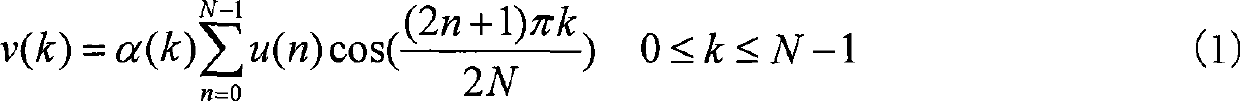Patents
Literature
1192 results about "Global information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
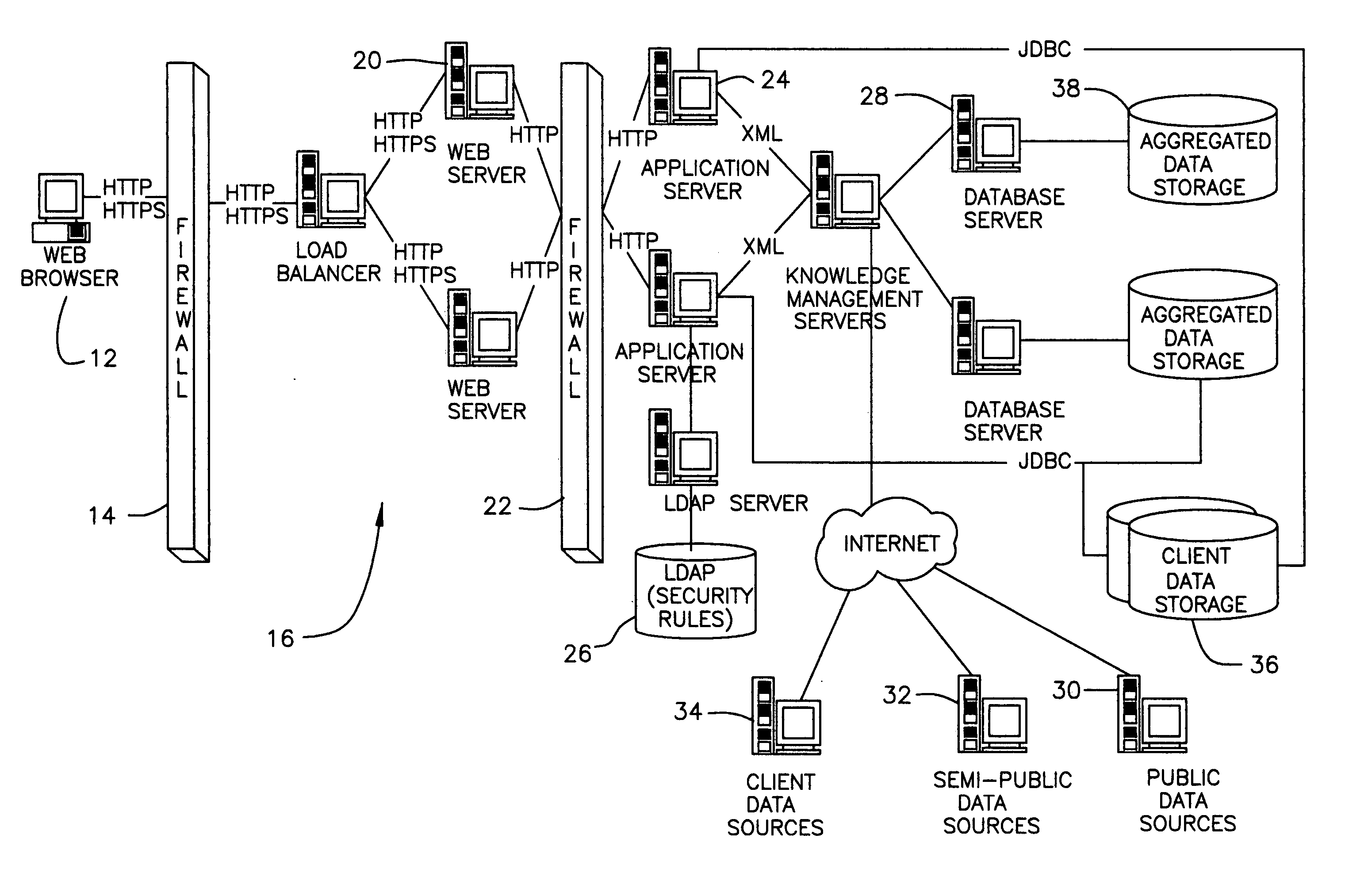
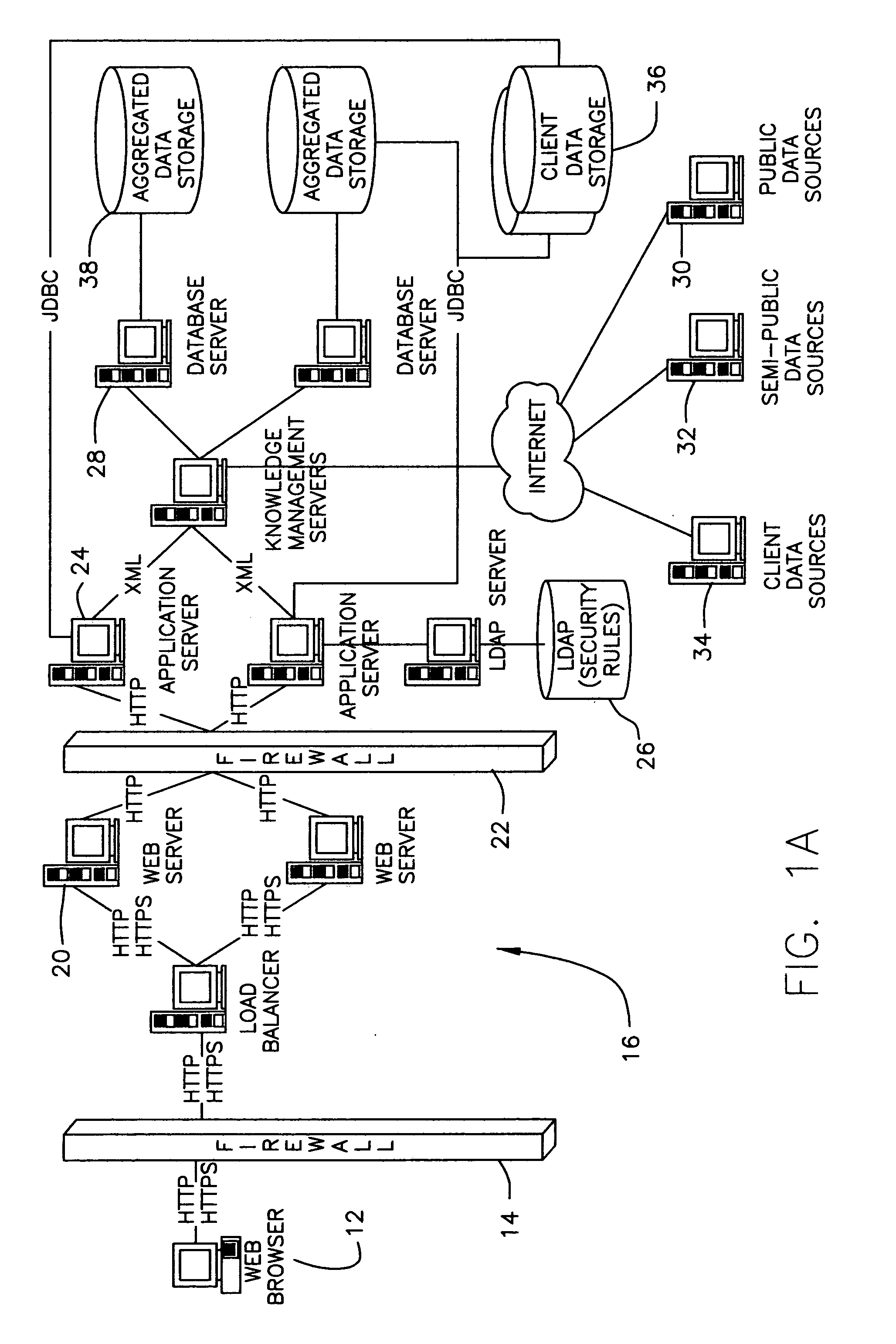
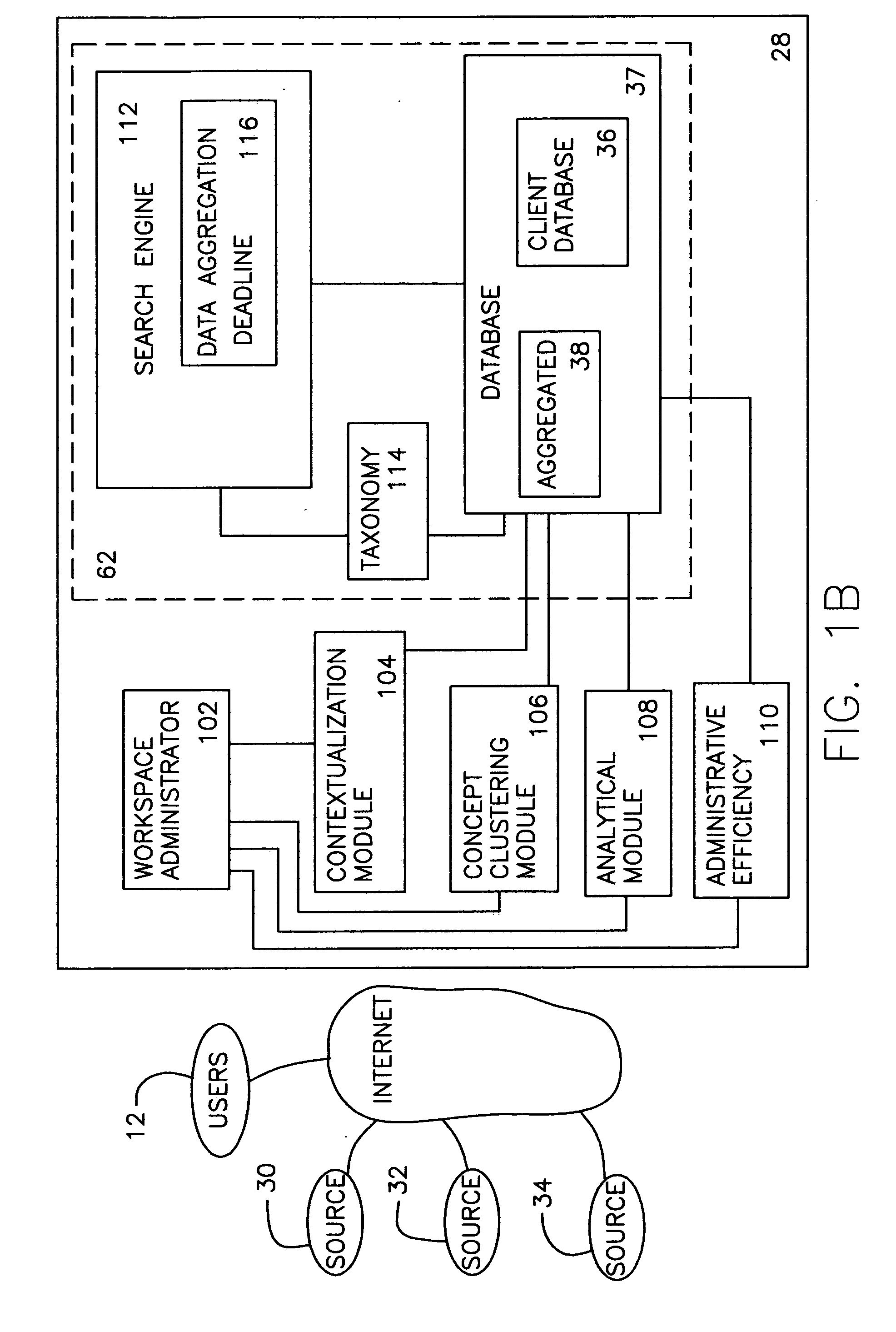
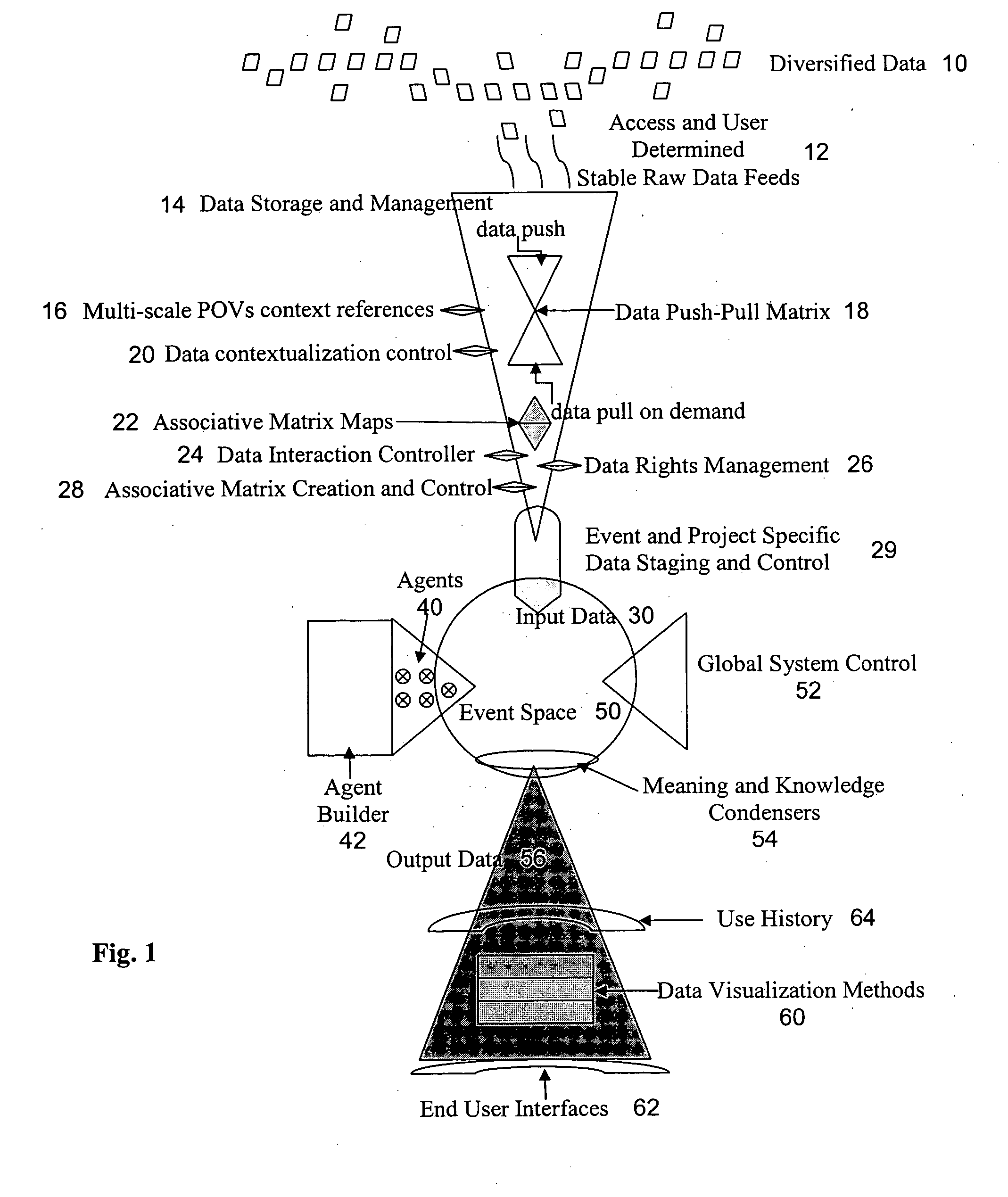
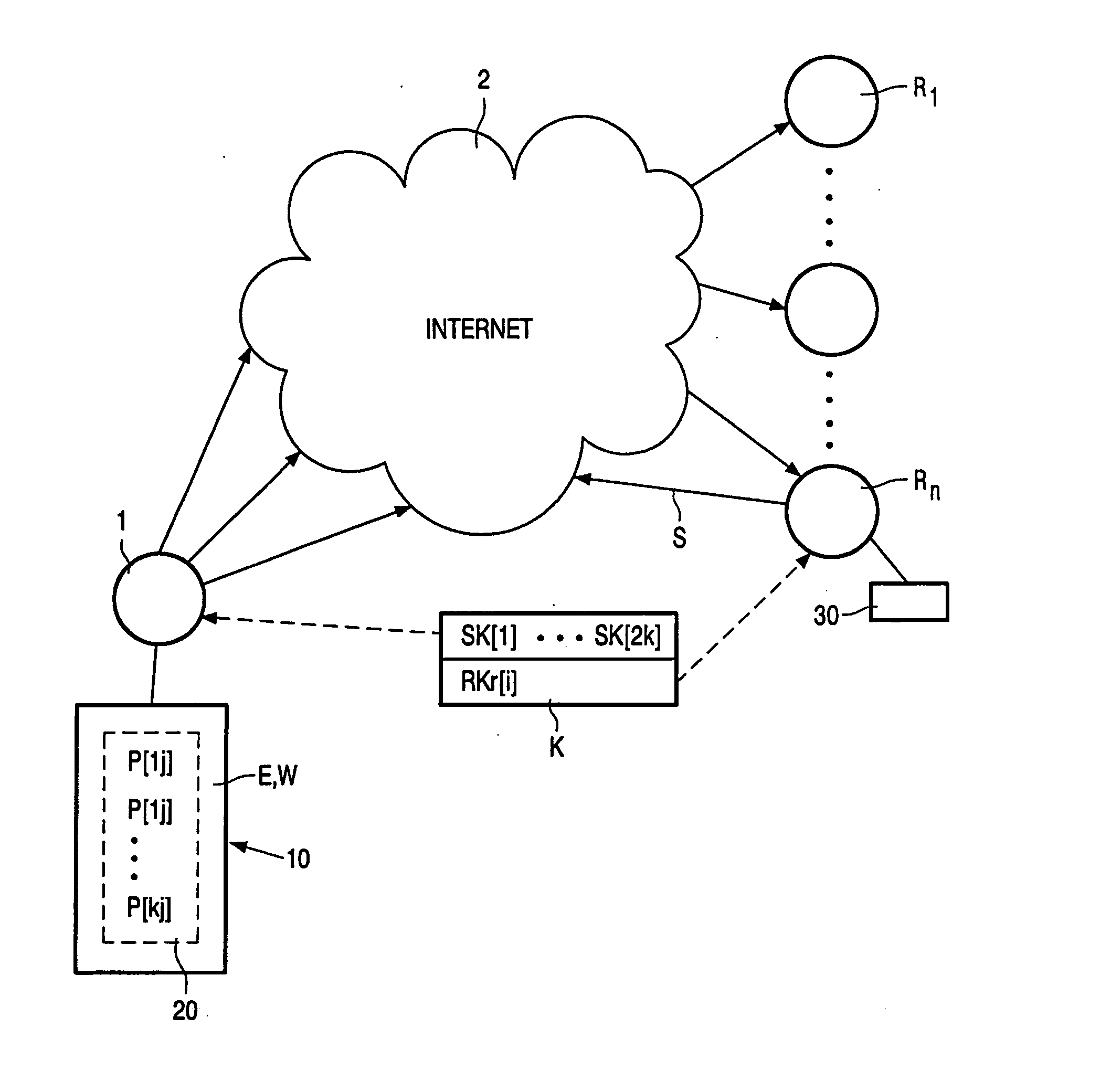
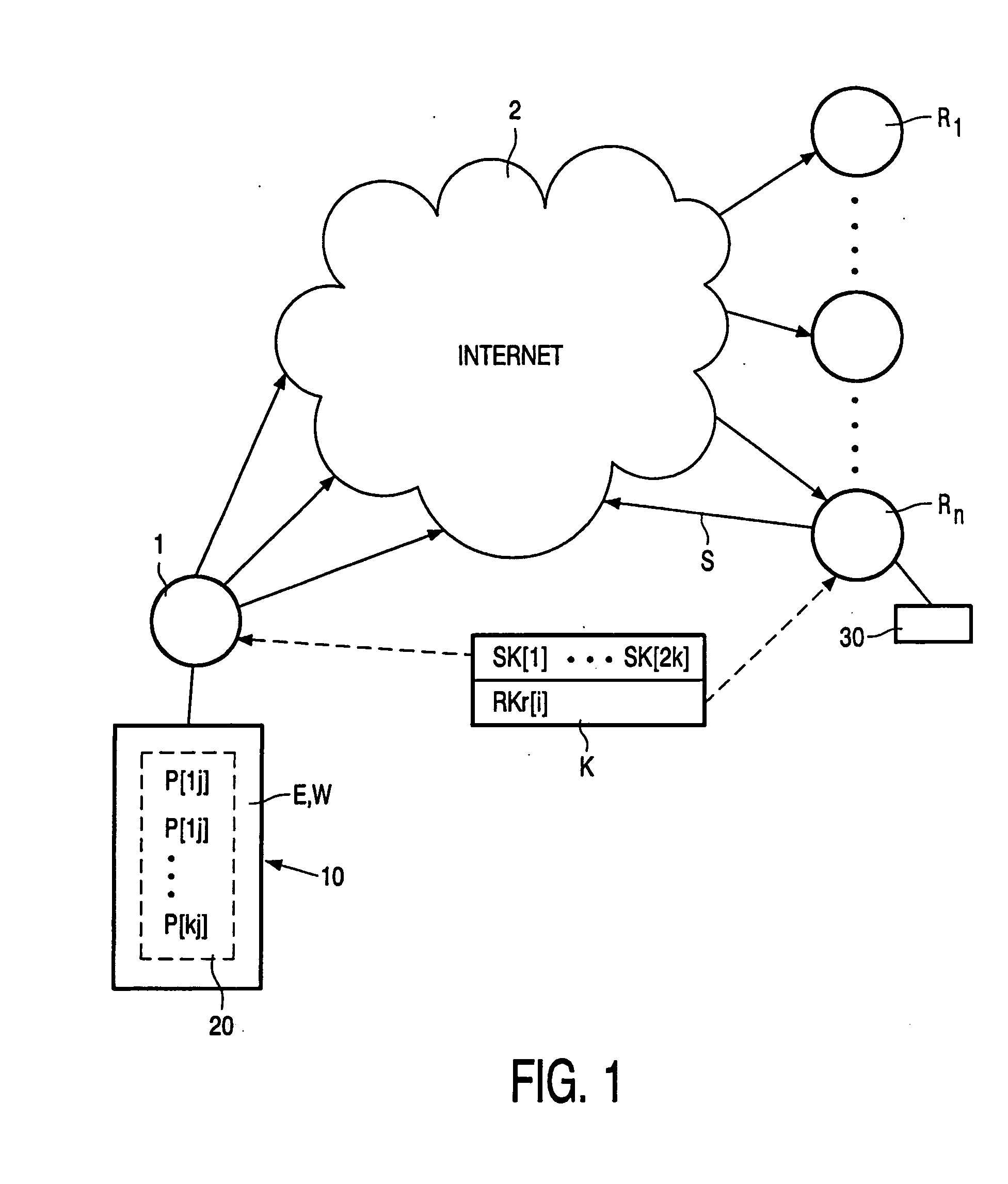
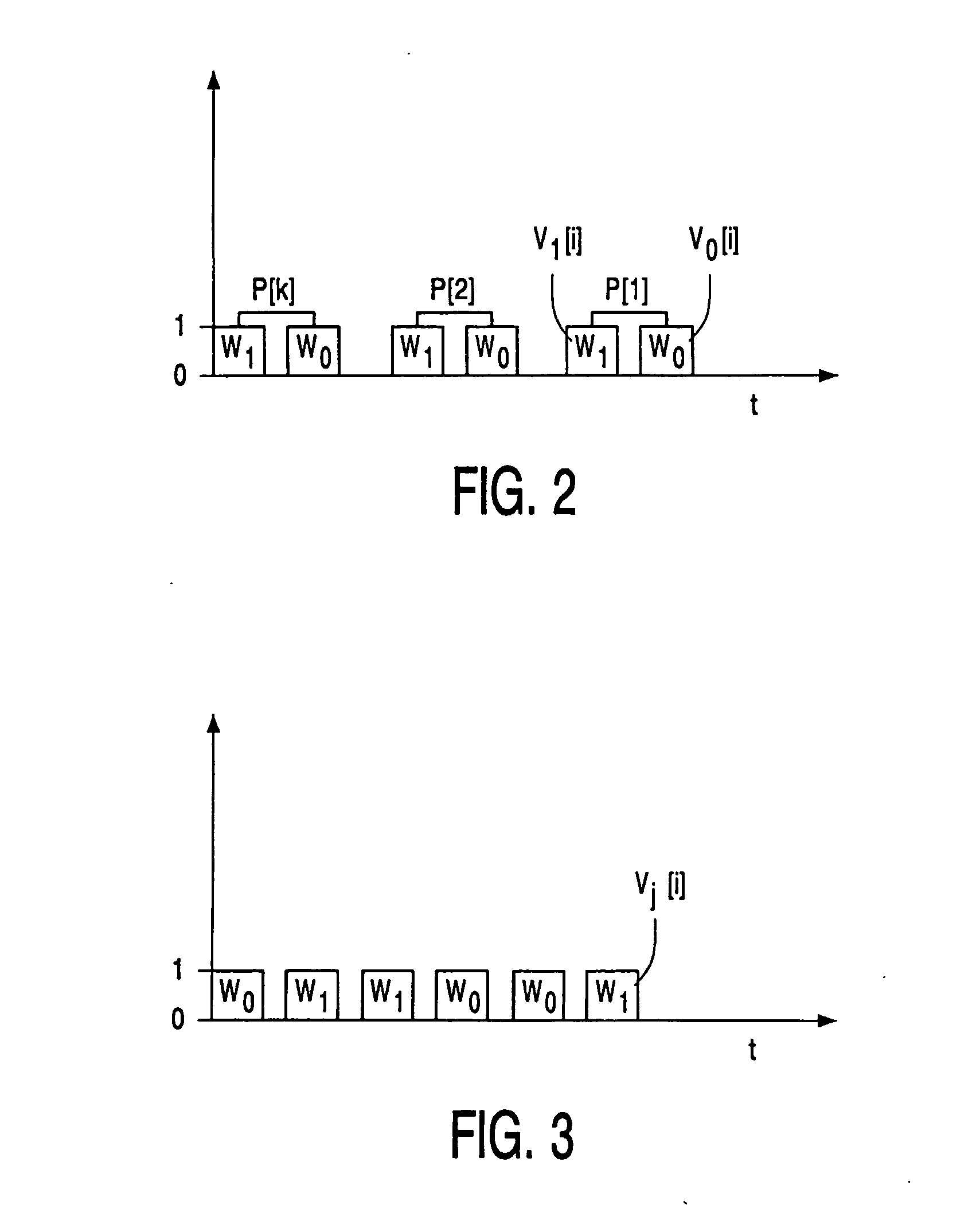
System and method for providing global information on risks and related hedging strategies
InactiveUS20050144114A1Increase productivityIncrease valueFinanceSpecial data processing applicationsAnalytic modelManagement tool
The present invention provides a system and method for information and data aggregation and analysis which provides risk managers, benefits managers, brokers, insurers and other insurance professional to have access to information resources, knowledge management tools, and powerful analytical models needed to increase their value and productivity. In accordance with one embodiment of the invention, the system and method provided is designed for information and data aggregation that allows for the compilation of data for mining and categorization by a knowledge management system, which stores all retrieved information in accordance with categories provided by a categorization engine referred to as a Taxonomy module. A contextualization module is configured to retrieve relevant information, based on various factors, including the user's profile, and the user's particular task. The system dynamically provides relevant information as the user interacts and conducts various tasks. The stored information is analyzed by a concept clustering module, so that various concepts relating to a particular topic can be uncovered and stored. In accordance with another embodiment of the invention, the system provides for various analytical tools that allow users to carry on with highly complex analysis of insurance related topics. The range of available analytical tool dynamically varies based on the user's needs and research topics. In accordance with yet another embodiment of the invention, the system provides for a unique interactive workspace that combines the features explained above in a logical manner. To this end, the system interface provides for various job templates, so as to enable the user's to carry various projects by a template driven task assignments. As the user navigates through the workspace, the range of available information to the user changes, based on the user's profile and navigation pattern.
Owner:ADVISEN
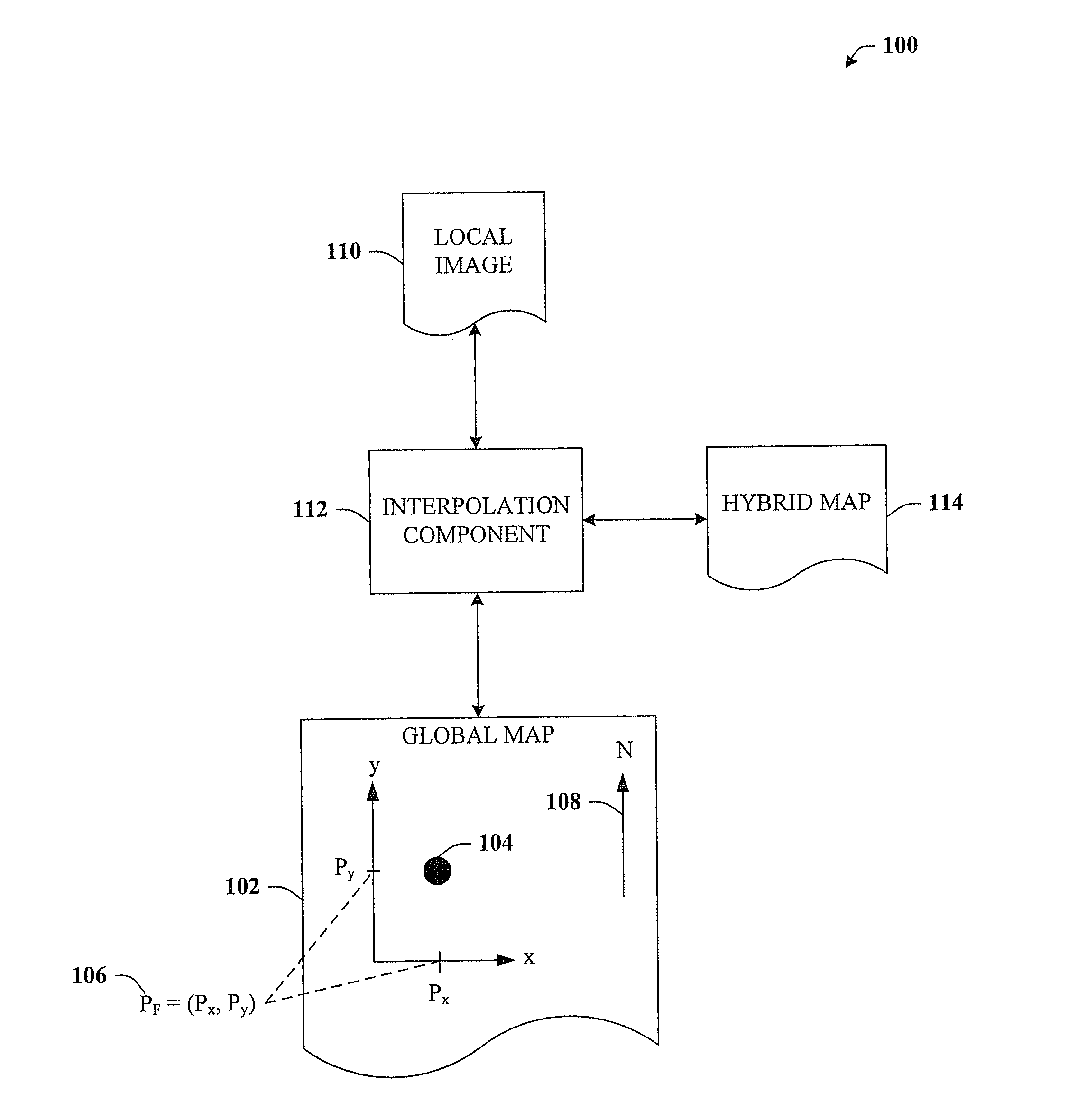
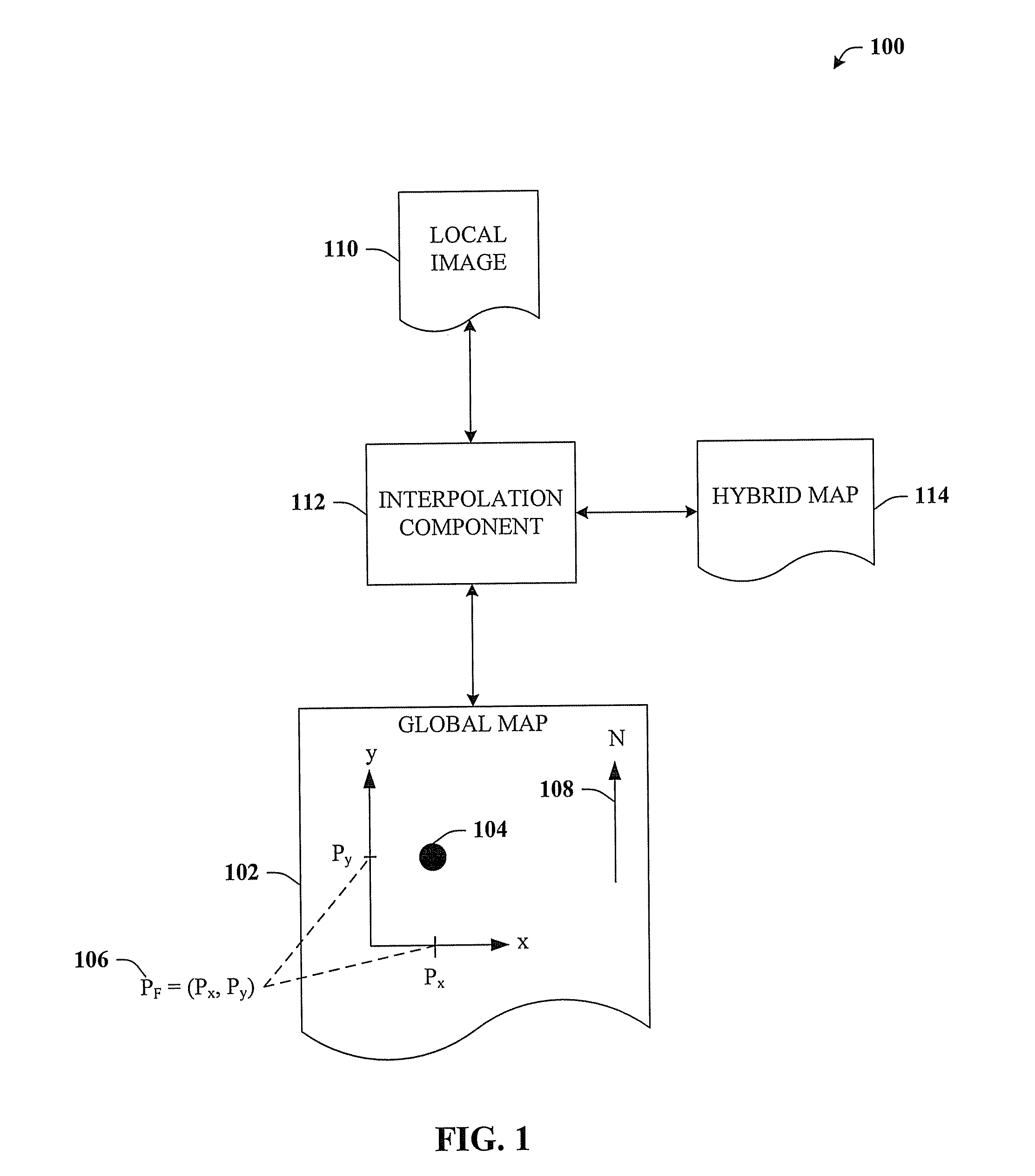
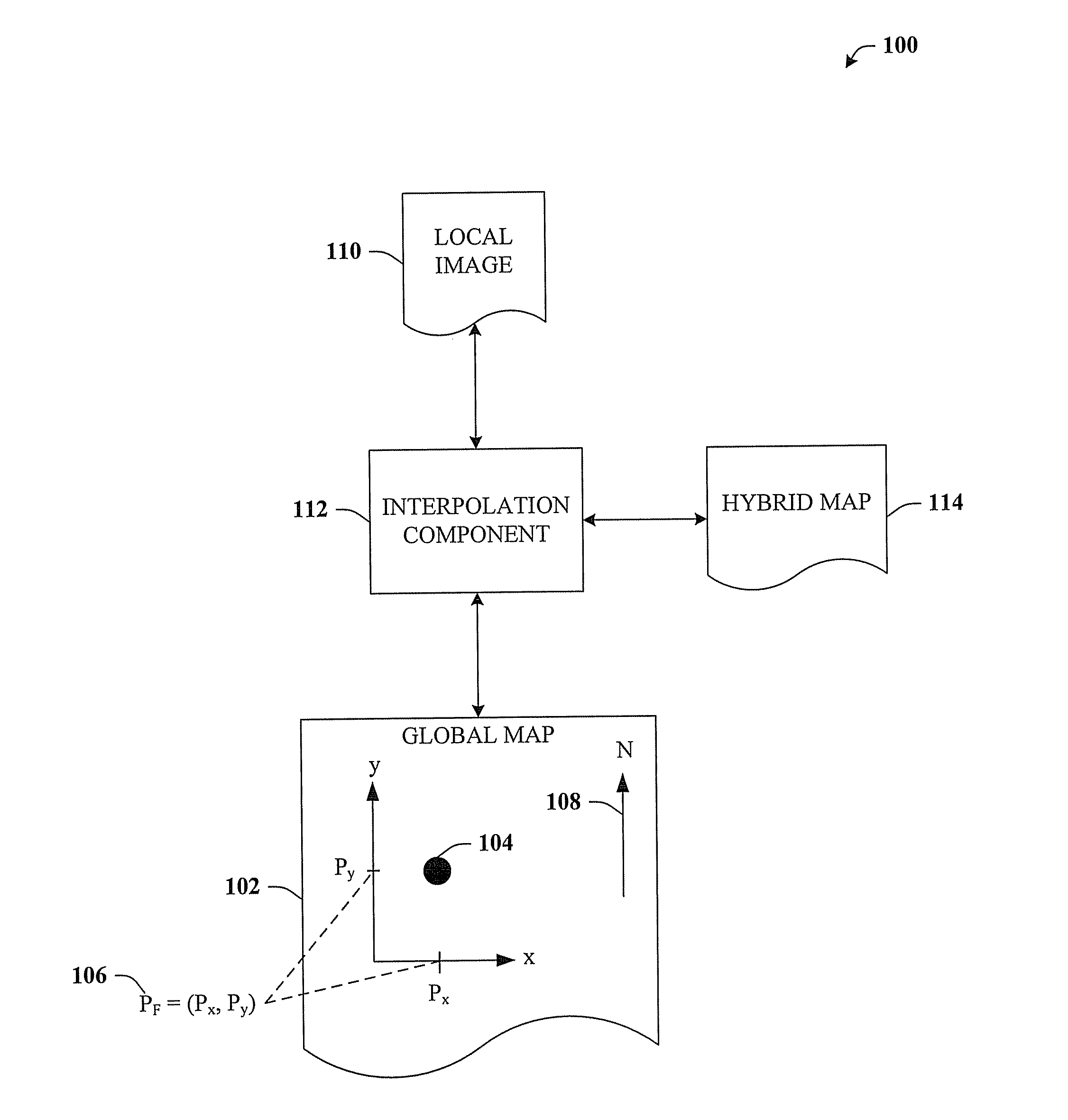
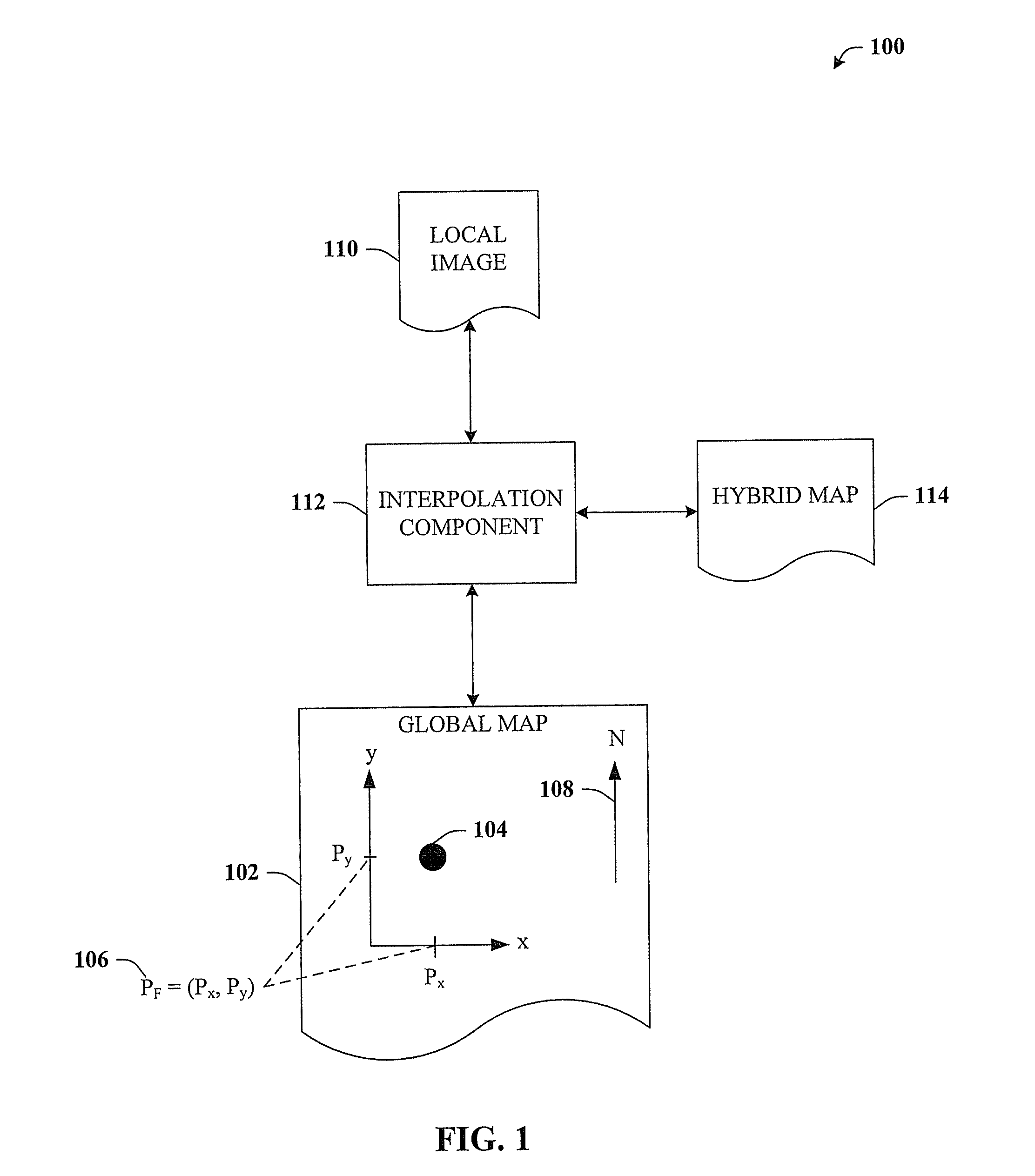
Street side maps and paths
ActiveUS20070076920A1Well formedColor signal processing circuitsGeometric image transformationMultiple perspectiveSubject matter
The claimed subject matter relates to a computer-implemented architecture that can generate a map. The map can be a hybrid between an orthographic projection map and street-side images, thus including useful aspects from both types of representations. For example, an orthographic projection map is very effective at presenting global relationships among the features of the map, but not effective at presenting local detail. In contrast, street-side images show excellent detail, but do not convey the global information of an orthographic projection map. The hybrid map can thus provide a richer set of information than conventional maps, and can also display objects / features of the hybrid map in multiple perspectives simultaneously on a single representation that is printable.
Owner:MICROSOFT TECH LICENSING LLC
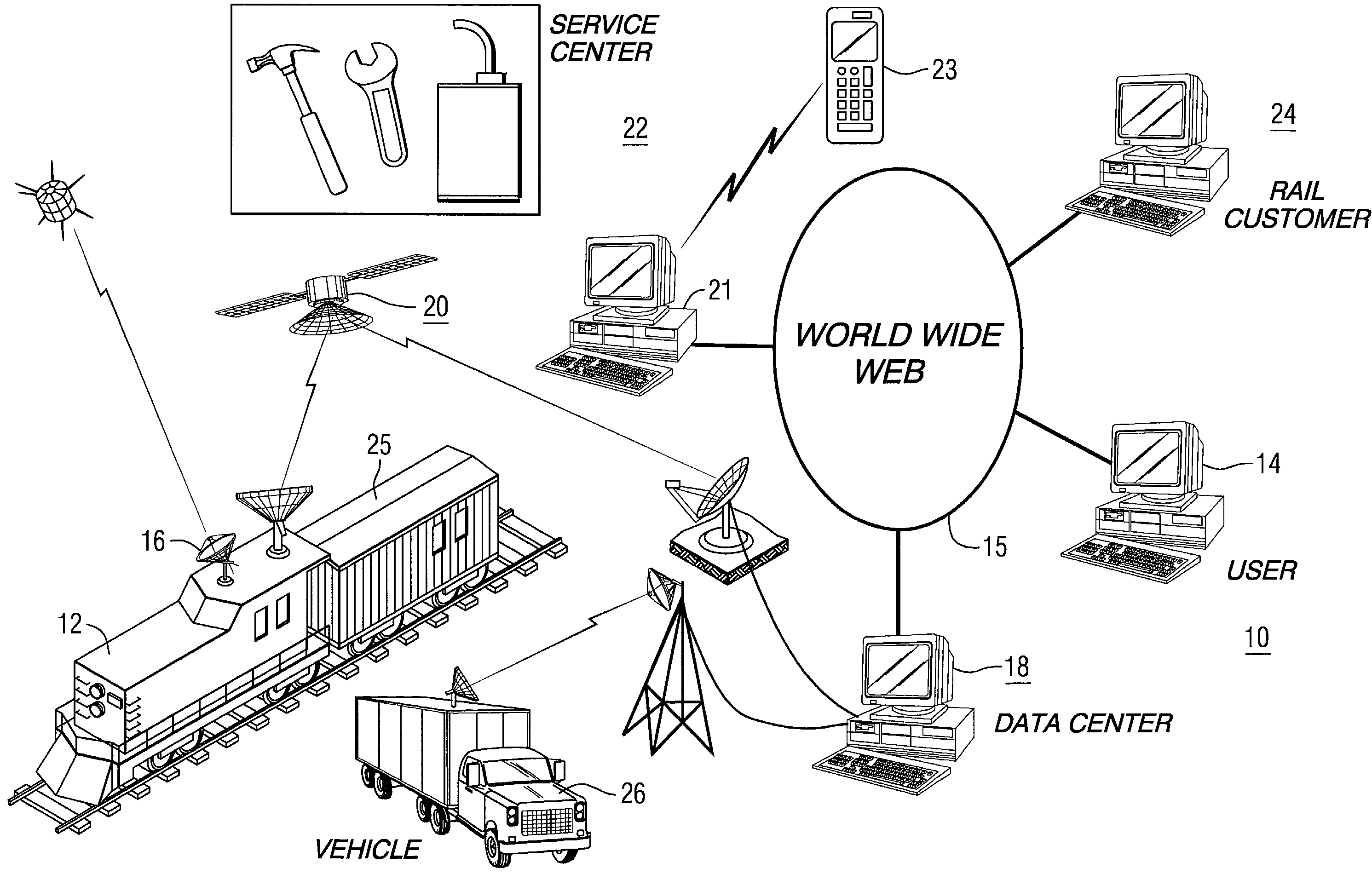
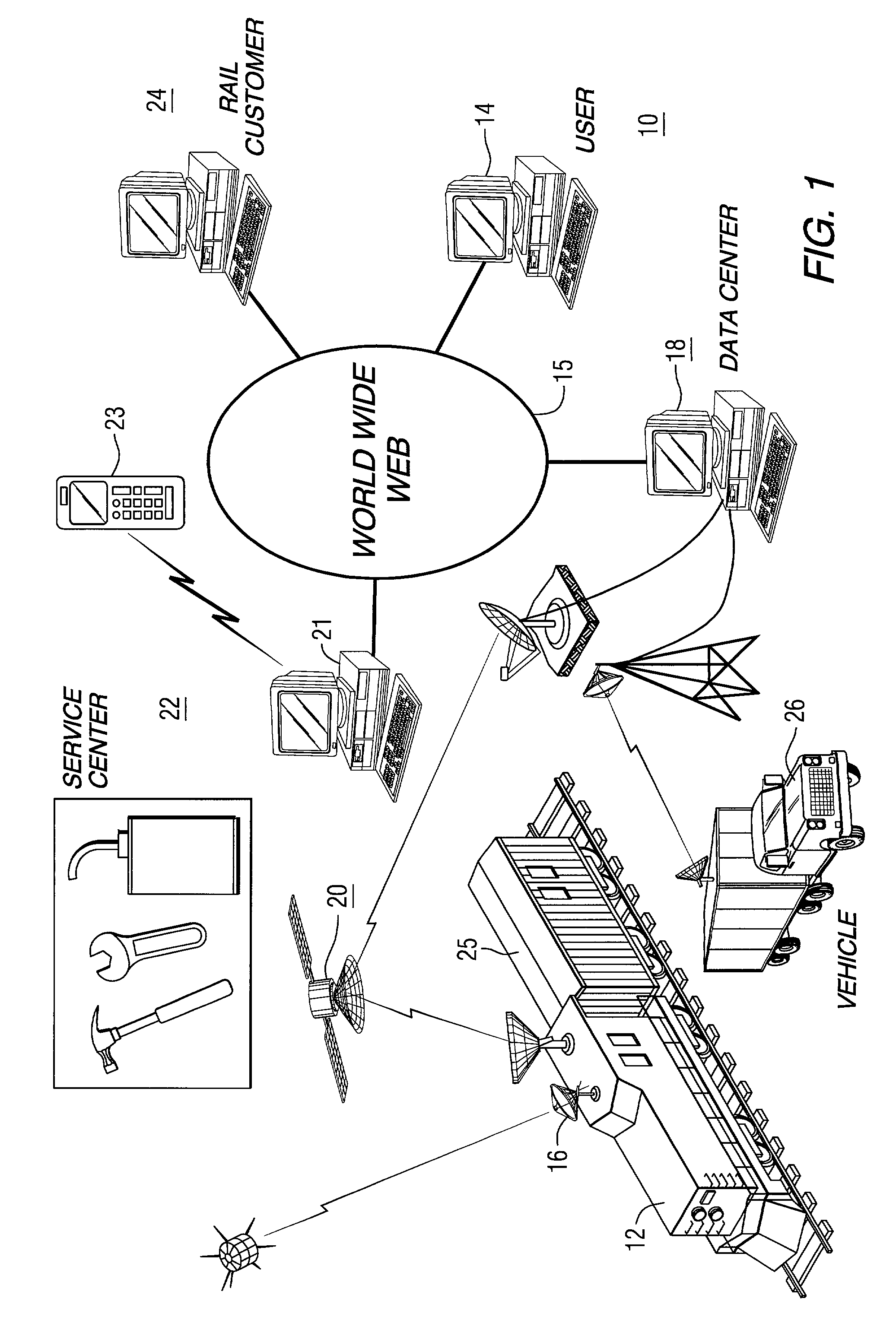
System and method for managing a fleet of remote assets
InactiveUS7783507B2Efficient integrationEasy to useRegistering/indicating working of vehiclesTrack side maintainanceGlobal informationComputer science
Method and system for managing a plurality of remote assets, such as a fleet mobile assets is provided. The method allows for collecting data regarding each of a plurality of remote assets. The collected data is used to develop historical information regarding actual usage of each remote asset. The information is distributed via a global information network.
Owner:WESTINGHOUSE AIR BRAKE TECH CORP
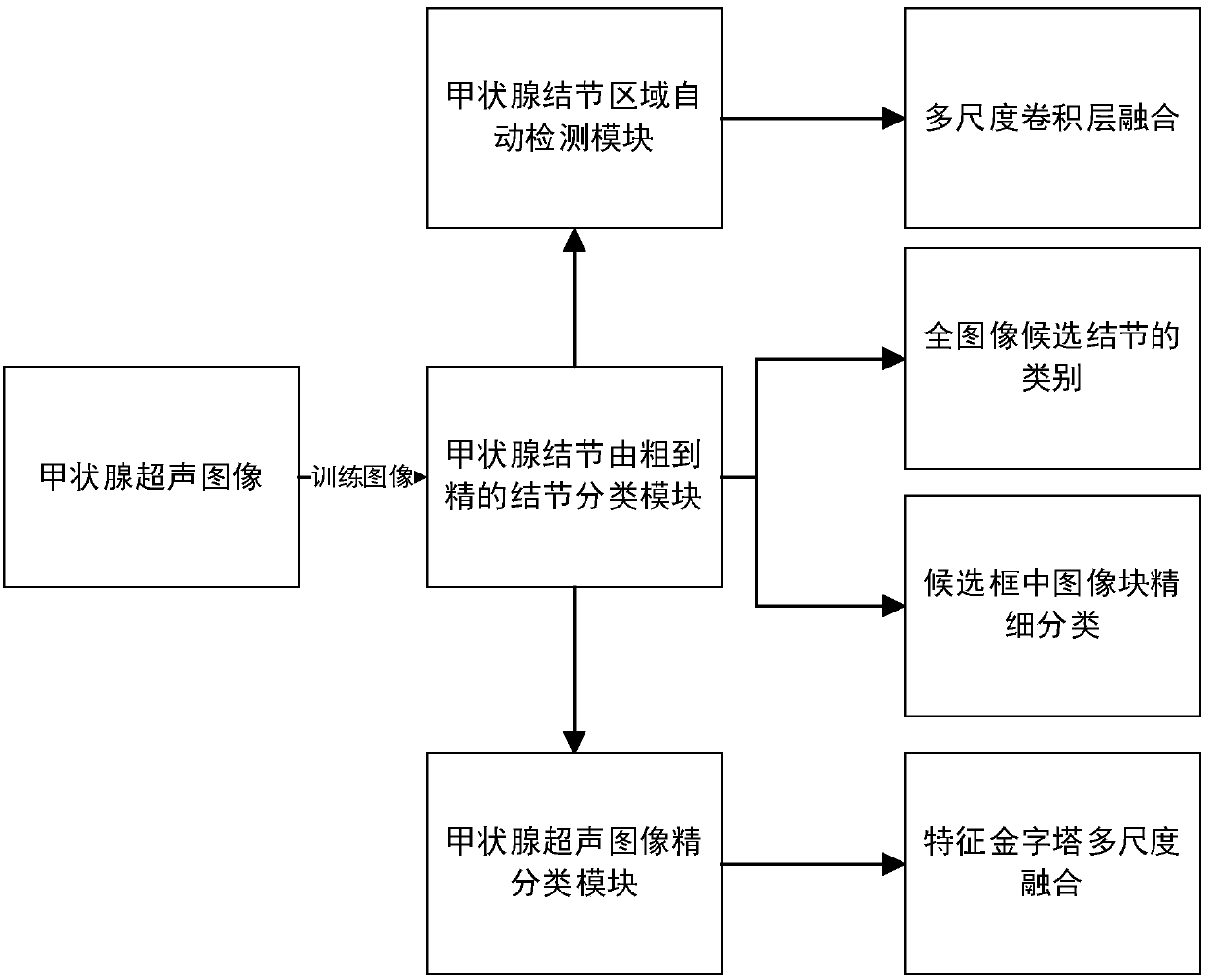
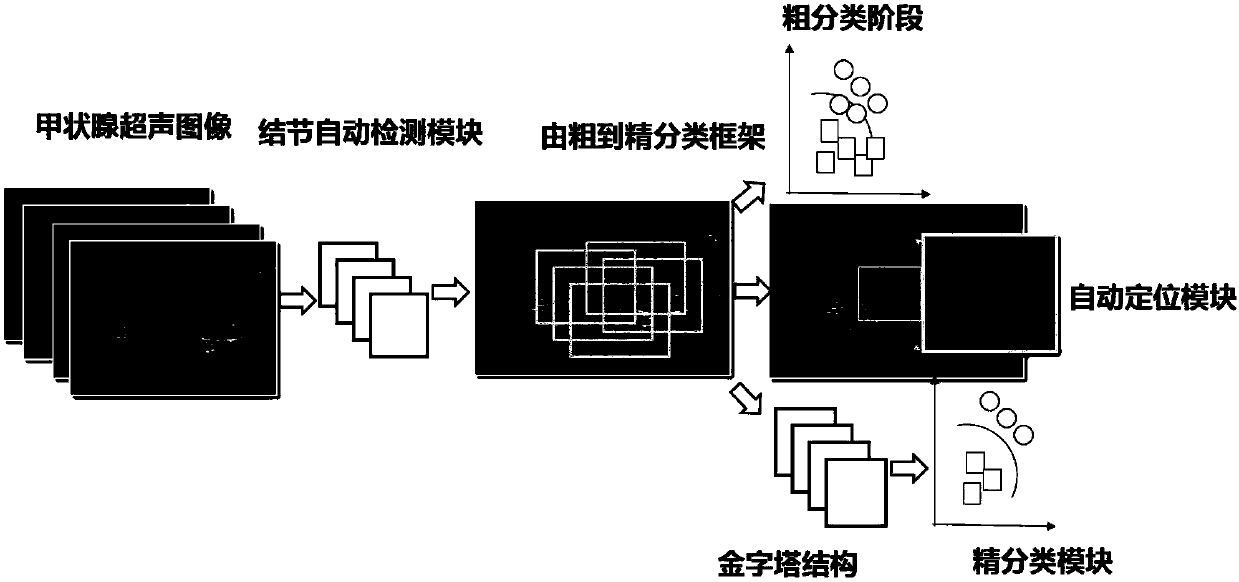
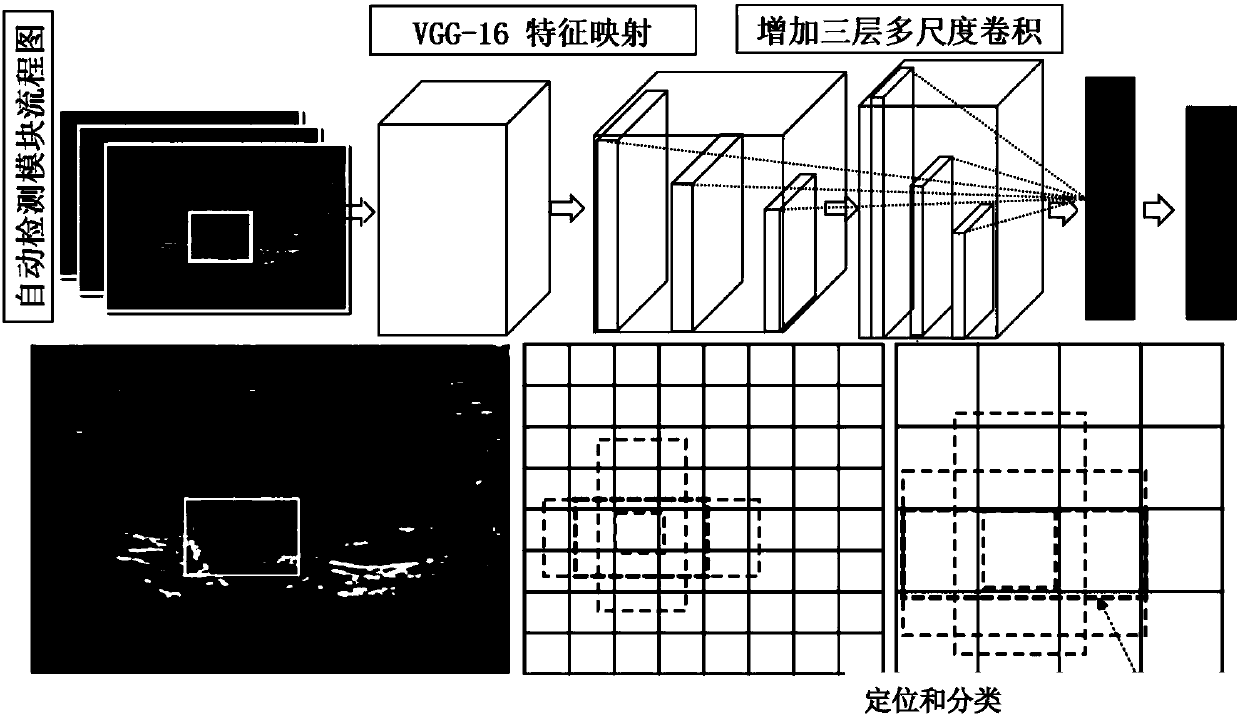
Thyroid ultrasound image nodule automatic diagnosis system based on multi-scale convolutional neural network
ActiveCN107680678AAccurate detectionAdapt to polymorphic automatic detectionImage enhancementImage analysisSemantic featureGlobal information
The invention provides a thyroid ultrasound image nodule automatic diagnosis system based on a multi-scale convolutional neural network. The system includes a thyroid nodule coarse-to-fine classification module, a thyroid nodule region automatic detection module, and a thyroid nodule fine classification module. The size features of different sensing regions are extracted through a multi-scale feature fusion convolutional neural network, and then, the context semantic features of a thyroid nodule can be extracted according to local and global information, and the thyroid nodule can be automatically located. Through multi-scale coarse-to-fine feature extraction based on a neural network and the design of a multi-scale fine classification AlexNet of a pyramid structure, the position of a focus and the probability that the focus is benign or malignant can be accurately predicted, doctors can be assisted in diagnosing a thyroid focus, and the objectivity of diagnosis is improved. The systemhas the characteristics of good real-time performance and high accuracy.
Owner:BEIHANG UNIV
Proxy methods for suppressing broadcast traffic in a network
ActiveUS20150058968A1Improve securityMultiple digital computer combinationsProgram controlBroadcast packetData pack
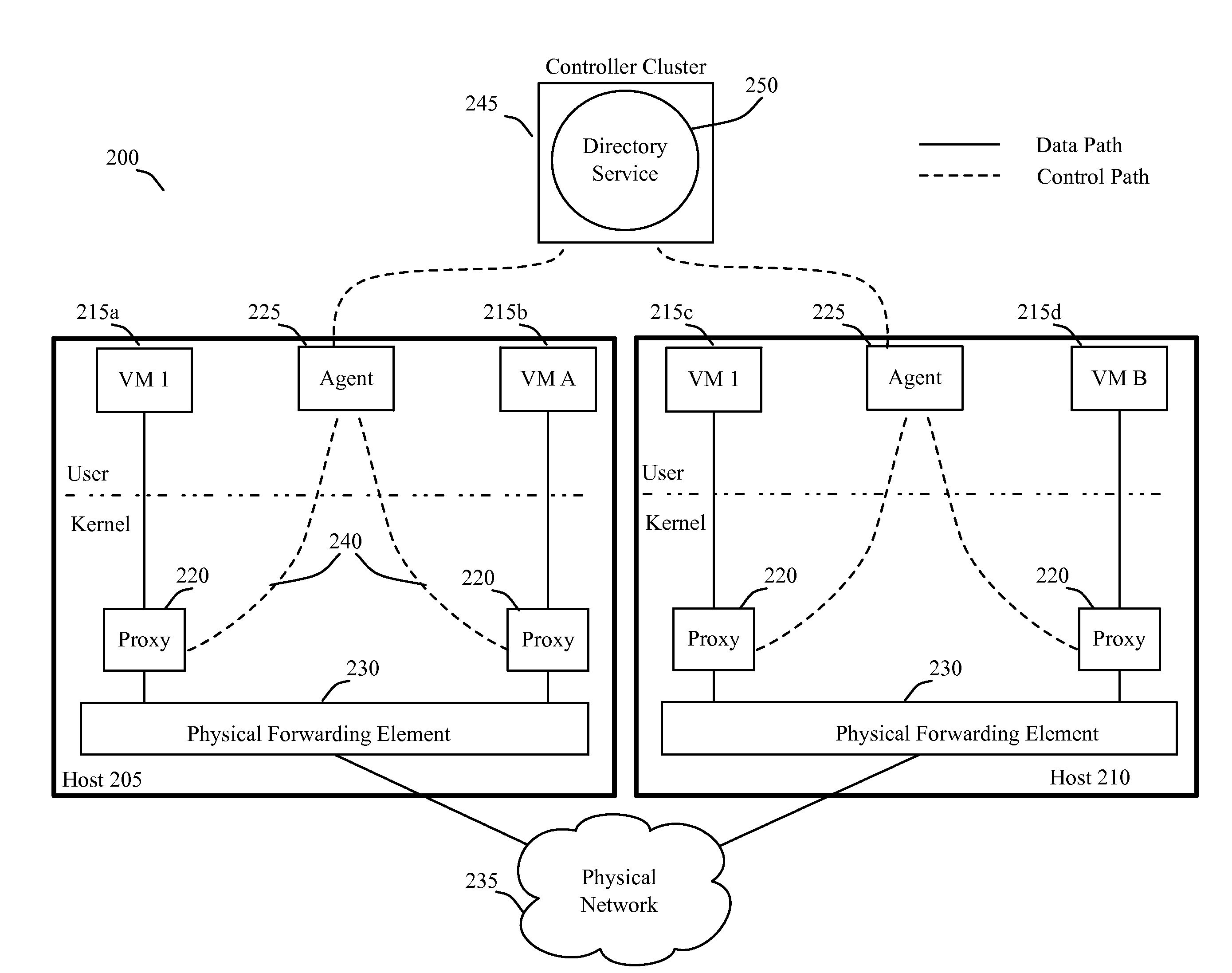
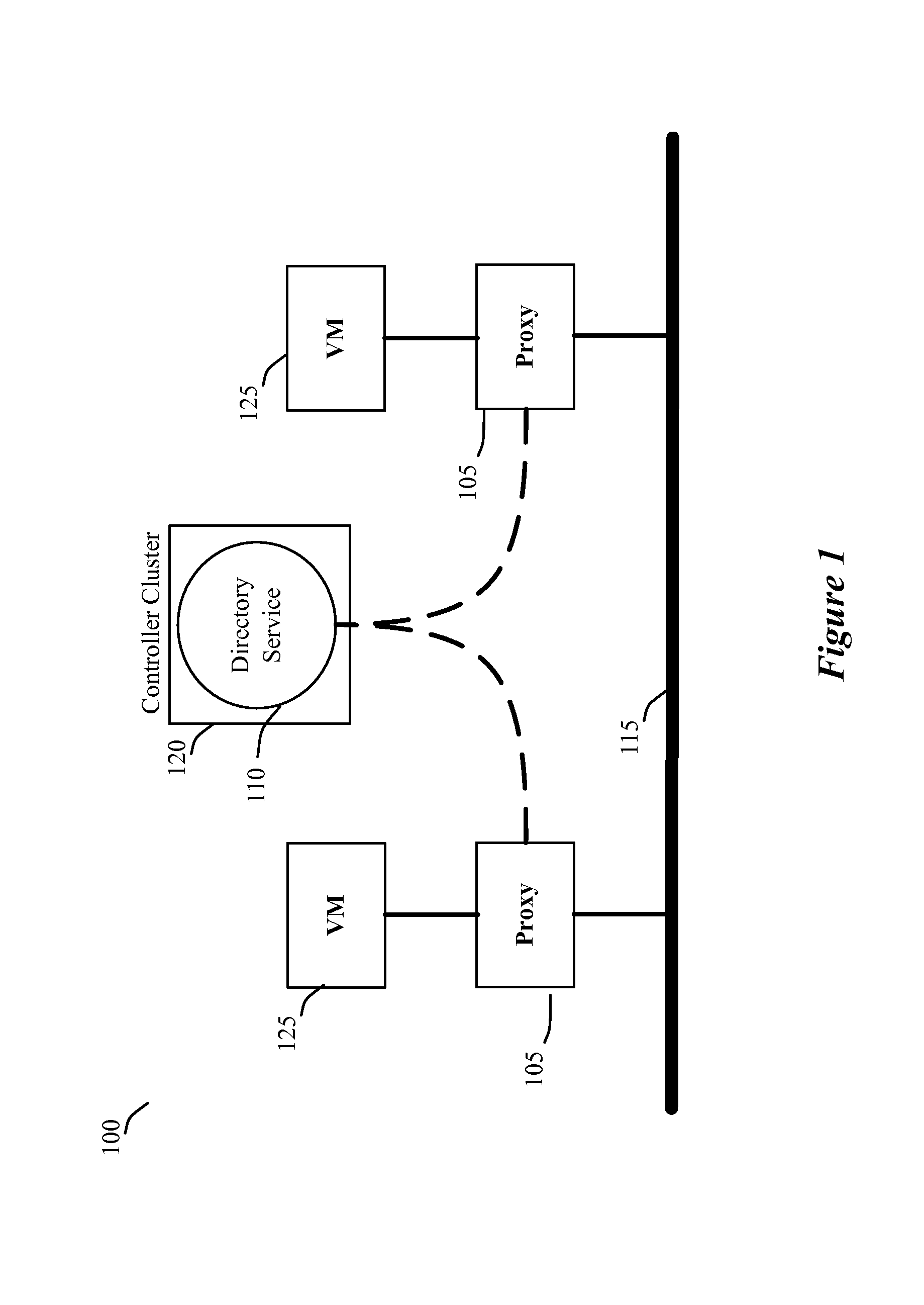
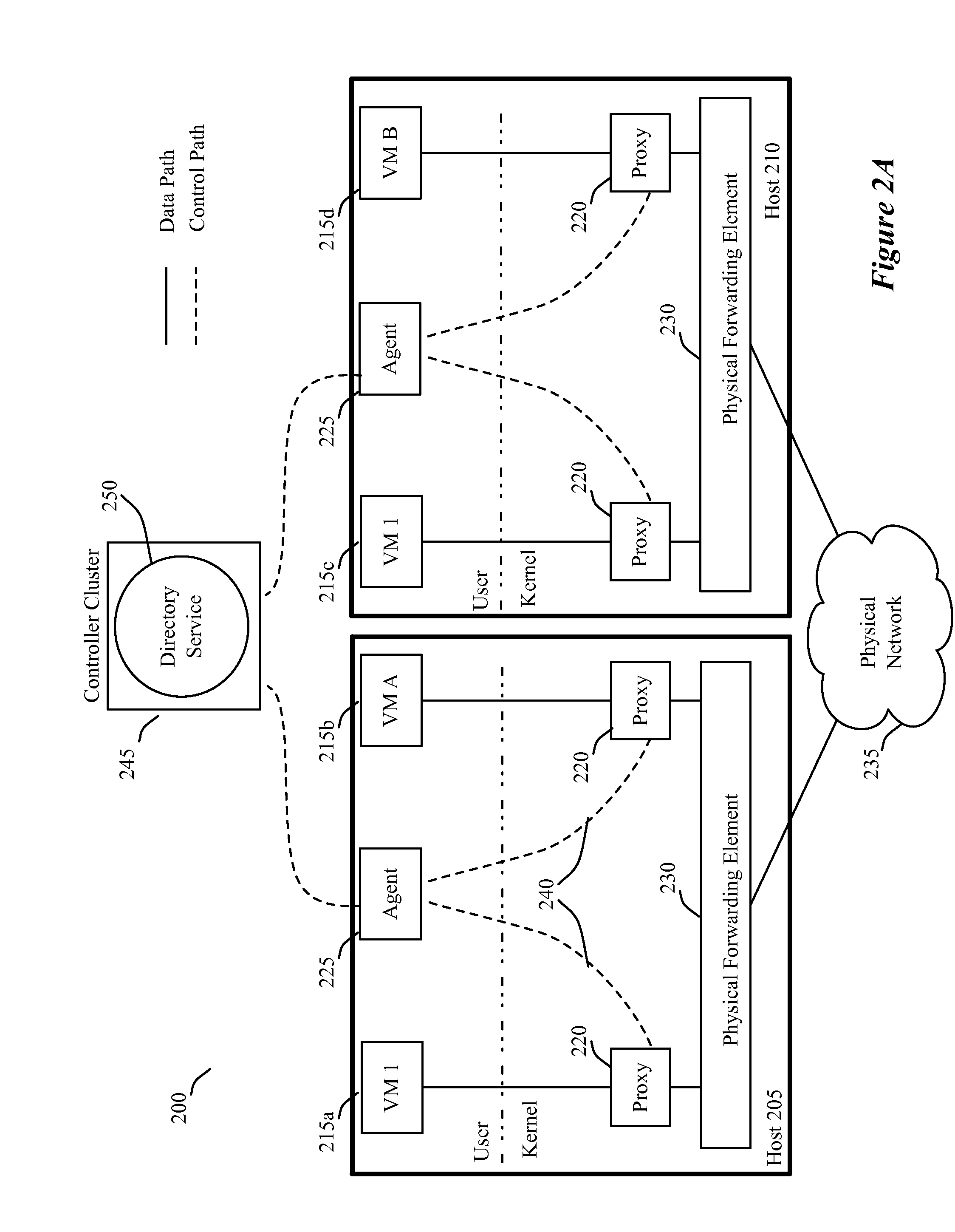
Some embodiments use proxies on host devices to suppress broadcast traffic in a network. Each host in some embodiments executes one or more virtual machines (VMs). In some embodiments, a proxy operates on each host between each VM and the underlying network. For instance, in some of these embodiments, a VM's proxy operates between the VM and a physical forwarding element executing on the VM's host. The proxy monitors the VM's traffic, and intercepts broadcast packets when it knows how to deal with them. The proxy connects to a set of one or more controllers that provides a directory service that collects and maintains global information of the network. By connecting to the controller cluster, the proxy can obtain information that it can use to resolve broadcast requests. In some embodiments, the connection between the proxy and the controller cluster is encrypted and authenticated, to enhance the security. Also, in some embodiments, the connection is an indirect connection through an agent that executes on the host device and connects the proxies of the host device with the controller cluster.
Owner:NICIRA
Method and apparatus for optimized centralized critical control architecture for switchgear and power equipment
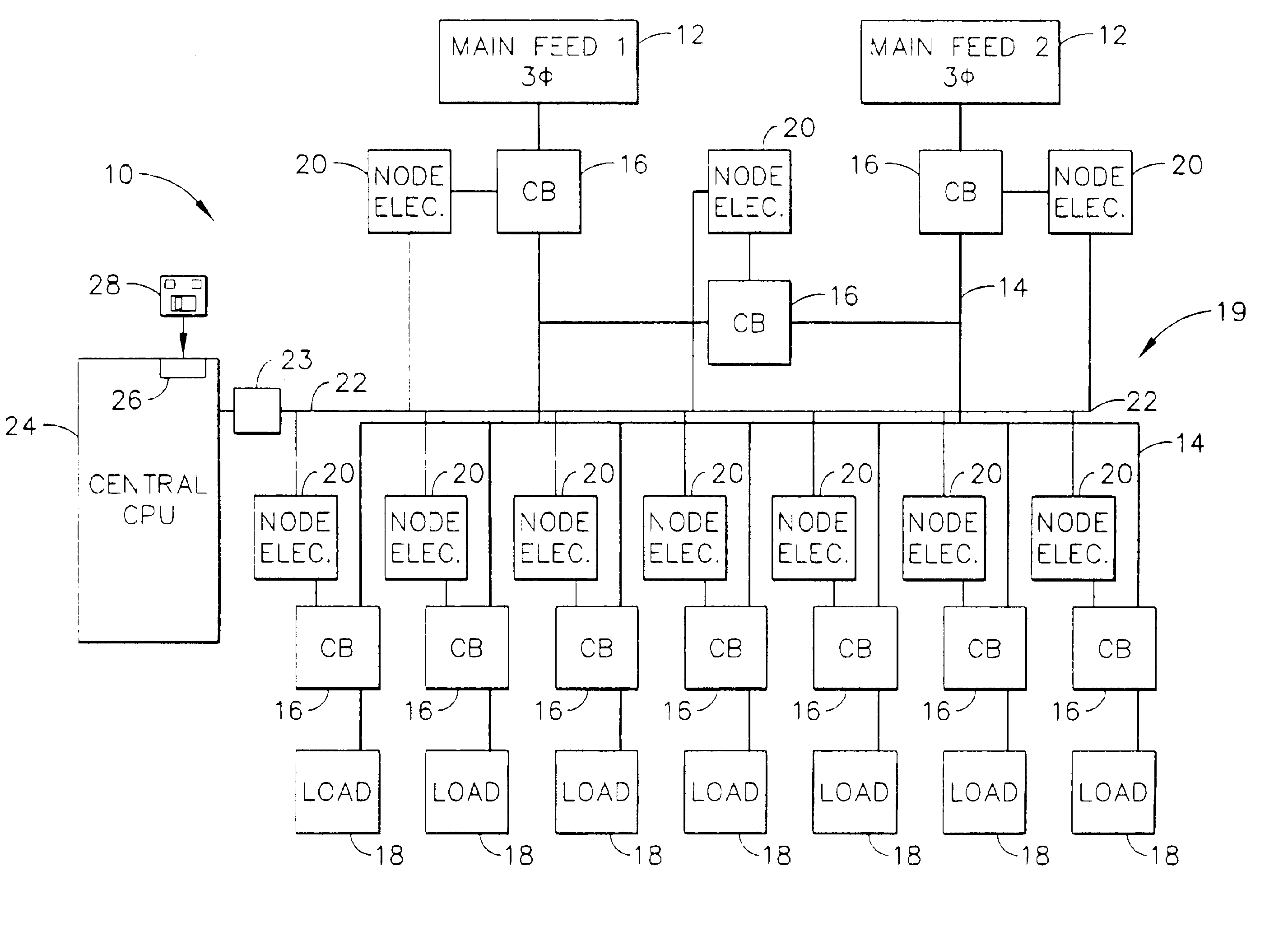
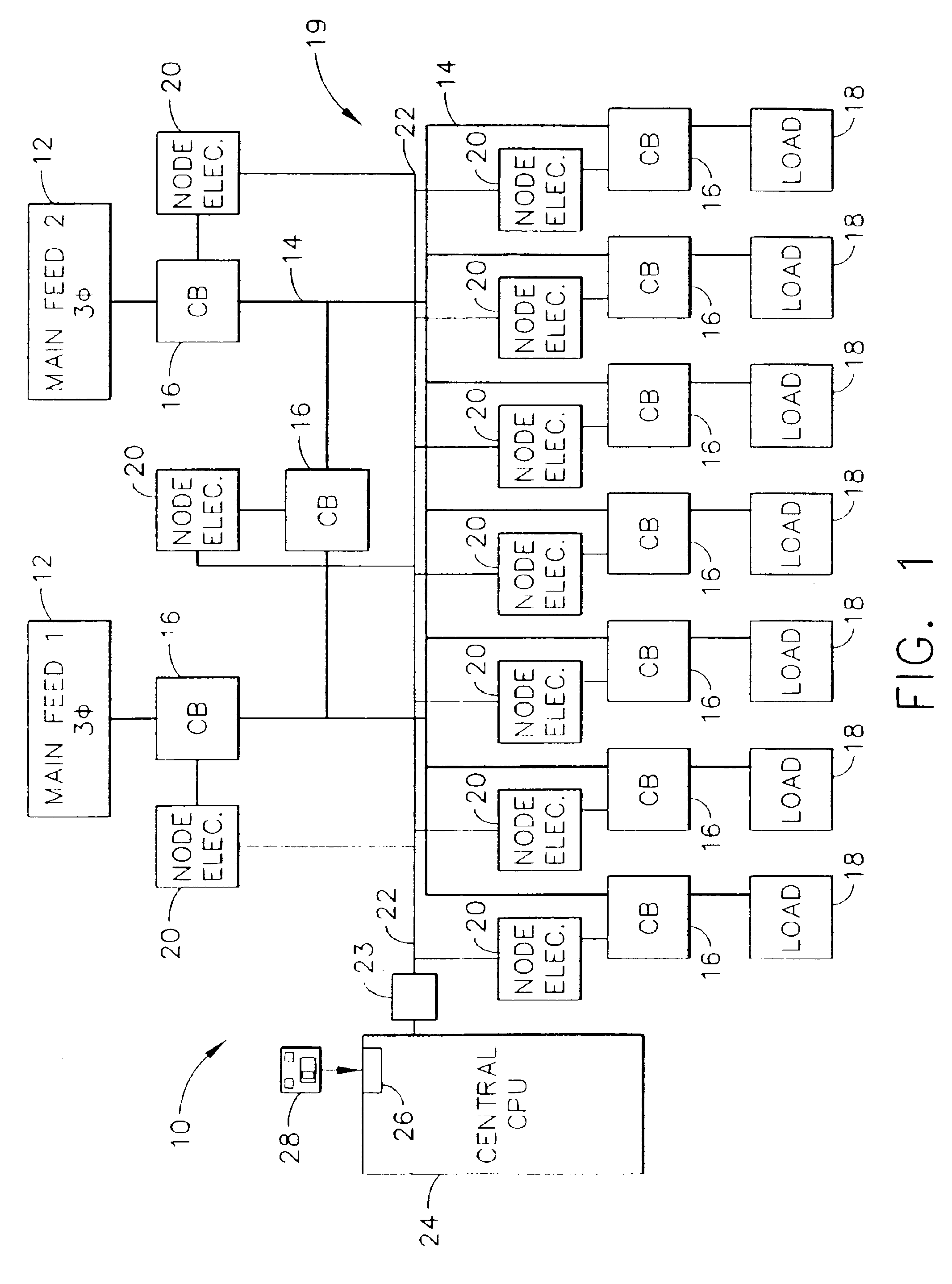
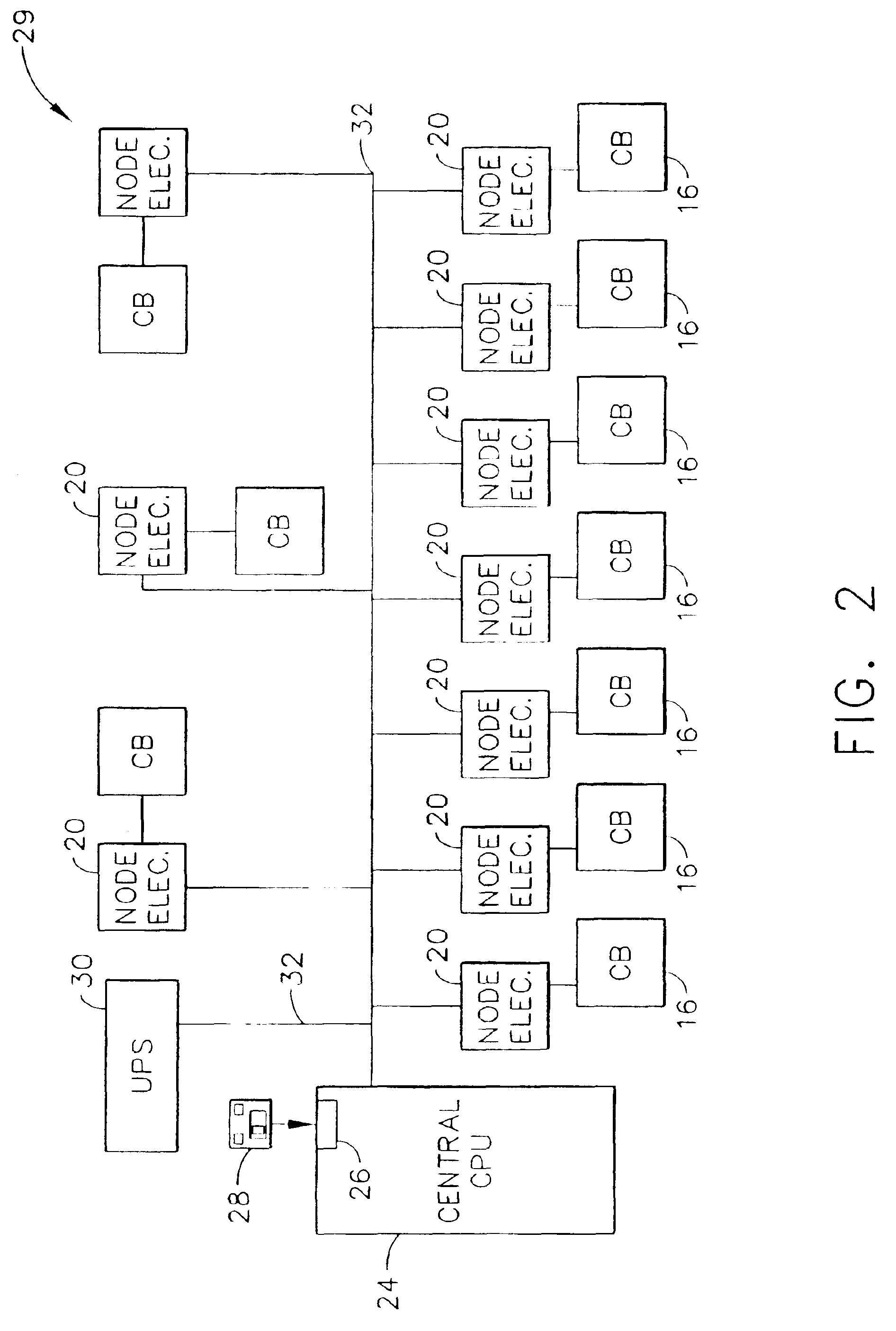
InactiveUS6892115B2Selective ac load connection arrangementsLevel controlElectricityDistribution power system
A method of monitoring and controlling a power distribution system is provided. The power distribution system includes a plurality of circuit breakers, a plurality of node electronic units, and wherein each associated circuit breaker is electrically coupled with each respective node electronic unit. The system also includes at least one digital network, and at least one central control processing unit (CCPU) wherein each CCPU includes a first power system global information set, and each CCPU is communicatively coupled to the plurality of node electronic units. The method includes transmitting at least one digital message from each node electronic unit to each CCPU over a respective network, determining an operational state of the power distribution system from the digital message, and transmitting at least one multicast message from each CCPU to each node electronic unit such that the circuit breakers are operable from each CCPU.
Owner:ABB (SCHWEIZ) AG
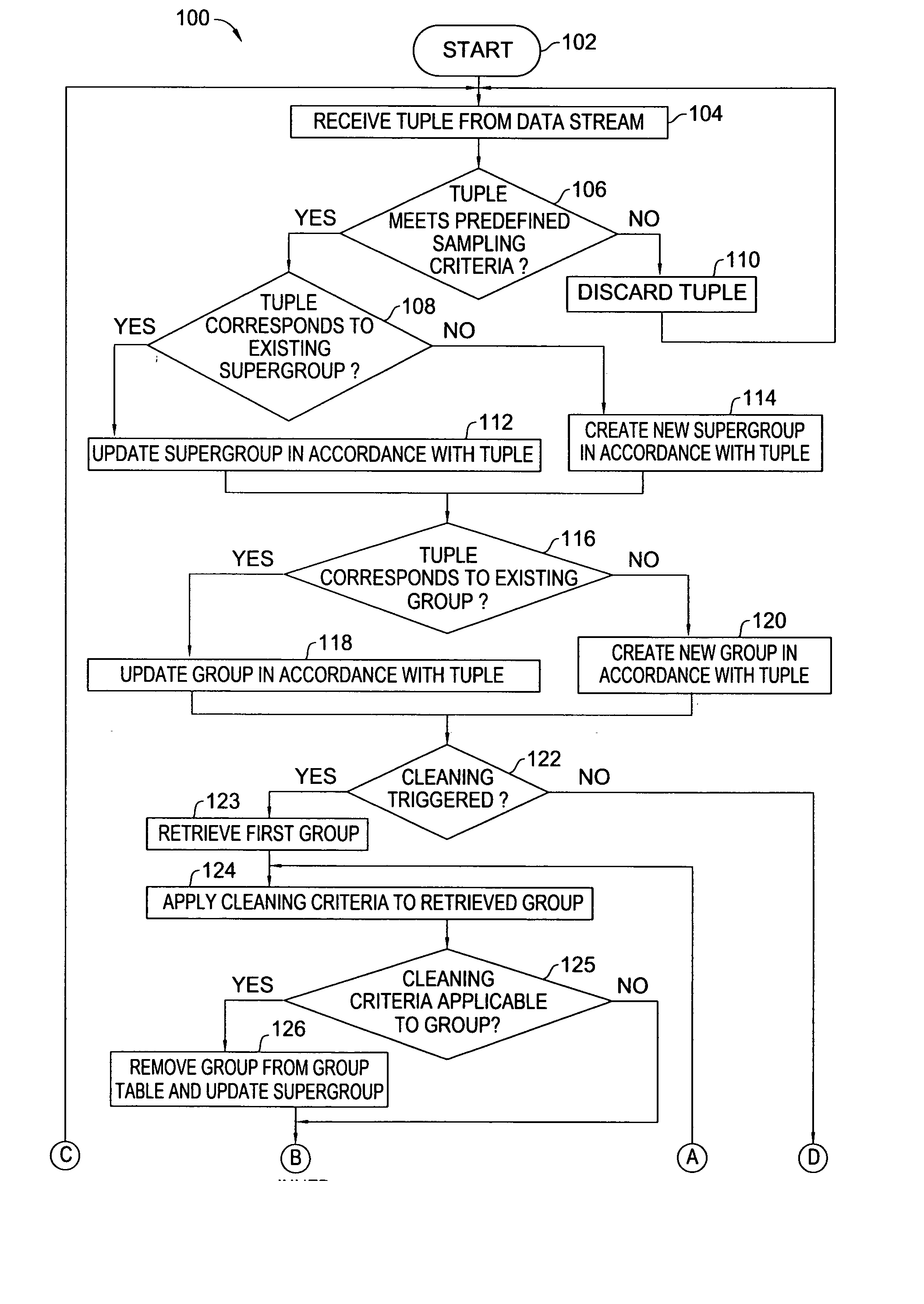
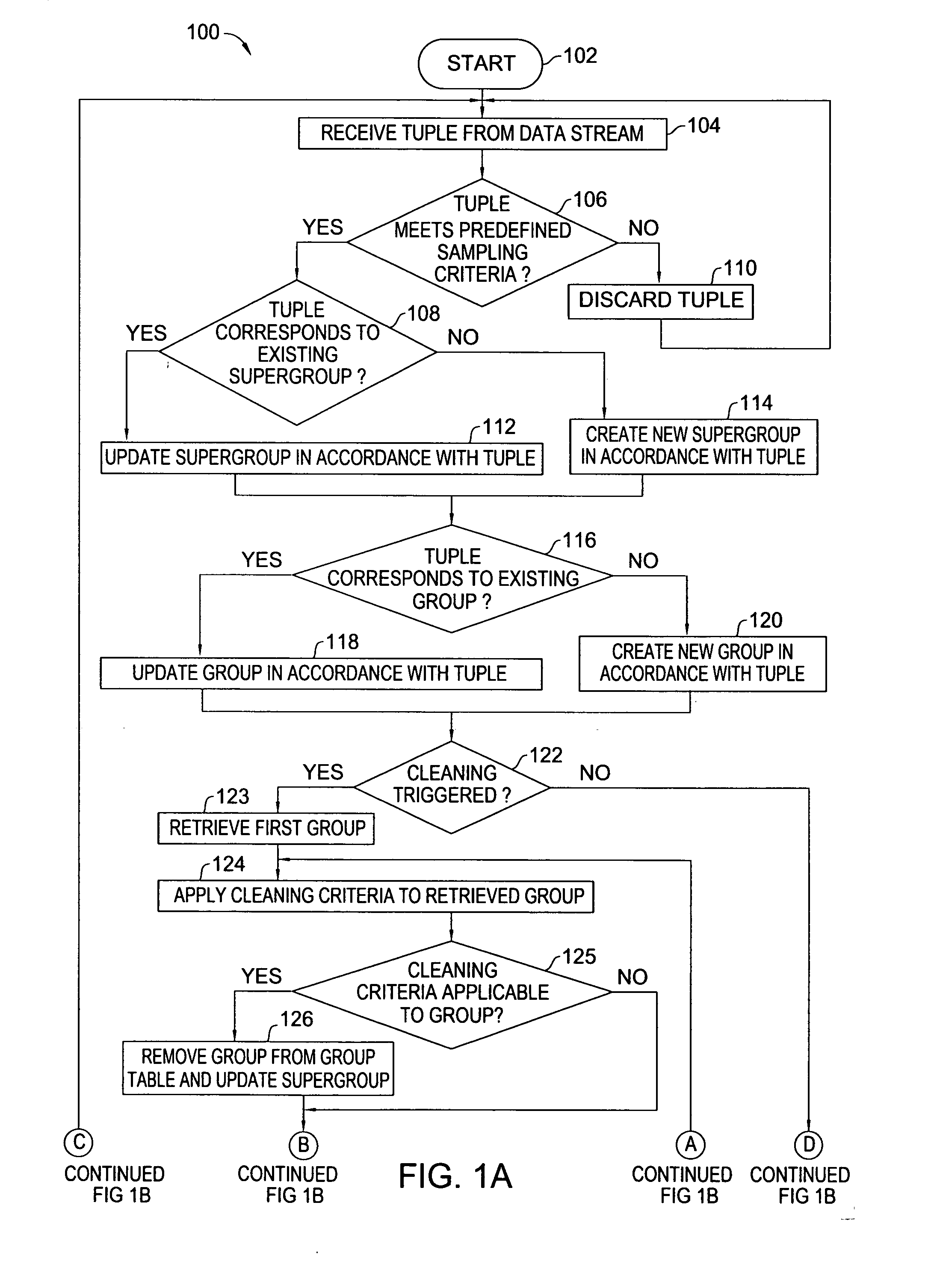
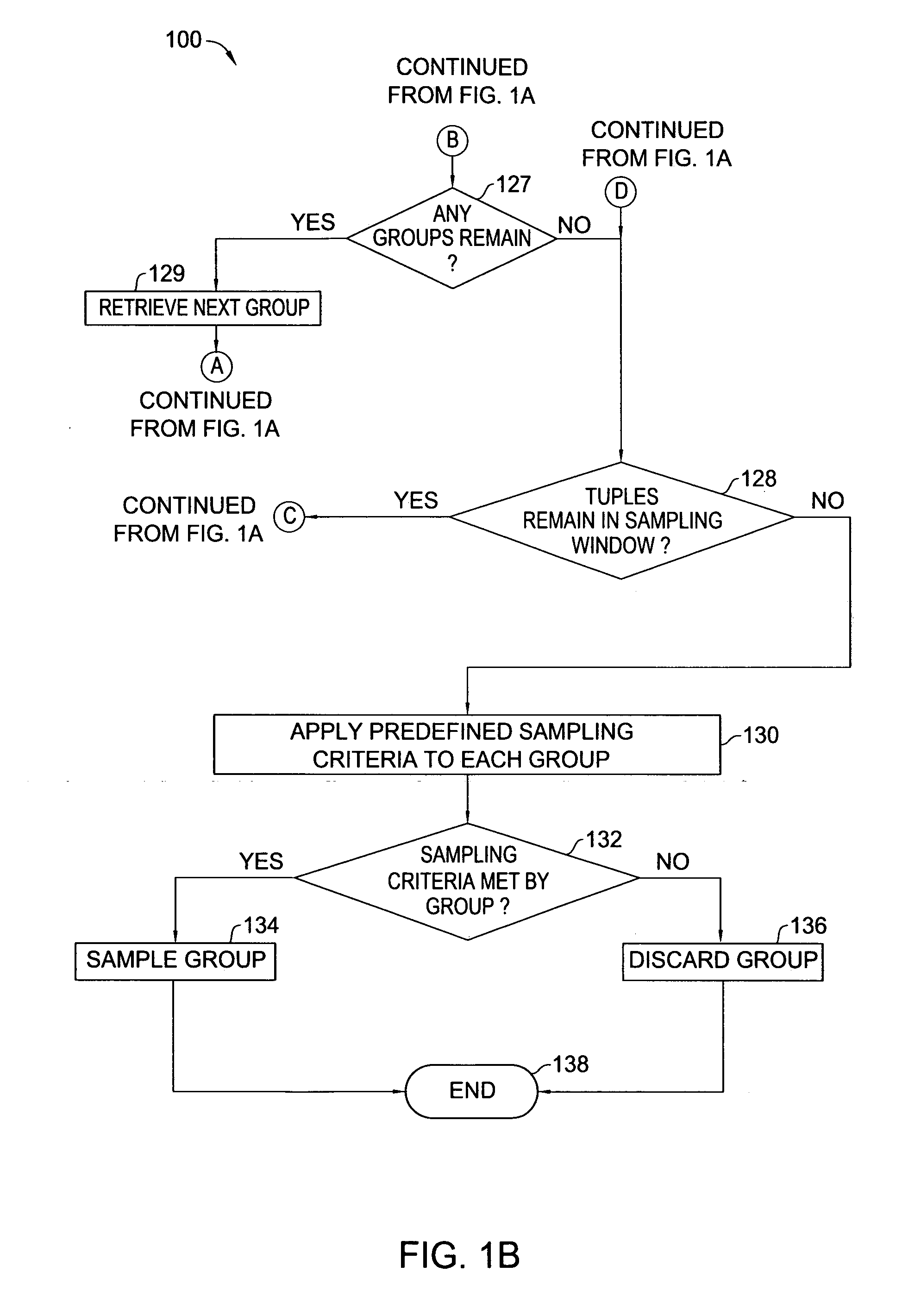
Method and apparatus for data stream sampling
In one embodiment, the present invention is a method and apparatus for data stream sampling. In one embodiment, a tuple of a data stream is received from a sampling window of the data stream. The tuple is associated with a group, selected from a set of one or more groups, which reflects a subset of information relating to a sample of the data stream. In addition, the tuple is associated with a supergroup, selected from a set of one or more supergroups, which reflects global information relating to the sample. It is then determined whether receipt of the tuple triggers a cleaning phase in which one or more tuples are shed from the sample. The operator can be implemented to execute a variety of different sampling algorithms, including well-known and experimental algorithms.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
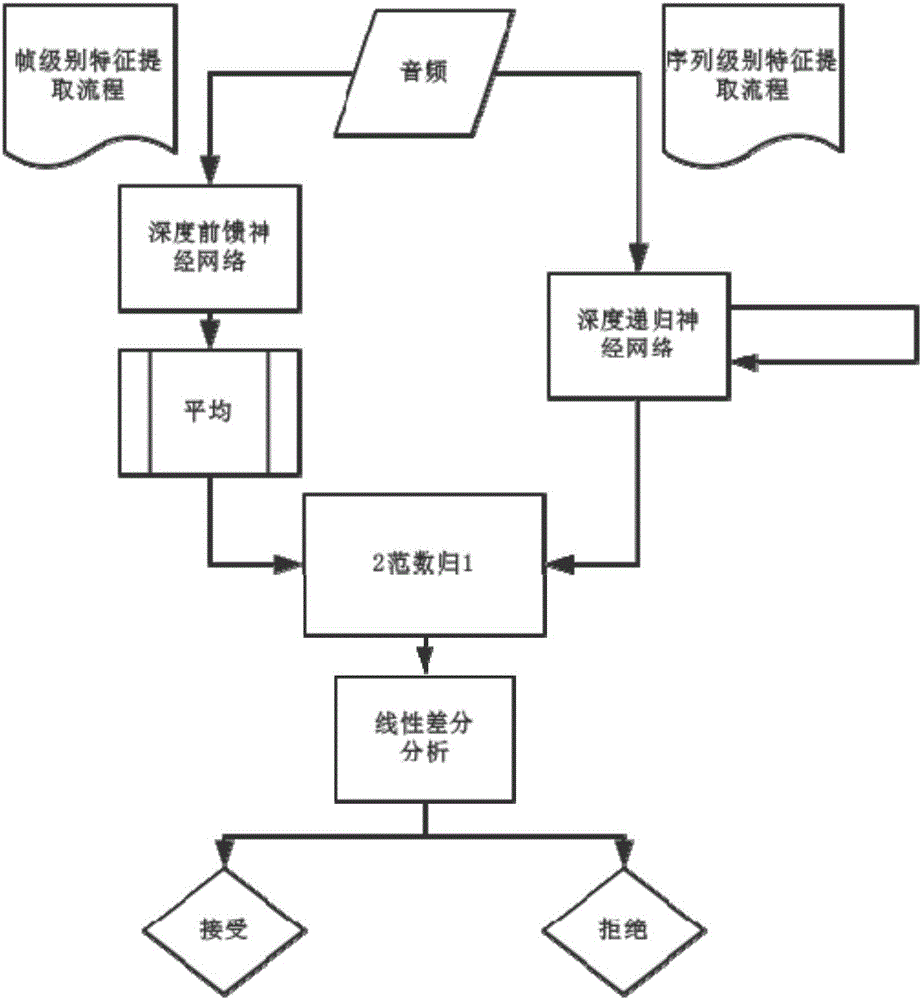
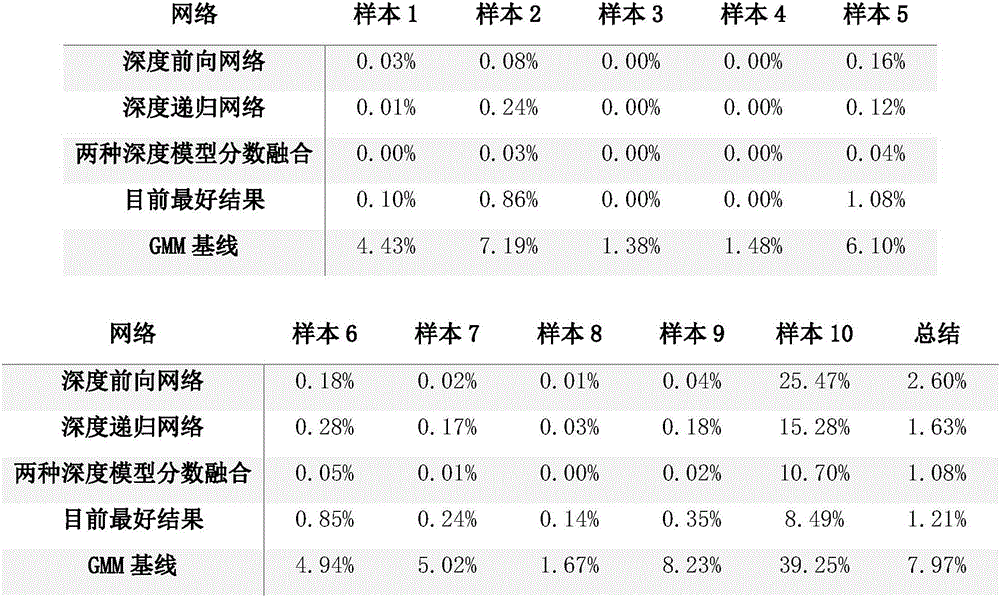
Method and system for detecting voice spoofing attack of speakers on basis of deep learning
The invention discloses a method and a system for detecting voice spoofing attack of speakers on the basis of deep learning. The method includes constructing audio-frequency training sets, initializing deep feed-forward neural networks and deep recurrent neural networks and respectively training the deep feed-forward neural networks and the deep recurrent neural networks by the aid of multi-frame feature vectors and single-frame vector sequences of the training sets; respectively leading frame level and sequence level feature vectors of to-be-tested audio frequencies into two trained linear differential analysis models in test phases, weighting two obtained result grades to obtain scores and comparing the scores to predefined threshold values so as to discriminate voice spoofing. The method and the system have the advantages that local features can be captured, and global information can be grasped; the linear differential analysis models are used as classifiers in identification and verification phases, the voice spoofing attack can be judged by means of grade fusion, and accordingly the voice spoofing detection accuracy can be greatly improved.
Owner:AISPEECH CO LTD
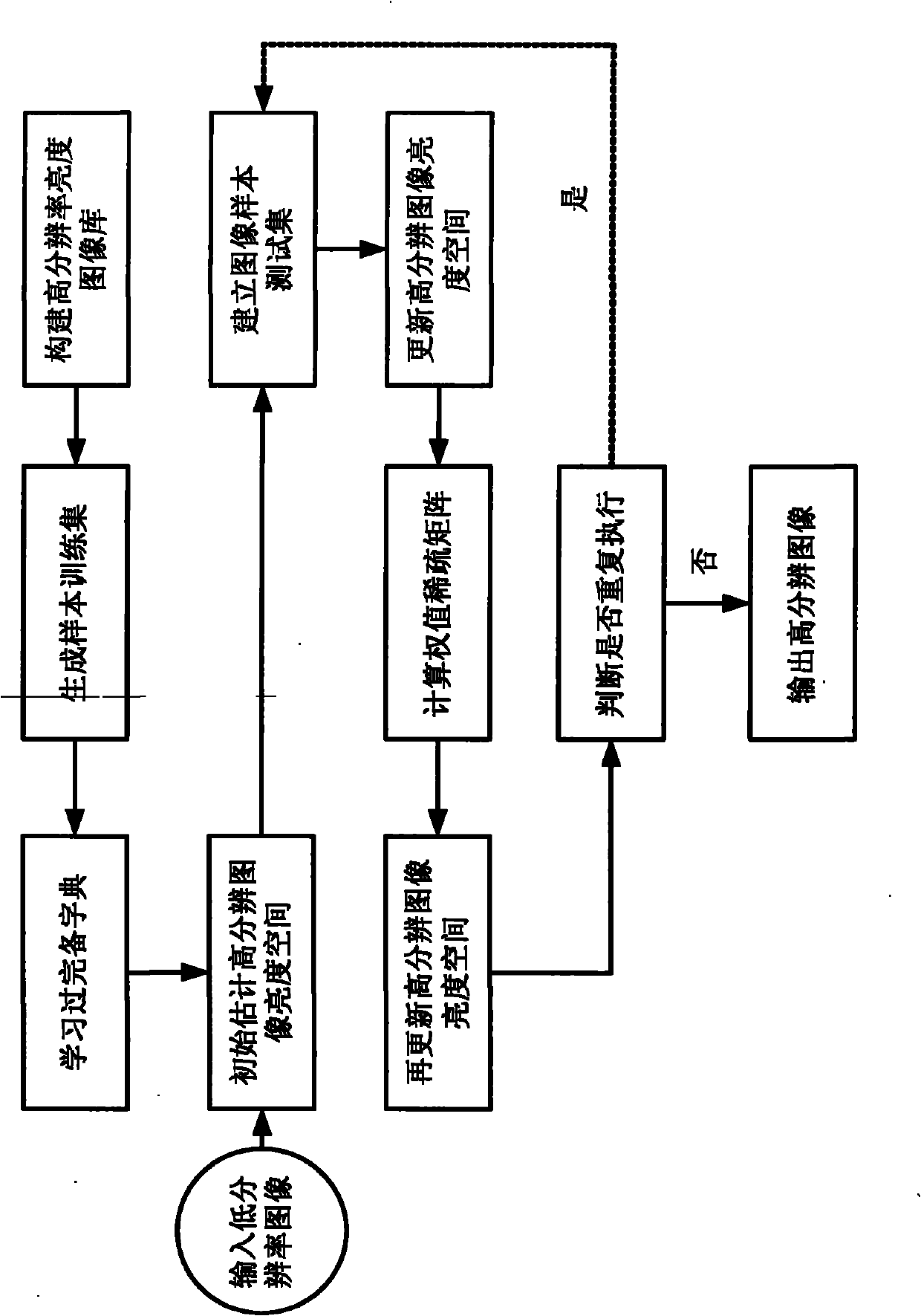
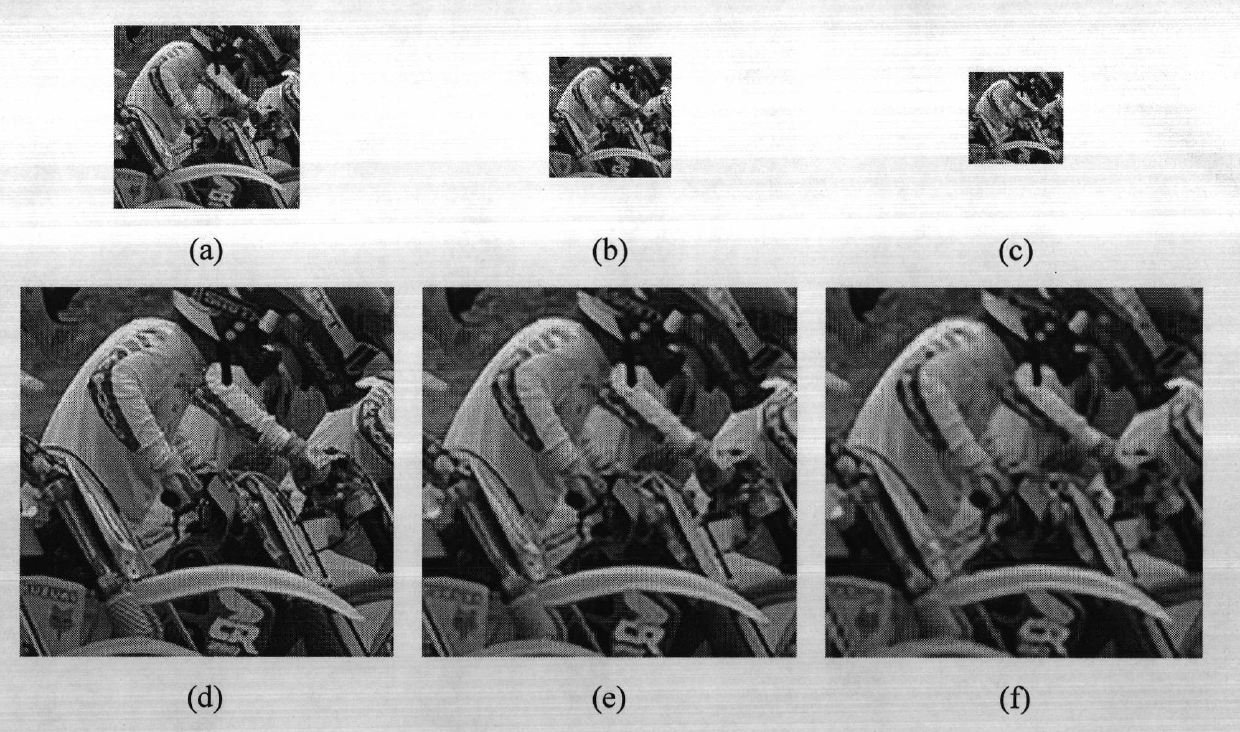
High-resolution dictionary based sparse representation image super-resolution reconstruction method
InactiveCN102142137ASharp edgeRich texture detailsImage enhancementCharacter and pattern recognitionReconstruction methodNon local
The invention discloses a high-resolution dictionary based sparse representation image super-resolution reconstruction method. The method comprises the following steps of: (1) constructing a high-resolution brightness image library; (2) generating a sample training set; (3) learning an over-complete dictionary; (4) primarily establishing a high-resolution image brightness space; (5) establishing an image sample test set; (6) updating the high-resolution image brightness space; (7) calculating a weight sparse matrix; (8) reupdating the high-resolution image brightness space; (9) judging whether to repeat execution; and (10) outputting a high-resolution image. The high-resolution over-complete dictionary learned by the invention can be applied to different amplification factors. Sparse representation, non-local prior and data fidelity constraint are fully utilized, so that local information and global information can be comprehensively utilized. The method has higher super-resolution capacity; and the reconstructed image is closer to an actual image.
Owner:XIDIAN UNIV
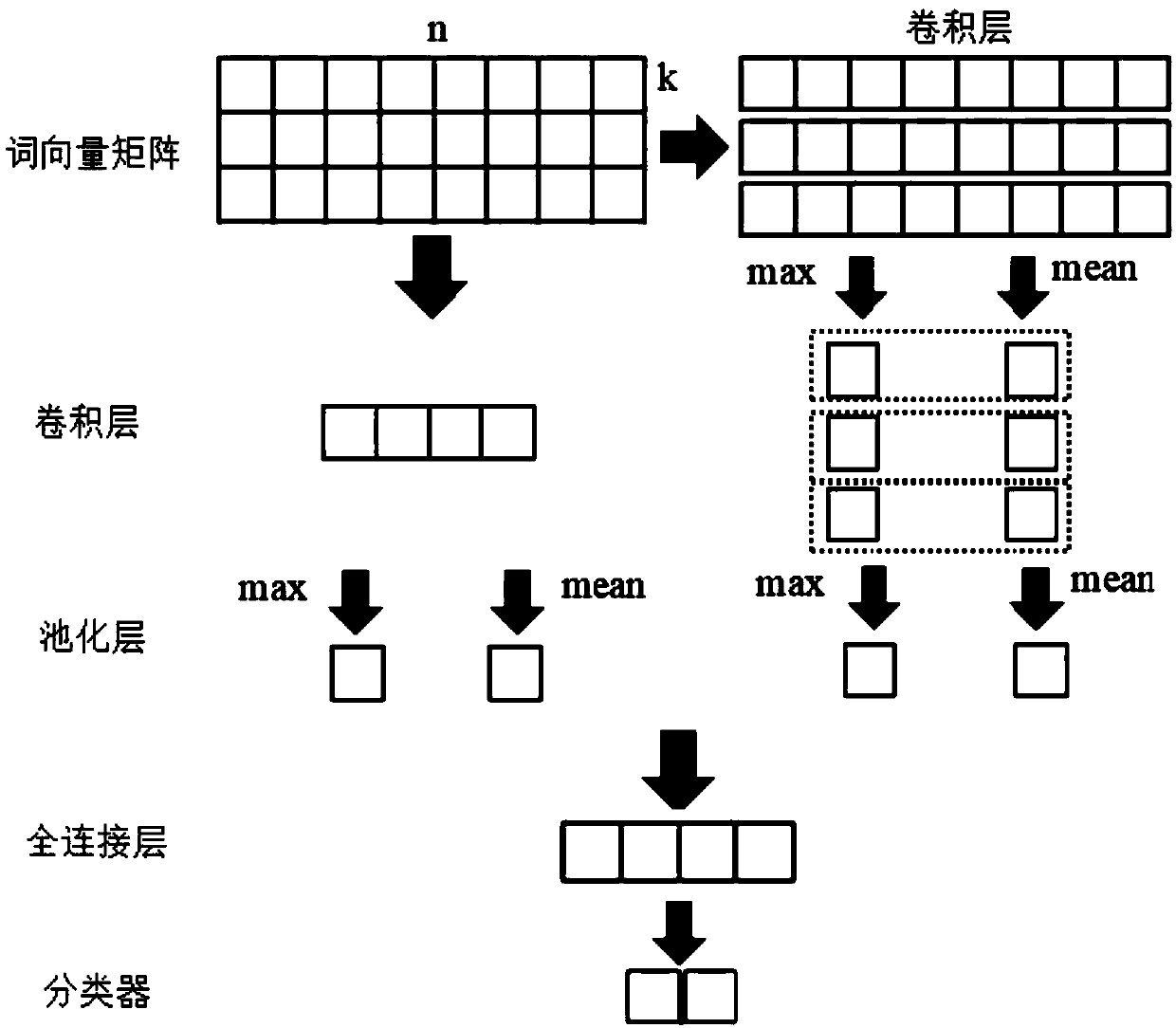
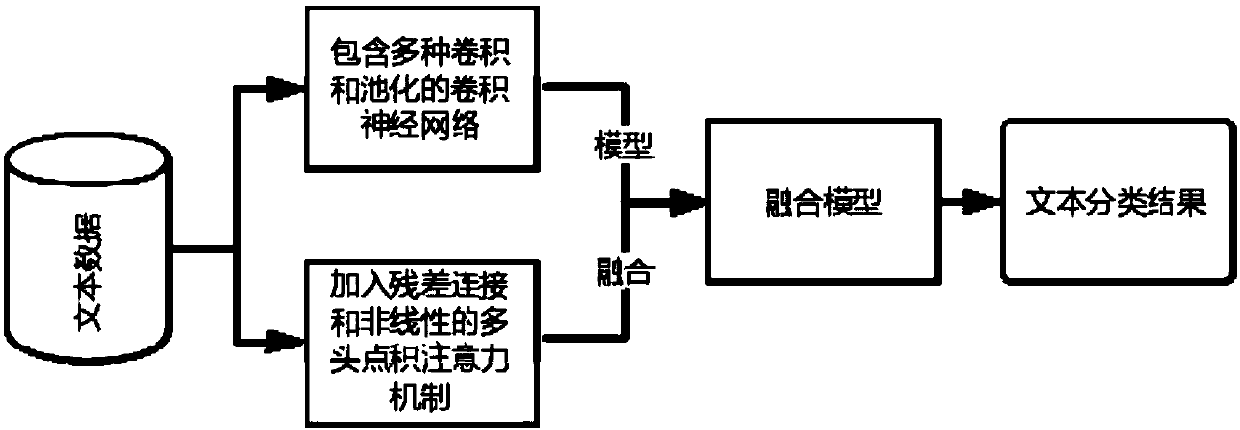
Text sentiment classification algorithm based on convolutional neural network and attention mechanism
ActiveCN108664632AFully captureFirmly connectedNatural language data processingNeural architecturesGranularityGlobal information
The invention discloses a text sentiment classification algorithm based on a convolutional neural network and an attention mechanism. The text sentiment classification algorithm comprises the steps of1, establishing the convolutional neural network comprising multiple convolutions and multiple kinds of pooling, and using sentiment classification text for training to obtain a first model; 2, establishing the multi-head point product attention mechanism into which residual connection and nonlinearity are added, and using the sentiment classification text for training to obtain a second model; 3, conducting model fusion on the two models to obtain sentiment classification of the text. Multiple granularity, the convolutions and multiple kinds of pooling are fused into the convolutional neuralnetwork, the residual connection and the nonlinearity are introduced into the attention mechanism, and attention is calculated several times to obtain two text sentiment classification models. Through a Bagging model fusion method, a fusion model is obtained, the text is classified, the advantages that the convolutional neural network can well capture local features and the attention mechanism can well capture global information can be combined, and the more comprehensive text sentiment classification models are obtained.
Owner:SOUTH CHINA UNIV OF TECH
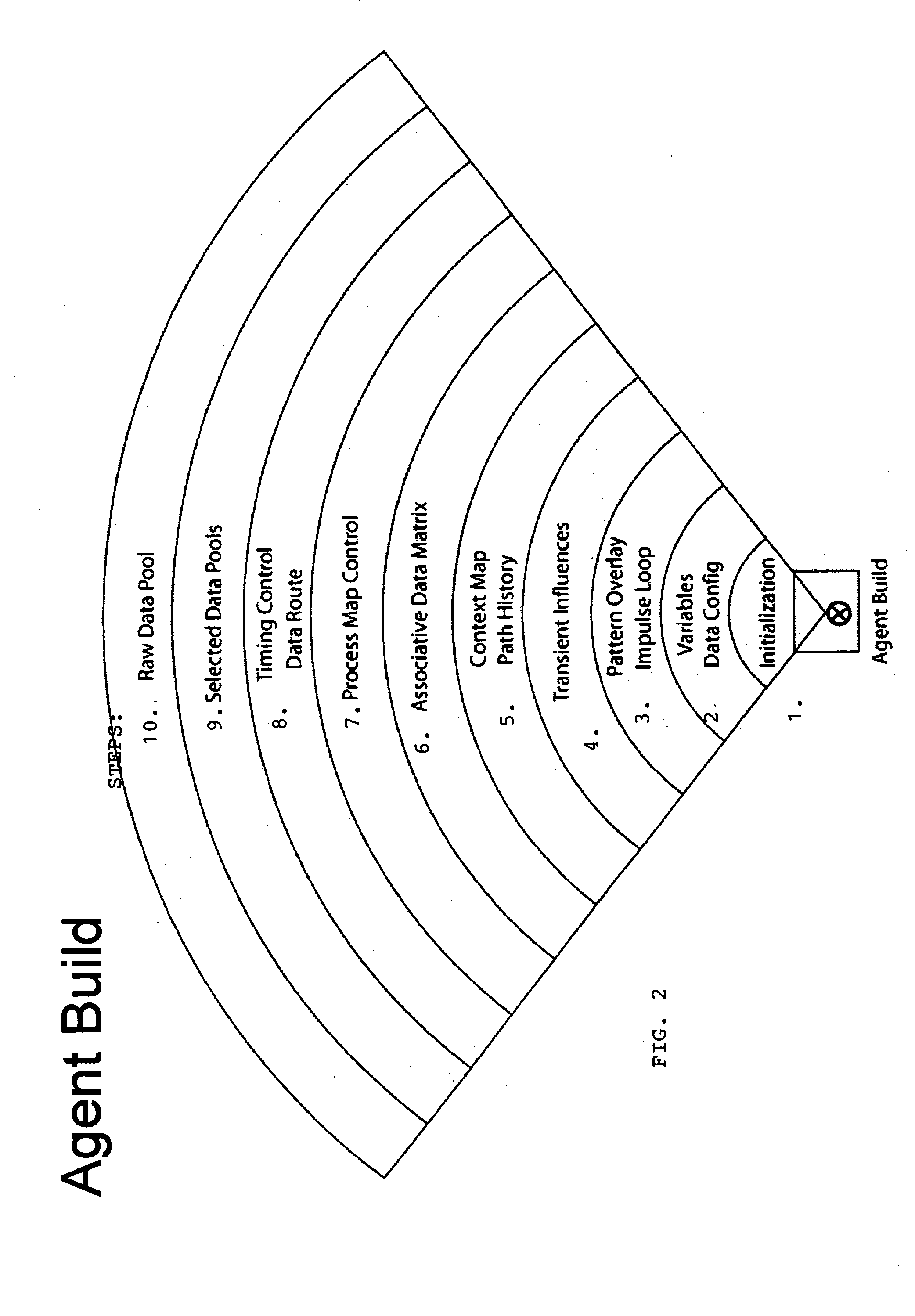
Cultural simulation model for modeling of agent behavioral expression and simulation data visualization methods
ActiveUS20040181376A1Accurately indicatedDrawing from basic elementsSpeech analysisVisual toolData visualization
A computer simulation method is provided for modeling the behavioral expression of one or more agents in an environment to be simulated, then running a simulation of the modeled agent(s) against real-world information as input data reflecting changing conditions of the environment being simulated, and obtaining an output based on the modeled agent(s) response(s). The simulation method models the underlying cultural, social, and behavioral characteristics on which agent behaviors and actions are based, rather than modeling fixed rules for the agent's actions. The input data driving the simulation are constituted by real-world information reflecting the changing conditions of the environment being simulated, rather than an artificial set of predefined initial conditions which do not change over time. As a result, the simulation output of the modeled agent's responses to the input information can indicate more accurately how that type of participant in the simulated environment might respond under real-world conditions. Simulations can be run on global networks for agent types of different cultures, societies, and behaviors, with global sources of information. Simulation environments can include problems and situations in a wide range of human activity. Robust new visual tools are provided for discerning patterns and trends in the simulation data, including waveform charts, star charts, grid charts, and pole chart series.
Owner:SEASEER R&D
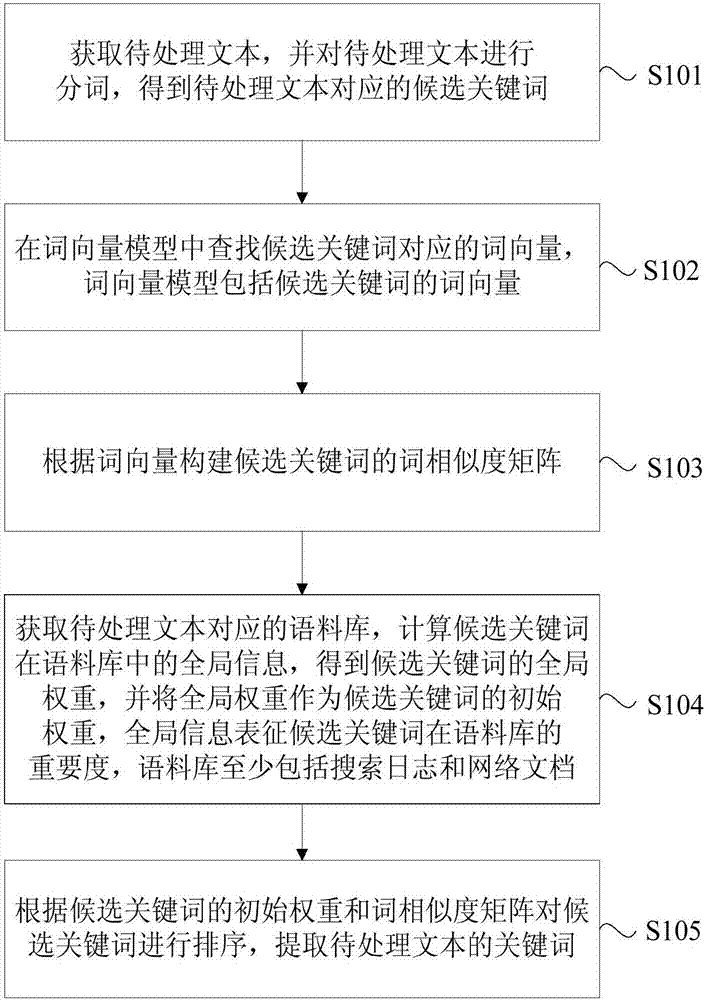
Method and device for extracting keyword based on graph model
ActiveCN107122413AAccurate extractionImprove accuracyNatural language data processingNeural learning methodsAlgorithmGlobal information
The embodiment of the invention provides a method and a device for extracting a keyword based on a graph model. The method comprises the steps of acquiring a to-be-processed text, and segmenting words of the to-be-processed text to obtain candidate keywords corresponding to the to-be-processed text; finding out word vectors corresponding to the candidate keywords from a word vector model, wherein the word vector model includes the word vectors of the candidate keyword; constructing a word similarity matrix of the candidate keywords according to the word vectors; acquiring a language database corresponding to the to-be-processed text, calculating global information of the candidate keywords in the language database to obtain a global weight of the candidate keywords, and taking the global weight as an initial weight of the candidate keywords, wherein the global information represents the importance degree of the candidate keywords in the language database, and the language database at least includes a search log and a network document; and ranking the candidate keywords according to the initial weight and the word similarity matrix of the candidate keyword, and extracting the keyword of the to-be-processed text. By use of the embodiment, the keyword extraction accuracy rate is effectively improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Ship intelligent identification tracking method
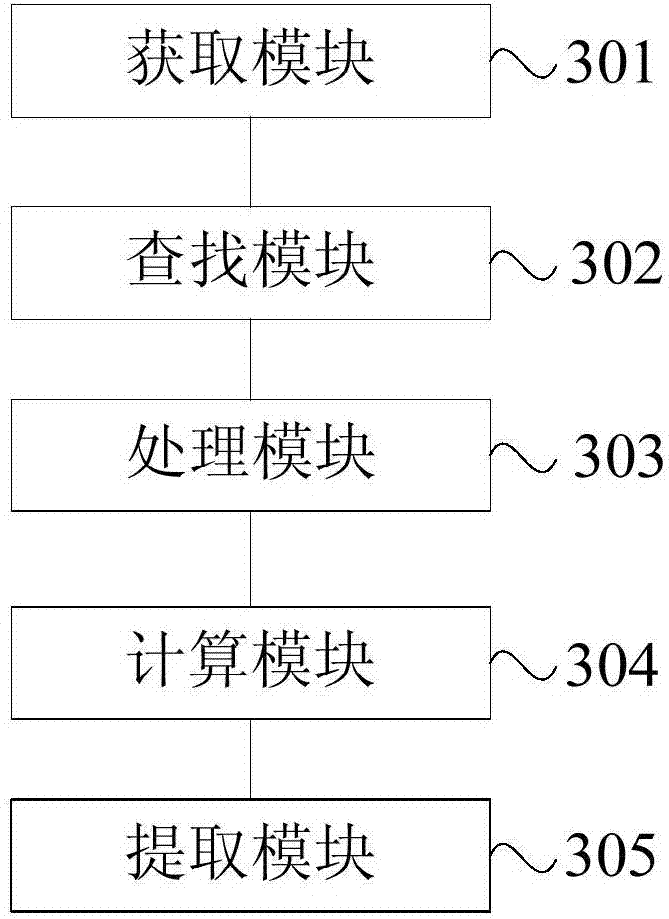
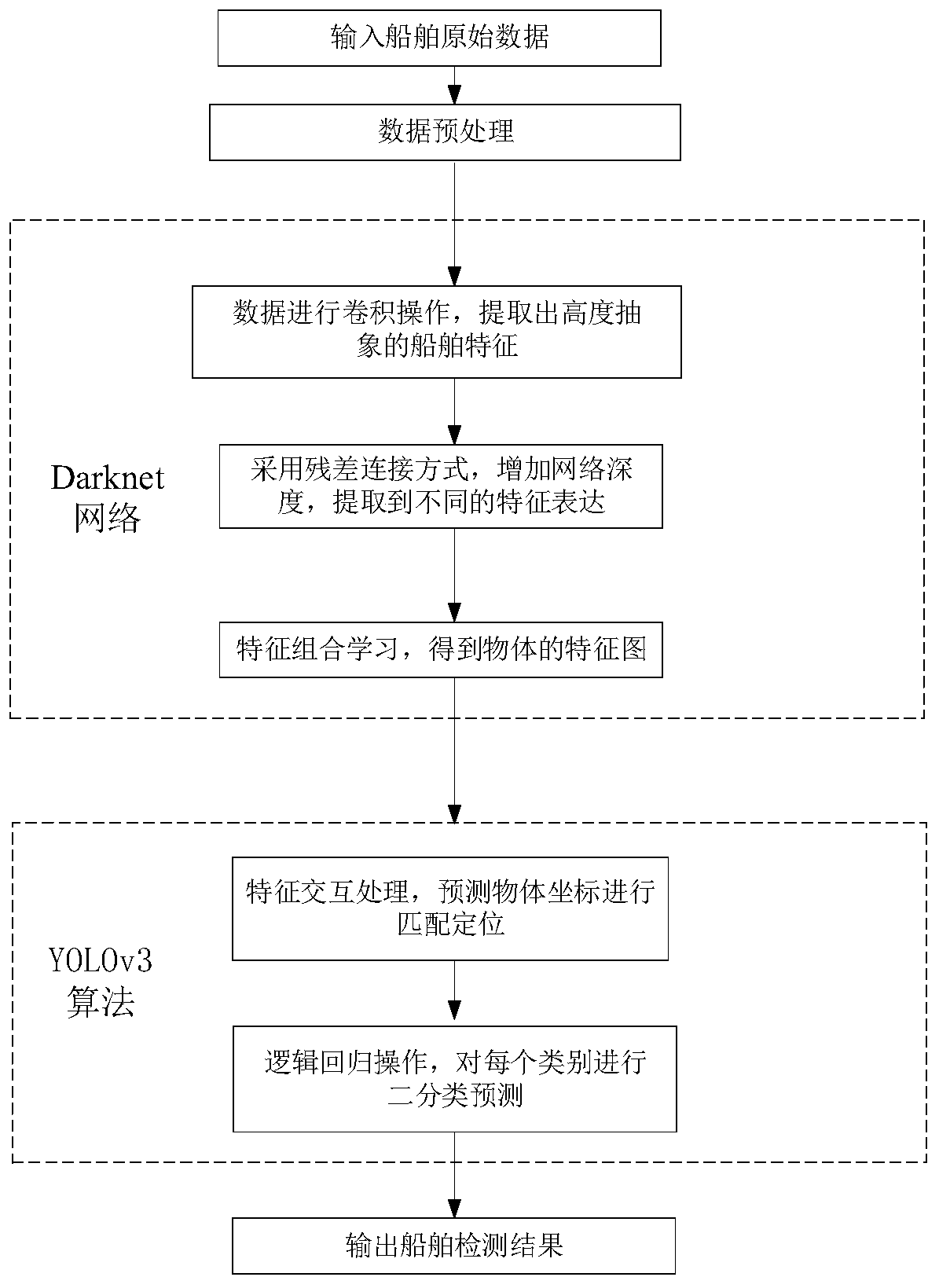
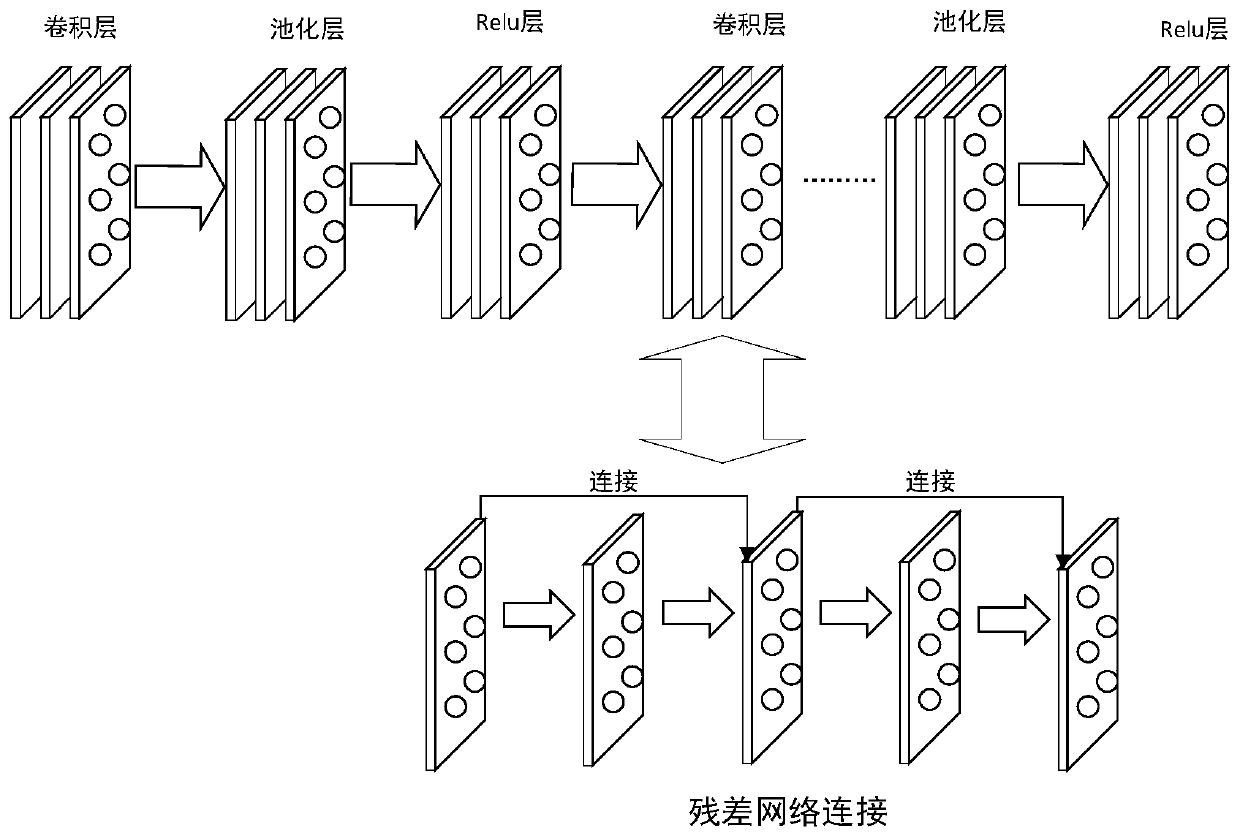
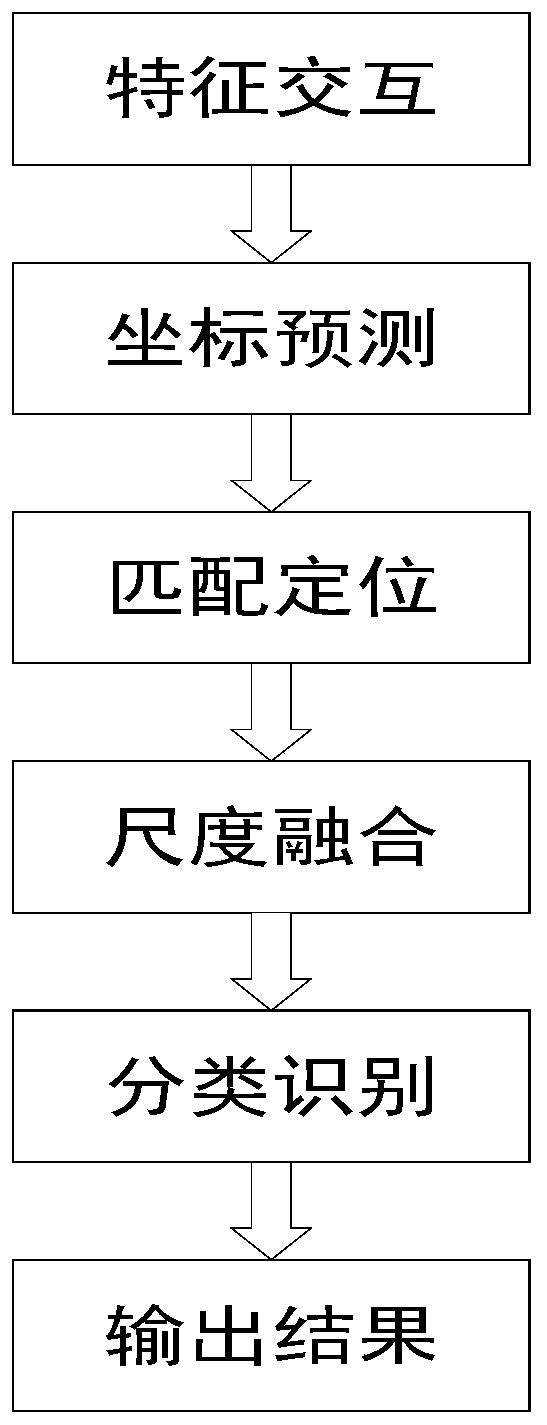
The invention provides a ship intelligent identification tracking method. For the ship intelligent identification tracking method, based on a deep learning algorithm based on computer vision, a basicclassification network structure and a multi-scale target prediction method in traditional deep learning are improved, and a Darknet network and a YOLOv3 algorithm are combined to track a ship and detect and identify the type of the ship in real time. According to the ship intelligent identification tracking method, the idea of a residual error network is introduced; a full convolution structure is adopted; the network depth is increased; the data feature learning capability is improved; and local feature interaction between the feature maps is achieved in a convolution kernel mode through a YOLOv3 algorithm, and matching and positioning of targets are conducted, and target area prediction and category prediction are integrated into a single neural network model on the basis, so that global information of the images is recognized as the targets. Experimental results show that compared with a traditional method, the algorithm provided by the invention not only has better real-time performance and accuracy, but also has better robustness for various environmental changes.
Owner:SHANGHAI MARITIME UNIVERSITY
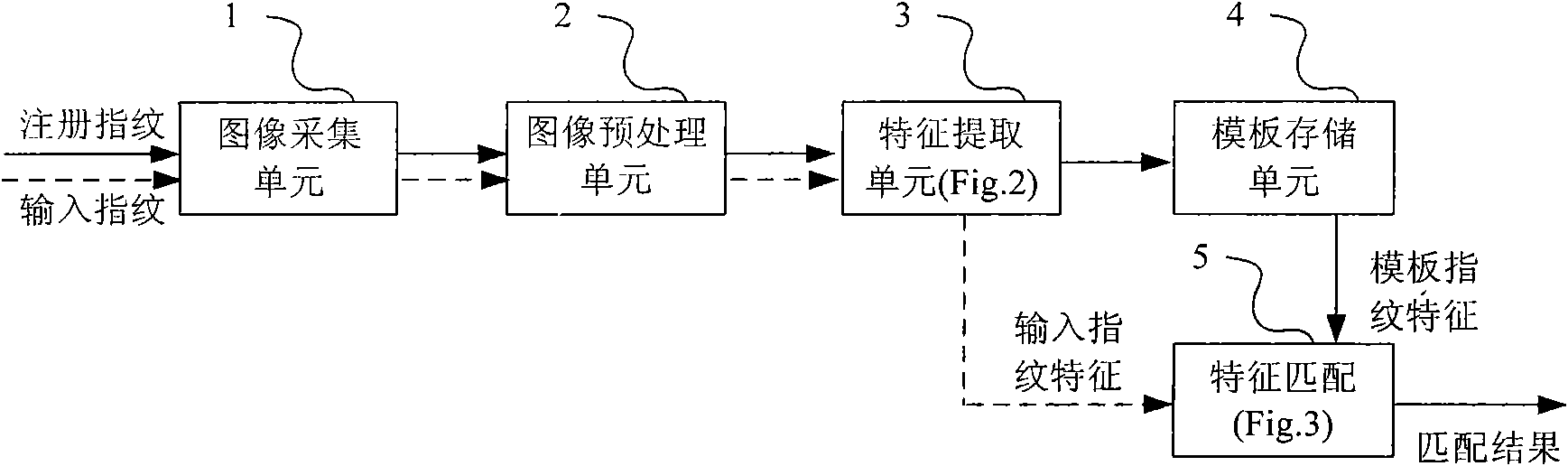
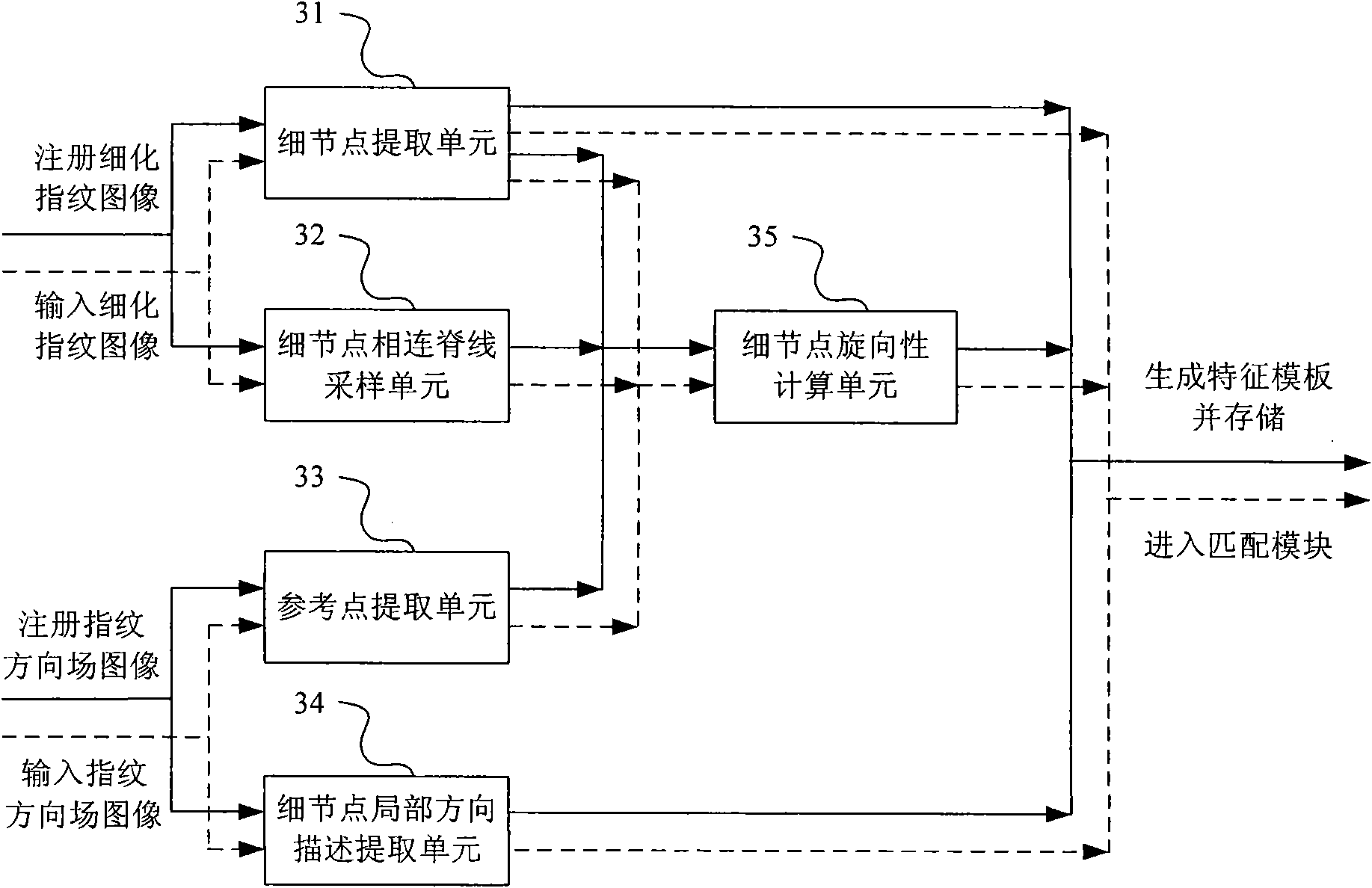
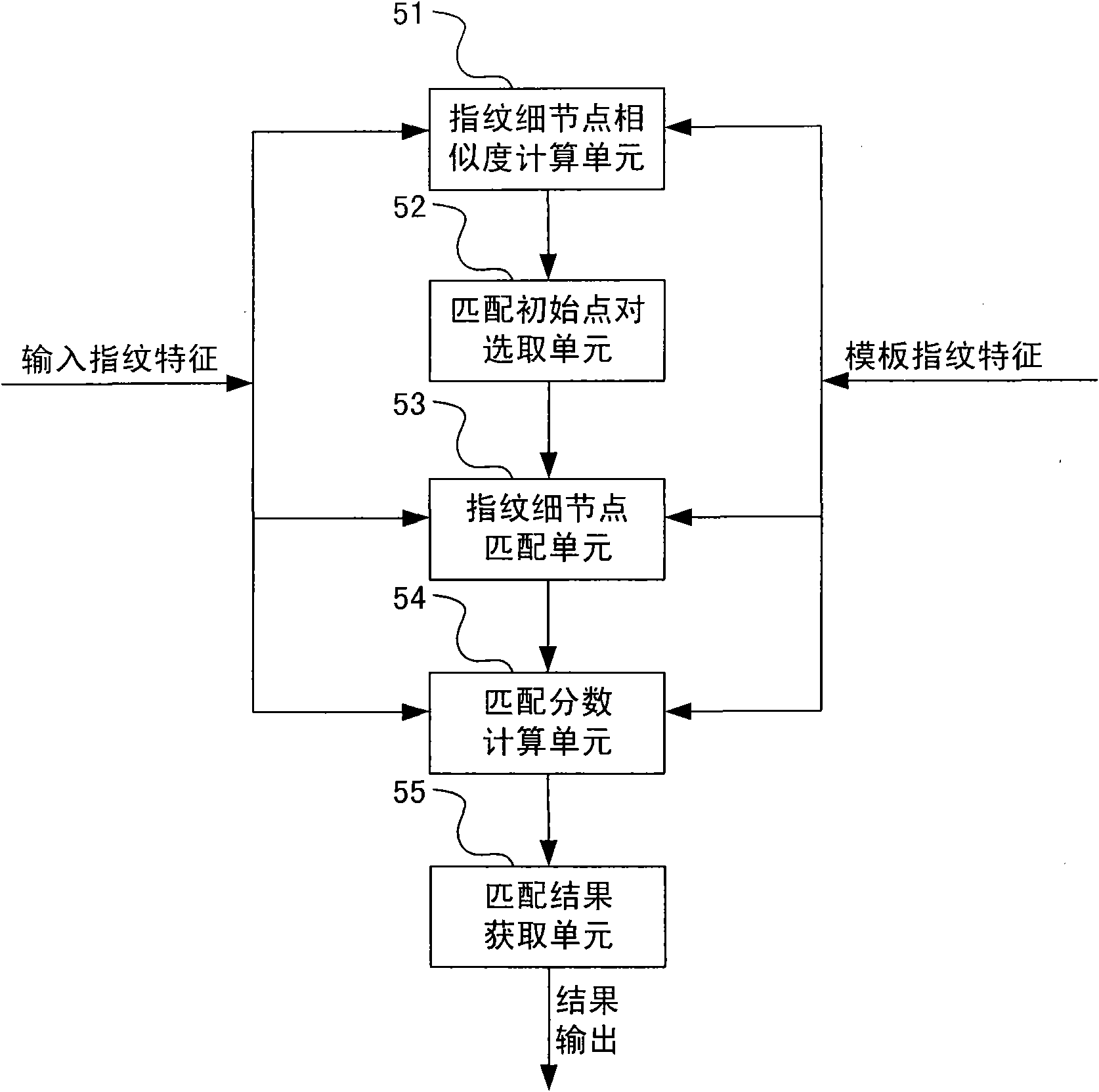
Fingerprint minutiae matching method syncretized to global information and system thereof
InactiveCN101777128AReduce false match rateAchieve integrationCharacter and pattern recognitionGlobal informationMinutiae
The invention provides a fingerprint minutiae matching method syncretized to global information and a system thereof. The system realizes the entire matching process by an image acquiring unit, an image pre-processing unit, a feature extracting unit, a template storing unit and a feature matching unit, which specifically comprises the following steps: from the feature extracting unit, extracting the feature including the globe information, that is, minutiae handedness, and regarding the minutiae handedness, minutiae information, and minutiae local direction description as the feature to represent the fingerprint; measuring the similarity between the minutiaes by the minutiae handedness and the minutiae local direction description; selecting several pairs of minutiaes having the greatest similarity as an initial dot pair; registering the fingerprint feature and obtaining the corresponding matching fractions with each group of initial dot pair as a reference; selecting the maximum matching fraction in matching fractions as the finial matching fraction; judging whether the input fingerprint feature and the template fingerprint feature are from the same finger based on the final matching fraction, thereby finishing the minutiae matching of the fingerprint.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Street-side maps and paths
ActiveUS7840032B2Color signal processing circuitsGeometric image transformationMultiple perspectiveSubject matter
Owner:MICROSOFT TECH LICENSING LLC
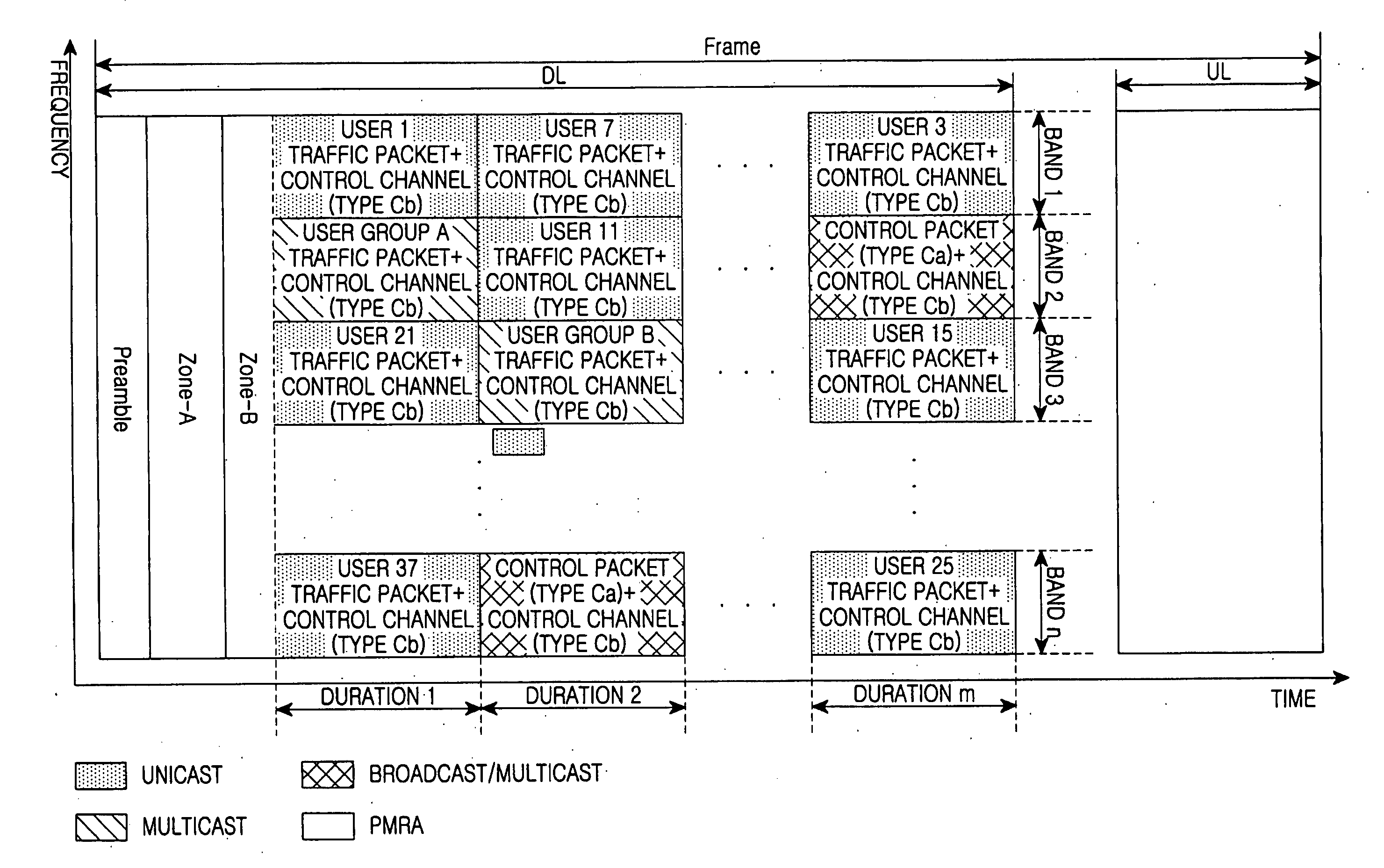
Method for generating a frame in an orthogonal frequency division multiple access communication system
ActiveUS20070058523A1Modulated-carrier systemsSignal allocationCommunications systemGlobal information
Disclosed is a method for generating a frame in an Orthogonal Frequency Division Multiple Access communication system. The method includes generating a frame having a global information zone and a local information zone, wherein the global information zone includes information that is necessary to be received commonly in all of user terminals; and the local information zone includes user terminal-by-user terminal or service-by-service traffic that is unnecessary to be received commonly in all of the user terminals.
Owner:HUAWEI TECH CO LTD
Method and system for blindly detecting a discontinuously transmitted shared channel, in particular blind high speed shared control channels detection
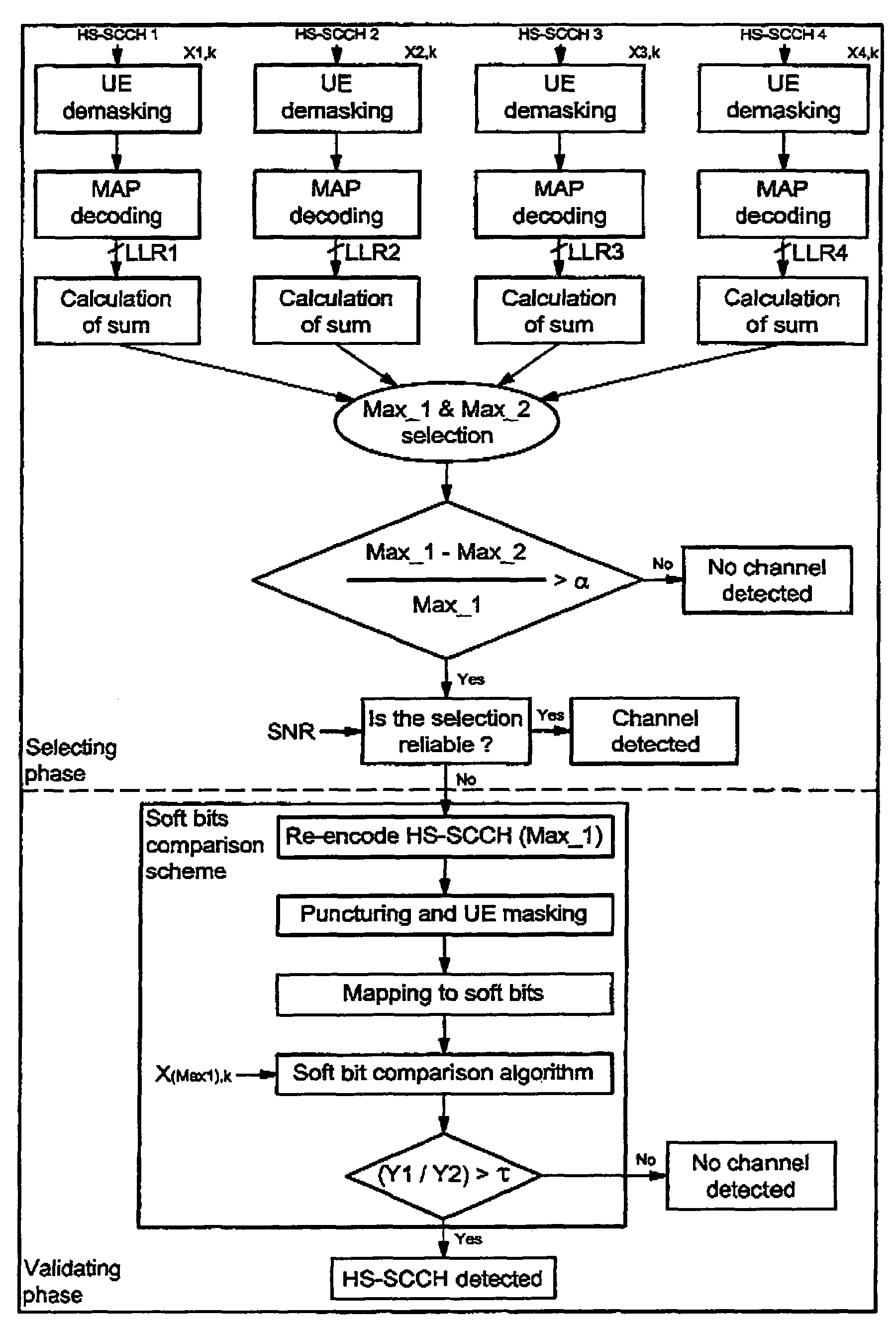
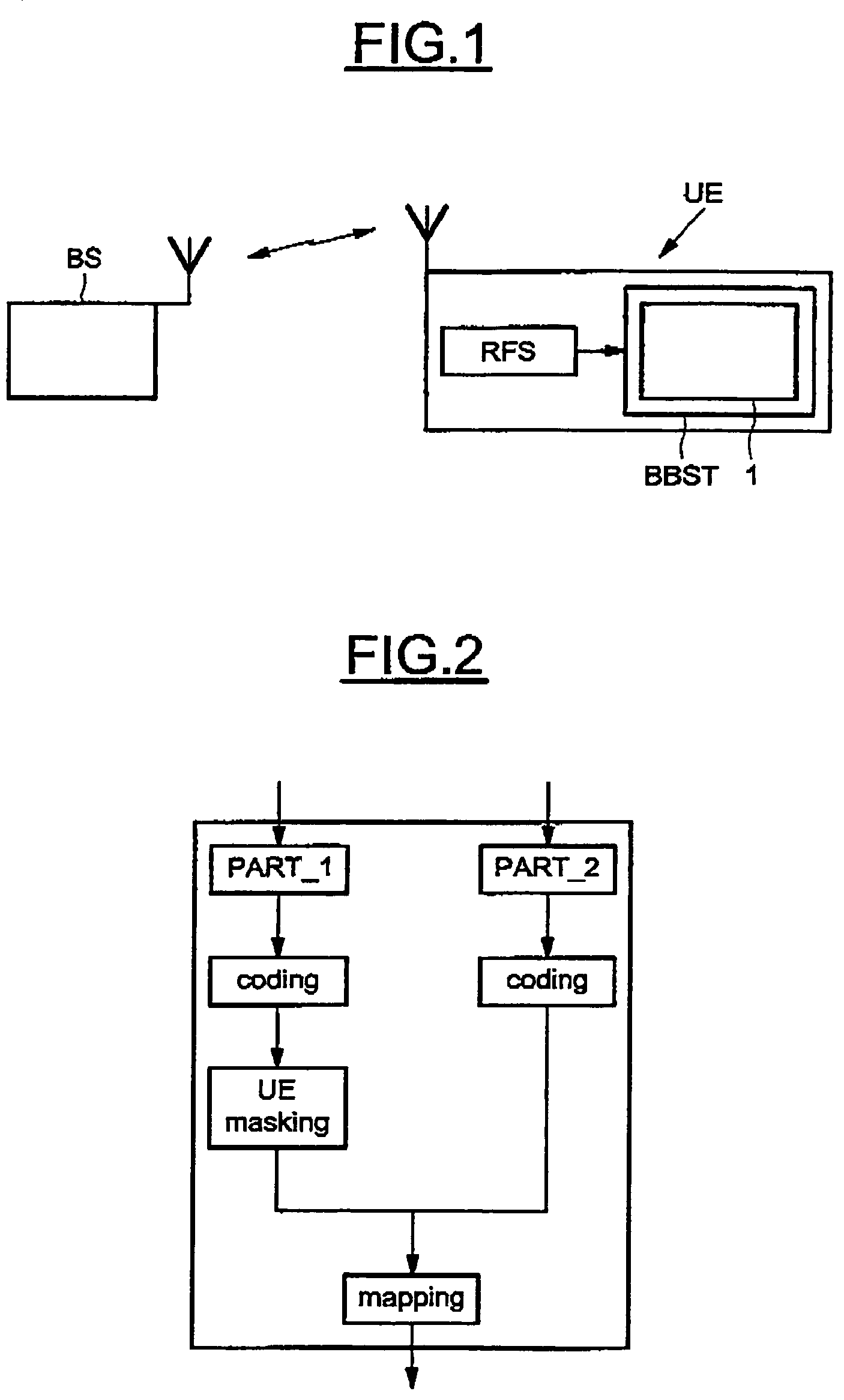
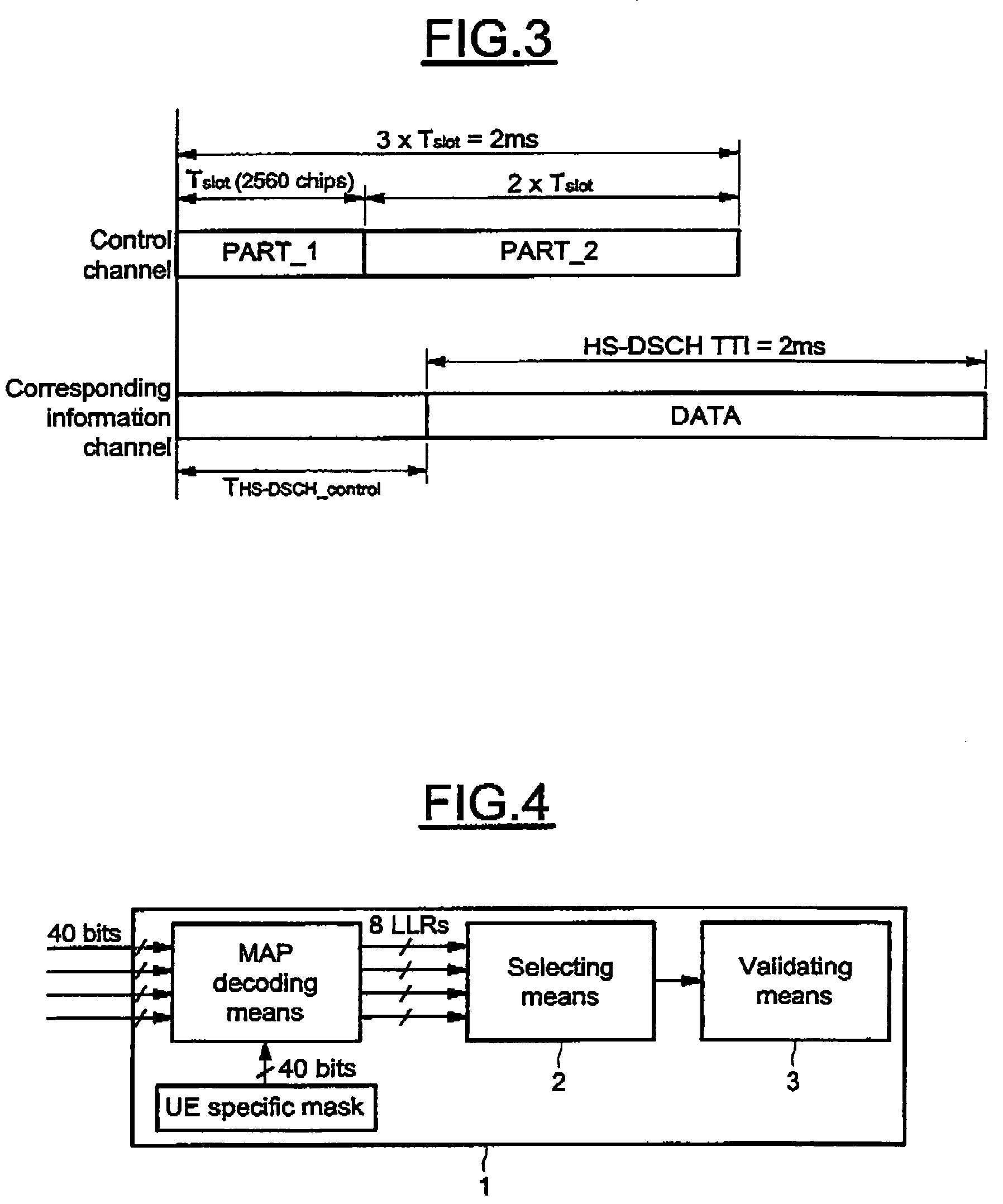
InactiveUS7688915B2Reduce loss rateReduce probabilityOther decoding techniquesCode conversionDigital dataControl channel
A method for detecting an eventual channel intended to a designated user equipment among n channels received by the designated user equipment during a given duration, each channel received during the duration carrying encoded data masked with an identifier associated to a user equipment. The method includes a selecting phase having a demasking step demasking the received masked encoded data of each channel with the identifier of the designated user equipment, a decoding step decoding the demasked encoded data of each channel to obtain a set of digital decoded data for each channel, a calculating step calculating, from each set of digital decoded data, a global information representative of a confidence in digital data received on the physical channel, and a detecting step detecting the channel from all the global information.
Owner:SNO WAY INT +1
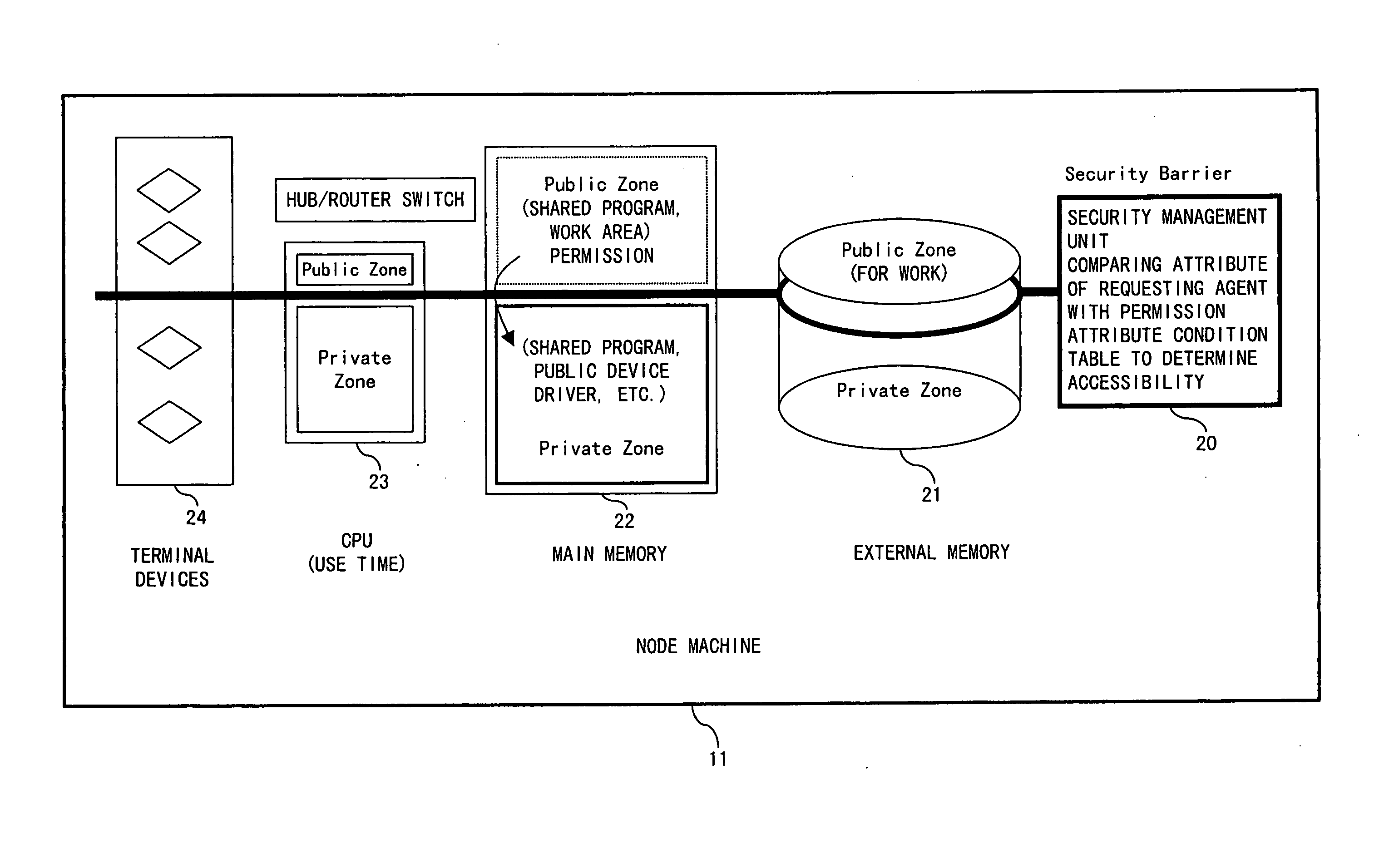
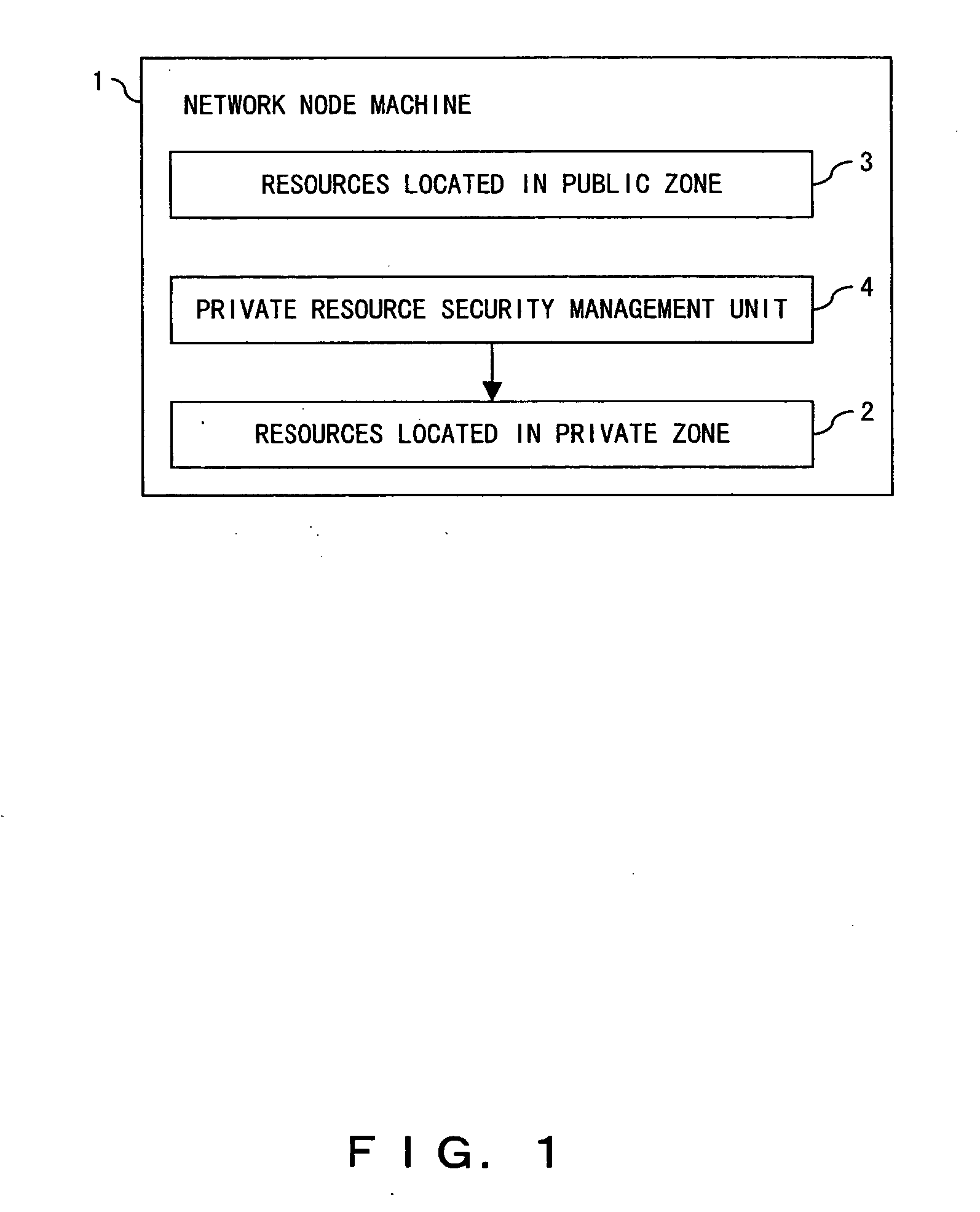
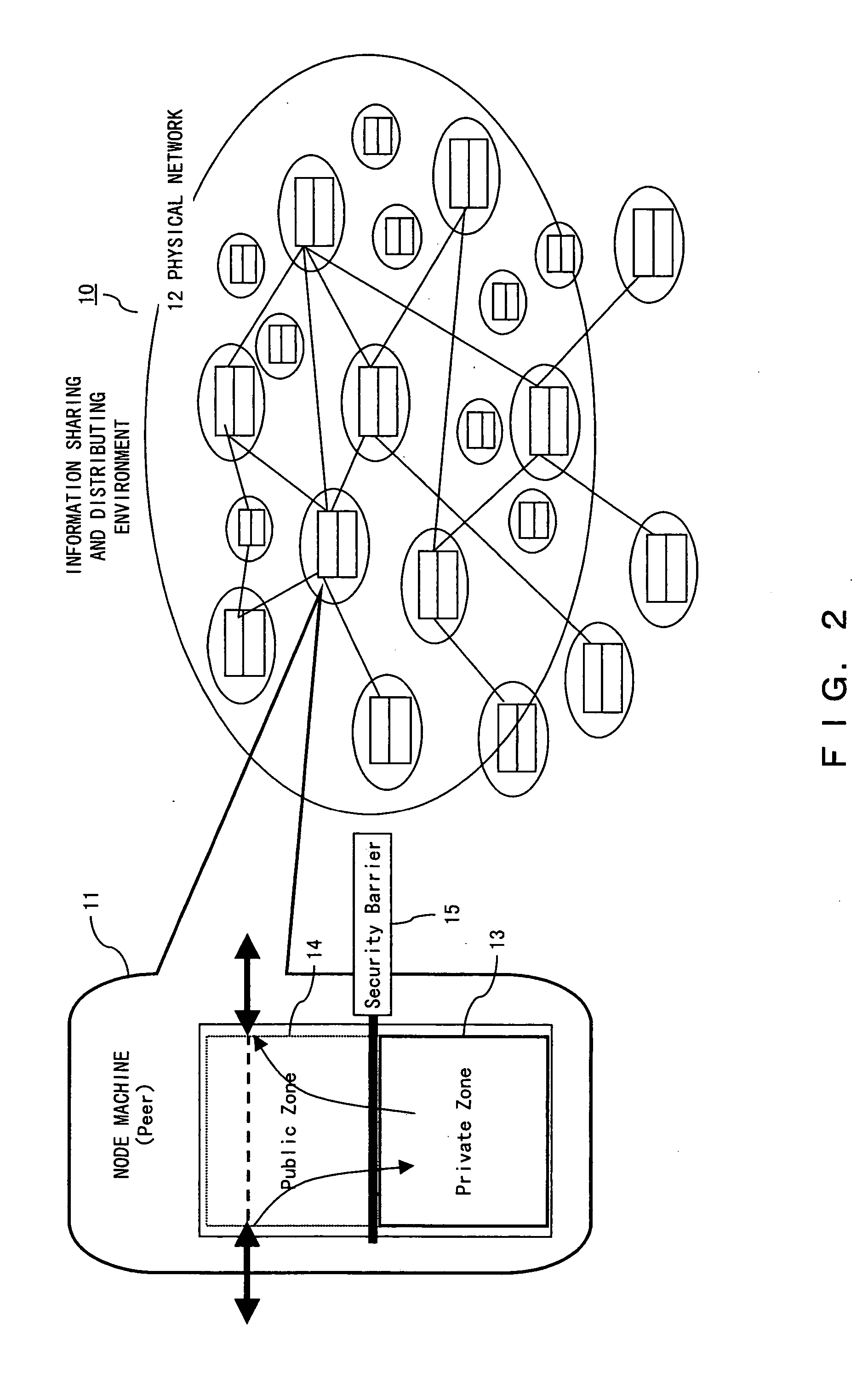
Network node machine and information network system
InactiveUS20050028012A1Easy to usePropelling public useDigital data processing detailsUnauthorized memory use protectionManagement unitResource security
In the global information sharing and distributing service system, the public use of idle resources can be propelled and sufficient security can be guaranteed on the resources for private use. A node machine configuring an information network includes resources located in a private zone available to private use, resources located in a public zone for public service use, and a private resource security management unit for management of the security of the resources located in the private zone.
Owner:FUJITSU LTD +1
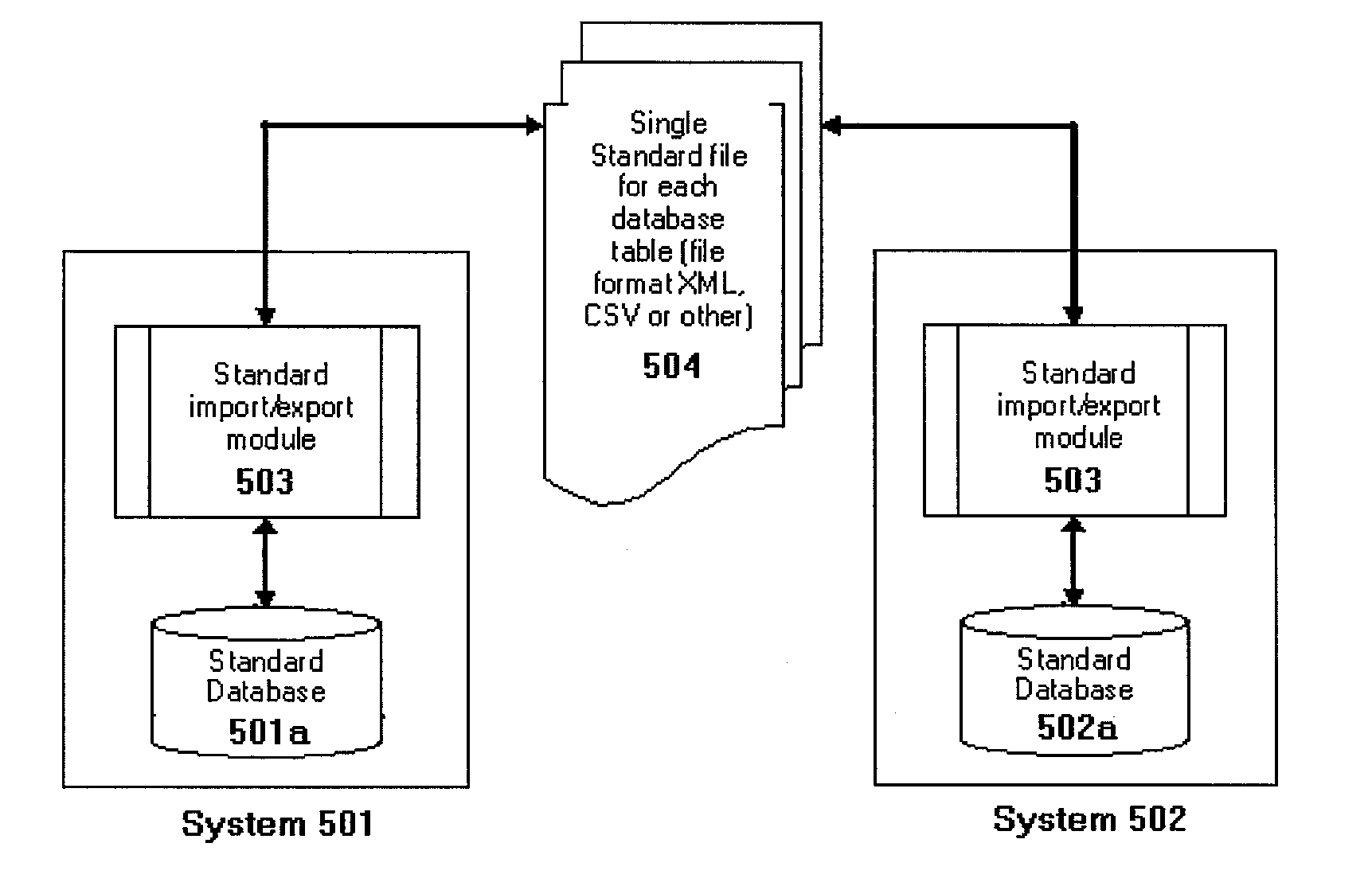
Global Information Management System and Method
ActiveUS20110320400A1Avoid repetitionDigital data processing detailsDatabase distribution/replicationRelational databaseGlobal information
A global information management system (GIMS) includes a collection of standards and methods that allow information management on a global scale. A GIMS computer network includes a central registration database (CRD) and one or more GIMS computer systems connected over a network. Each GIMS computer system includes a relational database having a set of standardized tables. The CRD may provide a GIMS network-unique system ID to each GIMS computer system. Each GIMS computer system uses the GIMS network-unique system ID as part of a primary key for each record generated by and stored in the set of standardized tables of the GIMS database. The GIMS enables global database normalization through the globally unique identification of database records.
Owner:NAMINI BORSU ASISI
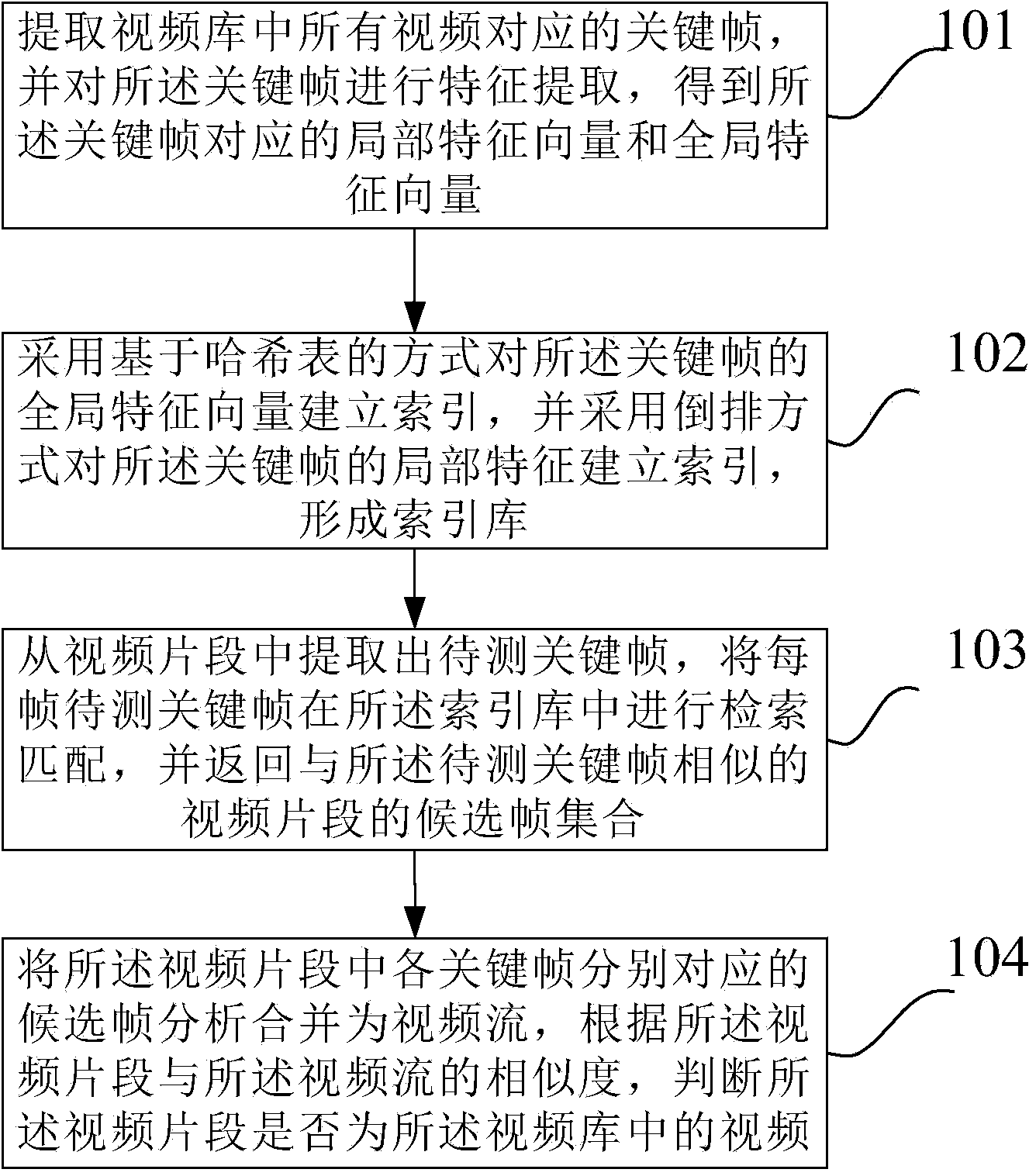
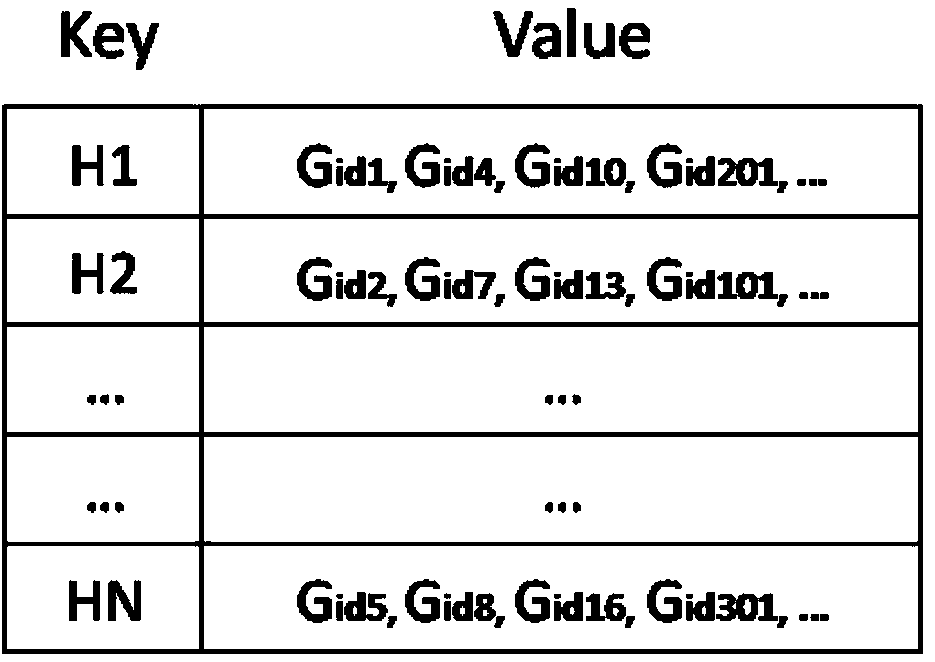
Video clip detecting method and device
InactiveCN104166685AImprove recallReduce match error rateSpecial data processing applicationsGlobal informationFeature fusion
The embodiment of the invention discloses a video clip detecting method and device, and belongs to the field of image processing. The video clip detecting method comprises the steps that a currently-input video file or real-time streaming video is used as an object to be detected, whether video in a video library appears in the current video stream or not is detected and recognized through the video analysis and retrieval method, the accurate position, in the stream to be detected, of a video clip is located and a detection result is output. Image features extracted through the video clip detecting method and device integrate image global information and image local information, the matching error rate is reduced while the high recall rate is guaranteed, robustness is kept for image content changes, therefore, accurate locating is conducted on video clips in real-time or off-line television programs or video programs and accurate detection and recognition of the video clips are kept on the conditions that frames of video streams are lost, mosaic blocks appear in the video streams, video resolution ratios and video frame rates are different and video contents change.
Owner:BEIJING JETSEN TECH
Human skeleton key point detection method and device
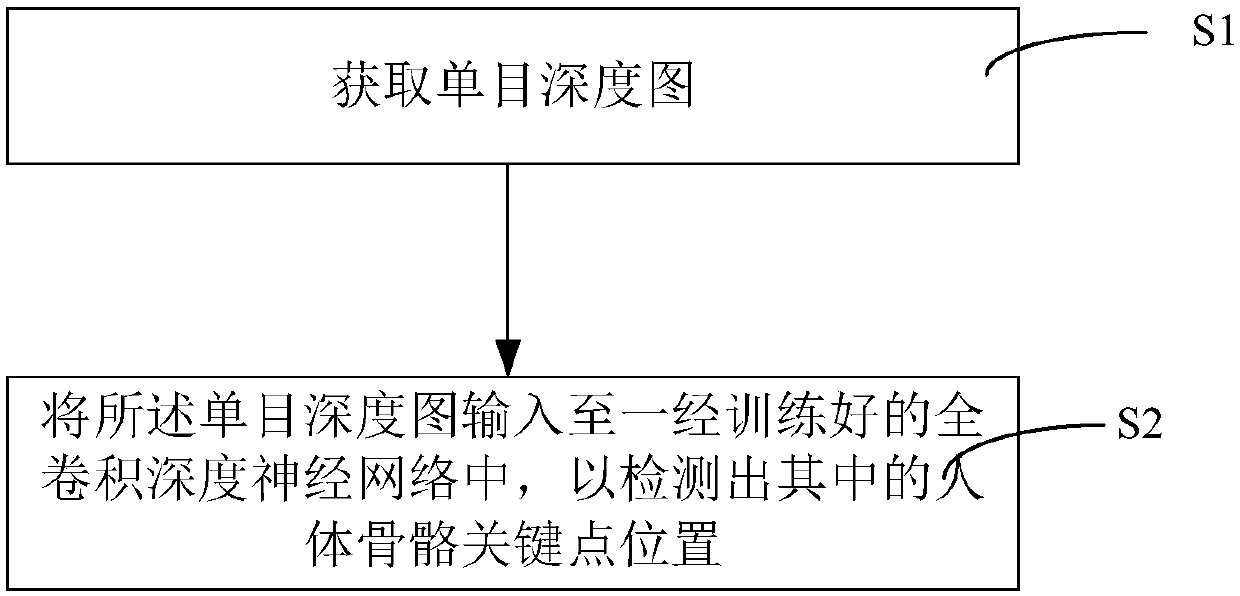
InactiveCN107767419APrecise positioningInput is validImage enhancementImage analysisPattern recognitionNerve network
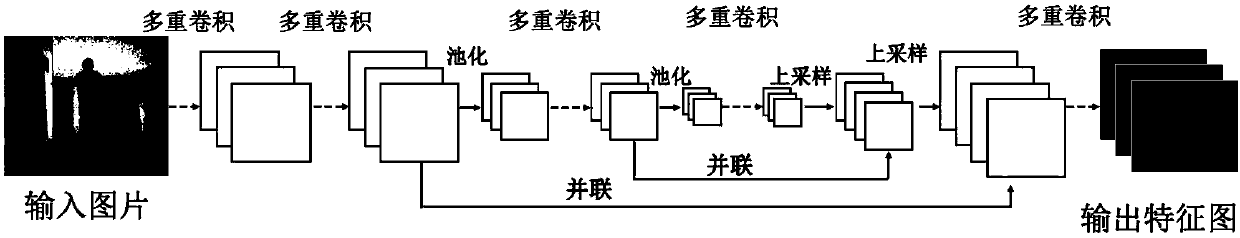
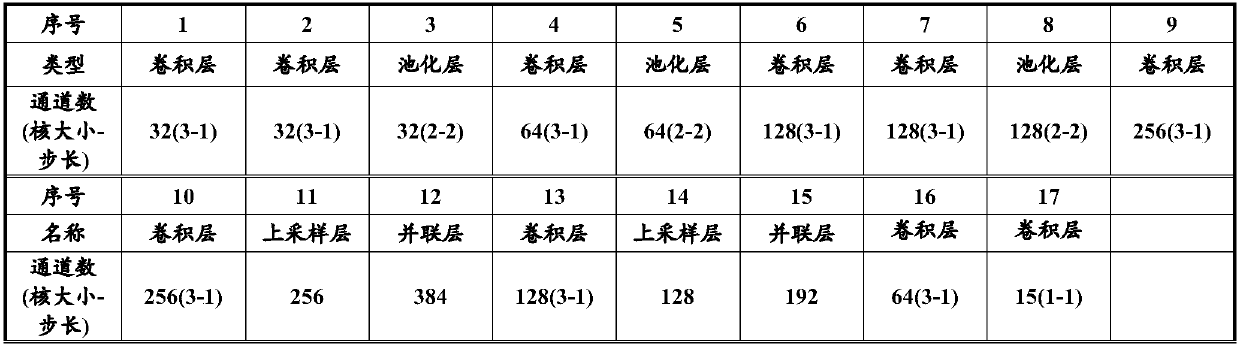
The invention discloses a human skeleton key point detection method and device. The method comprises the following steps that step one, a monocular depth map is acquired; and step two, the monocular depth map is inputted to a trained full convolutional deep neural network so as to detect the human skeleton key point position, wherein the network feed-forward low abstract early feature map and thehigh abstract later feature map are integrated by the full convolutional deep neural network, and the small feature map is enlarged to other feature maps by using up-sampling so that global information including the small feature map and feature information including the large feature map are inputted in the next convolution computation. The feature information can be effectively utilized with combination of the early and later feature information and the global and local information so that the more abundant feature information can be outputted and the skeleton key point locating effect can be enhanced.
Owner:广州深域信息科技有限公司
Method of controlling a display device, a display system, a display apparatus, and an electronic accessory device for controlling a display device
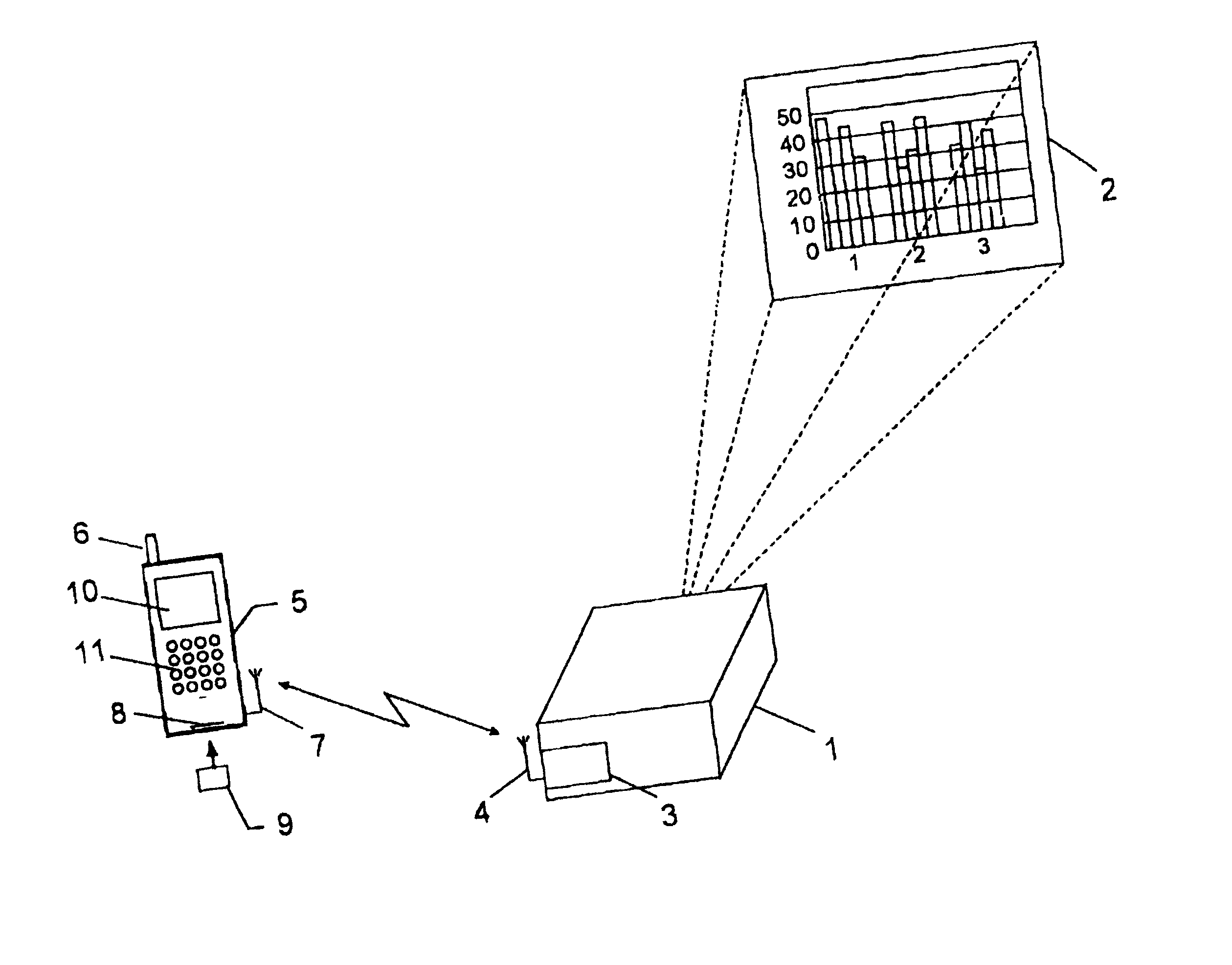
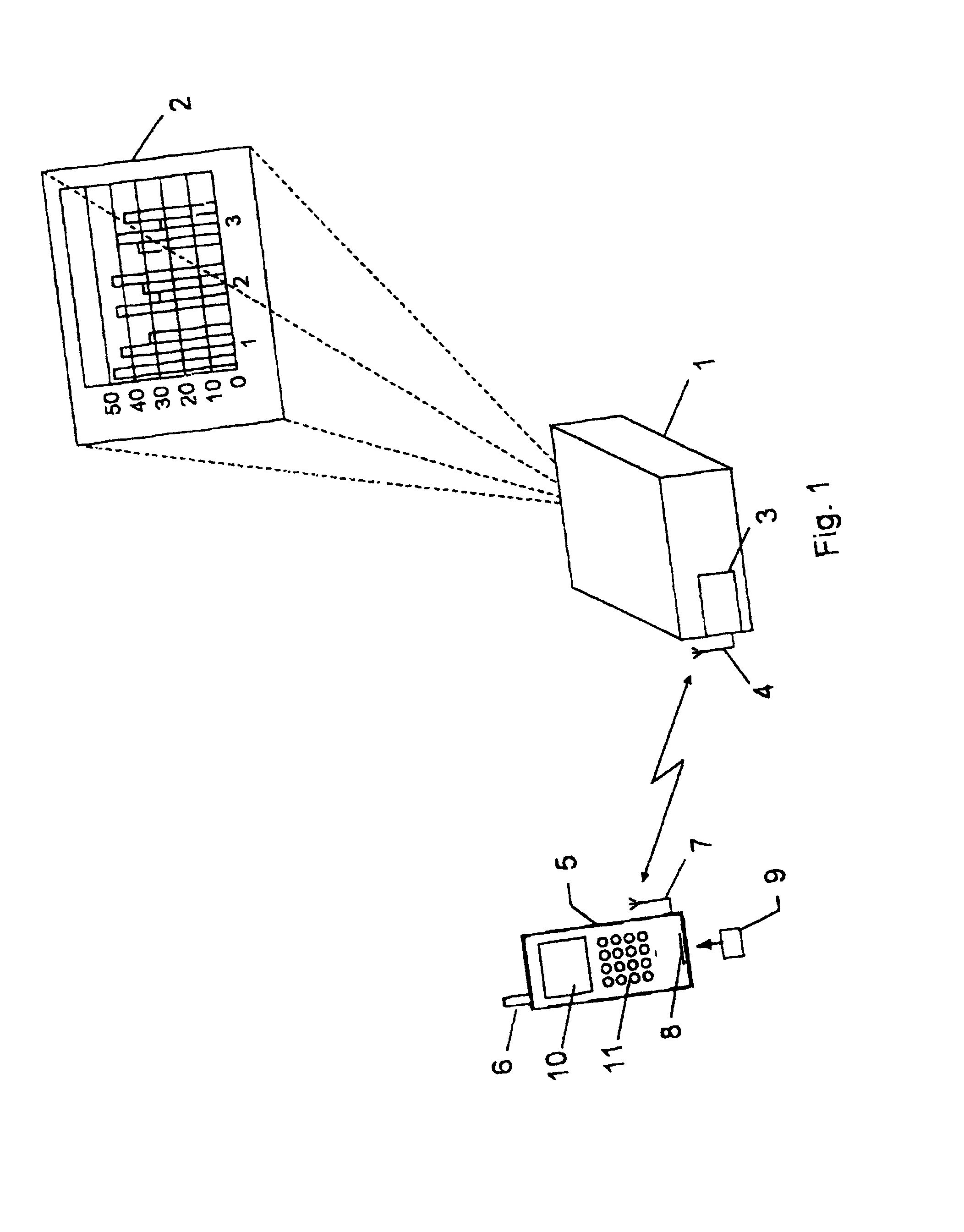
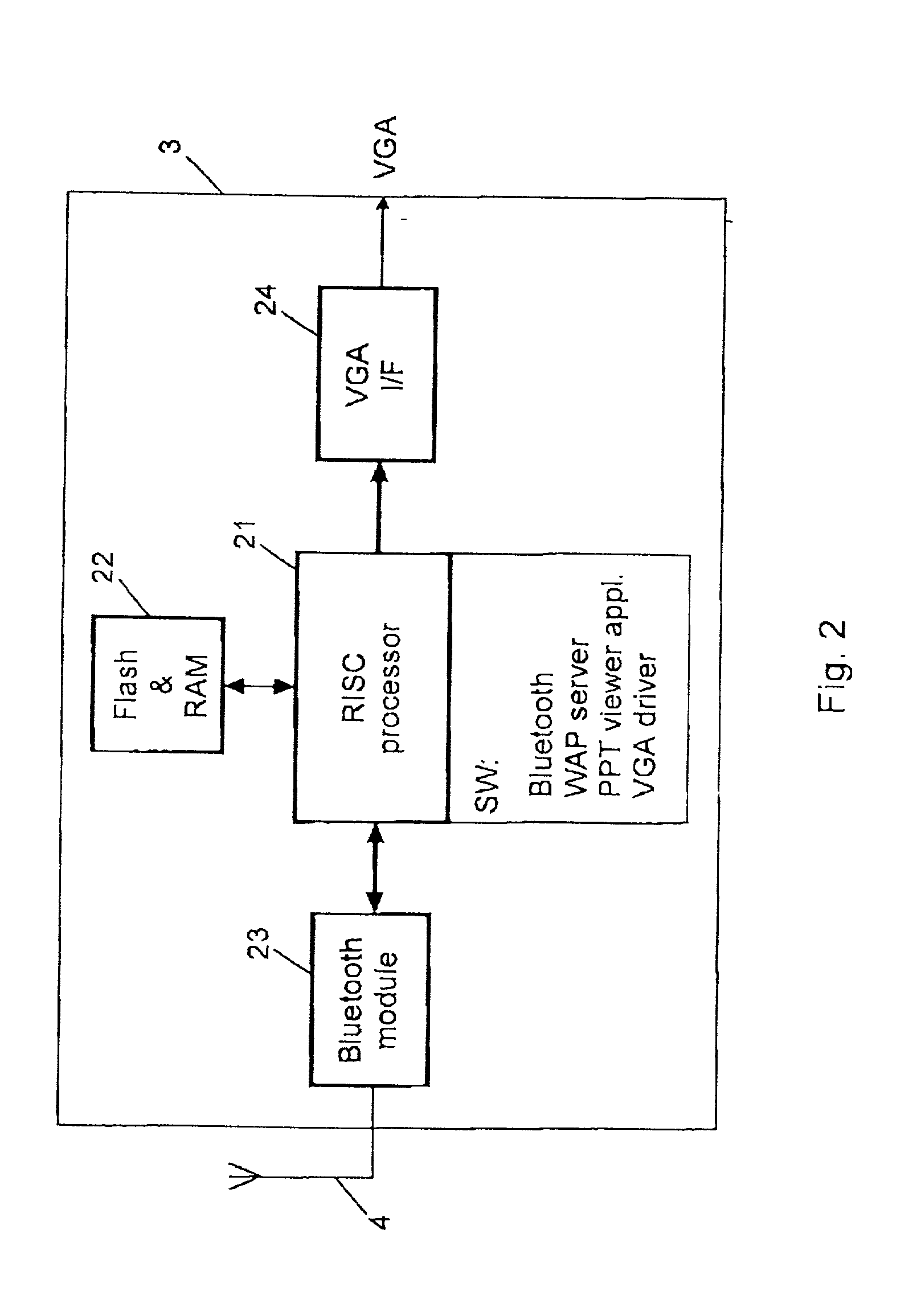
InactiveUS20020080090A1Avoid wire connectionsEasy to carryTransmission systemsInformation formatComputer hardwareInformation access
A display device (1;31), capable of providing visual displays (2) from electrical input signals, is controlled by means of a presentation application program adapted to convert data files representing images to be displayed into electrical input signals for the display device. Instructions are transmitted to said presentation application program from a portable telecommunications device (5;75) having an information access program for accessing a global information network, and a communication application program for communication with said information access program, and for controlling the presentation application program, is executed. In this way the display device can be controlled from the portable telecommunications device instead of a PC. A user does not have to carry a PC to the presentation location, and the need to struggle with a good deal of setting up before a presentation can be shown is avoided.
Owner:TELEFON AB LM ERICSSON (PUBL)
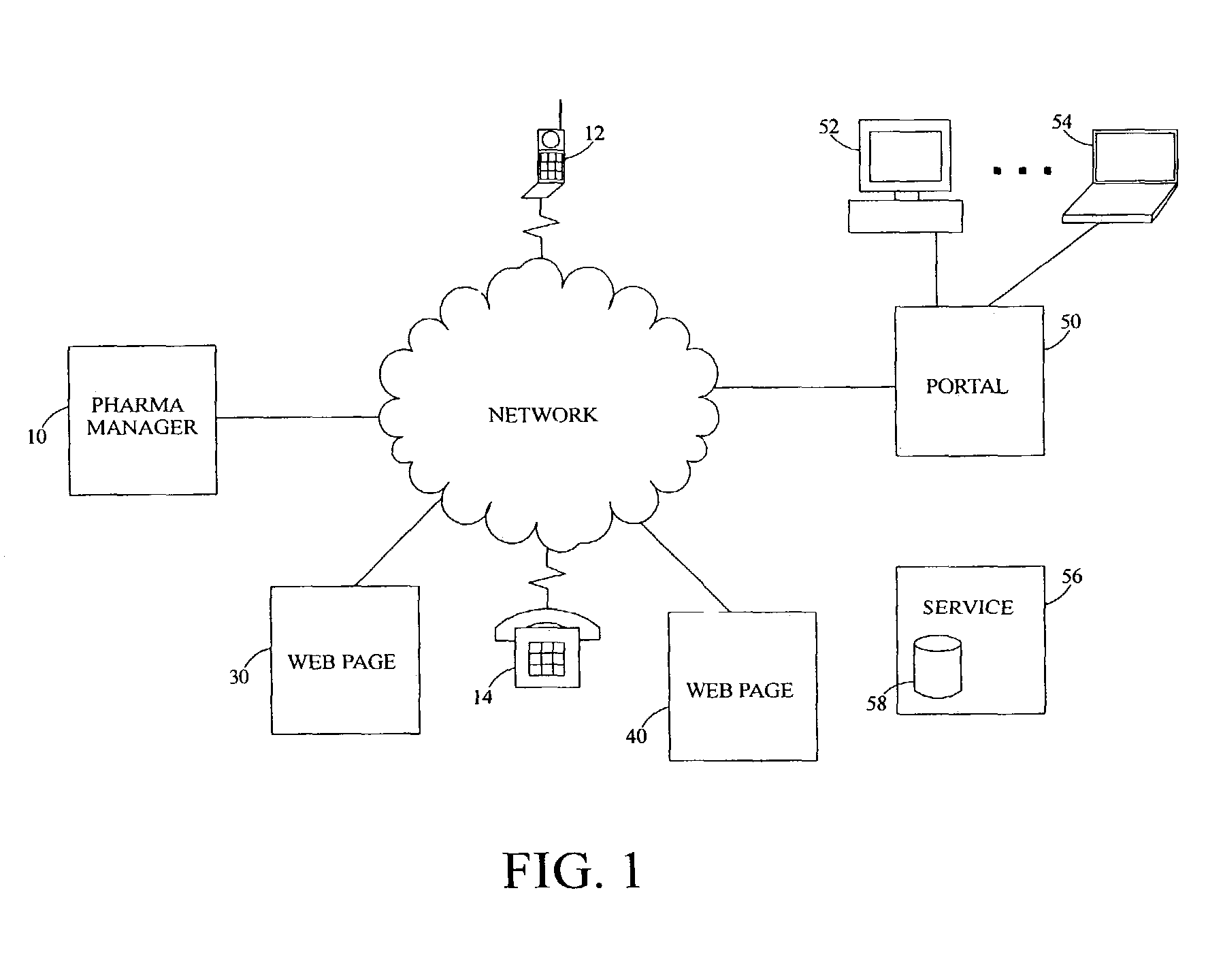
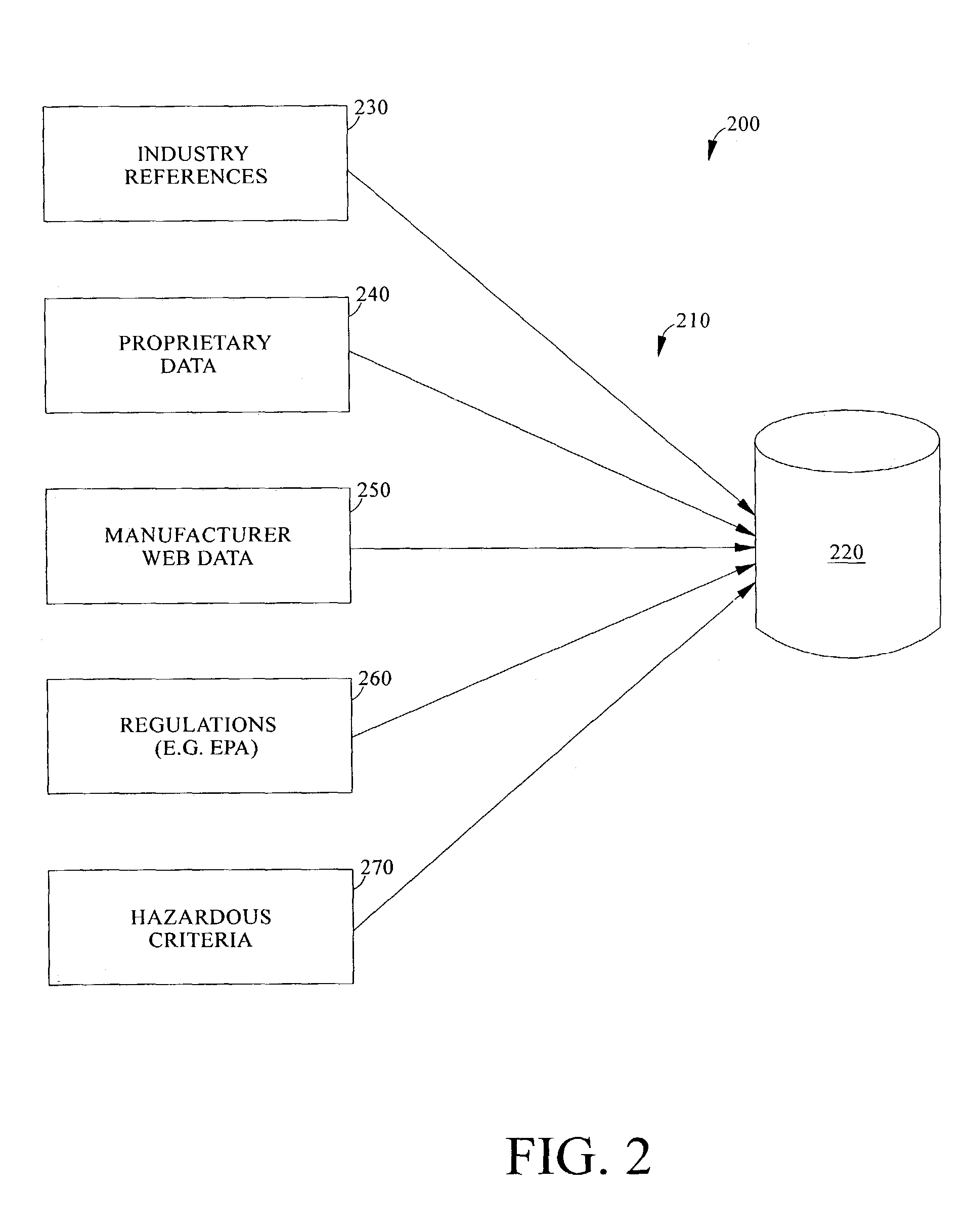
Pharmaceutical hazardous waste identification and management system
InactiveUS7096161B2Solid waste disposalDigital data processing detailsInformation repositoryEnvironmental toxicology
A pharmaceutical hazardous waste identification and management system integrates disparate information regarding pharmaceuticals to provide an indication of which pharmaceuticals are hazardous wastes as defined by respective national, international and state regulations and / or which are hazardous materials as defined by the US OSHA regulations. A subset of this information offers a global repository with respect to the occurrence, concentrations, and ecotoxicologic data of pharmaceuticals based on peer reviewed data provided by environmental toxicologists and related scientists.
Owner:WASTE MANAGEMENT NAT SERVICES INC
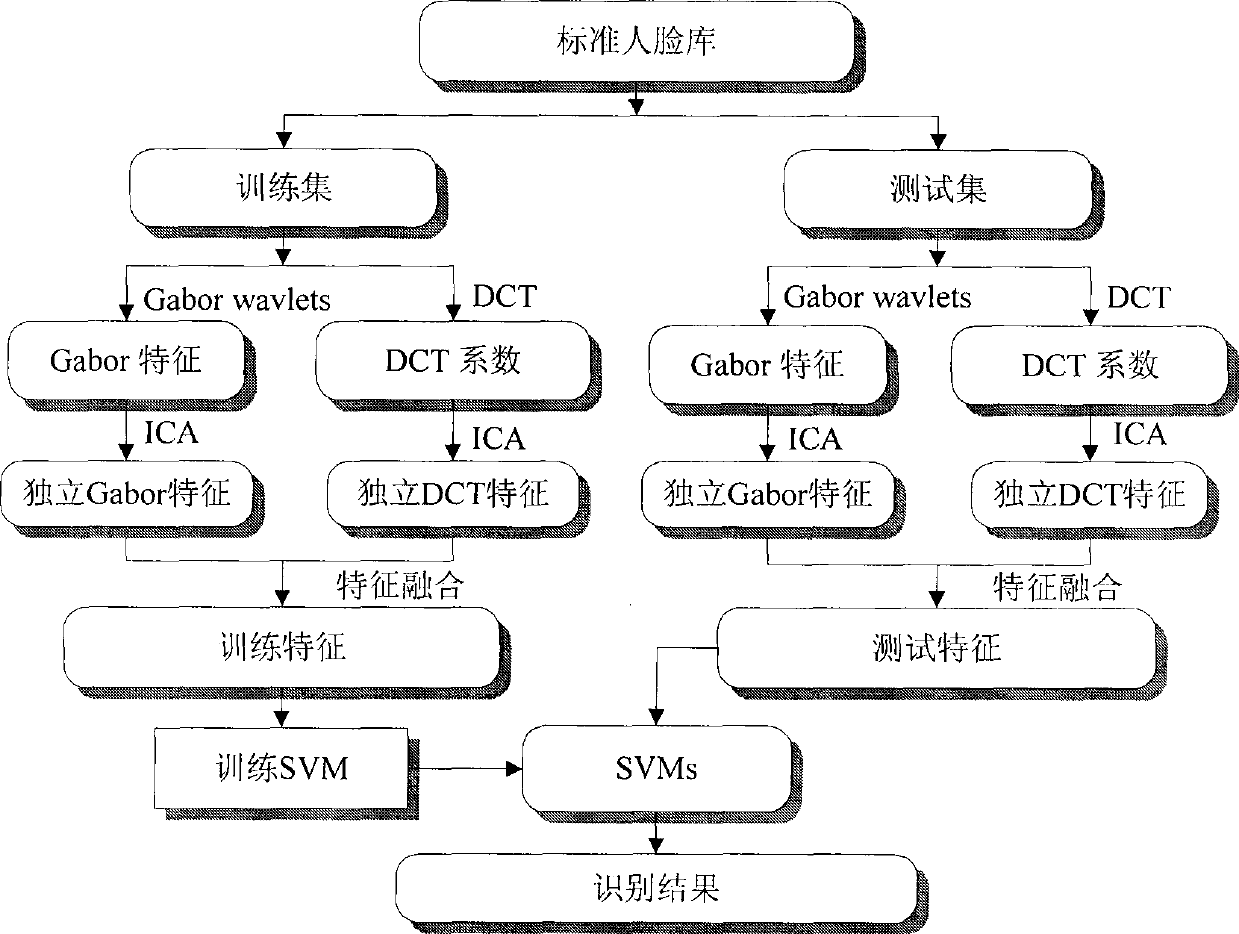
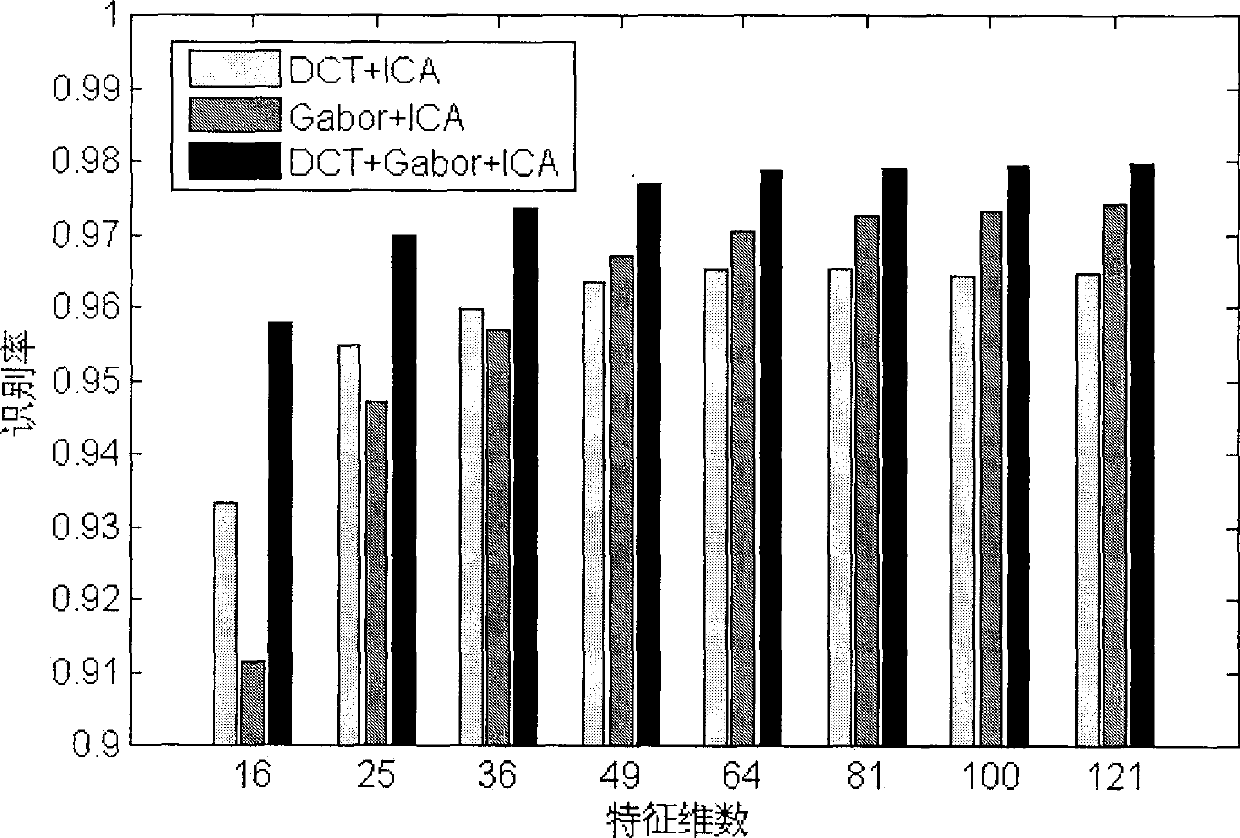
Human face identification method based on independent characteristic fusion
ActiveCN101388075ARemove redundant featuresReduce dimensionalityCharacter and pattern recognitionFeature vectorGlobal information
The invention discloses a face identification method which blends a global feature and a local feature based on an ICA. As a DCT can efficiently transit a high-dimensional face image into a low-dimensional space and reserves most of identifiable information of the image, the DCT is suitable for extracting the global feature of the image, while a Gabor wavelet transformation is suitable for extracting the local feature and the classification feature of the image, and the two features are widely applied to the face identification. Based on the two methods, we bring in the ICA technology to extract the independent Gabor feature and the independent DCT feature of the image, then efficiently blends the independent Gabor feature and the independent DCT feature to obtain a novel independent feature, enables the novel independent feature to have the local information of the Gabor feature and the global information of the DCT feature, efficiently reduces the dimension of a feature vector, and removes superfluous features. Finally, the blended independent feature is used for the SVM to realize the face classification identification.
Owner:DALIAN UNIV
Method for predicting dynamic risk and vulnerability under fine dimension
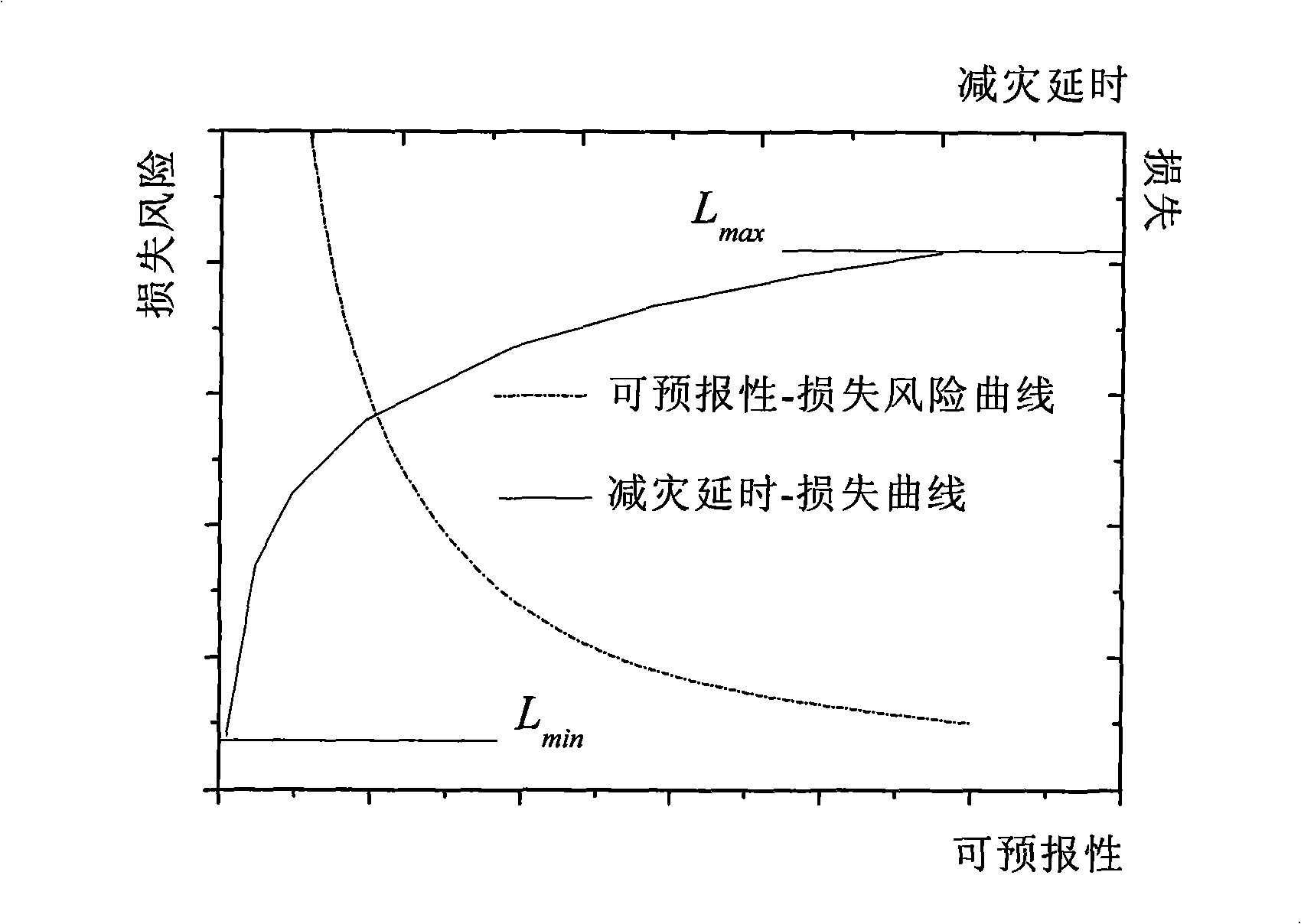
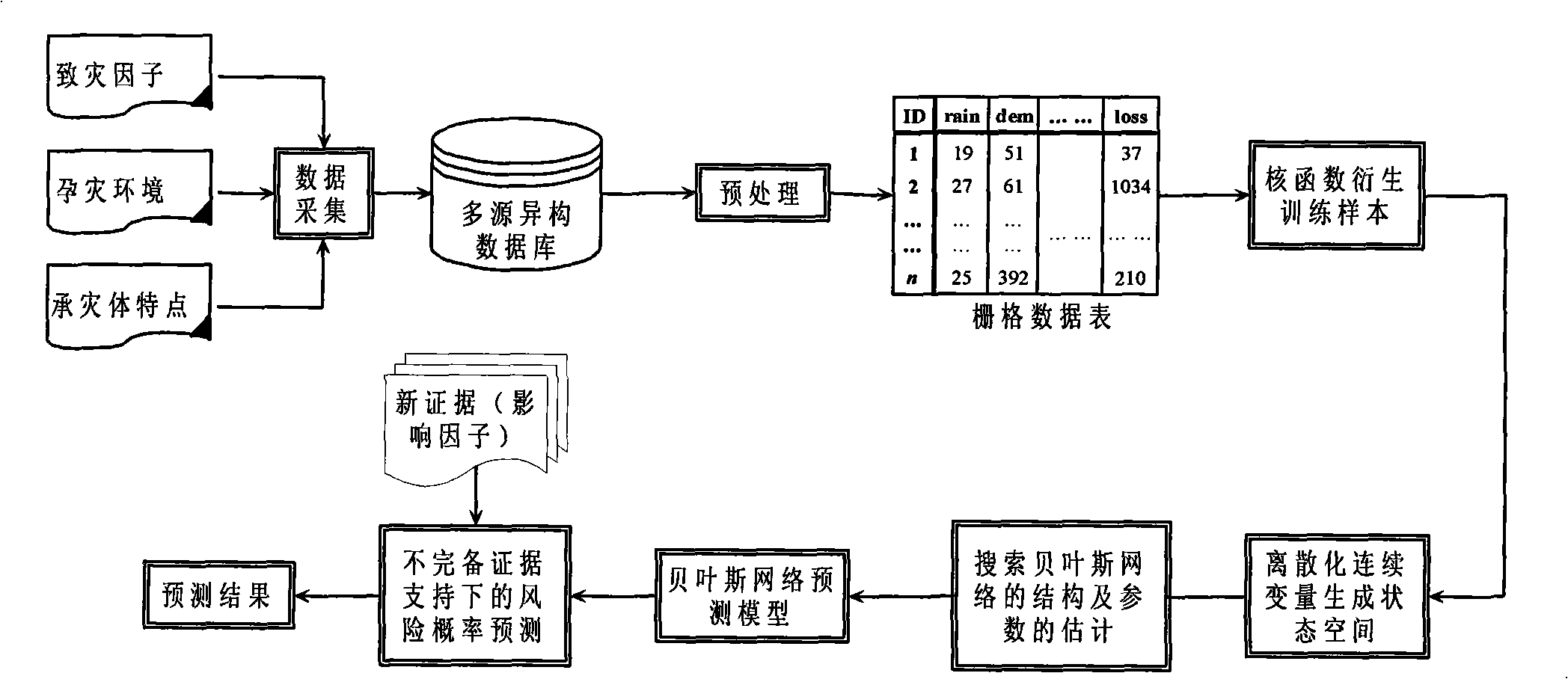
InactiveCN101354757AHigh information contentPowerfulInference methodsProbability estimationPredictive methods
The invention relates to a method for predicting dynamic risk and vulnerability at fine scale and belongs to the scientific field of global information. The method is mainly characterized in that an optimized Bayesian network is searched from multi-source heterogeneous spatiotemporal data on the basis of a grid format with certain resolution at fine scale; domain knowledge is combined to improve the network; therefore, the uncertain estimation of disaster risk and the vulnerability, namely probability estimation, is carried out. In the method, a nuclear density method is put forward to train a sample according to a sample derivative grid; an optimized discretization method is put forward to discretize continuous variables so as to provide discrete state space input for the network; a simulated annealing optimization algorithm is adopted to search an optimized network structure; and a method of accurate reasoning combined with approximate reasoning to predict the probabilities of risk and the vulnerability is adopted. The method provided by the invention can position the positions of the disaster risk and the vulnerability in real time at the fine spatial scale, estimate the spatial distribution of the risk probability and has important theoretical significance and practical value for improving the effects on the reduction and relief of disaster and building an intelligent public emergency pre-warning system by the state.
Owner:INST OF GEOGRAPHICAL SCI & NATURAL RESOURCE RES CAS
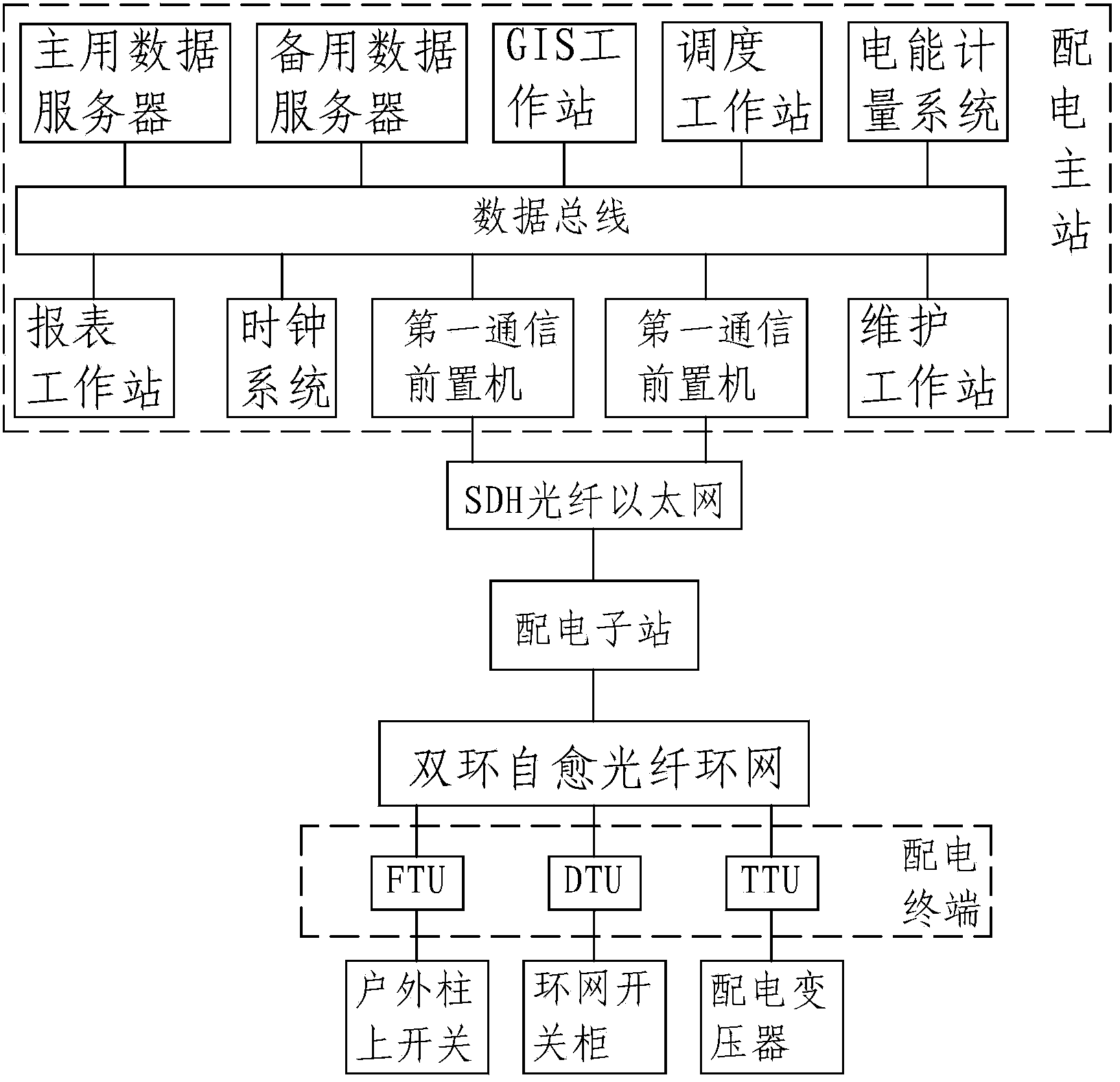
Distribution network automation system
InactiveCN104037945AEasy to planReduce line lossCircuit arrangementsInformation technology support systemData acquisitionDistribution power system
A distribution network automation system comprises a power distribution main station, power distribution substations and power distribution terminals. The power distribution main station is responsible for monitoring and managing global information and used for monitoring and acquiring data of a whole distribution network to complete fault handling within the whole network; the power distribution substations are used for managing distribution station terminal monitoring equipment such as switchgear cubicles for loop networks, switching stations for distribution networks and the like, acquiring, gathering and uploading signals of the power distribution terminals to the power distribution main station, and transmitting orders of the power distribution main station to the power distribution terminals; the power distribution terminals mainly used for acquiring data of primary equipment, controlling switchgears, detecting and recognizing faults and sending fault information to the power distribution substations and the power distribution main station. The distribution network automation system has the advantages that power supply reliability can be greatly improved, fault time can be greatly shortened, voltage quality can be greatly improved to provide optimal voltage for users, and labor intensity can be relieved for operators; management level of the whole power distribution system can be improved, working efficiency is improved, and user service level is improved.
Owner:STATE GRID CORP OF CHINA +1
Formation control method for unmanned aerial vehicles
The invention discloses a formation control method for unmanned aerial vehicles. The method comprises a formation generation step. The formation generation method comprises the following step that allthe unmanned aerial vehicles carry out formation change at appointed time after receiving information of a target reference formation, wherein firstly, all the unmanned aerial vehicles fly towards target formation positions closest to the unmanned aerial vehicles under the guidance of approach operation, and meanwhile, all the members in the formation obtain the positions and speeds of other surrounding unmanned aerial vehicles on the basis of the communication of an on-board detection system or a local area network within a limited detection range and process and utilize the information; secondly, the unmanned aerial vehicles generate respective target formation positions under virtual allocation operation and fly towards the respective target formation positions; finally, the unmanned aerial vehicles determine final target formation positions under the guidance of self-adaptive adjustment operation and fly towards the final target formation positions, so that the unmanned aerial vehicle cluster forms the target reference formation. By means of the method, the unmanned aerial vehicle formation members can form any formation without knowing global information, asynchronous triggering can be achieved, collisions can be avoided, and the formation control can also be implemented by memory even if the current communication is interrupted for a short time.
Owner:ARMY ENG UNIV OF PLA
Generation of a watermark being unique to a receiver of a multicast transmission of multimedia
InactiveUS20050141704A1Enhanced informationPrevent embeddingKey distribution for secure communicationMultiple keys/algorithms usageComputer networkUnique identifier
A method, apparatus and system for distributing multimedia data in an efficient way using multicast transmission, whereby each receiver is provided with his own unique identifier in the form of a watermark and also additional information, typically global information for instance to comply with DRM rules, in the same watermark.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
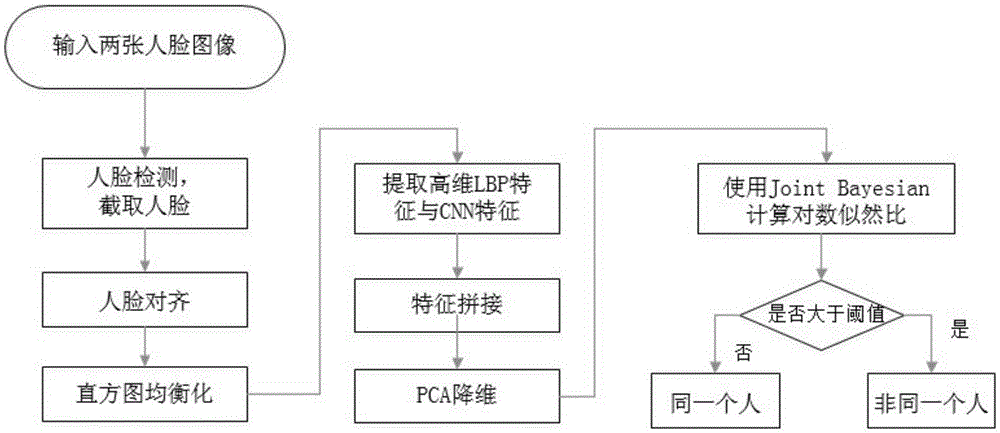
Face comparison method based on high-dimensional LBP (Local Binary Patterns) and convolutional neural network feature fusion
InactiveCN105550658AImprove accuracySolve the problem of weak generalization abilityCharacter and pattern recognitionDimensionality reductionPrincipal component analysis
The invention provides a face comparison method based on high-dimensional LBP (Local Binary Patterns) and convolutional neural network feature fusion. The method comprises the following steps: firstly, two types of face images are input, preprocessing is independently carried out, then, each image independently extracts the high-dimensional LBP features and the CNN (Convolutional Neural Network) features of the image, the two features are combined and are subjected to dimensionality reduction via PCA (Principal Component Analysis), and finally, a Joint Bayesian method is used for obtaining a similarity of the two images. In a feature extraction process, since the high-dimensional LBP extracts local information and the CNN extracts global information, two types of information are fused, and the information extracted by the features is complete. Compared with a method which separately uses the high-dimensional LBP or the CNN, the method is higher in accuracy and better in robustness and achieves a real-time face comparison rate.
Owner:王华锋 +6
Multi-person posture estimation method based on global information integration
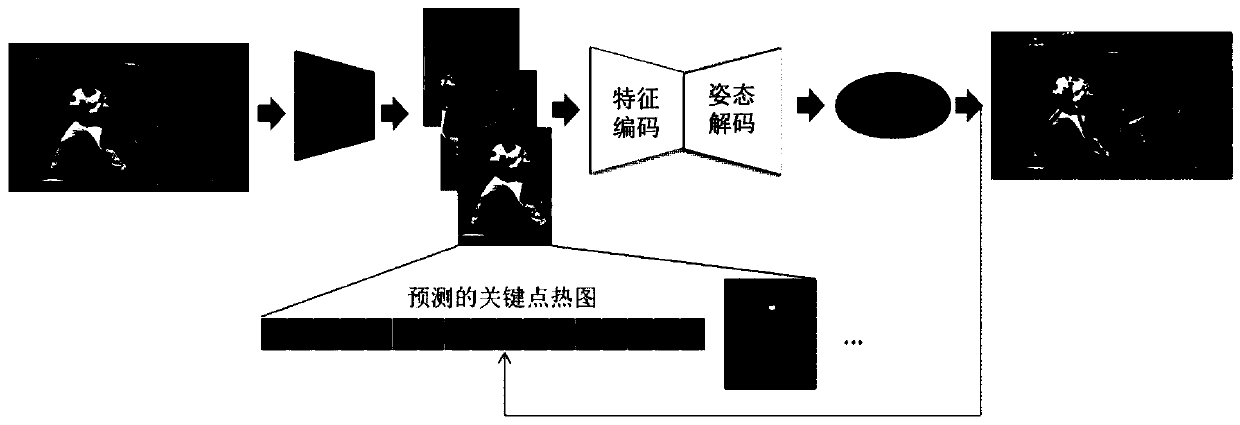
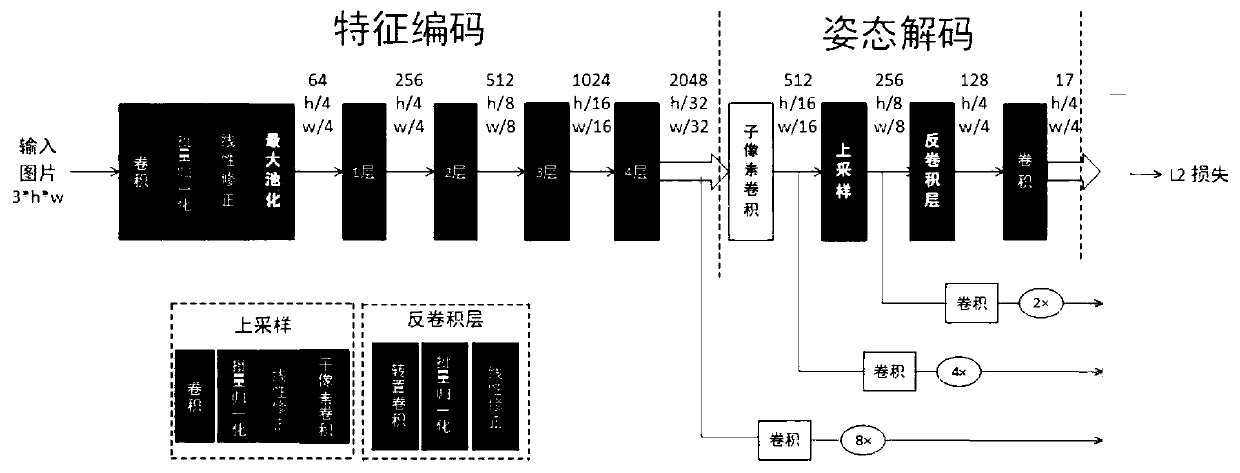
ActiveCN110135375AHigh precisionReduce misconnectionsCharacter and pattern recognitionNeural architecturesEstimation methodsAlgorithm
The invention discloses a multi-person posture estimation method based on global information integration. The multi-person posture estimation method comprises the following steps: carrying out pre-processing on an input image; generating a group of human body boundary frames through a human body detector, and inputting the obtained human body boundary frames into a'feature coding + posture decoding 'module to carry out model training; sequentially predicting the positioning of the key points of each person, and generating a plurality of key point heat maps to represent the position confidenceof each key point; and finally, eliminating redundant attitude estimation through an attitude non-maximum suppression module to obtain a final human body attitude.. By combining different normalization strategies with multi-layer information fusion, the accuracy of multi-person posture estimation can be remarkably improved, false connection can be effectively reduced by adopting a hyperedge geometric constraint strategy, and a posture estimation method which is difficult to encounter in scale change, shielding and complex multi-person scenes can be effectively improved.
Owner:NINGBO INST OF MATERIALS TECH & ENG CHINESE ACADEMY OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com