Patents
Literature
718 results about "Access token" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
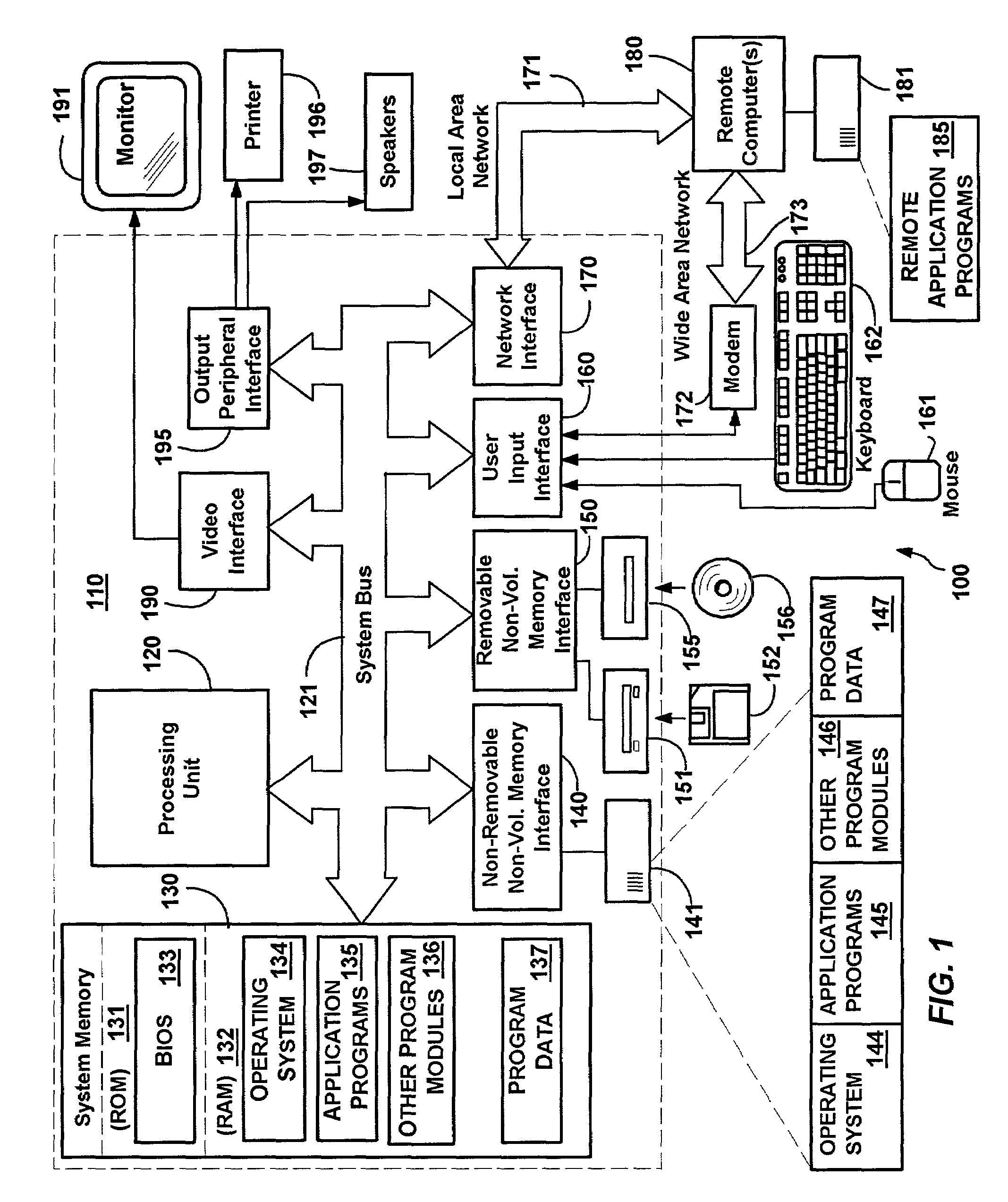
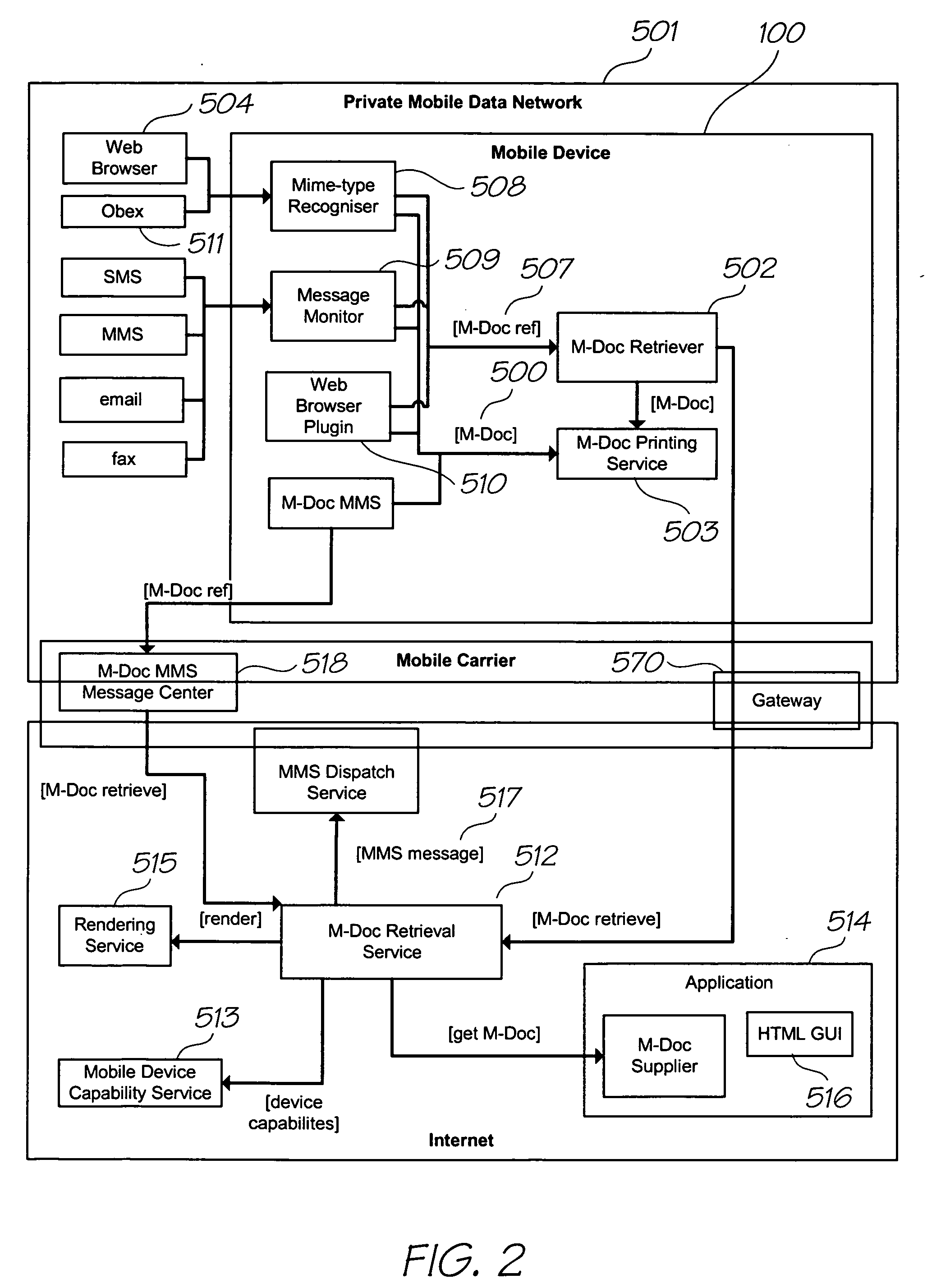
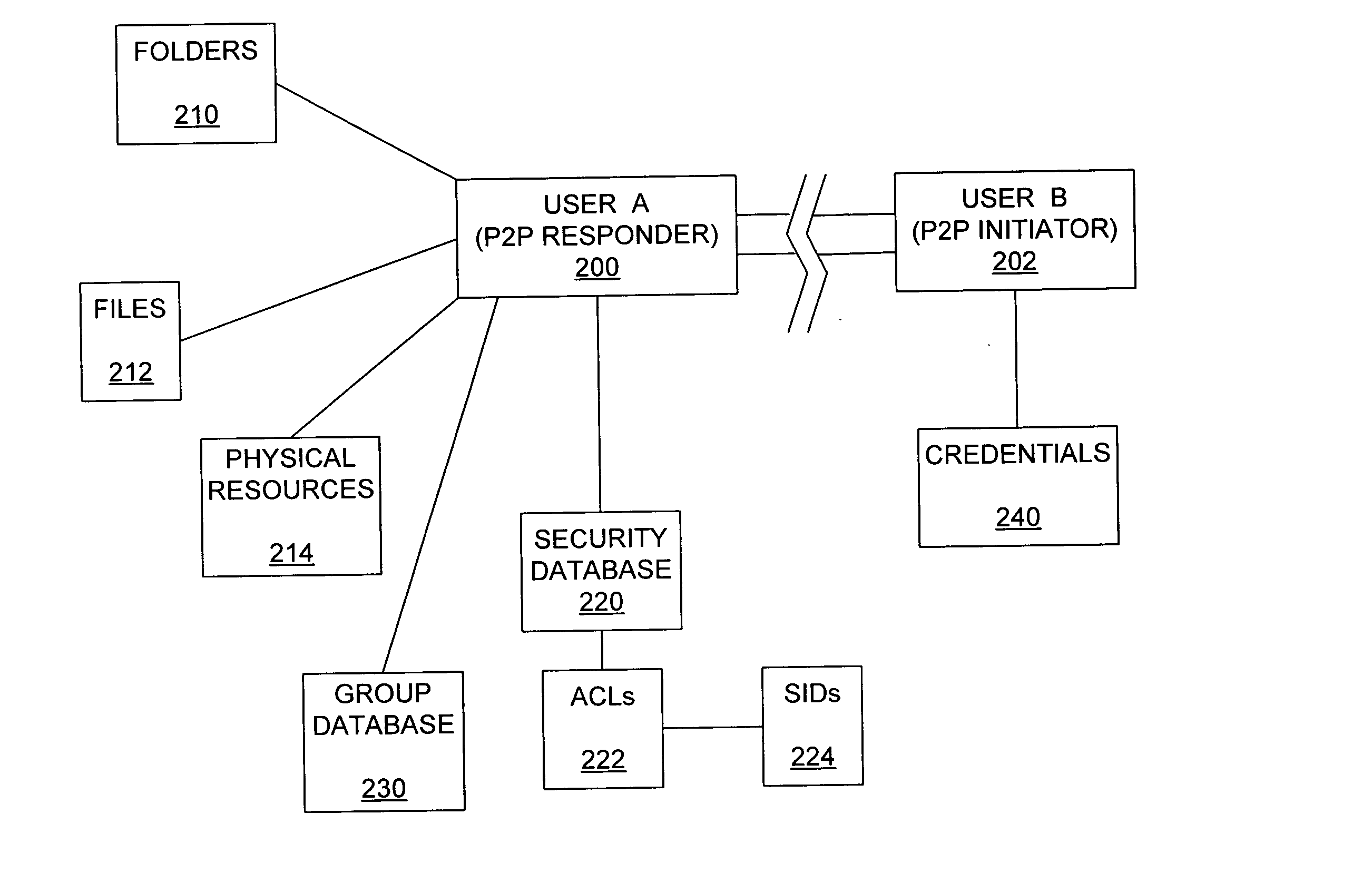
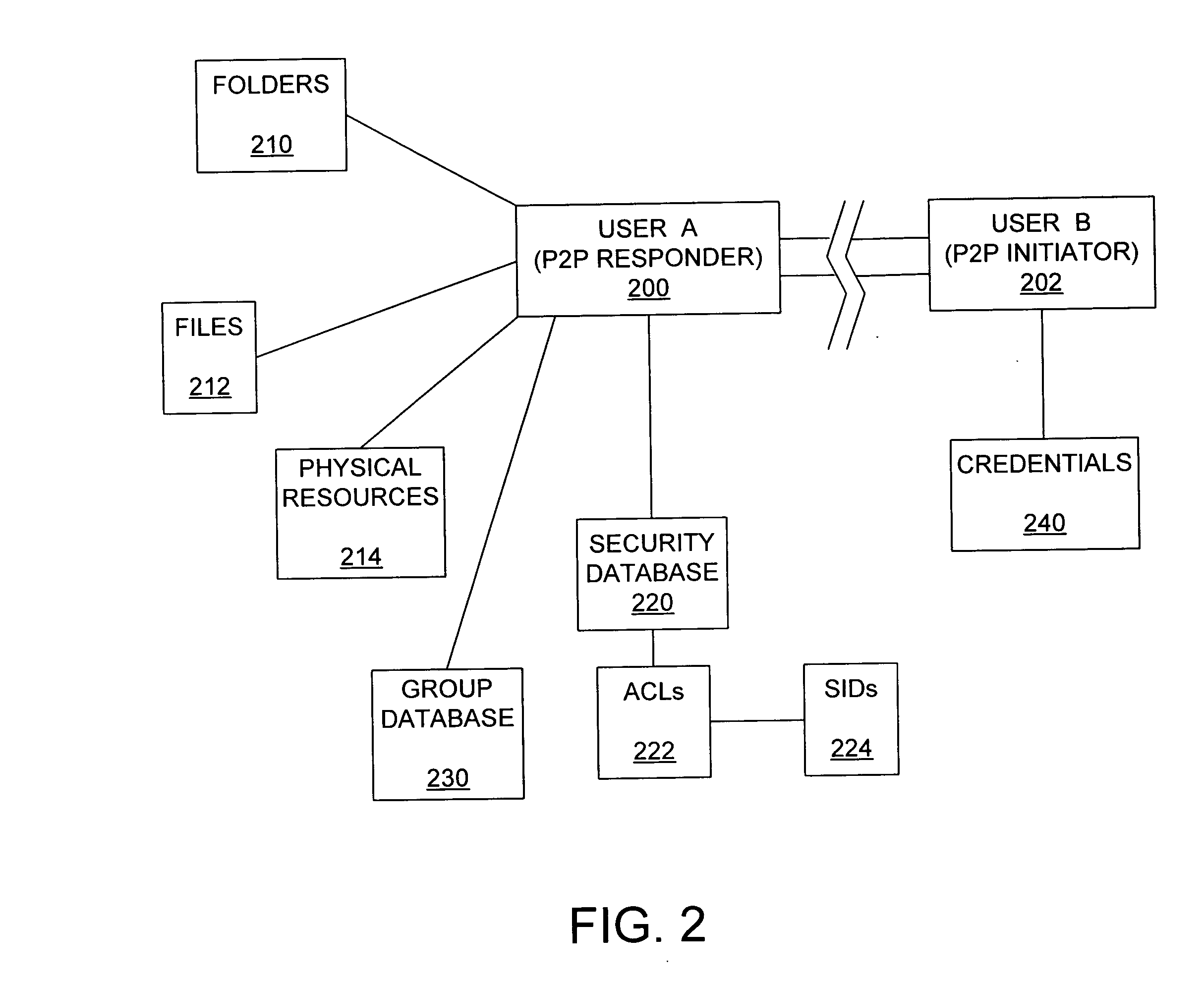
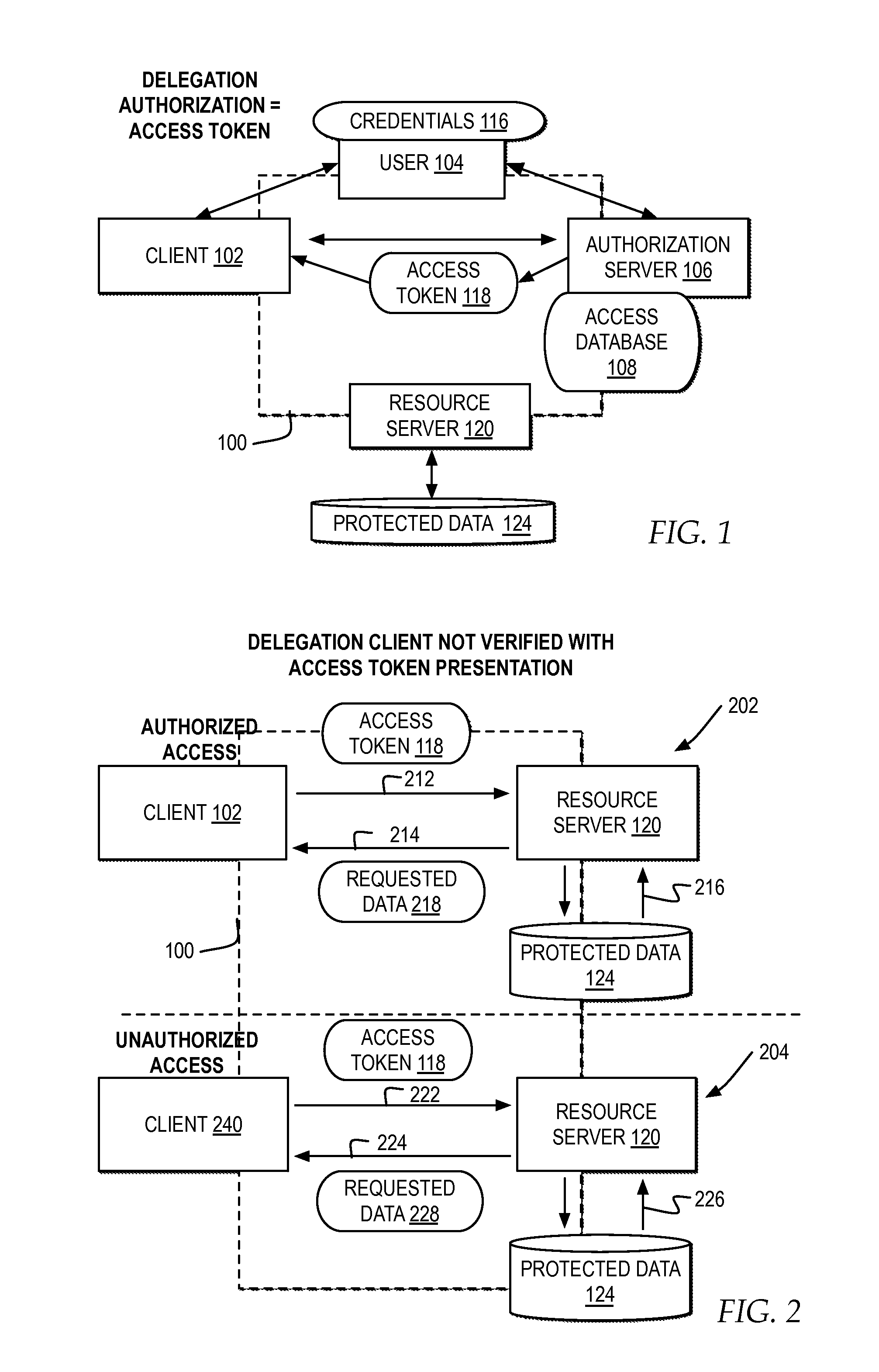
In computer systems, an access token contains the security credentials for a login session and identifies the user, the user's groups, the user's privileges, and, in some cases, a particular application. Typically one may be asked to enter the access token (for example a 40 character long gibberish) rather than the usual password (it therefore should be kept secret just like a password).
Bundled authorization requests
ActiveUS20150089569A1Easy to customizeDigital data processing detailsMultiple digital computer combinationsInternet privacyAccess token
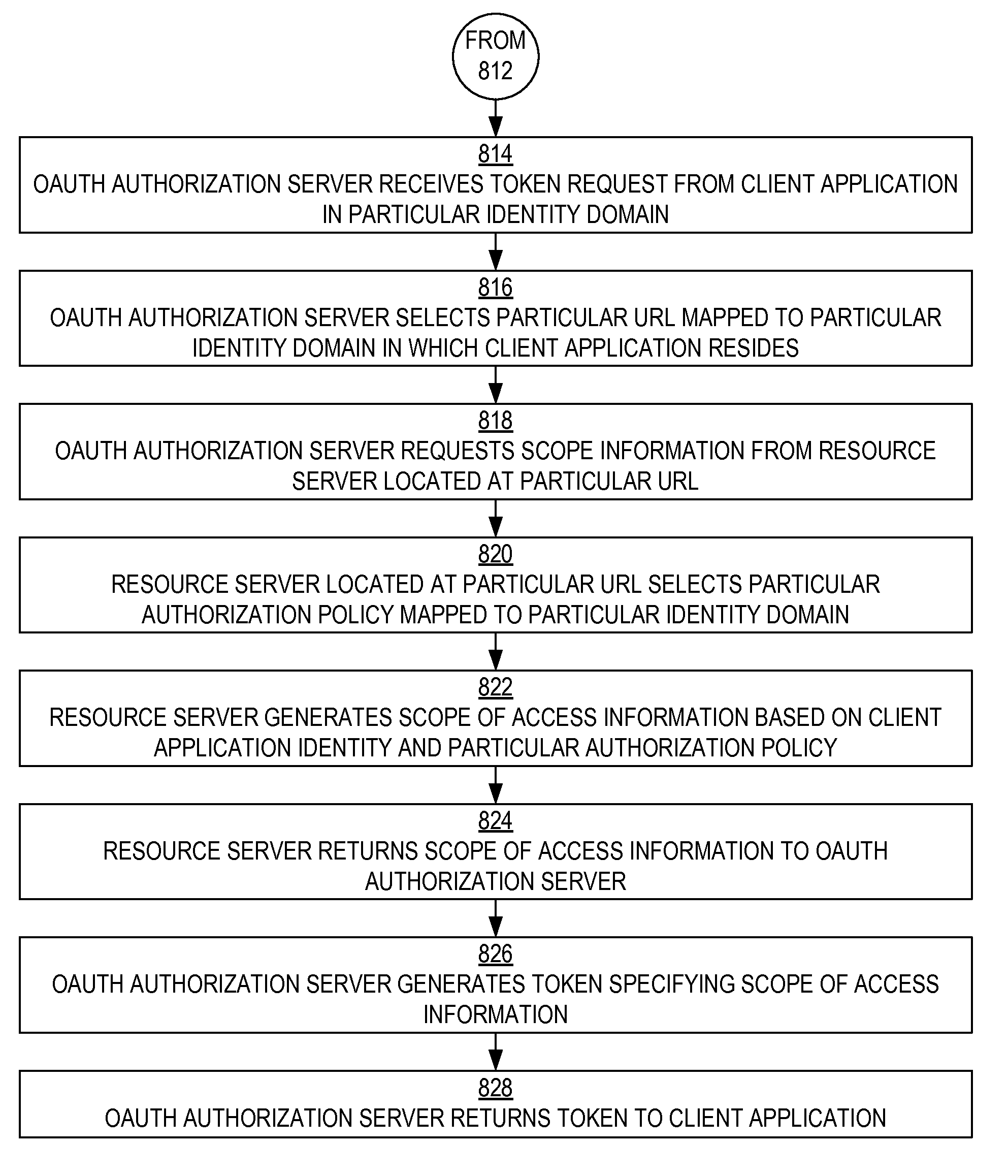
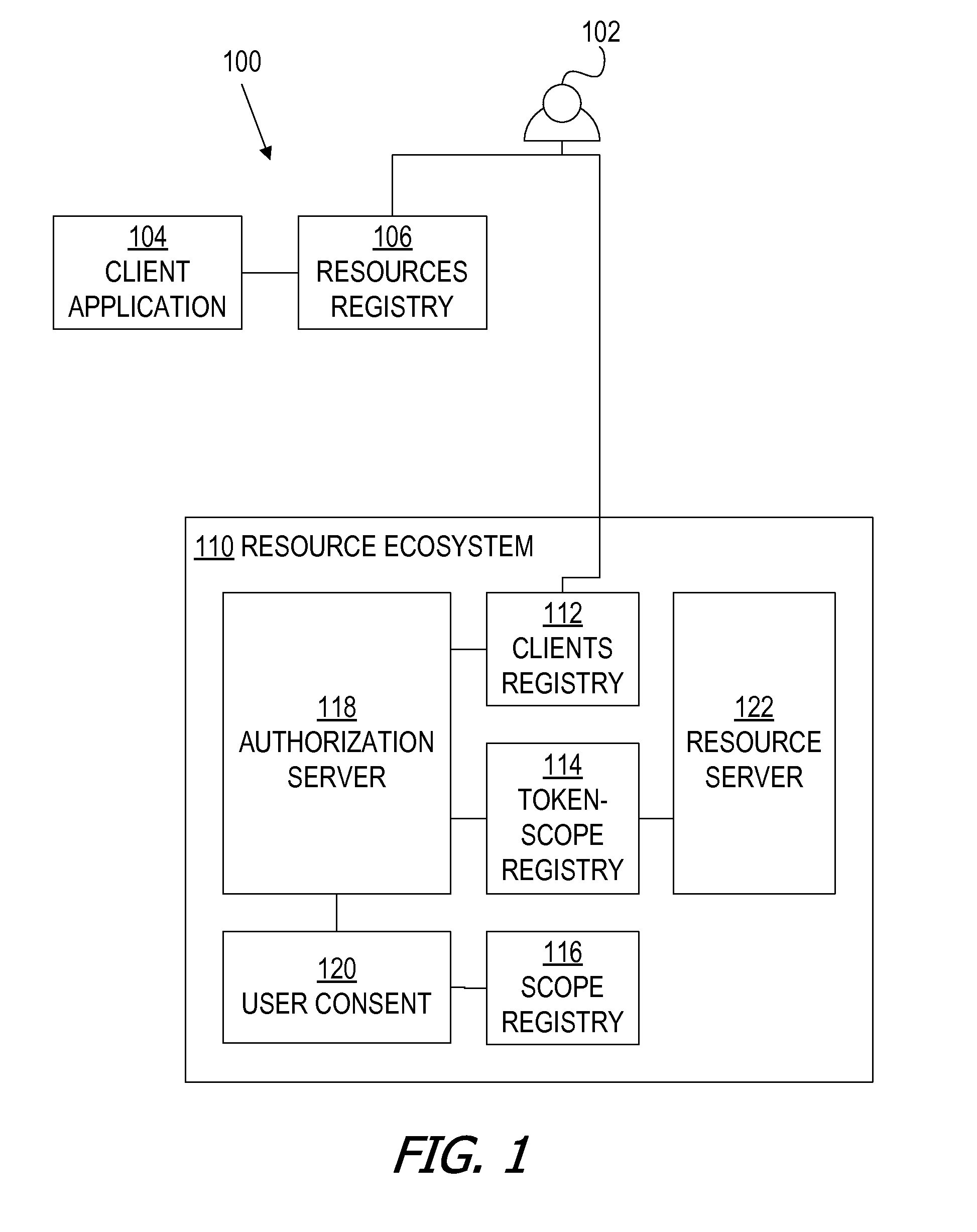
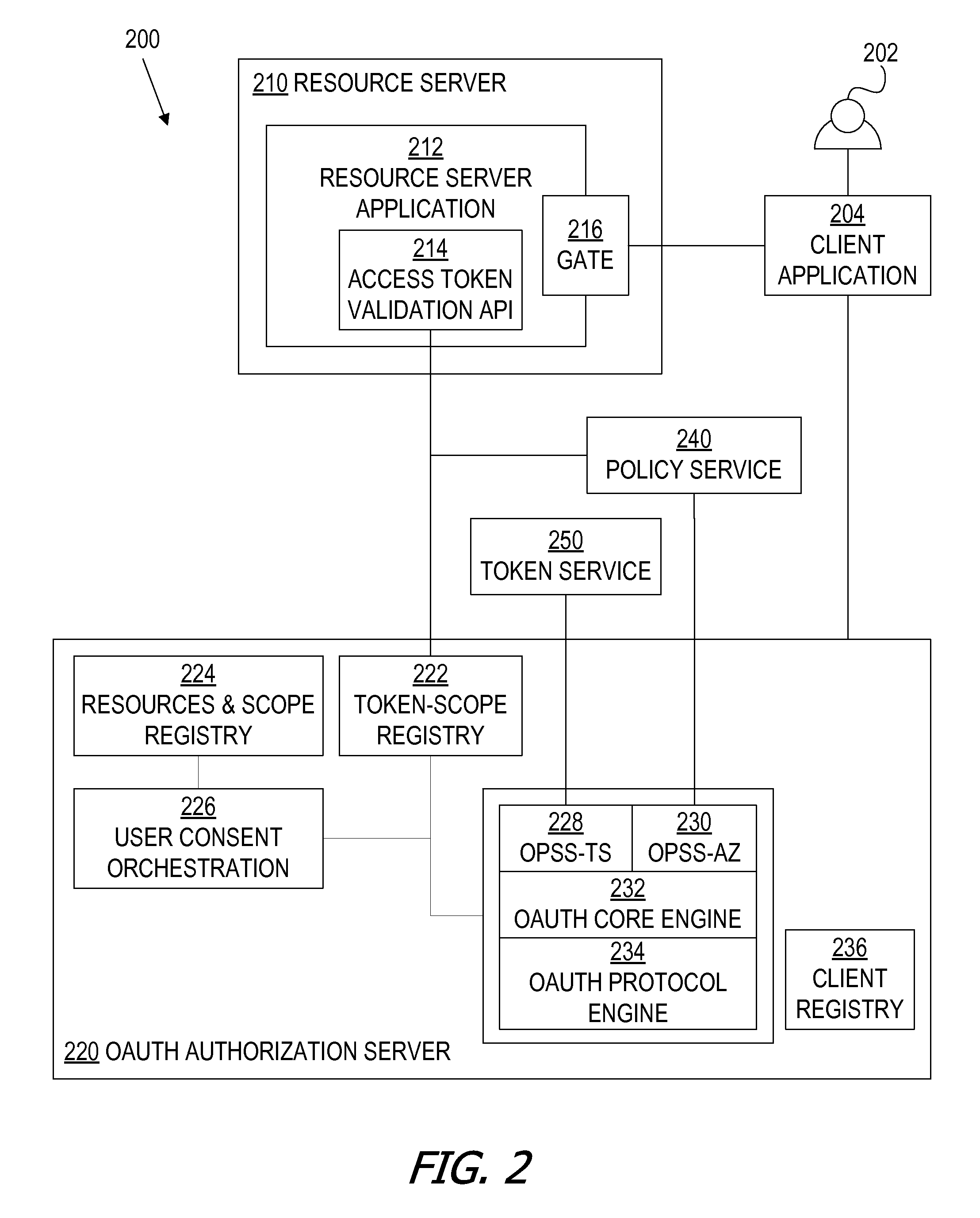
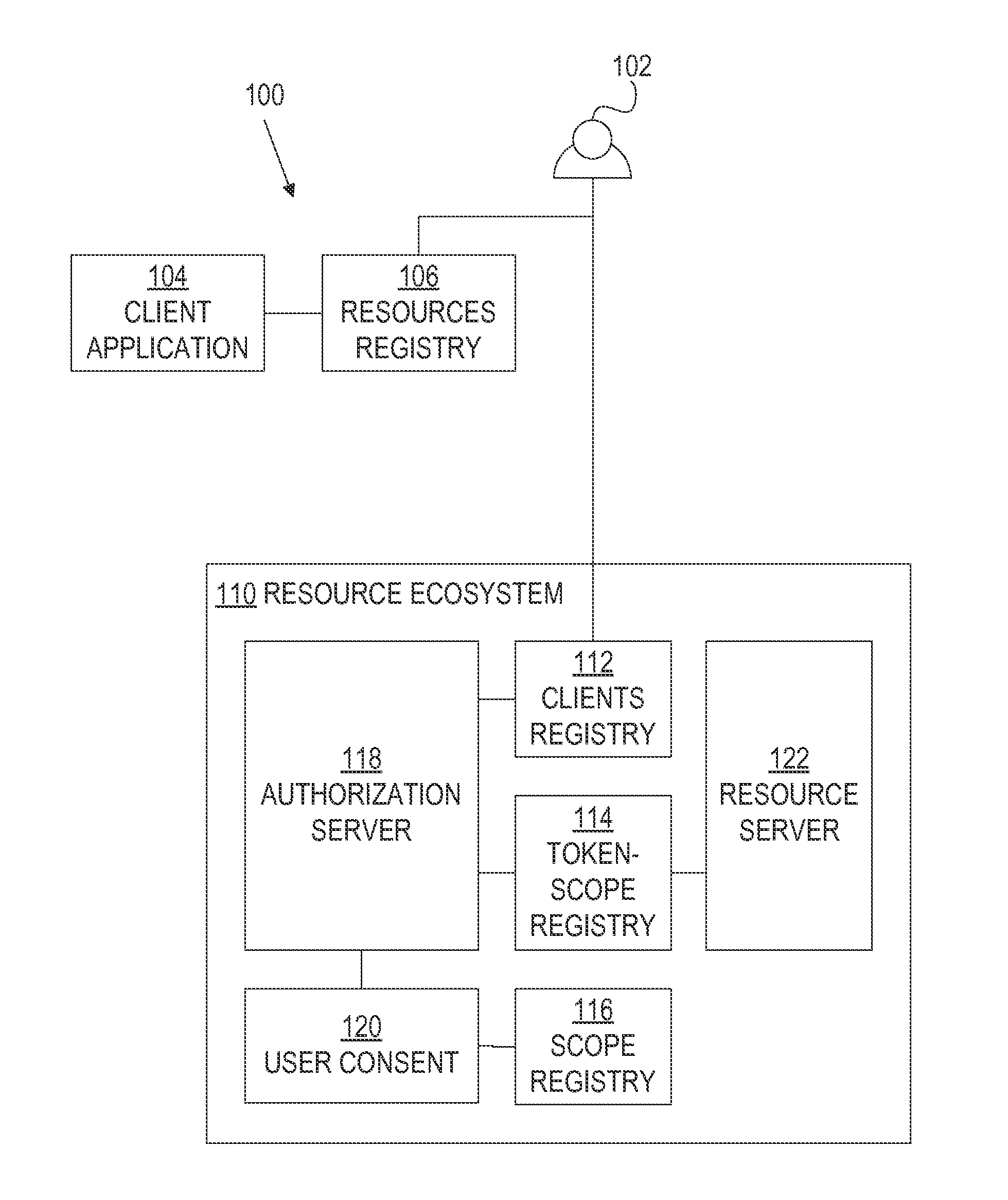
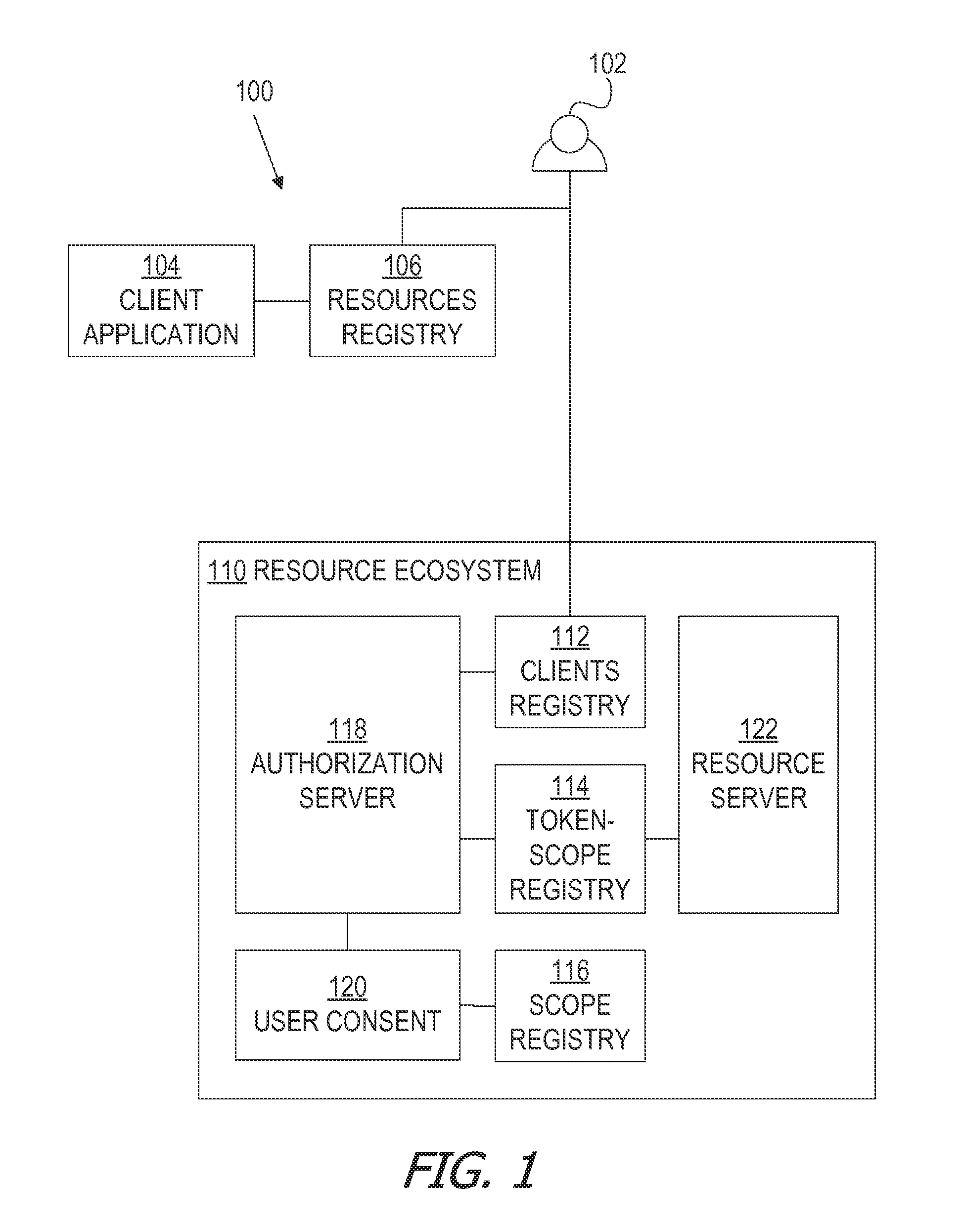
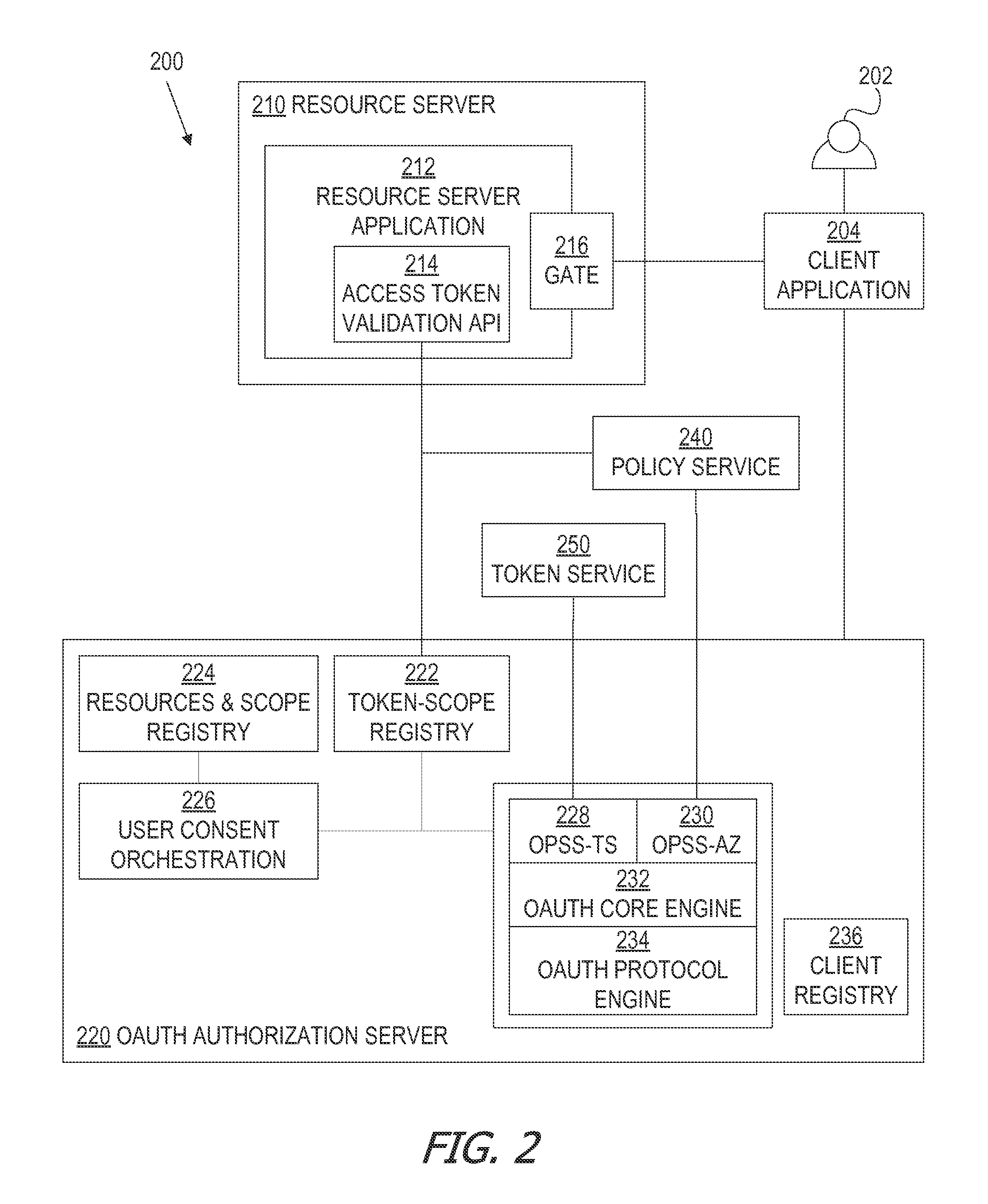
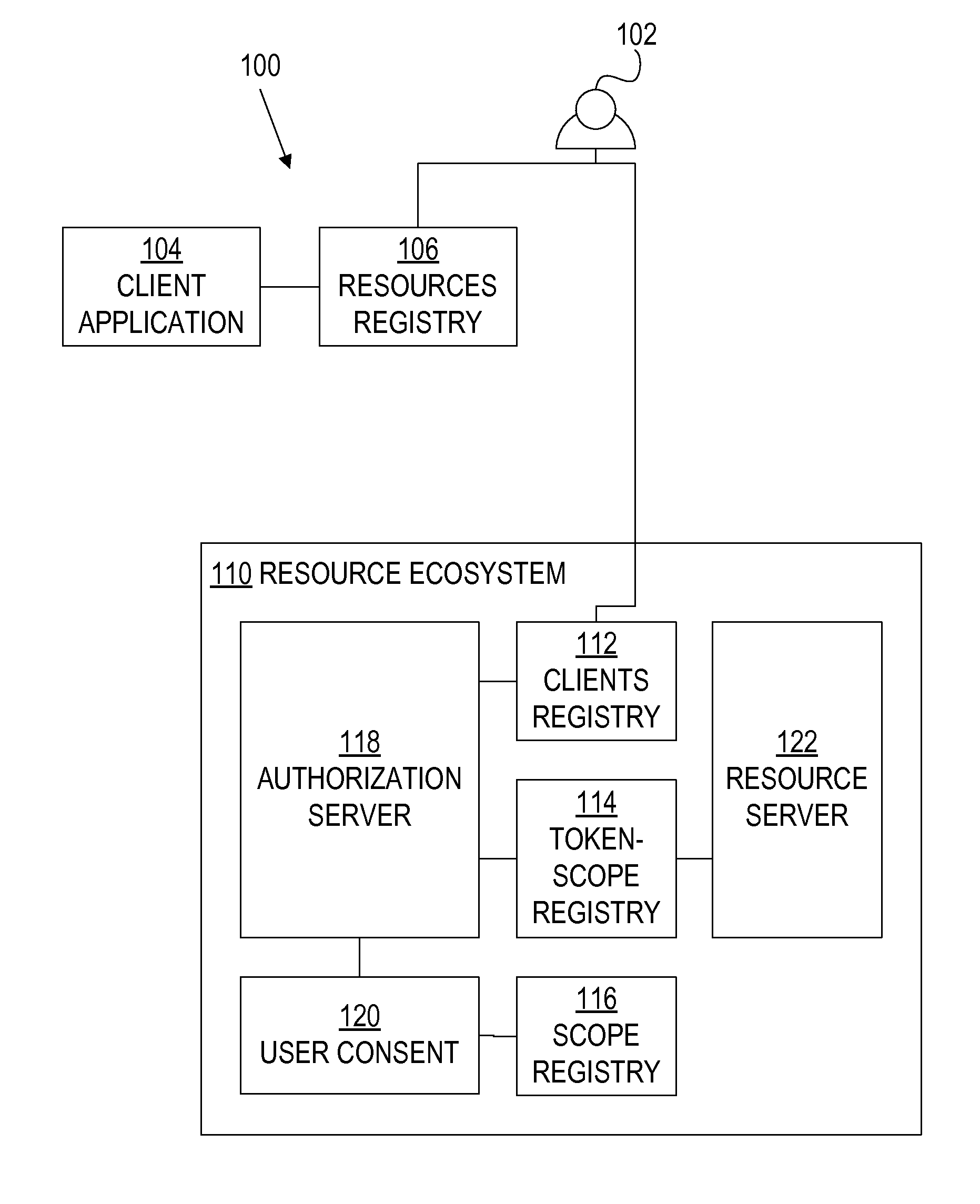
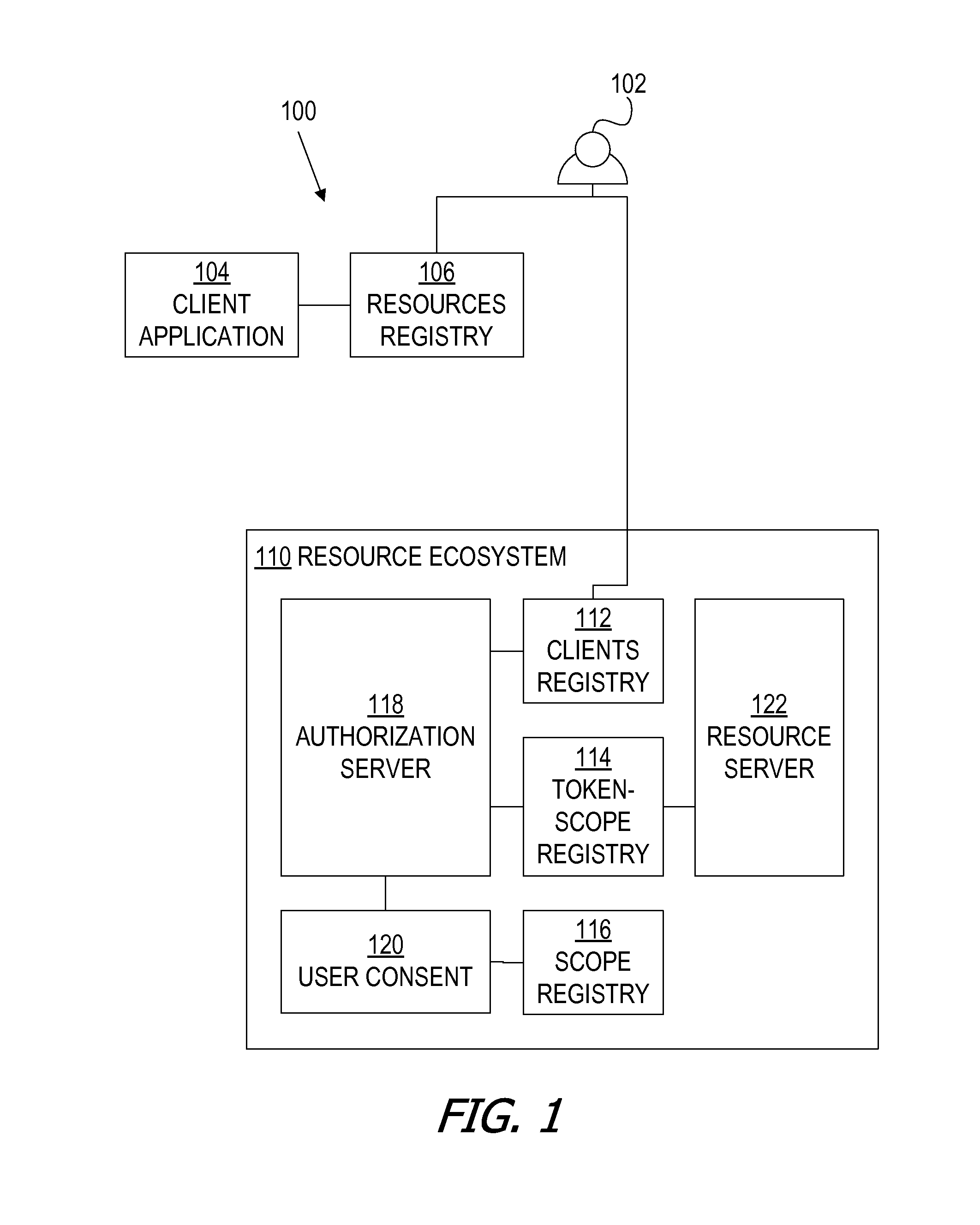
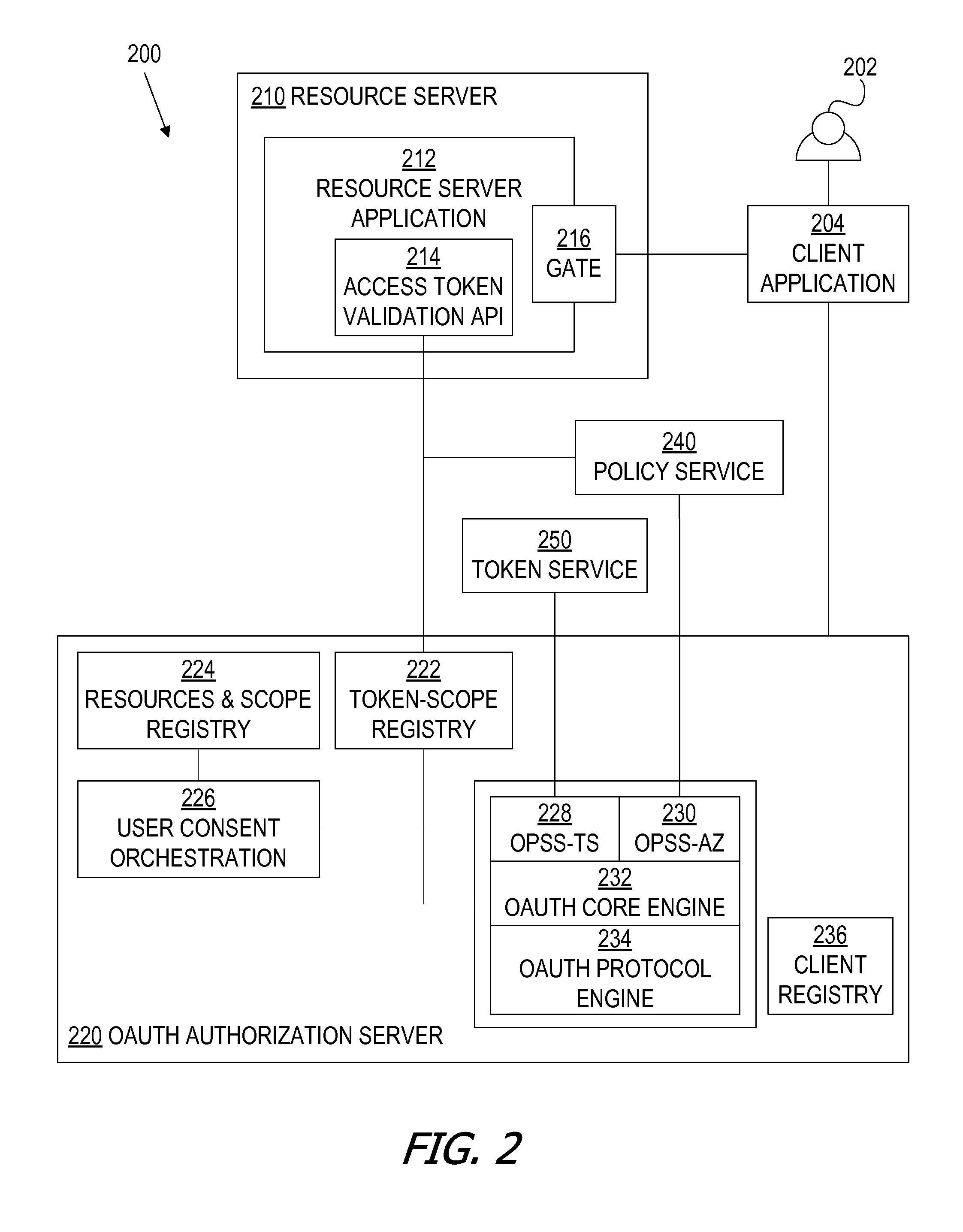
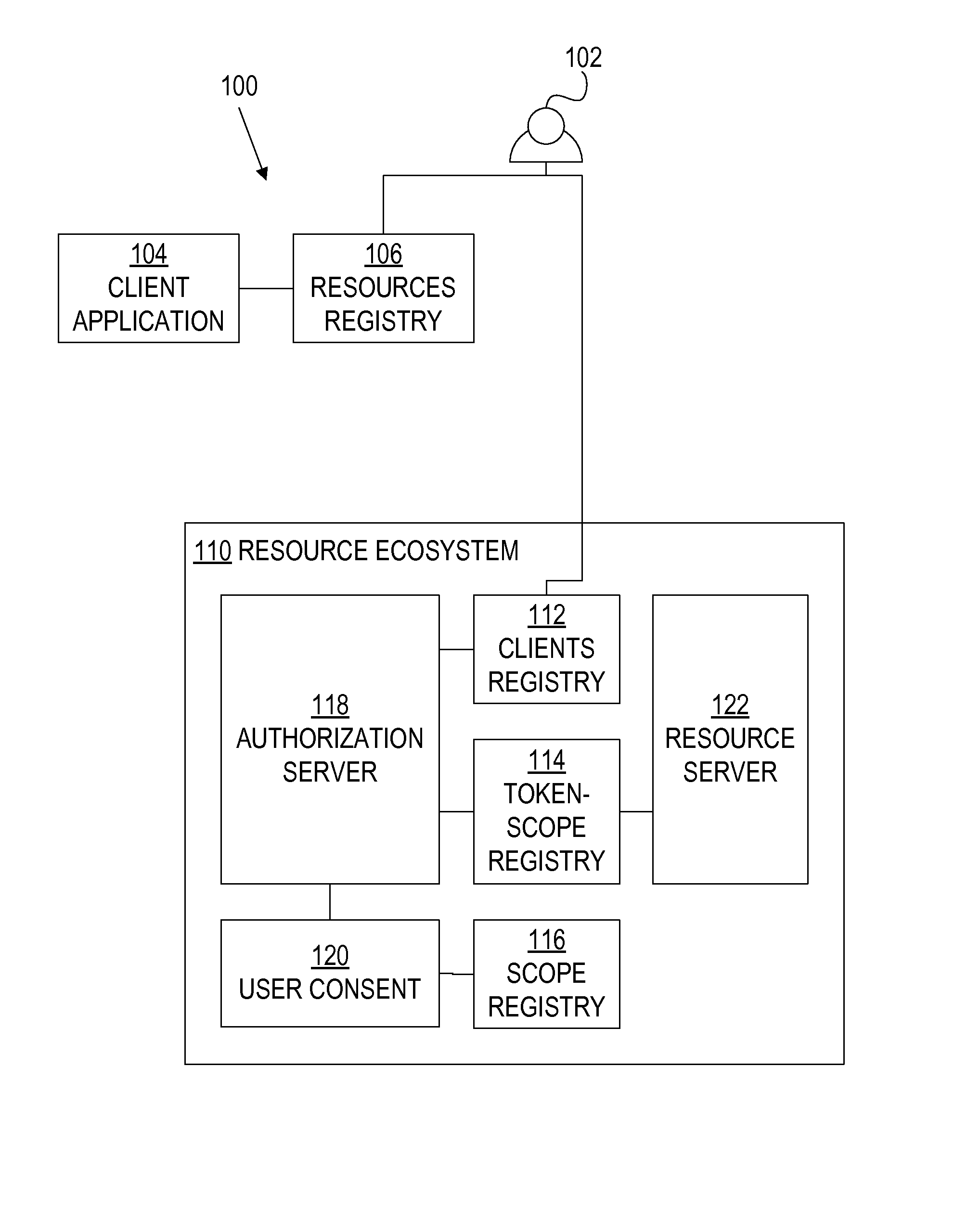
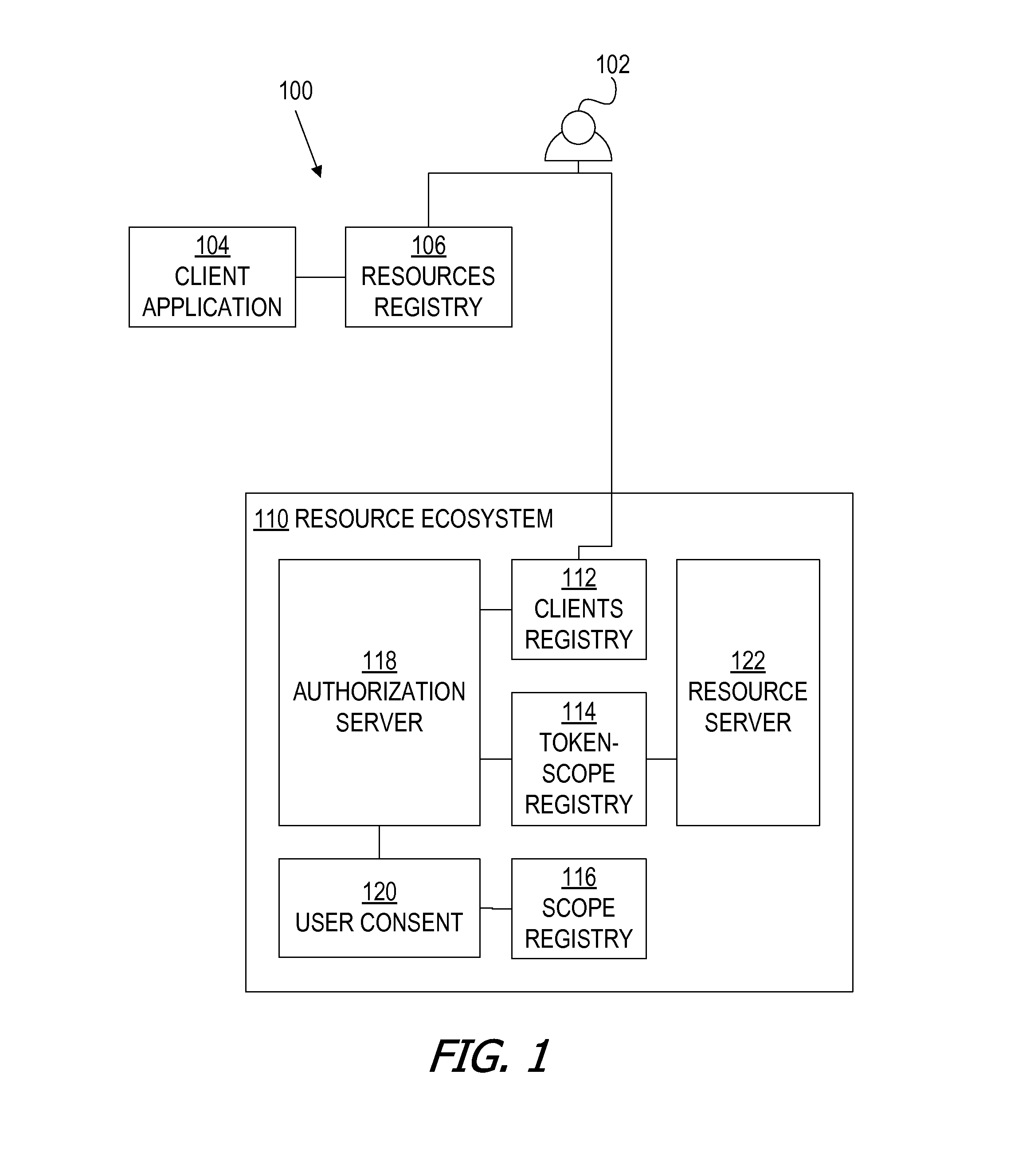
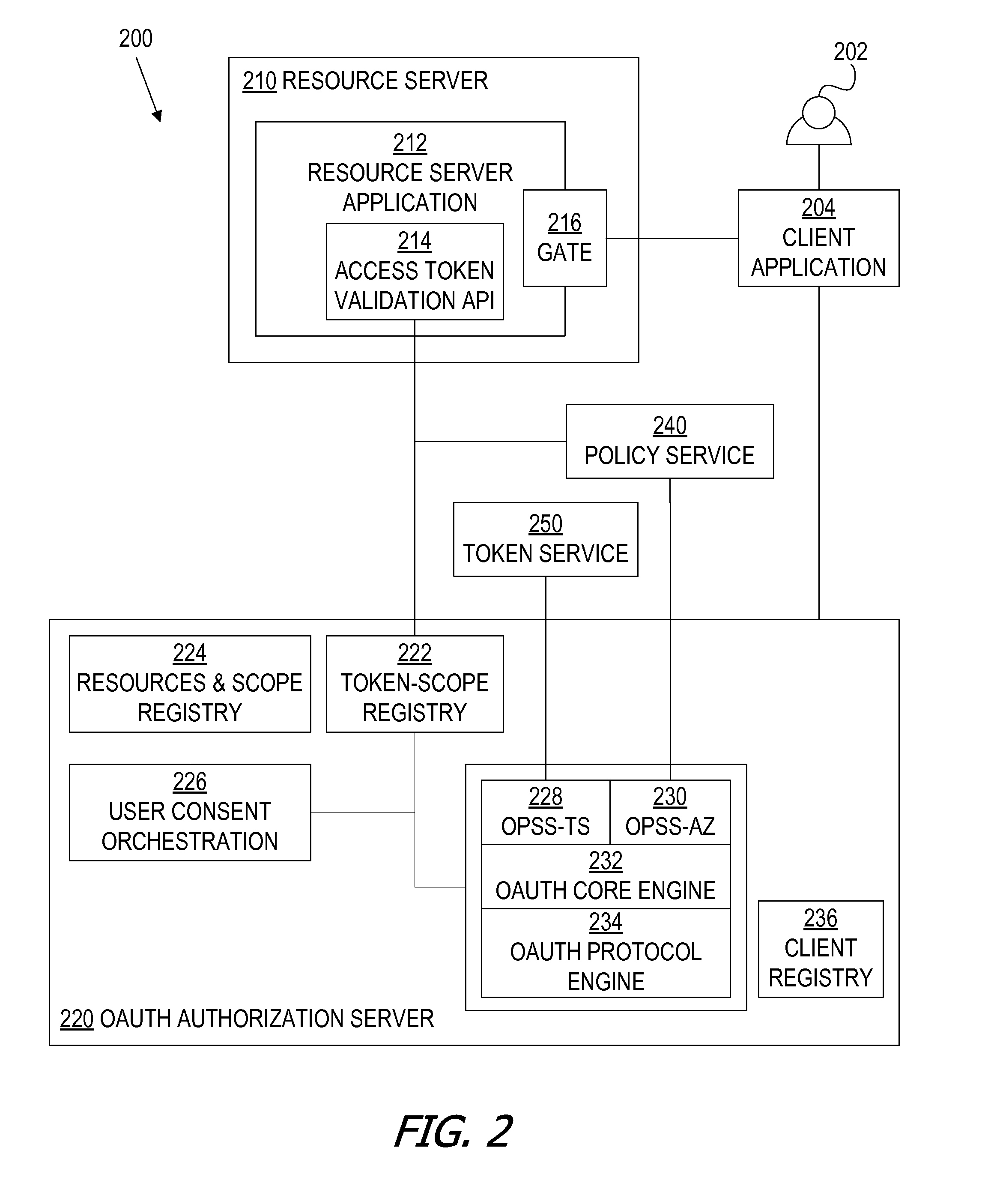
A framework, which conforms to the OAuth standard, involves a generic OAuth authorization server that can be used by multiple resource servers in order to ensure that access to resources stored on those resource servers is limited to access to which the resource owner consents. Each resource server registers, with the OAuth authorization server, metadata for that resource server, indicating scopes that are recognized by the resource server. The OAuth authorization server refers to this metadata when requesting consent from a resource owner on behalf of a client application, so that the consent will be of an appropriate scope. The OAuth authorization server refers to this metadata when constructing an access token to provide to the client application for use in accessing the resources on the resource server. The OAuth authorization server uses this metadata to map issued access tokens to the scopes to which those access tokens grant access.
Owner:ORACLE INT CORP
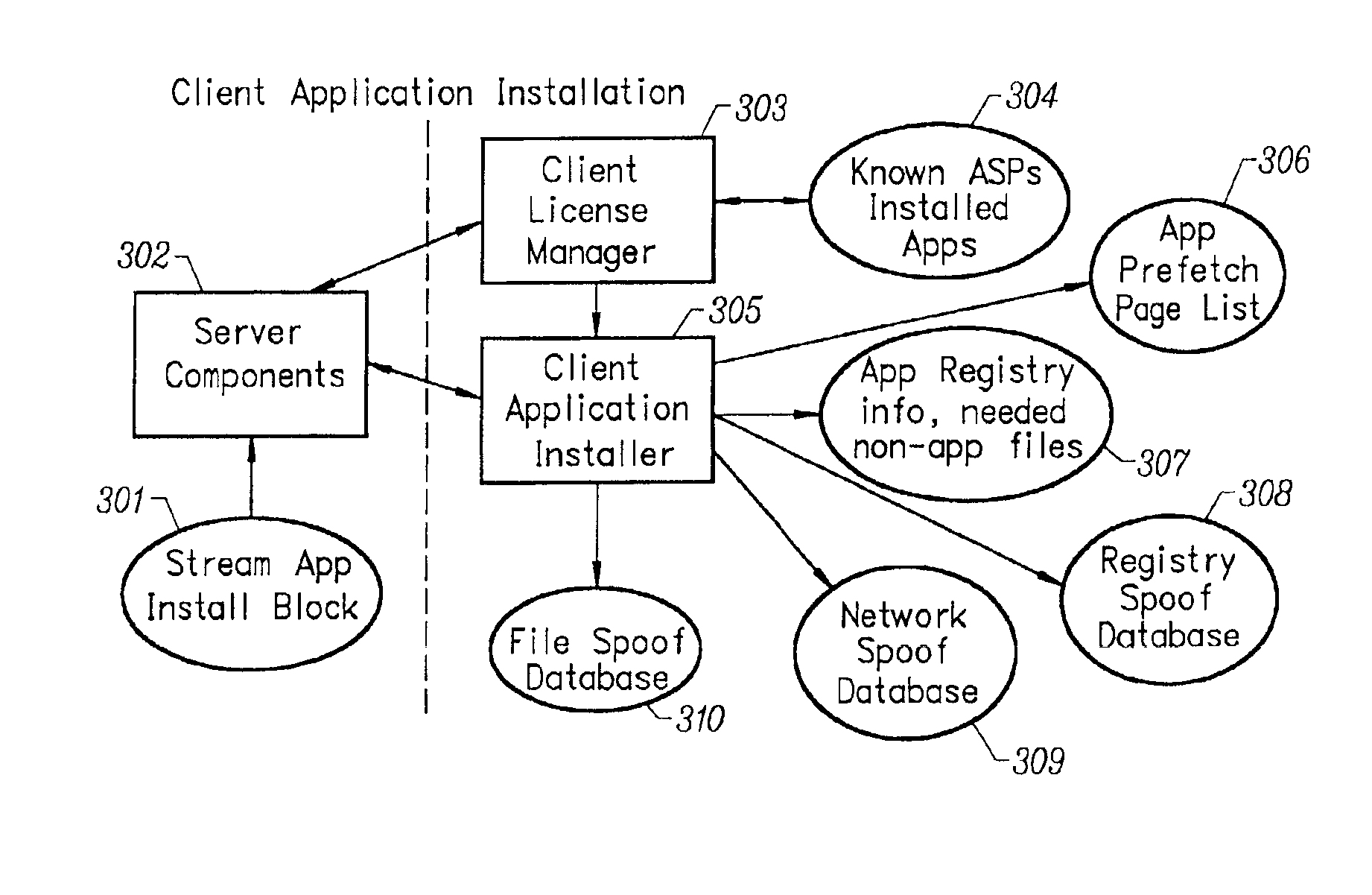
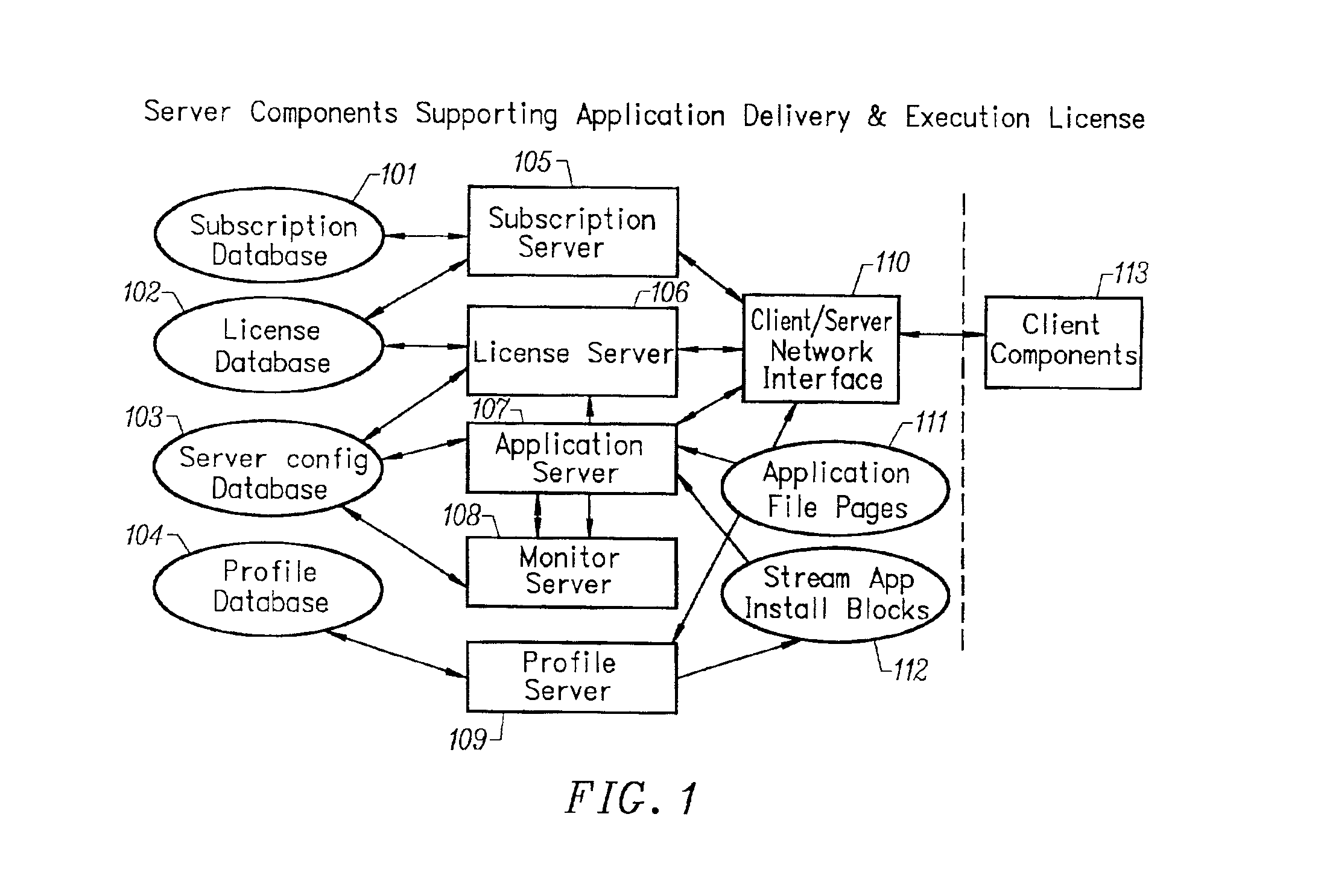
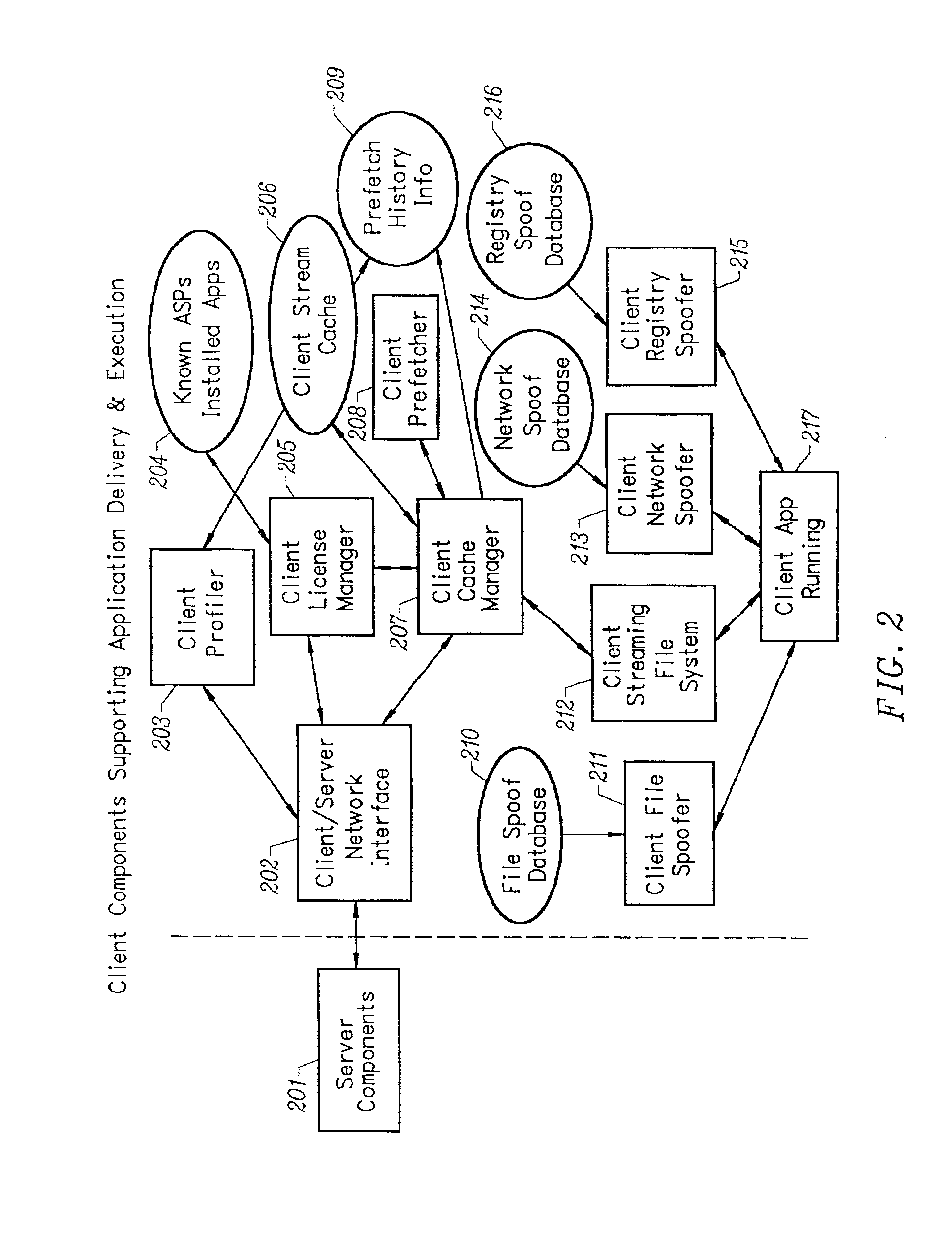
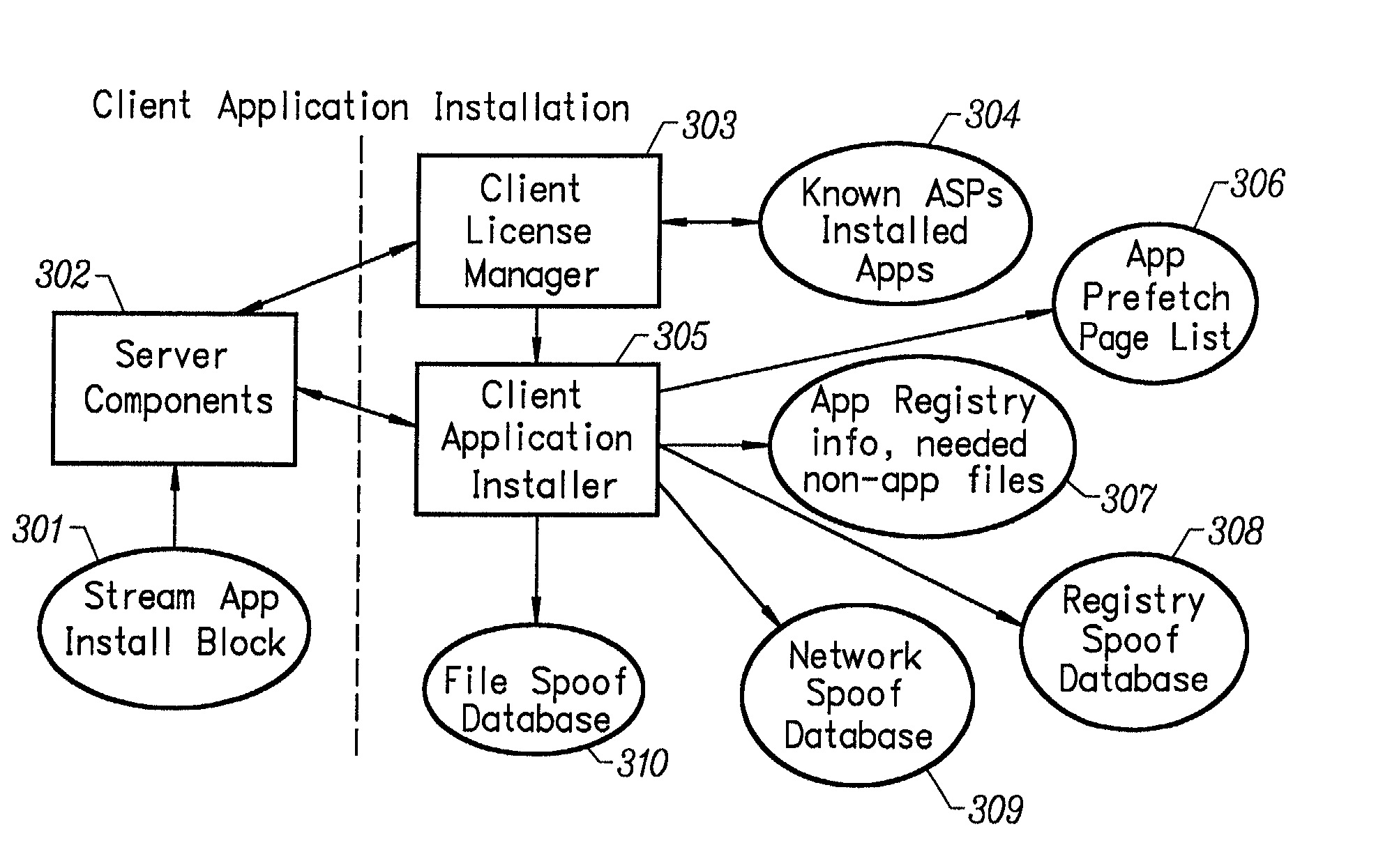
Client installation and execution system for streamed applications
InactiveUS6918113B2Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
Secure storage access using third party capability tokens
ActiveUS8042163B1Digital data processing detailsMultiple digital computer combinationsThird partyClient-side
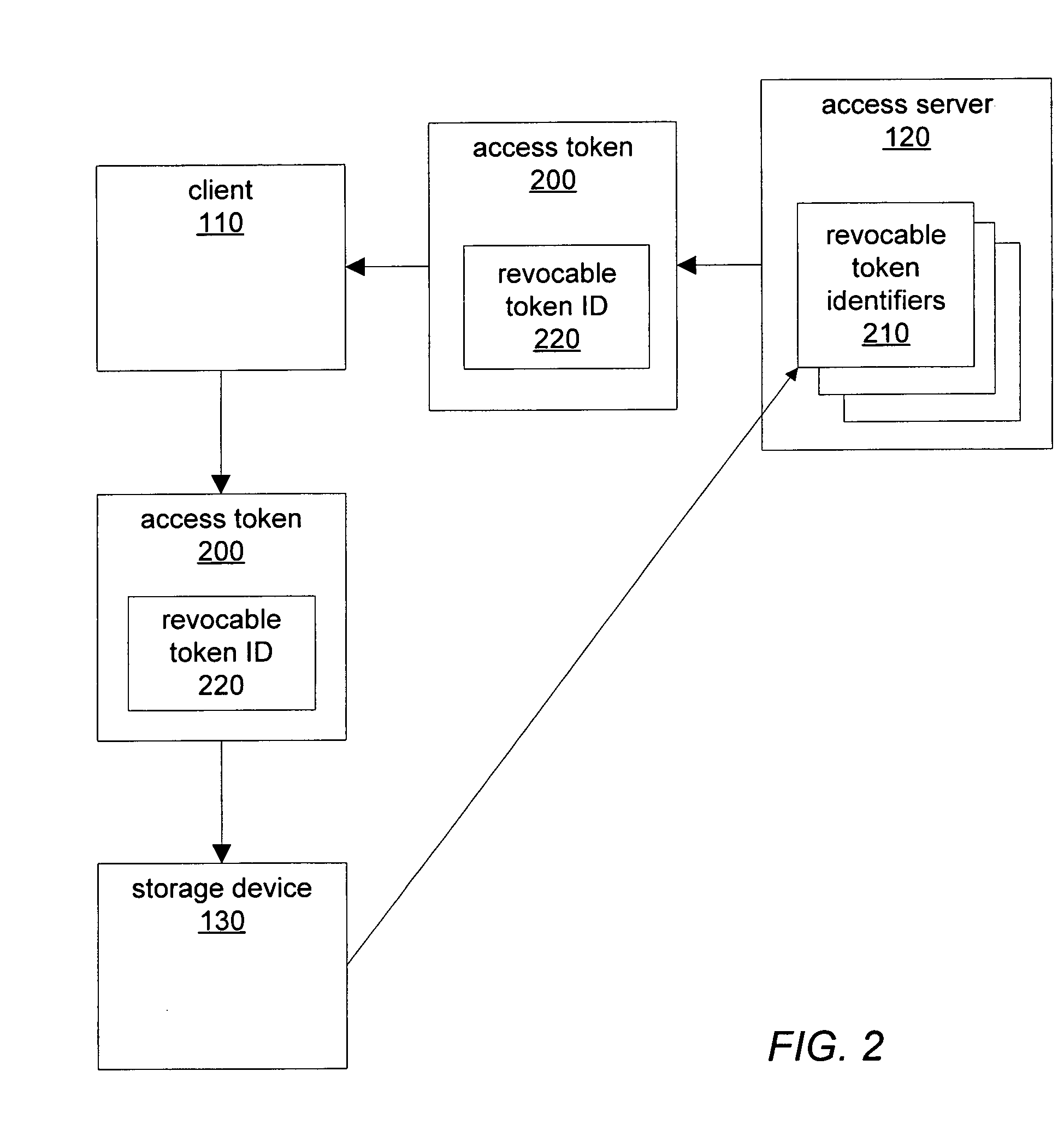
A method for revocable token identifiers may be employed in a shared storage environment. An access server may generate access tokens and include revocable token identifiers previously obtained from storage devices. When clients present access tokens to storage devices during storage requests, storage devices may check the validity of access tokens by verifying that the revocable token identifiers were previously issued to the access server. An access server may request that the storage device revoke revocable token identifiers. Storage devices may deny any future storage requests including revoked token identifiers. Additionally, an access token may include instructions specifying operations for a storage device to perform in conjunction with a storage request. A trusted server may issue grantor tokens granting permissions for access servers to use when issuing access tokens. An access server may then include such a grantor token in access tokens that it generates and issues to clients.
Owner:CA TECH INC
Intelligent network streaming and execution system for conventionally coded applications
InactiveUS7062567B2Multiple digital computer combinationsDigital data authenticationIntelligent NetworkApplication server
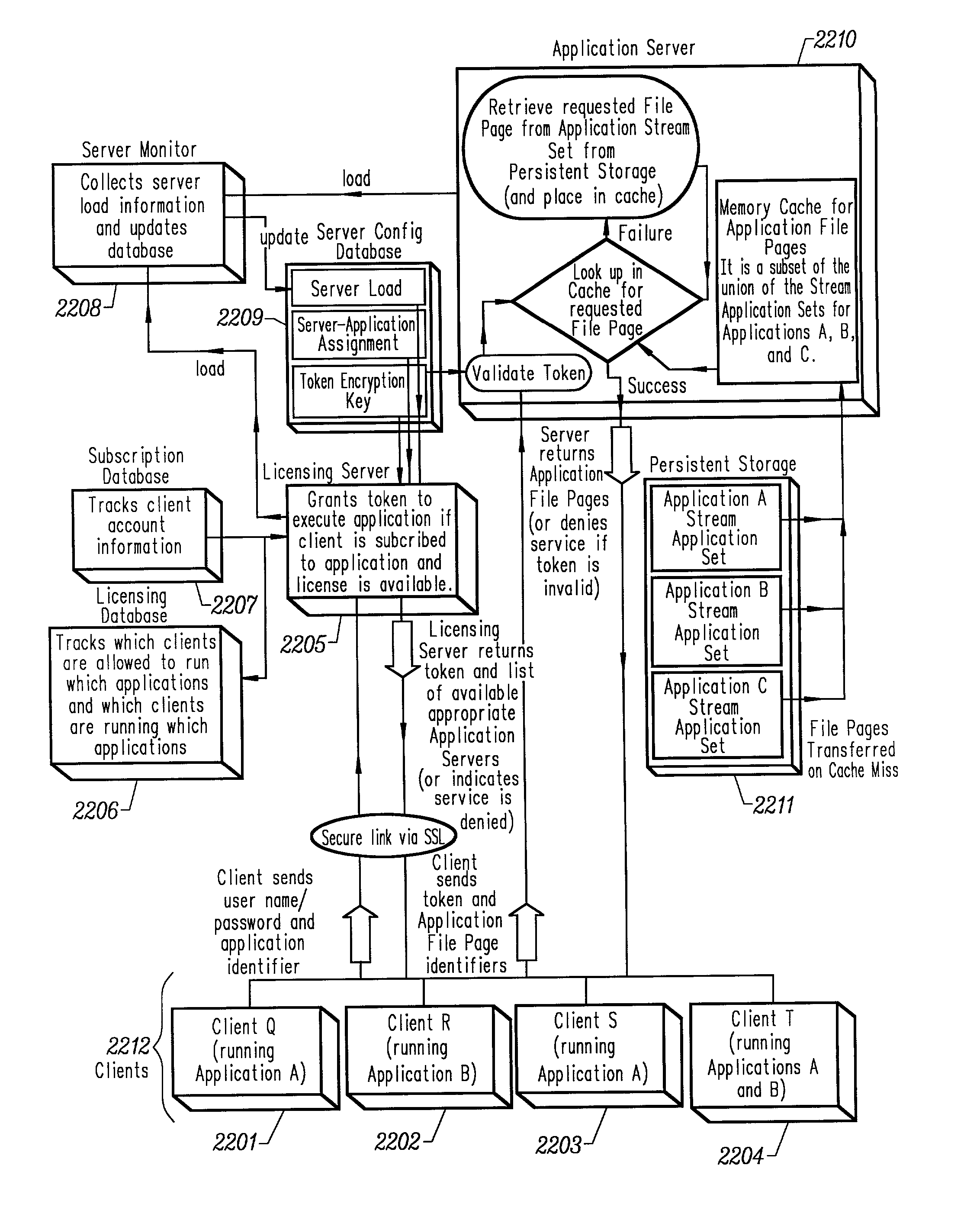
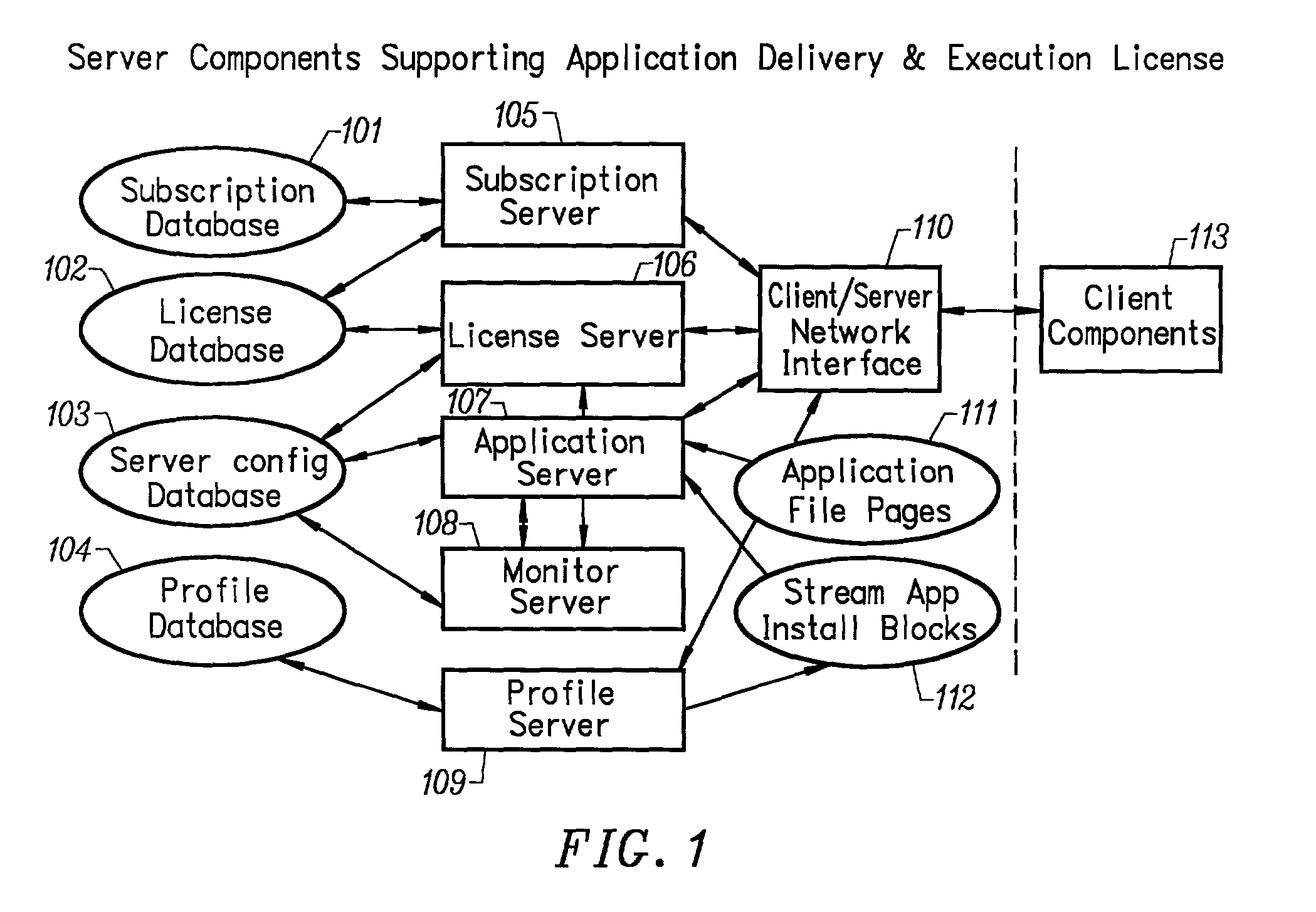
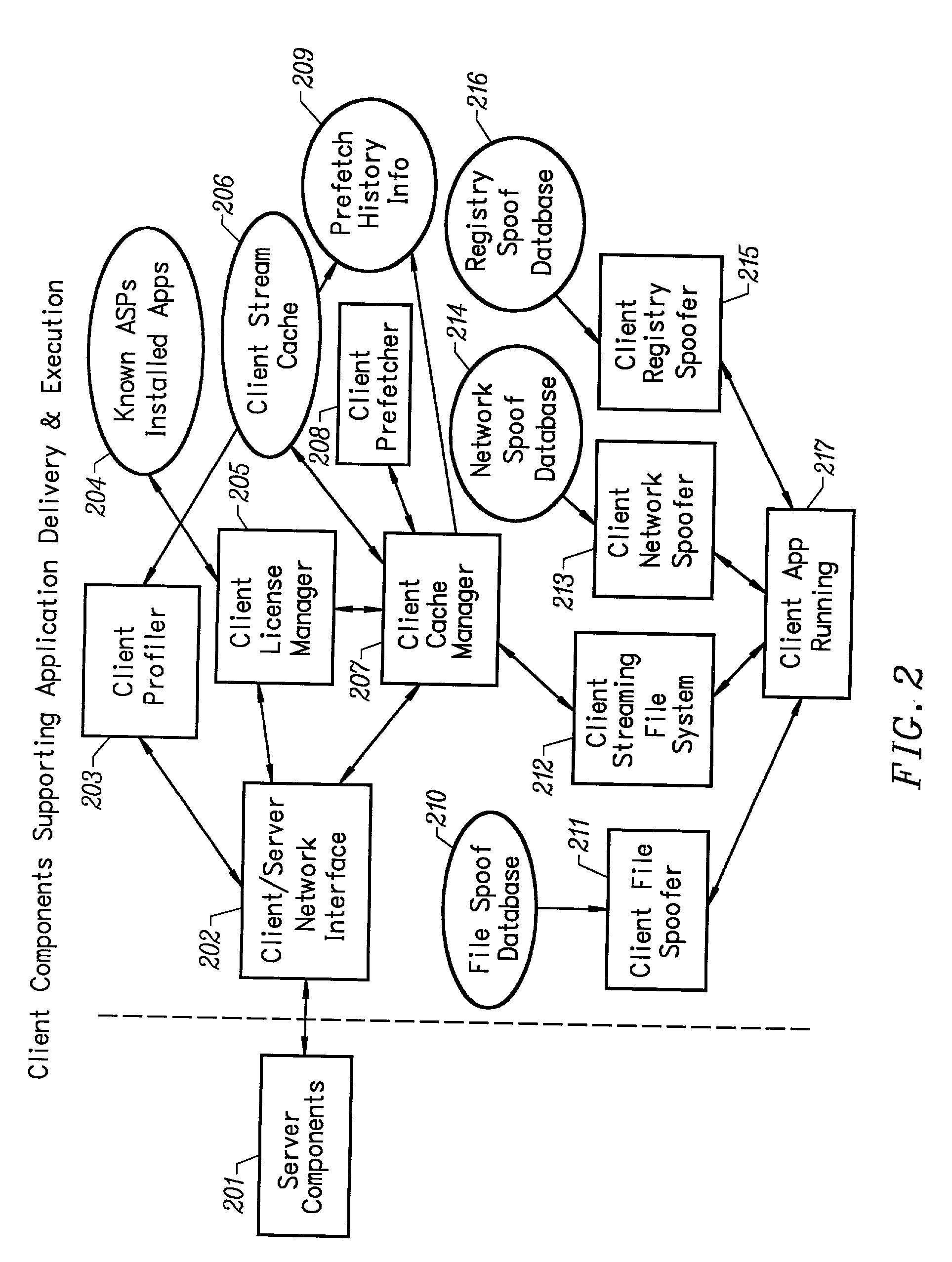
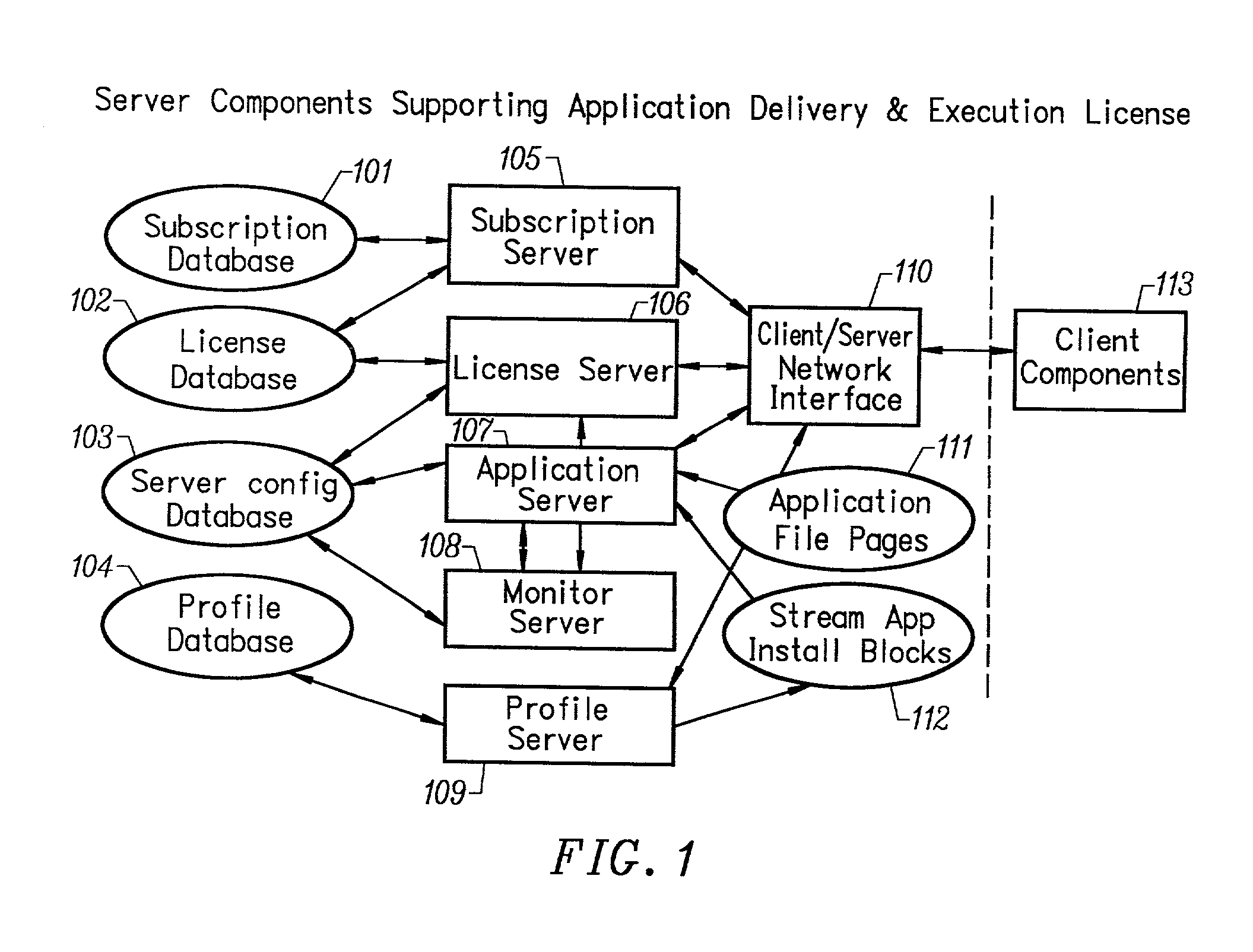
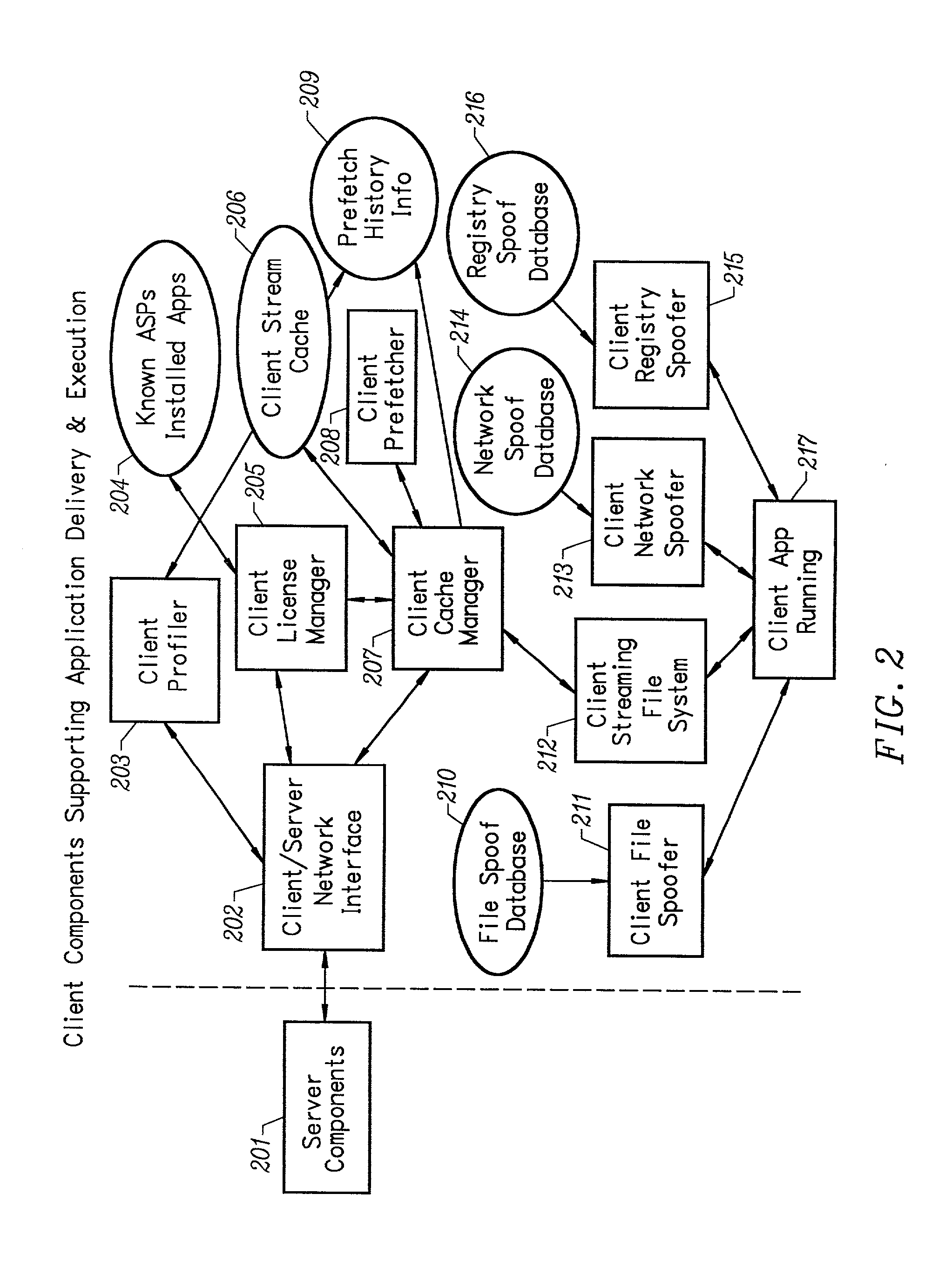
An intelligent network streaming and execution system for conventionally coded applications provides a system that partitions an application program into page segments by observing the manner in which the application program is conventionally installed. A minimal portion of the application program is installed on a client system and the user launches the application in the same ways that applications on other client file systems are started. An application program server streams the page segments to the client as the application program executes on the client and the client stores the page segments in a cache. Page segments are requested by the client from the application server whenever a page fault occurs from the cache for the application program. The client prefetches page segments from the application server or the application server pushes additional page segments to the client based on the pattern of page segment requests for that particular application. The user subscribes and unsubscribes to application programs, whenever the user accesses an application program a securely encrypted access token is obtained from a license server if the user has a valid subscription to the application program. The application server begins streaming the requested page segments to the client when it receives a valid access token from the client. The client performs server load balancing across a plurality of application servers. If the client observes a non-response or slow response condition from an application server or license server, it switches to another application or license server.
Owner:NUMECENT HLDG
Client installation and execution system for streamed applications
InactiveUS20020157089A1Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
Policies for secure software execution
InactiveUS7350204B2Efficiently constrain (or prevent from running) everything on a machineDigital data processing detailsUnauthorized memory use protectionFile systemDigital signature
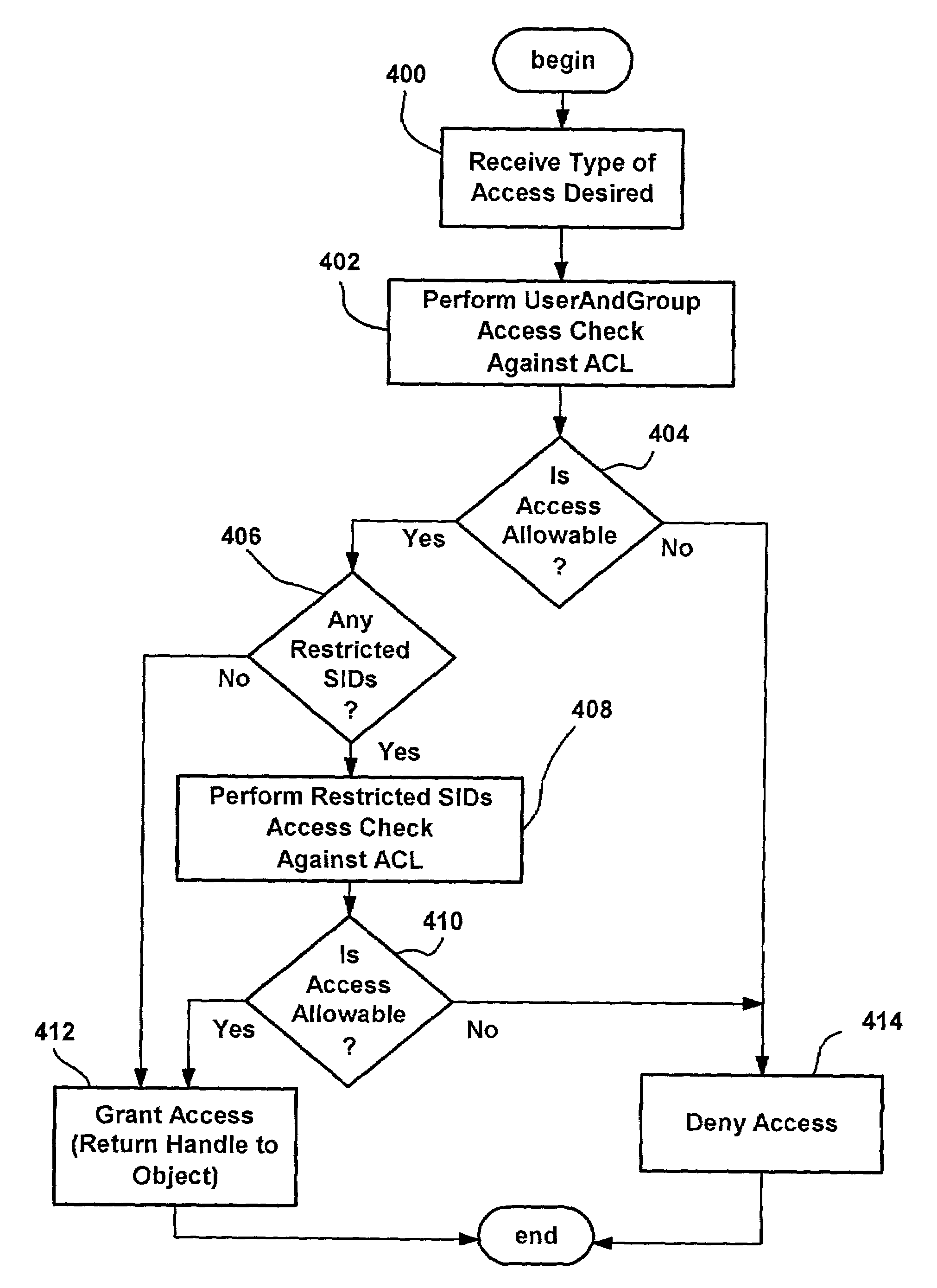
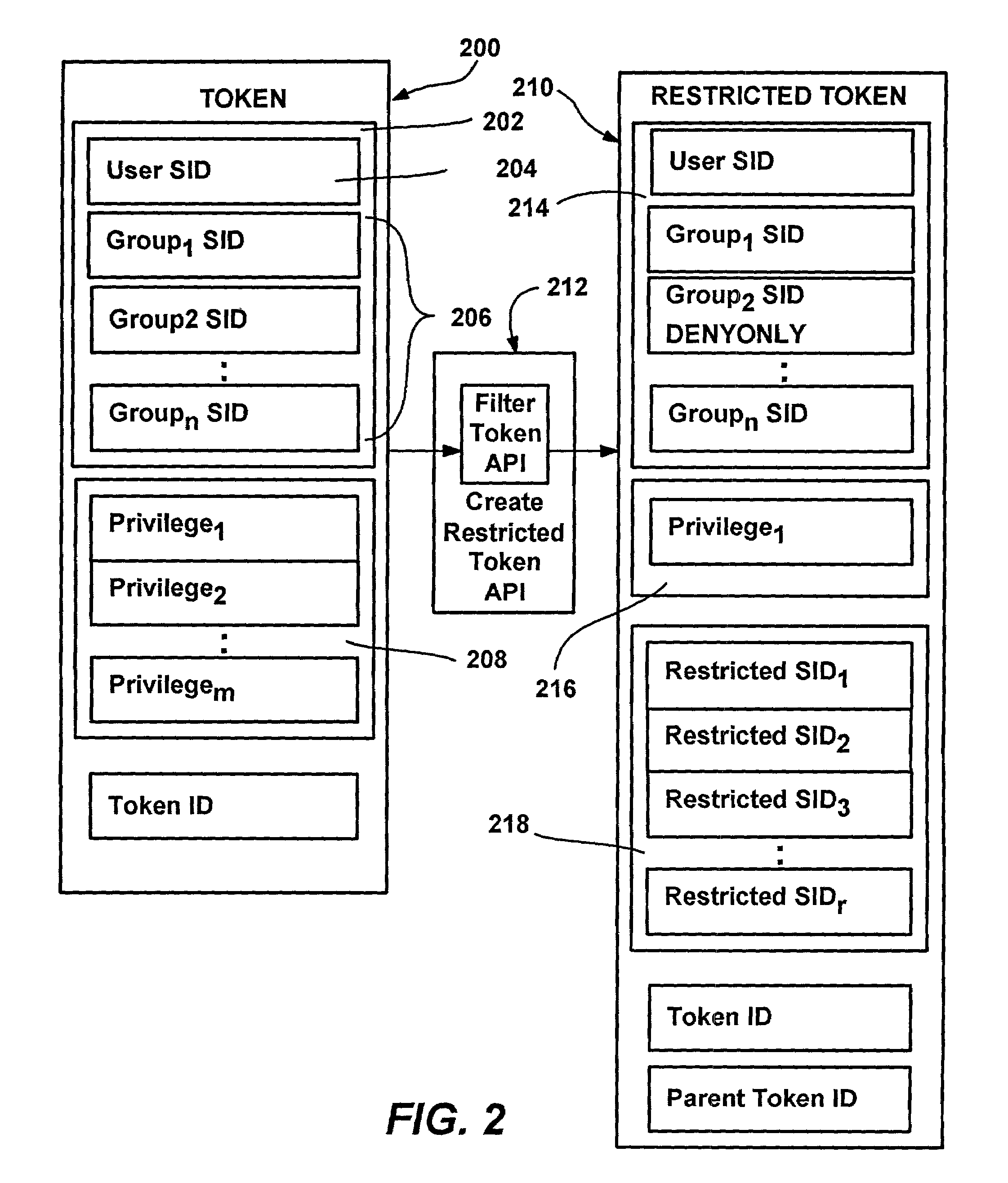
A system and method that automatically, transparently and securely controls software execution by identifying and classifying software, and locating a rule and associated security level for executing executable software. The security level may disallow the software's execution, restrict the execution to some extent, or allow unrestricted execution. To restrict software, a restricted access token may be computed that reduces software's access to resources, and / or removes privileges, relative to a user's normal access token. The rules that control execution for a given machine or user may be maintained in a restriction policy, e.g., locally maintained and / or in a group policy object distributable over a network. Software may be identified / classified by a hash of its content, by a digital signature, by its file system or network path, and / or by its URL zone. For software having multiple classifications, a precedence mechanism is provided to establish the applicable rule / security level.
Owner:MICROSOFT TECH LICENSING LLC
Oauth framework
ActiveUS20130086645A1More customizableEasy to customizeDigital data processing detailsMultiple digital computer combinationsClient-sideAccess token
A framework, which conforms to the OAuth standard, involves a generic OAuth authorization server that can be used by multiple resource servers in order to ensure that access to resources stored on those resource servers is limited to access to which the resource owner consents. Each resource server registers, with the OAuth authorization server, metadata for that resource server, indicating scopes that are recognized by the resource server. The OAuth authorization server refers to this metadata when requesting consent from a resource owner on behalf of a client application, so that the consent will be of an appropriate scope. The OAuth authorization server refers to this metadata when constructing an access token to provide to the client application for use in accessing the resources on the resource server. The OAuth authorization server uses this metadata to map issued access tokens to the scopes to which those access tokens grant access.
Owner:ORACLE INT CORP
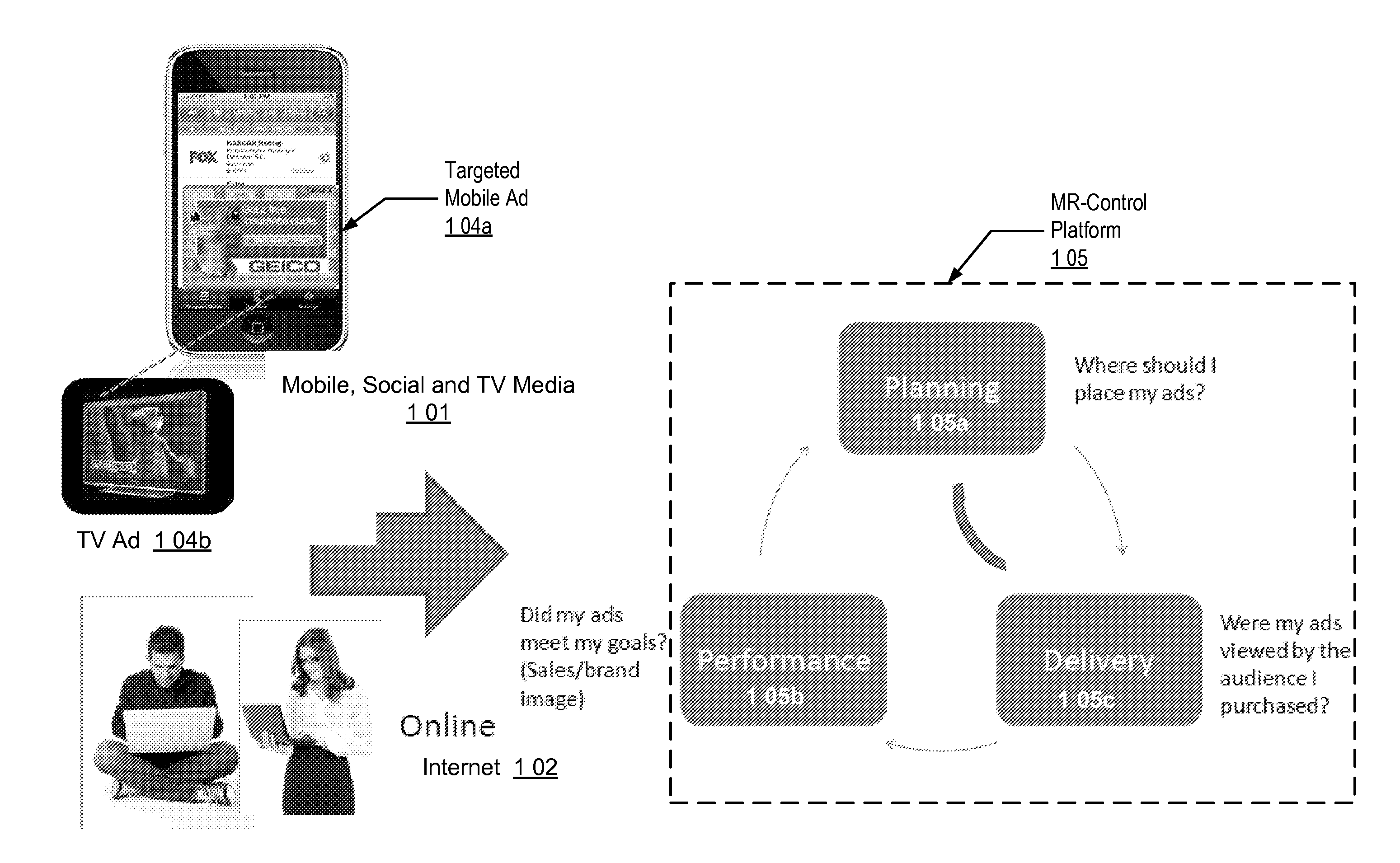
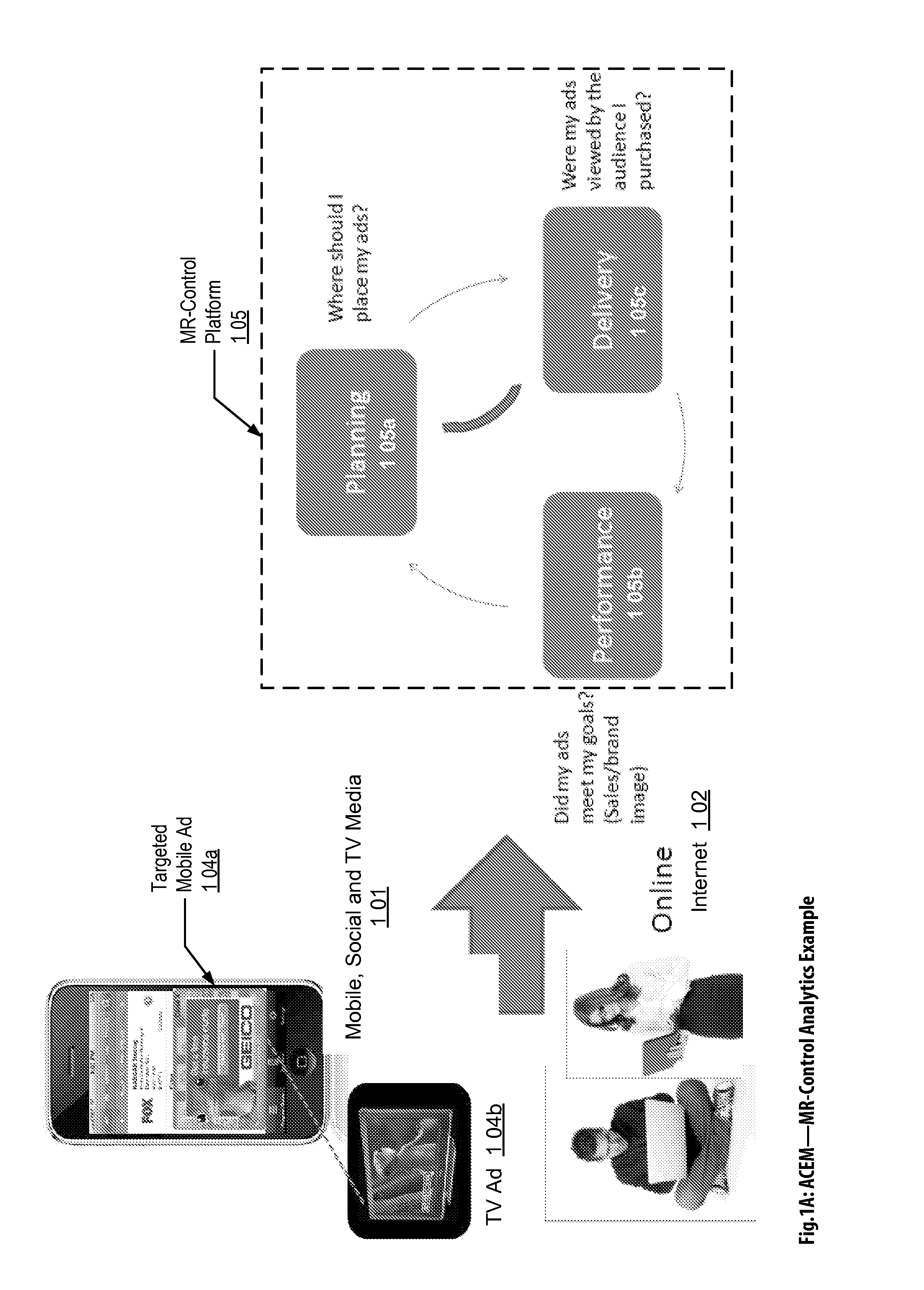
Audience Content Exposure Monitoring Apparatuses, Methods and Systems
ActiveUS20160007083A1Analogue secracy/subscription systemsBroadcast information monitoringSocial mediaMobile device
The Audience Content Exposure Monitoring Apparatuses, Methods and Systems (“ACEM”) transforms pulsing request (e.g., 1107), viewing status, purchase request, channel selection, survey request, sentiment request, atmospherics, social media posts, response events, data request and access token, app / device input monitoring, check-in, URL access, etc. inputs via ACEM components into atmospherics sampling record (e.g., 1106), ad contents (e.g., 1115), RT data / records, ad tags, media program, full page content outputs. In some embodiments, the ACEM provides a mobile metering system that configures the data collection of audience environment atmospherics to evaluate audience media exposure. In one implementation, the ACEM may employ media data collection technology using a combination of mobile device metering app and cloud hosted server side technology to determine when and how often a user mobile device should record and / or generate monitoring atmospherics of audience environment; and to determine what content the audience has been exposed to based on the collected monitoring data.
Owner:SYMPHONY ADVANCED MEDIA
Methods, Apparatuses, and Computer Program Products for Providing a Single Service Sign-On
InactiveUS20090271847A1Enhanced interactionImprove securityDigital data processing detailsUser identity/authority verificationPasswordSecret code
An apparatus may include a processor configured to receive a request for an access token from a remote entity, wherein the request includes an indication of a requested service. The processor may be further configured to determine a request type, wherein the request type may be a user identification and password combination, a request token exchange, or an access token exchange. The processor may be additionally configured to extract one or more parameters included in the request based upon the determined request type and to perform one or more security checks based at least in part upon the one or more extracted parameters. The processor may be further configured to create an access token based at least in part upon the results of the one or more security checks and to provide the access token to the remote entity.
Owner:NOKIA TECHNOLOGLES OY
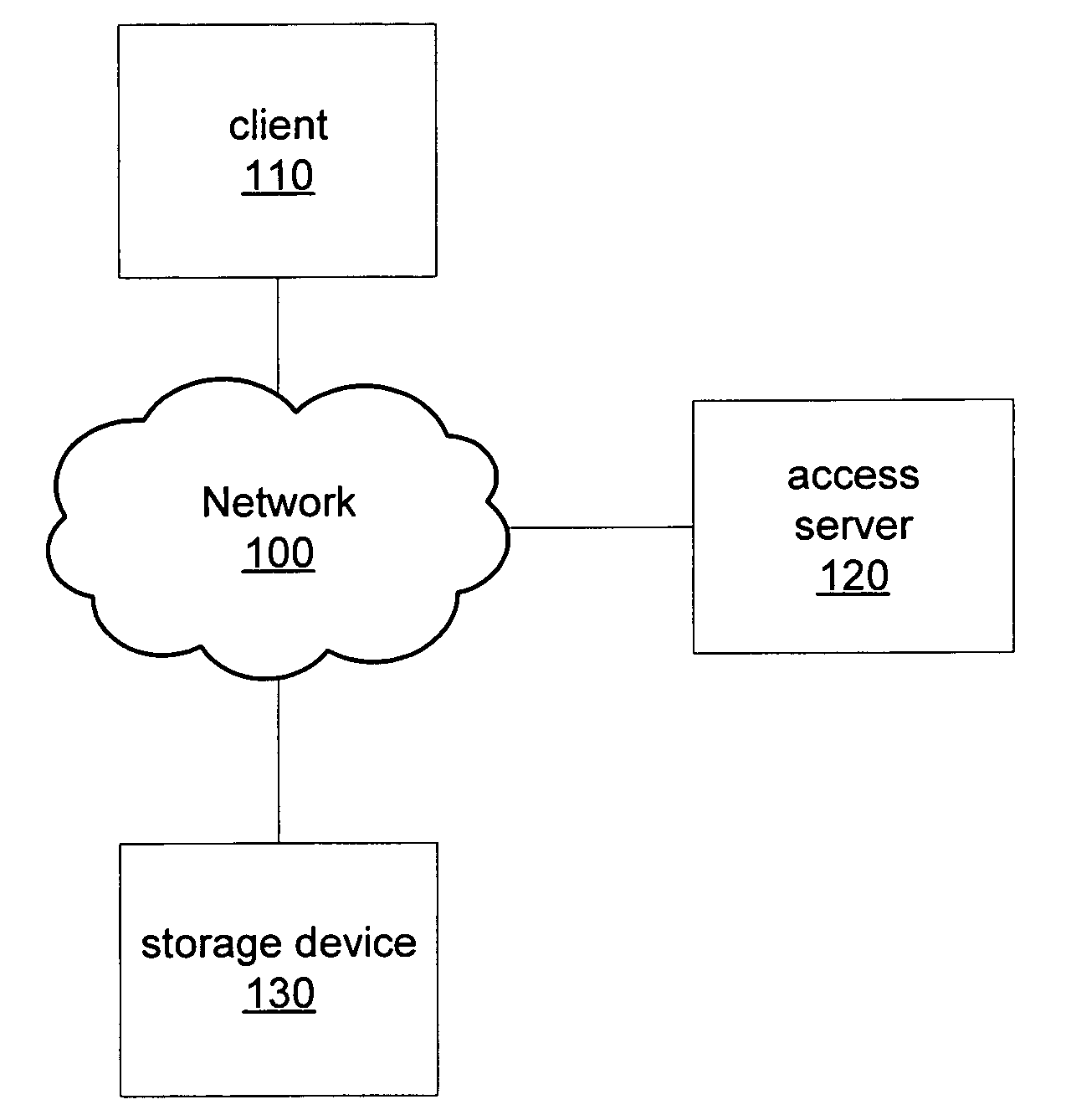
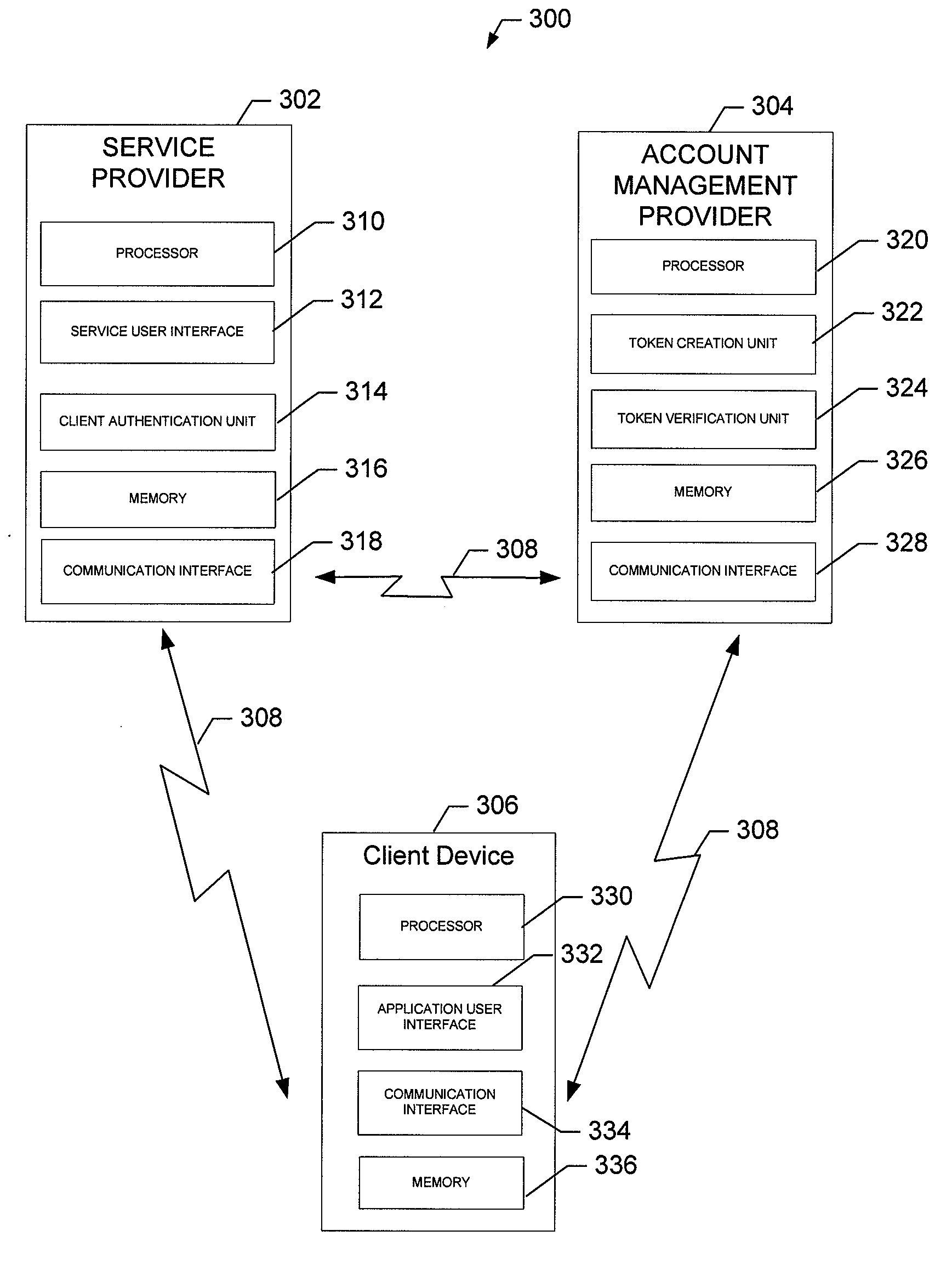
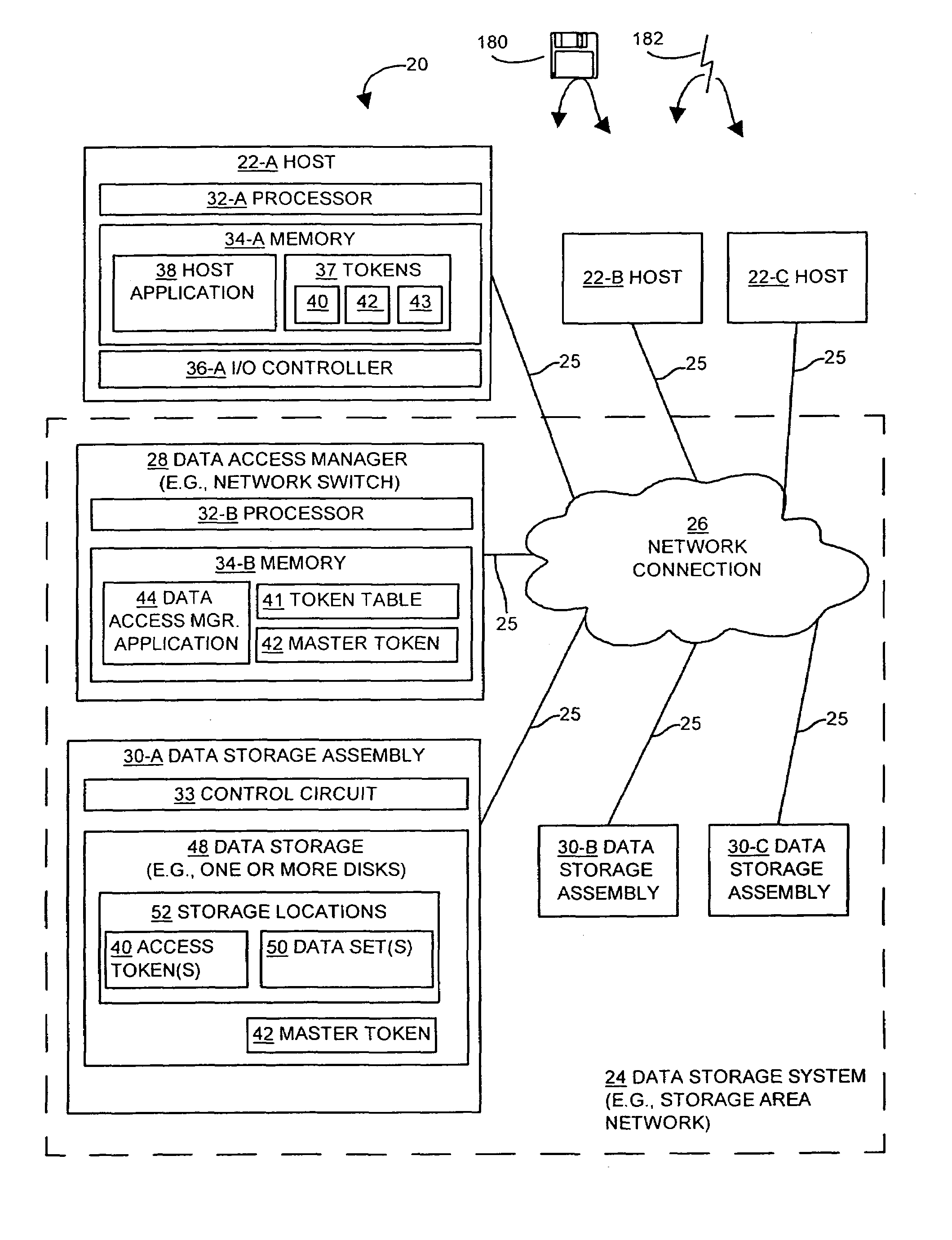
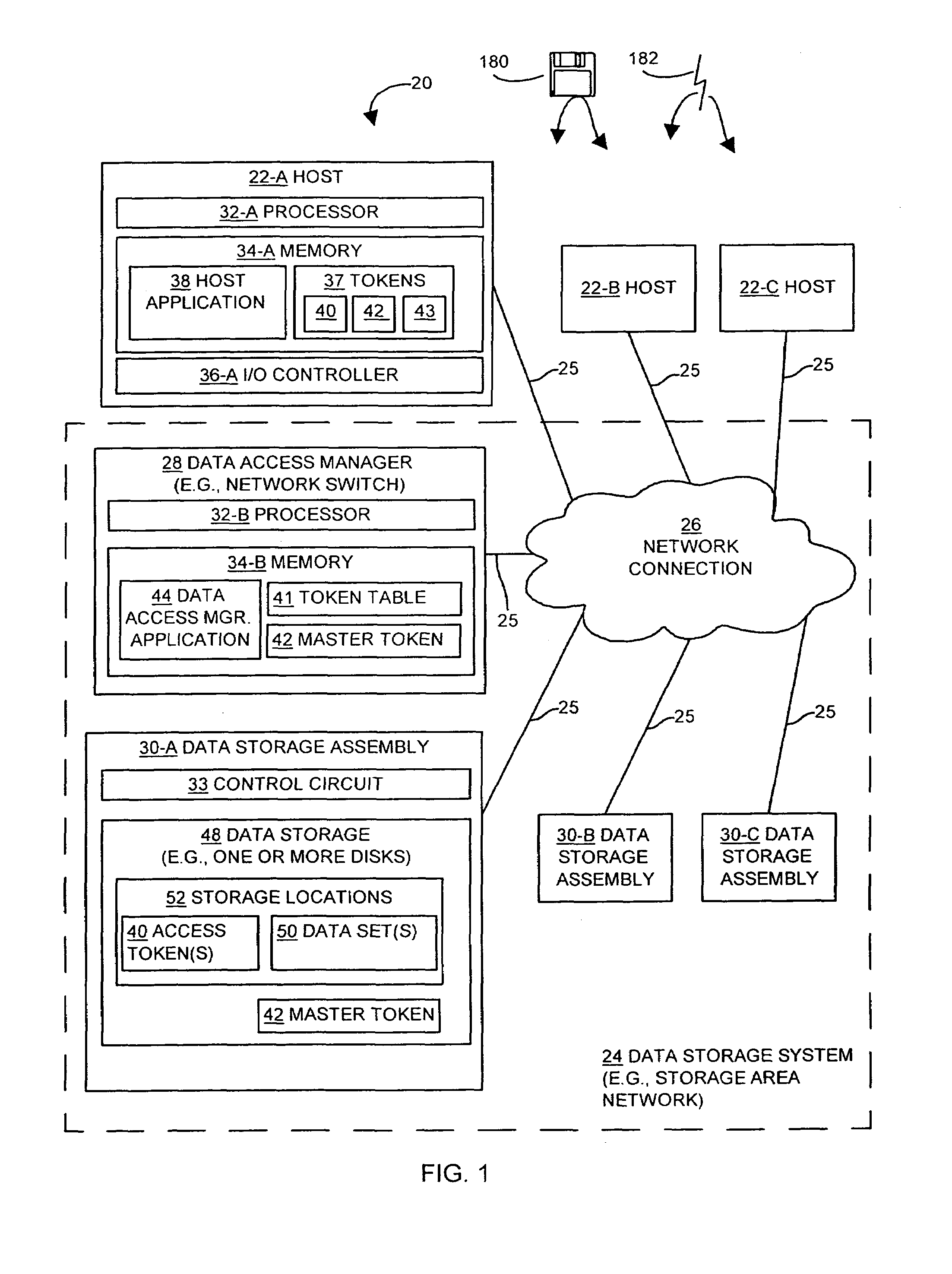
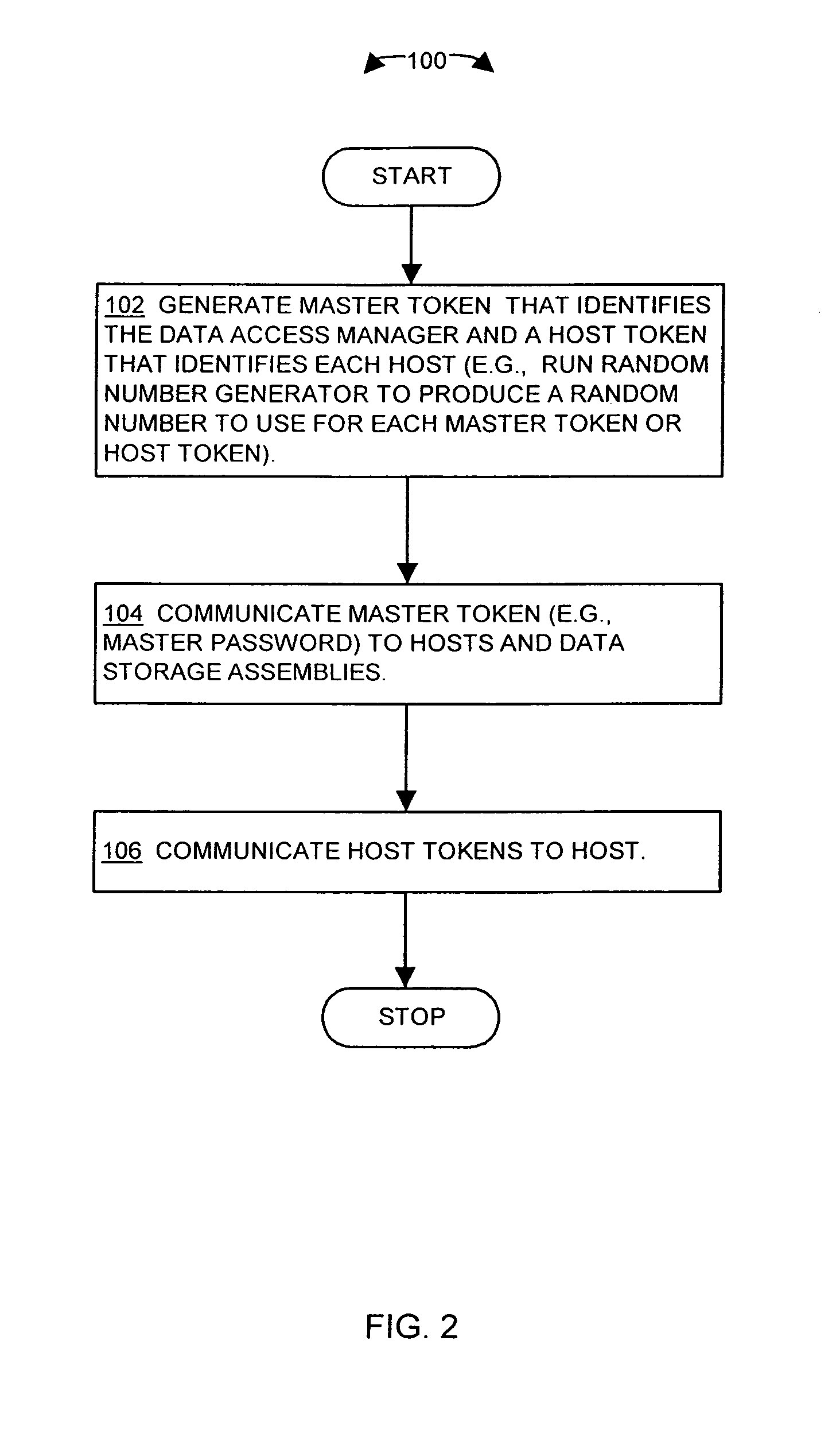
Methods and apparatus for providing security for a data storage system
InactiveUS7134138B2Digital data processing detailsUser identity/authority verificationData accessComputerized system
The invention is directed to techniques for providing security in data storage systems that provide access to data by other systems, such as host computer systems. A data access manager generates access tokens that it assigns to storage locations that store data in one or more data storage assemblies in the data storage system. A host that makes a request to access specific storage locations having data must obtain an access token associated with those storage locations from the data access manager, and provide the access token with the request to the data storage system. The data storage system then authenticates the request based on the access token.
Owner:EMC IP HLDG CO LLC
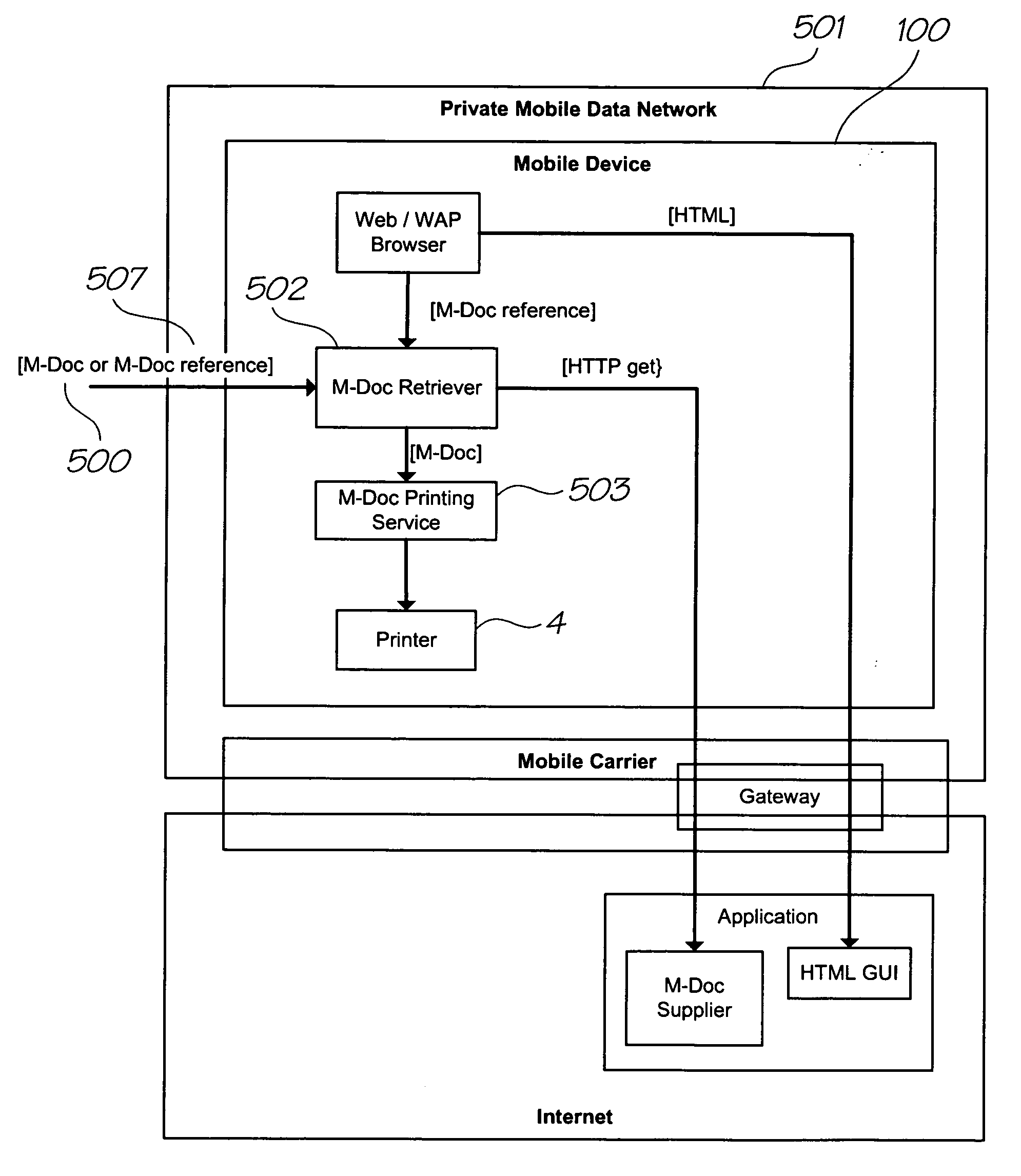
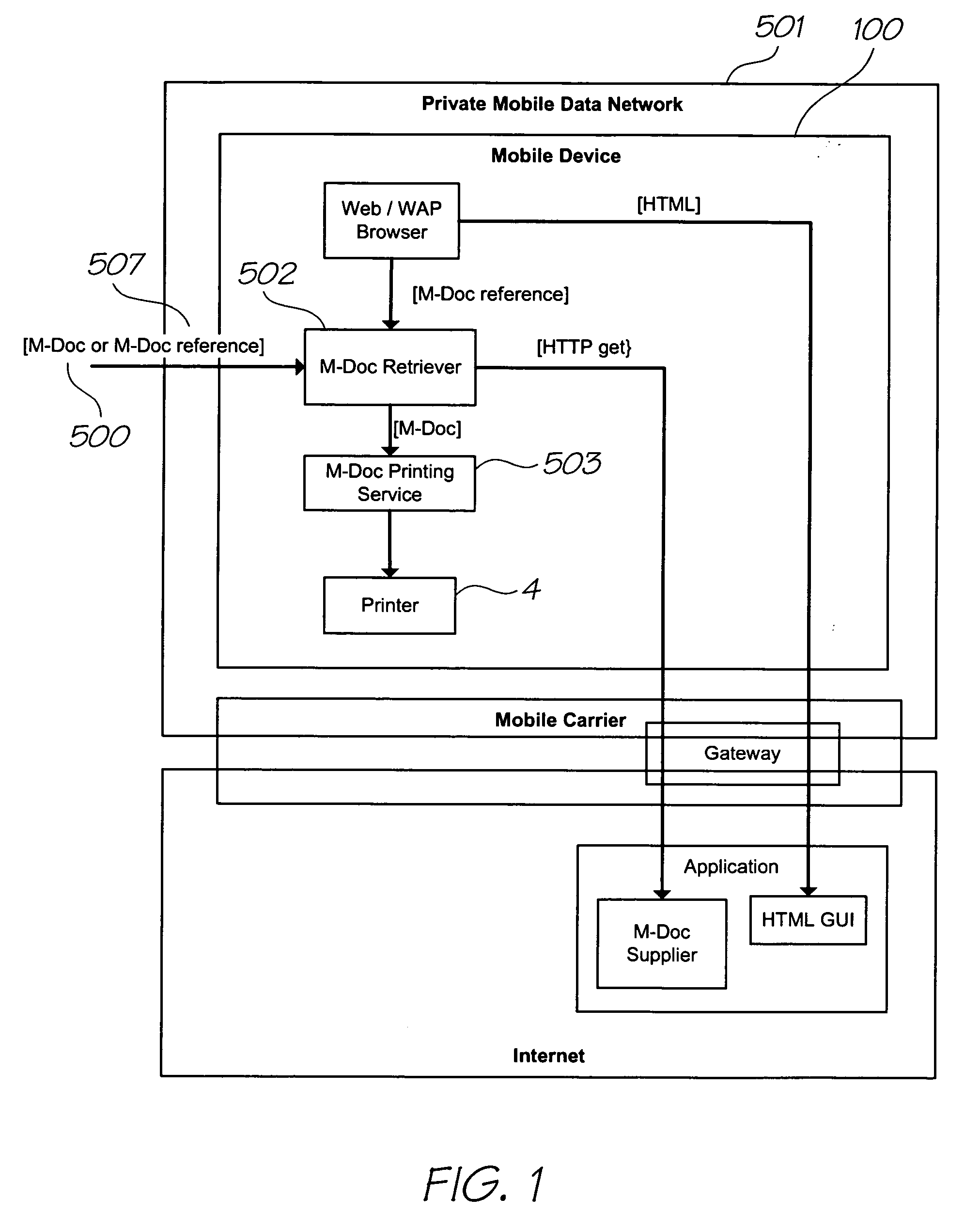
Retrieving an access token via a coded surface
InactiveUS20070067824A1Accurate explanationEasy to getDigital data processing detailsUser identity/authority verificationPrint mediaAccess token
A method of gaining access to a resource using an access token linked to a print medium, comprising the steps of: determining a print media identifier from the print medium using a sensor module of a mobile telecommunications device, the print media identifier having been linked to the access token; identifying, using the mobile telecommunications device and the print media identifier, the access token; and, causing the access token to be supplied to a system, wherein the system is configured to authenticate the access token and, if the authentication succeeds, provide access to the resource.
Owner:SILVERBROOK RES PTY LTD
Service profile-specific token attributes and resource server token attribute overriding
ActiveUS20150089623A1Easy to customizeDigital data processing detailsMultiple digital computer combinationsService profileService configuration
A framework, which conforms to the OAuth standard, involves a generic OAuth authorization server that can be used by multiple resource servers in order to ensure that access to resources stored on those resource servers is limited to access to which the resource owner consents. Each resource server registers, with the OAuth authorization server, metadata for that resource server, indicating scopes that are recognized by the resource server. The OAuth authorization server refers to this metadata when requesting consent from a resource owner on behalf of a client application, so that the consent will be of an appropriate scope. The OAuth authorization server refers to this metadata when constructing an access token to provide to the client application for use in accessing the resources on the resource server. The OAuth authorization server uses this metadata to map issued access tokens to the scopes to which those access tokens grant access.
Owner:ORACLE INT CORP
Portable computer system with hierarchical and token-based security policies
InactiveUS7111321B1Reduce the possibilityError detection/correctionVolume/mass flow measurementSource Data VerificationComputerized system
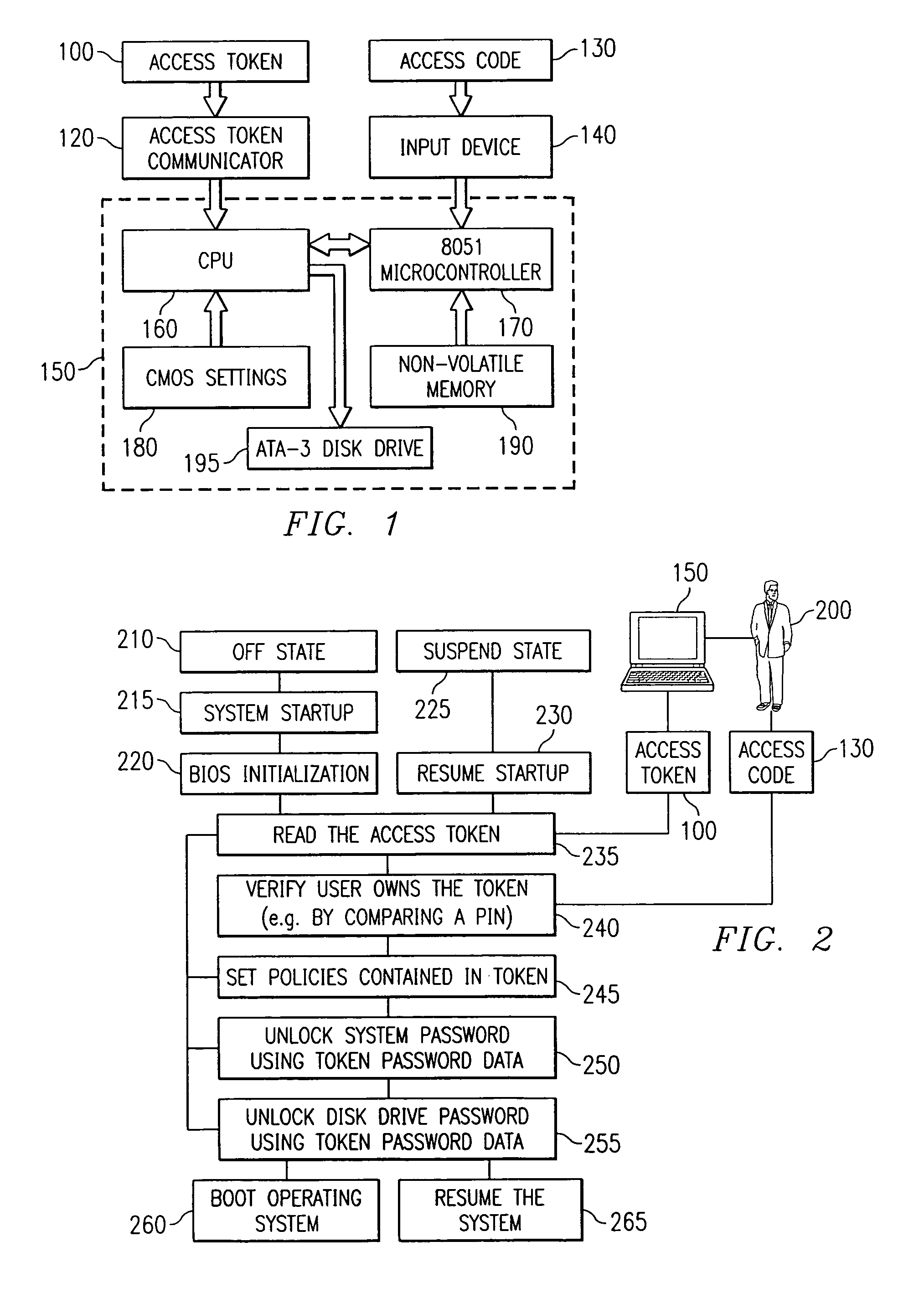
A computer system including a processor, an access token communicator capable of being coupled to the processor and adapted to read an access token, an input device coupled to the processor that is able to receive verification data that confirms authorized access of the access token, and software executable on the processor that includes instructions to control access to the processor and including code to access the access token and the verification data, code to verify the validity of the access token using the verification data, code to set security policies in the processor, and code to control access to resources in the processor based on the security policies. In addition, a method for reading an access token, verifying the validity of the access token, setting security policies in a computer system, and unlocking a computer system and a nonvolatile storage device attached to the computer system.
Owner:DELL PROD LP
Automated access data provisioning
ActiveUS20160173483A1Improve securityDigital data processing detailsMultiple digital computer combinationsComputer networkAccess token
A method is disclosed. The method includes transmitting by a computing device, an account creation request to a remote server computer. The method further includes automatically provisioning the computing device with an access token in response to receiving a request to create the account.
Owner:VISA INT SERVICE ASSOC
Multiple resource servers interacting with single oauth server
ActiveUS20160028737A1Easy to customizeDigital data processing detailsMultiple digital computer combinationsClient-sideAccess token
A framework, which conforms to the OAuth standard, involves a generic OAuth authorization server that can be used by multiple resource servers in order to ensure that access to resources stored on those resource servers is limited to access to which the resource owner consents. Each resource server registers, with the OAuth authorization server, metadata for that resource server, indicating scopes that are recognized by the resource server. The OAuth authorization server refers to this metadata when requesting consent from a resource owner on behalf of a client application, so that the consent will be of an appropriate scope. The OAuth authorization server refers to this metadata when constructing an access token to provide to the client application for use in accessing the resources on the resource server. The OAuth authorization server uses this metadata to map issued access tokens to the scopes to which those access tokens grant access.
Owner:ORACLE INT CORP
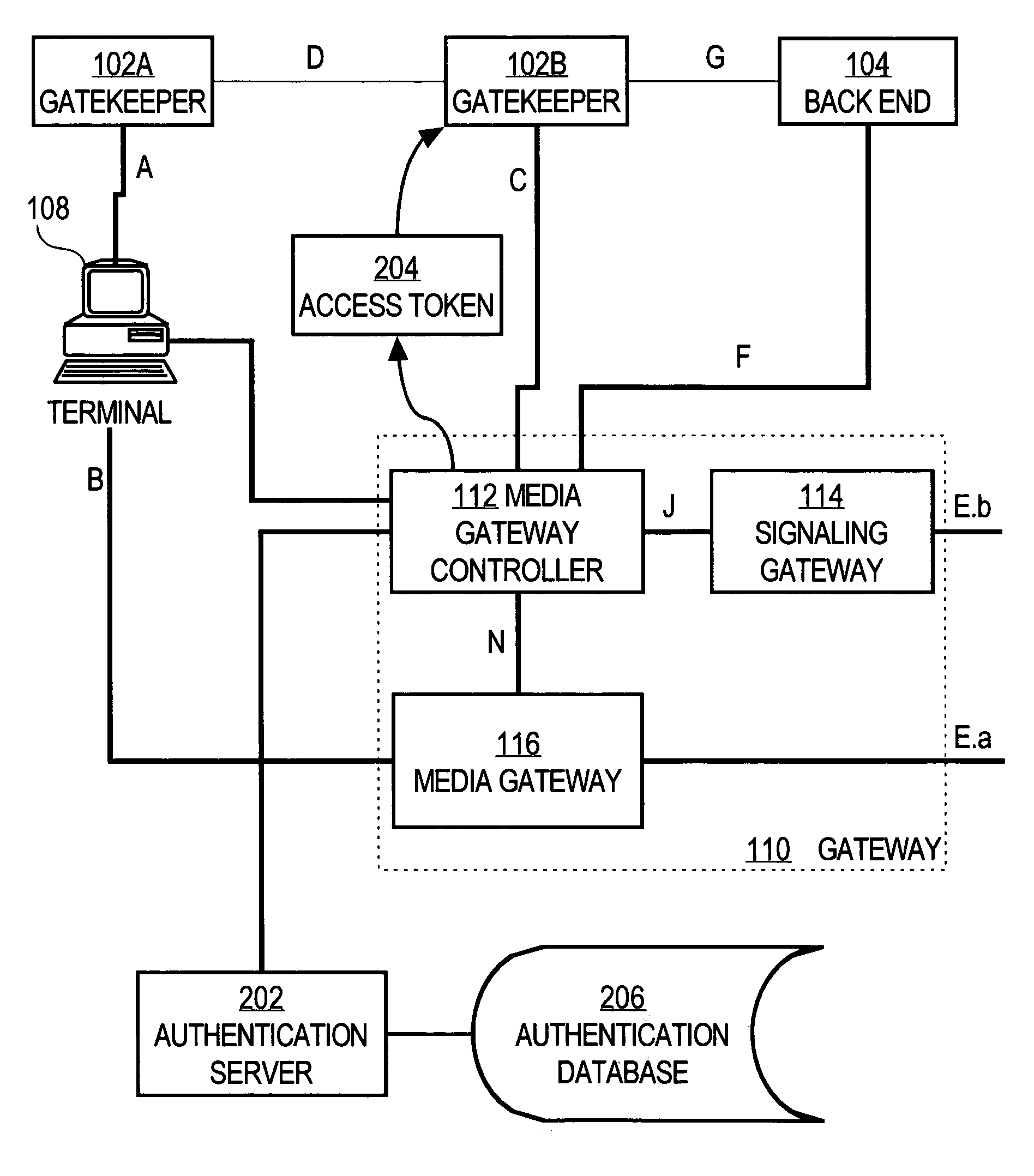
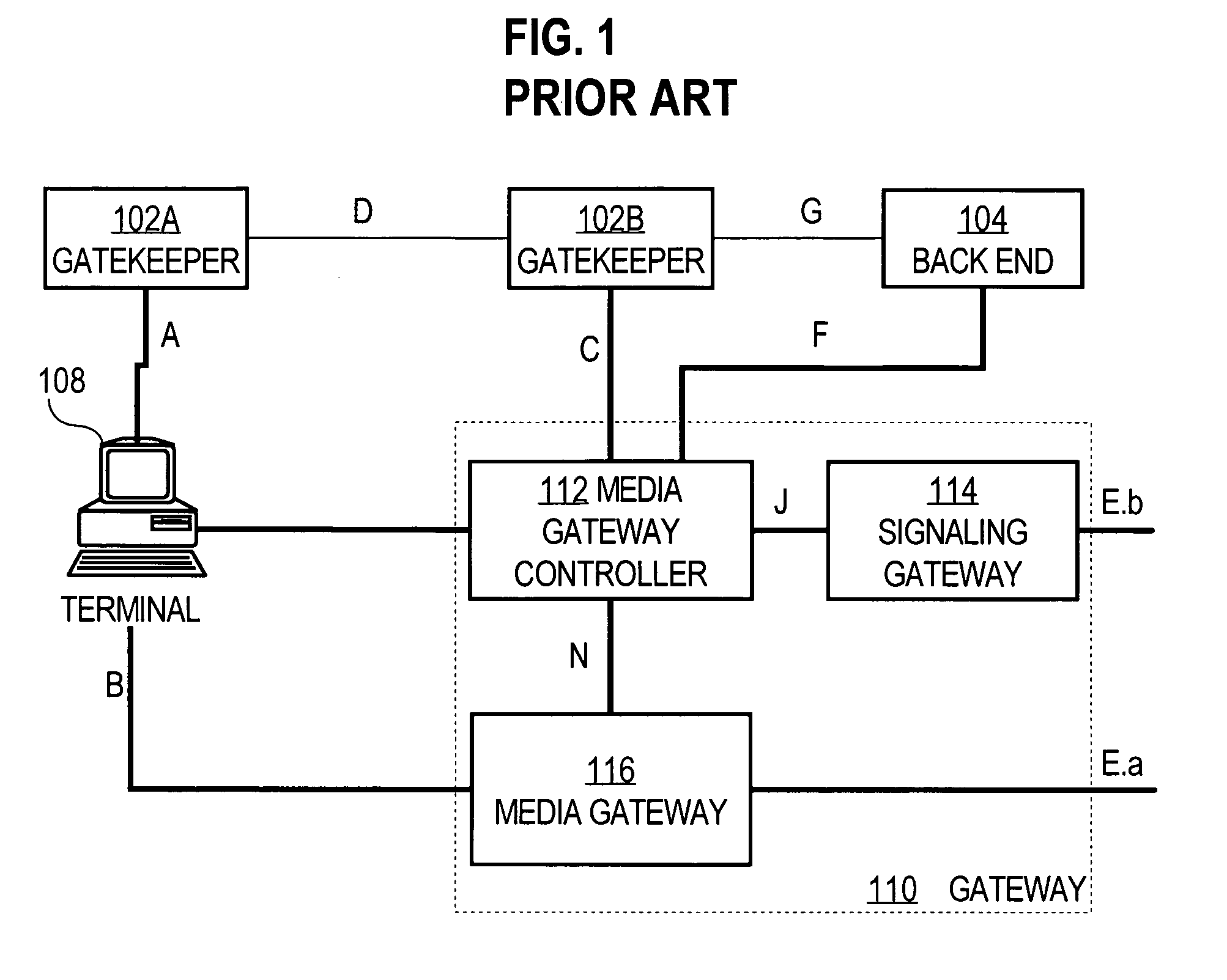
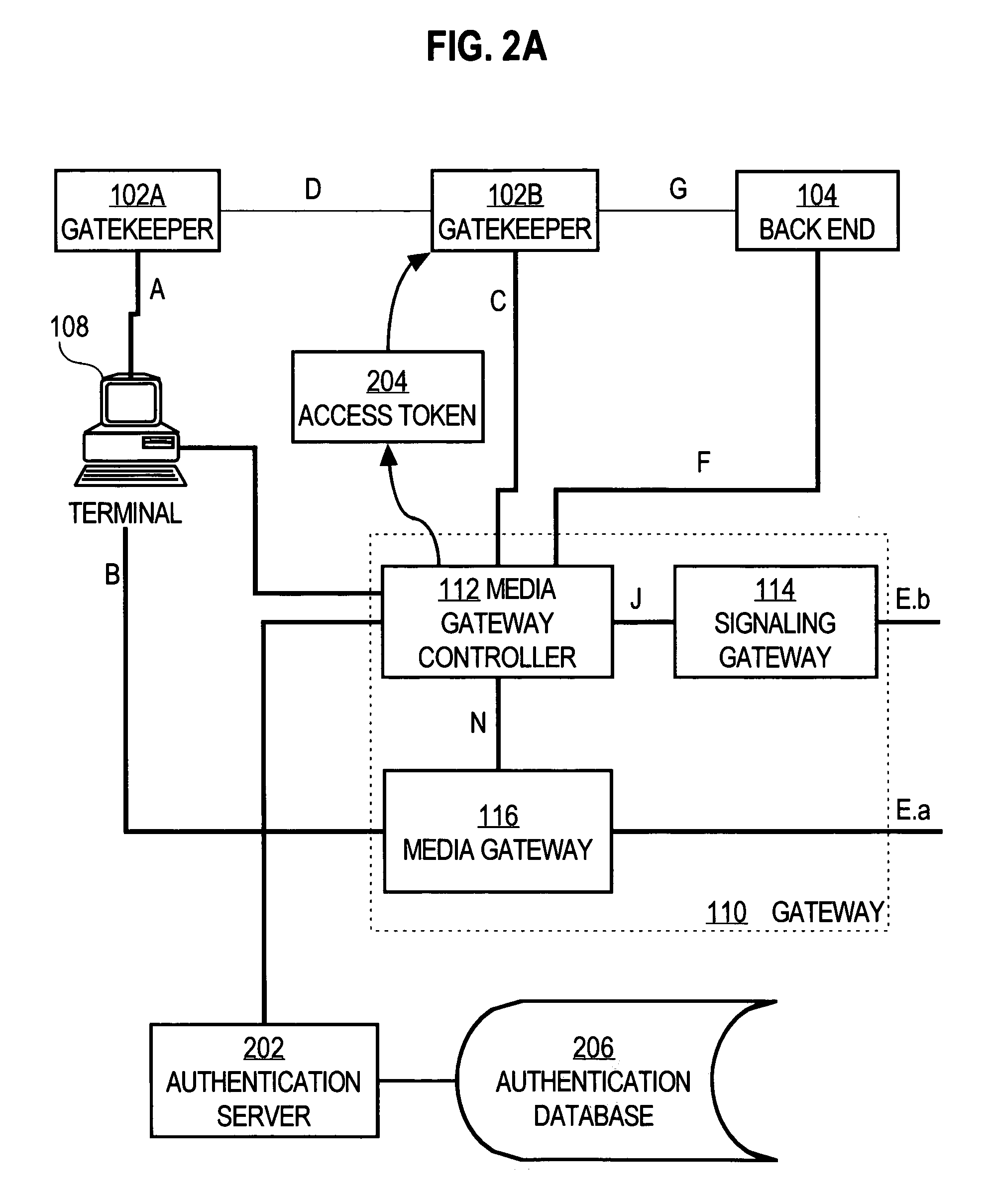
Authenticating endpoints of a voice over internet protocol call connection
InactiveUS6961857B1User identity/authority verificationMultiple digital computer combinationsInternet protocol suiteTimestamp
A method and apparatus for securely establishing voice over Internet Protocol calls are disclosed. In a Registration Security approach, a Gatekeeper sends an Access Token in all Registration Request messages. The Access Token contains information that authenticates the Gateway to the Gatekeeper. The Gatekeeper formats a message to an authentication server that will authenticate the information contained in the token, and the server responds with either an Access-Accept or Access-Reject message. The Gatekeeper responds to the Gateway with either a Registration Confirm message or a Registration Reject message. If a call is then placed from a successfully authenticated Gateway, that Gateway generates a new Access Token that is identical to the one generated during registration, except for the timestamp. The Gatekeeper uses the authentication server to authenticate the originating gateway, before sending the designation side Access Confirm message. As a result, a non-authenticated endpoint that knows a Gateway's address cannot use the Gateway address to circumvent security and access the telephone network to place unauthorized calls or free calls. In Admission or Per-Call Security, a Gateway is also required to include an Access Token in all originating side Admission Request messages. Such token contains information that identifies the user of the Gateway to the Gatekeeper, based on an account number and PIN obtained from the user. The Access Token is authenticated in the manner described above.
Owner:CISCO TECH INC
Peer-to-peer authorization method
ActiveUS20050044411A1Digital data processing detailsUnauthorized memory use protectionControl systemPeer to peer computing
Disclosed are peer-to-peer computer program products, methods, and systems in which a remote peer on a peer-to-peer network is granted or denied access to a resource based on the credentials presented by the remote peer. In accordance with the disclosed subject matter, an access token that includes one or more security identification values which represent respectively one or more access rights in an access control system is generated. An execution thread that is associated with the access token thus generated attempts to access the resource on behalf of the remote peer. In some embodiments, the access control system includes a generic user account, and the access token that is generated for the remote peer includes the security identification value associated with the generic user account in the access control system.
Owner:MICROSOFT TECH LICENSING LLC
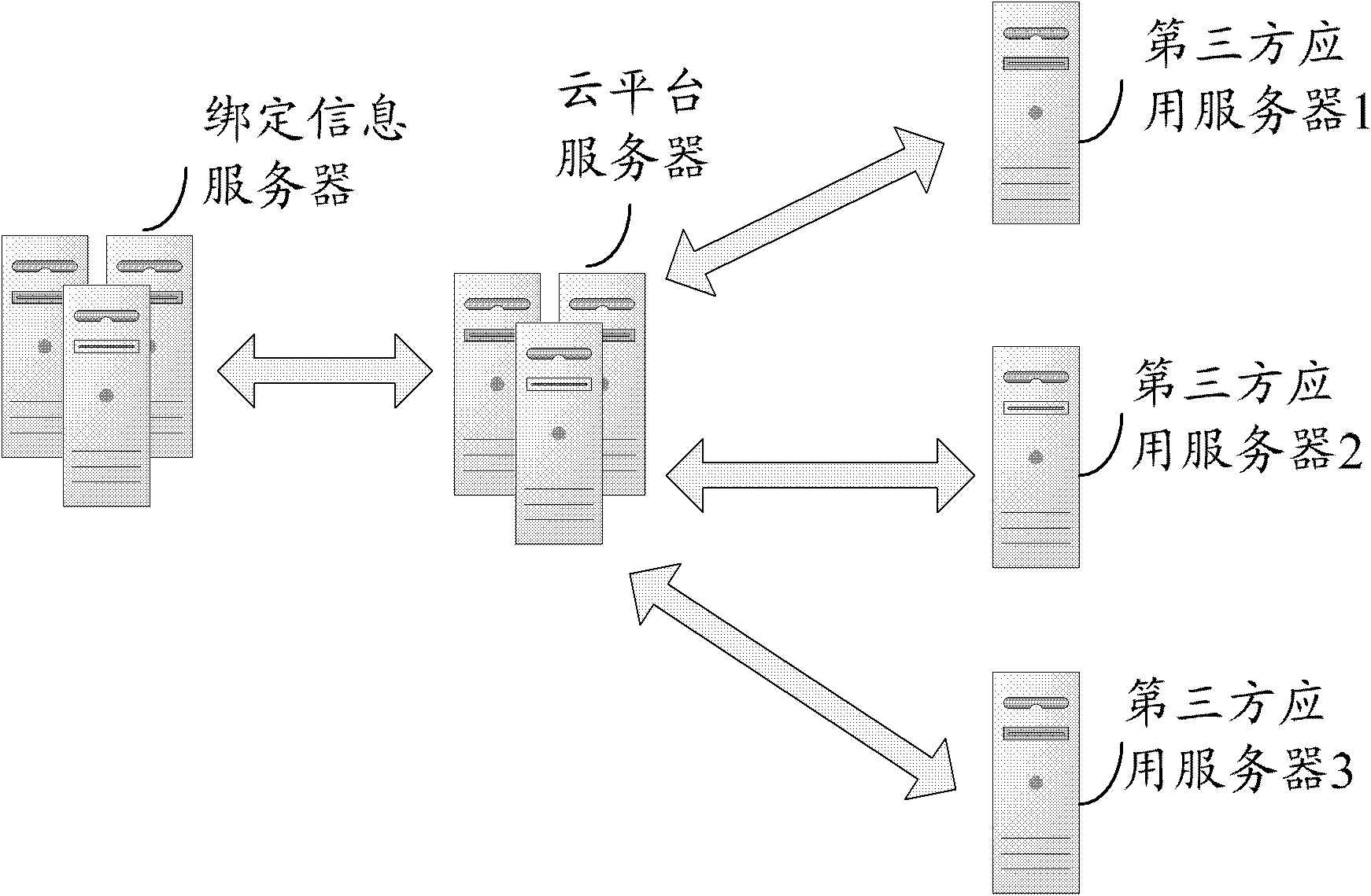
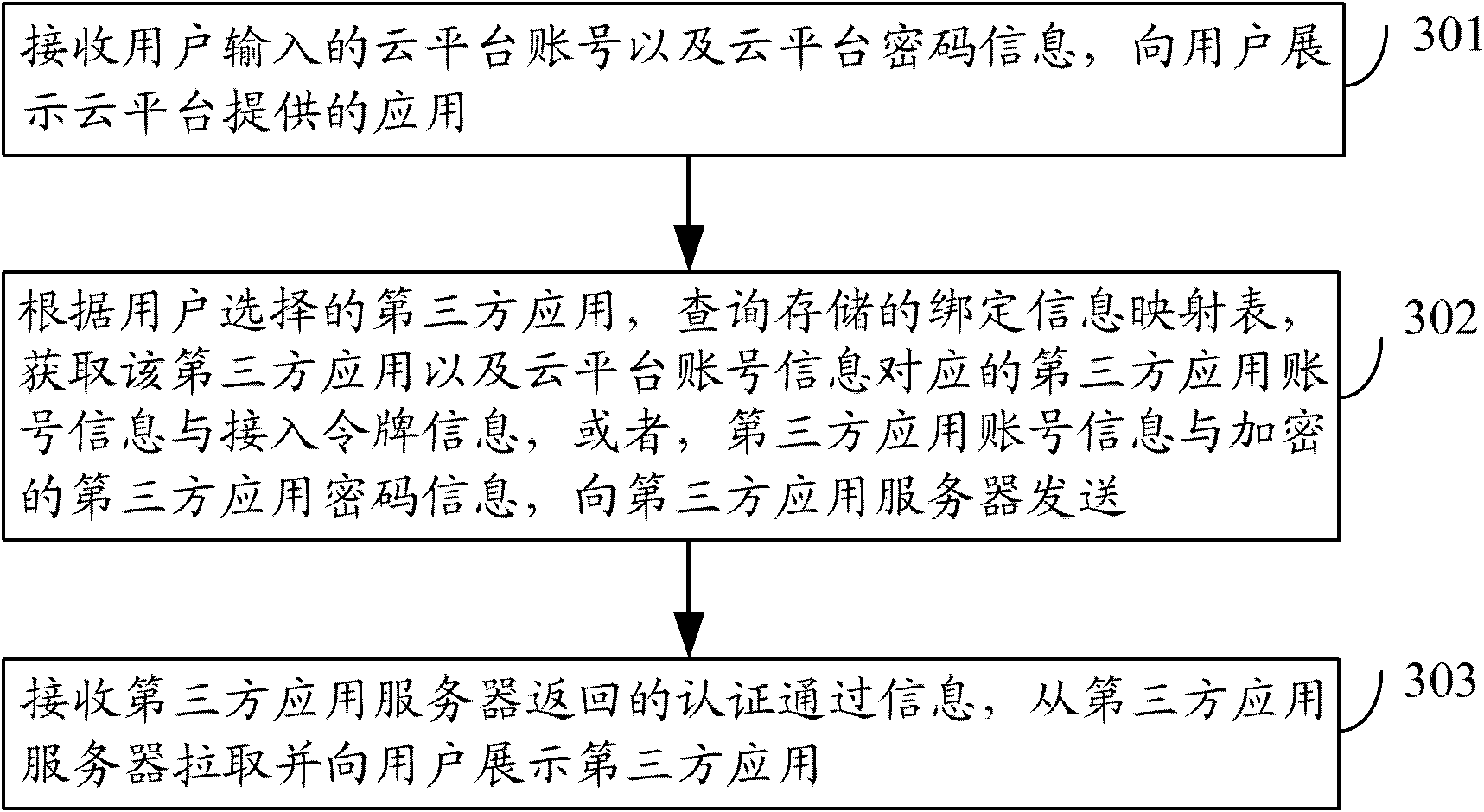
System and method for accessing third party application based on cloud platform
The invention discloses a system and a method for accessing a third party application based on a cloud platform. The method comprises the steps of receiving a cloud platform account and cloud platform password information, wherein the cloud platform account number and the cloud platform password information are input by a user, and displaying applications provided by the cloud platform to the user; according to the third party application selected by the user, querying a stored binding information mapping table, acquiring third party application account information and access token information corresponding to the third party application and cloud platform account information, or third party application account information and encrypted third party application password information corresponding to the third party application and the cloud platform account information, and sending the third party application account information and the access token information, or the third party application account information and the encrypted third party application password information to a third party application server; receiving authentication approval information returned by the third party application server, pulling the third party application from the third party application server and displaying the third party application to the user. With the application of the invention, the operation complexity of the frequent login of the user is reduced, and the security of the access to the third party application of the user is improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
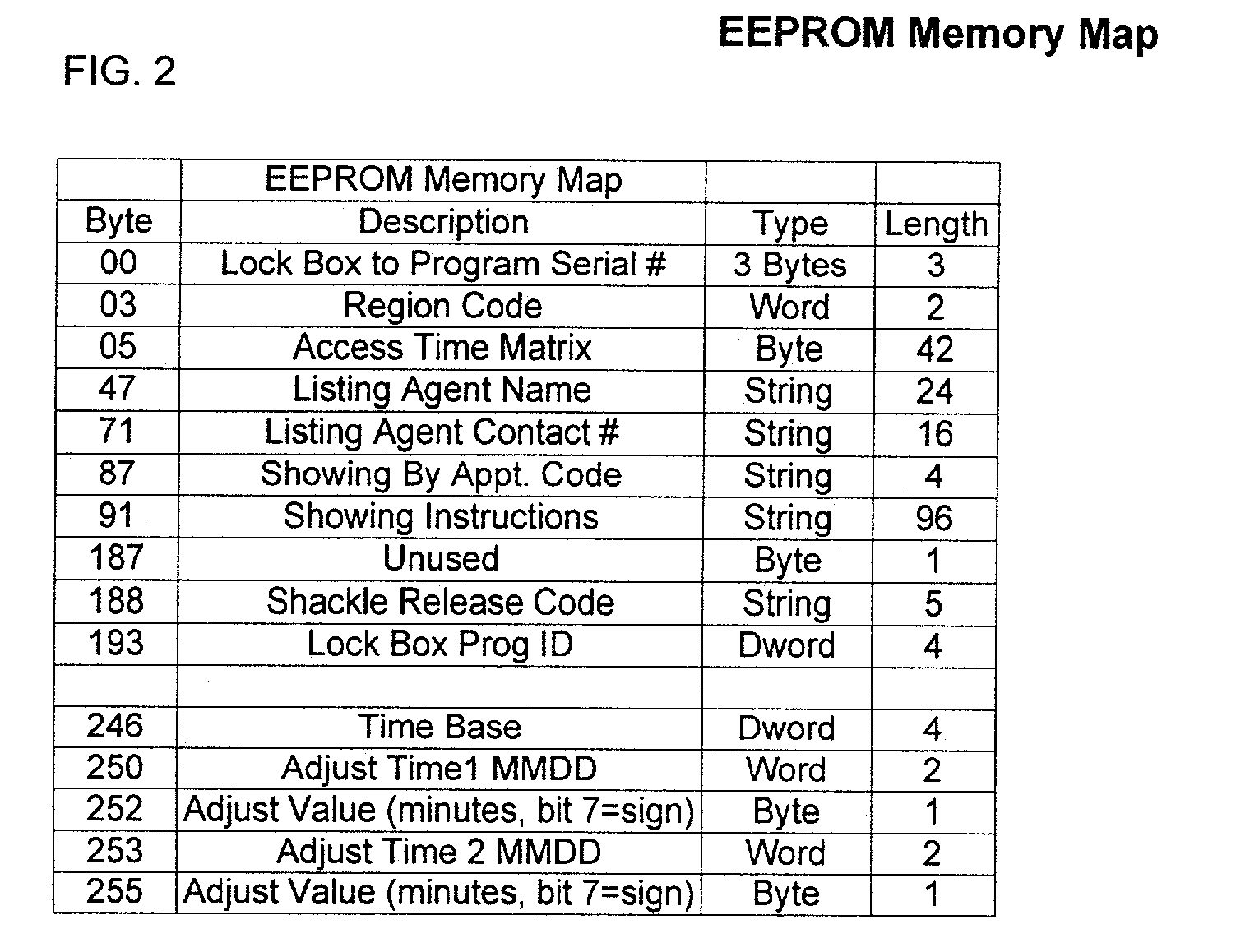
Electronic lock system and method for its use with card only mode
InactiveUS6989732B2Electric signal transmission systemsMultiple keys/algorithms usageMobile Telephone ServiceControl manner
An improved electronic lock system is provided for use with real estate lock boxes where there is the need for many people to access the secured compartment of the lock box in a controlled manner. Each user has an identification card with a non-volatile secure memory (known as a “smart card”), for exchanging data with the lock box, and with a portable computer capable of reading data from the smart card; or a cell phone can be used to gain access information from a central computer. The user first inserts the smart card into the connector attached to the lock box; the lock box reads the user's ID stored in the smart card memory and records this information in lock box memory. The lock box then transfers its access code information and other data to the smart card for further processing. The user then inserts the smart card in a portable card reader to learn the access code, or calls a central computer via a mobile phone system and interacts with the computer to elicit the necessary access code information. The access code is then manually keyed into the lock box keypad by the user to obtain access to the secure compartment. Other modes of operation include an “access token mode” and a “card only mode.”
Owner:SENTRILOCK
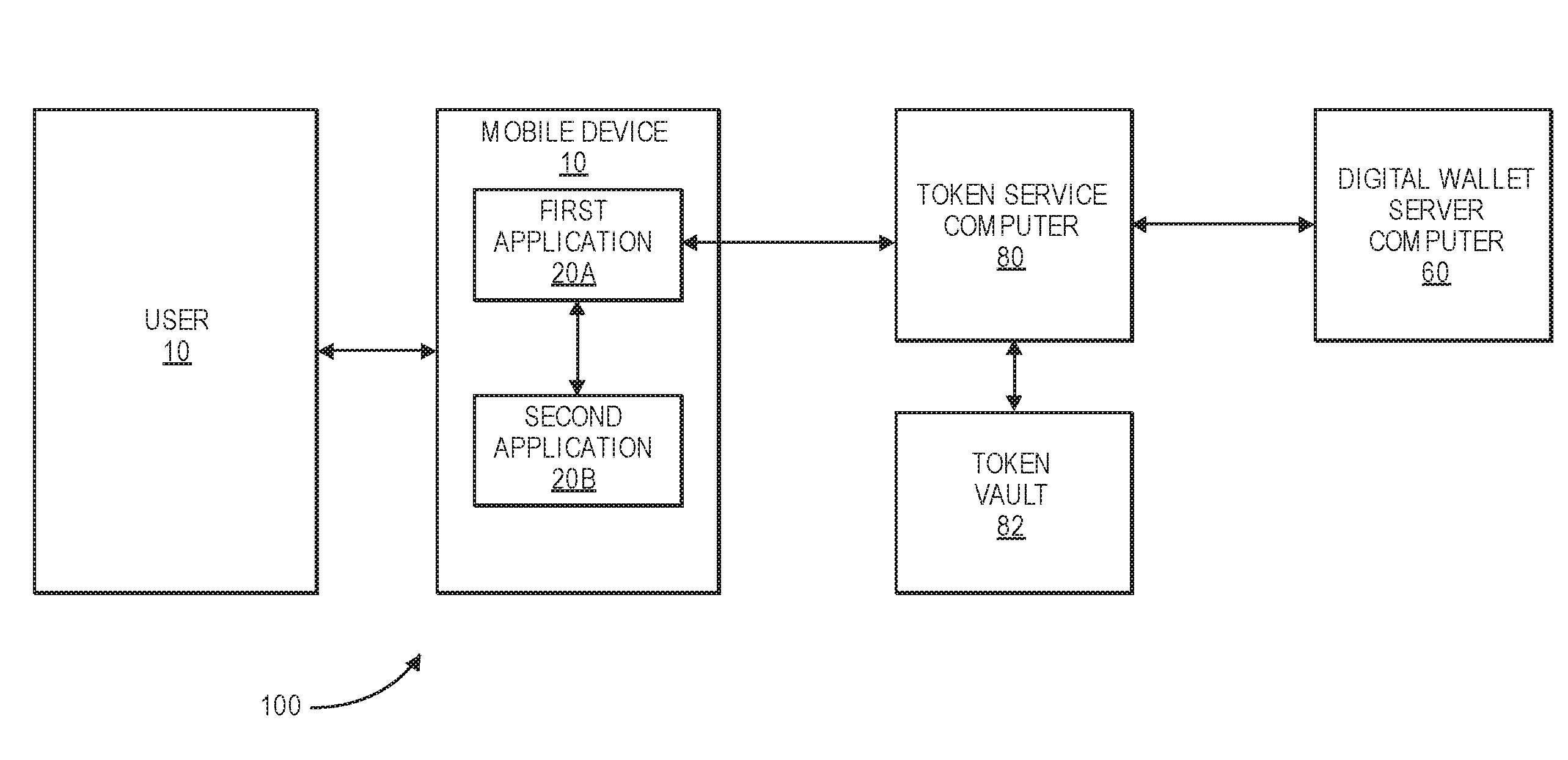
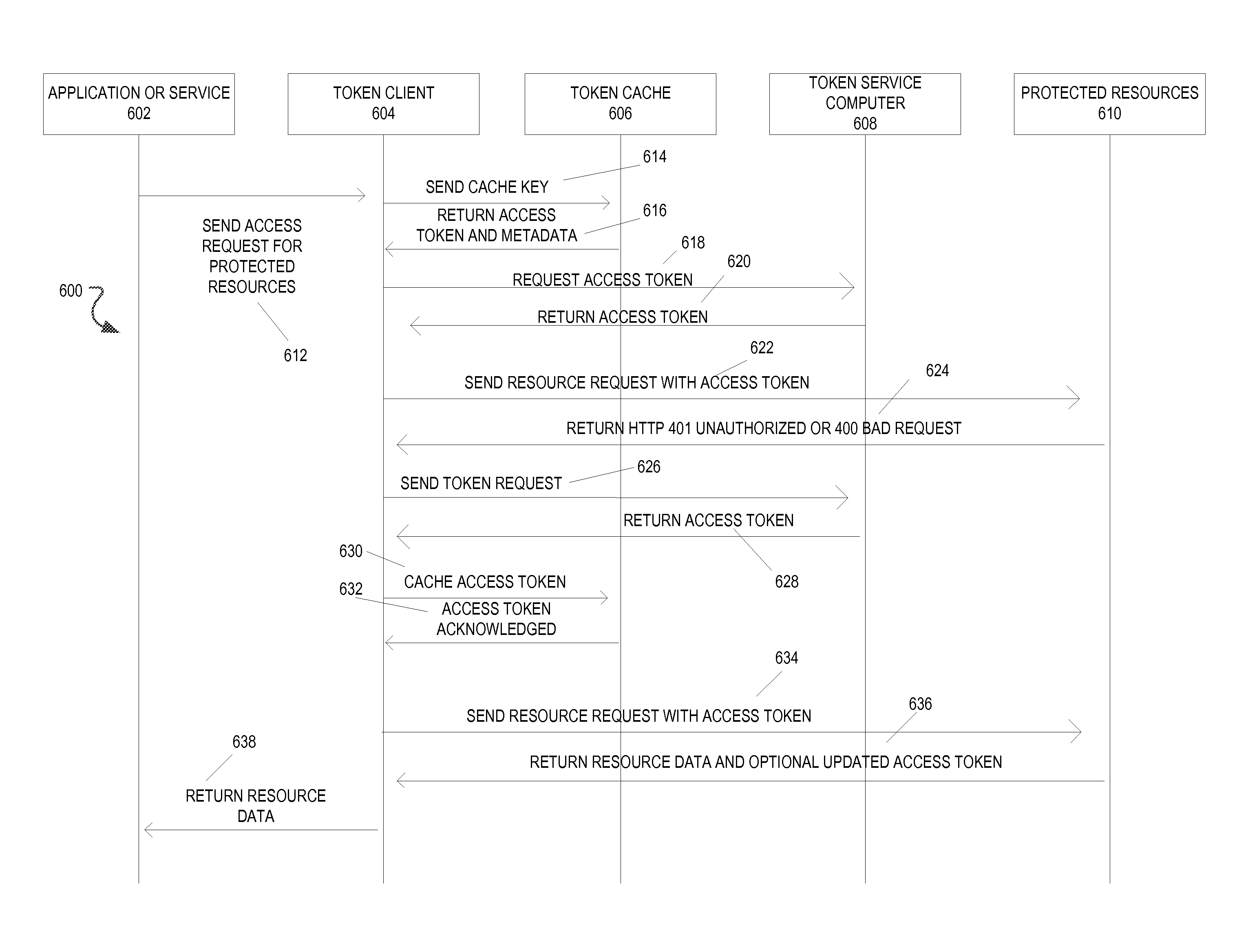
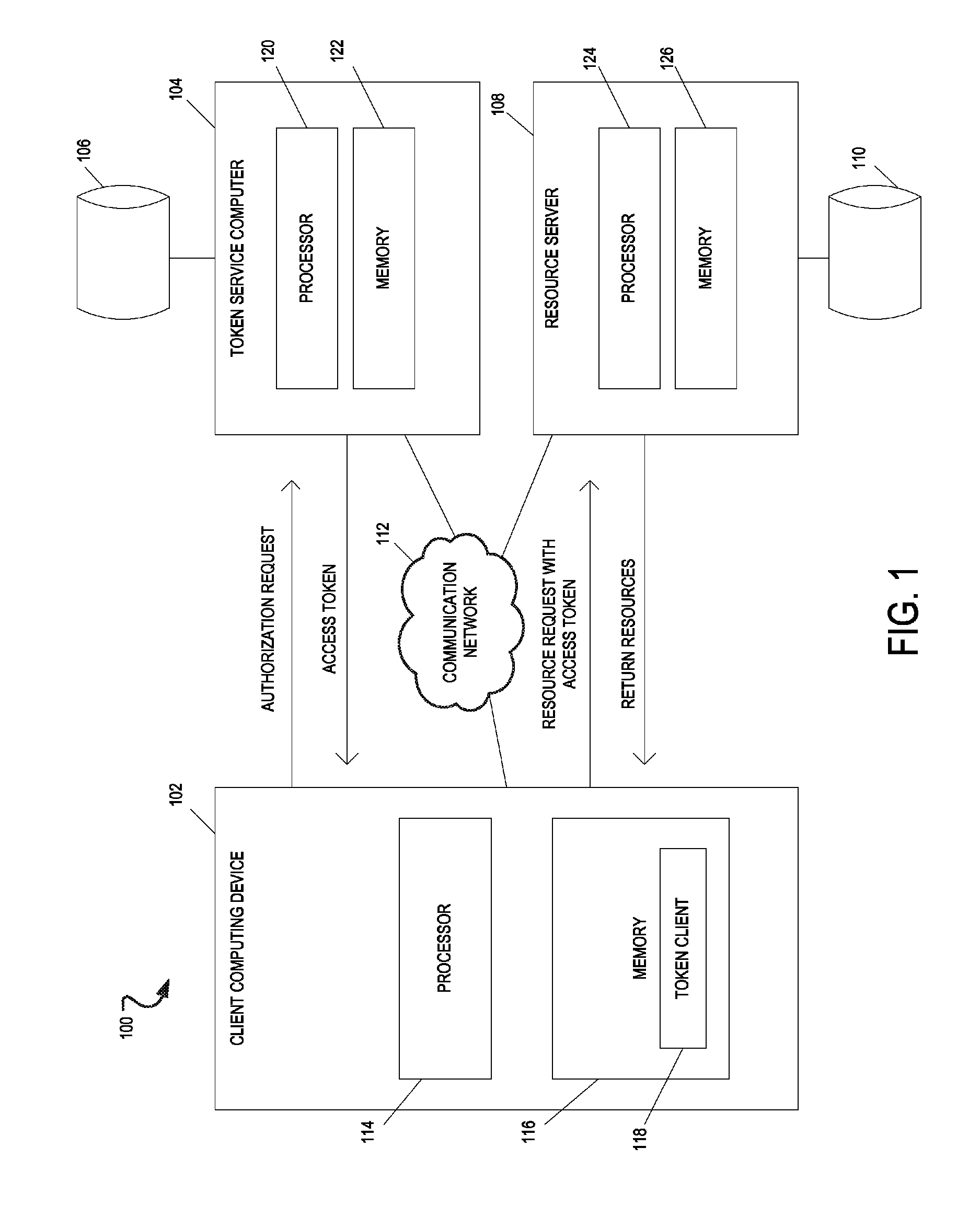
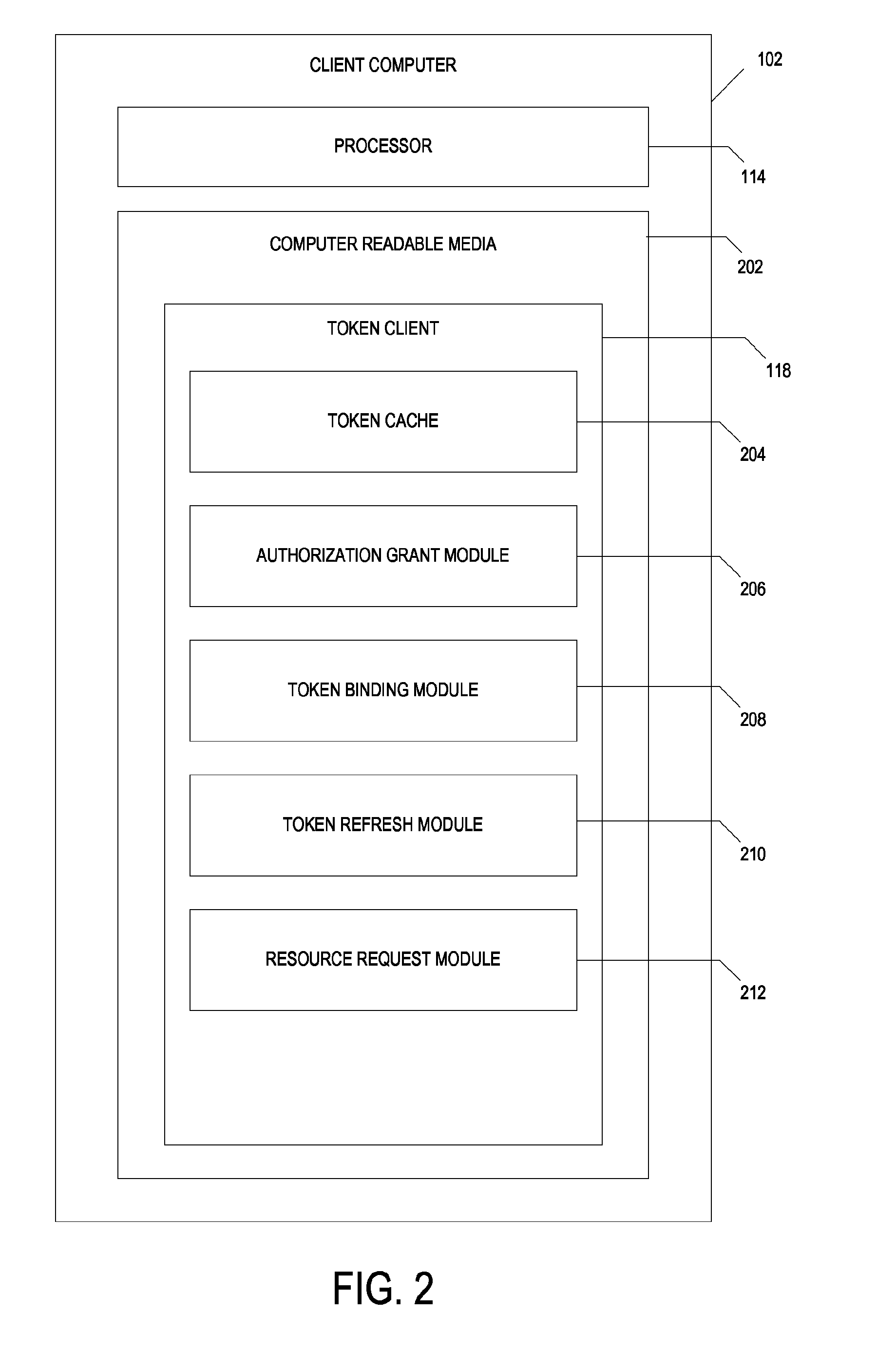
Authorization token cache system and method
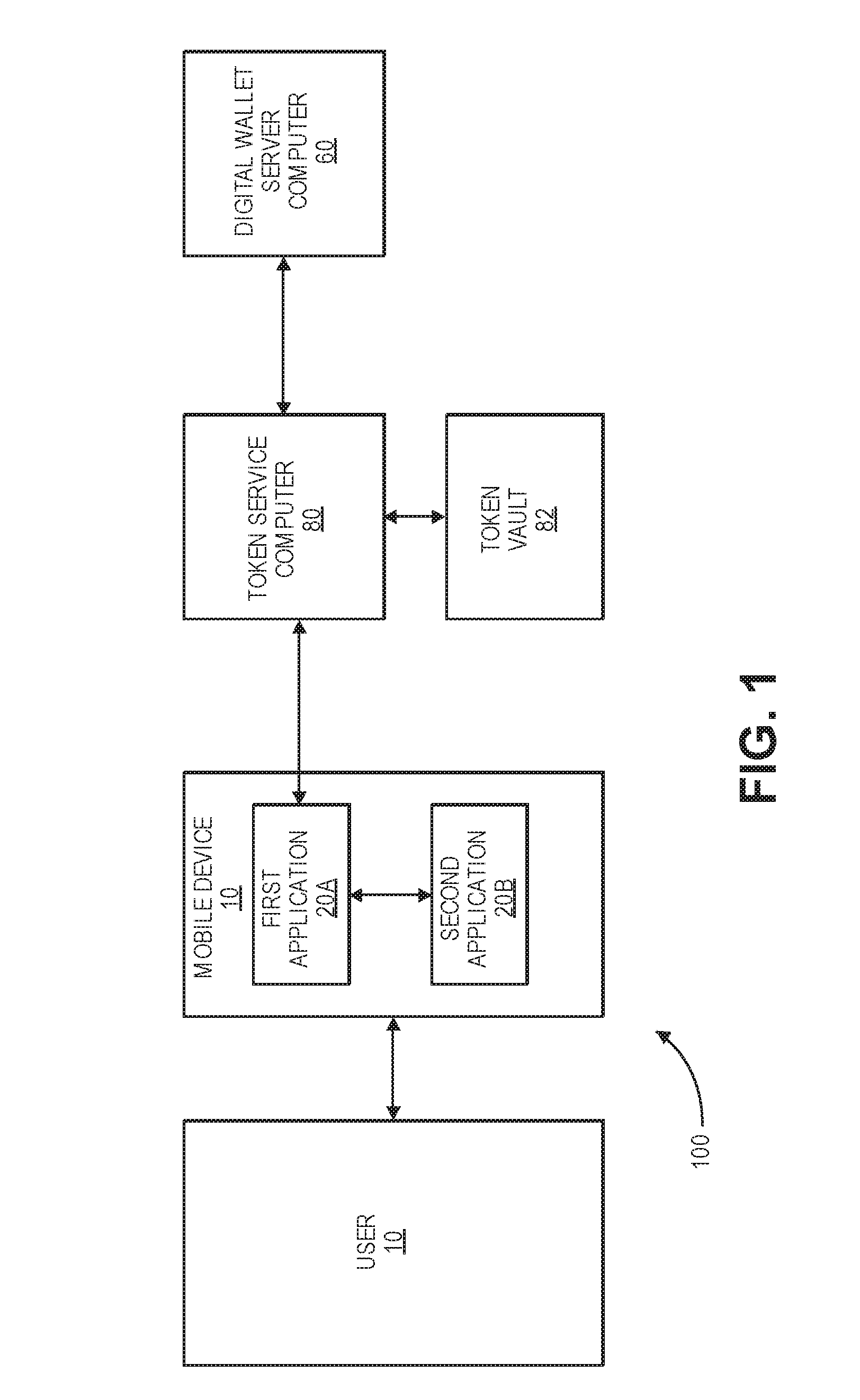
A system includes one or more processors to request access tokens from a token service computer, cache the access tokens and related information in a token cache, transmit the access tokens with a resource request to a resource server, and receive requested resources in response to the resource request. The resource server transmits representations of requested resources to computing devices having valid tokens. The access tokens and related information including credentials information and token metadata are stored in the token cache.
Owner:ORACLE INT CORP
Method, device and system for implementing authorization of third-party application based on open platform
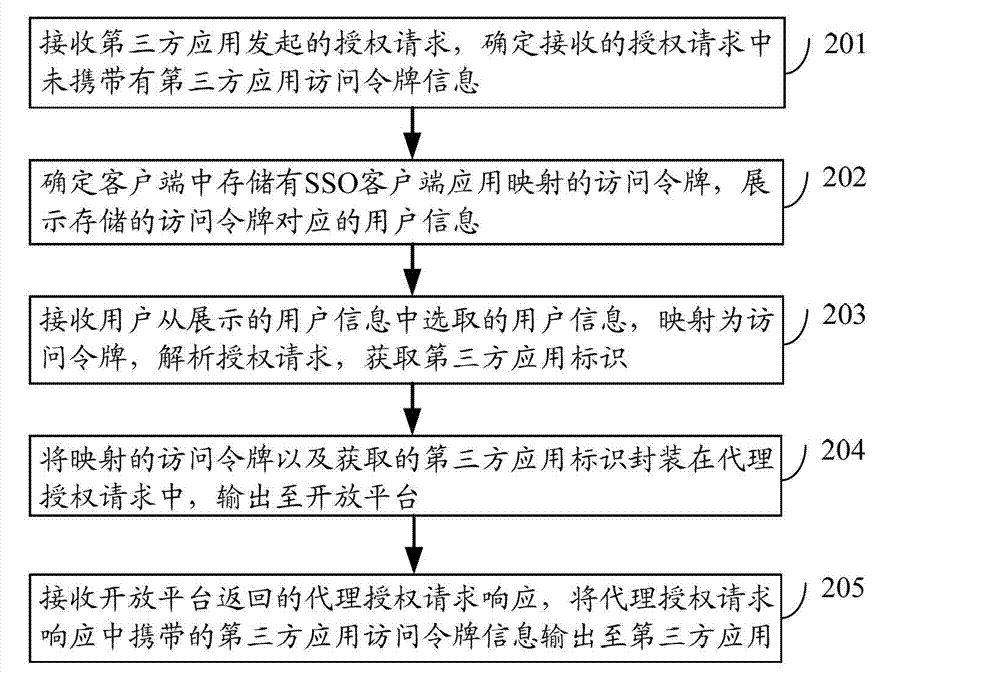
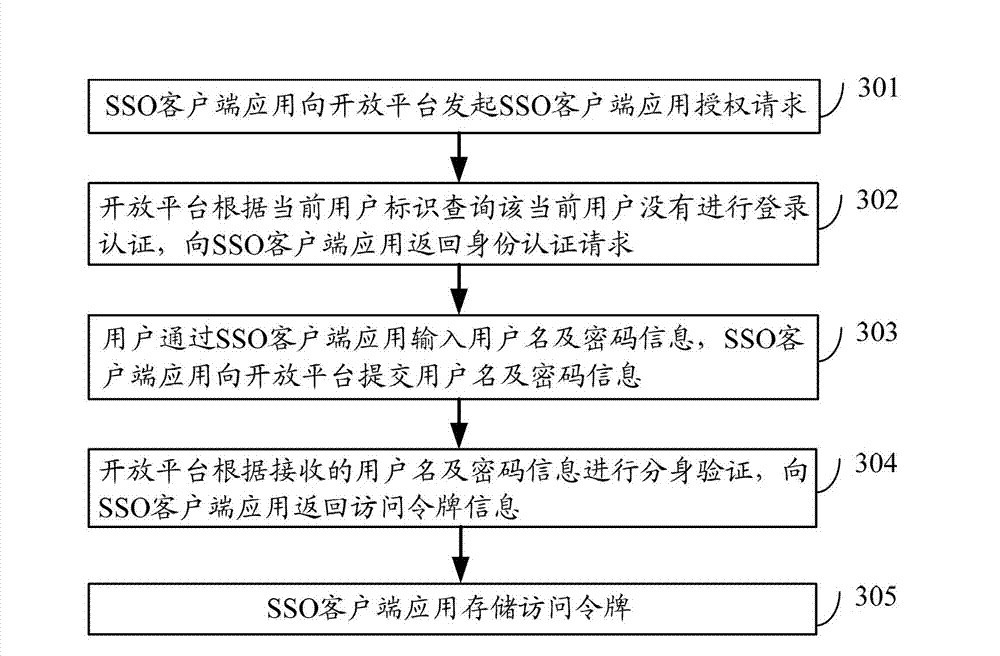
ActiveCN103051630AShorten the timeEasy to operateUser identity/authority verificationThird partyOpen platform
The invention discloses a method, a device and a system for implementing the authorization of a third-party application based on an open platform. The method comprises the following steps of: receiving an authorization request initiated by the third-party application, and determining that the received authorization request does not carry third-party application access token information; determining that an access token for single sign-on (SSO) client application mapping is stored in a client, and displaying user information corresponding to the stored access token; receiving user information which is selected from the displayed user information by a user, mapping the user information into the access token, analyzing the authorization request, and acquiring a third-party application identifier; packaging the mapped access token and the acquired third-party application identifier into an agent authorization request, and outputting the agent authorization request to the open platform; and receiving an agent authorization request response returned by the open platform, and outputting the third-party application access token information carried in the agent authorization request response to the third-party application. By the invention, application authorization efficiency can be improved.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
Identifying and destroying potentially misappropriated access tokens
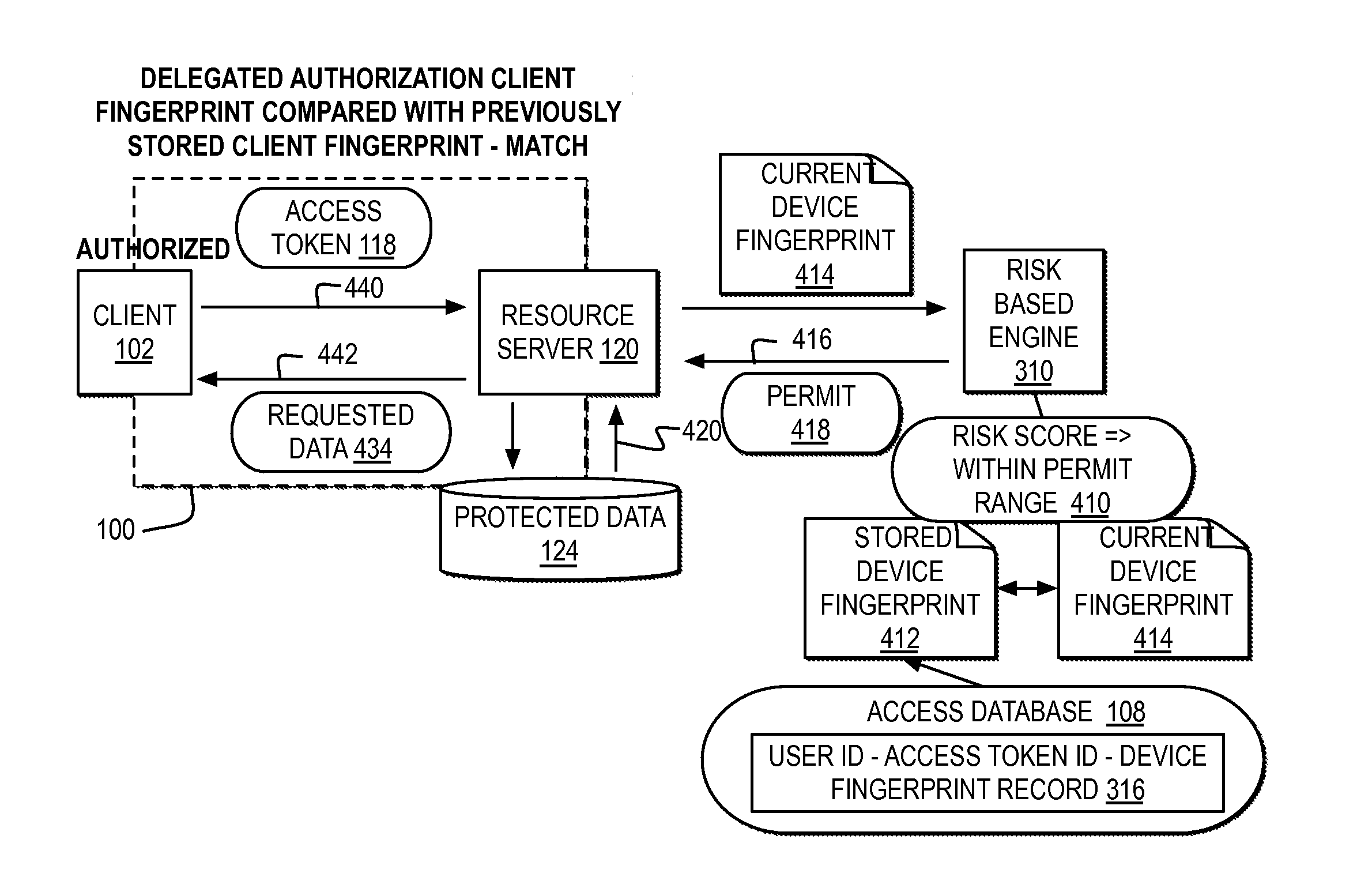
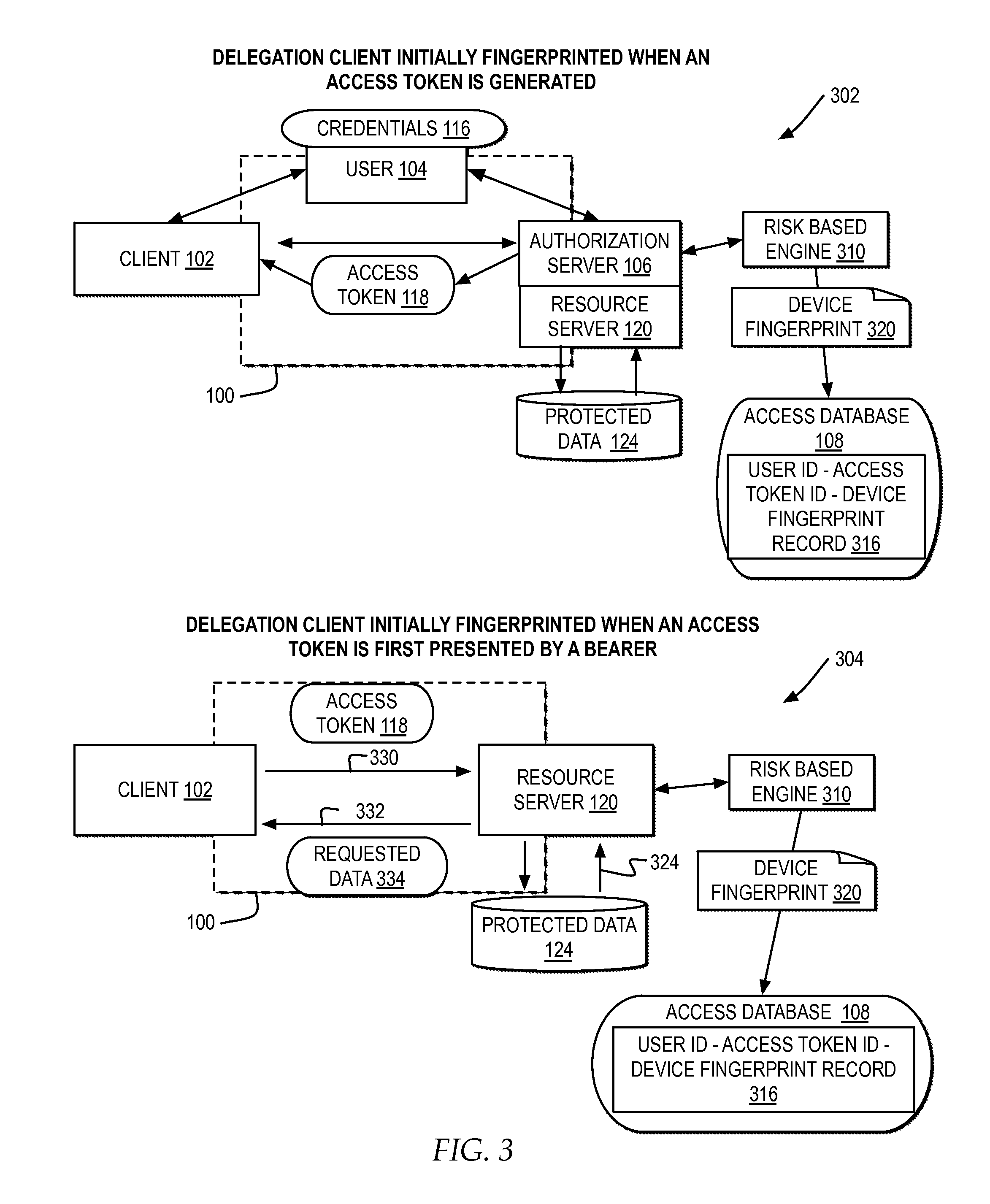
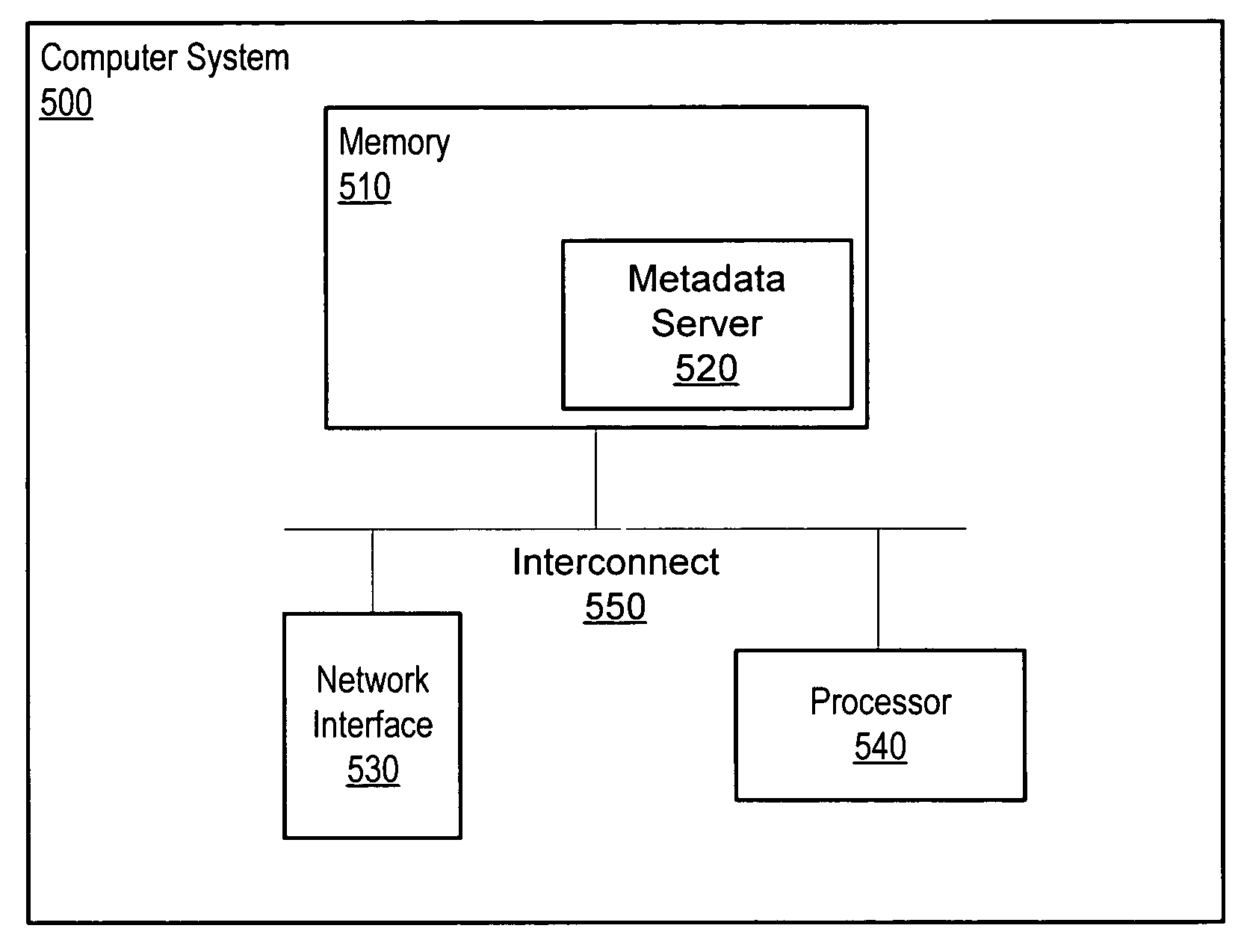
ActiveUS20150150110A1Digital data processing detailsMultiple digital computer combinationsAccess tokenDevice fingerprint
A computer receives a request for protected user data with an access token presented by a client as authorization for the client to access the protected user data in a delegated environment. The computer parses the request to create a device fingerprint identifying the device submitting the request for the client. The computer compares the device fingerprint of the request to a previously stored device fingerprint of an authorized device associated with the access token. The computer automatically determines whether to identify the access token as potentially misappropriated based on the comparison of the device fingerprint of the request to the previously stored device fingerprint.
Owner:IBM CORP
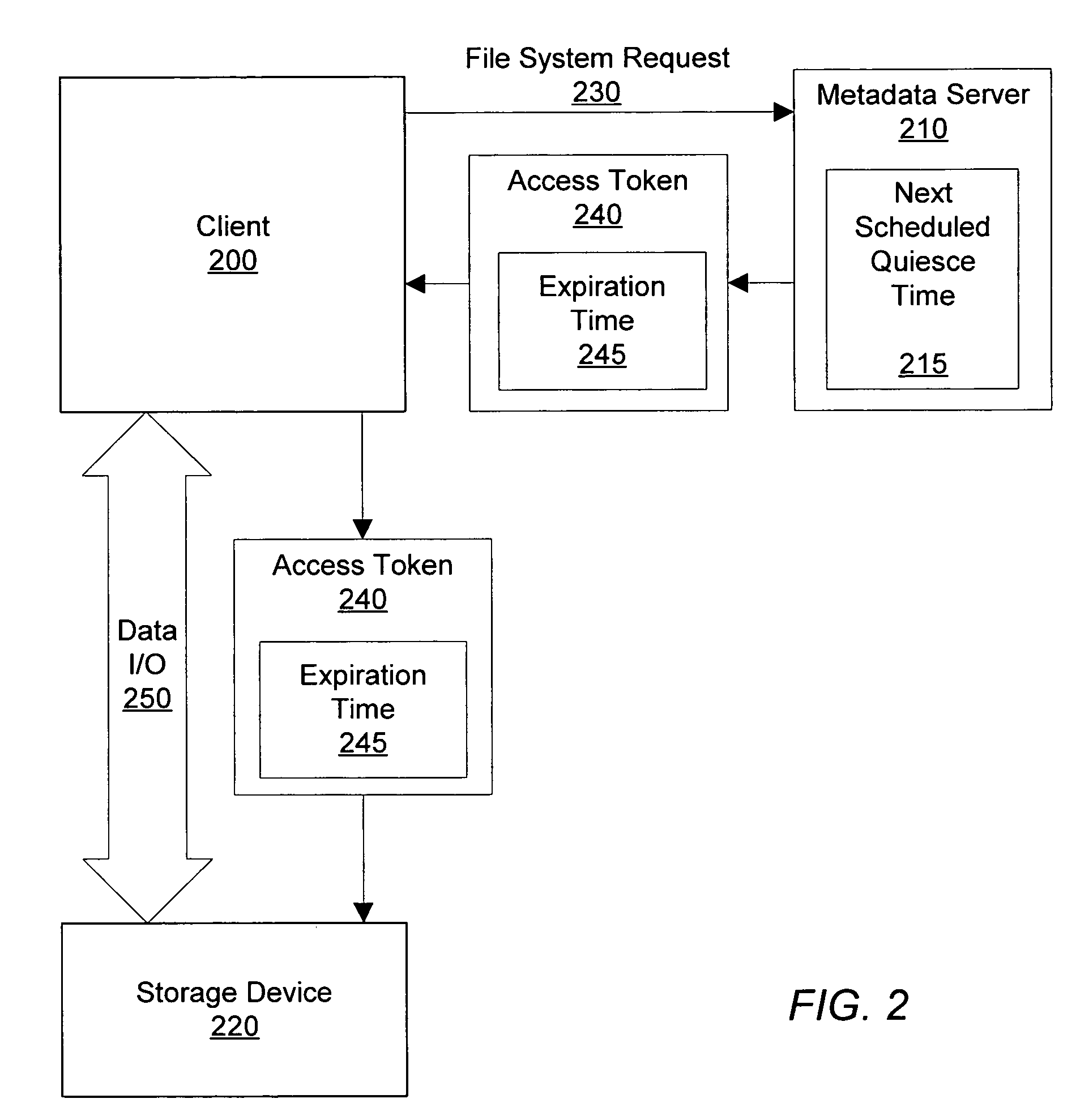
Expiration of access tokens for quiescing a distributed system
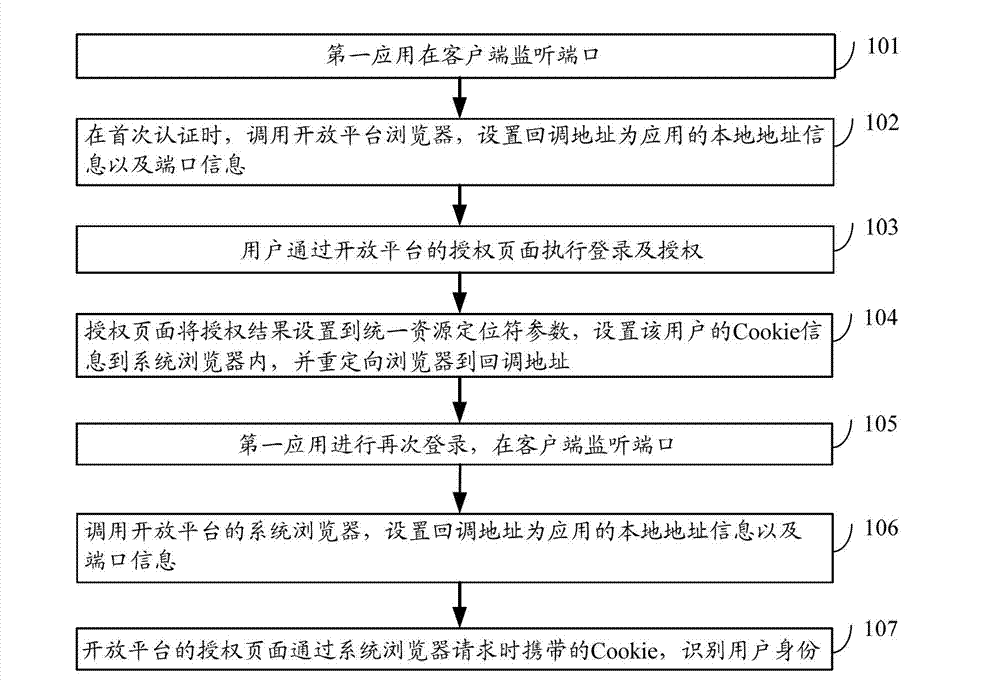
InactiveUS7720864B1Digital data information retrievalDigital data processing detailsExpiration TimeAccess token
A method, system and computer accessible medium for expiring access tokens in preparation for freezing file images. A metadata server may maintain a next scheduled quiesce time and may issue access tokens configured to expire before the next scheduled quiesce time. A metadata server may set an access token's expiration time to a maximum expiration time indicated by the next scheduled quiesce time or may set an access token's expiration time to a default expiration time if the default expiration time is earlier than the maximum expiration time. A storage device may recognize and enforce the access token's expiration time.
Owner:SYMANTEC OPERATING CORP
System and method for a directory secured user account
InactiveUS20050160276A1Access be reduced eliminatedDisadvantages can be reduced eliminatedComputer security arrangementsSecret communicationComputer networkAccess token
A system and method for providing network access includes identifying an available network resource, providing an access token to the available network resource, tracking the access token, and terminating the access token.
Owner:CAPITAL ONE FINANCIAL
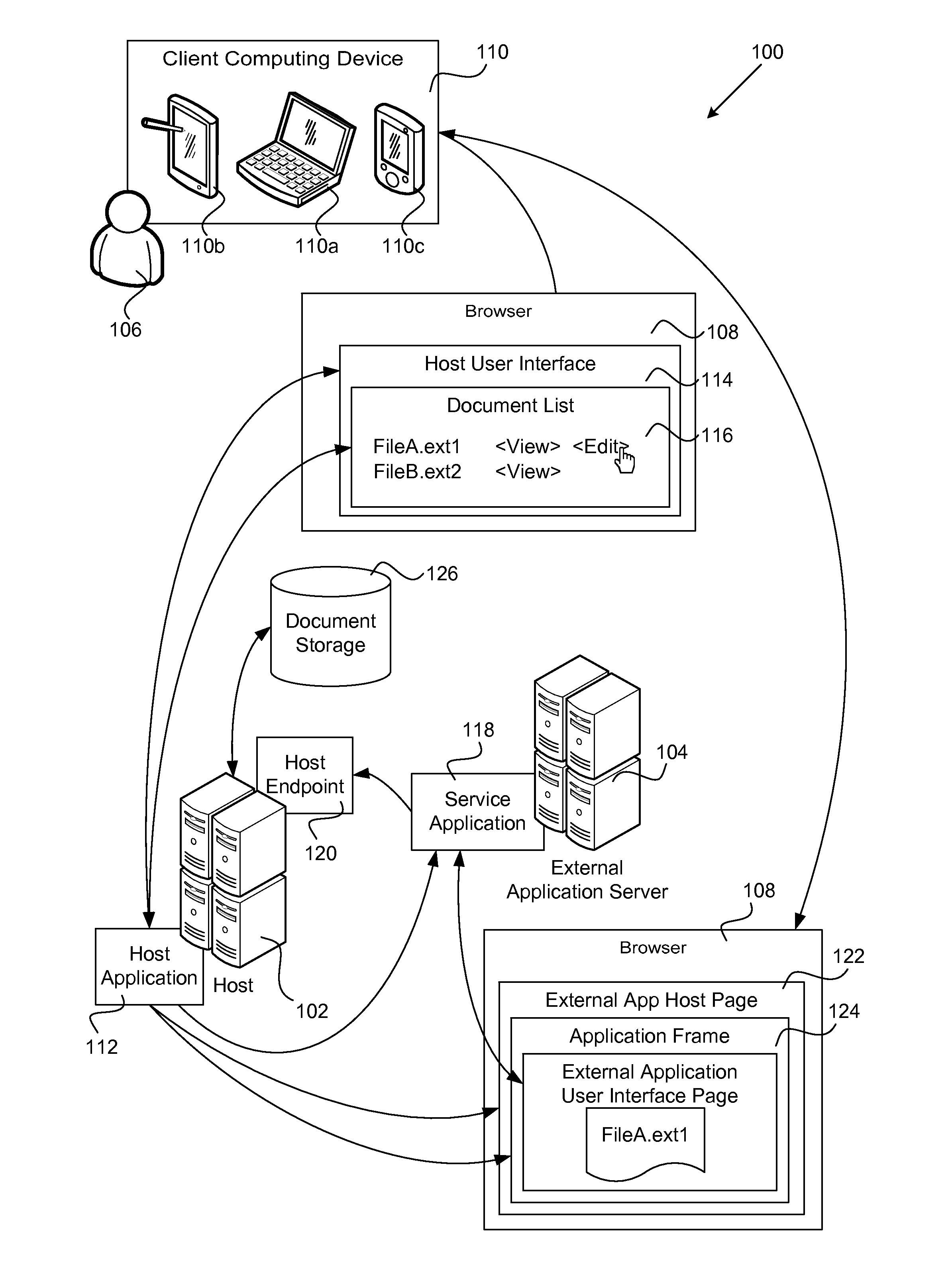
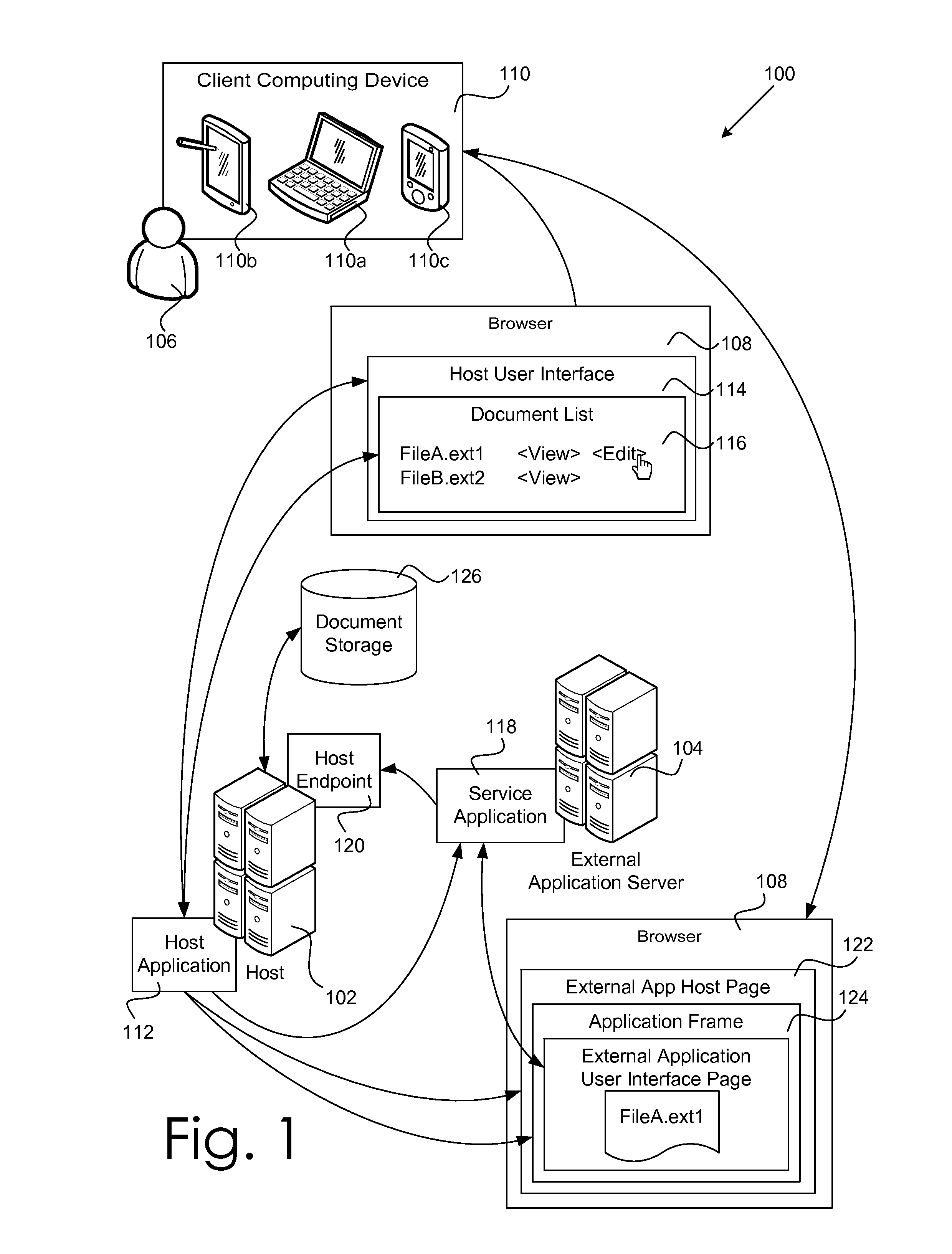
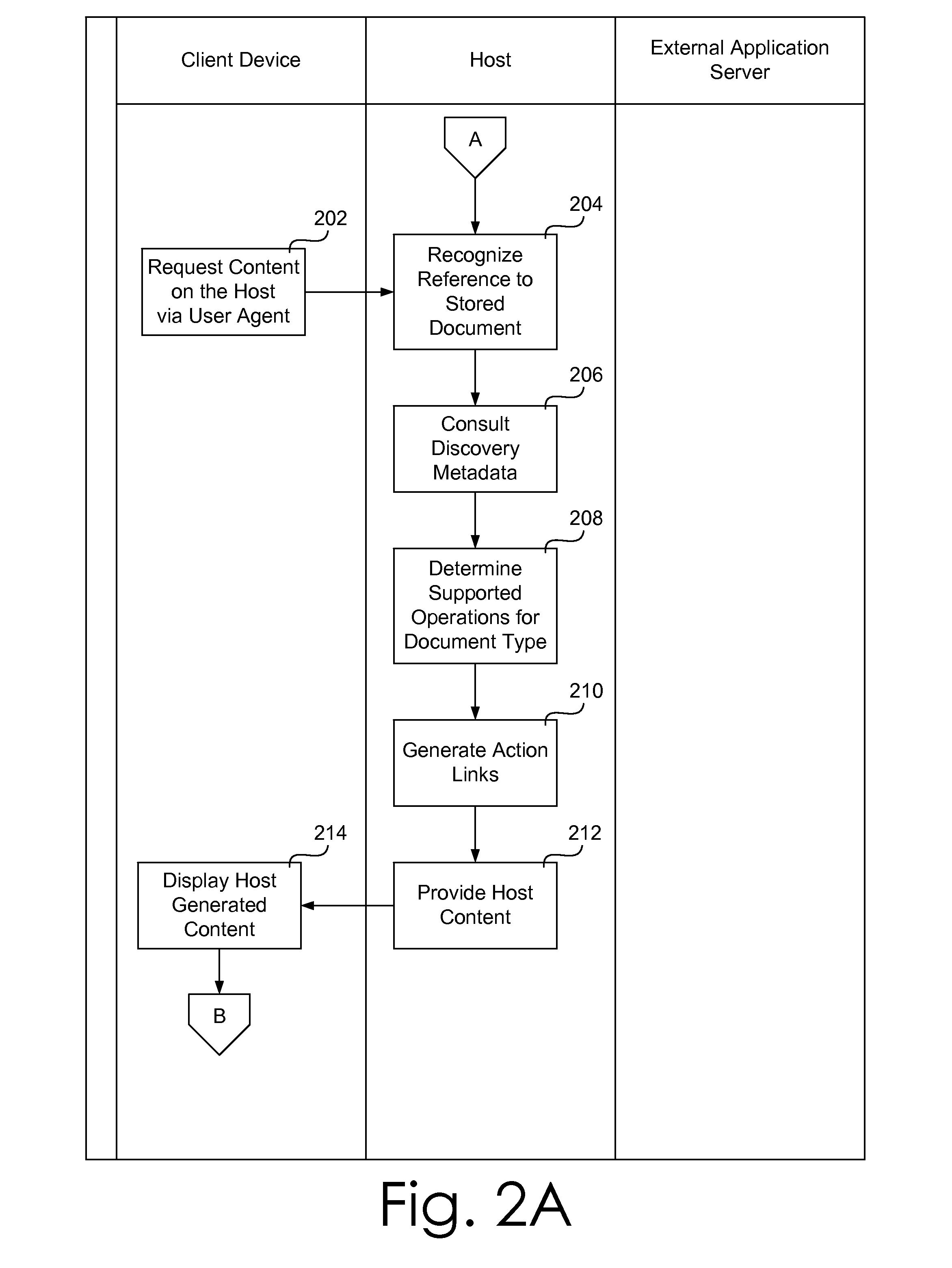
Host Agnostic Integration and Interoperation System
ActiveUS20130080785A1Improve the level ofEliminate needDigital data processing detailsUser identity/authority verificationOperational systemApplication server
A host agnostic integration and interoperation system. The host agnostic integration and interoperation system includes an open platform interface and the associated conventions that define the roles of and direct operations between a host and a service application running on an external application server and allow the host to discover and integrate the functionality provided by the service application. The open platform interface employs a limited number of easily implemented semantic methods allowing a host to expose and integrate the ability to view, edit, or otherwise manipulate a document using the host supported functionality of the service application from a standard user agent. The host agnostic integration and interoperation system handles user authentication at the host using an access token and establishes a trust relationship between the host and the external application server using a lightweight but secure proof key system.
Owner:MICROSOFT TECH LICENSING LLC
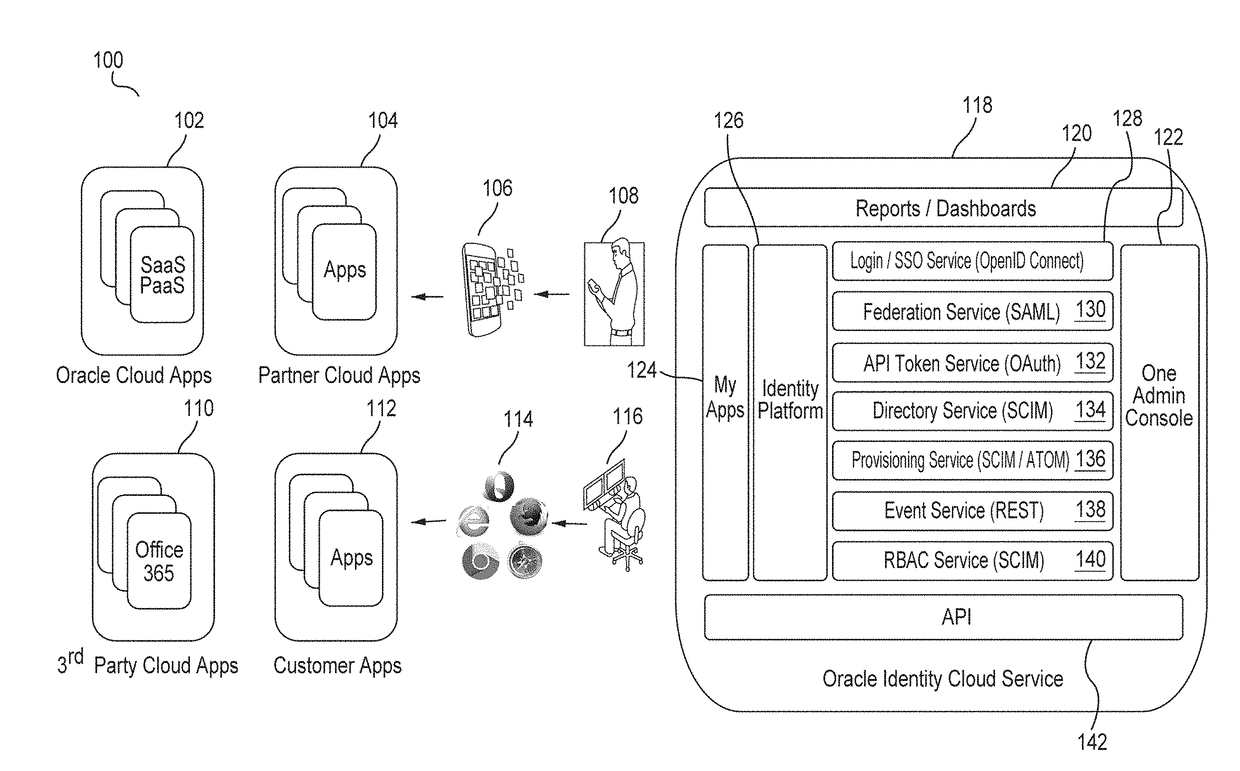
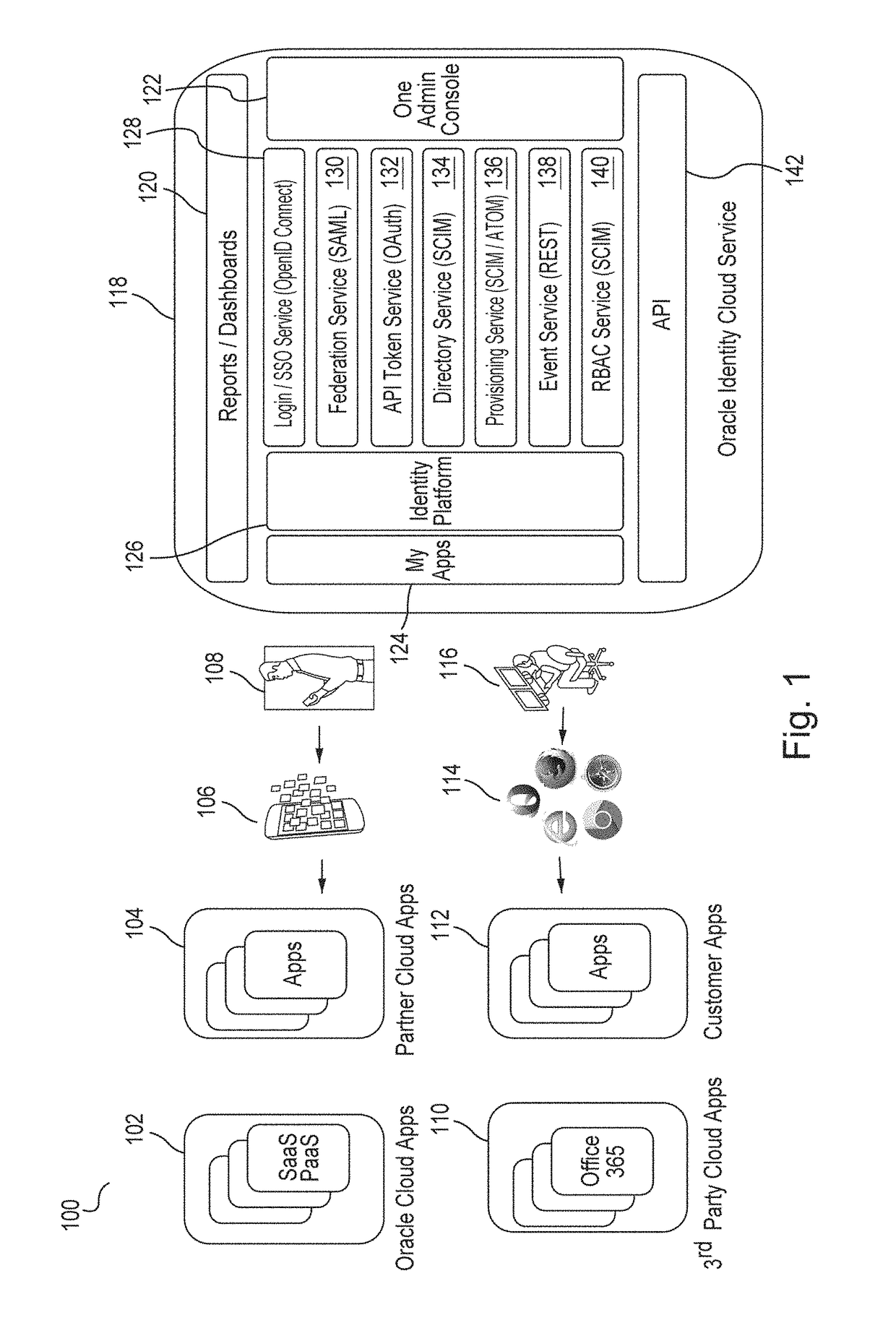
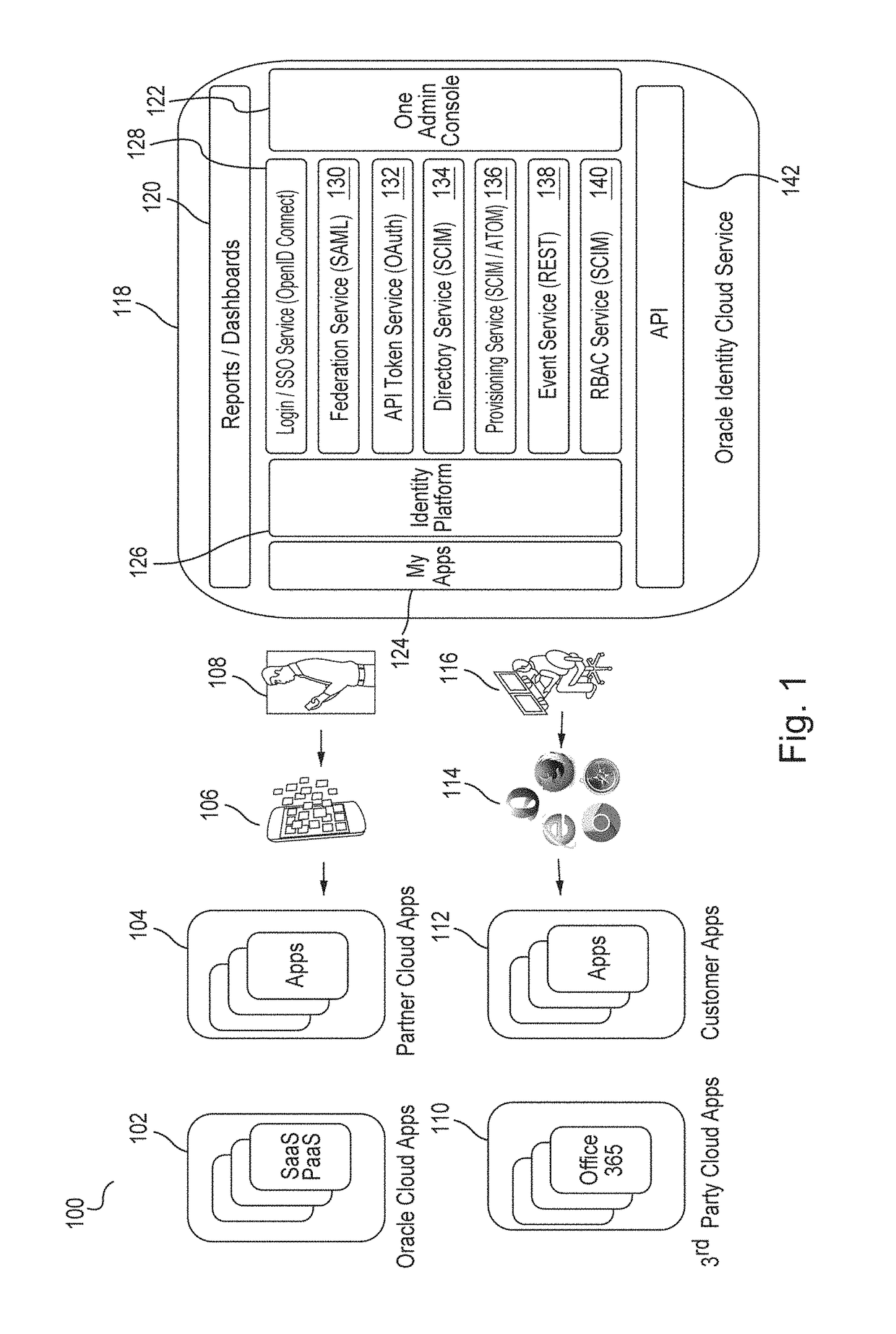
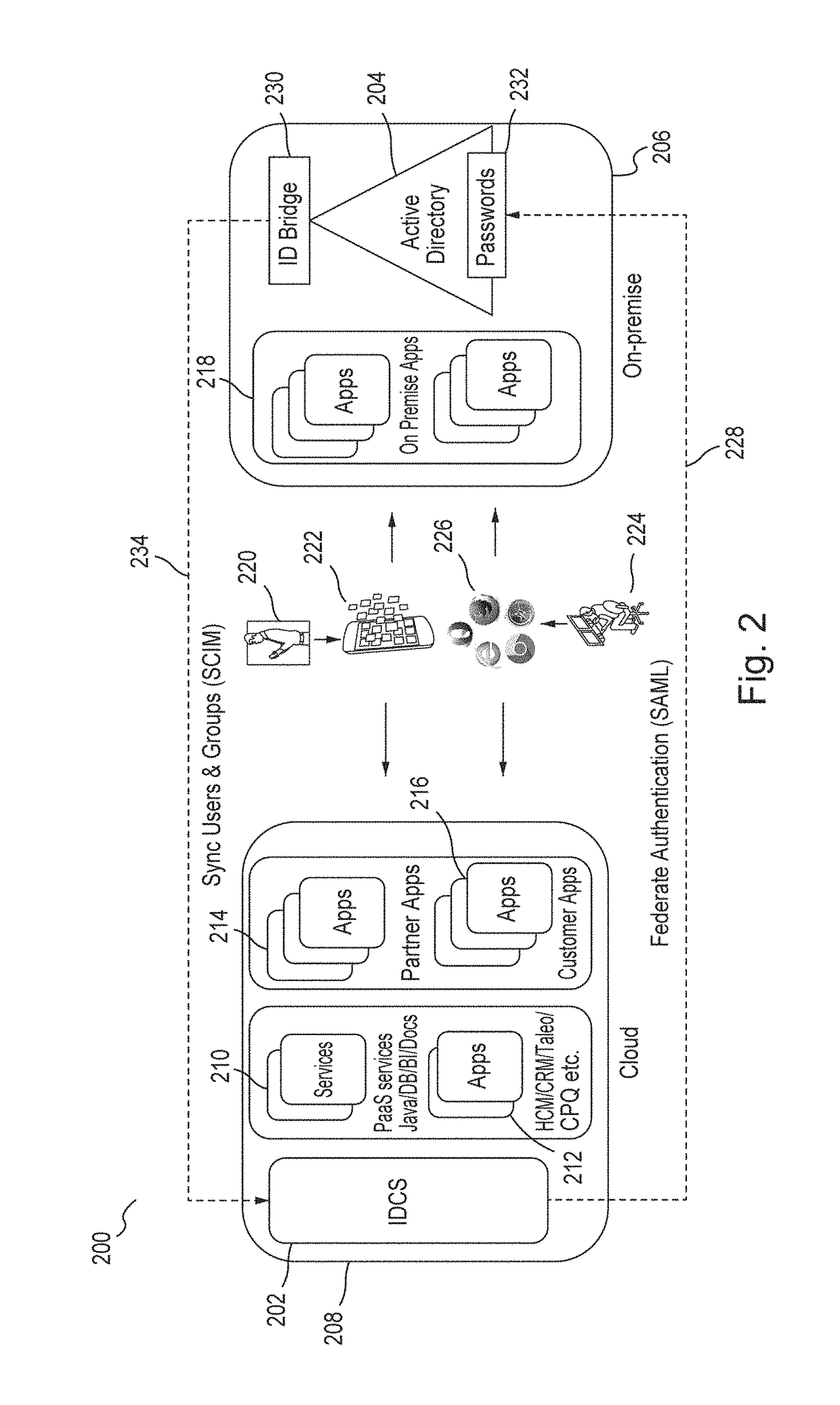
Generating derived credentials for a multi-tenant identity cloud service
A multi-tenant system that provides cloud-based identity management receives a request to execute a job, where the job has a scheduled start time, or a timeframe to complete, that exceeds the validity time of a request access token. The system generates the request access token corresponding to the job, where the request access token has access privileges. The system schedules the job and persists the request access token. The system triggers the job at the scheduled start time and generates a derived access token based on the request access token, where the derived access token includes the access privileges. The system then injects the derived access token during runtime of the job and calls a microservice using the derived access token to execute the job.
Owner:ORACLE INT CORP
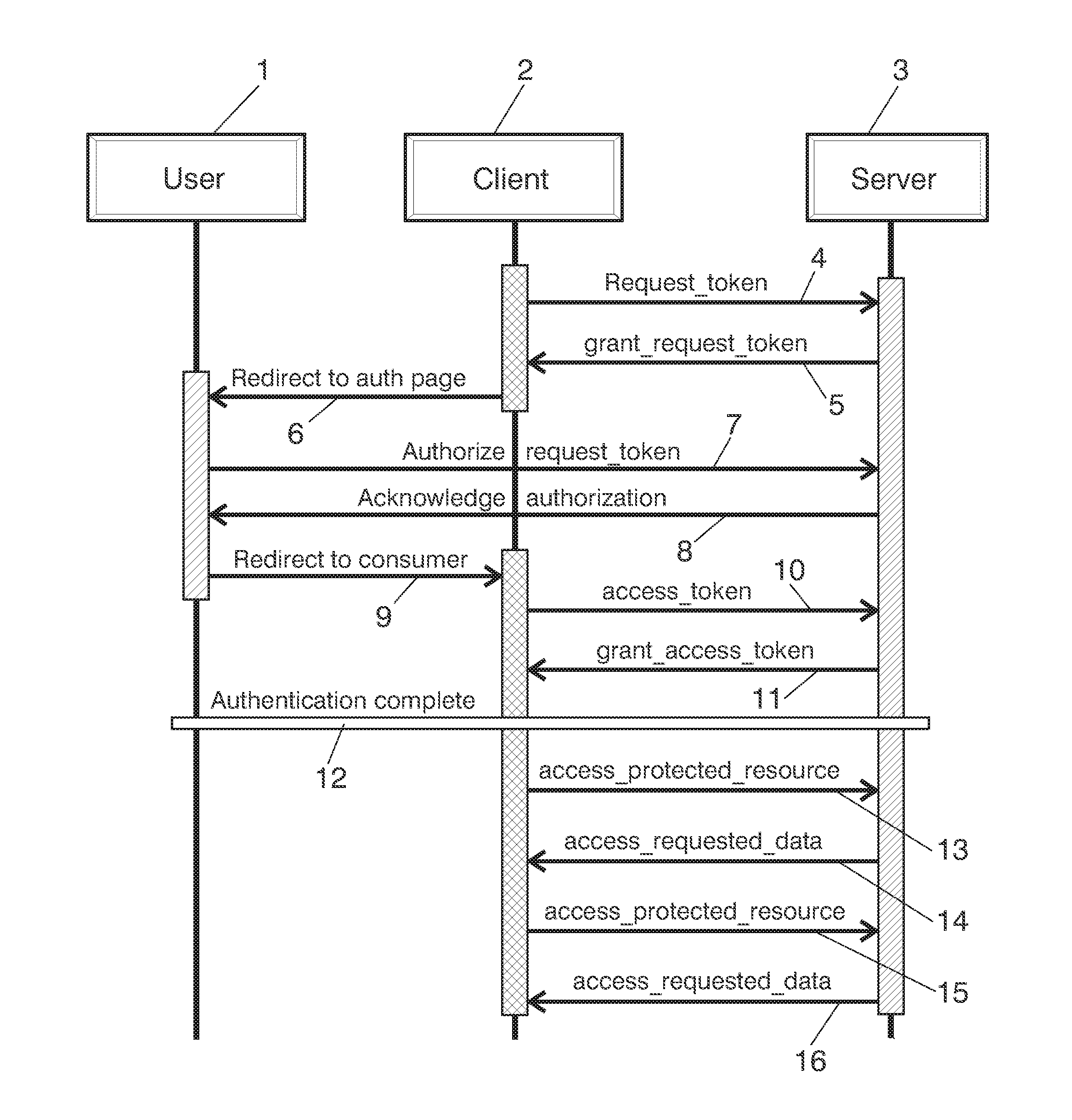
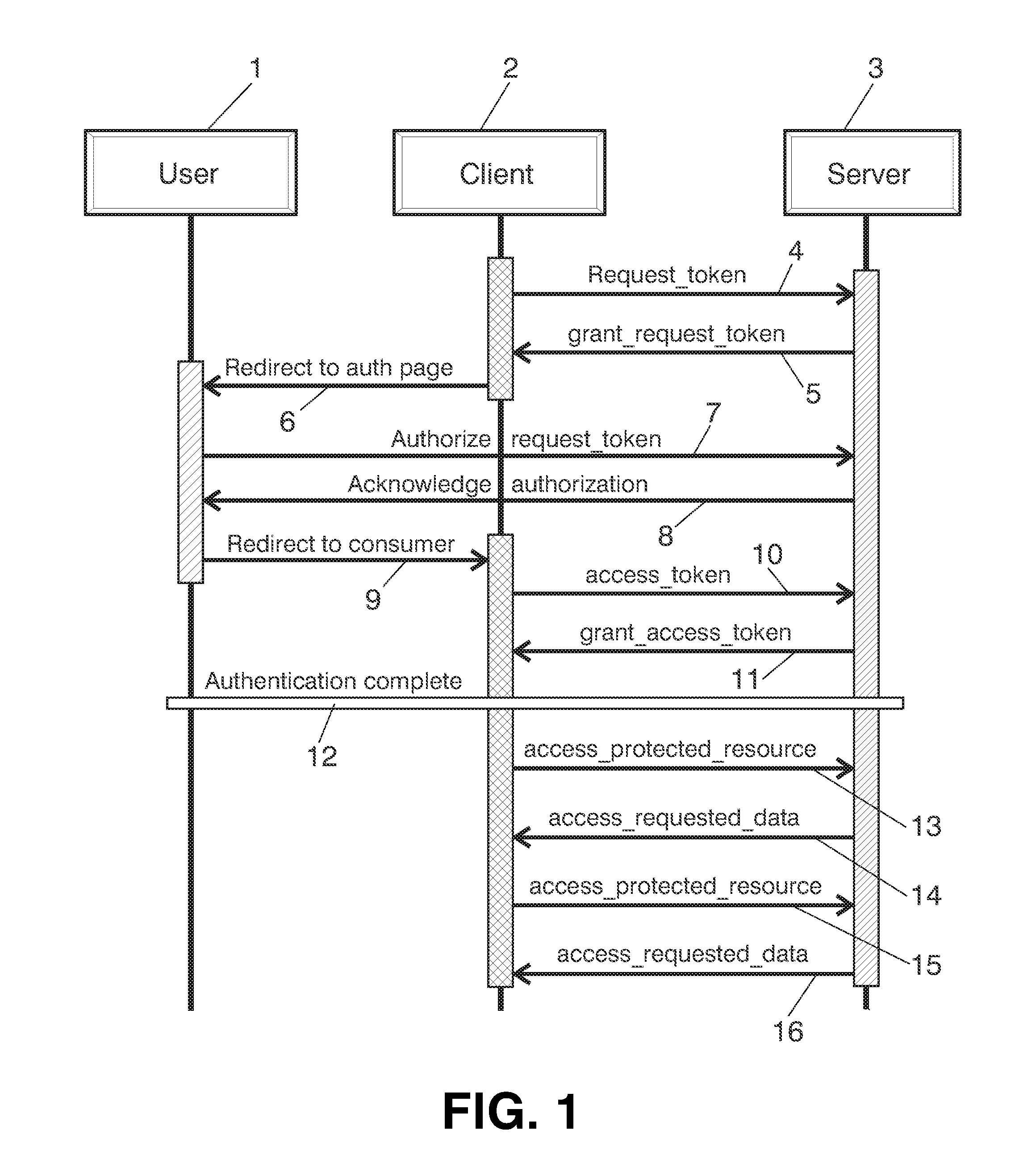
Method for authorizing access to protected content
ActiveUS20140068746A1User identity/authority verificationDigital data authenticationThird partyInternet privacy
The invention refers to a method for authorizing access to a third party application, called client (2), to protected resources owned by a user (1) and hosted in a server (3). The method comprising: the client being used by the user asking for a temporary token to the server; the server sending a first SMS to the user, said first SMS providing means to authenticate the user; authenticating the user by the means provided in previous two steps; the user authorizing the client; the server sending a second SMS to the user providing some information needed to obtain an access token; the client getting the information of the previous step from the user and the access token; the client accessing protected resources using the access token.
Owner:TELEFONICA SA
User data authorization method, device and system
ActiveCN102638473AImprove service experienceImprove service qualityUser identity/authority verificationThird partyApplication server
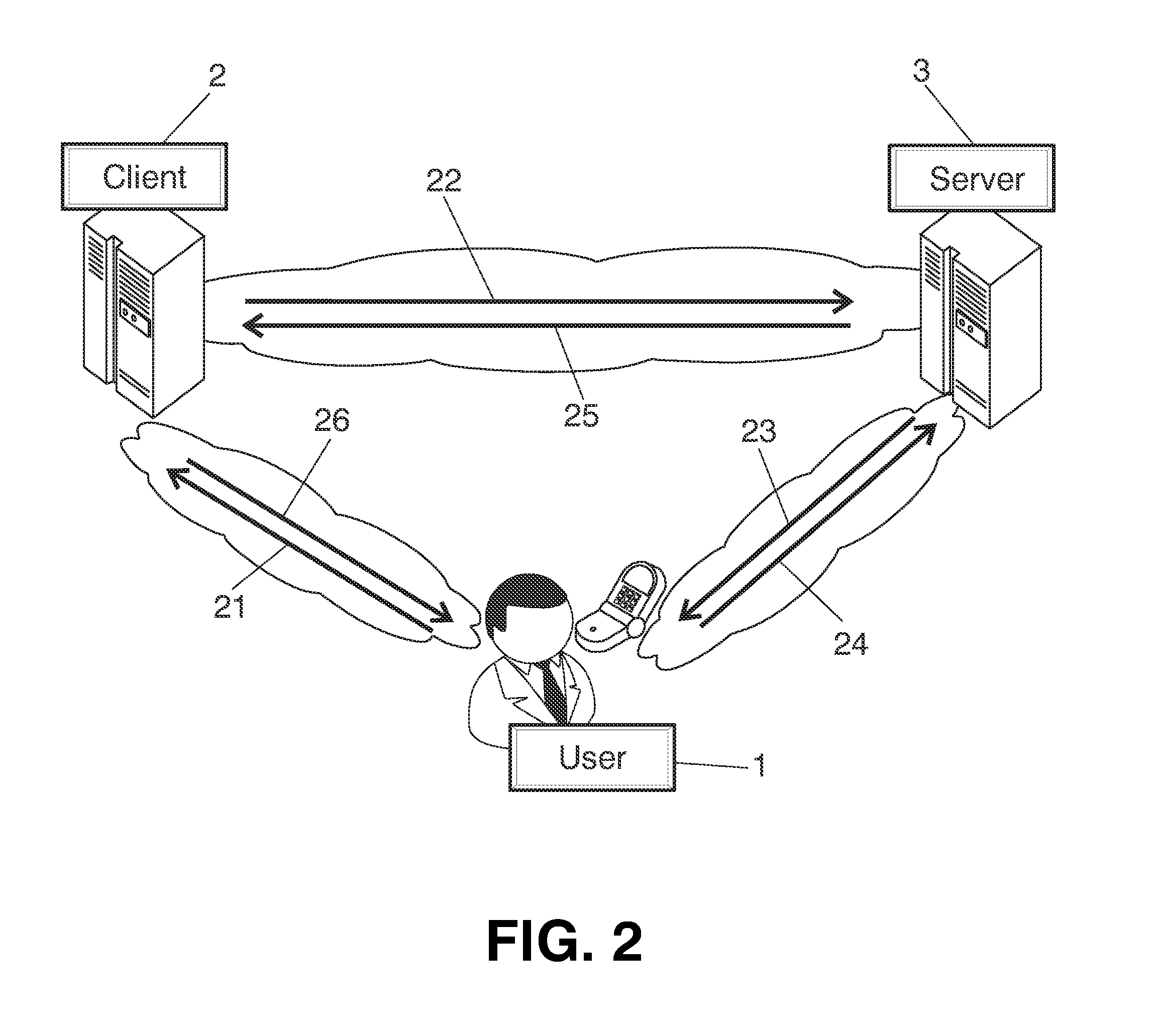
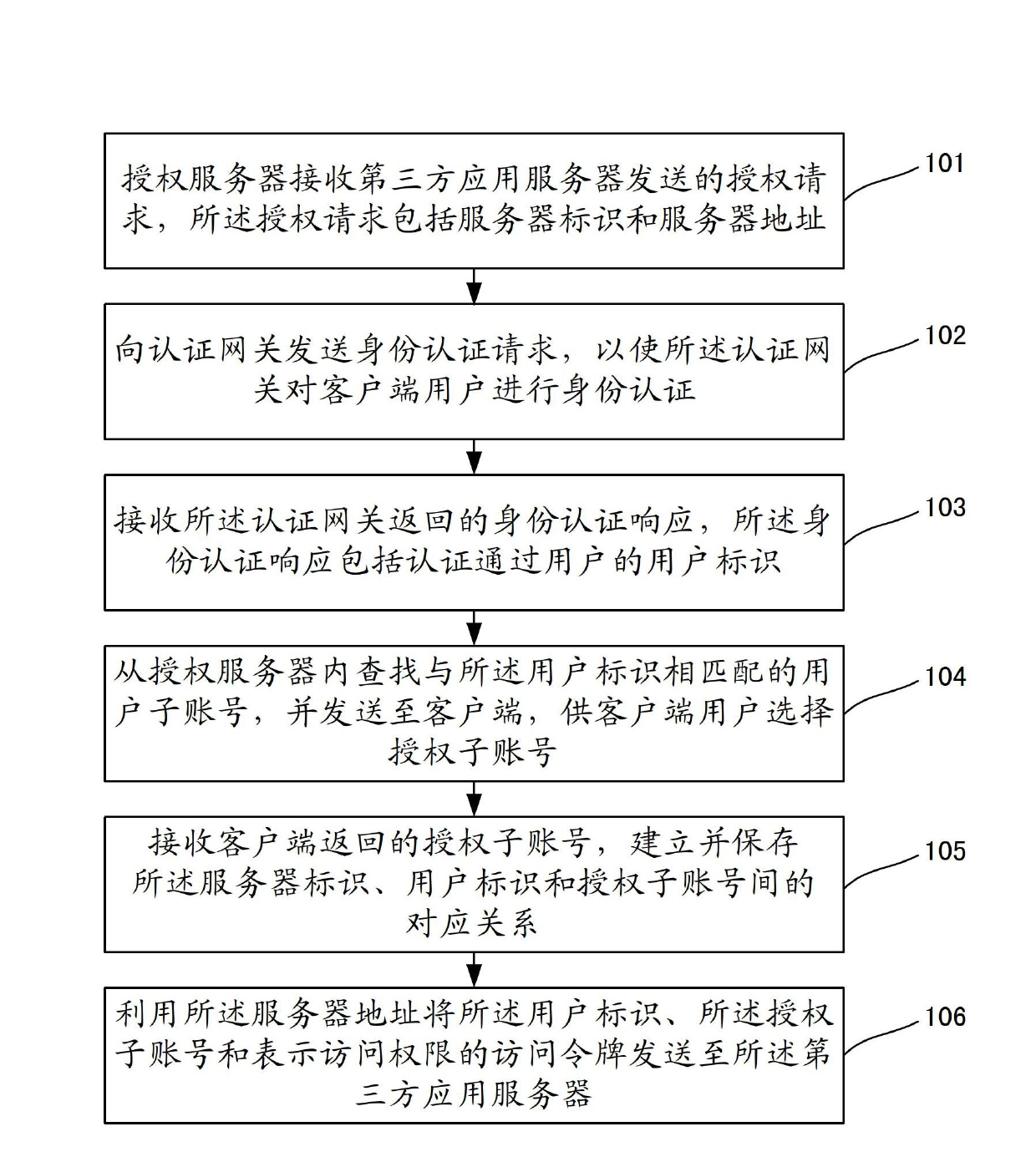
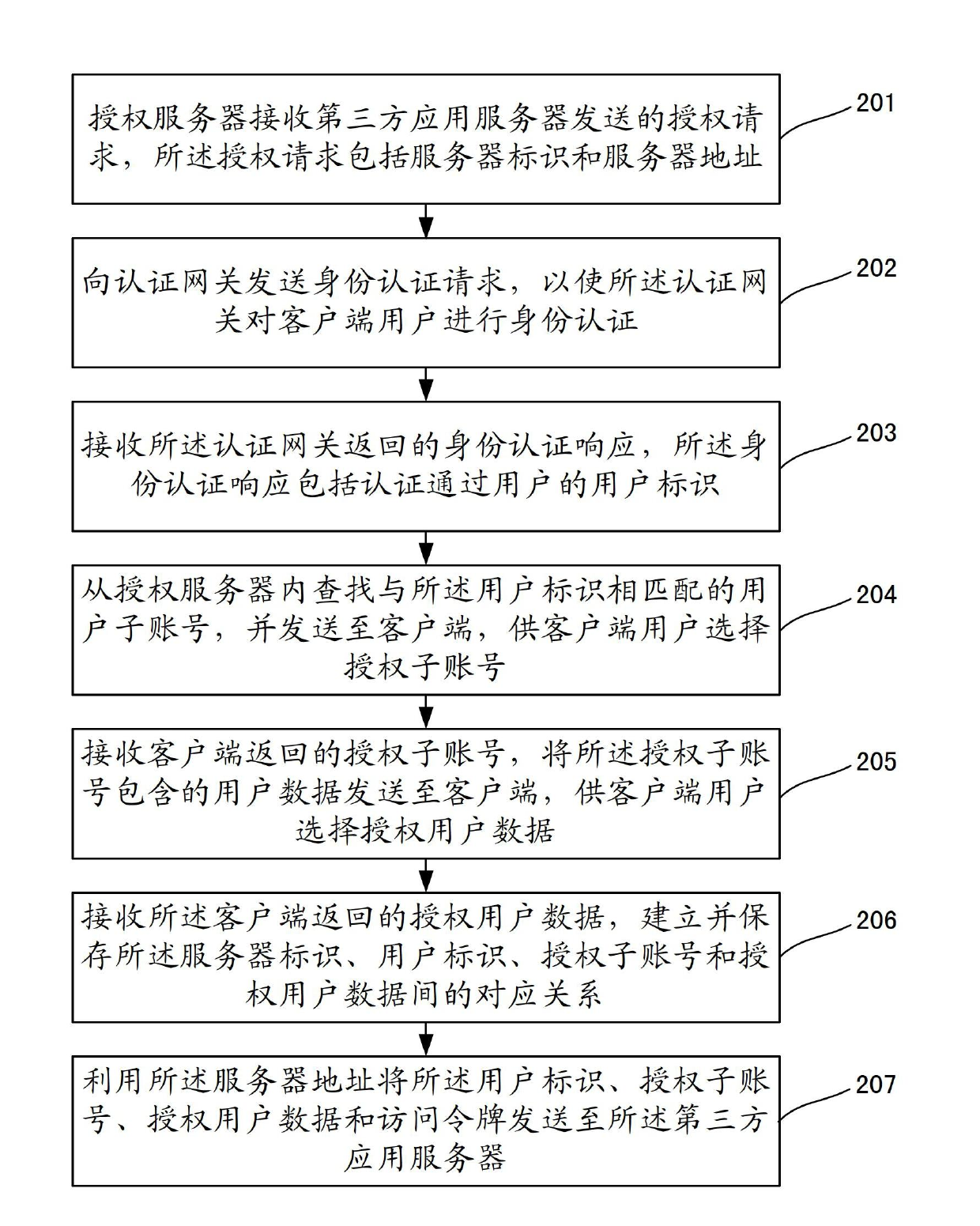
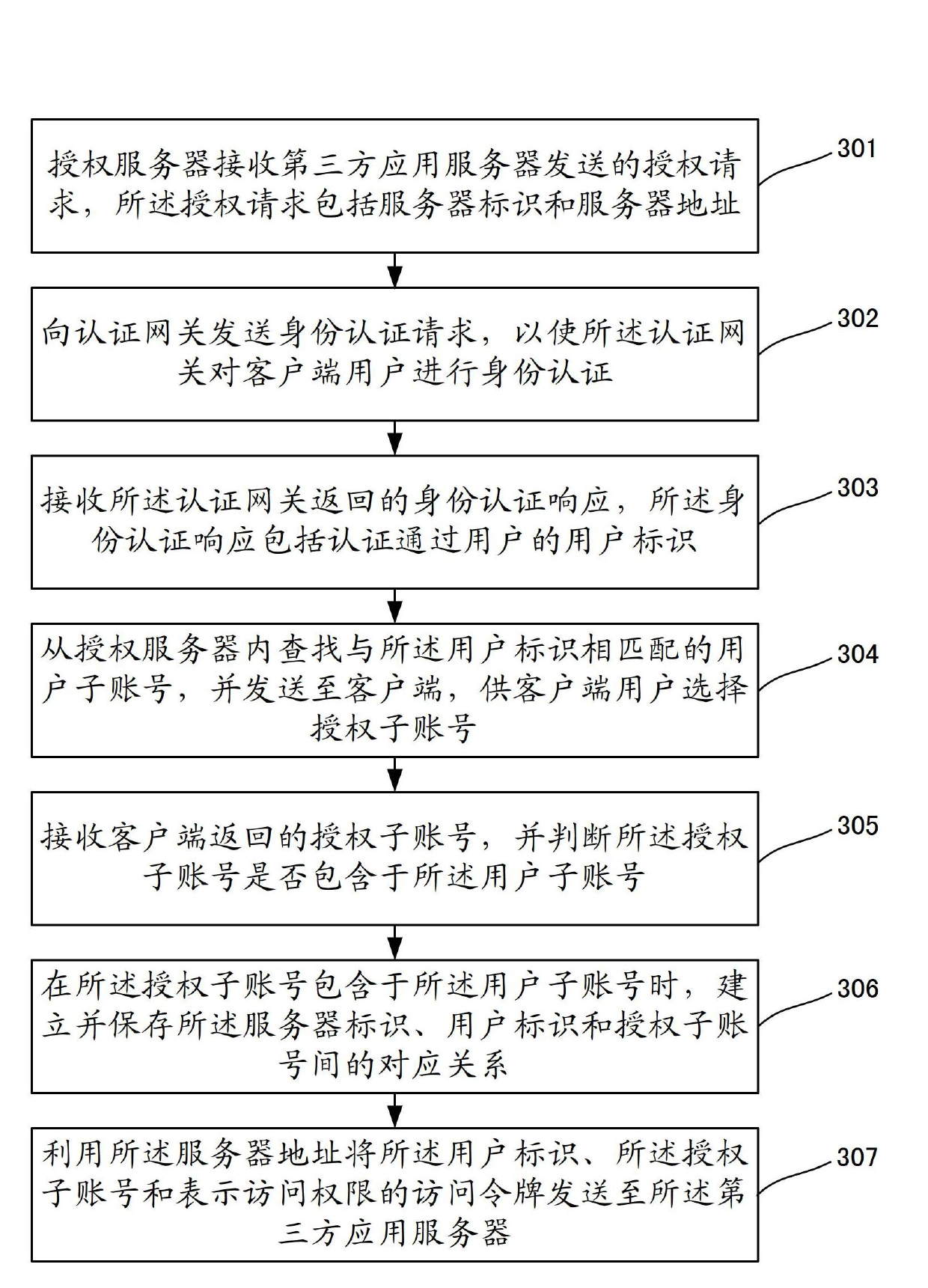
The invention discloses a user data authorization method, a user data authorization device and a user data authorization system. The method comprises the steps that an authorization server receives an authorization request transmitted by a third-party application server, wherein the authorization request comprises a server identifier and a server address; an identity authentication request is transmitted to an authentication gateway to authenticate the identity of a client user by the authentication gateway; an identity authentication response which is fed back by the authentication gateway is received, wherein the identity authentication response comprises an user identifier of the authenticated user; user sub-accounts which are matched with the user identifier are searched from the authorization server and are transmitted to a client for the client user to select an authorized sub-account; the authorized sub-account which is fed back by the client is received, and a corresponding relationship among the server identifier, the user identifier and the authorized sub-account is built and saved; and the user identifier, the authorized sub-account and an access token are transmitted to the third-party application server by using the server address. The third-party partial use authorization by the user is realized, the network service quality is improved and the service experience of the user is improved.
Owner:SHENGQU INFORMATION TECH SHANGHAI
Resource access authorization method
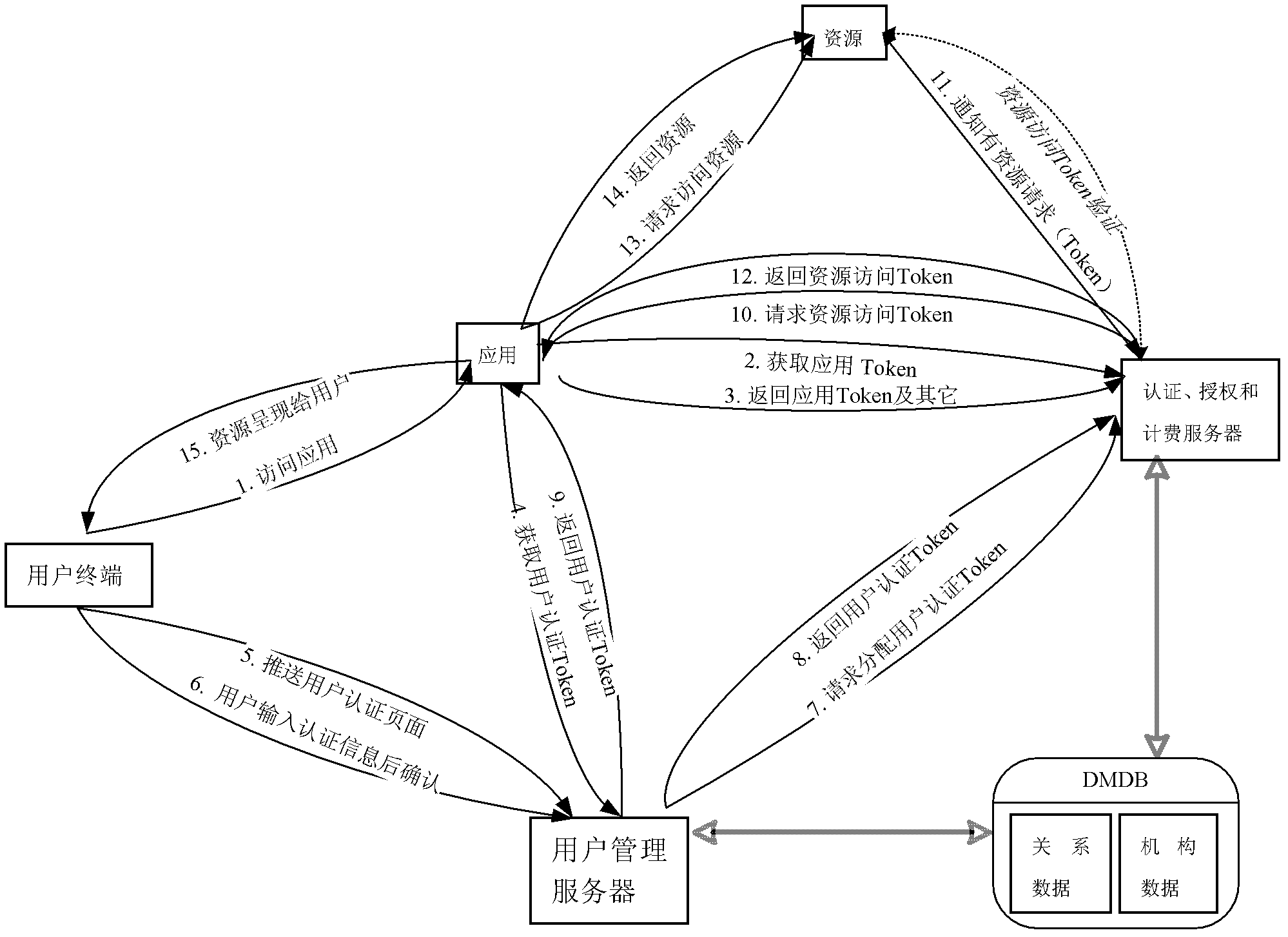
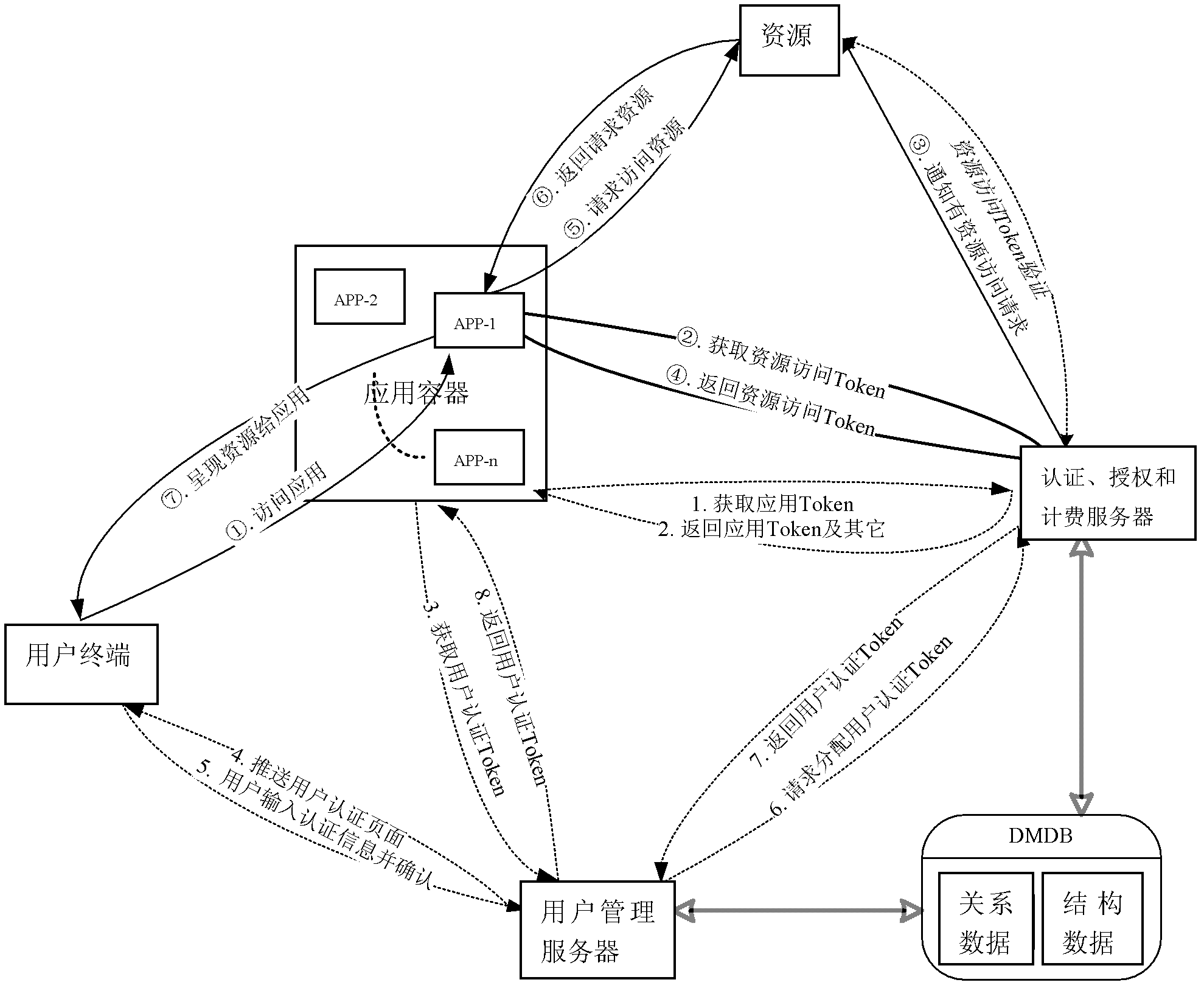
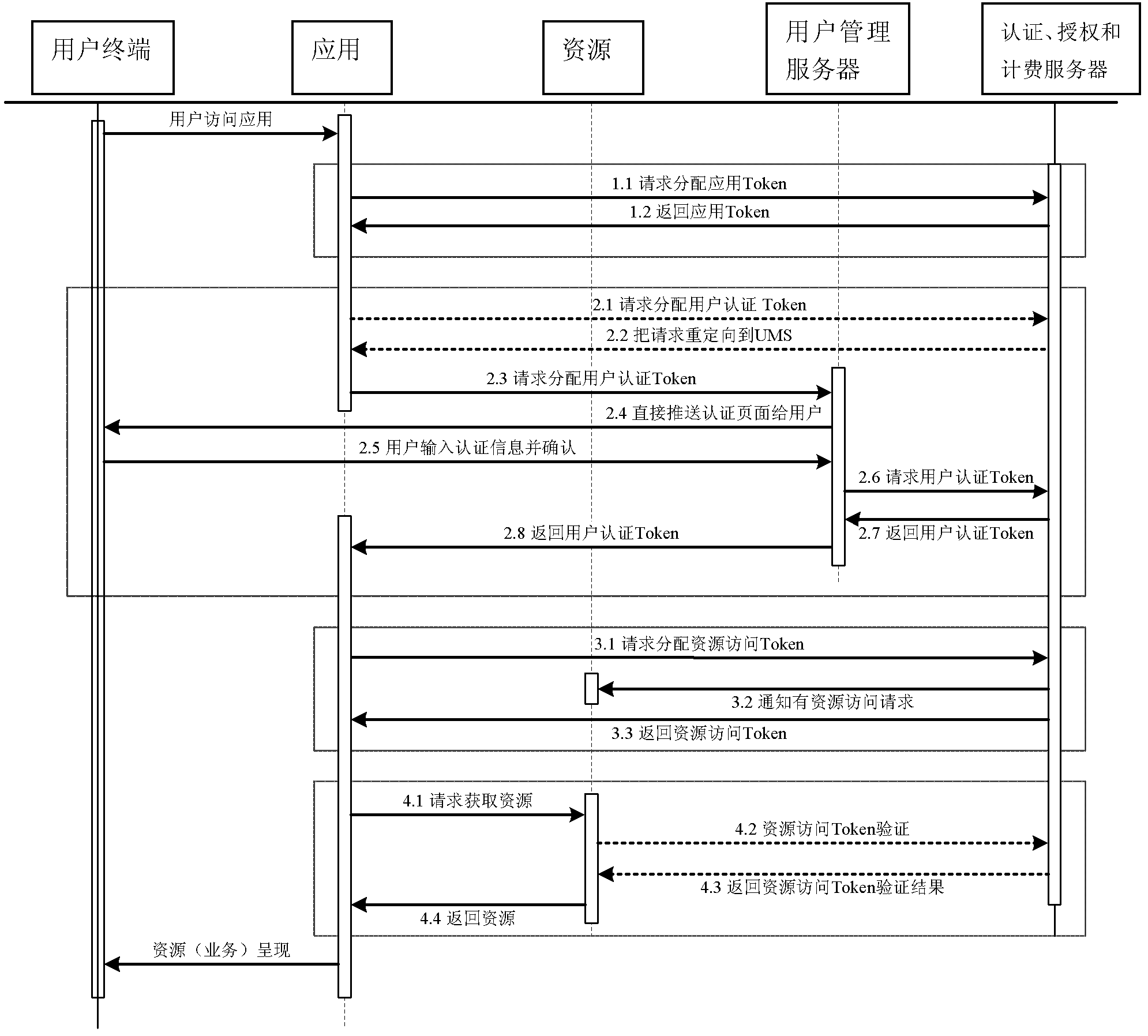
ActiveCN102546648AUser identity/authority verificationTelecommunications networkResource information
The invention relates to a resource access authorization method. The method concretely comprises the following steps: a user accesses or uses a specific application according to the following flows: the user accesses Widget application or other application in a terminal; the application acquires a user authentication token authenticated by the user from an application container and then initiates a resource access token request to an authentication, authorization and accounting server; the authentication, authorization and accounting server checks the user, the application, the application container and information of resources to be accessed by the application and generates a final resource access token after determining that the resources can be accessed; the authentication, authorization and accounting server gives the final resource access token to the application; the application initiates a resource access request to a resource server; the resource server checks a resource access token of the application; after the check is passed, the resources requested by the application are returned; and the application shows the resources to the terminal user. The resource access authorization method has the advantage that the method is suitable for resource access control and authorization of various terminals (a computer, a television / a set top box, a mobile phone, a mobile terminal and the like) in the fields of the Internet and tri-networks integration (the telecommunication network, the computer network and the cable television network).
Owner:优地网络有限公司
Identity cloud service authorization model with dynamic roles and scopes
ActiveUS20170329957A1Digital data authenticationProgram/content distribution protectionApplication softwareAccess token
A system for authorizing access to a resource associated with a tenancy in an identity management system that includes a plurality of tenancies receives an access token request for an access token that corresponds to the resource, the request including user information and application information, the user information including roles of a user and the application information including roles of the application. The system evaluates the access token request by computing dynamic roles and corresponding dynamic scopes for the access token including a second intersection between the dynamic roles of the user and the dynamic roles of the application. The system then provides the access token that includes the computed static scopes, where the scopes are based at least on the roles of the user and the roles of the application, and further including the computed dynamic roles and corresponding dynamic scopes.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com