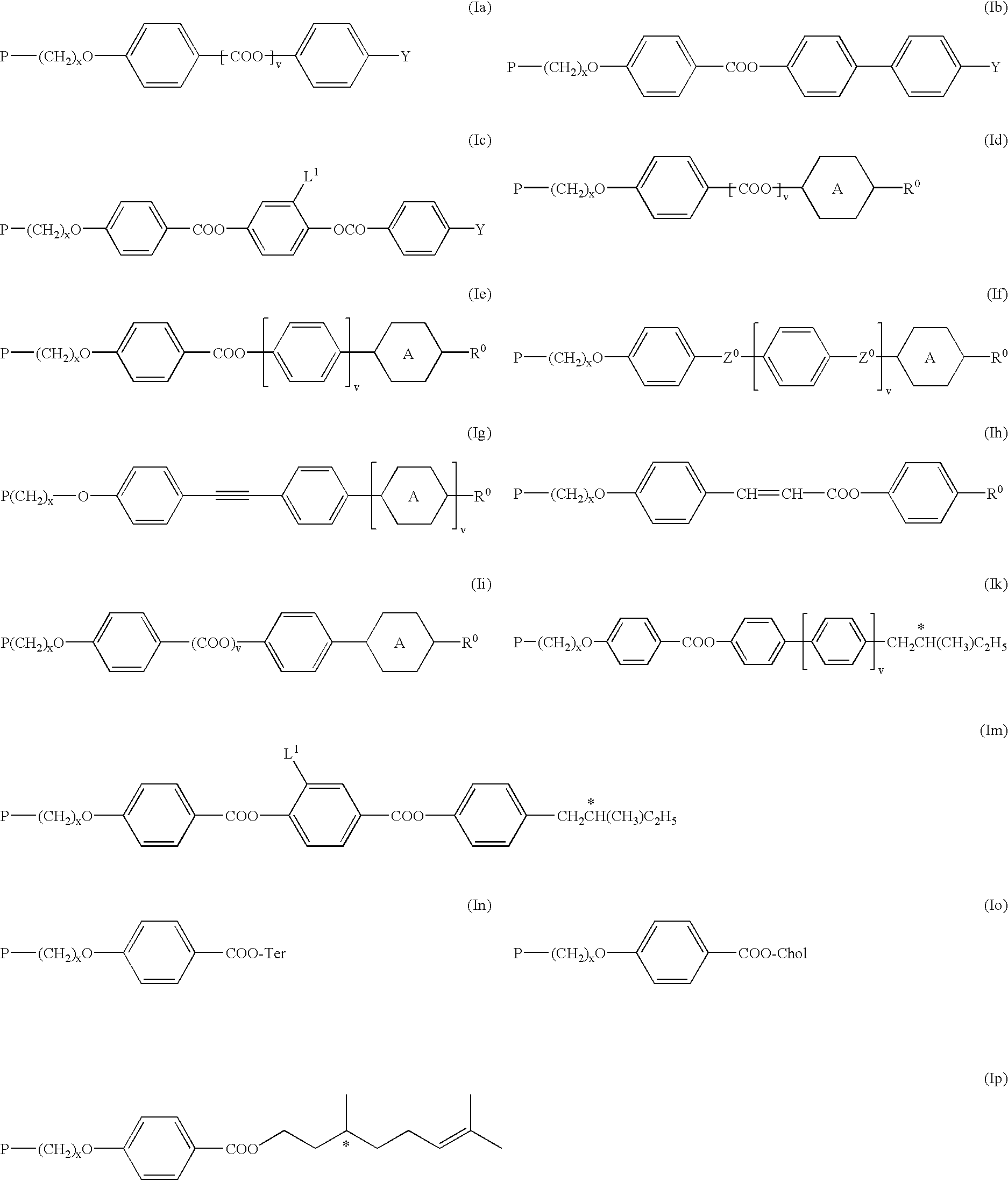Patents
Literature
161results about How to "Easy authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
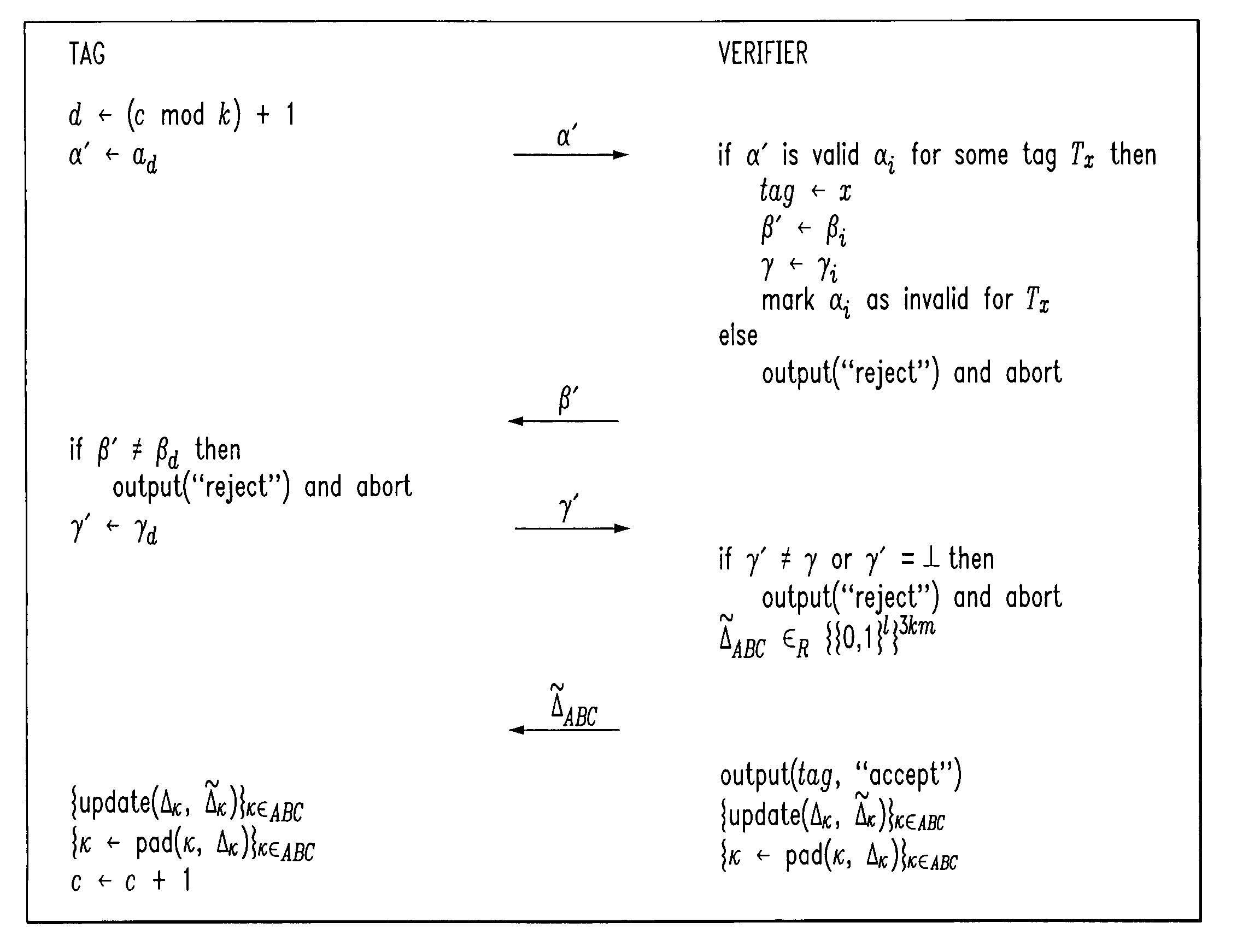
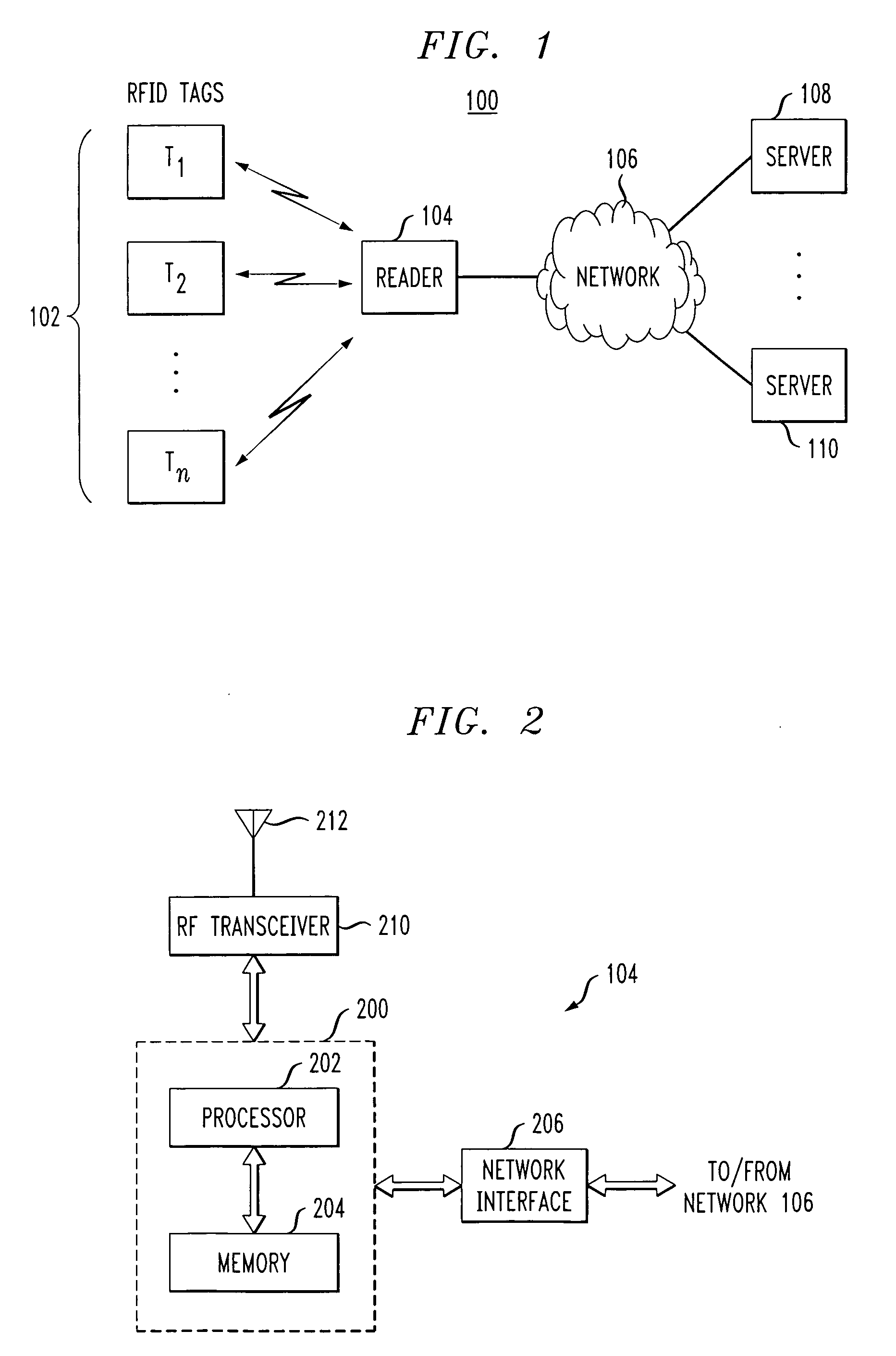
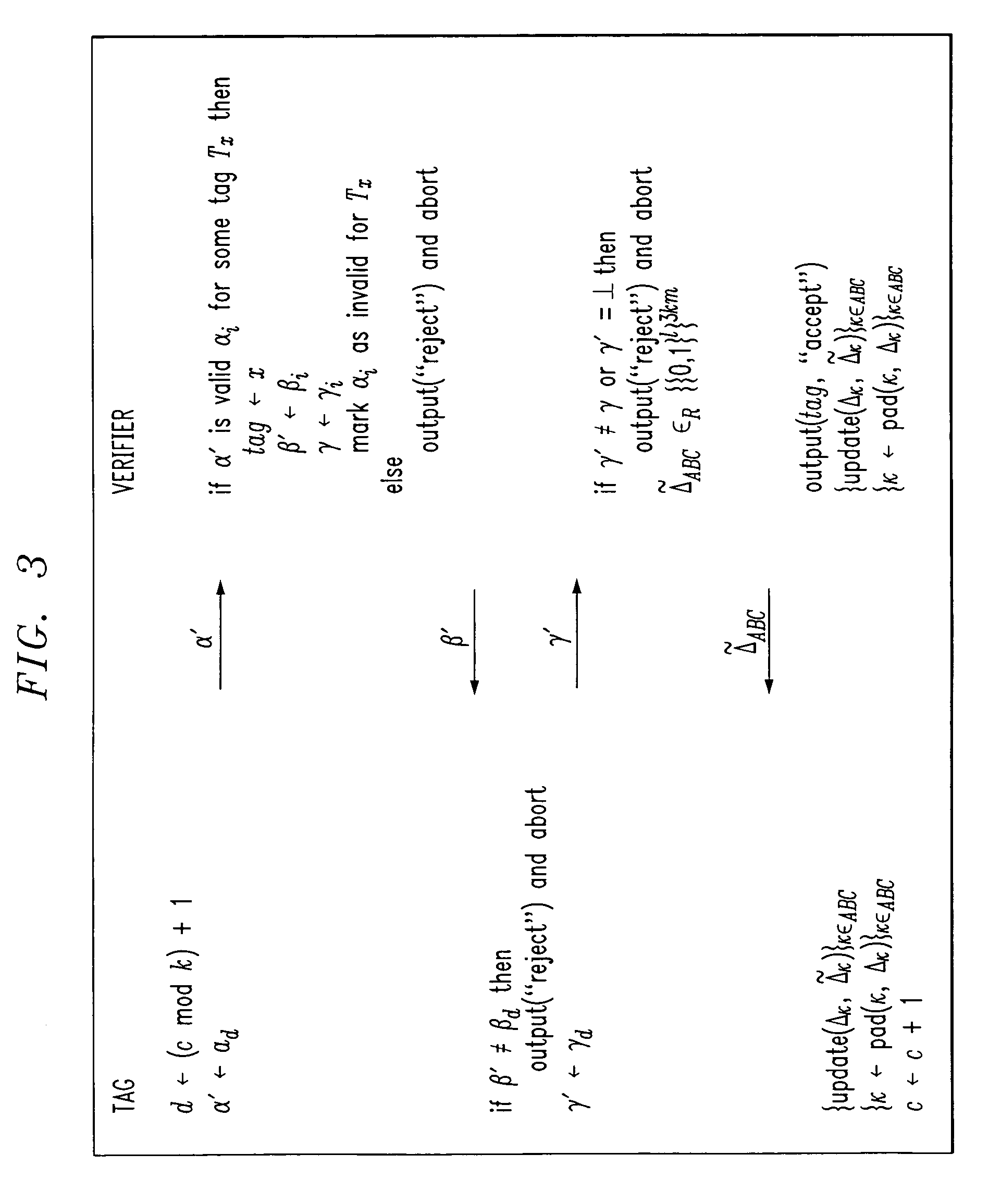
Low-complexity cryptographic techniques for use with radio frequency identification devices
ActiveUS7532104B2Easy authenticationElectric signal transmission systemsMultiple keys/algorithms usageComputer hardwareRadio frequency
Cryptographic techniques are provided having a complexity level which permits their implementation in inexpensive radio frequency identification (RFID) tags or other RFID devices. In an RFID system comprising one or more RFID devices and at least one reader that communicates with the devices, a plurality of pseudonyms is associated with a given one of the RFID devices. The RFID device transmits different ones of the pseudonyms in response to different reader queries, and an authorized verifier is able to determine that the different transmitted pseudonyms are associated with the same RFID device.
Owner:EMC IP HLDG CO LLC
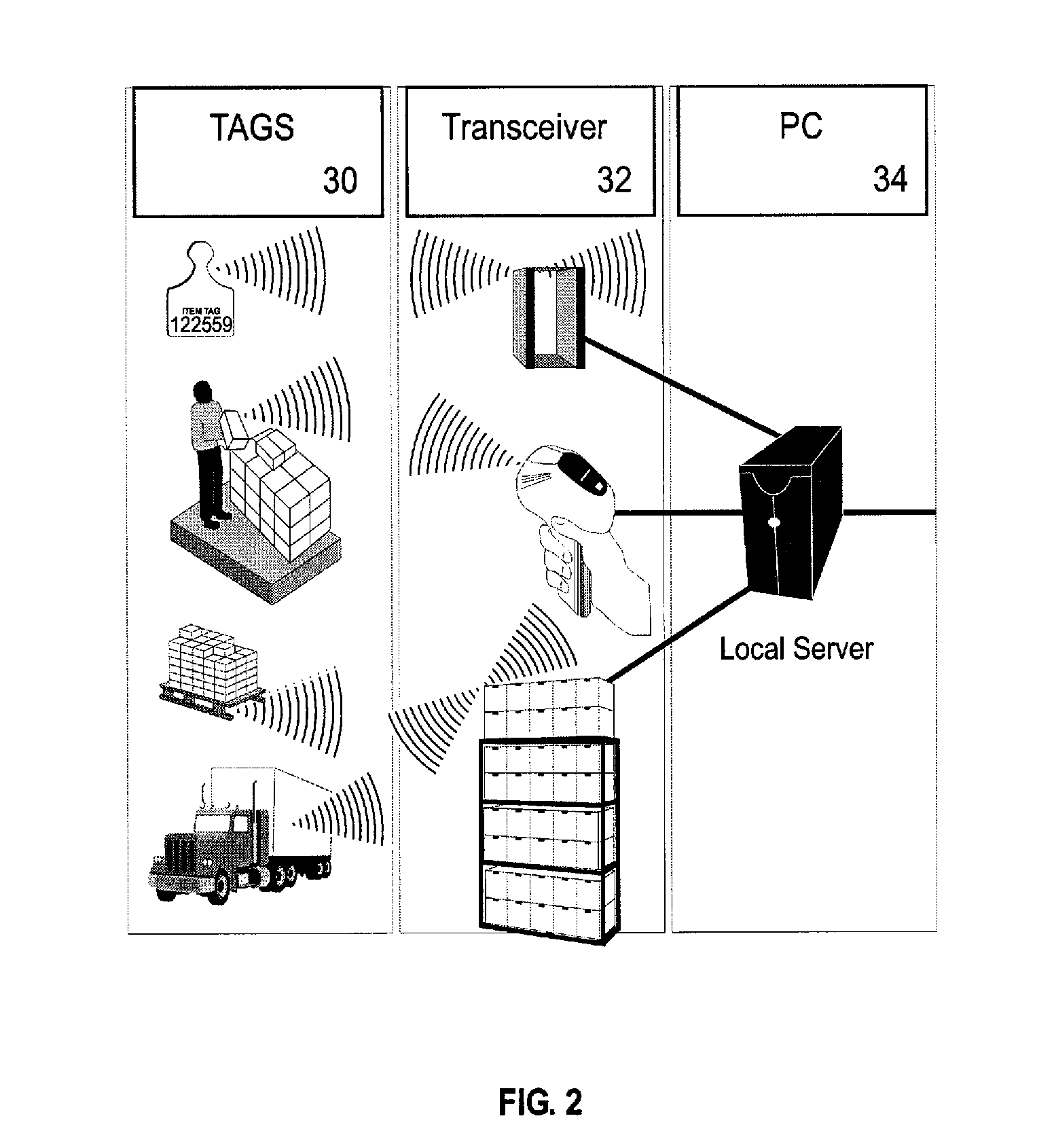
Method, apparatus, and system for tracking unique items
InactiveUS20070187266A1Improve protectionEasy authenticationContainer decorationsLevel indicationsInternet privacyRadio frequency
A method, apparatus, and system for double-sided scanning, tracking, registering, identification storing and further handling by trading or collecting unique items. Specifically, the invention relates to a method, apparatus, and system for locating and tracking unique objects utilizing a computer controlled radio frequency system and radio frequency tags that are associated with unique objects in a manner that facilitates both protection, up-loading to a unique and secure web-based service site allowing secure registration of identified, verified ownership and authentication of the unique objects.
Owner:HH TECH
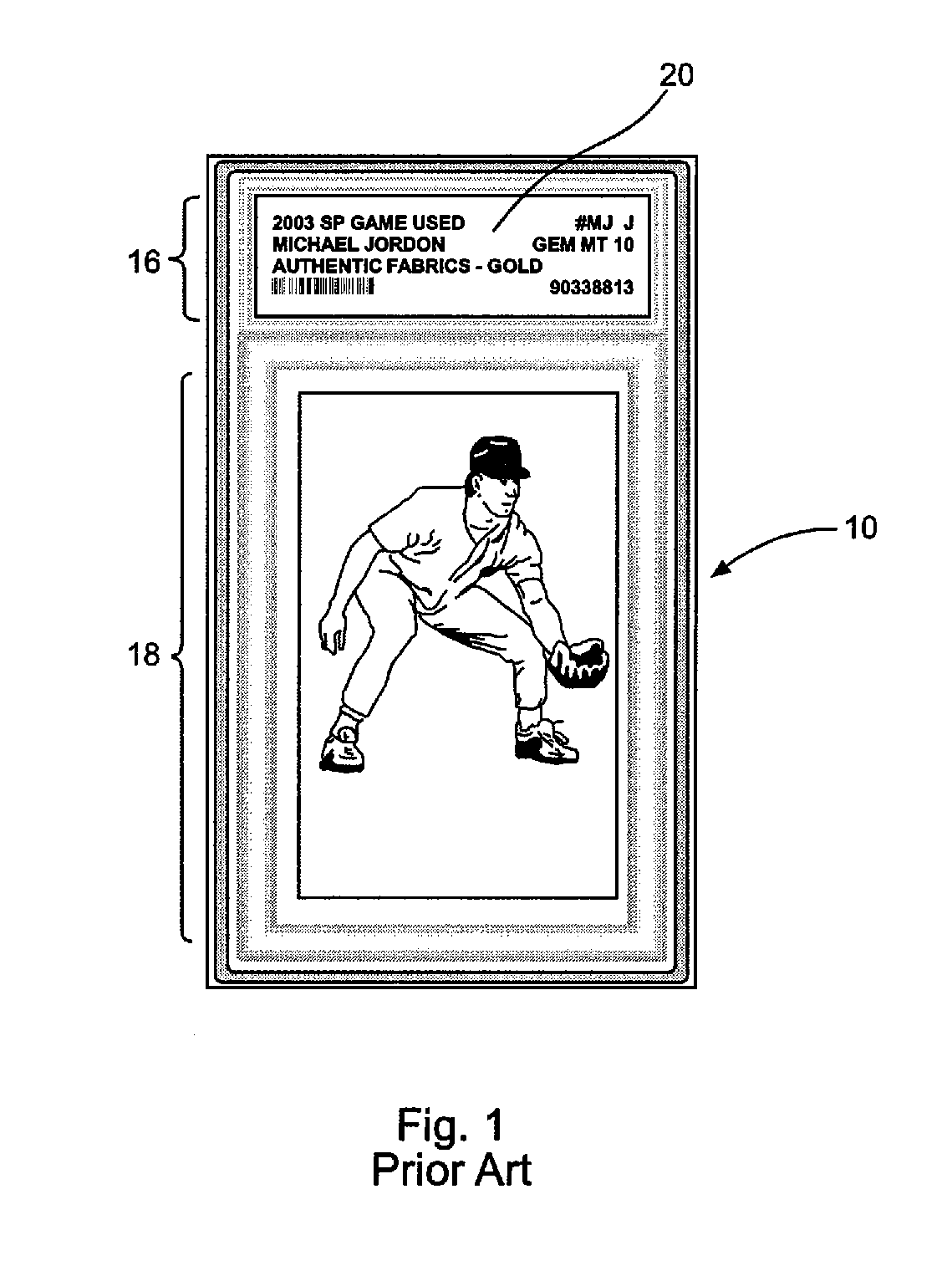
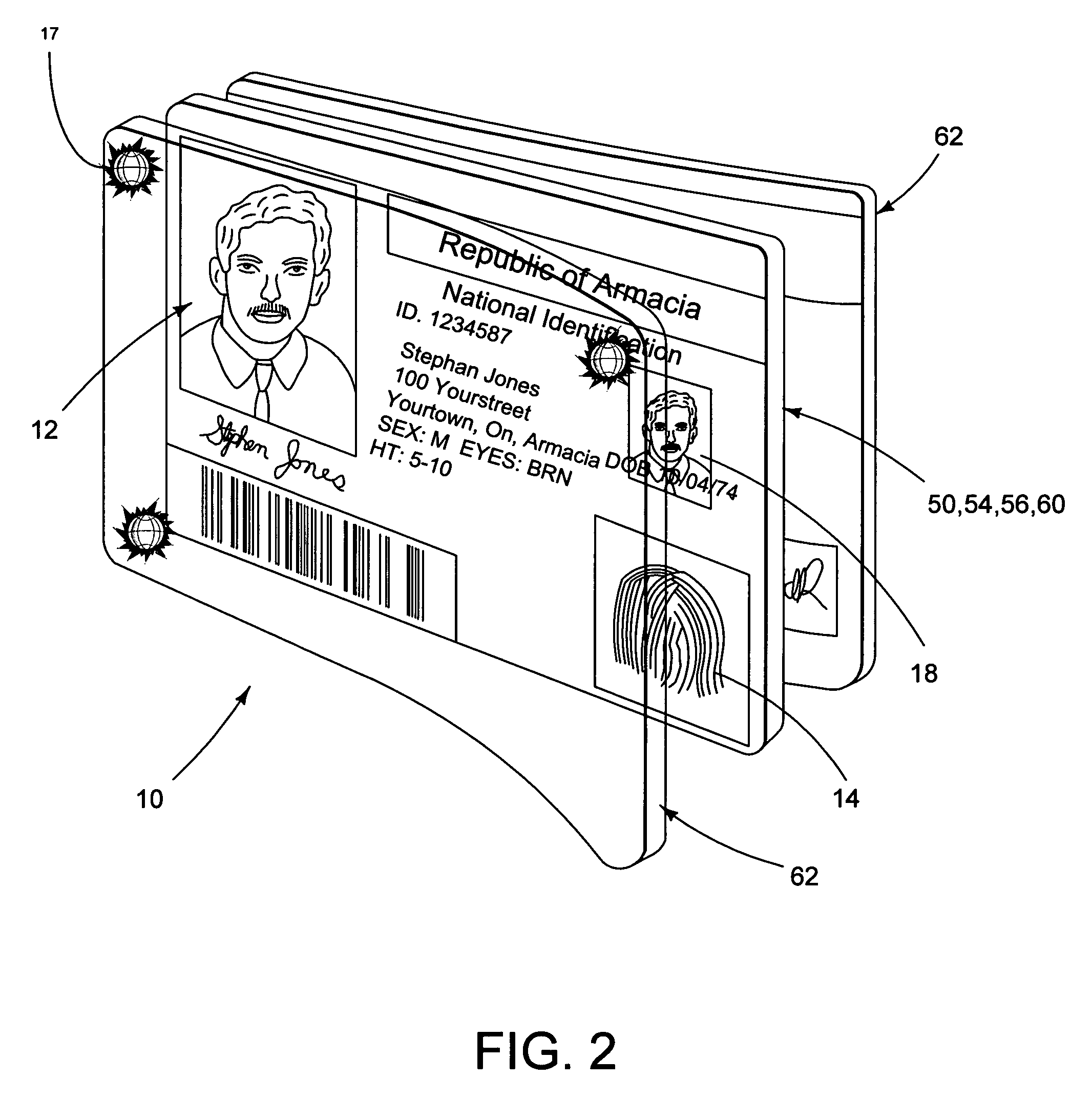
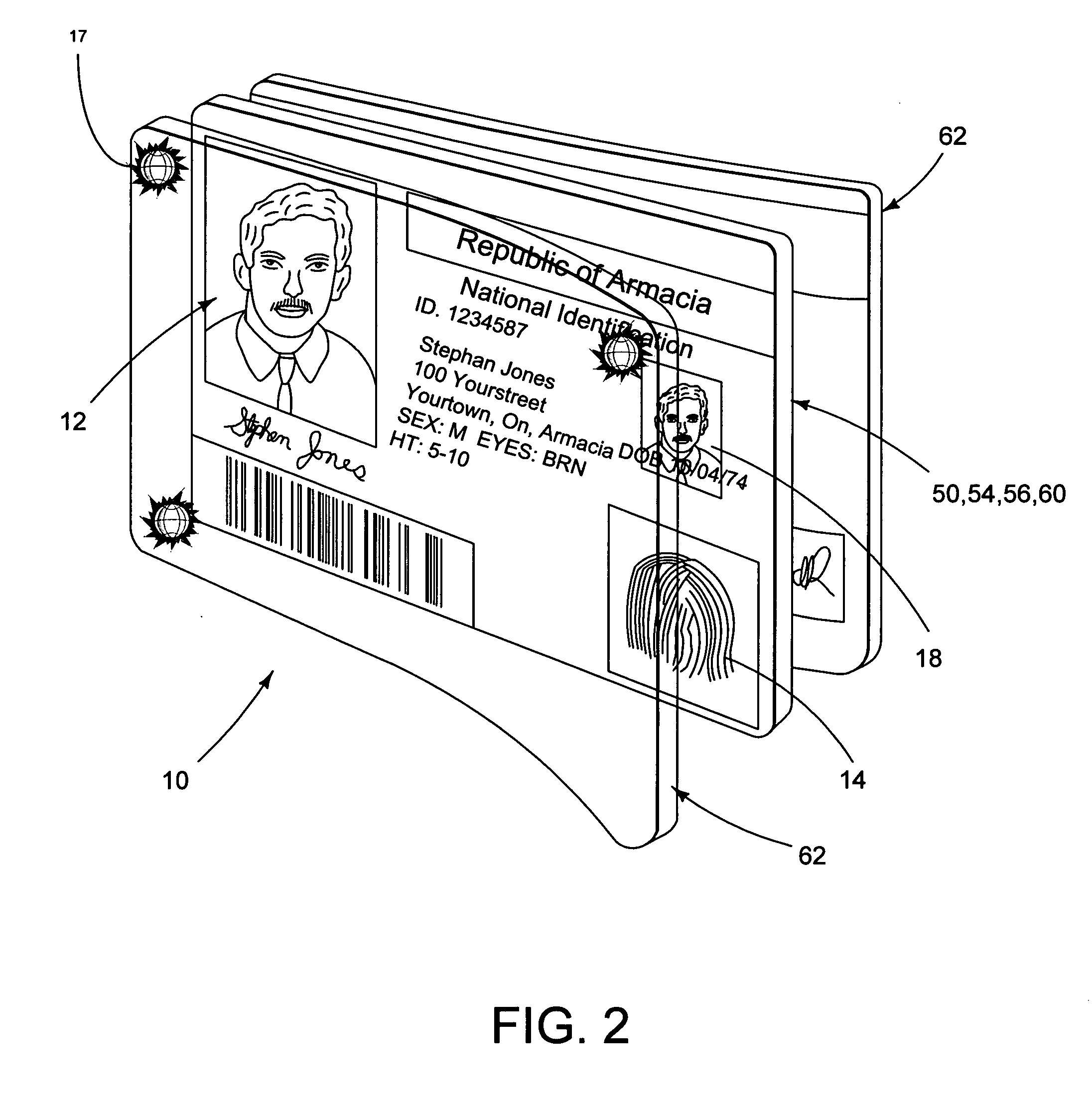
Identification document having intrusion resistance
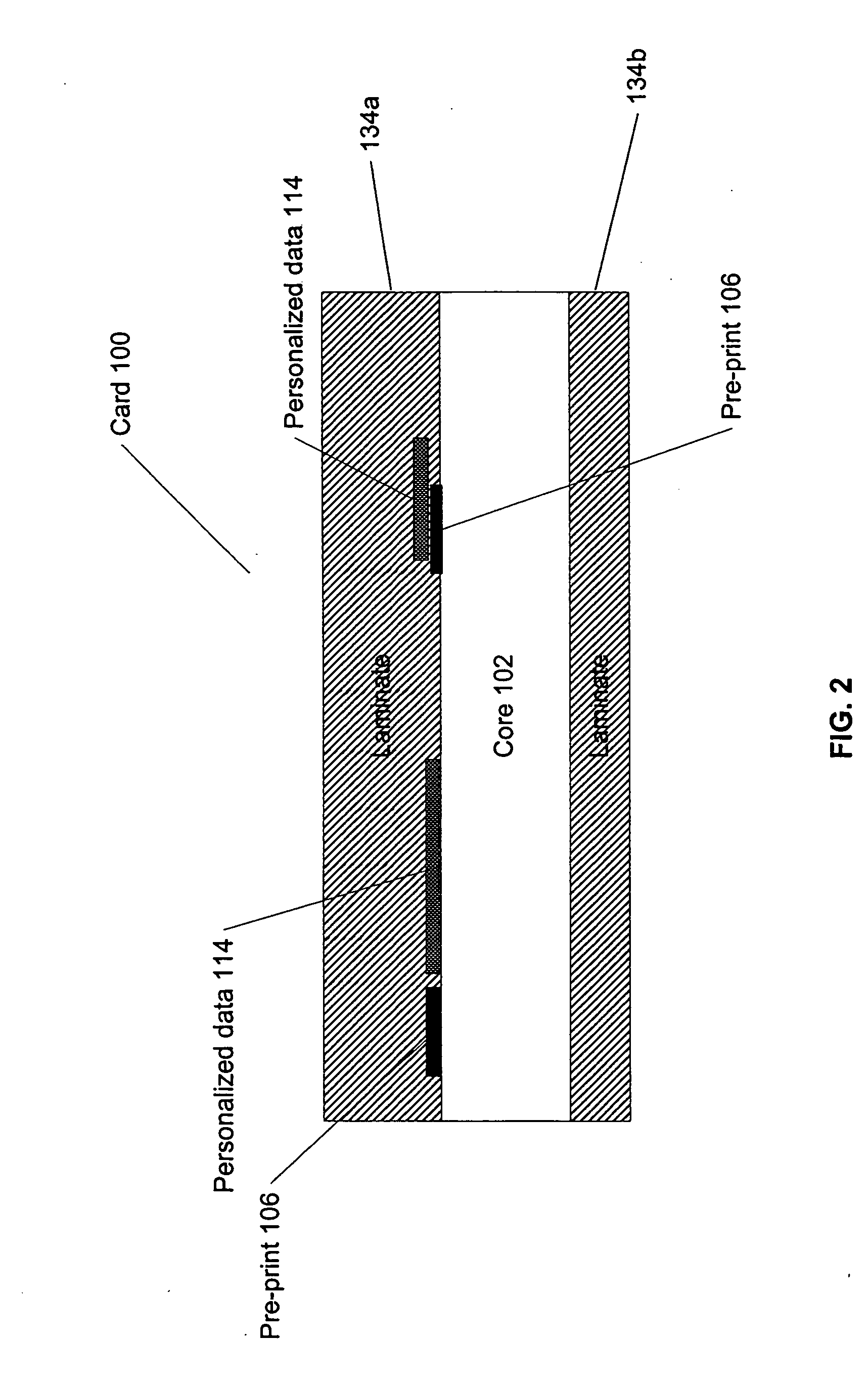
InactiveUS20050247794A1Improve security levelUltimate in durabilityOther printing matterRecord carriers used with machinesAdhesiveEngineering
An identification document is provided, comprising a core layer, such as TESLIN, laminated directly to a laminate layer, such as polycarbonate, without the use of an adhesive. The core layer has at least one indicium formed thereon and has a first surface. The first layer of laminate is affixed to the core layer by a press lamination process where the press lamination process is sufficient to couple the core layer to the first layer such that an attempt to separate the first layer from the core layer causes at least a partial destruction of the core layer.
Owner:DIGIMARC CORP
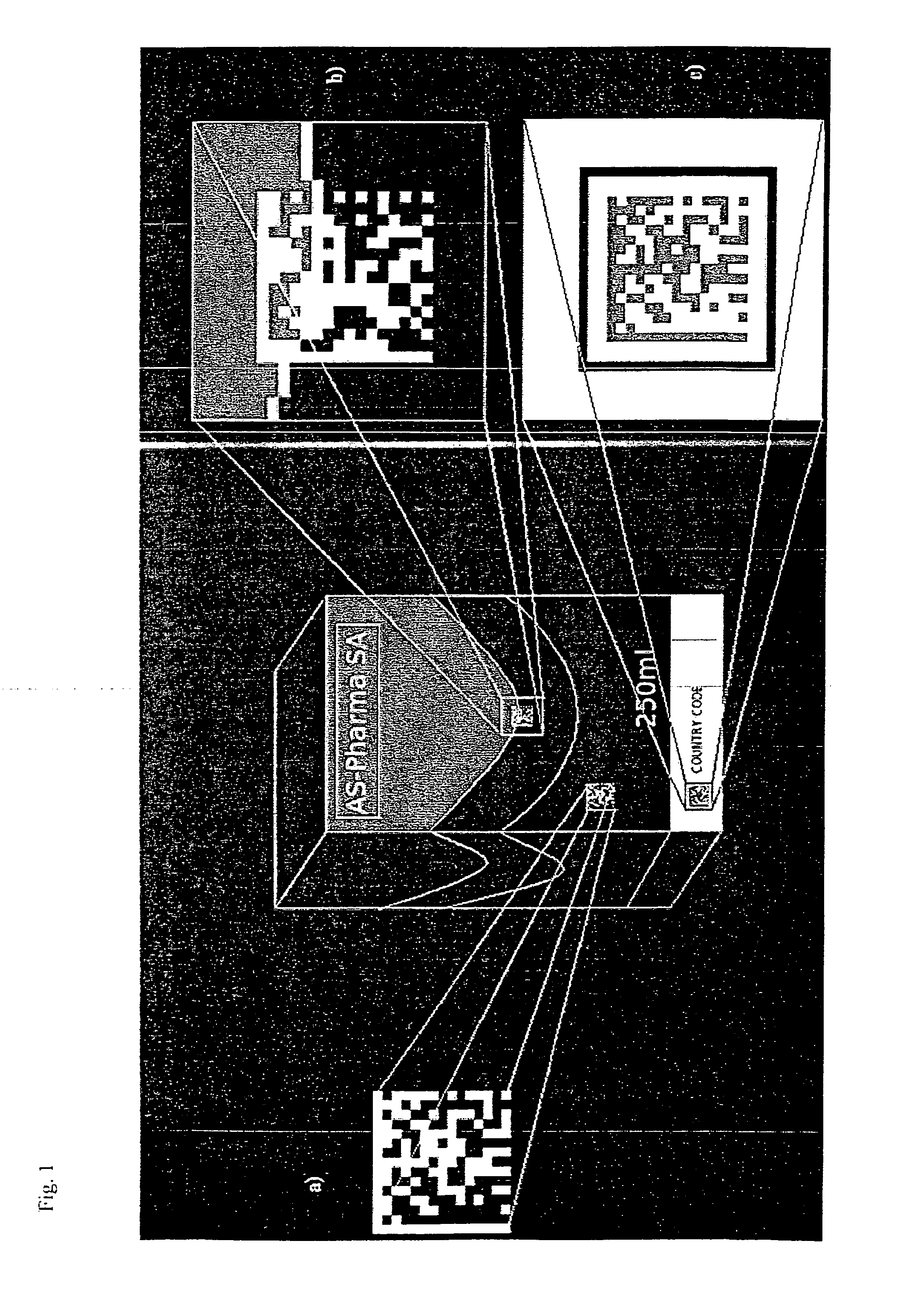
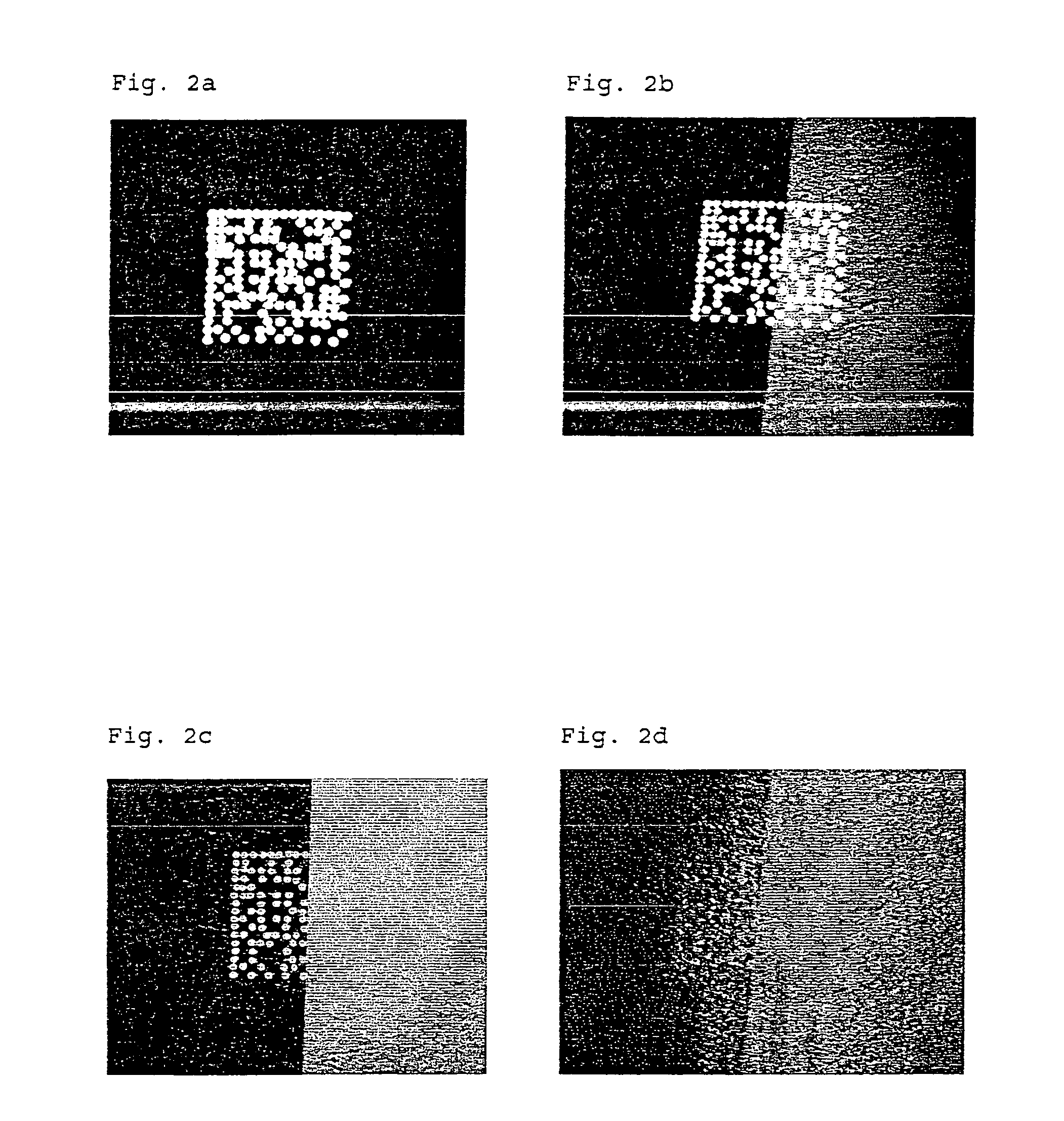
Identification and authentication using liquid crystal material markings
ActiveUS20110101088A1Easy authenticationIncrease contrastLiquid crystal compositionsStampsOptical propertyPolymeric liquid crystal
The present invention relates to a marking of polymeric liquid crystal material having determined optical characteristics allowing its authentication and reading by a machine and its authentication by the human eye. The marking is applied onto an item, good or article by a variable information printing process. The marking is in the form of indicia representing a unique code which allows for an easy authentication by the human eye and a secure tracking and tracing of the marked item, good or article throughout its life cycle.
Owner:SICPA HLDG SA
Method of preparing an anisotropic polymer film on a substrate with a structured surface
InactiveUS20030189684A1Easy authenticationLow temperature dependencePolarising elementsLight effect designsPolymer sciencePolymer
Owner:MERCK PATENT GMBH
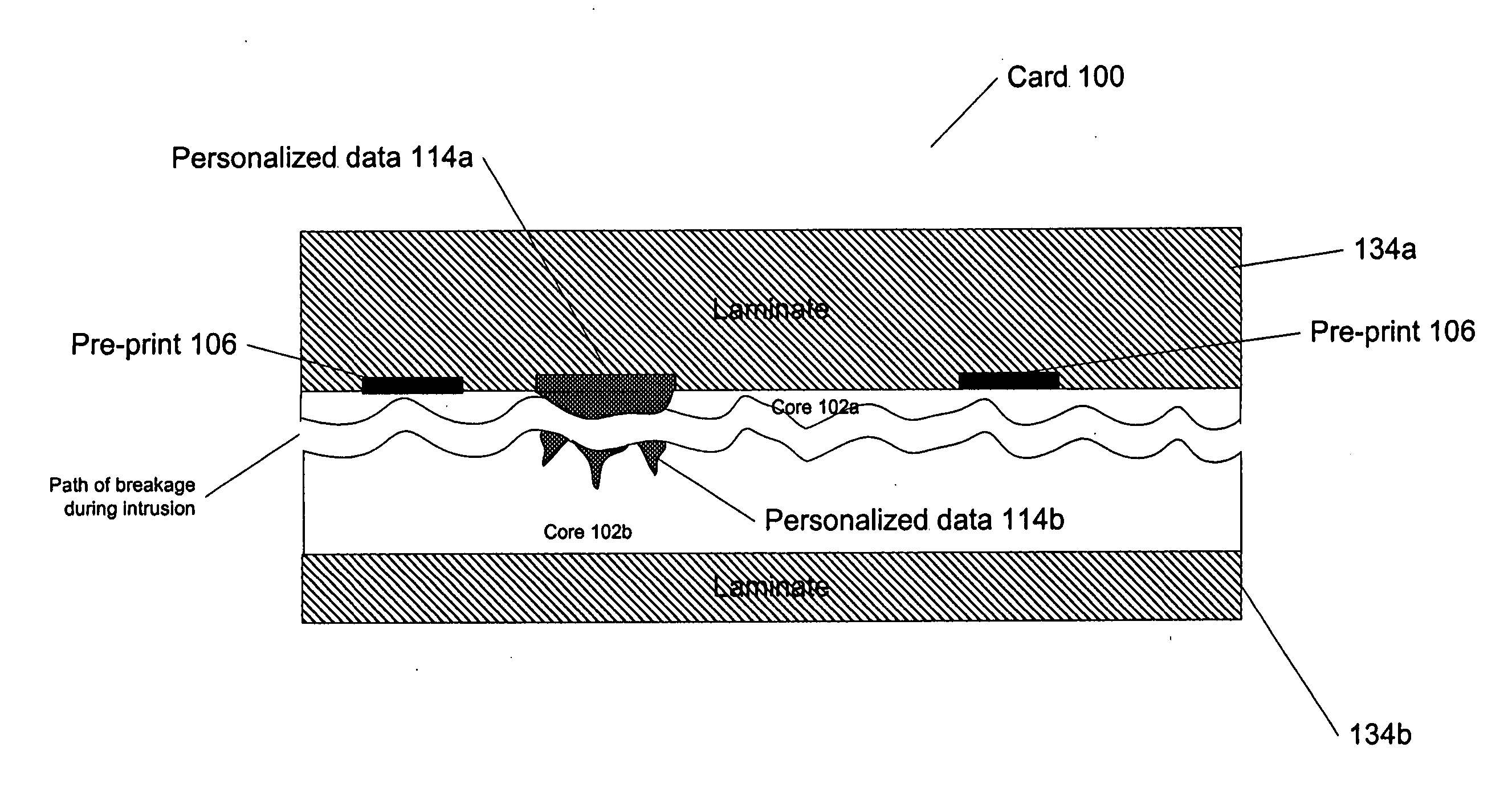
Tamper evident adhesive and identification document including same
InactiveUS7744002B2Easy authenticationEasy to identifyOther printing matterMacromolecular adhesive additivesMedicineAdhesive
A composition is provided for adhering a first article to a second article, the composition comprising a thermally active low Tg polymeric resin; and a multifunctional crystalline polymer. The thermally active low Tg polymeric resin can, for example, comprise 50-99% of the composition. The multifunctional crystalline polymer can, for example, comprise 1-50% of the composition. In one embodiment, the multifunctional crystalline polymer comprises 5-20% by weight of the composition. In one embodiment, the multifunctional crystalline polymer has a low molecular weight.
Owner:L 1 SECURE CREDENTIALING
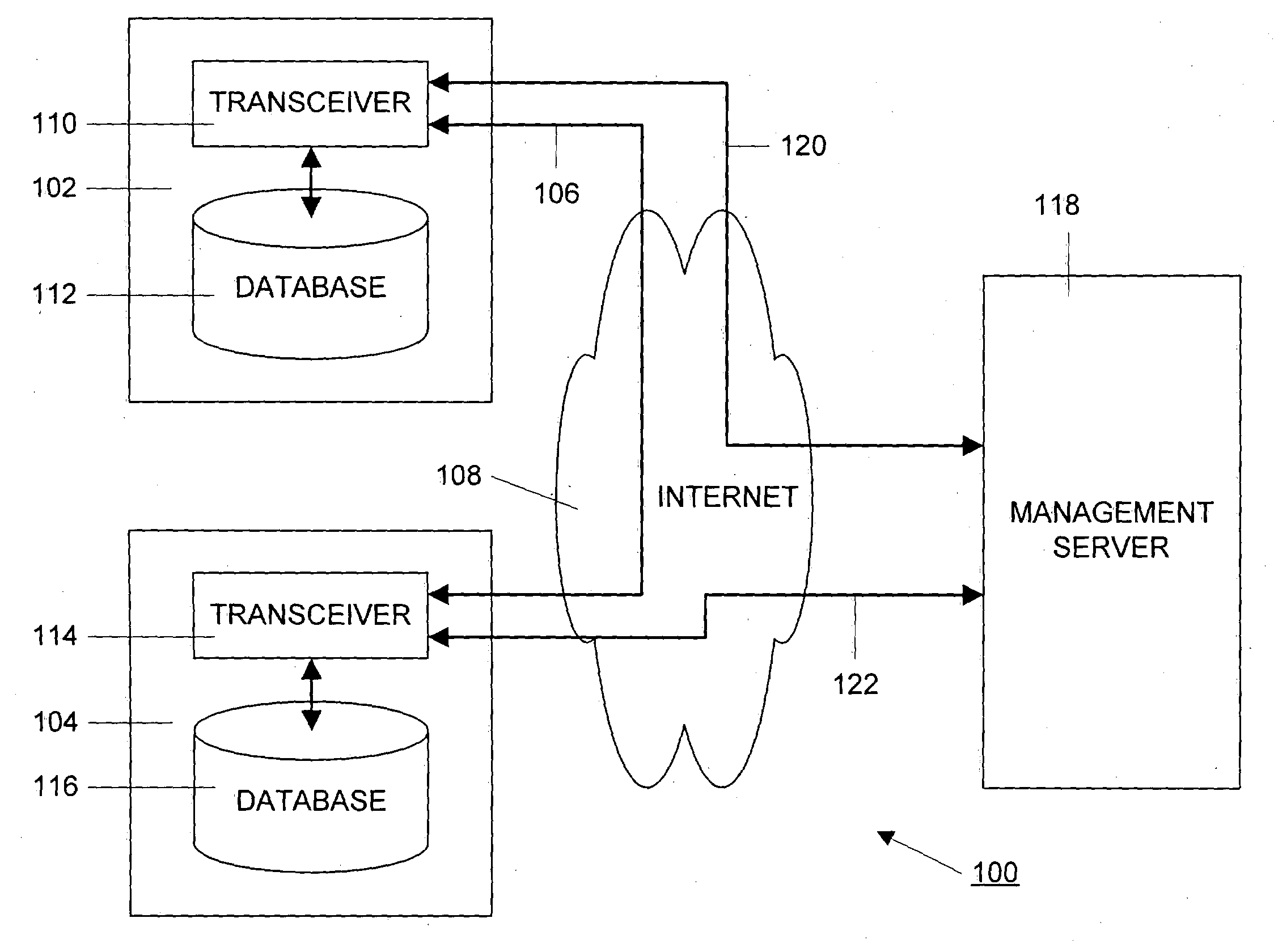
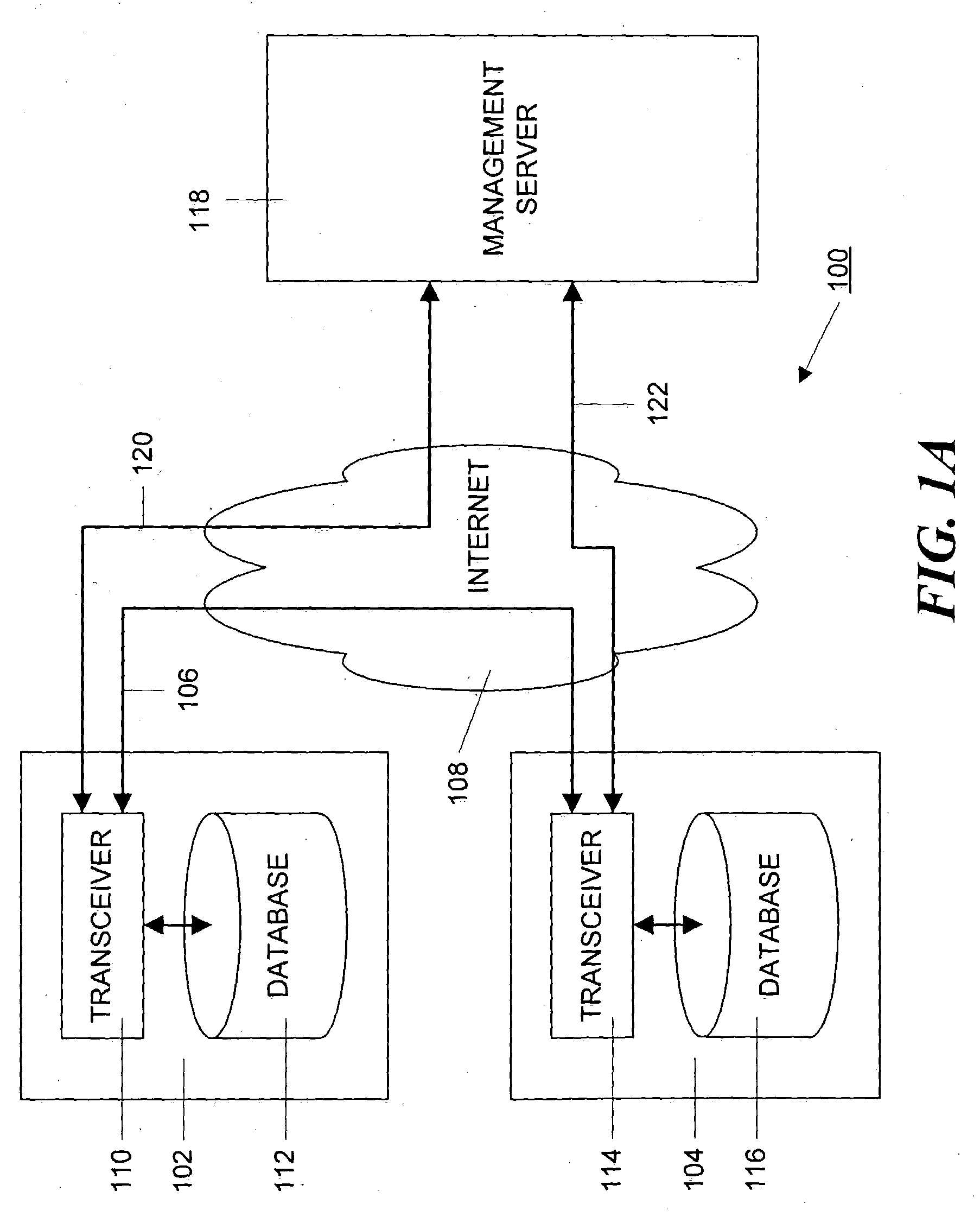
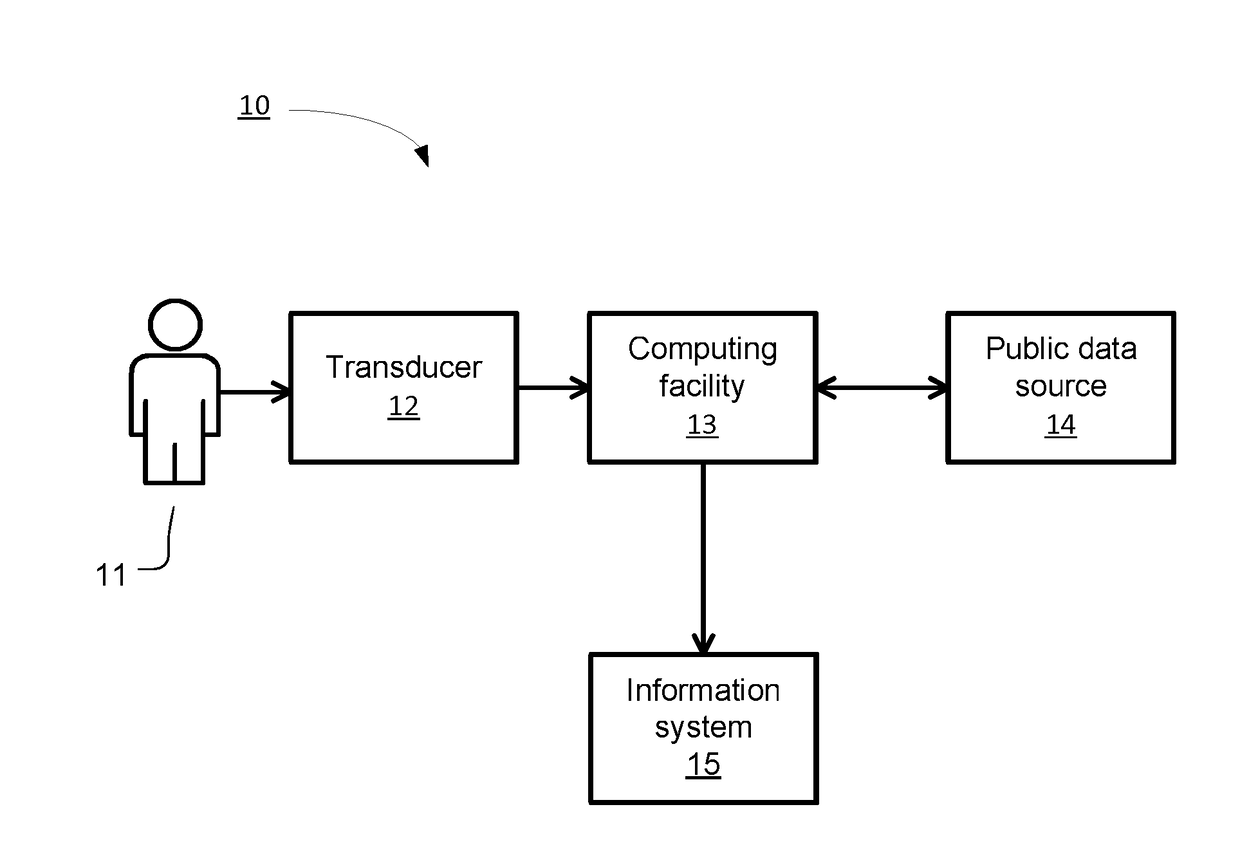
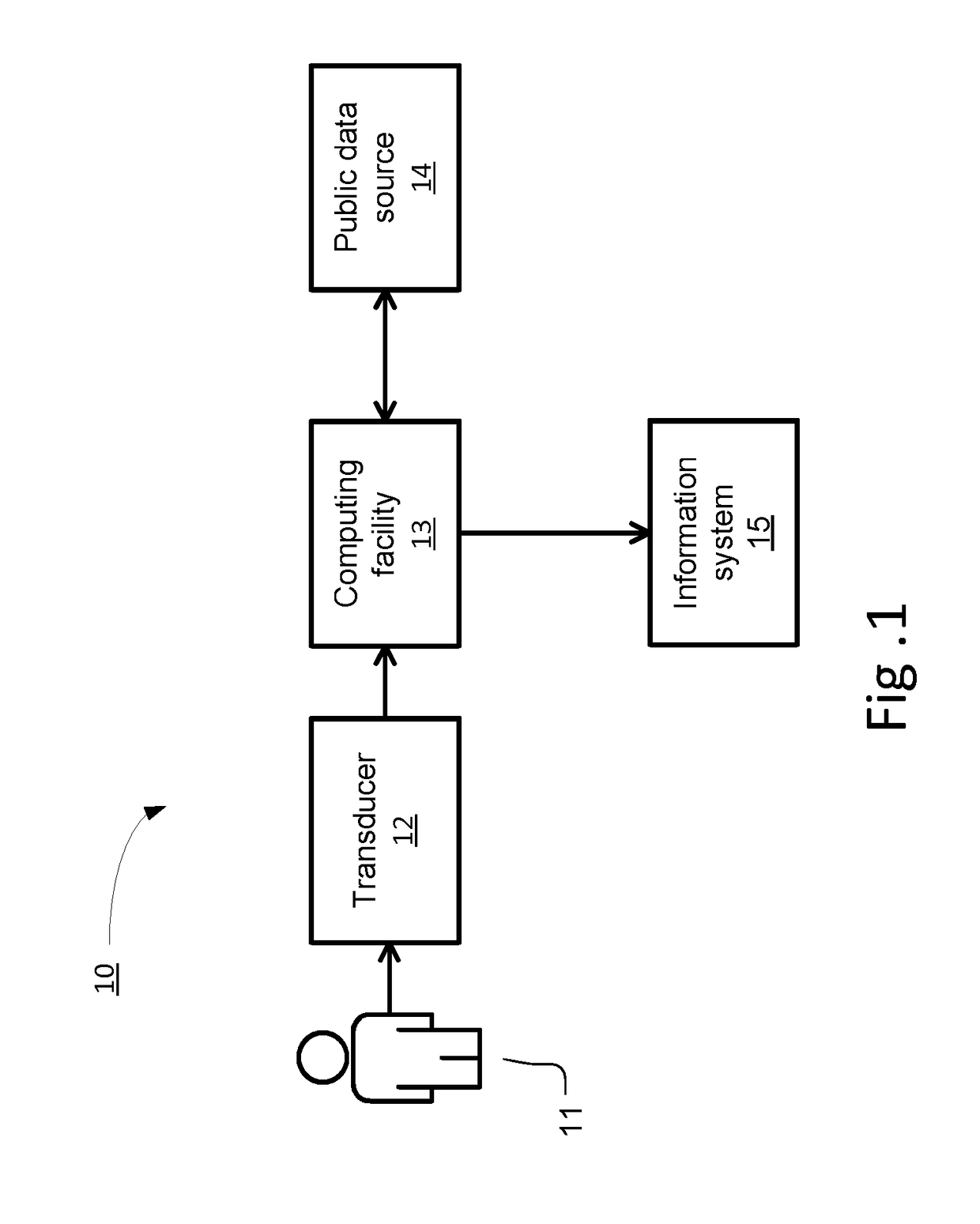
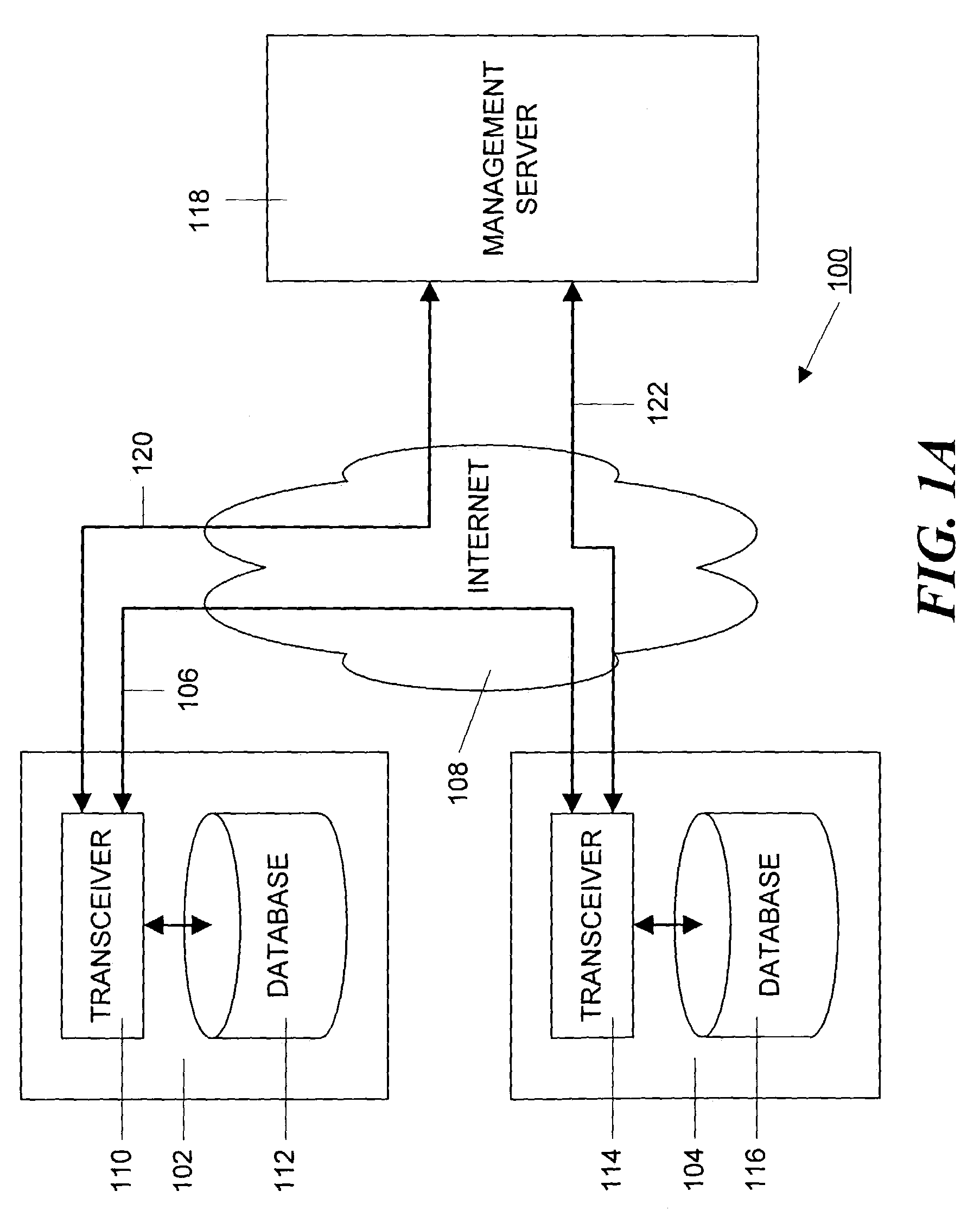
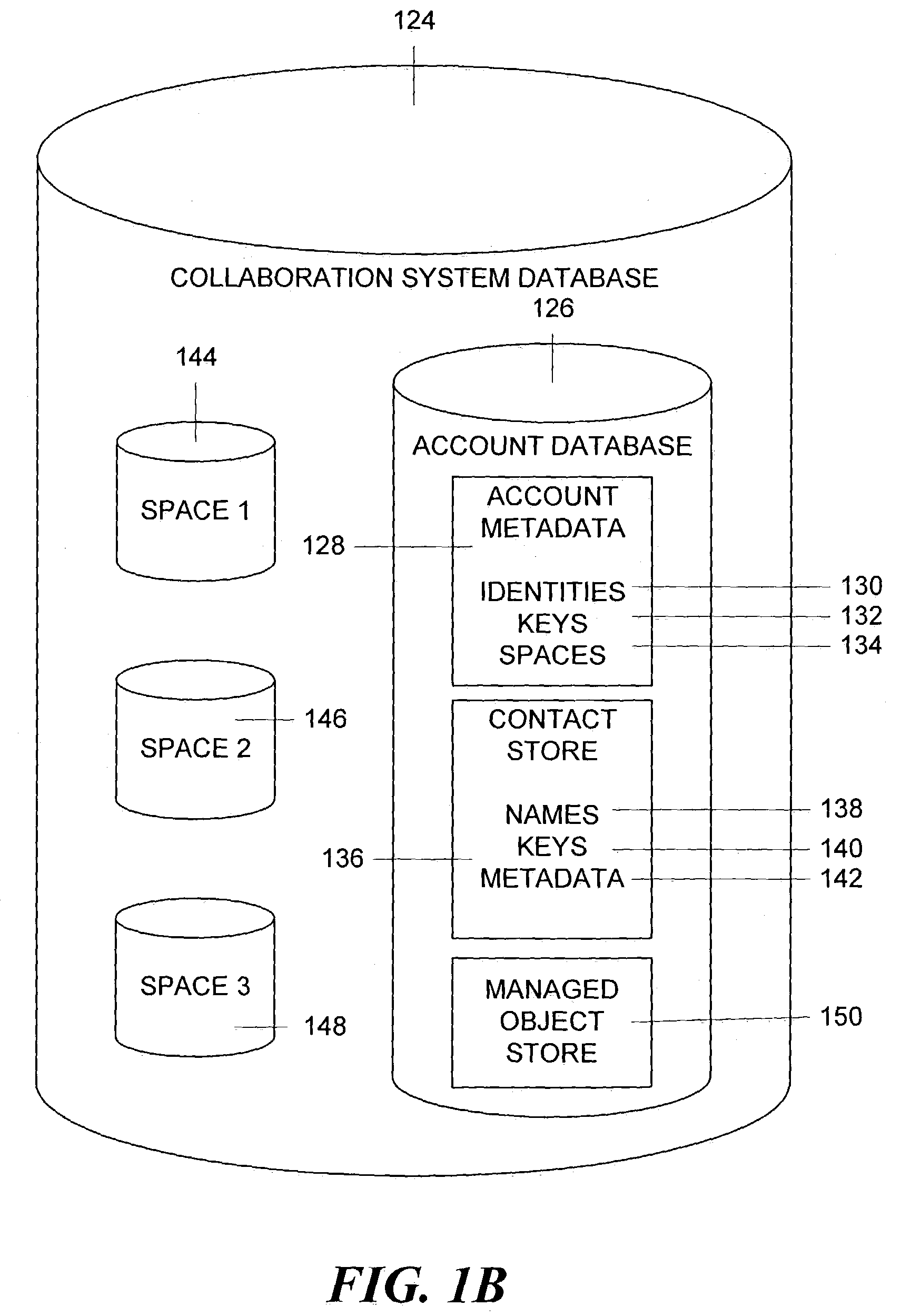
Method and apparatus for managing and displaying contact authentication in a peer-to-peer collaboration system
InactiveUS20090150968A1Easy authenticationDigital data processing detailsDigital computer detailsConfusionDisplay Name
Proper user-to-data associations are maintained in shared spaces created in a peer-to-peer collaborative system by means of a simplified and minimal user interface that permits users to easily authenticate other members of a shared space. In particular, support is provided for automatically building authenticated relationships even if users do not take the time to authenticate other users. When a user enters a shared space and views the contacts in that space, the display names of each contact are accompanied by distinctive icons that identify that authentication status of that contact. A mechanism is provided for resolving conflicts between contacts with the same display names to prevent confusion and contact “spoofing.” Security policies can be established to provide a uniform approach to authentication. These policies can be set by a user or, alternatively, the policies can be set by an administrator.
Owner:MICROSOFT TECH LICENSING LLC
Quick login to user profile on exercise machine
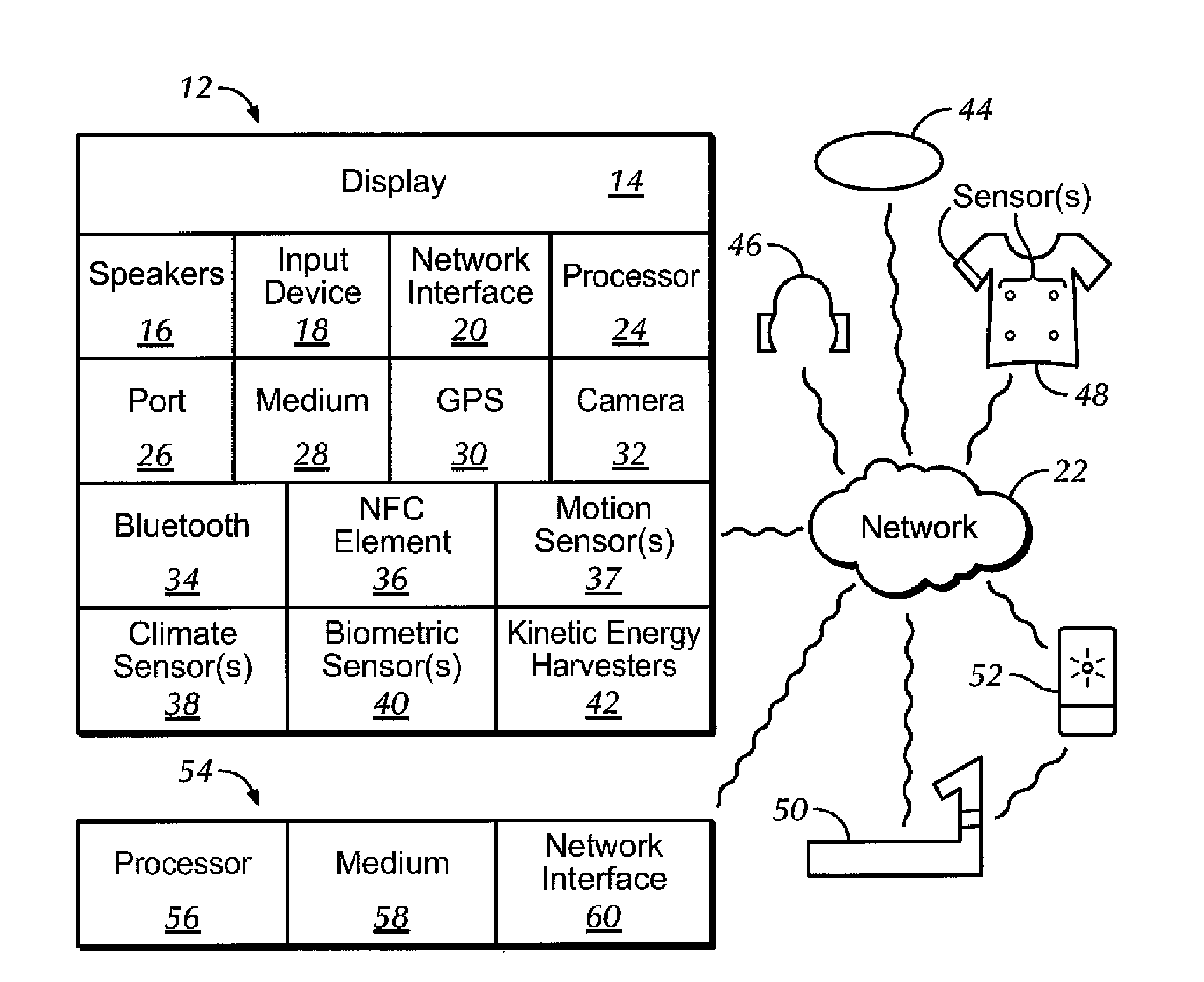
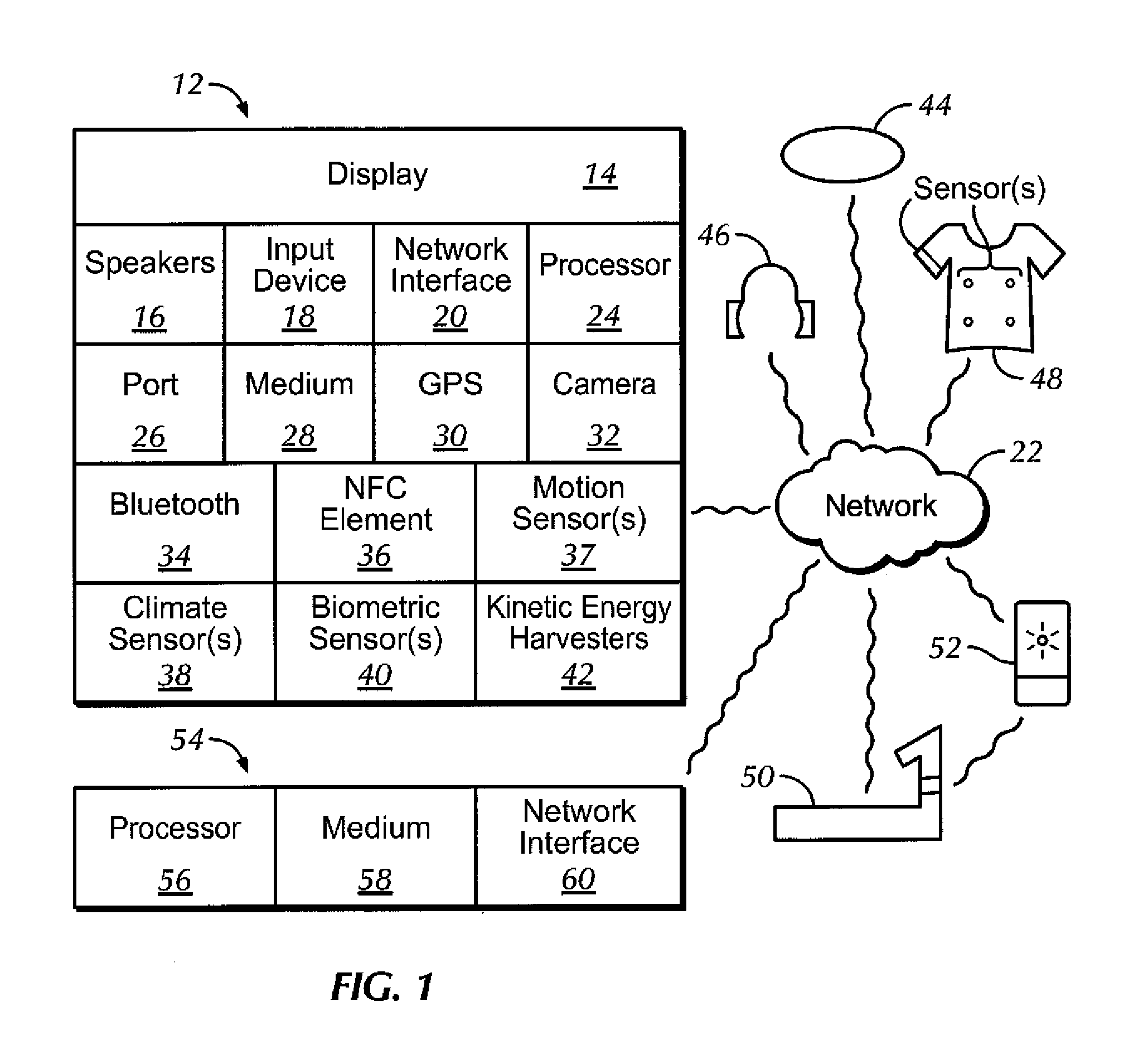
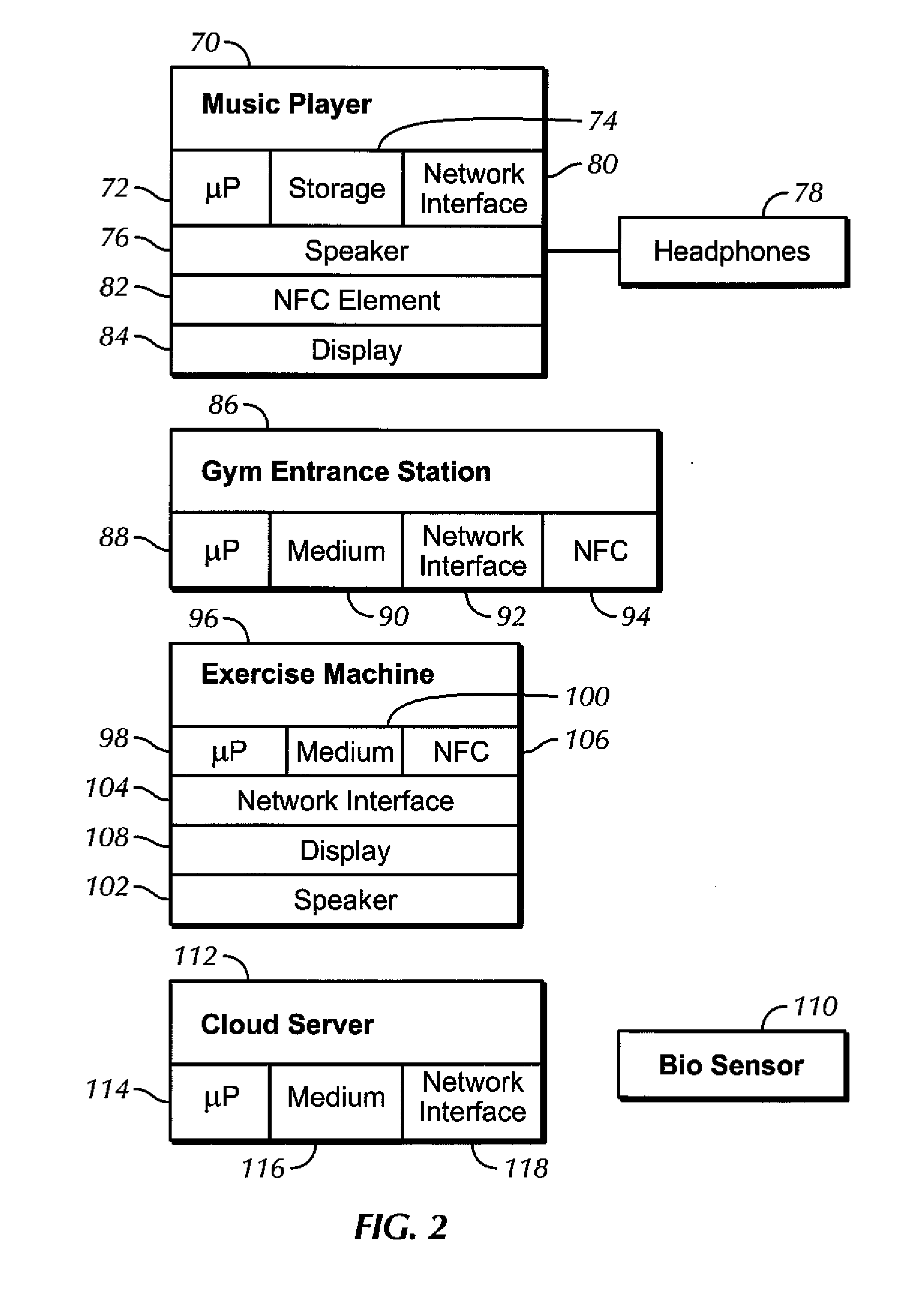
InactiveUS20150082408A1Easy authenticationQuick SetupPhysical therapies and activitiesDigital data processing detailsEngineeringMusic player
Owner:SONY CORP
System and method for verifying identity
InactiveUS9189788B1Easy to optimizeEasy authenticationProtocols using social networksProtocol authorisationIdentity recognitionUser authentication
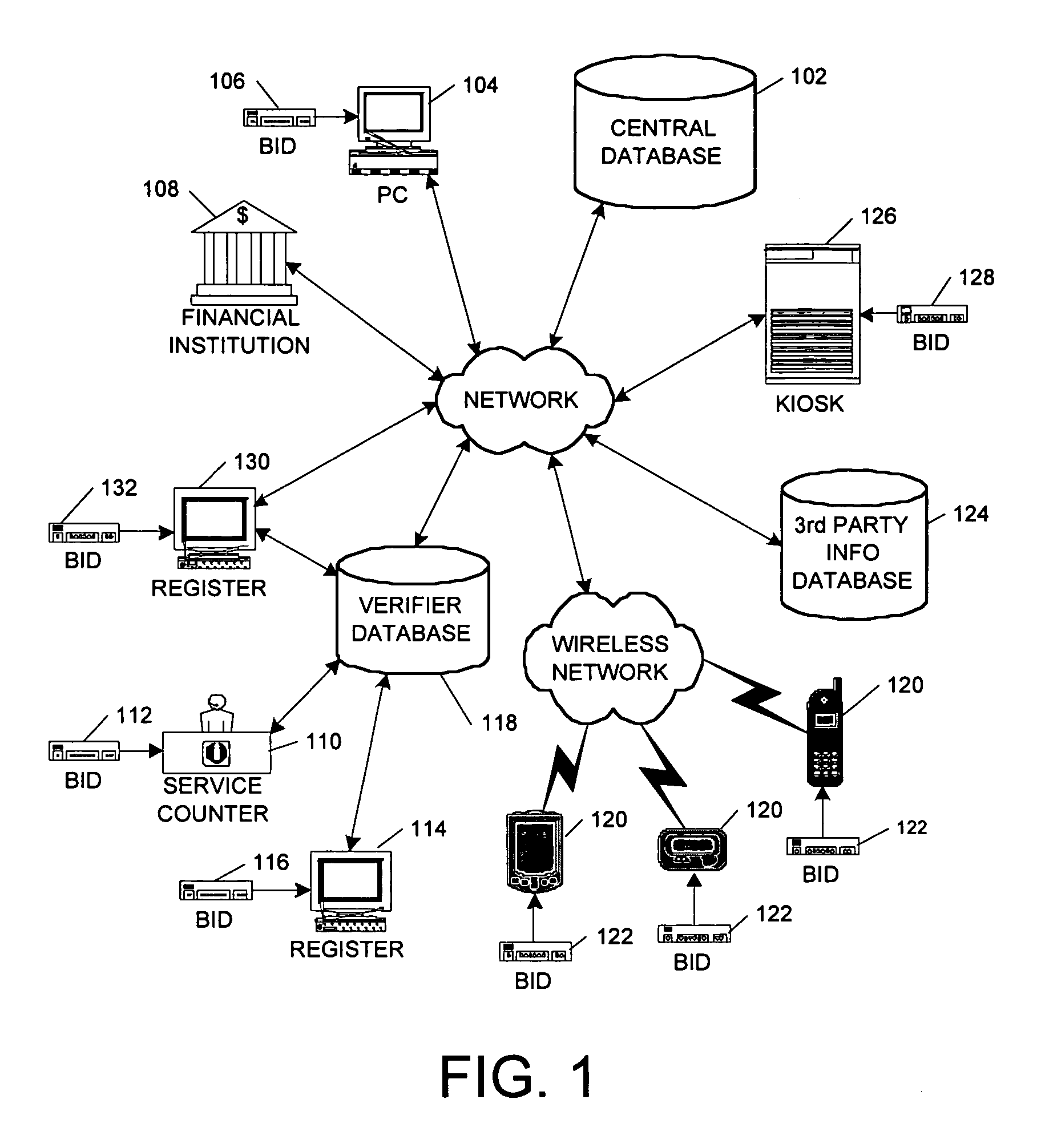
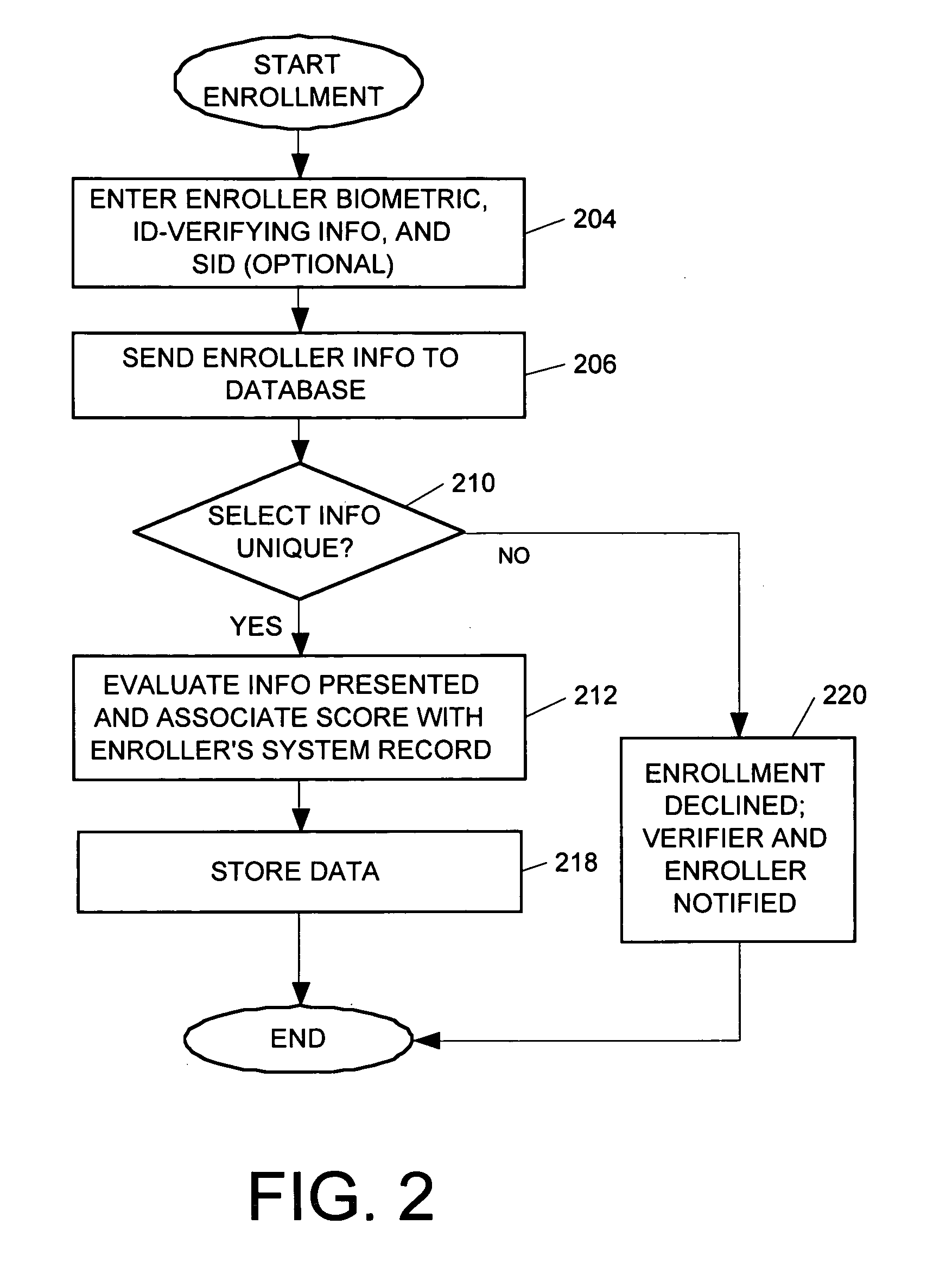
A system and method of identity verification at a point-of-identification verification (POV) using biometric-based identity recognition and an identity verifying score based upon a presenter's initial identification presentment and their subsequent action in the system. The system also provides tracking and evaluates verifier activity within the system through biometric-based identity recognition and a performance score based upon their actions and the results of their actions within the system. System users register at least one biometric identifier and personal and / or business identity-verifying data. Users present a biometric sample obtained from their person and their system ID number to conduct identification transactions. This data is used to authenticate the user's identity to a percentage of reliability and allows a user with consistently positive ID verifications to establish a higher ID score, strengthening their credibility within the system. Once enrolled, the system allows the user to be identified without presenting any token-based information, such as a driver's license or passport. In one embodiment, an identity verification score generated via the system can be employed in conjunction with online transactions, such as purchases, auctions, email, instant messaging, and the like.
Owner:OPEN INVENTION NEWTORK LLC
Method and system for digitally signing electronic documents
InactiveUS20070118732A1Prevent non-repudiationEasy authenticationUser identity/authority verificationComputer security arrangementsElectronic documentDigital signature
A method and apparatus for digitally signing an electronic document is provided. Data is inputted into the electronic document by a client. A signing process request is initiated by the client. The signing process request is then transmitted by the client to a server. An input field request, which is generated by the server, is then transmitted to the client. The server is then provided with user authentication credentials in response to the input field request. The user authentication credentials received from the client are verified by the server and the electronic document is digitally signed by the server on the basis of the verification of the user authentication credentials.
Owner:FORMATTA
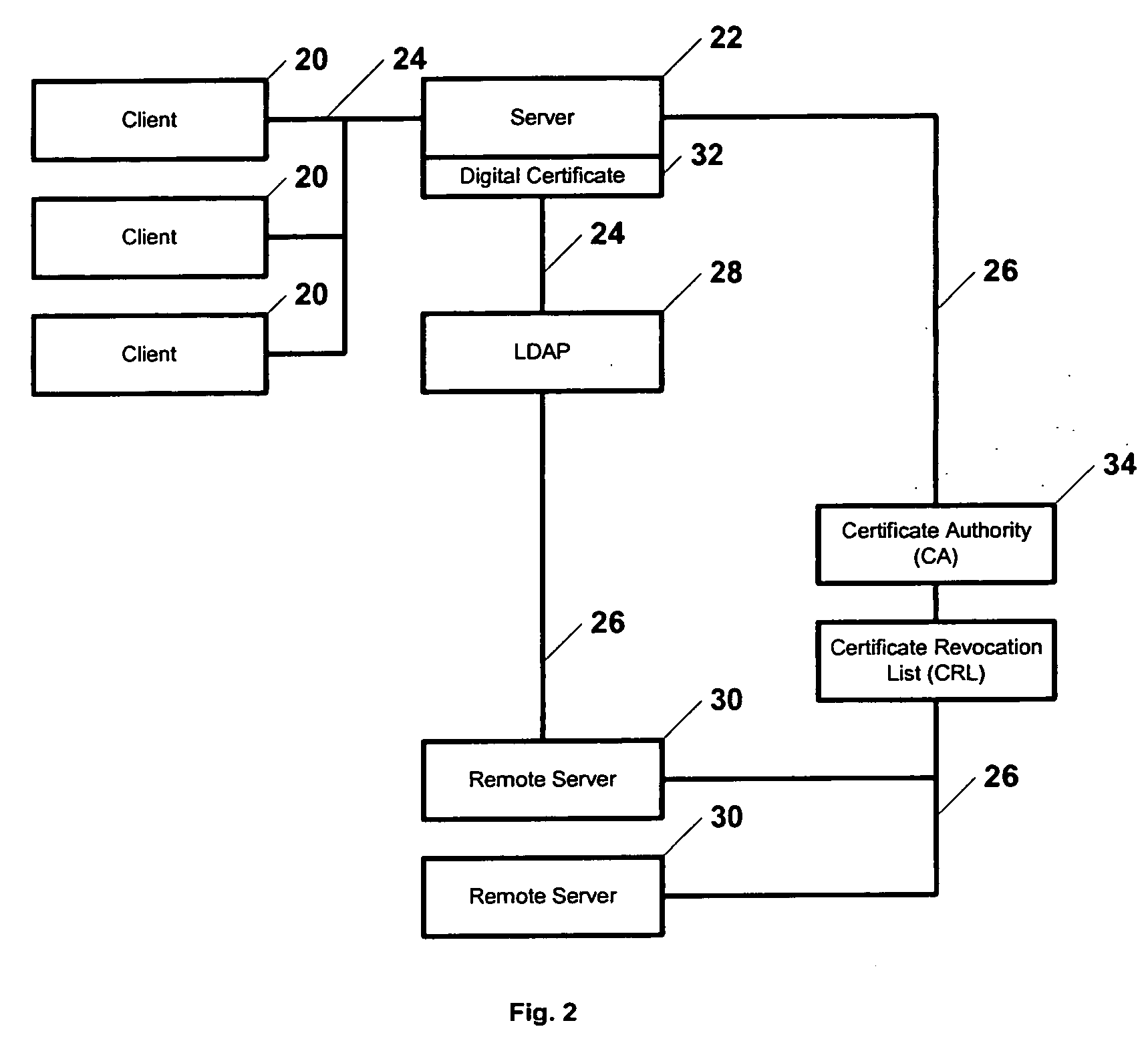
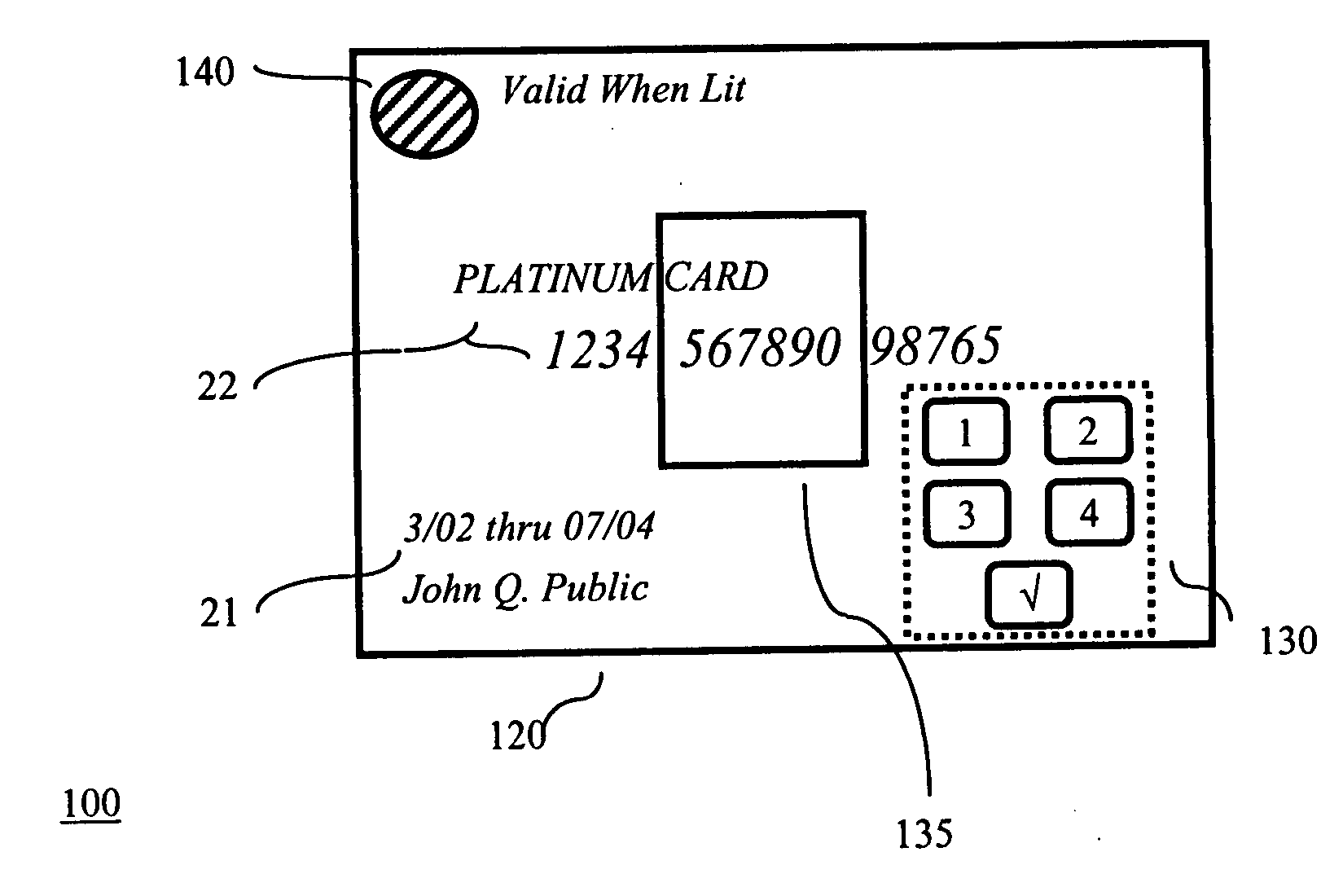
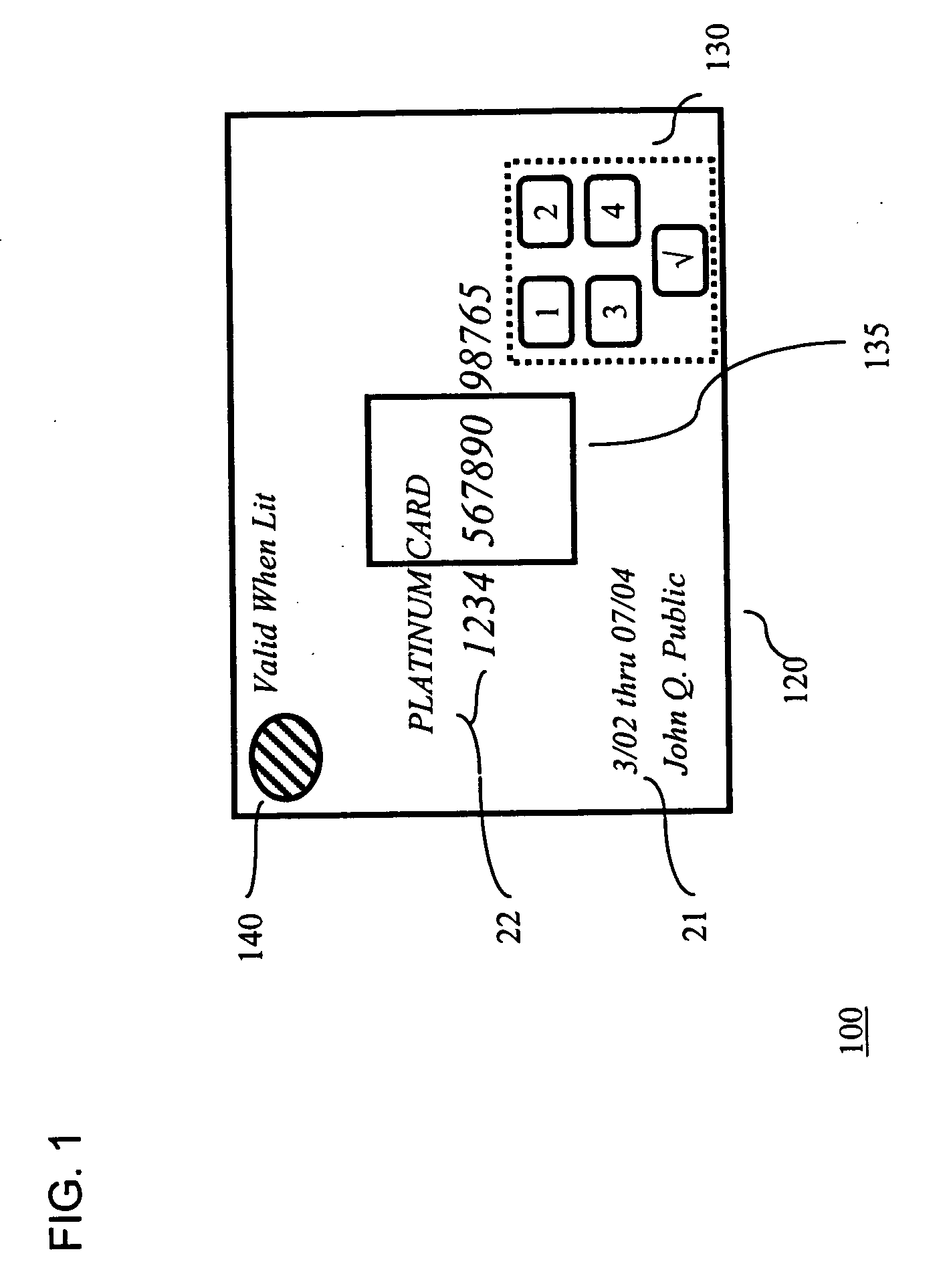
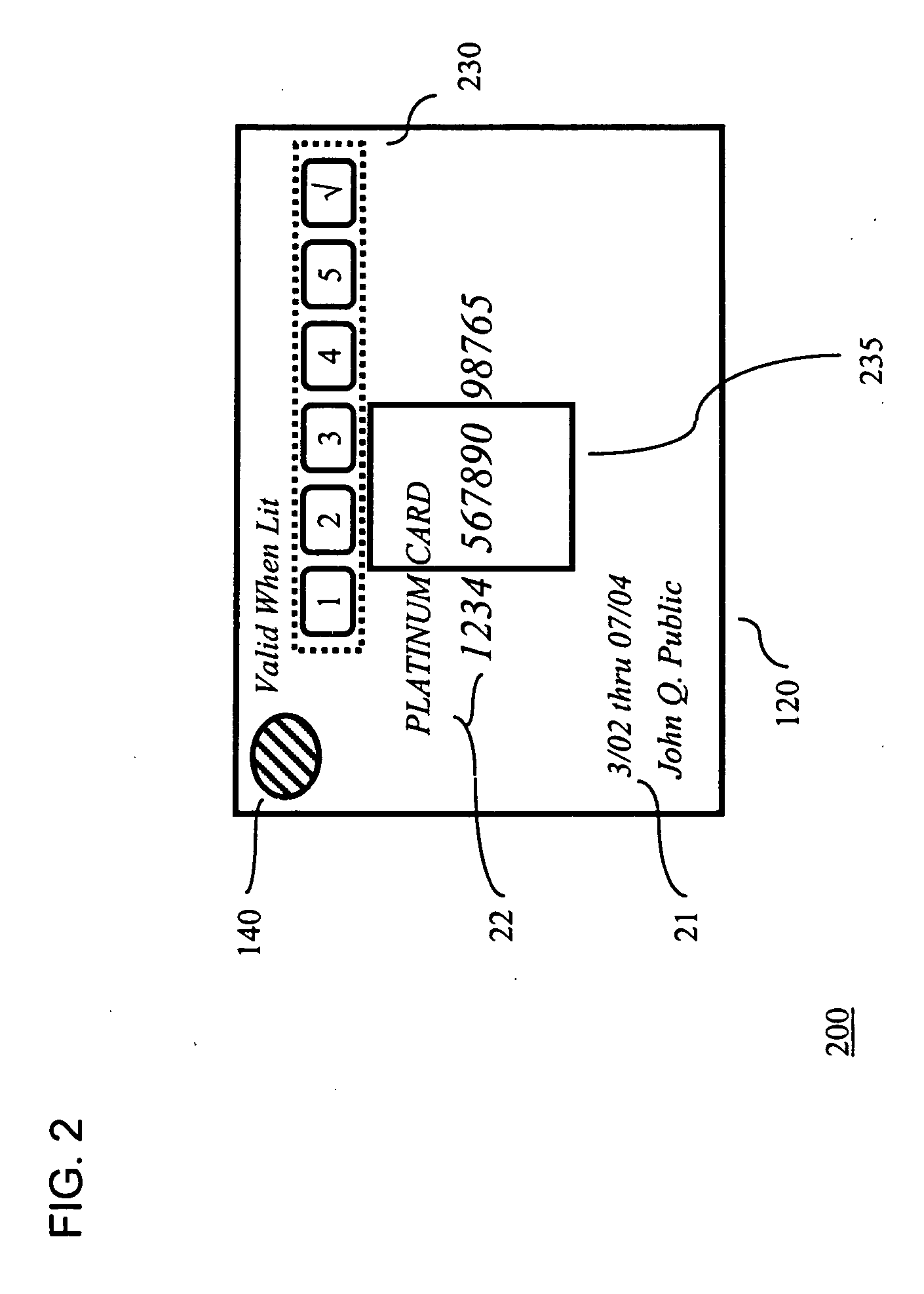
System for securing personal cards
InactiveUS20050211785A1Easy authenticationConvenient verificationSensing record carriersRecord carriers used with machinesCredit cardPersonal identification number
A credit card comprises a plastic layer, a processor, and a keypad. The keypad provides the ability to input a code (e.g., a personal identification number (PIN) code) to the processor as a part of validating the transaction. Illustratively, the entry of a valid PIN code may cause the processor to trigger an alerting device as an indicator to the merchant that the holder of the credit card is authorized for its use.
Owner:T INK INC
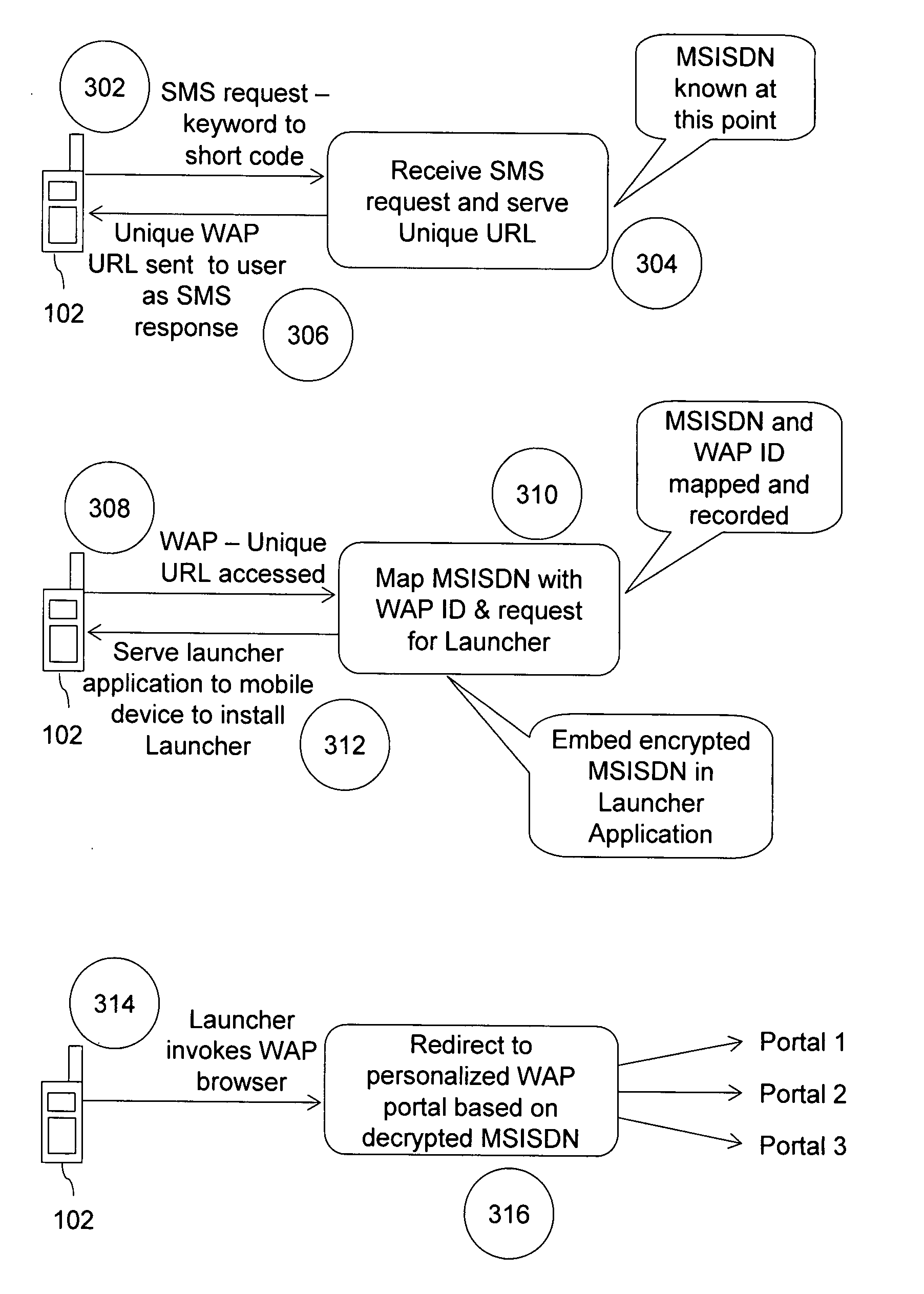
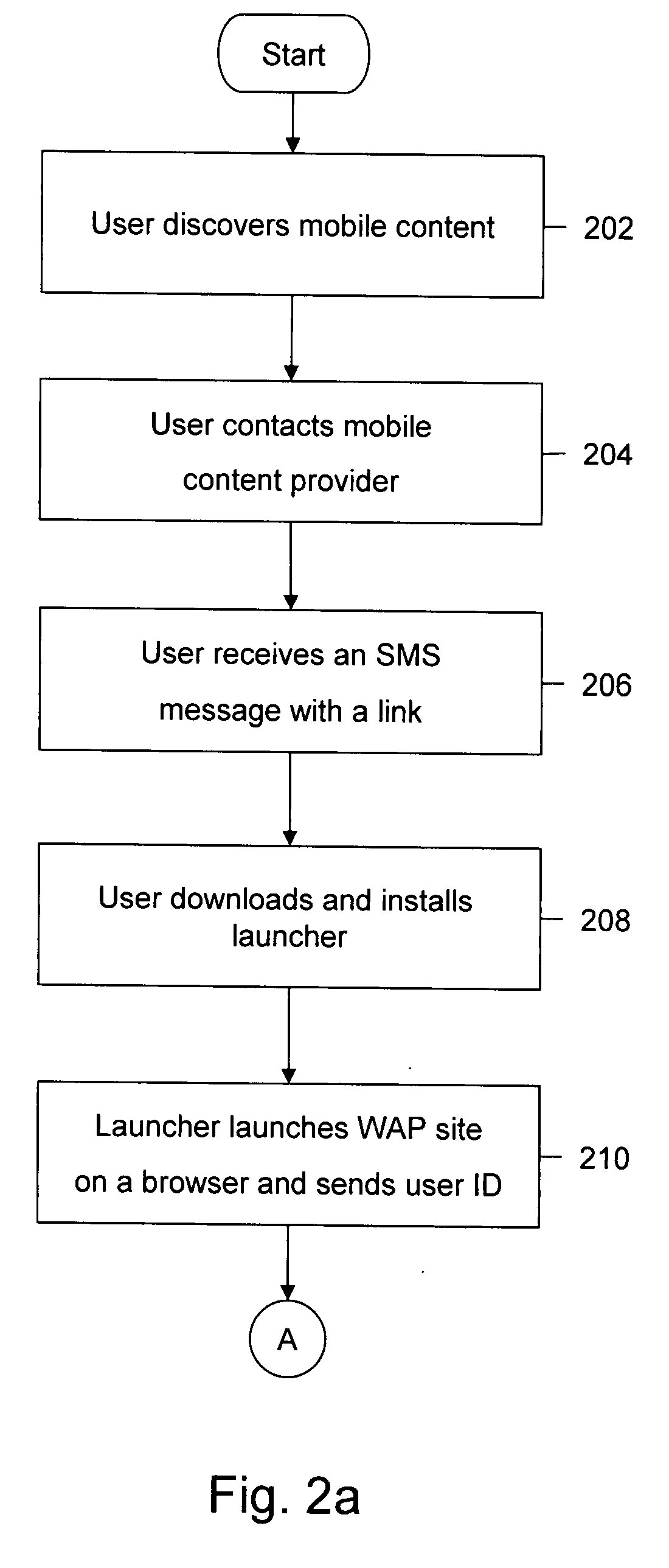
Method and computer program product for premium mobile service for discovery, payment, personalization and access of mobile content
InactiveUS20080160970A1Quick and convenient wayFacilitates personalized displaySpecial service for subscribersMarketingPaymentPersonalization
A method and computer program product for providing mobile content to a user of a mobile device. The mobile content is offered by a mobile content provider. Further, a launcher is provided and is installed on the mobile device. The launcher dynamically provides identity information associated with the user, context information about the user, and a dynamically-defined link to a Wireless Application Protocol (WAP) site of the mobile content provider. Subsequently, the WAP site is displayed when the launcher is activated on the mobile device. The WAP site provides the mobile content offered by the mobile content provider. The display of the WAP site is personalized on the basis of the context information. Thereafter, the purchased mobile content is downloaded by the user of the mobile device.
Owner:CISCO TECH INC
Identification and authentication using polymeric liquid crystal material markings
ActiveUS20120061470A1Easy authenticationIncrease contrastLiquid crystal compositionsOrganic chemistryOptical propertyComputer science
The present invention relates to a marking of polymeric liquid crystal material having determined optical characteristics allowing its authentication and reading by a machine and its authentication by the human eye. The marking is applied onto an item, good or article by a variable information printing process. The marking is in the form of indicia representing a unique code which allows for an easy authentication by the human eye and a secure tracking and tracing of the marked item, good or article throughout is life cycle.
Owner:SICPA HLDG SA
Security device
ActiveUS20100230615A1Easy to detectEasy authenticationNon-fibrous pulp additionPaper-money testing devicesColor shiftEmissivity
A security device for authenticating bank notes, documents and other items, comprises a luminescent material for producing luminescent radiation of first and second wavelengths. The security device includes an optically variable structure for controlling emission of luminescent radiation of at least one of the first and second wavelengths from the security device, the security device being arranged to permit, from an area of the optically variable structure, emission of luminescence of the first and second wavelengths from the security device. The optically variable structure causes the relative emissivity of the security device for luminescent radiation of the first and second wavelengths to change with a change in emission angle, so that the security device produces an angle-dependent colour shift in the emitted luminescent radiation. The optically variable structure may comprise an optical interference stack that controls transmission of luminescent radiation therethrough in response to the wavelength of luminescent radiation.
Owner:NANOTECH SECURITY
Portable health check apparatus and expiration analysis service method using the same
InactiveUS20060058697A1Easy authenticationNot burdenData processing applicationsPerson identificationHydrogenInformation analysis
A portable health check apparatus incorporating a highly sensitive and compact expiration analysis sensor and an expiration analysis service offered to a specified user at a specified time. Hydrogen is detected using tungsten oxide produced through metalorganic chemical vapor deposition process. The apparatus has a unit for performing personal authentication by using, for example, a voiceprint of a user. The apparatus is also arranged to call up a user at a predetermined time through a cellular phone. Further, a center server receives detection information of an expiration component via a communication circuit, analyzes or statistically processes the detection information, collates a result of the analysis or statistic process with advice information stored in a database and transmits advice information based on a result of the collation from the server to the cellular phone of the user.
Owner:HITACHI LTD
System and method for authentication in WLAN environment
InactiveUS20100313241A1Easy authenticationEasily performing authenticationDigital data processing detailsAssess restrictionAuthentication systemLocal area network
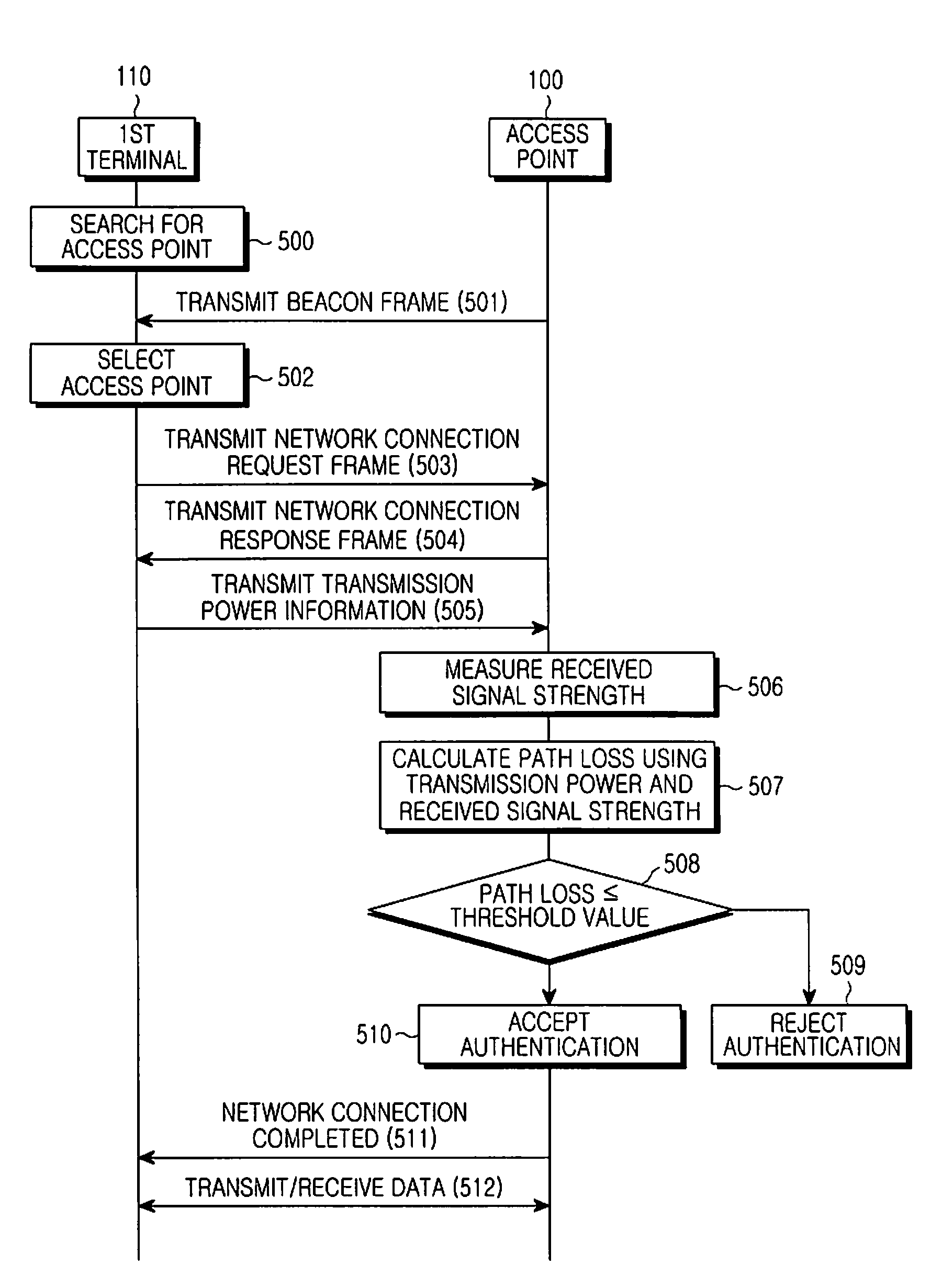
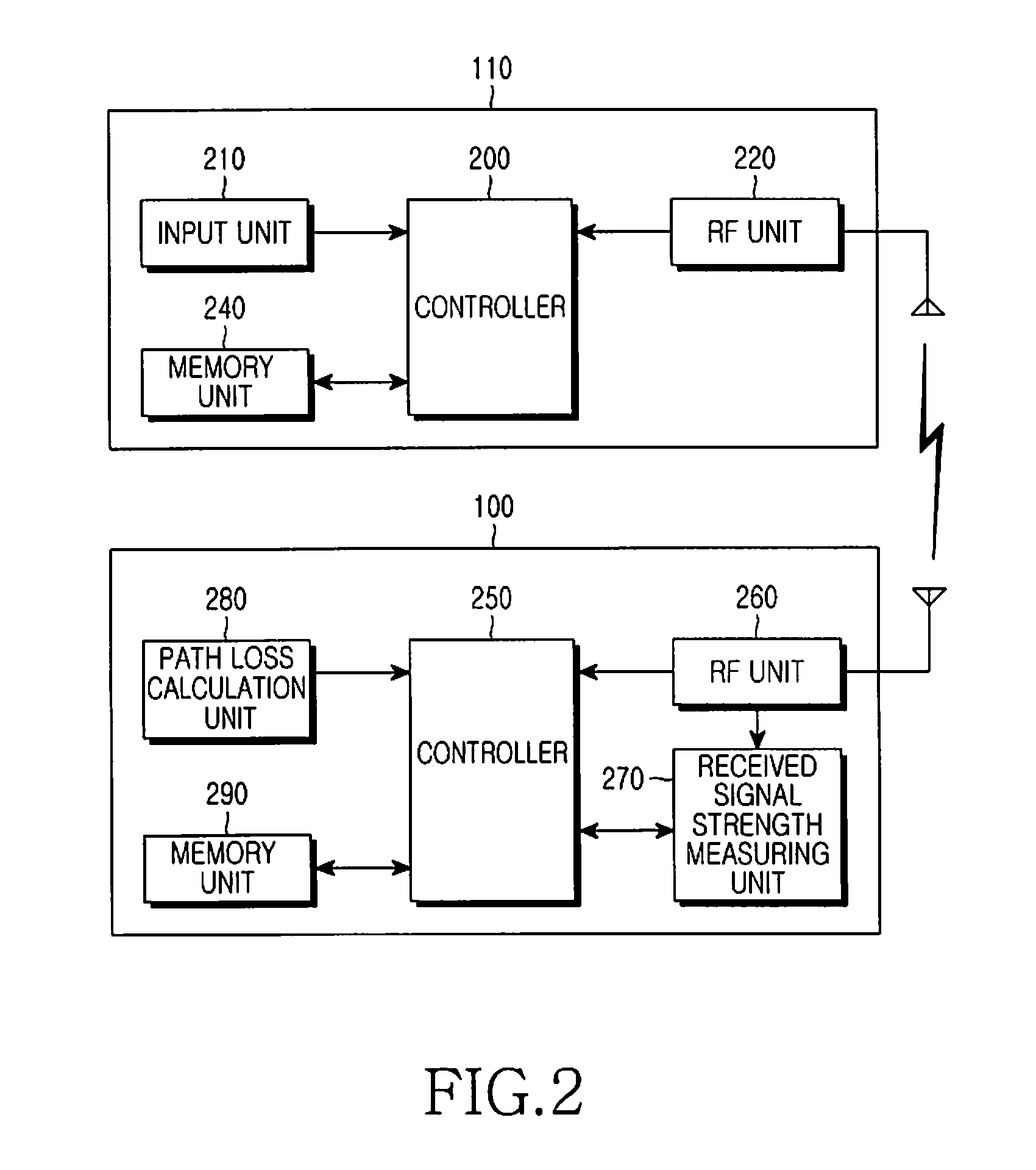
An authentication system and method in a wireless LAN (WLAN) environment. A terminal transmits an access authentication request to an access point of a WLAN which the terminal desires to access, and transmits its own transmission power information to the access point when receiving a response to the access authentication request from the access point, and the access point measures received signal strength, calculates a path loss value through the use of the received transmission power and the measured received signal strength, and performs access authentication of the terminal according to the calculated path loss value, so that a new terminal can easily access the WLAN where security has been set up.
Owner:SAMSUNG ELECTRONICS CO LTD
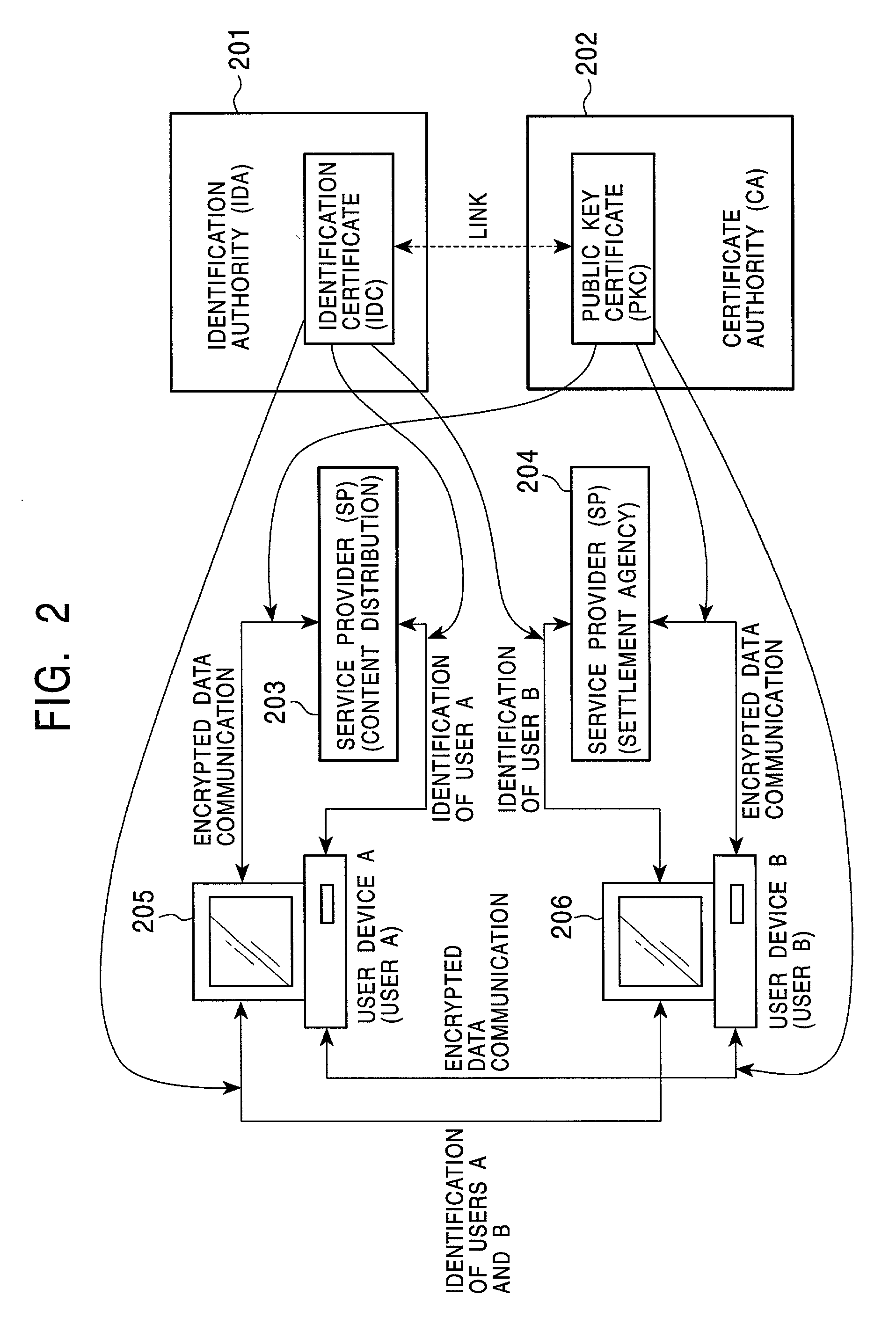
Public key certificate using system, public key certificate using method, information processing apparatus, and program providing medium
InactiveUS7100044B2Improve reliabilityEasy to useKey distribution for secure communicationDigital data processing detailsInformation processingPublic key certificate
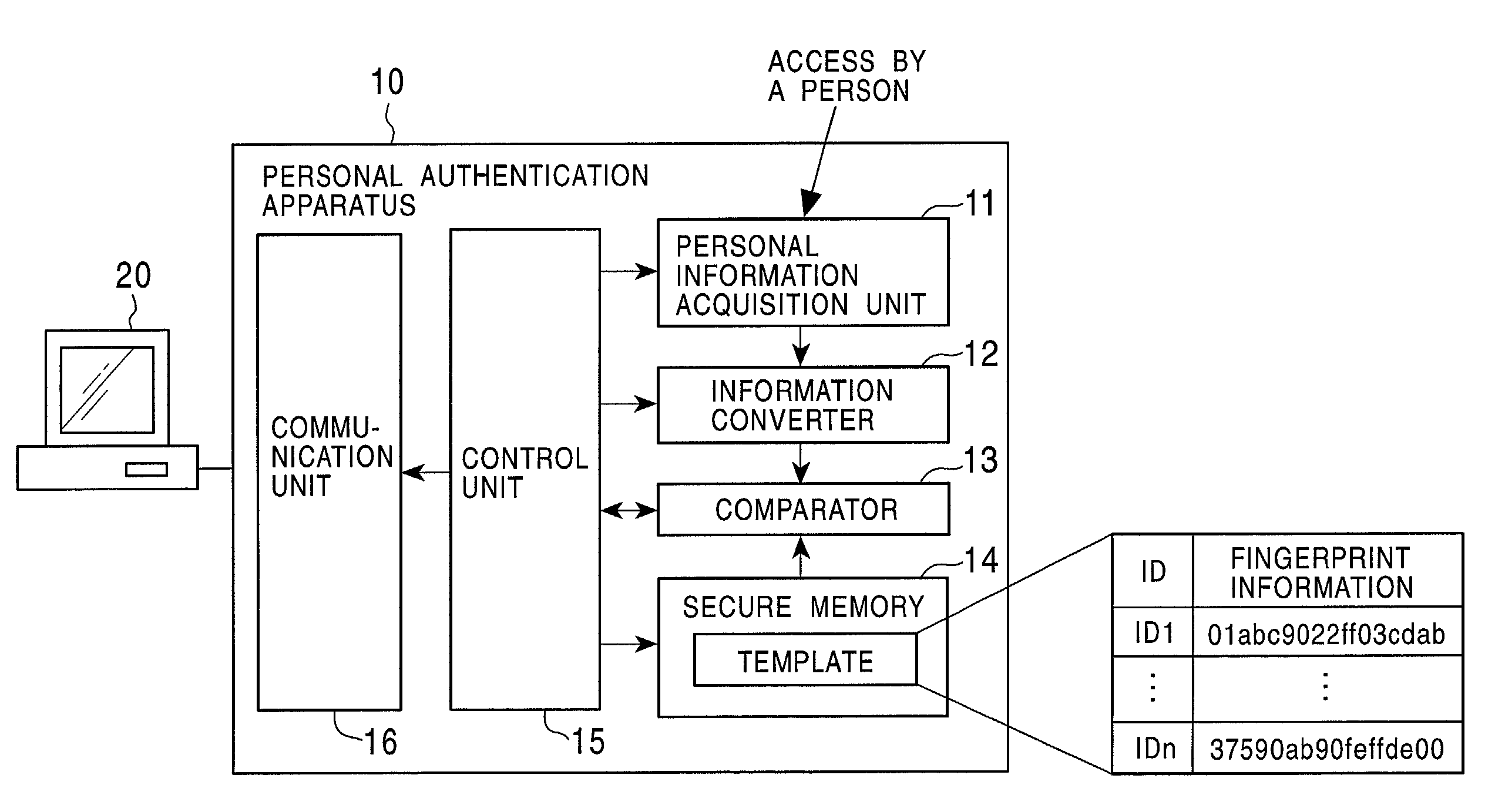
In a public key certificate using system, a template which serves as person identification data of a person requesting a public key certificate is obtained from a person identification certificate of the person, a person authentication is executed by comparing sampling information of the person against the template, and a public key certificate for the person is issued by a certificate authority on condition that the person authentication is established, thus reducing the load on the certificate authority for person authentication. The public key certificate issued to the user is deleted upon completion of a processing session involving use of the public key certificate, restricting the use of the public key certificate to the particular processing session.
Owner:SONY CORP
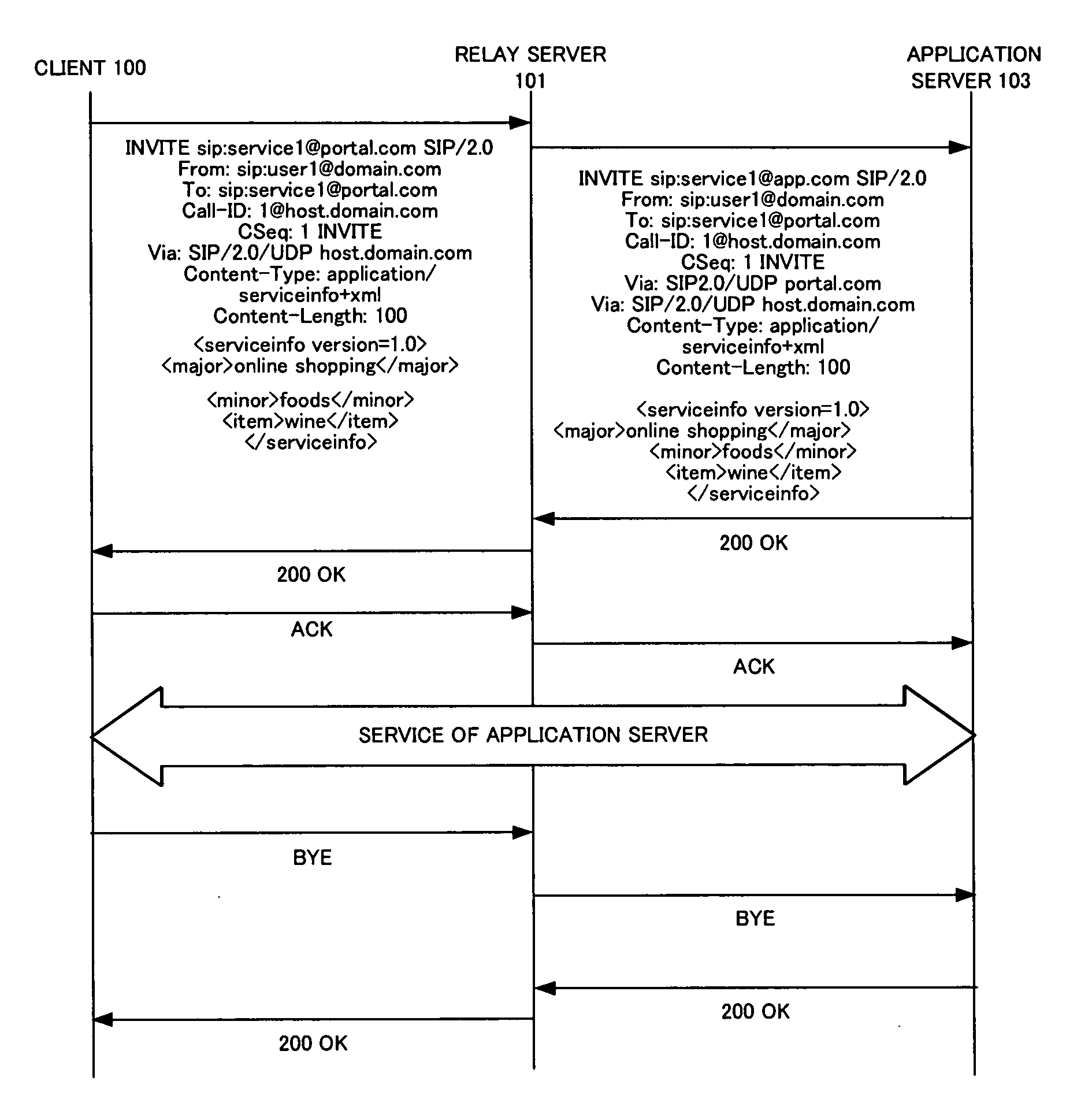
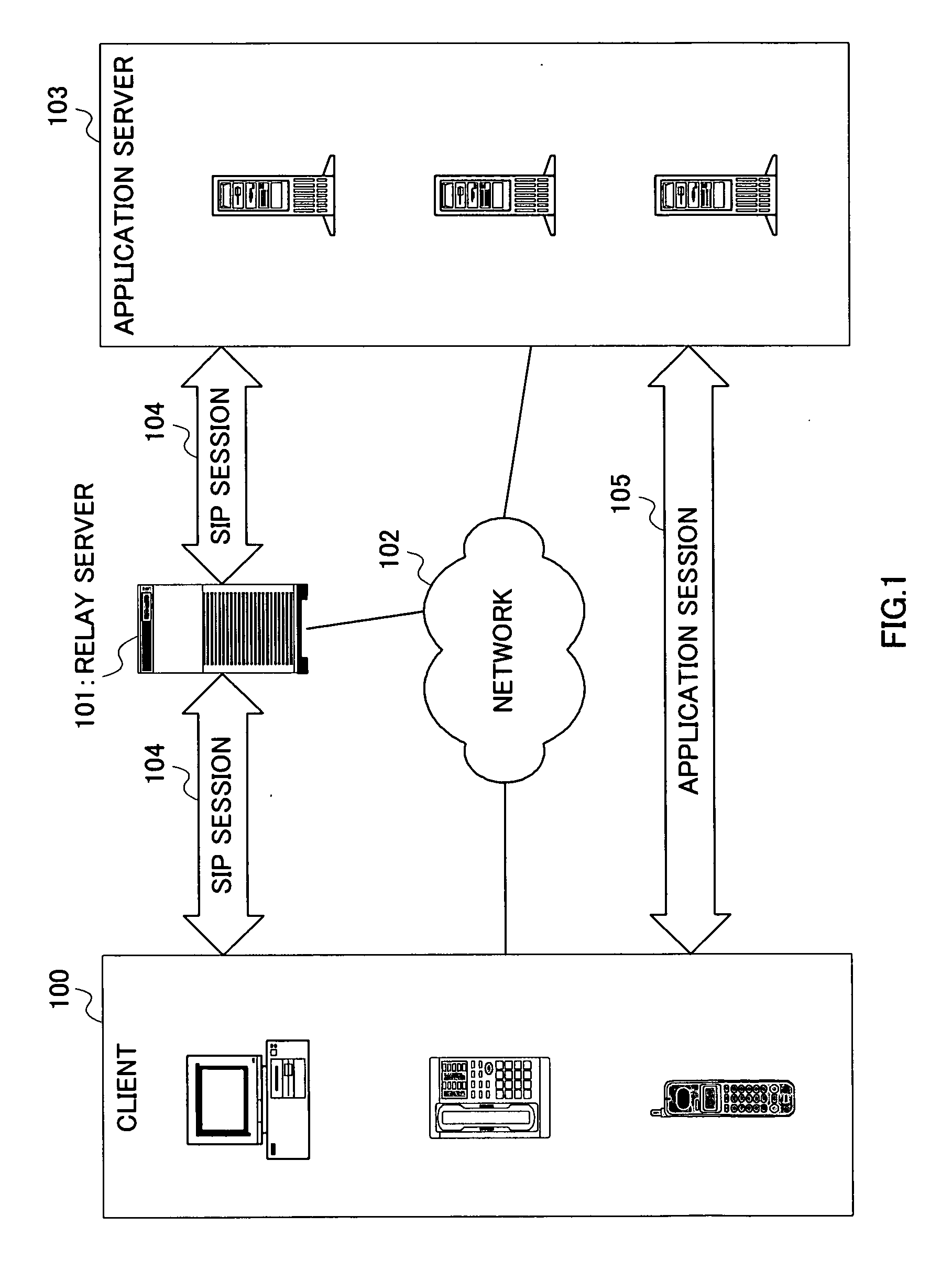
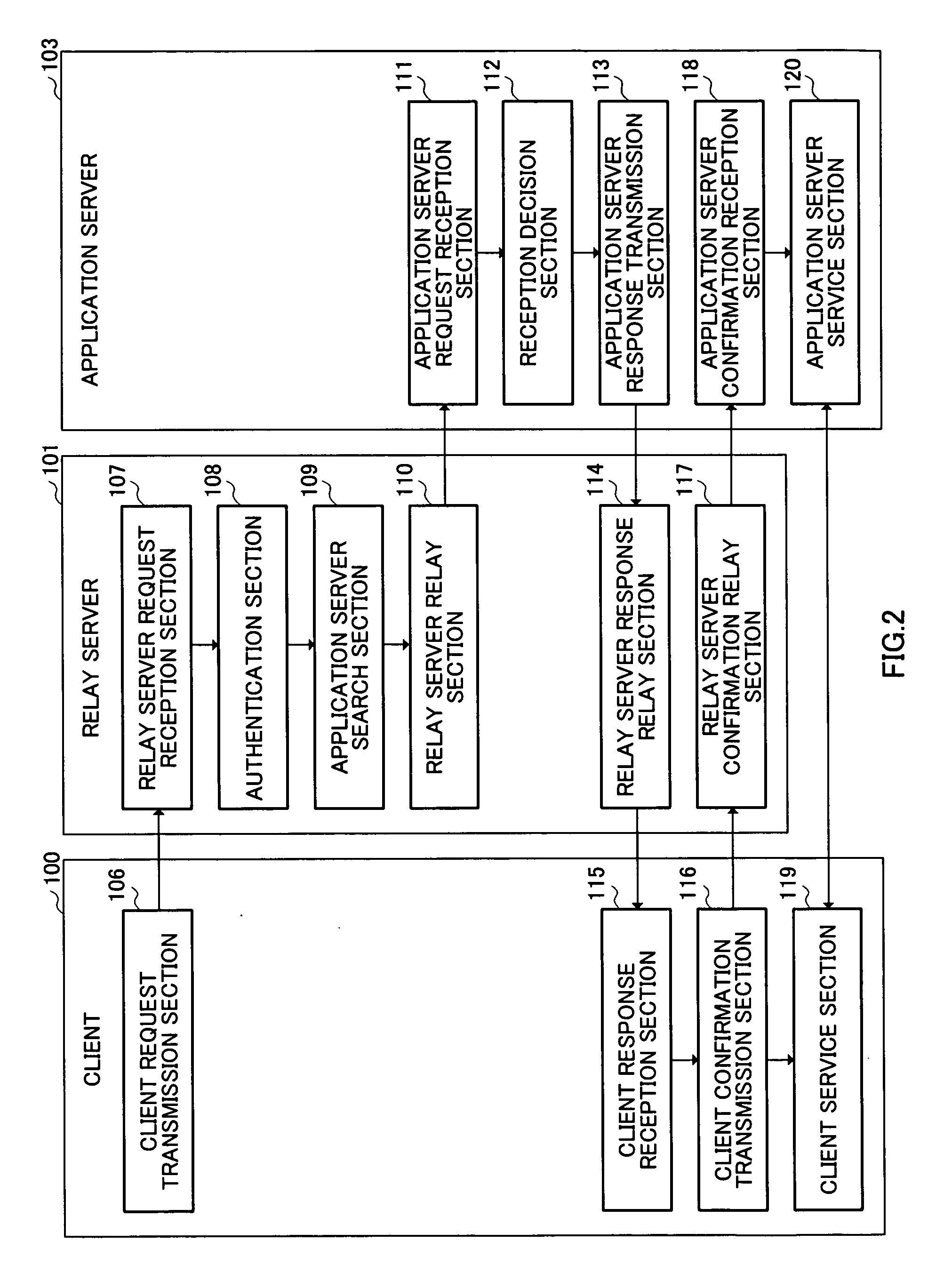
Relay server, relay server service management method, service providing system and program
InactiveUS20060095501A1Easy constructionImprove utilization efficiencyMultiple digital computer combinationsAutomatic exchangesPresent methodApplication server
An application service delivery method capable of making use of an existing SIP server function and easily carrying out authentication and billing. When a user who operates a client requests a service delivered by an application server, the present method establishes an SIP session between a client and application server using a standard SIP procedure via a relay server, and provides a direct service between the client and application server after establishment of the SIP session. The relay server carries out user authentication in the stage of establishment of the SIP session, which eliminates the necessity for the authentication function of the application server and makes it possible to easily construct the application server.
Owner:PANASONIC CORP
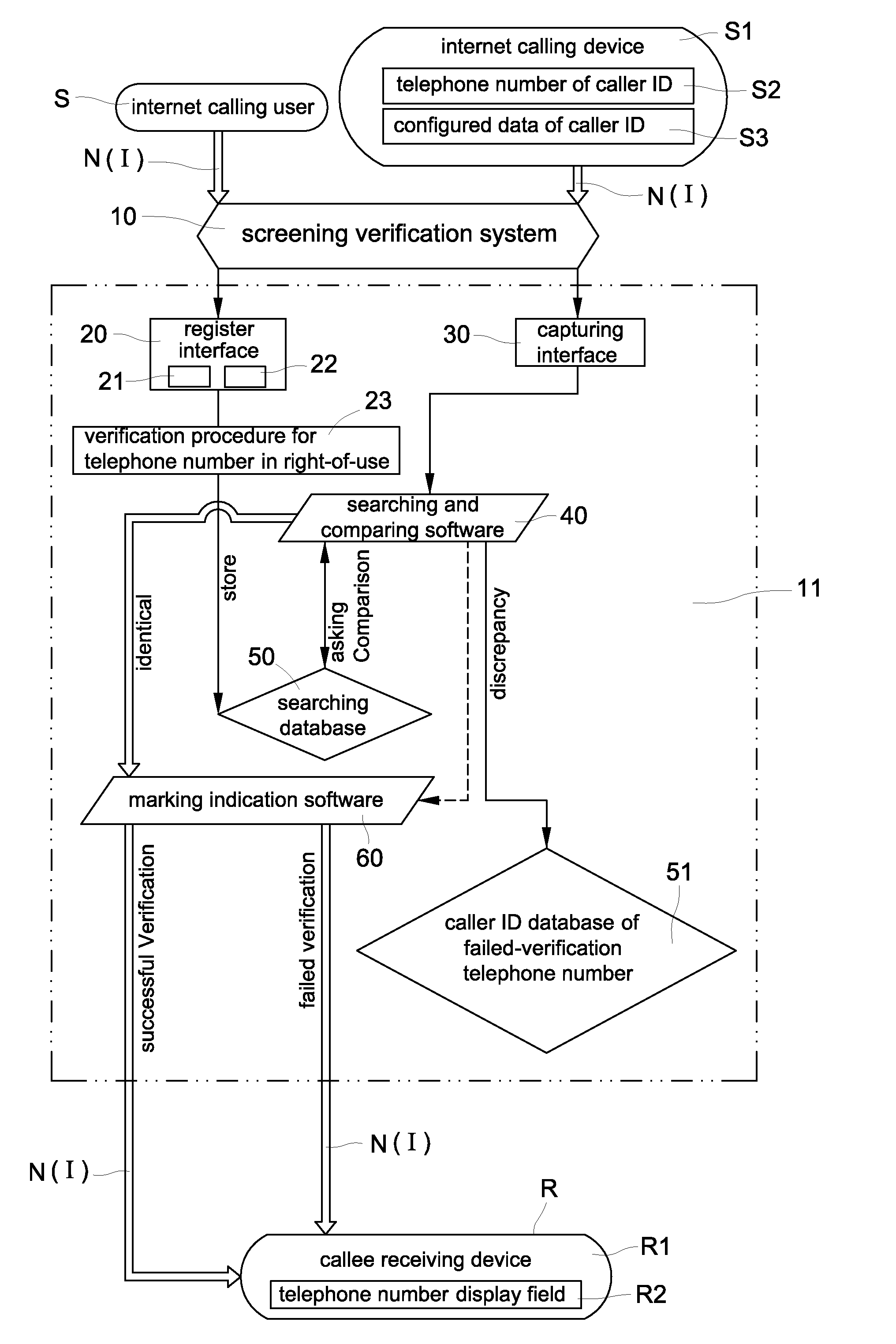
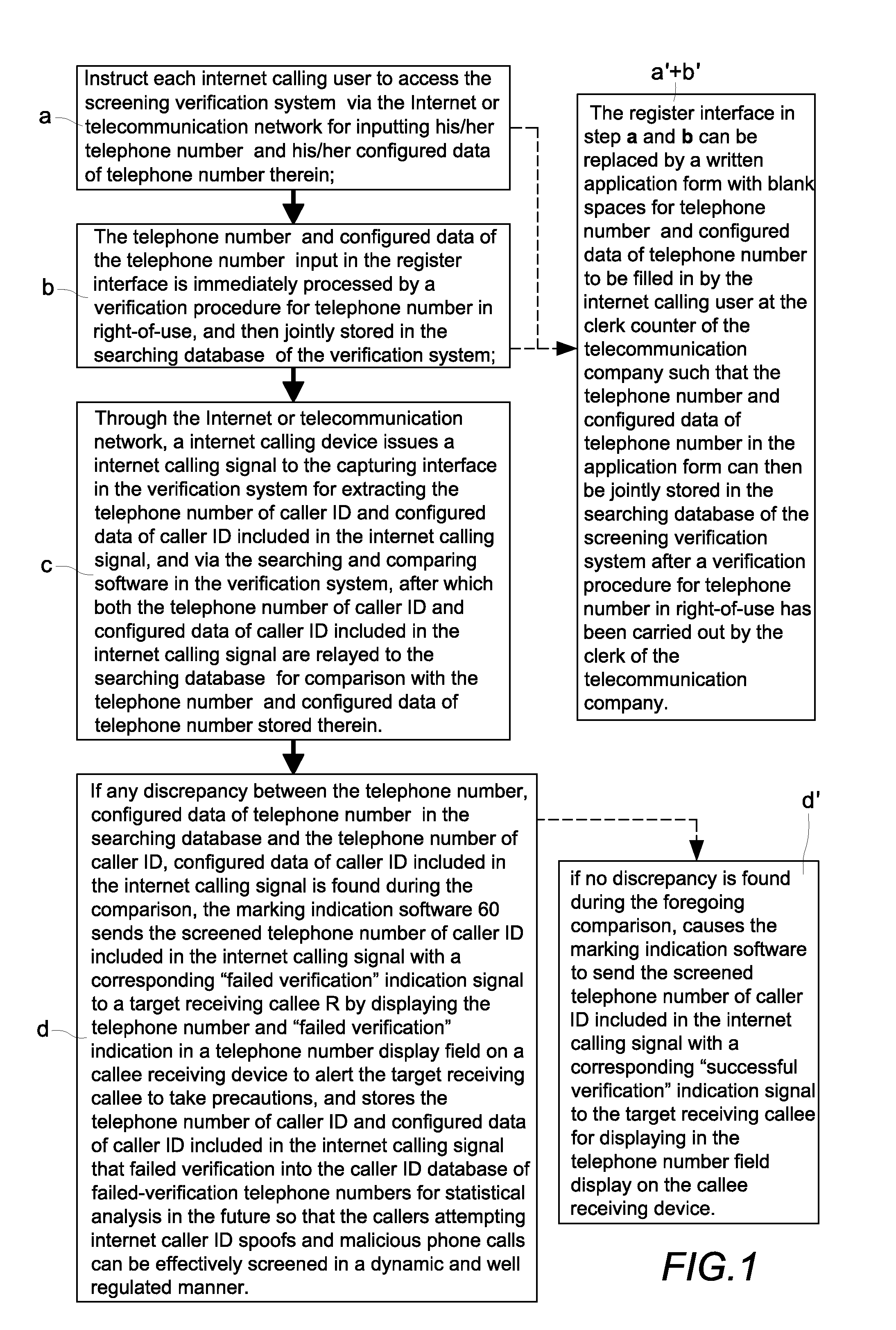
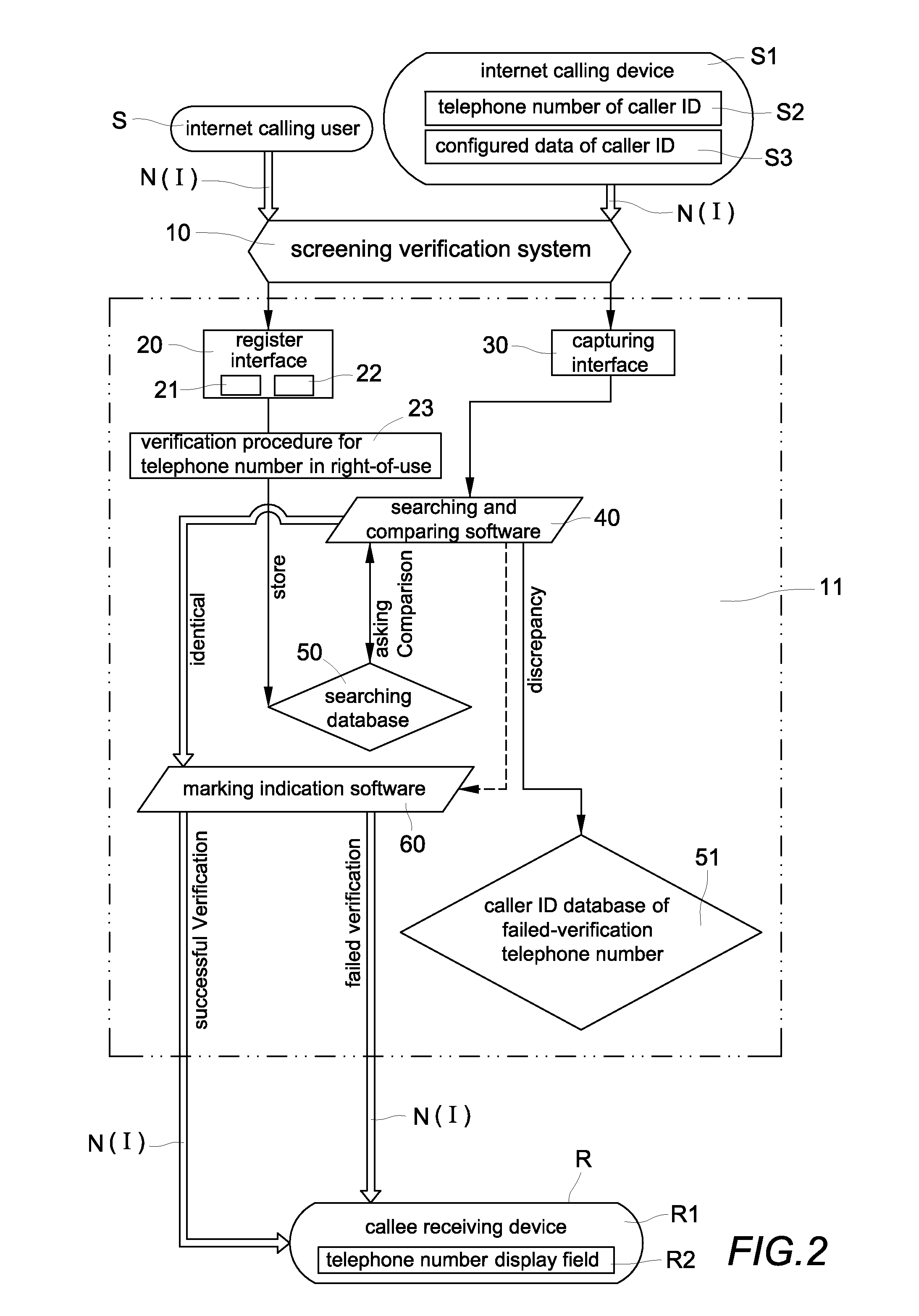
Verification method and system for screening internet caller id spoofs and malicious phone calls
InactiveUS20120287823A1Easy authenticationPrevent caller ID spoofing fraudSpecial service provision for substationMultiplex system selection arrangementsValidation methodsInternet users
A verification system for screening internet caller ID spoofs and malicious phone calls includes a server, a register interface, a capturing interface, a searching and comparing software, a searching database, a caller ID database of failed-verification telephone numbers, and marking indication software. The searching database stores a telephone number of caller ID and configured data of telephone number of every internet user. The searching and comparing software compares the telephone number of caller ID and configured data of caller ID included in the internet calling signal with a corresponding telephone number and configured data of the telephone number stored in the searching database. The marking indication software sends a verified result of the comparison with a corresponding indication signal to a target receiving callee so that the callee can easily take suitable measures to prevent becoming the victim of telephone fraud.
Owner:LIN CHUNG YU
Public/Private Key Biometric Authentication System
ActiveUS20170141920A1Meet the blocking requirementsAvoid the needMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesSecure communicationBiometric data
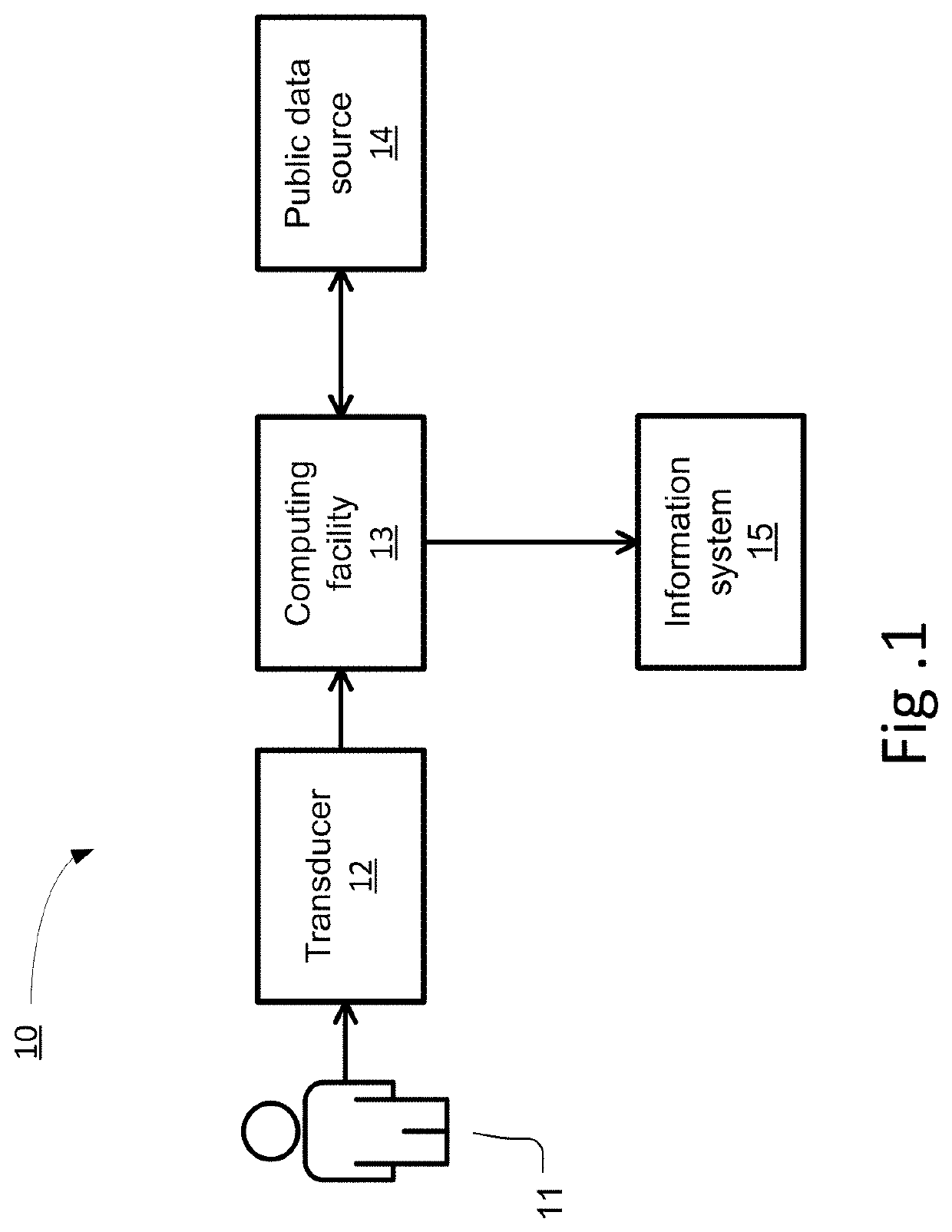
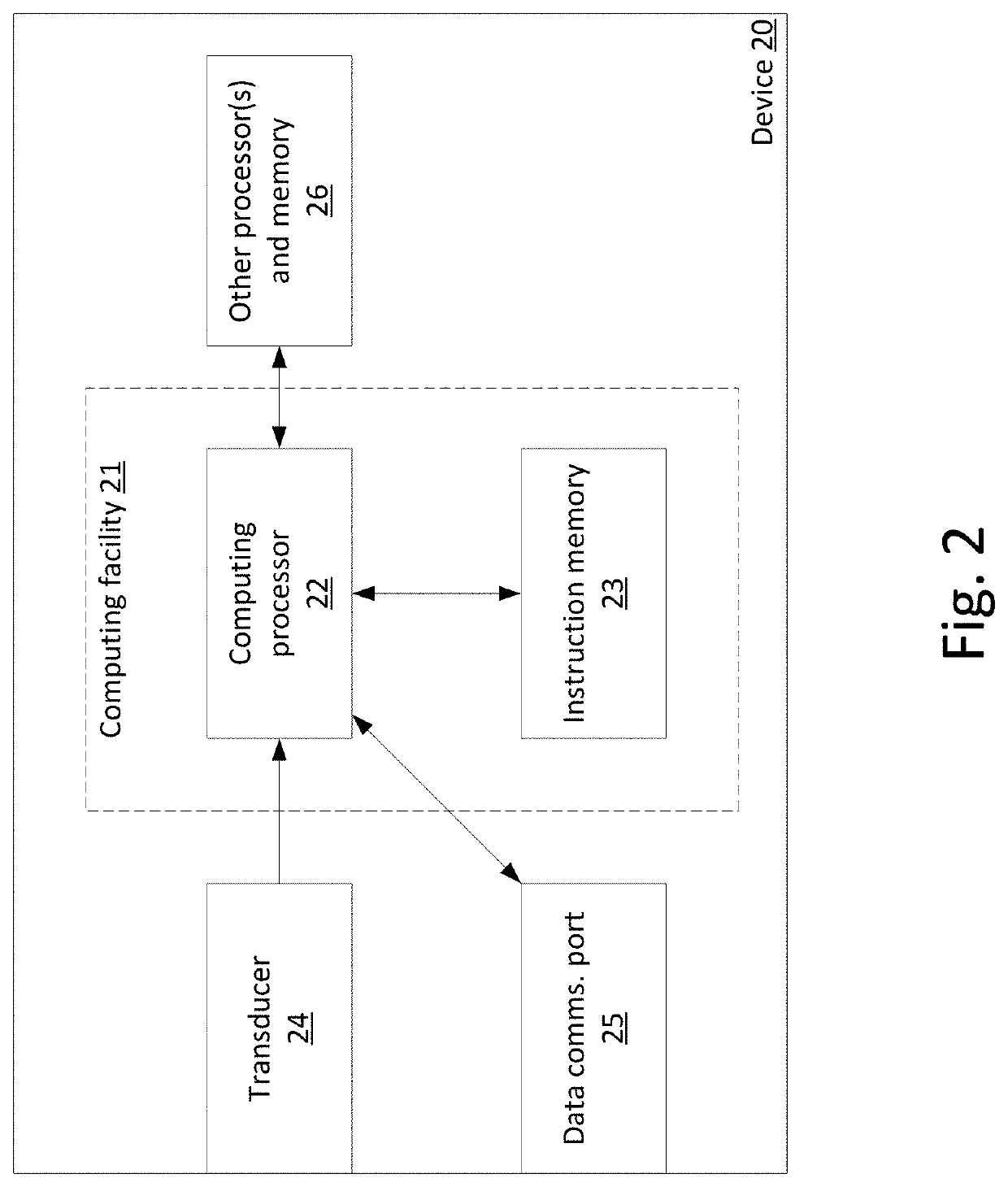
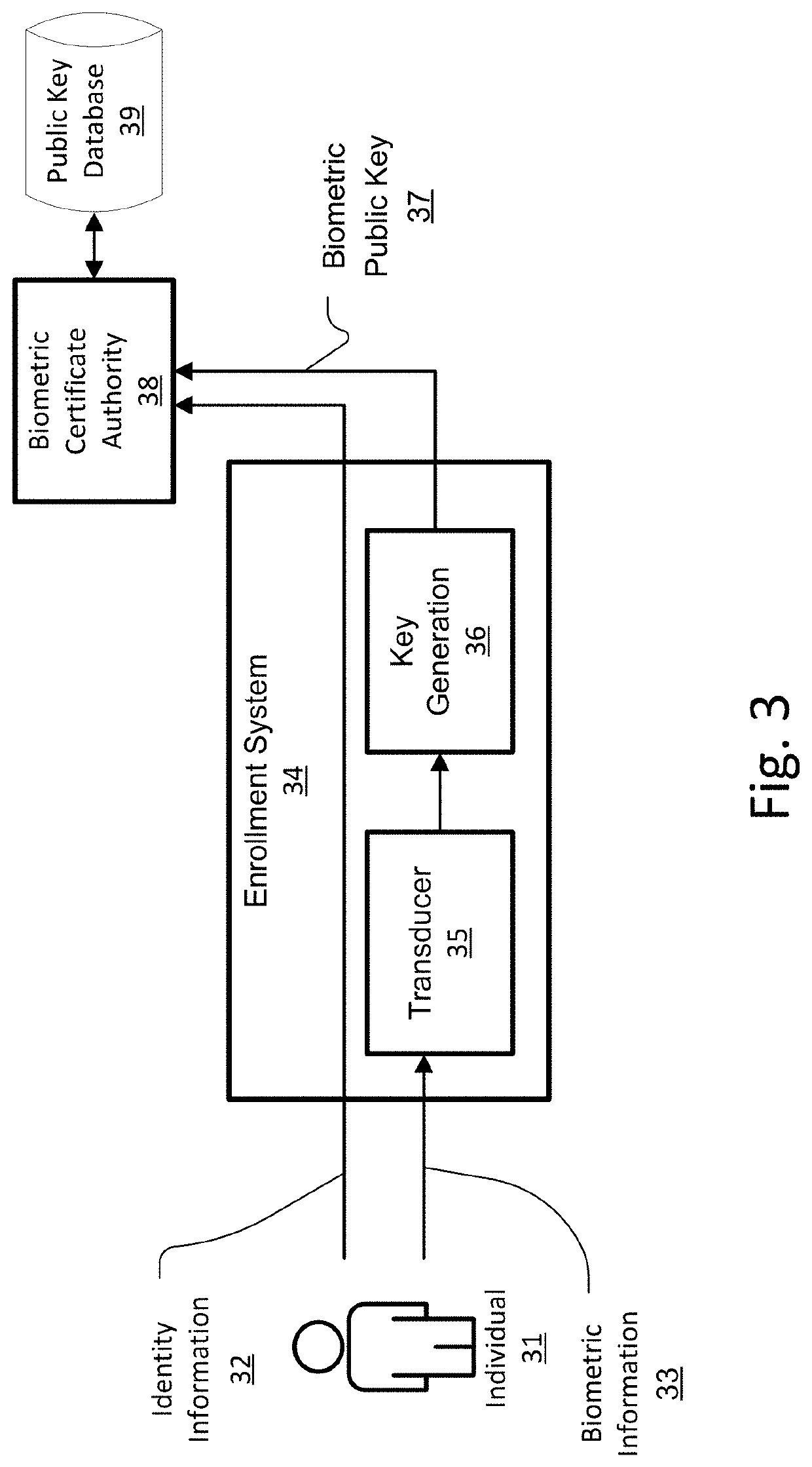
A device, method, and computer readable storage medium generate a biometric public key for an individual based on both the individual's biometric data and a secret, in a manner that verifiably characterizes both while tending to prevent recovery of either by anyone other than the individual. The biometric public key may be later used to authenticate a subject purporting to be the individual, using a computing facility that need not rely on a hardware root of trust. Such biometric public keys may be distributed without compromising the individual's biometric data, and may be used to provide authentication in addition to, or in lieu of, passwords or cryptographic tokens. Various use cases are disclosed, including: enrollment, authentication, establishing and using a secure communications channel, and cryptographically signing a message.
Owner:BADGE INC
Method and apparatus for managing and displaying contact authentication in a peer-to-peer collaboration system
InactiveUS7624421B2Easy authenticationDigital data processing detailsUser identity/authority verificationEngineeringSecurity policy
Owner:MICROSOFT TECH LICENSING LLC
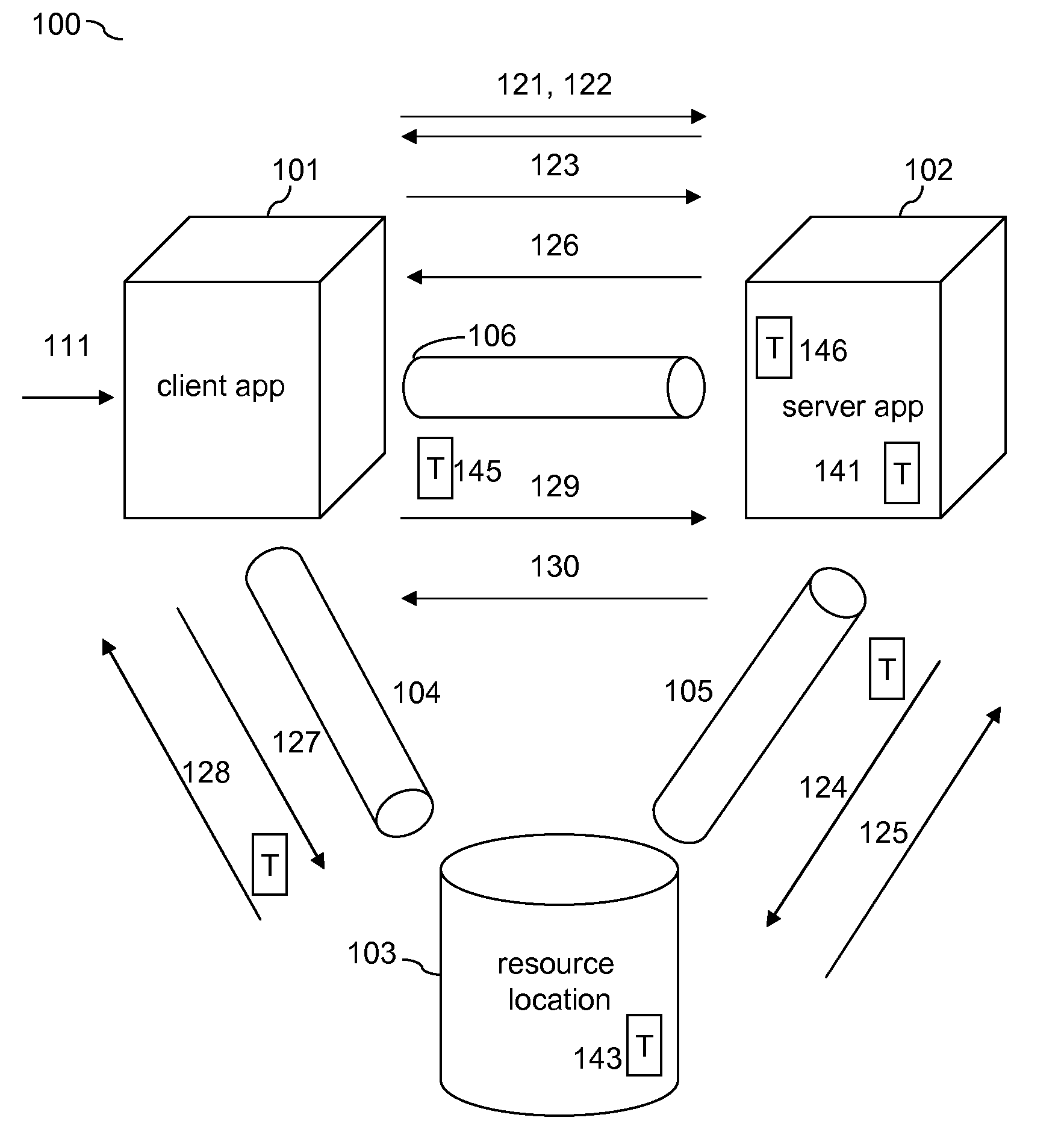
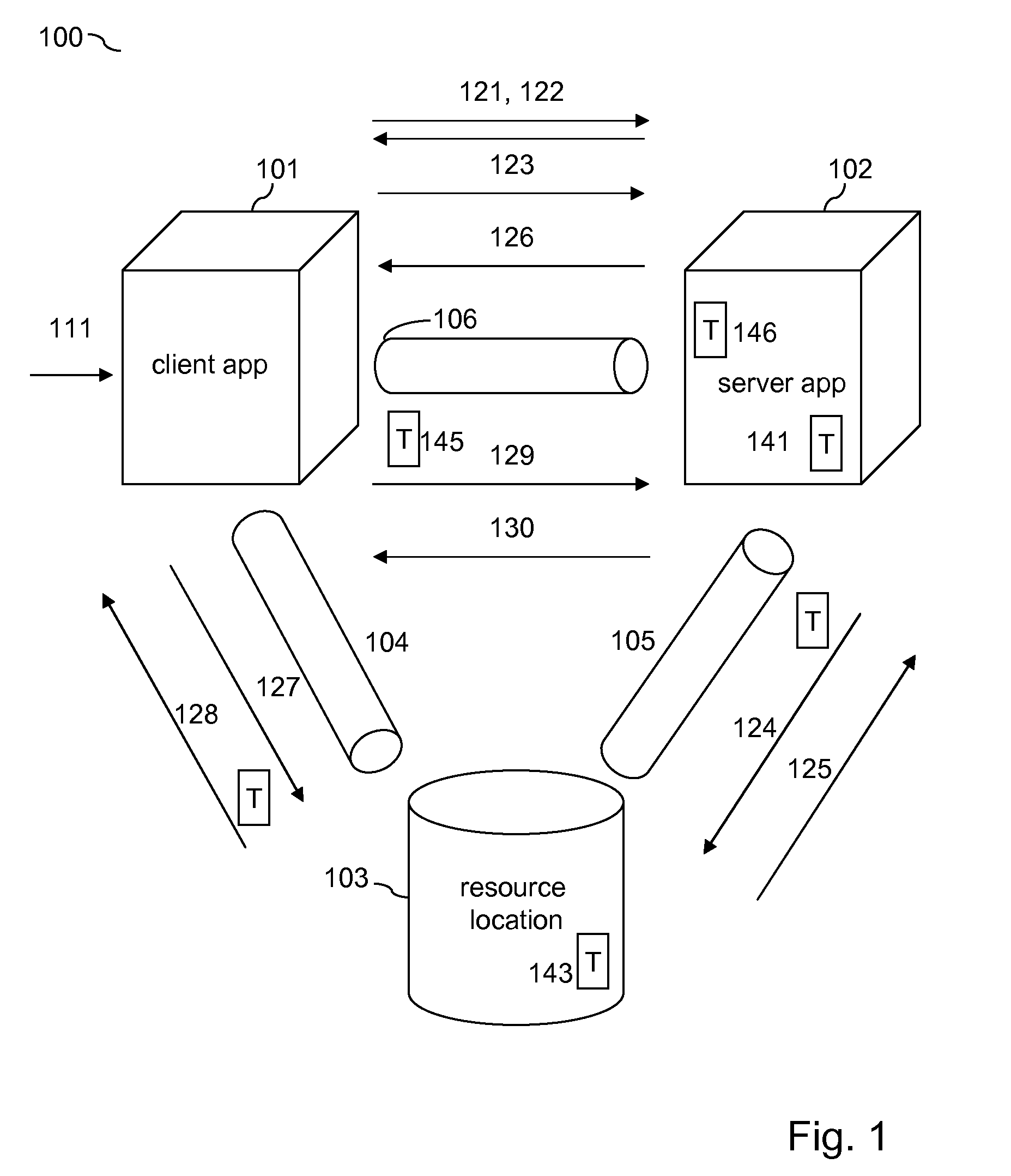
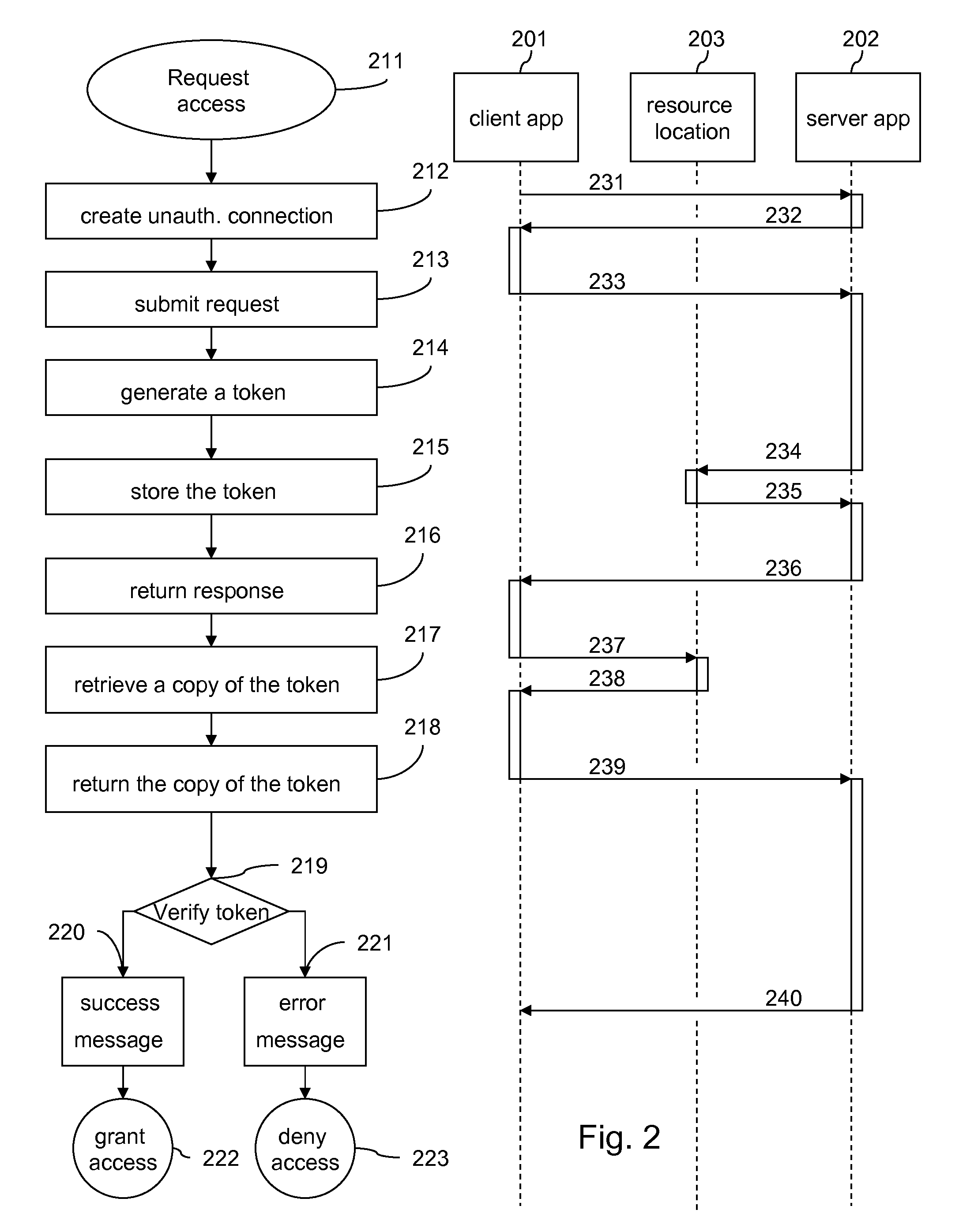
Token-Based Client To Server Authentication Of A Secondary Communication Channel By Way Of Primary Authenticated Communication Channels
InactiveUS20100138905A1Easy authenticationDigital data processing detailsUser identity/authority verificationClient-sideApplication software
The disclosure relates to authenticating a secondary communication channel between a client application and a server application when an authenticated primary communication channel has already been established between the client application and a resource application, on which the server application can store a generated authentication token that only privileged users including the client application user can read-access and send back to the server application by way of the secondary communication channel.
Owner:IBM CORP
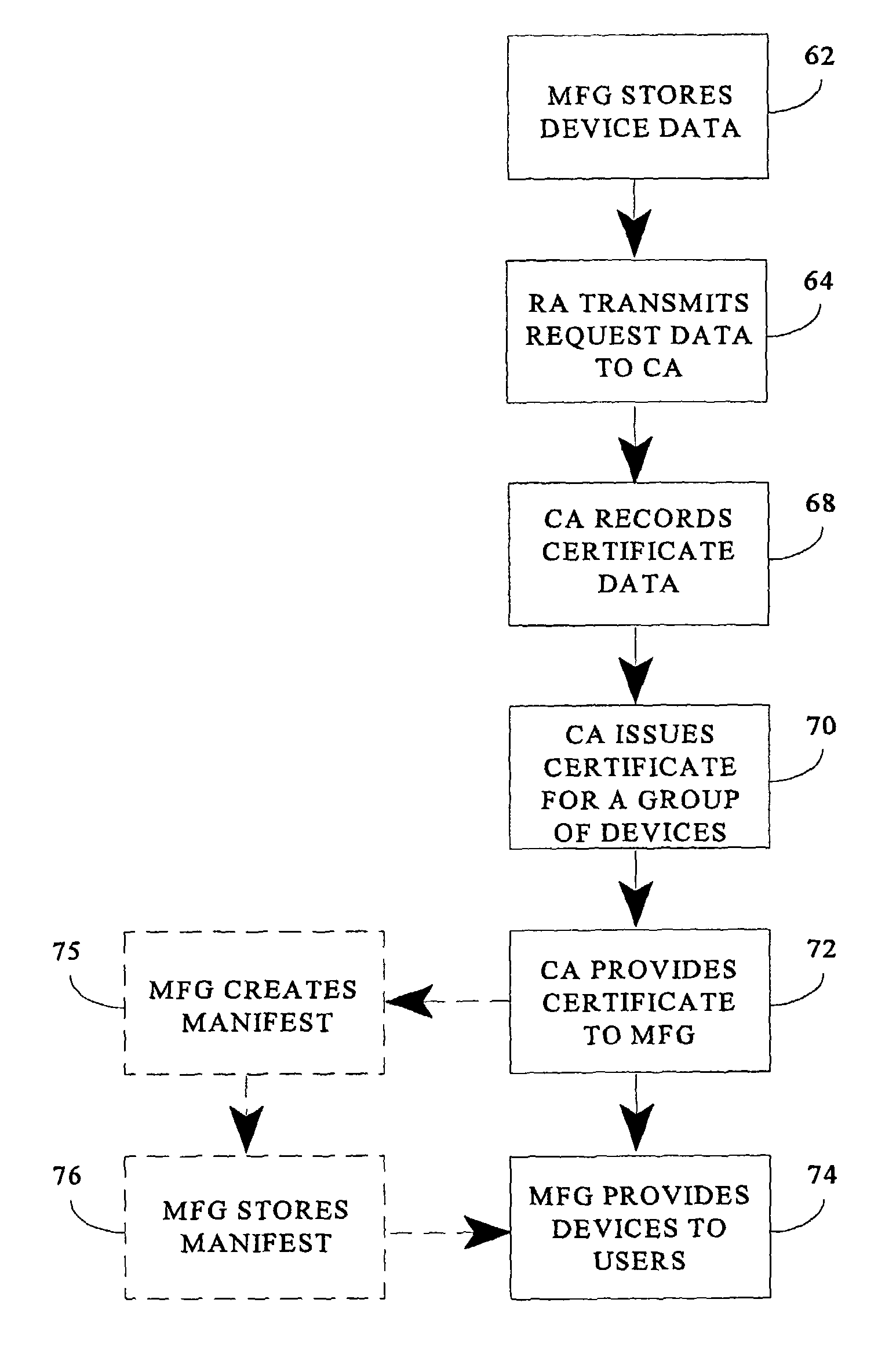
System and method for creating a trusted network capable of facilitating secure open network transactions using batch credentials
ActiveUS7925878B2Low costEasy authenticationUser identity/authority verificationBroadcast transmission systemsBiological activationComputer science
A system and method for creating a trusted network capable of facilitating secure transactions via an open network using batch credentials, such as batch PKI certificates, is presented. A certificate is bound to a group, or batch, or devices. This certificate is referenced by an activation authority upon processing a request for service by a device. Information regarding the device batch certificate is maintained in a permanent, or escrow, database. A user identity is bound to a device, as a device key is used to sign a user key created on the device in the presence of the user, and a copy of the device key is later used to decrypt the signed user key upon its transmission and receipt.
Owner:THALES DIS FRANCE SA
System and Method for Securing Personal Information Via Biometric Public Key
ActiveUS20190356491A1Avoid the needEasy authenticationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSecure communicationBiometric data
A device, method, and computer readable storage medium generate a biometric public key for an individual based on both the individual's biometric data and a secret, in a manner that verifiably characterizes both while tending to prevent recovery of either by anyone other than the individual. The biometric public key may be later used to authenticate a subject purporting to be the individual, using a computing facility that need not rely on a hardware root of trust. Such biometric public keys may be distributed without compromising the individual's biometric data, and may be used to provide authentication in addition to, or in lieu of, passwords or cryptographic tokens. Various use cases are disclosed, including: enrollment, authentication, establishing and using a secure communications channel, and cryptographically signing a message.
Owner:BADGE INC
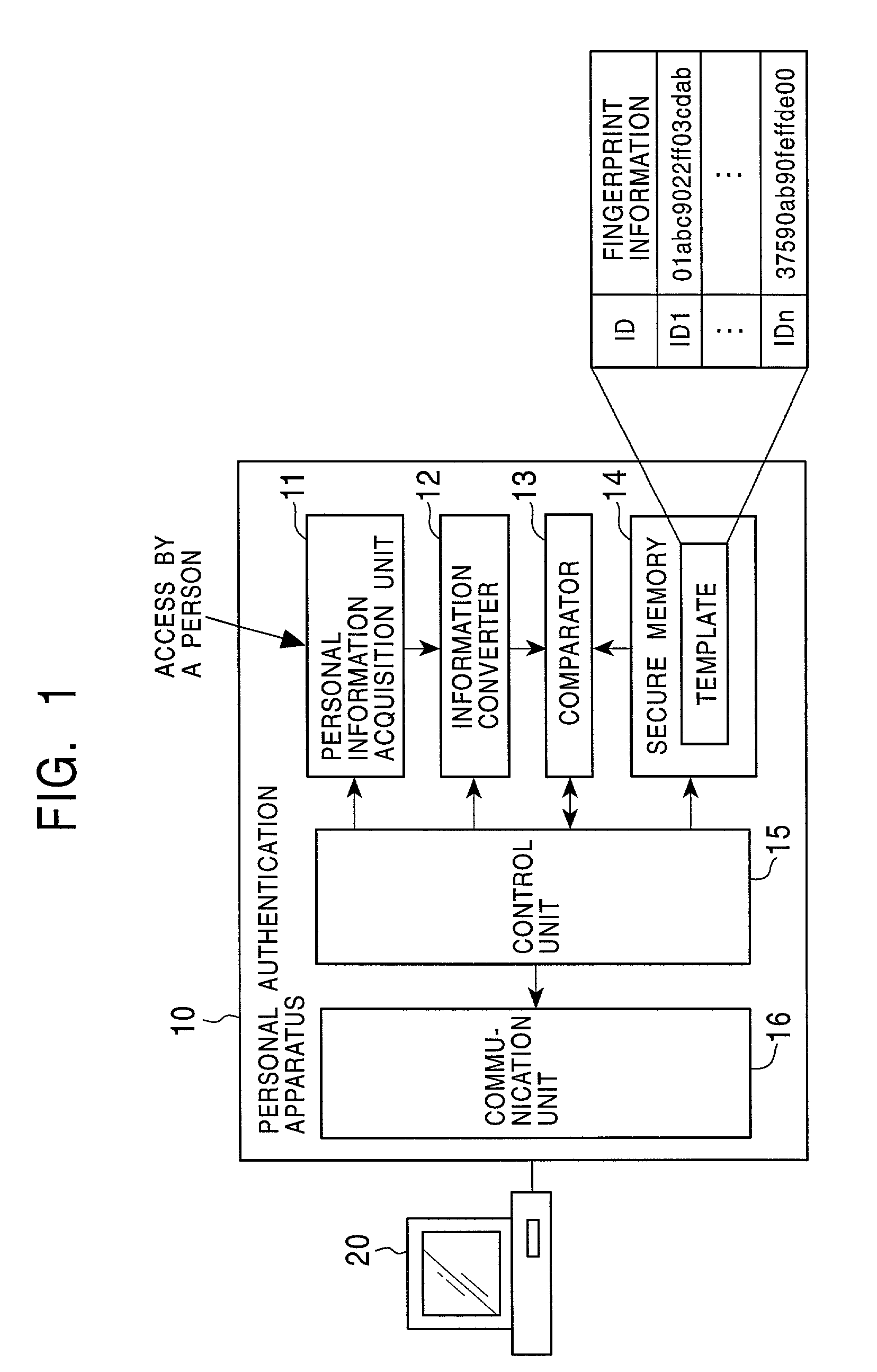
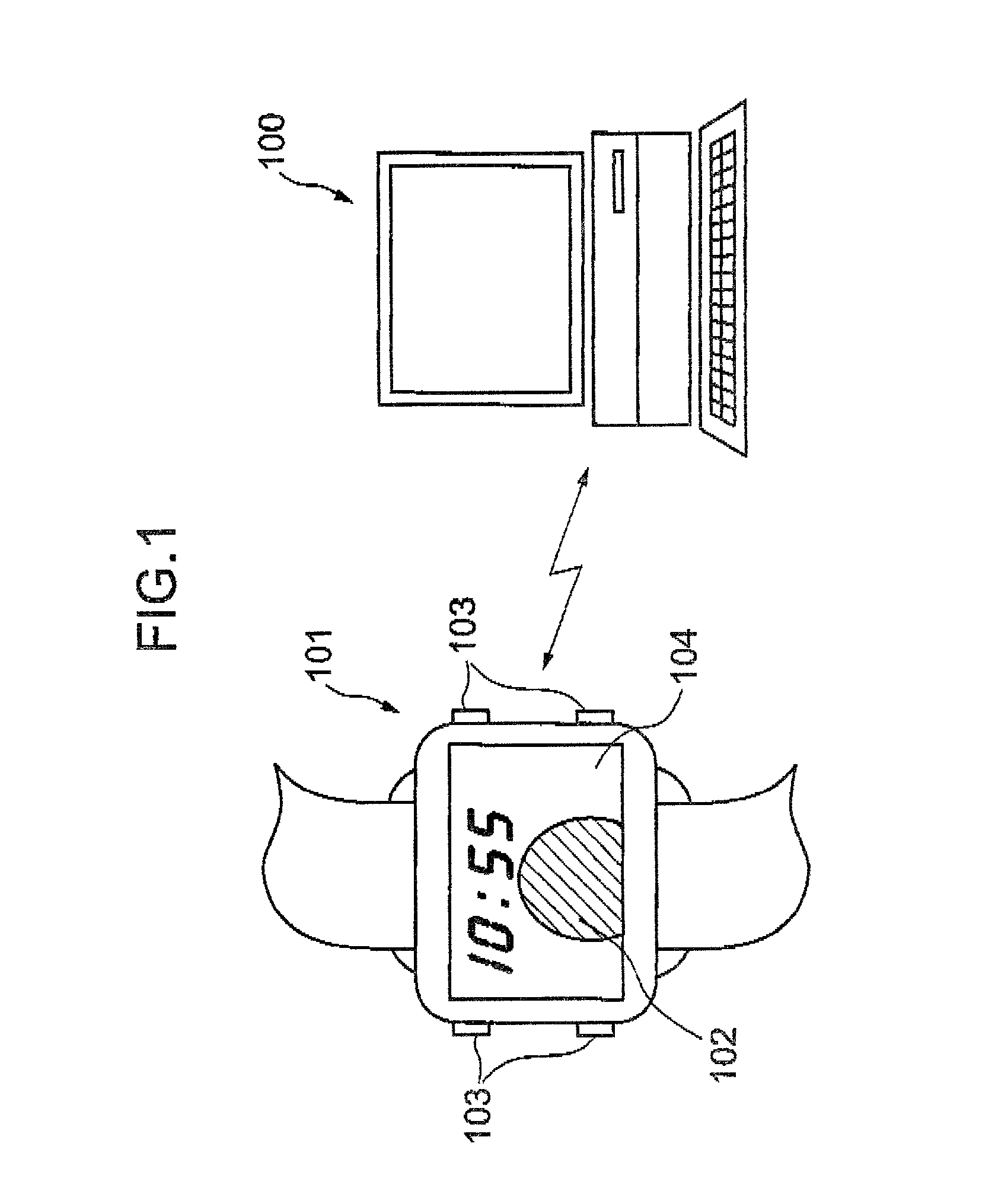
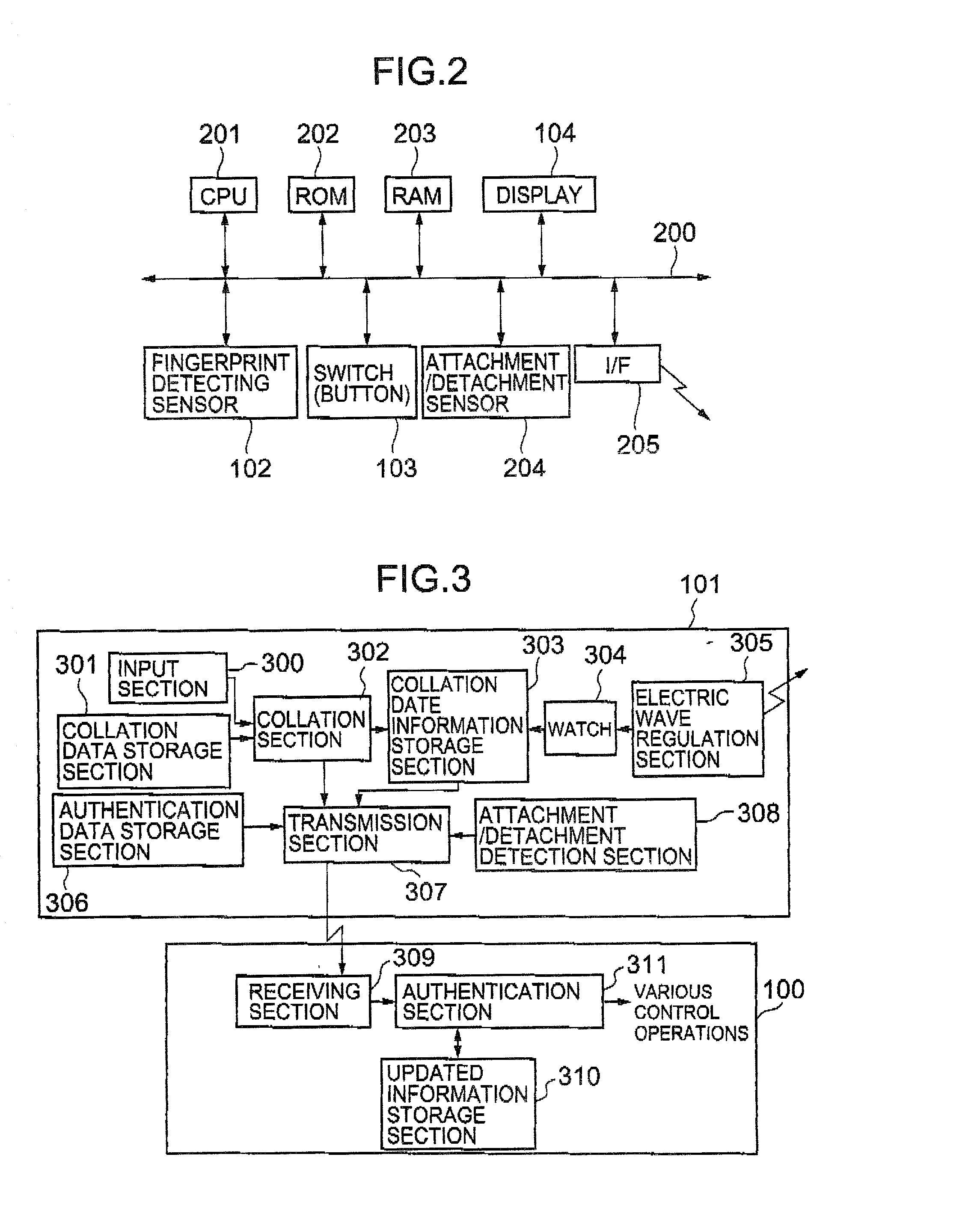
Information processor, personal authentication method, and computer-readable recording medium on which a program for executing the method by computer is recorded
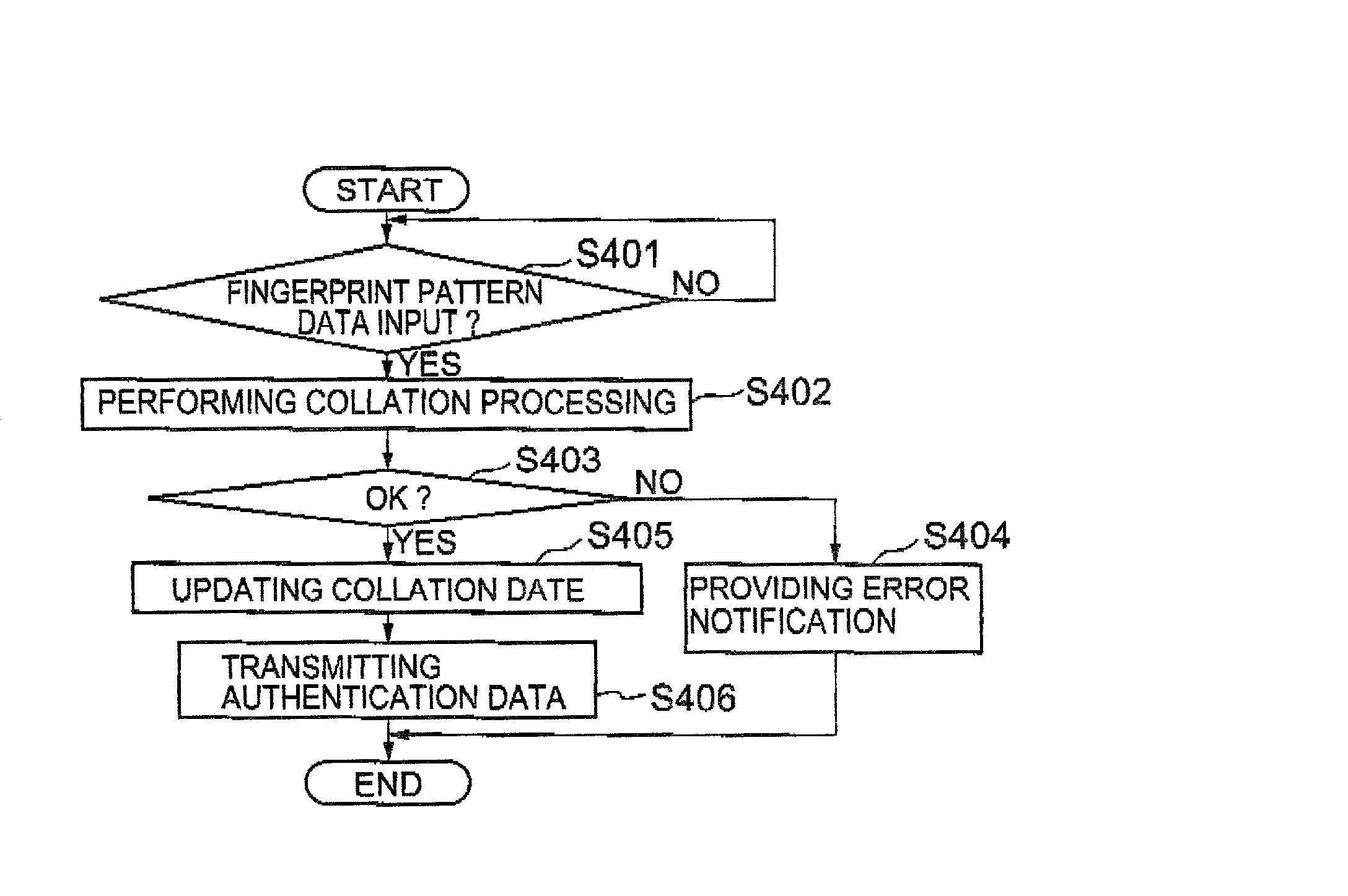
InactiveUS20020129268A1Easy authenticationAvoid dataImage analysisDigital data processing detailsComputer hardwareBiological body
An information processor and a personal authentication method arranged to easily and securely perform authentication using living-body information on a person whose identification is to be authenticated. The information processor has an input section for inputting living-body information (fingerprint pattern) representing a unique feature of a person whose identification is to be authenticated, a collation section for collating the input living-body information with living-body information registered in a collation data storage section in advance, and a transmission section for transmitting authentication data to an external unit on the basis of the result of the collation.
Owner:ITO TAKASHI +4
Tamper evident adhesive and identification document including same
InactiveUS20050242194A1Easy authenticationEasy to identifyOther printing matterMacromolecular adhesive additivesMedicineAdhesive
A composition is provided for adhering a first article to a second article, the composition comprising a thermally active low Tg polymeric resin; and a multifunctional crystalline polymer. The thermally active low Tg polymeric resin can, for example, comprise 50-99% of the composition. The multifunctional crystalline polymer can, for example, comprise 1-50% of the composition. In one embodiment, the multifunctional crystalline polymer comprises 5-20% by weight of the composition. In one embodiment, the multifunctional crystalline polymer has a low molecular weight.
Owner:L 1 SECURE CREDENTIALING
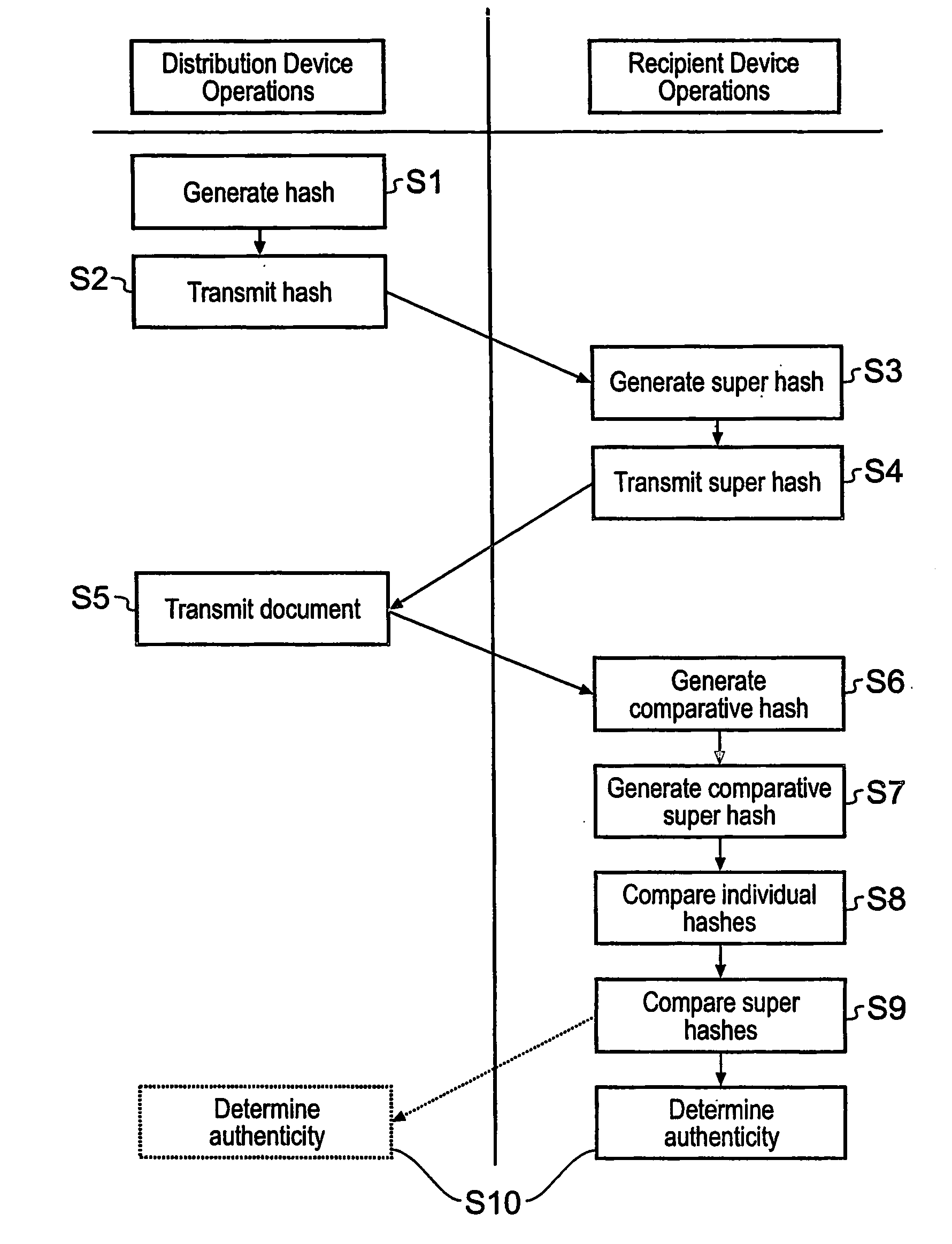
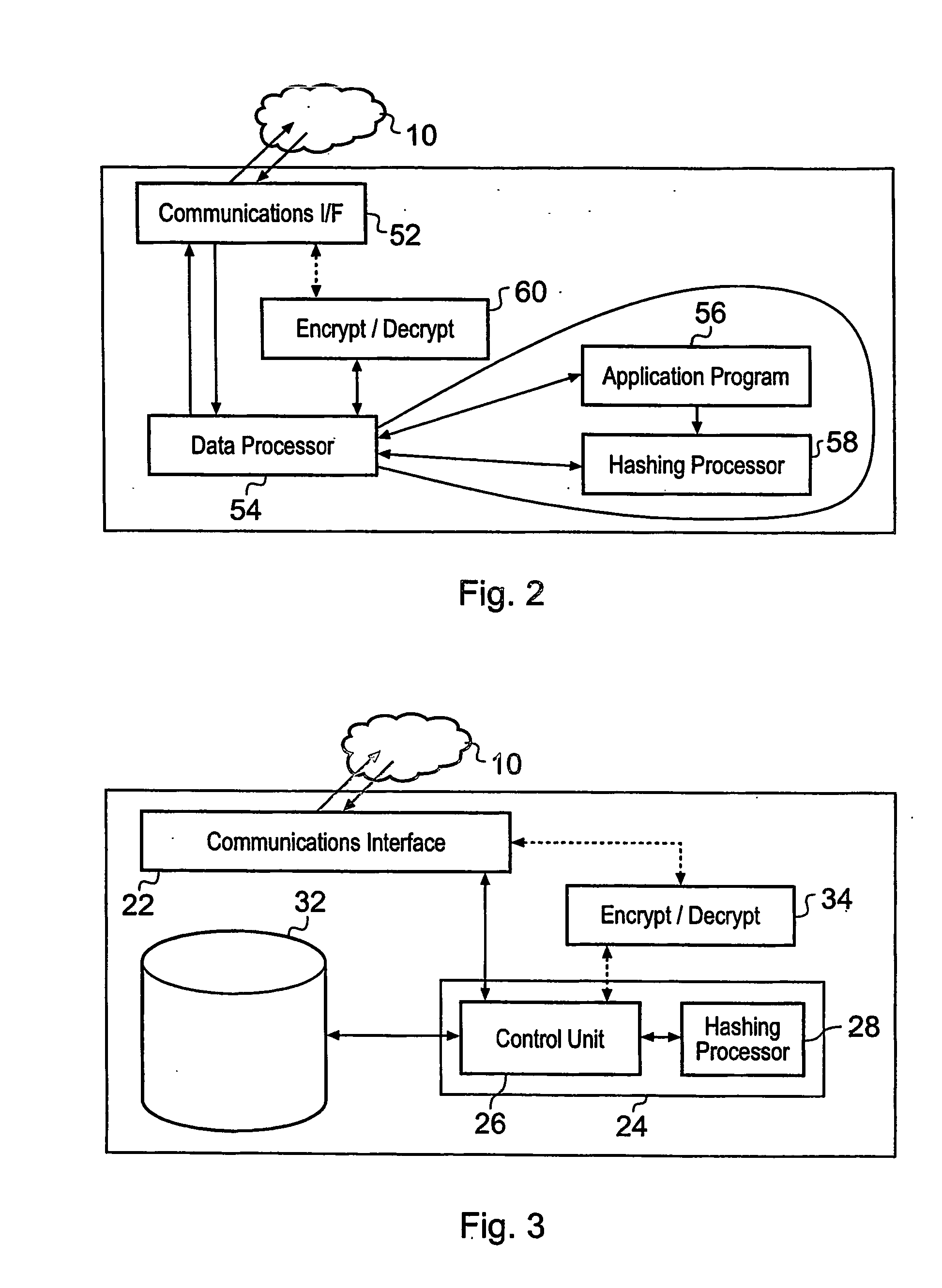
System and Method for Authenticating Documents
InactiveUS20080028439A1Easy authenticationDigital data processing detailsUser identity/authority verificationData processing systemData treatment
A data processing system for distributing and authenticating documents from a plurality of parties to a recipient data processing apparatus is disclosed. The system comprises a plurality of document distribution devices each configured to generate an original hash value from the content of a file containing a document to be distributed. A recipient data processing apparatus is configured to generate an original super hash value from the plurality of the original hash values, and to distribute the original super hash value to each of the document distribution devices. The system provides assurance that distributed documents have not been tampered with during communication, by an unscrupulous distributing party, or by an unscrupulous recipient by only submitting a hash value of the document to be distributed. The hash value provides for assurance at the eventual recipient of the document that no changes to the document have been made.
Owner:NEXTENDERS INDIA PVT
Electronic casino gaming system with improved play capacity, authentication and security
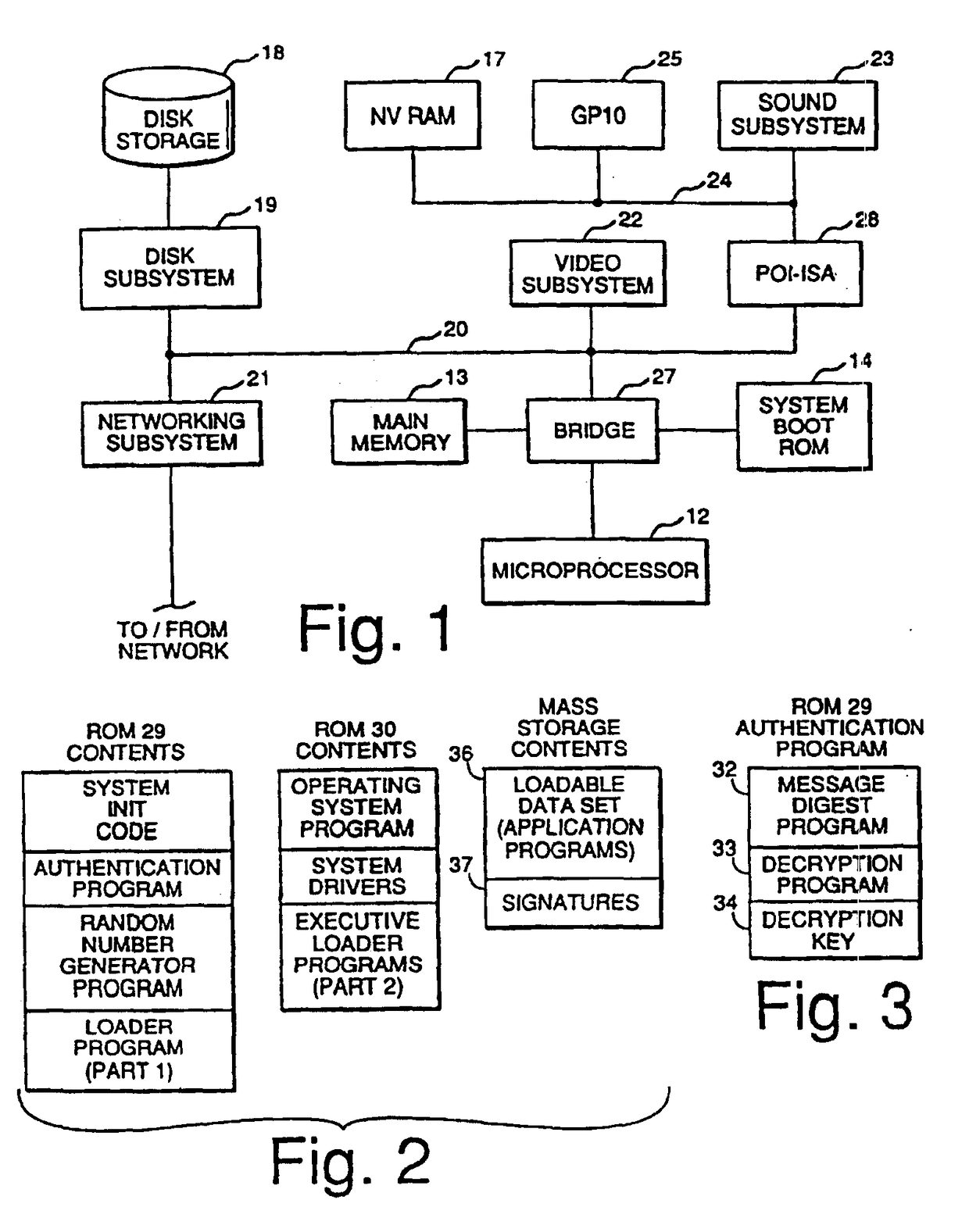
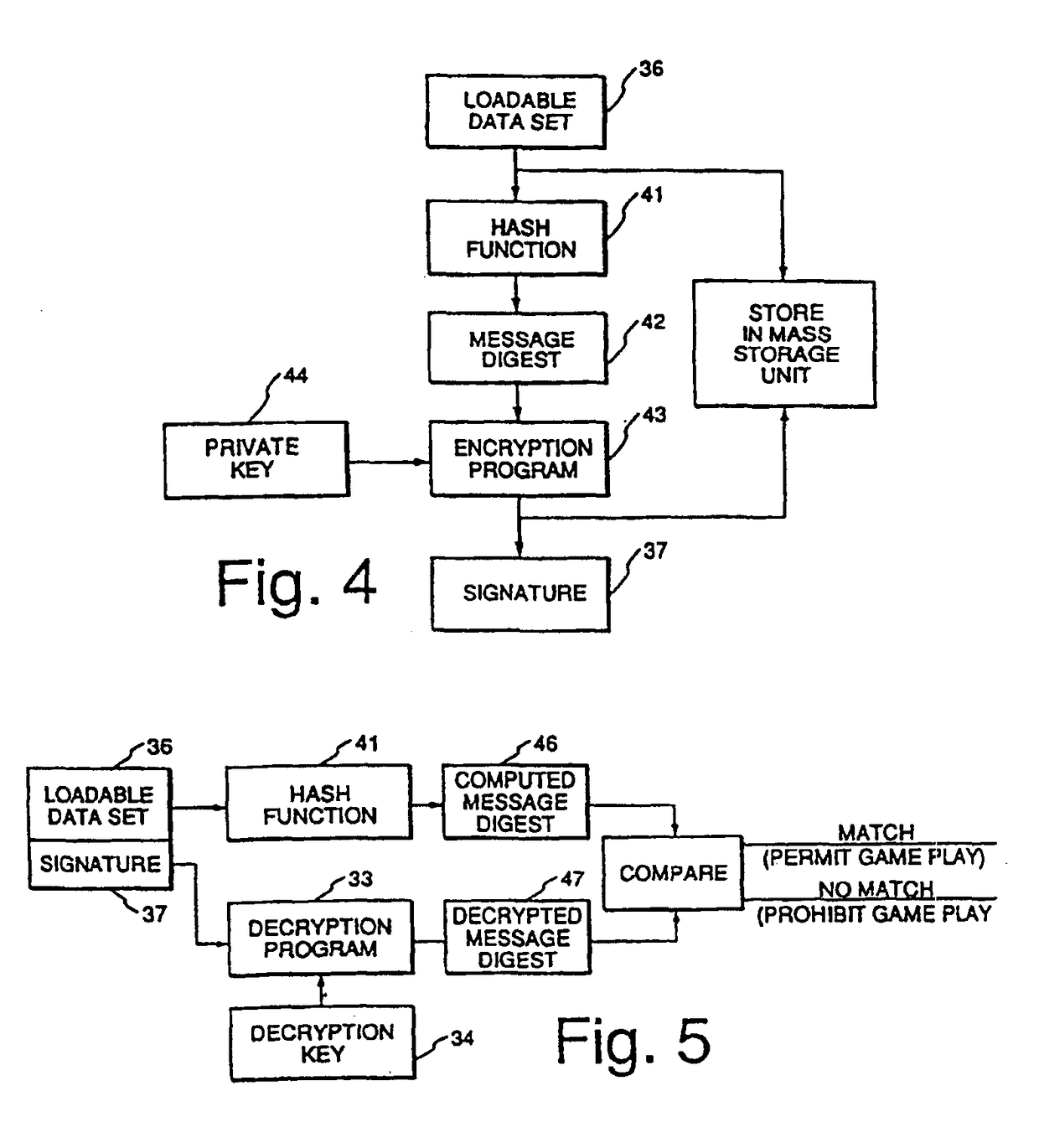
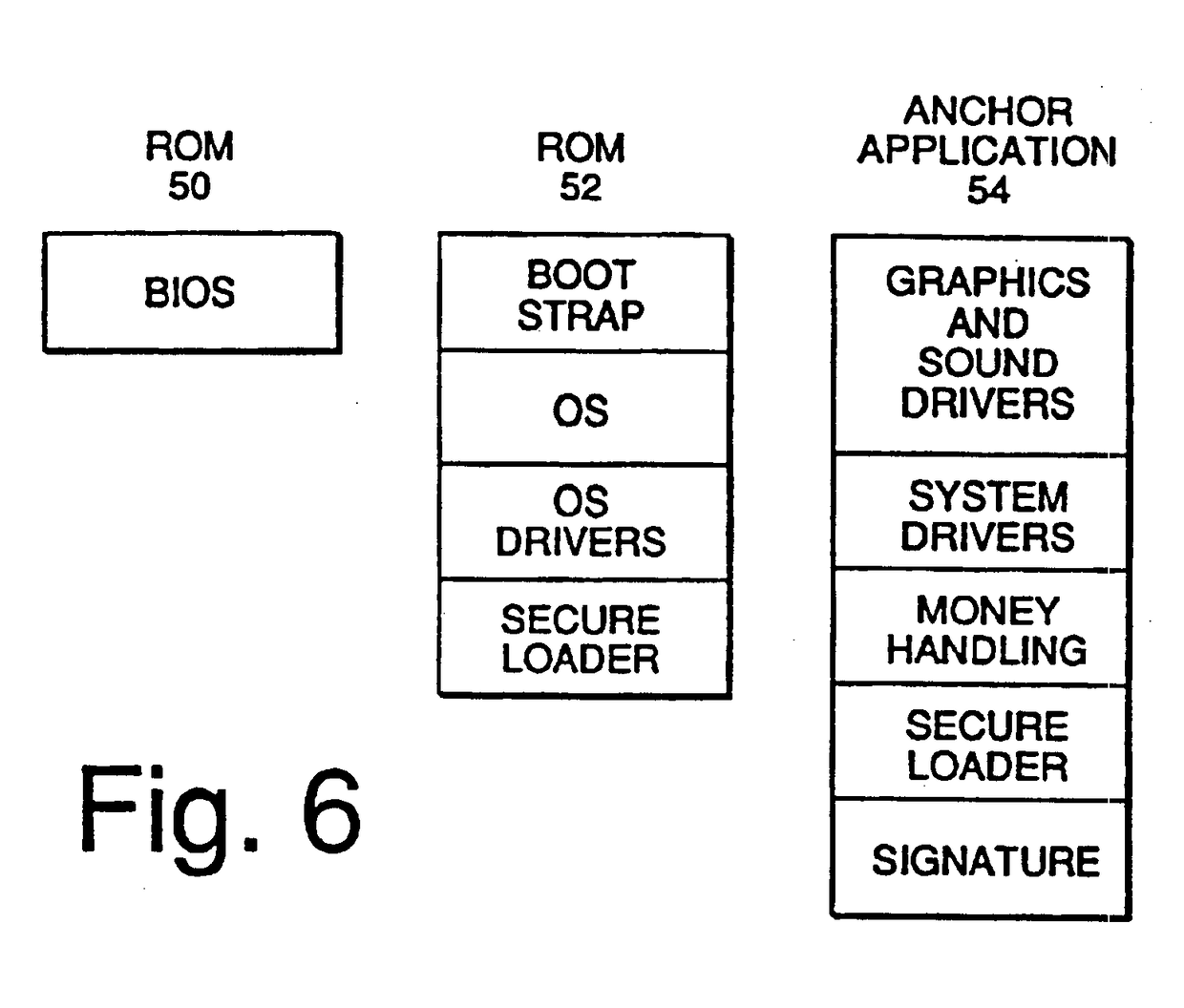
InactiveUSRE39368E1Expands casino game play capabilityImprove securityData processing applicationsDigital data processing detailsMass storageSCSI
The electronic casino gaming system consists of several system components, including a microprocessor (12), a main memory unit (13) that is typically a random access memory, and a system boot ROM (14). Also included in the electronic casino gaming system are a non-volatile RAM (17), a mass storage unit (18), a disk subsystem (19), and a PCI bus (20). The disk subsystem (19) preferably supports SCSI-2 with options of fast and wide. A video subsystem (22) is also included in the electronic casino gaming system and is coupled to the PCI bus (20) to provide full color still images and MPEG movies.
Owner:IGT
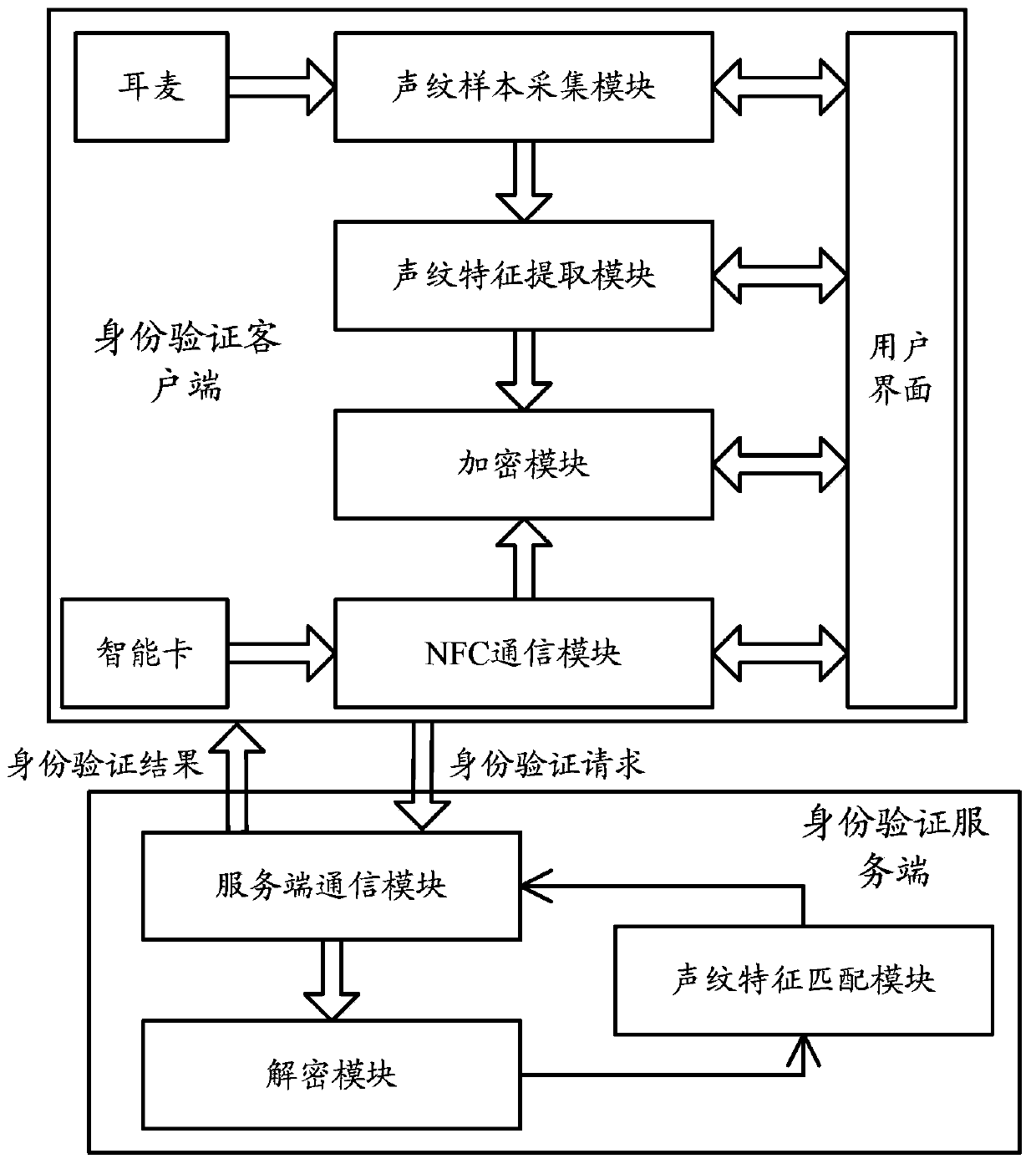
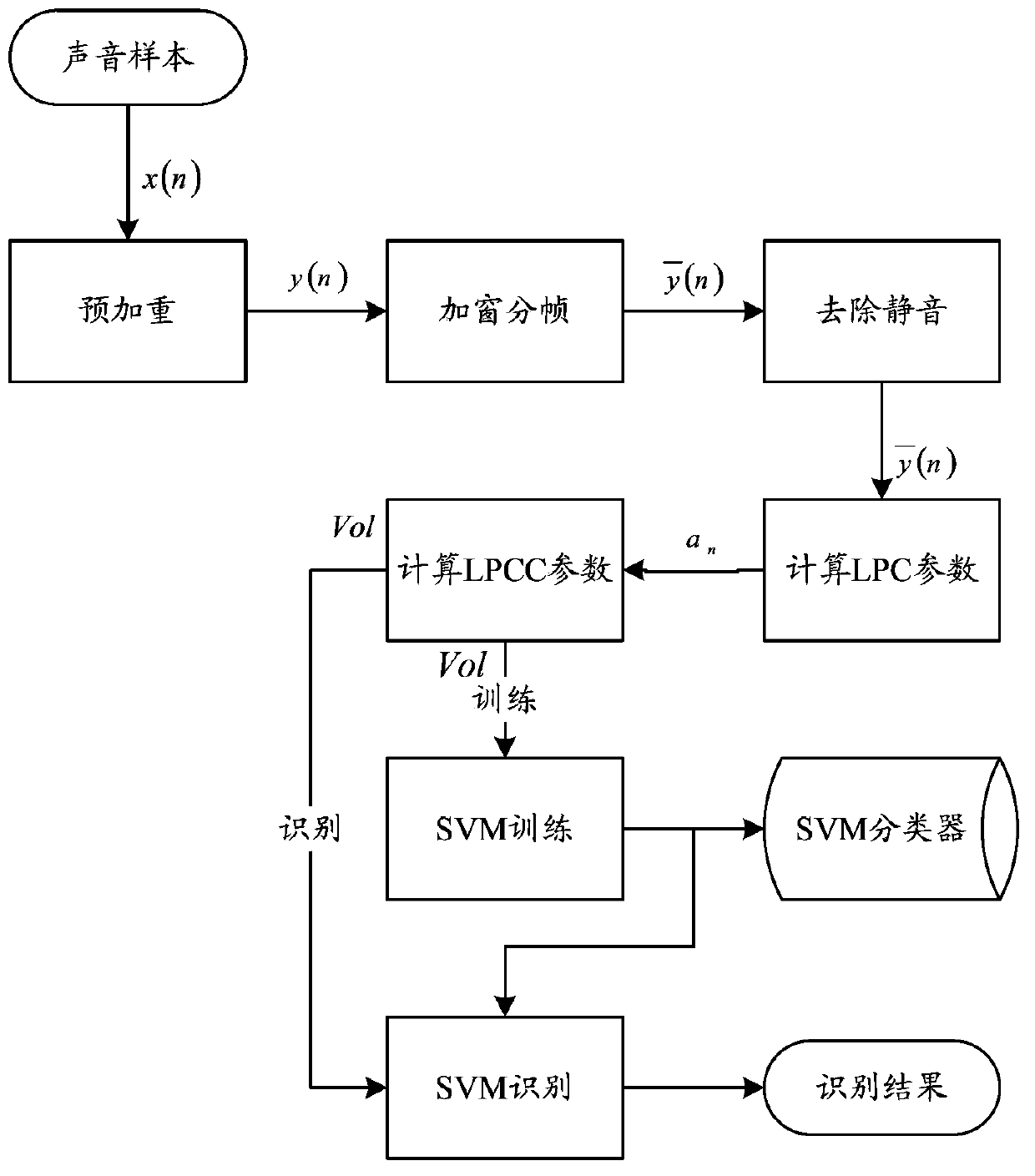
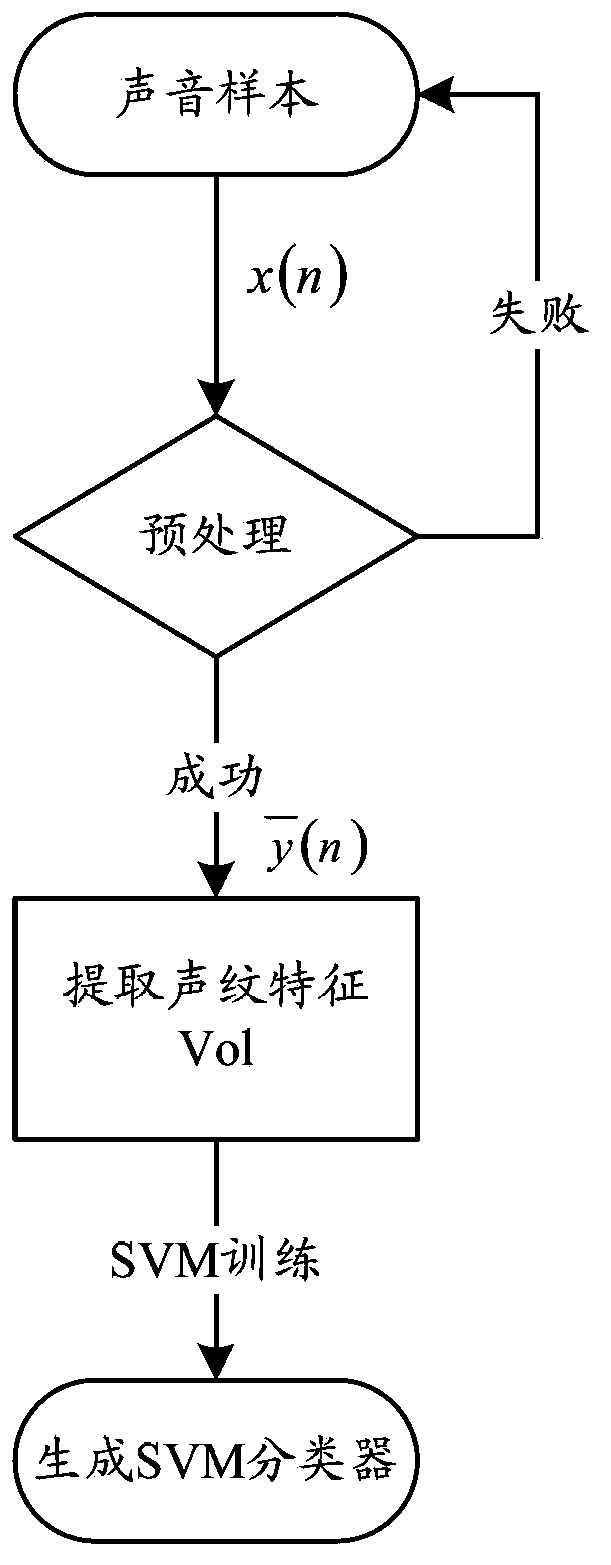
System and method for realizing smart card authentication based on voiceprint recognition
ActiveCN103391201AProtection securityGuaranteed to complete effectivelyUser identity/authority verificationSpeech analysisRead throughAuthentication server
The invention relates to a system for realizing smart card authentication based on voiceprint recognition. The system comprises an authentication client and an authentication server, wherein the authentication client comprises a voiceprint sample acquisition module, a voiceprint feature extraction module and an NFC (near field communication) module; the authentication server comprises a server communicating module and a voiceprint feature matching module; the server communicating module is used for receiving authentication request information sent by the authentication client and judging the validity of the authentication request and returning to an authentication result. The invention further relates to a method for realizing the smart card authentication based on the voiceprint recognition. With the adoption of the structure of the system and the method for realizing the smart card authentication based on the voiceprint recognition, related information on a smart card can be read through an NFC function, the irreplaceable, anti-theft and anti-lost characteristics of a voiceprint are used, the authentication can be guaranteed to be finished effectively, and a wider application range is provided.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
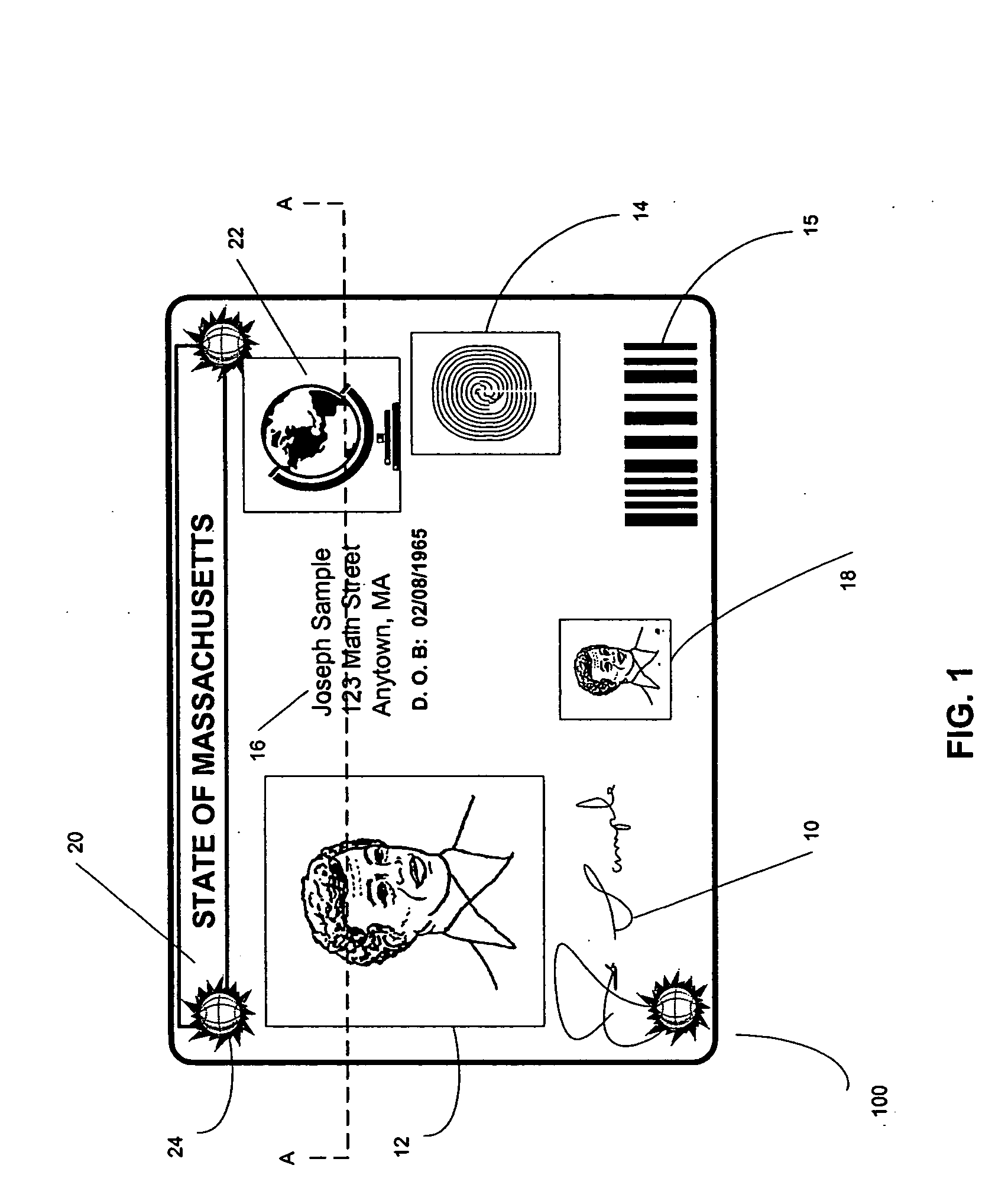
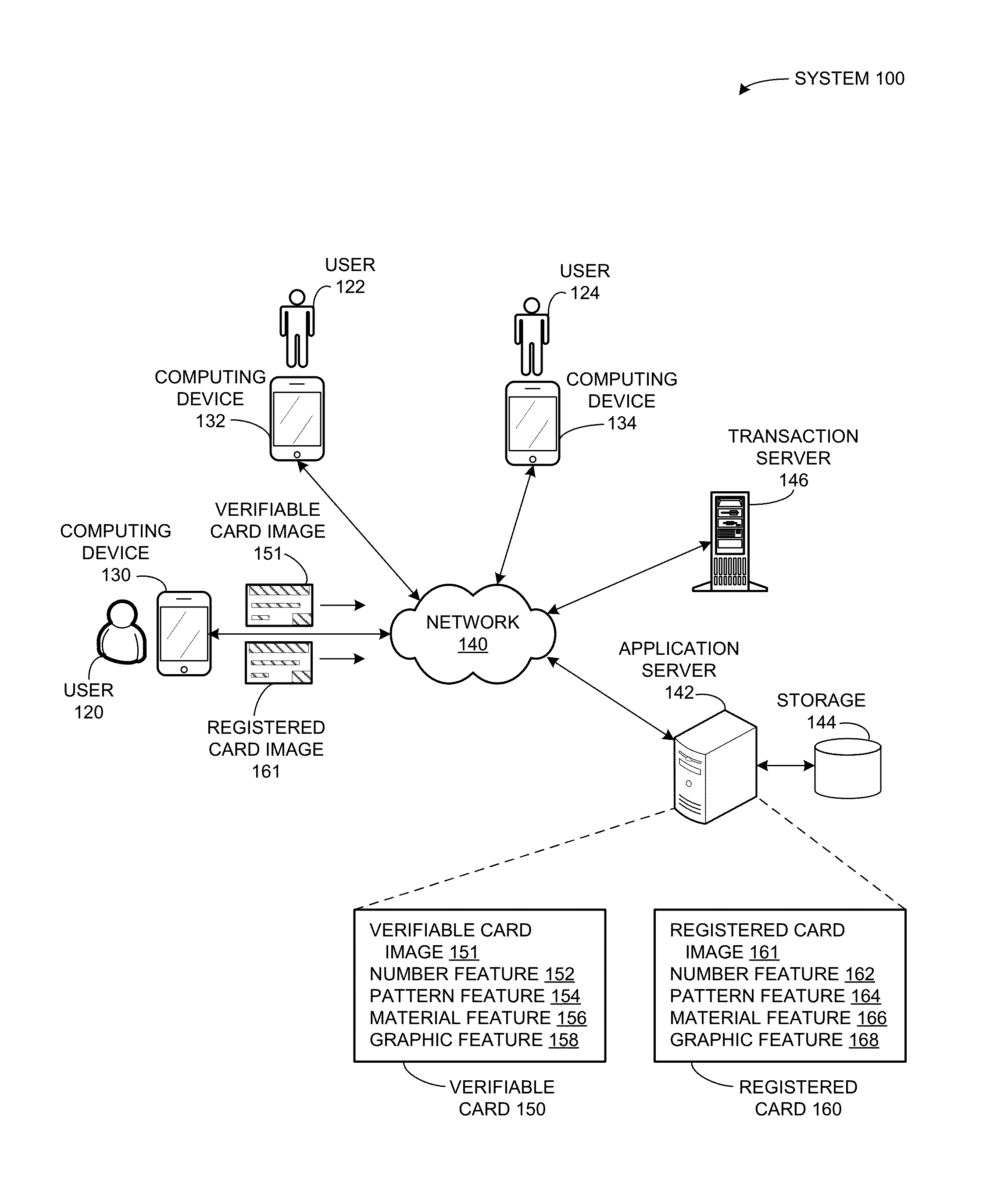
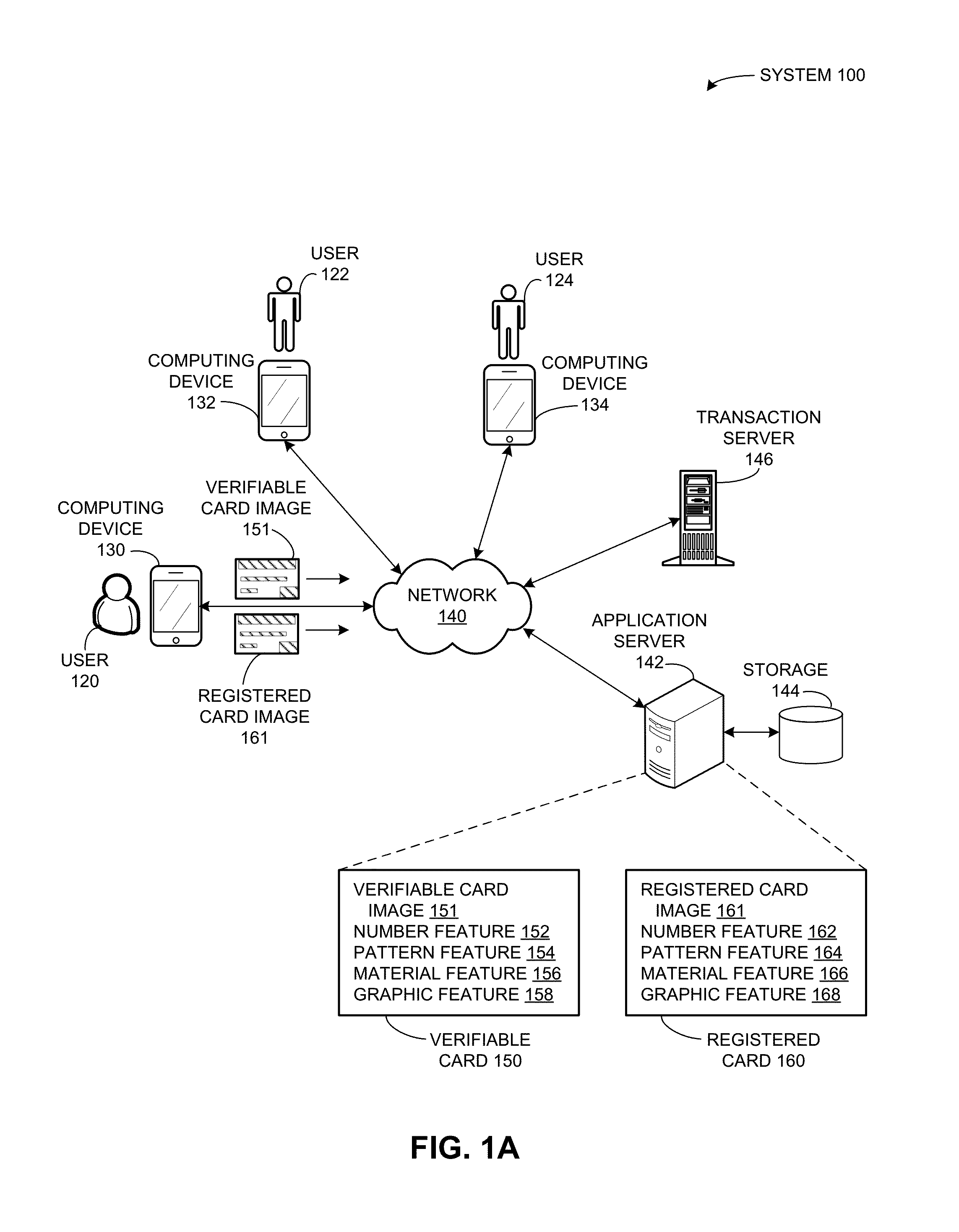
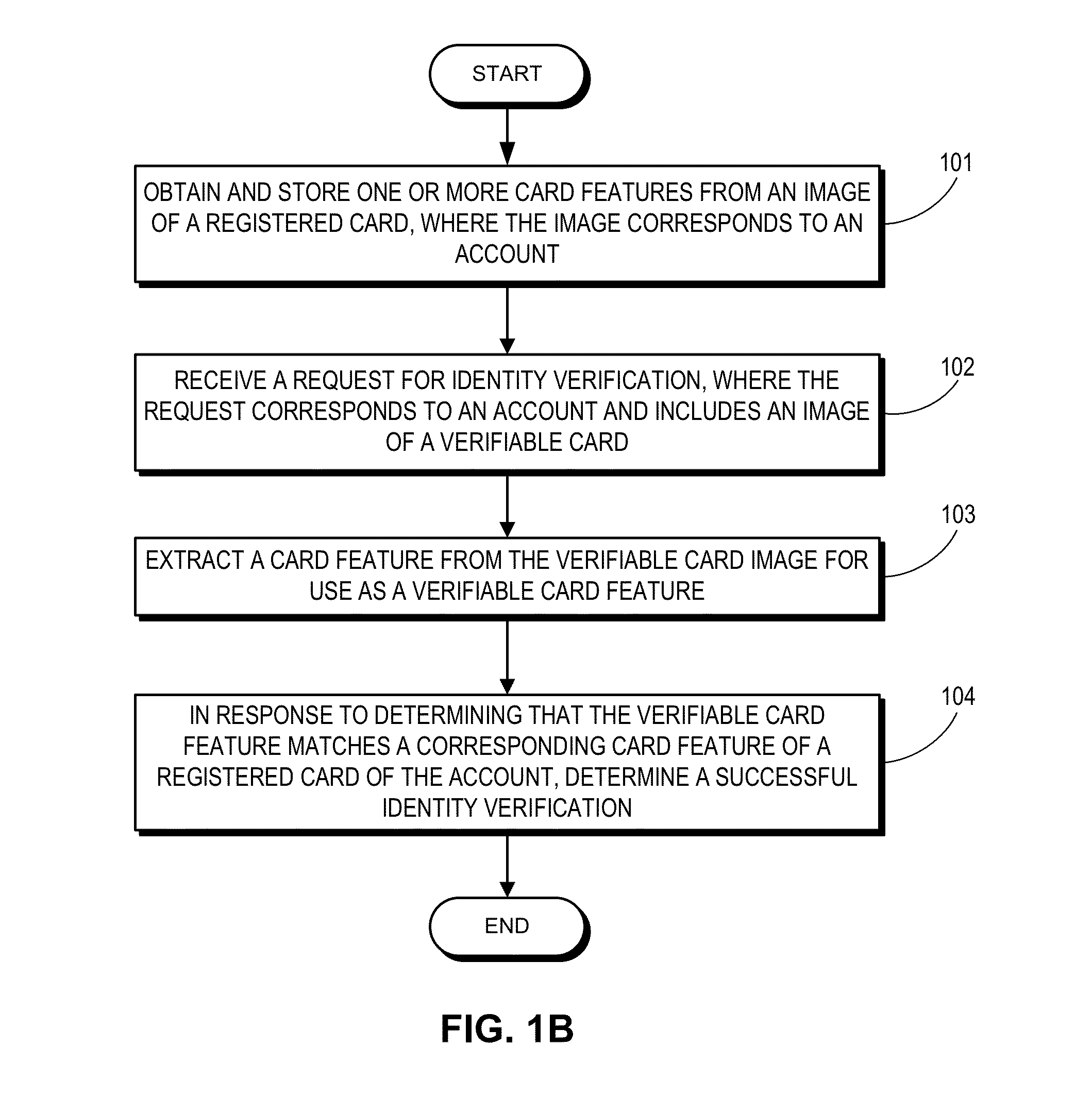
Method and system for verifying user identity using card features
ActiveUS20160048837A1Facilitates identity verificationEasy authenticationImage enhancementImage analysisComputer hardwareCard image
One embodiment of the present invention provides a system that facilitates identity verification based on various features of a card. During operation, a server receives a request for identity verification, where the request corresponds to an account and includes an image of a verifiable card. The server extracts a card feature from the verifiable card image for use as a verifiable card feature. In response to determining that the verifiable card feature matches a corresponding card feature of a registered card of the account, the server determines successful identity verification.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com