Patents
Literature
388 results about "Restricted access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
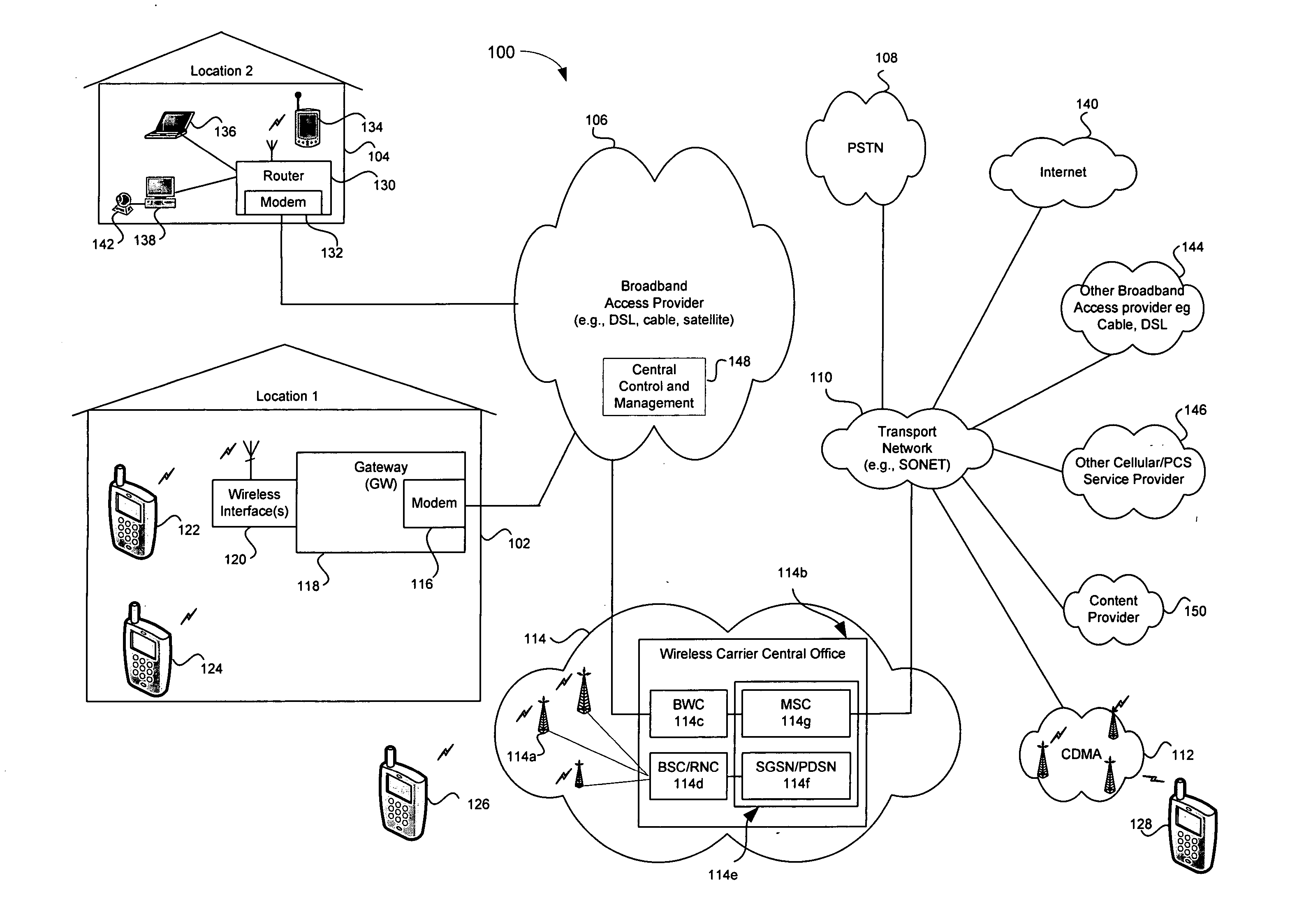
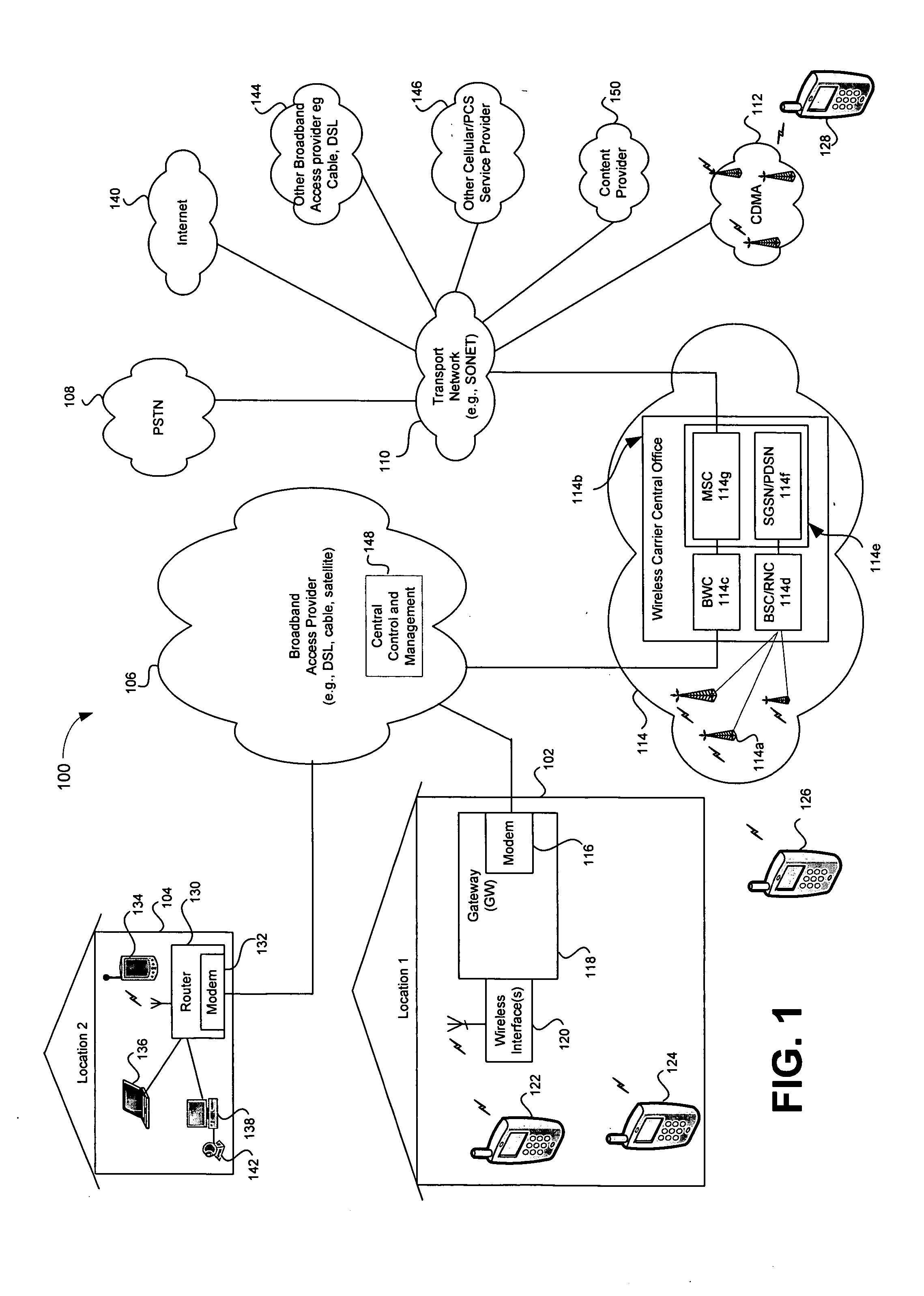
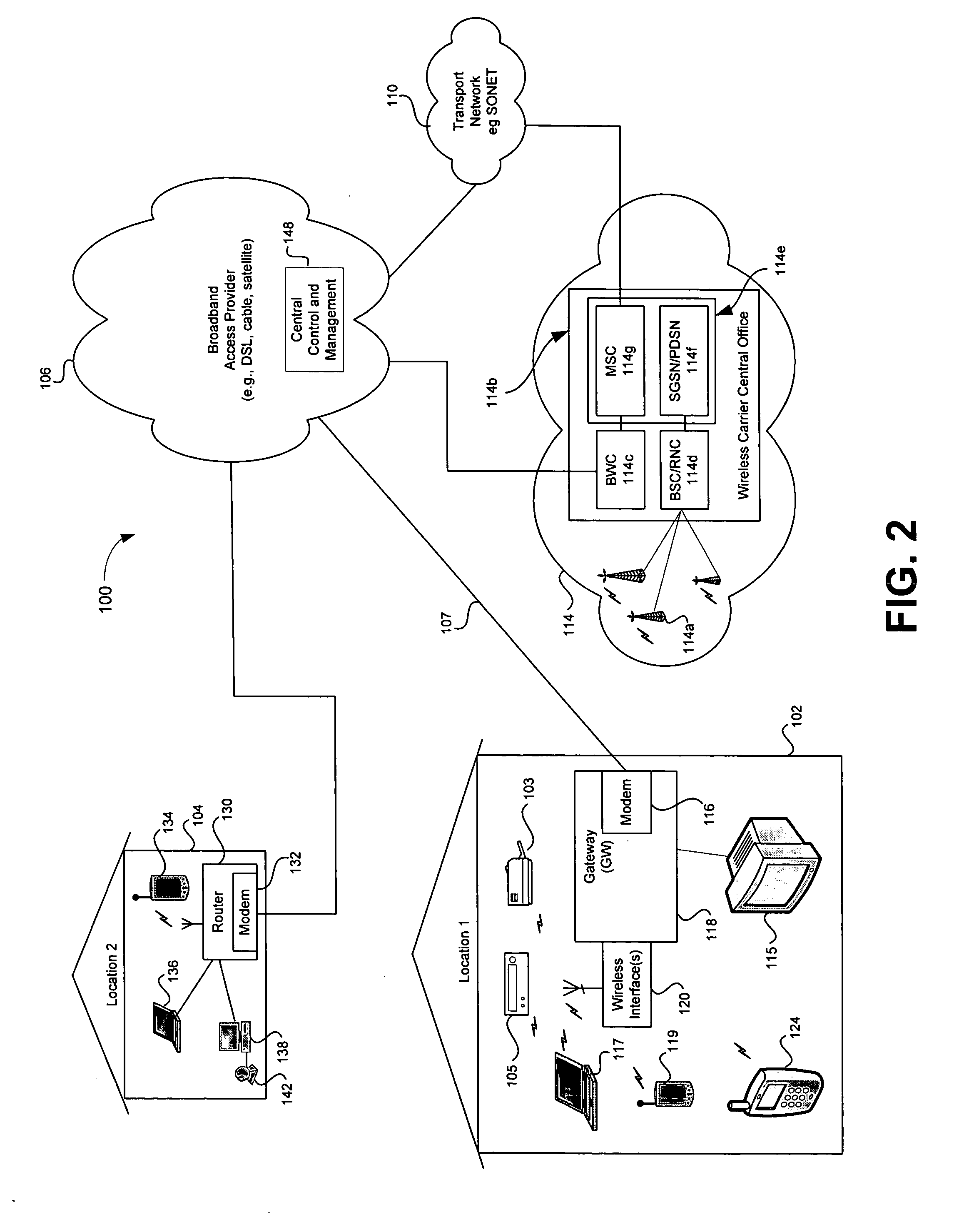
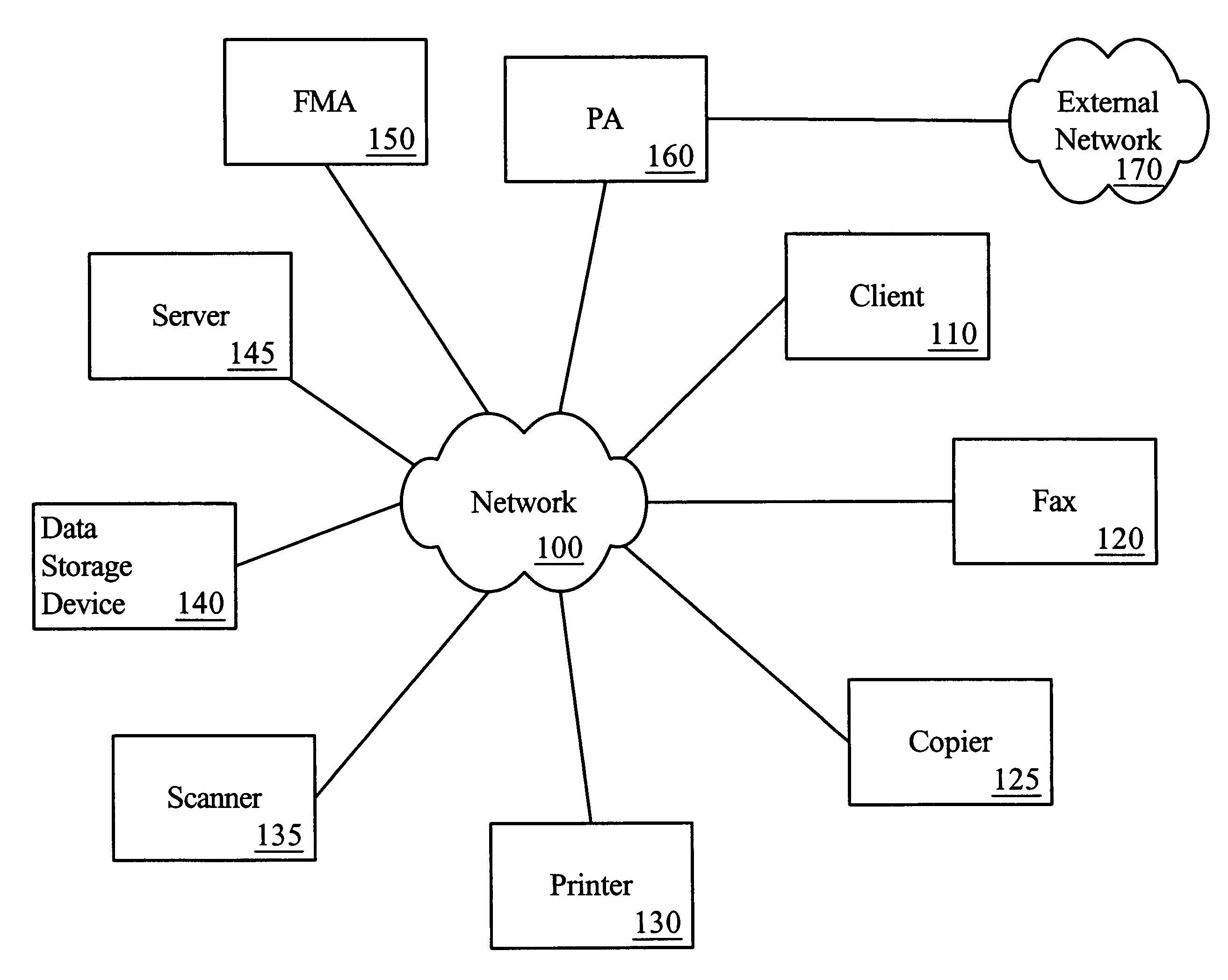
Method and system for providing registration, authentication and access via broadband access gateway
InactiveUS20050239445A1Television system detailsError preventionRestricted accessBroadband access networks
A system and method supporting user registration, authentication and access to multimedia services via a broadband access gateway is disclosed. A representative embodiment of the present invention may comprise a wireless interface and may be capable of exchanging multimedia communication between the wireless interface and a broadband network. The gateway may determine access to available media-related services based upon information that is provisioned in a broadband access gateway prior to the first access by a user of an access device. The gateway may automatically allow access to access devices that are pre-registered, and may support opportunistic registration for those users of access devices that have not been pre-registered. Restricted access to services and networks available through the gateway may be provided even when registration is not successful, or when the access device is not pre-registered. Interactive registration for gateway access may be supported, and one-button access using either soft or hard buttons may be provided.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
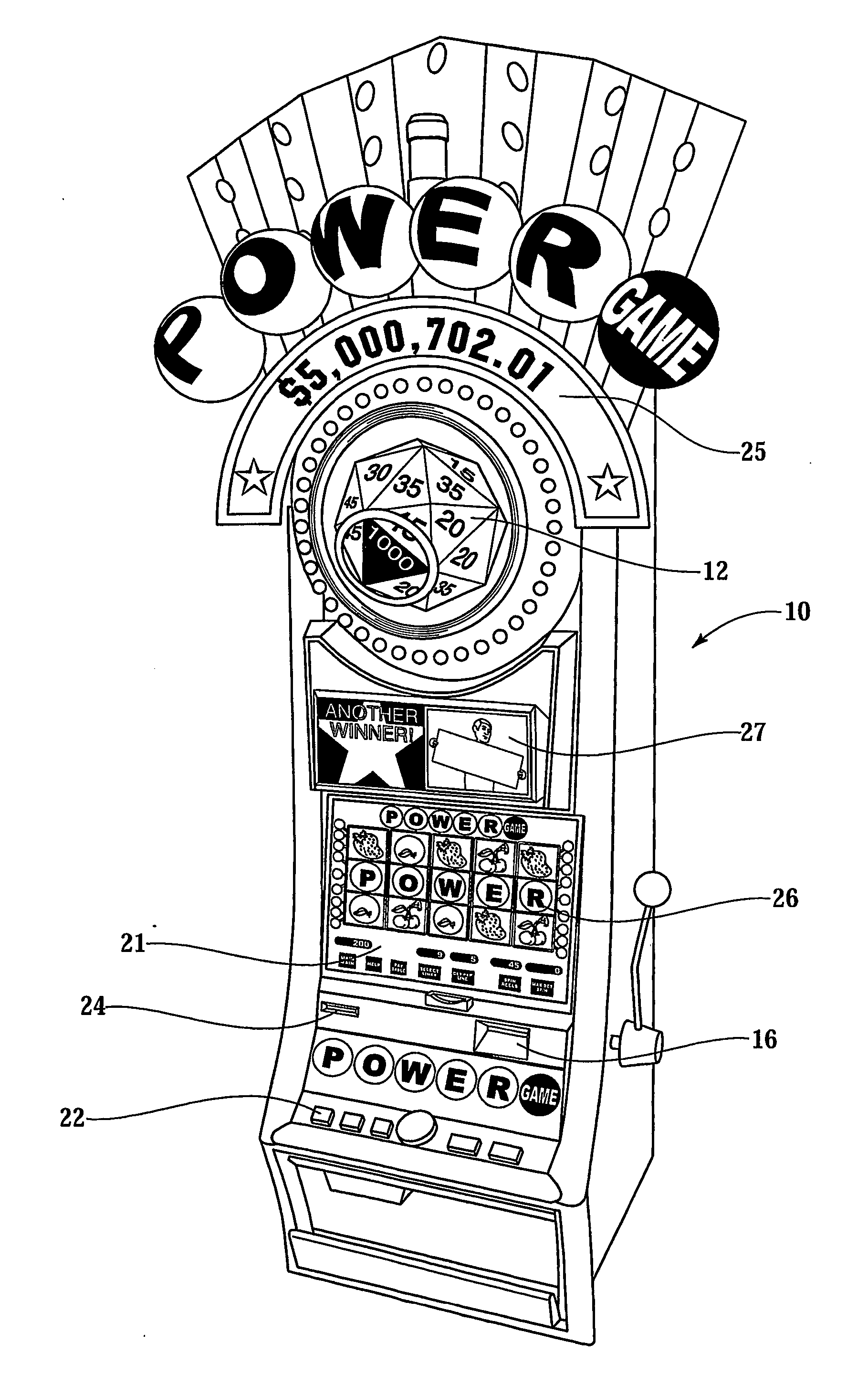
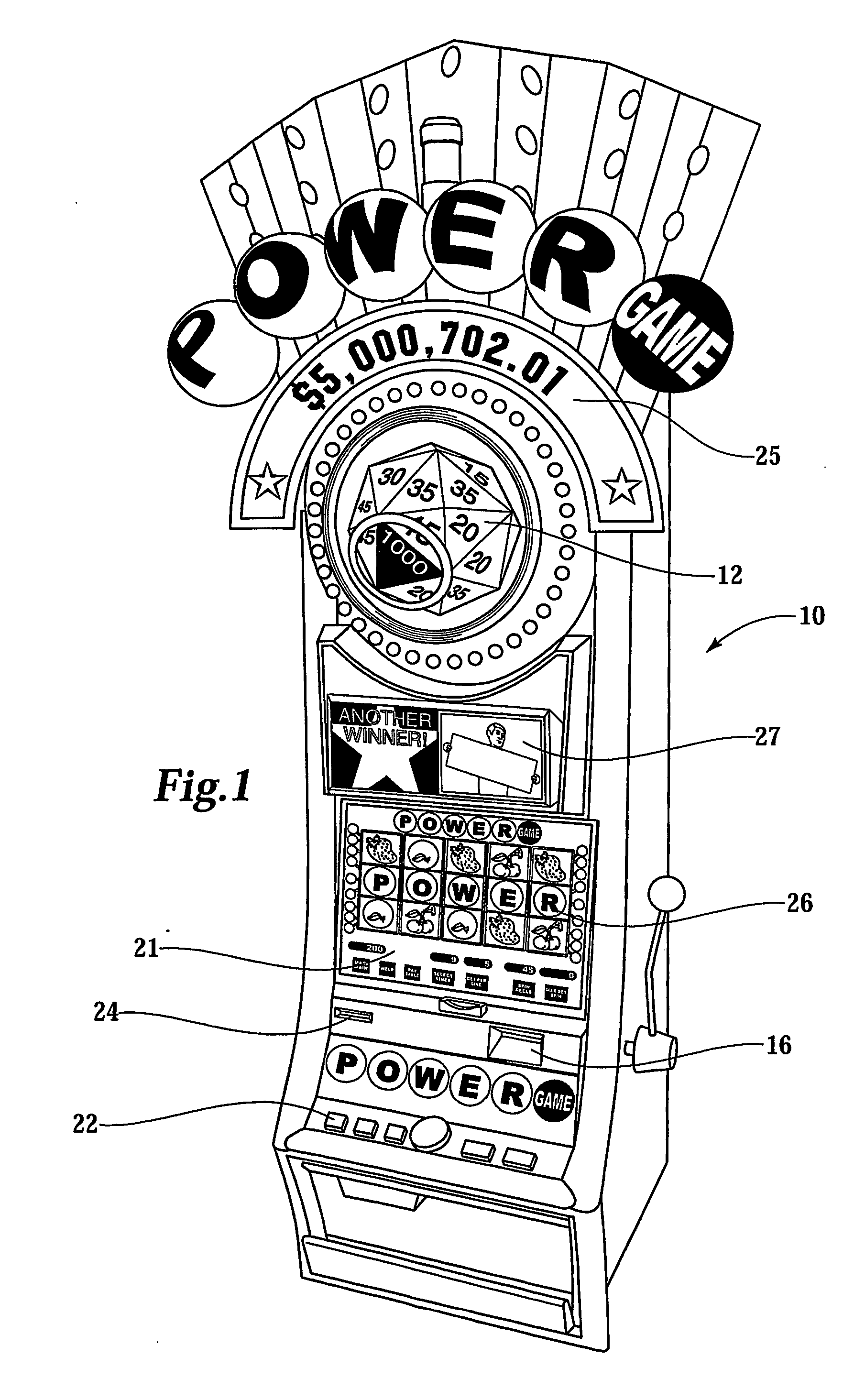
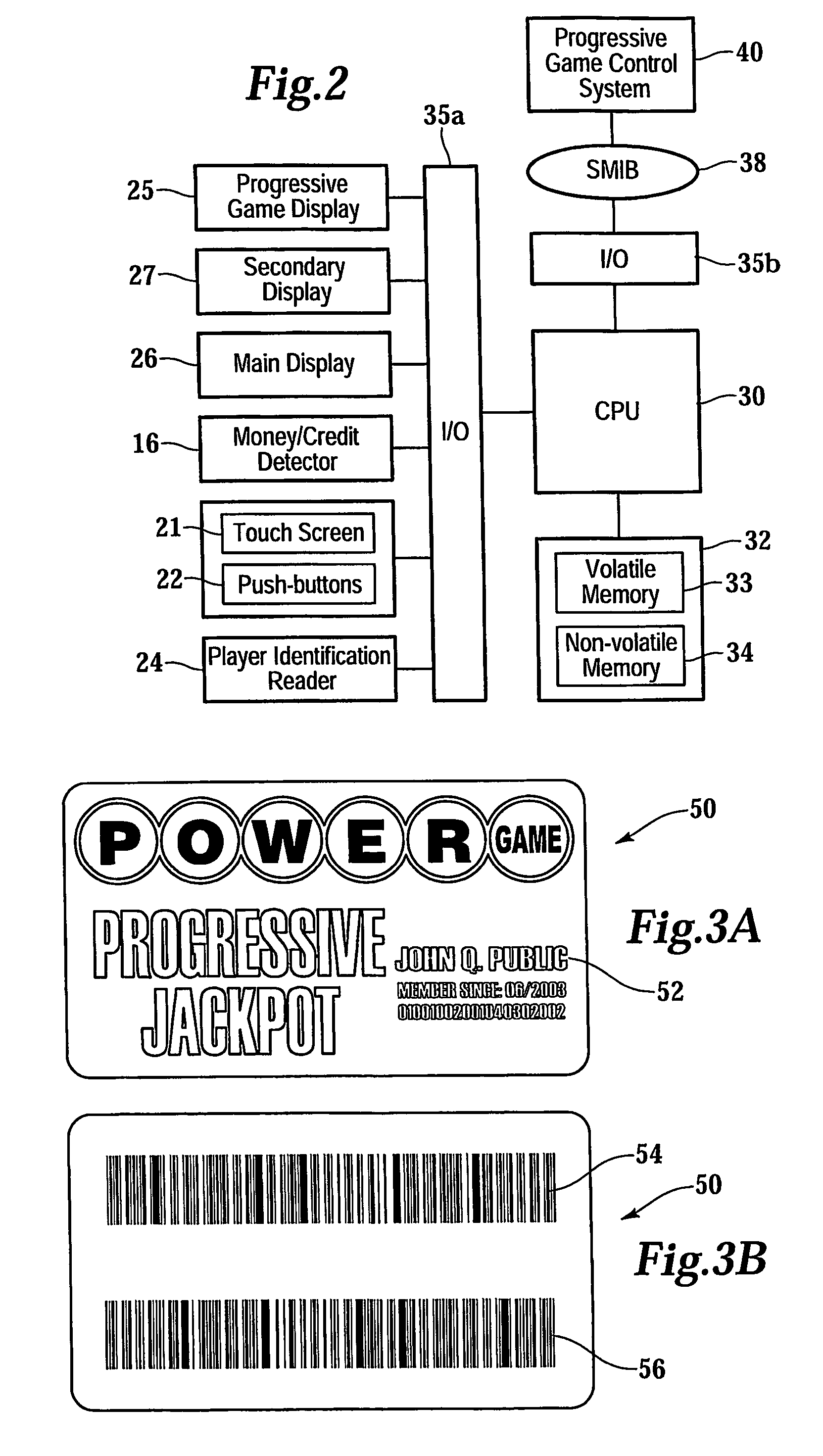
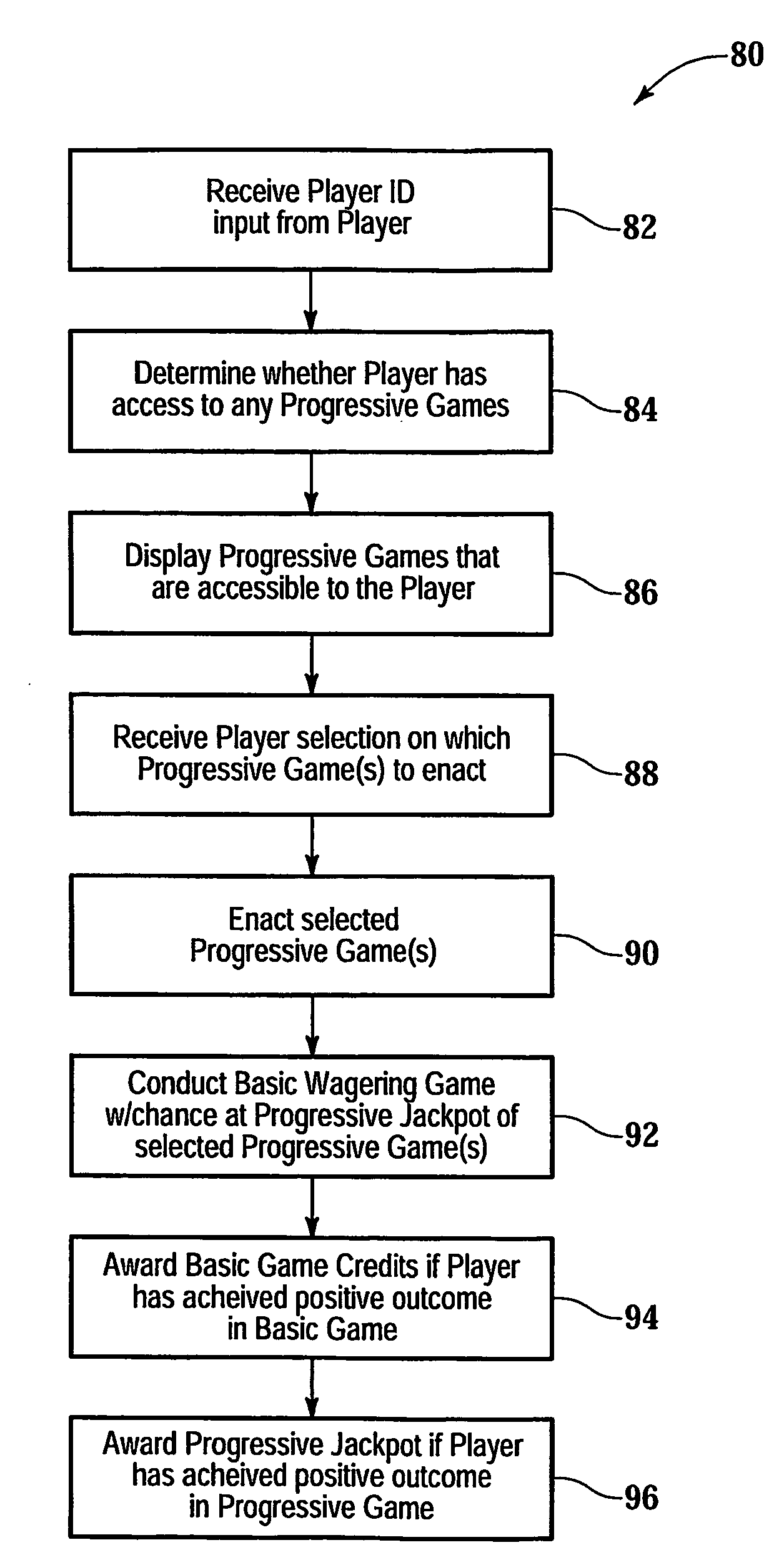
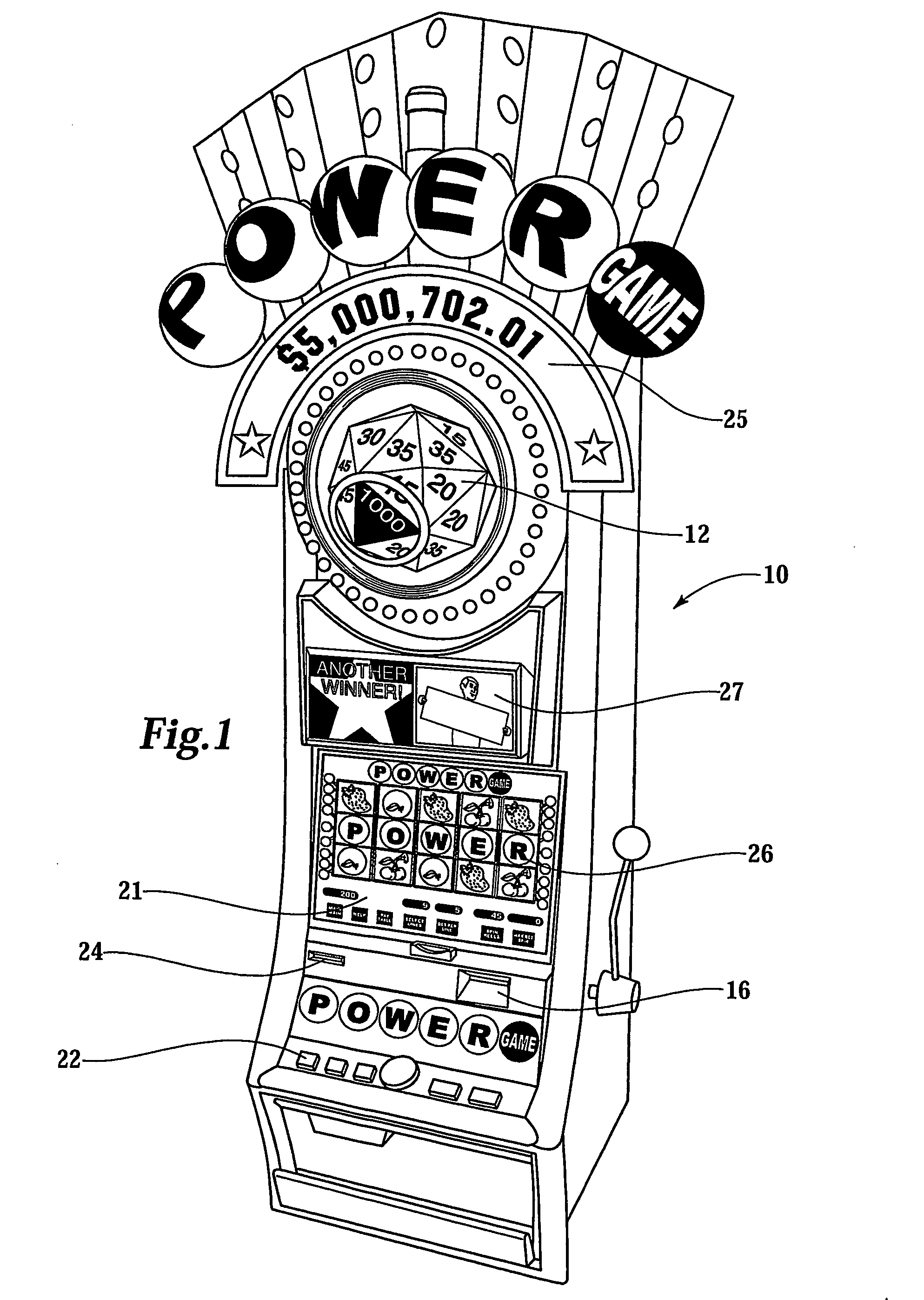
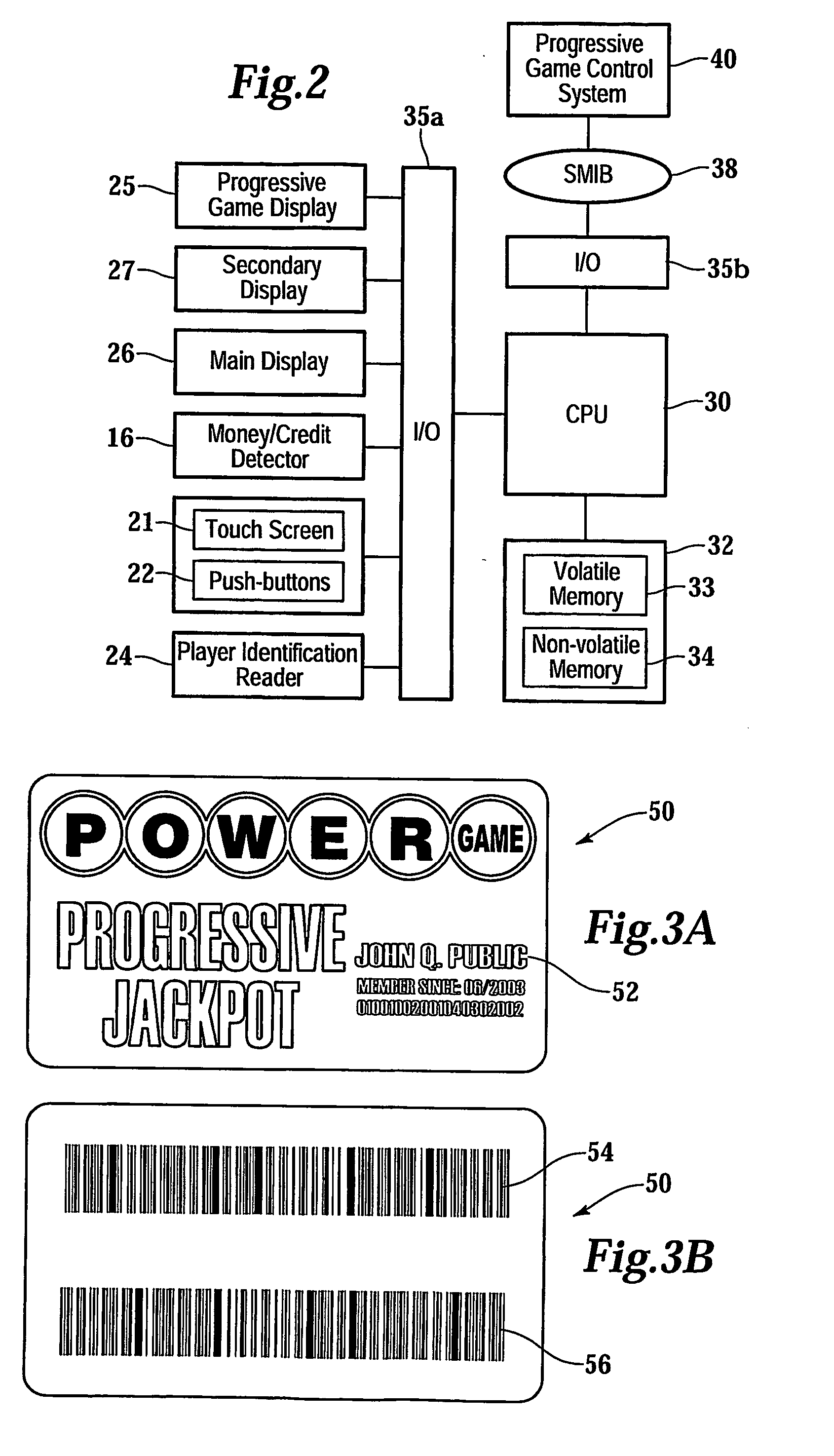
Gaming network for use in a restricted-access progressive game
InactiveUS20070060319A1Apparatus for meter-controlled dispensingVideo gamesComputer terminalIdentification device
A gaming system for playing a restricted-access progressive game comprises a database containing data, including a list of players having access to the restricted-access progressive game. The system includes a gaming terminal with a connection port for coupling the gaming terminal to the data-base. The gaming terminal has a player-identification device providing player information. The information is compared with data in the database to determine whether the restricted-access progressive game can be activated and game information displayed at the gaming terminal. A method of operating the progressive game comprises receiving a player-identification input at the gaming terminal and transmitting a player-identifier signal from the gaming terminal to a remotely located controller that determines accessibility to the progressive game. The method further includes receiving, at the gaming terminal, a progressive game accessibility signal from the remotely located controller and, if the signal is positive, allowing a player to conduct the progressive game.
Owner:BALLY GAMING INC
Policies for secure software execution
InactiveUS7350204B2Efficiently constrain (or prevent from running) everything on a machineDigital data processing detailsUnauthorized memory use protectionFile systemDigital signature
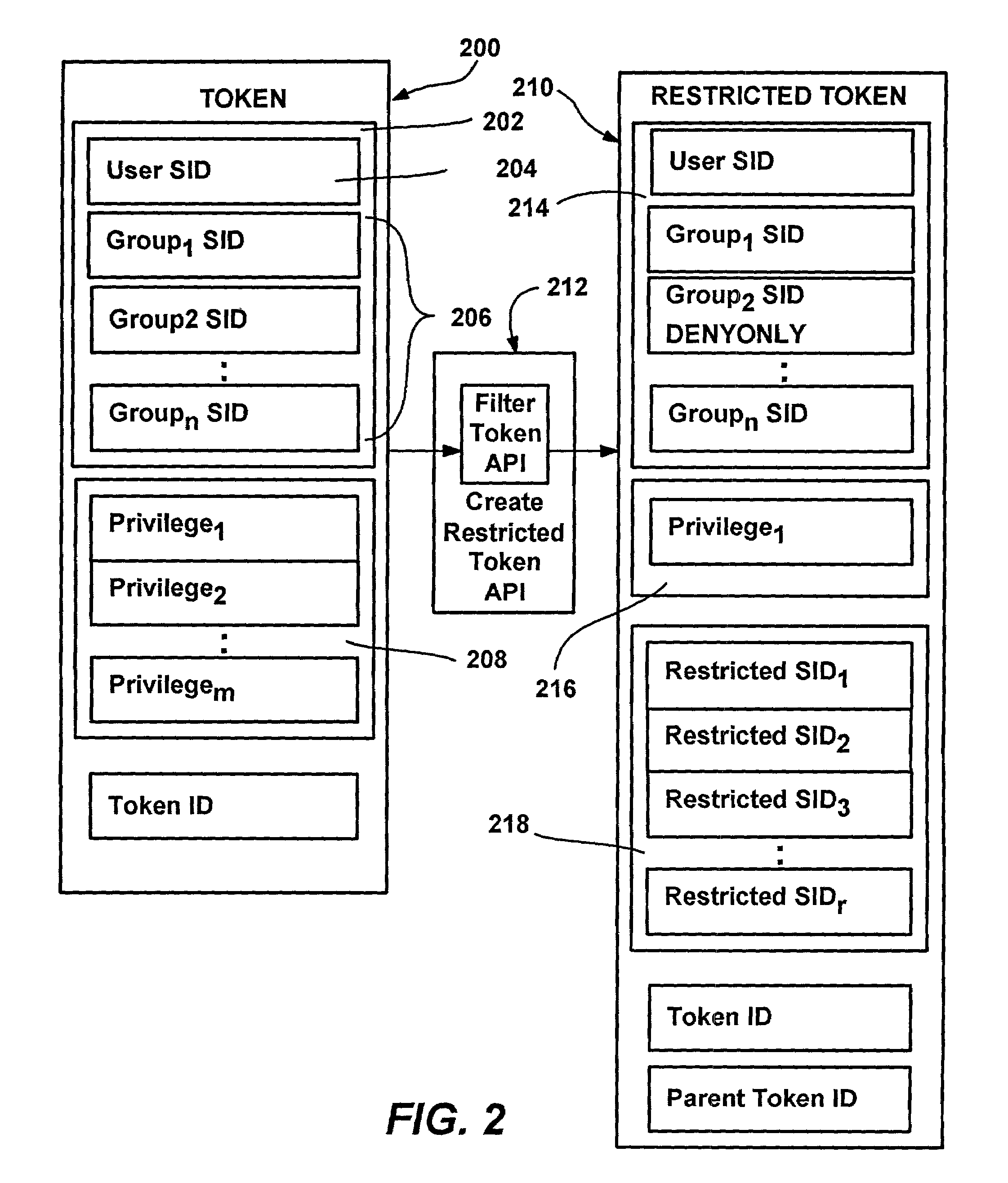
A system and method that automatically, transparently and securely controls software execution by identifying and classifying software, and locating a rule and associated security level for executing executable software. The security level may disallow the software's execution, restrict the execution to some extent, or allow unrestricted execution. To restrict software, a restricted access token may be computed that reduces software's access to resources, and / or removes privileges, relative to a user's normal access token. The rules that control execution for a given machine or user may be maintained in a restriction policy, e.g., locally maintained and / or in a group policy object distributable over a network. Software may be identified / classified by a hash of its content, by a digital signature, by its file system or network path, and / or by its URL zone. For software having multiple classifications, a precedence mechanism is provided to establish the applicable rule / security level.
Owner:MICROSOFT TECH LICENSING LLC
System and method to support gaming in an electronic network
InactiveUS6884162B2Apparatus for meter-controlled dispensingVideo gamesUser deviceRelevant information
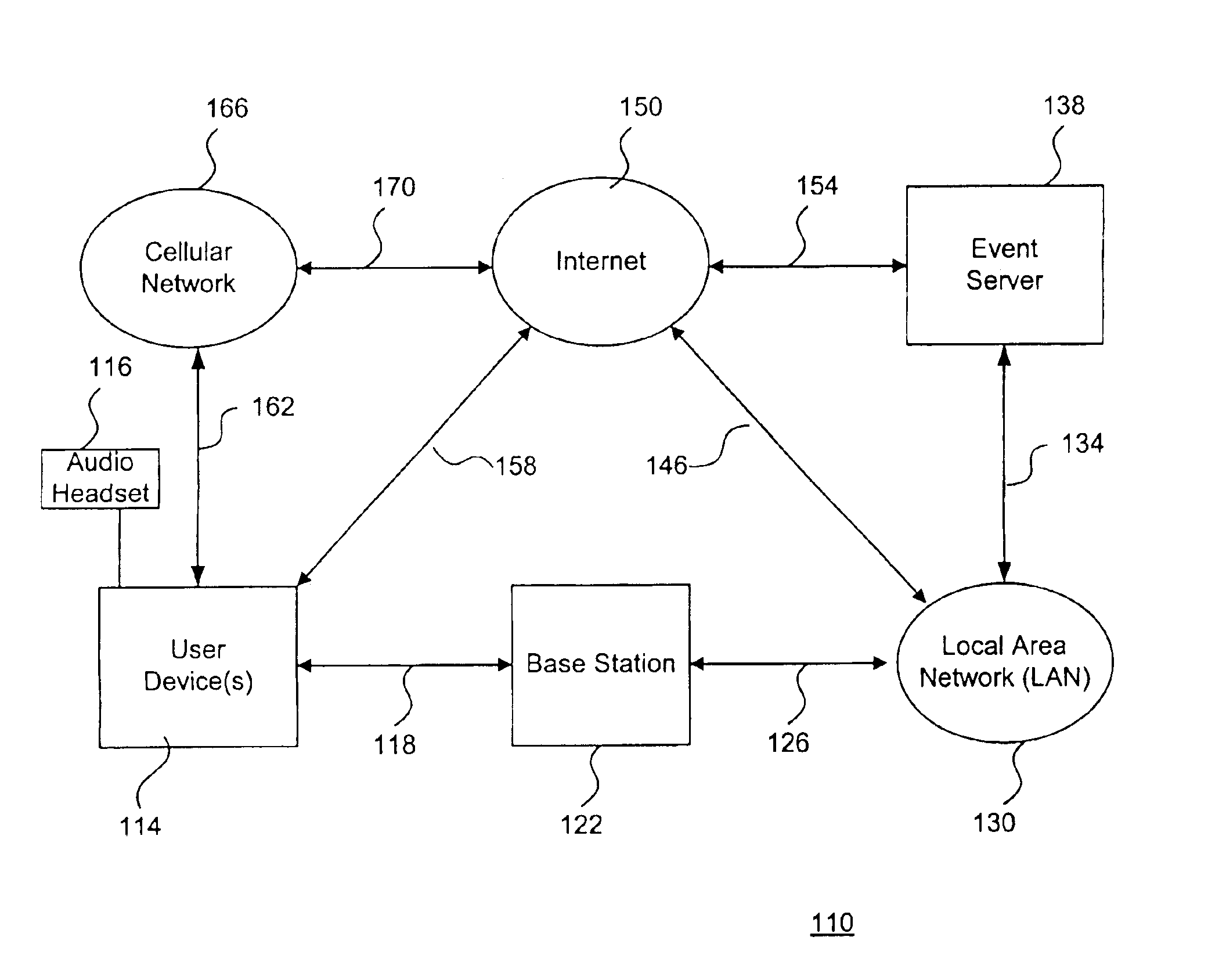
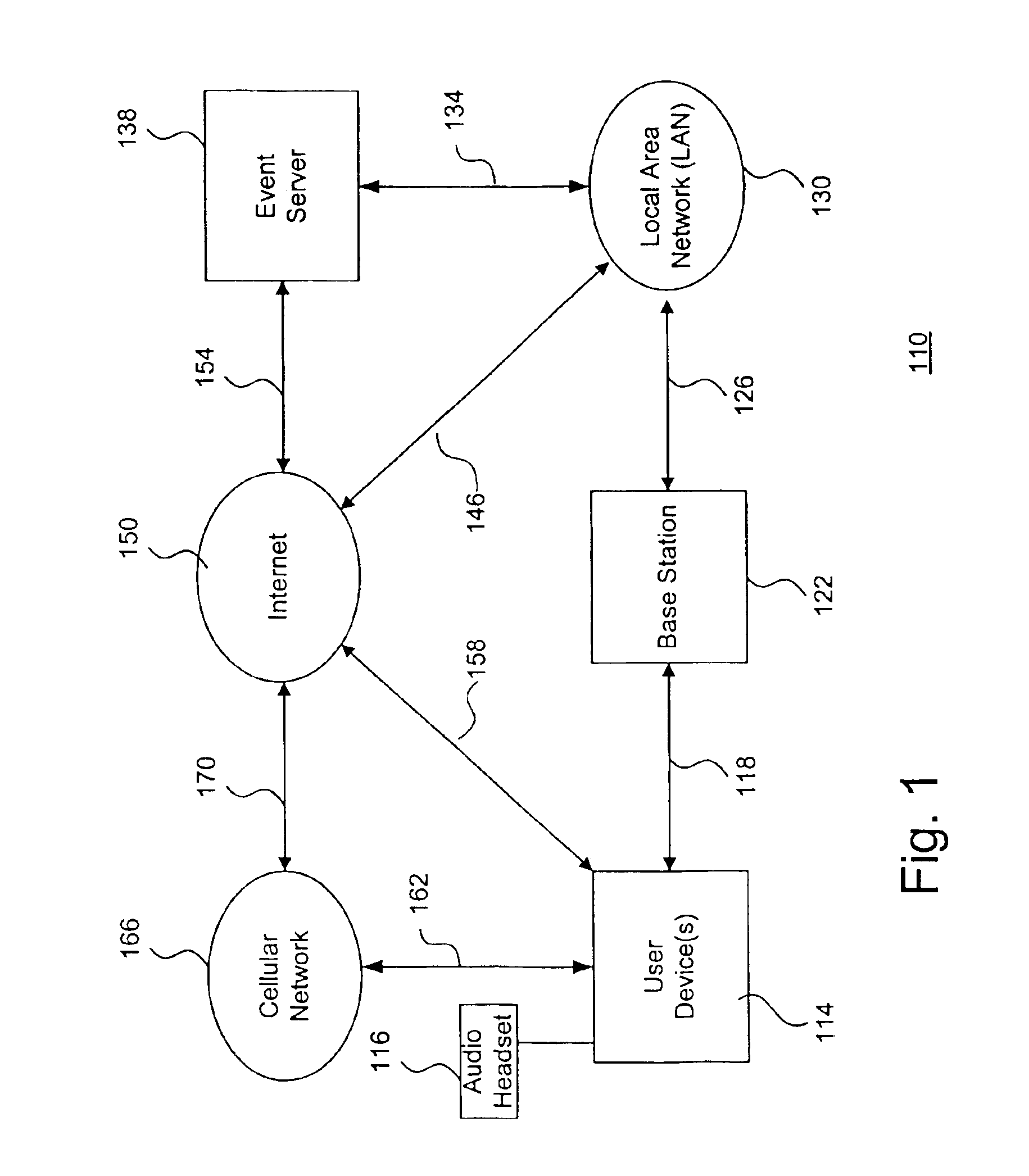
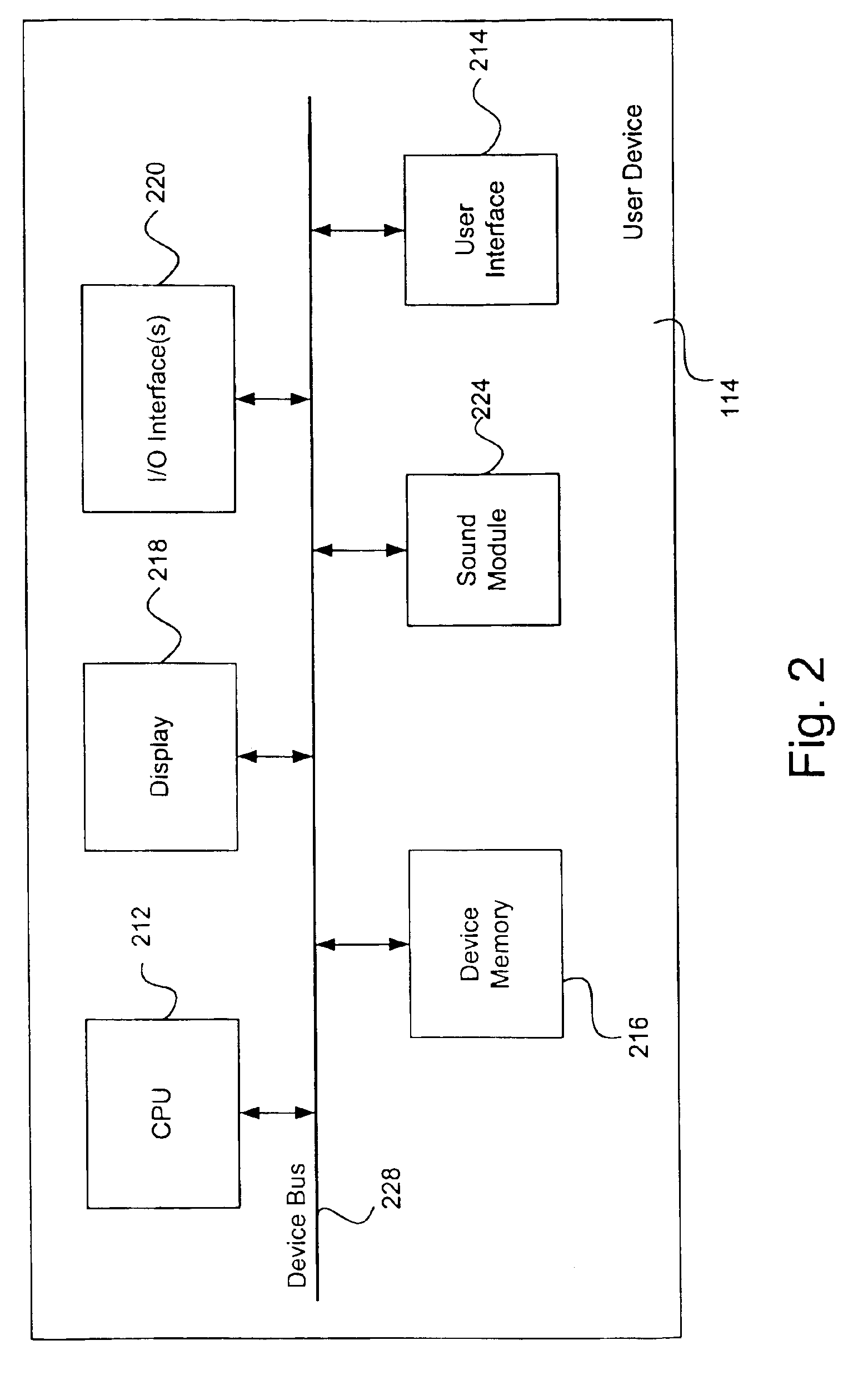
A system and method to support electronic gaming in an electronic network includes an event server that provides restricted access to various types of game services. One or more system users may utilize corresponding wireless portable user devices for connecting to the event server to thereby gain access to the foregoing game services as game participants. The system users may thereby utilize the user devices to access the event server for accessing appropriate gaming services and related information. In addition, a source system user may utilize a source user device to perform a transfer procedure for transferring ownership rights of an electronic certificate related to the electronic gaming to a target system user through a target user device. The foregoing transfer procedure may be conducted through the event server, or may occur directly from the source user device to the target user device.
Owner:SONY CORP +1
Restricted-access progressive game for a gaming machine
InactiveUS20070026941A1Apparatus for meter-controlled dispensingVideo gamesHuman–computer interactionRestricted access
Owner:BALLY GAMING INC
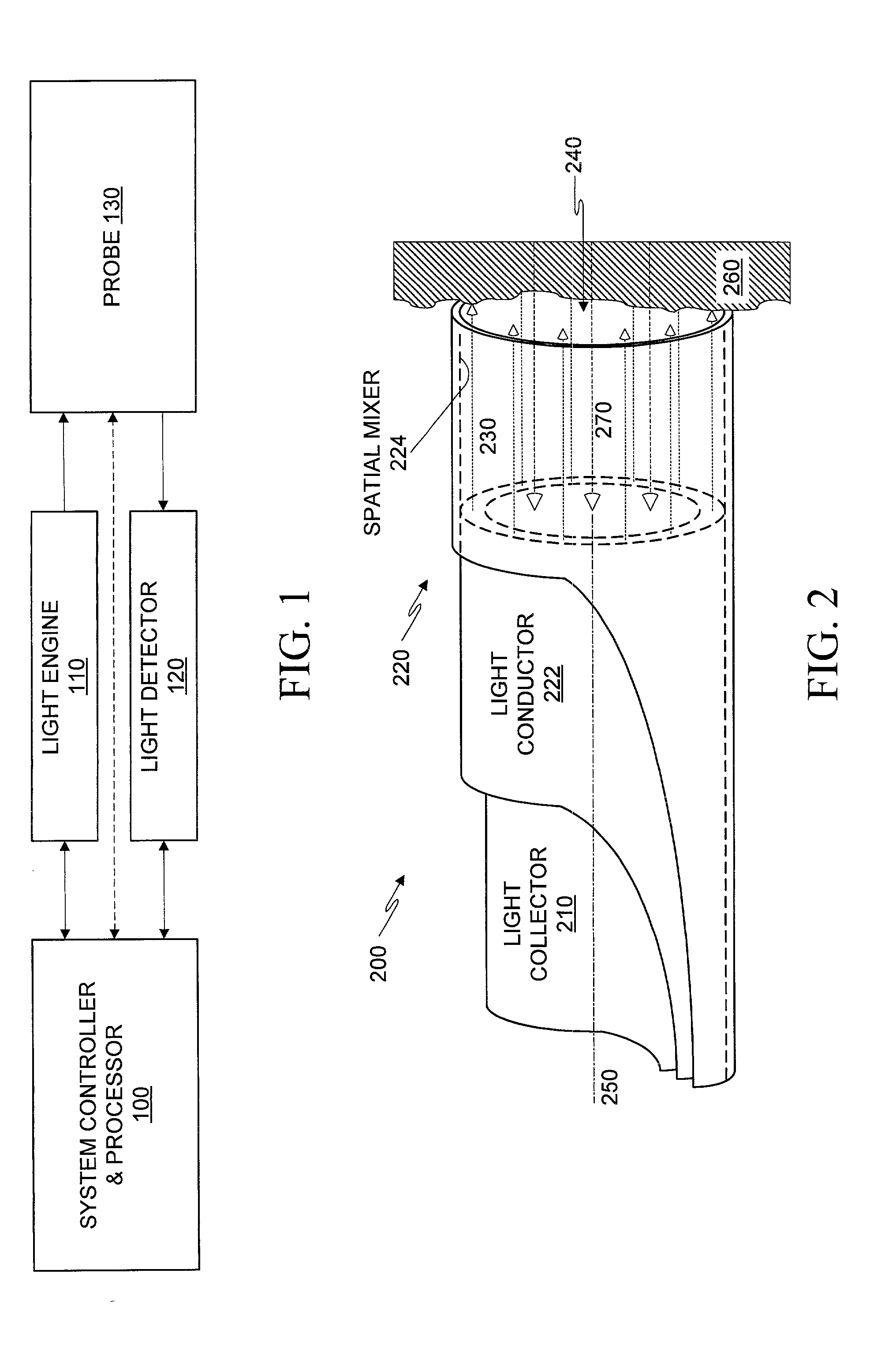
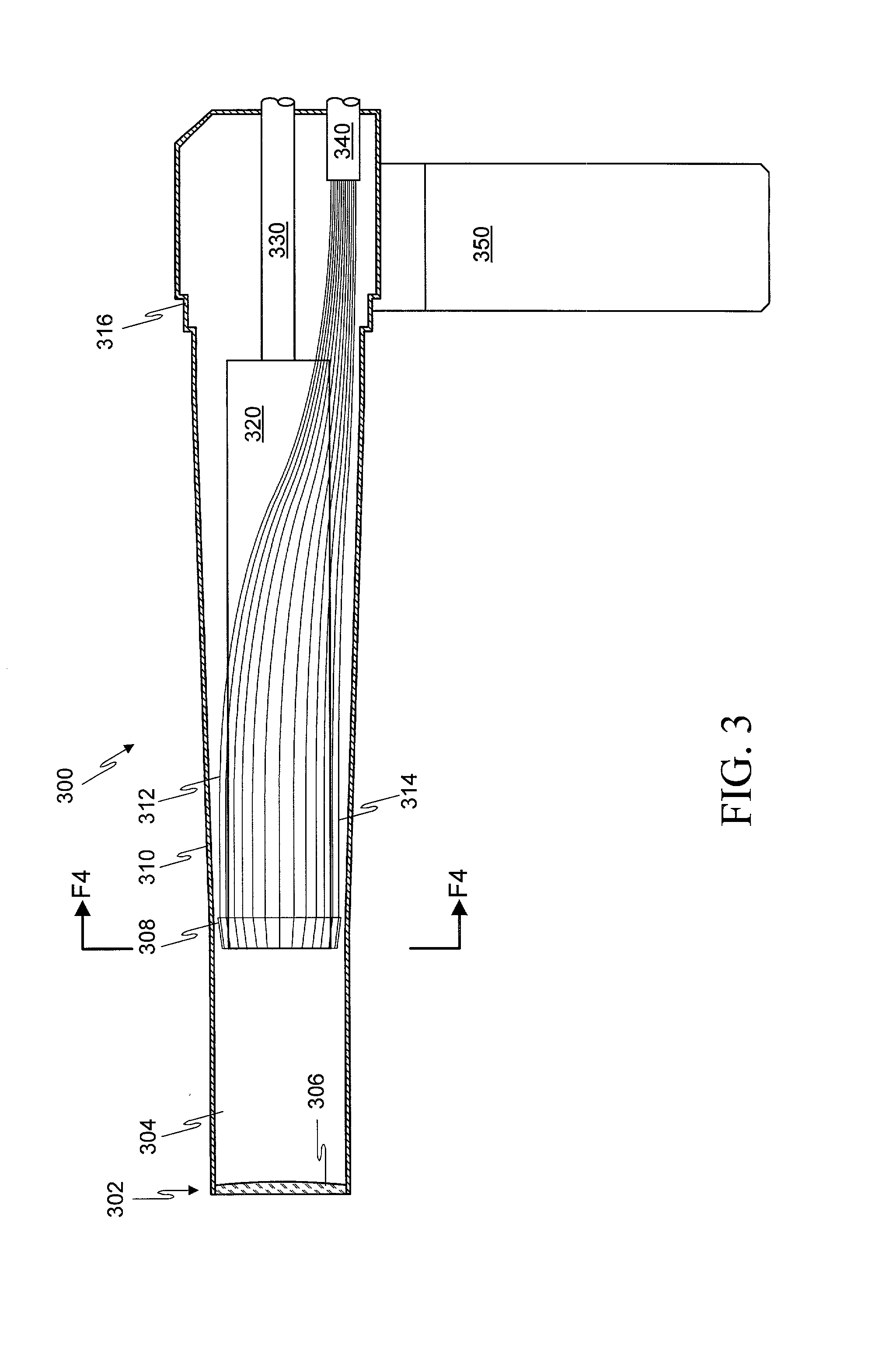
Optical probe having and methods for difuse and uniform light irradiation
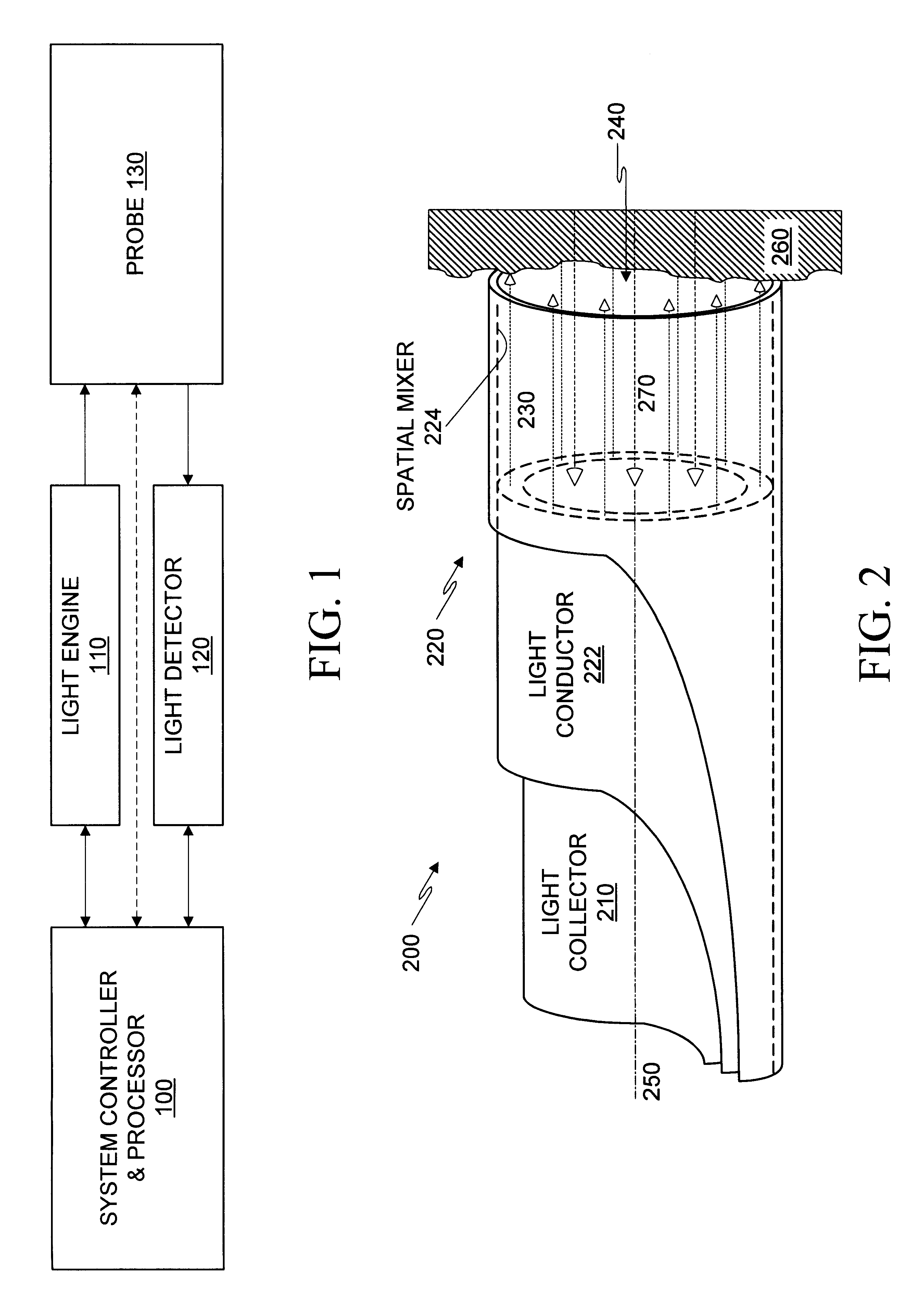
A variety of optical probes and methods have utility in the examination of various materials, especially materials in the interior of cavities having restricted access through orifices or passageways. One type of such optical probe is elongated and includes a distal optical window, a divergent light source, a spatial mixer, and a light collector. Light from the light source is mixed in the spatial mixer to achieve uniform diffuse light in the vicinity of the optical window. The light collector receives light from the target through the spatial mixer. The optical probe may be made of two sections, a reusable section and a disposable. The disposable is elongated and contains a mounting section, an inside surface suitable for the spatial mixing of light, and an optical element which helps to seal the reusable probe section from the target.
Owner:LIFESPEX
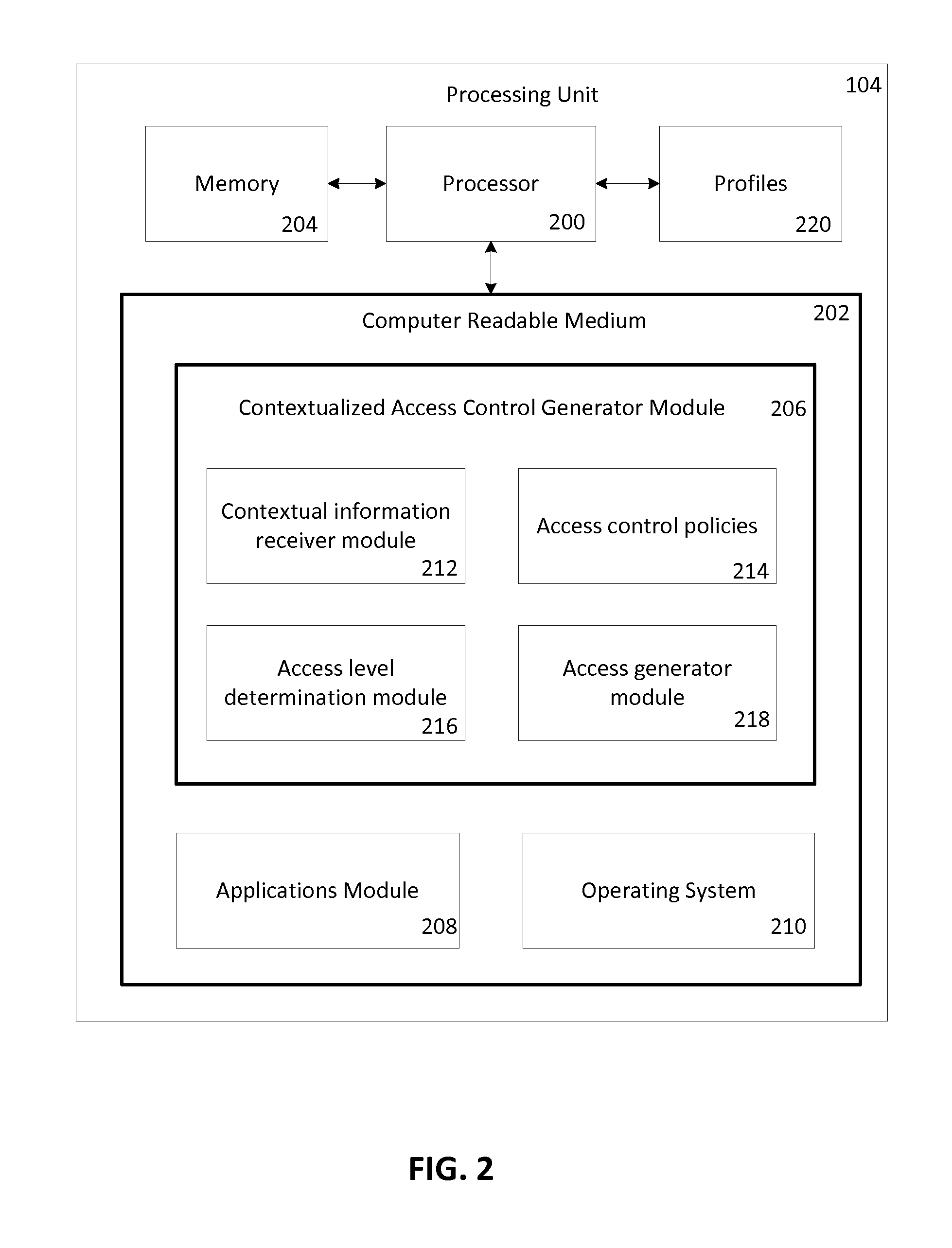
Contextualized Access Control
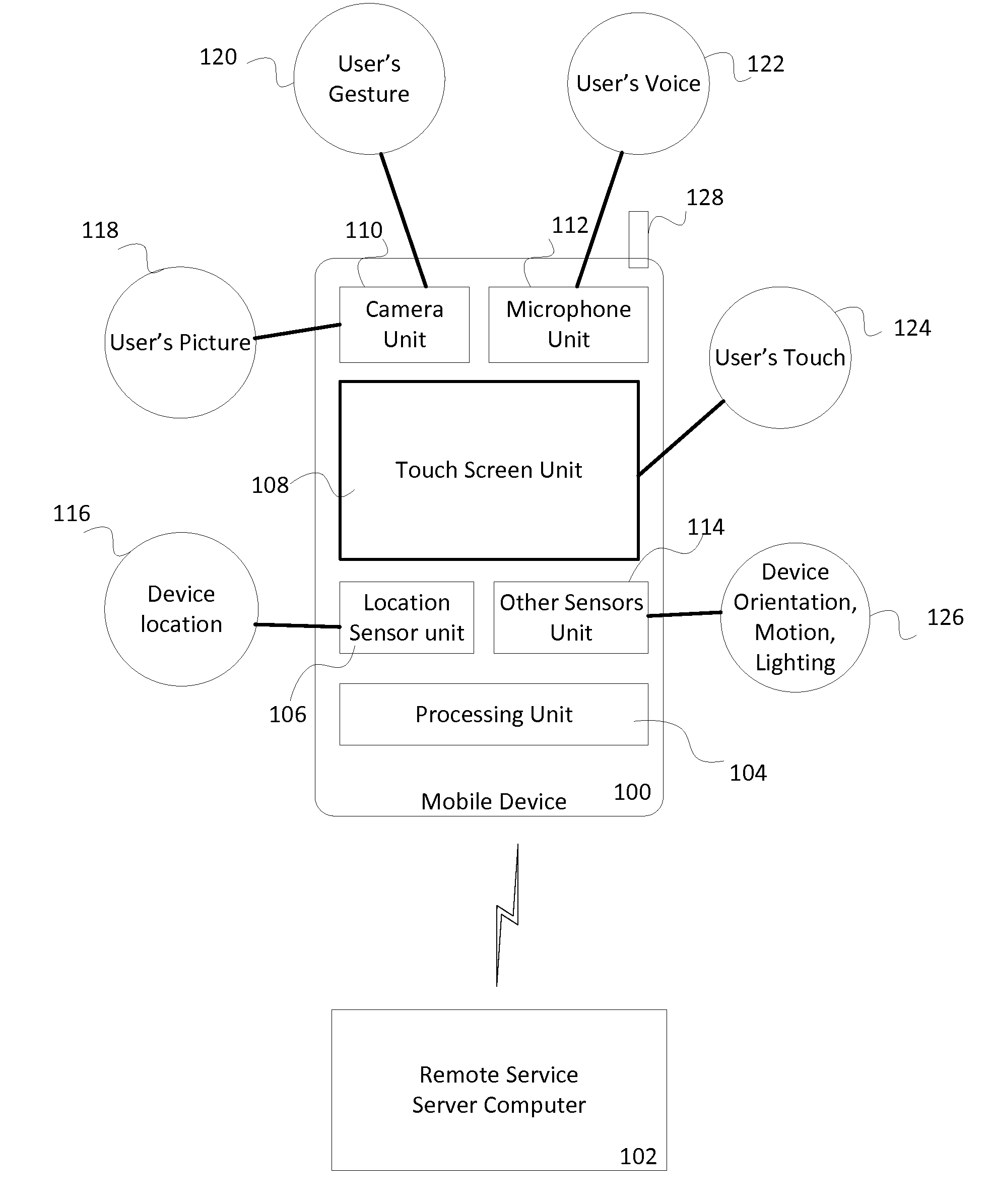
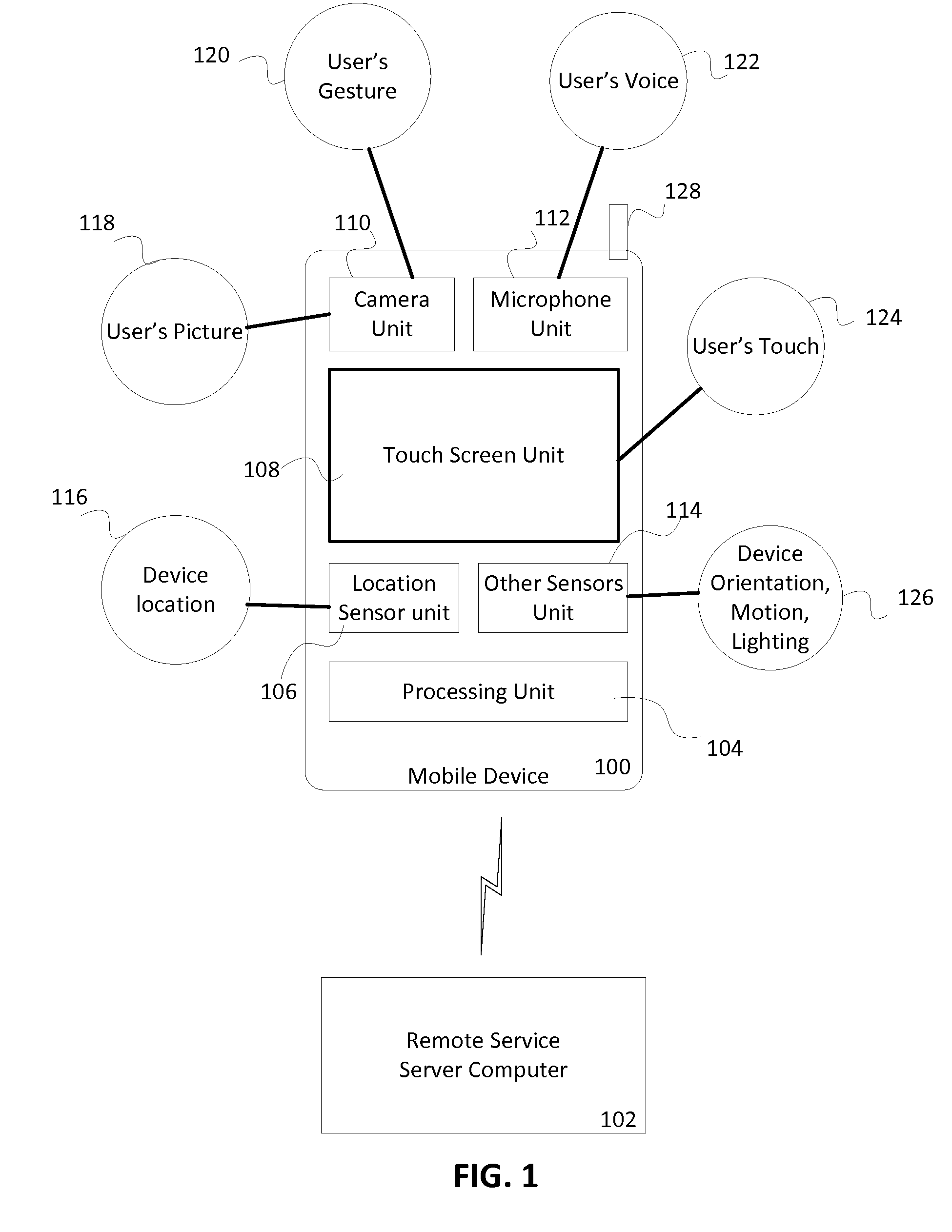
Contextual information associated with a mobile device can be automatically acquired using various sensors on the device. Based on the contextual information and an access control policy associated with an application on the mobile device, a level of access to the application can be determined. An entity may be identified, authenticated and authorized to gain full access, varying degree of restricted access or no access to the application based on the access control policy. Different applications may be provided different levels of access based on the access control policy associated with each application.
Owner:VISA INT SERVICE ASSOC
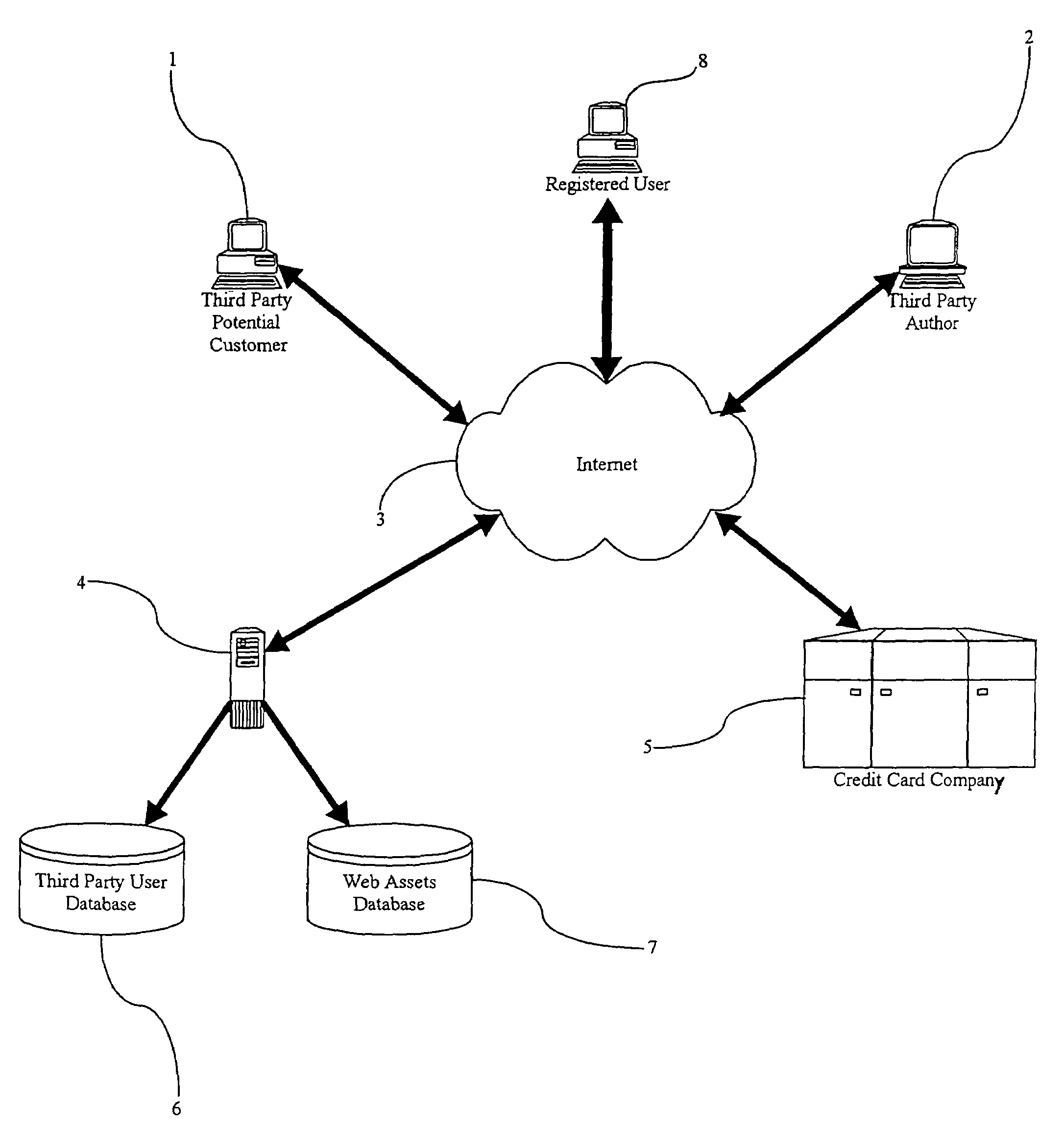
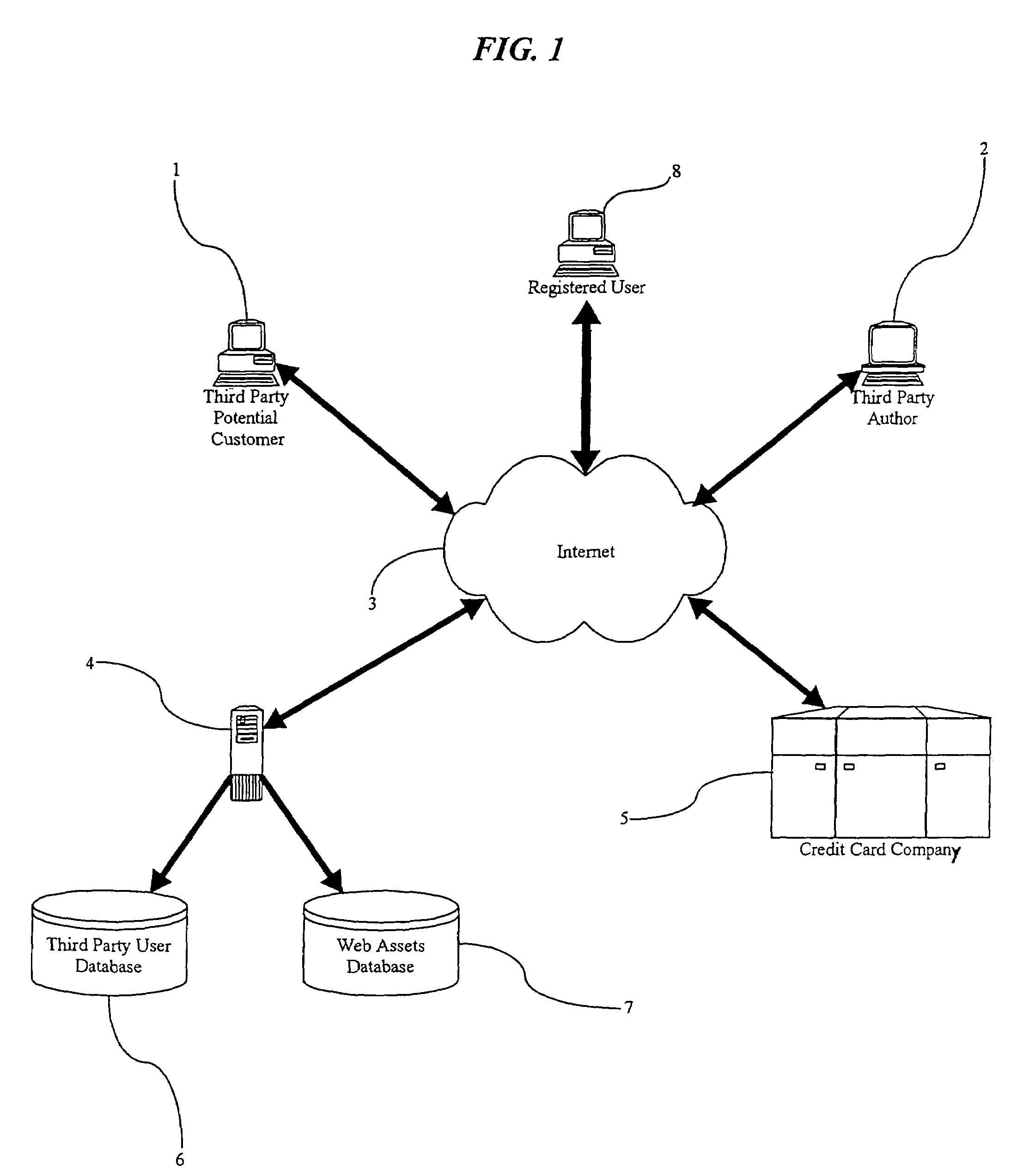
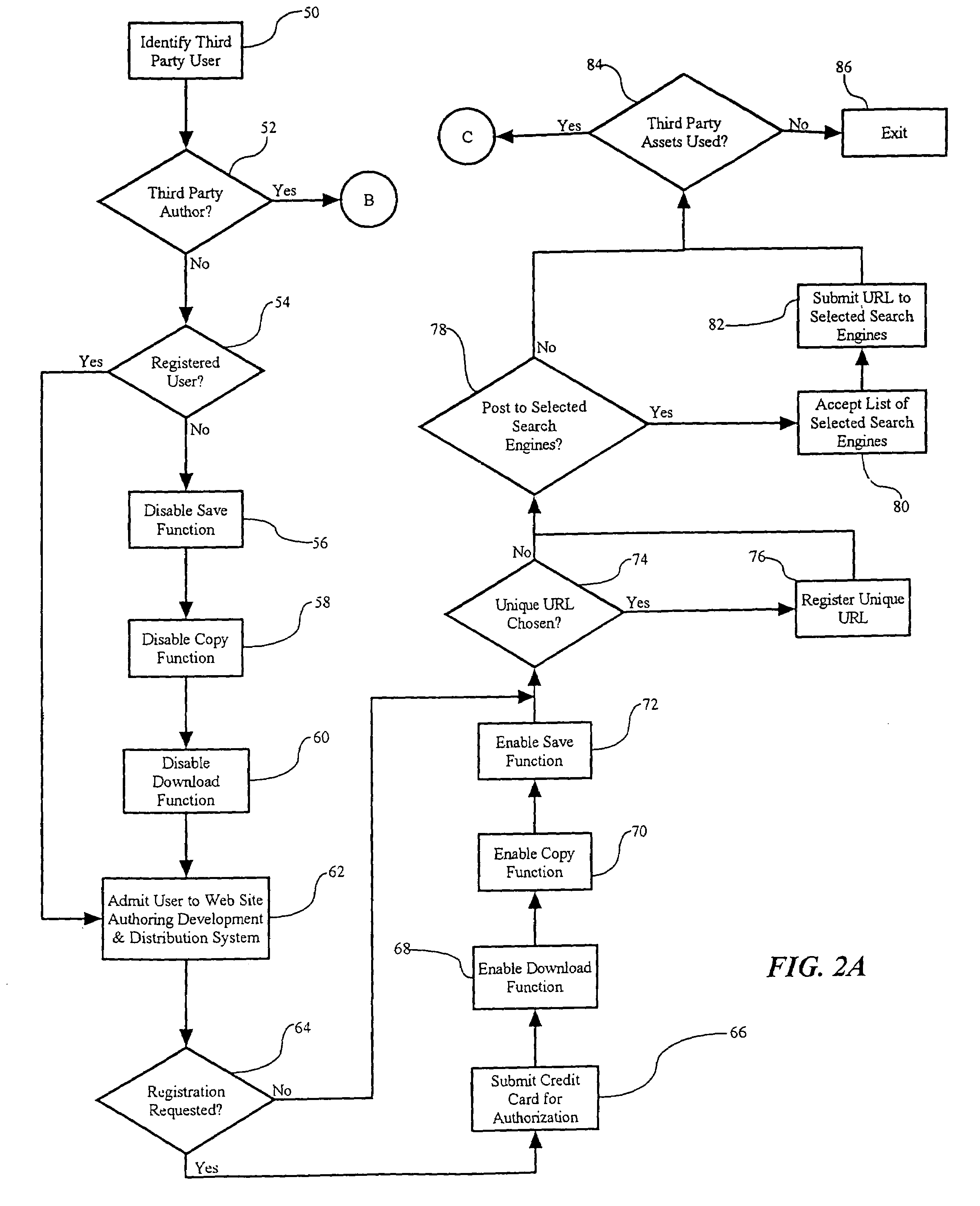
Method of moderating external access to an electronic document authoring development and distribution system
InactiveUS7353199B1Limited accessEfficient accessFinanceDigital computer detailsElectronic documentThird party
A method for moderating external access to an electronic document authoring, development and distribution system can comprise the steps of: identifying a third party requesting access to the system; permitting restricted access to the third party; and, eliminating all access restrictions imposed in the permitting step when the third party registers with the system. Thus, the inventive method provides to a third party potential customer access to the electronic document authoring, development and distribution system without risking the abuse of the system by the potential customer. The inventive method can encourage the submission of third party Web assets for use by registered users of the system. Specifically, the inventive method can further comprise the steps of: accepting electronic submissions of Web assets from the third party; storing the accepted Web assets in a Web asset database; and, compensating the third party for subsequent distribution of the Web assets.
Owner:PATENT TRUST +1
System and method for sending electronic data to inmates
InactiveUS20100299761A1Digital data processing detailsAnalogue secracy/subscription systemsLimited accessRelational database management system
The invention includes delivering and monitoring electronic letters to correction facility inmates while giving supervisory authorities the ability to screen the incoming mail. This may be achieved by providing a database having an entry for each inmate and having a plurality of fields, and by scanning an original letter as an electronic letter and storing each electronic letter sent to a specific inmate in a relational database management system (RDMS) table. Another aspect of the invention involves providing a computer-operated kiosk that may be used by individuals (e.g., inmates) in a restrained environment / restricted-access location (e.g., a prison) to browse through a catalog of available digital media or content, such as music, that may be purchase with credits earned based on work performed by the inmate or bought through some other means, for example by family members of the inmate.
Owner:SECURUS TECH
Optical probe having and methods for difuse and uniform light irradiation
A variety of optical probes and methods have utility in the examination of various materials, especially materials in the interior of cavities having restricted access through orifices or passageways. One type of such optical probe is elongated and includes a distal optical window, a divergent light source, a spatial mixer, and a light collector. Light from the light source is mixed in the spatial mixer to achieve uniform diffuse light in the vicinity of the optical window. The light collector receives light from the target through the spatial mixer. The optical probe may be made of two sections, a reusable section and a disposable. The disposable is elongated and contains a mounting section, an inside surface suitable for the spatial mixing of light, and an optical element which helps to seal the reusable probe section from the target.
Owner:LIFESPEX
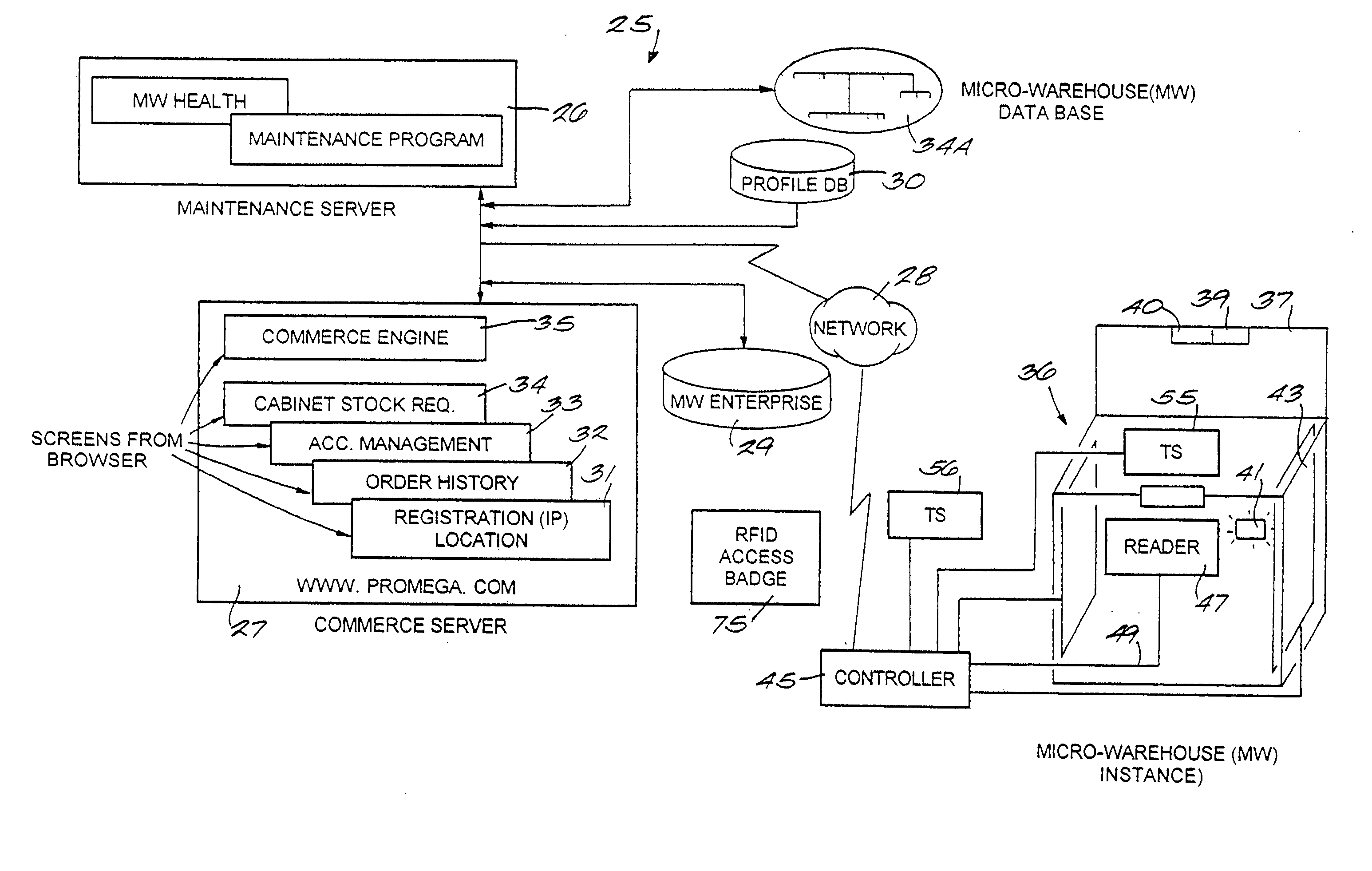
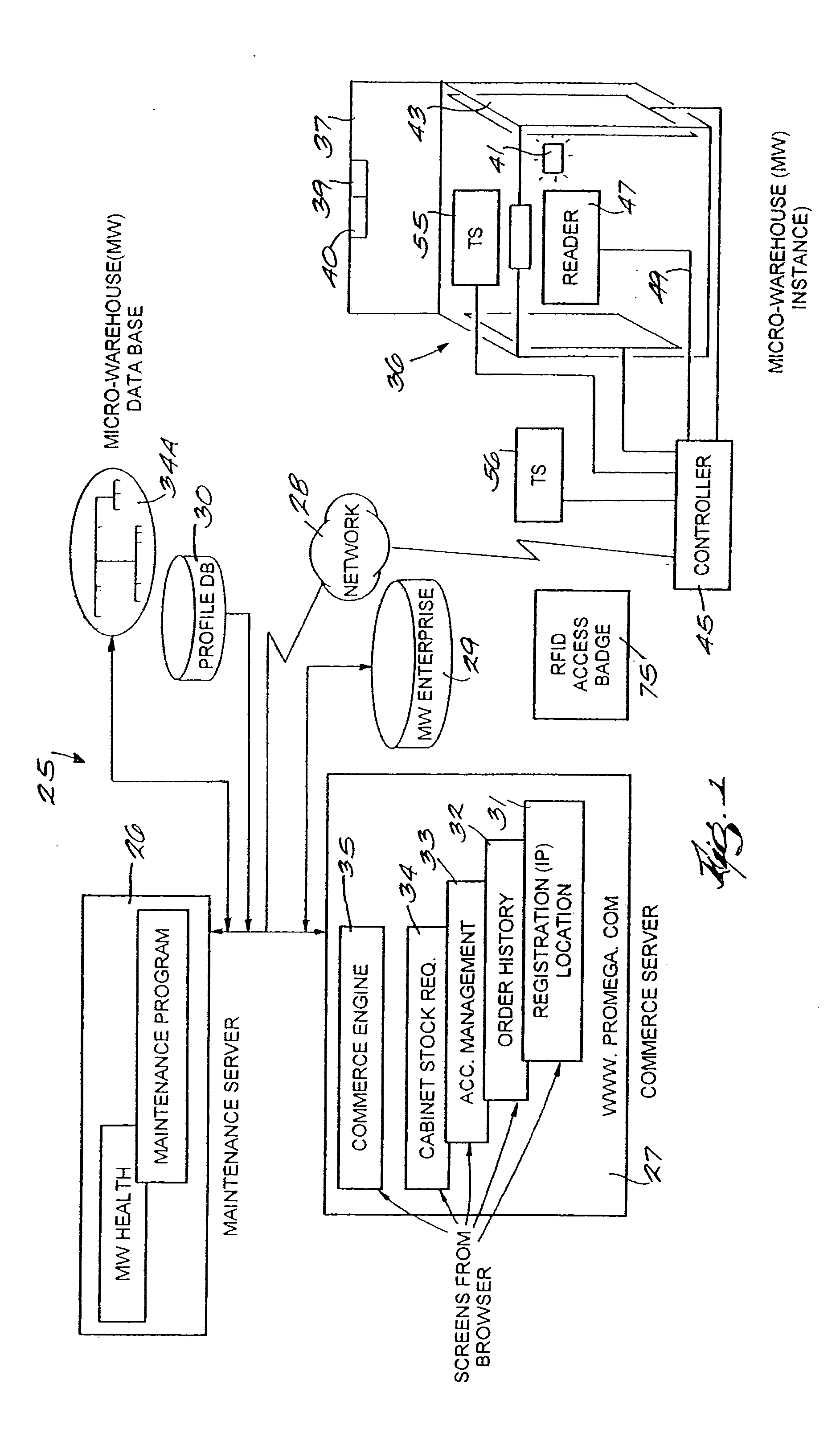
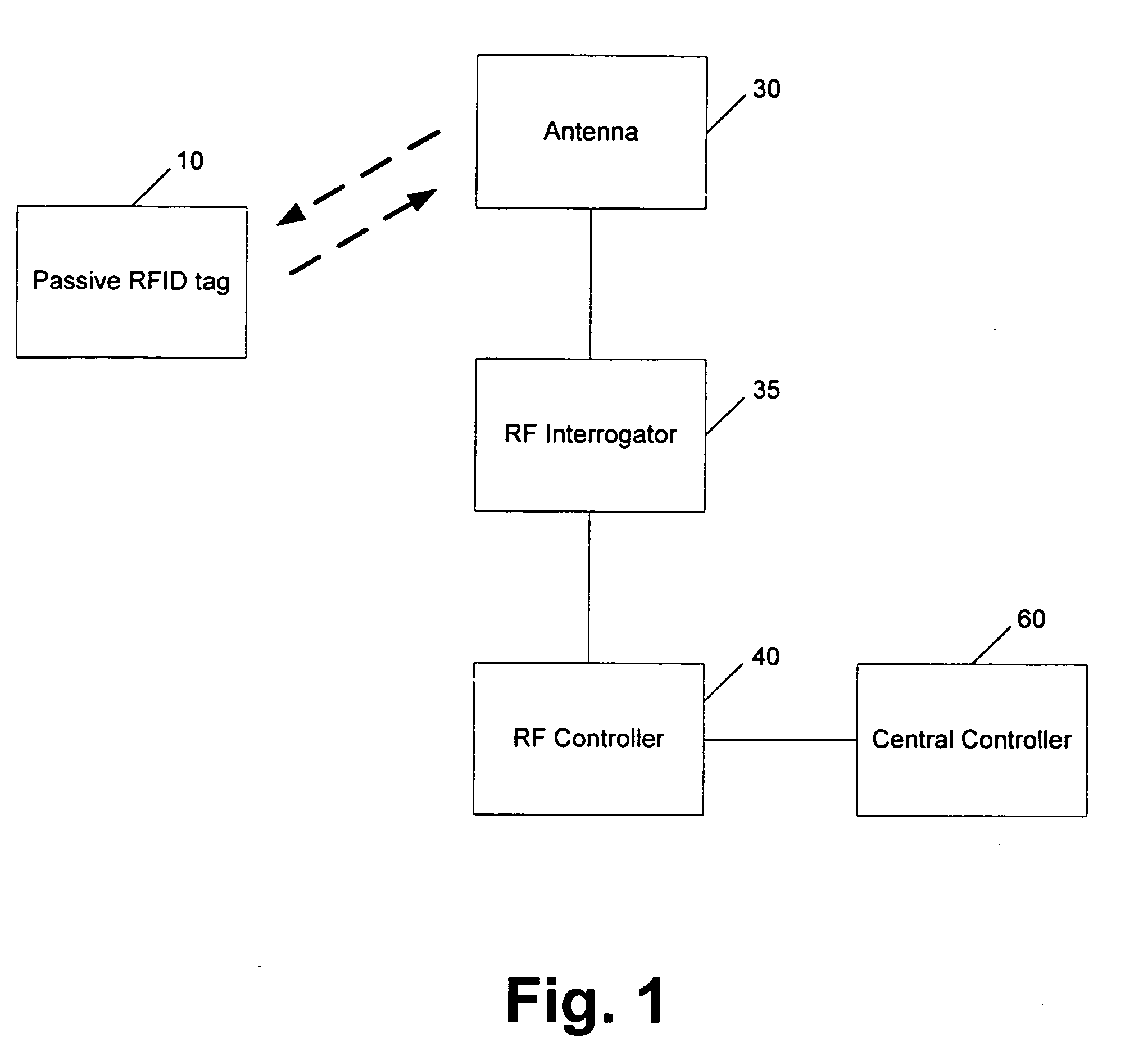
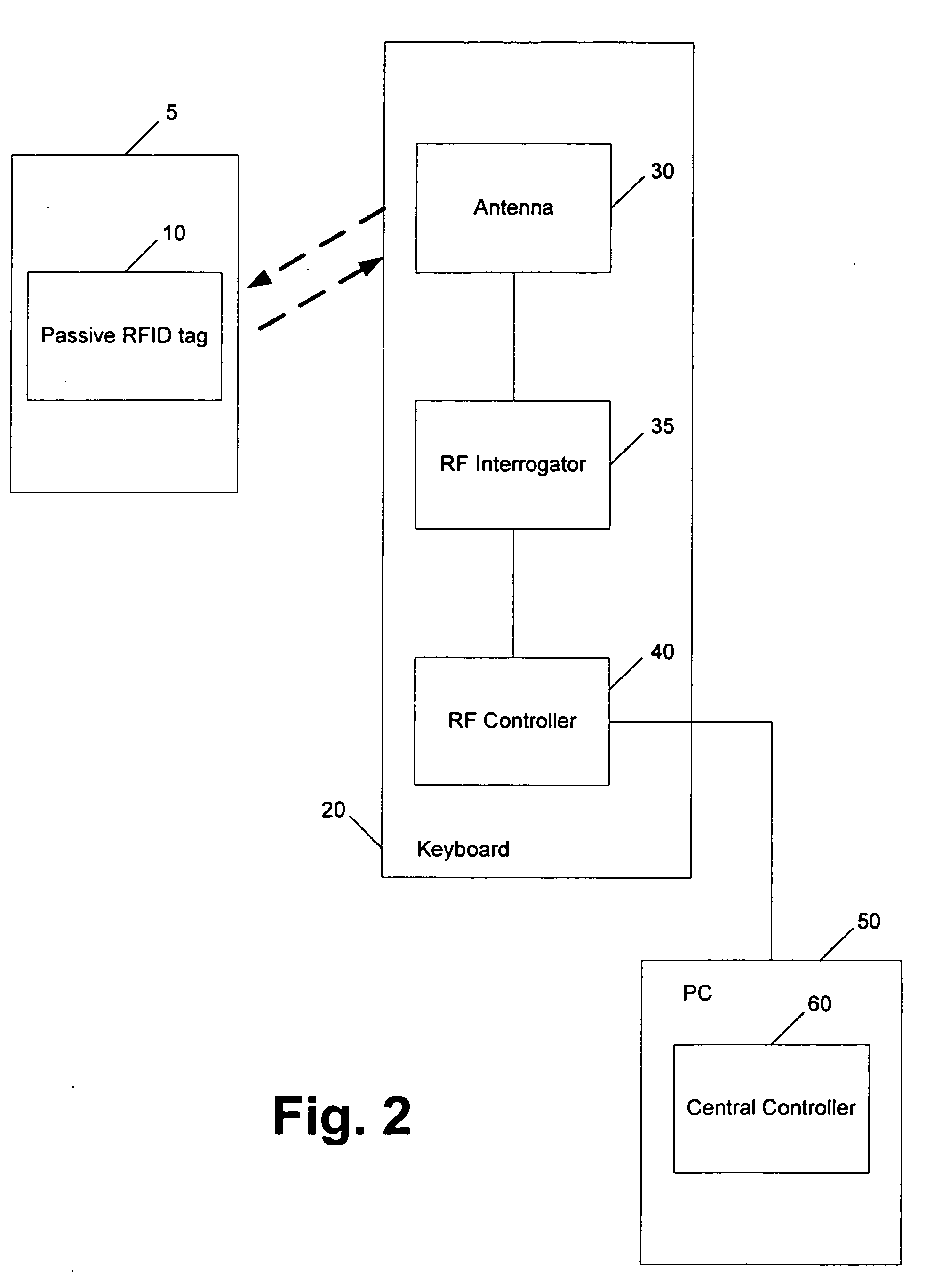
RF point of sale and delivery method and system using communication with remote computer and having features to read a large number of RF tags
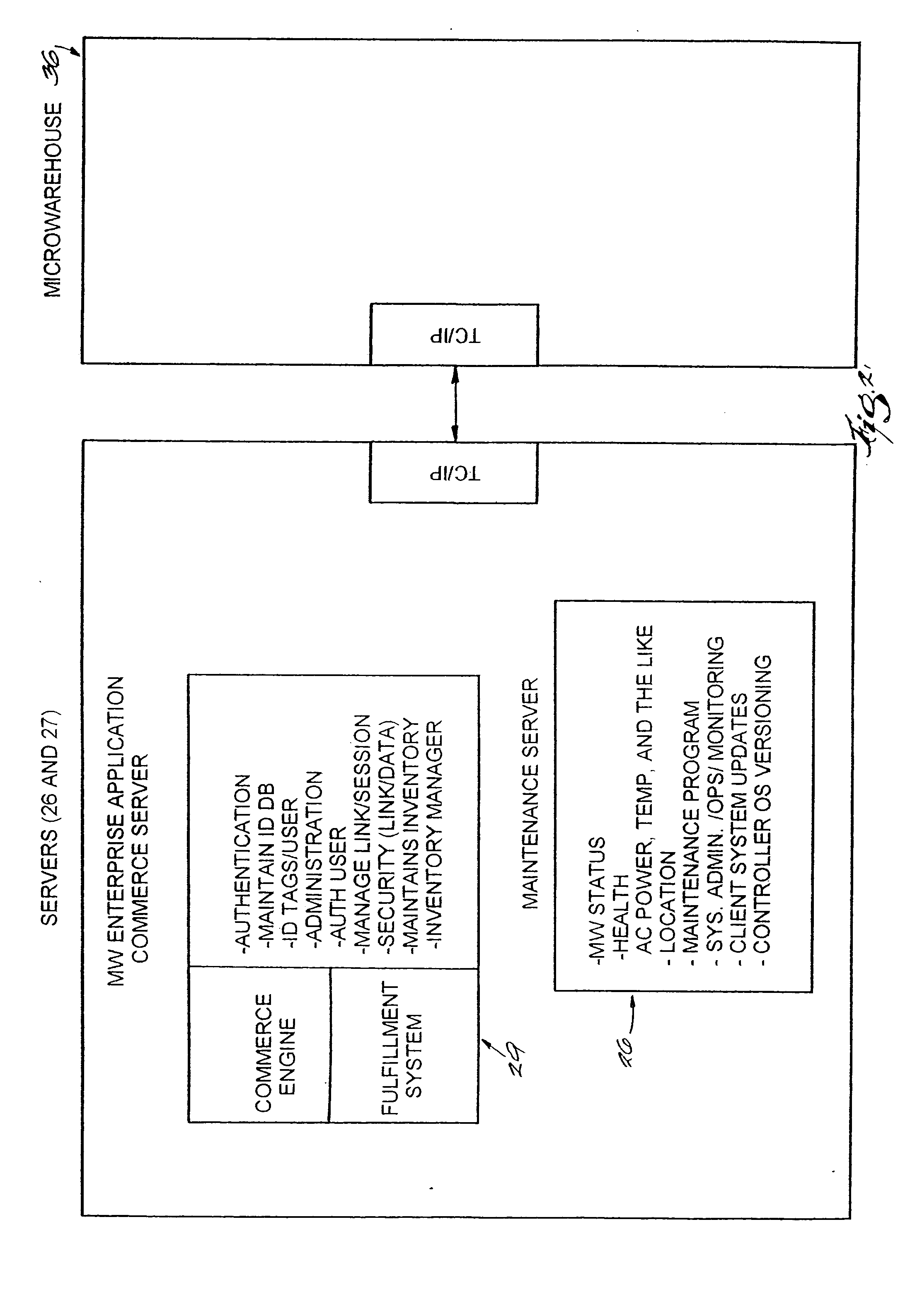
InactiveUS20050125312A1Credit registering devices actuationLighting and heating apparatusShadowingsEngineering
A method and system for providing point-of-sale and point-of-delivery and / or distribution of products in a restricted access unit near the customer. The method and system utilize products equipped with radio frequency tags and reduce the effects of energy sharing, shadowing, and nulls. In one embodiment, a plurality of RF tagged products are placed within a refrigerator, cabinet, or other micro-warehouse that has a door or opening that can detect access to the micro-warehouse. In one embodiment, one or more antennas are positioned within the door. Each antenna may have a transmission line of sight and be configured to emit a signal at predefined frequencies. Each antenna generates an electromagnetic field within the micro-warehouse. In one embodiment, the products are positioned in one or more bins, compartments, or similar devices located within the micro-warehouse such that at least two of the plurality of products are spaced a distance from each other to reduce energy sharing. The electromagnetic field is moved or altered within the micro-warehouse through the use of reflectors, devices that move the antennas, or other mechanisms.
Owner:PROMEGA CORP
Restricted access waste sorting system
ActiveUS20070278140A1Easy to classifyEncourages and facilitates complianceSustainable waste treatmentData processing applicationsMedical wasteRestricted access
A system for disposing of medical waste is generally configured to sort waste items into a plurality of containers according to applicable rules and regulations governing the handling and / or disposal of such items. In some embodiments, a system comprises sorting stations each of which houses a number of disposable containers. Each station can identify an item of waste, determine the most appropriate container for the item, and facilitate disposal of the item in the appropriate container. In some embodiments, a detection system for determining a presence and / or a quantity of waste items within a container is also provided. In some embodiments, access to discarded waste items is restricted once the waste items have been placed in a container.
Owner:CAREFUSION 303 INC
Security system for computer transactions
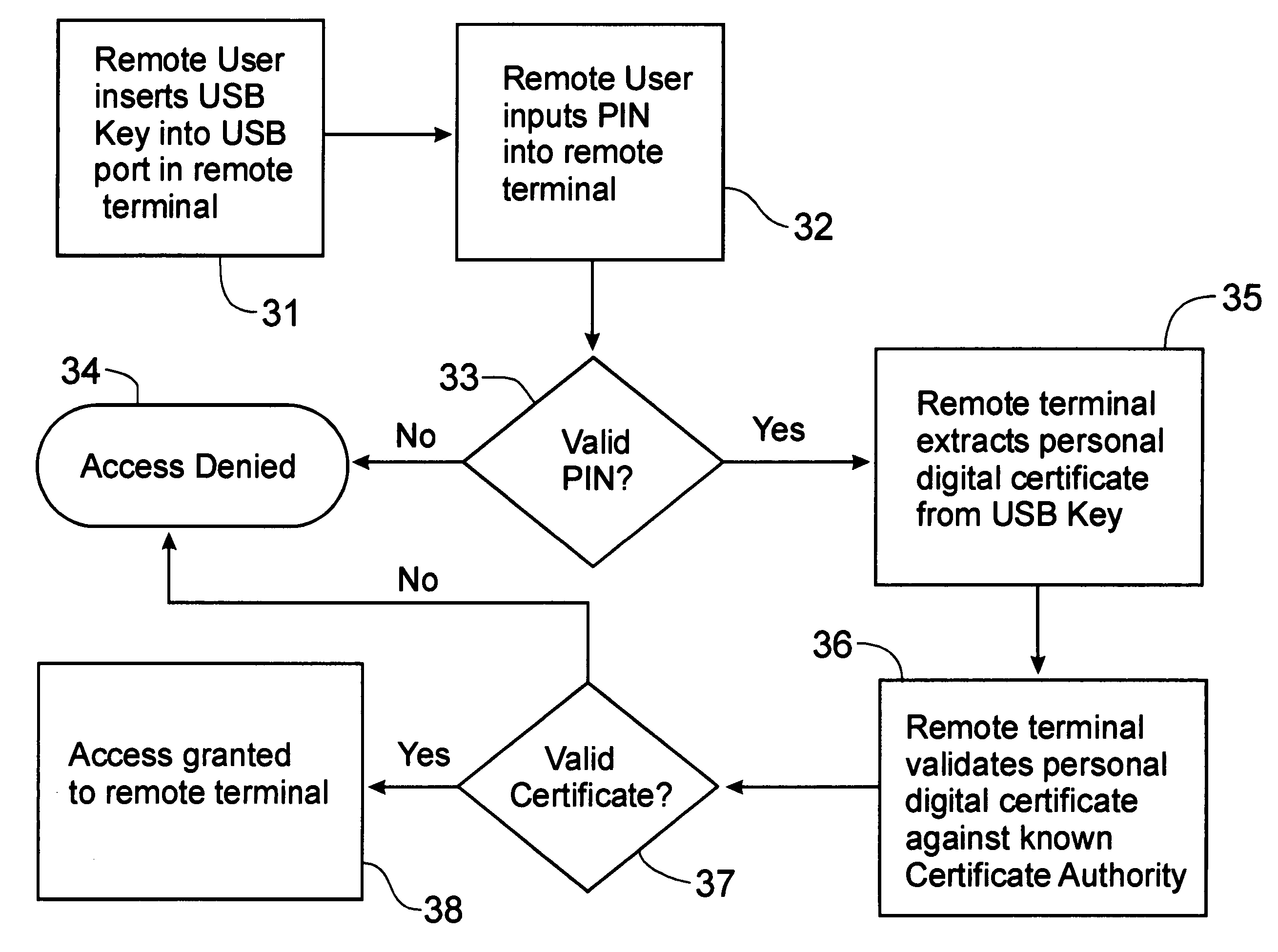
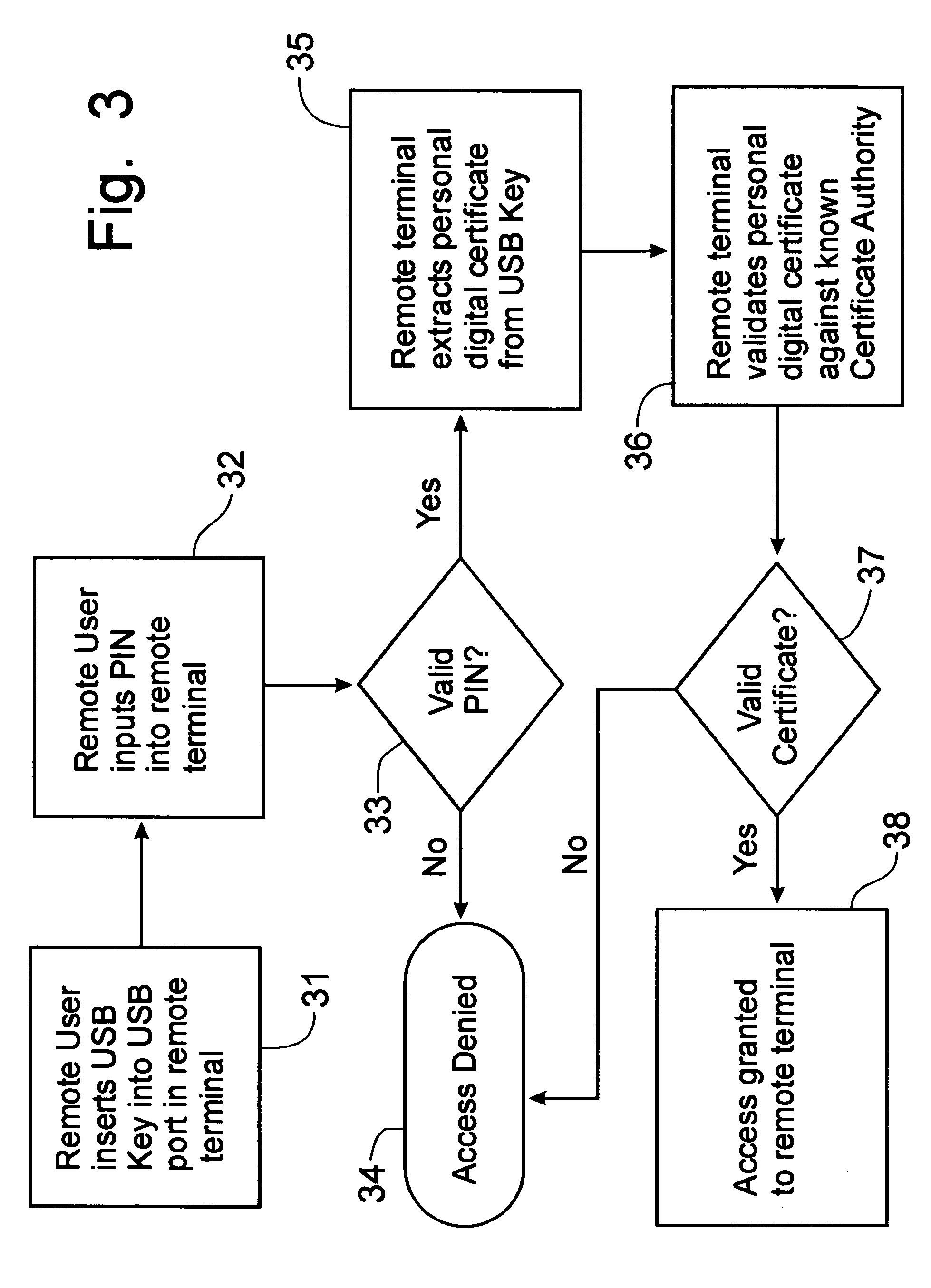
InactiveUS20060010325A1Rapid deploymentEasy to installUser identity/authority verificationDigital data authenticationPersonal identification numberIp address
A Security system for computer transactions incorporates a USB Security Key, a remote terminal and a secure access appliance to provide Security for a central computer. The USB Security Key is coded with a personal digital certificate and is required to be inserted into the remote terminal, along with the input of a personal identification number, before communications with the secure access appliance can be authenticated. The remote terminal is provided only with a central processing unit, random access memory, and restricted access, non-volatile flash memory storage device, which when used with a central computer, eliminates the need to store data on a permanent memory storage device. Software applications can be downloaded from the central computer for operation by the remote terminal. Since the IP address / name of the central computer is hidden by the secure access appliance, the central computer remains secure from unauthorized access and provides an audit trail.
Owner:DEVON IT
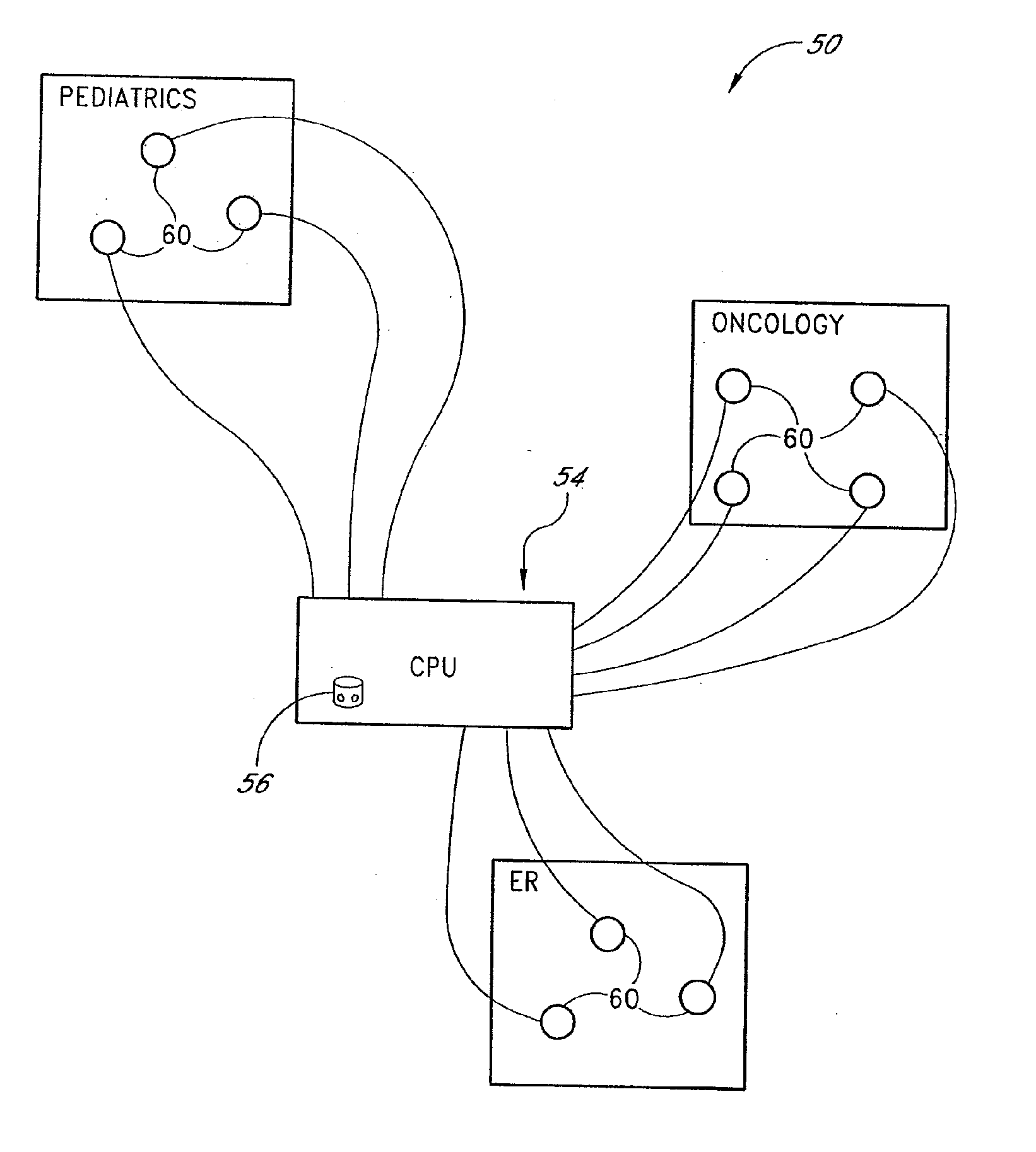
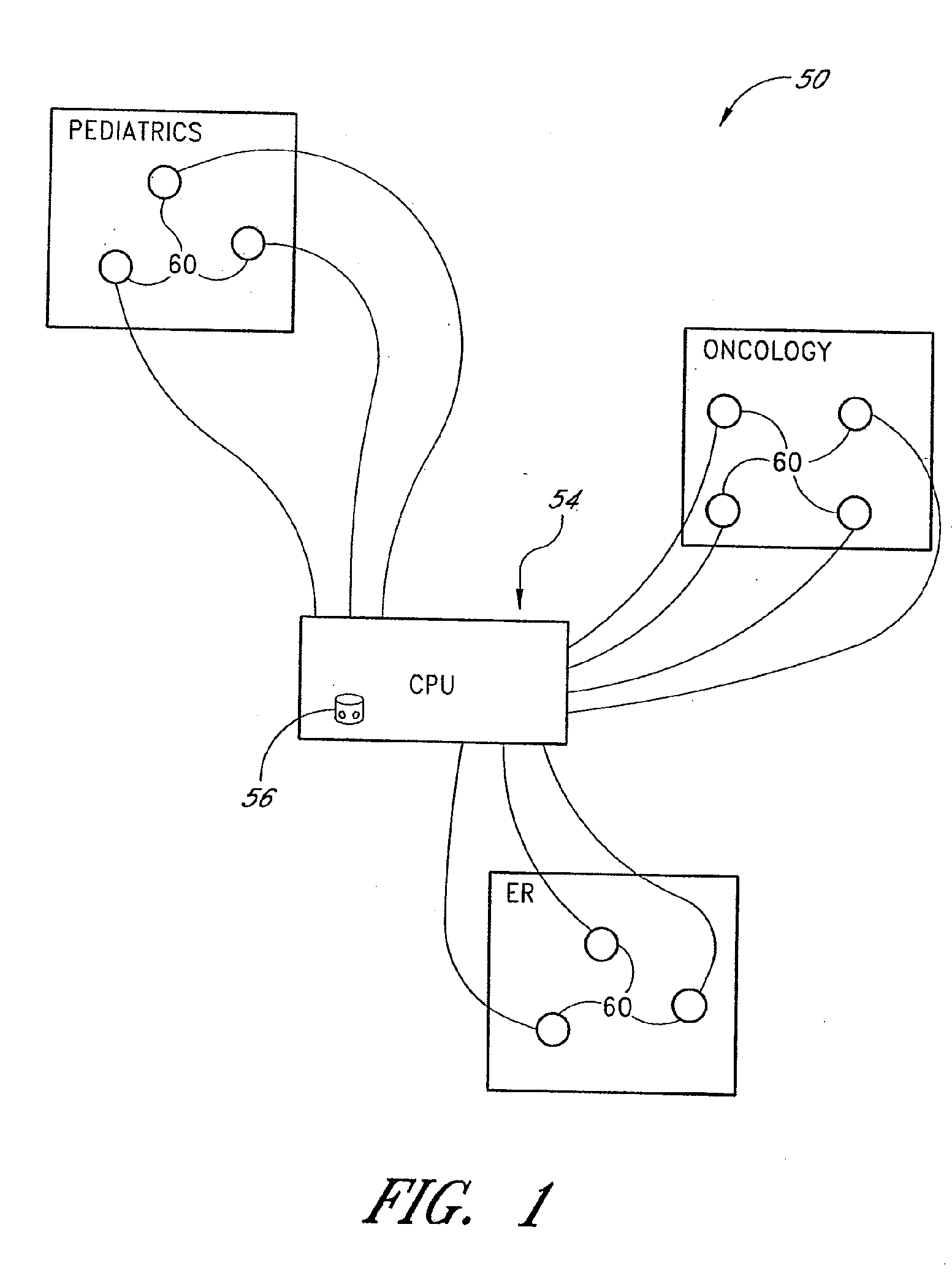
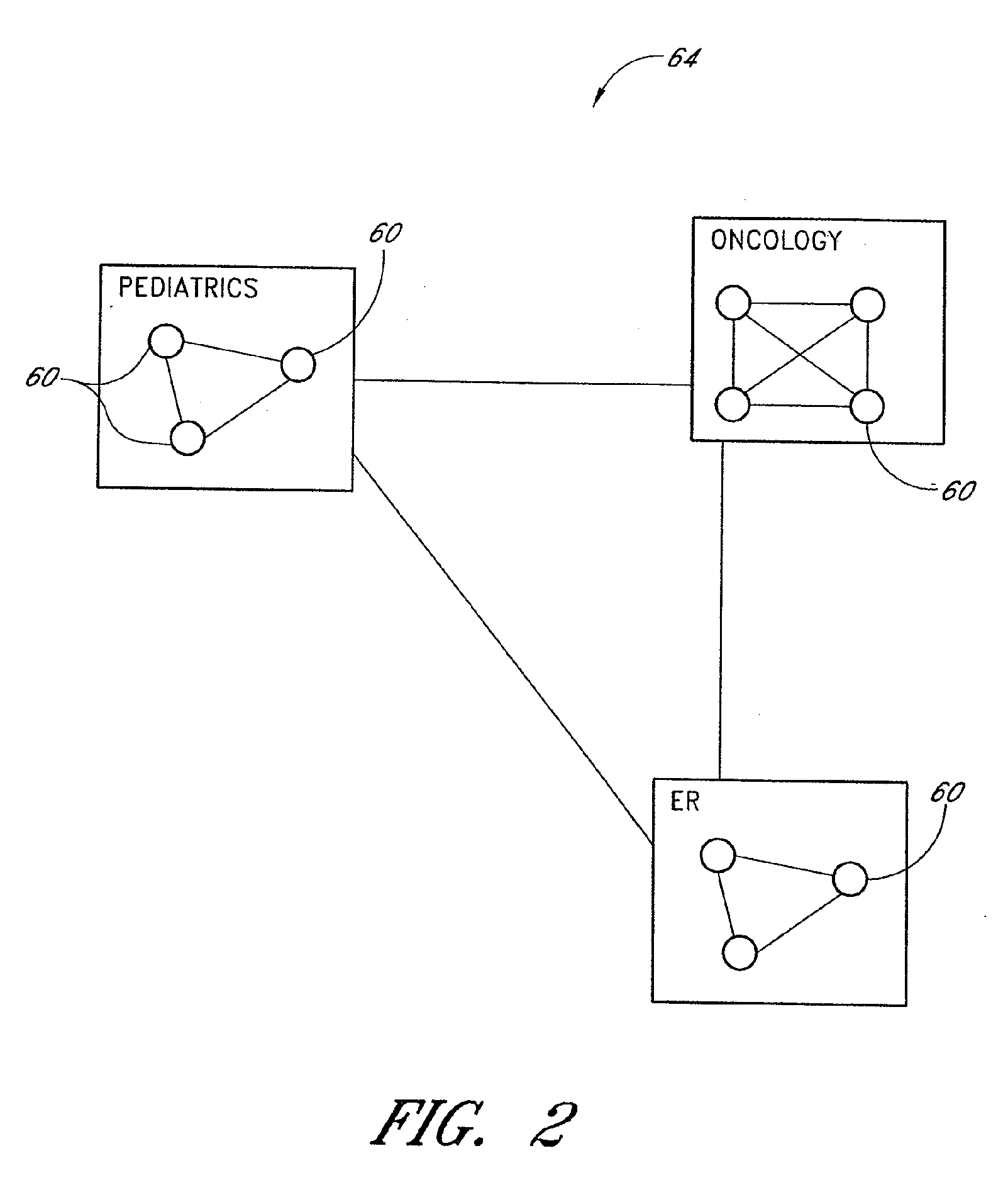
Finding location and ranging explorer
ActiveUS20050225427A1Guaranteed uptimeElectric signal transmission systemsMultiple keys/algorithms usageInteraction deviceRestricted access
An RFID tag is used to determine the presence or absence of a user. Rules or instructions responsive to this presence or absence are implemented to control a device or multiple devices accordingly. In this manner, a device can be maintained in a normal operating mode if a user is present, even though a user is not actively interacting with the device. Moreover, the device can be shut down or locked or be on restricted access if an authorized user is no longer in the presence of the device.
Owner:MICROSOFT TECH LICENSING LLC
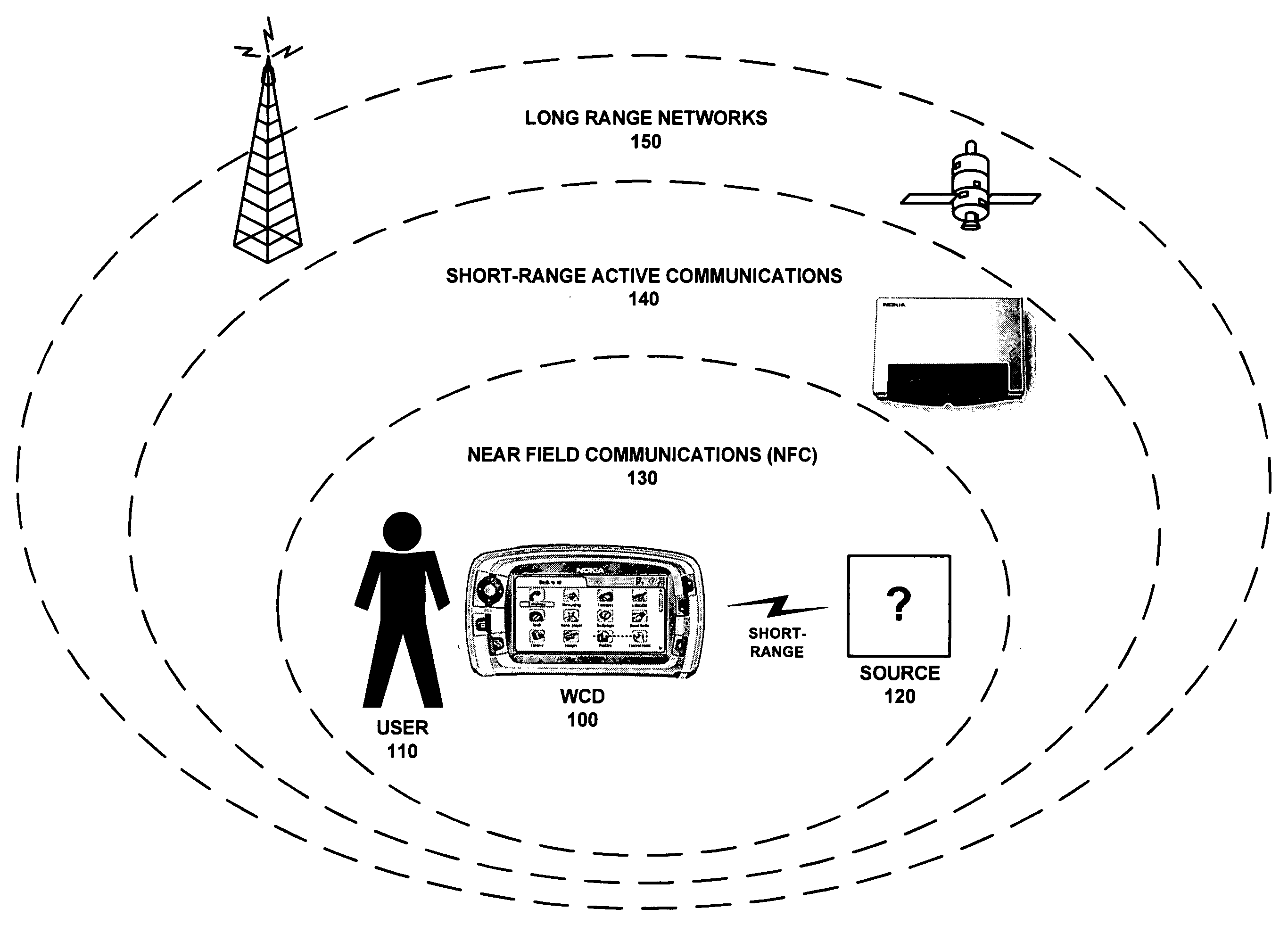
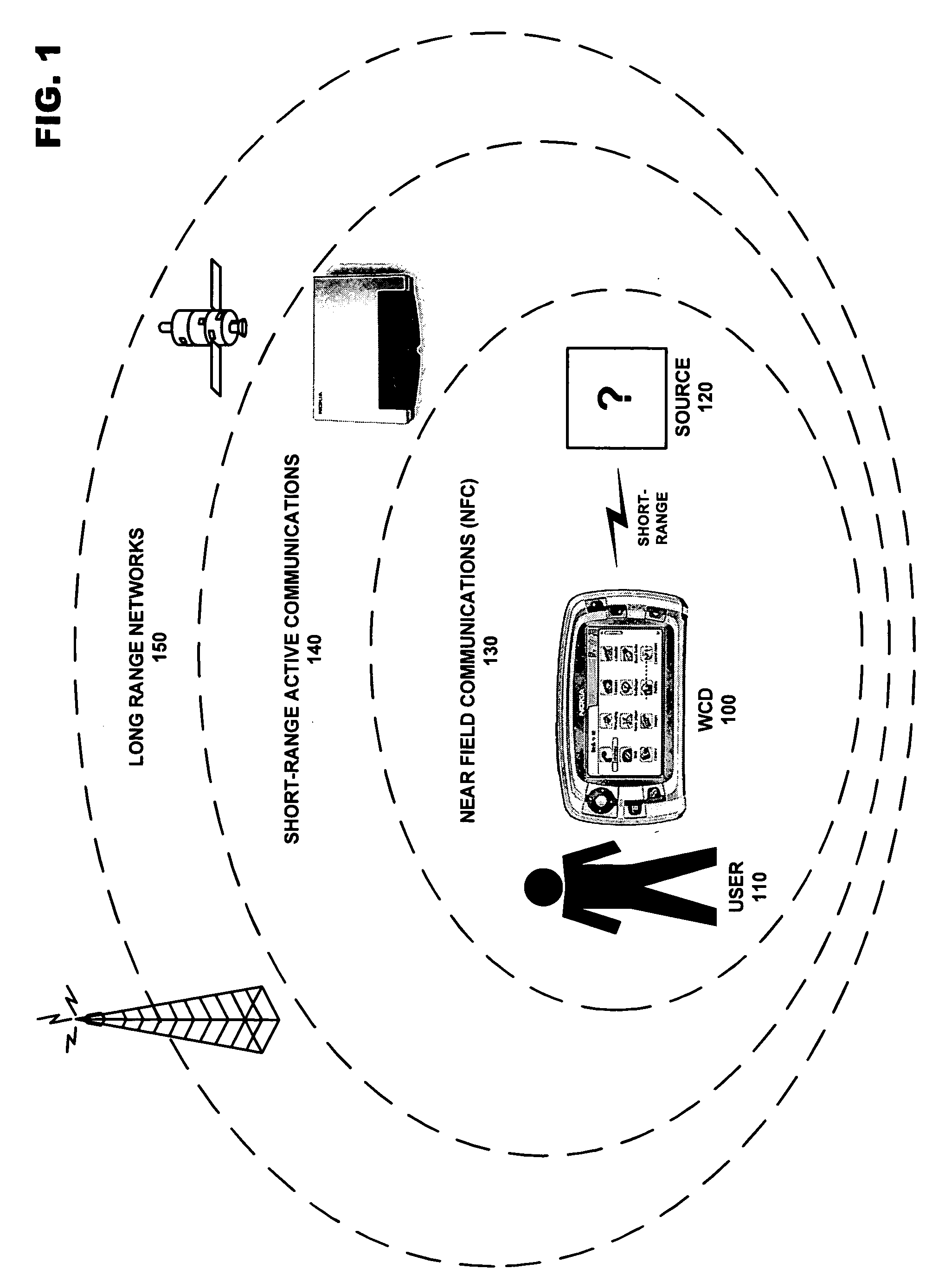
Conditional utilization of private short-range wireless networks for service provision and mobility
ActiveUS20080008140A1Without depletionWithout securityError preventionFrequency-division multiplex detailsTelecommunicationsService provision
A system for managing the integration of a private short-range wireless network into a service / mobility domain. The private short-range wireless network may be converted into a semi-private short range wireless network by managing access to the network in accordance with rules defined by a home user. These rules allow a home user to define how visitors will be granted access to the semi-private short-range network when the user is at home or away. Restricted access may be enforced when the home user is present, and security measures may force the semi-private short-range wireless network to enter a safe mode when a condition is met.
Owner:NOKIA TECHNOLOGLES OY
Method and system for providing restricted access to a storage medium
InactiveUS20090271586A1Digital data processing detailsUnauthorized memory use protectionFile systemData storing
A method of restricting file access is disclosed wherein a set of file write access commands are determined from data stored within a storage medium. The set of file write access commands are for the entire storage medium. Any matching file write access command provided to the file system for that storage medium results in an error message. Other file write access commands are, however, passed onto a device driver for the storage medium and are implemented. In this way commands such as file delete and file overwrite can be disabled for an entire storage medium.
Owner:KOM
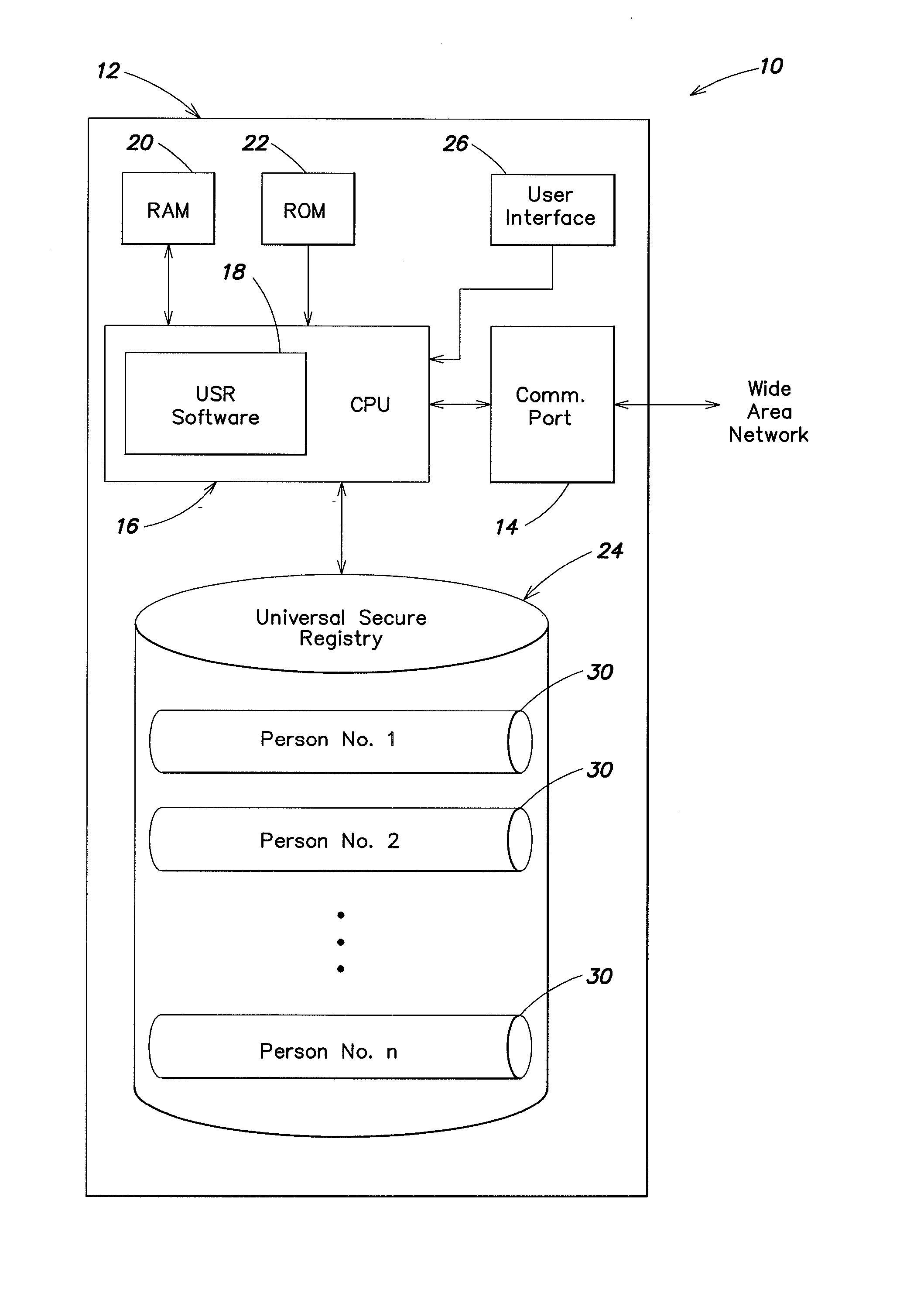
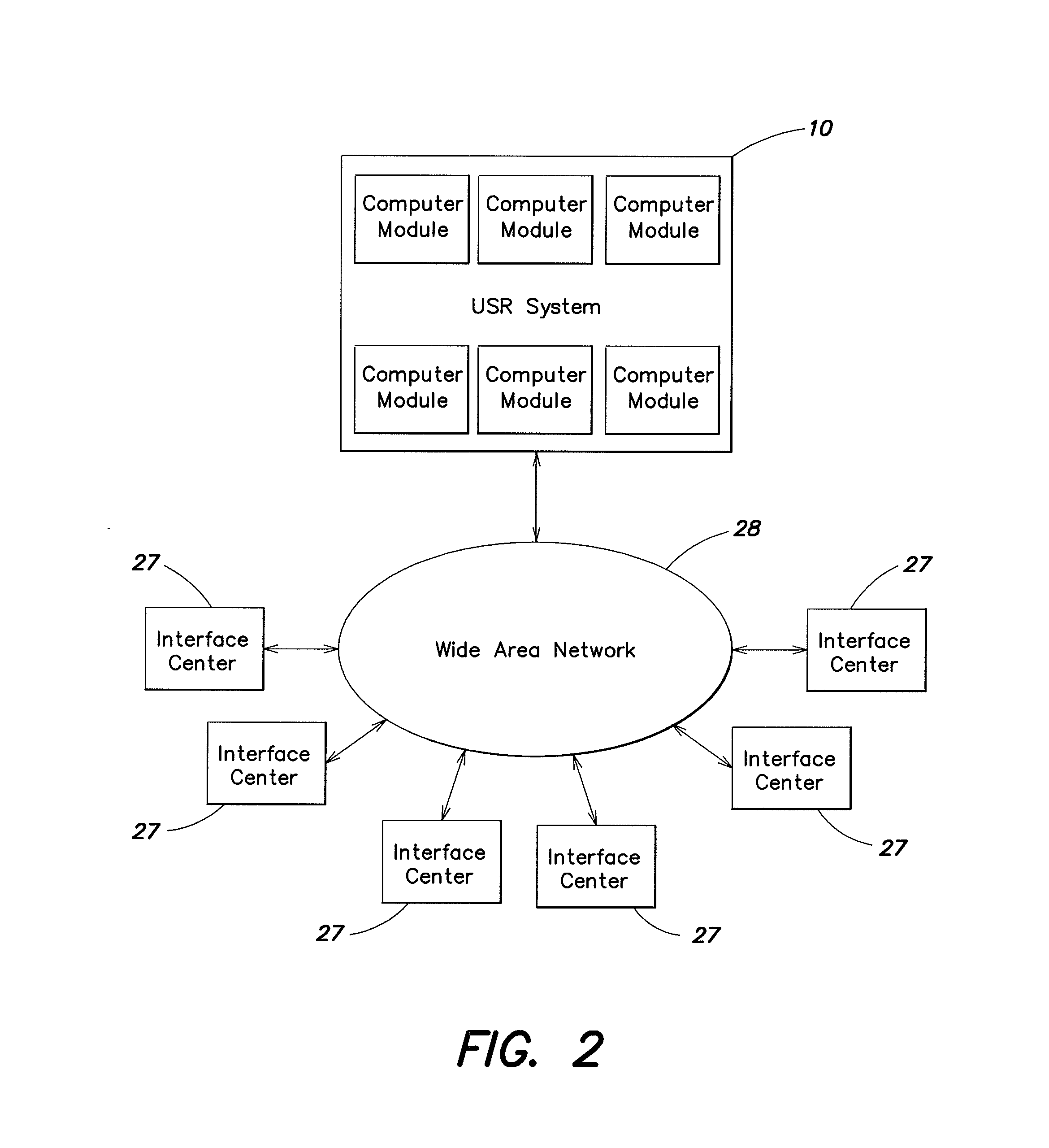
Universal secure registry
InactiveUS20080005576A1Easy to shapeCryptography processingUser identity/authority verificationRestricted accessBiological data
A secure registry system and method for the use thereof are provided which permits secure access to a database containing selected data on a plurality of entities, at least portions of which database has restricted access. Mechanisms are provided for controlling access to restricted access portions of the database are provided, such access being determined by at least one of the identity of the requesting entity and the entity's status. A multicharacter public code may be provided which the system can map to provide permit delivery of items, complete telephone calls and perform other functions for entities. The system may also be utilized to locate an individual based on limited biological data. Organizations utilizing the system may have custom software facilitating their access and use of the system.
Owner:UNIVERSAL SECURE REGISTRY
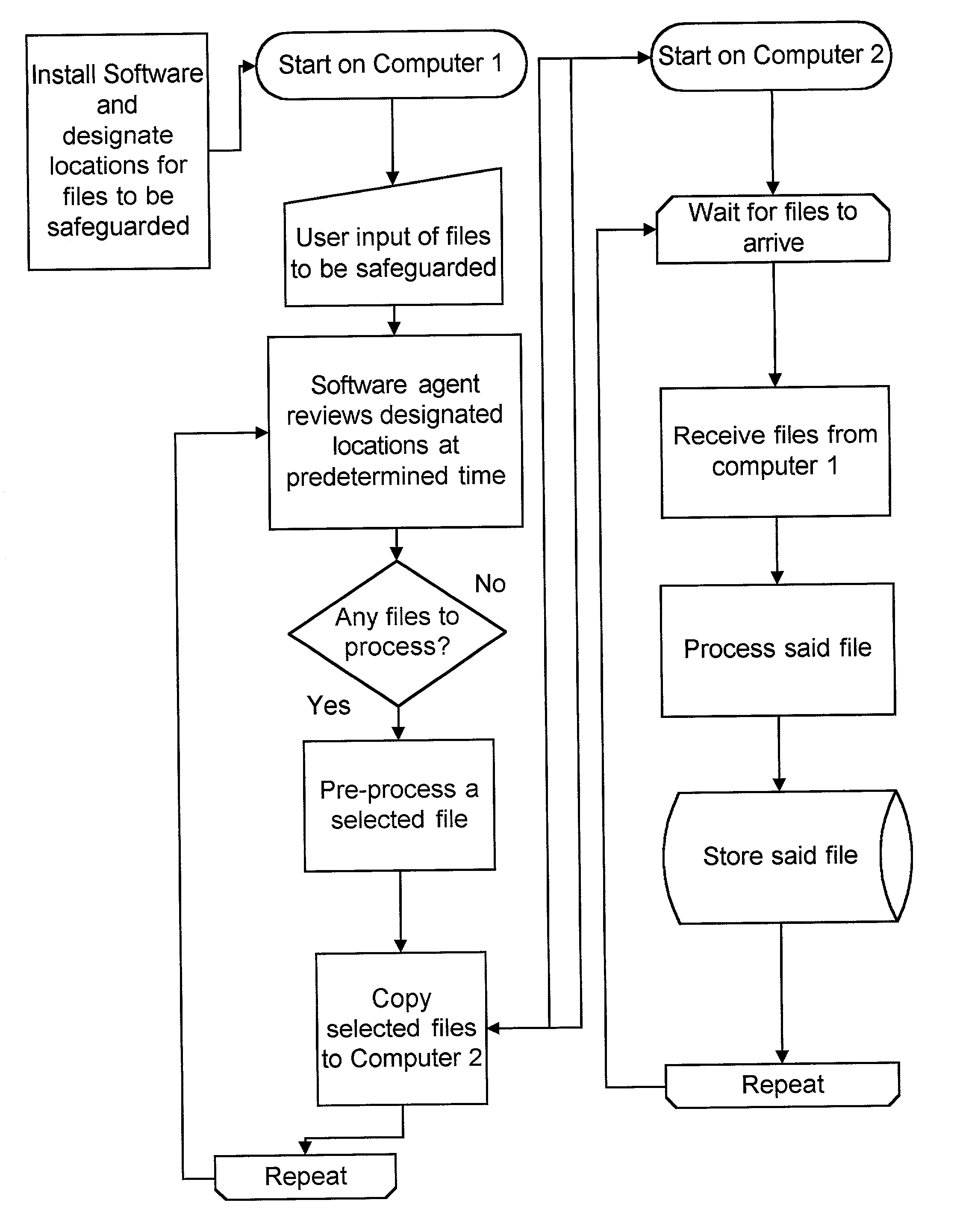
Method and apparatus for safeguarding files
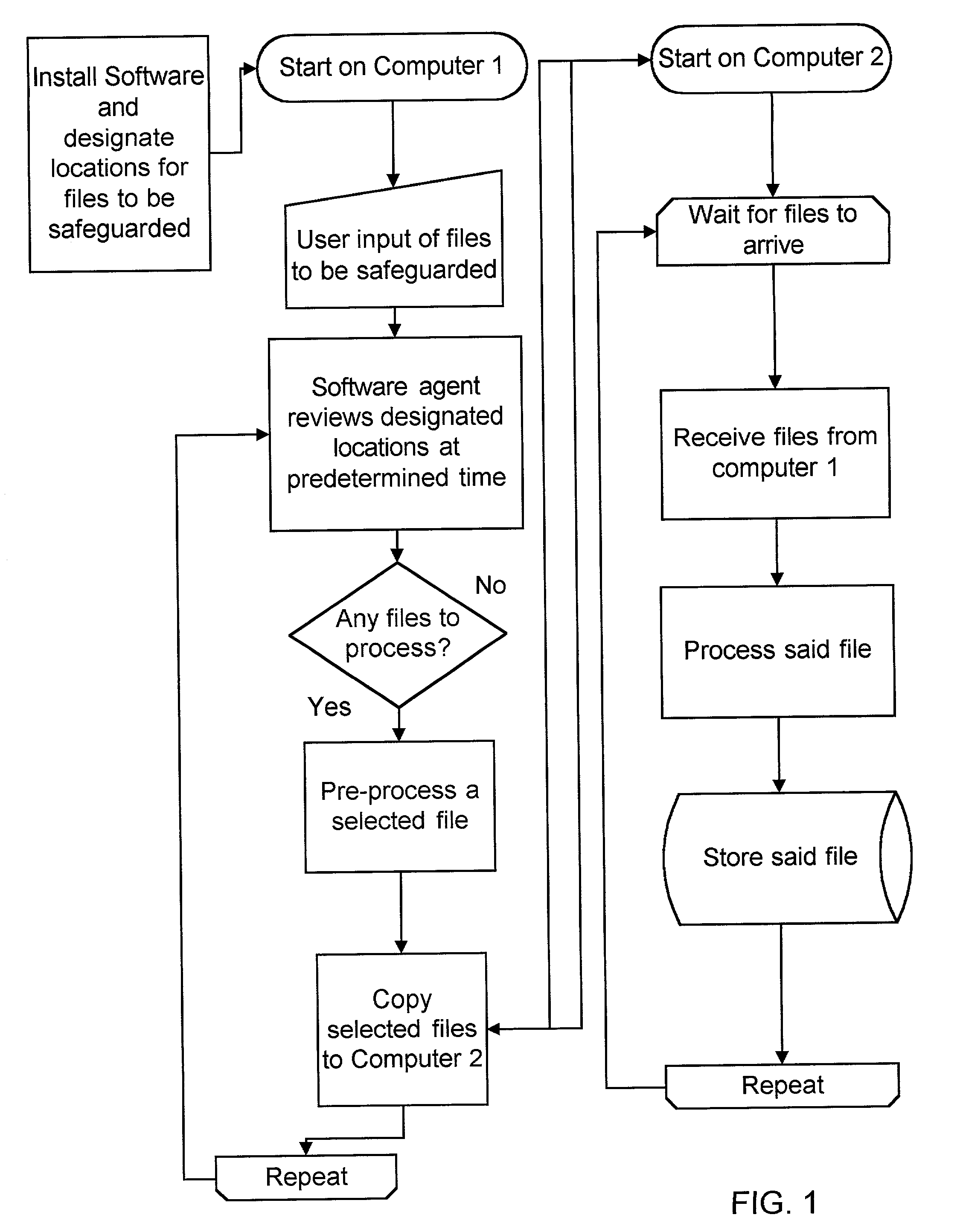
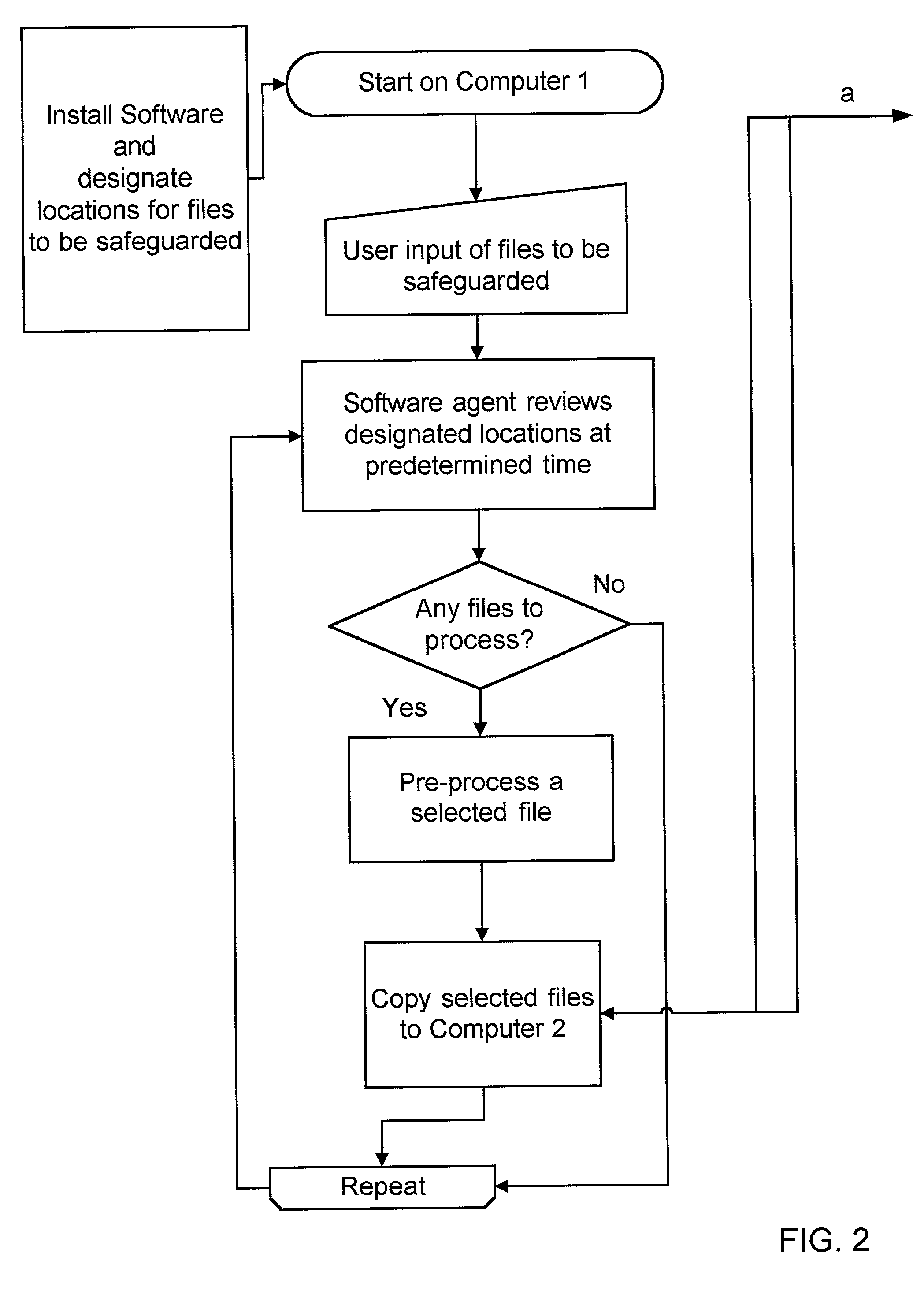
ActiveUS7174332B2Minimal interventionData processing applicationsUser identity/authority verificationSelection criterionRestricted access
A computer implemented method for safeguarding files, comprising the steps of designating a location on a first computer for storage of files to be safeguarded, selecting certain of the files to be safeguarded from the location based upon predetermined selection criteria, copying the selected files to be safeguarded to a second computer, deleting the selected files from the first computer, processing the selected files to be safeguarded on the second computer, and storing the selected files to be safeguarded in a restricted access database. In a second embodiment, the file is copied to a second computer, but not deleted from the first computer, in addition to all other steps of the method. The invention also includes an apparatus for carrying out the methods of the invention.
Owner:IP COM I
Method and system for providing restricted access to a storage medium
InactiveUS20130198474A1Unauthorized memory use protectionComputer security arrangementsFile systemData storing
A system, apparatus, method, or computer program product of restricting file access is disclosed wherein a set of file write access commands are determined from data stored within a storage medium. The set of file write access commands are for the entire storage medium. Any matching file write access command provided to the file system for that storage medium results in an error message. Other file write access commands are, however, passed onto a device driver for the storage medium and are implemented. In this way commands such as file delete and file overwrite can be disabled for an entire storage medium.
Owner:KOM
Method and network for selectively controlling the utility a target
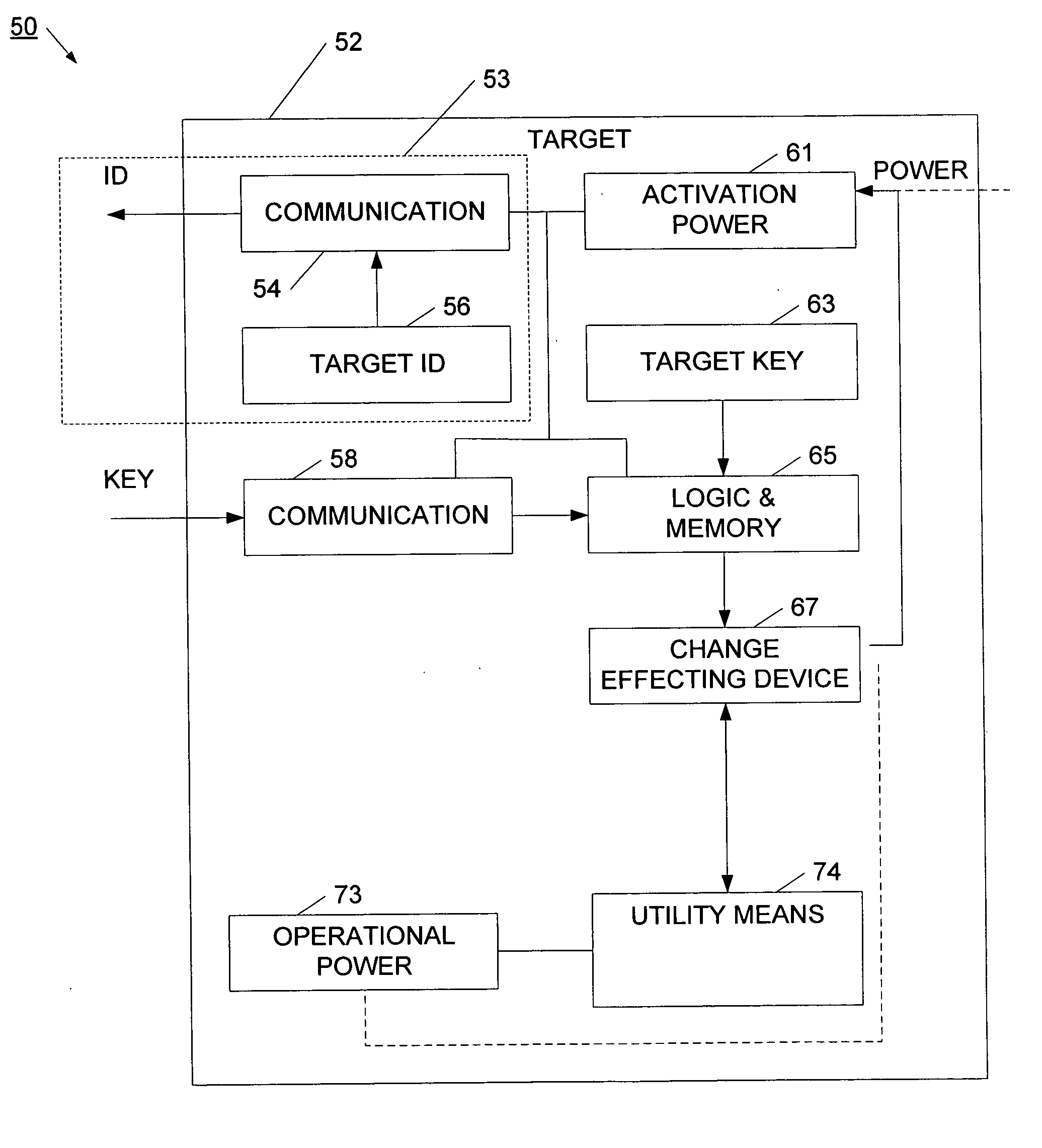
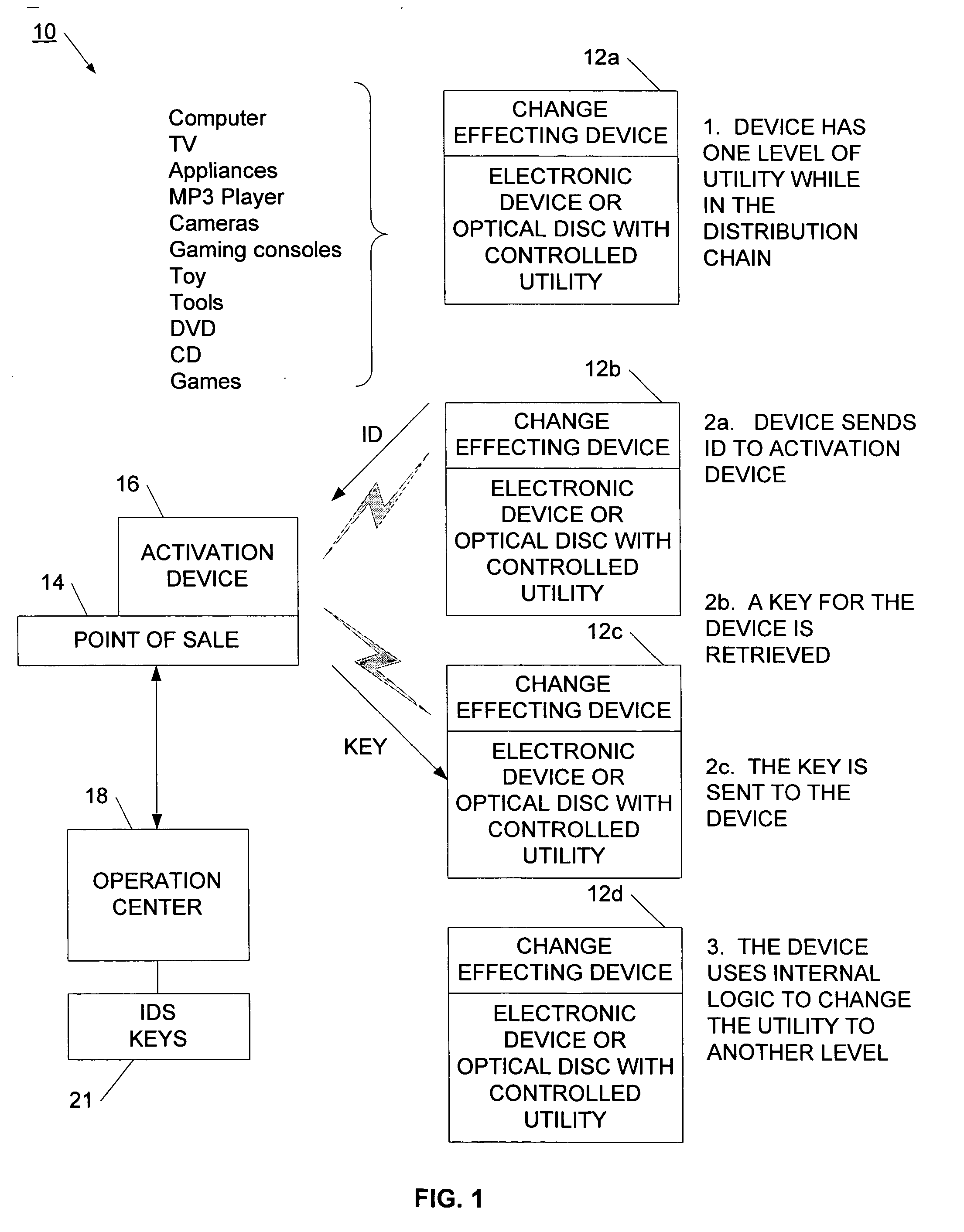
InactiveUS20060095385A1Reduce threatCompromise their utilityIndoor gamesUser identity/authority verificationDistribution controlBiological activation
A distribution control system is provided to support the controlled and selective changing of utility for a target. The target with controlled utility may be an electronic device, or alternatively, may be a tangible media, such as an optical disc. The distribution control system has a target with a change effecting device and a restricted access key. An activation device retrieves or generates an authorization key, and sends the authorization key to the target. The authorization key may be sent to the target wirelessly, for example, using a radio frequency signal. The target has logic that uses the restricted access key and the authorization key to change the utility of the target. In one example, the activation device retrieves the authorization key from a network operation center (NOC) by sending a target identifier to the NOC, and the NOC retrieves the authorization key for the identified target. The activation device may also connect to other systems for obtaining approval to change the utility of the target. For example, the authorization key may be sent to the target upon receiving payment, password, or other confirmation.
Owner:RPC IP HLDG
Methods and apparatuses for searching both external public documents and internal private documents in response to single search request
InactiveUS7386599B1Data processing applicationsDatabase queryingElectronic documentDocumentation procedure
Methods and apparatuses for both public documents and private documents in response to a single search request are disclosed. Public documents are electronic documents that are made available to large groups of people in by the publisher of the document. An example of a public document is a World Wide Web page. Private documents are documents that have restricted access. An example of a private document is a document that generated by members of an organization and is available only to members of the organization. As described in greater detail below, a portal appliance or other device can be used to search both public and authorized private electronic documents in response to a single search request thereby improving the results of the search and / or reducing the number of searches required to find the desired material.
Owner:RICOH KK
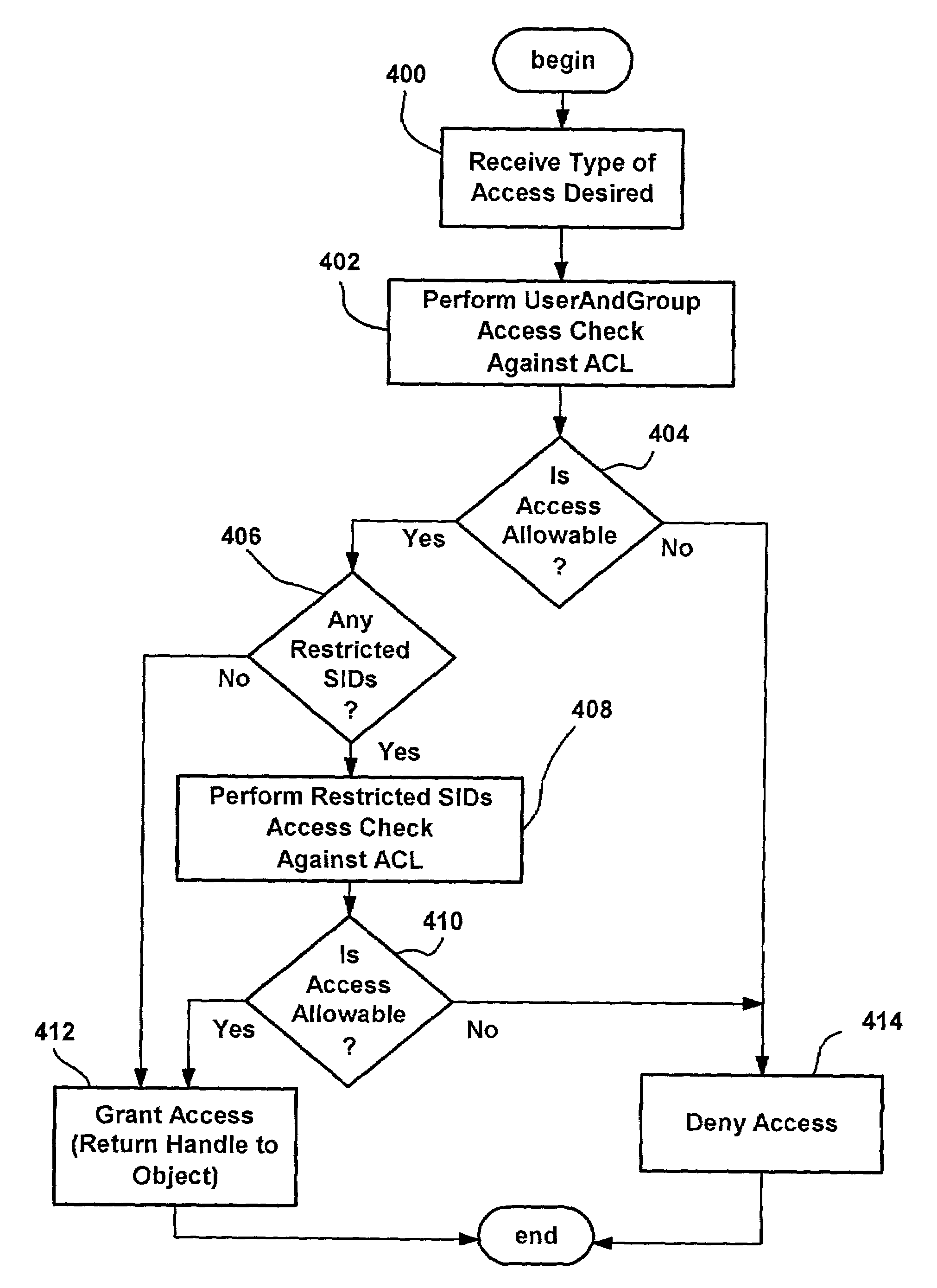
Method and apparatus for restricting access to a database according to user permissions
InactiveUS20030187848A1Easy to implementEasy maintenanceDigital data information retrievalDigital data processing detailsUser PrivilegeRights management
A method and apparatus for restricted access to a database according to user permissions are described. A user permissions file residing on a server includes information of permissions related to database records, and which of those permissions are associated with individual users. A permissions manager also residing on the server manages user queries either directly by generating restricted queries that reflect only authorized access to database records for the user generating the query, or indirectly by downloading a permissions filter or information for a restricted parameters screen to the user's client, so as to generate the restricted query on the client. In any case, a database management system residing on the server receives the restricted query and generates a result by accessing only authorized database records for the user, and communicates the result back to the user's client.
Owner:GHUKASYAN HOVHANNES +1
Methods for delivering a parcel to a restricted access area
ActiveUS9928749B2Reduce the required powerArresting gearLaunching/towing gearUncrewed vehicleRestricted access
Systems and methods include UAVs that serve to assist carrier personnel by reducing the physical demands of the transportation and delivery process. A UAV generally includes a UAV chassis including an upper portion, a plurality of propulsion members configured to provide lift to the UAV chassis, and a parcel carrier configured for being selectively coupled to and removed from the UAV chassis. UAV support mechanisms are utilized to load and unload parcel carriers to the UAV chassis, and the UAV lands on and takes off from the UAV support mechanism to deliver parcels to a serviceable point. The UAV includes computing entities that interface with different systems and computing entities to send and receive various types of information.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
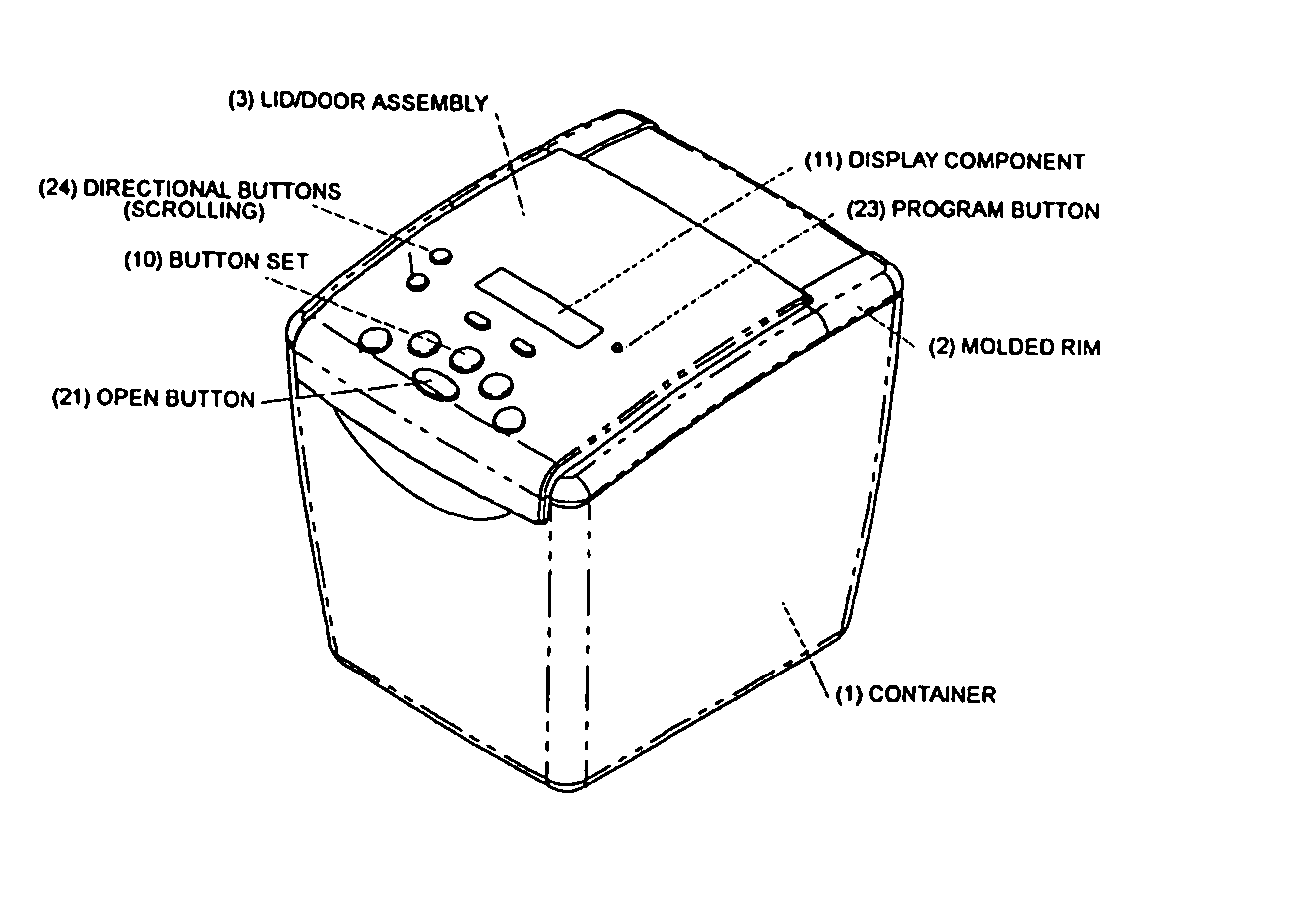
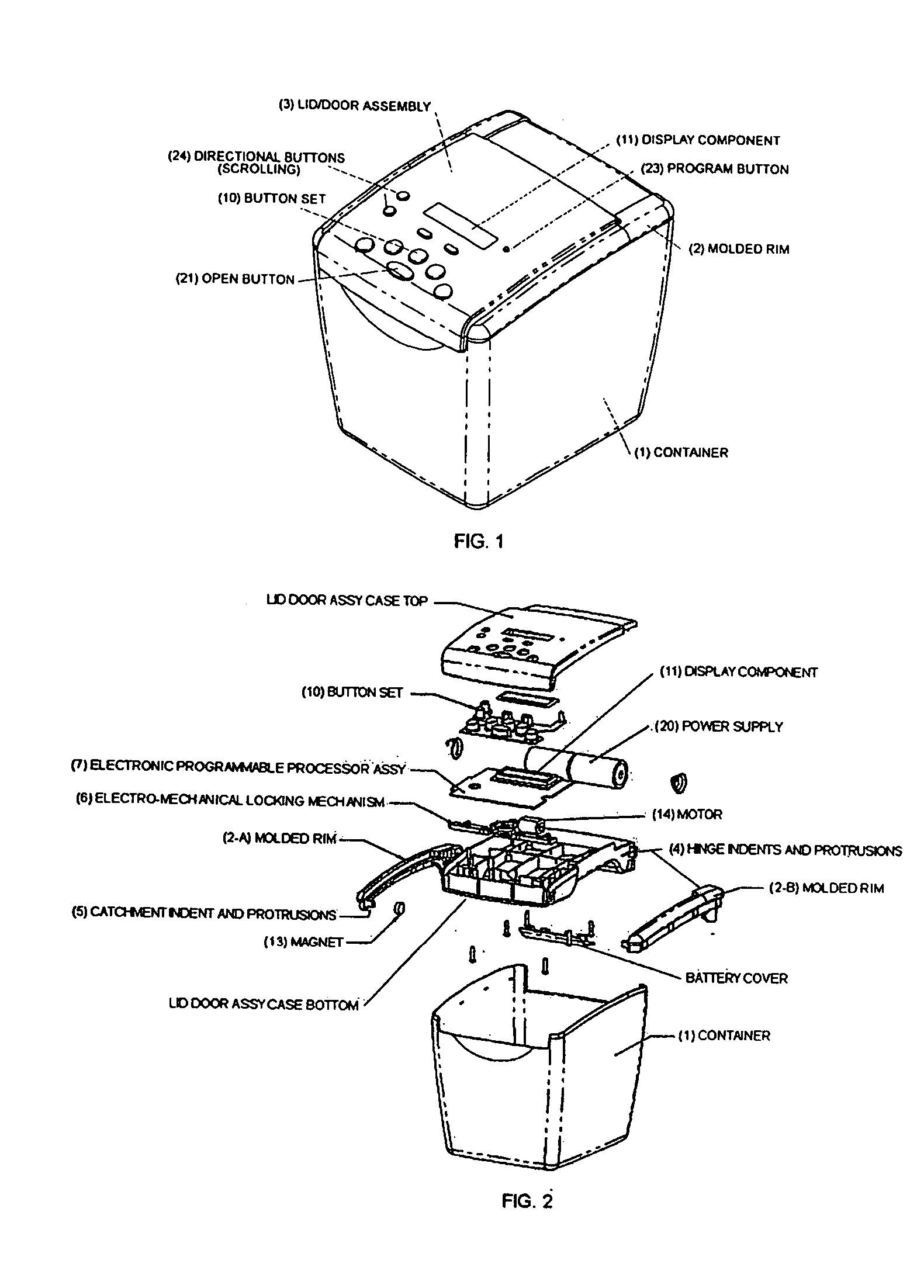
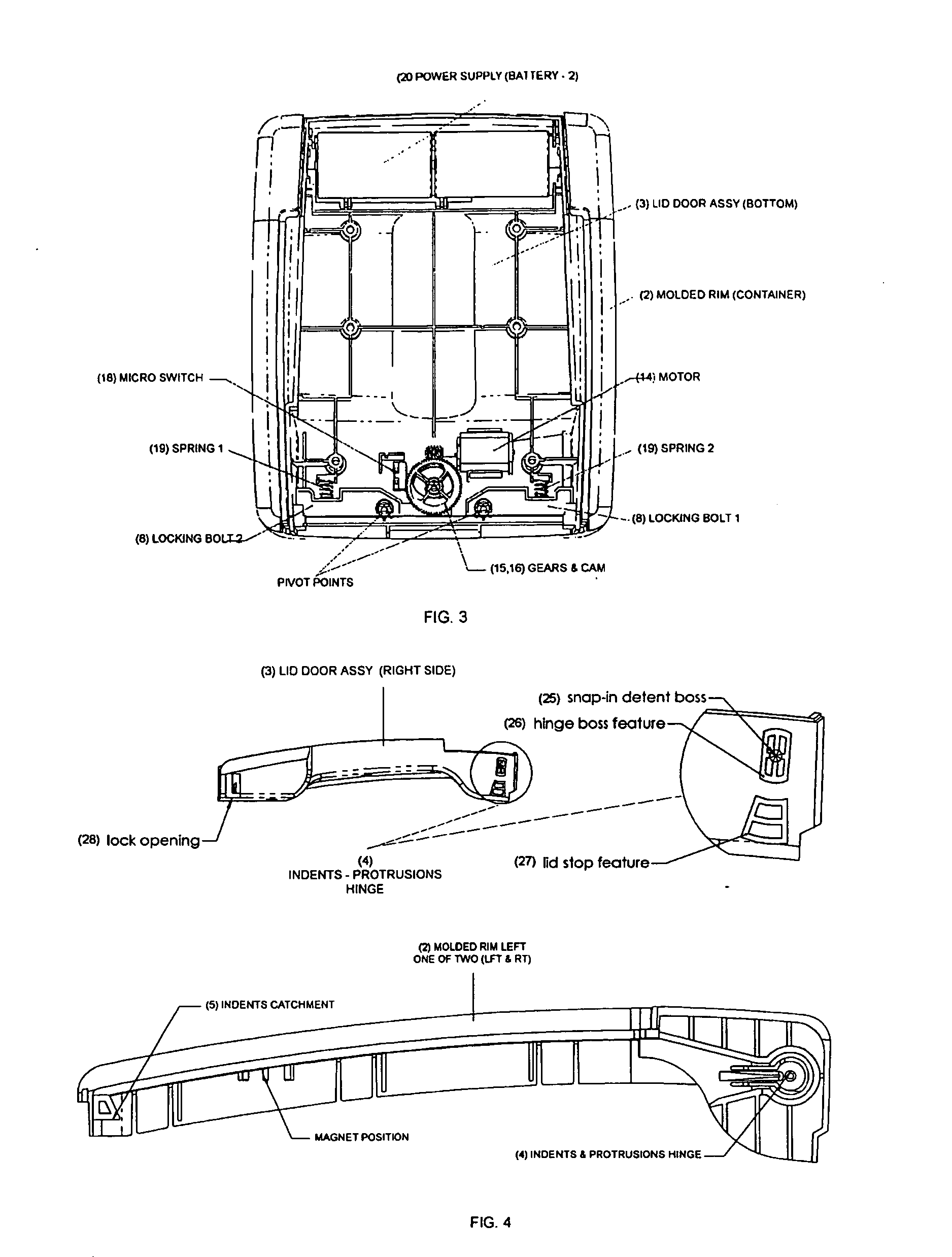
Programmable restricted access food storage container and behavior modification assistant
InactiveUS20050146419A1Reduce voltageGuaranteed to continue to useElectric signal transmission systemsMultiple keys/algorithms usageState of artLocking mechanism
A programmable food storage container and behavior modification assistant, having an automatically closing and locking lid / door, and a programmable lock mechanism able to accept and store multiple defined sequential periods of inaccessibility of variable duration and frequency, and multiple defined periods of accessibility of variable duration and frequency. Use of the device mandates compliance with, and reinforcement of behavior consistent with, the user's desire to develop and adhere to a pattern of controlled and limited consumption of any products stored within the container. Addressing the problem left unsolved in the prior art (i.e., the inability of some consumers to resist impulses to consume, and the finite and consumable capacity of people to resist temptation), the device eliminates temptations regarding its contents, and thus eliminates wasteful consumption of the consumer's finite supply of willpower, or capacity to successfully resist an impulse to consume.
Owner:PORTER MICHAEL
Systems and methods for secure sharing of information
ActiveUS20070113293A1Digital data processing detailsUser identity/authority verificationDigital signatureDistributed Computing Environment
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system. A method for providing secure restricted access to a digital asset includes: encrypting, by a first computing device, a digital asset; creating, by the first computing device, an executable file, the executable file comprising the encrypted digital asset, permission information associated with the digital asset, and executable code for decrypting and viewing the digital asset; creating, by the first computing device, a digital signature corresponding to the executable file; and transmitting, to a second computing device, the executable file and the digital signature. Corresponding systems and computer readable media with executable instructions are also described.
Owner:MICRO FOCUS LLC
Method and system for dynamically associating access rights with a resource
ActiveUS20080109912A1Digital data processing detailsUser identity/authority verificationClient-sideRestricted access
A method for dynamically associating, by a server, access rights with a resource includes the step of receiving, by the server, a request for a resource from a client. The server requests, from a policy engine, an identification of a plurality of access rights to associate with the resource, the plurality of access rights identified responsive to an application of a policy to the client. The server associates the resource with the plurality of access rights via a rights markup language. The server transmits the resource to the client with the identification of the associated plurality of access rights. An application program on the client makes an access control decision responsive to the associated plurality of access rights. The application program provides restricted access to the resource responsive to the access control decision.
Owner:CITRIX SYST INC
System and method of profitability analytics
InactiveUS20140172560A1Improve targetingMatched savings opportunity may improveDiscounts/incentivesFinanceFinancial transactionFinancial trading
Disclosed herein is a method to guide savings opportunities provided through a financial institution to their customers. The method comprising: analyzing financial transactions of customers to identify financial usage patterns, comparing usage patterns to available savings opportunities, reviewing available savings opportunities, identifying which savings opportunities are to be offered through the financial institution to customers and which are to have restricted access and enabling offered savings opportunities and restricted access savings opportunities for customers through the financial institution.
Owner:TRUAXIS
Method and System for Automatic Login Initiated Upon a Single Action with Encryption
InactiveUS20100211796A1Digital data processing detailsMultiple digital computer combinationsGraphicsWeb site
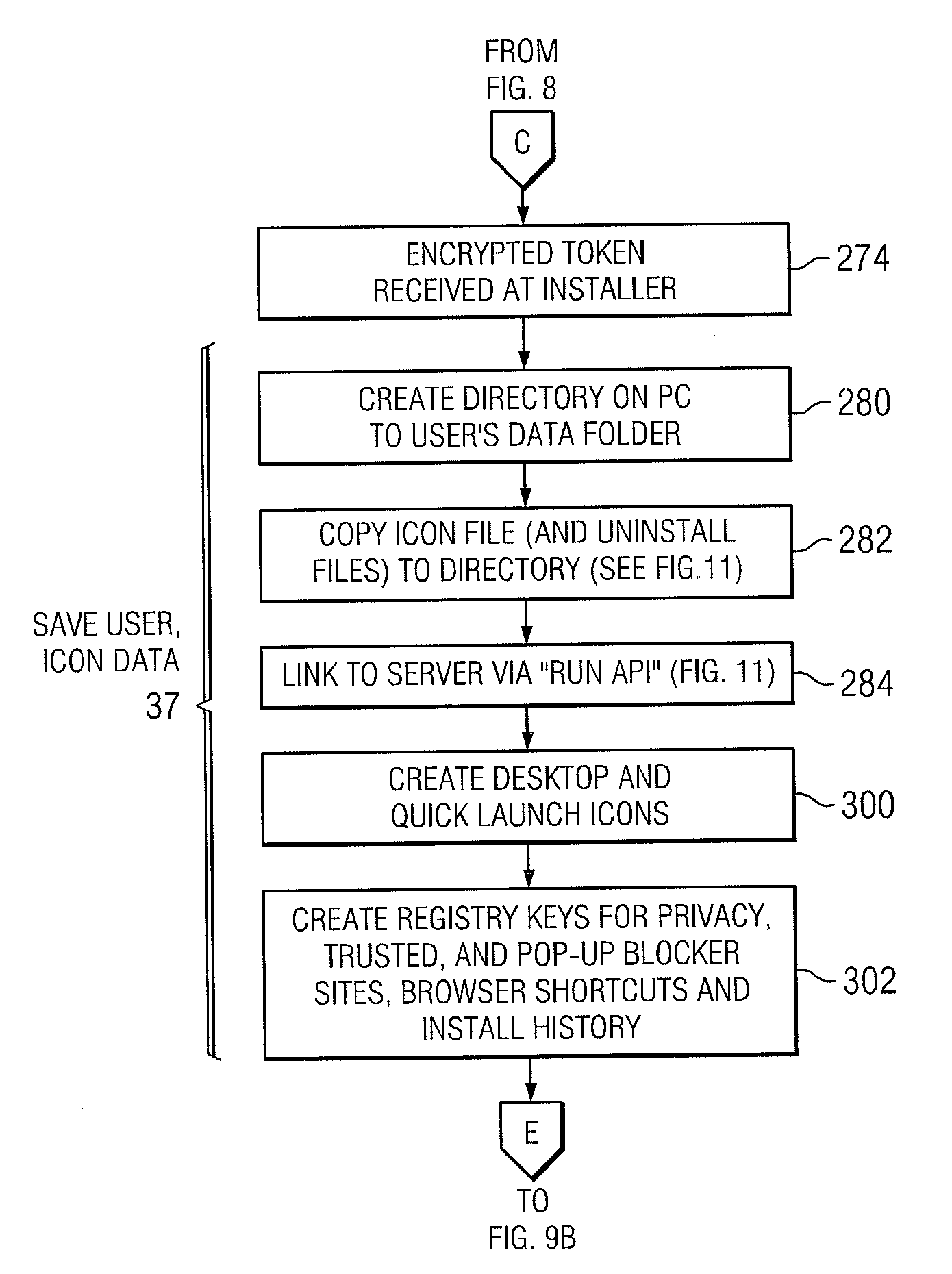
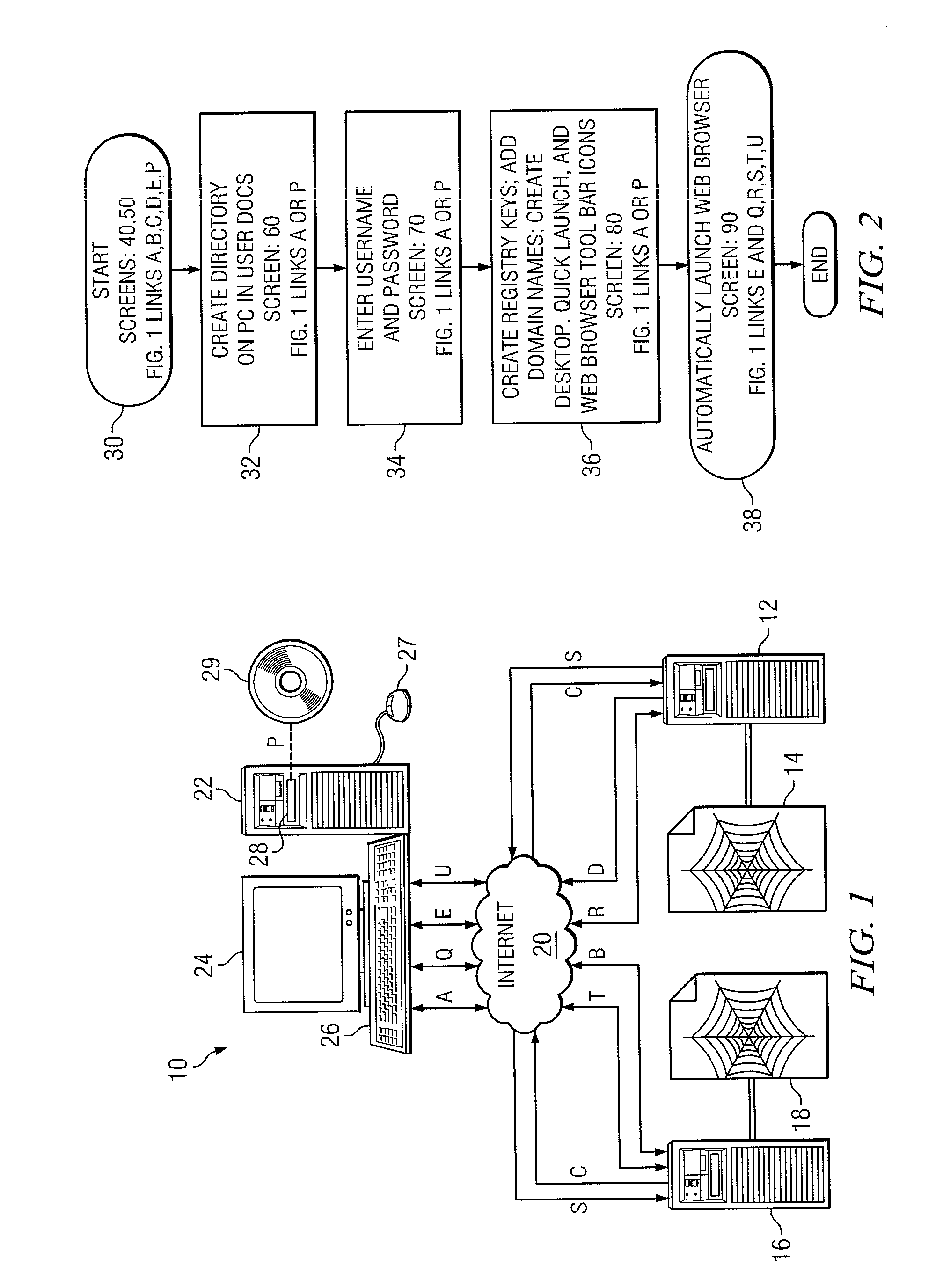
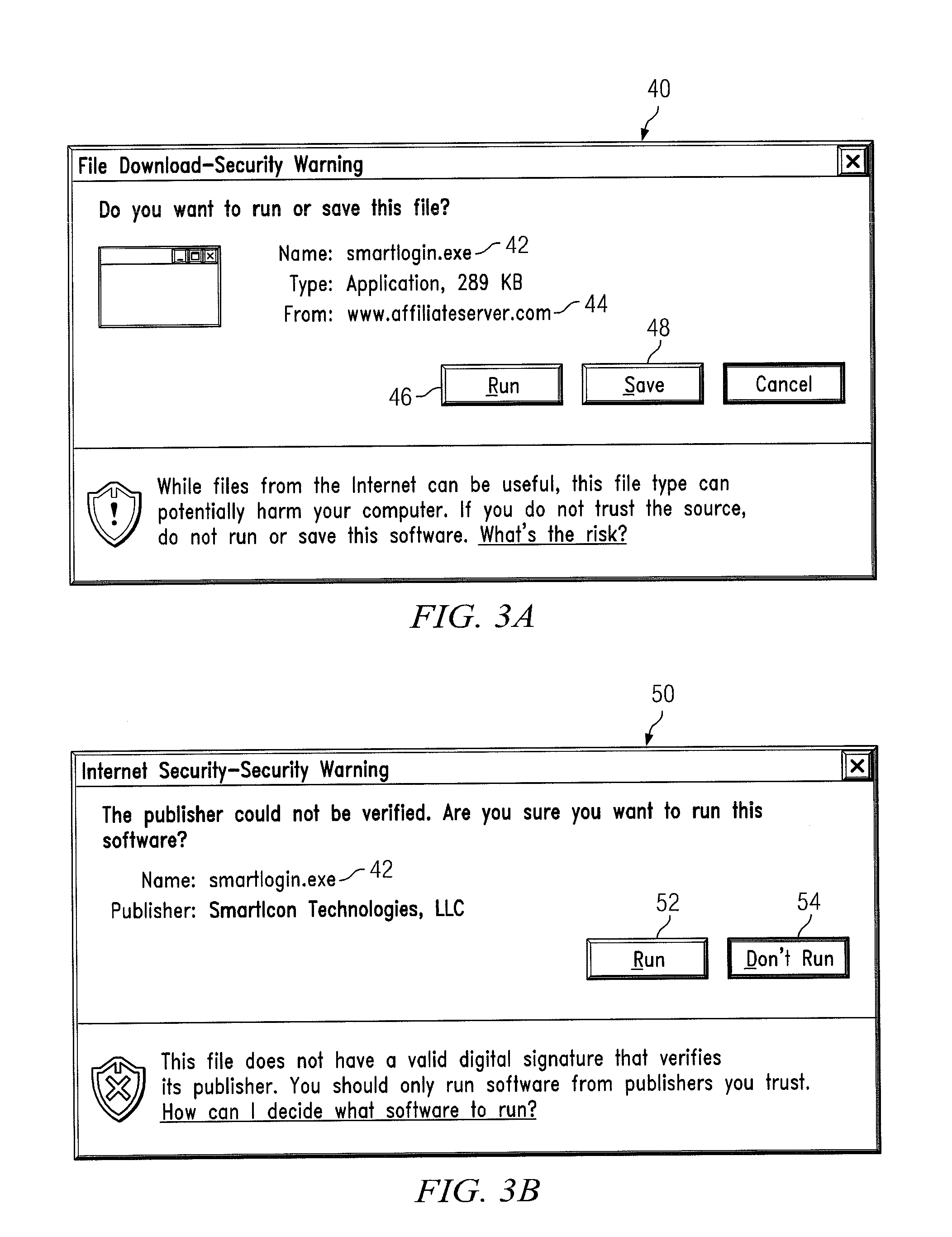
A method and system for secure automatic user login to a destination website in a single action, without the use of a file manager, cookies, or without storing user login information in a data folder having restricted access or that is external to the user PC. A user computer having a display, a mouse, and a browser is activated for establishing an Internet connection. The connection may be established from the user computer to the destination website with a single mouse click or a single touch on a displayed vendor icon or other symbol placed on a displayed graphic of the user PC display such as the desktop, task bar, or tool bar during a prior setup process. During the setup, an encrypted token is produced encrypting the user credential information. The encrypted token may be stored in the user data folder.
Owner:SMARTICON TECH
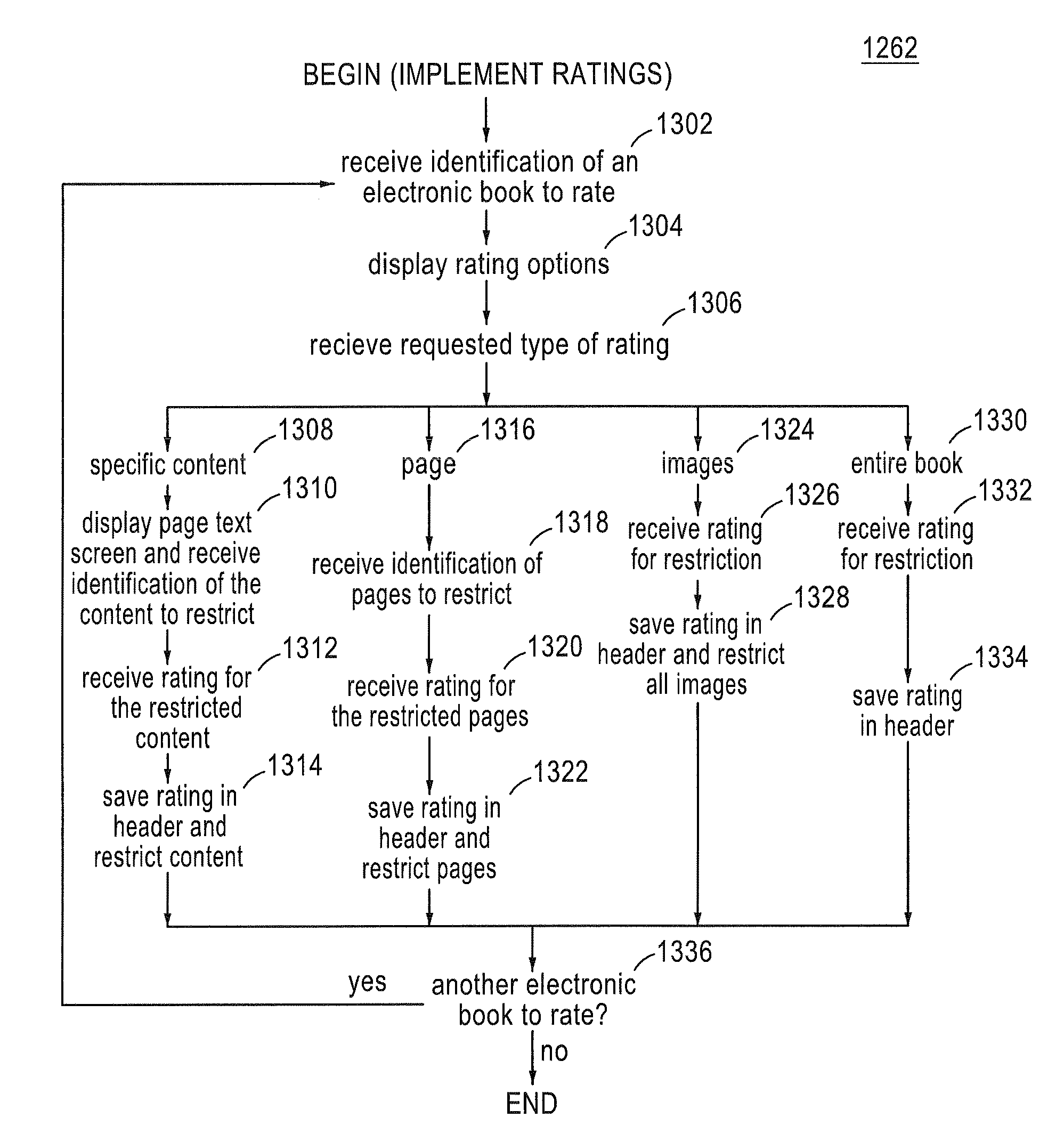
Electronic book with restricted access features
InactiveUS8095949B1Teaching processLimited accessTelevision system detailsDigital data processing detailsElectronic bookRestricted access
Owner:ADREA LLC
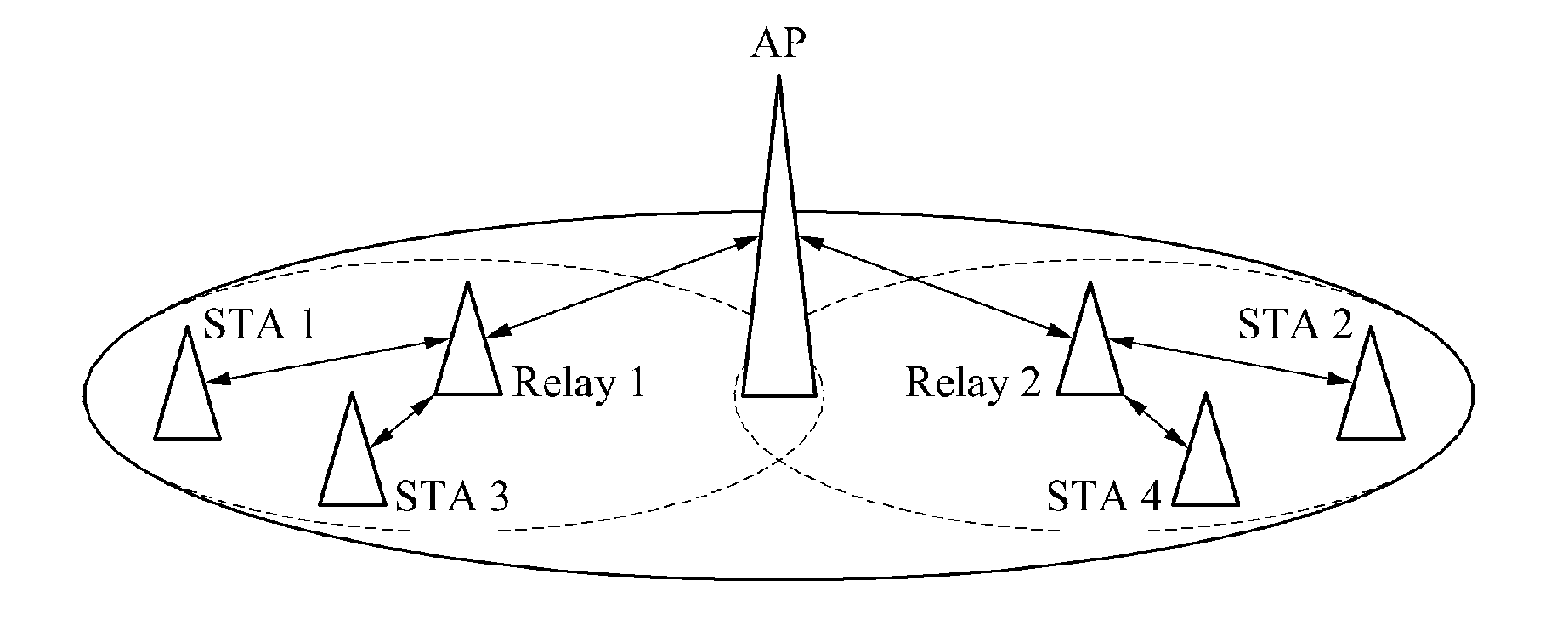
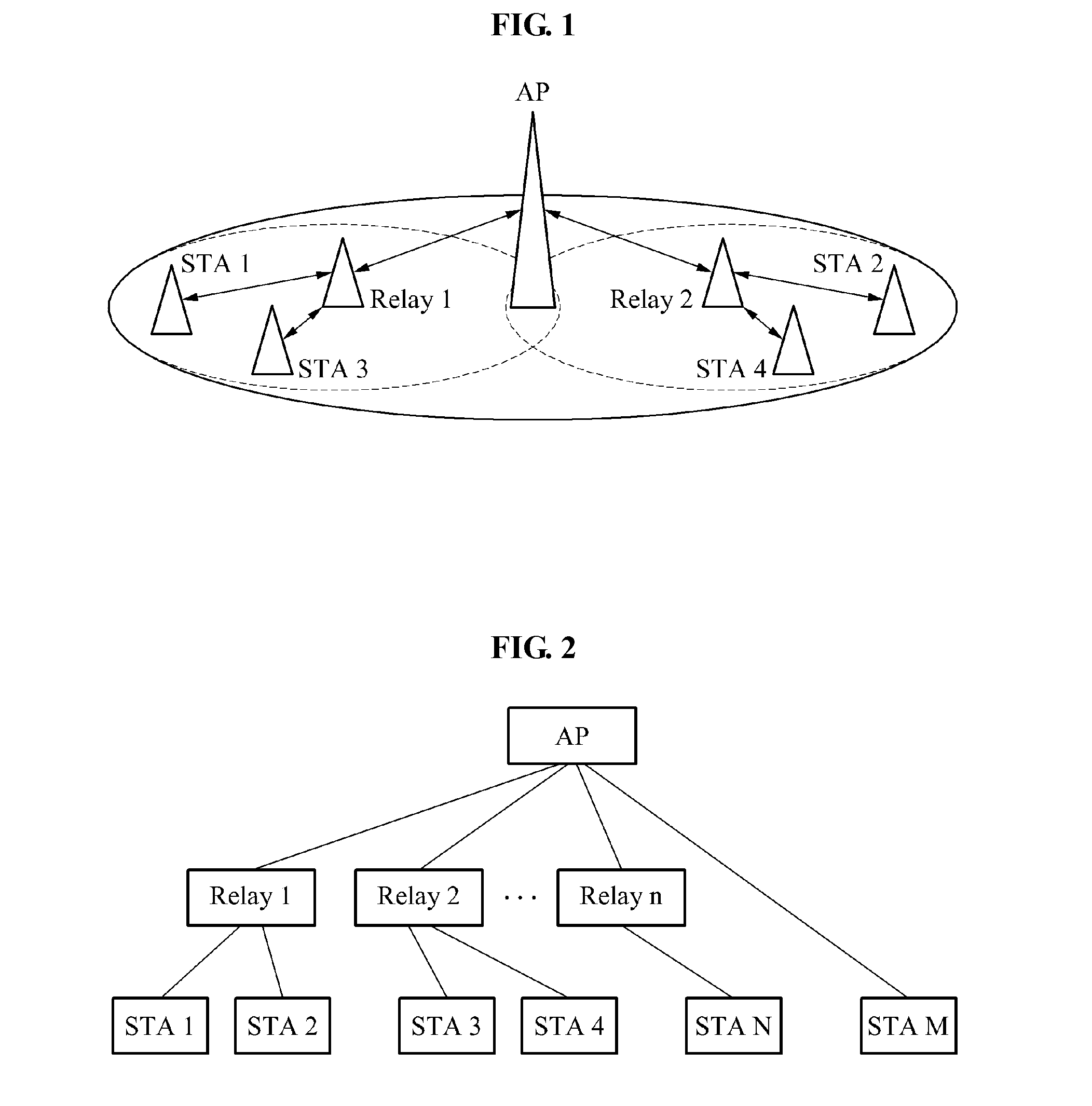
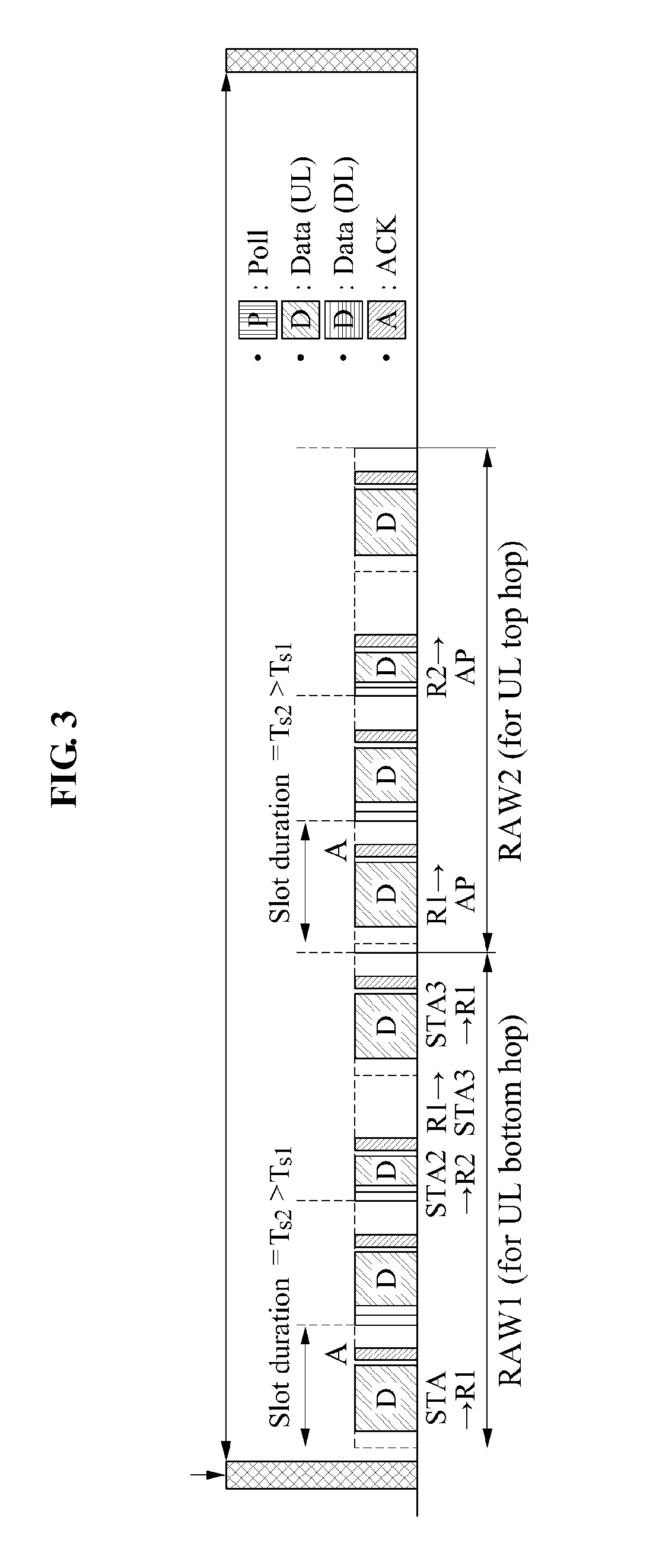
Method for allocating resources in wireless LAN system and wireless LAN system
Provided are a method of allocating resources in a wireless local area network (WLAN) system and the WLAN system including an access point (AP) to allocate a resource for communication between a relay and a station associated with the relay, the relay to allocate a restricted access window (RAW) or a slot for communication with a station based on the allocated resource, and the station to communicate with the relay based on the allocated RAW or the allocated slot.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com