Patents
Literature
145 results about "Request - action" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
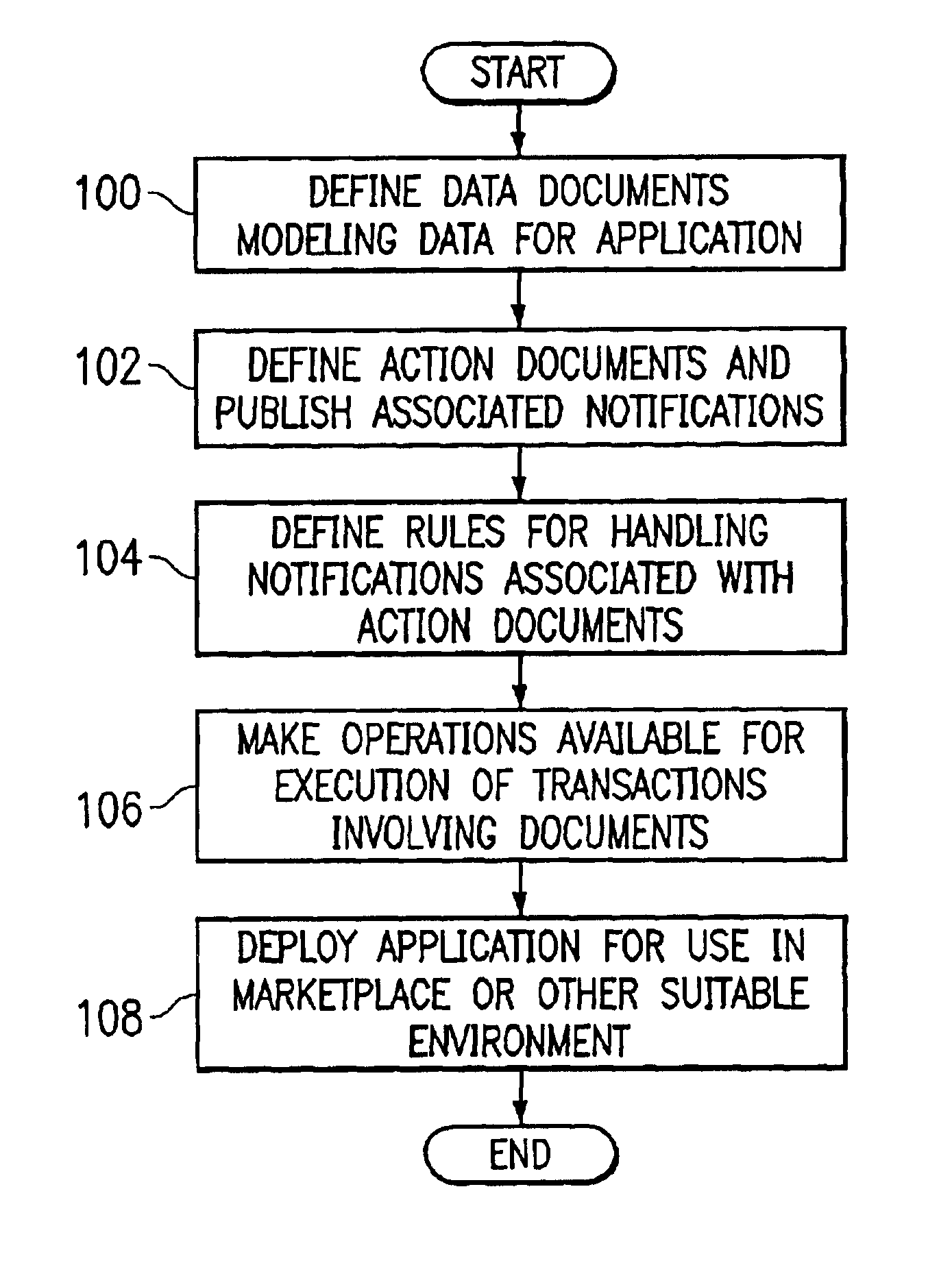
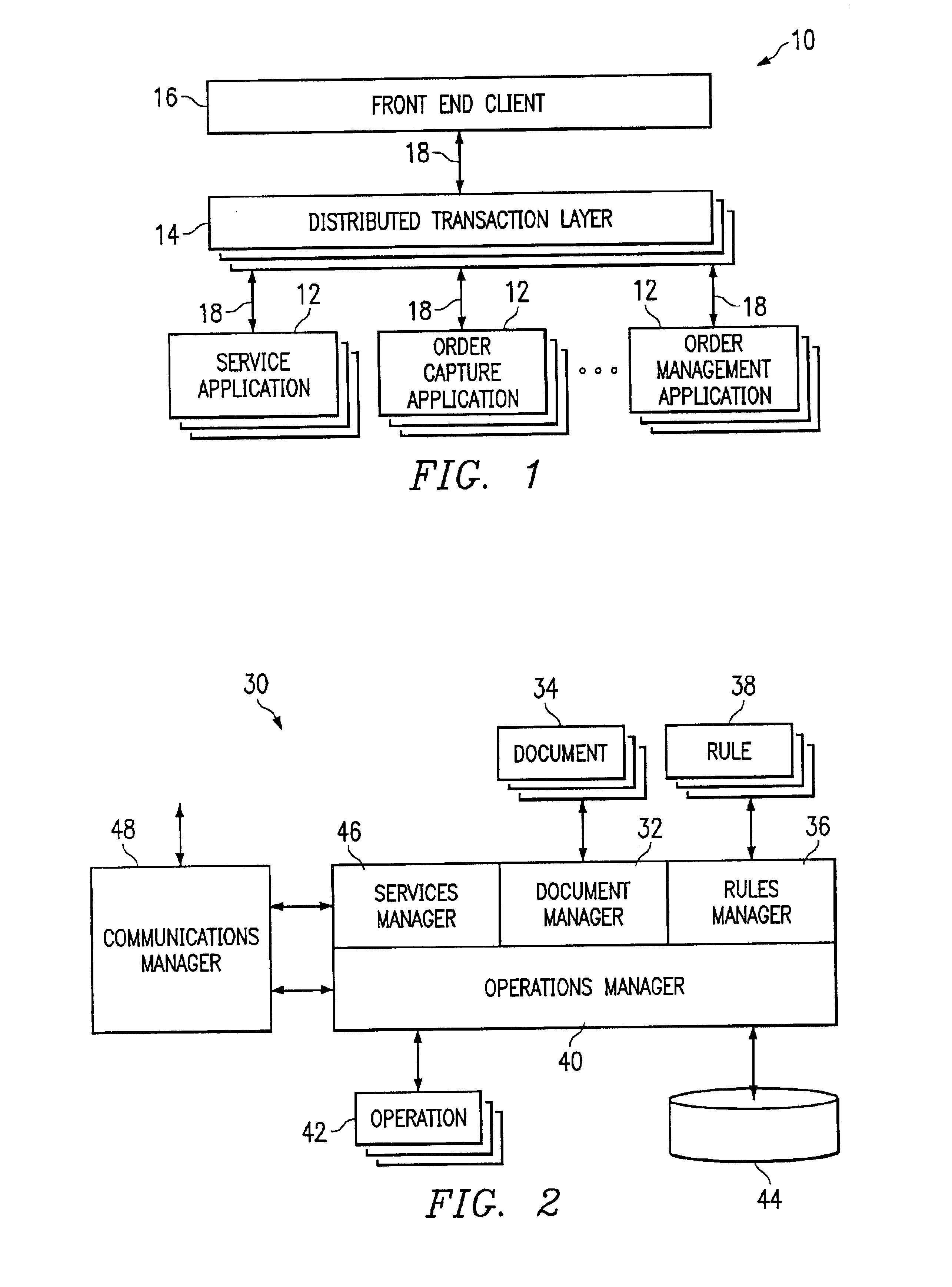
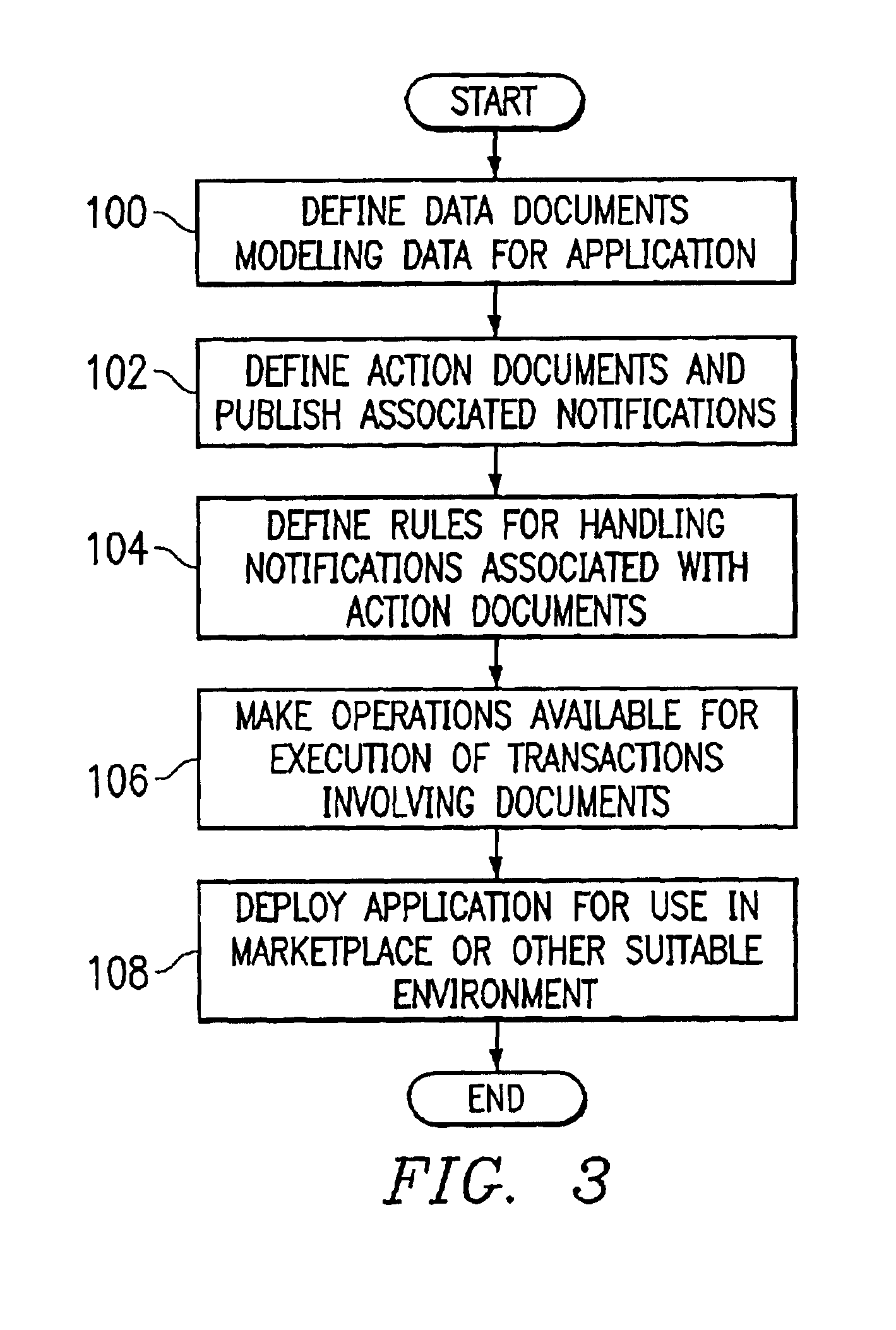
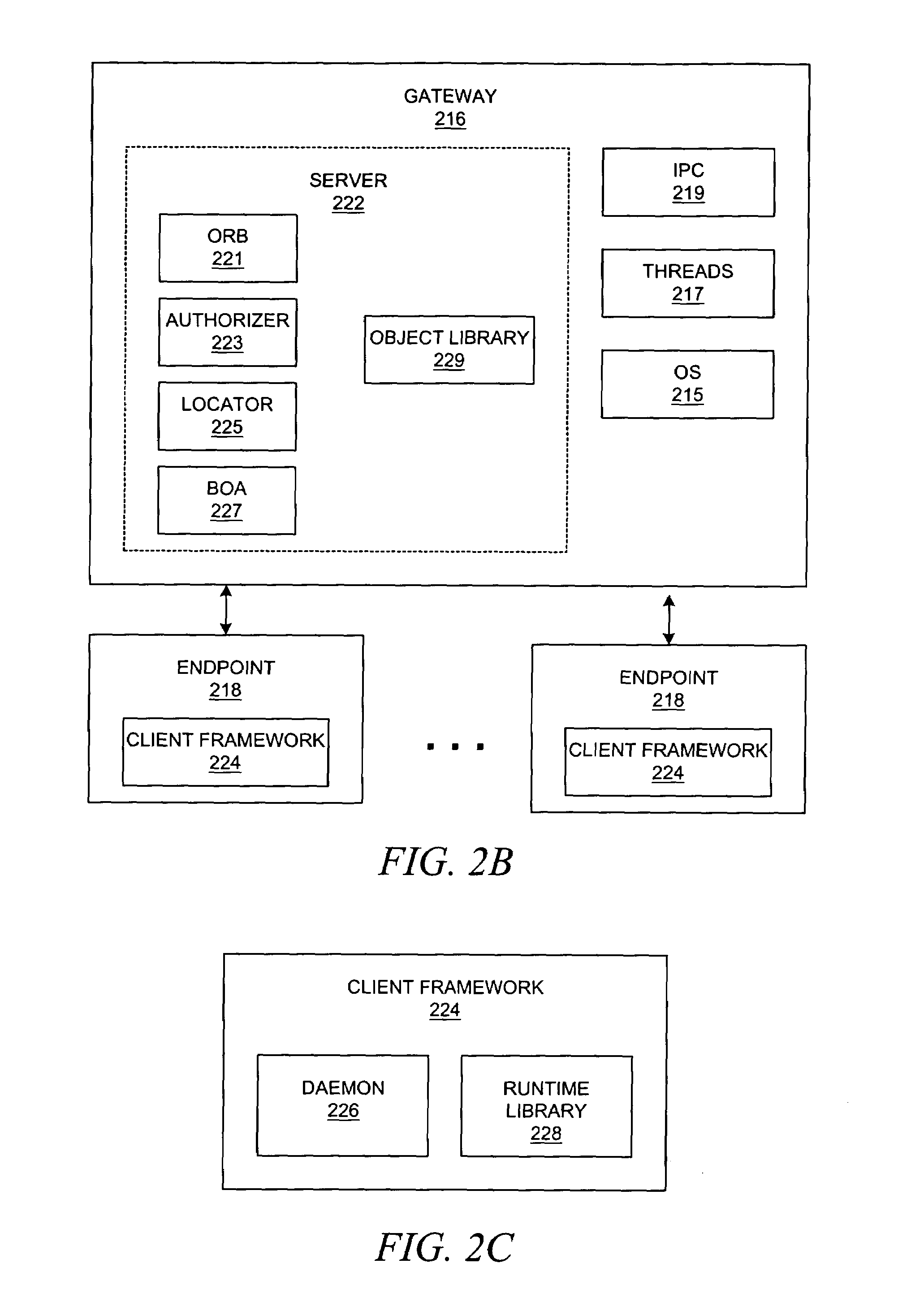
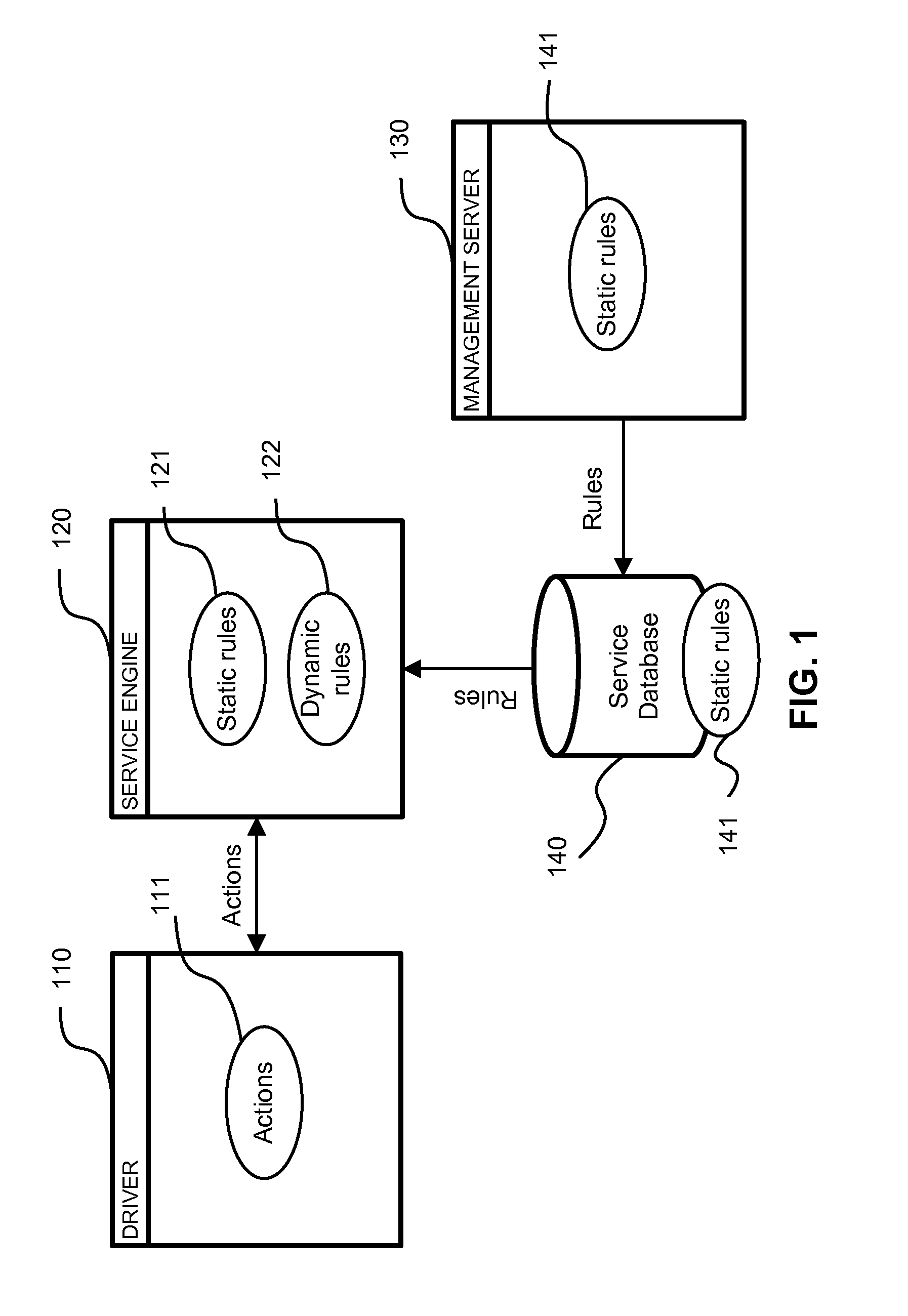
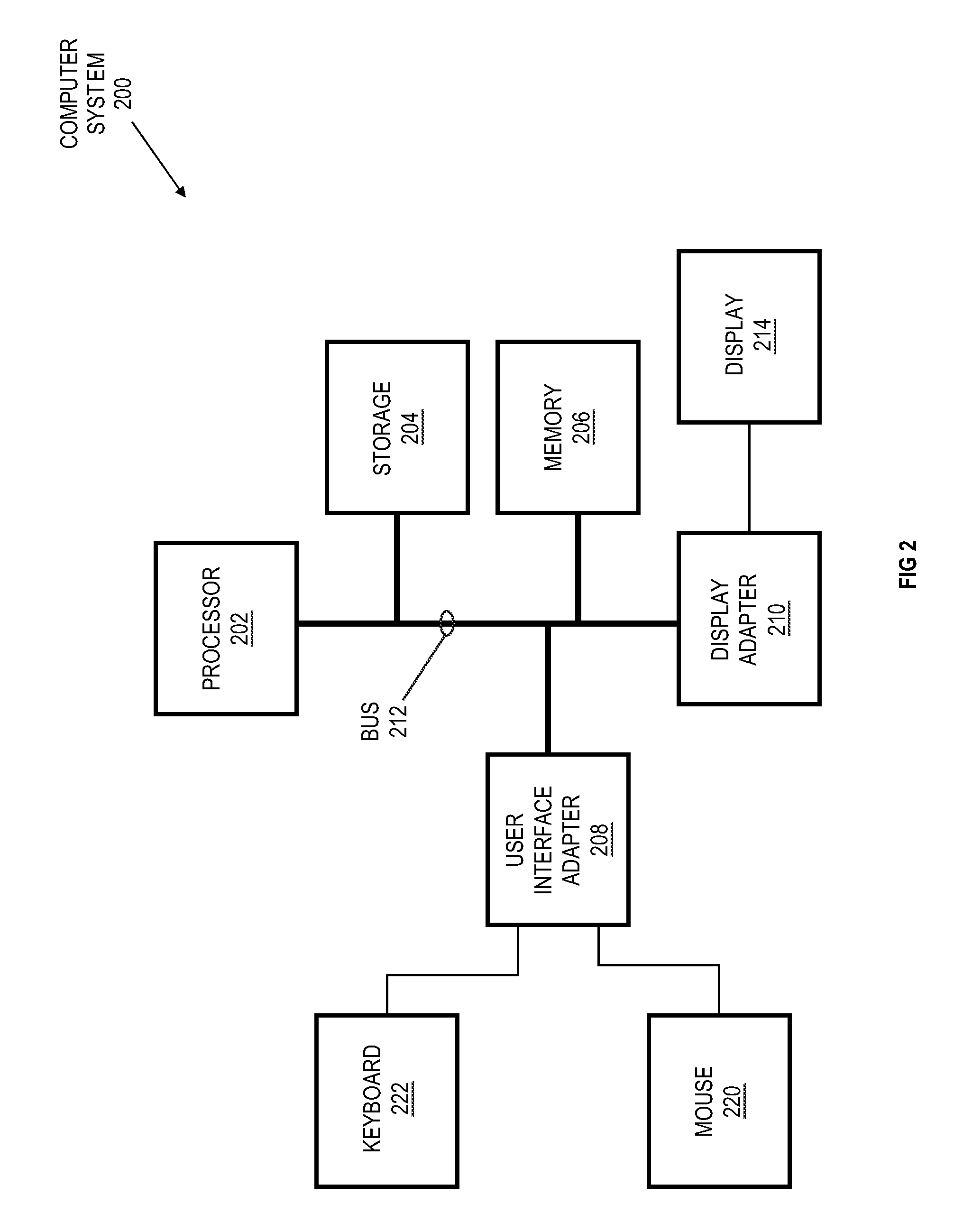
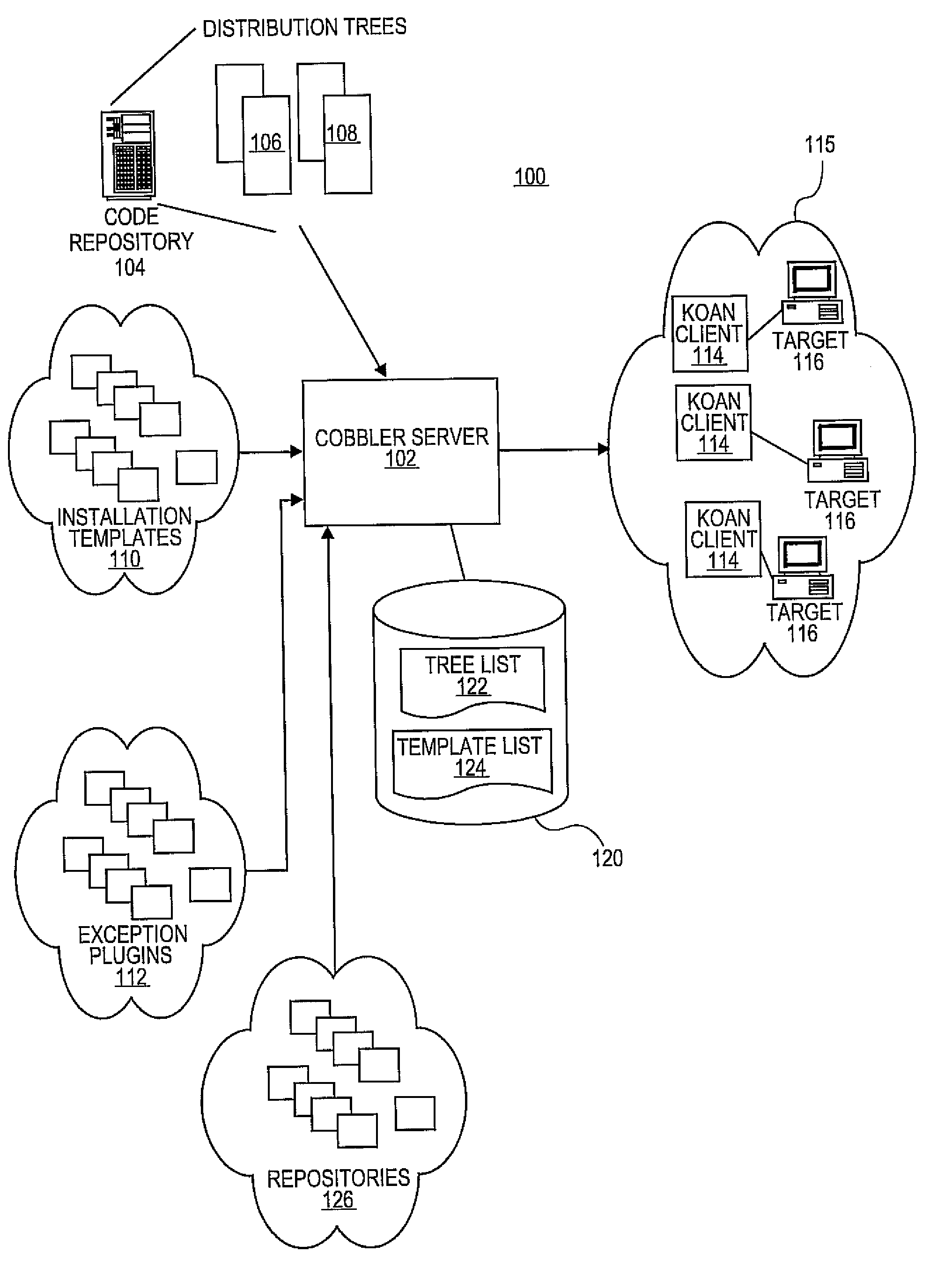
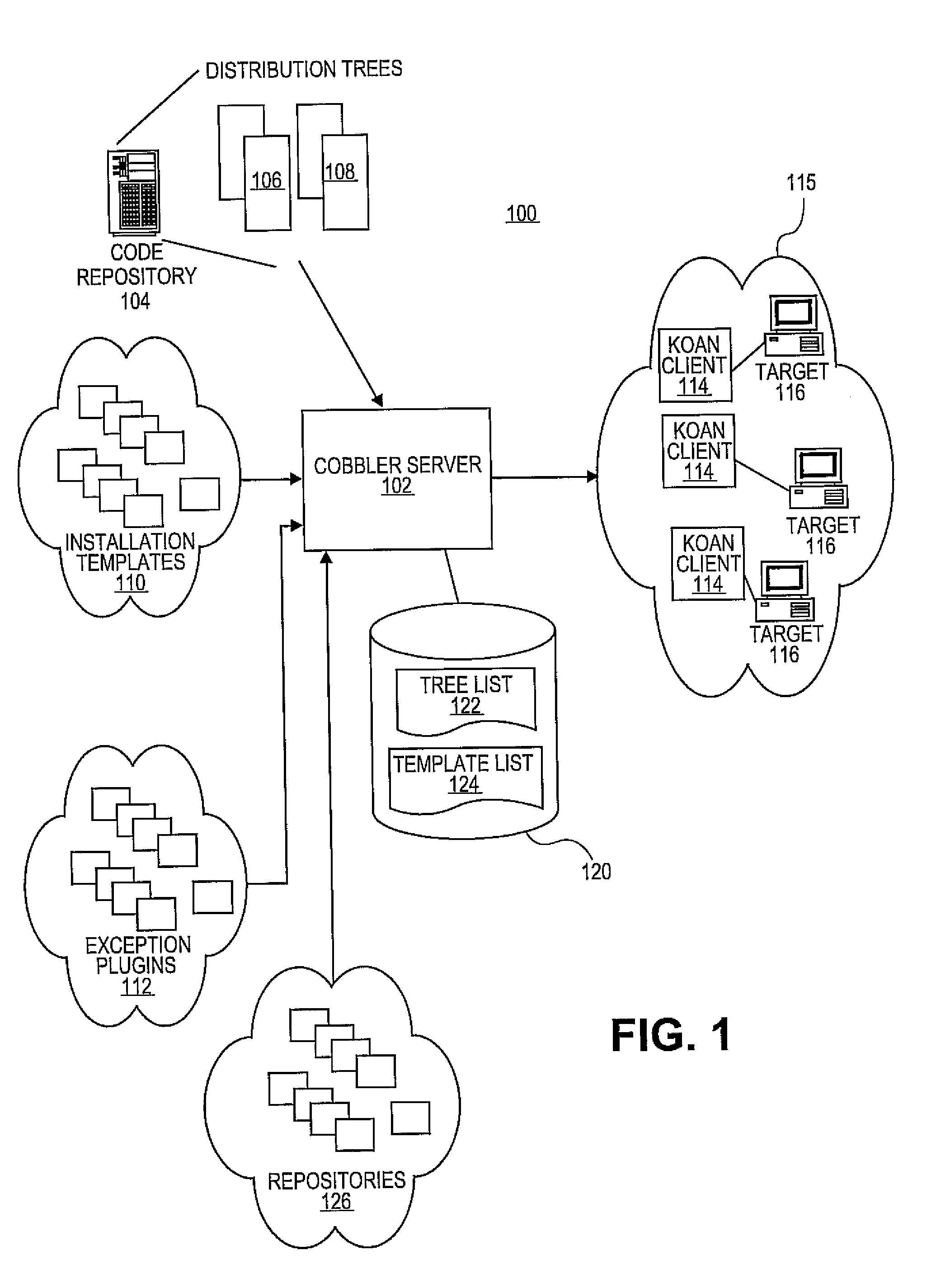
System and method for developing software applications using an extended XML-based framework
InactiveUS6845499B2Developing software applications have been substantially reduced or eliminatedShort development cycleSoftware designSpecific program execution arrangementsRequest - actionSoftware engineering
An XML-based framework (30) for developing software applications (12) includes a document manager (32) to manage activities relating to one or more XML-based data documents (34) associated with an application (12), each data document (34) modeling data associated with the application (12) and representing relationships between the data document (34) and one or more other data documents (34). The framework (30) includes a rules manager (36) to manage rules (38) specifying logic for handling notifications associated with XML-based action documents (34) received at the application (12), the notifications requesting actions involving data documents (34). The framework (30) also includes an operations manager (40) to manage the execution of transactions involving data documents (34) based on operations (42) defined for the application (12) during its development. The framework (30) provides a generic XML-based transaction engine, the application (12) being one of a plurality of distributed applications (12) each being an instance of the generic transaction engine. An electronic marketplace with a distributed transaction layer may include such a plurality of distributed applications (12), where the applications (12) interact with one another using the distributed transaction layer (14) to conduct electronic commerce within the marketplace.
Owner:JDA SOFTWARE GROUP
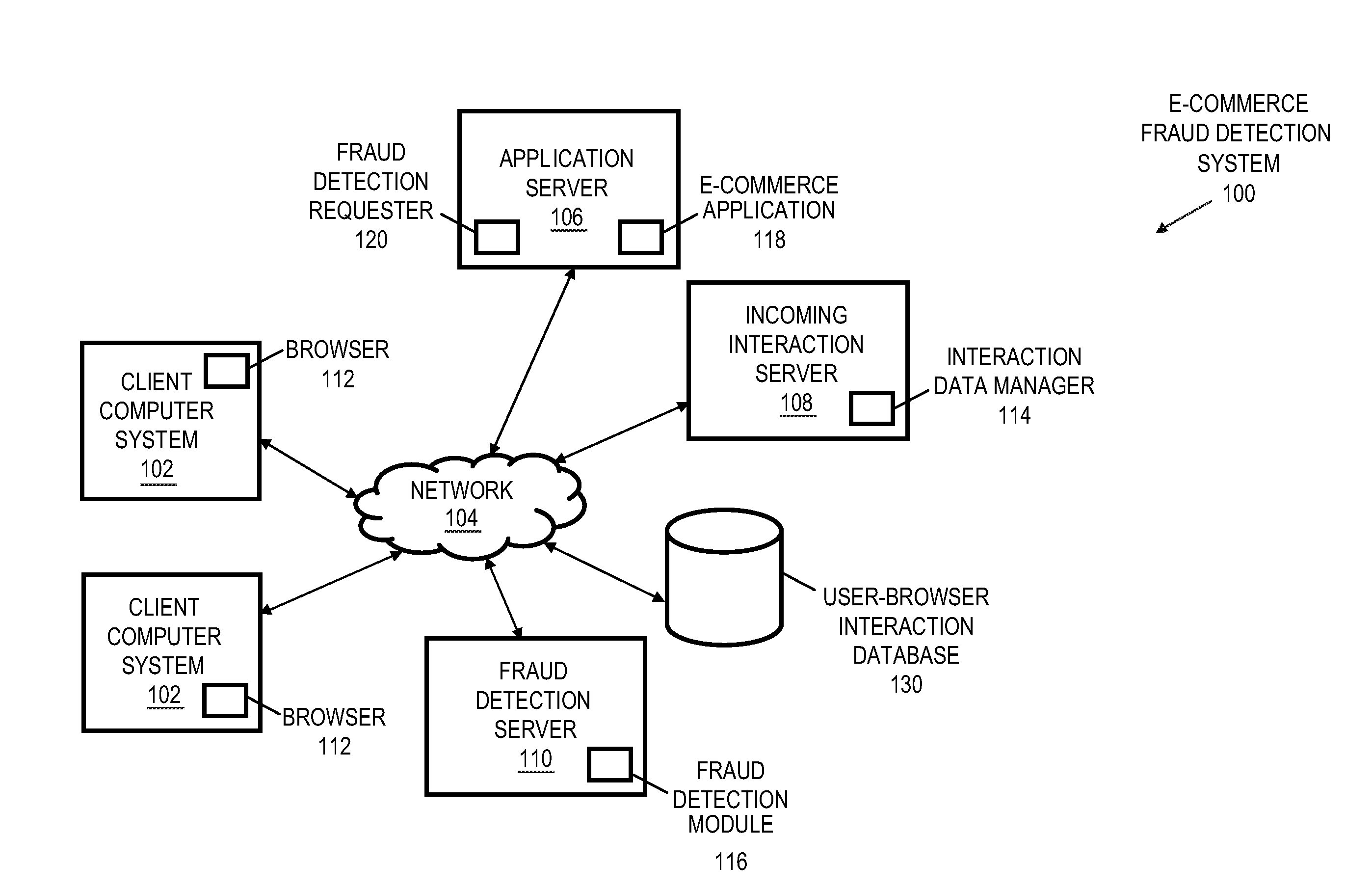
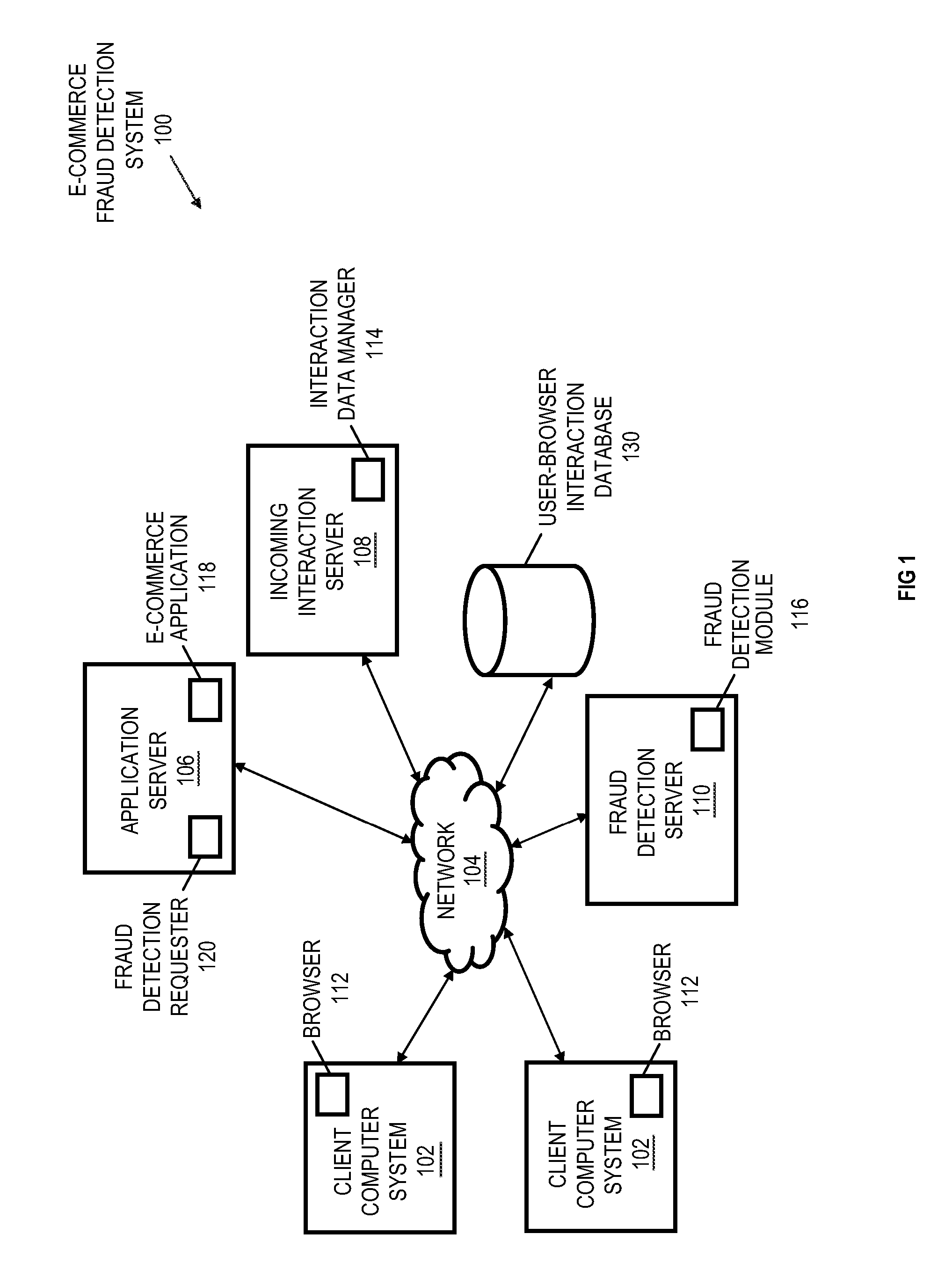
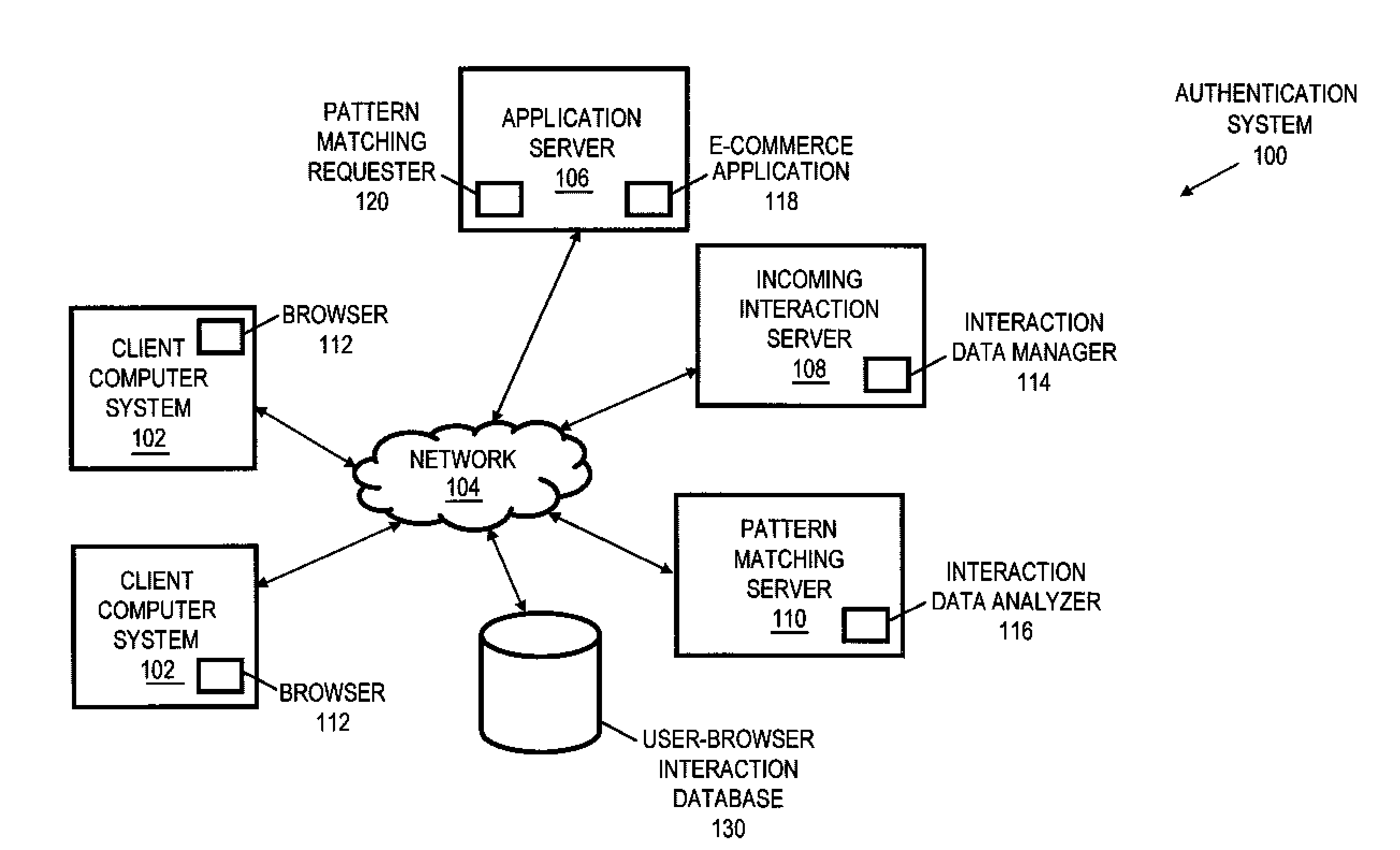
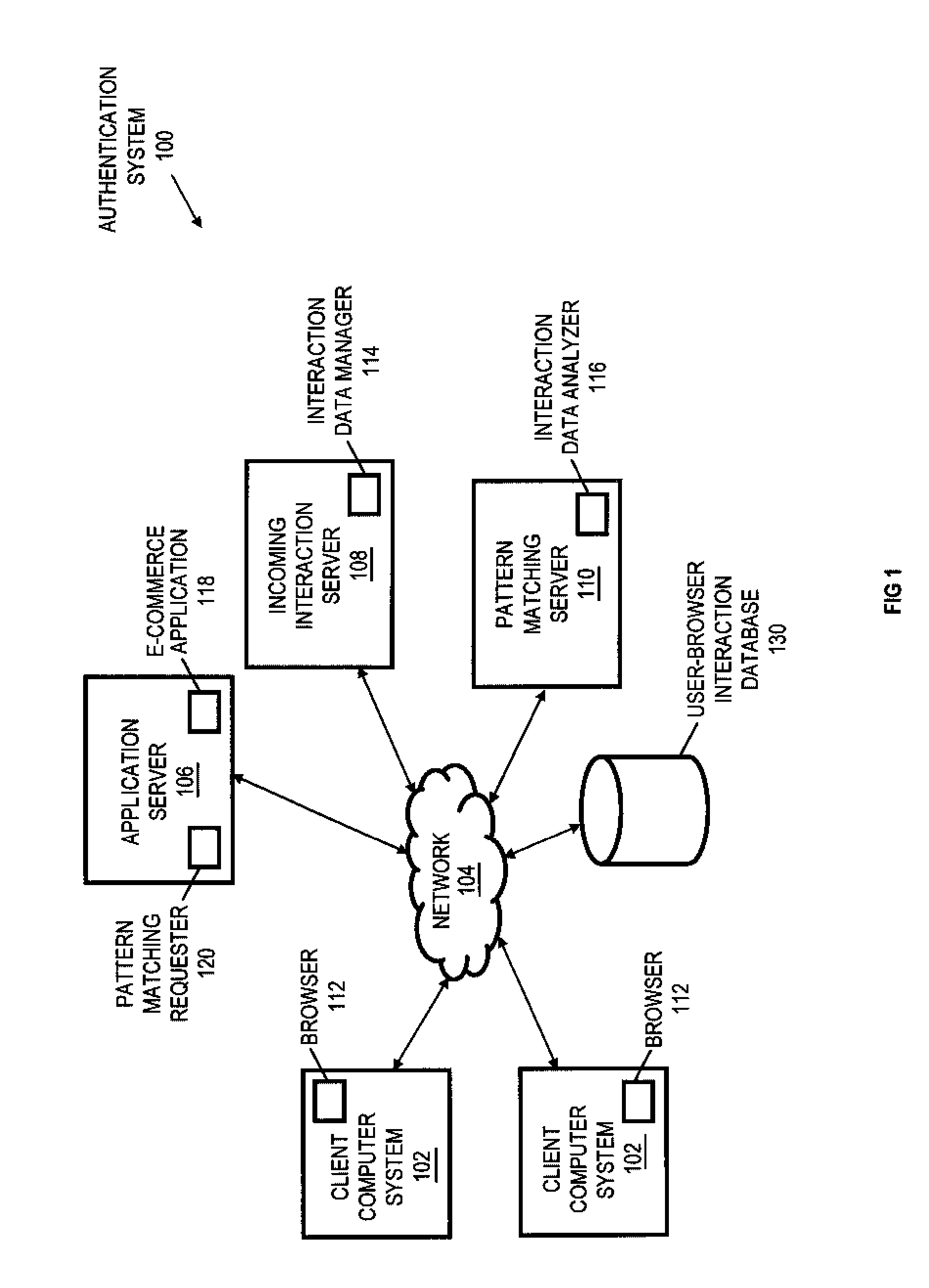
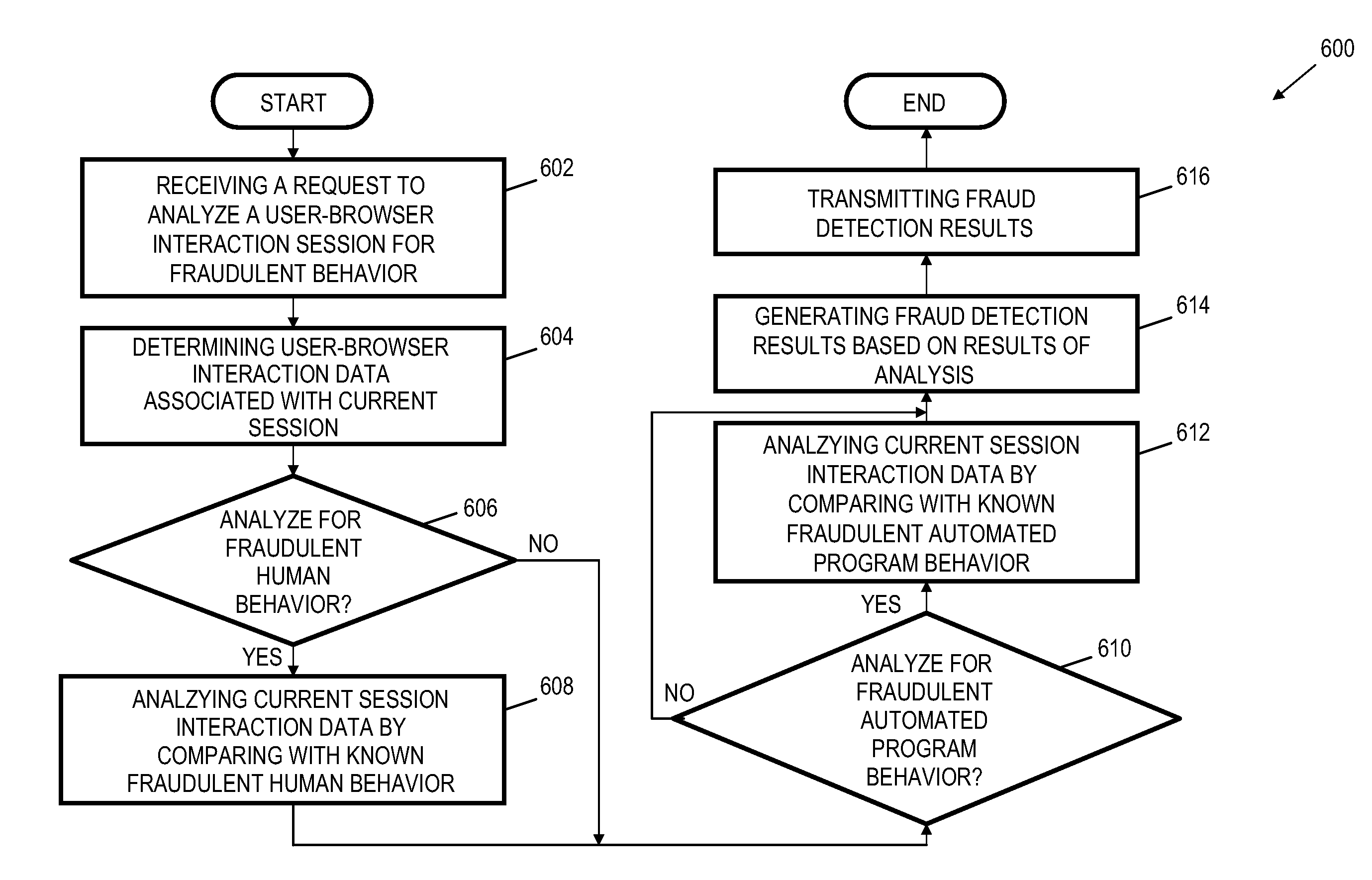
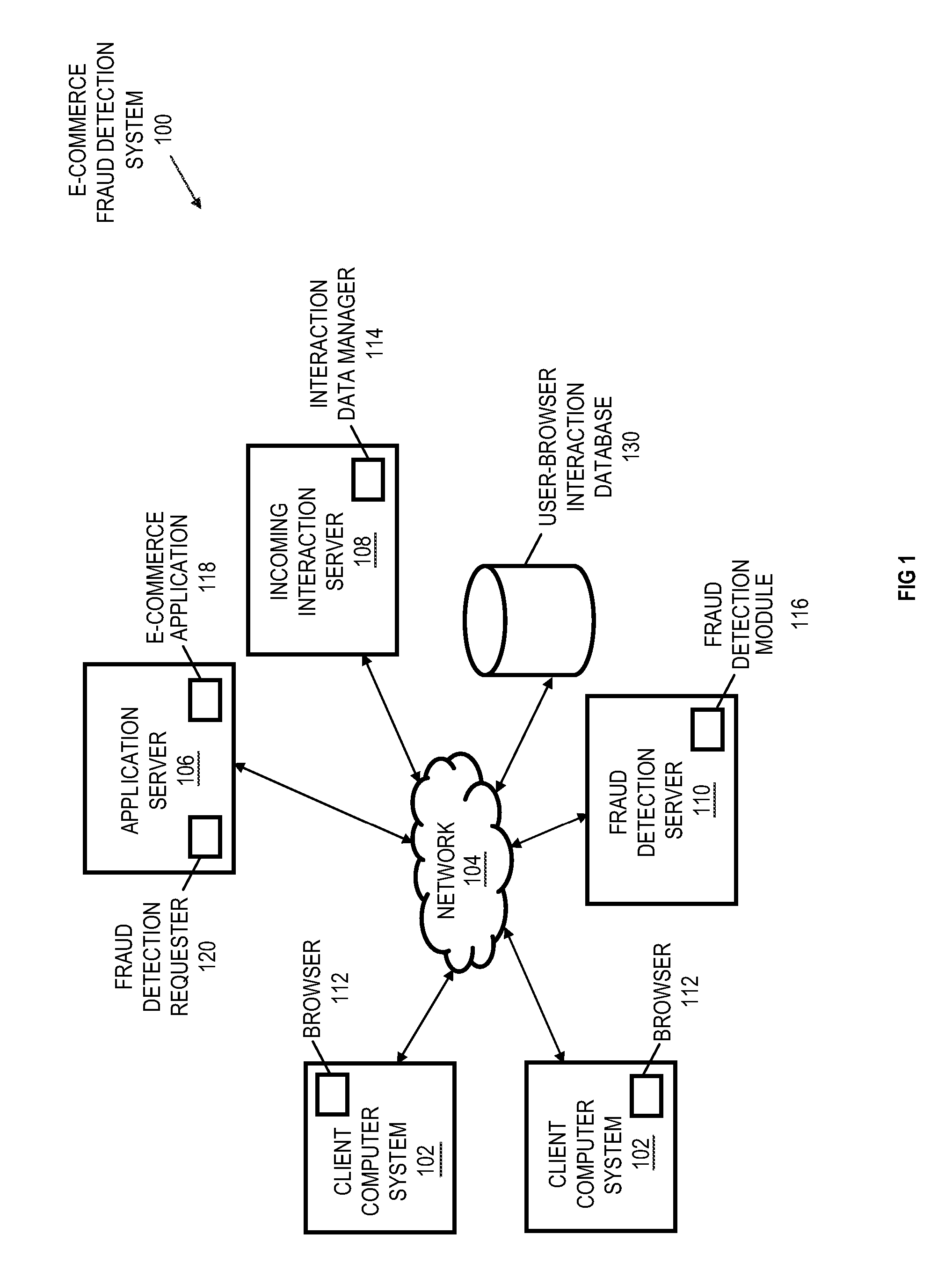
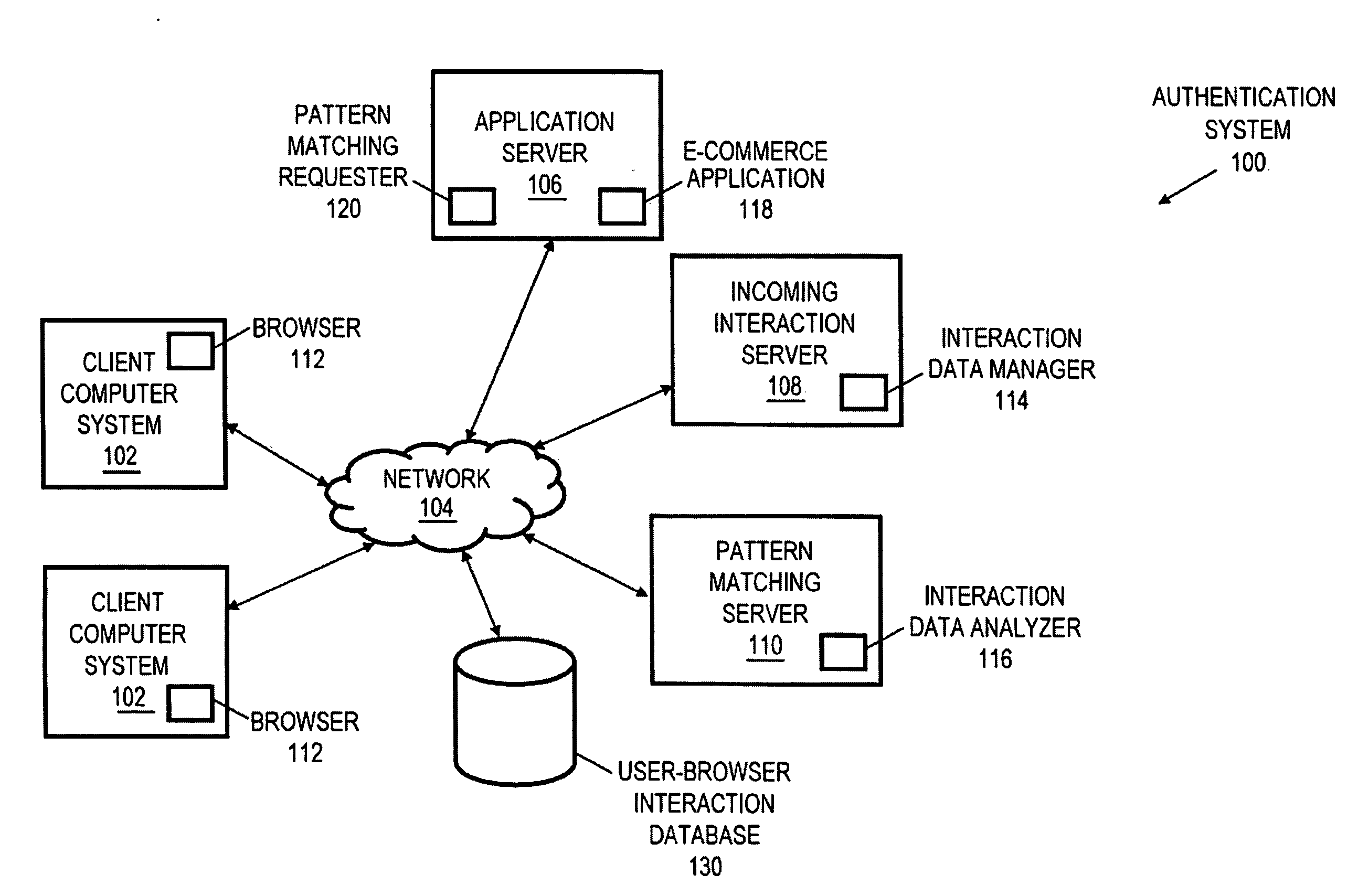
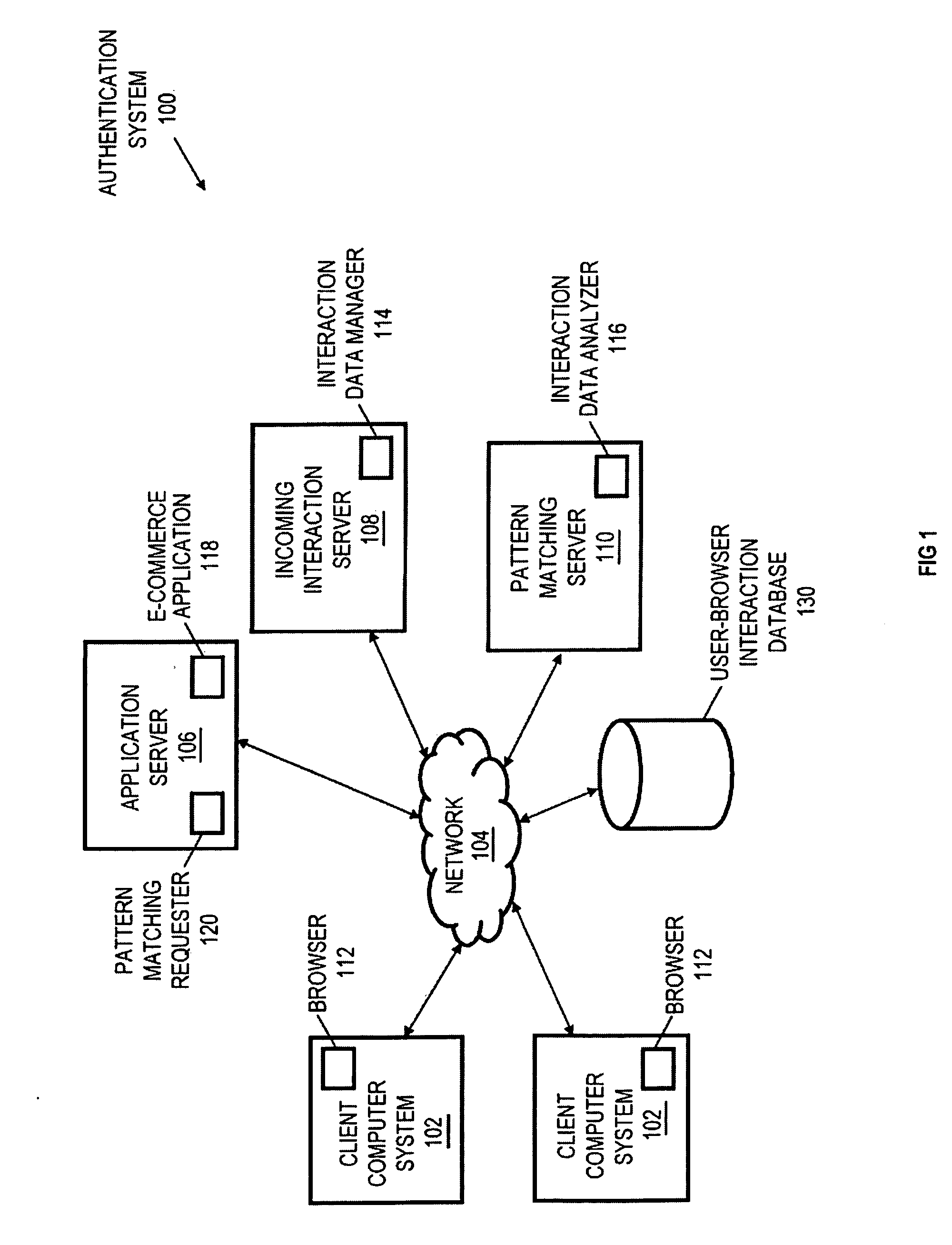
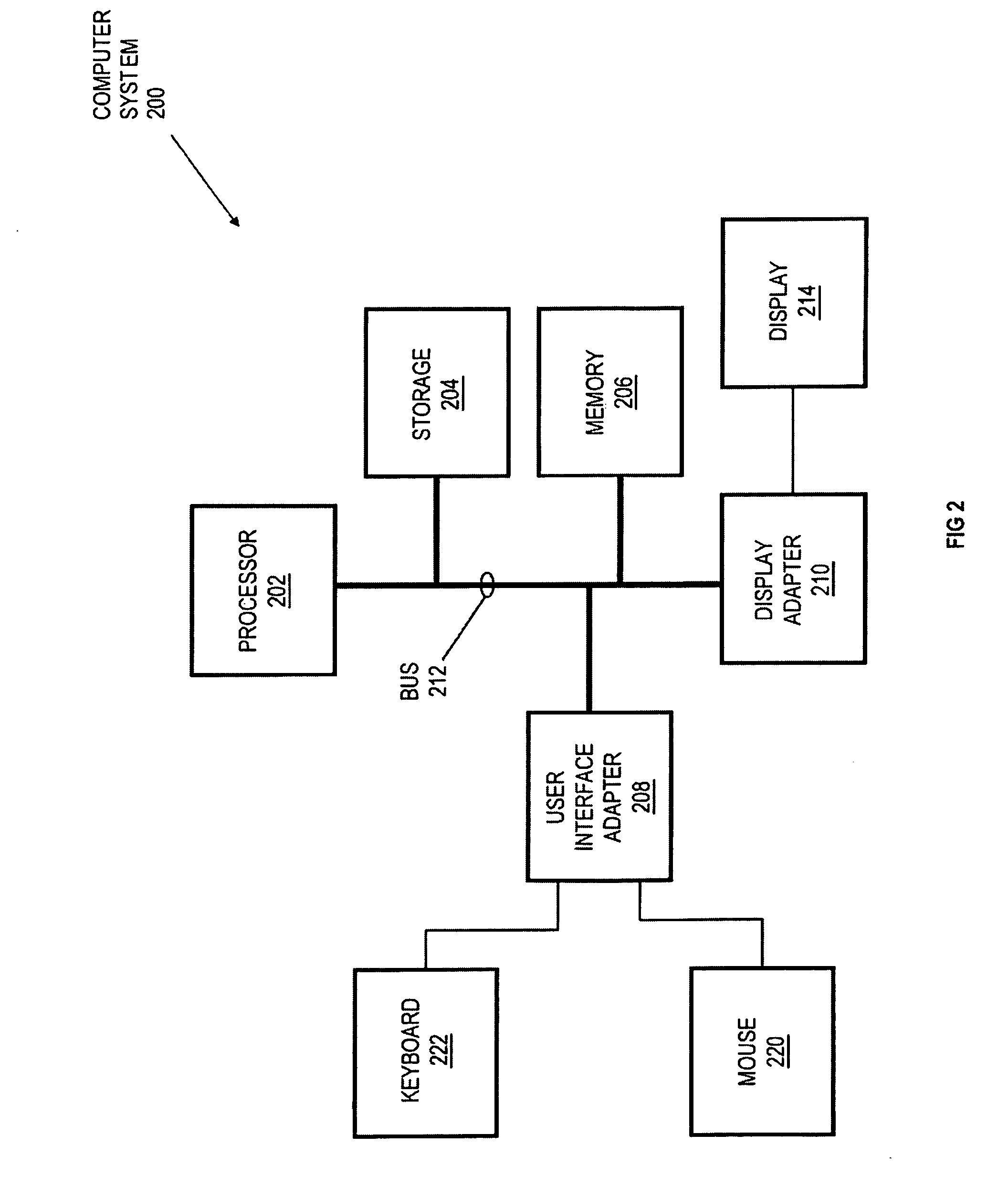
User-browser interaction-based fraud detection system
InactiveUS20070239604A1Payment architecturePlatform integrity maintainanceRequest - actionInternet privacy
Systems, methods and media for detecting fraudulent behavior during an Internet commerce session are disclosed. Embodiments of a method may include establishing an e-commerce session with a user and requesting fraud detection analysis of user-browser interaction during the e-commerce session. Embodiments may also include receiving fraud detection results for the e-commerce session, where the fraud detection results may provide an indication of a comparison between the user's interaction with a browser during the e-commerce session and known fraudulent behavior. Embodiments may also include performing an action based on the fraud detection results. Determining the fraud detection results may include determining user-browser interaction data associated with the session and comparing the user-browser interaction data to known fraudulent human or automated program behavior. Performing the action based on fraud detection results may include one or more of completing an e-commerce transaction, requesting additional authentication, denying the requested action, etc.
Owner:IBM CORP
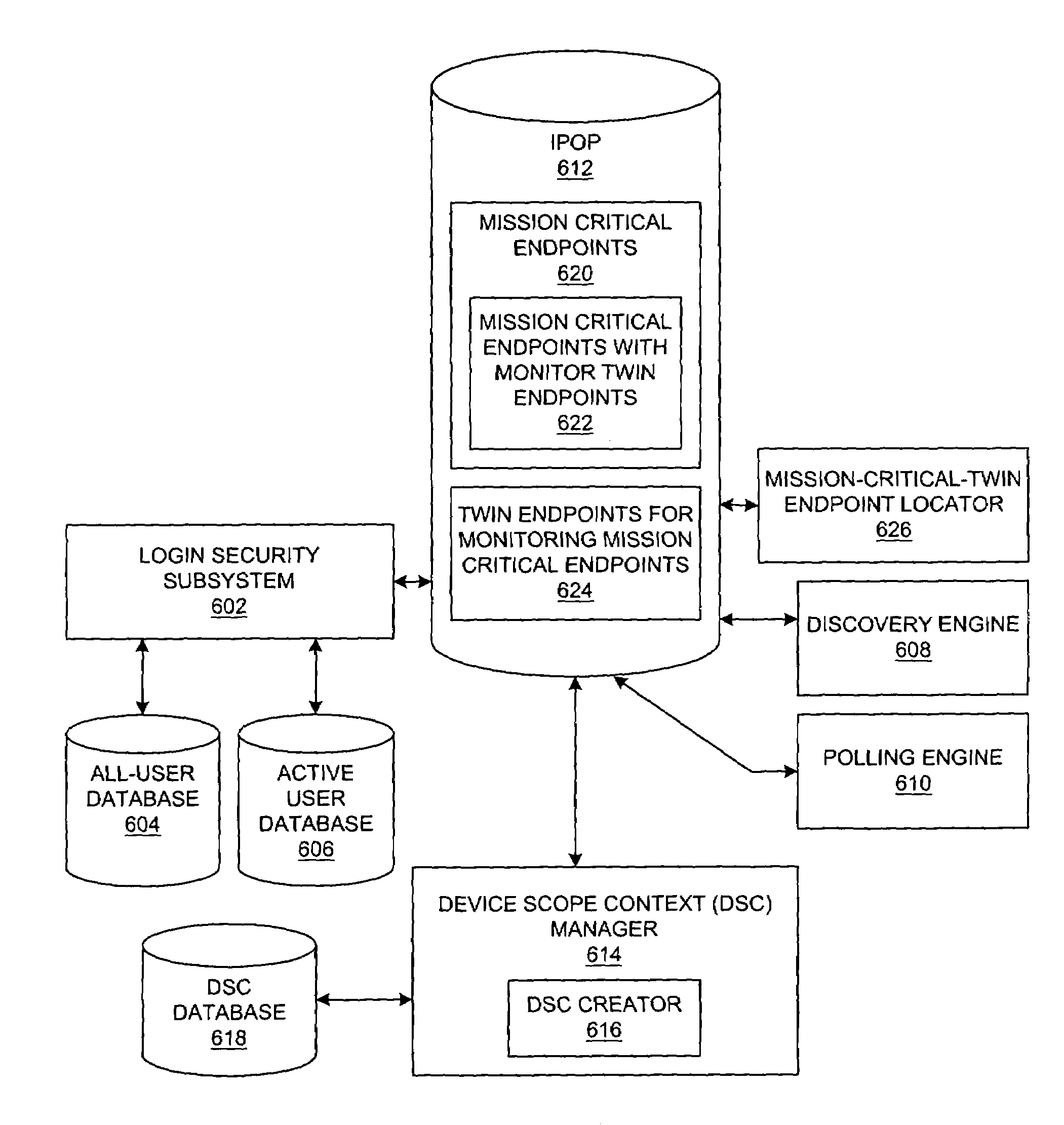
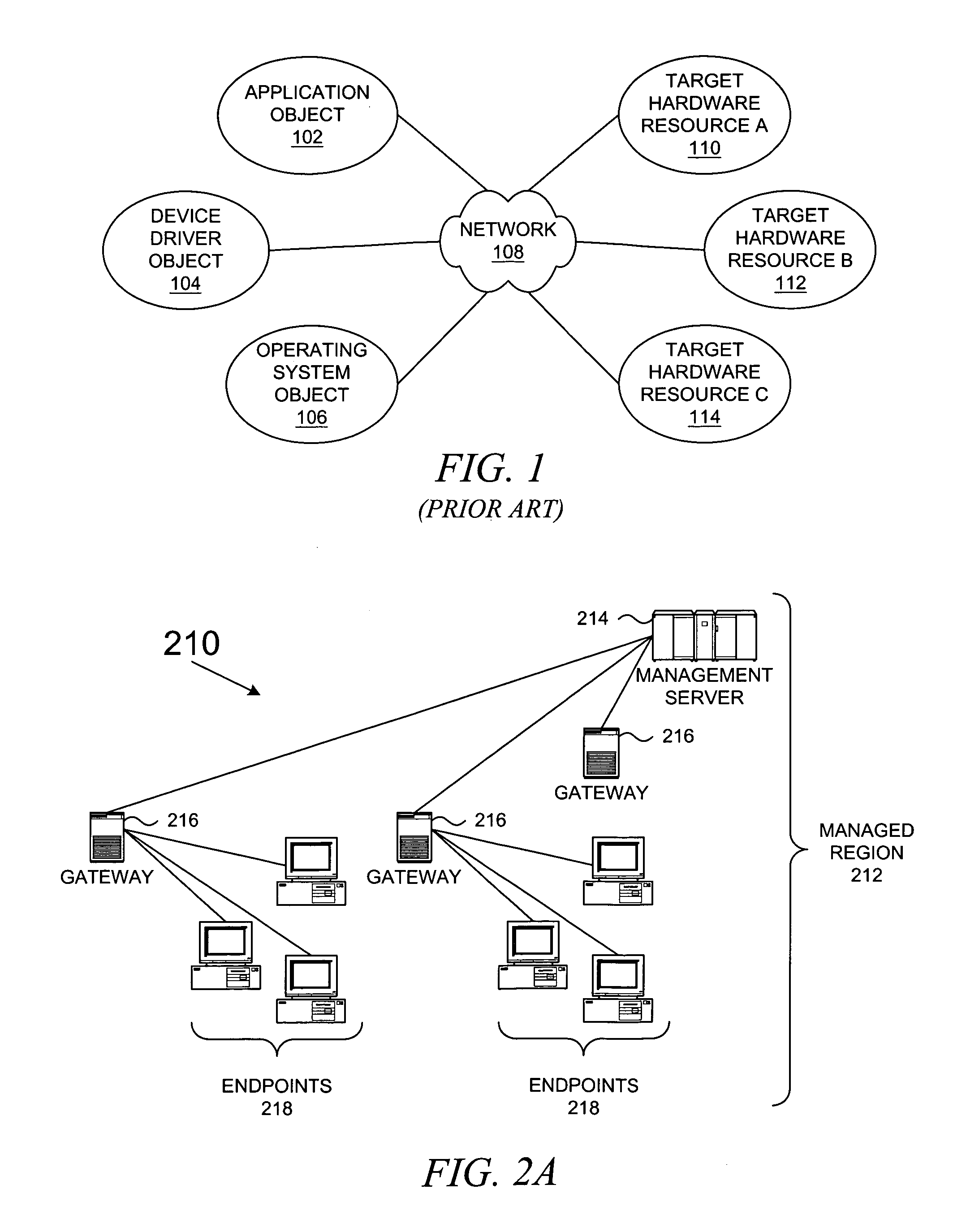
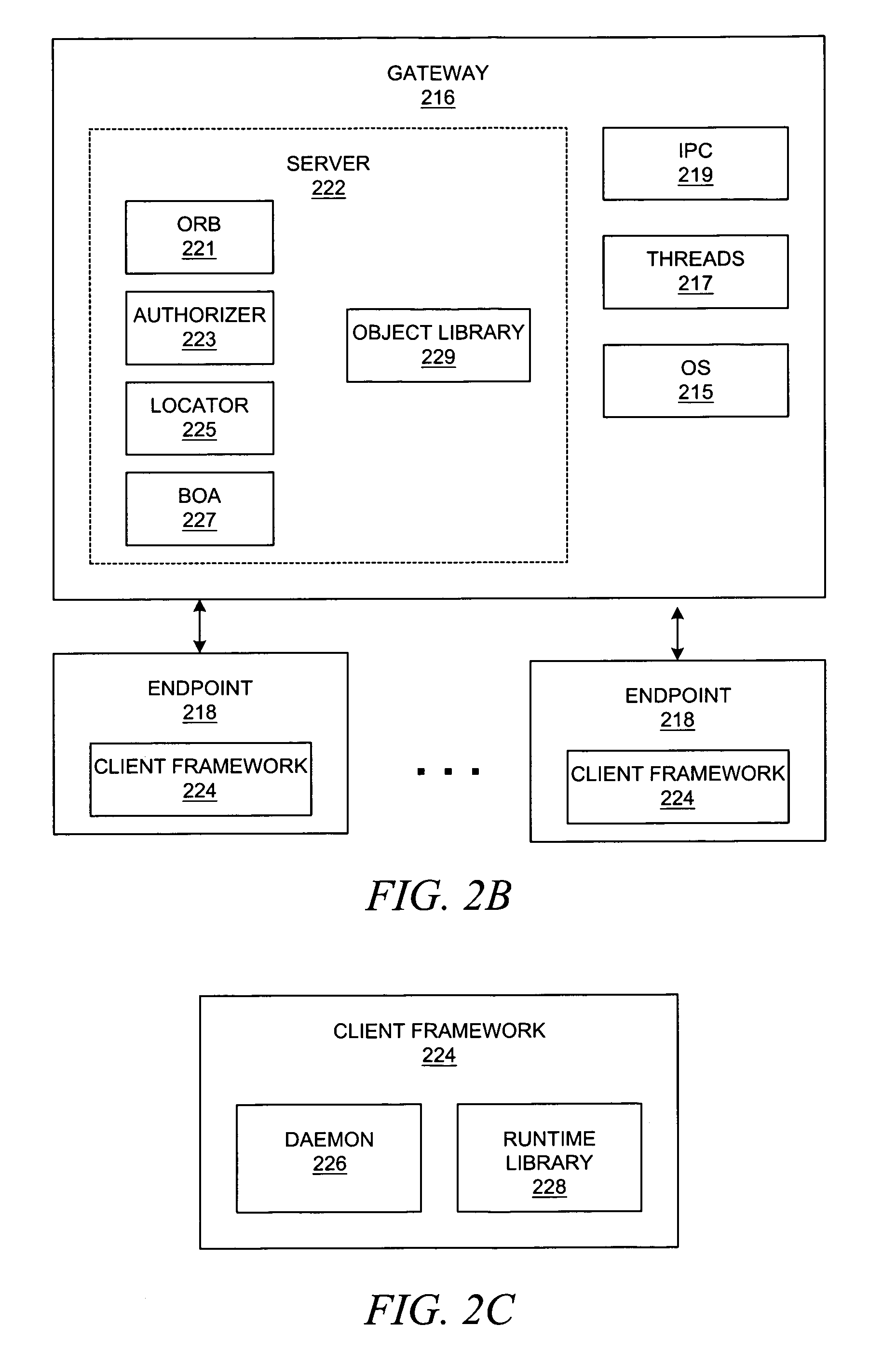
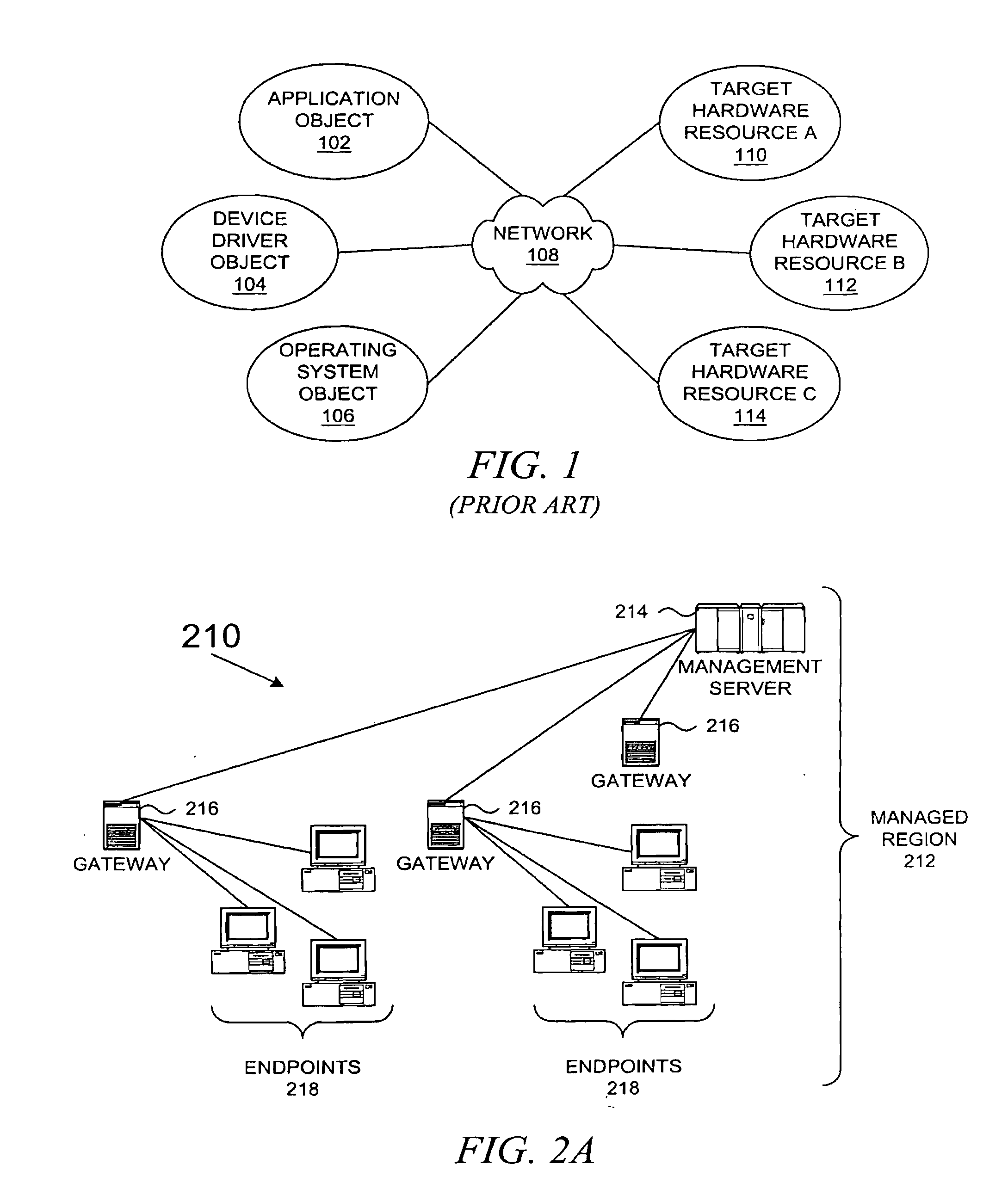
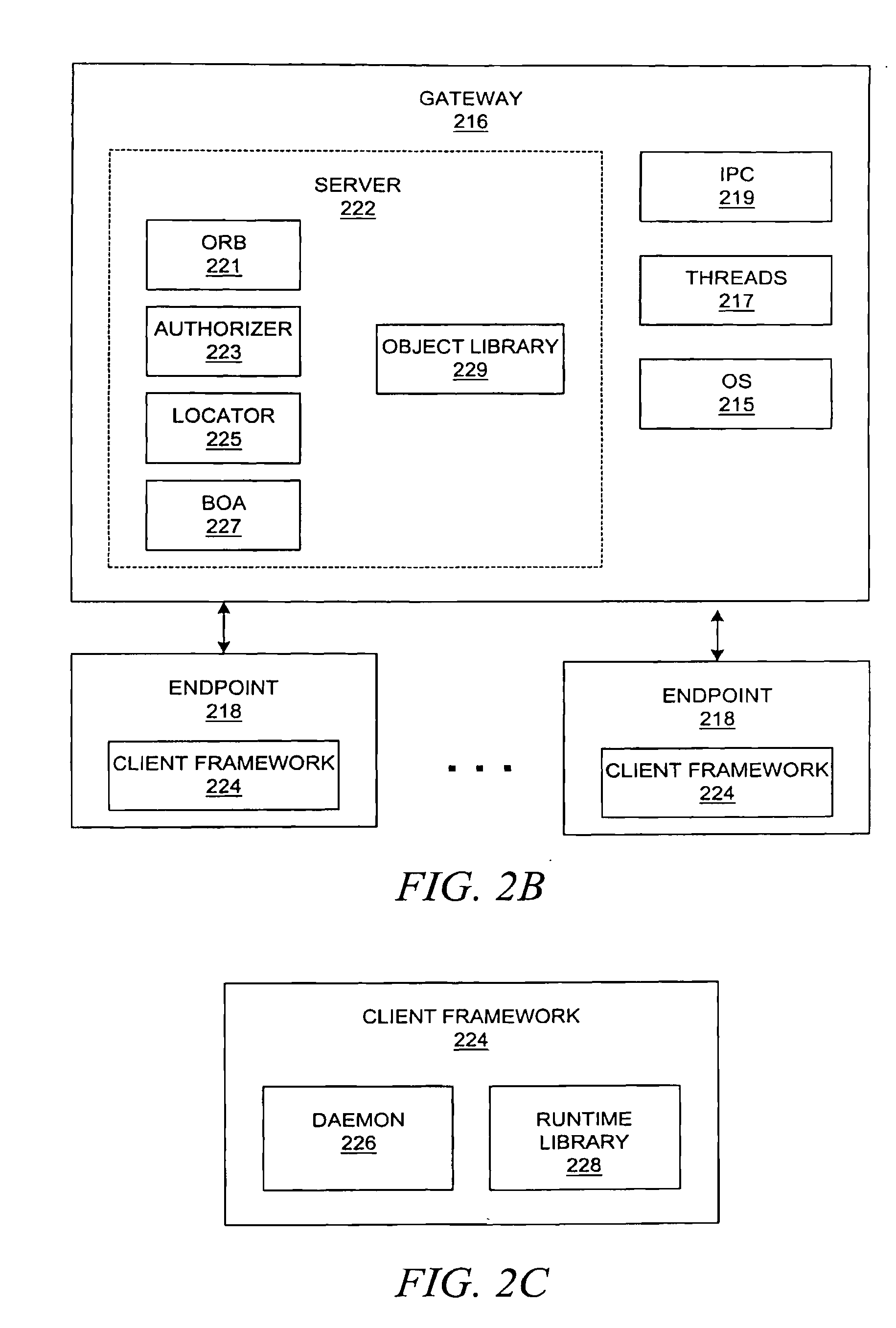
Method and system for network management with backup status gathering
A method, system, apparatus, and computer program product are presented for management of a distributed data processing system. Resources within the distributed data processing system are dynamically discovered, and the discovered resources are adaptively monitored using the network management framework. A network or system administrator configures some mission critical endpoints with multiple network interface cards (NICs) and specifies mission critical endpoints, non-mission critical actions, etc. During status collection activities associated with network or system management activities, the categorization of an endpoint as a mission-critical or non-mission critical endpoint affects the manner in which the status collection activity is performed. Applications can request the performance of actions at endpoints without regard to the categorization of the endpoint or without regard to the categorization of the requested action, and the network management system routes the action based on whether or not the specified endpoint is a mission critical endpoint. A non-mission-critical endpoint is associated with a mission-critical endpoint based on the non-mission-critical endpoint's communication history with the mission critical endpoint. The management system may use the status of a non-mission-critical endpoint as a reflection of the status of a mission-critical endpoint.
Owner:GOOGLE LLC
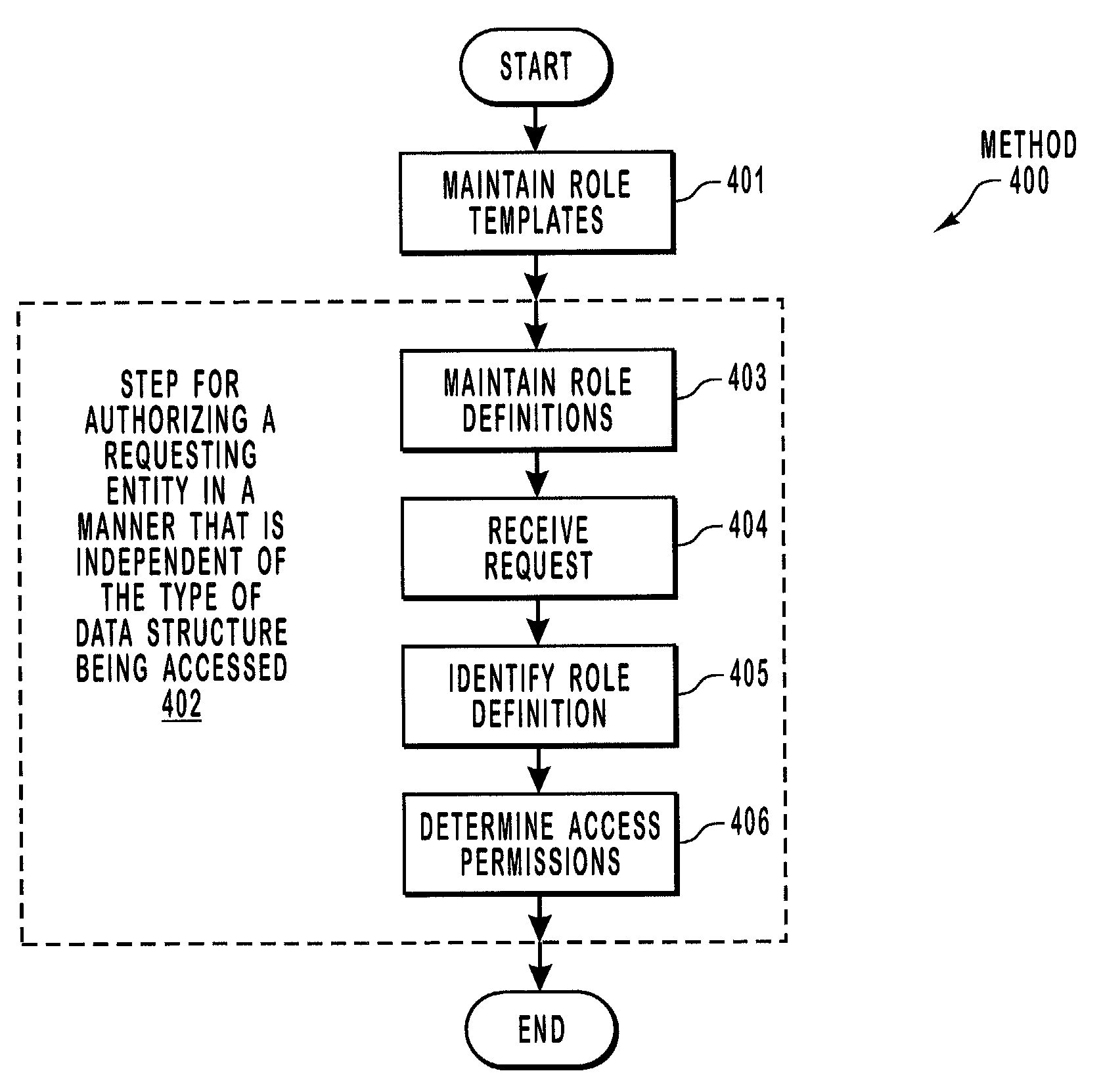
Authorizing a requesting entity to operate upon data structures
ActiveUS7284271B2High level of controlSpecial service provision for substationDigital data processing detailsRequest - actionAuthorization
Authorizing a requesting entity to have a service perform a particular action in a manner that is at least partially independent of the underlying target data structure. An authorization station maintains a number of role templates that each define basic access permissions with respect to a number of command methods. The authorization station also maintains a number of role definitions that each define access permissions for specific requesting entities by using one or more of the role templates. When the authorization station receives a request from the requesting entity, the authorization station then identifies the appropriate role definition. Using this role definition, the authorization station determines access permissions for the requesting entity with respect to the requested action.
Owner:MICROSOFT TECH LICENSING LLC
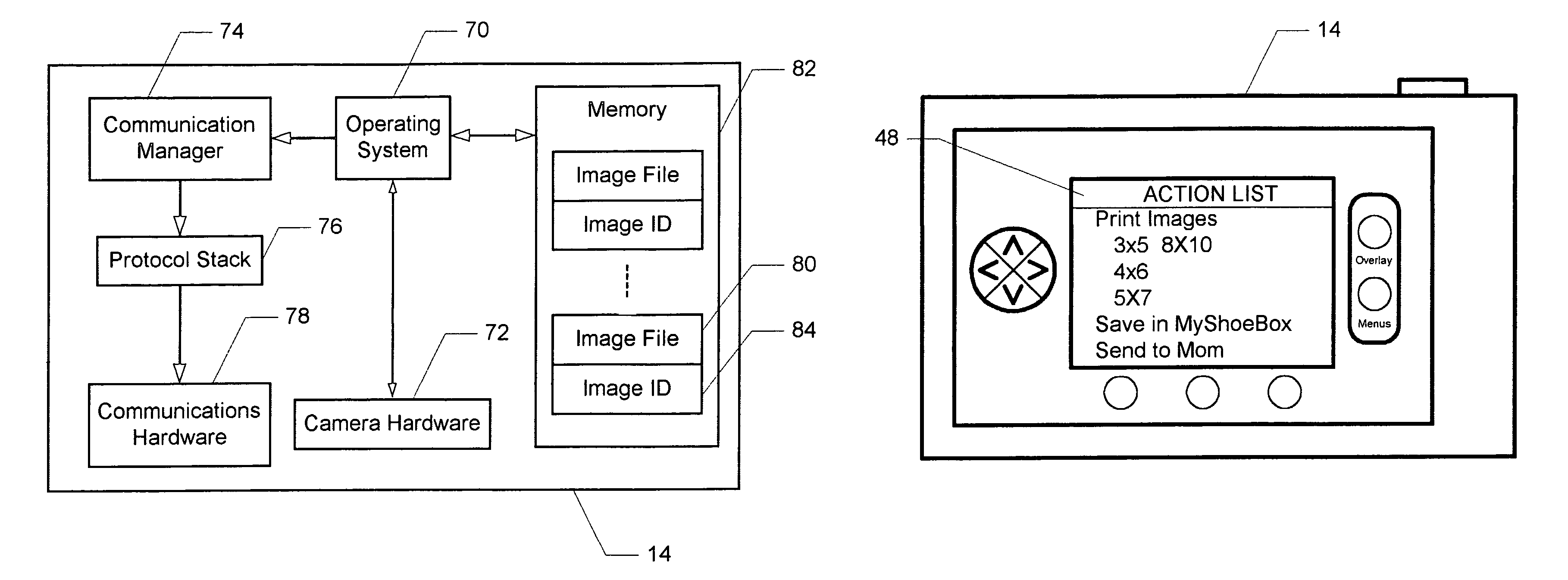
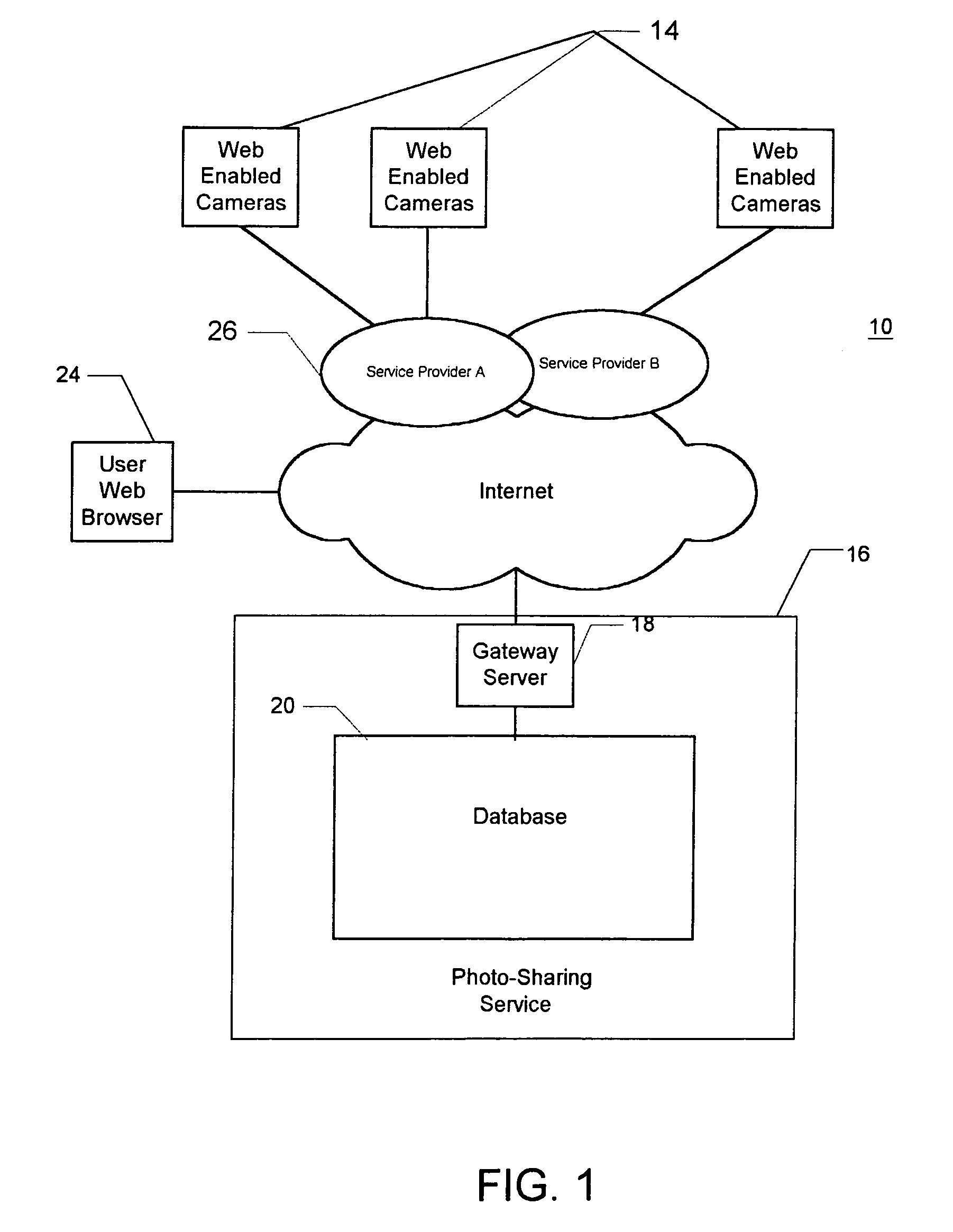
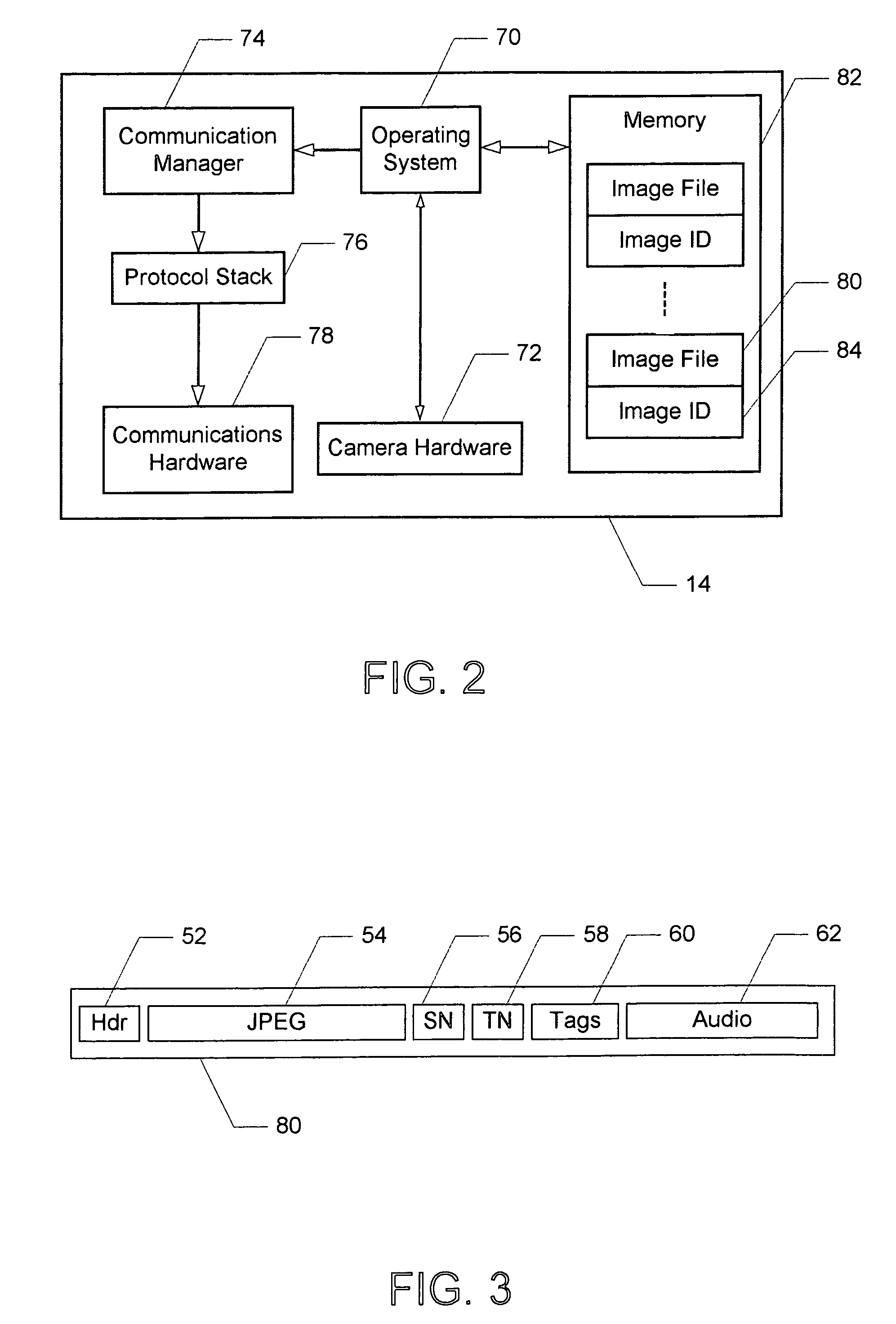
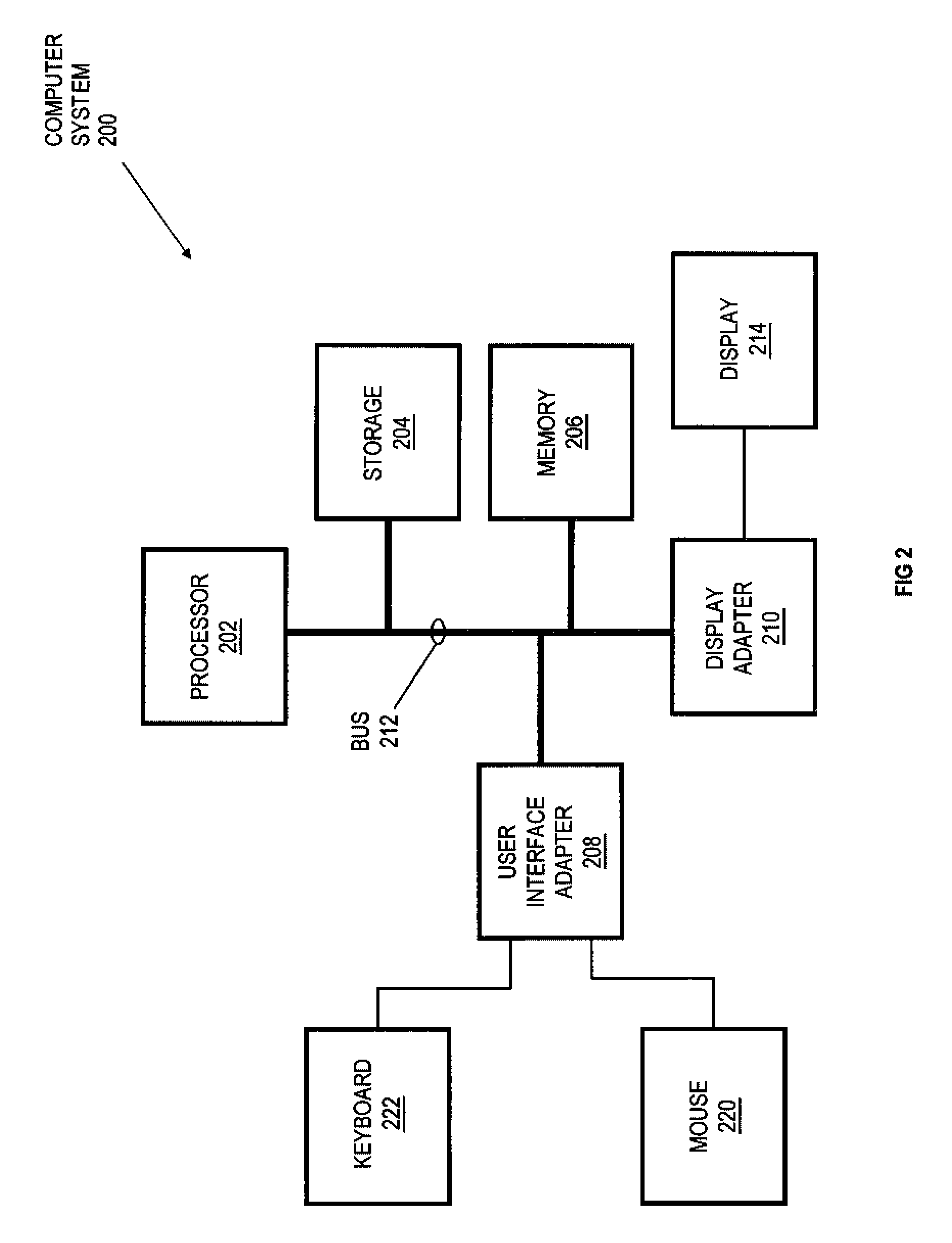
Transmission bandwidth and memory requirements reduction in a portable image capture device by eliminating duplicate image transmissions
InactiveUS7287088B1Reduce storageReduce transmission bandwidth requirementsMultiple digital computer combinationsTransmissionRequest - actionComputer hardware
A system and method for reducing storage and transmission bandwidth requirements of a portable image capture device capable of establishing a communications connection on a network are disclosed. The method includes assigning an image identifier to captured images uploaded to a server on a network, wherein each of the images is stored in an image file having a particular size. The size of each of the image files corresponding to the uploaded images on the image capture device may then be reduced, thereby reducing storage requirements. In response to a user request to apply an action to one of the uploaded images, only the image identifier of the image and the requested action are transmitted to the server, thereby eliminating the need to retransmit the image and reducing transmission bandwidth requirements.
Owner:DIGIMEDIA TECH LLC +1
User-browser interaction analysis authentication system
InactiveUS20070240230A1Digital data processing detailsUser identity/authority verificationRequest - actionPassword
Systems, methods and media for authenticating a user based on user-browser interaction are disclosed. Embodiments of a method may include, during an e-commerce session with a user, receiving a request for an action from the user and determining whether the requested action requires additional authentication. Embodiments may also include requesting analysis of user-browser interaction for the session, receiving a pattern matching score for the session, and performing an action based on the pattern matching score and the requested action. The pattern matching score may provide an indication of a comparison between the user's interaction with a browser during the session and a user-browser interaction profile for the user. The performed action may include completing an e-commerce transaction, accessing or modifying information, changing a password, requesting additional information, denying the requested action, or other action. Further embodiments may provide for authenticating the user with a first-level authentication.
Owner:IBM CORP
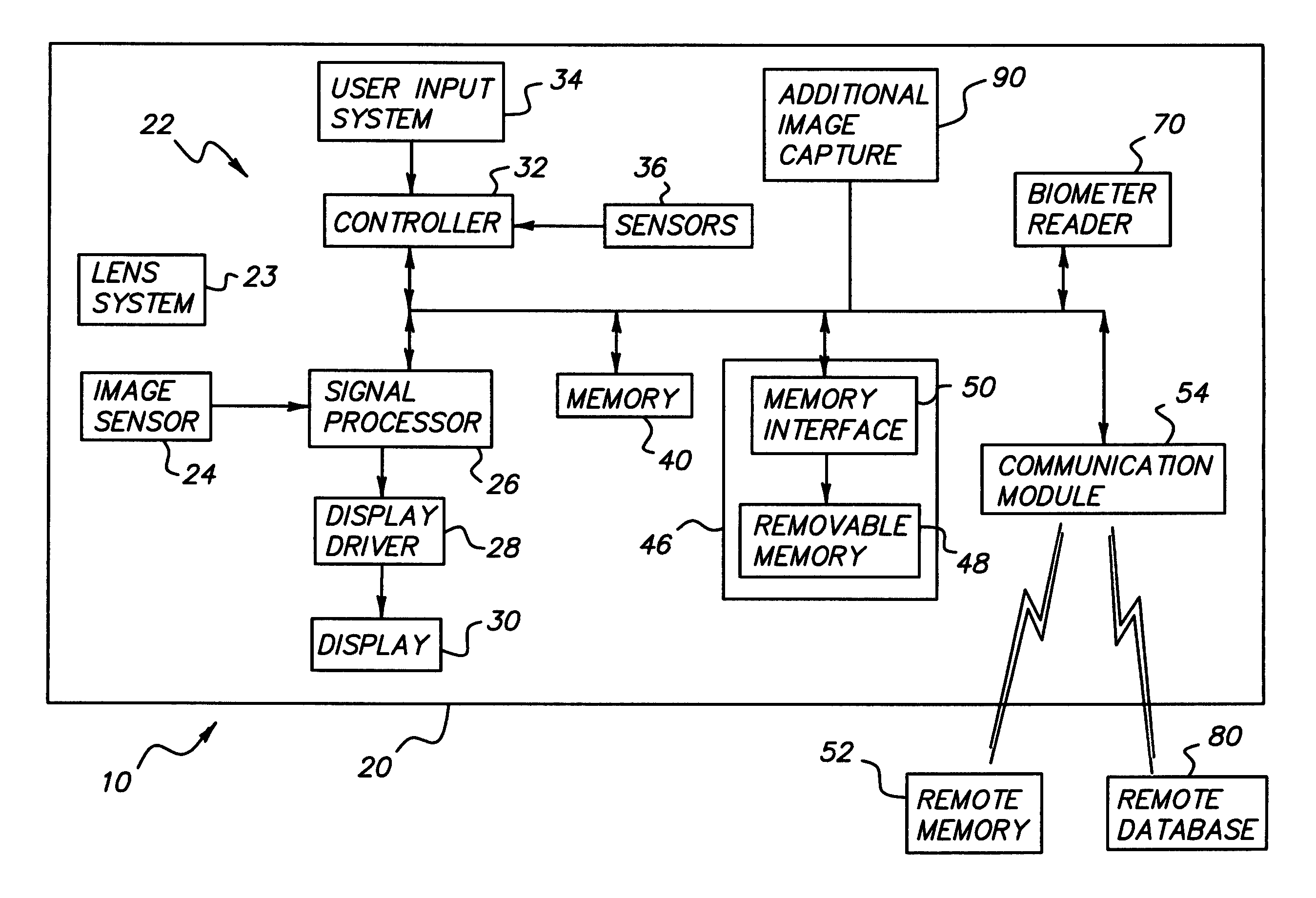
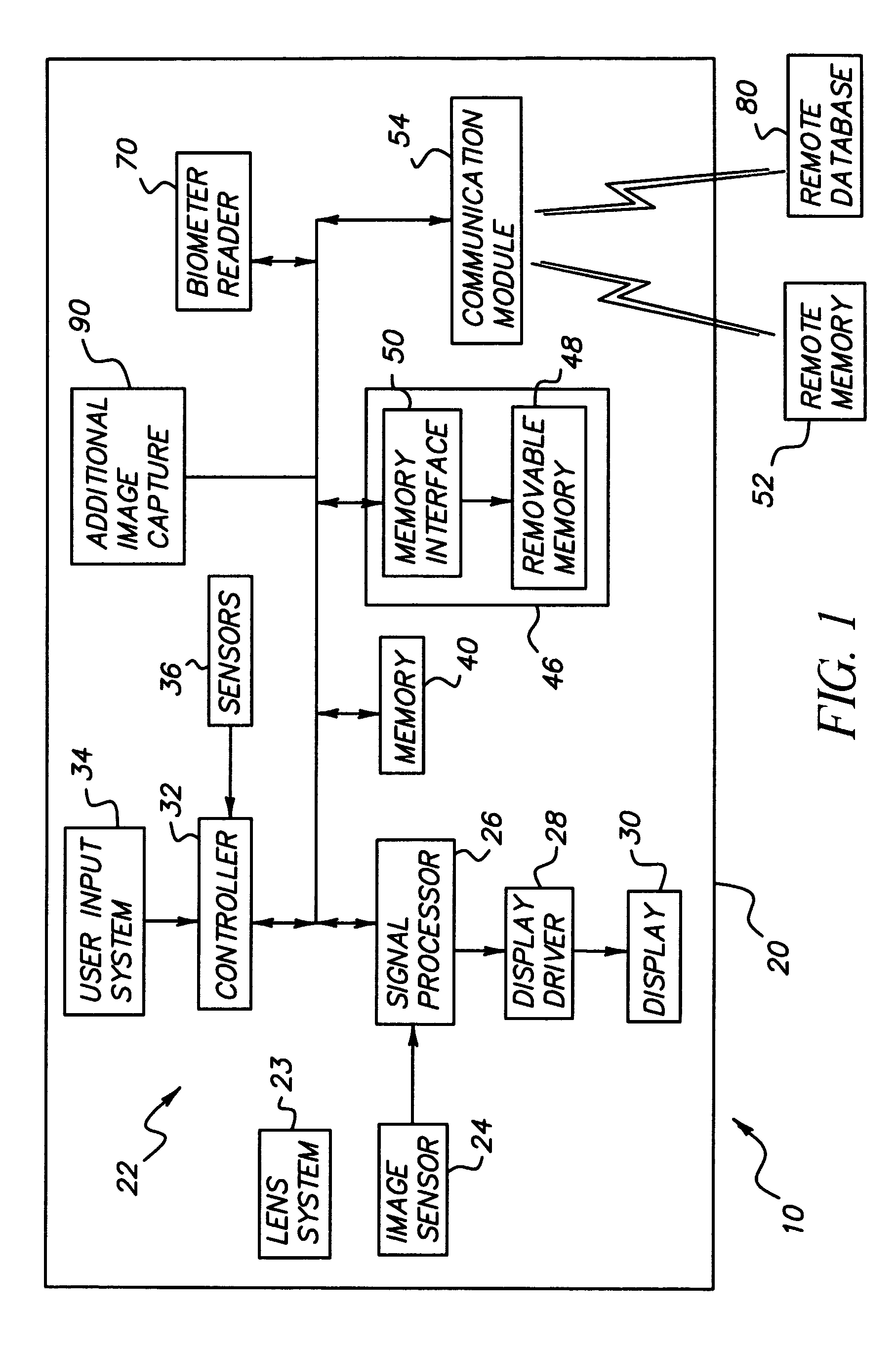
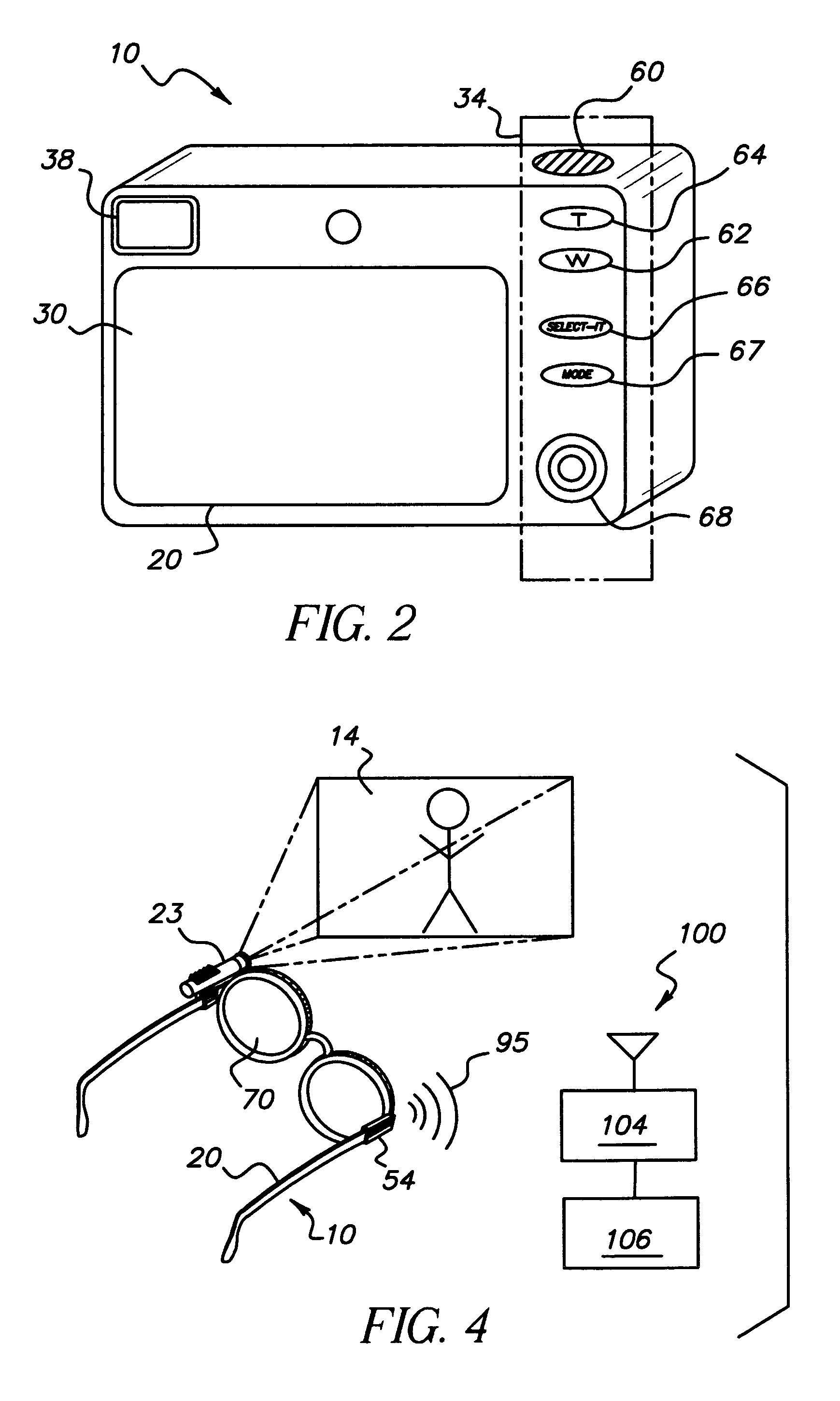
Wireless digital image capture device with biometric readers
InactiveUS20060104483A1Control over digital imagingTelevision system detailsElectric signal transmission systemsRequest - actionBiometric data
A digital image capture device and method for operating the same are provided. The digital image capture device has a digital image capture device comprising: a housing (20); a digital image capture system (22); a biometric reader (70) adapted to sense biometric data of a user; a wireless communication circuit (54) adapted to transmit wireless signals to a remote database and to receive authorization signals from the remote database; a processor (26) adapted to control and enable operation of the digital image capture system (22), the wireless communication circuit (54) and the biometric reader (70), wherein the processor (26): is adapted to cause biometric data to be read from a user, and wirelessly transmitted to a remote database so that the remote database can compare the sensed biometric data to stored biometric data and will transmit an authorization signal when the sensed biometric data corresponds to stored biometric data, said processor further being adapted to determine a set of authorized actions for a user of the digital image capture device based upon an authorization signal transmitted by the remote database; with said processor further being adapted to execute actions as requested by the user when the requested actions are within the set of authorized actions.
Owner:EASTMAN KODAK CO
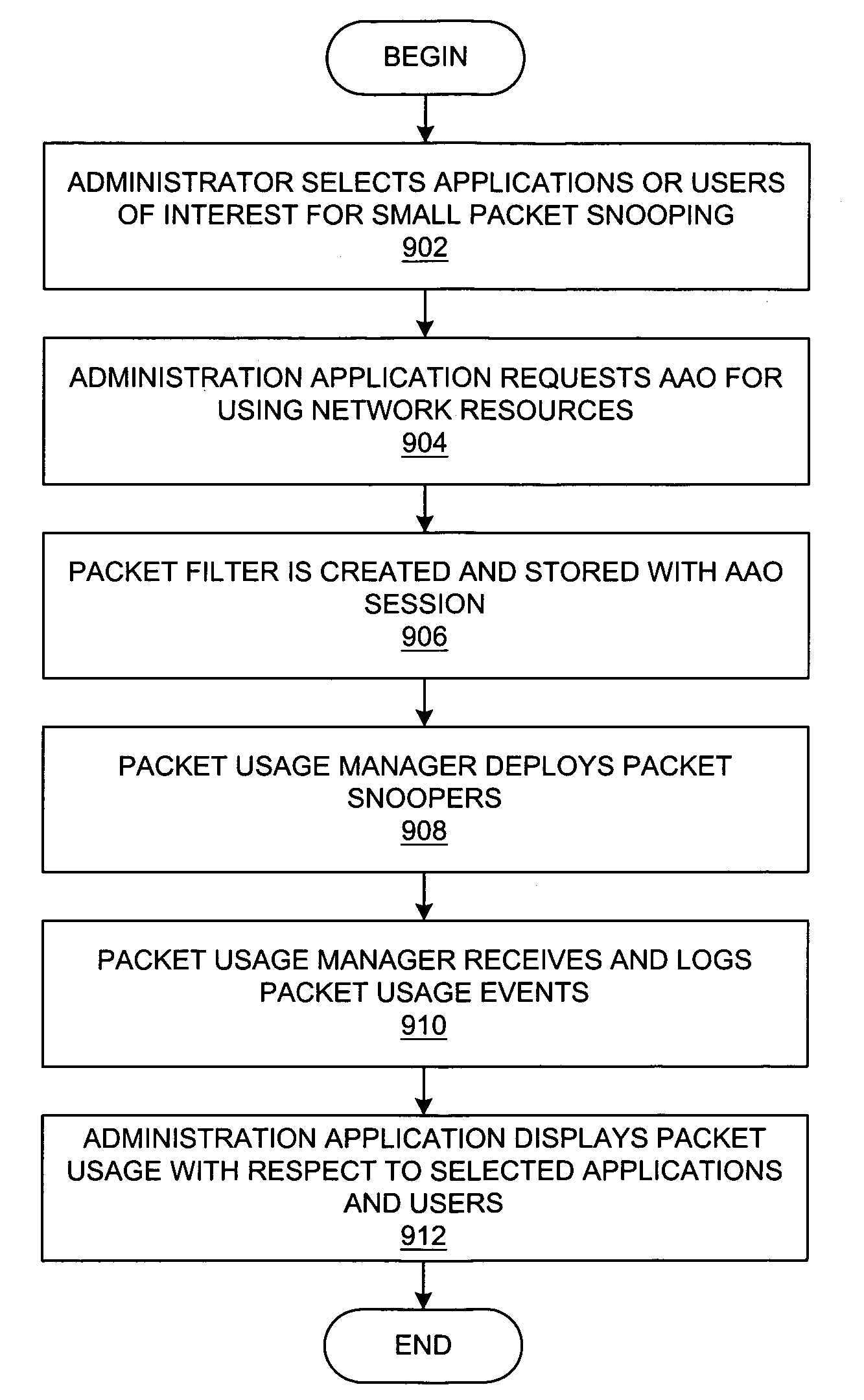
Method and system for network management providing access to application bandwidth usage calculations
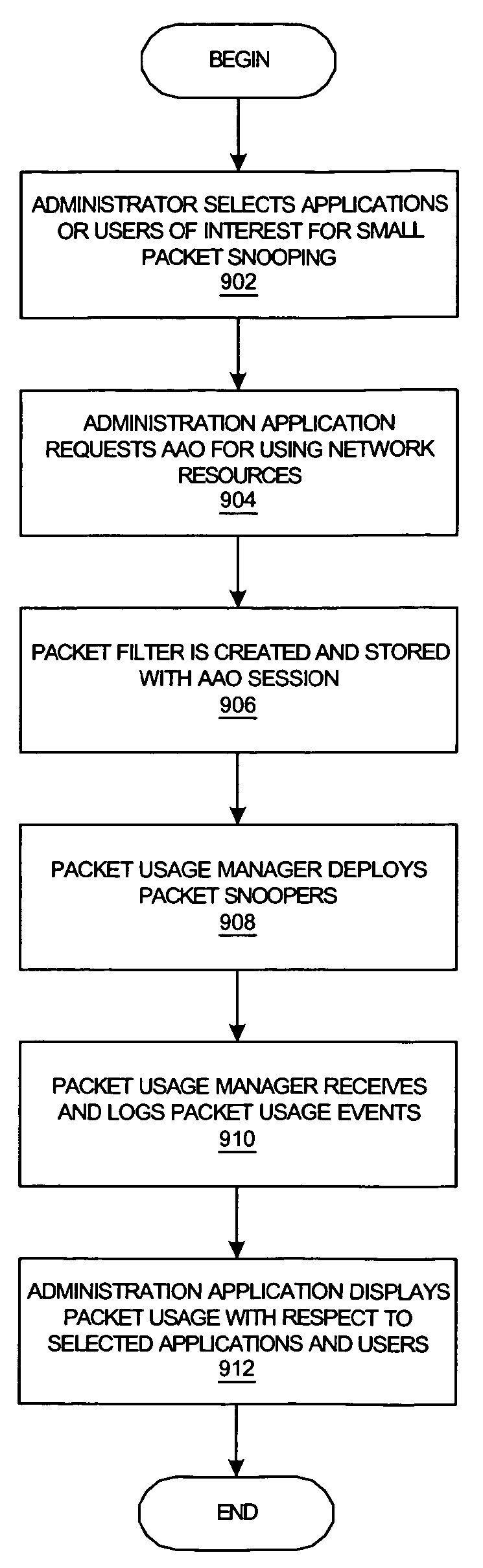
A method, system, apparatus, and computer program product is presented for management of a distributed data processing system. The network management framework is able to monitor multiple sources of network packets on various subnets within the distributed data processing system; distributed packet snoopers are deployed from a packet usage manager to monitor the multiple sources of network packets. The system administrator can request packet filtering based upon selected active users or active applications. A bandwidth history database is compiled from bandwidth usage data associated with multiple entities within the data processing system, including users, applications, and / or endpoints within the data processing system. In response to a requested action within the data processing system, bandwidth usage for the requested action can be predicted with reference to the bandwidth history database. The actual and predicted bandwidth usage of requested actions can be displayed to the system administrator in real time.
Owner:CITRIX SYST INT
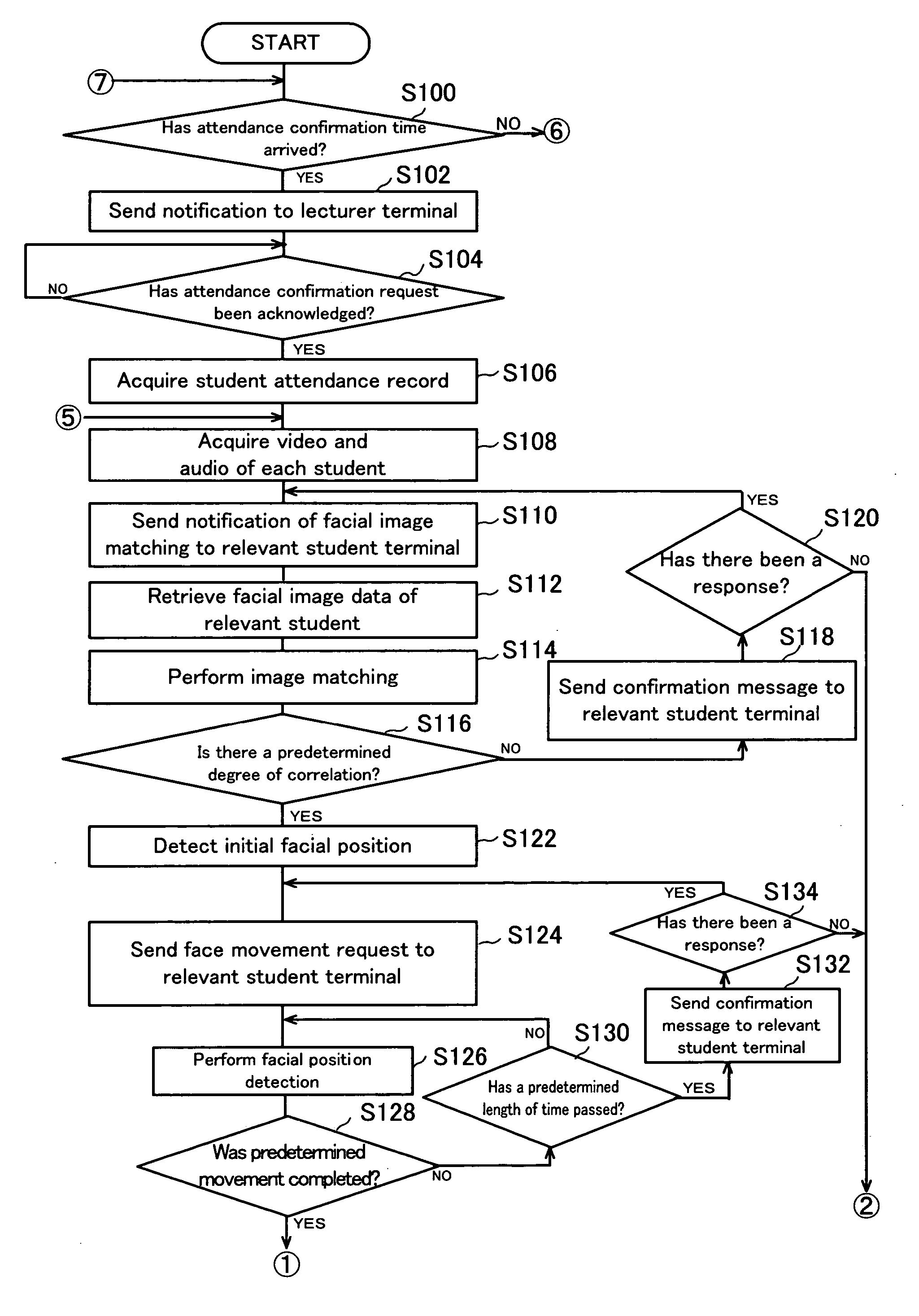
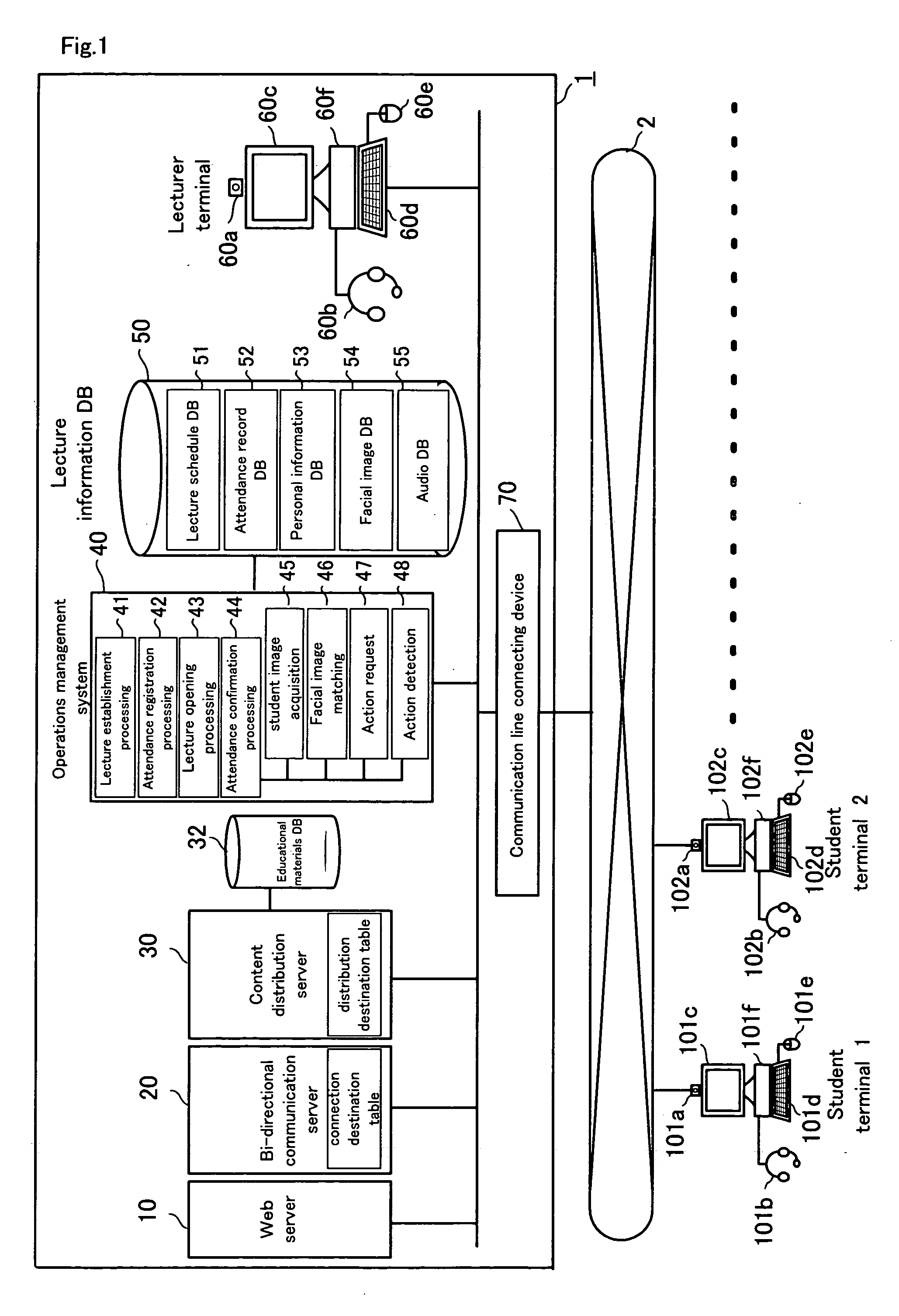
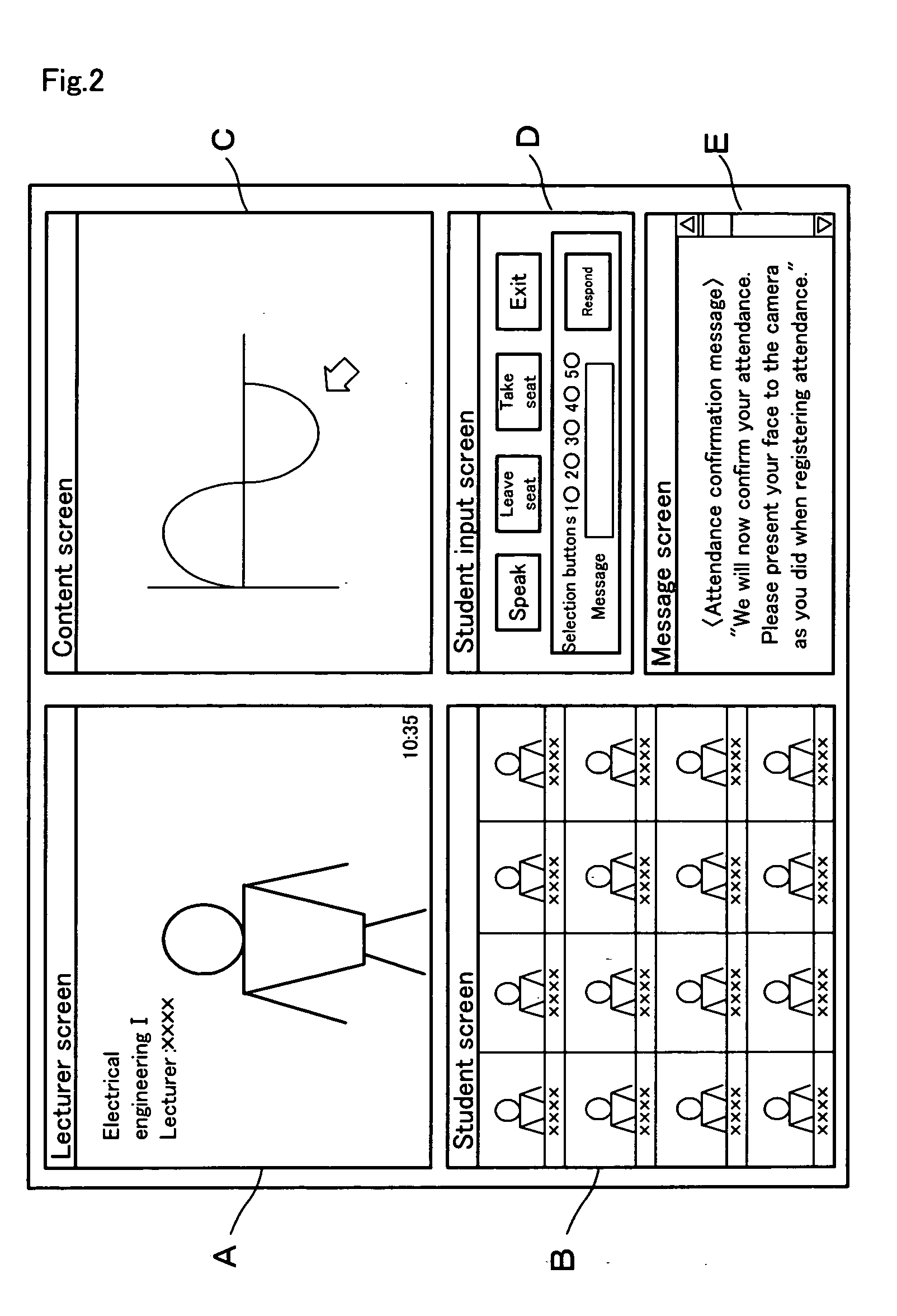
Remote education system, course attendance check method, and course attendance check program
InactiveUS20060057550A1Data processing applicationsTelevision conference systemsRequest - actionContent distribution
A remote education system includes a Web server, a bidirectional communication server, a content distribution server, an operations management system, a lecturer terminal, and a communication line connection device, and provides remote education to student terminals via the Internet. The operations management system includes a lecture information database for storing lecture schedules, attendance records, and personal information, facial images, and audio, of the students, and performs a lecture establishment processing, an attendance registration processing, a lecture opening processing, an attendance confirmation processing, and the like. The attendance confirmation processing includes a student image acquisition processing, a facial image matching processing, an action request processing, and an action detection processing, which match facial images of students, and detect image changes that occur in response to requested actions.
Owner:GINGANET CORP
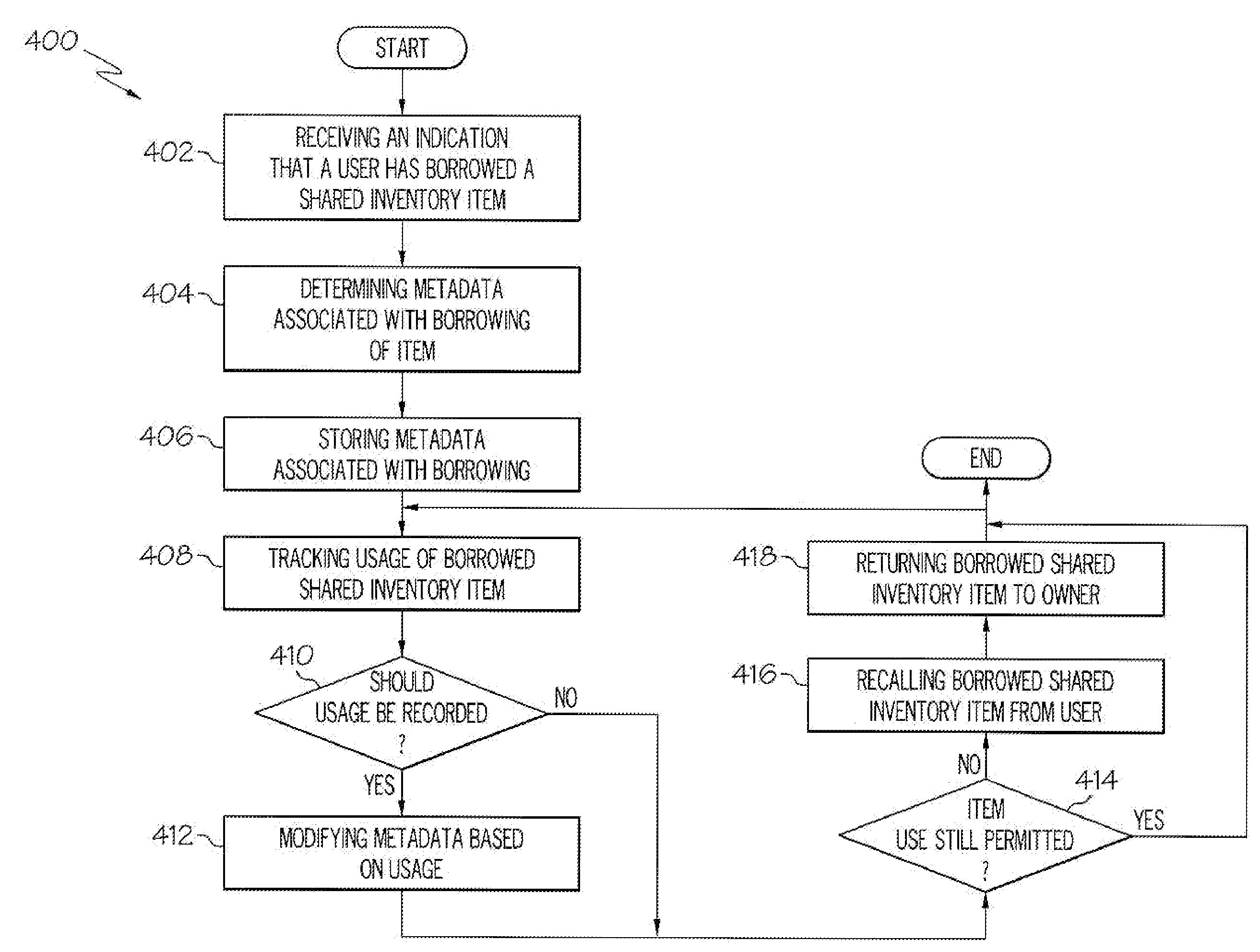
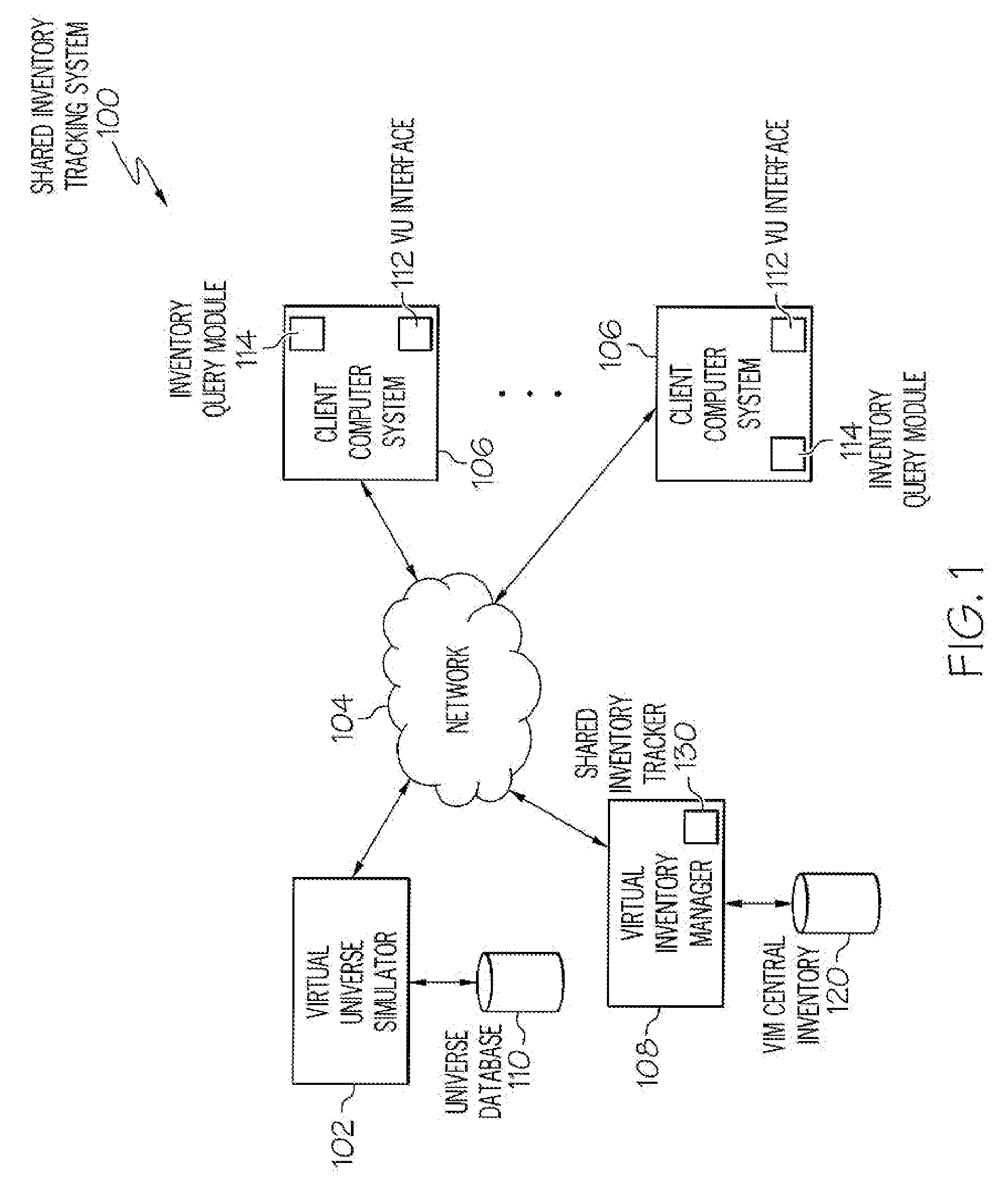
Tracking of Shared Inventory in a Virtual Universe
Generally speaking, systems, methods and media for tracking shared inventory in a virtual universe are disclosed. Embodiments of the method may include receiving indications that a plurality of users of a virtual universe have borrowed one or more shared inventory items, each shared inventory item having an associated item owner. Embodiments may also include determining and storing metadata associated with borrowing of the shared inventory items and tracking usage of the borrowed shared inventory items by the plurality of the users. Embodiments may also include receiving a query requesting performance of an action relating to one or more shared inventory items and performing the requested action relating to the one or more shared inventory items. In further embodiments, performing the requested action may include recalling the borrowed shared inventory item and returning it to an item owner associated with the borrowed shared inventory item.
Owner:KYNDRYL INC
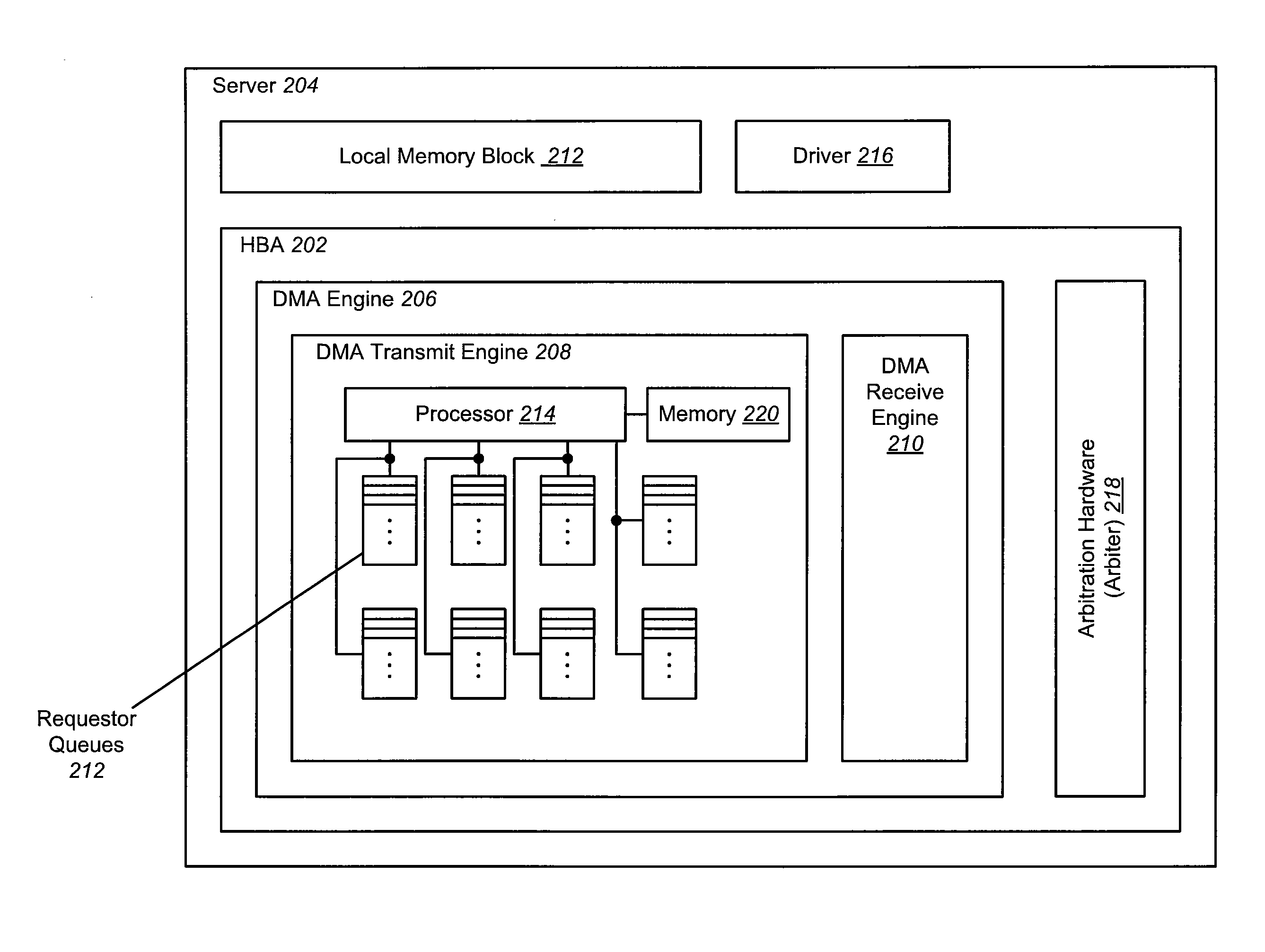
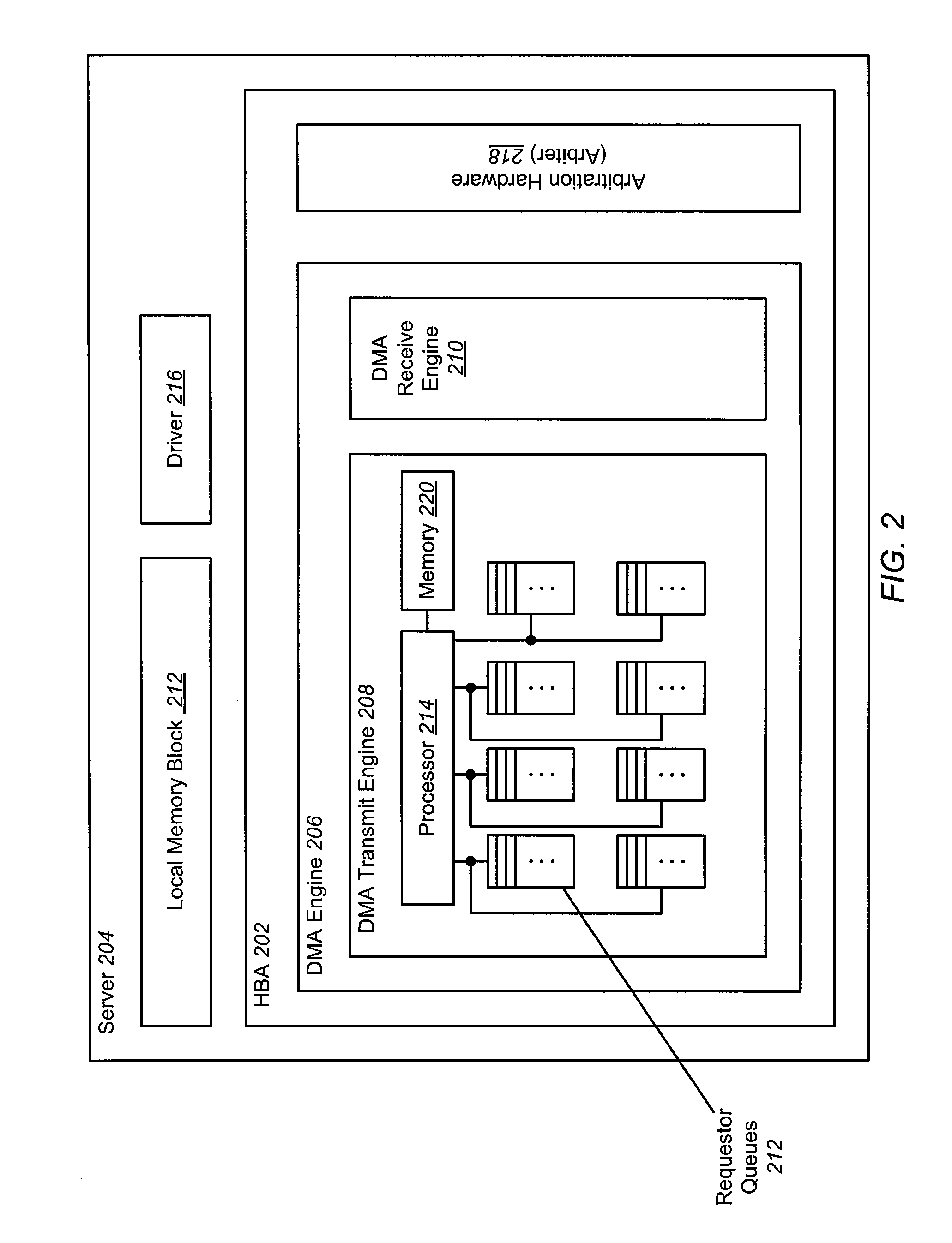
Dynamically Adjustable Arbitration Scheme
InactiveUS20100064072A1Raise priorityRaise the possibilityInput/output processes for data processingData conversionRequest - actionTimer
A network arbitration scheme is disclosed that manages device access fairness by selectively and dynamically increasing a requestor queue's likelihood of being serviced. A requestor queue increases its service priority by duplicating a request entry onto a set of priority rings maintained by arbitration hardware in a host bus adapter. Duplication occurs when (1) a requestor's queue fill count (the number of descriptors stored in the queue) exceeds a watermark level or (2) a requestor's queue timer times out. In the case of time-out, the requester in the lower priority ring will duplicate itself in the higher priority ring. Because the arbitration hardware services requesters using a round robin selection scheme, the likelihood of a requestor queue being serviced increases as the number of its duplicate request entries on a priority ring increases. Upon being serviced, the requester is able to perform the requested action.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Method for navigating in a multi-scale three-dimensional scene
InactiveUS7190365B2Cathode-ray tube indicatorsInput/output processes for data processingRequest - actionViewpoints
A method for navigating a 3D scene in a viewing area includes associating a point of interest with a reference shape, which is related to the shape of the 3D object, and displaying a scene according to a user-requested action, while keeping the point of interest within the reference shape and within the viewing area. The user-requested action may include translation, rotation, and zooming. The point of interest may include scene information such as a magnification factor, local orientation, and global orientation. The methods for performing a user-requested action in a 2D representation of a 3D object include determining a distance between a point of interest and a viewpoint; determining an amount of movement from a user input; and performing the user-requested action at a rate based on the amount of movement from the user input multiplied by a distance factor based on the distance between the point of interest and the viewpoint. A system for displaying a 3D object includes a 2D display for displaying the 3D object and a computer operatively coupled to the 2D display, the computer having a program to display the 3D object on the 2D display, the program adapted to enable translation, zoom, and rotation of the representation while restricting a point of interest within a reference shape and within a viewing window on the 2D display.
Owner:SCHLUMBERGER TECH CORP
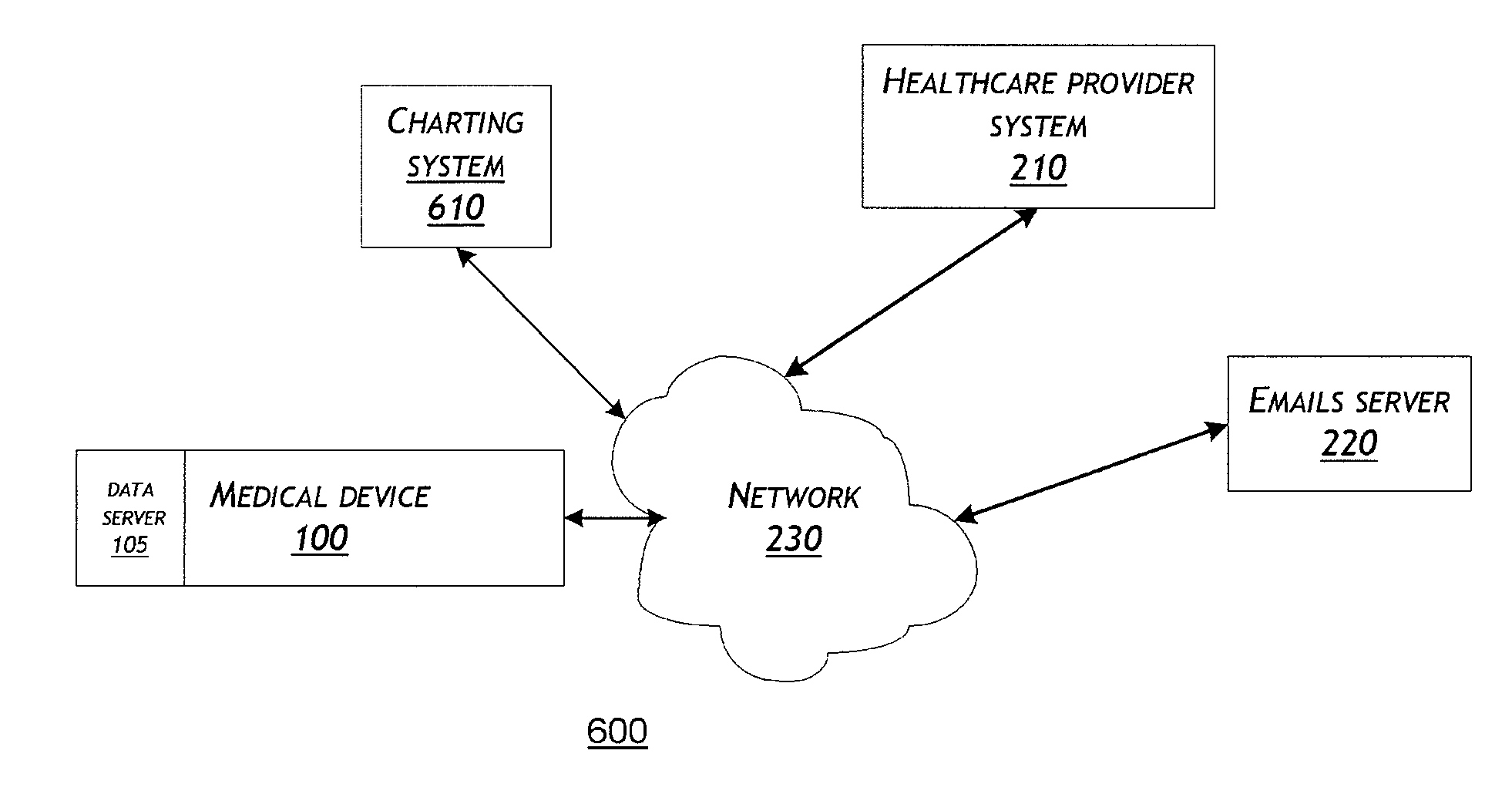
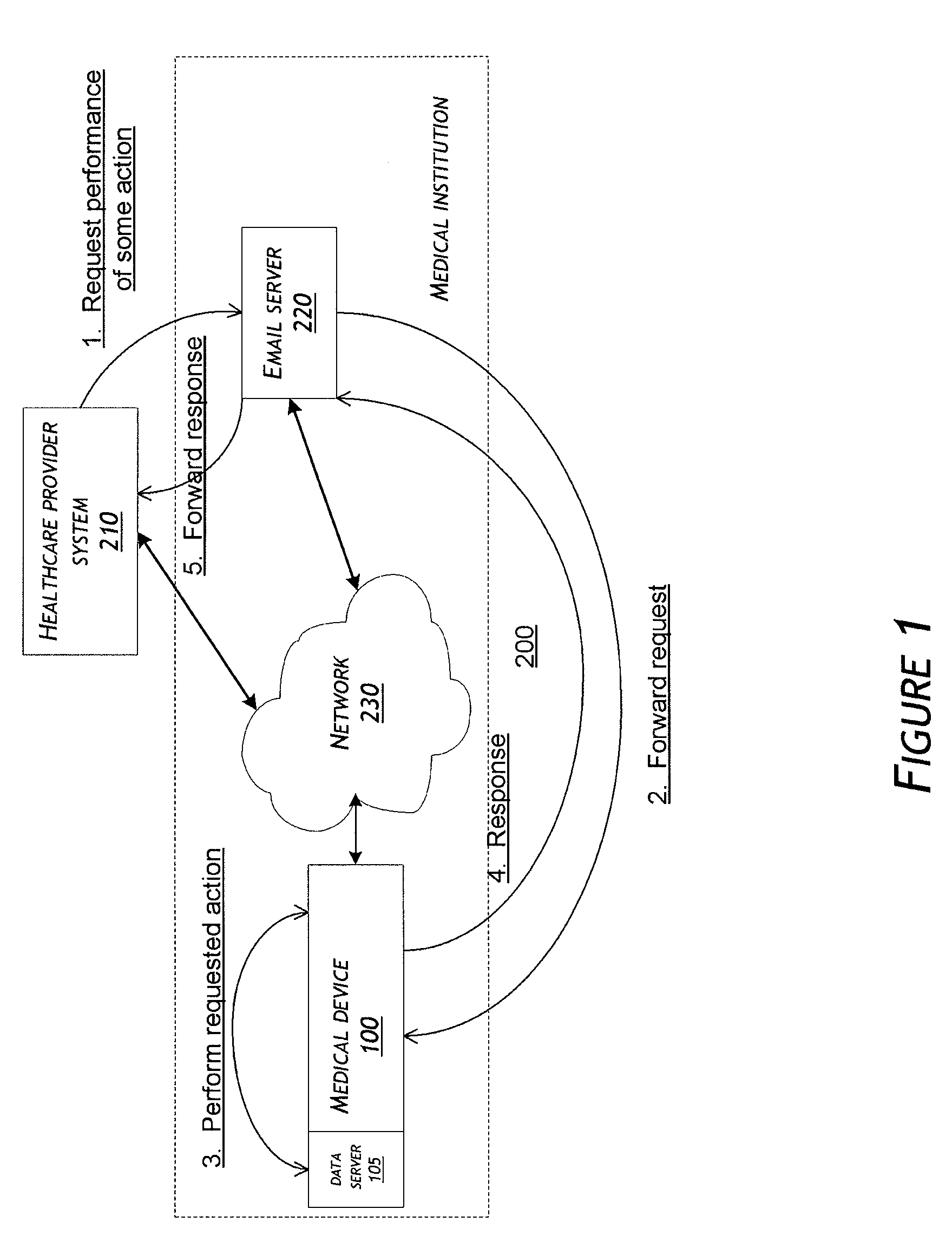
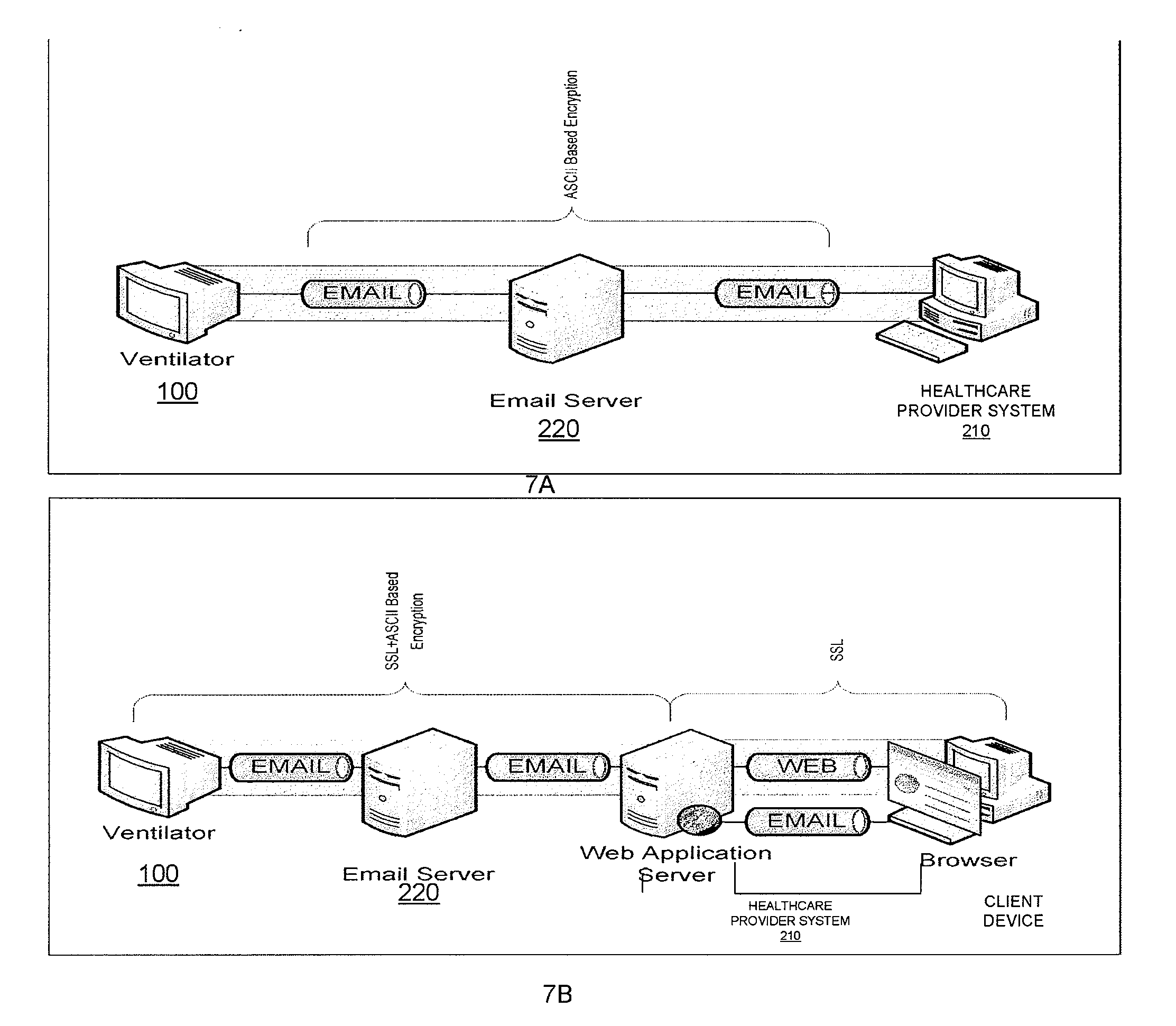
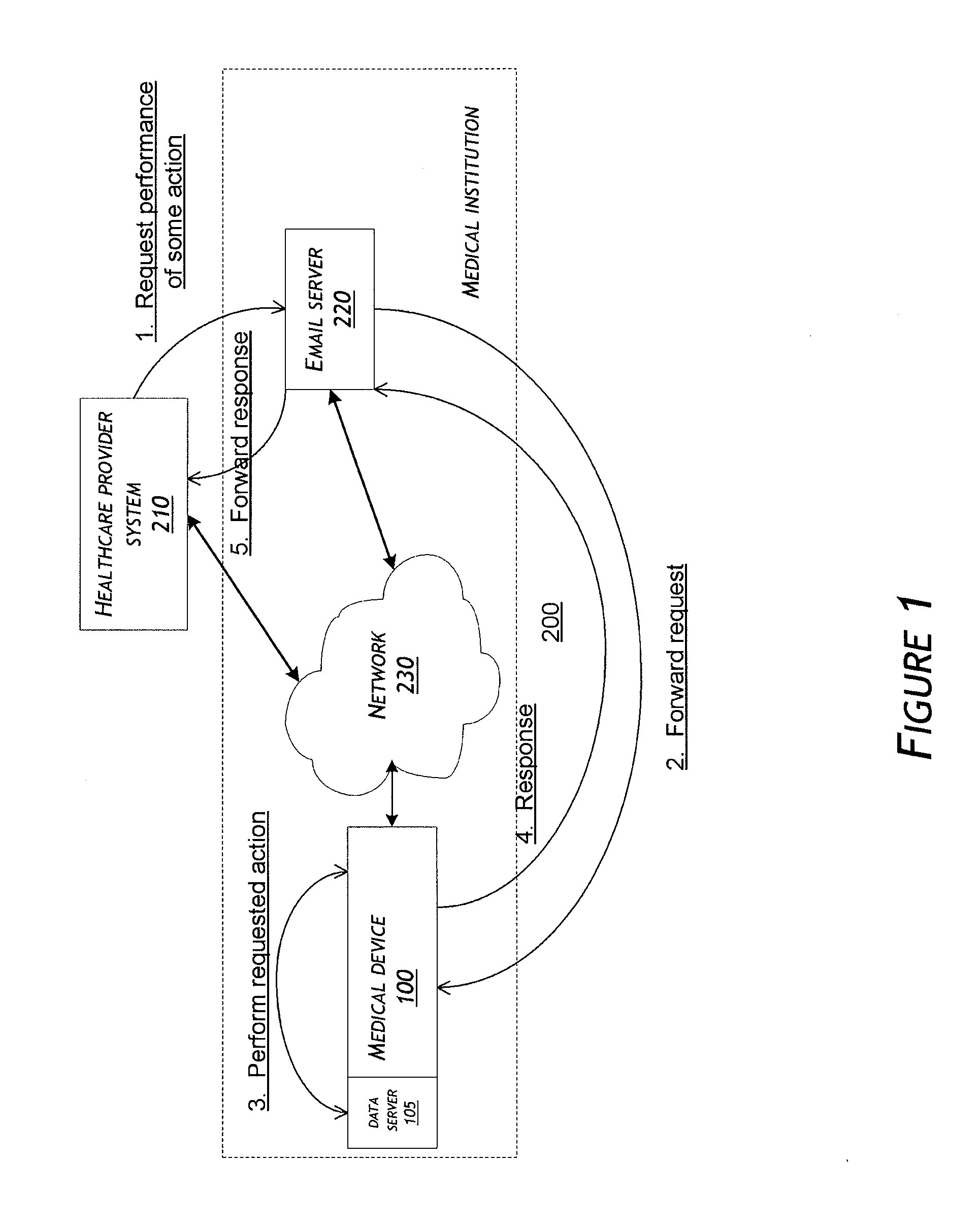
System and method for communicating over a network with a medical device
A medical device is provided that performs a requested action. The requested action may be communicated, for example, to the medical device via email messages. After performing the requested action, a response that is dependent upon the requested action is generated. The generated response is then sent on a network from the medical device as an email message.
Owner:EVENT MEDICAL
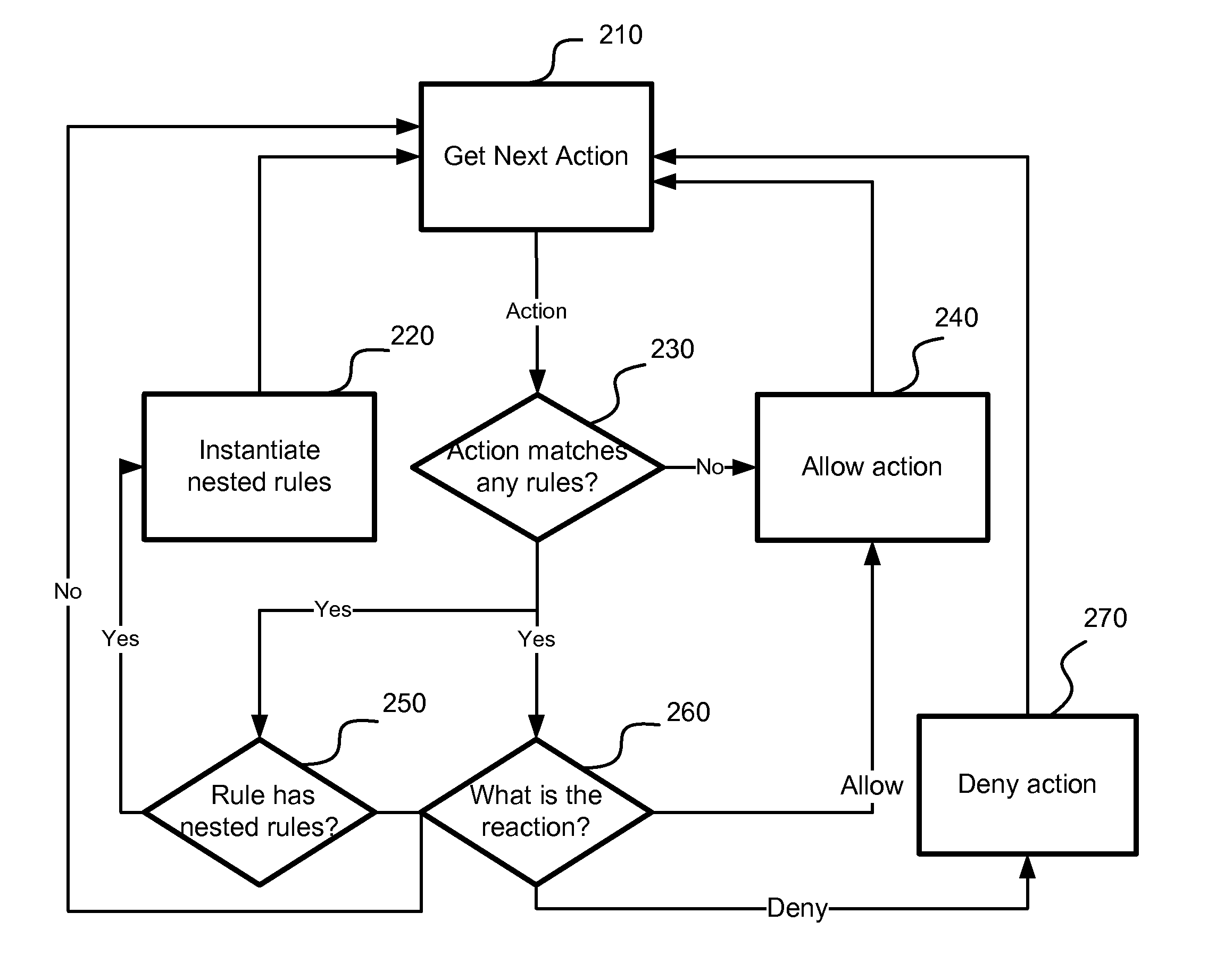
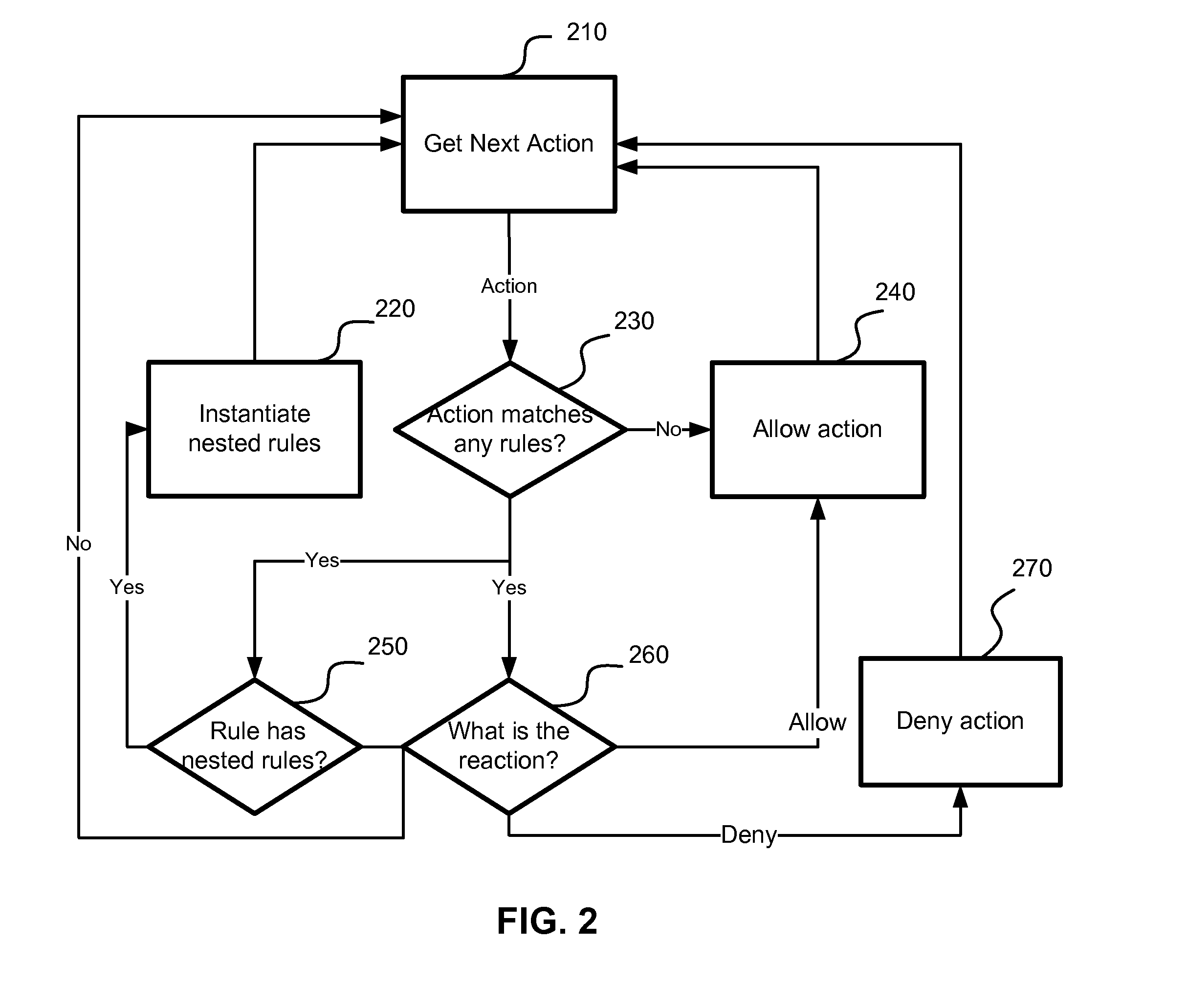
Application of nested behavioral rules for anti-malware processing
InactiveUS8850579B1Save system resourcesLarge actionMemory loss protectionError detection/correctionRequest - actionTheoretical computer science
A system, method and computer program product for implementing dynamic behavior rules for malware detection. A method of heuristic analysis of computer program execution is used. A behavior of a computer program is monitored, analyzed and blocked in runtime. Actions performed or triggered by each executable component are compared against a set of behavioral rules. The behavioral rules determine wherever the requested action is allowed or blocked, and which new behavioral rules are needed to be applied to future actions. Executed actions (allowed or blocked) introduce new dynamic behavioral rules to the computer system, which in turn can apply these rules for analyzing behavior of subsequent components executed on the computer system.
Owner:SAFE N SEC
User-browser interaction-based fraud detection system
InactiveUS8650080B2Payment architecturePlatform integrity maintainanceRequest - actionInternet privacy
Systems, methods and media for detecting fraudulent behavior during an Internet commerce session are disclosed. Embodiments of a method may include establishing an e-commerce session with a user and requesting fraud detection analysis of user-browser interaction during the e-commerce session. Embodiments may also include receiving fraud detection results for the e-commerce session, where the fraud detection results may provide an indication of a comparison between the user's interaction with a browser during the e-commerce session and known fraudulent behavior. Embodiments may also include performing an action based on the fraud detection results. Determining the fraud detection results may include determining user-browser interaction data associated with the session and comparing the user-browser interaction data to known fraudulent human or automated program behavior. Performing the action based on fraud detection results may include one or more of completing an e-commerce transaction, requesting additional authentication, denying the requested action, etc.
Owner:IBM CORP
Creation and management of service candidates for a service model
An apparatus, system, and method to facilitate the creation and management of service candidates in a service-oriented architecture (SOA). In one embodiment, a method includes receiving a user request for an action concerning a service candidate associated with a SOA service model, and displaying a user interface corresponding to the requested action. The method further includes receiving user input for the service candidate via the user interface, and updating the SOA service model based on the requested action and the received user input for the service candidate.
Owner:RED HAT
Achieving low latencies on network events in a non-real time platform
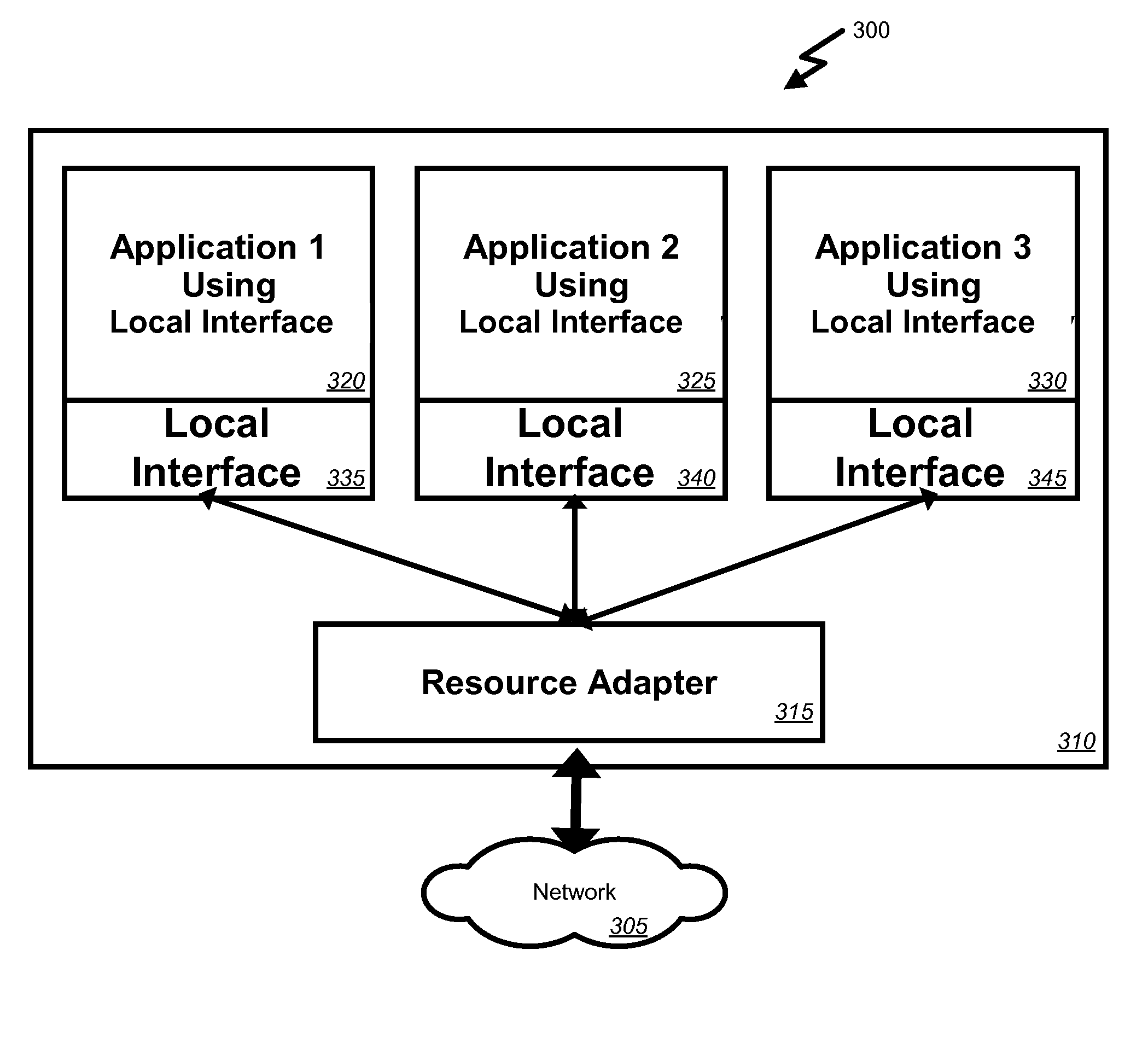
ActiveUS20080235327A1Low and predictable latencyImprove throughputMultiple digital computer combinationsTransmissionRequest - actionNon real time
Embodiments of the invention provide systems and methods for providing low-latency handling of events and / or requesting actions of external resources in a real time environment while utilizing non-real time components. According to one embodiment, a system for providing low-latency handling of events in a real time environment while utilizing non-real time components can comprise an external resource and a resource adapter communicatively coupled with the external resource. The resource adapter can be adapted to detect events of the external resource and / or request actions of the external resource. The system can also include at least one local application communicatively coupled with the resource adapter. The local application can have a local interface and the local application can interact with the resource adapter via the local interface.
Owner:ORACLE INT CORP
Method and system for network management providing access to application bandwidth usage calculations
InactiveUS7602808B2Digital computer detailsTime-division multiplexRequest - actionNetwork management
A method, system, apparatus, and computer program product is presented for management of a distributed data processing system. The network management framework is able to monitor multiple sources of network packets on various subnets within the distributed data processing system; distributed packet snoopers are deployed from a packet usage manager to monitor the multiple sources of network packets. The system administrator can request packet filtering based upon selected active users or active applications. A bandwidth history database is compiled from bandwidth usage data associated with multiple entities within the data processing system, including users, applications, and / or endpoints within the data processing system. In response to a requested action within the data processing system, bandwidth usage for the requested action can be predicted with reference to the bandwidth history database. The actual and predicted bandwidth usage of requested actions can be displayed to the system administrator in real time.
Owner:CLOUD SOFTWARE GRP SWITZERLAND GMBH
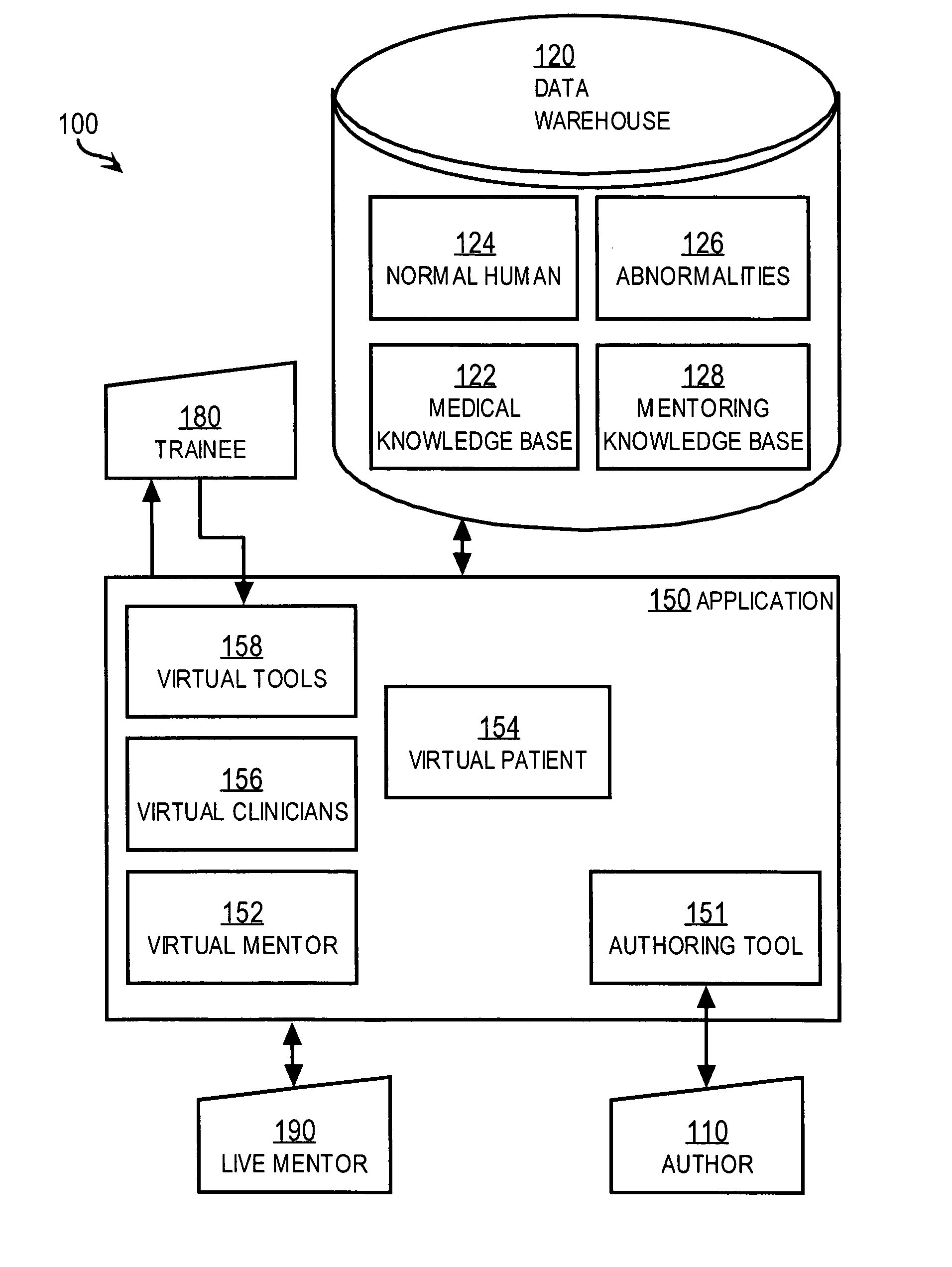
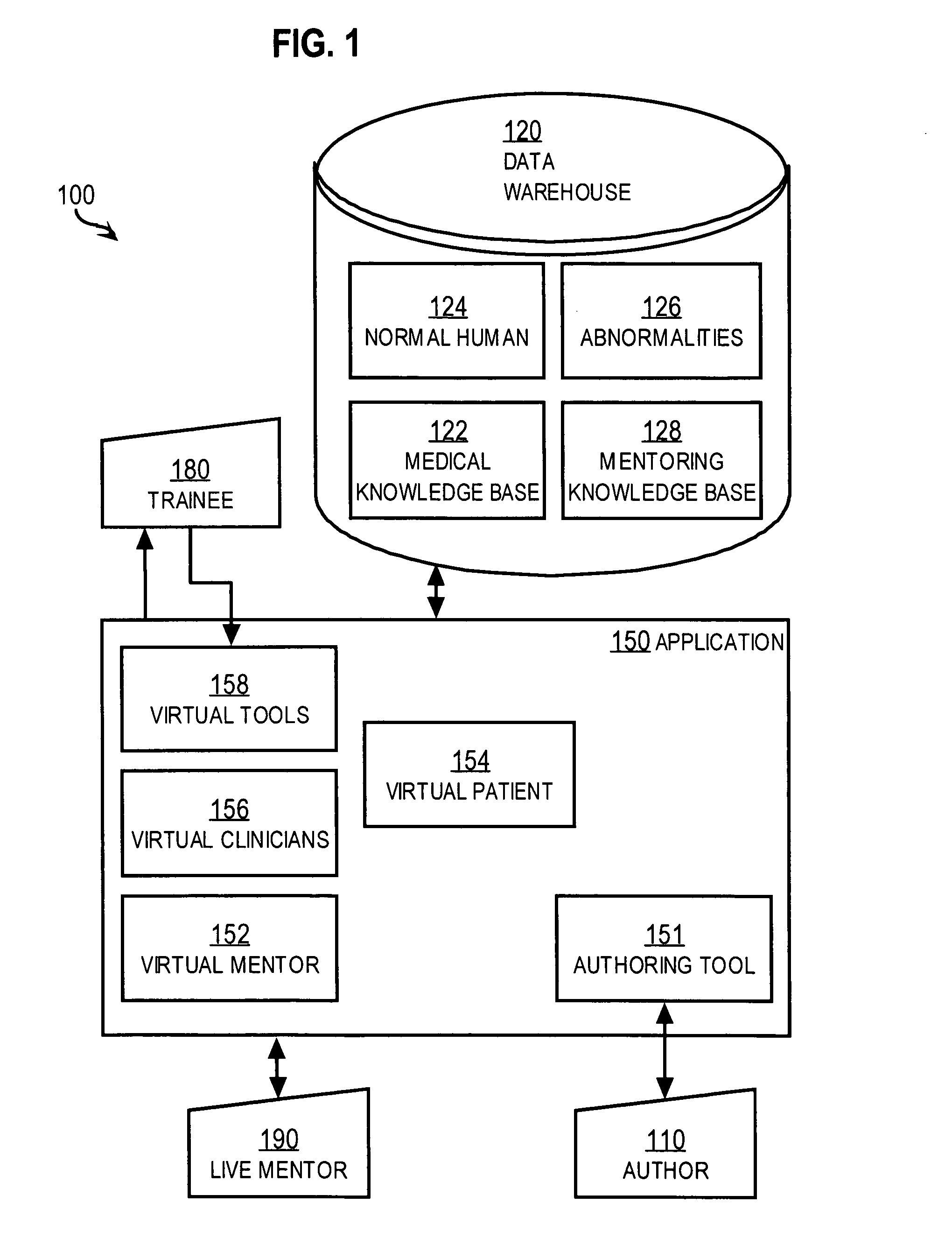
Techniques for delivering medical care by improving decision-making skills of medical personnel
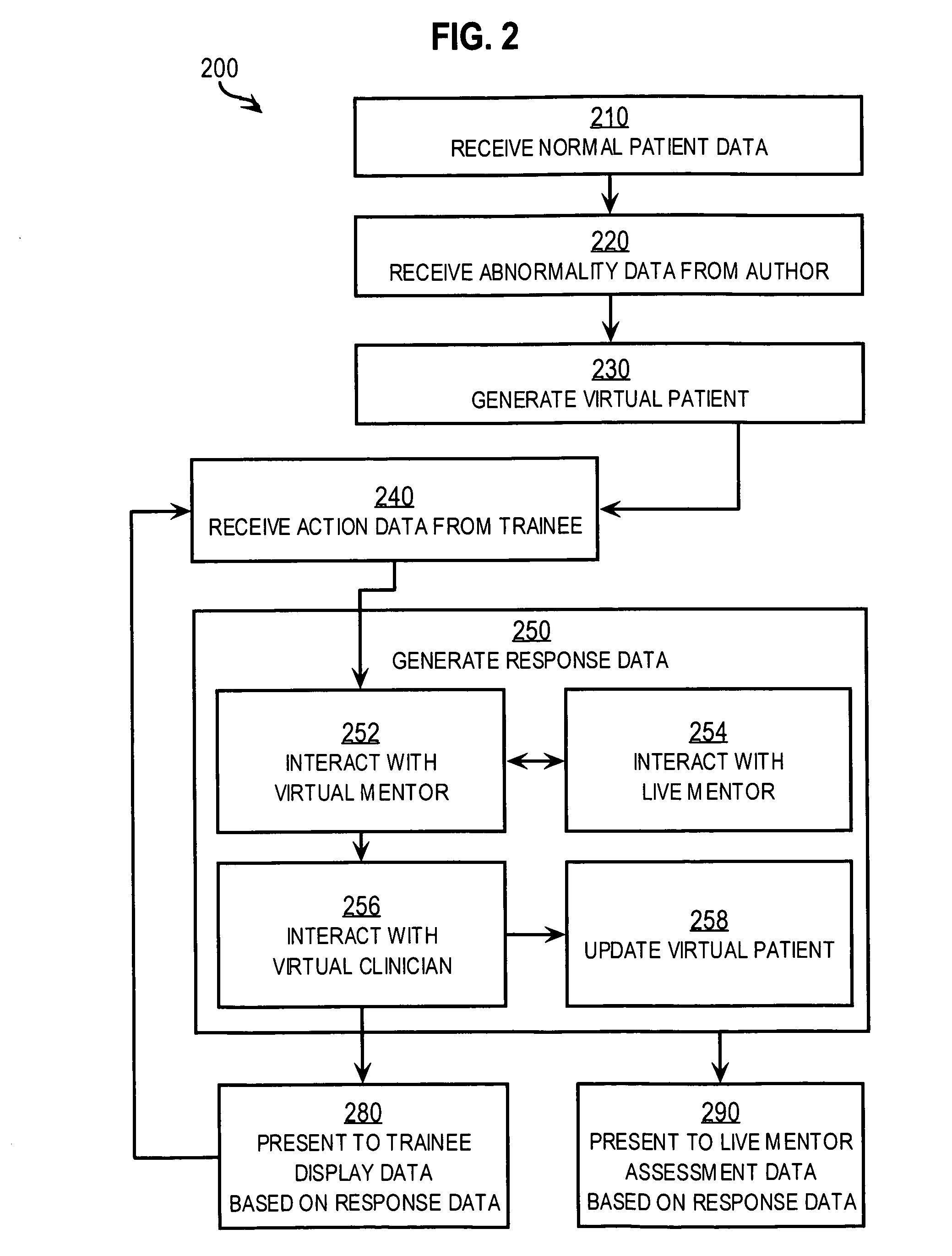
ActiveUS20050170323A1Improve decision makingSimple designEducational modelsRequest - actionSkill sets
Techniques for delivering medical care by improving decision making skills of medical personnel who deliver the care include receiving normal data that indicates normal conditions in a patient. Abnormality data is received from an author and indicates an abnormal condition in a patient. An instance of a virtual patient is generated based on the normal data and the abnormality data. The instance describes a sufficiently comprehensive physical state of a patient having the abnormal condition to simulate clinical measurements of the patient's condition. Action data is received from a trainee who is different from the author. Action data indicates a requested action relevant to dealing with the instance. Response data is generated based on the action data and the instance. Display data is presented to the trainee based on the response data. The display data indicates information about the instance available as a result of the requested action.
Owner:UNIV OF MARYLAND
System and method for communicating over a network with a medical device
A medical device is provided that performs a requested action. The requested action may be communicated, for example, to the medical device via email messages. After performing the requested action, a response that is dependent upon the requested action is generated. The generated response is then sent on a network from the medical device as an email message.
Owner:EVENT MEDICAL
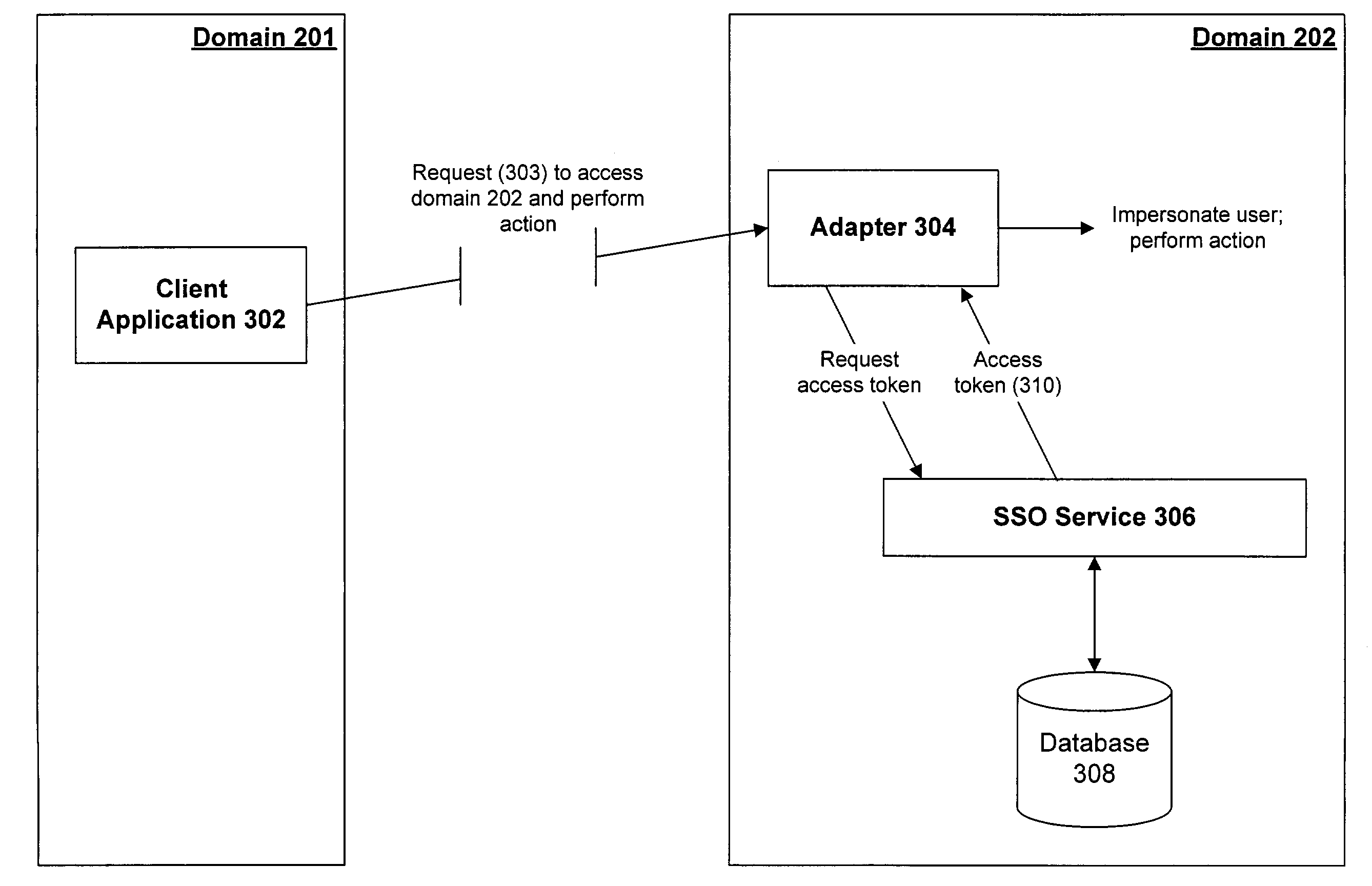
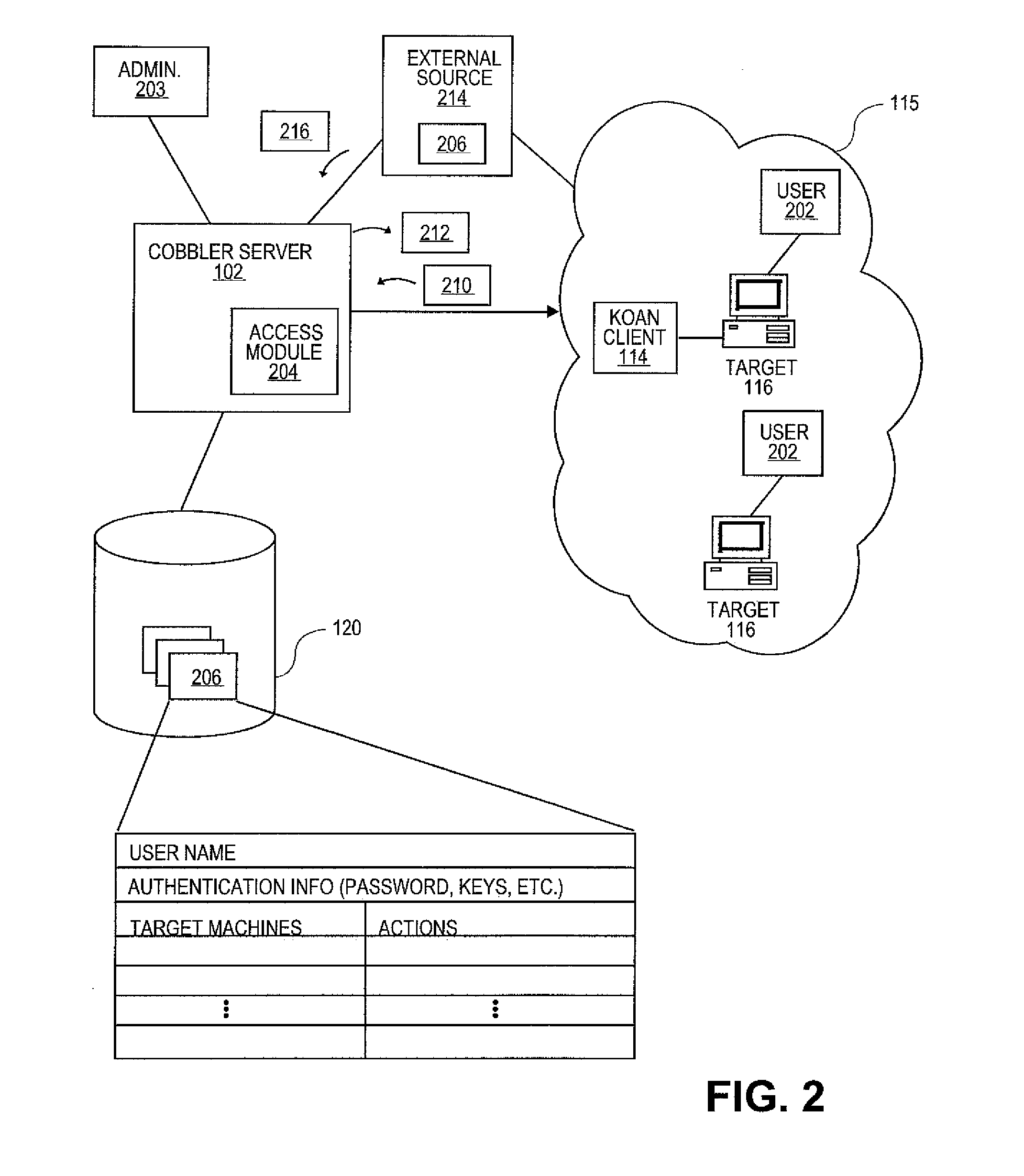
System and method for unified sign-on
InactiveUS7275259B2Digital data processing detailsUser identity/authority verificationRequest - actionAccess token
A system that allows a user of a first domain to access a second domain. A request originates in the first domain to perform an action in the second domain. The request indicates a user of the first domain on whose behalf the request was originated. The access request is received by an adapter in the second domain. The adapter requests an access token for a user of the second domain who corresponds to the user of the first domain. A mapping table is used to identify which user in the second domain corresponds to the user in the first domain. Once the correct user of the second domain is identified, an access token for that user is returned to the adapter. The adapter then carries out the requested action by using the access token to impersonate the user of the second domain.
Owner:MICROSOFT TECH LICENSING LLC
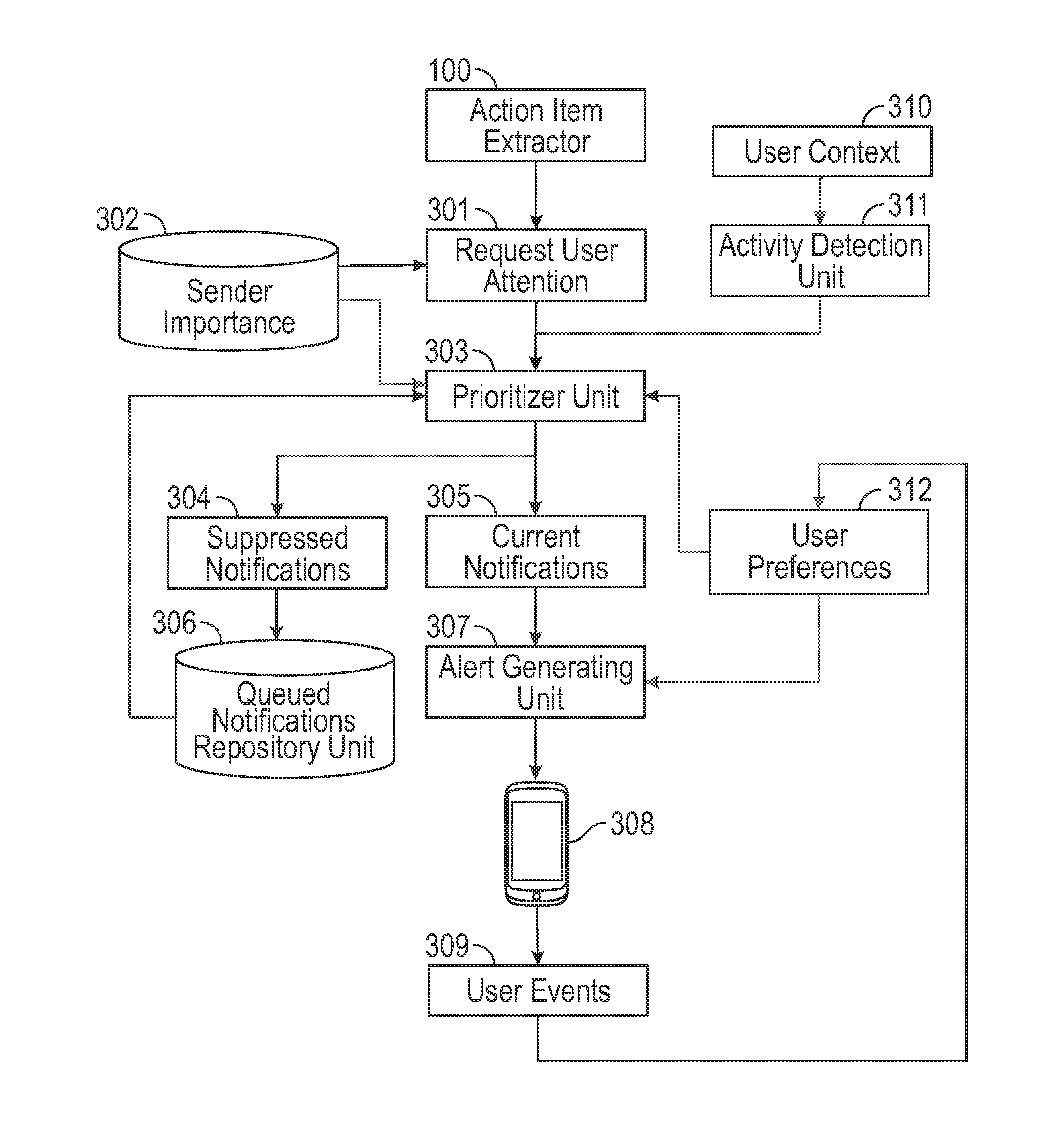
System and method for automatically mining corpus of communications and identifying messages or phrases that require the recipient's attention, response, or action
InactiveUS20150215253A1Rapid responseMathematical modelsDigital computer detailsRequest - actionProcess communication
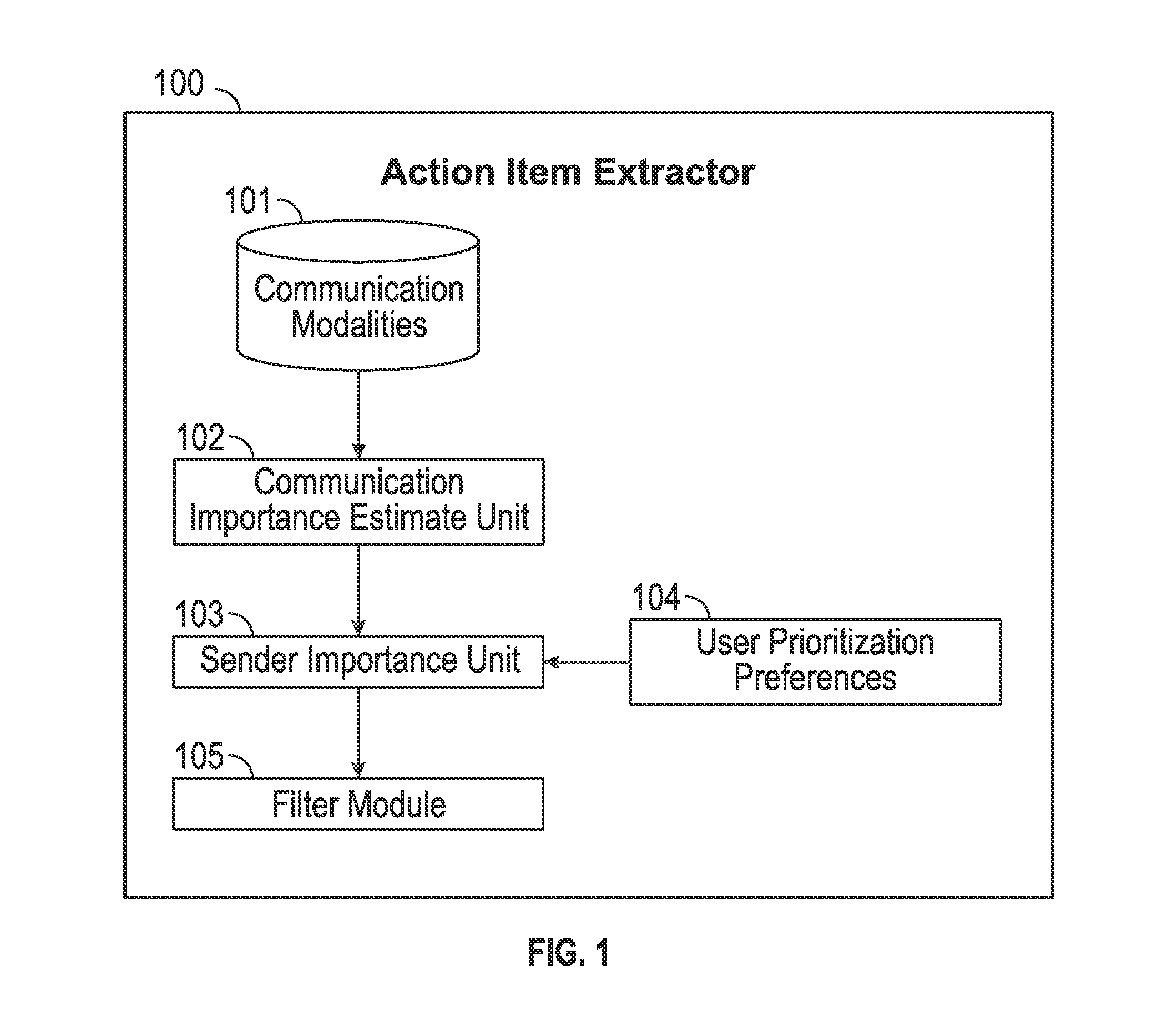
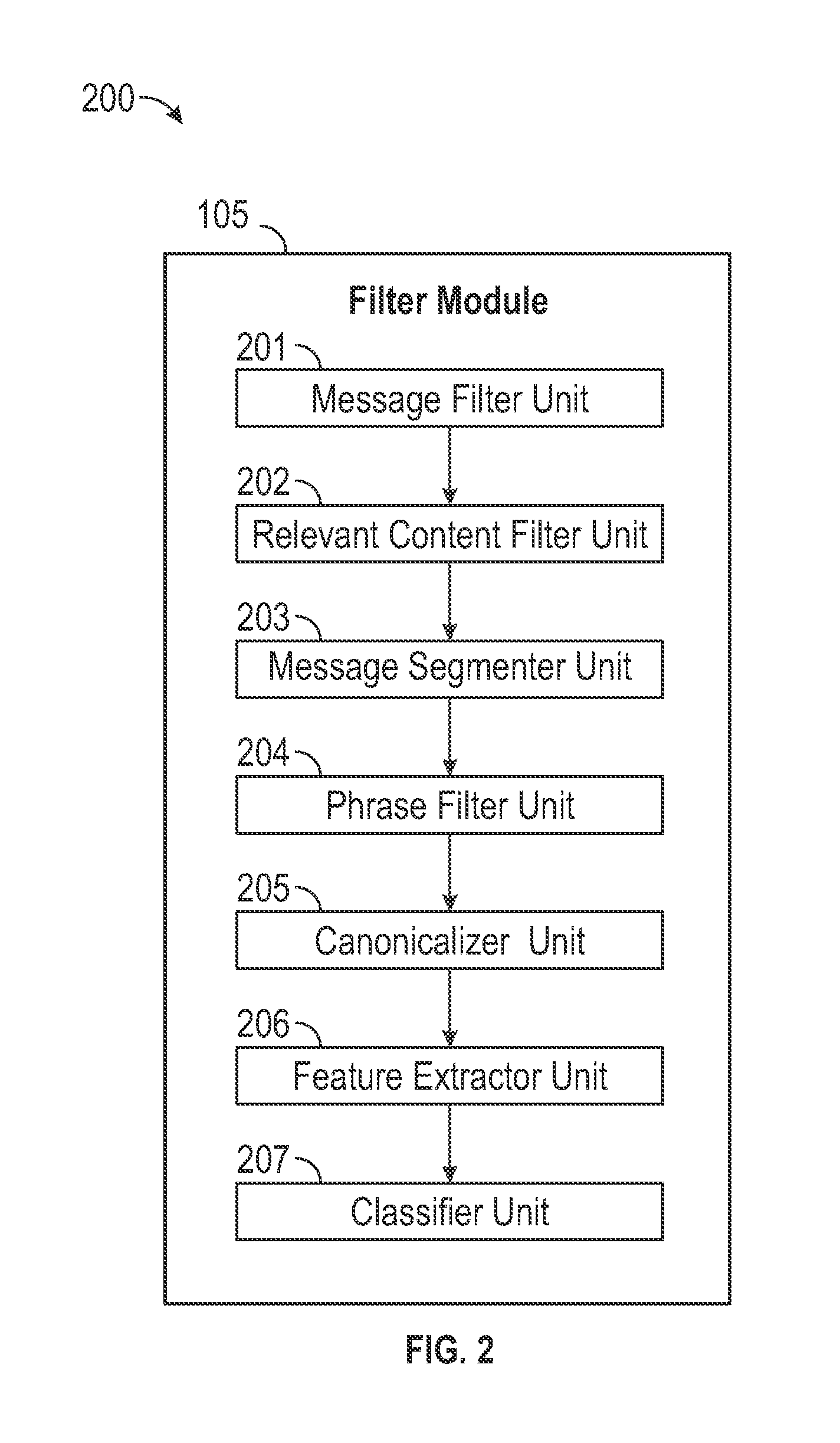
Exemplary embodiments of the present disclosure are directed towards a system for processing communications that detects just the portions of the communication requesting action, a response, or increased attention from a user, wherein said system comprises: (a) a message filter unit that analyzes the content and metadata of messages conveyed by various communication modalities and determines which portions of the messages request action, a response, or increased attention from the user; (b) a sender importance unit that determines from past communication patterns the perceived urgency that the user will afford to a new message from a particular sender; and (C) a user interface unit that alerts the user to detected items that require attention, response or action. Additionally, the disclosure describes a method for managing a list of tasks requiring attention automatically, where incoming messages are scanned and action items extracted and added to the list.
Owner:VEMURI SUNIL +2
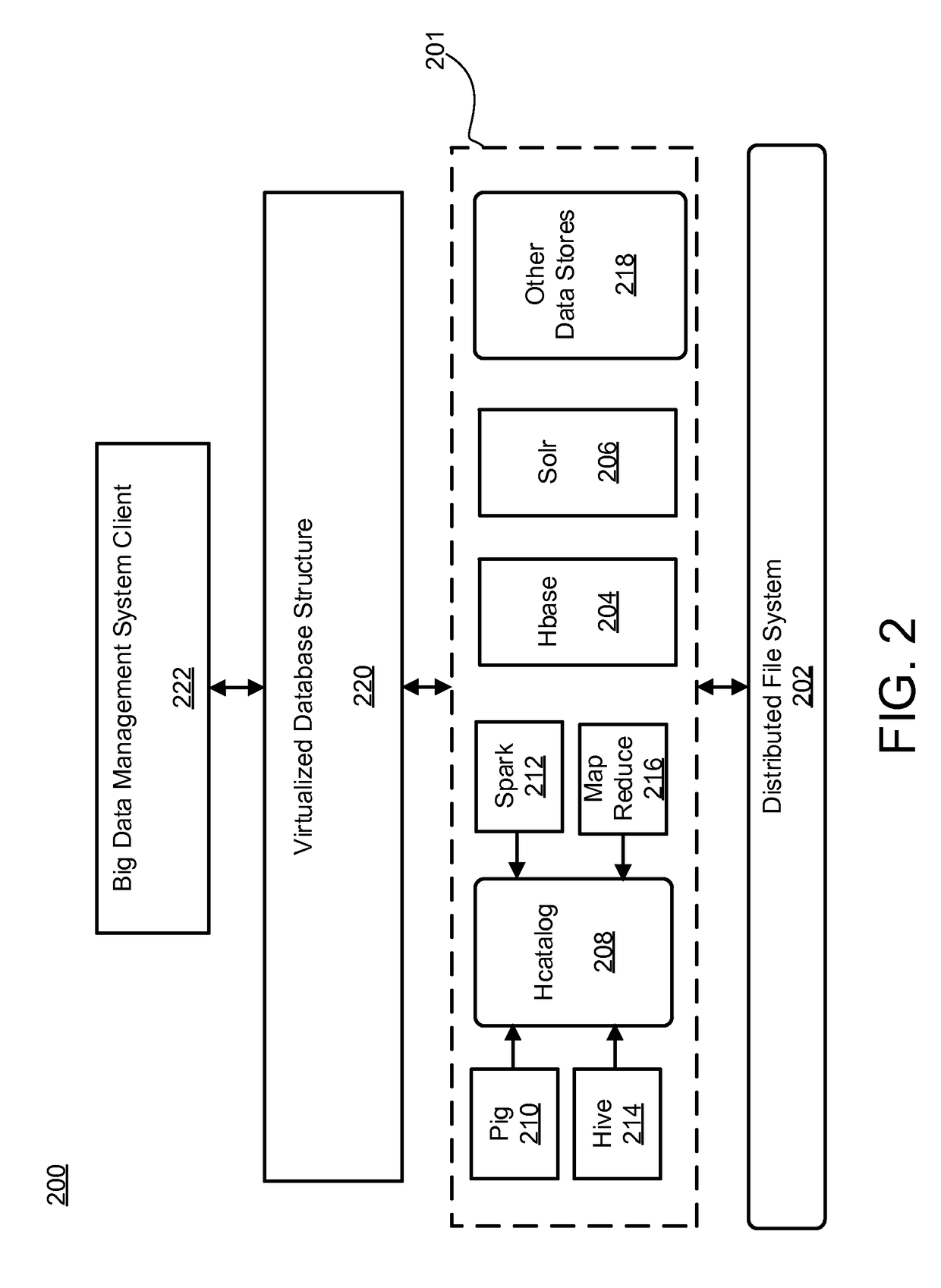
System and method for reading and writing to big data storage formats
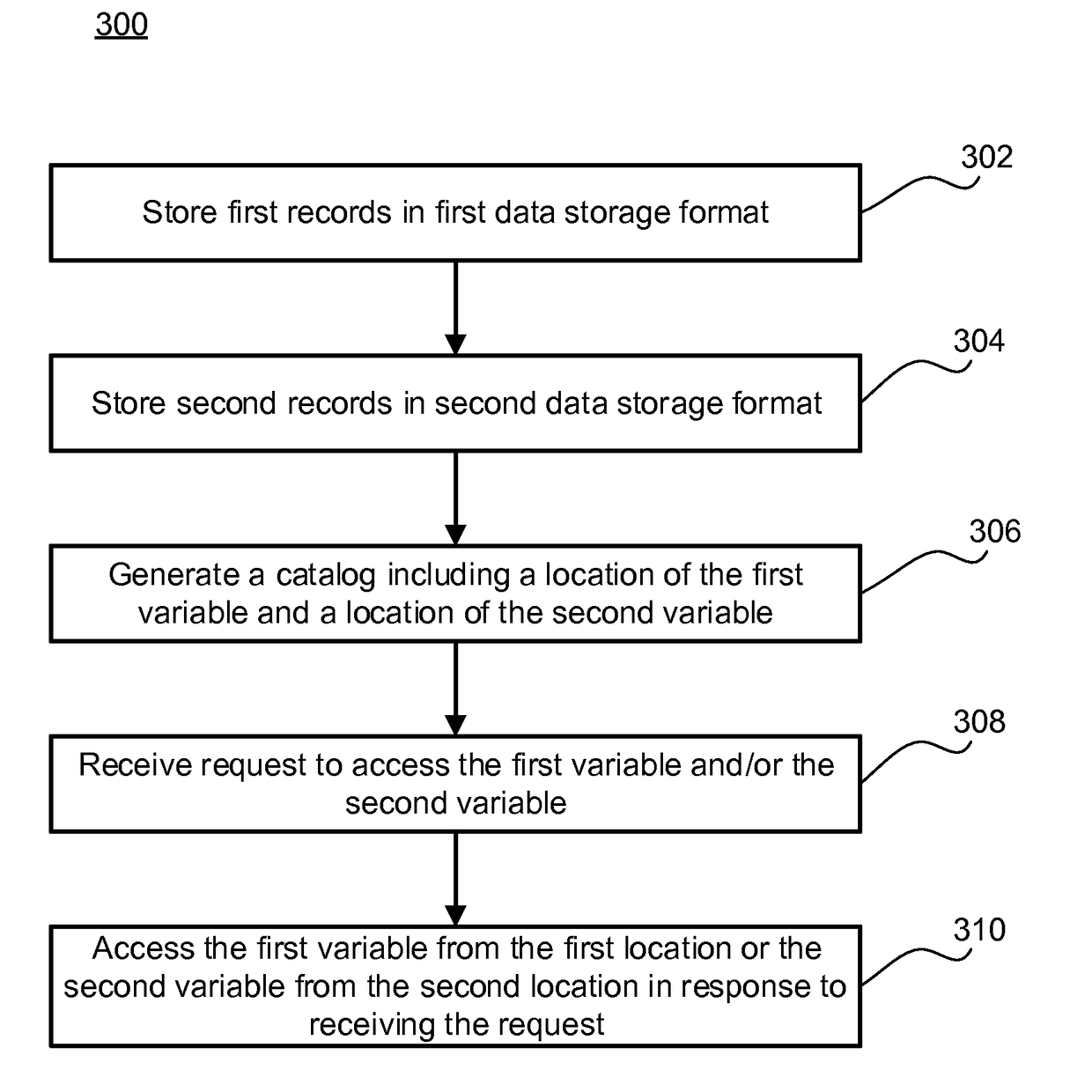
ActiveUS20170139997A1Digital data information retrievalDigital data protectionRequest - actionDatabase
A system may receive a request for access to a first variable. The request may include a requested action and a variable identifier for the first variable. The request may also have a syntax that is incompatible with first data storage format. The system may parse the request to capture the variable identifier from the request. The system may also look up a location of the first variable in a catalog using the variable identifier. The location of the first variable may include the first data storage format. The system may generate a query to access the first variable. The syntax of the query may be compatible with the first data storage format. The system may then submit the query to the first data storage format. The query may be configured to complete the requested action.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
User-Browser Interaction Analysis Authentication System
ActiveUS20080222712A1Digital data processing detailsUser identity/authority verificationRequest - actionPattern matching
Systems, methods and media for authenticating a user based on user-browser interaction are disclosed. Embodiments of a method may include, during an e-commerce session with a user, receiving a request for an action from the user and determining whether the requested action requires additional authentication. Embodiments may also include requesting analysis of user-browser interaction for the session, receiving a pattern matching score for the session, and performing an action based on the pattern matching score and the requested action. The pattern matching score may provide an indication of a comparison between the user's interaction with a browser during the session and a user-browser interaction profile for the user. The performed action may include completing an e-commerce transaction, accessing or modifying information, changing a password, requesting additional information, denying the requested action, or other action. Further embodiments may provide for authenticating the user with a first-level authentication.
Owner:INT BUSINESS MASCH CORP
Methods and systems for managing access in a software provisioning environment
ActiveUS20100058444A1Digital data processing detailsUser identity/authority verificationRequest - actionSoftware
A provisioning server can be configured to associate user actions with users that have access to perform the associated user actions. The user actions can include any user action performed within or by the provisioning server, such as configuring the provisioning server, modifying provisioning objects in the provisioning server, accessing provisioning processes by the provisioning server, and the like. The association can be based on the identity of the users or a type of user (administrator, client, guest, etc.). Once a request is received for a particular user action, the provisioning server can be configured to enable the requested action if the requested action is associated with the requesting user.
Owner:RED HAT
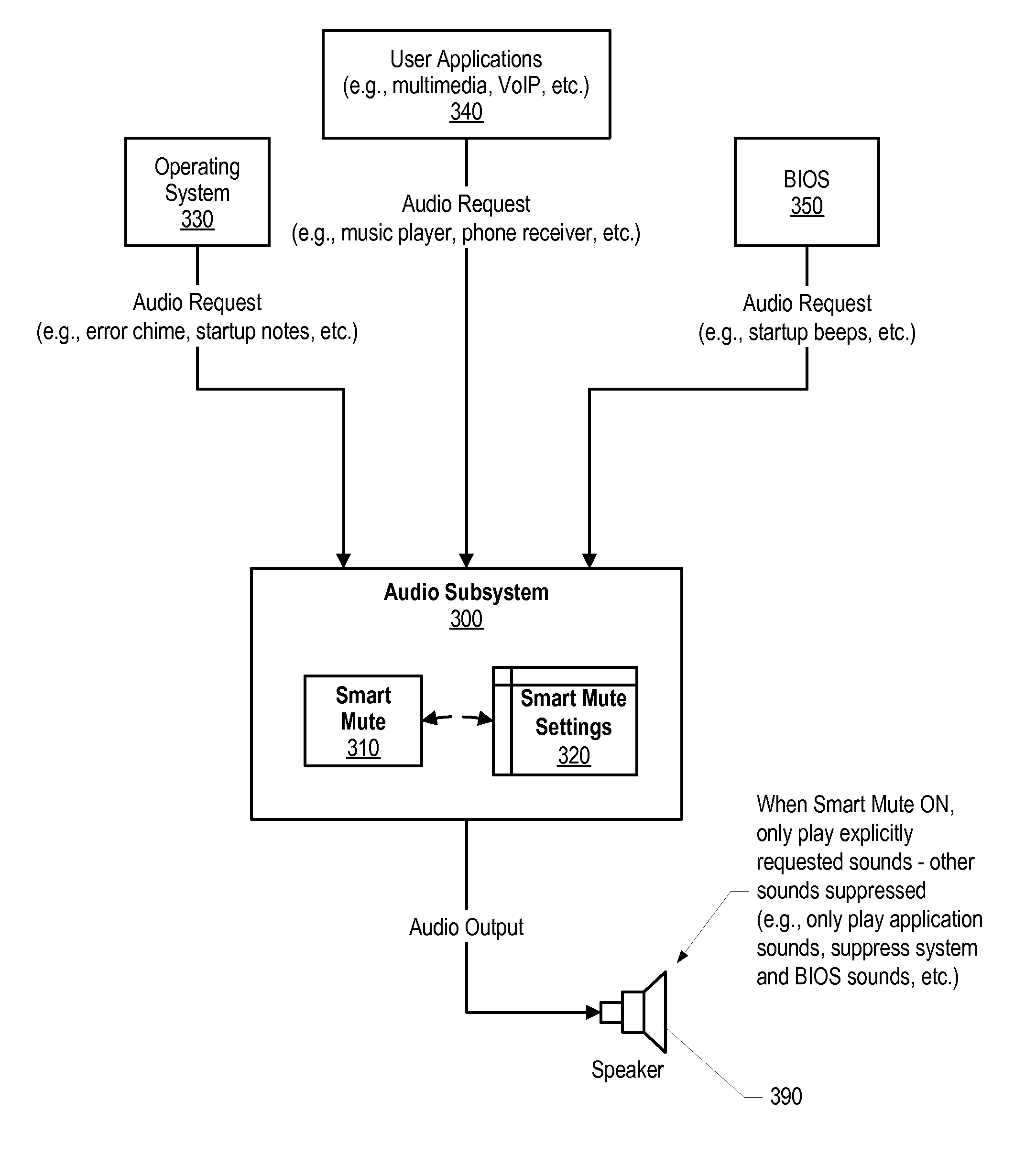
Intelligent Selective System Mute
Owner:LENOVO PC INT
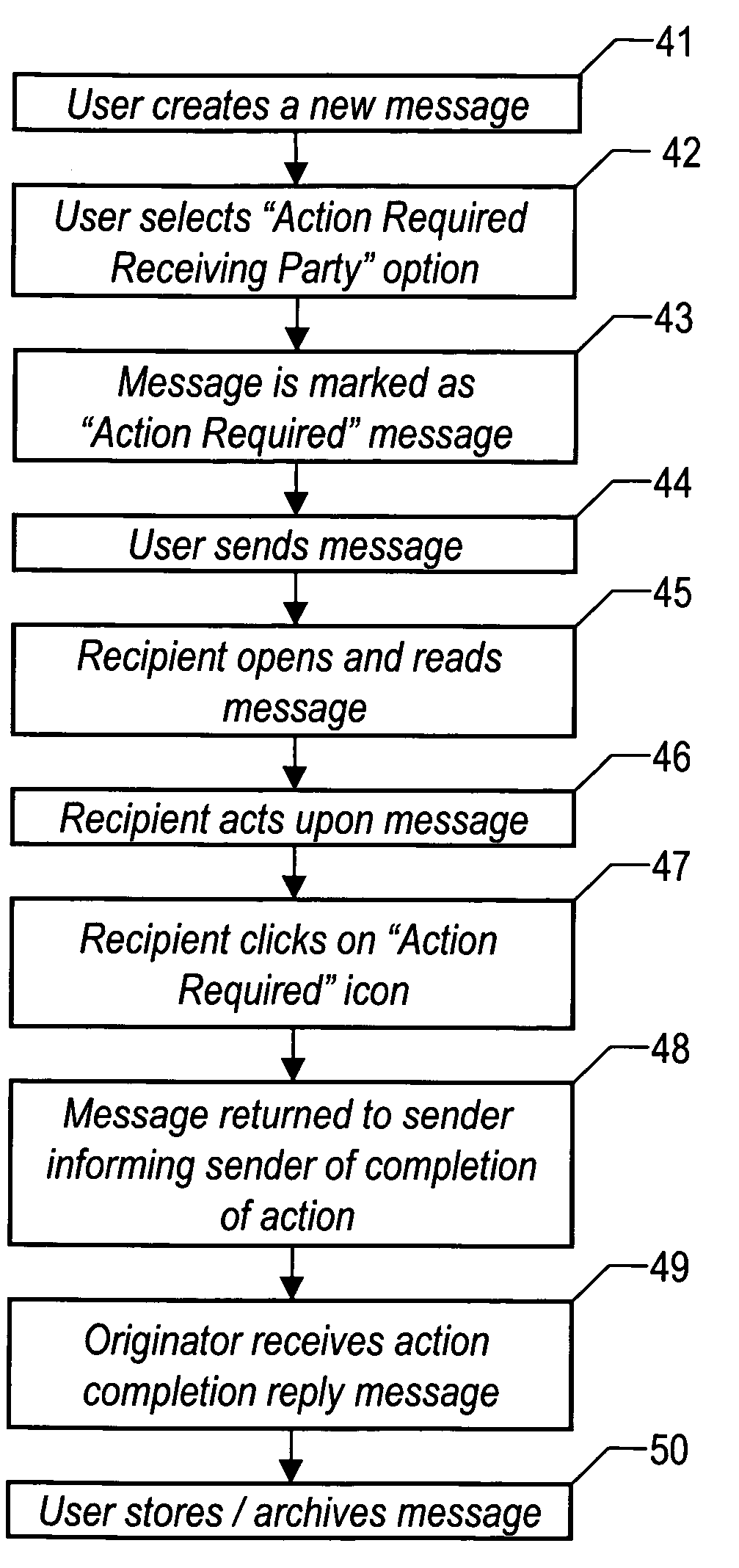
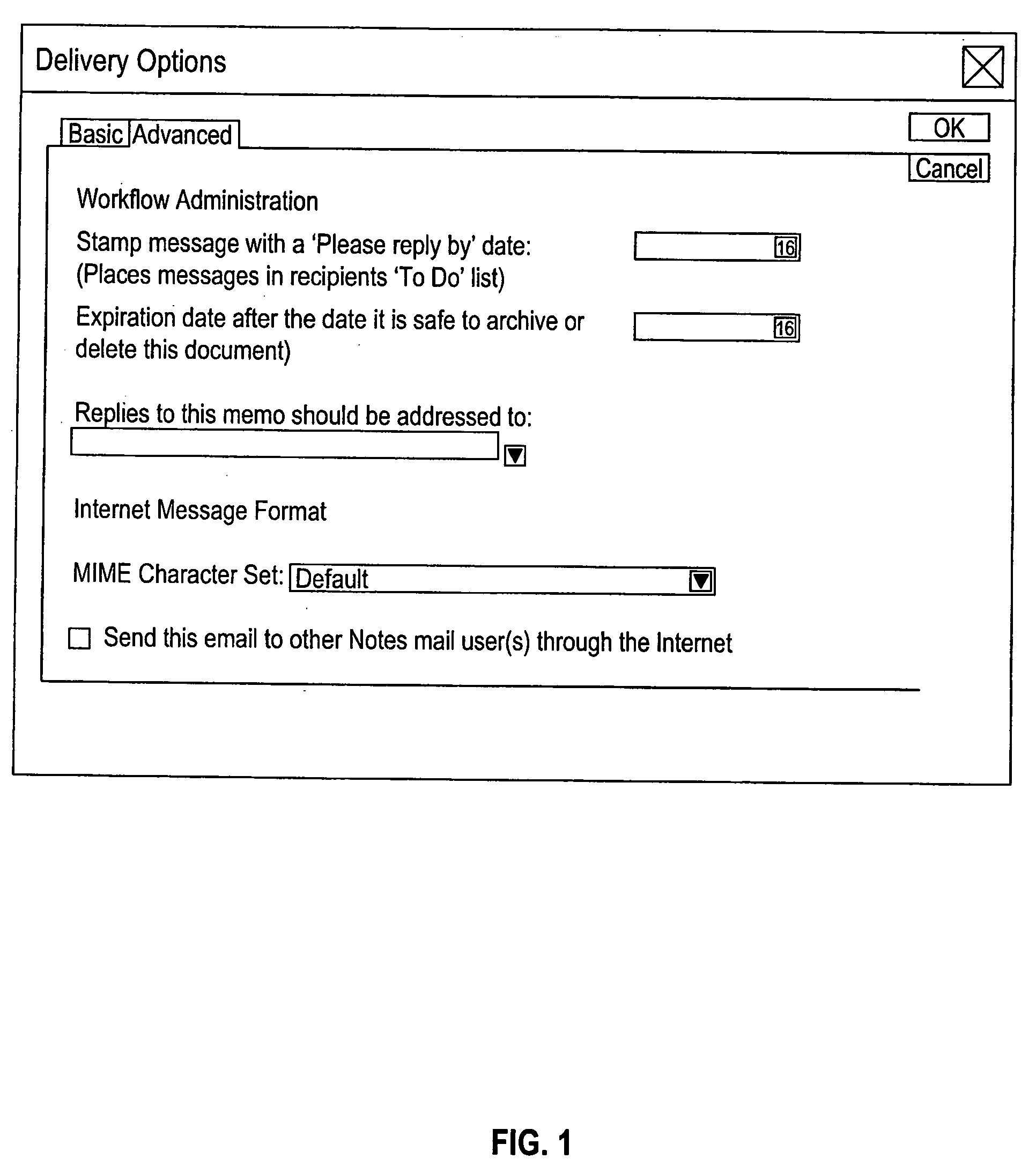
Method and system for notification of local action required to contents of electronic mail message
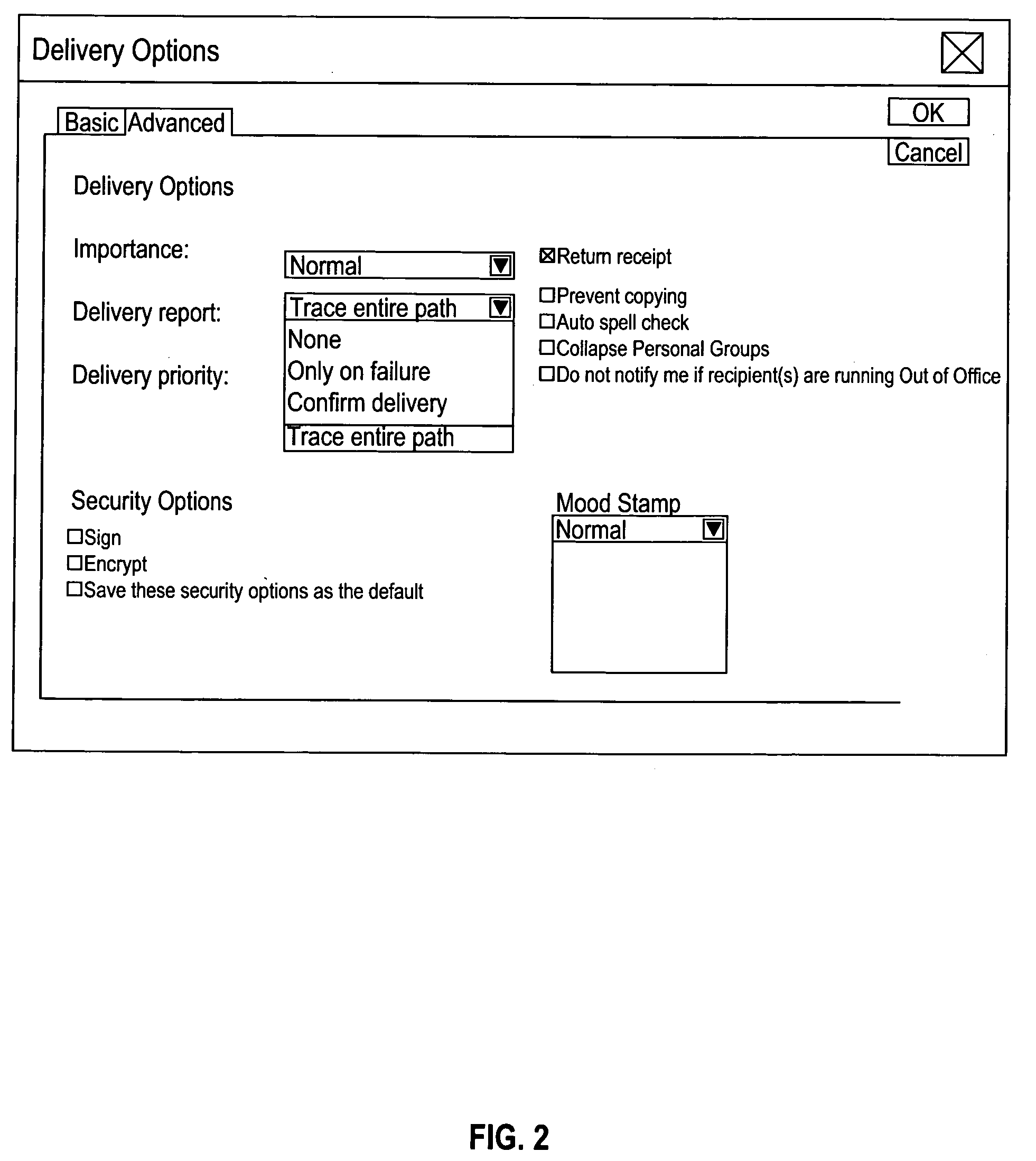
InactiveUS20050240655A1Maximum flexibilityEasy to manageMultiplex system selection arrangementsSpecial service provision for substationRequest - actionComputer science
The present invention provides a method and system to alert the recipient of an electronic message of some action that is required from the recipient. The invention also provides a method to alert the sender of the electronic message of the completion of the action required in the original electronic mail message. In the method of the present invention, the originator or recipient of an electronic mail message can choose to designate the message as one that requires an action by the message recipient. The recipient will notice the ‘Action Required’ icon and will be alerted to the fact that an action is required with this message. At the completion of the action, the sender of the original message will receive a notification that the requested action has been taken by the recipient.
Owner:HCL TECH LTD
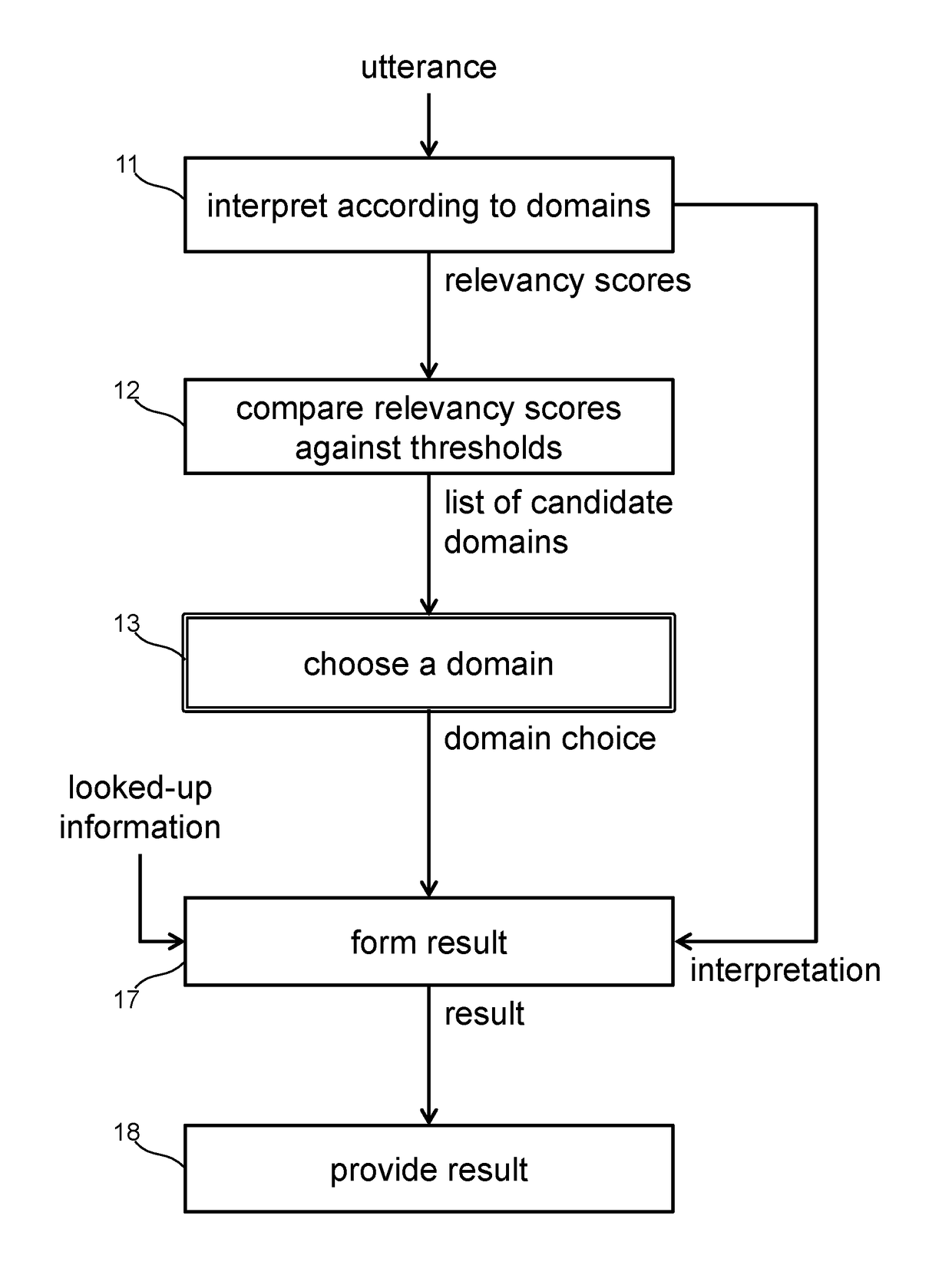
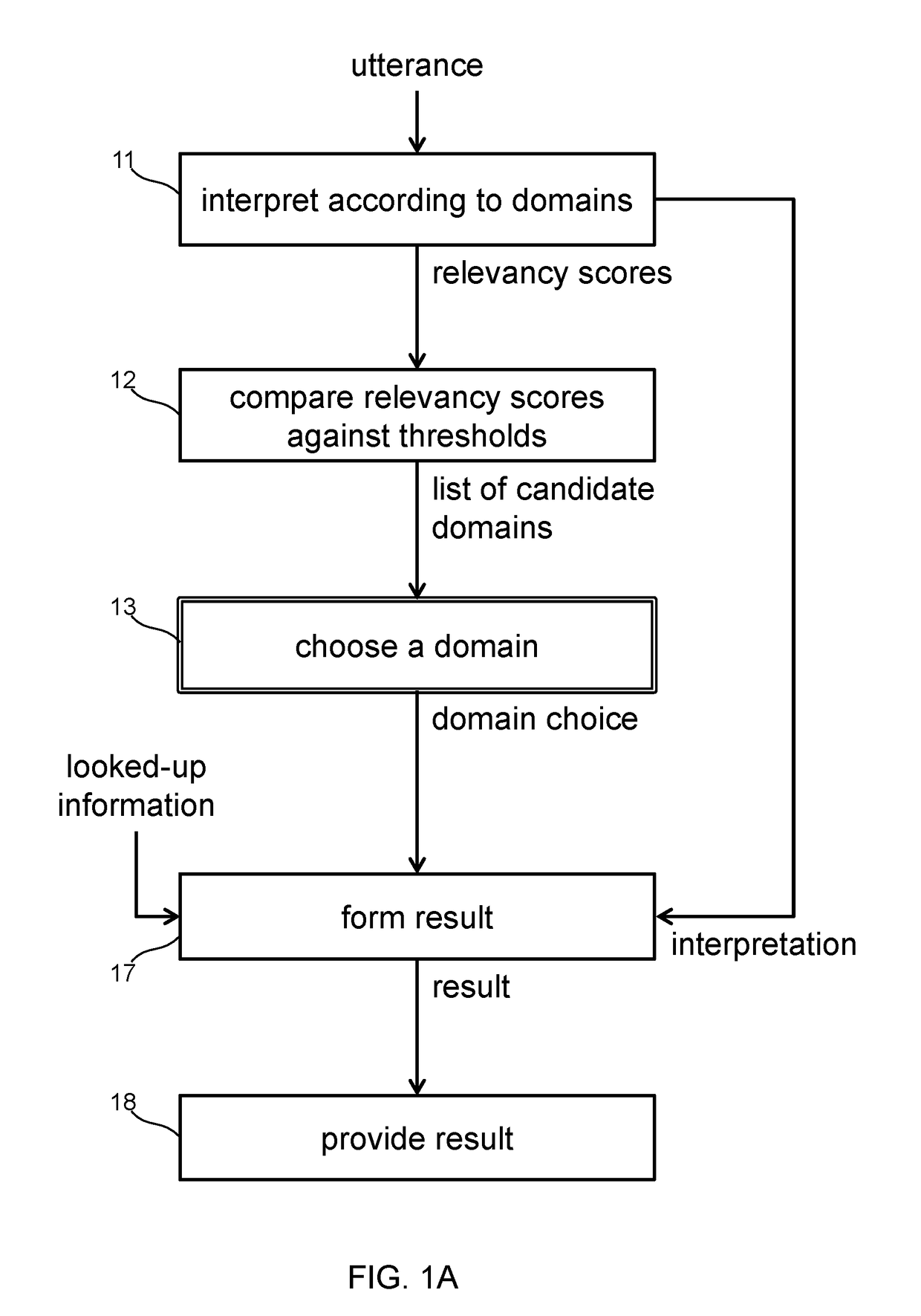
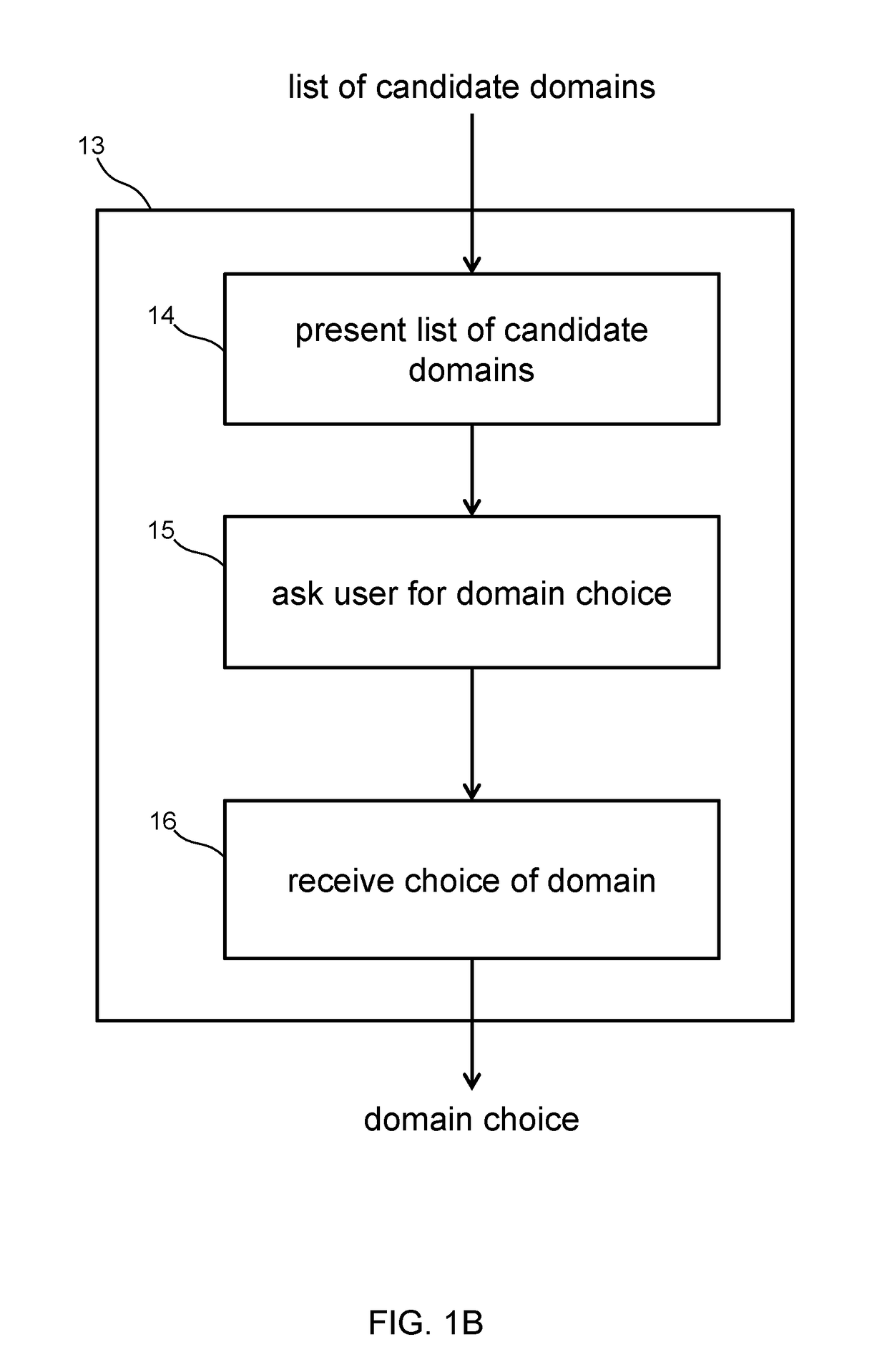
Speech-enabled system with domain disambiguation
Systems perform methods of interpreting spoken utterances from a user and responding to the utterances by providing requested information or performing a requested action. The utterances are interpreted in the context of multiple domains. Each interpretation is assigned a relevancy score based on how well the interpretation represents what the speaker intended. Interpretations having a relevancy score below a threshold for its associated domain are discarded. A remaining interpretation is chosen based on choosing the most relevant domain for the utterance. The user may be prompted to provide disambiguation information that can be used to choose the best domain. Storing past associations of utterance representation and domain choice allows for measuring the strength of correlation between uttered words and phrases with relevant domains. This correlation strength information may allow the system to automatically disambiguate alternate interpretations without requiring user input.
Owner:SOUNDHOUND AI IP LLC
Peer shared server event notification system and methods
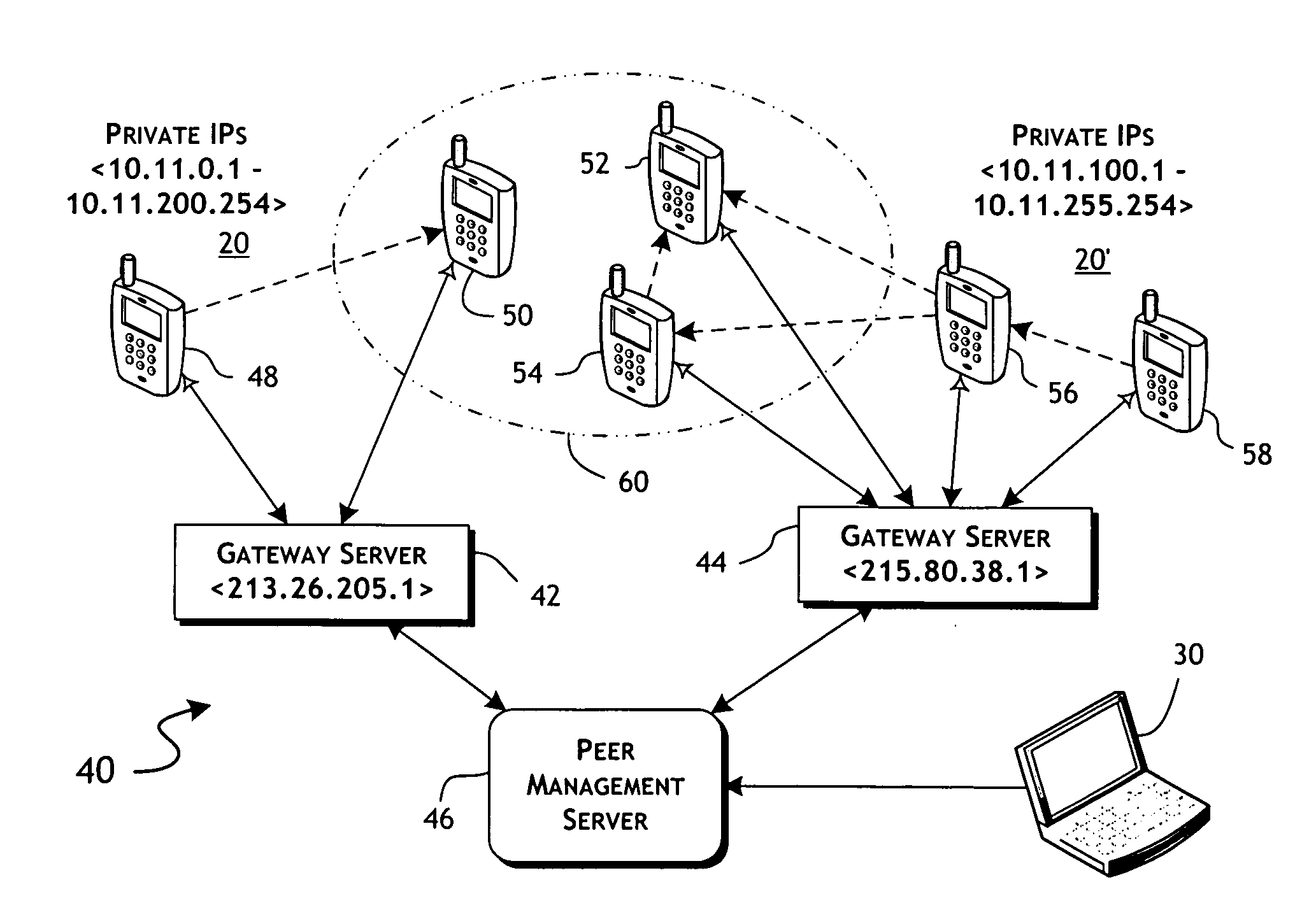
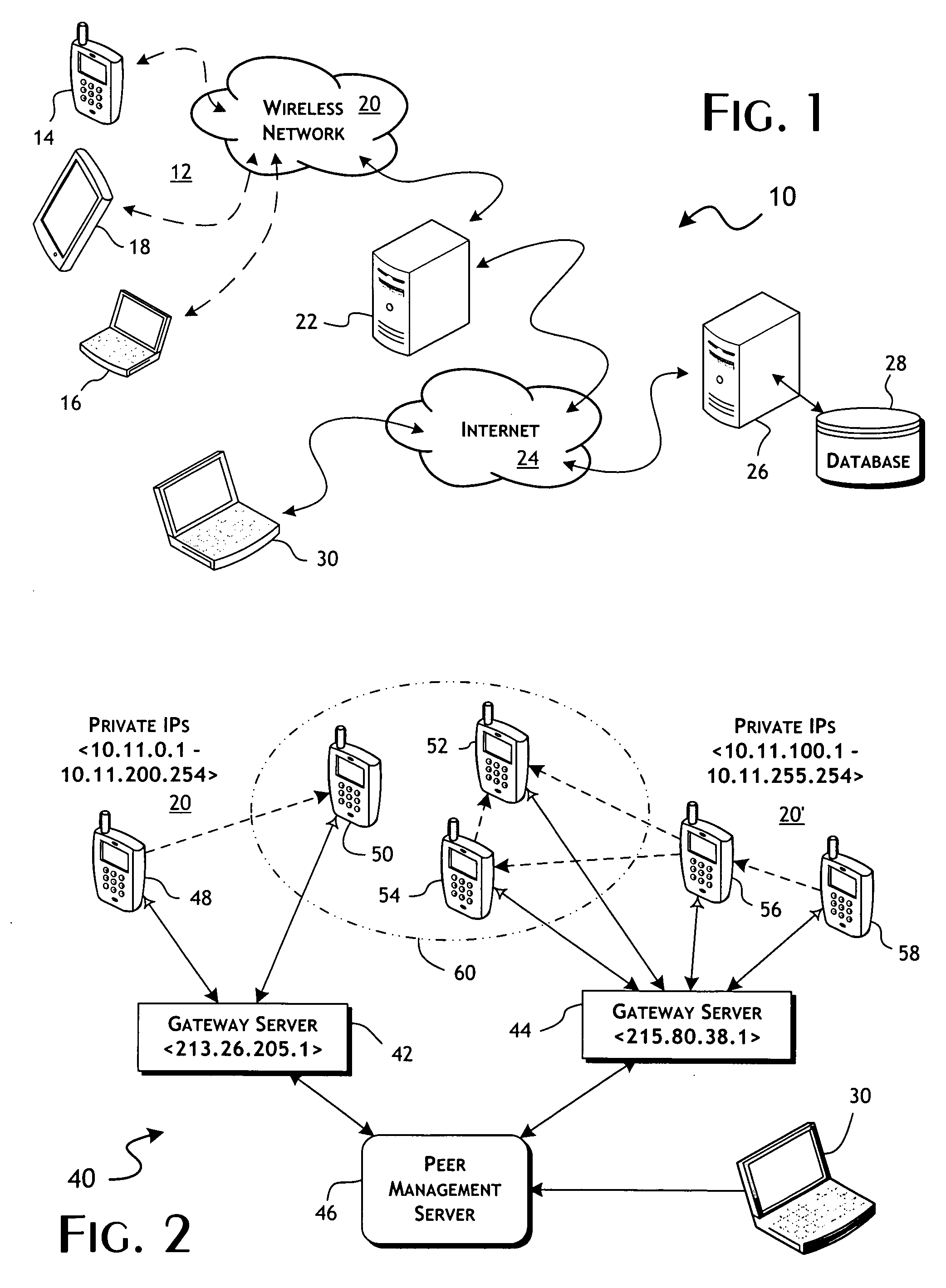
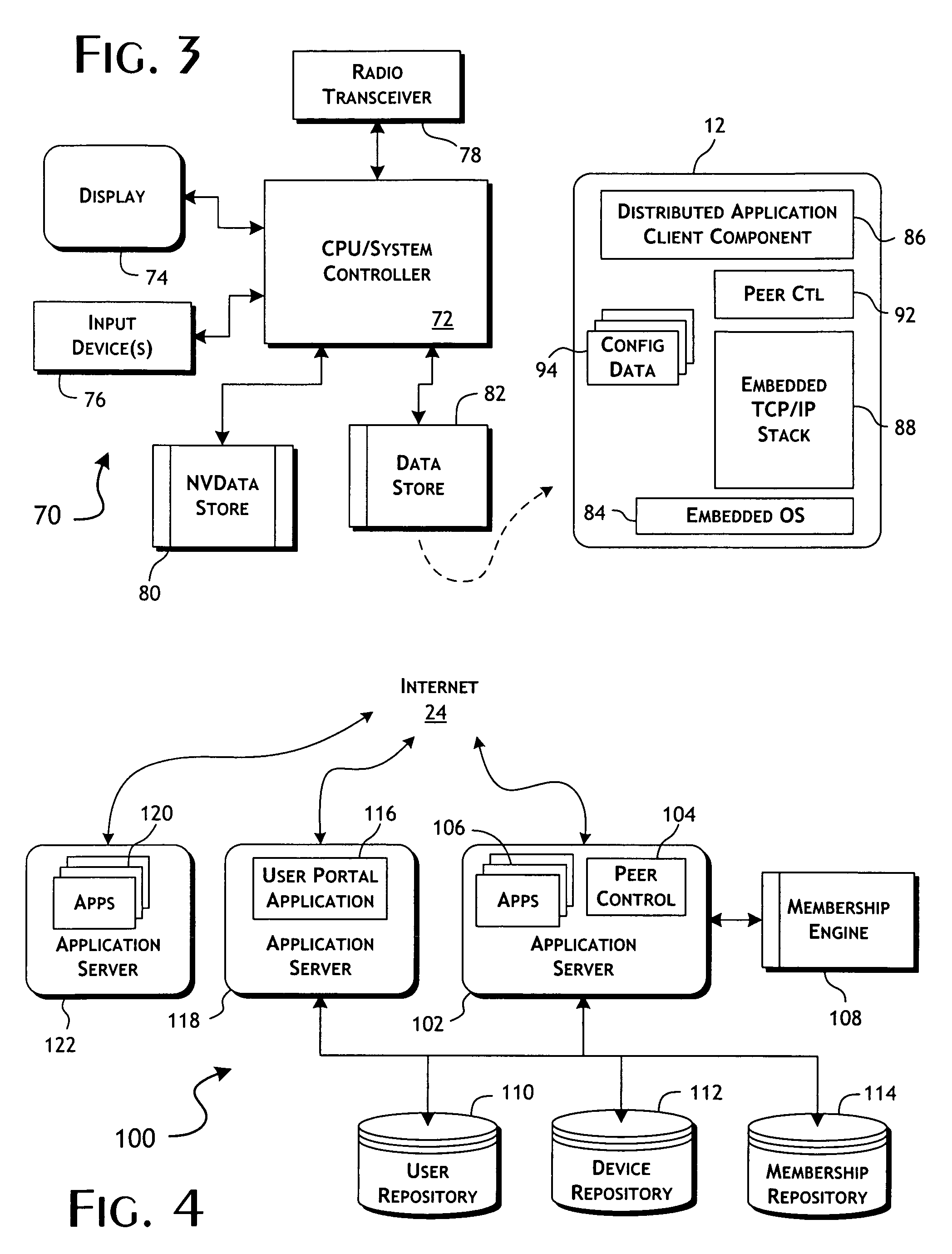
InactiveUS20090282123A1Efficient implementationConvenient timeMultiple digital computer combinationsData switching networksRequest - actionMobile device
Peer-communicated notices of requested actions are distributed to mobile devices on routing incompatible networks. A peer management server receives action requests for mobile devices communicated from a plurality of routing incompatible networks. In response to an action request, as received from a first mobile device, a set of one or more peer-shared notices are determined for delivery to a set of second mobile devices coupled to the same routing incompatible network. Selection of the deliverable notices is dependent on a policy identifier associated with the first mobile device. The set of notices are sent to said first mobile device for relay distribution to said set of second mobile devices utilizing the communications channel preferably as established by the first mobile device in communicating the action request. Delivery confirmation of individual peer relayed notices is preferably obtained upon receipt of an action request from the corresponding second mobile devices.
Owner:FUNAMBOL
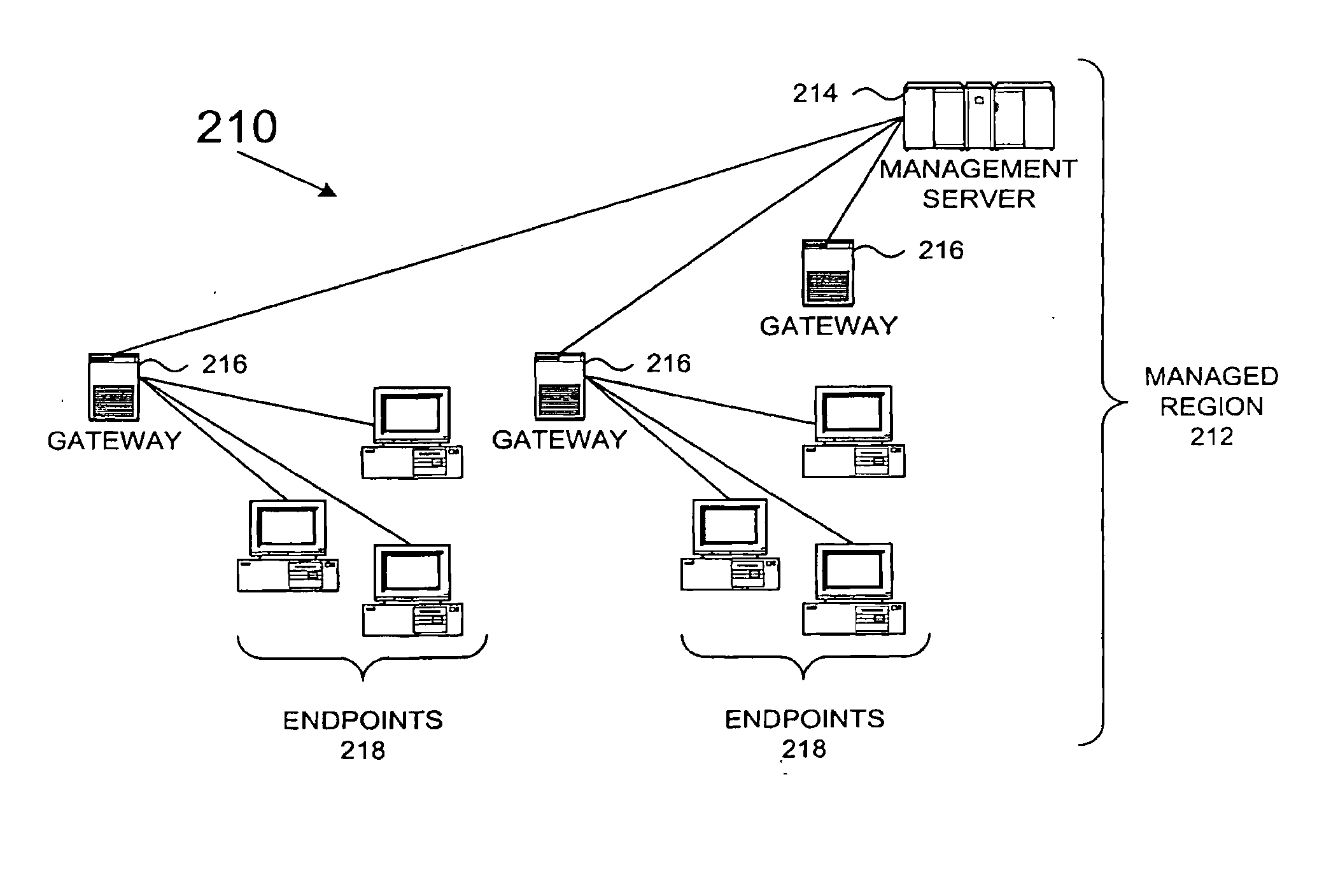
Method and System for Network Management with Platform-Independent Protocol Interface for Discovery and Monitoring Processes
InactiveUS20080301267A1Digital computer detailsData switching networksData processing systemTopology mapping
A method, system, apparatus, and computer program product is presented for management of a distributed data processing system. An action at a target device is requested, and the completion of the action depends upon communication protocol operations on a set of devices along a logical route through the distributed data processing system. A set of supported protocols that are common to the set of devices along the logical route are identified, and a subset of supported protocols in the set of supported protocols that can be used to complete the action is then identified. An allowable supported protocol is selected for the action based on the type of requested action, after which the requesting application may use the action in accordance with the selected allowable supported protocol, e.g., to monitor or discover the target device. A topology mapping is used to derive an endpoint-to-endpoint route for completing the requested action. A comparison of assigned priorities of each allowable supported protocol may be performed to choose the selected allowable supported protocol.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com