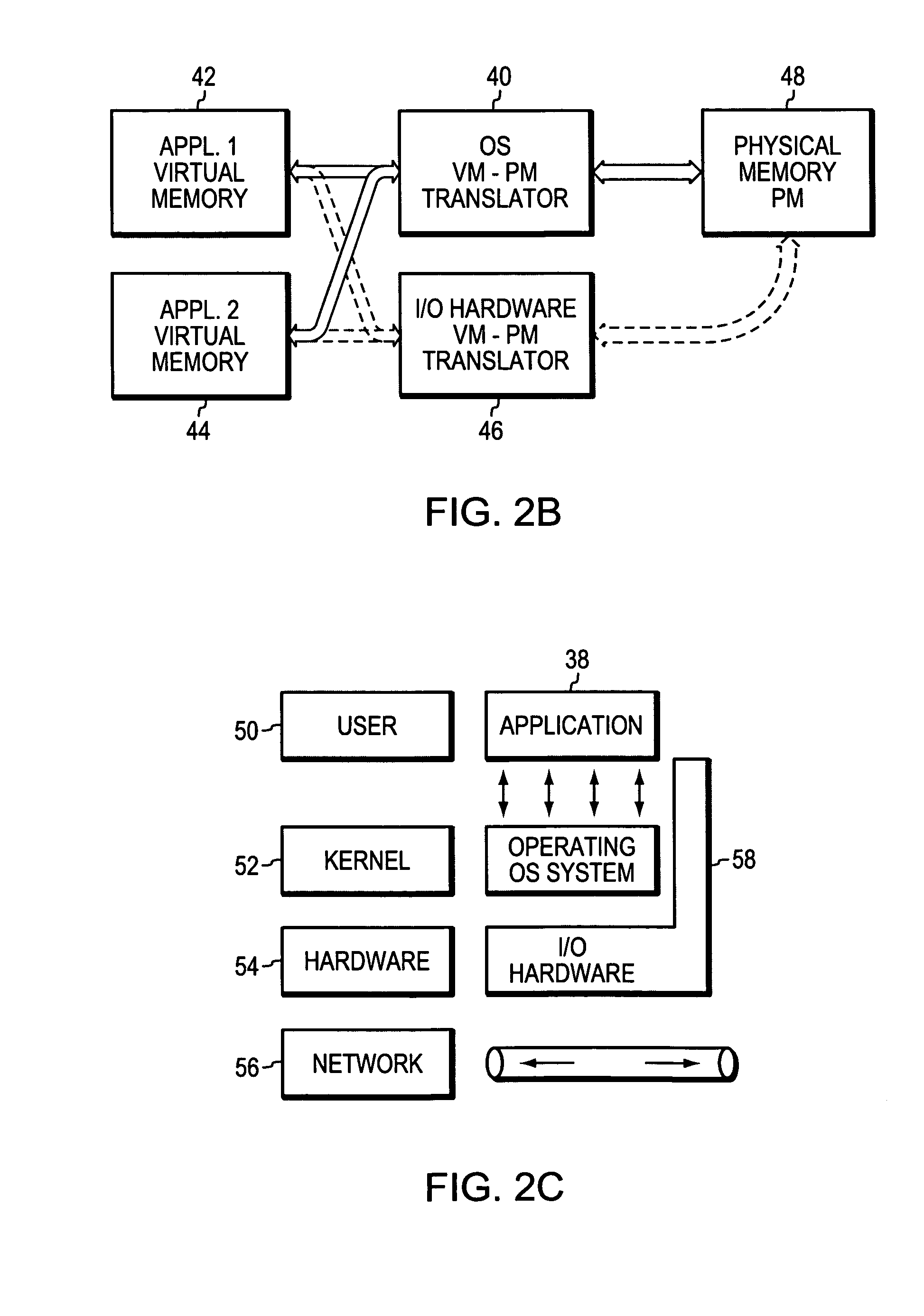
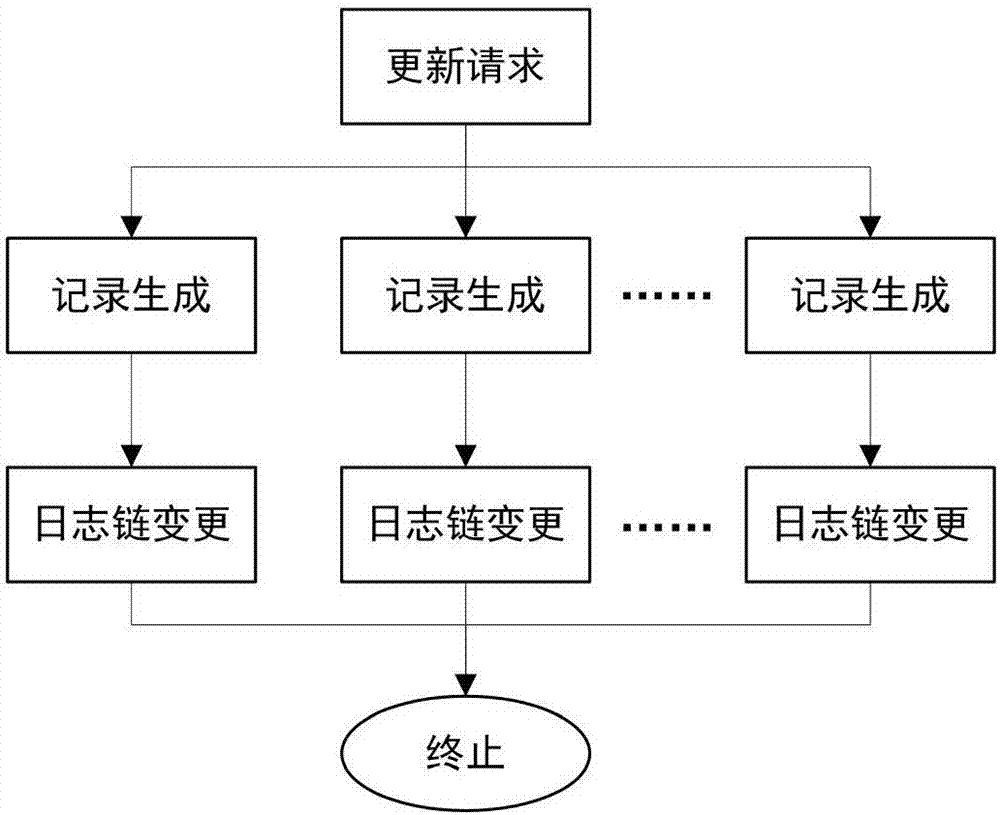
Patents
Literature
1274 results about "Key storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
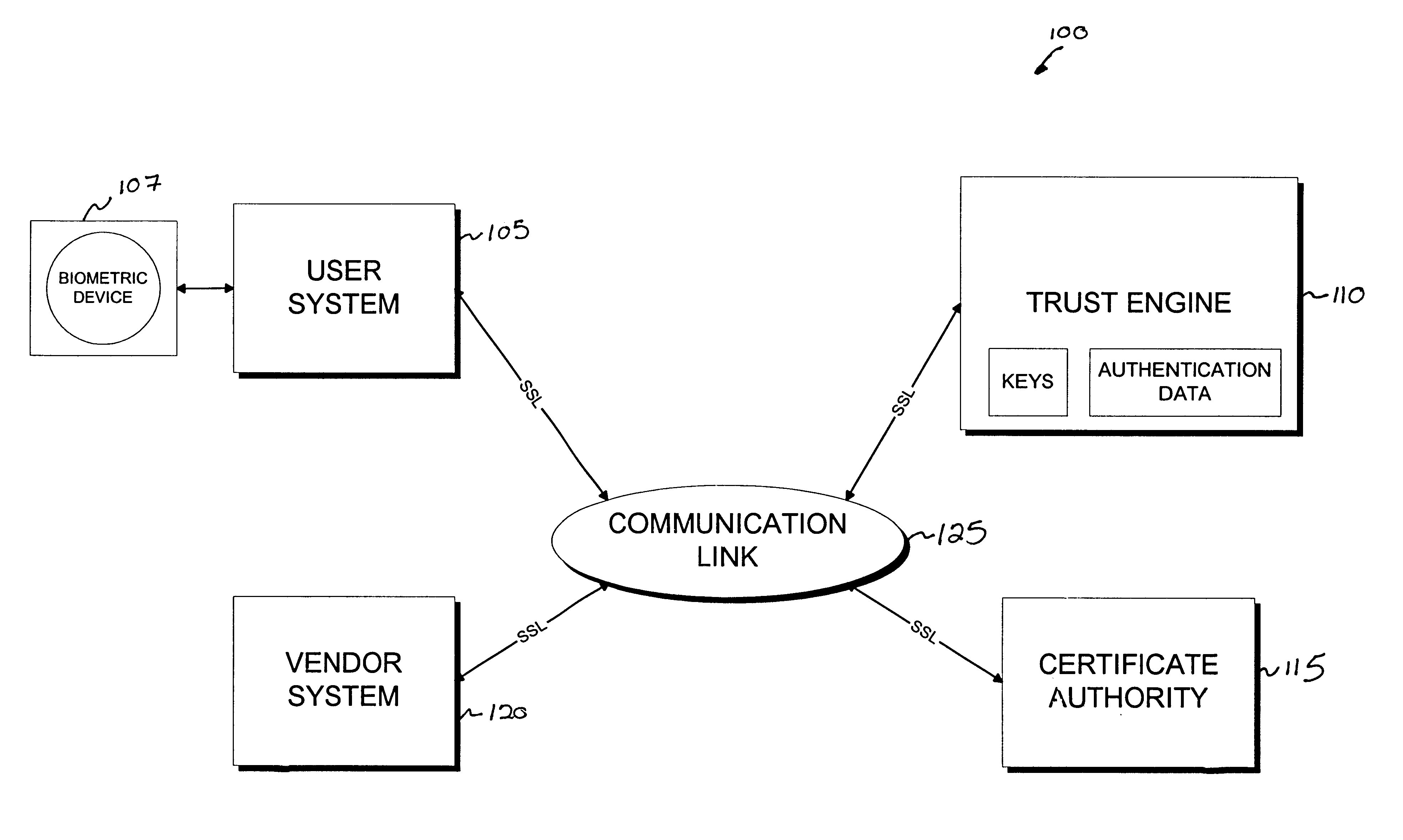
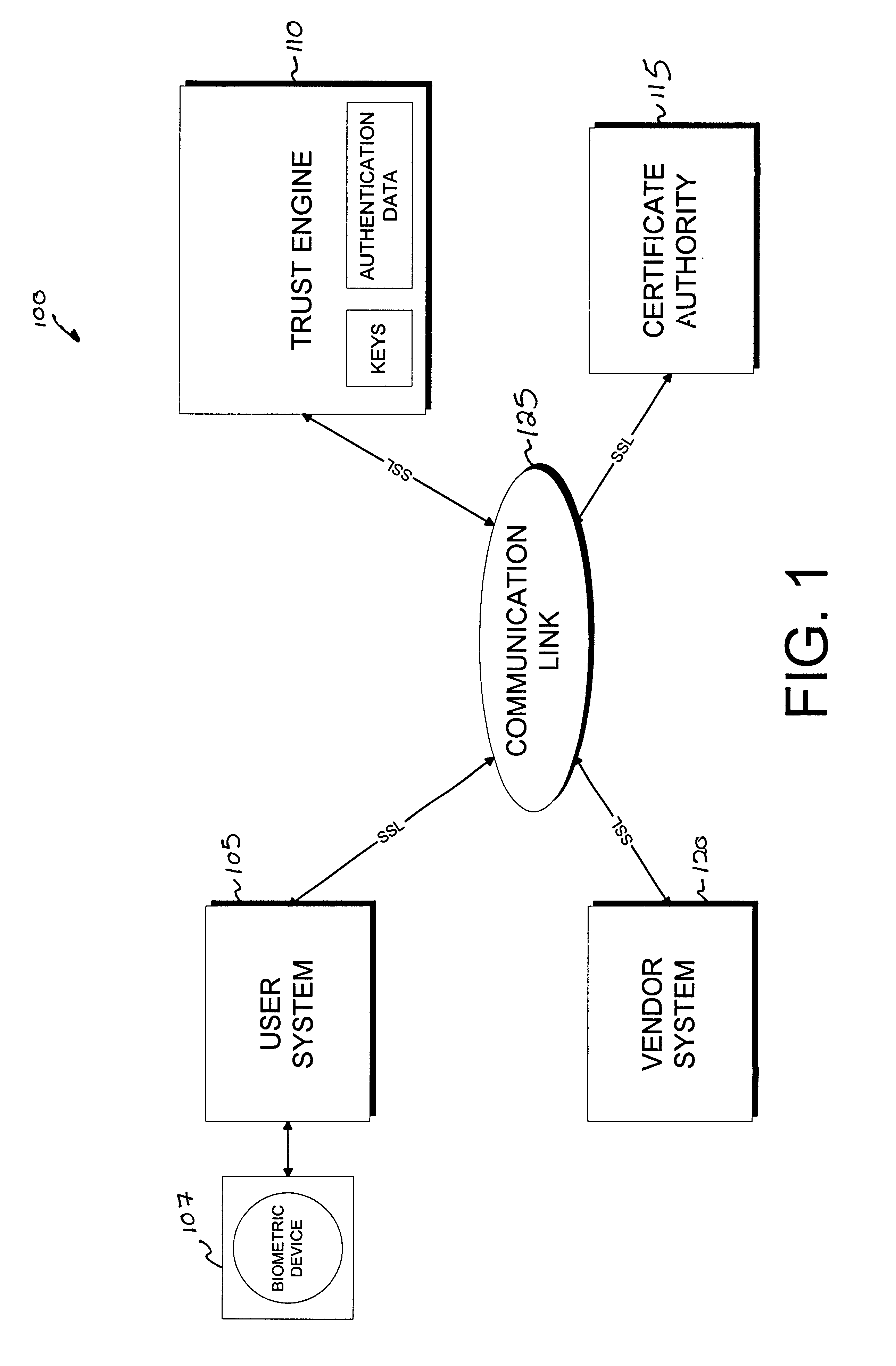
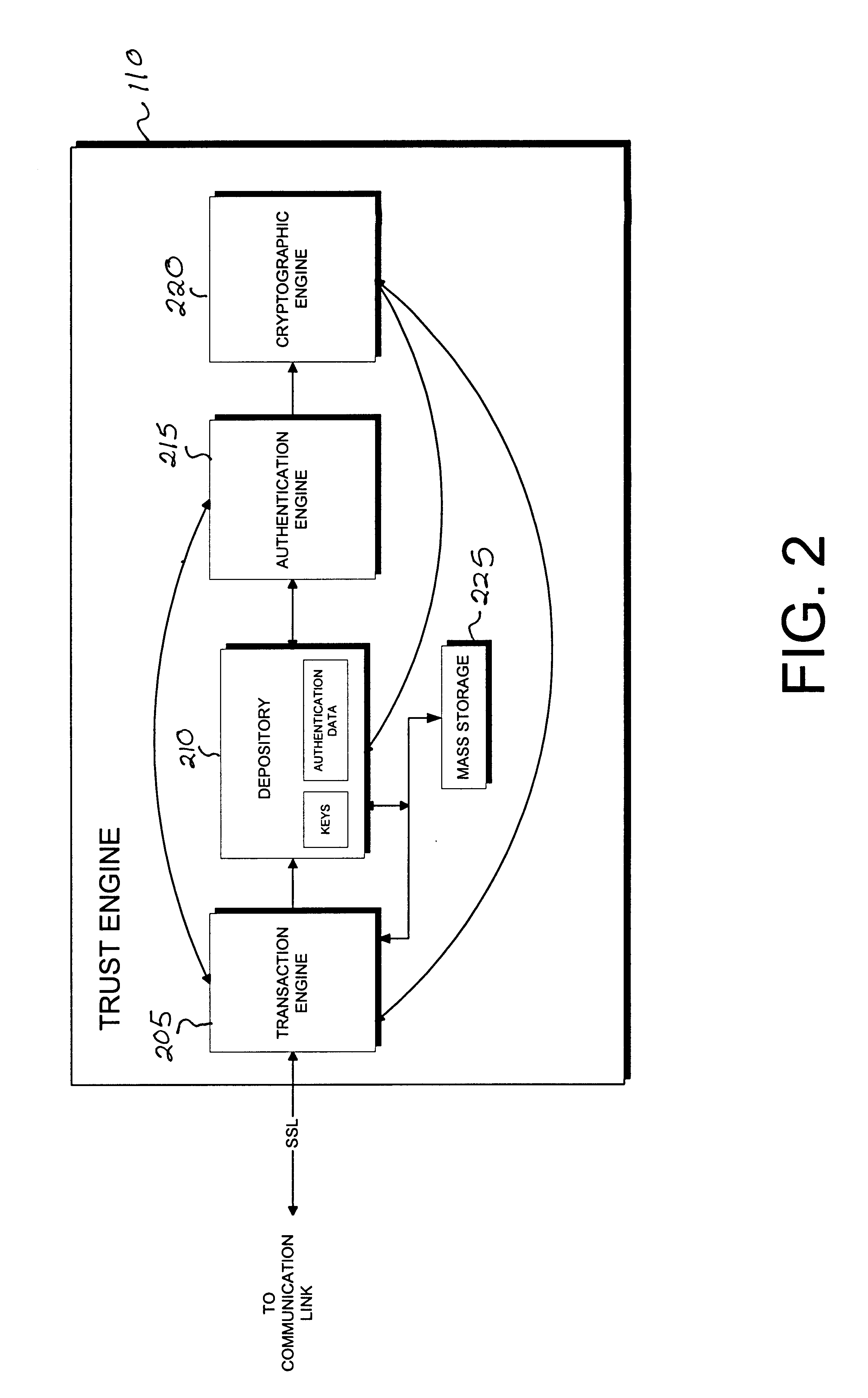
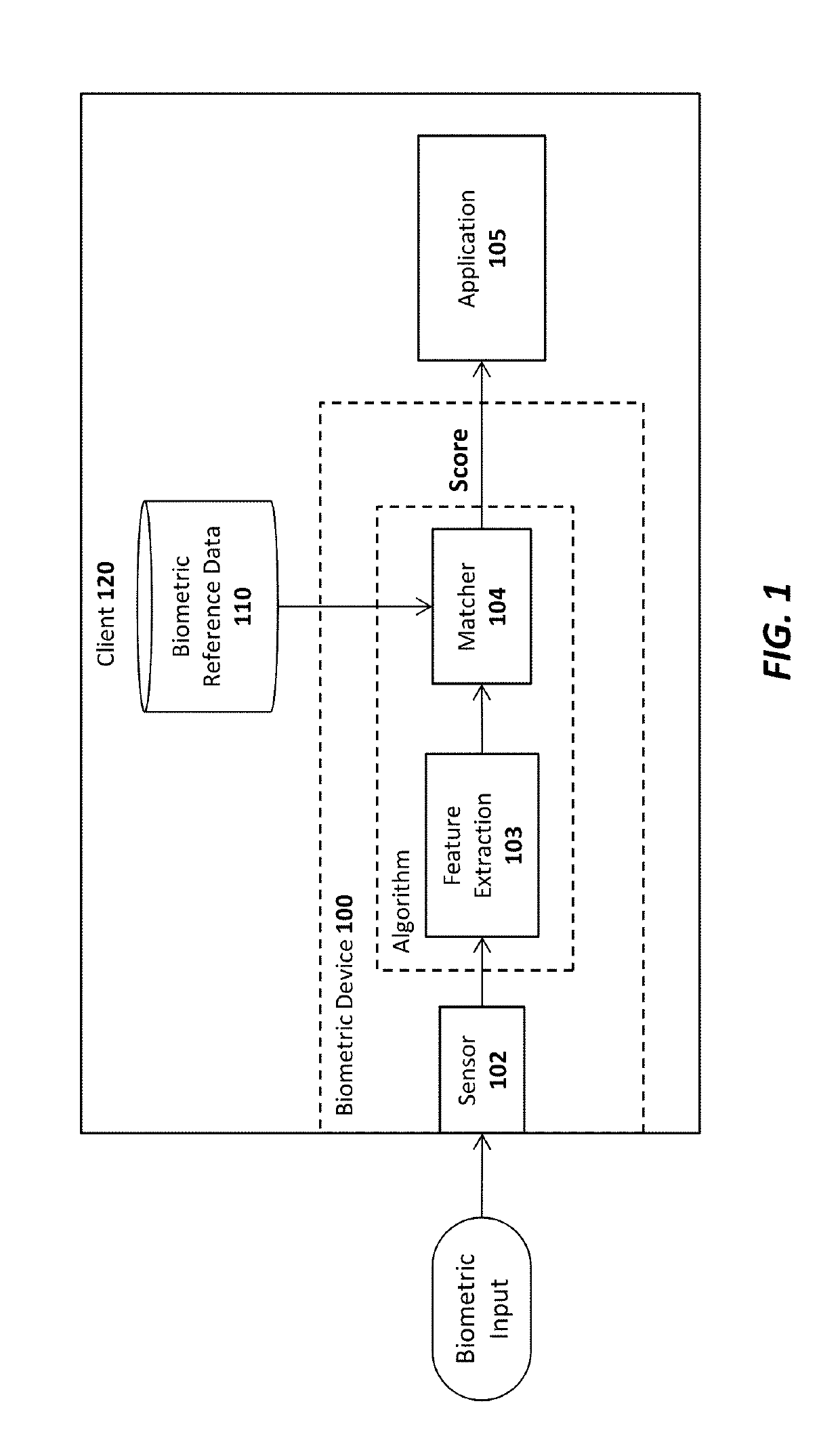
Cryptographic server with provisions for interoperability between cryptographic systems
InactiveUS6853988B1Reduce the number of timesMinimal compute resourceDigital data authenticationBuying/selling/leasing transactionsComputer hardwareKey storage
The invention is a cryptographic server providing interoperability over multiple algorithms, keys, standards, certificate types and issuers, protocols, and the like. Another aspect of the invention is to provide a secure server, or trust engine, having server-centric keys, or in other words, storing cryptographic keys on a server. The server-centric storage of keys provides for user-independent security, portability, availability, and straightforwardness, along with a wide variety of implementation possibilities.
Owner:SECURITY FIRST INNOVATIONS LLC
Data authentication system
InactiveUS20020169971A1Efficient verificationPossibility of leakageTelevision system detailsMultiple keys/algorithms usageKey storageMaster key
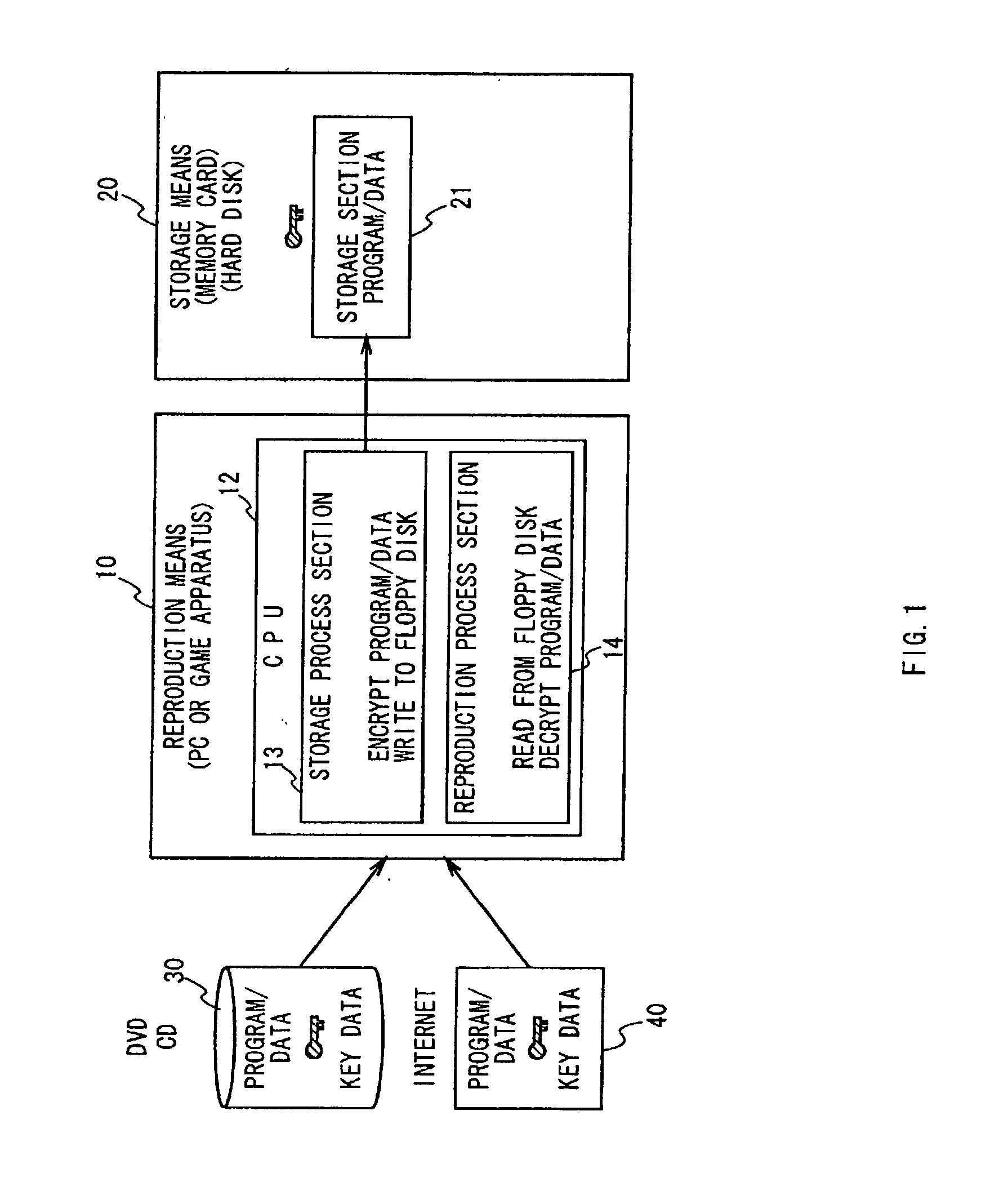
A data processing apparatus a data processing method efficiently ascertain that data are valid, prevent encryption processing key data from leaking, eliminate illegal use of contents data, restrict contents utilization, apply a different plurality of data formats to contents and efficiently execute reproduction processing of compressed data. The verification process of partial data is executed by collating the integrity partial data as check values for a combination of partial data of a content, and the verification process of the entirety of the combination of partial data is executed by collating partial-integrity-check-value-verifying integrity check values that verify the combination of the partial integrity check values. Master keys to generate individual keys necessary for a process of such as data encryption are stored in the storage section and keys are generated as required. An illegal device list is stored in the header information of a content and referred to when data is used. Keys specific to a data processing apparatus and common keys are stored and the keys are selectively used according to the content use restriction. Plural content blocks are coupled, and at least a part of the content blocks is applied to an encryption process by an encryption key Kcon, then encryption key data that is the encryption key Kcon encrypted by an encryption key Kdis is stored in the header section. A content data is made of compression data and an expansion processing program or a combination of types of compression programs and the reproducing apparatus can determine an expansion program applicable to a compressed content.
Owner:SONY CORP
Method and Apparatus for Hardware-Accelerated Encryption/Decryption
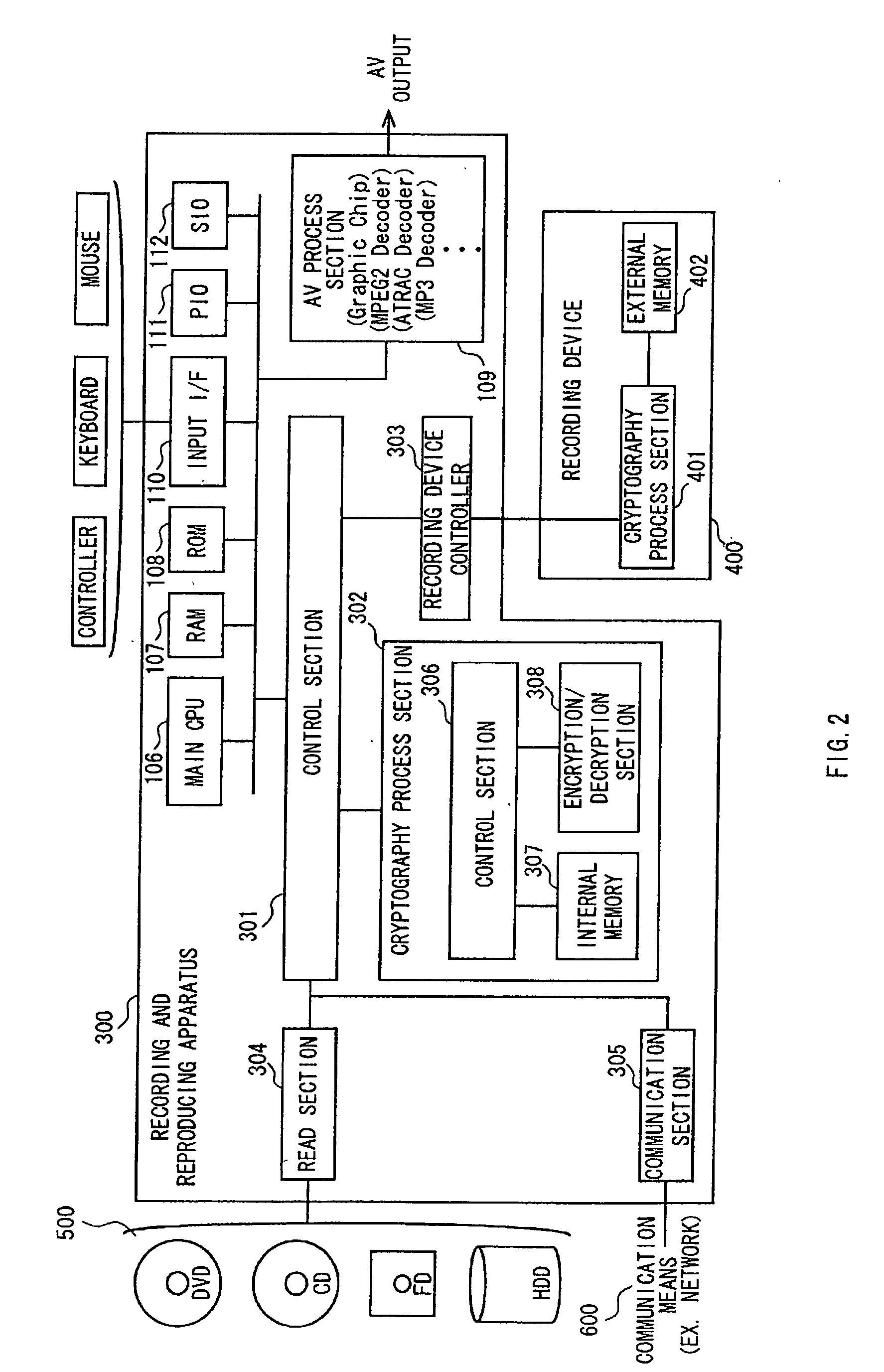
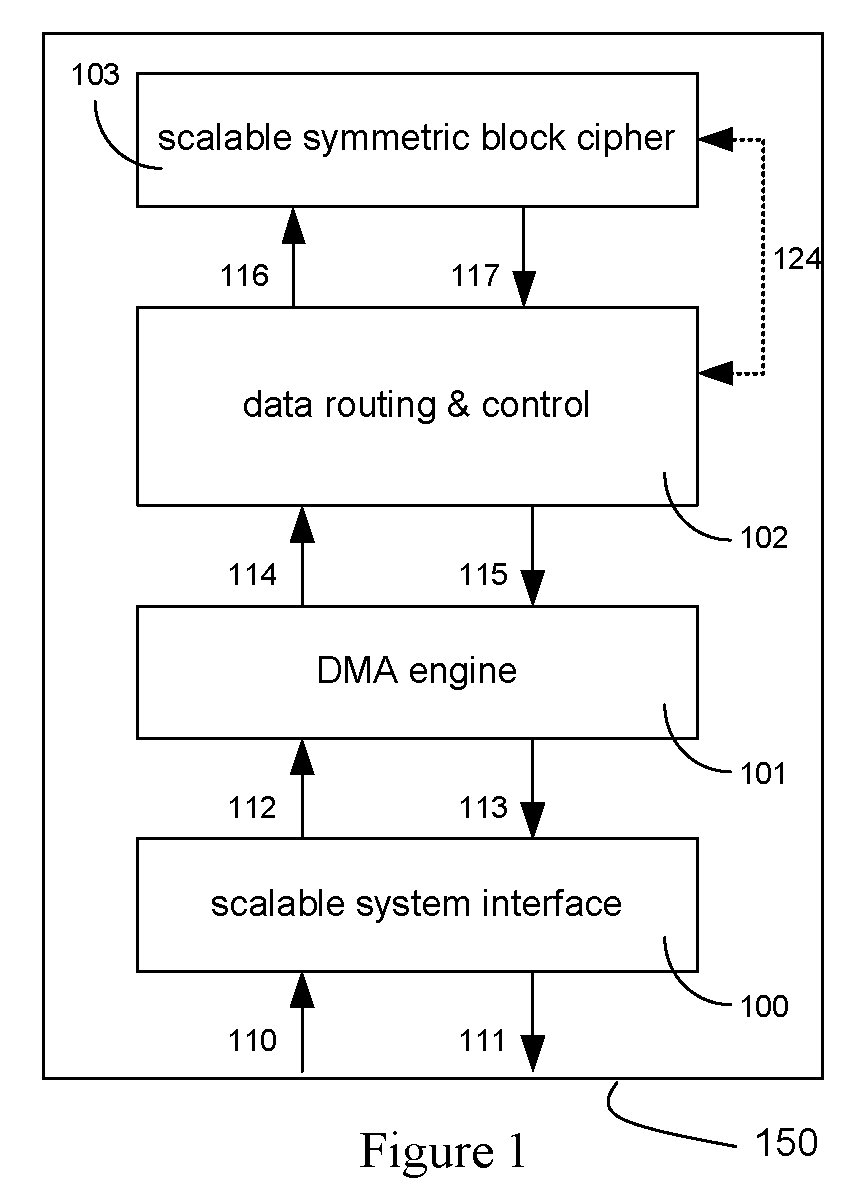
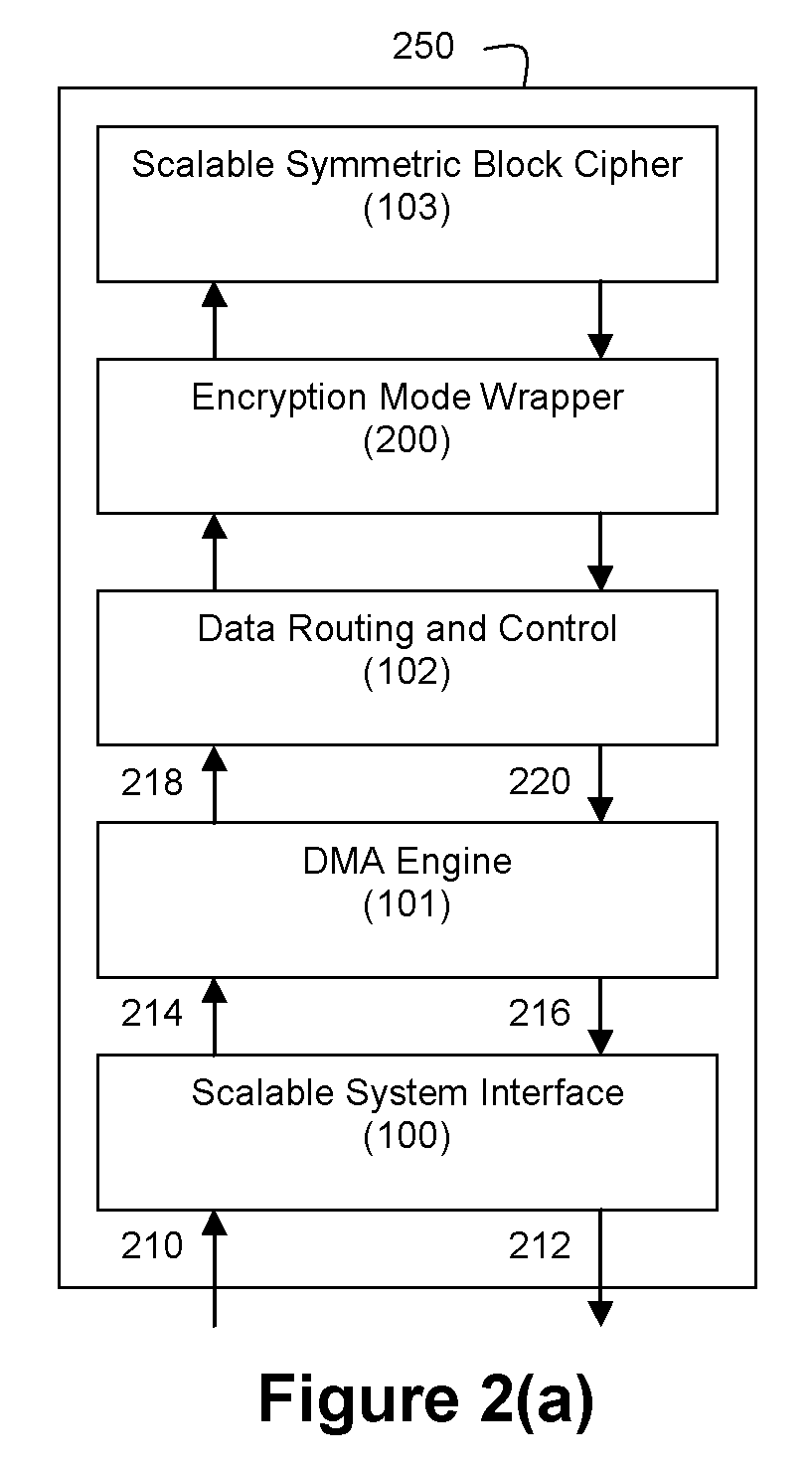
ActiveUS20090060197A1Avoid contactMaximize availabilityEncryption apparatus with shift registers/memoriesSecret communicationMultiple encryptionComputer hardware
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
Storage array password management
A system and method for generating passwords for secure login to a storage array. A randomly generated root secret is utilized along with a compartment ID to generate a root password for logging into a storage array with root privileges. The root secret is encrypted with the public key of a public-private key pair and stored on the storage array. The encrypted root secret is then stored in the storage array. When root access is needed, a private key stored externally to the storage array is utilized to decrypt the root secret. The decrypted root secret is then used along with the compartment ID to regenerate the root password.
Owner:PURE STORAGE
Distributed Network Encryption for Logical Network Implemented in Public Cloud
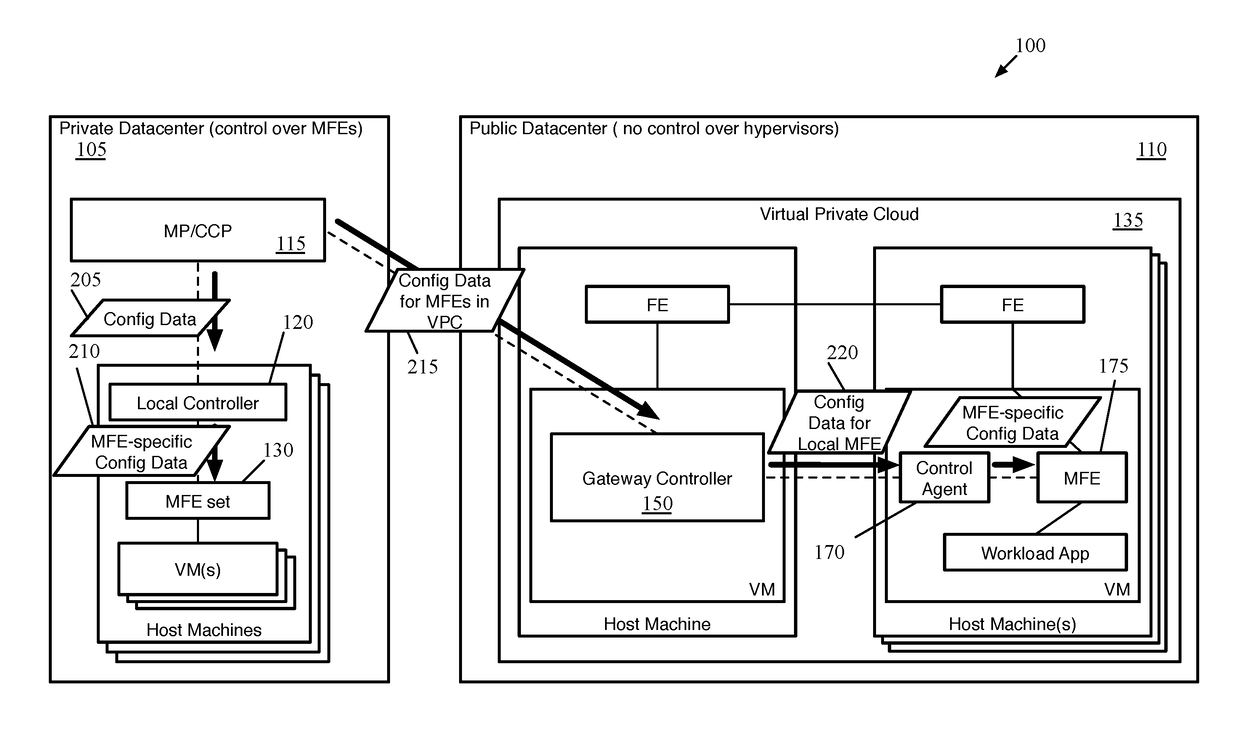
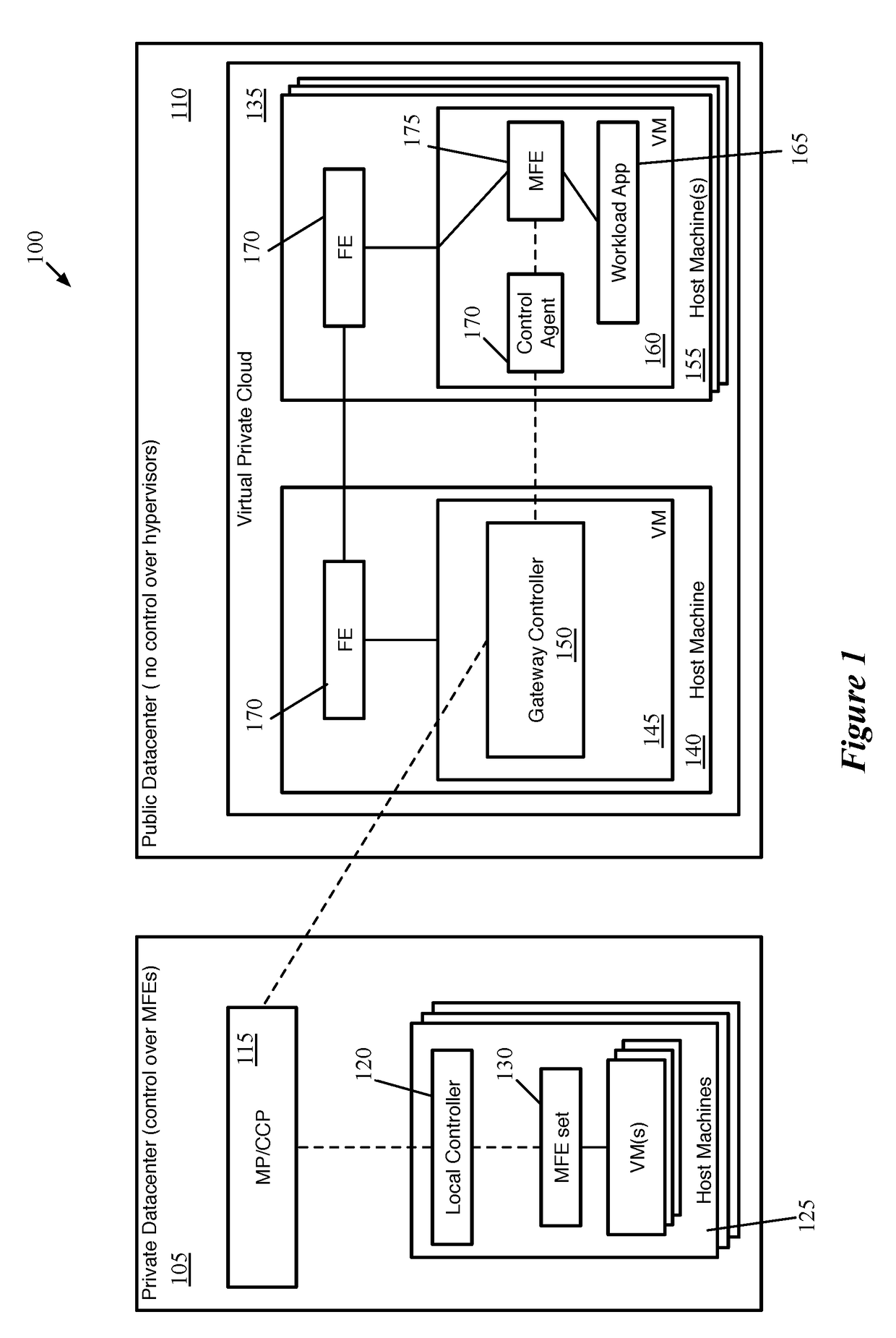
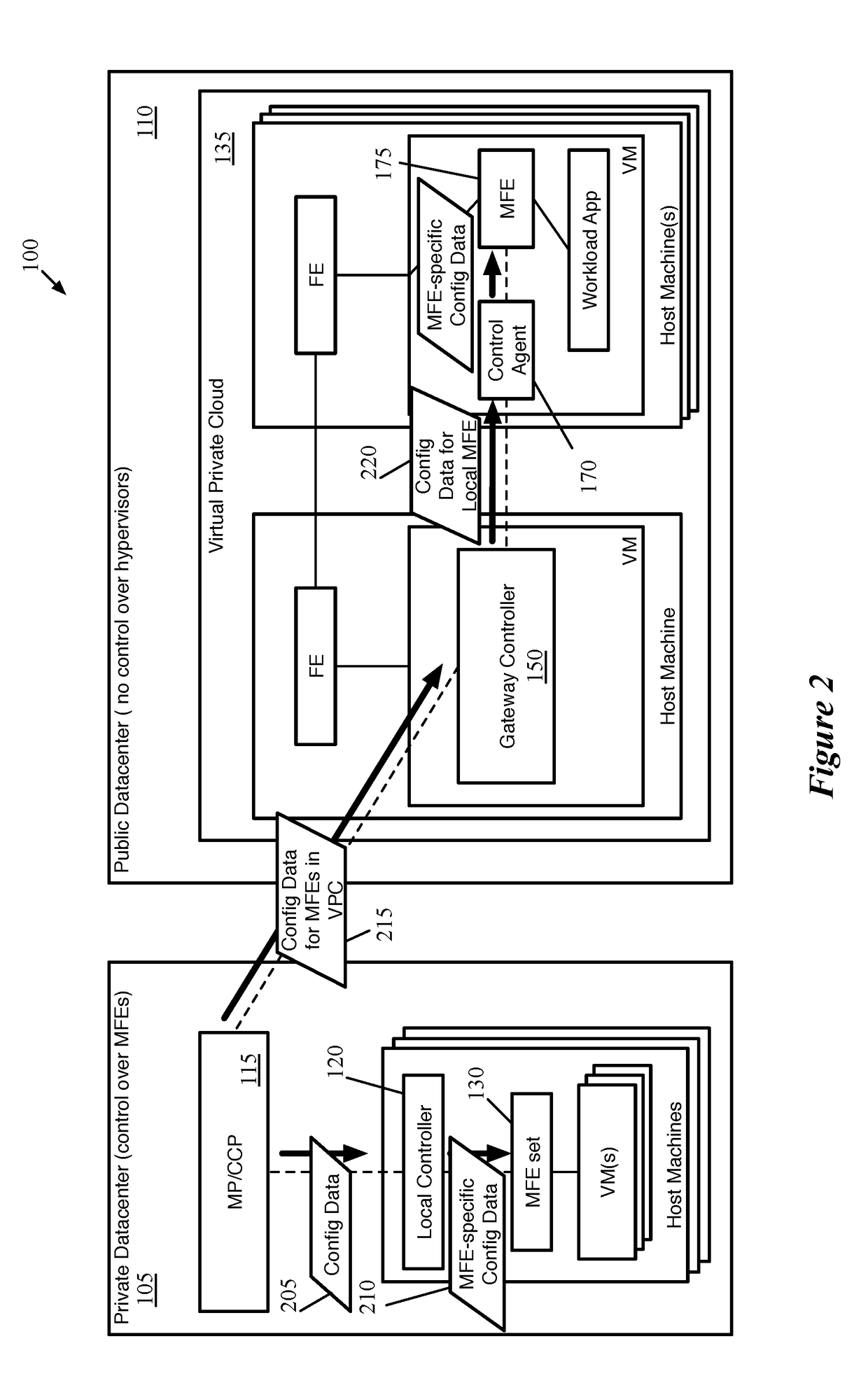
ActiveUS20180063193A1Key distribution for secure communicationUser identity/authority verificationKey distributionKey storage
Some embodiments provide a method for a first data compute node (DCN) operating in a public datacenter. The method receives an encryption rule from a centralized network controller. The method determines that the network encryption rule requires encryption of packets between second and third DCNs operating in the public datacenter. The method requests a first key from a secure key storage. Upon receipt of the first key, the method uses the first key and additional parameters to generate second and third keys. The method distributes the second key to the second DCN and the third key to the third DCN in the public datacenter.
Owner:NICIRA
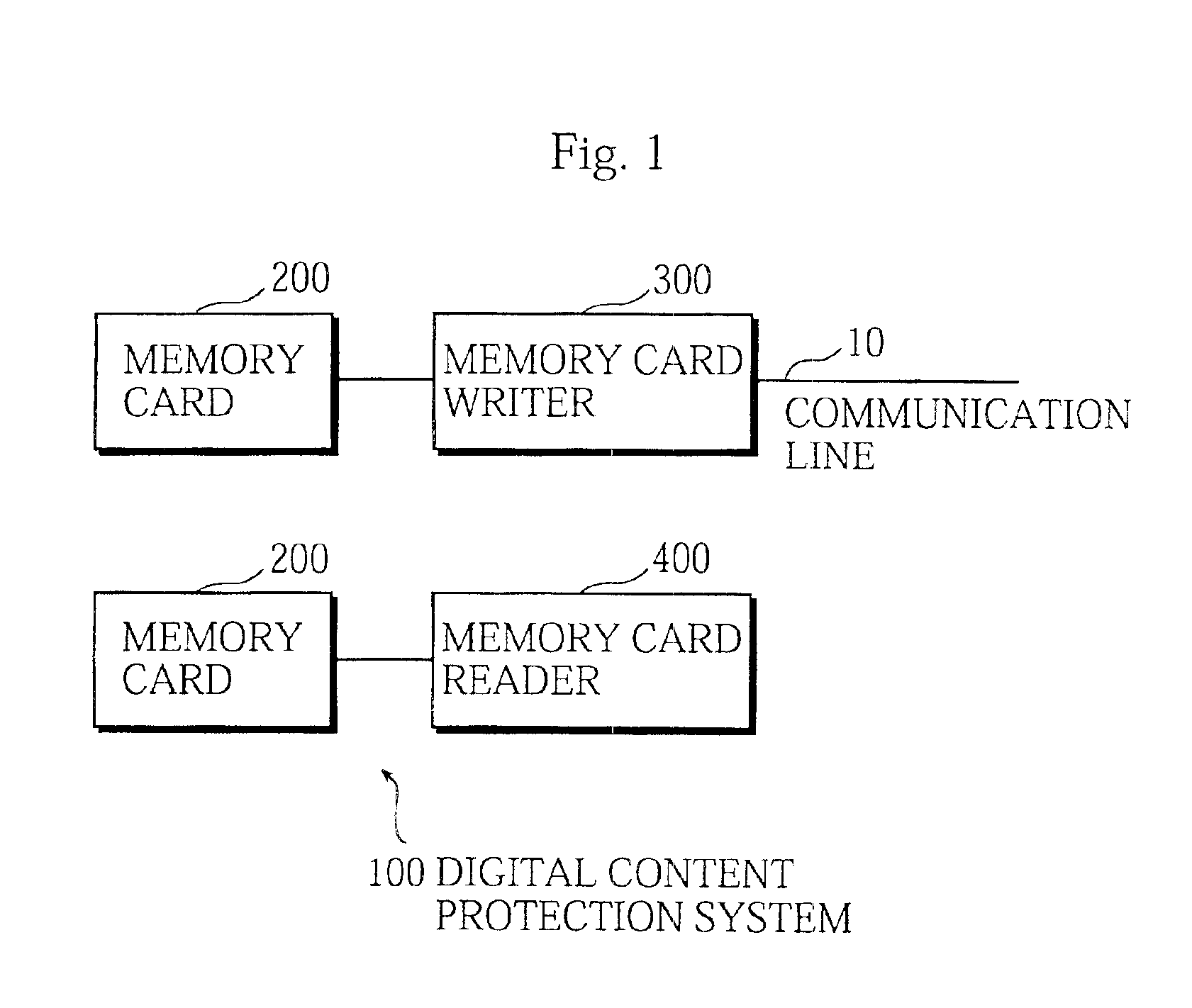
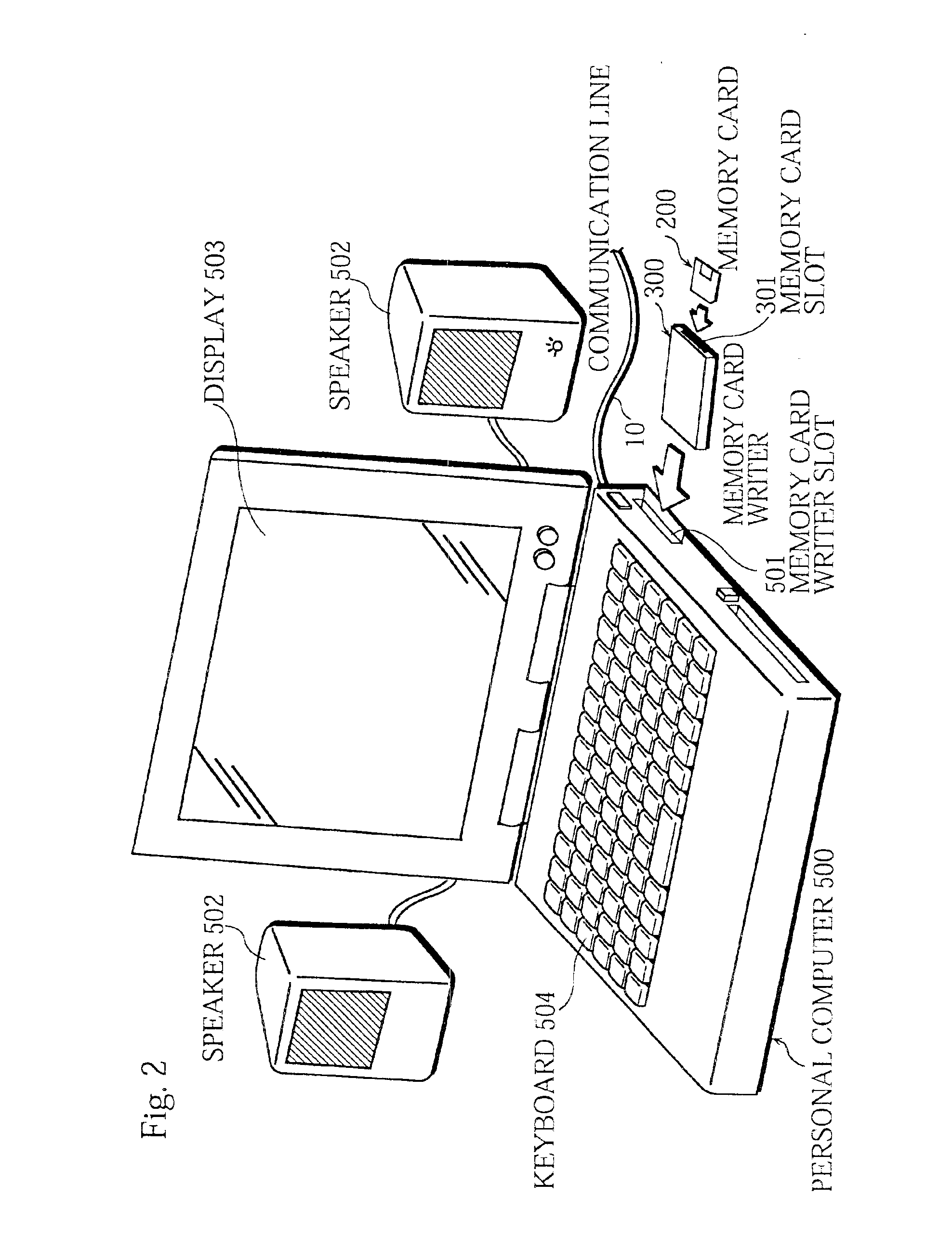
Digital content protection system
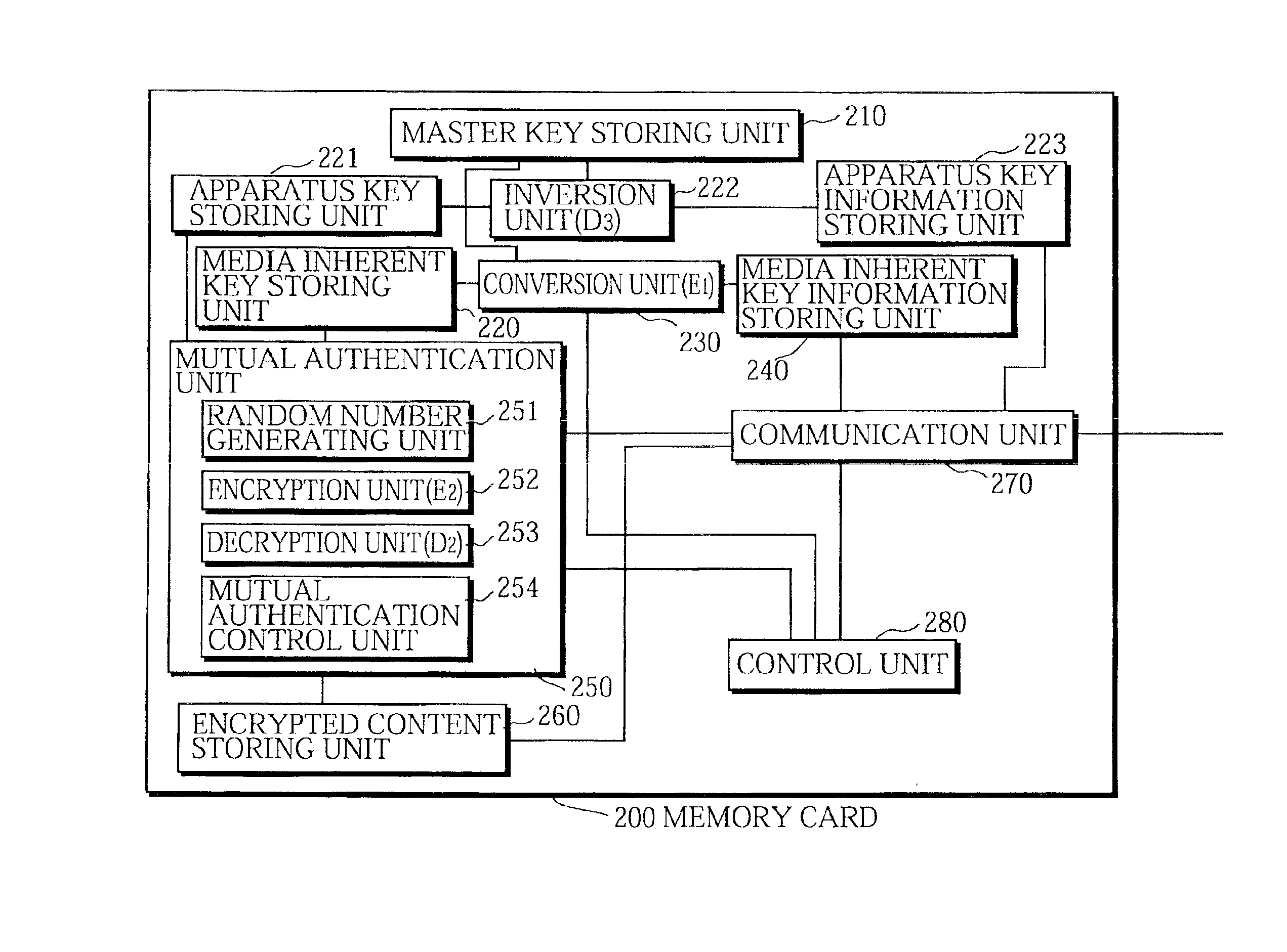
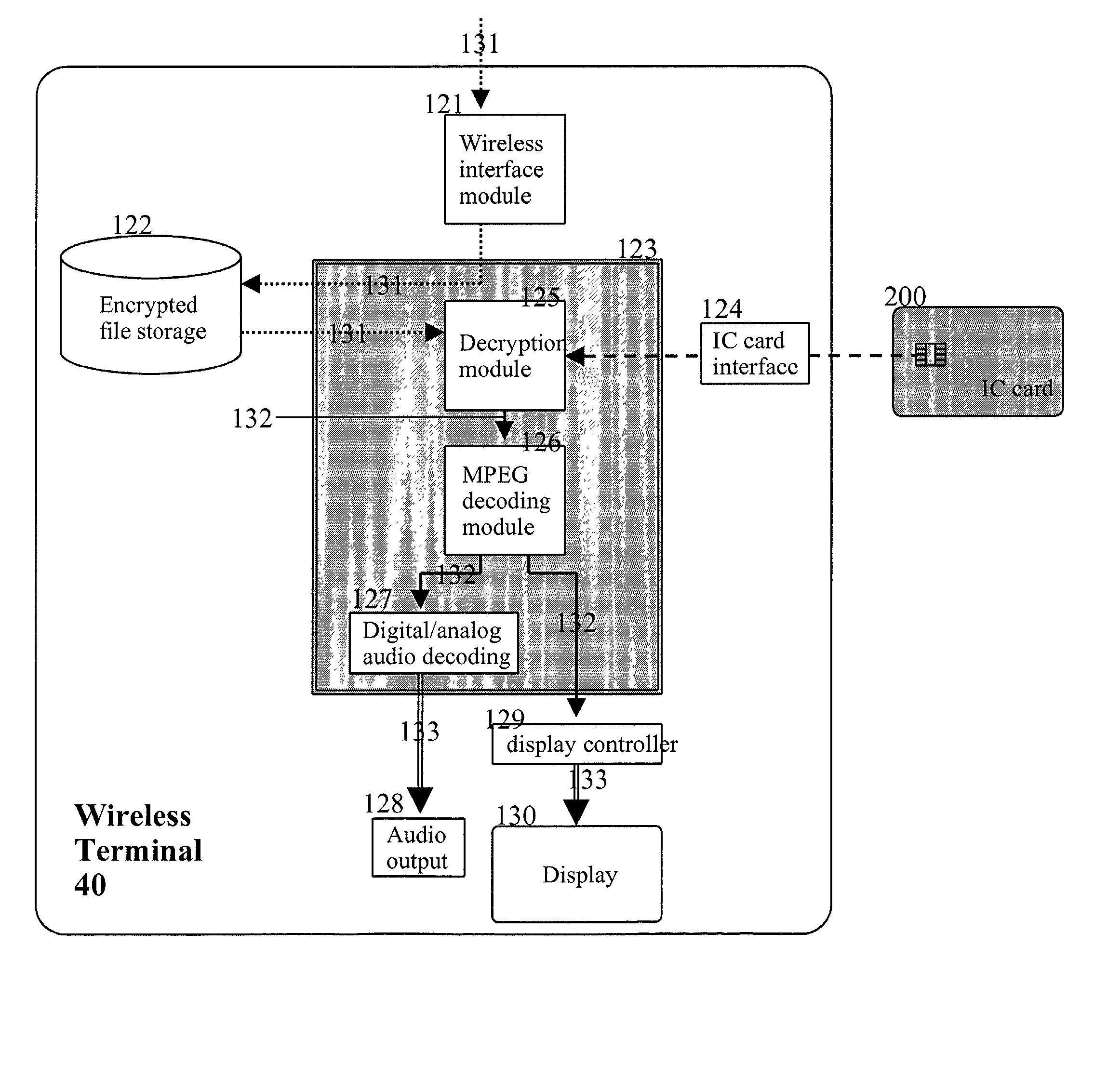
InactiveUS6859535B1Reduce scaleDigital data processing detailsUser identity/authority verificationDigital contentMediaFLO
The media inherent key storing unit 220 prestores an inherent key Ki, the conversion unit 230 generates an encrypted inherent key Ji from the inherent key read from the media inherent key storing unit 220, the random number generating unit 331 generates a random number R1, the encryption unit 252 generates an encrypted random number S1, the decryption unit 333 generates a random number R′1 from the encrypted random number R1, and the mutual authentication control unit 334 compares the random number R′1 with the random number R1 and, if the random number R′1 matches the random number R1, judges that the memory card 200 is an authorized device. If the memory card 200 and the memory card writer have successfully authenticated each other, the memory card writer encrypts a content using a decrypted inherent key. If the memory card 200 and the memory card reader have successfully authenticated each other, the memory card reader decrypts an encrypted content using the decrypted inherent key.
Owner:PANASONIC CORP
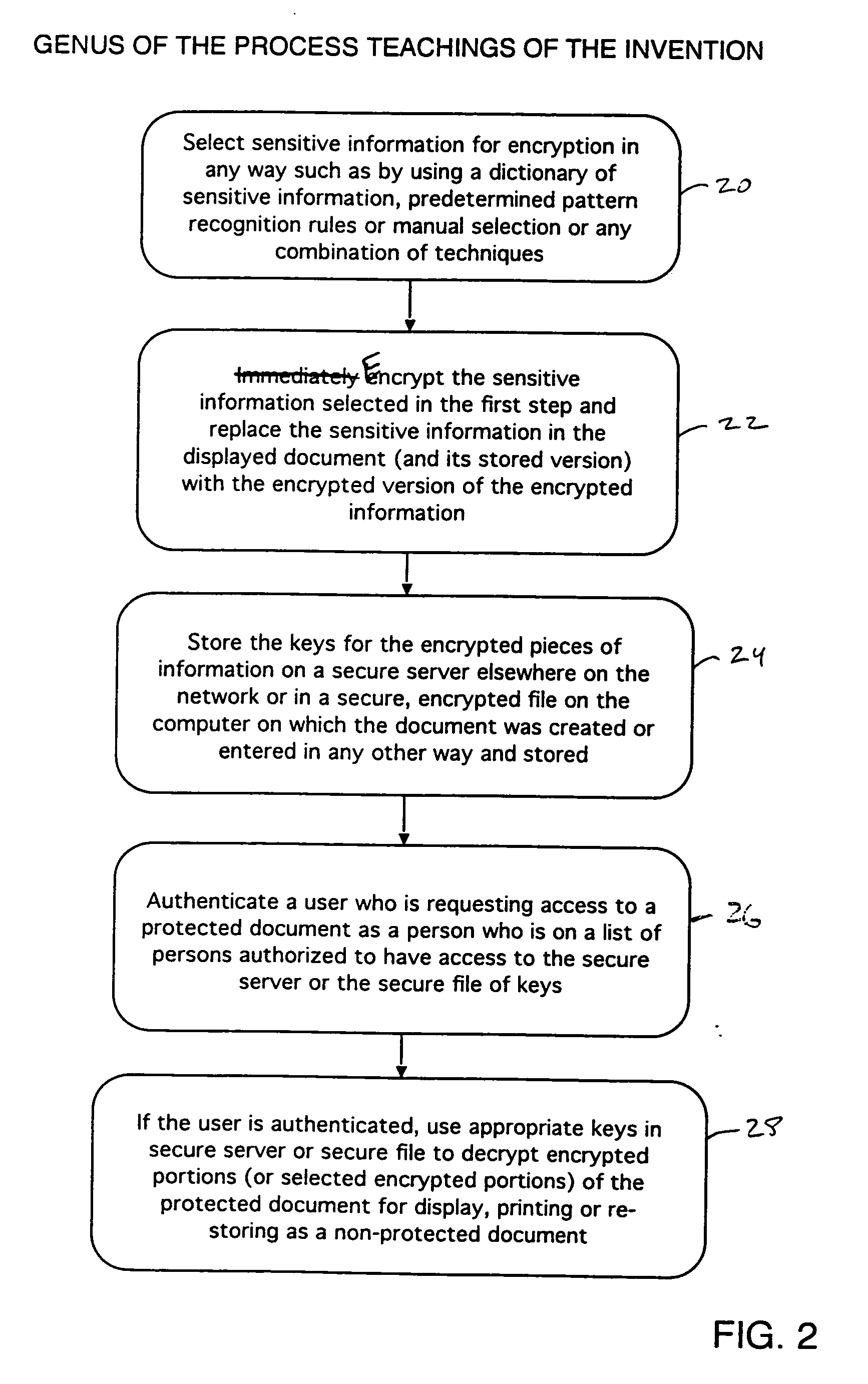
Method and apparatus for recognition and real time encryption of sensitive terms in documents
InactiveUS20060005017A1Function providedEliminated and reduced chanceComputer security arrangementsSecuring communicationPaper documentOverinclusion
A process for automatically selecting sensitive information in documents being displayed and / or generated on a computer to select sensitive information for encryption using pattern recognition rules, dictionaries of sensitive terms and / or manual selection of text. The sensitive text is automatically encrypted on the fly in the same manner as a spell checker works so that the sensitive information immediately is removed and replaced with the encrypted version or a pointer to where the encrypted version is stored. The keys used to encrypt the sensitive information in each document are stored in a table or database, preferably on a secure key server so that they do not reside on the computer on which the partially encrypted document is stored. Several learning embodiments that determine overinclusion and underinclusion errors in various ways and make adjustments to the rules and / or dictionary entries used to select sensitive information to reduce the errors are disclosed. Public-private key pair encryption algorithms and data structures to keep all the encryption keys stored such that they can be located is disclosed.
Owner:INFOSAFE
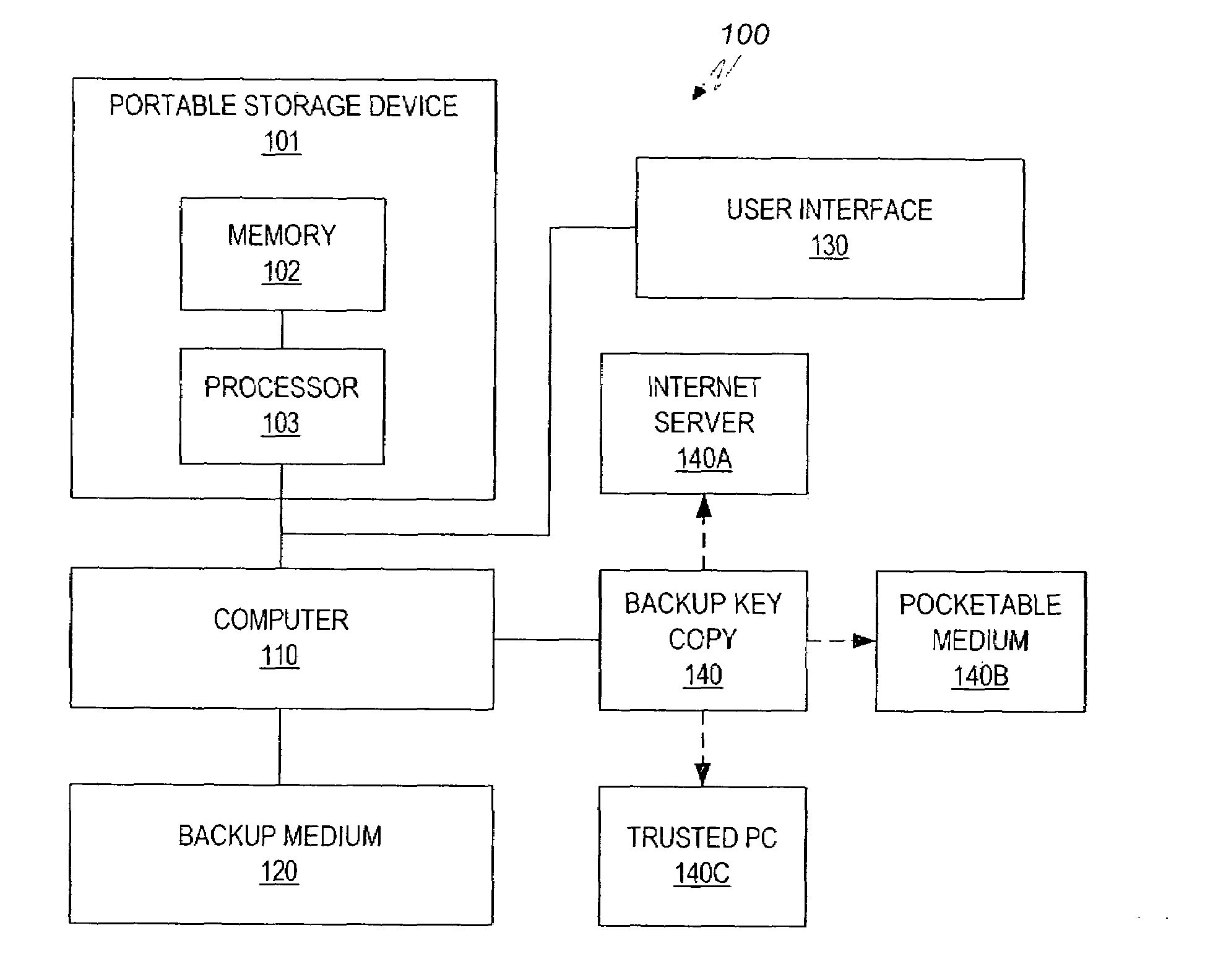
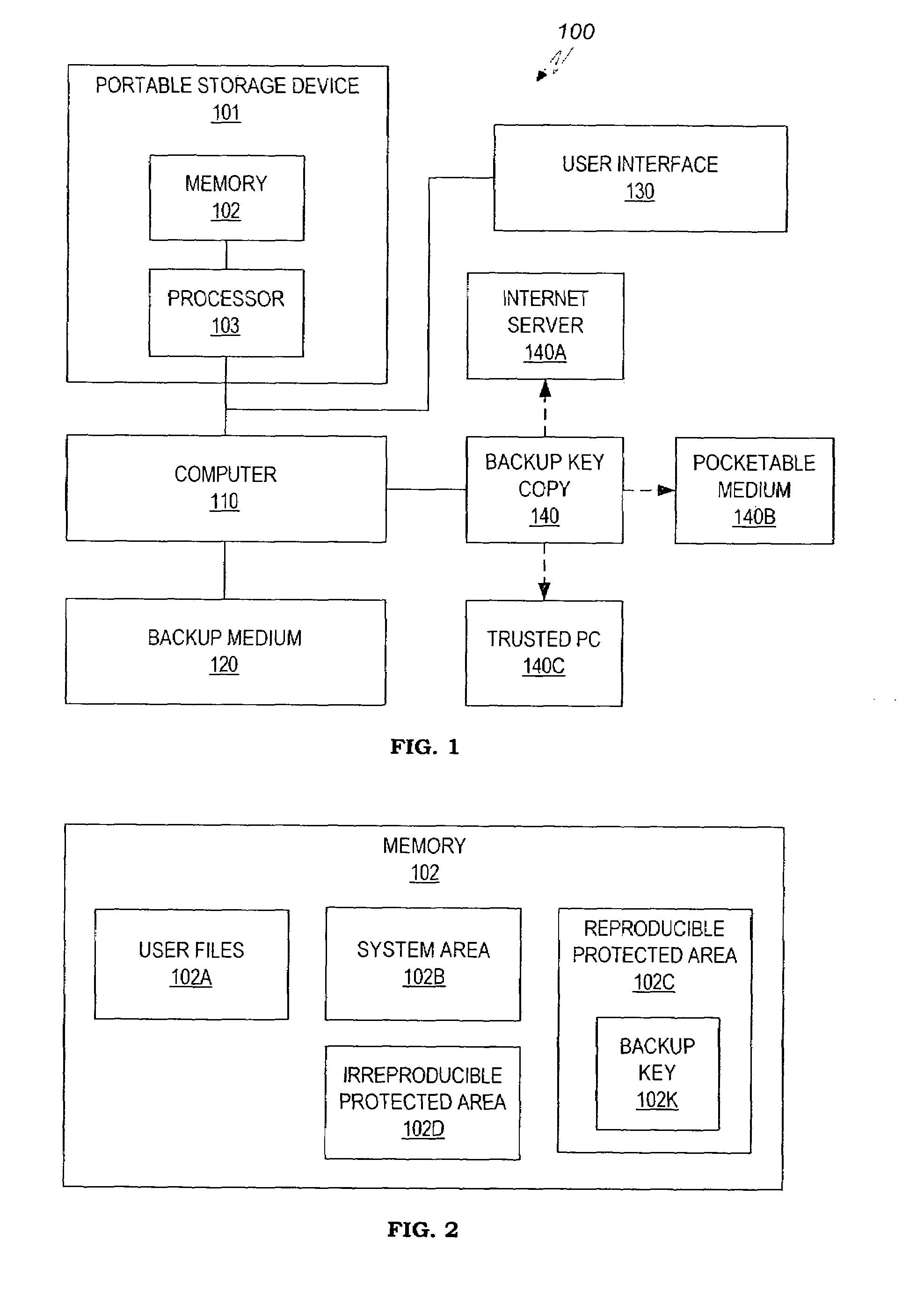
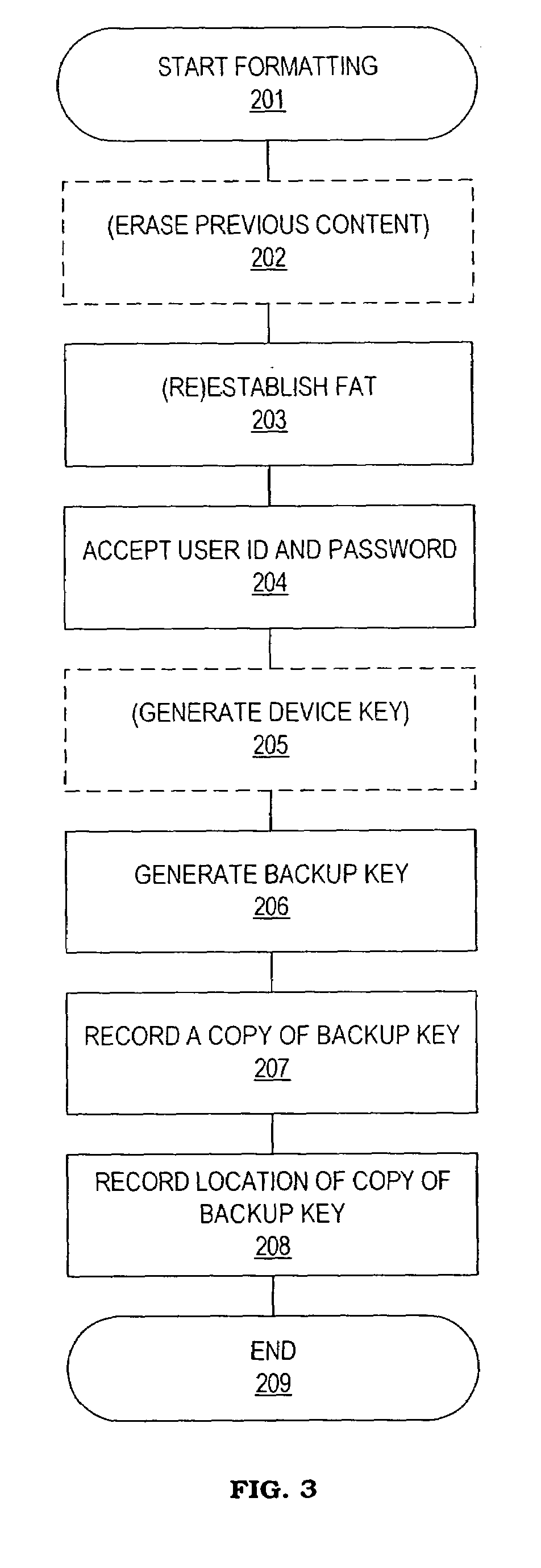
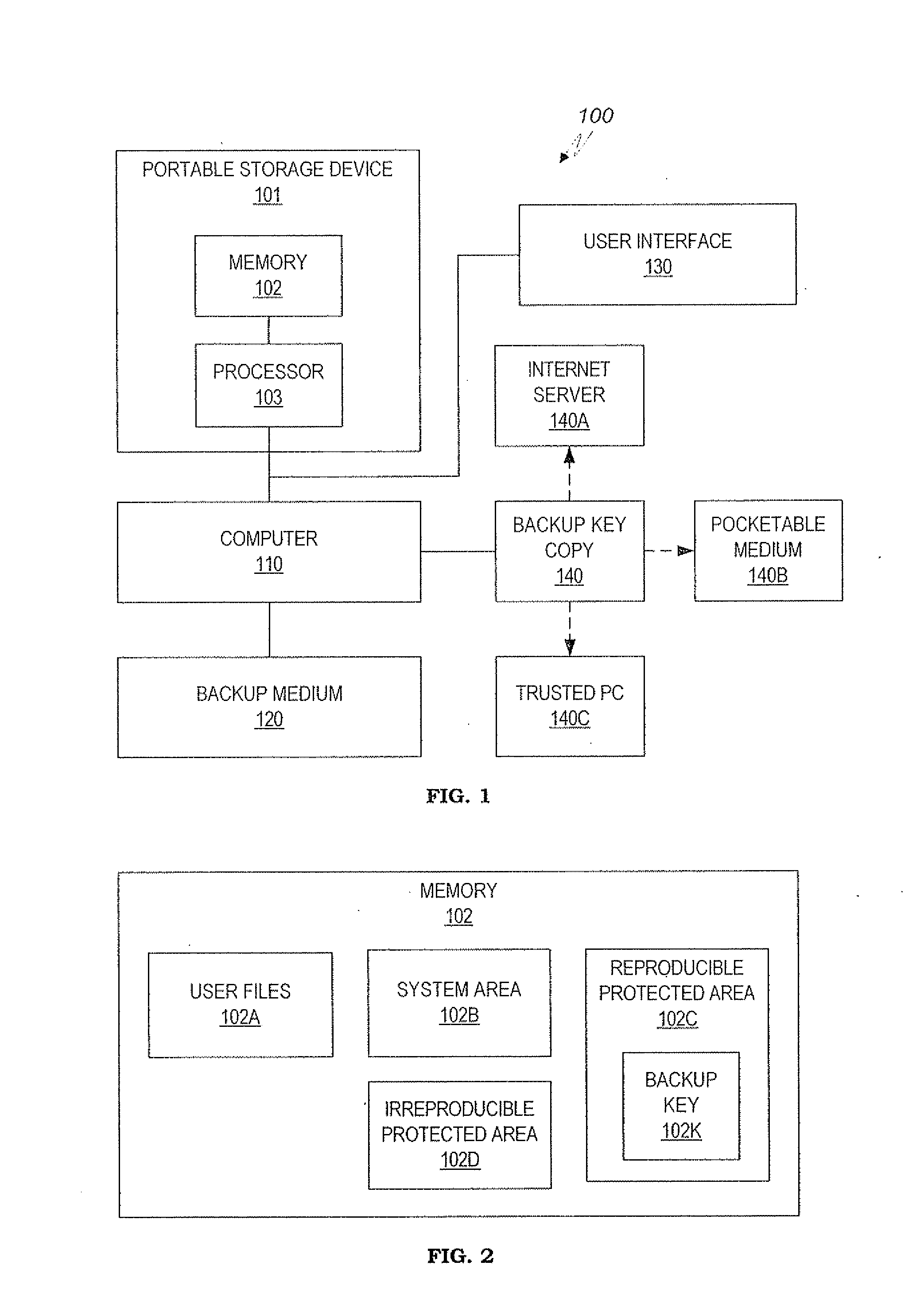
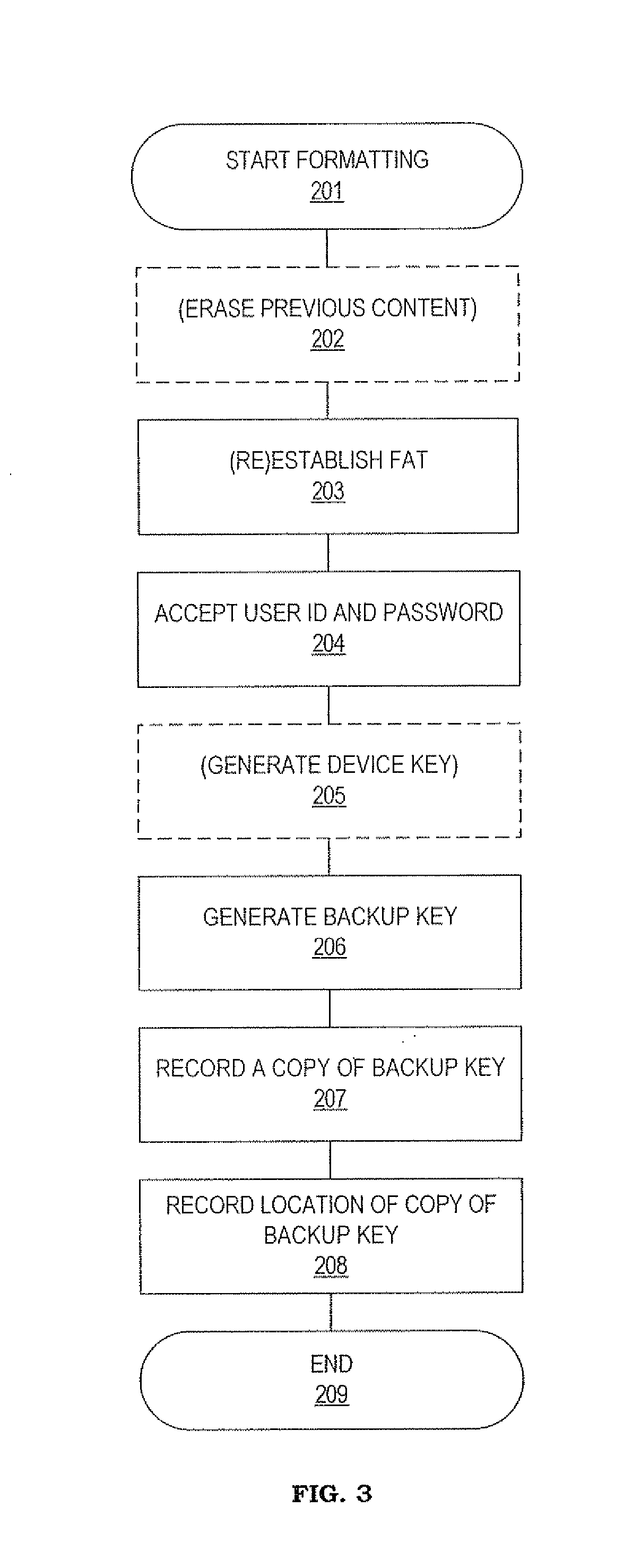
Method and system for maintaining backup of portable storage devices
ActiveUS7240219B2Safe storageEasy to carryUser identity/authority verificationUnauthorized memory use protectionPasswordTrusted Computing
Data stored in a portable storage device are encrypted, for example by a processor of the portable storage device itself, using a backup key and stored in a backup medium. The backup key is protected by being stored in a backup key storage medium, such as an internet server, a pocketable medium or a trusted computer, preferably after being encrypted using a password. As needed, the backup key is retrieved and used to decrypt the data from the backup medium. The decrypted data are restored to the original portable storage device or to a different portable storage device.
Owner:WESTERN DIGITAL ISRAEL LTD
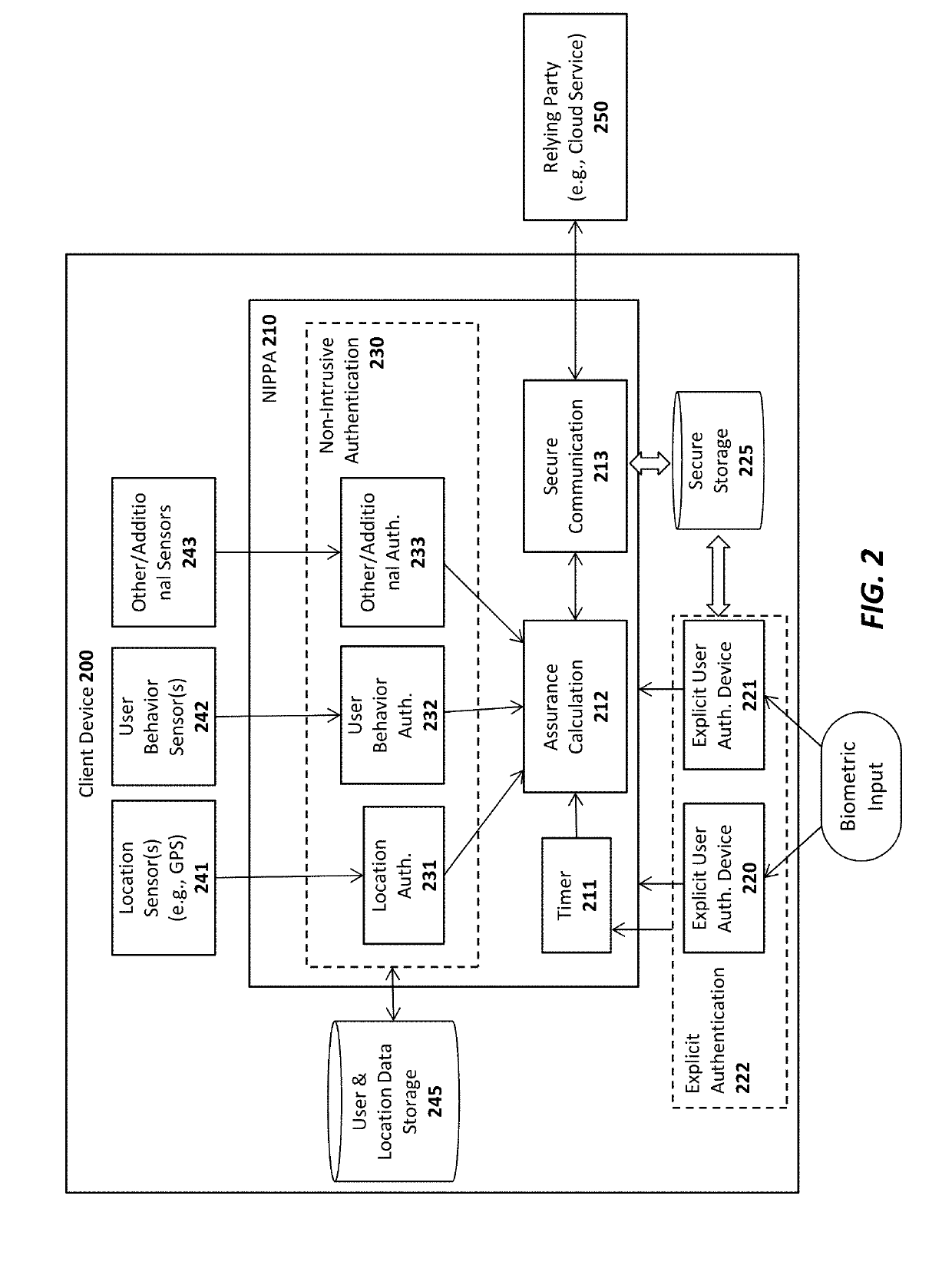
Extending a secure key storage for transaction confirmation and cryptocurrency
PendingUS20190164156A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesInternet privacyEngineering
A system, apparatus, method, and machine readable medium are described for secure authentication. For example, one embodiment of a system comprises: an authenticator on a client device to securely store one or more private keys, at least one of the private keys usable to authenticate a block of a blockchain; and an attestation module of the authenticator or coupled to the authenticator, the attestation module to generate a signature using the block and the private key, the signature usable to attest to the authenticity of the block by a device having a public key corresponding to the private key.
Owner:NOK NOK LABS
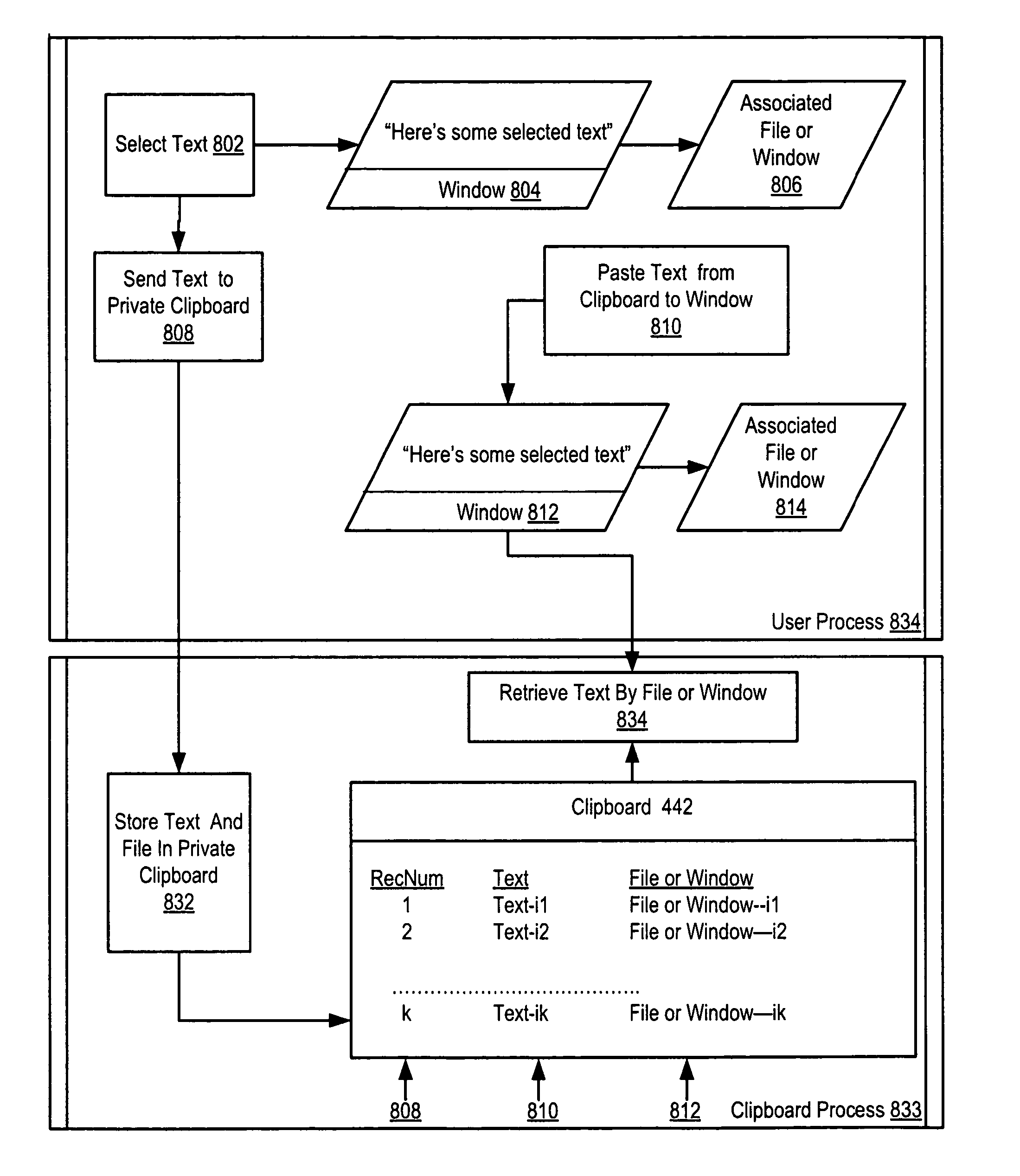
Secure clipboard function
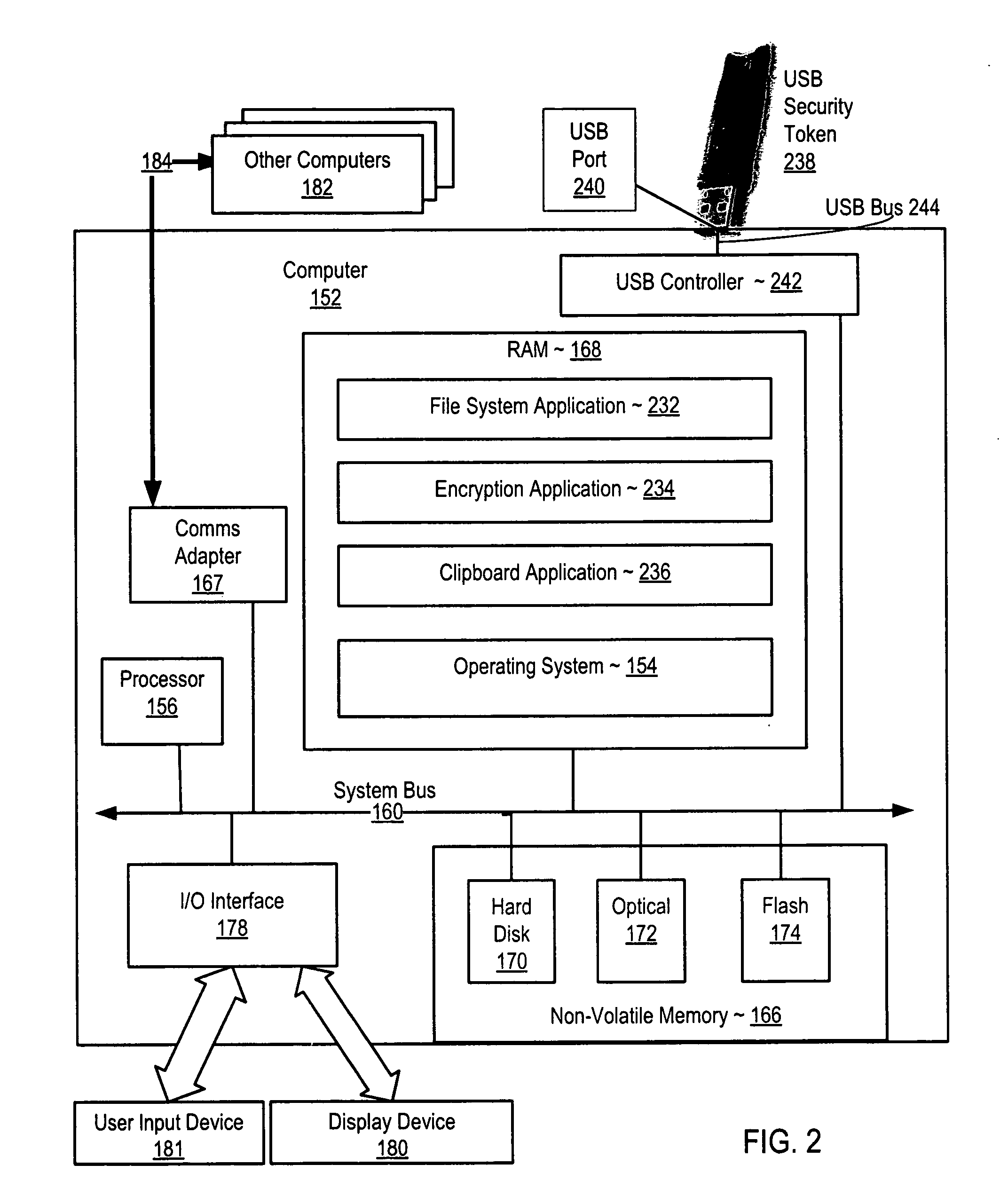
InactiveUS20070011749A1Digital data processing detailsUser identity/authority verificationFile systemUSB
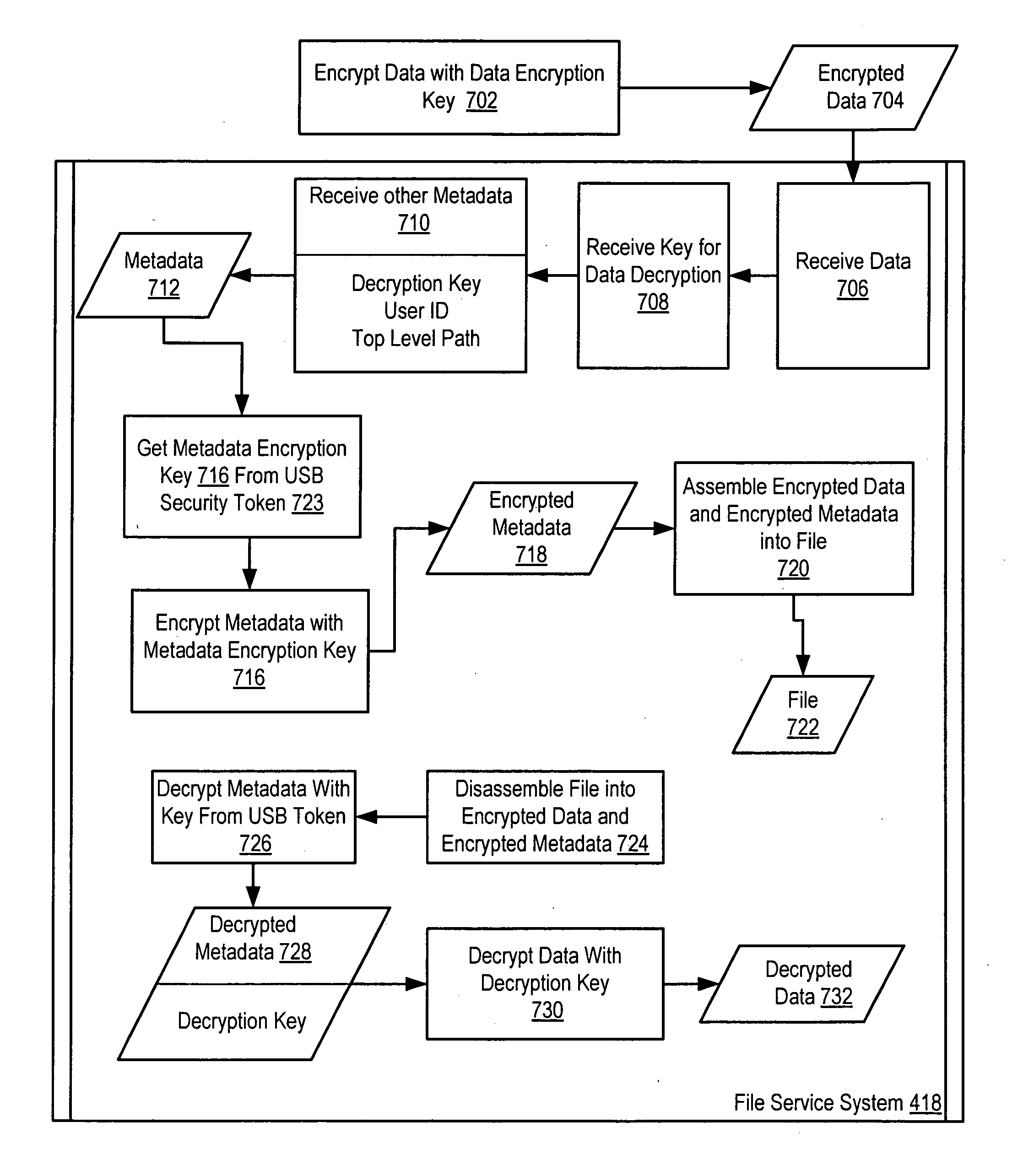
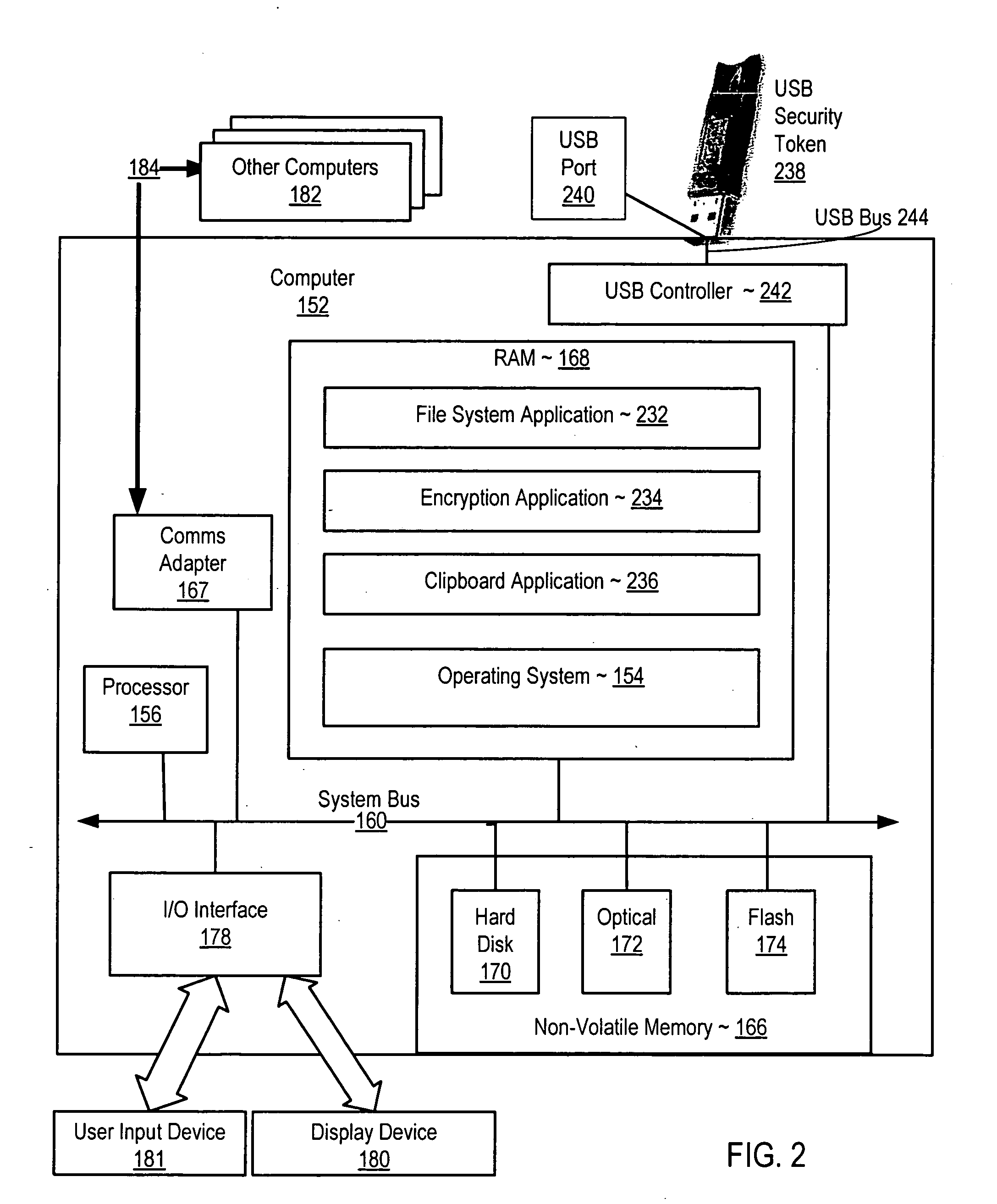
Securing computer files in which a publish permission is present in a file system. Upon receiving a request to write data from one file to another, the file system determines whether publish permission is needed. If so and the user lacks the publish permission, the request is rejected. Disclosed is securing computer files which include encrypting metadata about an encrypted file and storing both the encrypted file and the encrypted metadata. The metadata includes a key for decrypting the encrypted file. The key for decrypting the metadata is stored in a USB security token. Disclosed is securing computer files which include copying material from a window displaying the contents of a file to a clipboard application. The file or window is associated with the material. The clipboard application can deny a request to paste material associated with one file to a window displaying the contents of a different file.
Owner:SIMDESK TECH INC
Method for providing multimedia files and terminal therefor
InactiveUS20020076051A1Easy accessMechanically effected encryptionPayment architectureComputer hardwareData file
A method of and a system for securely distributing data files to a user. A first key is encrypted using a second key. The encrypted first key is stored on an integrated circuit card that is associated with the user. The integrated circuit card is provided to the user. Data files are encrypted using the first key to get an encrypted data file at a first party. The encryption parameters are exchanged between the first party and integrated circuit card.
Owner:NOKIA TECHNOLOGLES OY
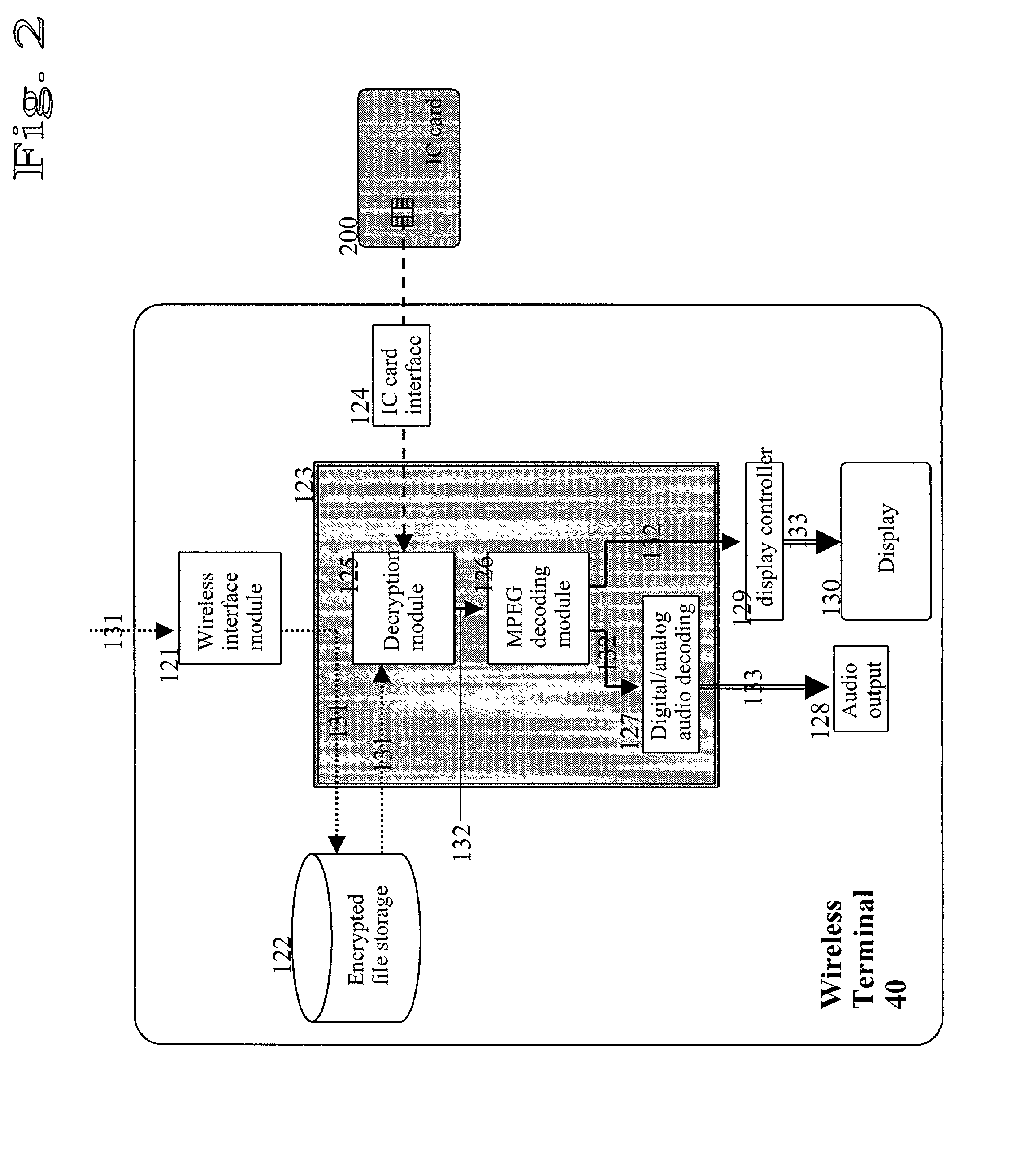
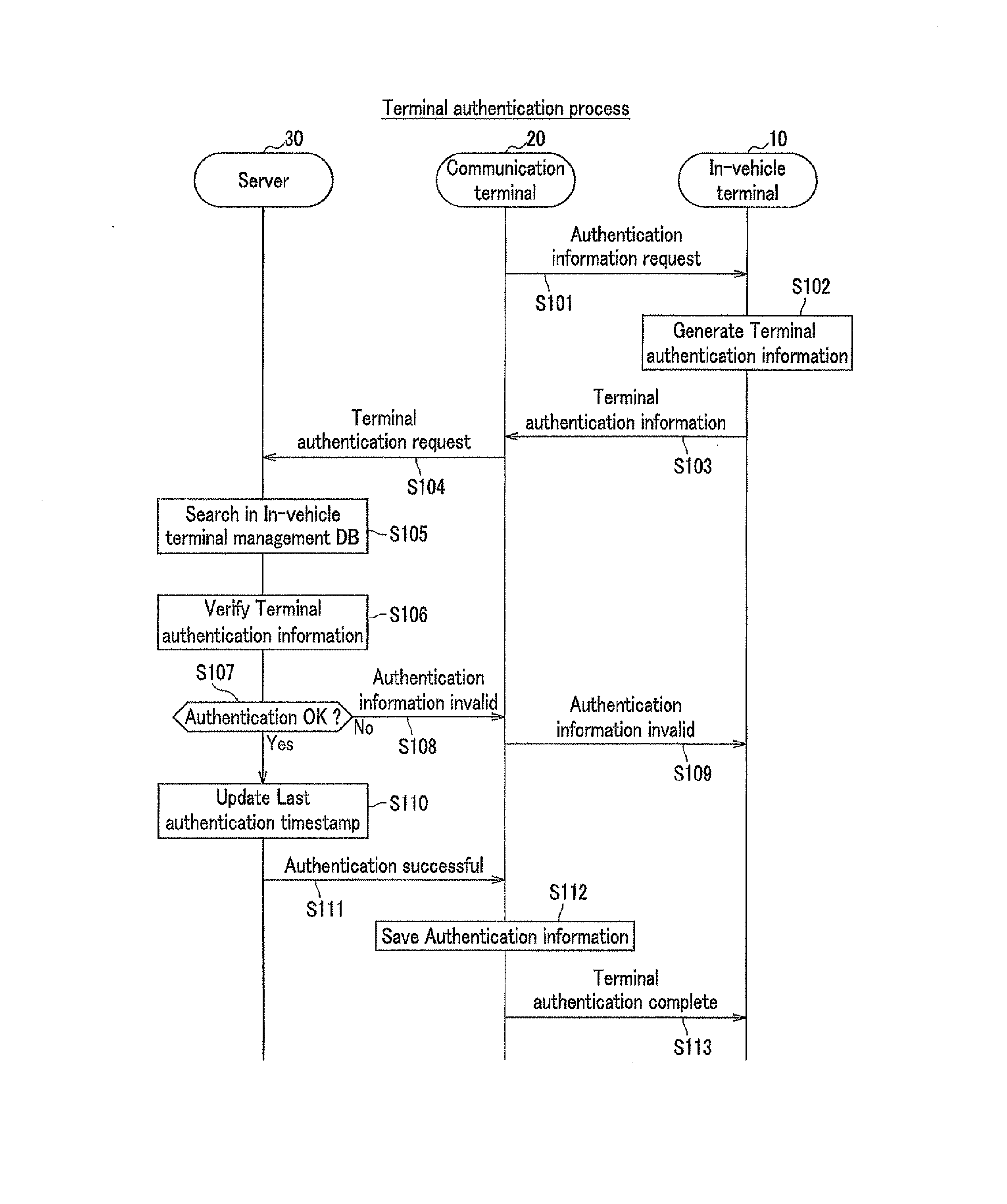
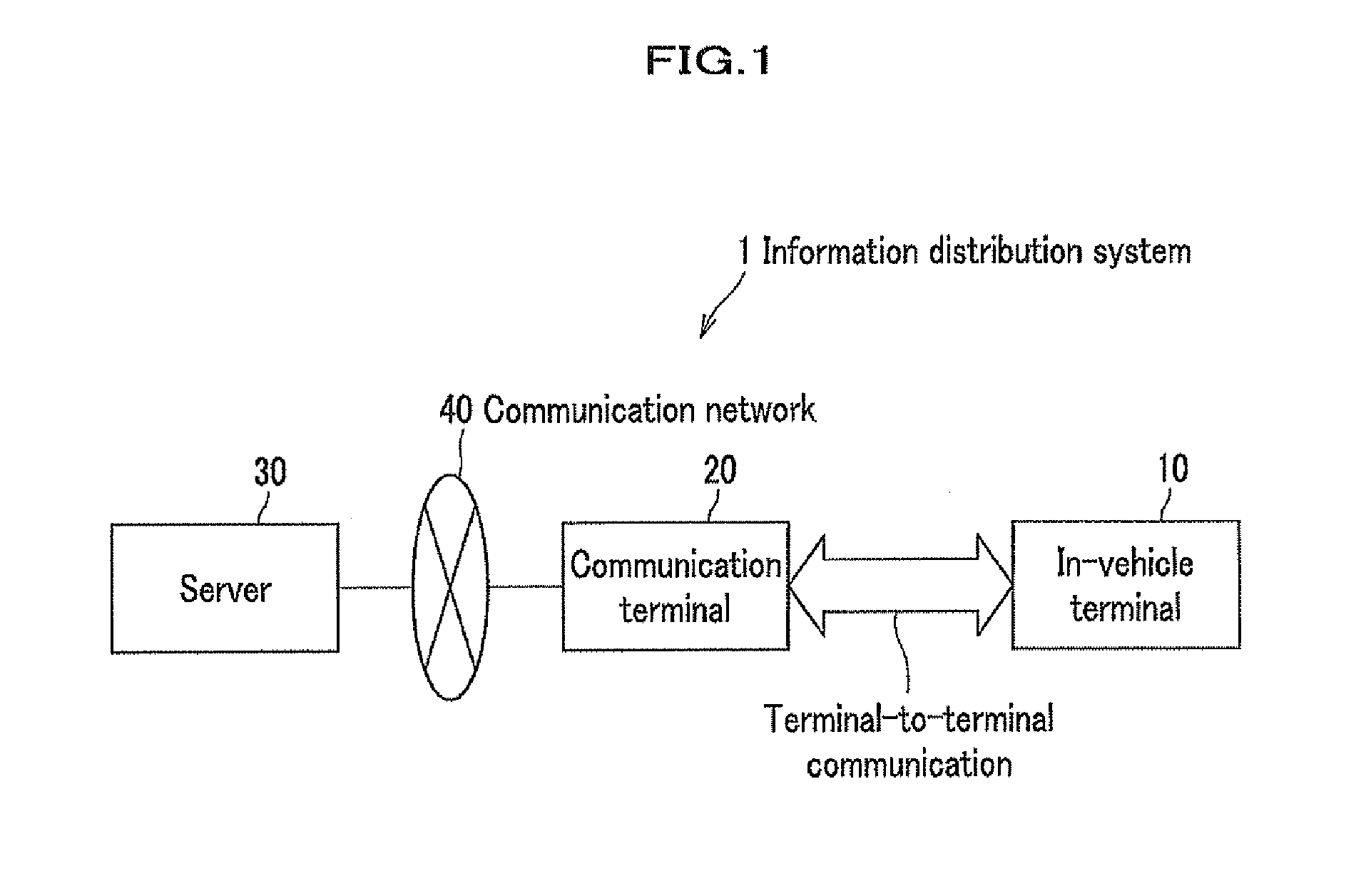
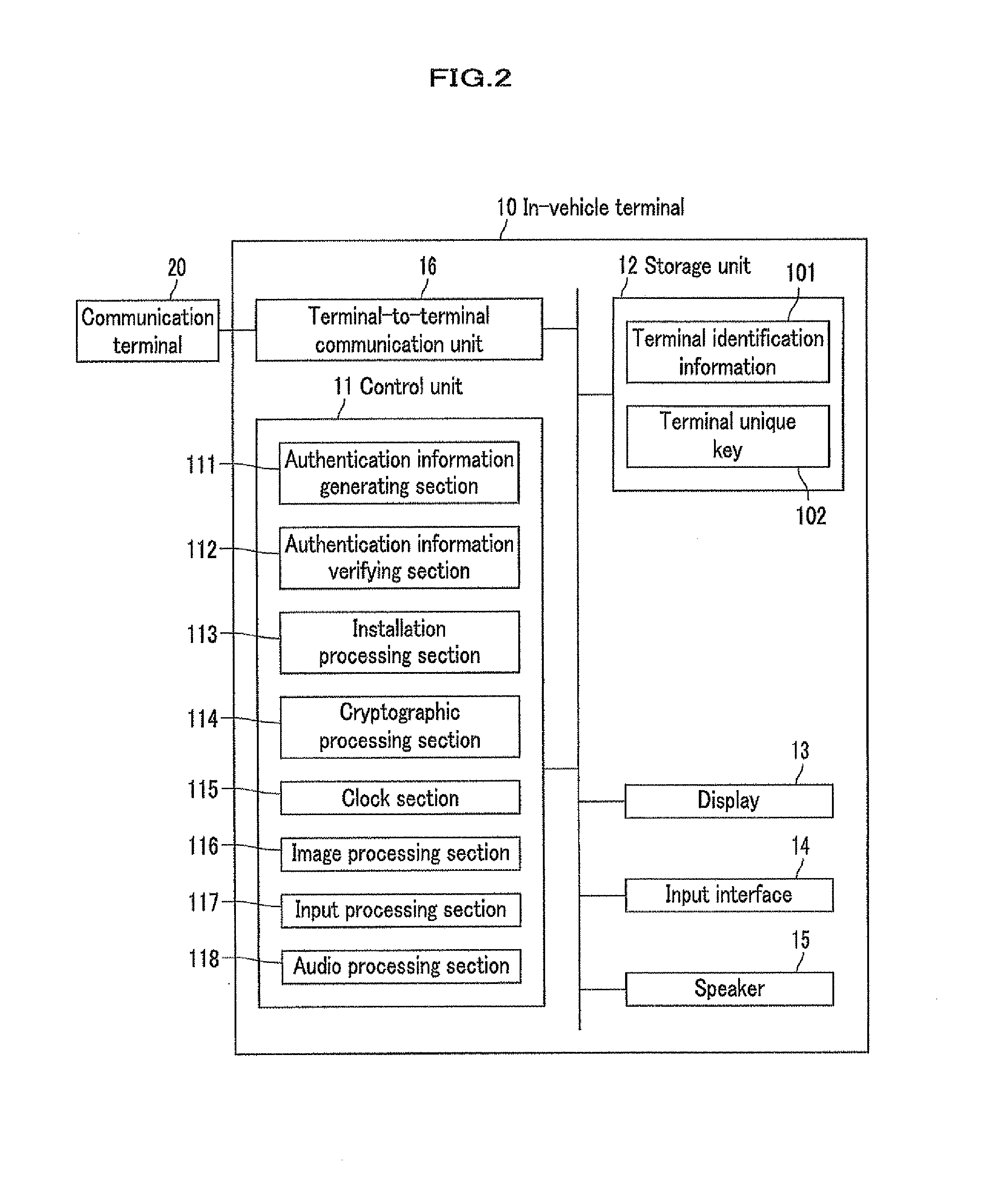
Information distribution method, information distribution system and in-vehicle terminal
ActiveUS20130179689A1Shorten the timeReduce effortService provisioningKey distribution for secure communicationDistribution methodIn vehicle
[Objective] When installing software into an in-vehicle terminal from a server, it is required to prevent the software from being installed into an unsuitable terminal, and to reduce time and efforts for data input and download, thereby improving the convenience of the user.[Solution] In an information distribution system, terminal identification information and a terminal unique key for an in-vehicle terminal are stored in a server as well as in itself. The in-vehicle terminal transmits the terminal identification information to the server for terminal authentication via a communication terminal after encrypting with the terminal unique key, and then the server transmits encrypted software to the communication terminal. The communication terminal transmits the encrypted software to the in-vehicle terminal, which in turn obtains a software unique key encrypted with the terminal unique key from the server and decrypts the encrypted software for installation using the software unique key.
Owner:CLARION CO LTD
Method and system for delegation of security procedures to a visited domain
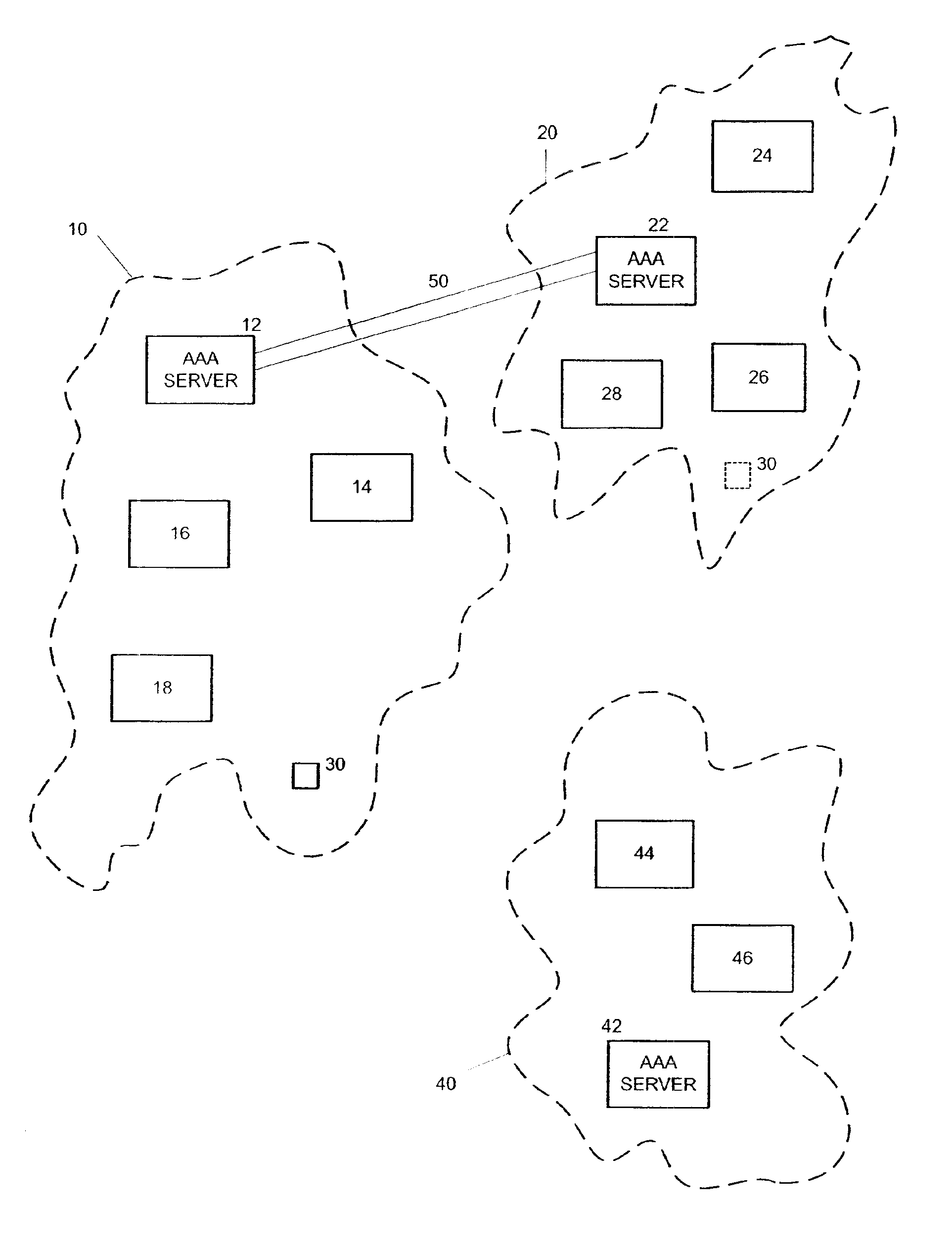
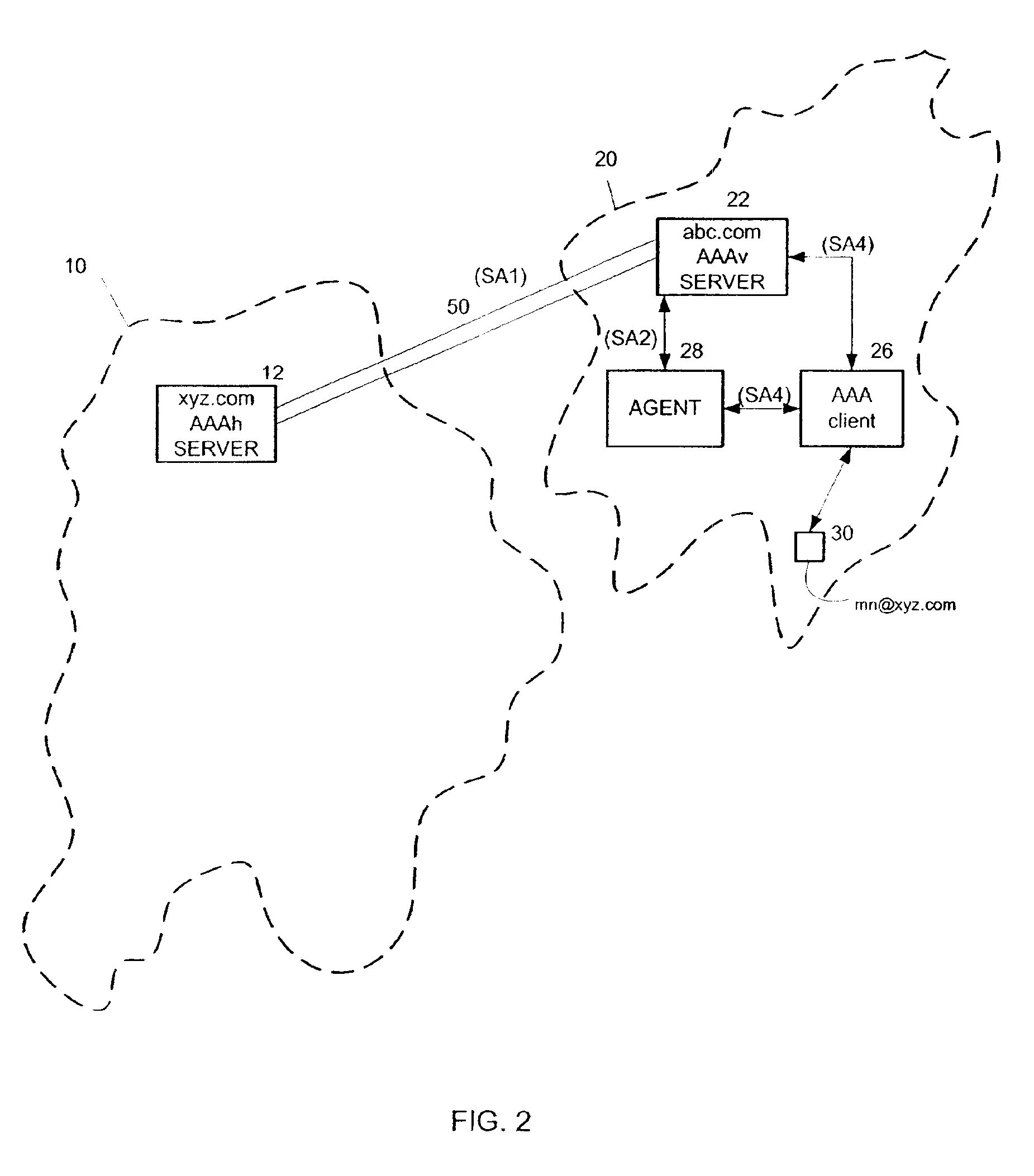
InactiveUS6879690B2User identity/authority verificationSecret communicationDerivation procedureKey storage
A method and system for delegation of security procedures to a second domain. A first key is generated for a mobile node. The first key is stored at the mobile node and at a home domain of the mobile node. The mobile node is moved to the second domain. A request is sent from the second domain to the home domain to authenticate the mobile node. A second key is generated at the home domain using the first key and a random number. The random number and the second key are sent to the second domain. The random number is sent to the mobile node by the second domain. The mobile node generates the second key using the random number and the first key. The second key is used for authentication procedures and / or key derivation procedures between the mobile node and the second domain.
Owner:NOKIA TECHNOLOGLES OY
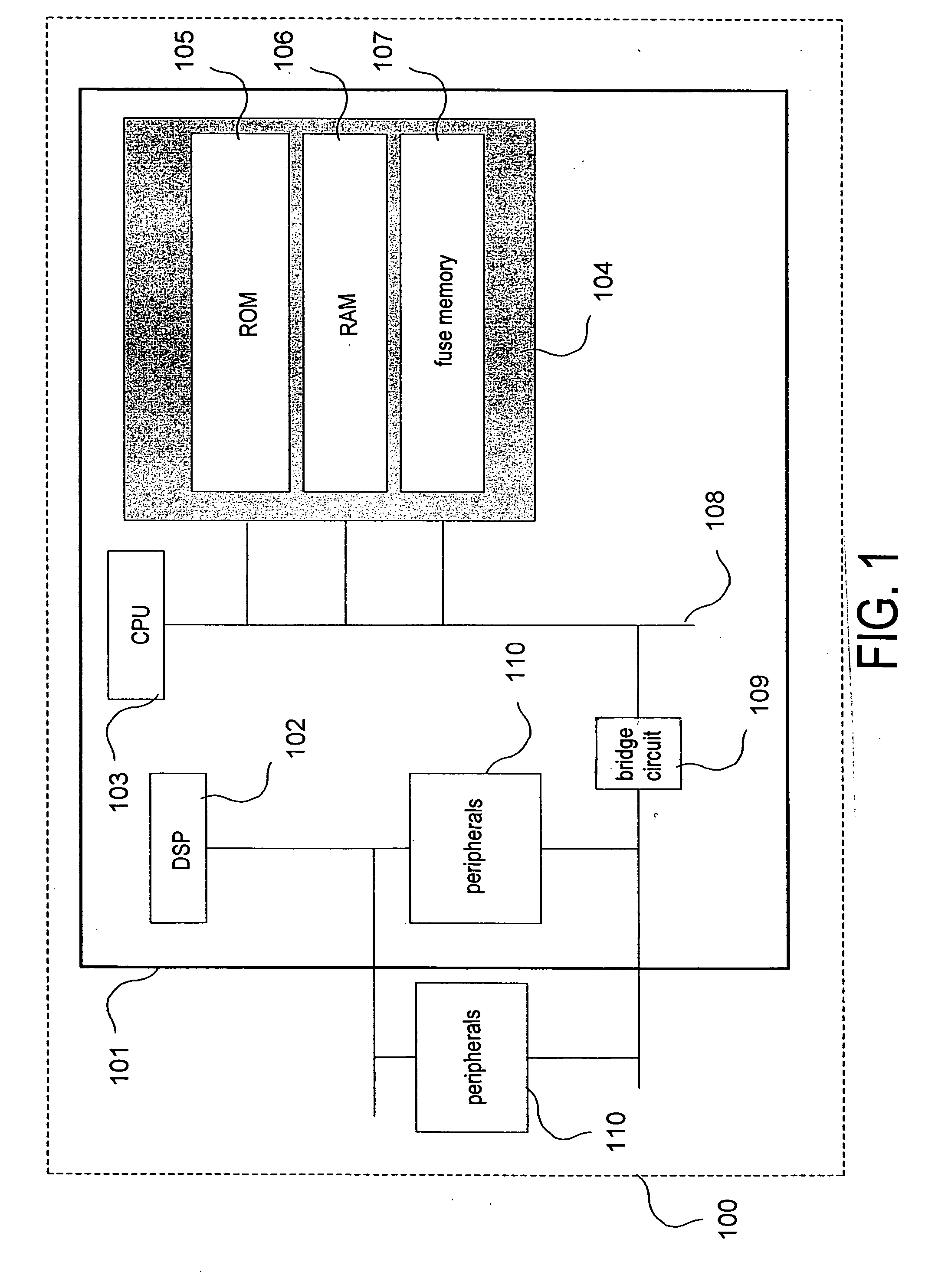
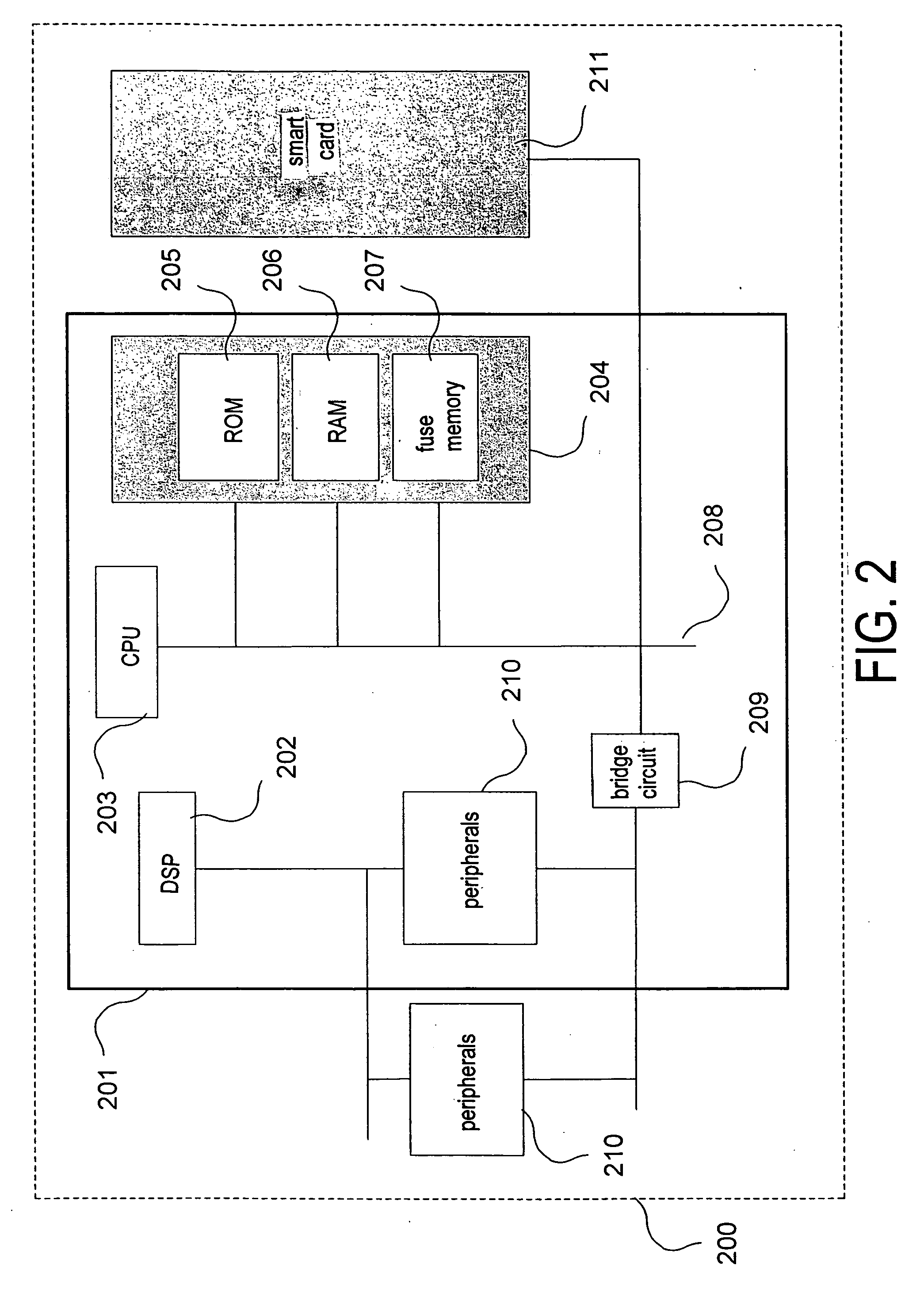
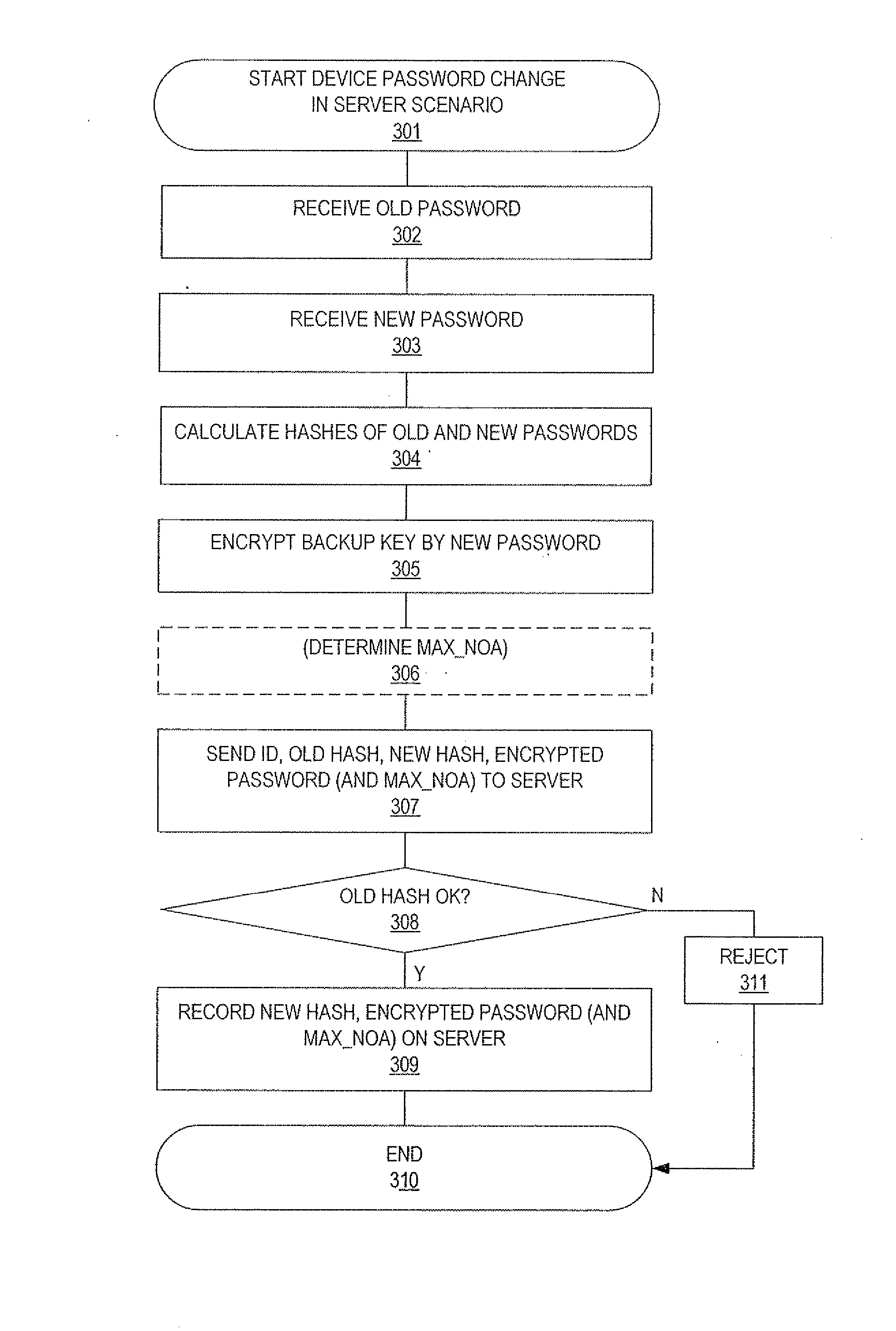
Key storage administration
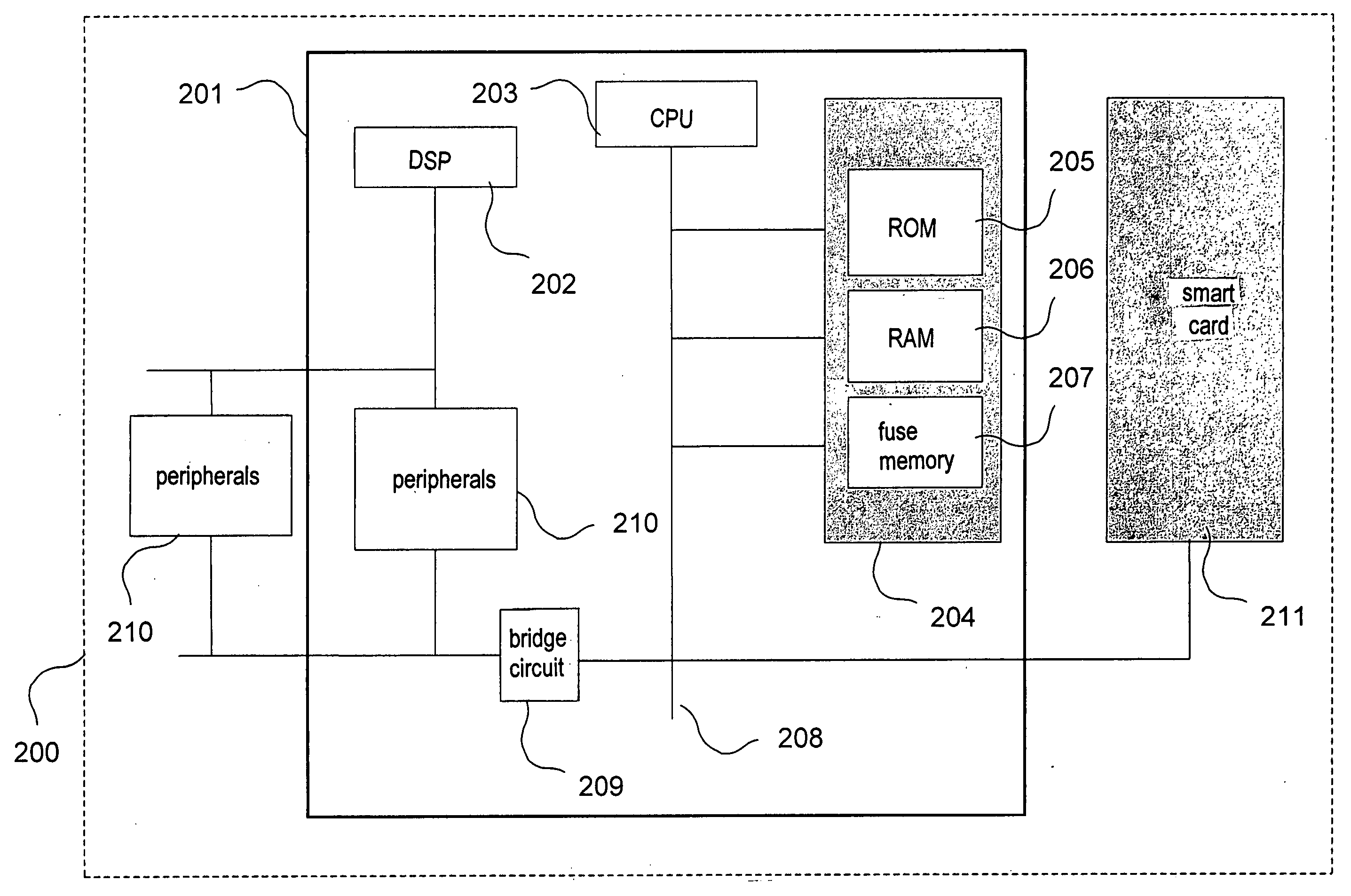
ActiveUS20050044375A1Avoid excessive computationAccurate identificationDigital data processing detailsUser identity/authority verificationPasswordSoftware engineering
The present invention relates to a method and a system for allowing multiple applications to manage their respective data in a device (100, 200) having a secure environment (104, 204, 211) to which access is strictly controlled. The idea of the invention is that a storage area is allocated (301) within the secure environment (104, 204, 211) of a device (100, 200). The storage area is associated (302) with an identity of an application, the associated identity is stored (303) in the secure environment (104, 204, 211) and access to the storage area is controlled (304) by verifying correspondence between the associated identity and the identity of an accessing application. This is advantageous, since it is possible for the accessing application to read, write and modify objects, such as cryptographic keys, intermediate cryptographic calculation results and passwords, in the allocated storage area.
Owner:NOKIA TECHNOLOGLES OY
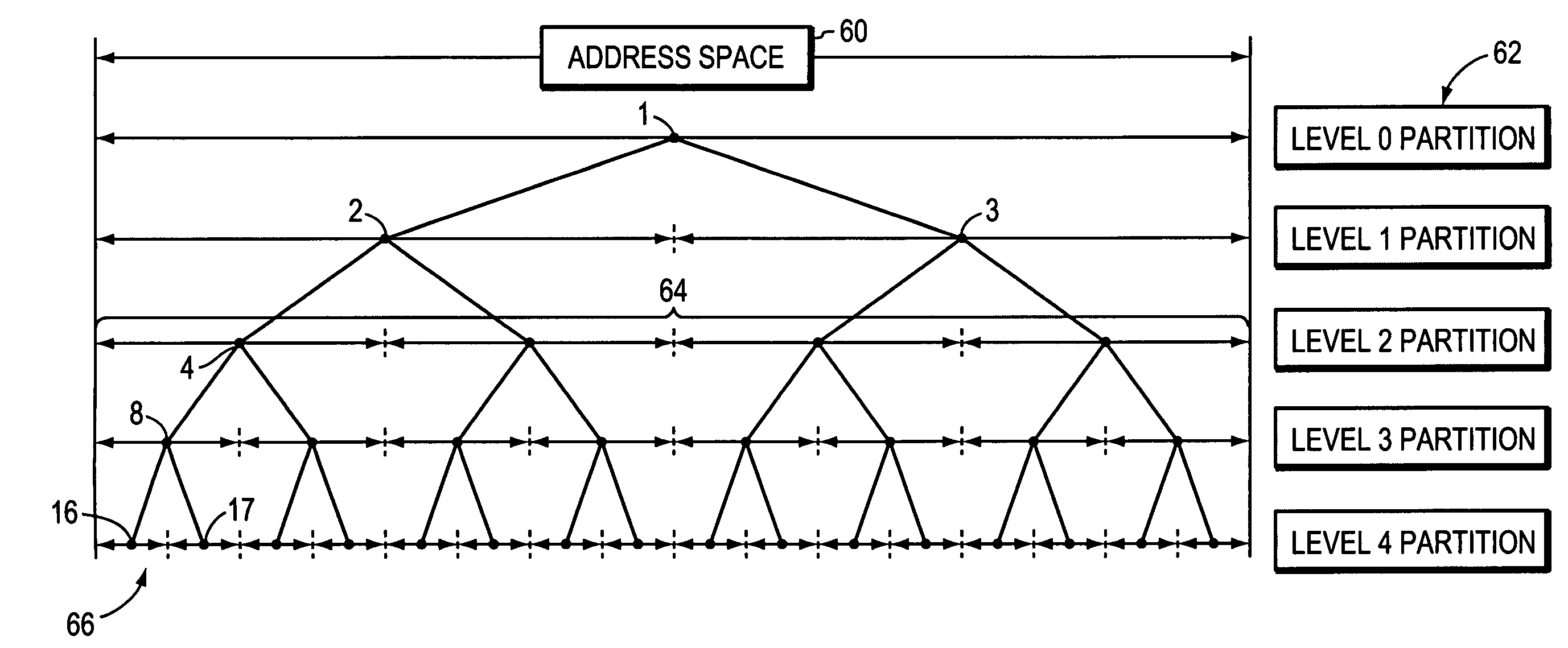
Method and apparatus for determining if stored memory range overlaps key memory ranges where the memory address space is organized in a tree form and partition elements for storing key memory ranges
ActiveUS7251663B1Efficient of system resourceEffective timeData processing applicationsDigital data processing detailsMemory addressTheoretical computer science
An efficient method and apparatus for storing and retrieving memory ranges is disclosed. A key range that is stored or to be stored is associated with a node in the tree hierarchy encompassing the entire memory address space. All previously stored ranges are listed or otherwise associated with each node, and all possible nodes that may contain ranges that overlap the key range, regardless of starting or ending locations or range length, are found. Partitions are developed in the tree structure of the available address space and the width of the key range (w), the widths of the partitions (d), and the range of offsets in the starting location of the key range with respect to a partition (o) are used to develop a formula that finds a partition suitable for storing the key range. Hashing and dynamic tree building may be used.
Owner:NETWORK APPLIANCE INC
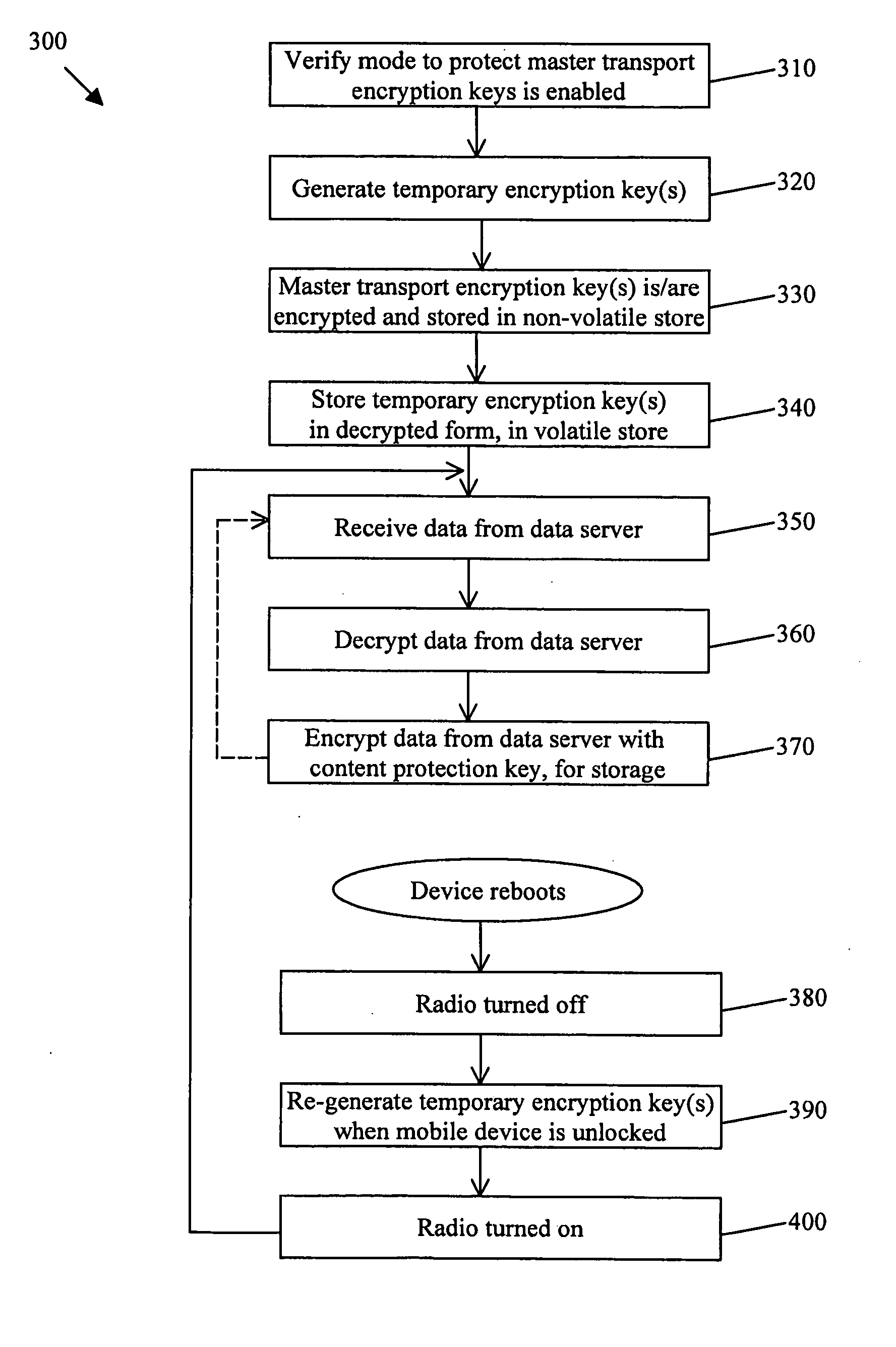
System and method for protecting master encryption keys
ActiveUS20070165844A1Key distribution for secure communicationDigital data processing detailsMobile deviceEncryption
A system and method for protecting master transport encryption keys stored on a computing device. Master transport encryption keys are used to secure data communications between computing devices. In one example embodiment, there is provided a method in which a copy of a master transport encryption key is generated and stored in a volatile store of a first computing device (e.g. a mobile device). This copy of the master transport encryption key can be used to facilitate the decryption of data received at the first computing device from a second computing device (e.g. a data server), even while the first computing device is locked. The method also comprises encrypting the master transport encryption key, with a content protection key for example, and storing the encrypted master transport encryption key in a non-volatile store of the first computing device.
Owner:MALIKIE INNOVATIONS LTD
Secure local storage of files
InactiveUS20070011469A1User identity/authority verificationUnauthorized memory use protectionFile systemUSB
Securing computer files in which a publish permission is present in a file system. Upon receiving a request to write data from one file to another, the file system determines whether publish permission is needed. If so and the user lacks the publish permission, the request is rejected. Disclosed is securing computer files which include encrypting metadata about an encrypted file and storing both the encrypted file and the encrypted metadata. The metadata includes a key for decrypting the encrypted file. The key for decrypting the metadata is stored in a USB security token. Disclosed is securing computer files which include copying material from a window displaying the contents of a file to a clipboard application. The file or window is associated with the material. The clipboard application can deny a request to paste material associated with one file to a window displaying the contents of a different file.
Owner:SIMDESK TECH INC
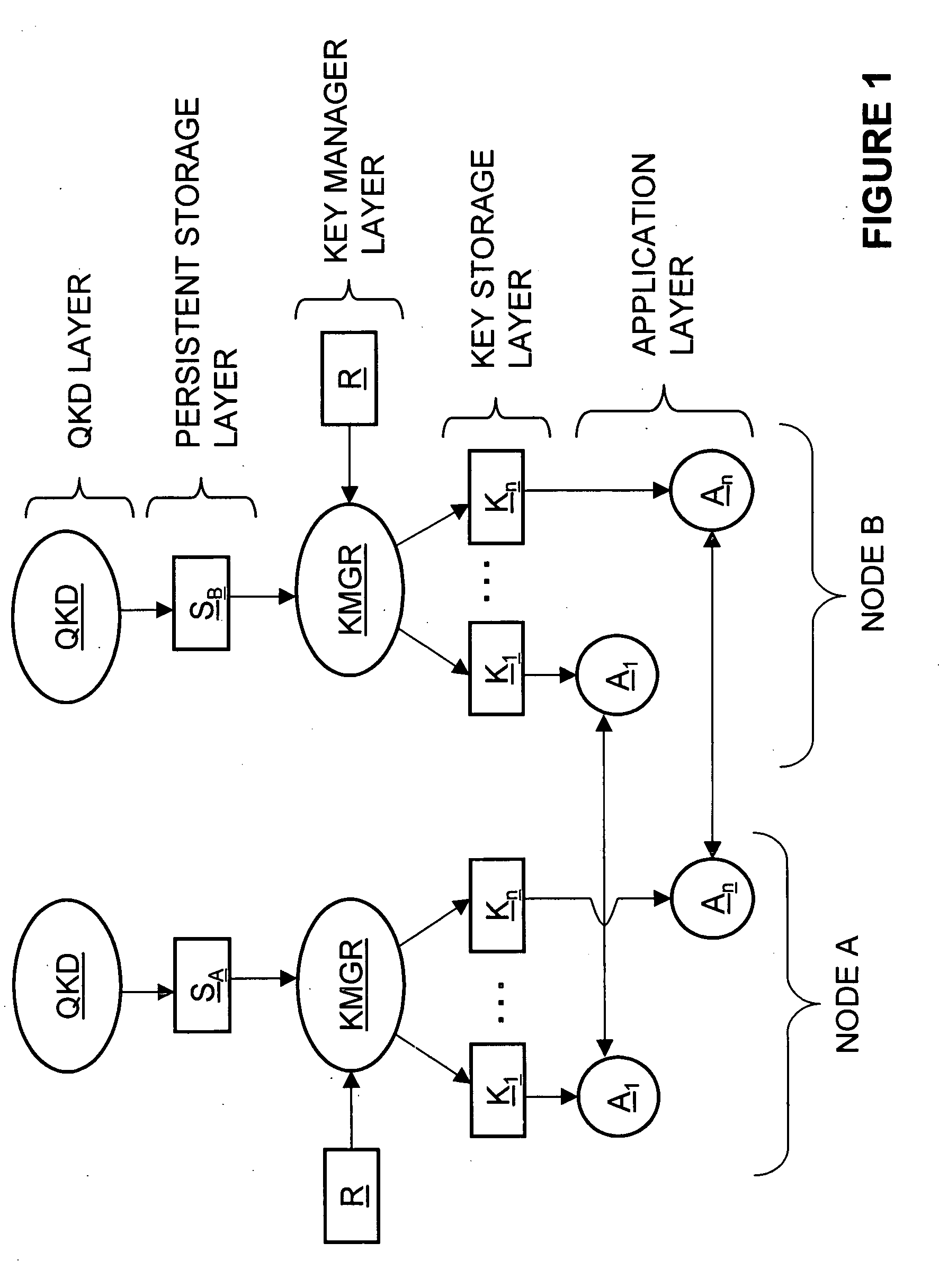
Key manager for QKD networks
ActiveUS20060062392A1Key distribution for secure communicationUser identity/authority verificationNetwork keyKey storage
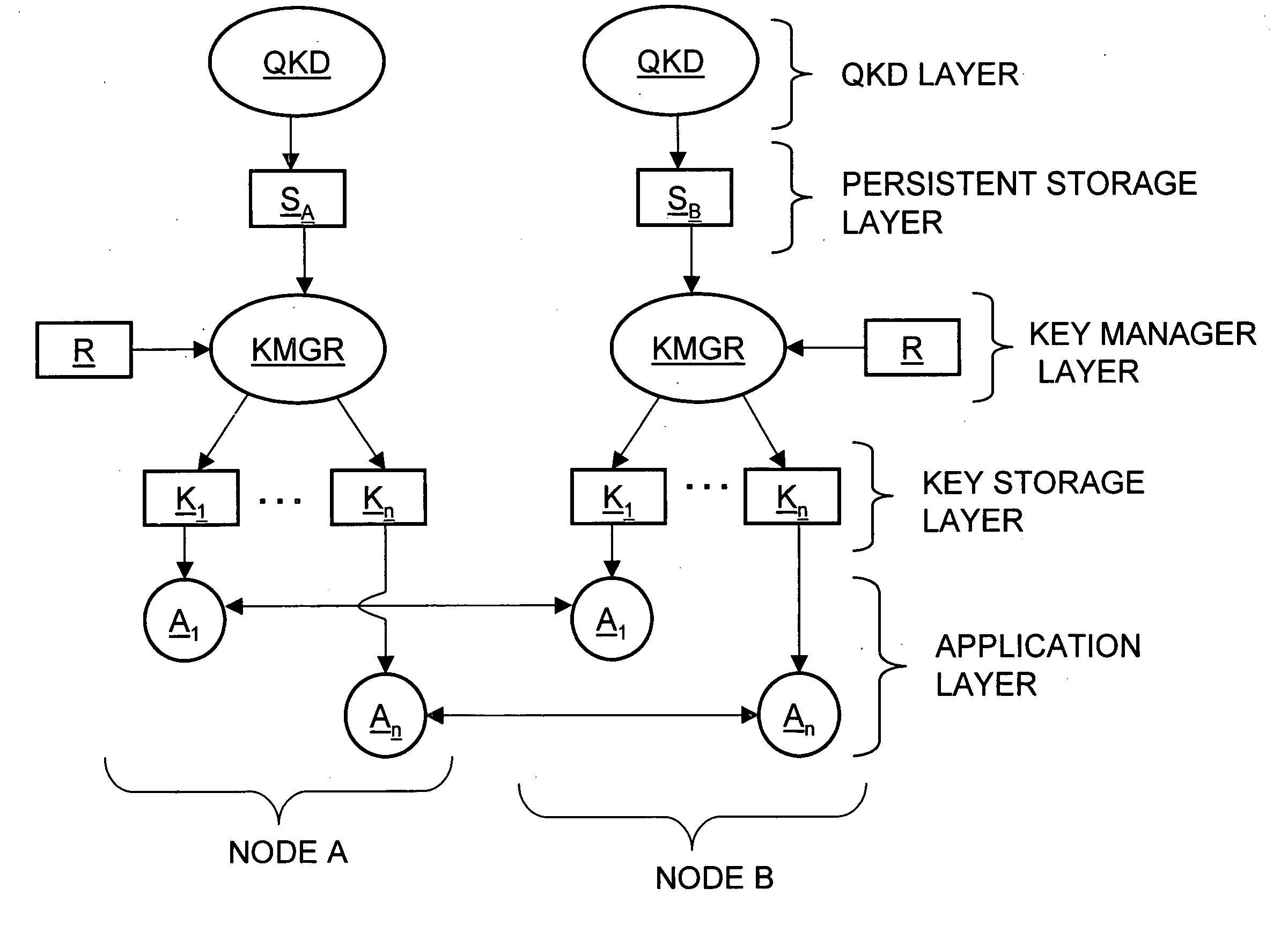
Key manager systems and methods for a QKD-based network are disclosed. The system includes a QKD layer that generates quantum encryption keys, a persistent storage layer that stores the quantum encryption keys, and a key management layer. The key management layer generates an application registration record that includes a list of multiple applications that use the quantum encryption keys. The key management layer also generates a corresponding key storage layer. The multiple applications reside in an applications layer. The applications in each node remove keys from the key storage layer so that each node can encrypt / decrypt data using quantum encryption keys. The methods also include secure QKD system boot-up and authentication that facilitate implementing a commercial QKD system in real-world environments.
Owner:MAGIQ TECH INC
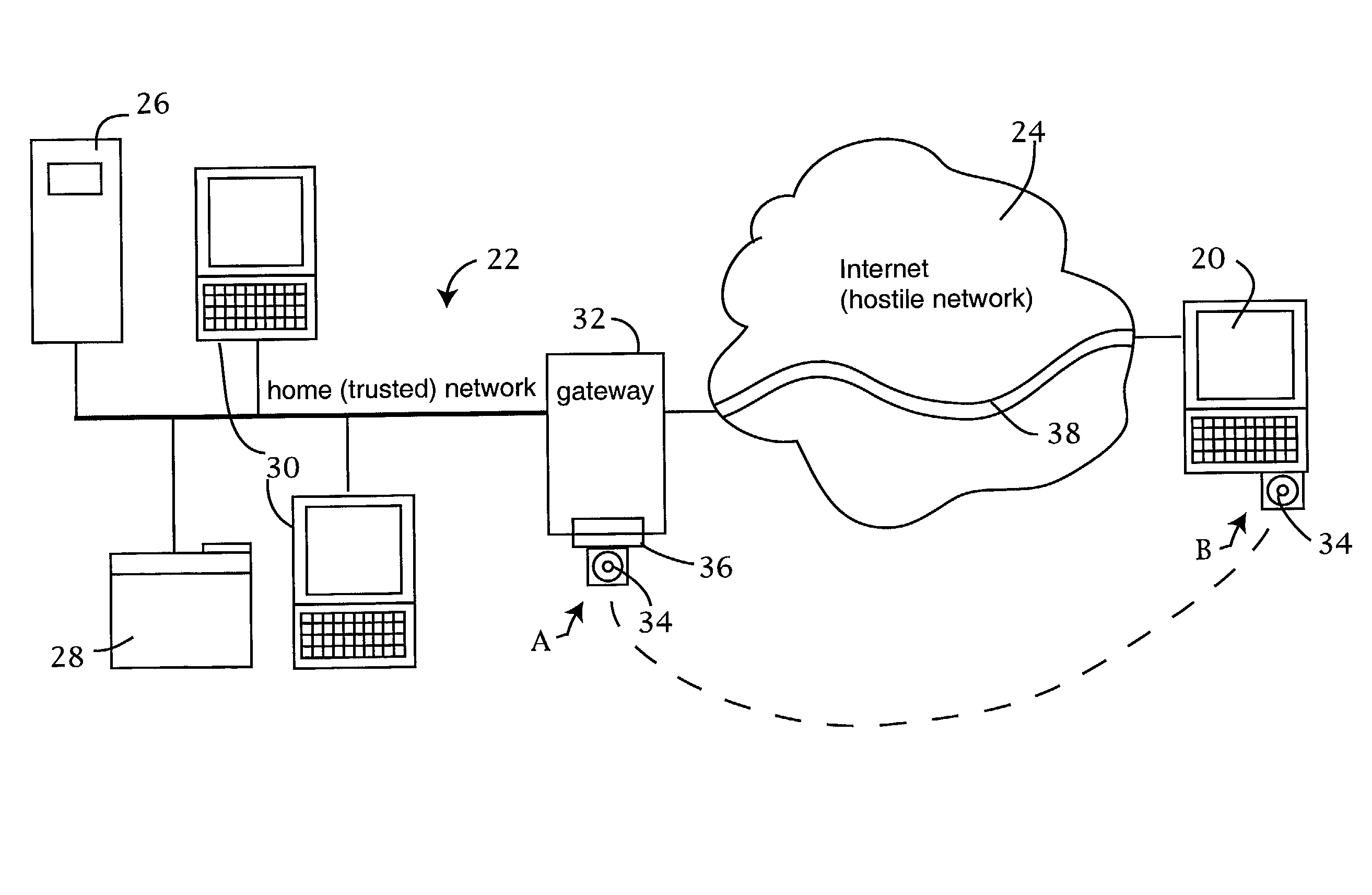
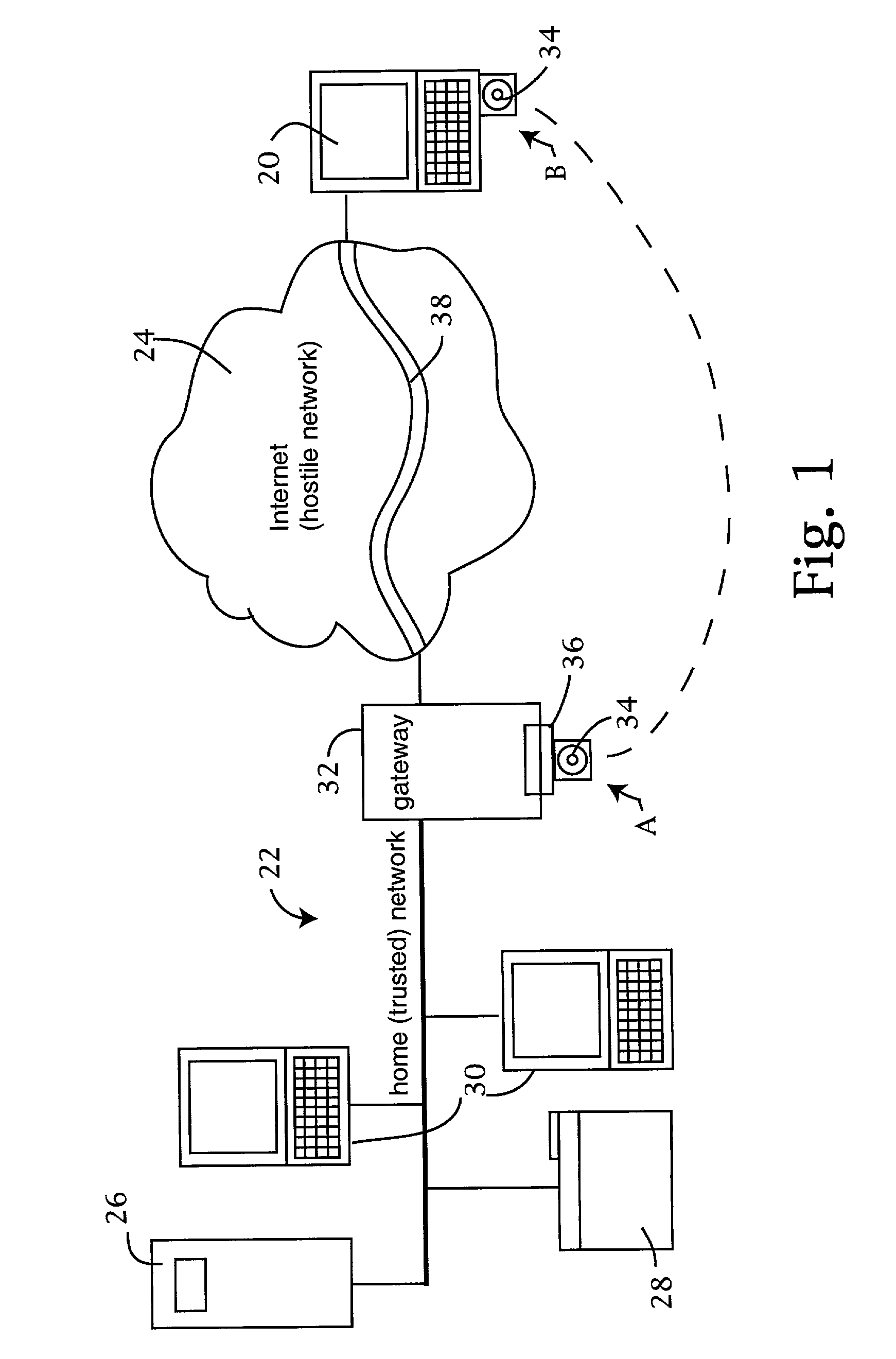
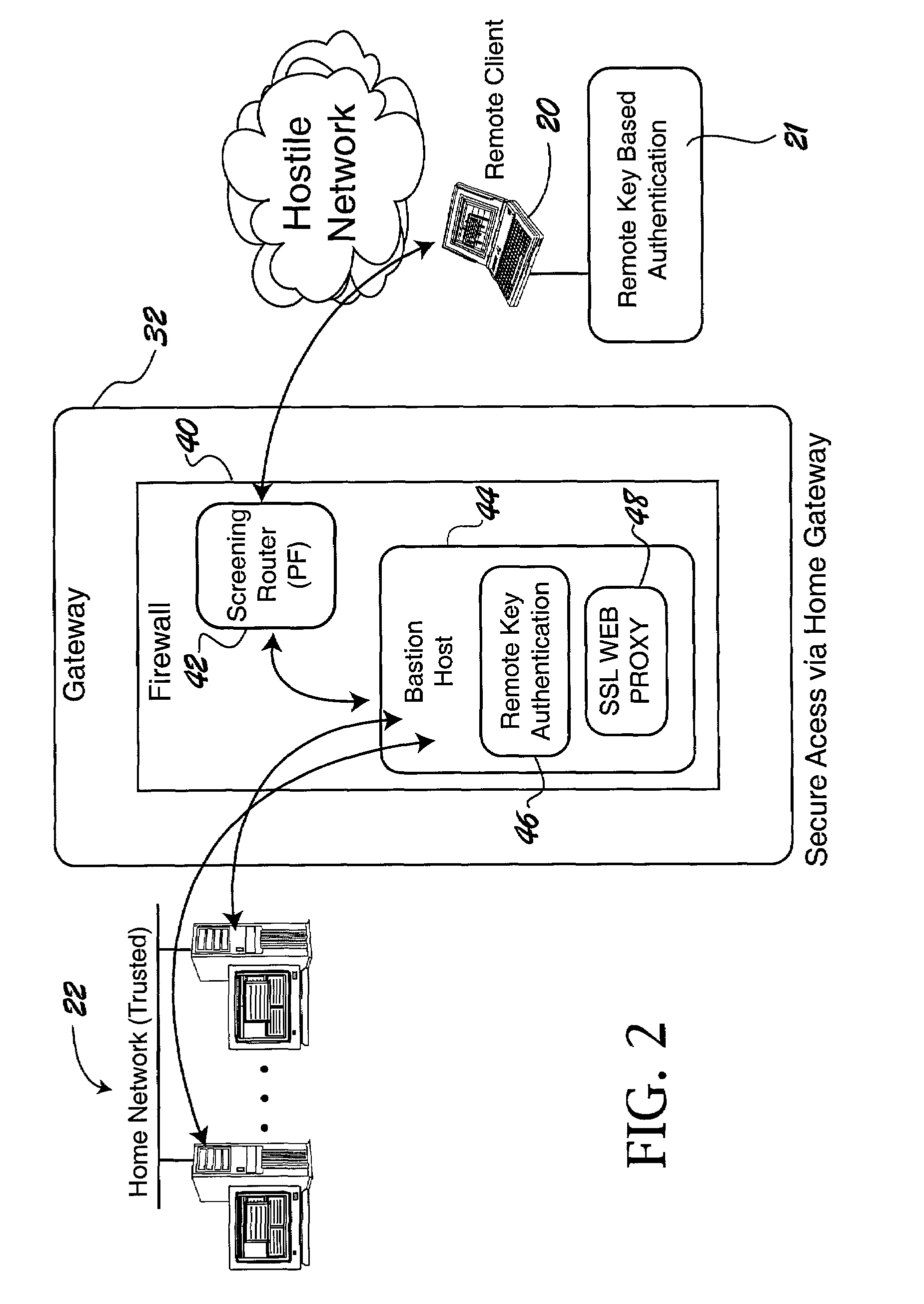
Computer network security system employing portable storage device
ActiveUS7228438B2Easy to useRaise security concernsUser identity/authority verificationUnauthorized memory use protectionUniform resource locatorClient machine
The trusted computer network is protected behind a gateway that includes a bastion host and screening router which blocks all URLs associated with the trusted network. The bastion host includes a remote client authentication mechanism and web proxy component that verifies and translates incoming URL requests from authenticated remote clients. Authentication is performed using one-time passwords that are stored on a portable storage device. The user configures the portable storage device by operating configuration software from the protected side of the gateway. The portable storage device also stores plug-in software to enable the client computer to properly retrieve the one-time password and exchange authentication messages with the bastion host. Further security is obtained by basing the one-time password on an encrypted version of the user's PIN. A symmetric key used to encrypt the PIN is stored in a protected area within the portable storage device.
Owner:SOVEREIGN PEAK VENTURES LLC
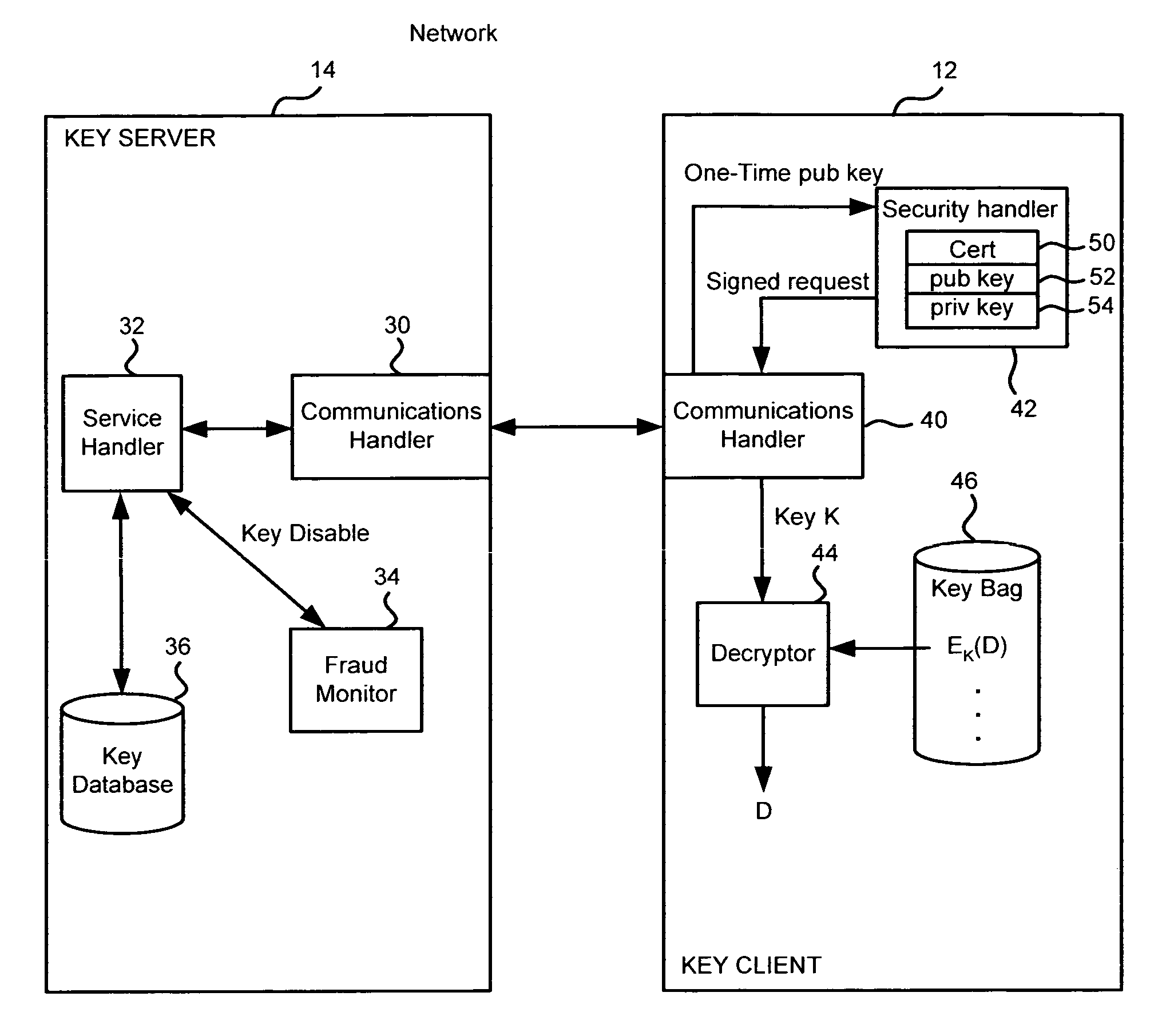
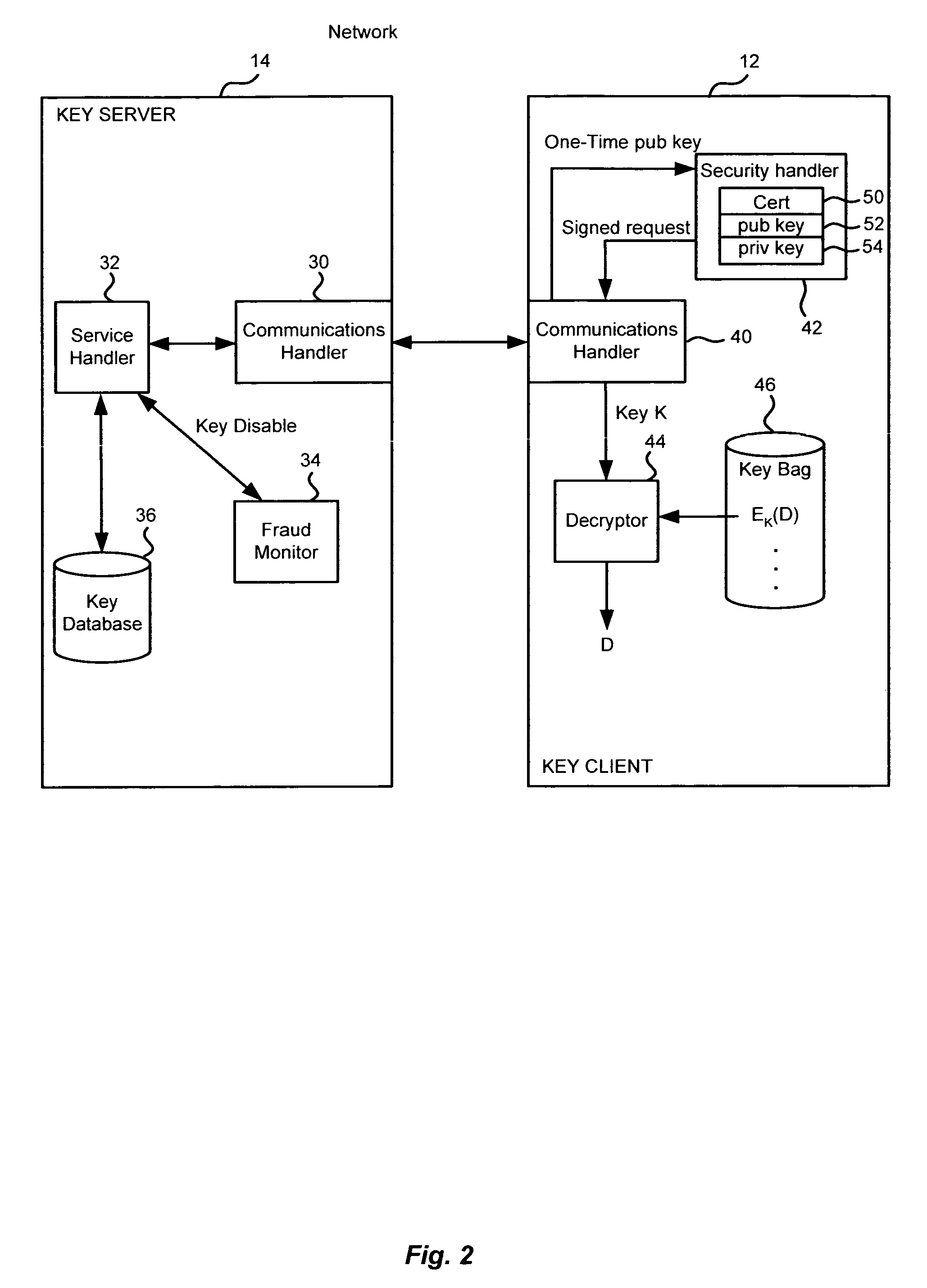
Method and apparatus for cryptographic key storage wherein key servers are authenticated by possession and secure distribution of stored keys
InactiveUS7711122B2Key distribution for secure communicationPublic key for secure communicationKey storageData storing
A key management system includes secured data stored on a first system secured by a control key stored securely on a key server. The secured data is secured against attacks such as unauthorized use, modification or access, where authorization to access the secured data is determined by knowledge of an access private key of an access key pair. When an authorized user is to access the secured data, the first system generates a request to the key server, signed with the access private key, wherein the request is for a decryption control key and the request includes a one-time public key of a key pair generated by the first system for the request. The first system can decrypt the decryption control key from the response, using a one-time private key. The first system can then decrypt the secured data with the decryption control key remaining secured in transport.
Owner:CA TECH INC
Strong authentication token usable with a plurality of independent application providers
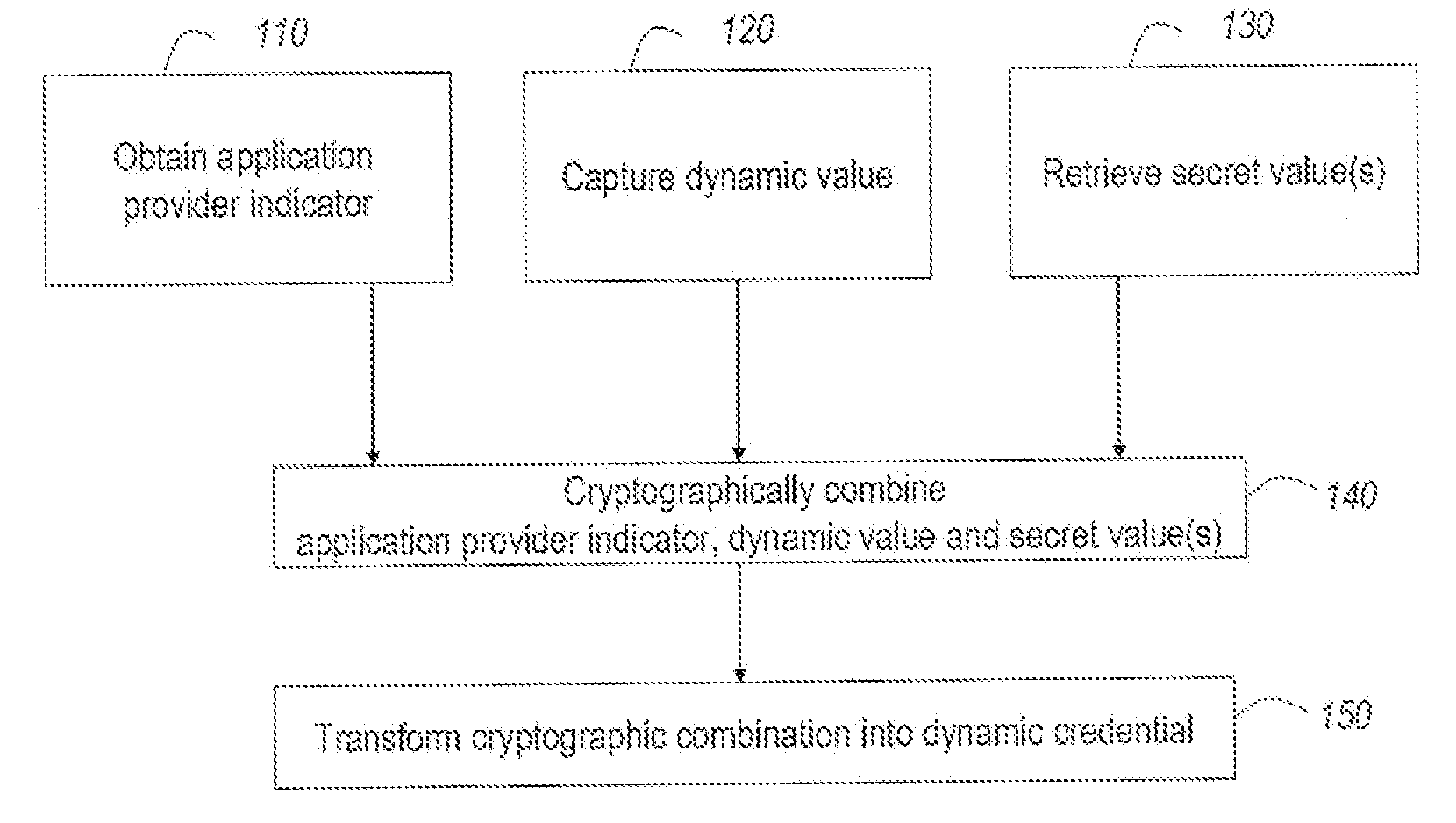
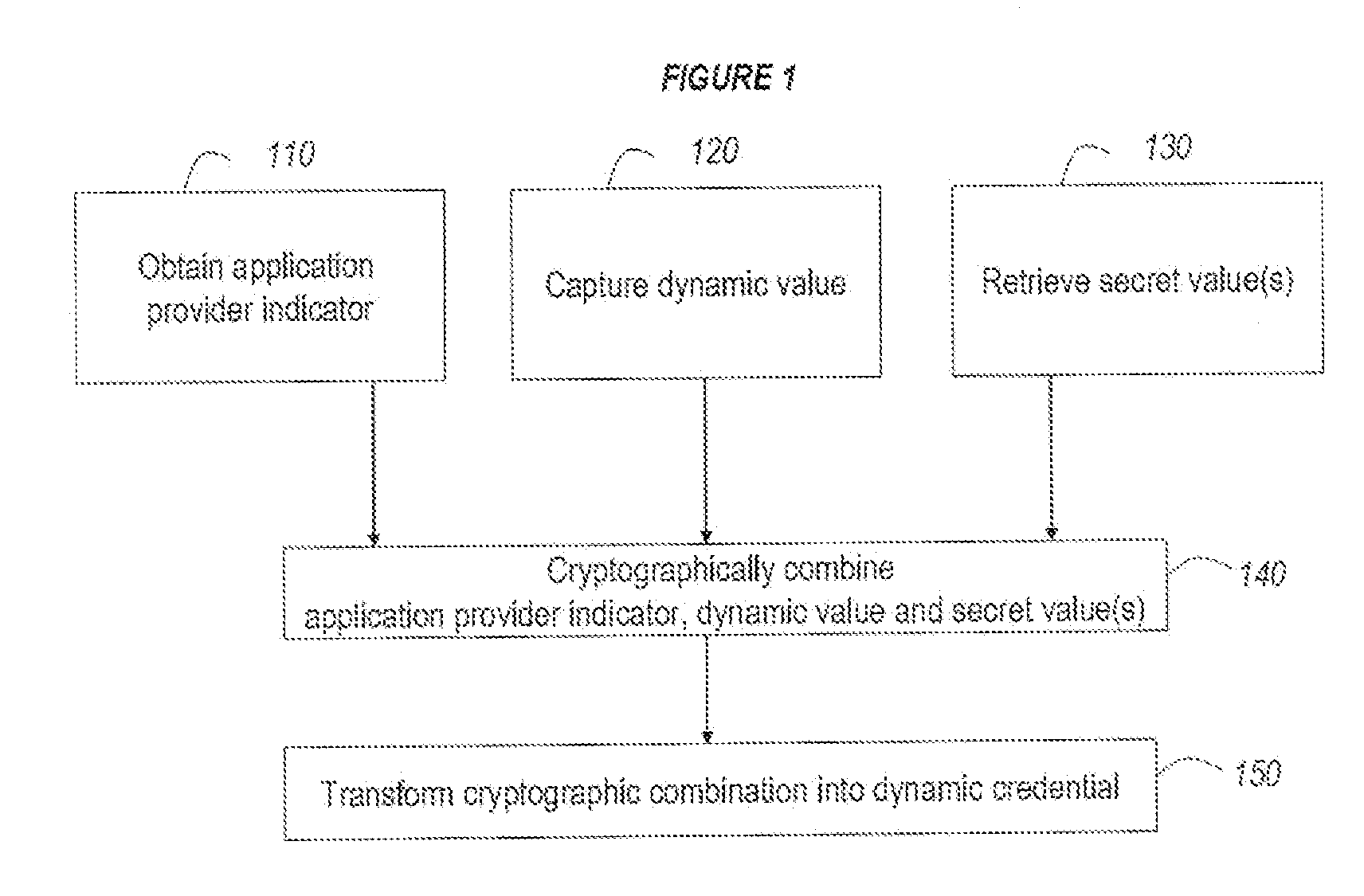
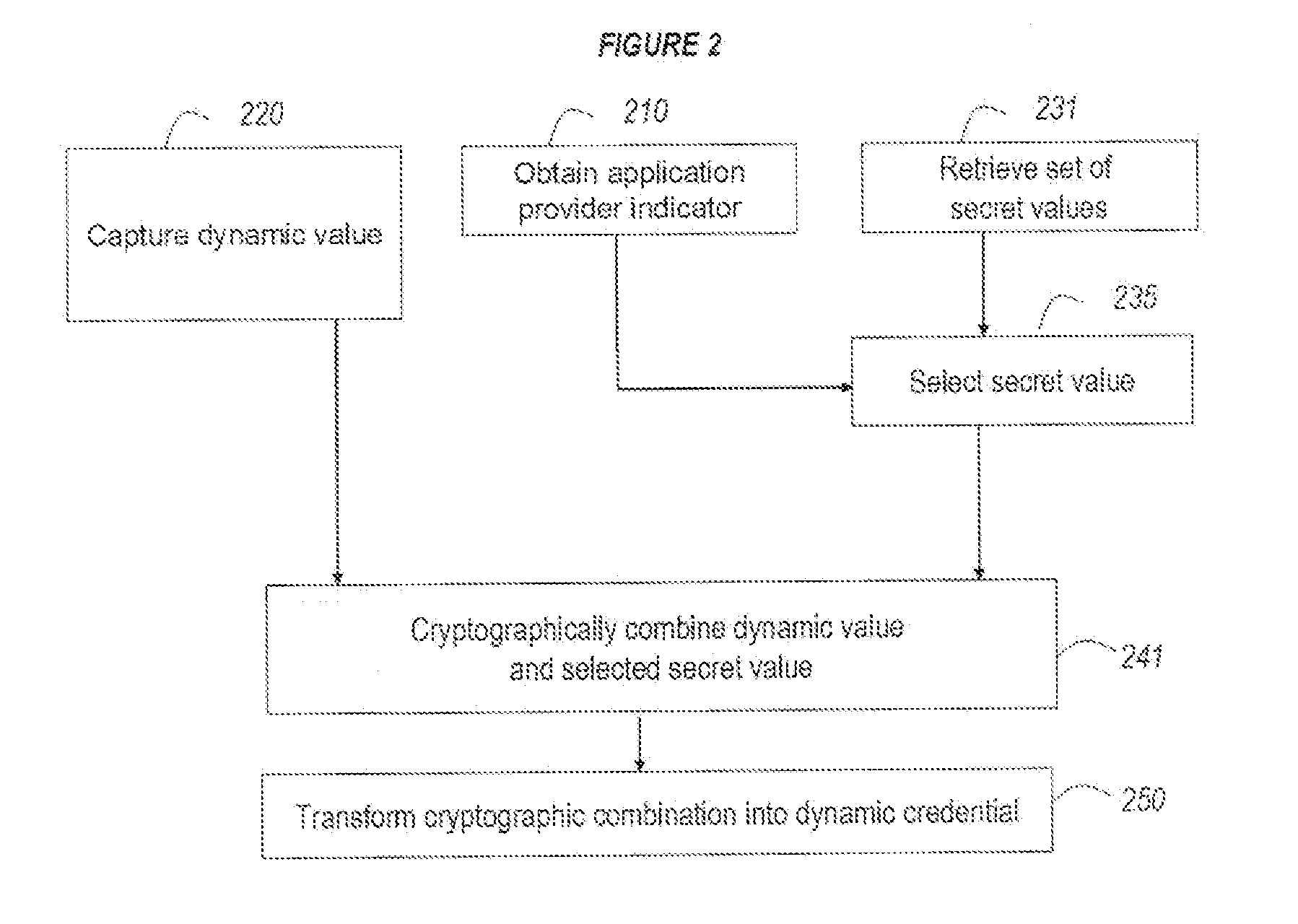
ActiveUS20110099384A1Low costCost can be dividedMultiple keys/algorithms usageDigital data processing detailsPersonalizationUnique identifier
Owner:ONESPAN NORTH AMERICA INC
Decentralized public key management method and system based on trusted network
ActiveCN107070644AEfficient verificationEfficient queryKey distribution for secure communicationStructure of Management InformationUser identifier
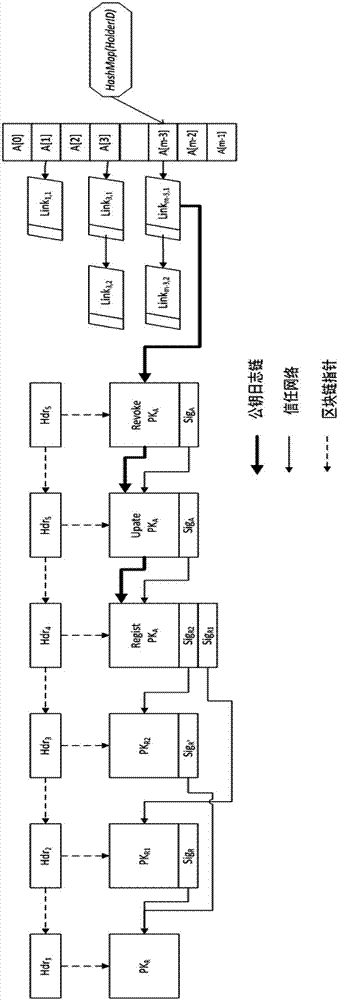
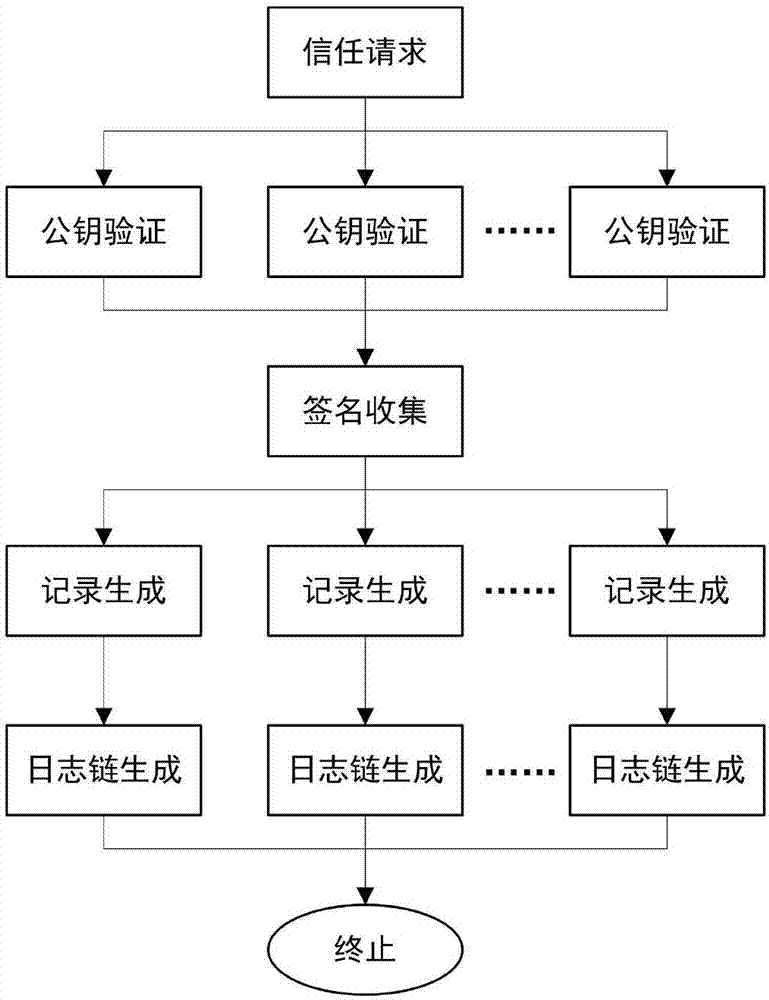
The invention mainly belongs to the technical field of information security, and specifically relates to a novel decentralized public key management method and a trusted model. The method is constructed on distributed data network platforms such as a block chain and P2P (Peer to Peer) in order to ensure that all nodes in the platforms can participate in maintenance of whole-life-cycle management of public keys of users, and the changes of the public keys of the users in various states in a life cycle are recorded in a bill form. Through the method, public keys passing verification can be recorded and added into a consistent public key storage structure of a platform to be saved; a public key log chain is generated for all public key records of the same user according to a time sequence, and an authentication chain and a trusted network are formed on the basis of a referrer signature; and efficient search of the public keys can be realized on the basis of user identifiers. Through adoption of the method, the public keys of the users can be issued and acquired conveniently and accurately, and the effectiveness, correctness, consistency and non-fraudulence of acquired public keys are ensured. The method can be taken as an infrastructure supporting authentication, encryption, integrity and accountability services.
Owner:UNIV OF SCI & TECH BEIJING
System and method for secure transaction process via mobile device
ActiveUS20140214688A1Overcome disadvantagesAcutation objectsPayment protocolsSecurity domainKey storage
A secure element with a user security domain thereon, the user security domain constituted of: a security domain control circuitry; an encoder / decoder functionality responsive to the security domain control circuitry; and a secured keys storage in communication with the security domain control circuitry, the encoder / decoder functionality arranged to: encode data responsive to at least one first key stored on the secured keys storage, and output an encoded data; and decode received data responsive to at least one second key stored on the secured keys storage, and output a decoded data.
Owner:PING IDENTITY
Apparatus and method for encrypting and decrypting data recorded on portable cryptographic tokens
InactiveUS20020129261A1Provide securitySecure transmissionKey distribution for secure communicationPublic key for secure communicationEmbedded securitySecure transmission
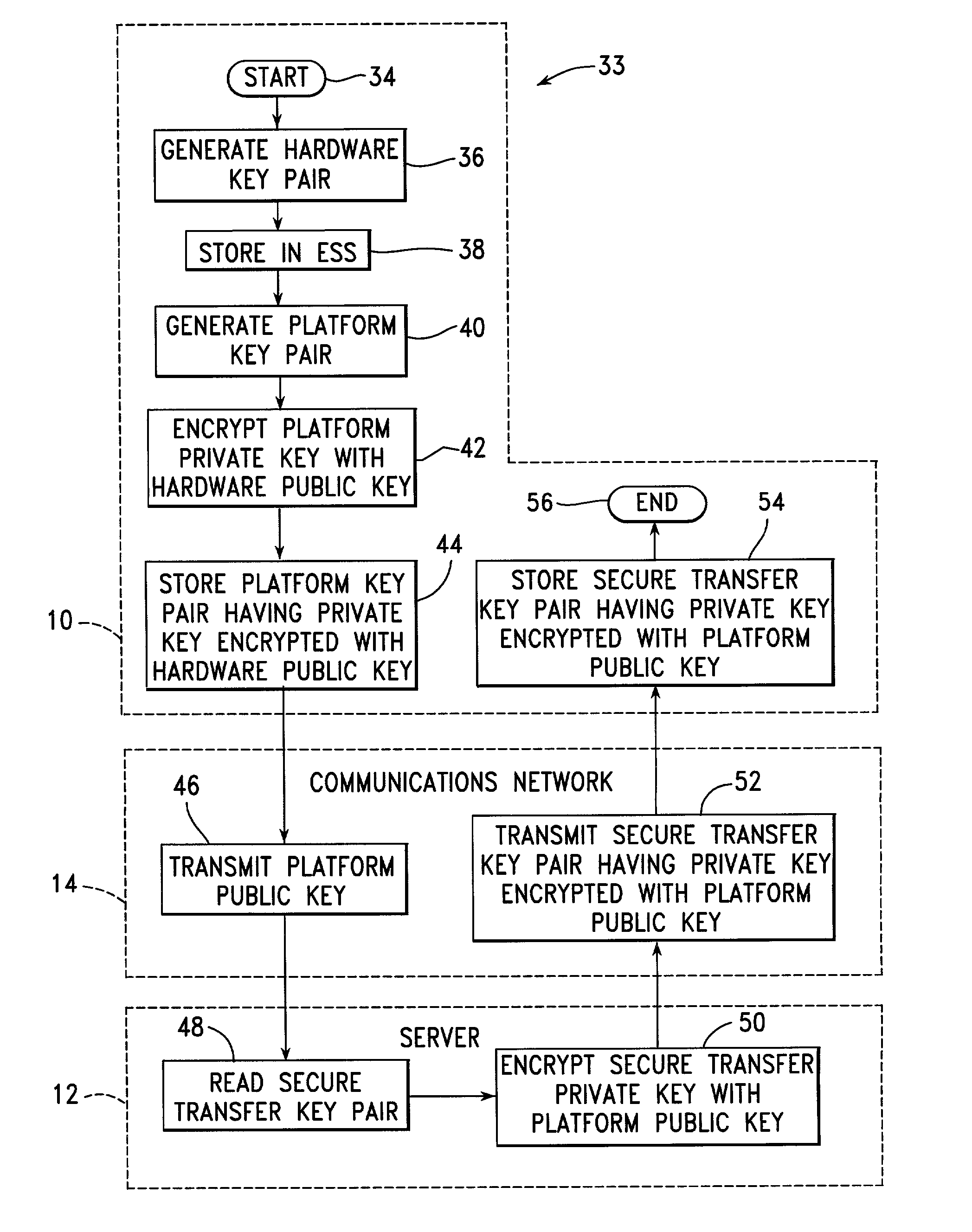
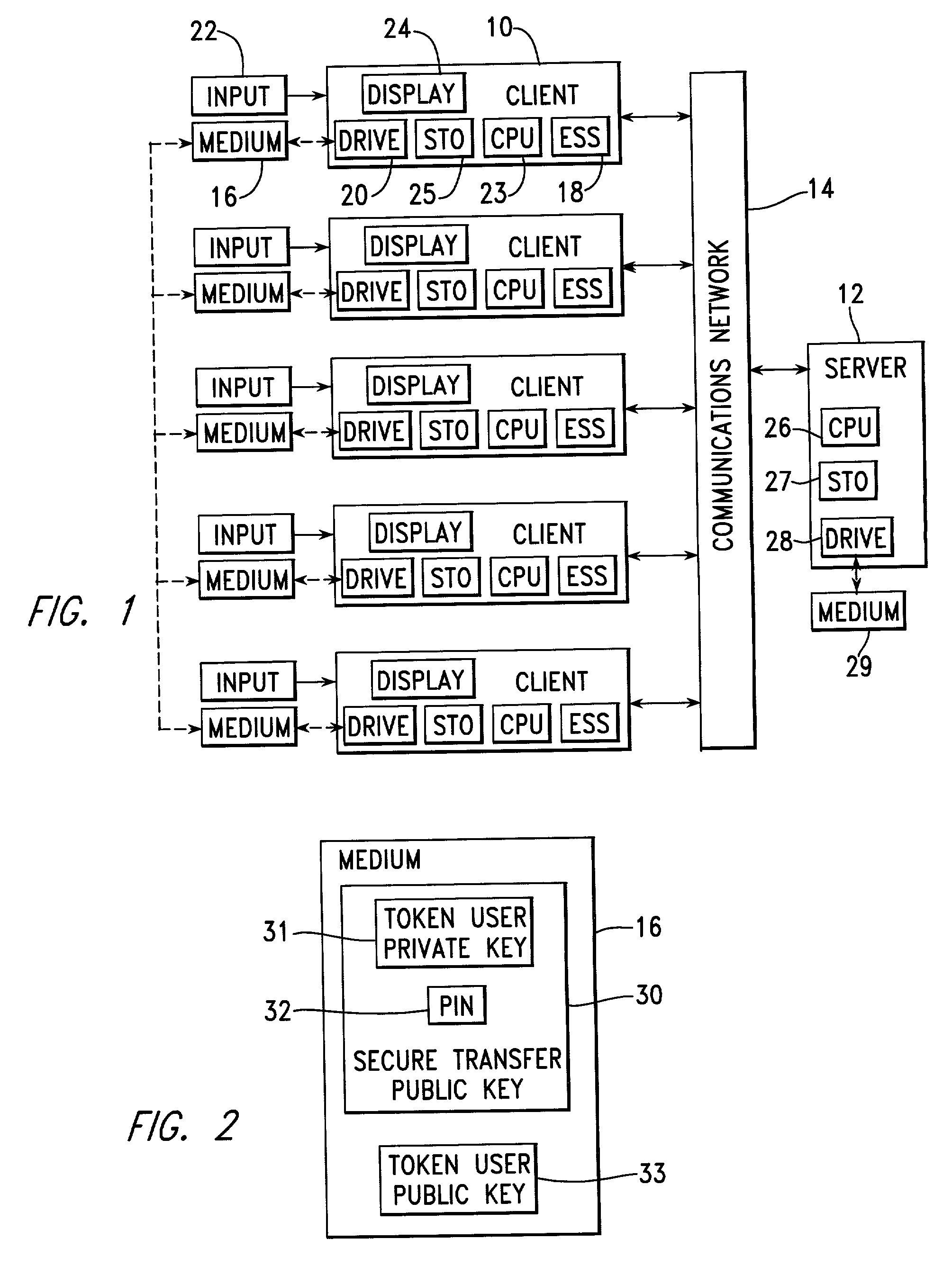
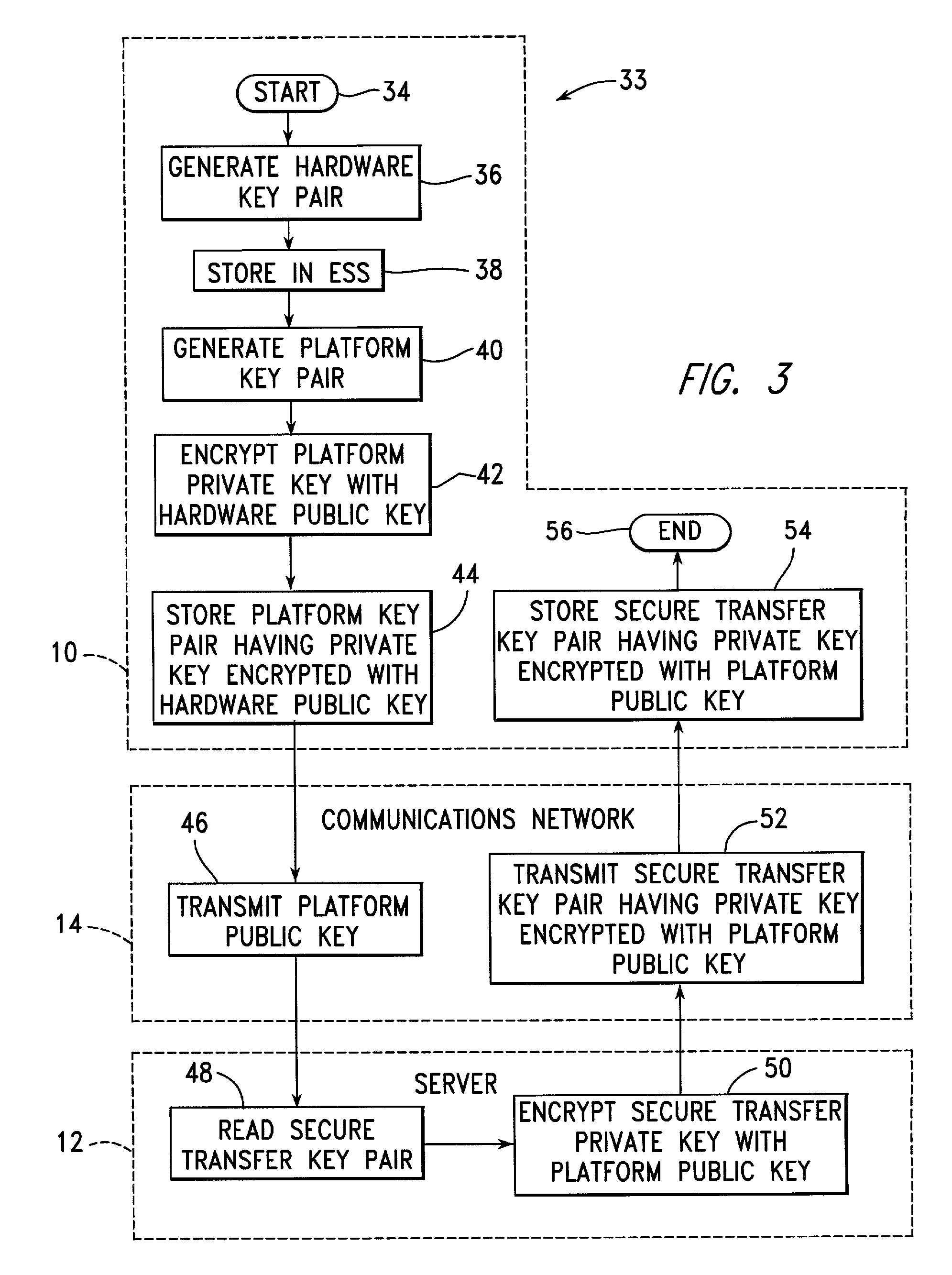
A number of client systems receive a common secure transfer key pair from a server during initialization. The secure transfer private key is encrypted in the server with a platform public key sent to the server from the client system. Each client system is then able to encrypt data, using a secure transfer public key, to be recorded on a computer readable medium, and subsequently to decrypt such data using a secure transfer private key. Preferably, each client system includes an embedded security subsystem (ESS) performing cryptographic processes and providing secure key storage. Then, the secure transfer private key is stored as encrypted, and is decrypted using a private key within the ESS. Preferably, the platform private key is also stored encrypted, to be decrypted within the ESS using a hardware private key.
Owner:IBM CORP
Method and apparatus for distributing, interpreting, and storing heterogeneous certificates in a homogenous public key infrastructure
InactiveUS6895501B1Avoid less flexibilityUser identity/authority verificationWeb browserDigital signature
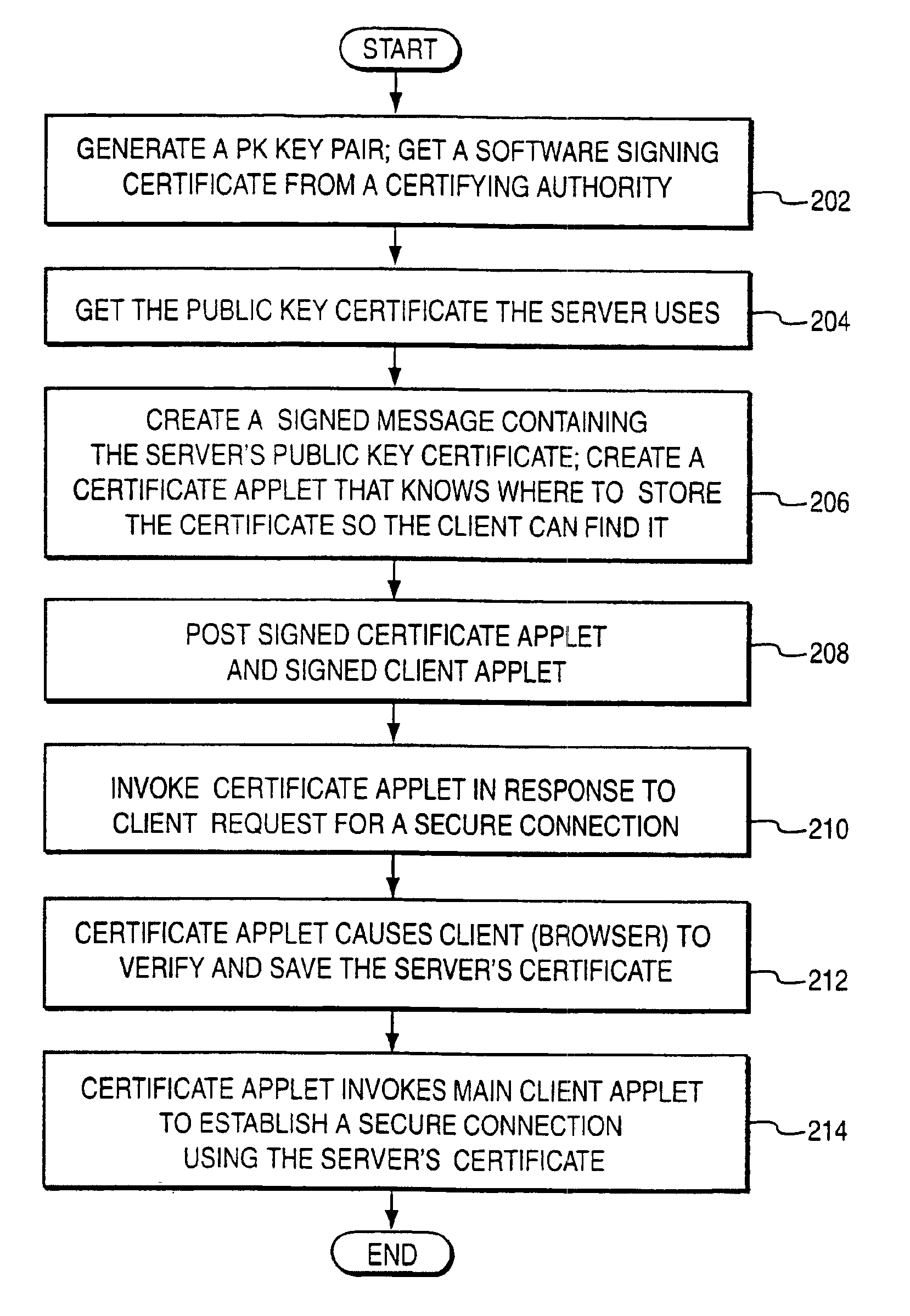
A connection is established between a server and a web browser having access to a first, trusted public key. The server downloads a digitally signed archive to the browser, the archive including a second public key. The browser verifies the digitally signed archive using the first public key, and stores the second public key in response to the verification. The browser then uses the stored second public key to authenticate the server and establish a secure connection with the server. The second public key and its chain of trust need not be known by the browser beforehand, and the archive may include program fragments that store the key in an area where the browser (or an applet running under the browser) can access and use it. The archive may also include a program fragment that performs certificate validation for the client—enabling the client to handle certificate types it does not know about. Advantages include allowing the archive to be transmitted over any insecure connection since it is integrity protected and authenticated; and allowing the client to make a direct connection to the server without having to access certificate stores on the platform.
Owner:ATTACHMATE
Cryptographic server with provisions for interoperability between cryptographic systems
InactiveUS20050102244A1Minimal compute resourceAvoid the needDigital data authenticationBuying/selling/leasing transactionsComputer hardwareKey storage
Owner:SECURITY FIRST INNOVATIONS LLC
Processing system using internal digital signatures
InactiveUS20060015732A1User identity/authority verificationUnauthorized memory use protectionDigital signatureHandling system
A preferred embodiment of the invention uses local or internal public and private keys for signatures. The keys are obtained and managed internally by a kernel process having access to a secure key storage area. The kernel process is booted within a trusted platform and is the only process that is allowed to access the key storage area. The internal keys can be used in addition to external keys for both internal key-based and external key-based signatures on a single digital item. In a preferred embodiment, the kernel process also maintains revocation lists and is synchronized with other entities by having the same criteria (e.g., time-based) for revoking or expiring known internal keys
Owner:SONY CORP +1
CPK credibility authorization system
InactiveCN1832403AEliminate Collusion AttacksImprove securityUser identity/authority verificationKey exchangeHash function
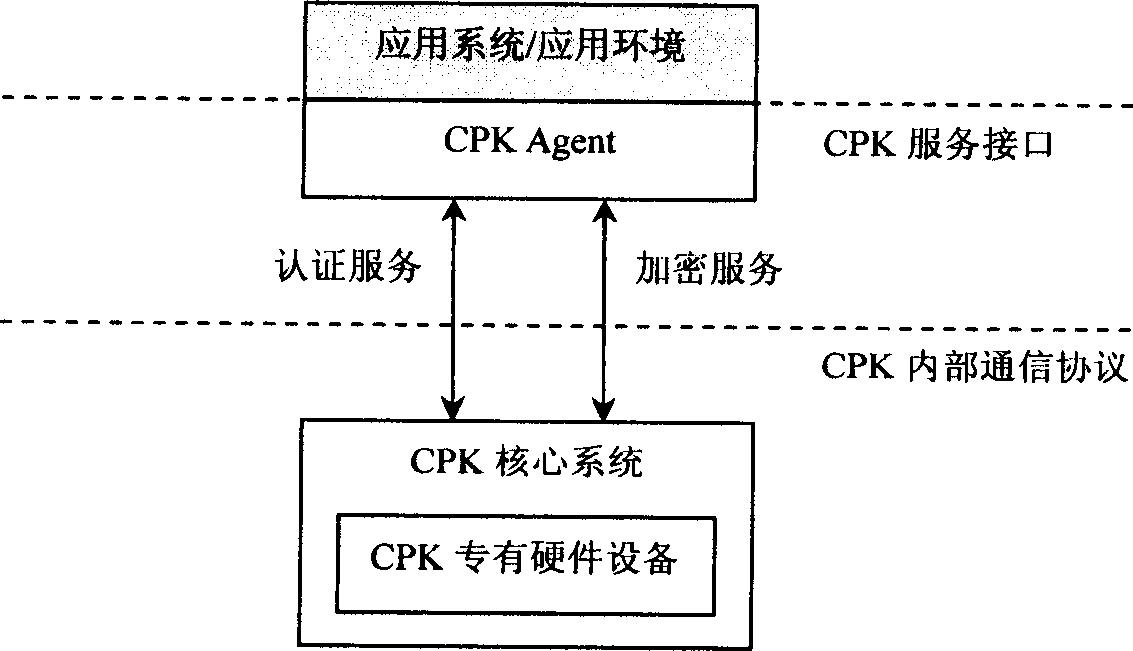
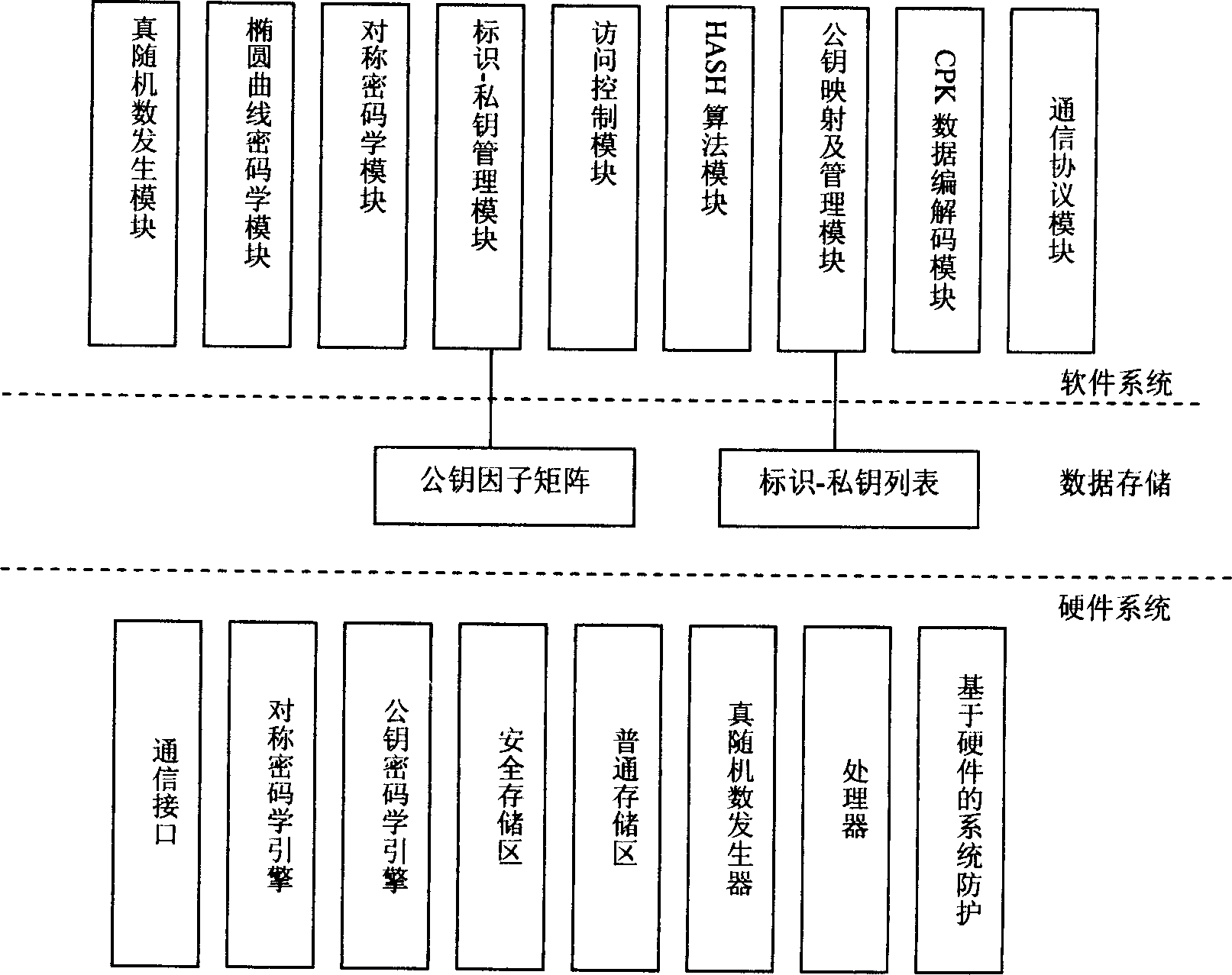
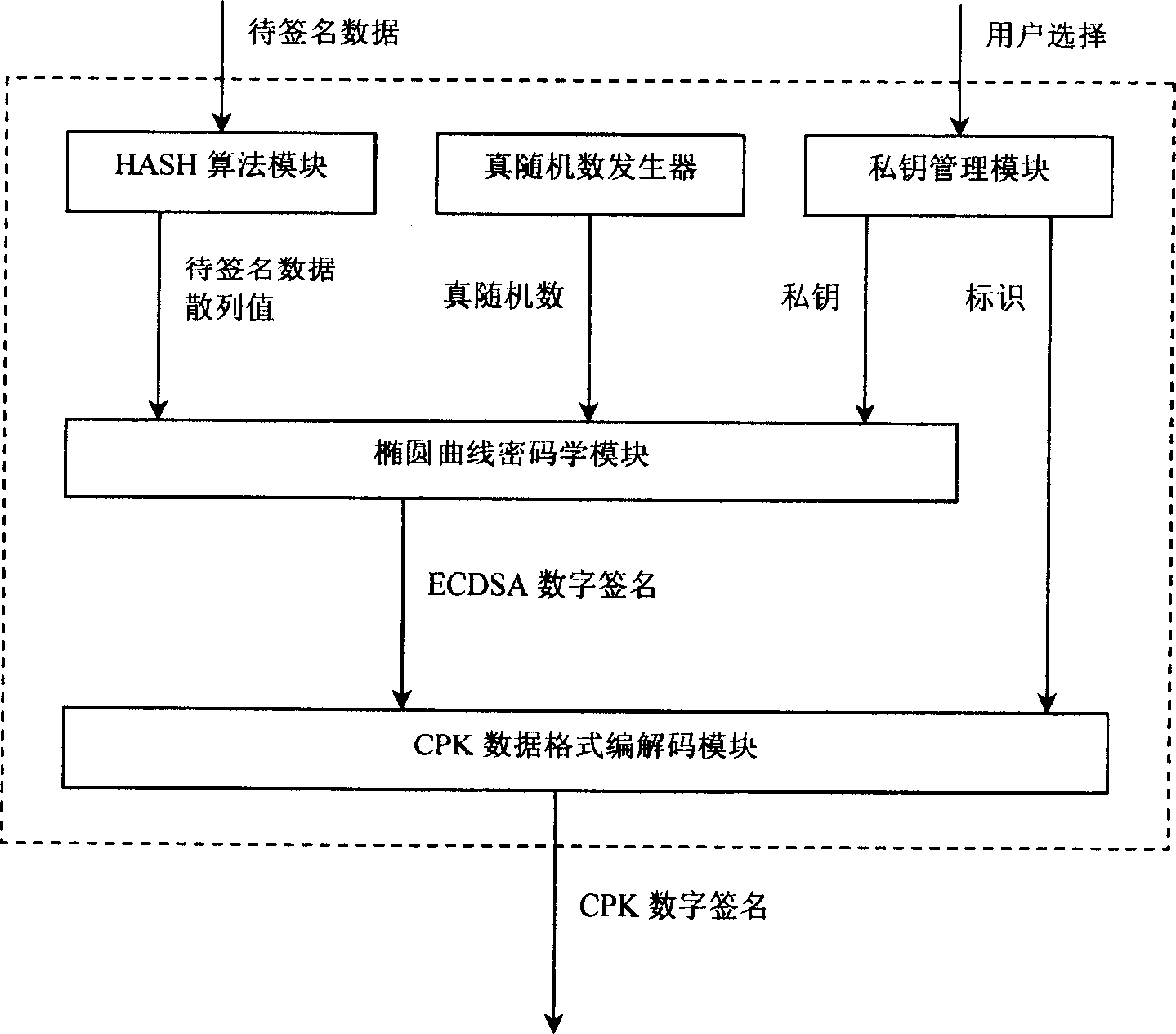
This invention discloses a CPK trustable certification system with a chip including special COS, CPK algorithm, ID certificates, signature protocol, a cryptographic key exchange protocol, a ciphering algorithm and HASH function and divided into intelligent card, USB Key, Flash card and cell phone SIM card. One chip can bear the functions of a cipher machine, signature verification, cryptographic key storage and management.
Owner:BEIJING E HENXEN AUTHENTICATION TECH
Method And System For Maintaining Backup Of Portable Storage Devices
InactiveUS20080077808A1Safe storageEasy to carryVolume/mass flow measurementUnauthorized memory use protectionPasswordTrusted Computing
Data stored in a portable storage device are encrypted, for example by a processor of the portable storage device itself, using a backup key and stored in a backup medium. The backup key is protected by being stored in a backup key storage medium, such as an internet server, a pocketable medium or a trusted computer, preferably after being encrypted using a password. As needed, the backup key is retrieved and used to decrypt the data from the backup medium. The decrypted data are restored to the original portable storage device or to a different portable storage device.
Owner:WESTERN DIGITAL ISRAEL LTD
Key storage and organization unit
InactiveUS20050199628A1Access is deniedProgramme controlComputer controlLocking mechanismEngineering
A key storage and organization unit includes a lockbox and a set of key file cards for retaining and storing keys in an organized manner. The lockbox includes a base and a cover that are secured by two closure latching members. When the two closure latching members are applied to the base and cover, a single locking mechanism can be applied to secure the lockbox. The lockbox is designed to receive multiple locking mechanisms, each capable of securing access to the lockbox.
Owner:MASTER LOCK COMANY LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com