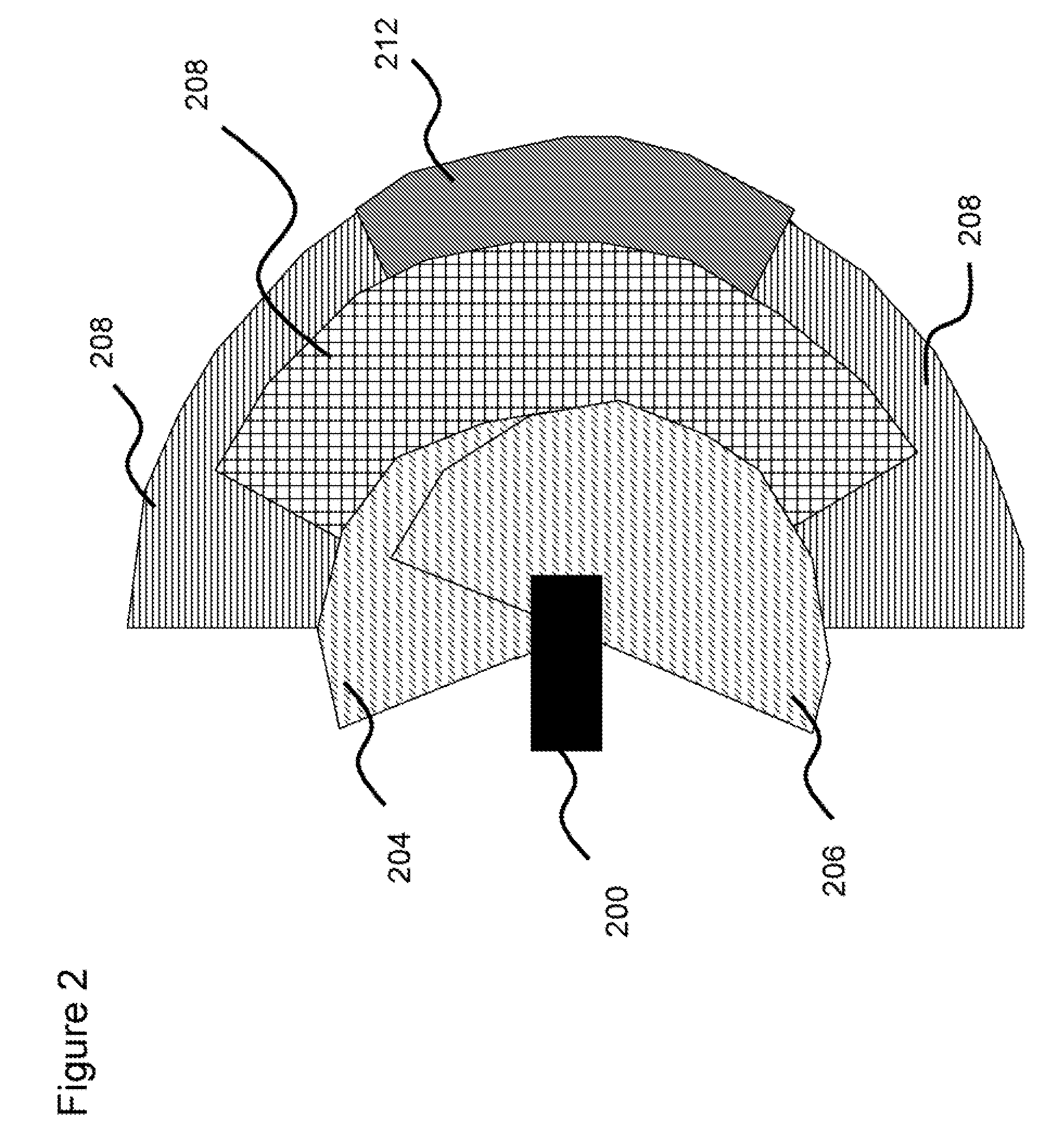
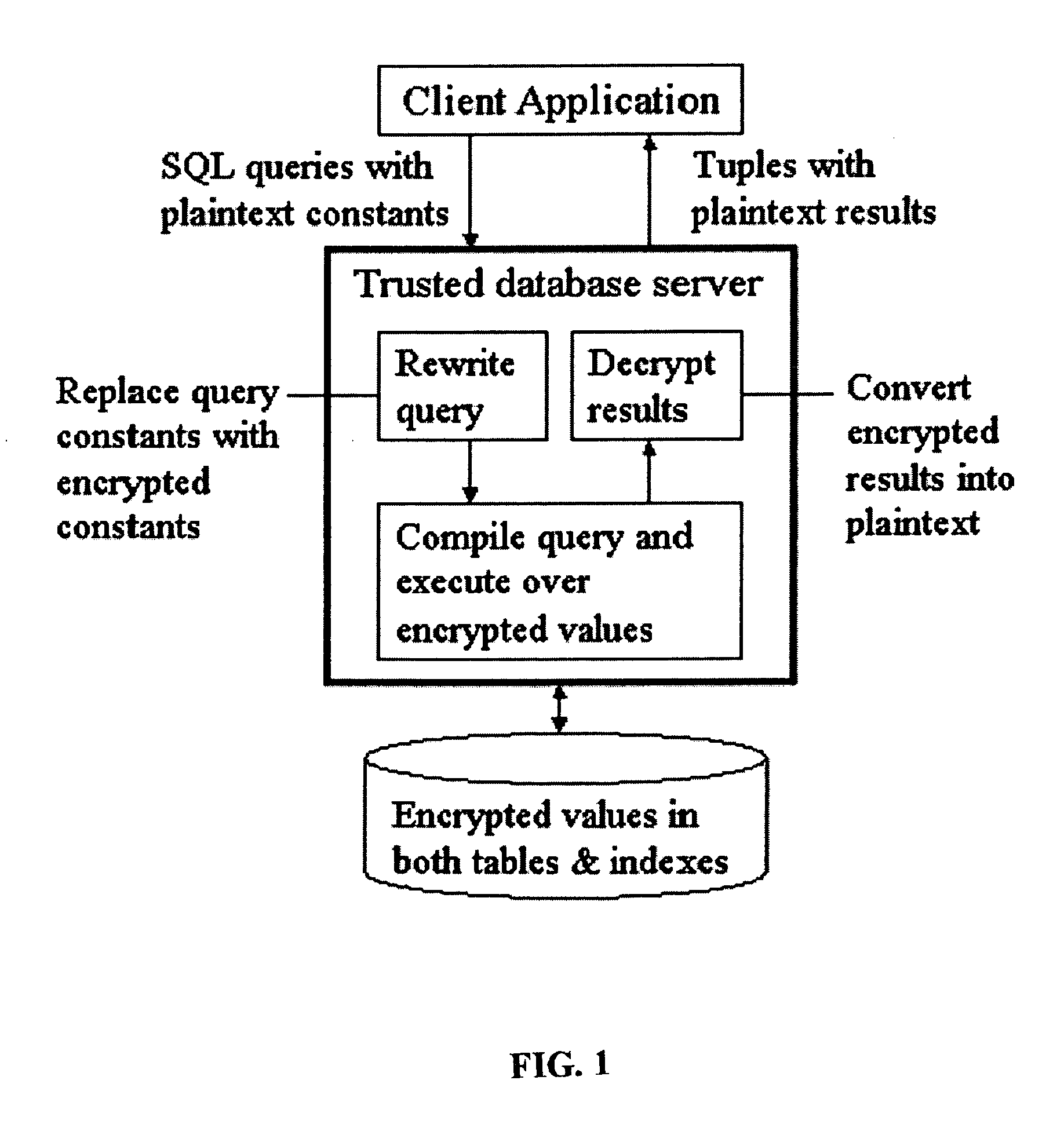
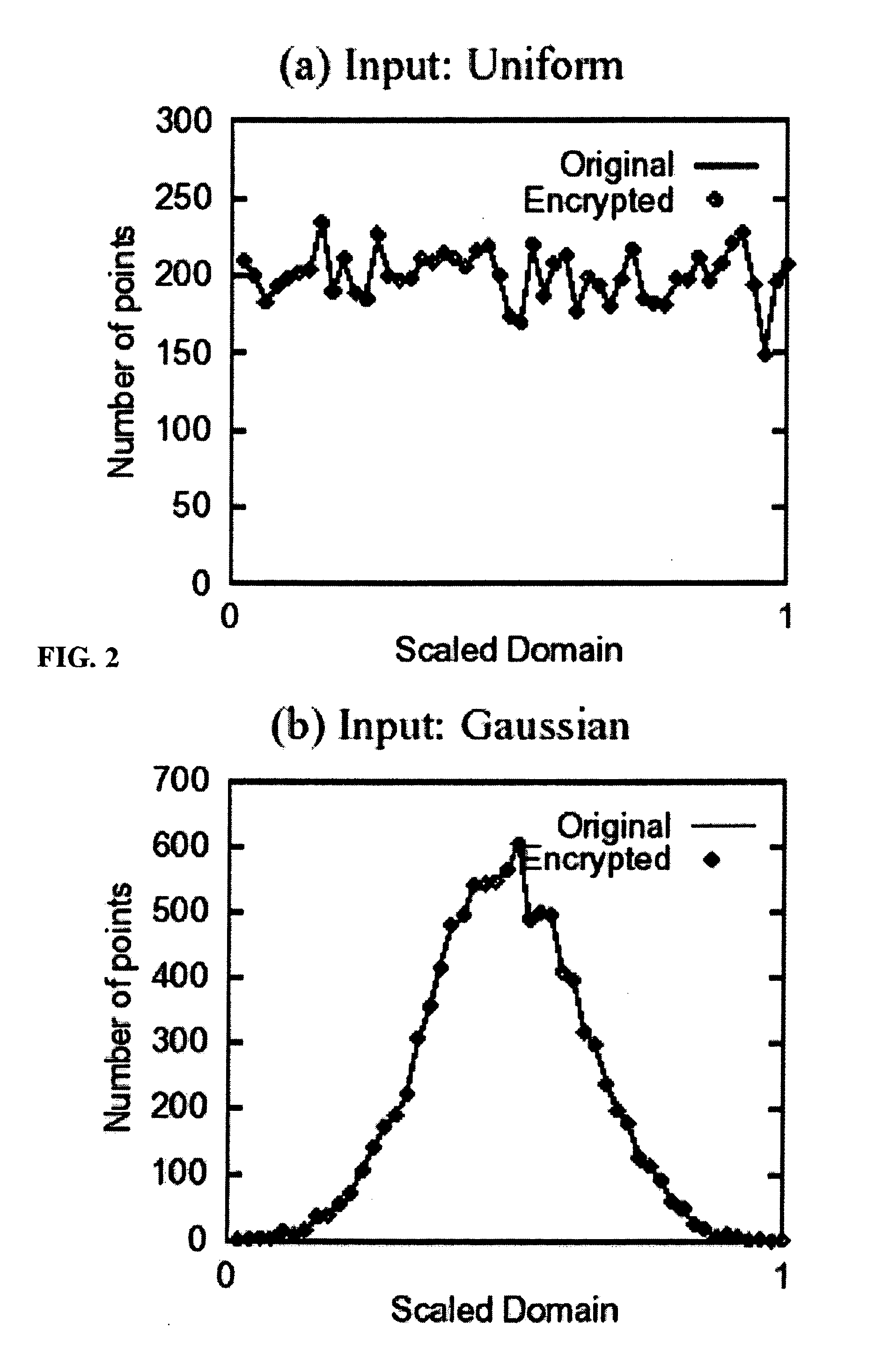
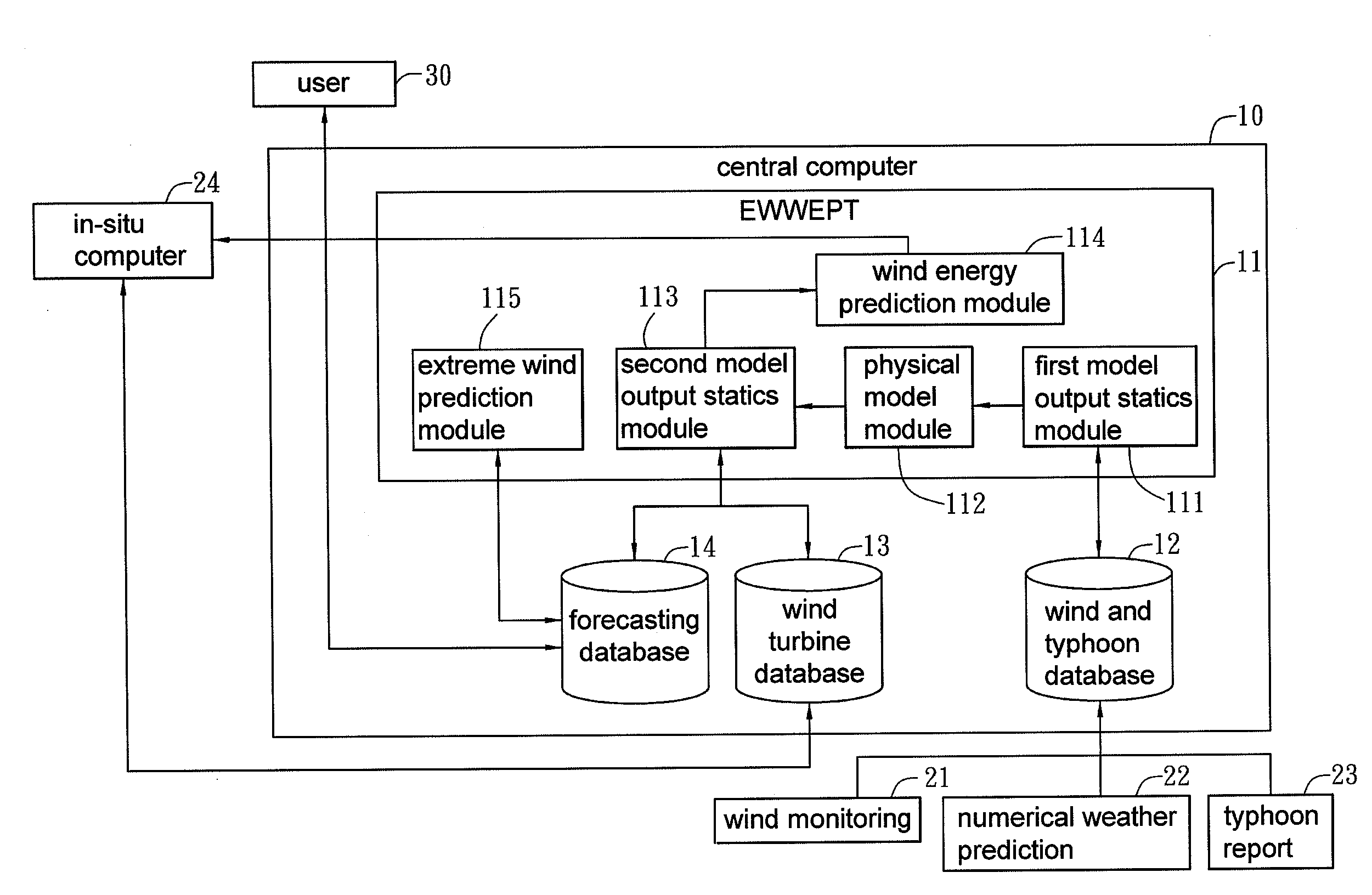
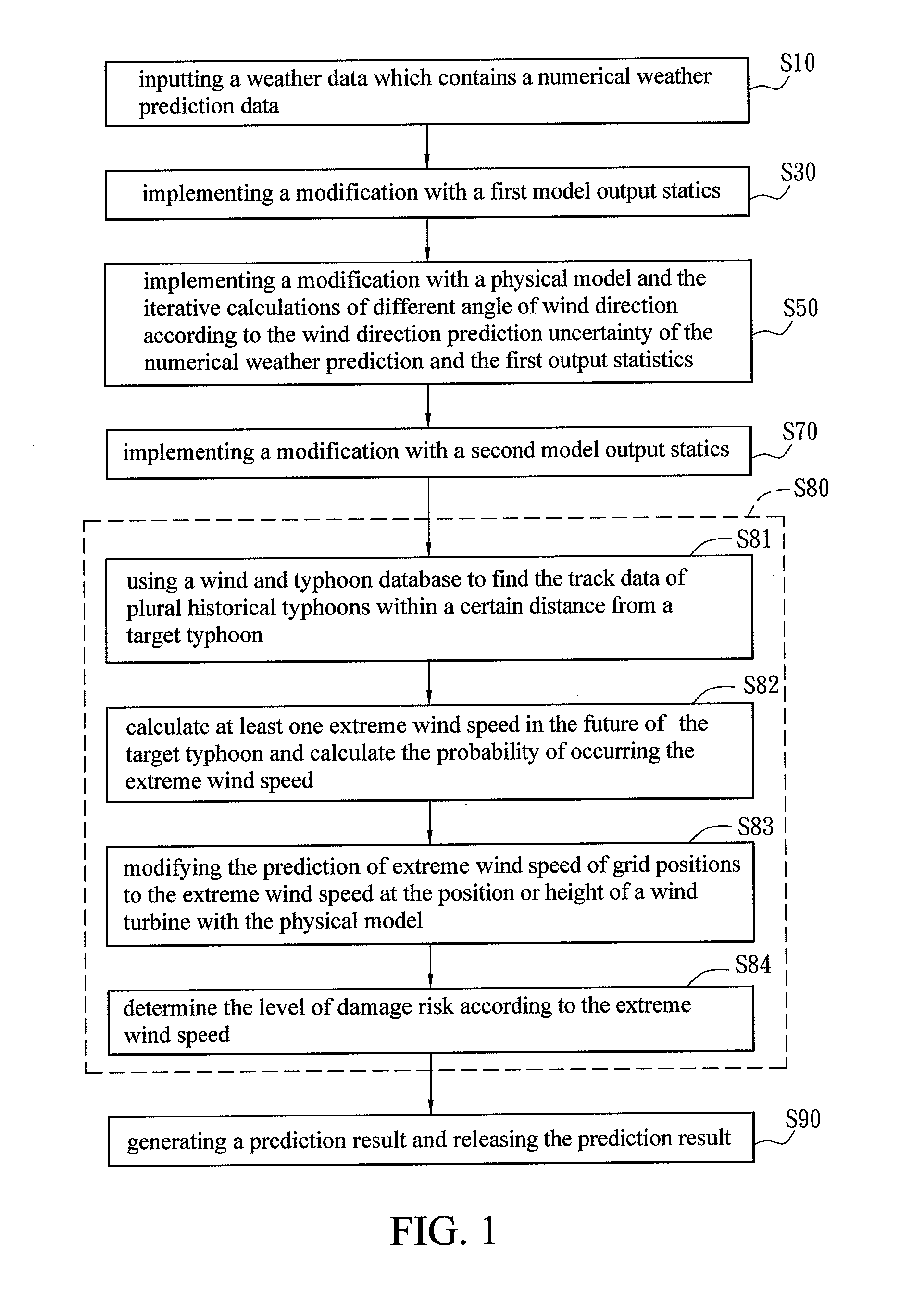
Patents
Literature
4908 results about "Numeric Value" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
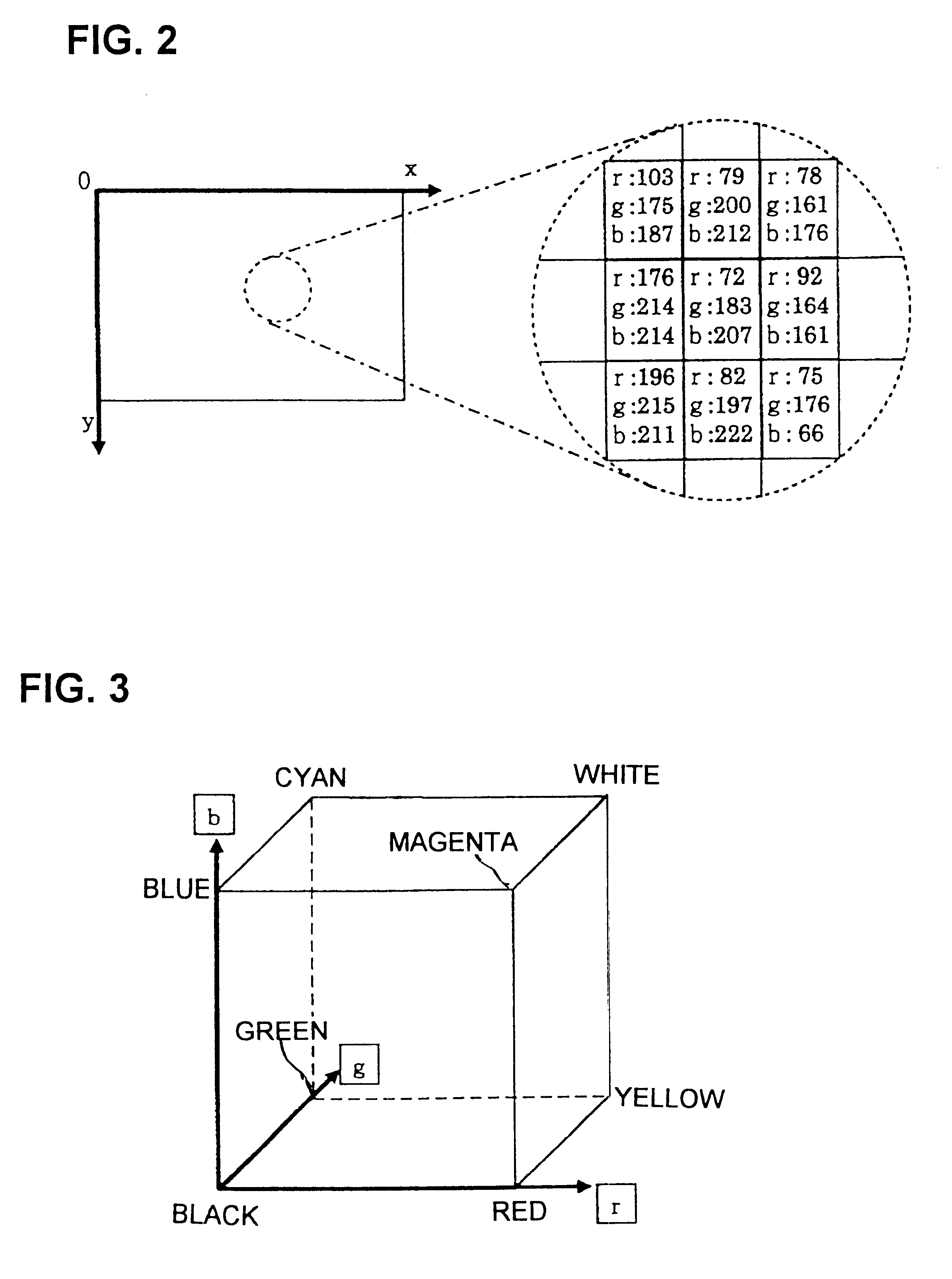
Information in the form of a numeral contained in a data field.
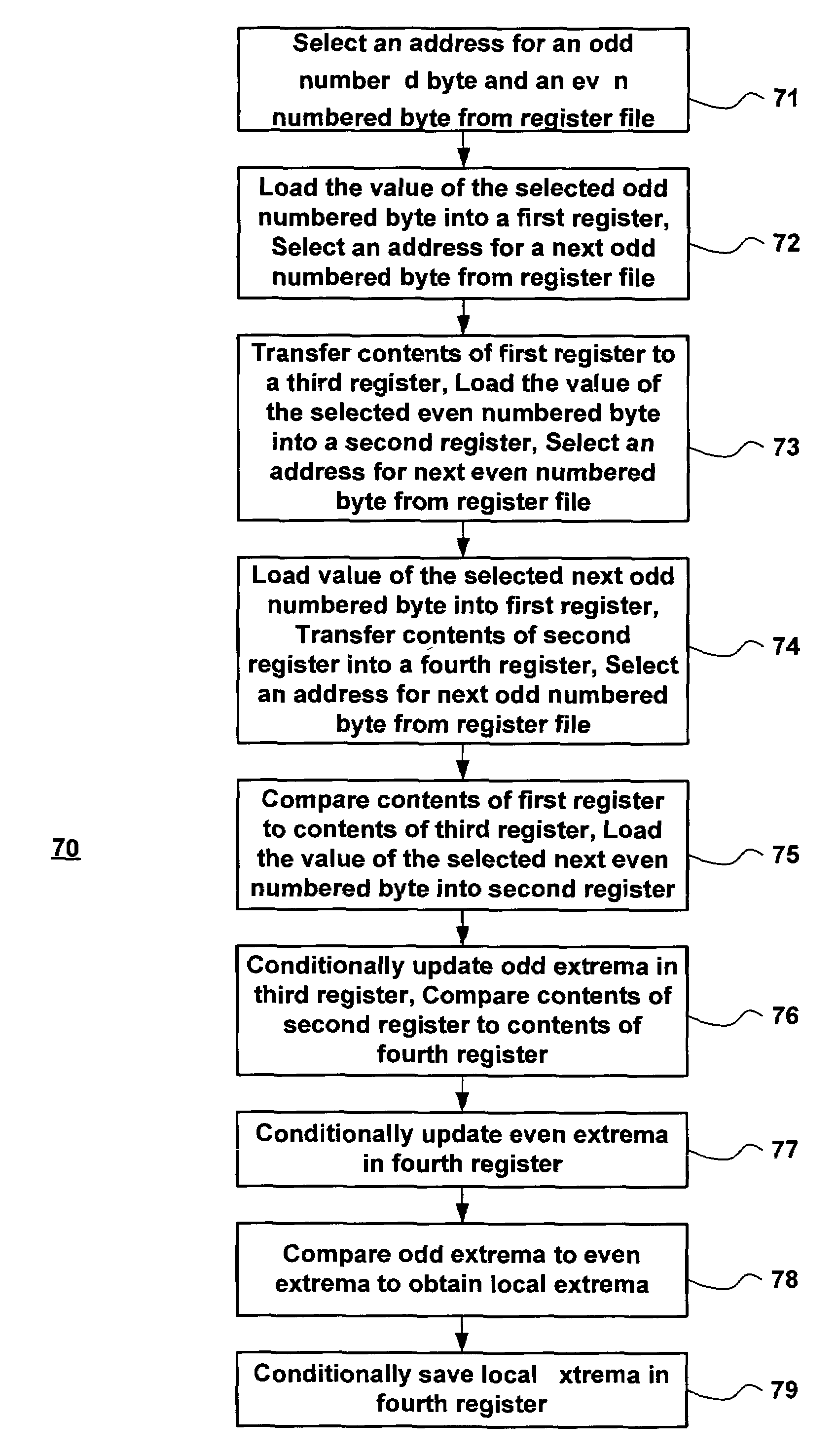
Method for finding local extrema of a set of values for a parallel processing element
ActiveUS7454451B2Digital data processing detailsDigital computer detailsTheoretical computer scienceProcessing element
A method for finding a local extrema for a single processing element having a set of values associated therewith includes separating the set of values into an odd set of values and an even set of values, determining a first extrema from the odd set of values, determining a second extrema from the even set of values, and determining the local extrema from the first extrema and the second extrema. The first extrema is found by comparing each odd-numbered value in the set to each other odd-numbered value in the set and the second extrema is found by comparing each even-numbered value in the set to each other even-numbered value in the set.
Owner:MICRON TECH INC
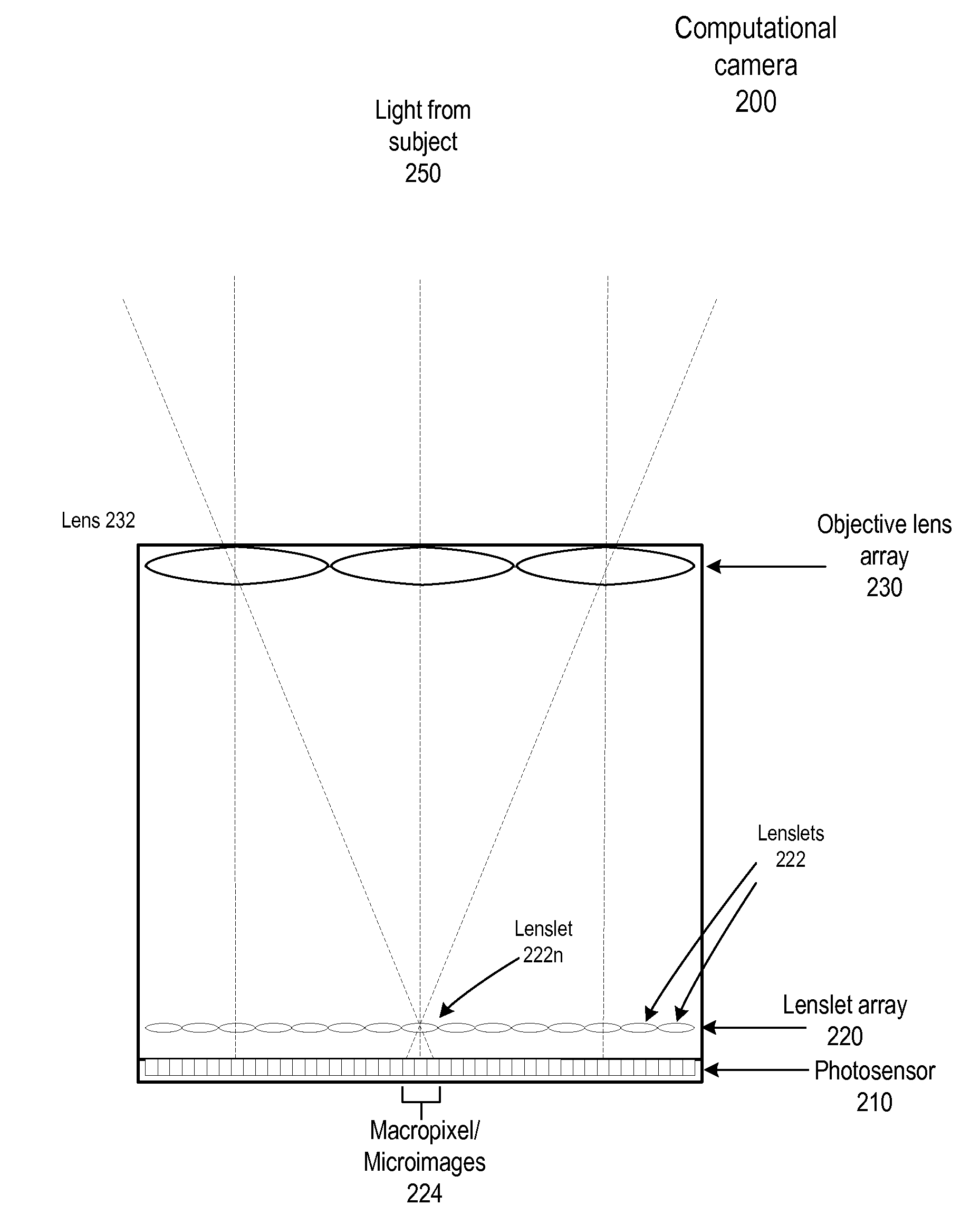
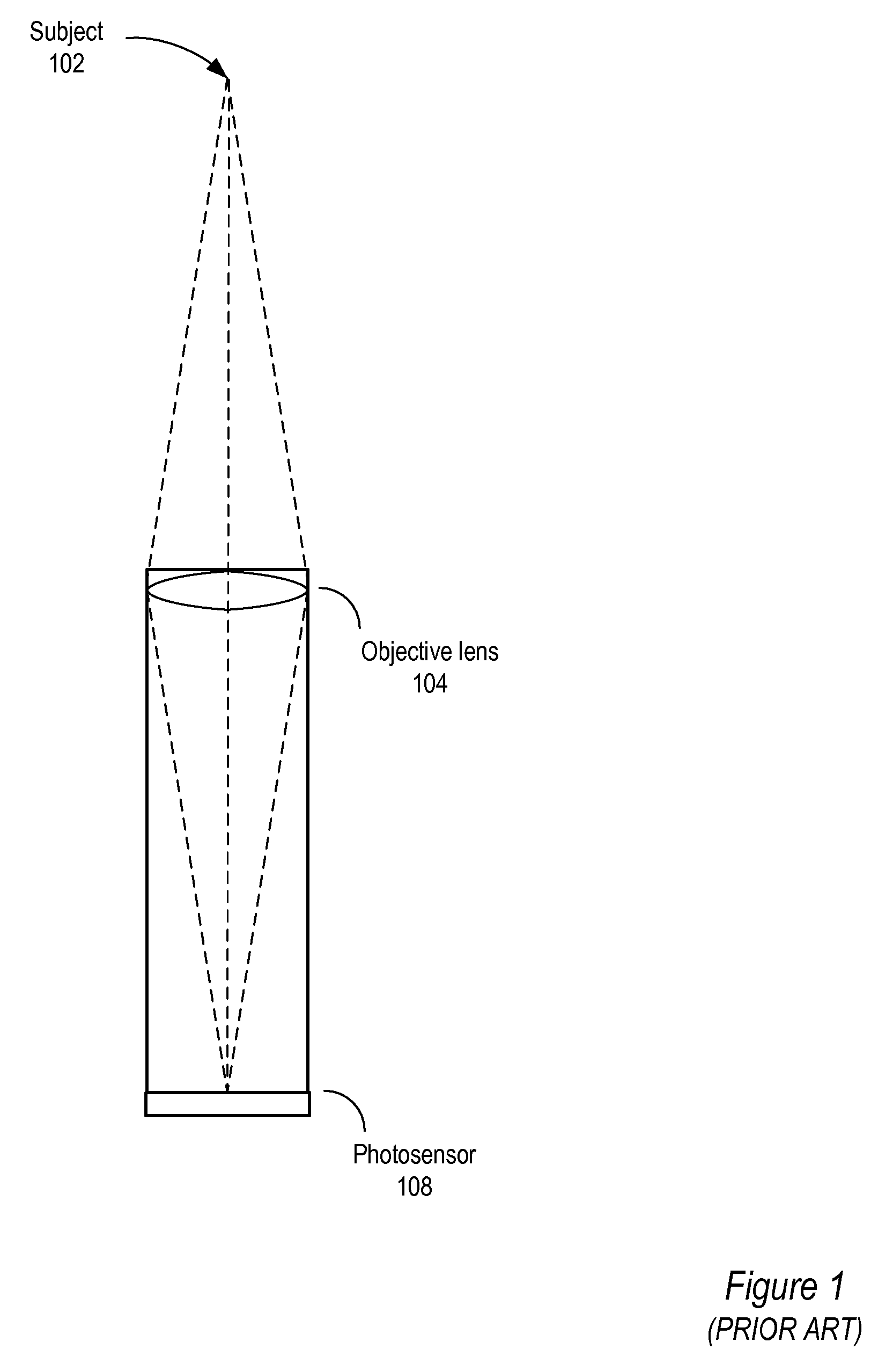
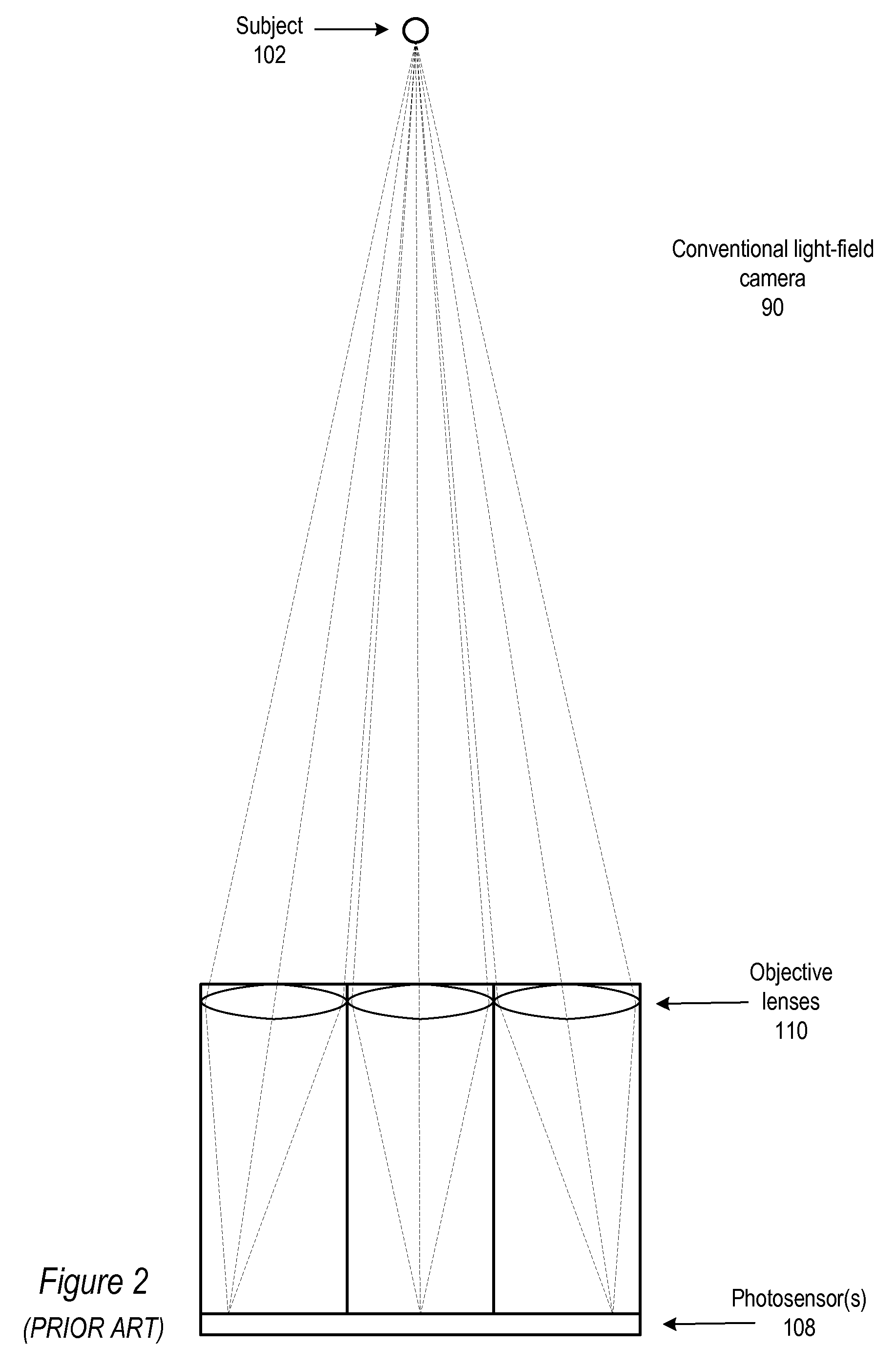
Fast Computational Camera Based On Two Arrays of Lenses
ActiveUS20090102956A1Less expenseQuality improvementTelevision system detailsTelevision system scanning detailsRadianceInformation capture
Method and apparatus for a fast (low F / number) computational camera that incorporates two arrays of lenses. The arrays include a lenslet array in front of a photosensor and an objective lens array of two or more lenses. Each lens in the objective lens array captures light from a subject. Each lenslet in the lenslet array captures light from each objective lens and separates the captured light to project microimages corresponding to the objective lenses on a region of the photosensor under the lenslet. Thus, a plurality of microimages are projected onto and captured by the photosensor. The captured microimages may be processed in accordance with the geometry of the objective lenses to align the microimages to generate a final image. One or more other algorithms may be applied to the image data in accordance with radiance information captured by the camera, such as automatic refocusing of an out-of-focus image.
Owner:ADOBE INC
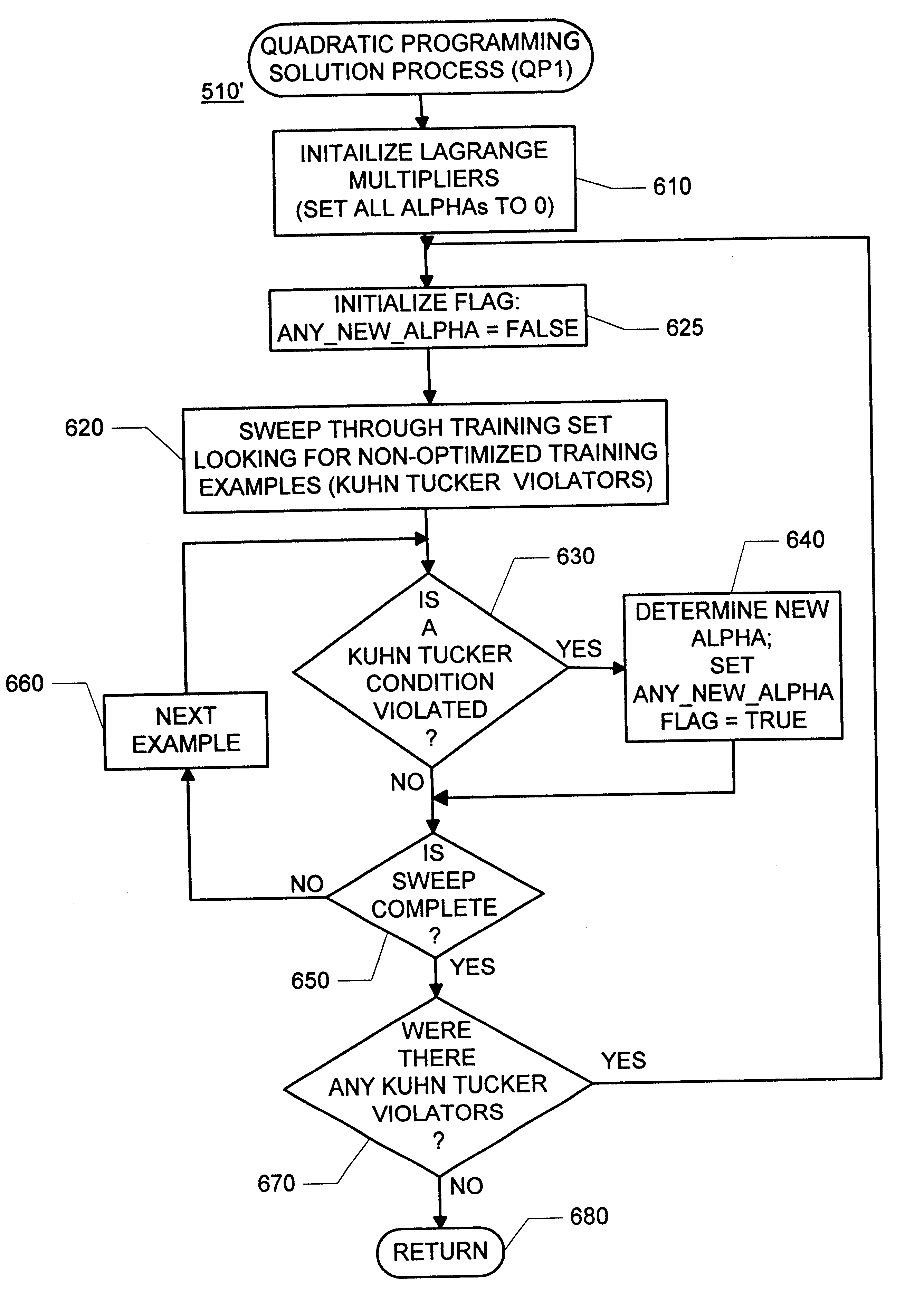
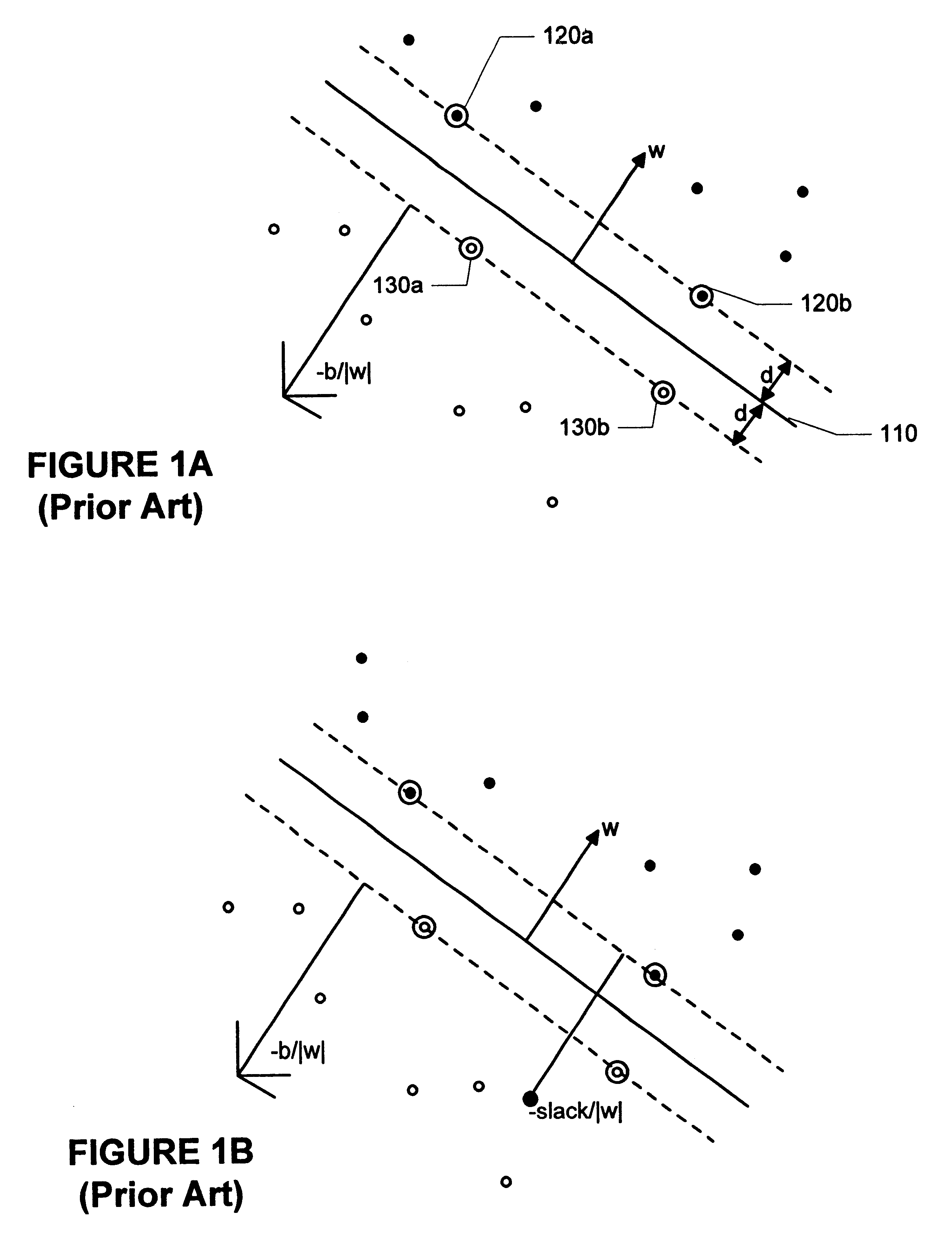
Methods and apparatus for building a support vector machine classifier
InactiveUS6327581B1Quick fixDigital computer detailsCharacter and pattern recognitionNumeric ValueTraining Supports
Solving a quadratic programming problem involved in training support vector machines by sweeping through a set of training examples, solving small sub-problems of the quadratic programming problem. Each of these sub-problems has an analytic solution, which is faster that the numerical quadratic programming solutions used in the prior art. In one embodiment, training examples with non-optimal Lagrange multipliers are adjusted, one at a time, until all are optimal (e.g. until all examples fulfill the Kuhn-Tucker conditions). In another embodiment, training examples with non-optimal Lagrange multipliers are paired and then adjusted, until all are optimal.
Owner:MICROSOFT TECH LICENSING LLC +1
Statistical classification of high-speed network data through content inspection
InactiveUS20050060295A1Good marginEasy to separateData switching networksSpecial data processing applicationsFeature extractionStatistical classification
A network data classifier statistically classifies received data at wire-speed by examining, in part, the payloads of packets in which such data are disposed and without having a priori knowledge of the classification of the data. The network data classifier includes a feature extractor that extract features from the packets it receives. Such features include, for example, textual or binary patterns within the data or profiling of the network traffic. The network data classifier further includes a statistical classifier that classifies the received data into one or more pre-defined categories using the numerical values representing the features extracted by the feature extractor. The statistical classifier may generate a probability distribution function for each of a multitude of classes for the received data. The data so classified are subsequently be processed by a policy engine. Depending on the policies, different categories may be treated differently.
Owner:INTEL CORP +1
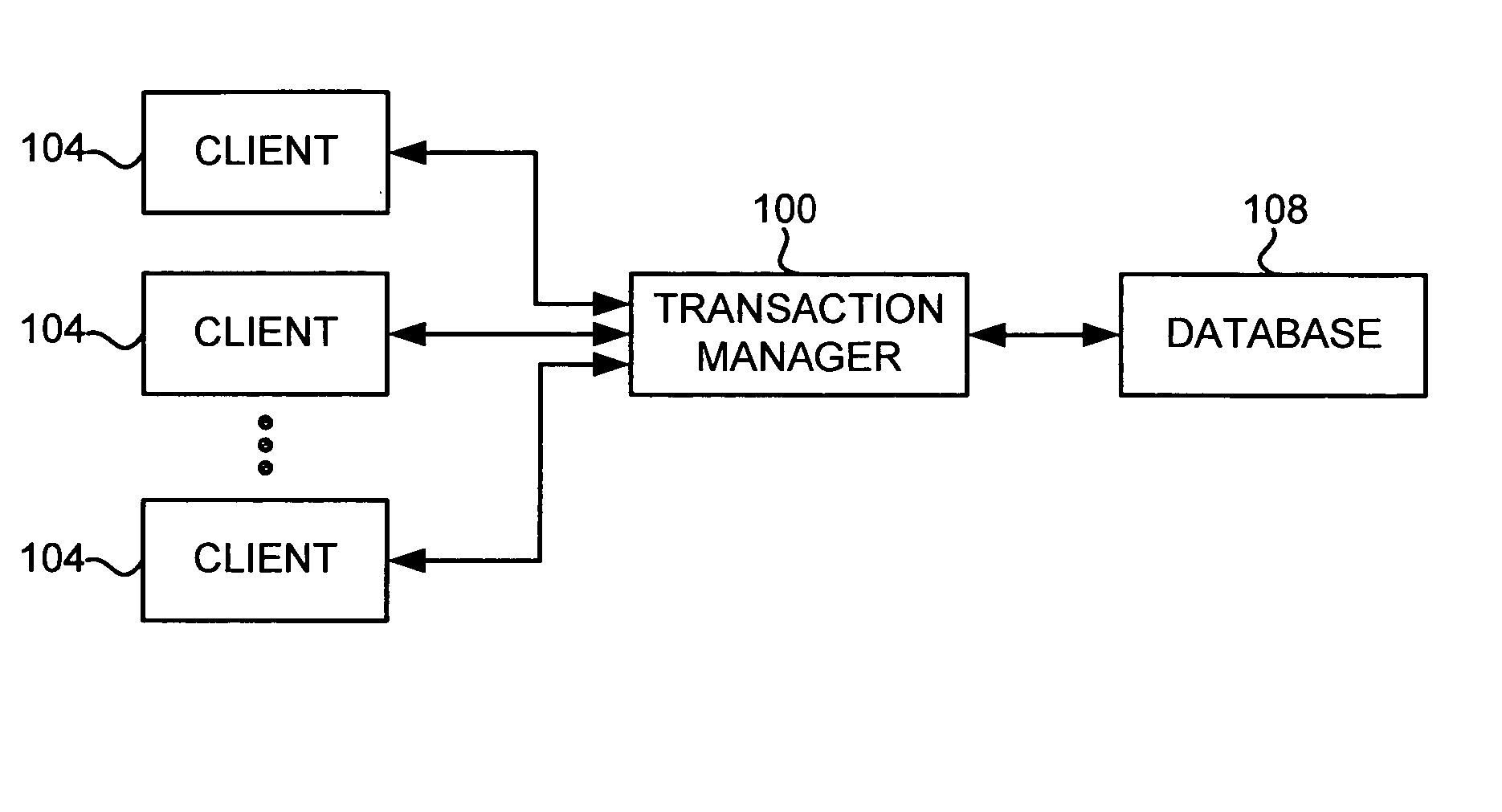
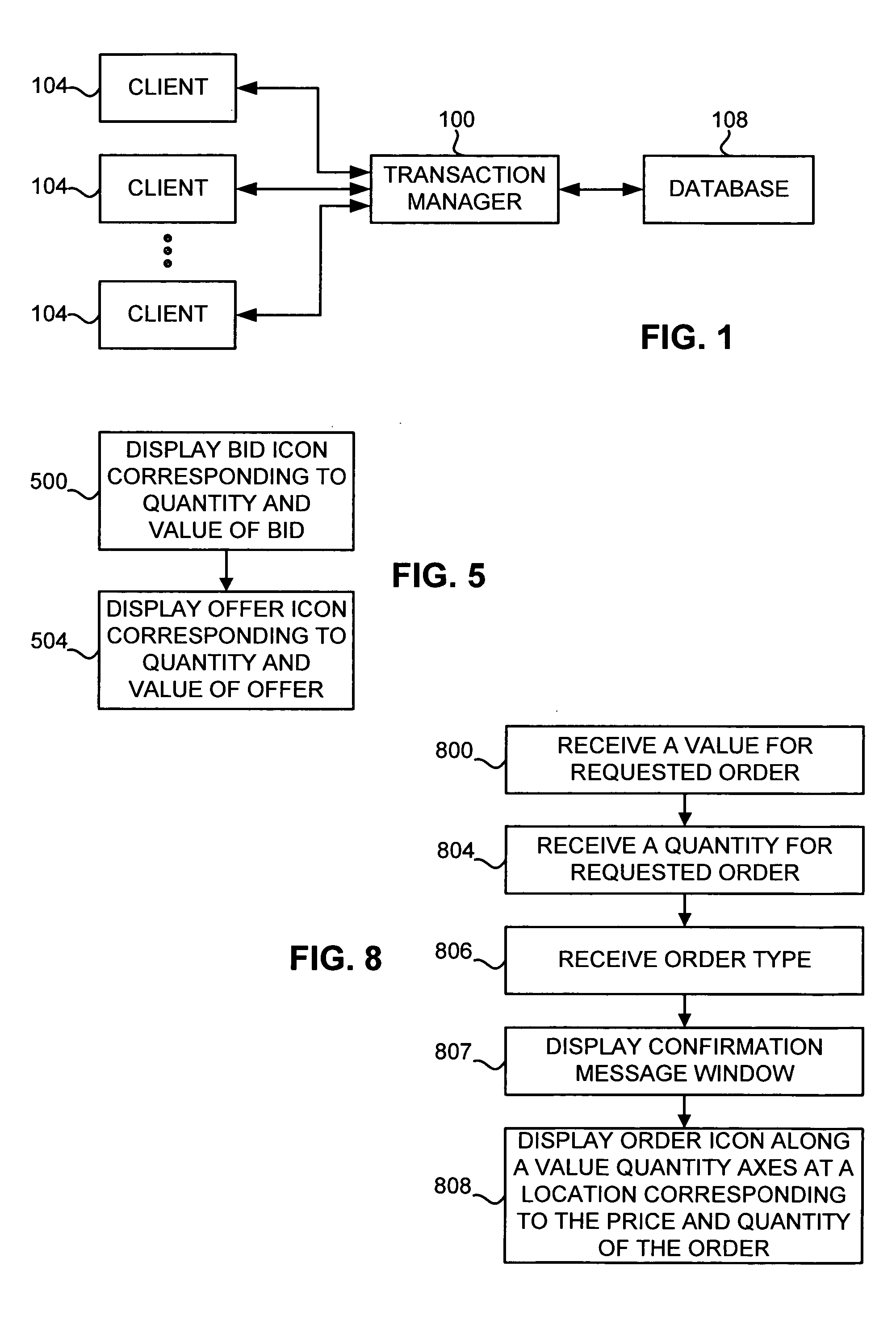
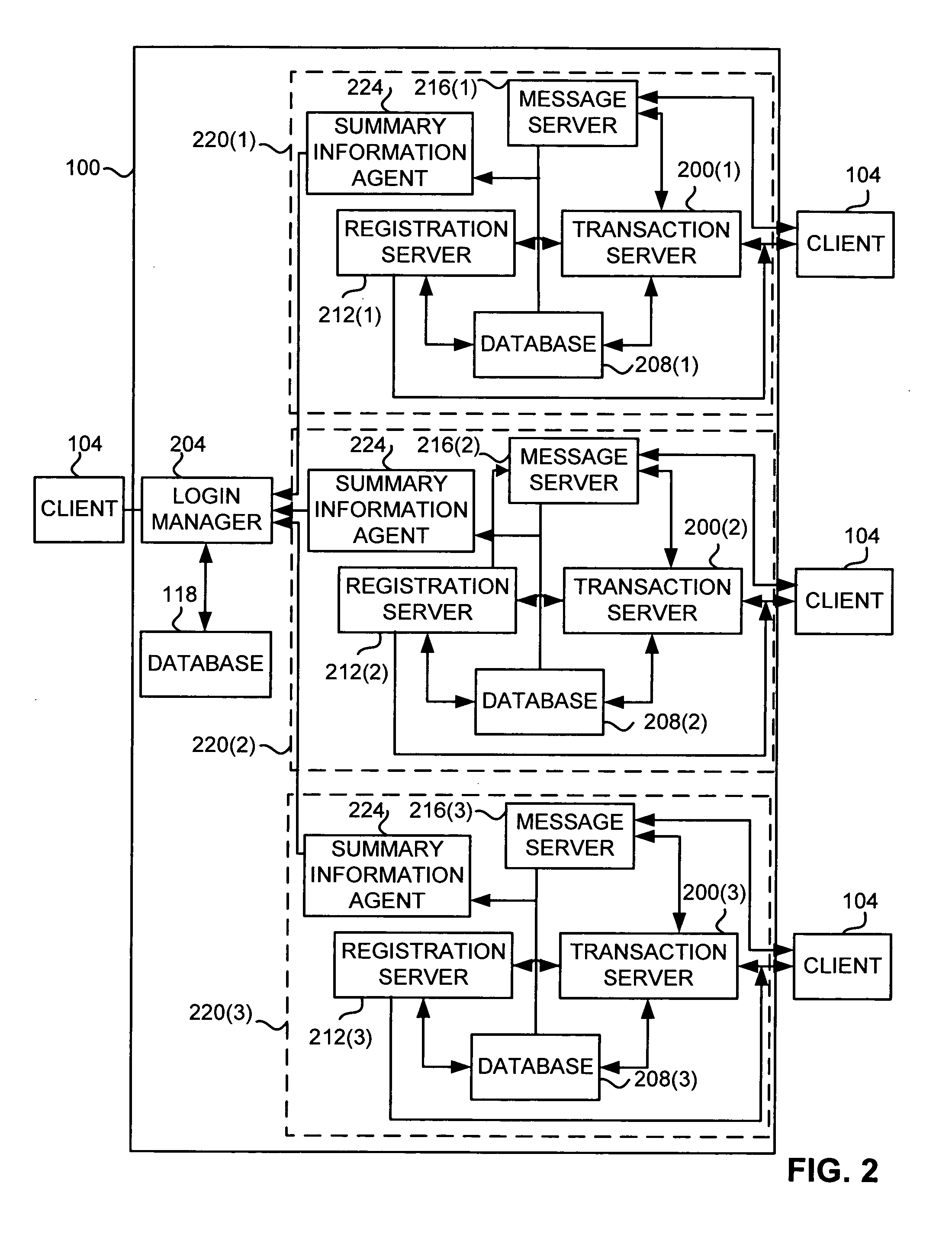
User interface for semi-fungible trading
InactiveUS20060059083A1Efficient and effective tradingTraded efficientlyFinancePayment architectureHuman–computer interactionUser interface
A user interface and method are disclosed for providing trading between a plurality of semi-fungible and non-fungible goods. A plurality of book axes are displayed in a single interface, each book axis representing a market for a particular good. Orders for goods are displayed as marks on the axes to display the relative value of the orders. A value axis is provided that relates the value of the goods from each market to each other. Thus, a single interface provides the means to relate the values of different semi-fungible goods. The value axis may be displayed in units of price, or a custom value designated by a user or pre-defined by the interface. Quantity information is represented in the interface through the display of a dimension of an order icon. Precise information about each order is displayed either in a panel view or a pop-up window.
Owner:TRADING TECH INT INC
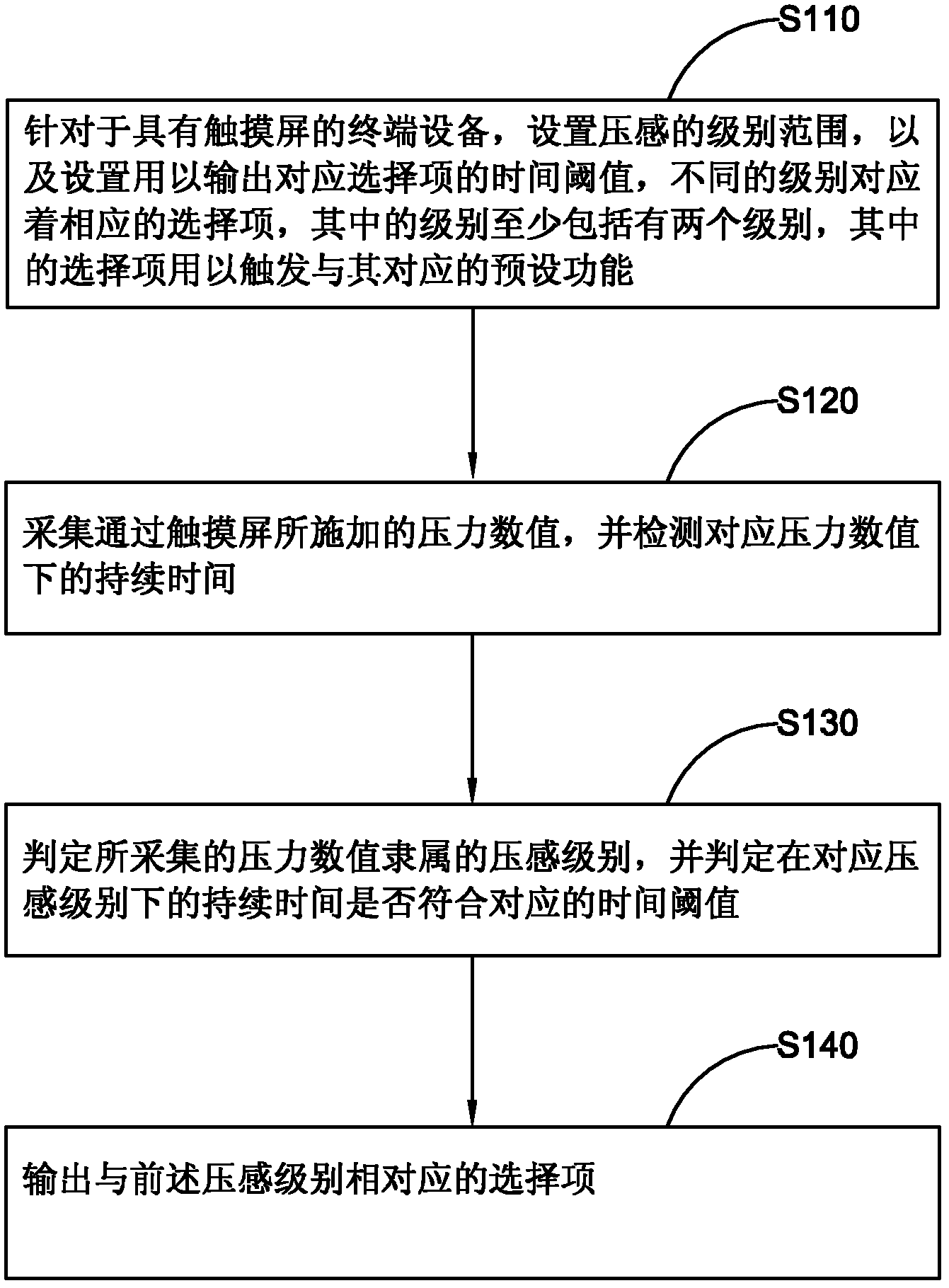
Method and terminal for obtaining options by pressing
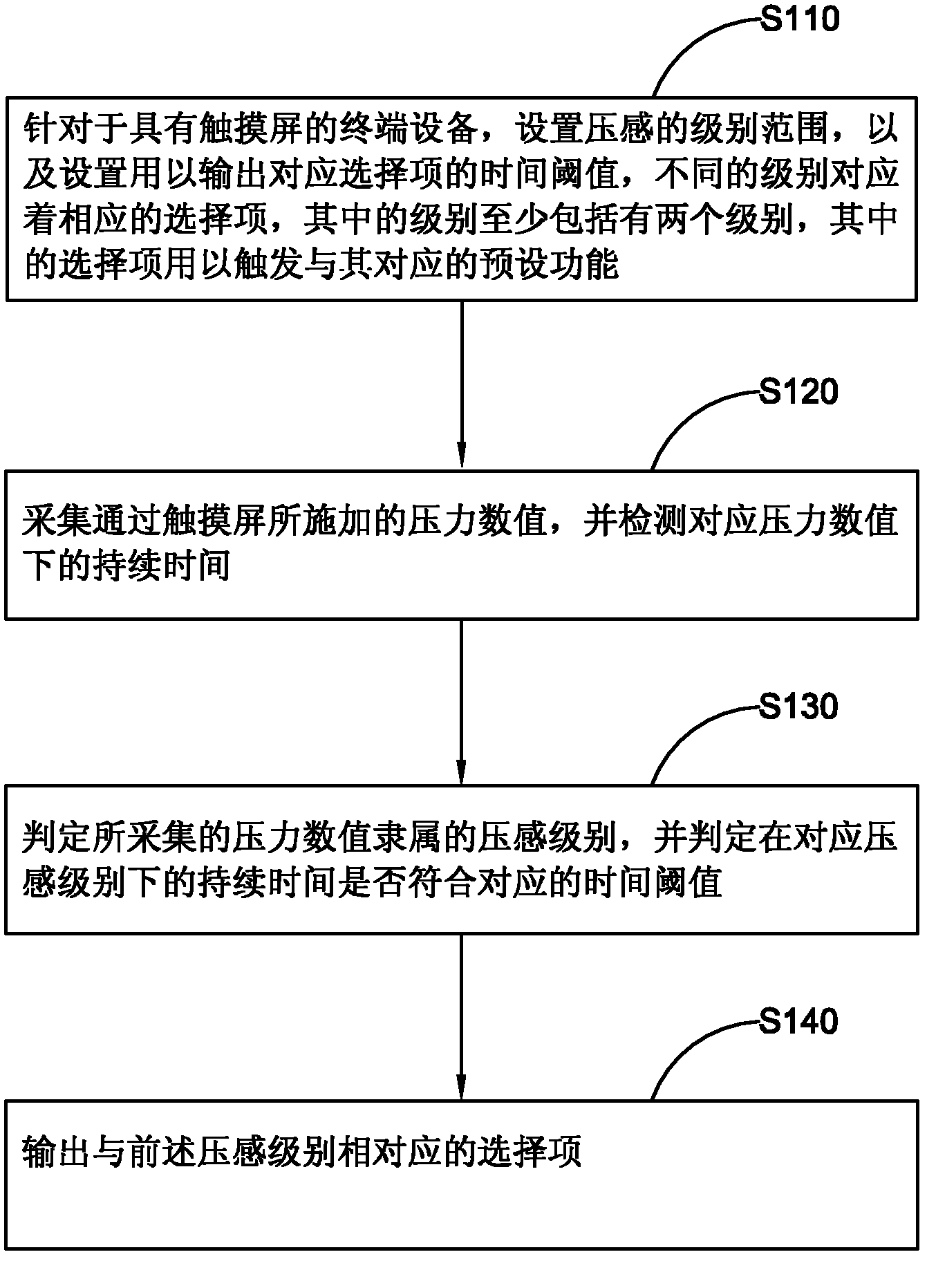
The invention provides a method and a terminal for obtaining options by pressing, belonging to the technical field of electronic devices and software. The method comprises the steps of: for a terminal device with a touch screen, setting pressure level range, setting time threshold for outputting corresponding options, wherein different levels are corresponding to corresponding options; at least two levels are included; the options are used for triggering corresponding preset functions; 2, collecting pressure value applied by the touch screen, detecting duration under the corresponding pressure value; 3, judging pressure level subordinating to the collected pressure value and time threshold; entering the next step on the corresponding condition; and 4, outputting options corresponding to the pressure level. The method can obtain the options corresponding to the preset function by collecting different pressure values applied on the touch screen by the user.
Owner:SHANGHAI LIANGMING TECH DEV
Software architecture for high-speed traversal of prescribed routes
InactiveUS20080059015A1Reduce computing loadImprove abilitiesPlatooningVehicle position/course/altitude controlTerrainLocal environment
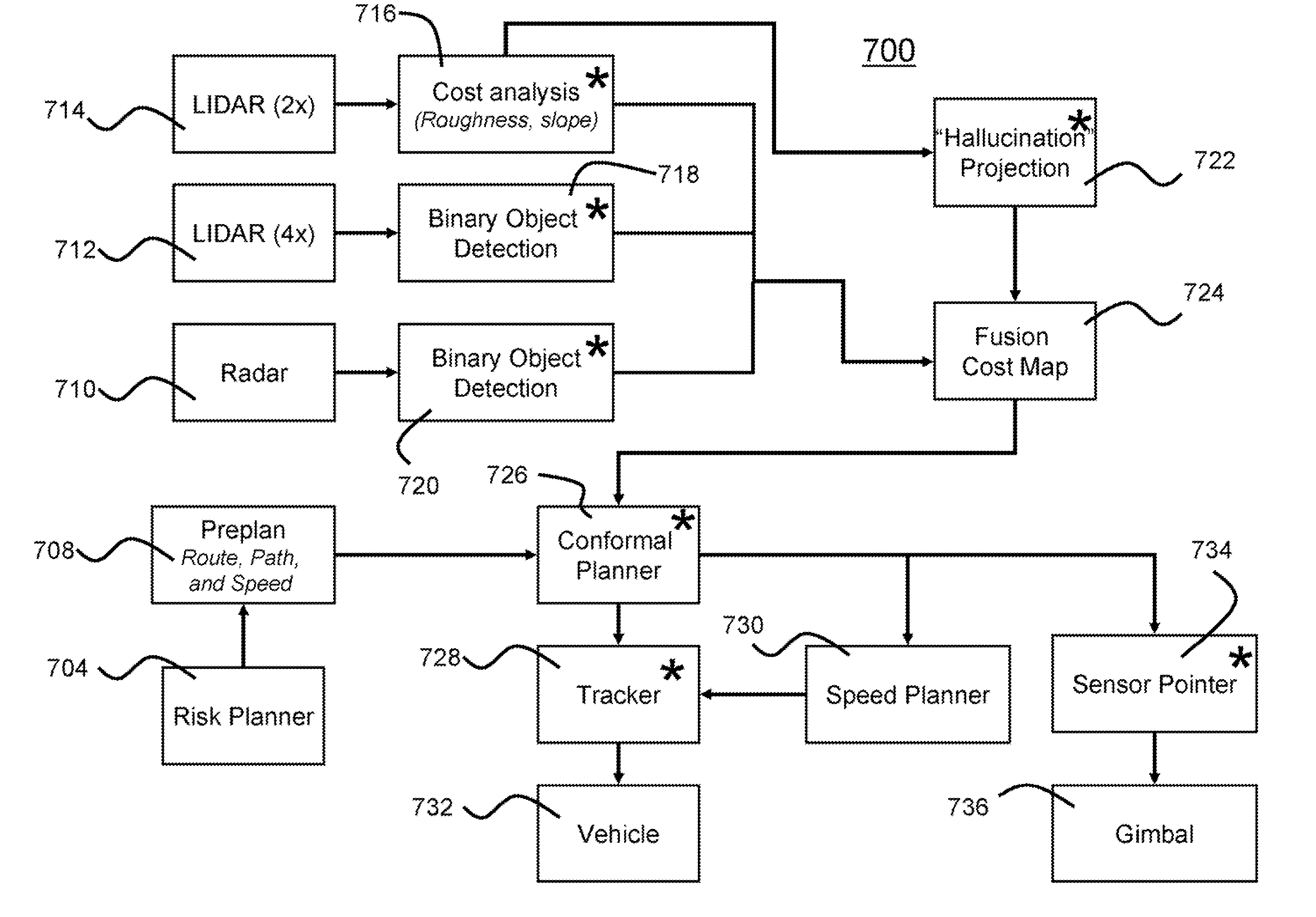
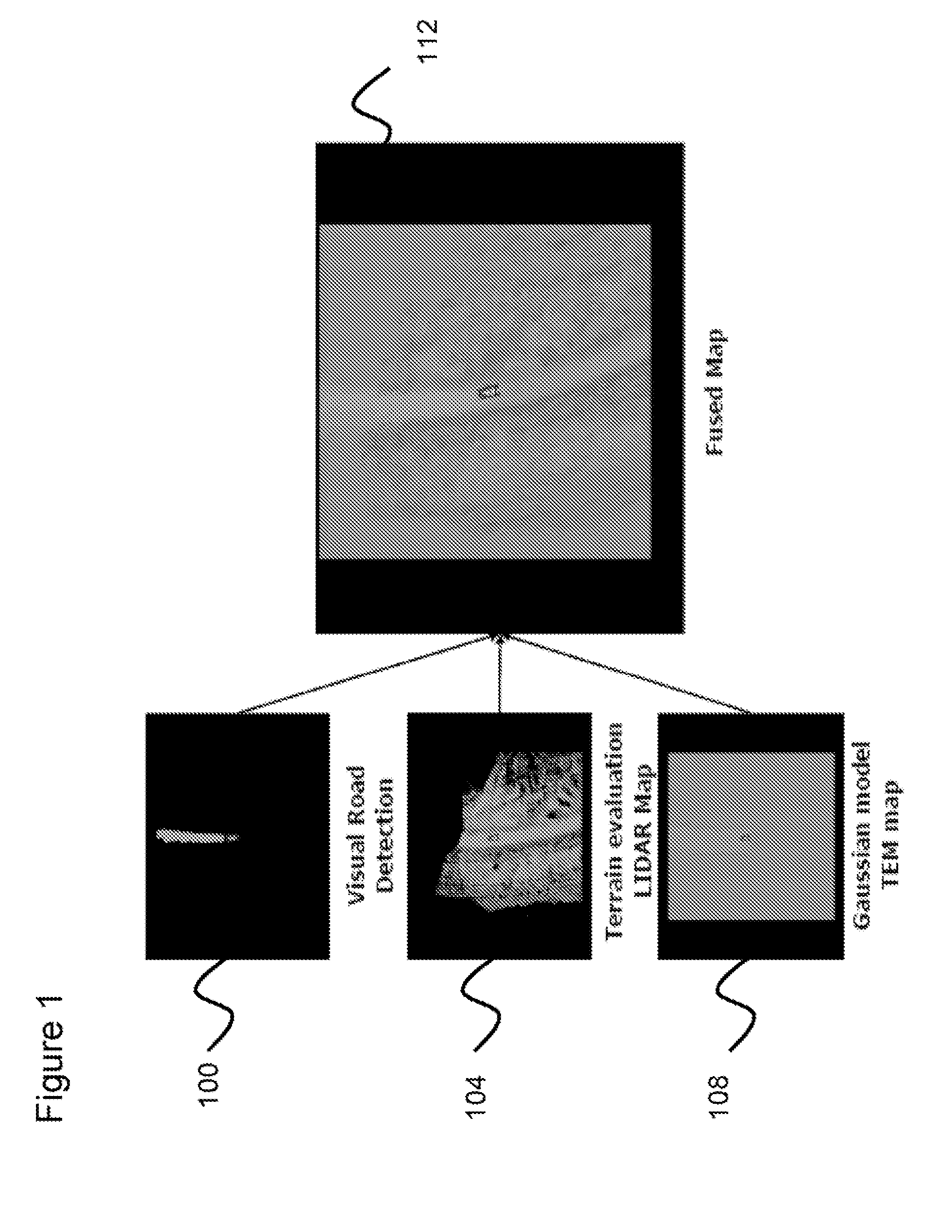
Systems, methods, and apparatuses for high-speed navigation. The present invention preferably encompasses systems, methods, and apparatuses that provide for autonomous high-speed navigation of terrain by an un-manned robot. By preferably employing a pre-planned route, path, and speed; extensive sensor-based information collection about the local environment; and information about vehicle pose, the robots of the present invention evaluate the relative cost of various potential paths and thus arrive at a path to traverse the environment. The information collection about the local environment allows the robot to evaluate terrain and to identify any obstacles that may be encountered. The robots of the present invention thus employ map-based data fusion in which sensor information is incorporated into a cost map, which is preferably a rectilinear grid aligned with the world coordinate system and is centered on the vehicle. The cost map is a specific map type that represents the traversability of a particular environmental area using a numeric value. The planned path and route provide information that further allows the robot to orient sensors to preferentially scan the areas of the environment where the robot will likely travel, thereby reducing the computational load placed onto the system. The computational ability of the system is further improved by using map-based syntax between various data processing modules of the present invention. By using a common set of carefully defined data types as syntax for communication, it is possible to identify new features for either path or map processing quickly and efficiently.
Owner:CARNEGIE MELLON UNIV
Methods of creating a dictionary for data compression
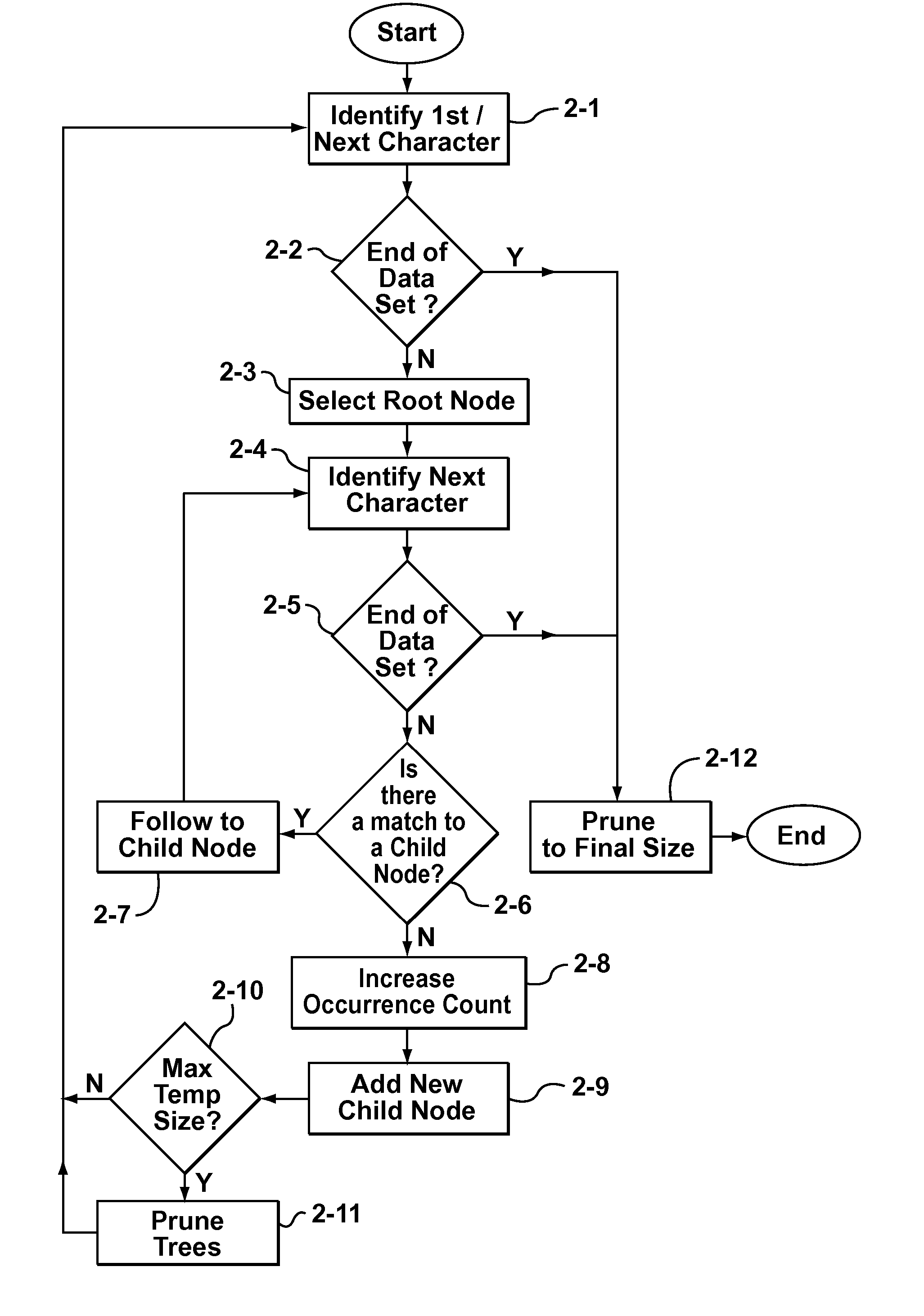
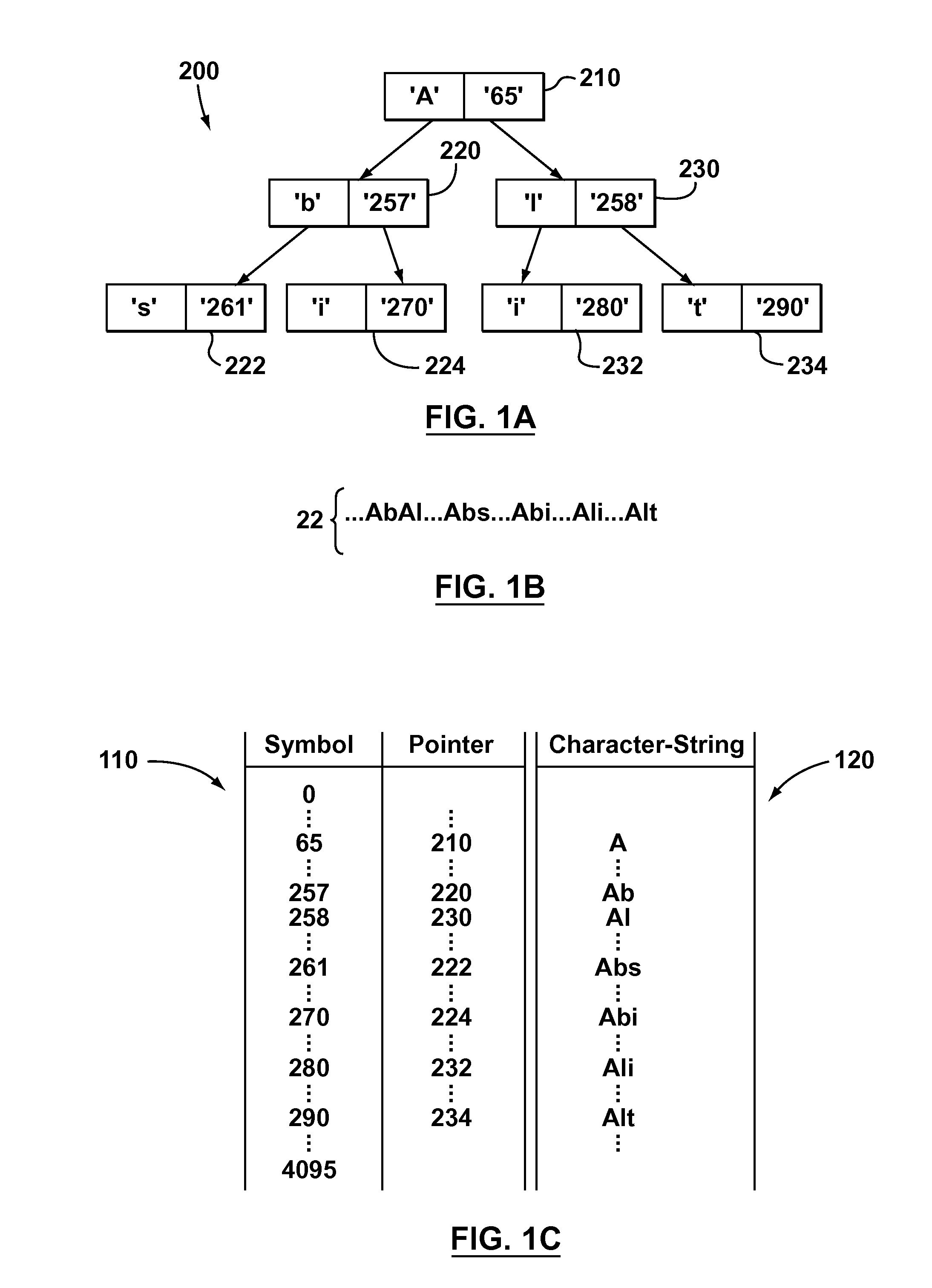
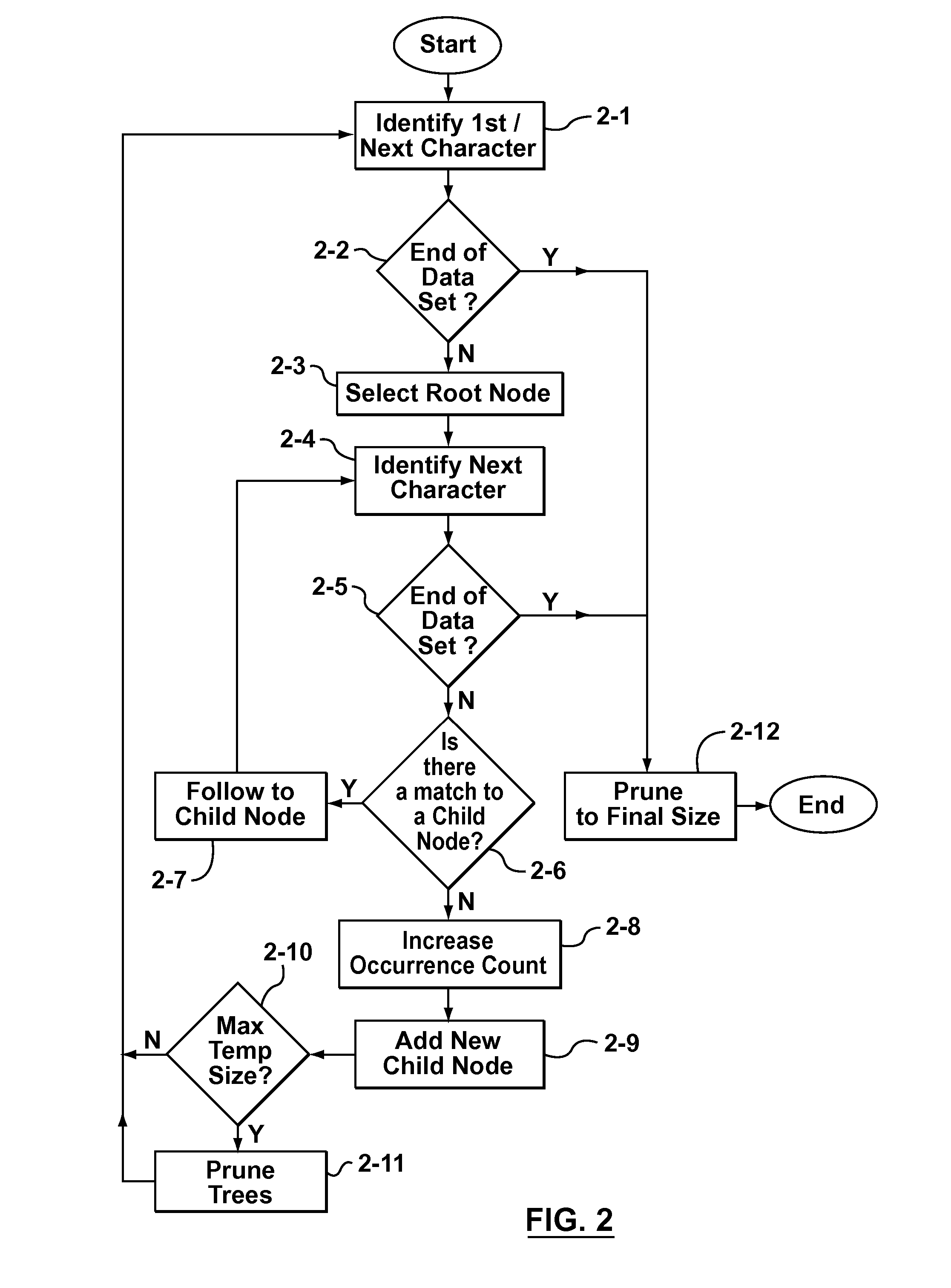
Some aspects of the invention provide methods, systems, and computer program products for creating a static dictionary in which longer byte-strings are preferred. To that end, in accordance with aspects of the present invention, a new heuristic is defined to replace the aforementioned frequency count metric used to record the number of times a particular node in a data tree is visited. The new heuristic is based on counting the number of times an end-node of a particular byte-string is visited, while not incrementing a count for nodes storing characters in the middle of the byte-string as often as each time such nodes are visited. The result is an occurrence count metric that favours longer byte-strings, by being biased towards not incrementing the respective occurrence count values for nodes storing characters in the middle of a byte-string.
Owner:GLOBALFOUNDRIES INC
Sample discriminating method
InactiveUS7122111B2Easy to useWeather/light/corrosion resistanceMicrobiological testing/measurementGlucose sensorsMedicine
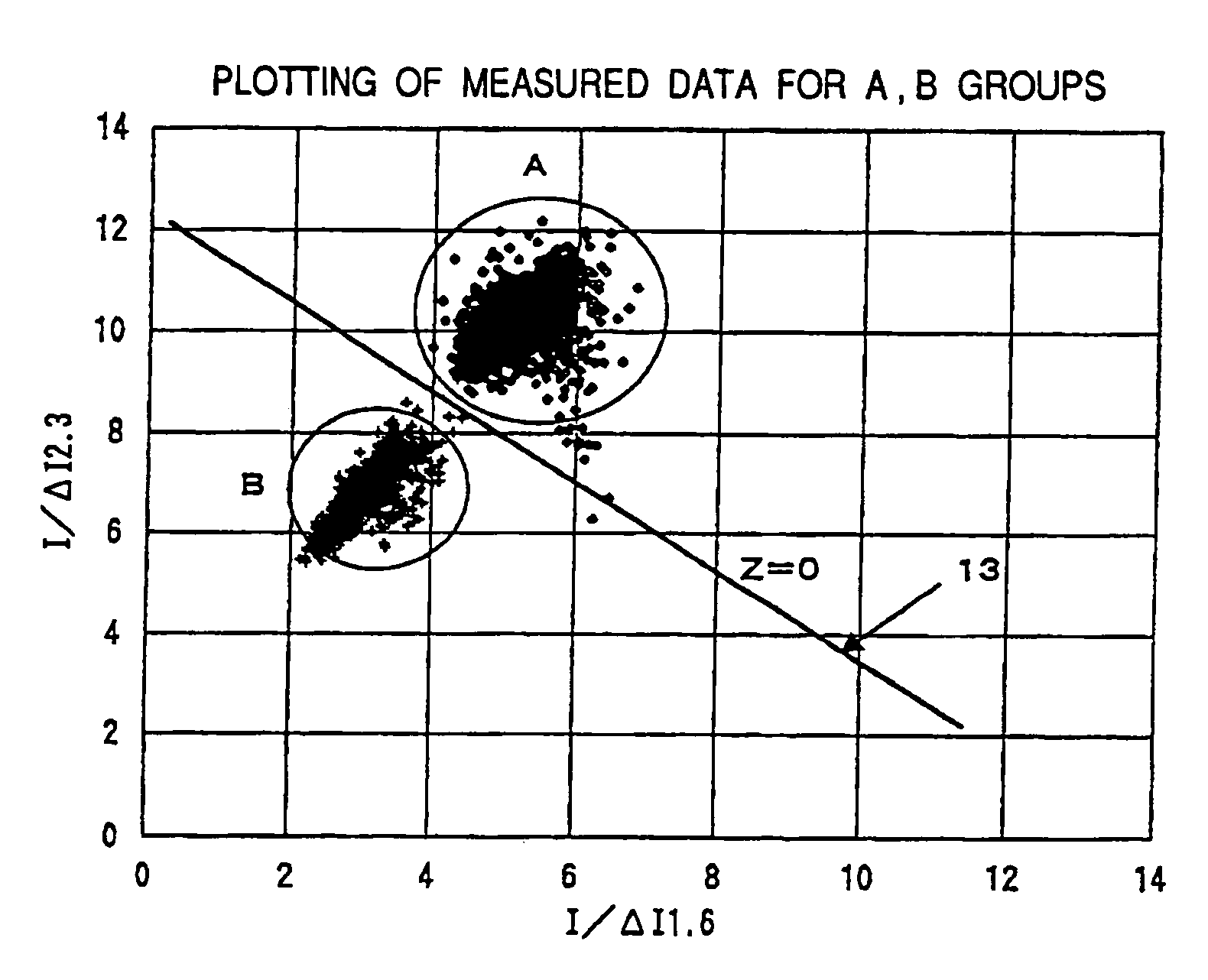
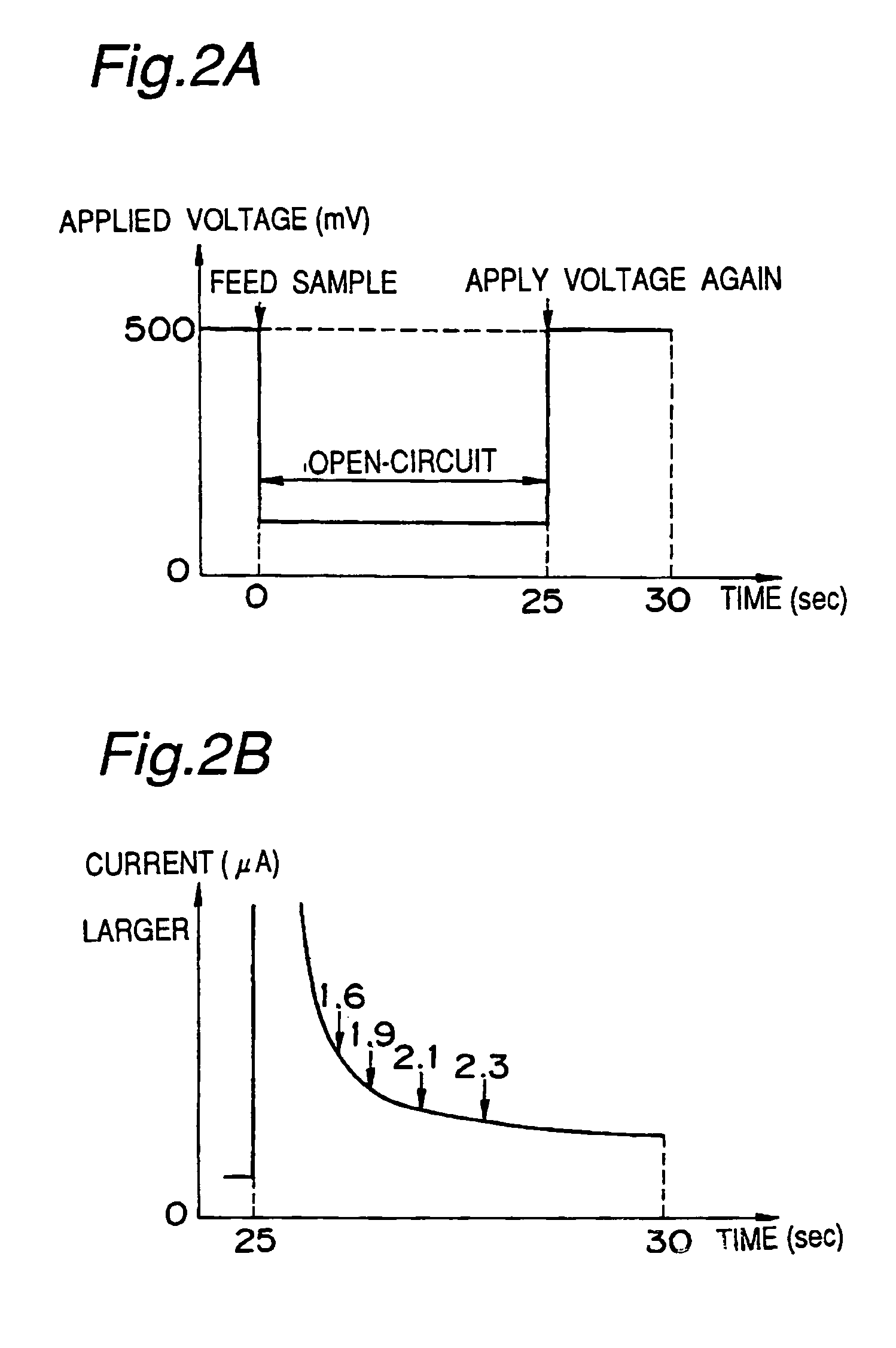
A glucose sensor system comprising the steps of using as a sample discriminating parameter a ratio (I / ΔI) of a measured current value I to the time-differential value of the current value ΔI, defining a discrimination function that discriminates whether a sample is blood or control fluid and uses the discriminating parameter as an independent variable, quantitating as a discriminating index a numeric value obtained by substituting a discriminating parameter value into this discrimination function, and automatically discriminating, based on this index, whether the sample is blood or a control fluid, whereby a kind of the sample can be automatically quantitated by measuring electric current when a sensor system is used for quantitating the concentration of an analysis object in the sample.
Owner:PHC CORP
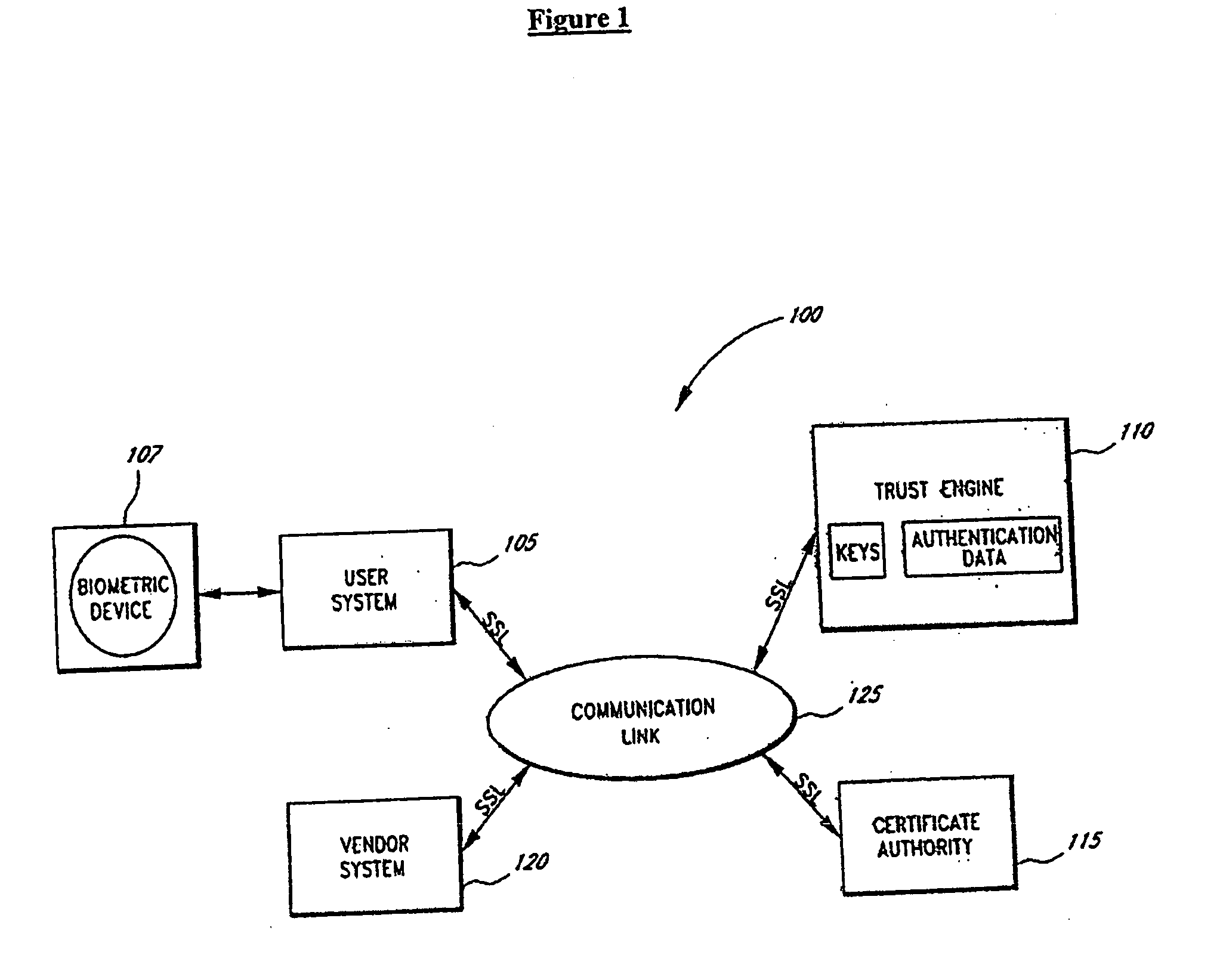
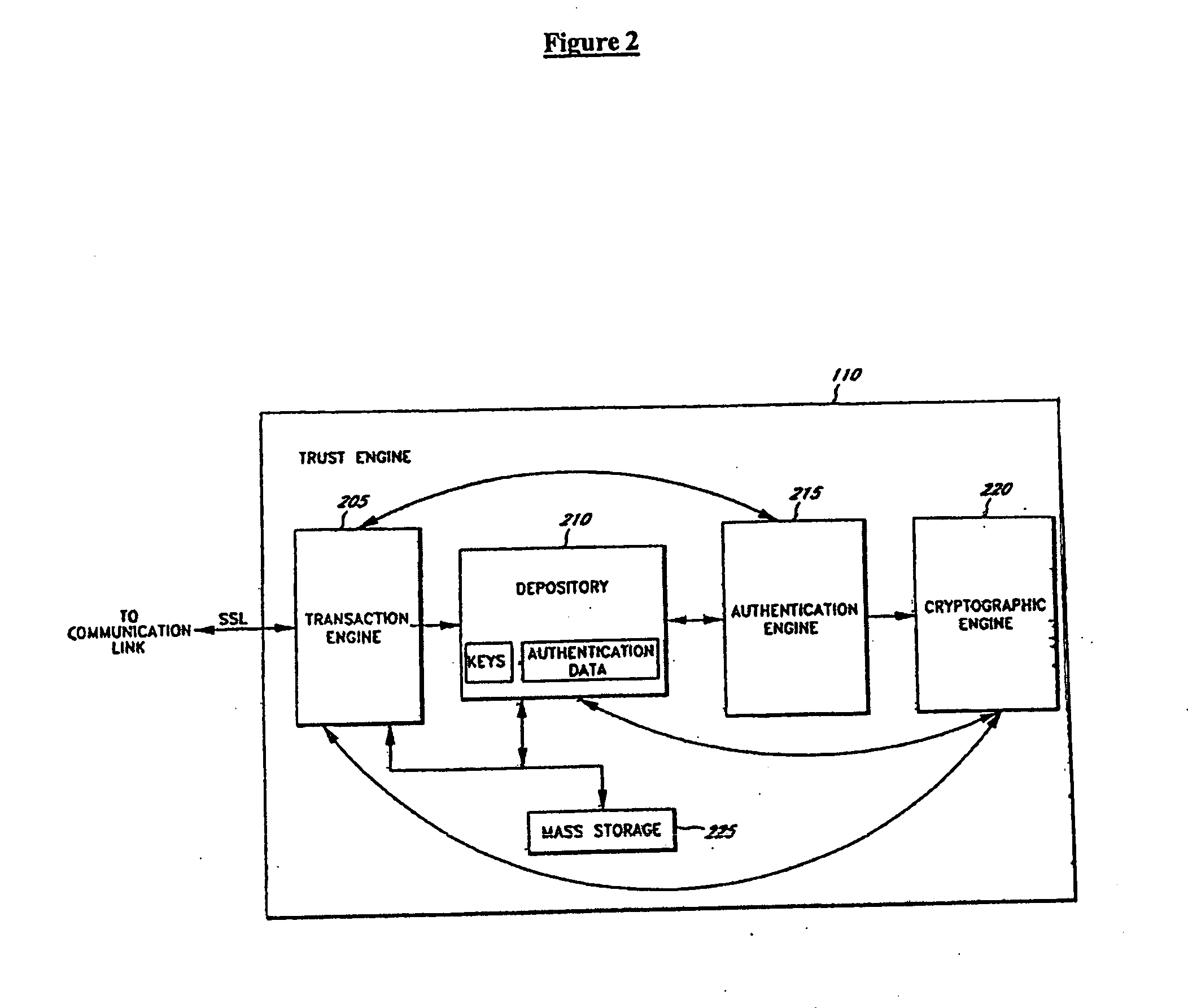
Systems and methods for distributing and securing data
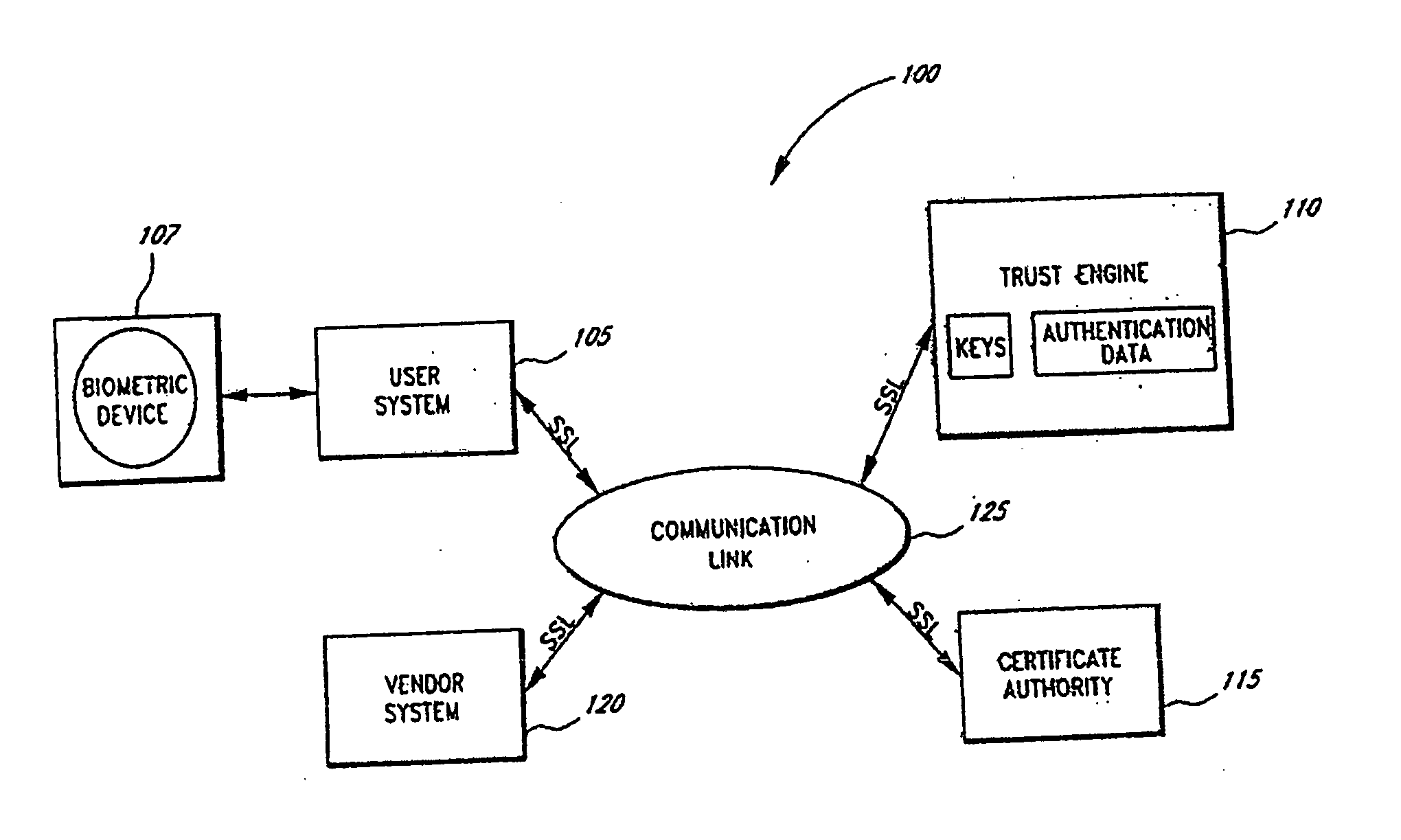
ActiveUS20080137857A1Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
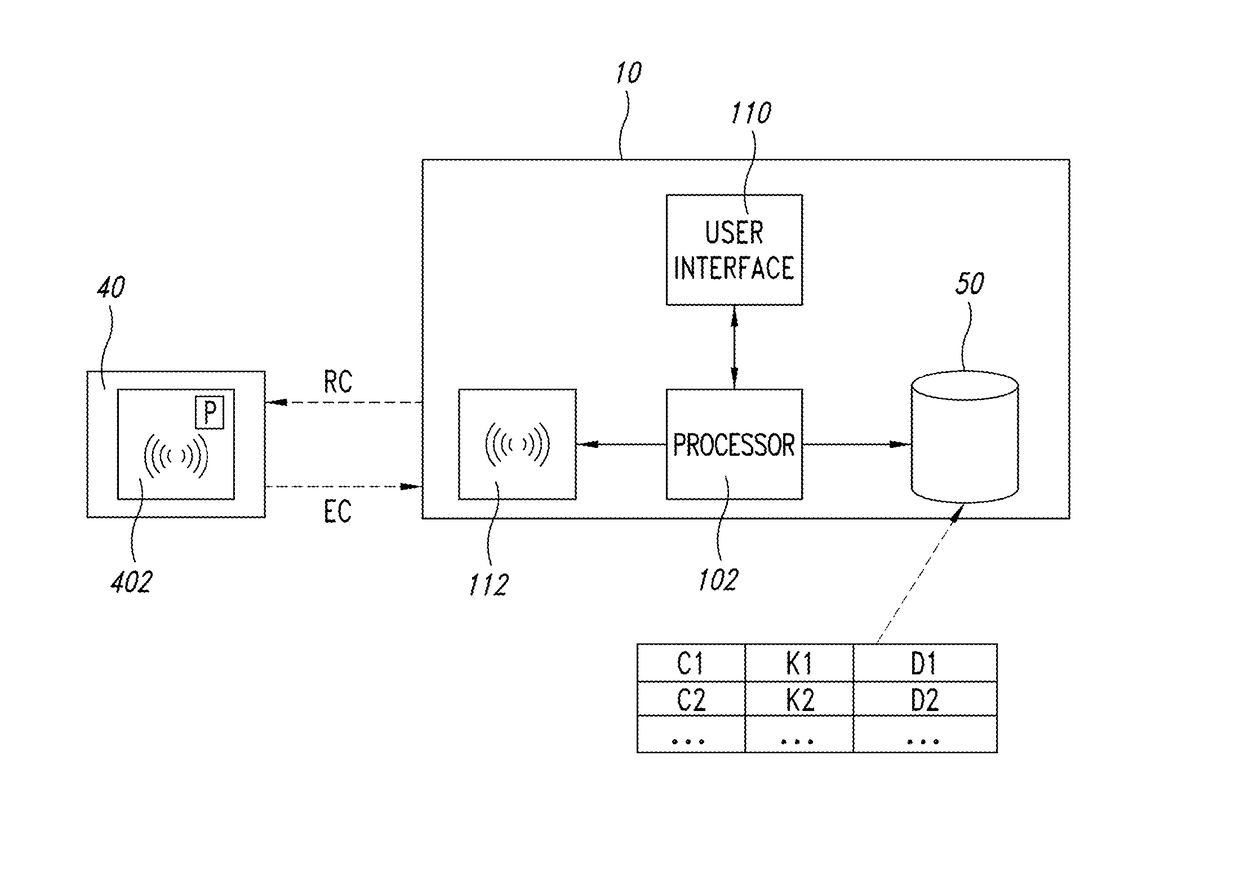
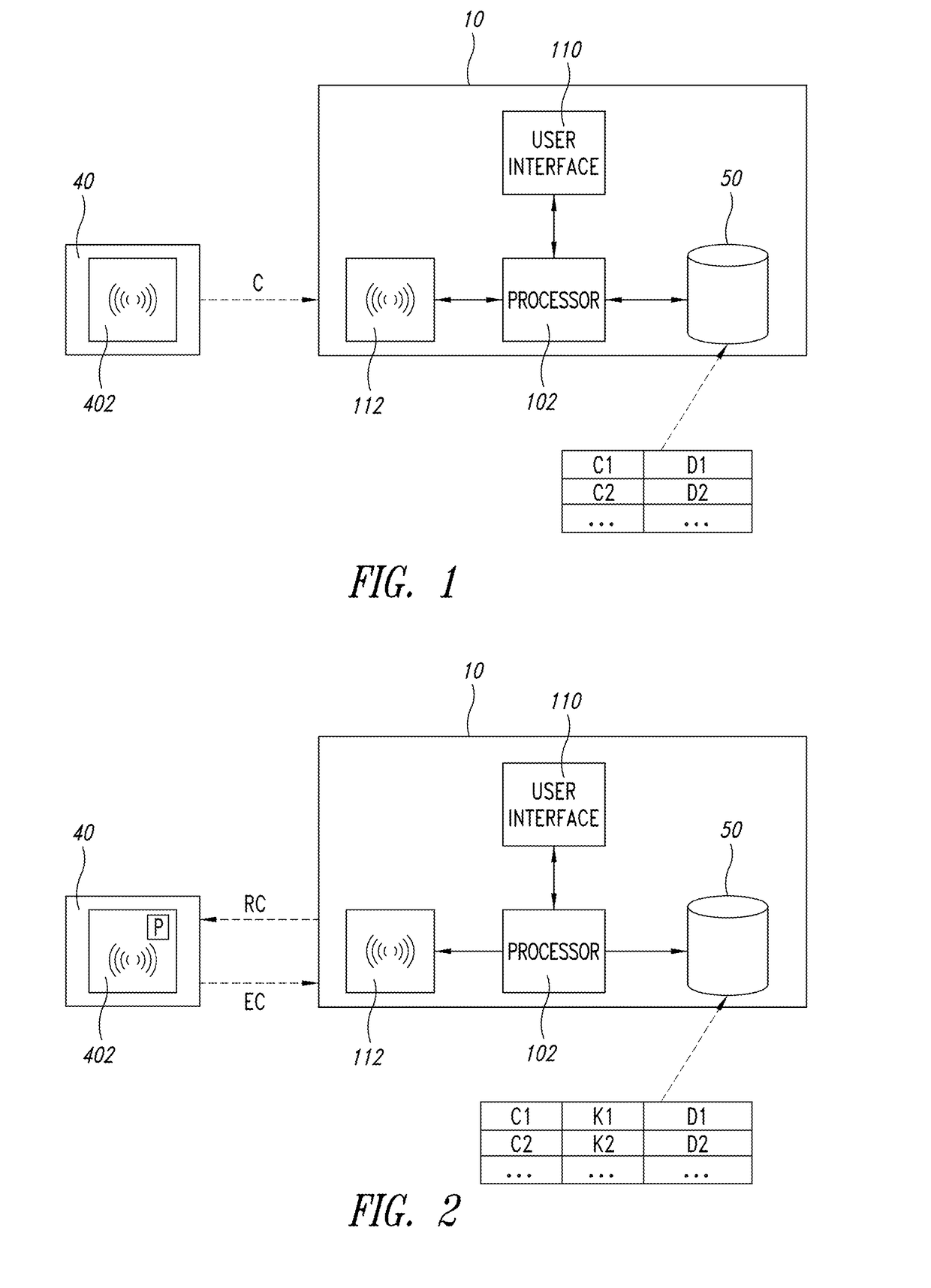
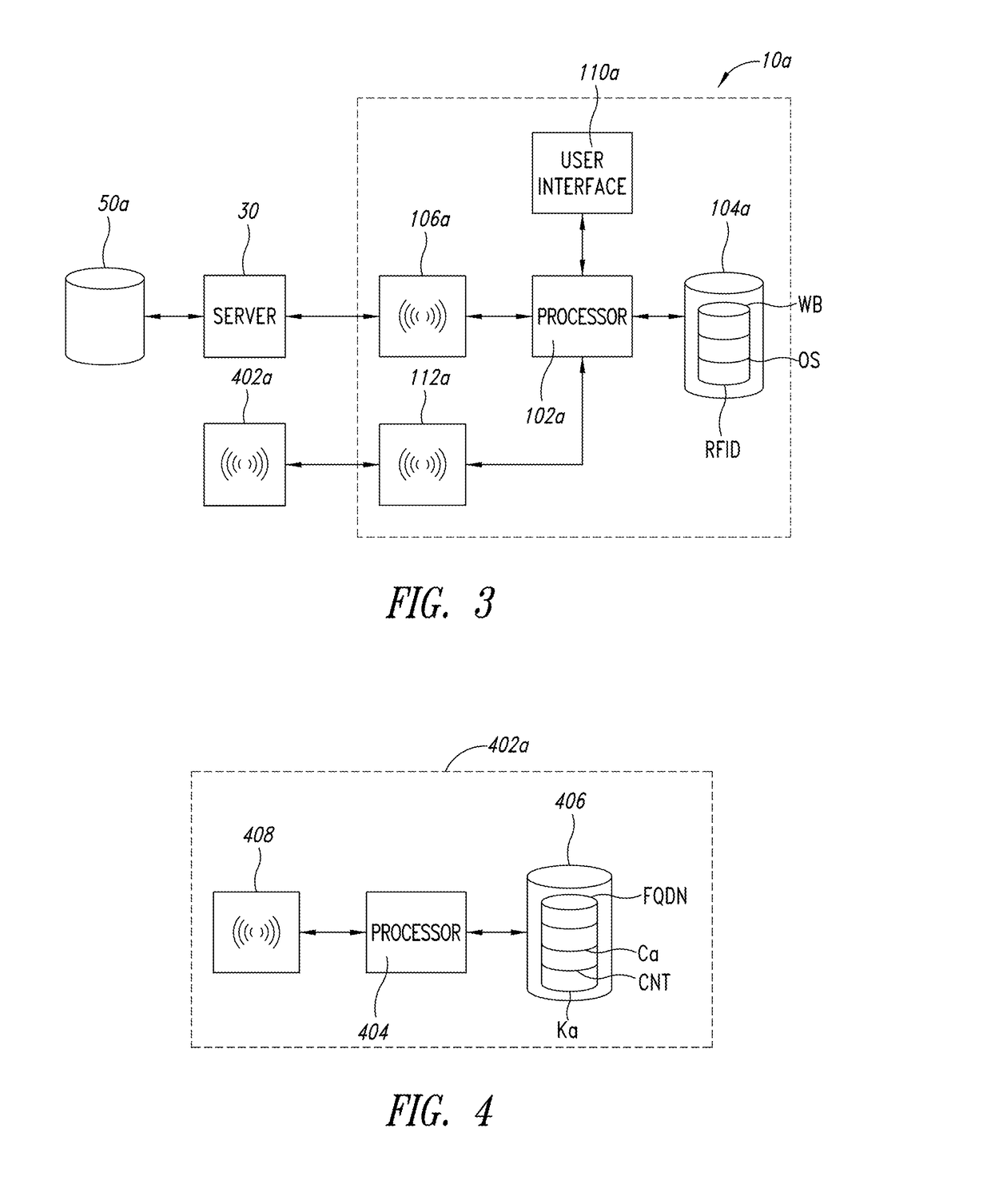
Tag, related method and system for identifying and/or authenticating objects
ActiveUS20170116447A1Easy to identifyEasy authenticationEncryption apparatus with shift registers/memoriesSensing by electromagnetic radiationCommunication interfaceUniform resource locator
Owner:STMICROELECTRONICS SRL
Systems and methods for enhancing dimensioning, for example volume dimensioning
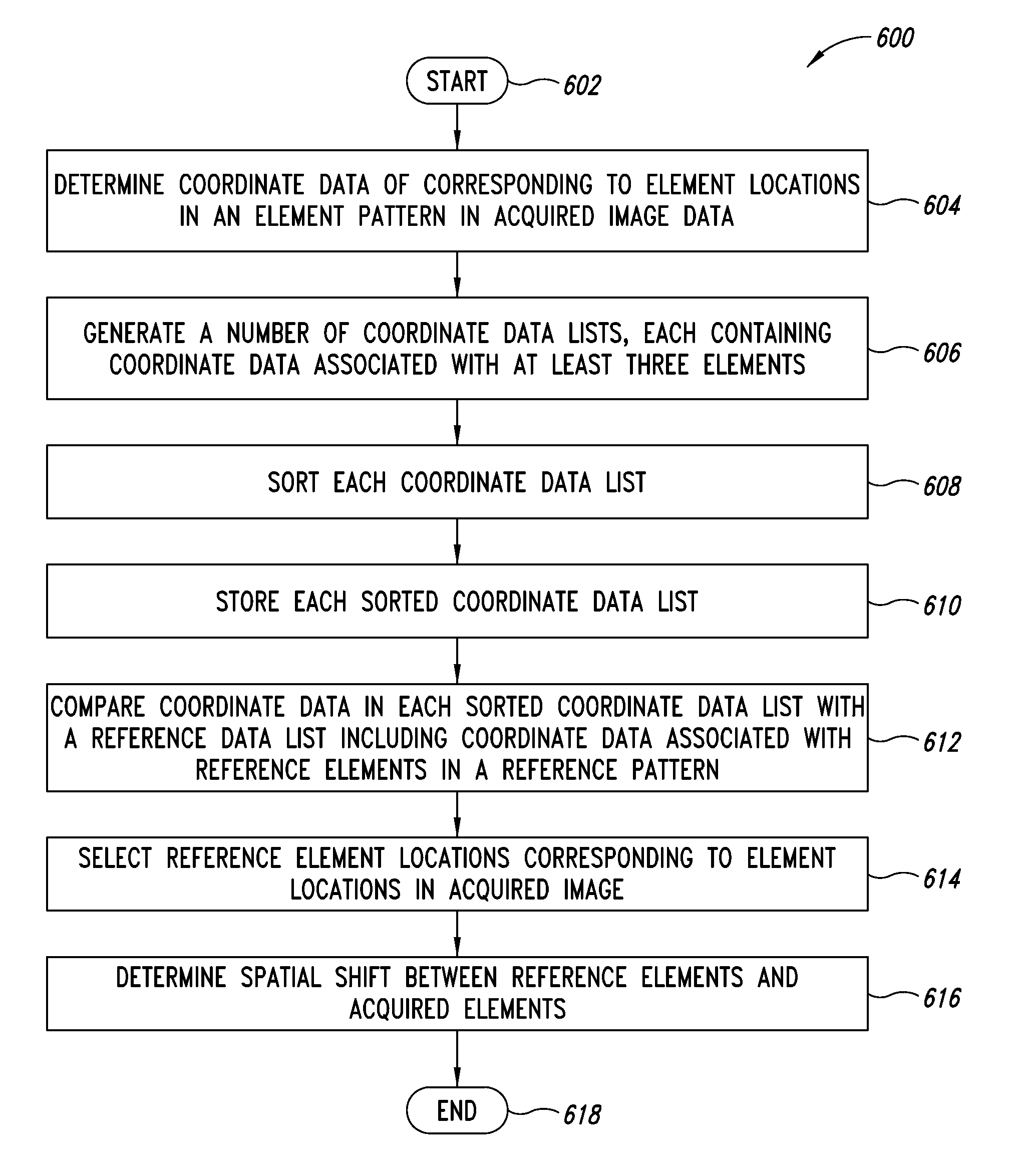
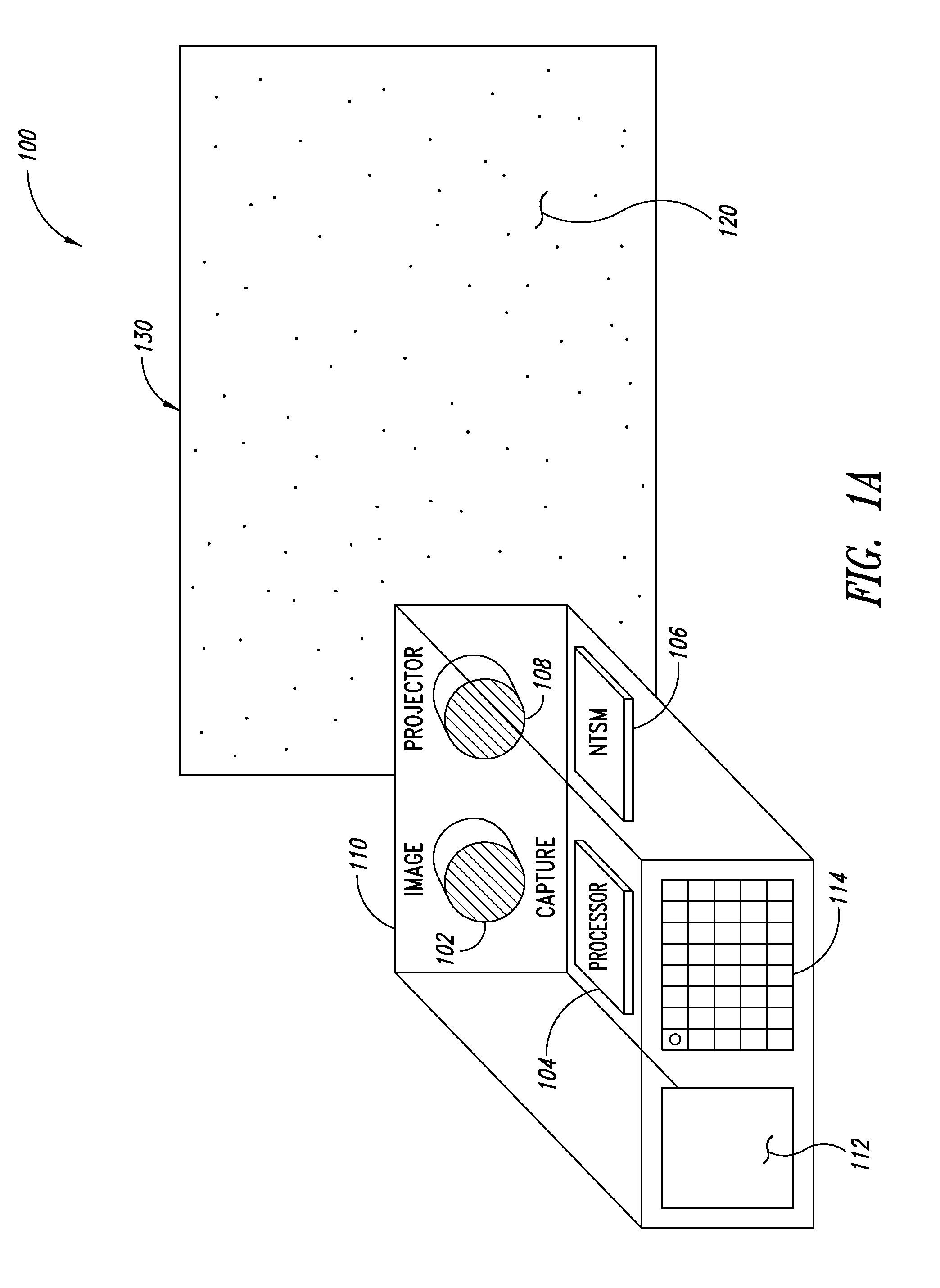
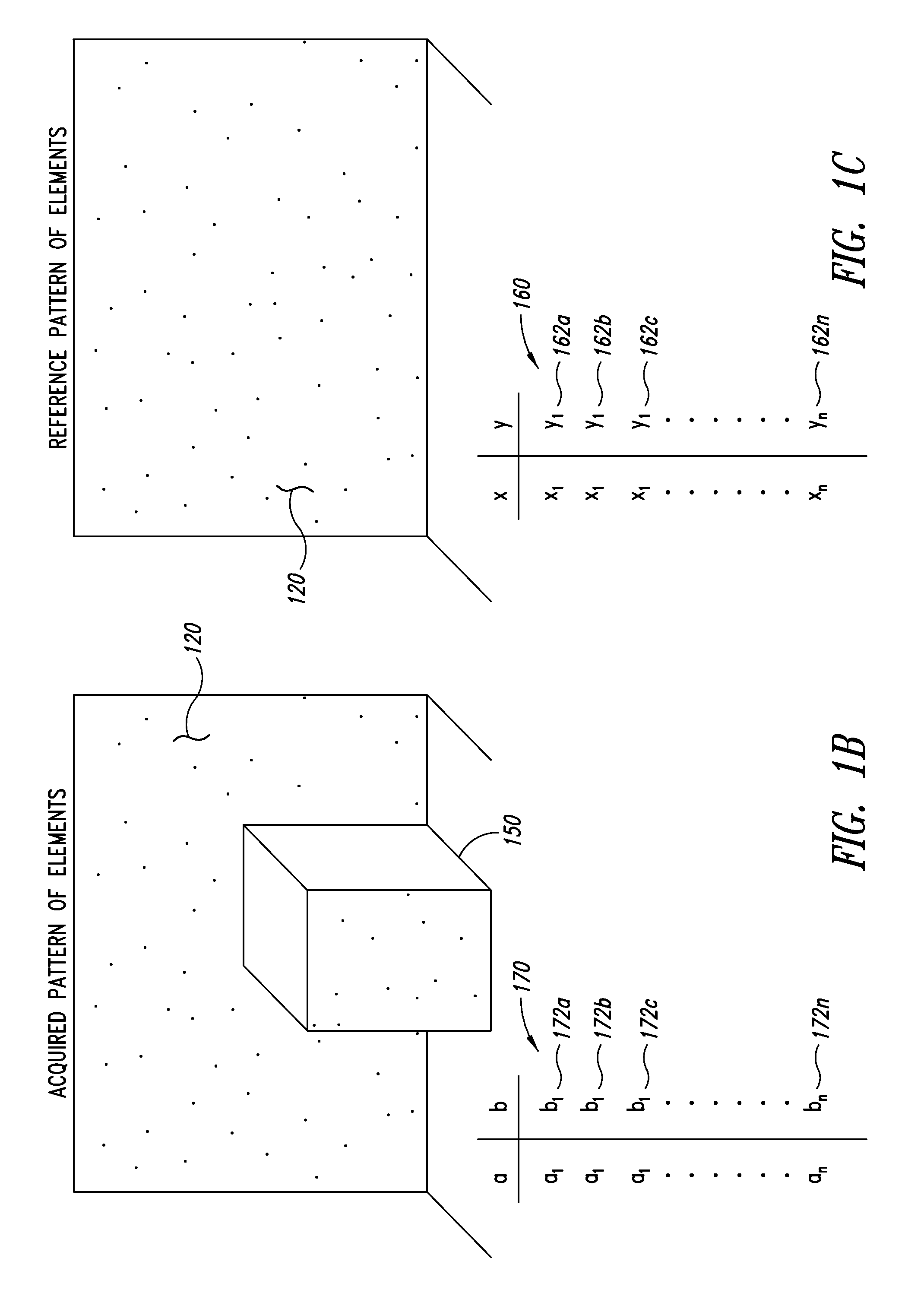
ActiveUS9080856B2Processing speedAccurate dataImage analysisCharacter and pattern recognitionSpatial correlationGraphics
A dimensioning system can include stored data indicative of coordinate locations of each reference element in a reference image containing a pseudorandom pattern of elements. Data indicative of the coordinates of elements appearing in an acquired image of a three-dimensional space including an object can be compared to the stored data indicative of coordinate locations of each reference element. After the elements in the acquired image corresponding to the reference elements in the reference image are identified, a spatial correlation between the acquired image and the reference image can be determined. Such a numerical comparison of coordinate data reduces the computing resource requirements of graphical comparison technologies.
Owner:INTERMEC IP
System and Method for Auditing a Security Policy
ActiveUS20090138938A1Reduce vulnerabilityImprove performanceComputer security arrangementsTransmissionComputerized systemSecurity policy
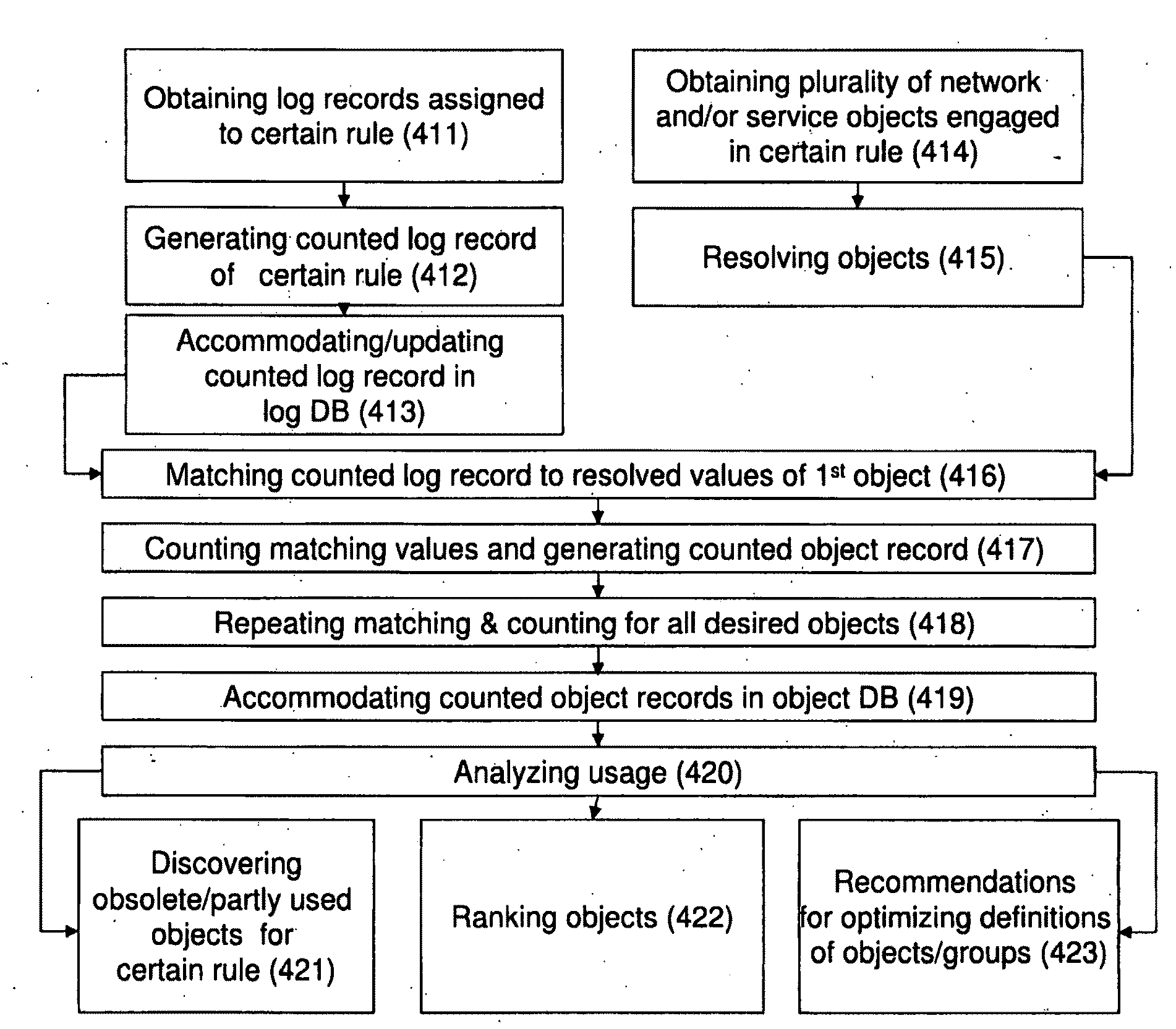
Provided a computerized system and method of automated auditing a range of rules associated with an enforced security policy. The method comprises automated obtaining log records assigned to a first rule within the range of rules and logged during a counted period, each said log record comprising a unique rule identifier and recorded values of respective arguments comprised in the rule; counting a number of records matching certain recorded values and logged within certain time intervals within the counted period (counted values); and automated generating a counted log record assigned to said rule, said record comprising the unique rule identifier, the counted period, recorded values of the rule arguments and respective counted values. The method further comprises obtaining a plurality of objects engaged in said first rule; resolving a first object among said plurality of objects to a set of resolved values; matching said resolved values to the recorded values of the respective arguments, said recorded values comprised in the counted log record assigned to said rule; counting each match in accordance with respective counted value, thus giving rise to a plurality of matching values of the resolved values; and using the plurality of matching values for analysis related to usage of the first object.
Owner:TUFIN SOFTWARE TECH
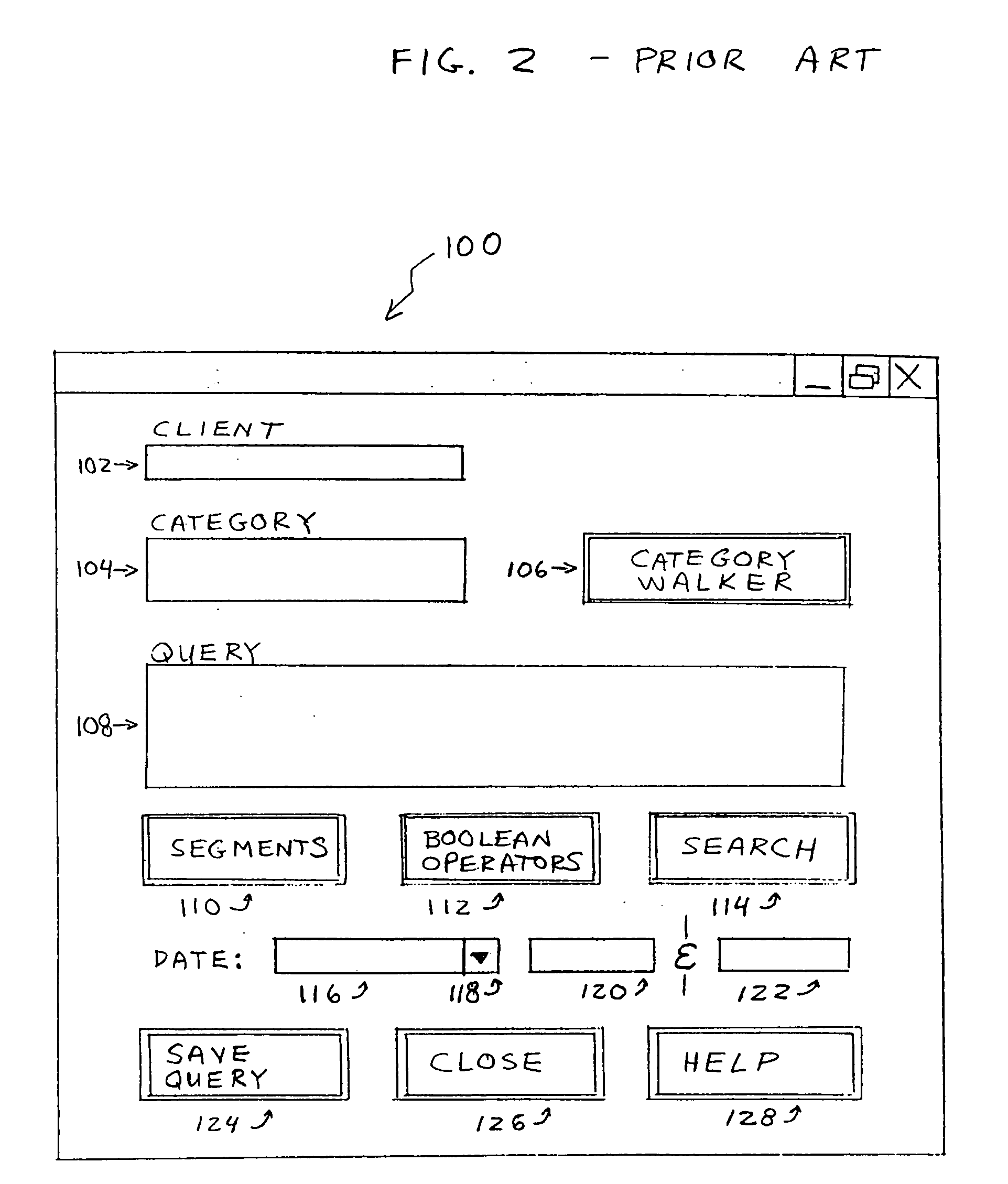
Graphical user interface for building boolean queries and viewing search results
InactiveUS20050192953A1Communication Latency MinimizedDigital data information retrievalData processing applicationsThe InternetNative client
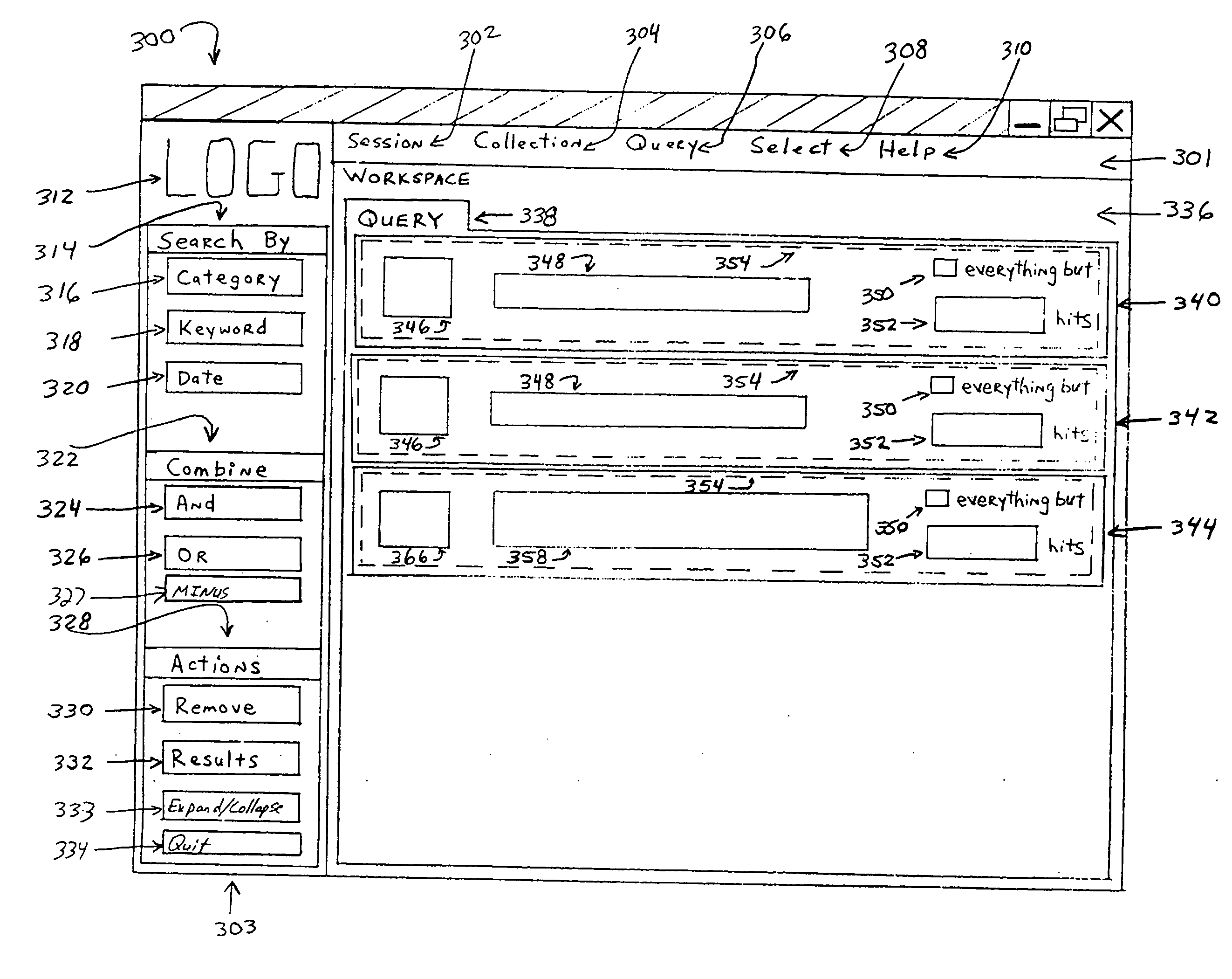
A graphical user interface is for building Boolean queries and viewing search results using search cells, combination cells, a toolbar, and a menu bar. The search cells are movable within a workspace and preferably contain a text field, a facet type designation, an advanced button and a hit count. Search cells can search records by a category, keyword, date or numeric value. Categories are preferably chosen with the assistance of a category walker. The combination cells are movable within the workspace and preferably contain a combine icon, a hit count and an expression field. The combination cell is a Boolean combination of two or more selected search cells. In the preferred embodiment of the invention, the Boolean logic is graphically depicted with the use of combination brackets. The contents of each combination bracket is controllable by the use of movable graphical pins that are located between each pair of search cells. The combination bracket can be represented by use of a rectangular bracket, a square bracket, or a curly brace. In an alternative embodiment of the invention, the Boolean query is depicted in a folder tree hierarchy. Search folders and combination folders are used to depict search cells and combination cells, respectively. Search folders contain the same information as search cells, but search folders can be toggled to appear as small folder icons within the workspace. Combination folders are represented as small folder icons containing a logical AND icon, a logical OR icon or a logical MINUS icon. Search folders are shown to be included within combination folders through the use of the folder tree hierarchy, just as computer files are shown to be included within a folder in a typical file manager program. In the preferred embodiment, the invention runs an internet browser and is coupled to a remote server through the internet. To minimize communication delays across the internet, an applet can be run on the local client to perform most graphical display manipulations prompted by the searches manipulation of the search cells, the combination cells, the toolbar, and the menu. The remote server is used to execute queries received over the internet from the local client and deliver search results back to the local client over the internet. Optionally, the client can take on some or all of the tasks of the server in executing queries over the internet.
Owner:ROMAN KENDYL A +1
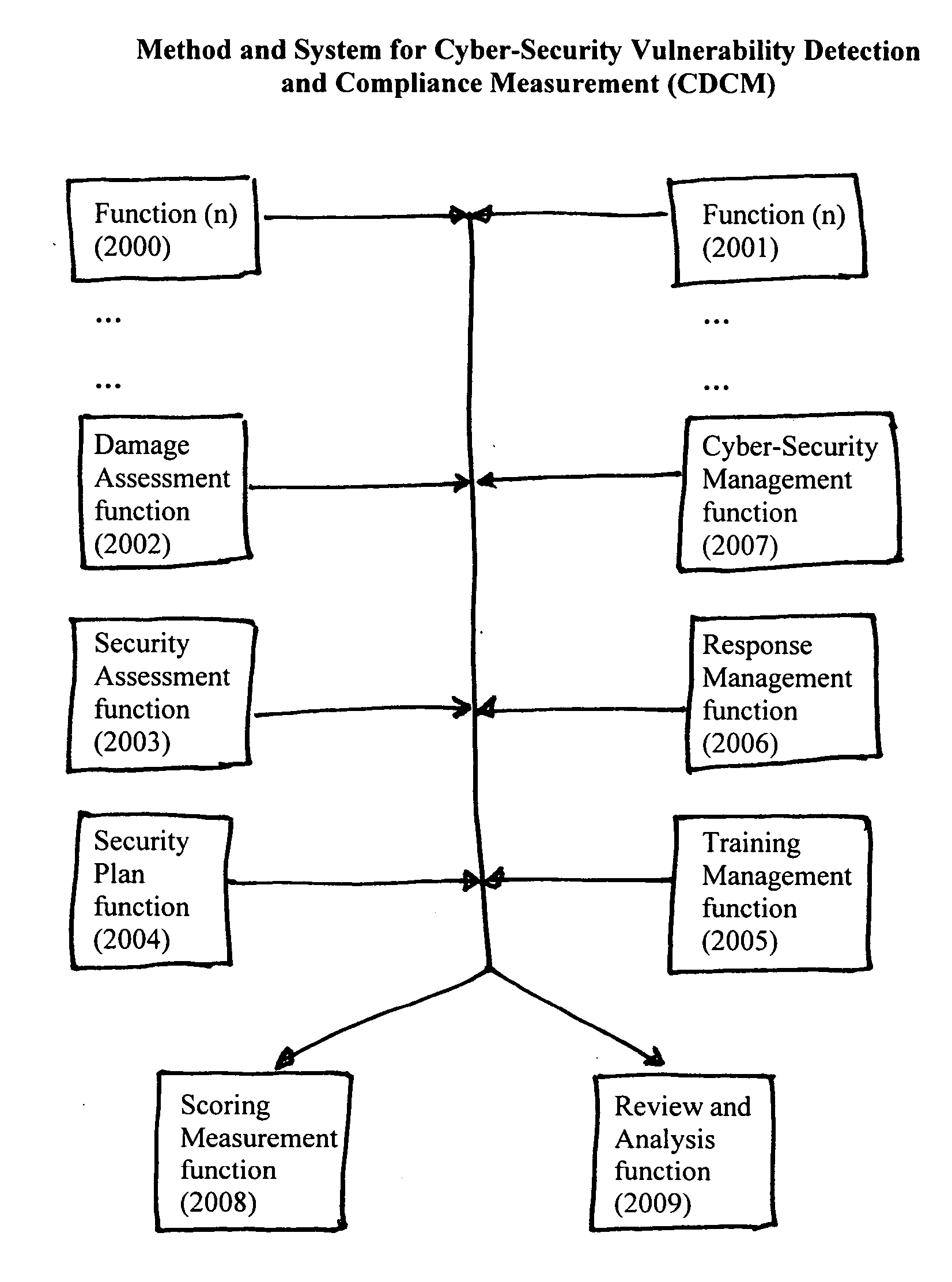
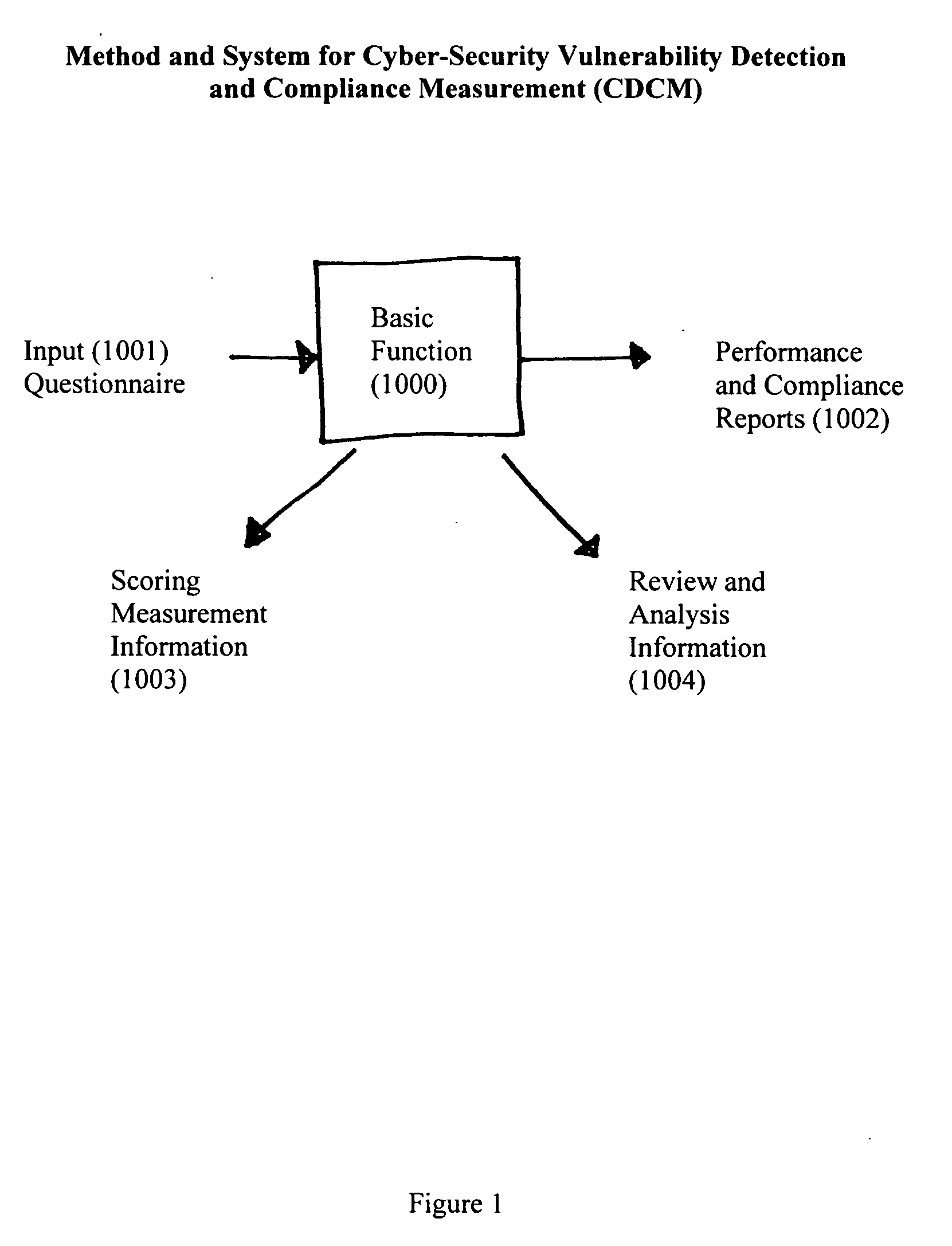
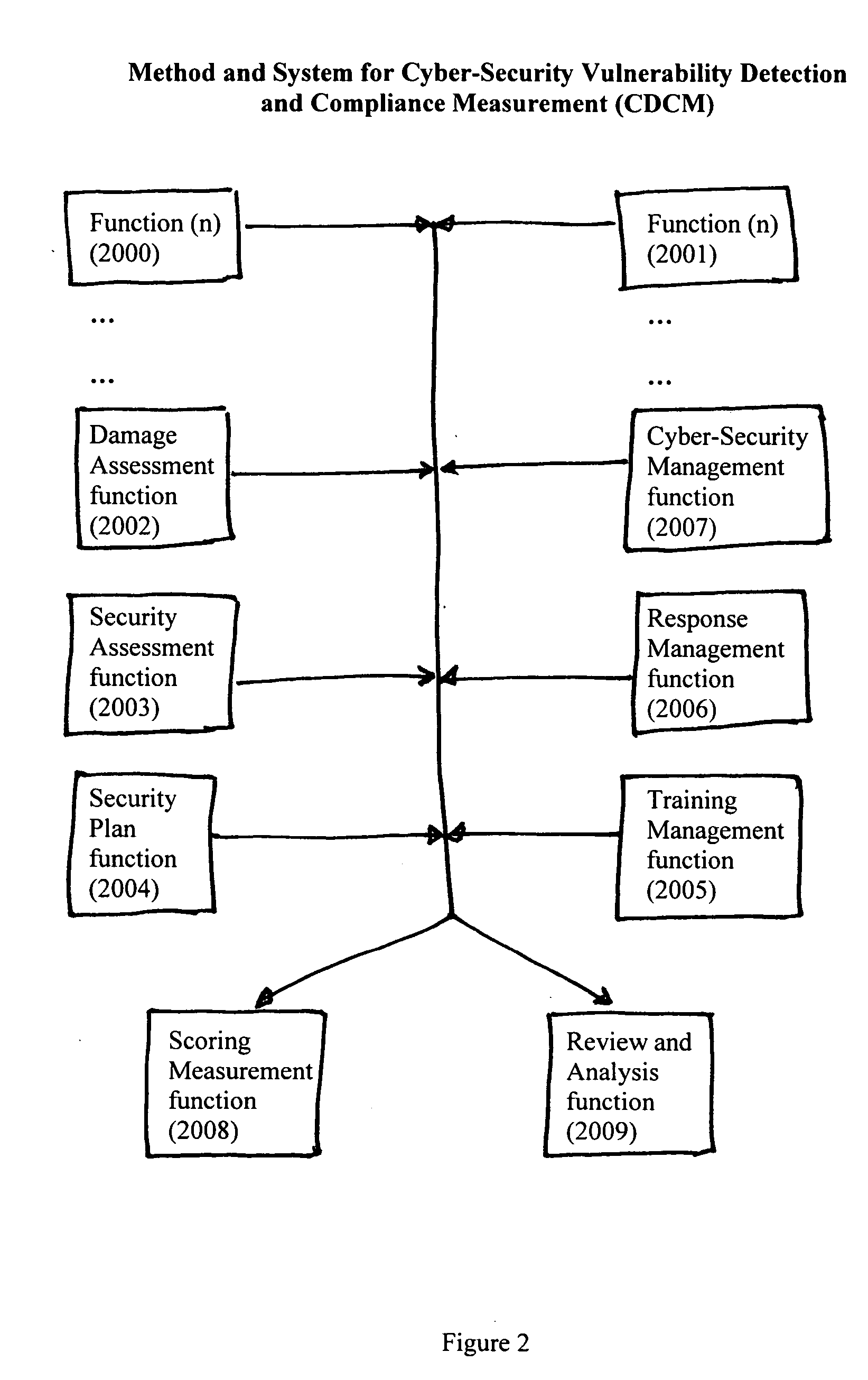
Method and system for cyber-security vulnerability detection and compliance measurement (CDCM)
InactiveUS20050132225A1Improve abilitiesDigital data processing detailsUser identity/authority verificationProgram planningHandling system
Method and System for Cyber-Security Vulnerability Detection and Compliance Measurement (CDCM) provides any entity, organization or individual with access to or possession of sensitive, confidential or secret information, defined as “protected information,” in digital format that is received, processed, stored or distributed by a computer, computer system or digital processing equipment with the capability to detect and respond to cyber security vulnerabilities and to measure compliance with cyber-security requirements as established by the Federal Security Information Management Act (FISMA) for the security of protected information and certain additional related desirable or mandatory cyber-security requirements. In one sample embodiment of the invention, the method utilizes a damage assessment function; a security assessment function; a security plan or planning function; a training management function; a response management function; a cyber-security management function; a scoring measurement function; and a review and analysis function; to establish a quantifiable and definitive numerical measurement of the relative compliance of a specific processing system, at a specific point in time, to a defined and established threshold value of performance, or compliance acceptance, and to provide, assemble and be capable of archiving the supporting parameters, status, states and analysis that is specifically associated with the numerical value which represents the specific processing system's state of compliance at the specified time and to utilize various intermediate values and parameters to manage and enhance the performance of the specific system thereby improving the systems compliance score and numerical performance measurement value.
Owner:GEARHART GLENN
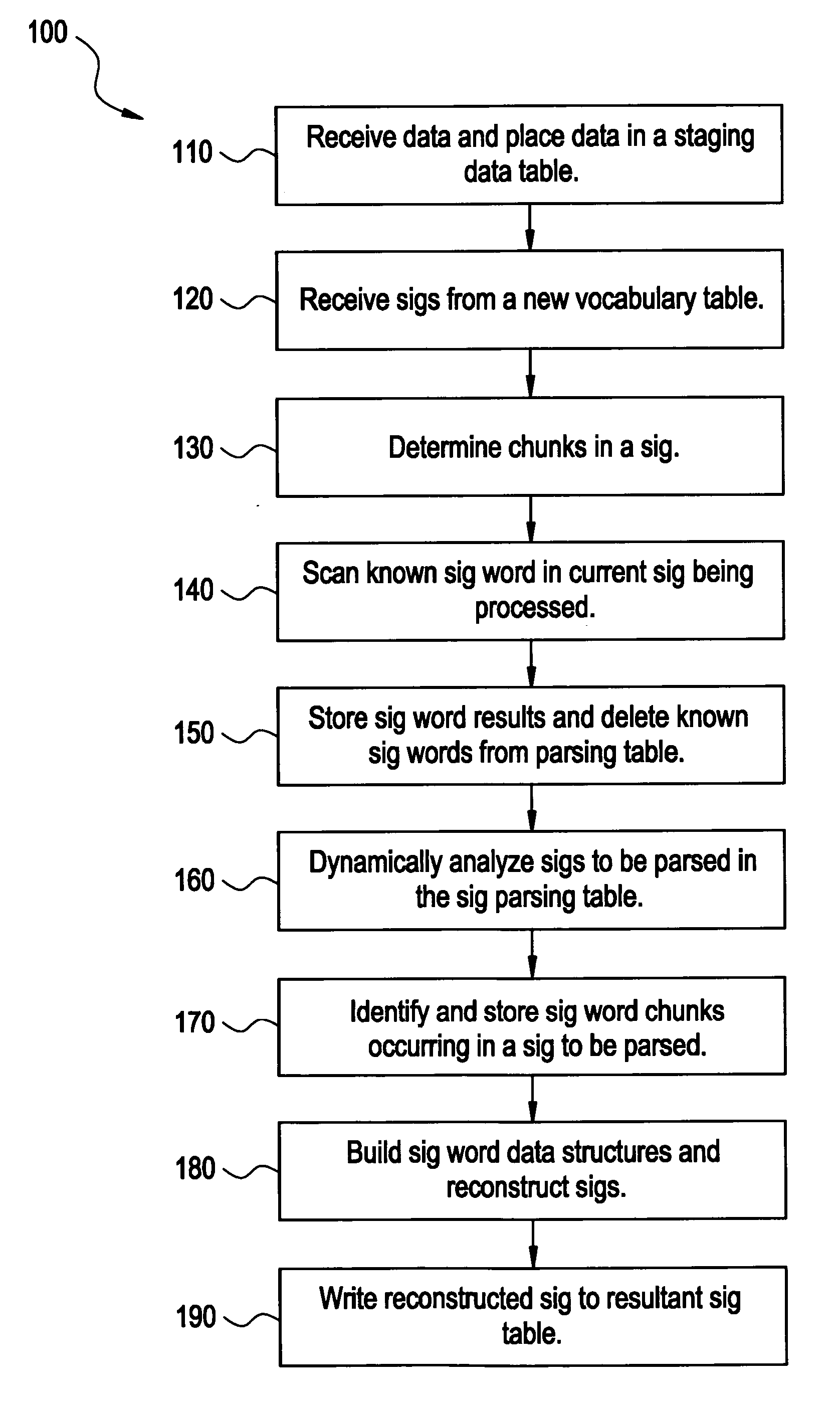
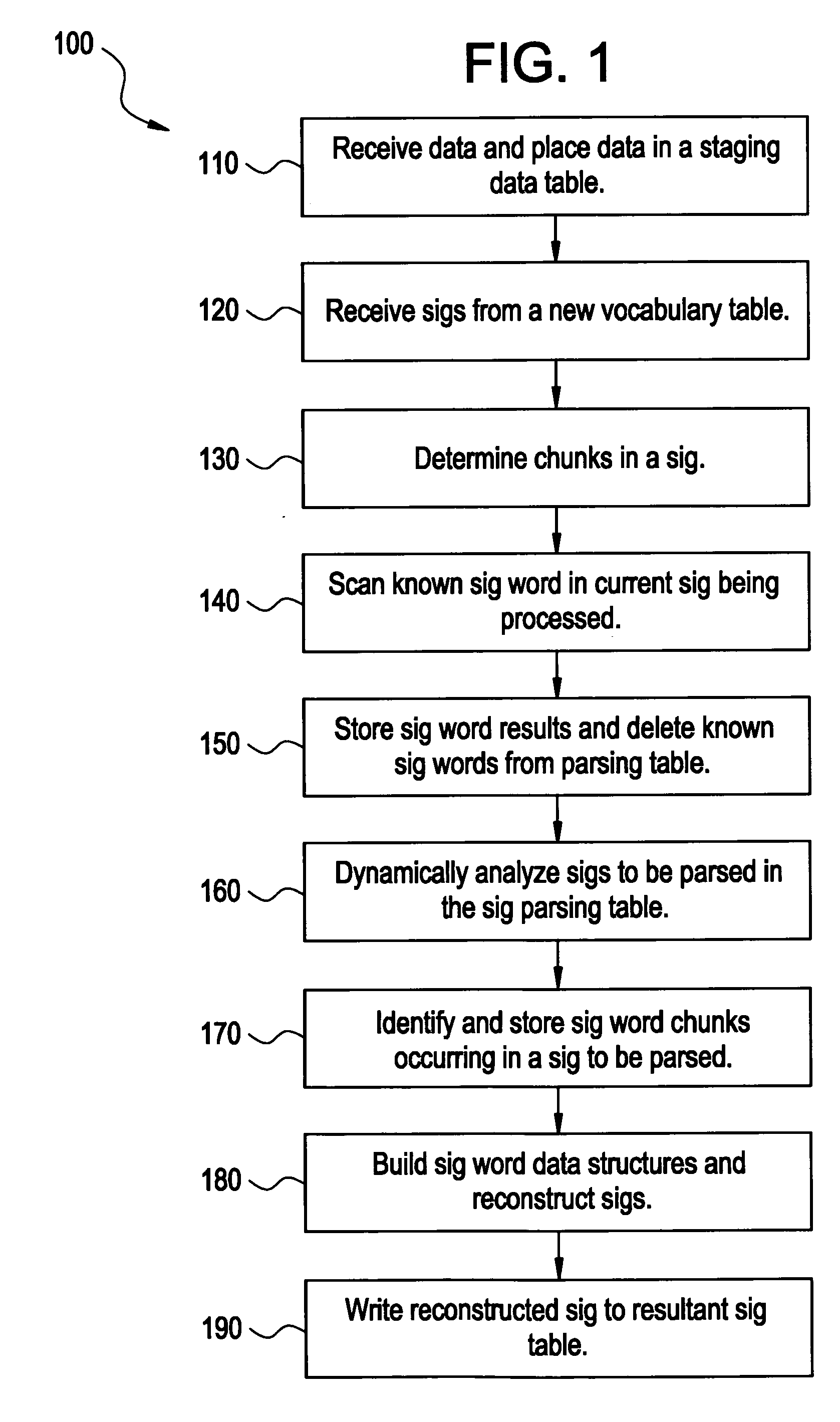
System and method for parsing medical data
InactiveUS20060235881A1Simple methodDrug and medicationsDigital data processing detailsText stringWorld Wide Web
Certain embodiments of the present invention provide a system and method for processing medical data. The method includes the steps of identifying text strings in medical data, associating the text strings with standardized identifiers from a library, and outputting the standardized identifiers associated with the text strings. In an embodiment, a report and / or an order including the standardized identifiers associated with the text strings may be printed and / or stored. In an embodiment, the library may be modified to accommodate the text strings. A user and / or software program may be used to review the text strings to associate the standardized identifiers with the text strings, for example. In an embodiment, the text strings may be deconstructed into a plurality of sub-strings. A standardized identifier is then associated with each sub-string. The standardized identifiers may be numeric values, for example.
Owner:GENERAL ELECTRIC CO
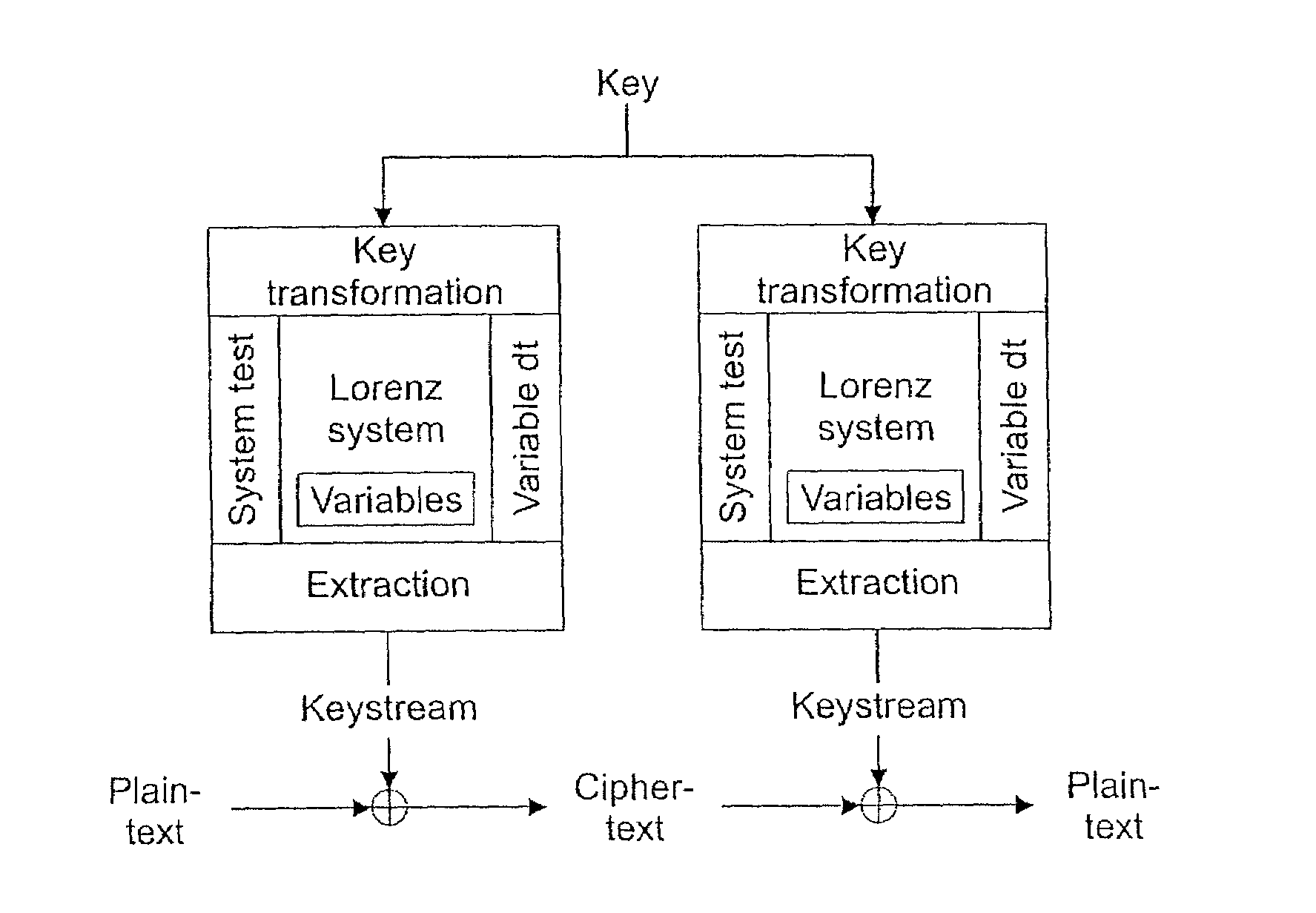
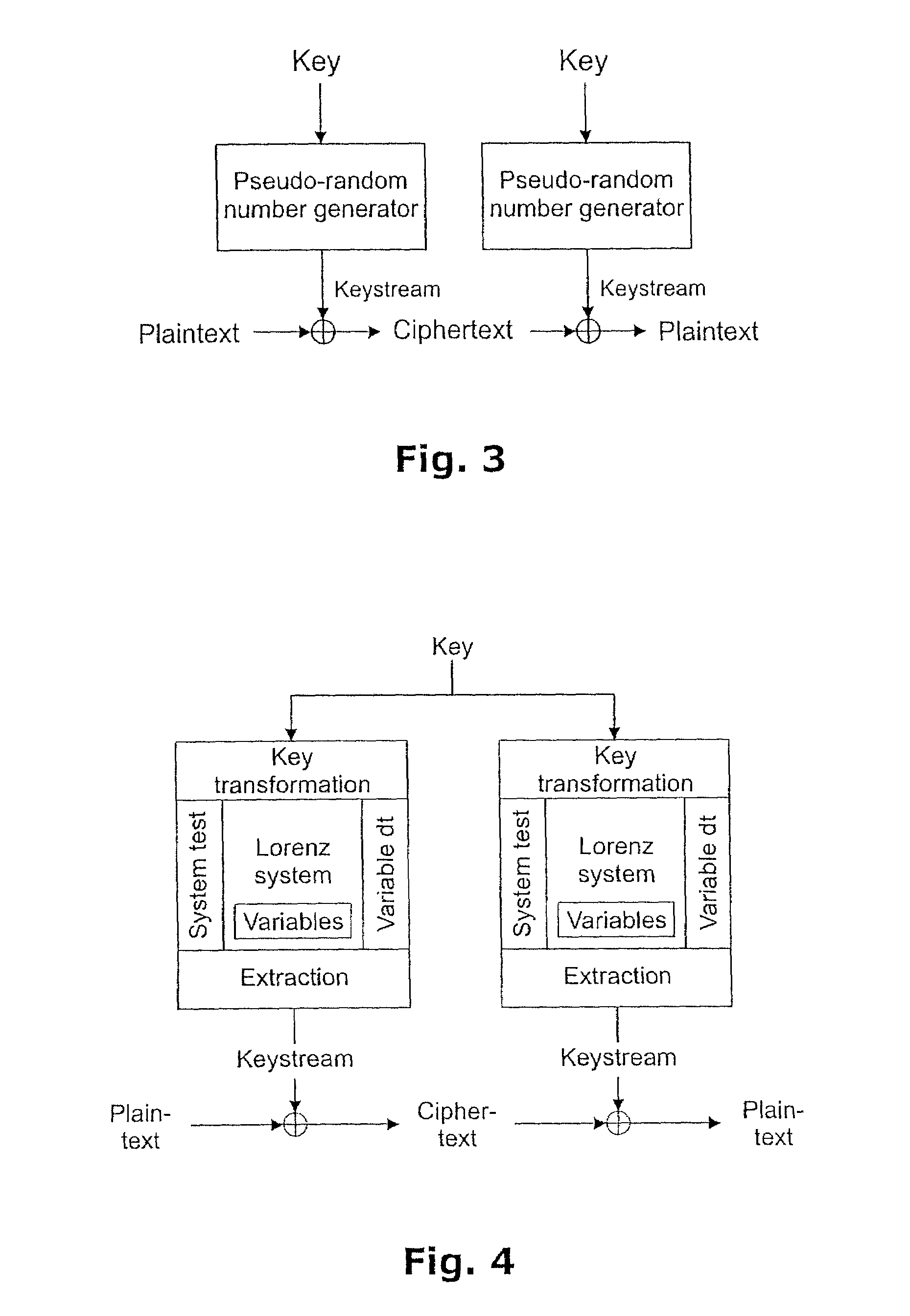
Method of generating pseudo-random numbers in an electronic device, and a method of encrypting and decrypting electronic data
InactiveUS7170997B2Compromise safetyQuick buildRandom number generatorsSecret communicationTheoretical computer scienceElectronic data
A method of performing numerical computations in a mathematical system with at least one function, including expressing the mathematical system in discrete terms, expressing at least one variable of the mathematical system as a fixed-point number, performing the computations in such a way that the computations include the at least one variable expressed as a fixed-point number, obtaining, from the computations, a resulting number, the resulting number representing at least one of at least a part of a solution to the mathematical system, and a number usable in further computations involved in the numerical solution of the mathematical system, and extracting a set of data which represents at least one of a subset of digits of the resulting number, and a subset of digits of a number derived from the resulting number.
Owner:CRYPTICO
Identification information issuing system
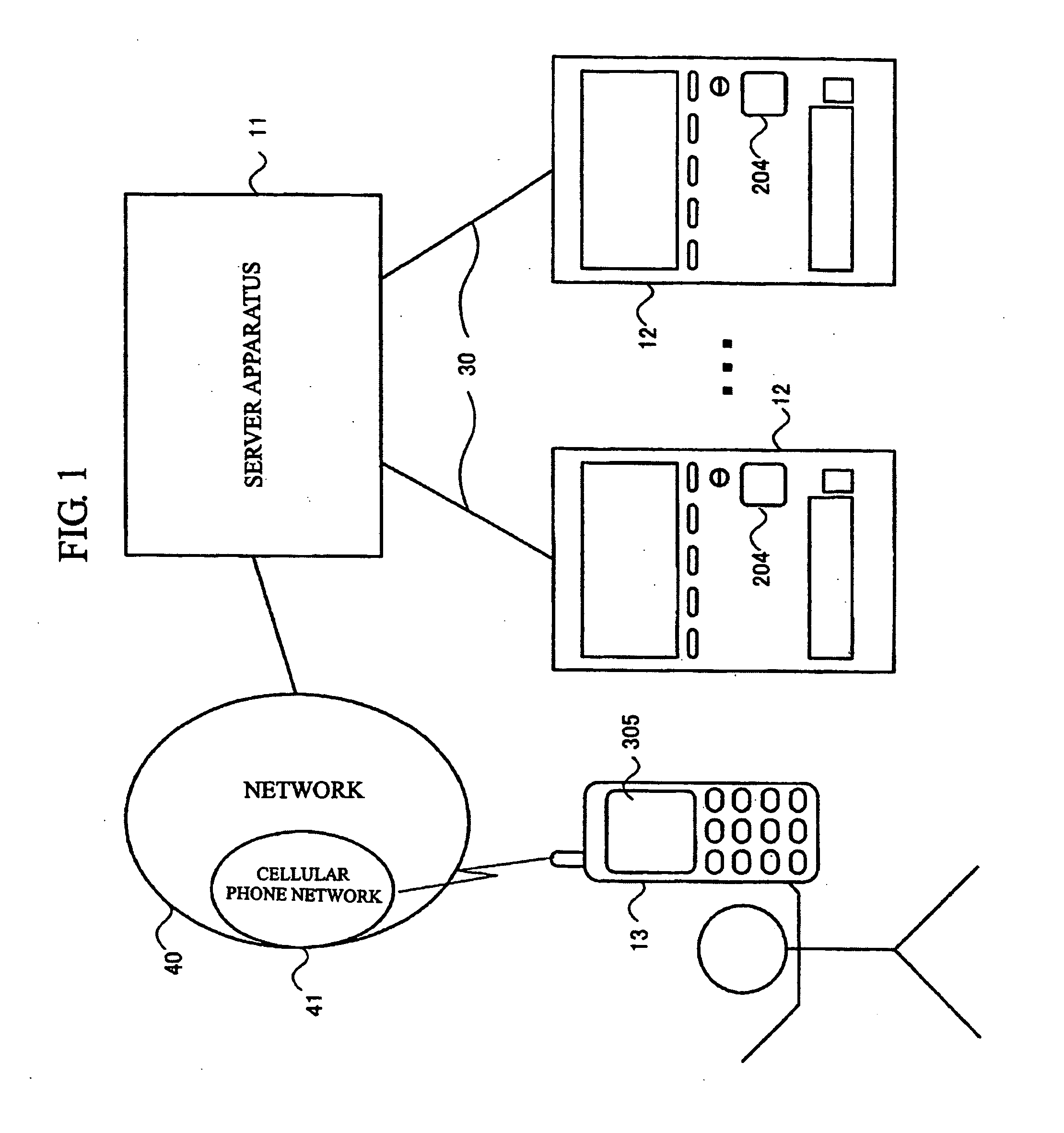
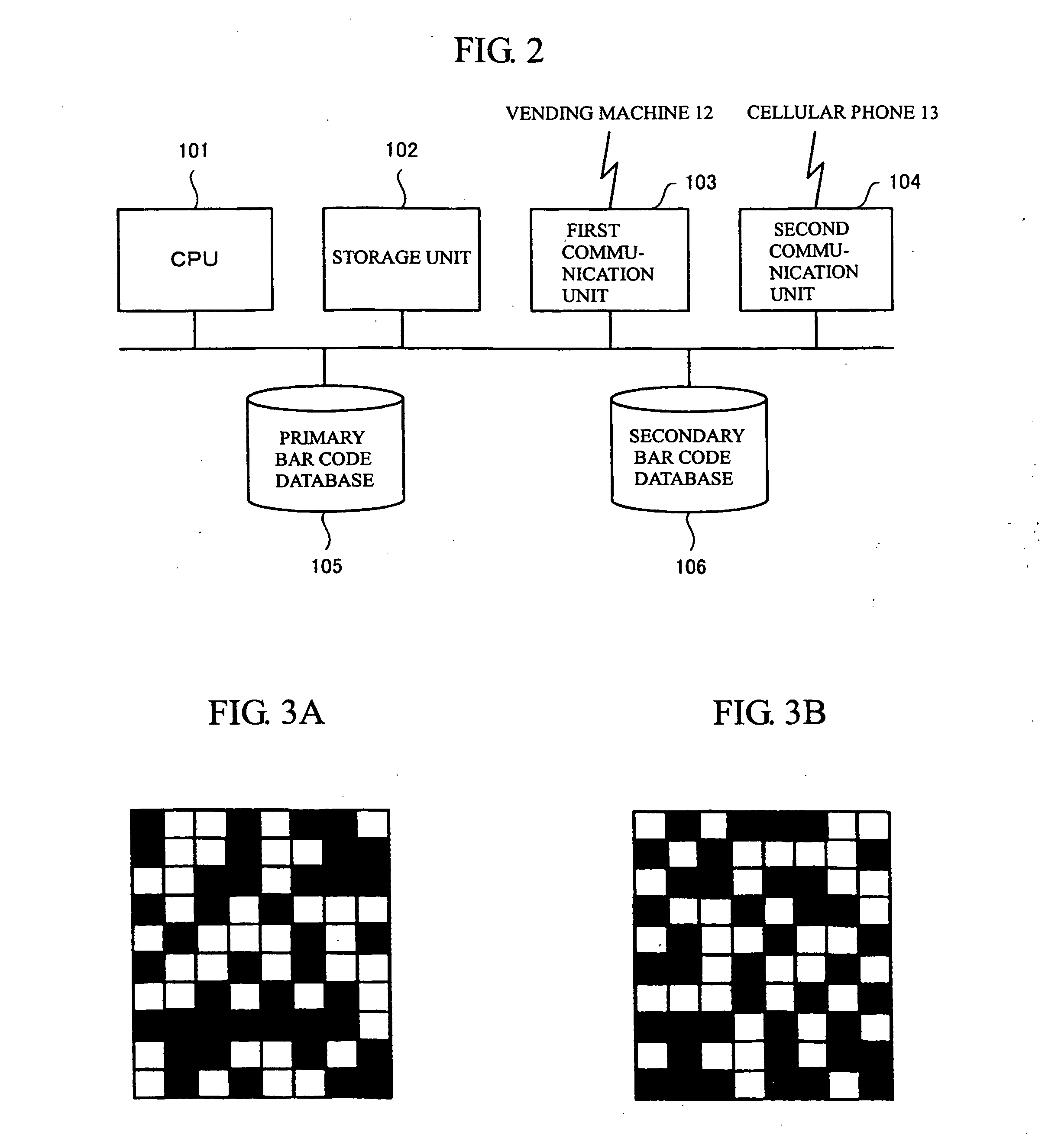
InactiveUS20050059339A1Attempt have been hamperedDigitally marking record carriersUser identity/authority verificationProgramming languageBarcode
When image data of a bar code displayed on a cellular phone and read by a vending machine or the like are sent to a server apparatus, the apparatus converts the code to a numerical value. The apparatus divides the code value by divisor A to obtain remainder a, and divides the code value by divisor B to obtain remainder b. The least common multiple for the numeric value A and the numeric value B is greater than the difference between the maximum and minimum values that the bar code value assumes. The apparatus refers pointers registered in a storage position corresponding to remainder a in the first table and pointers registered in a storage position corresponding to remainder b in the second table. The apparatus authenticates the user when the same user information in a user database can be accessed from both the first table and the second table.
Owner:CODECOM
Image recognition method and apparatus utilizing edge detection based on magnitudes of color vectors expressing color attributes of respective pixels of color image
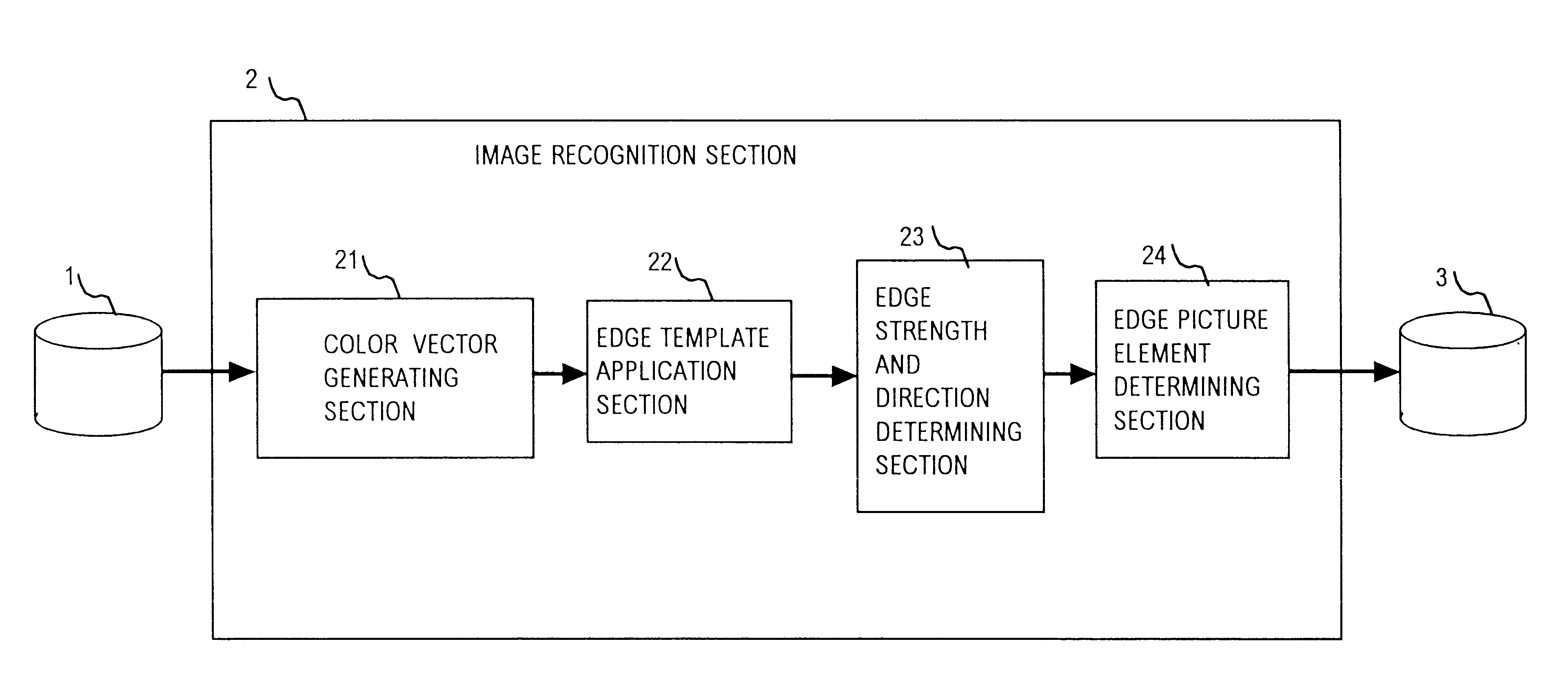
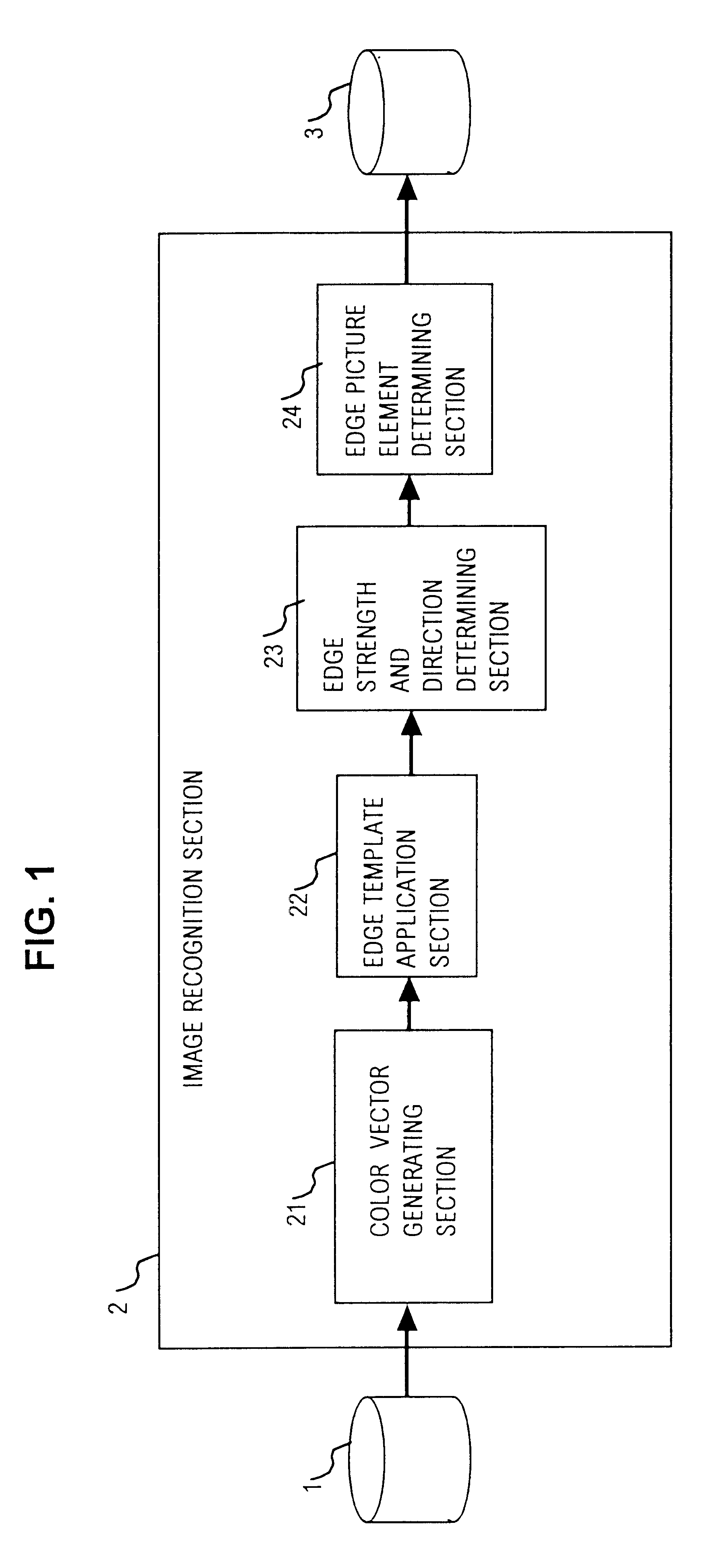
InactiveUS6665439B1Easy to identifyReduce precisionImage enhancementImage analysisColor imageArray data structure
An image recognition apparatus operates on data of a color image to obtain an edge image expressing the shapes of objects appearing in the color image, the apparatus including a section for expressing the color attributes of each pixel of the image as a color vector, in the form of a set of coordinates of an orthogonal color space, a section for applying predetermined arrays of numeric values as edge templates to derive for each pixel a number of edge vectors each corresponding to a specific edge direction, with each edge vector obtained as the difference between weighted vector sums of respective sets of color vectors of two sets of pixels which are disposed symmetrically opposing with respect to the corresponding edge direction, and a section for obtaining the maximum modulus of these edge vectors as a value of edge strength for the pixel which is being processed. By comparing the edge strength of a pixel with those of immediately adjacent pixels and with a predetermined threshold value, a decision can be reliably made for each pixel as to whether it is actually located on an edge and, if so, the direction of that edge.
Owner:PANASONIC CORP
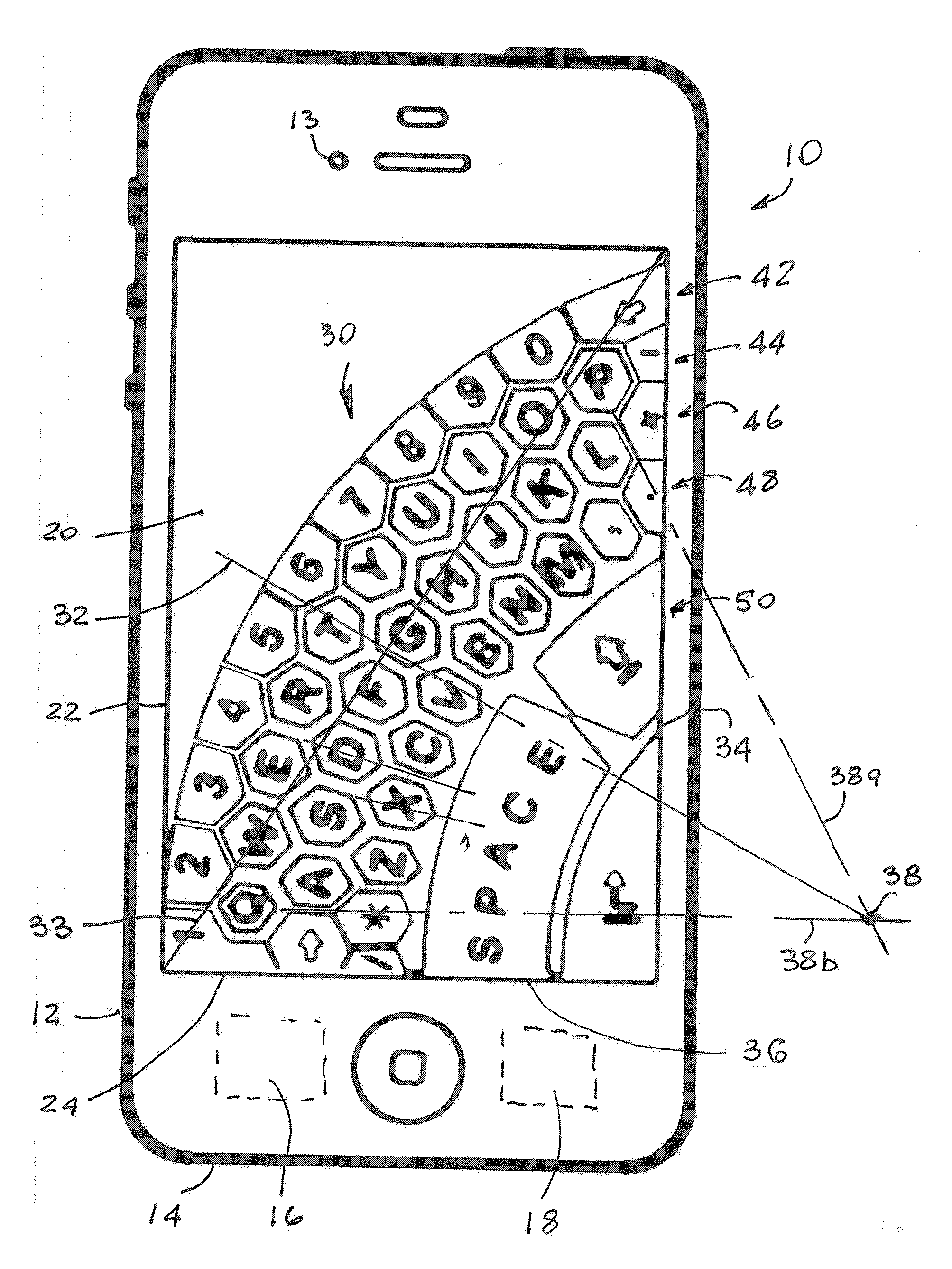
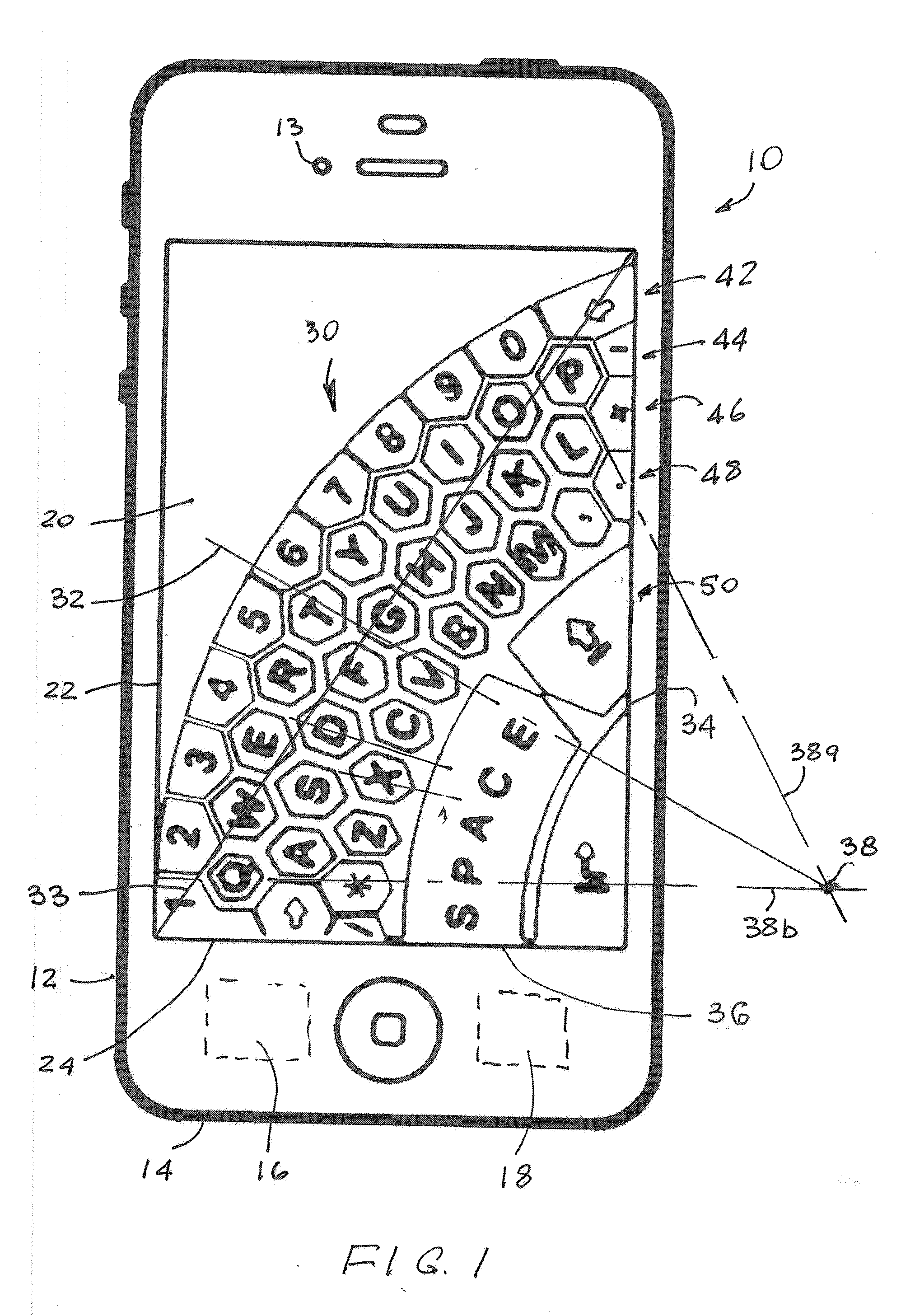
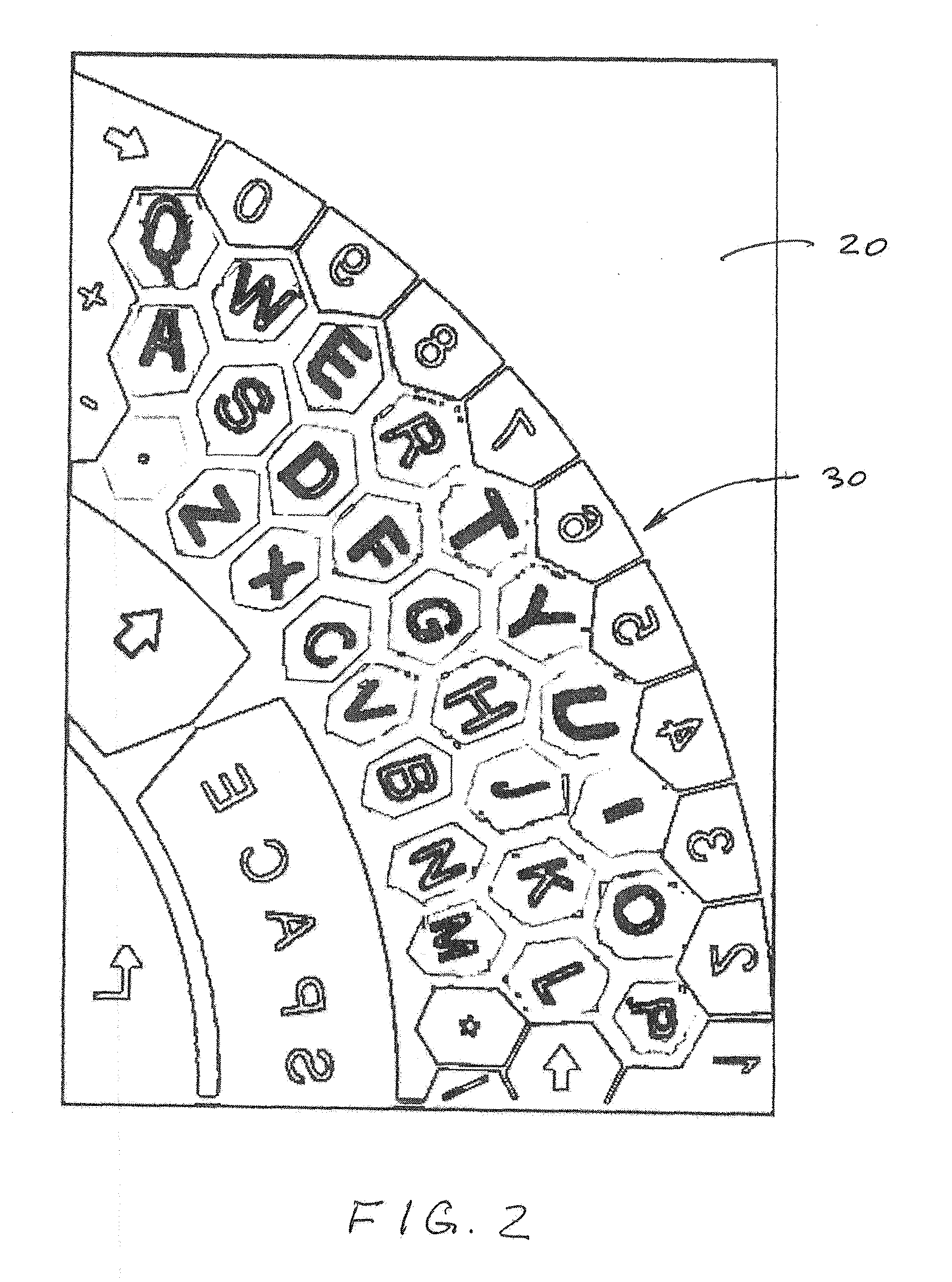
On-Screen Diagonal Keyboard
ActiveUS20130234949A1Easy to reachEasy to useInput/output for user-computer interactionCathode-ray tube indicatorsDiagonalSharp angle
Owner:CHORNENKY TODD E
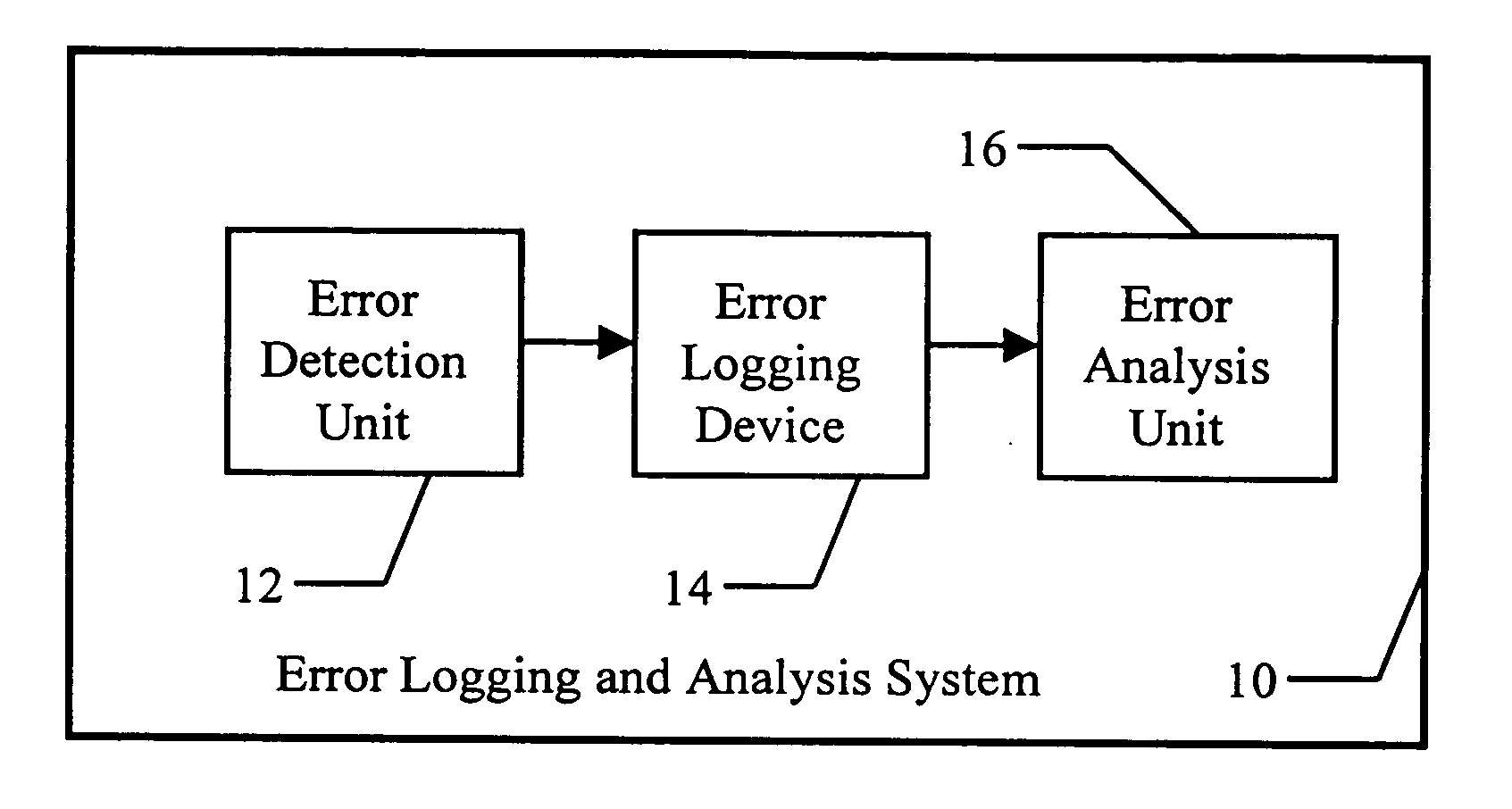
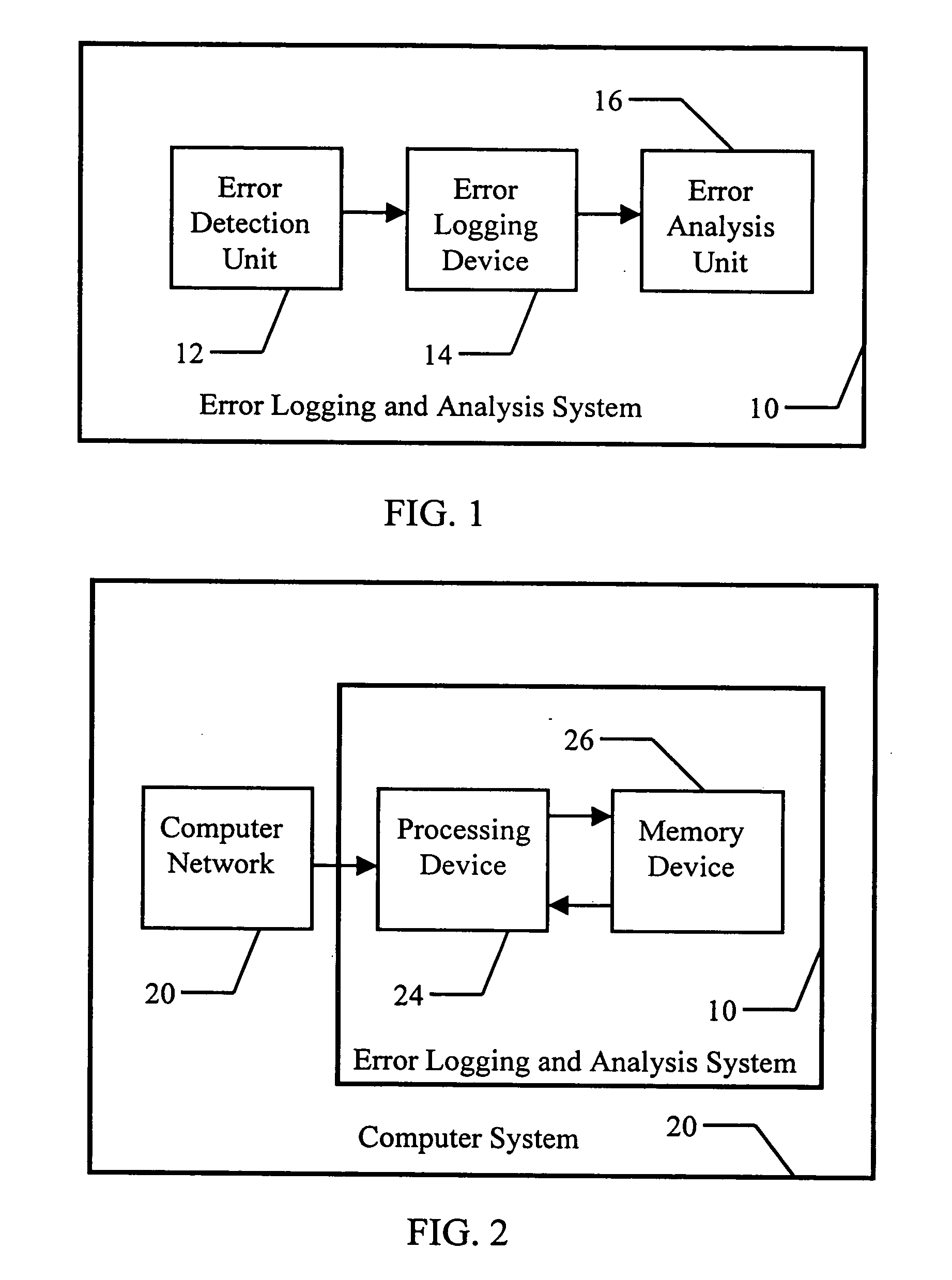
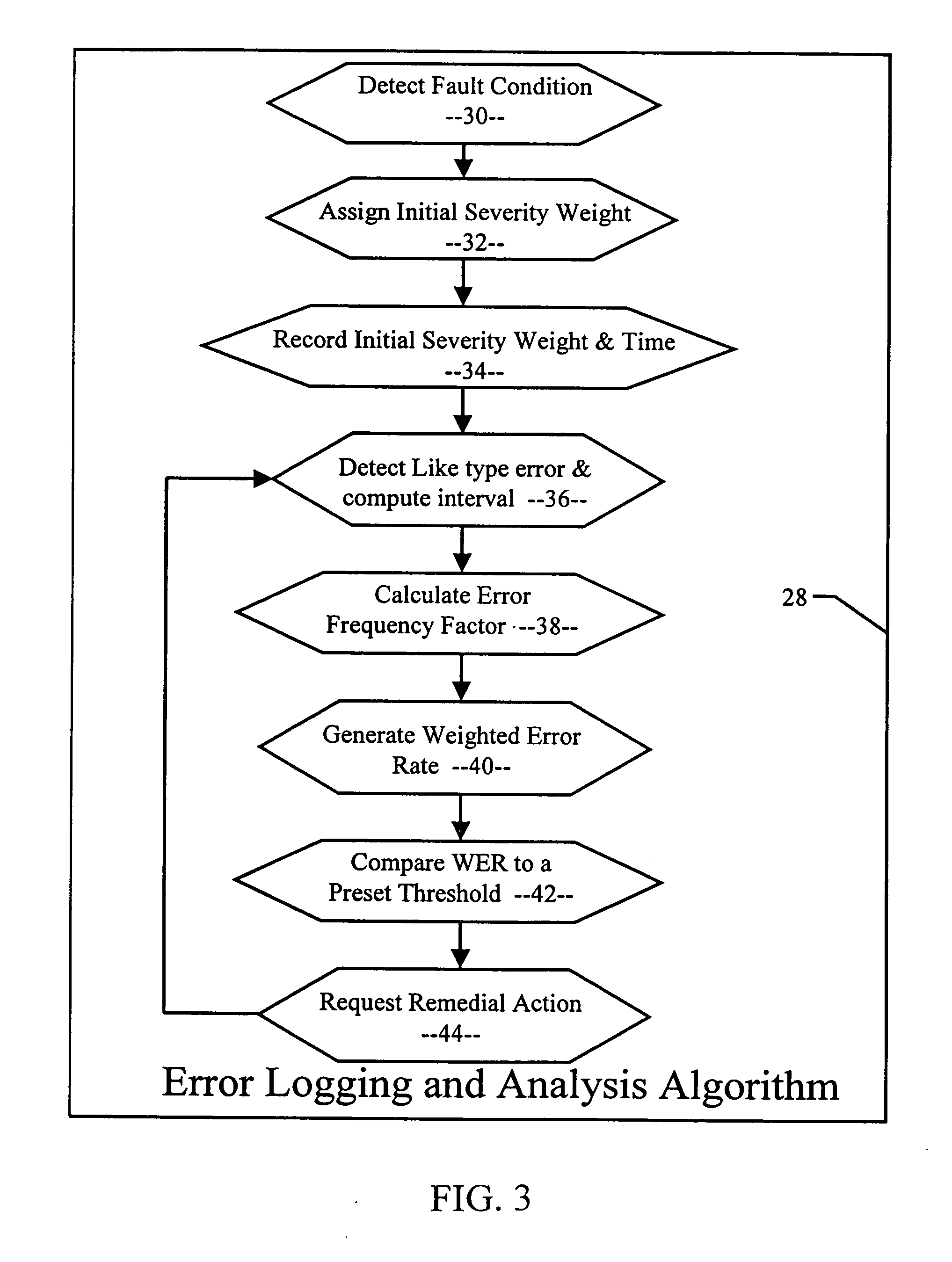
Efficient real-time analysis method of error logs for autonomous systems
An error logging and analysis system is used to detect a type of error condition, assign a numeric value corresponding to the severity of the error condition, record the time of the error condition, and determine the frequency between subsequent error conditions of the same type. A weighted error rate is generated as a function of the severity of the initial error condition, the frequency of subsequent error conditions, and a percentage of any preceding weighted error rates. These weighted error rates are compared to a predetermined threshold to determine if the error condition is statistically significant.
Owner:IBM CORP
System and method for order-preserving encryption for numeric data
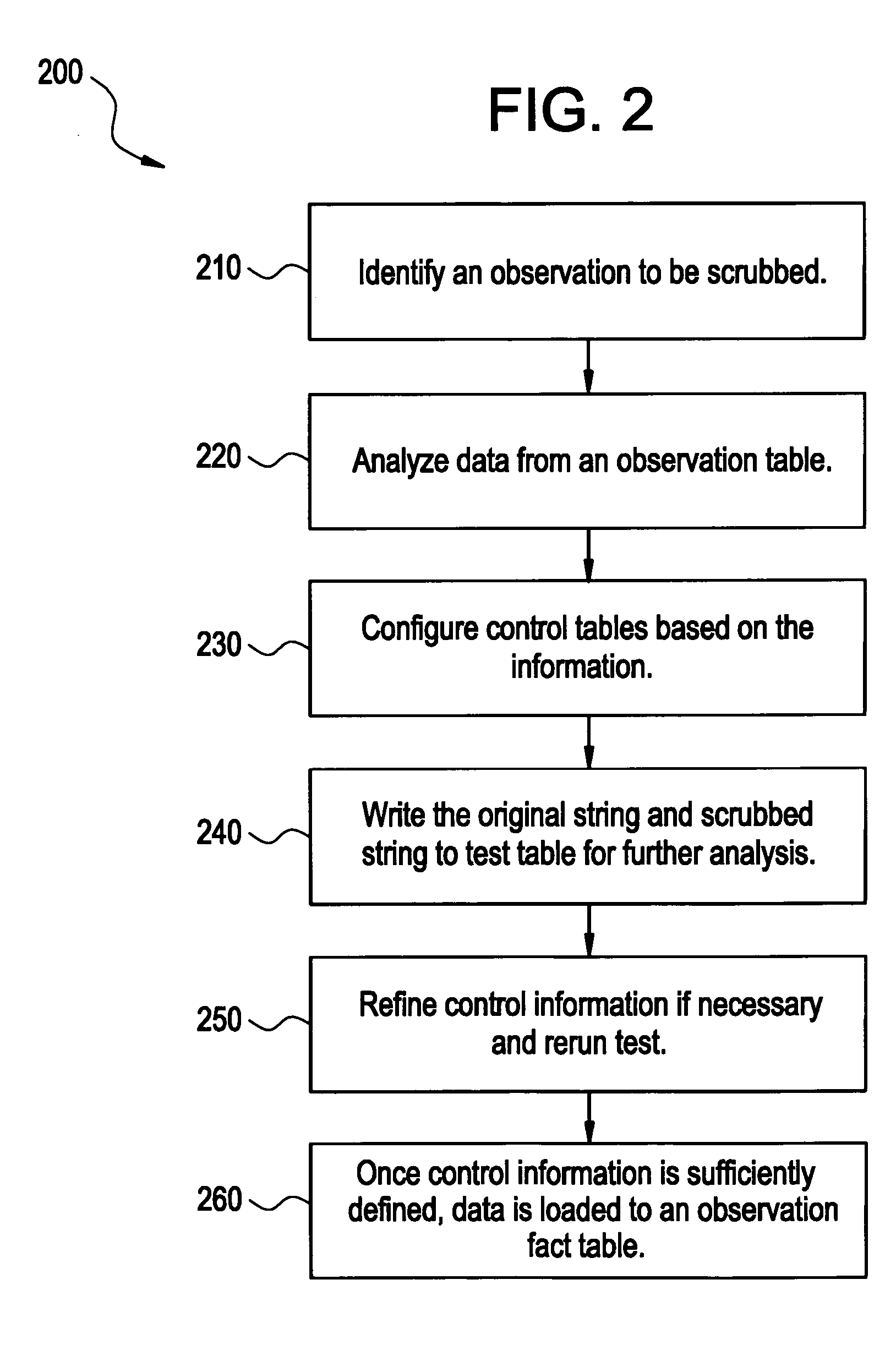
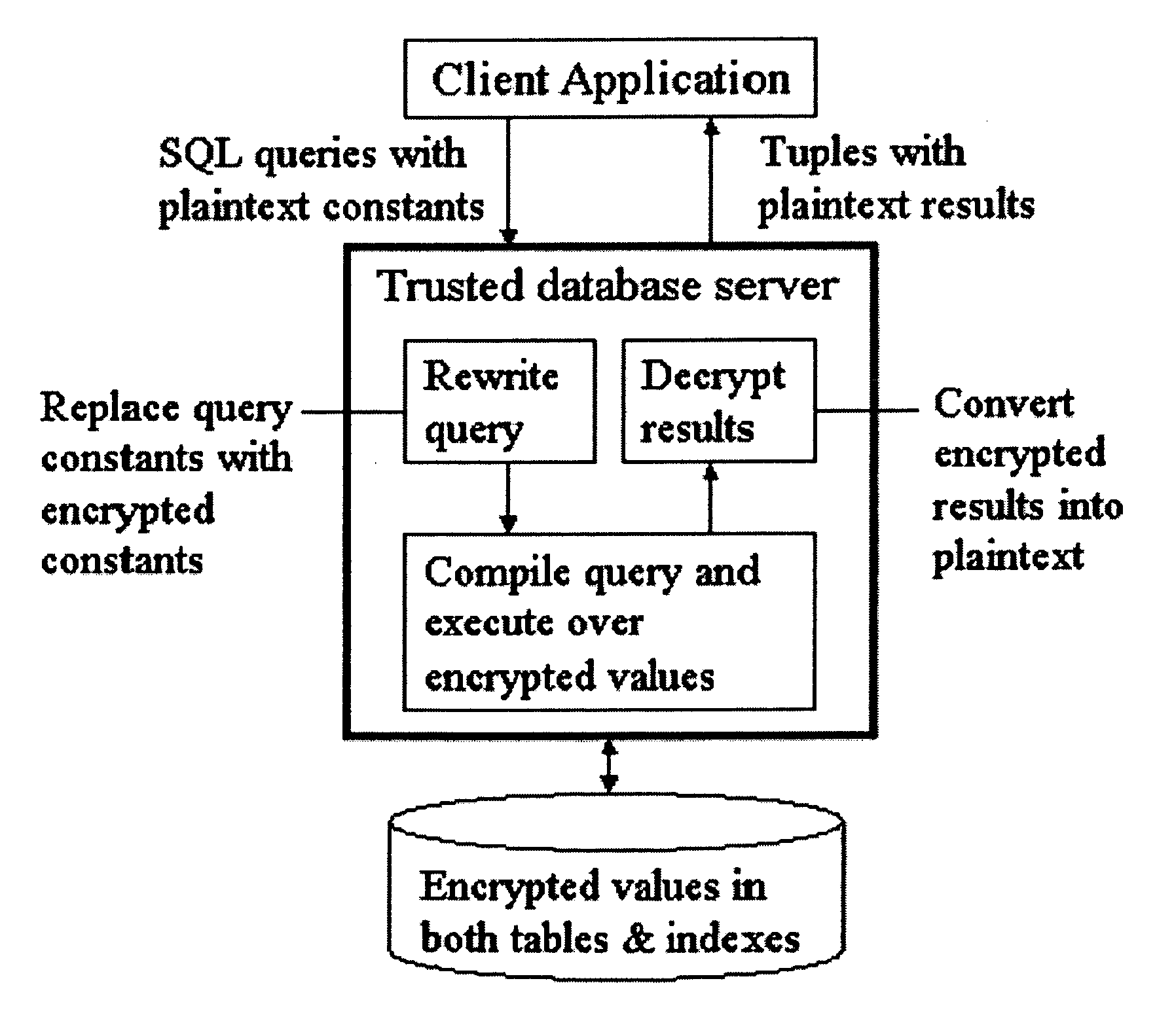
InactiveUS20050147240A1Digital data processing detailsAnalogue secracy/subscription systemsGrowth phaseData set
A system, method, and computer program product to automatically eliminate the distribution information available for reconstruction from a disguised dataset. The invention flattens input numerical values into a substantially uniformly distributed dataset, then maps the uniformly distributed dataset into equivalent data in a target distribution. The invention allows the incremental encryption of new values in an encrypted database while leaving existing encrypted values unchanged. The flattening comprises (1) partitioning, (2) mapping, and (3) saving auxiliary information about the data processing, which is encrypted and not updated. The partitioning is MDL based, and includes a growth phase for dividing a space into fine partitions and a prune phase for merging some partitions together.
Owner:IBM CORP
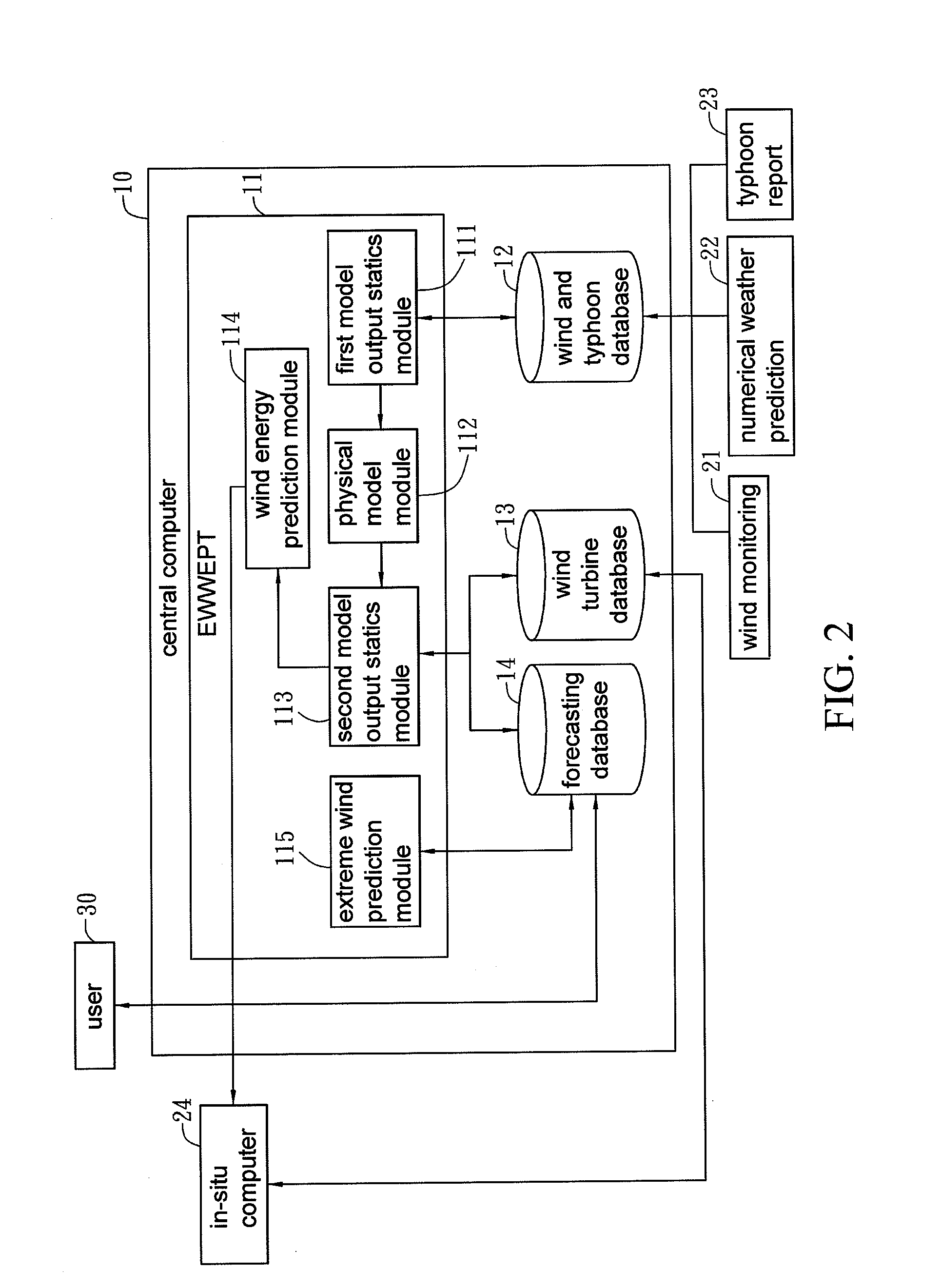
Wind energy forecasting method with extreme wind speed prediction function
InactiveUS20120046917A1Improve efficiencyProcess safetyWeather condition predictionEngine fuctionsNumerical weather predictionPhysical model
A wind energy forecasting method with extreme wind speed prediction function cooperated with a central computer, comprising the steps of: inputting a weather data which contains a numerical weather prediction data; implementing a modification with a first model output statistics; implementing a modification with a physical model in accordance with the output of the first model output statistics that can iteratively calculate the results by varying the angles of wind direction; implementing a modification with a second model output statistics; and implementing a prediction of extreme wind speed caused by typhoon, which comprises the following sub-steps of: using a wind and typhoon database to find track data of plural historical typhoons within a certain distance from a target typhoon; using an extreme wind and wind energy prediction tool to calculate at least one extreme wind speed in the future of the target typhoon and calculate the probability of occurring the extreme wind speed; and modifying the extreme wind speed with the physical model to the extreme wind speed at the position or height of a wind turbine.
Owner:INST NUCLEAR ENERGY RES ROCAEC
System and method for determining cybersecurity rating and risk scoring
A system for deriving a rating representative of a level of cybersecurity of a user is configured to execute steps of a method comprising (i) requesting, from the user, identifying information about the user; (ii) requesting, from the user, input in response to a set of predetermined questions provided to the user based on the identifying information about the user; (iii) collecting, based on at least the identifying information, public domain data about the user and data from the user's digital assets; and (iv) computing, based on the collected data and the input to the set of predetermined questions provided by the user, a numerical value defining the cybersecurity rating.
Owner:CYBERLAB
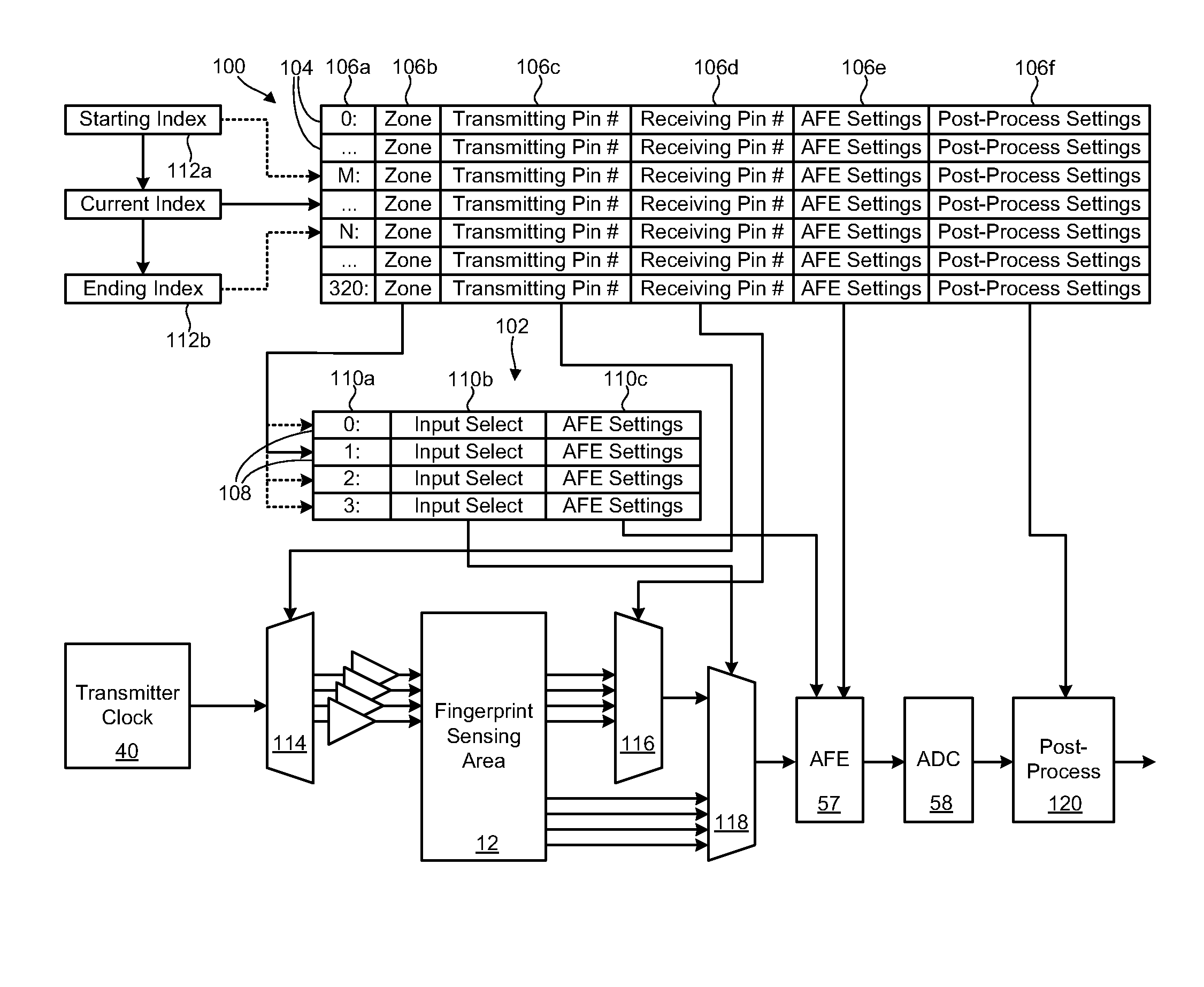
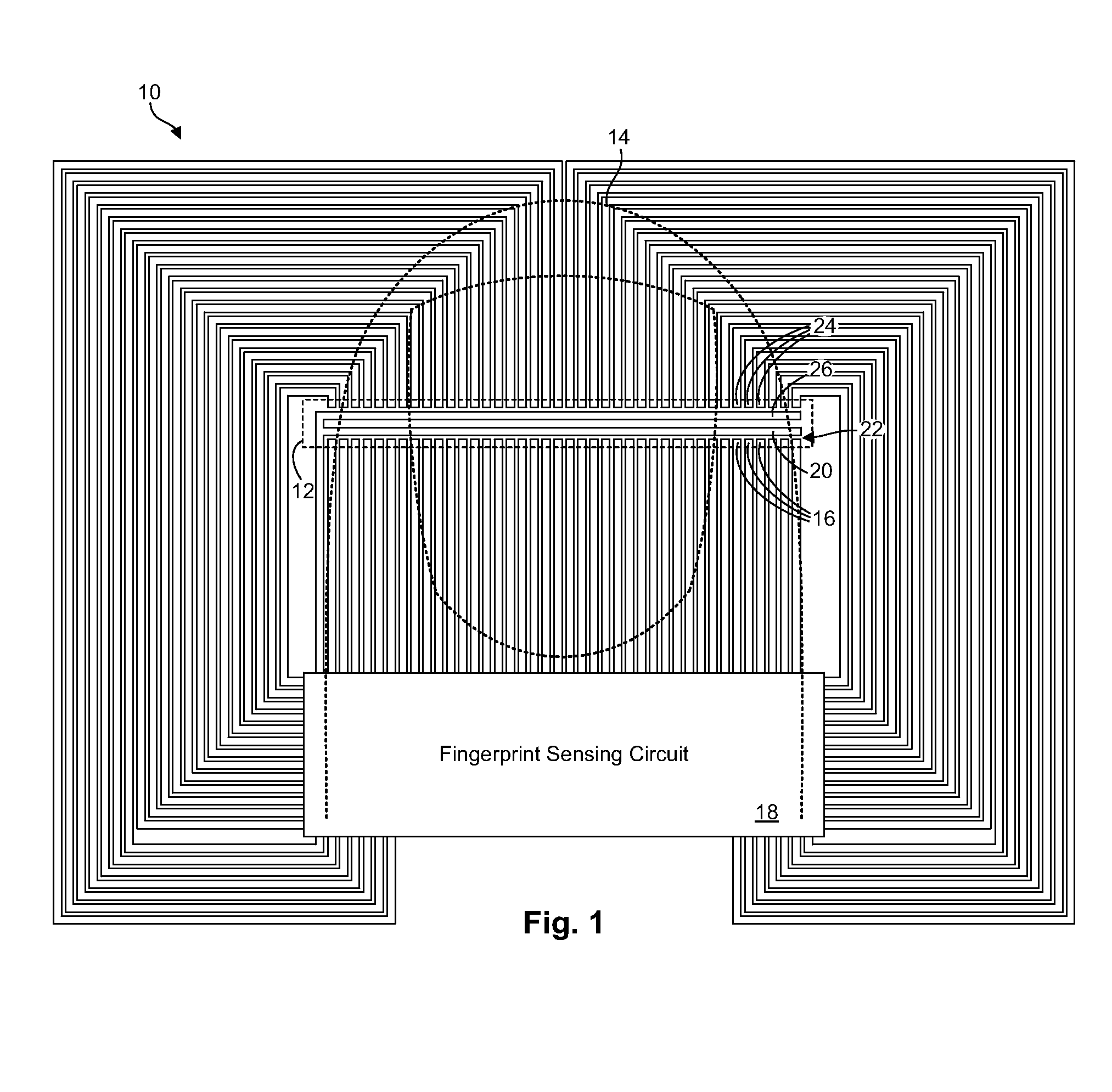
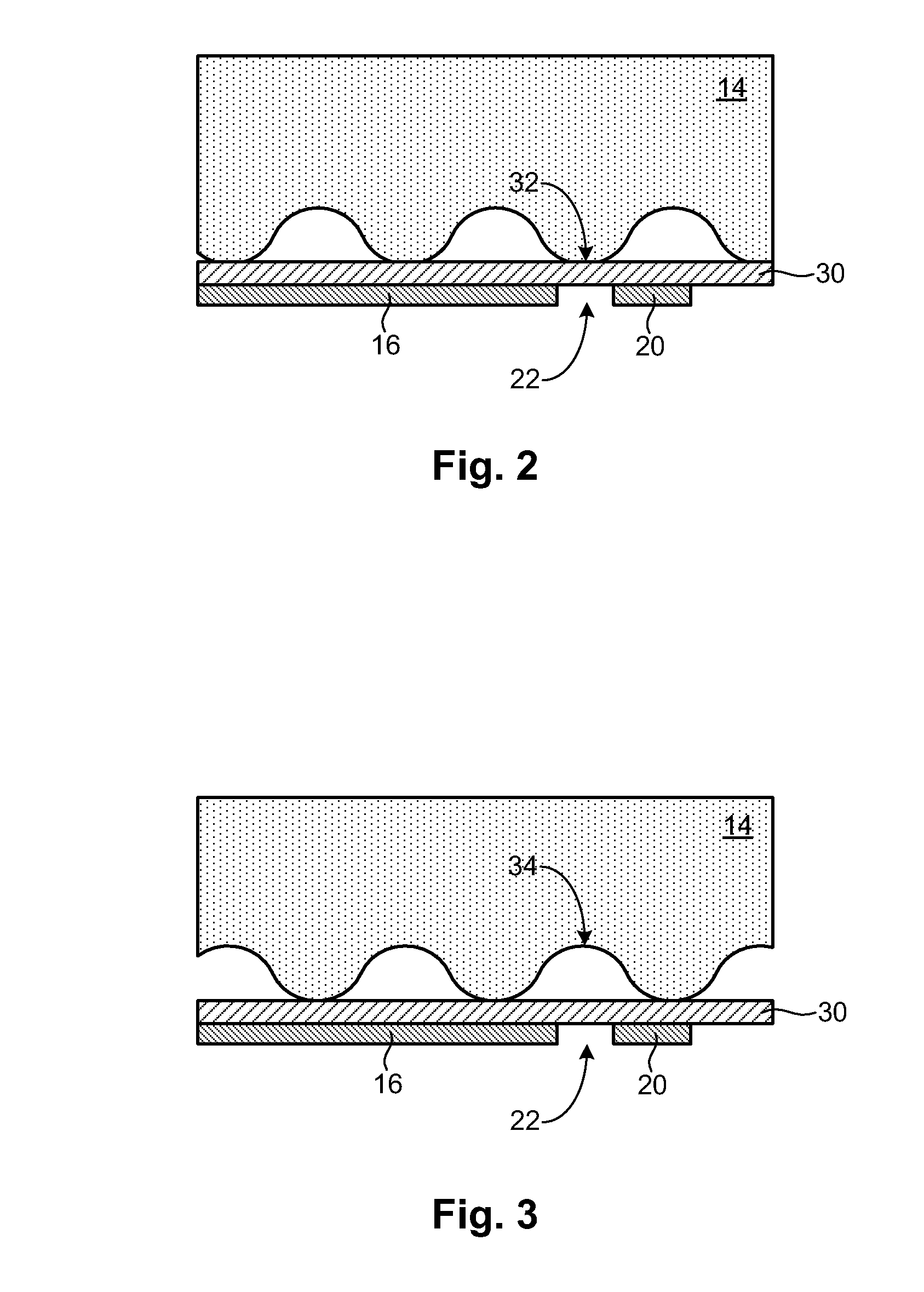
Fingerprint sensing circuit having programmable sensing patterns
A fingerprint sensor with programmable sensing patterns is disclosed in one embodiment of the invention as including a fingerprint sensing circuit having multiple I / O interconnects. The I / O interconnects are configured to sequentially drive a plurality of fingerprint sensing elements. A memory device may be operably coupled to the fingerprint sensing circuit. A programmable data structure, such as a table, file, character string, numeric value, array, or the like may be stored in the memory device to designate a pattern for driving the fingerprint sensing elements. The fingerprint sensing circuit is configured to drive the fingerprint sensing elements according to the designated pattern. In selected embodiments, the fingerprint sensing elements may include transmitting elements, receiving elements, or a combination thereof.
Owner:SYNAPTICS INC
Generating sufficiently sized, relatively homogeneous segments of real property transactions by clustering base geographical units
InactiveUS20080288312A1More accuracyMore precisionMarket predictionsSpecial data processing applicationsUnit systemFinancial transaction
Systems and methods for generating segments of real property transactions by clustering base geographic units are provided. According to one embodiment, information regarding real property transactions is received, each transactions corresponds to a base geographic unit based on a physical location of a real property associated with the transaction at issue. For each value of a clustering function represented within the real property transactions, relatively homogeneous segments of transactions are built by aggregating transactions of the base geographic units into clusters based on a predetermined similarity function evaluating corresponding numerically valued attributes associated with the base geographic units until each segment has a sufficient number of transactions to provide desired accuracy, reliability or usefulness in the context of desired numerical modeling or analysis and all real property transactions have been assigned to a segment. Then, the desired numerical modeling or analysis can be performed based on the resulting segments.
Owner:INTELLIREAL
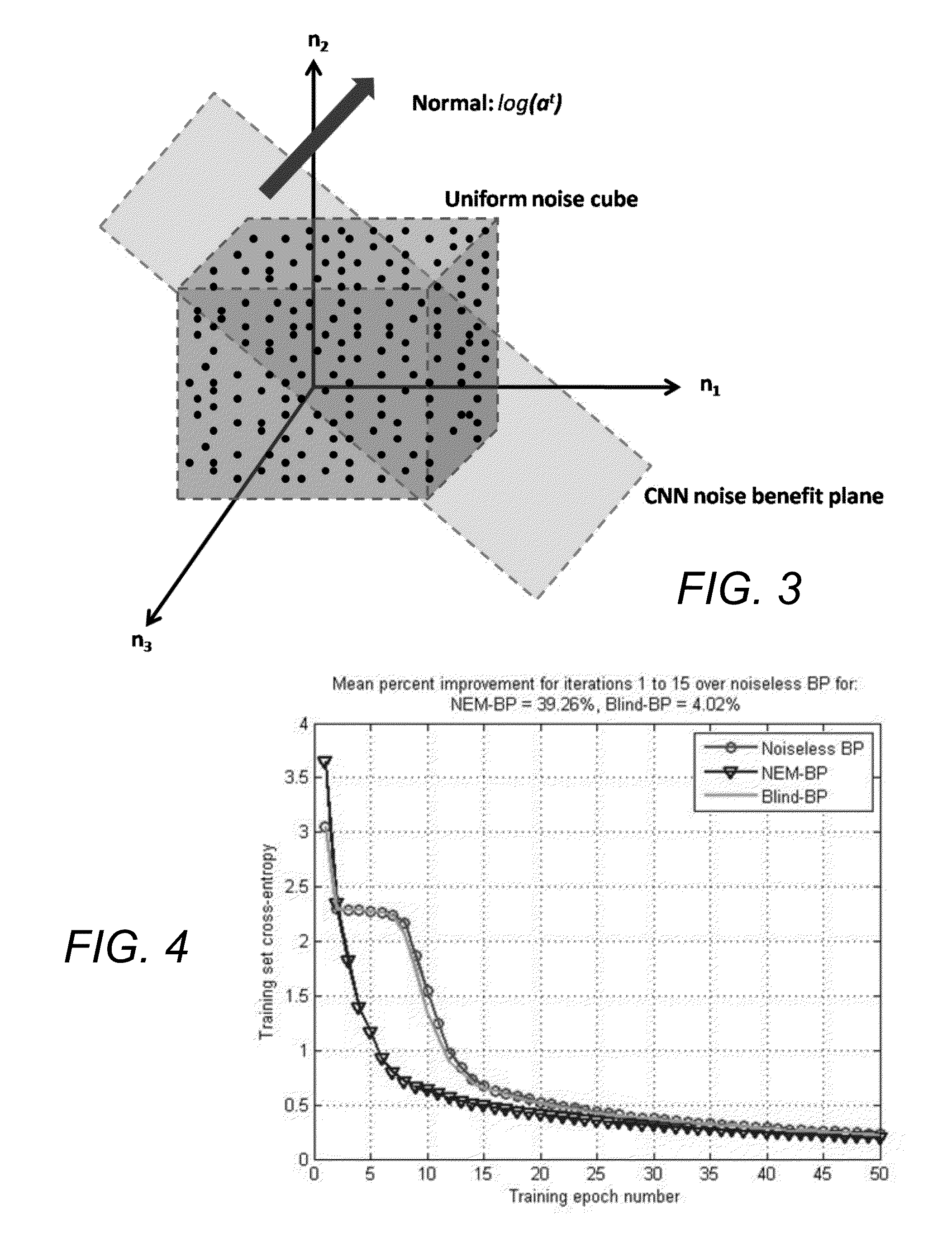
Noise-enhanced convolutional neural networks
ActiveUS20160019459A1Learning speedImprove accuracyMathematical modelsDigital computer detailsData processing systemComputerized system
A learning computer system may include a data processing system and a hardware processor and may estimate parameters and states of a stochastic or uncertain system. The system may receive data from a user or other source; process the received data through layers of processing units, thereby generating processed data; apply masks or filters to the processed data using convolutional processing; process the masked or filtered data to produce one or more intermediate and output signals; compare the output signals with reference signals to generate error signals; send and process the error signals back through the layers of processing units; generate random, chaotic, fuzzy, or other numerical perturbations of the received data, the processed data, or the output signals; estimate the parameters and states of the stochastic or uncertain system using the received data, the numerical perturbations, and previous parameters and states of the stochastic or uncertain system; determine whether the generated numerical perturbations satisfy a condition; and, if the numerical perturbations satisfy the condition, inject the numerical perturbations into the estimated parameters or states, the received data, the processed data, the masked or filtered data, or the processing units.
Owner:UNIV OF SOUTHERN CALIFORNIA
Extending the range of lithographic simulation integrals
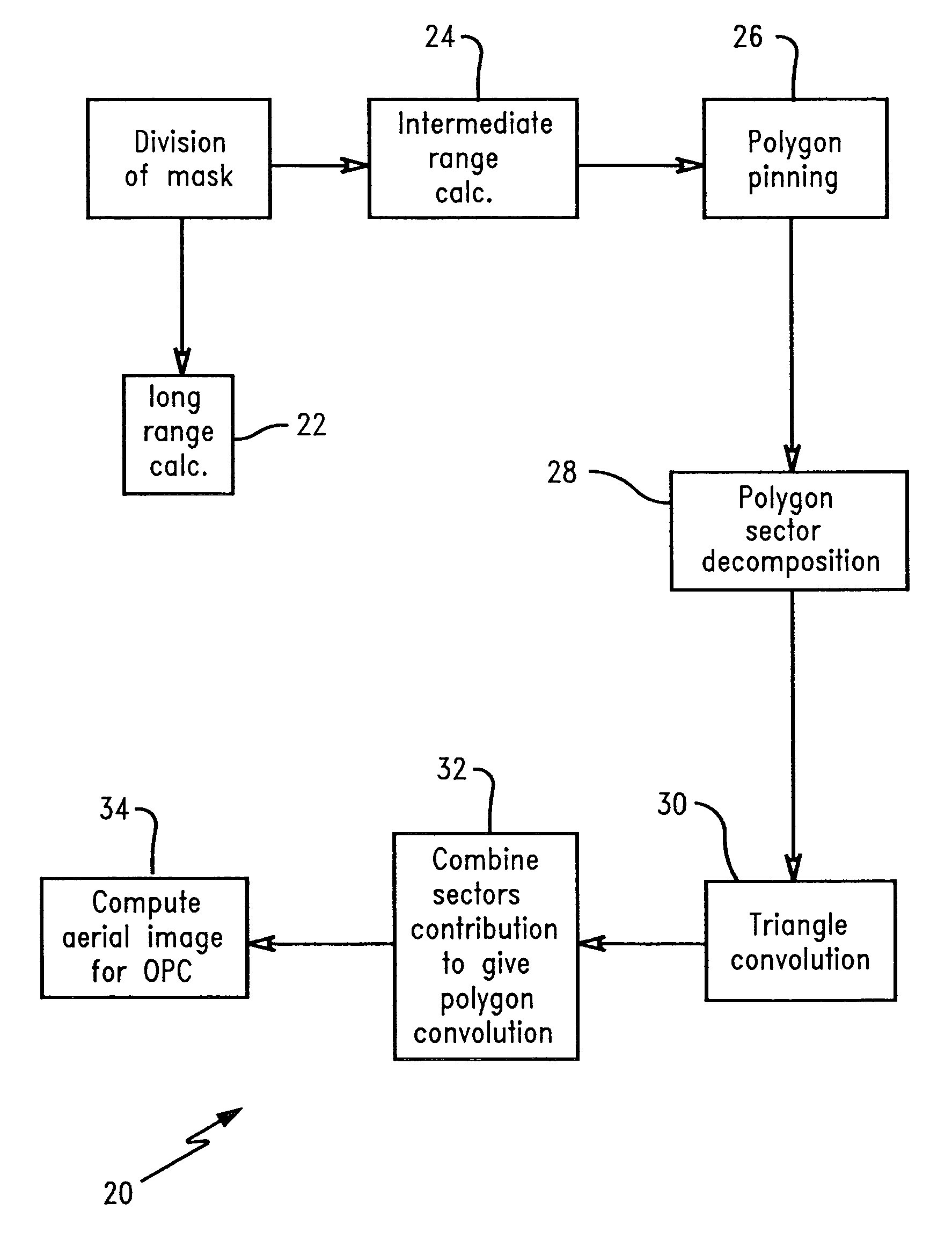
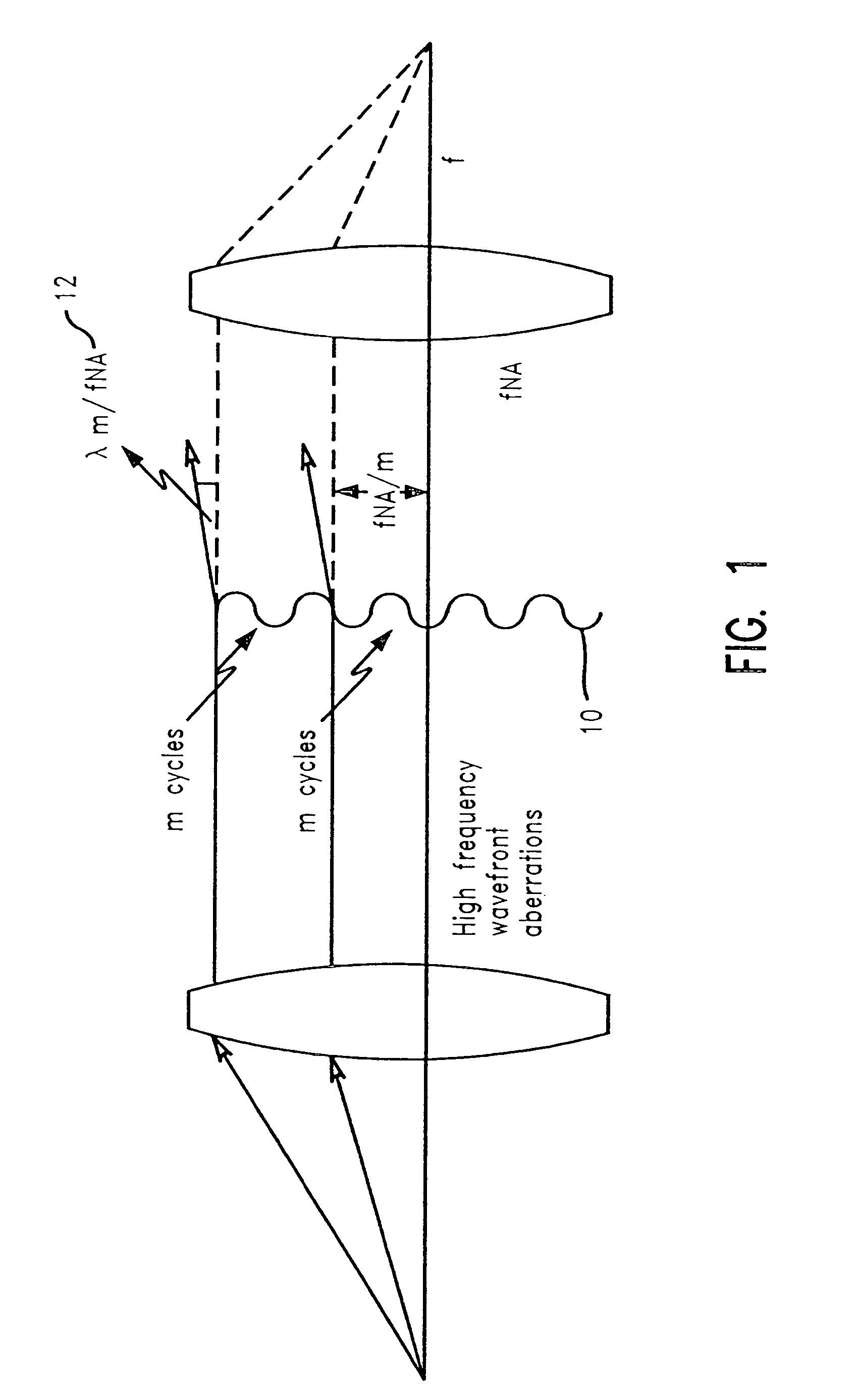
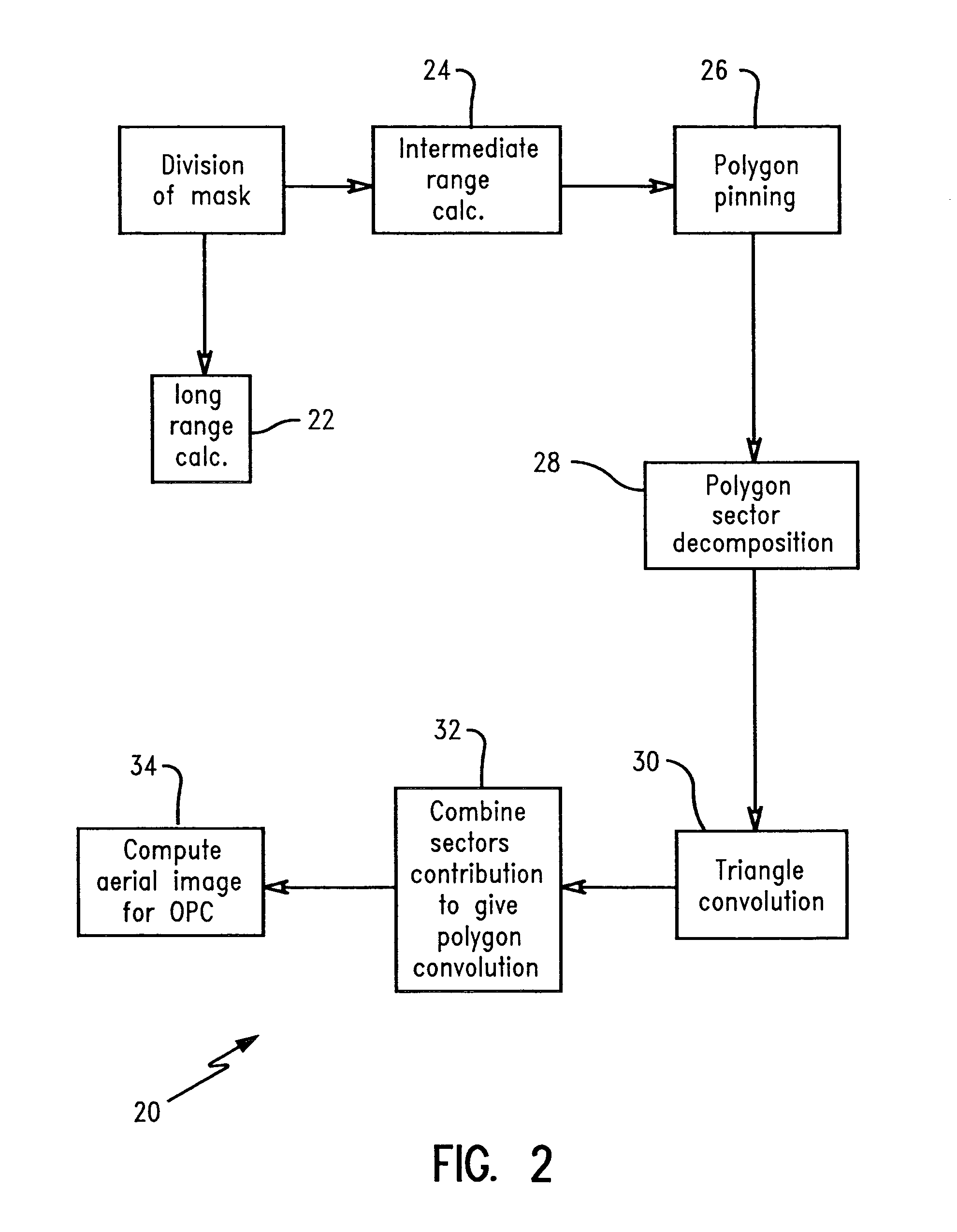
ActiveUS7010776B2Semiconductor/solid-state device manufacturingCharacter and pattern recognitionLithographic artistAnalytical expressions
Owner:GLOBALFOUNDRIES U S INC
Data processing method, data processing apparatus, semiconductor device, and electronic apparatus
InactiveUS20060013485A1Analogue/digital conversionTelevision system detailsDevice materialData treatment
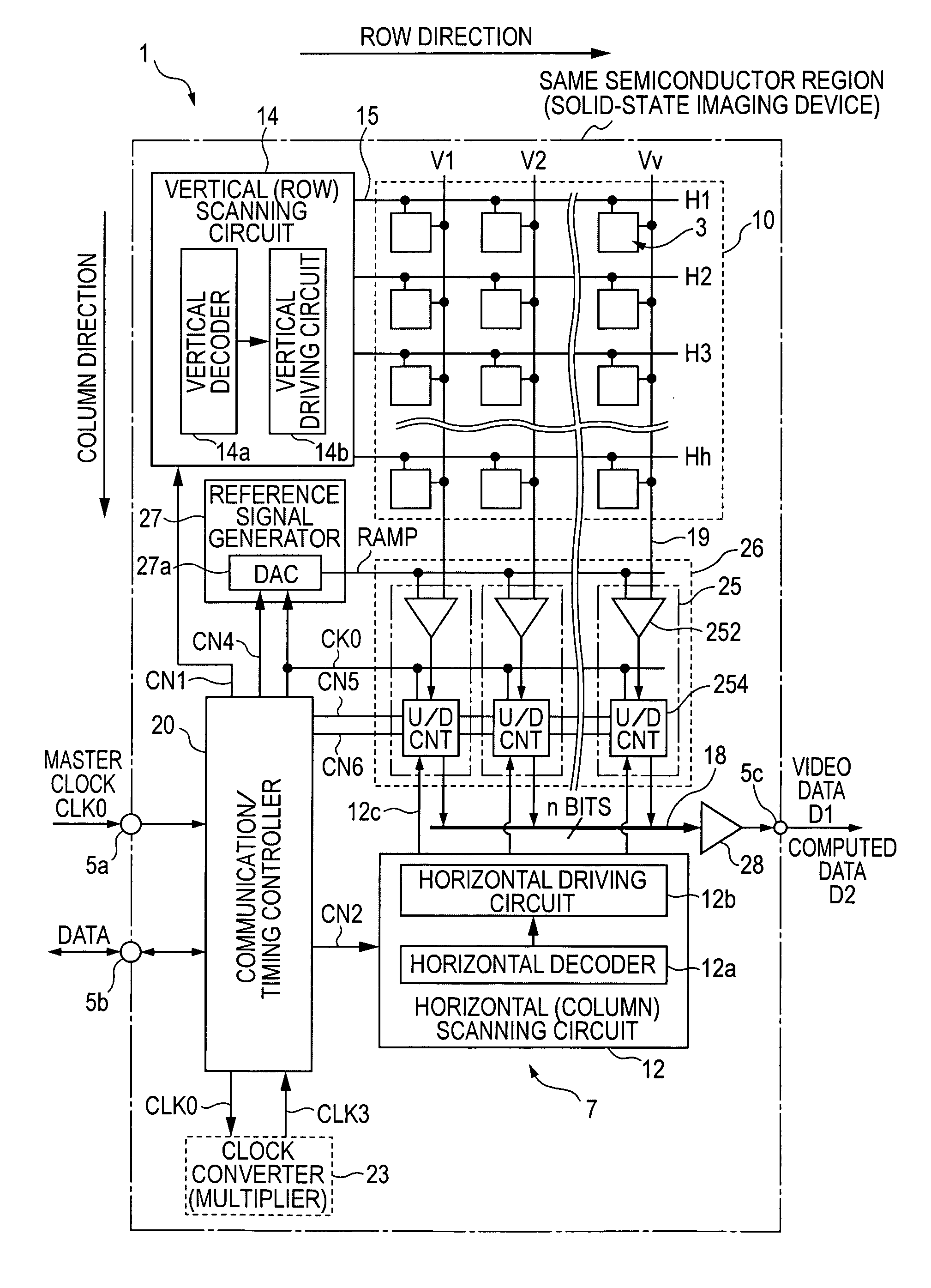
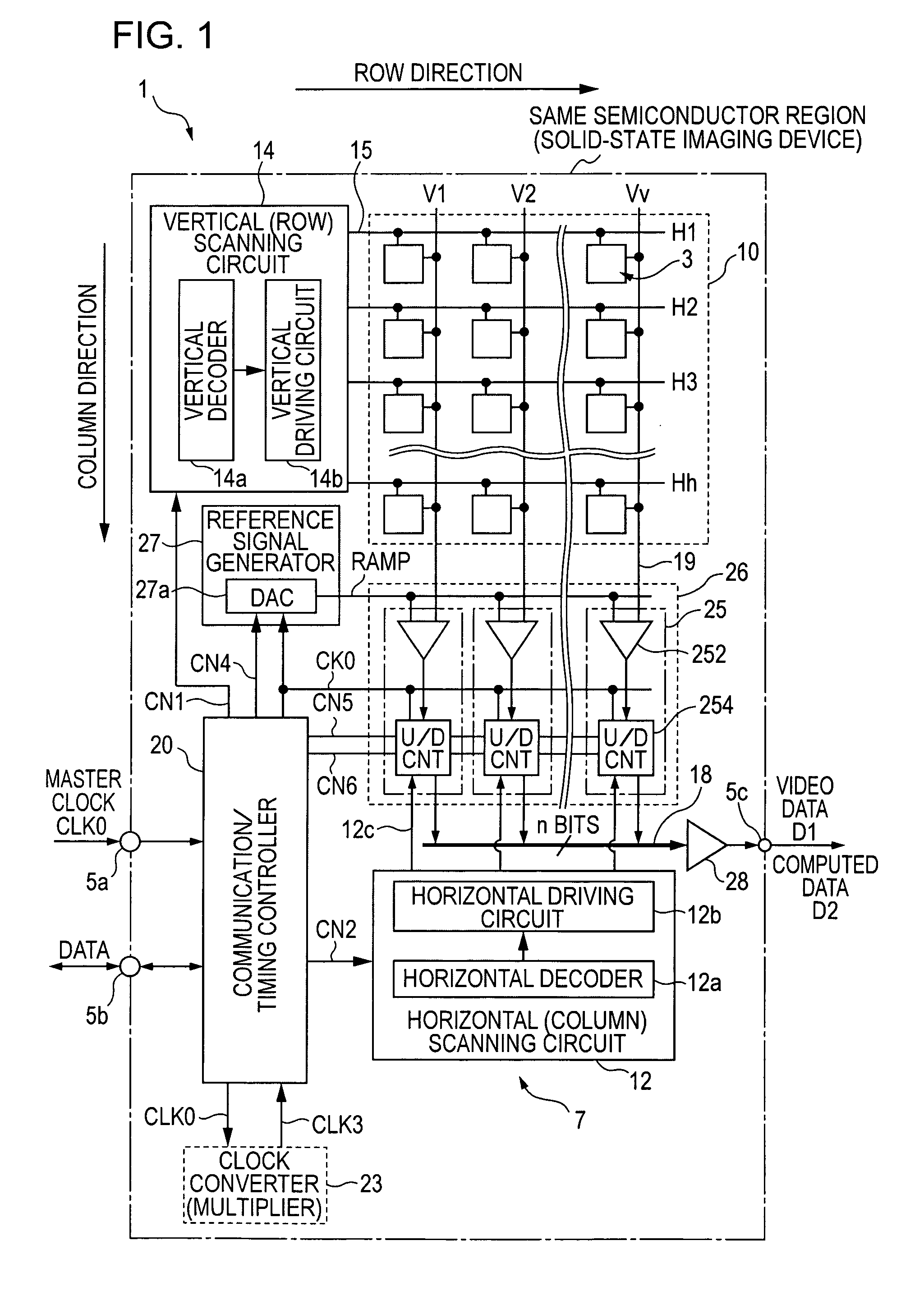
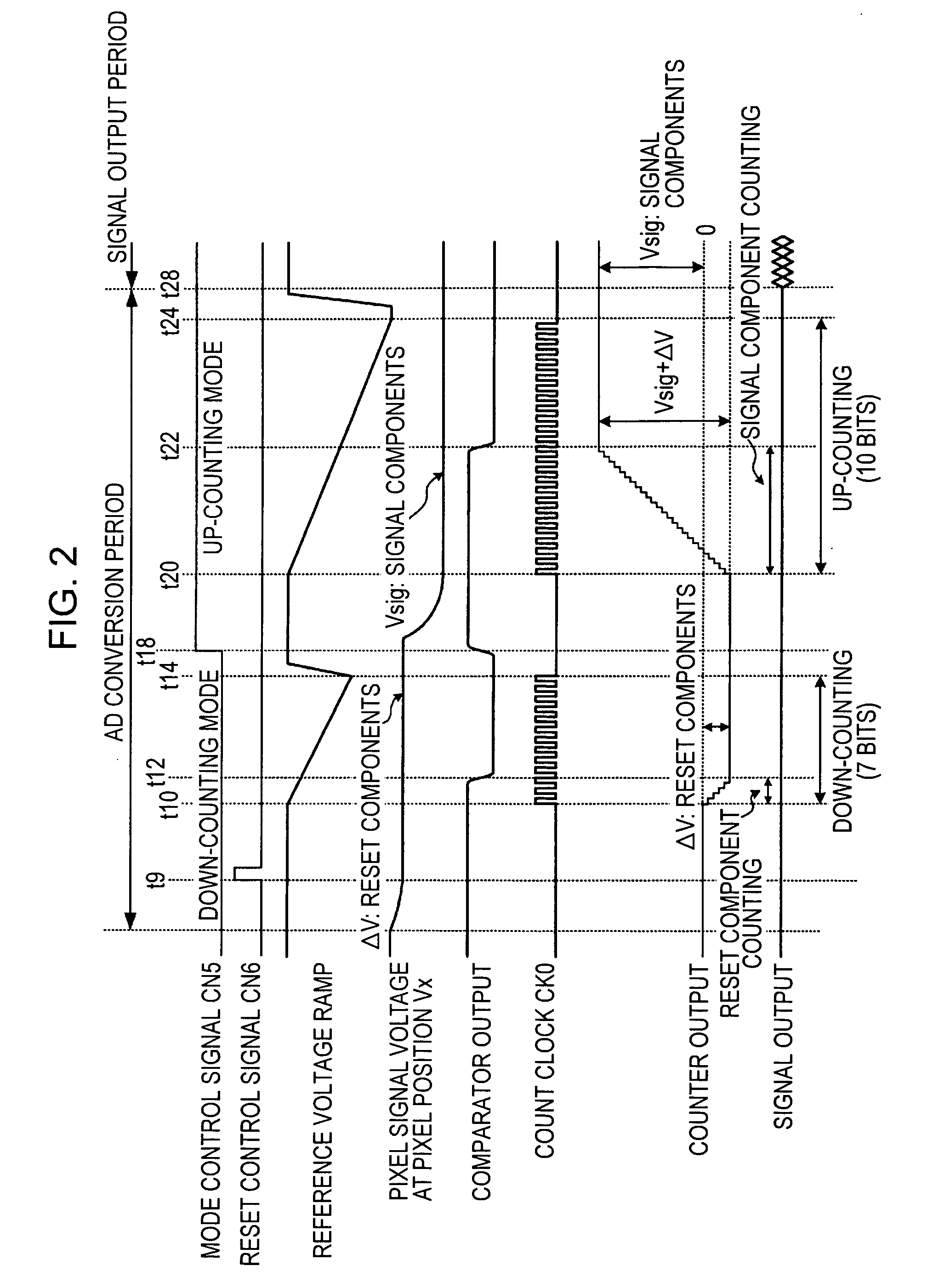
In a solid-state imaging device with an AD converter mounted on the same chip, to enable an efficient product-sum operation while reducing the size of the circuit scale and the number of transmission signal lines. A pixel signal during an n-row readout period is compared with a reference signal for digitizing this pixel signal, and a counting operation is performed in one of a down-counting mode and an up-counting mode while the comparison processing is being performed, and then, the count value when the comparison processing is finished is stored. Subsequently, by using the n-row counting result as the initial value, a pixel signal during an (n+1)-row readout period is compared with the reference signal for digitizing this pixel signal, and also, the counting operation is performed in one of the down-counting mode and the up-counting mode, and then, the count value when the comparison processing is finished is stored. If the count mode for the n+1 row is set to be opposite to the count mode for the n row, the count value obtained by the counting operation for the n+1 row is a subtraction result. If the count modes for the n+1 row and the n row are set to be the same, the count value obtained by the counting operation for the n+1 row is an addition result
Owner:SONY CORP
Fixed-point method and system for floating-point operation
ActiveCN107451658AReduce precision lossImprove efficiencyPhysical realisationNeural learning methodsNumerical rangeParallel computing
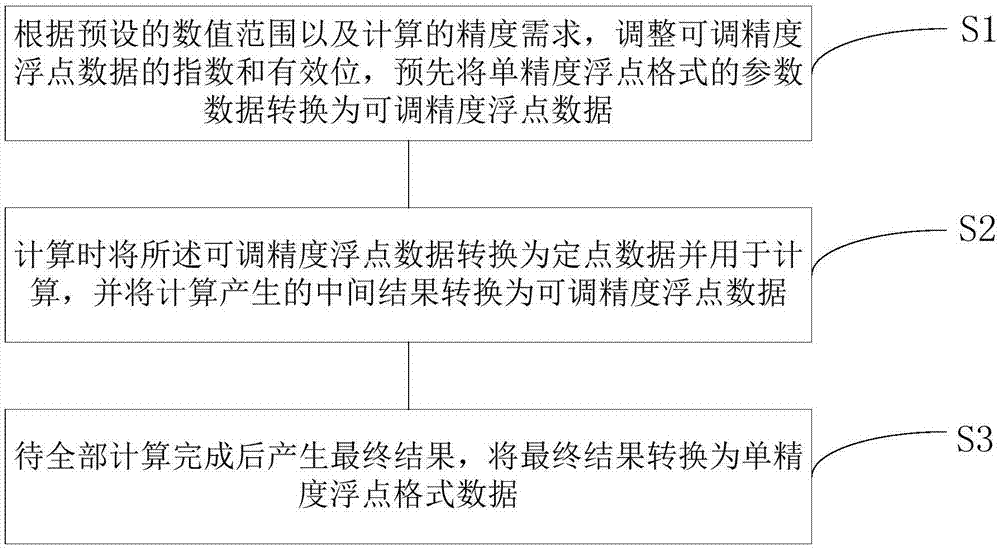
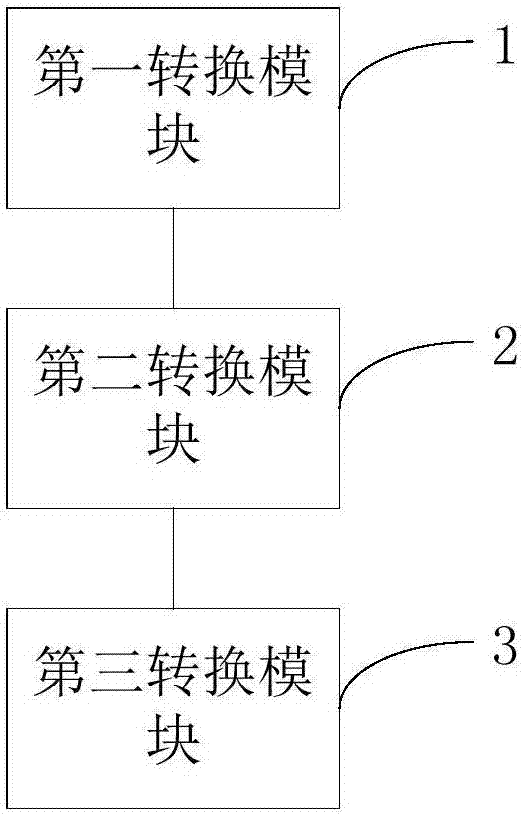
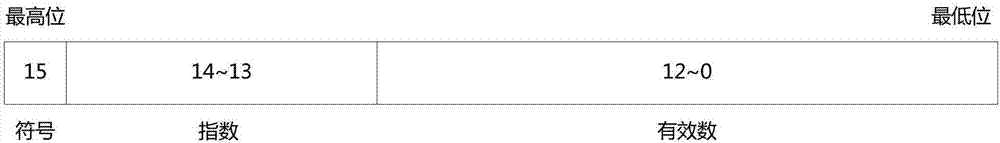
The invention discloses a fixed-point method for a floating-point operation. The method comprises the steps that according to a preset numerical range and the calculation precision requirement, the exponents and significant bits of adjustable-precision floating-point data are adjusted, and the parameter data in a single-precision floating-point format are converted into adjustable-precision floating-point data; when calculating is carried out, the adjustable-precision floating-point data are converted into fixed-point data and used for calculation, and an intermediate result generated by calculation is converted into adjustable-precision floating-point data; a final result is generated after all calculation; and the final result is converted to data in the single-precision floating-point format. According to the invention, standard floating-point data can be represented with a 16-bit bit width or a smaller bit width to realize fixed-point conversion of the floating-point operation; the storage space is saved; the operation performance is improved; and the calculation precision is not influenced.
Owner:HANGZHOU FEISHU TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com