Patents
Literature
4332 results about "Data operations" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
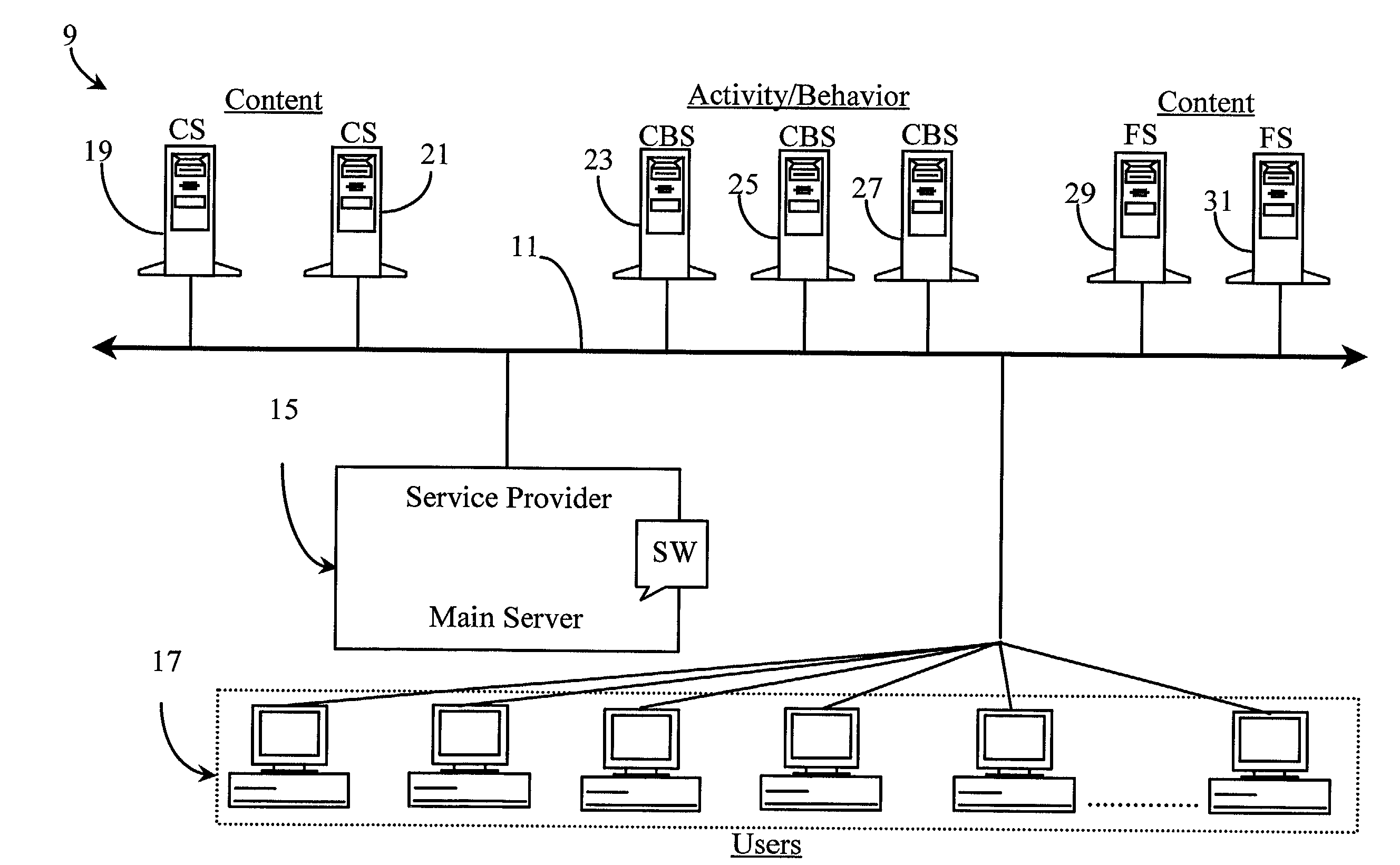
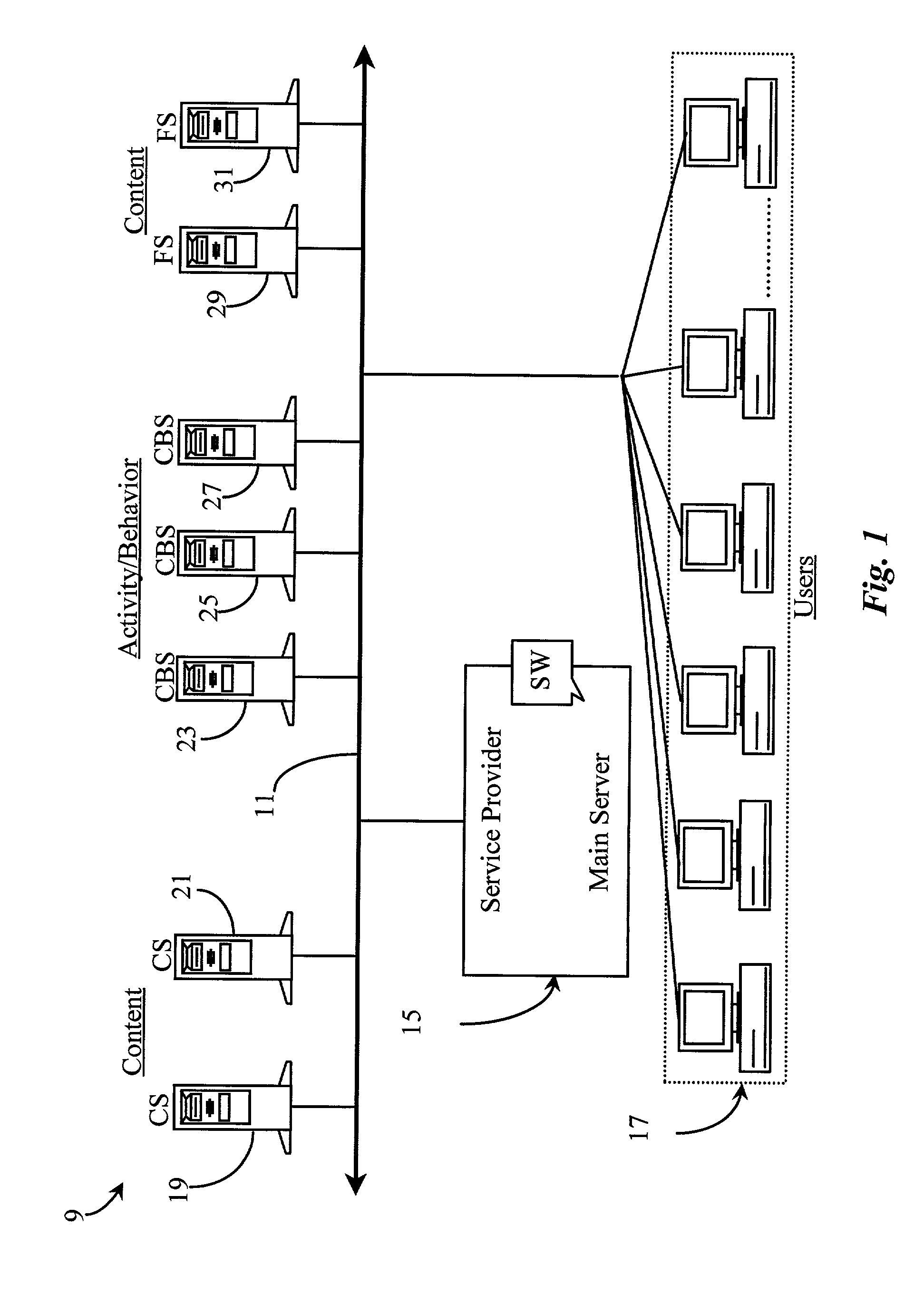
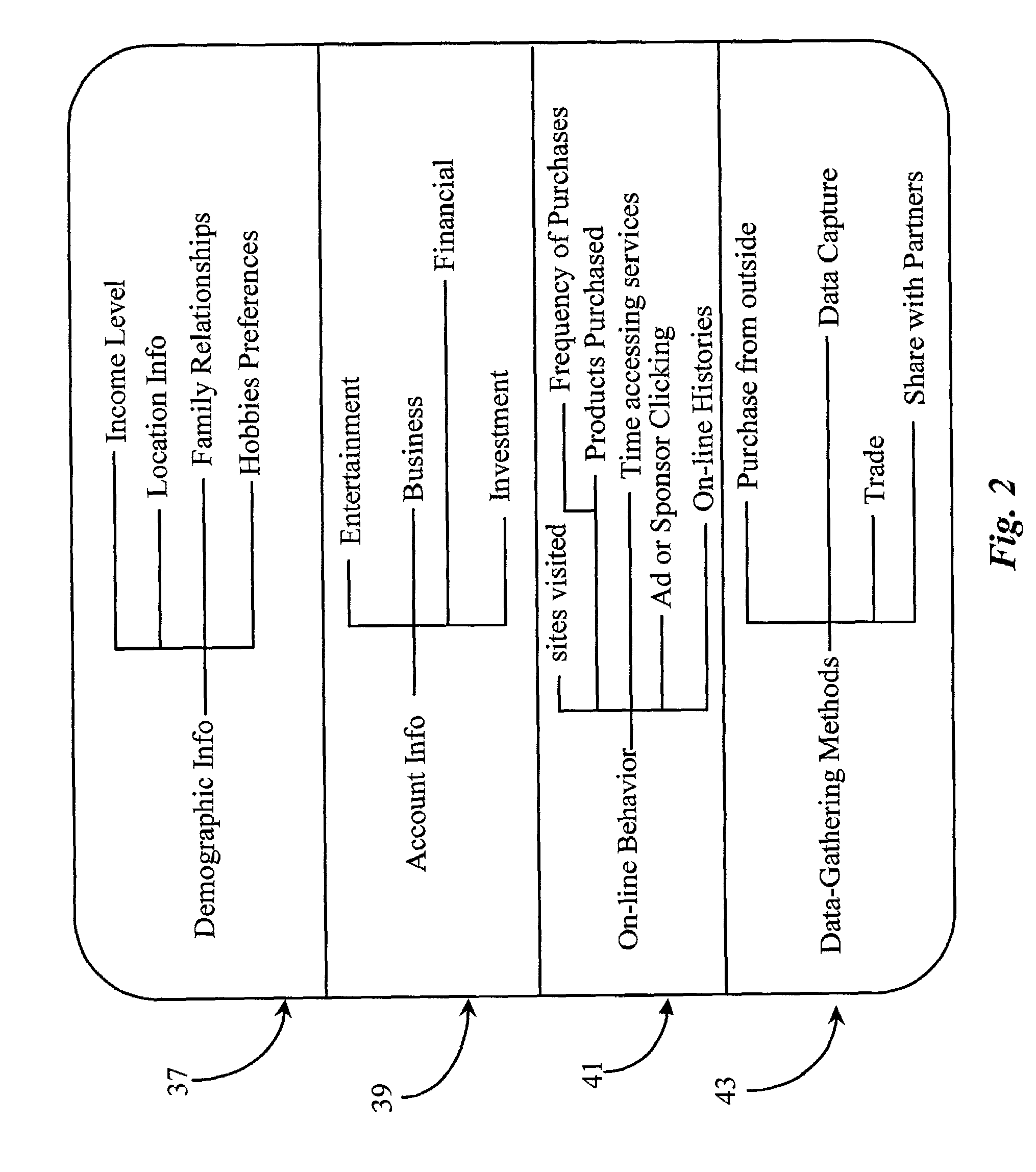
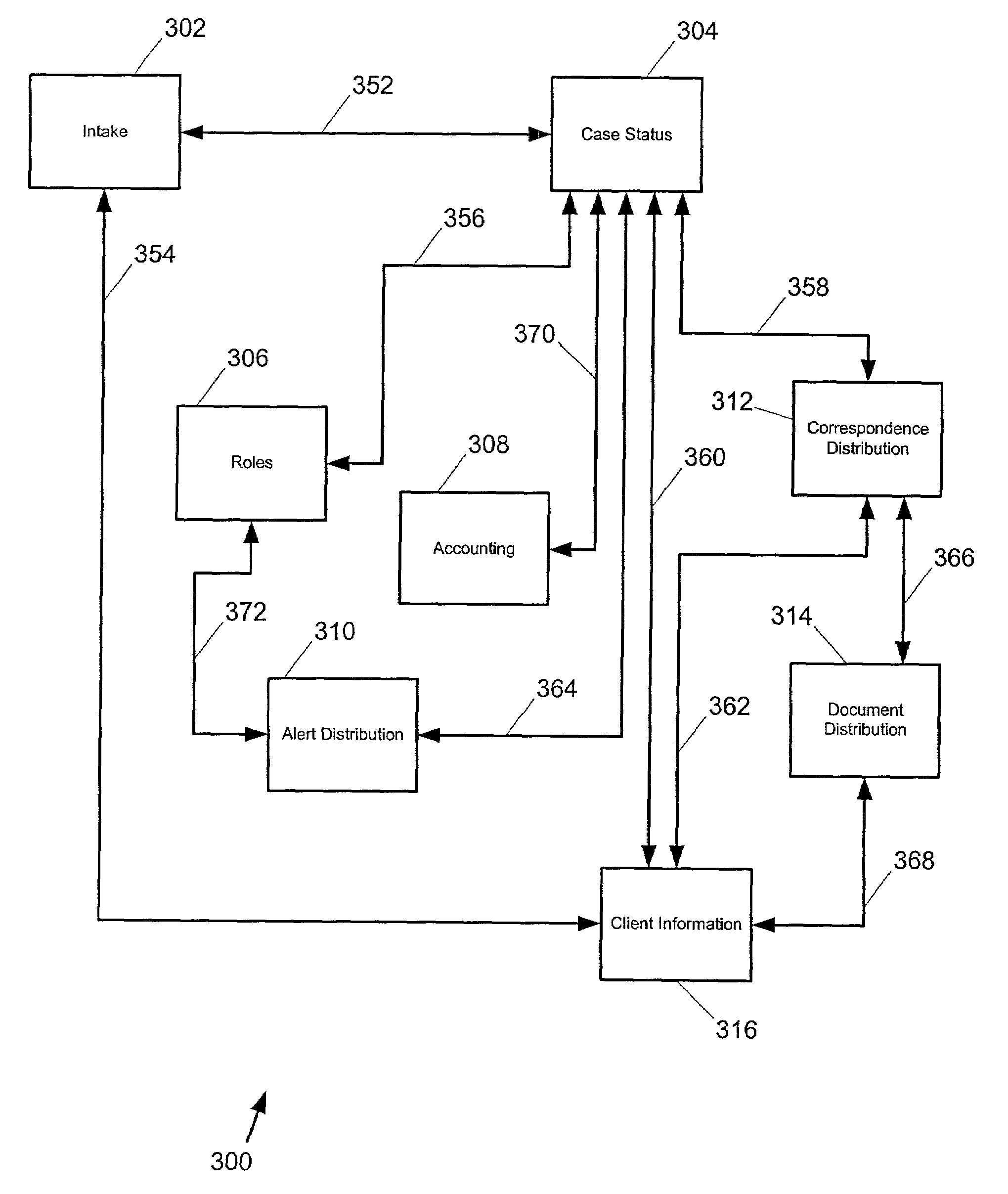
Data Operations. The Data Operation Category focuses on where patient demographic data comes from, how it is used in a system, and the staff members who have access to enter, modify, archive, or delete patient demographic data.
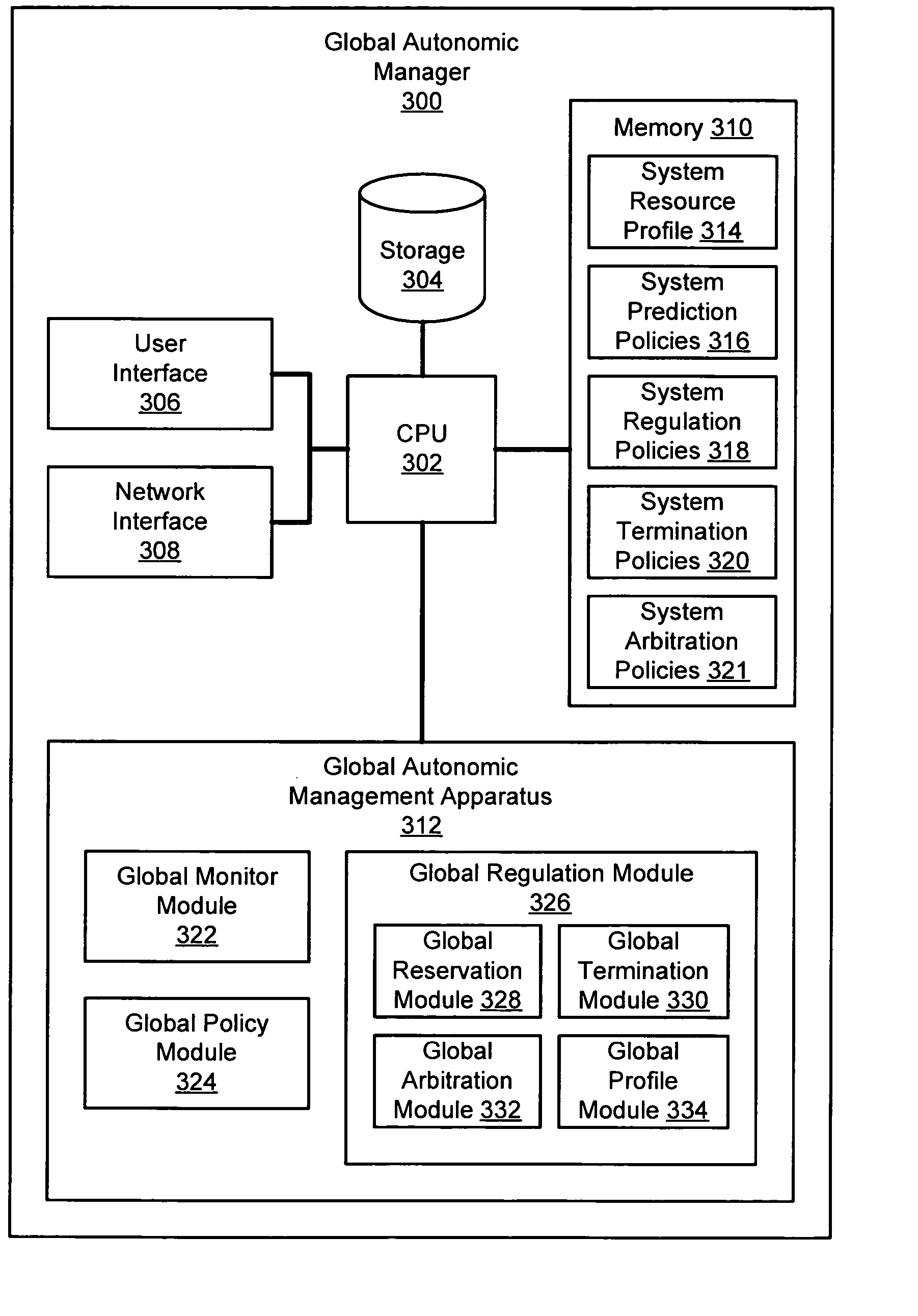
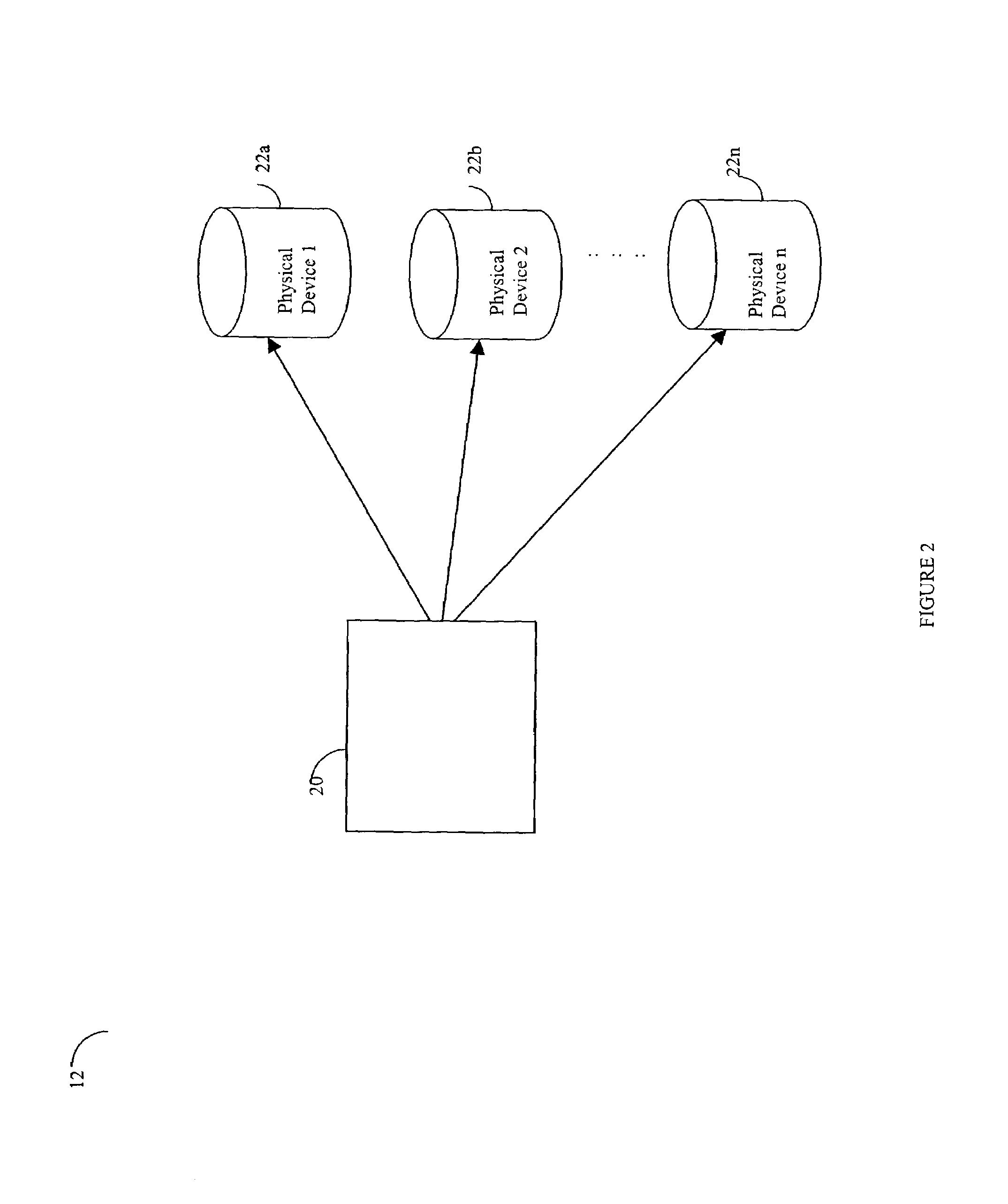
Apparatus, system, and method for autonomic control of grid system resources
ActiveUS20050131993A1Resource allocationMultiple digital computer combinationsAutomatic controlData operations
An apparatus, system, and method are disclosed for autonomic management of data operations and performance resources on a grid computing system. An autonomic management apparatus includes a monitor module, a policy module, and a regulation module. The monitor module is configured to monitor the grid computing system for a trigger event. The policy module is configured to access one of a plurality of system policies. Each of the plurality of system policies corresponds to an operational control parameter of a system resource of the grid computing system. The regulation module is configured to autonomically regulate the system resource in response to a recognized trigger event according to one of the plurality of system policies. The trigger event may be a prediction trigger event, an initiation trigger event, a regulation trigger event, or a termination trigger event.
Owner:WESTERN DIGITAL TECH INC
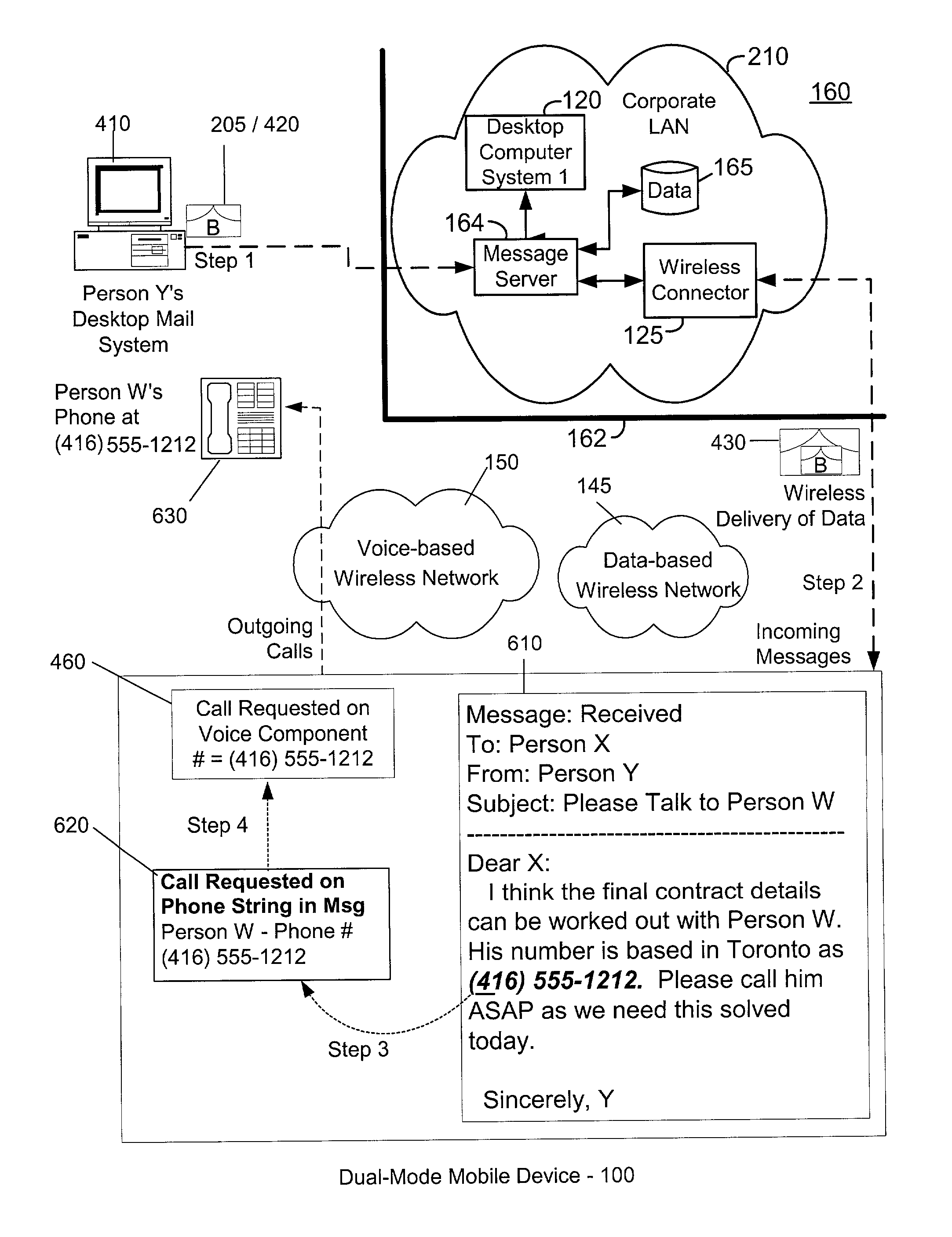
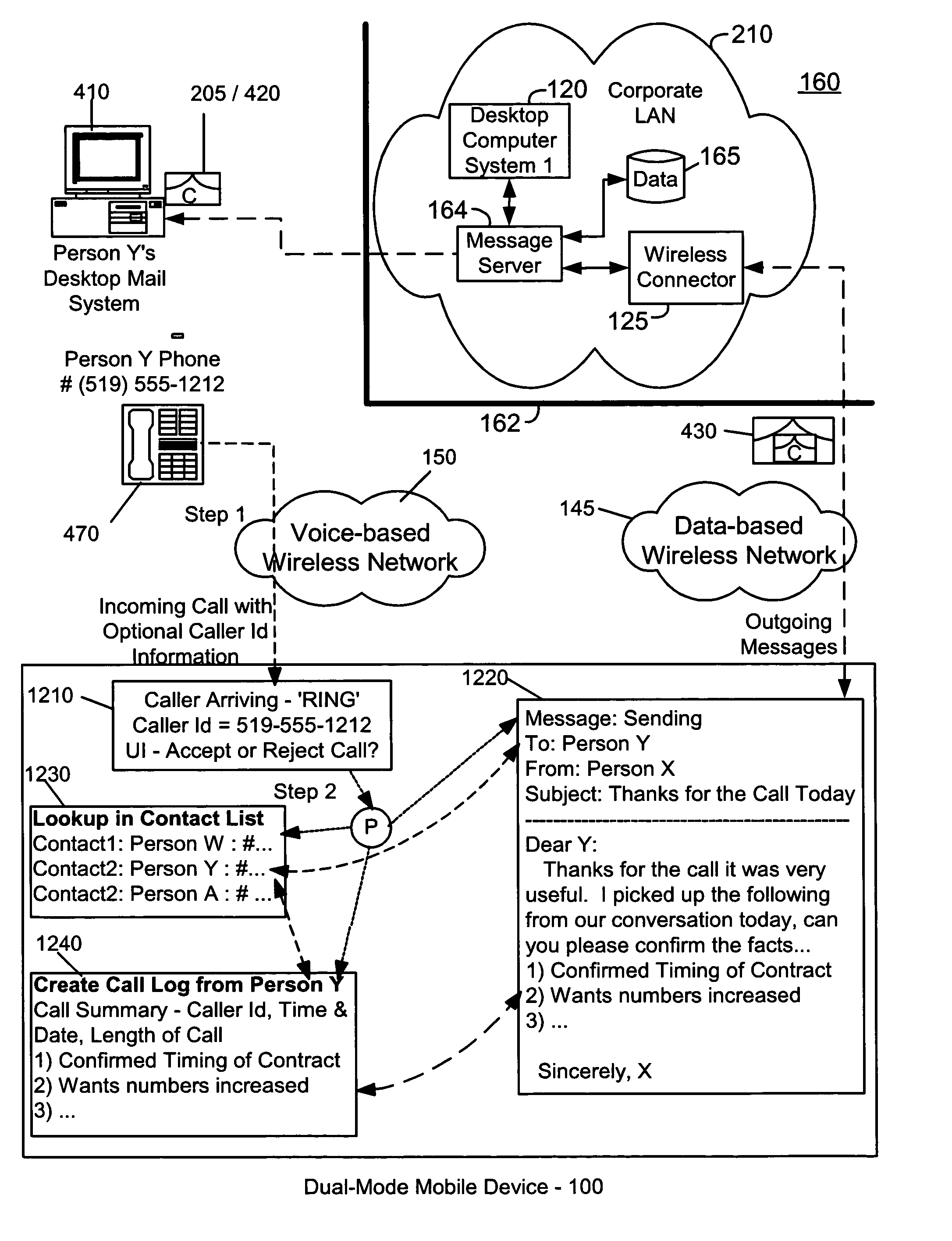
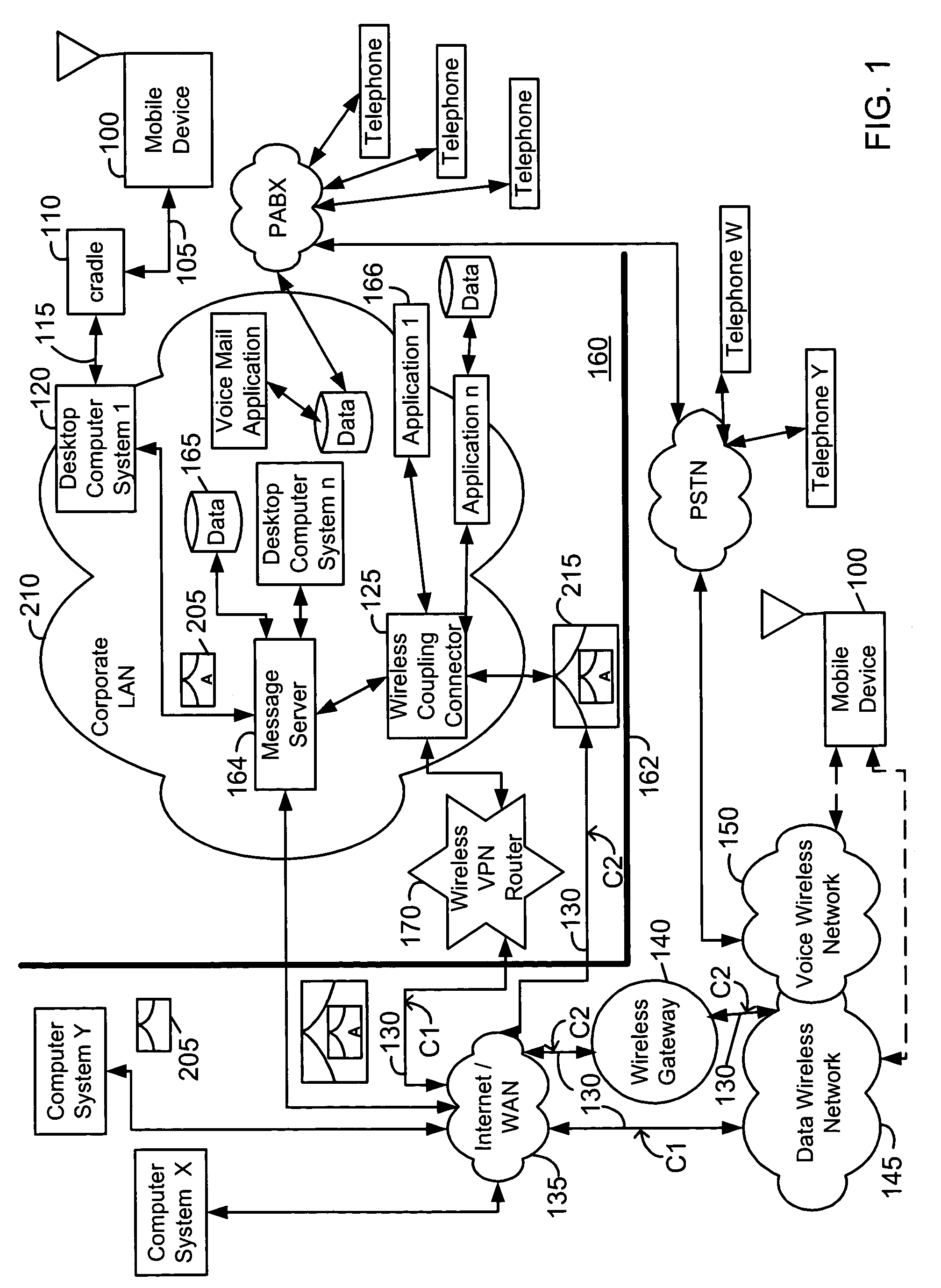
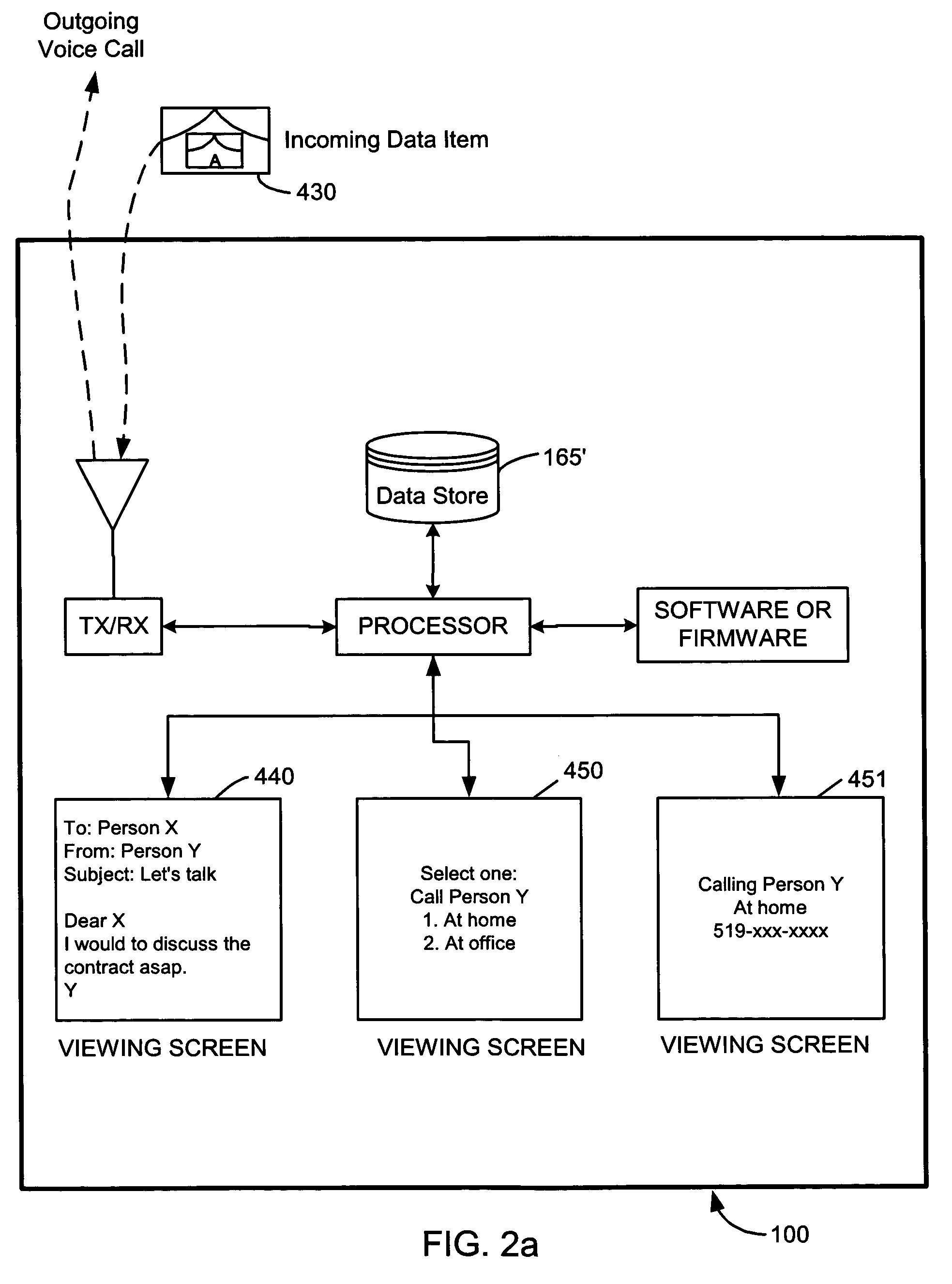
Advanced voice and data operations in a mobile data communication device
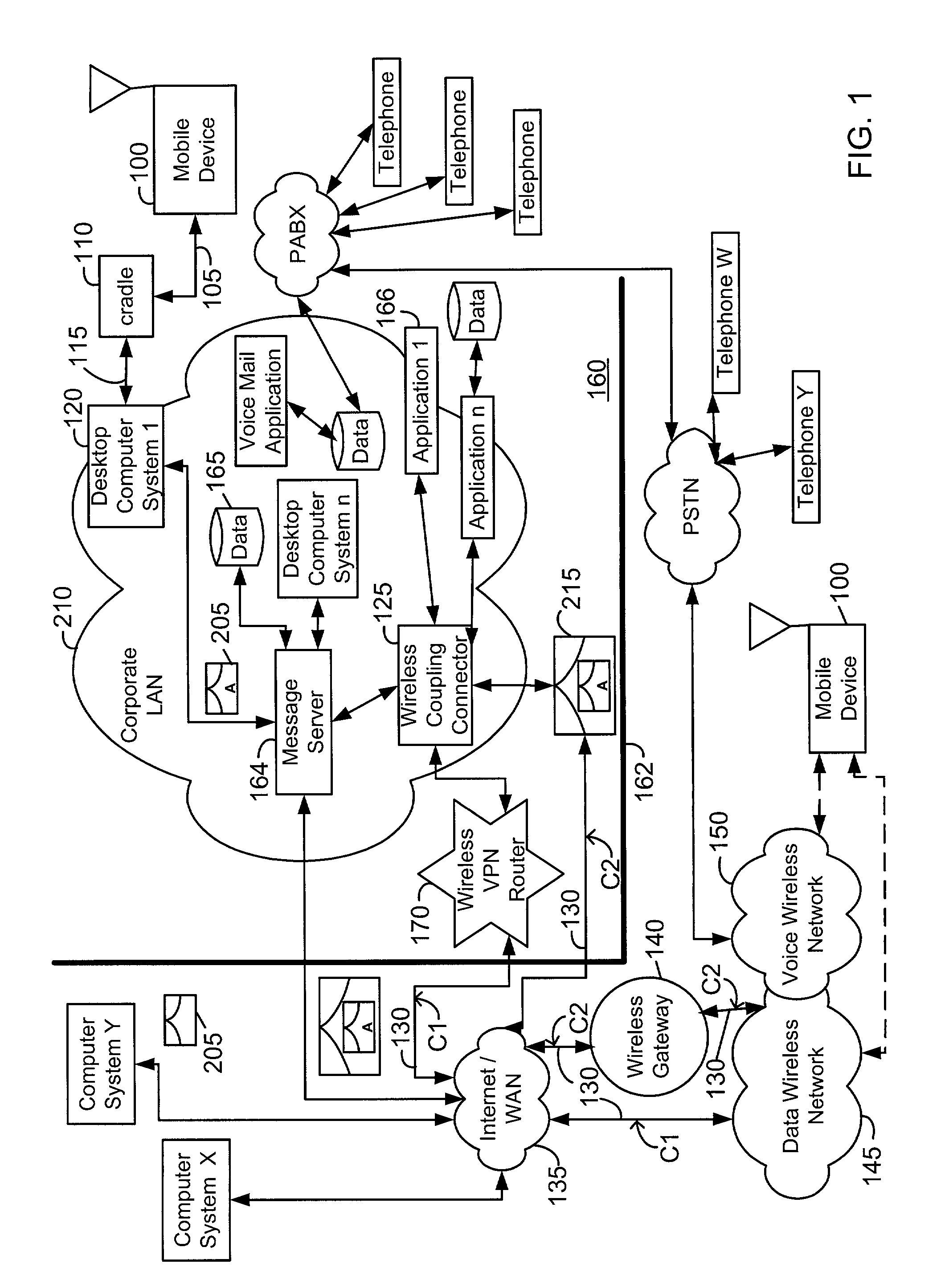
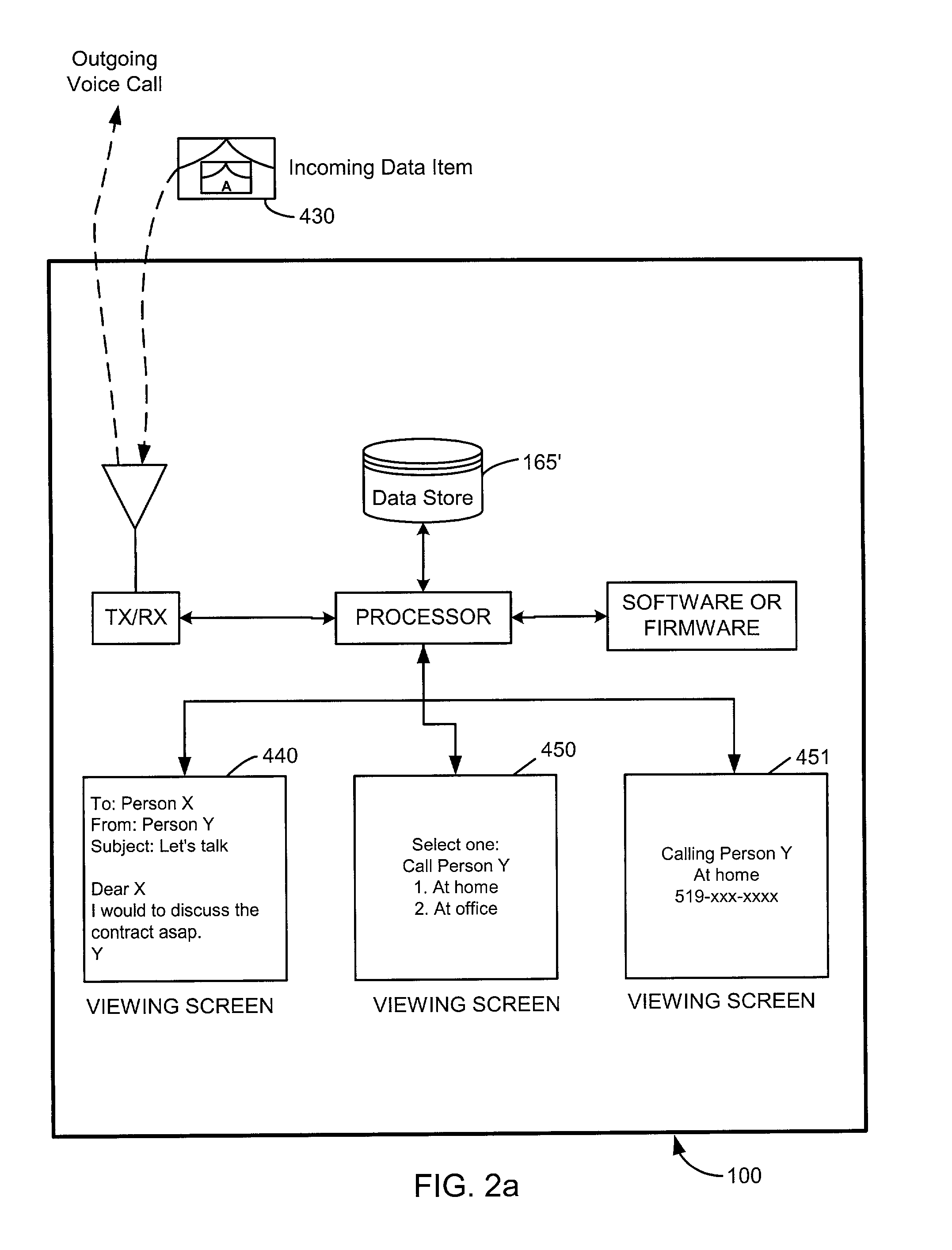
InactiveUS20020128036A1Data processing applicationsSpecial service for subscribersData operationsData center
A system and method for integrating voice and data operations into a single mobile device capable of simultaneously performing data and voice actions. The mobile device working in a network capable of exchanging both cell phone calls and data items to the mobile device. By wearing an earphone or an ear-bud device the user is capable of dealing with voice conversations while working with data centric information related to the current caller. By providing a data-centric device with voice capabilities there is a new range of features that allow incoming data events to trigger outgoing voice events.
Owner:MALIKIE INNOVATIONS LTD
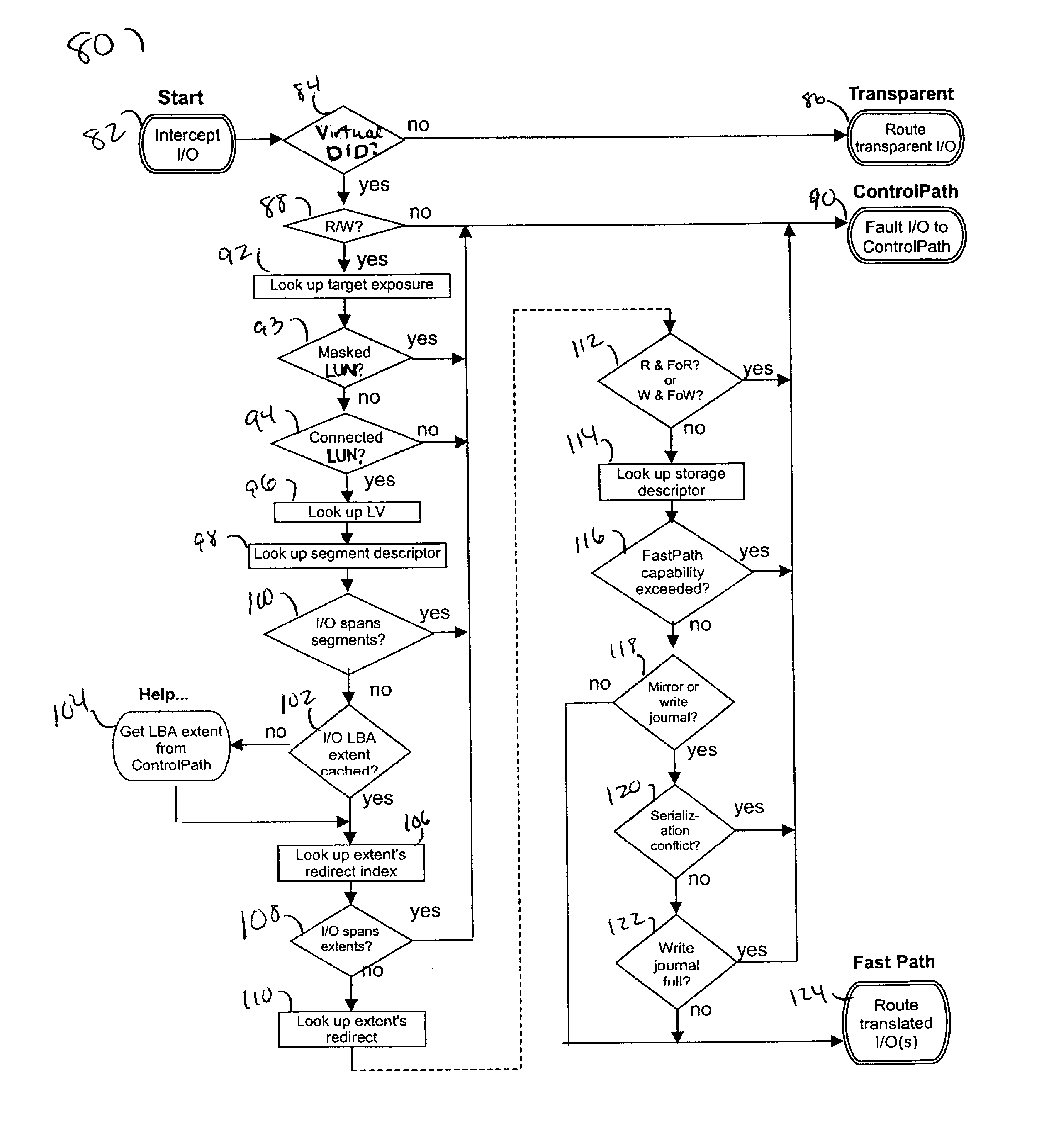
Locking technique for control and synchronization
InactiveUS6973549B1Digital data information retrievalMultiprogramming arrangementsFast pathLocking mechanism
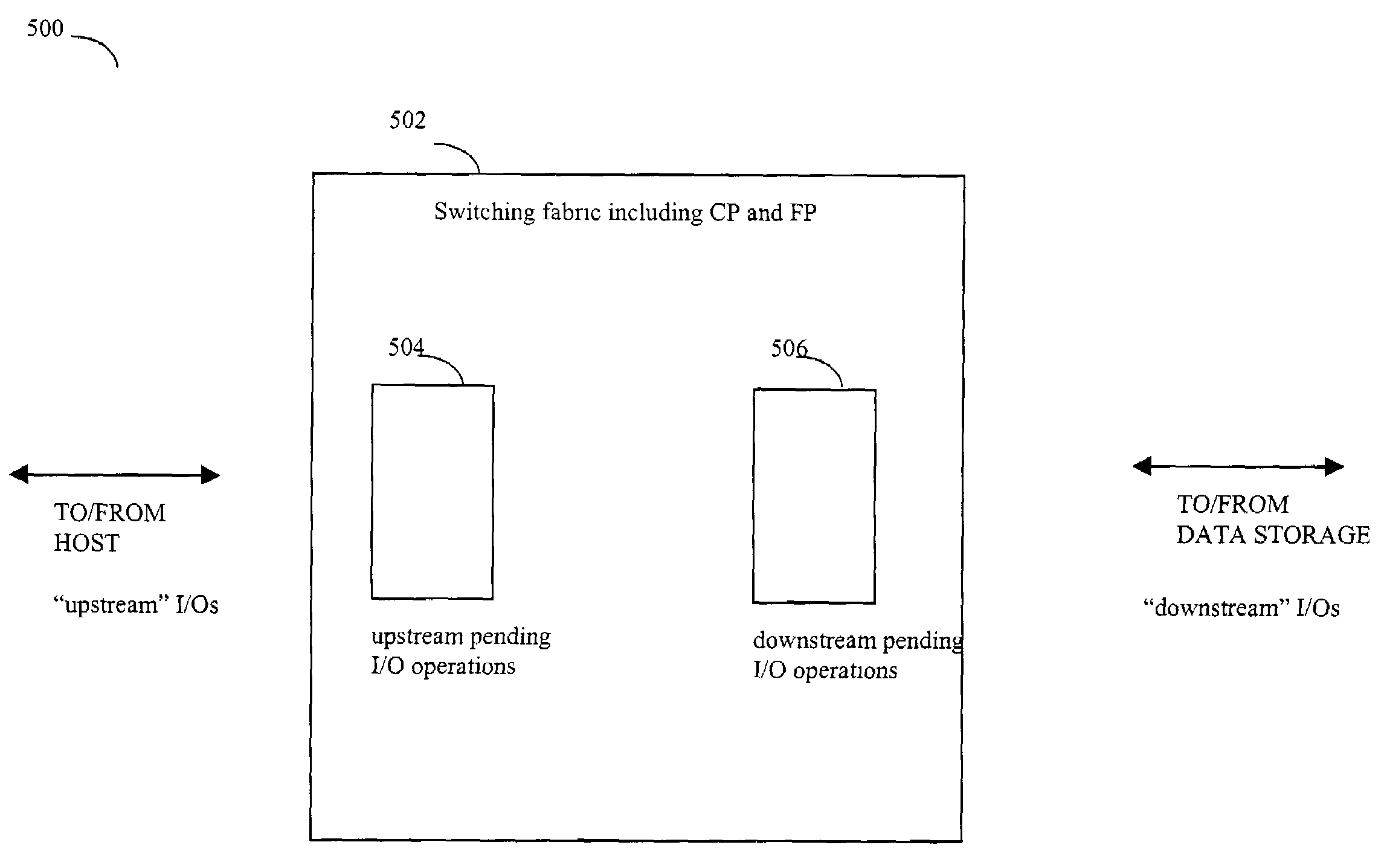
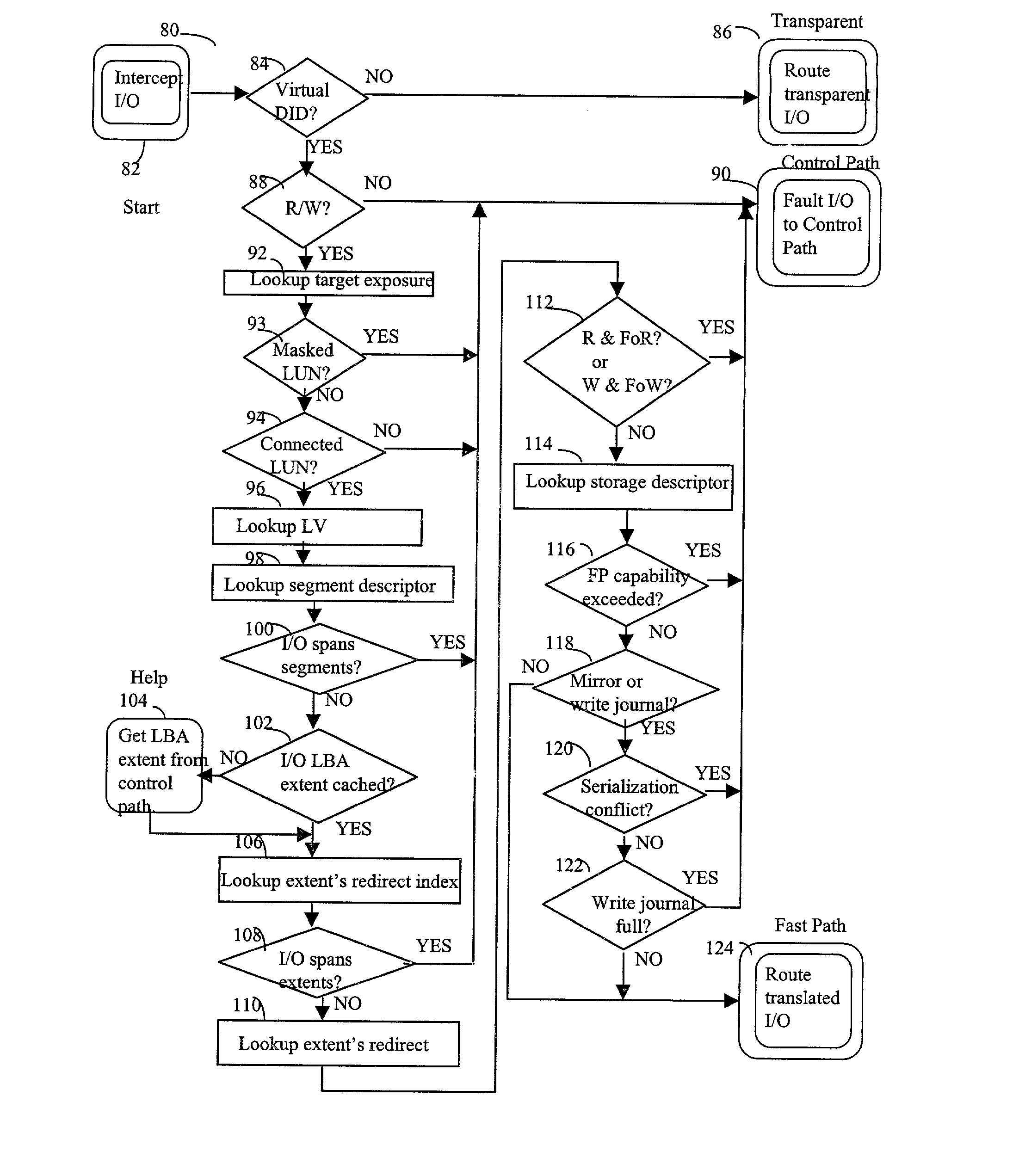
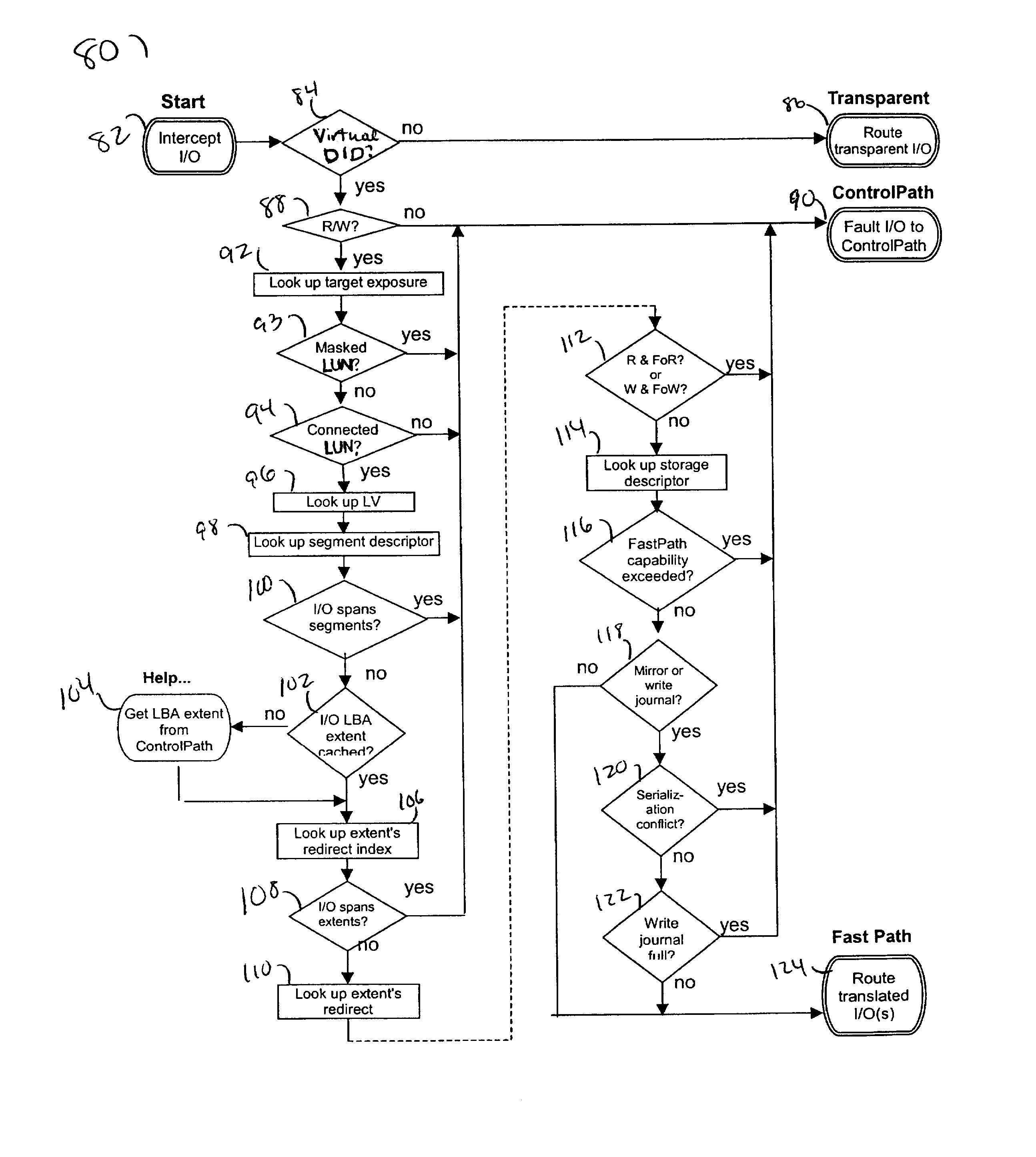
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
Intelligent device connection for wireless media ecosystem
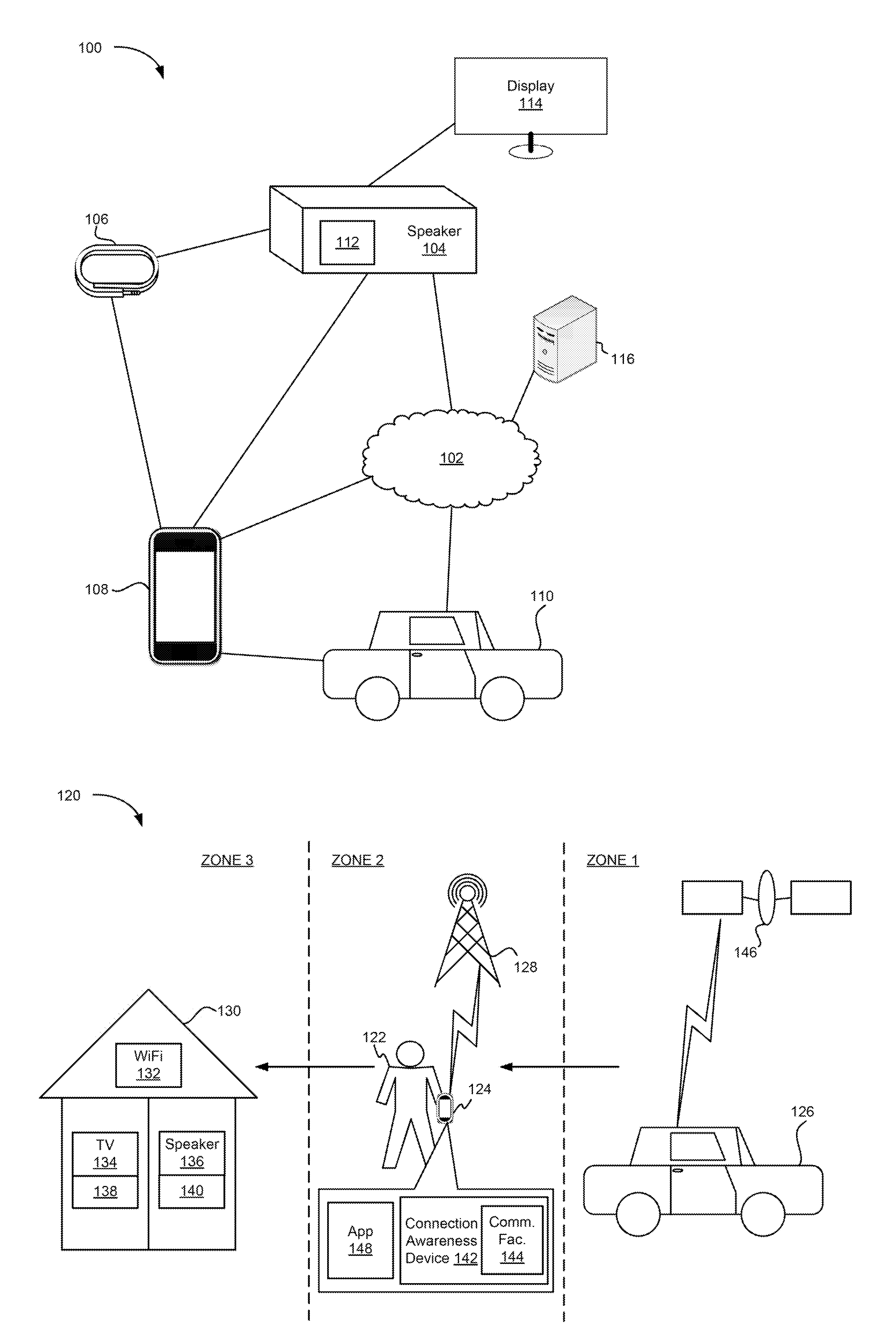
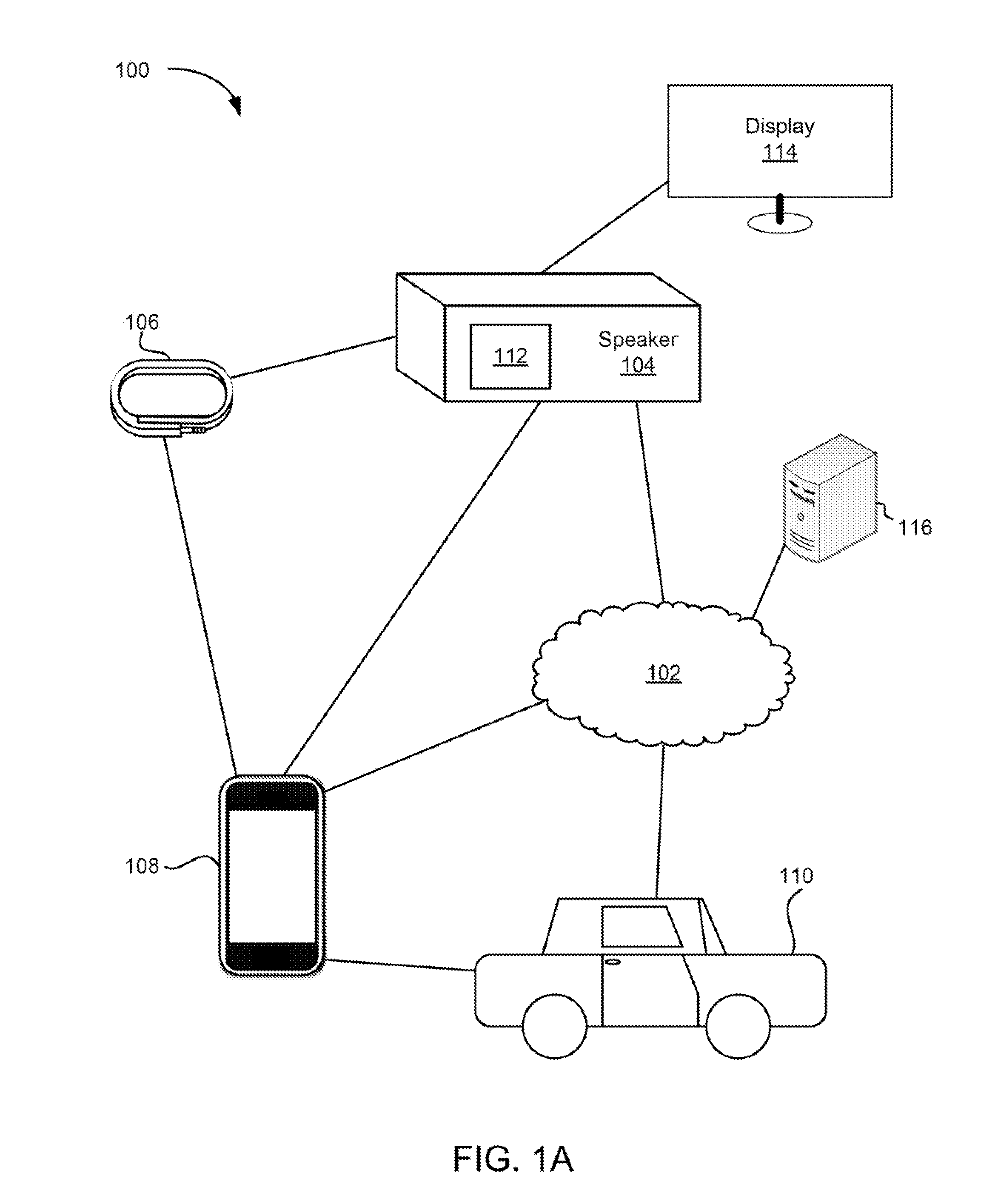
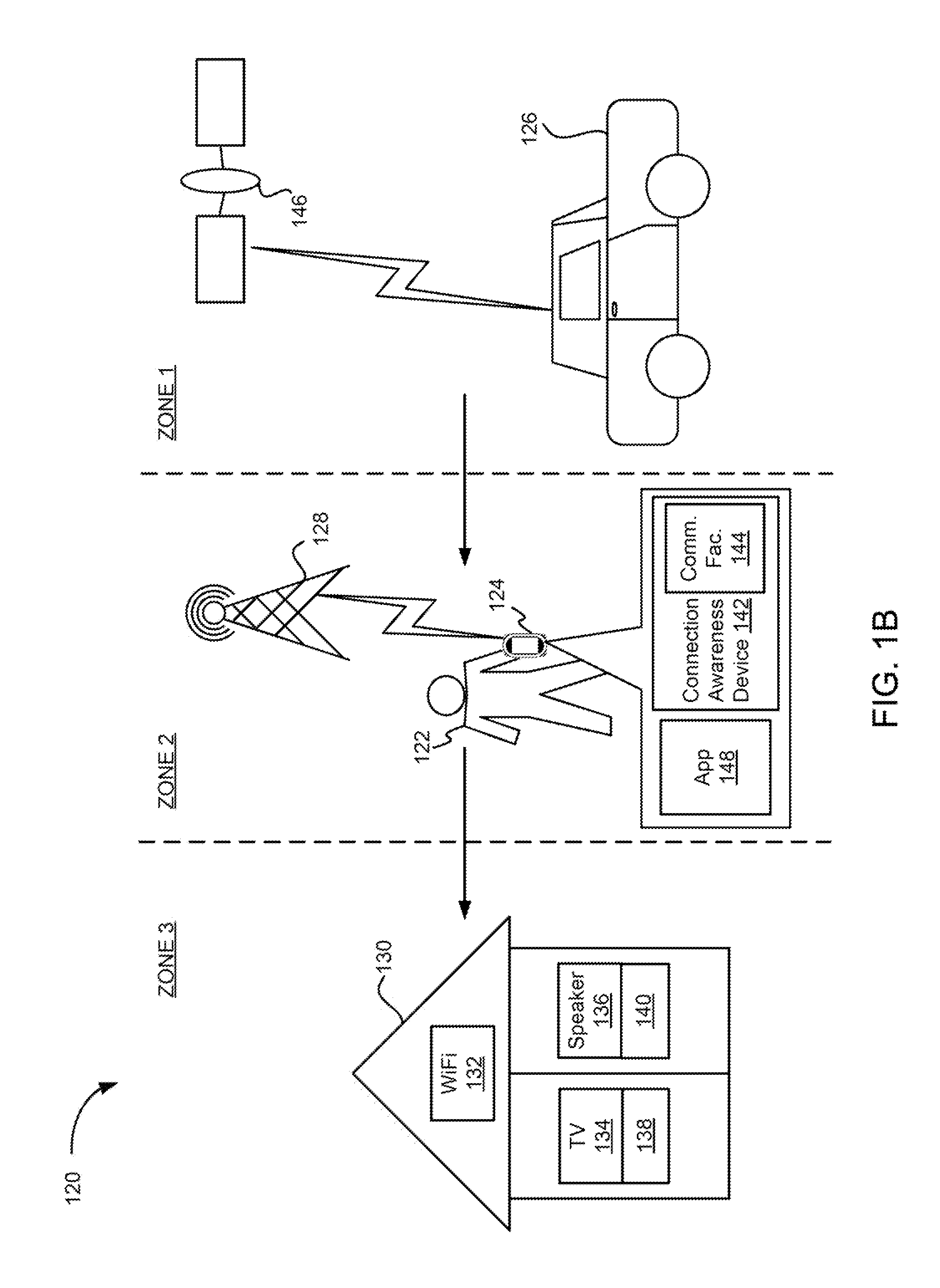
Techniques associated with intelligent device connection for wireless media ecosystem are described, including detecting, using an antenna implemented in a connection awareness device, a radio signal emitted by a wireless device, generating proximity data indicating a proximity of the wireless device to the antenna, providing the proximity data to an intelligent communication facility coupled to the antenna, determining the proximity passes within a threshold proximity, determining the wireless device is compatible with an output device coupled to the connection awareness device, sending to the wireless device data comprising a query associated with an operation, receiving a response indicating the wireless device is performing the operation, sending a first control signal to the output device, synchronizing a performance of the operation by the output device with another performance of the operation by the wireless device, and sending a second control signal to the wireless device to stop performing the operation.
Owner:JAWBONE INNOVATIONS LLC
Target information generation and ad server
InactiveUS7155508B2Increase ratingsGreater profit margin for ad companiesDigital computer detailsTransmissionMass storageApplication software
An advertisement selection and delivery system for selecting advertisements based on profile information and rendering the advertisements as accessible to a user operating a network-capable appliance connected to a data-packet-network is provided. The system comprises, a first server node connected to the network, the first server node functioning as a user access point on the network, a mass storage repository accessible to the first server node, the repository for storing and serving user profile data, a second server node connected to the network, the second server node for generating user preference data, at least one advertisement server connected to the network, the advertisement server for serving advertisement data, a software application for generating user preference lists and performing advertisement selection and at least one network-capable appliance connected to the network the network-capable appliance for receiving the advertisement data. A user operating the network-capable appliance accesses the first server node and receives the advertisement data, the advertisement data selected for service by matching the user preference data to stored advertisements and rendered accessible to the user during the time of user access to the system from the network-capable appliance.
Owner:YODLEE COM INC
Churn prediction and management system
ActiveUS20070156673A1Avoid erosionFacilitates efforts to retain high profitability customersSpecial data processing applicationsMarketingCustomer attritionData operations
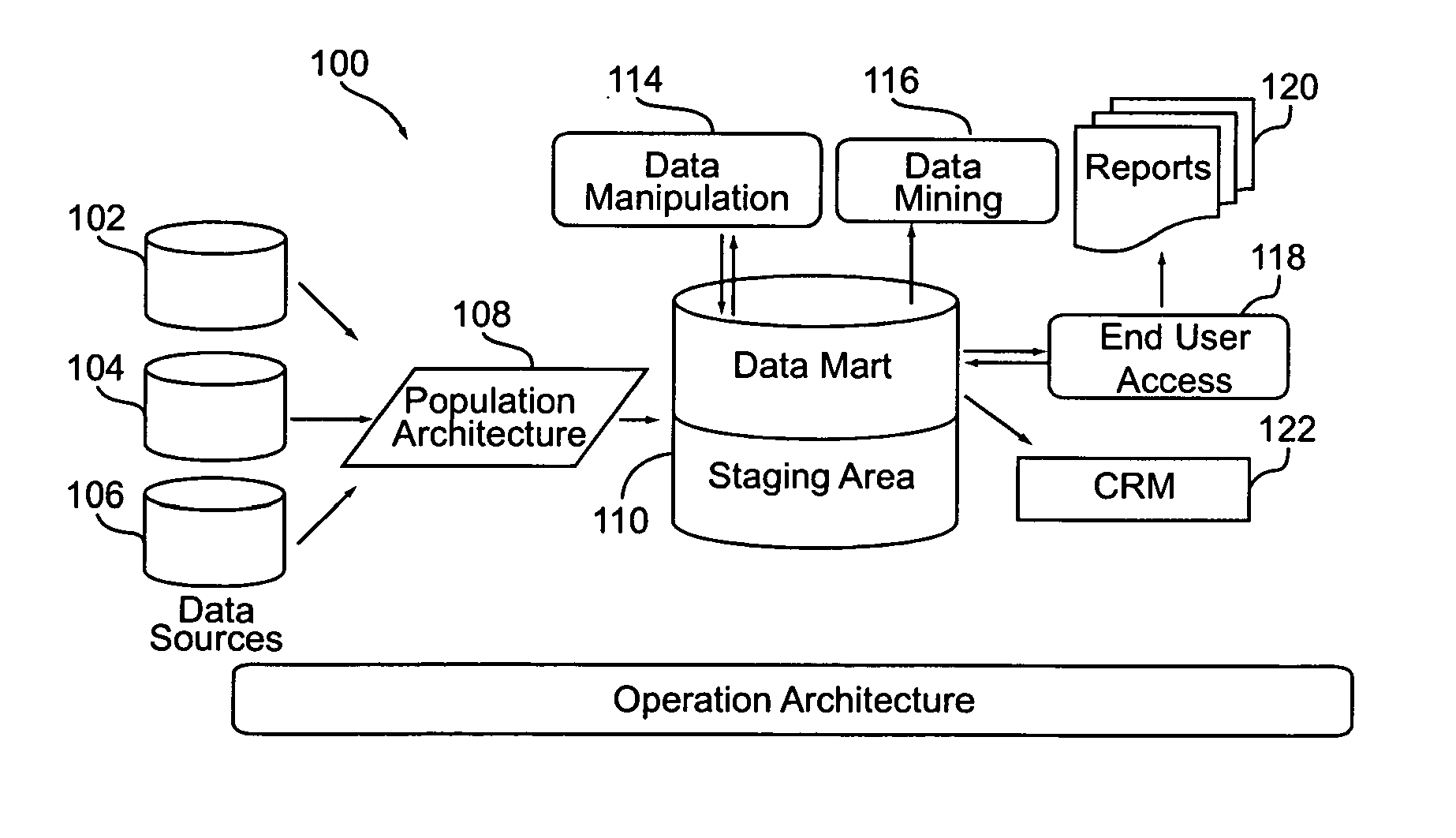
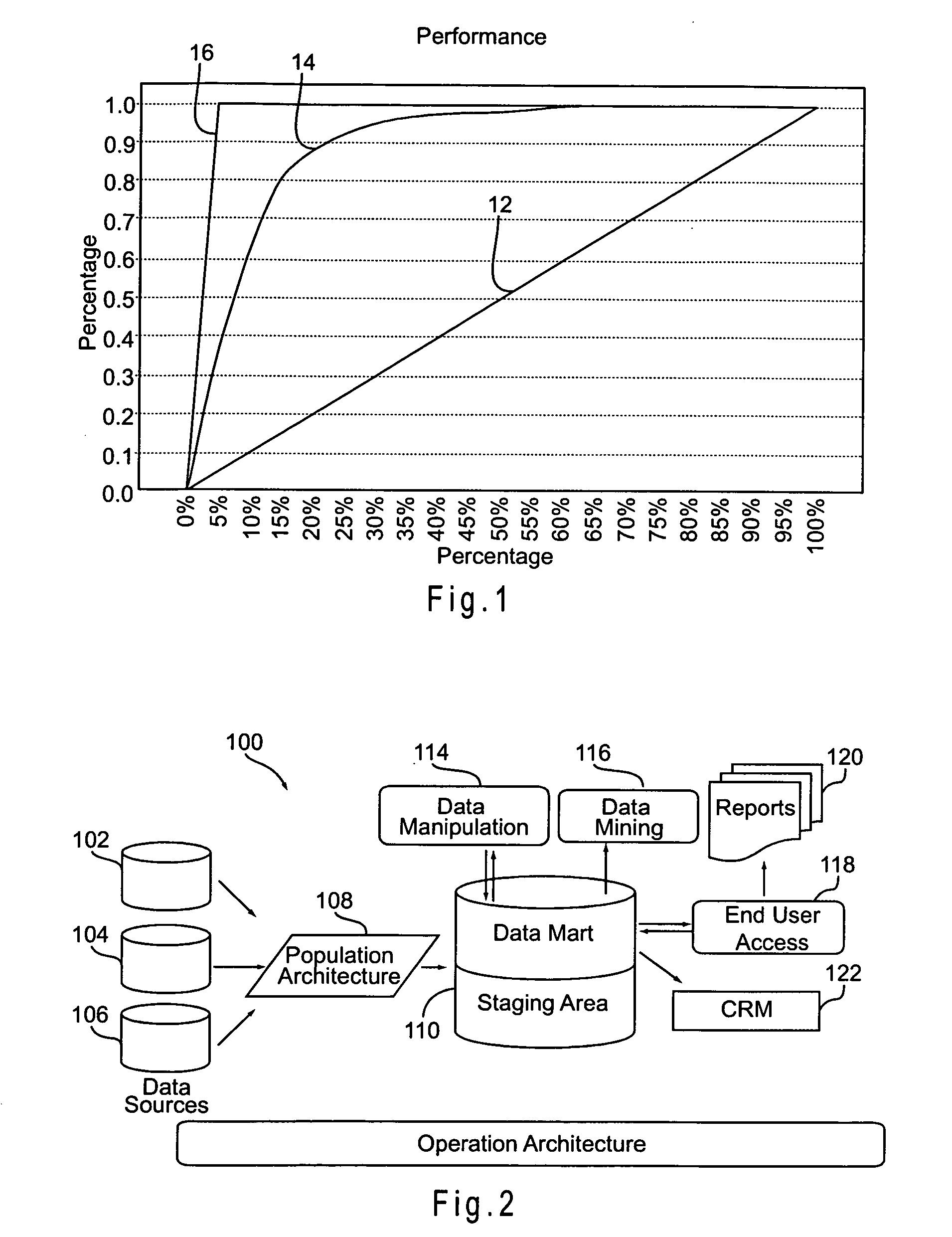
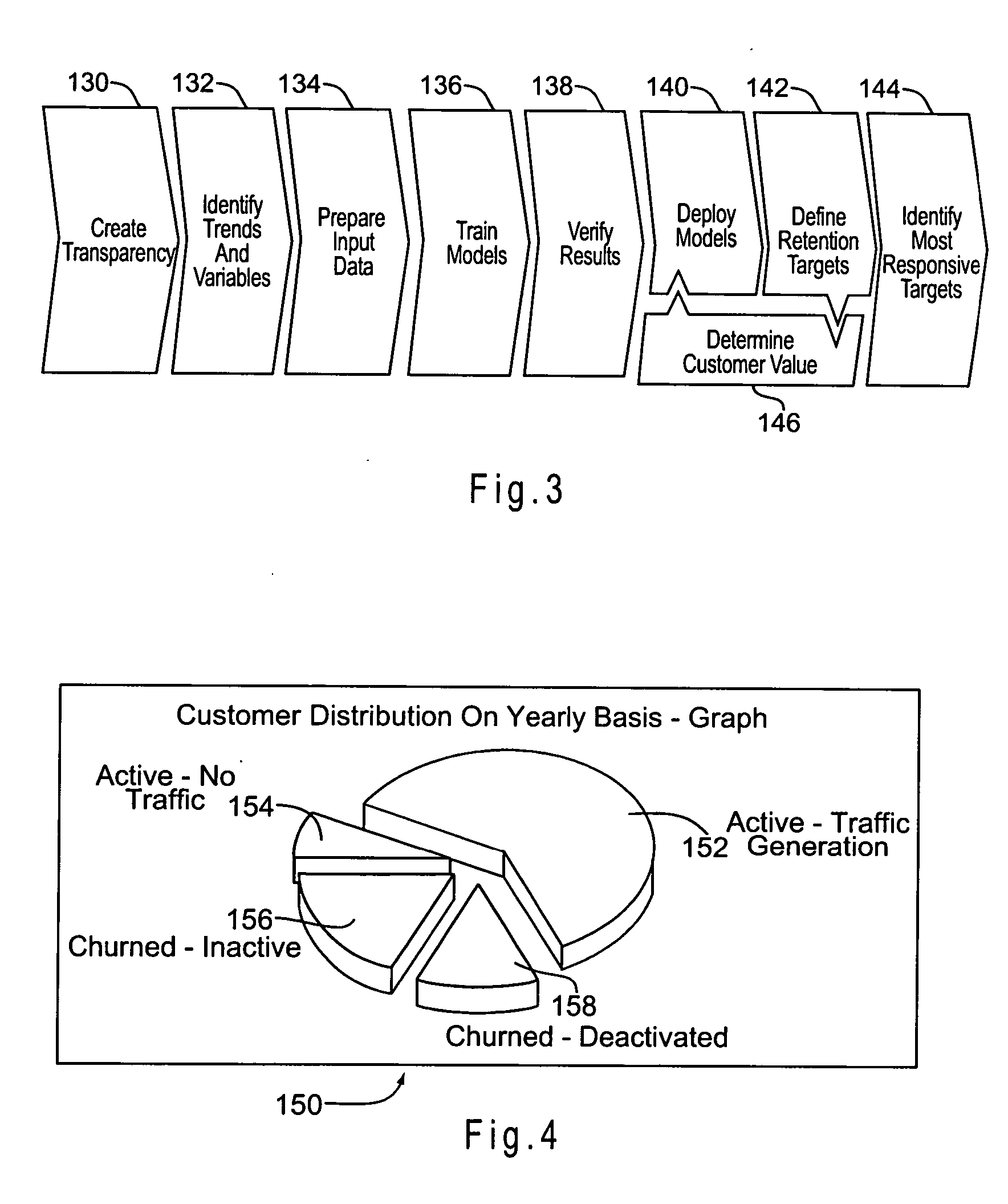
A system and method for managing churn among the customers of a business is provided. The system and method provide for an analysis of the causes of customer churn and identifies customers who are most likely to churn in the future. Identifying likely churners allows appropriate steps to be taken to prevent customers who are likely to churn from actually churning. The system included a dedicated data mart, a population architecture, a data manipulation module, a data mining tool and an end user access module for accessing results and preparing preconfigured reports. The method includes adopting an appropriate definition of churn, analyzing historical customer to identify significant trends and variables, preparing data for data mining, training a prediction model, verifying the results, deploying the model, defining retention targets, and identifying the most responsive targets.
Owner:ACCENTURE GLOBAL SERVICES LTD
Method and storage and manipulation of storage system metrics
InactiveUS7082441B1Promote generationEasy accessData processing applicationsError detection/correctionData operationsData description
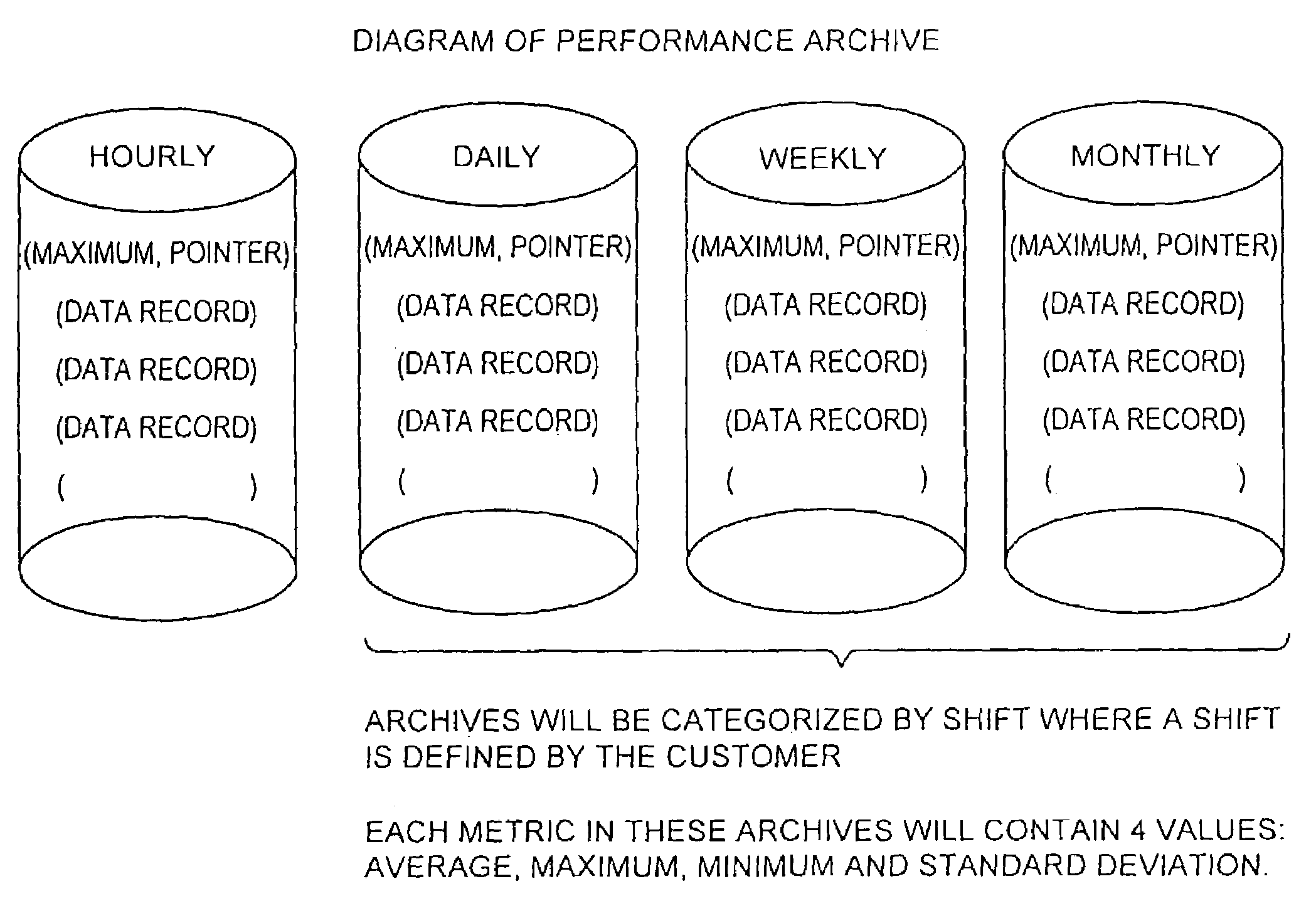
A method for storage and manipulation of storage system metrics incorporates a self-describing format wherein each data file includes a header block that contains the description and order of the periodic data. The header block is followed by a data block in which the data items are presented in the order that they appear in the data description block for that category. Two types of data are managed, including Base Metrics and Derived Metrics. Base Metrics are metrics that appear in the data file sent by an agent. Derived Metrics are computed based on a set of functions that derive new metrics from the base metrics as well as from previously defined derived metrics. A subset of the data block or file describes the configuration of the storage system at the time that the data file was created. Thus the data file contains a header section that in addition to describing the metrics also describes the configuration. A performance view component a user interface that facilitates access to the archives, and data manipulation effecting enhanced performance analysis, workload characterization and capacity planning. The performance view component facilitates generation of factory and user defined views of monitored metrics / parameters. Metrics from a storage system can be correlated using the performance view features, and parameters across machines can be correlated as well. System configuration(s) can be viewed and changed via the performance view user interface.
Owner:EMC IP HLDG CO LLC
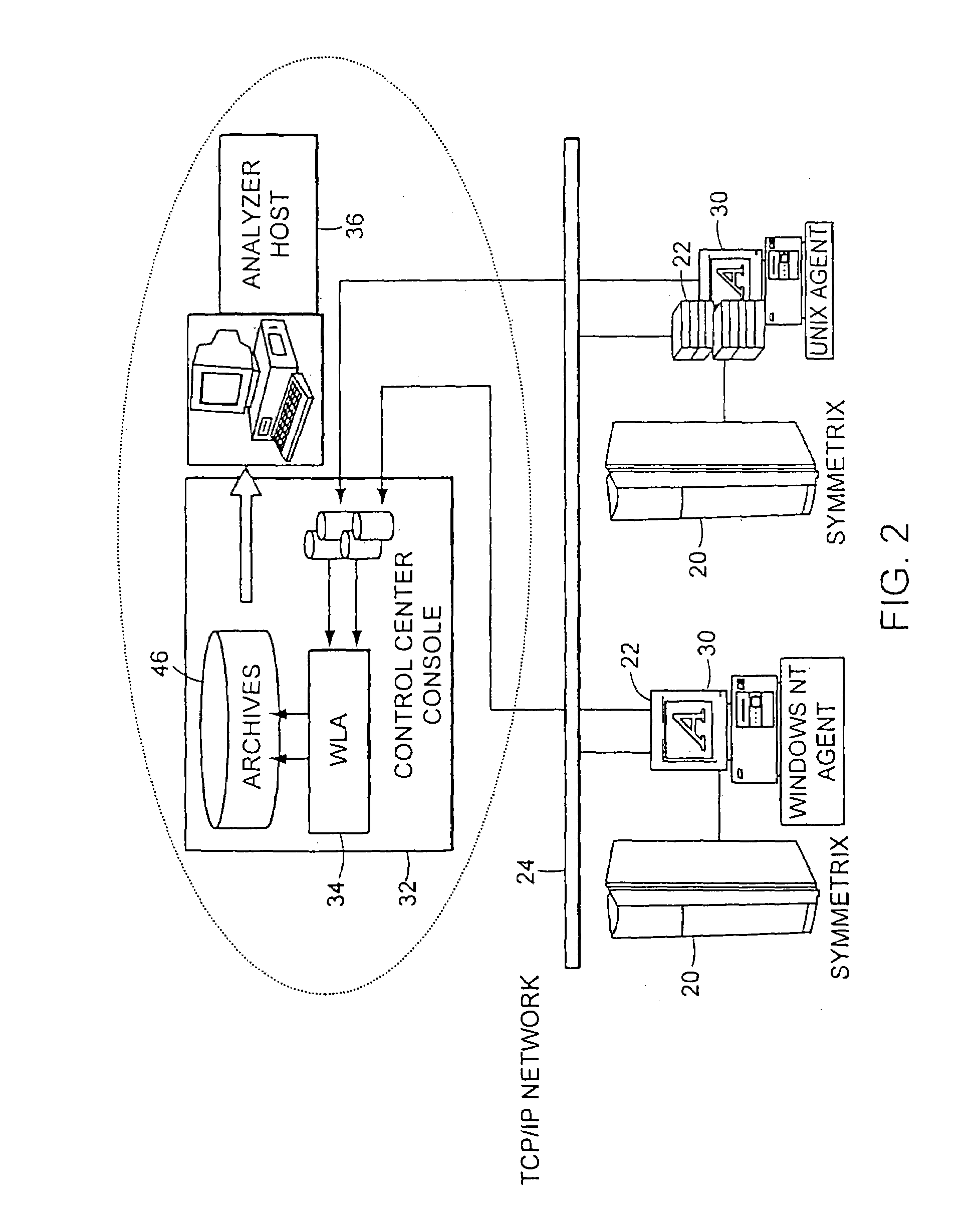
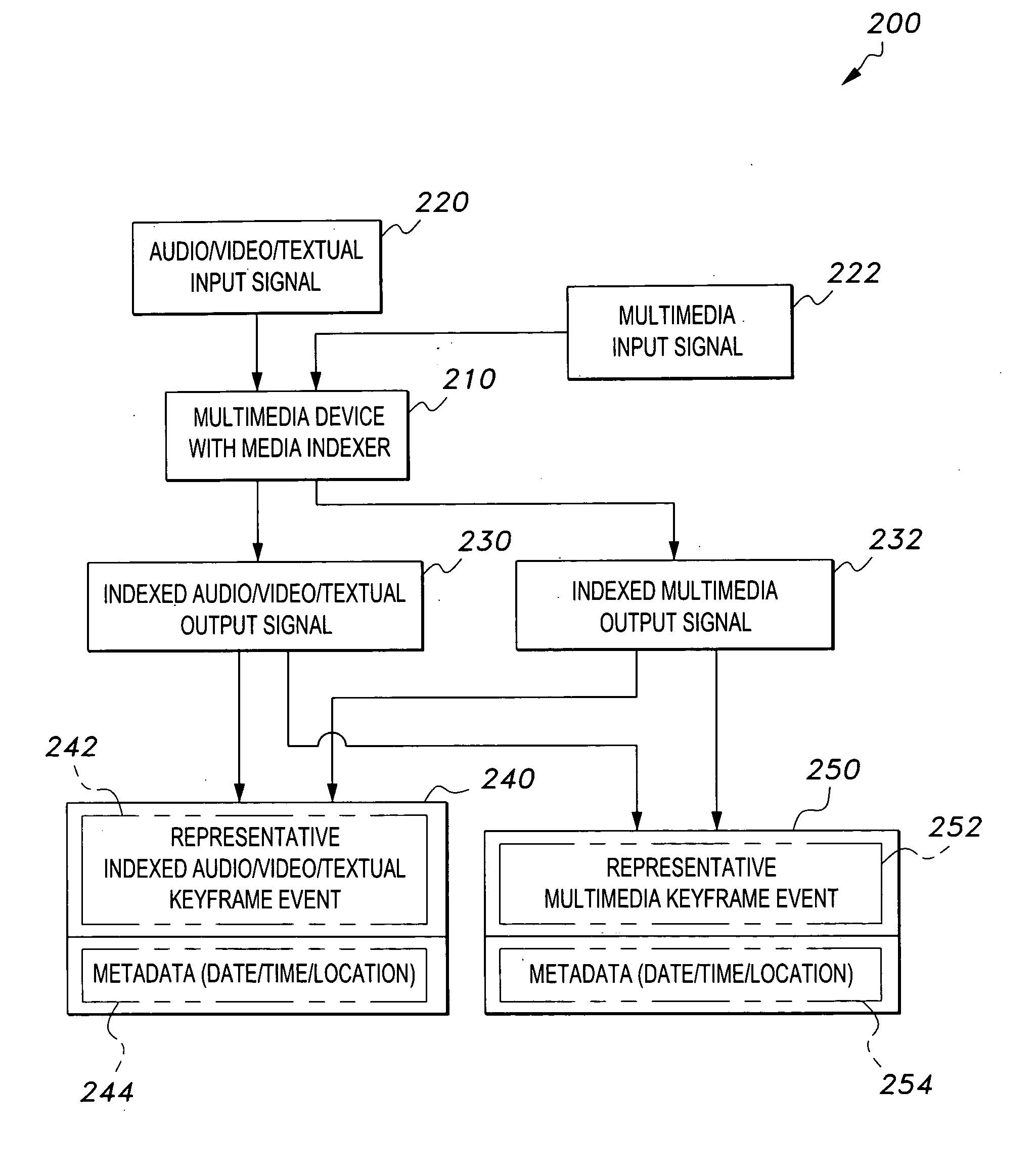
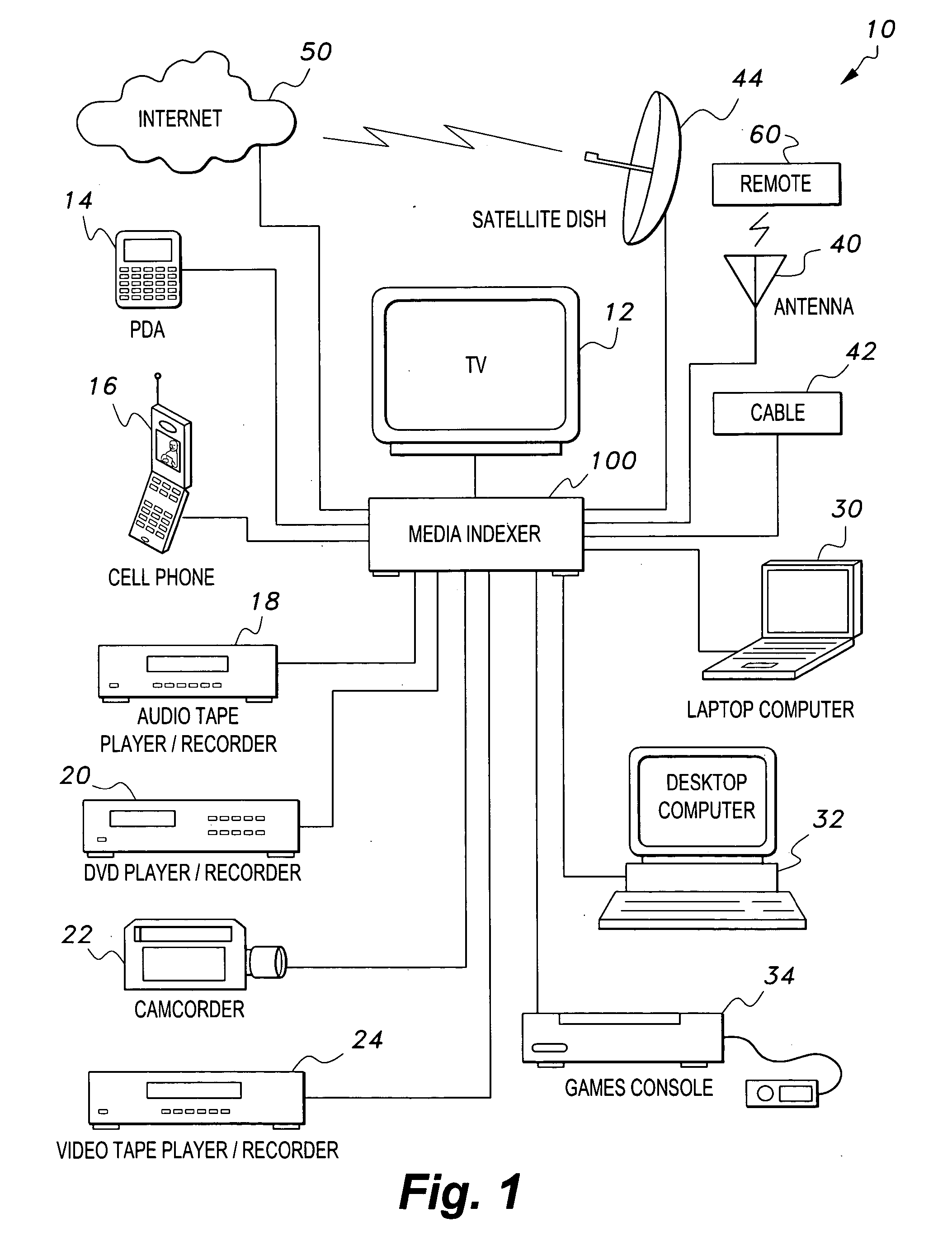
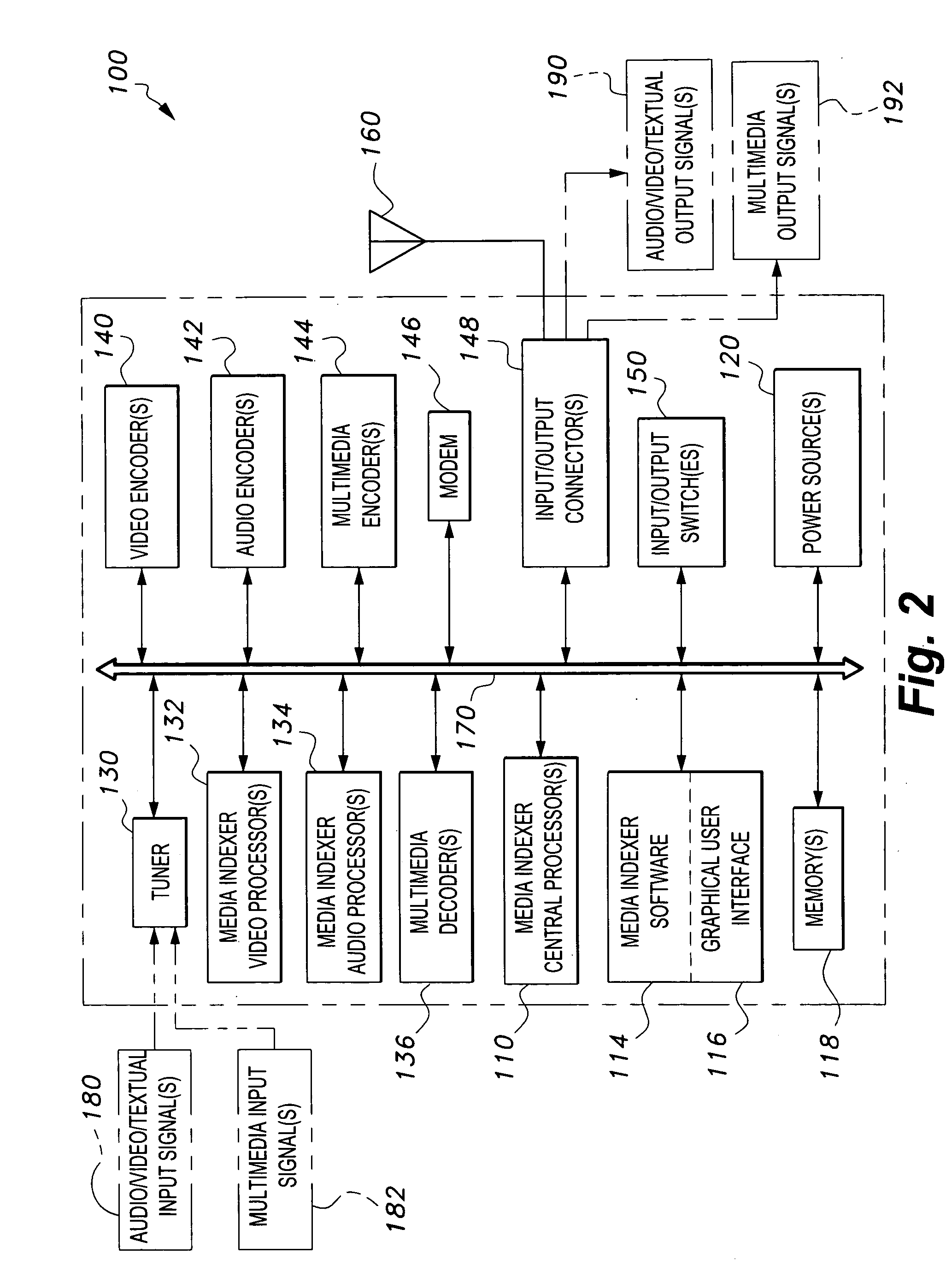
Media indexer
InactiveUS20050033758A1Inexpensive and dependable and fully effectiveTelevision system detailsPeptide/protein ingredientsData operationsFile sharing
A media indexer method, a media indexer, and / or a media indexer computer useable medium. The media indexer includes a central processor and a memory carrying thereon media indexer software which carries out steps including receiving a media signal, identifying keyframes of the media signal, establishing metadata for each identified keyframe, tagging each identified keyframe with metadata established for the associated keyframe, and outputting the media signal in a form unchanged from the received media signal, and / or a form including identified keyframes of the received media signal, each identified keyframe including a representative media keyframe event with metadata associated with the corresponding media keyframe event. The media indexer can generate parallel index signals that are synchronized to the time rate of the received media signal, and can input and output data using standard compatible file formats for file sharing and data manipulations with other compatible files and software.
Owner:BAXTER BRENT A
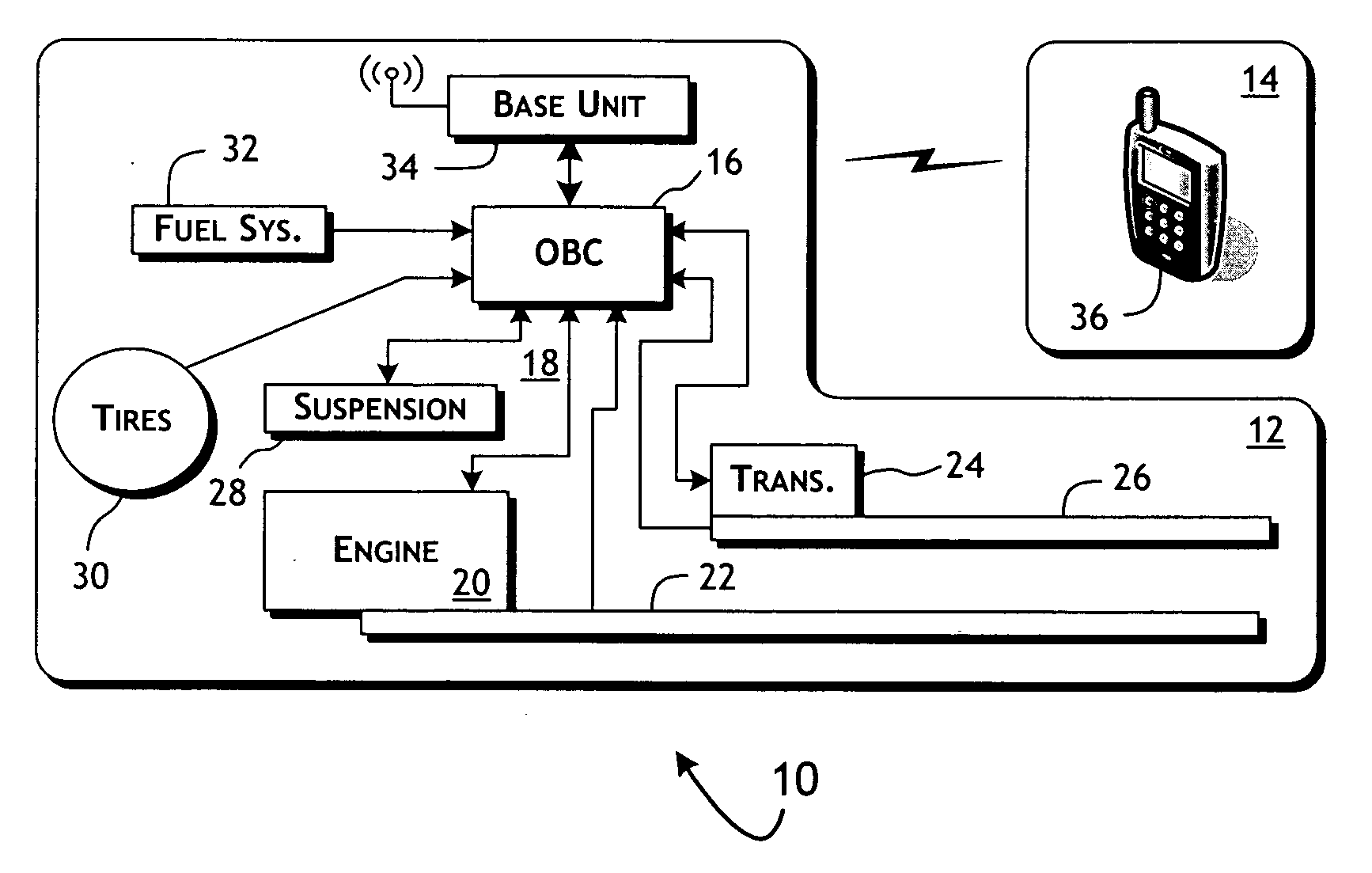
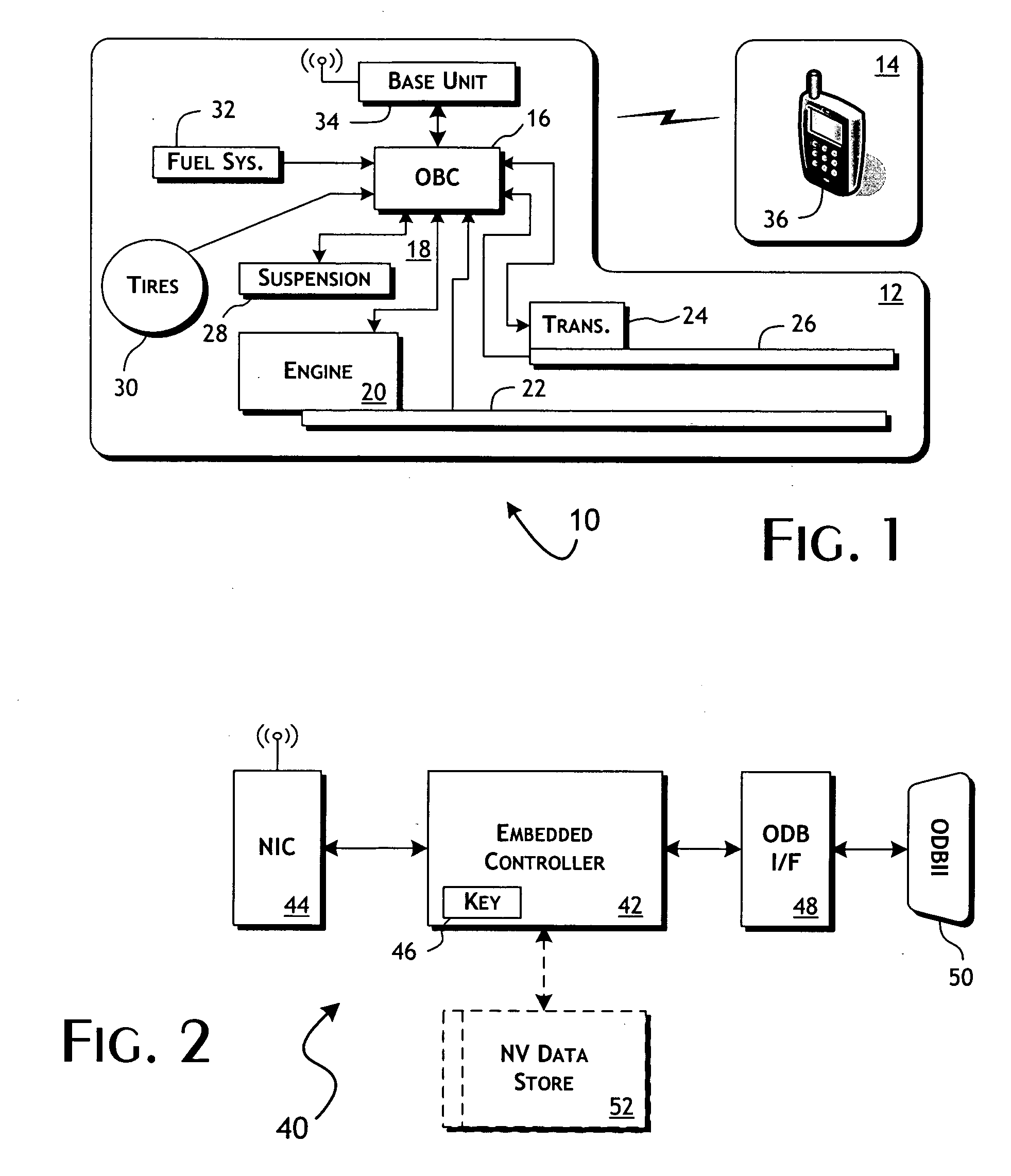
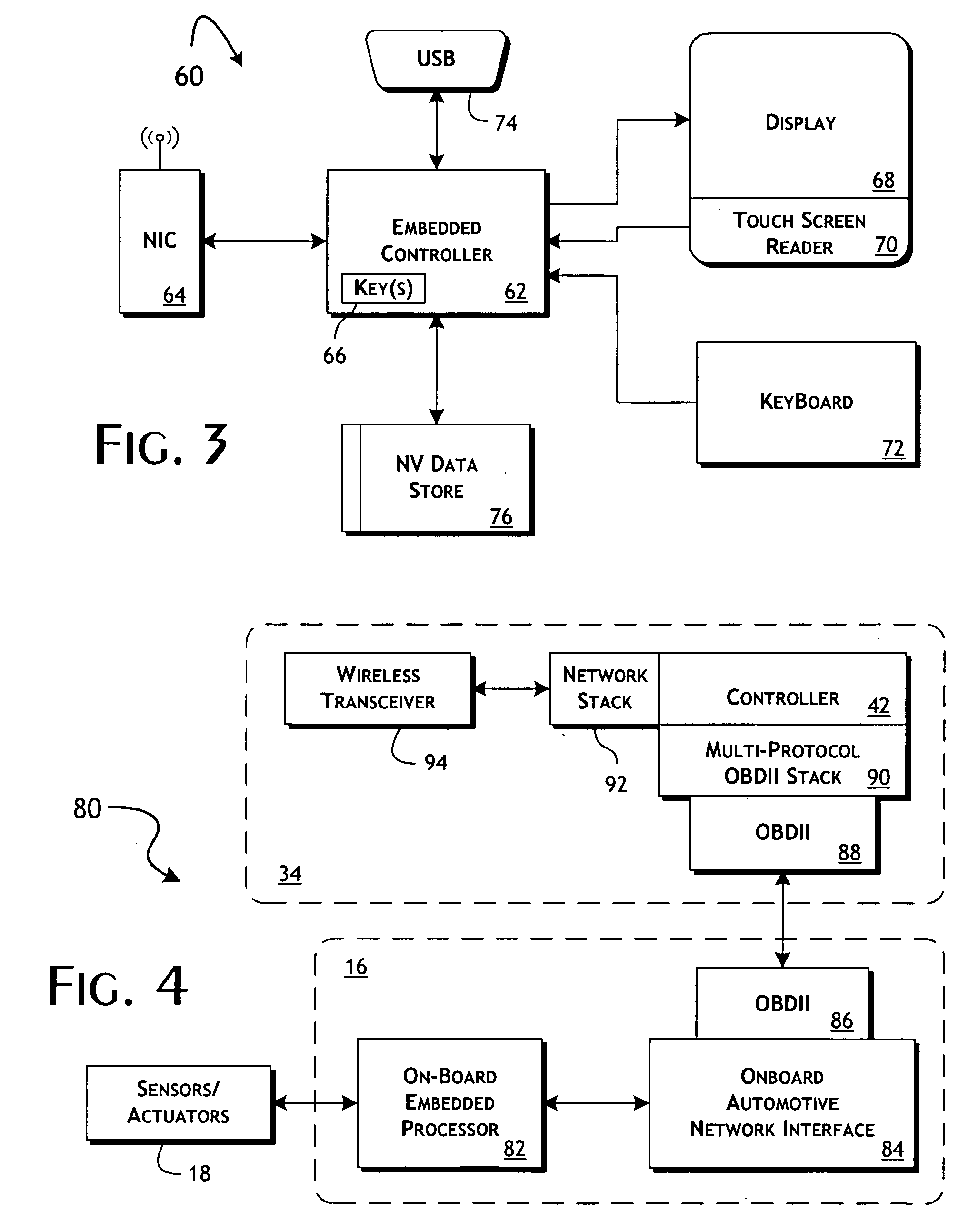
System and methods of performing real-time on-board automotive telemetry analysis and reporting
InactiveUS20060229777A1Readily and safely performedImprove abilitiesVehicle testingInternal-combustion engine testingDiagnostic testControl system
Active diagnosis of current operating and potential fault conditions in the operation of the vehicle is implemented using a diagnostic controller interoperating with an on-board vehicle control system as installed within a vehicle. The diagnostic controller supports autonomous execution of diagnostic tests initiated dependent on the operational state of the vehicle. The control system includes a diagnostics control manager that autonomously selects test routines for execution at defined operational states, including in-service operational states, a monitor, responsive to sensor data retrieved in real-time from the on-board vehicle control system, operative to detect a current instance of the in-service operational state of the vehicle, and a diagnostic test scheduler operative to initiate execution of the diagnostic test routine upon detection of the current instance of the in-service operational state of the vehicle.
Owner:HUDSON MICHAEL D +1
Fast path caching
InactiveUS20030140209A1Input/output to record carriersMemory adressing/allocation/relocationFast pathData operations
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
Vehicle communication, analysis and operation system
InactiveUS20130024060A1Instruments for road network navigationDigital data processing detailsFuel conservationOperational system
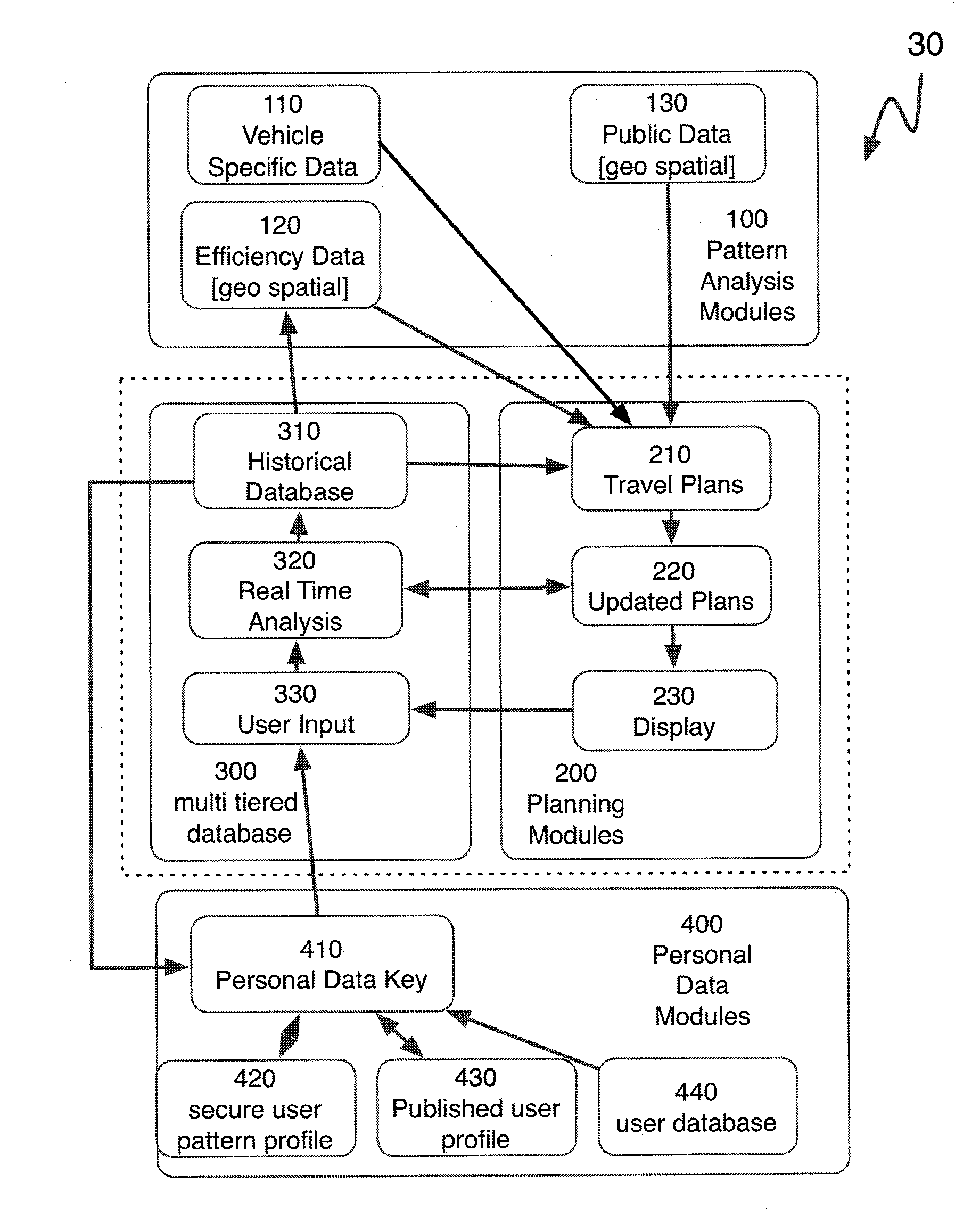
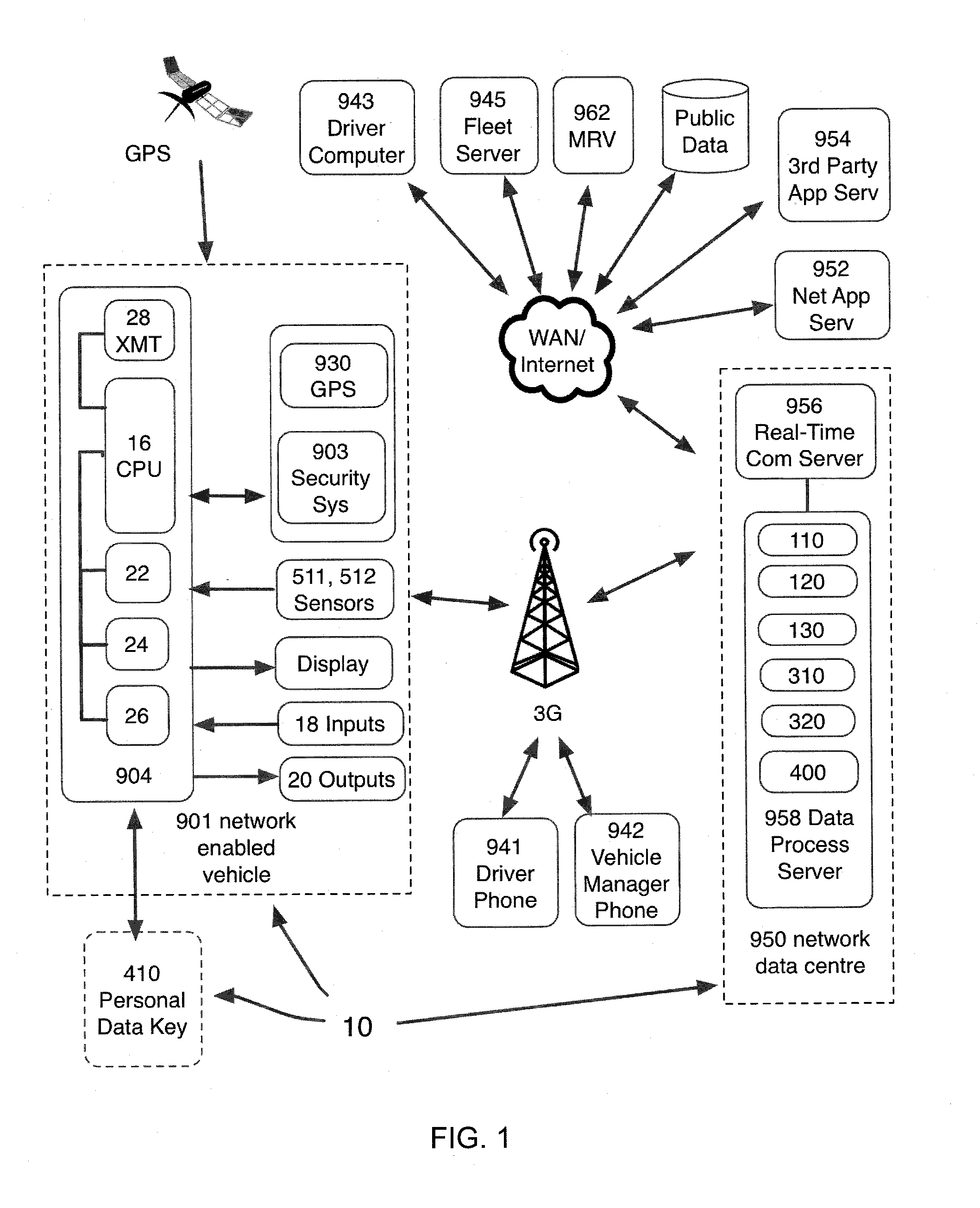
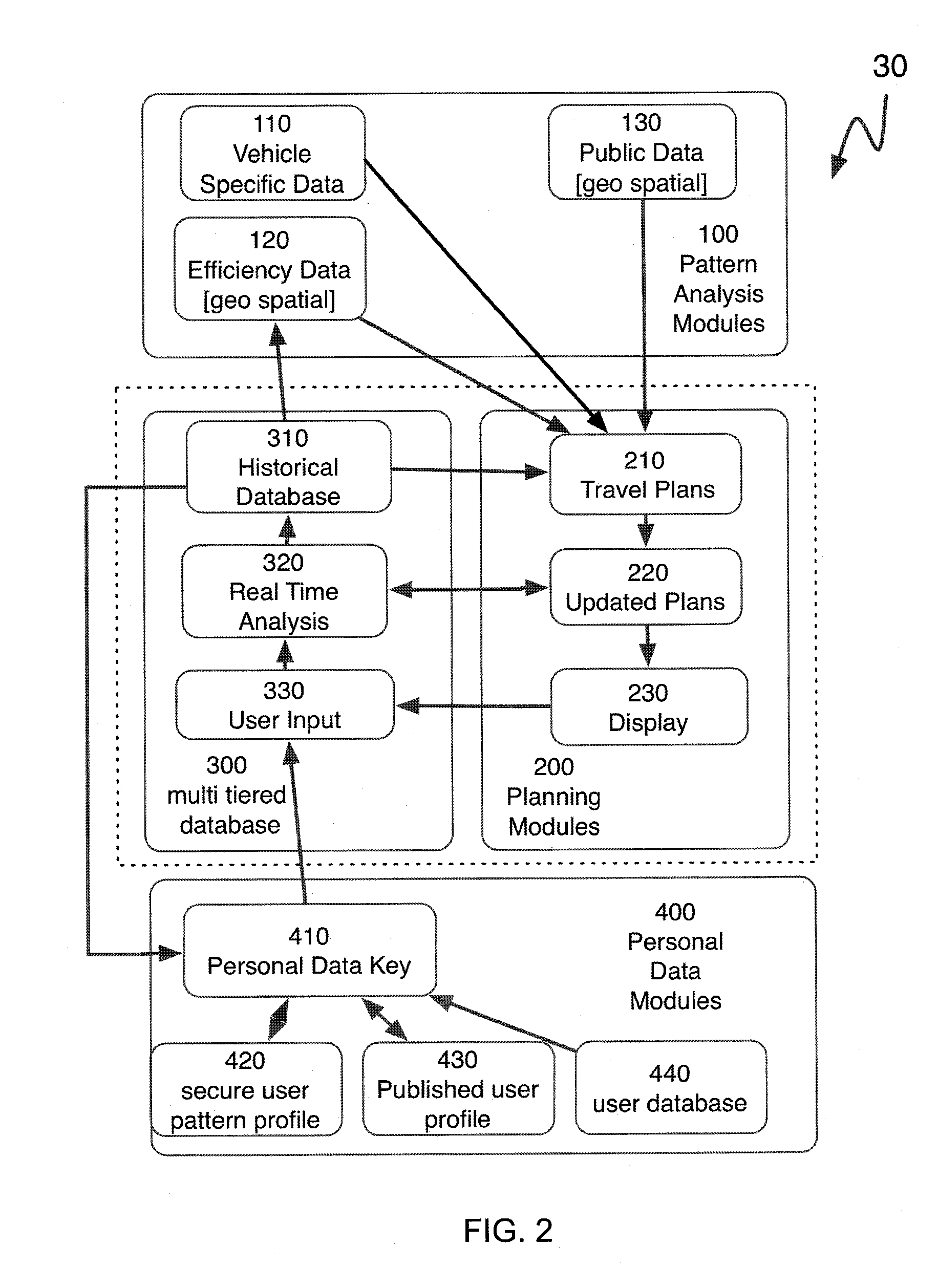
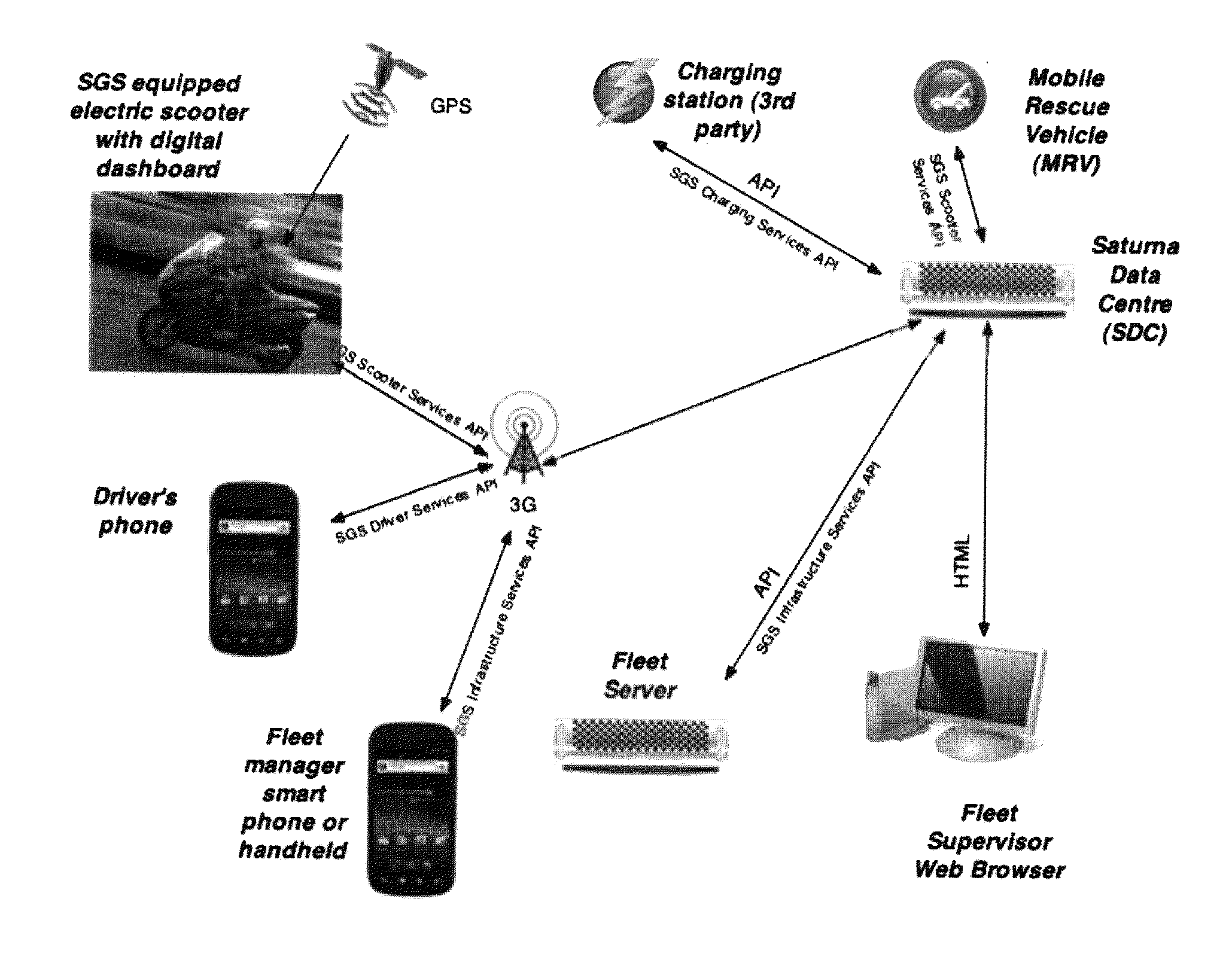
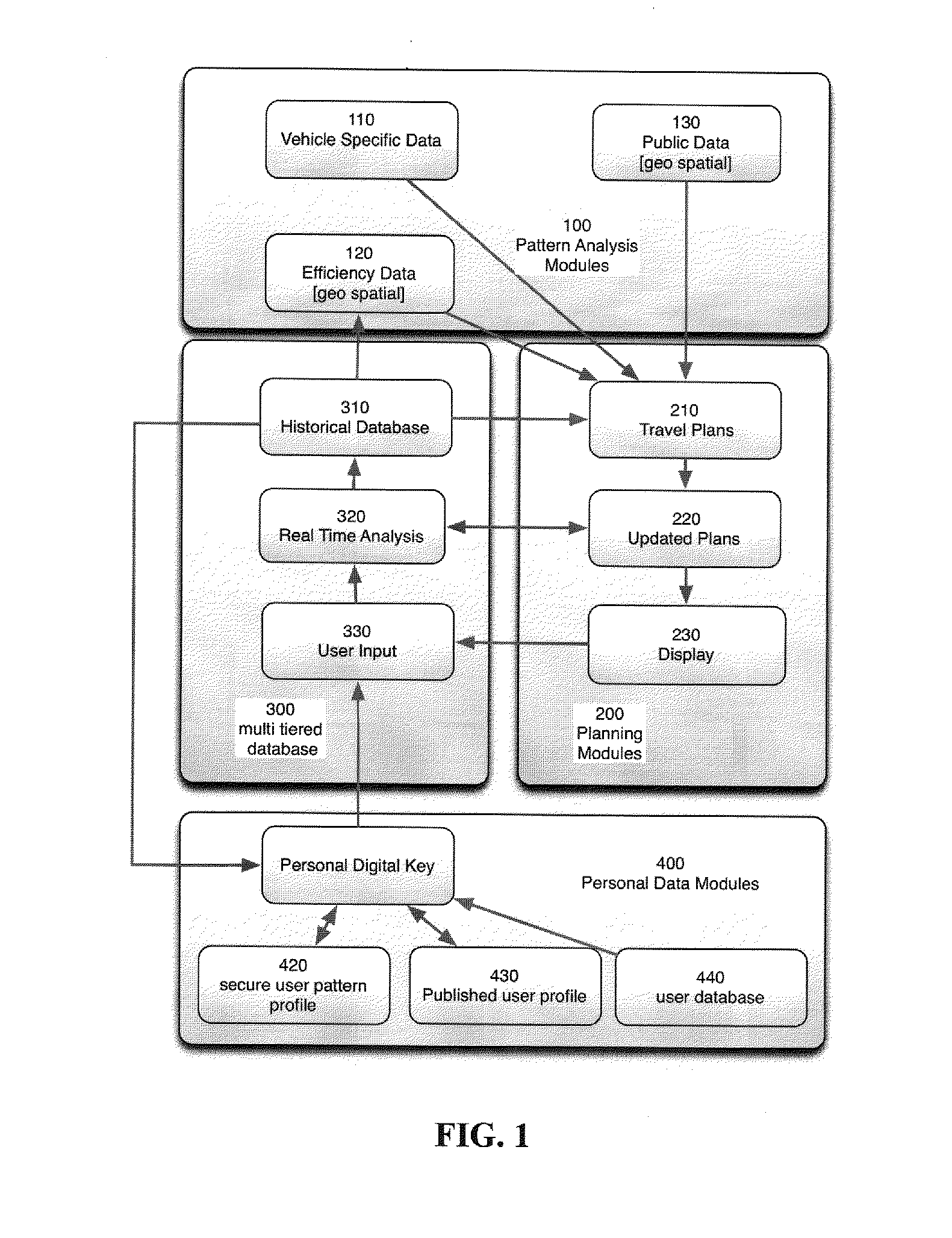
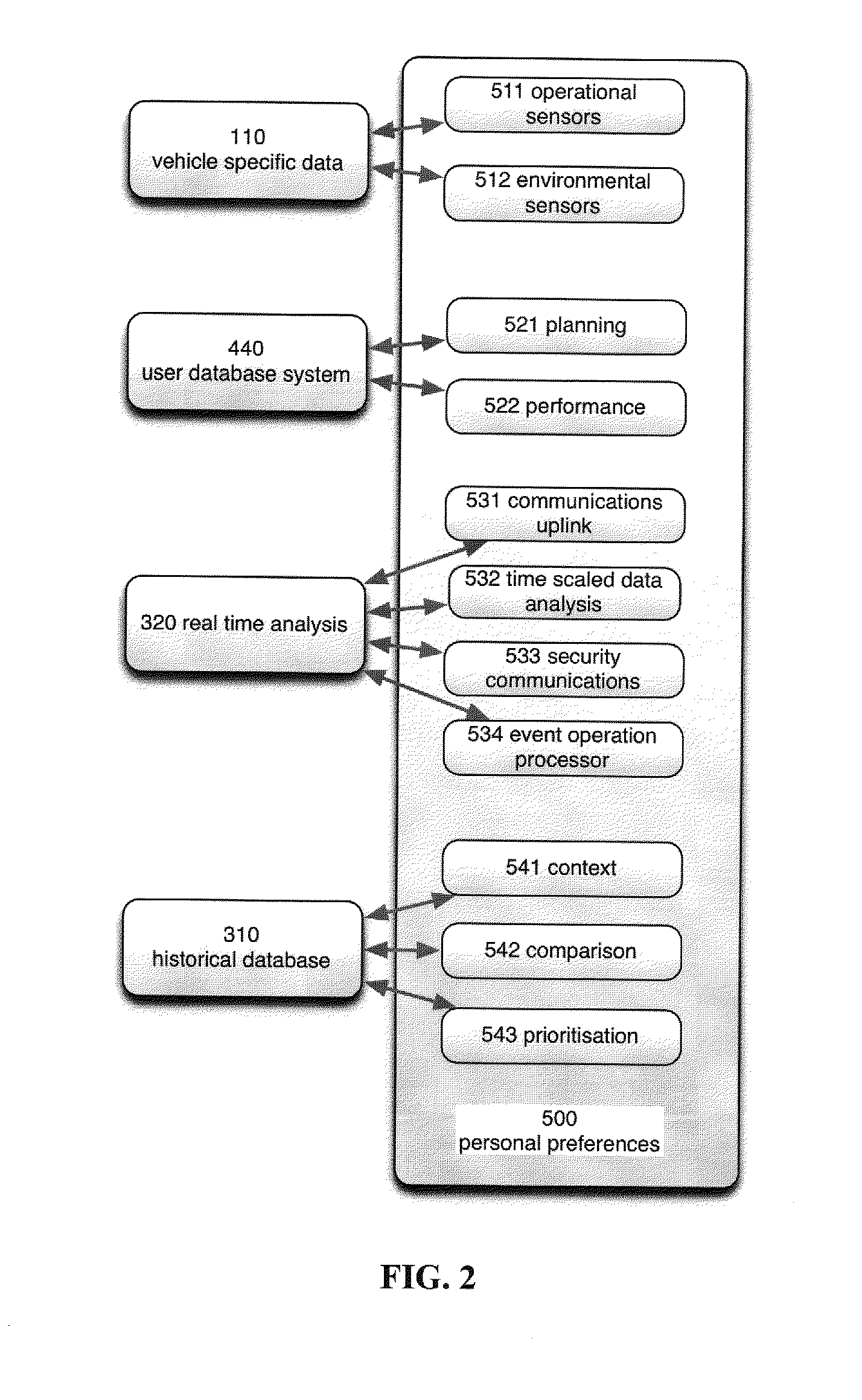
A communication and analysis system can manage data operations with a vehicle centric system. A vehicle that is in a communications link with a network can also manage its activities based on real-time, historical and predictive knowledge, without having this knowledge processing on-board. Such data processing includes the geo-spatial, internal functions and operator specific requirements. The rule based system also incorporates the use patterns of a specific vehicle, or a specific user. A use pattern can be transferred from one operator to another or be shared to assist with navigation and operations. A vehicle operator or vehicle multiple operators can share or upload information that can assist with efficient operations, including fuel conservation and time management. Use patterns can be assigned to geospatial regions and be used for comparative analysis for such activities as efficient operation, safe travel and navigation.
Owner:SATURNA GREEN SYST
Security infusion pump with bar code reader
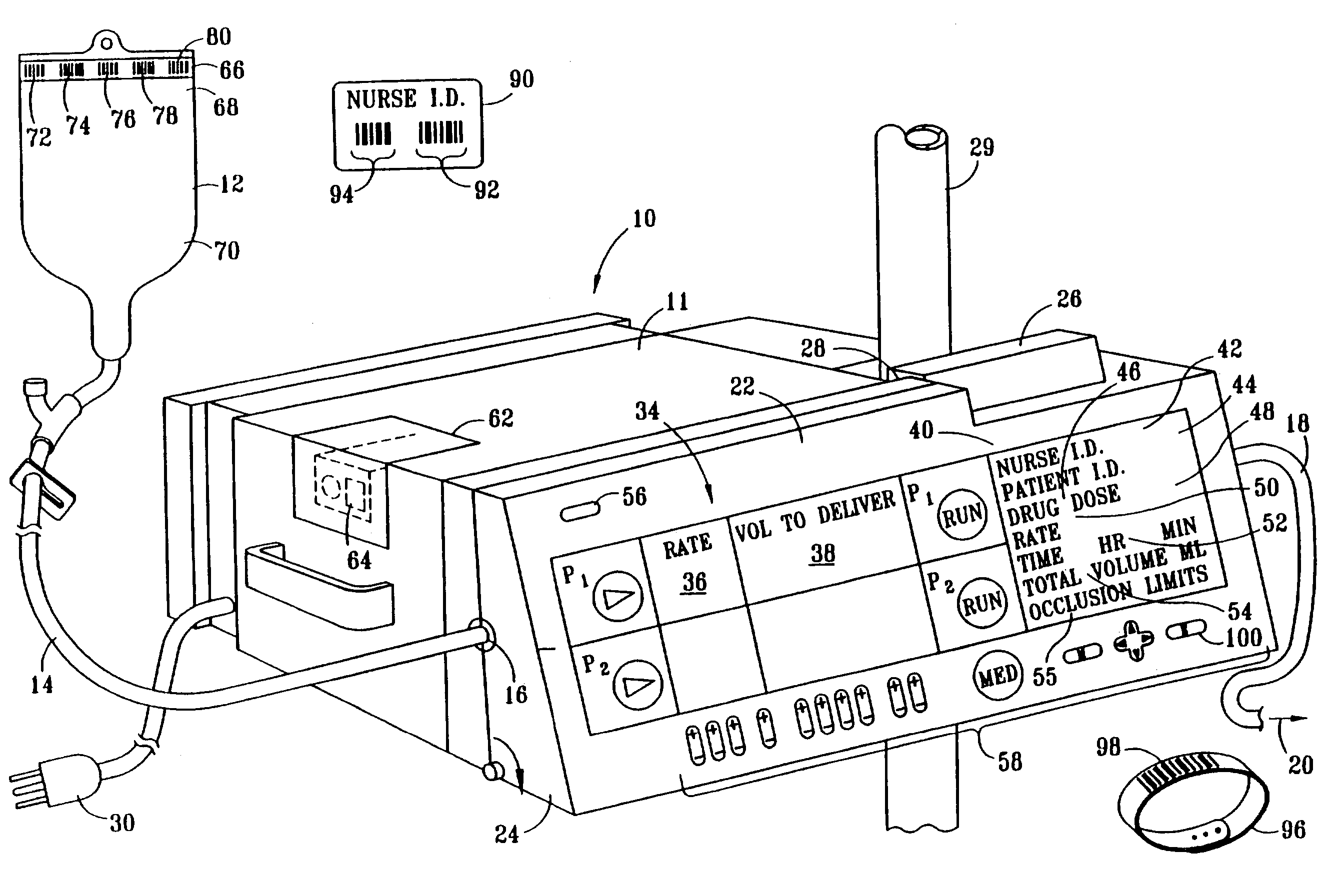
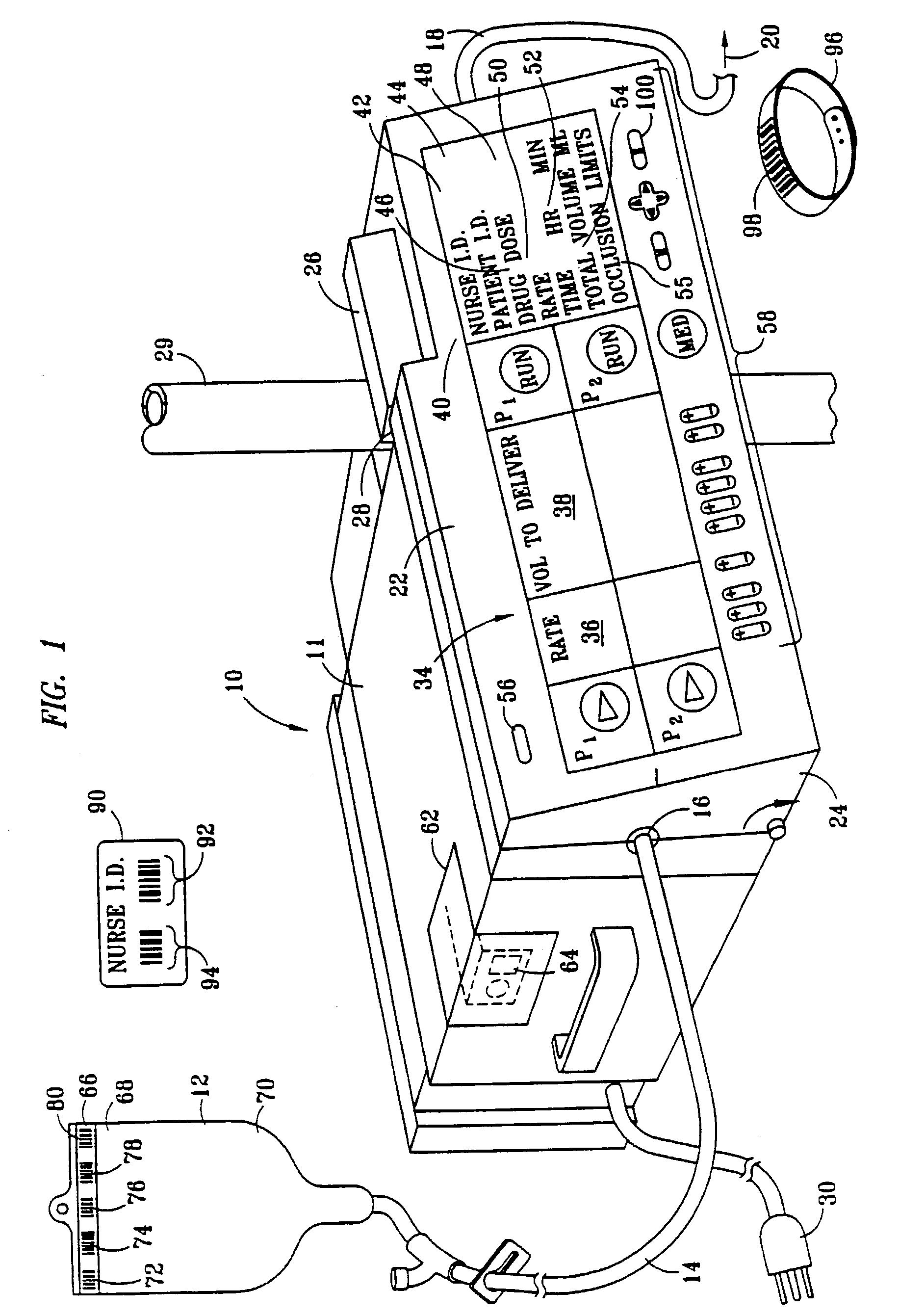
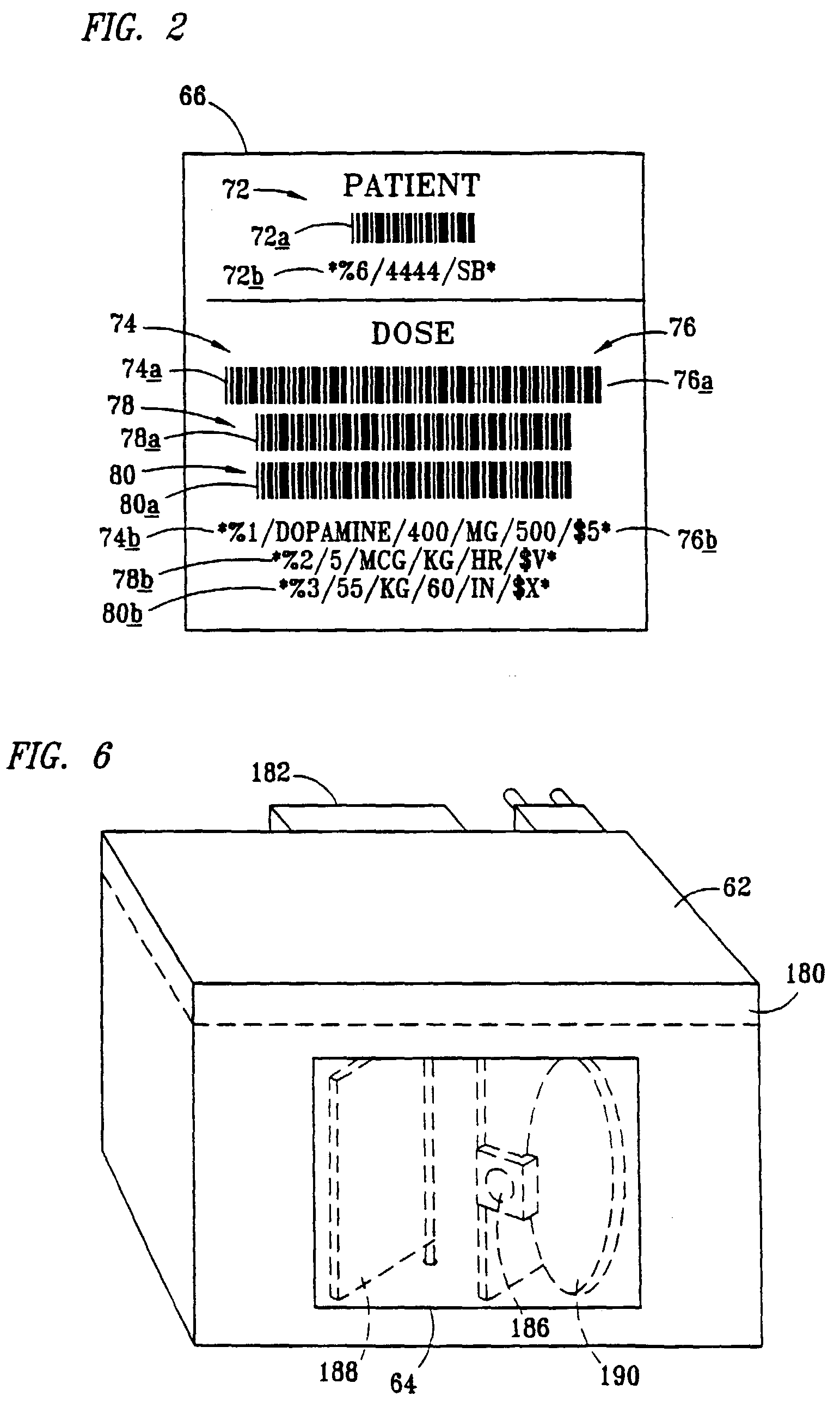
InactiveUS7236936B2Improve accuracyImprove securityDrug and medicationsMedical devicesData operationsBarcode
A medical infusion pump with a bar code reader having simplified and enhanced security features. The infusion pump with bar code reader is comprised of an infusion pump with a housing, a control display screen and control software for operating the infusion pump according to input infusion data. A bar code reader is contained in the infusion pump housing and operatively attached to communicate scanned bar code infusion data to the pump display screen and to the control software. At least one initialization button for starting execution of a bar code scanning program is operatively connected through circuitry in the pump, the program activating the bar code reader to scan for an authorized user code, for an authorized user ID code, for a patient ID code, and for infusion data compatible for operating the infusion pump. A confirmation program and confirmation buttons manually operable by the authorized user. Acceptable scanning of authorization code, authorized user ID code, patient ID code and infusion data must be manually confirmed by the authorized user prior to activating the pump to infuse fluids according to the infusion data.
Owner:B BRAUN MEDICAL
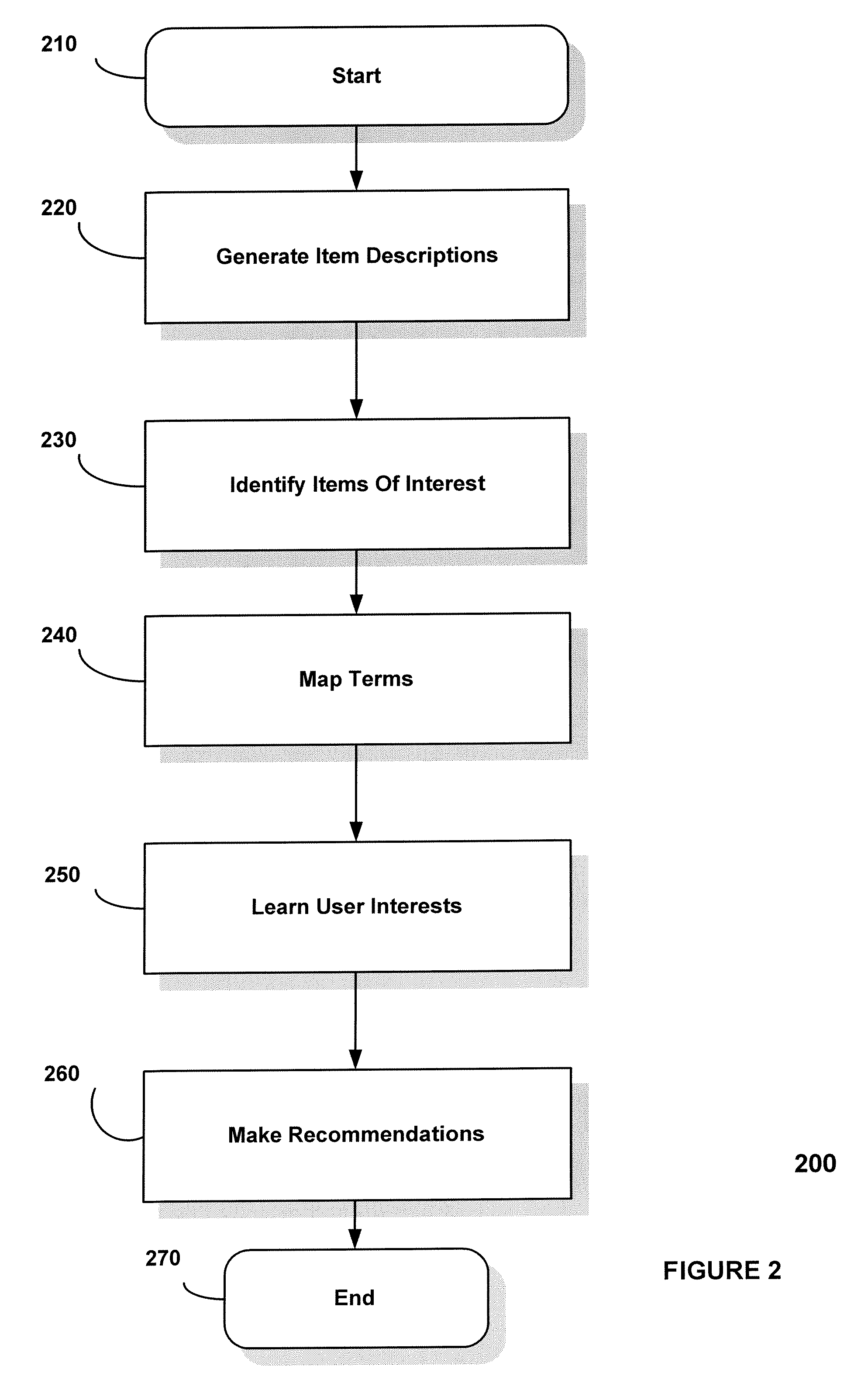
System and method for recommending items of interest to a user
ActiveUS20070078849A1Improve privacyDigital data information retrievalSelective content distributionPersonalizationDecision taking
A system and method is disclosed for recommending items to individual users using a combination of clustering decision trees and frequency-based term mapping. The system and method of the present invention is configured to receive data based on user action, such as television remote control activity, or computer keyboard entry, and when a new item data is made available from sources such as television program guides, movie databases, deliverers of advertising data, on-line auction web sites, and electronic mail servers, the system and method analytically breaks down the new item data, compares it to ascertained attributes of item data that a user liked in the past, and produces numeric ranking of the new item data dynamically, and without subsequent user input, or data manipulation by item data deliverers, and is tailored to each individual user. A embodiment is disclosed for learning user interests based on user actions and then applying the learned knowledge to rank, recommend, and / or filter items, such as e-mail spam, based on the level of interest to a user. The embodiment may be used for automated personalized information learning, recommendation, and / or filtering systems in applications such as television programming, web-based auctions, targeted advertising, and electronic mail filtering. The embodiment may be structured to generate item descriptions, learn items of interest, learn terms that effectively describe the items, cluster similar items in a compact data structure, and then use the structure to rank new offerings. Embodiments of the present invention include, by way of non-limiting example: allowing the assignment of rank scores to candidate items so one can be recommended over another, building decision trees incrementally using unsupervised learning to cluster examples into categories automatically, consistency with “edge” (thick client) computing whereby certain data structures and most of the processing are localized to the set-top box or local PC, the ability to learn content attributes automatically on-the-fly, and the ability to store user preferences in opaque local data structures and are not easily traceable to individual users.
Owner:FOURTHWALL MEDIA
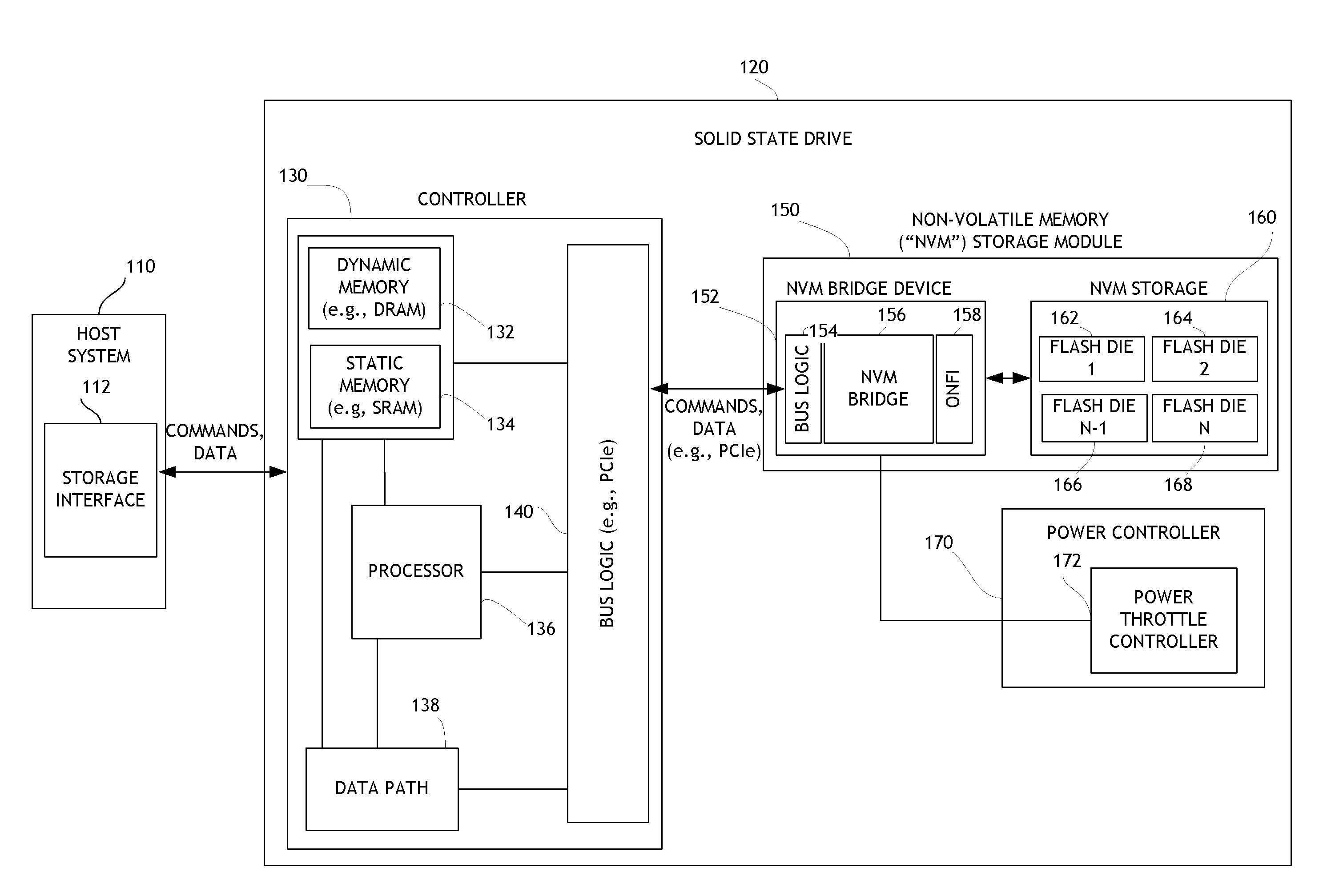
Systems and methods for detailed error reporting in data storage systems
ActiveUS8713357B1Efficient discoveryEasy to understandInput/output to record carriersFault responseData operationsData access
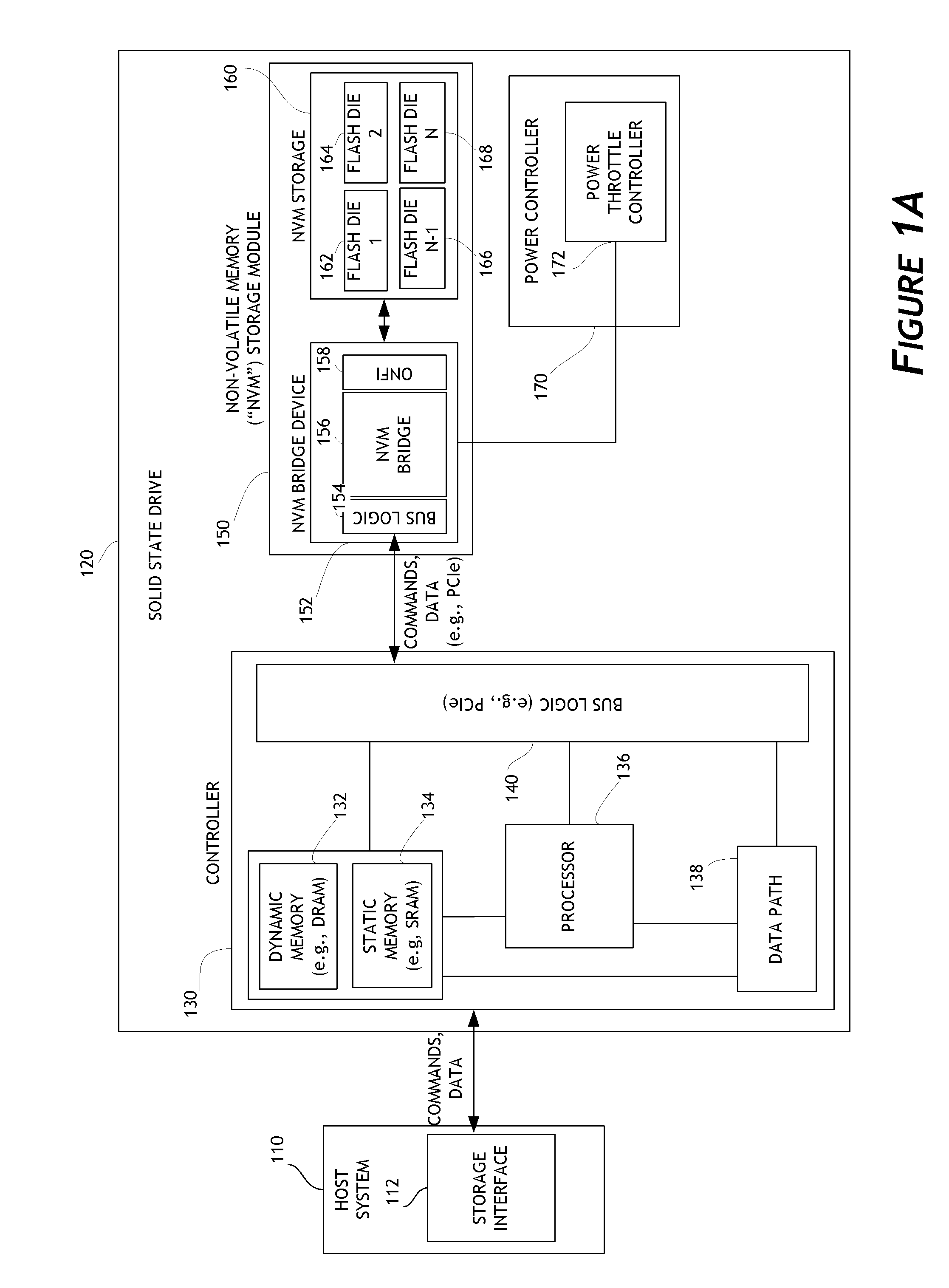
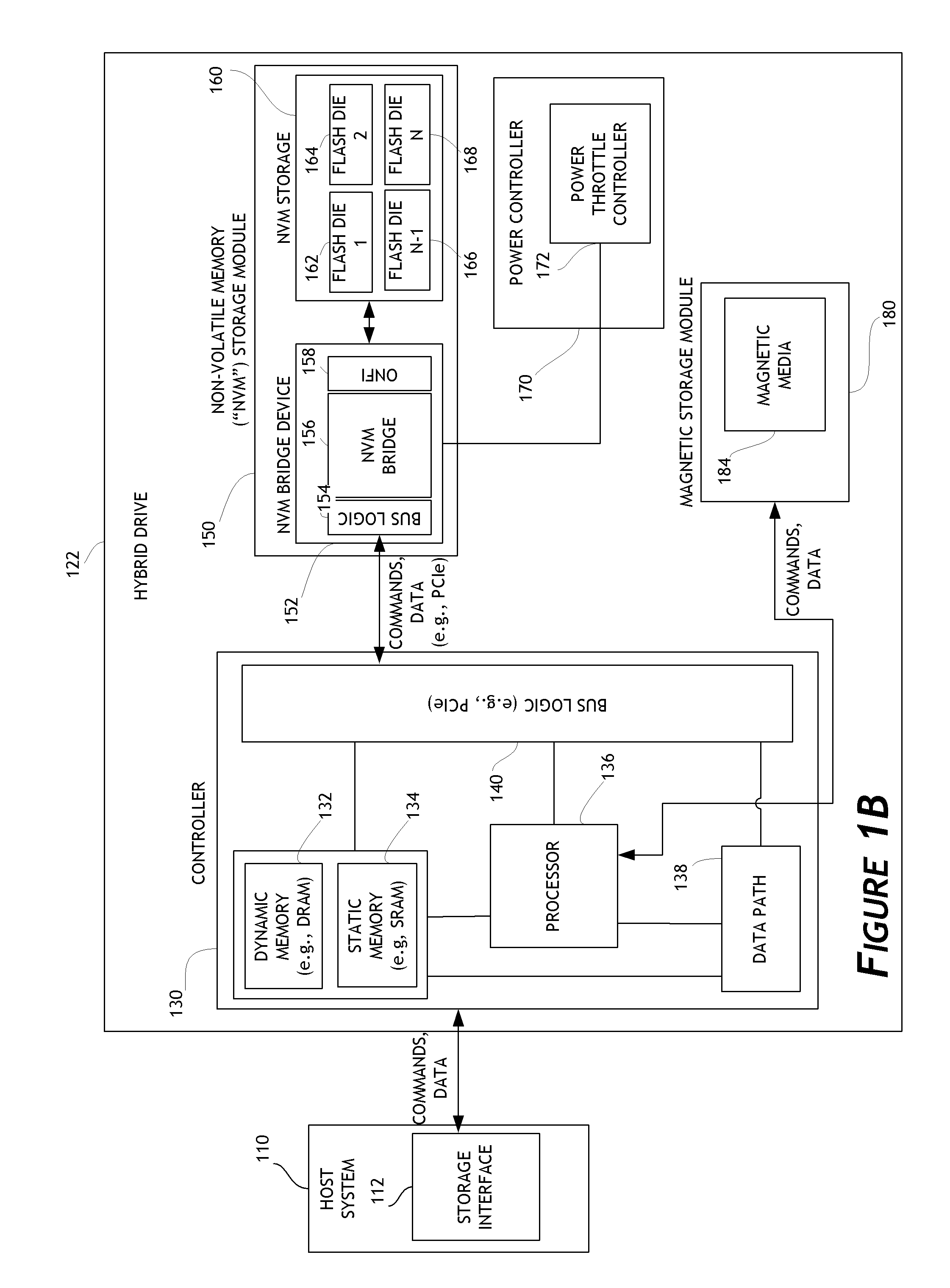
Embodiments of the invention are directed to providing detailed error reporting of data operations performed on a NVM storage device. In one embodiment, a controller interfaces with a NVM storage device including NVM storage coupled with a bridge. In one embodiment, the controller is provided physical, page-level access to the NVM via the bridge, and the bridge provides detailed error reporting of the data operations that the bridge performs on the NVM on behalf of the controller. For example, the bridge may provide page level reporting indicating which page(s) failed during a read operation. Detailed error reporting allows the controller to better understand the failures that occurred in a data access operation in the NVM. It also enables the controller to manage the flash media at the physical page / block level. In one embodiment, detailed error reporting also enables the return of discontinuous ranges of data with the error portions removed.
Owner:WESTERN DIGITAL TECH INC
I/O primitives
InactiveUS7013379B1Error detection/correctionMemory adressing/allocation/relocationFast pathLocking mechanism
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
Dynamic and variable length extents
InactiveUS20030140210A1Input/output to record carriersMemory adressing/allocation/relocationVariable-length codeFast path
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
Fast path for performing data operations
InactiveUS20070016754A1Multiplex system selection arrangementsUnauthorized memory use protectionFast pathData operations
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
Dynamic, hierarchical data exchange system
InactiveUS7165073B2Overcome limitationsOptimize locationData processing applicationsDigital data information retrievalRelational algebraData operations
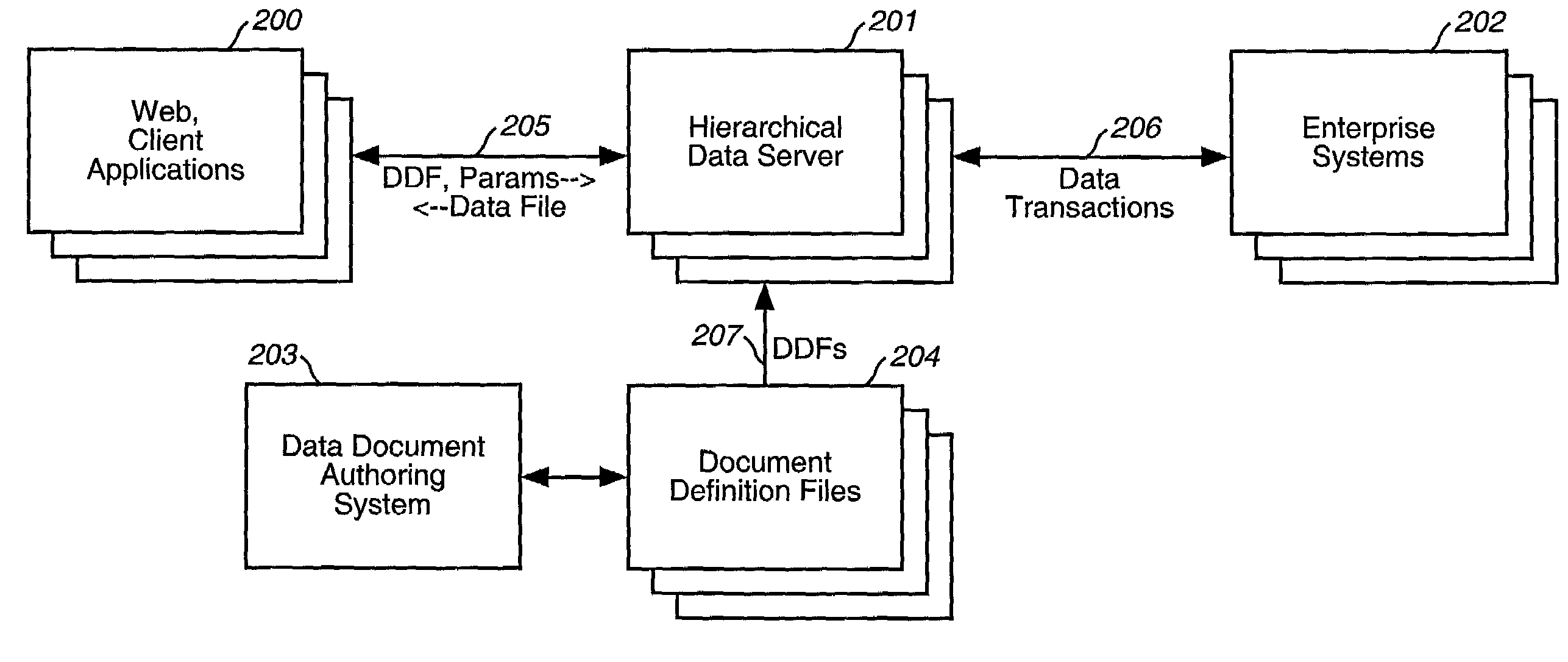
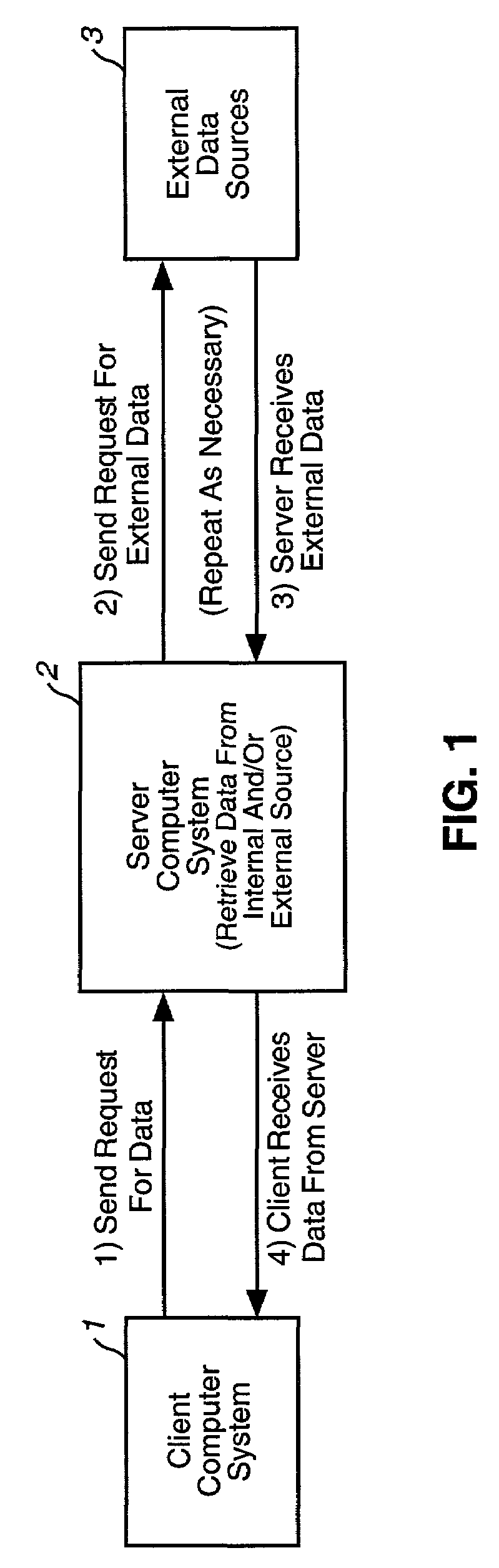
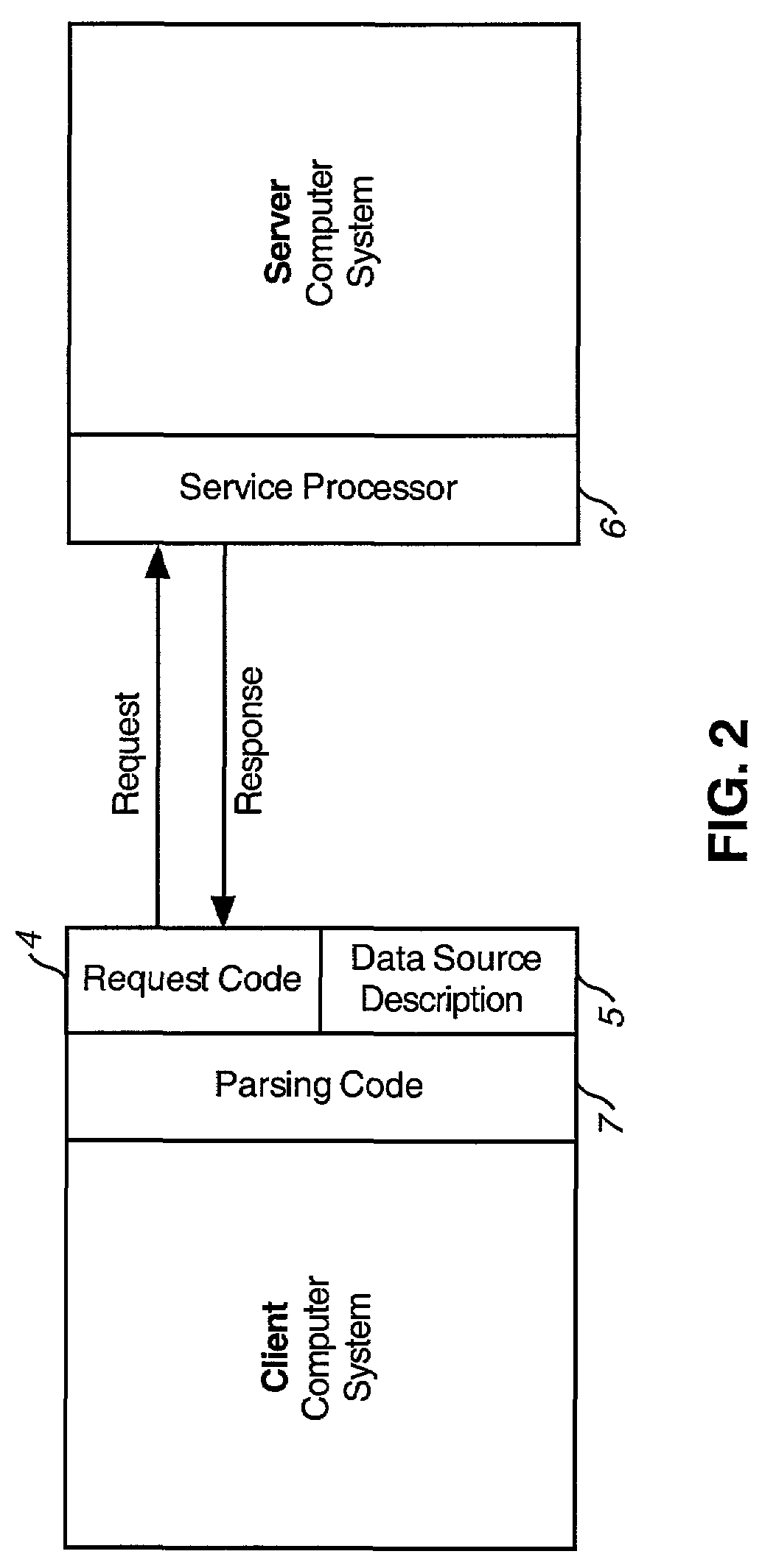
A computer system provides the ability to construct and edit a Data Definition File (DDF) containing hierarchically related elements of data, some of which are dynamic in that they must execute in order to produce or retrieve data. A client computer system having knowledge of a DDF appropriate for its uses sends a request to a server, which contains or can retrieve the DDF requested by the client. The request contains parameters used by the server to customize the resulting keyed data file for the client's purposes. Upon receipt of the request, the server copies the DDF into a coupled memory, performs requested parameter substitutions, and executes dynamic elements to produce resulting data elements. The process is repeated recursively for all elements of the hierarchical structure, until no dynamic elements remain, then the resulting keyed data file is returned to the client for its uses. Data elements may be derived from a plurality of sources, and these sources may be combined and manipulated using a plurality of data operations, including relational algebra or structured query language, enabling joins and merges between multiple sources and formats. An Authoring System is provided which assists in the construction and validation of DDFs.
Owner:X AWARE
Vehicle communication, analysis and operation system
InactiveUS20130079964A1Minimizes computation loadLoad minimizationDigital data processing detailsNavigation instrumentsFuel conservationOperational system
The present invention provides a communication and analysis system that can manage data operations with a vehicle centric system with a planned route path. A vehicle that is in a communications link with a network can also manage its activities based on real time, historical and predictive knowledge, without having this all knowledge processing on board. Such data processing would include a cluster analysis of geo-spatial, internal functions and operator specific requirements. The rule based system would also incorporate the use patterns of a specific vehicle, or a specific user. A vehicle operator or vehicle multiple operators could share or upload information that would assist with efficient data processing and display, including fuel conservation and time management. Cluster weighting patterns can be assigned based on activities as efficient operation, safe travel and navigation.
Owner:SATURNA GREEN SYST
Fast path caching
InactiveUS6986015B2Input/output to record carriersMemory adressing/allocation/relocationFast pathData operations
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:INT BUSINESS MASCH CORP
Advanced voice and data operations in a mobile data communication device
InactiveUS7096009B2Special service for subscribersCalled number recording/indicationData operationsData center
A system and method for integrating voice and data operations into a single mobile device capable of simultaneously performing data and voice actions. The mobile device working in a network capable of exchanging both cell phone calls and data items to the mobile device. By wearing an earphone or an ear-bud device the user is capable of dealing with voice conversations while working with data centric information related to the current caller. By providing a data-centric device with voice capabilities there is a new range of features that allow incoming data events to trigger outgoing voice events.
Owner:MALIKIE INNOVATIONS LTD
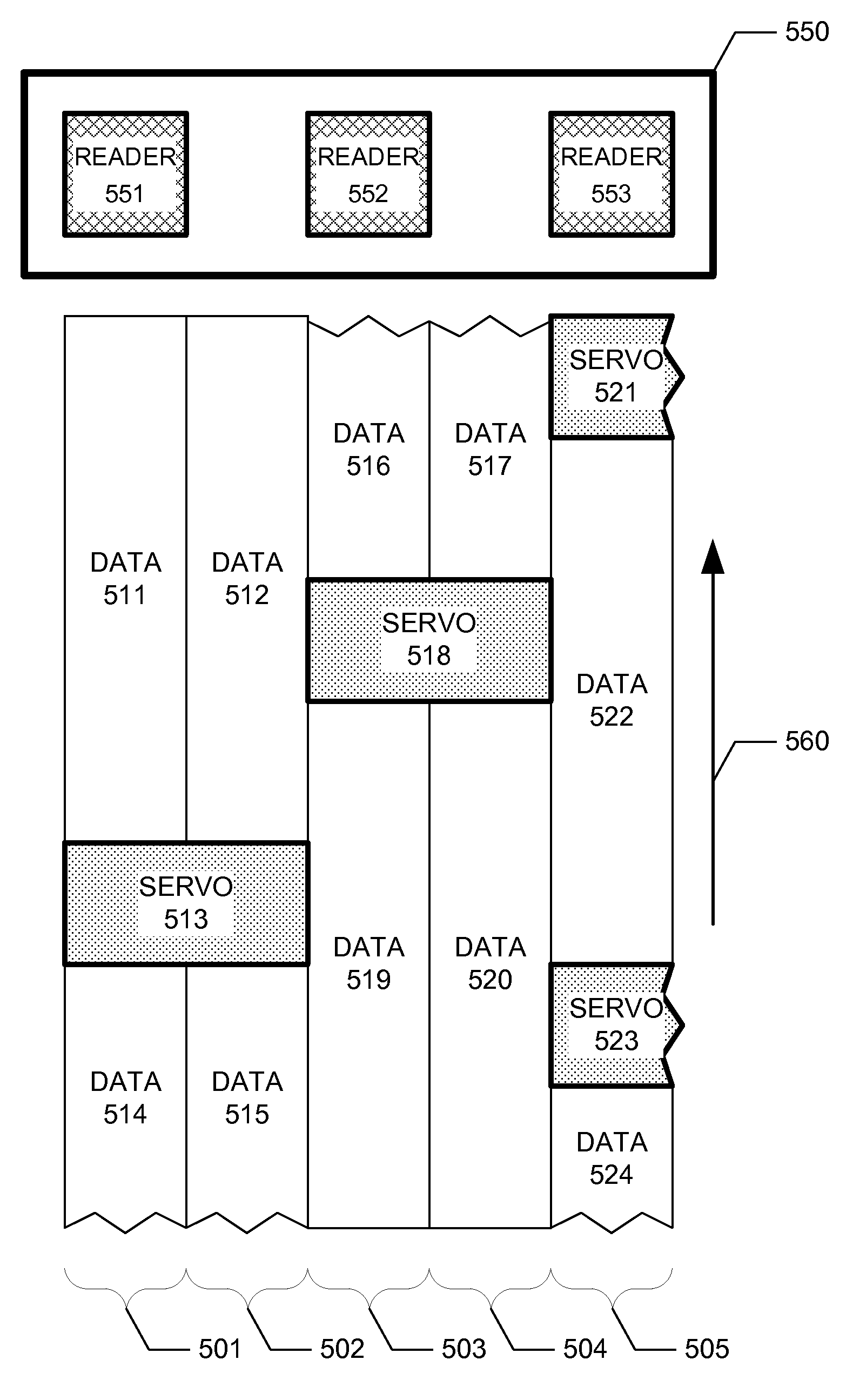
Servo design in data storage media
InactiveUS8203800B2Good synchronizationRecord information storageAlignment for track following on disksData operationsReal-time computing
A data storage medium comprises a plurality of data regions, and a plurality of servo regions configured to provide positioning information to a reading device. Each of the plurality of data regions corresponds to more than one of the plurality of servo regions. The more than one of the plurality of servo regions are configured to provide positioning information to the reading device at discrete times corresponding to a data operation of a corresponding data region.
Owner:WESTERN DIGITAL TECH INC
Extended storage capacity for a network file server
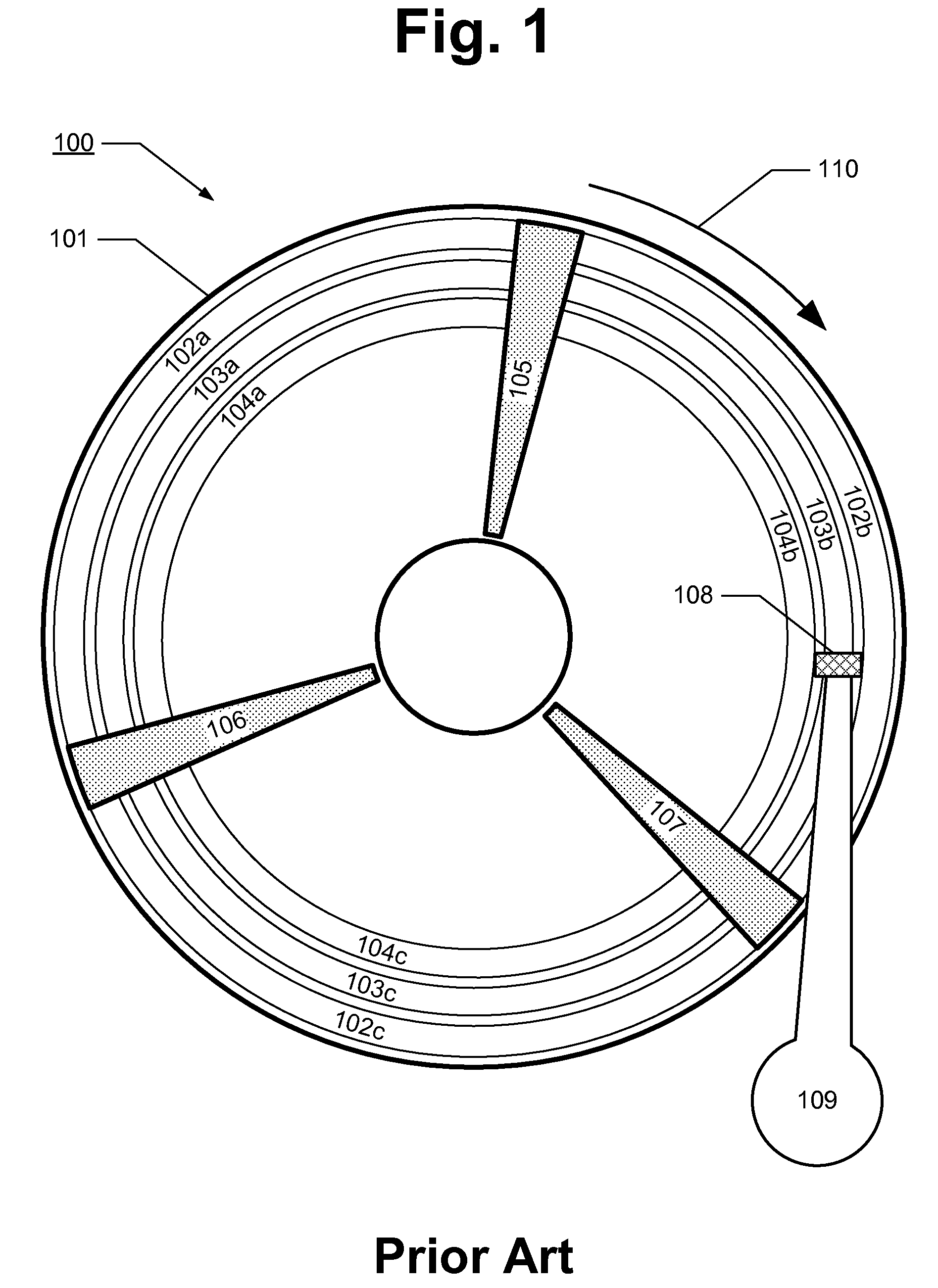
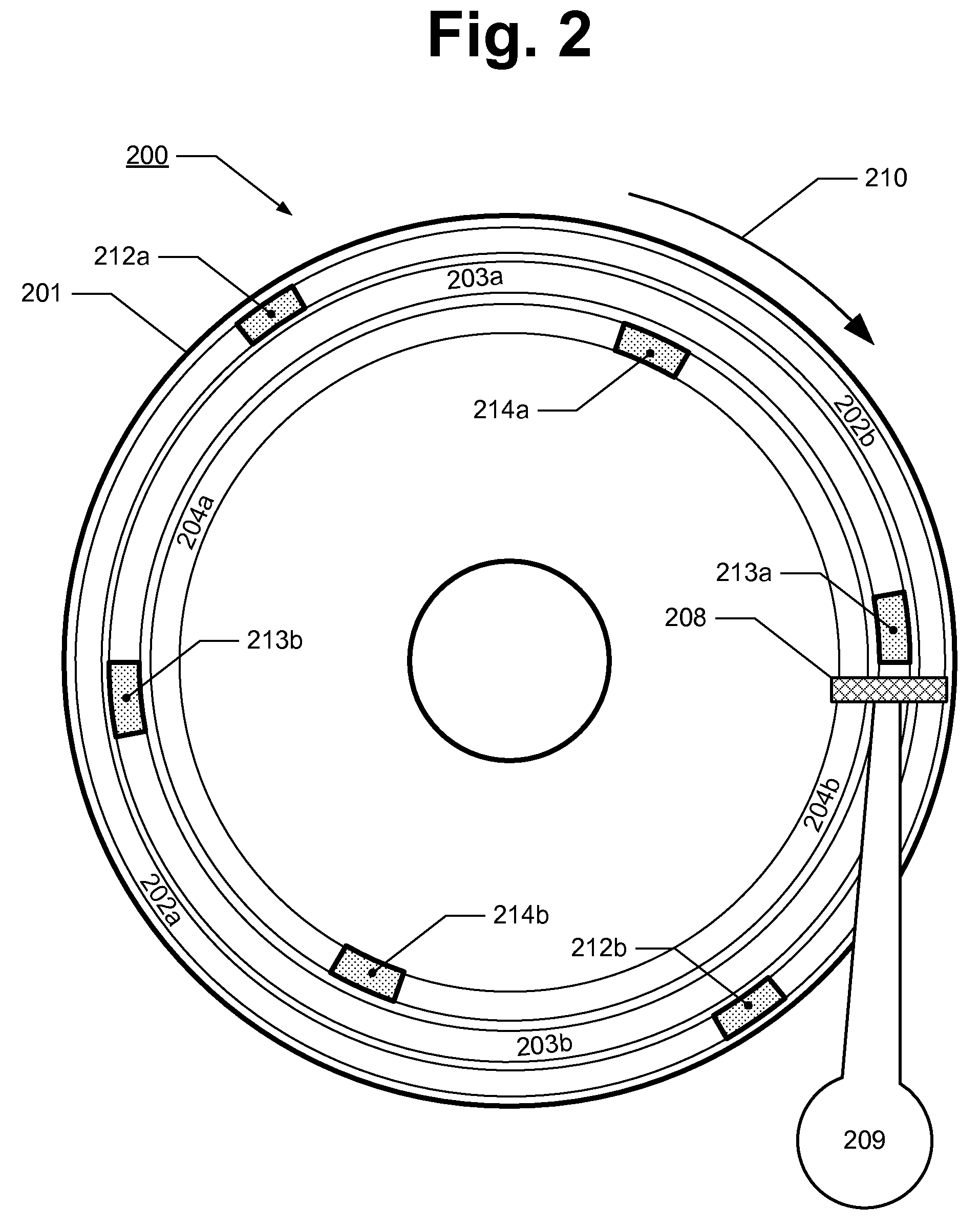
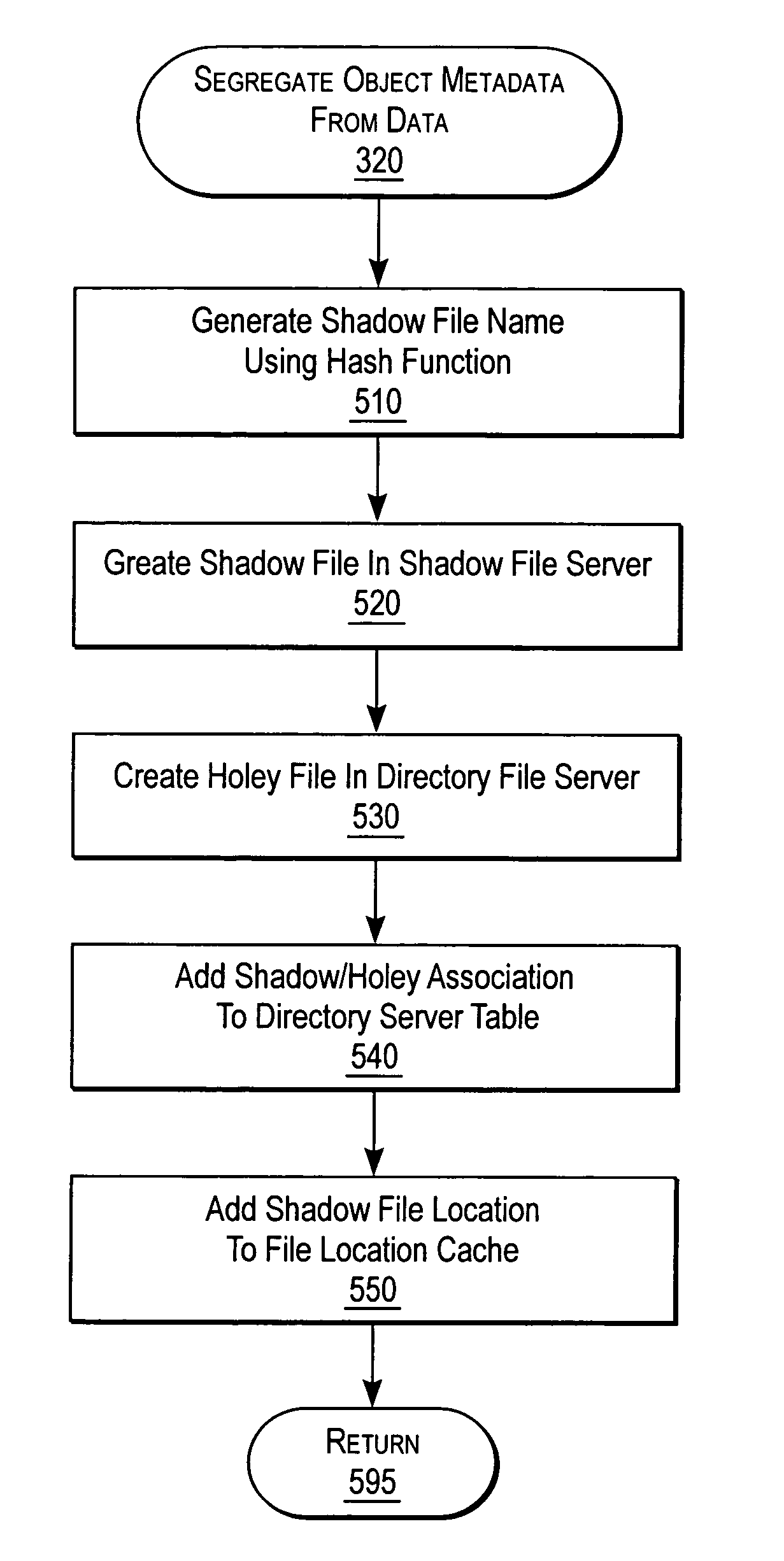
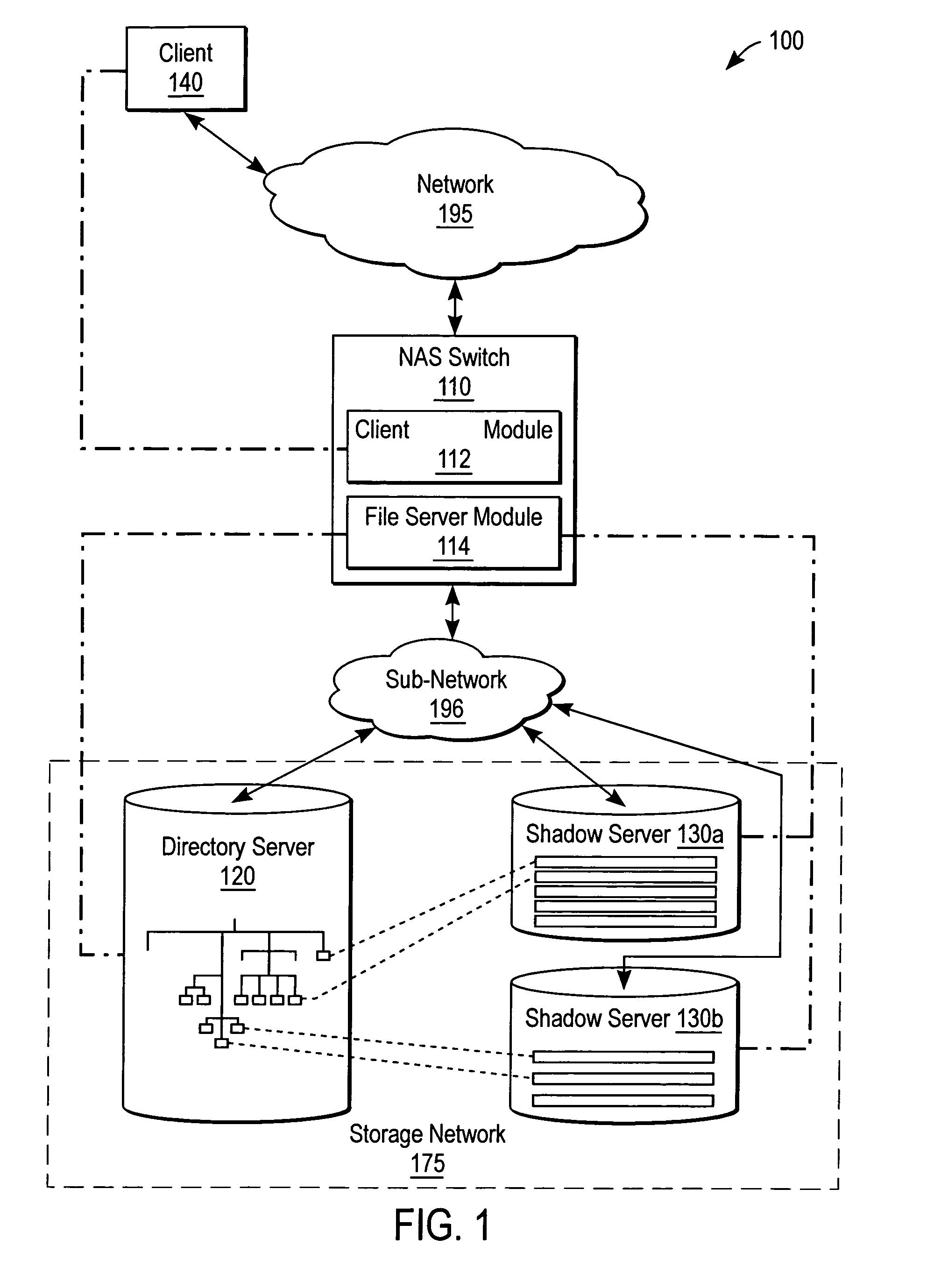
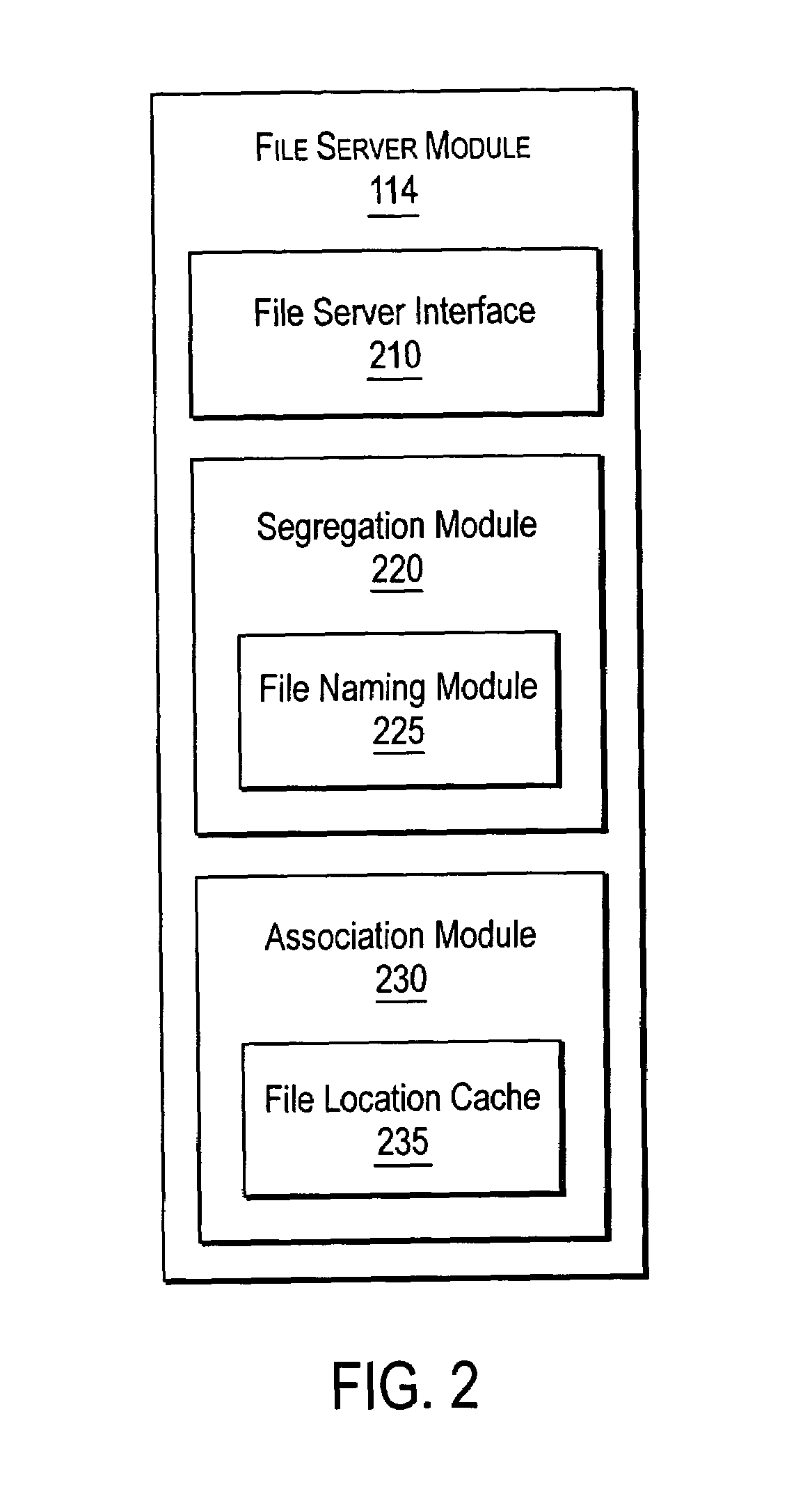
ActiveUS7072917B2Data processing applicationsDigital data processing detailsServer replicationData operations
A NAS switch provides extended storage capacity to a file server in a decentralized storage network such as a NAS (Network Attached Storage) storage network. The NAS switch sits in the data path of a client on the front end and a directory file server and shadow file servers on the back end. A segregation module in the NAS switch replicates data from the directory file server to a shadow file server, and then replaces the data in the directory file server with holey files. Holey files, which store a range of consecutive values such as zero with negligible storage space, retain the attributes of the data without retaining its storage consumption. Thus, the directory file server can server as a single directory hierarchy for several shadow file servers containing data beyond a capacity of the directory file server. When the NAS switch receives operations from the client, an association module forwards directory operations to the directory file server and data operations to the shadow file server. The NAS switch also provides services to several shadow file servers from a single directory file server.
Owner:CISCO TECH INC
Adaptively modifying pre-read operations within a rotating media storage device
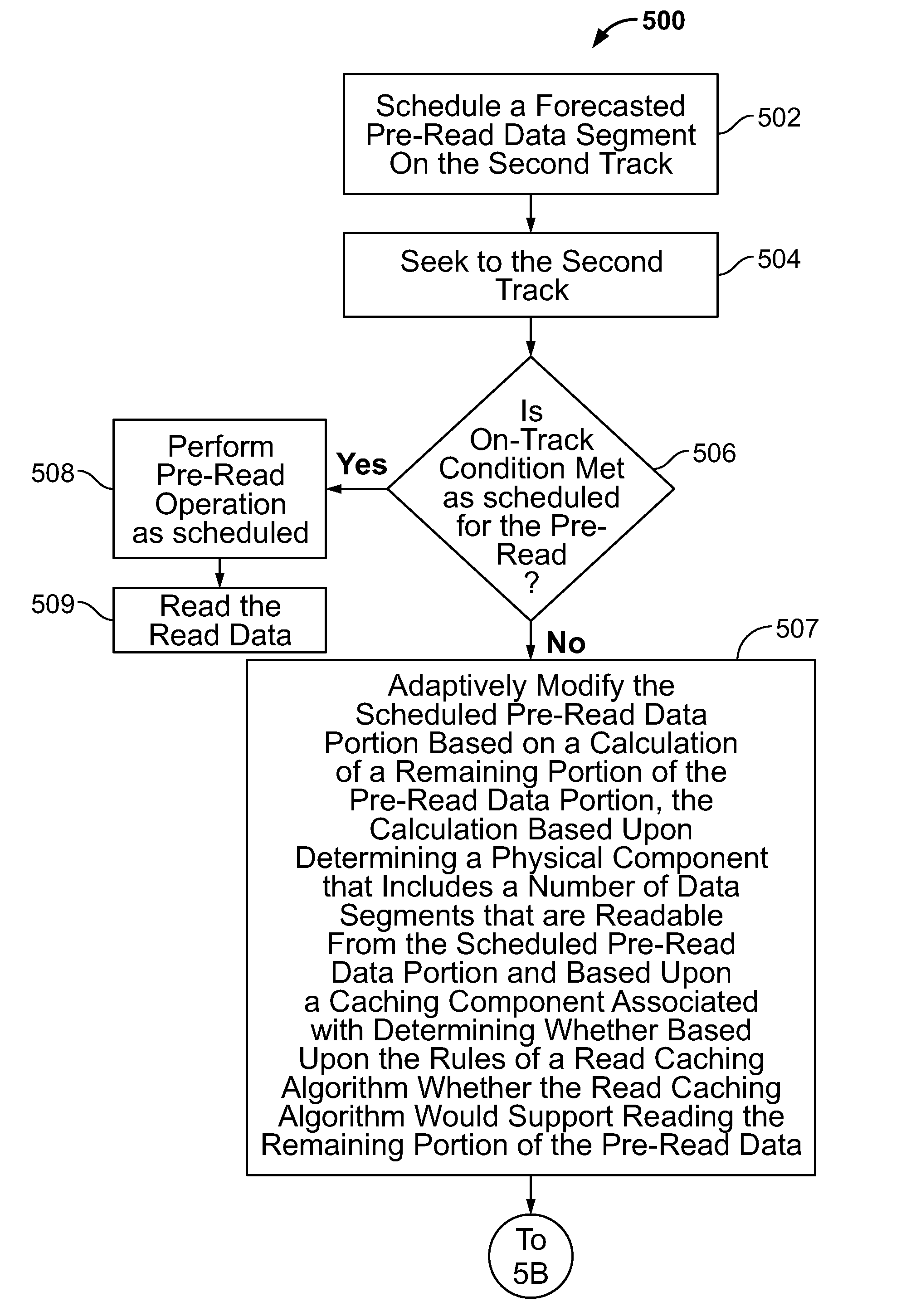
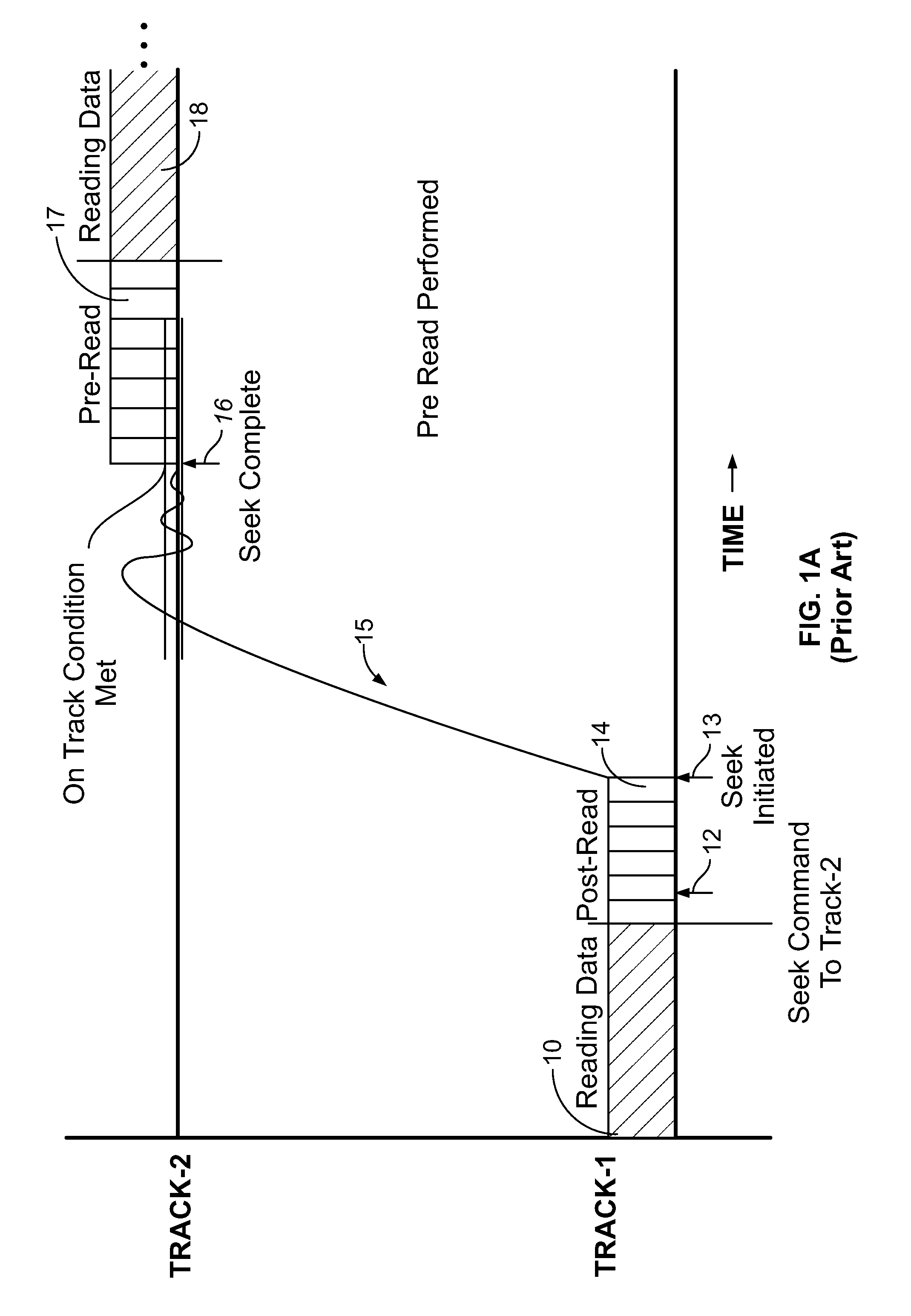
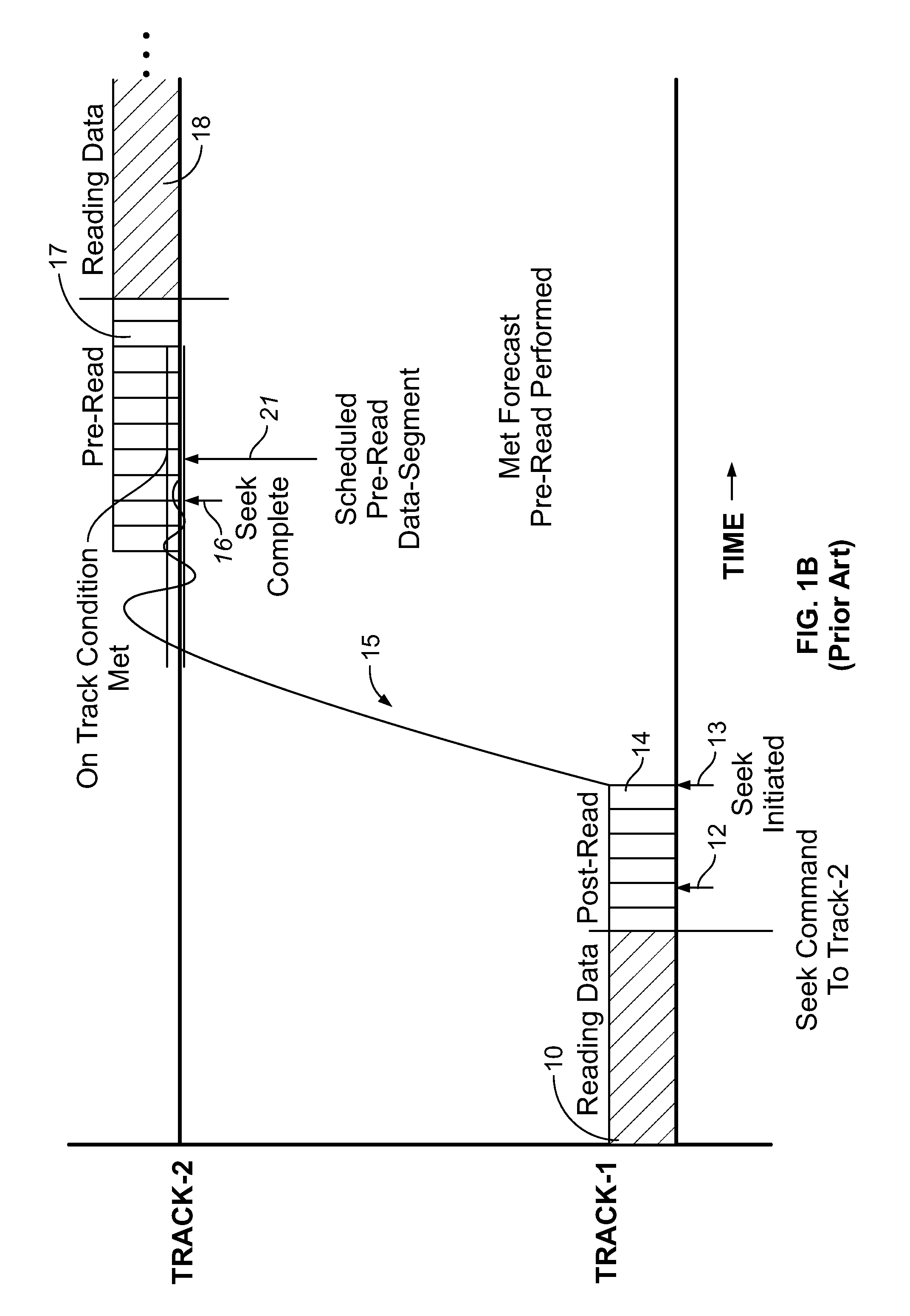
InactiveUS8307156B1Efficient switchingInput/output to record carriersDriving/moving recording headsData segmentData operations
A rotating media storage device (RMSD) that adaptively modifies pre-read operations is disclosed. The RMSD schedules a pre-read data segment on a second track of disk, commands a movable head to seek to the second track, and if an on-track condition is not met for the scheduled pre-read data segment, modifies the pre-read operation. In one example, modifying the pre-read operation includes canceling the pre-read operation and then performing a read data operation.
Owner:WESTERN DIGITAL TECH INC
Fast path for performing data operations
InactiveUS7280536B2Multiplex system selection arrangementsData switching by path configurationFast pathPathPing
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:INT BUSINESS MASCH CORP
Method and apparatus for accelerating data access operations in a database system
InactiveUS20050198062A1Accelerating data access operationEfficiently streamedDigital data information retrievalSpecial data processing applicationsData operationsData access
Data access operations in a database system may be accelerated by allowing the memory cache to be supplemented with a disk cache. The disk cache can store data that isn't able to fit in the memory cache and, since it doesn't contain the primary copy of the data for the database, may organize the data in such a way that the data is able to be streamed from the disks in response to data read operations. The reduced number of read data operations allows the data to be read from the disk cache faster than it could be served from the primary storage facilities, which might not allow the data to be organized in the same manner. The cache hit ratio may be increased by compressing data prior to storing it in the cache. Additionally, where a particular portion of data stored on the disk cache is being used heavily, that portion may be pulled into memory cache to accelerate access to that portion of data.
Owner:SHAPIRO RICHARD B
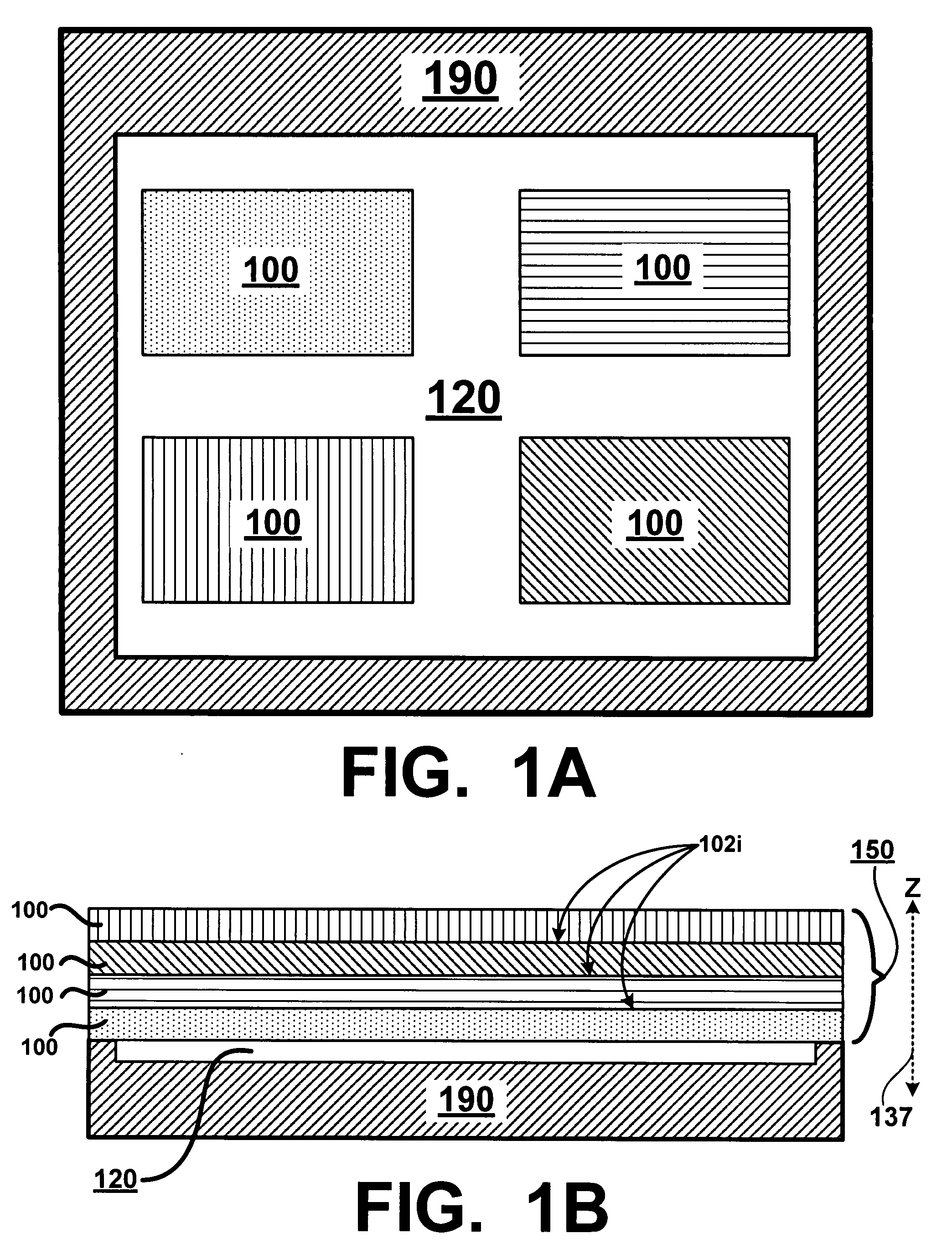
Threshold device for a memory array
A threshold device including a plurality of adjacent tunnel barrier layers that are in contact with one another and are made from a plurality of different dielectric materials is disclosed. A memory plug having first and second terminals includes, electrically in series with the first and second terminals, the threshold device and a memory element that stores data as a plurality of conductivity profiles. The threshold device is operative to impart a characteristic I-V curve that defines current flow through the memory element as a function of applied voltage across the terminals during data operations. The threshold device substantially reduces or eliminates current flow through half-selected or un-selected memory plugs and allows a sufficient magnitude of current to flow through memory plugs that are selected for read and write operations. The threshold device reduces or eliminates data disturb in half-selected memory plugs and increases S / N ratio during read operations.
Owner:UNITY SEMICON
Cryptographic control for mobile storage means
ActiveUS20090217385A1Digital data processing detailsAnalogue secracy/subscription systemsData operationsCryptographic protocol
A system and method that regulates the various operations between computing stations and storage devices. Storage devices are the storage means that are contained upon devices that are able to have data stored upon them. Any operation that involves or may lead to the exchange or accessing of content (data) between a storage device and computing station may be regulated by means of a policy which comprise a set of rules. Rules may be defined according to specific criteria, including the type of storage device, the type of content, the attributes of the content, and other attributes associated with the storage device and / or the content. The policy will be dynamically installed upon a computing station for specific user(s) and will regulate the data operations that may take place between the computing stations and storage devices based on evaluation of the policy. Based on the evaluation of the policy, the requested operation is permitted, restricted in some areas, or denied.
Owner:CRYPTOMILL
Method, apparatus and system for processing compliance actions over a wide area network
ActiveUS6985922B1Easy to processFacilitate storage and manipulation of dataDigital data processing detailsMultiple digital computer combinationsData operationsDatabase engine
The method, apparatus and system are provided for obtaining information regarding compliance with local laws via client computers to upload information to a centralized server preferably over a wide area network. The data is obtained through interaction with a client device and the data is stored on a server. The server has access to a database engine which provides triggering and alarming capabilities for the tracking of applicable dates and events. The server system is provided with software and / or hardware necessary to perform manipulation of the data provided by the client and enable reconfiguration of the data for investigative and reporting purposes.
Owner:S J BASHEN
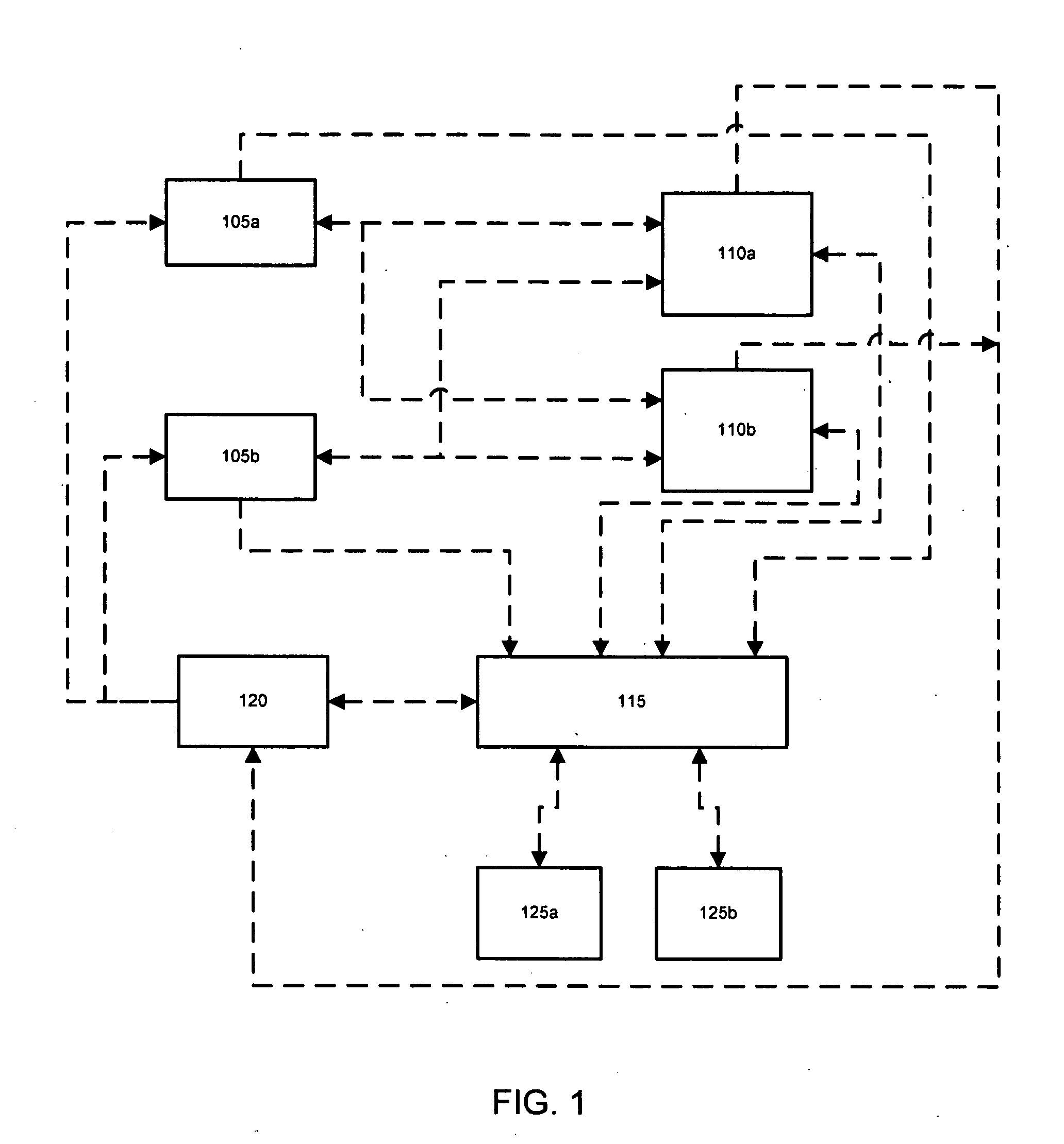
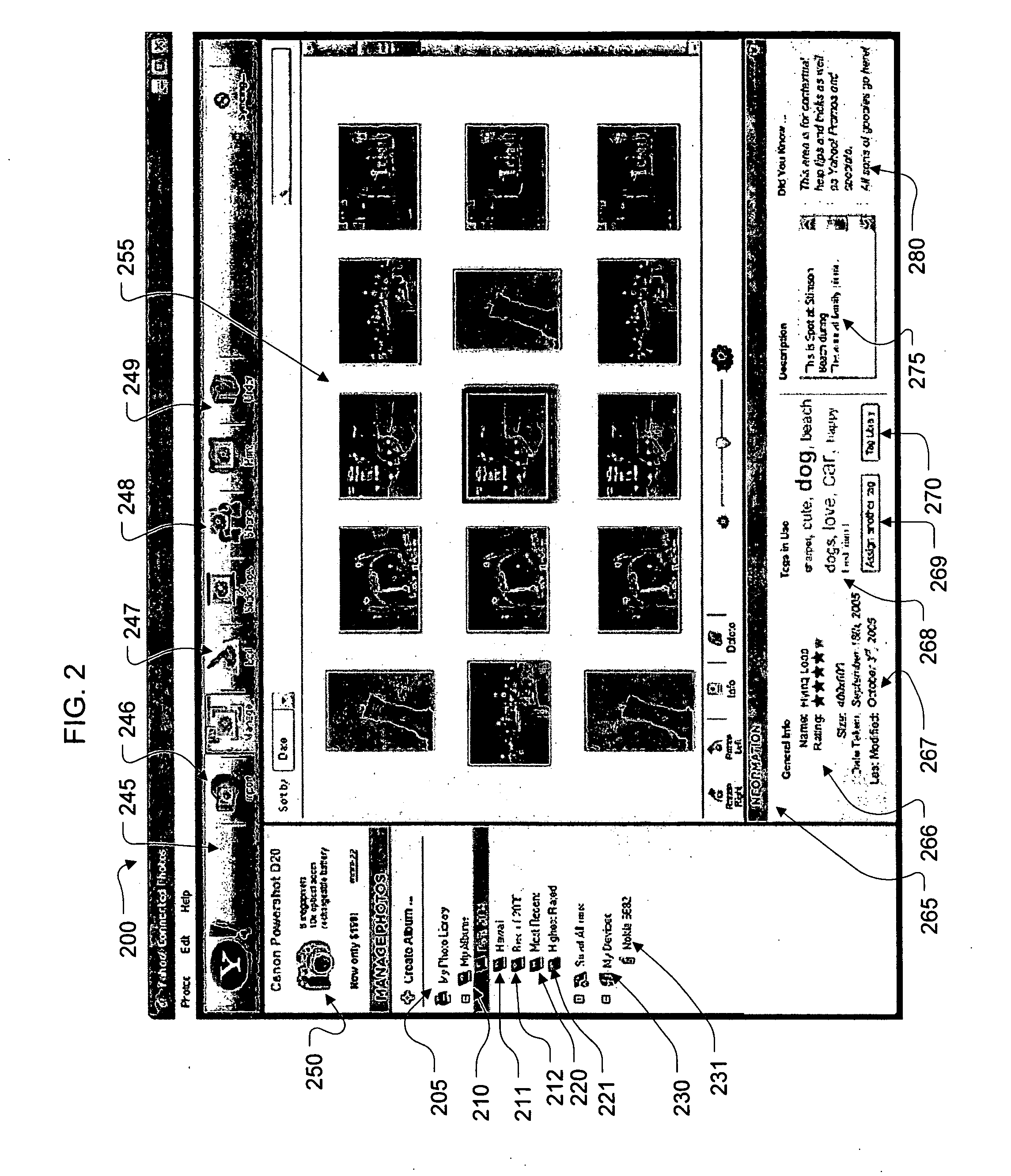
Synchronizing image data among applications and devices
For providing synchronization of image data among diverse devices and applications, exemplary systems include a direct client application providing a user interface operable to allow a user to organize image data according to albums, and to select one or more albums for synchronization with one or more server interfaces that provide various image data manipulation, sharing, and features related thereto. Systems also include an intermediary system to assist in synchronization of select albums with handheld devices, and a notification server to provide scalable notifications of album updates made at server interfaces by users. Exemplary methods include steps providing for selection, from direct client applications, of albums to synchronize with devices, including handheld devices, and various steps of providing updates and notifications among appropriate system components.
Owner:VERIZON PATENT & LICENSING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com