Patents
Literature
3172 results about "On the fly" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
On the fly is a phrase used to describe something that is being changed while the process that the change affects is ongoing. It is used in the automotive, computer, and culinary industries. In cars, on the fly can be used to describe the changing of the cars configuration while it is still driving. Processes that can occur while the car is still driving include switching between two wheel drive and four wheel drive on some cars and opening and closing the roof on some convertible cars. In computing, on the fly CD writers can read from one CD and write the data to another without saving it on a computer's memory. Switching programs or applications on the fly in multi-tasking operating systems means the ability to switch between native and/or emulated programs or applications that are still running and running in parallel while performing their tasks or processes, but without pausing, freezing, or delaying any, or other unwanted events. Switching computer parts on the fly means computer parts are replaced while the computer is still running. It can also be used in programming to describe changing a program while it is still running. In restaurants and other places involved in the preparation of food, the term is used to indicate that an order needs to be made right away.
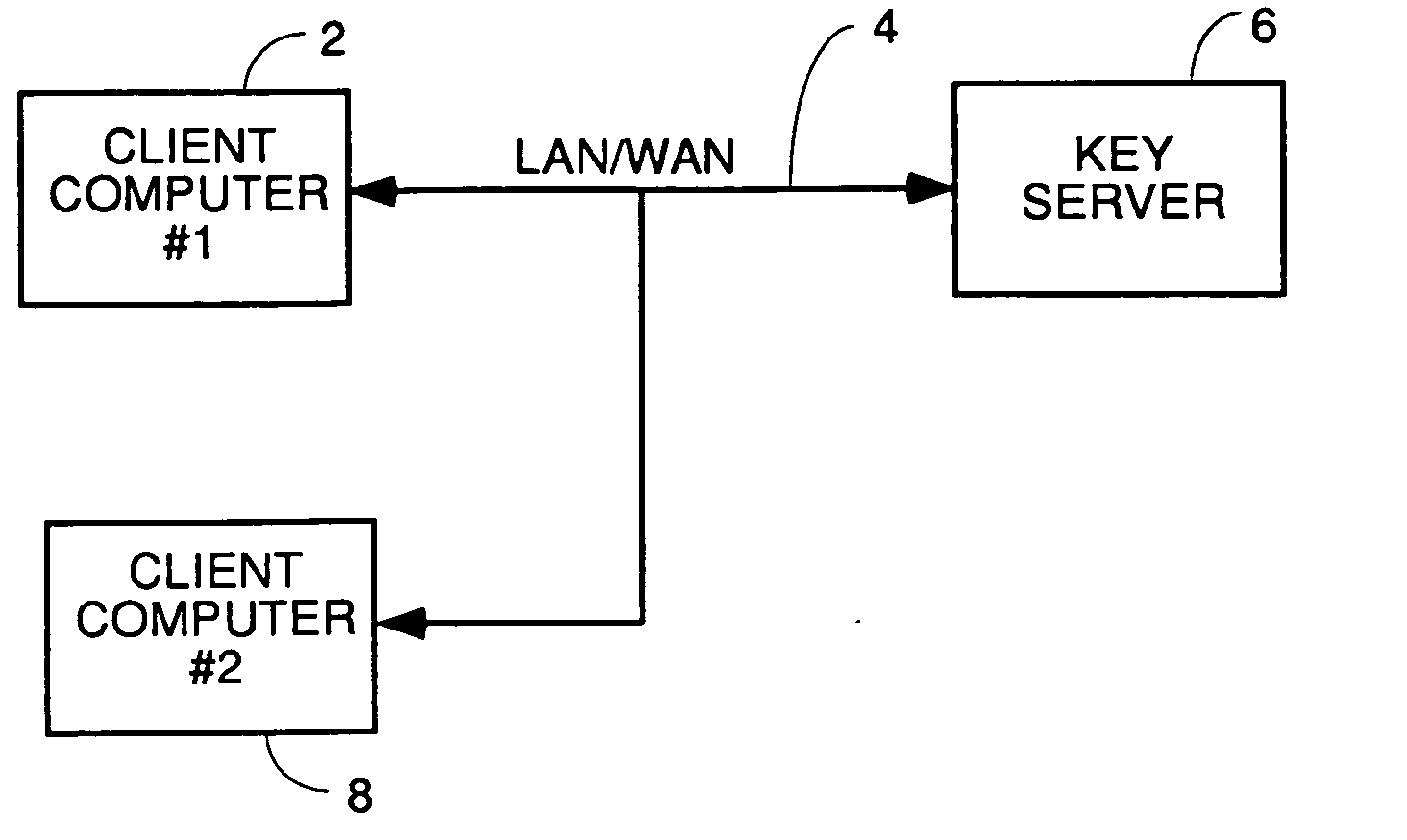
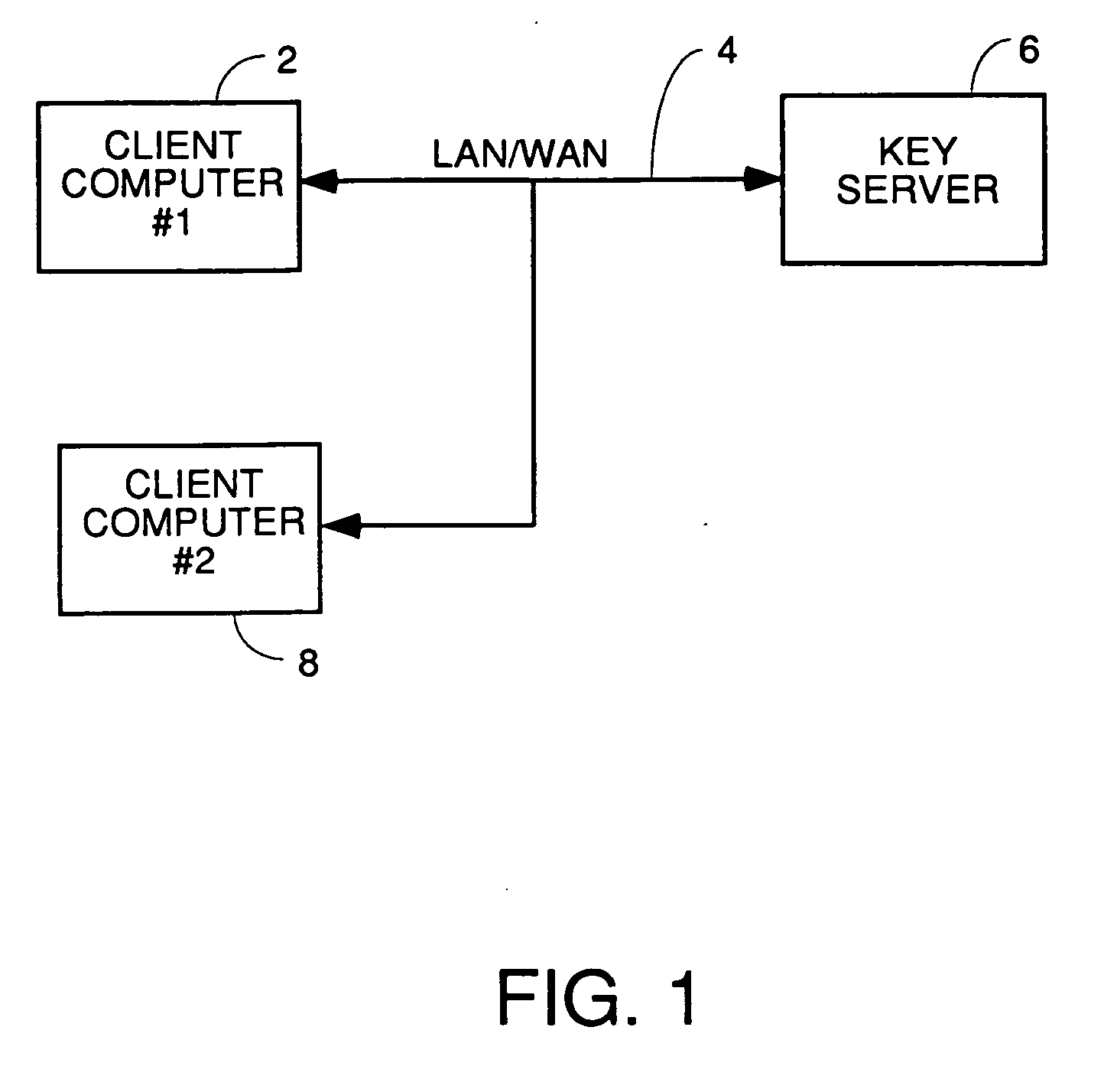
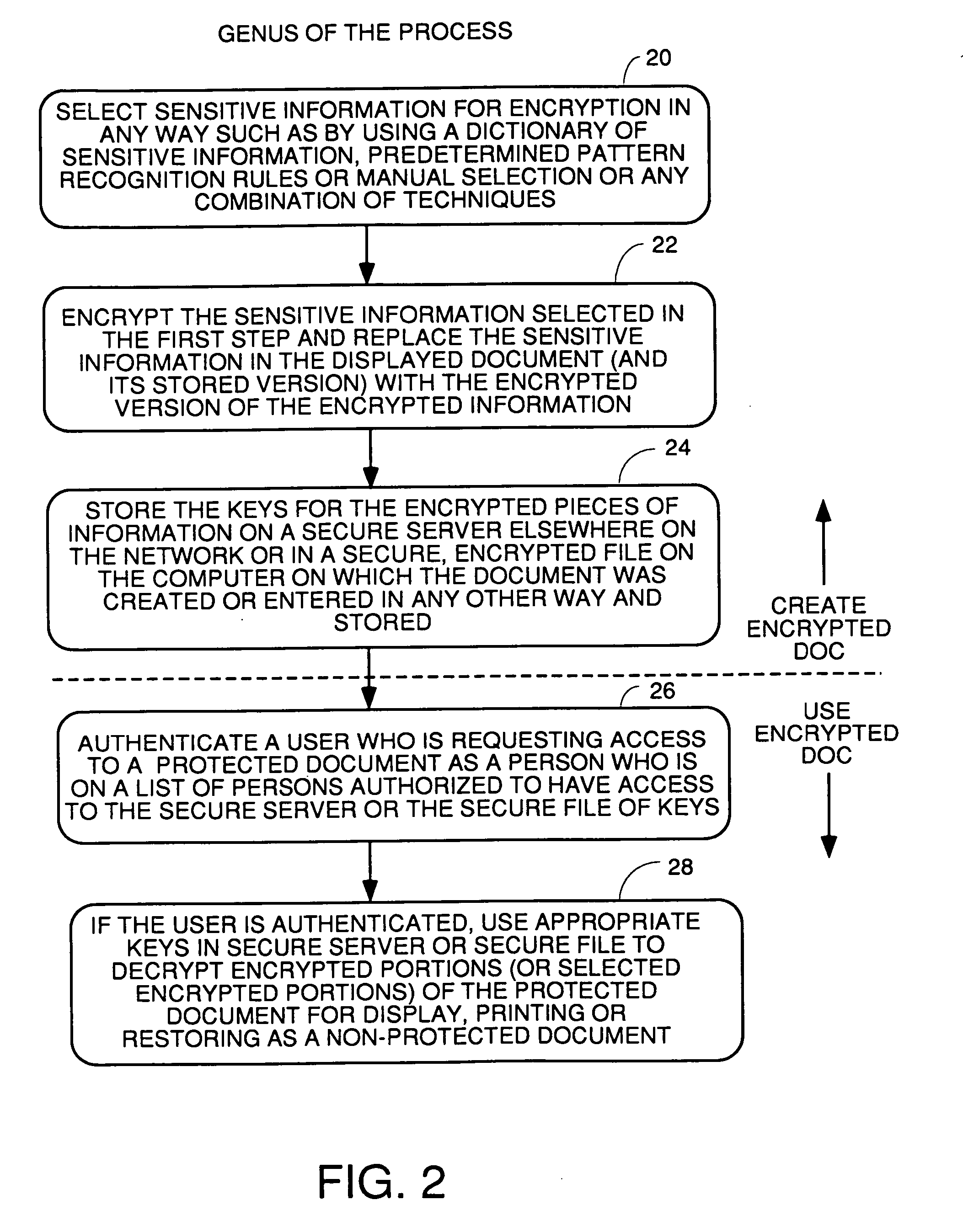
Method and apparatus for recognition and real time protection from view of sensitive terms in documents
InactiveUS20060075228A1Computer security arrangementsSecuring communicationInternet privacyClient-side
A process for automatically selecting sensitive information in any form of document being displayed and / or generated on a computer to select sensitive information for protection by encryption, redaction or removal of only the sensitive text. Selection is done by using pattern recognition rules, dictionaries of sensitive terms and / or manual selection of text. The sensitive text is automatically protected on the fly in the same manner as a spell checker works so that the sensitive information immediately is removed and replaced with the encrypted or redacted version or a space and a pointer to where the decryption key or the original of the redacted or removed text is stored. Other embodiments require manual approval of automatically selected text prior to protection. For encryption embodiments, the keys used to encrypt the sensitive information in each document are stored in a table or database, preferably on a secure key server so that they do not reside on the computer on which the partially redacted document is stored. Embodiments to protect the body of emails and attachments in either the email client or web mail environment are also disclosed.
Owner:INFOSAFE
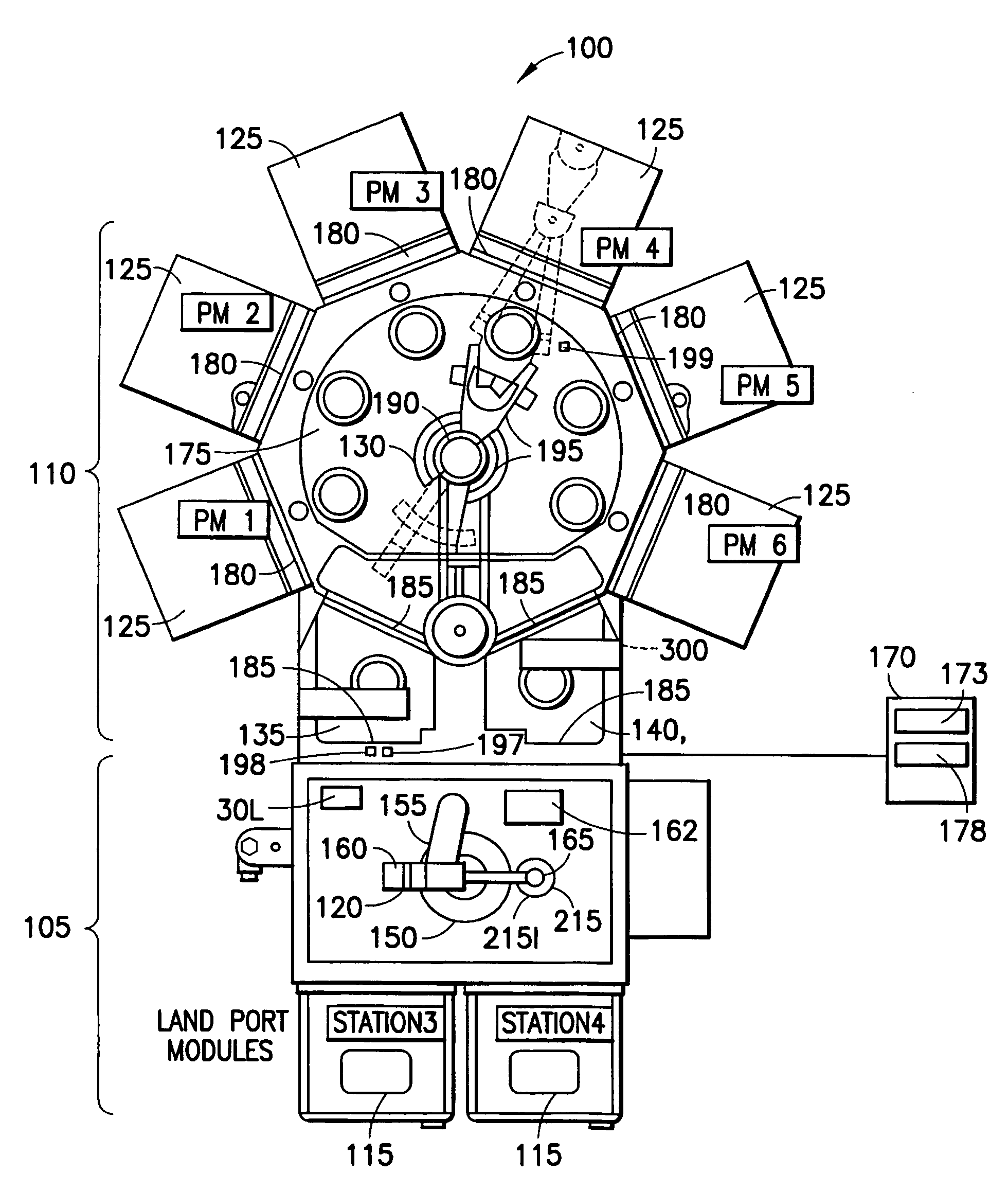
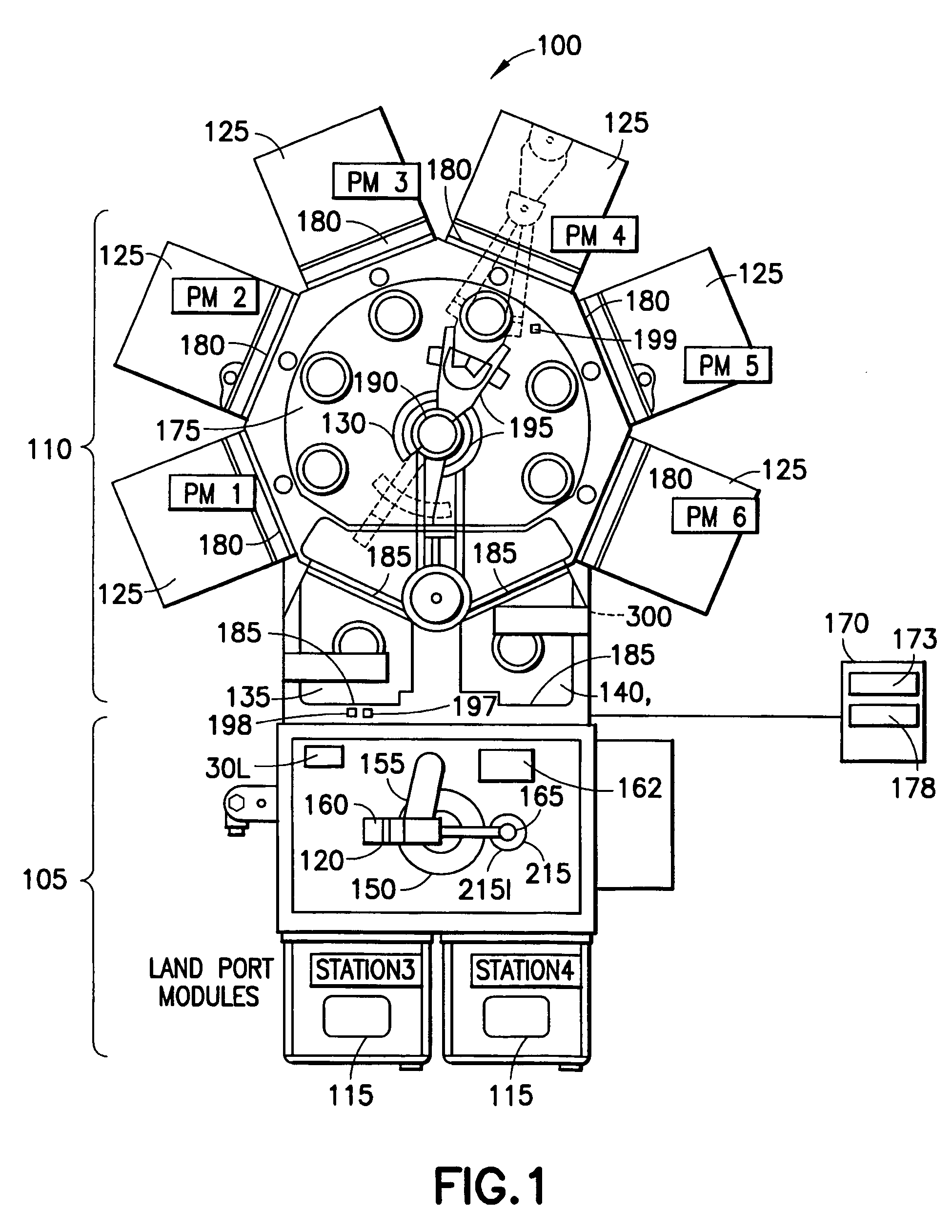
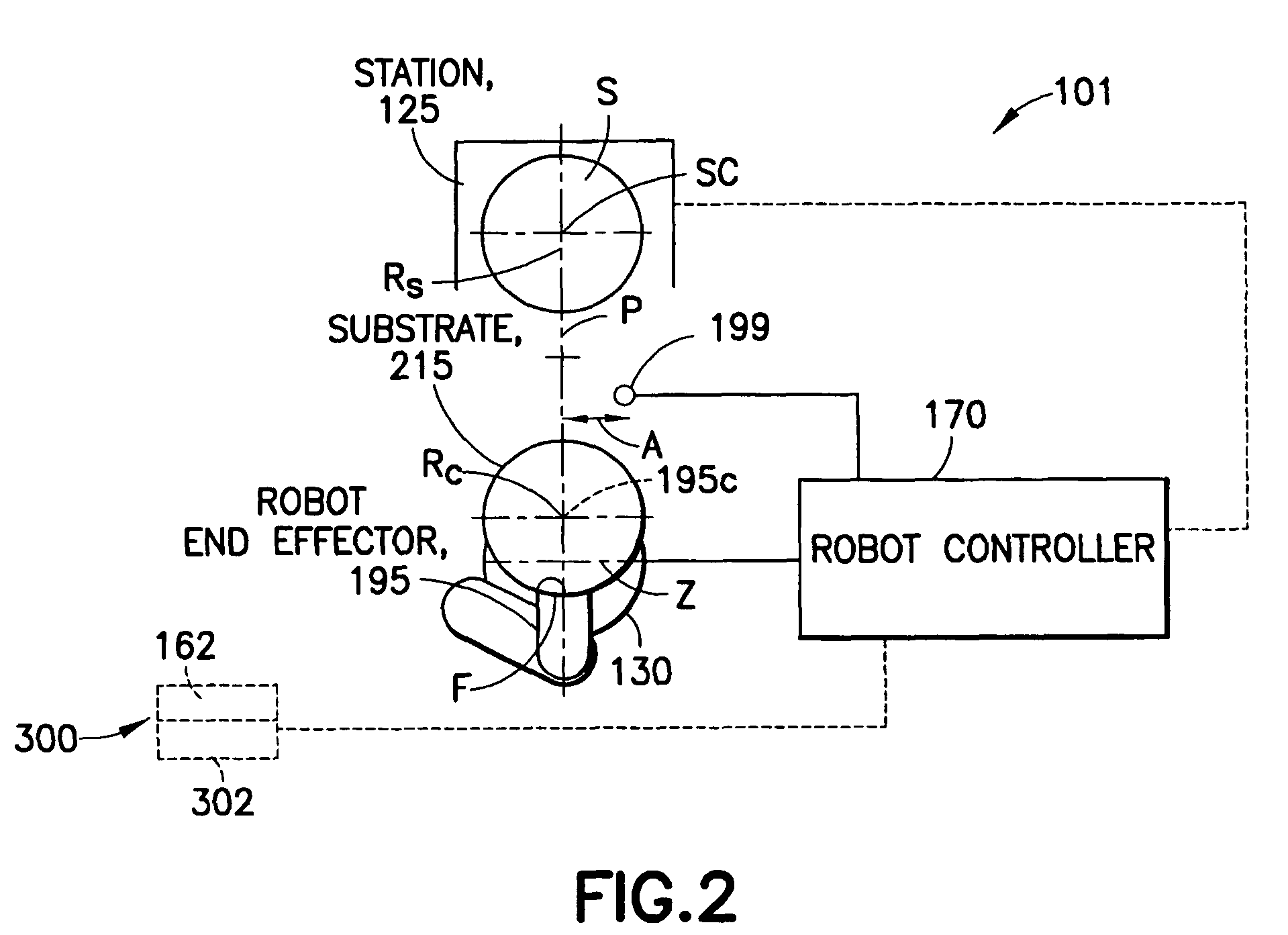
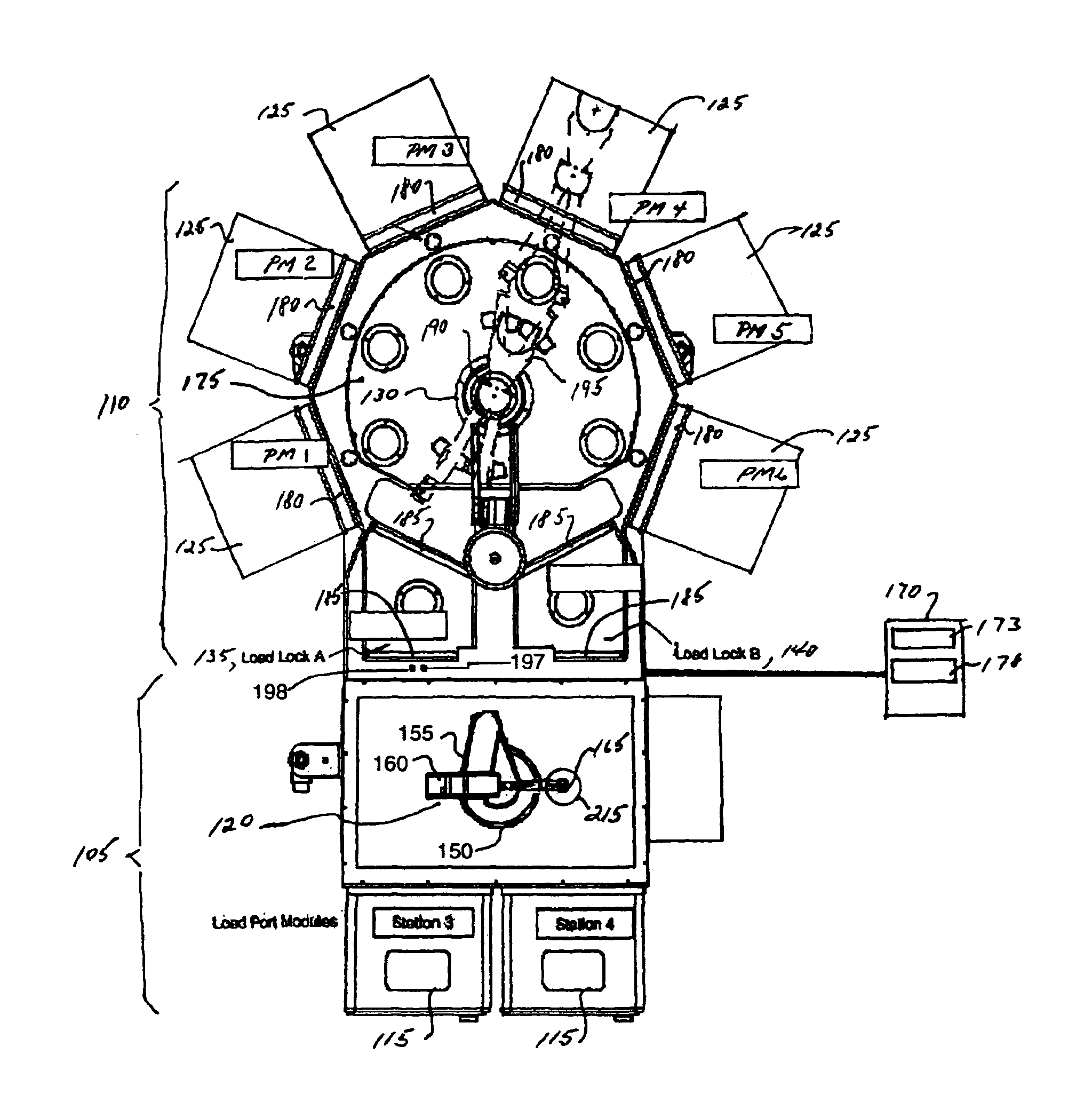
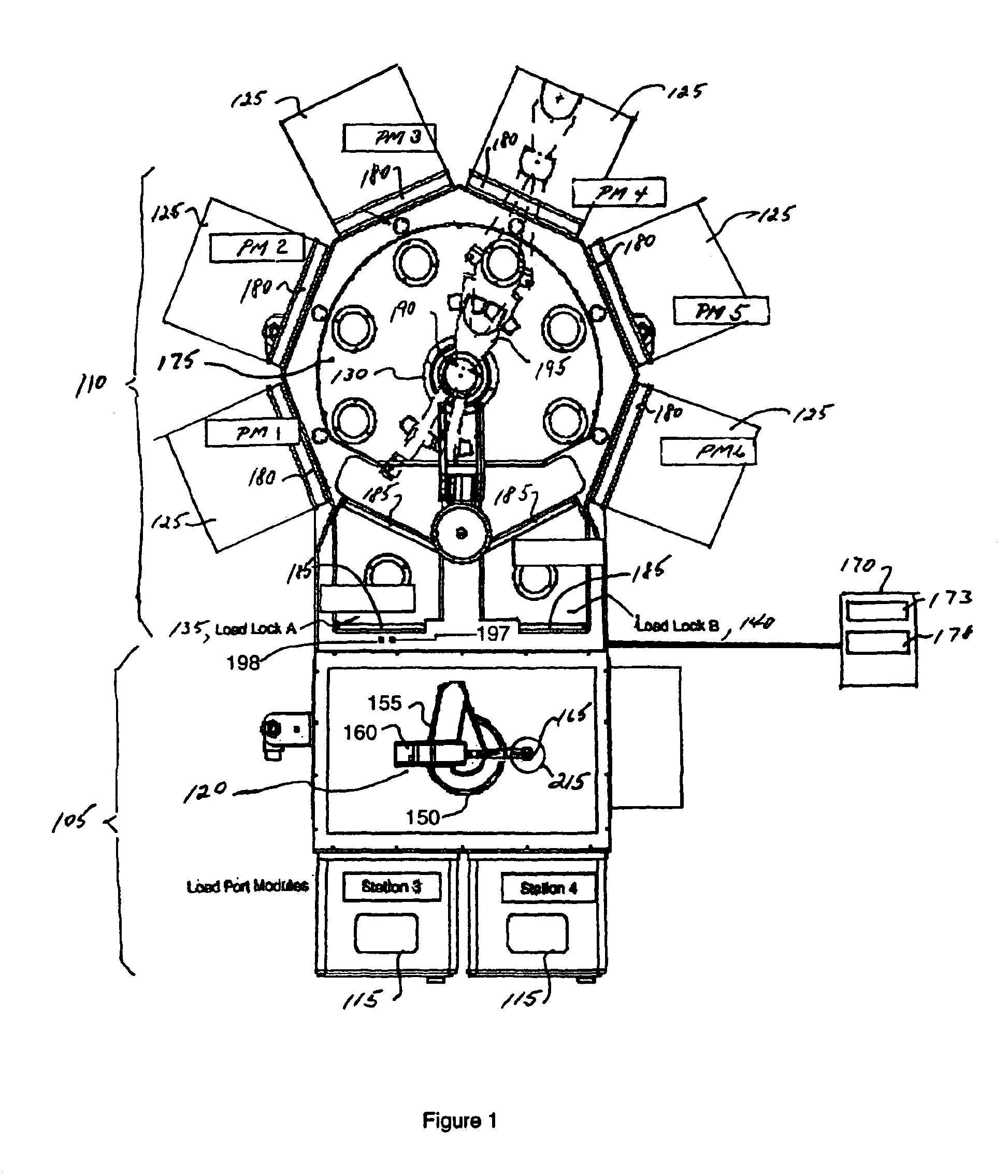
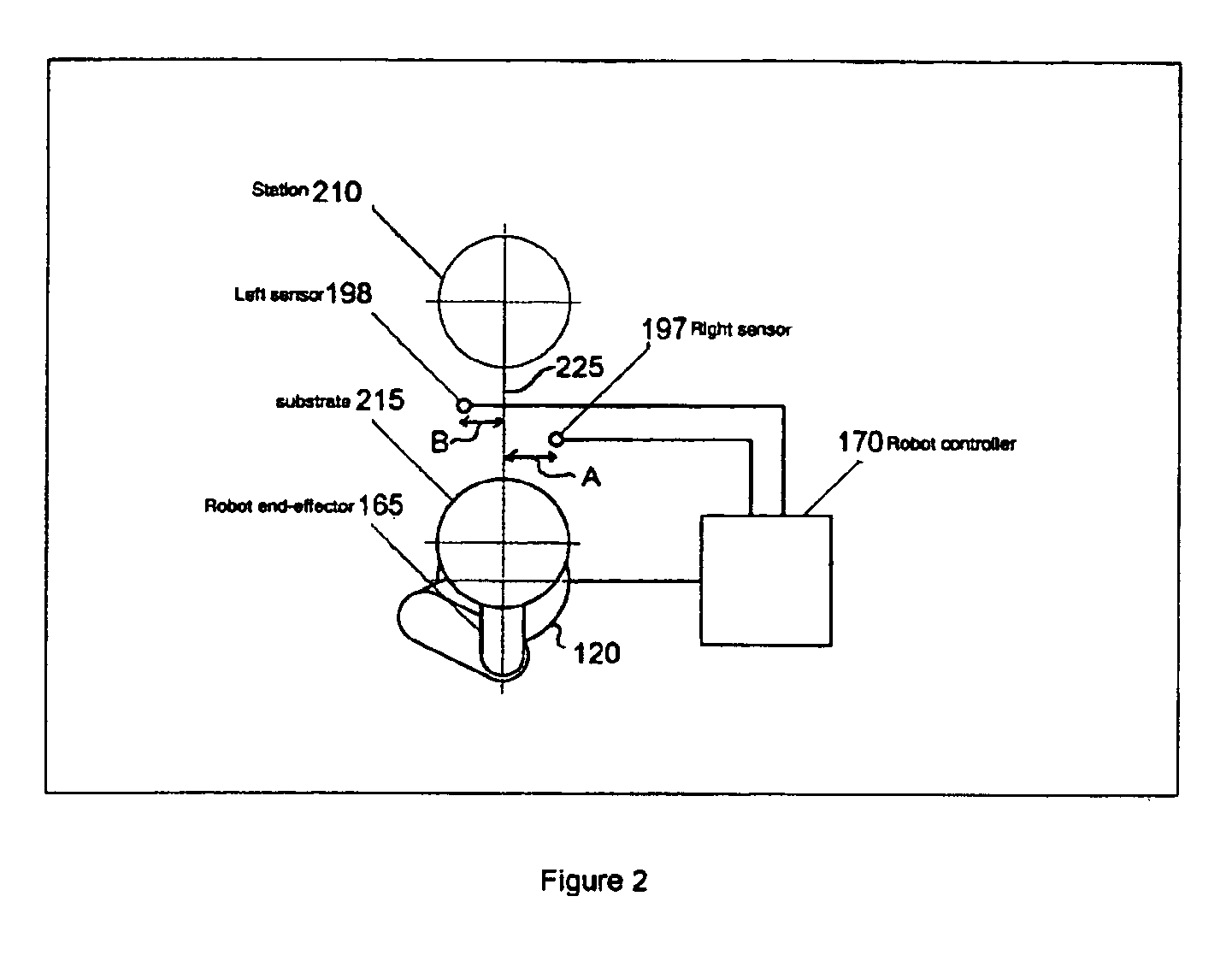
Process apparatus with on-the-fly workpiece centering
ActiveUS7925378B2Digital data processing detailsSemiconductor/solid-state device manufacturingEngineeringElectrical and Electronics engineering
A substrate processing apparatus having a transport apparatus, at least one sensor connected to the transport apparatus and a controller. The transport apparatus is adapted for transporting the substrate between processing stations of the processing apparatus. The sensor is capable of sensing the substrate transported by the transporting apparatus. The sensor is arranged for sending at least one signal in response to sensing the substrate. The controller is communicably connected to the sensor and arranged to determine alignment of the substrate in at least two directions, angled relative to each other, relative to a predetermined location. The controller is capable of determining alignment from the at least one signal identifying no more than two points on the substrate and independent of radial variances between substrates.
Owner:BOOKS AUTOMATION US LLC
System and method for on-the-fly eccentricity recognition
Owner:BOOKS AUTOMATION US LLC
Locking technique for control and synchronization
InactiveUS6973549B1Digital data information retrievalMultiprogramming arrangementsFast pathLocking mechanism
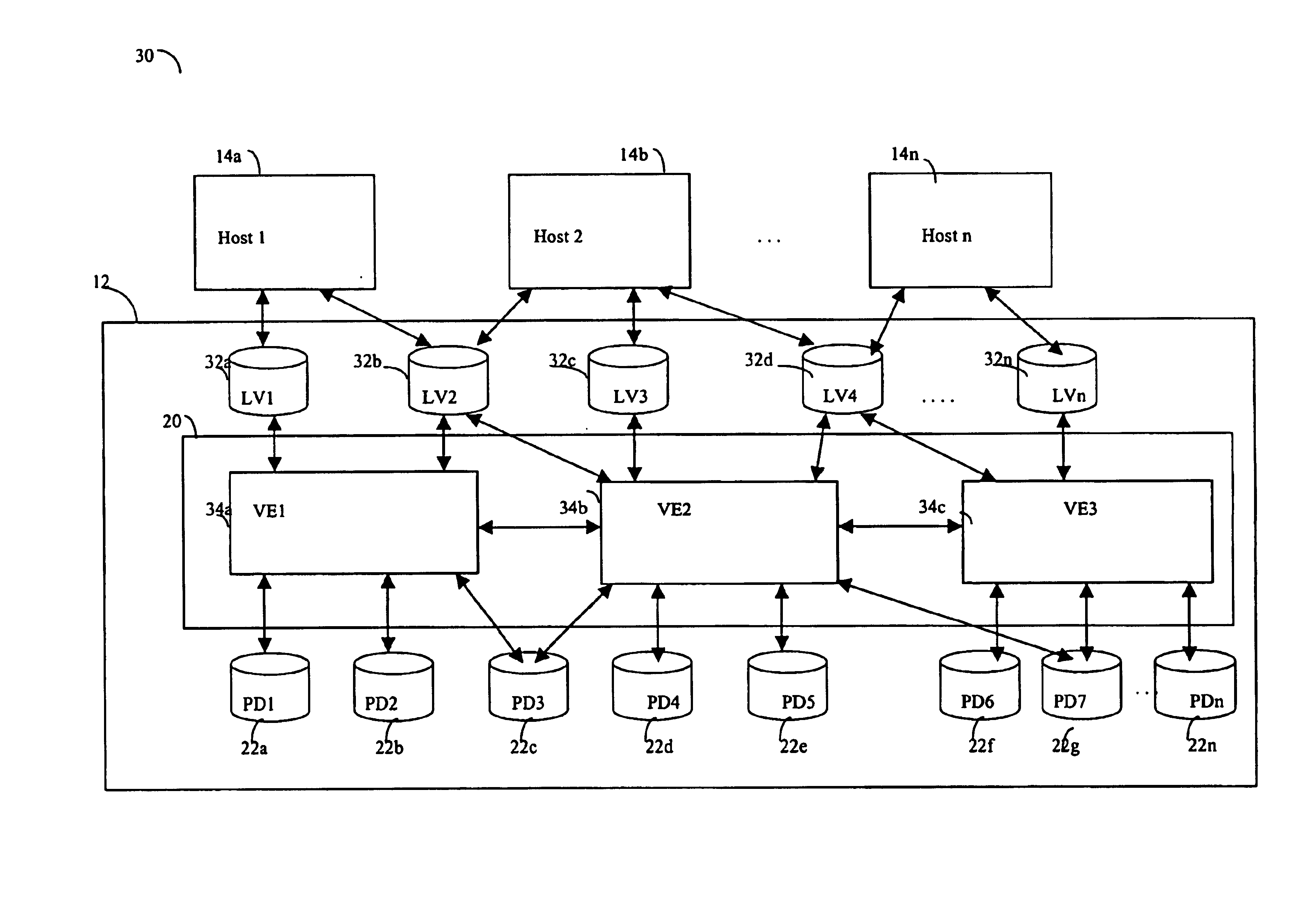
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
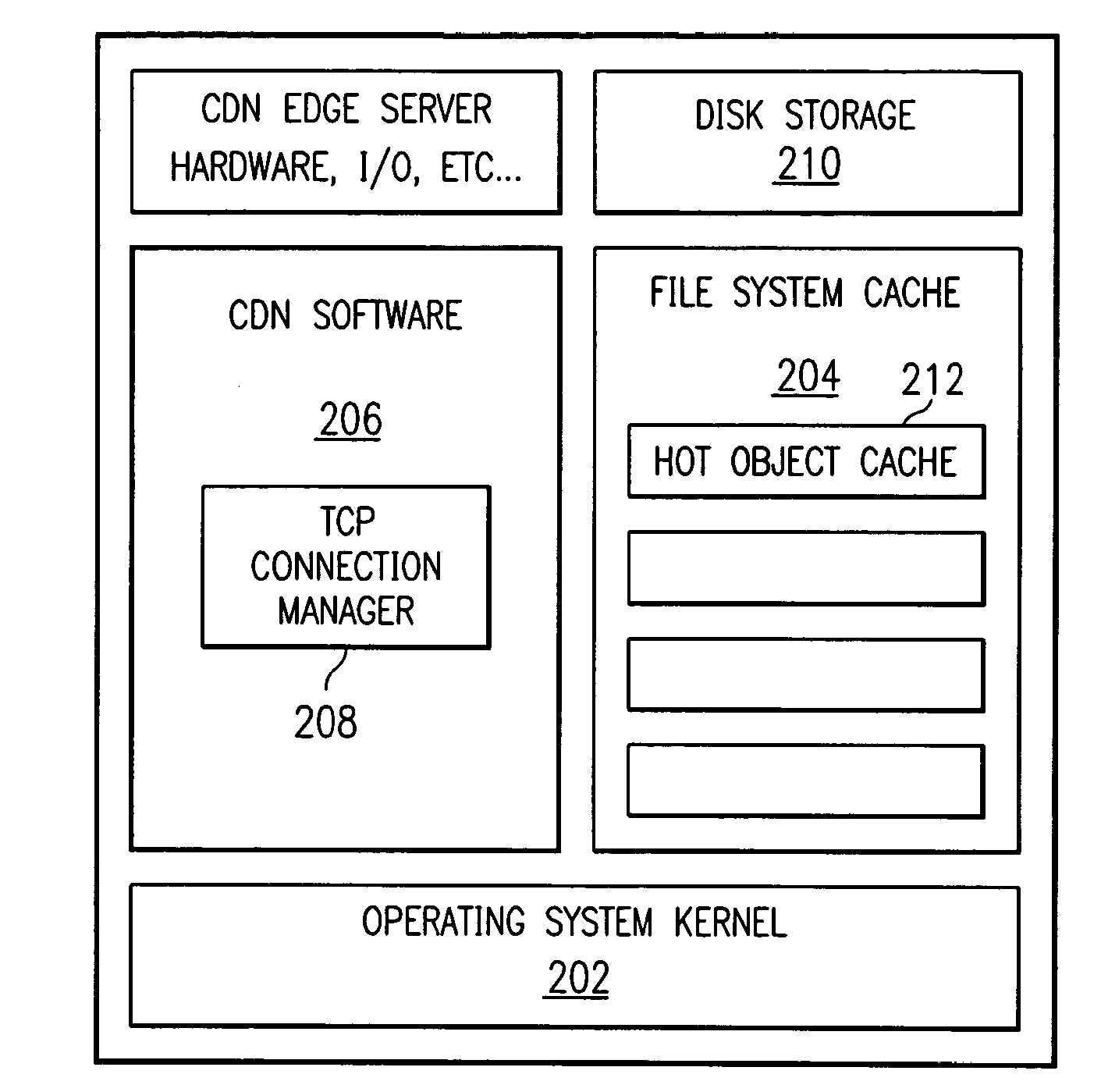
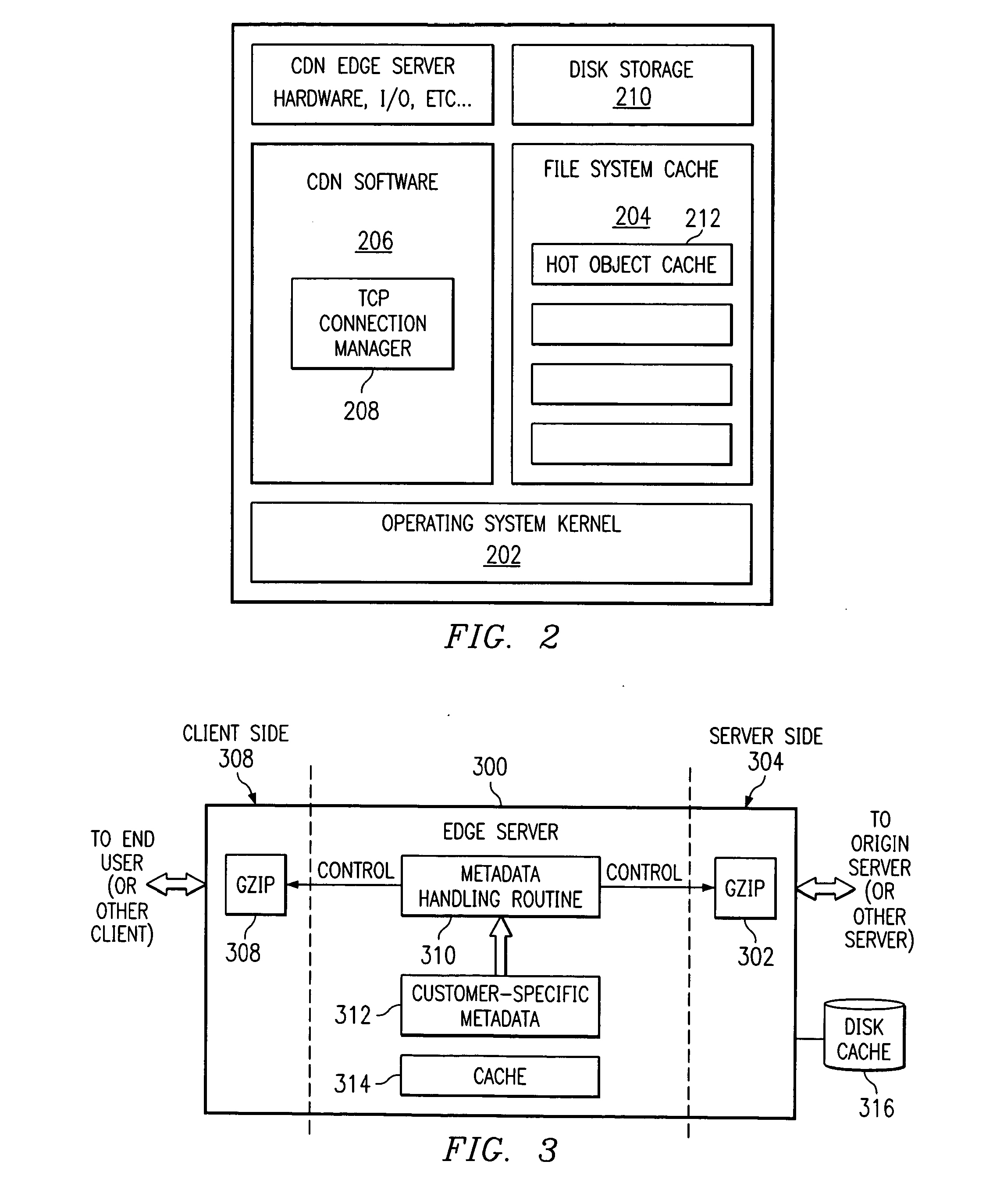
Method for caching and delivery of compressed content in a content delivery network
InactiveUS20080046596A1Easy to useReduce transfer timeDigital data information retrievalMultiple digital computer combinationsEdge serverComputer science
A content delivery network (CDN) edge server is provisioned to provide last mile acceleration of content to requesting end users. The CDN edge server fetches, compresses and caches content obtained from a content provider origin server, and serves that content in compressed form in response to receipt of an end user request for that content. It also provides “on-the-fly” compression of otherwise uncompressed content as such content is retrieved from cache and is delivered in response to receipt of an end user request for such content. A preferred compression routine is gzip, as most end user browsers support the capability to decompress files that are received in this format. The compression functionality preferably is enabled on the edge server using customer-specific metadata tags.
Owner:AFERGAN MICHAEL M +3
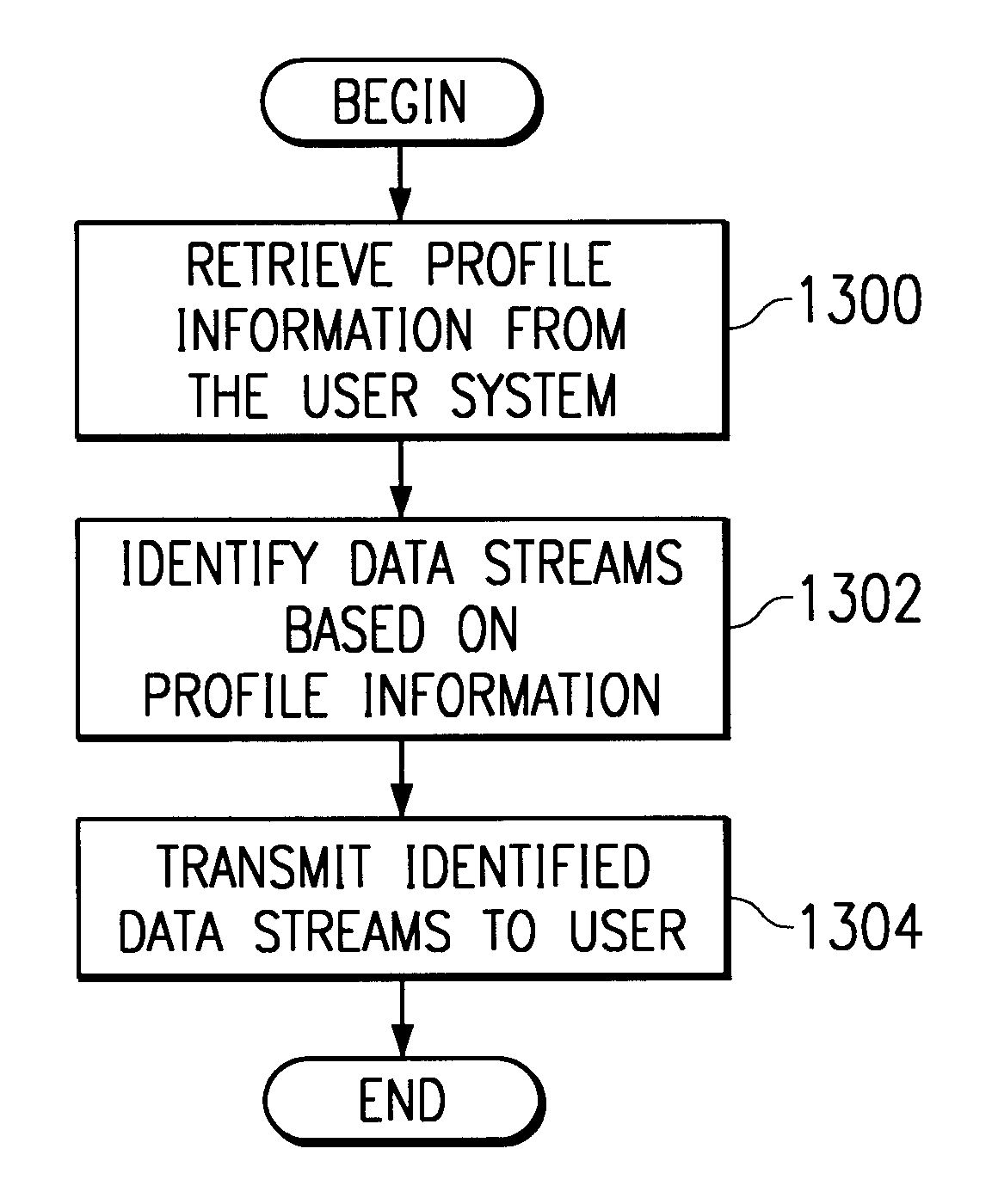
Method and apparatus for dynamic distribution of controlled and additional selective overlays in a streaming media
A method and apparatus for providing a tailored content stream to respective clients from a server. A client profile is generated for each of the respective clients. From a plurality of related streams, streams are selected to send to each respective client based on the respective client profile. Each respective client is sent only the respective selected streams for the client.
Owner:RPX CORP
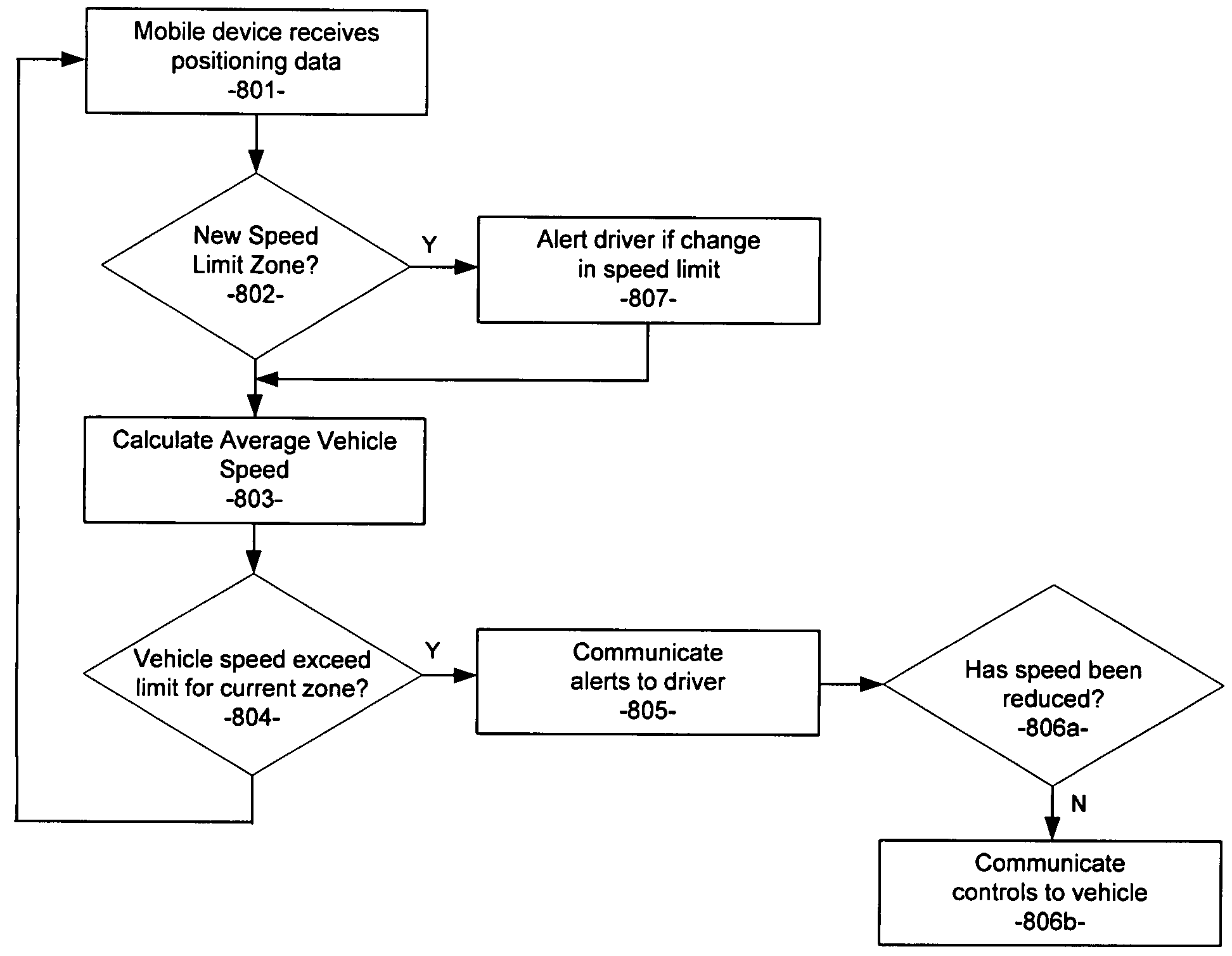
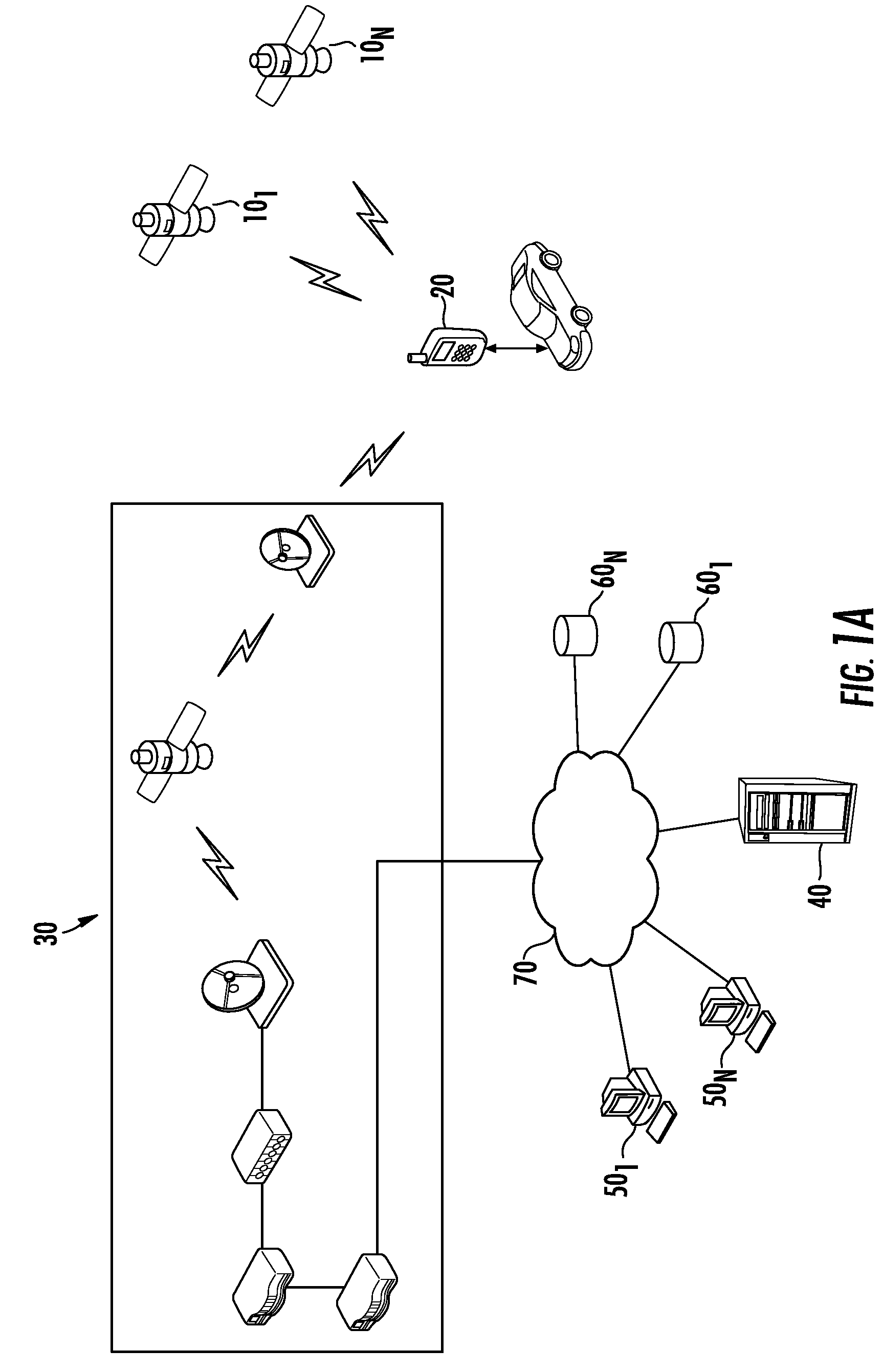
Systems and methods for remotely configuring vehicle alerts and/or controls
InactiveUS20090079555A1Easy to useReduce transmission costsRegistering/indicating working of vehiclesDigital data processing detailsData feedExternal data
The present invention provides systems and methods for remotely configuring a mobile device communicatively coupled with a vehicle. The mobile device receives current GPS and vehicle information and transmits the information to a remote server. The remote server displays vehicle and / or driver information to remote users via a user interface. The user interface provides remote users the ability to remotely configure the mobile device according to user-customizable settings. In embodiments, configurations may be made in real-time and / or on-the-fly. In further embodiments, the server receives data feeds from a variety of external data sources and integrates the data to provide recommended vehicle configurations.
Owner:GNI INT LLC
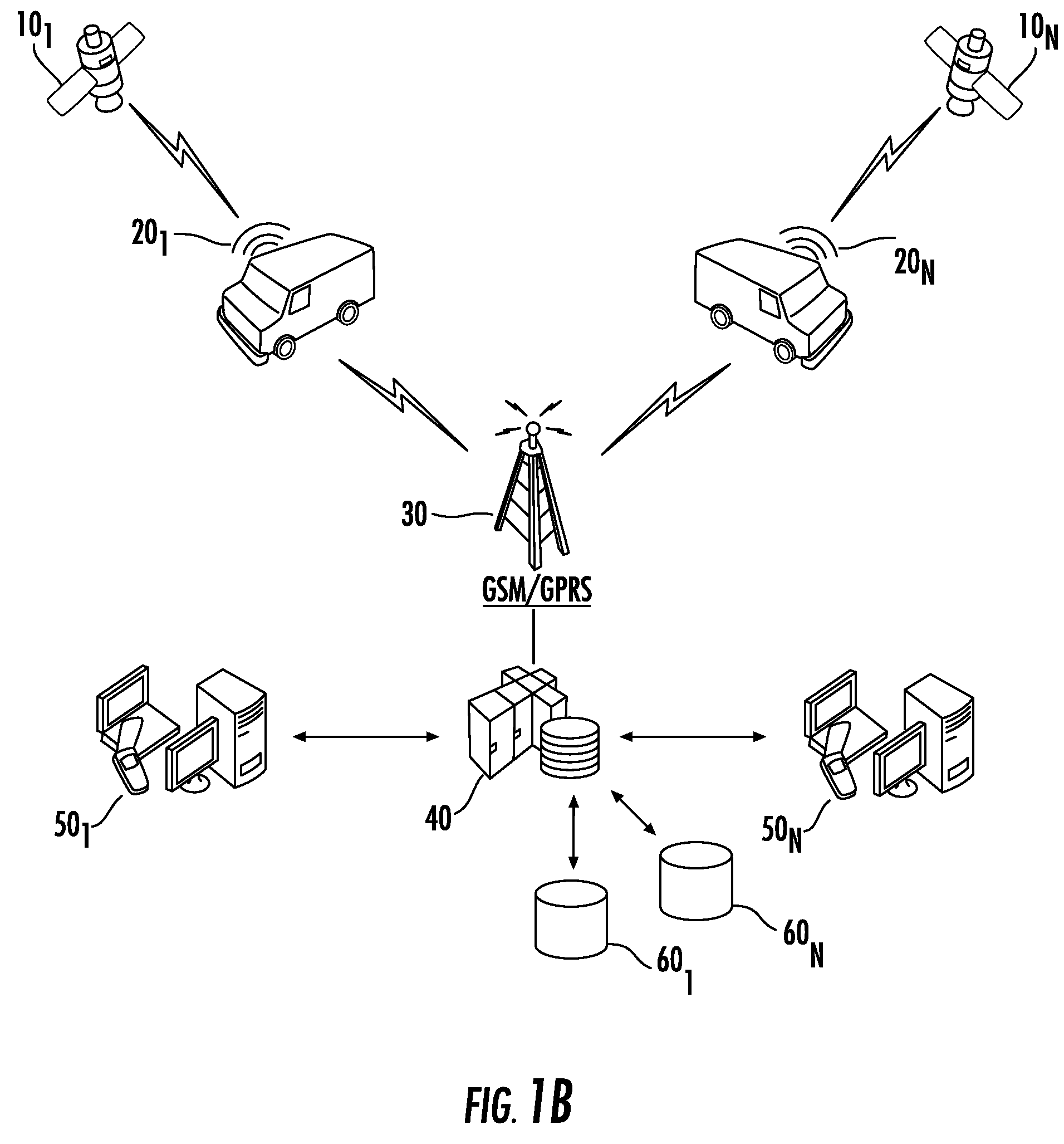
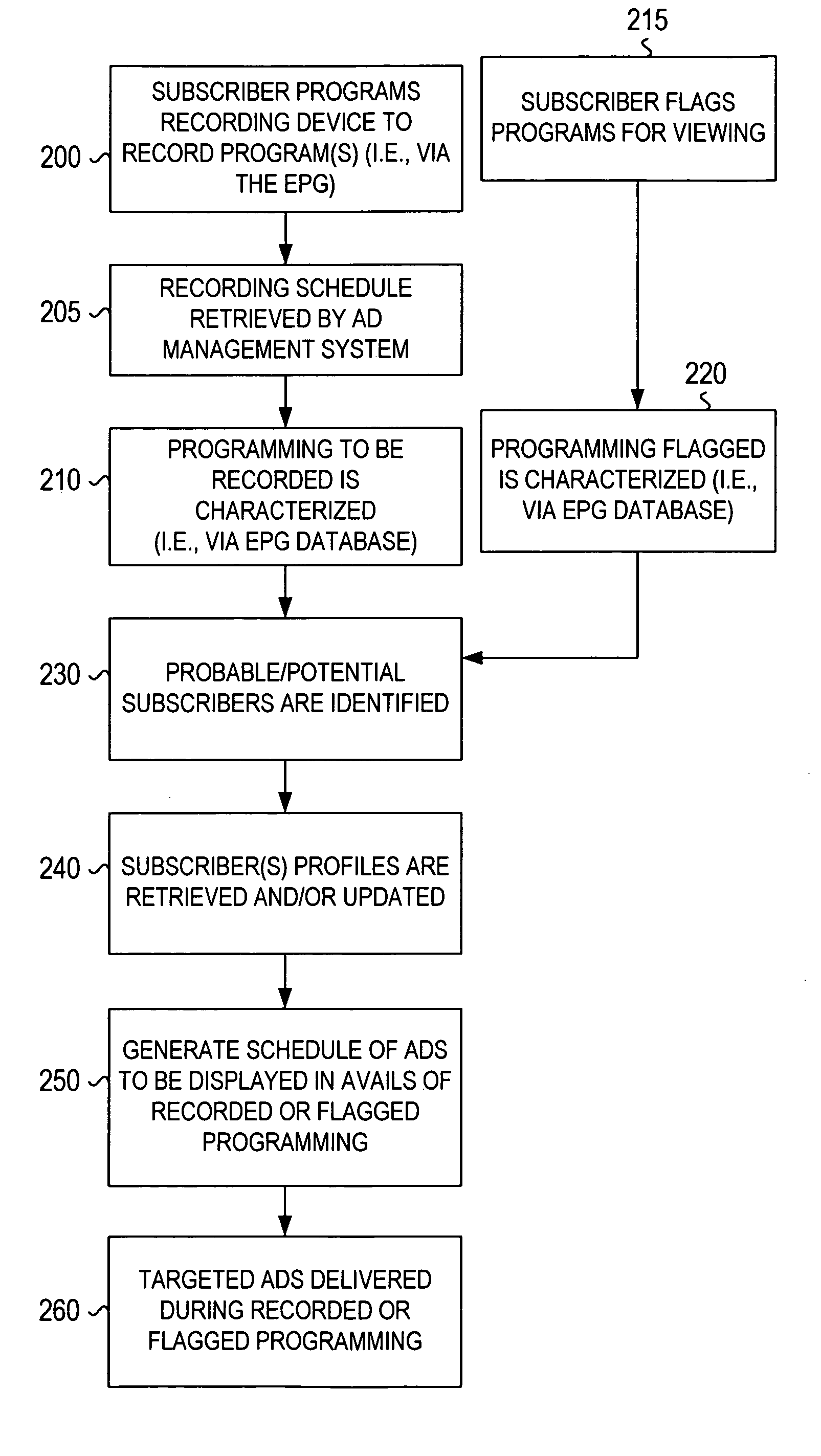
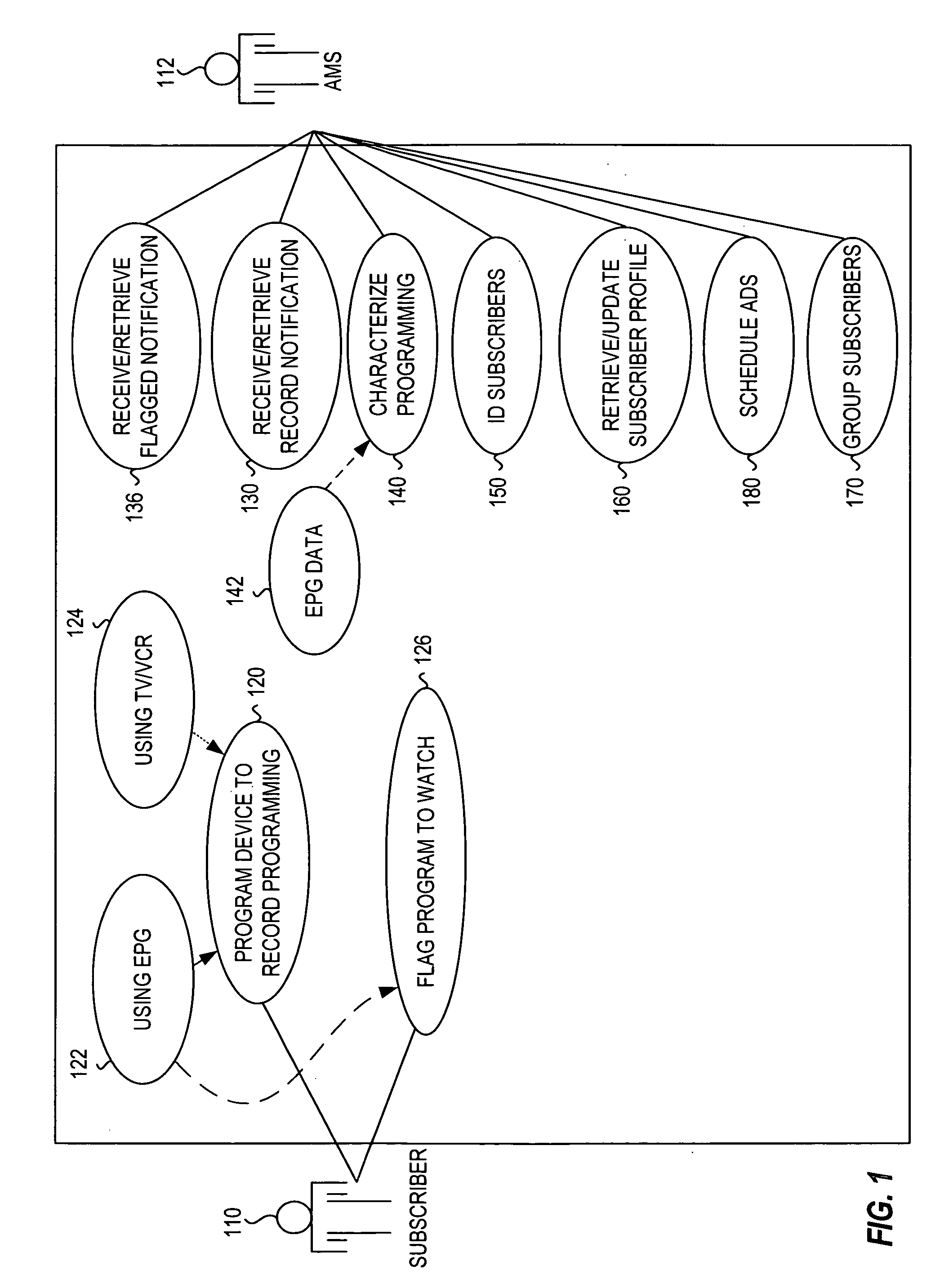
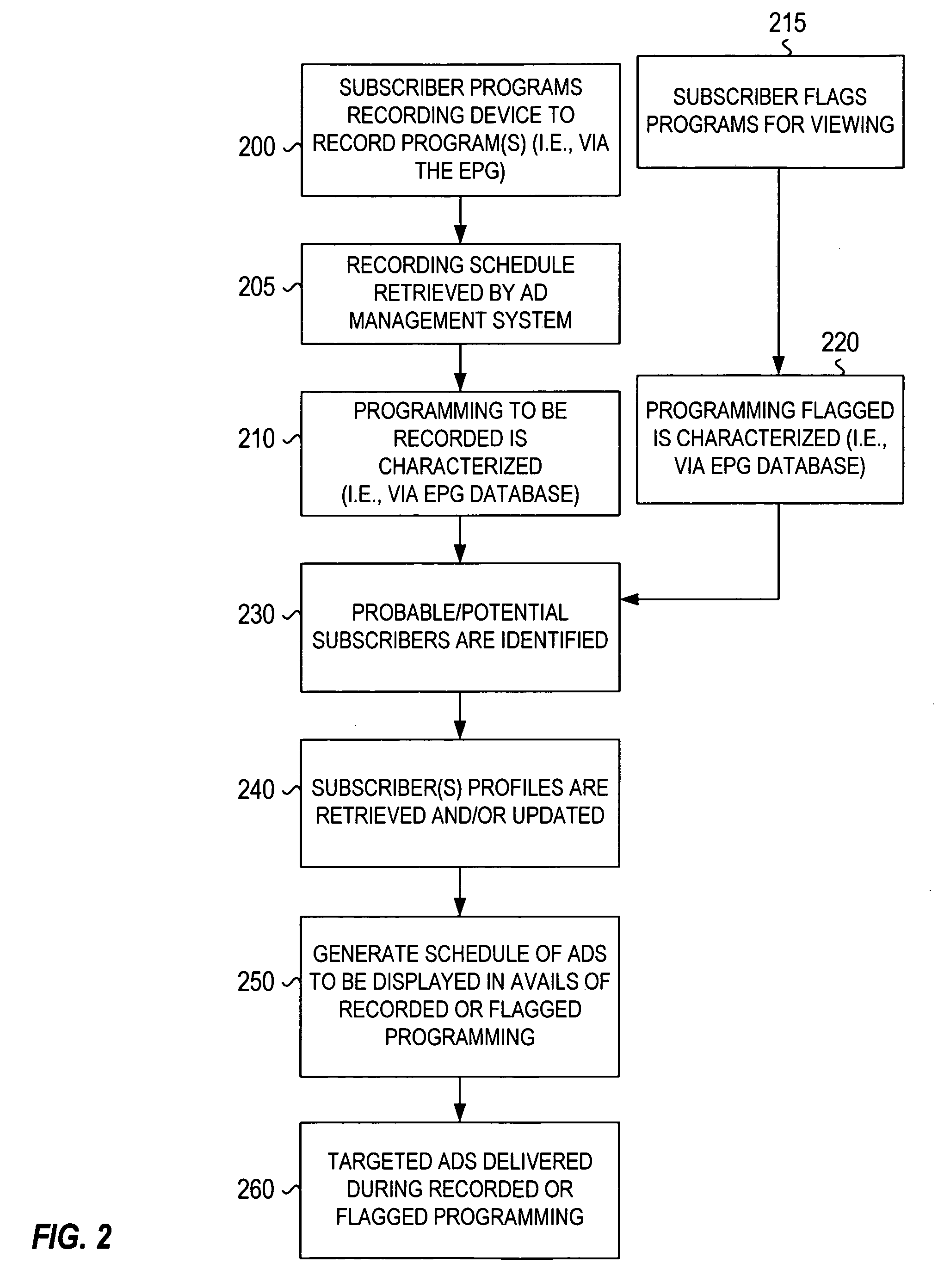
Method and system for addressable and program independent advertising during recorded programs
InactiveUS20050283796A1Television system detailsColor television detailsTargeted advertisingDatabase
A system and method for delivering addressable or targeted advertising to subscribers during programming that the subscribers have recorded identifies the timing and characterization of programs to be recorded and the probable subscriber of those programs. Using the subscriber profiles of those subscribers, either already developed or generated on-the-fly based on program selection, and ad characterizations / profiles, the system generates a schedule of advertisements to be inserted into the avails (advertising opportunities) of the programming as it is recorded. The schedule generated can depend on correlations or matching between the ad profiles and the subscribers' profile, scheduling requirements (i.e., contracts and sales with advertisers) and timing. This system allows for targeted advertising to be delivered to subscribers during recorded programming and thus provides for additional opportunities for advertisers to reach subscribers in a highly addressable fashion.
Owner:PRIME RES ALLIANCE E LLC
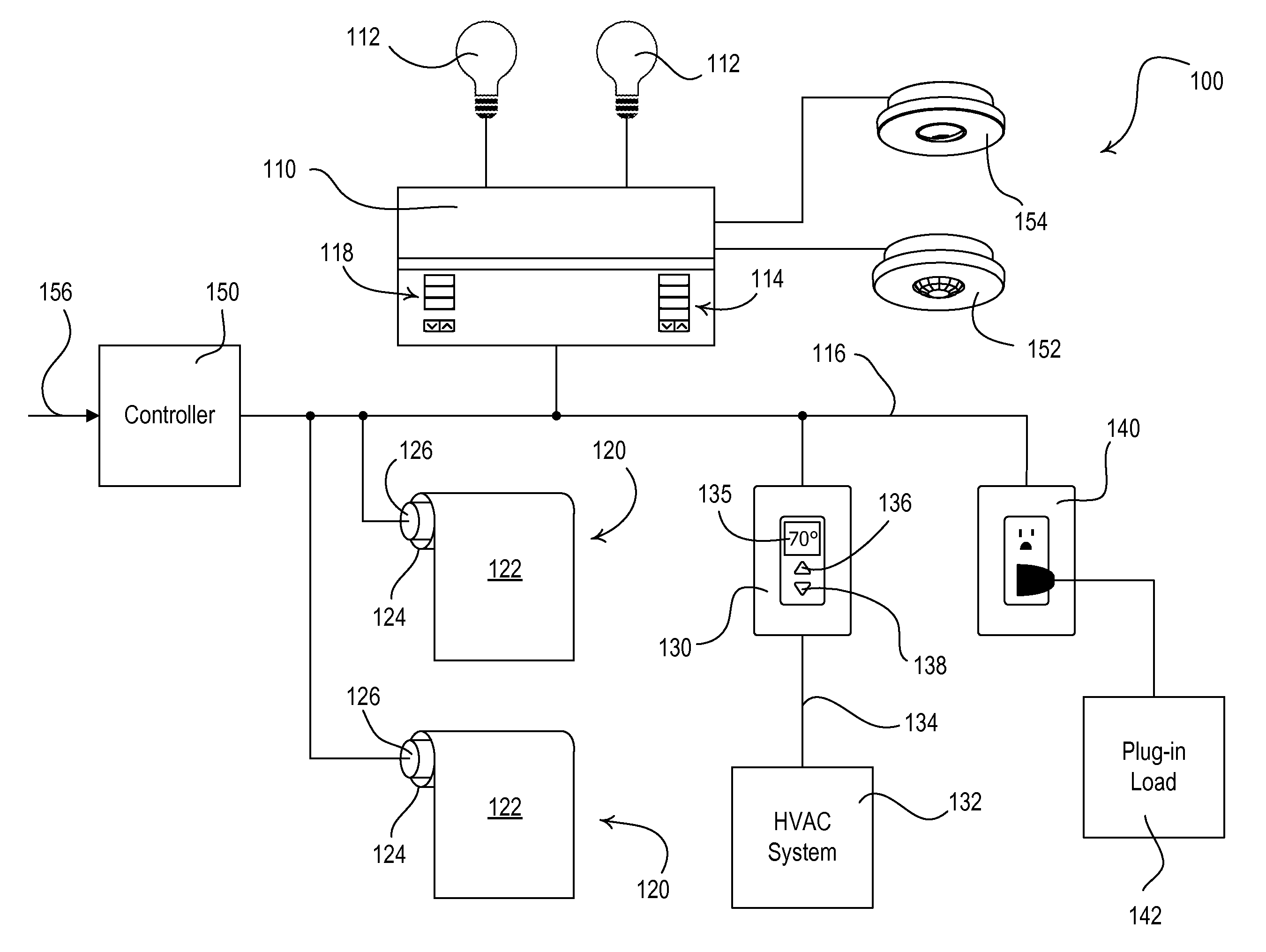
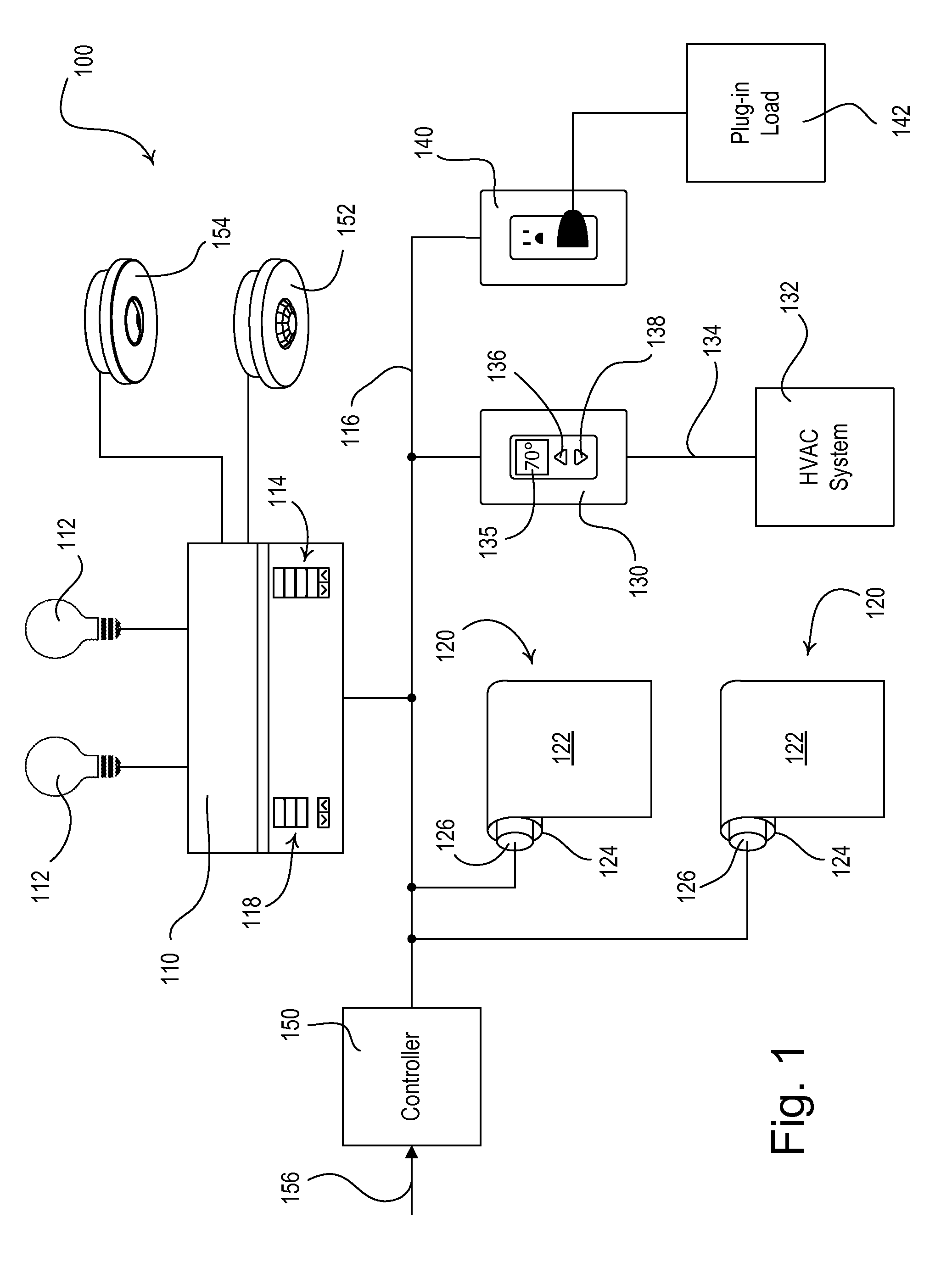
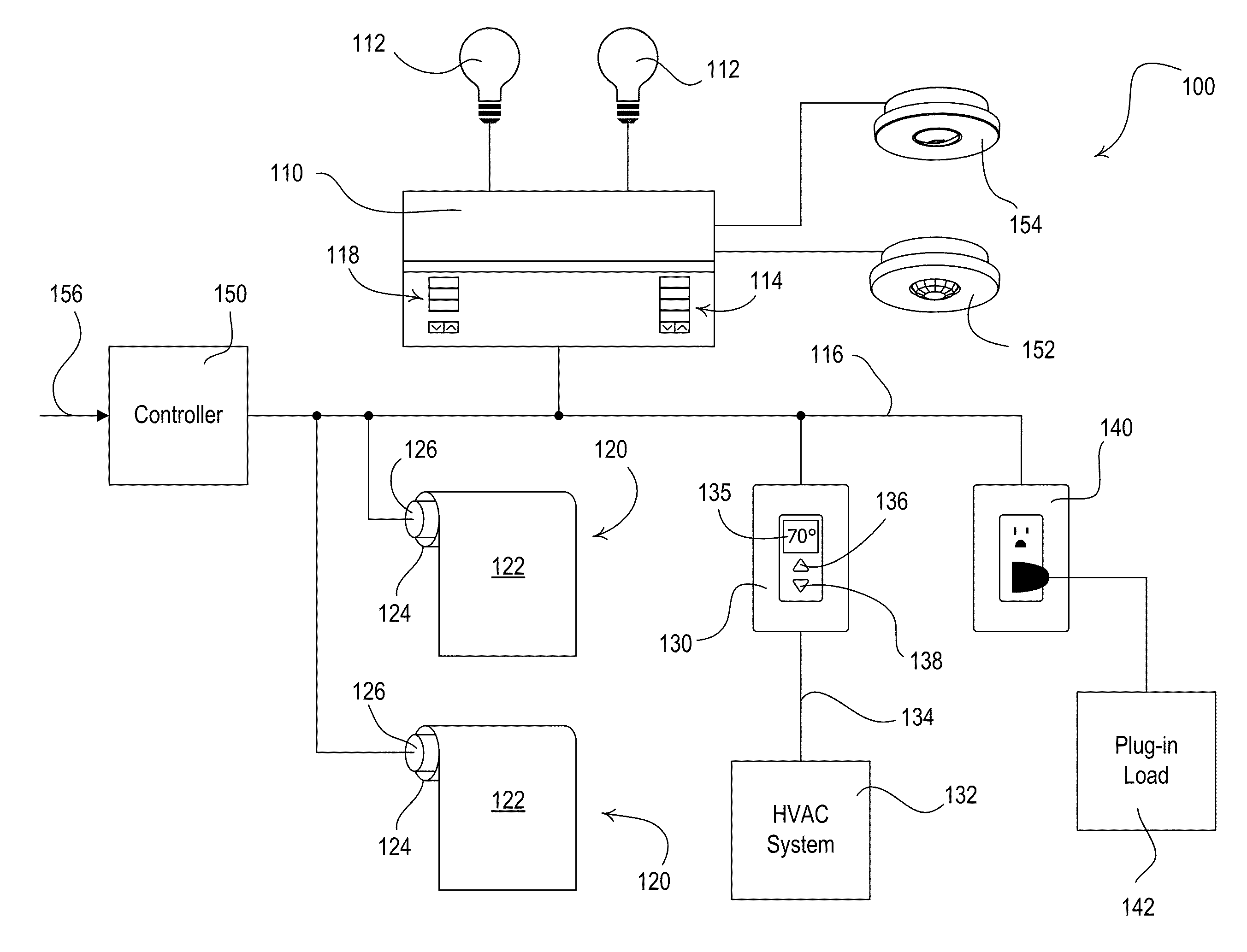
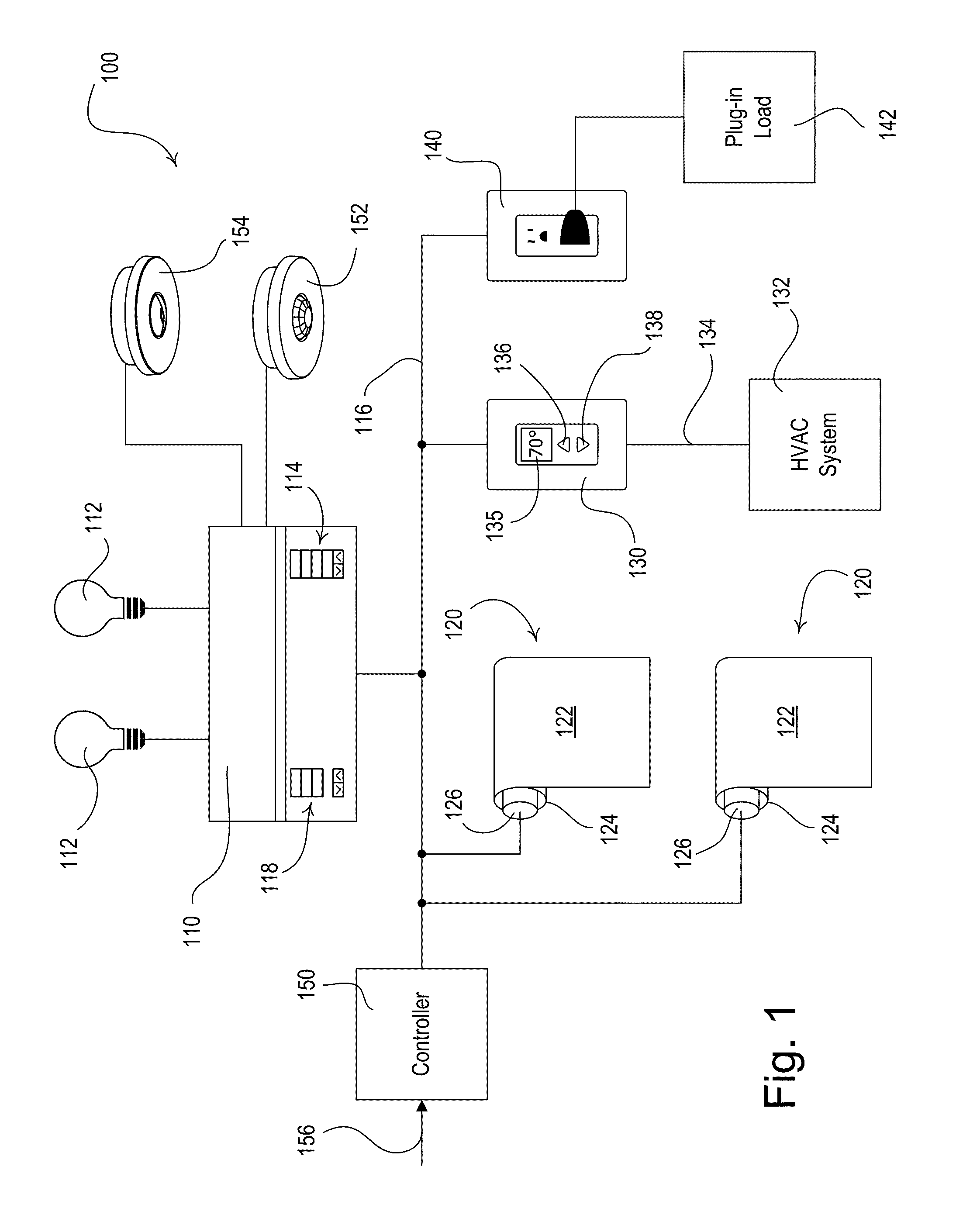
Dynamic Keypad for Controlling Energy-Savings Modes of a Load Control System
ActiveUS20120095601A1Reduce the amount of powerIncrease setpoint temperatureSampled-variable control systemsMetering/charging/biilling arrangementsTemperature controlOperating energy
A load control system for a building having a lighting load, a window, and a heating and cooling system comprises a lighting control device for controlling the amount of power delivered to the lighting load, a motorized window treatment comprising a window treatment fabric for covering the window, a temperature control device for controlling a setpoint temperature of the heating and cooling system to thus control a present temperature in the building, and a dynamic keypad comprising a visual display and operable to receive a user input. The dynamic keypad allows a user to select, adjust, and monitor a plurality of energy-savings modes of the load control system. For example, the dynamic keypad allows the user to enable and adjust a setback temperature of the temperature control device on-the-fly.
Owner:LUTRON TECH CO LLC
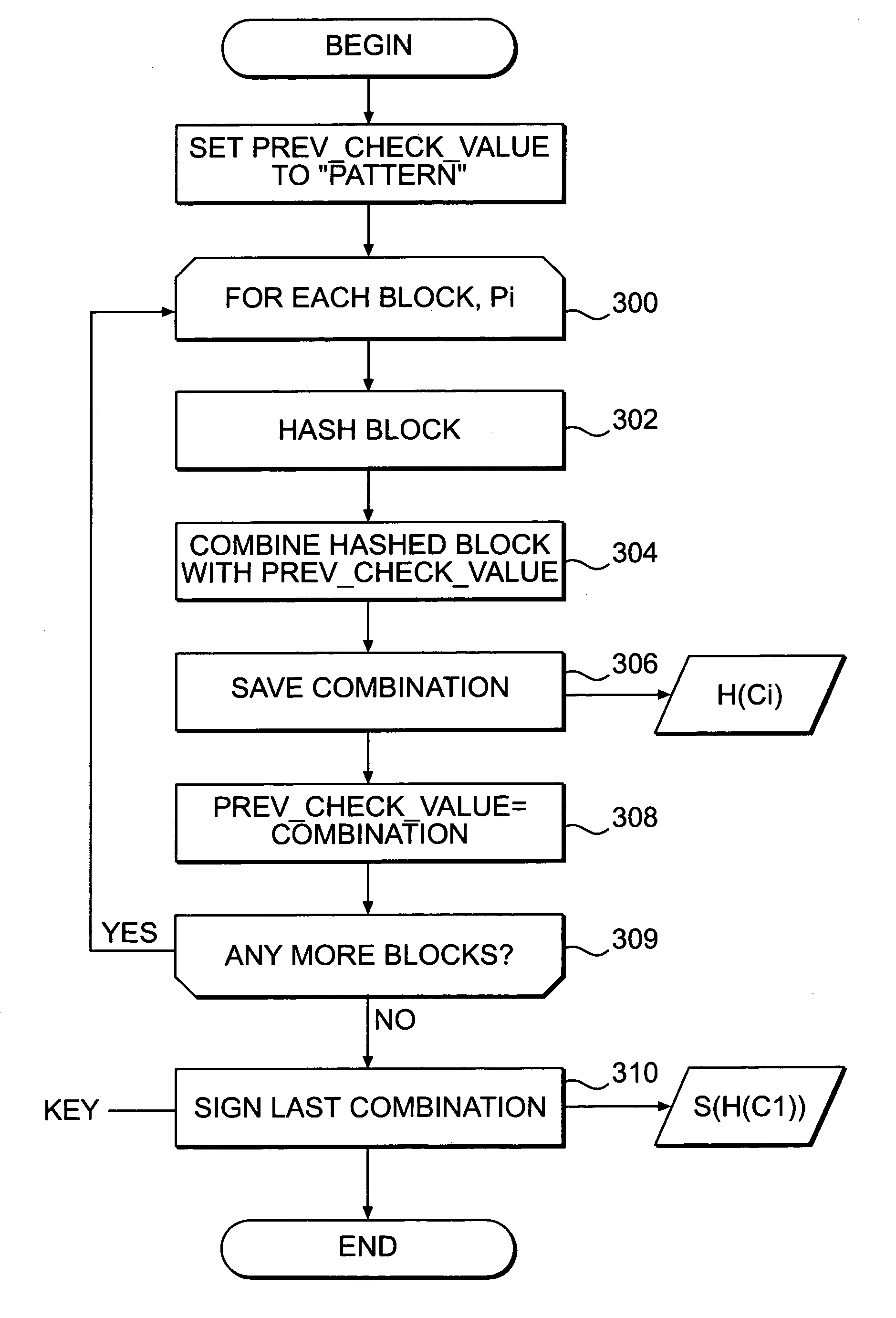
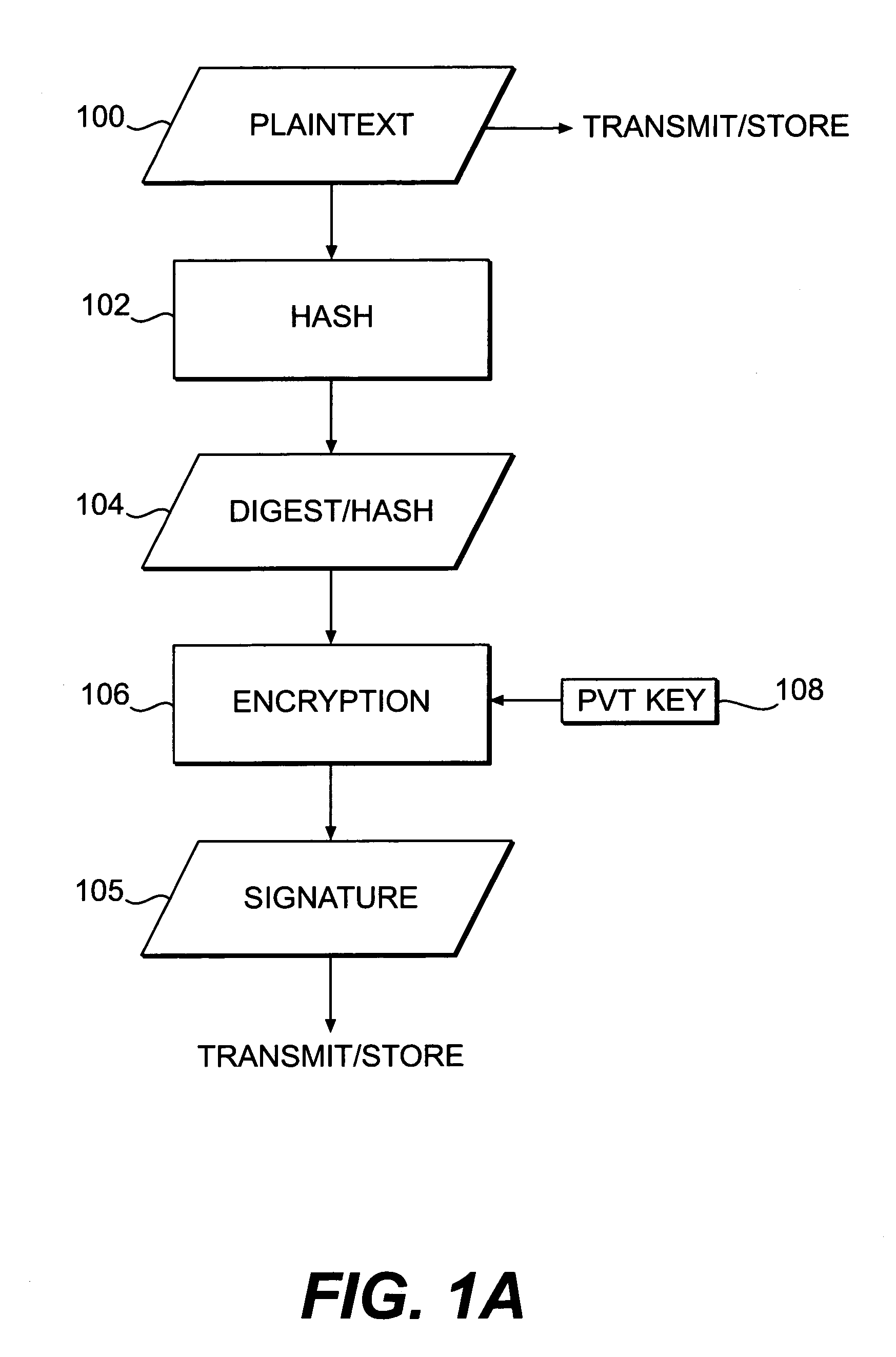
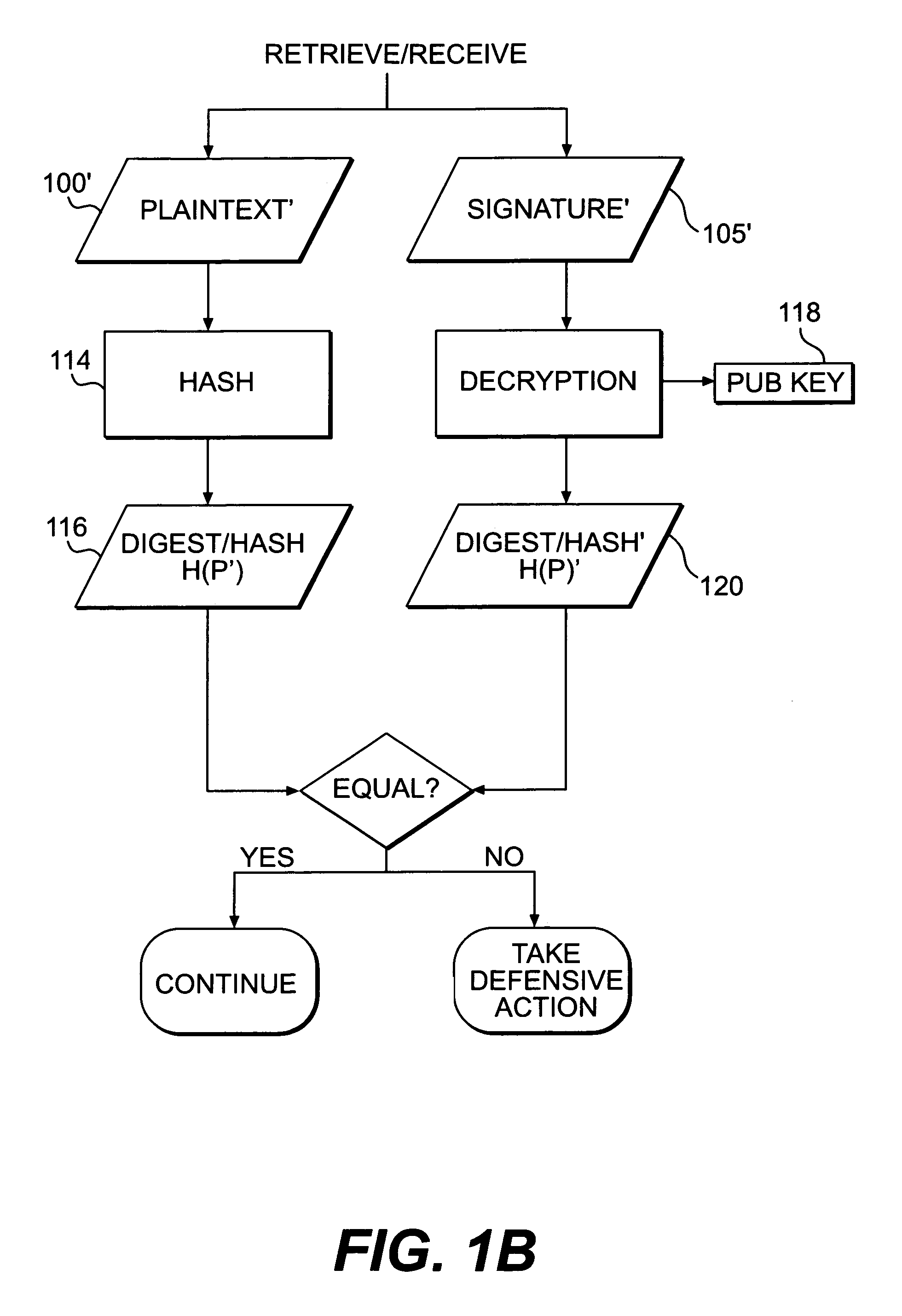
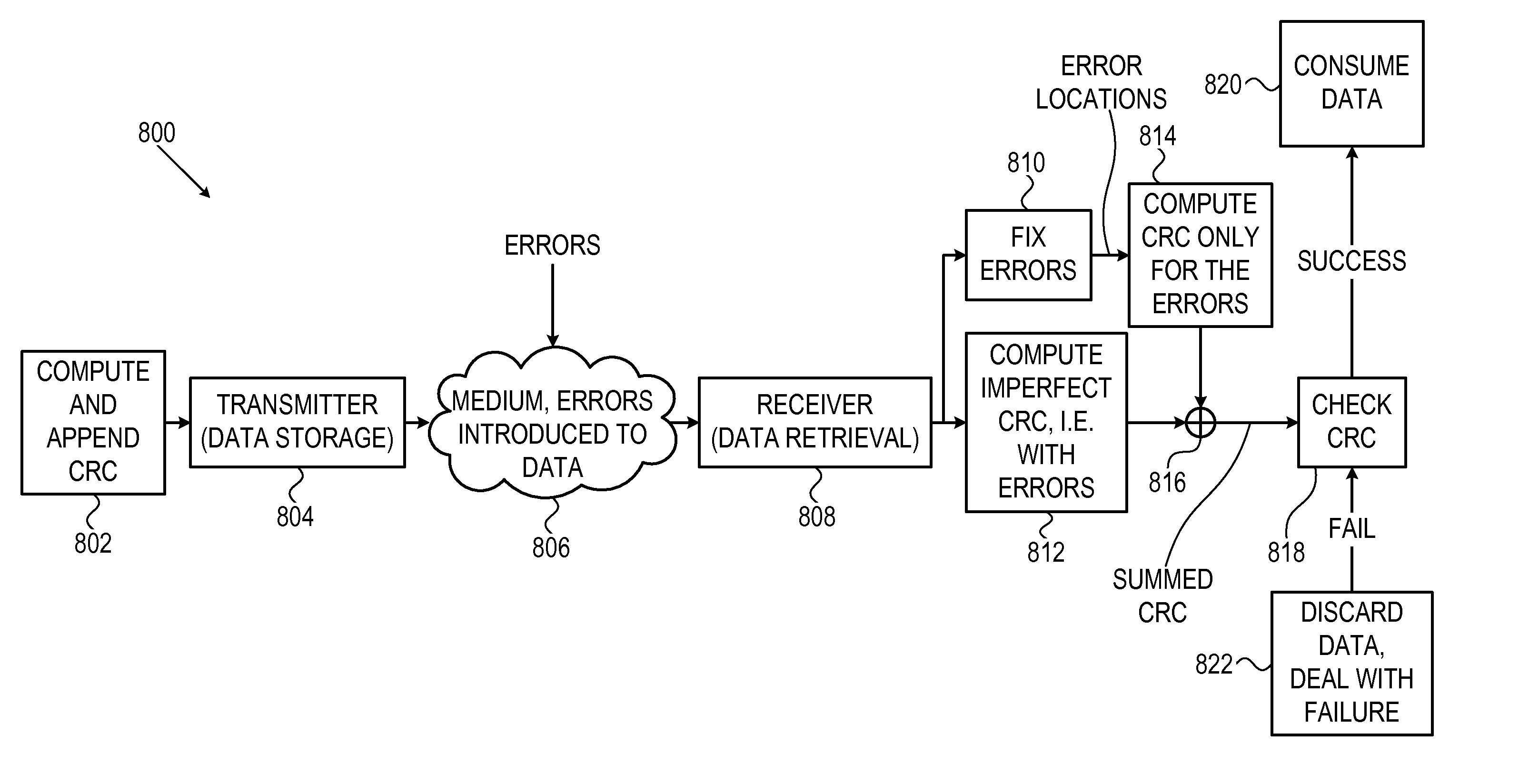
Systems and methods for authenticating and protecting the integrity of data streams and other data
InactiveUS6959384B1Authentication is convenientDetecting errorUser identity/authority verificationDigital data protectionError checkFault tolerance
Systems and methods are disclosed for enabling a recipient of a cryptographically-signed electronic communication to verify the authenticity of the communication on-the-fly using a signed chain of check values, the chain being constructed from the original content of the communication, and each check value in the chain being at least partially dependent on the signed root of the chain and a portion of the communication. Fault tolerance can be provided by including error-check values in the communication that enable a decoding device to maintain the chain's security in the face of communication errors. In one embodiment, systems and methods are provided for enabling secure quasi-random access to a content file by constructing a hierarchy of hash values from the file, the hierarchy deriving its security in a manner similar to that used by the above-described chain. The hierarchy culminates with a signed hash that can be used to verify the integrity of other hash values in the hierarchy, and these other hash values can, in turn, be used to efficiently verify the authenticity of arbitrary portions of the content file.
Owner:INTERTRUST TECH CORP
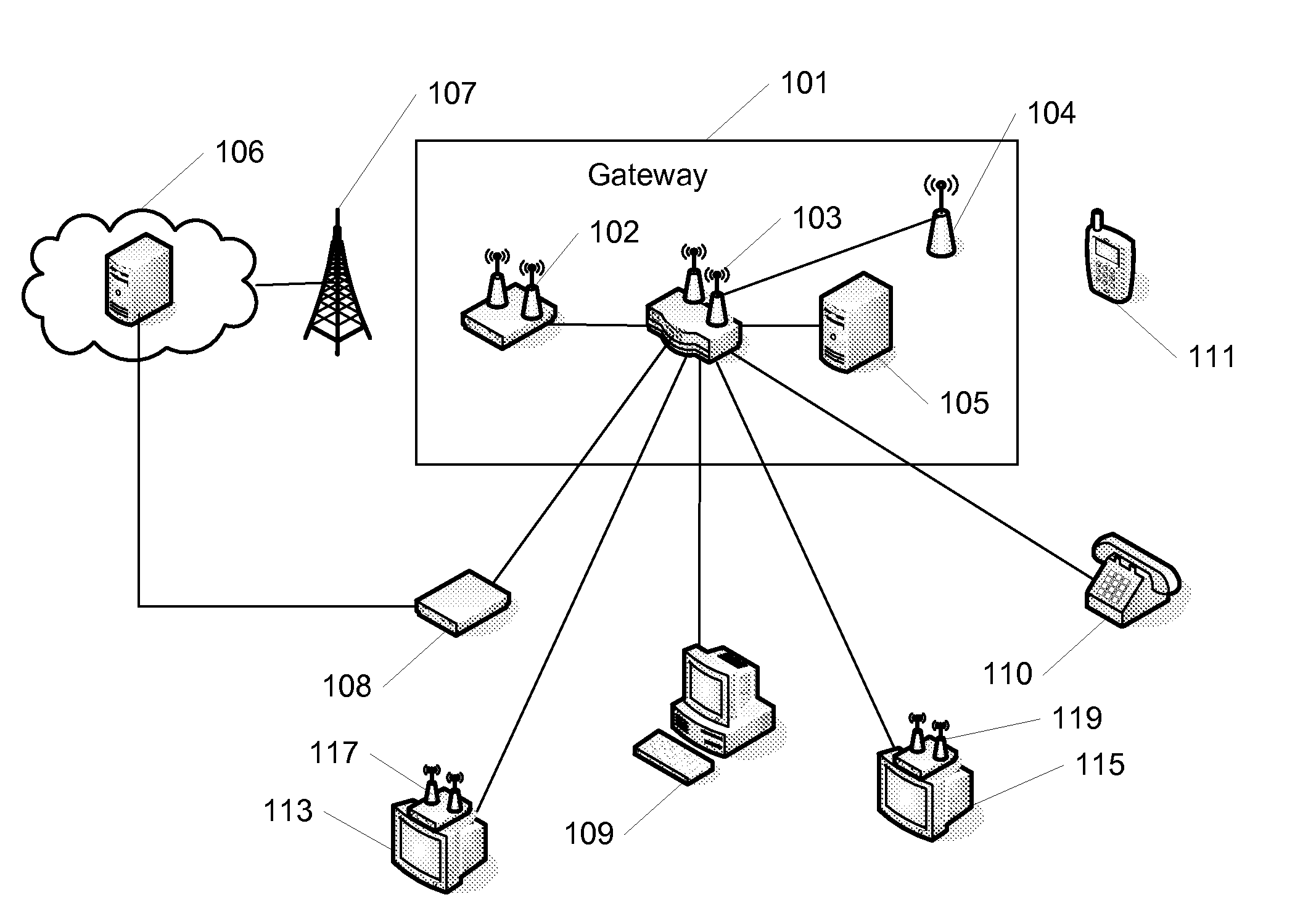
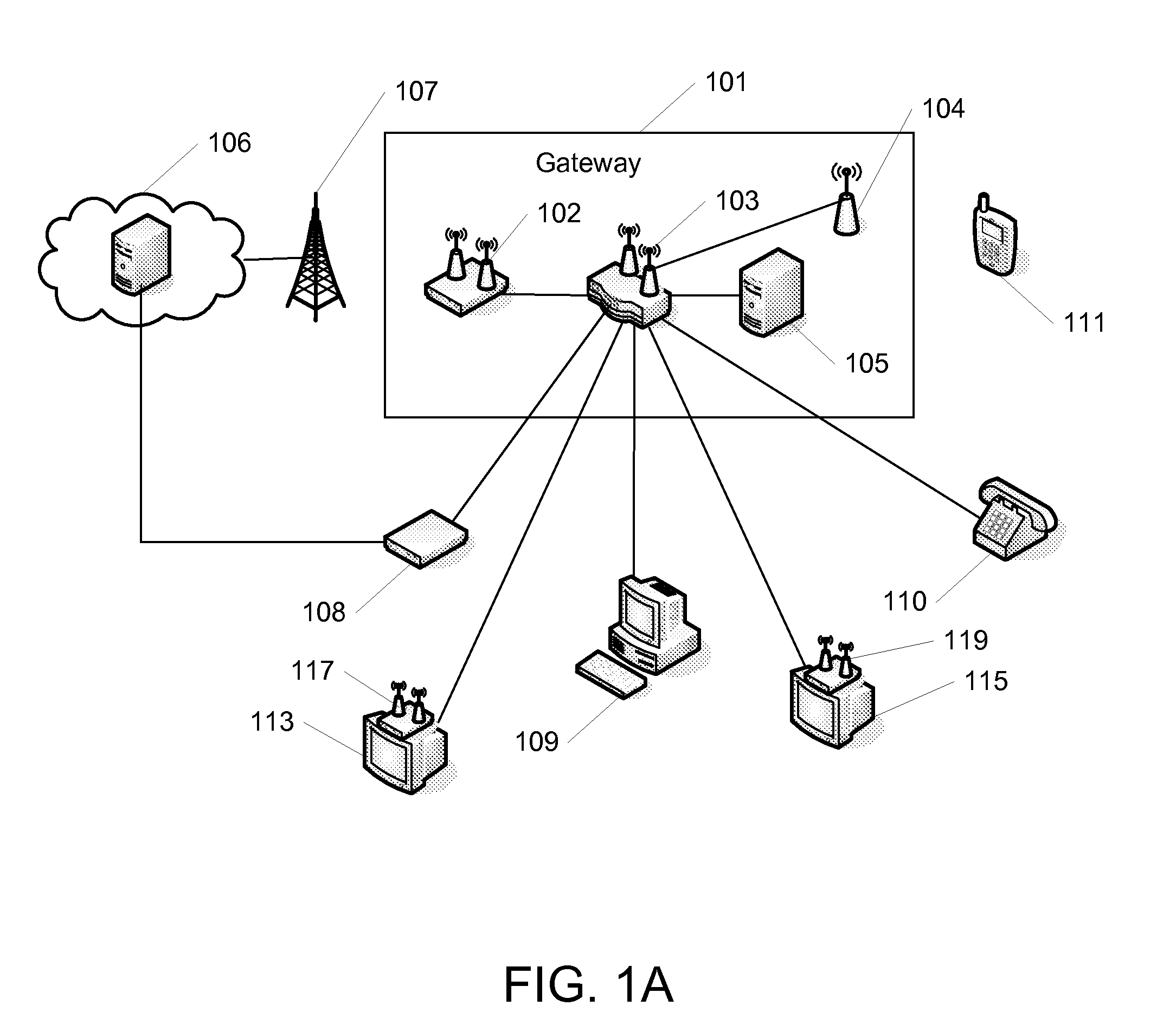
System and method for personal content access
InactiveUS20080235733A1Television system detailsColor television detailsContent distributionOn the fly
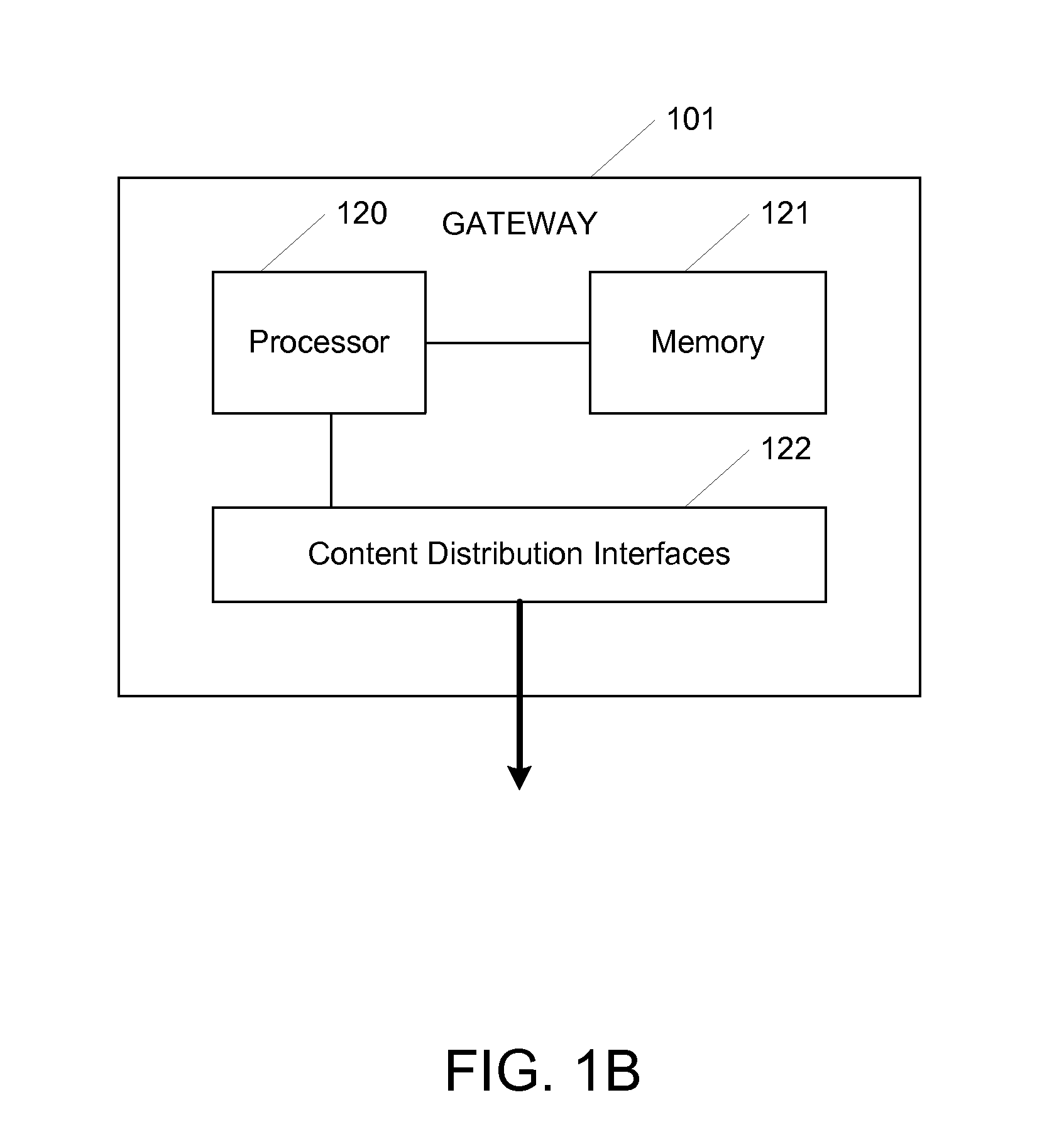
A method and system for integrated personal content access have been disclosed. The system includes a gateway which is able to communicate across devices, coordinating media content distribution among the devices and users. The gateway can seamlessly switch or copy content streams from one device to another, even if the devices use different formats or protocols. Tags for adding embellishments to content on the fly for viewing by the user or by others. Tokens for indicating the identity and source of content, along with a location within the content, can also be used when sharing content or when switching content viewing between devices. Additionally, a network of gateways is possible, where content may be shared between devices connected to different gateways.
Owner:MONUMENT BANK OF INTPROP LLC
Method and apparatus for seismic data acquisition
InactiveUS20050052951A1Avoid entrapmentMinimize the possibilityTransducer detailsSeismic signal receiversOcean bottomRubidium
A marine seismic exploration method and system comprised of continuous recording, self-contained ocean bottom pods characterized by low profile casings. An external bumper is provided to promote ocean bottom coupling and prevent fishing net entrapment. Pods are tethered together with flexible, non-rigid, non-conducting cable used to control pod deployment. Pods are deployed and retrieved from a boat deck configured to have a storage system and a handling system to attach pods to cable on-the-fly. The storage system is a juke box configuration of slots wherein individual pods are randomly stored in the slots to permit data extraction, charging, testing and synchronizing without opening the pods. A pod may include an inertial navigation system to determine ocean floor location and a rubidium clock for timing. The system includes mathematical gimballing. The cable may include shear couplings designed to automatically shear apart if a certain level of cable tension is reached.
Owner:MAGSEIS FF LLC
On-the fly coating of acid-releasing degradable material onto a particulate
ActiveUS20050034861A1Reduce molecular weightLiquid surface applicatorsFluid removalParticulatesPlasticizer
The present invention relates to methods and compositions for treating subterranean formations, and more specifically, to improved methods and compositions for degrading filter cake deposited on a subterranean formation. One embodiment of the present invention provides a method of creating particulates coated with acid-releasing degradable material on-the-fly comprising the step of: combining an acid-releasing degradable material with a solvent or a plasticizer to create a coating solution; and, coating the coating solution onto a particulate on-the-fly to create coated particulates. Another embodiment of the present invention provides a gravel pack comprising gravel particles coated on-the-fly with an acid-releasing degradable material.
Owner:HALLIBURTON ENERGY SERVICES INC
Preventing illegal distribution of copy protected content
InactiveUS20070033408A1User identity/authority verificationProgram/content distribution protectionComputer networkAnalysis data
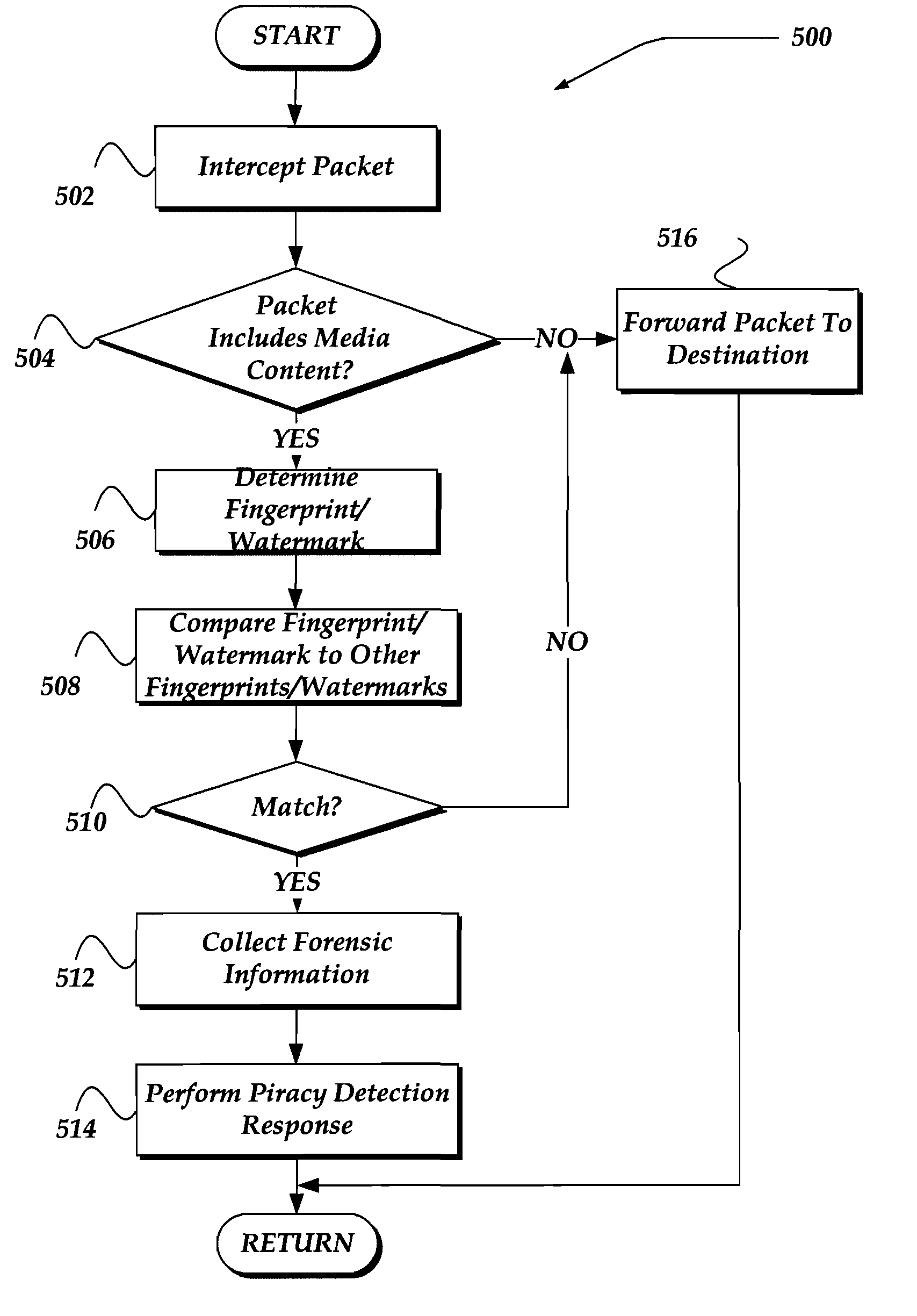
Method and devices are directed to invention is directed towards analyzing packets on-the-fly for pirated content. Packets are intercepted and analyzed to determine if the packets include media content. If media content is detected, a comparator determines a fingerprint associated with the media content. The comparator then compares the determined fingerprint to other fingerprints within a data store. If a match is found, forensic information may be collected. Piracy detection responses may also be performed, including: blocking transmission of the media content, providing a piracy alert message, degrading a quality of the media content, or including within the media content a watermark and / or fingerprint. In one embodiment, the packet analysis and the comparator may reside within a same or different device within a path between a source device and a destination device to enable piracy detection to be performed in real-time.
Owner:GOOGLE LLC
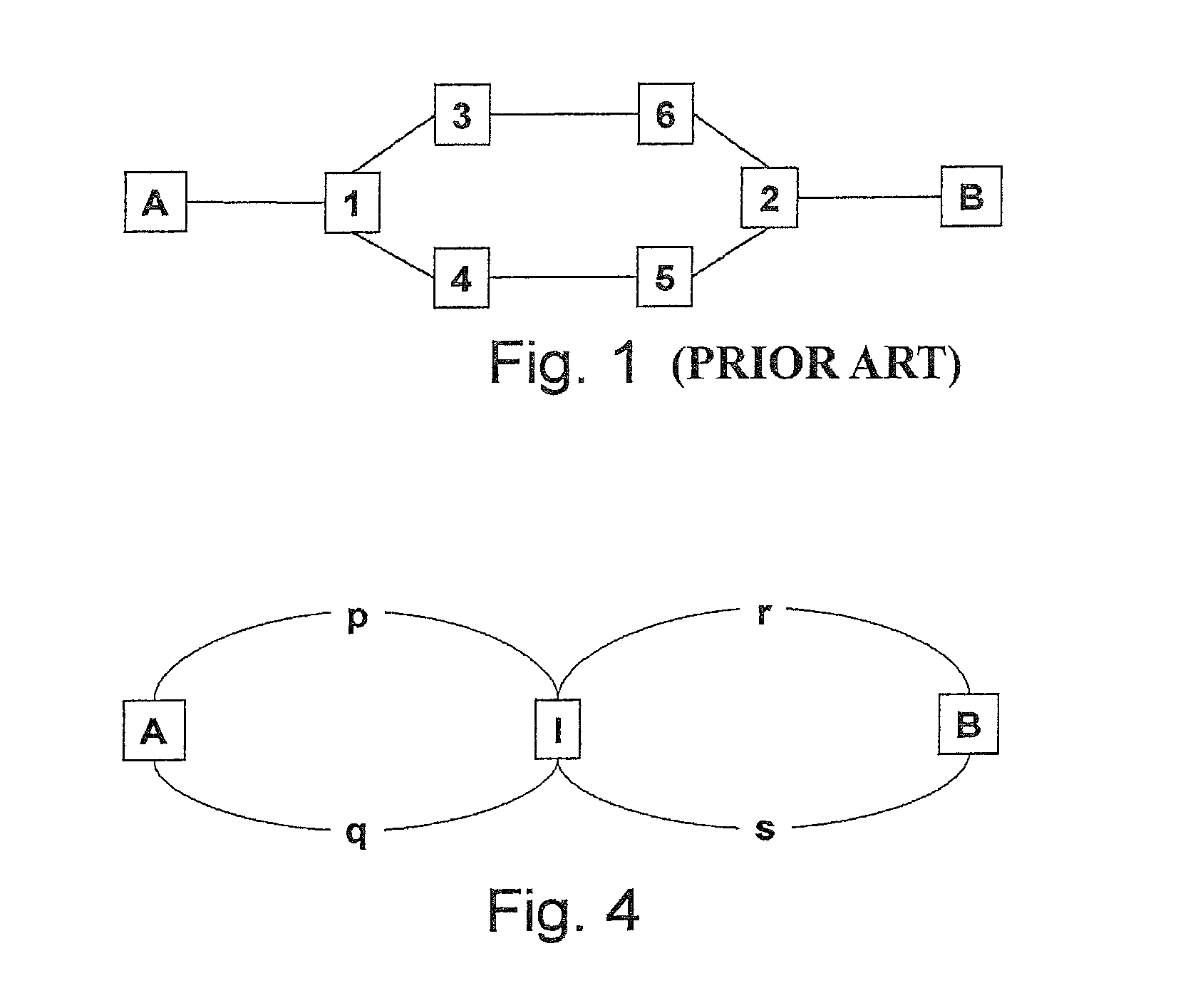
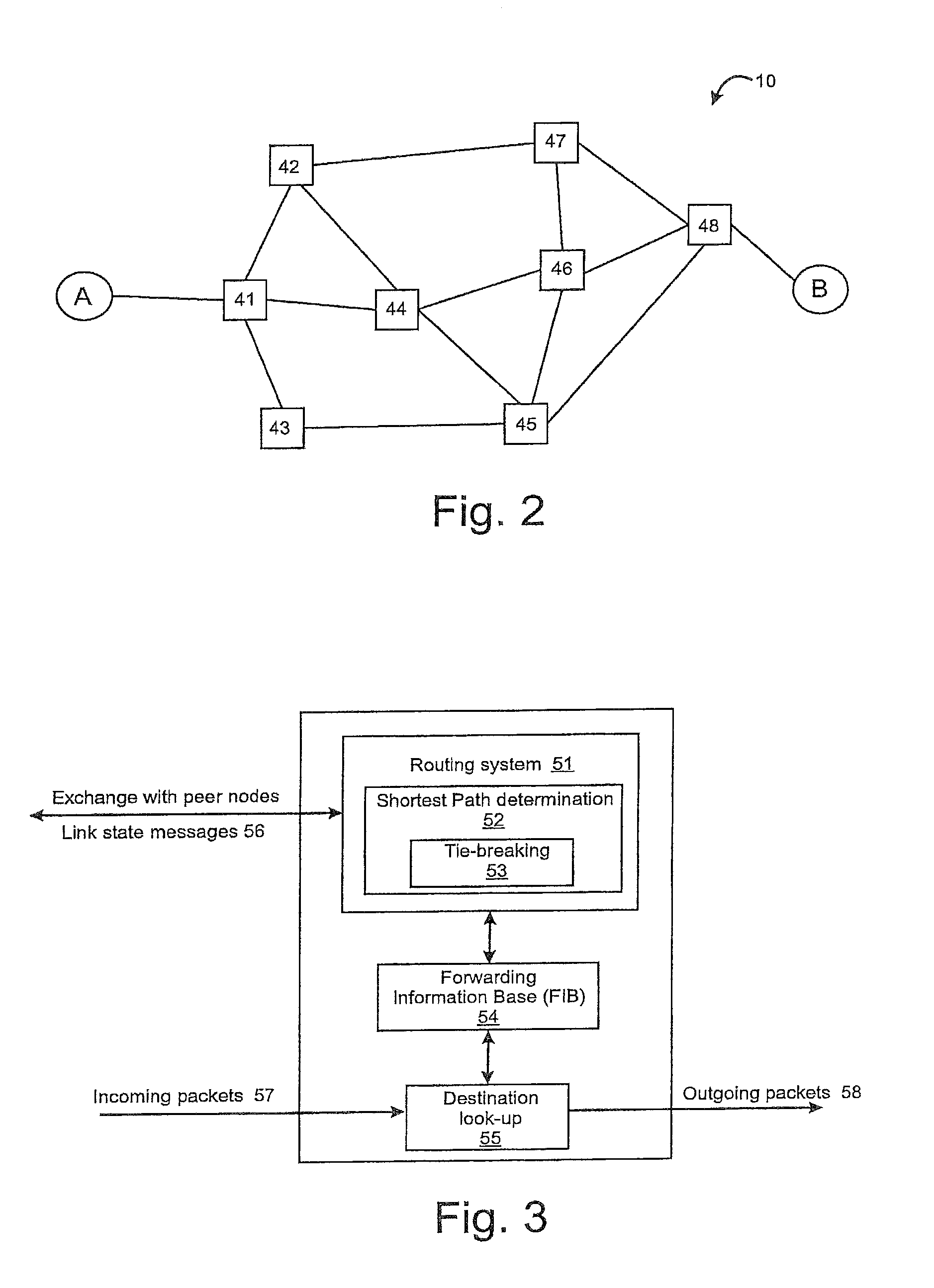
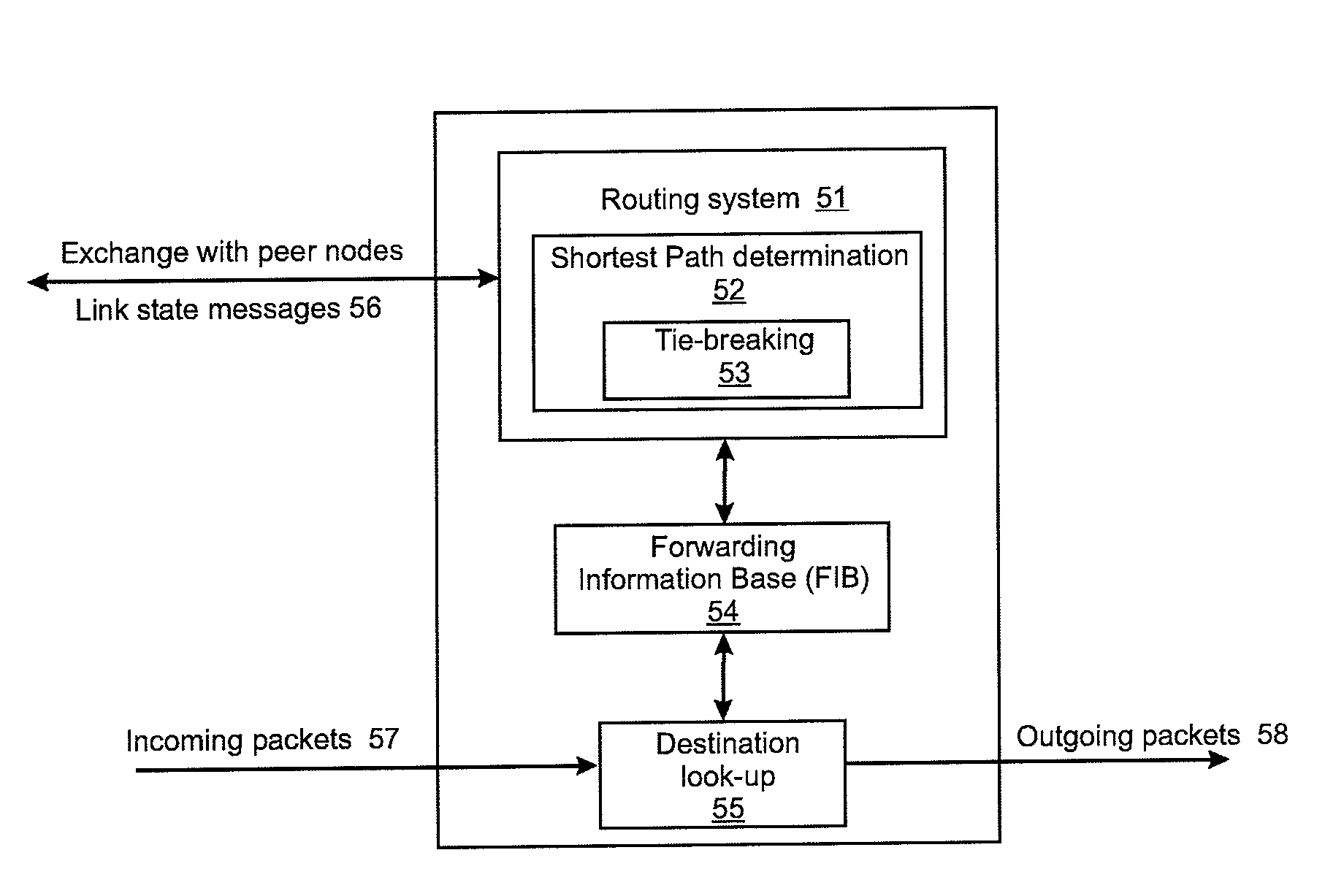
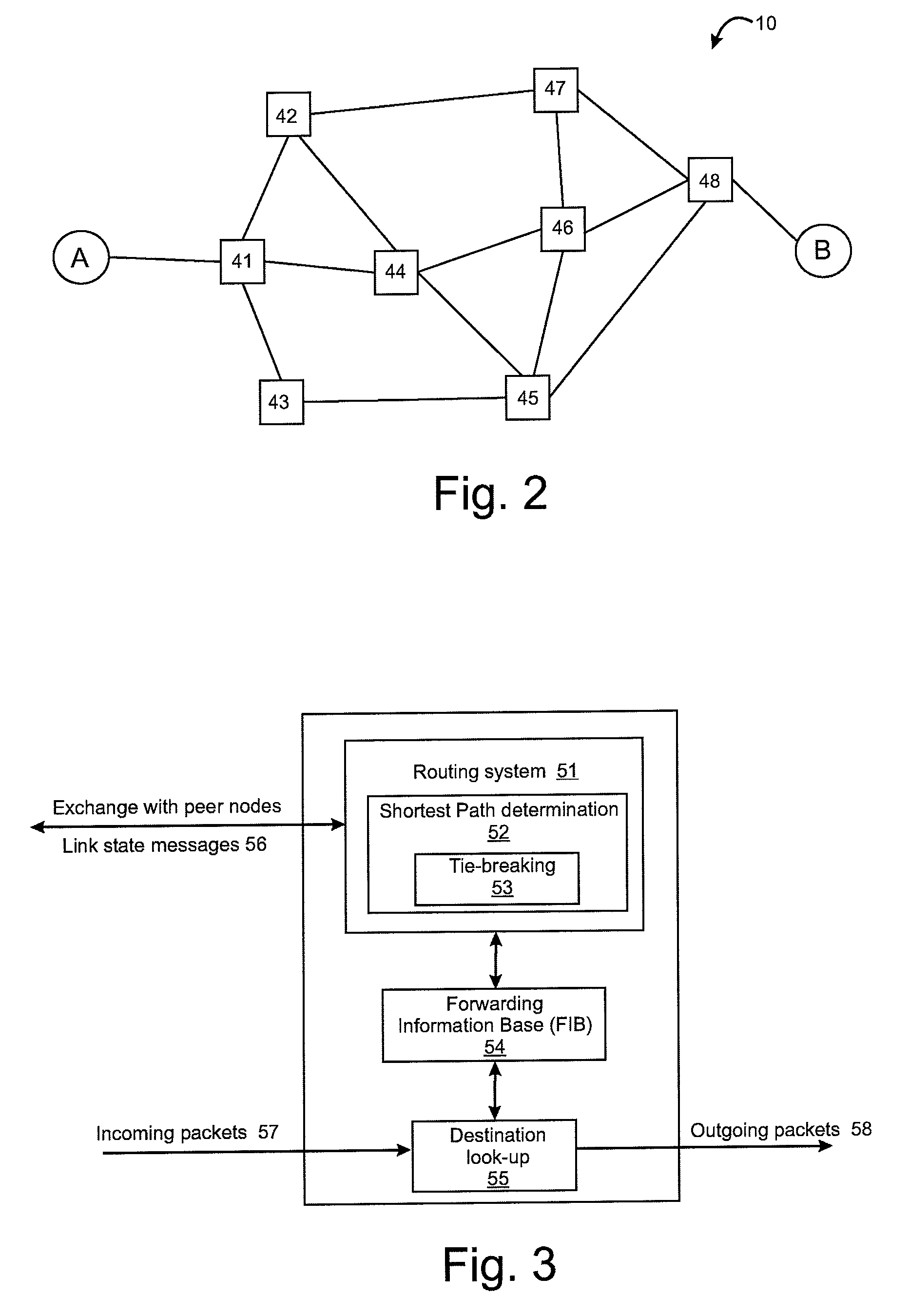
Tie-breaking in shortest path determination
InactiveUS8761022B2Simple calculationLower requirementError preventionTransmission systemsTraffic flowOrder set
A consistent tie-breaking decision between equal-cost shortest (lowest cost) paths is achieved by comparing an ordered set of node identifiers for each of a plurality of end-to-end paths. Alternatively, the same results can be achieved, on-the-fly, as a shortest path tree is constructed, by making a selection of an equal-cost path using the node identifiers of the diverging branches of the tree. Both variants allow a consistent selection to be made of equal-cost paths, regardless of where in the network the shortest paths are calculated. This ensures that traffic flow between any two nodes, in both the forward and reverse directions, will always follow the same path through the network.
Owner:RPX CLEARINGHOUSE
Triggering applications based on a captured text in a mixed media environment
ActiveUS7672543B2Facilitate methodMultimedia data indexingSpecial data processing applicationsElectronic formDigital content
A Mixed Media Reality (MMR) system and associated techniques are disclosed. The MMR system provides mechanisms for forming a mixed media document that includes media of at least two types (e.g., printed paper as a first medium and digital content and / or web link as a second medium). In one particular embodiment, the MMR system includes an action processor and method, and MMR documents with an associated action. The MMR document structure is particularly advantageous because the ability to specify different actions for different MMR documents, combined with the ability to create any number of MMR documents for a particular location on any media, allows the MMR architecture to serve as a universal trigger or initiator for additional processing. In other words, addition processing or actions can be triggered or initiated based on MMR recognition. The action processor receives the output of the MMR recognition process which yields an MMR document including at least one action. The action processor executes that action which includes various commands to the MMR system or other systems coupled to the MMR system. The MMR system architecture is advantageous because an action can be executed by pointing the capture device at a block of text, and the action is performed. Example actions include retrieving the text in electronic form to the capture device, retrieving the specification for the action, inserting data to a MMR document, transferring data between documents, purchasing items, authoring actions or reviewing historical information about actions. The MMR system includes a variety of user applications (one or more actions) initiated by the MMR recognition of a text patch such as information retrieval for a travel guide book, stock listings or advertisements; information capture such as recording content from a conference, recording and storing multimedia associated with the document, capturing information for a calendar and on the fly authoring; purchasing media files for storage on any part of an MMR document.
Owner:RICOH KK
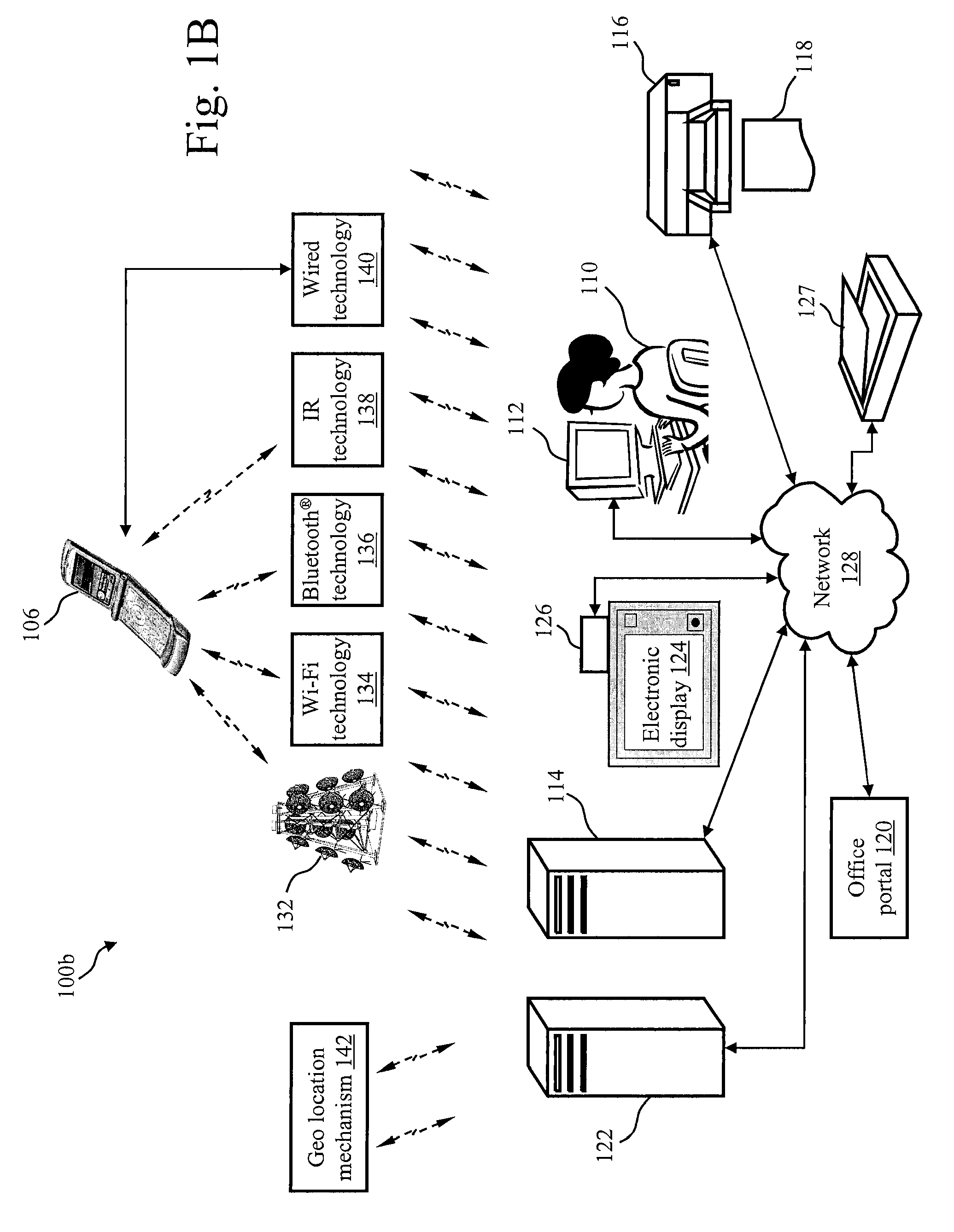
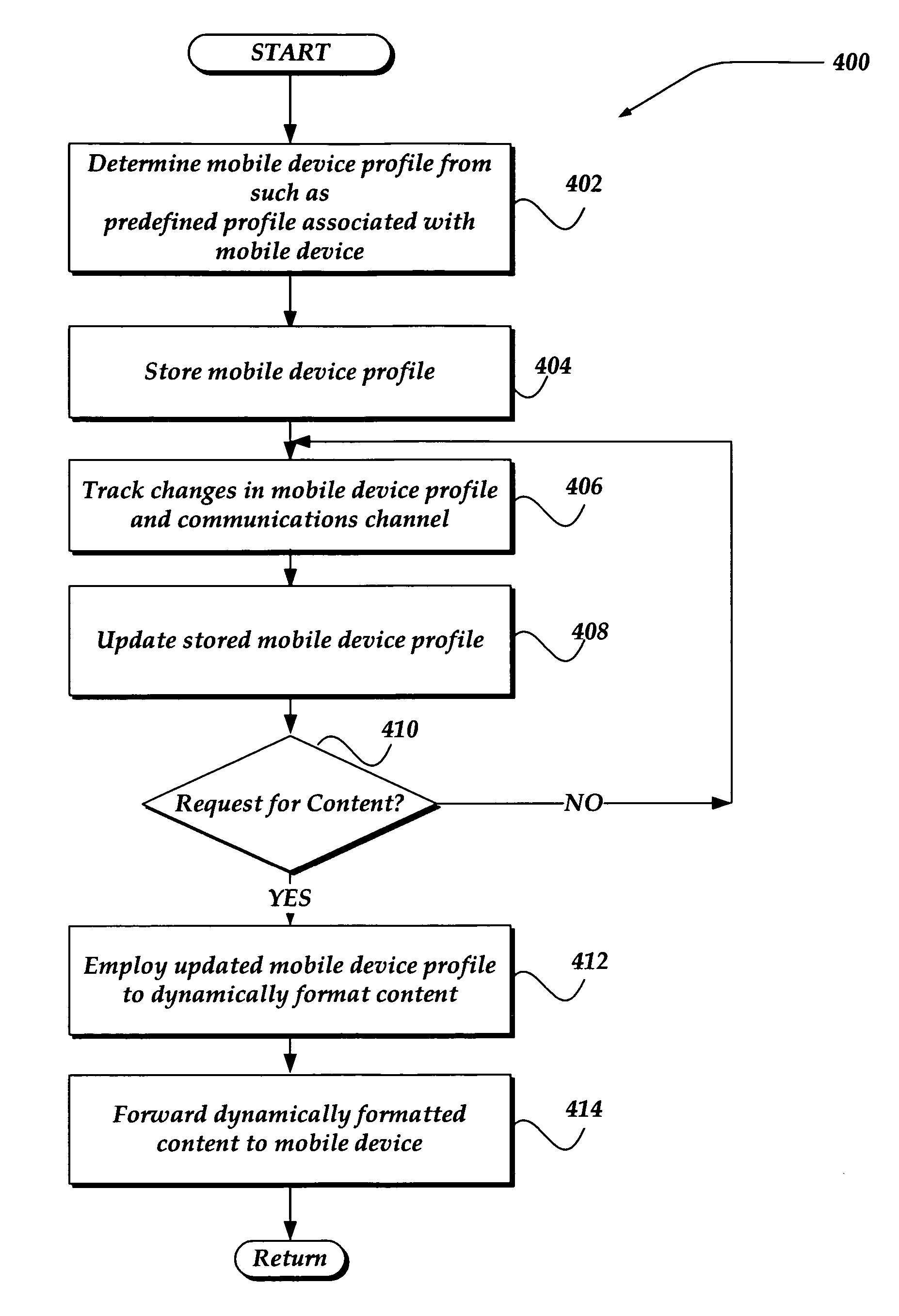
Dynamically generating content based on capabilities of a mobile device
InactiveUS20060274869A1Digital data information retrievalInformation formatConnection typeSpecific test
A system, apparatus, and method is directed to dynamically generating content on the fly based on at least one characteristic of a computing device requesting the content, including a characteristic of a network connection. The invention may receive information from a variety of sources, including a manufacturer of the computing device, a header sent by the computing device, and specific test results performed on computing devices similar to the requesting computing device. The information may include screen size, screen resolution, memory size, browser capabilities, applications supported, and so forth. The network connection information may include bandwidth, delays, degradation, connection type, and so forth. The information may be combined to determine an overall device profile. When a request for content is made, the server may employ the device profile to dynamically format the content and provide it optimized for the computing device.
Owner:OATH INC
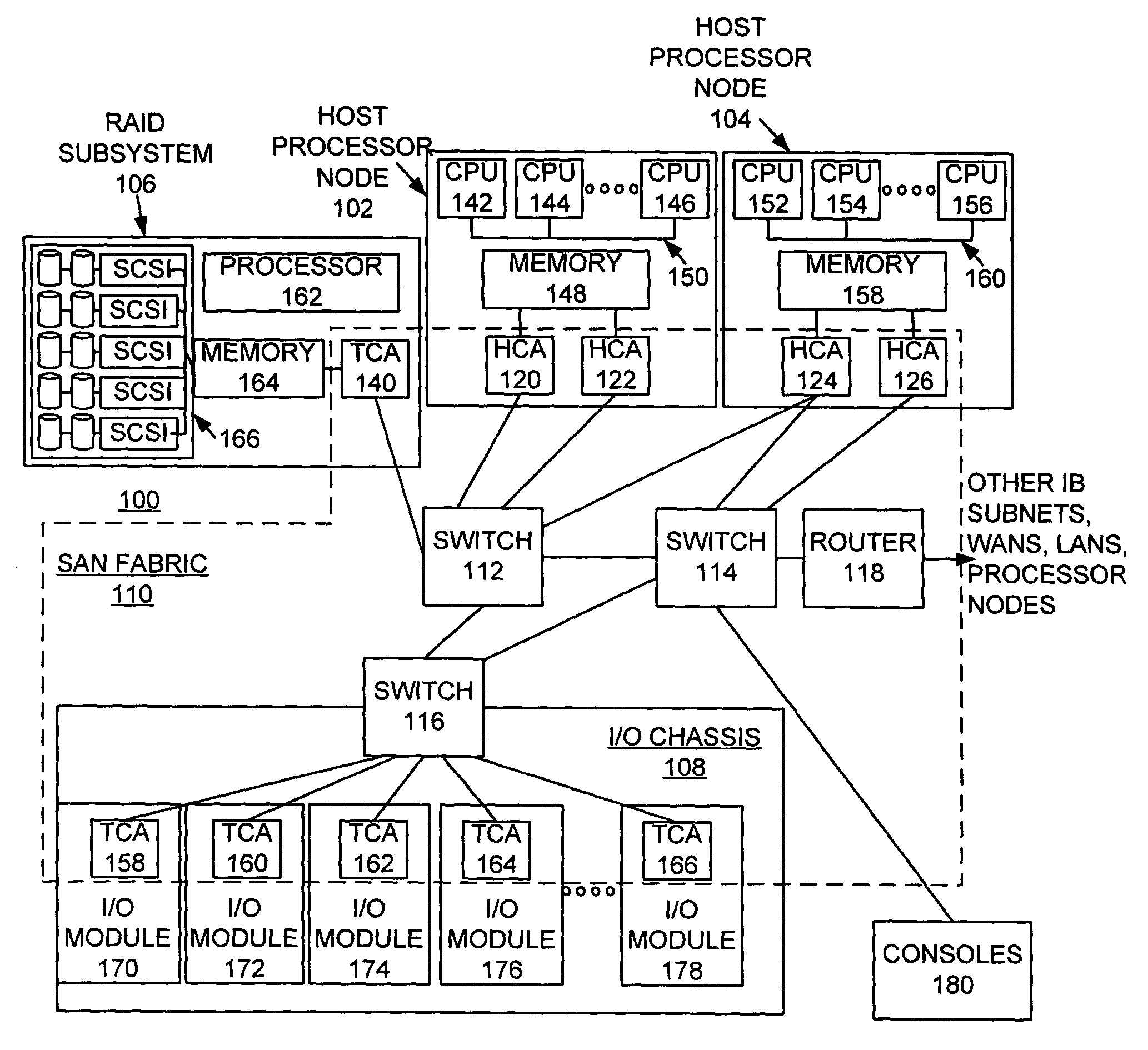
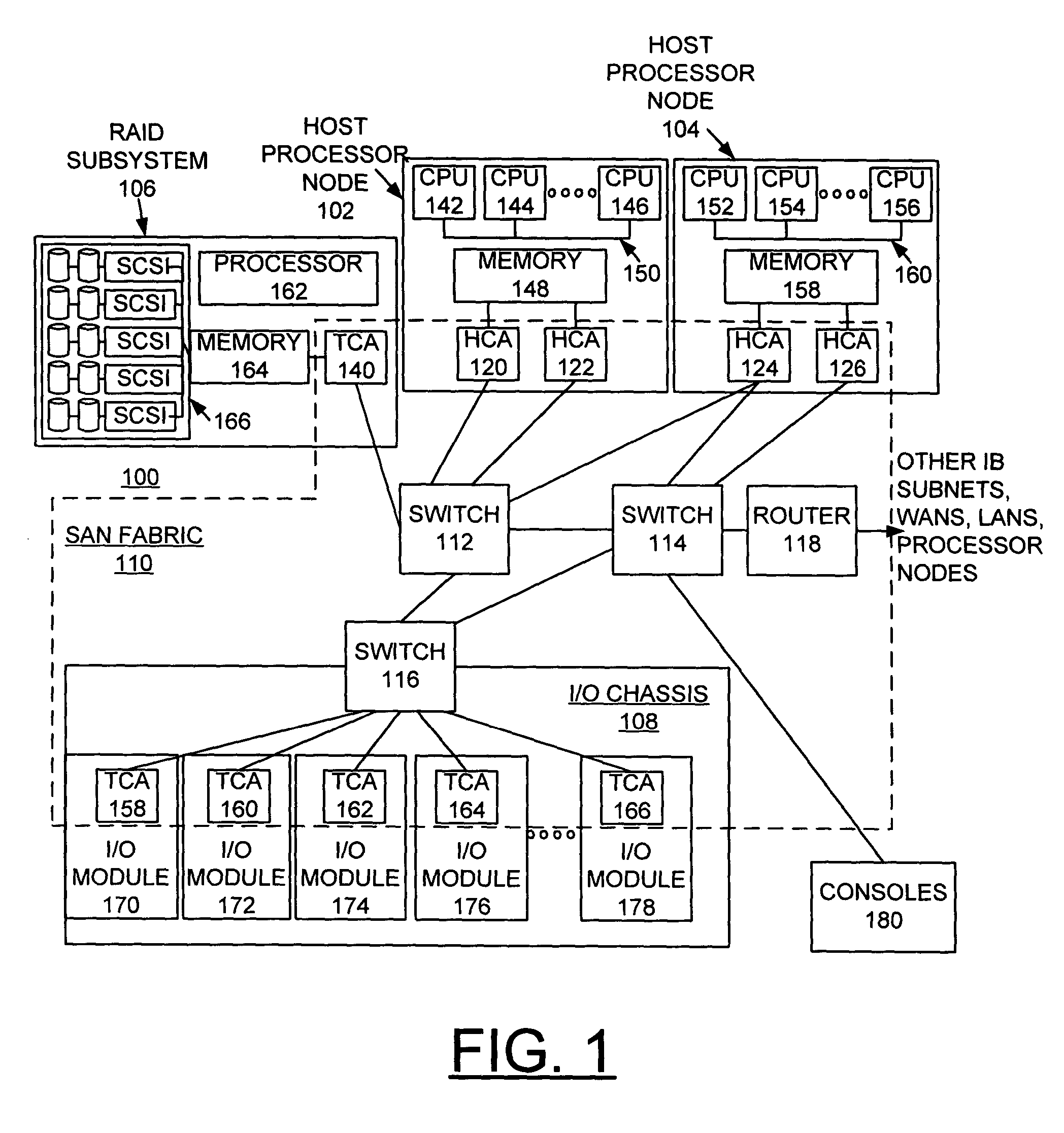
Method for implementing dynamic virtual lane buffer reconfiguration
InactiveUS20050060445A1Without effectOvercome disadvantagesData switching networksInput/output processes for data processingProcessor registerChange request
A method, apparatus and computer program product are provided for implementing dynamic Virtual Lane buffer reconfiguration in a channel adapter. A first register is provided for communicating an adapter buffer size and allocation capability for the channel adapter. At least one second register is provided for communicating a current port buffer size and one second register is associated with each physical port of the channel adapter. A plurality of third registers is provided for communicating a current VL buffer size, and one third register is associated with each VL of each physical port of the channel adapter. The second register is used for receiving change requests for adjusting the current port buffer size for an associated physical port. The third register is used for receiving change requests for adjusting the current VL buffer size for an associated VL.
Owner:IBM CORP
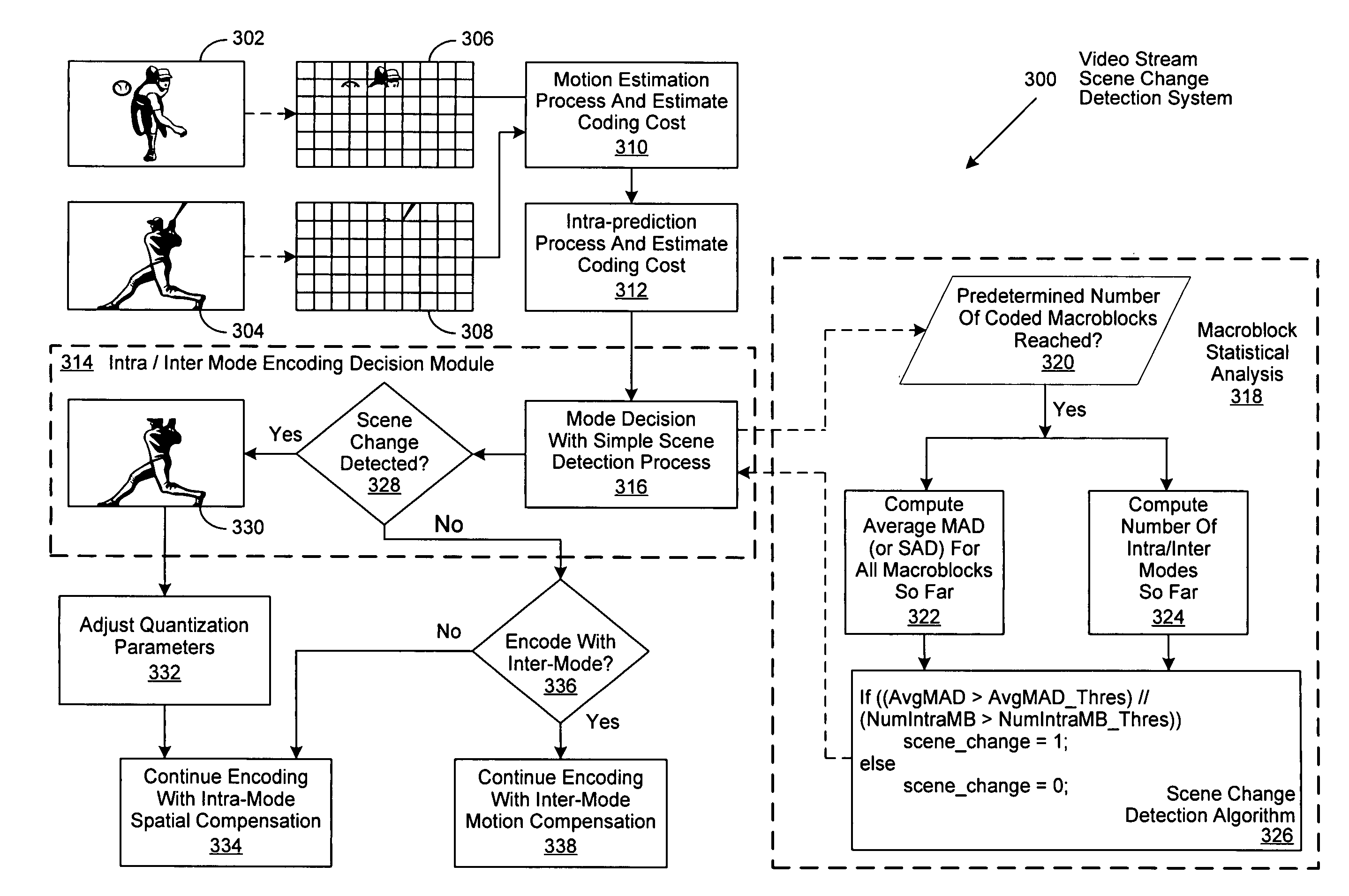
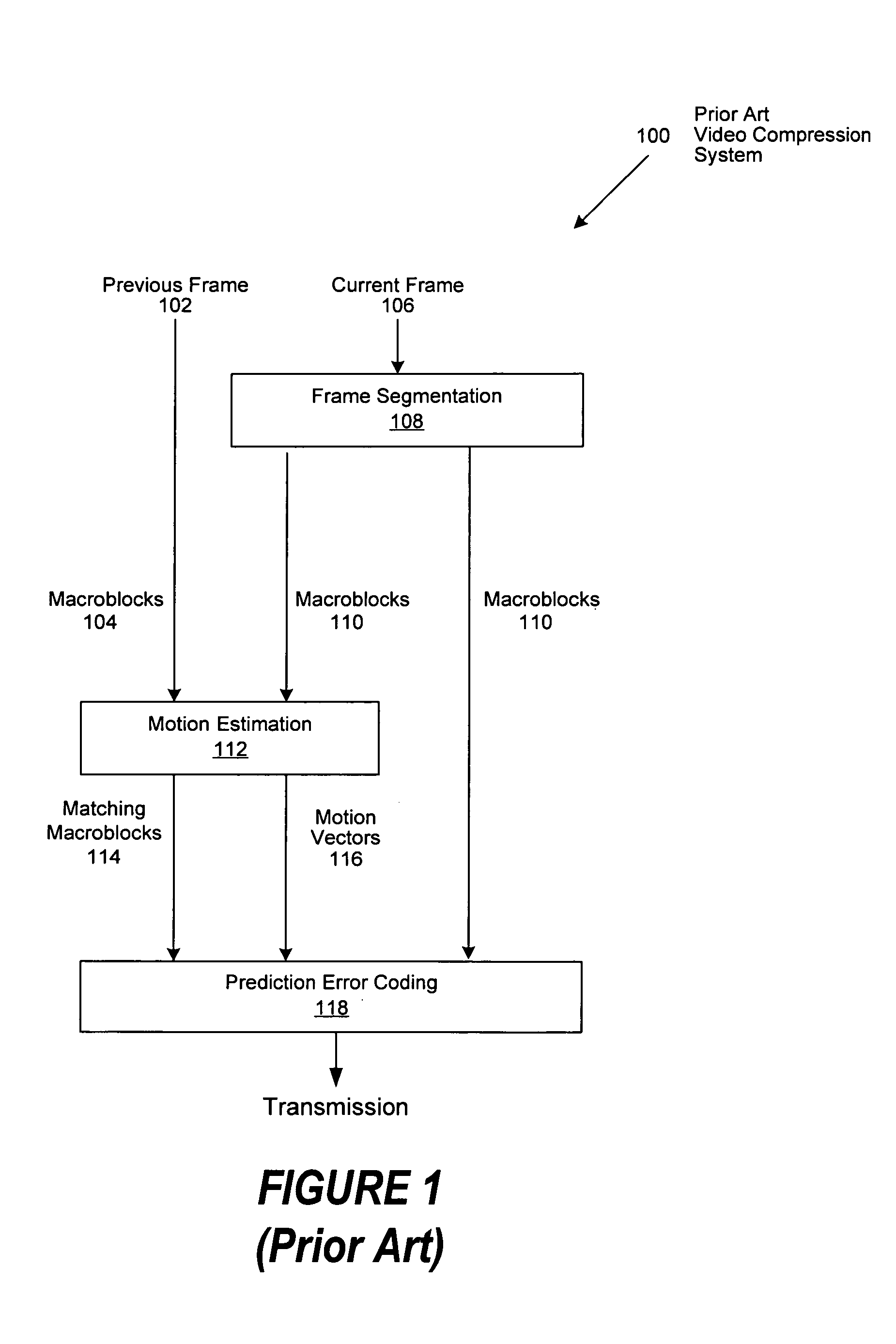
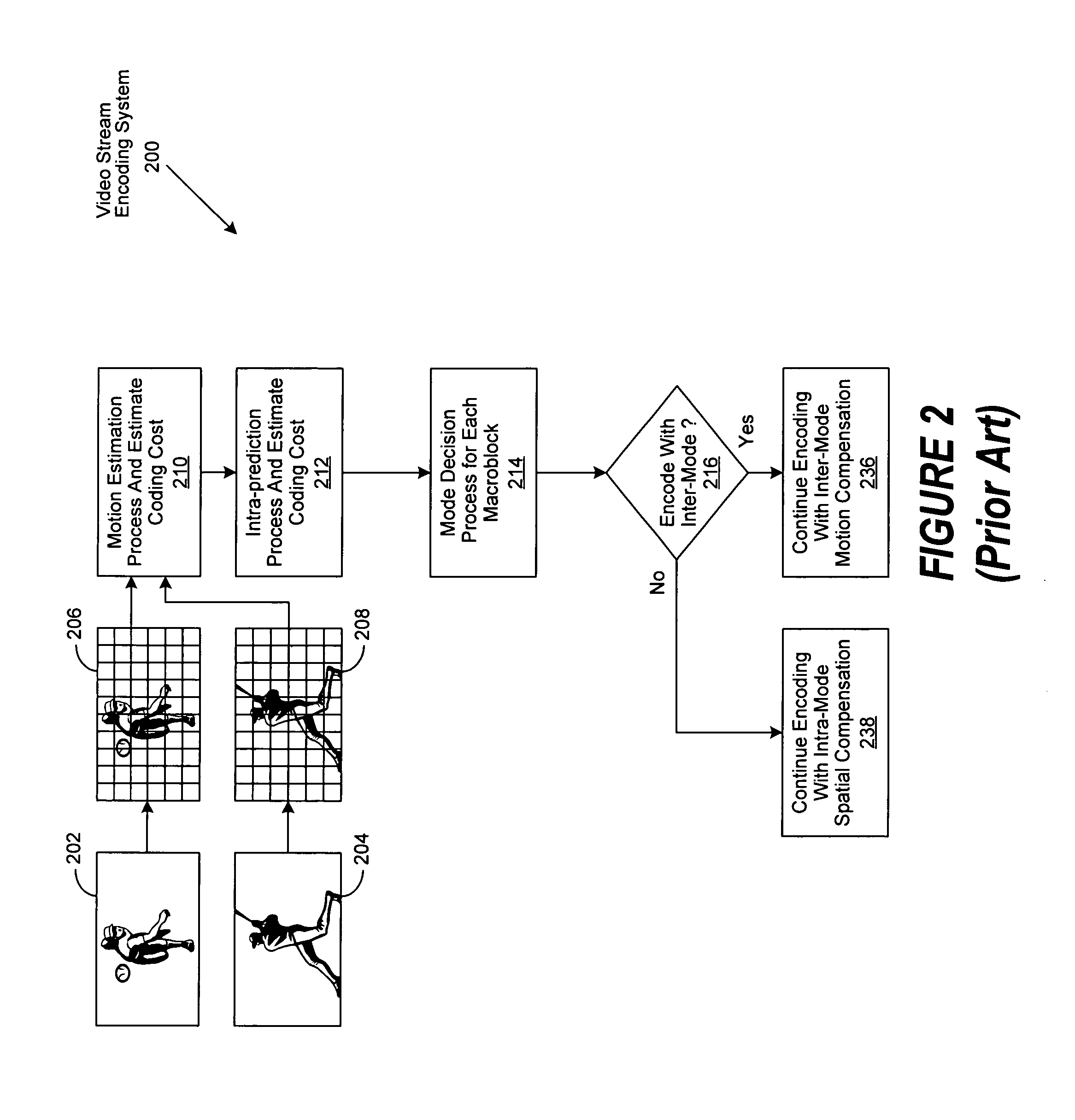
Method of increasing coding efficiency and reducing power consumption by on-line scene change detection while encoding inter-frame
InactiveUS20070274385A1Television system detailsColor television with pulse code modulationPattern recognitionComputation complexity
A system and method for on-the-fly detection of scene changes within a video stream through statistical analysis of a portion of the macroblocks comprising each video frame as they are processed using inter-frame coding. If the statistical analysis of the selected macroblocks of the current frame differs from the previous frame by exceeding predetermined thresholds, the current video frame is assumed to be a scene change. Once a scene change is detected, the remainder of the video frame is encoded as an intra-frame, intra-macroblocks, or intra slices, through implementation of one or more predetermined or adaptively adjusted quantization parameters to reduce computational complexity, decrease power consumption, and increase the resulting video image quality. As decoding is the inverse of encoding, these improvements are similarly recognized by a decoder as it decodes a resulting encoded video stream.
Owner:NXP USA INC
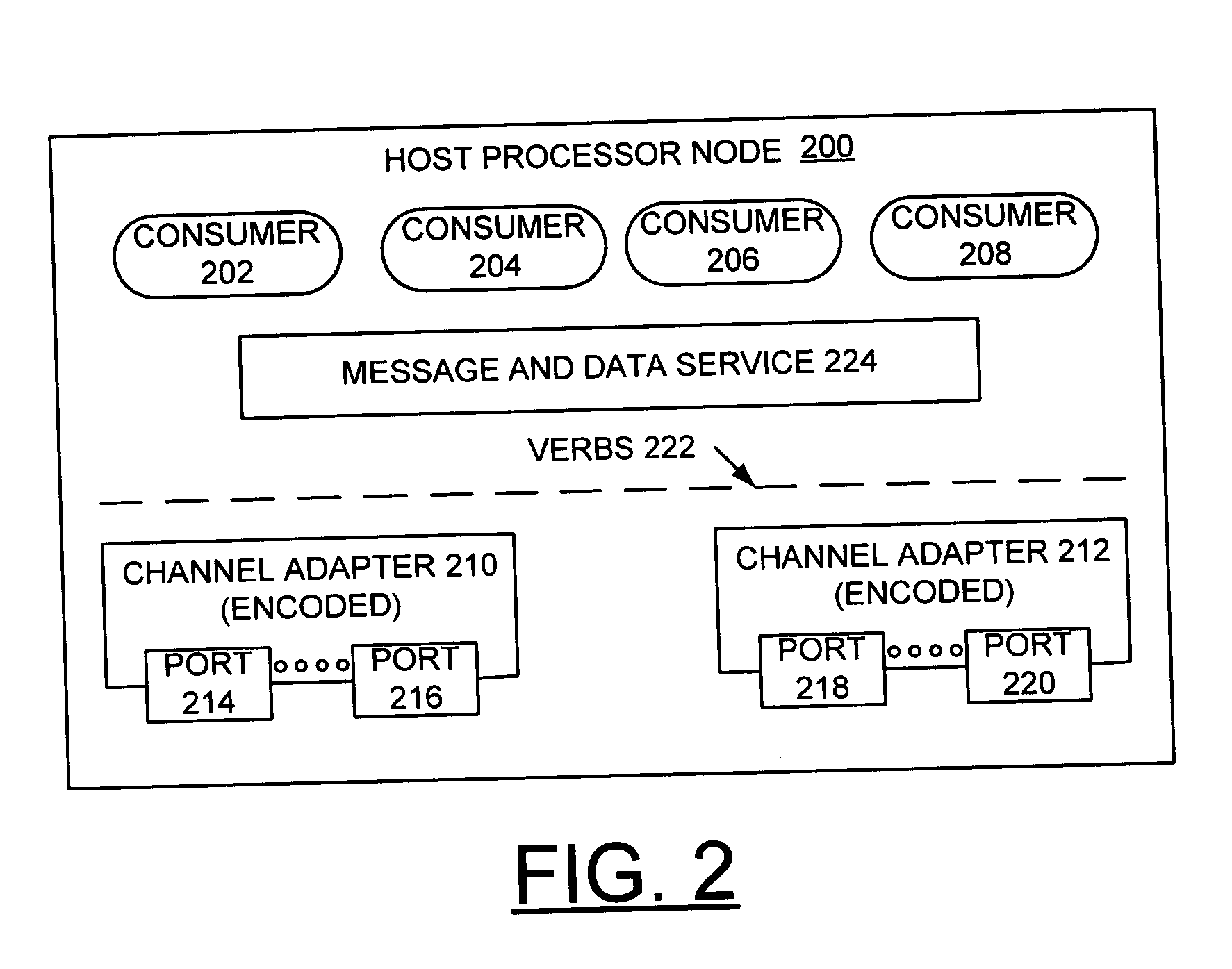
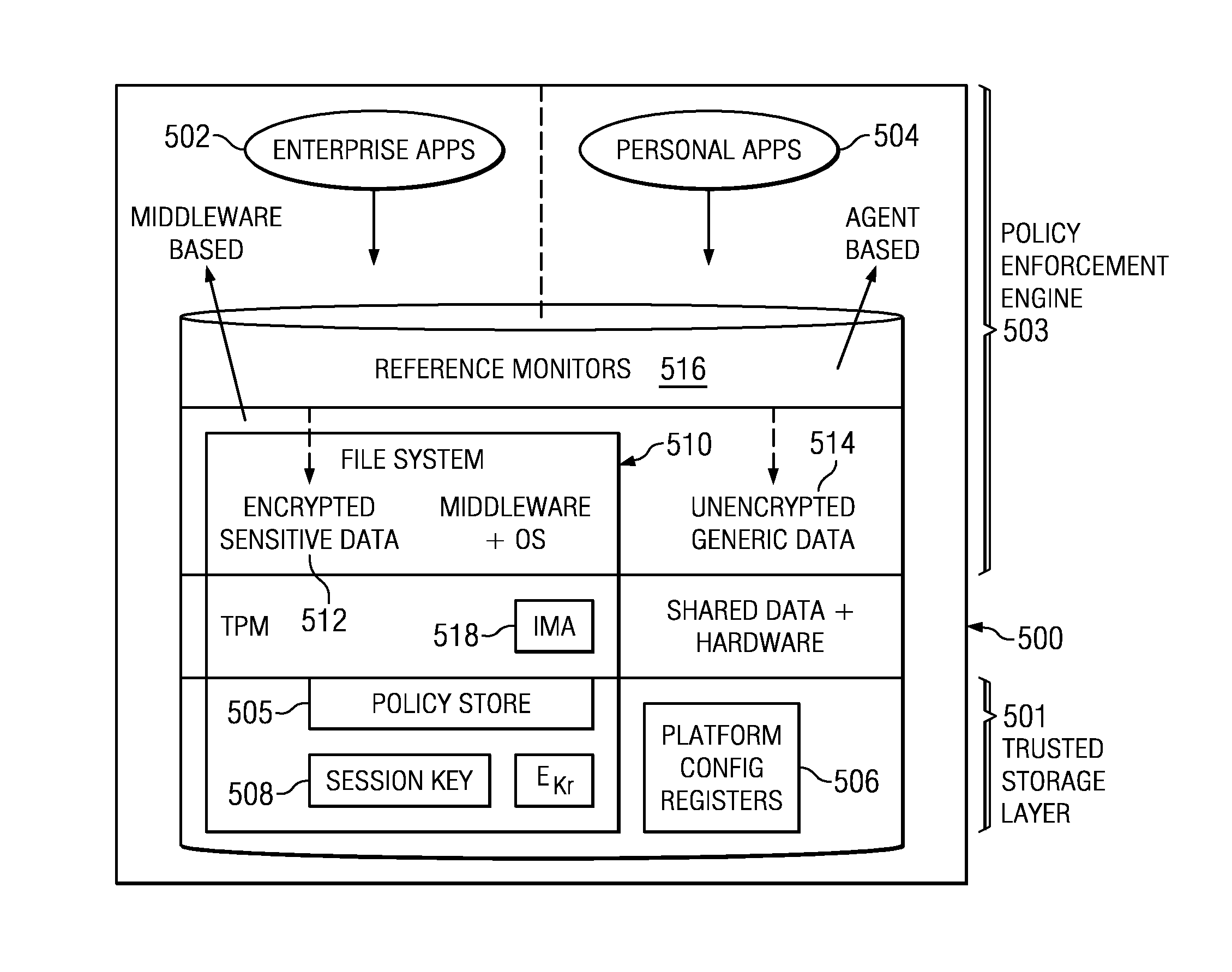
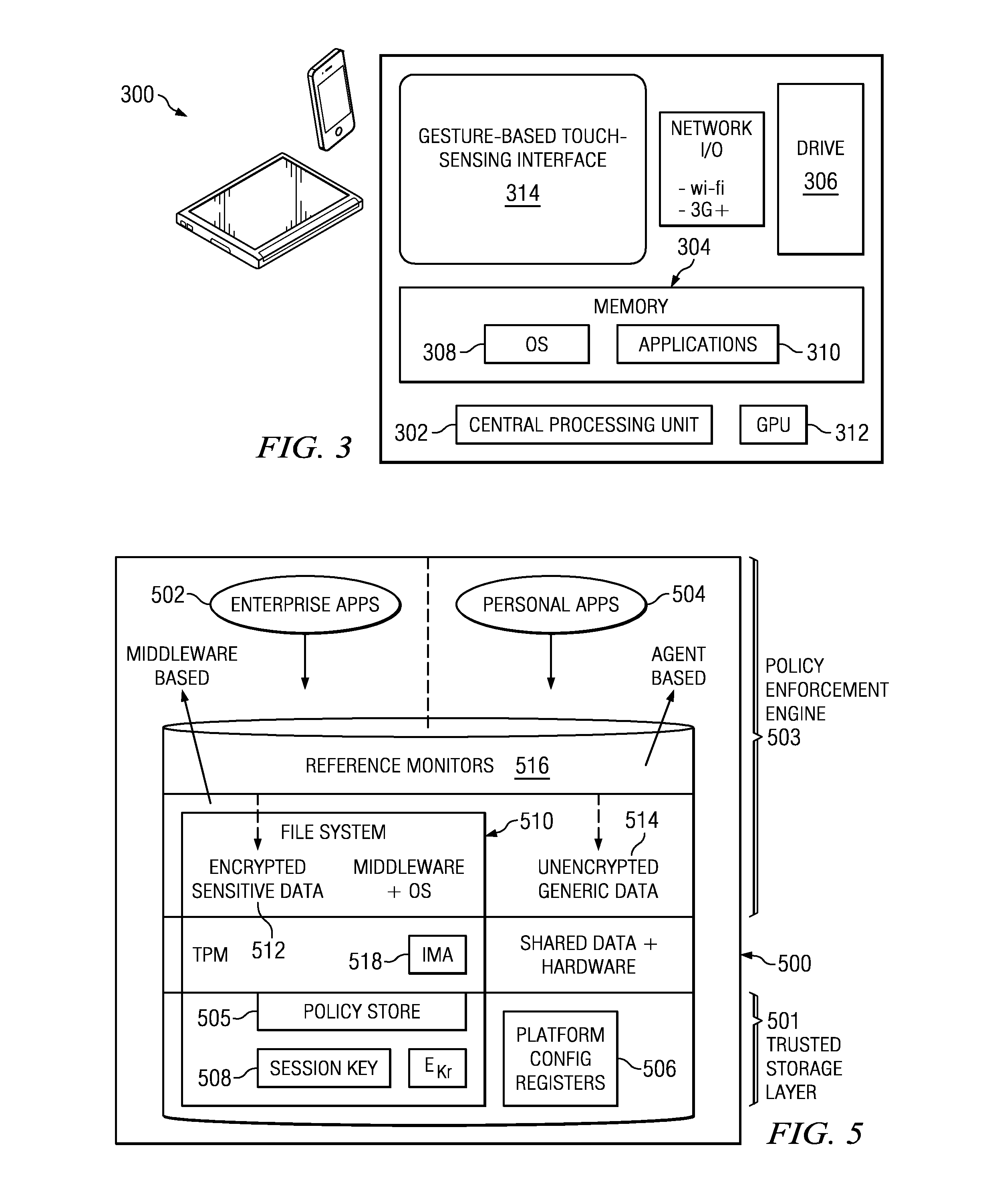
Policy-based dynamic information flow control on mobile devices
ActiveUS20130290709A1User identity/authority verificationComputer security arrangementsInternet privacyData access
A method and system are provided for securing data on a mobile device that supports both enterprise and personal applications. According to the method, information flows and data accesses are tracked on the device at run-time to enable access control decisions to be performed based on a policy, such as an enterprise privacy policy that has been distributed to the device from an enterprise server. The policy may be updated by events at the device as well as at the enterprise server.
Owner:IBM CORP
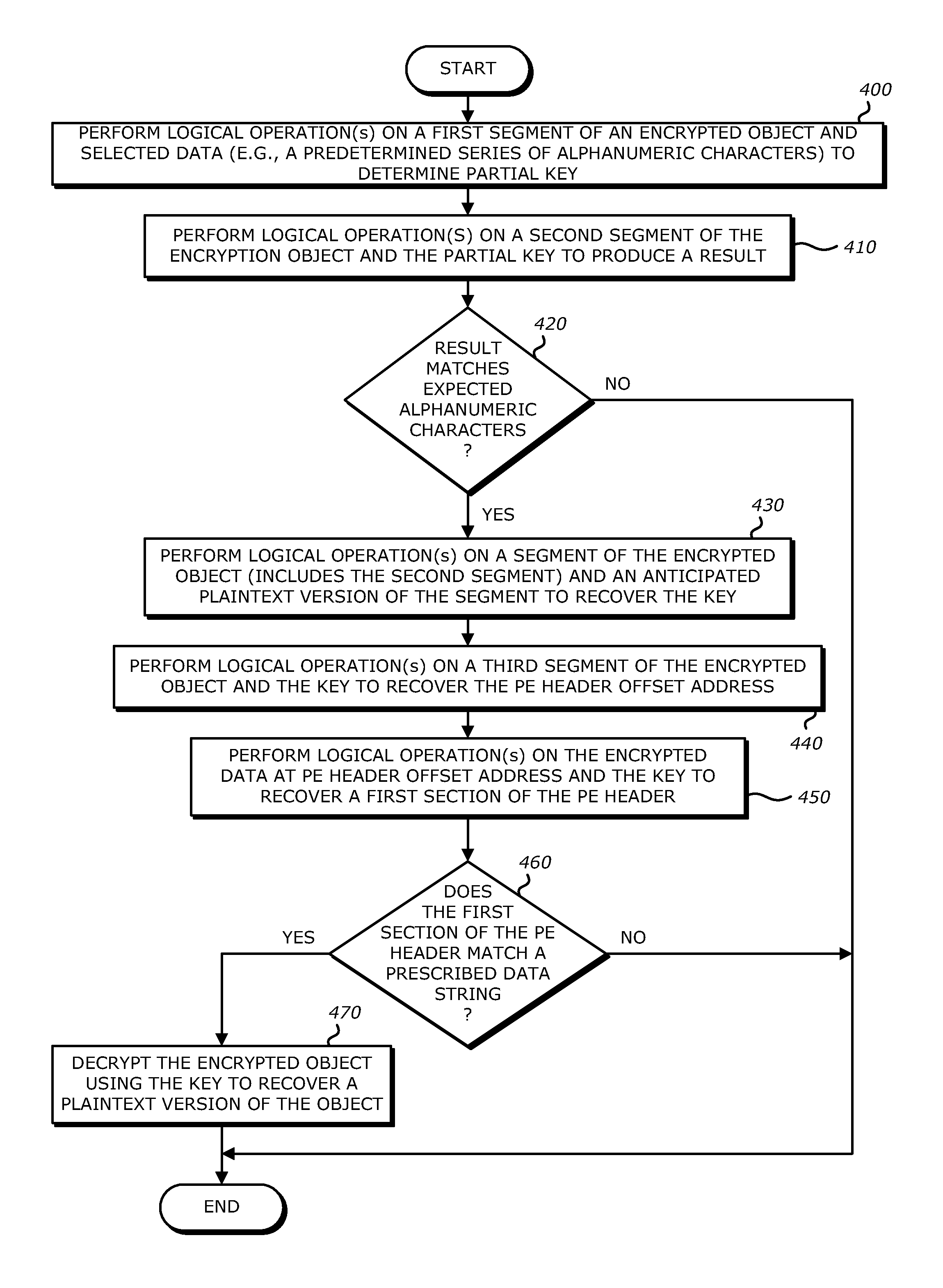
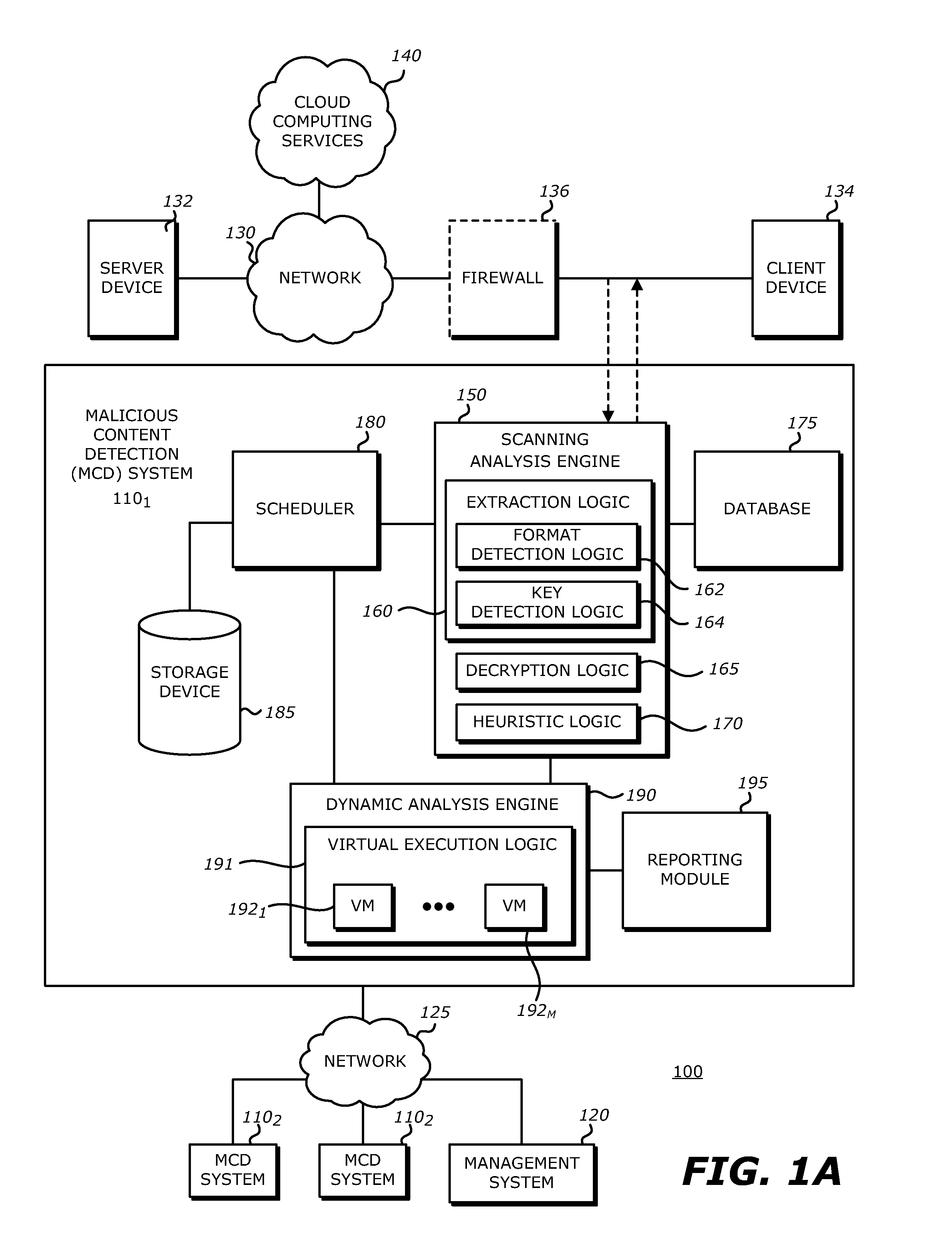
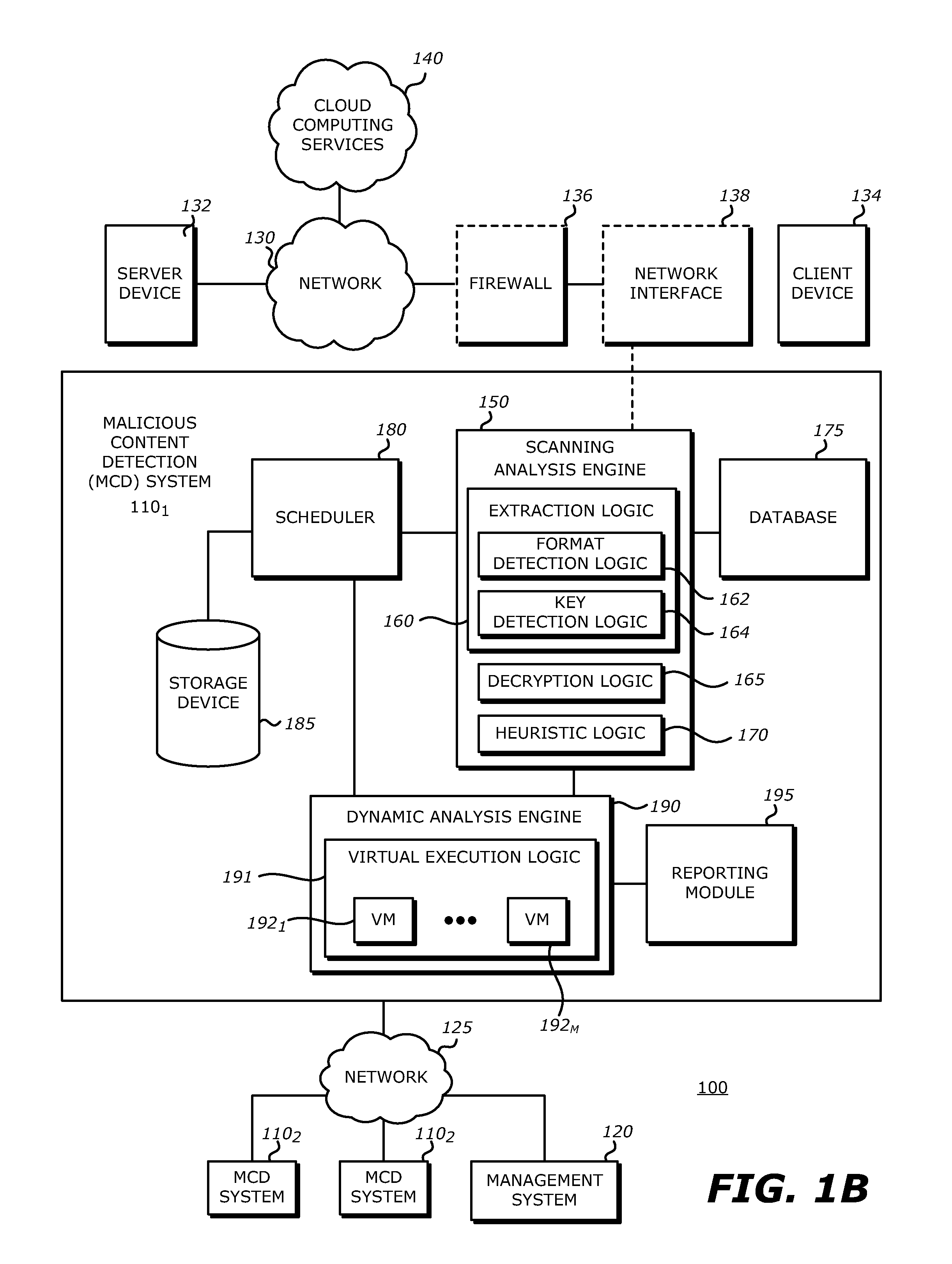
System, apparatus and method for conducting on-the-fly decryption of encrypted objects for malware detection
ActiveUS9560059B1Key distribution for secure communicationData stream serial/continuous modificationComputer hardwareLogical operations
A decryption scheme for recover of a decrypted object without a cryptographic key is described. First, logical operation(s) are conducted on data associated with a first data string expected at a first location within an object having the predetermined format and data within the encrypted object at the first location to recover data associated with a portion of a cryptographic key from the encrypted object. Thereafter, logical operation(s) are conducted on that data and a first portion of the encrypted object at a second location to produce a result. Responsive to the result including data associated with the plaintext version of the second data string, logical operation(s) are conducted on a second portion of the encrypted object and the data associated with the plaintext version of the second data string to recover data associated with the cryptographic key. Thereafter, the encrypted object may be decrypted using the cryptographic key.
Owner:FIREEYE SECURITY HLDG US LLC +1
Magnetic recording head with dynamic fly height heating and having thermally controlled pole tip protrusion to control and protect reader element
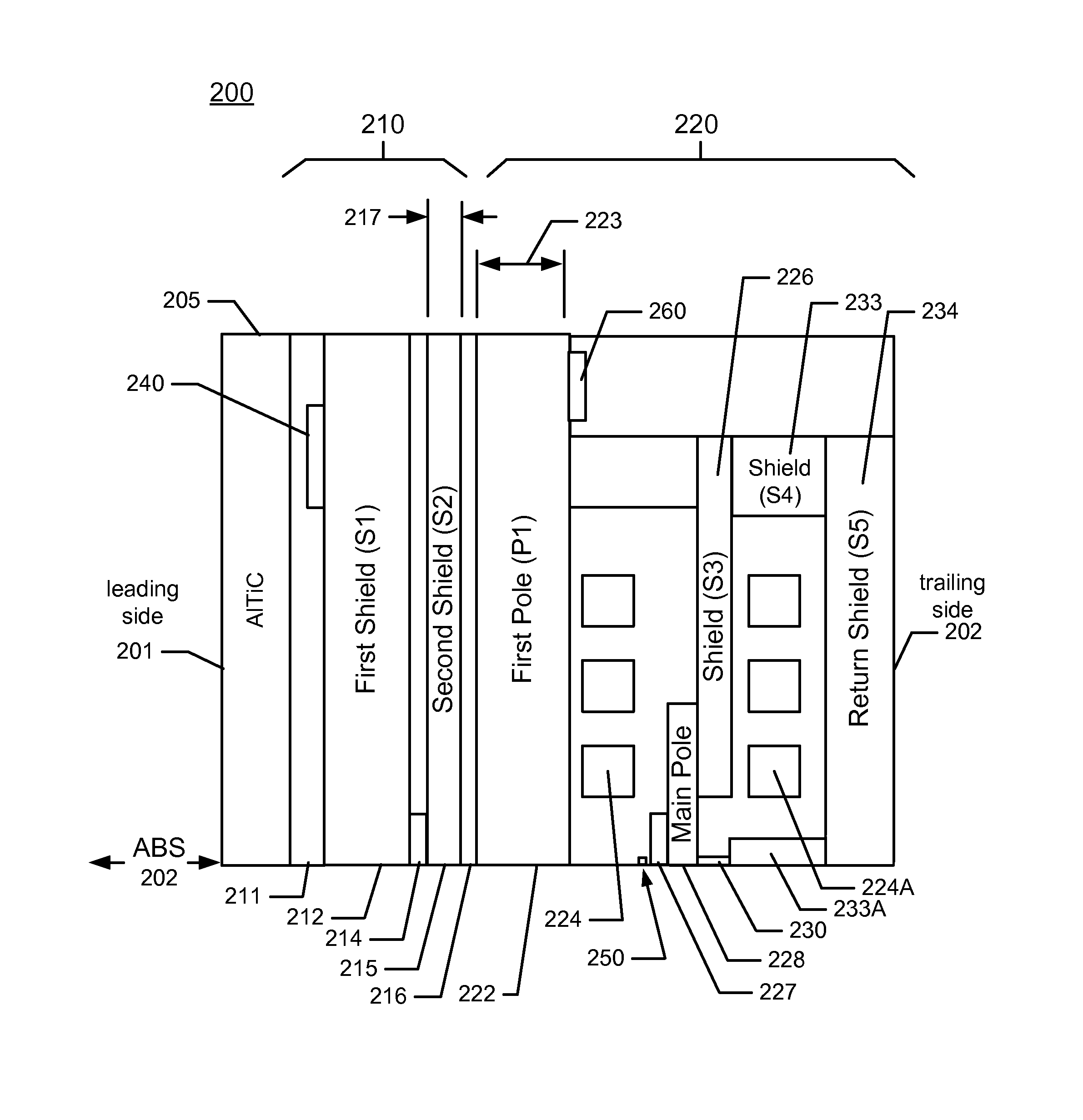
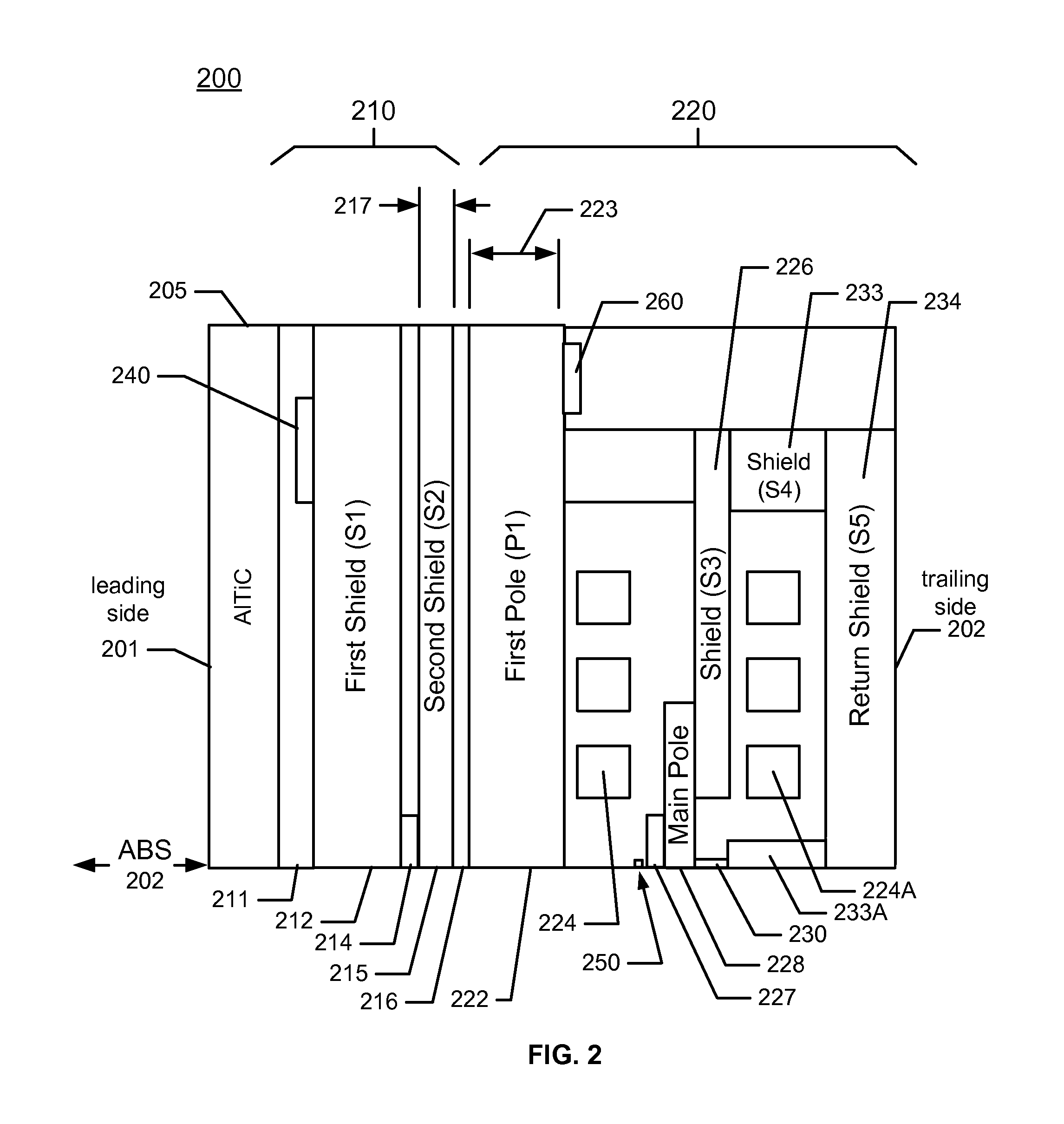
ActiveUS8749920B1Record information storageHeads for perpendicular magnetisationsHard disc driveMagnetic transducers
A magnetic recording device includes a slider having an air bearing surface (ABS), a leading side, and a trailing side and a head residing on the slider. The head has a first magnetic transducer and a first heater for heating an area proximal to the first magnetic transducer. A first shield (S1) comprising a first material is on the leading side of the first magnetic transducer and a second shield (S2) comprising the first material is on the trailing side of the first magnetic transducer. A first pole (P1) comprising the first material is on the trailing side of the second shield (S2), and the first pole (P1) is between 0.6 micron and 2.0 micron thick; and the second shield (S2) is less than 0.6 micron thick. A hard disk drive includes the magnetic recording device.
Owner:WESTERN DIGITAL TECH INC
Dynamic keypad for controlling energy-savings modes of a load control system
ActiveUS8866343B2Reduce the amount requiredReduce power consumptionElectric signal transmission systemsMetering/charging/biilling arrangementsTemperature controlUser input
A load control system for a building having a lighting load, a window, and a heating and cooling system comprises a lighting control device for controlling the amount of power delivered to the lighting load, a motorized window treatment comprising a window treatment fabric for covering the window, a temperature control device for controlling a setpoint temperature of the heating and cooling system to thus control a present temperature in the building, and a dynamic keypad comprising a visual display and operable to receive a user input. The dynamic keypad allows a user to select, adjust, and monitor a plurality of energy-savings modes of the load control system. For example, the dynamic keypad allows the user to enable and adjust a setback temperature of the temperature control device on-the-fly.
Owner:LUTRON TECH CO LLC
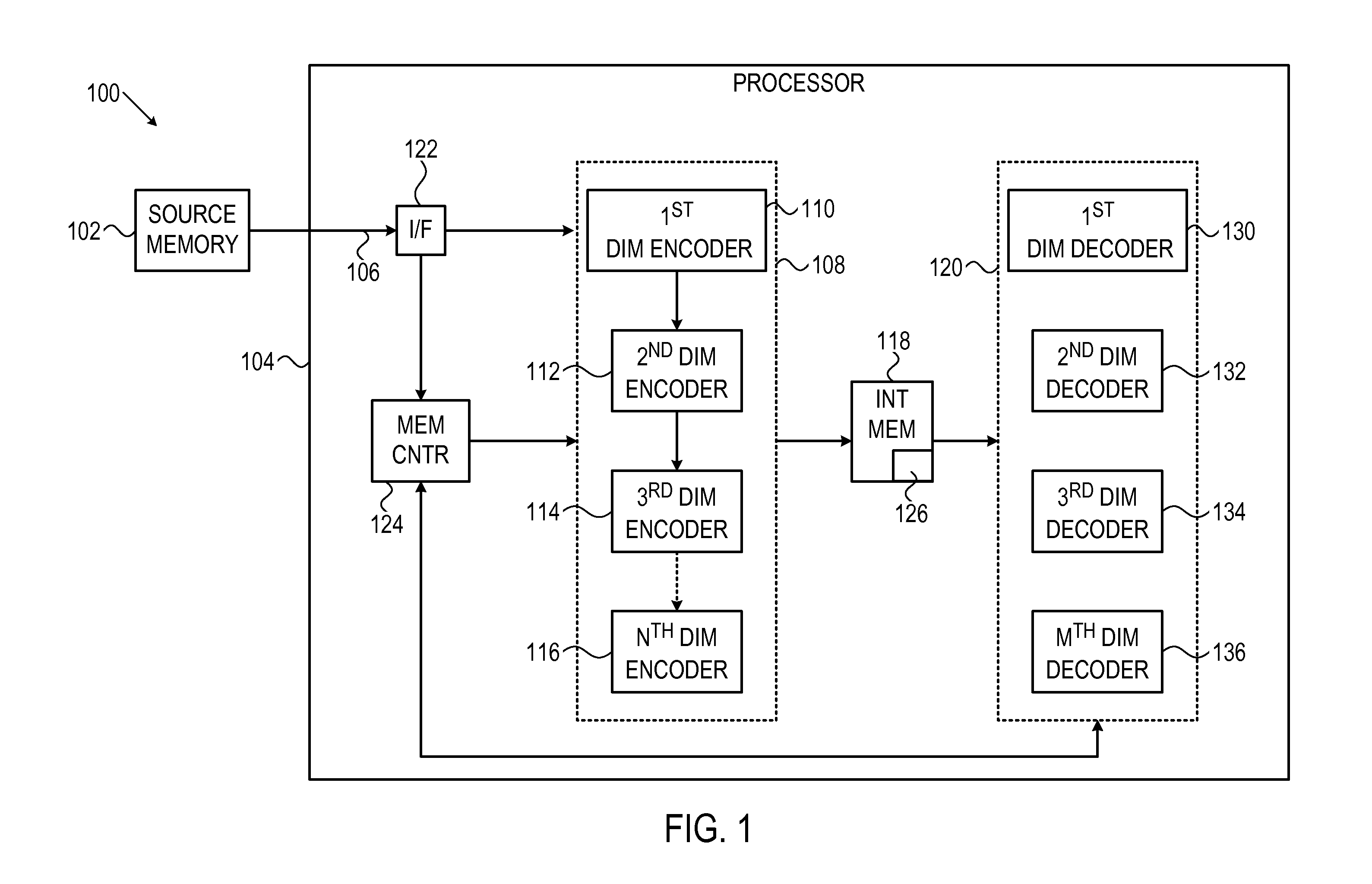
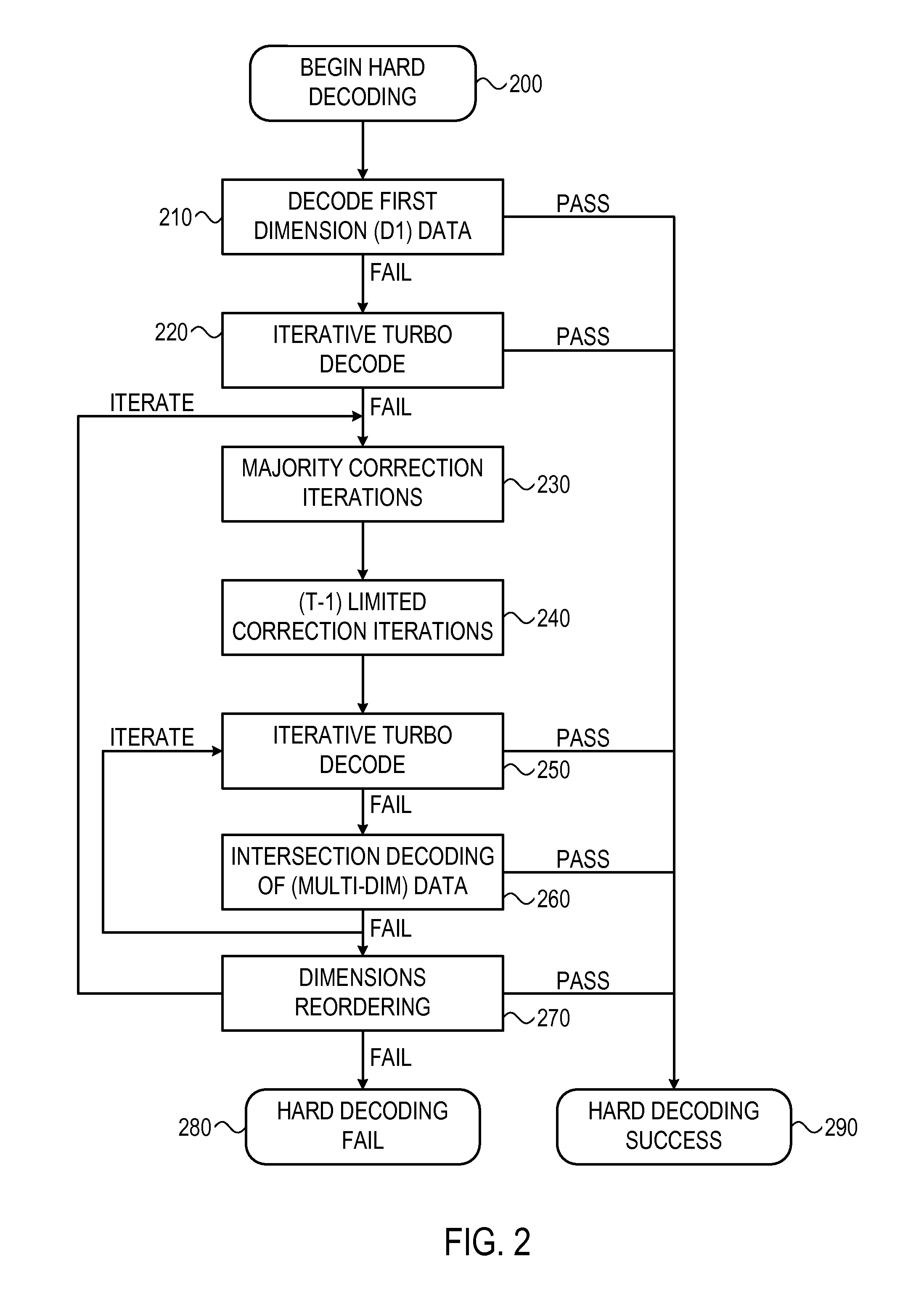
System and method for multi-dimensional encoding and decoding
ActiveUS20120005560A1Error correction/detection using convolutional codesOther decoding techniquesHypothesisDependability
A system and method is provided for decoding a set of bits using a plurality of hypotheses, for example, each independently tested on-the-fly. Initial bit states and associated reliability metrics may be received for the set of bits. A current hypothesis may be decoded for correcting the set of bits, wherein the current hypothesis defines different bit states and associated reliability metrics for the set of bits. If decoding the current hypothesis is not successful, a subsequently ordered hypothesis may be decoded, wherein the hypotheses are ordered such that their associated reliability metric is a monotonically non-decreasing sequence. Decoding may proceed iteratively until the current hypothesis is successful.
Owner:AVAGO TECH INT SALES PTE LTD
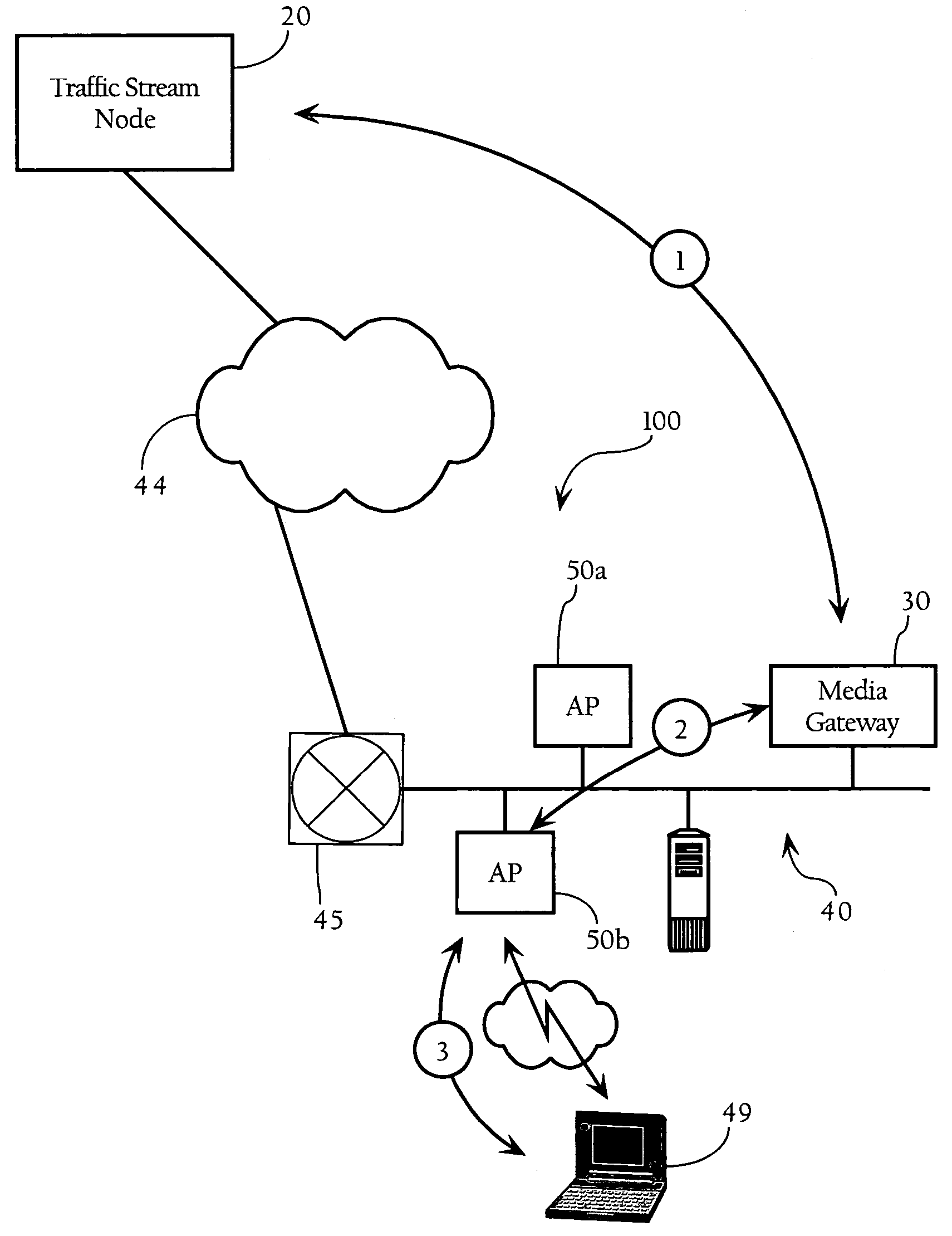
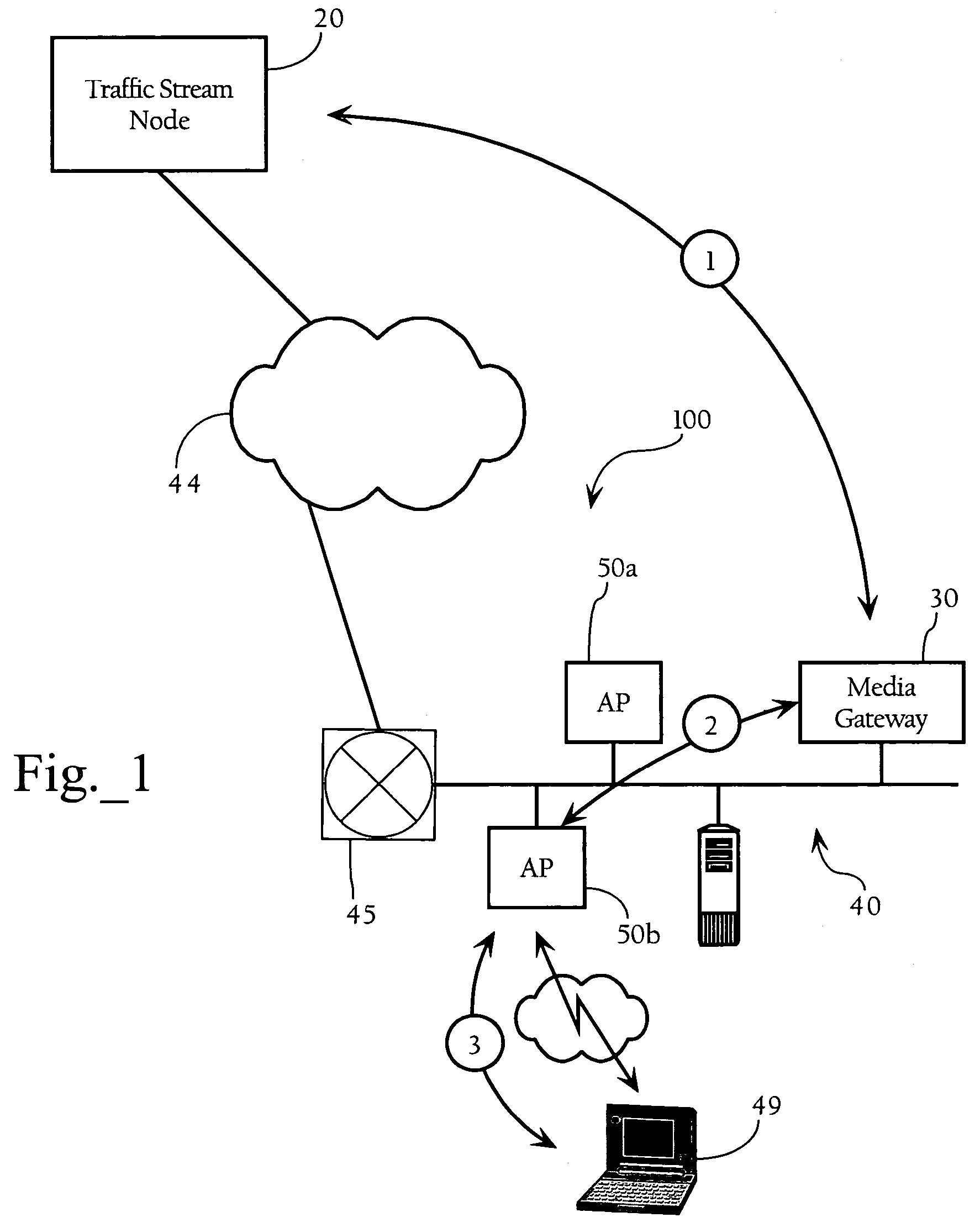
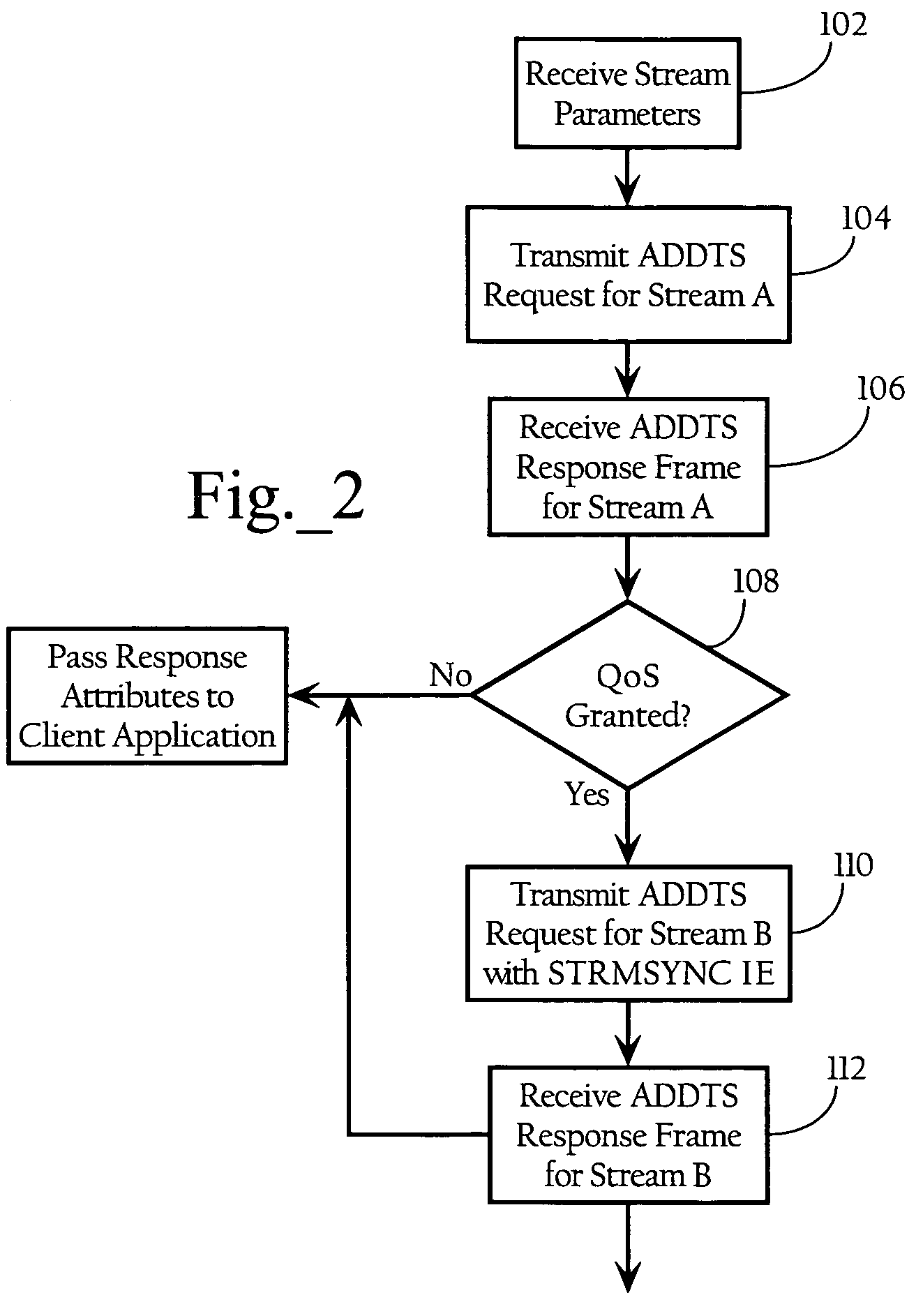
Method and system for media synchronization in QoS-enabled wireless networks
ActiveUS7486658B2Improve performanceGood synchronizationSynchronisation arrangementError preventionData synchronizationWireless mesh network
Owner:CISCO TECH INC
Method and apparatus for cache control
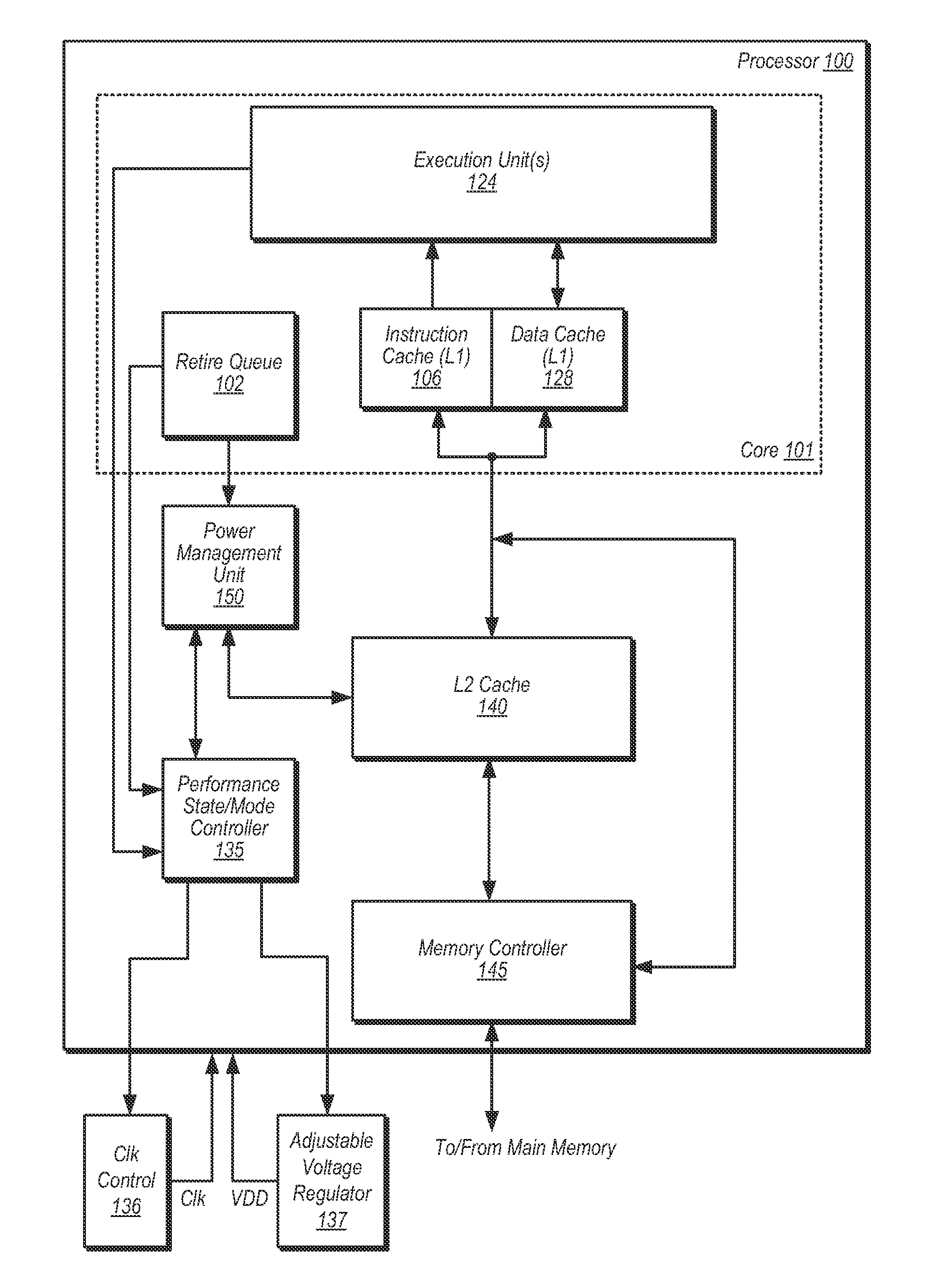
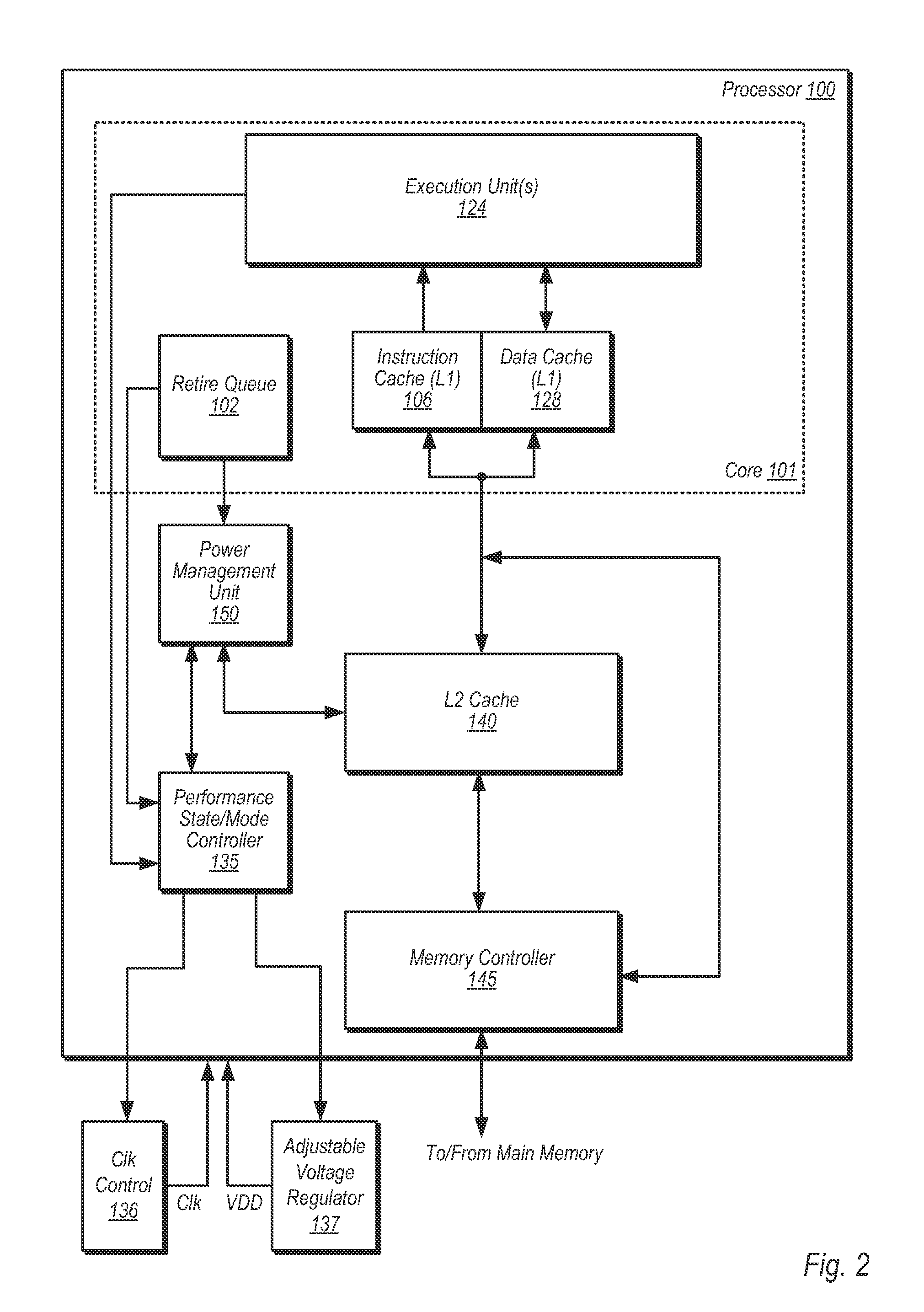
ActiveUS20110283124A1Memory architecture accessing/allocationEnergy efficient ICTOperating pointParallel computing
A method and apparatus for dynamically controlling a cache size is disclosed. In one embodiment, a method includes changing an operating point of a processor from a first operating point to a second operating point, and selectively removing power from one or more ways of a cache memory responsive to changing the operating point. The method further includes processing one or more instructions in the processor subsequent to removing power from the one or more ways of the cache memory, wherein said processing includes accessing one or more ways of the cache memory from which power was not removed.
Owner:ADVANCED MICRO DEVICES INC
Adding multi-tenant awareness to a network packet processing device on a Software Defined Network (SDN)
“Multi-tenant awareness” is added to a set of one or more packet processing devices in a Software Defined Network (SDN) having a controller. For each of one or more tenants, information in a table associates network protocol address attributes with an Internet Protocol (IP) address unique to the tenant. The table is associated with a multiple-layer translation layer being managed by the SDN controller. As a data packet traverses the translation layer, network protocol address attributes are translated according to values in the table to enable logical routing of the packet (to a given PPD. This translation occurs dynamically (or “on-the-fly”) as packets are “on route” to their destination. By implementing a multi-layer network address translation (NAT), one layer may be used to translate network protocol address source attributes, while a second layer may be used to translate network protocol address destination attributes.
Owner:IBM CORP
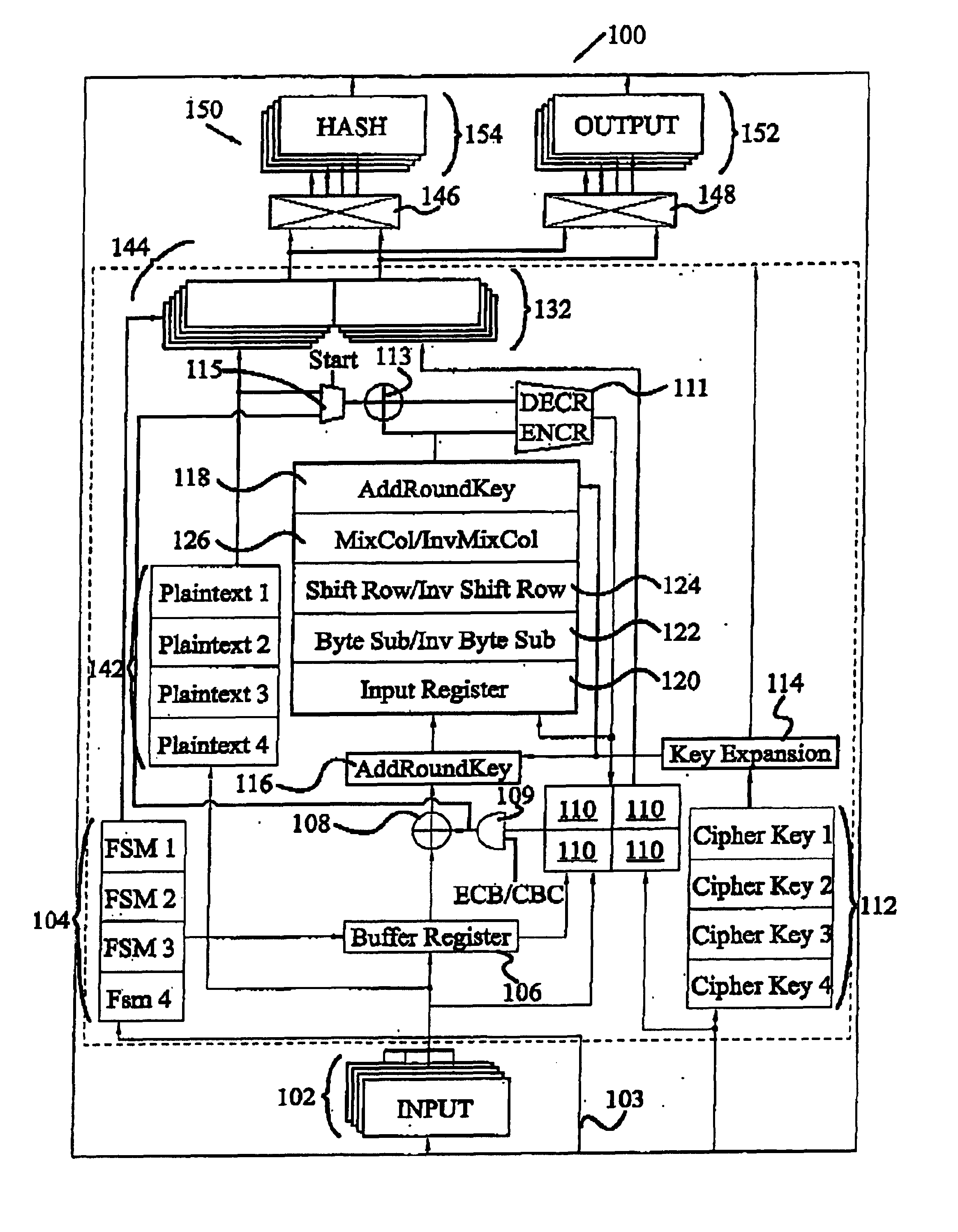
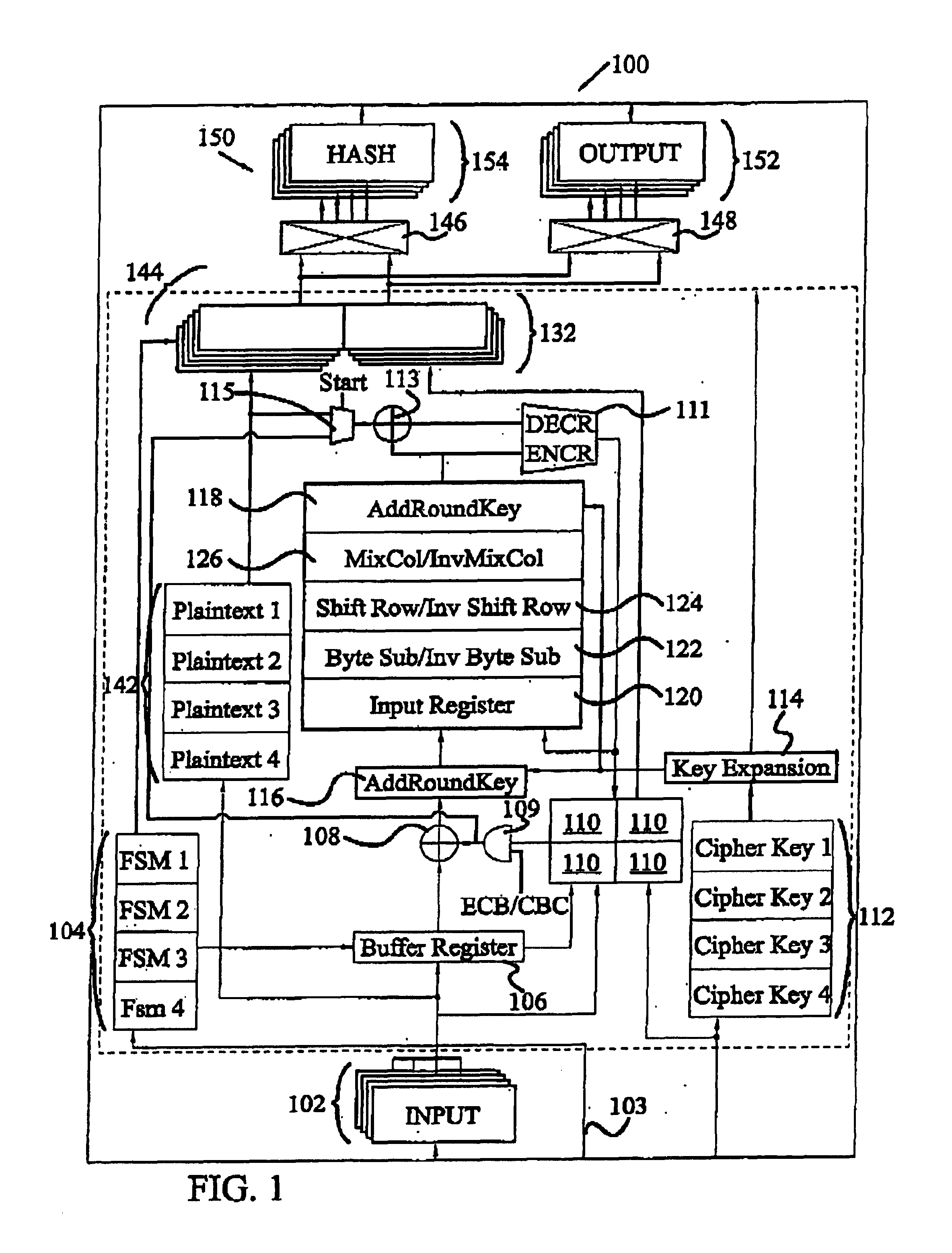
Circuit and method for implementing the advanced encryption standard block cipher algorithm in a system having a plurality of channels
InactiveUS6937727B2Efficient implementationGenerate efficientlyEncryption apparatus with shift registers/memoriesUser identity/authority verificationS-boxAdvanced Encryption Standard
A circuit includes a single circuit portion for implementing the Advanced Encryption Standard (AES) block cipher algorithm in a system having a plurality of channels. The circuit portion includes a circuit for individually generating, on the fly, the round keys used during each round of the AES block cipher algorithm. The circuit portion also includes shared logic circuits that implement the transformations used to encrypt and decrypt data blocks according to the AES block cipher. The single circuit portion encrypts or decrypts data blocks from each of the plurality of system channels in turn, in round-robin fashion. The circuit portion also includes a circuit for determining S-box values for the AES block cipher algorithm. The circuit additionally implements an efficient method for generating round keys on the fly for the AES block cipher decryption process.
Owner:EXCELIS INC
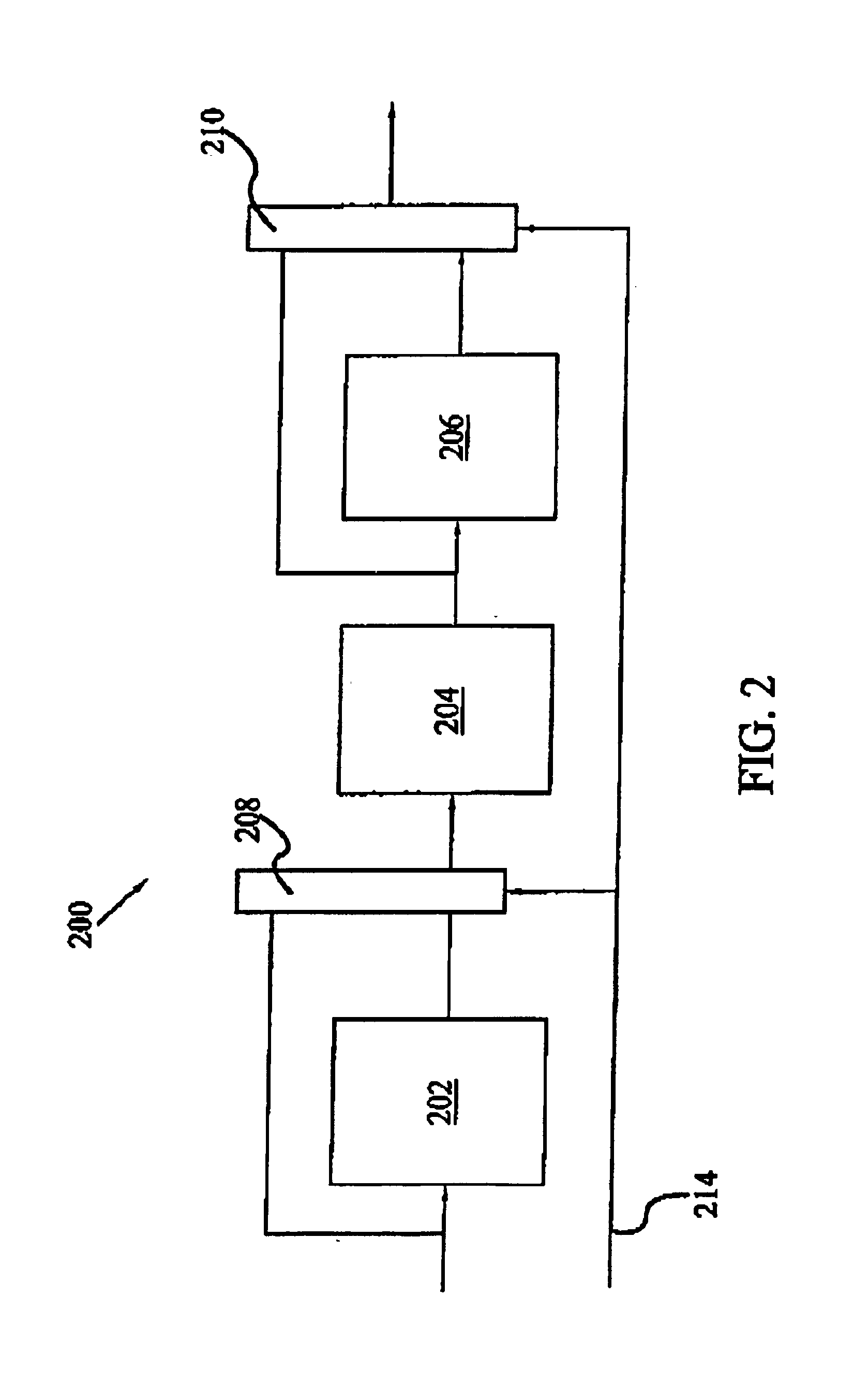
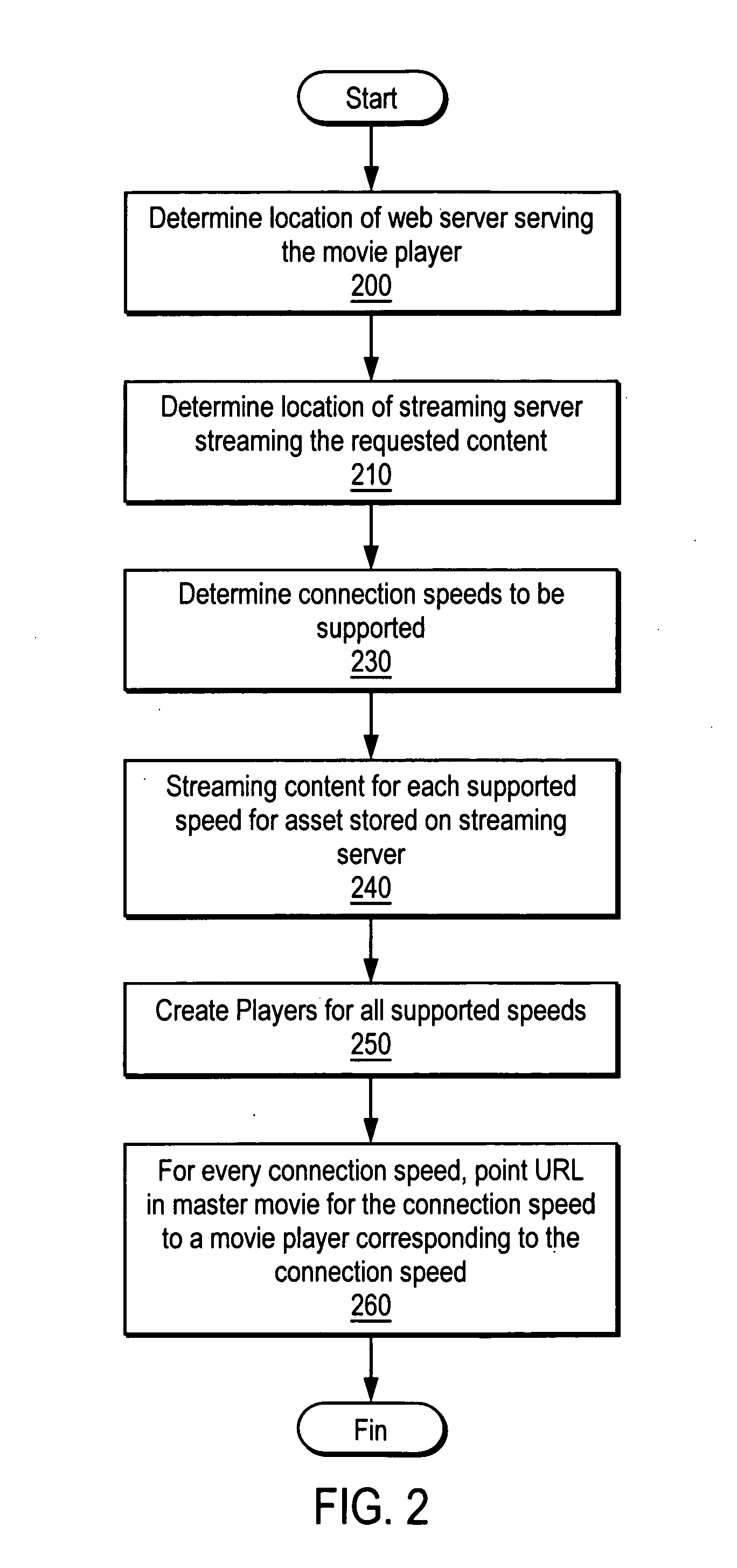
Method and apparatus for creating a connection speed detecting movie and rich media player customization on the fly
InactiveUS7178161B1Improve performanceTelevision system detailsColor television detailsComputer hardwareOn the fly
A master movie and player are created on the fly. The master movie is created based on characteristics of a movie or other asset to be viewed by the player. The player is constructed from a template having rudimentary player capabilities for a predetermined connection speed. Tracks selected by suppliers and user / e-tailers are added to customize the player. Different players are constructed for various predetermined connection speeds. When an asset is to be viewed, a server downloads the master movie matching a content viewer's request to the content viewer's machine. The master movie determines the connection speed and send a message back to the server. The server then downloads the player for the asset requested by the content viewer and matching the content viewer's connection speed. The requested asset is then streamed to the content viewer.
Owner:TENTOE SURFING
Tie-Breaking in Shortest Path Determination
InactiveUS20090168768A1Simple calculationLower requirementData switching by path configurationTraffic flowDistributed computing
A consistent tie-breaking decision between equal-cost shortest (lowest cost) paths is achieved by comparing an ordered set of node identifiers for each of a plurality of end-to-end paths. Alternatively, the same results can be achieved, on-the-fly, as a shortest path tree is constructed, by making a selection of an equal-cost path using the node identifiers of the diverging branches of the tree. Both variants allow a consistent selection to be made of equal-cost paths, regardless of where in the network the shortest paths are calculated. This ensures that traffic flow between any two nodes, in both the forward and reverse directions, will always follow the same path through the network.
Owner:RPX CLEARINGHOUSE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com