Patents
Literature
6064 results about "Systems management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Systems management refers to enterprise-wide administration of distributed systems including (and commonly in practice) computer systems. Systems management is strongly influenced by network management initiatives in telecommunications. The application performance management (APM) technologies are now a subset of Systems management. Maximum productivity can be achieved more efficiently through event correlation, system automation and predictive analysis which is now all part of APM.
Virtual systems management
Automatic configuration management of a network is provided by determining an inventory of resources at a virtualization layer of a node of the network, assigning prioritization to members of a set of network configuration elements, allocating virtual resources among the set of network configuration elements, establishing a network configuration. The configuration is managed by determining real time performance metrics for the configuration, producing a reallocation of the virtual resources based on the performance metrics that are estimated to change the established configuration, change the performance metrics, and initiating the reallocation of the virtual resources. This Abstract is provided for the sole purpose of complying with the Abstract requirement that allows a reader to quickly ascertain the subject matter of the disclosure contained herein. This Abstract is submitted with the understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:TOUTVIRTUAL
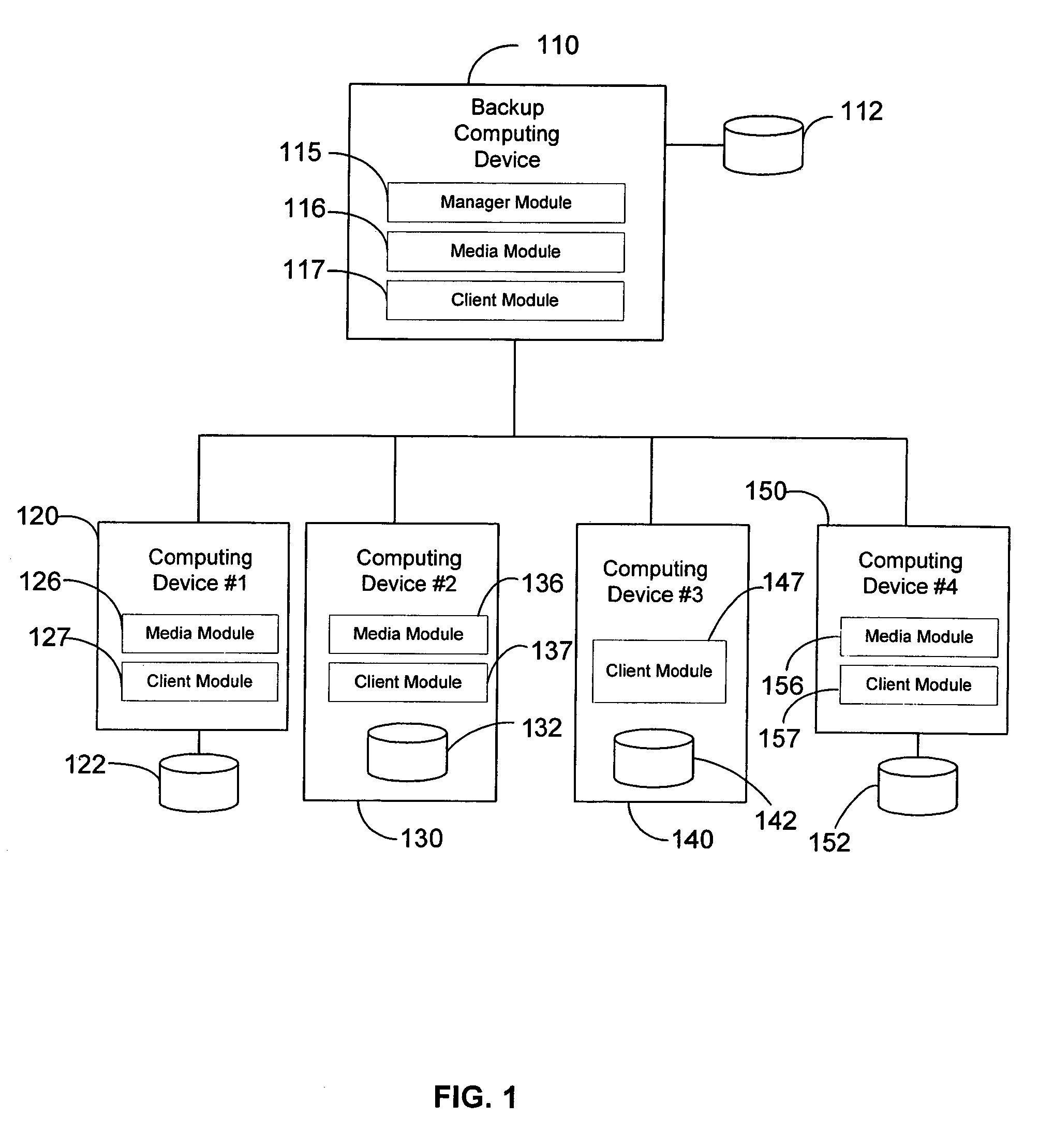
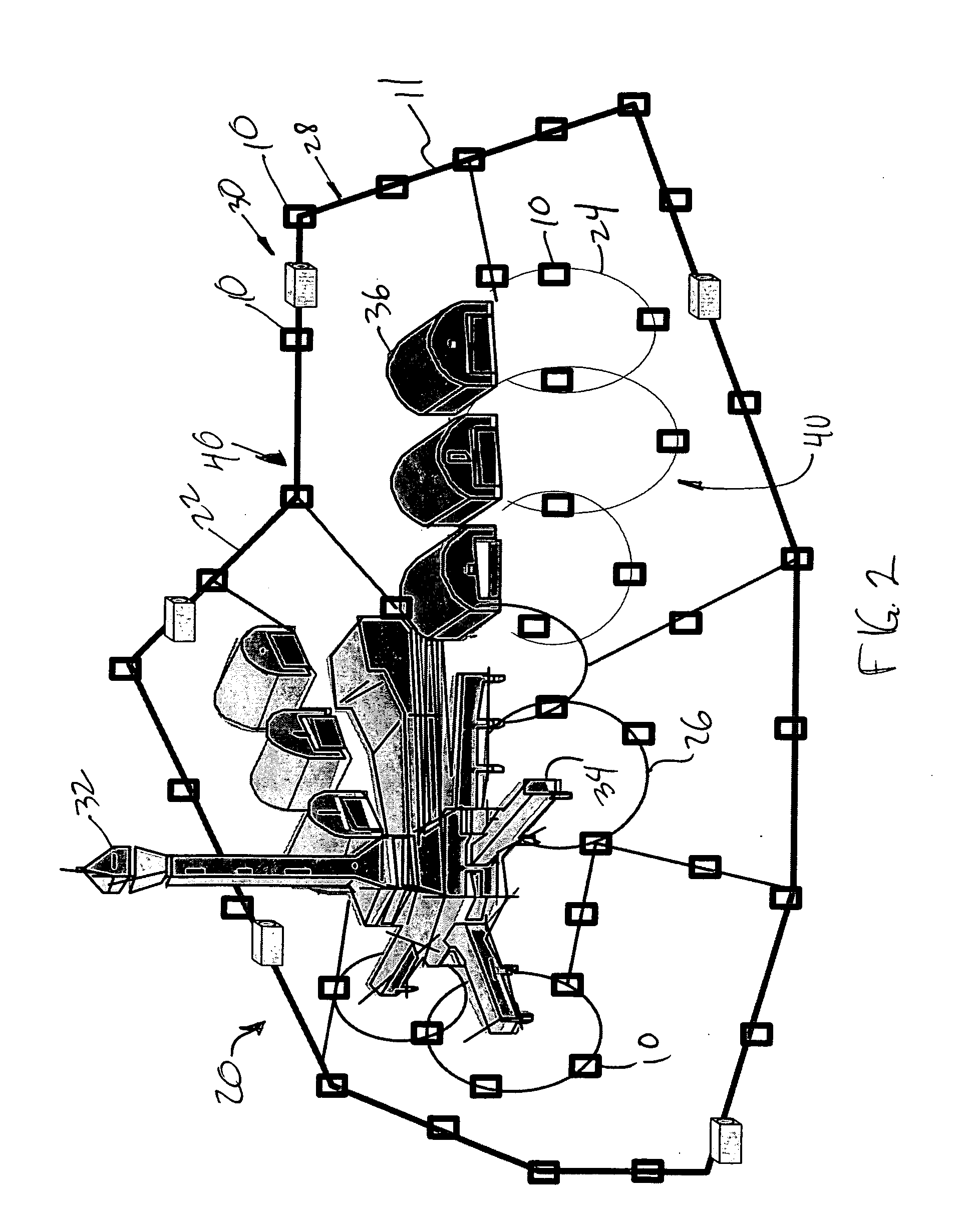
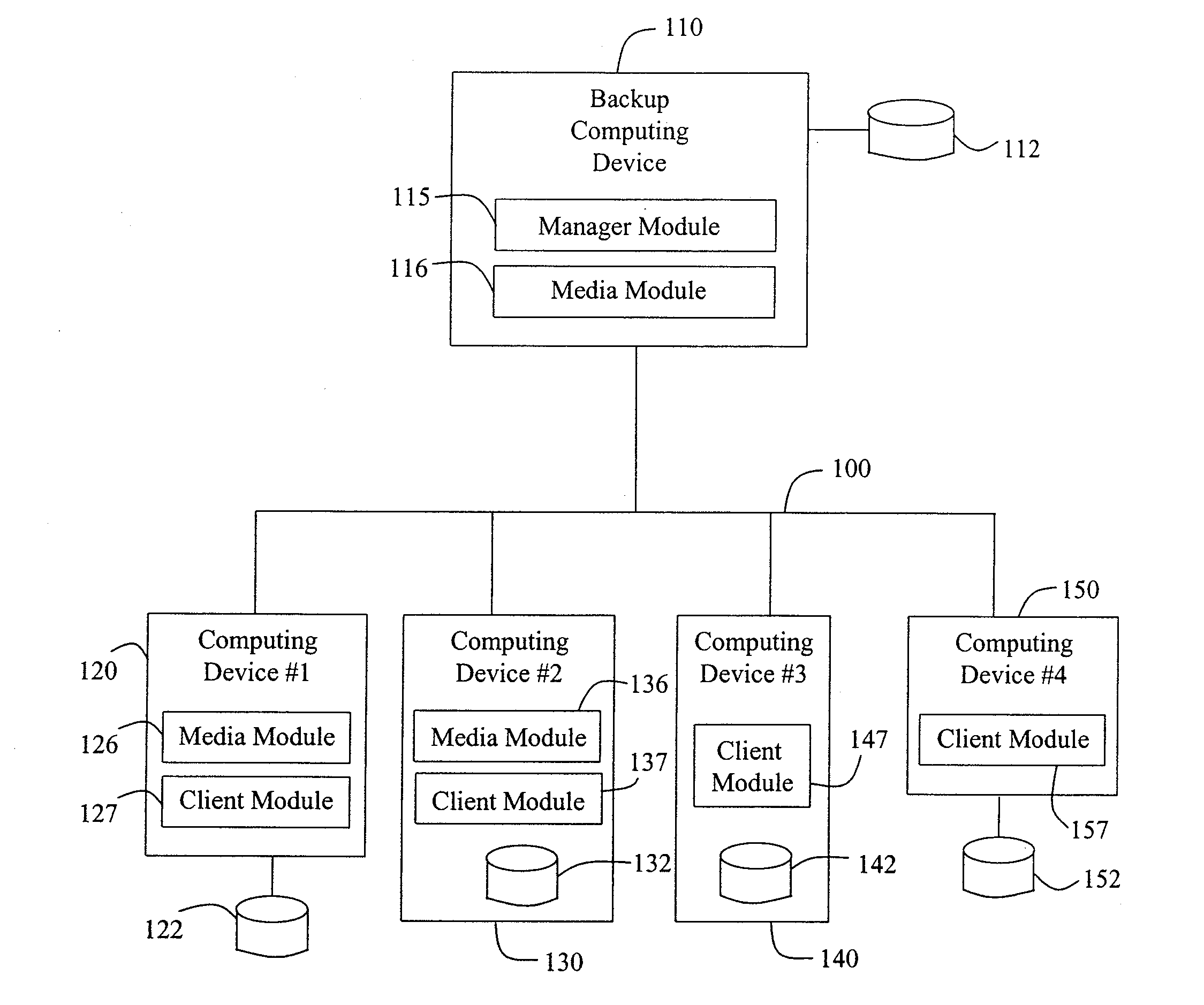
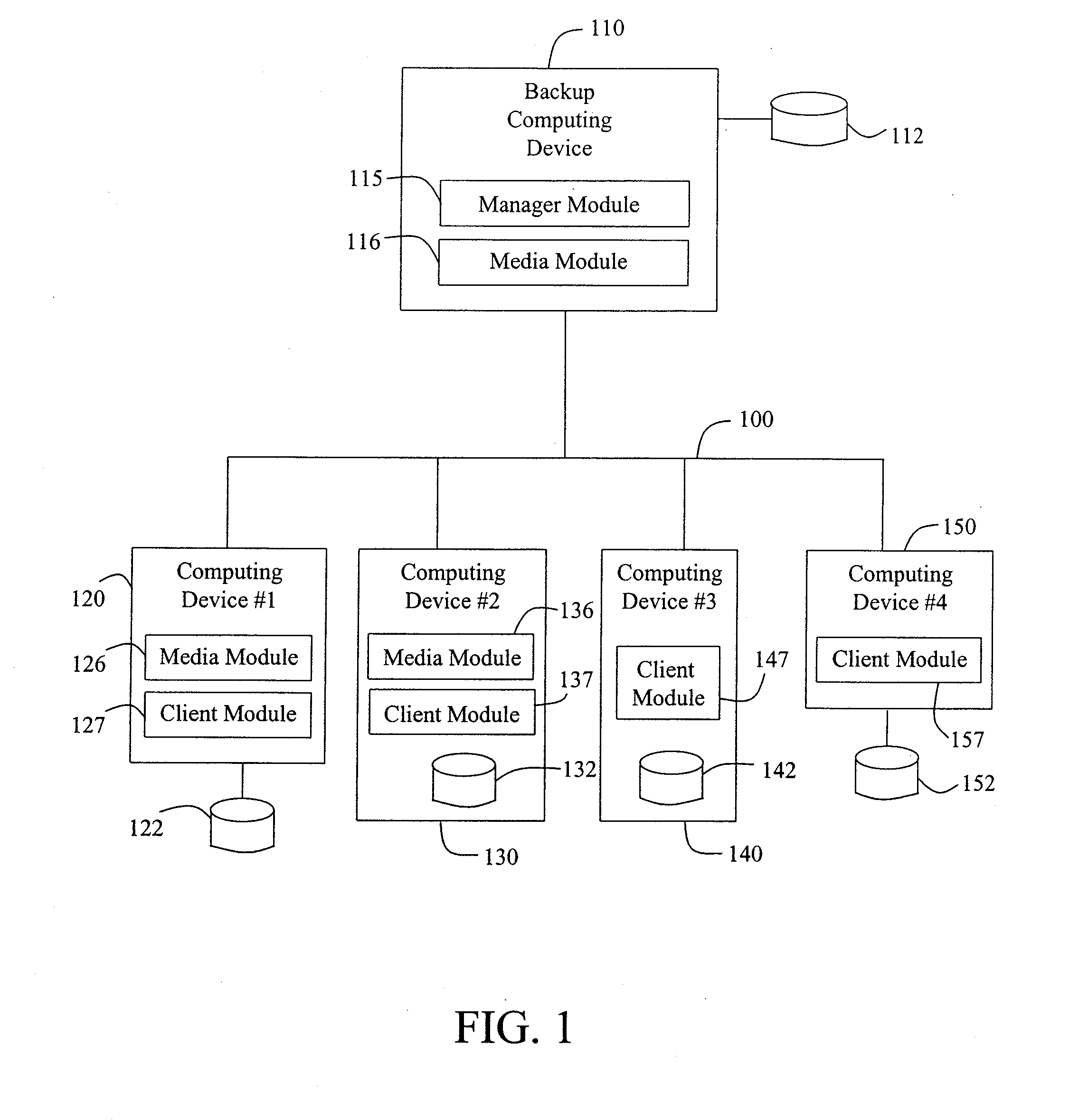
Modular backup and retrieval system
InactiveUS7389311B1Data processing applicationsDigital data processing detailsSystems managementModularity
Owner:COMMVAULT SYST INC
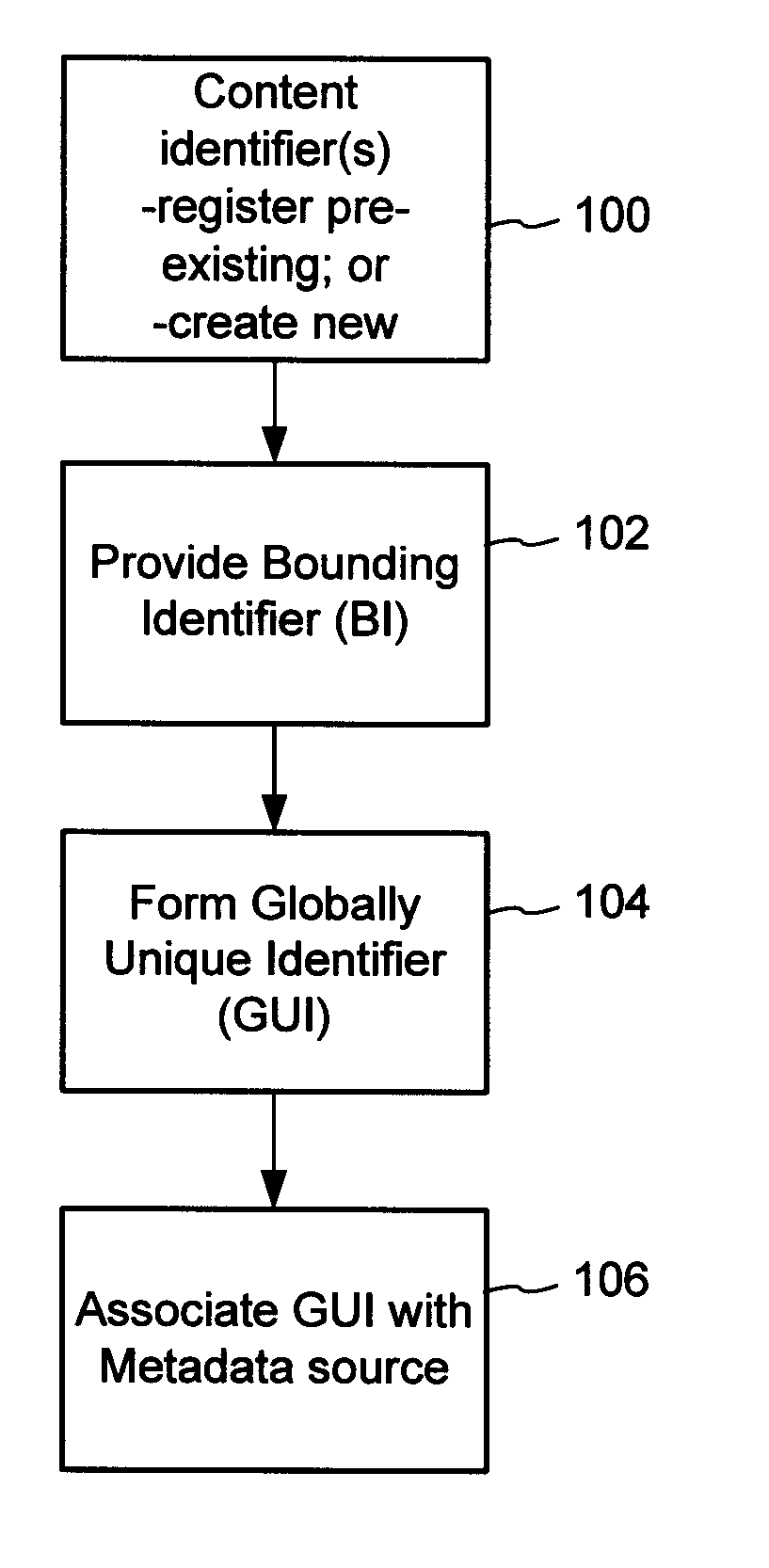
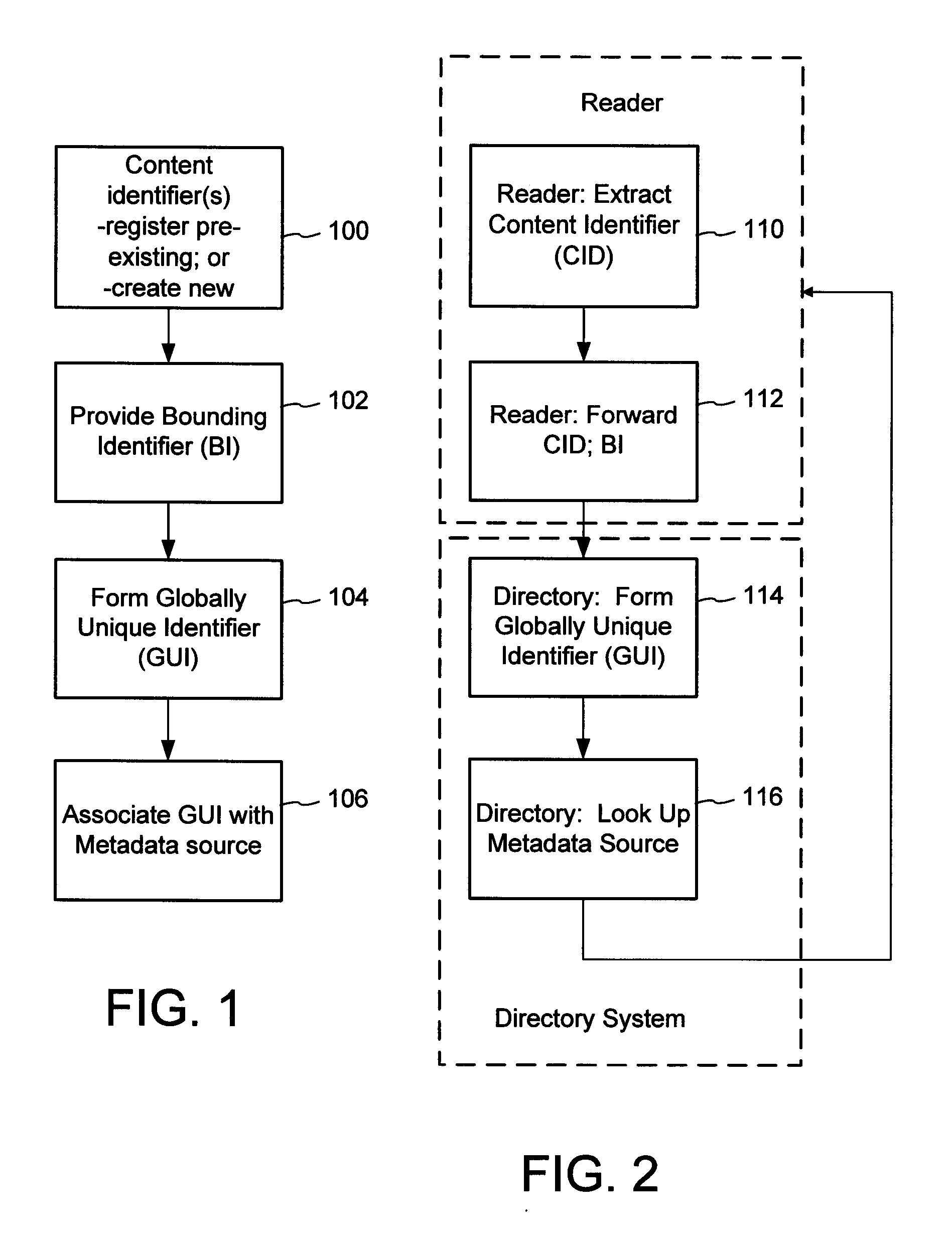
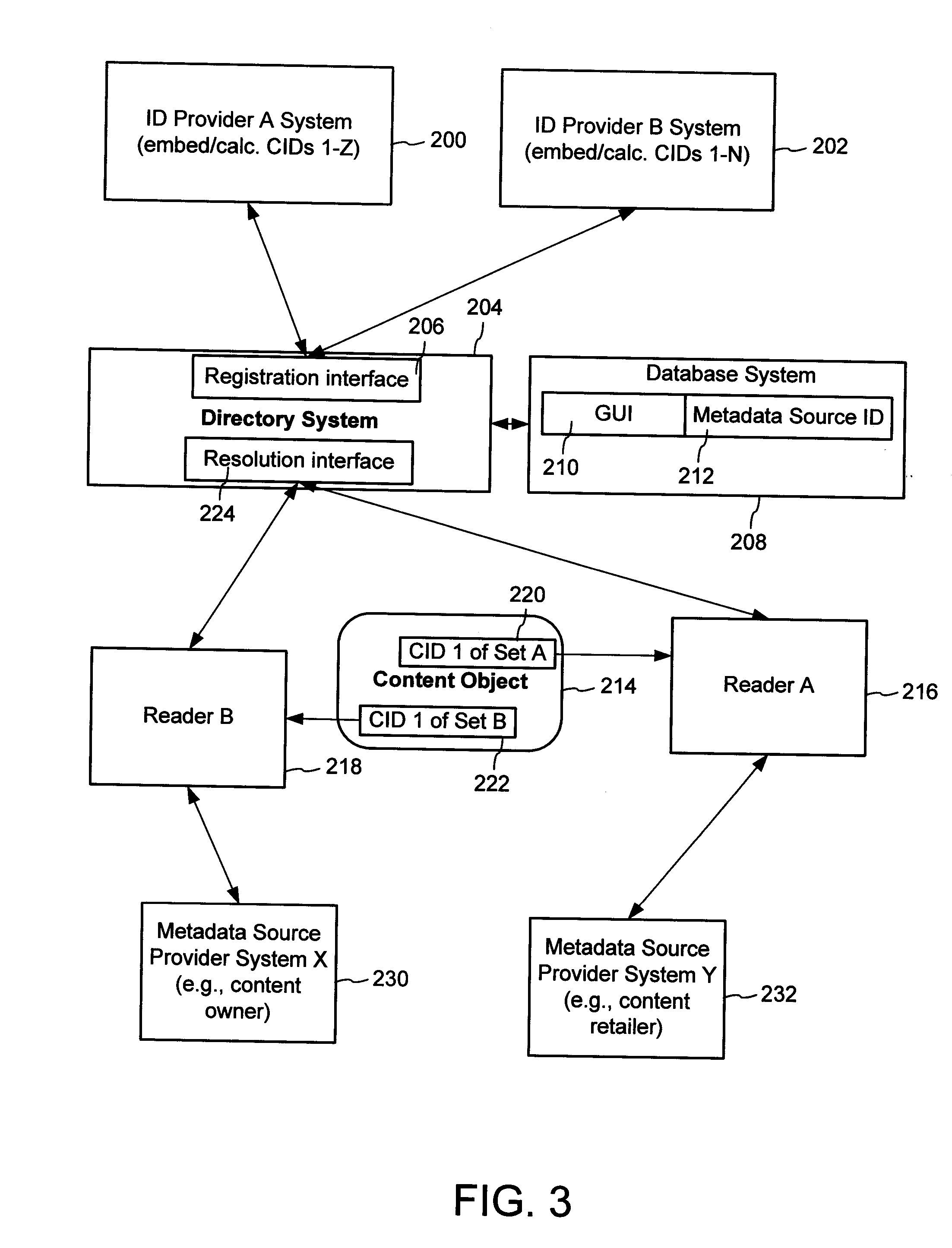
Content Metadata Directory Services
ActiveUS20070156726A1Improve interoperabilityIncrease the number ofMultimedia data indexingDigital data processing detailsContent IdentifierSystems management
The content metadata directory system connects consumers of identified content to managed metadata databases and other digital resources. The system manages links between identifiers in content objects and metadata sources. It supports a variety of different type of content identifiers and allows for overlap among different content identification schemes. One method of associating a content object with metadata uses a combination of a content identifier and a bounding identifier to enable handling of disparate sets of content identifiers for content objects with potentially conflicting content identifiers. The method receives a content identifier for a content object from among a set of content identifiers and provides a unique bounding identifier for the set of content identifiers. This unique bounding identifier is used in combination with the content identifier to form a globally unique identifier for the content object. This globally unique identifier is associated with a metadata source, which enables routing of a user to the metadata source.
Owner:DIGIMARC CORP
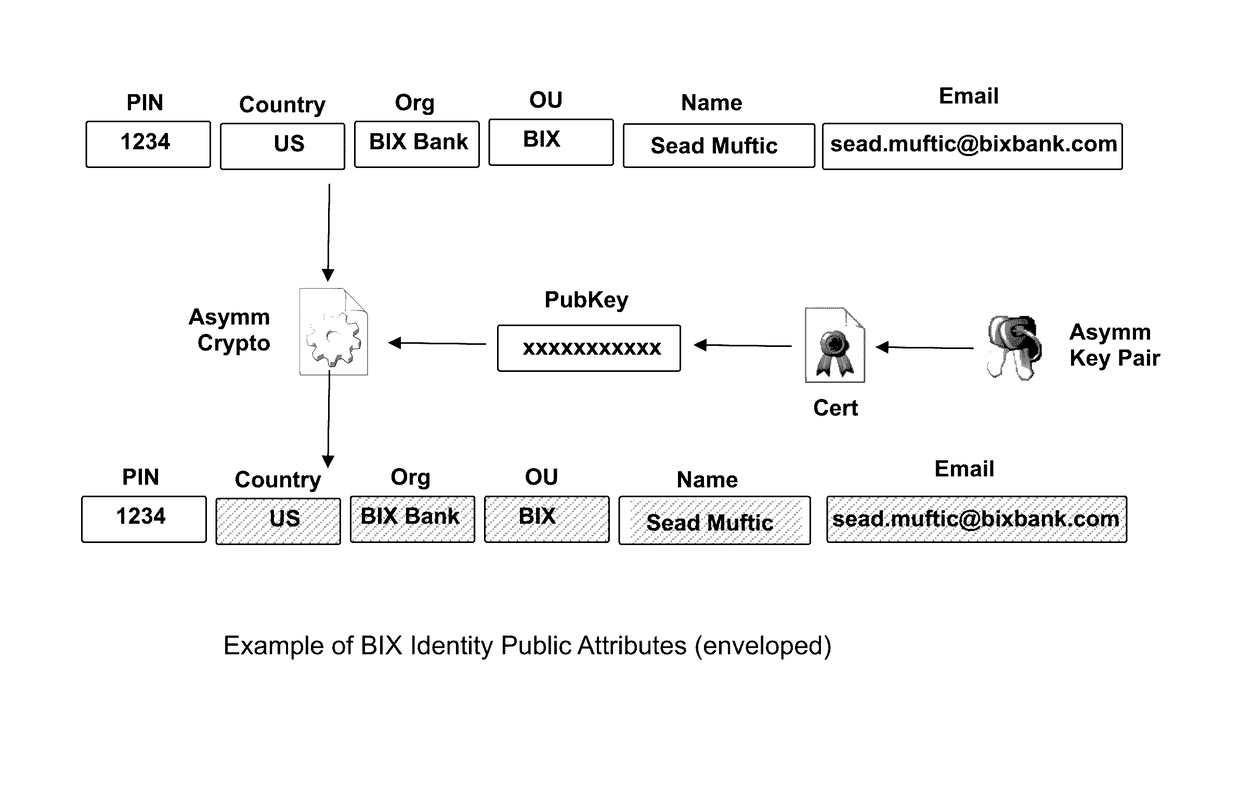
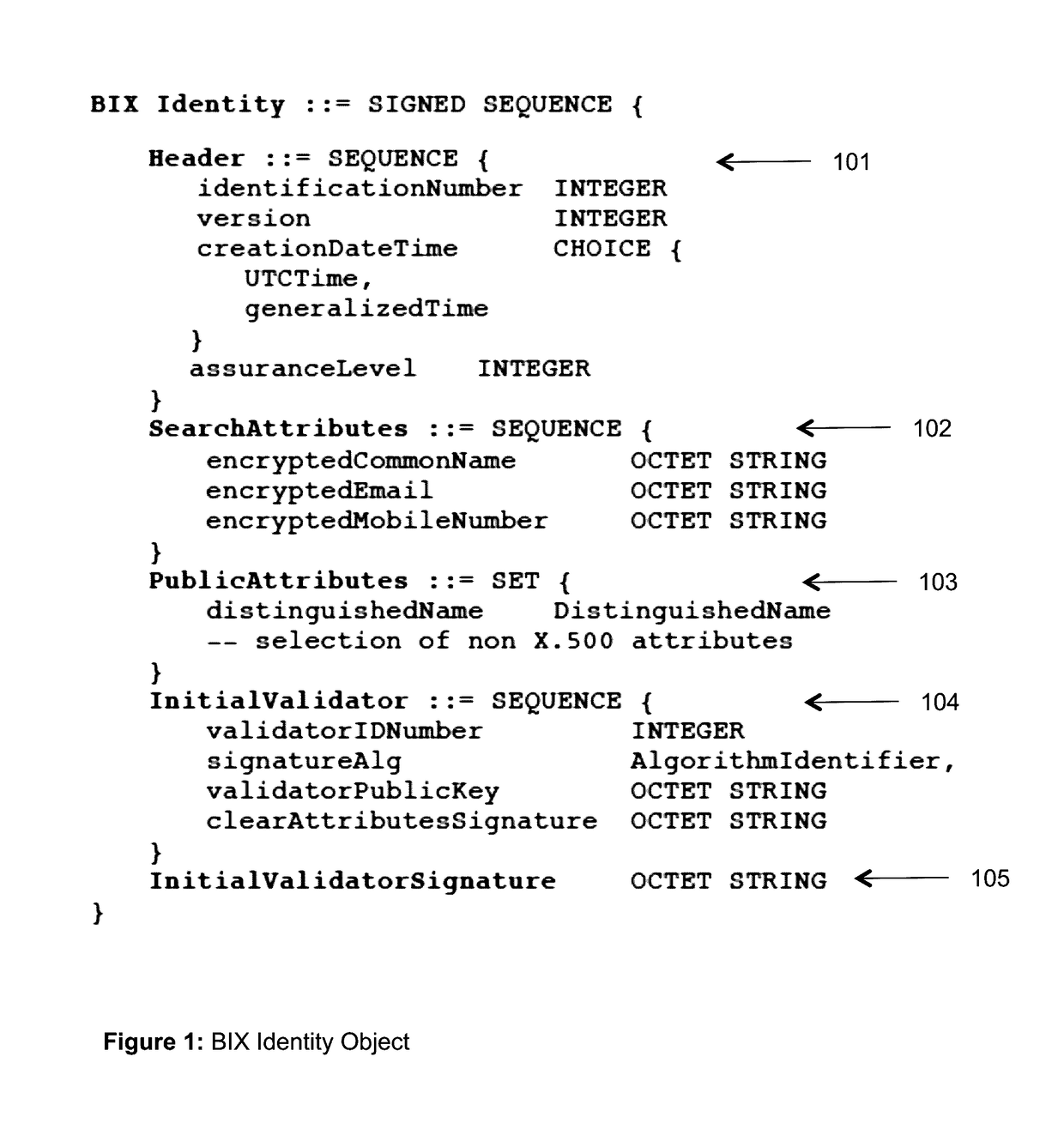
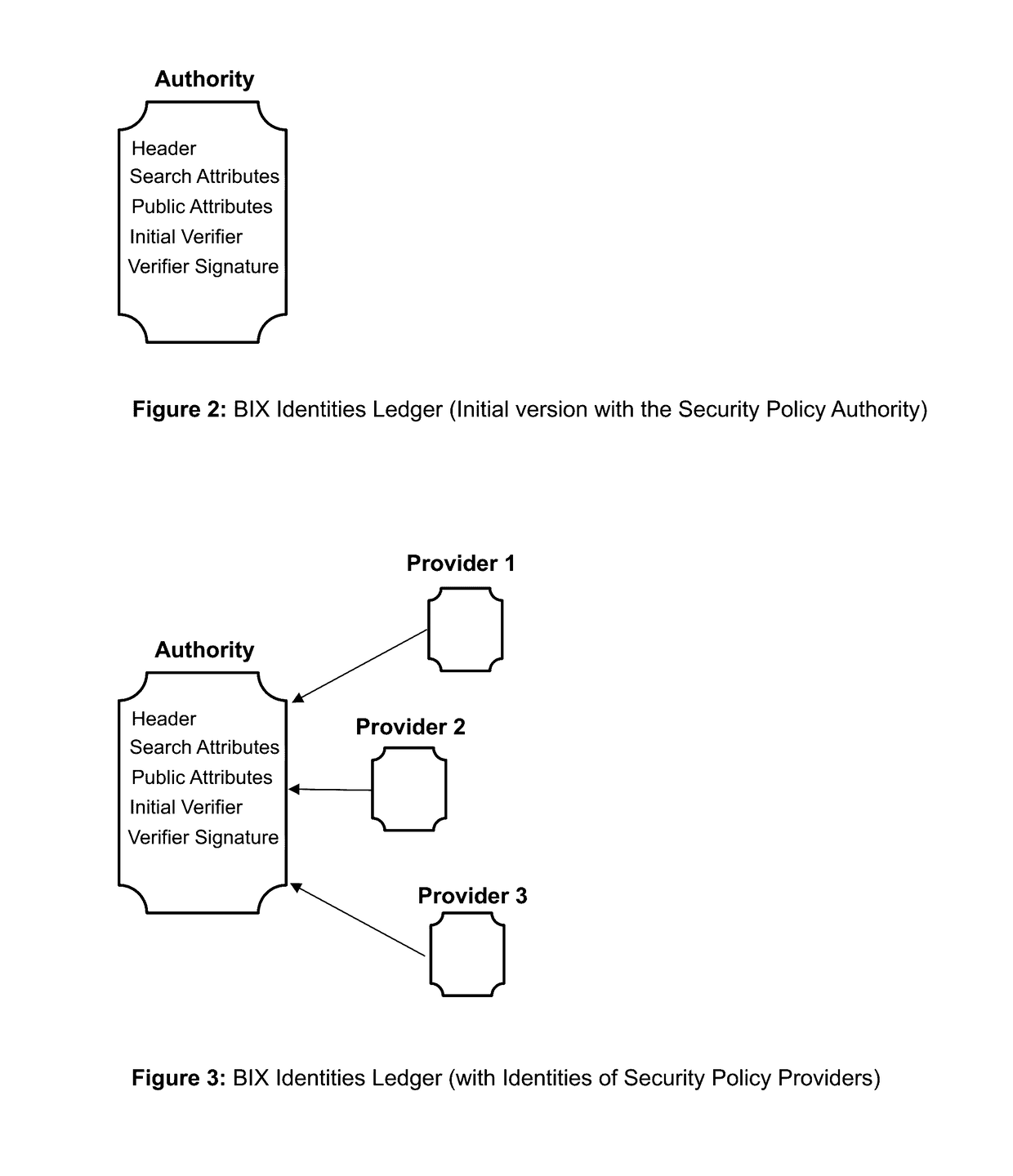
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
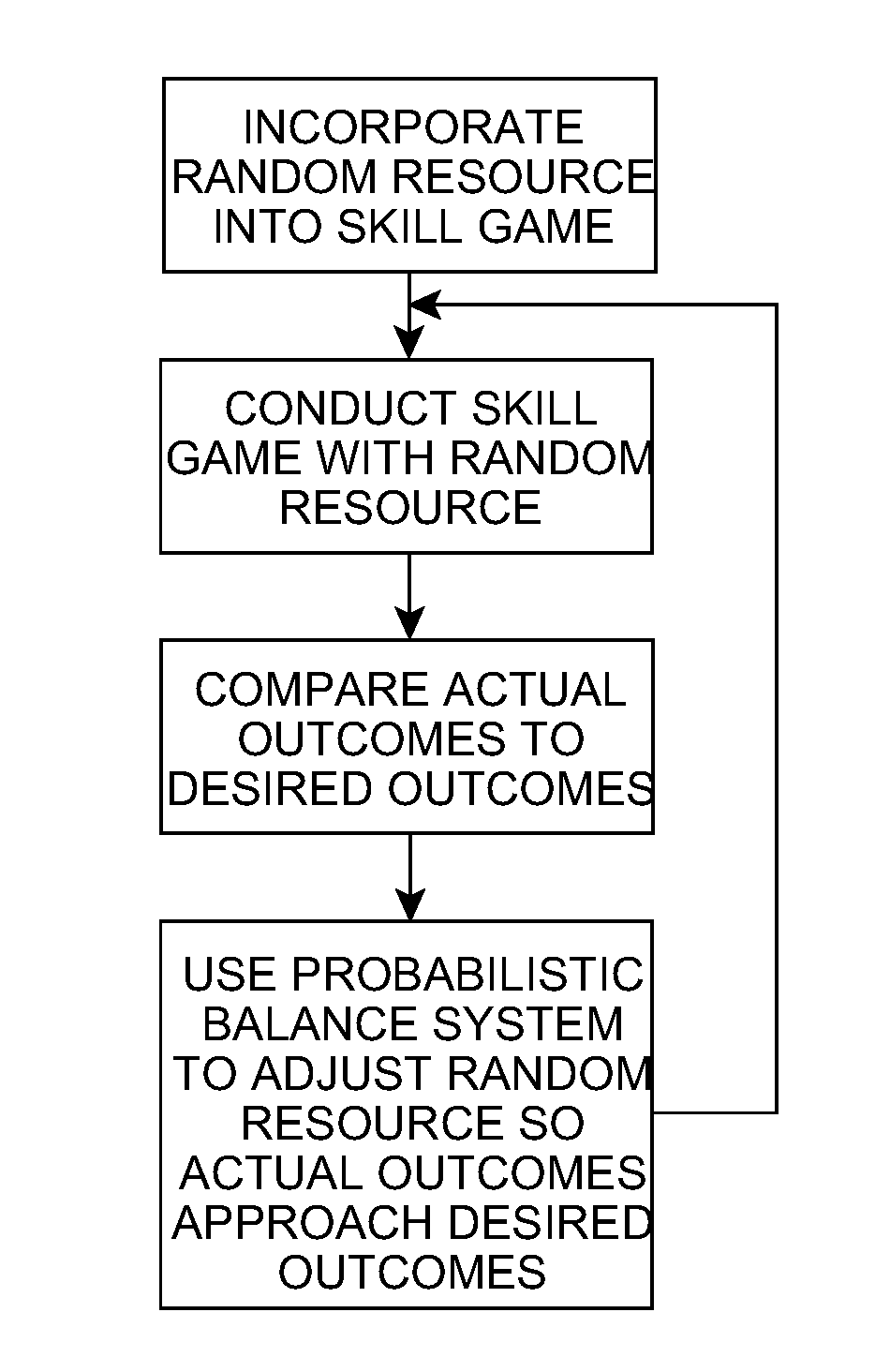
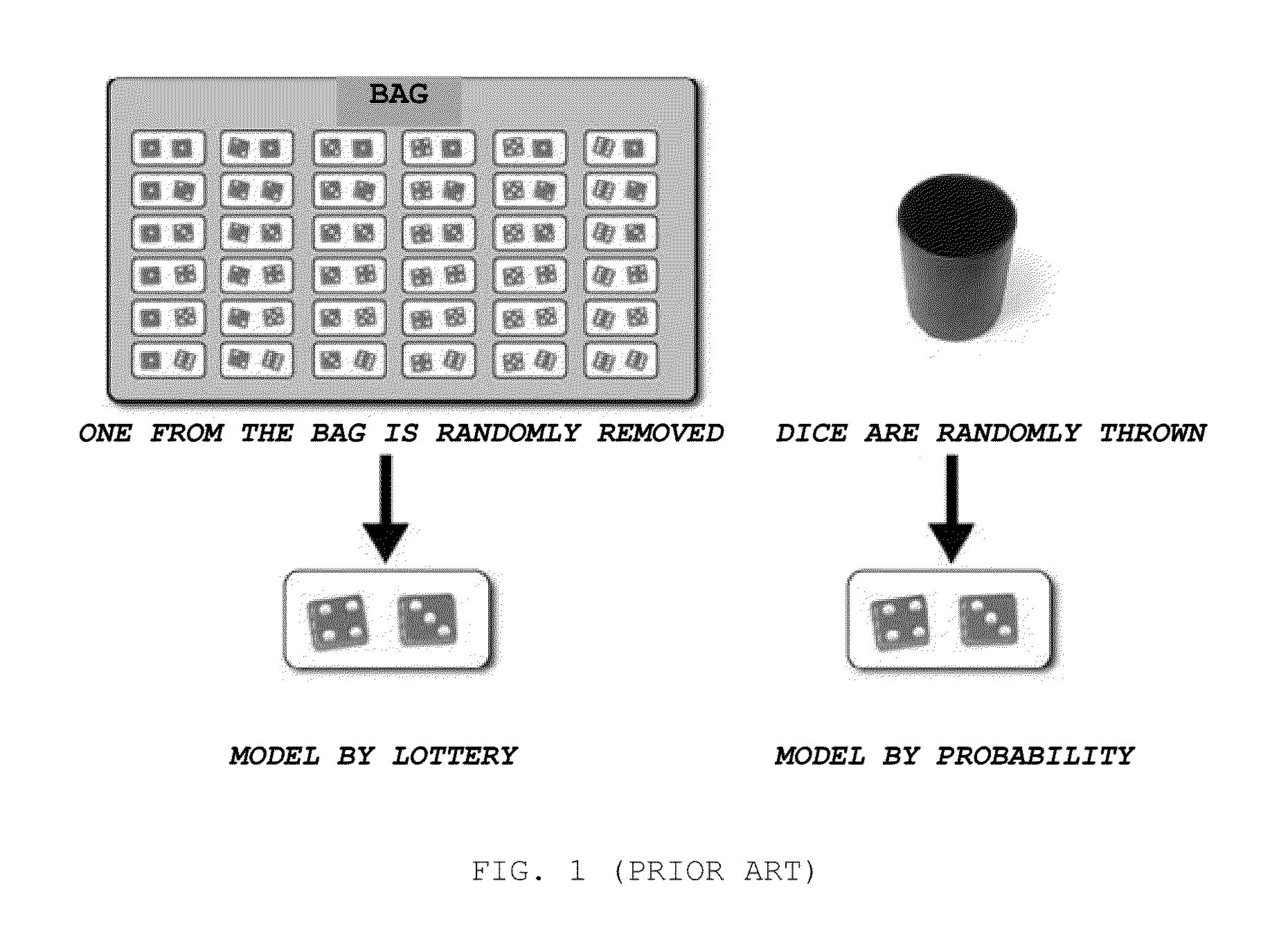
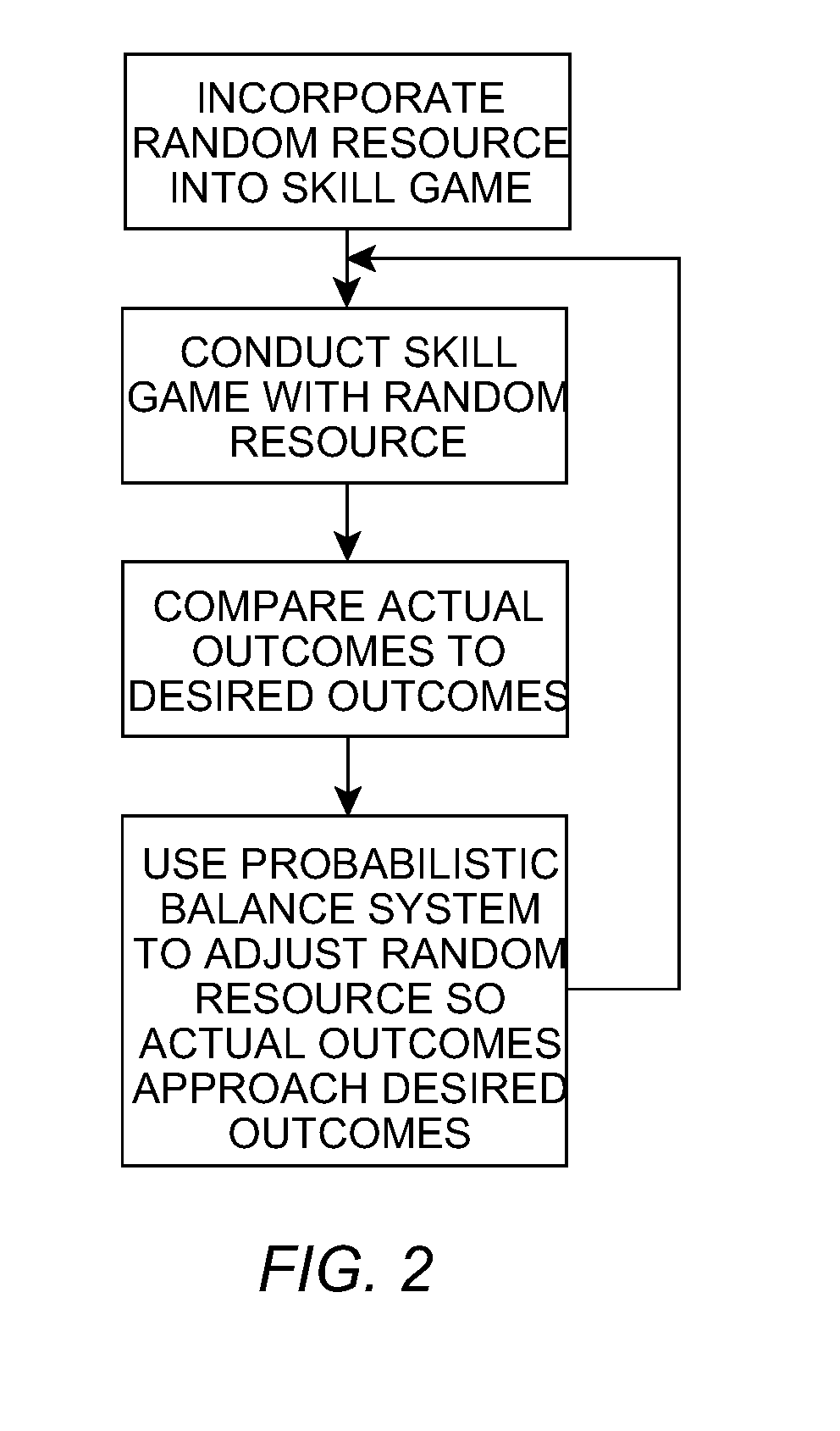
System for Incorporating Chance Into Interactive Games Requiring the Application of Intellectual or Motor Skills
InactiveUS20110009178A1Apparatus for meter-controlled dispensingVideo gamesMaximum levelSystems management
The invention refers to digital interactive games operable from specific terminals, video game consoles, personal computers, cell phones, digital interactive television, even when they include an initial bit of chance for their usual development, in order to incorporate the possibility to get a prize (including cash payments), besides of simply diversion. It comprises the incorporation of at least one random resource capable of sustaining a mathematical balance between winners and losers equivalent to that governing games of pure chance, keeping the condition that, for the resolution of each game, it requires the participation of the person, his / her with and his / her visual, motor, spatial, and linguistic skills, besides to his / her knowledge. The incorporated random resource is managed by a probabilistic balance system that ensures the proper ratio between winners and losers in terms of the predetermined “payout”. The incorporated random resource could be either a lottery of maximum results including the previous draw of the maximum result the player can reach (although he / she plays it perfectly), or a lottery of levels of difficulty that draws the level of difficulty set for each game between a maximum level (virtually impossible to overcome) and a minimum level (very easy to overcome), or a combination of both of them.
Owner:IPARK ENTRETENIMENTOS S L U
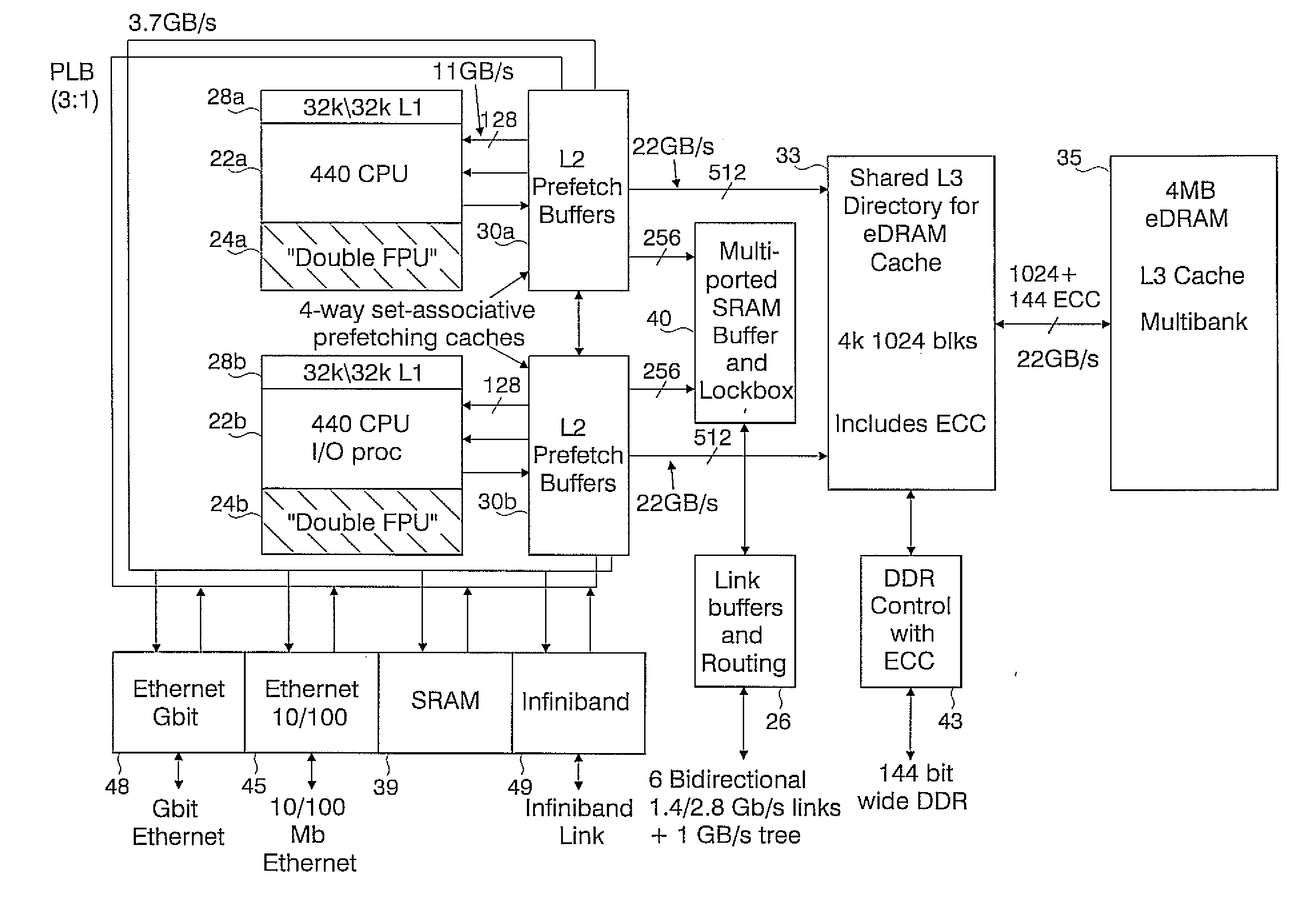
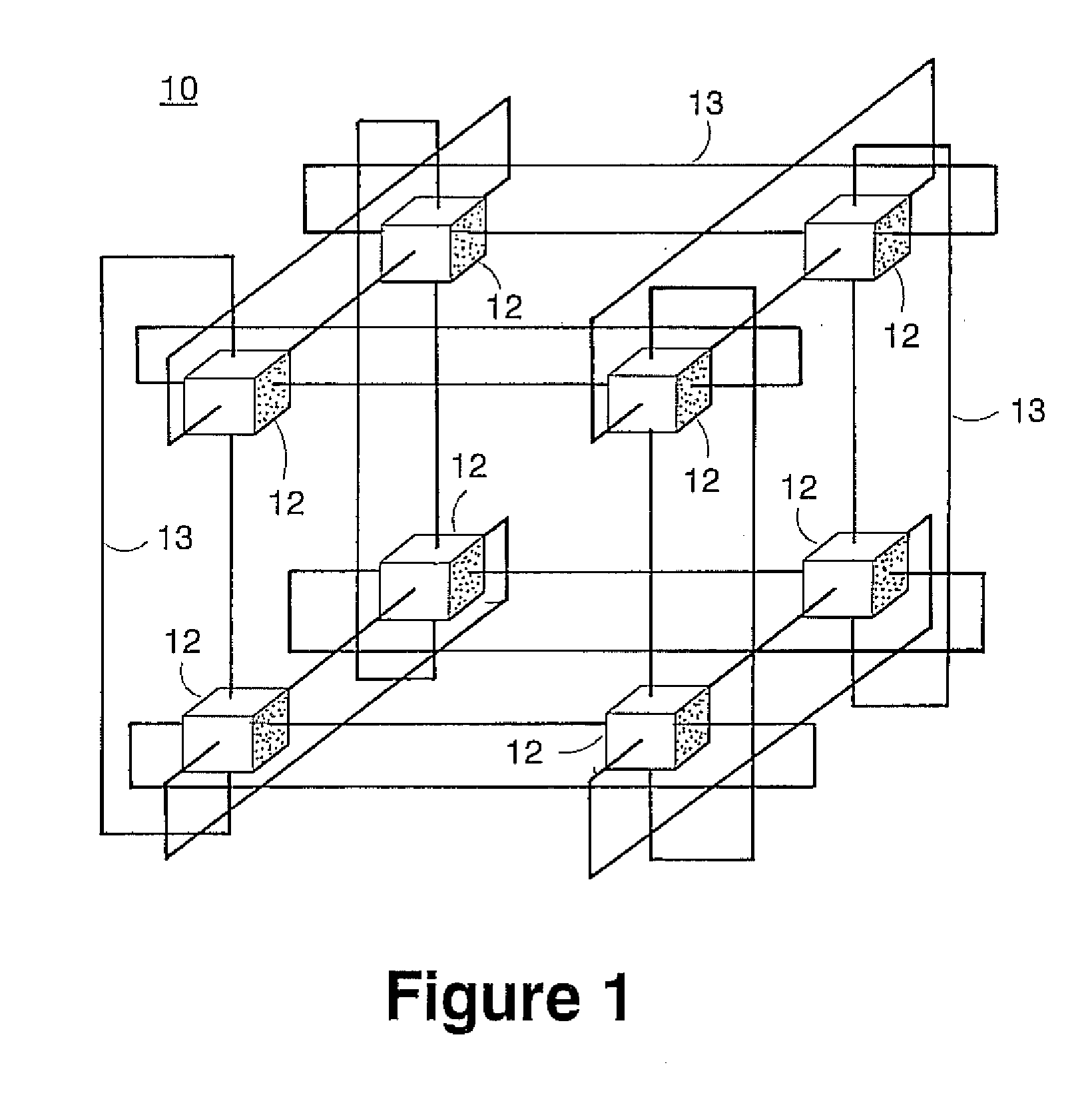
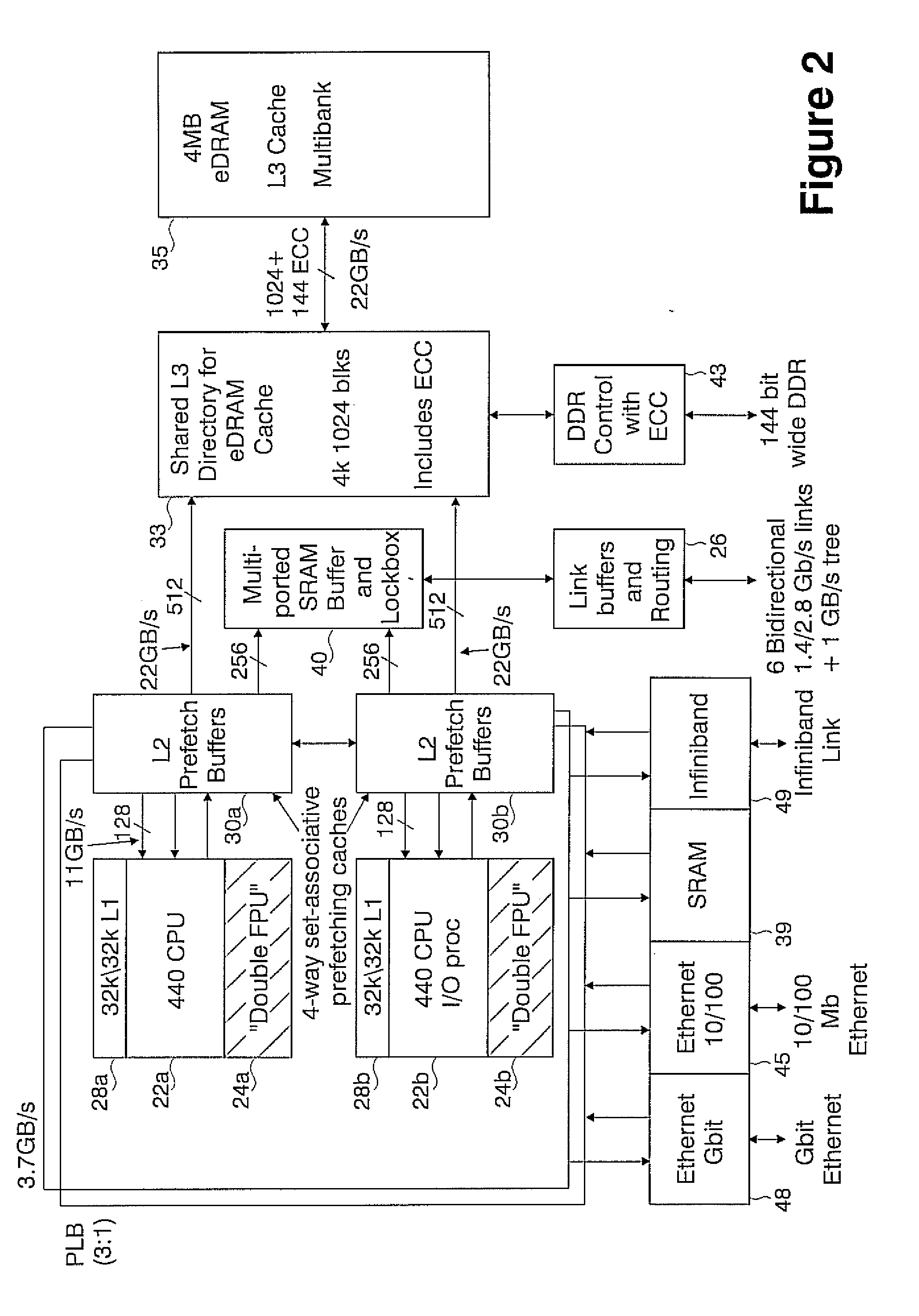
Novel massively parallel supercomputer
InactiveUS20090259713A1Low costReduced footprintError preventionProgram synchronisationSupercomputerPacket communication
Owner:INT BUSINESS MASCH CORP
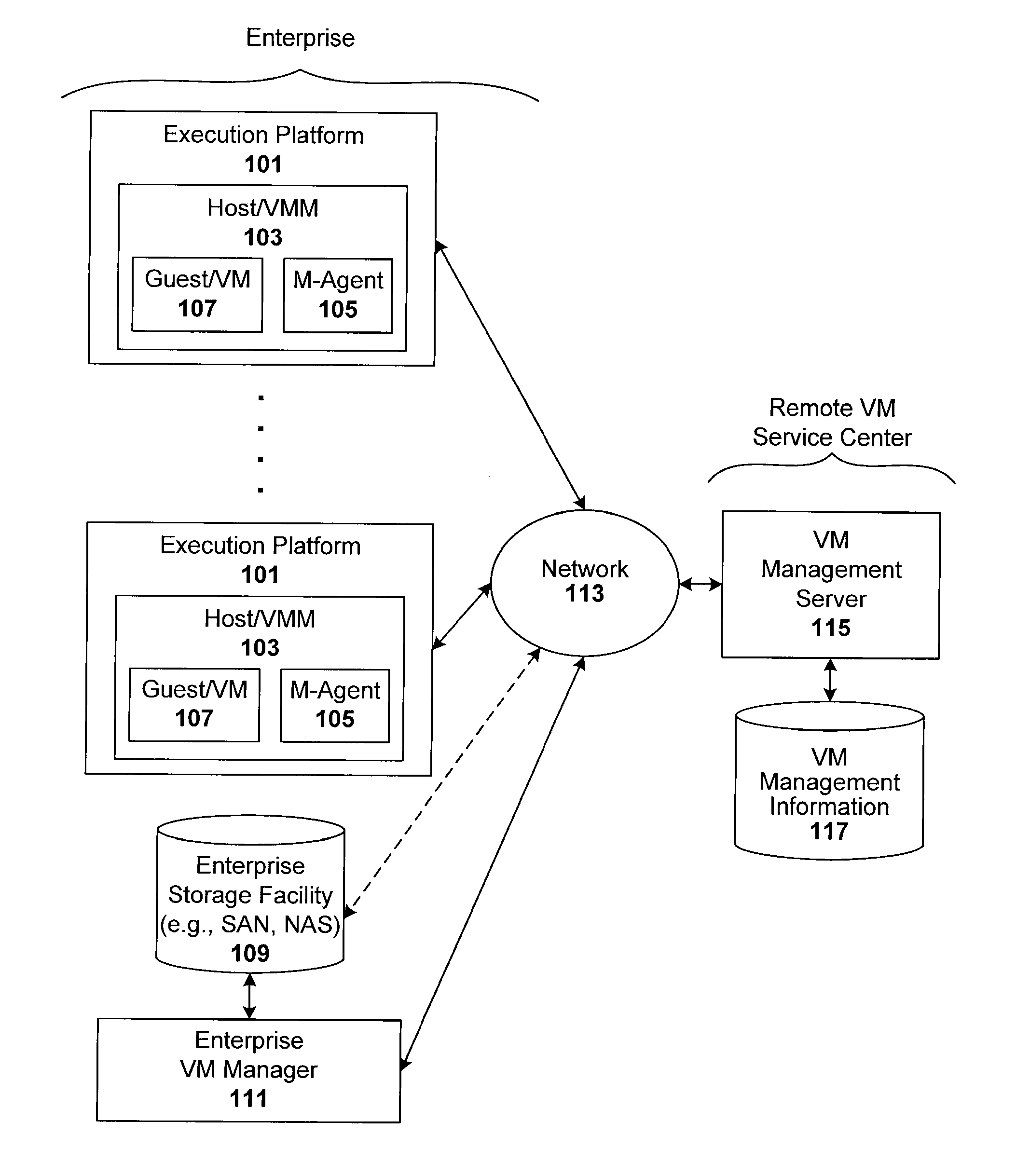
Compliance-based adaptations in managed virtual systems
ActiveUS8234640B1Removing malwareDisabling malwareMemory loss protectionError detection/correctionVirtual file systemConsistency test
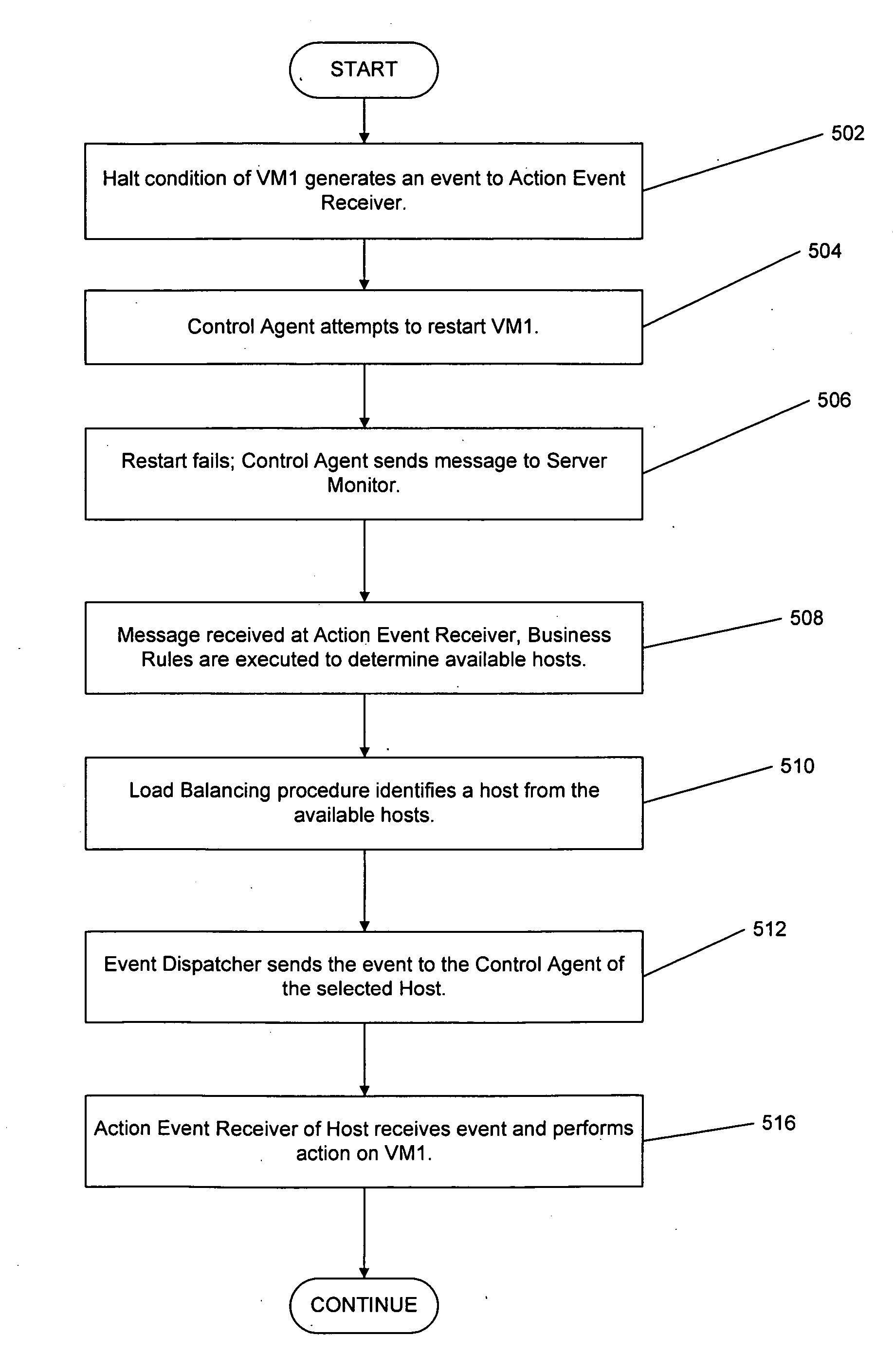
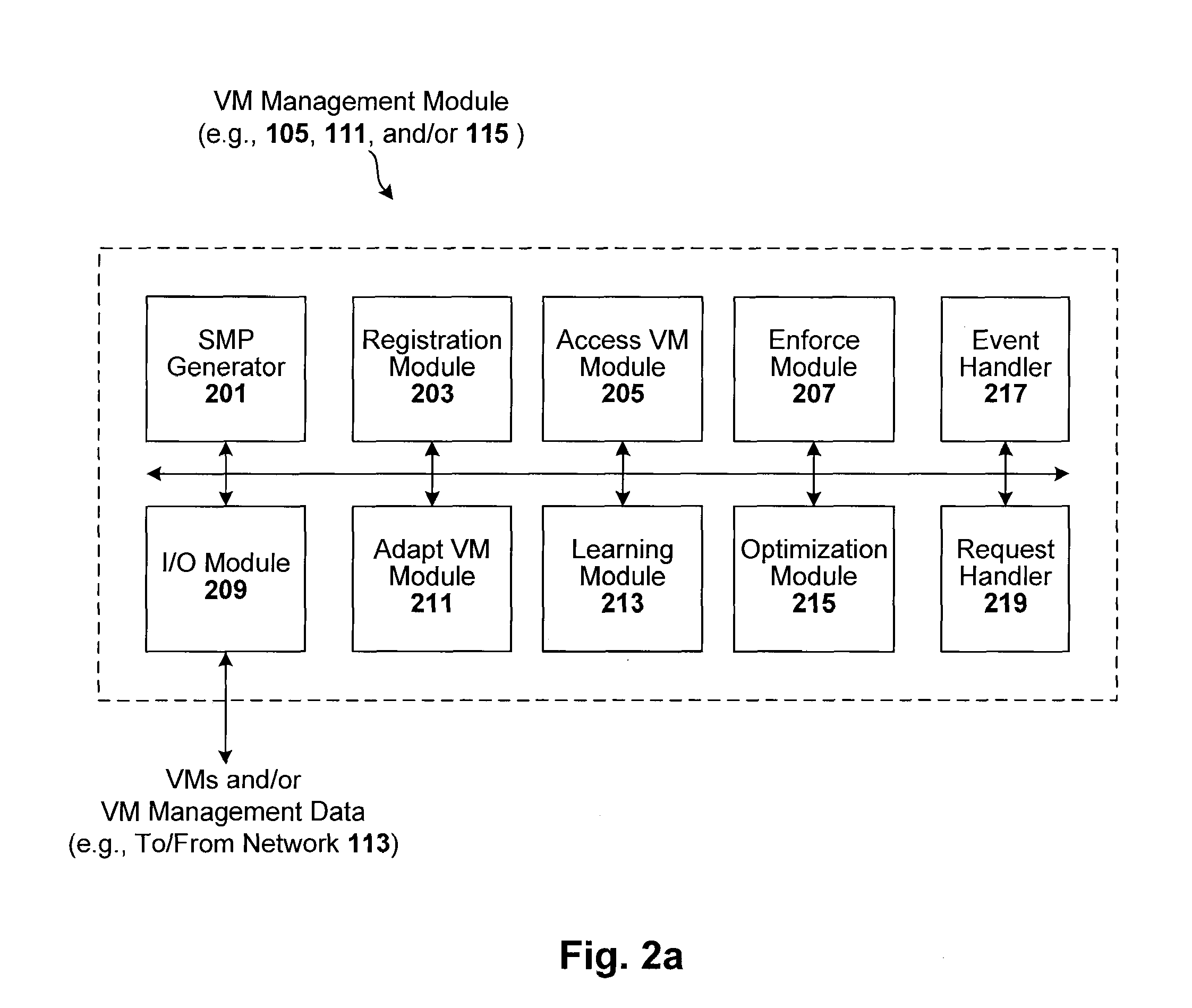
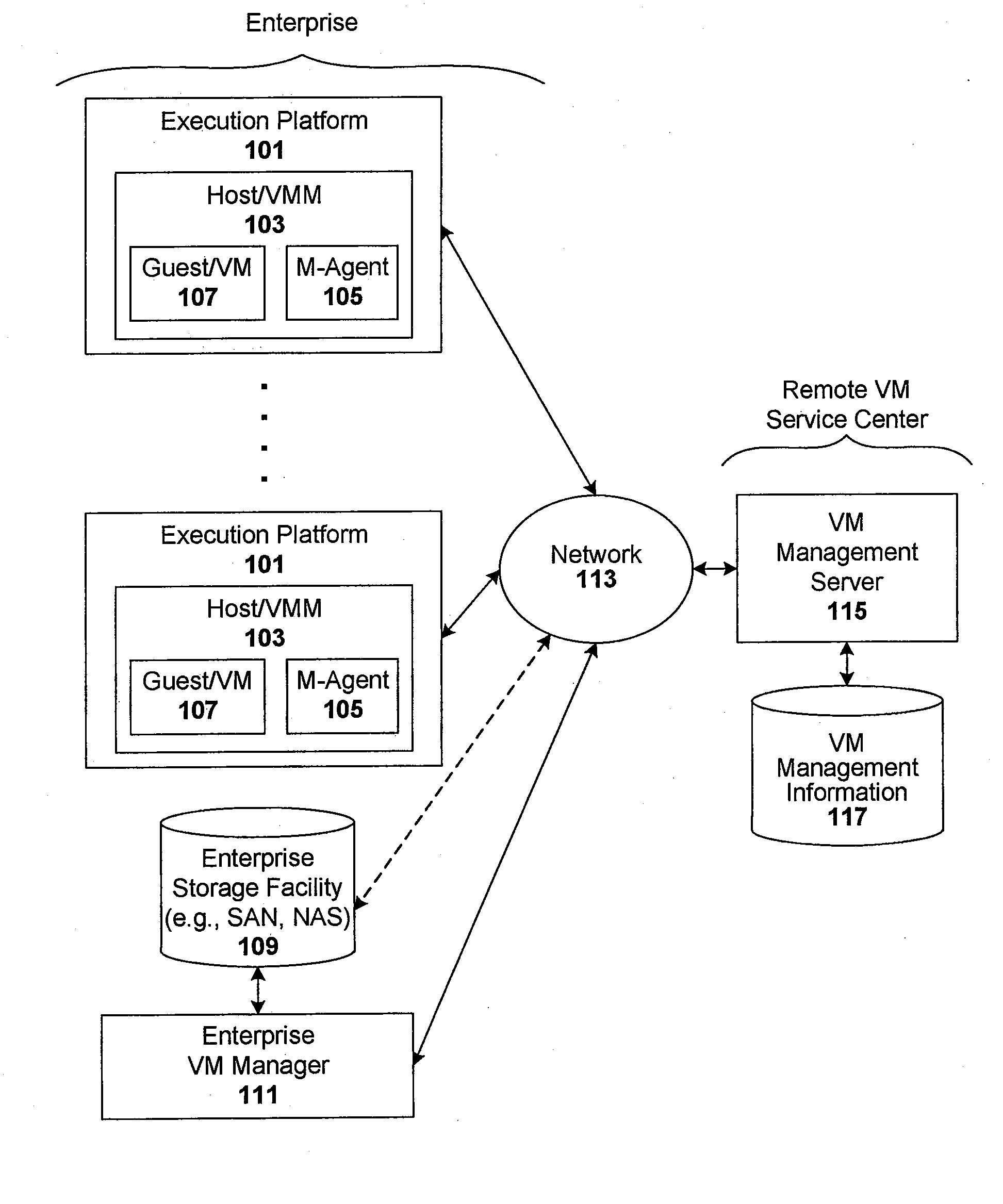
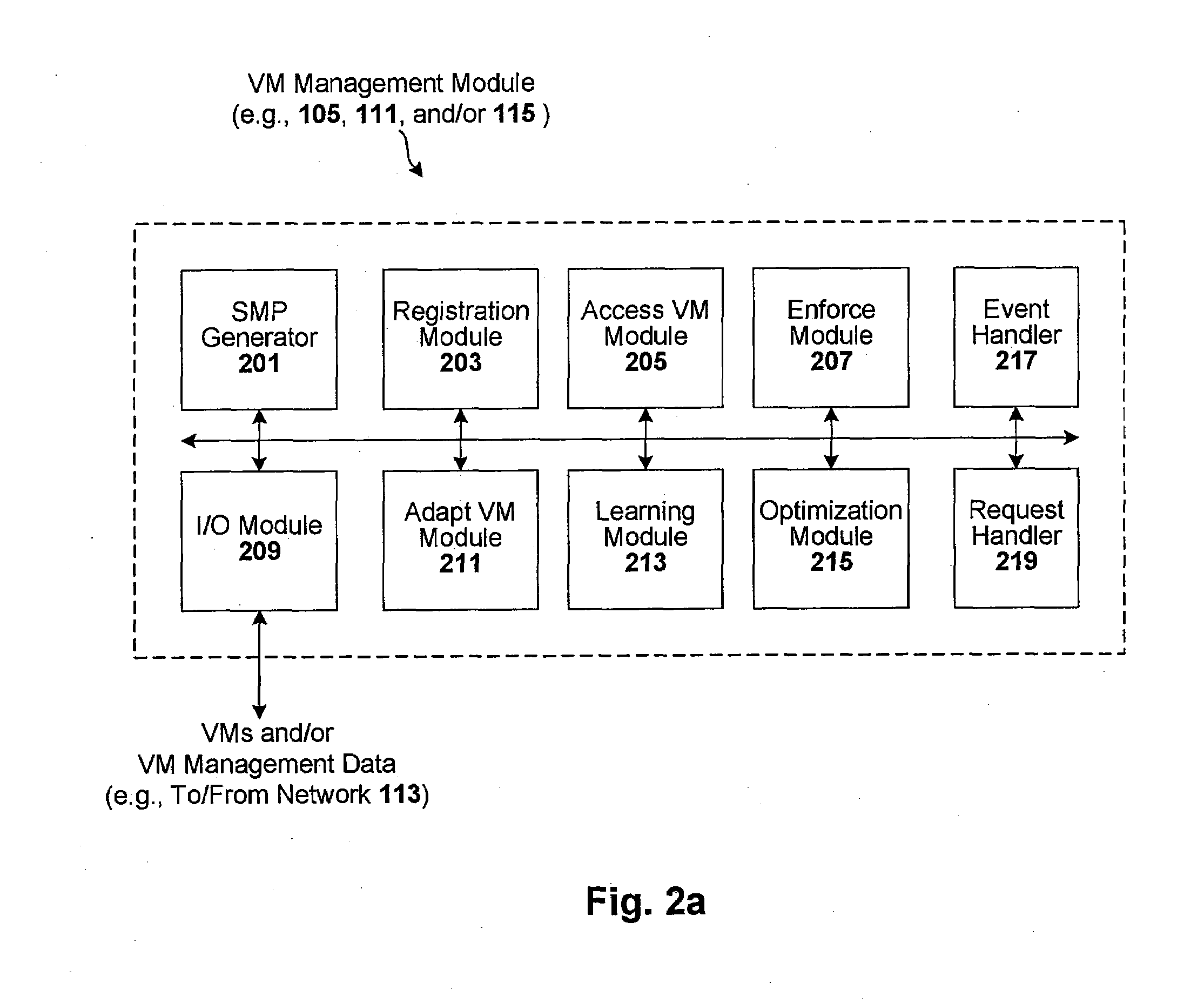
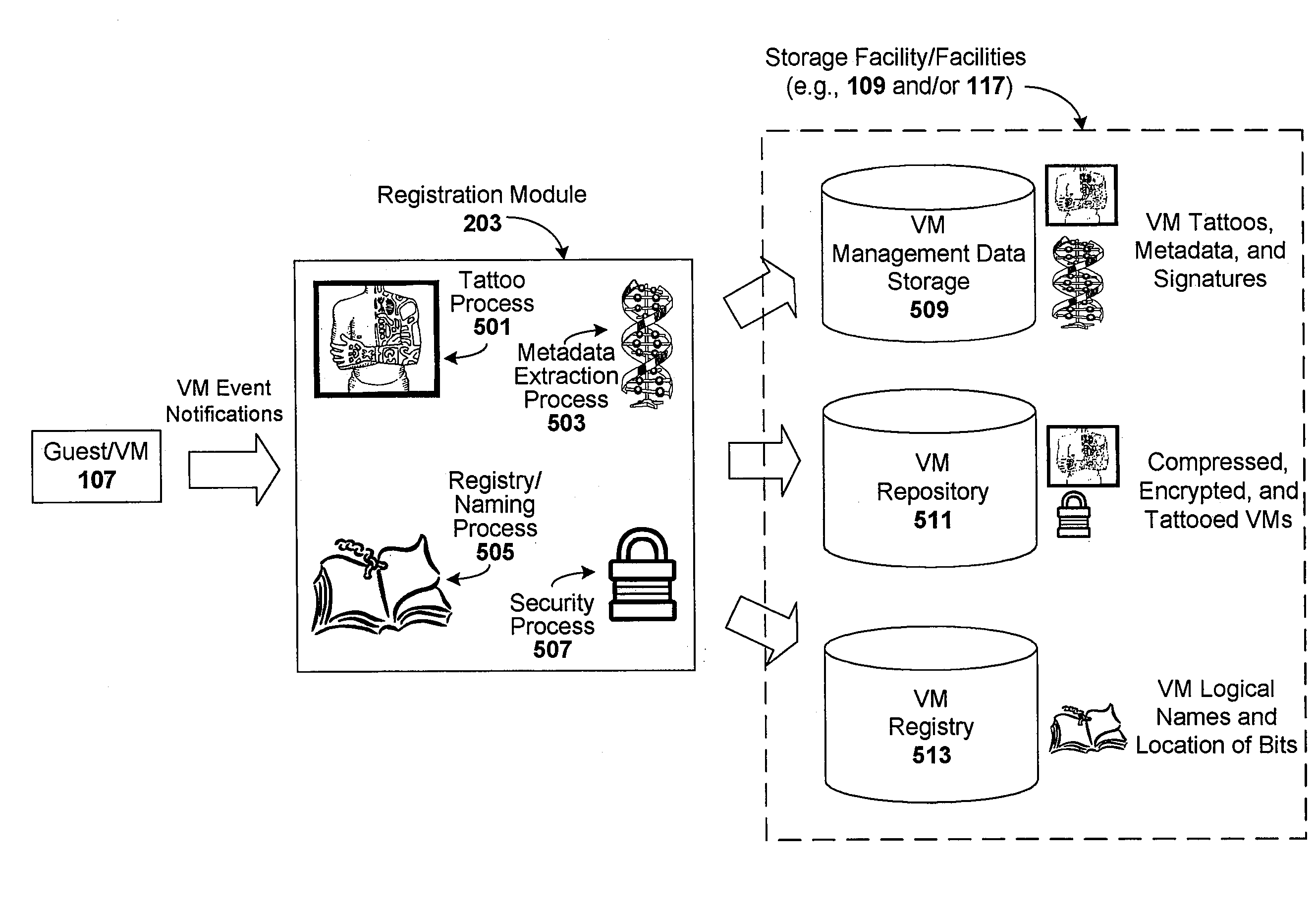
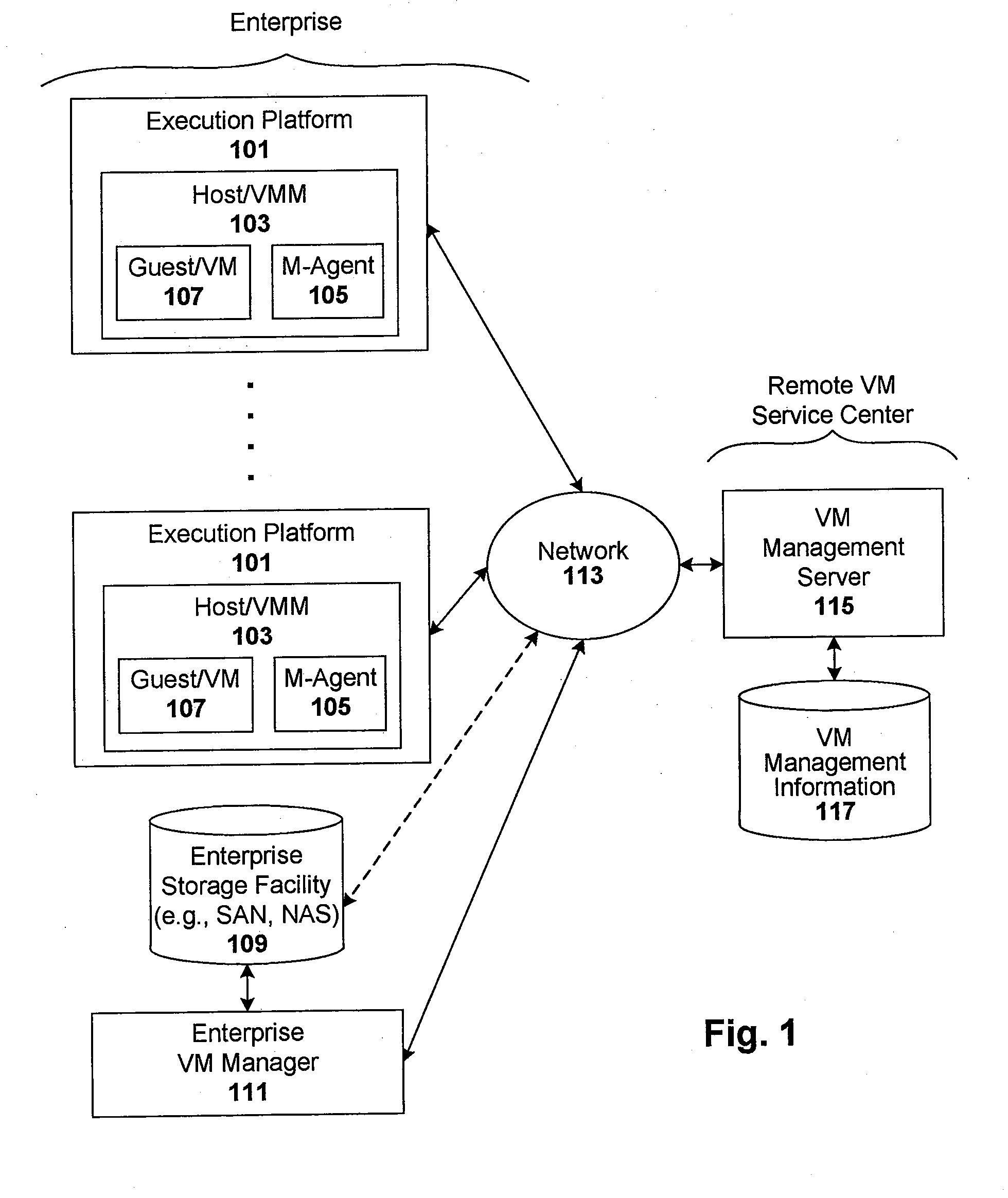
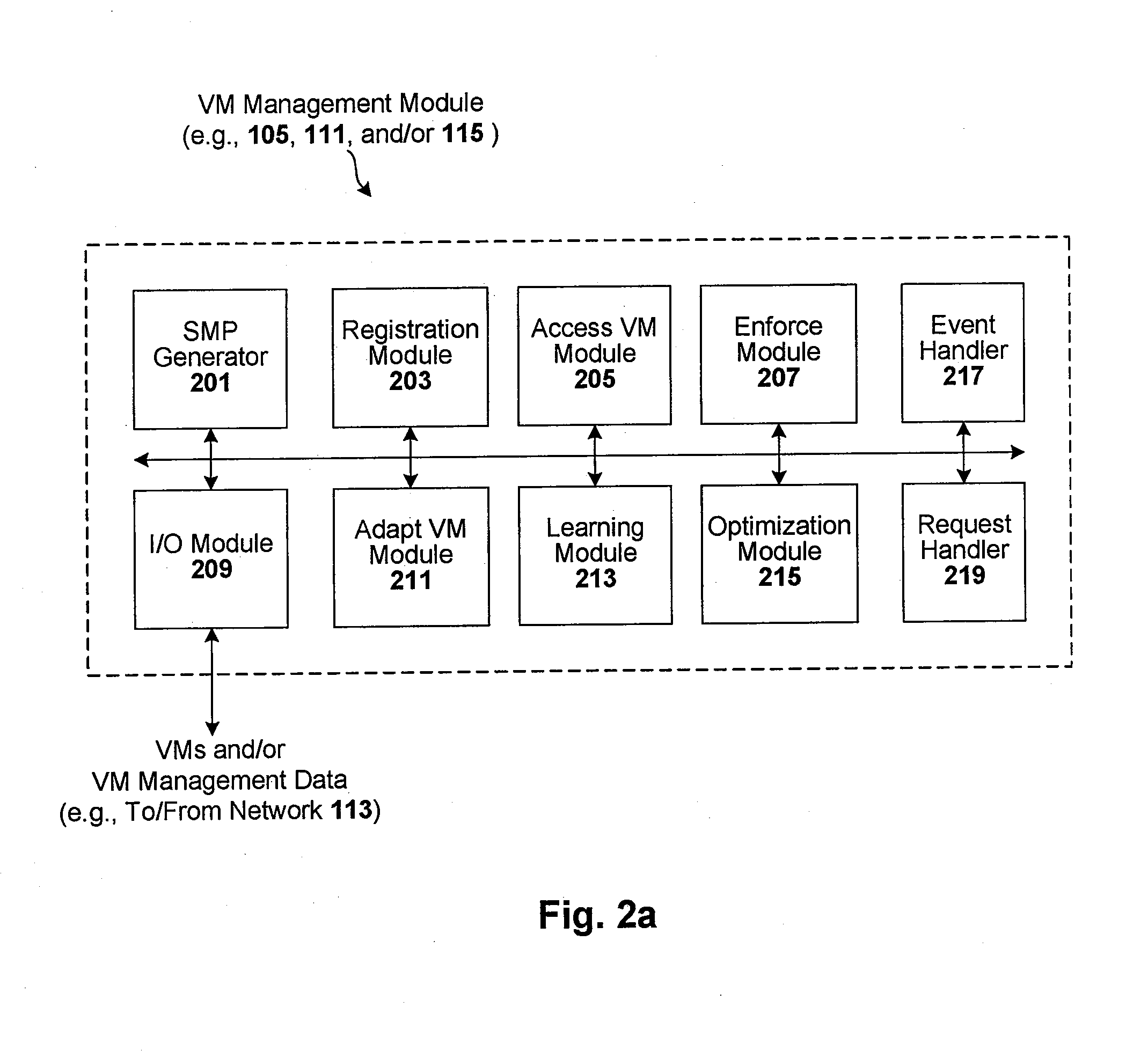
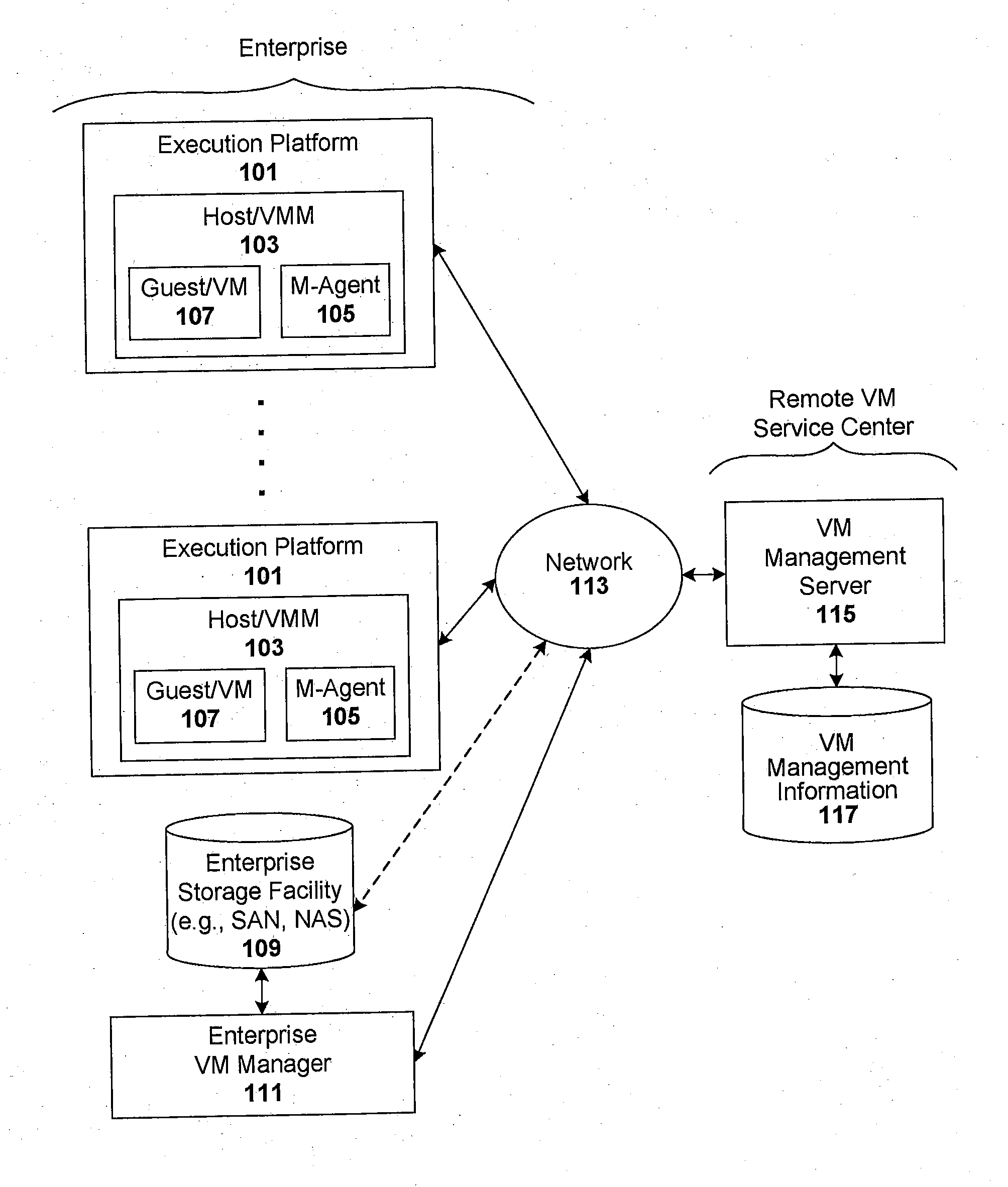
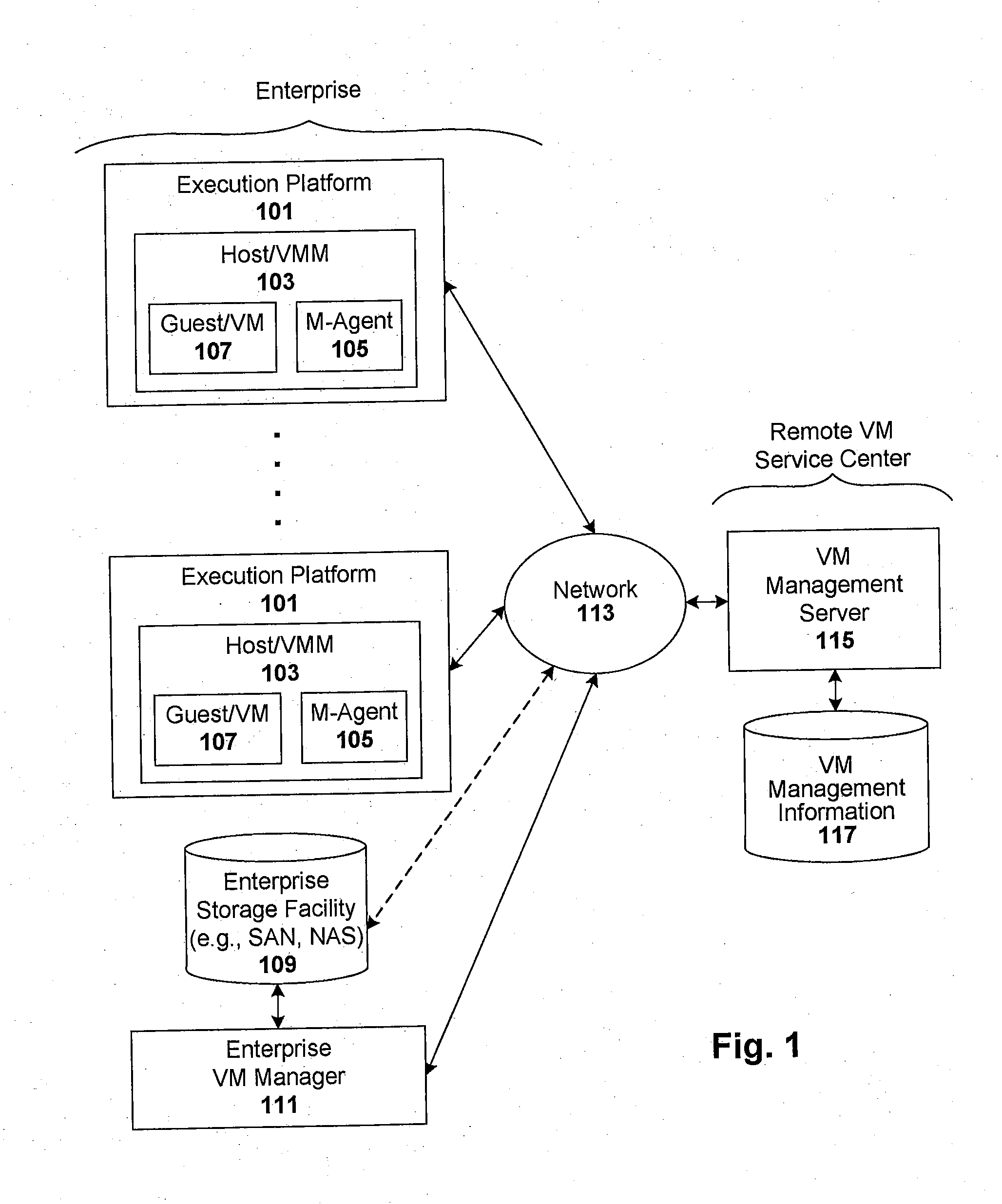
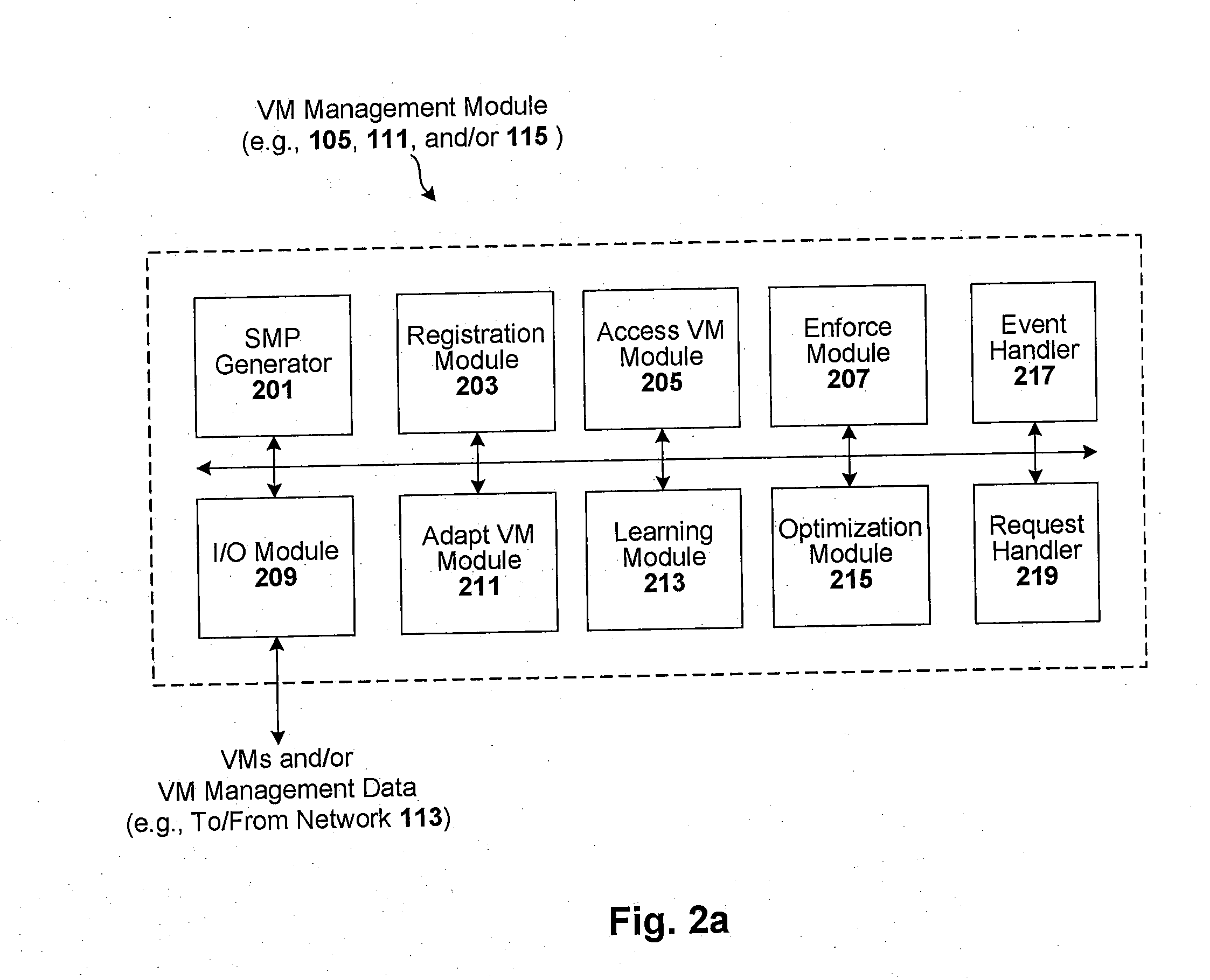
Techniques are disclosed for controlling and managing virtual machines and other such virtual systems. VM execution approval is based on compliance with policies controlling various aspects of VM. The techniques can be employed to benefit all virtual environments, such as virtual machines, virtual appliances, and virtual applications. For ease of discussion herein, assume that a virtual machine (VM) represents each of these environments. In one particular embodiment, a systems management partition (SMP) is created inside the VM to provide a persistent and resilient storage for management information (e.g., logical and physical VM metadata). The SMP can also be used as a staging area for installing additional content or agentry on the VM when the VM is executed. Remote storage of management information can also be used. The VM management information can then be made available for pre-execution processing, including policy-based compliance testing.
Owner:RED HAT
Systems and methods for recovering electronic information from a storage medium
ActiveUS7472238B1Error detection/correctionMemory adressing/allocation/relocationSystems managementEngineering
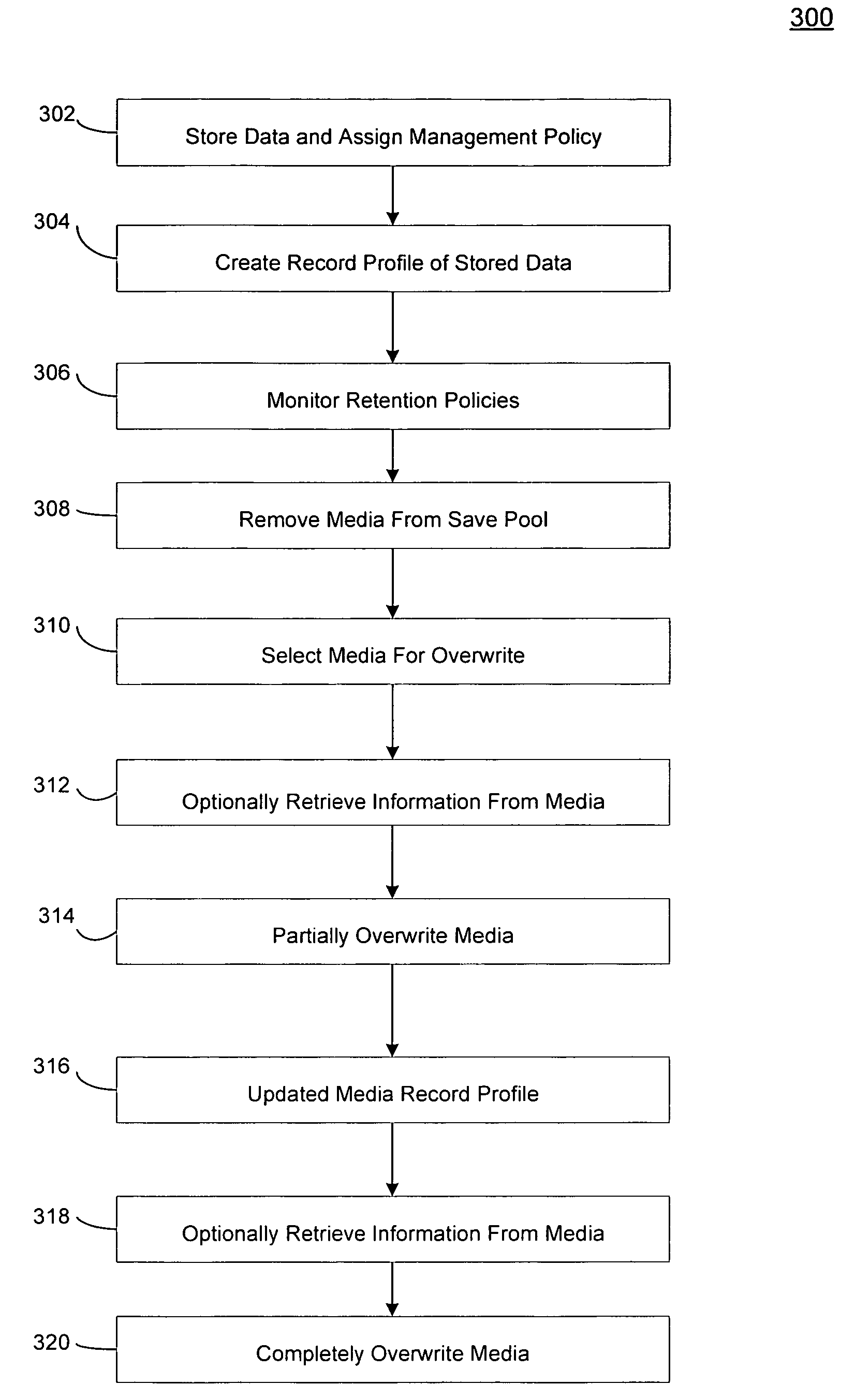
In one embodiment of the invention, a method is provided for retrieving certain electronic information previously stored on certain storage media after a threshold set in the storage retention criteria has been exceeded in an electronic information storage system that stores electronic information on storage media in accordance with a storage retention criteria is provided. The method includes storing a record in a memory associated with a system manager that assigns the storage retention criteria to the certain electronic data, designating the storage media available for overwrite after the threshold set in the storage retention policy has been exceeded, identifying the certain storage media available for overwrite, and retrieving information from the certain media after the threshold set in the storage retention policy has been exceeded.
Owner:COMMVAULT SYST INC
Methods and systems for managing security policies
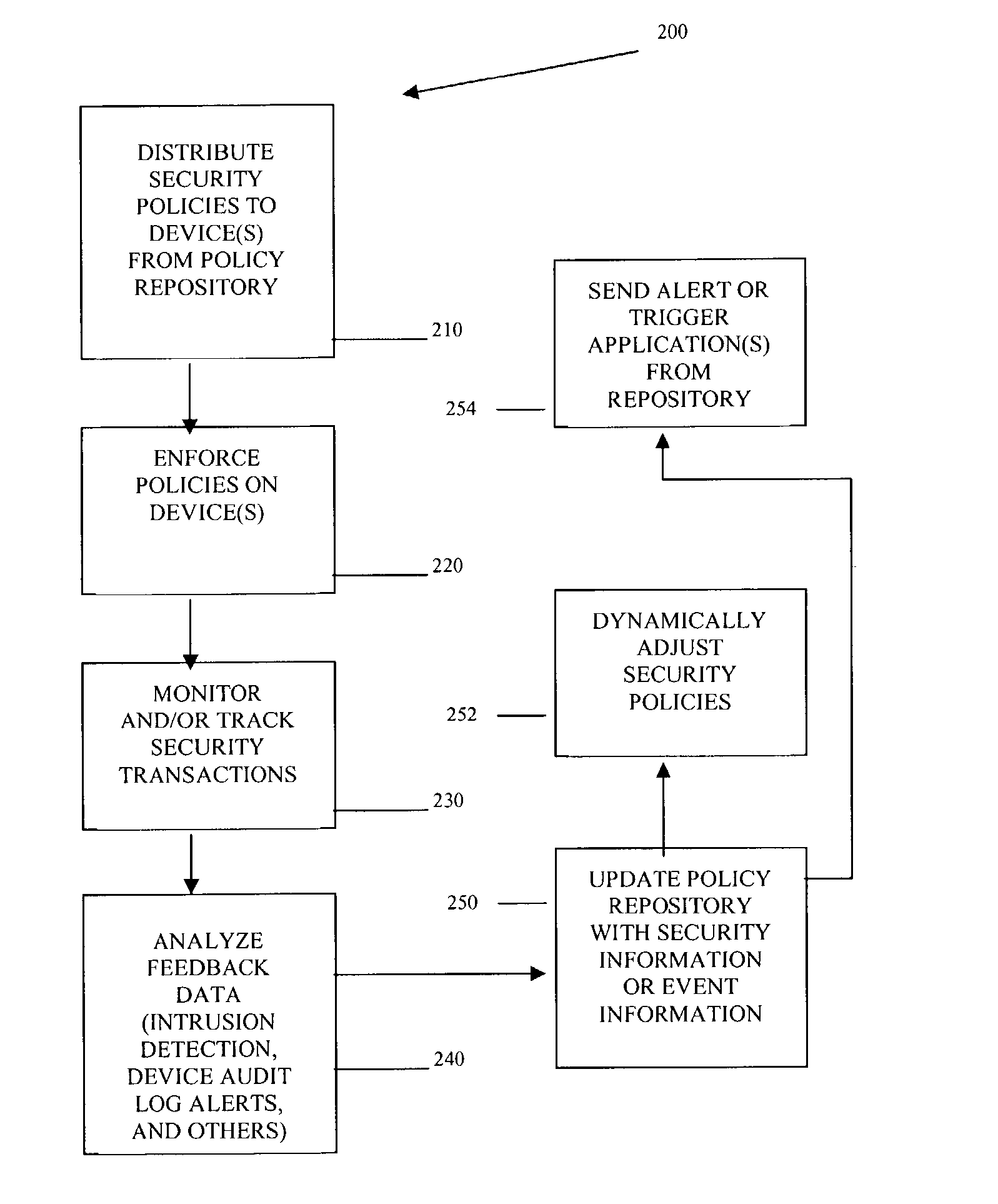
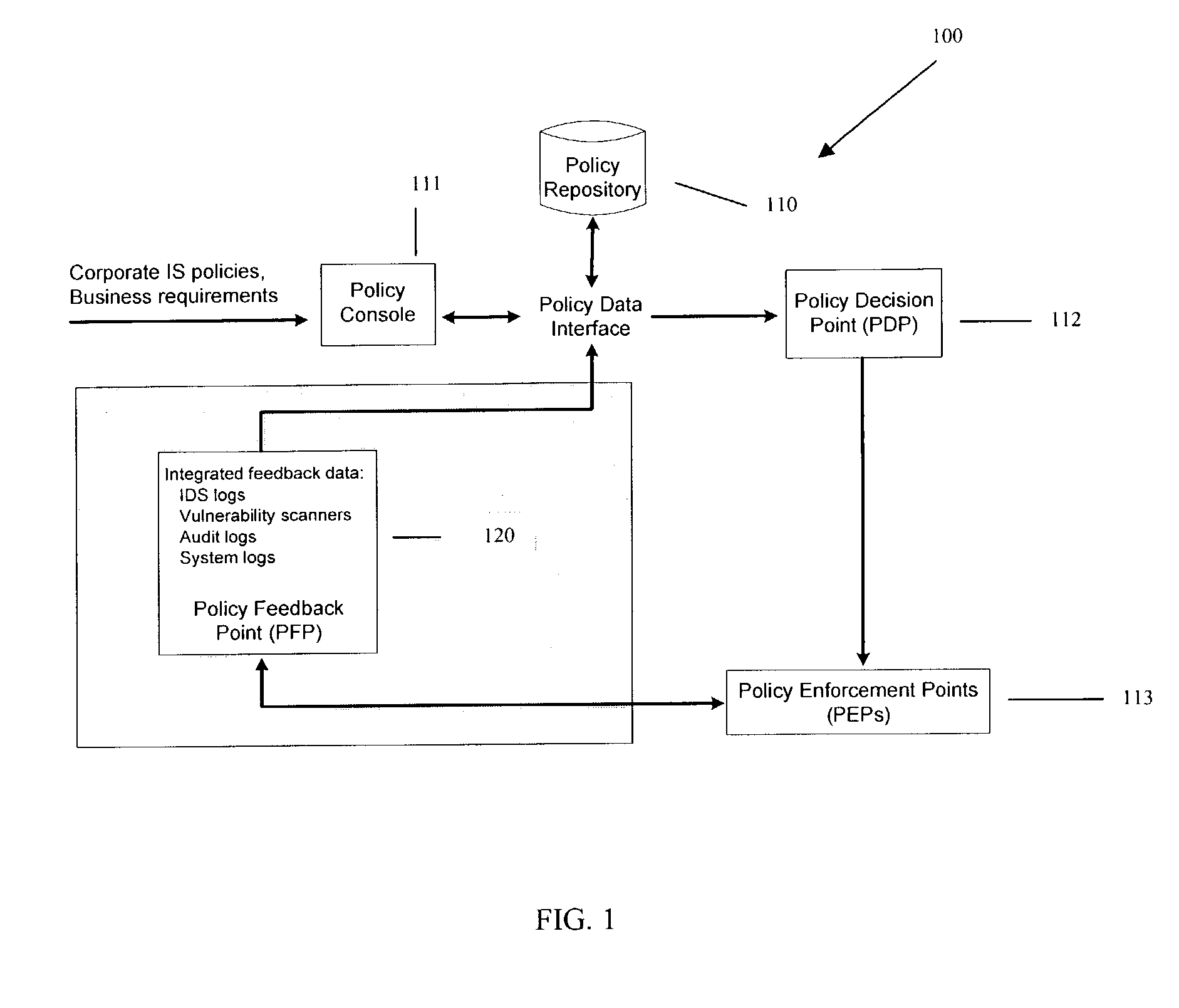
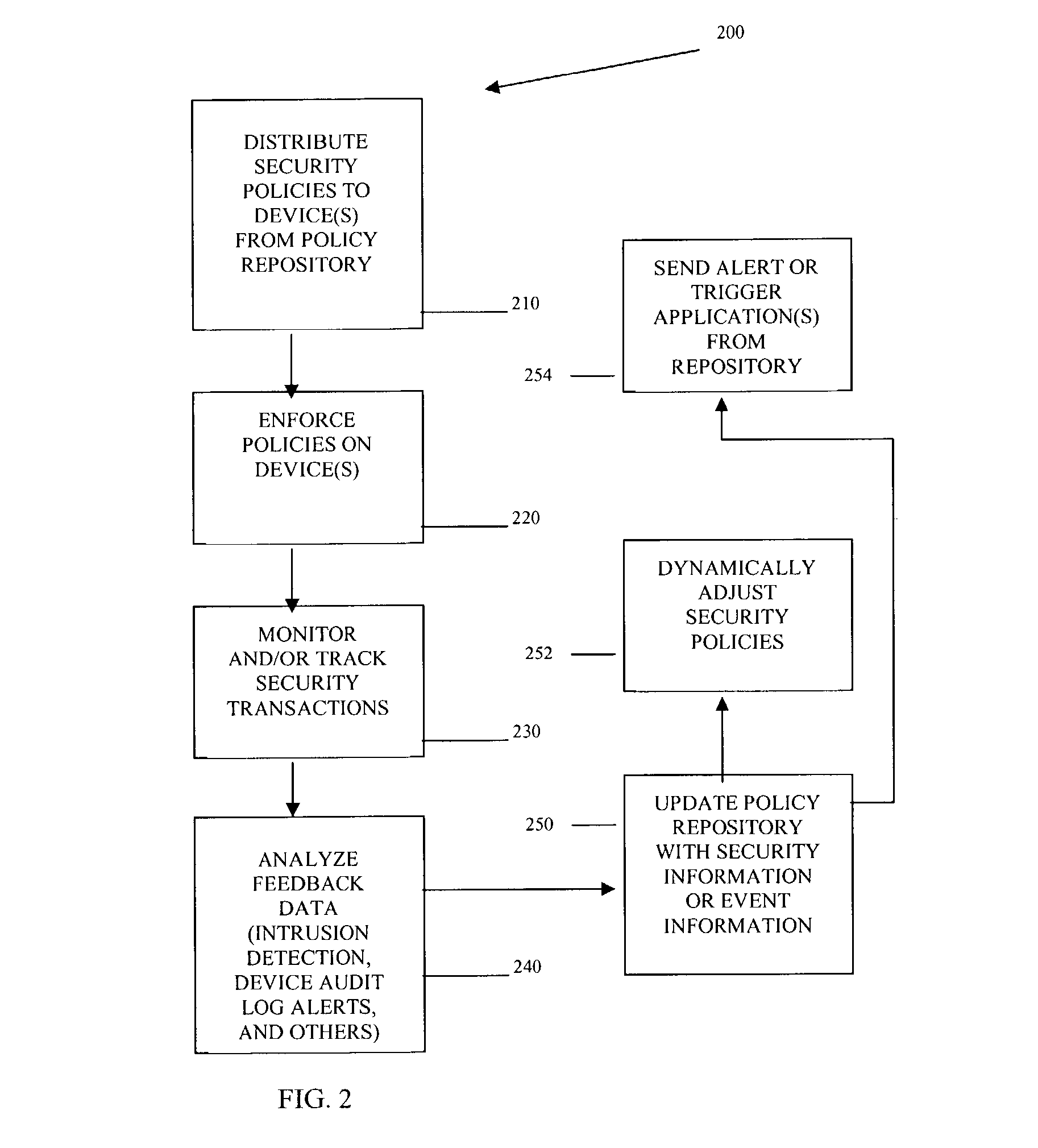
InactiveUS20040193912A1Data taking preventionDigital data processing detailsPolicy decisionSystems management
Methods, machines, and systems manage security policies of heterogeneous infrastructure and computing devices of a network. Security policy repository houses security policies that are pushed over the network by a policy decision point PDP to appropriate security-enabled devices (policy enforcement points (PEPs)) for enforcement. Using a closed feedback loop, a policy feedback point (PFP) collects and processes data from intrusions, alerts, violations, and other abnormal behaviors from a variety of PEPs or logs produced from PEPs. This data is sent as feedback to the policy repository. The PDP detects the data and analyzes it to determine if policy updates (which can be dynamic and automatic) need to be adaptively made and dynamically pushed to PEPs. The PDP can also send console messages or alerts to consoles or administrators.
Owner:INTEL CORP
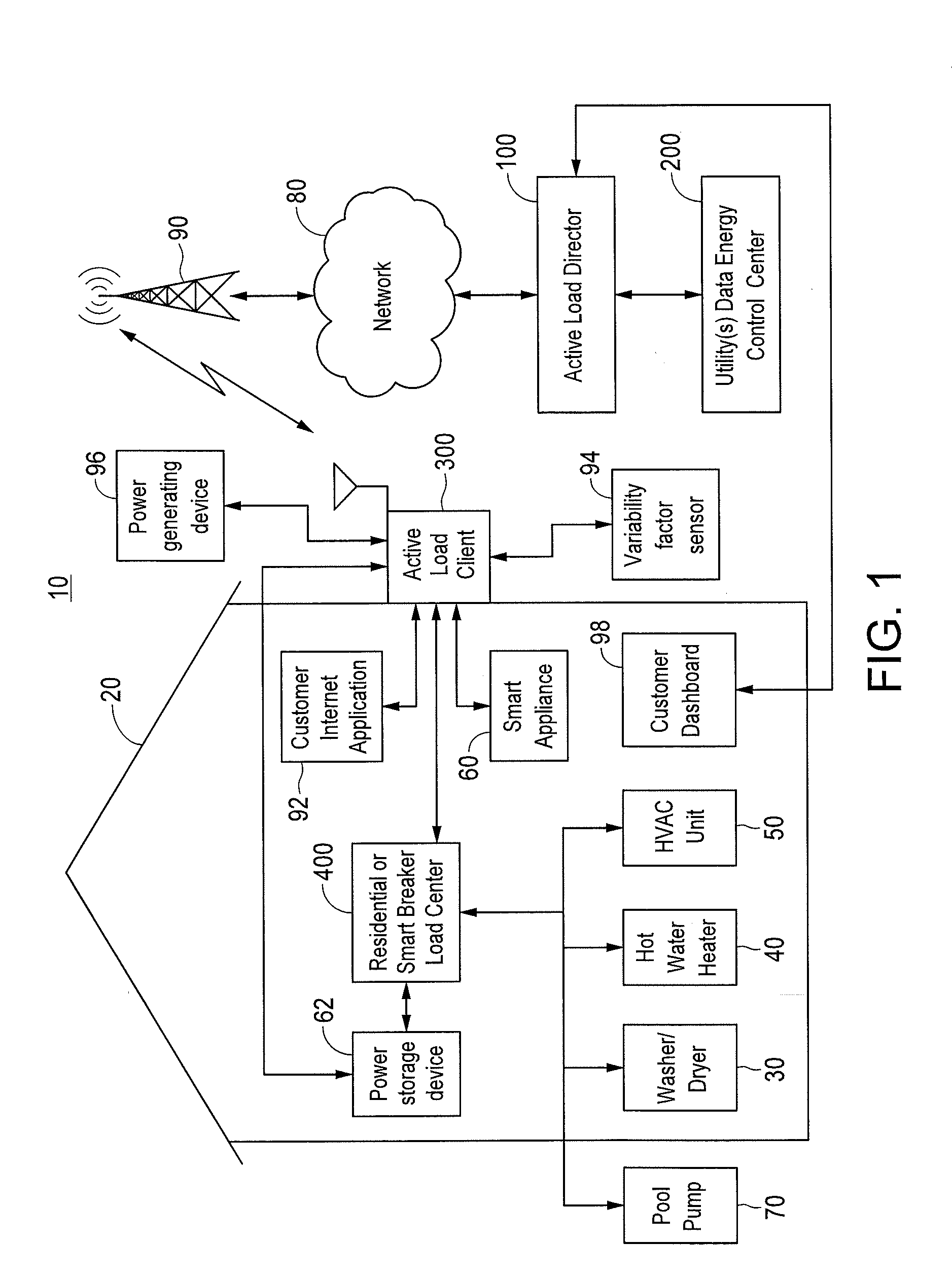
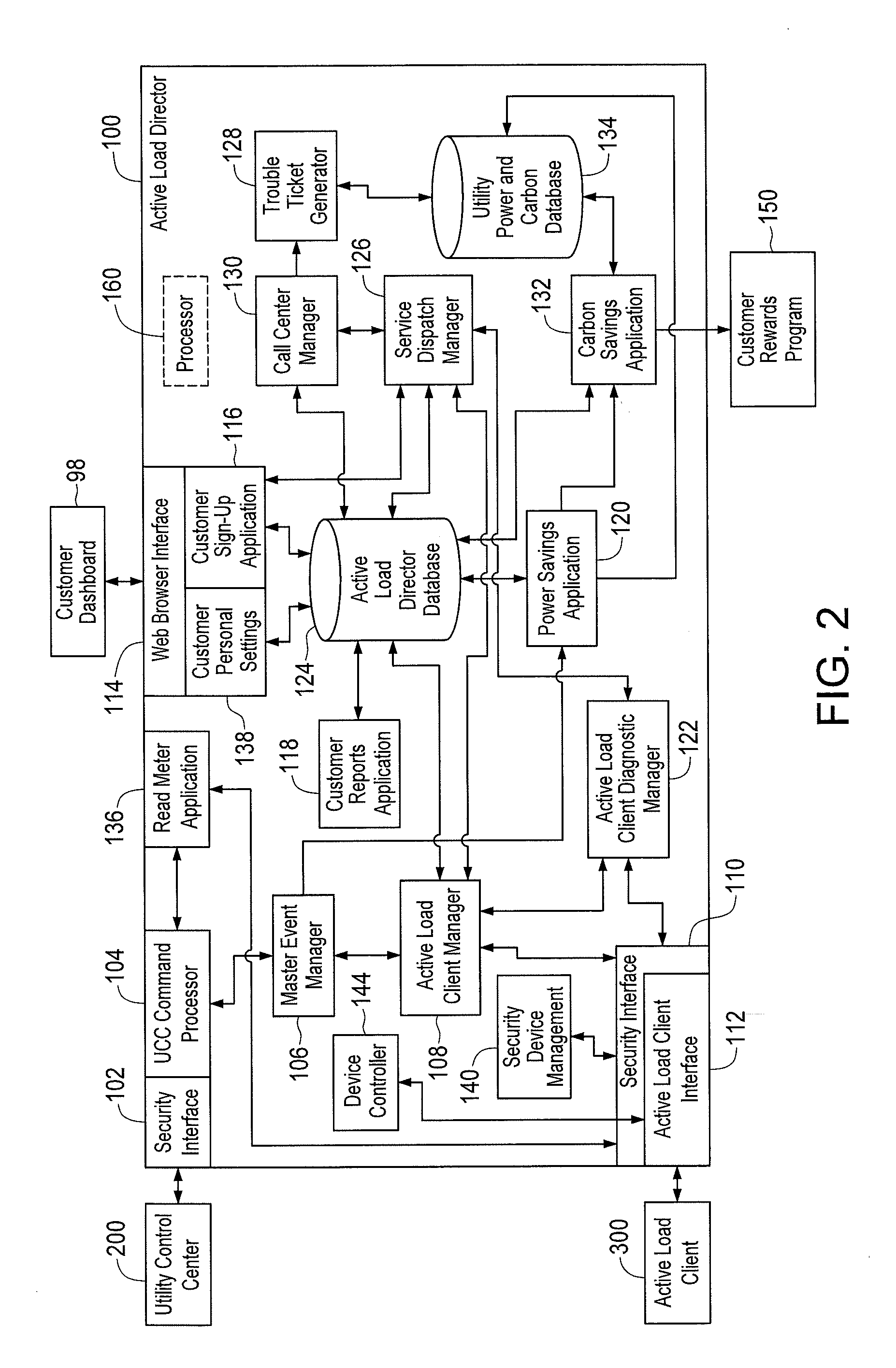
Method and Apparatus for Actively Managing Consumption of Electric Power Supplied by One or More Electric Utilities
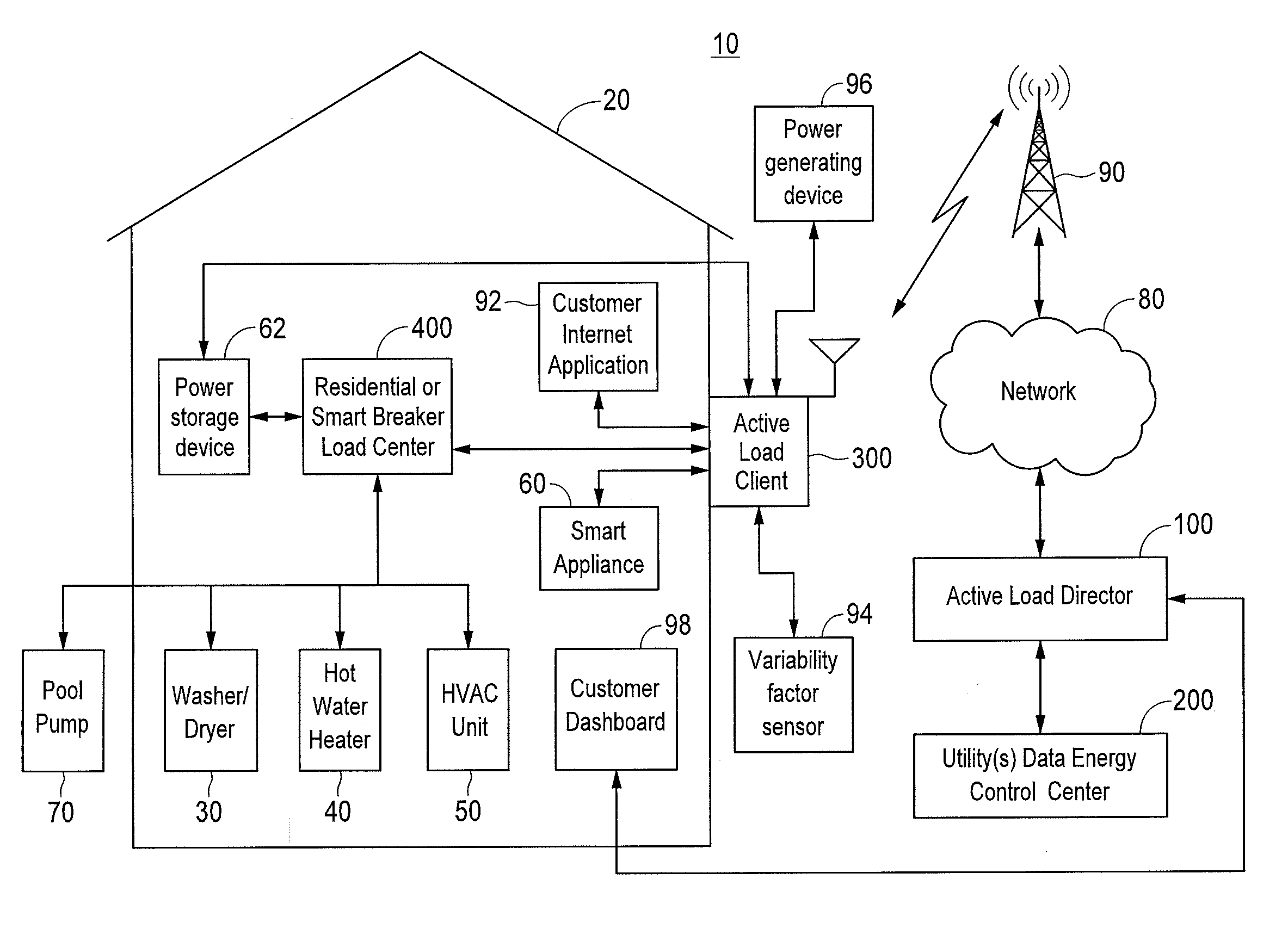
ActiveUS20110172841A1Detrimental changeEnergy efficient ICTLevel controlPower flowSystems management
A system manages consumption of power supplied by at least one electric utility to multiple power consuming devices. Power flow to the power consuming devices is enabled and disabled by controllable devices controlled by one or more client devices. According to one embodiment, a group of one or more client devices to which to communicate a power control message is determined. The power control message indicates at least one of an amount of electric power to be reduced and an identification of one or more controllable devices to be instructed to disable a flow of electric power to one or more associated power consuming devices. The power control message is communicated to the determined group of client devices to initiate a power reduction event. Subsequent to initiation of the power reduction event, a determination is made that at least one controllable device has prematurely exited the power reduction event.
Owner:LANDISGYR INNOVATIONS INC +1
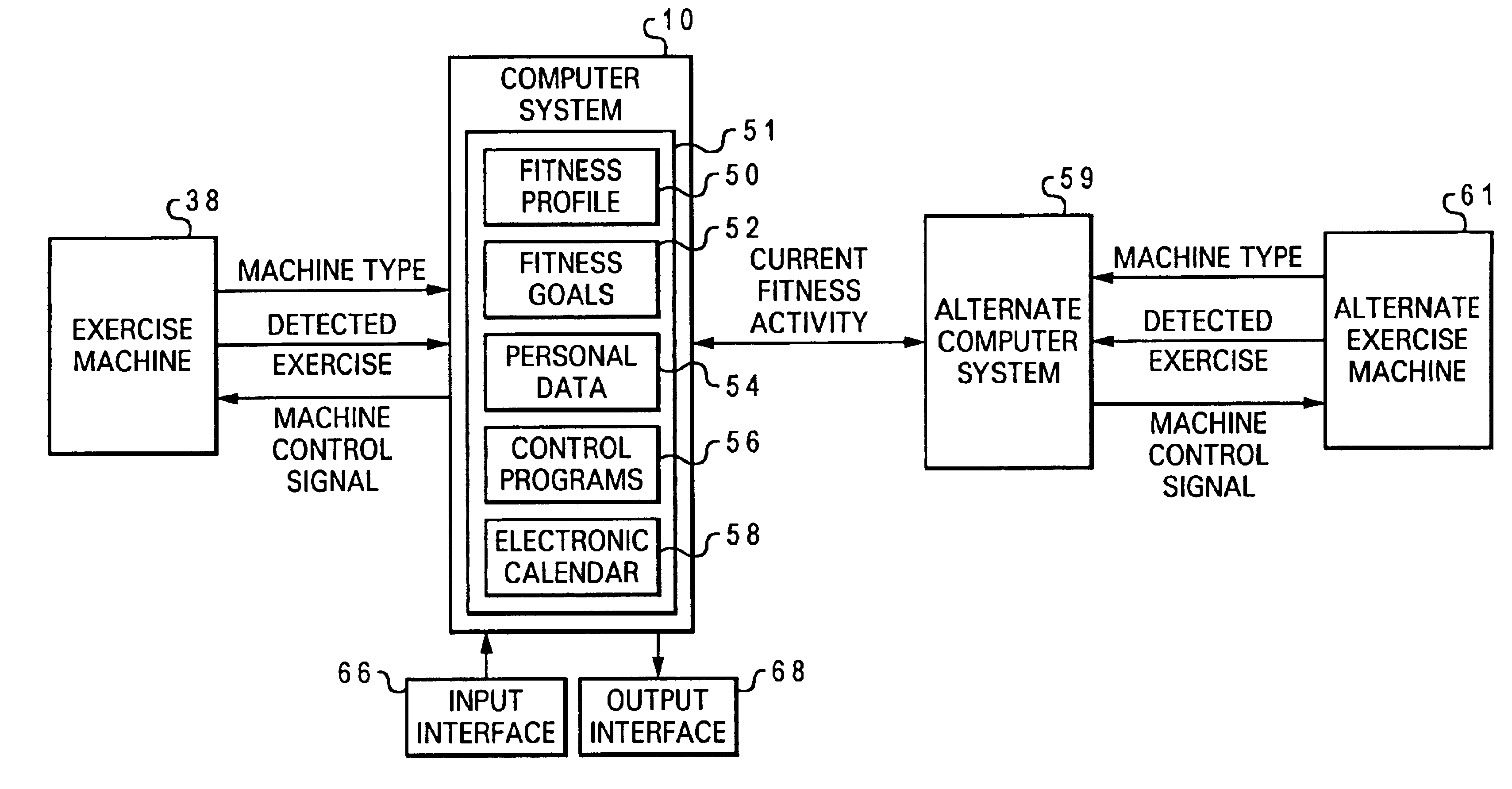
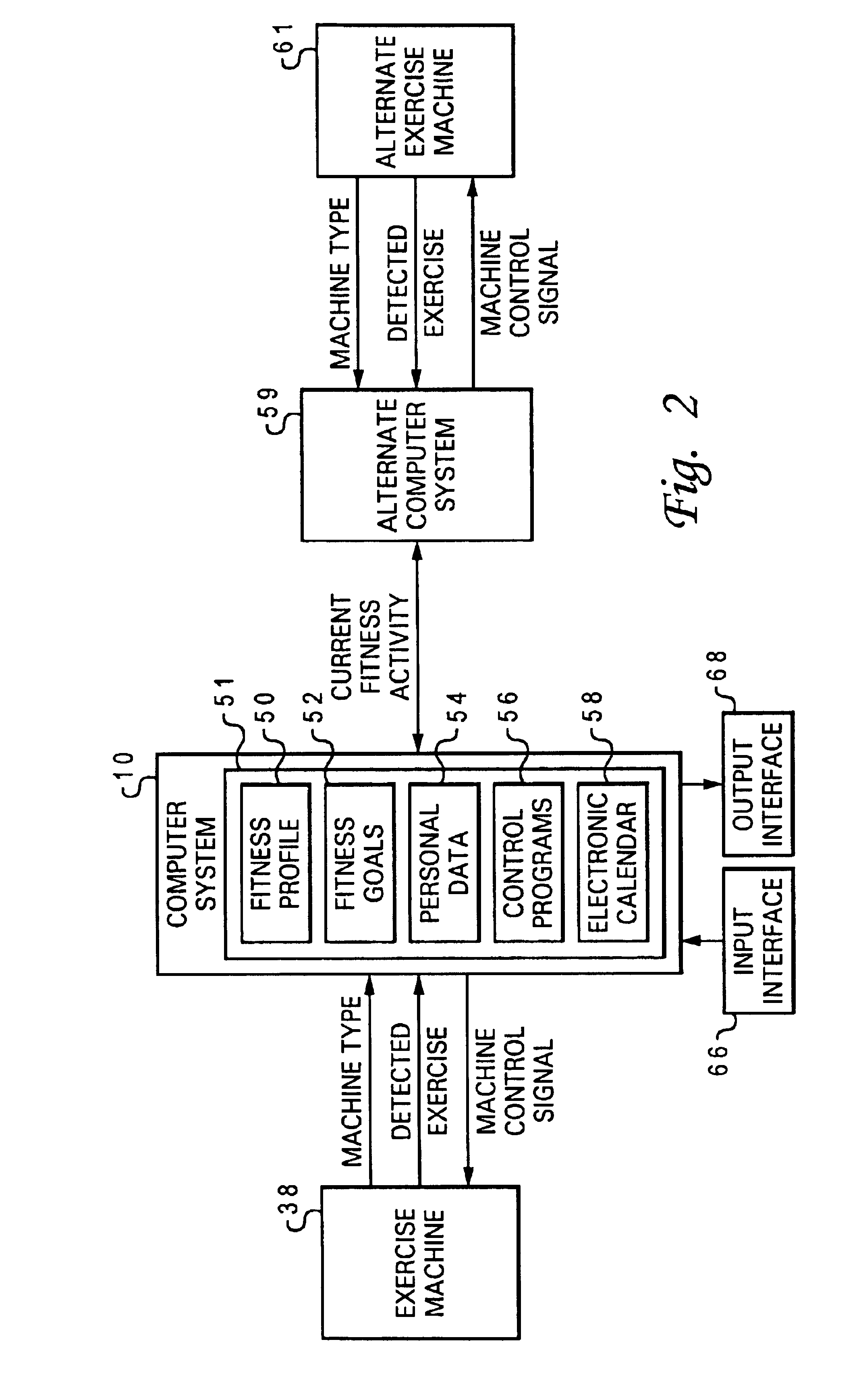
Managing fitness activity across diverse exercise machines utilizing a portable computer system
In accordance with the method, system and program of the present invention, at least one type of exercise indicator signal associated with exercise performed by a particular user is received from a particular exercise machine in a common transmittable data format at a portable computer system provided the particular user. Cumulative fitness activity is computed and stored for the particular user at the portable computer system utilizing the at least one type of exercise indicator signal and previously accumulated fitness activity data at the portable computer system, such that an independent portable computer system associated with the particular user monitors the real-time cumulative fitness activity of the particular user from at least one type of exercise indicator signal received from at least one exercise machine over a period of time.
Owner:ICON HEALTH & FITNESS INC
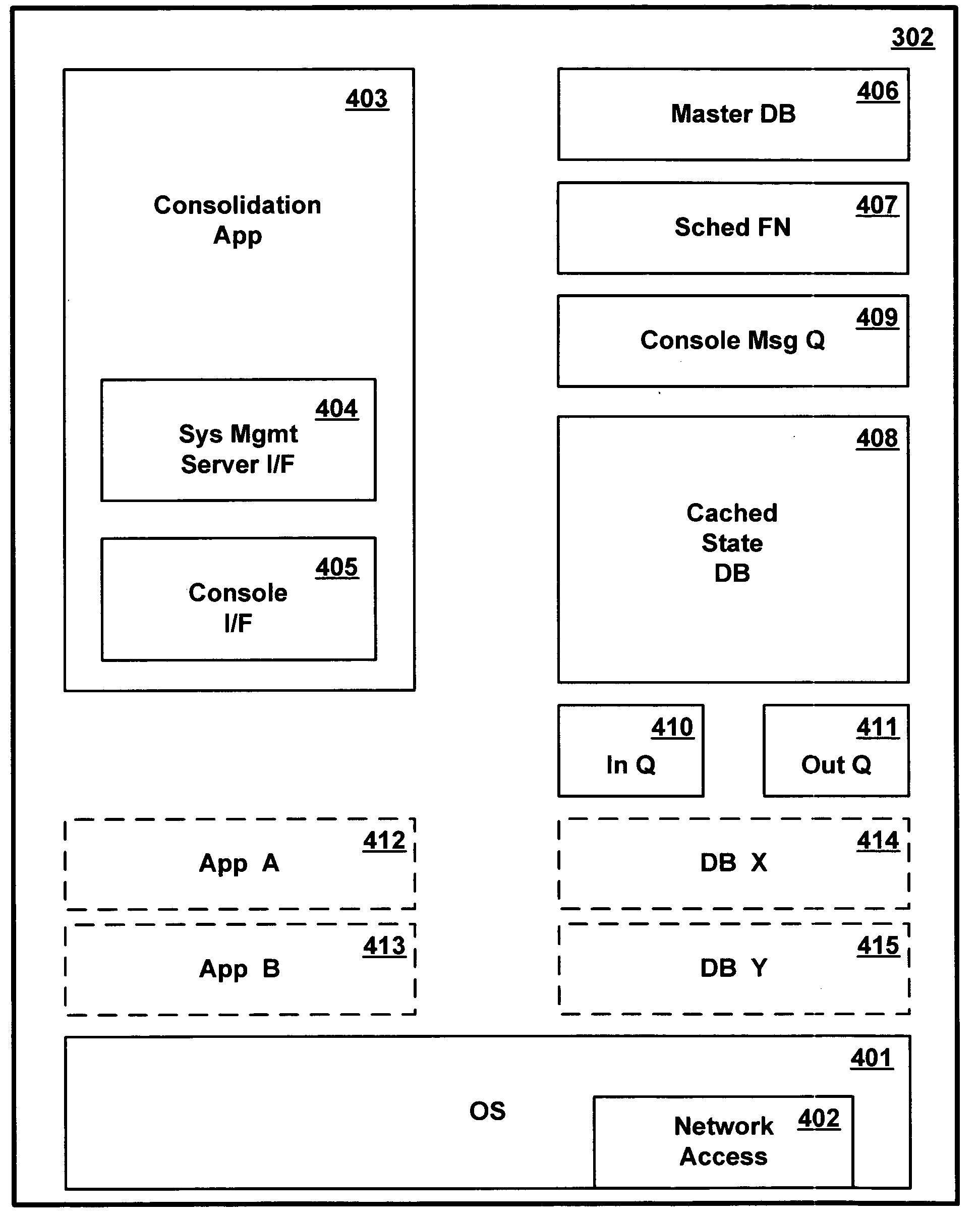
Method and apparatus for managing multiple data processing systems using existing heterogeneous systems management software
InactiveUS20050102683A1Less expensiveMultiprogramming arrangementsMultiple digital computer combinationsPublic interfaceData processing system
A common consolidation management application provides an interface to the multiple different system management software applications and at least one user input console. An adapter in each of the system management software applications supports communication with the consolidation application. A system administrator issues requests to different system management software applications using a common interface provided by the consolidation application. The consolidation application can be installed over an existing complex of computer systems managed by different management applications, without modifying the managed systems or replacing the management applications.
Owner:IBM CORP
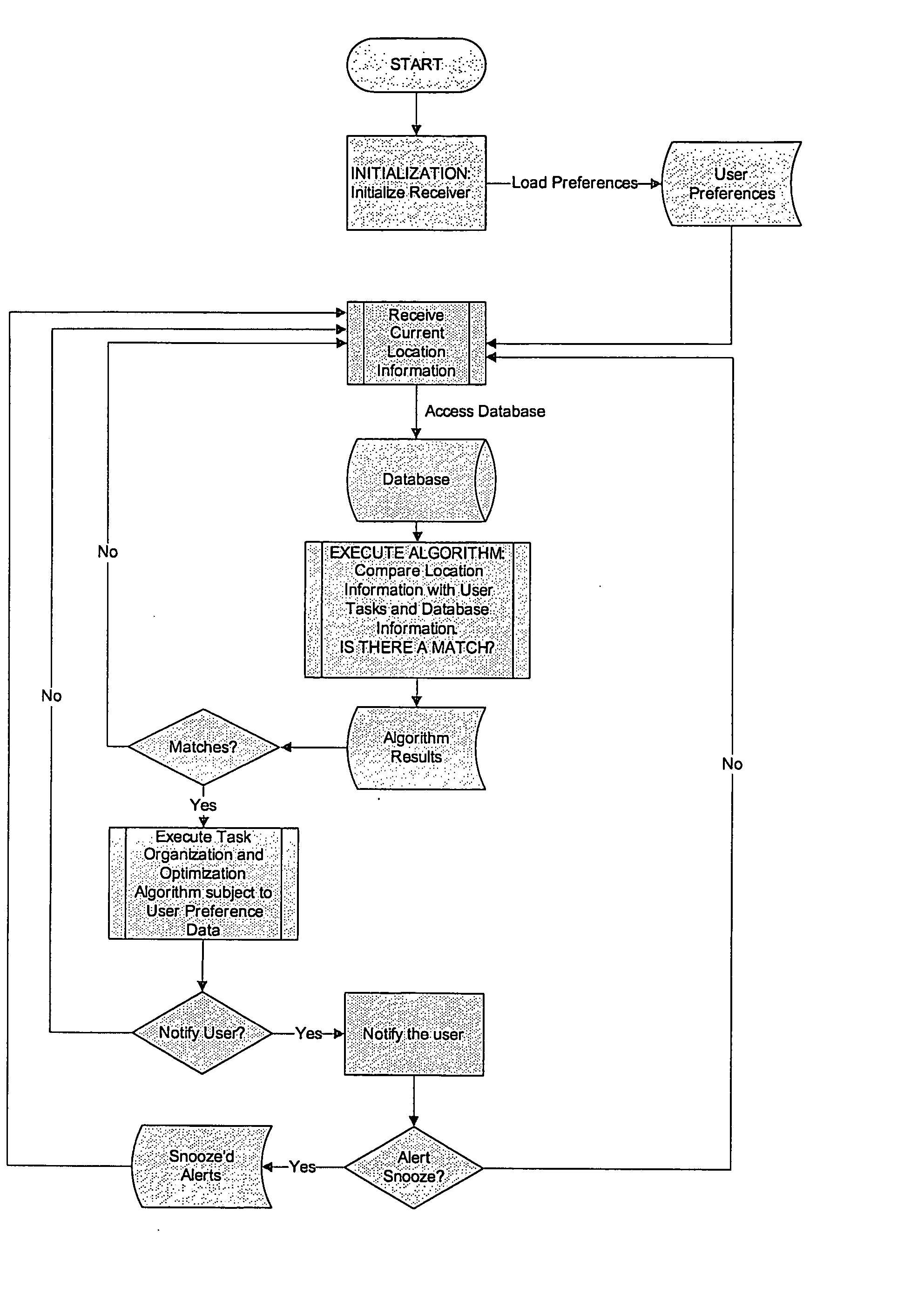
Recordable location-based reminder system organizer
An organization system using location information, possibly in conjunction with time based information for tasks, with the purpose of optimizing user travel distance and / or time to complete specified tasks. Task organization may include alternate criteria such as importance, or sharing and assigning of tasks over groups to optimize in terms of the time / location / schedule of other members of the group. The mobile system may alert users of some tasks based on the user proximity to those tasks, alert of other tasks based on both time and location, or others based solely on the current time and the time of the task. The system can provide a dynamic schedule, changing based on time estimates of the user tasks as well as actual time to complete user tasks, estimates of travel time between tasks, as well as other criteria.
Owner:BLASS MELANIE MAGDOLNA
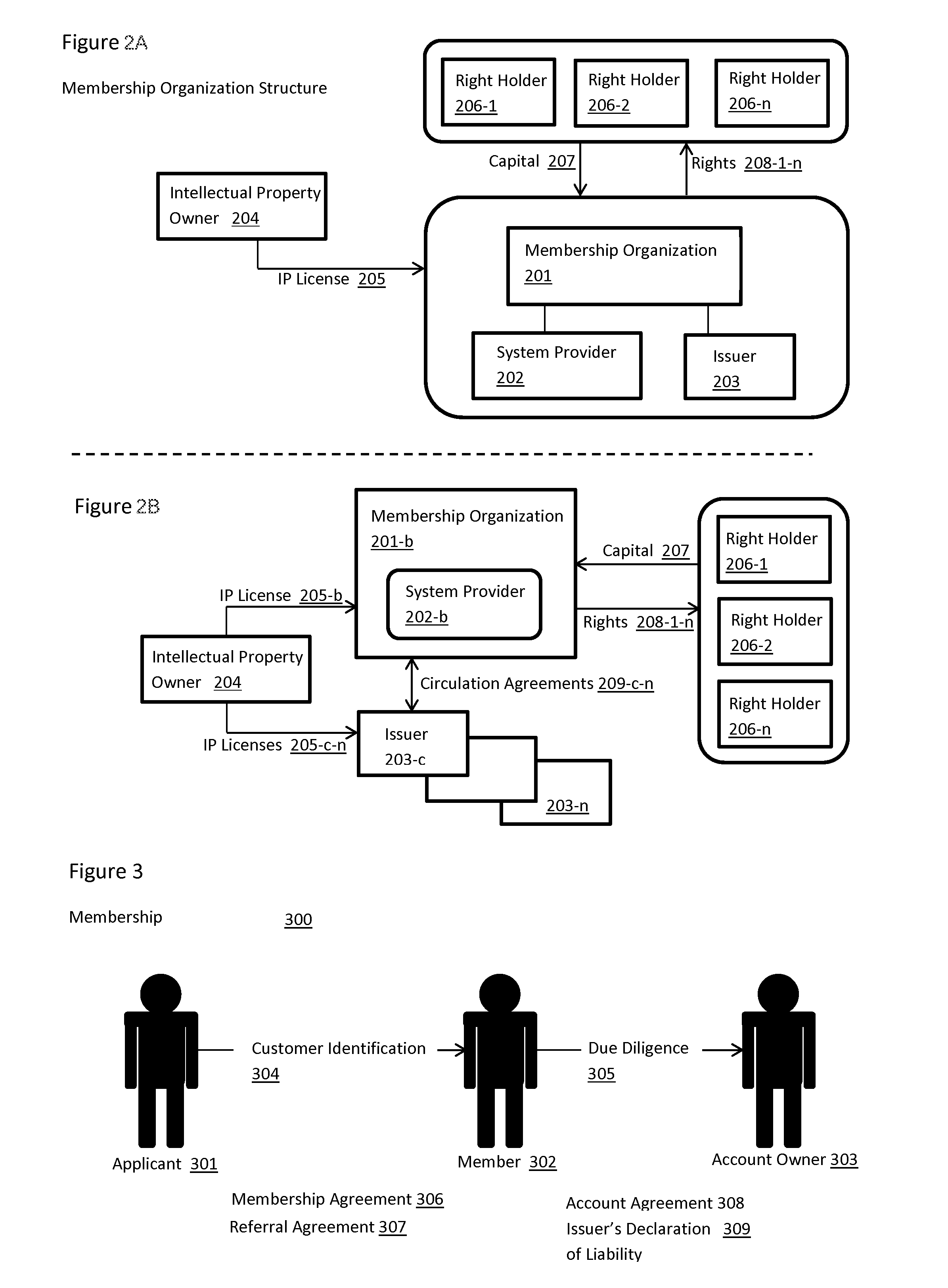
Systems and methods for a private sector monetary authority
InactiveUS20140279540A1Facilitate commercial successFacilitate emergenceFinanceCurrency conversionSystems managementComputer science
Embodiments of the present invention may provide systems and methods for administering a private sector Monetary Authority. The systems and methods may include providing access to End Users; and enabling performance of specialized Roles required for the administration of the system. The systems and methods may be self-contained for creation, holding, circulation and retirement of the Base Money such that outside money or value cannot be transmitted into or out of the system.
Owner:FULCRUM IP
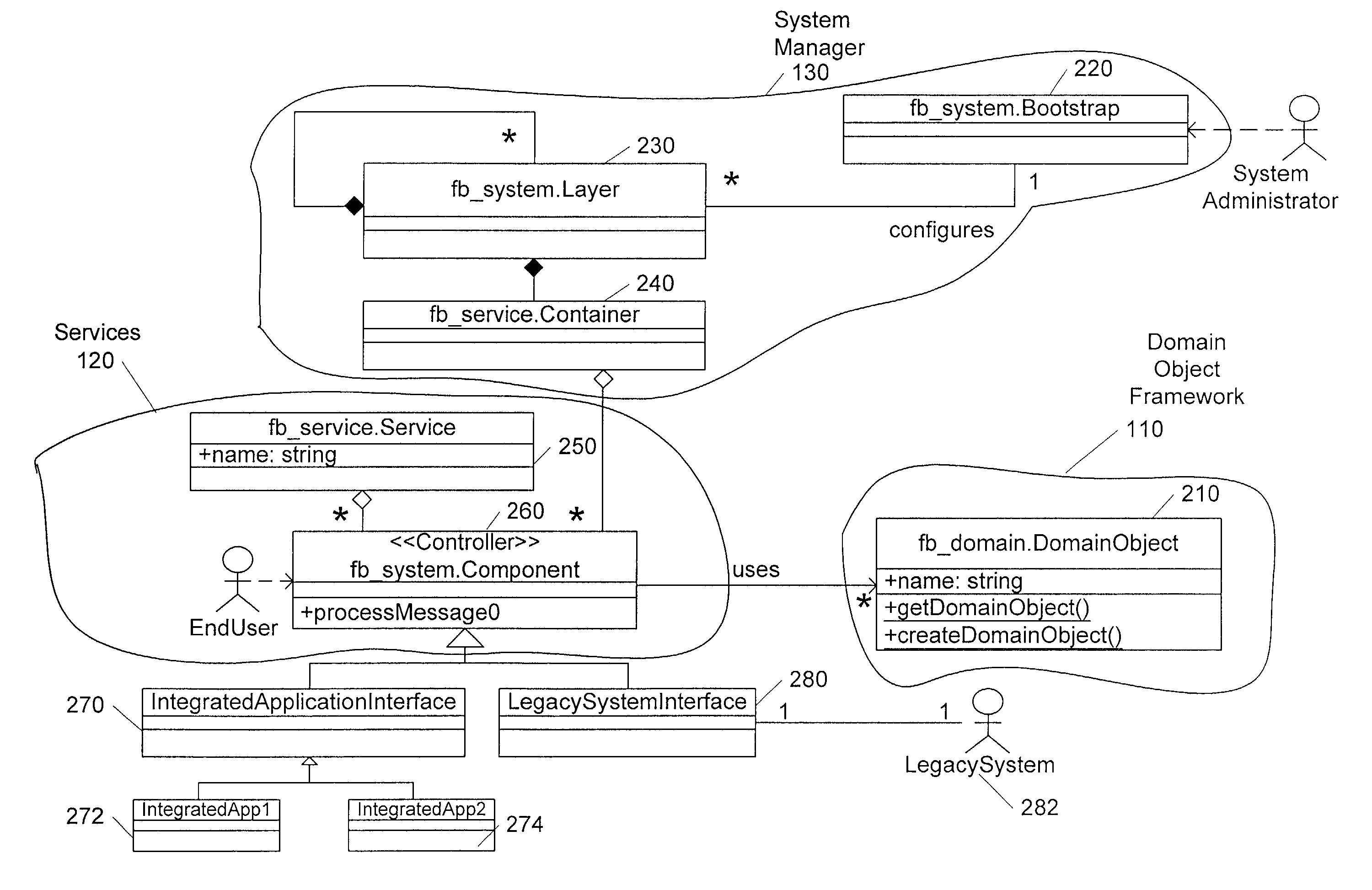
System for integrating data between a plurality of software applications in a factory environment
InactiveUS7047517B1Reduce complexityEasy to modifySpecific program execution arrangementsSpecial data processing applicationsService provisionSystems management
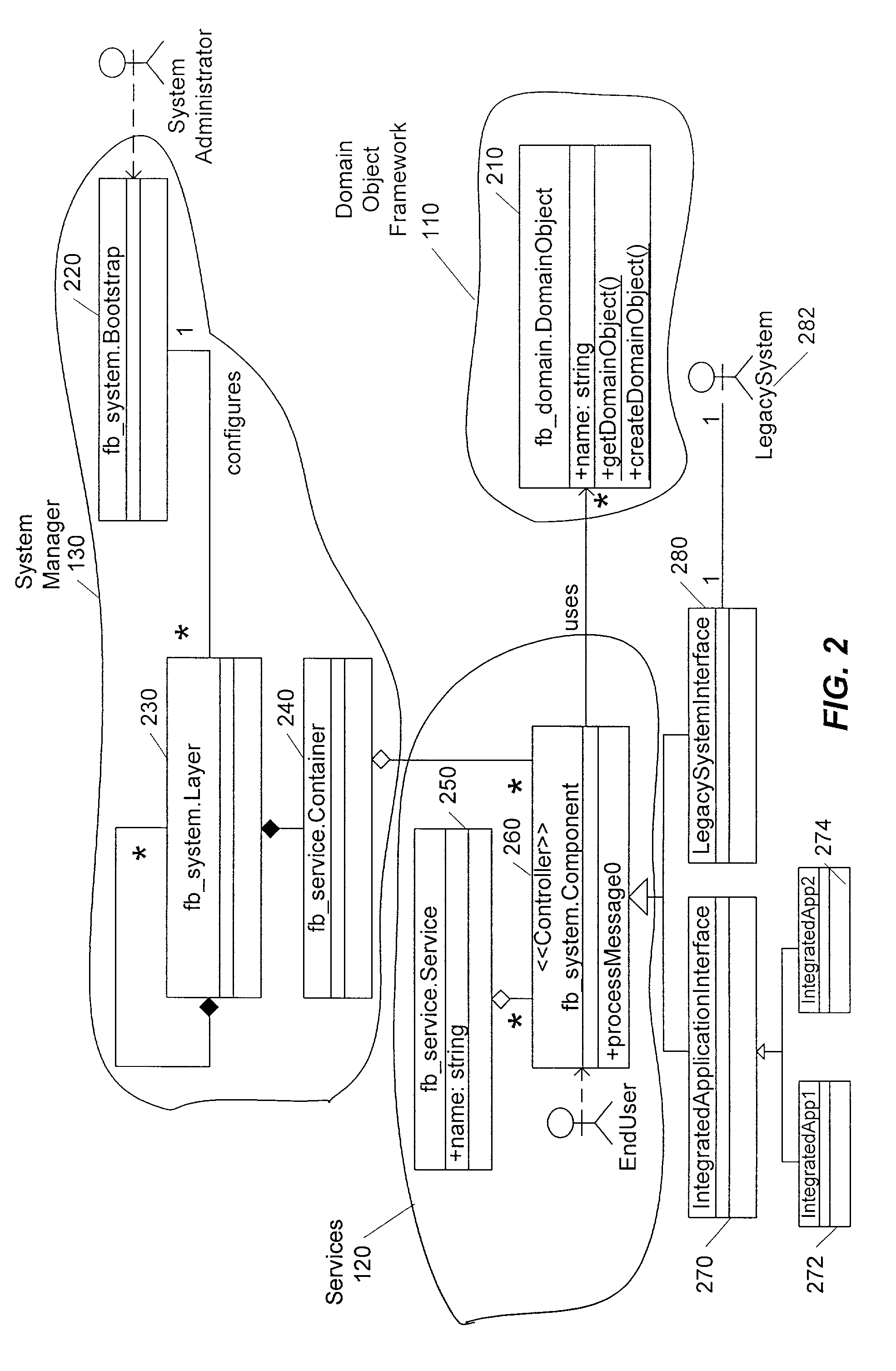
An architecture for integrating data between a plurality of software applications in a factory environment comprises a factory system and a domain application. The factory system comprises a domain object superclass and at least two first-level subclasses of the domain object superclass. An instantiation of one of the first-level subclasses corresponds to a domain object, which represents an item in a factory. The factory system also includes a service, which provides an operation related to the domain object. The service comprises at least one component, where each component is operable to perform the operation related to the domain object. The architecture also includes a domain application, which implements a component of the service of the factory system to perform the operation related to the domain object. The architecture can optionally include a system manager for managing hardware and software in the factory.
Owner:ADVANCED MICRO DEVICES INC
Registering and accessing virtual systems for use in a managed system
ActiveUS20080134175A1Platform integrity maintainanceSoftware simulation/interpretation/emulationConsistency testVirtual file system
Techniques are disclosed for controlling and managing virtual machines and other such virtual systems. VM execution approval is based on compliance with policies controlling various aspects of VM. The techniques can be employed to benefit all virtual environments, such as virtual machines, virtual appliances, and virtual applications. For ease of discussion herein, assume that a virtual machine (VM) represents each of these environments. In one particular embodiment, a systems management partition (SMP) is created inside the VM to provide a persistent and resilient storage for management information (e.g., logical and physical VM metadata). The SMP can also be used as a staging area for installing additional content or agentry on the VM when the VM is executed. Remote storage of management information can also be used. The VM management information can then be made available for pre-execution processing, including policy-based compliance testing.
Owner:RED HAT
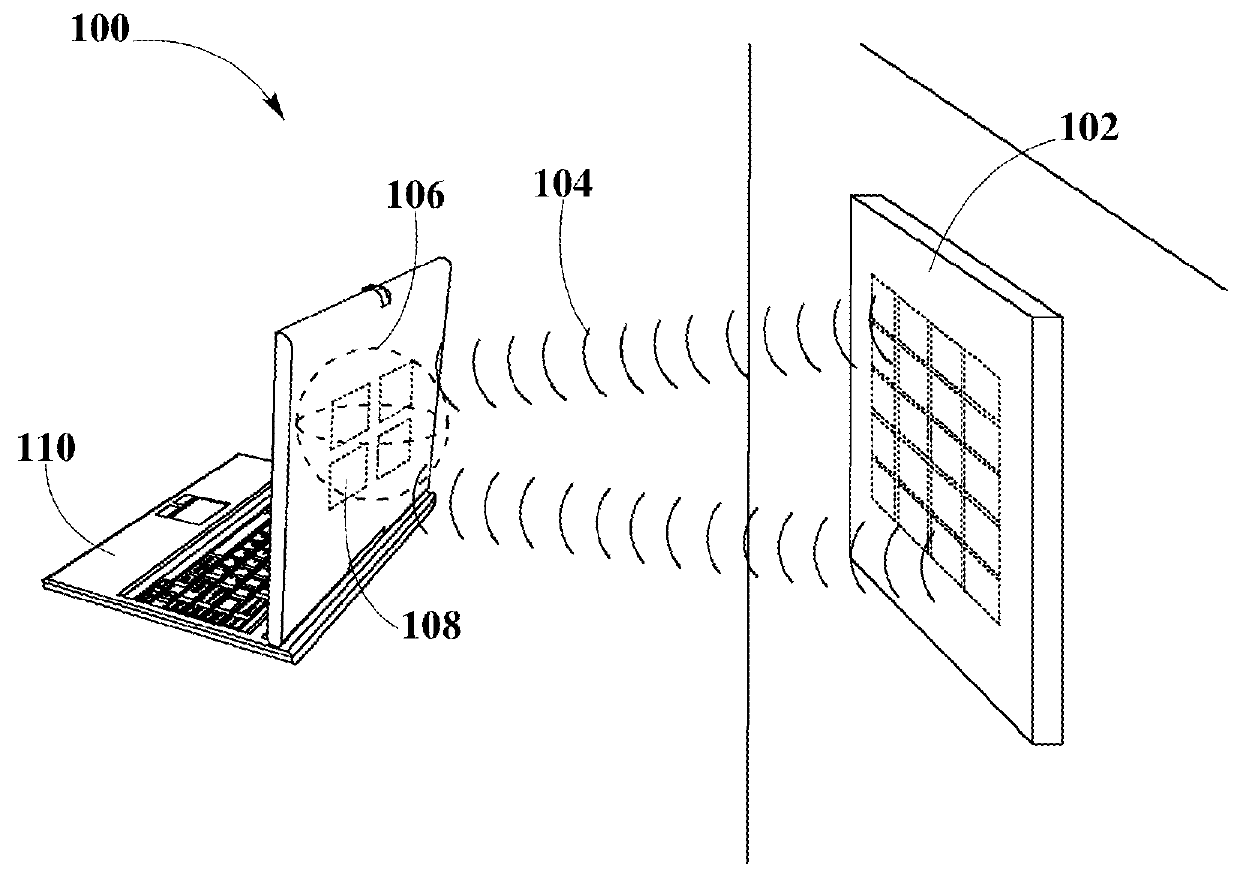
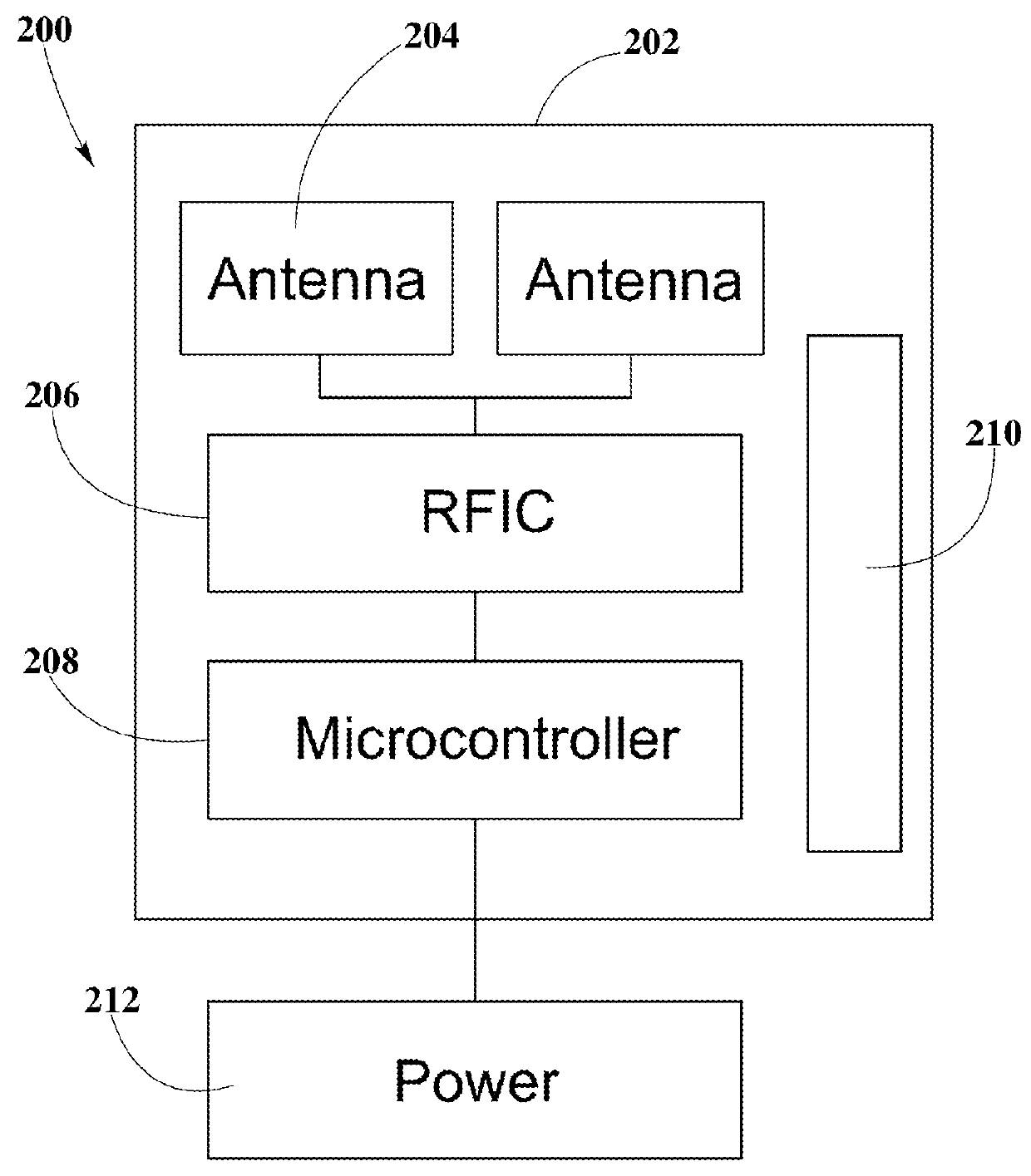
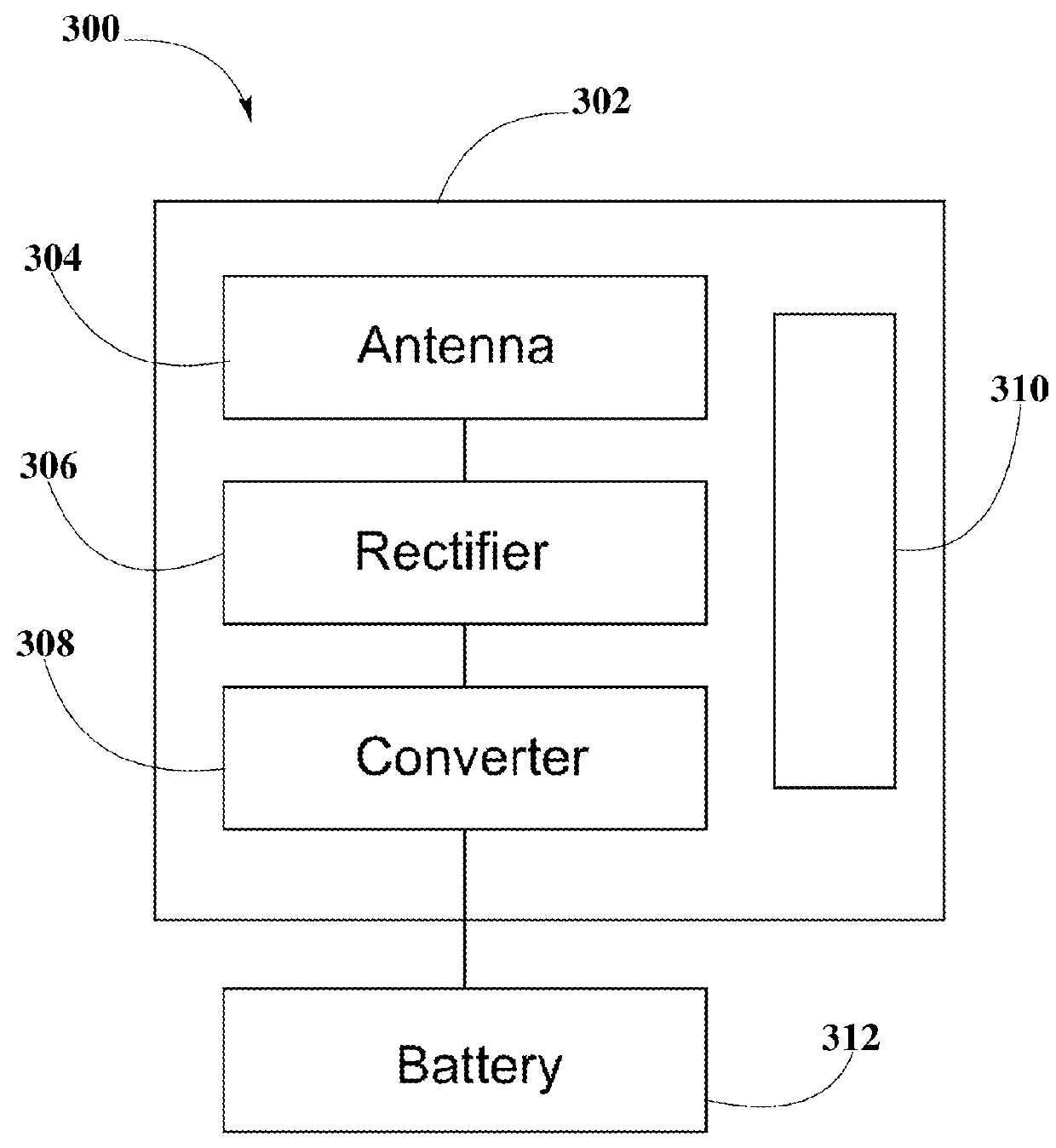
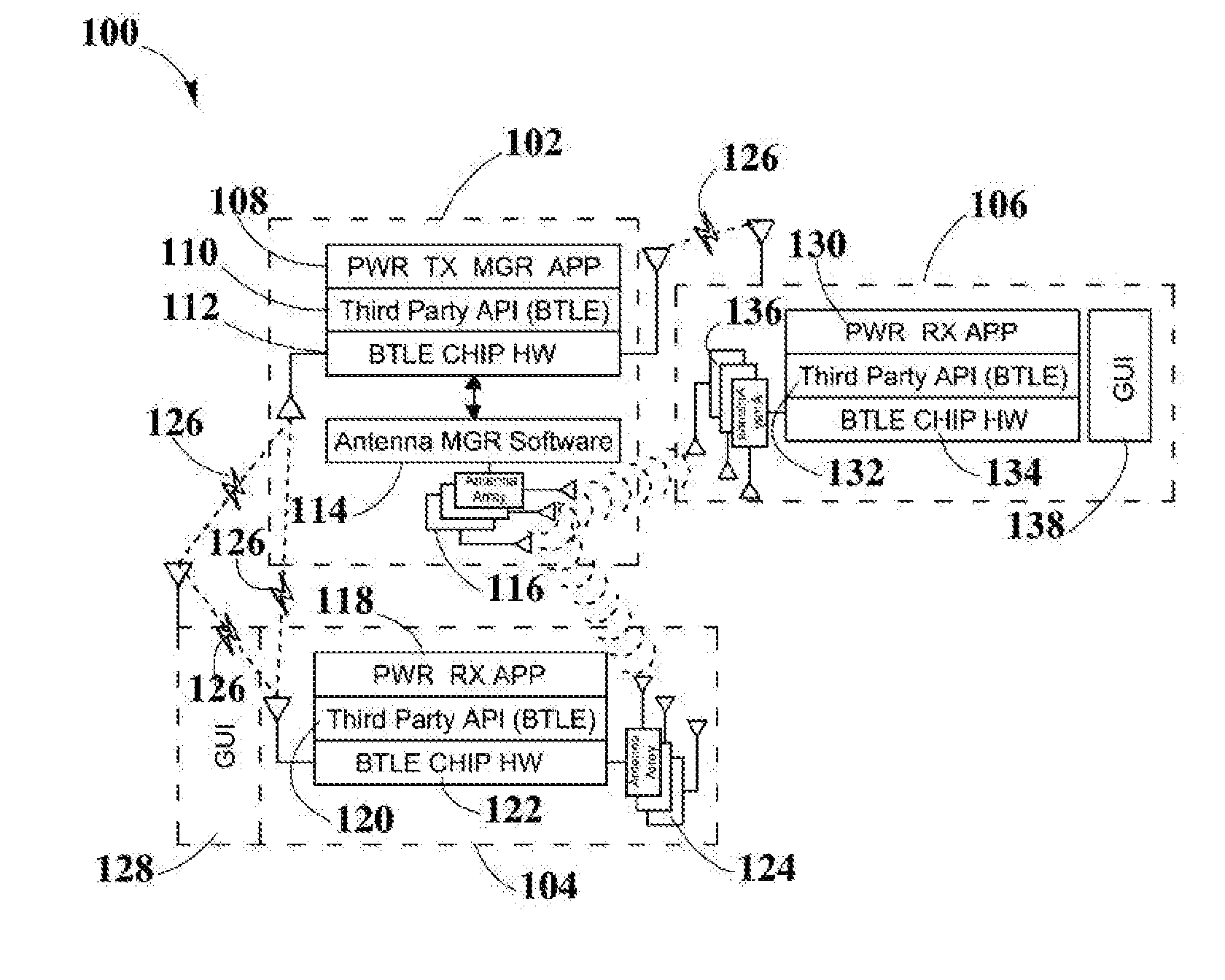
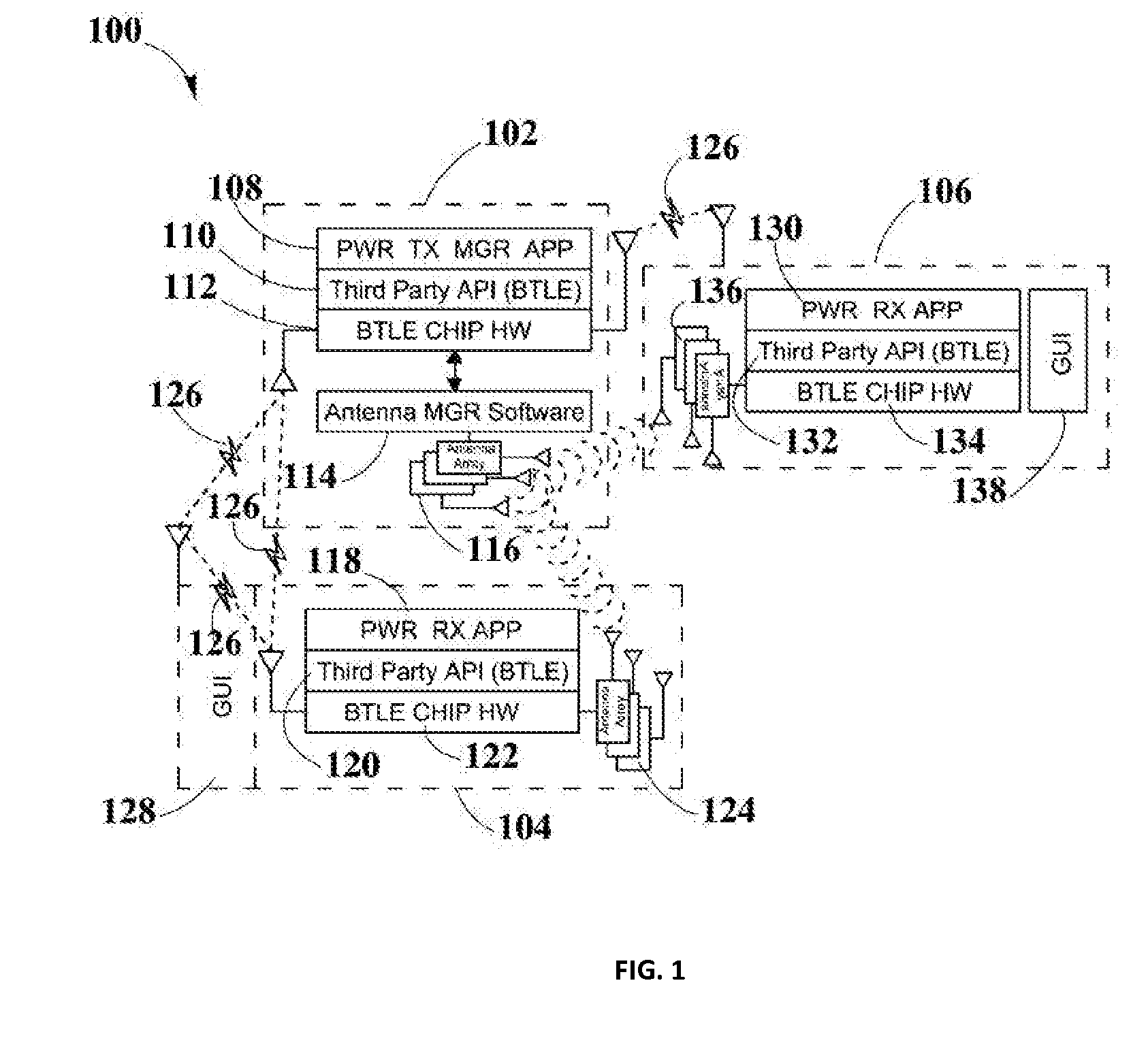
Systems and Methods for Tracking the Status and Usage Information of a Wireless Power Transmission System
InactiveUS20160056635A1Improve concentrationImprove accuracyVolume/mass flow measurementPower supply for data processingElectric power transmissionElectric force
Disclosed here are methods and systems to generate and distribute information about the status and usage of a wireless power transmission system. Specifically, the present disclosure may describe a process to generate information through various software running in different components of the wireless power transmission system. Additionally, the disclosure may also include a wireless power transmission system architecture which may include components, such as a remote information service, a remote information service manager, a remote information service database, one or more authorized computing devices, and a plurality of system information generators. System information generator may refer to components, such as wireless power transmitters, computing devices / non computing devices (coupled with power receiver devices), a system management service, and distributed system database. The aforementioned components within the wireless power transmission system may be used to automatically and autonomously generate, store, transmit, and distribute system status, usage, and statistics or metrics information in order to be edited or reported by authorized and authenticated users. The information may also be used to increase the accuracy of strategic marketing, sales focus, to alert customer service of system problems and performance issues, and for billing end users.
Owner:ENERGOUS CORPORATION
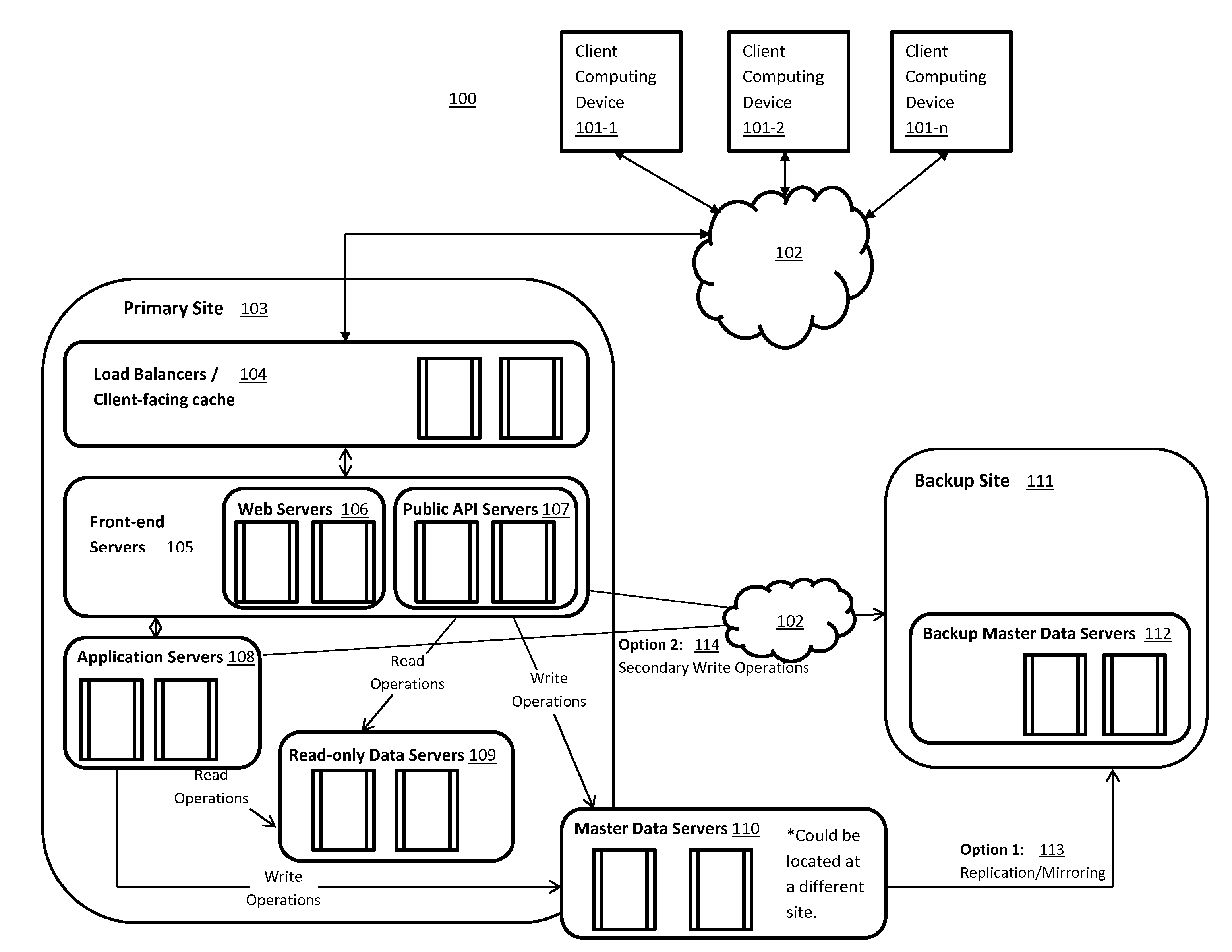
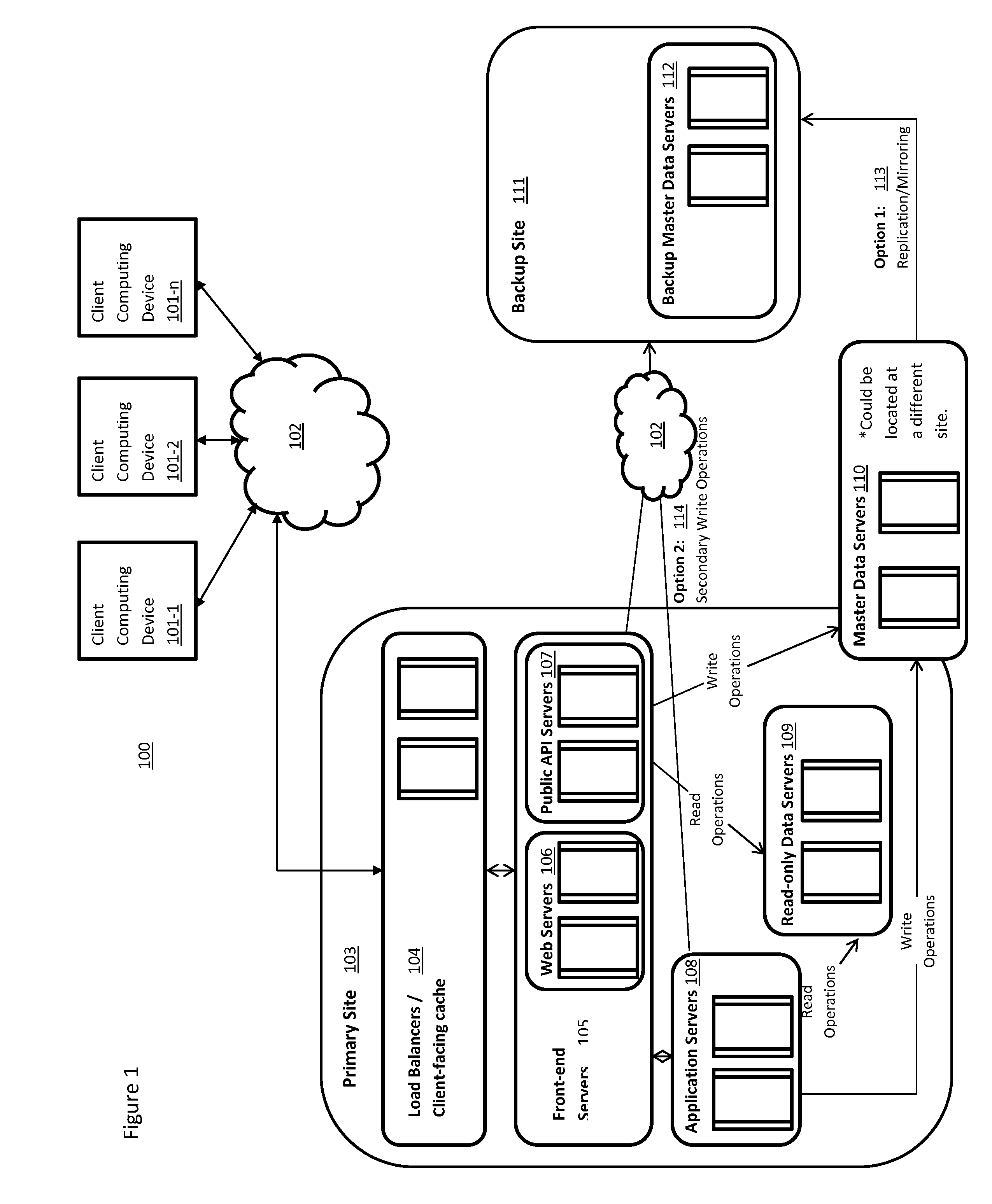
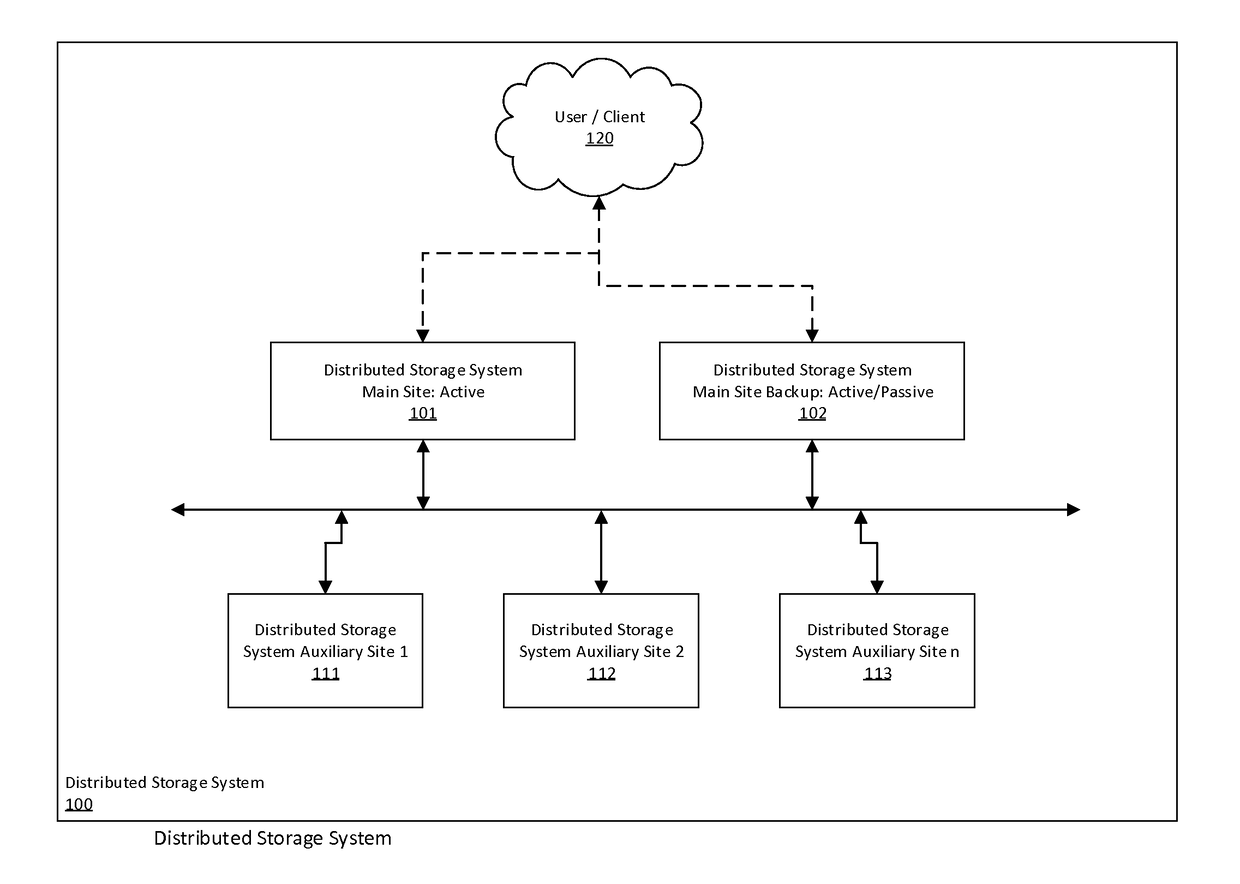
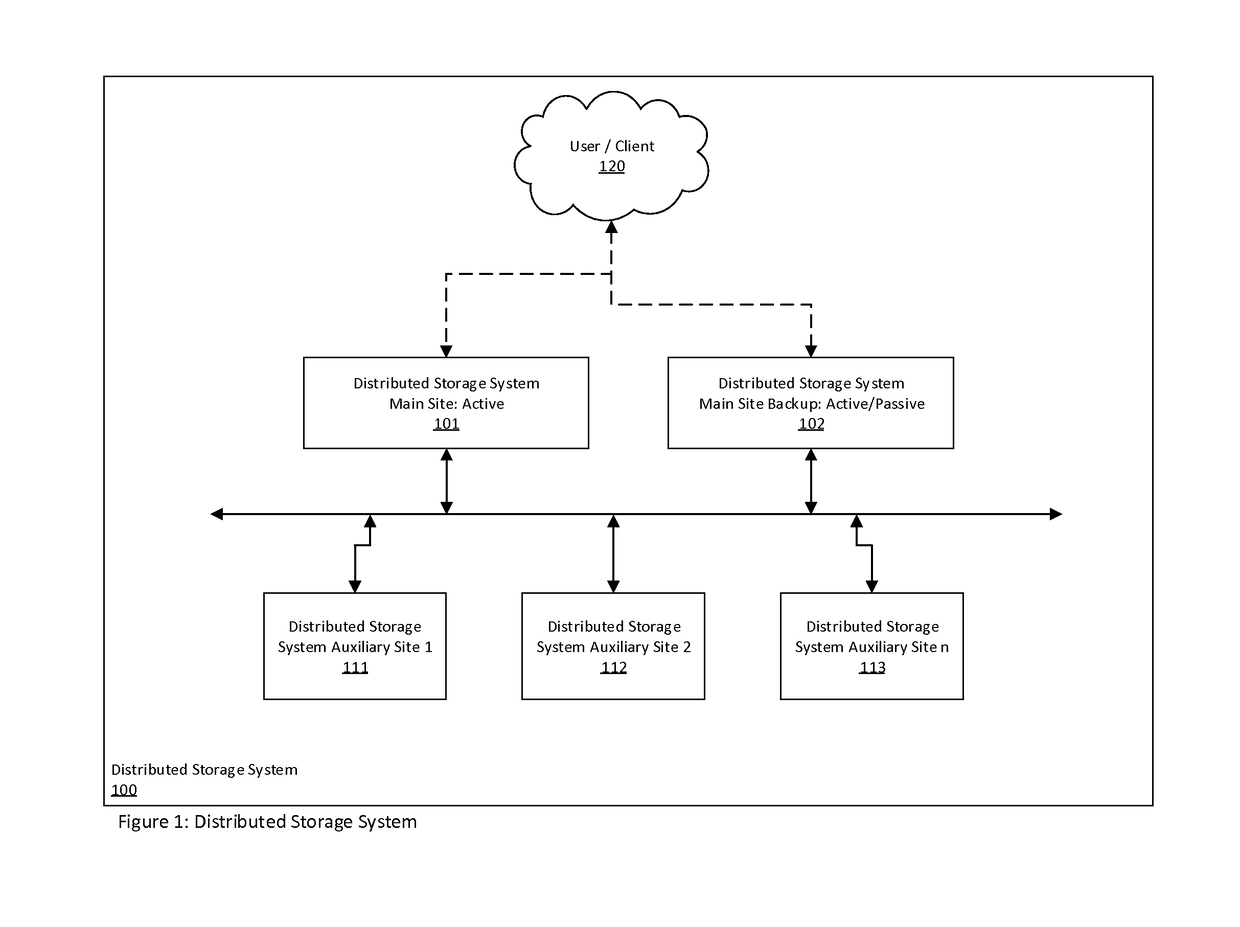
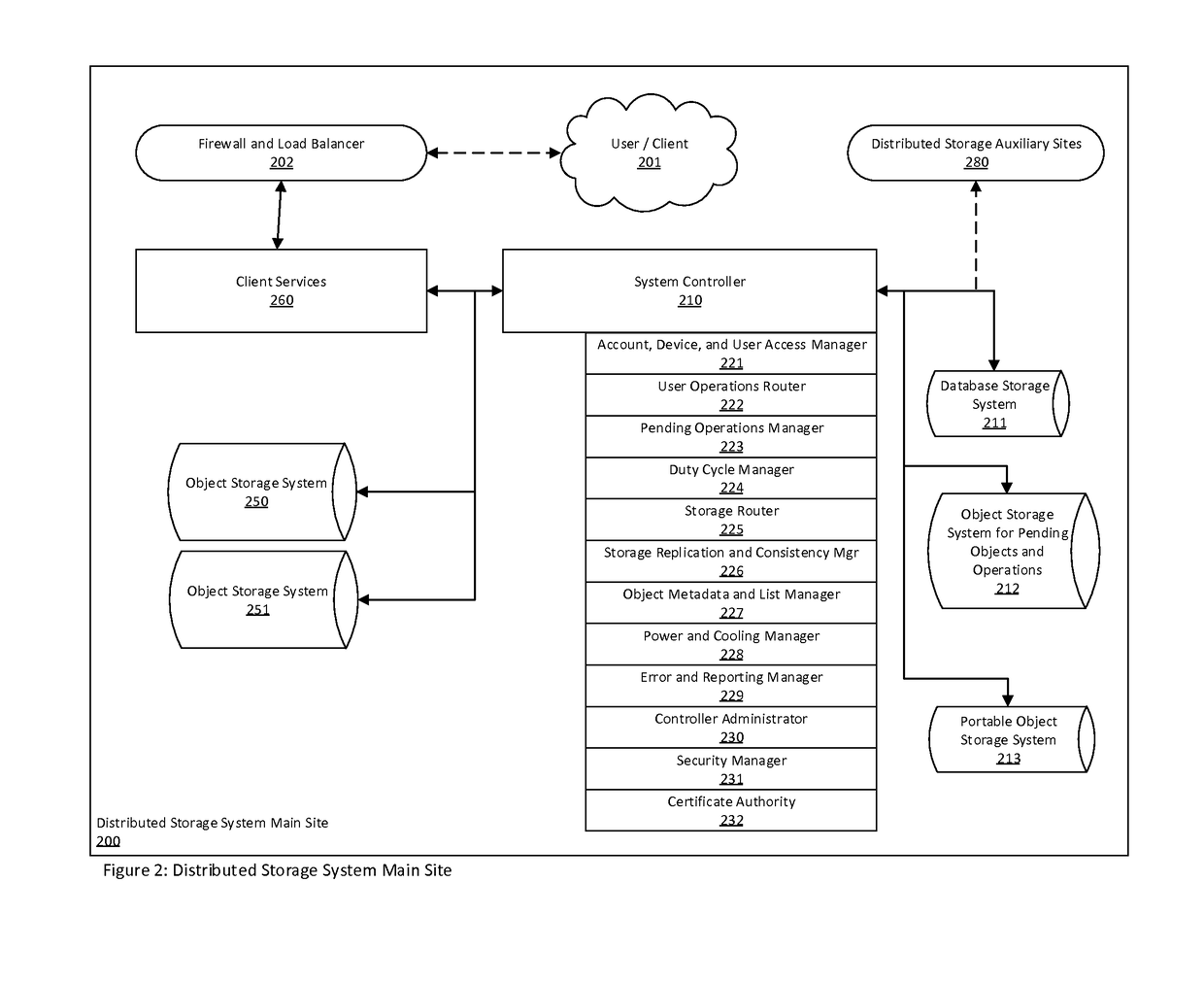
Distributed storage system for long term data storage
A distributed storage system for the long-term storage of data objects that is implemented utilizing one or more distinct storage sites that may be comprised of system controllers and object storage systems that act in concert to embody a single distributed storage system. A system may include a one or more types and / or instances of object storage systems in which replicas of objects are stored in at least two of the said object storage systems. A system may further include system controllers associated with logical and / or physical sites that coordinate object, user, device, and system management functionally.
Owner:SMITH DAVID LANE
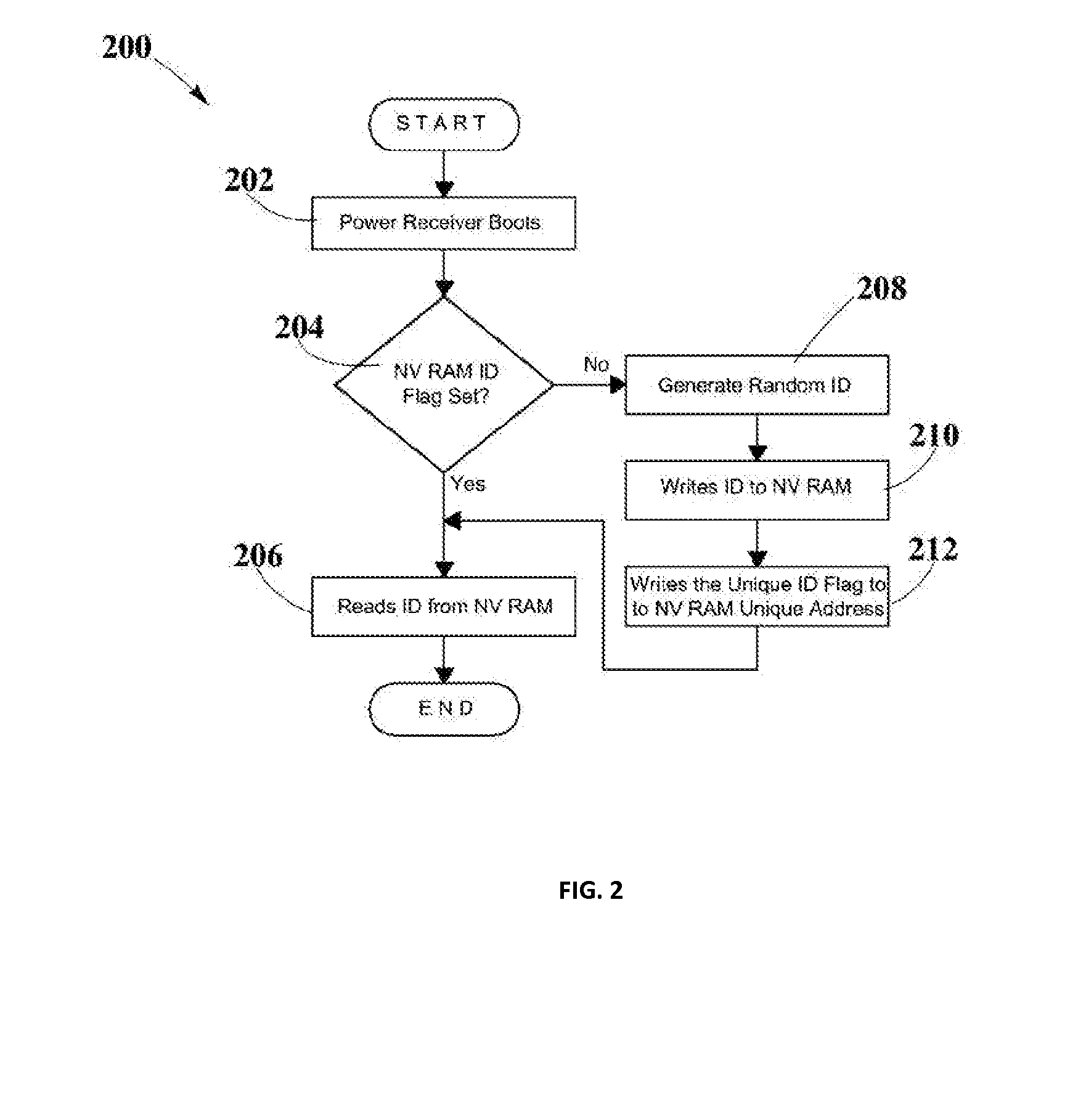
System and Method for Generating a Power Receiver Identifier in a Wireless Power Network
ActiveUS20150340911A1Easy to associateEasily associated to userElectromagnetic wave systemTransformersSystems managementUnique identifier
Embodiments in the present disclosure may be directed to a system and method that may be used to generate a unique identifier for one or more wireless power devices such as one or more wireless power receivers, wireless power transmitters, GUI management devices, and system management servers among others, within a wireless power network. The method may use automated software embedded on a chip that may run when a wireless power device boots up for the first time. The unique ID may allow easy associations of wireless power devices with user defined names.
Owner:ENERGOUS CORPORATION
Systems and methods for managing the development and manufacturing of a drug
InactiveUS20070192715A1Easy to optimizeManagement complexityComputer-assisted medical data acquisitionTechnology managementGraphicsChemical reaction
Graphical user interfaces, computer readable media, and computer systems for monitoring a chemical process. An administration module sets a plurality of user preferences associated with the chemical process. A people management module defines a user role in the chemical process. An organization module defines an organizational structure of an organization that runs the chemical process. An equipment module defines equipment used in the chemical process. A material module controls a chemical used in the chemical process. A process module defines a chemical reaction in the chemical process.
Owner:ORACLE INT CORP
Method and apparatus for achieving dynamic capacity and high availability in multi-stage data networks using adaptive flow-based routing
ActiveUS20050091396A1Multiplex system selection arrangementsError preventionSystems managementHigh availability
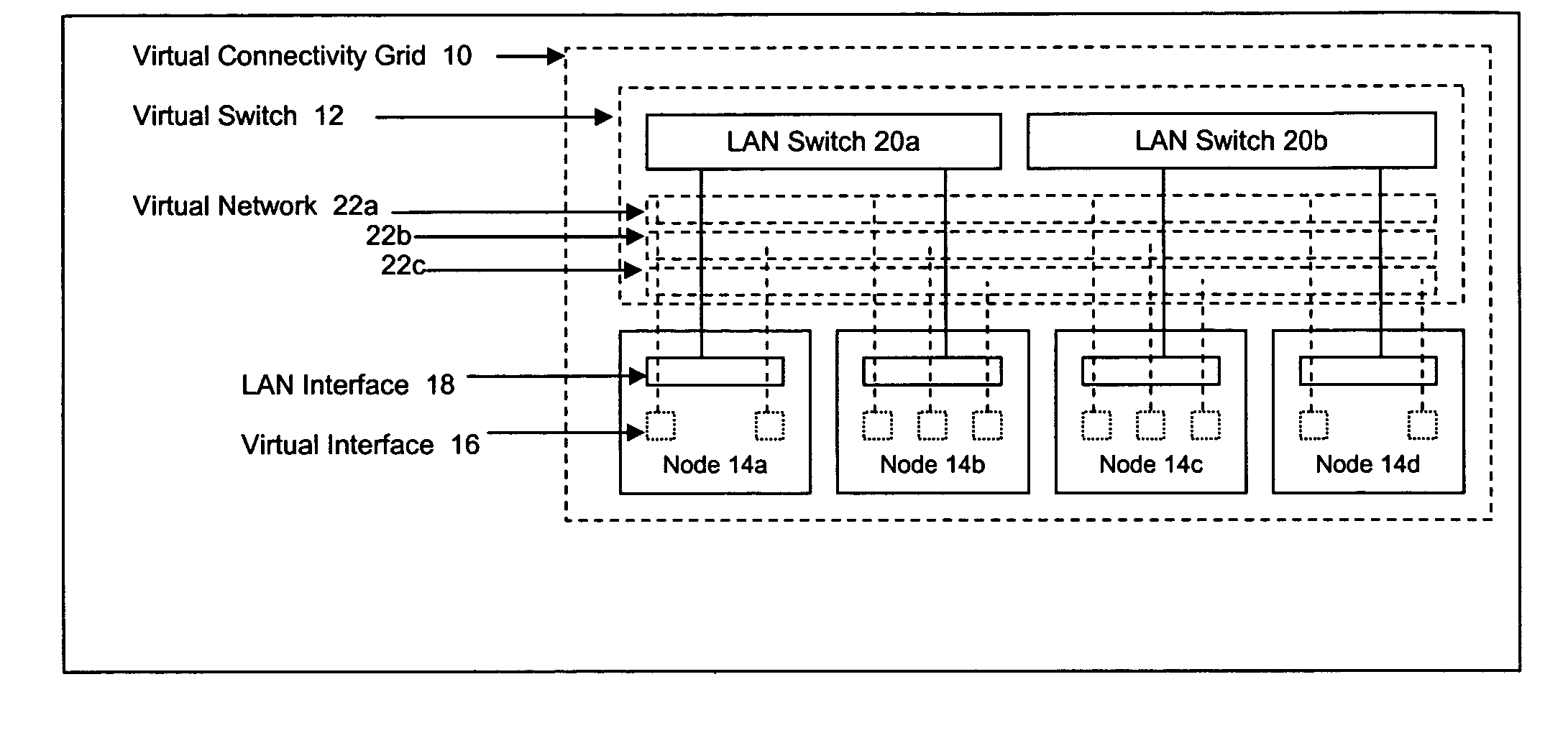
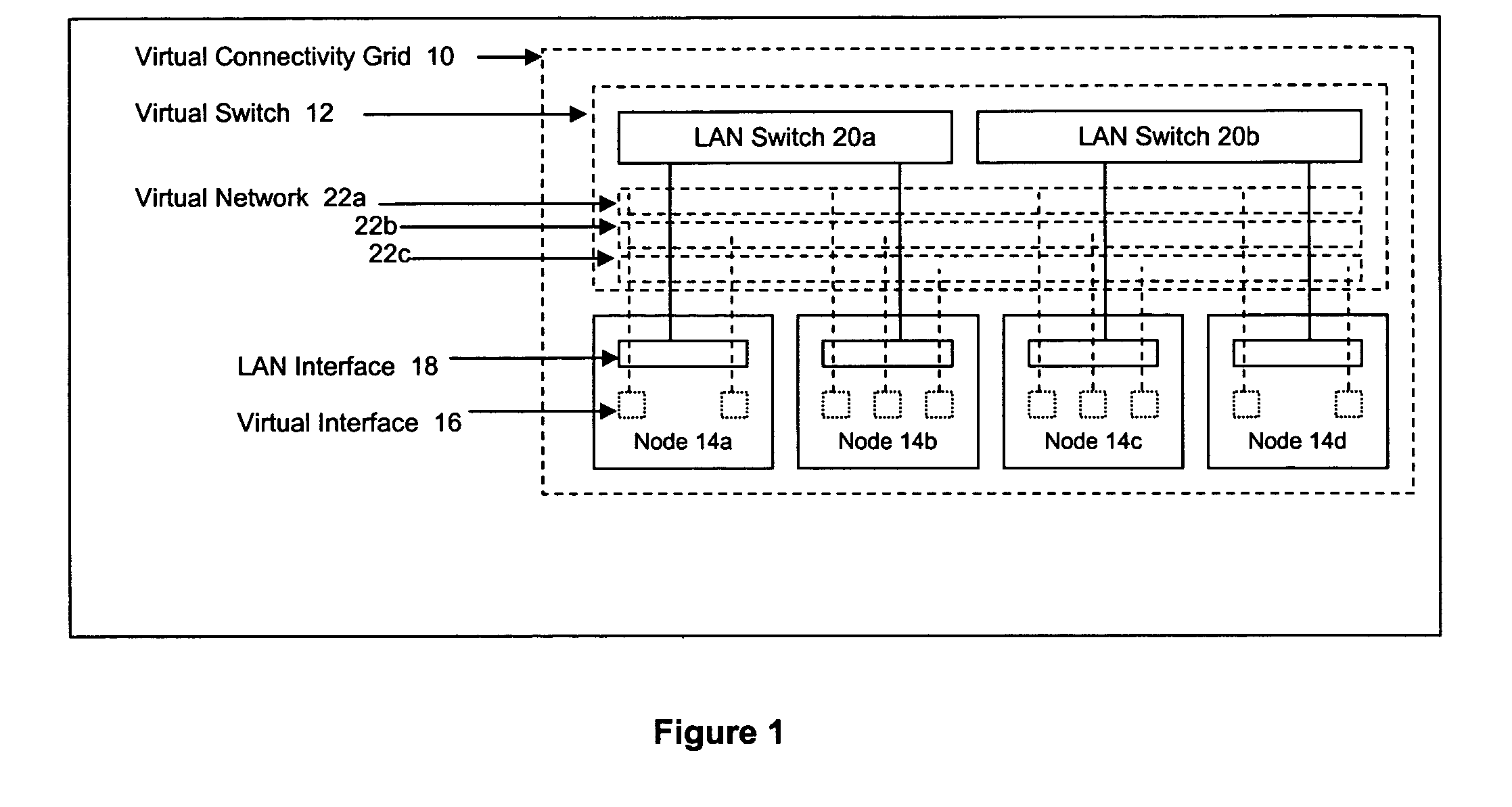
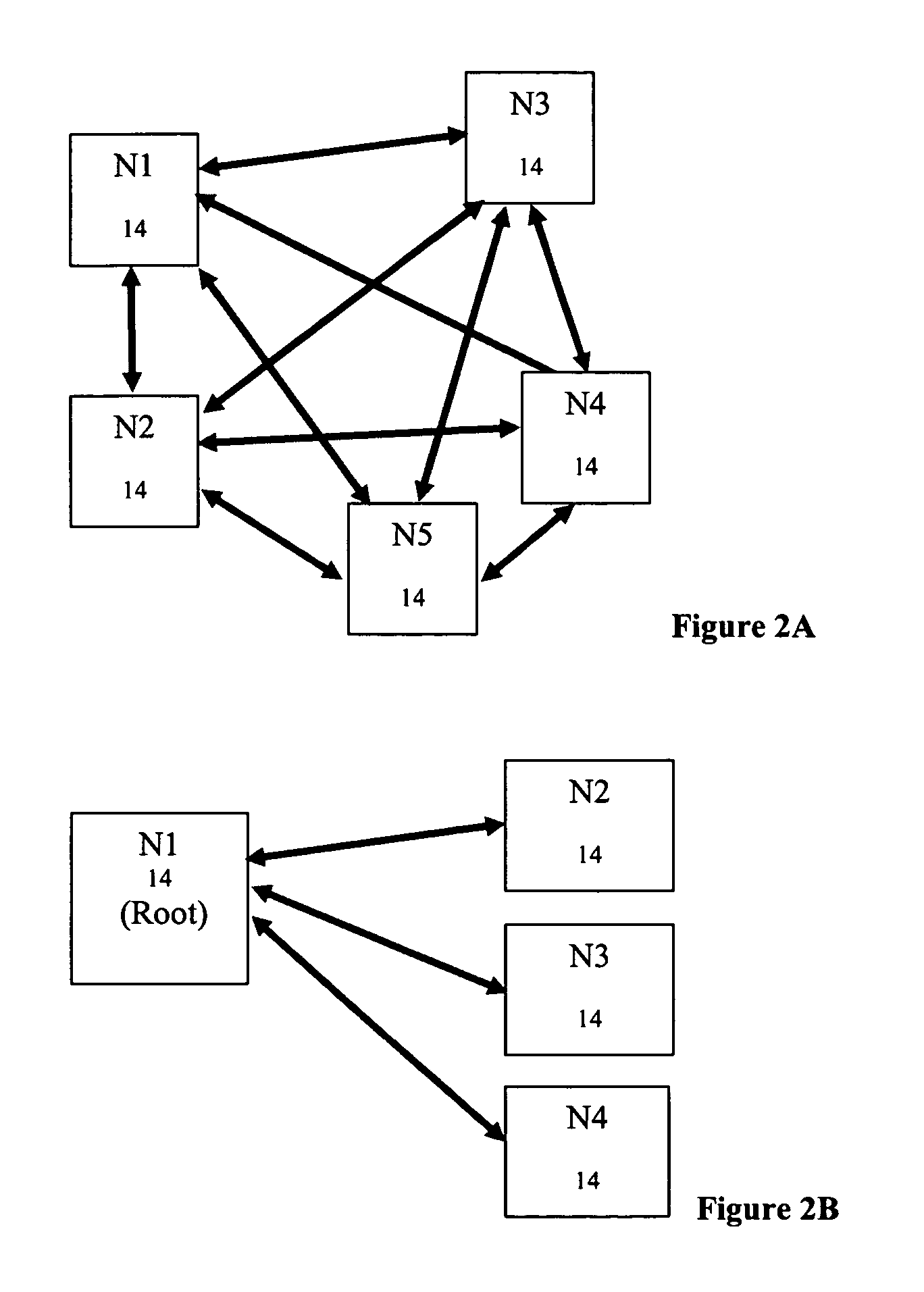
Methods and systems for determining paths for flows within a multi-stage network made up of clusters of processing nodes. The flow paths may be determined without knowledge of whether or not packets of a particular flow will actually traverse specific ones of the clusters within the multi-stage network. In various implementations, the nodes of the multi-stage network may be coupled to one or more physical network switches through respective physical interfaces and a virtual connectivity grid superimposed thereon and configured through the use of a flow routing framework and system management framework to group the nodes into a number of clusters. The nodes of each cluster are configured to perform similar packet processing functions and the clusters are interconnected through virtual networks to which the nodes are communicatively coupled via virtual interfaces overlaid on top of the physical network interfaces.
Owner:DELL PROD LP
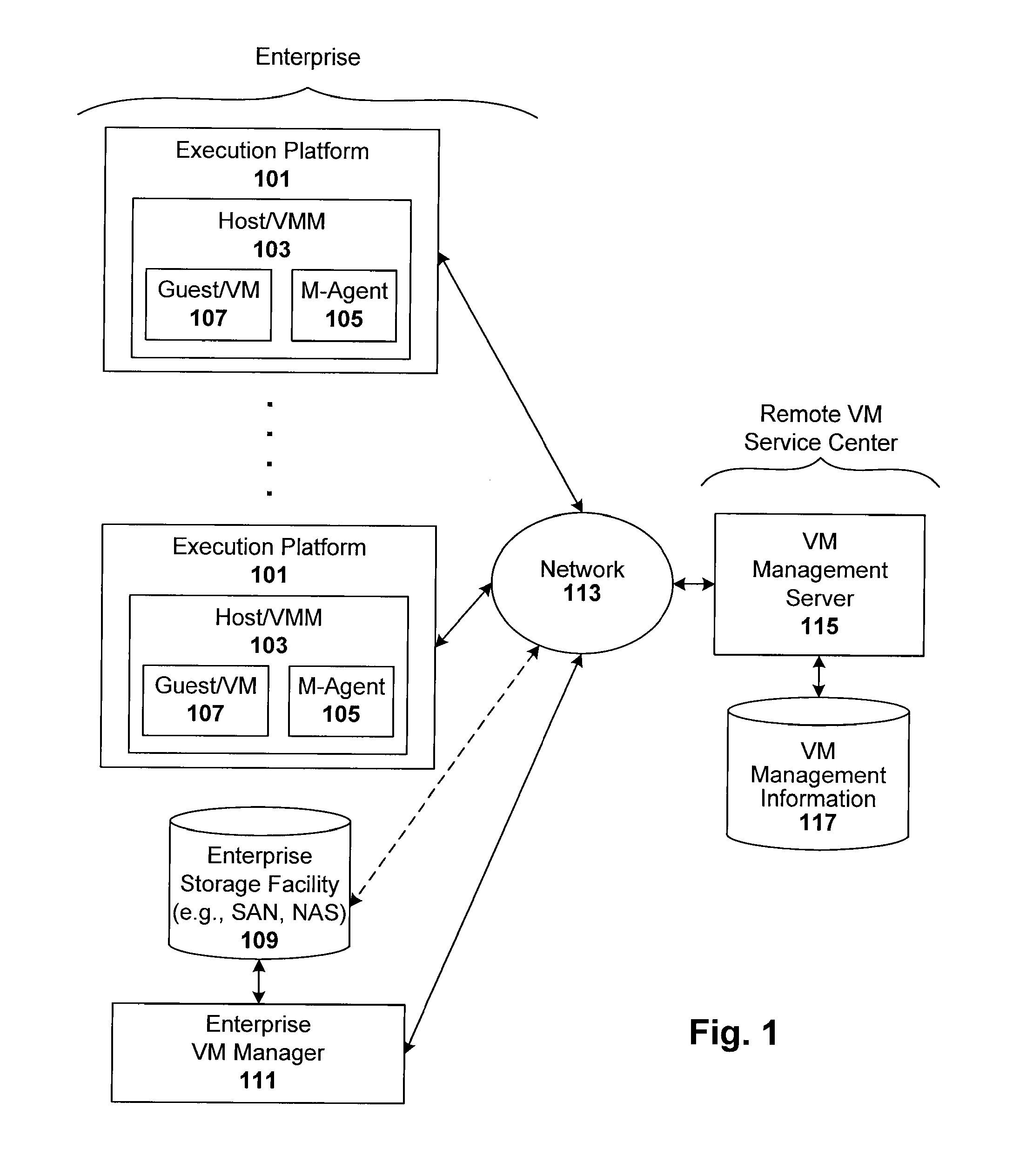
Enforcement of compliance policies in managed virtual systems
ActiveUS20080134176A1Preventing executionNon-redundant fault processingSoftware simulation/interpretation/emulationSystems managementMetadata
Techniques are disclosed for controlling and managing virtual machines and other such virtual systems. VM execution approval is based on compliance with policies controlling various aspects of VM. The techniques can be employed to benefit all virtual environments, such as virtual machines, virtual appliances, and virtual applications. For ease of discussion herein, assume that a virtual machine (VM) represents each of these environments. In one particular embodiment, a systems management partition (SMP) is created inside the VM to provide a persistent and resilient storage for management information (e.g., logical and physical VM metadata). The SMP can also be used as a staging area for installing additional content or agentry on the VM when the VM is executed. Remote storage of management information can also be used. The VM management information can then be made available for pre-execution processing, including policy-based compliance testing.
Owner:RED HAT
Facilities management system
InactiveUS20050078006A1Improve securityEffective time managementIndividual entry/exit registersBurglar alarm electric actuationActive monitoringSystems management
A system is described for management of an operations area. The management system includes a central processing component with one or more central processors. An active monitoring system component is connected to the central processor. The active monitoring system includes tags and readers for individual identification of one or more tagged entities. The active monitoring system component is arrayed to create a management zone. The tags and readers are linked to the central processing component such that information from the tags and readers is received and analyzed by the central processing component. A passive monitoring system component is connected to the central processor. The passive monitoring system identifies non-tagged entities entering the management zone and additional information is communicated to the central processing component for analysis.
Owner:HUTCHINS J MARC +1
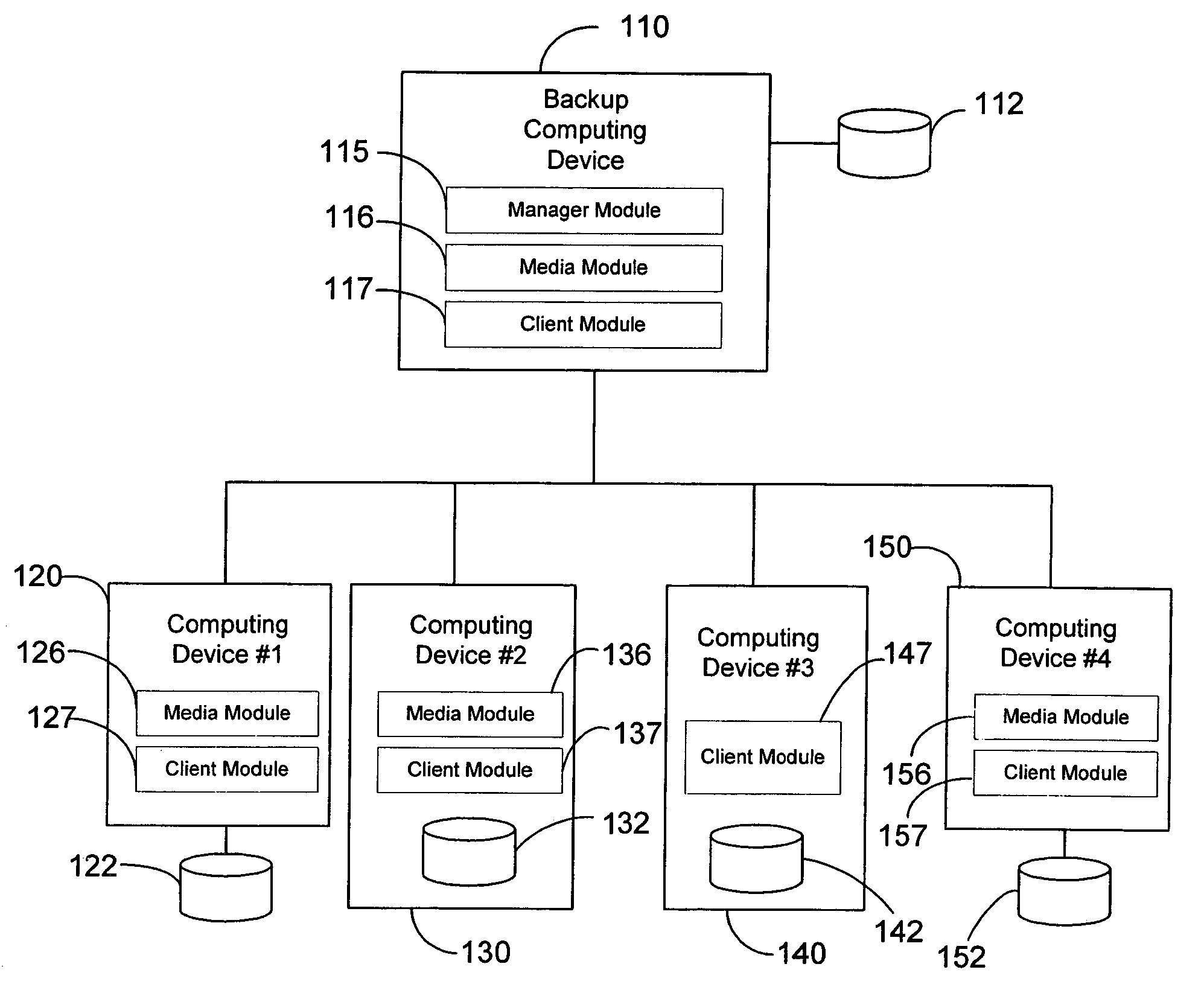
Modular systems and methods for managing data storage operations
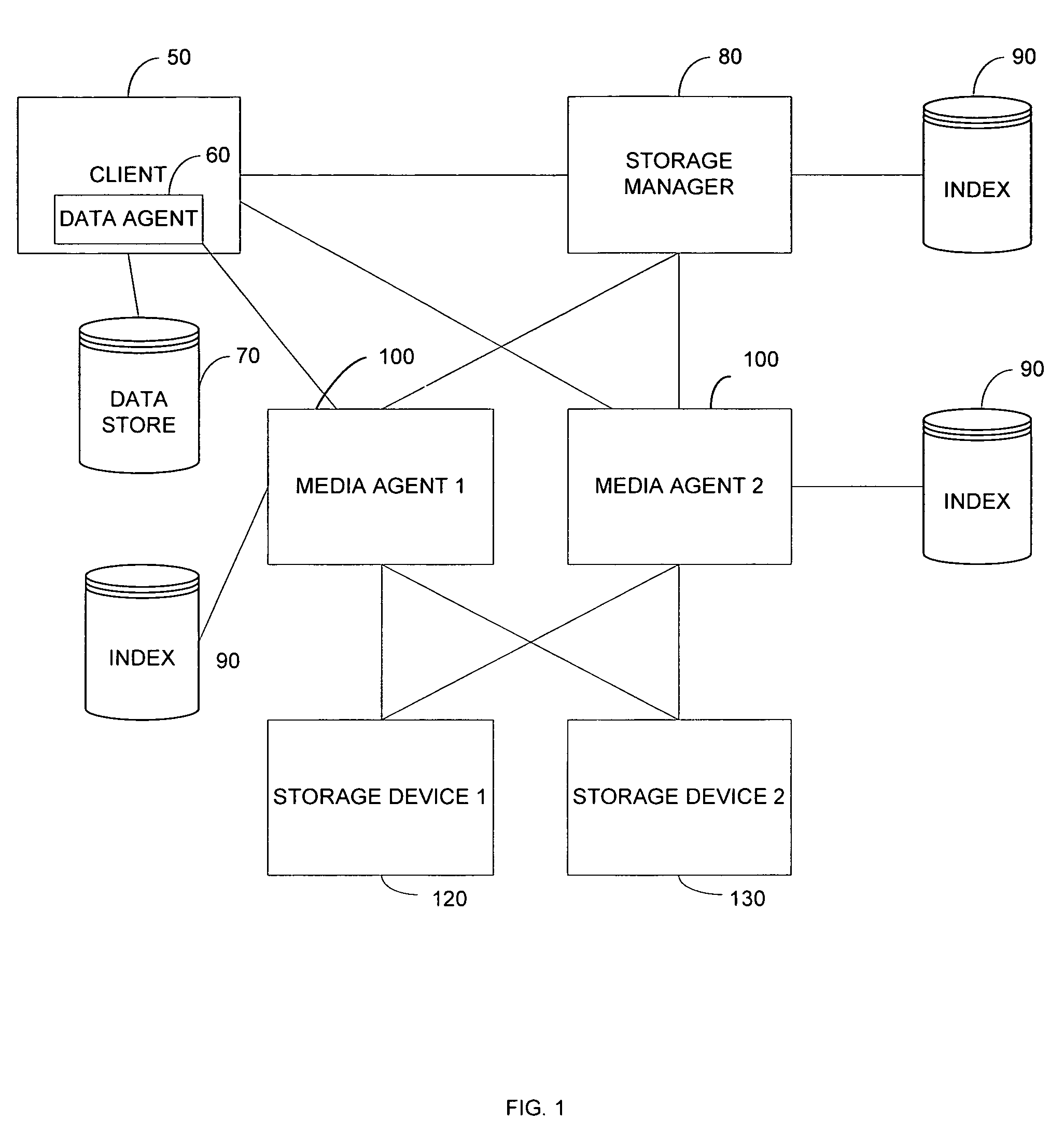
InactiveUS20080244177A1Data processing applicationsDigital data processing detailsRegimenSystems management
The invention is a modular backup and retrieval system. The software modules making up the backup and retrieval system run independently, and can run either on the same computing devices or on different computing devices. The modular software system coordinates and performs backups of various computing devices communicating to the modules. At least one module on one of the computing devices acts as a system manager for a network backup regimen. A management component acts as a manager for the archival and restoration of the computing devices on the network. It manages and allocates library media usage, maintains backup scheduling and levels, and supervises or maintains the archives themselves through pruning or aging policies. A second software module acts as a manager for each particular library media.
Owner:COMMVAULT SYST INC
Automatic optimization for virtual systems
ActiveUS20080184225A1Memory loss protectionError detection/correctionConsistency testVirtual file system
Techniques are disclosed for controlling and managing virtual machines and other such virtual systems. VM execution approval is based on compliance with policies controlling various aspects of VM. The techniques can be employed to benefit all virtual environments, such as virtual machines, virtual appliances, and virtual applications. For ease of discussion herein, assume that a virtual machine (VM) represents each of these environments. In one particular embodiment, a systems management partition (SMP) is created inside the VM to provide a persistent and resilient storage for management information (e.g., logical and physical VM metadata). The SMP can also be used as a staging area for installing additional content or agentry on the VM when the VM is executed. Remote storage of management information can also be used. The VM management information can then be made available for pre-execution processing, including policy-based compliance testing.
Owner:RED HAT
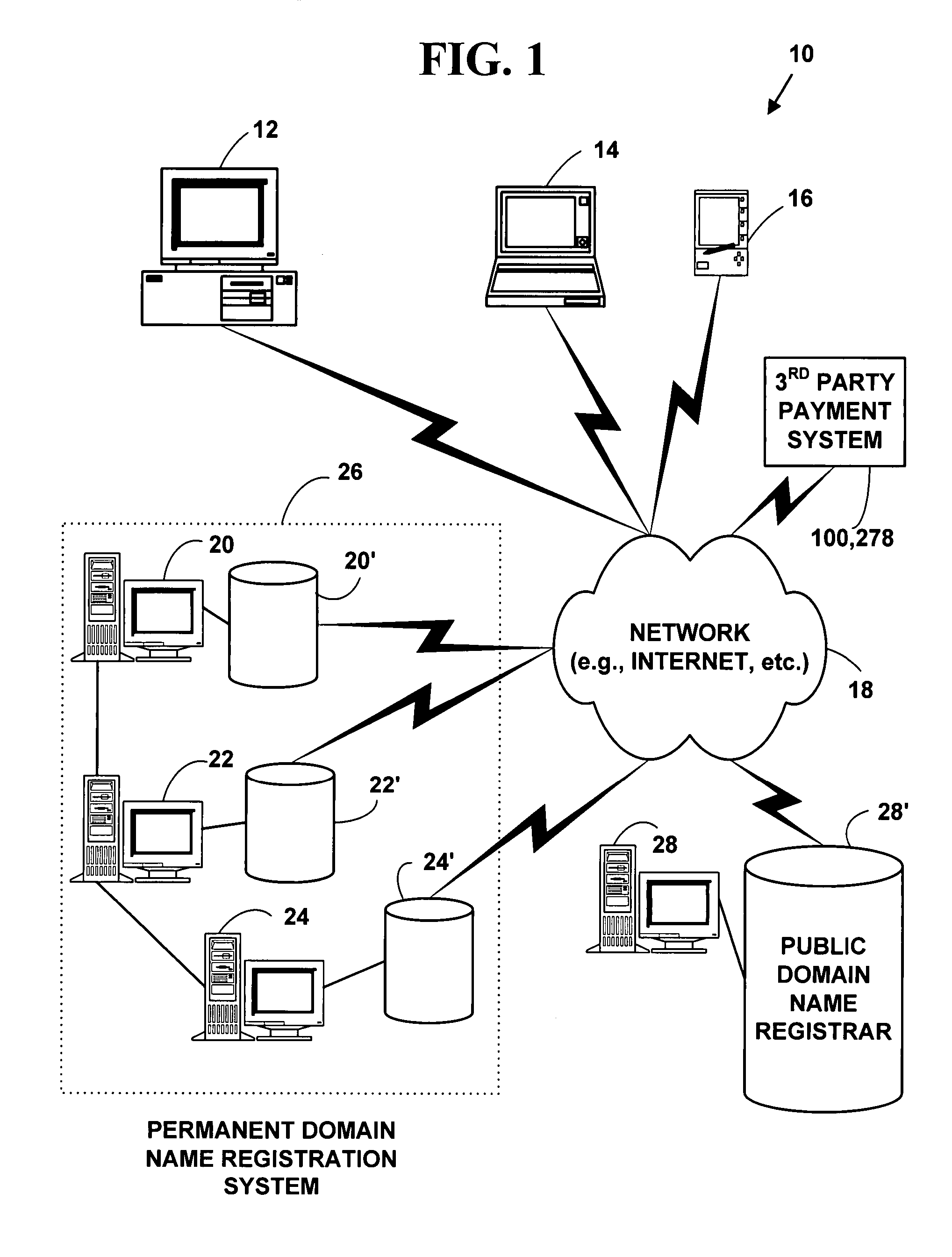
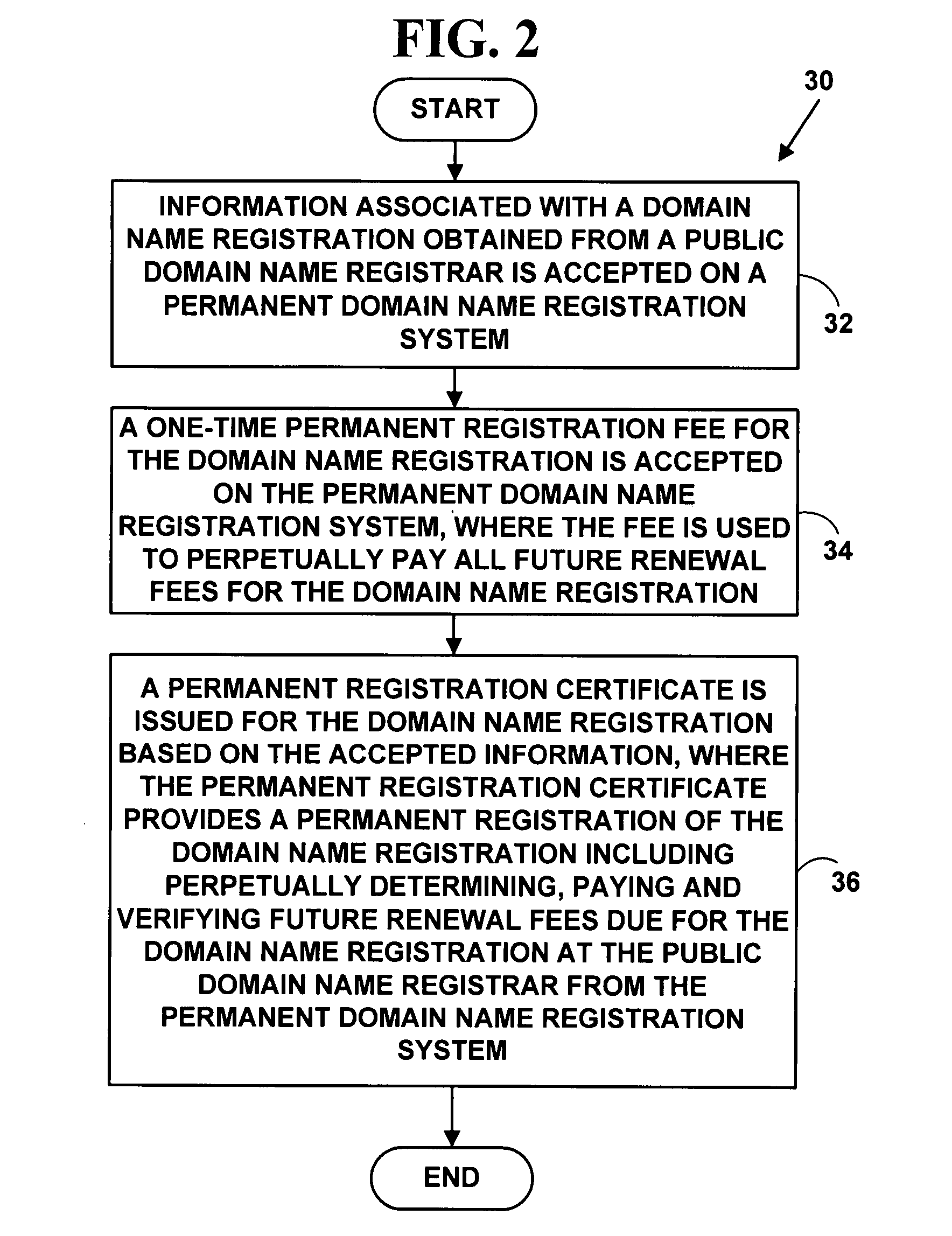
Method and system for protecting domain names via third-party systems
InactiveUS20080046340A1Digital data authenticationBuying/selling/leasing transactionsThird partyDomain name
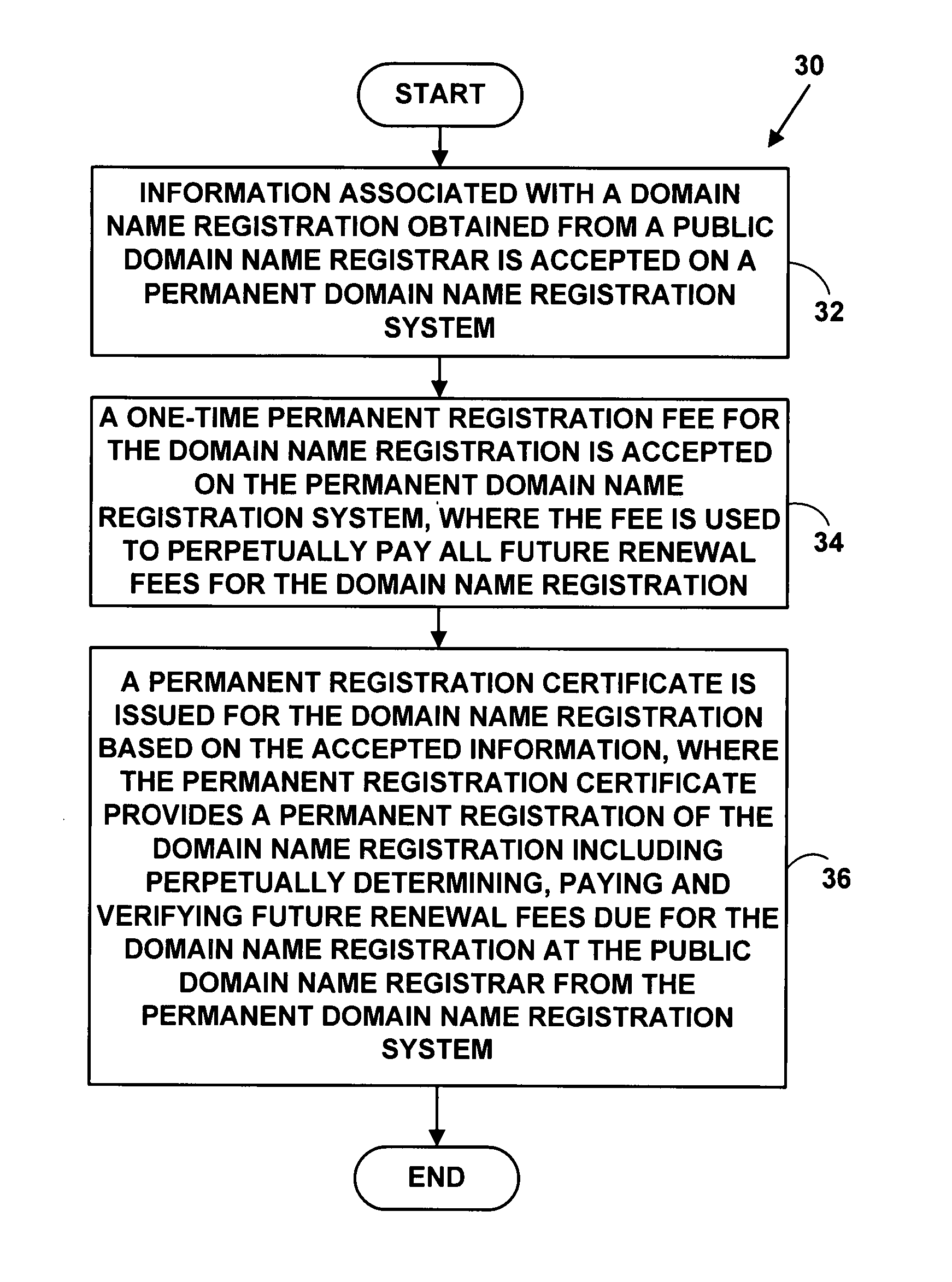
A method and system for extending a permanent domain name registration service and / or website hosting service by third-party payment system. A third-party payment system enables a domain name / website hosting account holder to accept third-party payments; third parties may then view a payment section on their website and choose to make a payment for a specified period. The third-party payment system manages the funds and tracks the need to accept third-party payments and to make timely payments to the service provider. A beneficiary contact and a third-party contact method are included as means to help manage a website that may operate unattended and may remain online indefinitely thereby providing permanent domain name registration or permanent website hosting.
Owner:BROWN CHARLES P
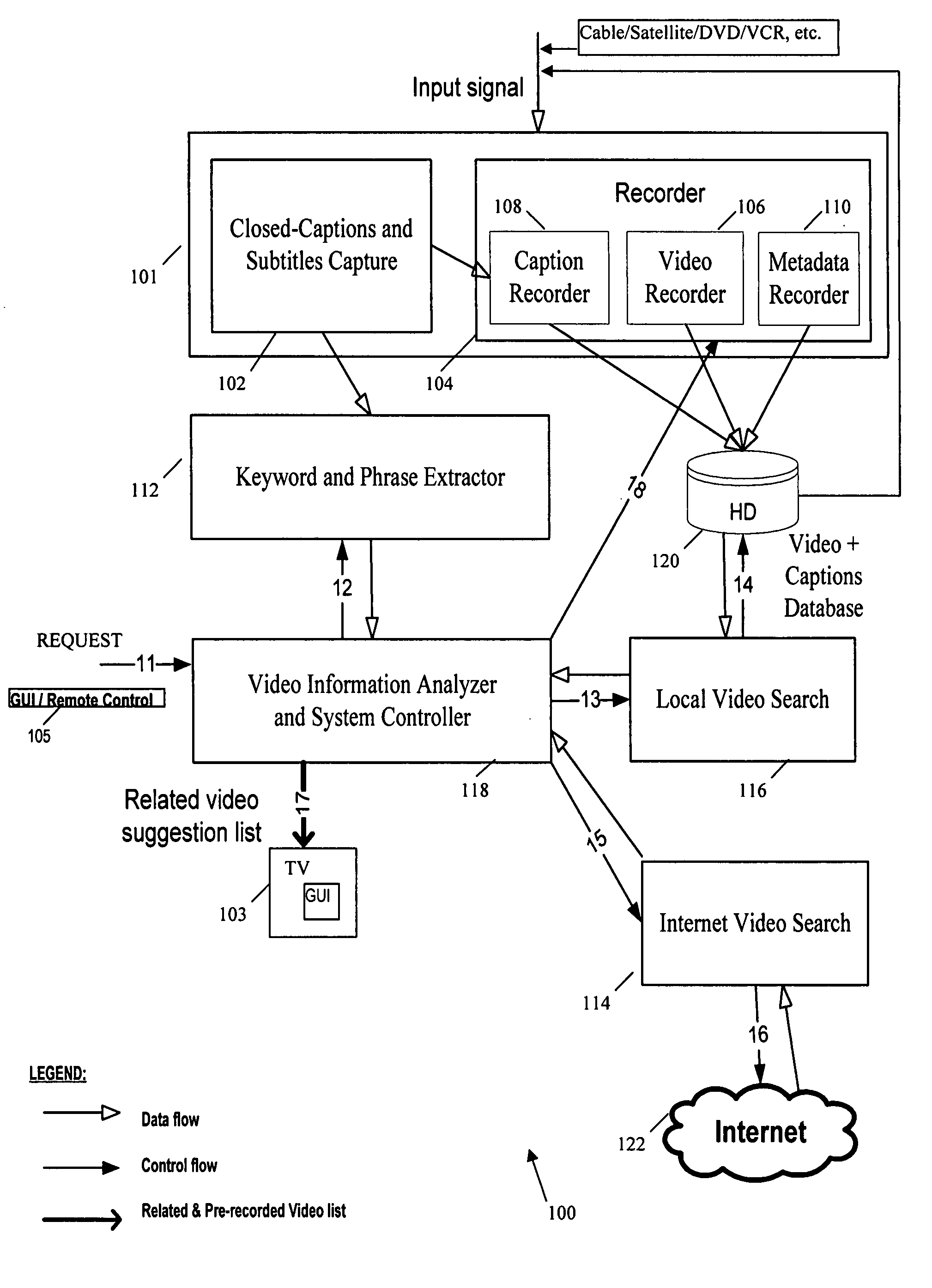
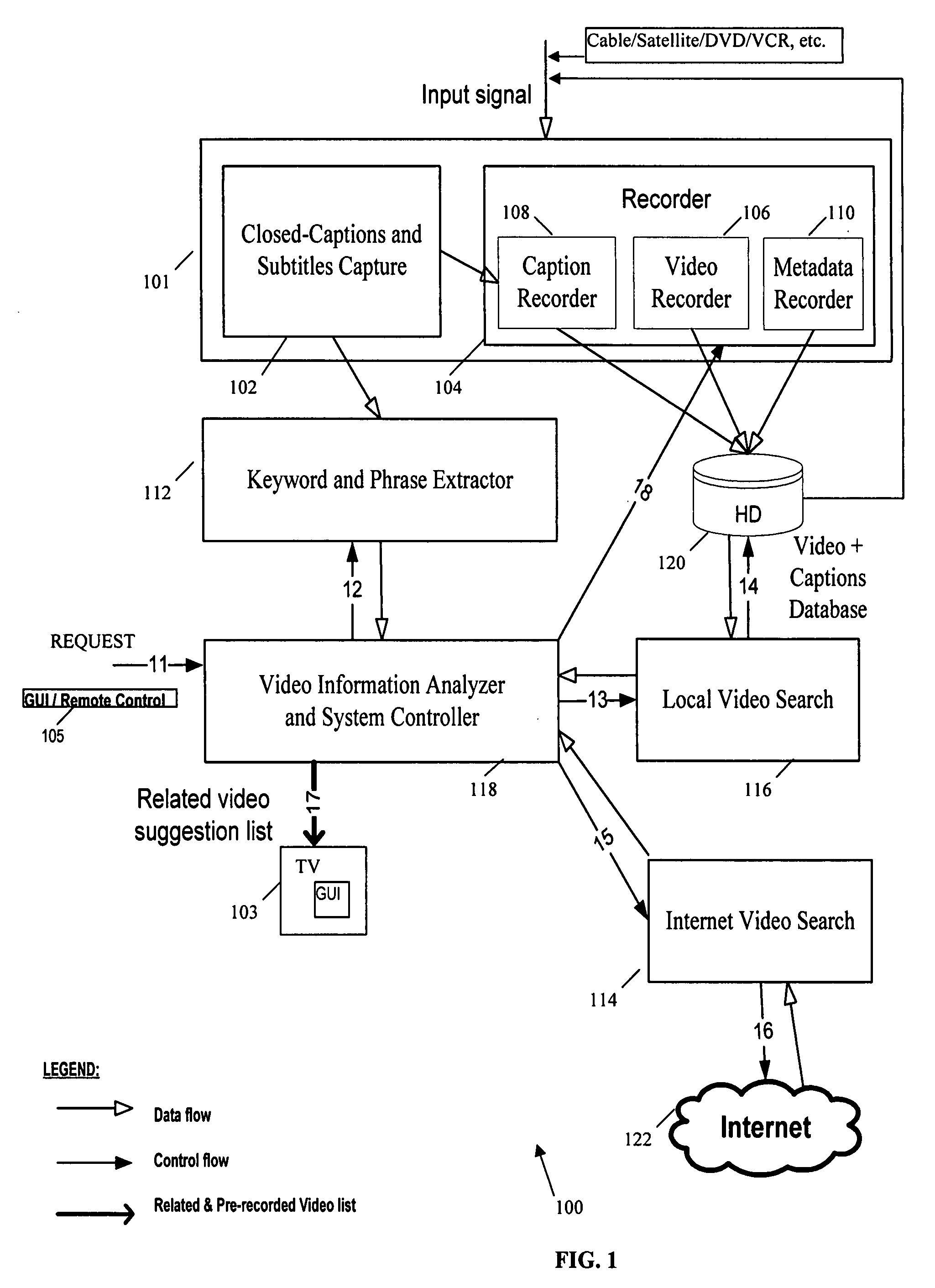
Method and system for managing information on a video recording device
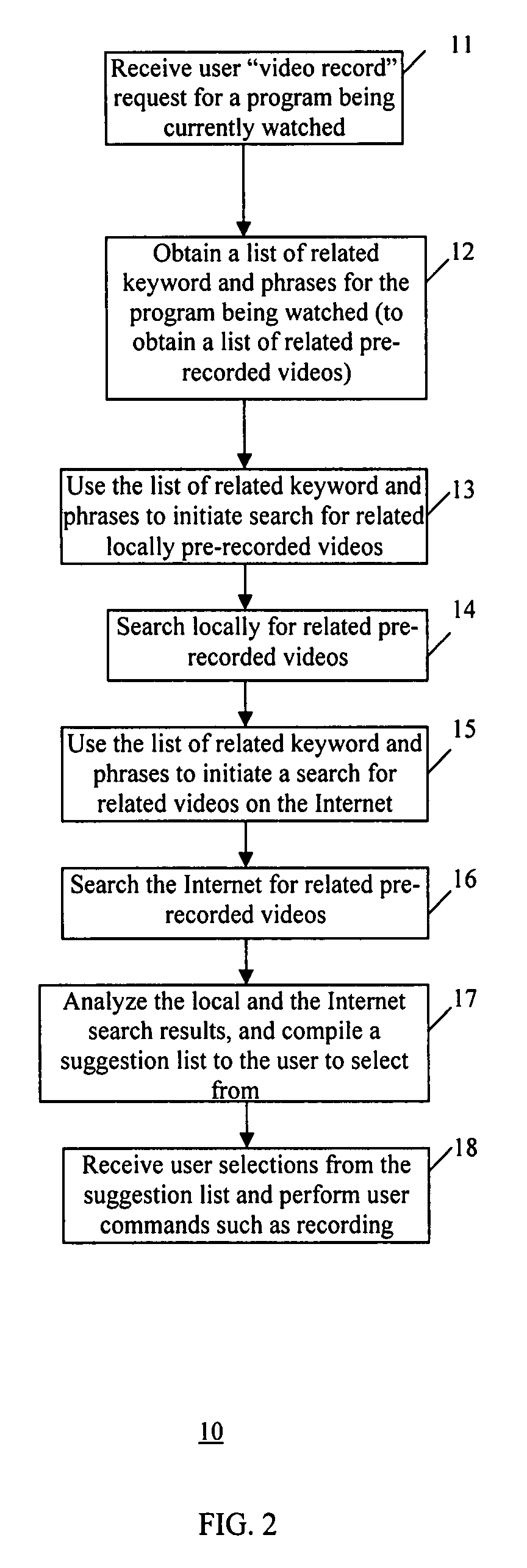
InactiveUS20070214488A1Television system detailsMetadata video data retrievalComputer graphics (images)Management process
A method and system that implement a process for managing video information on a video recording device. The management process involves receiving a video input signal including a video stream, obtaining content information corresponding to the video stream, associating the content information with the video stream, and storing the video stream and associated content information in a database as a searchable index for the video stream. The searchable index includes location of the stored video stream and identifies the associated content information. Then, content information from an input signal corresponding to a video stream is captured for analysis and searching the index to identify stored video streams related to the video program for suggestion to the user.
Owner:SAMSUNG ELECTRONICS CO LTD
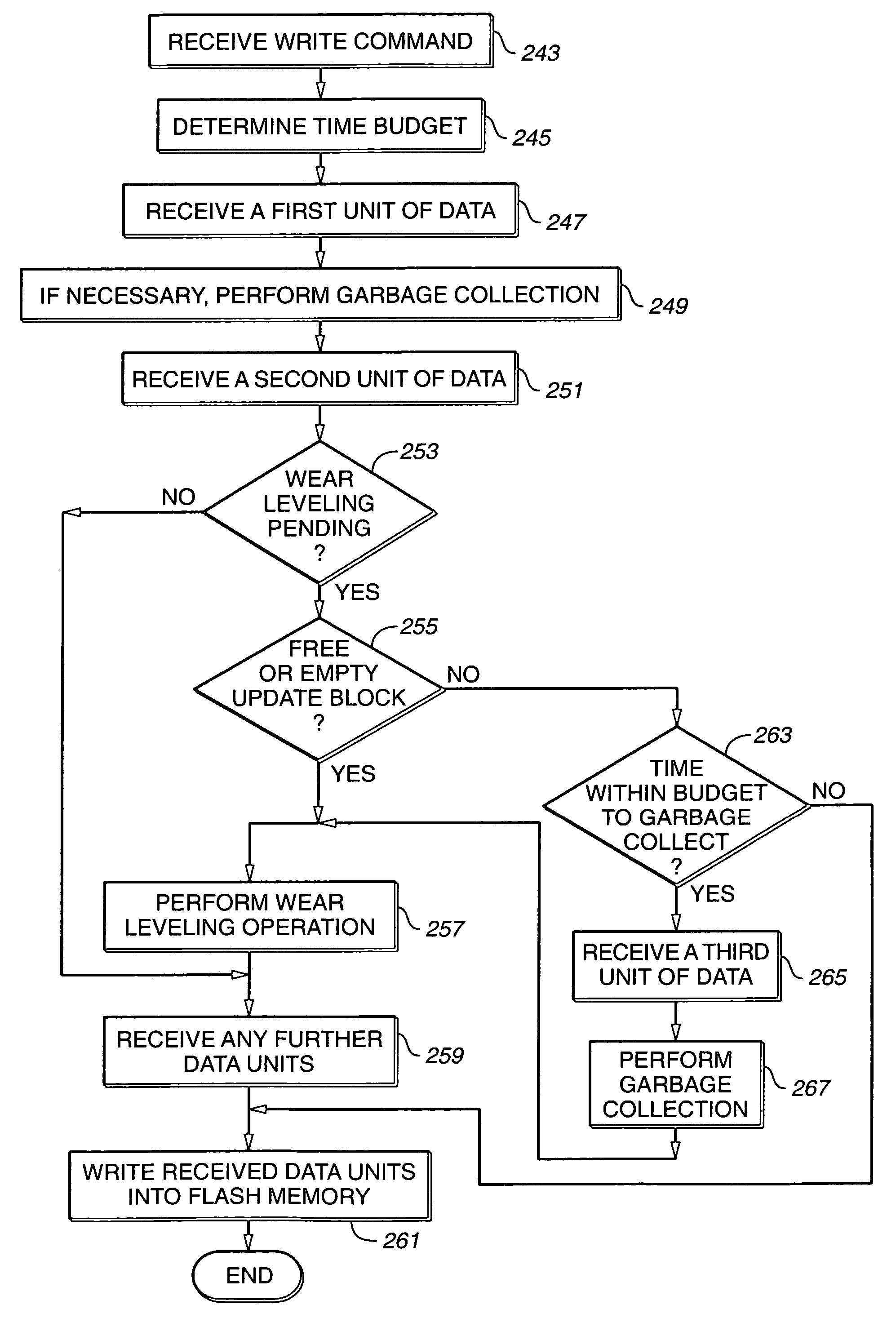
Scheduling of housekeeping operations in flash memory systems
InactiveUS20060161724A1Improved performance characteristicsMaximum countMemory architecture accessing/allocationMemory systemsSystems managementNon-volatile memory
A re-programmable non-volatile memory system, such as a flash EEPROM system, having its memory cells grouped into blocks of cells that are simultaneously erasable is operated to perform memory system housekeeping operations in the foreground during execution of a host command, wherein the housekeeping operations are unrelated to execution of the host command. Both one or more such housekeeping operations and execution of the host command are performed within a time budget established for executing that particular command. One such command is to write data being received to the memory. One such housekeeping operation is to level out the wear of the individual blocks that accumulates through repetitive erasing and re-programming.
Owner:SANDISK TECH LLC
Lottery management system
InactiveUS20030228910A1Easy to integrateImprove reliabilityPaper-money testing devicesPayment architectureSystems managementSoftware development
A lottery management system provides the ability to integrate various lottery system types into a single lottery management solution so as to allow the customized deployment of various lottery system attributes. In one embodiment, lottery system attributes include game types, reporting functions, system administration, point-of-sale integration, device and network-specific interfaces and retail management. The present invention can include a lottery transaction server, a message exchange component, thin client components, thick client components and software development kits.
Owner:GTECH RHODE ISLAND CORP
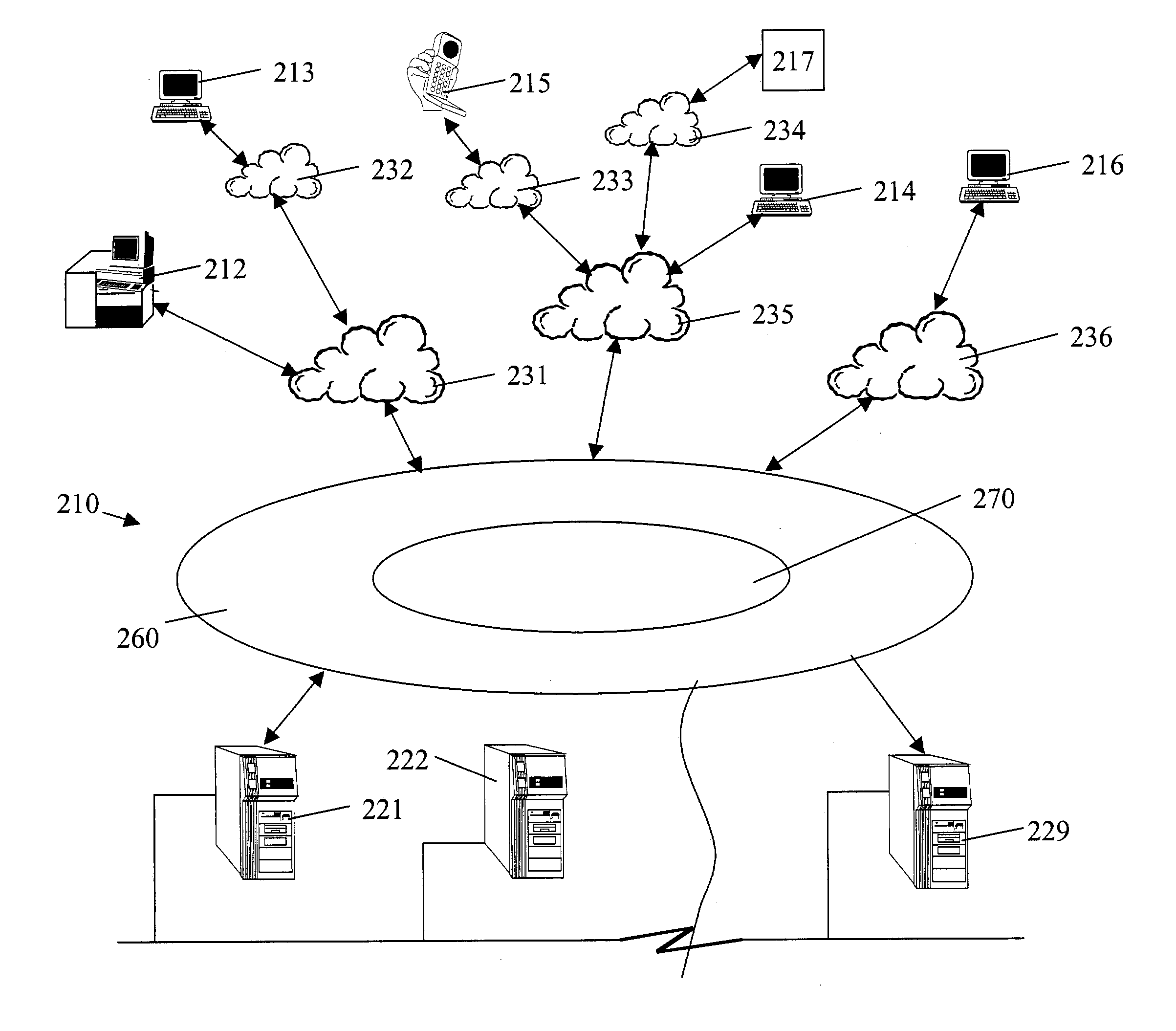
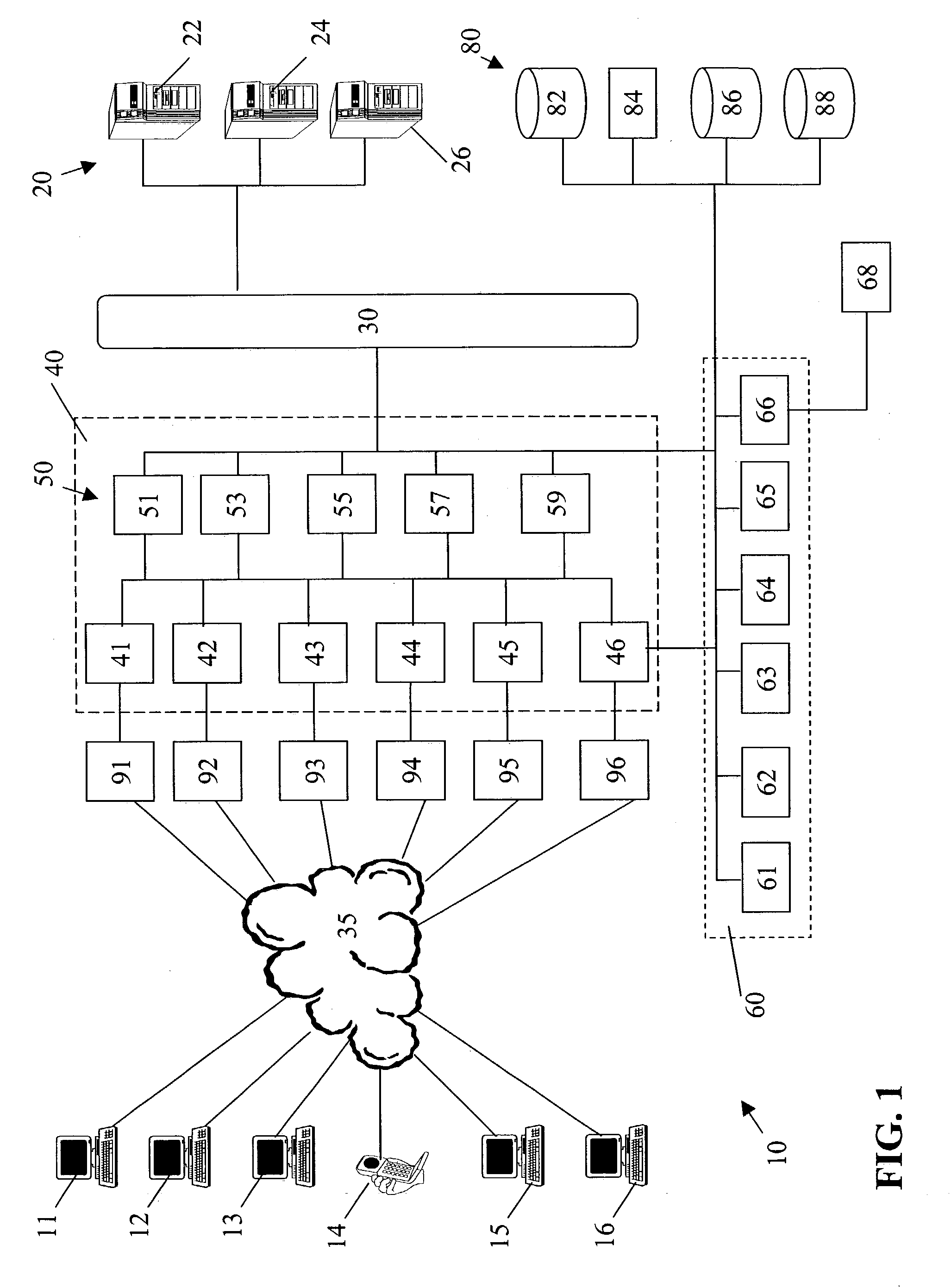
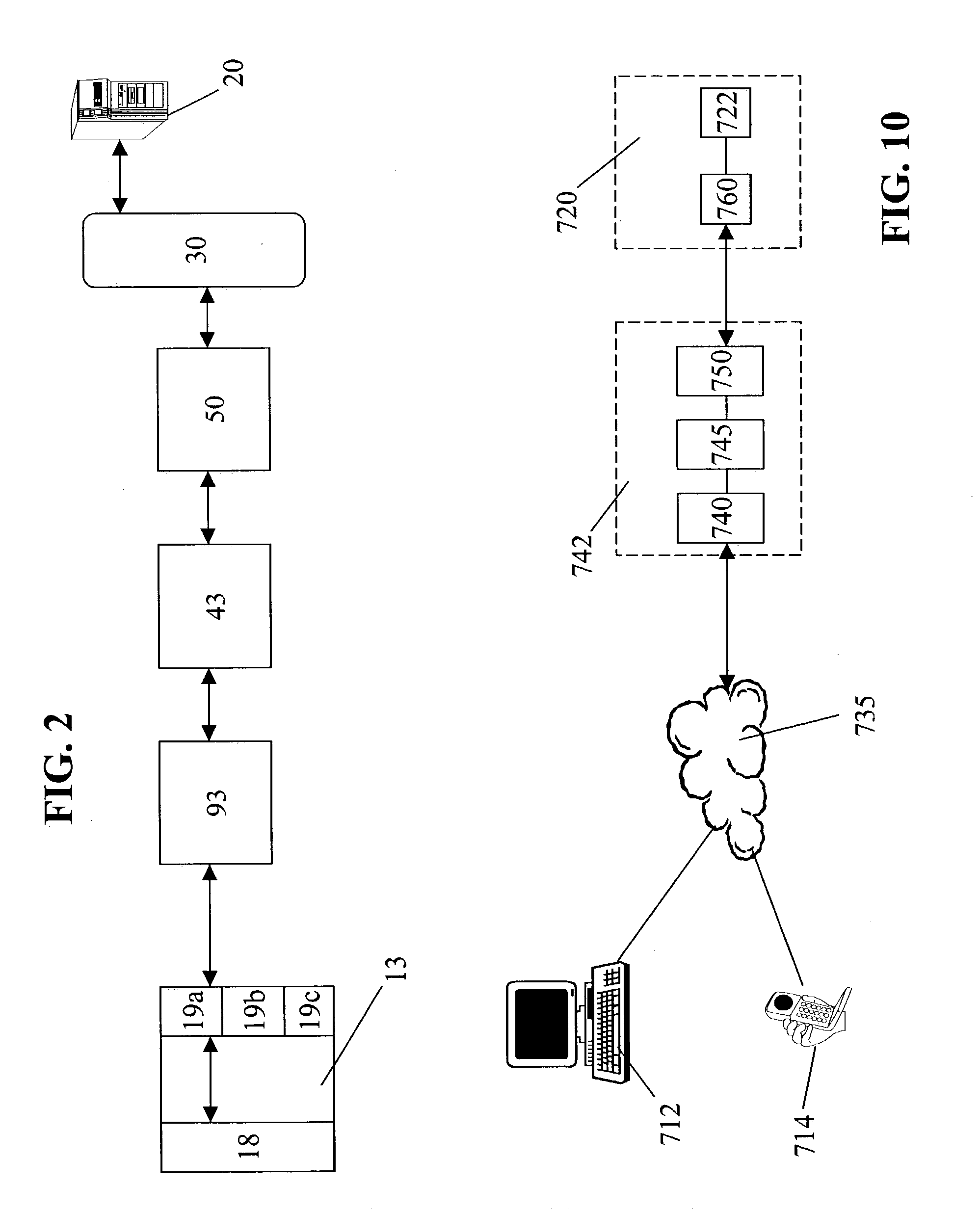
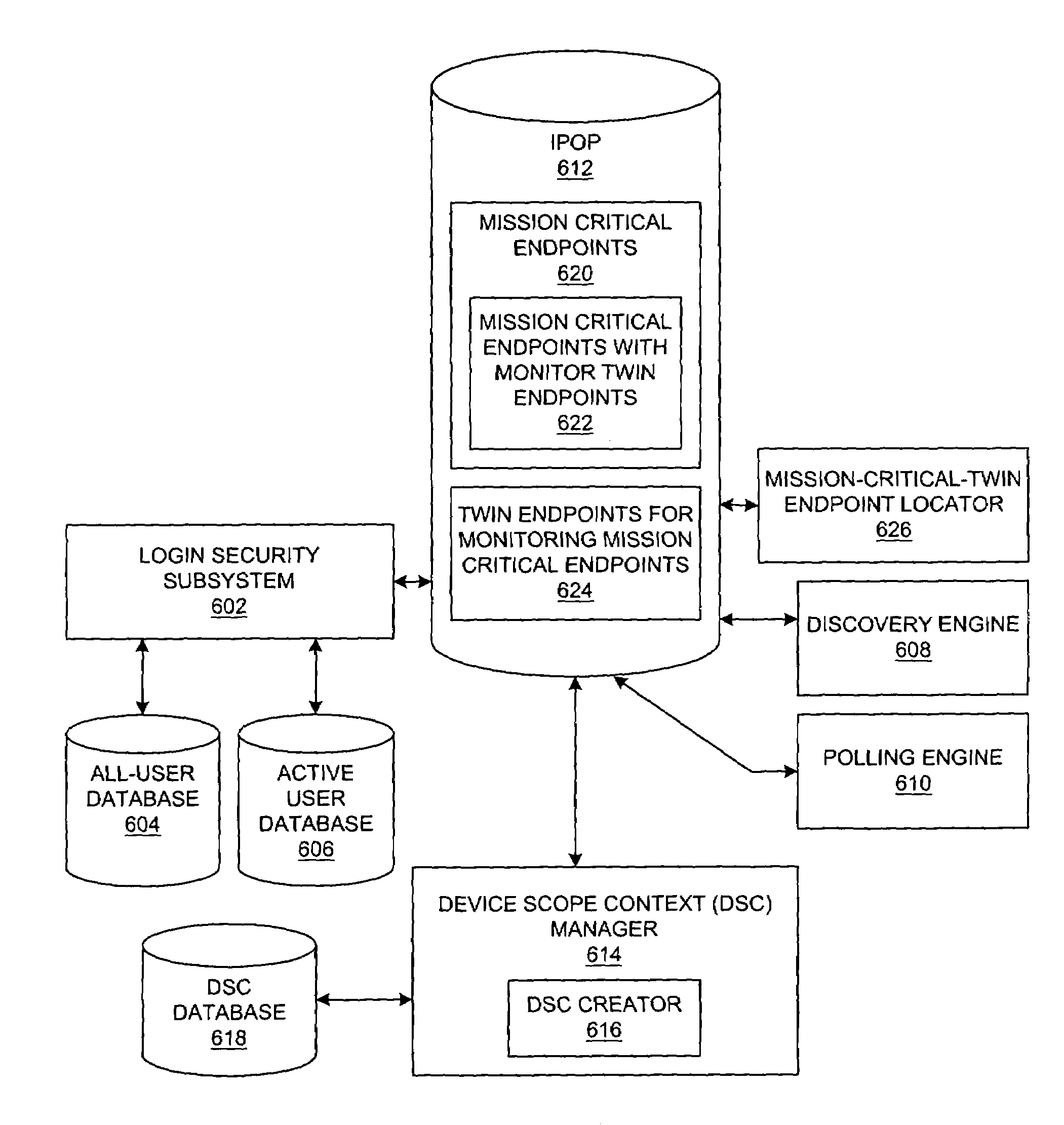
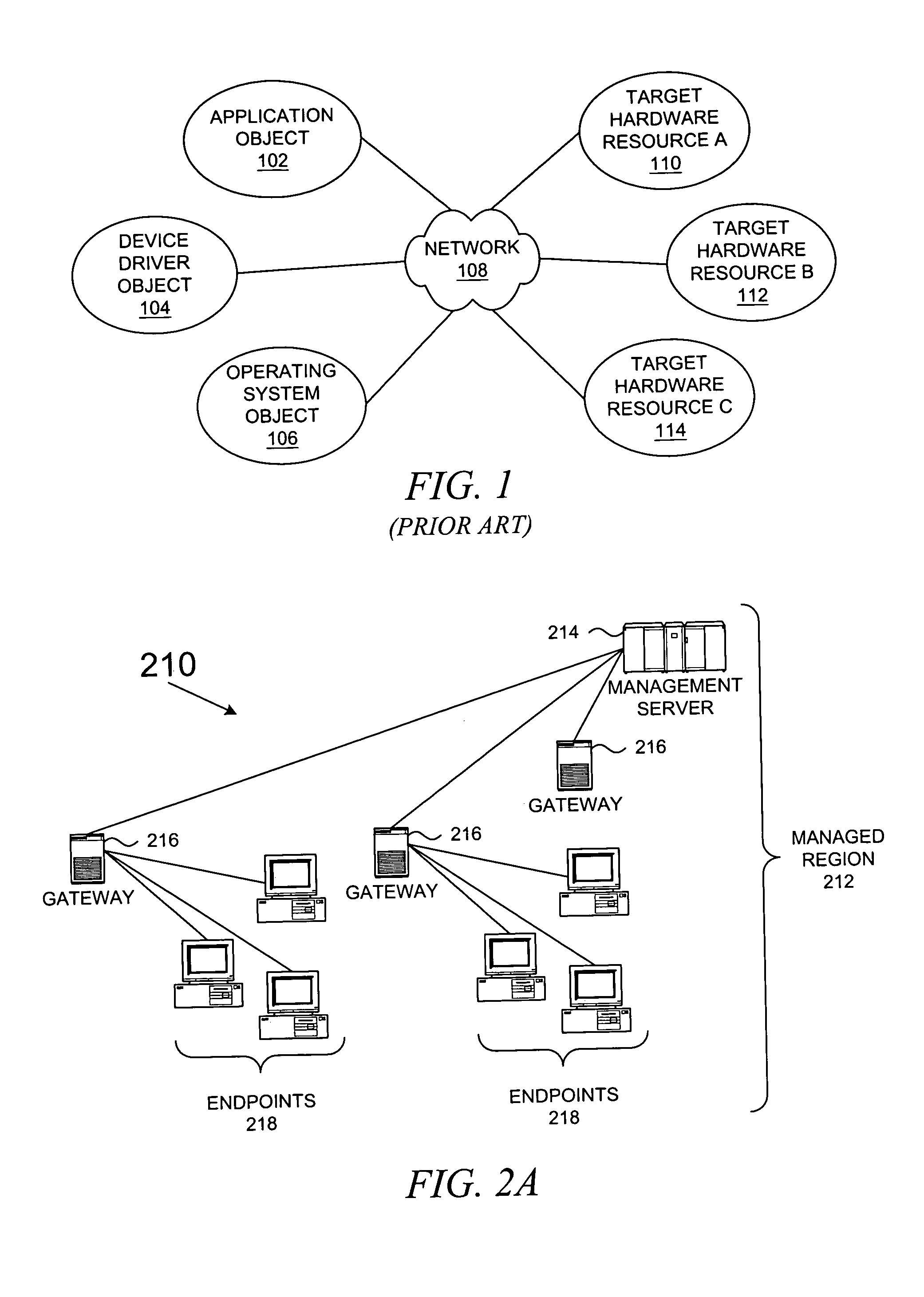
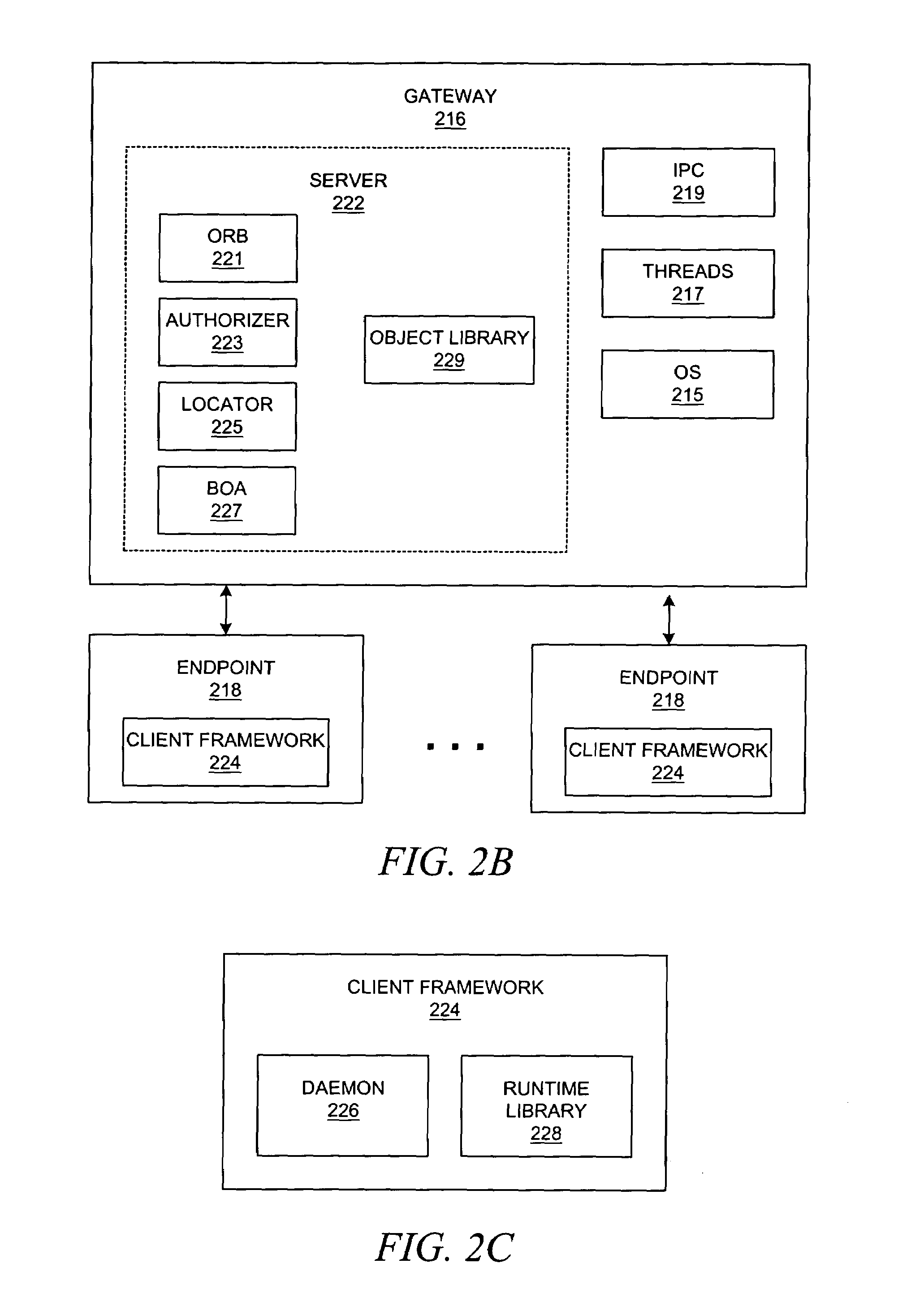
Method and system for network management with backup status gathering
A method, system, apparatus, and computer program product are presented for management of a distributed data processing system. Resources within the distributed data processing system are dynamically discovered, and the discovered resources are adaptively monitored using the network management framework. A network or system administrator configures some mission critical endpoints with multiple network interface cards (NICs) and specifies mission critical endpoints, non-mission critical actions, etc. During status collection activities associated with network or system management activities, the categorization of an endpoint as a mission-critical or non-mission critical endpoint affects the manner in which the status collection activity is performed. Applications can request the performance of actions at endpoints without regard to the categorization of the endpoint or without regard to the categorization of the requested action, and the network management system routes the action based on whether or not the specified endpoint is a mission critical endpoint. A non-mission-critical endpoint is associated with a mission-critical endpoint based on the non-mission-critical endpoint's communication history with the mission critical endpoint. The management system may use the status of a non-mission-critical endpoint as a reflection of the status of a mission-critical endpoint.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com