Patents
Literature
454 results about "Management agent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Management agent is a software agent that runs on a managed node (example: a router) and provides an interface to manage it. It can perform operations on managed objects in the node and can also forward notifications to the manager (EMS).
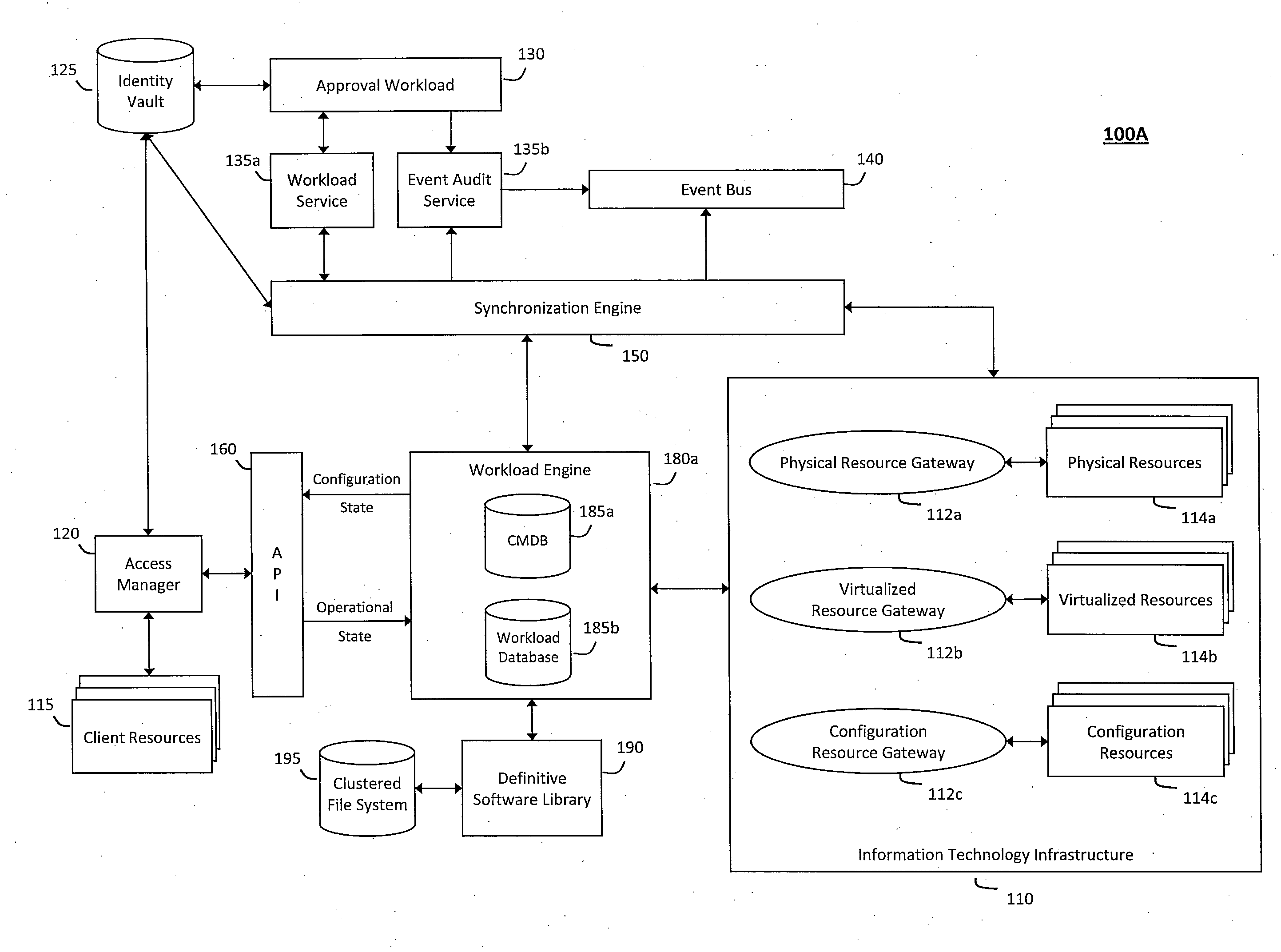
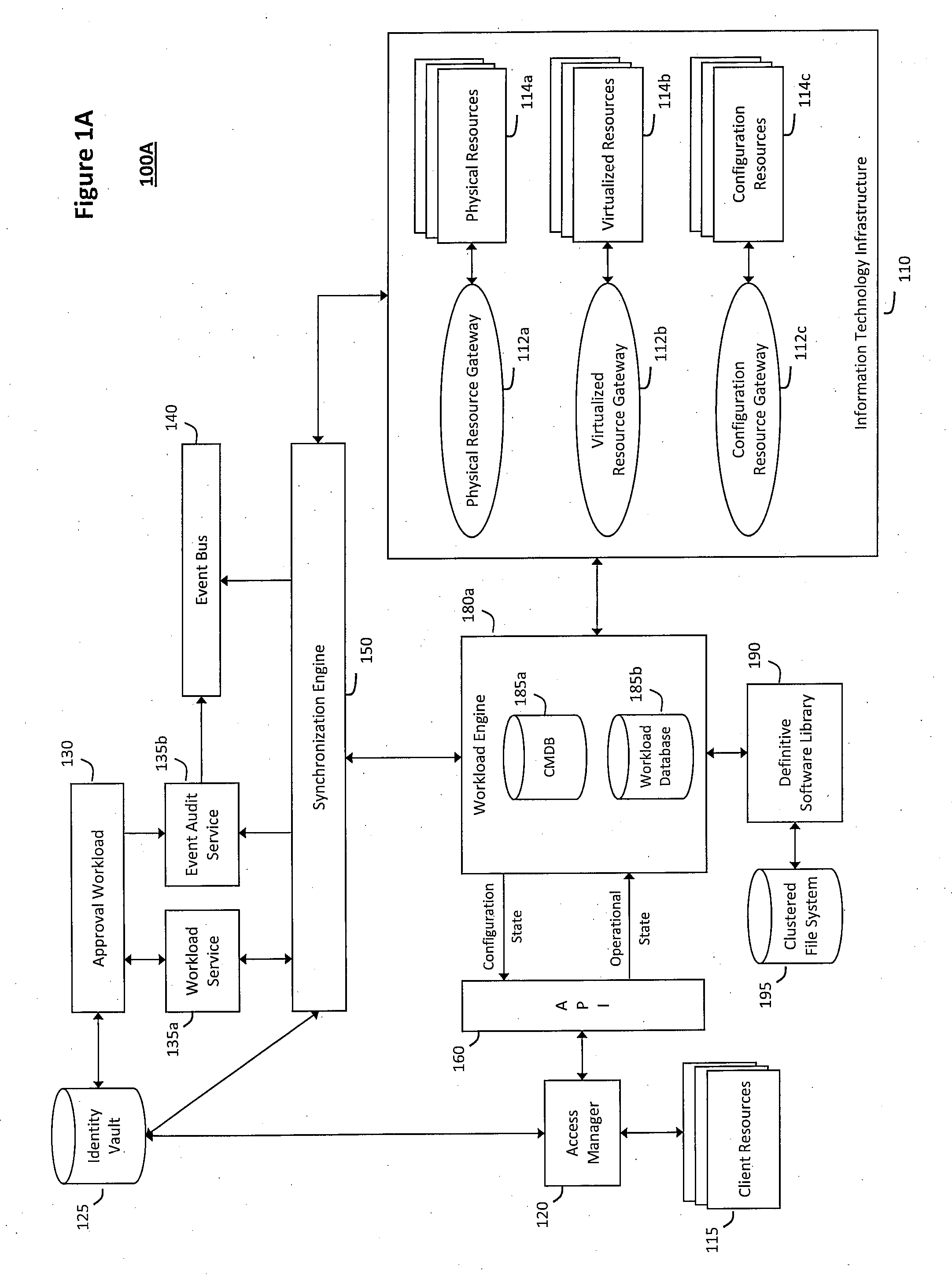
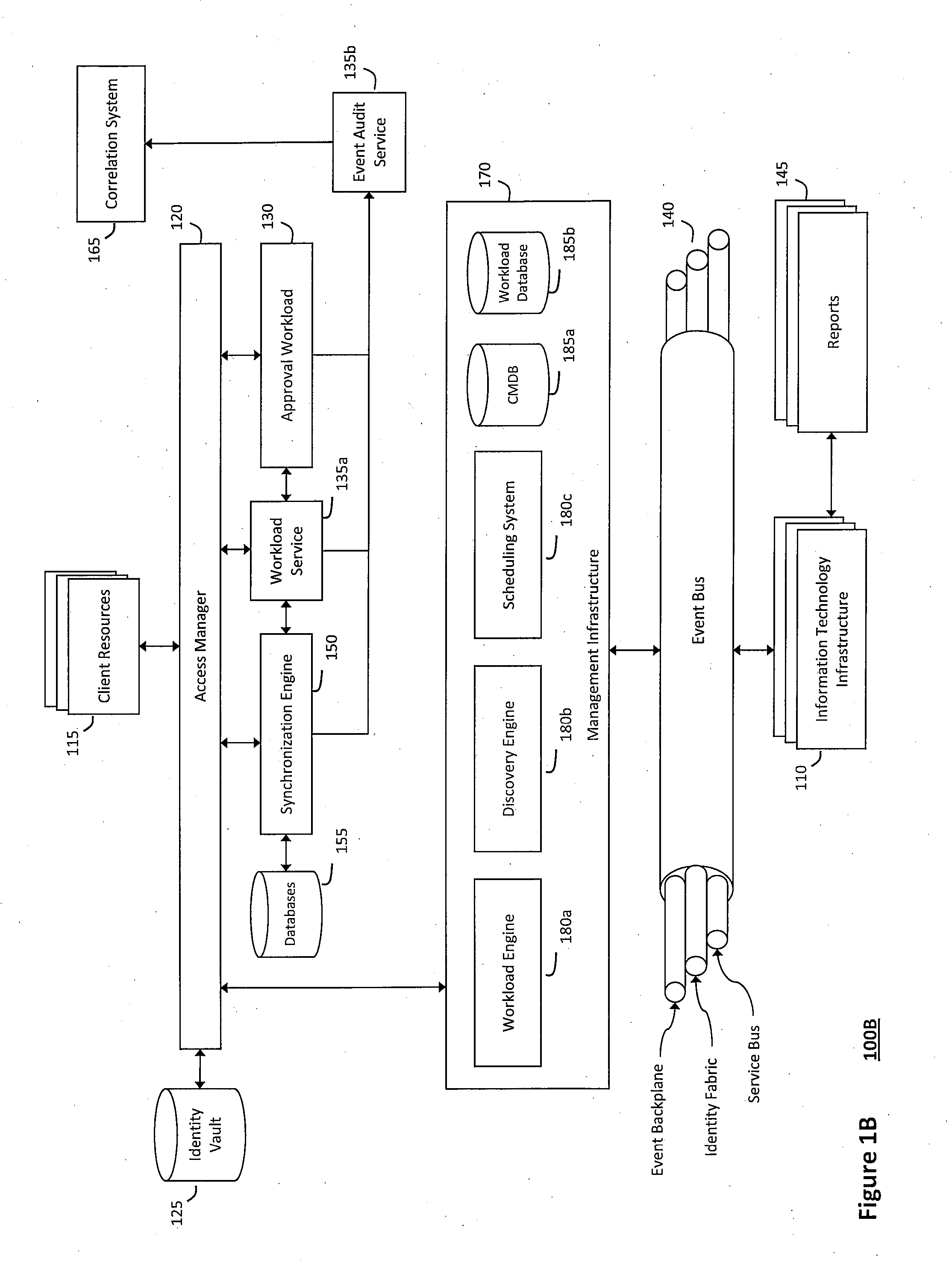
System and method for controlling cloud and virtualized data centers in an intelligent workload management system
InactiveUS20110126197A1Free computational resourceAgile and flexible managementDigital computer detailsDigital data authenticationData centerService-oriented architecture
The system and method for controlling cloud and virtualized data centers described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, and further to creating cloud images having embedded management agents and identity services for validating the cloud images prior to deployment into the cloud and virtualized data centers and controlling, monitoring, and auditing activity associated with the cloud images following deployment into the cloud and virtualized data centers.
Owner:MICRO FOCUS SOFTWARE INC
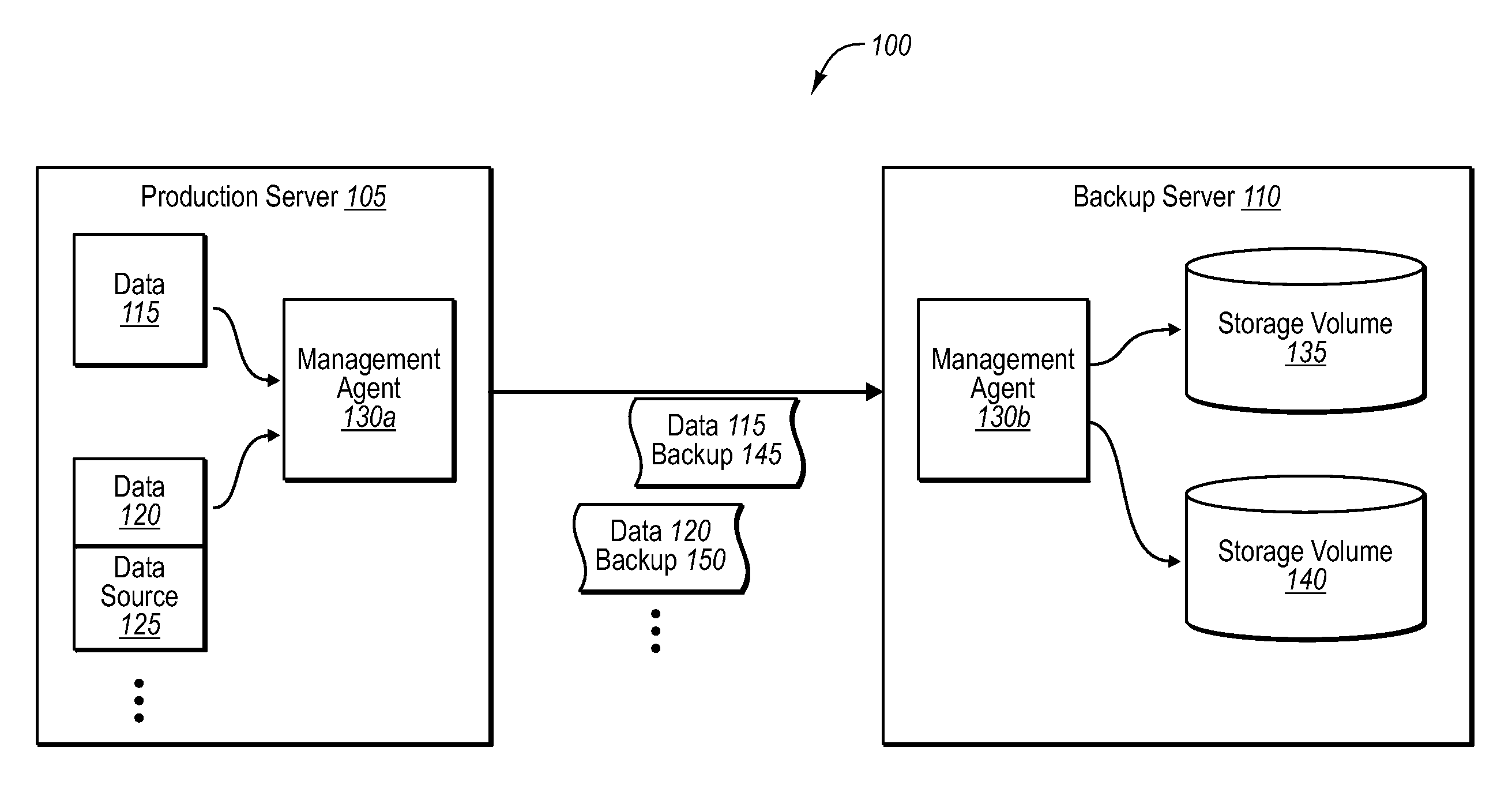
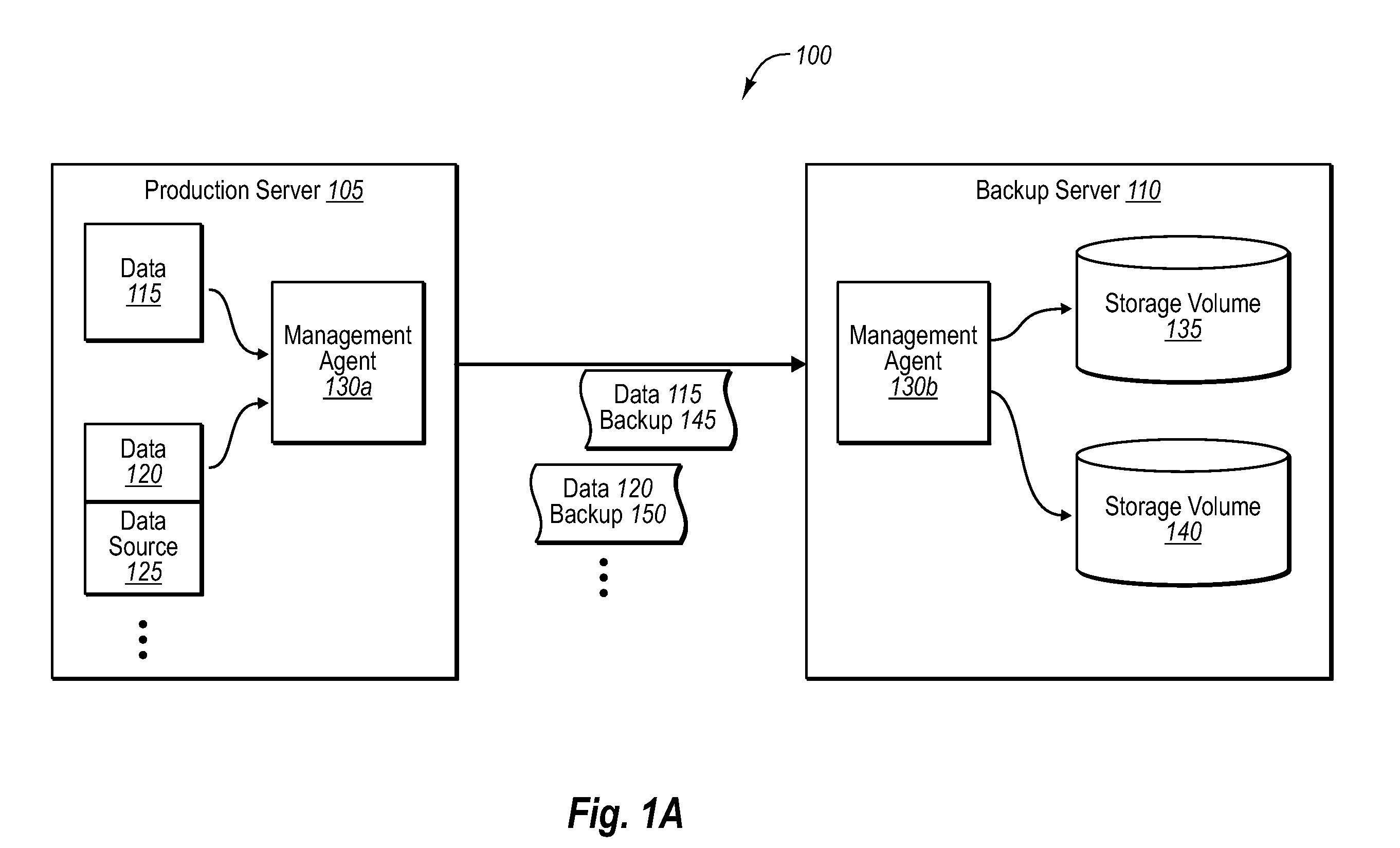
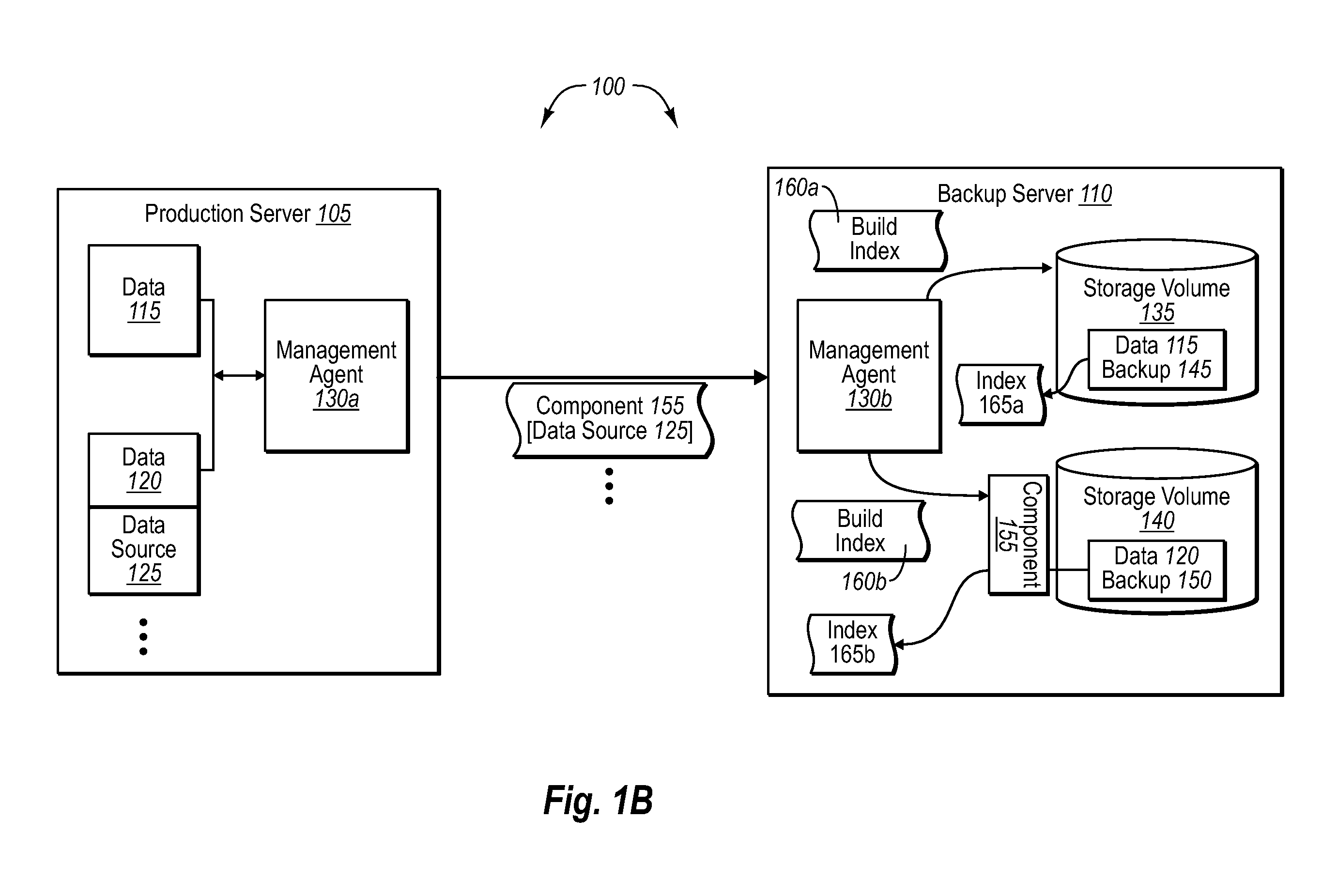
Managing data with backup server indexing
ActiveUS20070288536A1Efficient managementEasy retrievalData processing applicationsDigital data information retrievalBackupManagement agent
Indexing functionality can be shifted to one or more backup servers in a backup system. In one implementation, a backup server can receive one or more data backups from one or more production servers. The backup server can then build or create one or more indexes at the backup server, which correspond to the contents of the one or more data backups. In one implementation, one or more management agents can also identify any appropriate components that might be needed to read the backup data at the backup server pursuant to building the one or more indexes. In either case, the one or more indexes can be used for a wide range of purposes, such as to manage data usage quotas at the one or more production servers, as well as to retrieve data from the backup server based on specific file requests.
Owner:MICROSOFT TECH LICENSING LLC
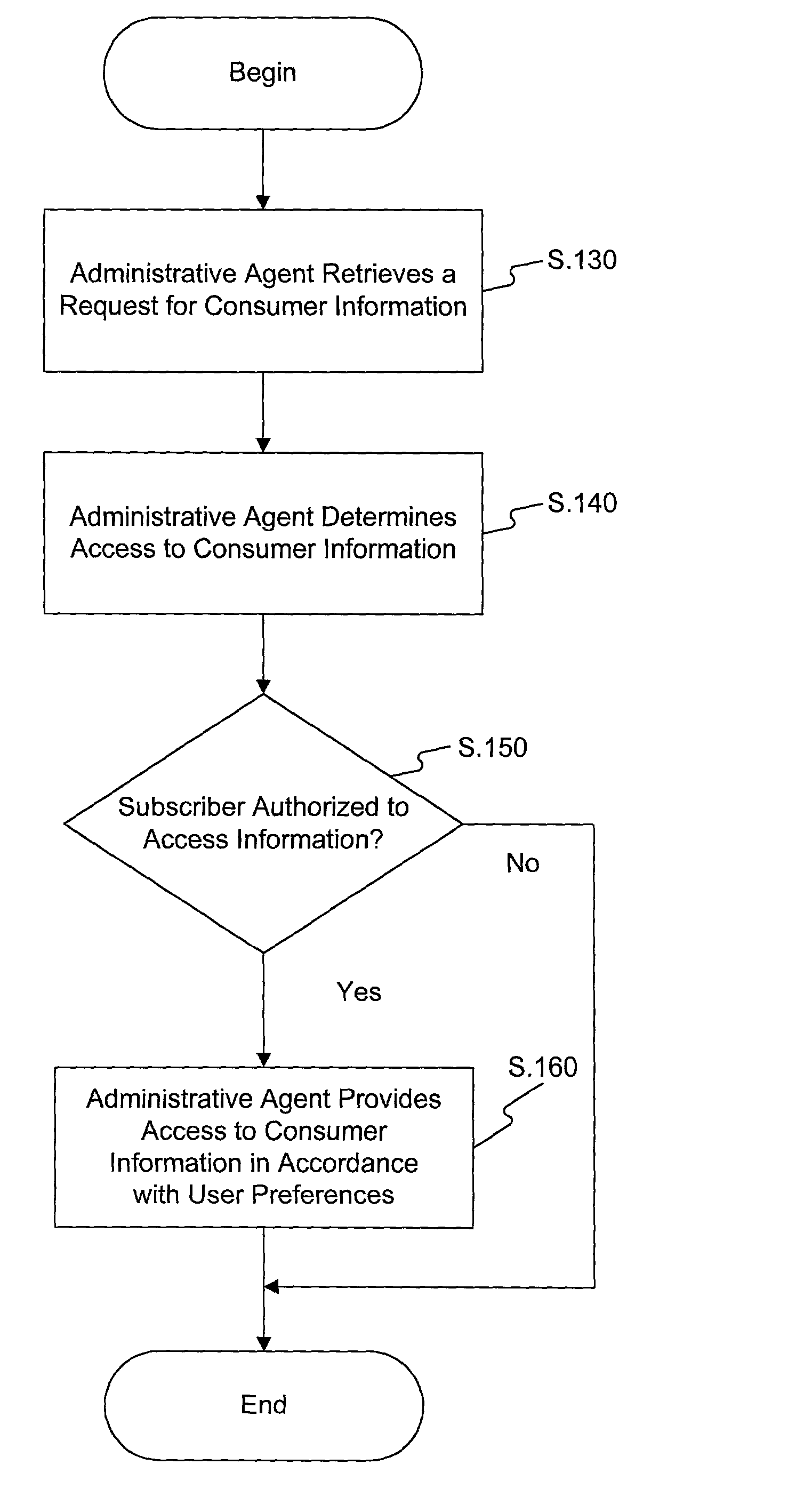
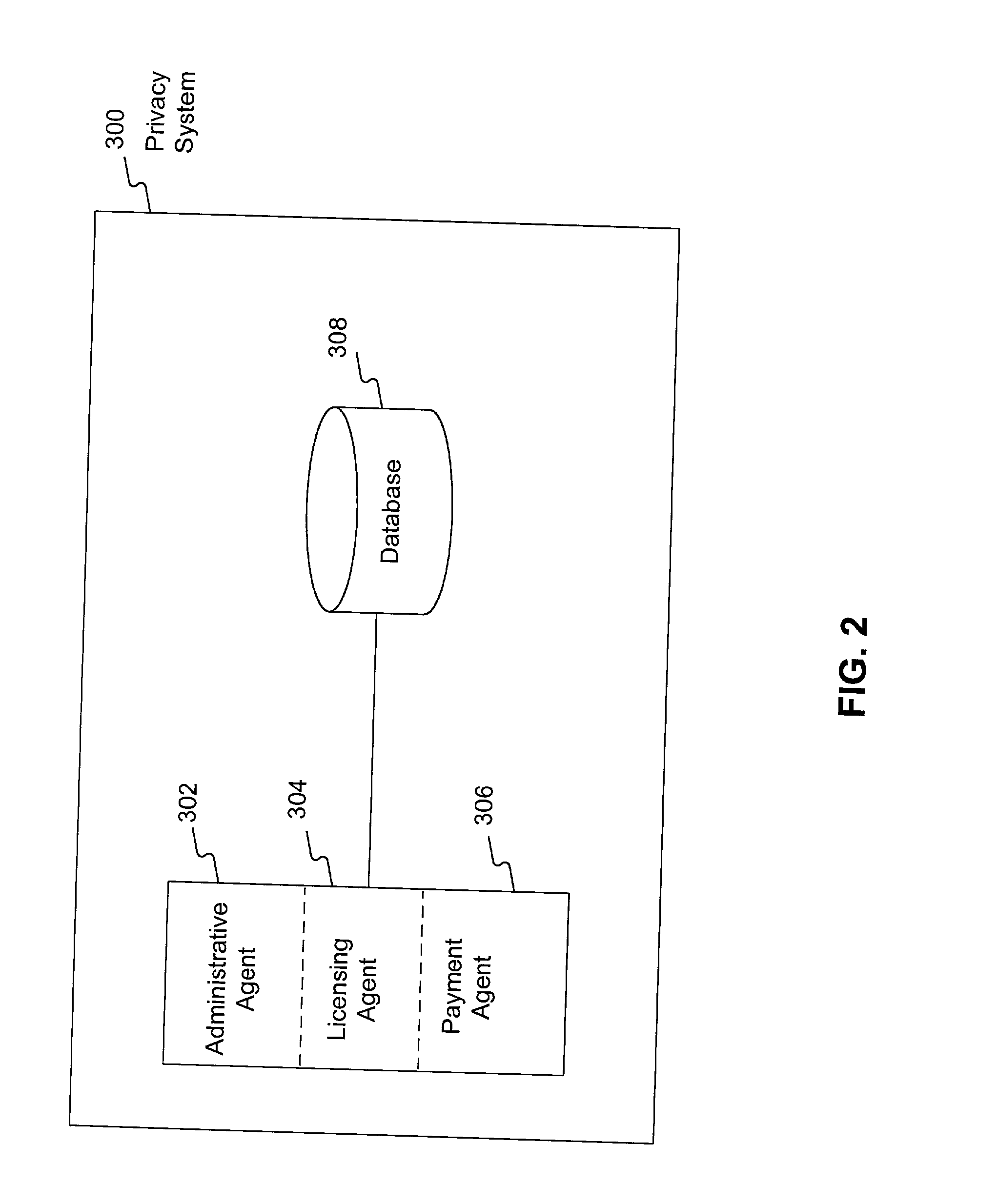
System and method for managing consumer information
InactiveUS20020111816A1Facilitating management and sharingComputer security arrangementsElectric/magnetic computingPaymentControl manner
A system and method are provided for managing consumer information, which permit sharing of consumer information in a controlled manner. In accordance with the disclosed system, at least one database is provided that contains consumer information related to at least one user. An administrative agent is also provided for establishing access to the consumer information contained in the database based on preferences expressed by the user. The system also includes a licensing agent for setting at least one licensing fee schedule for each user based on a set of licensing rules, and a payment agent for paying each user. In accordance with a disclosed method, a database is created of consumer information related to at least one user and access to the consumer information contained in the database is established based on each user's preferences. The method also includes setting a licensing fee schedule based on a set of licensing rules and paying the customer based on a set of payment rules.
Owner:CAPITAL ONE SERVICES
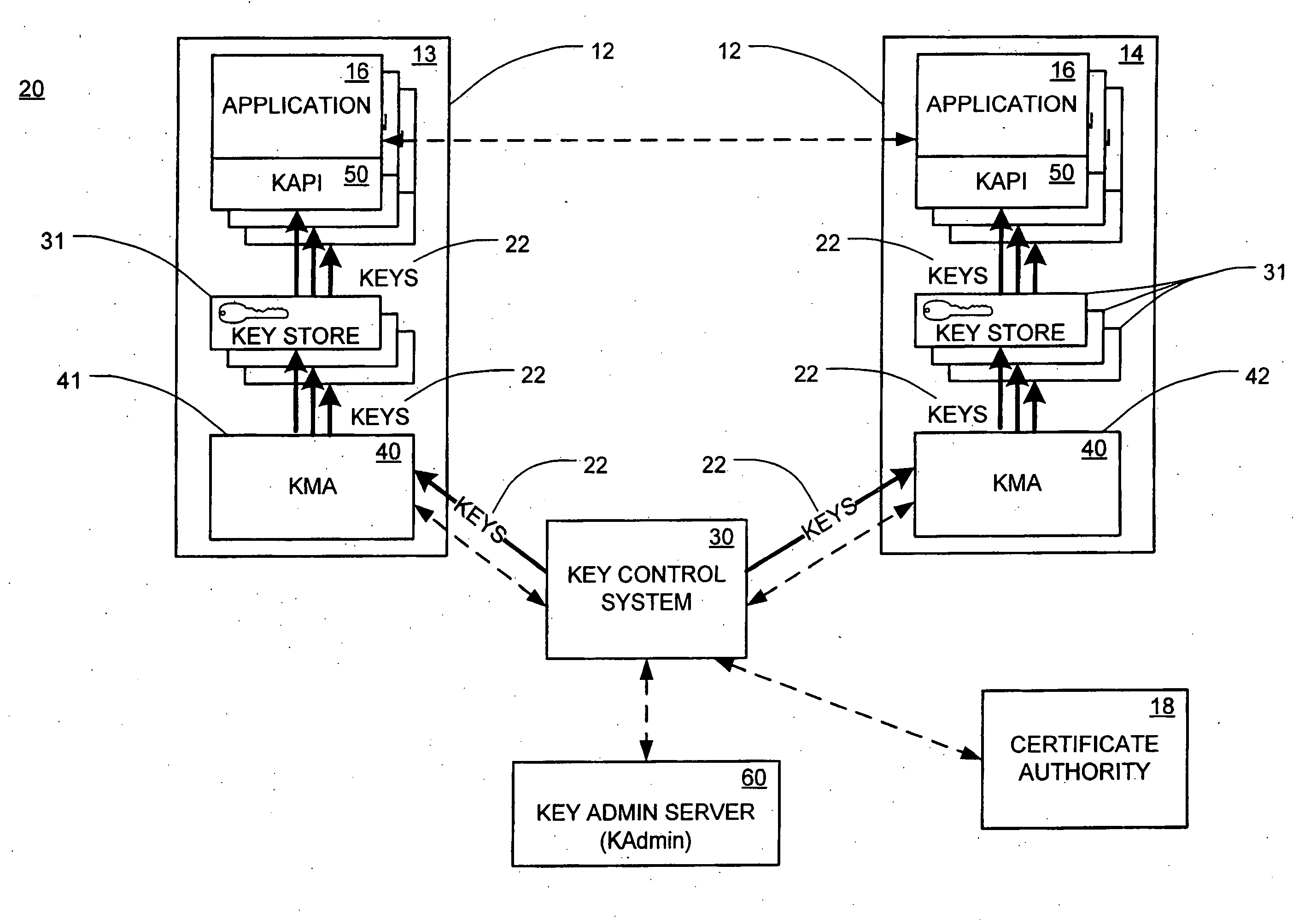
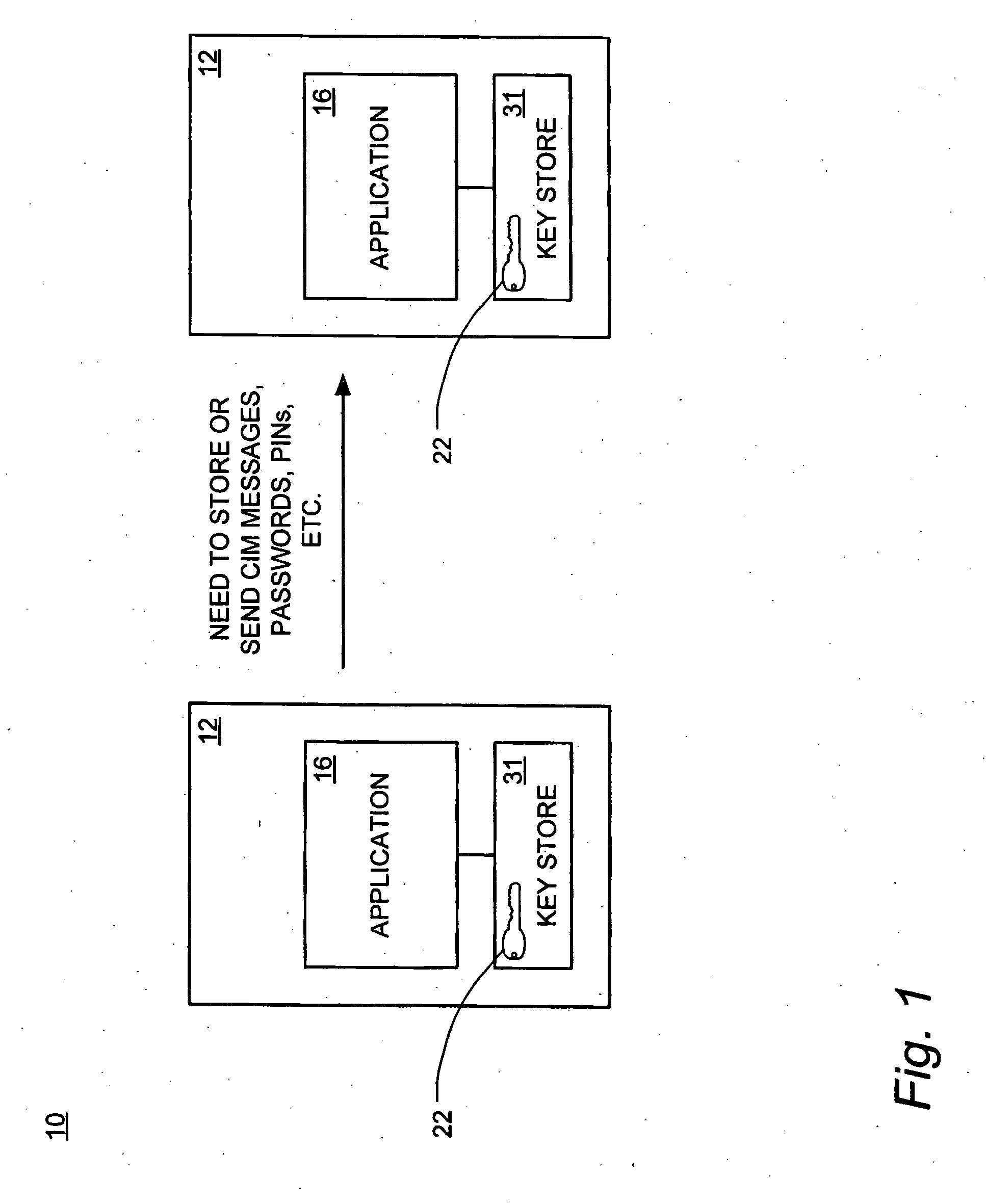
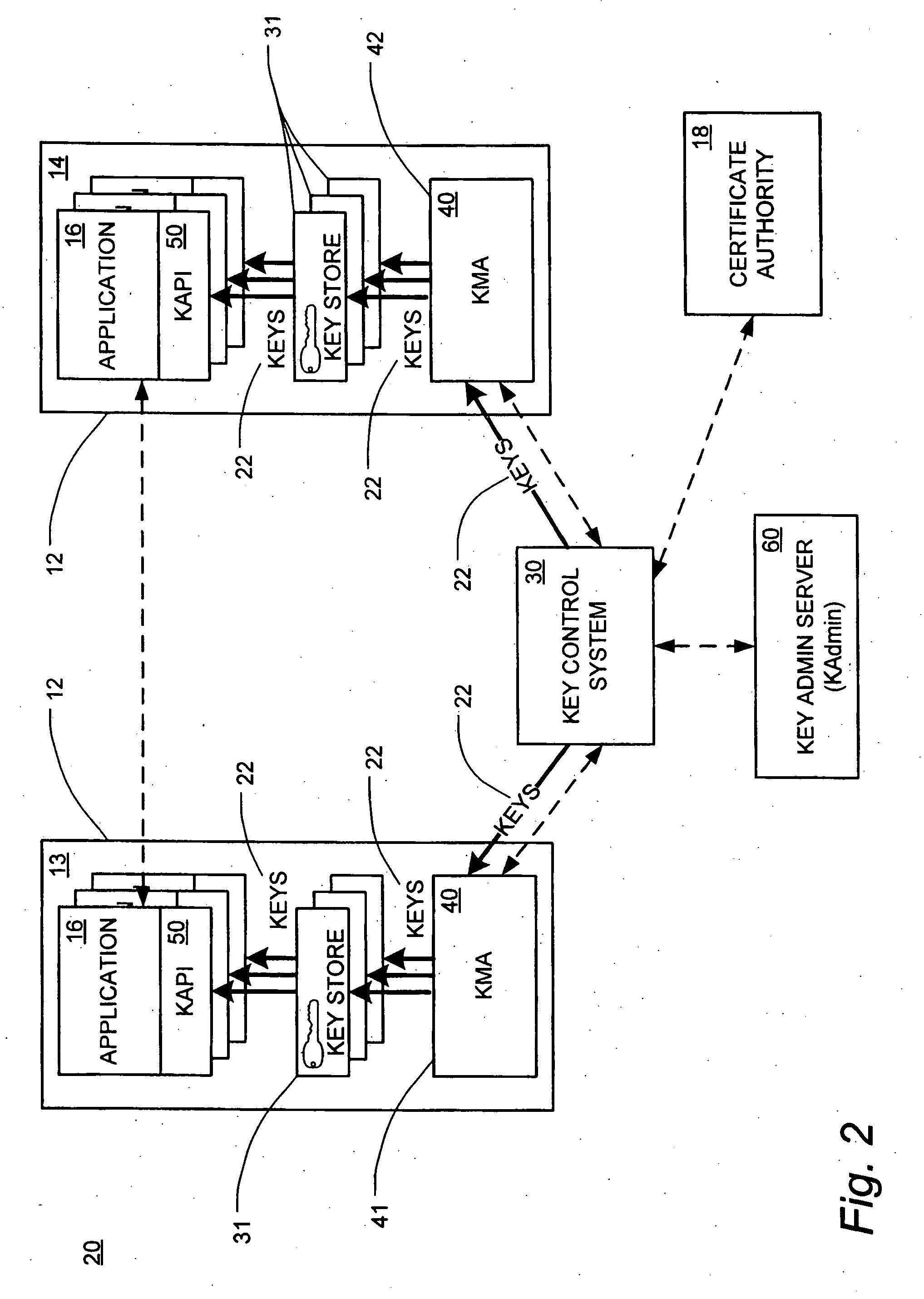
Automated key management system
ActiveUS20060291664A1Suitable for useKey distribution for secure communicationUnauthorized memory use protectionControl systemKey management
A system for automated cryptographic key management comprises a key control system, a key management agent system, and a key system application program interface. A method for automated cryptographic key management is also disclosed. The method comprises the automatic generation of cryptographic keys by the key control system and distribution of such keys by the key control system to the key management agent system.
Owner:WELLS FARGO BANK NA
Authentication for computer system management
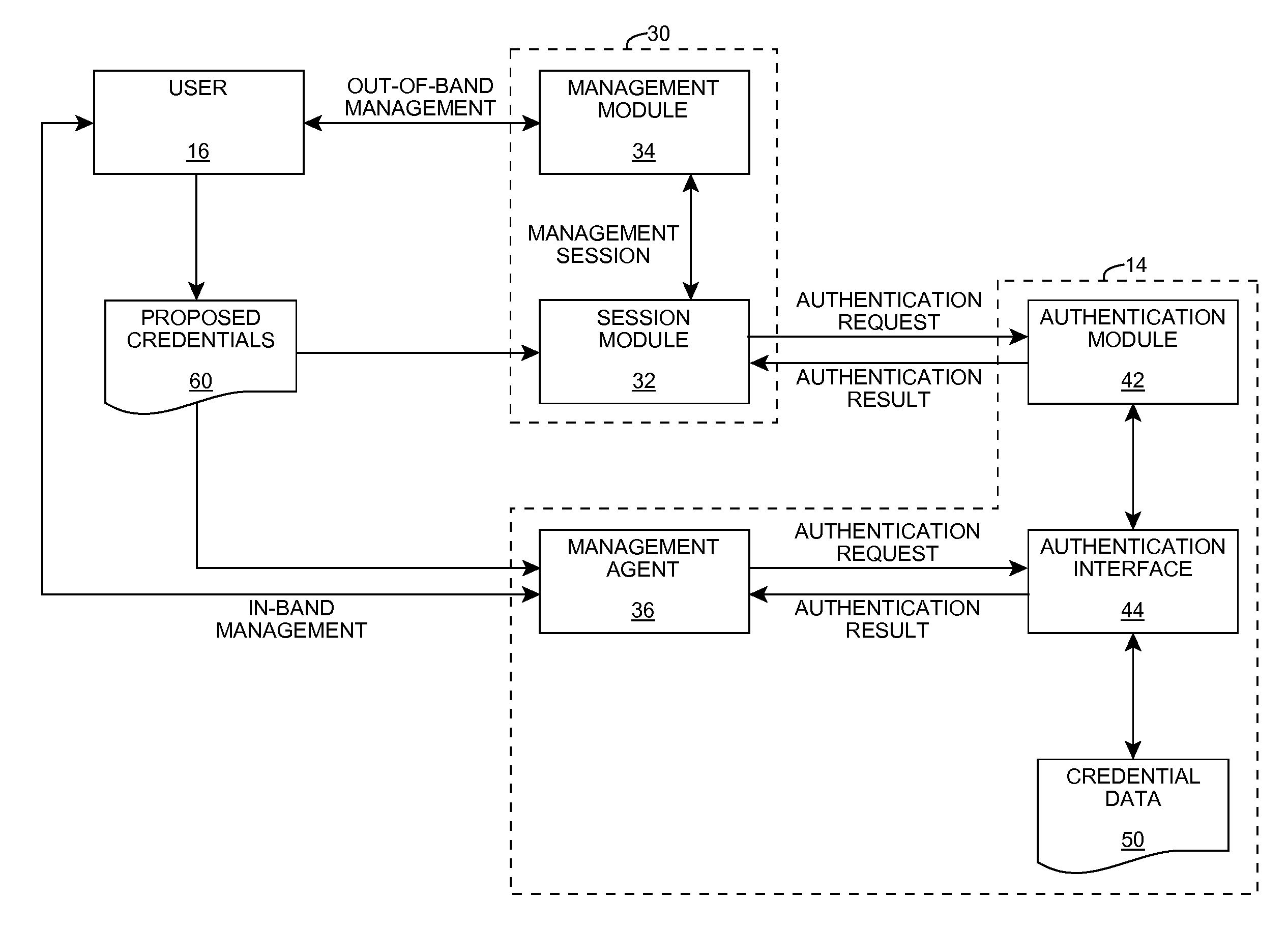
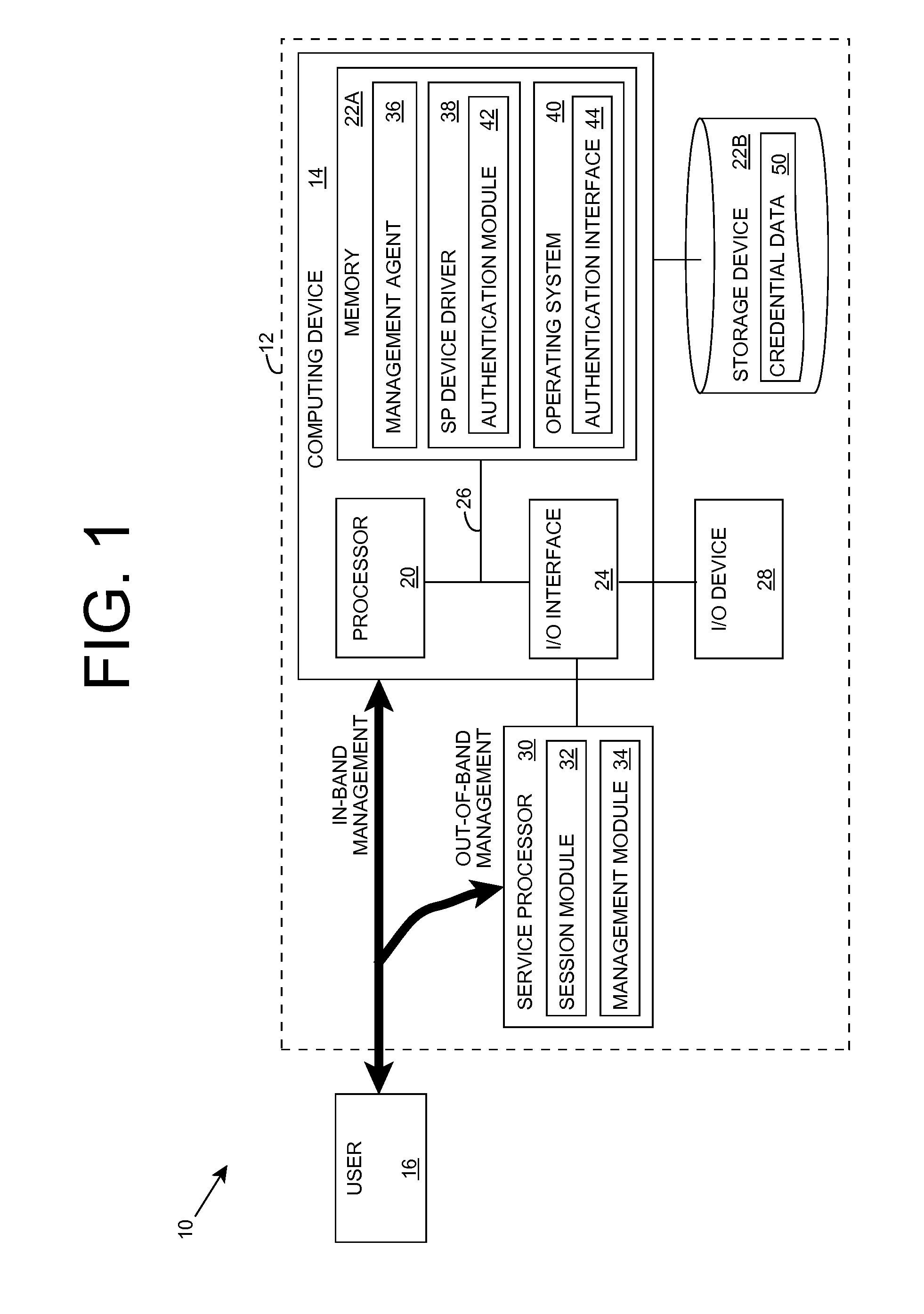
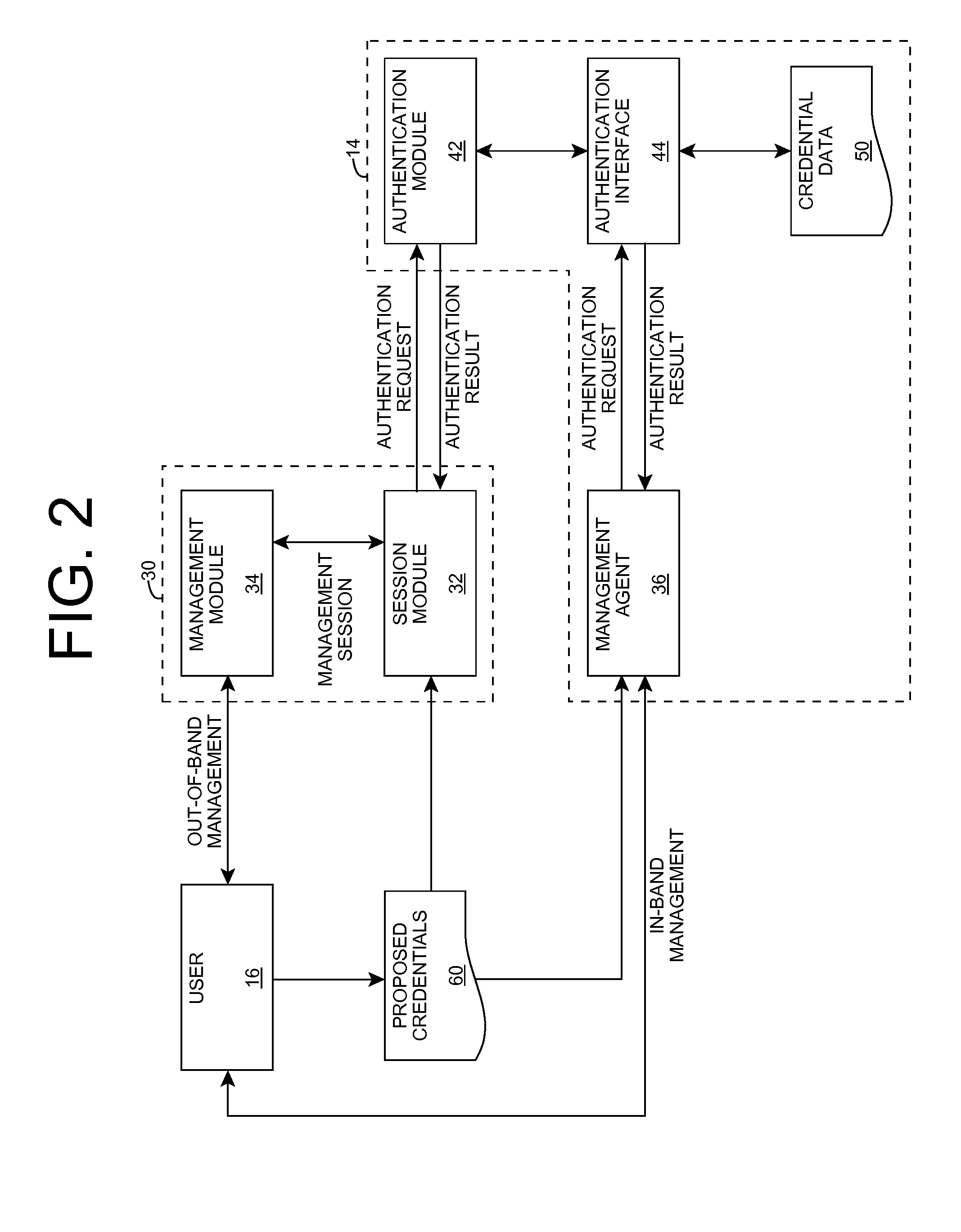
ActiveUS8347378B2Error detection/correctionDigital data processing detailsOperational systemInternet privacy
An improved solution for authenticating a user seeking to manage a computer system is provided according to aspects of the invention. A user seeking to perform out-of-band management of the computer system can provide a set of credentials to a service processor, which in turn provides them to the computer system for authentication. Additionally, a user seeking to perform in-band management of the computer system can provide a set of credentials to a management agent executing on the computer system for authentication. In either case, the computer system can authenticate the set of credentials, e.g., using an operating system interface.
Owner:LENOVO GLOBAL TECH INT LTD
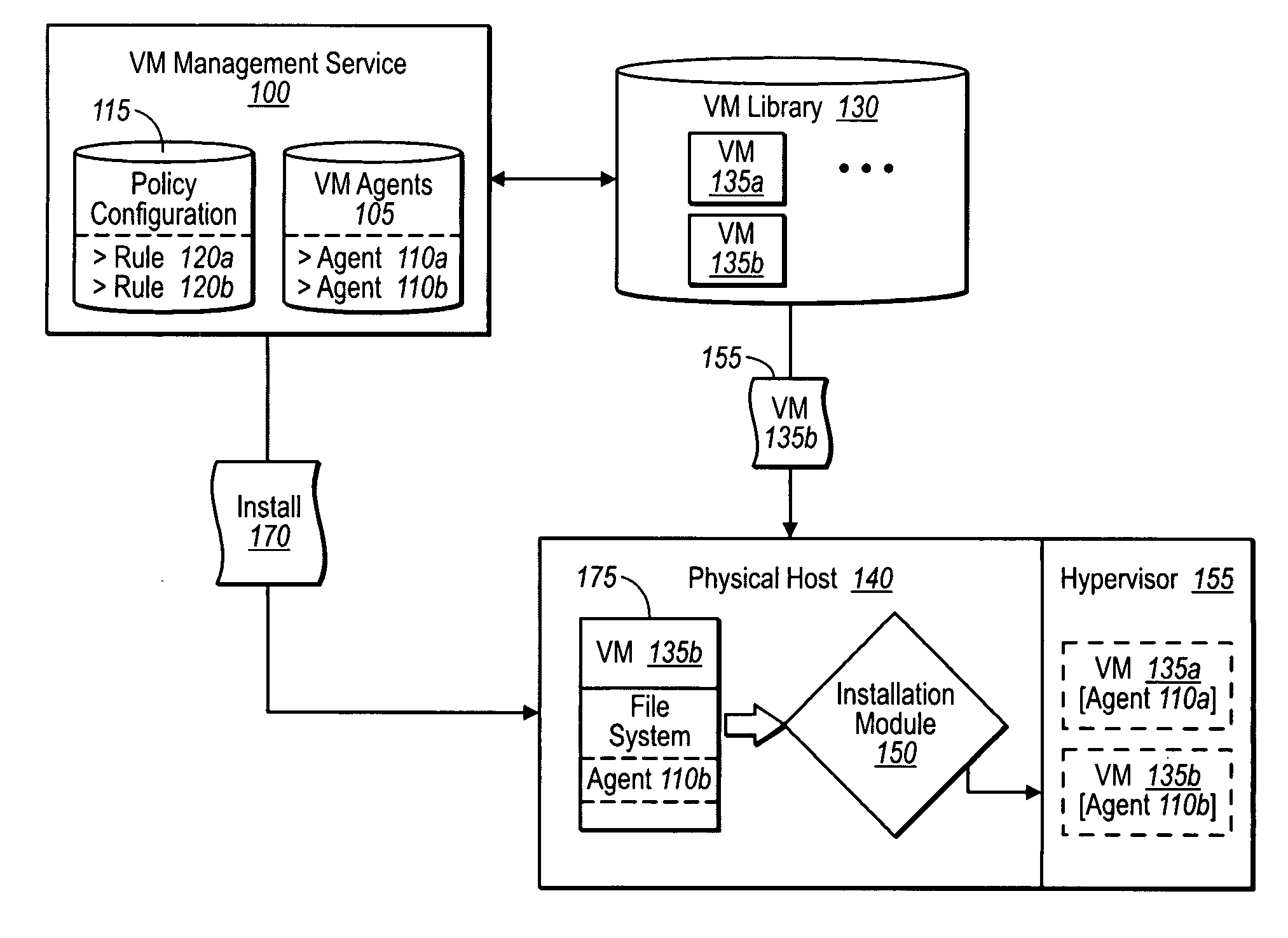
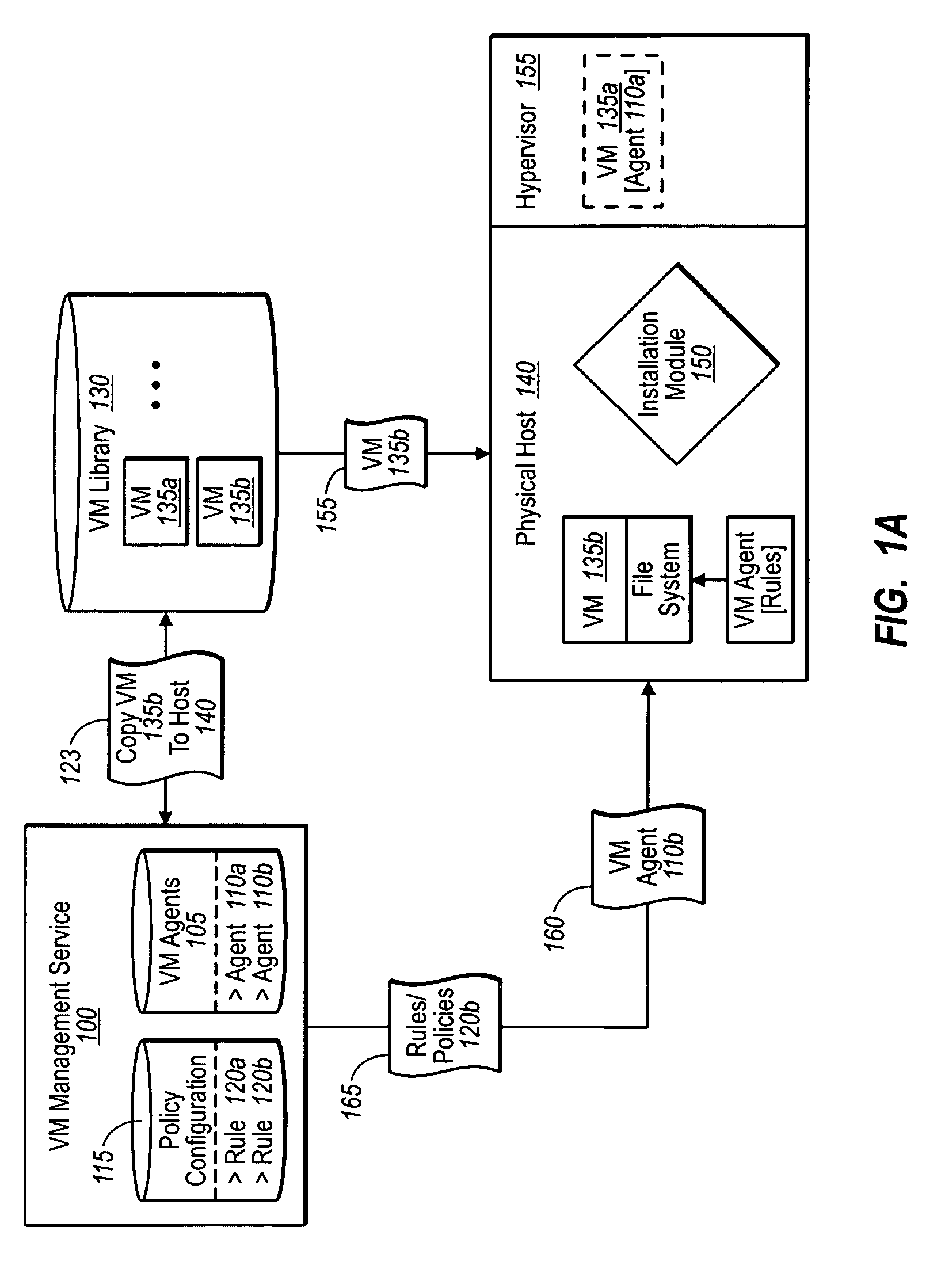
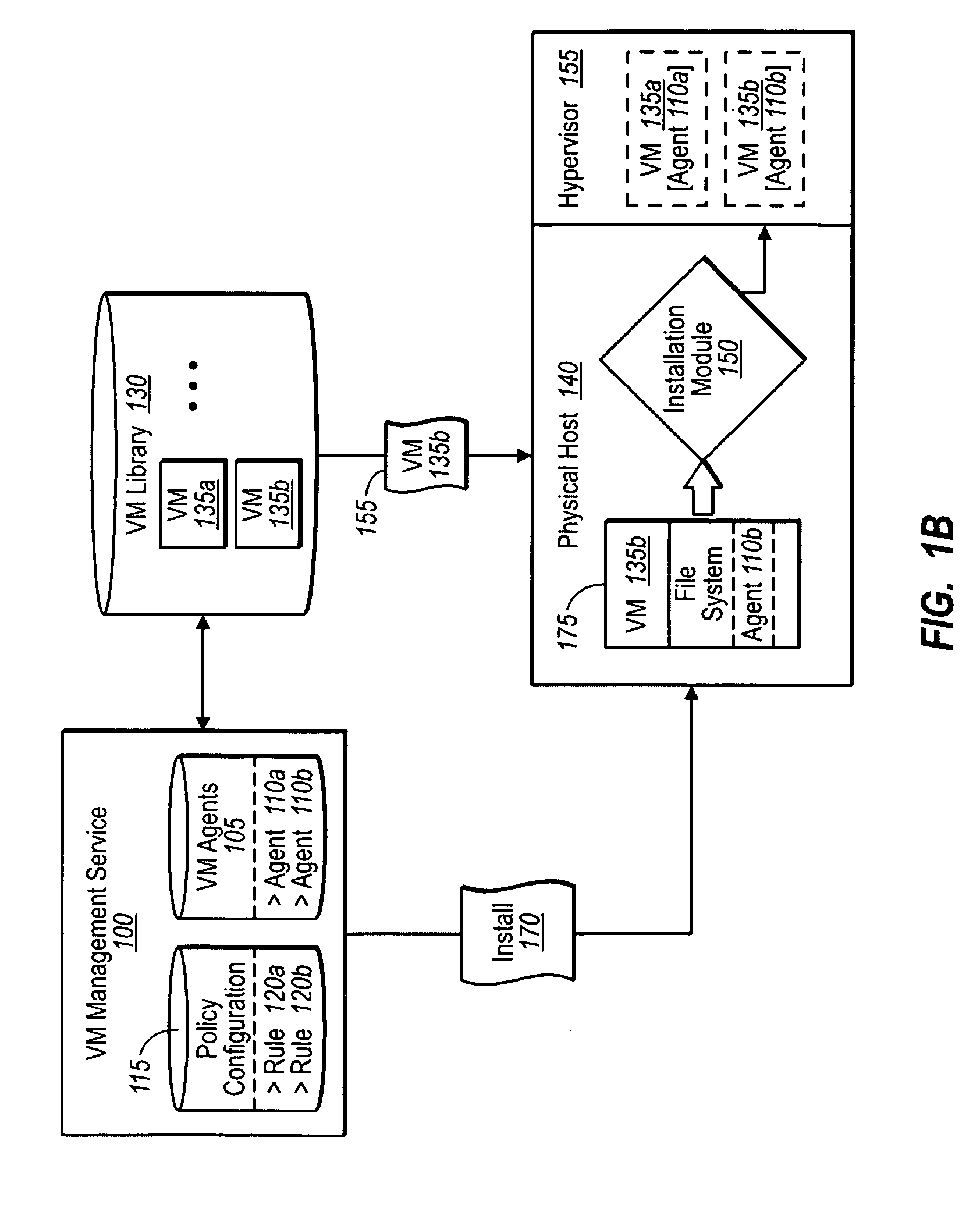
Installing a management agent with a virtual machine
InactiveUS20090328030A1Easy to installReliable fashionDigital computer detailsProgram loading/initiatingThird partyOperational system
A management service can install one or more third-party agents and any number of customizations for an operating system / virtual machine at the same as the system / machine is installed. In one implementation, a management service places (e.g., from a remote location) an operating system / virtual machine image in a mounting location. Before installing the corresponding system (OS or virtual machine), the management service also inserts one or more third-party agents into the image, as well as any number or type of policies and customizations. The management service then directs installation of the combined image (including rules, policies, and customizations) so that the operating system, third-party agents, and provided customizations, are all installed together during the same installation process. Accordingly, the management service allows for agents to reliably and immediately begin executing with installation of the operating system / virtual machine.
Owner:MICROSOFT TECH LICENSING LLC
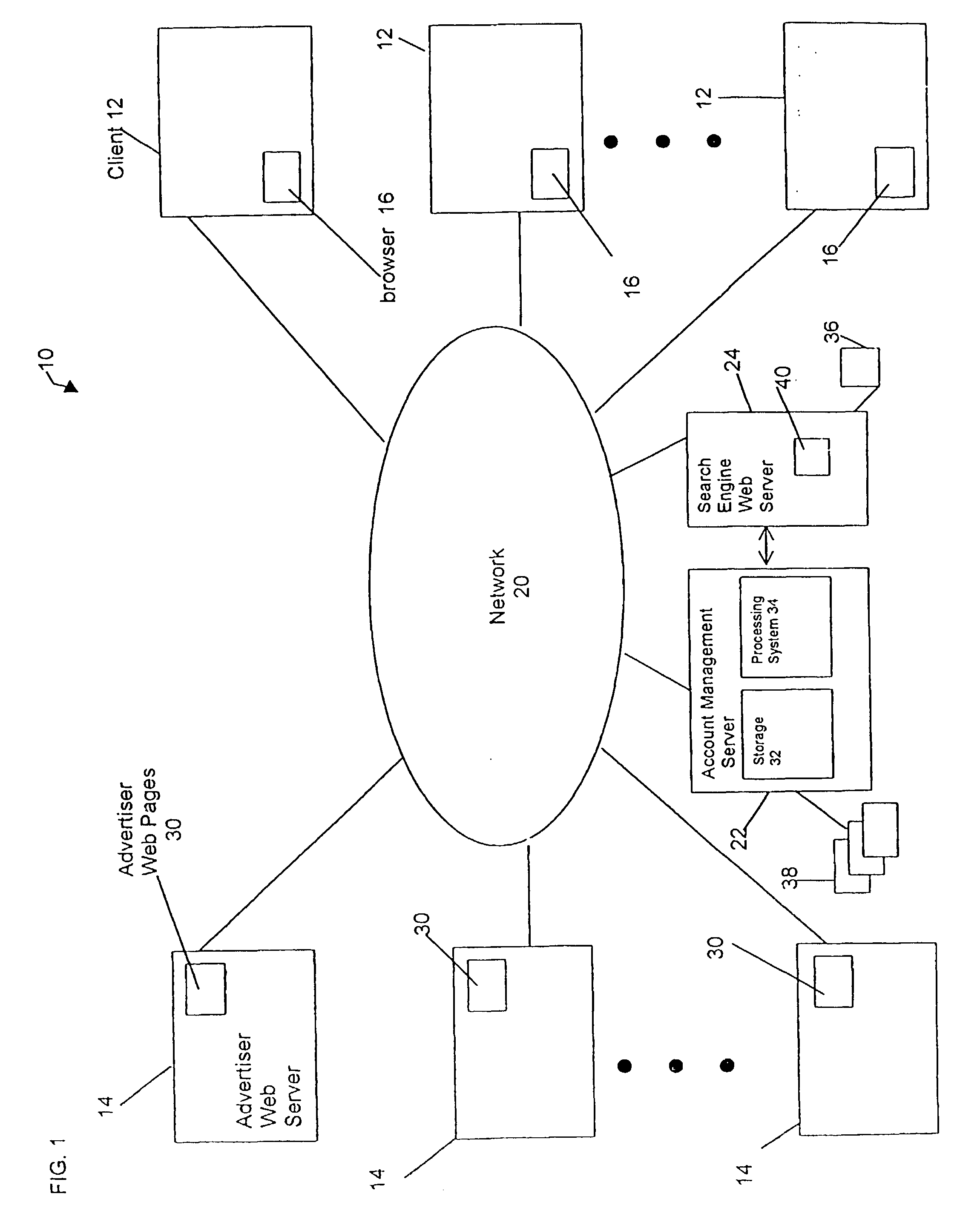
Automatic flight management in an online marketplace
InactiveUS20060190328A1Maximizing total number of clickConstant flight budgetWeb data indexingAdvertisementsWeb search queryData mining
Owner:R2 SOLUTIONS
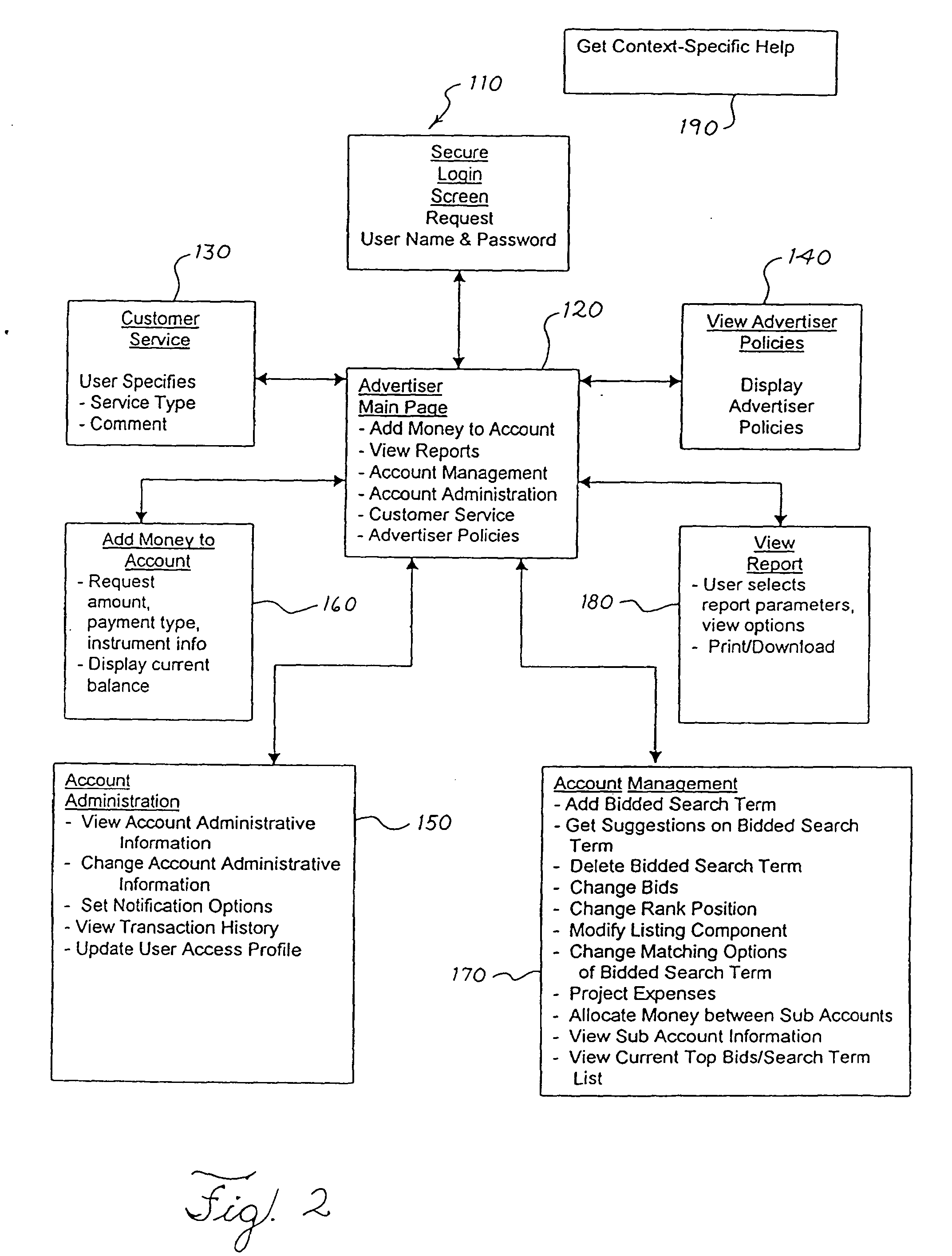
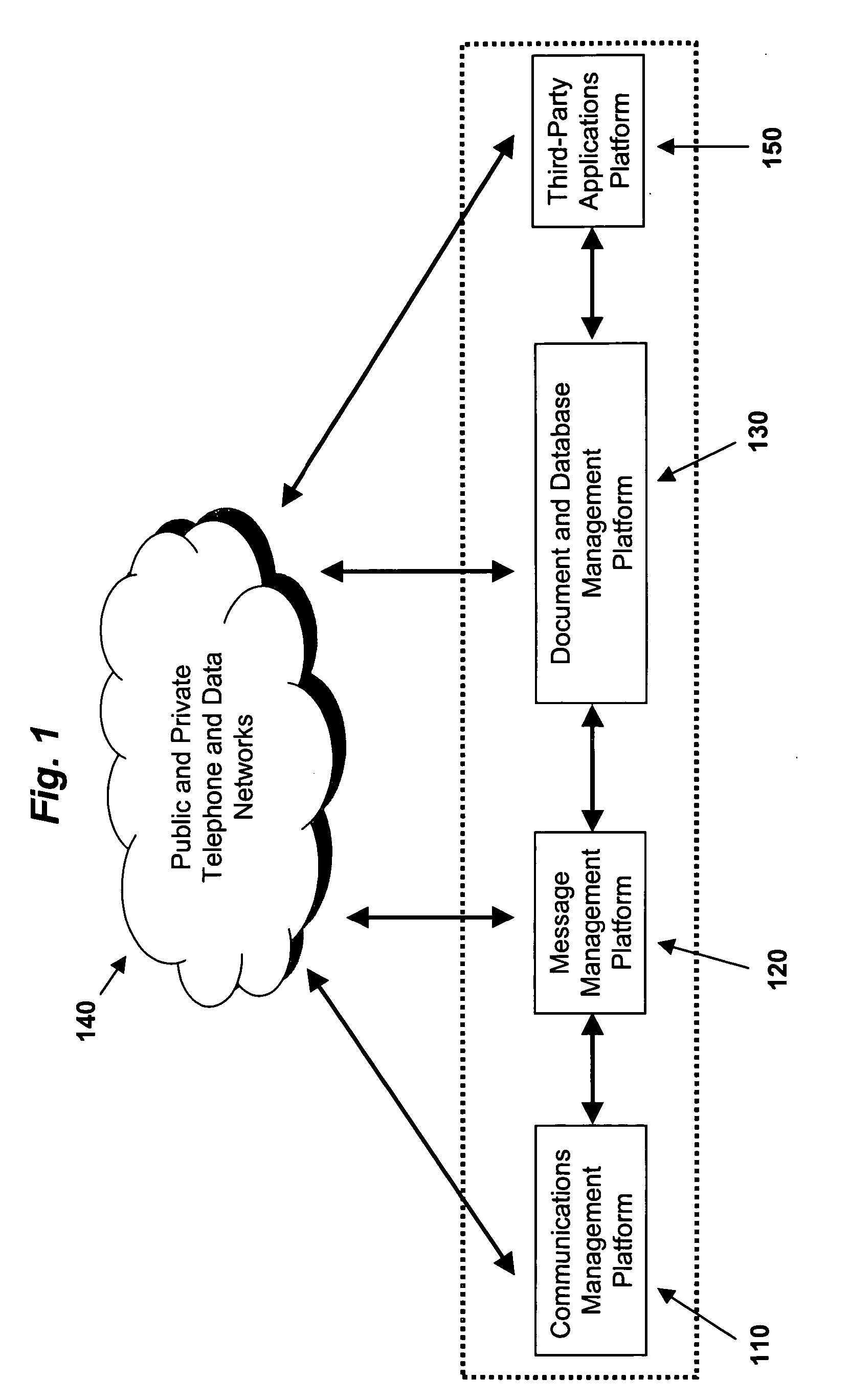
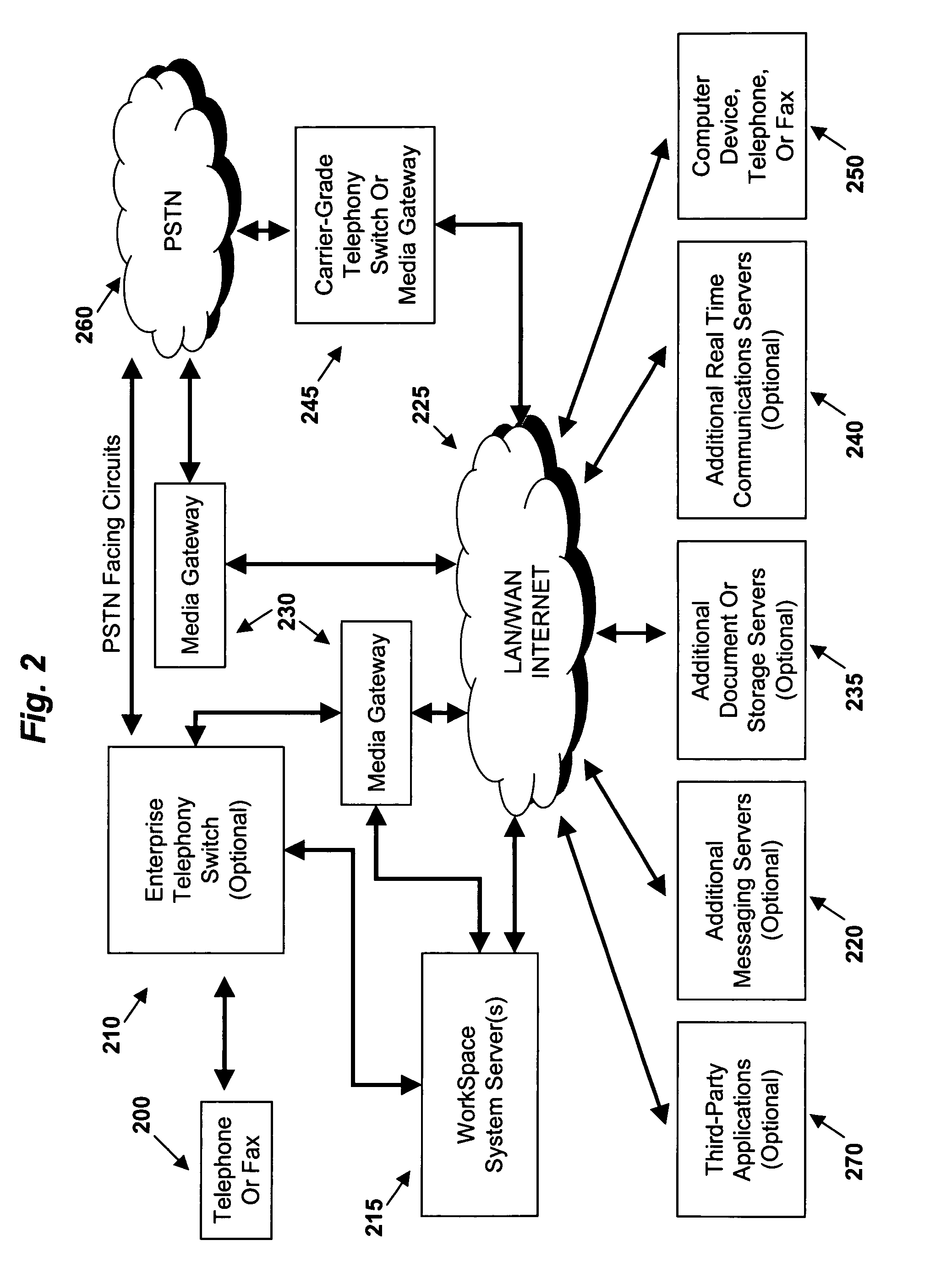
Agent architecture employed within an integrated message, document and communication system
InactiveUS20050060638A1Multiplex communicationMultiple digital computer combinationsCommunications systemAgent architecture
A system is described for managing messages, communications and / or documents comprising: a plurality of task agents, each task agent to perform one or more specified message processing actions, document processing actions, and / or communications processing actions on different types of messages, documents and / or communication channels, respectively; and one or more manager agents to coordinate the actions of the plurality of task agents responsive to a plurality of message and / or document processing rules.
Owner:CATALYSTWEB
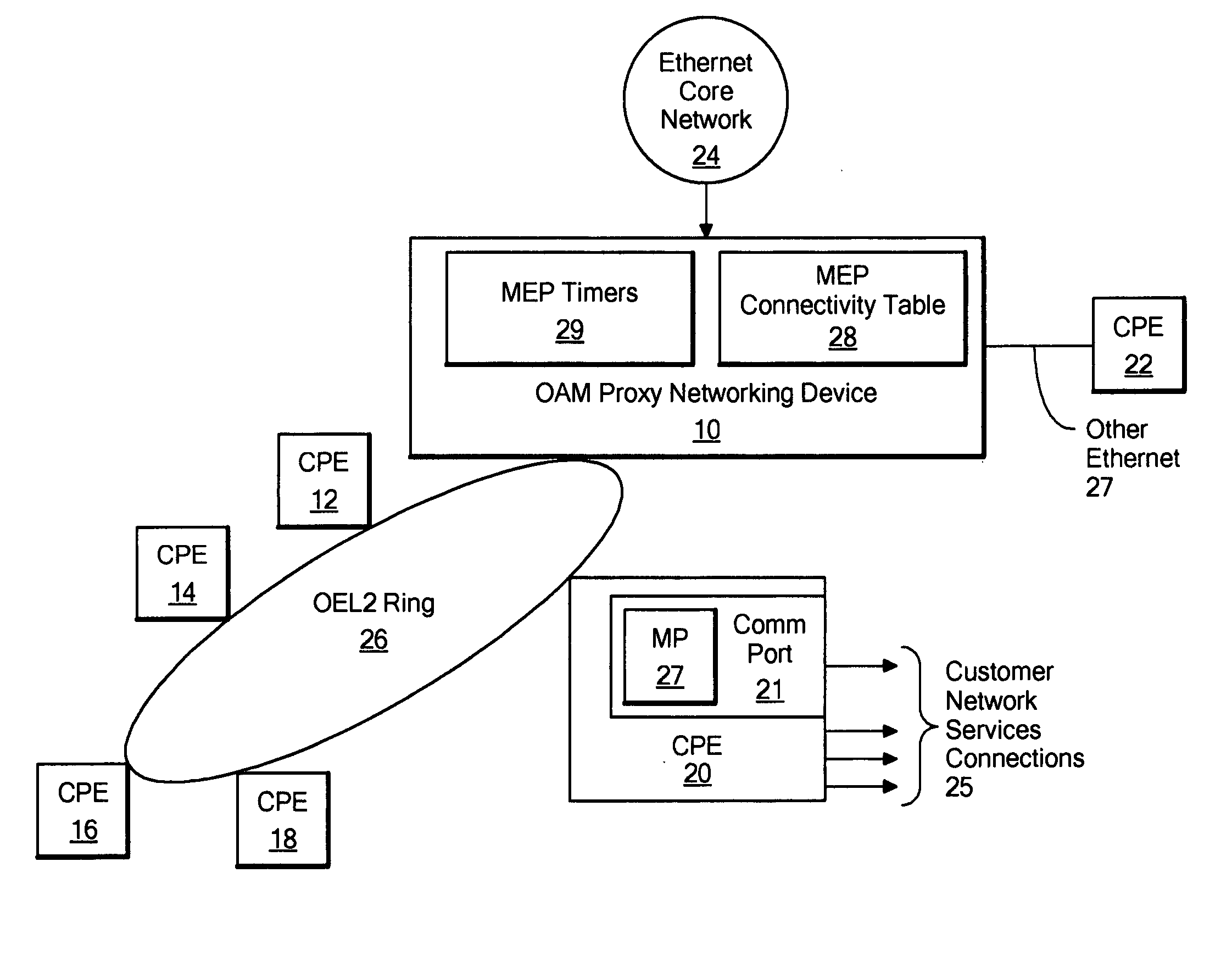
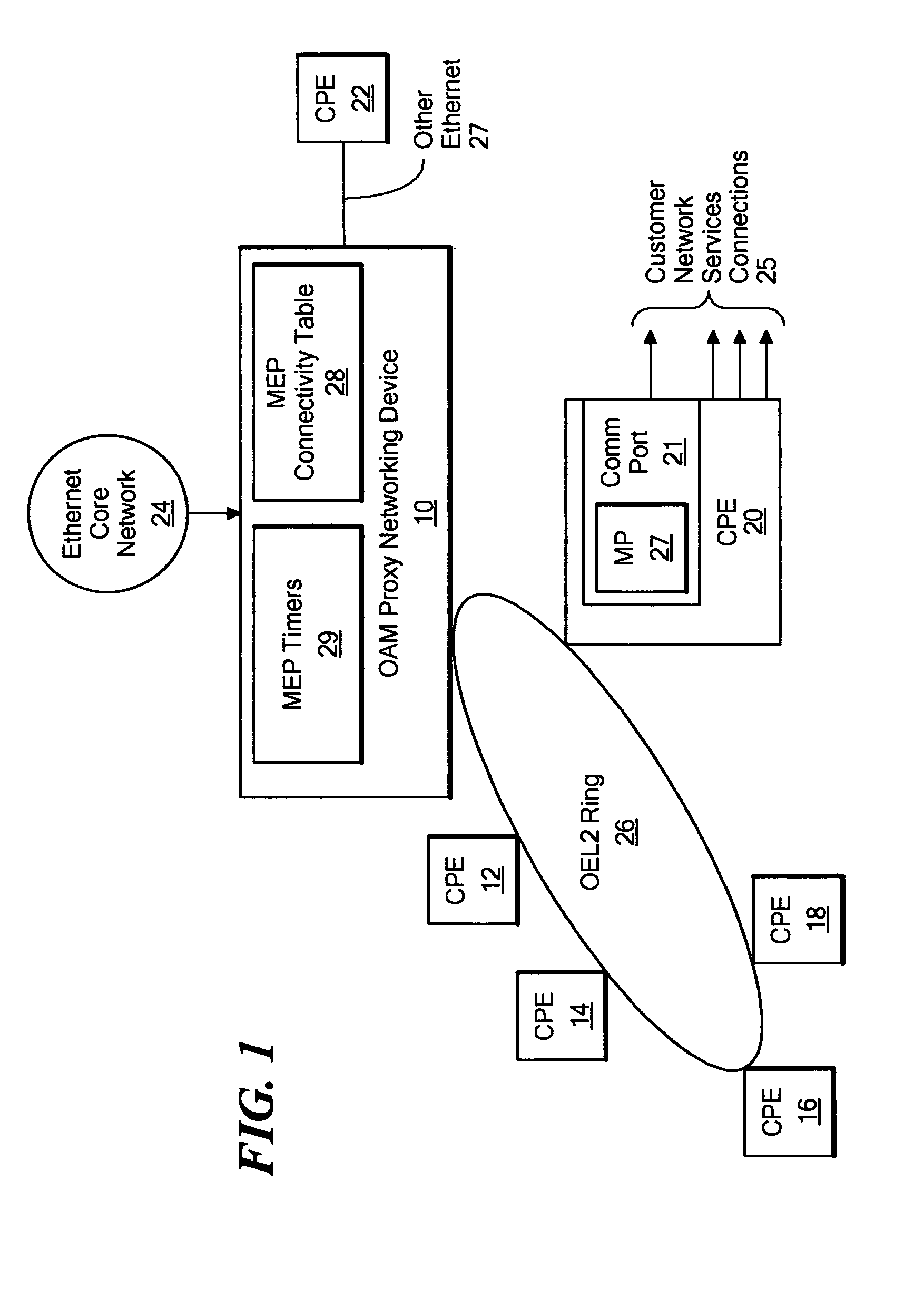
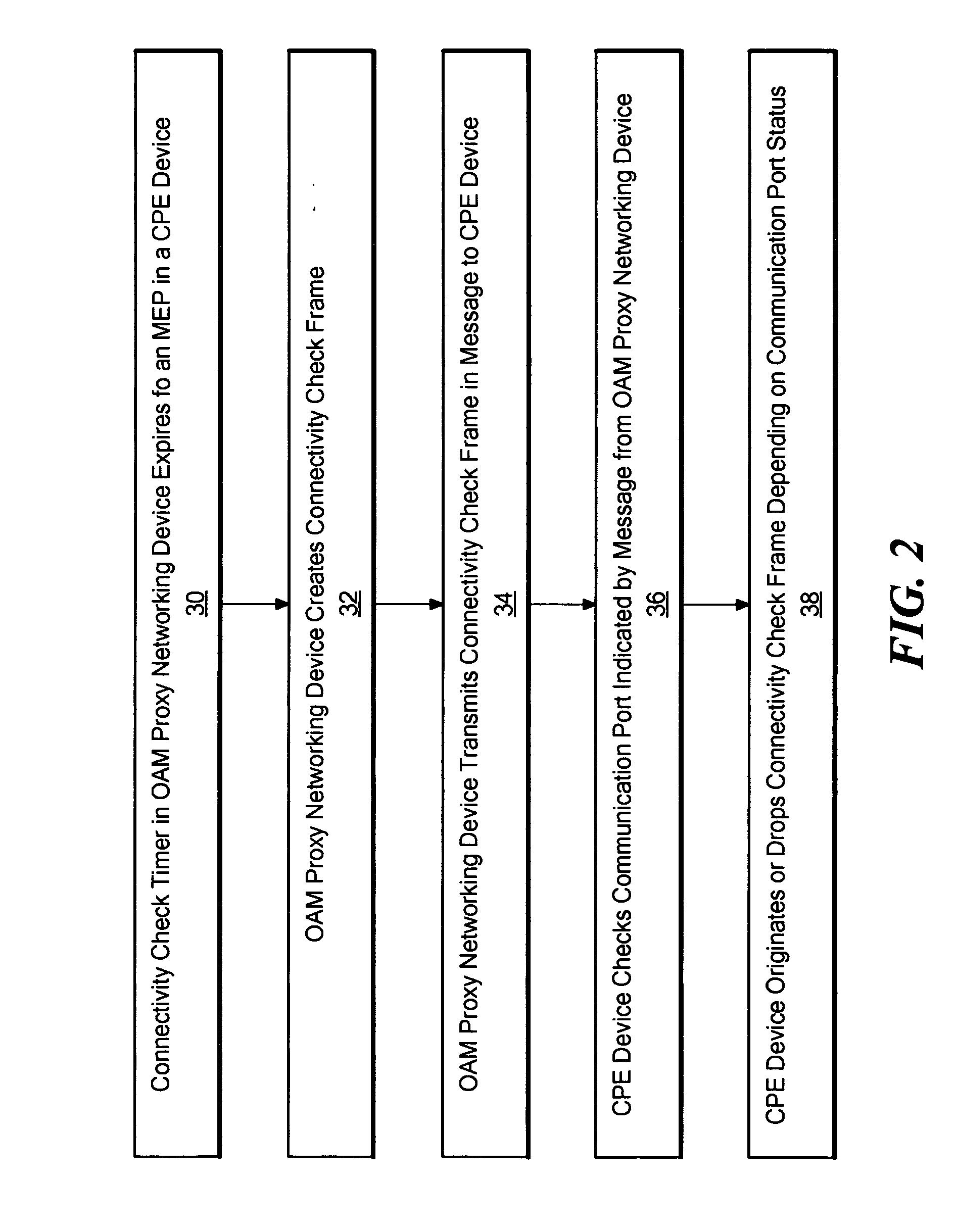
Method and system for originating connectivity fault management (CFM) frames on non-CFM aware switches
InactiveUS20070140126A1Effective expansionAvoid a lotError preventionFrequency-division multiplex detailsOperations, administration and managementOperability
A system for originating connectivity fault management (CFM) frames on non-CFM aware switches is disclosed. In the disclosed system, an OAM (Operations Administration and Management) proxy networking device connected to a core Ethernet network operates with one or more CPE (Customer Premises Equipment) devices to which it is communicably connected to support CFM out to the CPE devices without requiring that the CPE devices themselves implement CFM functionality. The OAM proxy networking device generates Connectivity Check (CC) frames, Loopback reply frames, and Linktrace reply frames for MEPs (Maintenance End Points) or MIPs (Maintenance Intermediate Points) contained in communication ports on the CPEs. These CFM frames generated by the OAM proxy networking device are then sent within messages from the OAM proxy networking device to the appropriate CPE. When the CPE device receives a message from the OAM proxy networking device containing one of these CFM frames, it checks the operability of a communication port indicated by the message. If the port is operable, the CPE device extracts the CFM frame from the message and originates it through the OAM proxy networking device into the core Ethernet network. The OAM proxy networking device further operates to process Connectivity Check frames received from the core Ethernet network and addressed to the CPE devices by maintaining an MEP connectivity database. As a result, these received Connectivity Check frames are dropped without forwarding to the CPE devices.
Owner:RPX CLEARINGHOUSE
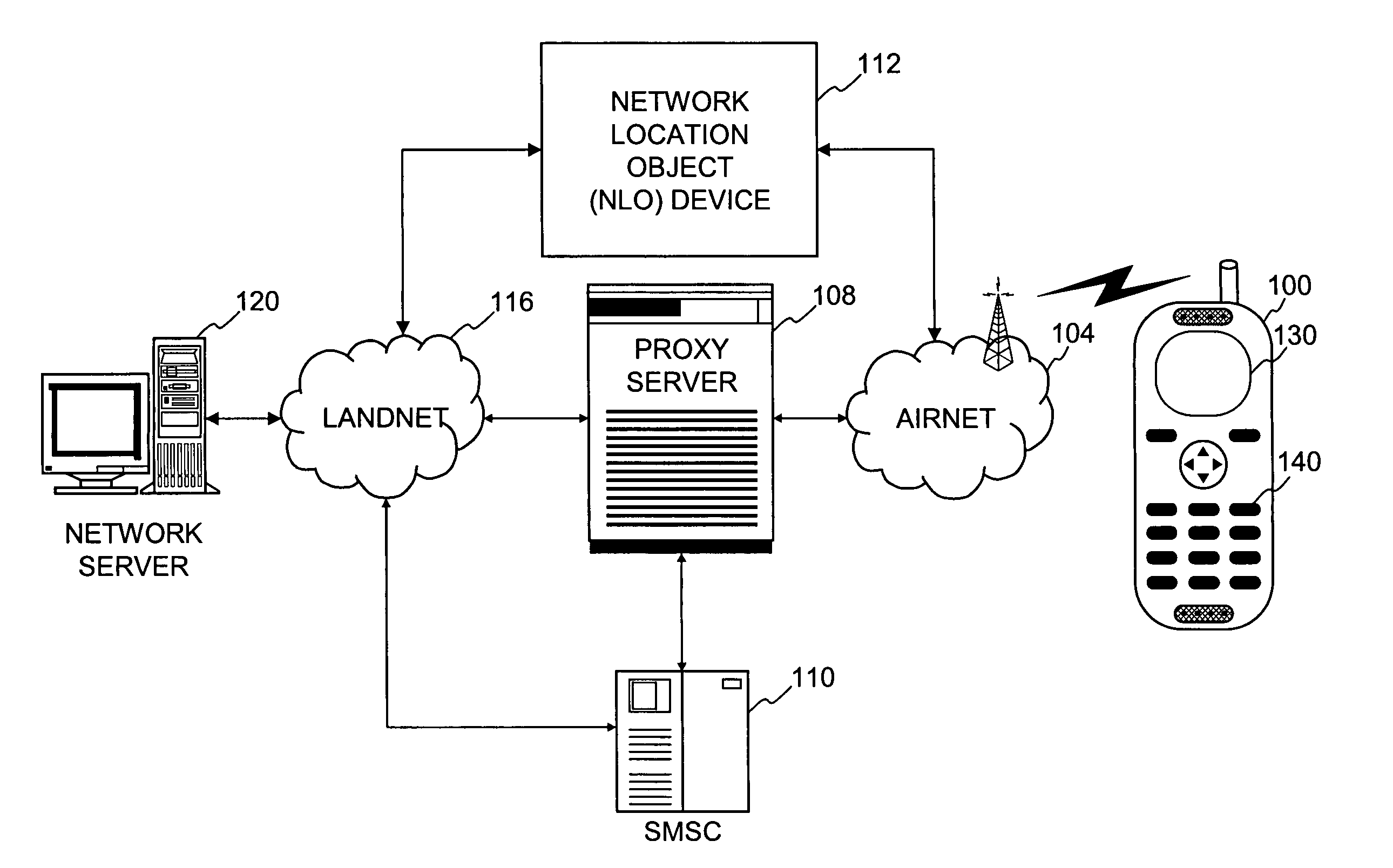
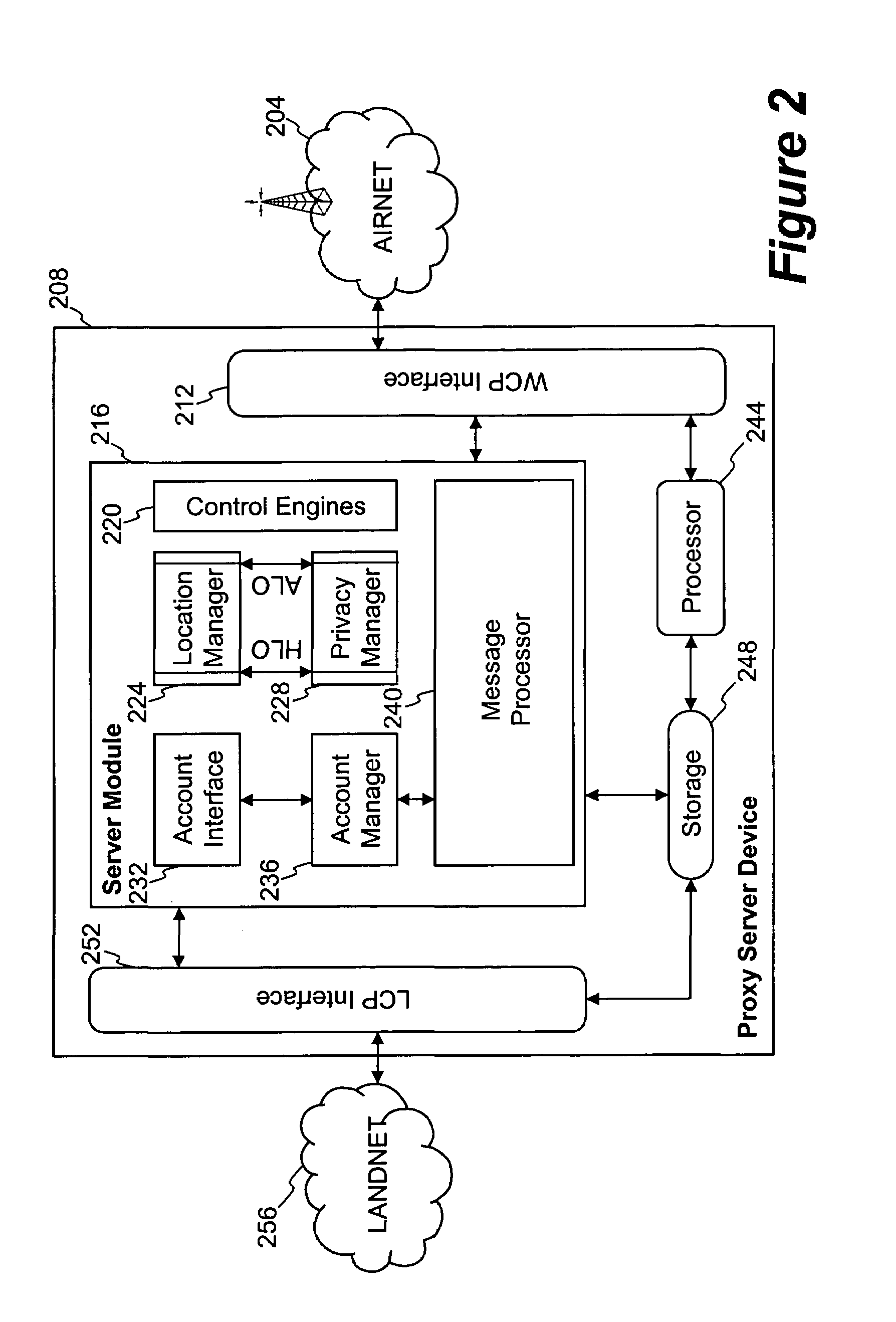
Method and system for exchanging sensitive information in a wireless communication system
InactiveUS7093286B1Control releaseEnhanced informationNetwork traffic/resource managementDigital data processing detailsCommunications systemInternet privacy
Improved techniques that enable the exchange of sensitive information between client devices and server devices are disclosed. The exchange, as well as the use and nature, of sensitive information released can be governed by one or more privacy agreements established between the principle parties, namely, a client device and a content server. A proxy server can be used to establish privacy agreements with content servers (service providers).
Owner:UNWIRED PLANET
Automatic flight management in an online marketplace
InactiveUS7231358B2Maximizing total number of clickConstant flight budgetAdvertisementsWeb data indexingWeb search queryData mining
A database search system includes a database of search terms, each search term associated with a bid amount payable by an advertiser of a plurality of advertisers and a search engine responsive to search queries from searchers for searching the database. A flight management agent is responsive to advertiser-specified parameters for adjusting bid amounts of search listings to manage expenditures over a time interval.
Owner:R2 SOLUTIONS
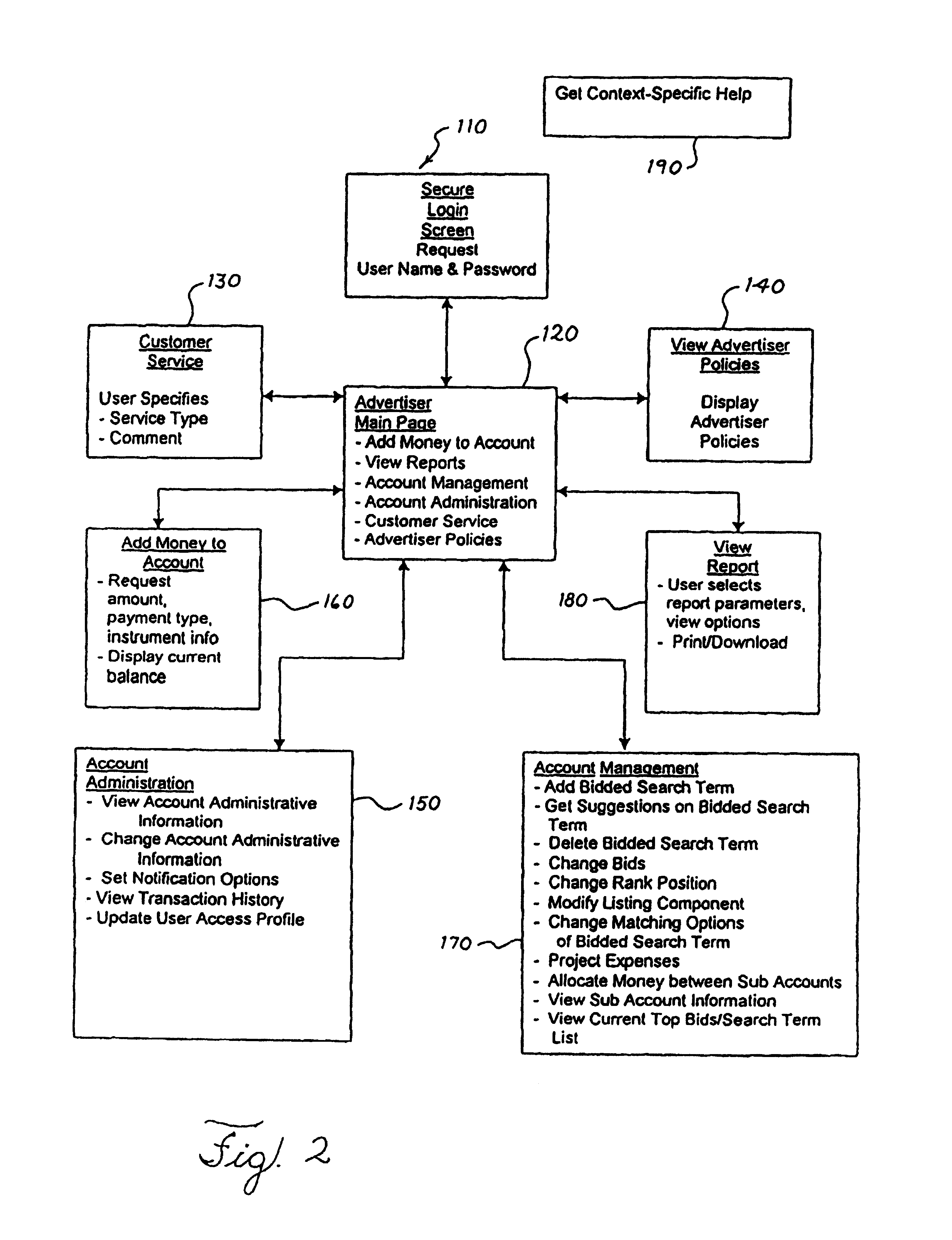
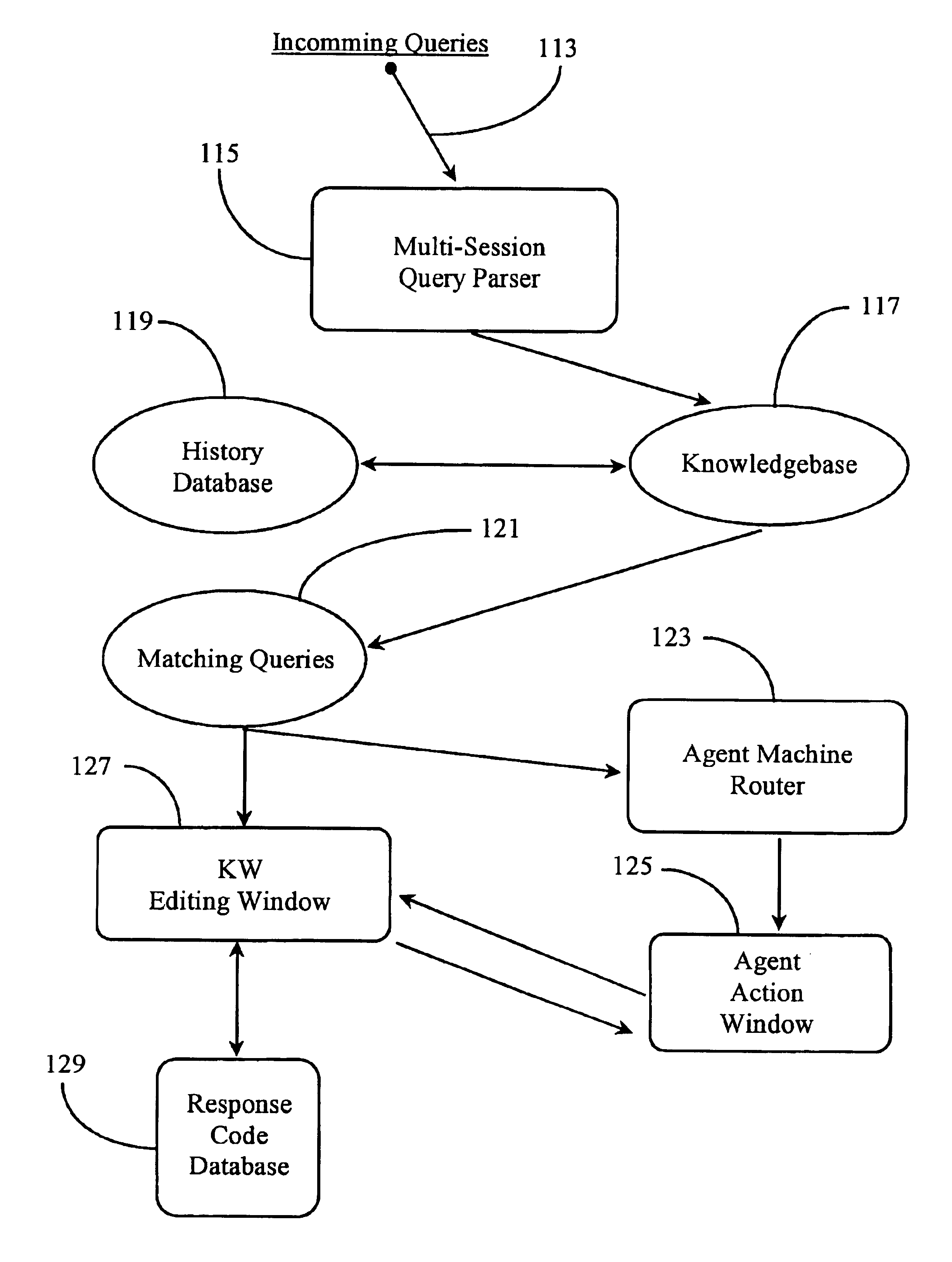
Method and apparatus for auto-assisting agents in agent-hosted communications sessions
InactiveUS6922689B2Reduce workloadMetadata text retrievalData processing applicationsParsingDatabase
A communication center has a system for managing agent-hosted sessions including systems for storing queries and responses to queries in sessions in associated pairs, and for comparing newly-arriving queries with stored query-response pairs. In the event of a match or near match, stored responses to oft-repeated queries are provided to agents for use, relieving agents of the tasks of responding manually to often-repeated queries. Parsing and sentence structure tools are used, and in some cases aid stations with knowledge workers are provided to allow editing and extra help for agents.
Owner:ALCATEL LUCENT SAS +1
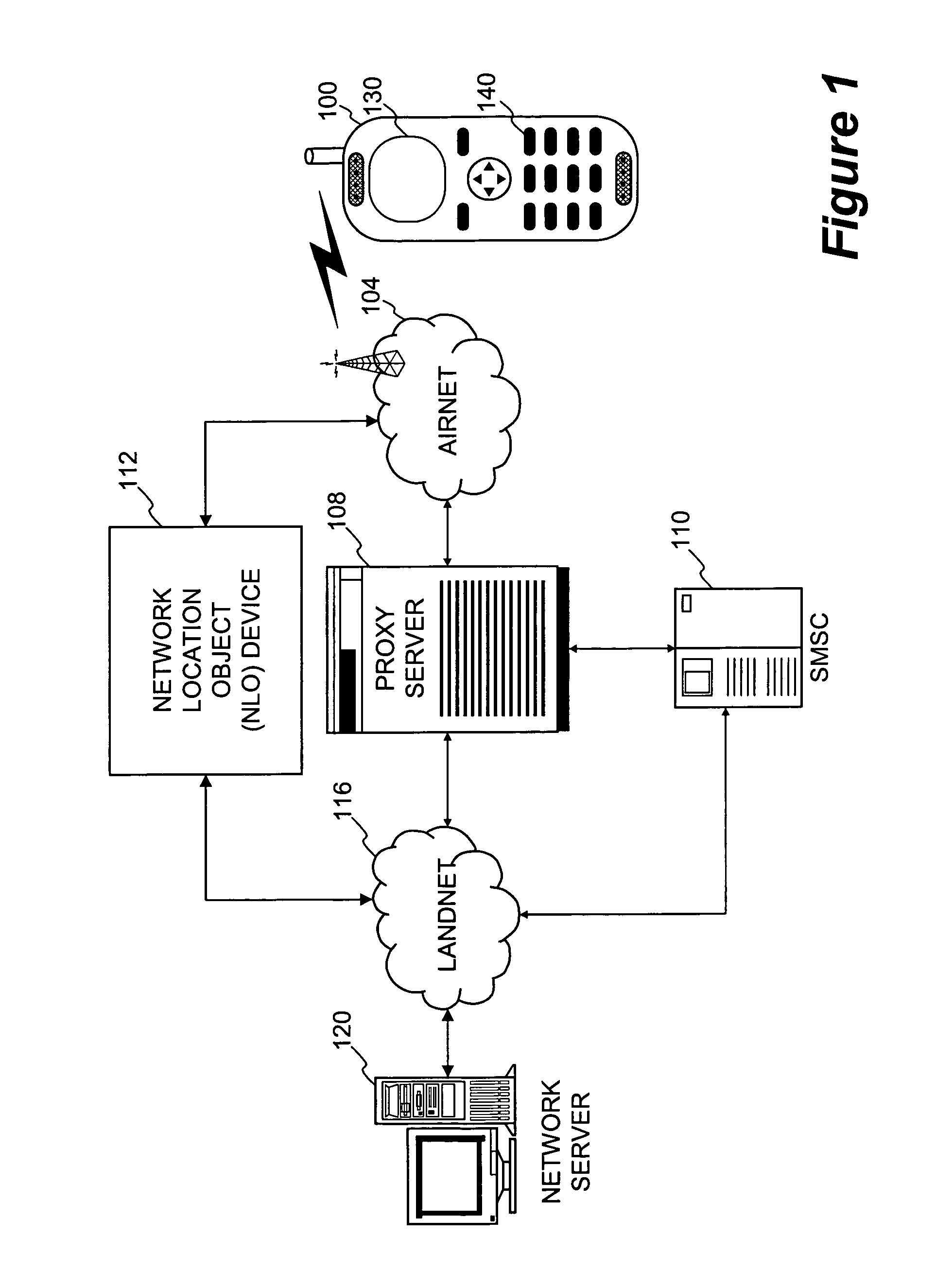
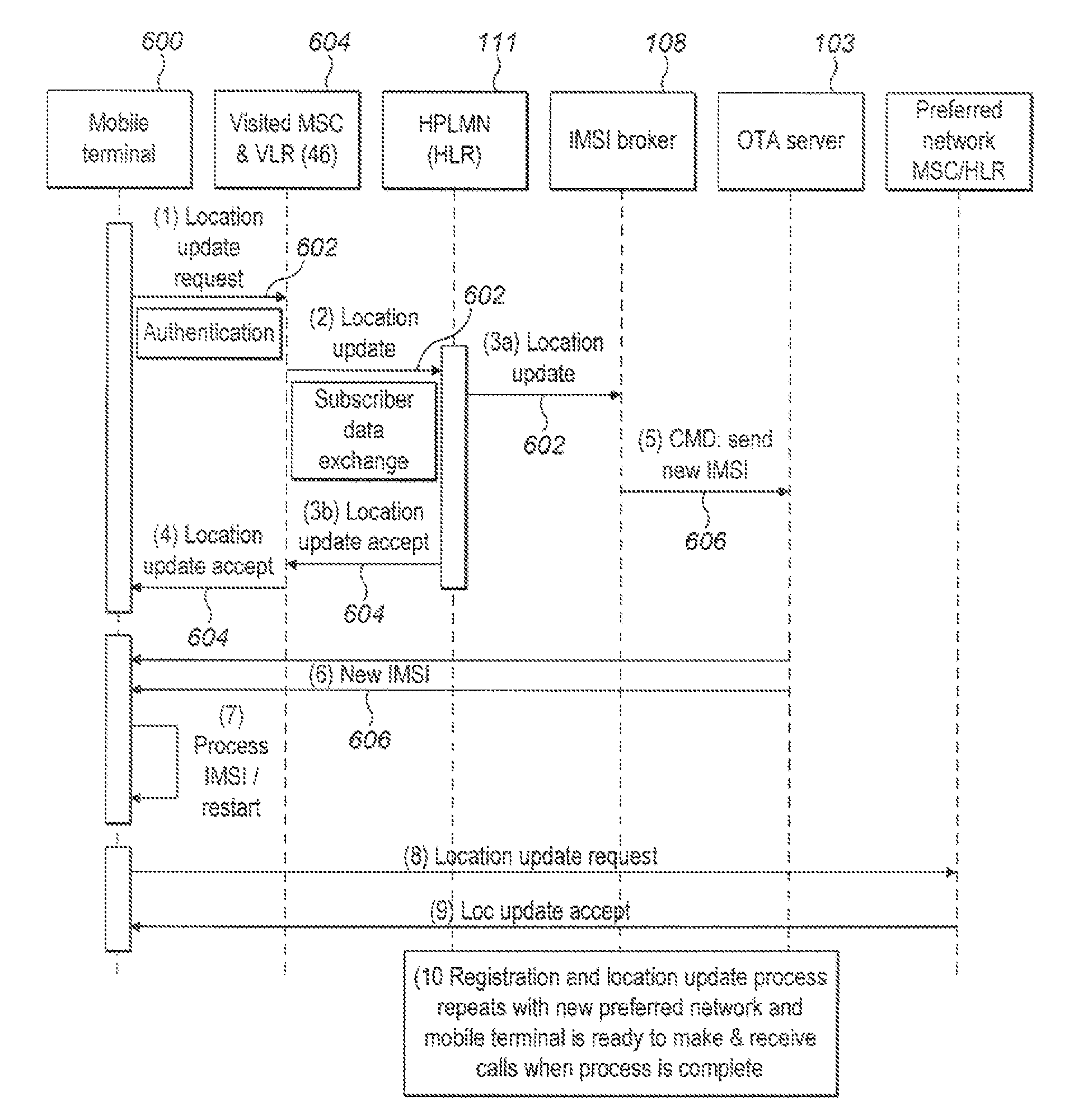
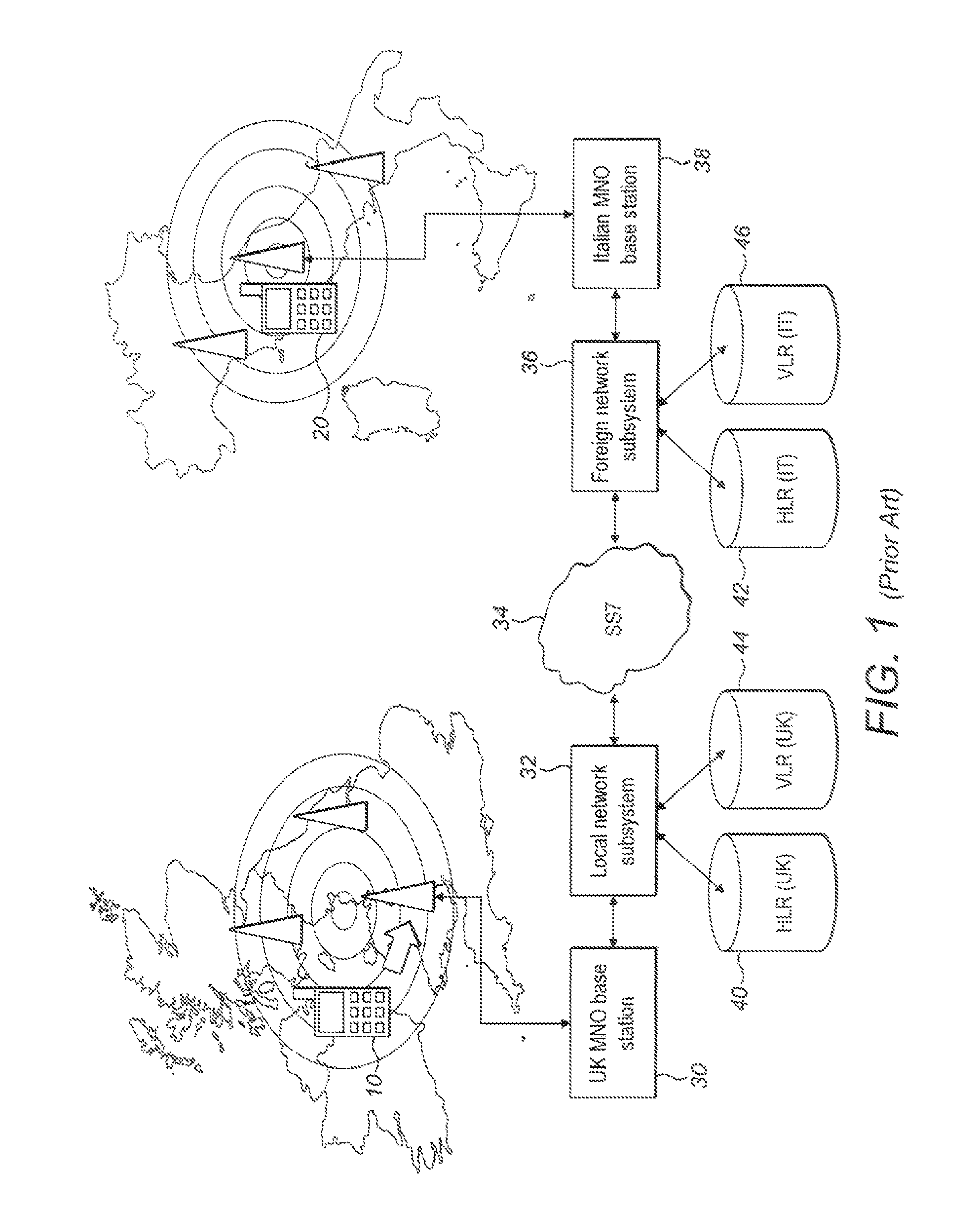
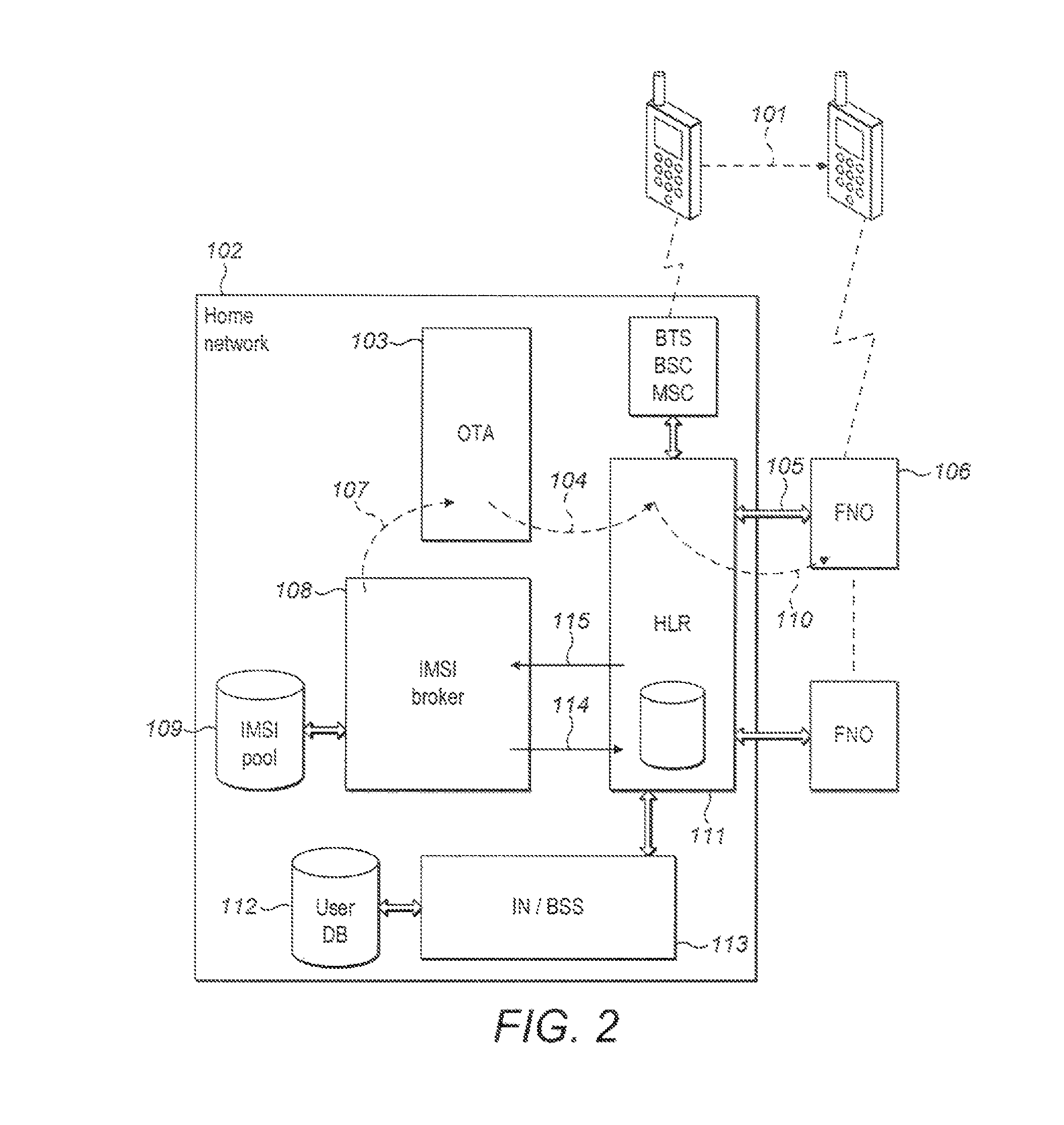
Subscriber identification management broker for fixed/mobile networks
ActiveUS8406758B2Low costEliminate chargeAssess restrictionWireless commuication servicesMobile WebCommunication device
There present invention relates to a method for managing the automatic provision of a subscriber network identifier from a central network server to a subscribed communication device, the method comprising receiving notification at the central server relating to a change in the current location for the subscribed device, and determining from the notification whether a new subscriber network identifier is to be provisioned from the central server. The method further comprises selecting a subscriber network identifier on the basis of the current location, if the determining step has determined that a new subscriber network identifier is to be provisioned, and outputting the selected subscriber network identifier for transmission to the subscribed device. The present invention also relates to managing the automatic connection of a subscribed communication device to a network, where a preferred network and preferred subscriber network identifier may be used.
Owner:TRUPHONE
Automatic flight management in an online marketplace
InactiveUS20030149622A1Reduce computing timeReduce spacingWeb data indexingAdvertisementsWeb search queryData mining
A database search system includes a database of search terms, each search, term associated with a bid amount payable by an advertiser of a plurality of advertisers and a search engine responsive to search queries from searchers for searching the database. A flight management agent is responsive to advertiser-specified parameters for adjusting bid amounts of search listings to manage expenditures over a time interval.
Owner:R2 SOLUTIONS
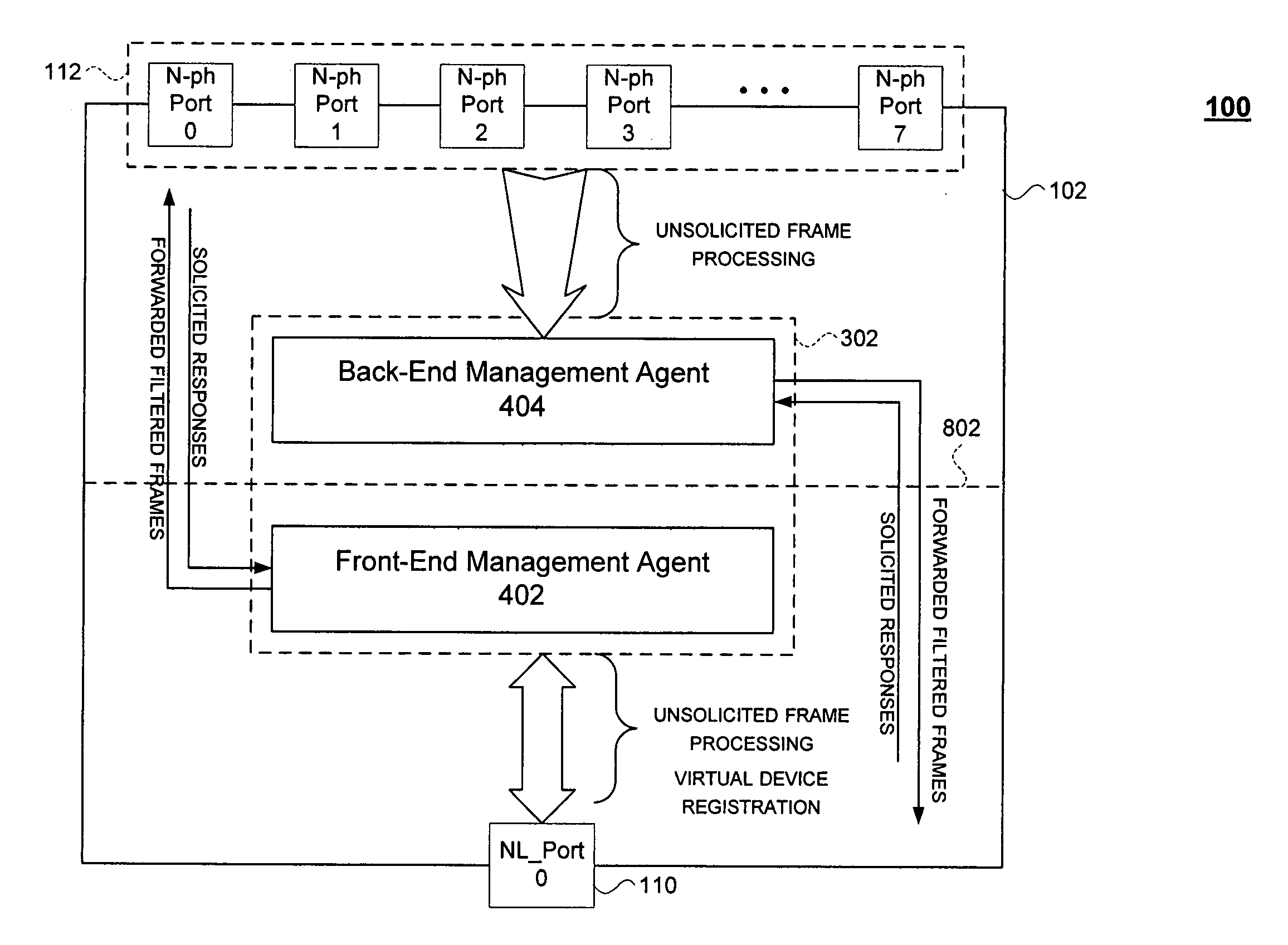
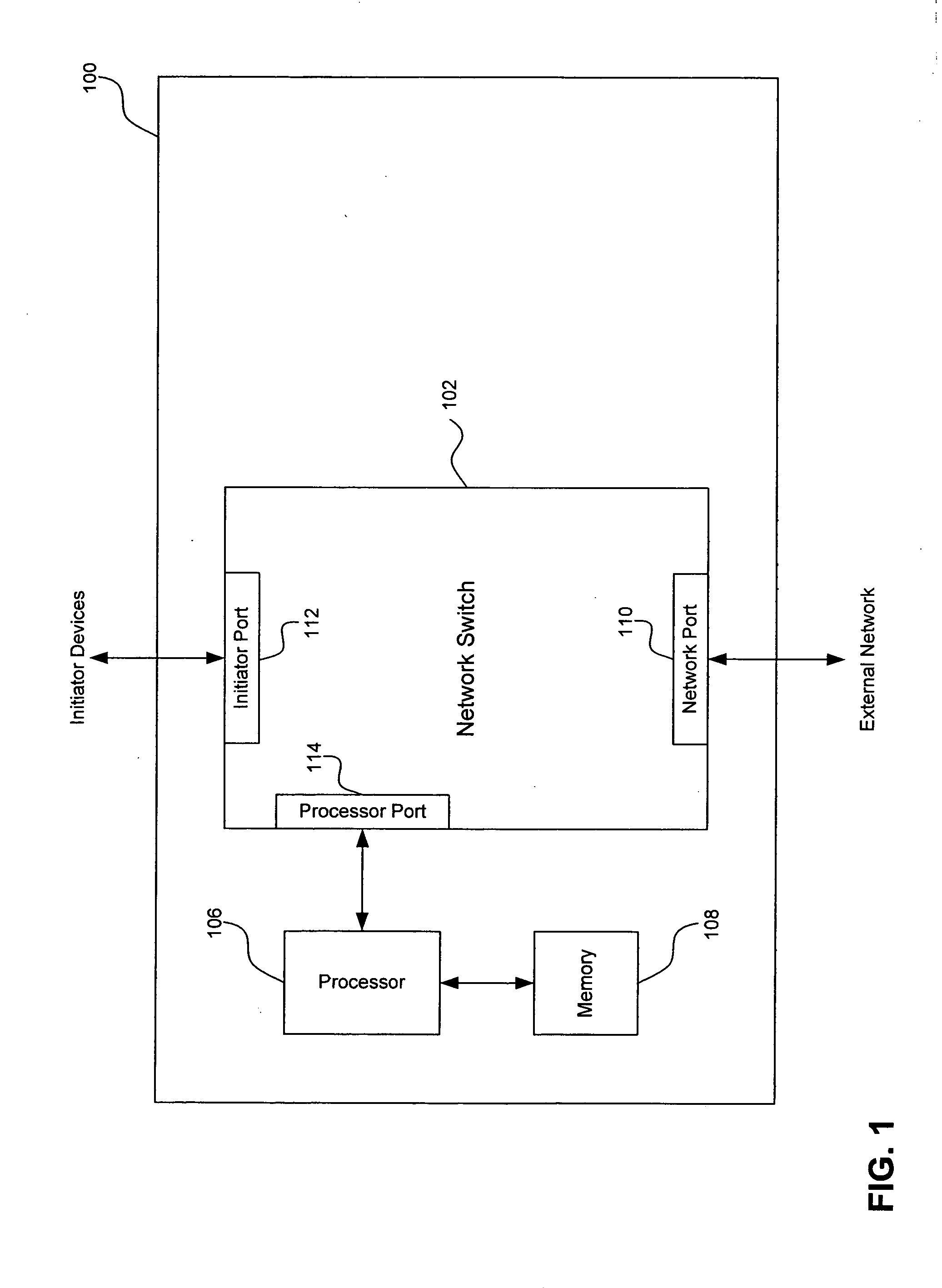
Apparatus and system for coupling and decoupling initiator devices to a network using an arbitrated loop without disrupting the network
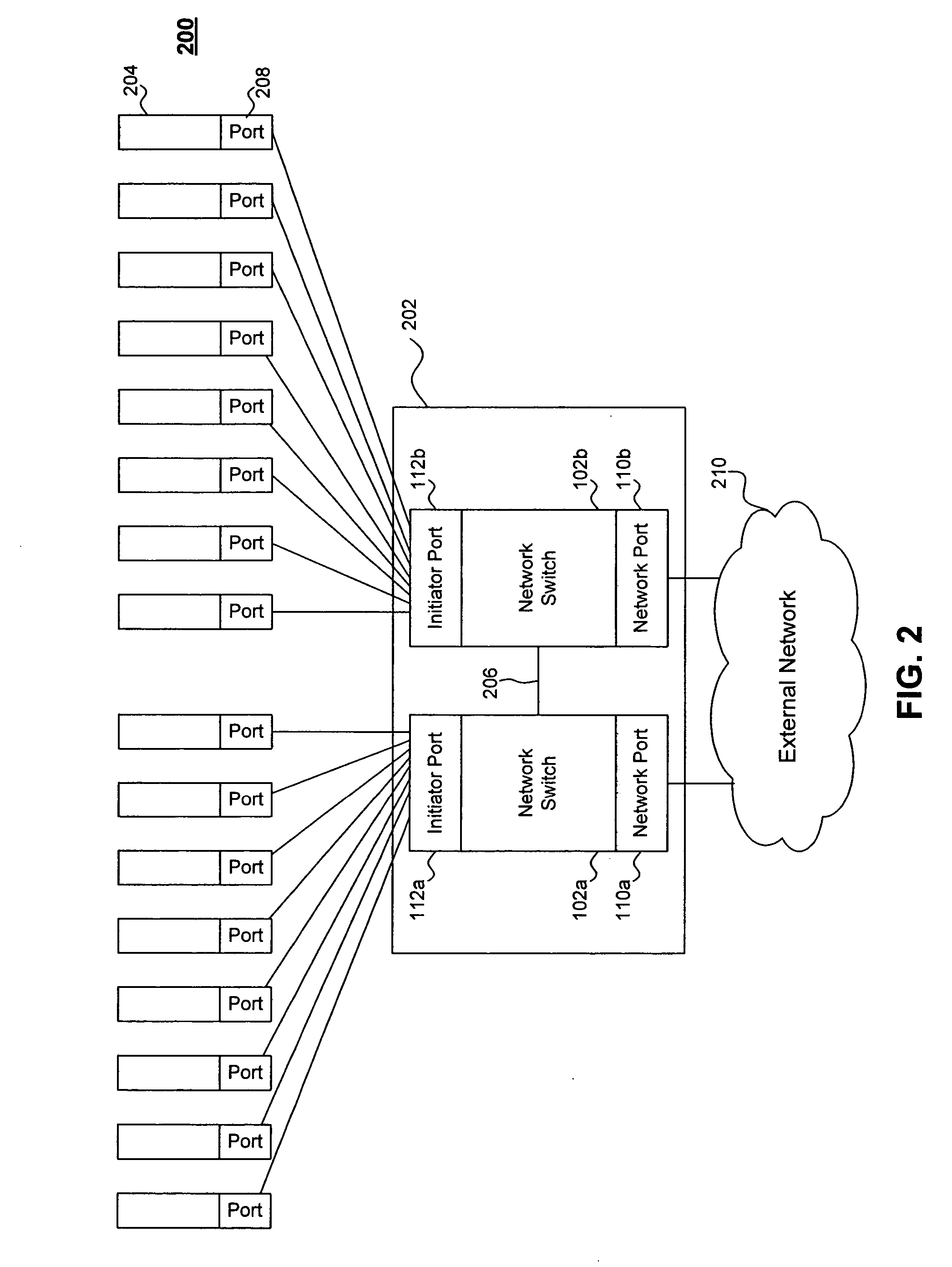
InactiveUS20060034192A1Easy to switchMinimal numberMultiplex system selection arrangementsData switching by path configurationEngineeringManagement agent
The present invention enables the coupling and decoupling of multiple processing devices to a network without disrupting the network. In an embodiment, the invention provides a switch having a network port and several initiator ports each configured for coupling to a processing device. The switch is configured to route data from the network port to the initiator ports and from the initiator ports to the network port. A management agent facilitates operation of the switch by processing port initializations, replying to device registration requests, and processing predetermined unsolicited discovery commands. During operation, the management agent enables configuration changes caused, for example, by the coupling and / or decoupling of processing device to initiator ports.
Owner:AVAGO TECH INT SALES PTE LTD
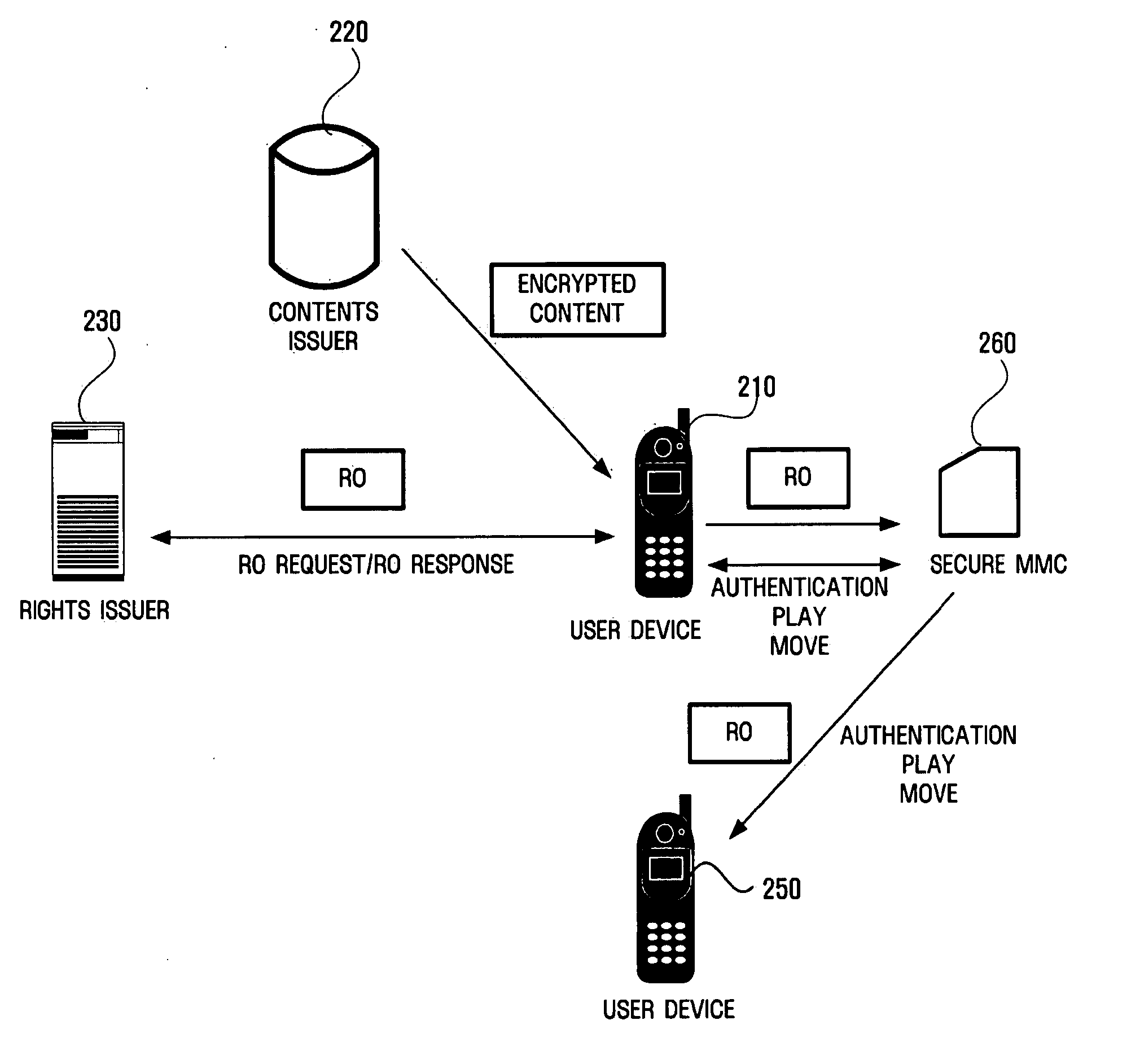
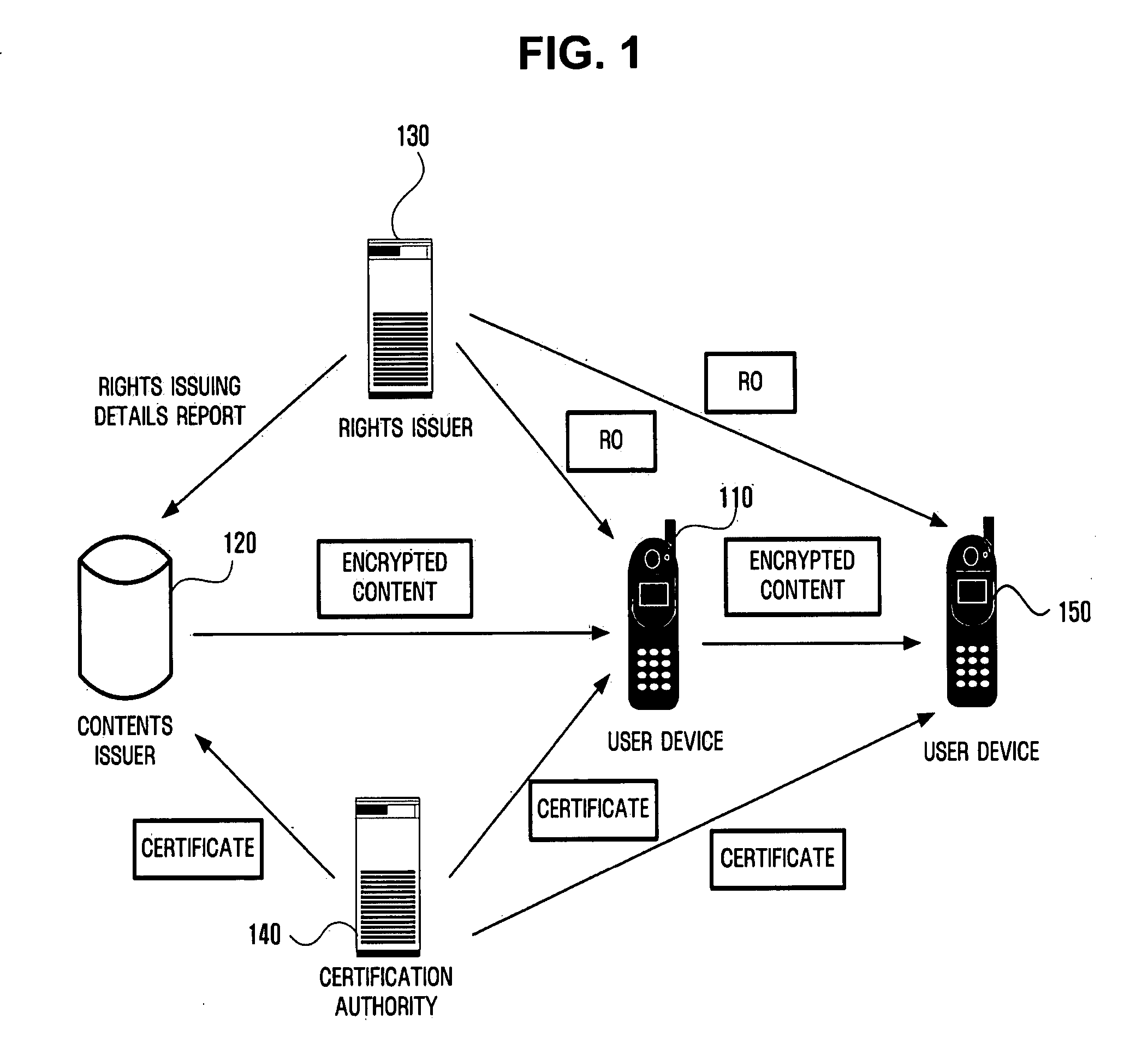
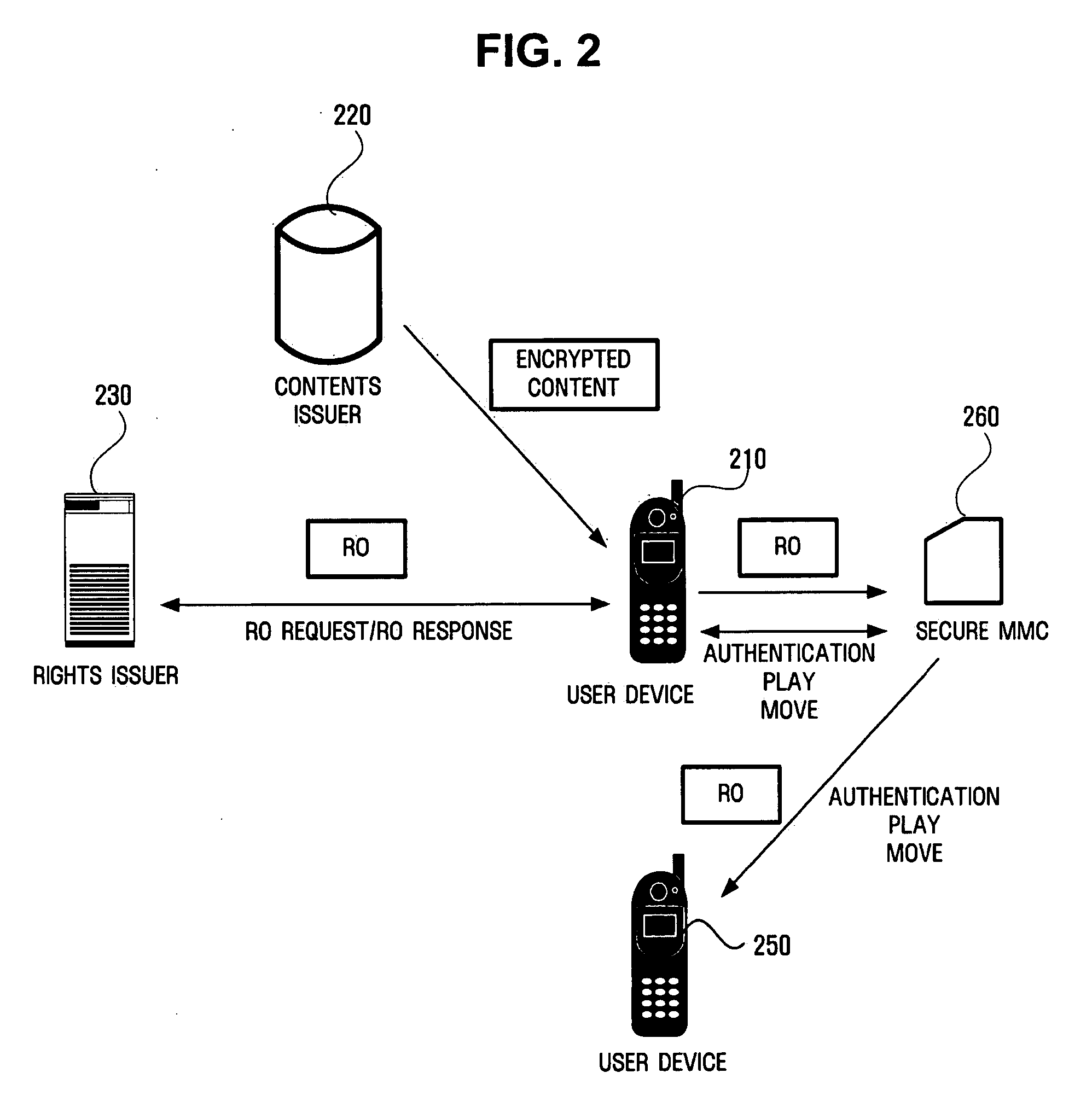
Apparatus and method for sending and receiving digital rights objects in converted format between device and portable storage
InactiveUS20050267845A1Reduce loadImprove data transfer efficiencyKey distribution for secure communicationUser identity/authority verificationComputer hardwareTransceiver
An apparatus and method for sending and receiving a digital rights object (RO) in a converted format between a device and a portable storage are provided. The device includes a transceiver module receiving a RO from a rights issuer, an RO converter module converting the RO received by the transceiver module into a format for communication with a portable storage, an interface module for connection with the portable storage, a public-key encryption module authenticating with the portable storage connected through the interface module, a session key generation module generating a session key shared with the authenticated portable storage, and a digital rights management (DRM) agent providing the RO in the format converted by the RO converter module to the portable storage and receiving a RO in the converted format from the portable storage. The device converts the format of the RO to communicate with the portable storage.
Owner:SAMSUNG ELECTRONICS CO LTD
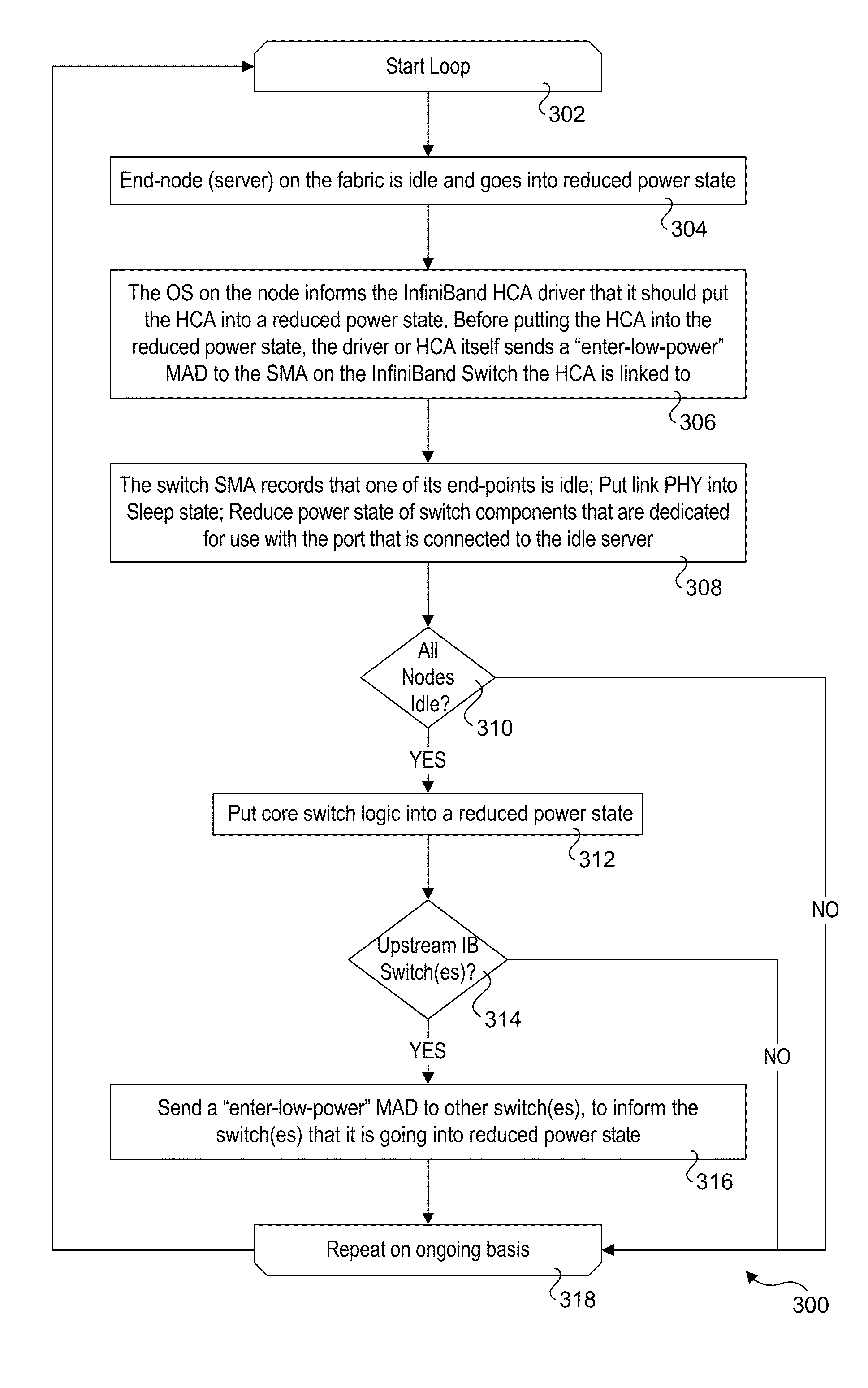
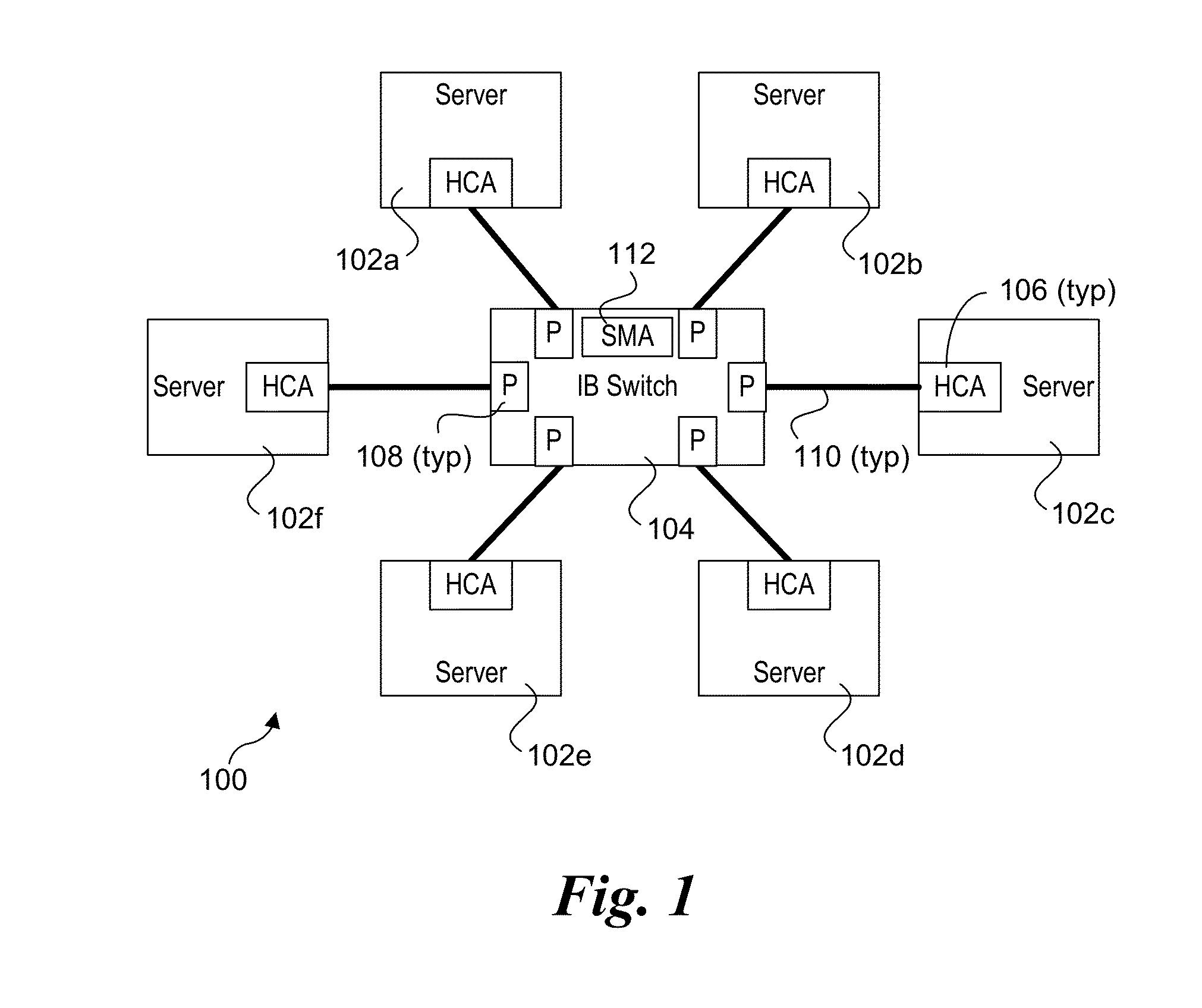
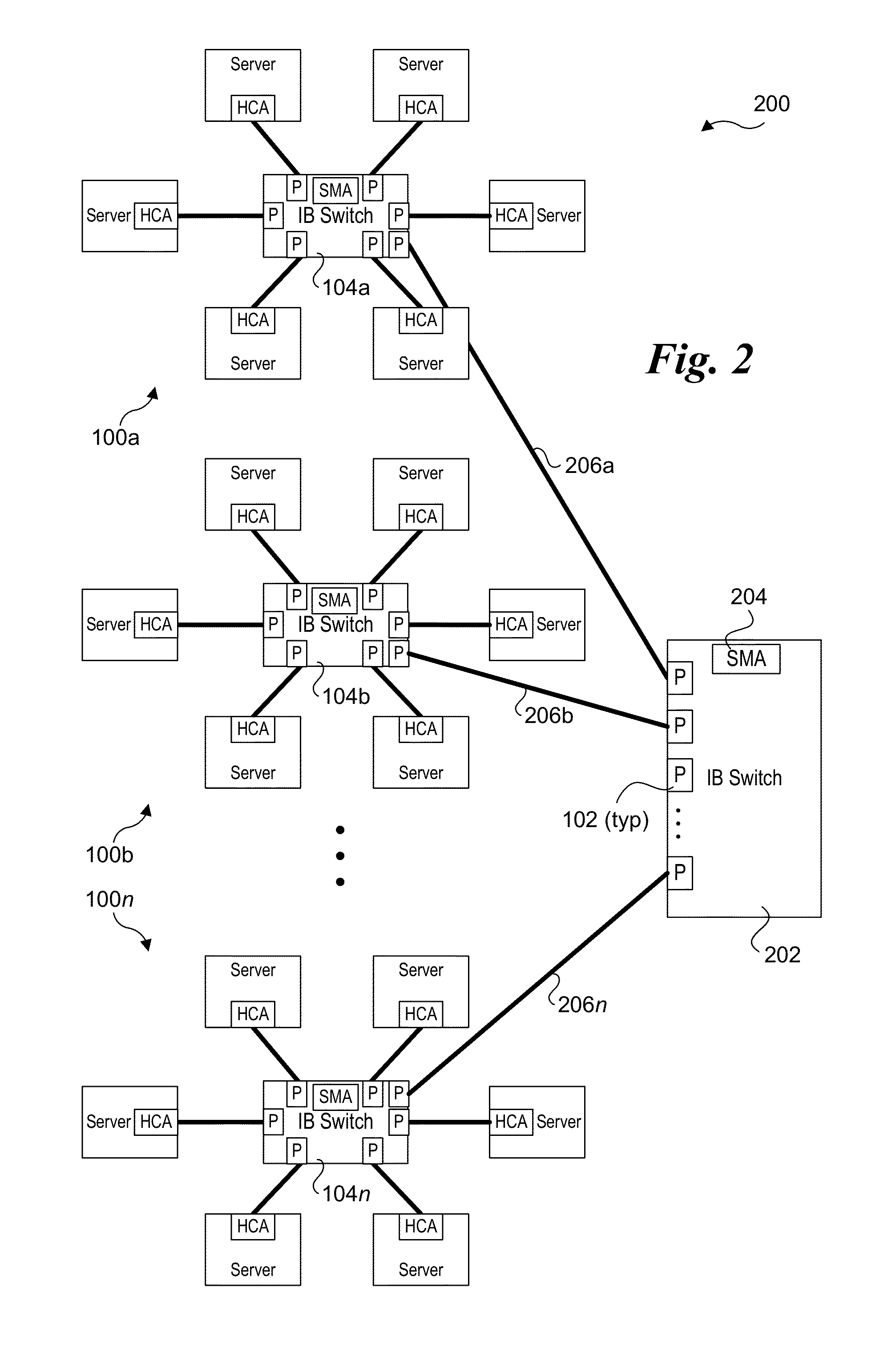
Power management of infiniband switches
ActiveUS20150338909A1Power supply for data processingEnergy efficient computingMulti portComputer science
Methods for performing power management of InfiniBand (IB) switches and apparatus and software configured to implement the methods. Power management datagrams (MADs) are used to inform IB switches that host servers connected to the IB switch's ports are to transition to a reduced-power or offline state or have returned to a normal operating state. A subnet management agent (SMA) on the IB switch receives the power MADs from the host servers and tracks each server's operating state. In response to power down MADs, the SMA coordinates power reduction of the switch's ports and other switch circuitry. For switches with multi-port IB interfaces, a multi-port interface is caused to enter a reduced-power state when all of its ports are connected to host servers that are idle or offline. Additionally, when all of a switch's ports are connected to idle or offline servers the SMA may put the switch's core switch logic into a reduced-power state. Power MADs are also used to inform upstream IB switches when a switch is to transition to a reduced power state or has returned to a normal operating state.
Owner:INTEL CORP
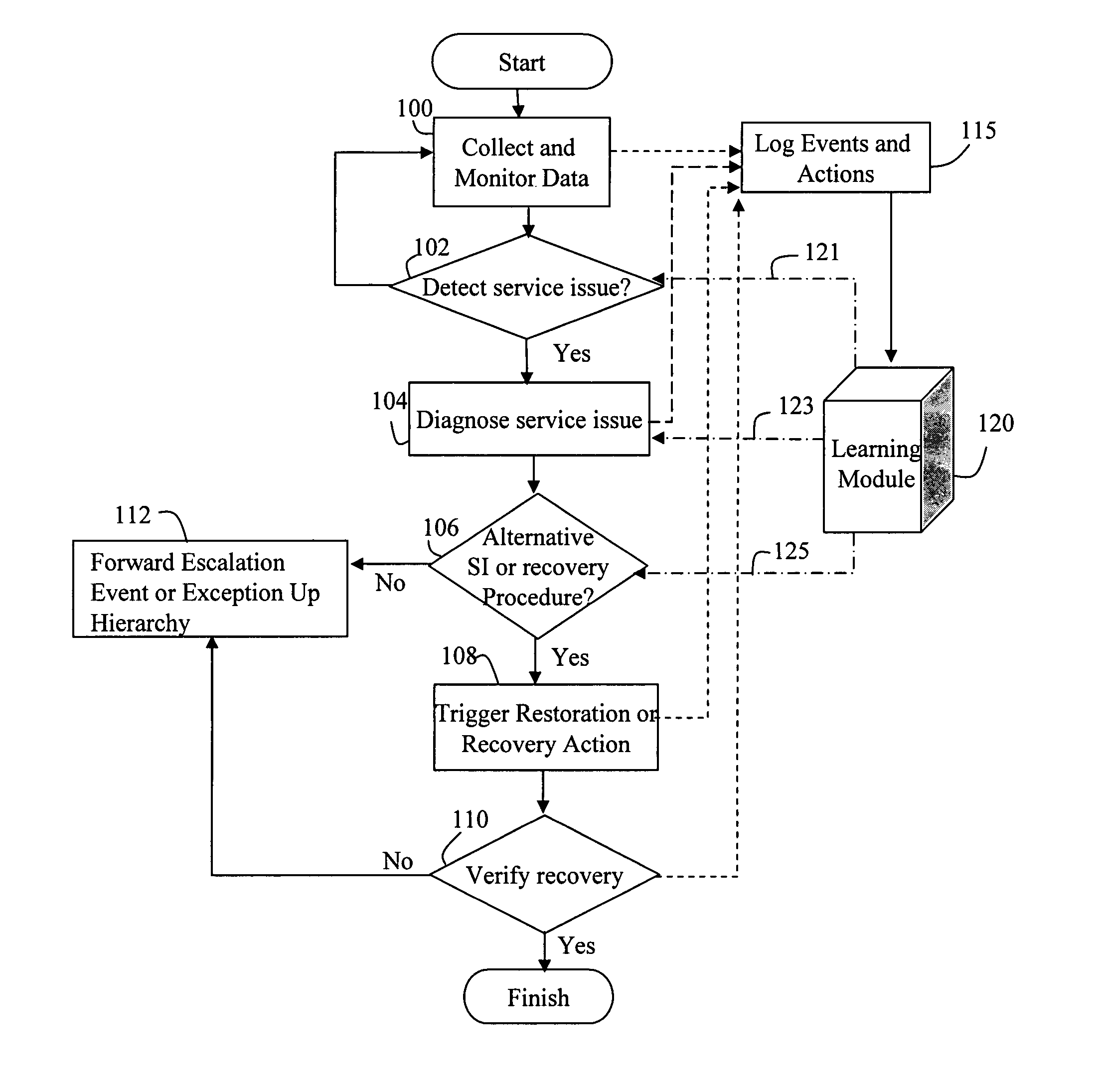
Method and apparatus for enabling dynamic self-healing of multi-media services
ActiveUS7580994B1Enabling recoveryEnabling restorationDigital computer detailsTransmissionSelf-healingService component
In the service architecture of the invention, each service is viewed as a hierarchical arrangement of service components. At least one management agent is associated with each layer, and is used to manage and preserve the expected performance of the service components. The management agents cooperatively exchange management information regarding the service components at their layers to permit service self-management and self-healing, enabling restoration and recovery with minimum or no human intervention.
Owner:GENBAND US LLC
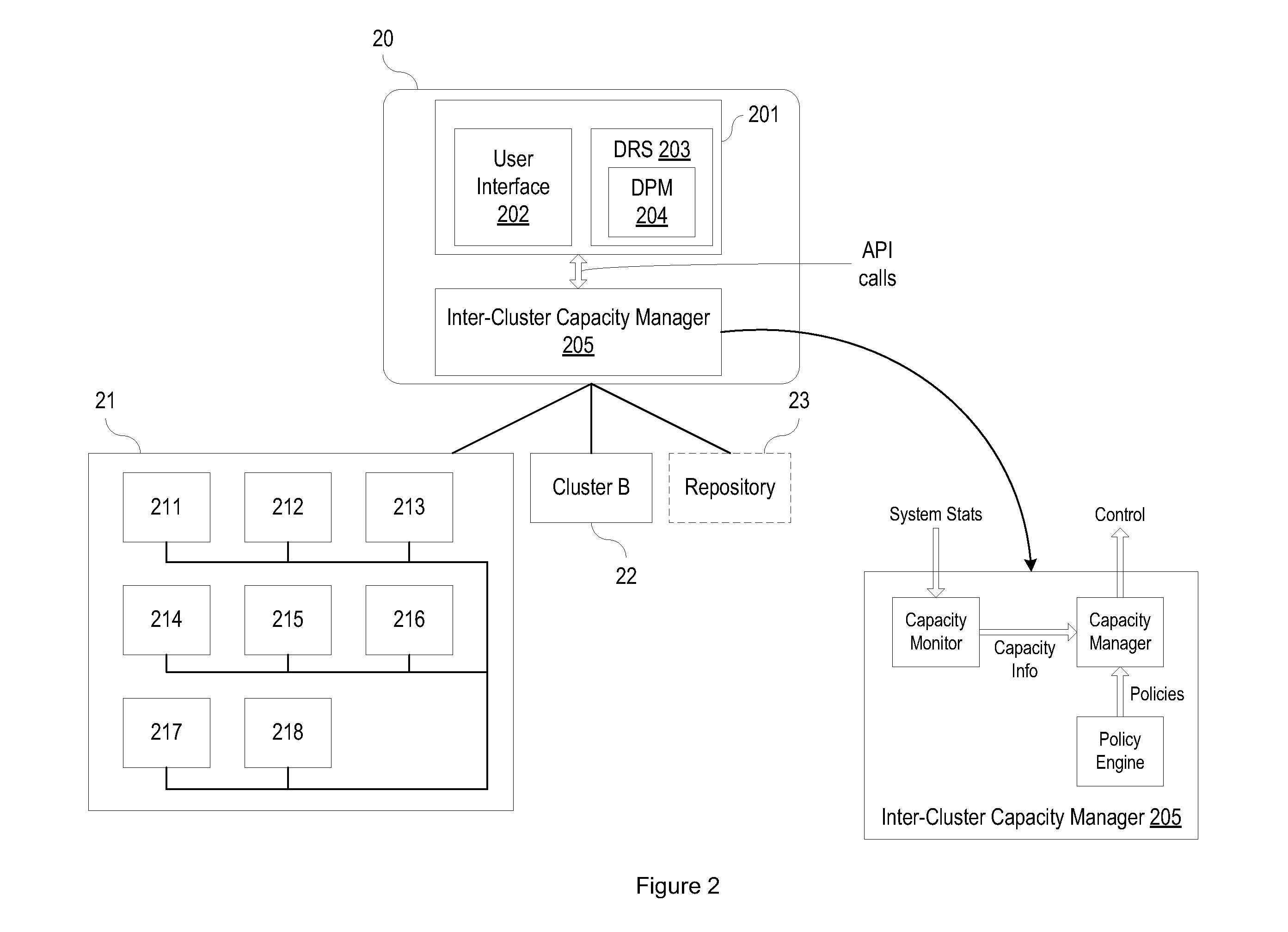
System and Method for Automatically Optimizing Capacity Between Server Clusters
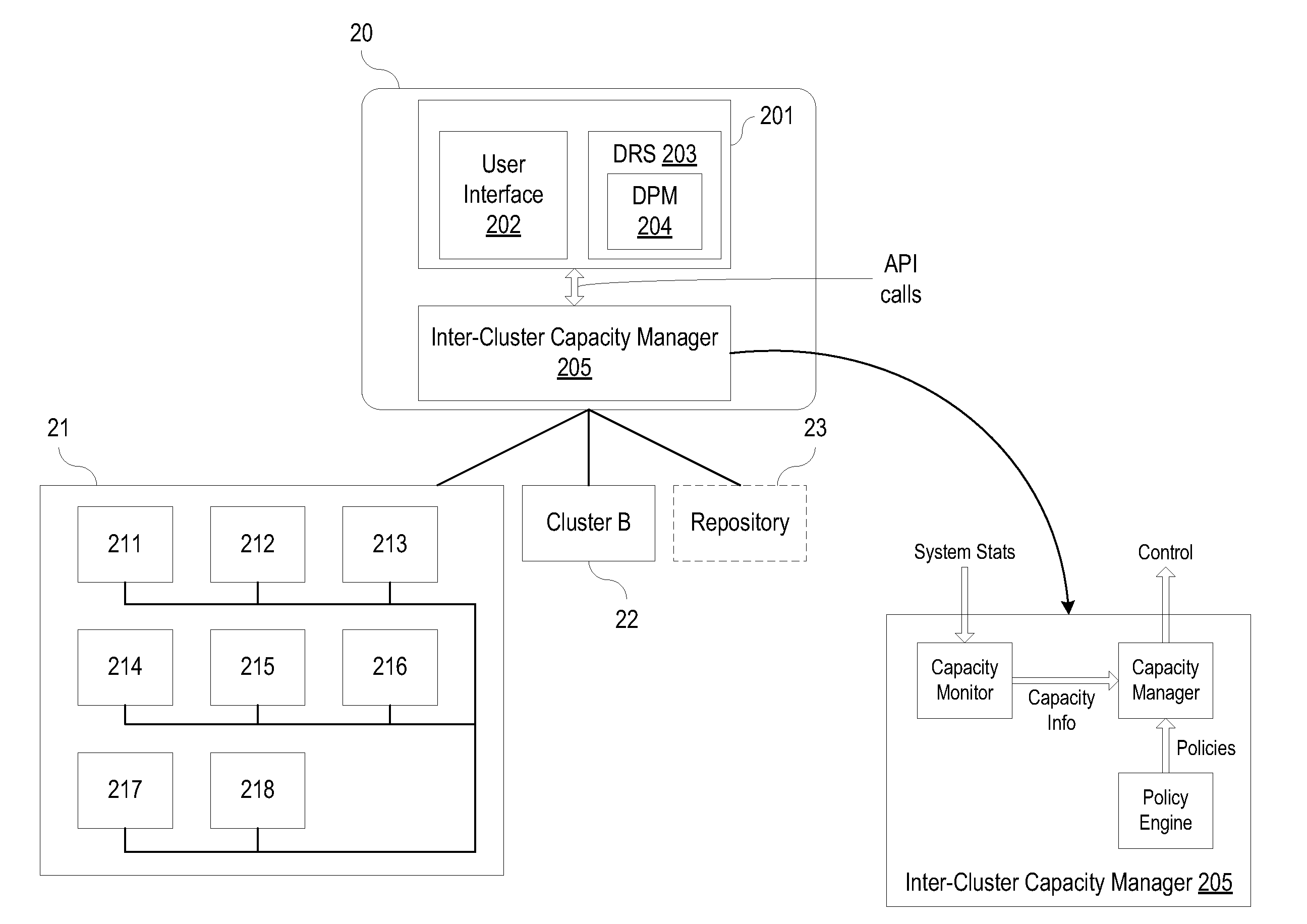
ActiveUS20110191477A1Automatically optimizing capacityEnable balancingError detection/correctionDigital computer detailsResource Management SystemDistributed computing
A resource management system for a virtual machine computing environment includes a software component that optimizes capacity between server clusters or groups by monitoring the capacity of server clusters or groups and automatically adding and removing host systems to and from server clusters or groups. The software component may be implemented at a server cluster management level to monitor and execute host system moves between server clusters and / or at a higher level in the resource management hierarchy. At the higher level, the software component is configured to monitor and execute host system moves between sets of server clusters being managed by different server cluster management agents.
Owner:VMWARE INC
Method and apparatus for modifying a computer program in a trusted manner
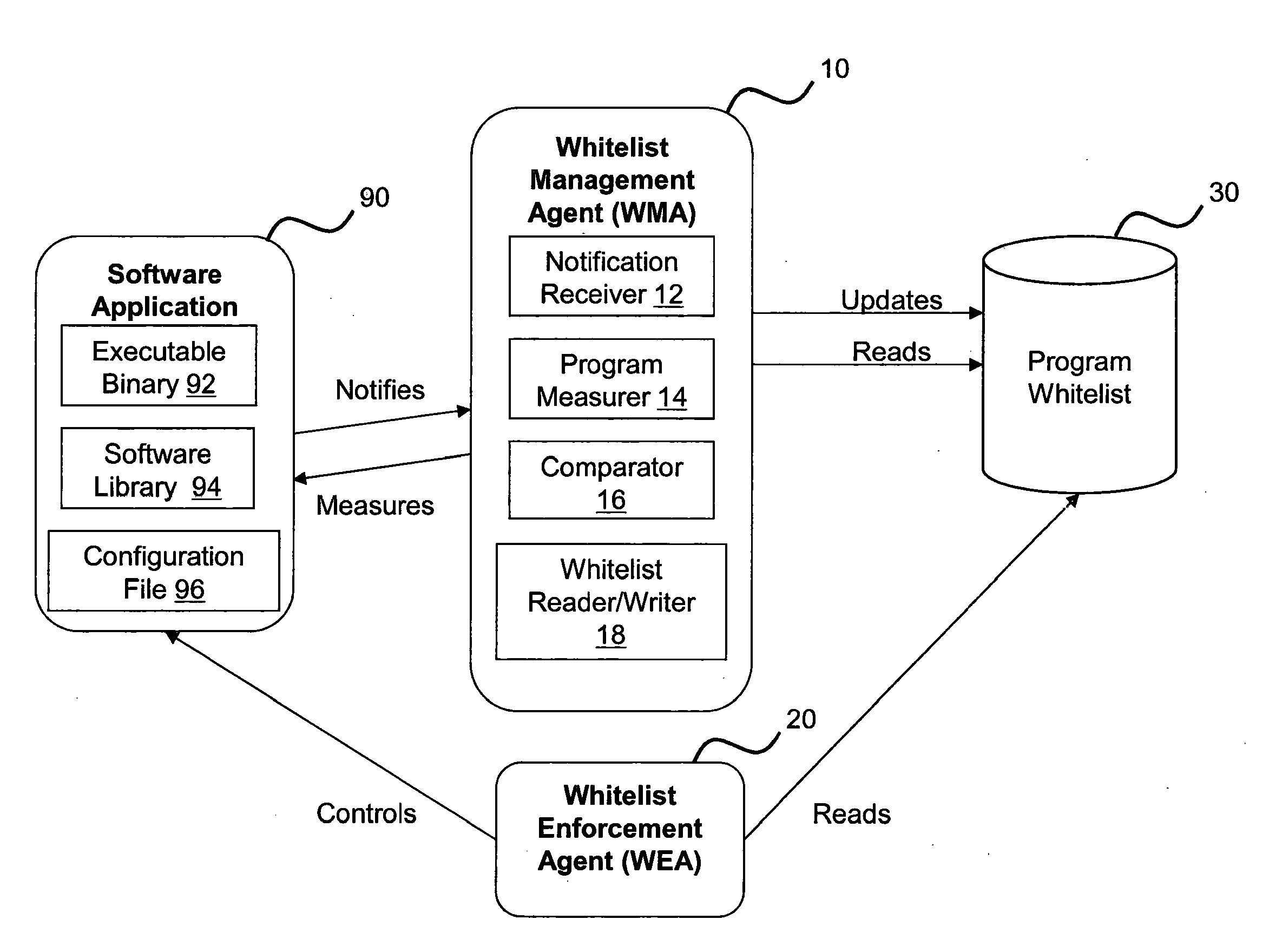
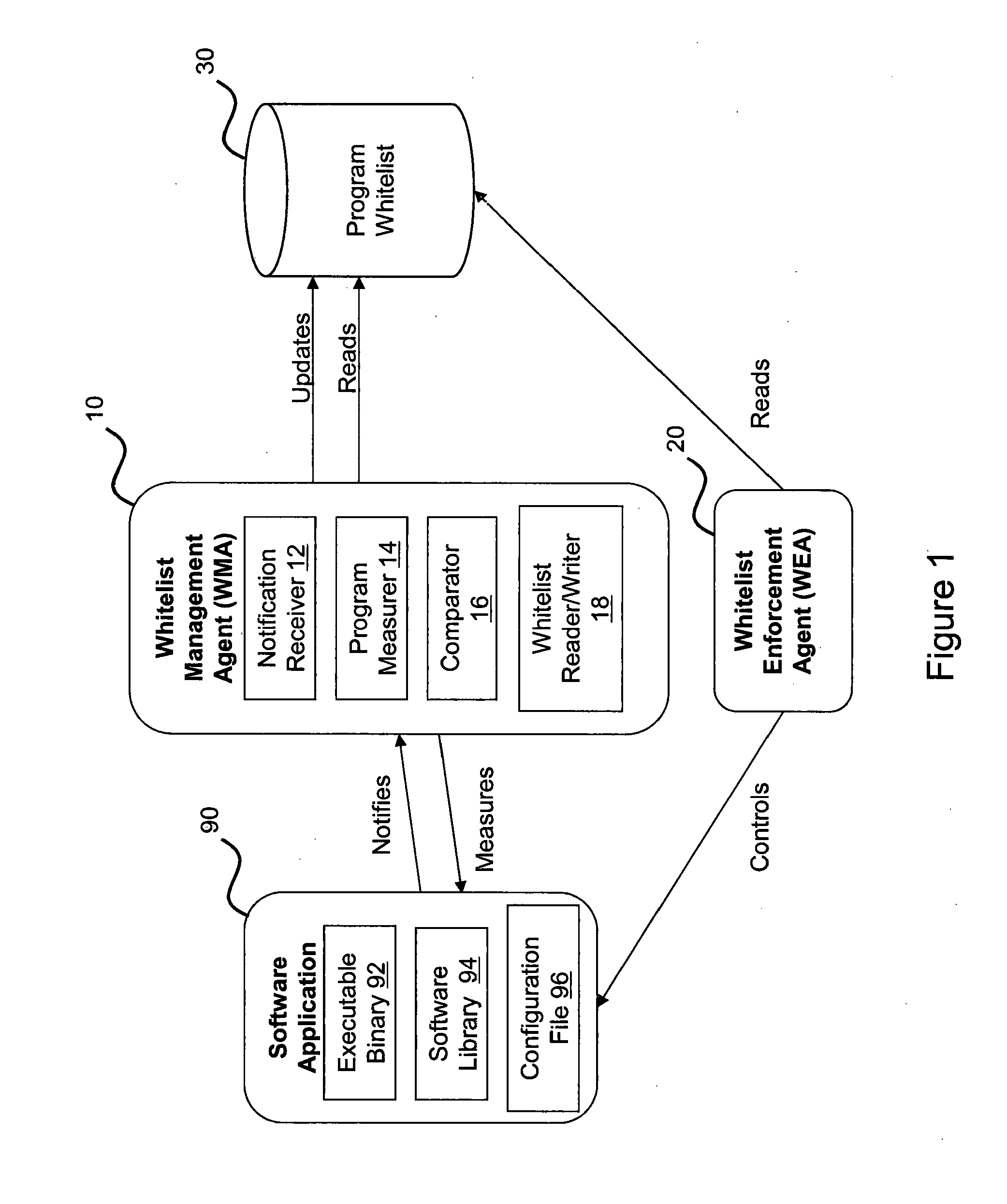
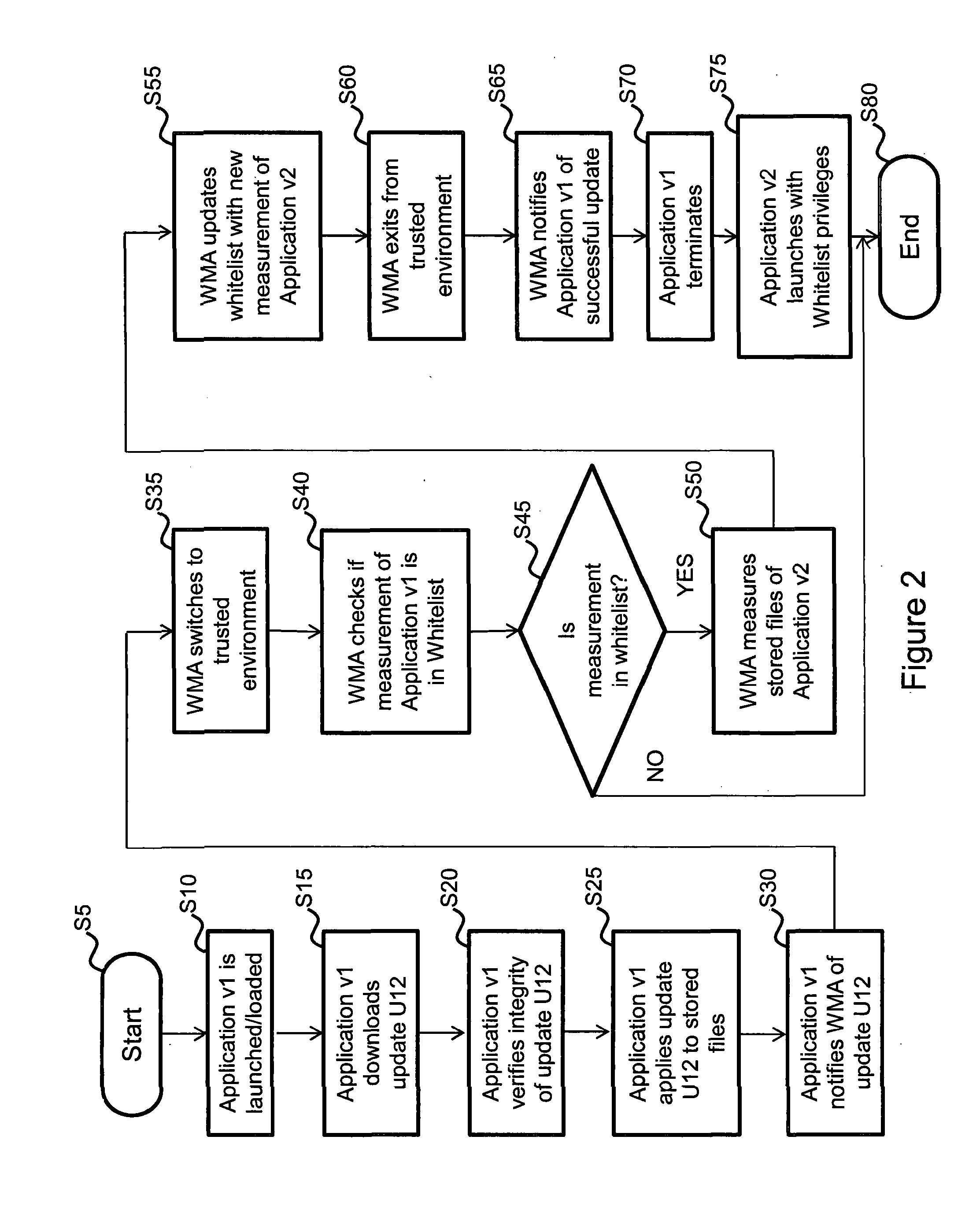
ActiveUS20160203313A1Delay minimizationIncreased complexityMemory loss protectionError detection/correctionNotification ReceiverComputer module
A computer system having a system memory and being arranged to permit a target program (90) installed on the system to be modified in a trusted manner. The system comprises a White-list Management Agent, WMA, module (10) for receiving, at a notification receiver (12), a notification that the target program (90) which is loaded into the system memory of the computer system has performed an update operation on the target program resulting in the generation and storage of a modified version of the target program on a storage device associated with the computer system. The WMA module is operable, upon receipt of a target program update notification, to determine if the program (90) as loaded into the system memory is in a trusted state by measuring the program (90) using a program measurer module (14) and comparing this, using a comparator (16), with a pre-stored value contained in a program whitelist (30), the pre-stored value being obtained from the program whitelist (30) using a whitelist reader / writer (18). If the determination is positive, the WMA module (10) generates a hash code of the modified version of the target computer program as stored on the storage device using the program measurer module (14) and stores this generated hash code as a new trusted hash code for the target program in the program whitelist (30), in order to permit subsequent verification of the modified version of the target program as being in a trusted state.
Owner:BRITISH TELECOMM PLC
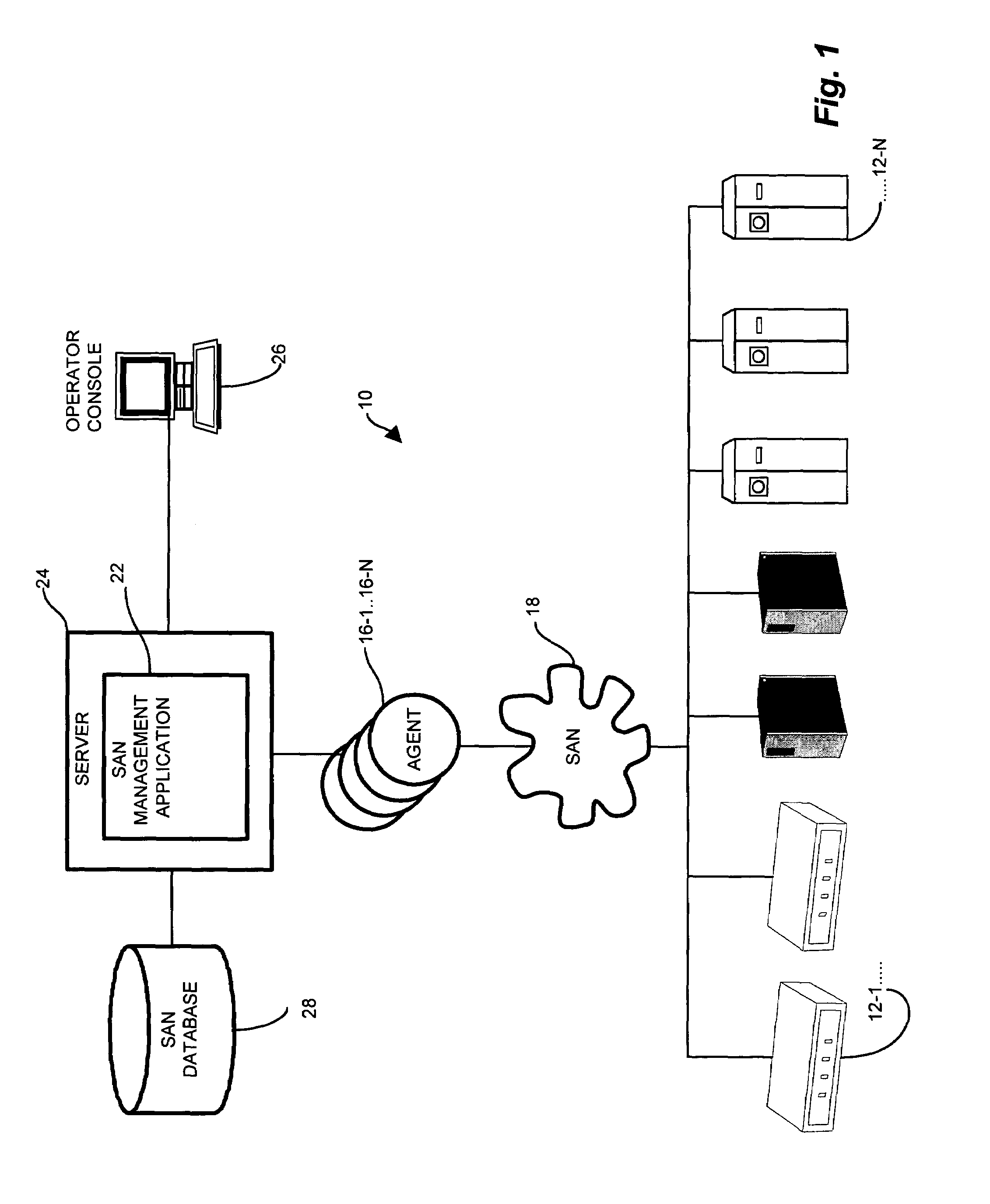
Universal computer management interface
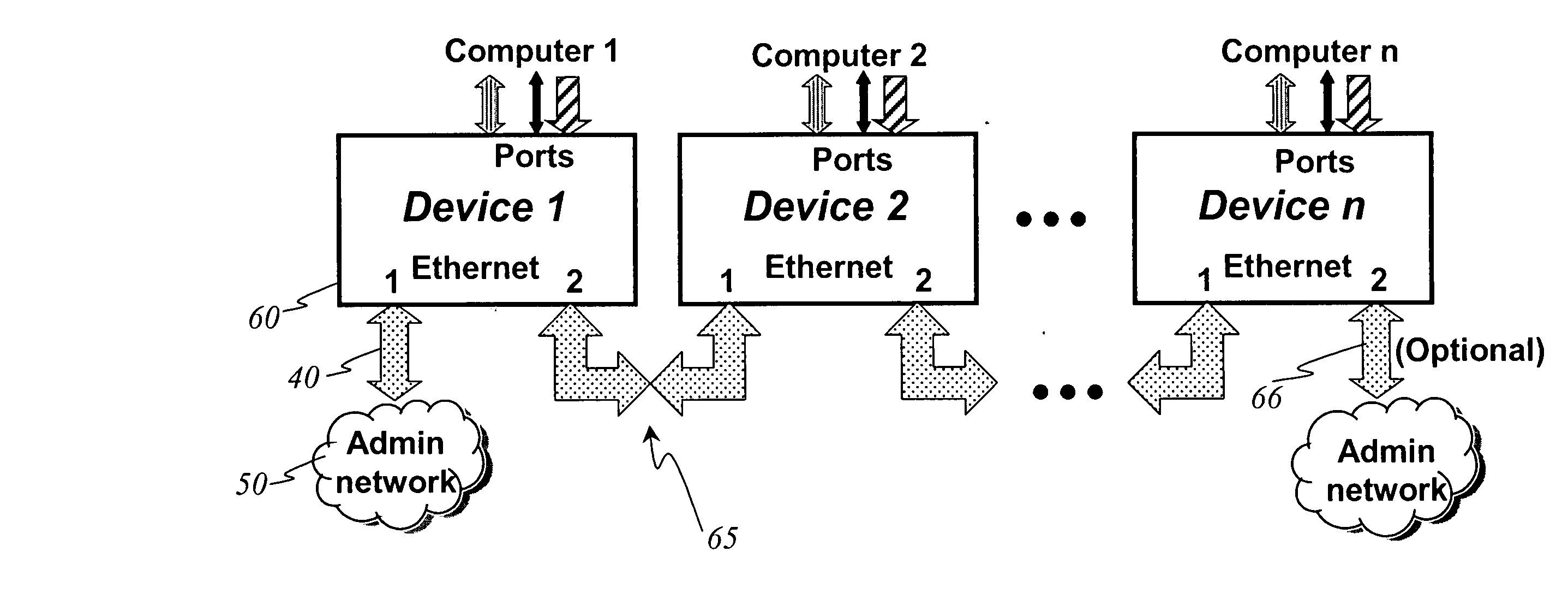
ActiveUS20070206630A1Efficient cablingEliminate needDigital computer detailsTime-division multiplexOperational systemNetwork connection
An integrated computer management apparatus allowing a networked administrator to manage a computer via multiple connection types and protocols. A preferred embodiment of the device has a network connection for the administrative users, coupled via an internal Ethernet switch and a processor to keyboard-video-mouse, serial, and Ethernet computer connections. Depending on hardware characteristics, operational status, OS, and administrator preferences any of these may be used to provide remote computer system management functions. Software running on the processor can provide direct logical connection between the remote administrator and a management port; may serve web pages graphically interpreting data gleaned from one or more of the connections; can provide protocol translation or proxy services; or locally execute an intelligent management agent. The device can be physically small enough to be supported by its connecting cables, and receives power from the attached computer.
Owner:LANTRONIX
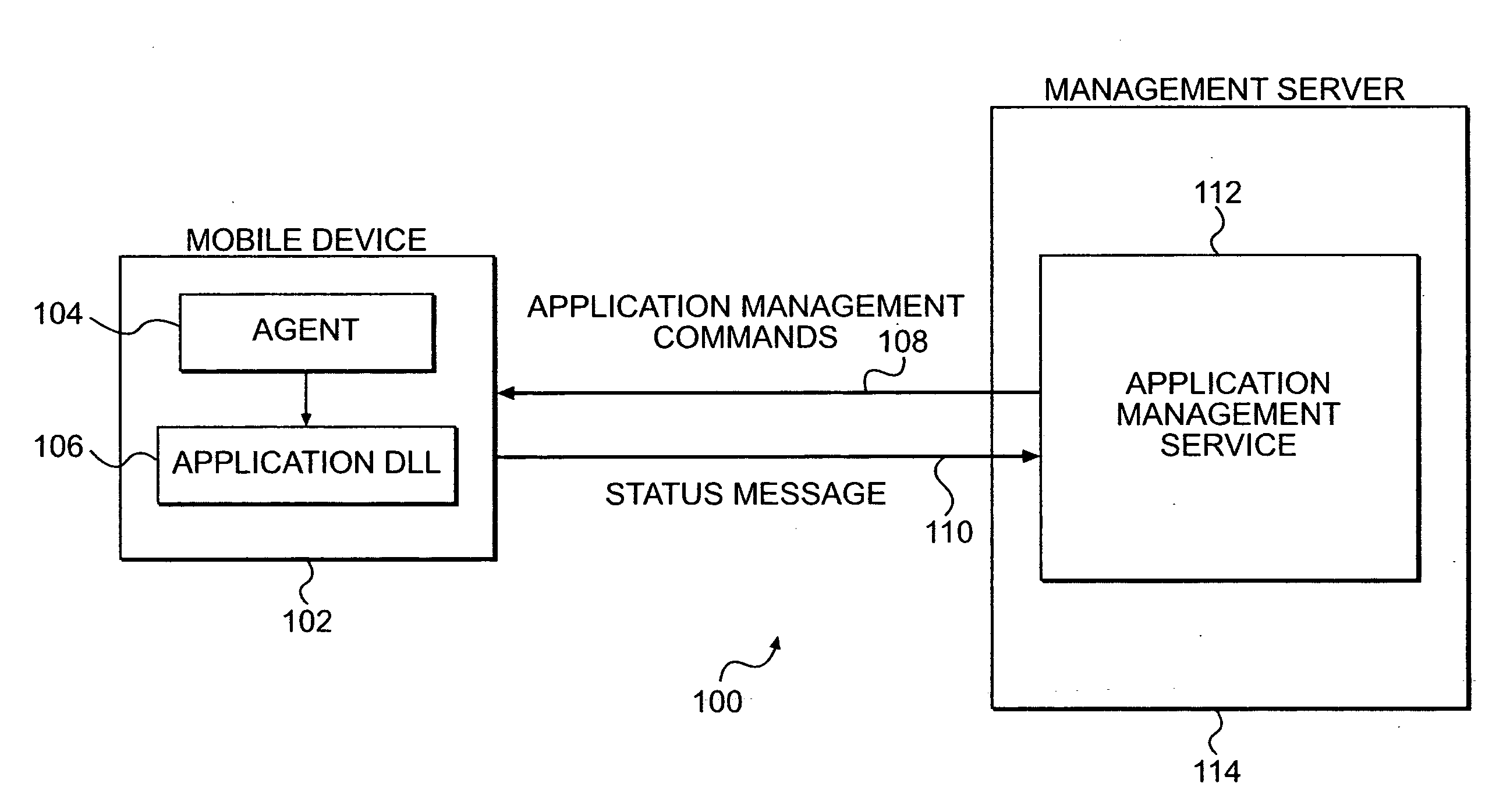
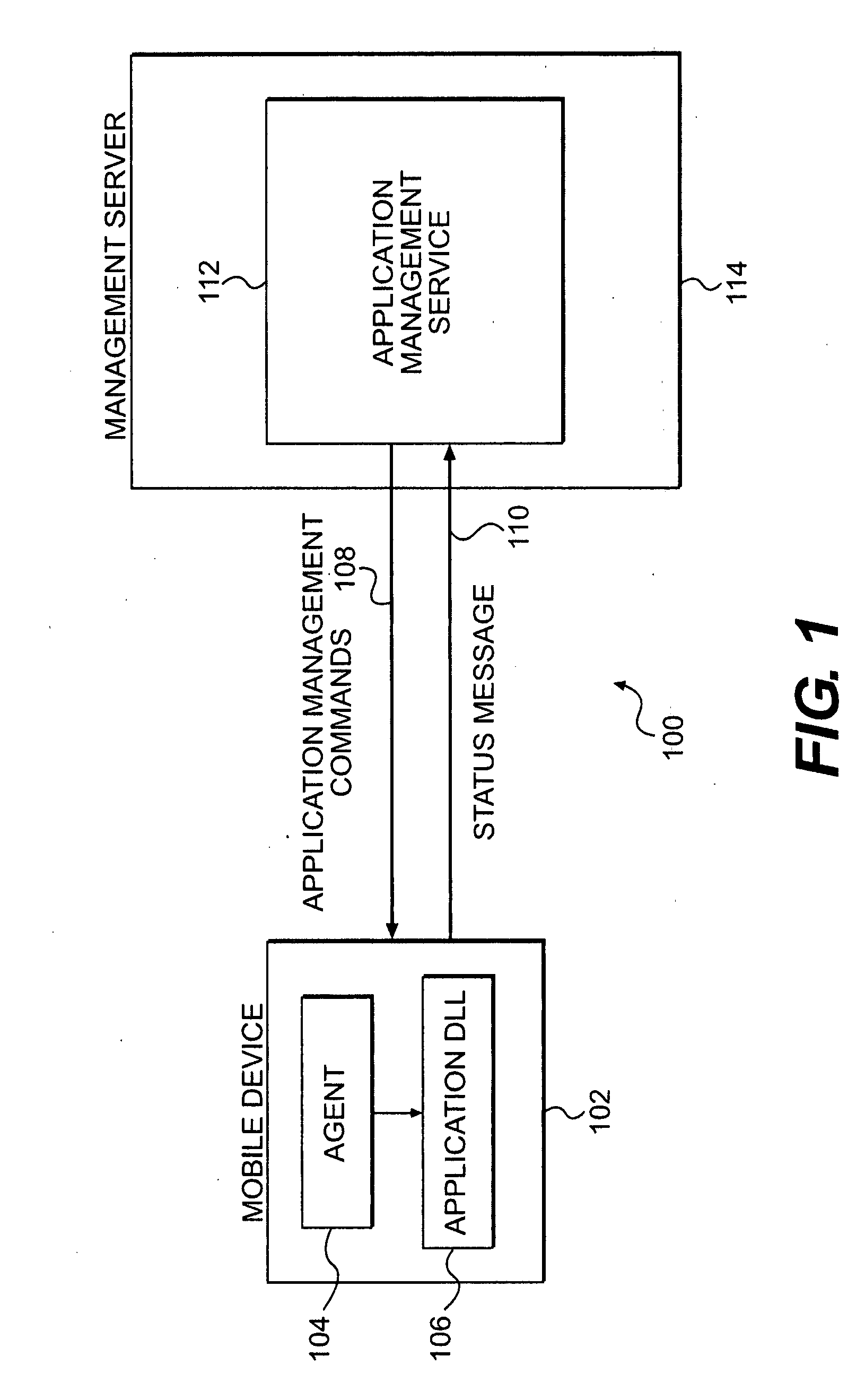
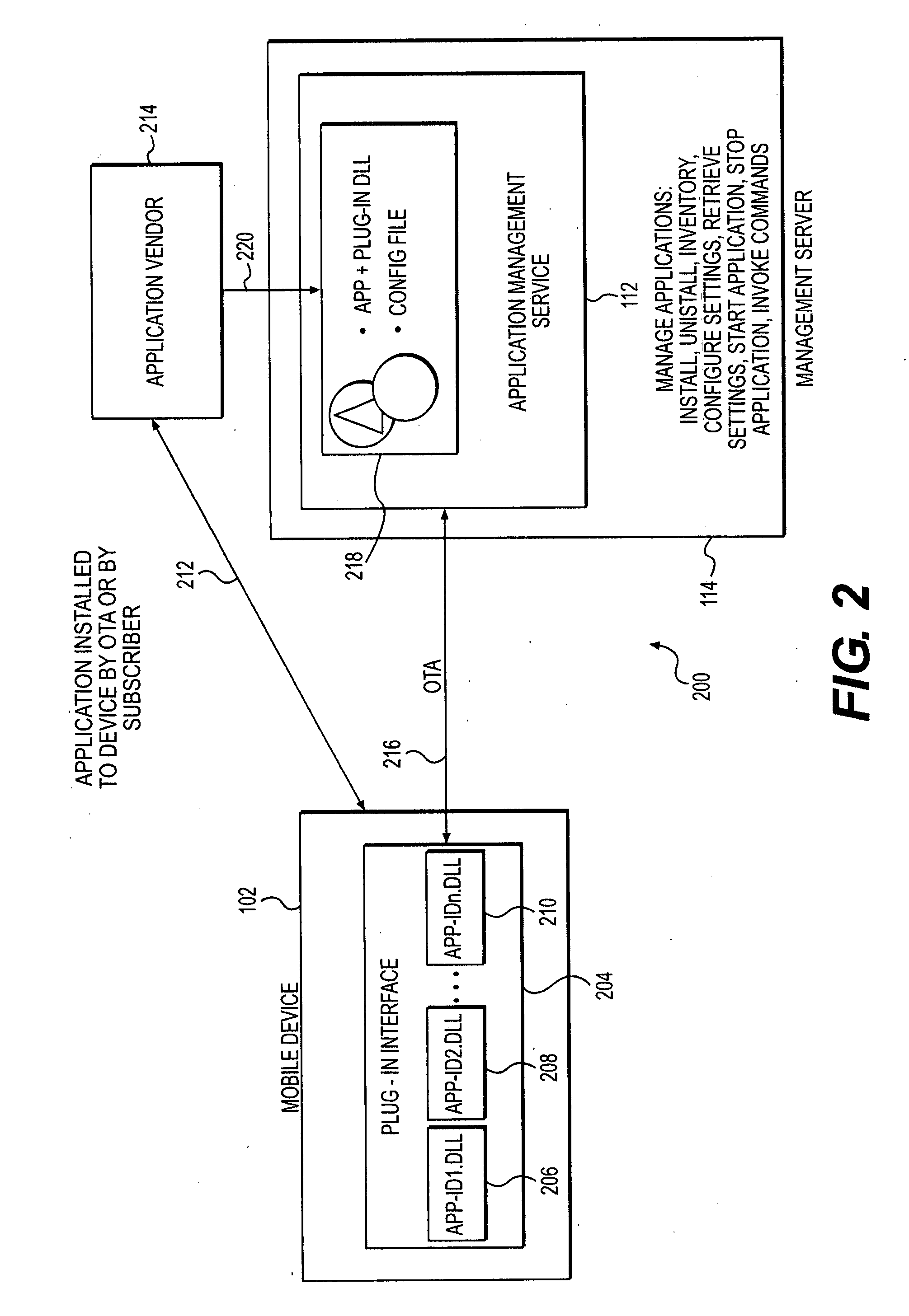
System and method to provide application management on wireless data terminals by means of device management agent and dynamic link libraries
ActiveUS20080064383A1Supporting applicationIncrease valueSubstation equipmentAutomatic exchangesThird partyApplication lifecycle management
The present invention relates to a system and method of remote application management on wireless data terminals using a device management agent and dynamic link libraries provided by the application. Third party applications on a wireless device can communicate and be controlled by a remote management server via a management client plug-in interface.
Owner:ALCATEL LUCENT SAS +1
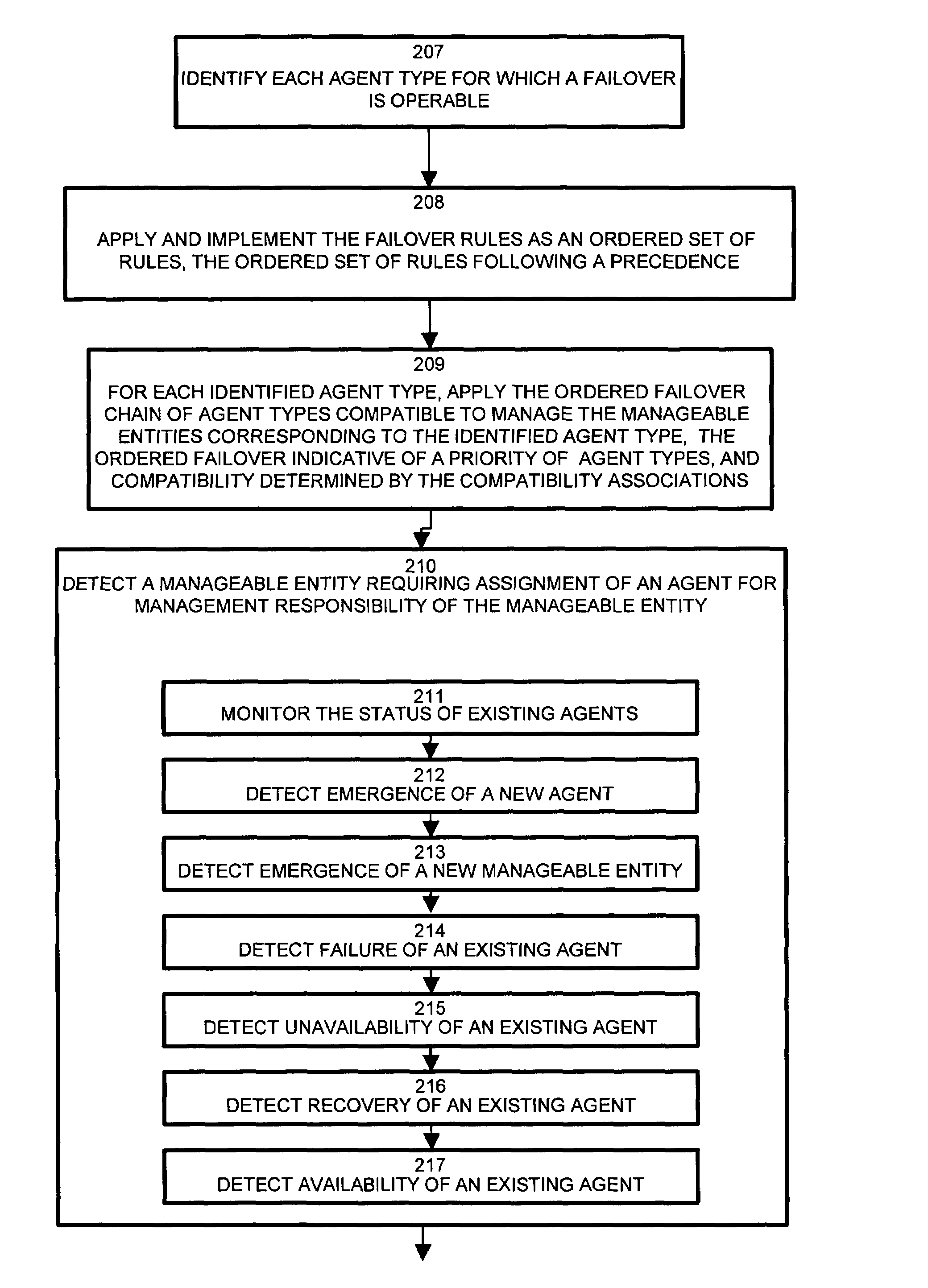
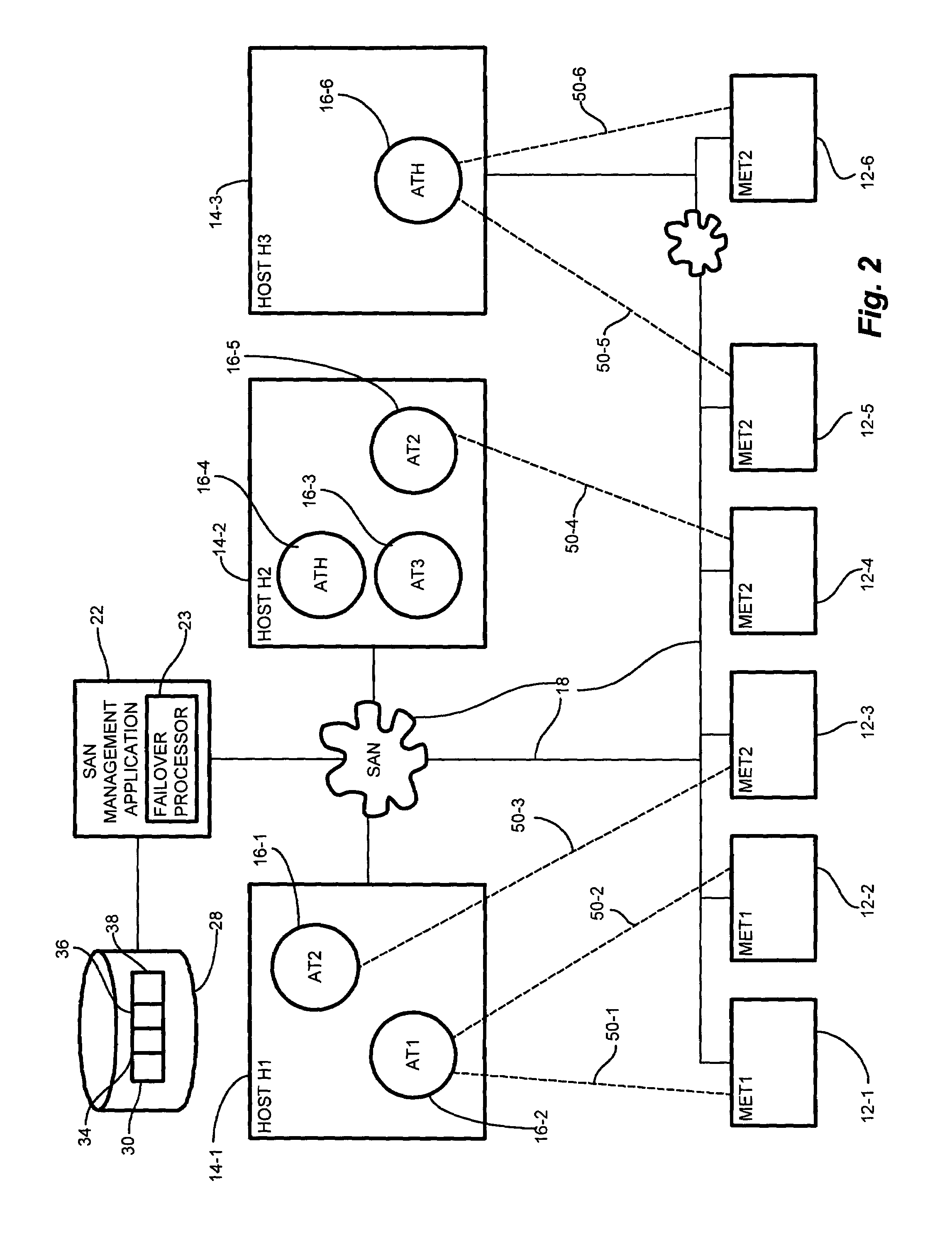
System and methods for failover management of manageable entity agents
In a managed information network, unavailable agents have a detrimental effect on user access to manageable entities. Intelligent, optimal assignment of manageable entities to available agents becomes a formidable task, particularly in a large storage area network. The task becomes especially complex when there are deployed agents of different types capable to manage a different scope of functionality of managed elements of the same type. A failover processor provides reliable, rule based methods for initial assignment of manageable entities (elements) to best available management agents, and a reliable, dynamic, rule based mechanism to reallocate manageable entities to a best management agent in case when current agent, responsible for element management, become unavailable or new best agent for element management starts up. A prioritized list of failover rules specifies metrics for determining alternate agents for manageable entities in the event agents become unavailable. A failover chain, or list of agent types, identifies preferential agent types to which the reassigned manageable entities correspond. Successive prioritization rules apply in the event that multiple candidate agents of the failover chain selection are available.
Owner:EMC IP HLDG CO LLC
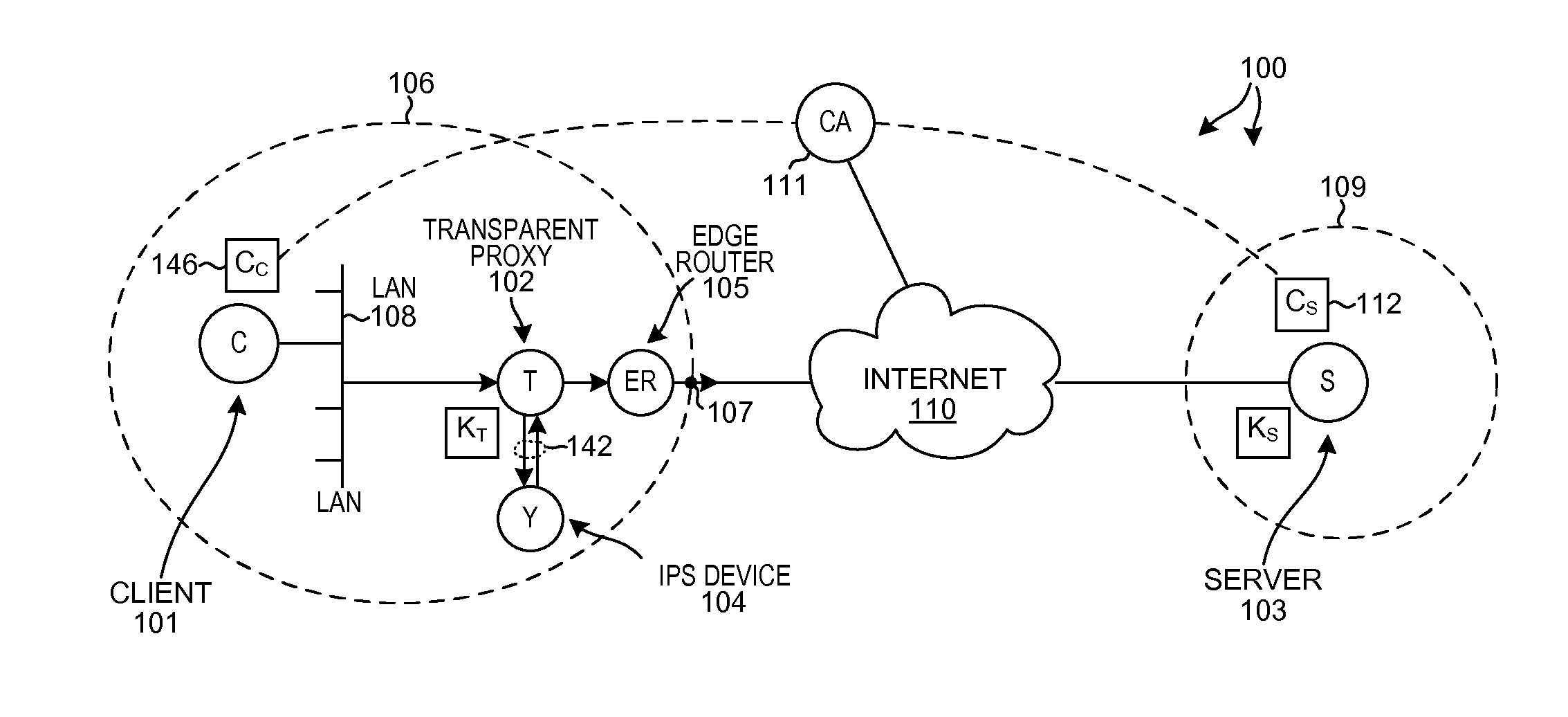
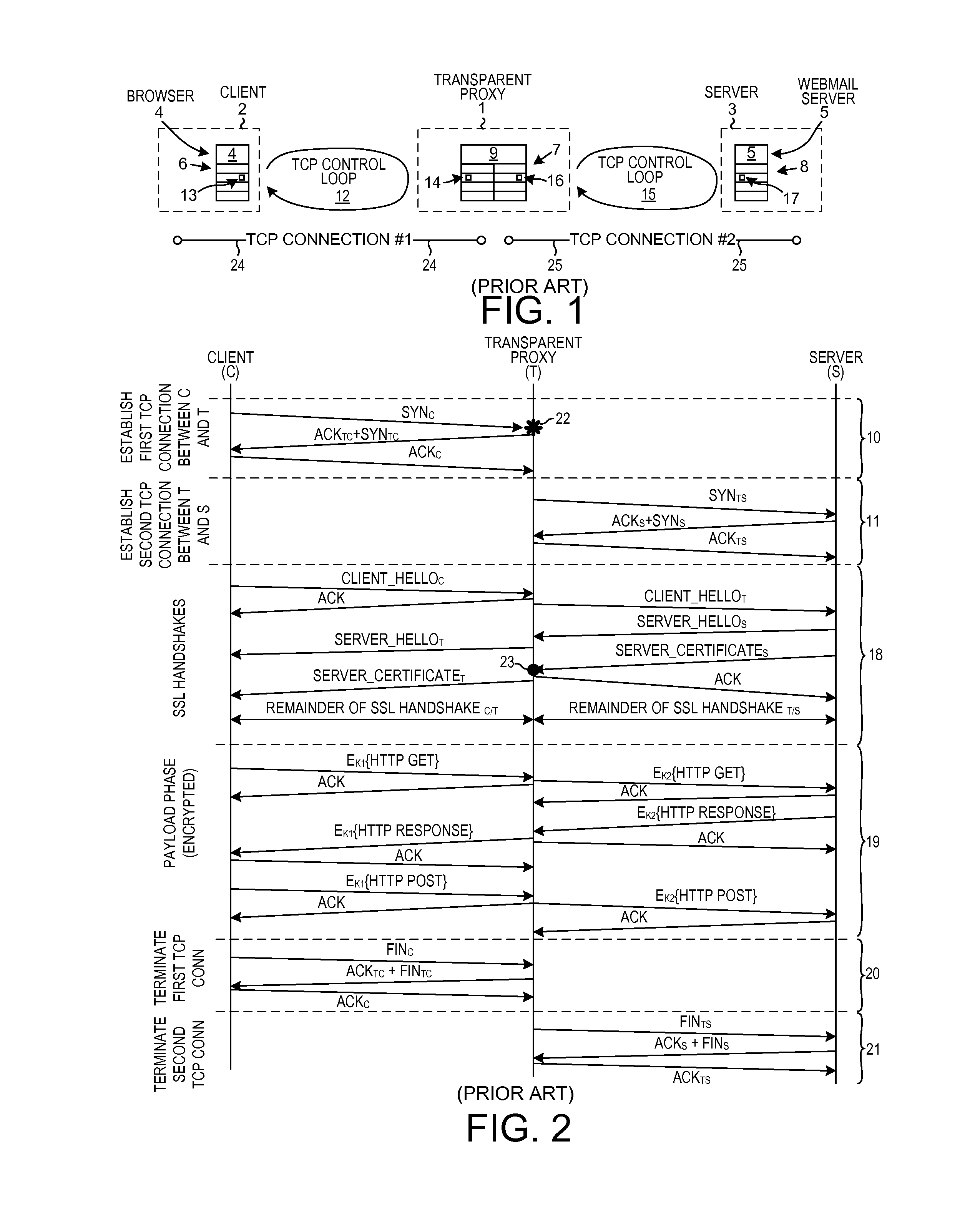
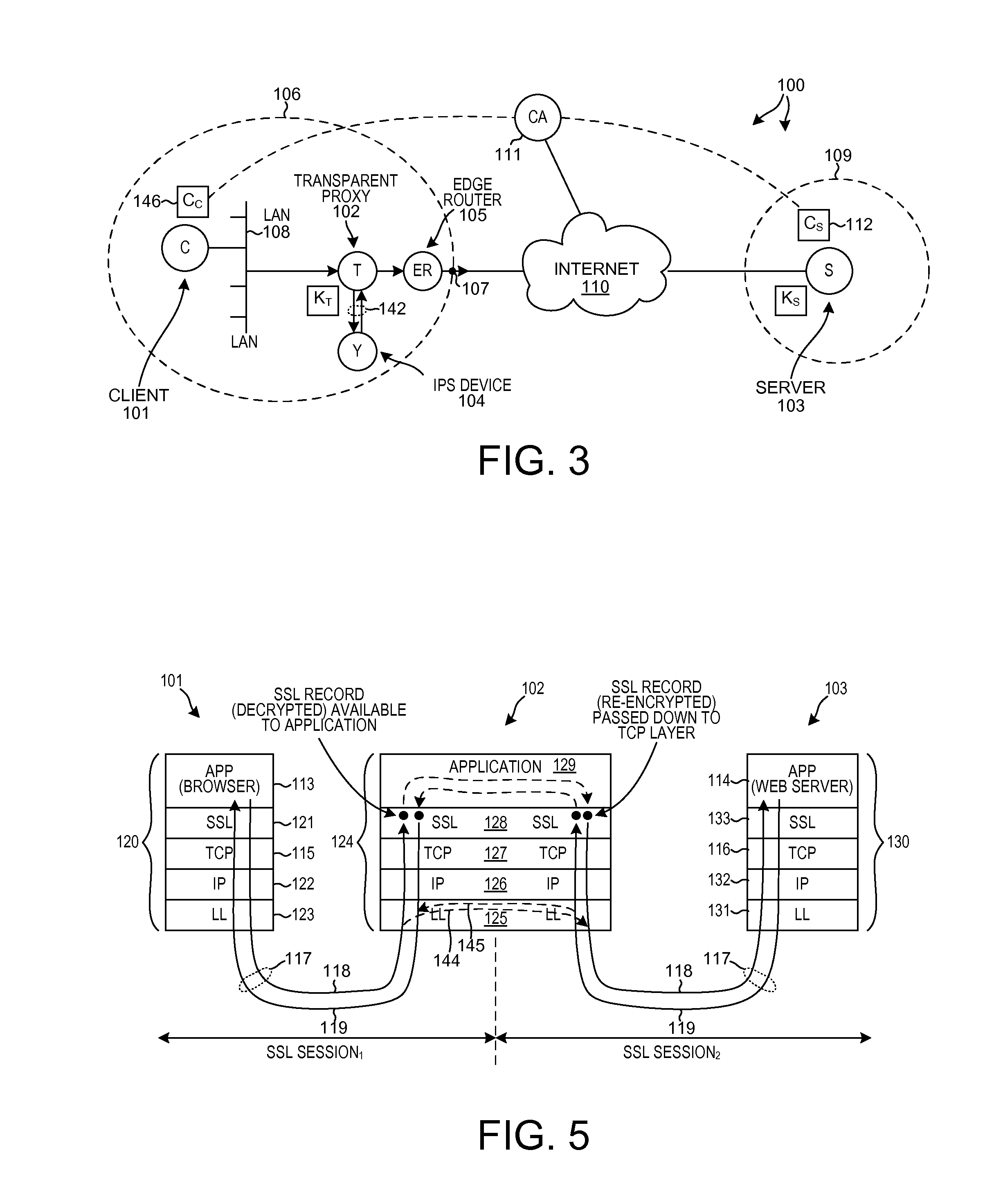
Efficient intercept of connection-based transport layer connections
A TCP connection is established between a client and a server, such that packets communicated across the TCP connection pass through a proxy. Based at least in part on a result of monitoring packets flowing across the TCP connection, the proxy determines whether to split the TCP control loop into two TCP control loops so that packets can be inspected more thoroughly. If the TCP control loop is split, then a first TCP control loop manages flow between the client the proxy and a second TCP control loop manages flow between the proxy and the server. Due to the two control loops, packets can be held on the proxy long enough to be analyzed. In some circumstances, a decision is then made to stop inspecting. The two TCP control loops are merged into a single TCP control loop, and thereafter the proxy passes packets of the TCP connection through unmodified.
Owner:NETRONOME SYST
Method and apparatus for redirecting transactions based on transaction response time policy in a distributed environment
InactiveUS20060167891A1Performance issueFinanceError detection/correctionDistributed computingComputer program
A method, system, and computer program instructions for using existing performance monitoring solutions to detect performance issues in an enterprise, and providing and executing a corrective action on any server being monitored in the enterprise to correct the performance issue. When a management agent on a monitored server detects a threshold violation, the management agent sends a violation event to the management server. Upon receiving the violation event, the management server distributes a corrective action associated with the threshold violation to a set of defined management agents involved in the transaction. Each management agent then runs the corrective action to remedy the performance problem.
Owner:IBM CORP
Multi-line/Multi-state Virtualized OAM Transponder
ActiveUS20160048403A1Function increaseAvoid lostTransmissionSoftware simulation/interpretation/emulationVirtualizationProgram management
Novel tools and techniques might provide for implementing applications management, based at least in part on operations, administration, and management (“OAM”) information. A host computing system might comprise a dedicated OAM management agent. While normal application frame flow might be sent or received by VMs running on the host computing system, OAM frame flow might be sent or received by the OAM management agent, which might also serve as an OAM frame generator. Alternatively, or additionally, based on a determination that at least one OAM frame has changed (in response to a change in address of far-end and / or near-end OAM server functions), the OAM management agent might update a list associating the at least one OAM frame that has changed with corresponding at least one VM of the one or more VMs, without restarting any of the at least one VM, the OAM management agent, and / or the host computing system.
Owner:CENTURYLINK INTPROP
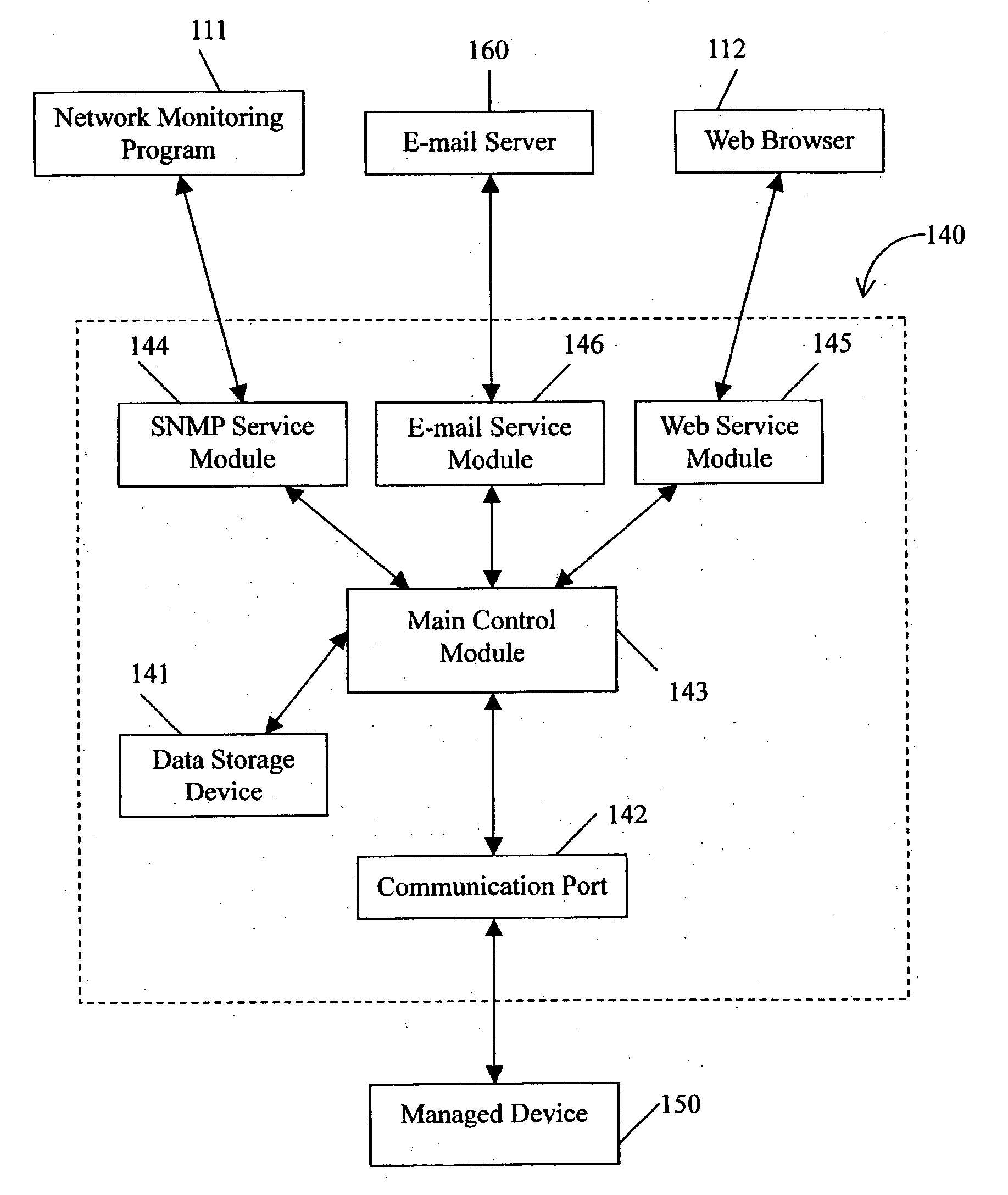
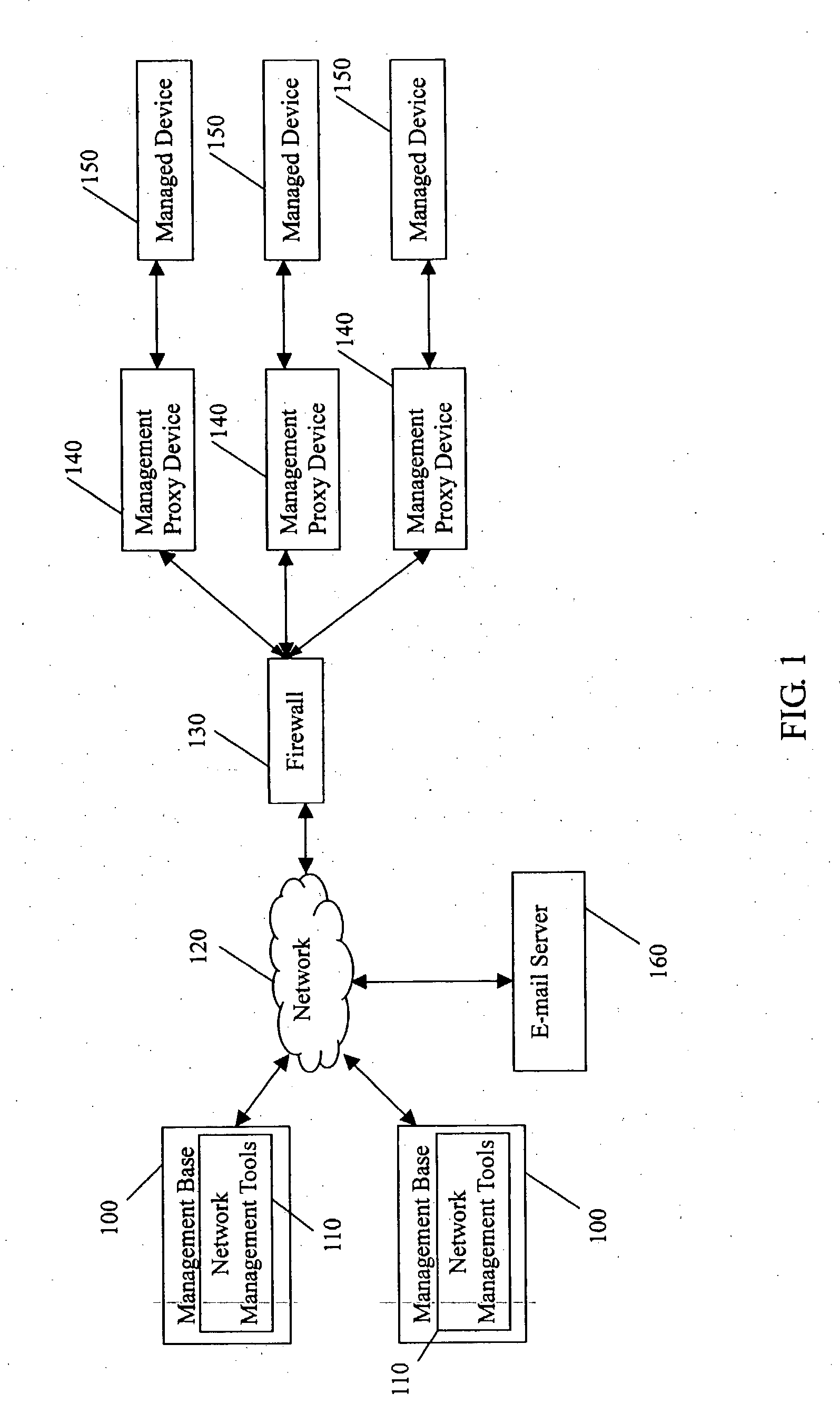
System and method for managing network devices via e-mail
InactiveUS20040093383A1Multiple digital computer combinationsData switching networksManagement toolComputer module
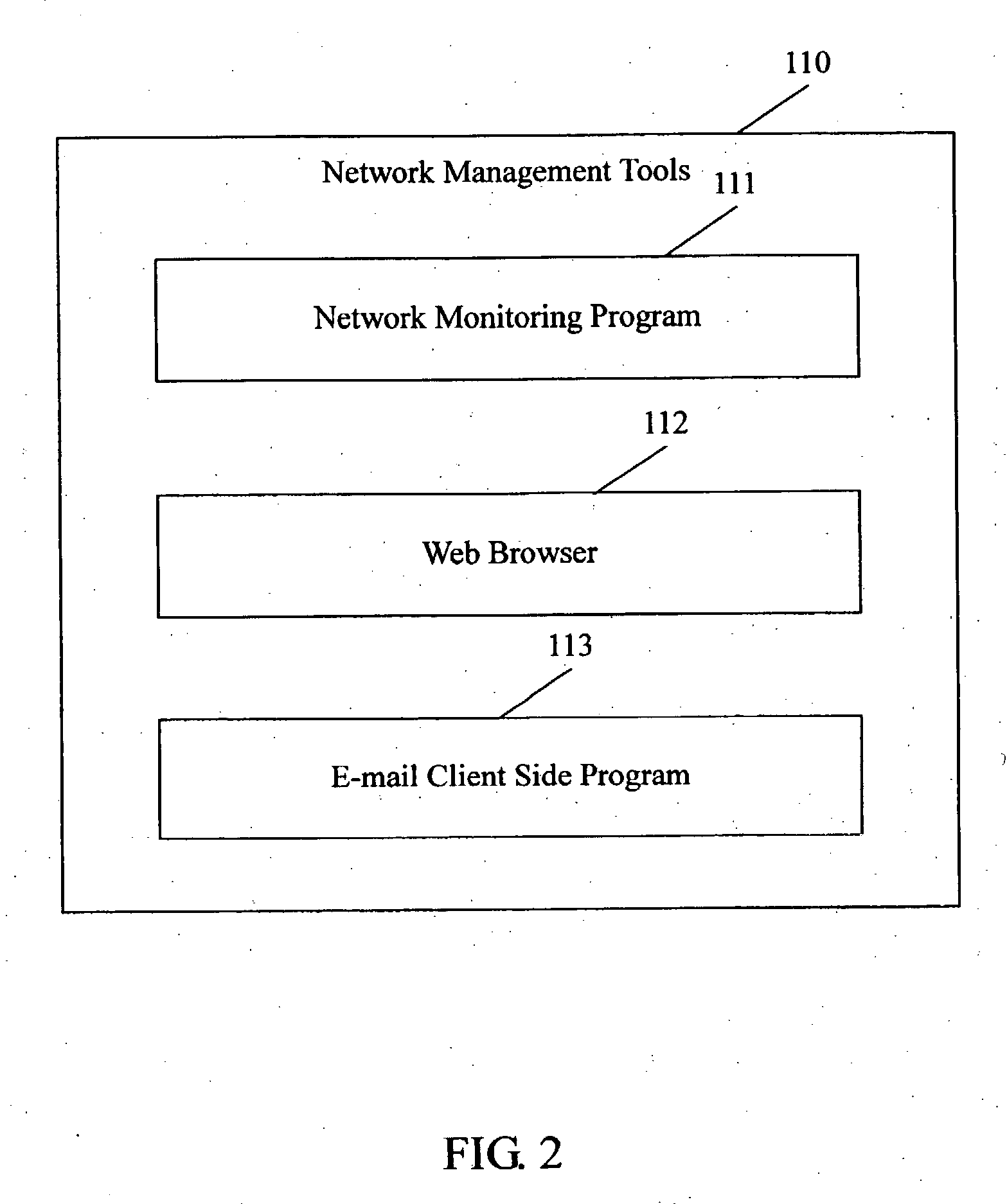
A system and method for managing network devices via e-mail that accomplishes sending management commands to the management proxy device (140) and receiving status information on the managed device (150) via e-mail in a network management system. The system for managing network devices via e-mail comprised: at least one management base (100) that runs an e-mail client side program (113) as a network management tool to send e-mails containing management commands; at least one management proxy device that runs an e-mail service module (146) for receiving and analyzing e-mails containing management commands, and for sending e-mails containing status information on a managed device, said e-mail service module comprising an e-mail receiving sub-module (1461), a decryption sub-module (1462), a status information reporting sub-module (1463) and an e-mail sending sub-module (1464); and an e-mail server (160) that receives e-mails from the management base and the management proxy device.
Owner:HON HAI PRECISION IND CO LTD
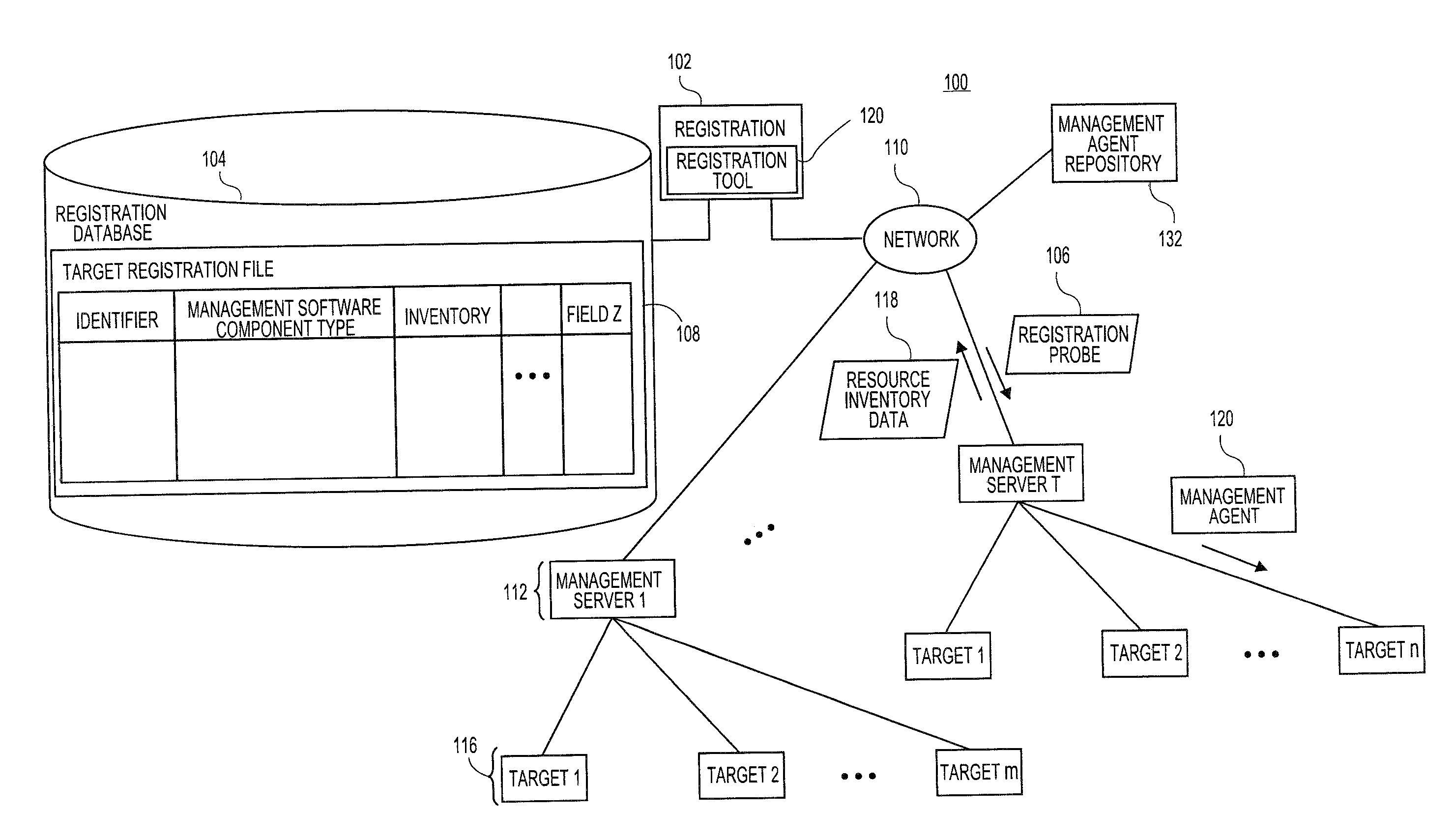
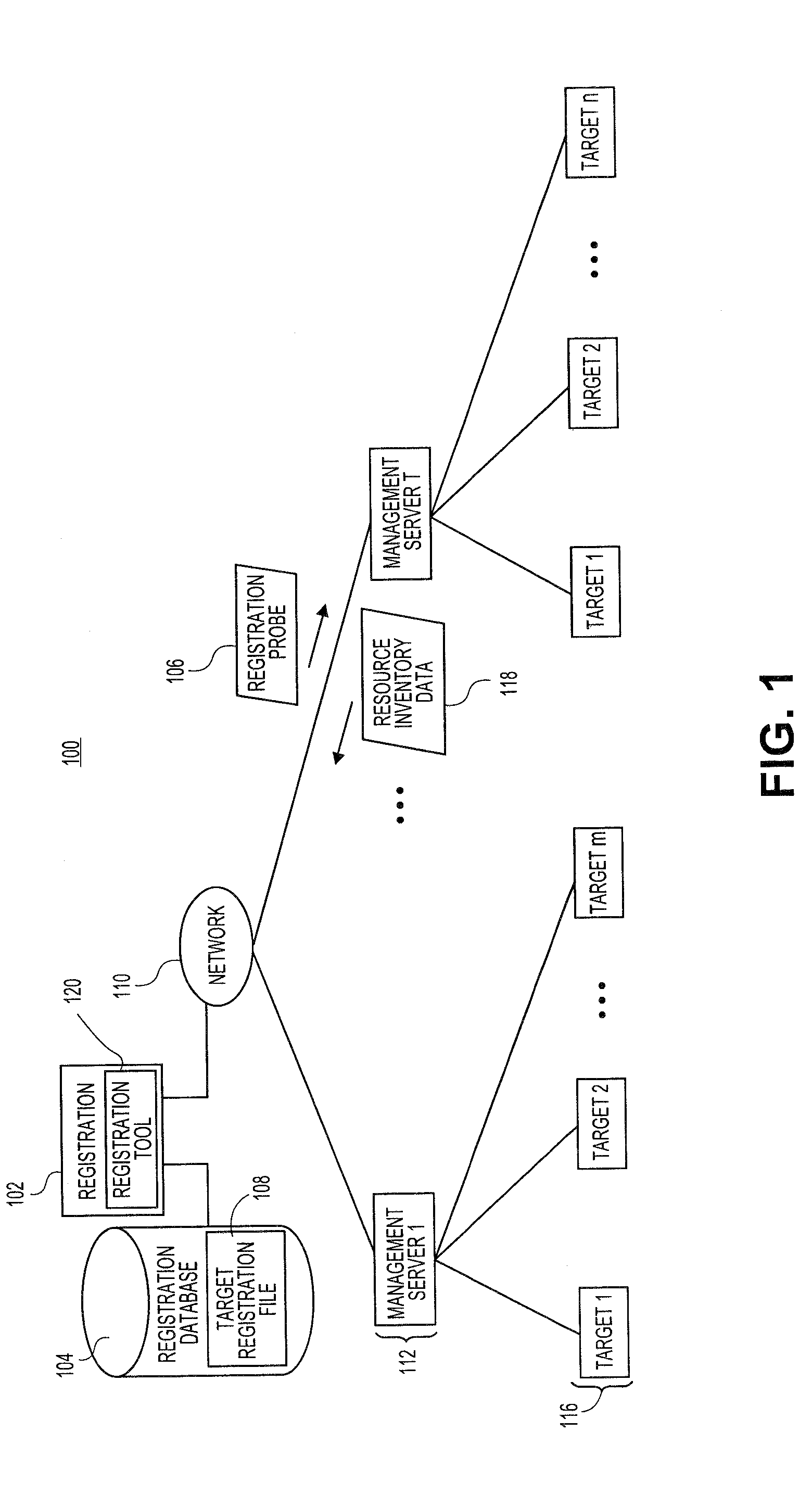
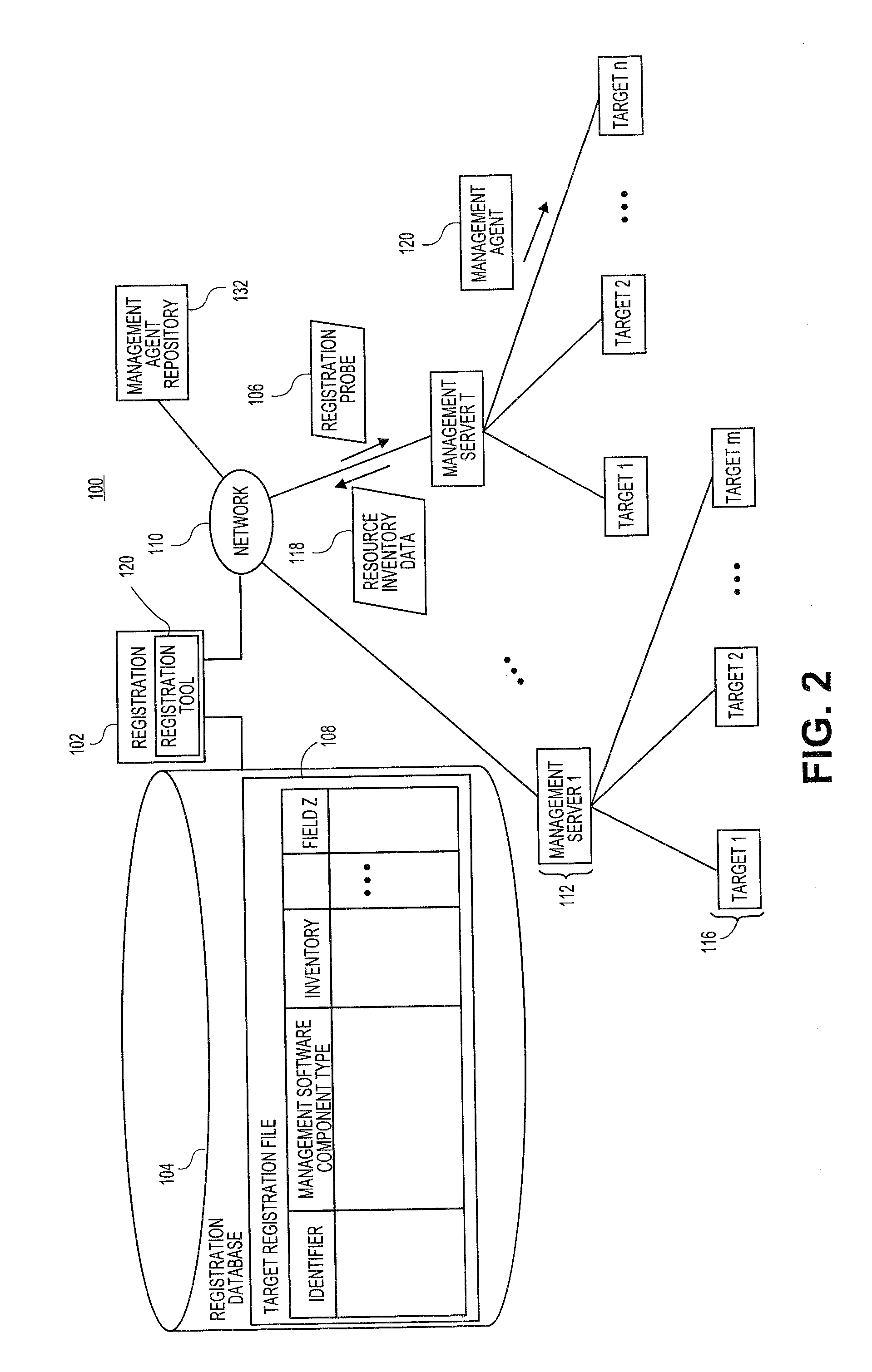
Systems and methods for generating management agent installations
Embodiments relate to systems and methods for installation of management agents on target machines. In embodiments, a central management server can scan a managed network to identify different types and configurations of target machines. Different types of target machines may require different types of management agent software in order to invoke different types of management services, such as configuration management or performance monitoring services. The necessary types of management agent may depend, for instance, on the operating system and / or applications installed on individual targets. In embodiments, different types or classes of management agents can register or communicate with different types of remote management servers. The management agent(s) on individual targets can thereby initiate and manage the installation of agents or other resources that may be needed to register to the remote network services, without a requirement to install or use specific package management tools for specific products.
Owner:RED HAT
Open platform for managing an agent network
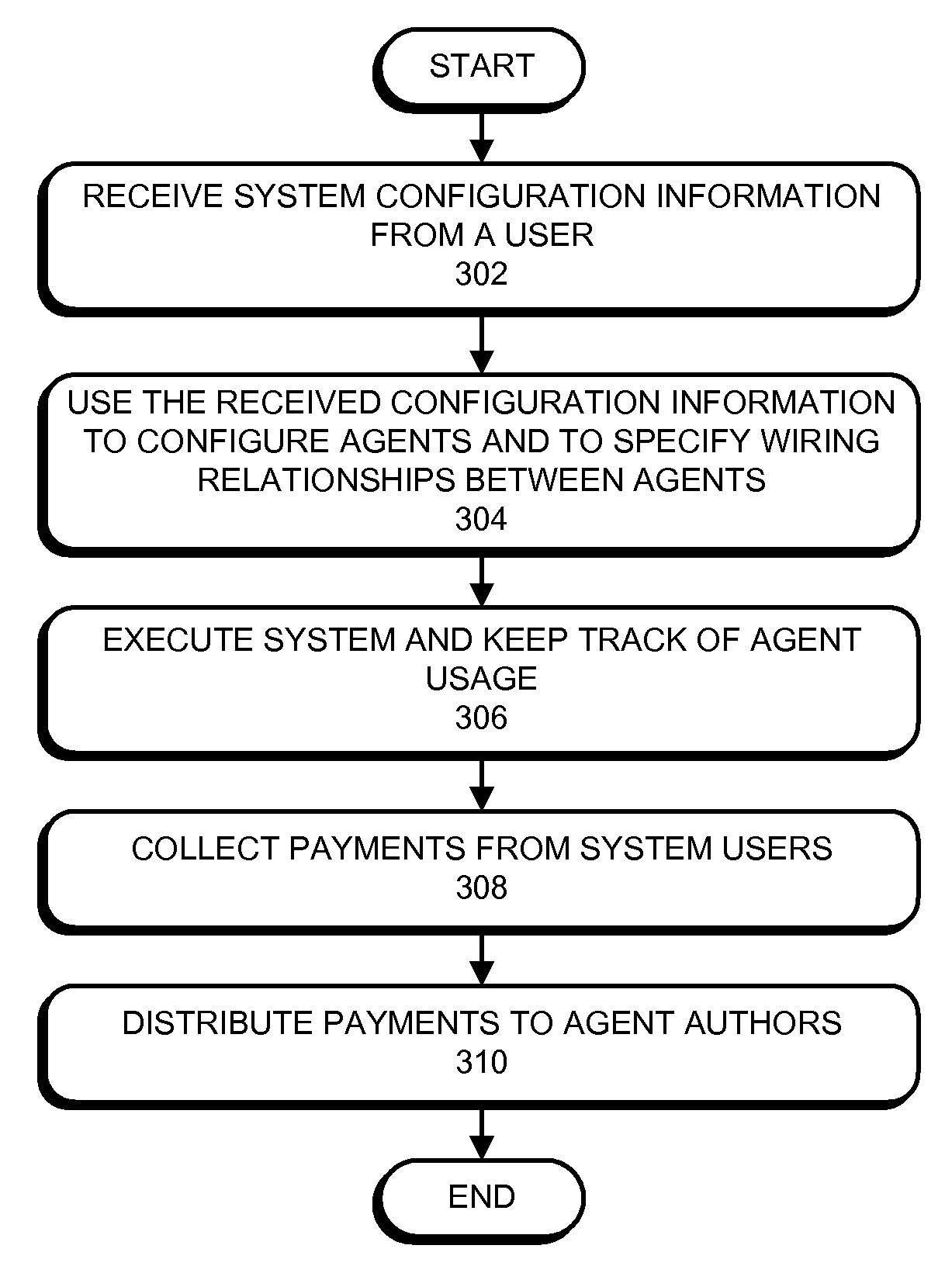
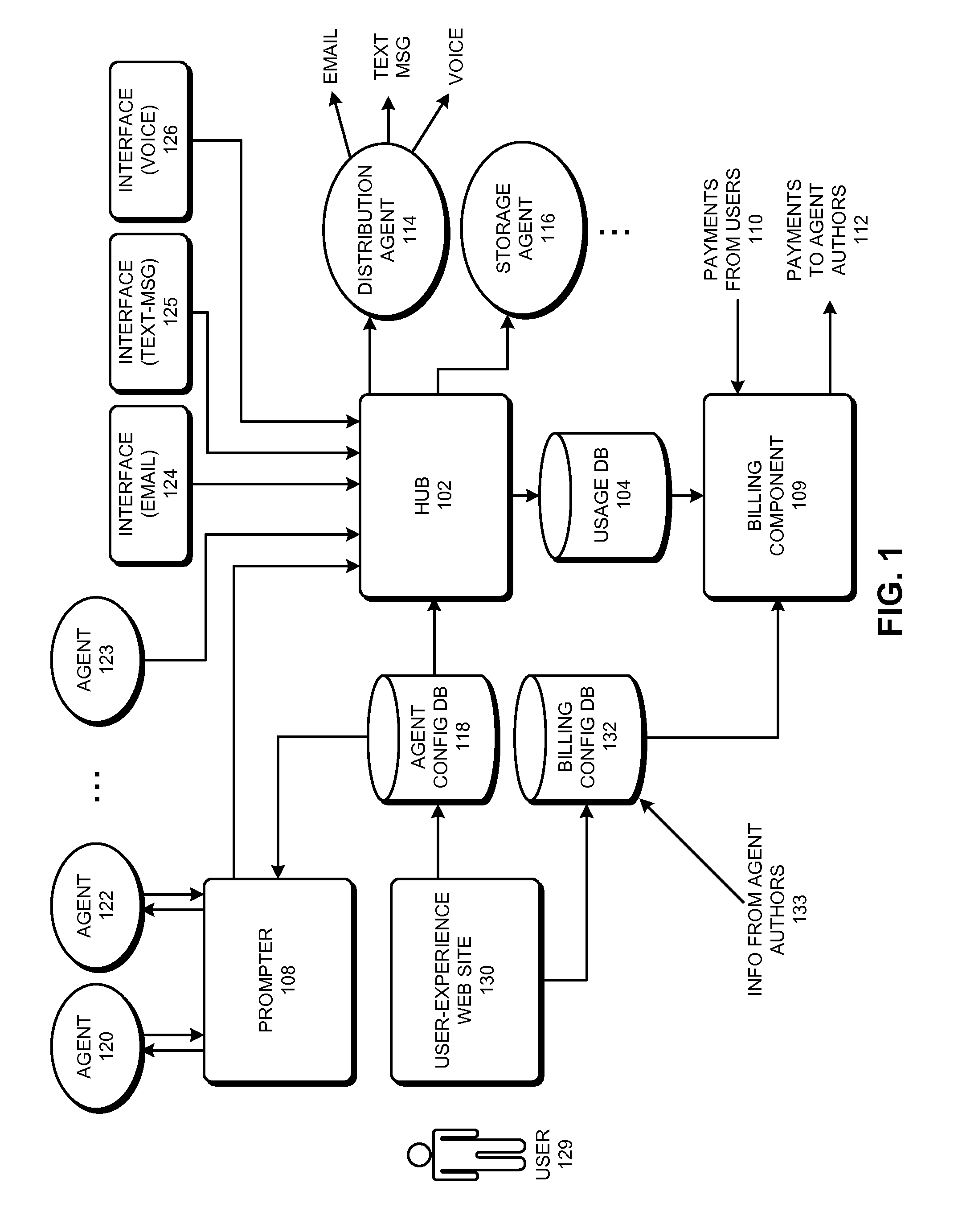
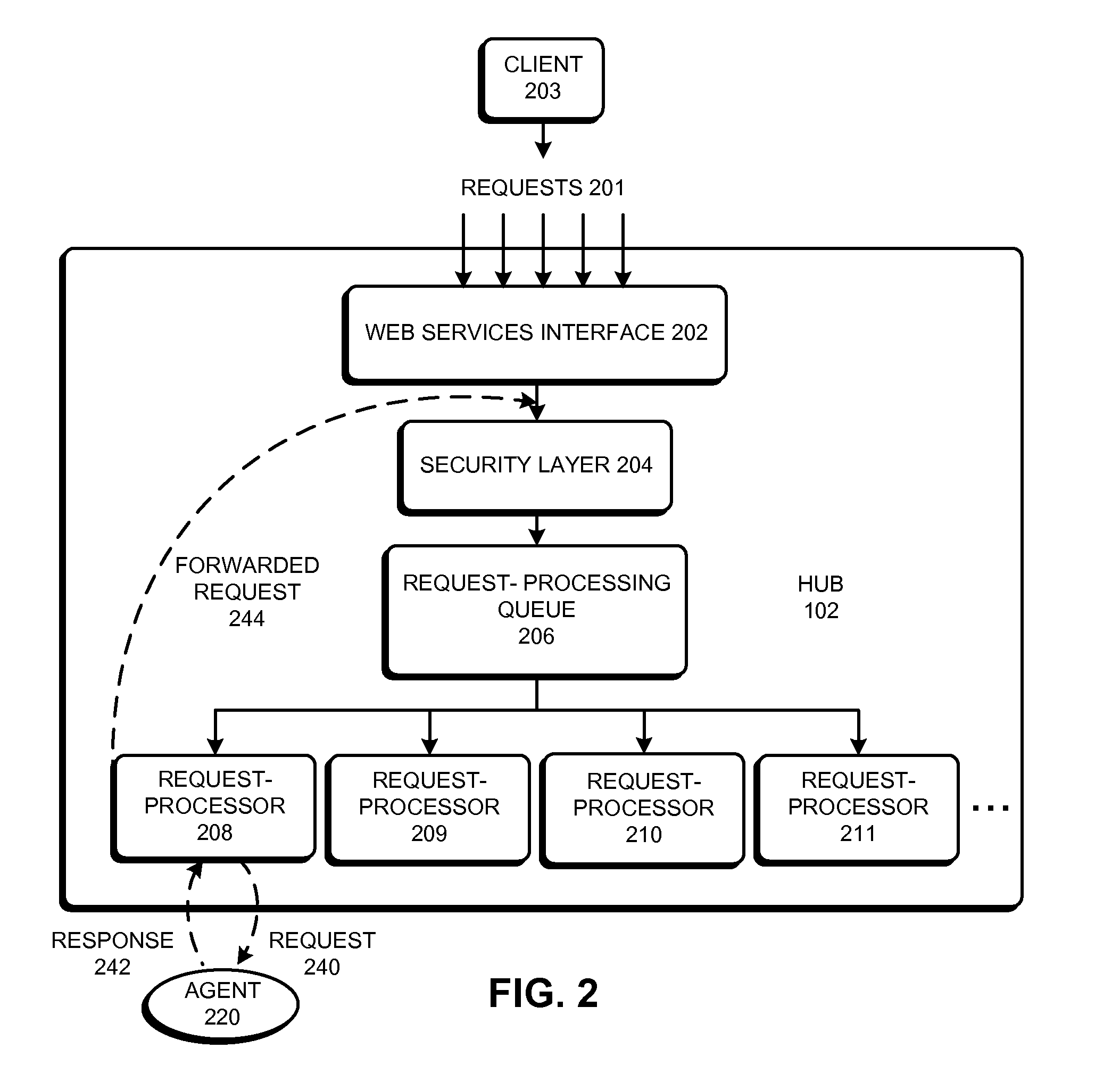
ActiveUS20090125618A1Metering/charging/biilling arrangementsError detection/correctionOpen platformSystem usage
Some embodiments of the present invention provide a system for managing software agents. This system enables a user to configure agents and to specify wiring relationships between the agents and other system components. This system also includes a hub component, which is configured to route communications to and from the agents in accordance with user-specified wiring relationships.
Owner:INTUIT INC
Systems and methods for providing managed services
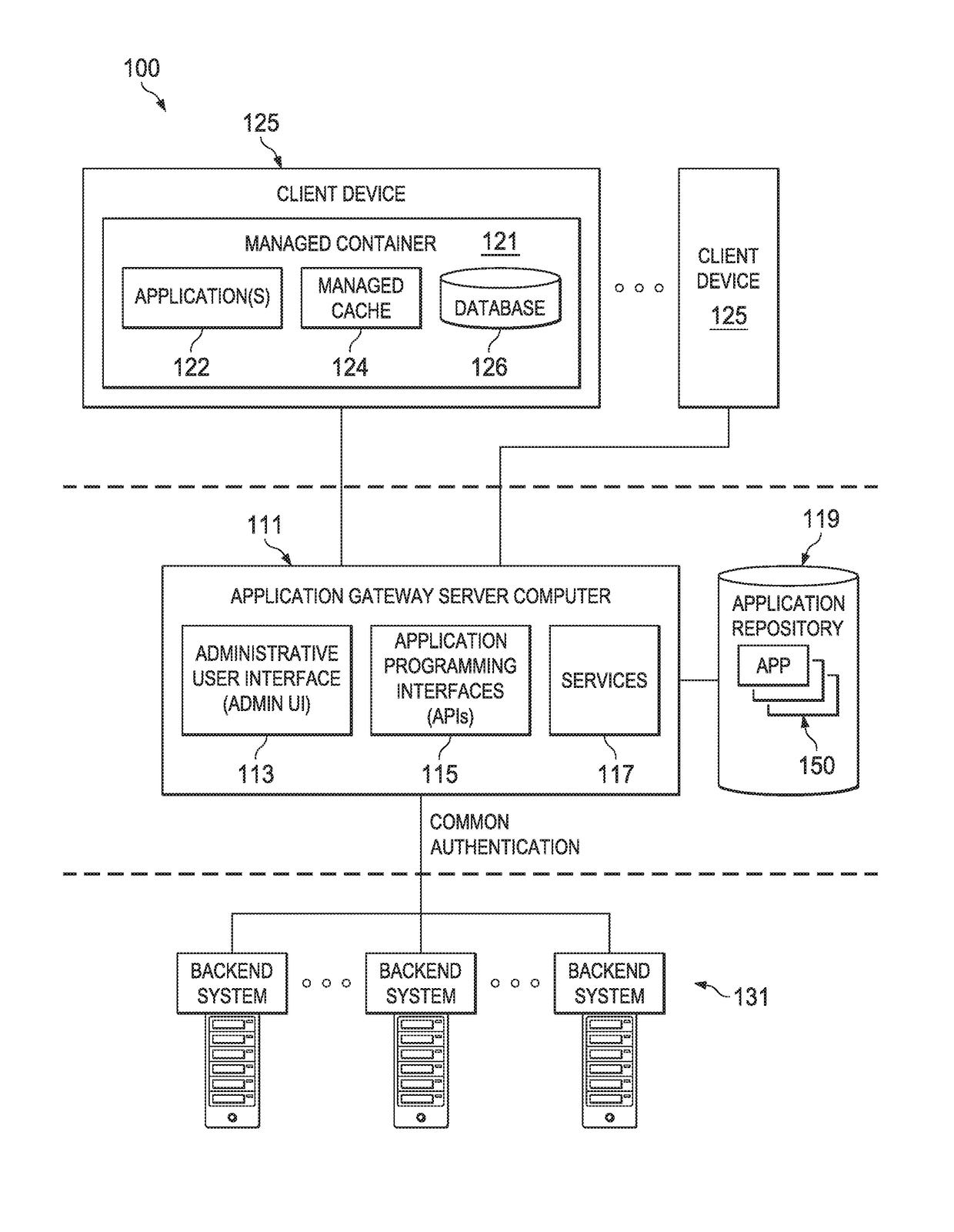
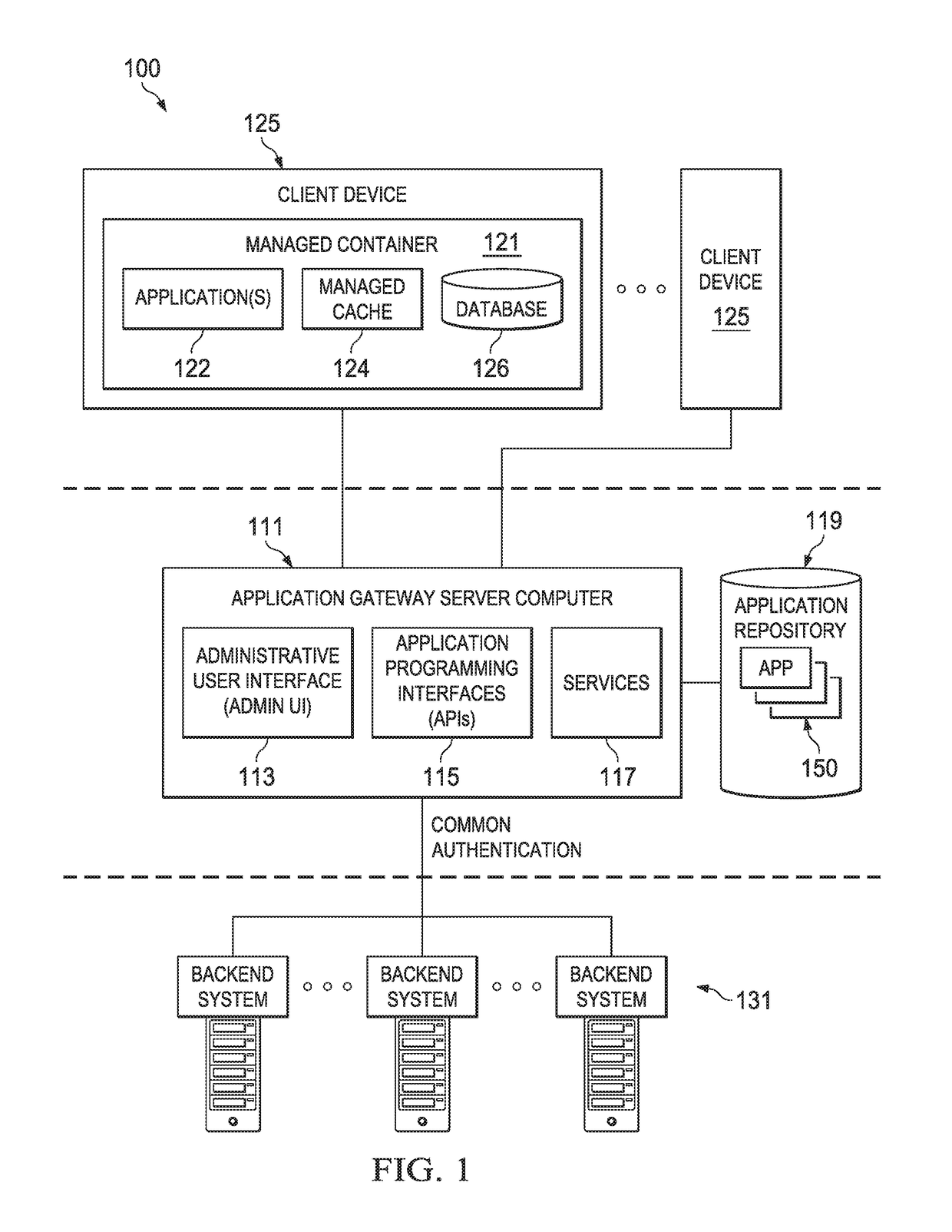
ActiveUS20170250853A1Many solutionsInterprogram communicationPlatform integrity maintainanceUser deviceApplication software
Embodiments improve application gateway architecture by pushing secure managed service boundaries. Managed services that were previously available directly in application gateway code are separated from application gateway code and exposed to service clients in a controlled, secured manner via a RESTful API layer dedicated to the management and interaction of deployed managed services. The separation can be realized in management agents. A management agent receives a service request from an application and makes an API call to the dedicated management API layer of the managing application gateway. The application may run within a managed container on a user device. Responsive to the API call, the application gateway sends a control or configuration message to the management agent over HTTP. The management agent controls or configures the managed service to function or behave as dictated by the application gateway.
Owner:OPEN TEXT SA ULC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com