Patents
Literature
313 results about "File manager" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
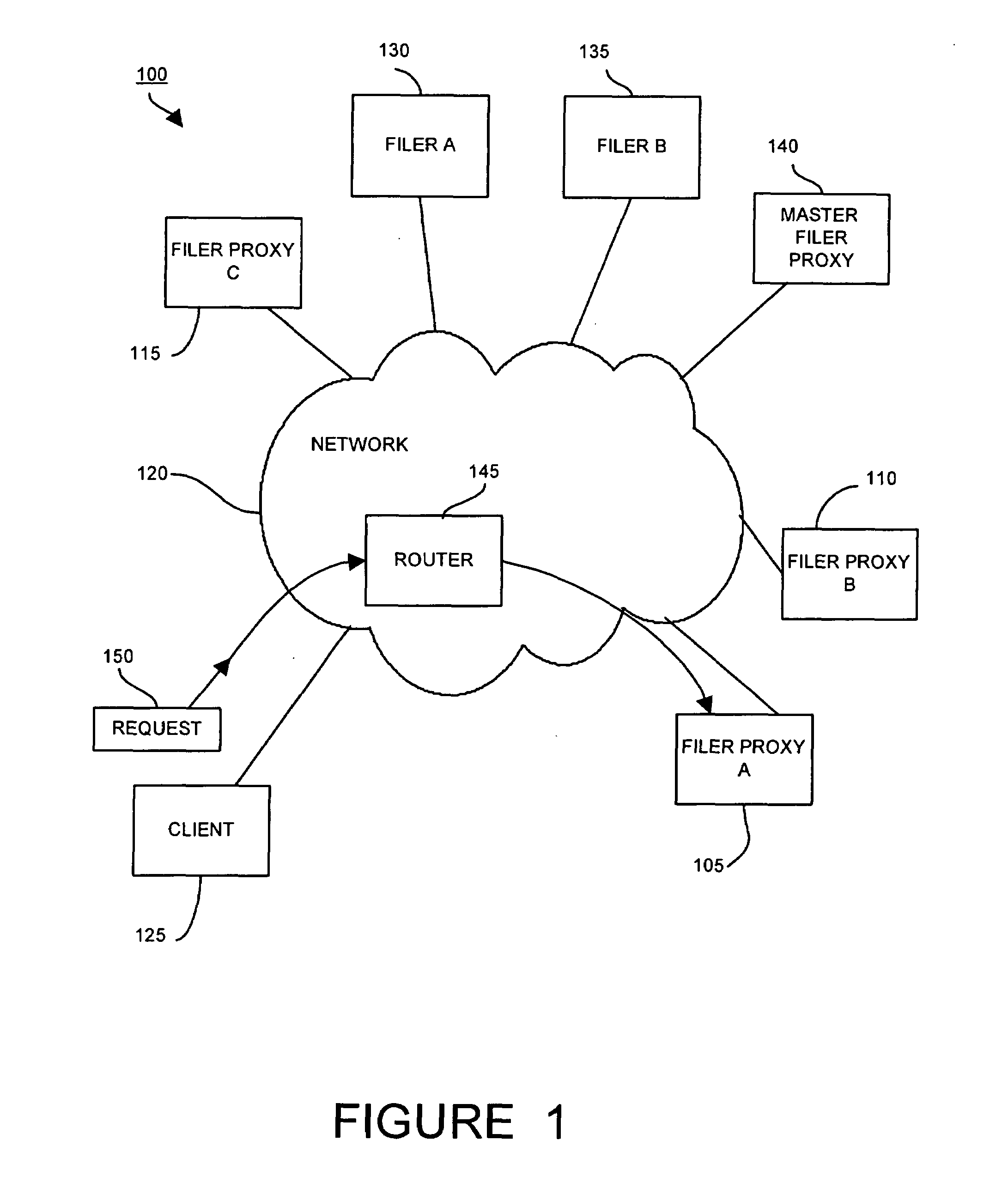
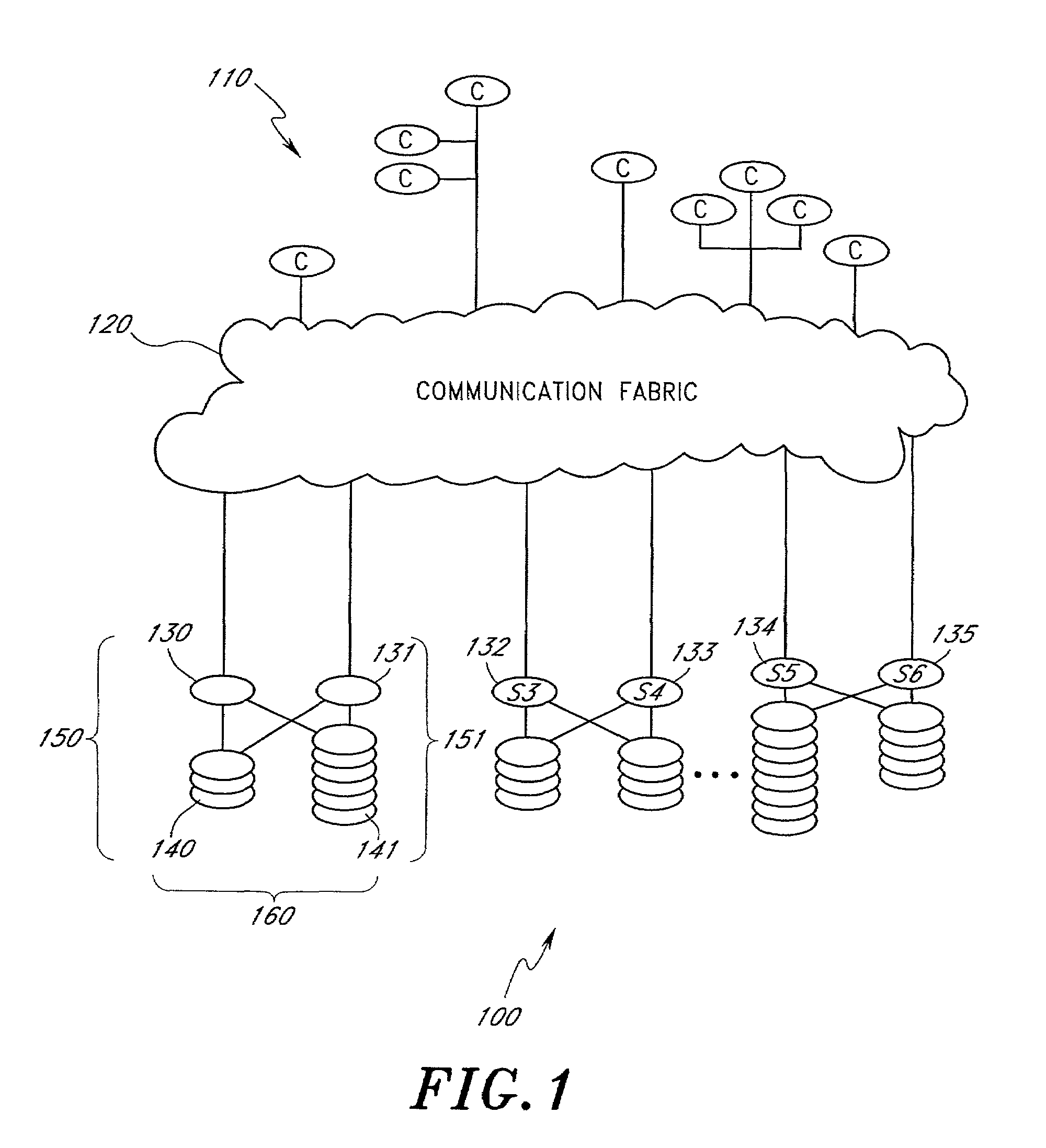
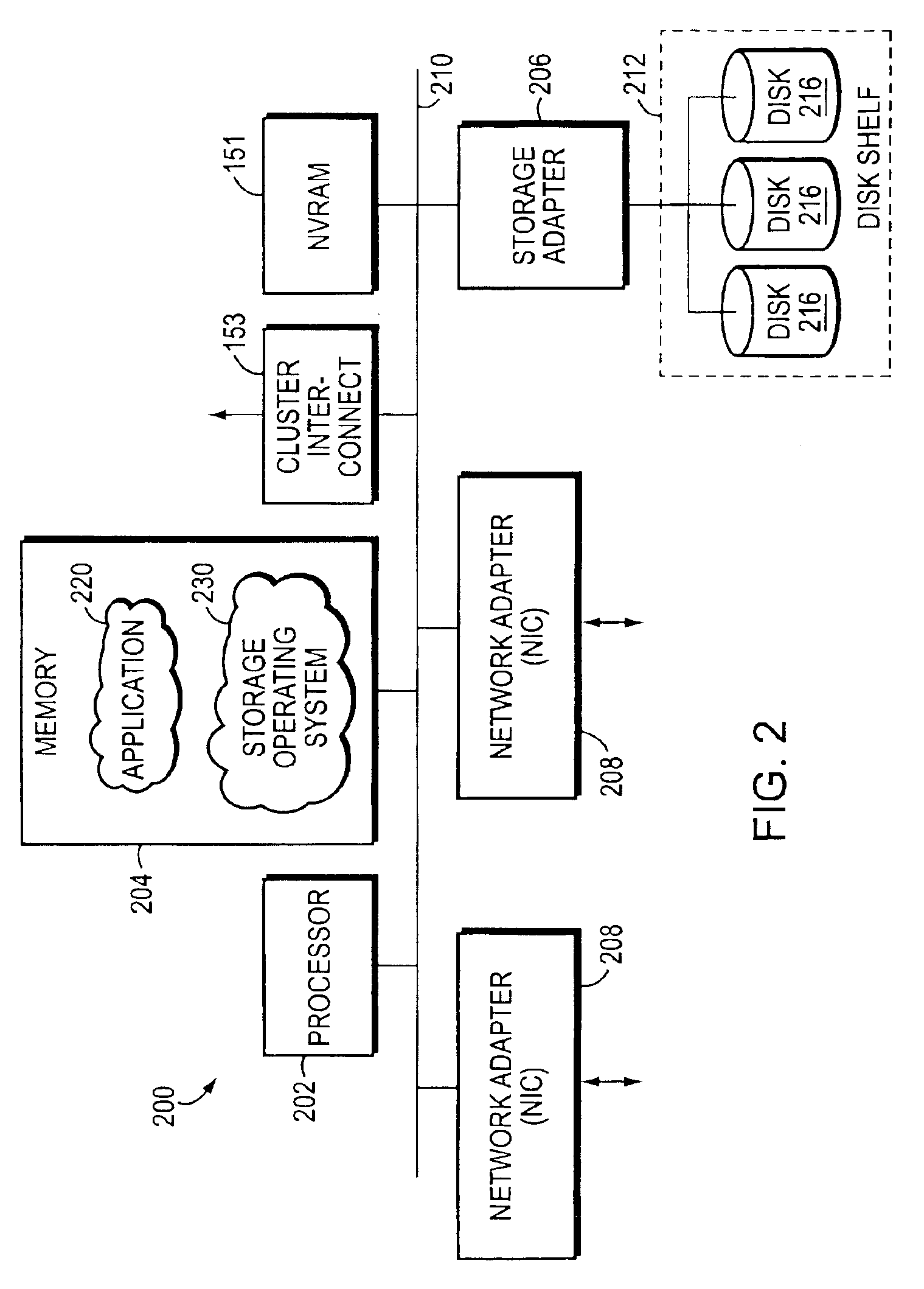
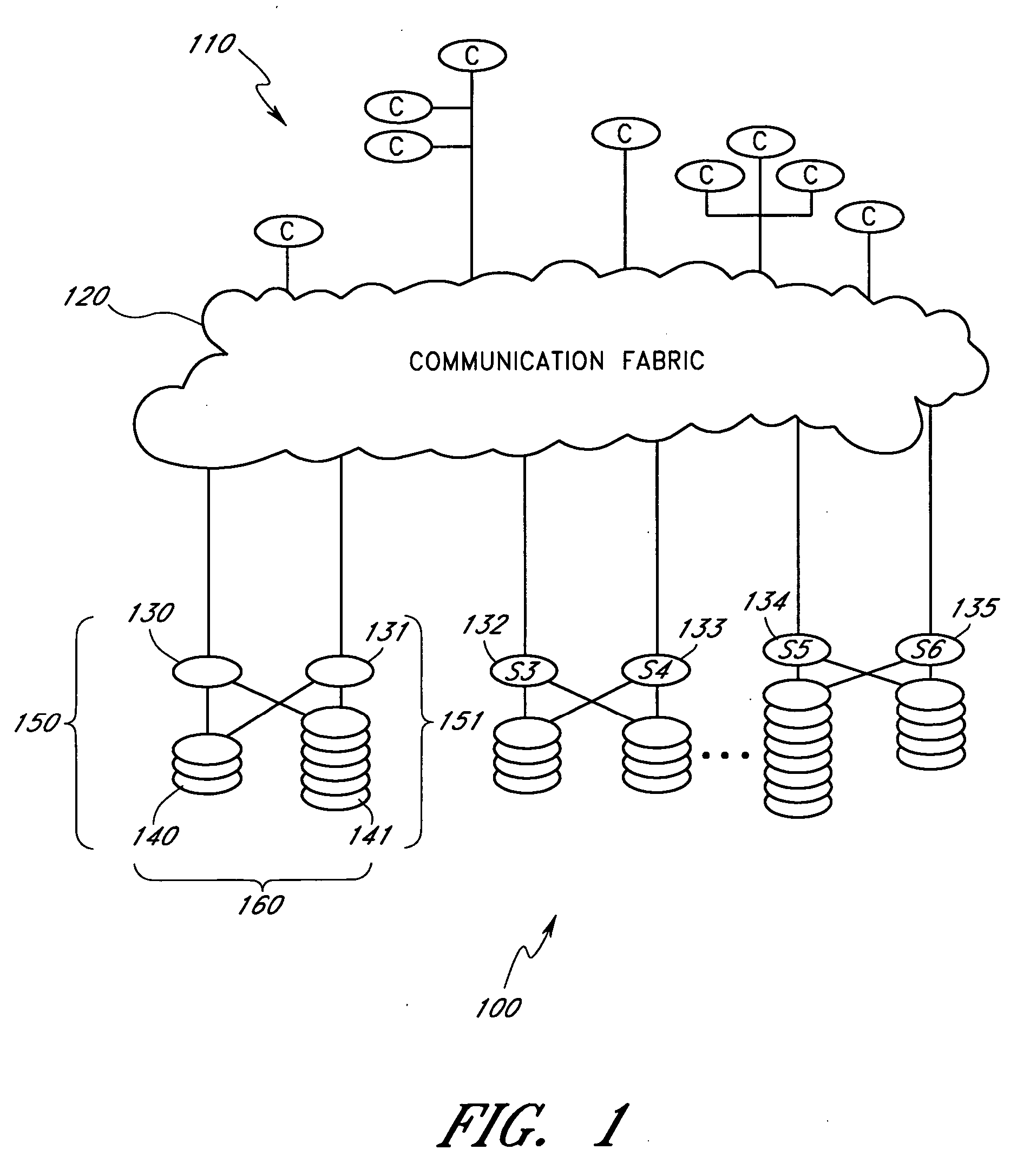
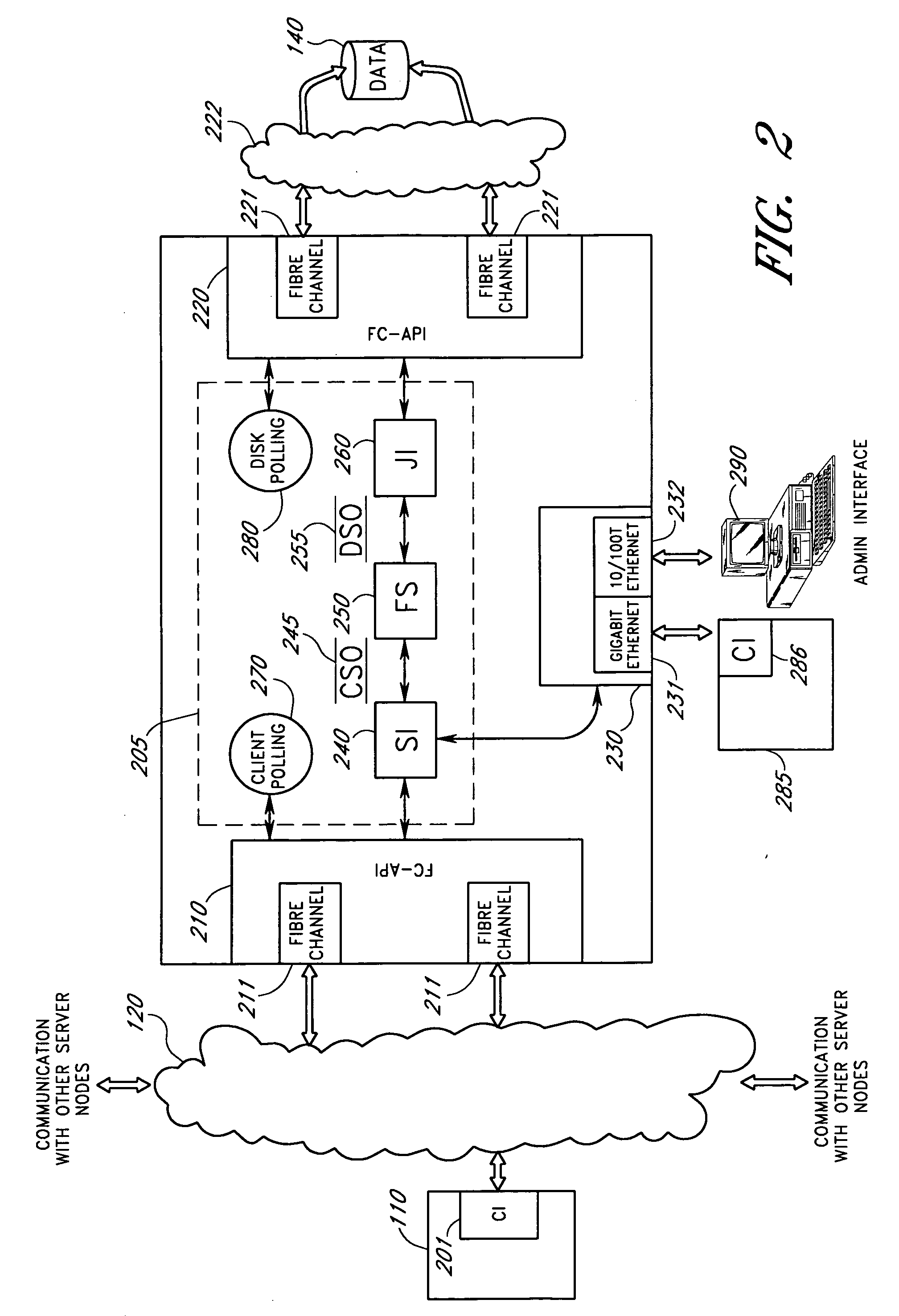
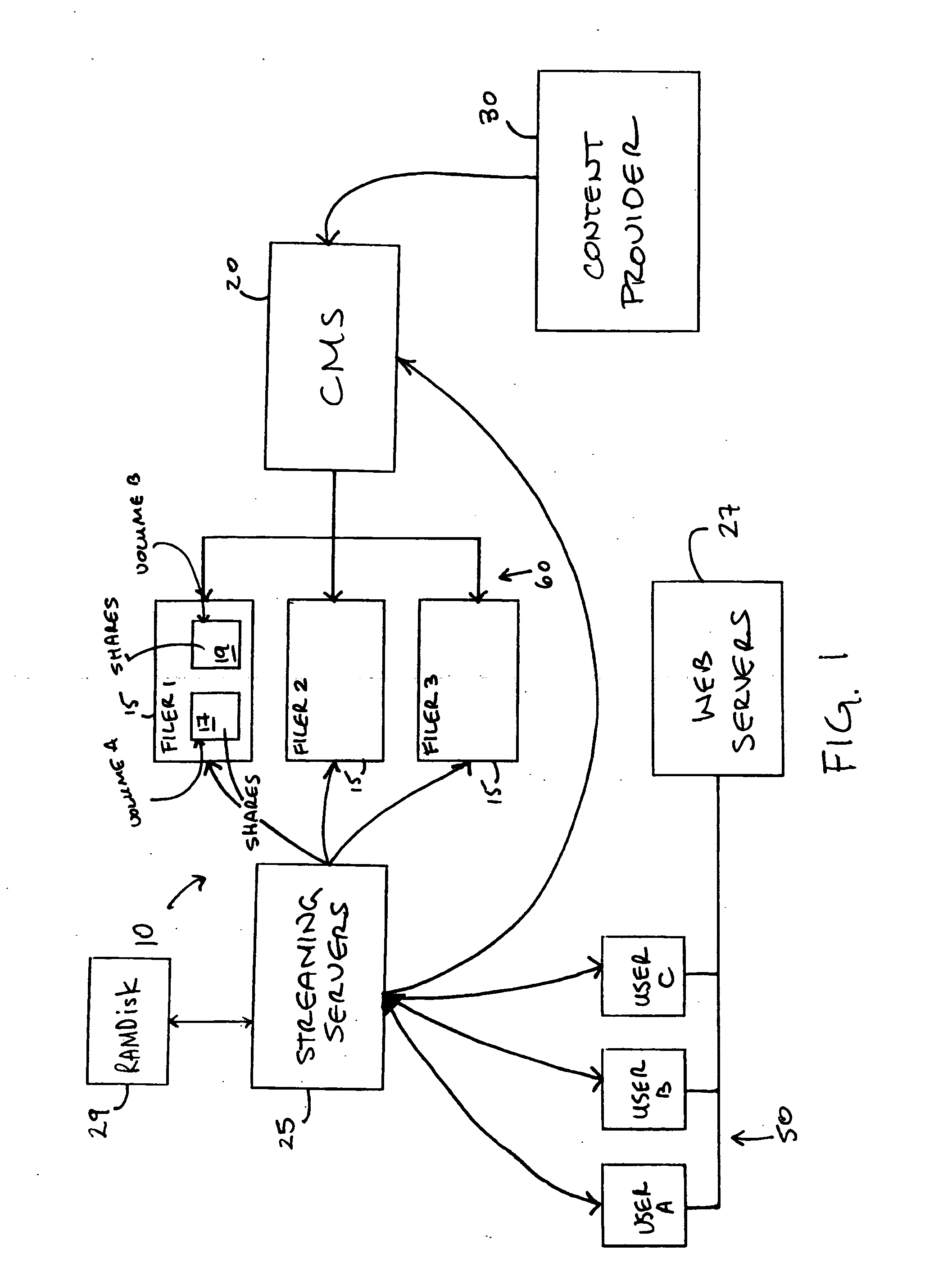
Method and apparatus for transparent distributed network-attached storage with web cache communication protocol/anycast and file handle redundancy
ActiveUS7254636B1Data processing applicationsDigital data processing detailsContent distributionNetwork connection
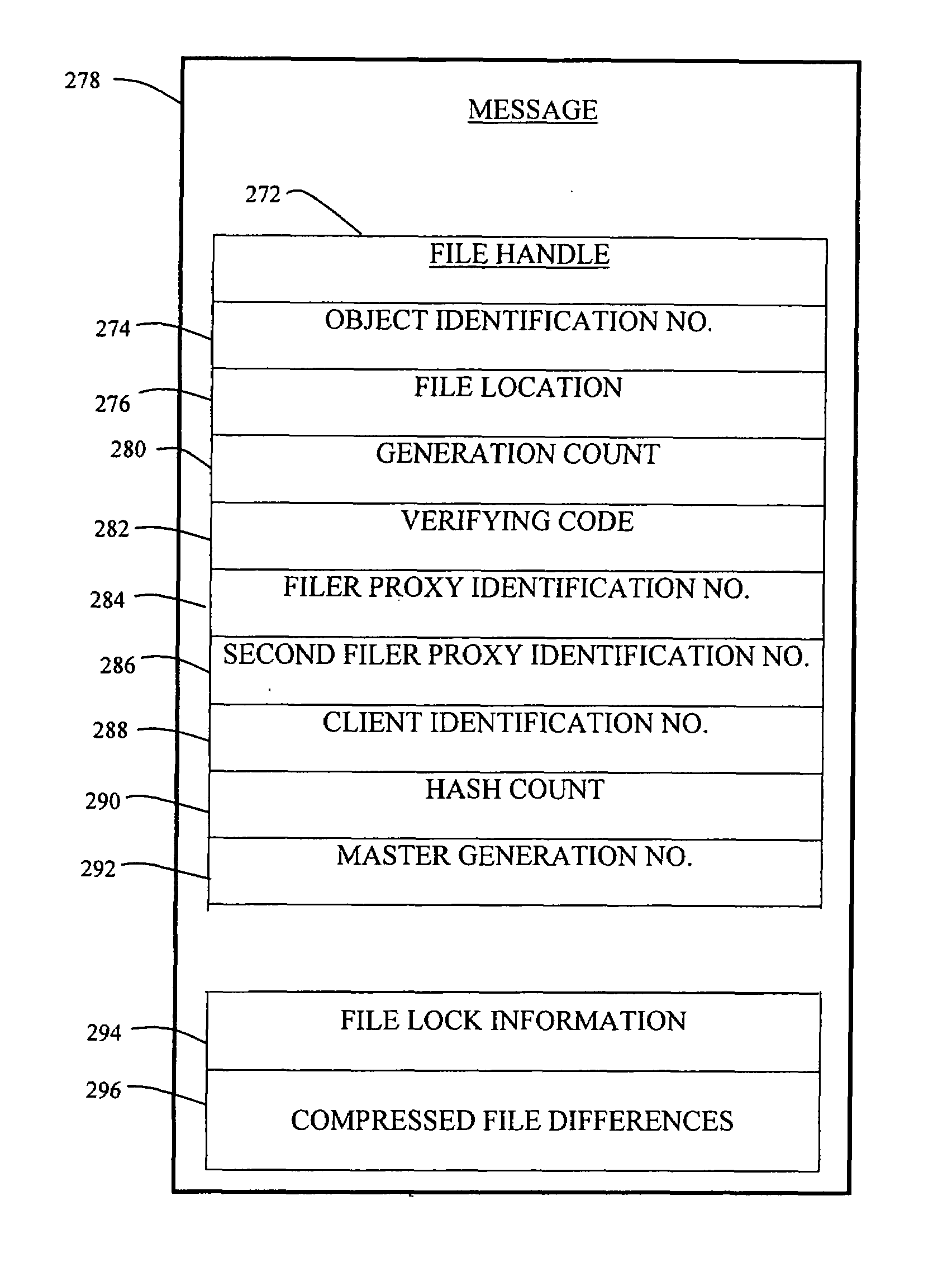
A distributed network-attached storage network provides content distribution using conventional file transfer protocols such as NFS and CIFS. A filer proxy accepts a client request and translates the client request to a file transfer protocol accepted at the file system having the file requested in the client request. The filer proxy generates a file handle for the file containing redundant filer proxy information to be used for failover to a backup filer proxy in the event of a network error or failure of an original filer proxy. The file handle also contains information for network security purposes such as detection of forged file handles.
Owner:CISCO TECH INC
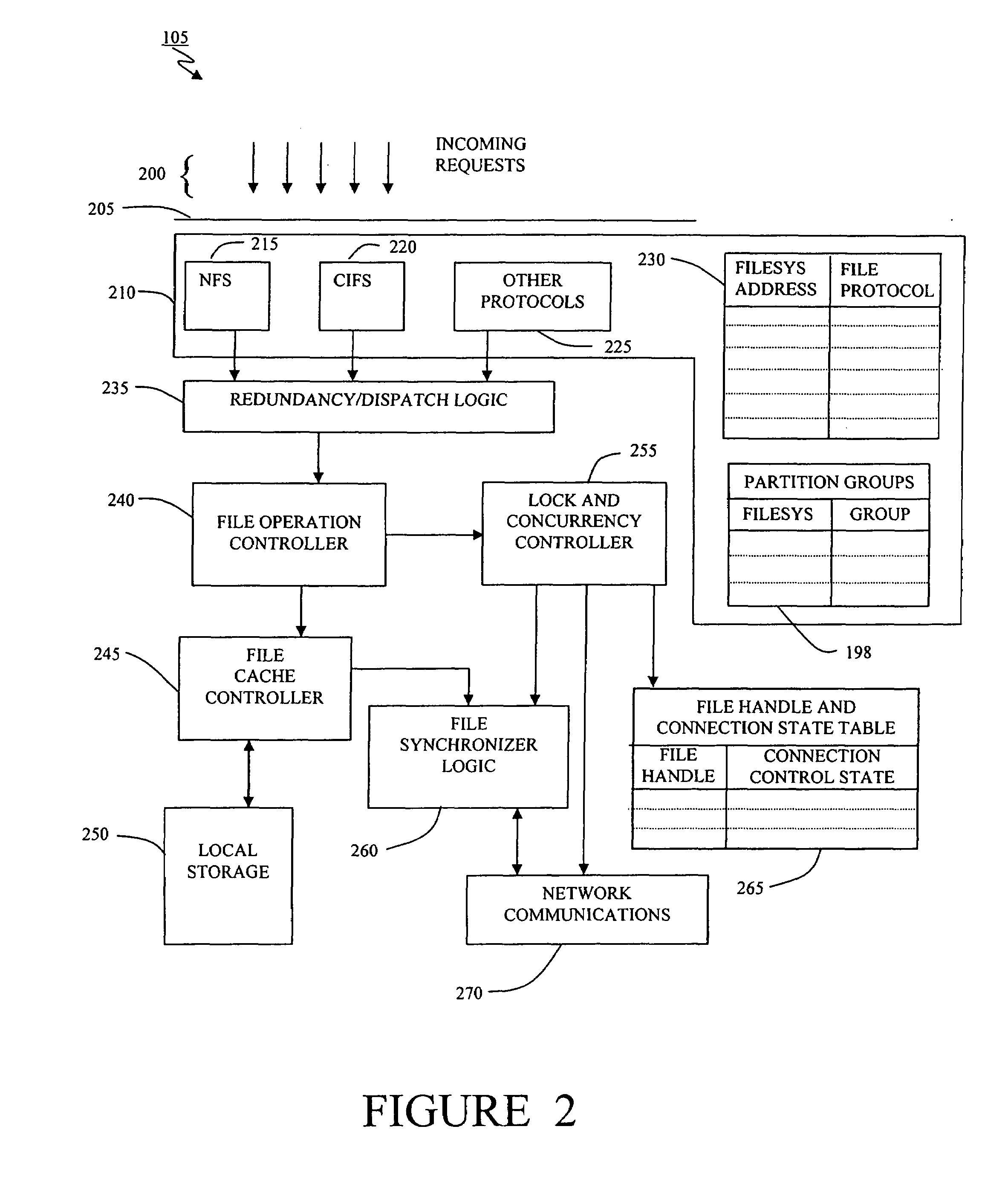
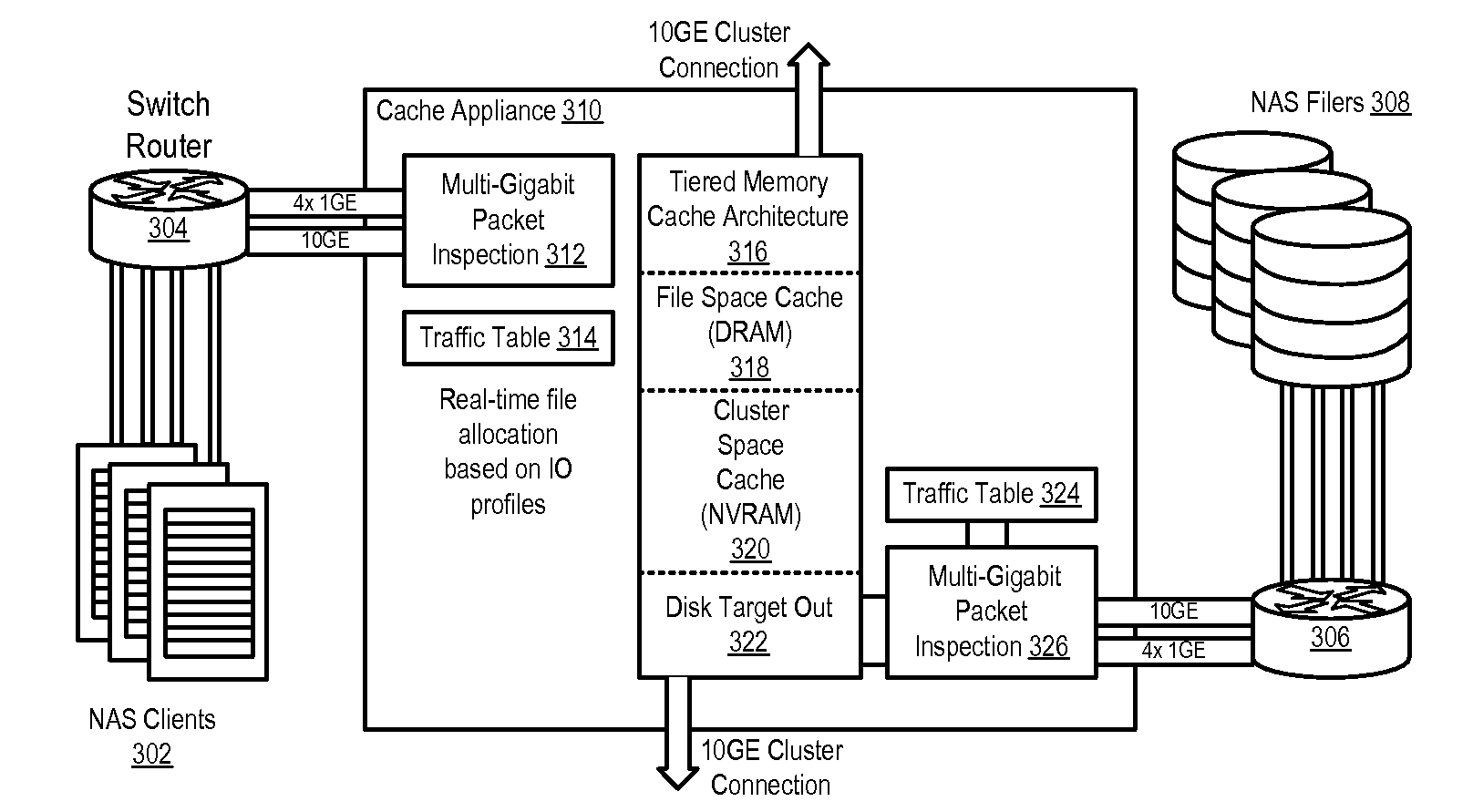
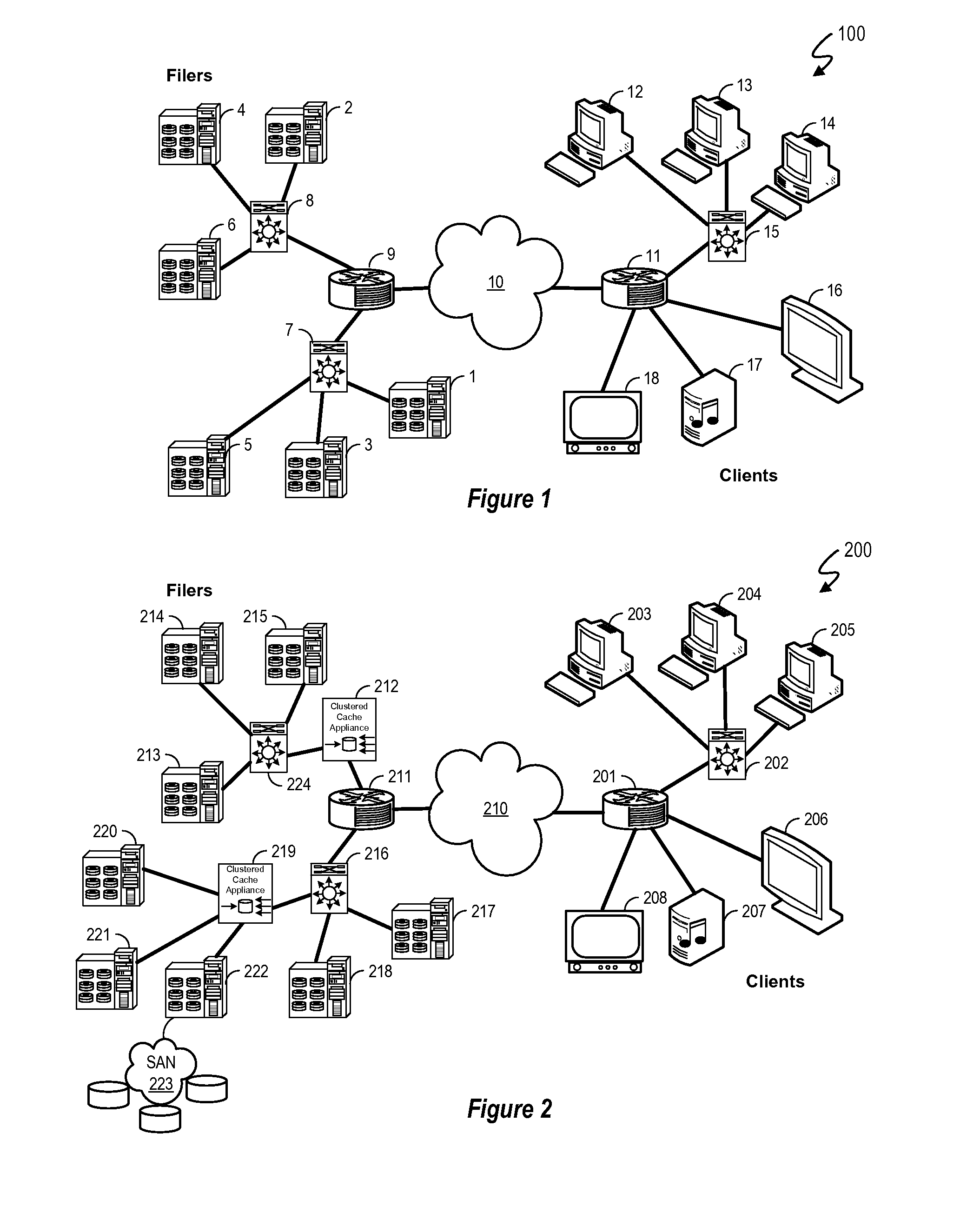
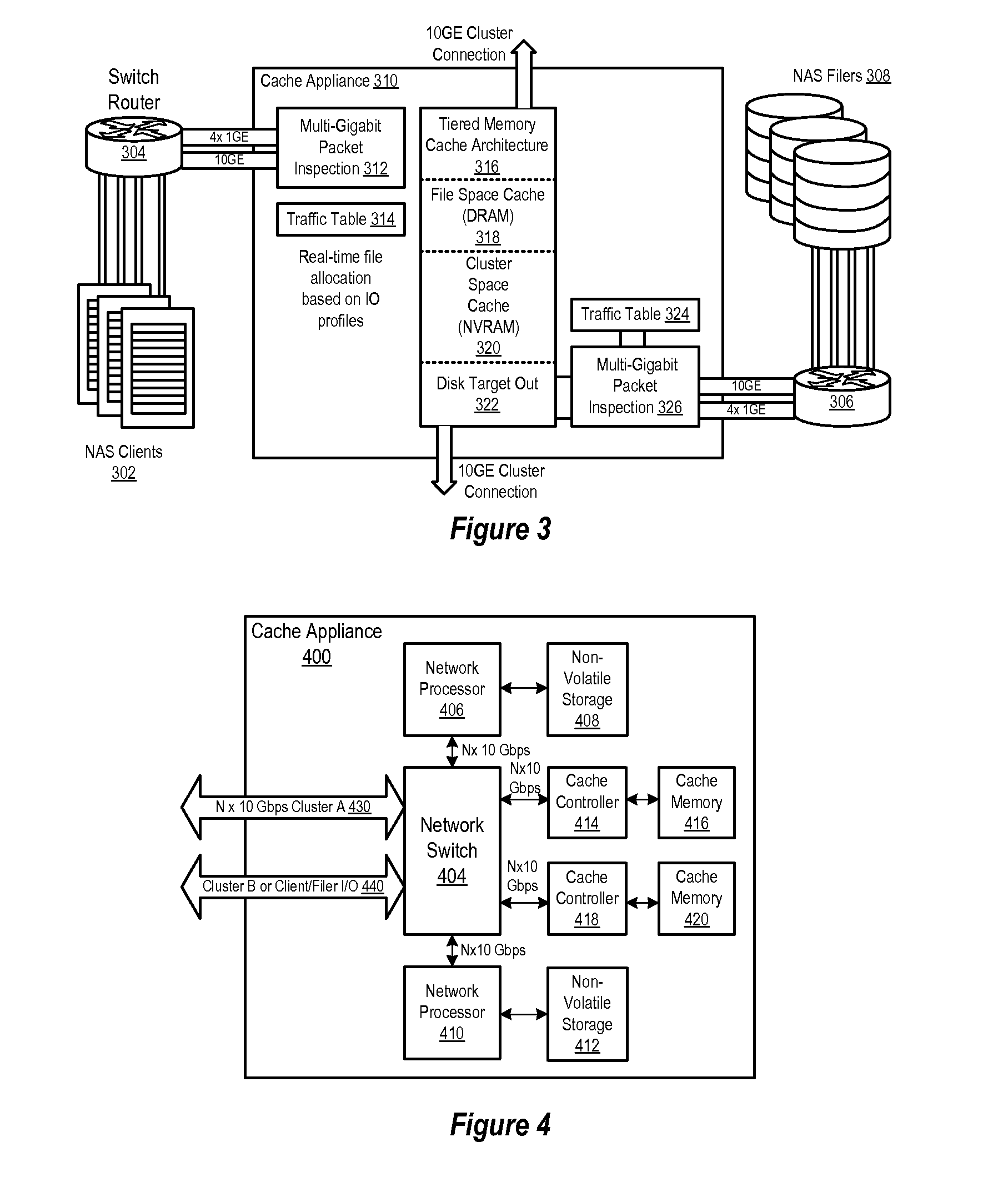
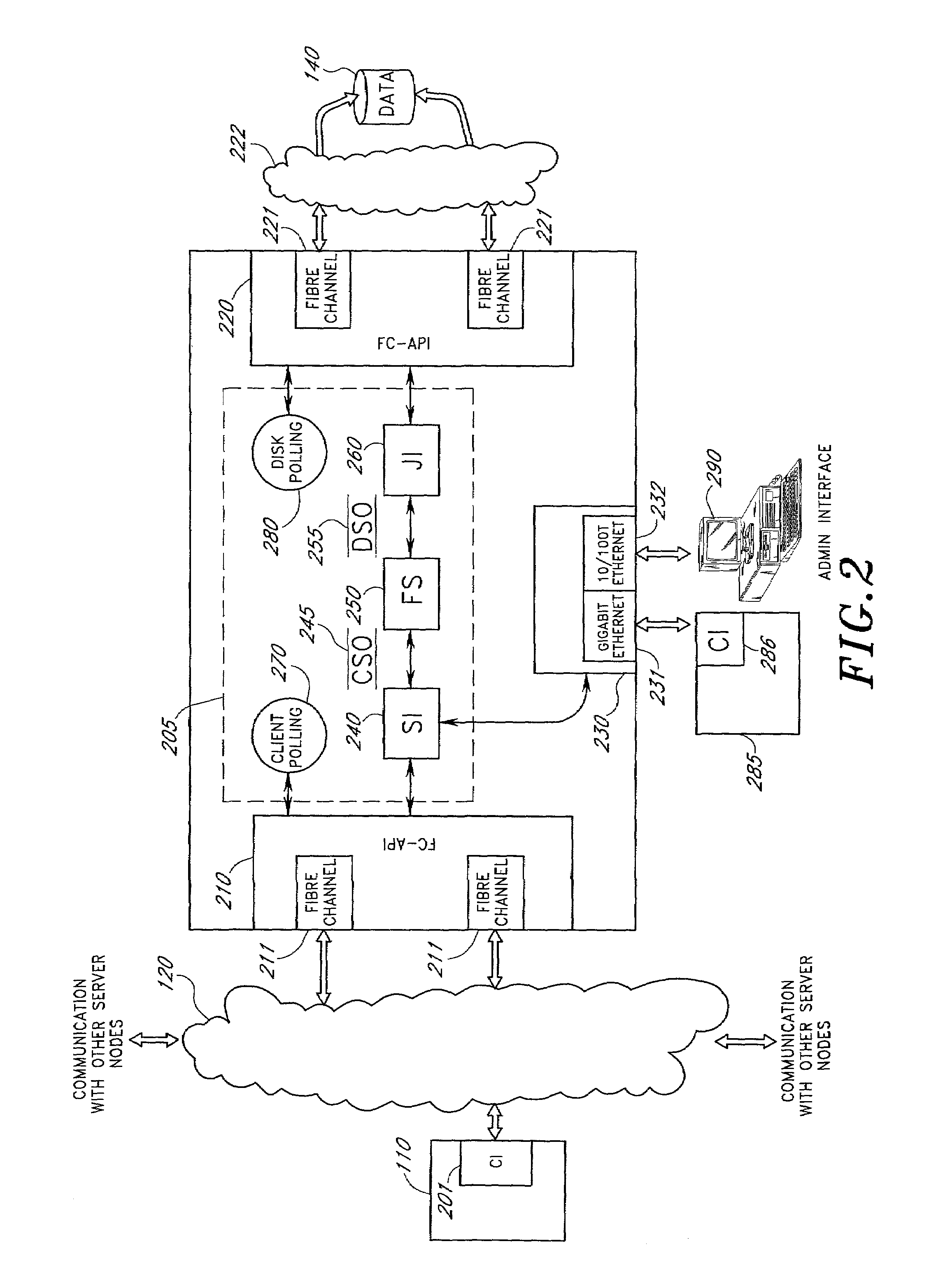
Clustered cache appliance system and methodology
ActiveUS20090182945A1Memory adressing/allocation/relocationTransmissionAccess timeLatency (engineering)
A method, system and program are disclosed for accelerating data storage by providing non-disruptive storage caching using clustered cache appliances with packet inspection intelligence. A cache appliance cluster that transparently monitors NFS and CIFS traffic between clients and NAS subsystems and caches files using dynamically adjustable cache policies provides low-latency access and redundancy in responding to both read and write requests for cached files, thereby improving access time to the data stored on the disk-based NAS filer (group).
Owner:NETWORK APPLIANCE INC
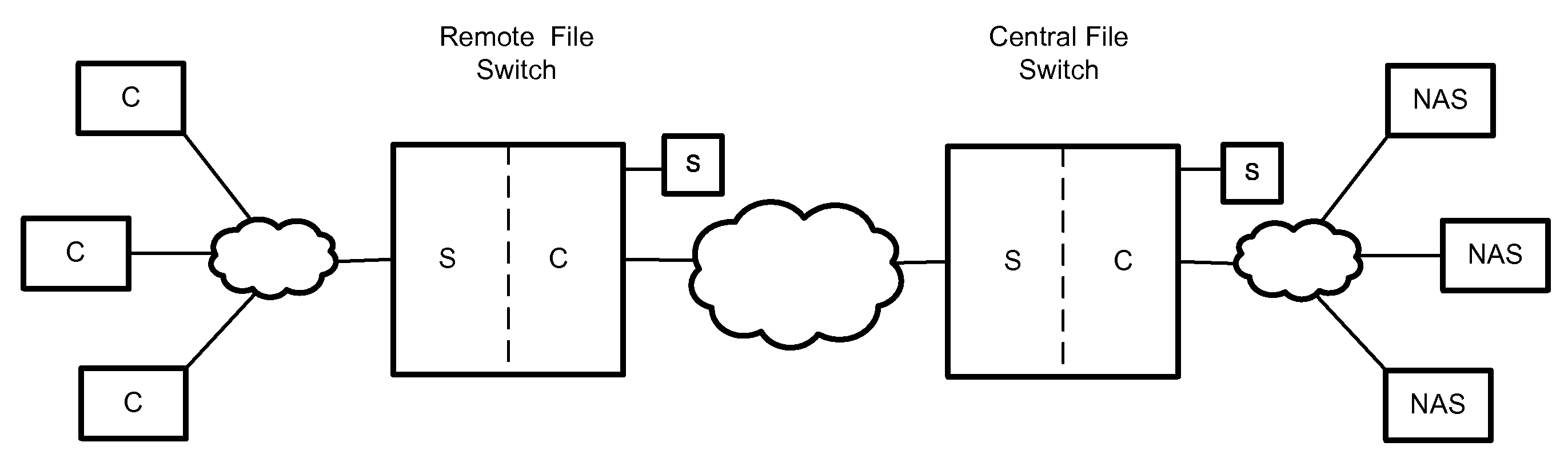
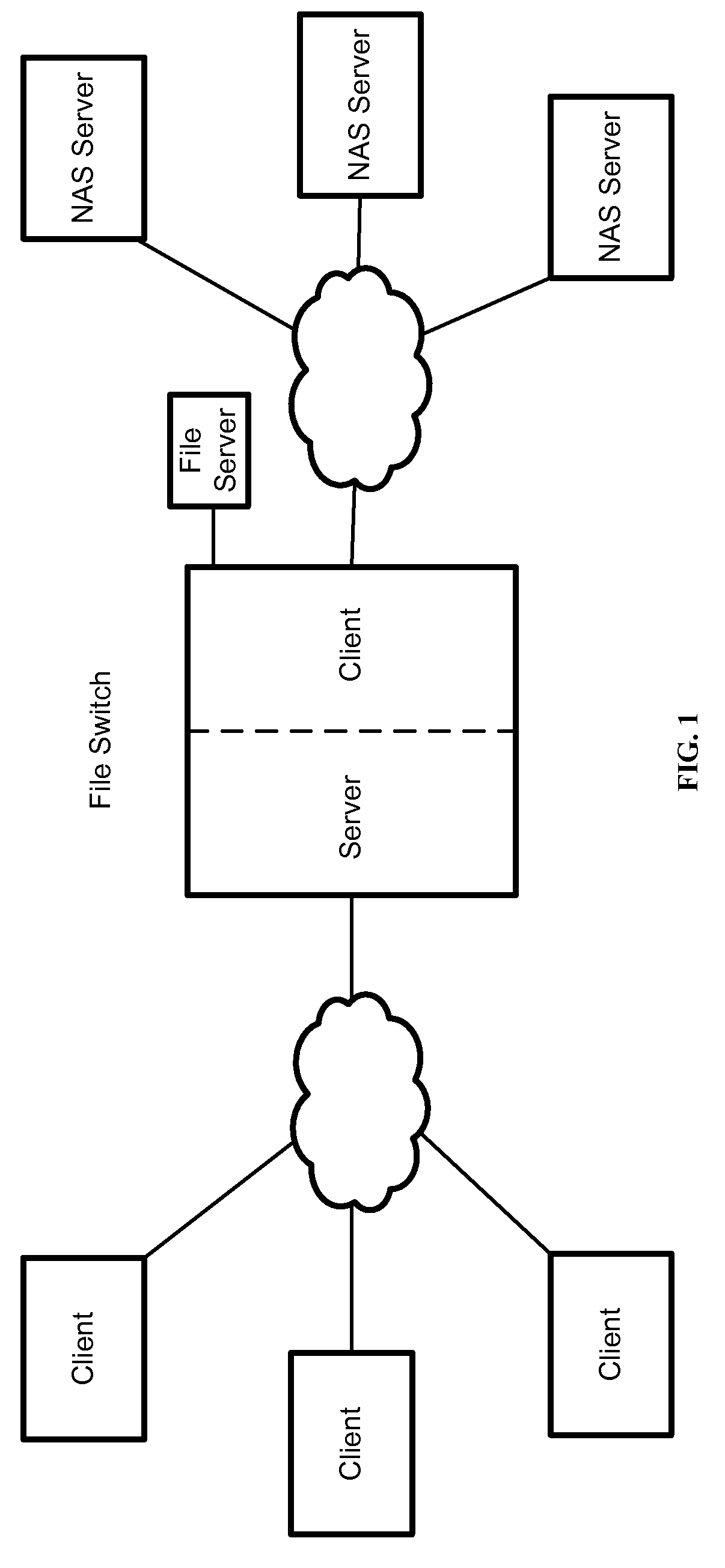
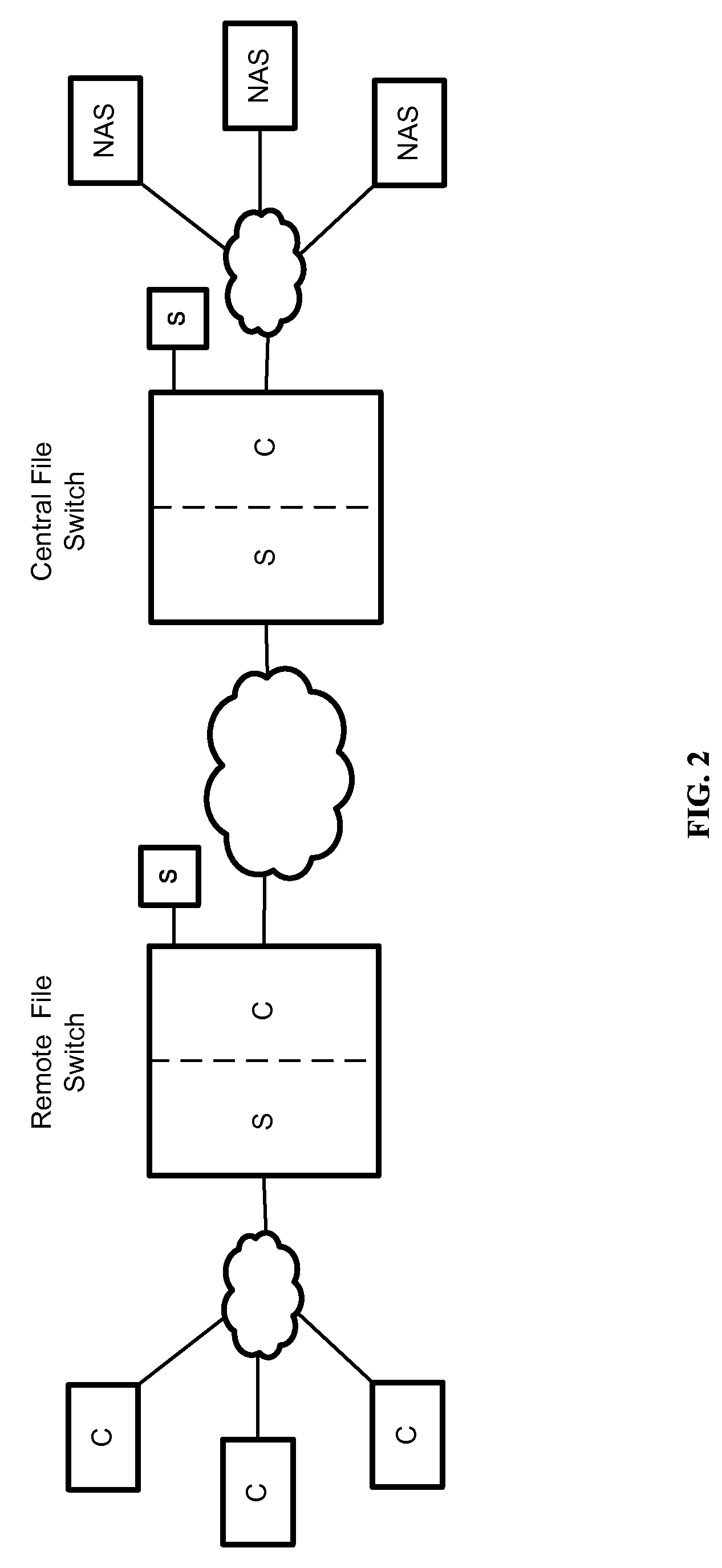
Remote File Virtualization in a Switched File System
A plurality of network file manager switches interoperate to provide remote file virtualization. Copies of file data and / or metadata are maintained at a central site and at one or more remote sites. The network file manager switch at the remote site may satisfy certain client requests locally without having to contact the network file manager switch at the central site. A global namespace is maintained and is communicated to all network file manager switches.
Owner:RPX CORP
Hierarchal data management
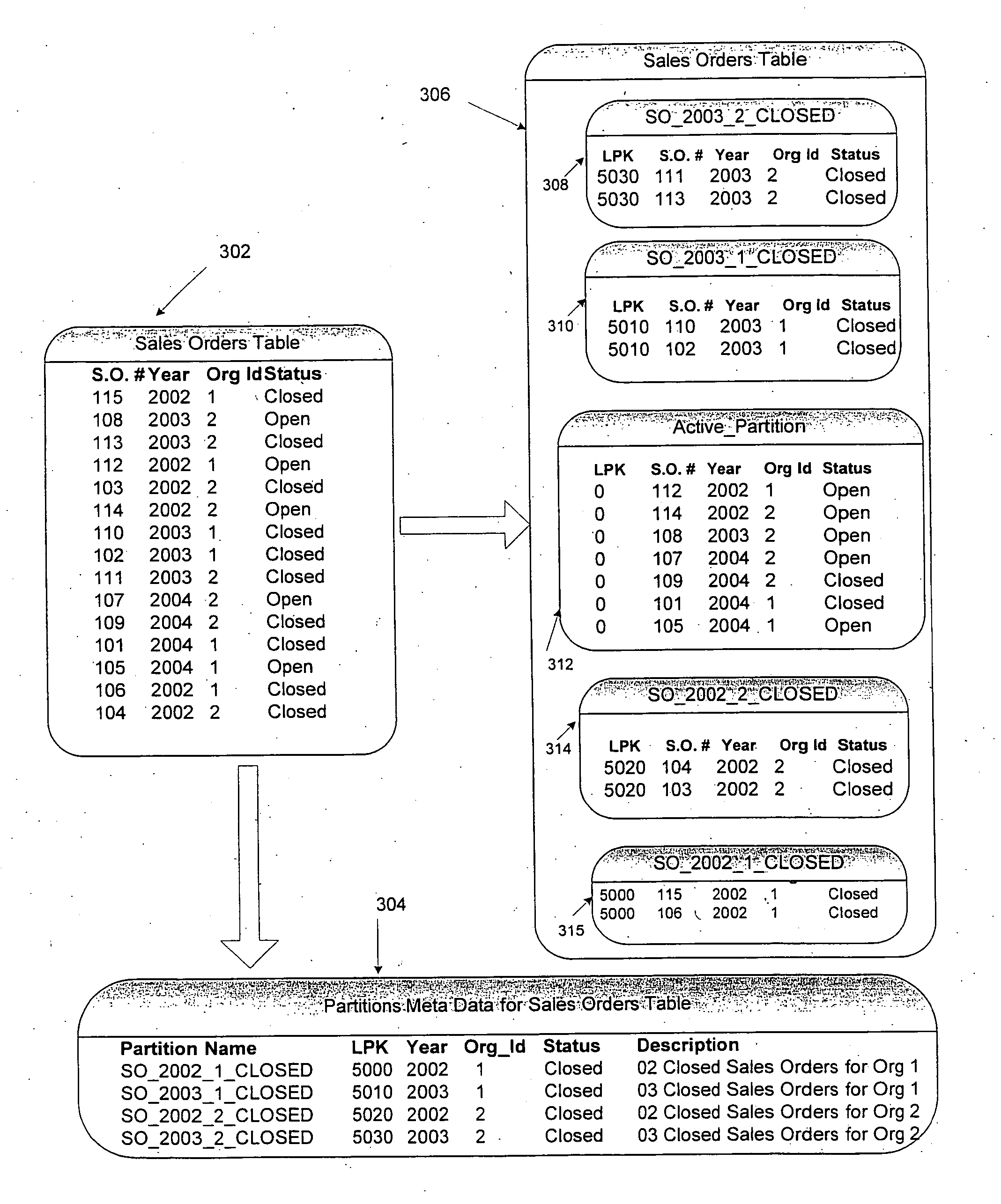
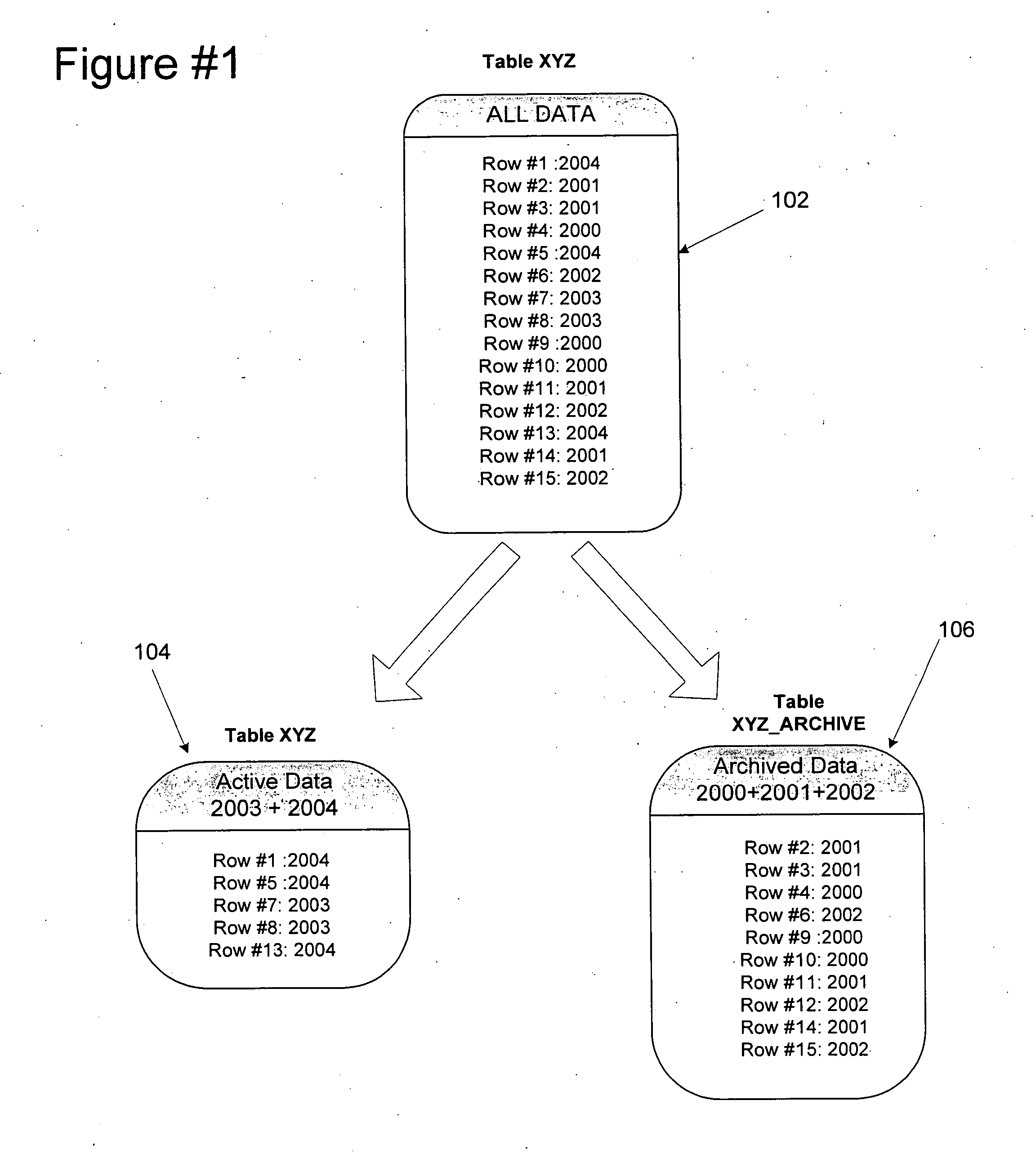
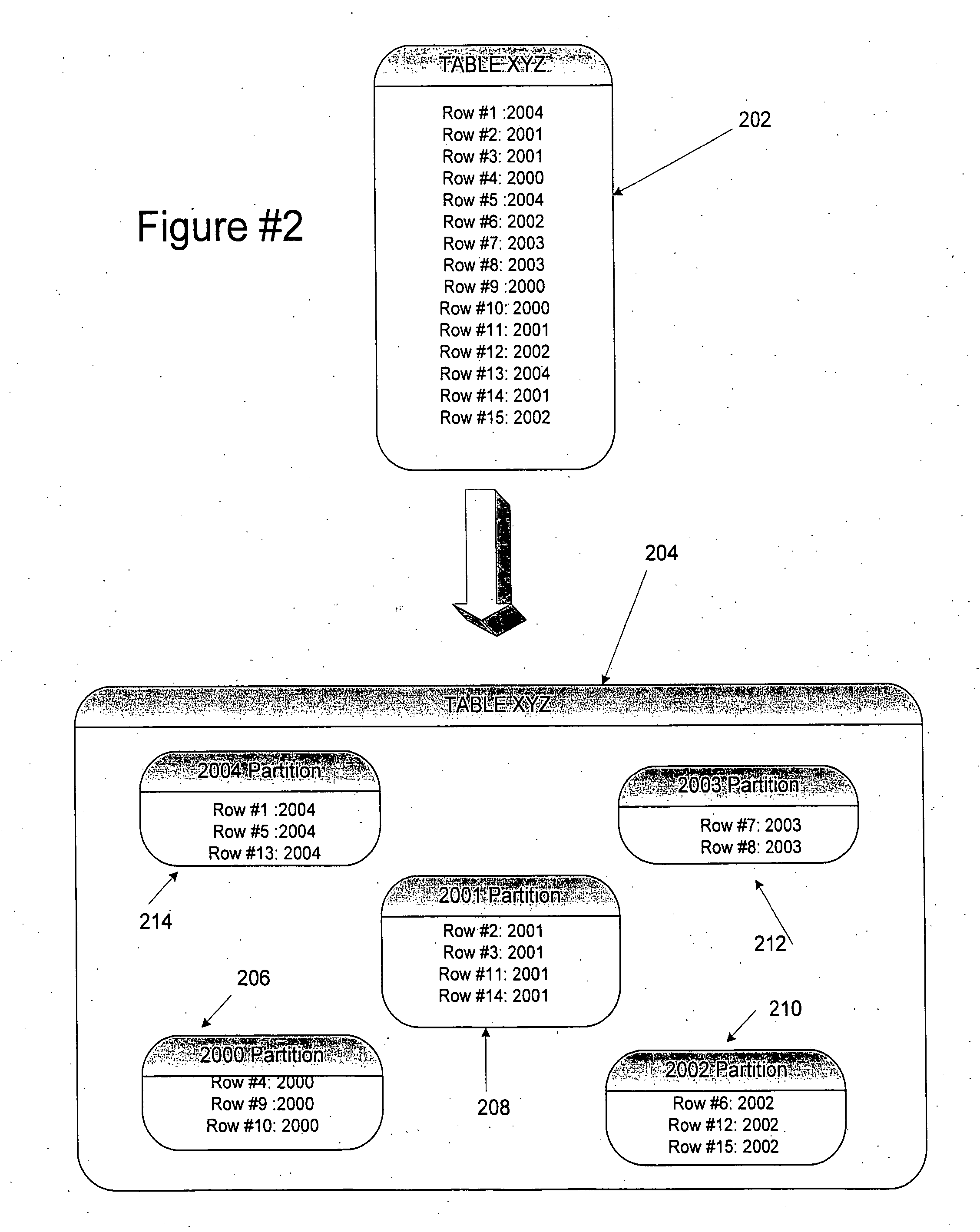
InactiveUS20060206507A1Improve system performanceLow costDigital data processing detailsRelational databasesData classData management
A hierarchal data management system for a storage device includes an entity relationship discover to generate meta data from a business object, a file manager to create a partition based on the metadata, a data mover to generate a logical partitioning key and to store the logical partitioning key in the metadata for the partition. The file manager includes a data management policy to define a data class and a storage policy to map the data class to the storage device to form a partition table.
Owner:DAHBOUR ZIYAD M
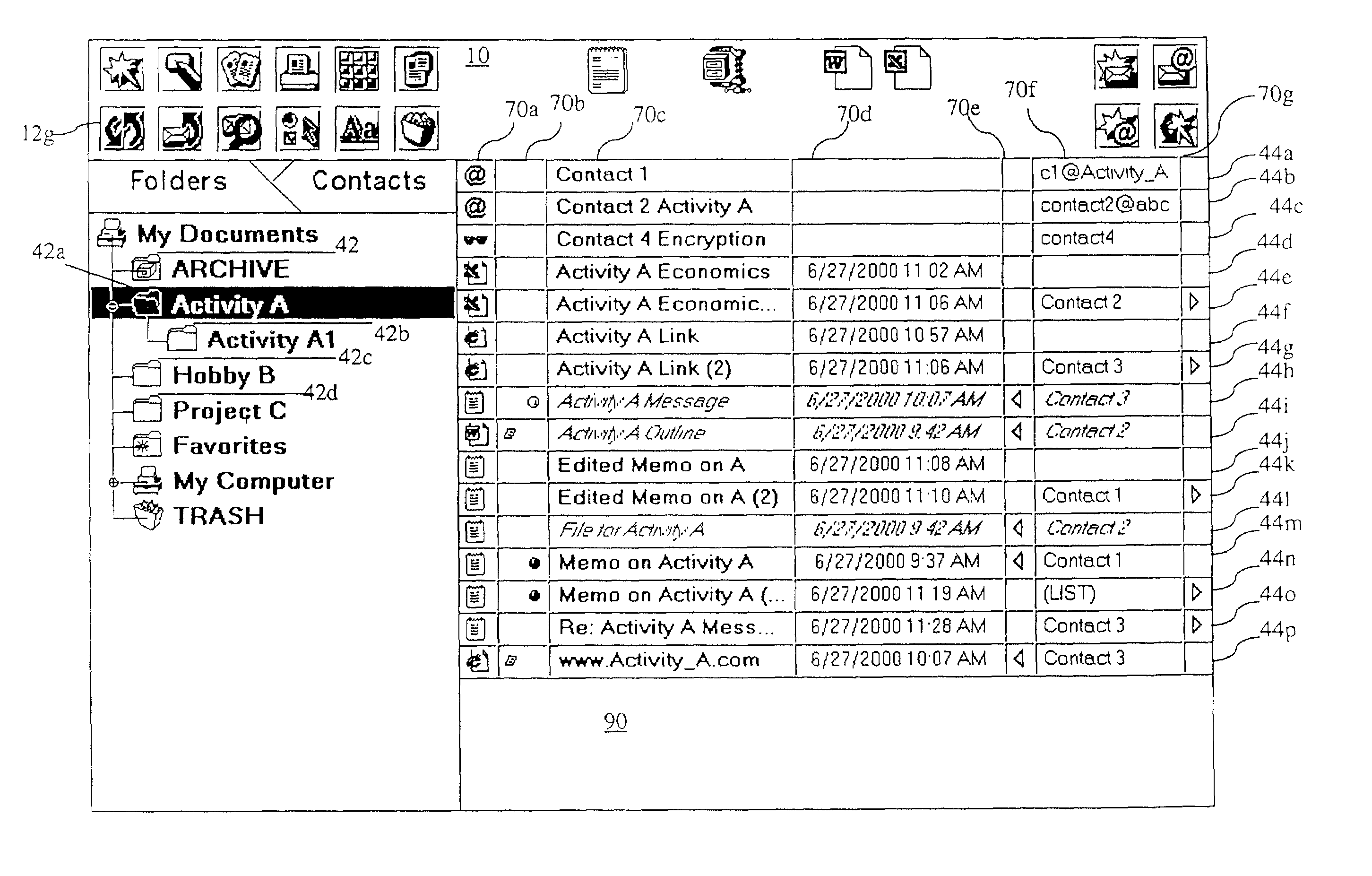
System and method for organizing, managing, and manipulating desktop objects with an activity-oriented user interface
InactiveUS7219302B1Avoid excessive clicking on a mouseStrong advantageData processing applicationsDigital data processing detailsCommunications managementEngineering
An email client and file manager provides combined file management and communications management in a single interface. An interface allows documents, email messages, contact information, web links or pages, and user-attached notes to be stored in the same folders. This facilitates communication by email and fax. The interface permits the user to combine this data in folders which the user categorizes according to a folder tree created by the user. In one embodiment of the invention, the client, in its email function, communicates with a dedicated host which in turn communicates with external servers according to standard internet protocol.
Owner:EVEREZ SYST
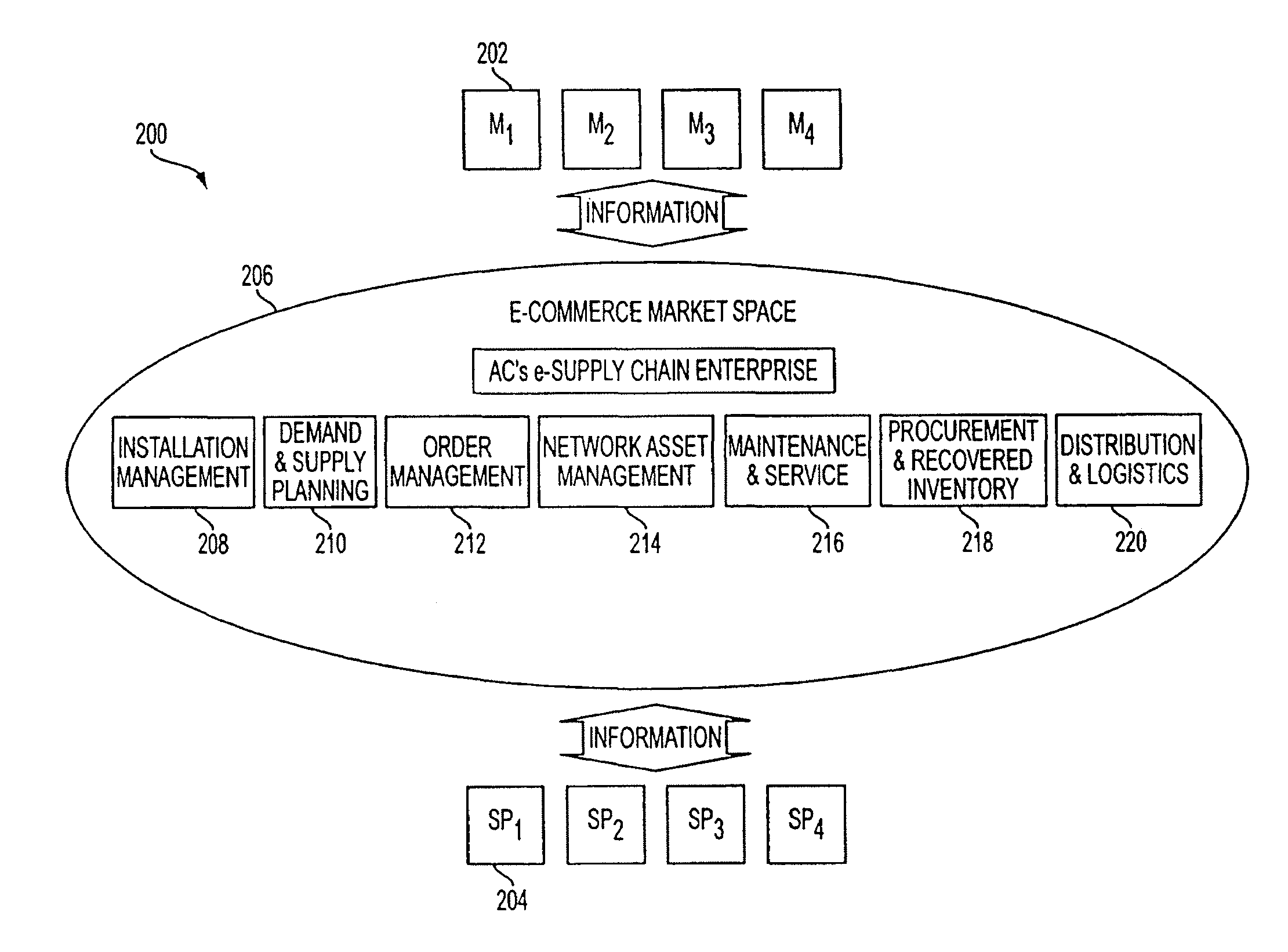
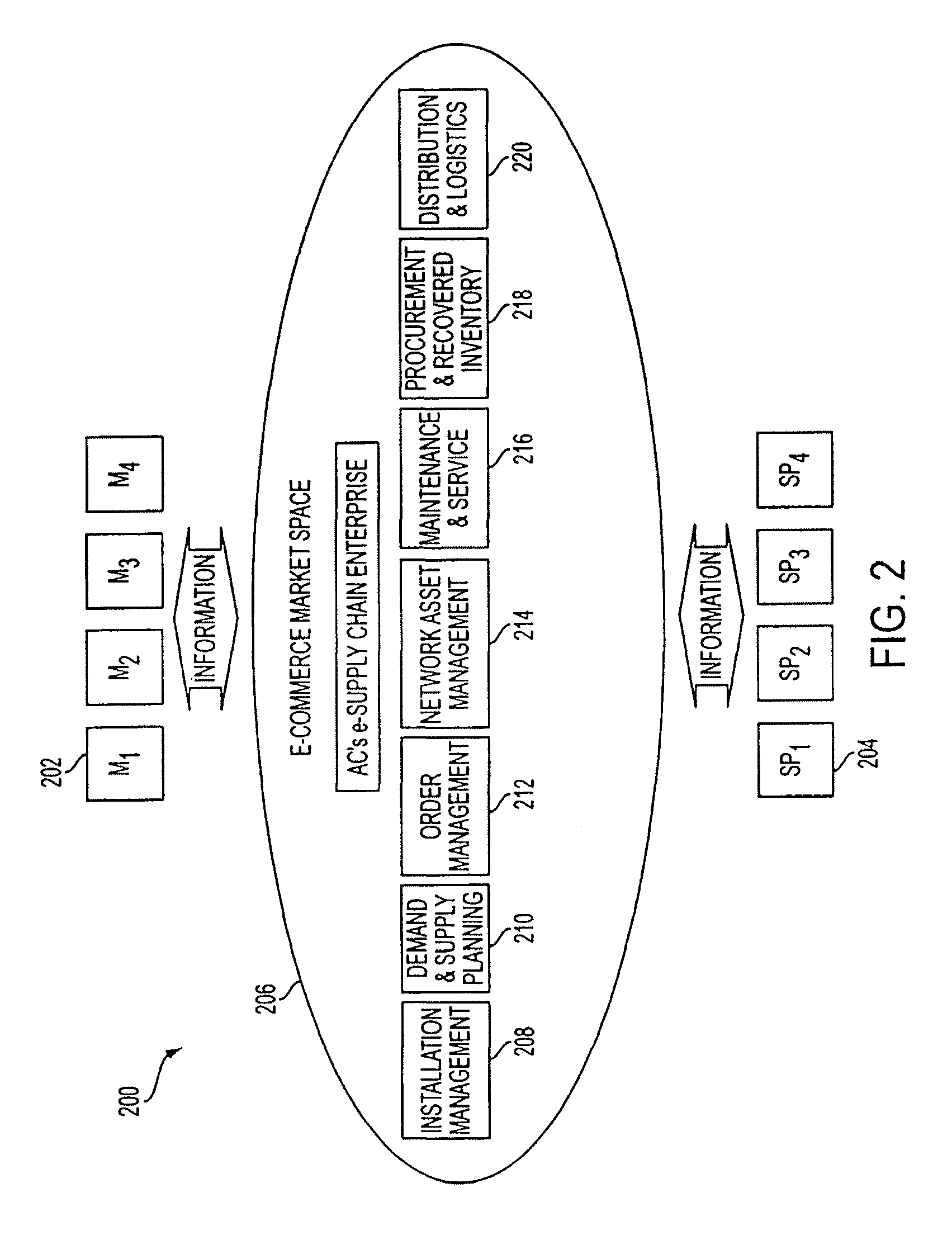
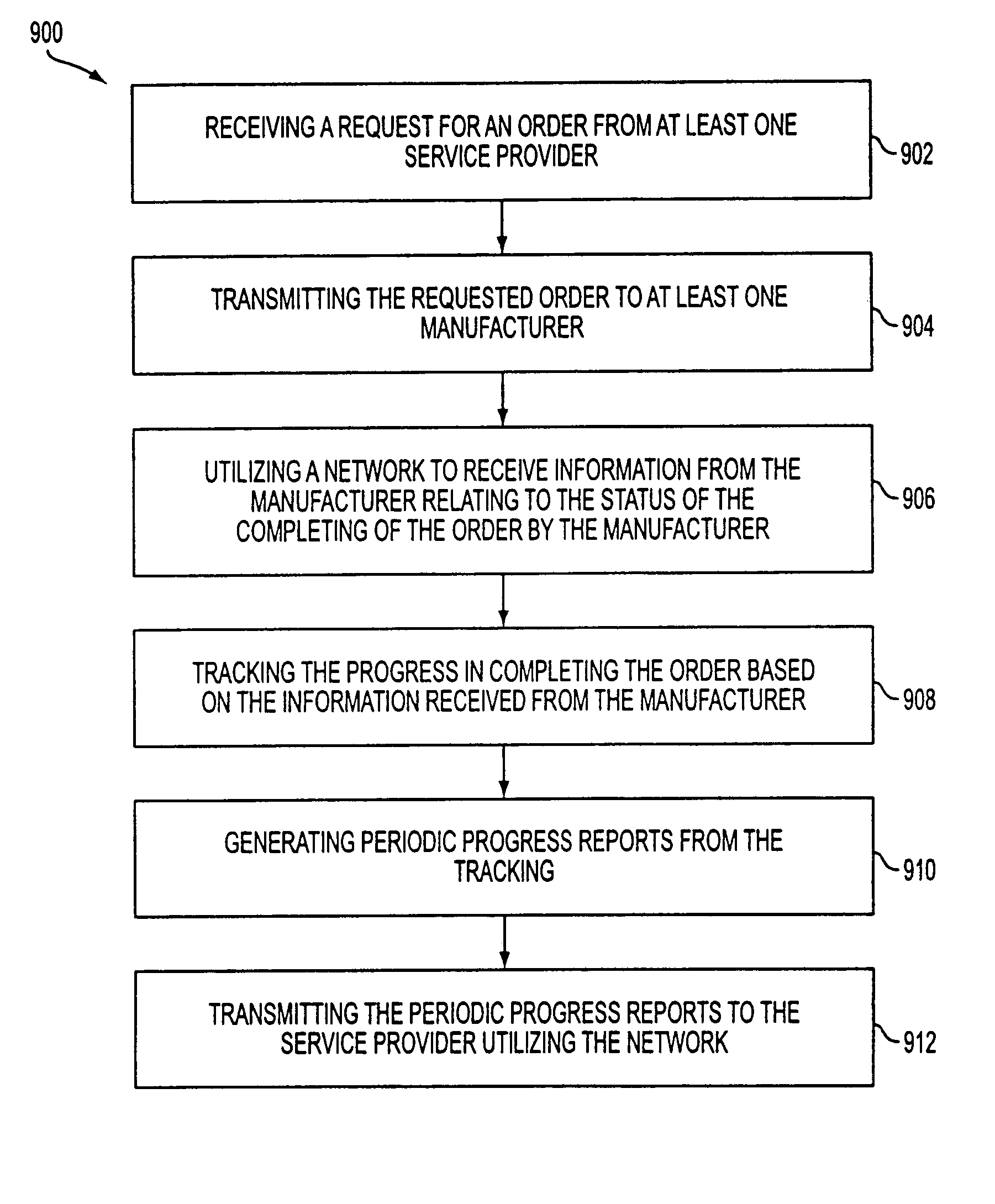
Technology sharing during demand and supply planning in a network-based supply chain environment
A system, method, and article of manufacture are provided for technology sharing during demand and supply planning in a network-based supply chain environment. Steps included are providing locator and mapping capabilities utilizing the network. Technology that includes streaming audio, stereo audio and video data is also shared utilizing the network. Encryption capabilities for the technology are also included. Further, searching capabilities are provided utilizing the network in addition to logging events and passive user profiling. The event logging includes logging network operations. User profile data is automatically received and stored. User profile data includes user identity, state, preferences and interests. User profile data is also automatically exported to an active profile manager which automatically adds additional user profile data. Additional user profile data includes information related to whether the user is a service provider or a manufacturer and the location of user.
Owner:ACCENTURE GLOBAL SERVICES LTD
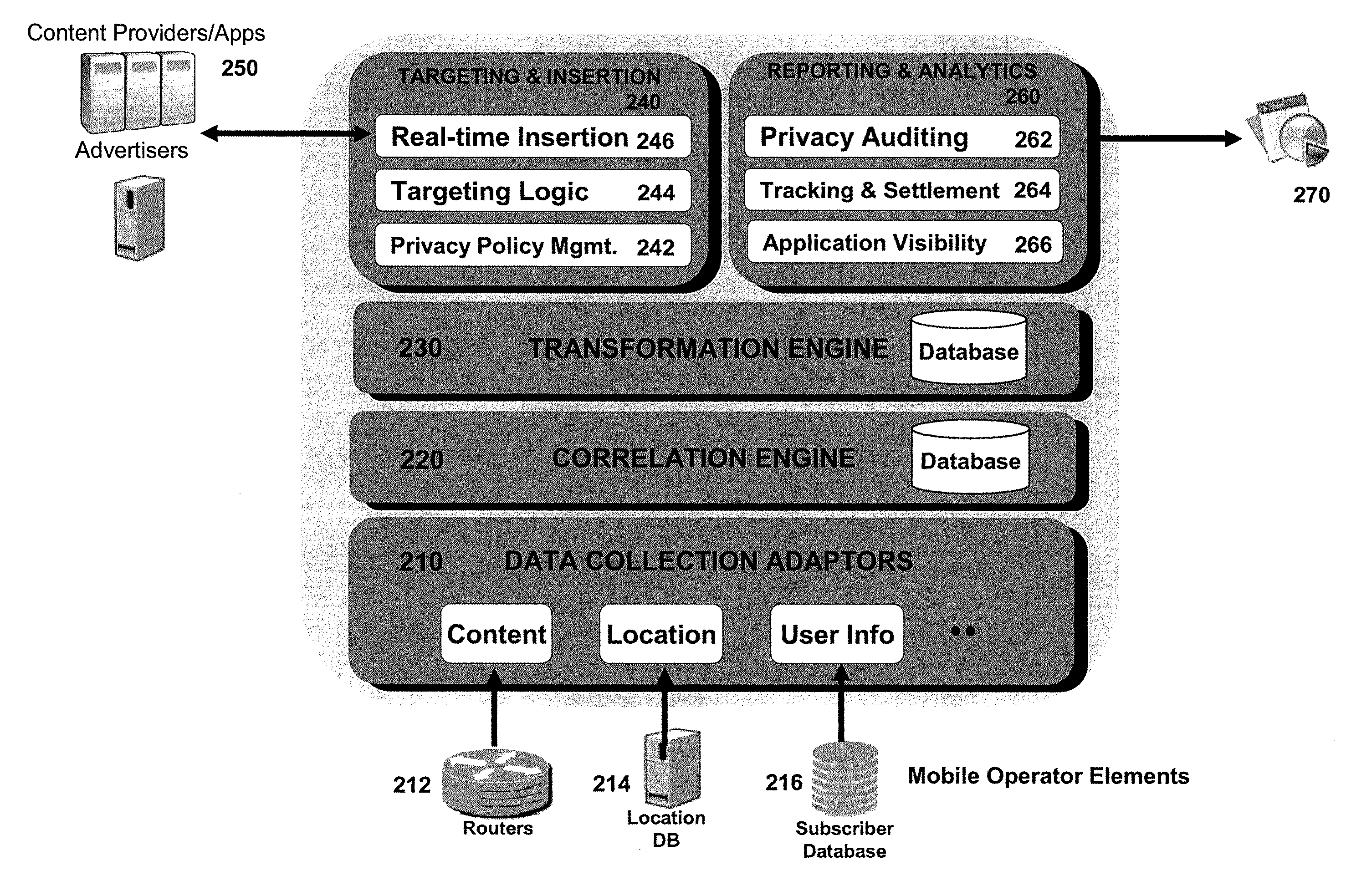
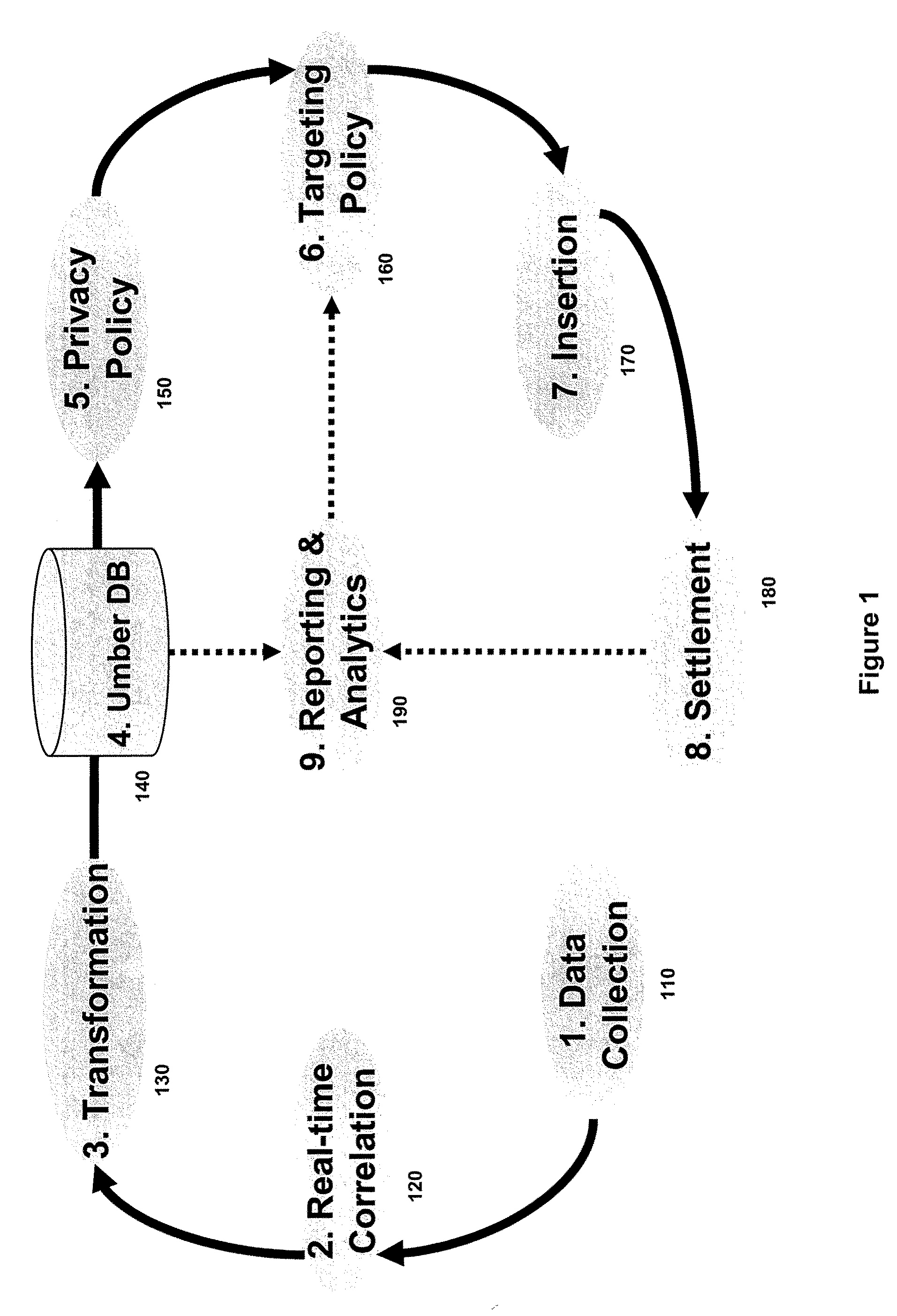
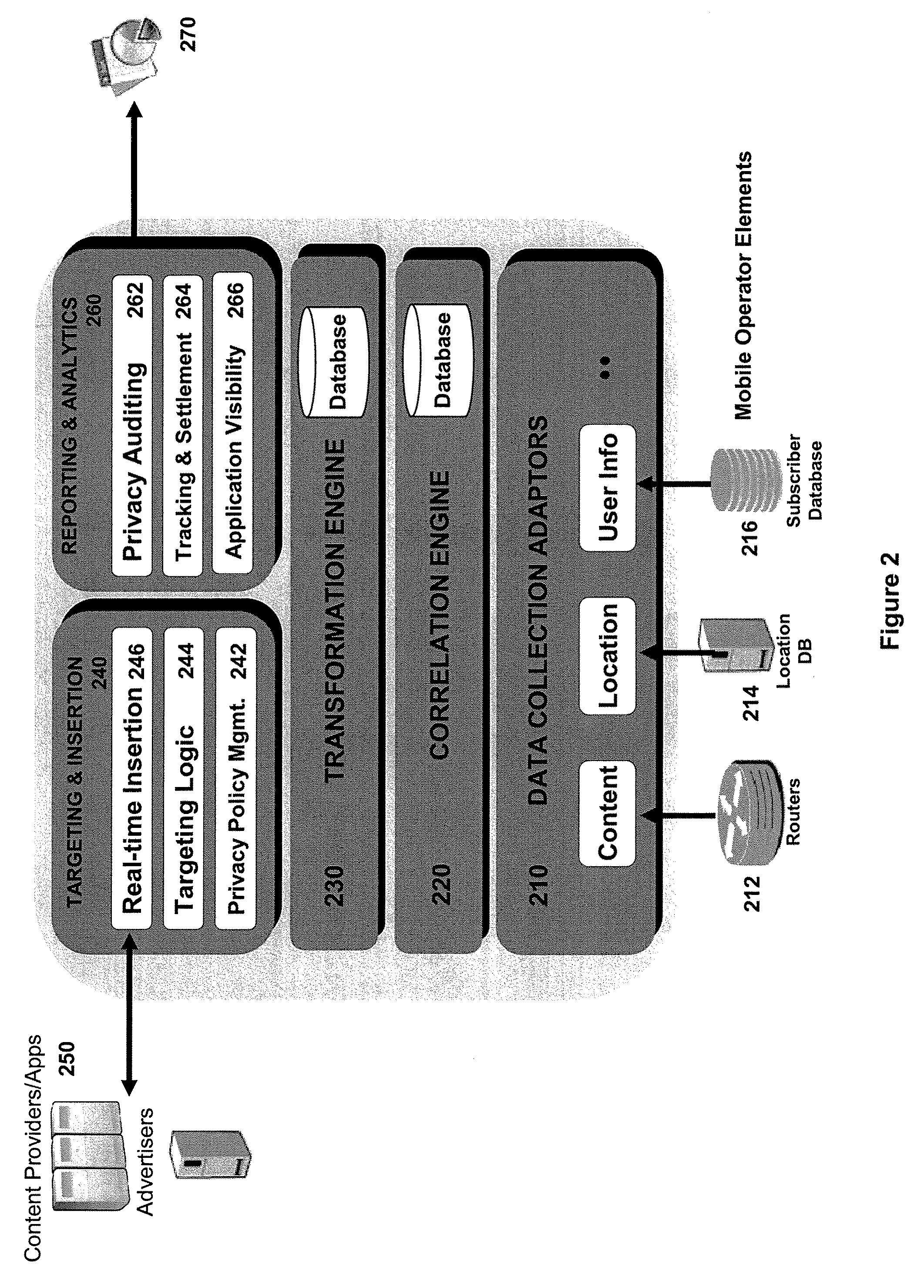
System and Method for Creating Anonymous User Profiles from a Mobile Data Network
InactiveUS20090247193A1Services signallingLocation information based serviceIp addressCollector device
A mobile network device creates and continuously modifies an anonymous user profile from collected network data and subsequently shares the profile with content providers. The mobile network device includes multiple collector devices that monitor data from routers on the mobile data network for application-level activity and a corresponding IP address or mobile phone number. The collectors then analyze the content involved with the activity and correlate it to an IP-address-phone-number pair to create a user profile. Each collector then modifies the user profile with the user's location information at the time the activity was requested. Each collector subsequently transforms the user profile into an anonymous user profile vector and shares it with the profile manager. By repeating this process over time, the collectors create and modify an anonymous user profile vector that can be shared with content providers for targeted advertising.
Owner:ZETTICS
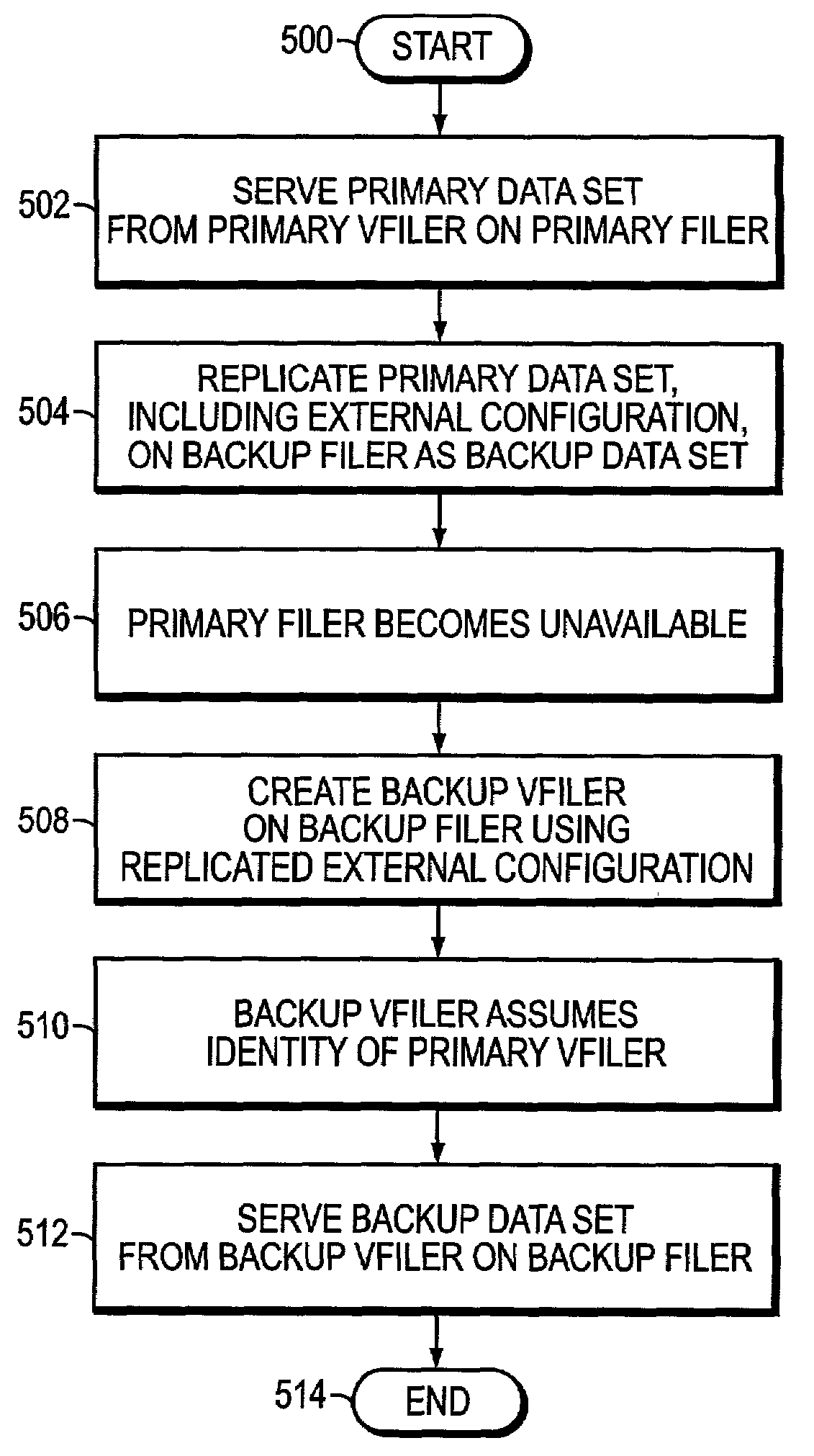
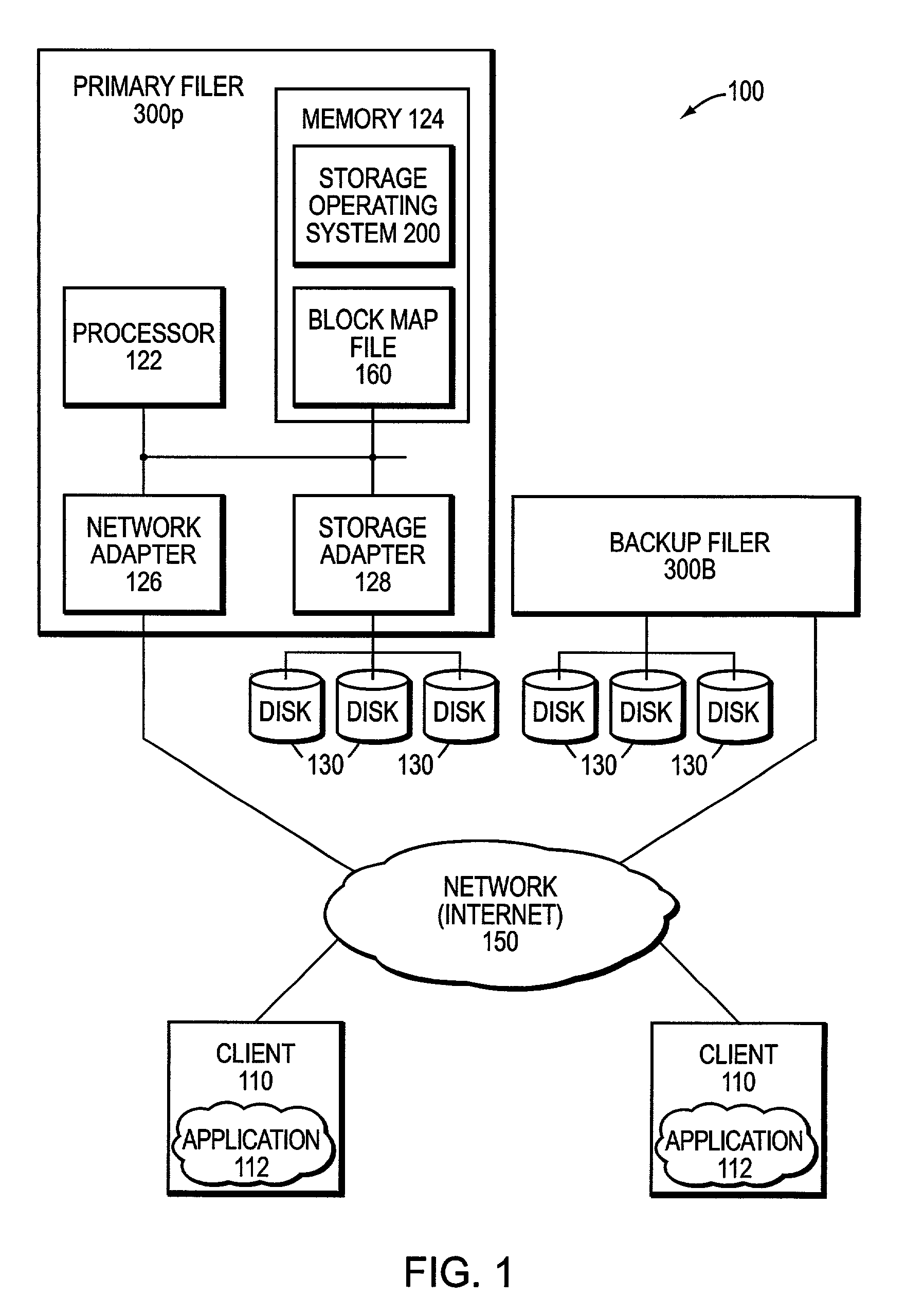
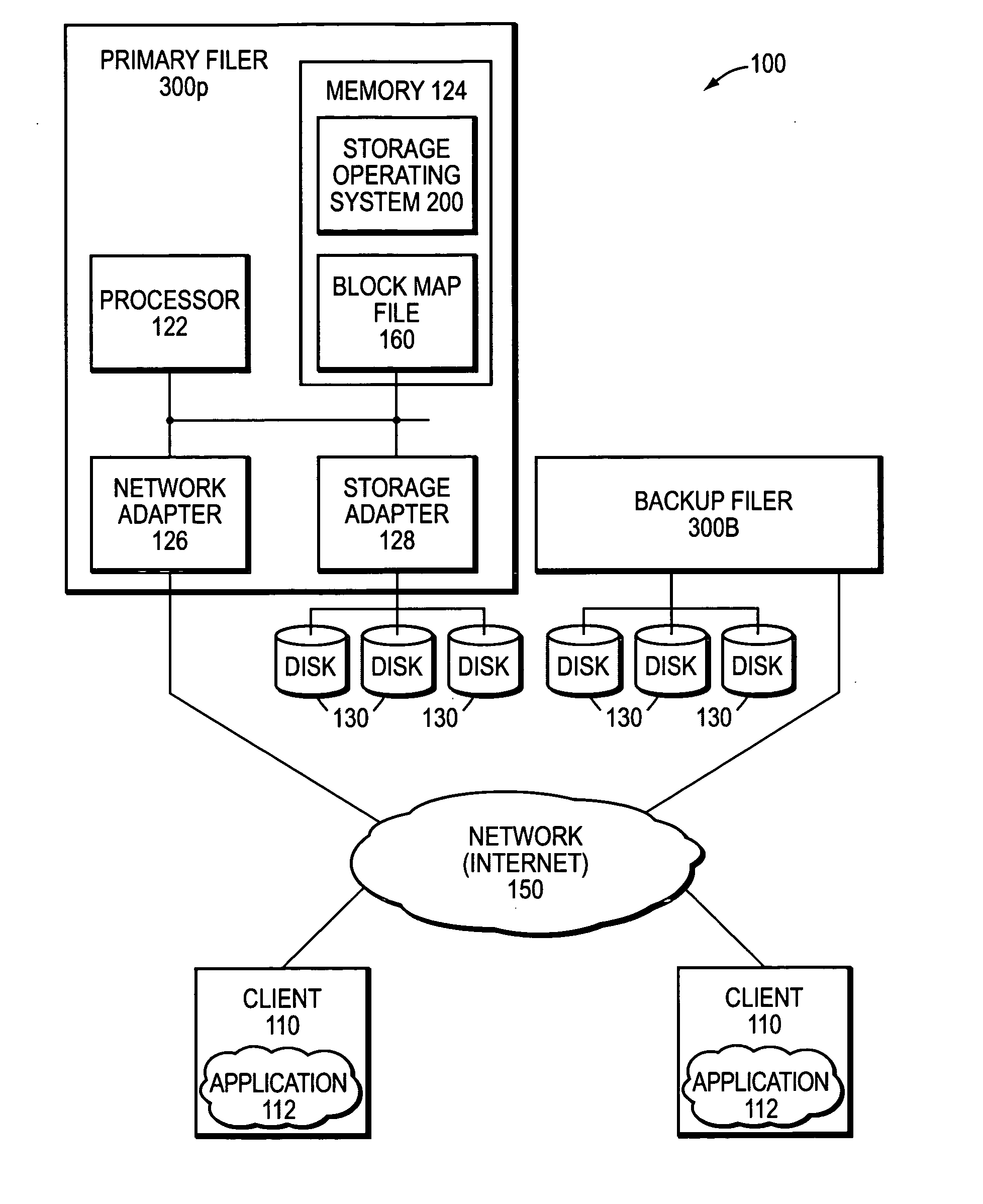
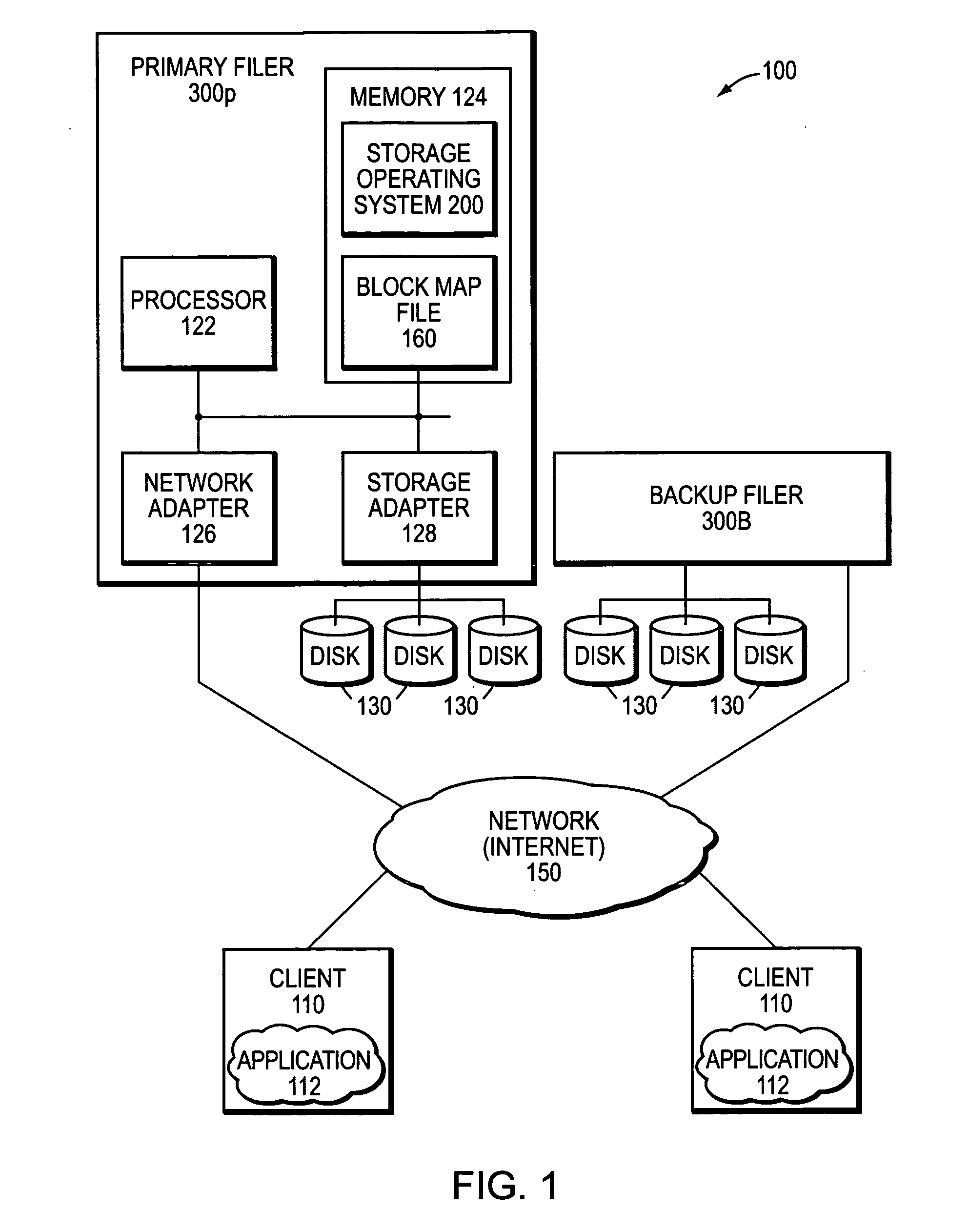
Remote disaster recovery and data migration using virtual appliance migration
A technique efficiently creates and serves a backup data set on a backup filer located at a remote site from a primary filer by essentially moving an entire operating environment of a primary data set to the backup filer. The primary filer is organized into one or more virtual filers (vfilers), one of which (the primary vfiler) is configured to serve data, such as the primary data set, for a client. In the event that the primary filer or primary vfiler becomes unavailable, the technique may be implemented as a disaster recovery or data migration sequence to enable efficient instantiation of a backup vfiler to serve the backup data set for the client.
Owner:NETWORK APPLIANCE INC
System and method for indexing a backup using persistent consistency point images
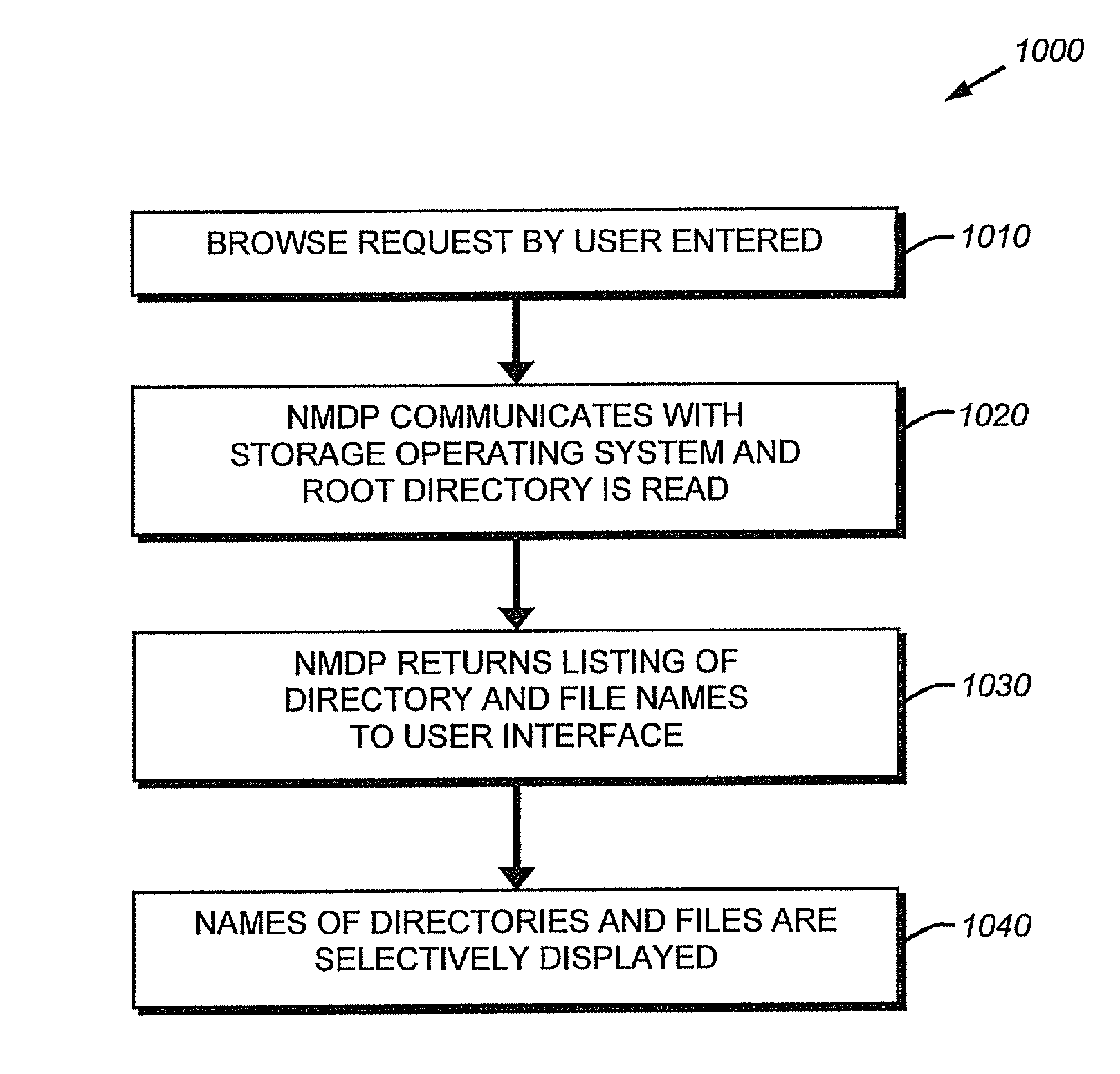
ActiveUS7966293B1Through simpleGood flexibilityData processing applicationsError detection/correctionCommand-line interfaceApplication software
This invention provides a system and method for managing backup and restore operations on a storage system, typically between source storage system and destination storage system using a backup management client that employs a version of the Network Data Management Protocol to interface with the destination file server and generate an “index” of data structures (such as directories and files) from directly from scanning the trees of PCPIs stored on the destination. The management client includes a command line interface for entry of instructions by a user or application and a web-based user interface and allows the index to be displayed as a series of web pages on a graphical user interface. The index can be browsed and selected data structures can be restored to a source filer / file server as desired. All back-ups / PCPIs can be contemporaneously browsed, allowing greater flexibility in selecting a best backup image to restore.
Owner:NETWORK APPLIANCE INC
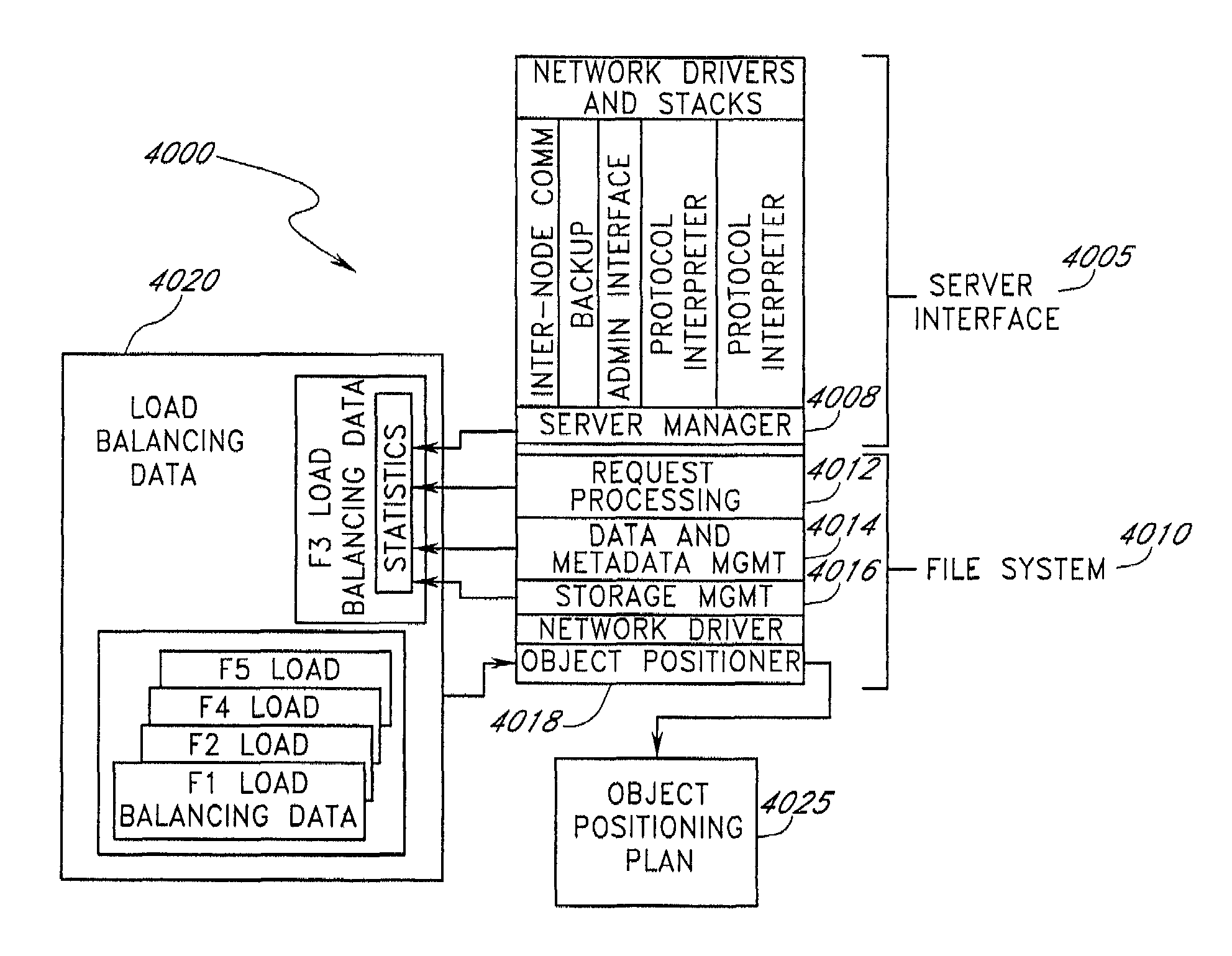
Server-independent object positioning for load balancing drives and servers
ActiveUS6990667B2Increase capacityImprove throughputMemory adressing/allocation/relocationDigital computer detailsFile systemClient-side
A file system that balances the loading of filers and the capacity of drives that are associated with the filers is described. The file system includes a first disk drive that includes a first unused capacity and a second disk drive that includes a second unused capacity, wherein the second unused capacity is smaller than the first unused capacity. The file system further includes a first filer that is configured to fill requests from clients through access to at least the first disk drive. The file system further includes a second filer that is configured to fill requests from clients through access to at least the second disk drive. The second filer is configured to select an infrequently accessed file from the second disk drive and to push the infrequently accessed files to the first disk drive, thereby improving a balance of unused capacity between the first and second disk drives without substantially affecting a loading for each of the first and second filers.
Owner:OVERLAND STORAGE
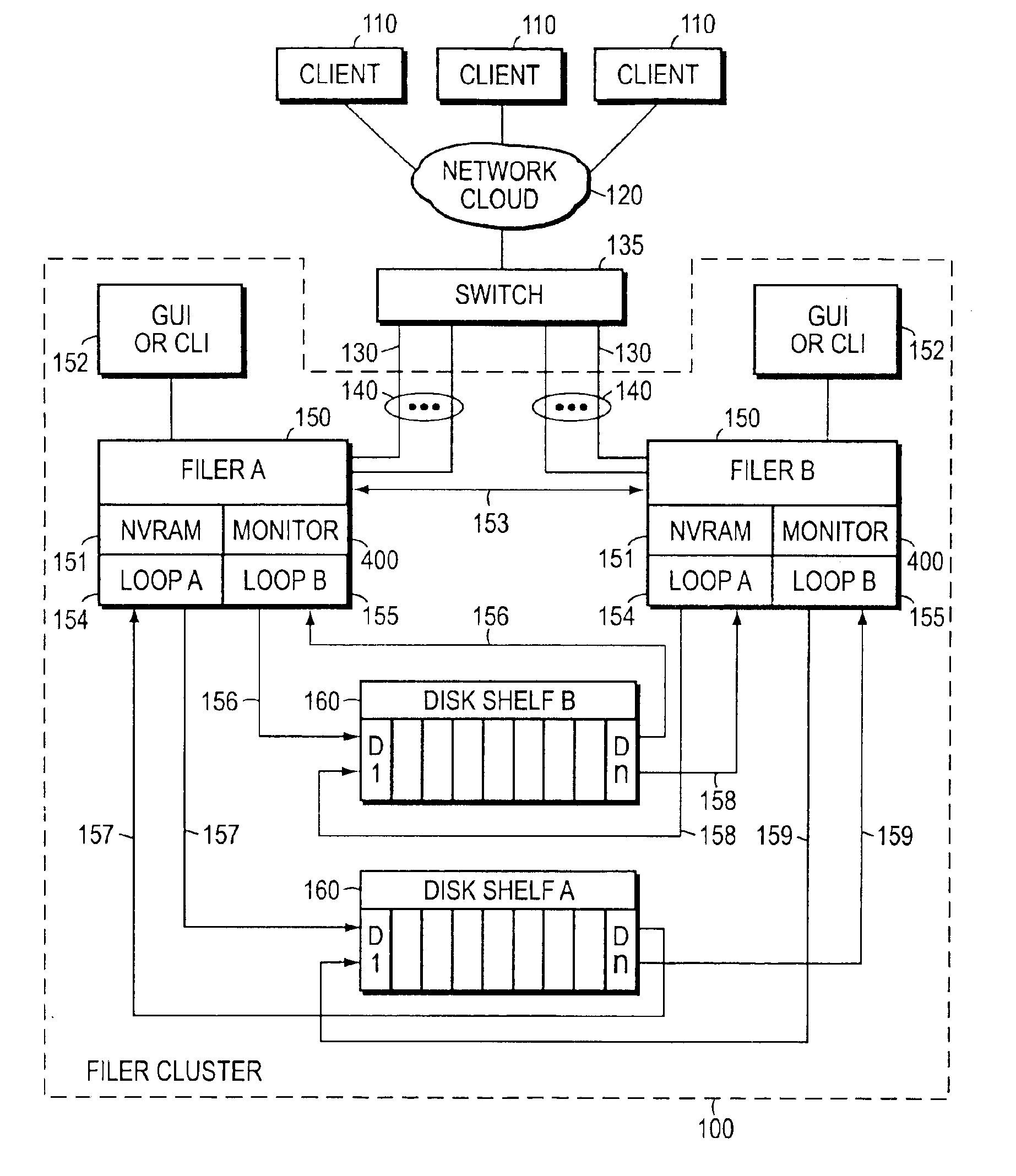
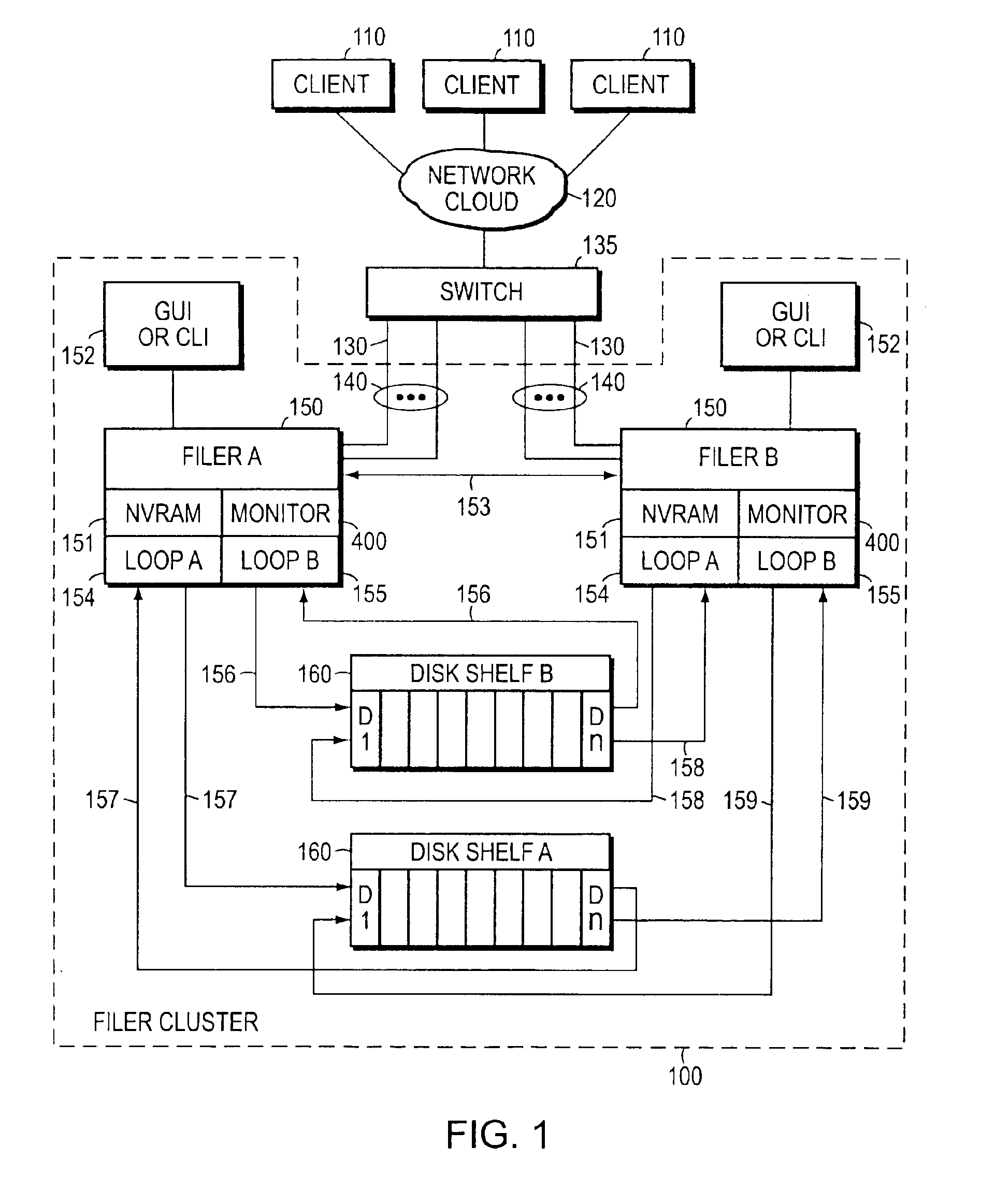
Negotiated graceful takeover in a node cluster
InactiveUS6920580B1Minimizes problemRedundant hardware error correctionNode clusteringNetwork addressing
The invention is a method for operating a file server system in a cluster mode that provides for relatively rapid and reliable takeover of a failed file server in the cluster by a partner file server when the failed file server has detected a fault that will cause it to shut down. This is done by the failed file server requesting the one file server to take over its file services after detecting the fault in its operations, the one file server letting the failed file server complete existing file service requests from clients, refusing further file service requests addressed to the failed file server, and the one file server taking over by transferring file service requests to the one file server. As part of this takeover the one file server takes on the identity of the failed filer and activates network interfaces and network addresses that replicate the failed server's network addresses.
Owner:NETWORK APPLIANCE INC
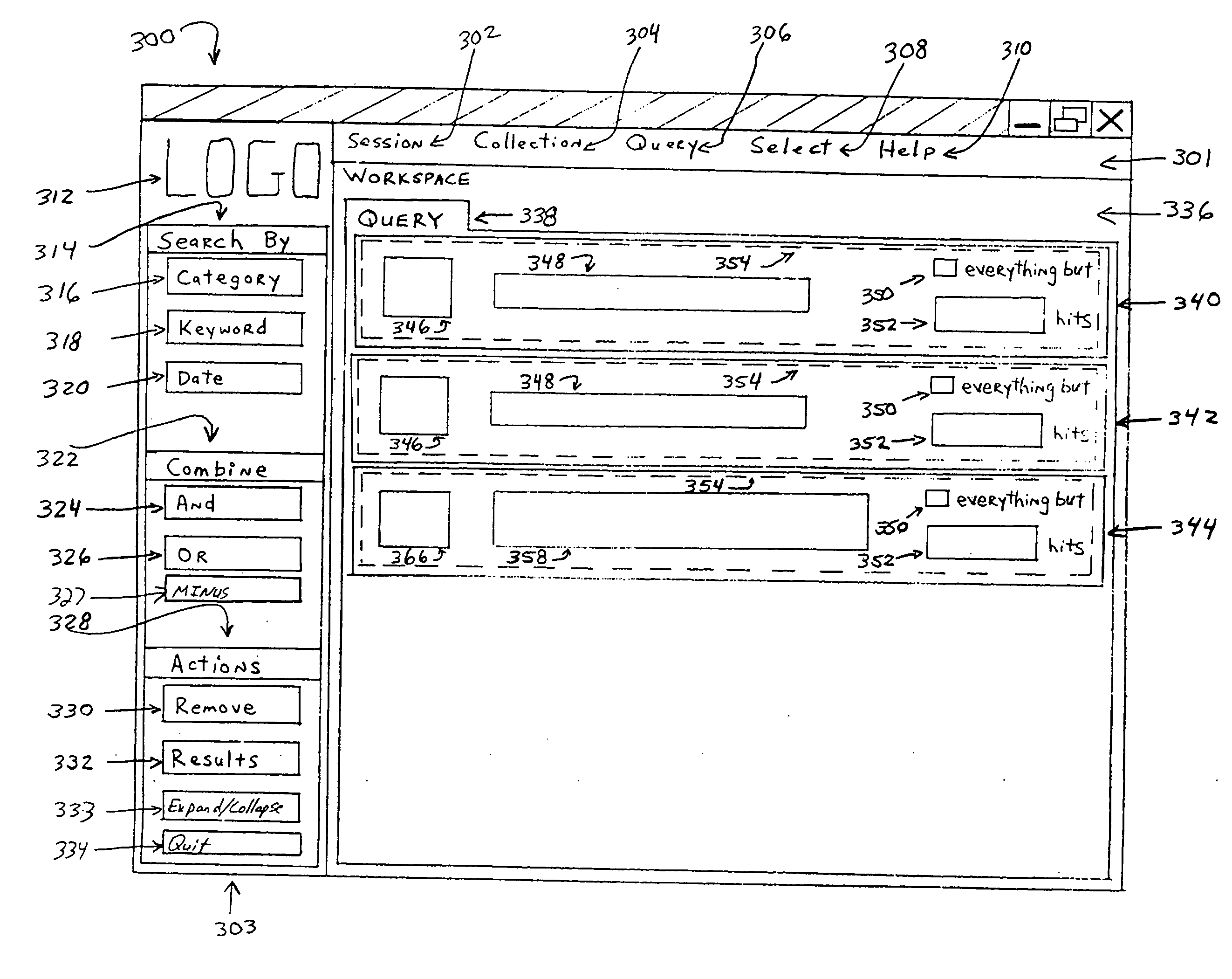
Graphical user interface for building boolean queries and viewing search results
InactiveUS20050192953A1Communication Latency MinimizedDigital data information retrievalData processing applicationsThe InternetNative client
A graphical user interface is for building Boolean queries and viewing search results using search cells, combination cells, a toolbar, and a menu bar. The search cells are movable within a workspace and preferably contain a text field, a facet type designation, an advanced button and a hit count. Search cells can search records by a category, keyword, date or numeric value. Categories are preferably chosen with the assistance of a category walker. The combination cells are movable within the workspace and preferably contain a combine icon, a hit count and an expression field. The combination cell is a Boolean combination of two or more selected search cells. In the preferred embodiment of the invention, the Boolean logic is graphically depicted with the use of combination brackets. The contents of each combination bracket is controllable by the use of movable graphical pins that are located between each pair of search cells. The combination bracket can be represented by use of a rectangular bracket, a square bracket, or a curly brace. In an alternative embodiment of the invention, the Boolean query is depicted in a folder tree hierarchy. Search folders and combination folders are used to depict search cells and combination cells, respectively. Search folders contain the same information as search cells, but search folders can be toggled to appear as small folder icons within the workspace. Combination folders are represented as small folder icons containing a logical AND icon, a logical OR icon or a logical MINUS icon. Search folders are shown to be included within combination folders through the use of the folder tree hierarchy, just as computer files are shown to be included within a folder in a typical file manager program. In the preferred embodiment, the invention runs an internet browser and is coupled to a remote server through the internet. To minimize communication delays across the internet, an applet can be run on the local client to perform most graphical display manipulations prompted by the searches manipulation of the search cells, the combination cells, the toolbar, and the menu. The remote server is used to execute queries received over the internet from the local client and deliver search results back to the local client over the internet. Optionally, the client can take on some or all of the tasks of the server in executing queries over the internet.
Owner:ROMAN KENDYL A +1
Method and system for digital privacy management
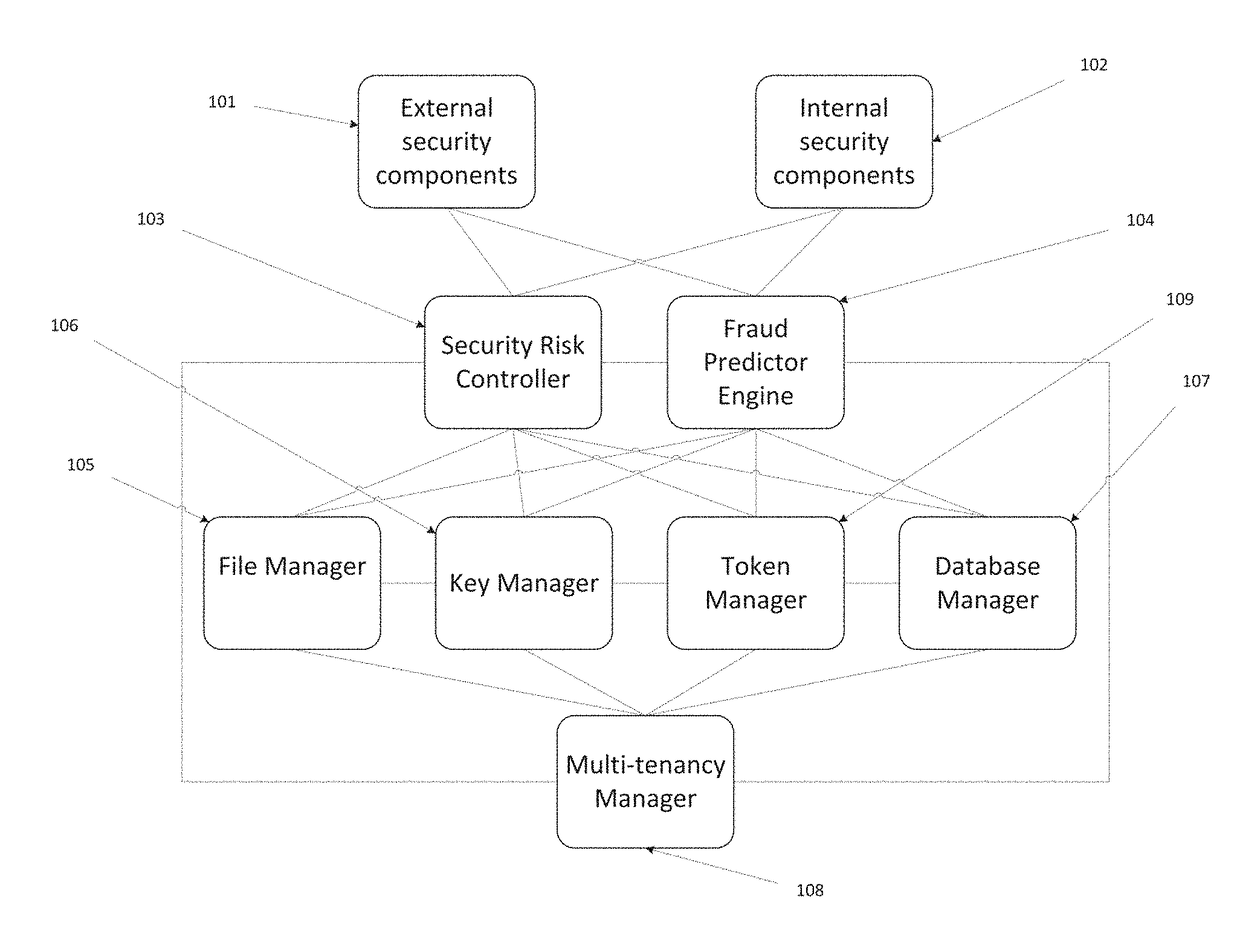
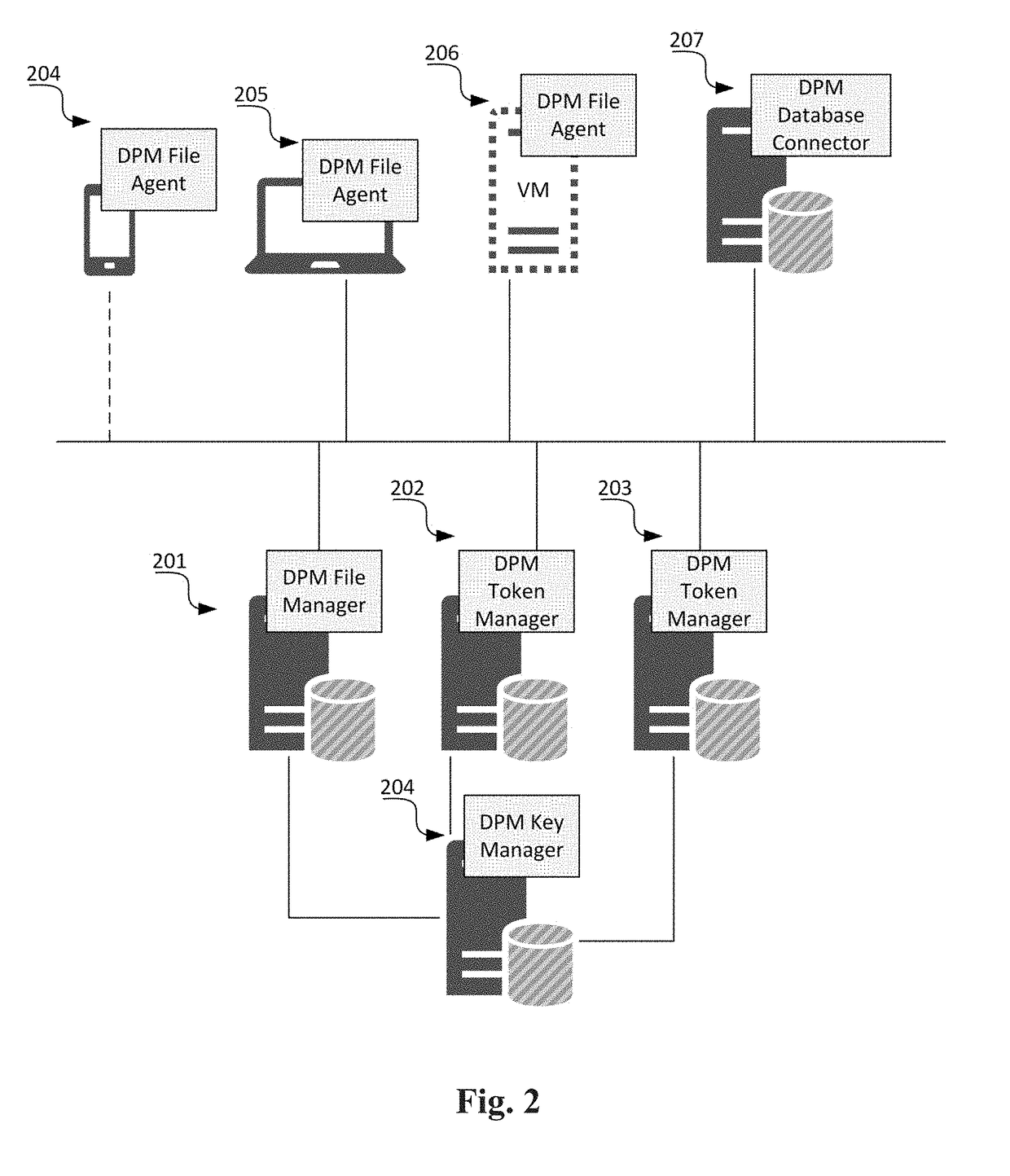
Data Privacy Manager (DPM) solution includes a number of different components performing data security procedures (encryption, masking, tokenization, Anonymization, etc.) at the folder, file, email, application, database and column levels. These include components such as Key Manager, File Manager, File Agent, Email Agent, Database Manager, Database Connector, the Token Manager, Security Risk Controller and Fraud Predictor. All these components can be managed through a management console.
Owner:ADHAR VIRESHWAR K
Systems and methods for load balancing drives and servers
InactiveUS20060031287A1Increase capacityImprove reliabilityError detection/correctionMultiple digital computer combinationsFile systemClient-side
A file system that balances the loading of filers and the capacity of drives that are associated with the filers is described. The file system includes a first disk drive that includes a first unused capacity and a second disk drive that includes a second unused capacity, wherein the second unused capacity is smaller than the first unused capacity. The file system further includes a first filer that is configured to fill requests from clients through access to at least the first disk drive. The file system further includes a second filer that is configured to fill requests from clients through access to at least the second disk drive. The second filer is configured to select an infrequently accessed file from the second disk drive and to push the infrequently accessed files to the first disk drive, thereby improving a balance of unused capacity between the first and second disk drives without substantially affecting a loading for each of the first and second filers.
Owner:OVERLAND STORAGE INC
Technology sharing during demand and supply planning in a network-based supply chain environment
A system, method, and article of manufacture are provided for technology sharing during demand and supply planning in a network-based supply chain environment. Steps included are providing locator and mapping capabilities utilizing the network. Technology that includes streaming audio, stereo audio and video data is also shared utilizing the network. Encryption capabilities for the technology are also included. Further, searching capabilities are provided utilizing the network in addition to logging events and passive user profiling. The event logging includes logging network operations. User profile data is automatically received and stored. User profile data includes user identity, state, preferences and interests. User profile data is also automatically exported to an active profile manager which automatically adds additional user profile data. Additional user profile data includes information related to whether the user is a service provider or a manufacturer and the location of user.
Owner:ACCENTURE GLOBAL SERVICES LTD
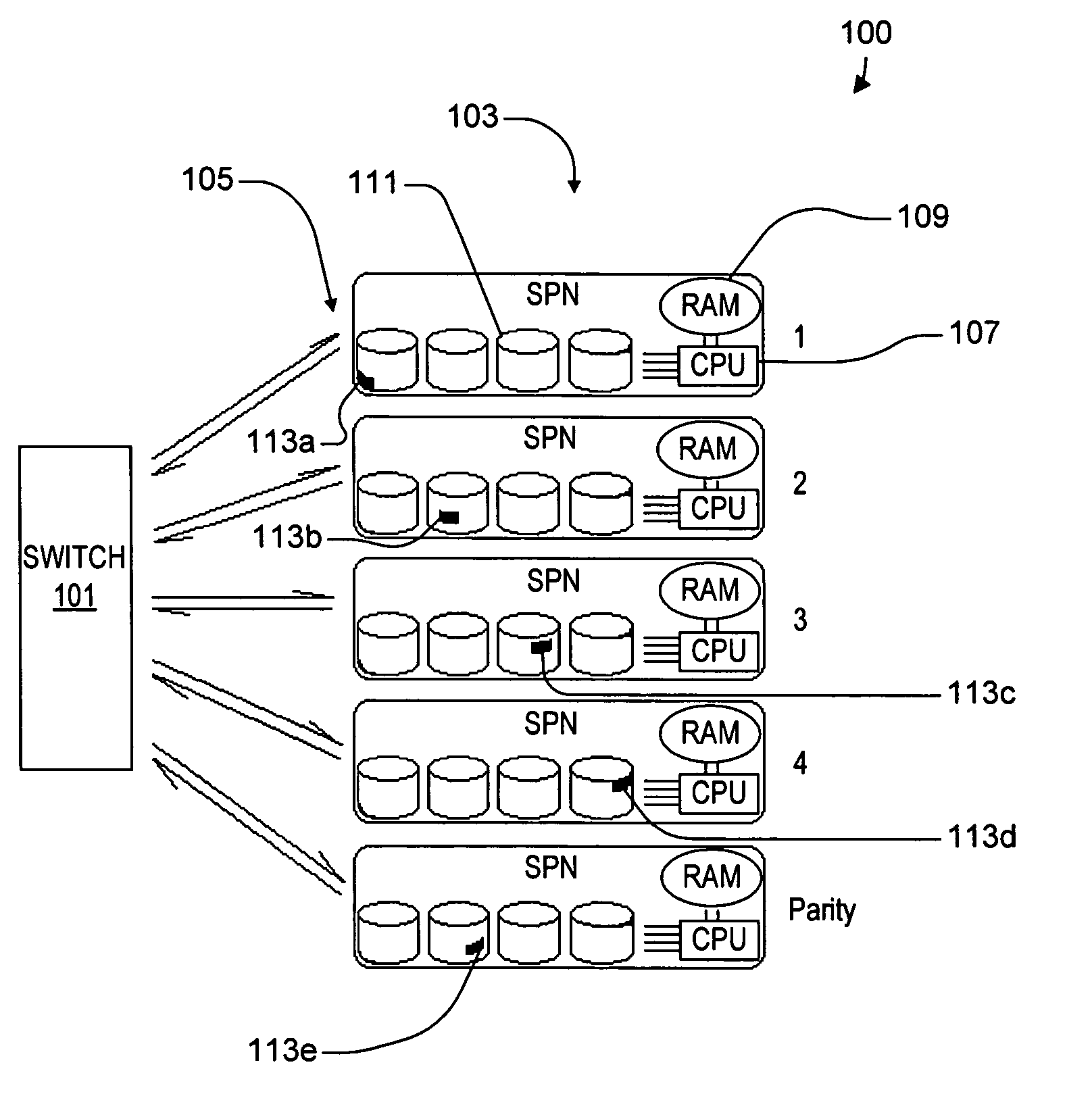
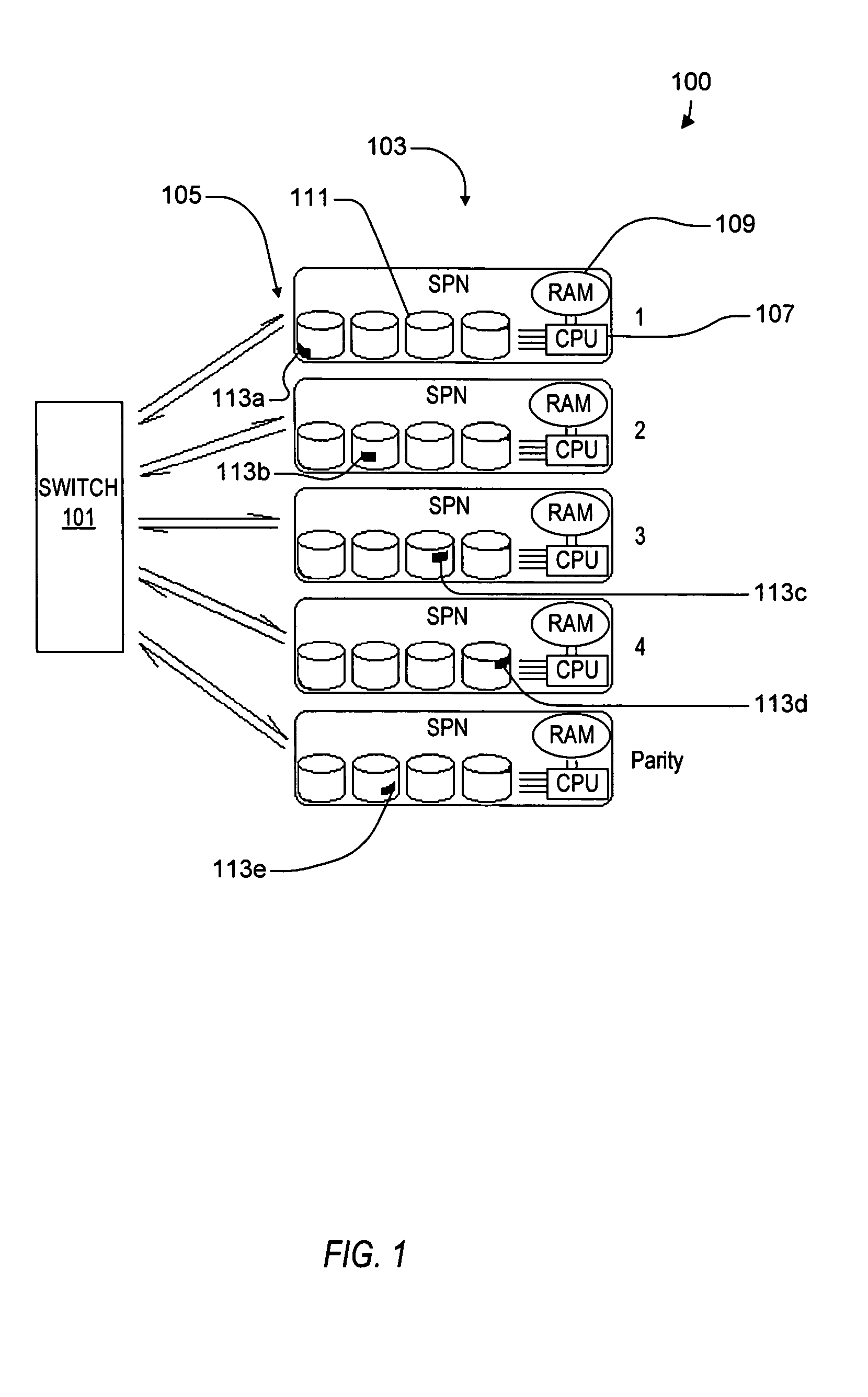
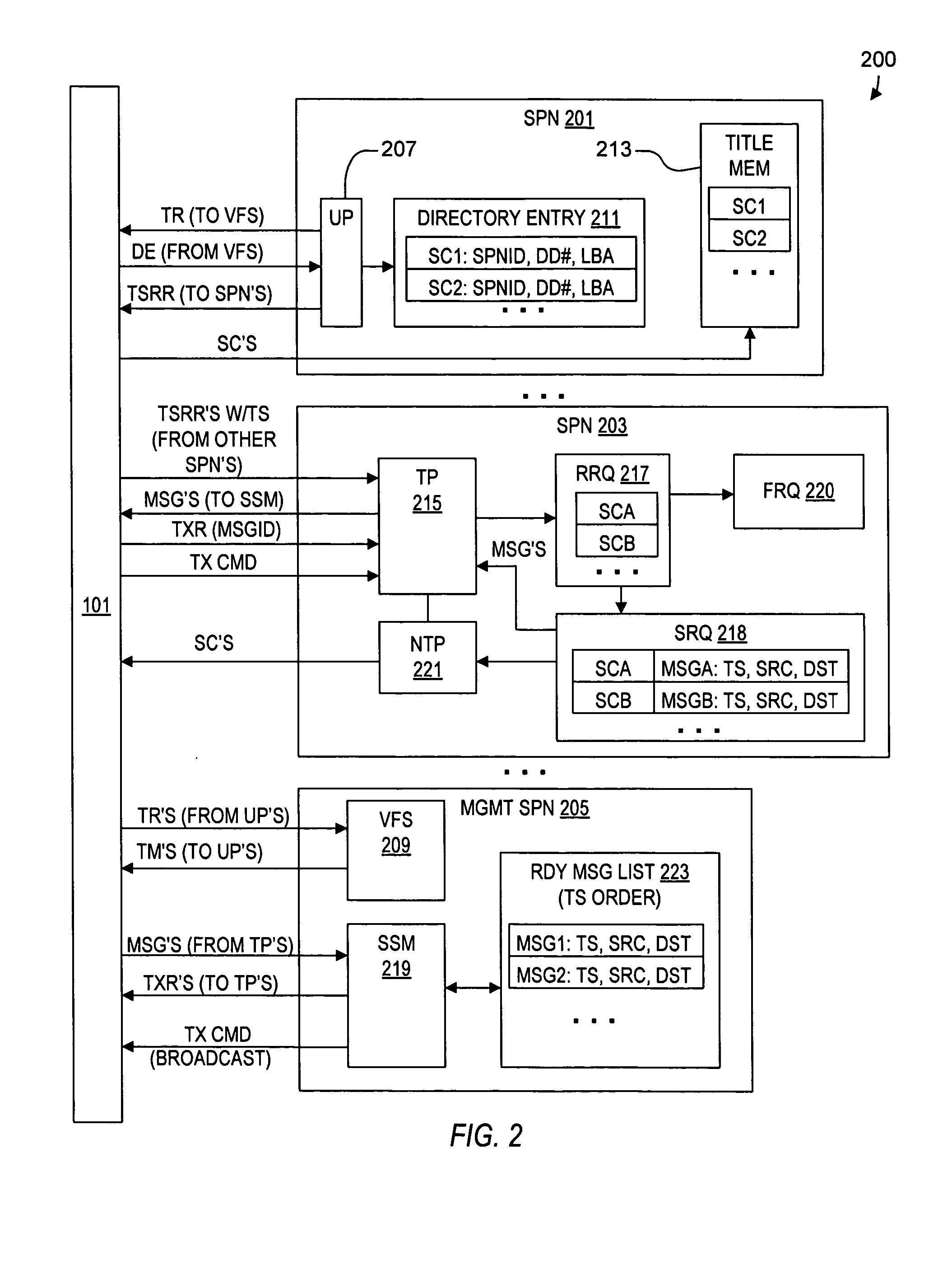
Virtual file system
ActiveUS20050114350A1Input/output to record carriersRecording by optical meansVirtual file systemProcessor node
A virtual file system including multiple storage processor nodes including a management node, a backbone switch, a disk drive array, and a virtual file manager executing on the management node. The backbone switch enables communication between the storage processor nodes. The disk drive array is coupled to and distributed across the storage processor nodes and stores multiple titles. Each title is divided into data subchunks which are distributed across the disk drive array in which each subchunk is stored on a disk drive of the disk drive array. The virtual file manager manages storage and access of each subchunk, and manages multiple directory entries including a directory entry for each title. Each directory entry is a list of subchunk location entries in which each subchunk location entry includes a storage processor node identifier, a disk drive identifier, and a logical address for locating and accessing each subchunk of each title.
Owner:INTERACTIVE CONTENT ENGINES LLC
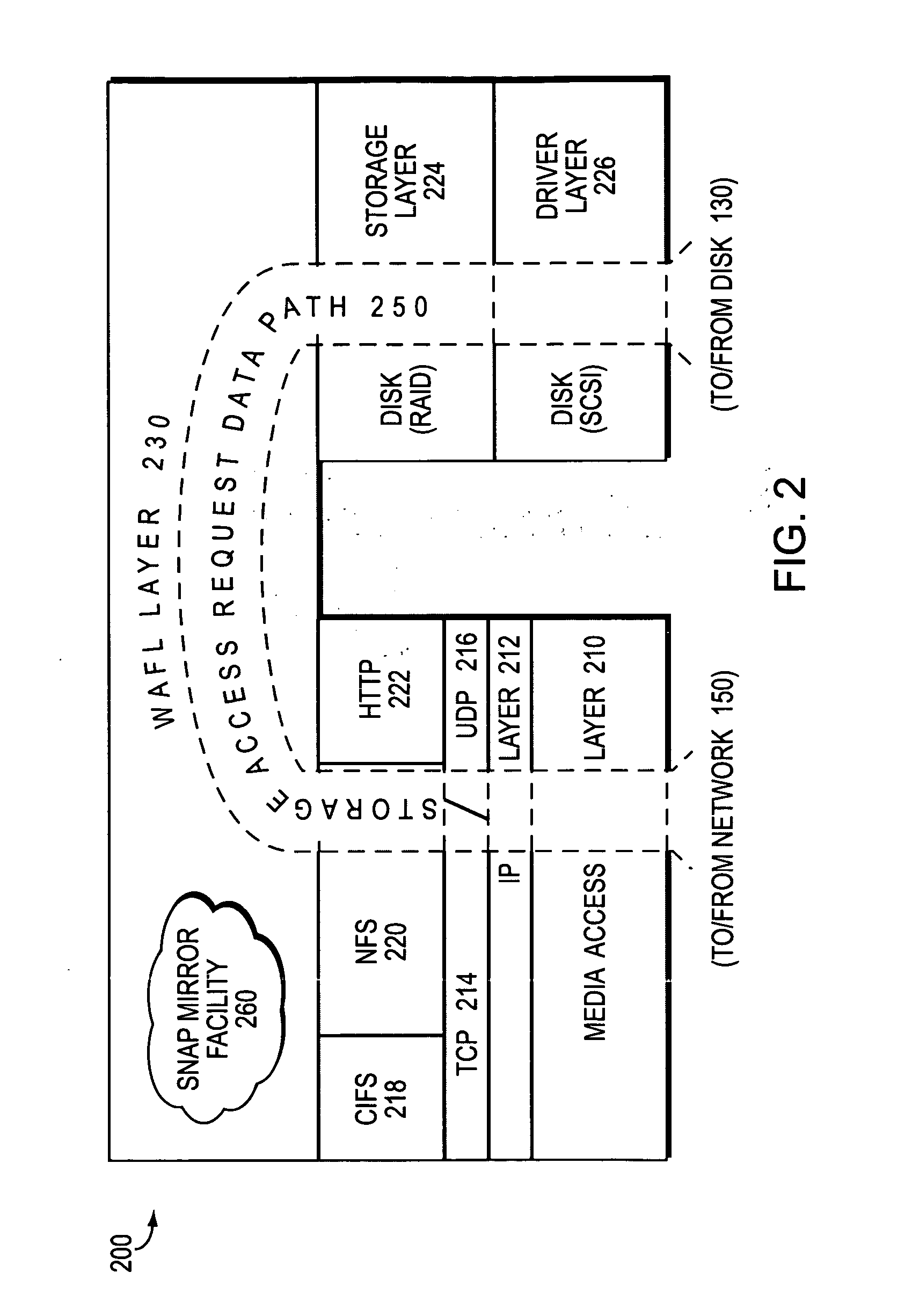
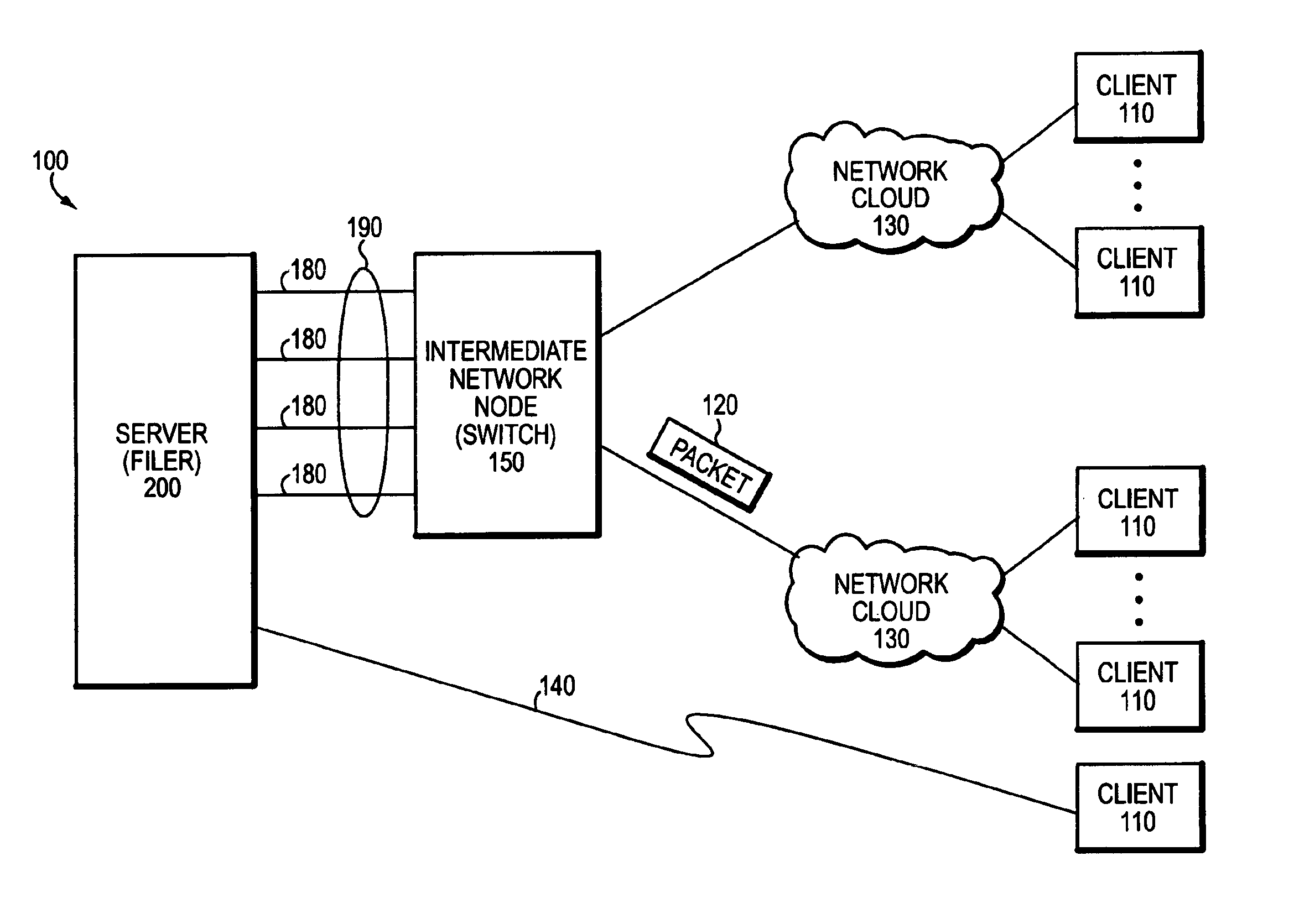
Highly available DNS resolver and method for use of the same
ActiveUS7426576B1Network degradationReliance has been minimizedMultiple digital computer combinationsTransmissionDomain nameOperational system
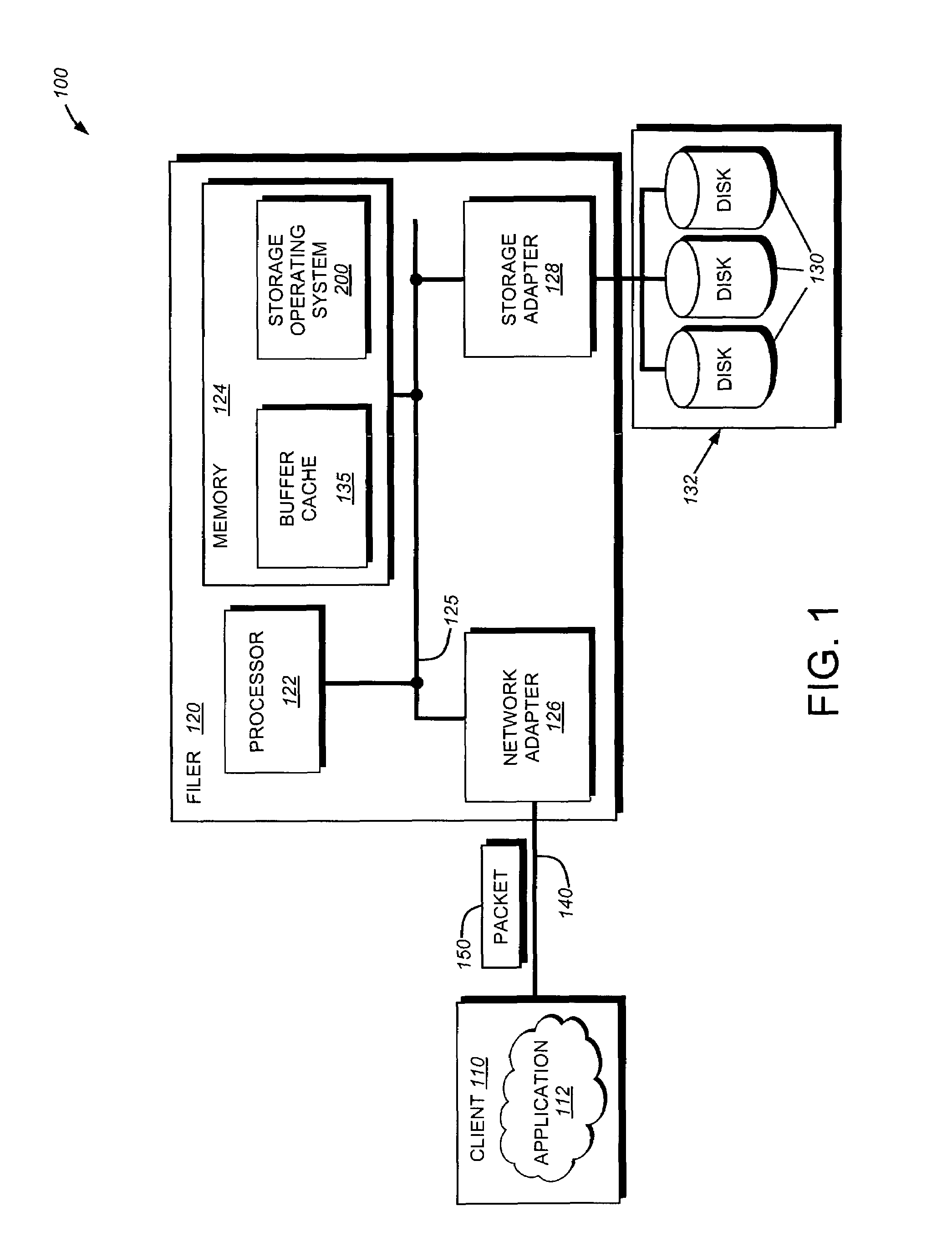
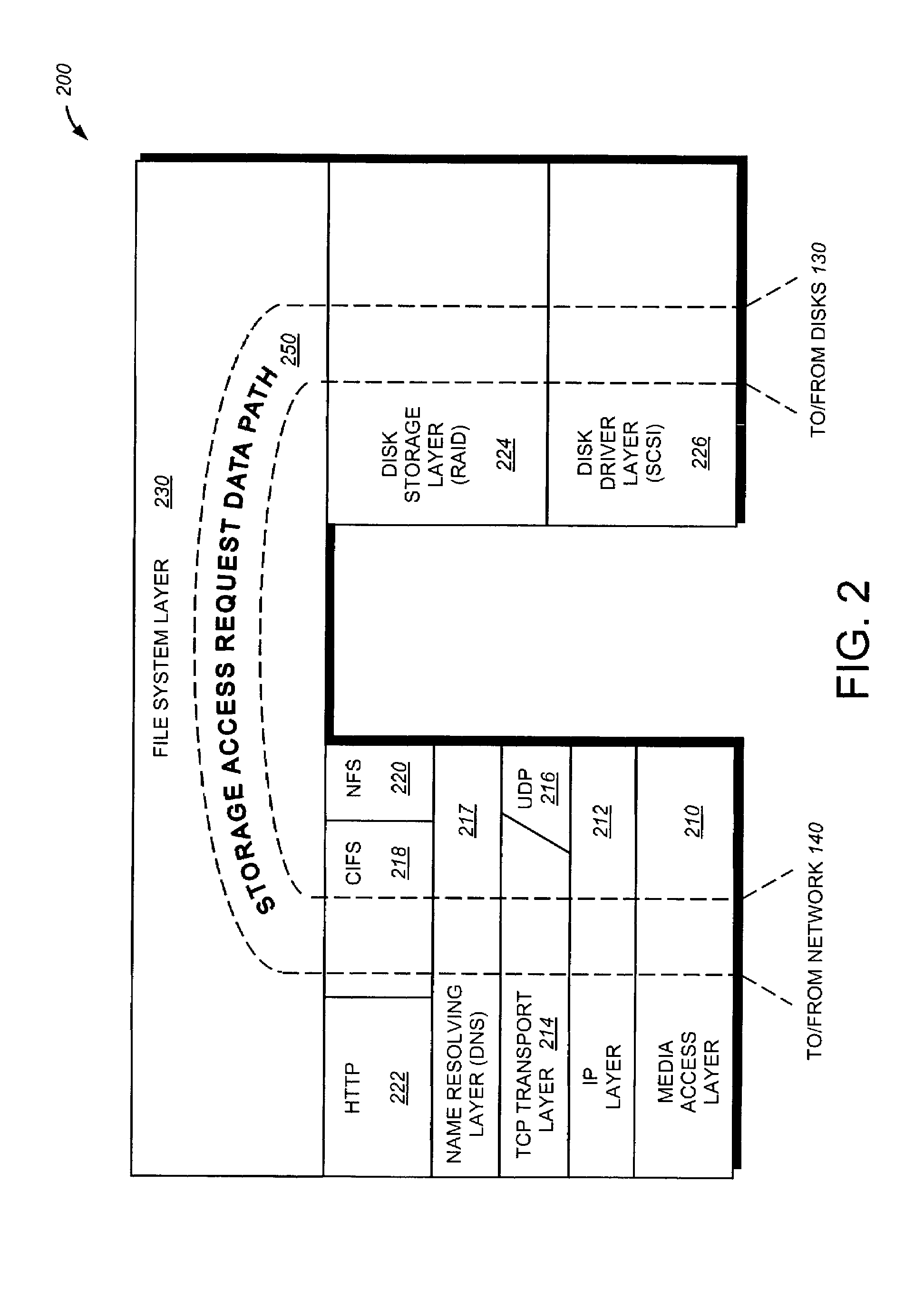
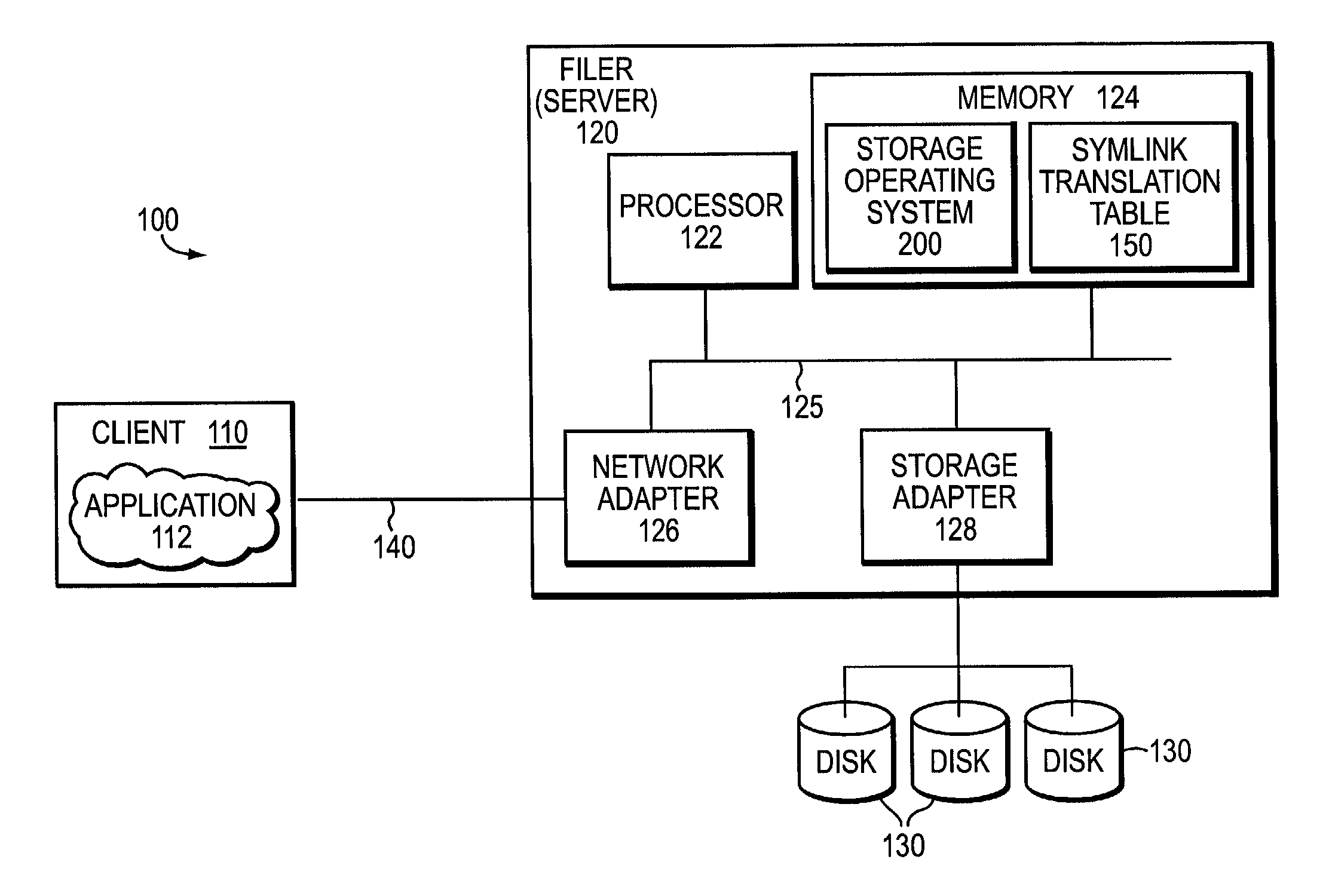
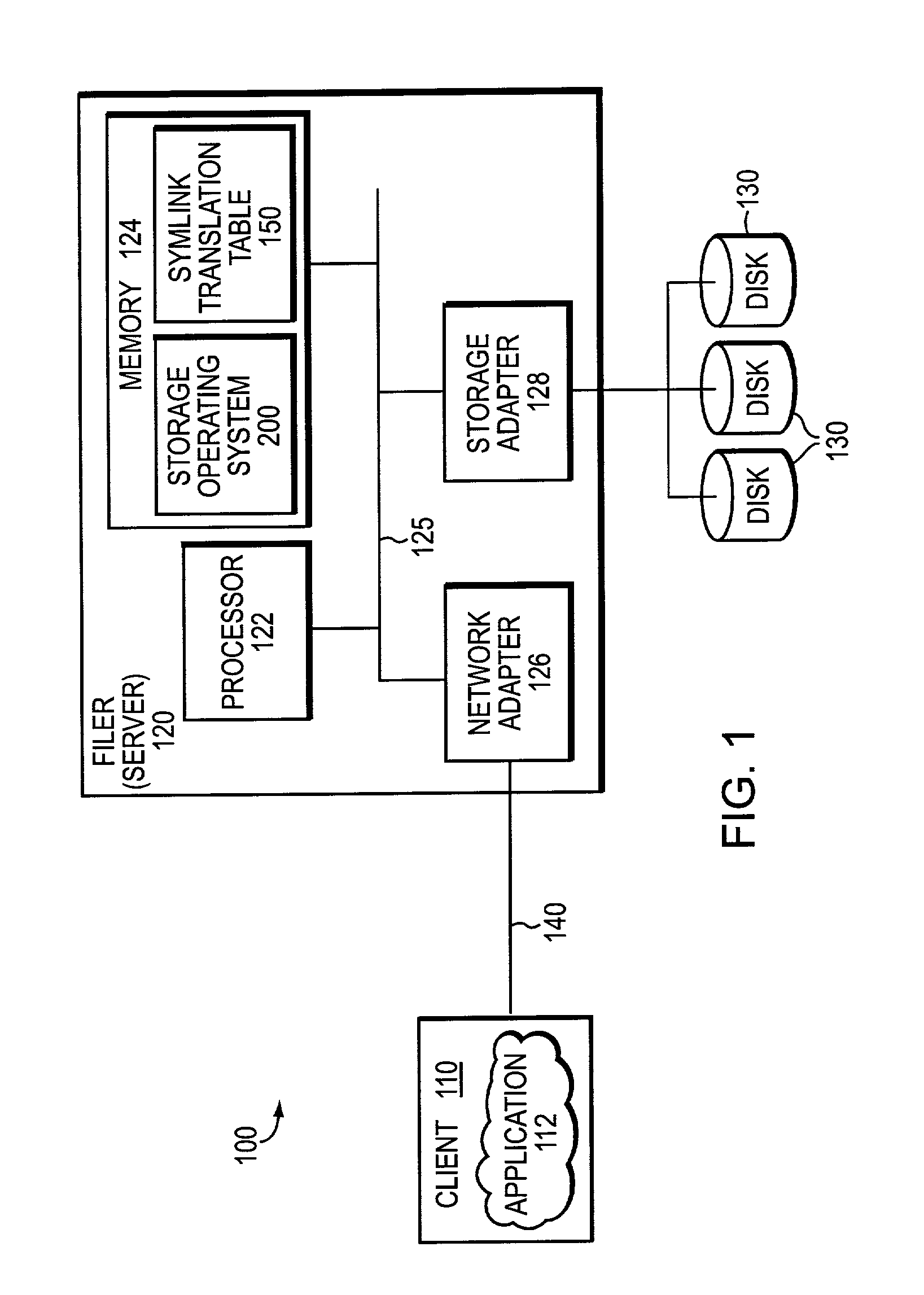
The present invention relates to an enhanced DNS resolver architecture configured to operate in high availability environments, such as the Internet. Specifically, the DNS resolver code of the present invention may be implemented by a storage operating system in a filer. The resolver code modifies a conventional resolver algorithm so as to reduce the time necessary to map IP addresses to alphanumeric domain names and vice versa. Advantageously, the enhanced resolver code keeps track of non-responsive or “dead” DNS servers as well as non-resolvable or “bad” domain names and IP addresses.
Owner:NETWORK APPLIANCE INC
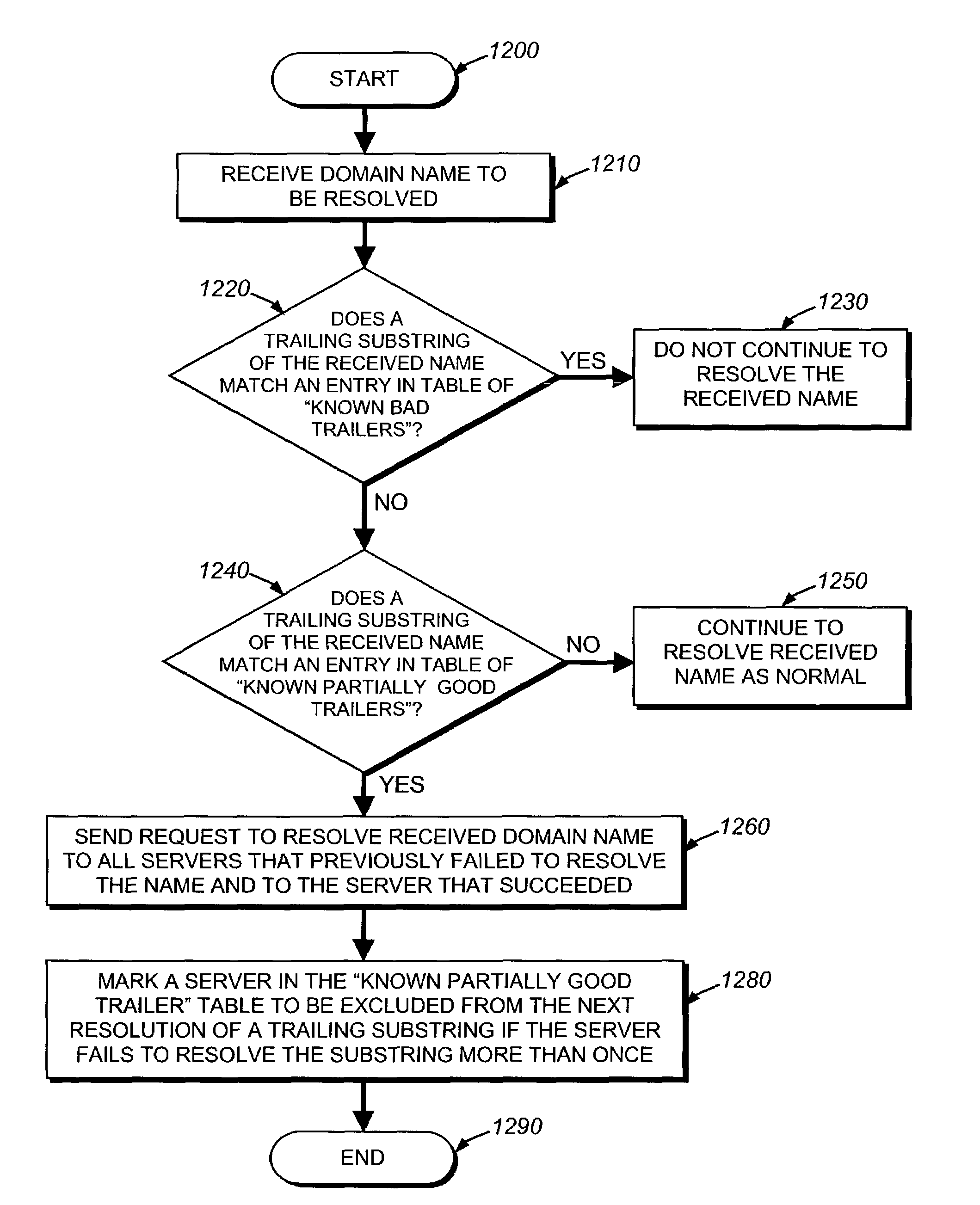
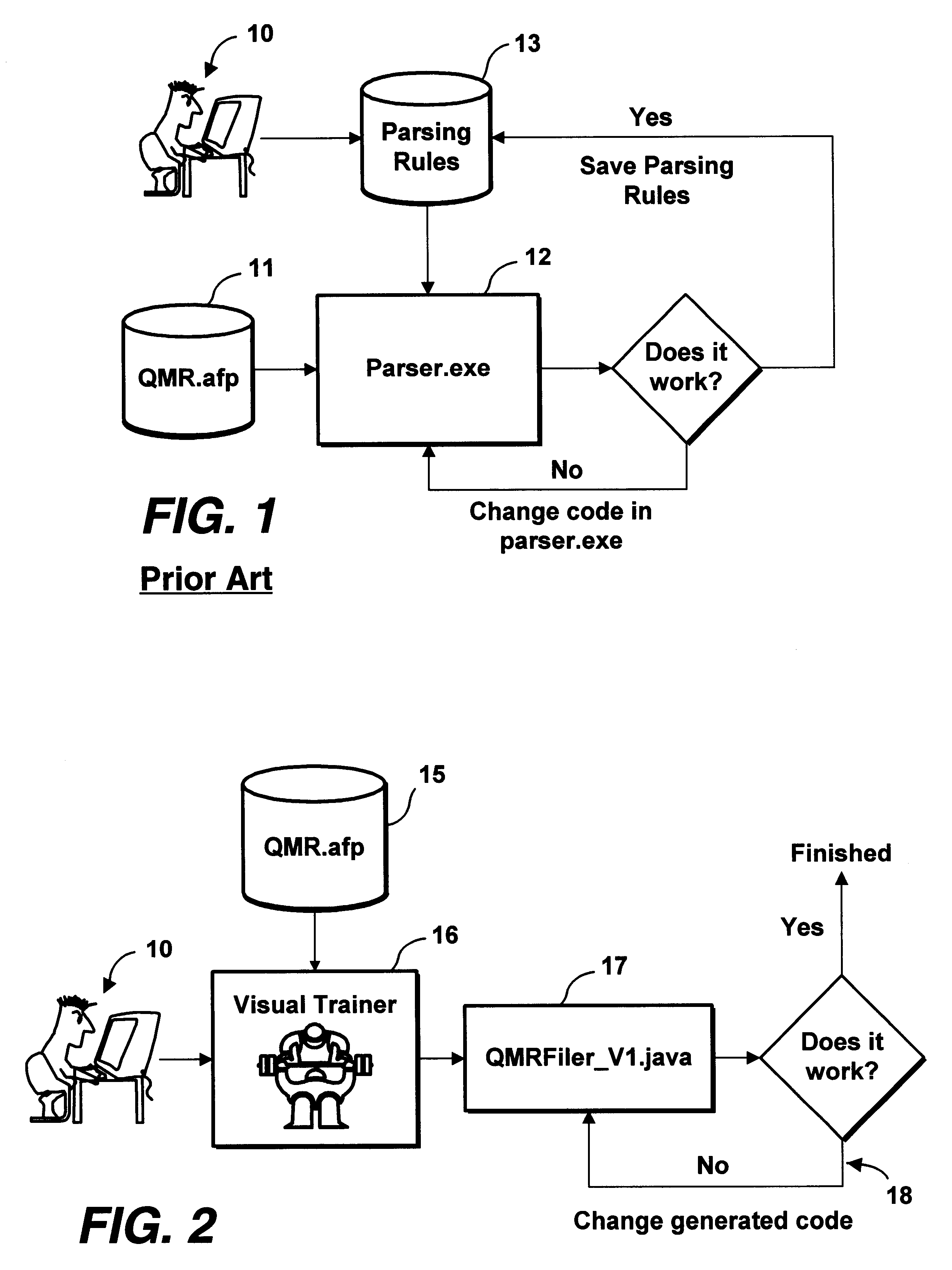
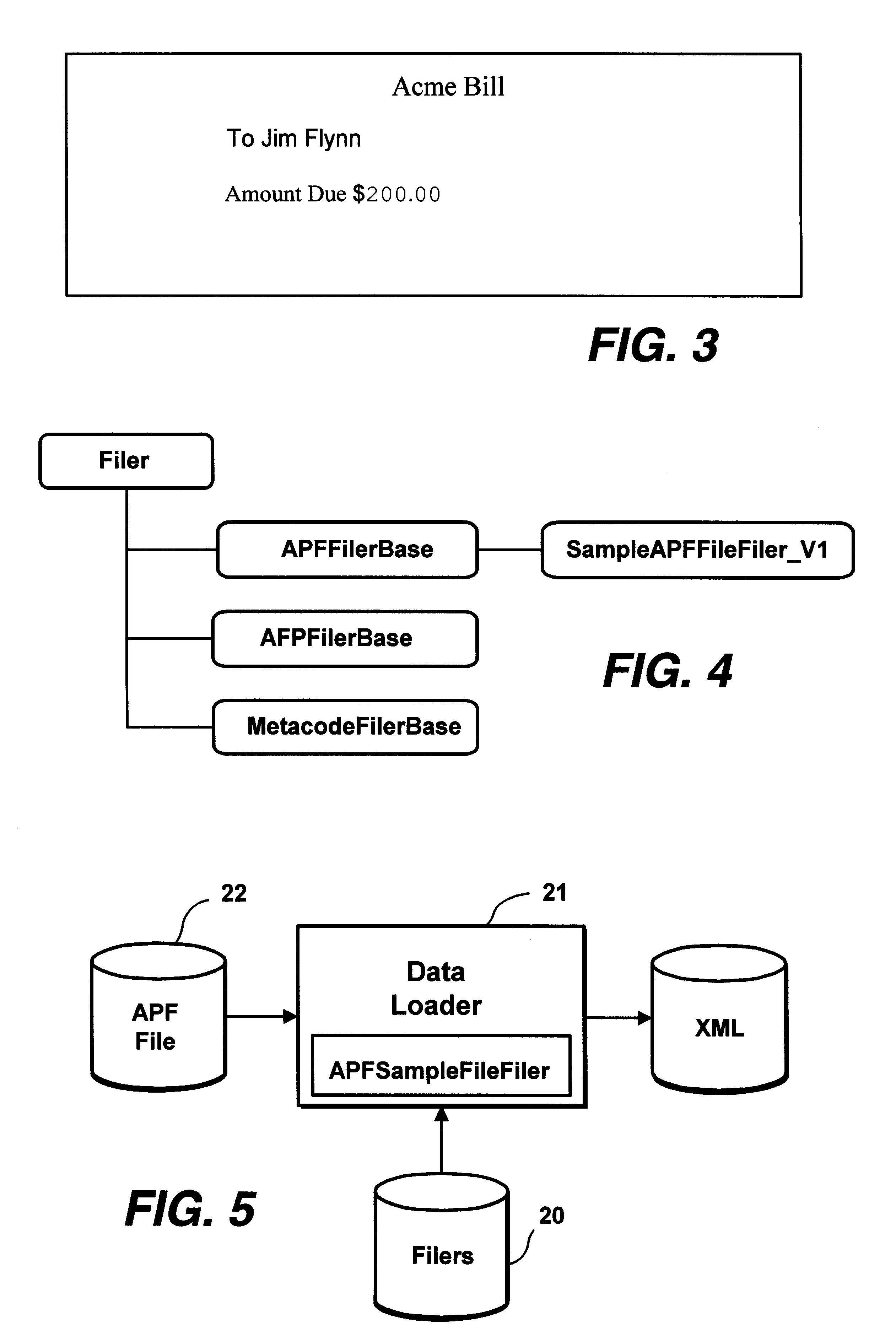
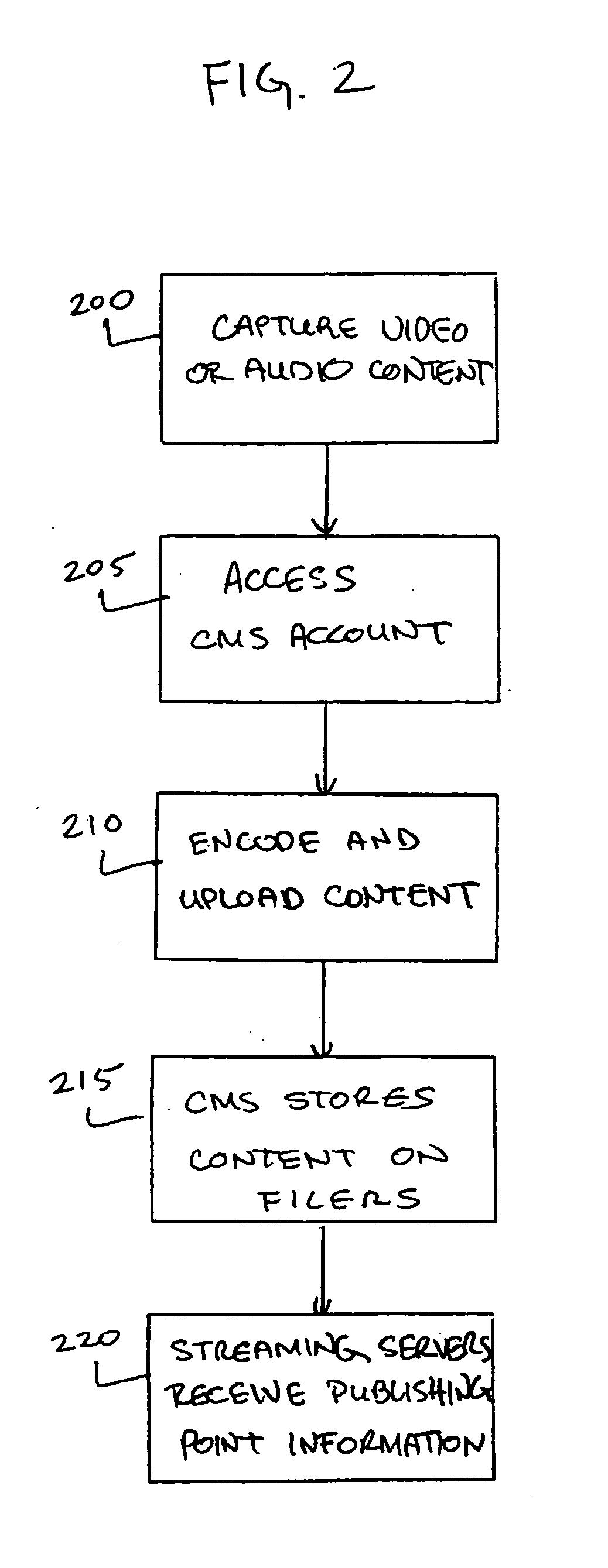
Method facilitating data stream parsing for use with electronic commerce
InactiveUS6850950B1Avoid disadvantagesNatural language data processingBilling/invoicingData setData stream
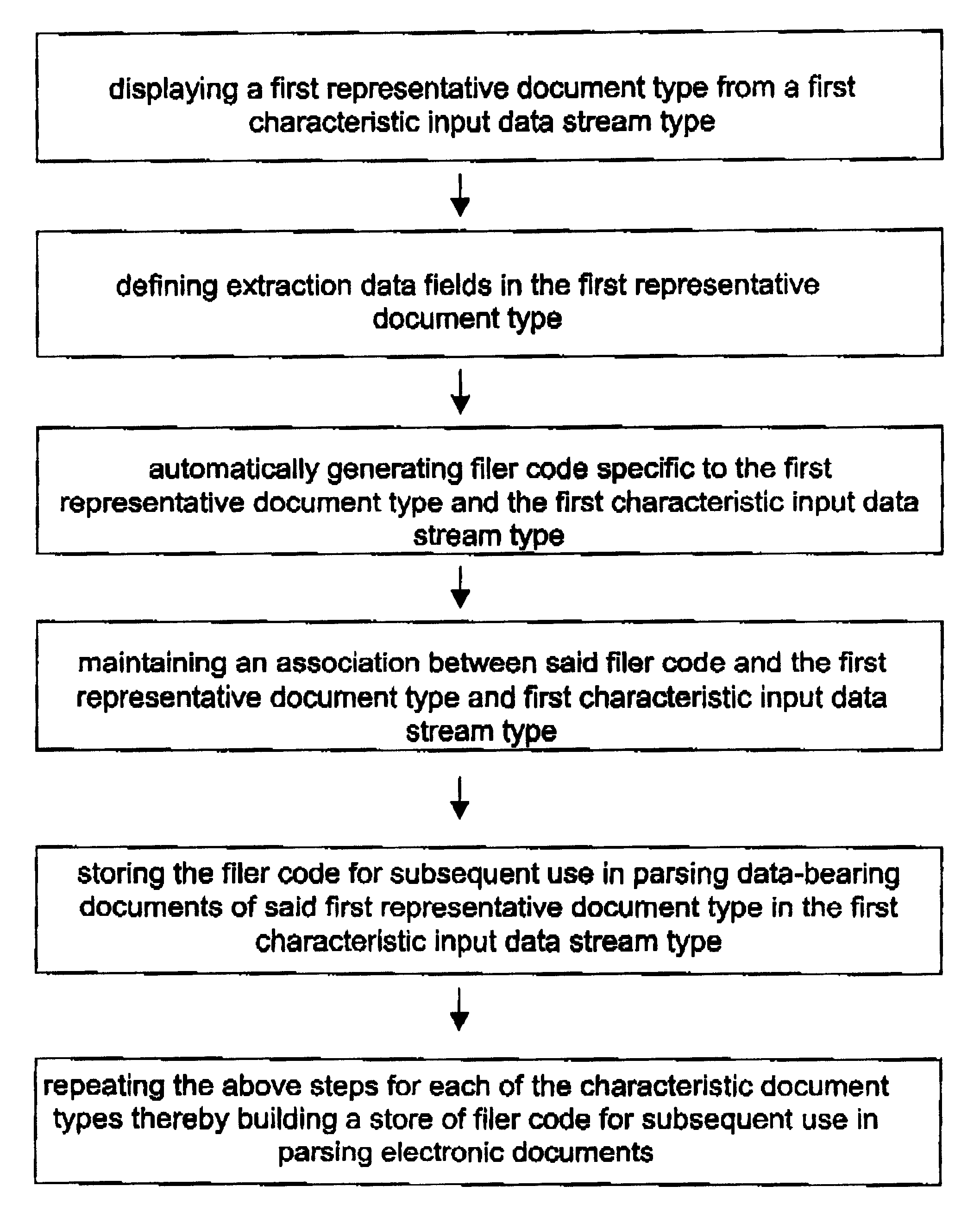
A parsing technique suitable for use in electronic commerce that avoids the disadvantages of known monolithic parsers. The parsing system generates code specific to each input document and data stream type, which may then be updated as needed to handle document-specific idiosyncrasies without requiring modifications to the core parser code. As a user (10) defines parsing rules for extracting data from a representative sample document (15), a visual trainer (16) automatically generates code in the background, referred to as a filer (17), that is specific to that document and that embodies the rules for extracting data from that particular document. The generated code may be modified manually (18) as needed to account for any idiosyncratic conditions associated with the document. Each representative document has associated with it its own filer. A parsing engine (20, 21) comprises a collection of such individual filers appropriate for the types of documents that arise in any given organization. A mapping or other association is maintained between representative document types and their filers. In regular operation, a user selects a data set to be extracted from certain documents. When the parsing engine receives a document in an input data stream, the associated filer is loaded and parses that document for the selected data set. Then another filer is loaded in response to another input document, and so on. The filers may be especially efficiently generated using an object-oriented approach and then dynamically instantiated at run time as may be conveniently achieved, for example, in the Java programming language.
Owner:PITNEY BOWES INC
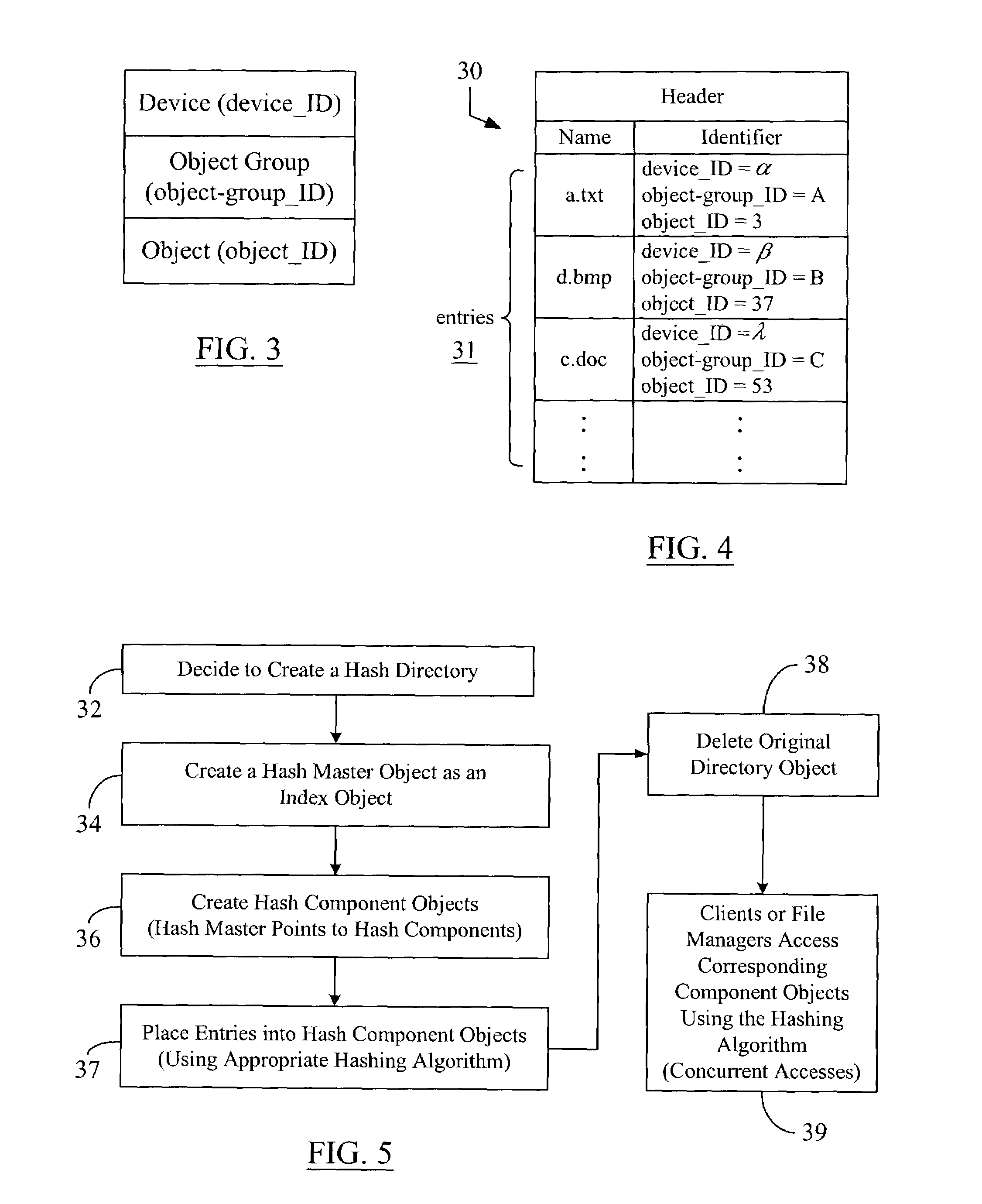
Hashing objects into multiple directories for better concurrency and manageability
ActiveUS7007024B2Decreases manageabilityReduce decreaseData processing applicationsDigital data processing detailsComputer hardwareClient-side
A data storage methodology wherein a hashing algorithm is applied to break a directory object experiencing frequent concurrent accesses from a number of client or manager applications into a predetermined number of hash component objects and a hash master object that manages the component objects. The hash master object and the hash components, together, constitute a hash directory, which replaces the original non-hashed directory object. Each hash component object contains a portion of the entries contained in the original directory object. Each hash component is managed by only one file manager. The entries in the original directory object are distributed among the hash component objects using a predefined hashing algorithm. The creation of hash components and the hash master allows more than one client application or file manager to concurrently write corresponding hash components without the need for access coordination on each access.
Owner:PANASAS INC
Remote disaster recovery and data migration using virtual appliance migration
InactiveUS20070038887A1Create efficientlyEfficiently servingError detection/correctionData setClient-side
A technique efficiently creates and serves a backup data set on a backup filer located at a remote site from a primary filer by essentially moving an entire operating environment of a primary data set to the backup filer. The primary filer is organized into one or more virtual filers (vfilers), one of which (the primary vfiler) is configured to serve data, such as the primary data set, for a client. In the event that the primary filer or primary vfiler becomes unavailable, the technique may be implemented as a disaster recovery or data migration sequence to enable efficient instantiation of a backup vfiler to serve the backup data set for the client.
Owner:NETWORK APPLIANCE INC
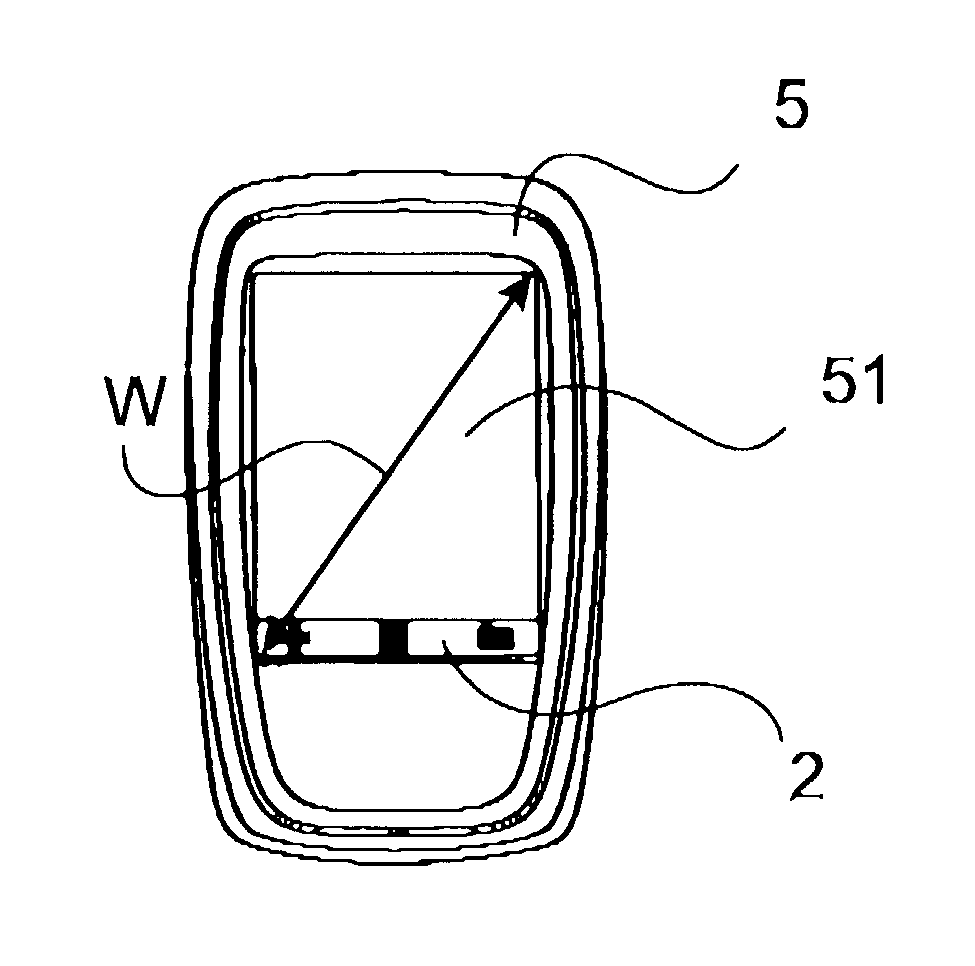
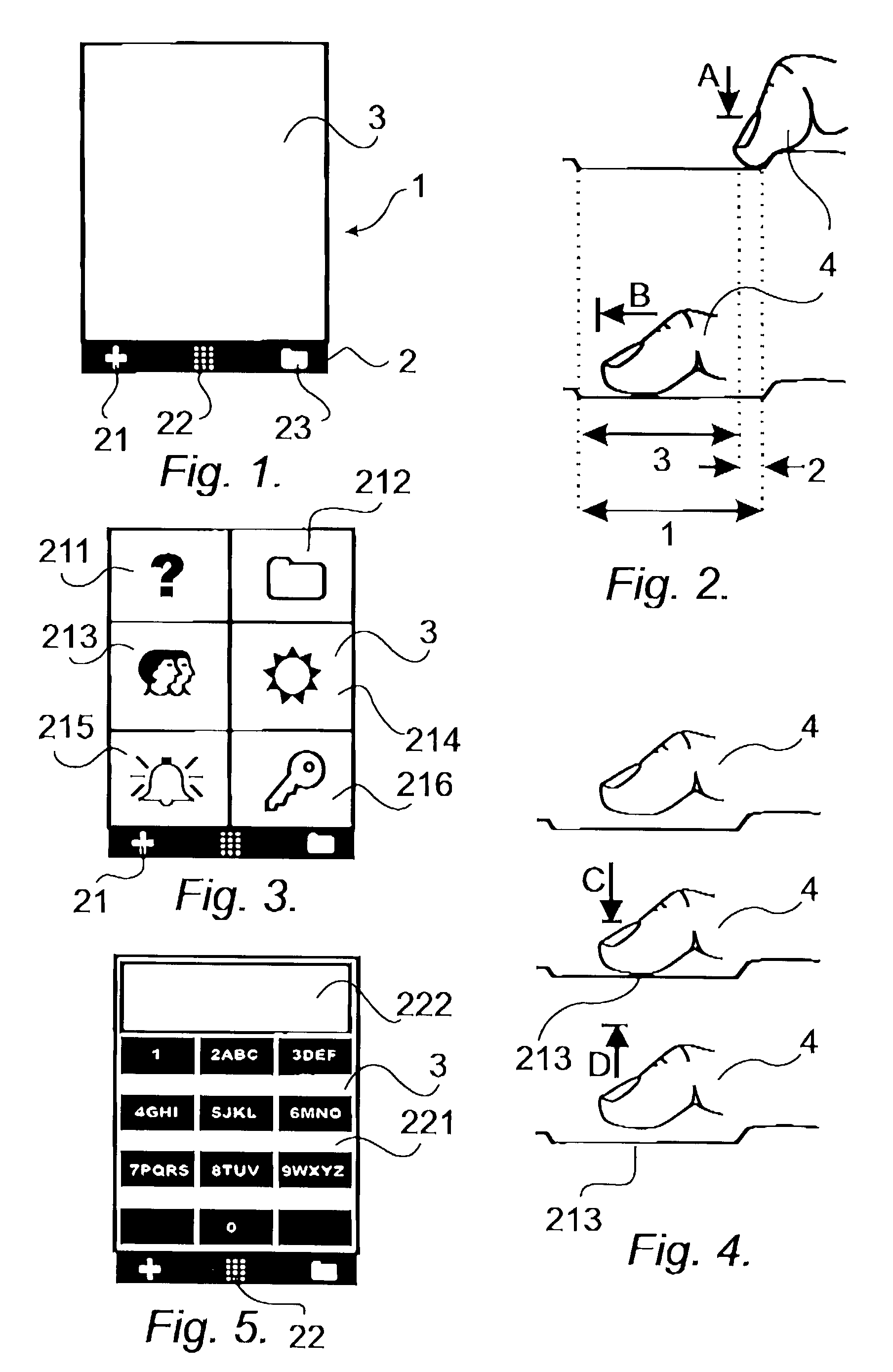
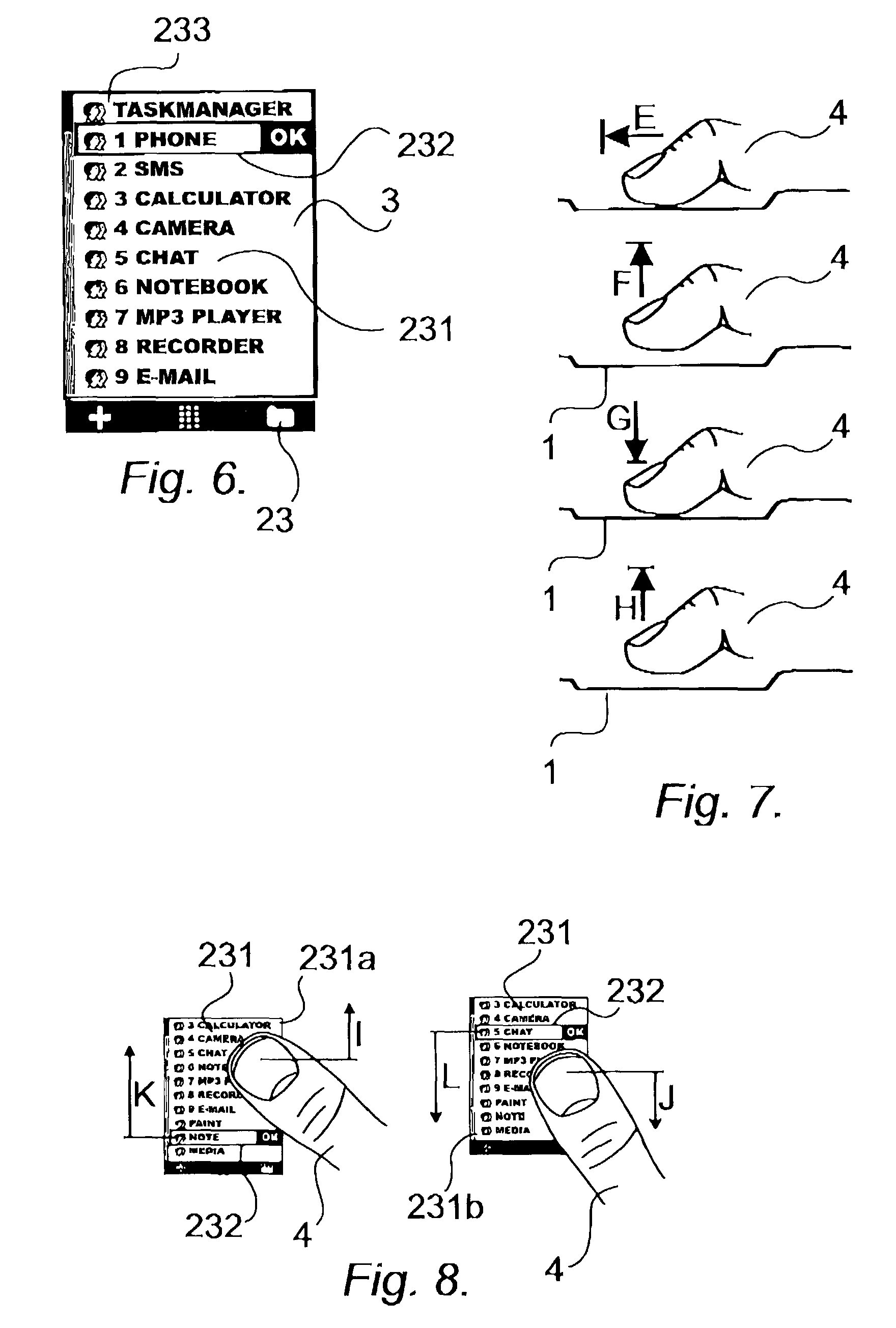
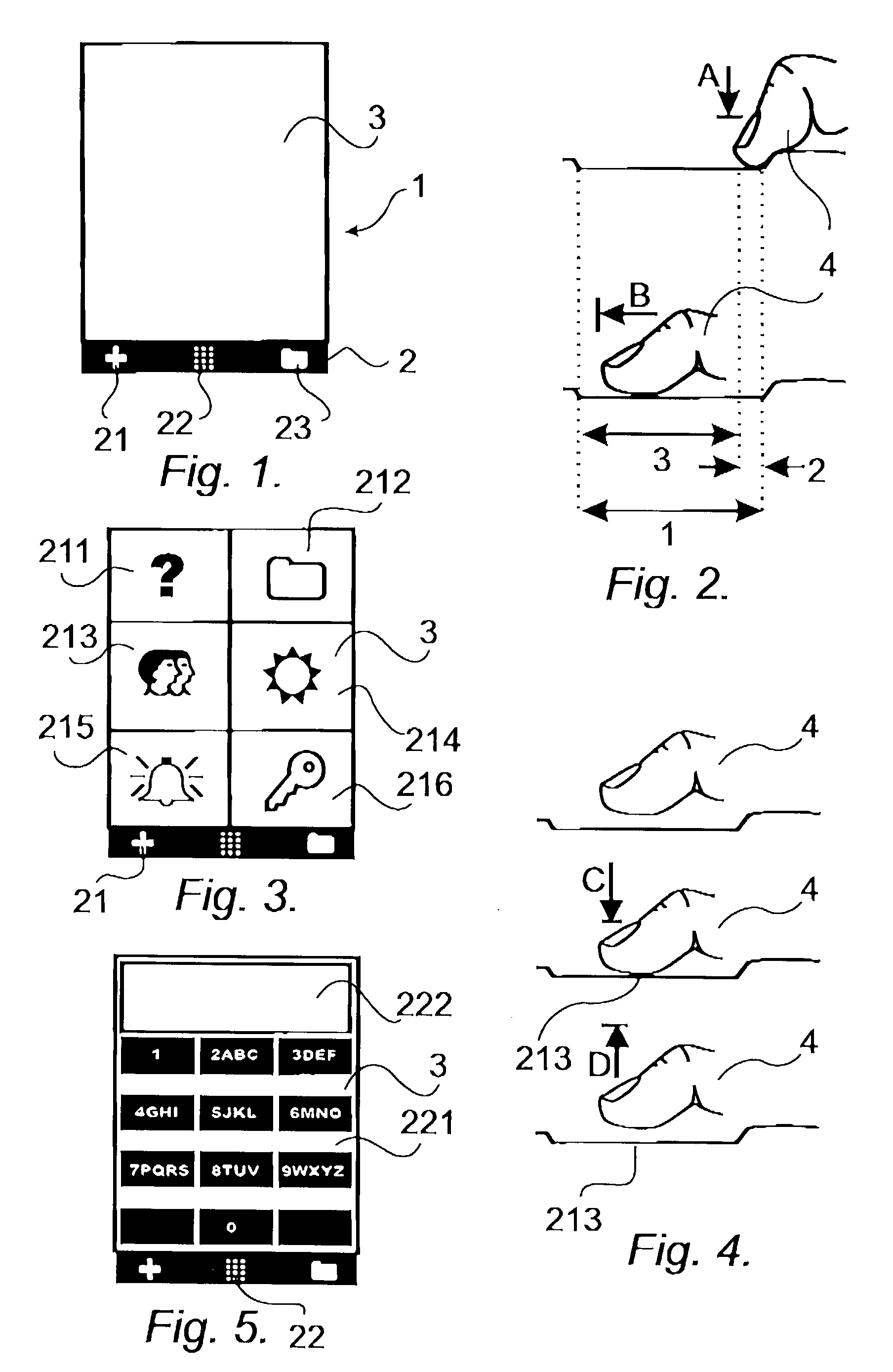
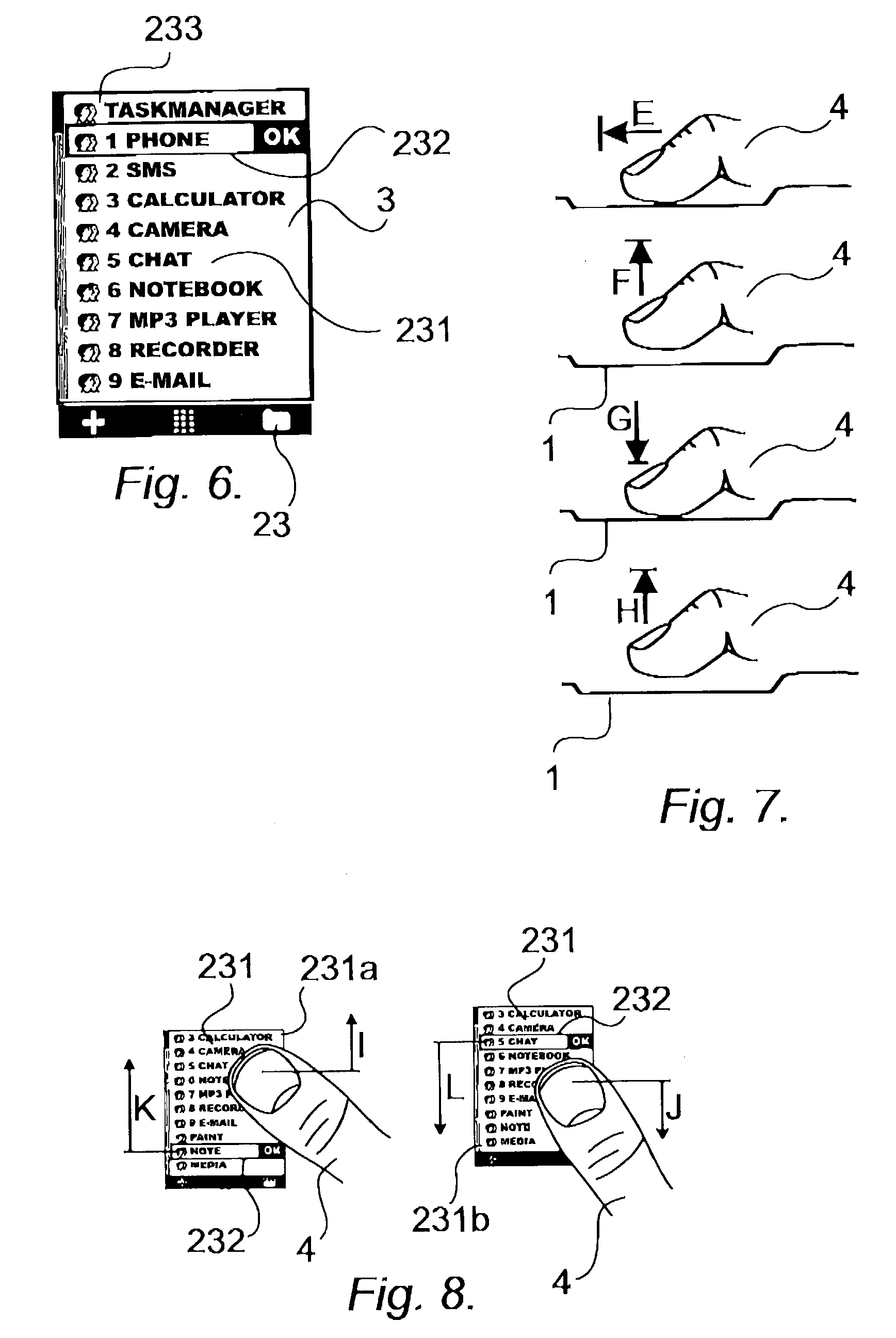
User interface for mobile handheld computer unit
ActiveUS8095879B2Input/output for user-computer interactionCathode-ray tube indicatorsEngineeringHand Held Computer
The present invention relates to a user interface for a mobile handheld computer unit, which computer unit comprises a touch sensitive area (1), which is divided into a menu area (2) and a display area (3). The computer unit is adapted to run several applications simultaneously and to present an active application on top of any other application on the display area (3). The menu area (2) is adapted to present a representation of a first (21), a second (22) and a third predefined (23) function. The first function (21) is a general application dependent function, the second function (22) is a keyboard function, and the third function (23) is a task and file manager. Any one of these three functions can be activated when the touch sensitive area (1) detects a movement of an object with its starting point within the representation of the function on the menu area (2) and with a direction from the menu area (2) to the display area (3).
Owner:NEONODE SMARTPHONE LLC
Streaming media content delivery system and method for delivering streaming content
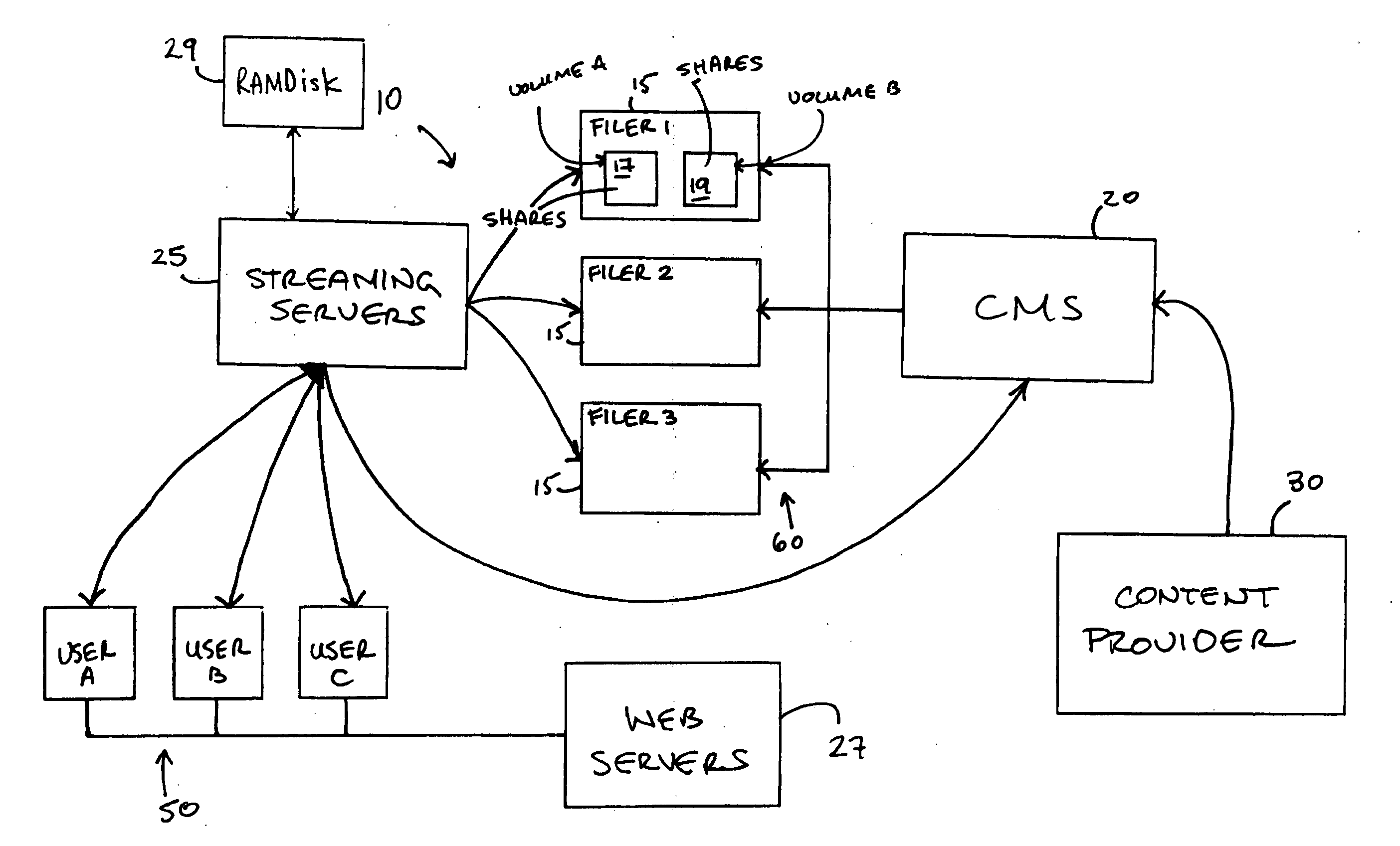
ActiveUS20060230170A1Reduce needReduce in quantityMultiple digital computer combinationsTelevision systemsMedia serverComputer science
A method for delivering streaming media files to a plurality of end users from a streaming media delivery system including a filer for storing the media files and a streaming server for serving the media files generally includes the steps of monitoring demand for the streaming media files, identifying at least one of the streaming media files to be cached when demand for the at least one of the streaming media files reaches a pre-defined threshold, copying the streaming media file to a streaming server from a media storage device, and streaming the streaming media file using the copy stored locally on the streaming server.
Owner:YAHOO ASSETS LLC
User interface
ActiveUS20040109013A1Highly simplifiedSimplify the viewing processInput/output for user-computer interactionCathode-ray tube indicatorsHand Held ComputerHuman–computer interaction
The present invention relates to a user interface for a mobile handheld computer unit, which computer unit comprises a touch sensitive area (1), which is divided into a menu area (2) and a display area (3). The computer unit is adapted to run several applications simultaneously and to present an active application on top of any other application on the display area (3). The menu area (2) is adapted to present a representation of a first (21), a second (22) and a third predefined (23) function. The first function (21) is a general application dependent function, the second function (22) is a keyboard function, and the third function (23) is a task and file manager. Any one of these three functions can be activated when the touch sensitive area (1) detects a movement of an object with its starting point within the representation of the function on the menu area (2) and with a direction from the menu area (2) to the display area (3).
Owner:NEONODE SMARTPHONE LLC
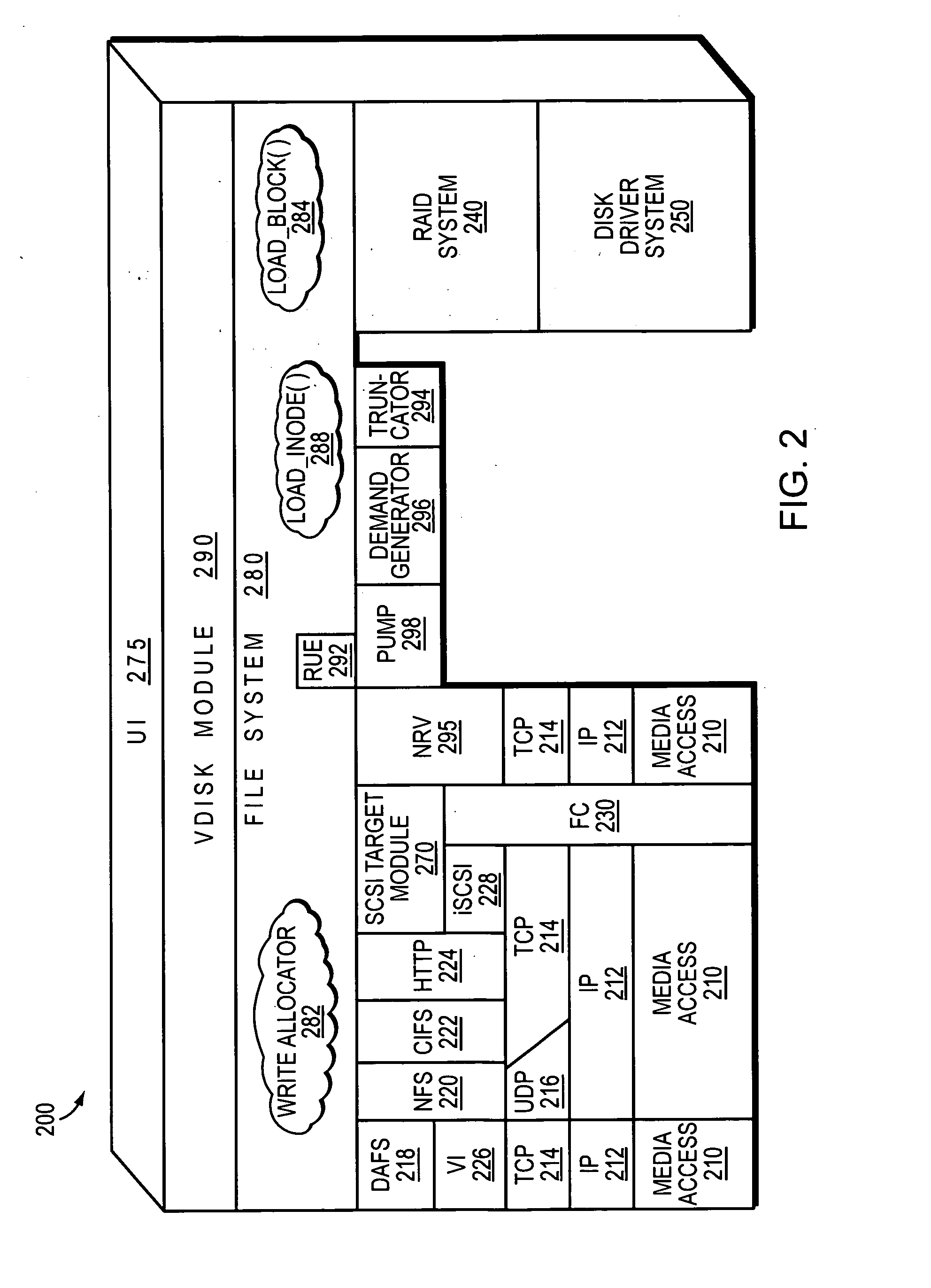
Technique to enable support for symbolic link access by windows clients
ActiveUS6968345B1Solve problemsEnhanced levelData processing applicationsMultiple digital computer combinationsDistributed File SystemSymbolic link
A widelink directive provides an enhanced level of indirection with respect to a resource, such as a unit of storage, attached to a destination, such as a storage system. The widelink has a scope of indirection that is “wider” than a conventional symbolic link (“symlink”). The novel widelink directive is similar to the distributed file system (DFS) facility that allows DFS-enabled common internet file system clients to resolve uniform naming convention paths to locations that may or may not be on an original storage system, such as a multi-protocol filer, or original protocol server of the filer. By taking advantage of clients that support the DFS facility, the widelink directive is quite flexible in that it can be used to resolve symlinks that “leave” a share.
Owner:NETWORK APPLIANCE INC
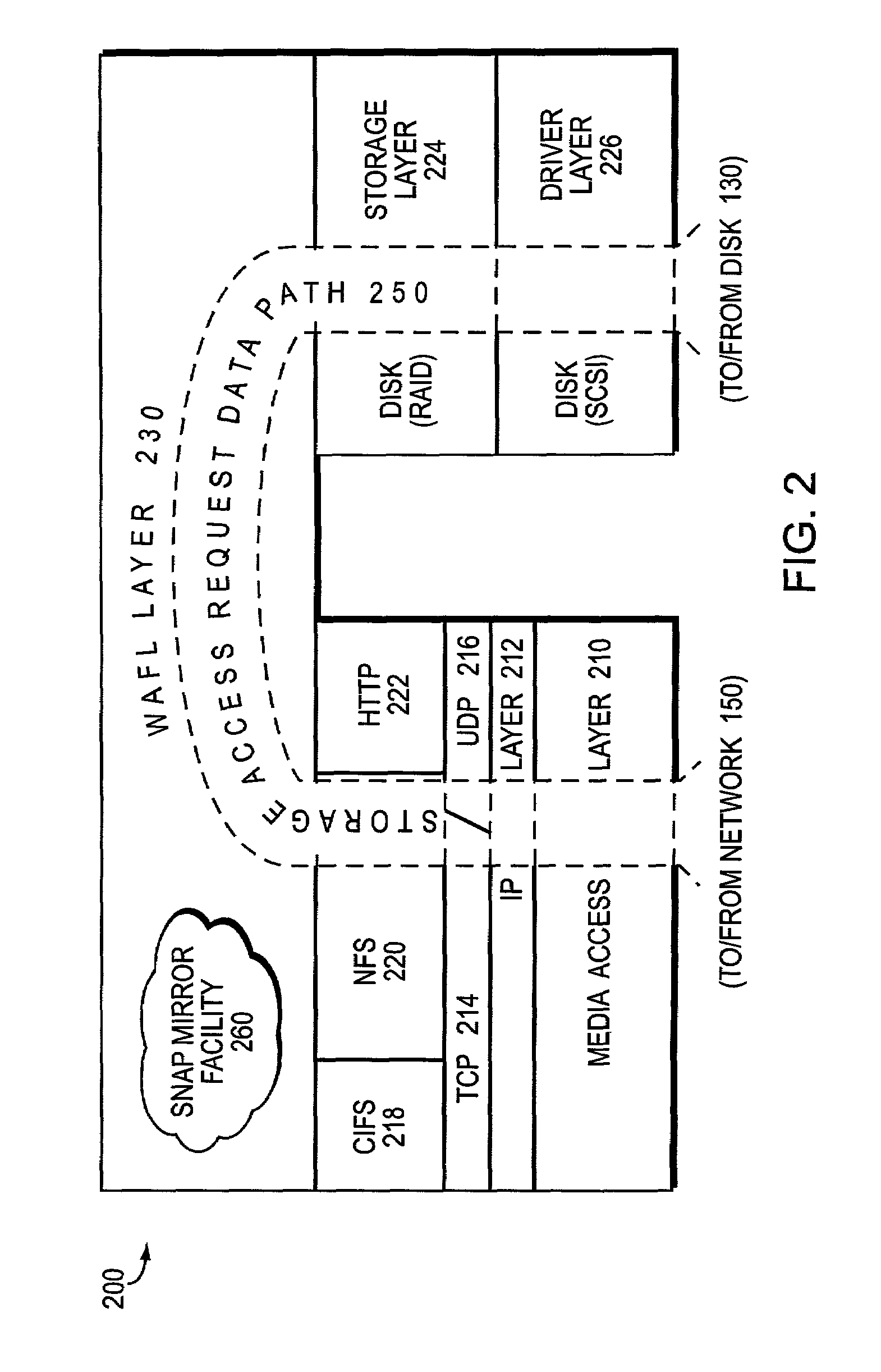
System and method for caching network file systems
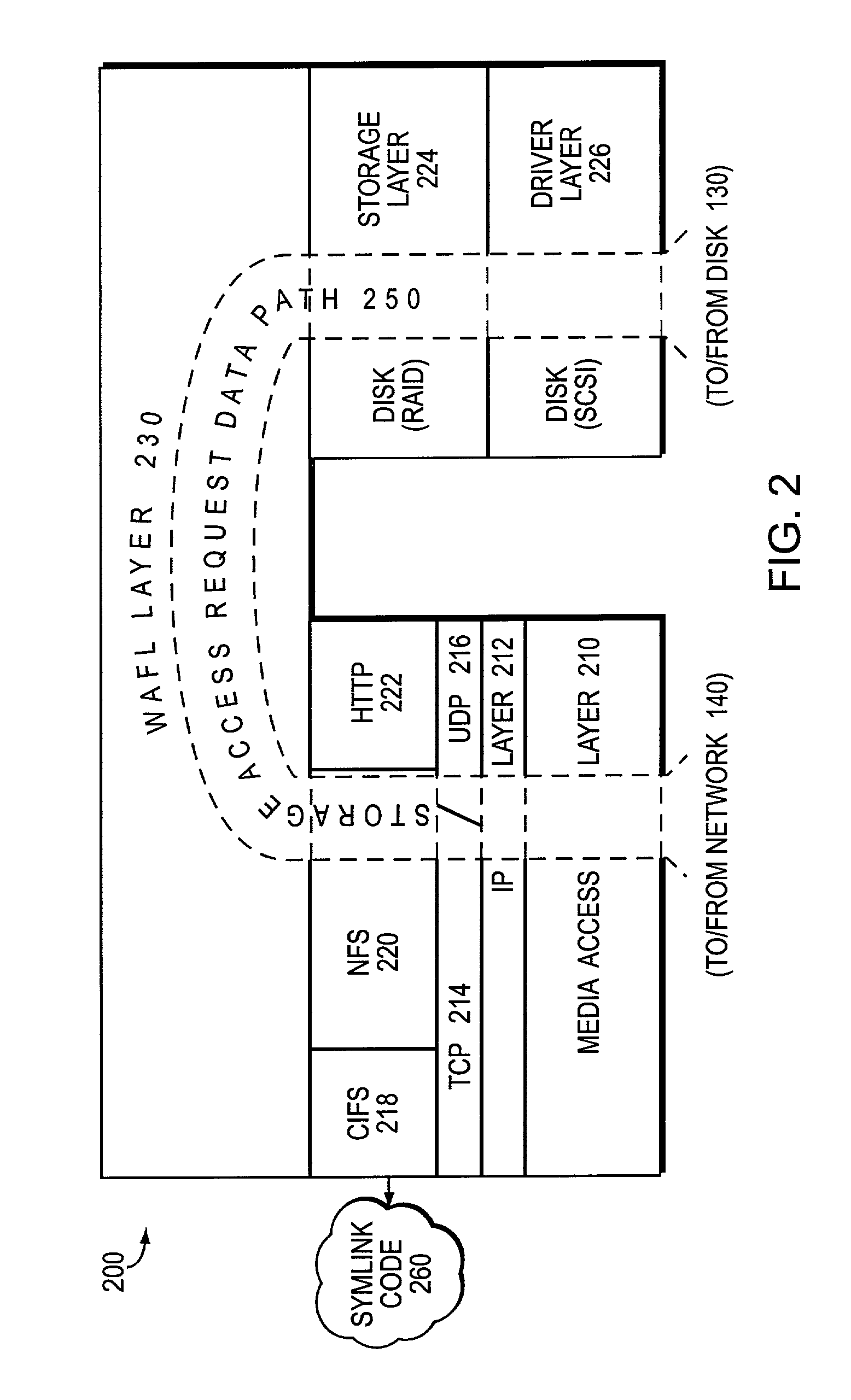
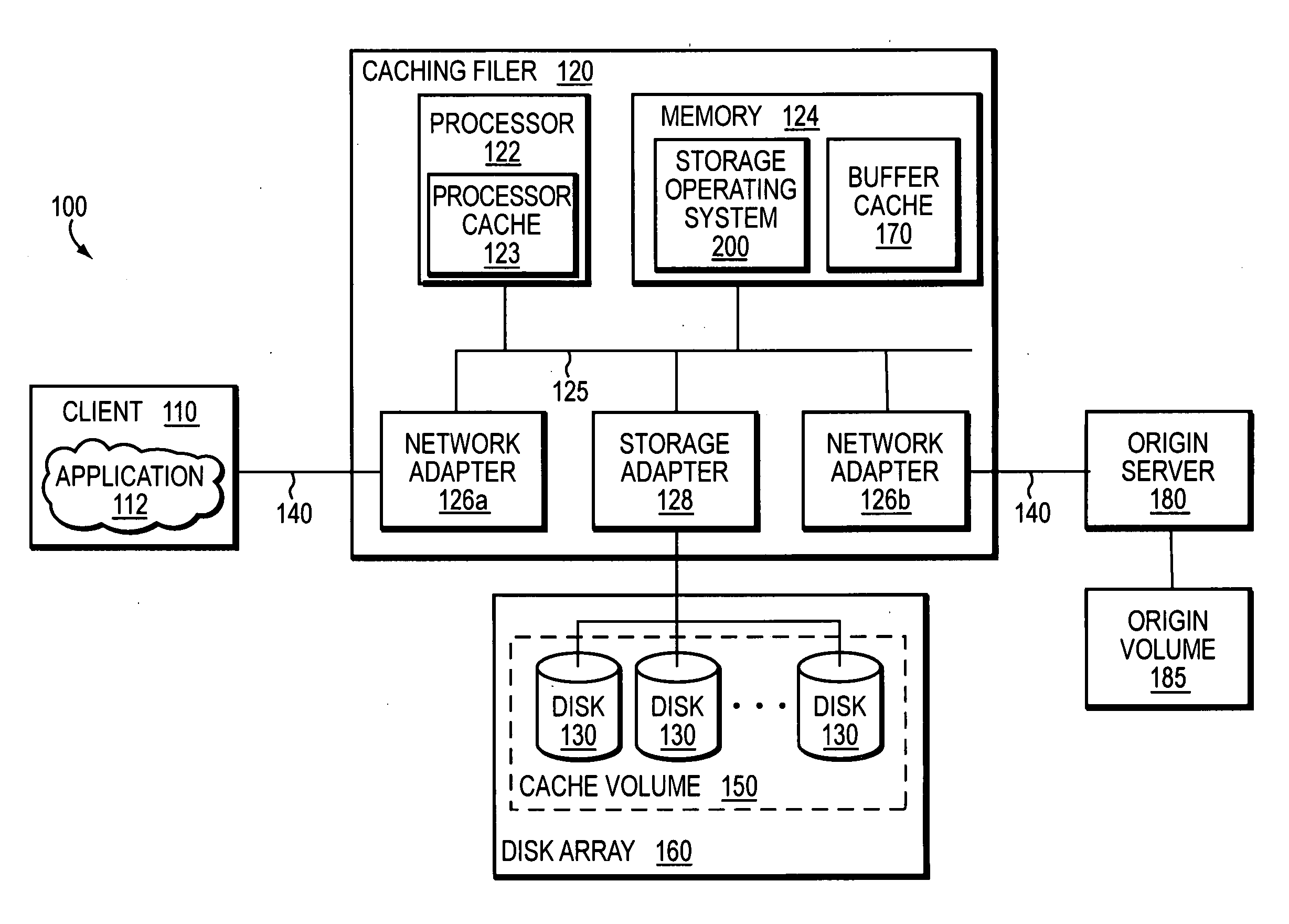
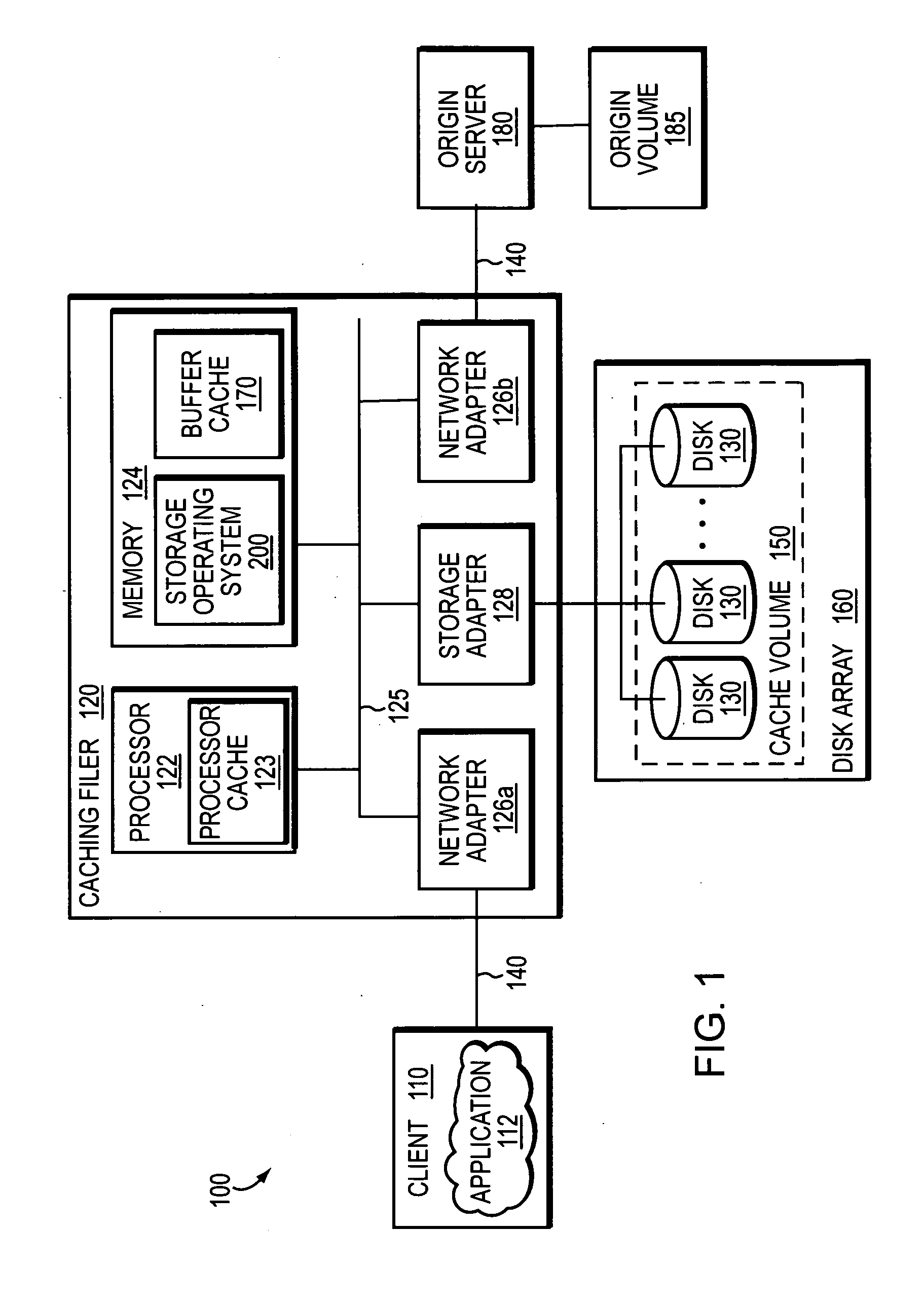
ActiveUS20070250552A1Fast and efficient client accessDigital computer detailsTransmissionPrimitive operationFile system
A network caching system has a multi-protocol caching filer coupled to an origin server to provide storage virtualization of data served by the filer in response to data access requests issued by multi-protocol clients over a computer network. The multi-protocol caching filer includes a file system configured to manage a sparse volume that “virtualizes” a storage space of the data to thereby provide a cache function that enables access to data by the multi-protocol clients. To that end, the caching filer further includes a multi-protocol engine configured to translate the multi-protocol client data access requests into generic file system primitive operations executable by both the caching filer and the origin server.
Owner:NETWORK APPLIANCE INC
Technique for enabling multiple virtual filers on a single filer to participate in multiple address spaces with overlapping network addresses
InactiveUS6895429B2Improve performanceDigital computer detailsSecuring communicationOperational systemRouting table
A technique enables a server, such as a filer, configured with a plurality of virtual servers, such as virtual filers (vfilers), to participate in a plurality of private network address spaces having potentially overlapping network addresses. The technique also enables selection of an appropriate vfiler to service requests within a private address space in a manner that is secure and distinct from other private address spaces supported by the filer. An IPspace refers to each distinct address space in which the filer and its storage operating system participate. An IPspace identifier is applied to translation procedures that enable the selection of a correct vfiler for processing an incoming request and an appropriate routing table for processing an outgoing request.
Owner:NETWORK APPLIANCE INC
System and method for supporting block-based protocols on a virtual storage appliance executing within a physical storage appliance
InactiveUS20050228835A1Input/output to record carriersComputer security arrangementsOperational systemSecurity domain
An architecture provides the ability to create and maintain multiple instances of virtual servers, such as virtual filers (vfilers), within a server, such as a storage appliance. A vfiler is a logical partitioning of network and storage resources of the storage appliance platform to establish an instance of a multi-protocol server. Each vfiler is allocated a subset of dedicated units of storage resources, such as volumes or logical sub-volumes (qtrees), and one or more network address resources. Each vfiler is also allowed shared access to a file system resource of a storage operating system. To ensure controlled access to the allocated and shared resources, each vfiler is further assigned its own security domain for each access protocol. A vfiler boundary check is performed by the file system to verify that a current vfiler is allowed to access certain storage resources for a requested file stored on the filer platform.
Owner:NETWORK APPLIANCE INC
Multi-protocol lock manager
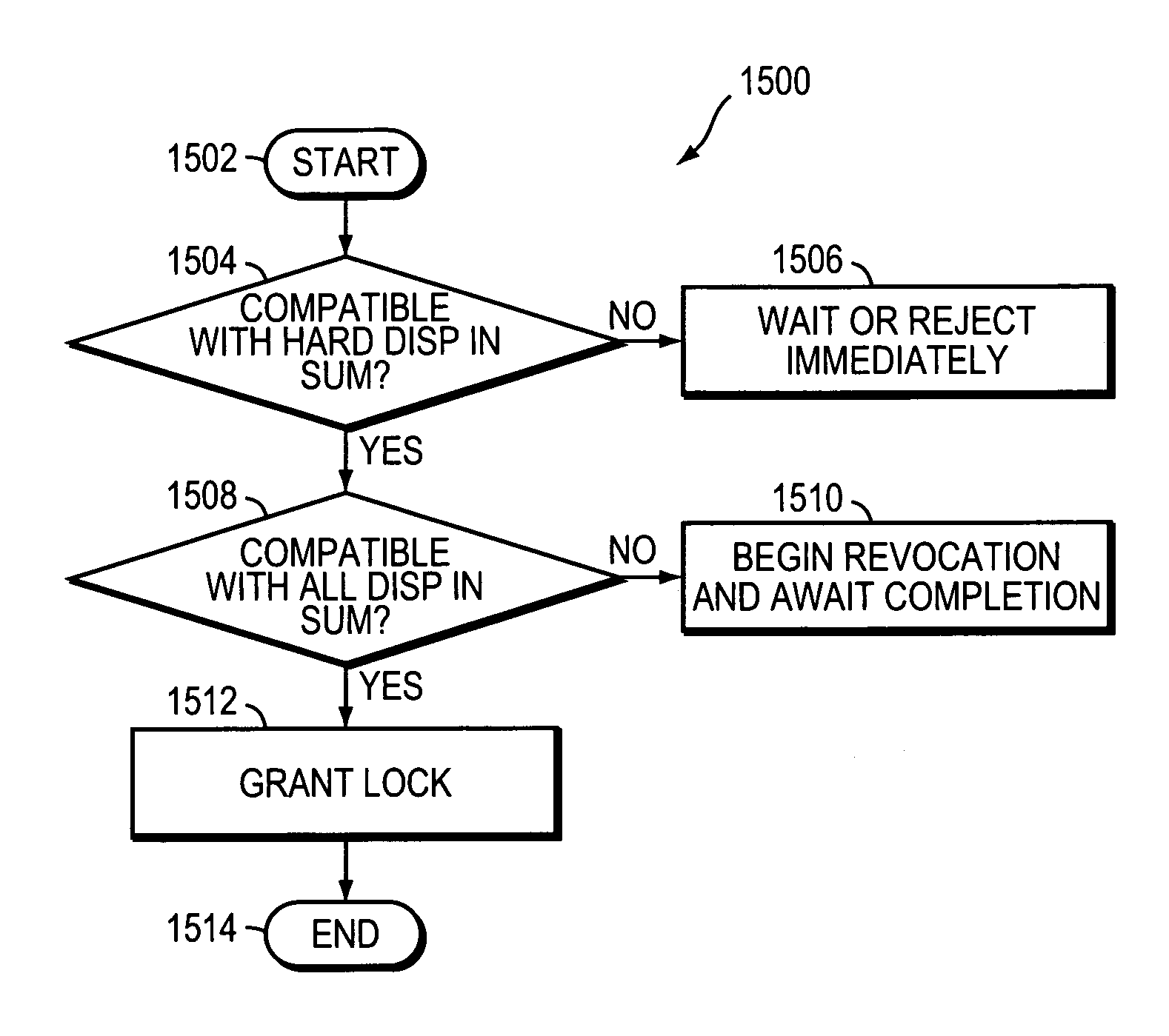
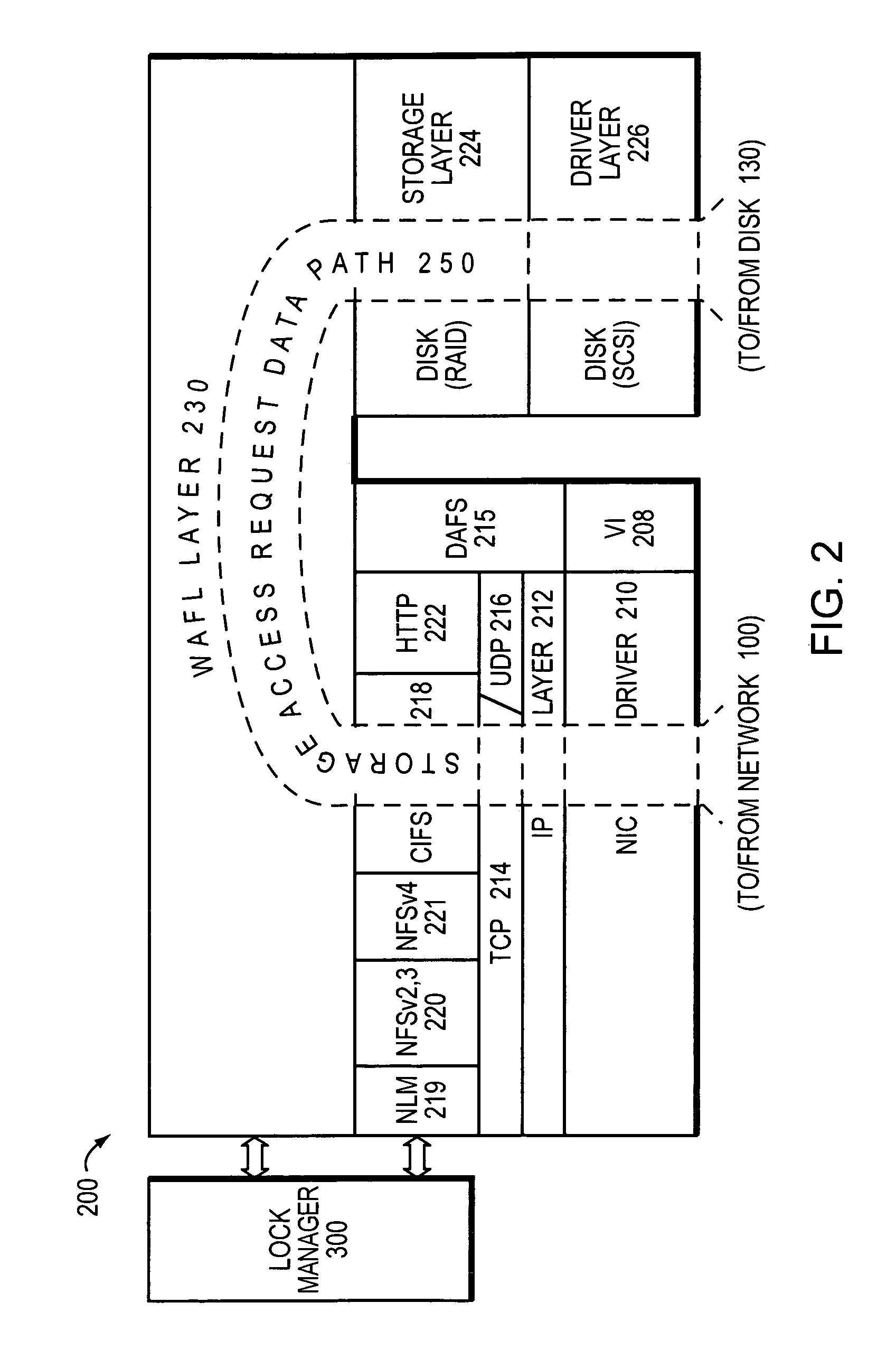
ActiveUS7313557B1Data processing applicationsDigital data information retrievalLock managerSemantics
A multi-protocol lock manager efficiently manages granting, revoking and releasing of various types of locks on files or regions of files located on a file server, such as a filer. The various locks are associated with multiple different file access protocols, each having its own semantics. The multi-protocol lock manager allows the filer to take appropriate actions with respect to locking requests and other file access operations, while ensuring that the actions taken are always consistent with semantic requirements for each lock, as established by the associated file access protocol.
Owner:NETWORK APPLIANCE INC
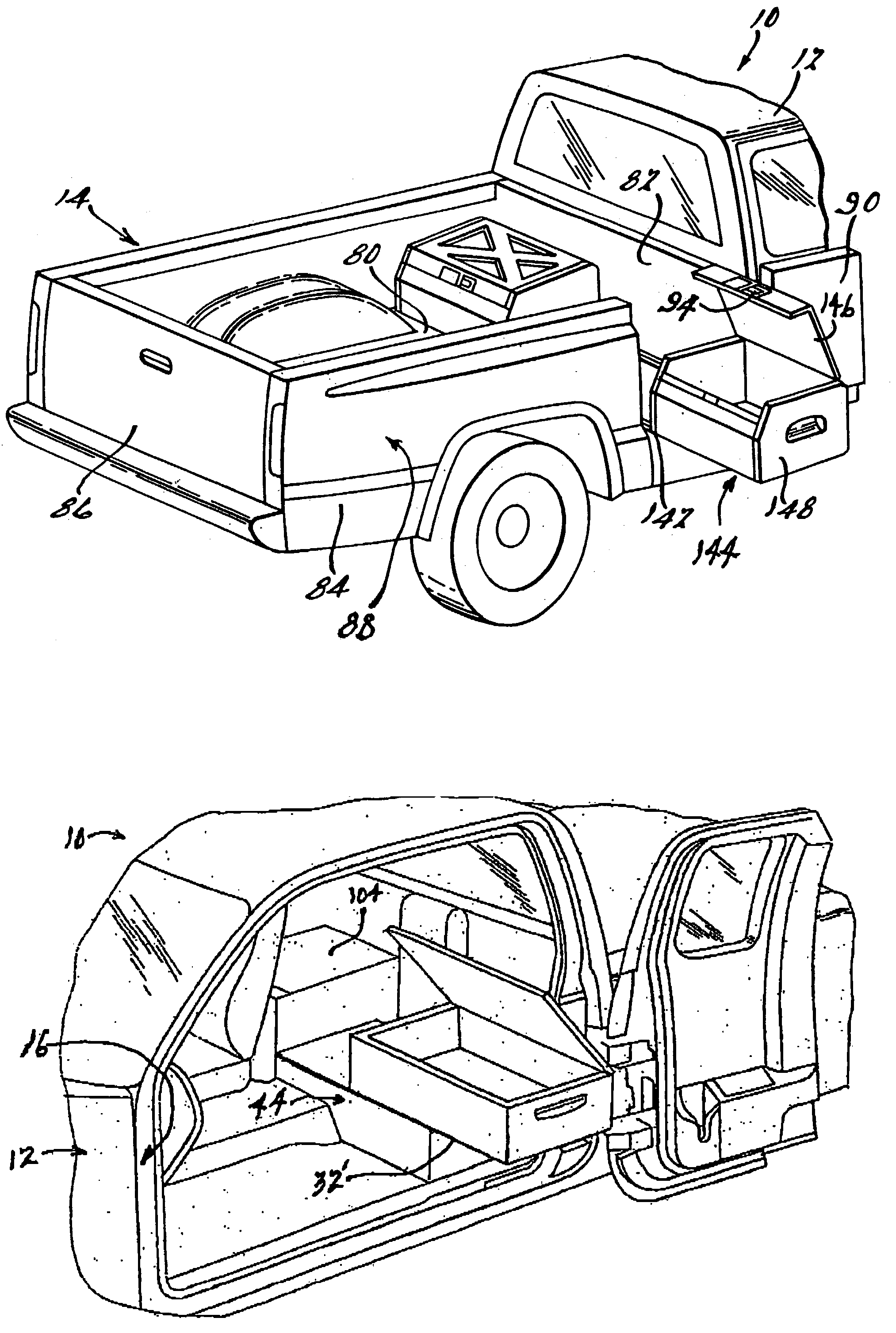
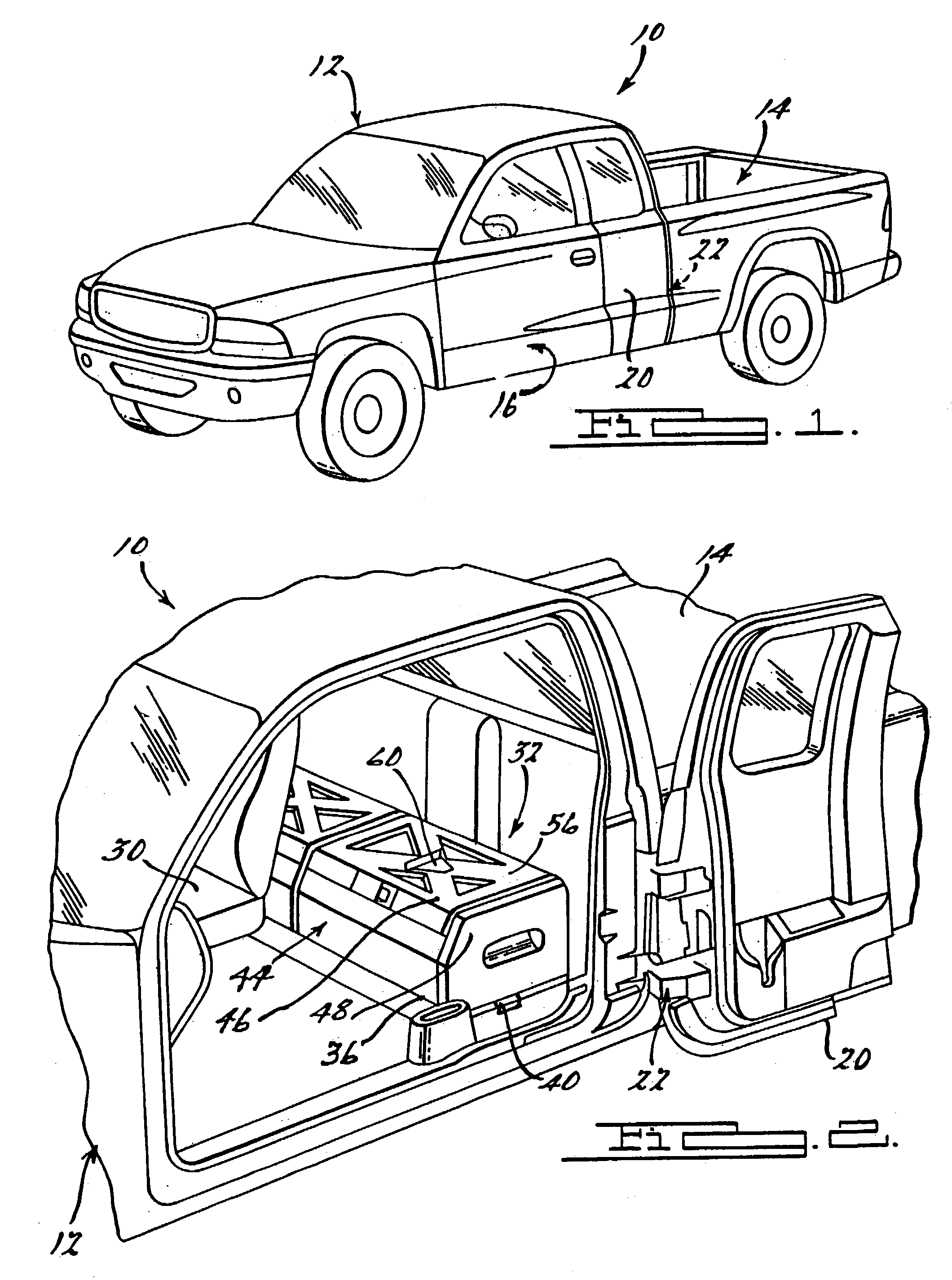
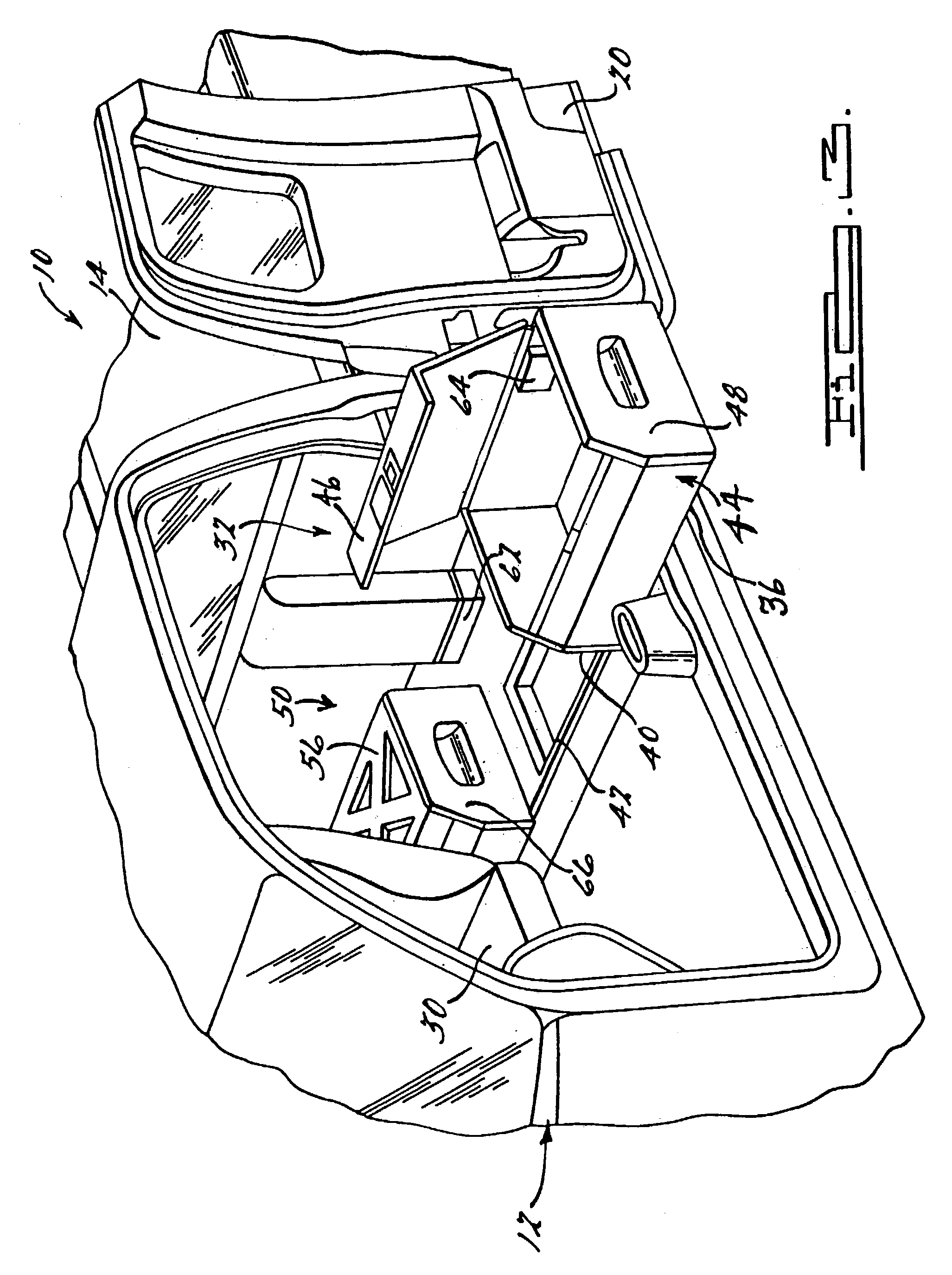
Vehicle mobile work station
A mobile work station assembly for a vehicle. The work station incorporates a docking station, toolbox, file organizer, power inverter, storage container and a mobile phone assembly on a sliding load floor that can extend outwardly from the interior of the vehicle. The work station is removably attached to the load floor. The work station is adapted for mounting in a vehicle interior or within a pickup truck bed.
Owner:FCA US
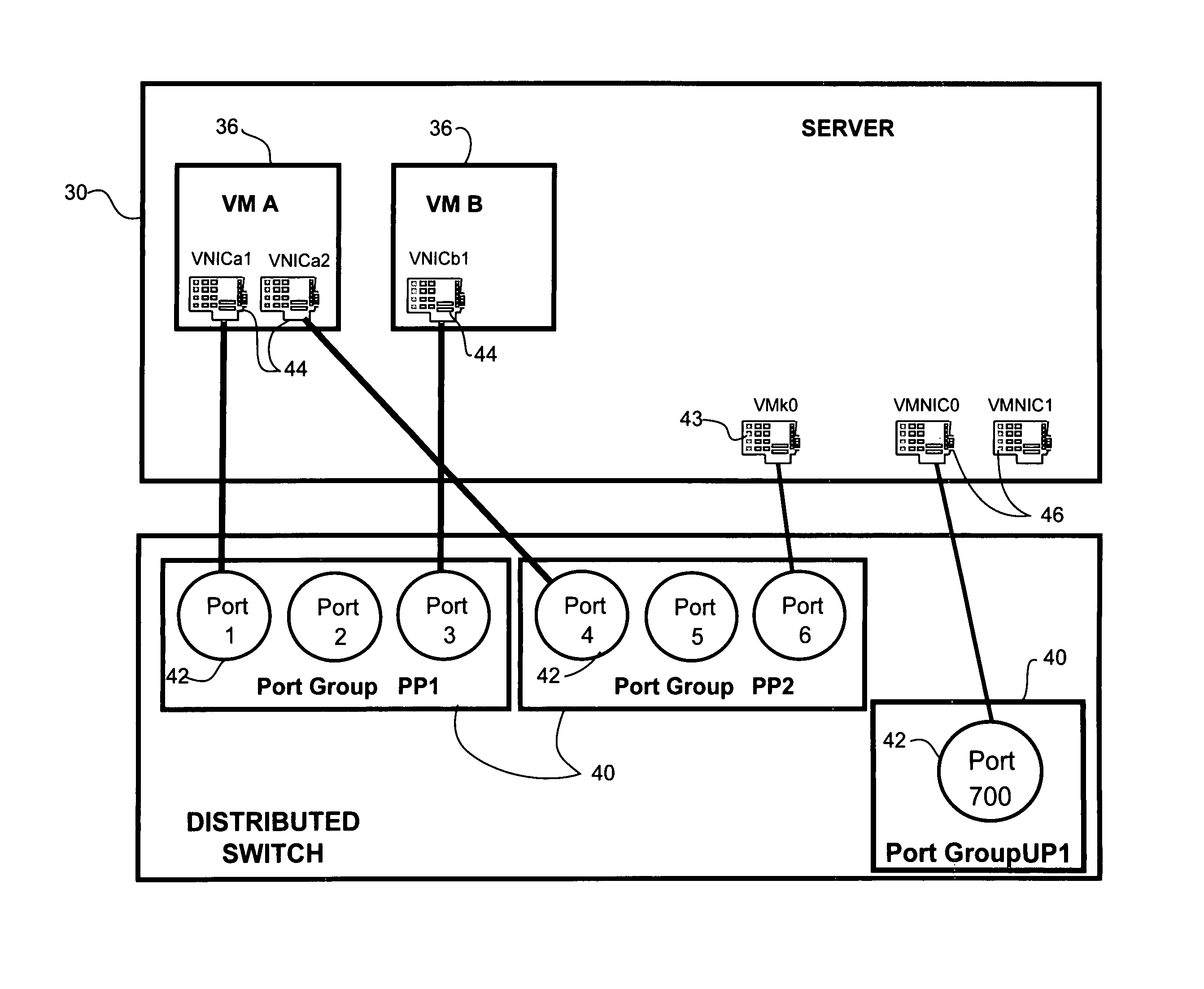
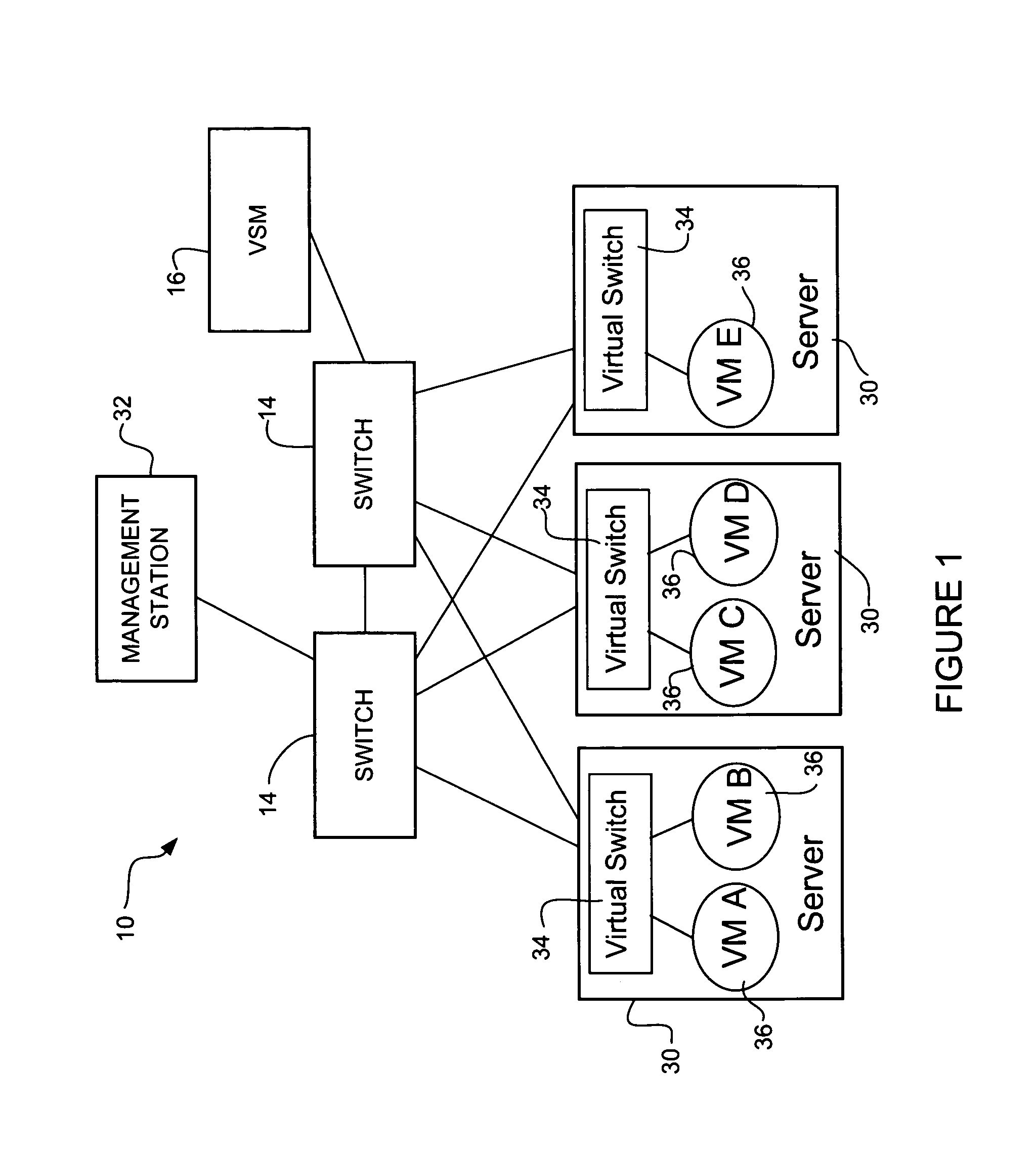
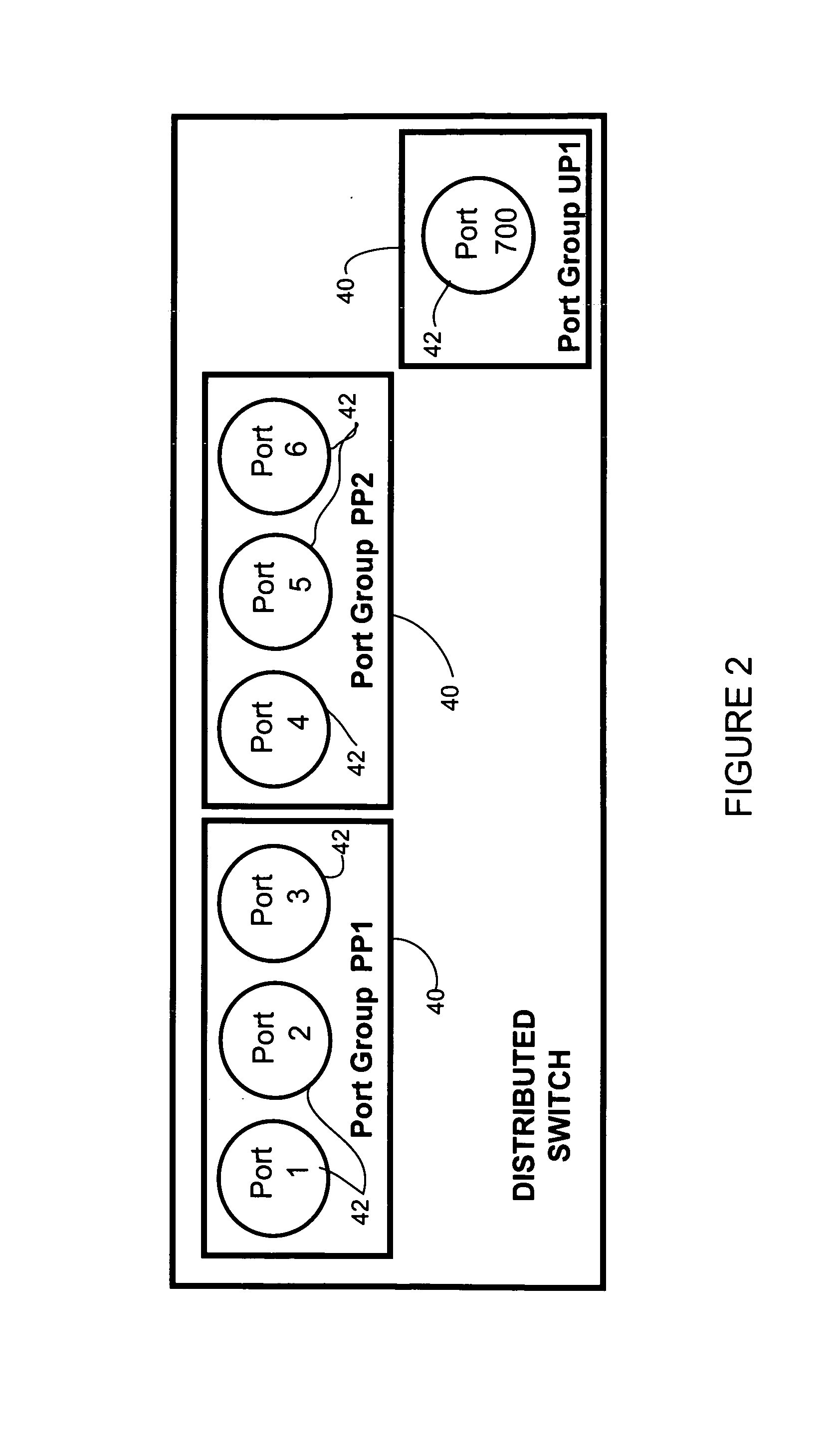
Policy based configuration of interfaces in a virtual machine environment
In one embodiment, an apparatus includes a port profile manager for receiving a port configuration policy and creating a port profile for the port configuration policy. The apparatus further includes a management interface for transmitting the port profile to a management station operable to receive input mapping the port profile to one or more interfaces associated with virtual machines. The port profile manager receives and stores the mapping input at the management station, for use in configuring the interfaces according to the port configuration policy. A method for policy based configuration of interfaces in a virtual machine environment is also disclosed.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com