characteristics analysis module and a process fault analysis module. The process fault analysis device and the method provided by the invention can be employed for identifying the key parts of the process system, reducing the process monitoring variables and solving the problem that the selection of monitoring point position depends on people's knowledge or experience; meanwhile, the invention makes the best of real-time data information of the process industry process system, thereby ensuring monitoring over the process fault is more instantaneous and accurate; and the utilization of the system domain knowledge improves the fault recognition and separation capability of the traditional PCA monitoring method.
Owner:XI AN JIAOTONG UNIV
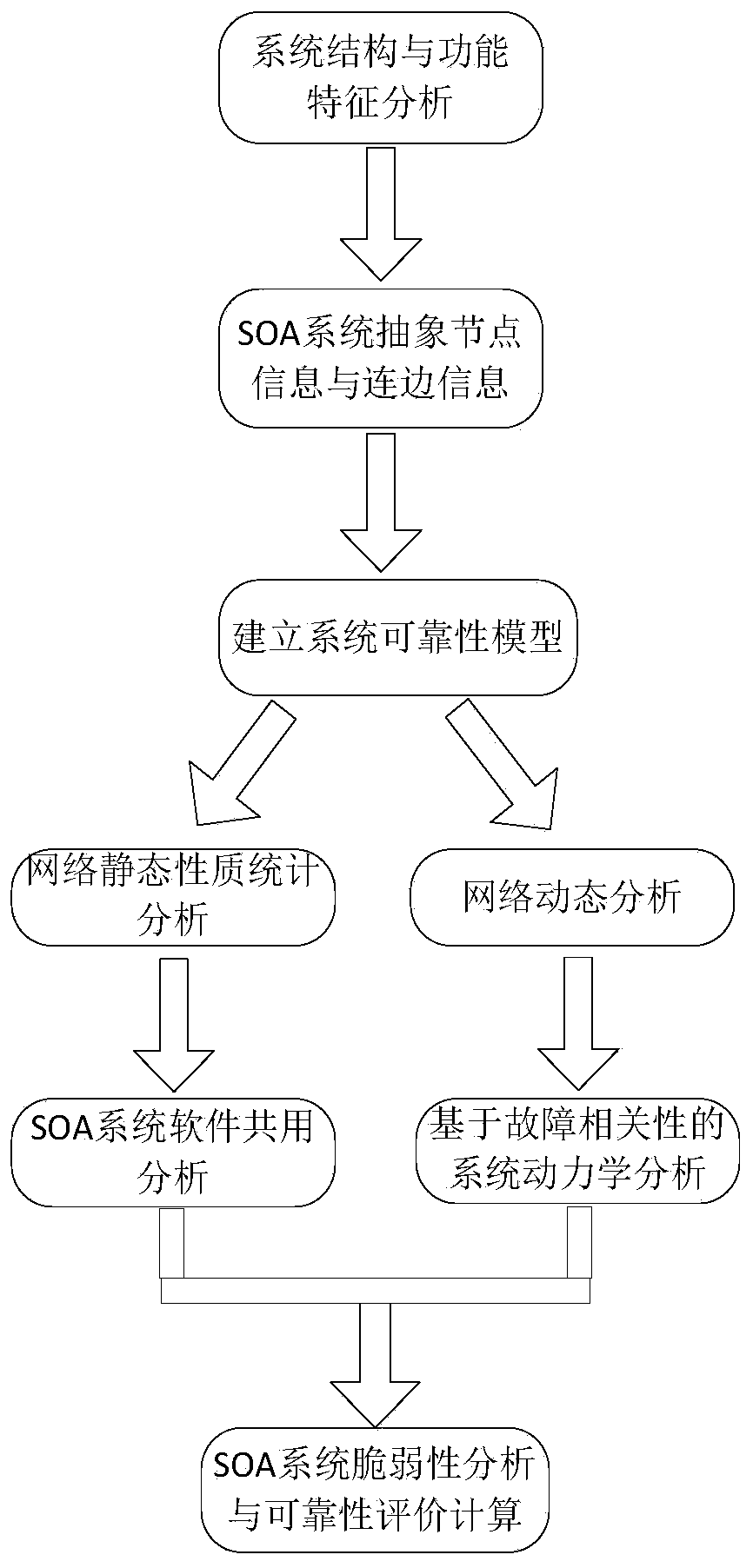
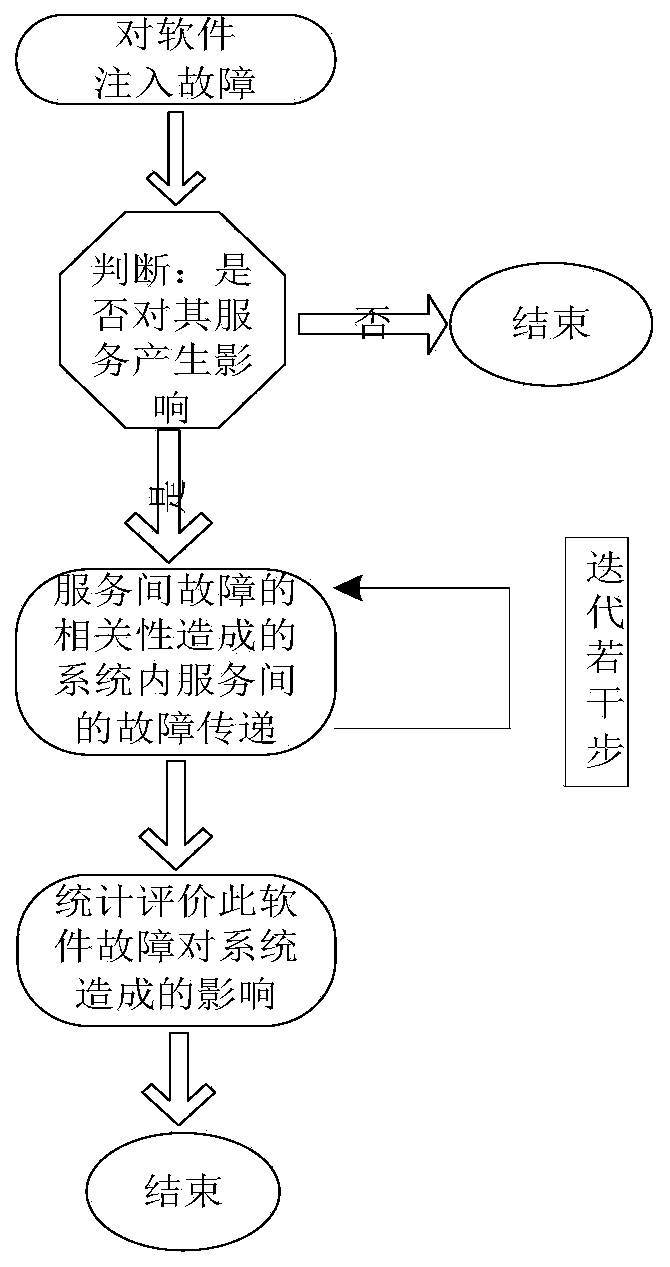
SOA system reliability evaluation method based on complex network theory
ActiveCN104298593AEmphasis on topological featuresEasy to operateSoftware testing/debuggingCascading failureStructure and function
An SOA system reliability evaluation method based on a complex network theory comprises four steps, belongs to the technical field of complex system reliability and aims at solving the problem that an SOA system is complex in structure and function and a traditional reliability analysis method is difficult to implement and even cannot be implemented and putting forward a methodology for effectively analyzing the reliability of the complex SOA system. The SOA system reliability evaluation method is characterized in that the method is innovatively integrated with the complex network theory, objects in the SOA system and the mutual effect of the objects are abstracted to be nodes and connecting lines in a complex network so as to establish a complex network failure model, a cascading failure model for the SOA system is put forward, and reliability analysis work is completed by utilizing a Monte Carlo simulation experiment on the basis so as to find key software and a weak structure influencing the system reliability. The SOA system reliability evaluation method is not limited by system scale, and increase of the system scale does not enable the calculation complex degree of the method to be remarkably improved. The SOA system reliability evaluation method is clear in physical significance and easily operated and implemented by engineers.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com