Network node machine and information network system
a network node machine and information network technology, applied in the field of network node machines and information network systems, can solve the problems of insufficient security of information resources through integral methods, inability to ensure the security of resources, and insufficient management of access security, so as to achieve the effect of effective use of computer resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
second embodiment
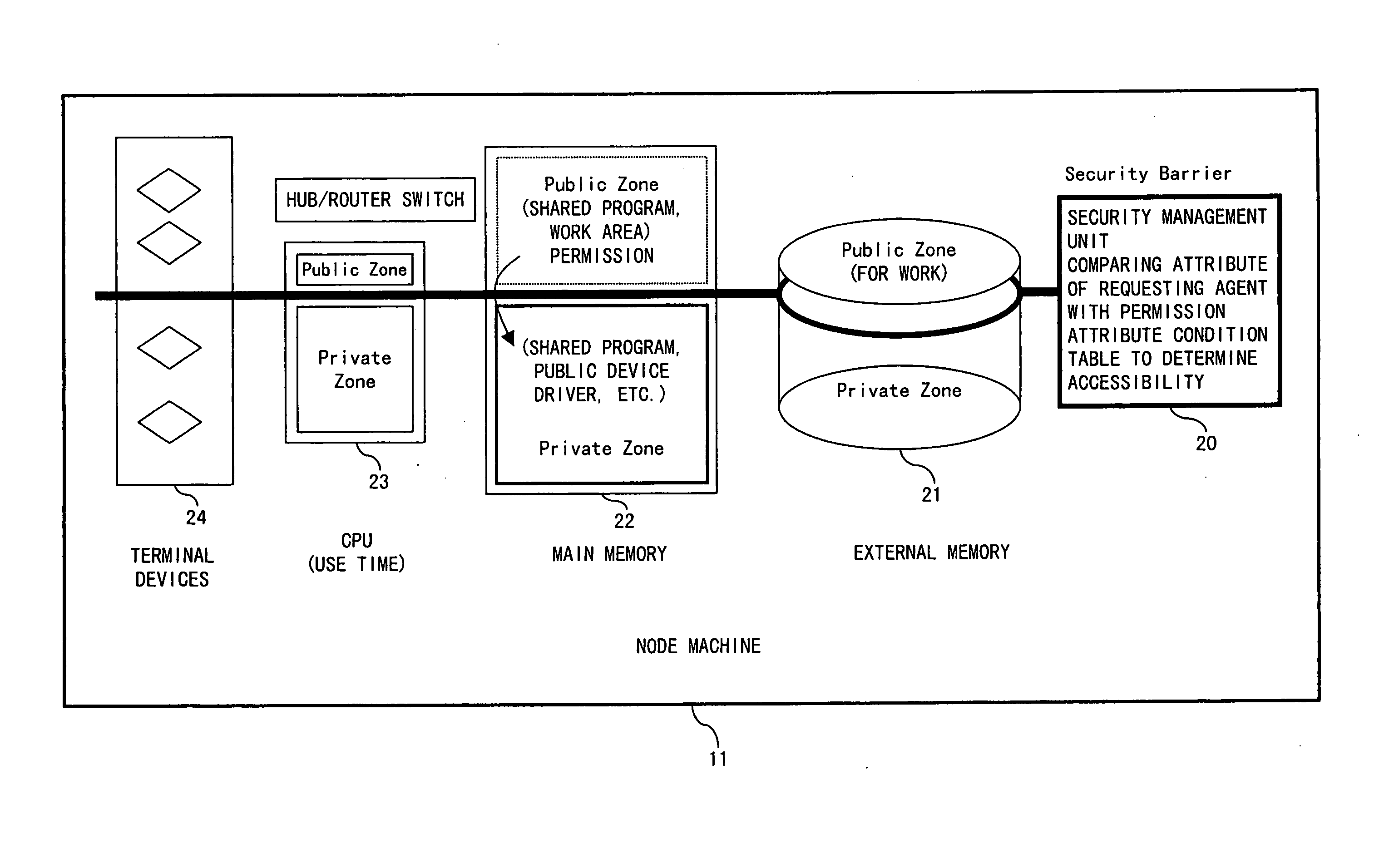
[0069] A security barrier is provided in a portal agent as described in the Practically, a security management device or a software routine is provided in a node machine having a portal agent function so that the security management unit in each portal agent can manage the security using the device or the routine.
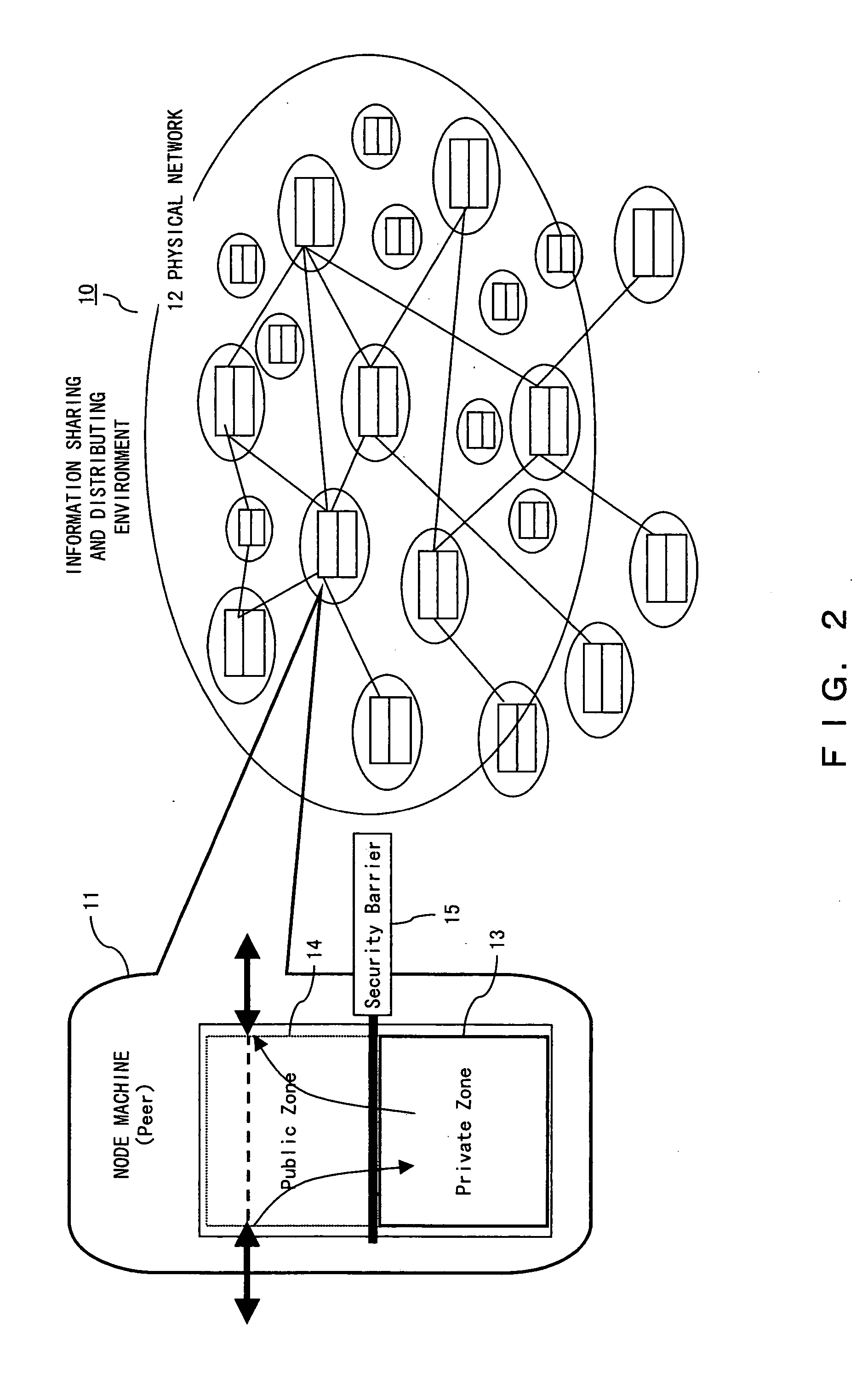
[0070]FIG. 3 is an explanatory view of a public zone and a private zone.
[0071] The node machine 11 in the physical network 12 comprises the private zone 13 and the public zone 14. The private zone and the public zone are respectively set in a logical network management unit (community management agent) and in a physical network management unit (ACC).
[0072] A public zone is an open area, and offers a public application service as described below.
[0073] Address search of other service sites (node machine) [0074] Address caching [0075] Routing [0076] Transferring a message [0077] Distributing a message [0078] Caching related information [0079] Others
[0080] In a private zo...
third embodiment
[0161] Then, the relationship between the community when the agent joins the community and the public policy is explained below as the It is necessary for an agent to join a community, any qualification (attribute) is required. After it joins the community, it has to present any contribution (offer a service) to the community. The framework is realized by the system of an attribute and a public policy.
[0162] A public policy is represented by the description of a service rule to be presented by an agent when it joins a community. For example, it is presented in, for example, a predicate logic format.
[0163] The operation of an agent when it joins a community is described below.
[0164] (1) An agent presents its own agent attribute and a part of the attribute of the node (machine environment in which the agent operates) to the portal agent of the community.
[0165] (2) The portal agent compares the community subscription condition with the attribute of the agent requesting to join a co...
fourth embodiment
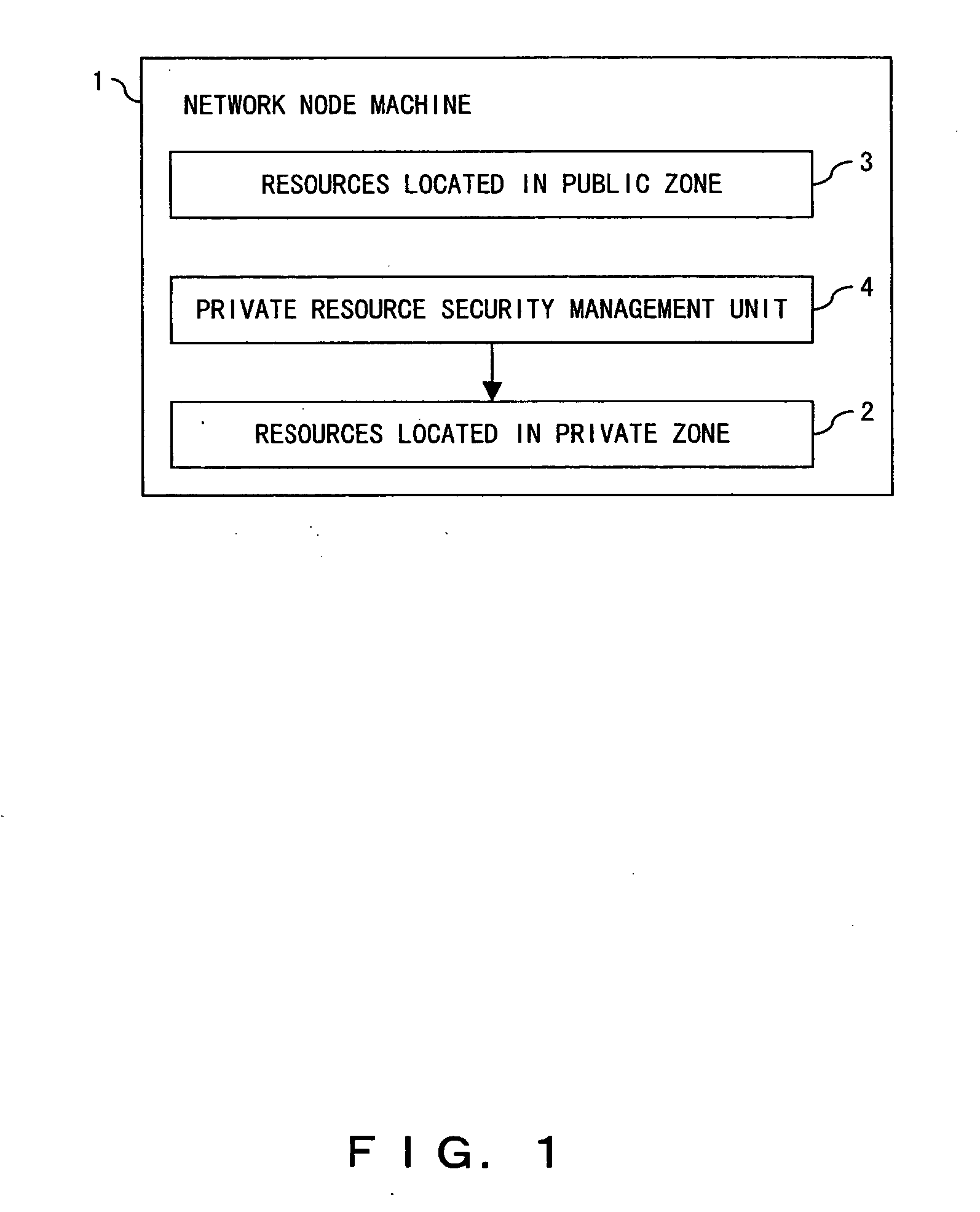
[0179] Finally, the control of the access from an agent in another community to the private resources is described below as the When a plurality of agents (nodes) communicate with one another, information is communicated through a public object operating in each public zone. Normally, a public object can access the public resources only by the access control of the public execution environment, and cannot access the private resources in the private zone. However, depending on the attribute of an agent, the private resources of the communication partner agent can be accessed. This system is realized by comparing the private policy with the agent attribute of the communication partner. A private policy is a rule described in a predicate logic, etc. in which an agent attribute corresponds to the accessibility to the resources. The private policy can be defined by the user, or can be added to the resources themselves. Described below is the operation procedure of the system.
[0180] In t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com