Patents
Literature
7032results about "Multiple keys/algorithms usage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
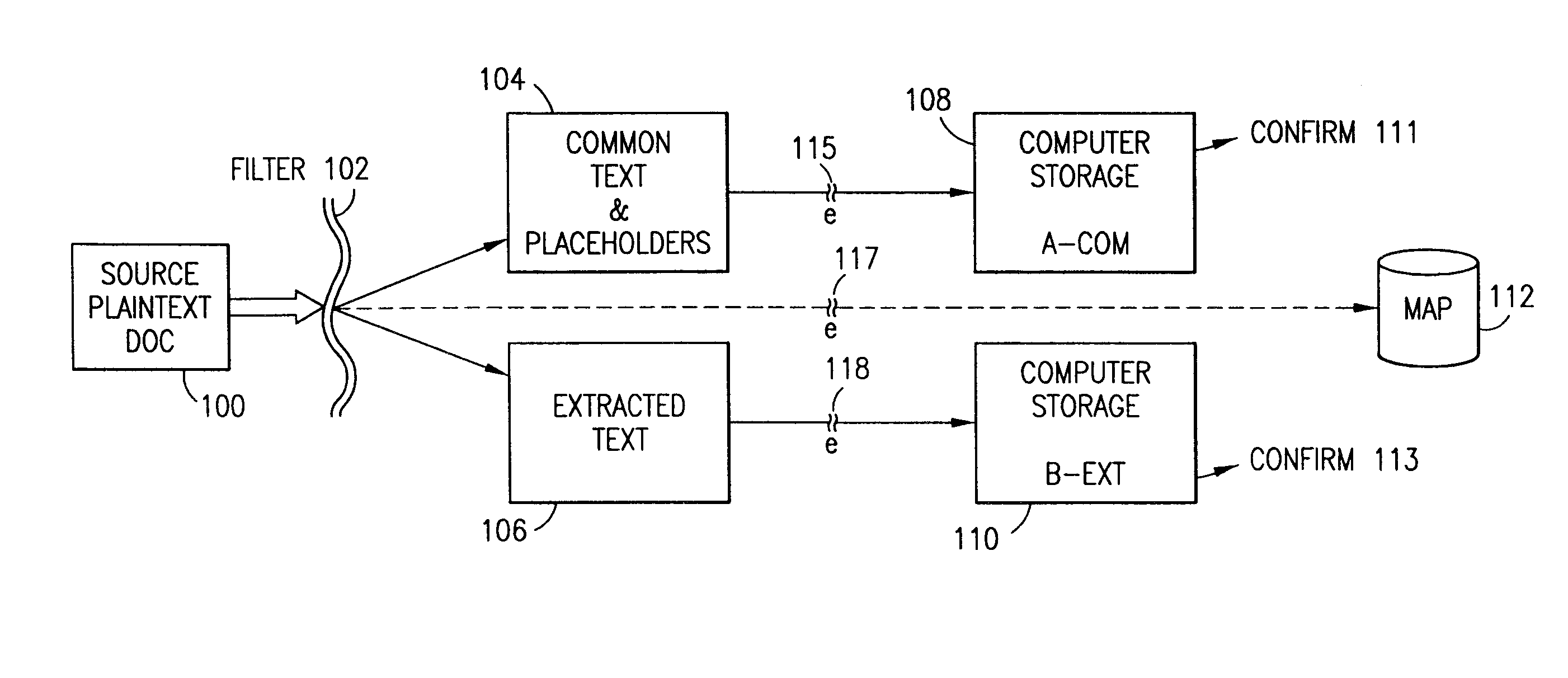
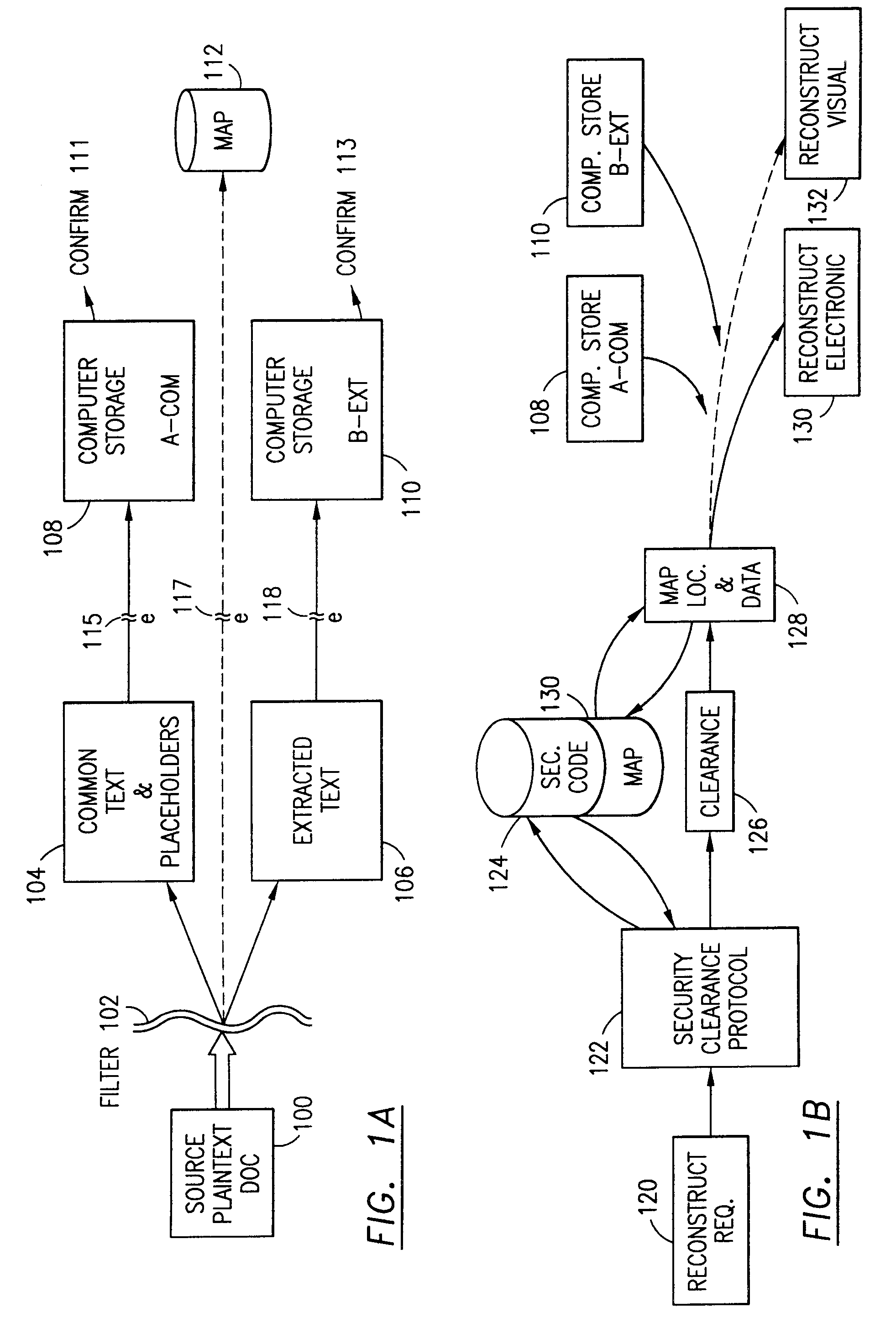
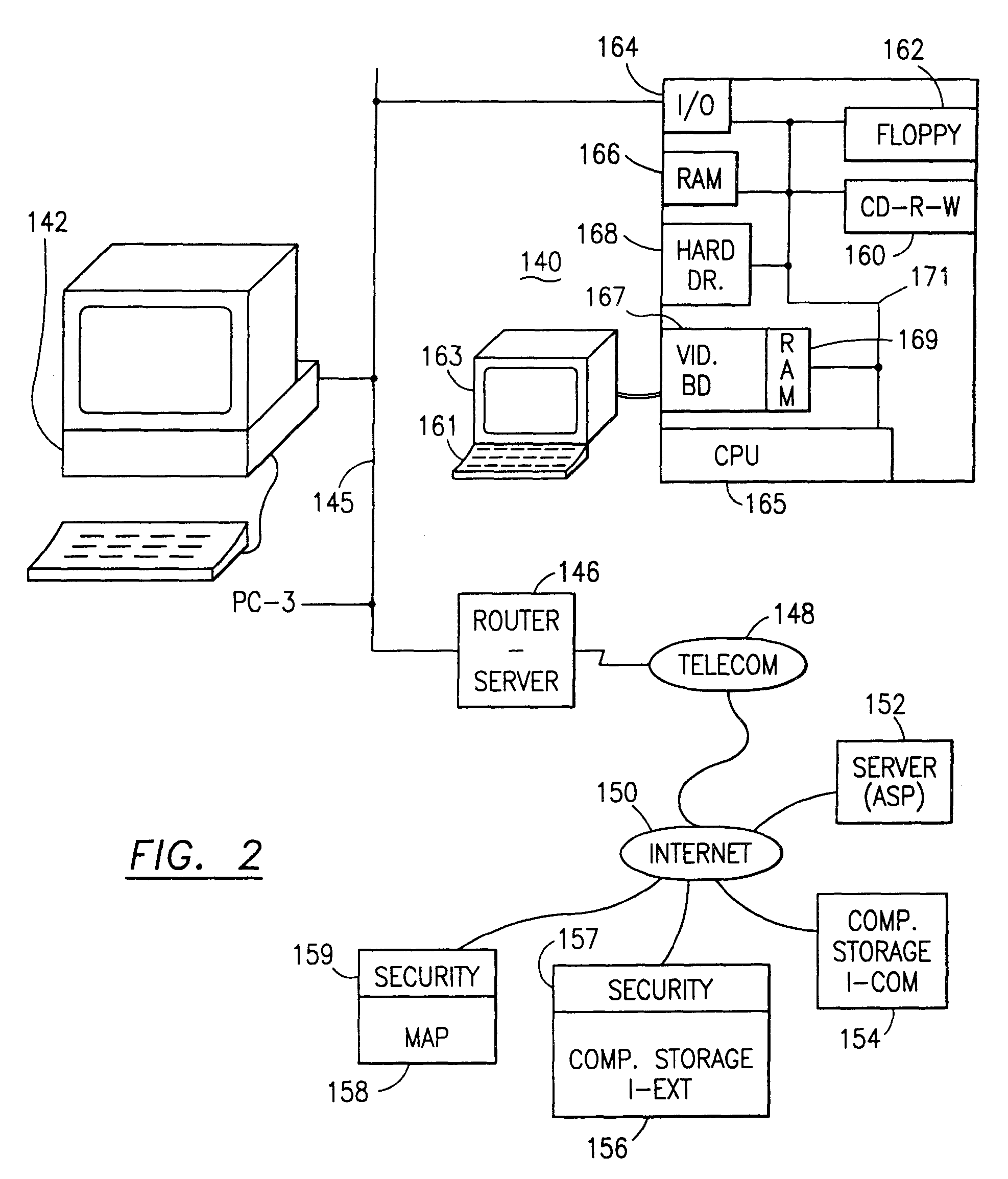
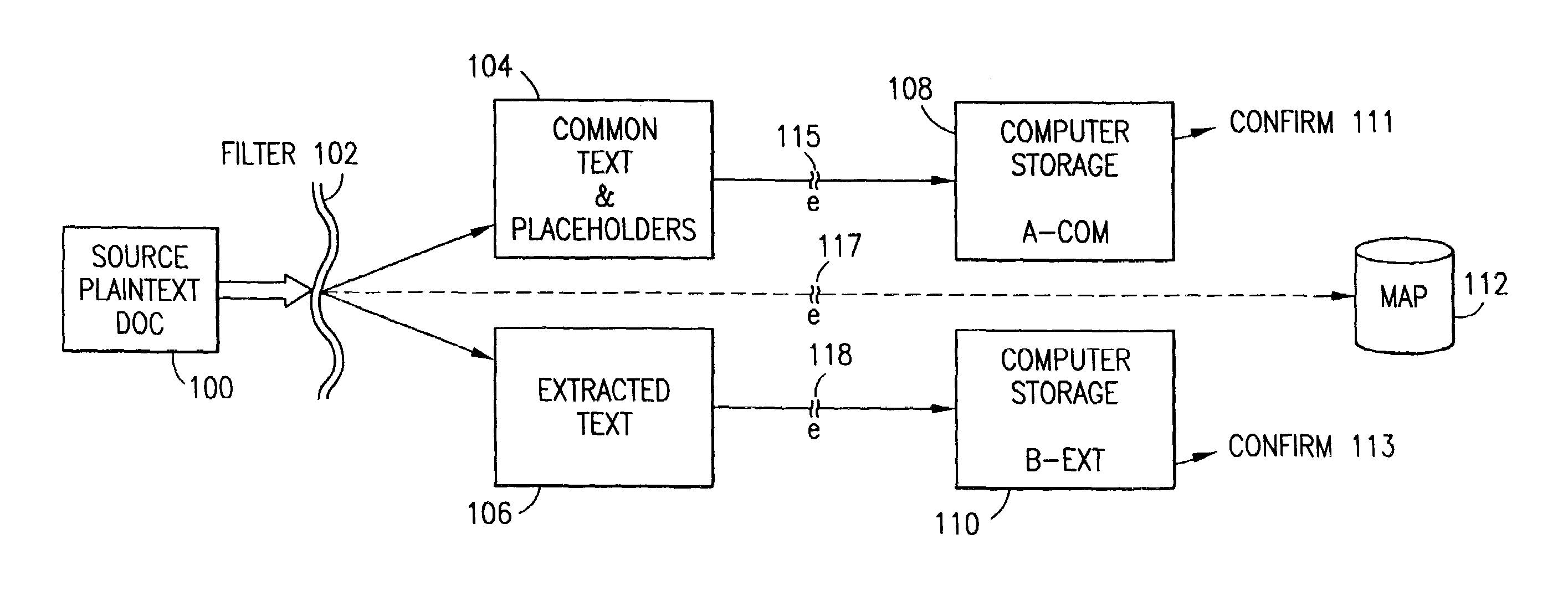
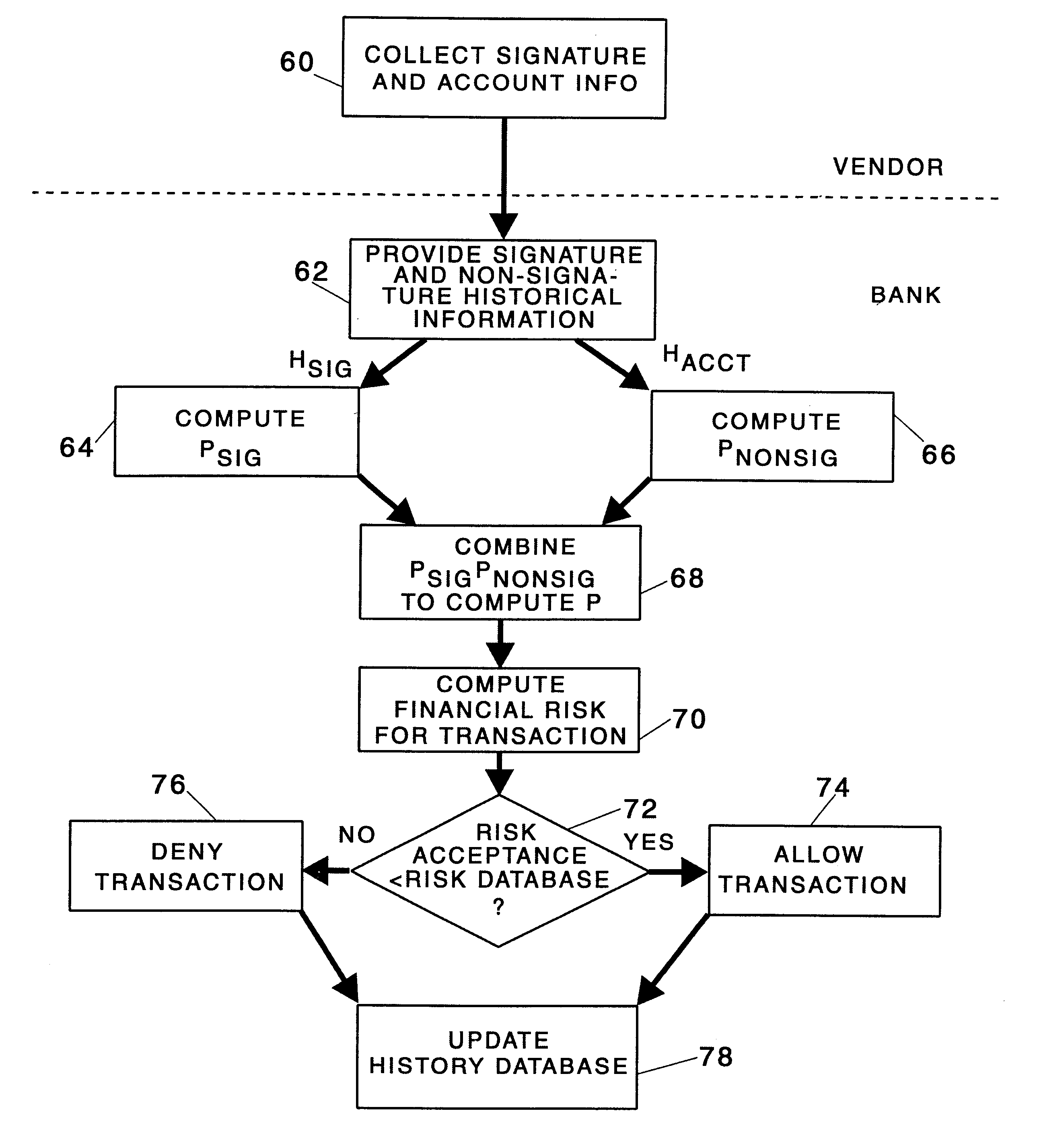
Data security system and method for separation of user communities
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
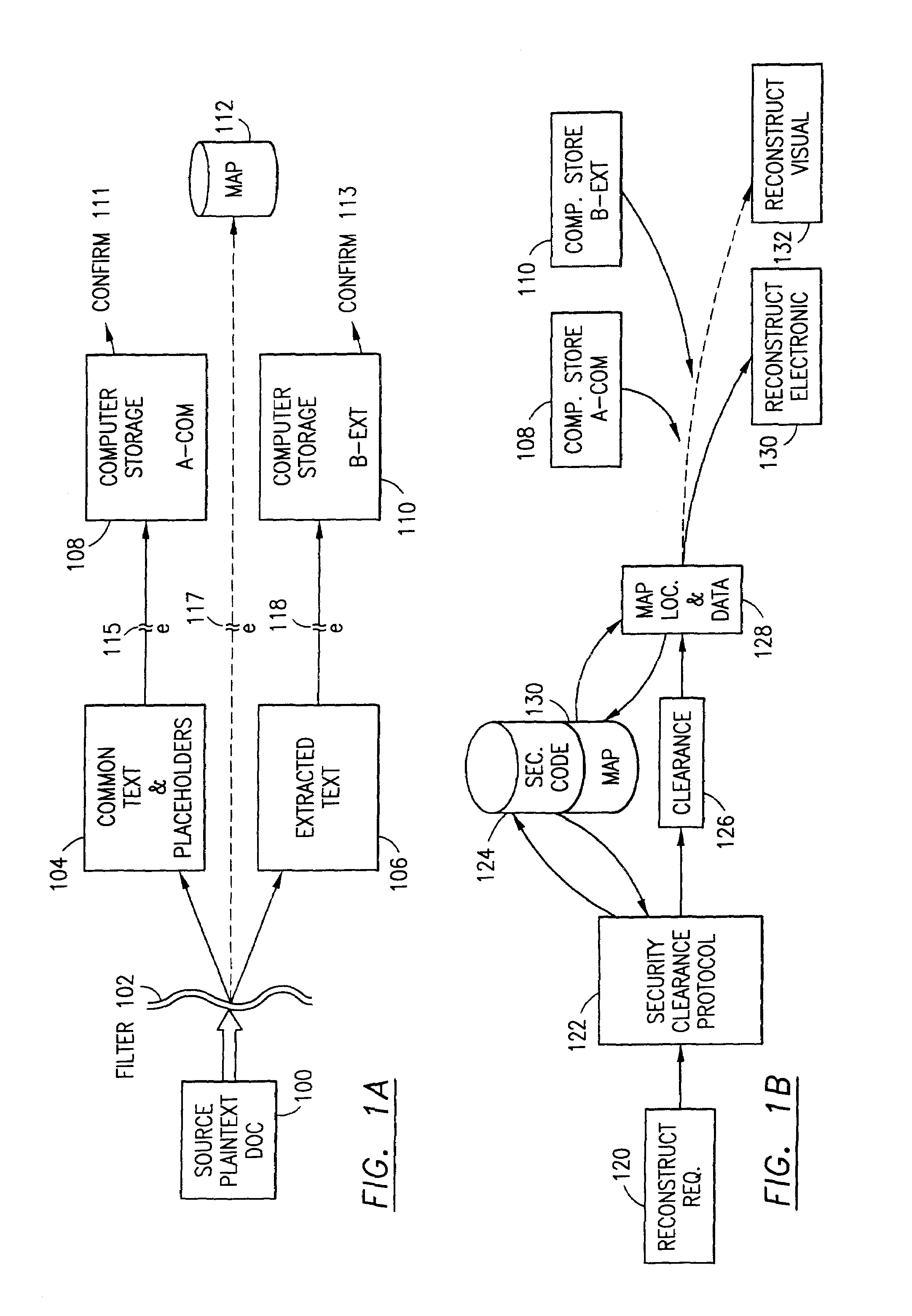
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
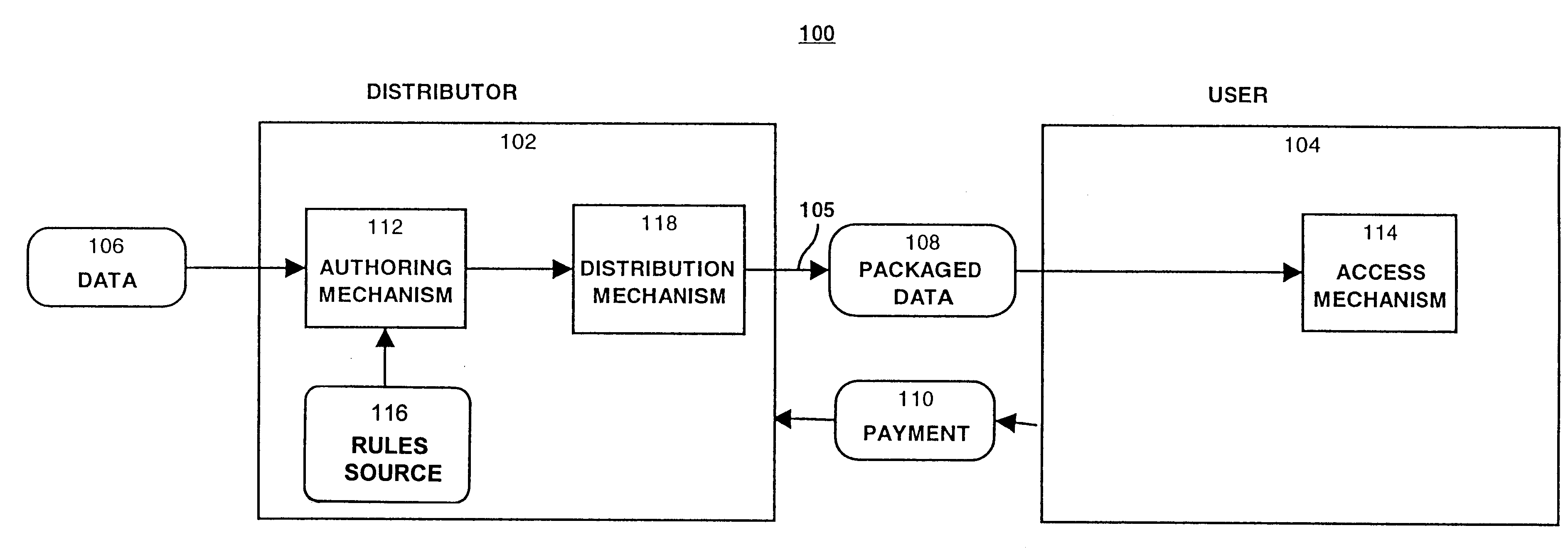
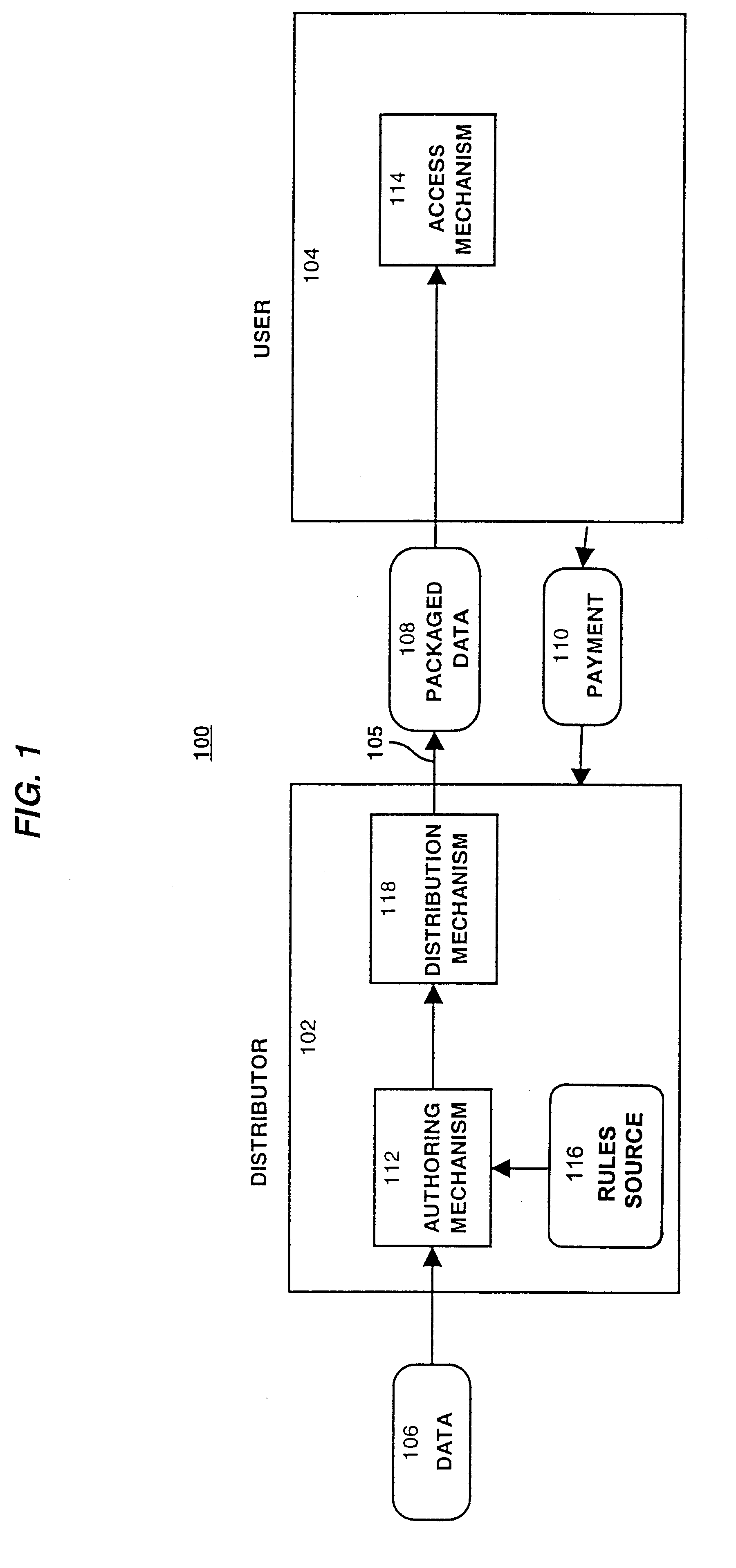
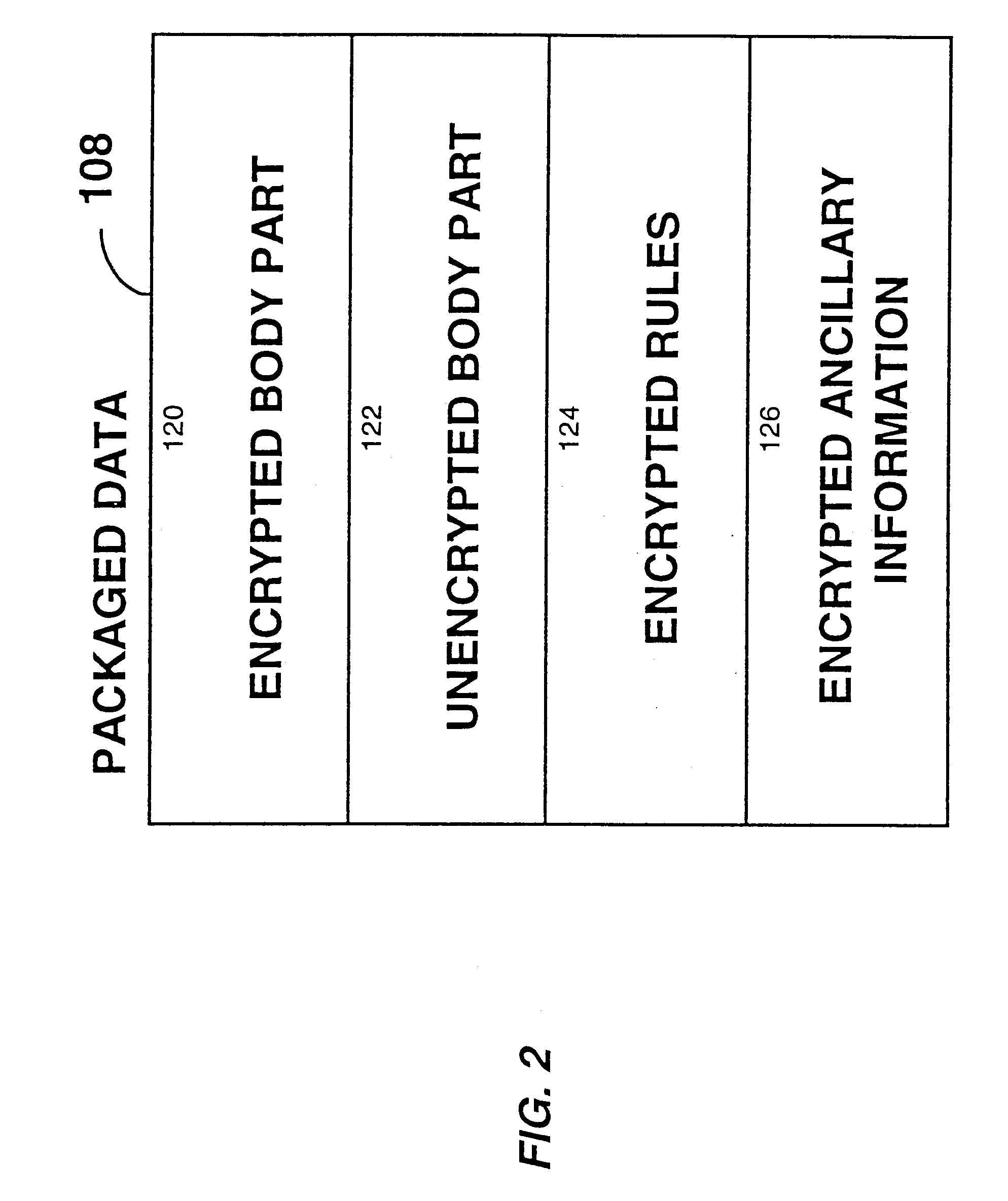
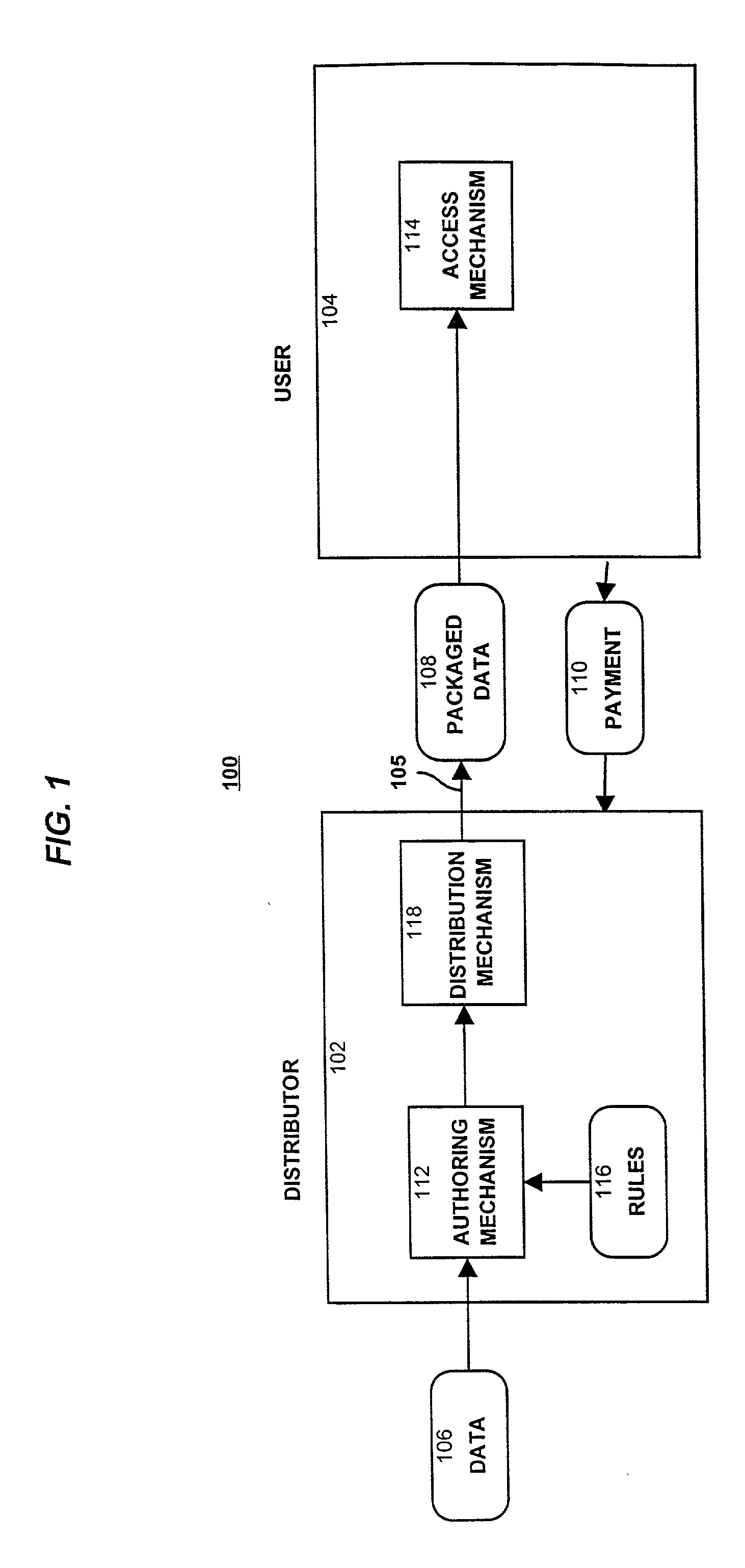
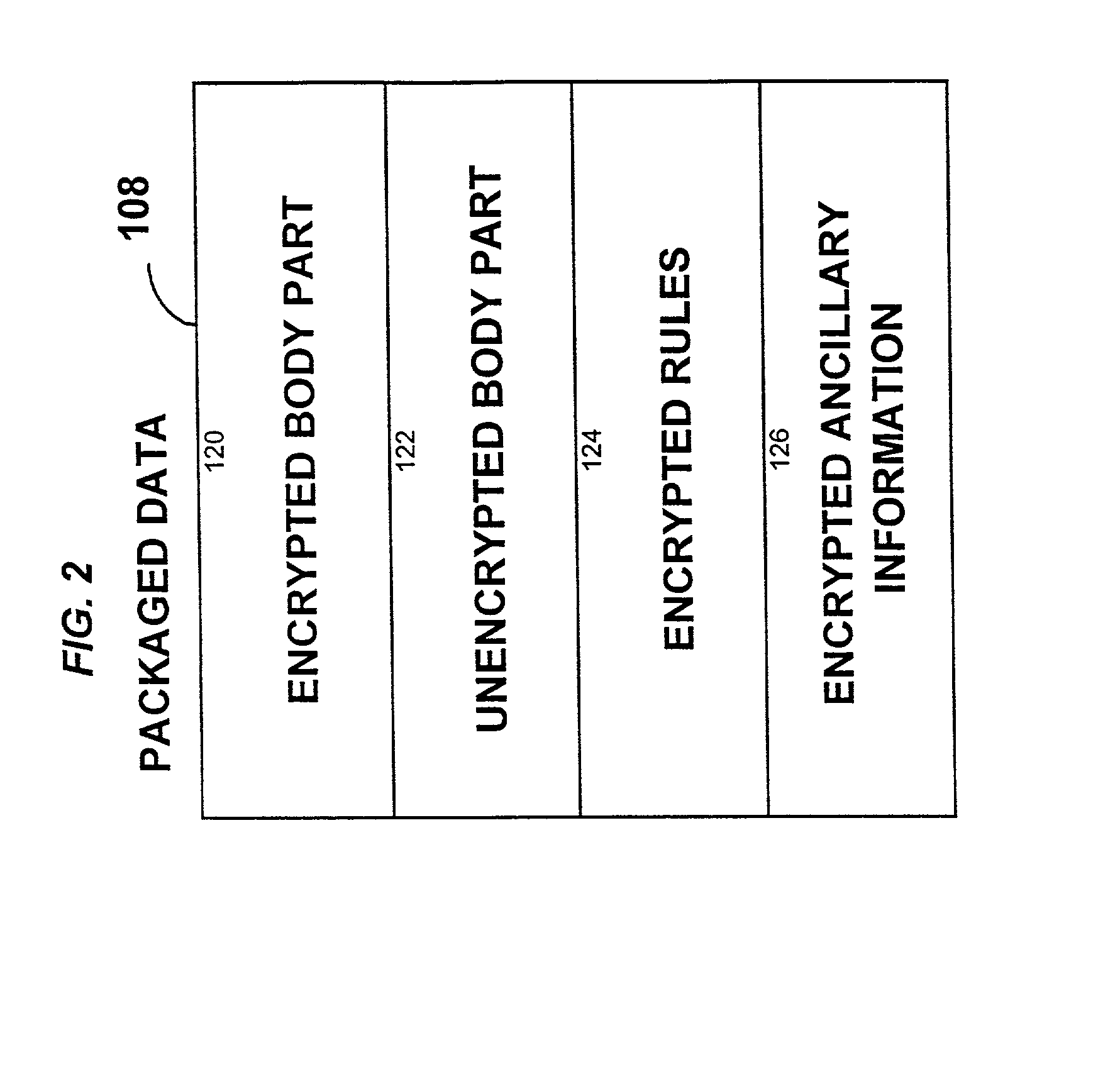
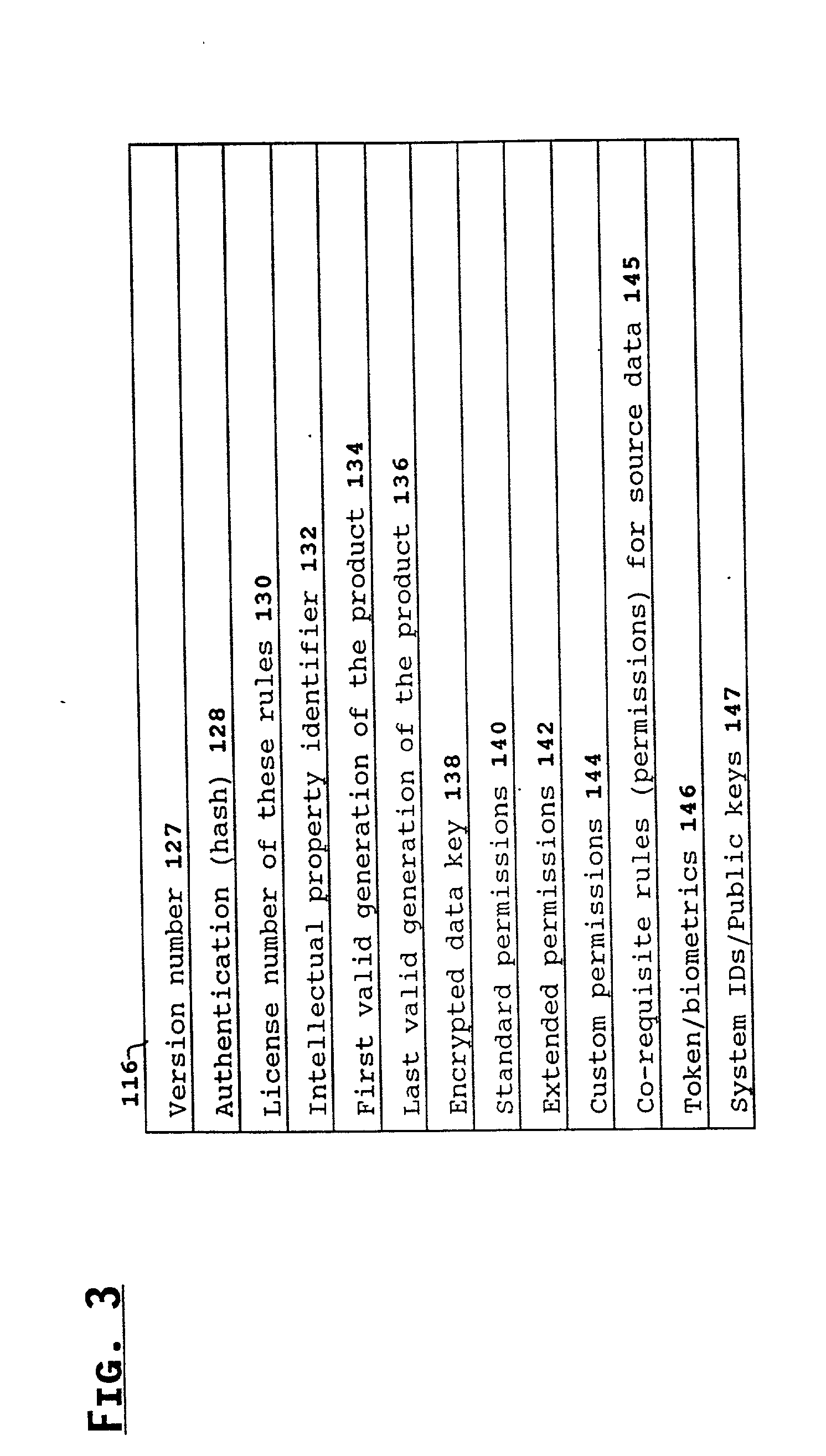
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
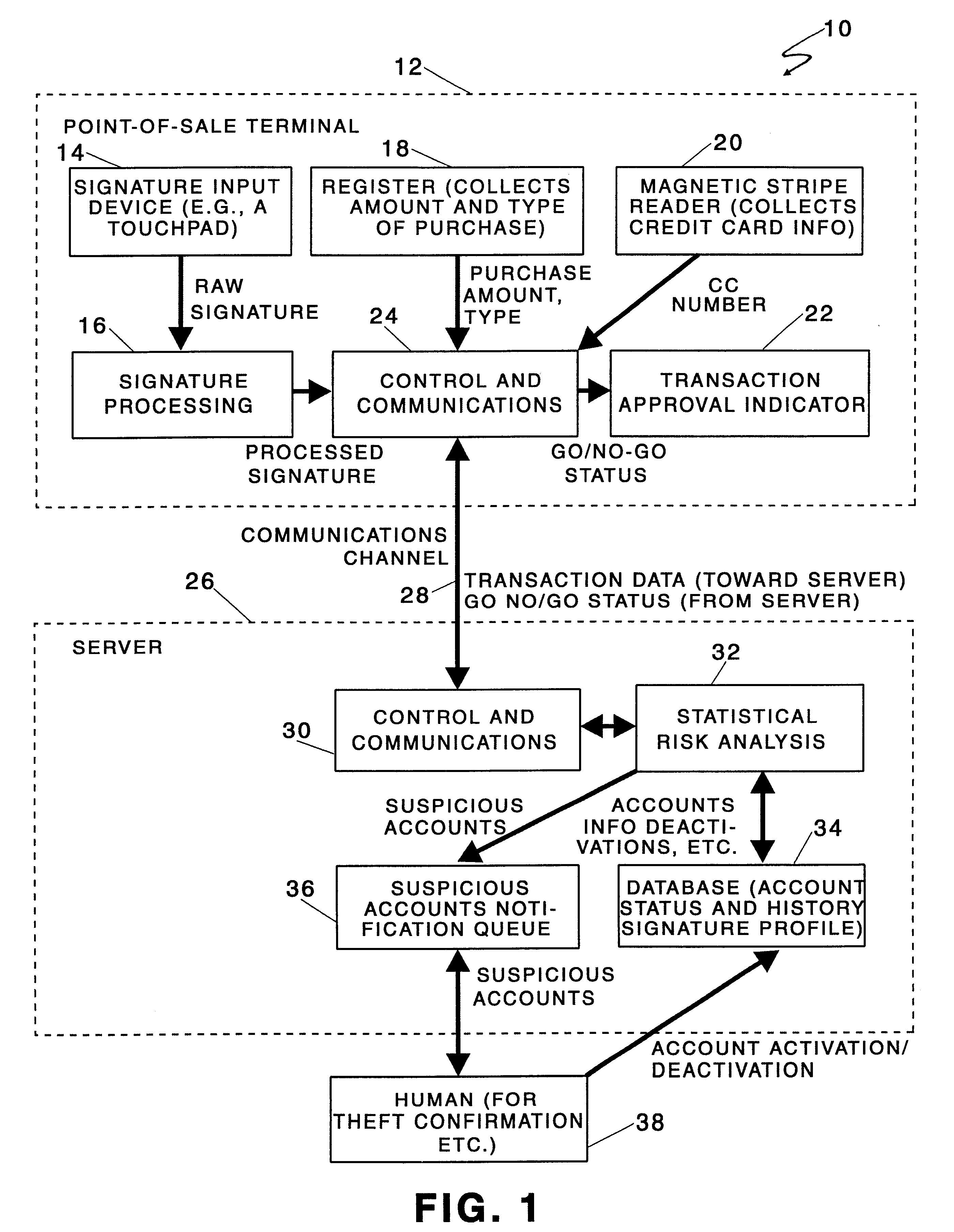
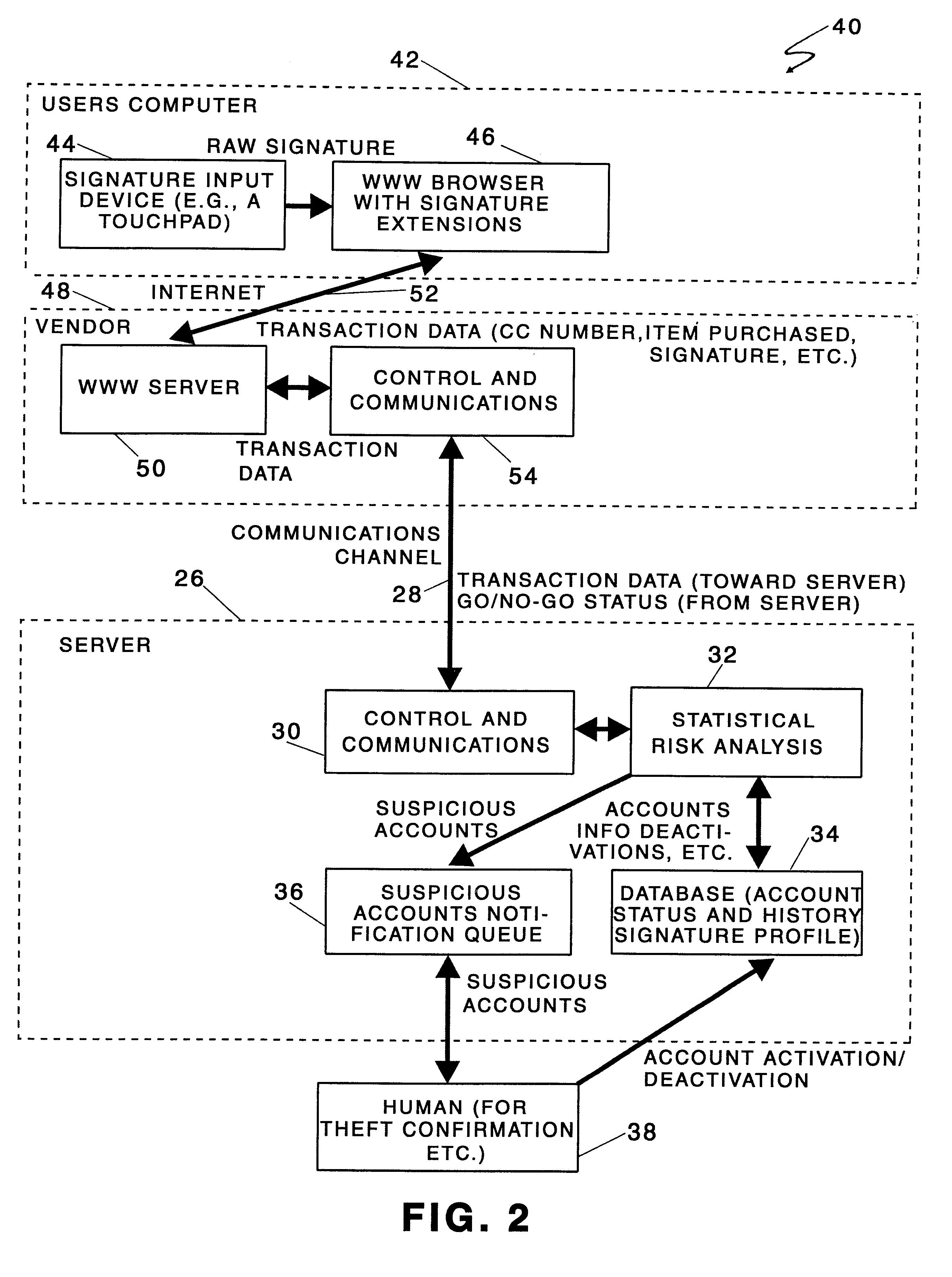
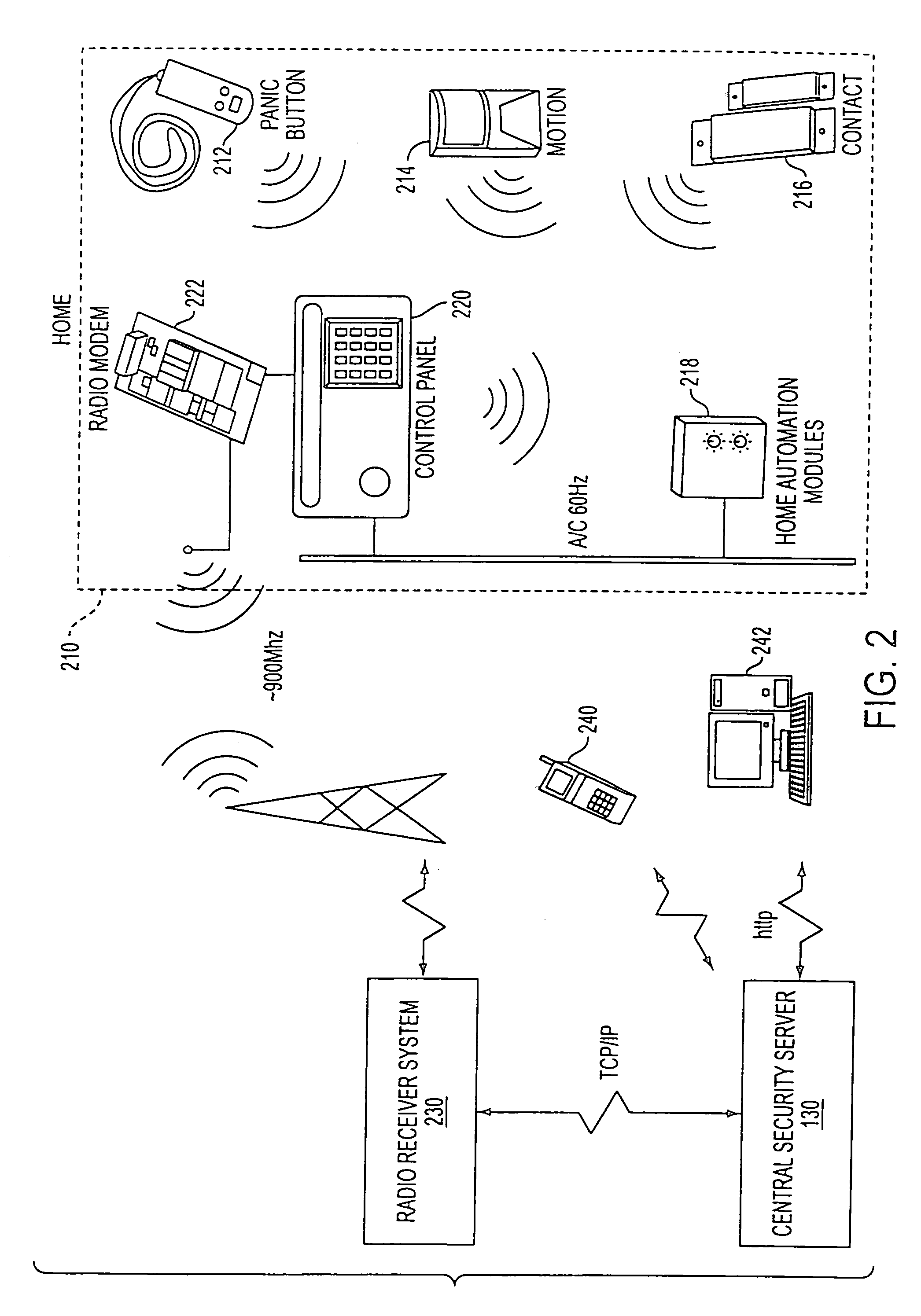
System and method for connecting security systems to a wireless device
InactiveUS7113090B1Electric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
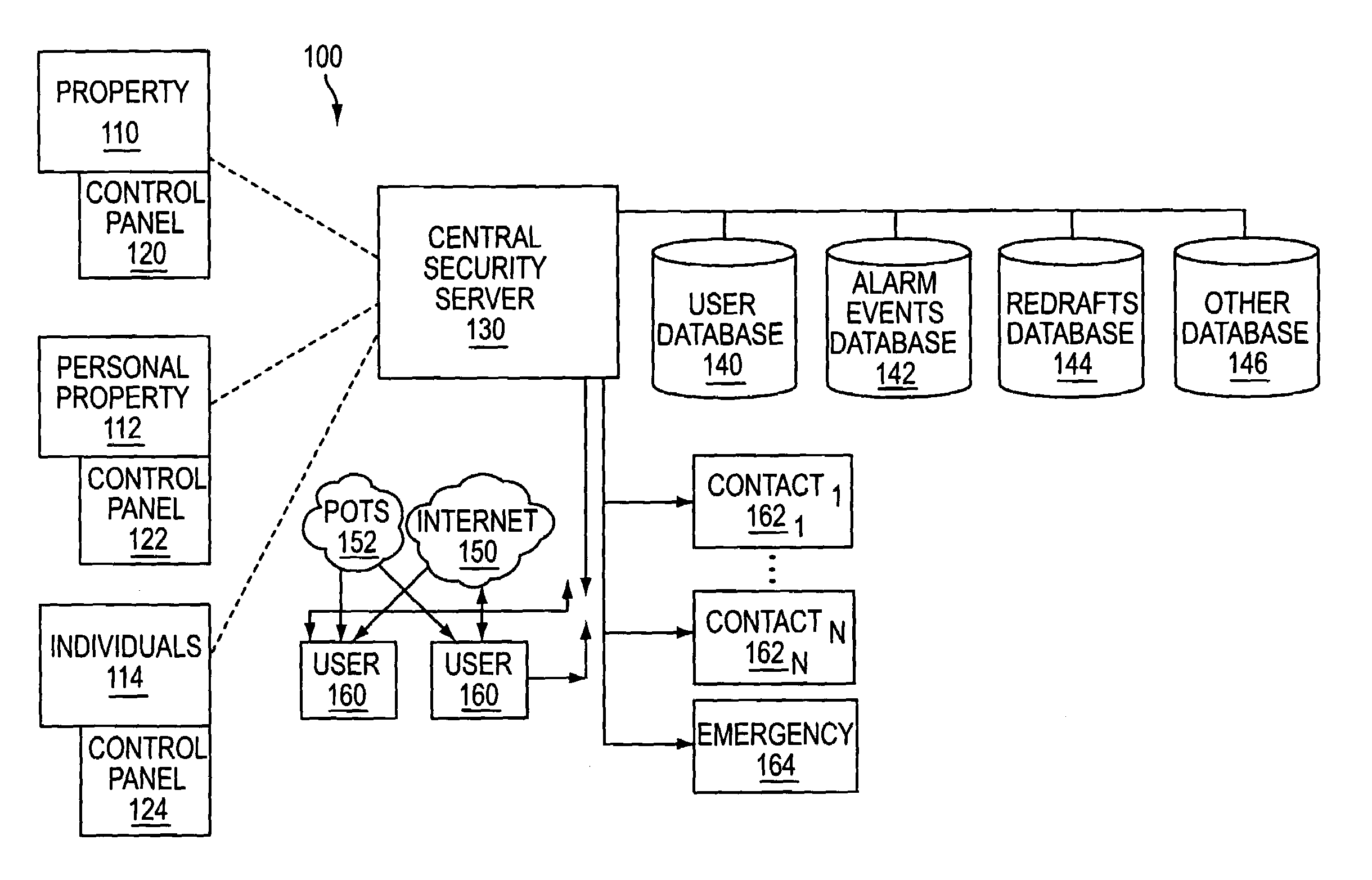
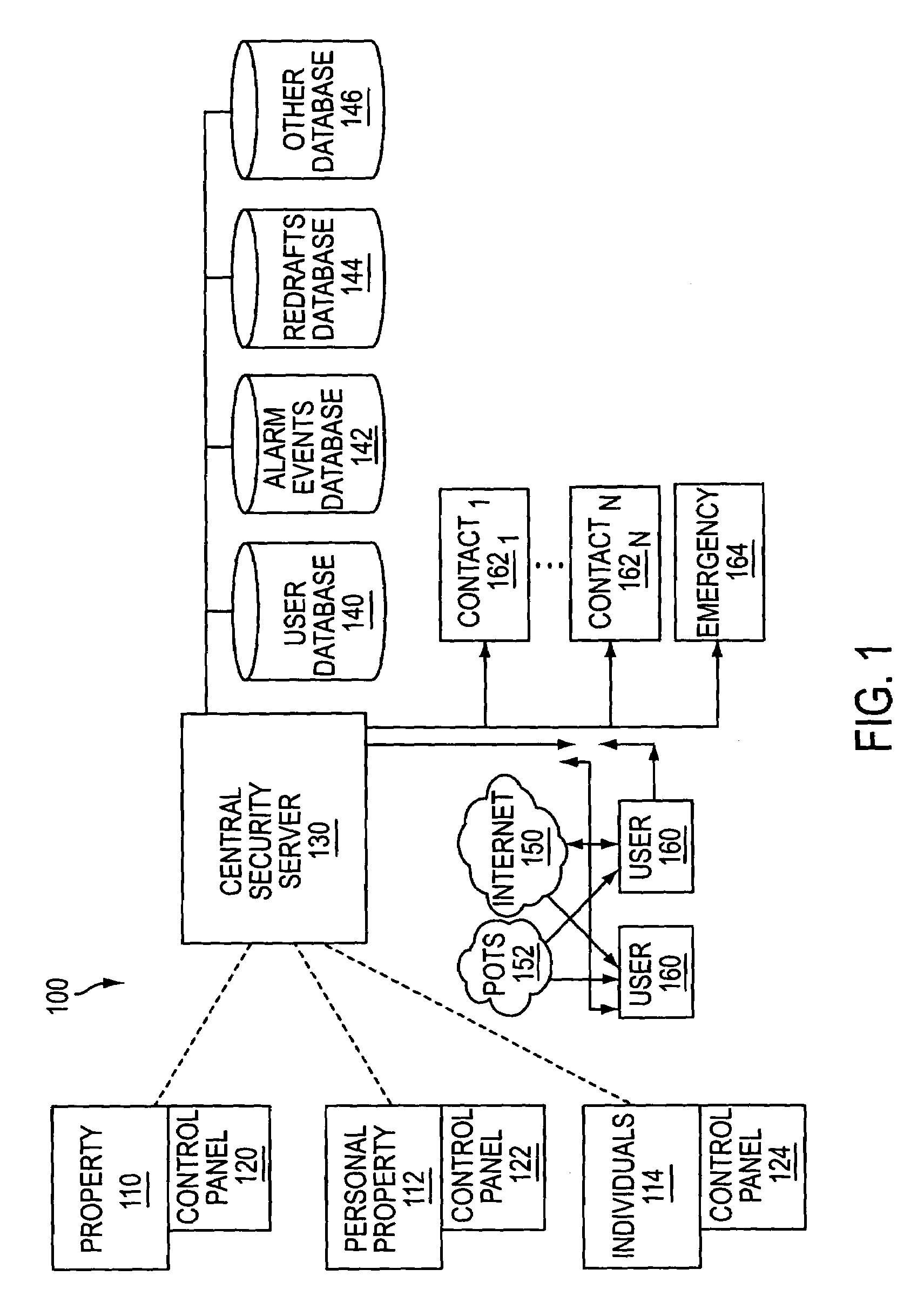
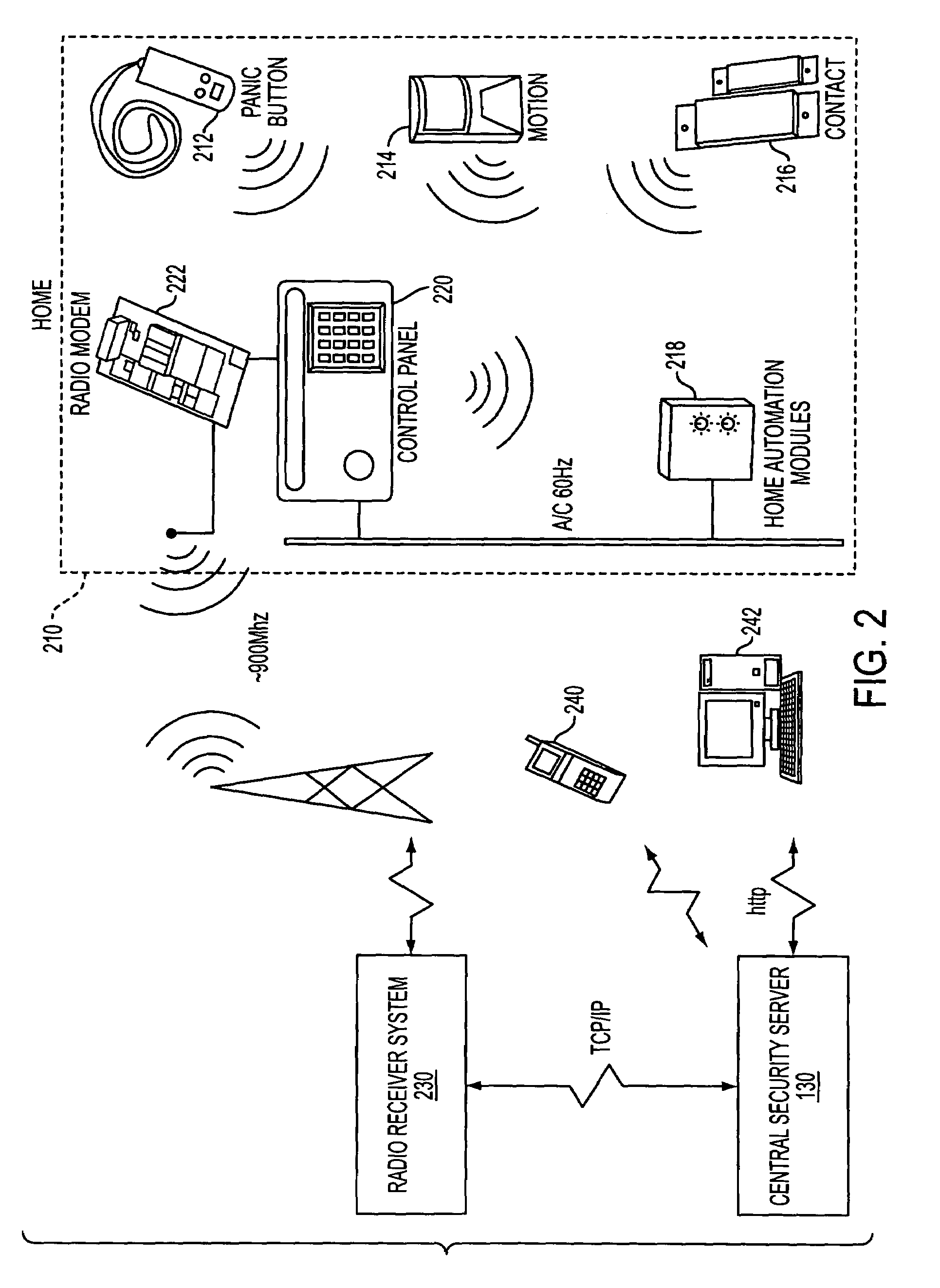
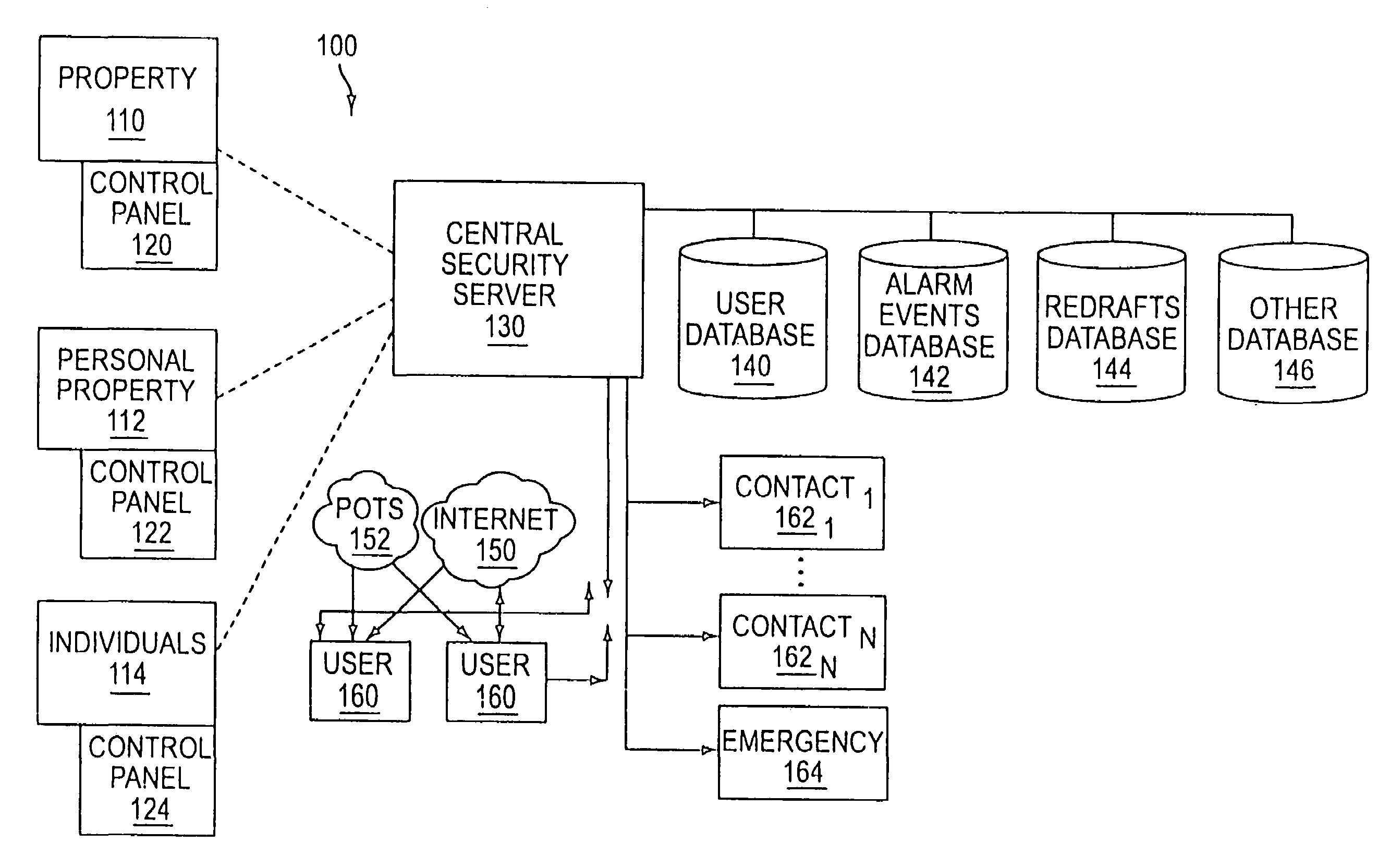
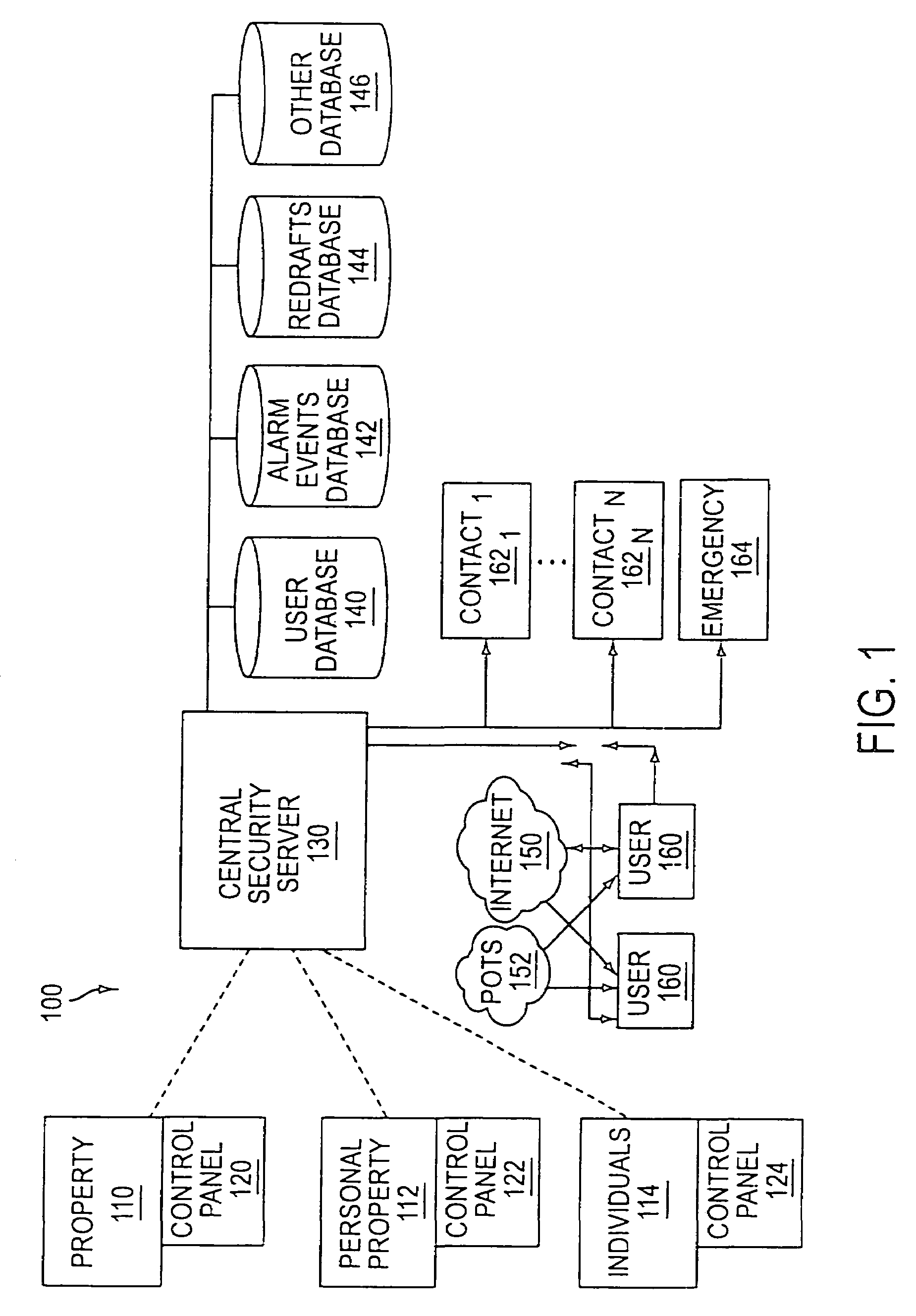
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
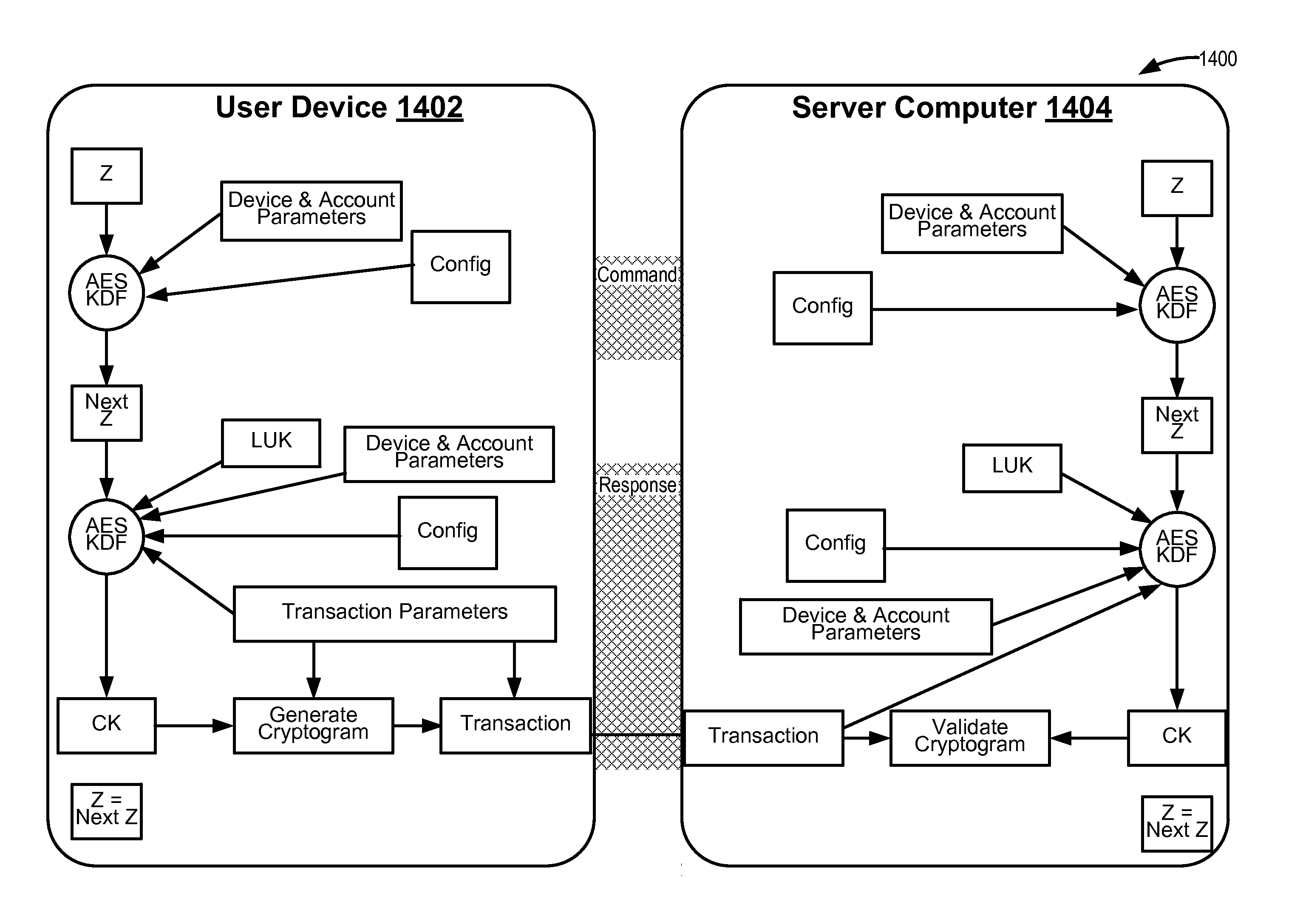
Methods for secure cryptogram generation
ActiveUS20160065370A1Avoid attackKey distribution for secure communicationMultiple keys/algorithms usageSecure communicationUser device
Embodiments of the invention introduce efficient methods for securely generating a cryptogram by a user device, and validating the cryptogram by a server computer. In some embodiments, a secure communication can be conducted whereby a user device provides a cryptogram without requiring the user device to persistently store an encryption key or other sensitive data used to generate the cryptogram. For example, the user device and server computer can mutually authenticate and establish a shared secret. Using the shared secret, the server computer can derive a session key and transmit key derivation parameters encrypted using the session key to the user device. The user device can also derive the session key using the shared secret, decrypt the encrypted key derivation parameters, and store the key derivation parameters. Key derivation parameters and the shared secret can be used to generate a single use cryptogram key. The cryptogram key can be used to generate a cryptogram for conducting secure communications.
Owner:VISA INT SERVICE ASSOC
Secure Dynamic Communication Network And Protocol
ActiveUS20160219024A1Increase the difficultyUsefulness of their knowledge would be short-livedMultiple keys/algorithms usageData taking preventionDigital dataData segment
In a secure cloud for transmitting packets of digital data, the packets may be repeatedly scrambled (i.e., their data segments reordered) and then unscrambled, split and then mixed, and / or encrypted and then decrypted as they pass through media nodes in the cloud. The methods used to scramble, split, mix and encrypt the packets may be varied in accordance with a state such as time, thereby making the task of a hacker virtually impossible inasmuch as he or she may be viewing only a fragment of a packet and the methods used to disguise the data are constantly changing.
Owner:LISTAT LTD
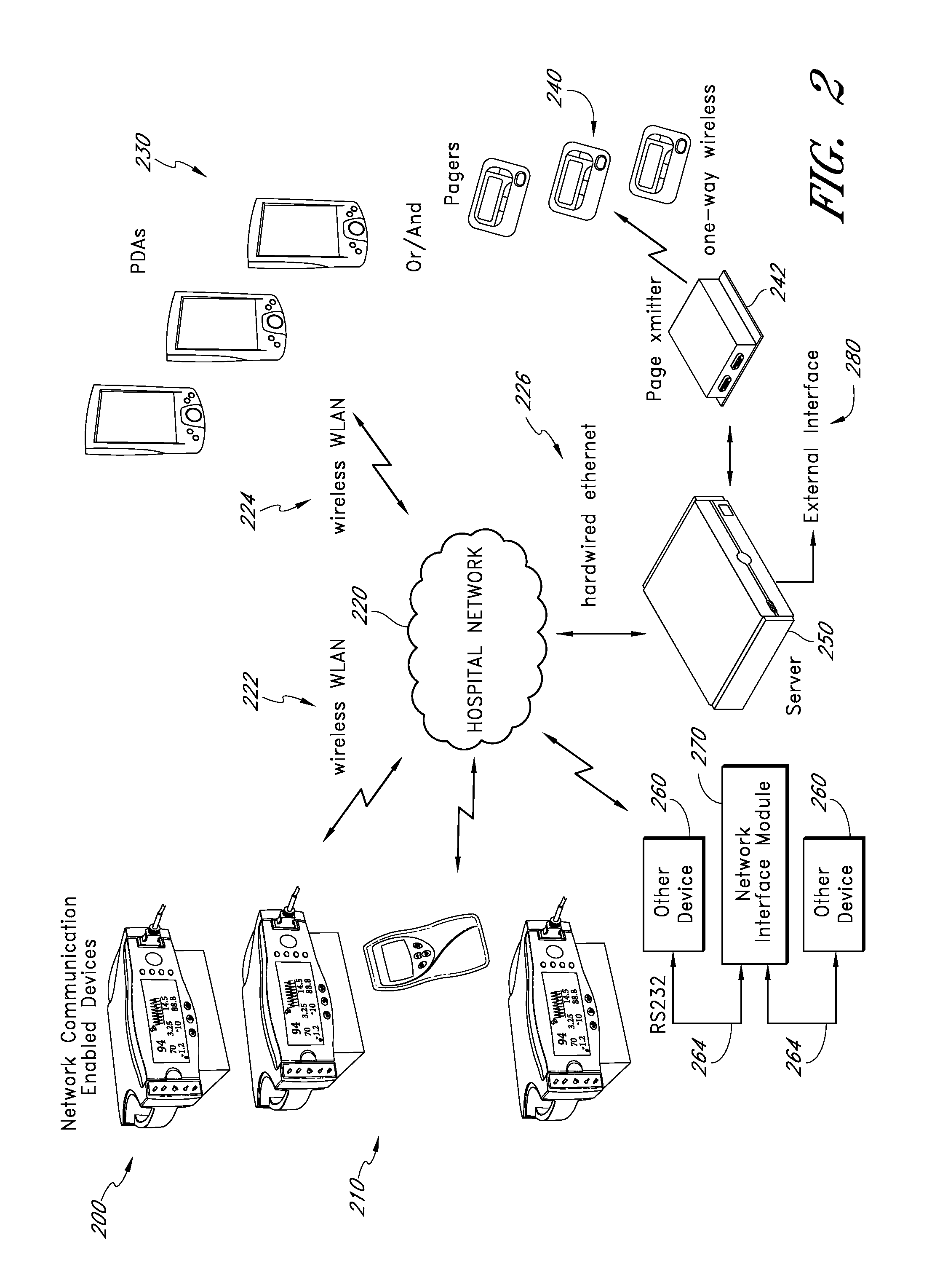
System and method for locating and communicating with personnel and equipment in a facility
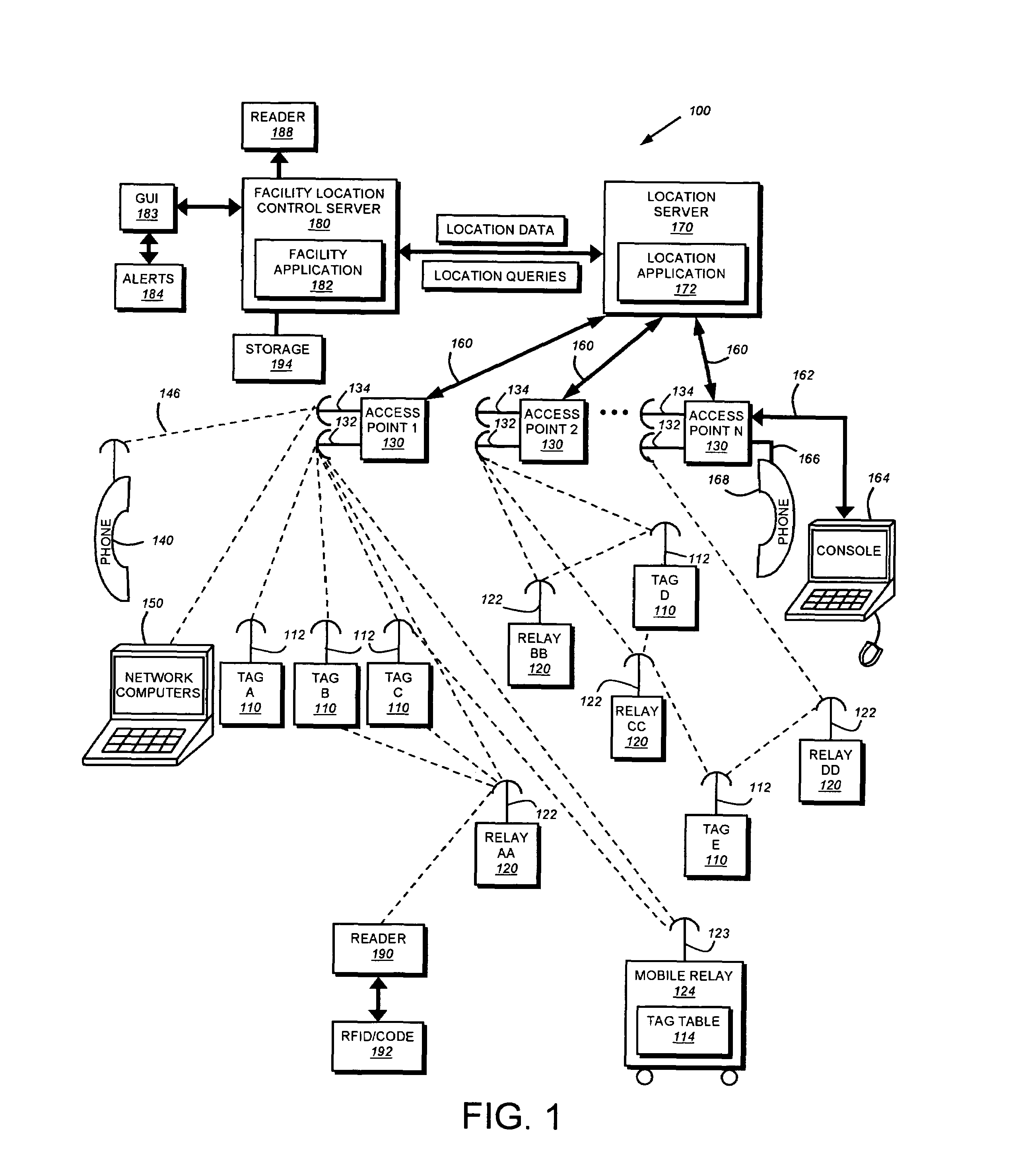
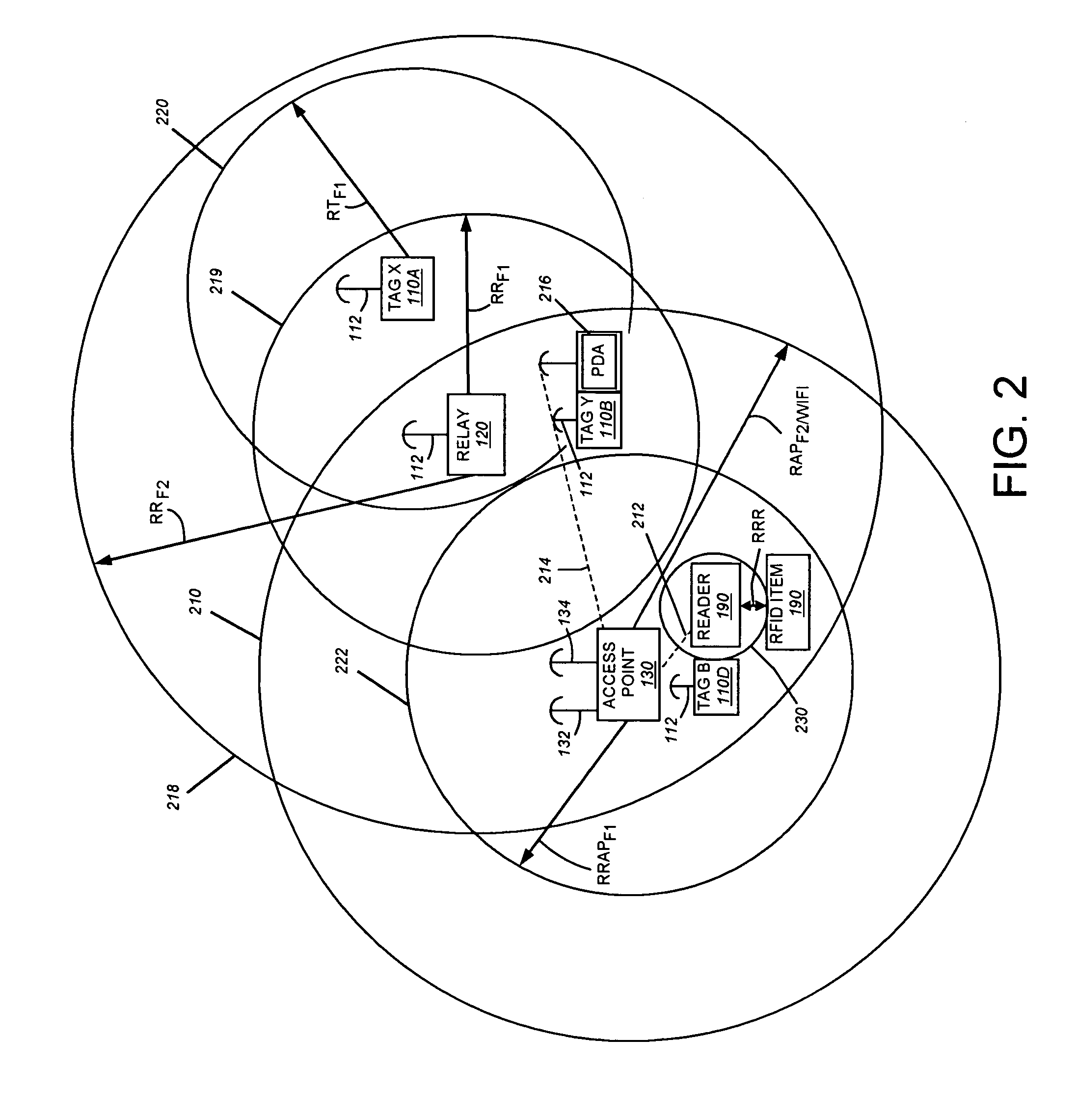
InactiveUS7323991B1Increase redundancyQuickly and frequently and continuously updatedElectric signal transmission systemsTicket-issuing apparatusTransceiverWireless data
This invention provides a system and method for identifying, locating, authorizing by proximity and communicating with equipment and personnel in a facility that generally employs a series of limited range transceivers for location determination and a distributed wireless data network for data transfer. The system employs unique RF transceiver tags on personnel and equipment that are each uniquely identified and registered with a facility control application that oversees activities in the facility. The tags are tracked by RF communication based upon their proximity to one or more fixed-base networked access points and relays (which transfer location data by RF back to access points) within four range zones. Location data on all tags is uploaded periodically to a location server that interfaces with the facility control server. Tag data is monitored by the facility control server to track, authorize and deauthorize certain data transfers, movements and activities in accordance with rules established for each tag (or type of tag) within the facility control server's application. Wireless networking (WiFi, for example), in combination with the RF-derived location information, allows the facility control server to correlate and transmit data to staff in conjunction with location and proximity. WiFi can transmit authorizations, deauthorizations and general data based upon triggers established by proximity and location. Likewise, data can be transmitted over WiFi from readers etc. from personnel and equipment located and identified by the system.
Owner:TIDEWATER HLDG
Limited-use keys and cryptograms
ActiveUS20150178724A1Promote generationImprove securityMultiple keys/algorithms usageCryptography processingCryptogramCommunication device
Techniques for enhancing the security of a communication device when conducting a transaction using the communication device may include encrypting account information with a first encryption key to generate a second encryption key, and encrypting key index information using the second key to generate a limited-use key (LUK). The key index information may include a key index having information pertaining to generation of the LUK. The LUK and the key index can be provided to the communication device to facilitate generation of a transaction cryptogram for a transaction conducted using the communication device, and the transaction can be authorized based on the transaction cryptogram generated from the LUK.
Owner:VISA INT SERVICE ASSOC
Electronic apparatus, electronic camera, electronic device, image display apparatus, and image transmission system
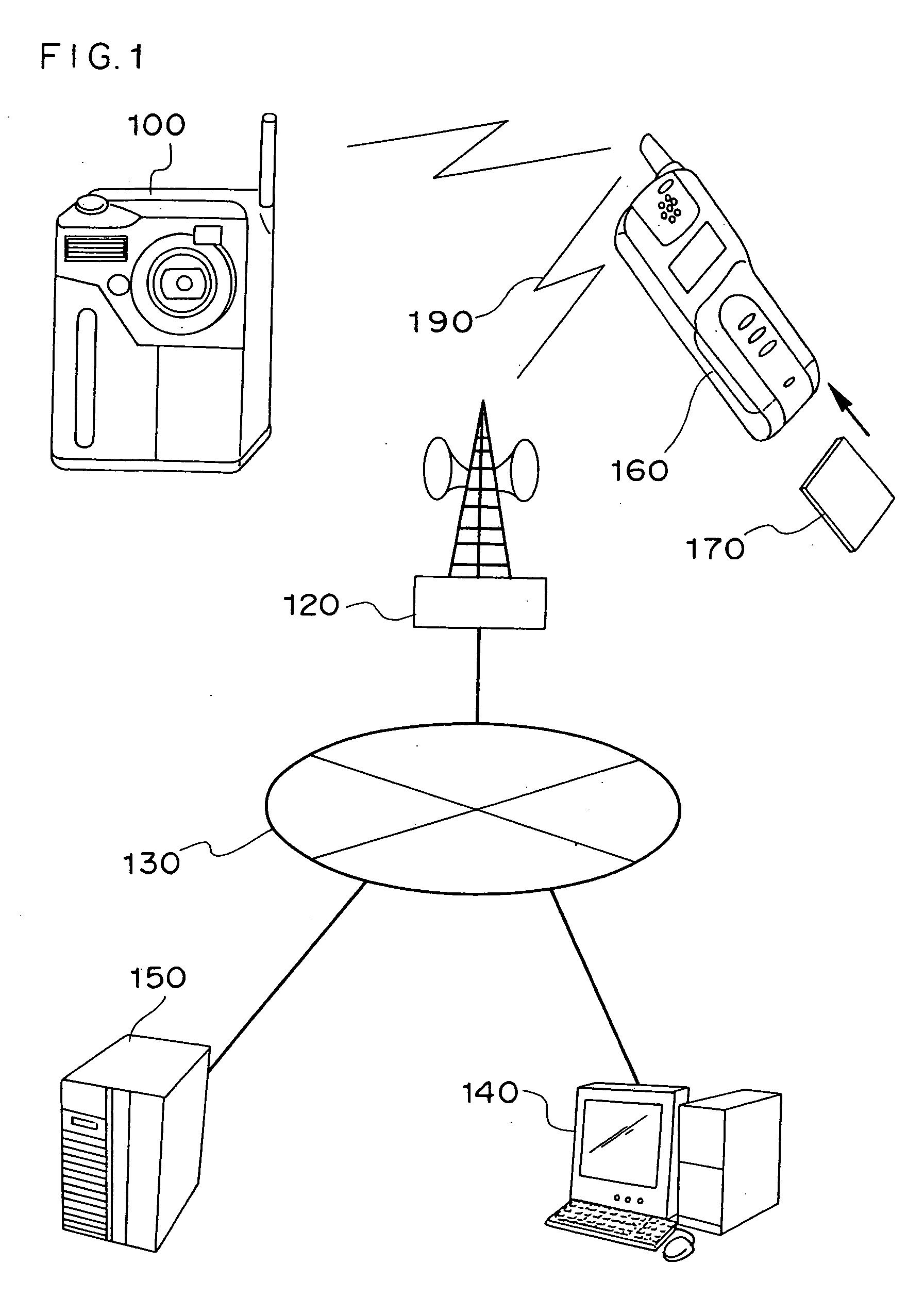
ActiveUS20050001024A1Speed up user identificationAvoid mistakesTelevision system detailsElectric signal transmission systemsComputer hardwareTransfer system
In an electronic apparatus having a user identification function or in a user identification method, an electronic apparatus and an electronic instrument having stored therein user personal information communicate in wireless with each other so as to enable the electronic apparatus to automatically identify the electronic apparatus user. If the electronic apparatus identifies a plurality of possible users, the electronic apparatus automatically selects the user by executing specific user identification processing.
Owner:NIKON CORP
Intelligent home automation
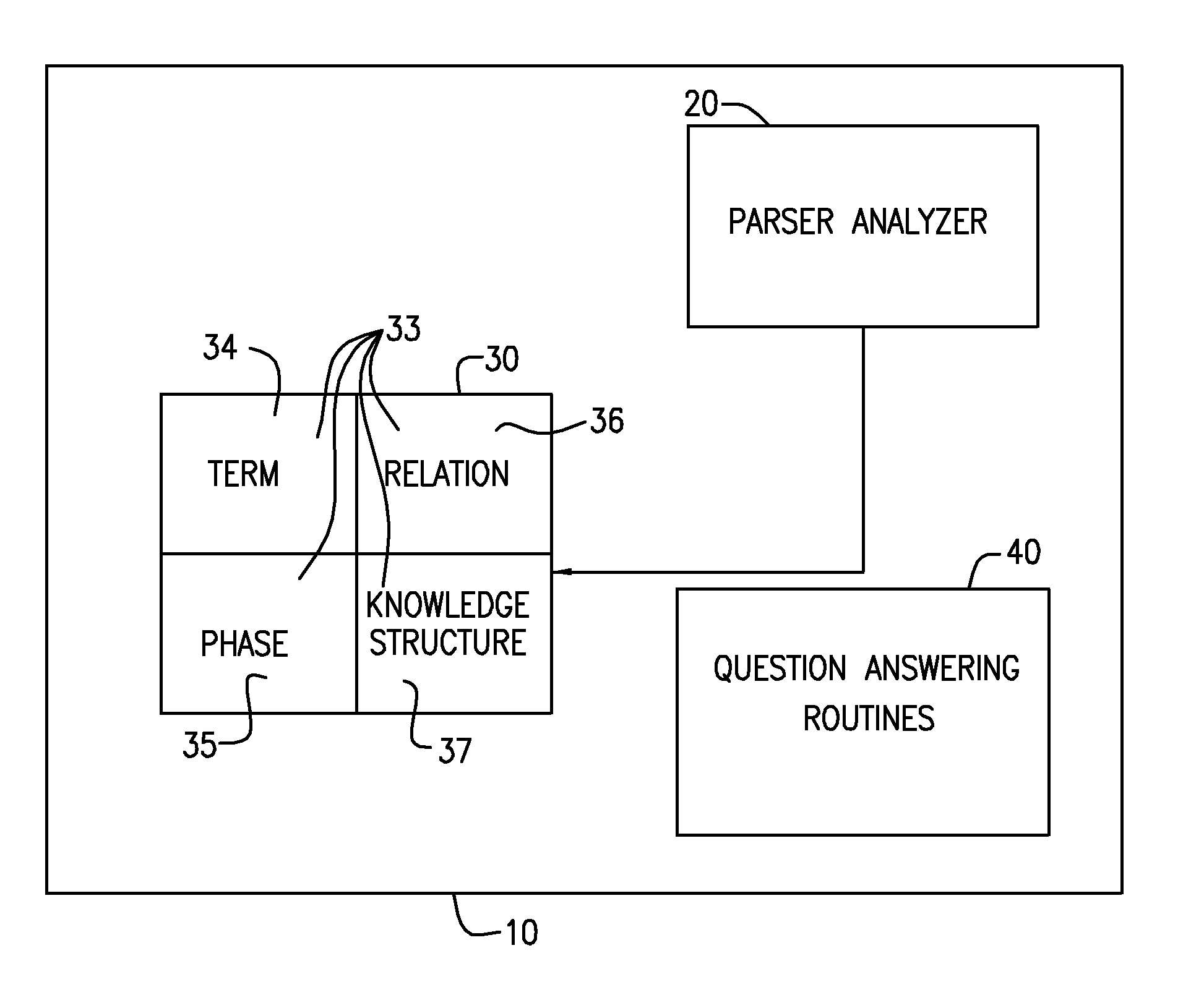
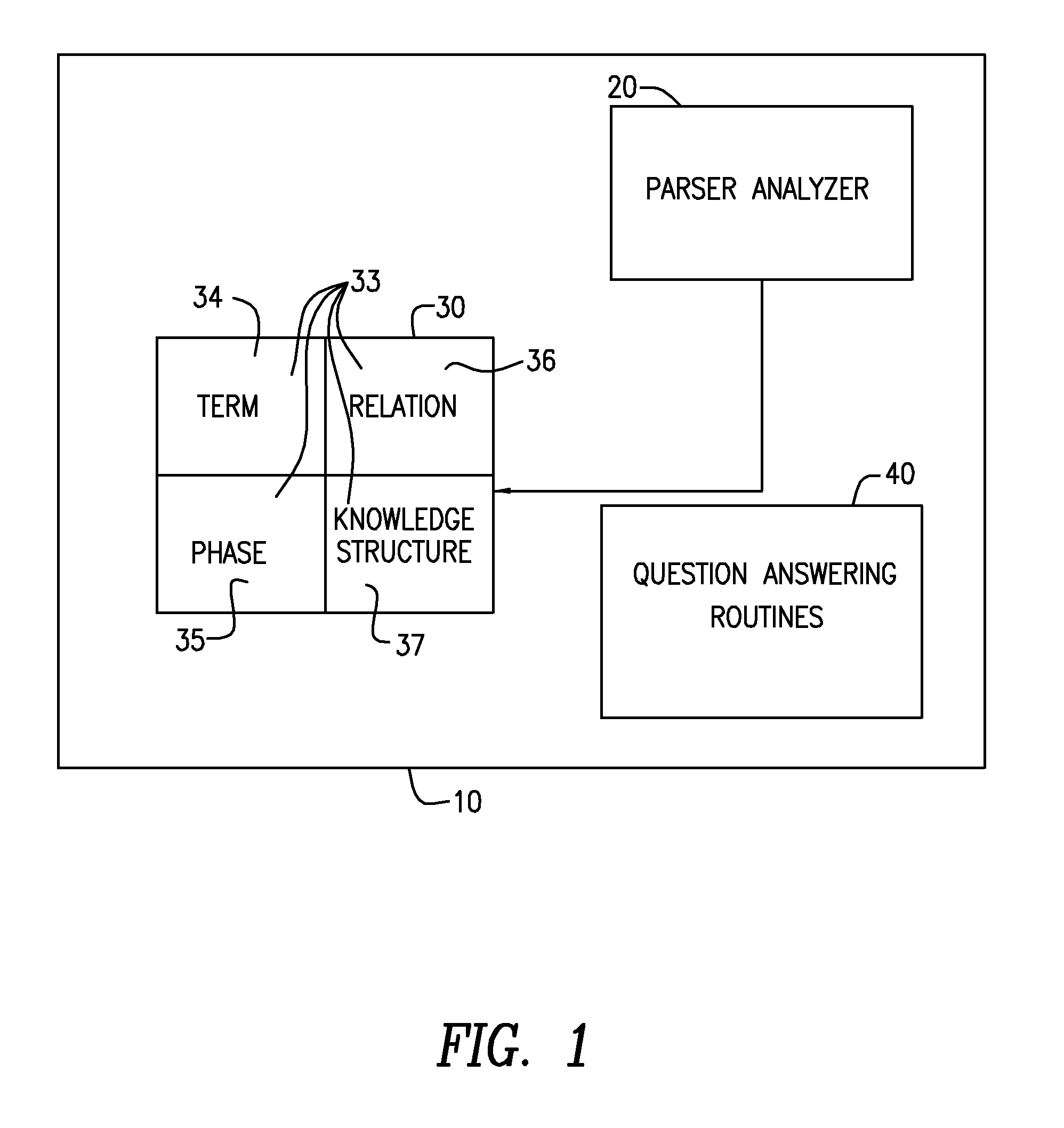
InactiveUS20100332235A1Electric signal transmission systemsMultiple keys/algorithms usageSpoken languageThe Internet
An intelligent home automation system answers questions of a user speaking “natural language” located in a home. The system is connected to, and may carry out the user's commands to control, any circuit, object, or system in the home. The system can answer questions by accessing the Internet. Using a transducer that “hears” human pulses, the system may be able to identify, announce and keep track of anyone entering or staying in the home or participating in a conversation, including announcing their identity in advance. The system may interrupt a conversation to implement specific commands and resume the conversation after implementation. The system may have extensible memory structures for term, phrase, relation and knowledge, question answering routines and a parser analyzer that uses transformational grammar and a modified three hypothesis analysis. The parser analyzer can be dormant unless spoken to. The system has emergency modes for prioritization of commands.
Owner:DAVID ABRAHAM BEN
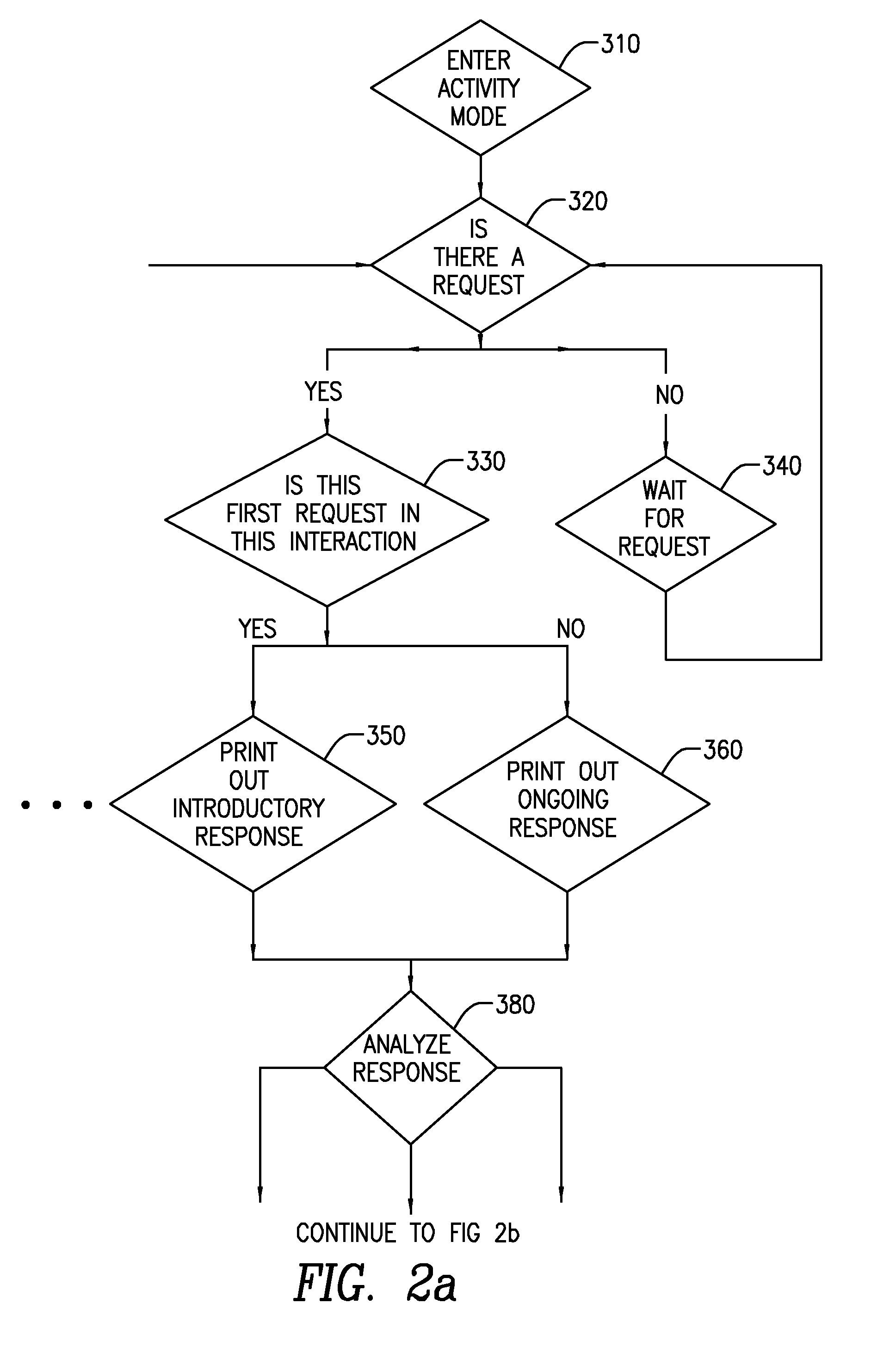
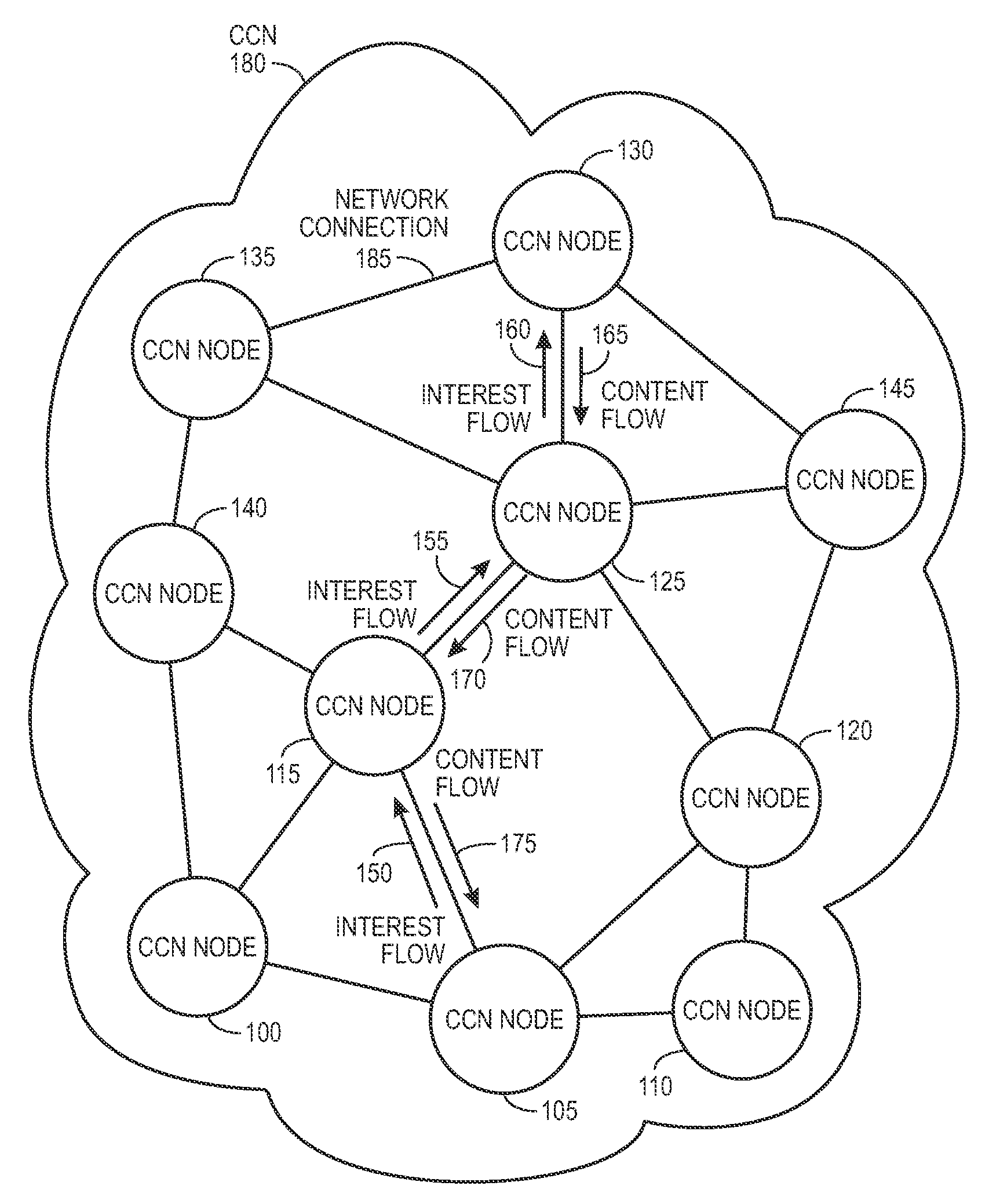
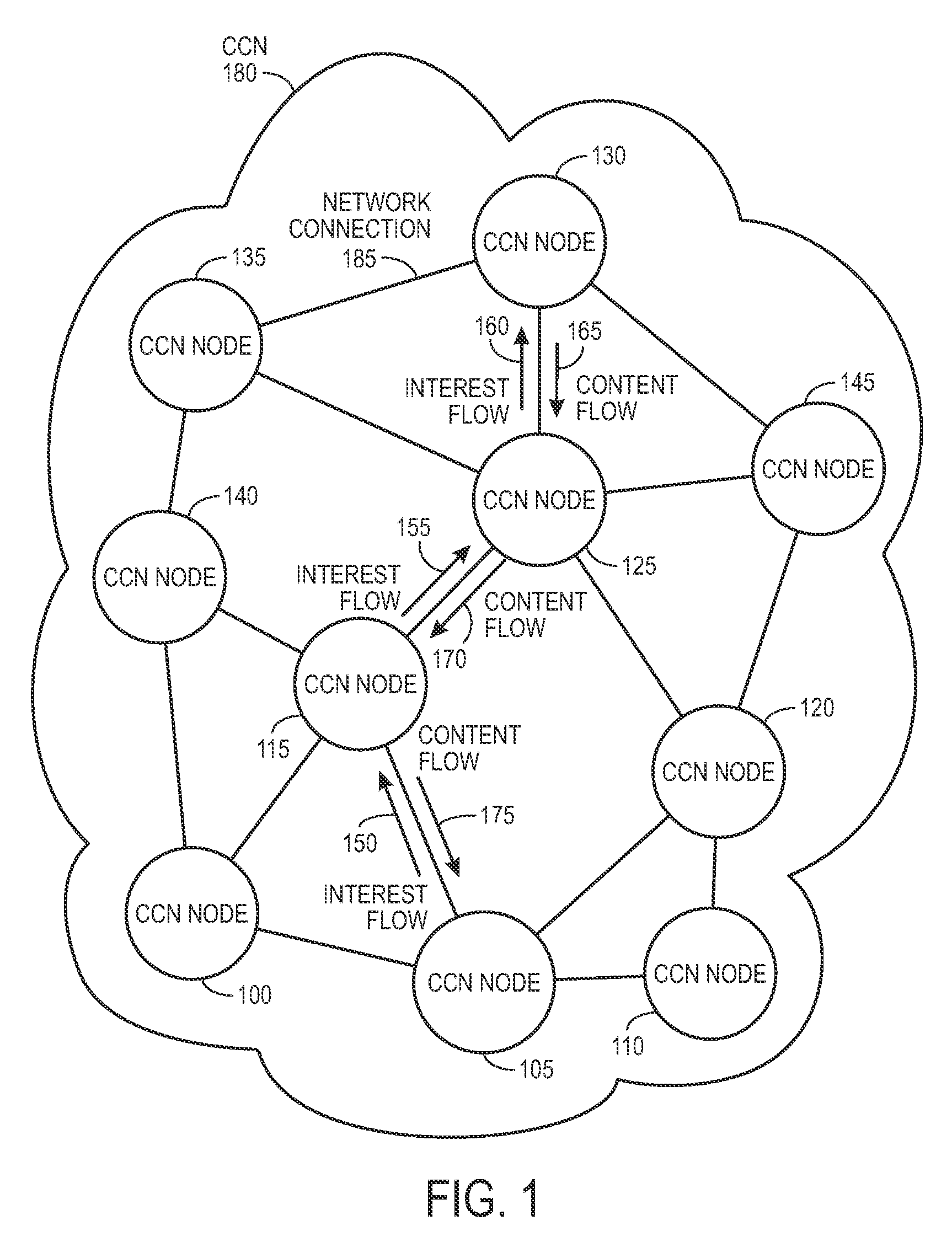
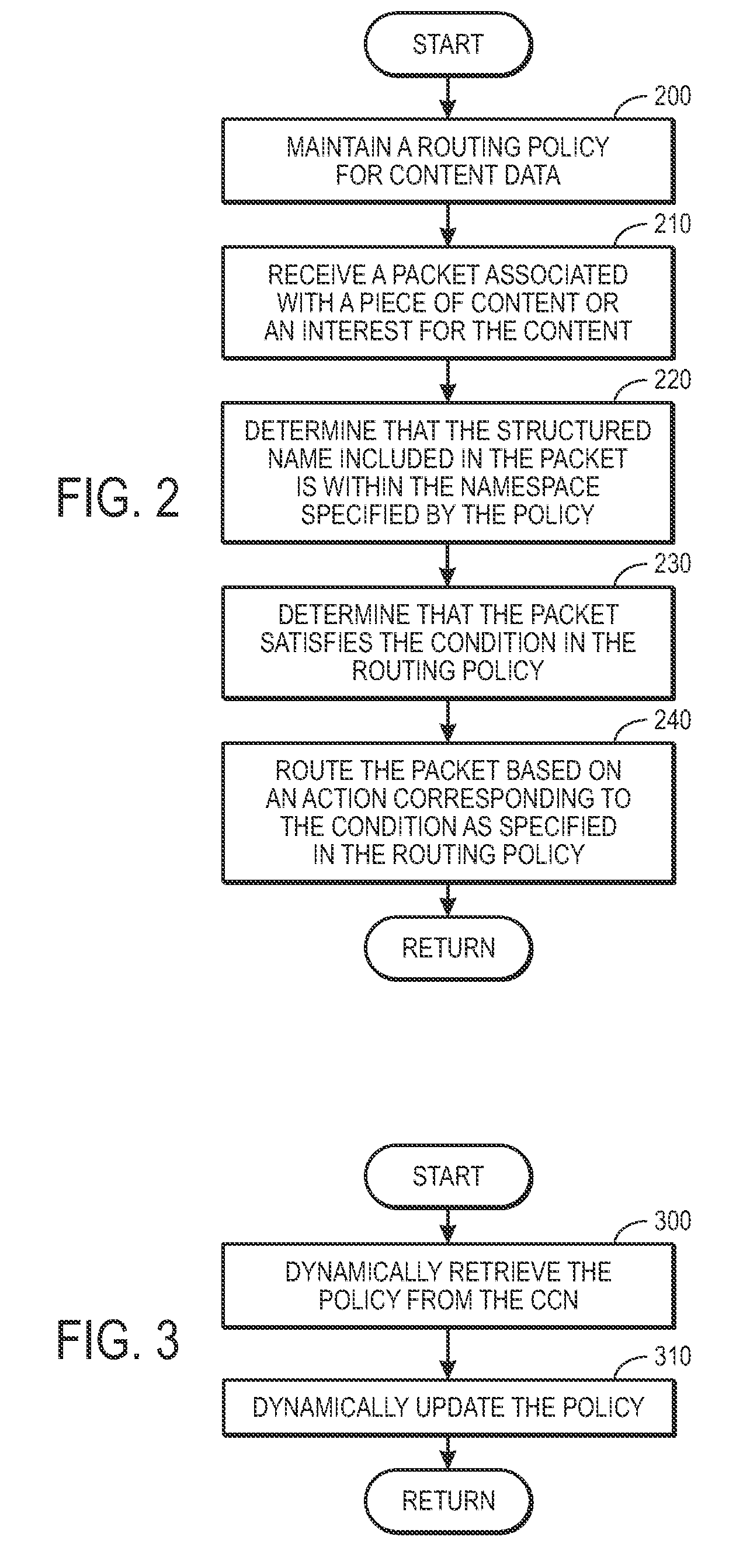
Controlling the spread of interests and content in a content centric network
ActiveUS20090288163A1Easy flow controlExpected levelMemory loss protectionMultiple keys/algorithms usageContent centricSystem maintenance
One embodiment of the present invention provides a system for controlling the spread of interests and content in a content centric network (CCN). During operation, the system maintains a routing policy for content data. The system also receives a packet associated with a piece of content or an interest for the content. Next, the system determines that the structured name included in the packet is within the namespace specified in the routing policy. The system further determines that the packet satisfies the condition in the routing policy. Subsequently, the system routes the packet based on in part the action corresponding to the condition as specified in the routing policy.
Owner:CISCO TECH INC
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
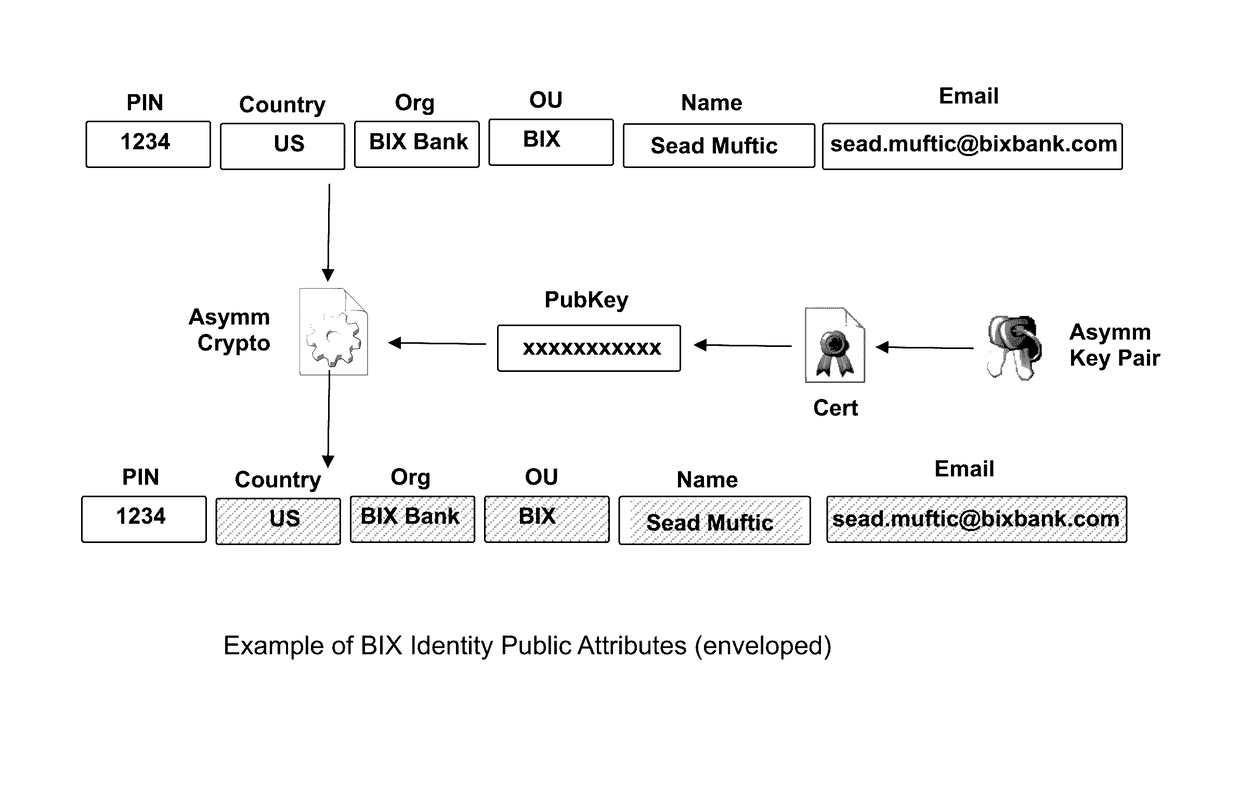
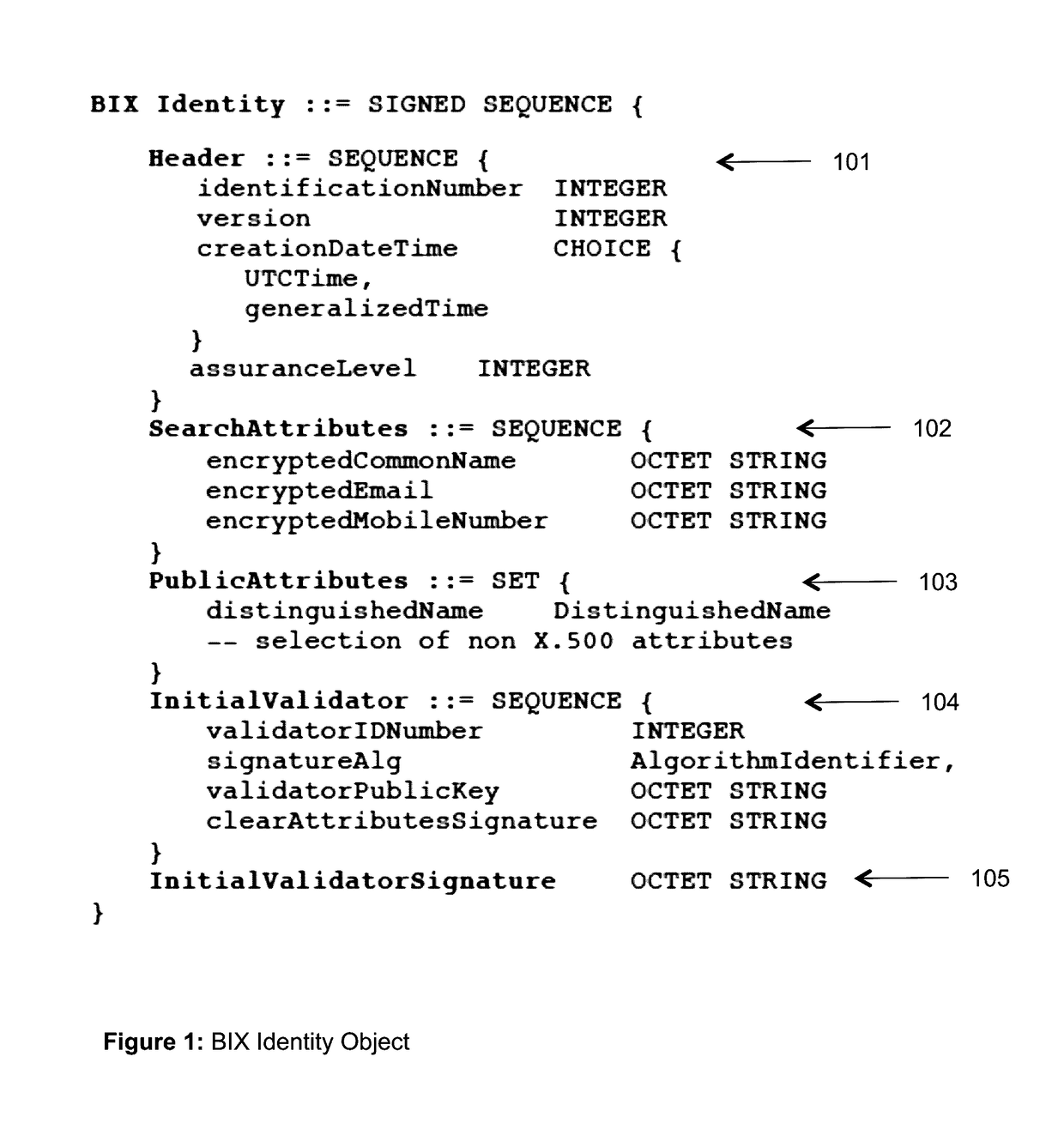
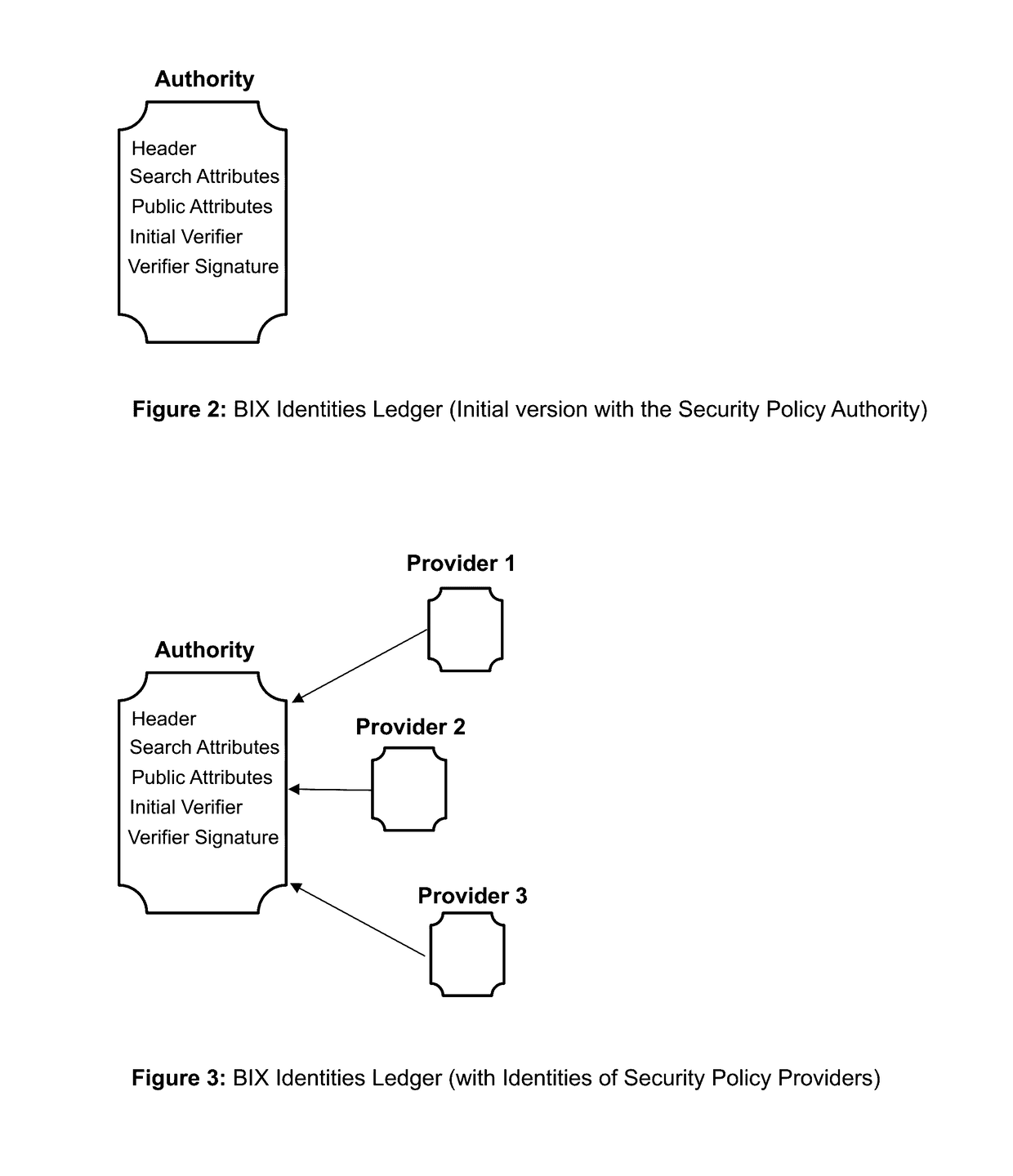
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
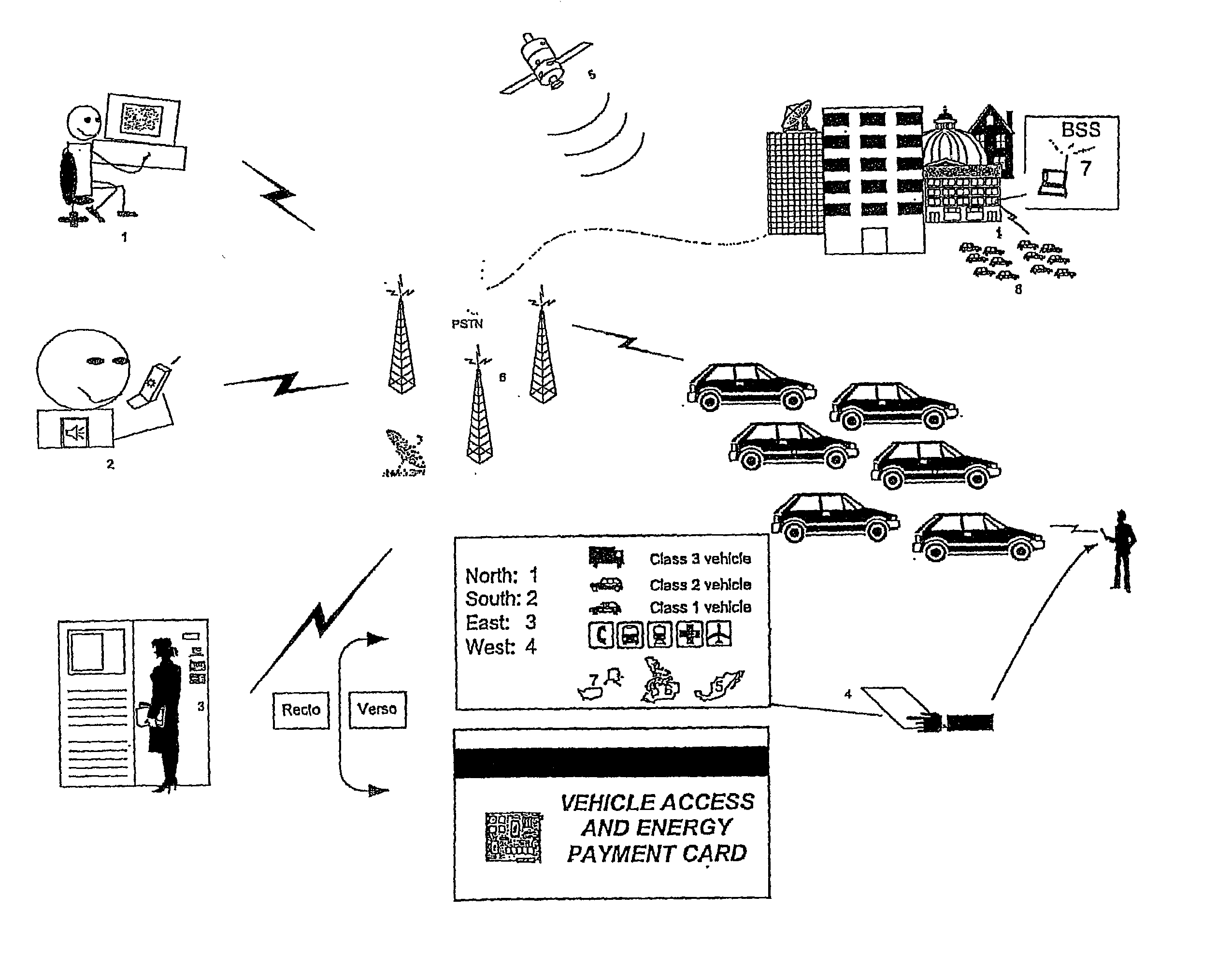
System and method for automating a vehicle rental process
InactiveUS20020186144A1Eliminate needLower the thresholdElectric signal transmission systemsTicket-issuing apparatusCommunication unitOn board
The present invention concerns an automated vehicle rental system for a fleet of rental vehicles, where the vehicles are geographically distributed and normally locked when not rented. At least one of the vehicles, when not in use, is parked in an unguarded location. The system has a vehicle communications unit for enabling communication to and from the vehicle, user-carried electronic devices, or other readers, and for interfacing with the user. An on-board unit (OBU) is located on each of the vehicles for interfacing with the vehicle communications unit, and with a door unlocking mechanism. The system further has a central reservations, management and location system (CRMLS) in communication through a communications network with each OBU, the CRMLS performing all reservations and management functions, and being linked to a database containing a location and availability of each of thr vehicles and a rate for rental, the CRMLS also being provided with an allocation manager system for geographically allocating vehicles. In order to access the vehicle, the system also includes a key being borne by the user. The system minimizes the human intervention in the rental process, and is more user-friendly.
Owner:ZOOP MOBILITY NETWORK
Radio frequency identification system and method
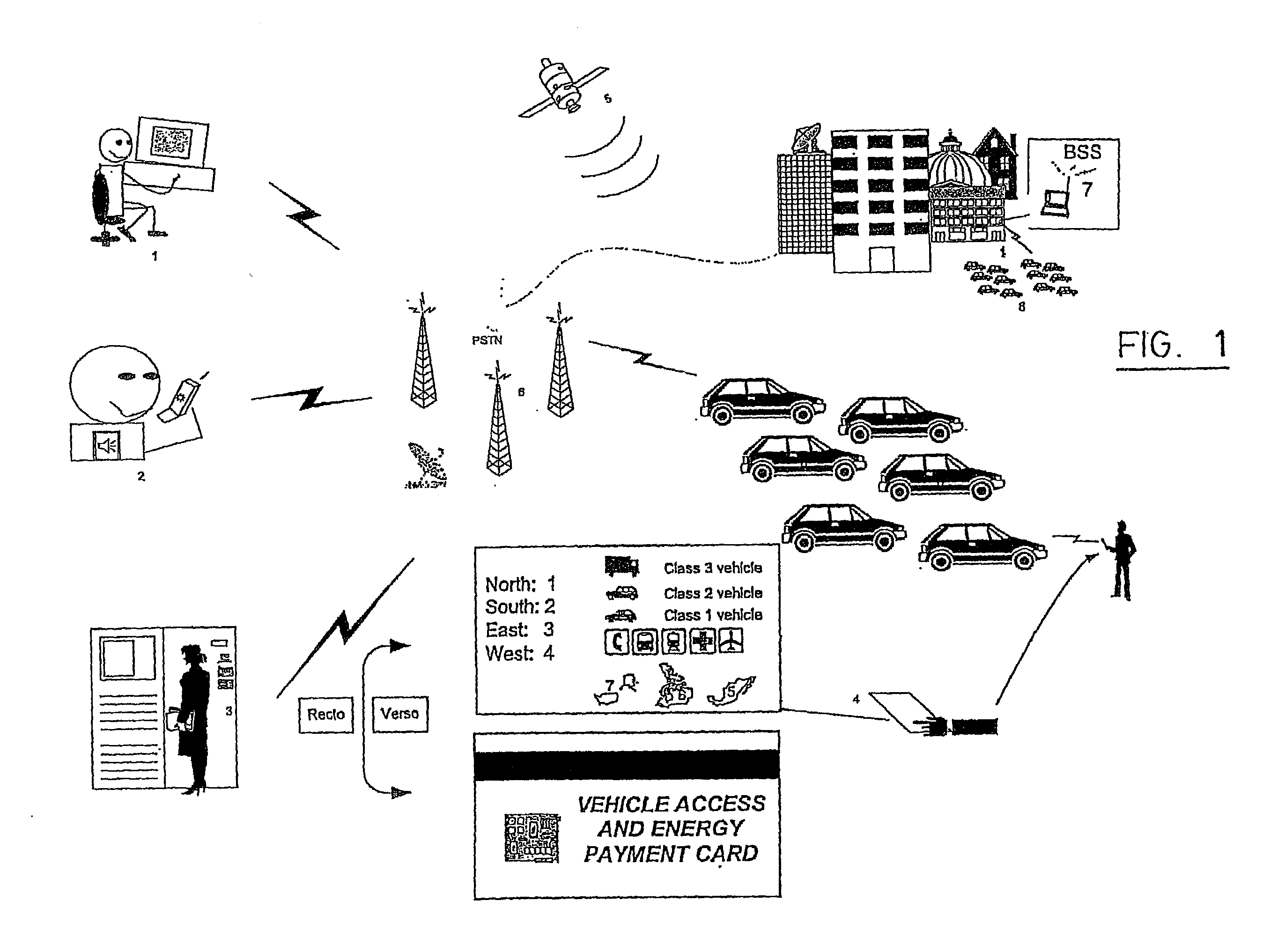
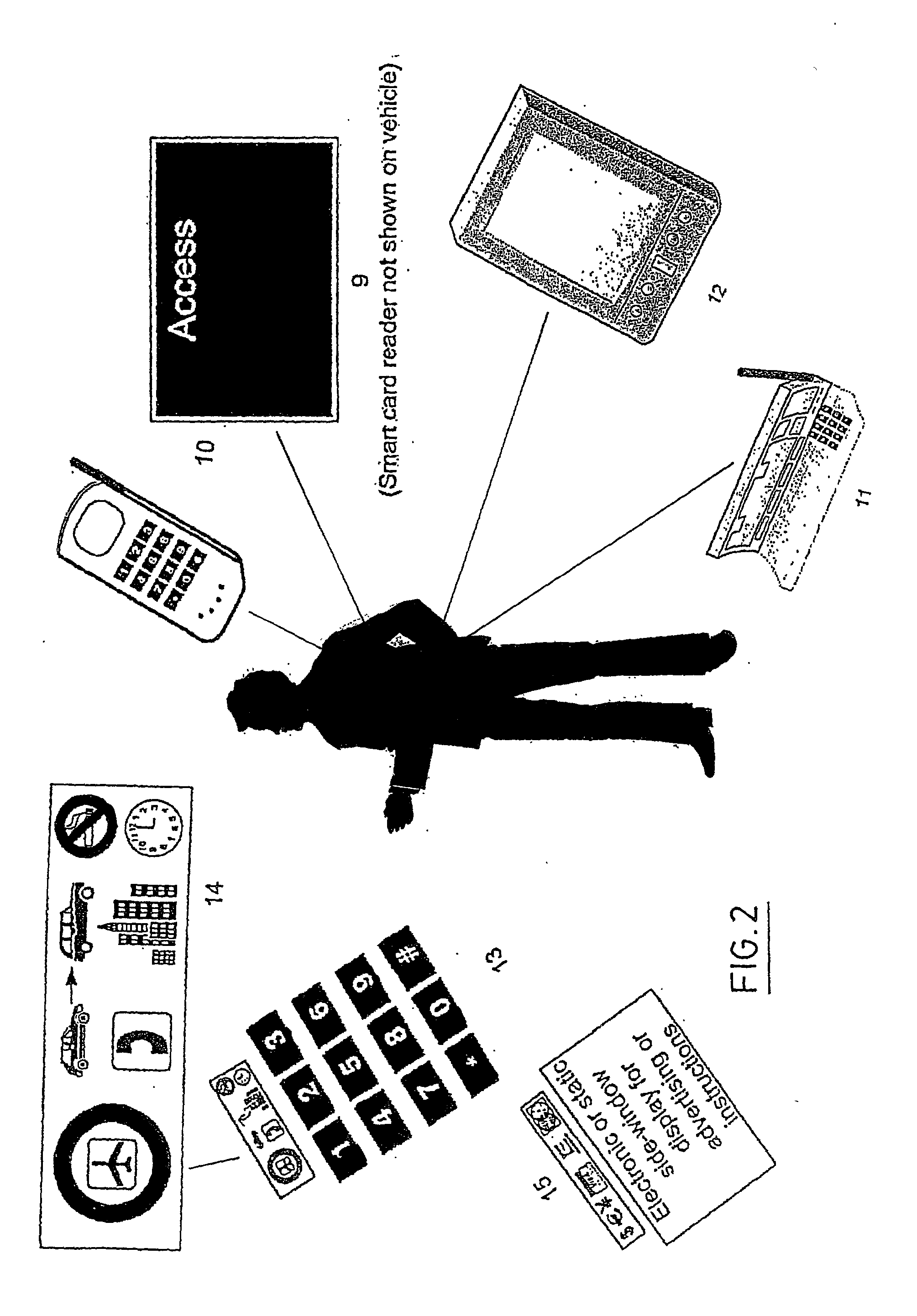
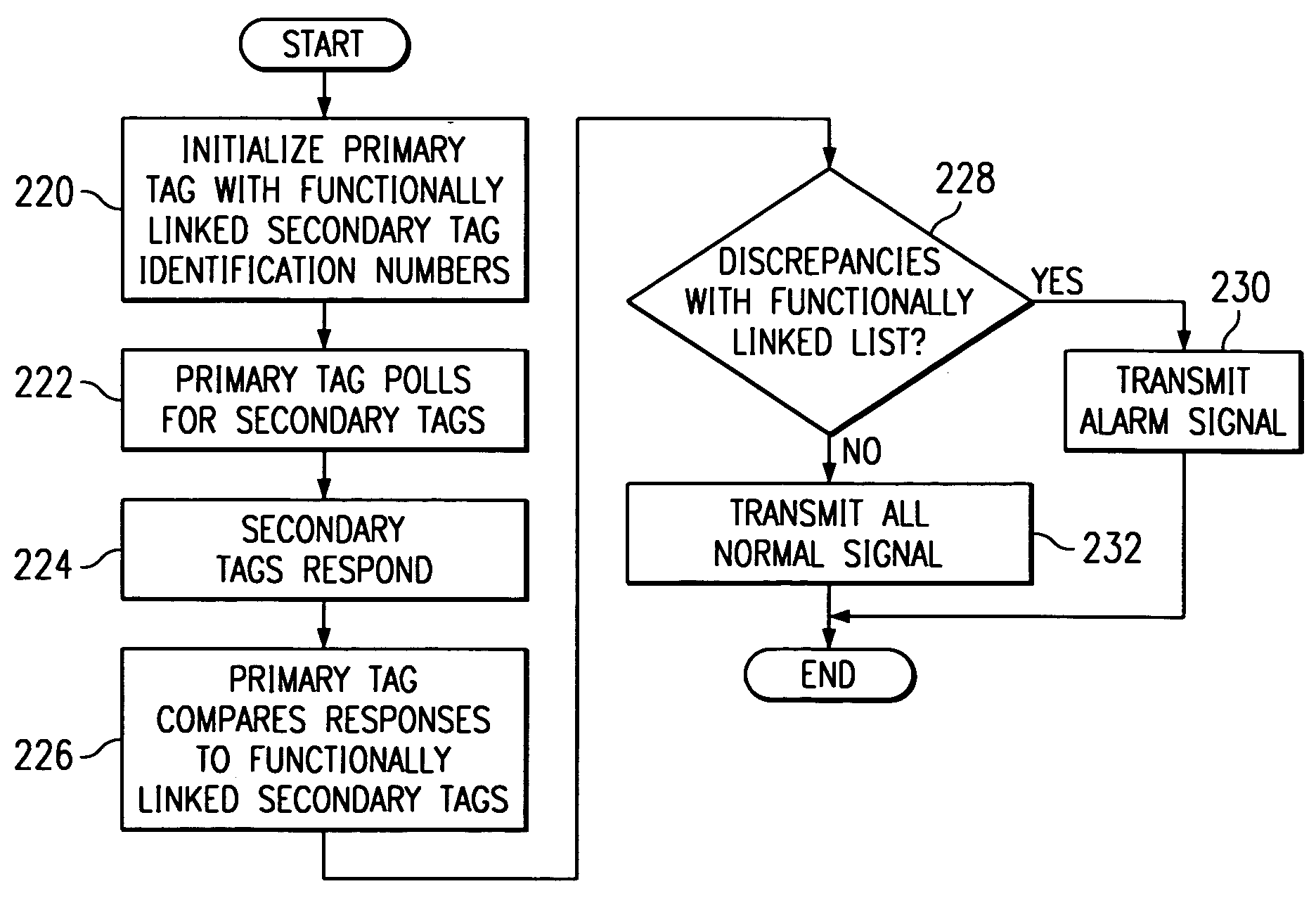
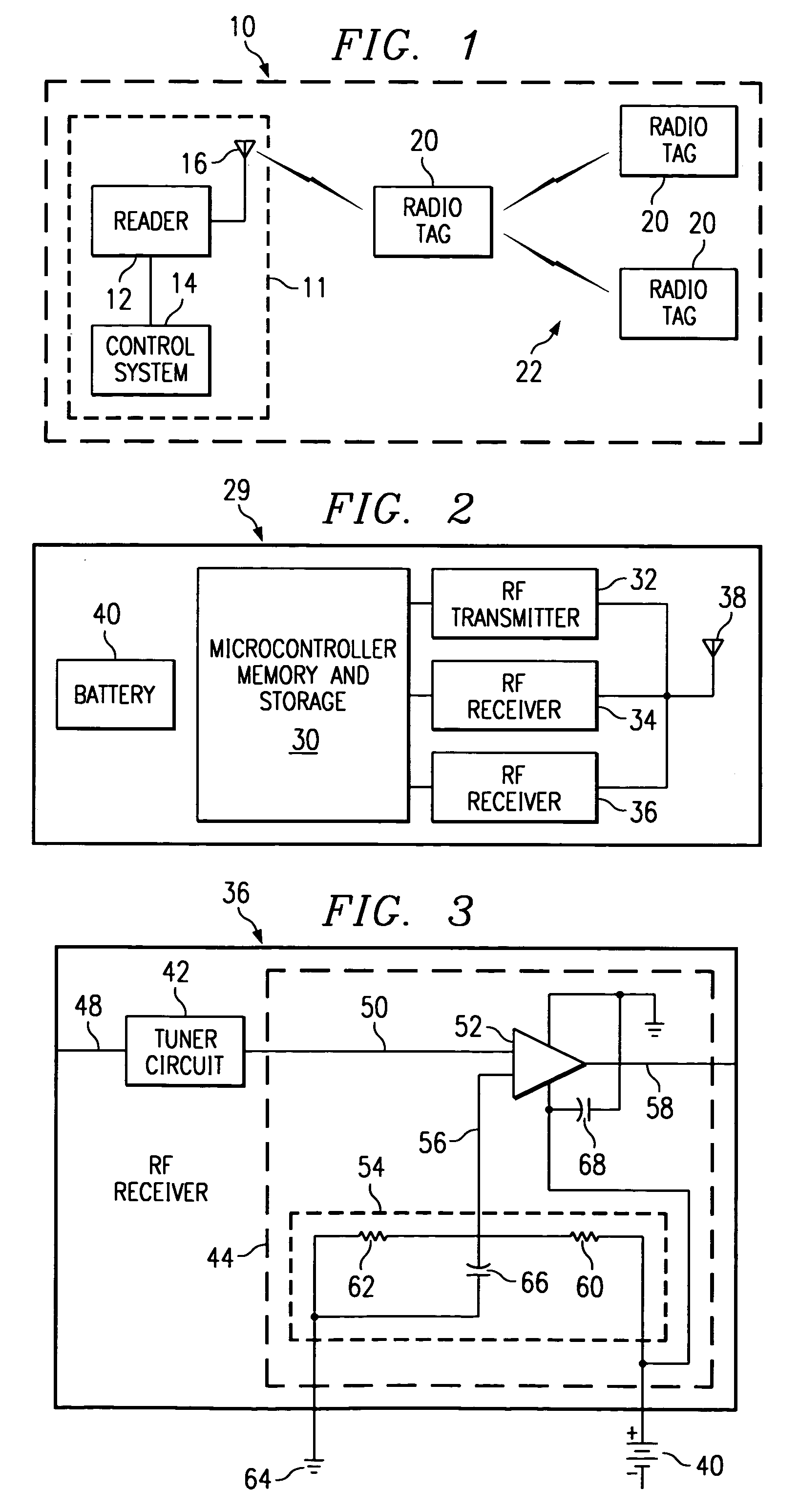
InactiveUS7005985B1Eliminate and reduce disadvantageEliminate and reduce and problemElectric signal transmission systemsMultiple keys/algorithms usageRadio frequencyWorld Wide Web
A method and system for monitoring assets using radio frequency tags is provided that includes a plurality of primary tags. Each primary tag stores an identification of each linked tag associated with the primary tag. The primary tag receives a polling event and transmits a query message for linked tags within an operational range of the primary tag. Each linked tag receiving the query message transmits a response message that includes an identification of the linked tag. The primary tag receives the response messages and compares the identifications in the response messages to the identifications stored for each linked tag. Based on the comparison, the primary tag determines a monitored asset status.
Owner:AXCESS INT INC
Automated Access, Key, Certificate, and Credential Management
ActiveUS20150222604A1Effective rotationLow costMultiple keys/algorithms usagePublic key for secure communicationCredential managementTrust relationship
Certain embodiments provide means for managing automated access to computers, e.g., using SSH user keys and other kinds of trust relationships. Certain embodiments also provide for managing certificates, Kerberos credentials, and cryptographic keys. Certain embodiments provide for remediating legacy SSH key problems and for automating configuration of SSH keys, as well as for continuous monitoring.
Owner:SSH COMMUNICATIONS SECURITY
Identity verification methods
Owner:SYNAPTICS INC
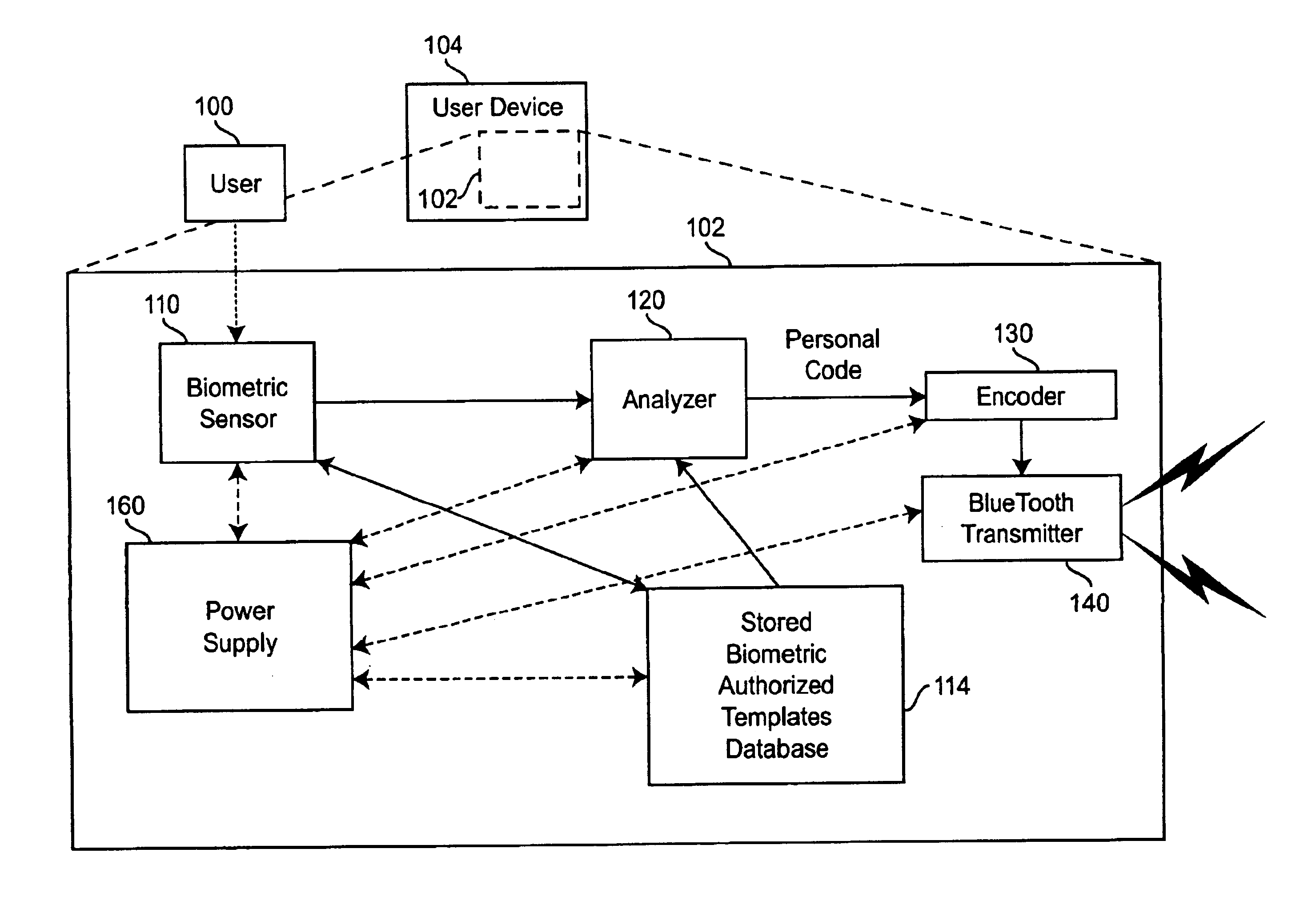
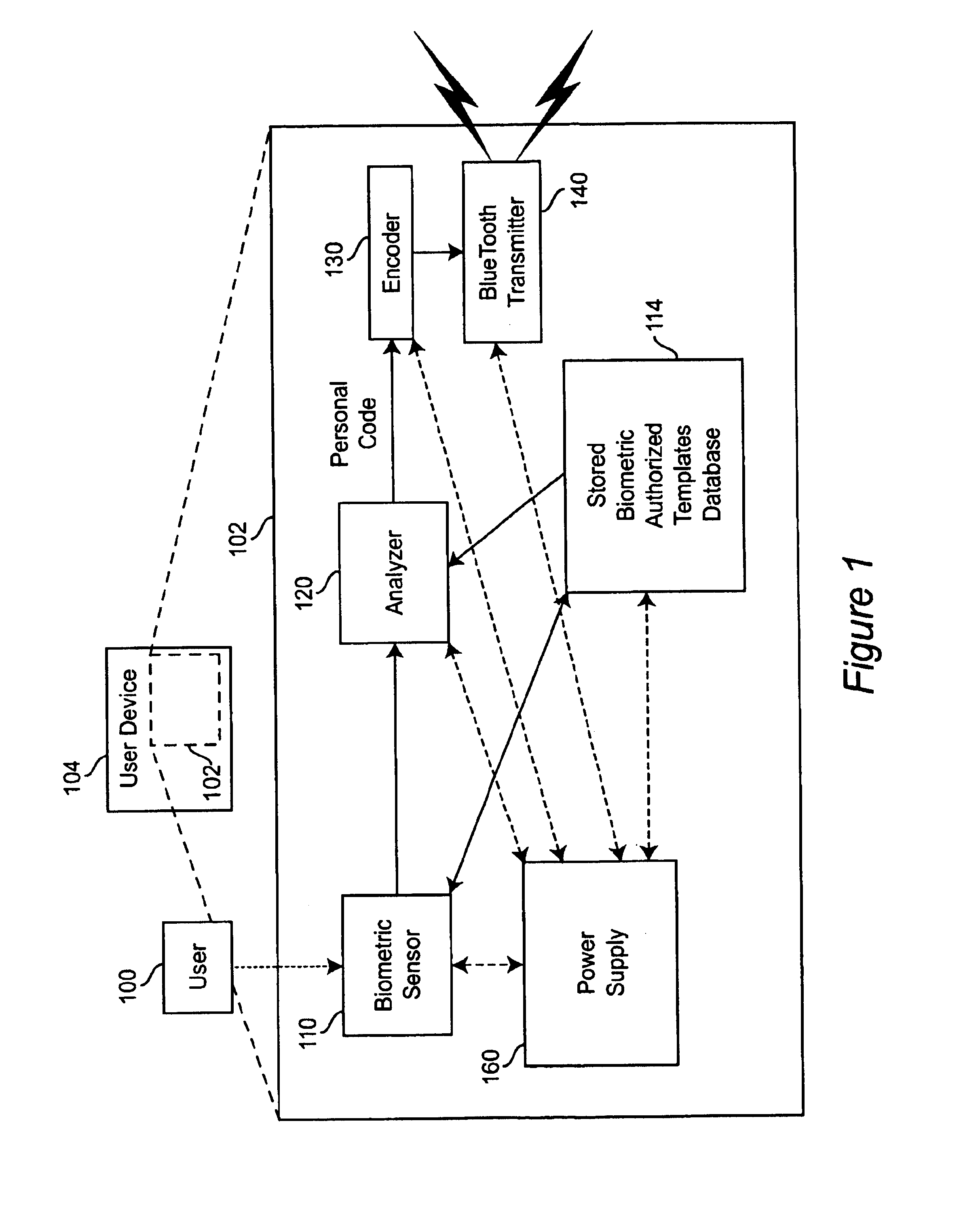
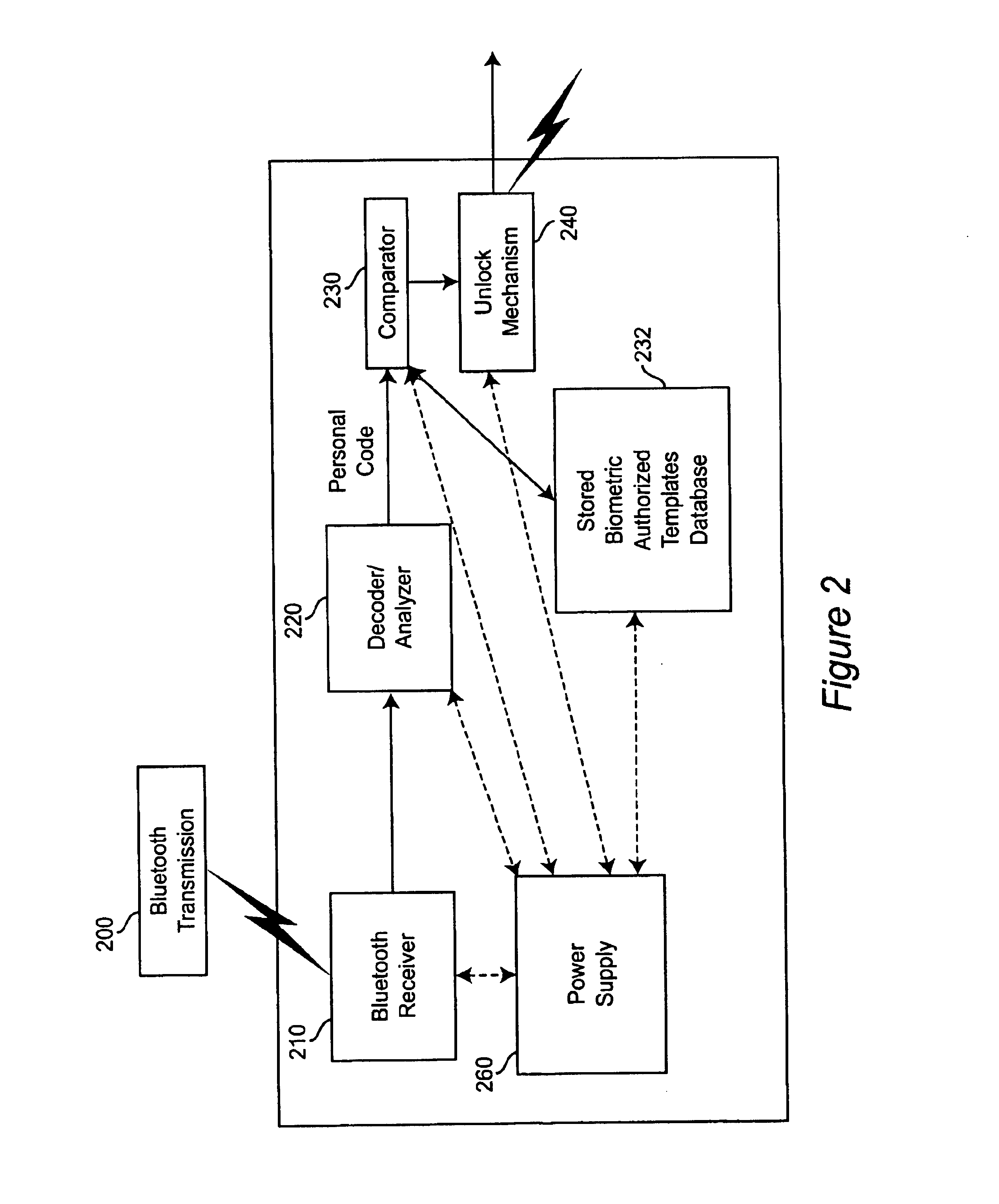
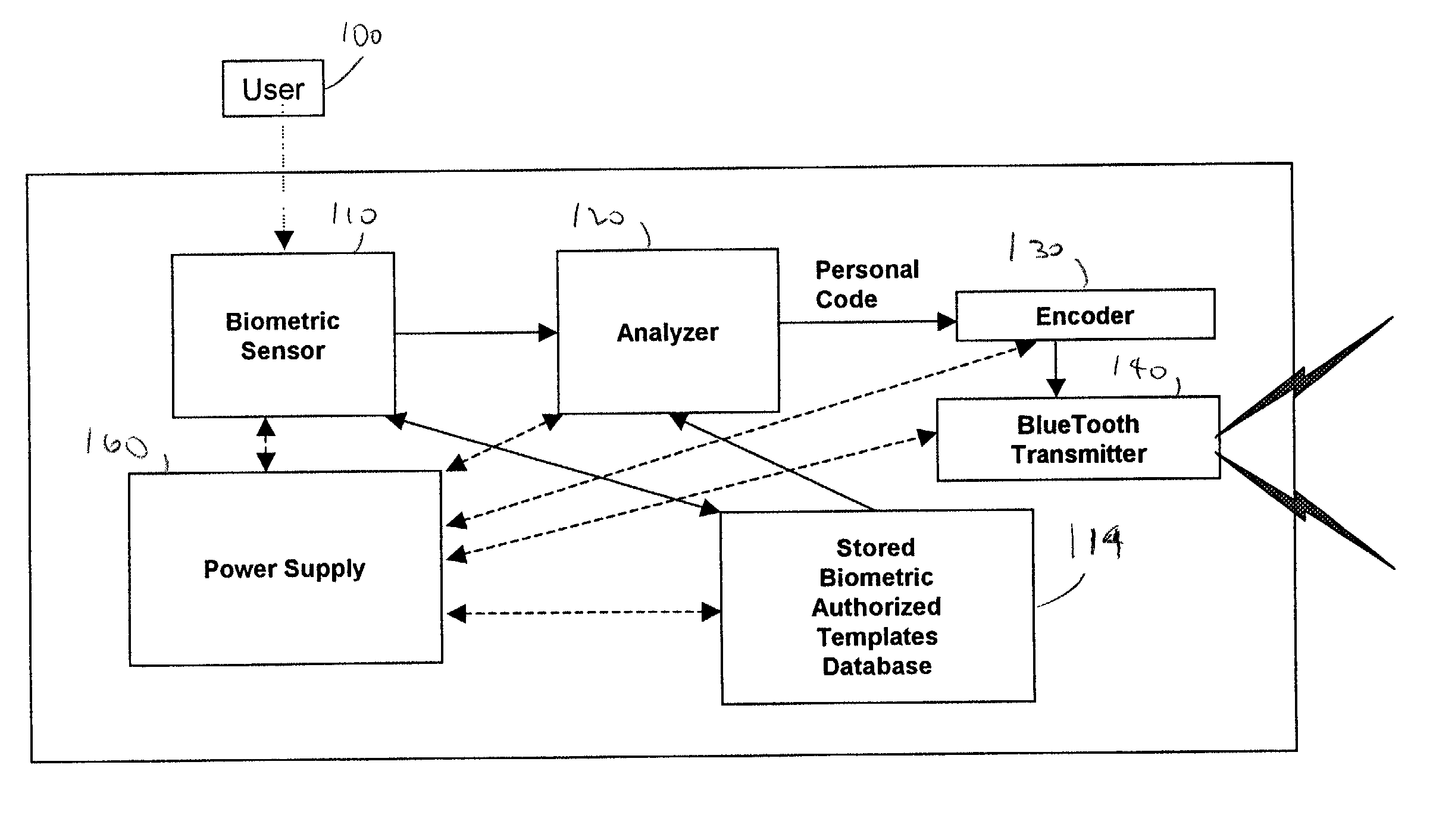
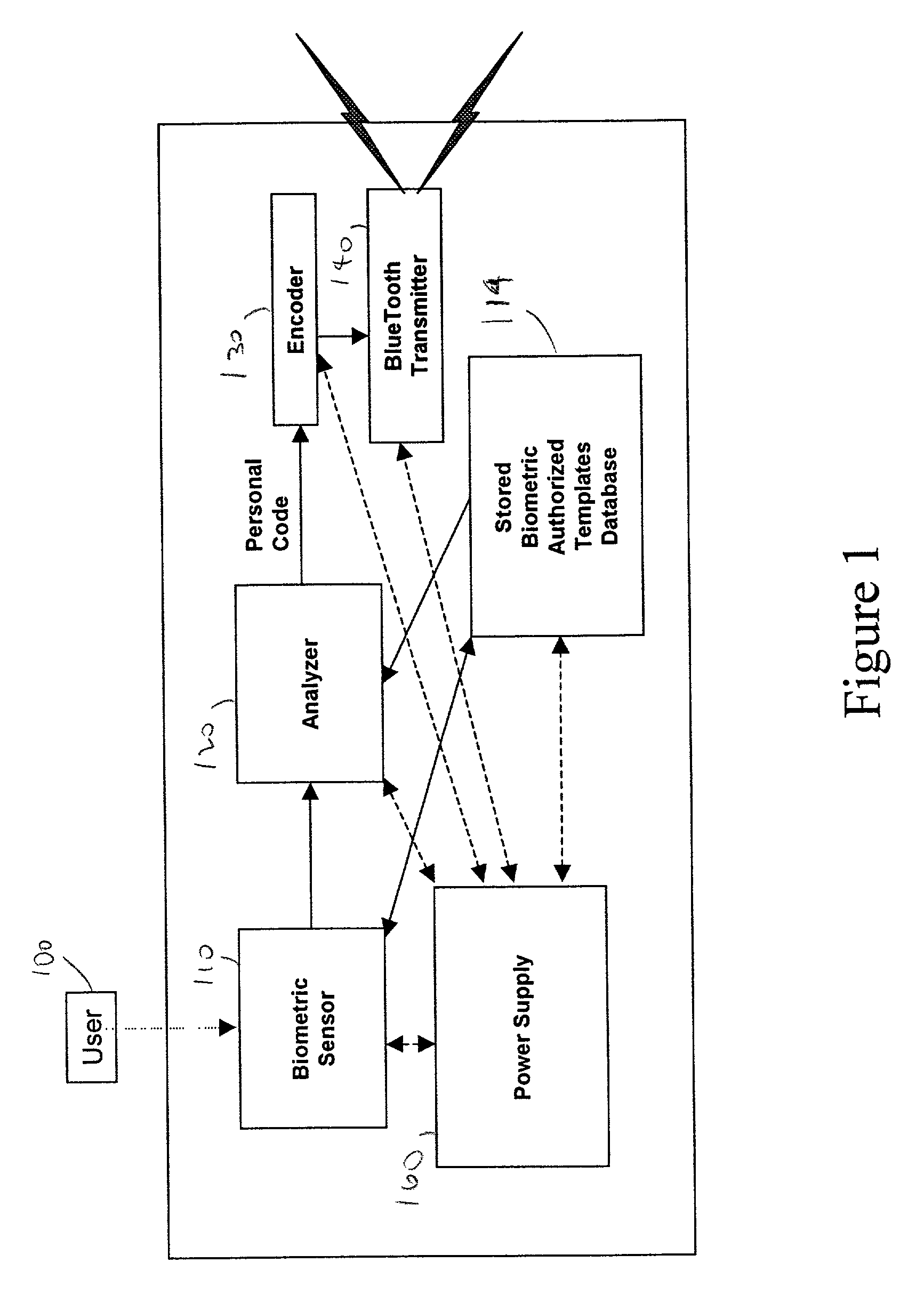
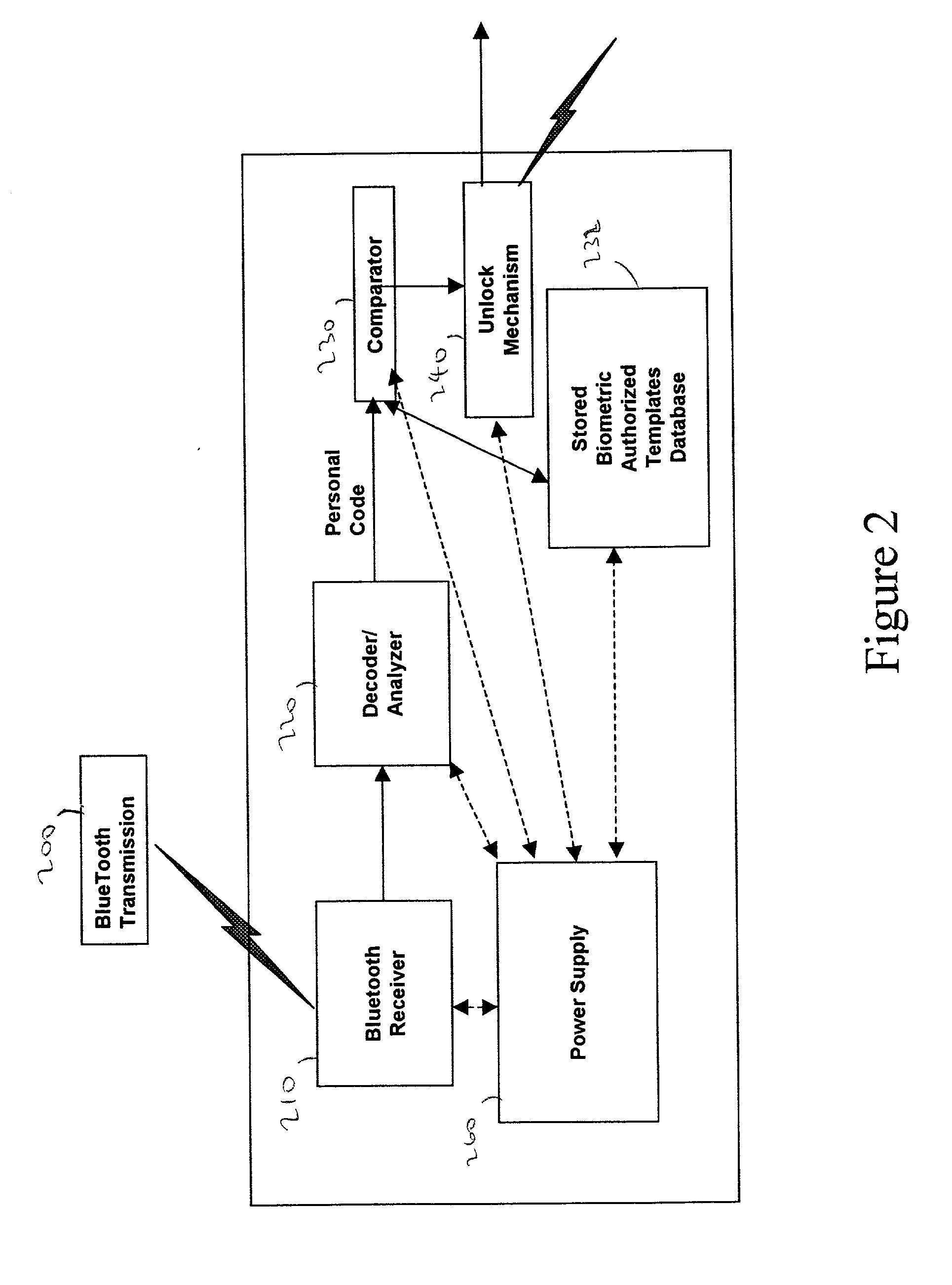
Personal biometric key
InactiveUS6850147B2Reliable resultsEasy to compressElectric signal transmission systemsImage analysisComputer hardwareCommunications system
A personal biometric key system uses a personal identity code transmitted to a universal biometric electronic lock via a communication system and using a clock or GPS chip and allows a person to select one or more personal biometric methods and to be personally responsible for the maintenance of the sensor and its availability. The selection can be tailored to the particular needs and circumstances of the person using the key. The person can also change the personal biometric sensor when needs and circumstances change. The organization being accessed by the key can set minimum levels for what type sensor data they will accept and for level of services they will provide for a given type sensor.
Owner:MIKOS
System and method for connecting security systems to a wireless device
InactiveUS6965313B1Not be preventElectric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
Personal biometric key
InactiveUS20020140542A1Electric signal transmission systemsImage analysisComputer hardwareCommunications system
A personal biometric key system uses a personal identity code transmitted to a universal biometric electronic lock via a communication system and using a clock or GPS chip and allows a person to select one or more personal biometric methods and to be personally responsible for the maintenance of the sensor and its availability. The selection can be tailored to the particular needs and circumstances of the person using the key. The person can also change the personal biometric sensor when needs and circumstances change. The organization being accessed by the key can set minimum levels for what type sensor data they will accept and for level of services they will provide for a given type sensor.
Owner:MIKOS
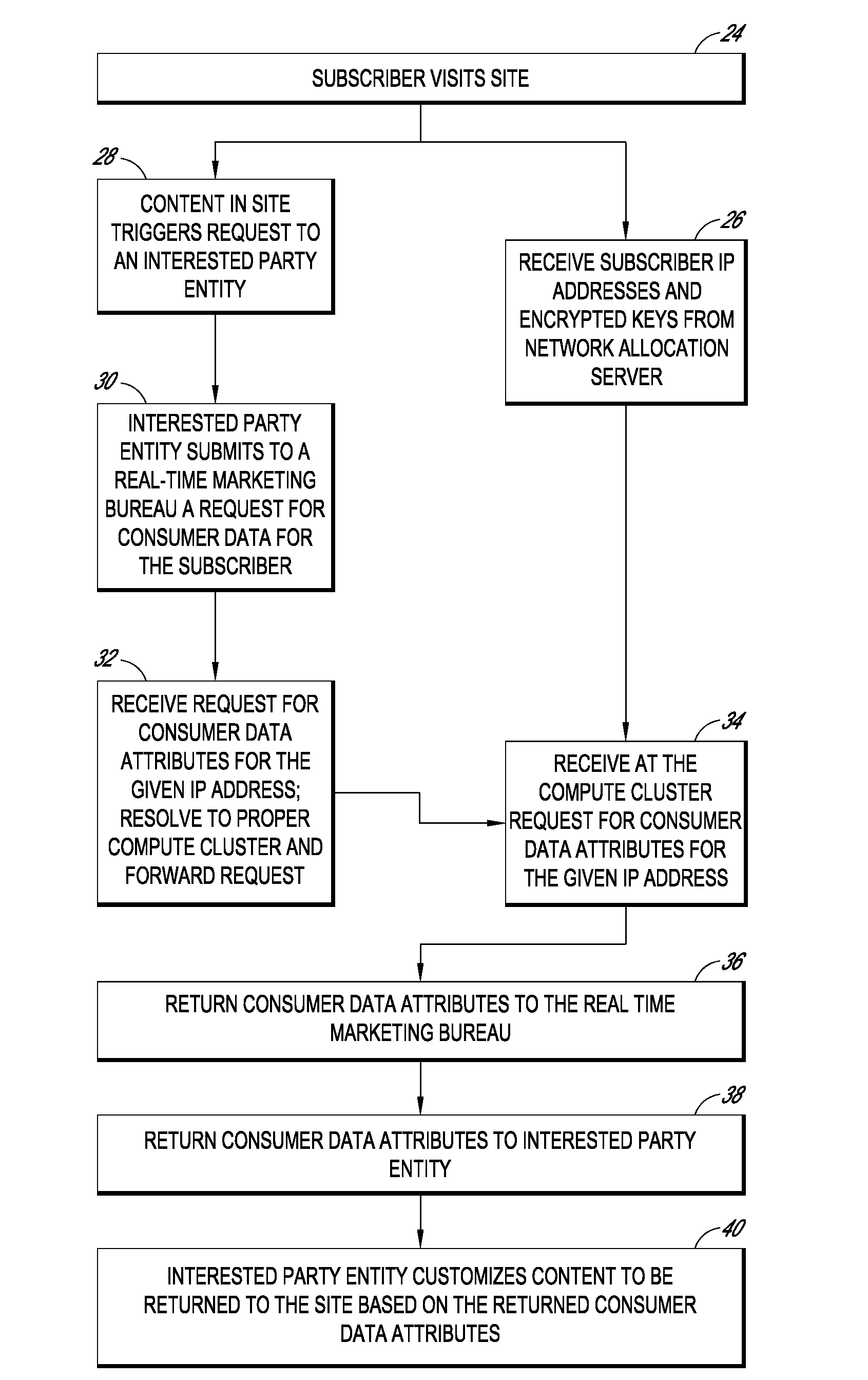
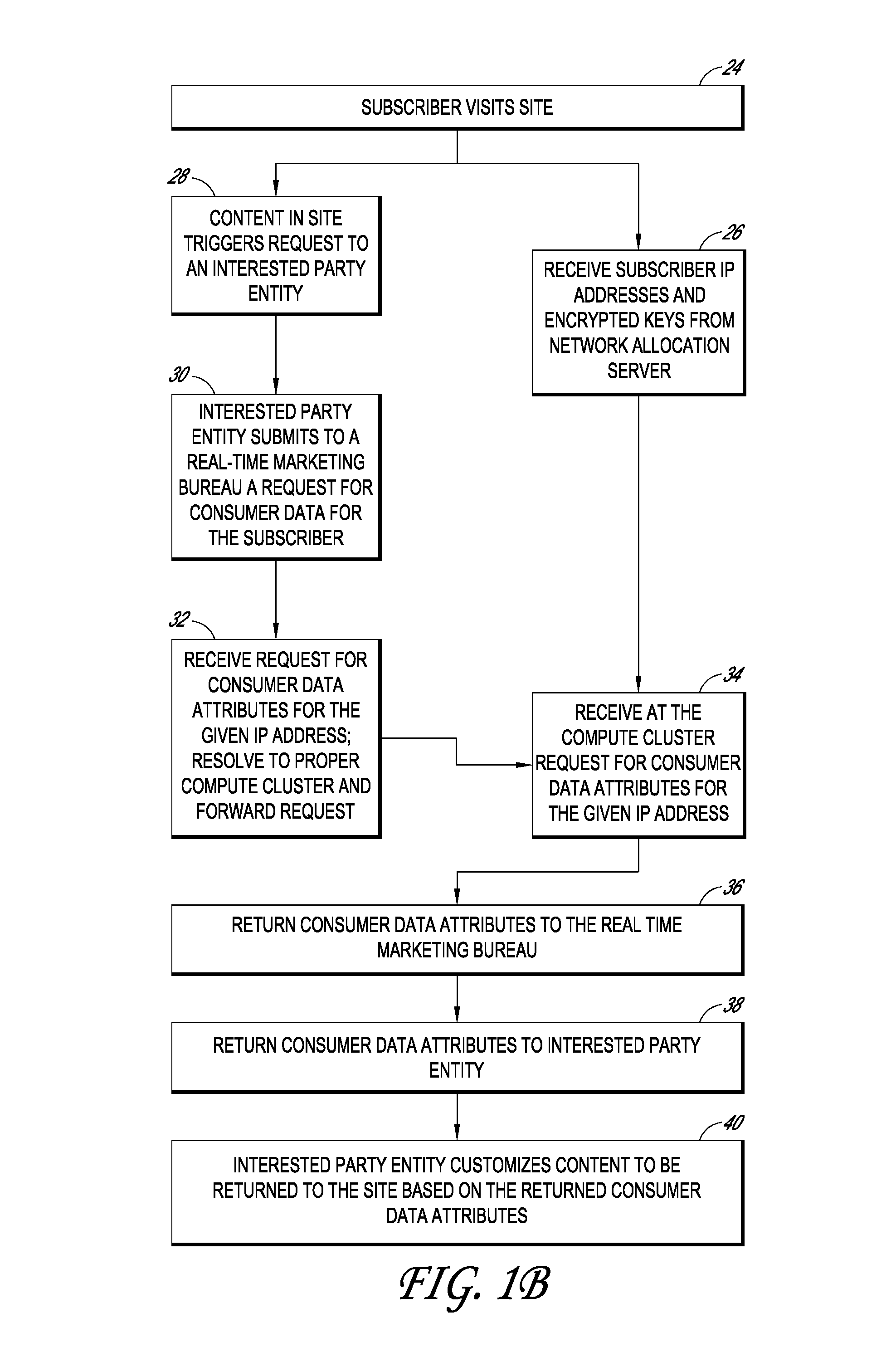
Systems and methods for providing real time anonymized marketing information
InactiveUS20100094758A1Protects consumer privacyPrivacy protectionMultiple keys/algorithms usageComputer security arrangementsReal-time marketingThird party
Embodiments disclosed herein are directed to systems and methods for enabling the matching of third party data with access providers' subscriber data in a privacy compliant manner, and then connecting an internet user to that third party data for use by marketers, content providers, or other interested parties in a manner that protects consumer privacy at all times. In one embodiment, an access provider such as an ISP sends its subscriber data to a double blind processor that generates an encrypted key for each subscriber. The key is then used to find matching consumer data, for example, consumer segments that represent previously collected or modeled consumer attitudinal, habit, or financial data. The key may be forwarded to a real time marketing bureau, which may use the matched data in subsequent real-time or substantially real-time operations to provide consumer or business data to advertisers, content providers, and other interested parties.
Owner:EXPERIAN MARKETING SOLUTIONS
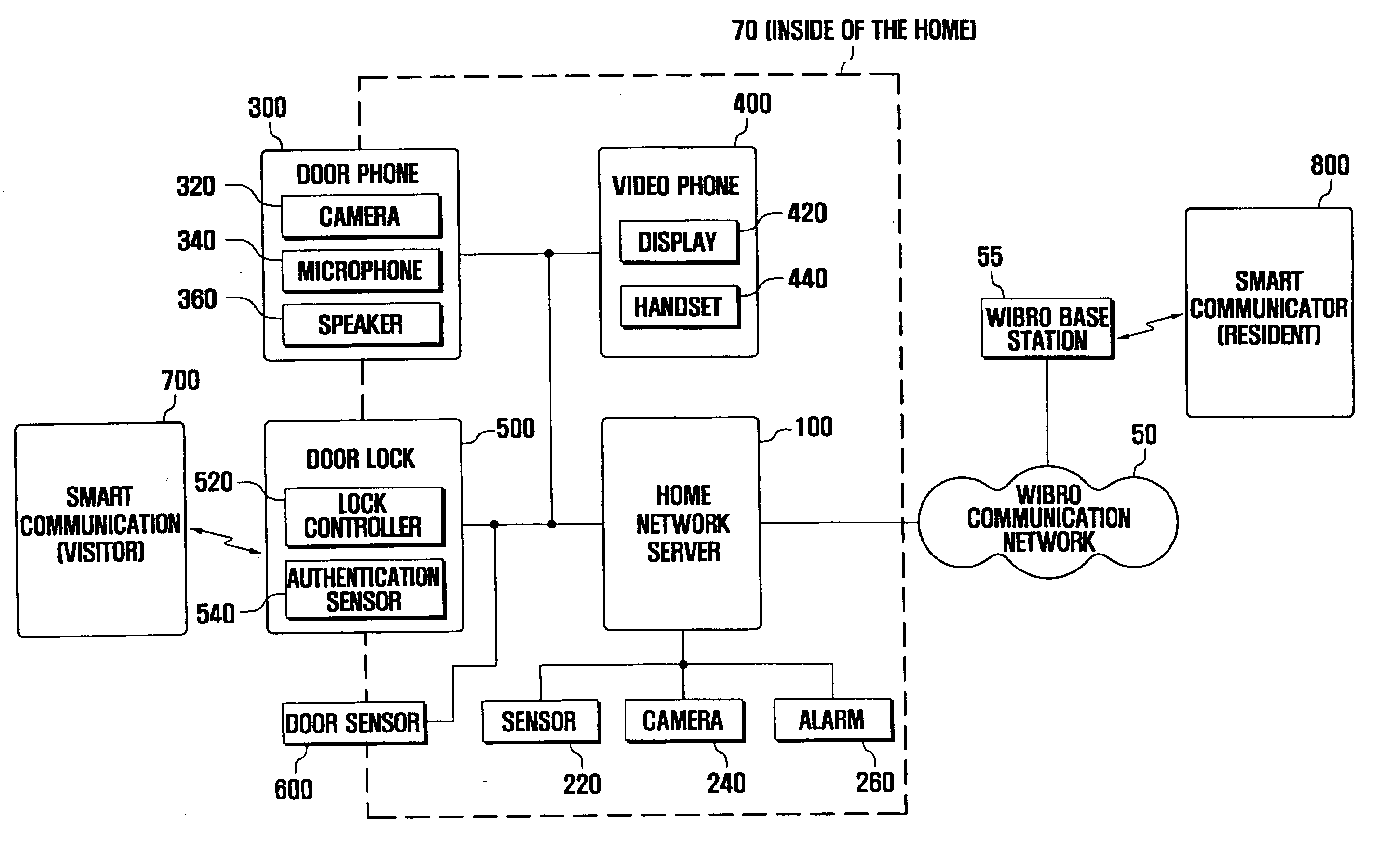
Access authentication system and method using smart communicator
ActiveUS20070216764A1Electric signal transmission systemsMultiple keys/algorithms usageCommunication controlAuthentication system
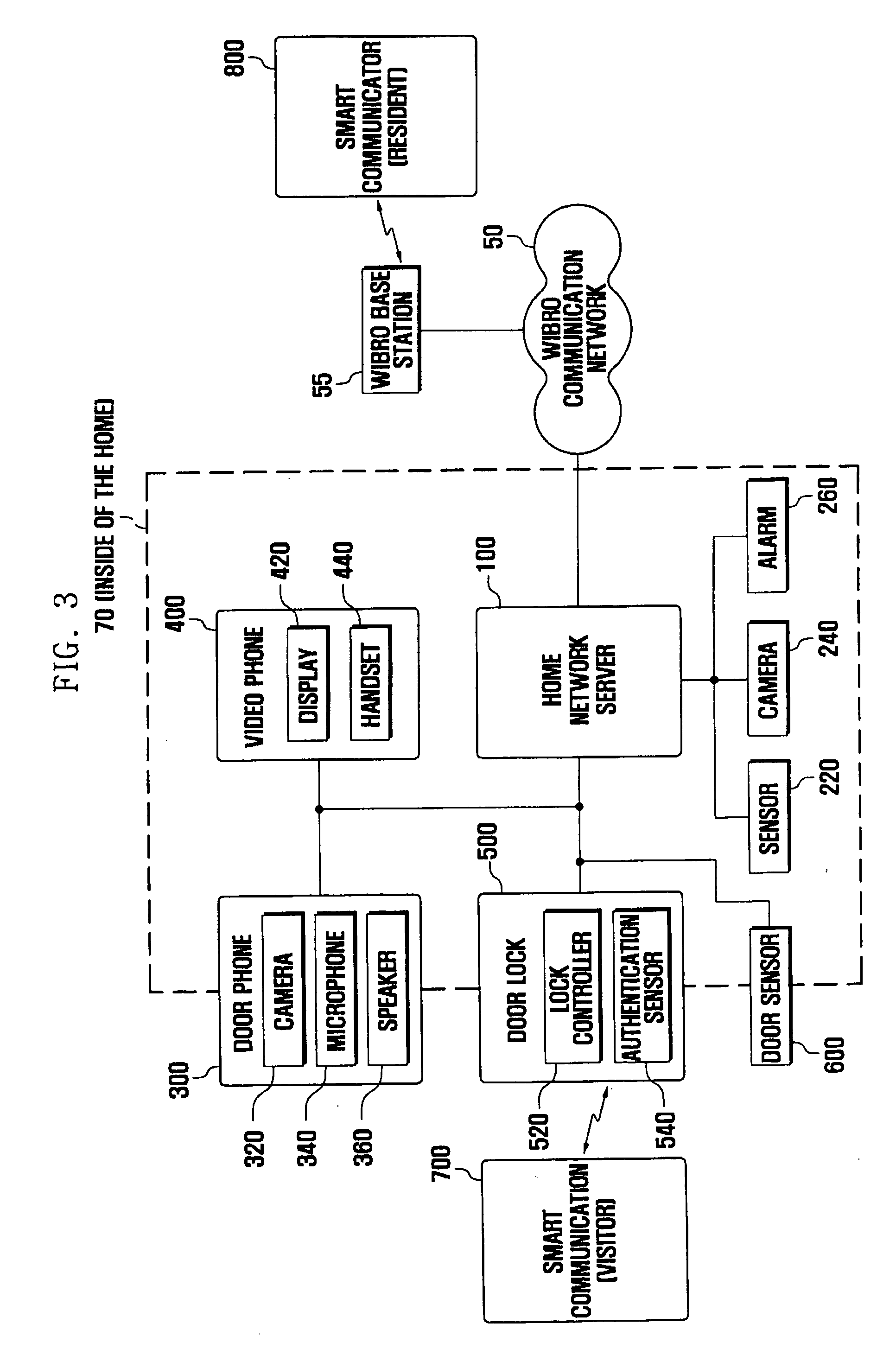
Disclosed is an intelligent access authentication system and method. The intelligent access authentication system includes a door lock that can be locked and released in a predetermined manner, a door phone for communicating with the visitor; a smart communicator which configures access approval levels of expected visitors and access authentication information for each access approval level, communicates with the visitor, and controls the door lock, and a home network server which stores the access approval levels of expected visitors and access authentication information for each access approval level received from the smart communicator, checks the access approval level of the visitor attempting to release the door lock by referring to previously stored information, and transmits a door lock operating command to the door lock according to the access approval level of the visitor. In the present invention, the resident can check the visitor and control the door lock to be released according to the access approval level of the visitor, even at a remote location.
Owner:HUAWEI TECH CO LTD
Health care sanitation monitoring system
ActiveUS20130045685A1Electric signal transmission systemsMultiple keys/algorithms usageMonitoring systemMedical emergency
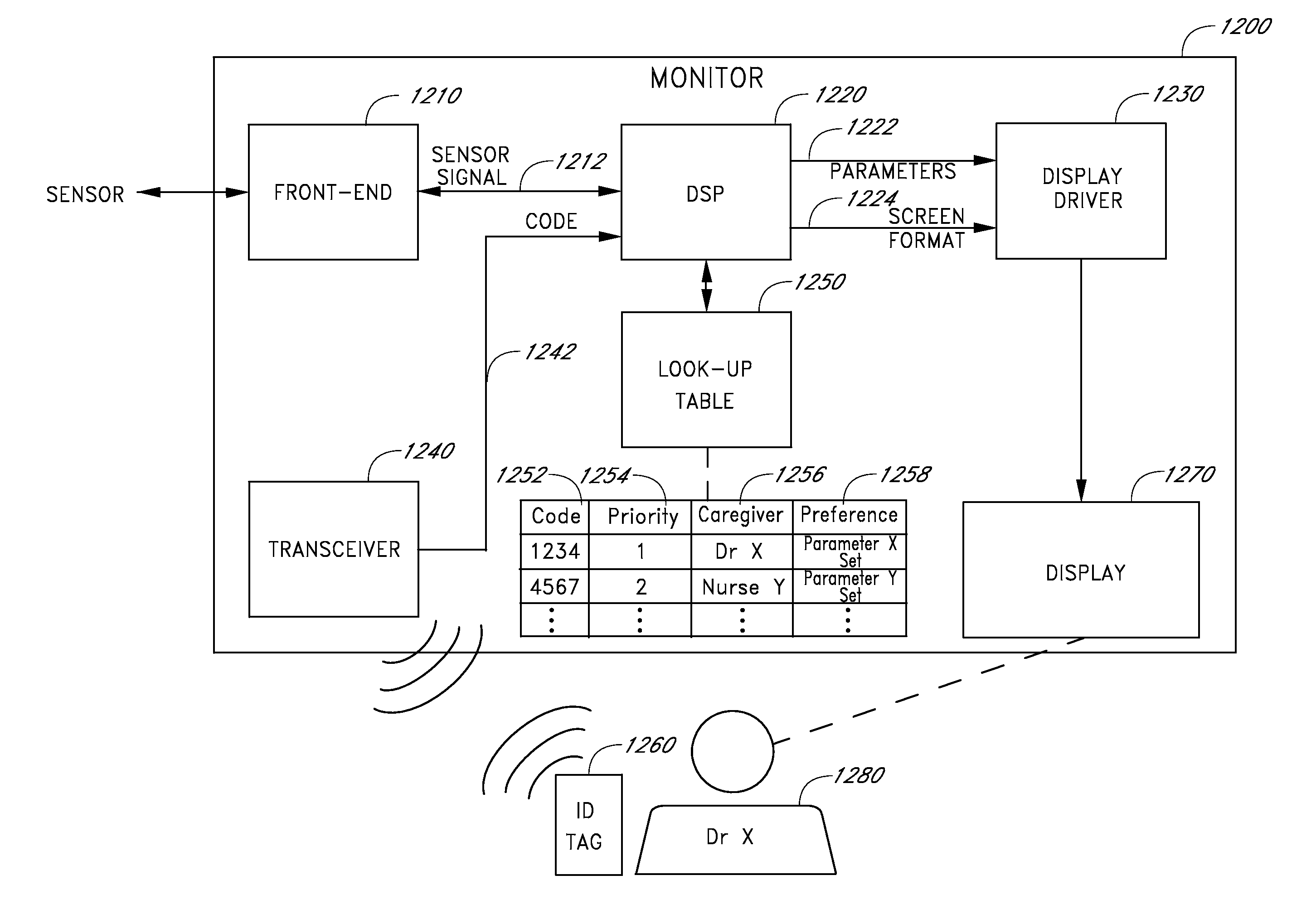
A medical sanitation device may include a detector for detecting the physical presence of a clinician token within a detection area in the vicinity of the medical sanitation device. The clinician token may be indicative of the identity of a clinician. The medical sanitation device also includes a sanitation module configured to be used by the clinician to perform a sanitation task. Detection of a clinician in proximity to the medical sanitation device may be used to at least partially control access to, or operation of, a medical patient monitoring device.
Owner:JPMORGAN CHASE BANK NA
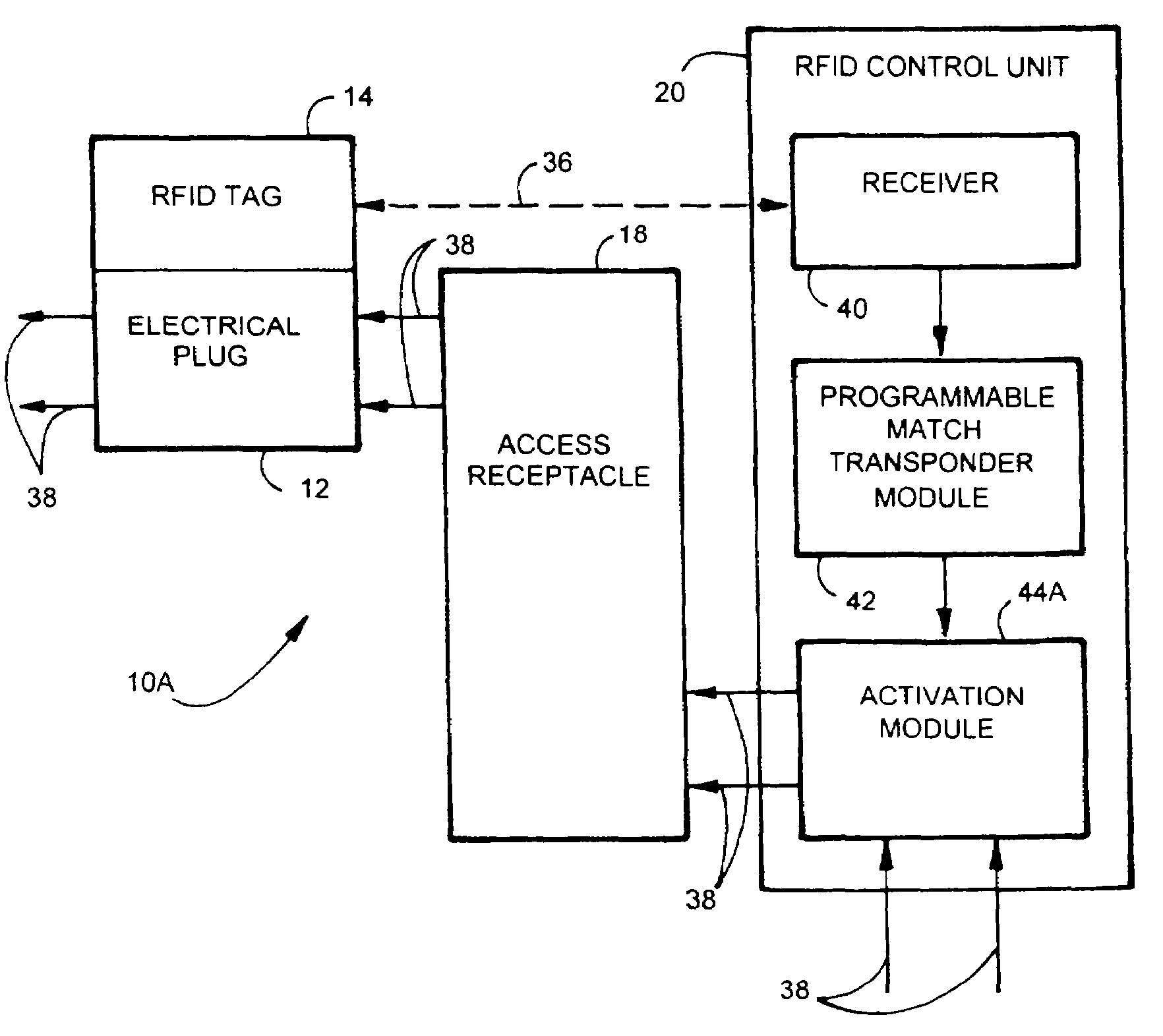
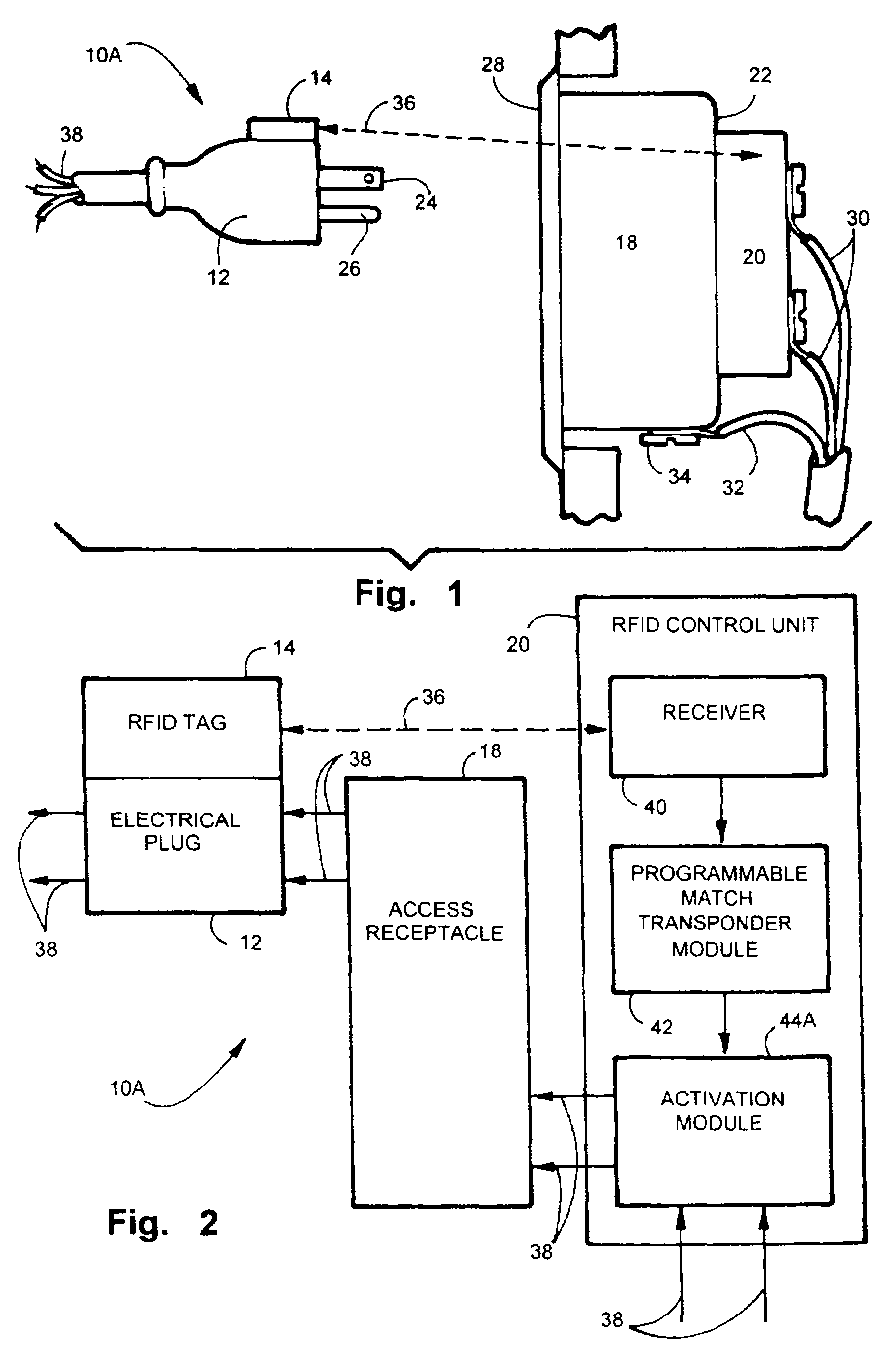
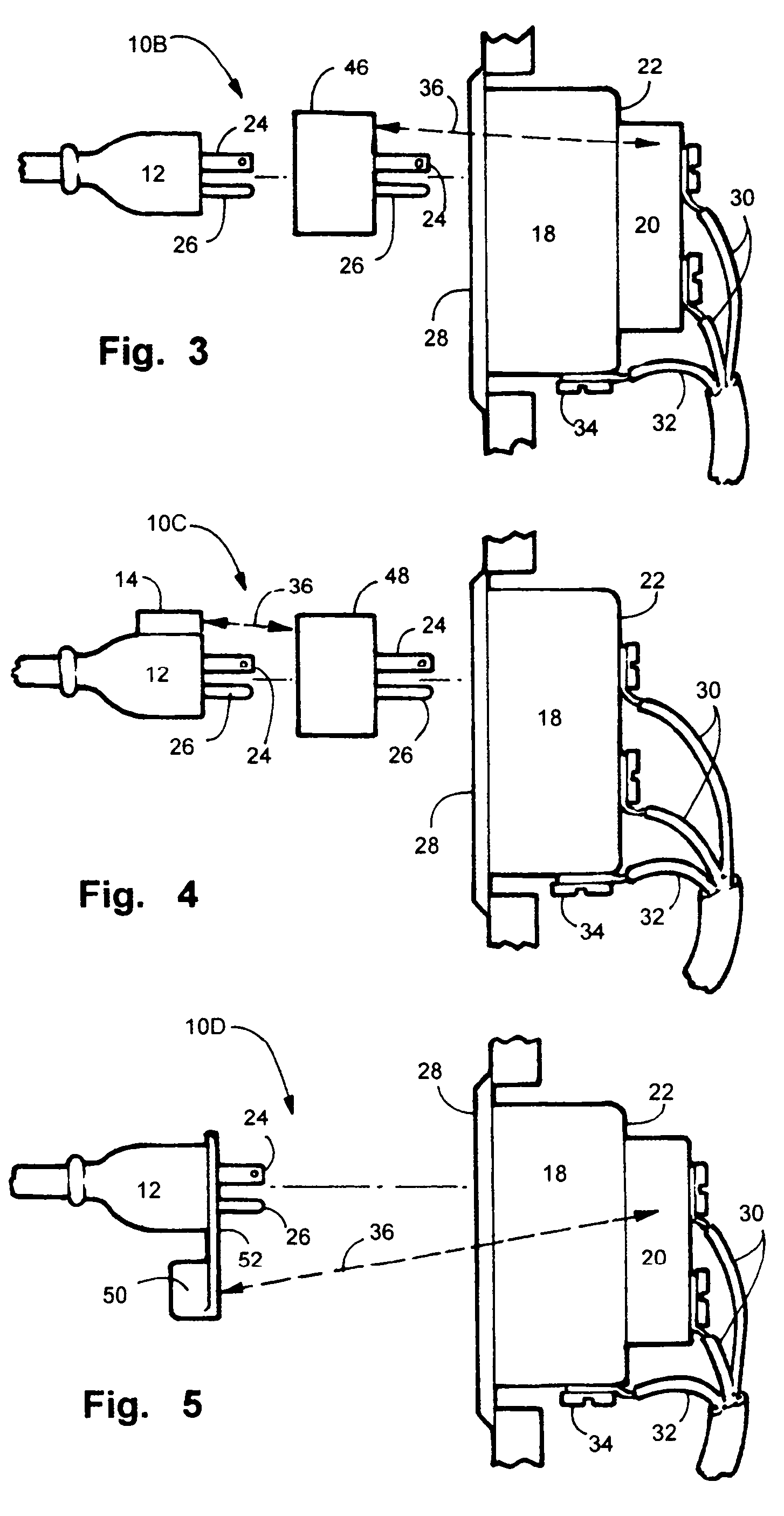
Electric, telephone or network access control system and method
InactiveUS7167078B2EasilyEasy to installElectric signal transmission systemsMultiple keys/algorithms usageElectricityControl system
An apparatus and method for controlling user access to electrical receptacles and telephone and network communications receptacles. The device features a short range radio receiver and one or a plurality of RF energized radio identification tags with transmittable identification transponder codes. The receptacle contains circuitry that detects the immediate presence of energized transponders with proper identification codes and only enables the electric, telephone or network access from the receptacle to become active if the correct matching transponder identification code is present. The tag is a small flexible device having one side that may be attached to the plug or the receptacle or interfaced therebetween. Access to the power or network is allowed for a defined duration of time or only so long as the transponder remains energized and transmits the identification code.
Owner:POURCHOT SHAWN C
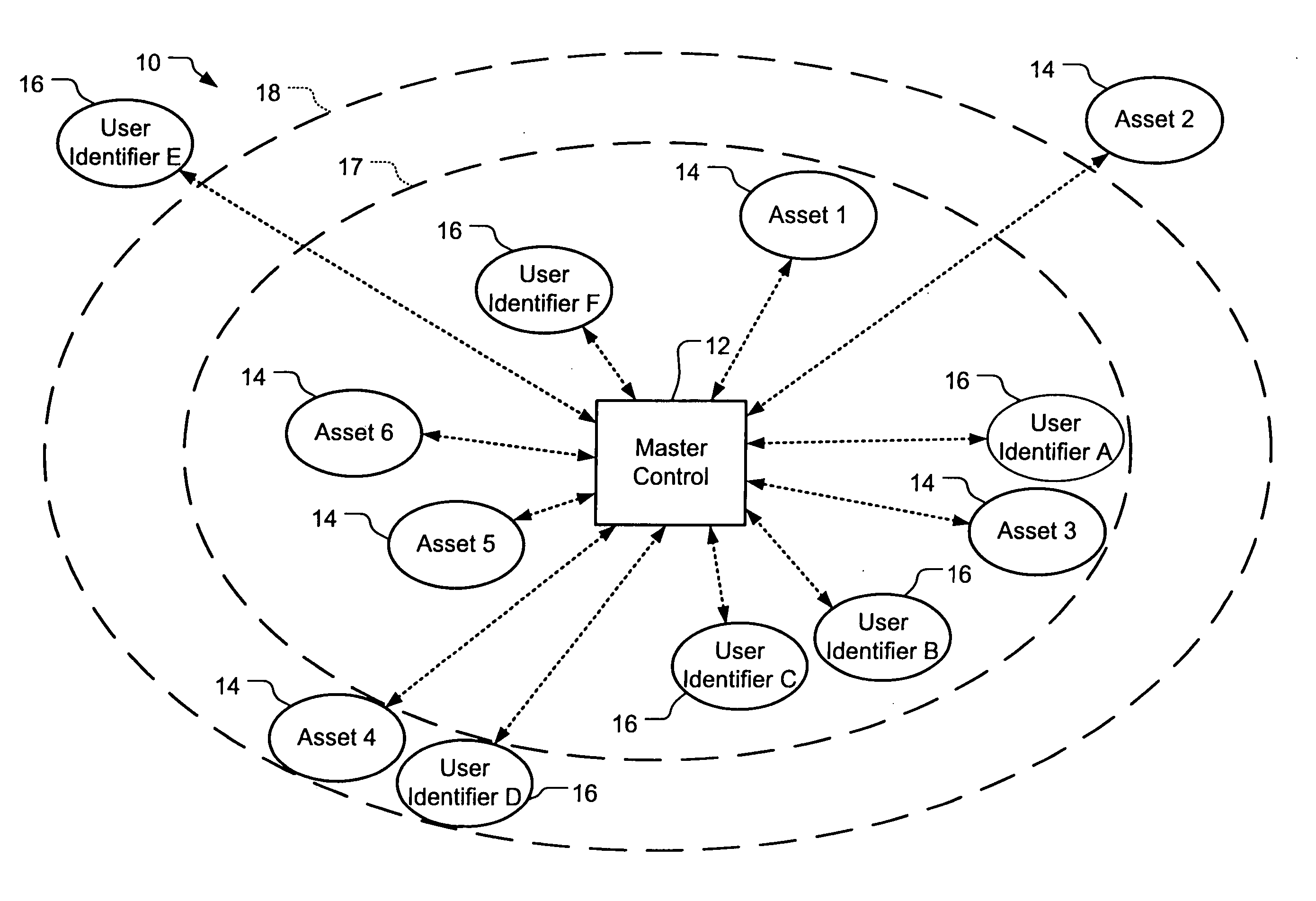
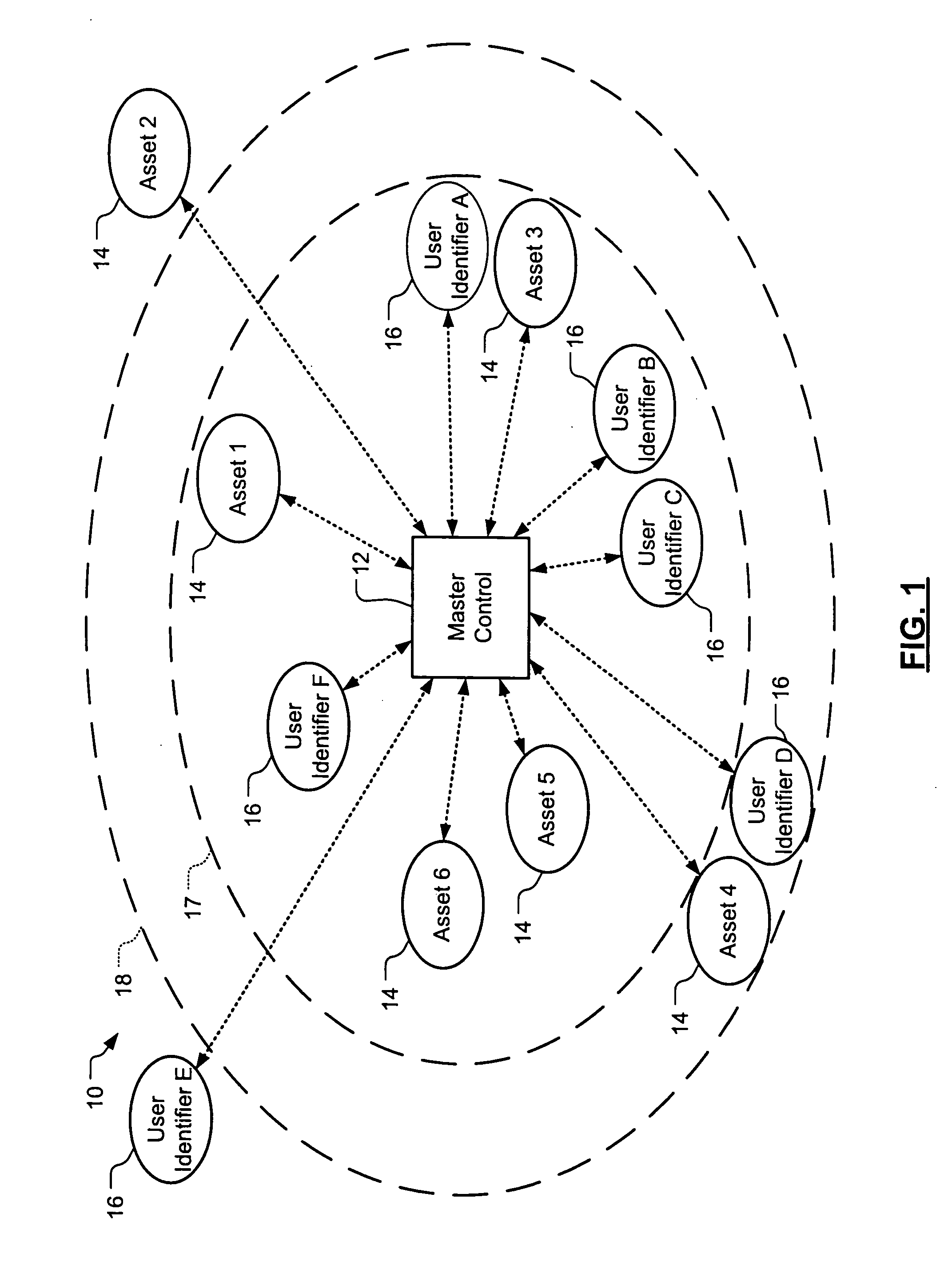
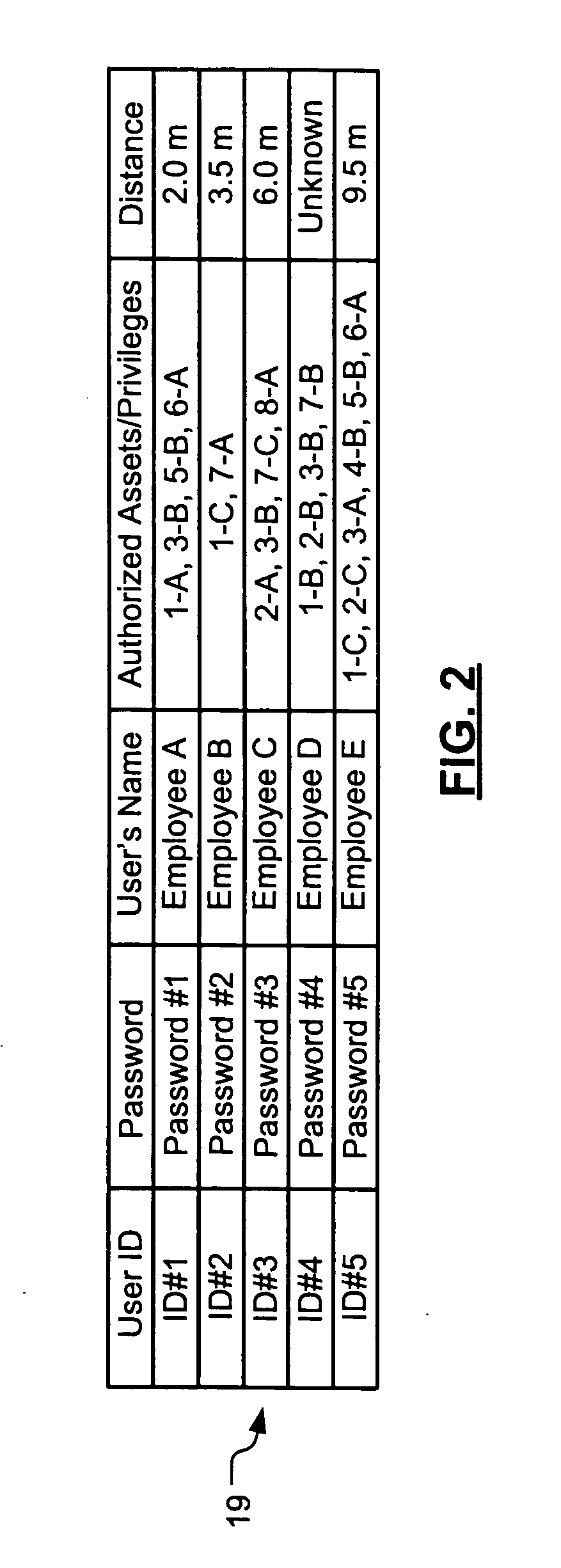
Wireless asset monitoring and security system
InactiveUS20050128083A1Electric signal transmission systemsMultiple keys/algorithms usageLocking mechanismUnique identifier
An asset monitoring and security system includes at least one asset assigned a unique identifier and operable wirelessly transmit an identification signal embodying the identifier. A data store maintains a list of the assets and privileges associated with the assets for authorized users of the assets. A control unit is adapted to receive identification signals from the assets and monitor positions of the assets within a defined area. The control unit communicates with the data store and is further operable to initiate an alarm event when privileges associated with a given asset for authorized users of the asset are exceeded. Each of the assets includes a lock-out mechanism that impedes use of the asset when the lock-out mechanism is activated. The control unit activates the lock-out mechanism of a given asset when the privileges associated with the asset for authorized users of the asset are exceeded.
Owner:BLACK & DECKER INC
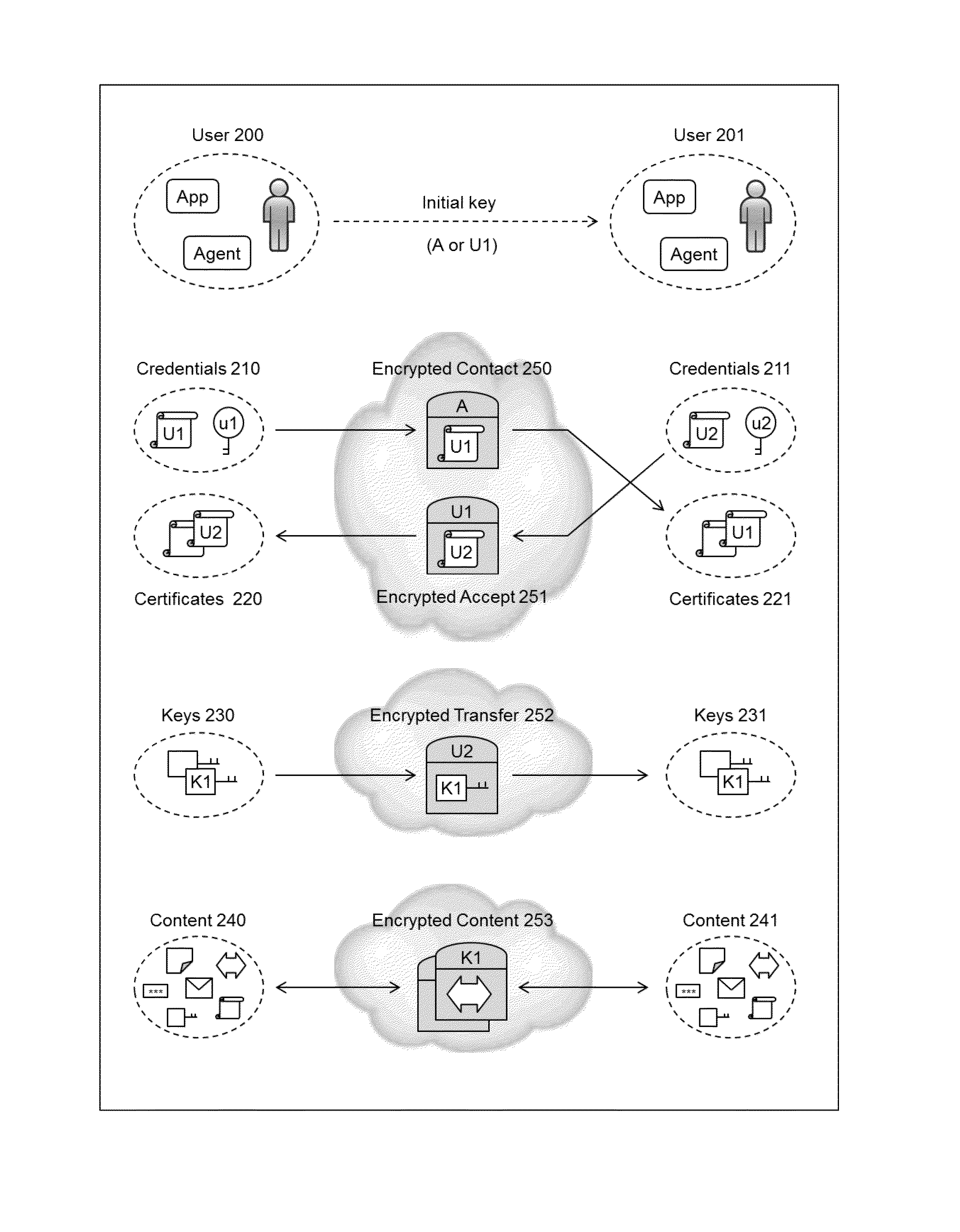
Cryptographic method and system
InactiveUS20140164776A1Easy to useImprove abilitiesKey distribution for secure communicationMultiple keys/algorithms usageInformation sharingInternet privacy
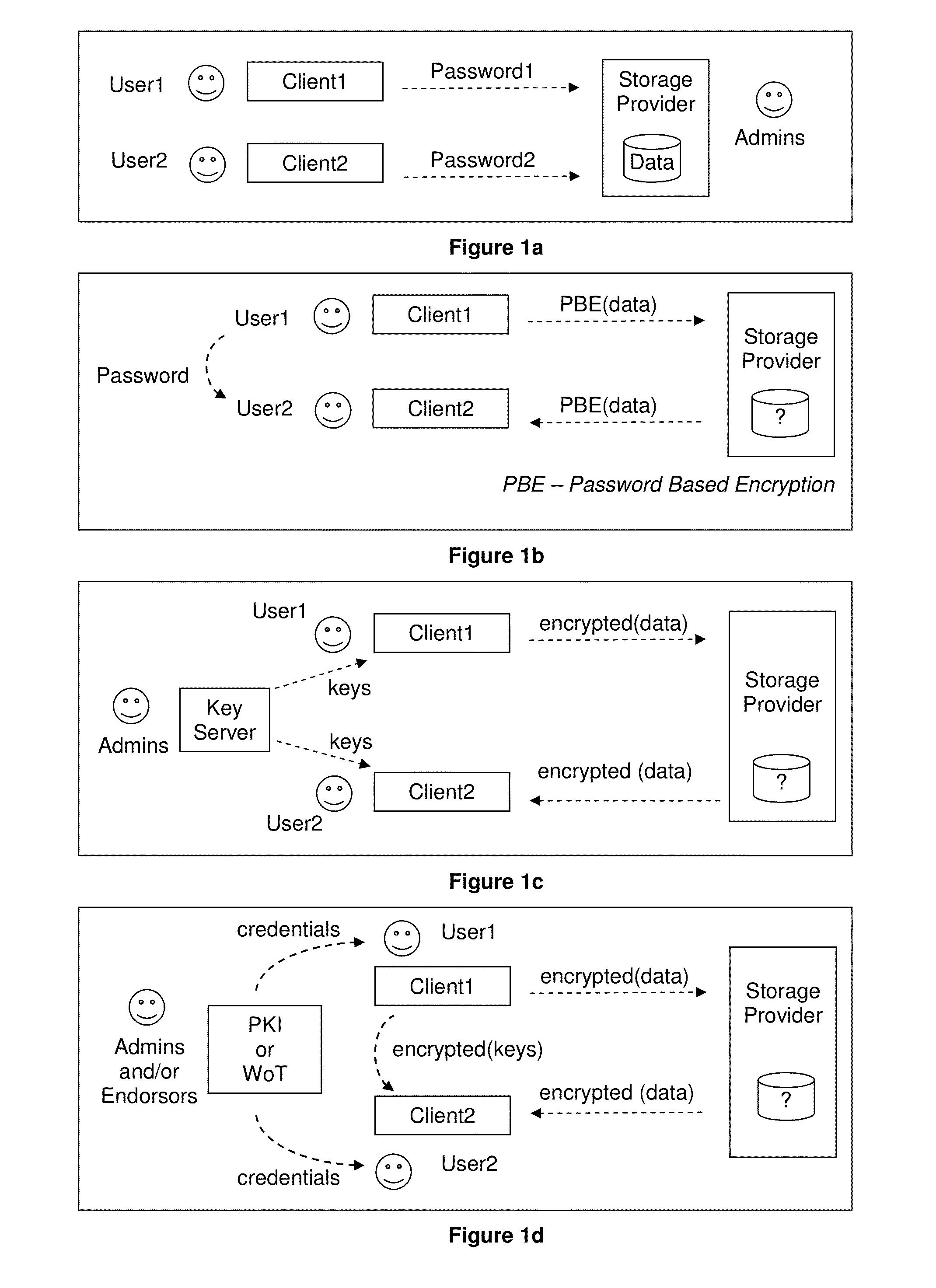
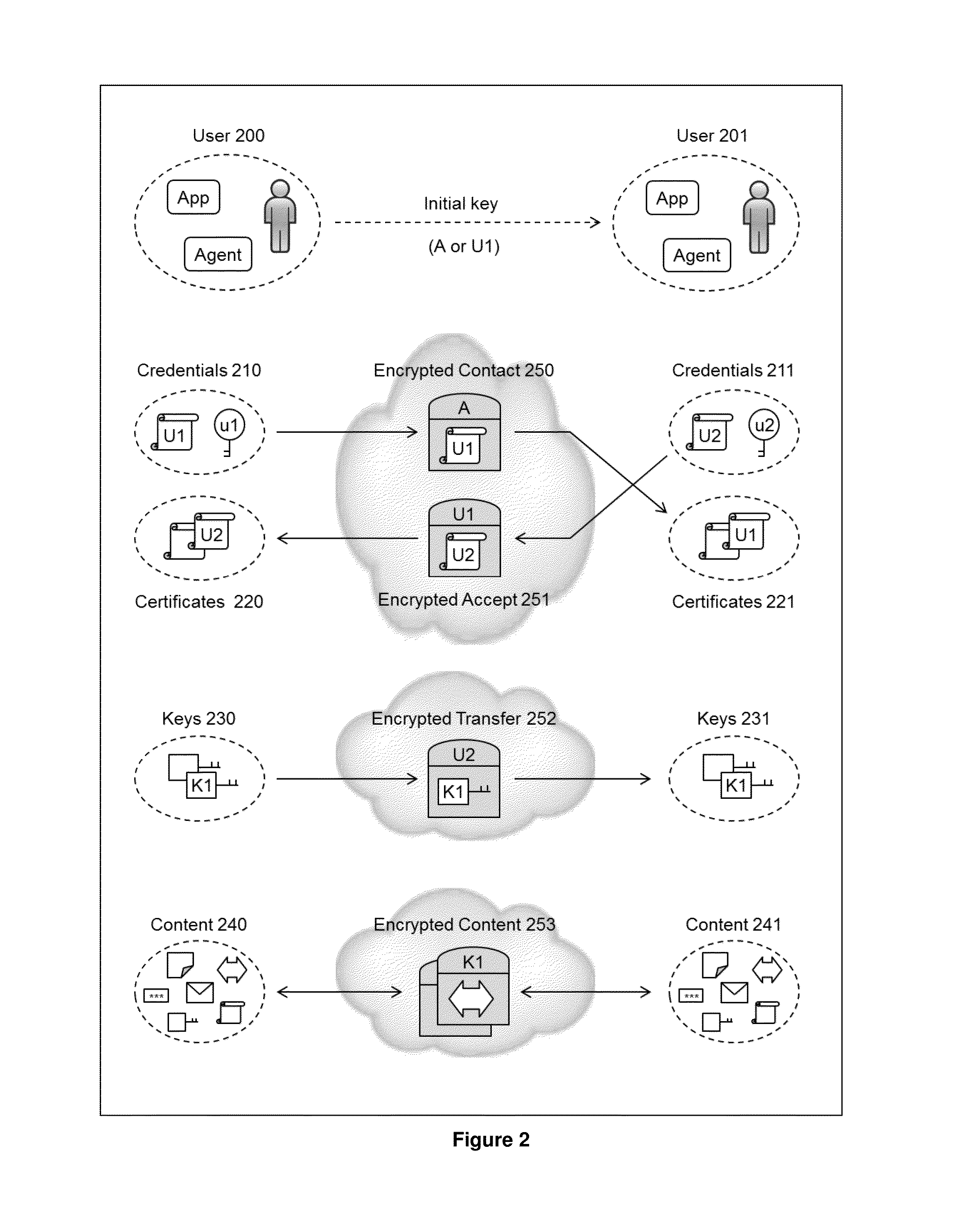
The present invention relates to the field of security of electronic data and / or communications. In one form, the invention relates to data security and / or privacy in a distributed and / or decentralised network environment. In another form, the invention relates to enabling private collaboration and / or information sharing between users, agents and / or applications. Embodiment(s) of the present invention enable the sharing of key(s) and / or content between a first user and / or agent and a second user and / or agent. Furthermore, embodiment(s) of the present invention have application in sharing encrypted information via information sharing services.A number of inventions, aspects and embodiments are disclosed herein.
Owner:LOCK BOX
System and method for secure electronic communication services
InactiveUS20090198997A1Easy accessSecure transmissionKey distribution for secure communicationMultiple keys/algorithms usageScalable systemEmail address
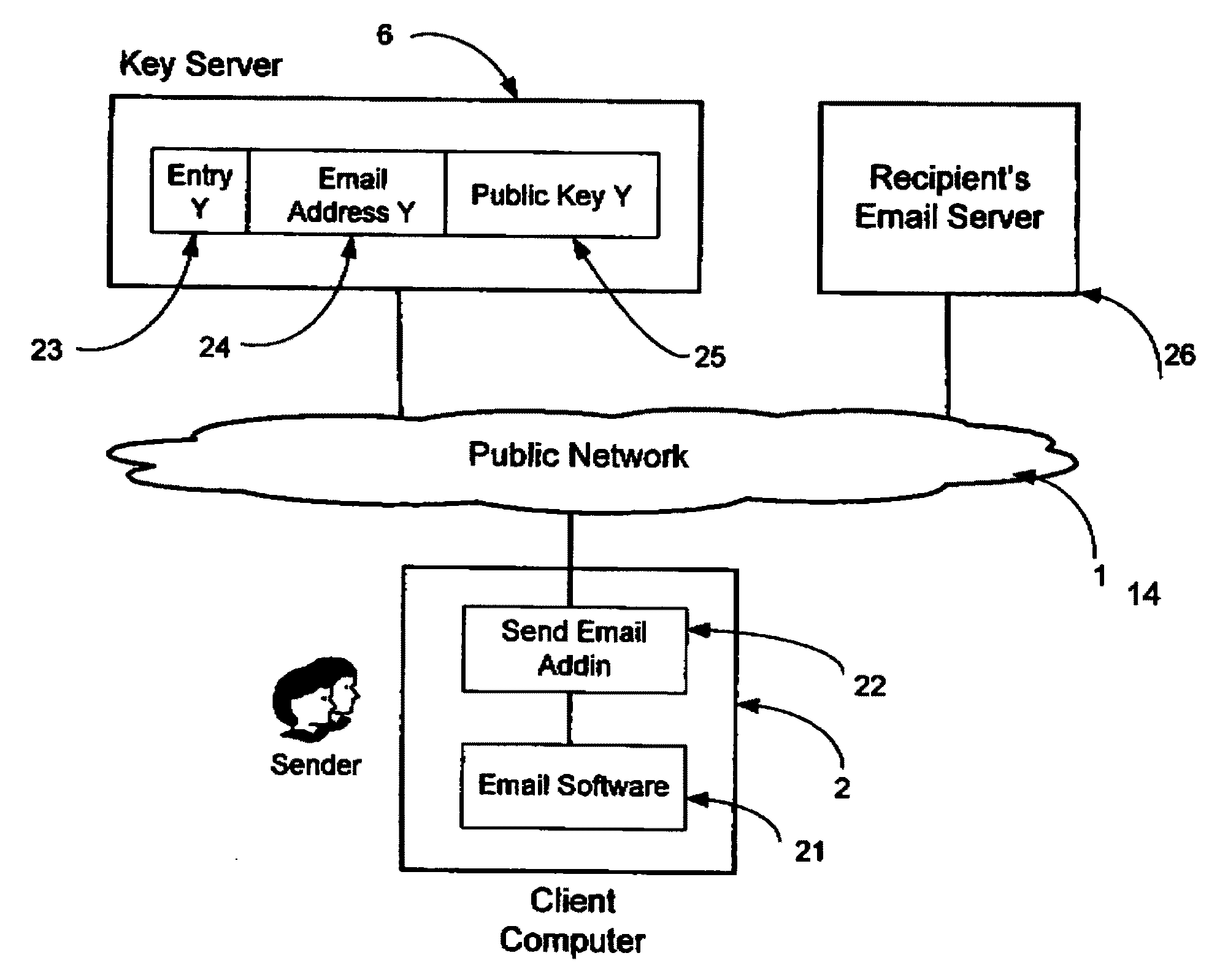
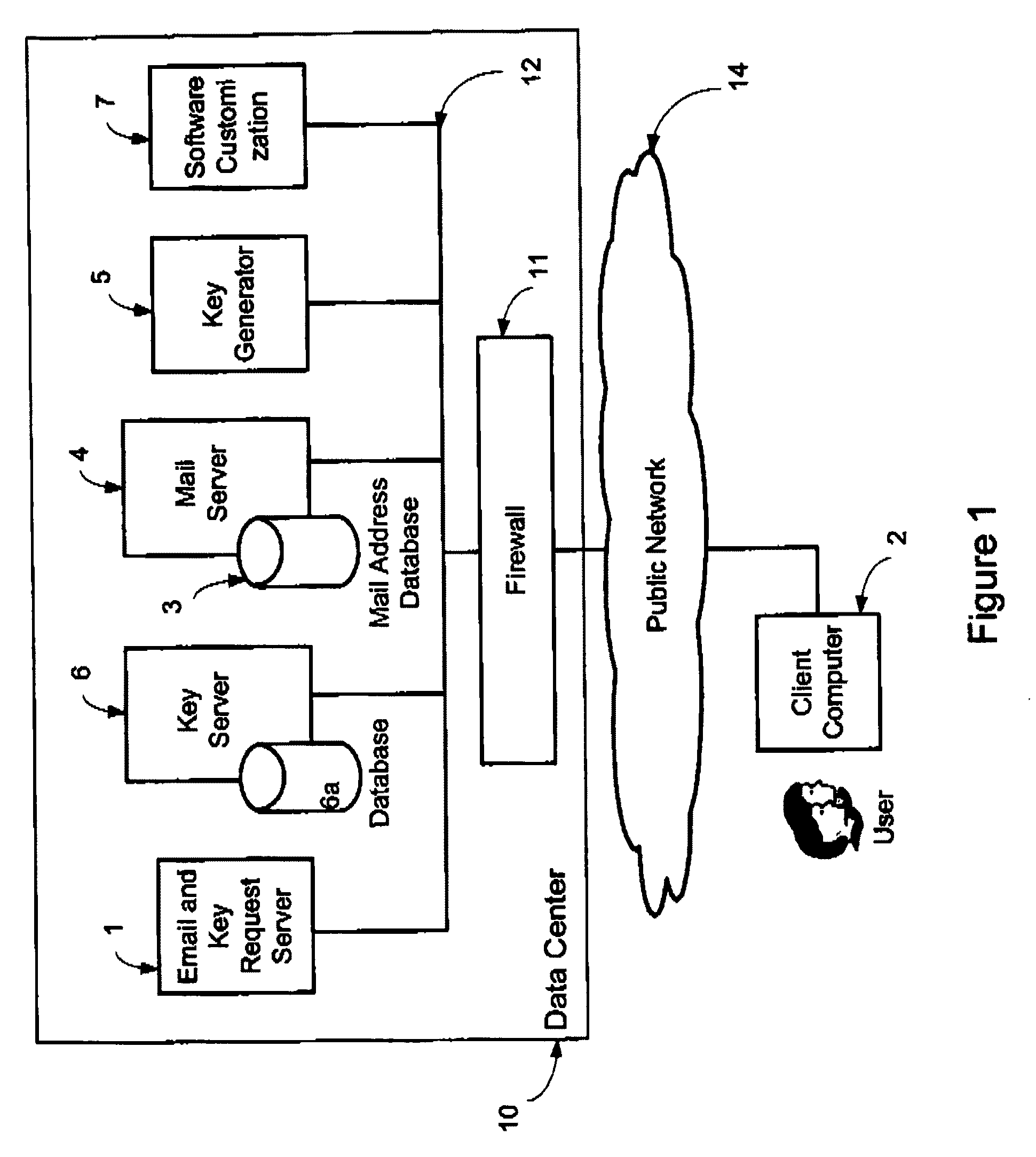
A system, method and software module for secure electronic communication services, wherein a public key (25) of private-public-key pair (30,25) is associated with an email address (24), internet name or other registered unique identifier; the registered user of the unique identifier holds the private-key (30) securely, and the respective public-key (25) is made accessible on a key server (6) for look-up and retrieval by other users, for encryption of communications to be sent to the holder of the private-key, and optionally for message confidentiality, message integrity and authentication of sender and recipient, without requiring certificates. A distributed and scalable system is provided by a server network (600; 401, 501) for registration, key distribution and management preferably using a kDNS server hierarchy (601,602,603) or a key-DNS server hierarchy (701,702,) and associated protocols so that public-keys of recipients can be searched and retrieved over the internet based on the recipients email address or other unique identifier, thus facilitating secure communication between users in different network domains and organizations.
Owner:TOPOSIS CORP
System for controlling access and distribution of digital property
InactiveUS20010021926A1Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
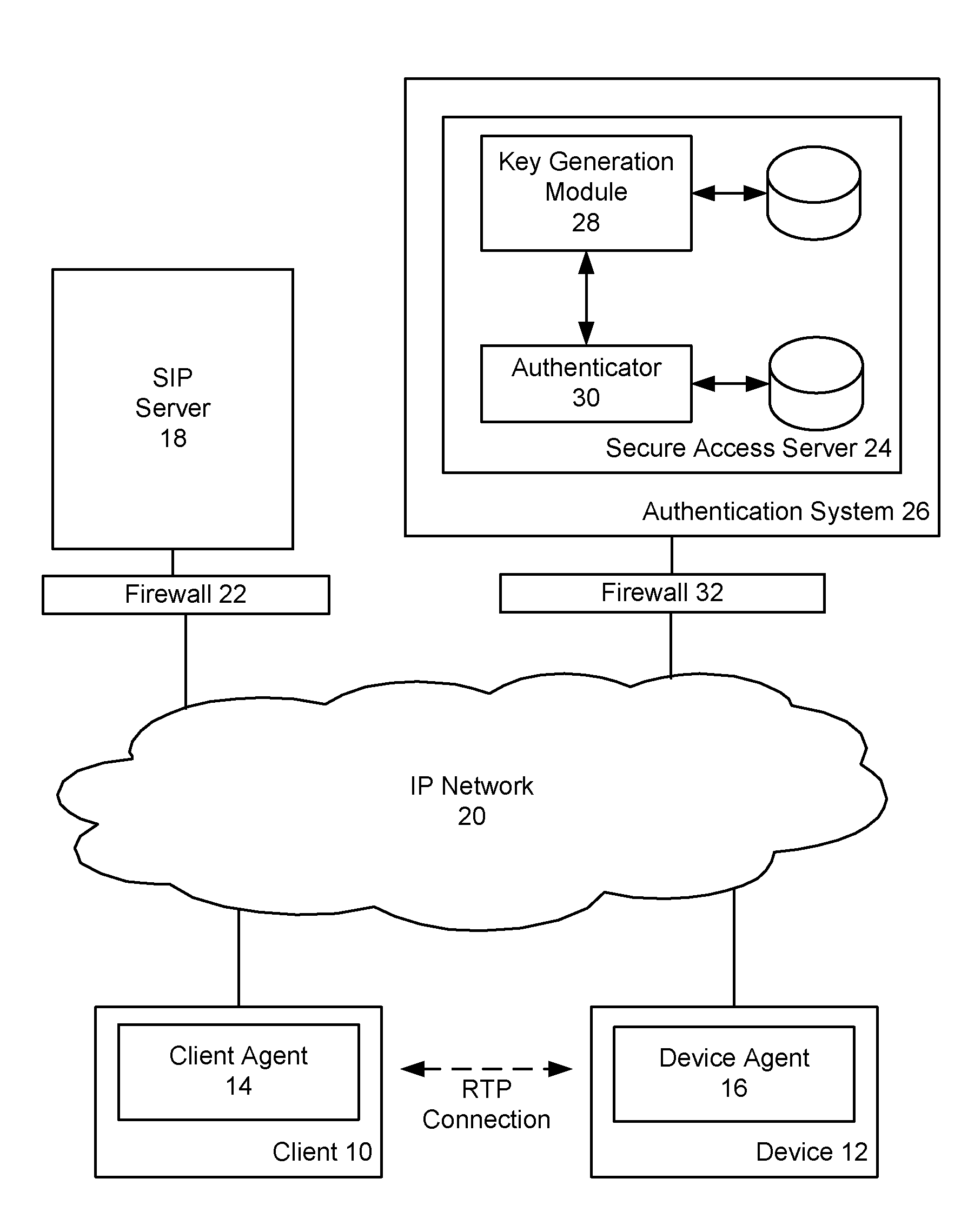
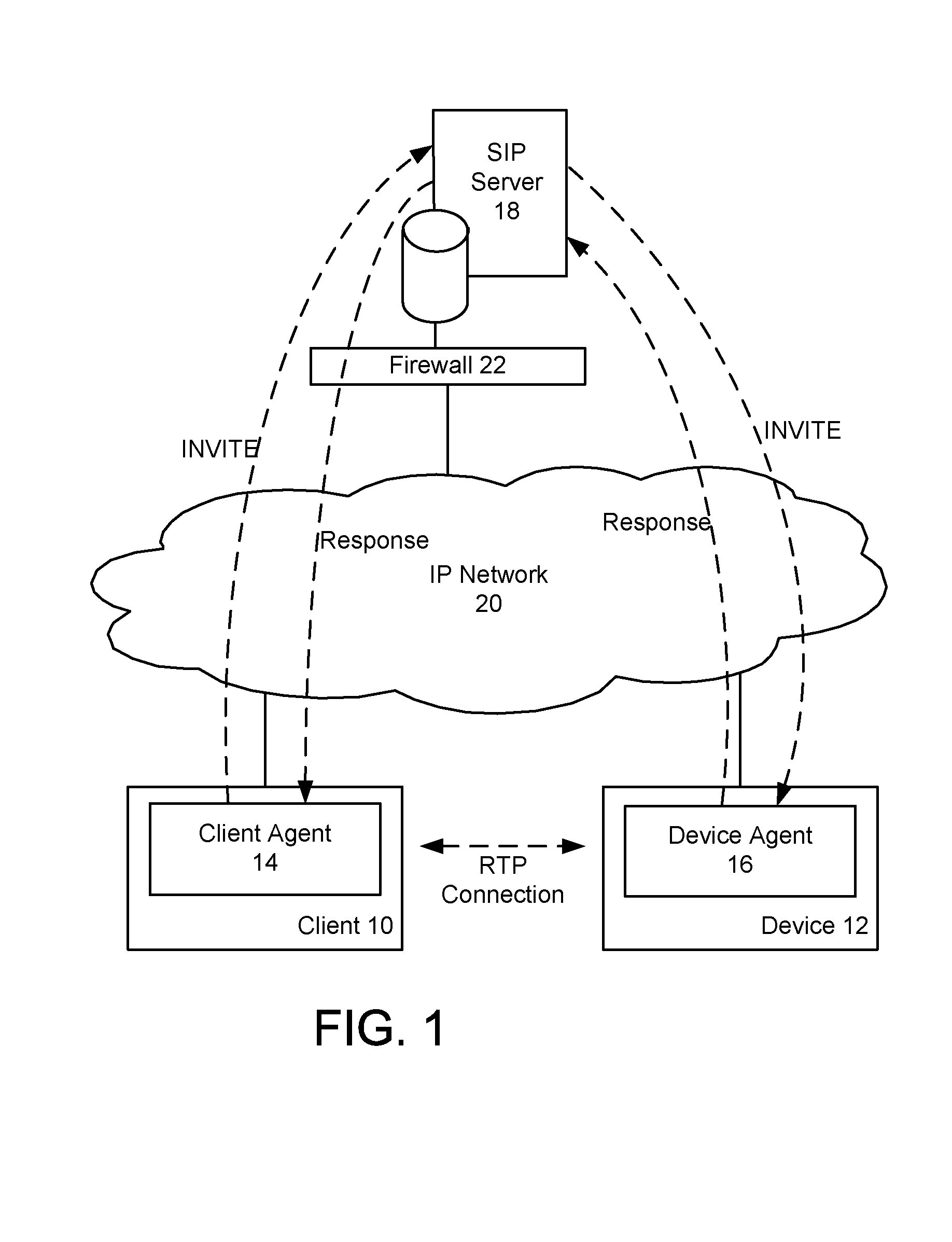
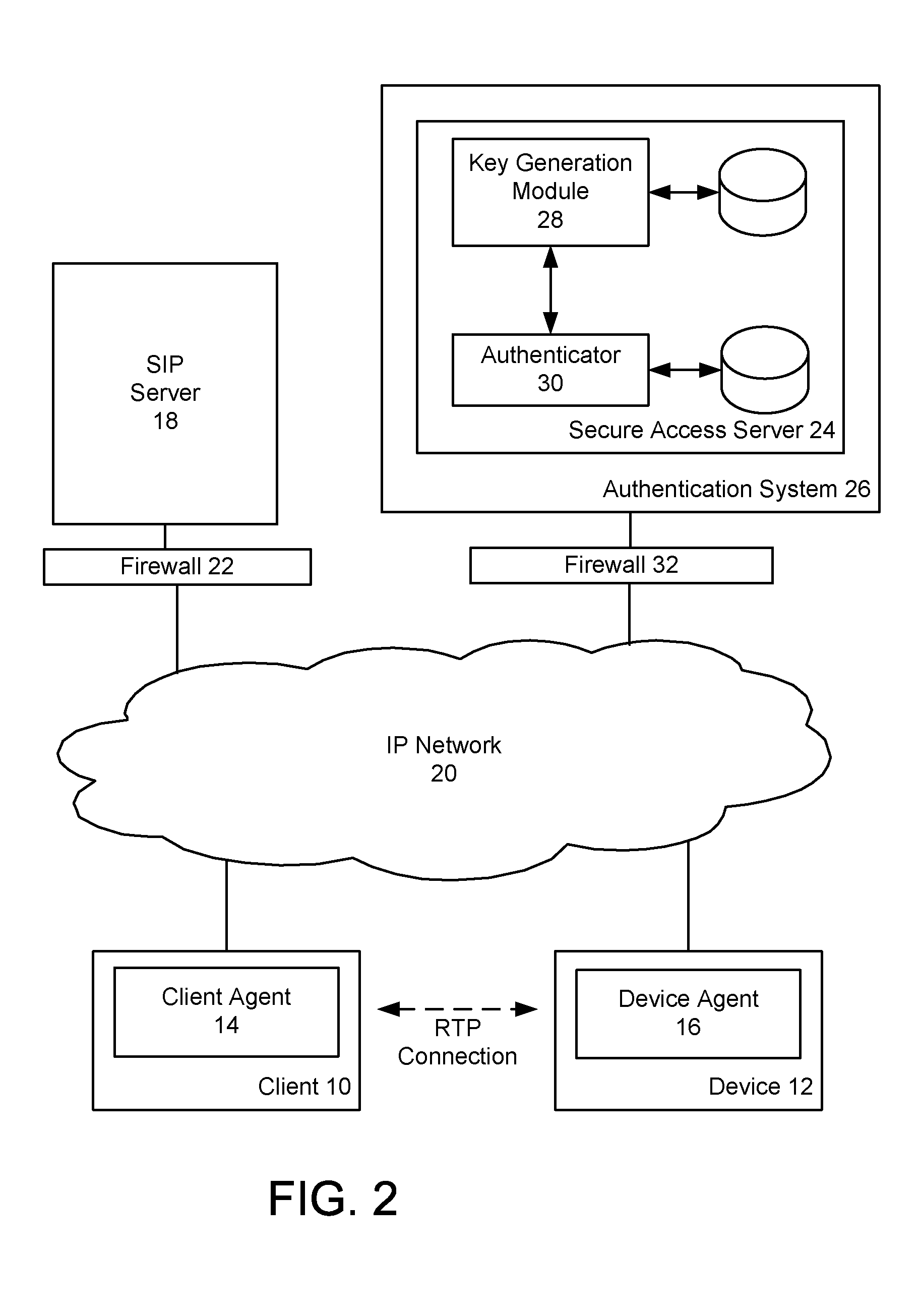
Device authentication and secure channel management for peer-to-peer initiated communications
ActiveUS20080235511A1Multiple keys/algorithms usageUser identity/authority verificationKey exchangeSignaling protocol
A method and system for providing secure access to a device initiating communications using a peer-to-peer signaling protocol, such as a SIP or H.323. In a device registration phase, the device contacts a secure access server, and authenticates to the secure access server by providing an identification, such as its factory ID. The secure access server then issues a device ID and private key to the authenticated device. A client can then initiate a further communication session and be authenticated by the secure access server. The secure access server returns the device identification and the device's public key to the client. The client and device can then perform a symmetrical key exchange for their current communication session, and can communicate with appropriate encryption. The device's private key can be set to expire after one or more uses.
Owner:BCE
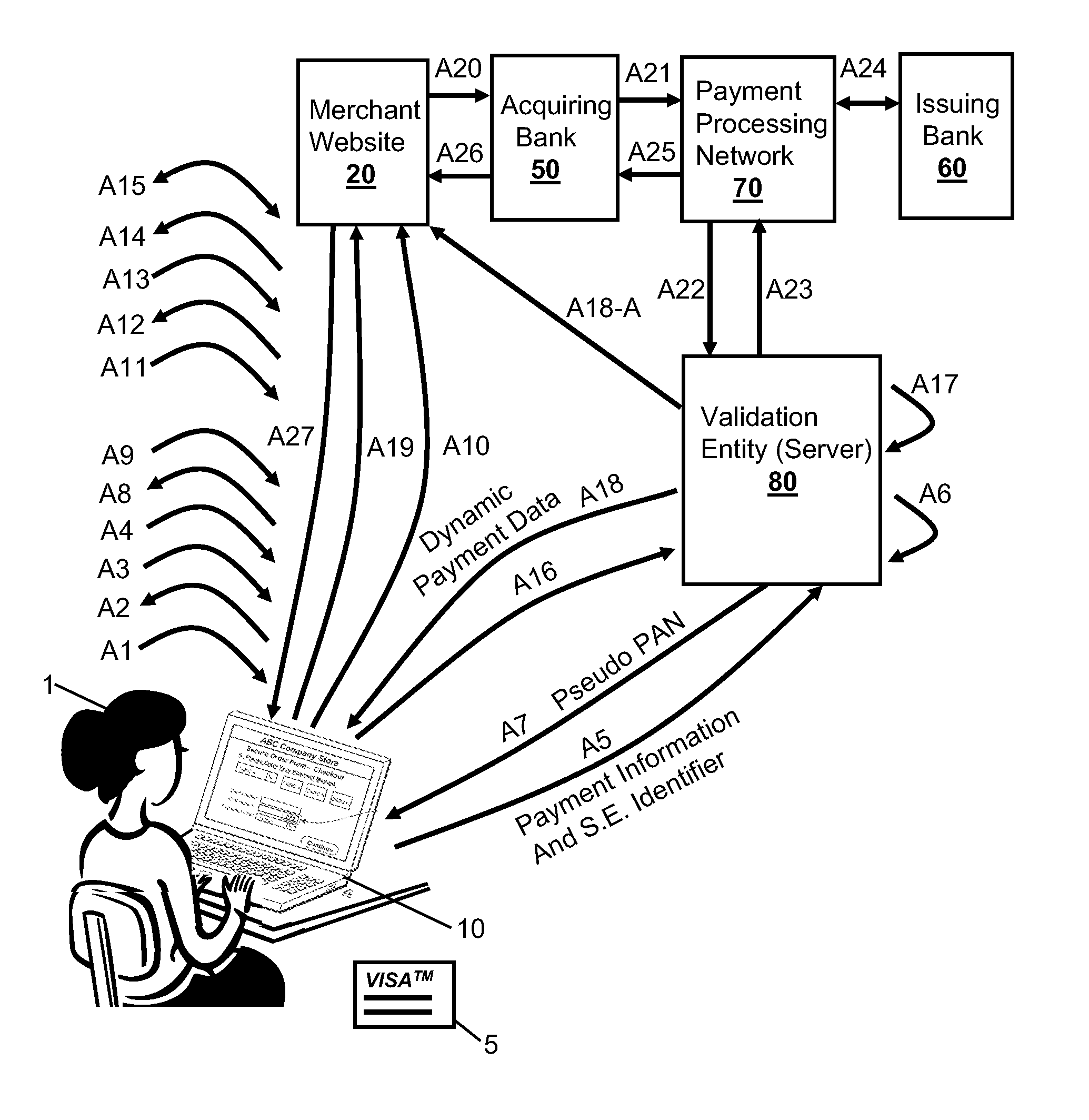
Integration of Payment Capability into Secure Elements of Computers
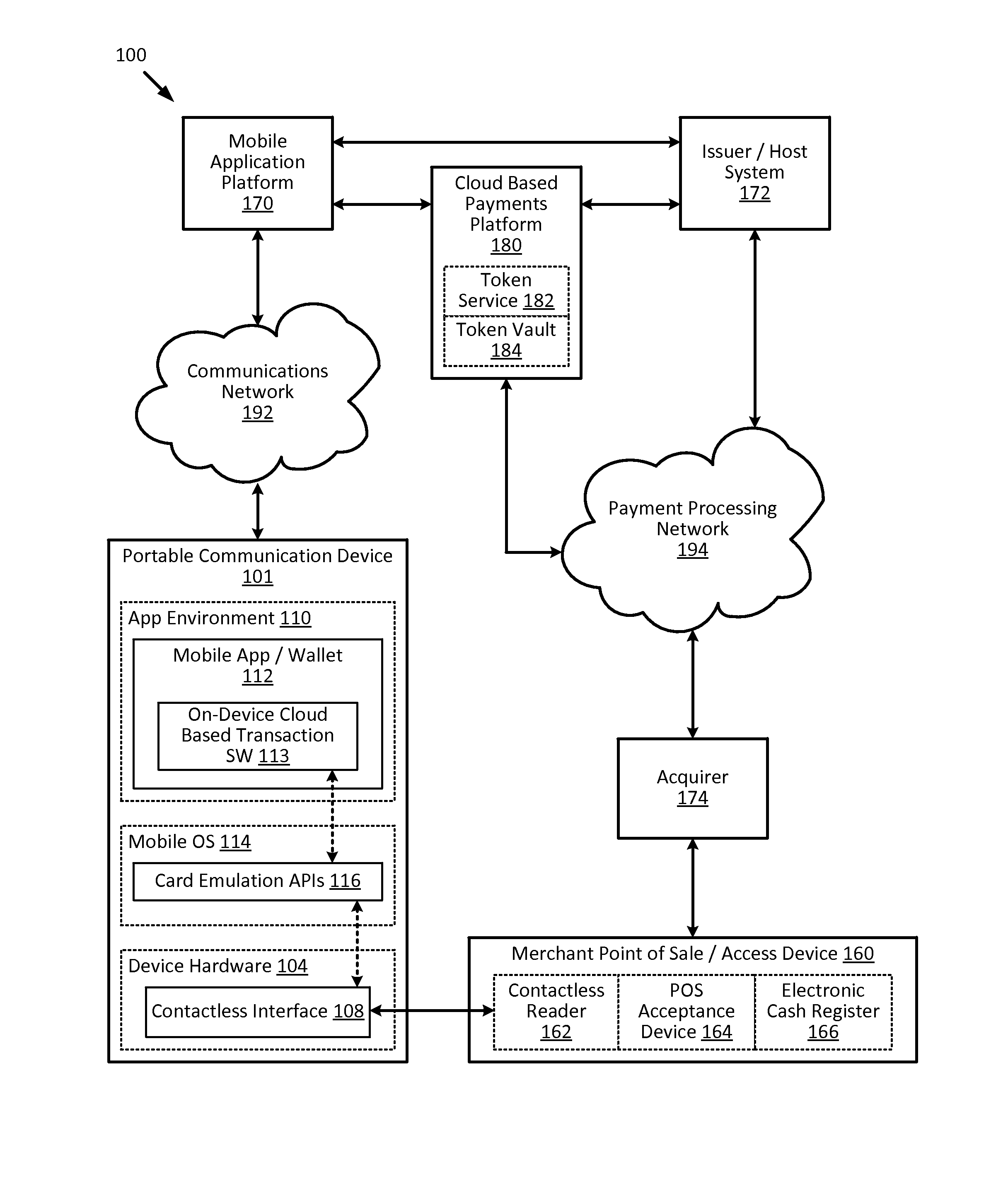
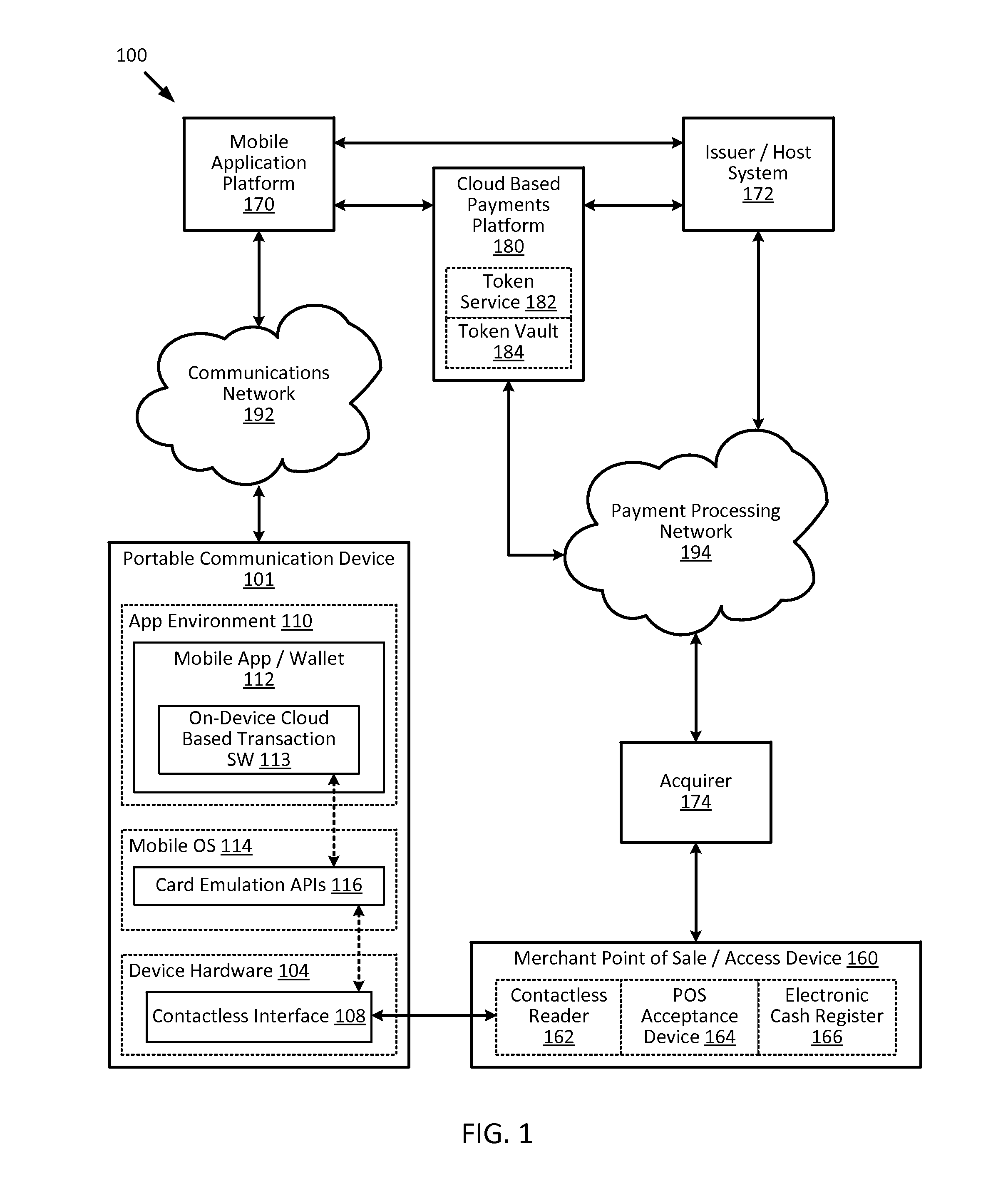
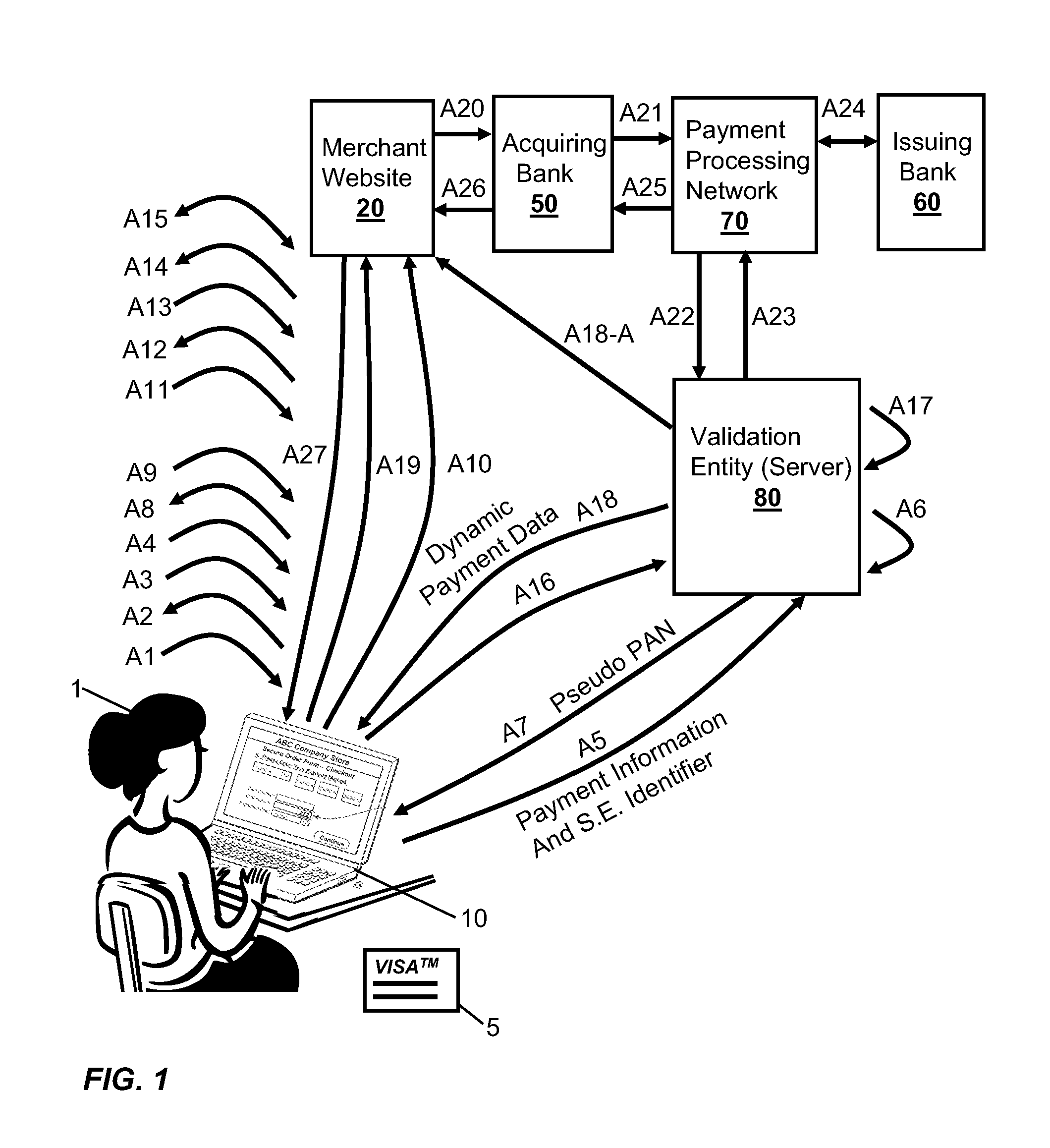
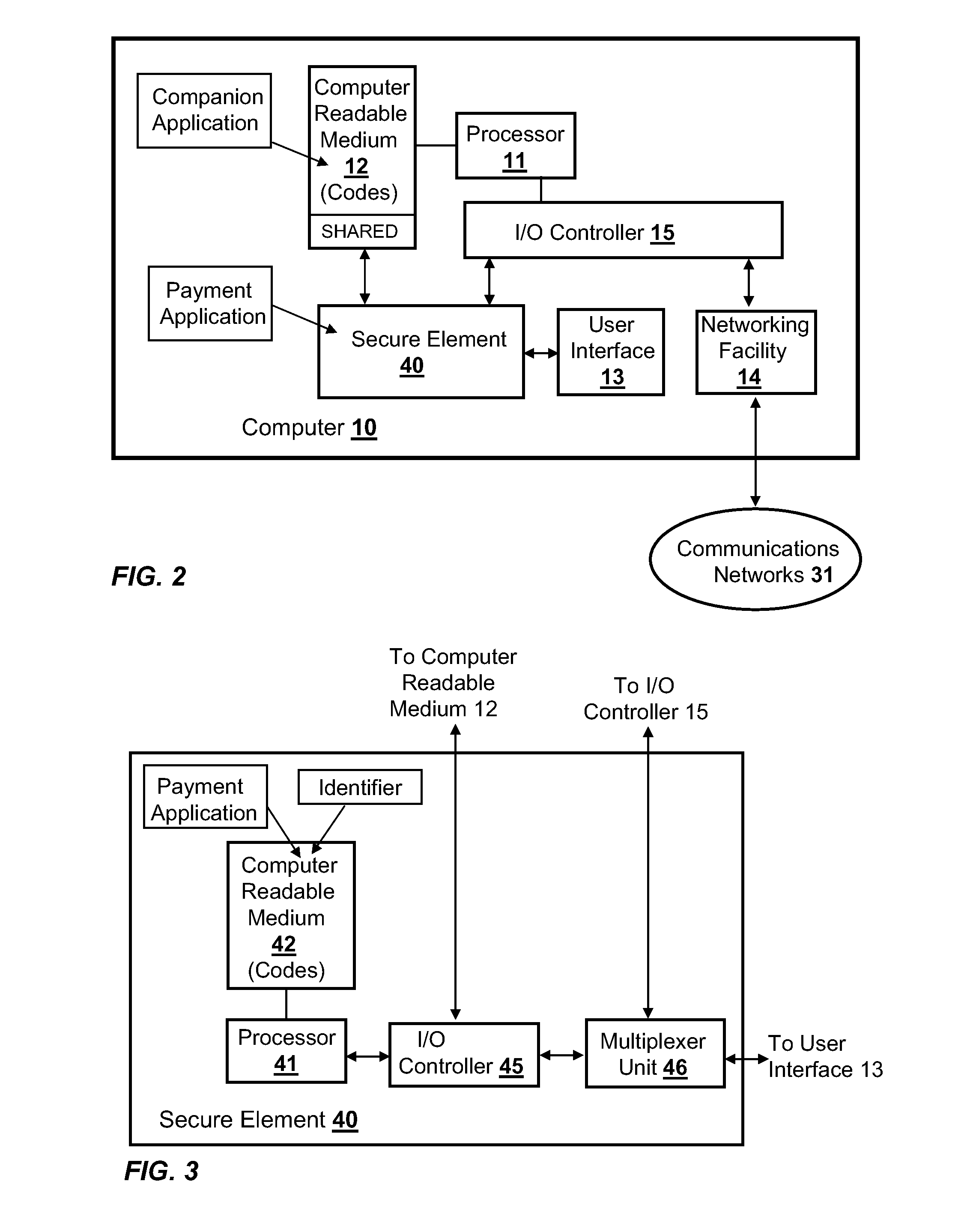
Methods, secure elements, validation entities, and computer program products for effecting secure communication of payment information to merchants for Internet-based purchases. Payment information for a user's real payment information is installed in a secure element of a computer, the payment information may comprise a pseudo PAN number for the portable consumer device provided by a validation entity. The secure element is shielded from the computer's operating system to thwart hacker attacks. The user accesses the secure element to make a purchase. In response, the secure element contacts the validation entity with the pseudo account number, and in response obtains dynamic payment information that the secure element can used to effect the payment. The dynamic payment information comprises an account number that is different from the pseudo PAN, and which has at least one difference which respect to the user's real payment information.
Owner:VISA INT SERVICE ASSOC
Data authentication system
InactiveUS20020169971A1Efficient verificationPossibility of leakageTelevision system detailsMultiple keys/algorithms usageKey storageMaster key
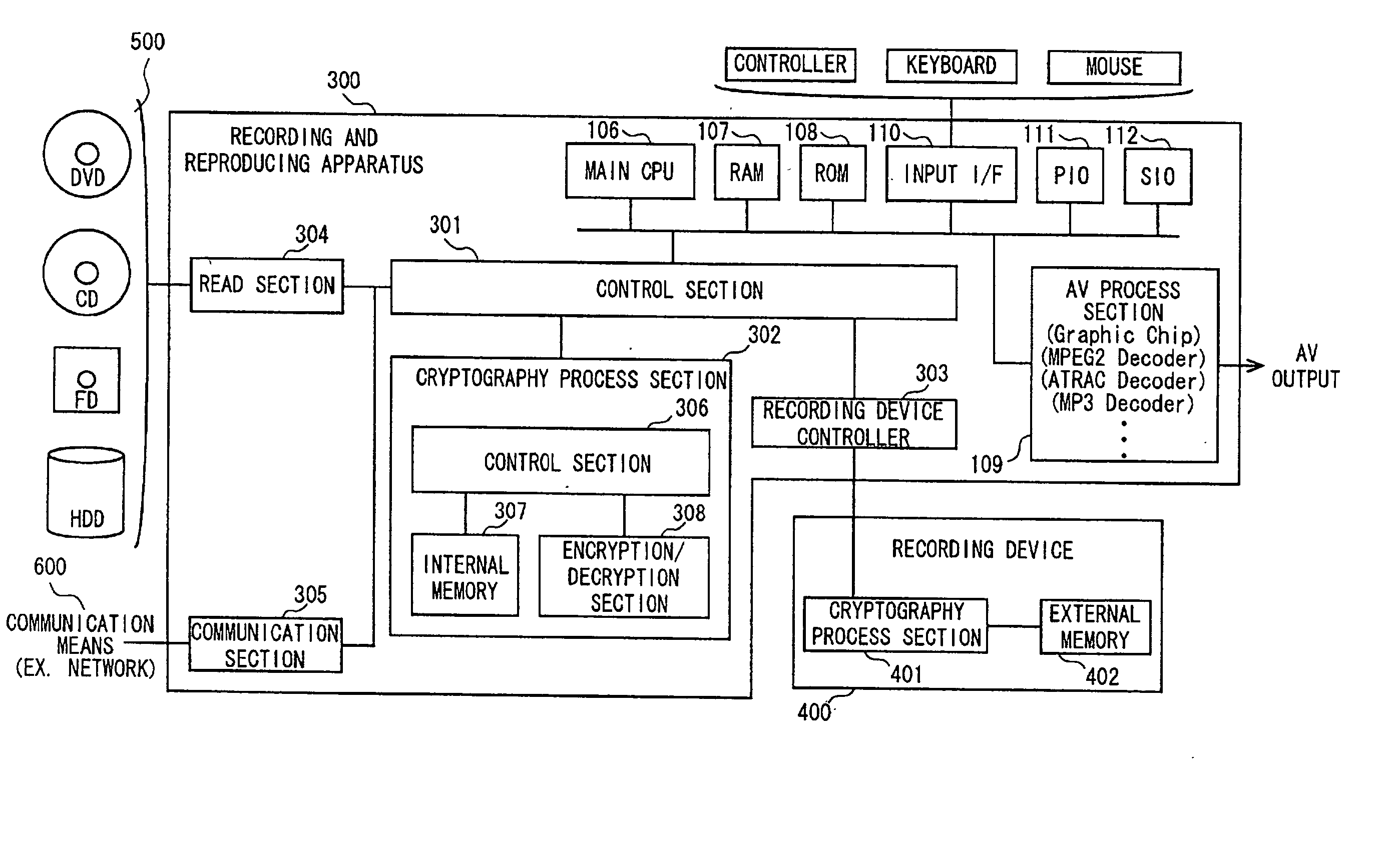
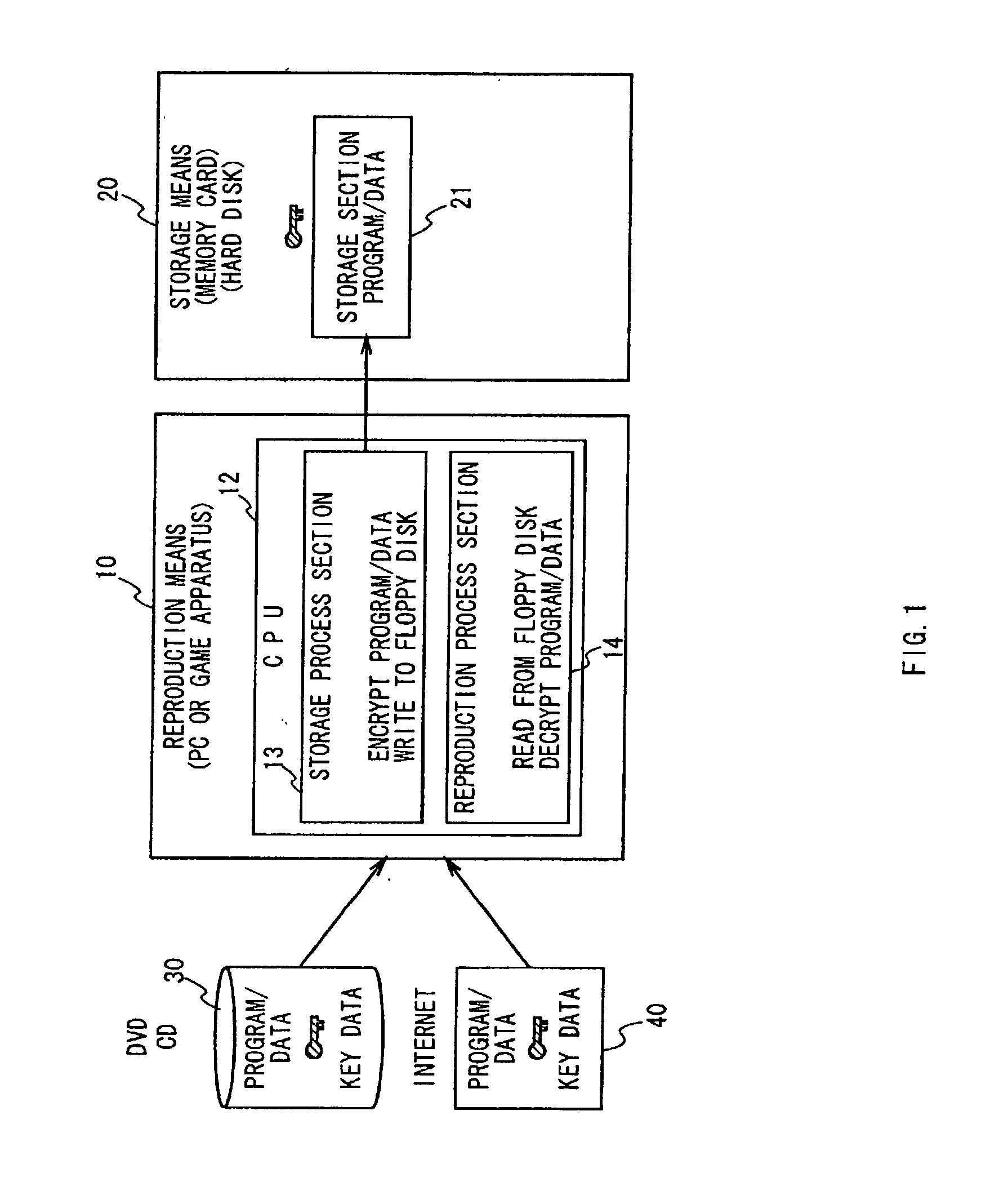
A data processing apparatus a data processing method efficiently ascertain that data are valid, prevent encryption processing key data from leaking, eliminate illegal use of contents data, restrict contents utilization, apply a different plurality of data formats to contents and efficiently execute reproduction processing of compressed data. The verification process of partial data is executed by collating the integrity partial data as check values for a combination of partial data of a content, and the verification process of the entirety of the combination of partial data is executed by collating partial-integrity-check-value-verifying integrity check values that verify the combination of the partial integrity check values. Master keys to generate individual keys necessary for a process of such as data encryption are stored in the storage section and keys are generated as required. An illegal device list is stored in the header information of a content and referred to when data is used. Keys specific to a data processing apparatus and common keys are stored and the keys are selectively used according to the content use restriction. Plural content blocks are coupled, and at least a part of the content blocks is applied to an encryption process by an encryption key Kcon, then encryption key data that is the encryption key Kcon encrypted by an encryption key Kdis is stored in the header section. A content data is made of compression data and an expansion processing program or a combination of types of compression programs and the reproducing apparatus can determine an expansion program applicable to a compressed content.
Owner:SONY CORP
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com