Patents
Literature
12467 results about "Data file" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
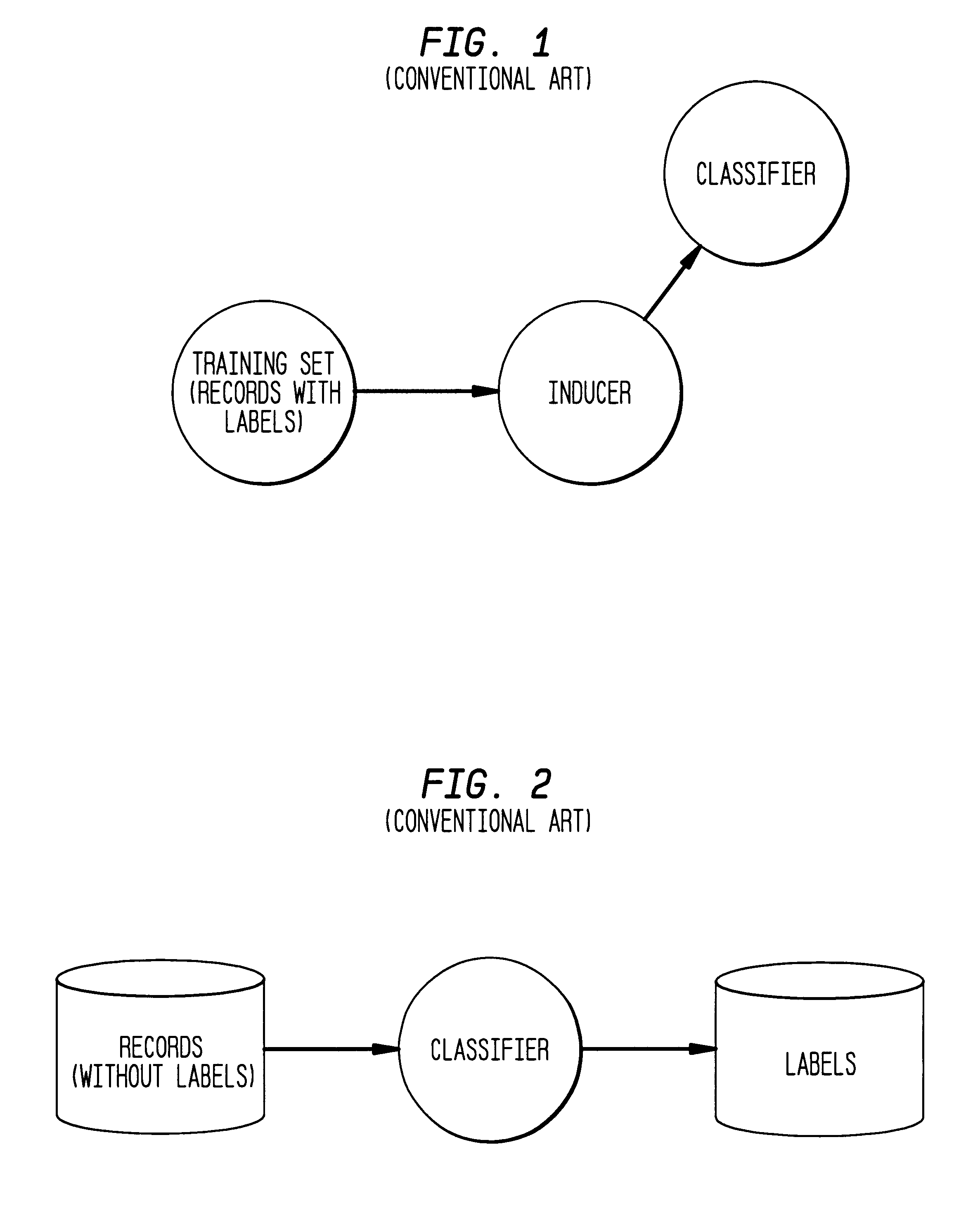
A data file is a computer file which stores data to be used by a computer application or system, including input and output data. A data file usually does not contain instructions or code to be executed (that is, a computer program).
Database management system which synchronizes an enterprise server and a workgroup user client using a docking agent
InactiveUS6092083AData processing applicationsDatabase distribution/replicationData fileTransaction log
Method of and apparatus for collecting, storing, and retrieving data in a database management system. The database management system has an enterprise server and at least one workgroup user client. The method includes creating a transaction in a local database resident on said workgroup user client, entering the transaction into a transaction log resident on the workgroup user client, and creating a transaction file corresponding to the transaction log in an outbox of the workgroup user client. The workgroup user client transaction log is read, skipping those transactions which originate at the enterprise server, data files are created corresponding to the entries. The data files corresponding to transactions originating at the workgroup user client are read to an inbox on the enterprise server, thus updating the transactions into an enterprise database on the enterprise server.
Owner:ORACLE INT CORP
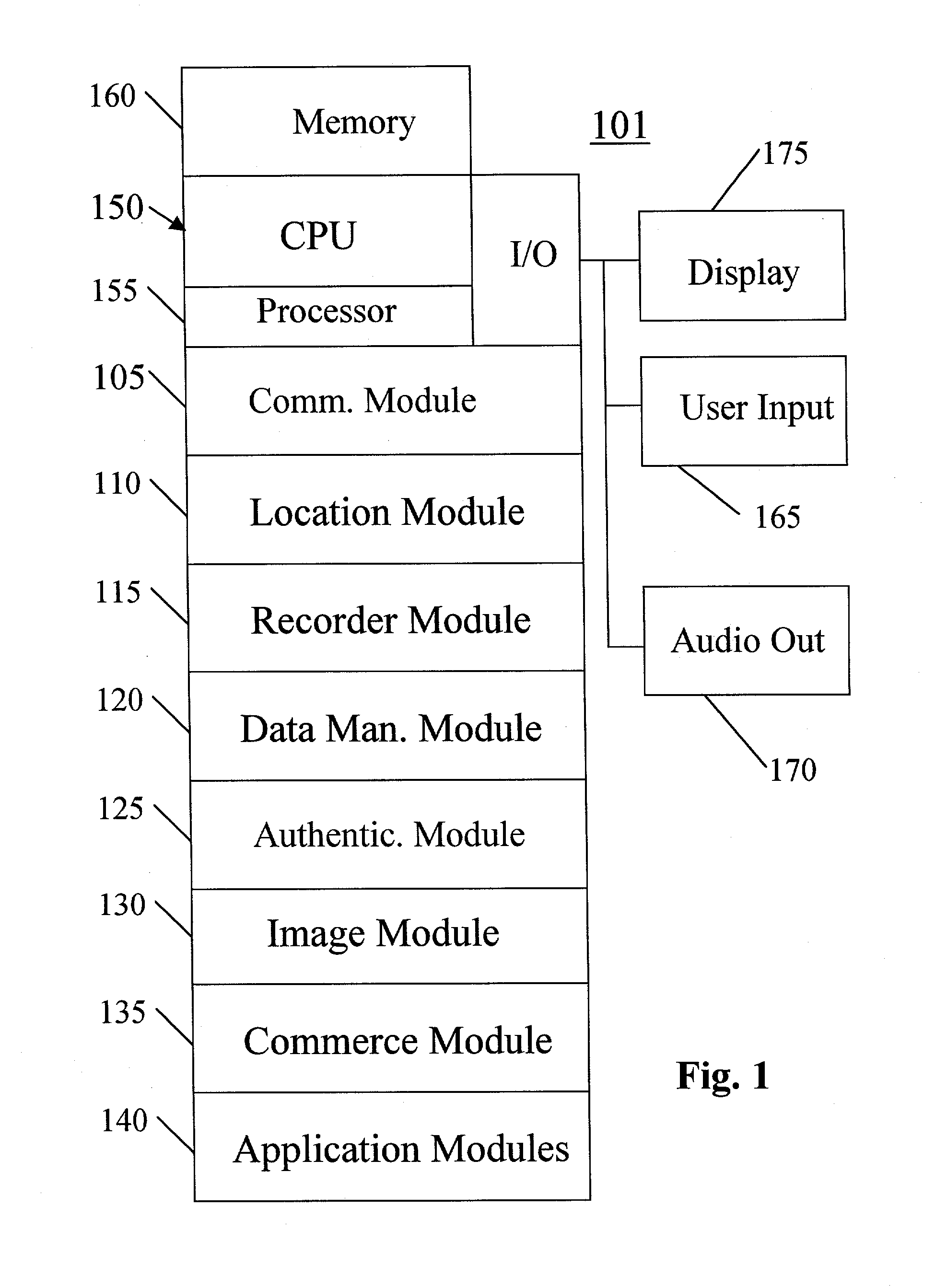
System, method, and computer program product for providing location based services and mobile e-commerce
ActiveUS20030220835A1Facilitating localized e-commerceFacilitate communicationAdvertisementsReservationsData fileDisplay device
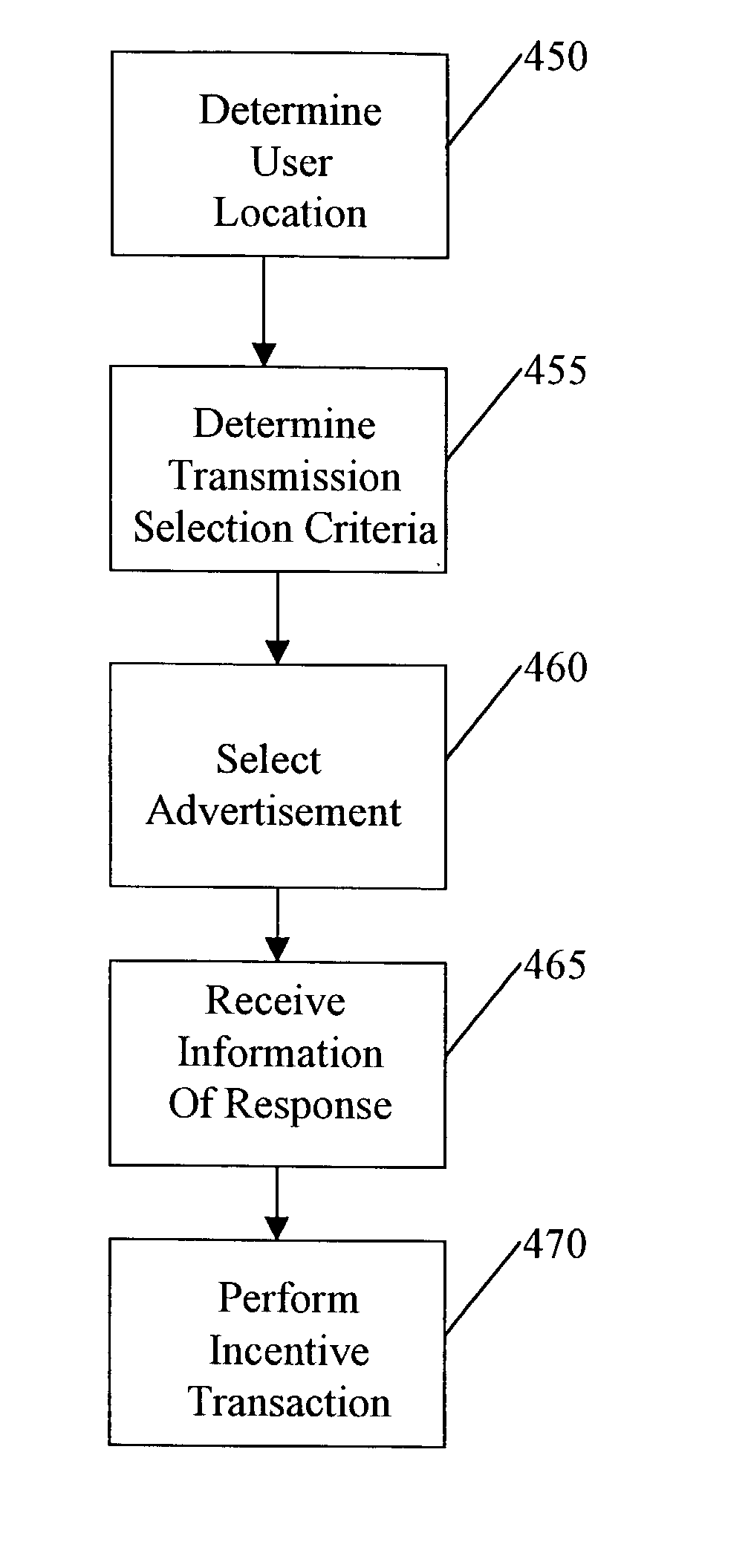
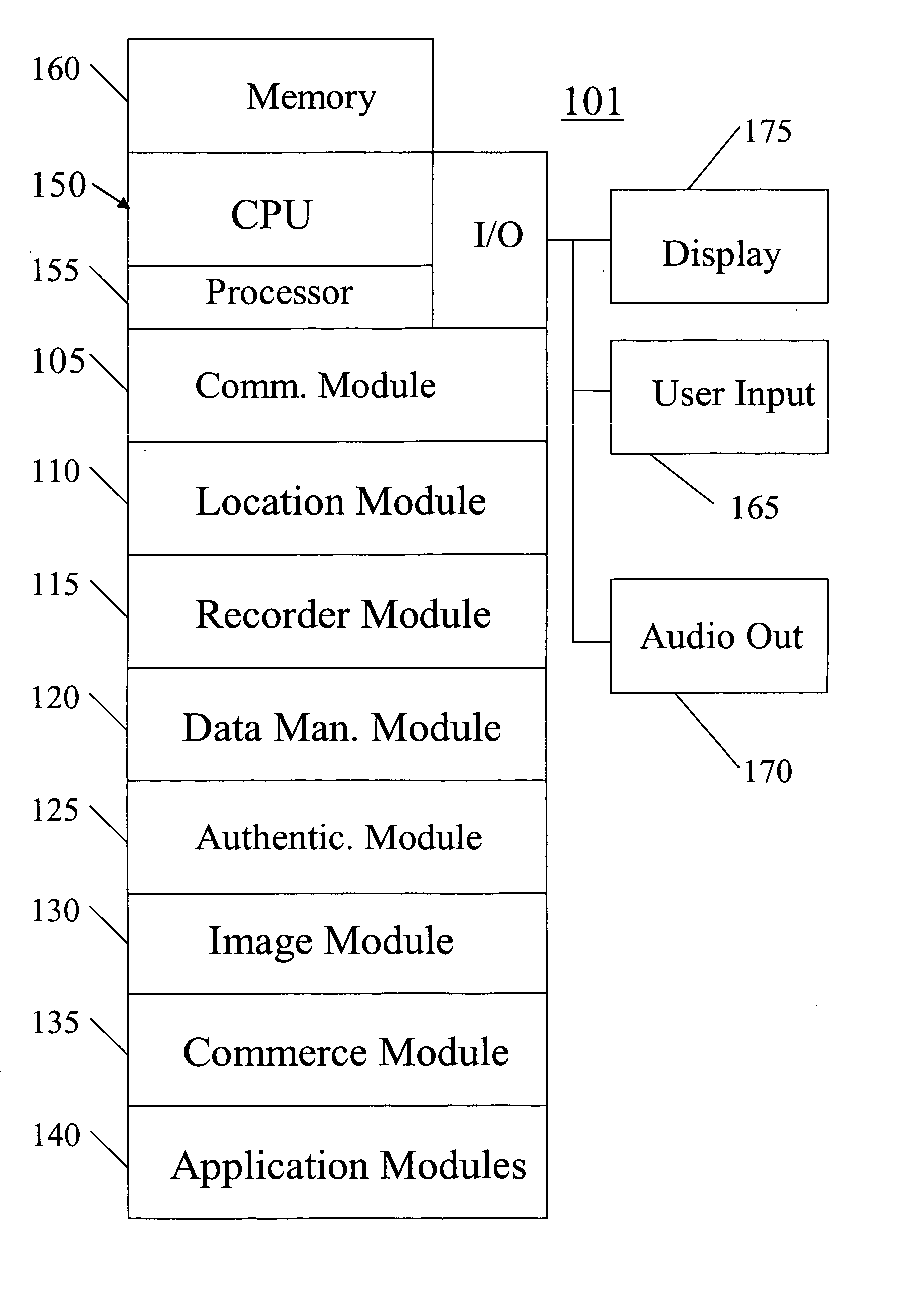
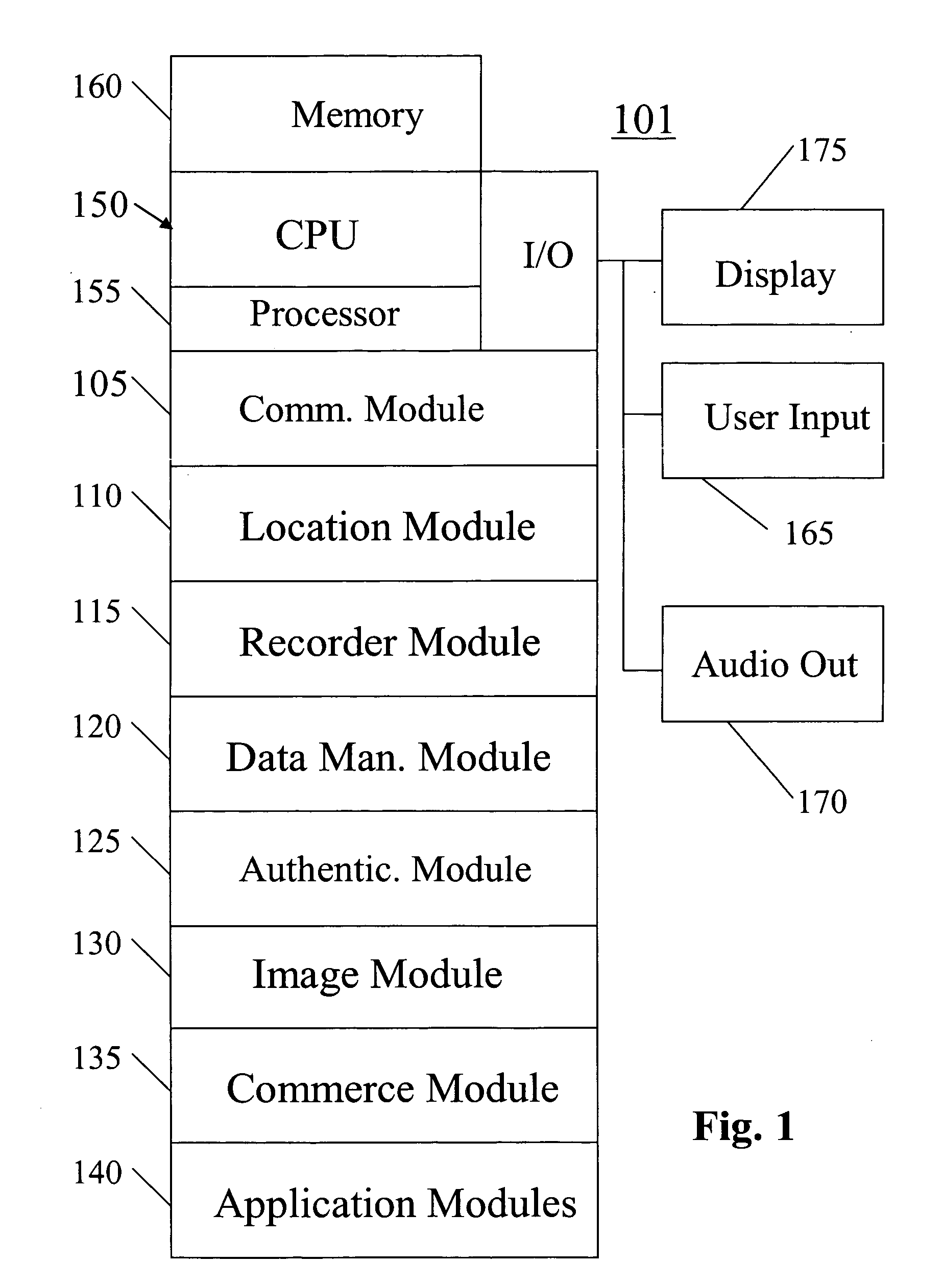
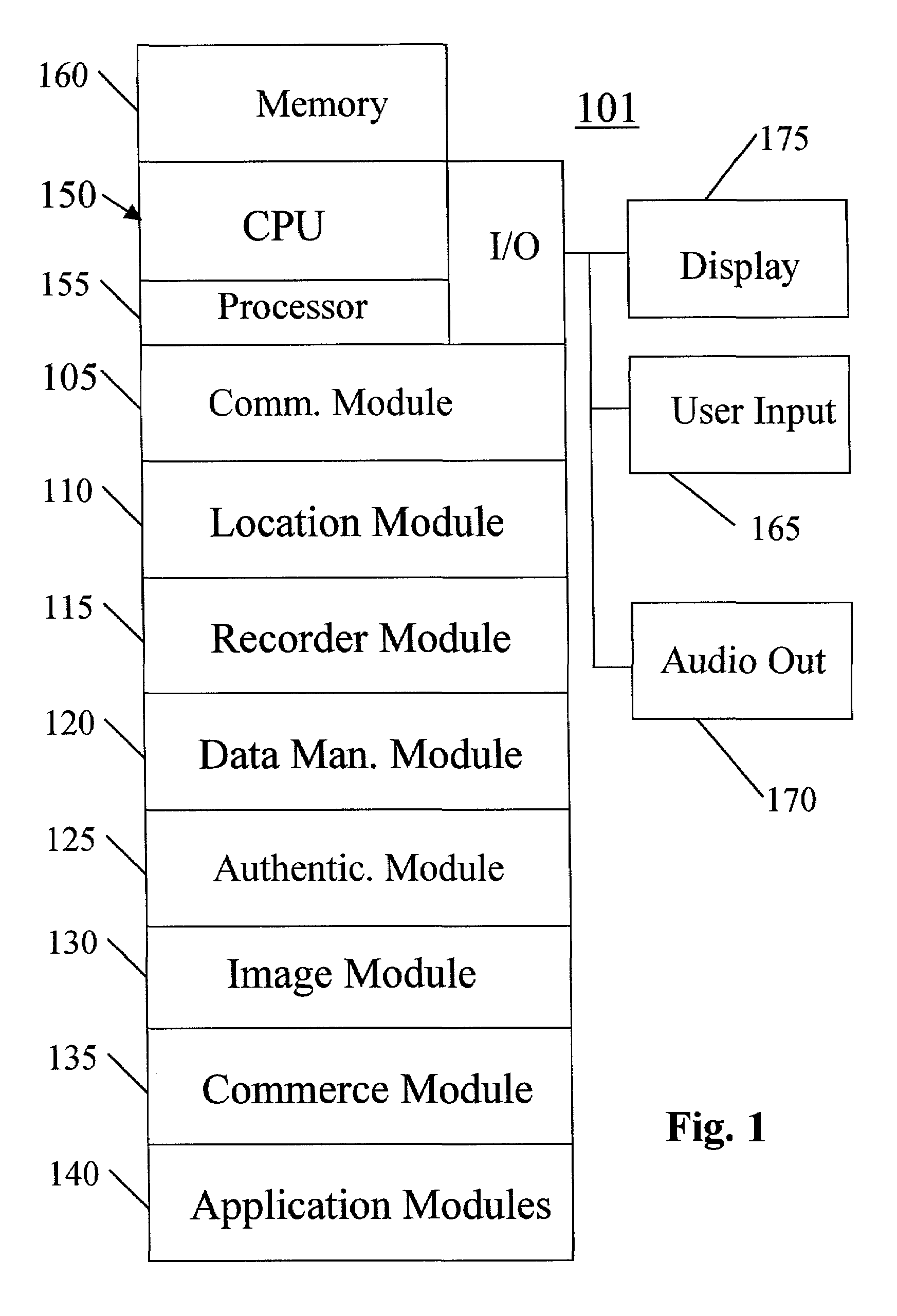
A system, method, apparatus and computer program product for providing location based functions and mobile e-commerce comprising a central processing unit including a processor, a storage device, and programming stored in the storage device, a display device, an audio input device, an audio output device, a communications module, a commerce module, an image module, and a location module. The programming controls the operation of the present invention to provide functions based on location data, to facilitate commercial exchanges by wirelessly exchanging payment and product information with venders, to identify services such as venders meeting selection criteria, to wirelessly exchange select information with other users and systems, to restrict and / or monitor the use of the device based on authorized user parameters, selecting one of a plurality networks through which to communicate, detecting a trigger for performing an action based on a change in location and sensed data, storing a voice annotation with a computer data file, determining service providers and associated communication parameters, contemporaneously maintaining a wireless voice and data link, providing a system for selecting and delivering mobile advertisements, and many other functions and services that are described herein.
Owner:GULA CONSULTING LLC
System, method, and computer program product for providing location based services and mobile e-commerce
ActiveUS20030065805A1Facilitating localized e-commerceFacilitate communicationTelevision system detailsColor television detailsDisplay deviceData file
A system, method, apparatus and computer program product for providing location based functions and mobile e-commerce comprising a central processing unit including a processor, a storage device, and programming stored in the storage device, a display device, an audio input device, an audio output device, a communications module, a commerce module, an image module, and a location module. The programming controls the operation of the present invention to provide functions based on location data, to facilitate commercial exchanges by wirelessly exchanging payment and product information with venders, to identify services such as venders meeting selection criteria, to wirelessly exchange select information with other users and systems, to restrict and / or monitor the use of the device based on authorized user parameters, selecting one of a plurality networks through which to communicate, detecting a trigger for performing an action based on a change in location and sensed data, storing a voice annotation with a computer data file, determining service providers and associated communication parameters, contemporaneously maintaining a wireless voice and data link, providing a system for selecting and delivering mobile advertisements, and many other functions and services that are described herein.
Owner:GULA CONSULTING LLC
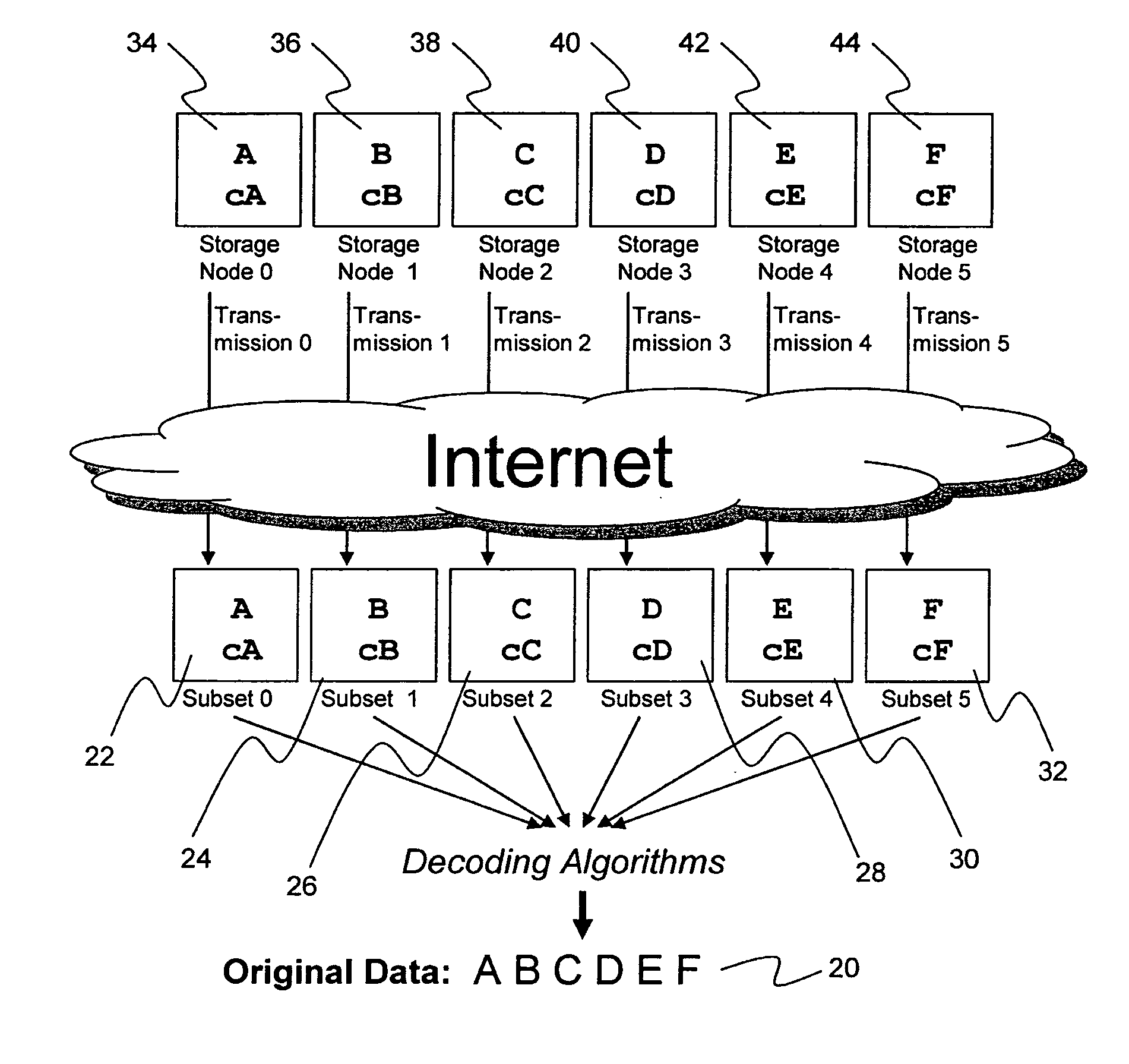
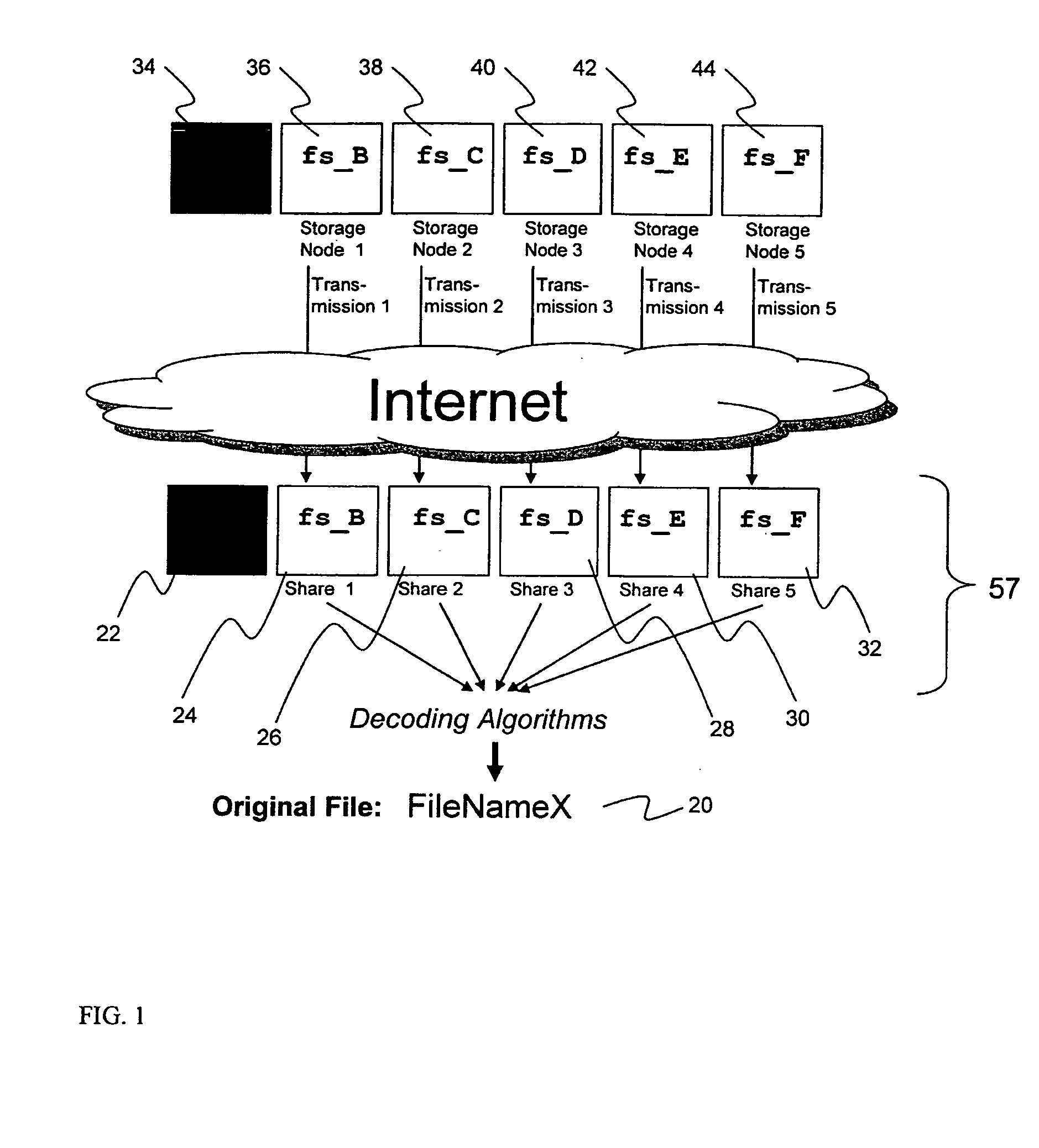
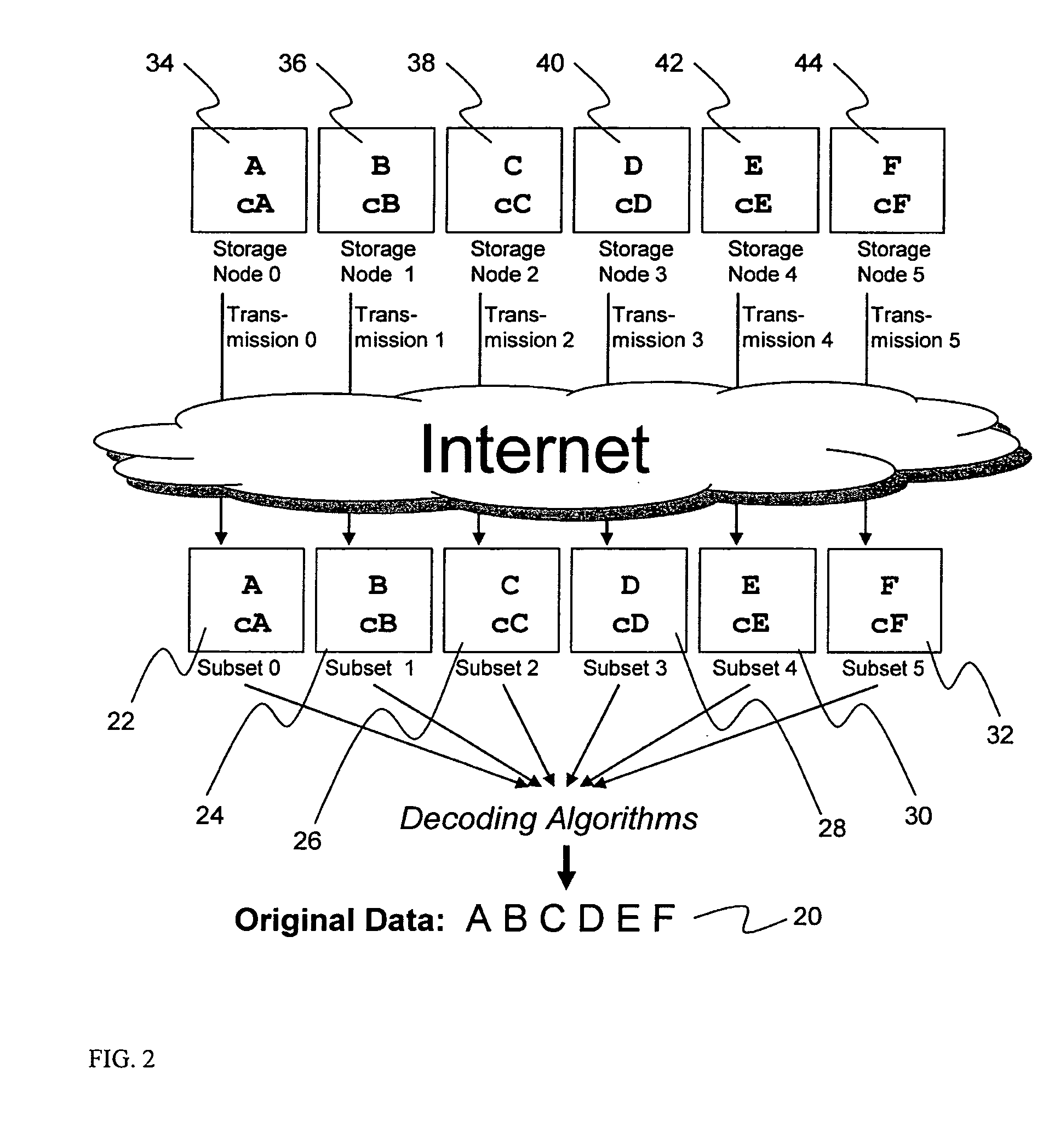
System for rebuilding dispersed data
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
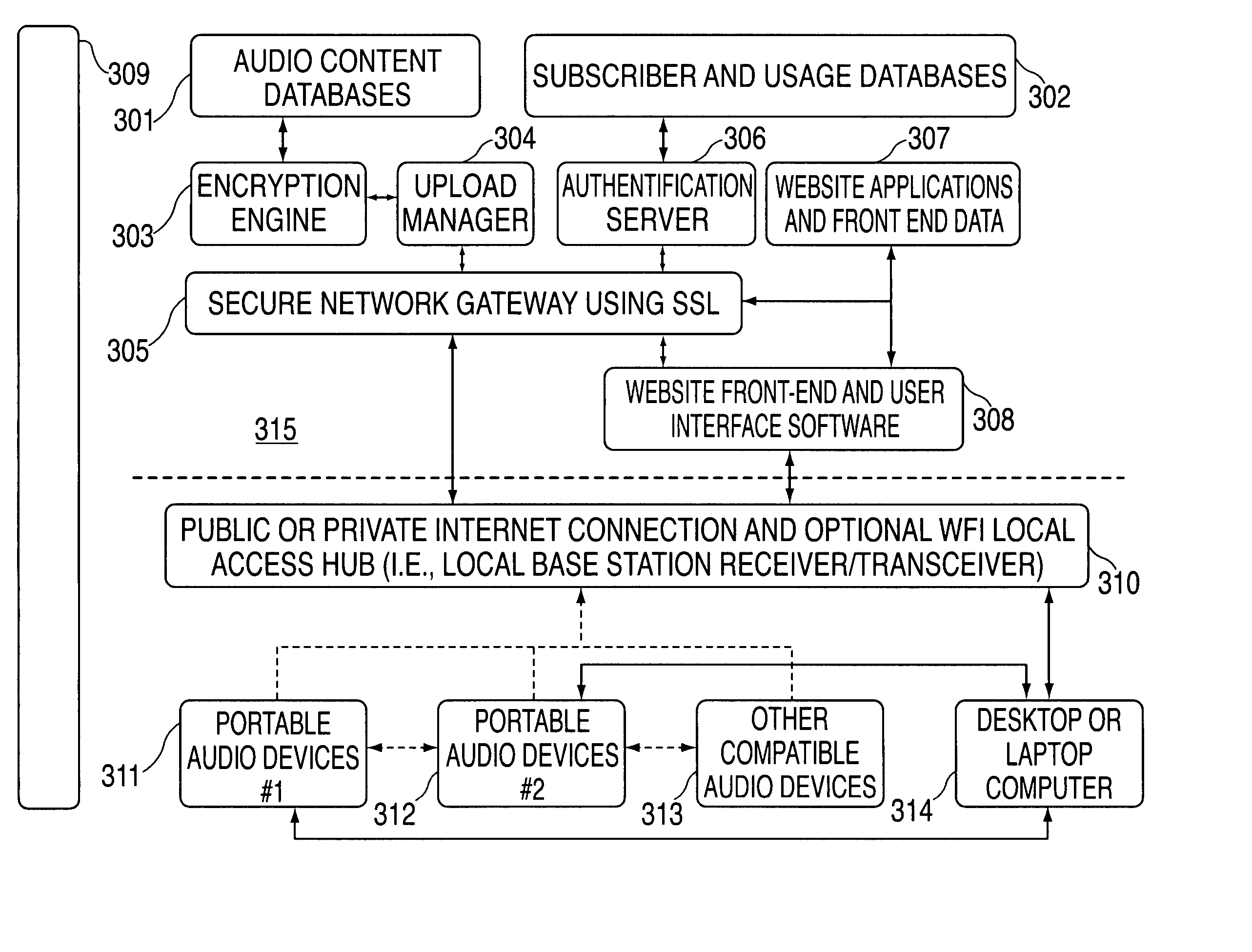
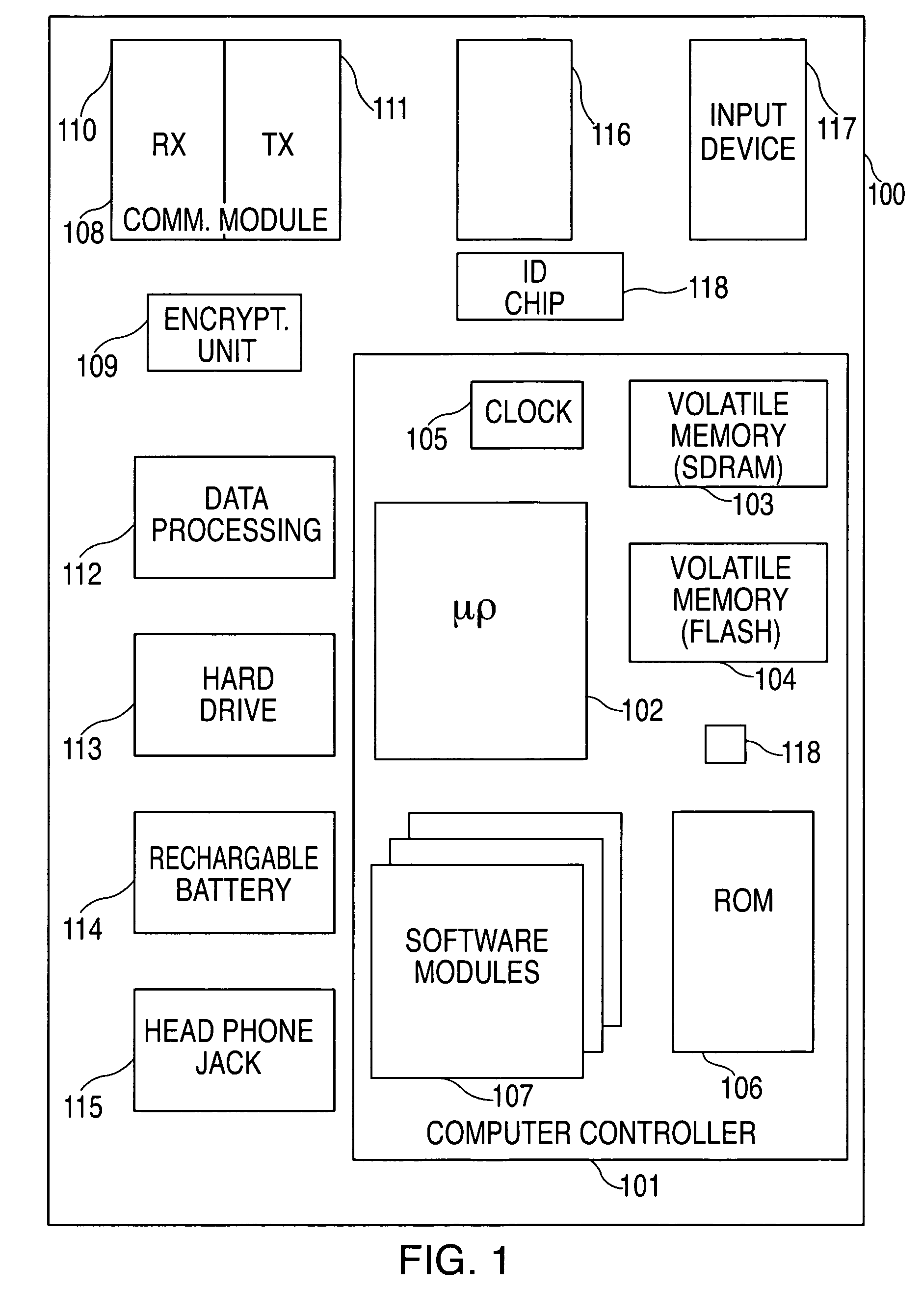
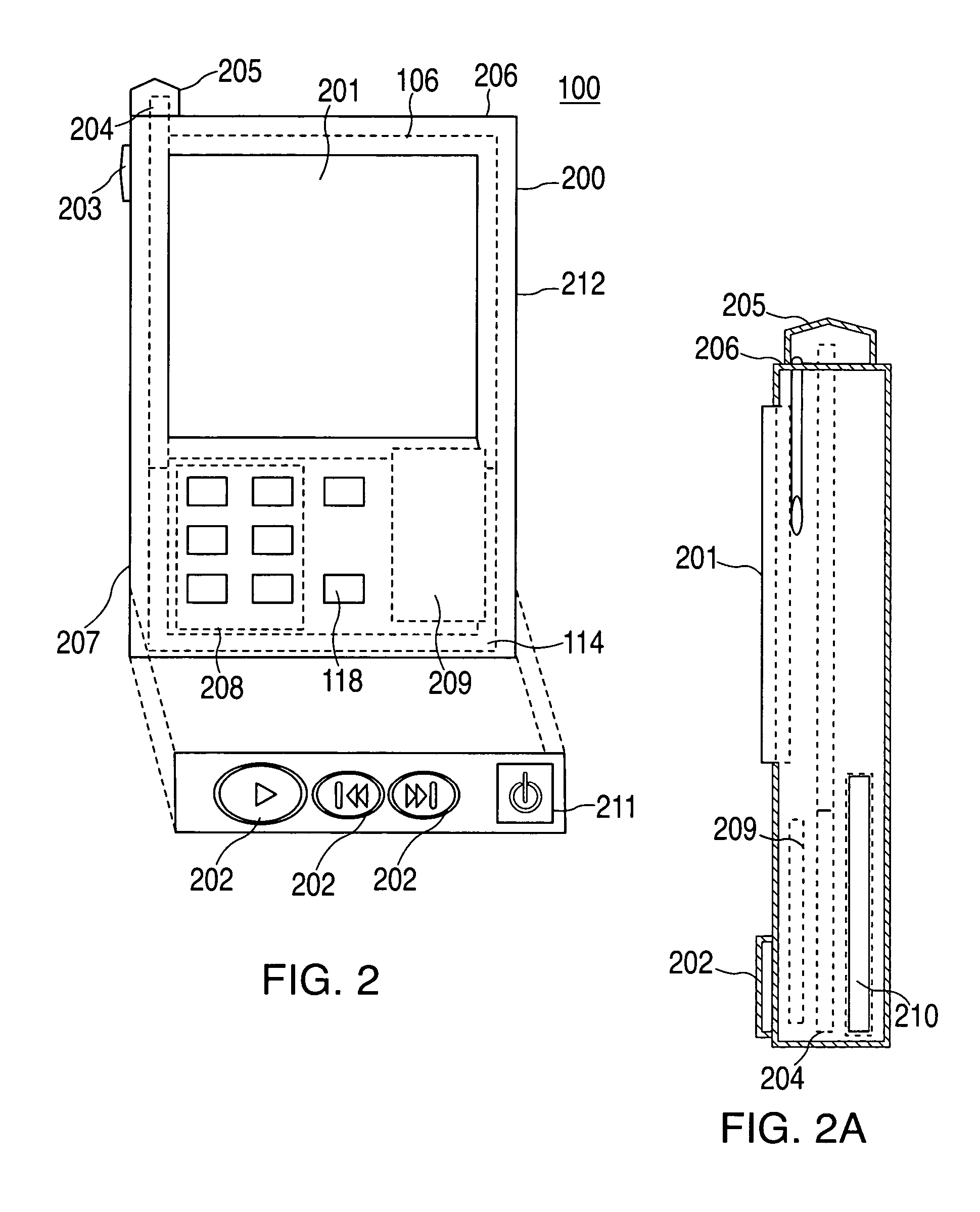
Audio visual player apparatus and system and method of content distribution using the same
InactiveUS20060008256A1None of methods is secureTelevision system detailsColor television signals processingContent distributionVideo player
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
Automatic, personalized online information and product services
InactiveUS6981040B1Improve performanceManage efficiently enormousDigital data information retrievalMultiple digital computer combinationsLearning machinePersonalized search
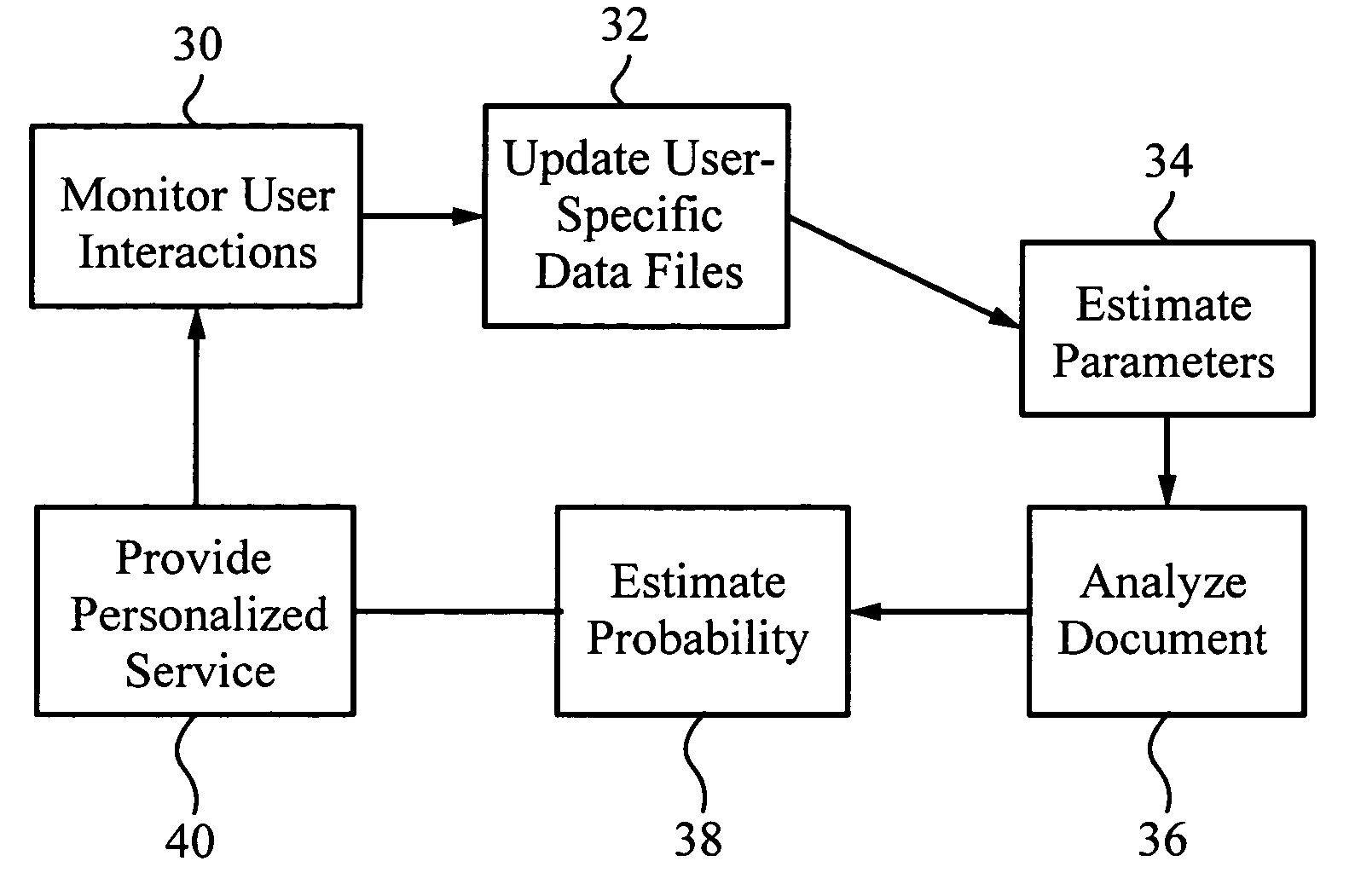
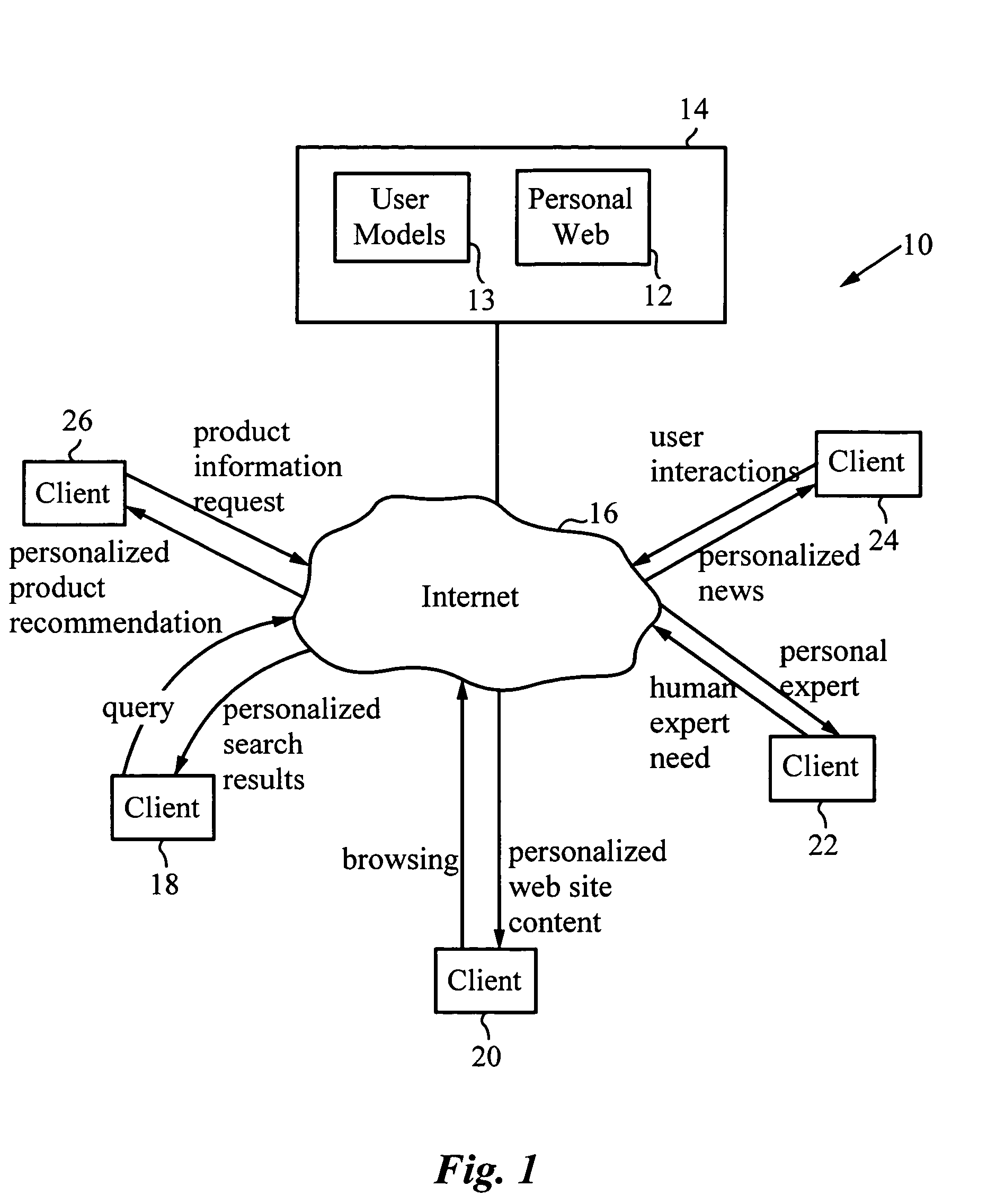
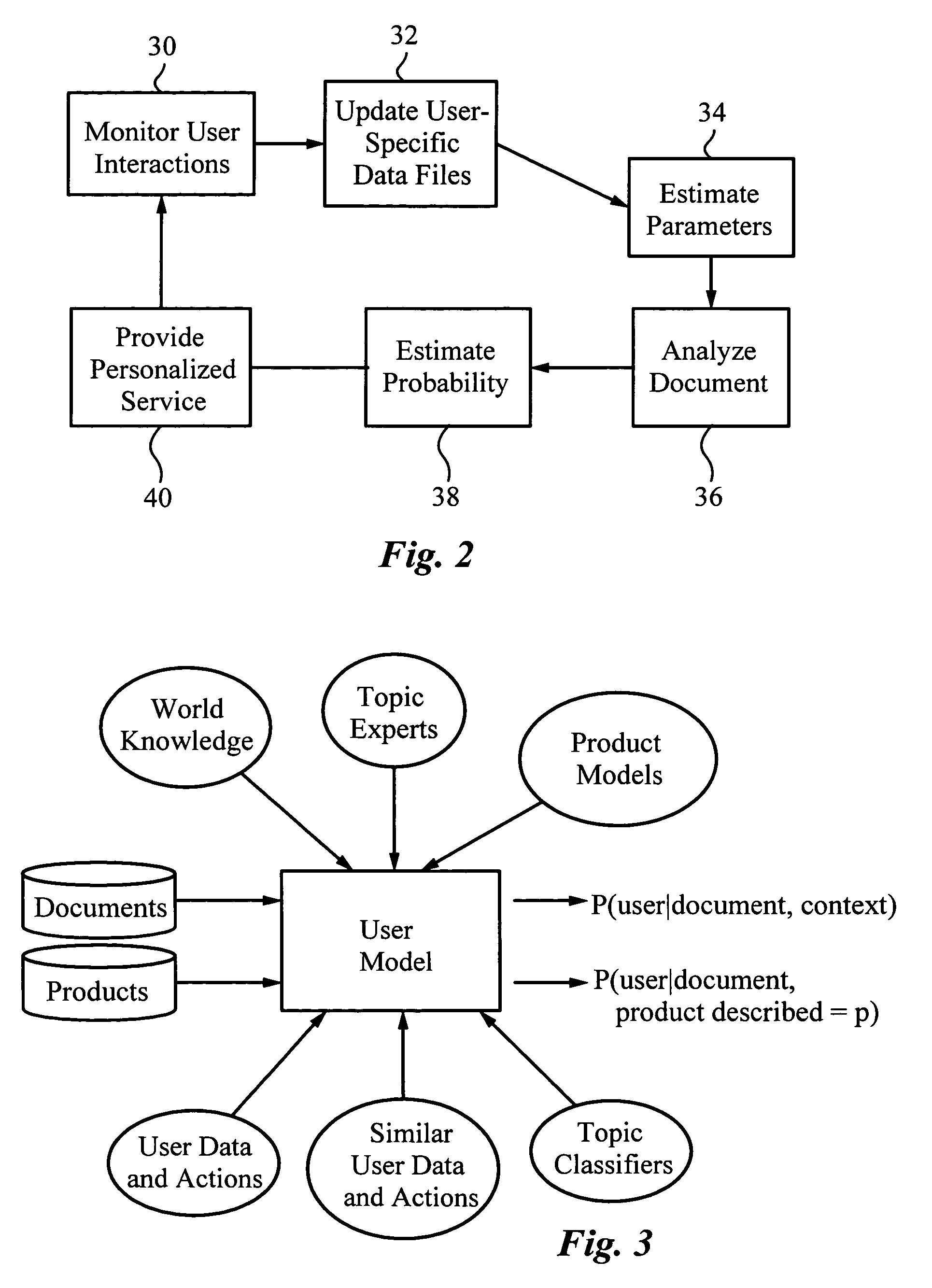
A method for providing automatic, personalized information services to a computer user includes the following steps: transparently monitoring user interactions with data during normal use of the computer; updating user-specific data files including a set of user-related documents; estimating parameters of a learning machine that define a User Model specific to the user, using the user-specific data files; analyzing a document to identify its properties; estimating the probability that the user is interested in the document by applying the document properties to the parameters of the User Model; and providing personalized services based on the estimated probability. Personalized services include personalized searches that return only documents of interest to the user, personalized crawling for maintaining an index of documents of interest to the user; personalized navigation that recommends interesting documents that are hyperlinked to documents currently being viewed; and personalized news, in which a third party server customized its interaction with the user. The User Model includes continually-updated measures of user interest in words or phrases, web sites, topics, products, and product features. The measures are updated based on both positive examples, such as documents the user bookmarks, and negative examples, such as search results that the user does not follow. Users are clustered into groups of similar users by calculating the distance between User Models.
Owner:PERSONALIZED USER MODEL PUM
Portable communications device and method of use
A system, method, apparatus and computer program product for providing location based functions and mobile e-commerce comprising a central processing unit including a processor, a storage device, and programming stored in the storage device, a display device, an audio input device, an audio output device, a communications module, a commerce module, an image module, and a location module. The programming controls the operation of the present invention to provide functions based on location data, to facilitate commercial exchanges by wirelessly exchanging payment and product information with venders, to identify services such as venders meeting selection criteria, to wirelessly exchange select information with other users and systems, to restrict and / or monitor the use of the device based on authorized user parameters, to select one of a plurality networks through which to communicate, to detect a trigger for performing an action based on a change in location and sensed data, to store a voice annotation with a computer data file, to determine service providers and associated communication parameters, to contemporaneously maintain a wireless voice and data link, to provide a system for selecting mobile advertisements, and many other functions and services that are described herein.
Owner:WOUNDER
System, method, and computer program product for providing location based services and mobile e-commerce
ActiveUS7487112B2Facilitate communicationTelevision system detailsColor television detailsData fileDisplay device
A system, method, apparatus and computer program product for providing location based functions and mobile e-commerce comprising a central processing unit including a processor, a storage device, and programming stored in the storage device, a display device, an audio input device, an audio output device, a communications module, a commerce module, an image module, and a location module. The programming controls the operation of the present invention to provide functions based on location data, to facilitate commercial exchanges by wirelessly exchanging payment and product information with venders, to identify services such as venders meeting selection criteria, to wirelessly exchange select information with other users and systems, to restrict and / or monitor the use of the device based on authorized user parameters, selecting one of a plurality networks through which to communicate, detecting a trigger for performing an action based on a change in location and sensed data, storing a voice annotation with a computer data file, determining service providers and associated communication parameters, contemporaneously maintaining a wireless voice and data link, providing a system for selecting and delivering mobile advertisements, and many other functions and services that are described herein.
Owner:GULA CONSULTING LLC
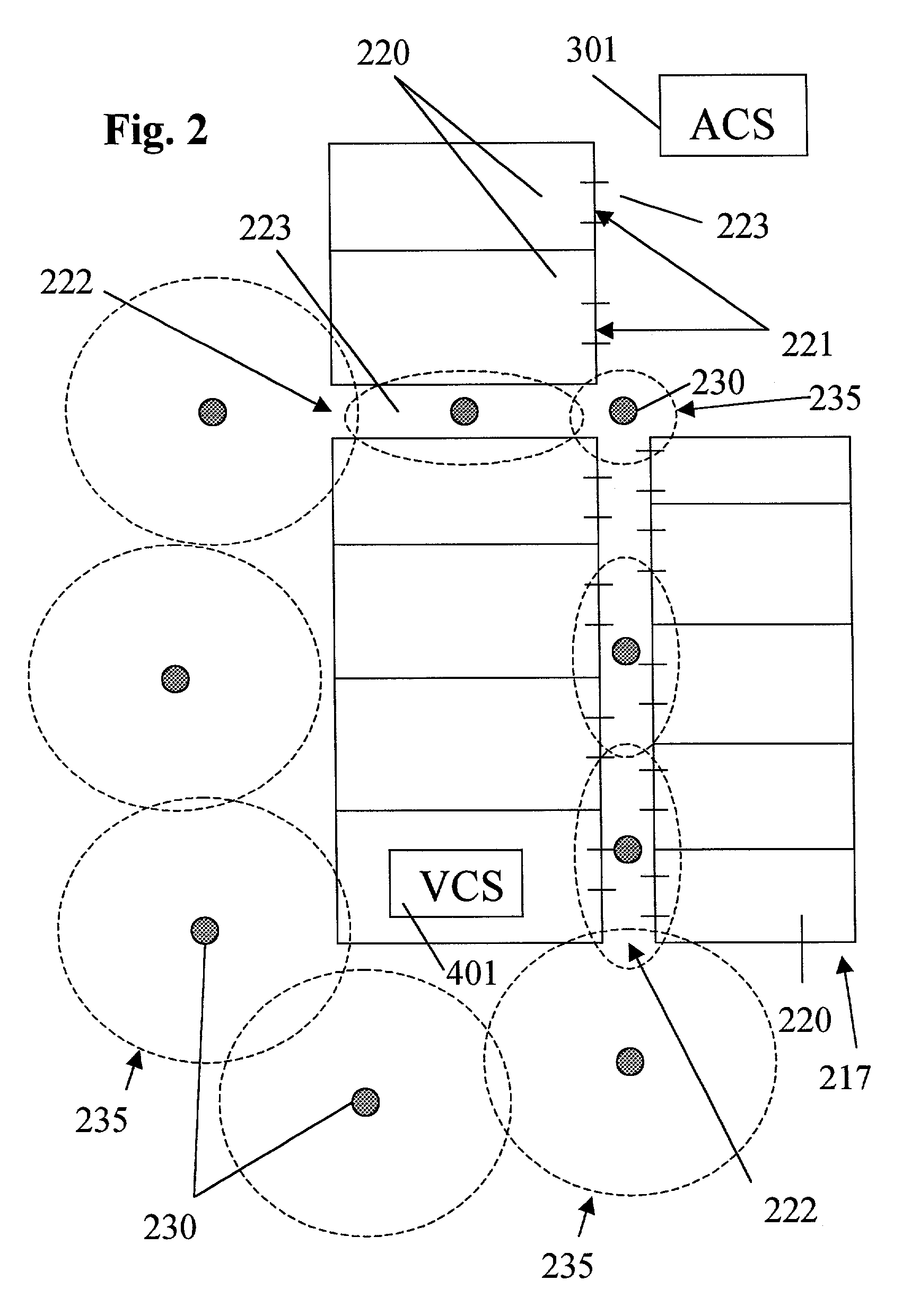
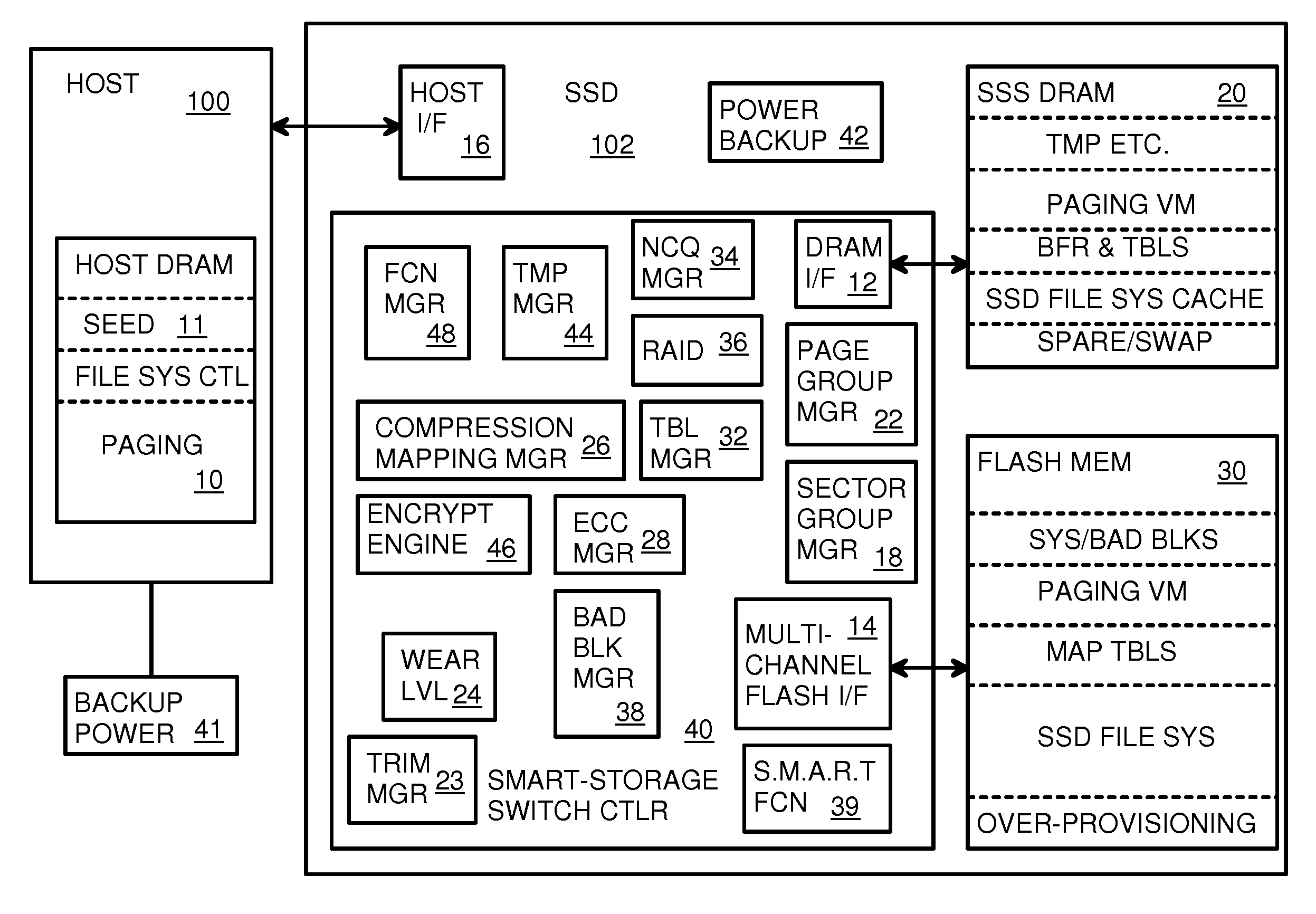
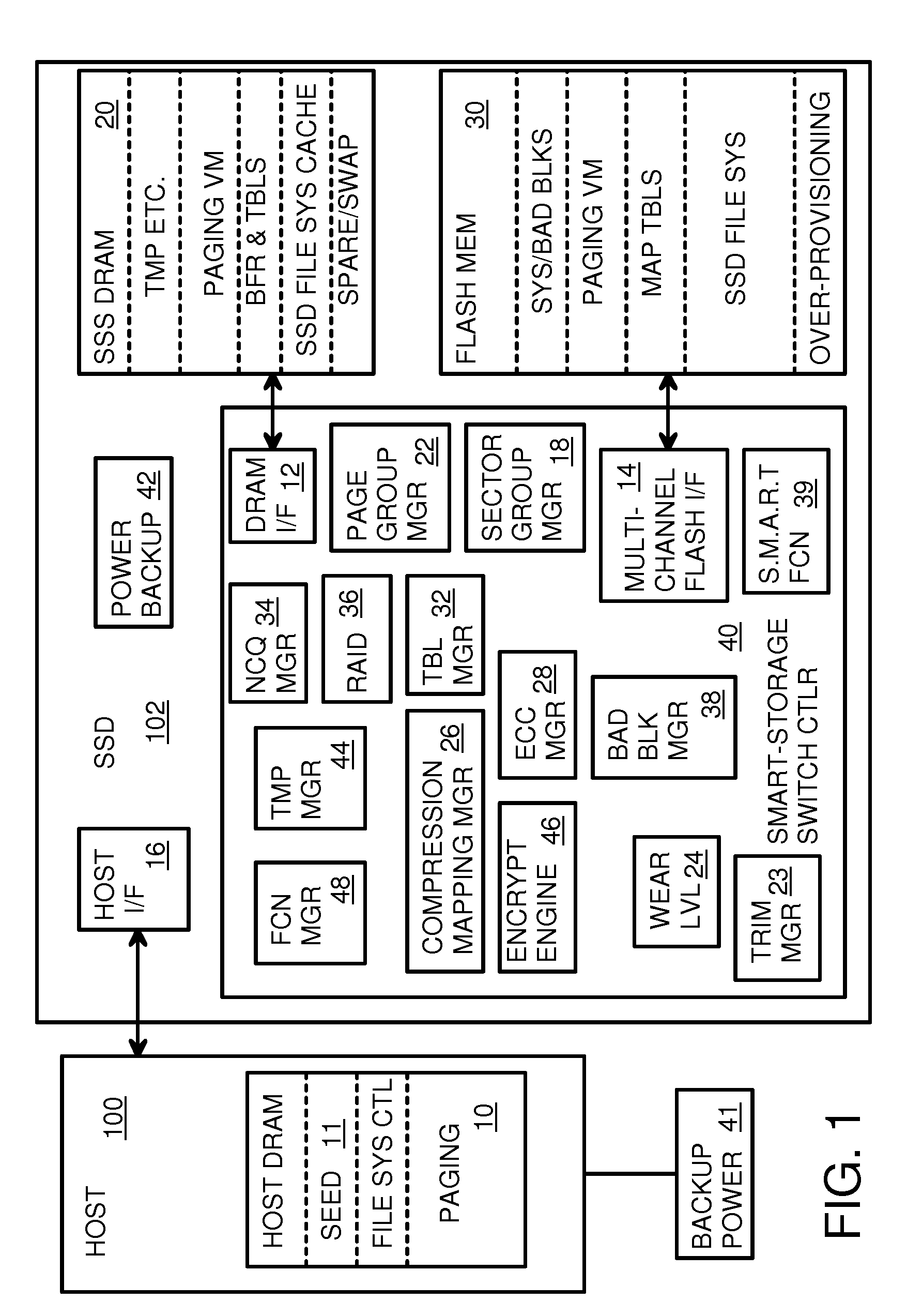
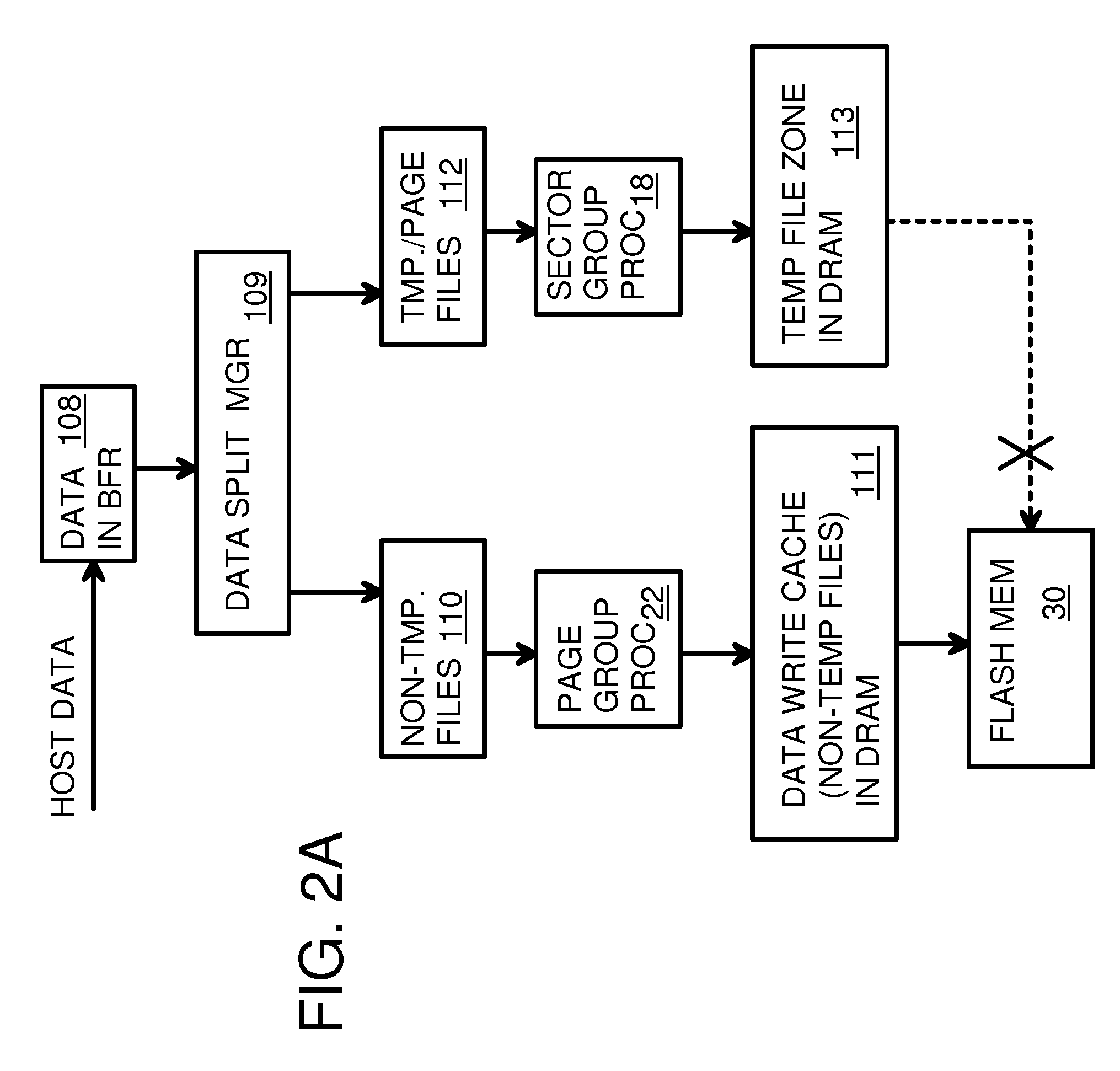
Super-Endurance Solid-State Drive with Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear
ActiveUS20120284587A1Memory architecture accessing/allocationDigital storageFilename extensionData file
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
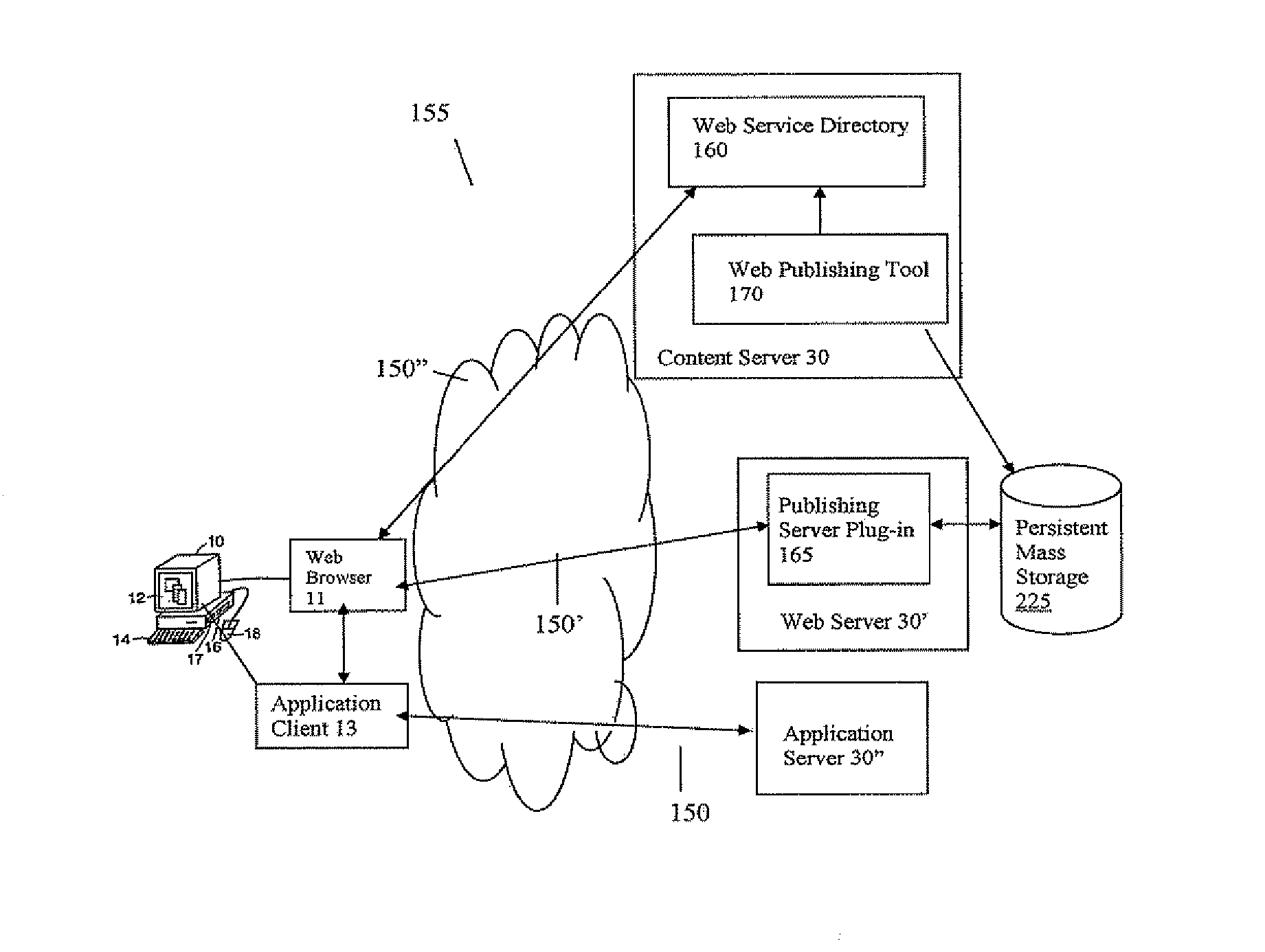
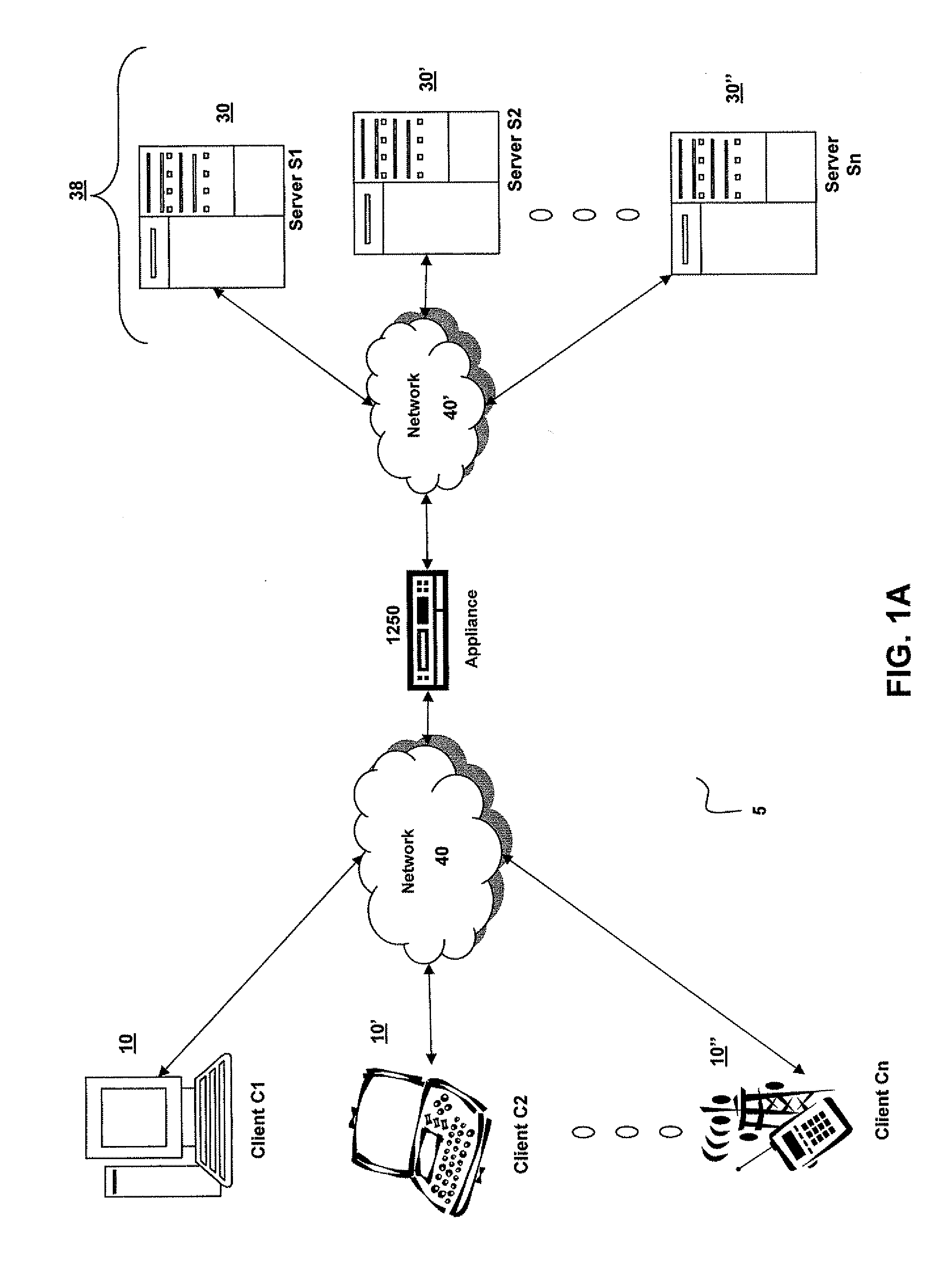
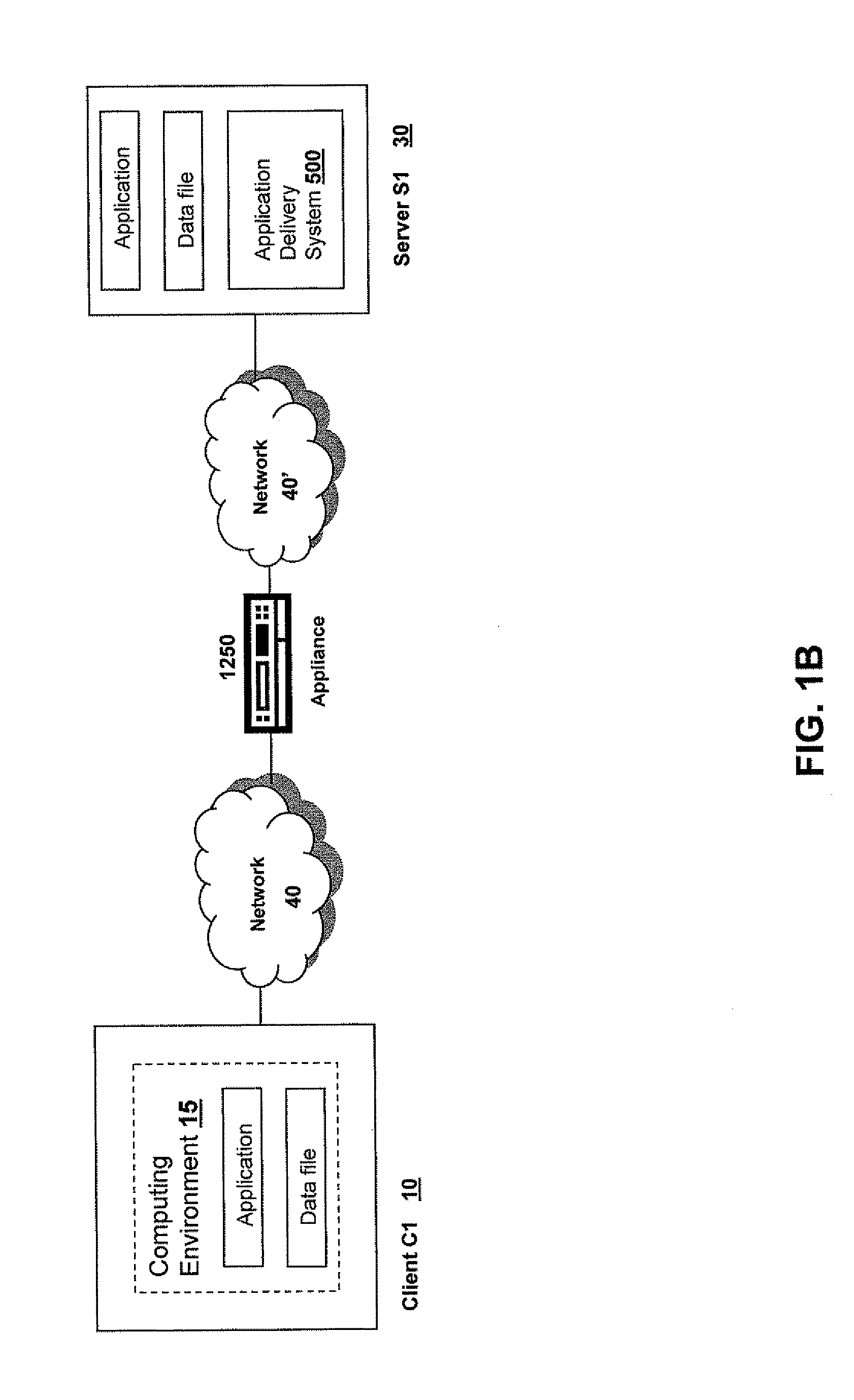
Systems and Methods for Accelerating Delivery of a Computing Environment to a Remote User
ActiveUS20070244987A1Reduce deliveryFacilitate communicationMultiple digital computer combinationsData switching networksNetwork connectionData file
The present invention is directed towards the acceleration of delivery of a computing environment to a remote user of a client at a remote location. The computing environment may include an application and a data file used or processed by the application. The application and data file may be stored or provided via a server remote to the client. The user can request a computing environment from the server that provides for execution of the application by the user via the remote computer. For example, the server may stream the application to the remote client. The client and server may communicate via an appliance that accelerates communications between the client and server. For example, the appliance may accelerate the streaming of the application to the remote user. In some cases, the application or remote user may also request a data file from the server, and the appliance accelerates the delivery of the data file to the remote user. As such, users at remote locations obtain accelerated access via any network connected device to applications and data files located remotely to the user.
Owner:CITRIX SYST INC
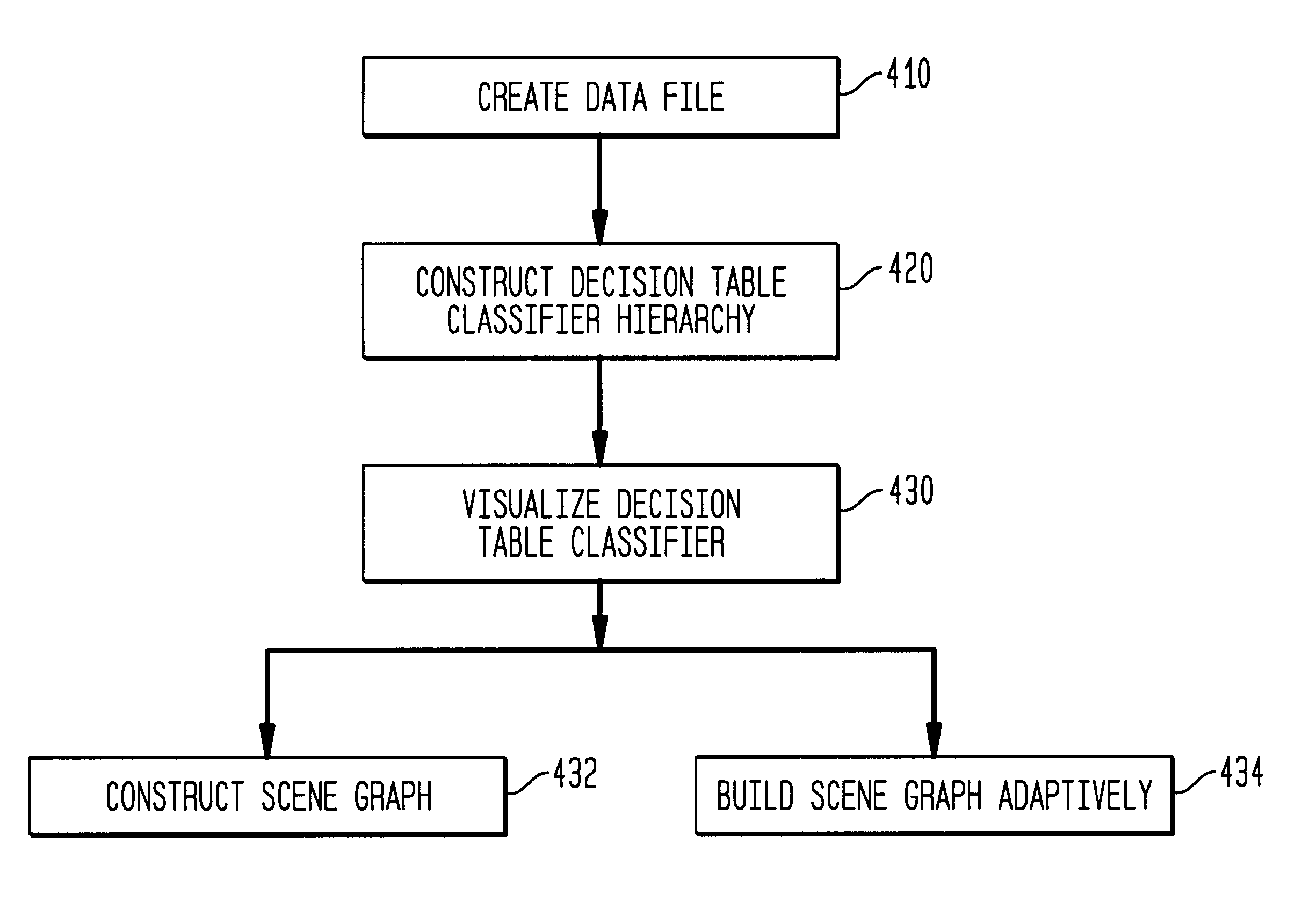
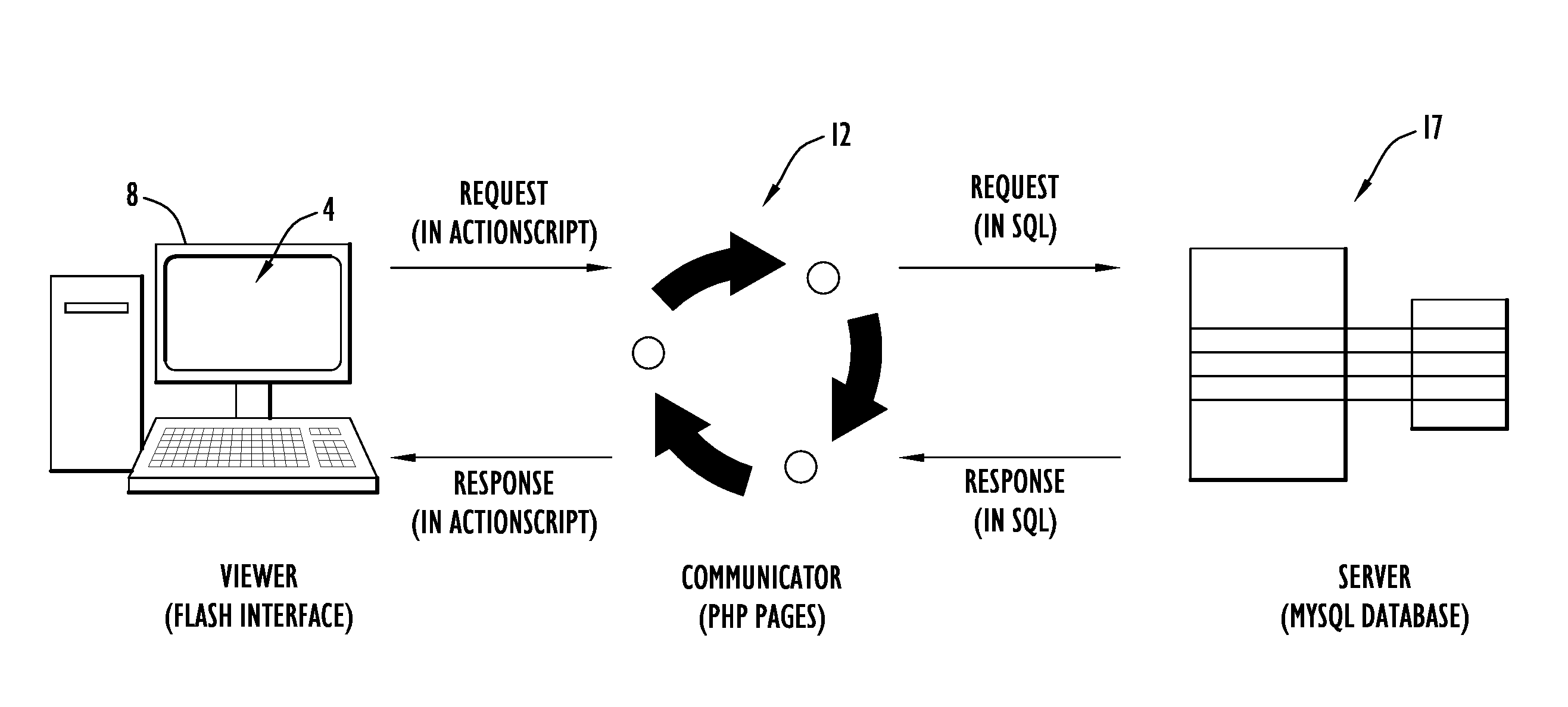
Method, system, and computer program product for visualizing a data structure
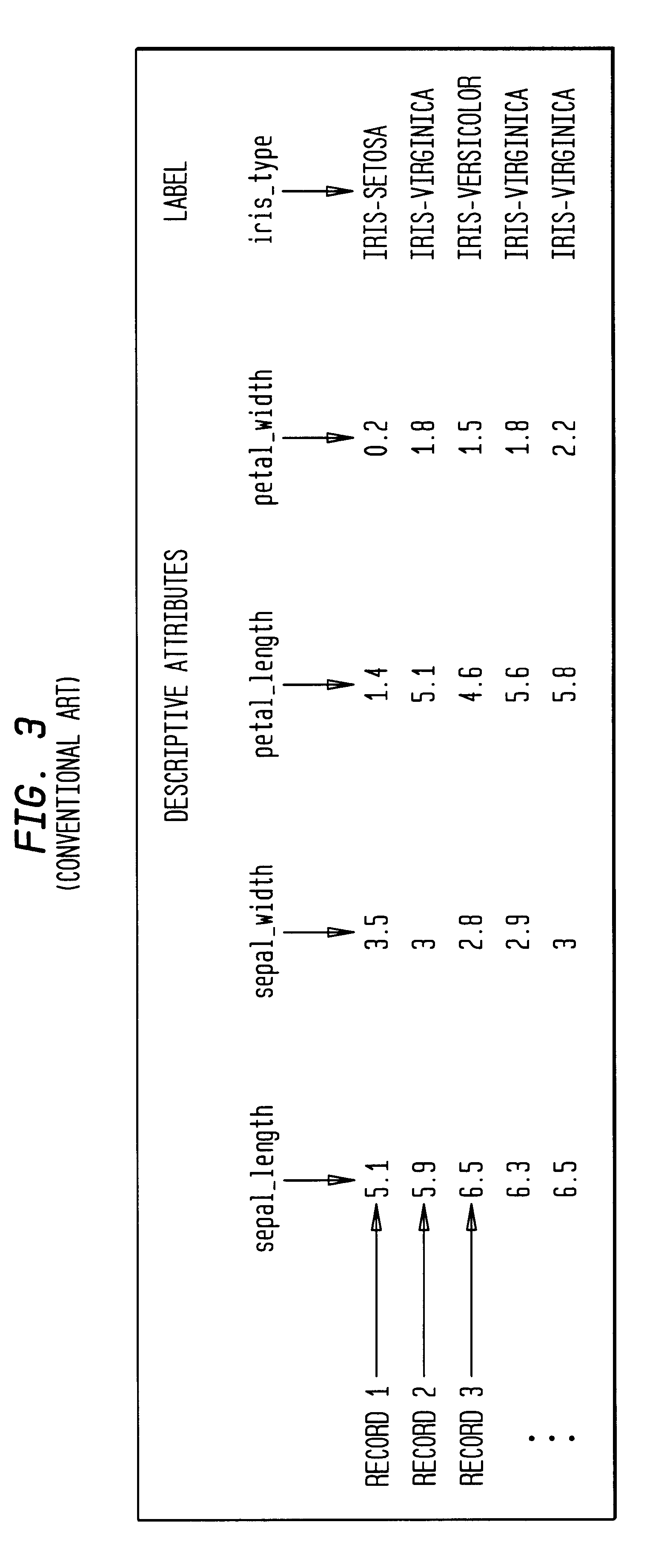
A data structure visualization tool visualizes a data structure such as a decision table classifier. A data file based on a data set of relational data is stored as a relational table, where each row represents an aggregate of all the records for each combination of values of the attributes used. Once loaded into memory, an inducer is used to construct a hierarchy of levels, called a decision table classifier, where each successive level in the hierarchy has two fewer attributes. Besides a column for each attribute, there is a column for the record count (or more generally, sum of record weights), and a column containing a vector of probabilities (each probability gives the proportion of records in each class). Finally, at the top-most level, a single row represents all the data. The decision table classifier is then passed to the visualization tool for display and the decision table classifier is visualized. By building a representative scene graph adaptively, the visualization application never loads the whole data set into memory. Interactive techniques, such as drill-down and drill-through are used view further levels of detail or to retrieve some subset of the original data. The decision table visualizer helps a user understand the importance of specific attribute values for classification.
Owner:RPX CORP +1
Card dispensing shoe with scanner apparatus, system and method therefor
The present invention is directed to a playing card dispensing shoe apparatus, system and method wherein the shoe has a card scanner which scans the indicia on a playing card as the card moves along and out of a chute of the shoe by operation of the dealer. The scanner comprises an optical-sensor used in combination with a neural network which is trained using error back-propagation to recognize the card suits and card values of the playing cards as they are moved past the scanner. The scanning process in combination with a central processing unit (CPU) determines the progress of the play of the game and, by identifying card counting systems or basic playing strategies in use by the players of the game, provides means to limit or prevent casino losses and calculate the Theoretical Win of the casino, thus also providing an accurate quality method of the amount of comps to be given a particular player. The shoe is also provided with additional devices which make it simple and easy to access, record and display other data relevant to the play of the game. These include means for acconunodating a "customer-tracking card" which reads each player's account information from a magnetic stripe on the card, thus providing access to the player's customer data file stored on the casino's computer system, and one or more alpha-numeric keyboards and LCD displays used to enter and retrieve player and game information. Also included are keyboards on the game table so that each player can individually select various playing or wagering options using their own keyboard.
Owner:PROGRESSIVE GAMING INT
Method and apparatus for the management of data files
InactiveUS6263330B1Easy retrievalEasy accessData processing applicationsTelemedicineMedical recordData file
The present invention provides a network system for storage of medical records. The records are stored in a database on a server. Each record includes two main parts, namely a collection of data elements containing information of medical nature for the certain individual, and a plurality of pointers providing addresses or remote locations where reside other medical data for that particular individual. Each record also includes a data element indicative of the basic type of medical data found at the location pointed to by a particular pointer. This arrangement permits a client workstation to download the record along with the set of pointers which link the client to the remotely stored files. The identification of the basic type of information that each pointer points to allows the physician to select the ones of interest and thus avoid downloading massive amounts of data where only part of that data is needed at that time. In addition, this record structure allows statistical queries to be effected without the necessity of accessing the data behind the pointers. For instance, a query can be built based on keys, one of which is the type of data that a pointer points to. The query can thus be performed solely on the basis of the pointers and the remaining information held in the record.
Owner:BESSETTE LUC
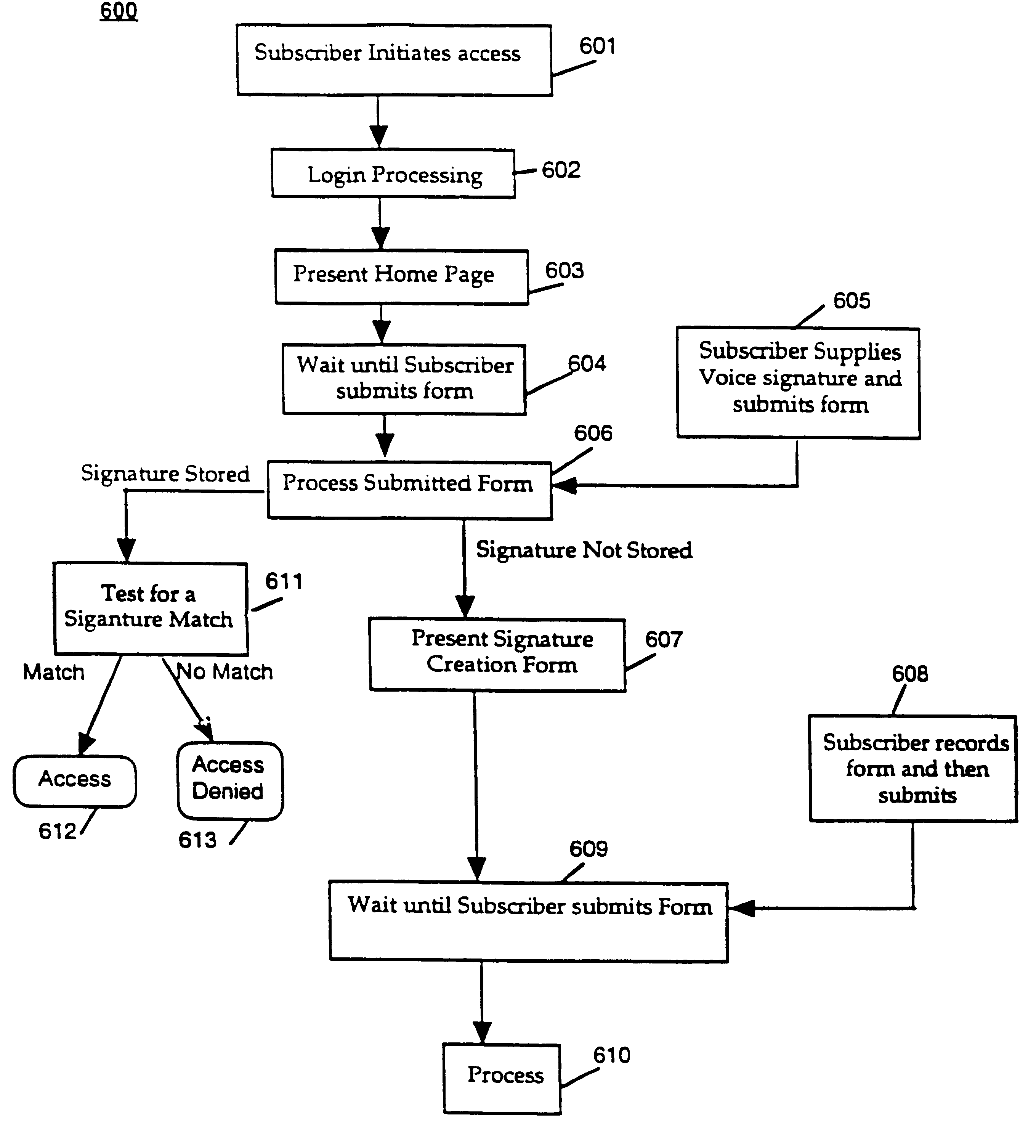
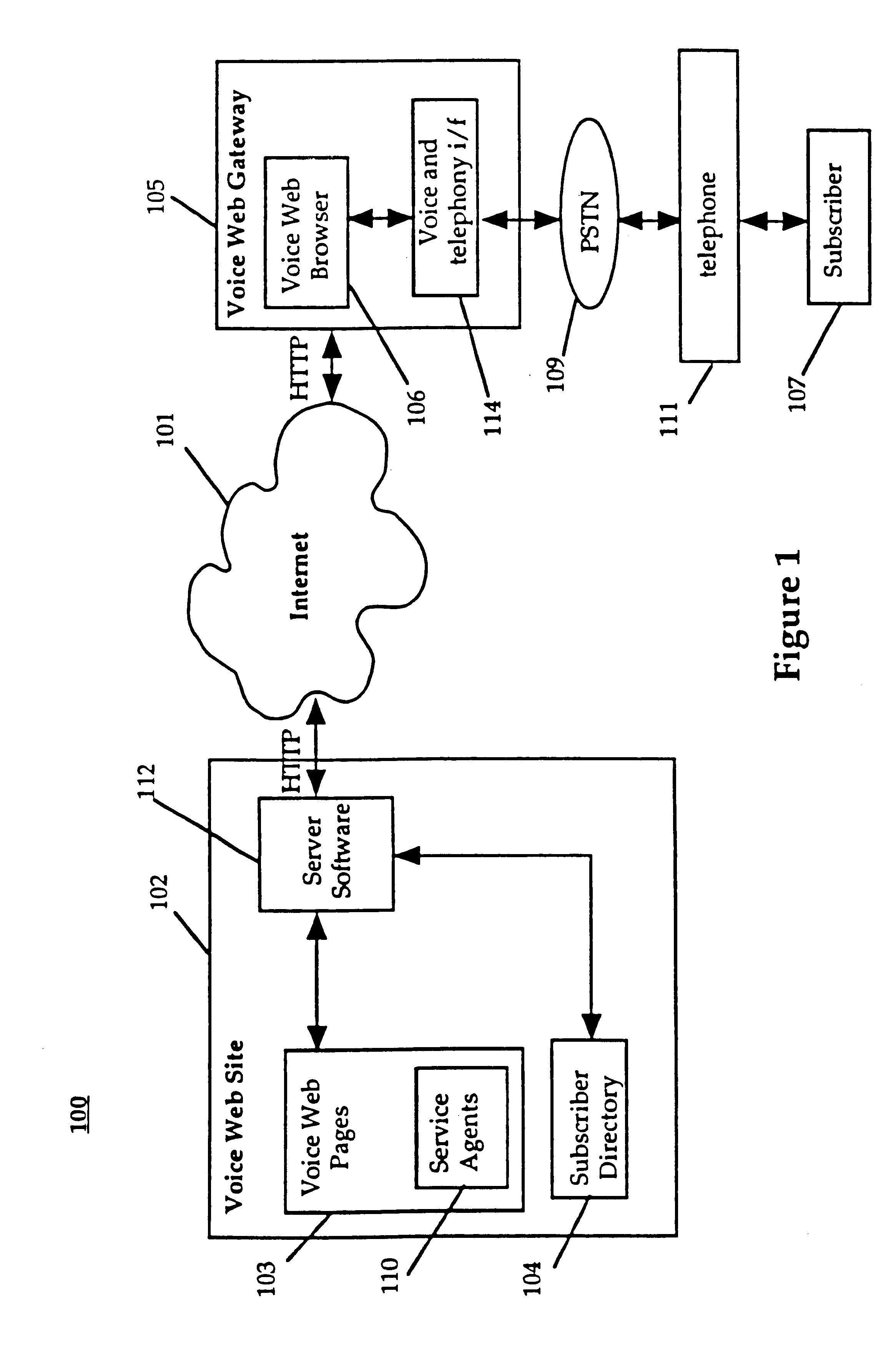
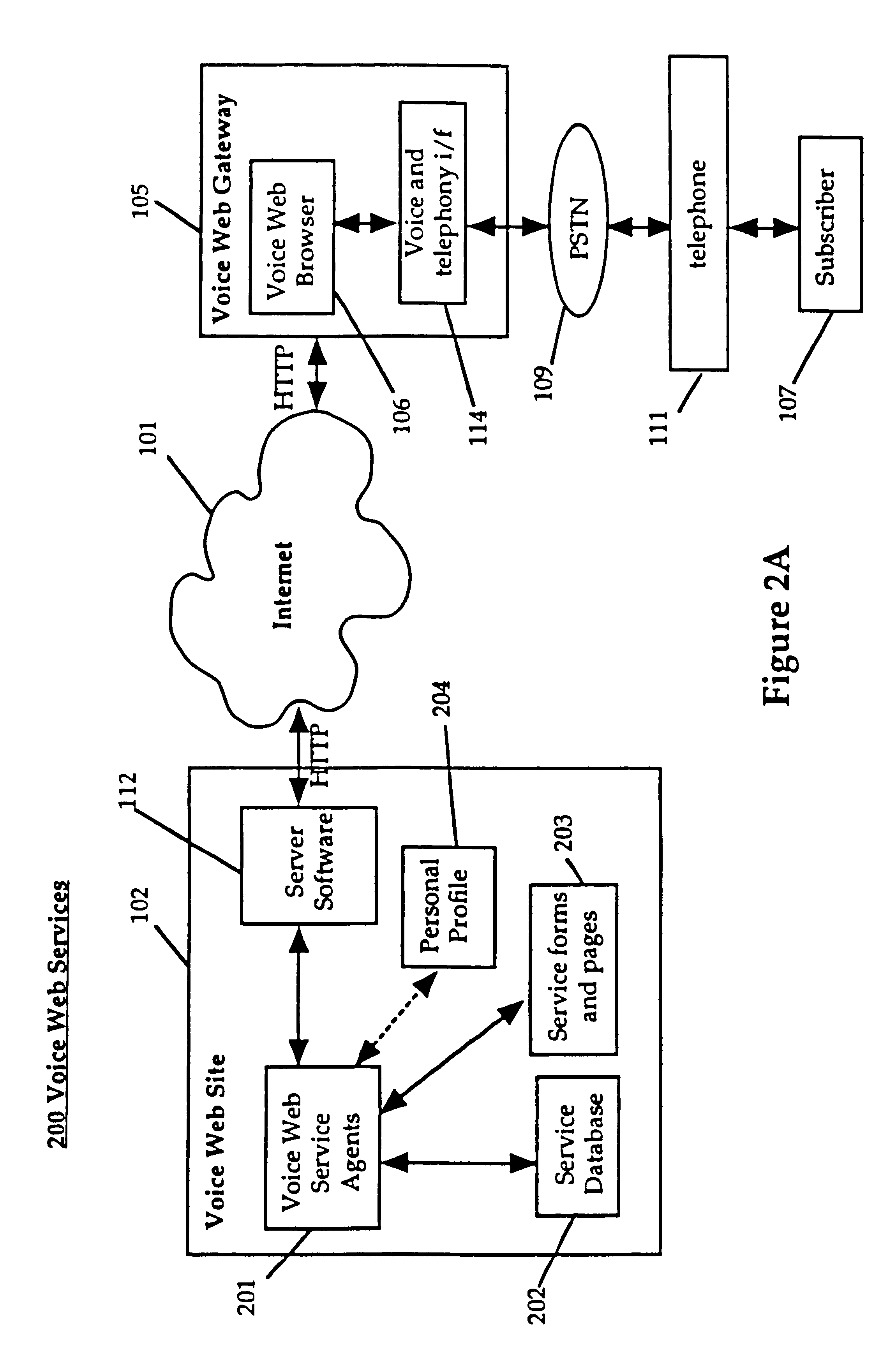
System and method for providing and using universally accessible voice and speech data files
InactiveUS6400806B1Automatic call-answering/message-recording/conversation-recordingAutomatic exchangesSpeech trainingHyperlink
A system and method provides universal access to voice-based documents containing information formatted using MIME and HTML standards using customized extensions for voice information access and navigation. These voice documents are linked using HTML hyper-links that are accessible to subscribers using voice commands, touch-tone inputs and other selection means. These voice documents and components in them are addressable using HTML anchors embedding HTML universal resource locators (URLs) rendering them universally accessible over the Internet. This collection of connected documents forms a voice web. The voice web includes subscriber-specific documents including speech training files for speaker dependent speech recognition, voice print files for authenticating the identity of a user and personal preference and attribute files for customizing other aspects of the system in accordance with a specific subscriber.
Owner:NUANCE COMM INC
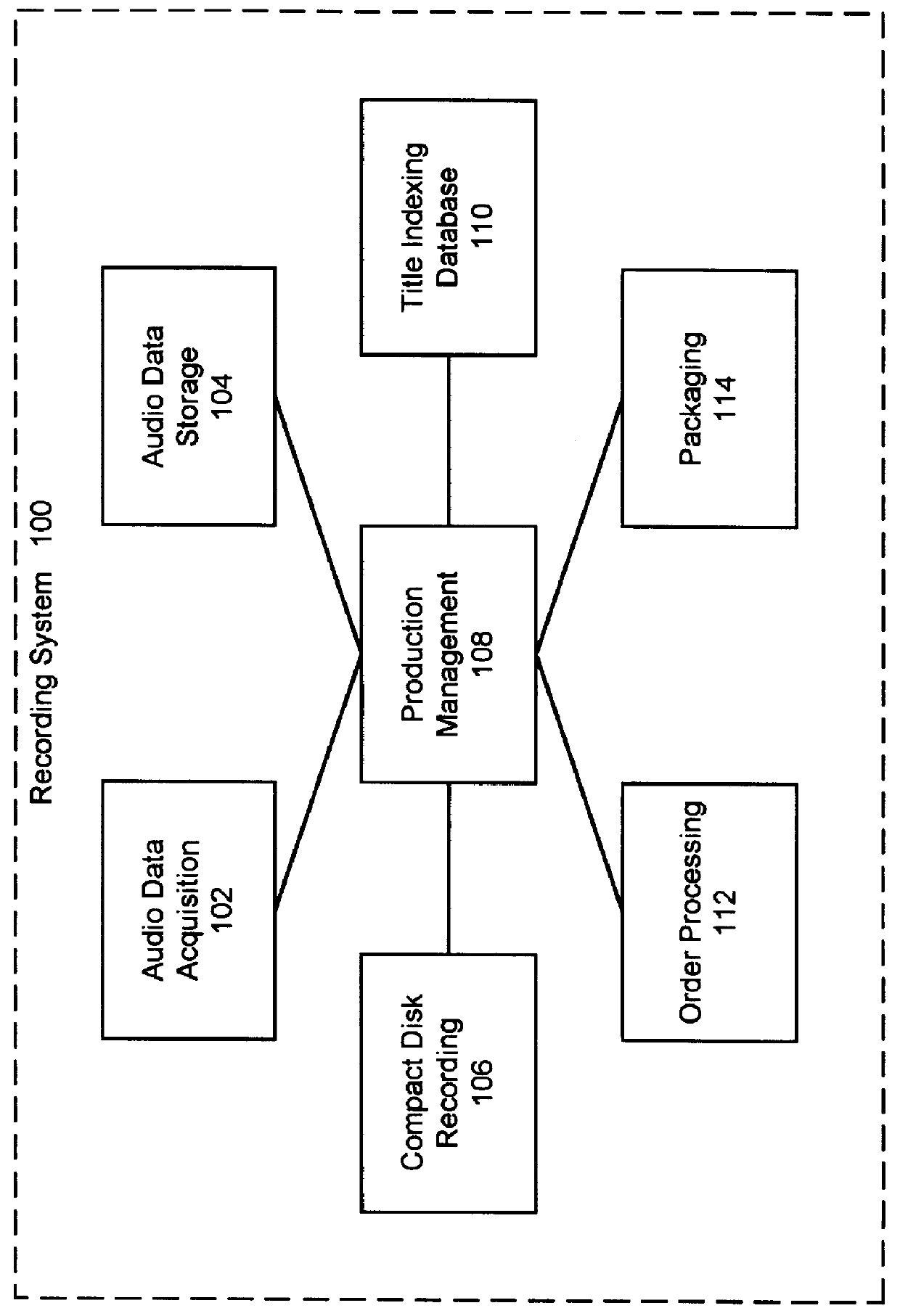
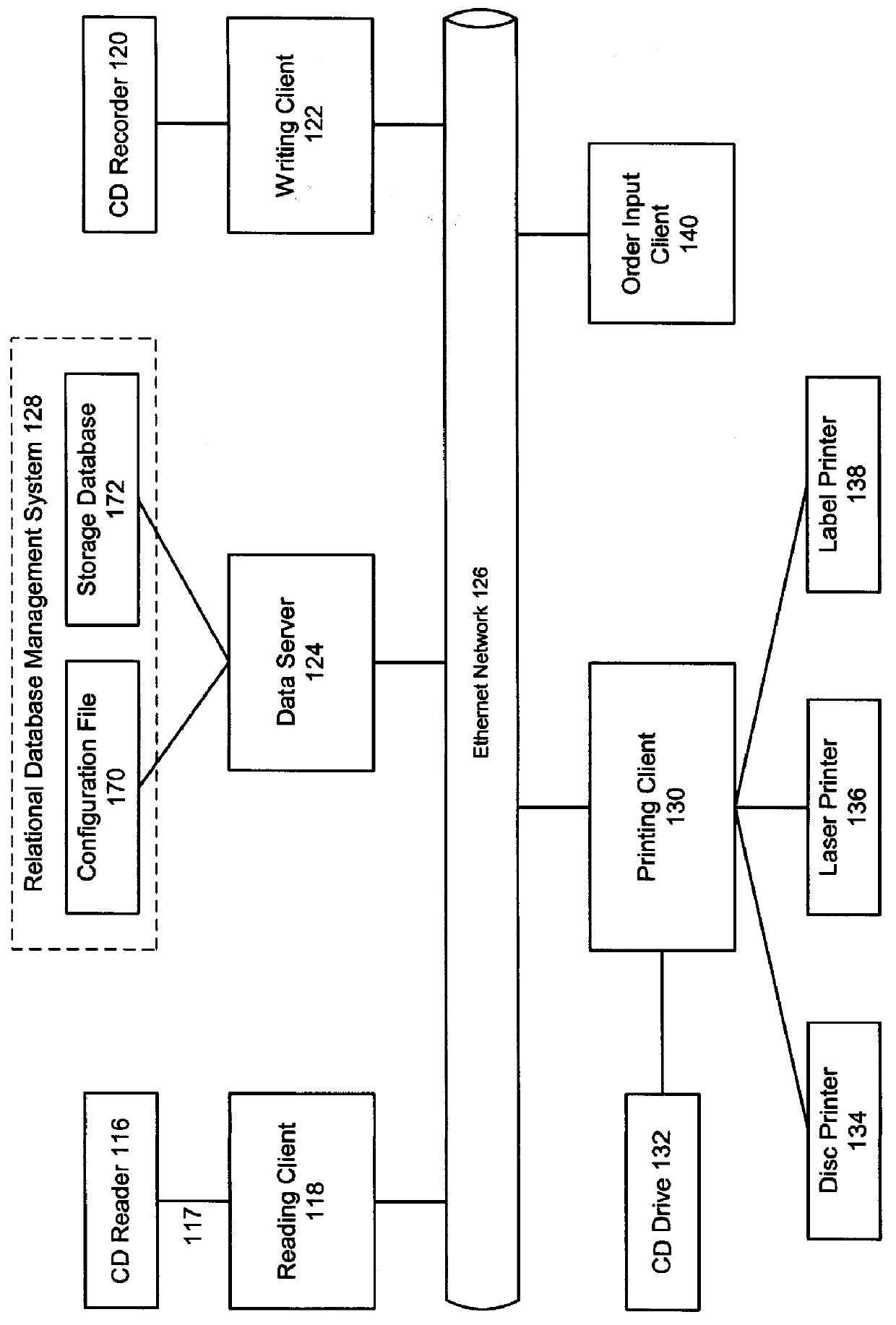
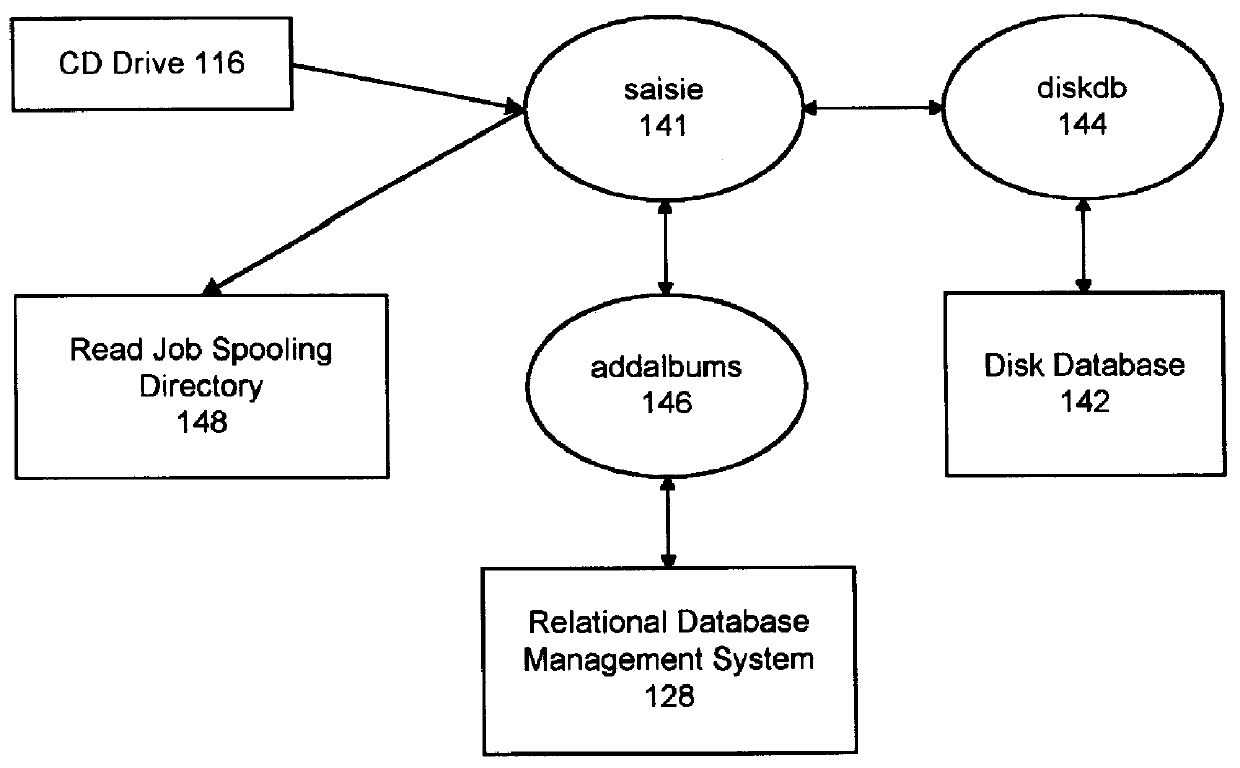
System and method for production of compact discs on demand
InactiveUS6011758ALayered productsElectronic editing digitised analogue information signalsDigital dataCompact disc
A system and method for production of customized compact discs (CD) includes compiling a collection of digital data files from source CDS, receiving customer orders and processing those customer orders by writing customer-selected digital data files onto a CD. Data files are read from the source CDs by an acquisition station and stored in a storage subsystem distributed over a number of data servers. A order input client receives and logs orders from customers. The customer orders are then processed by data servers transferring the cuistomer-selected data files to a writing station. The writing station records the data onto a destination CD. A printing station then prints content description information on the CD and jacket and also prints invoices and shipping labels.
Owner:MUSICMAKER COM
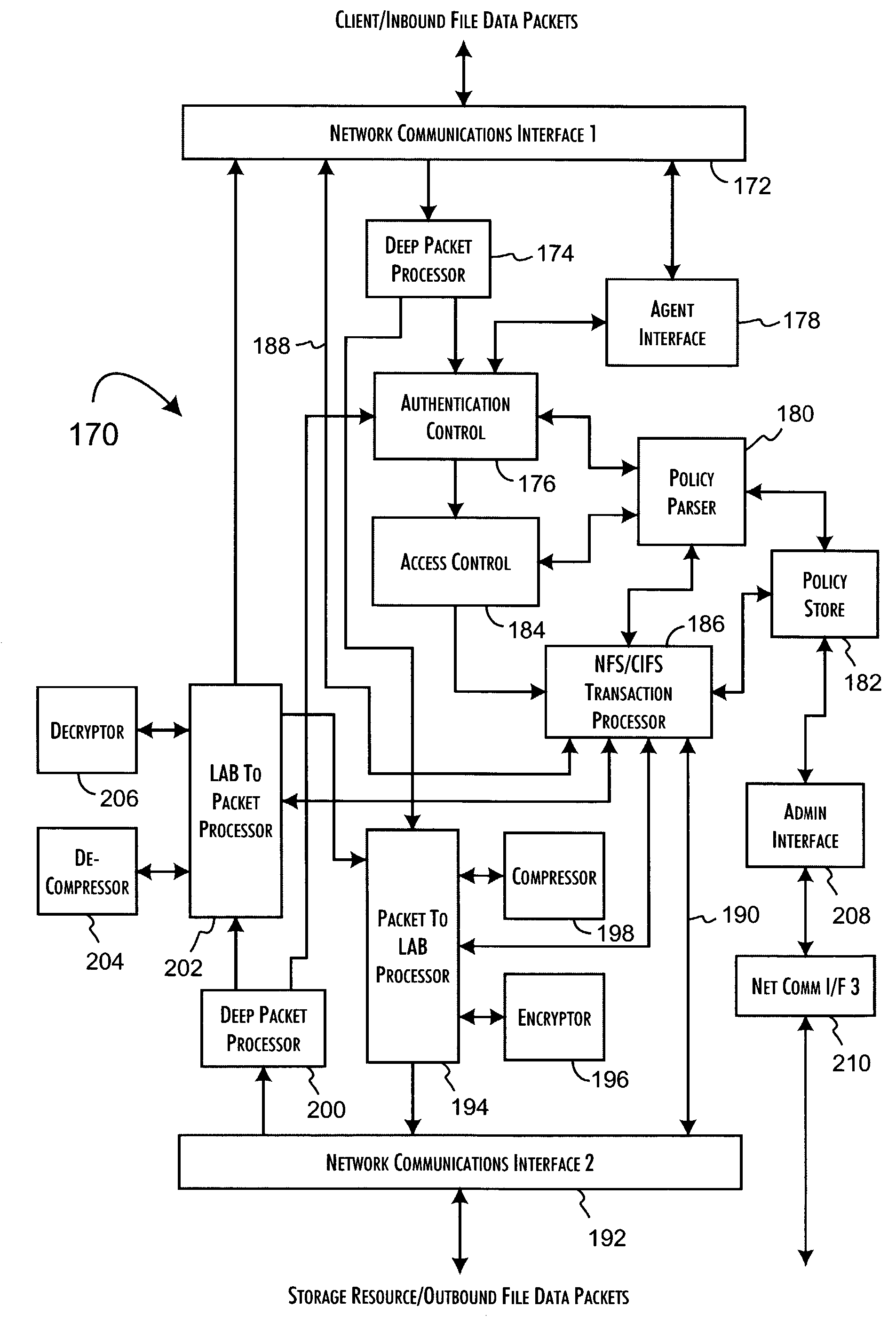
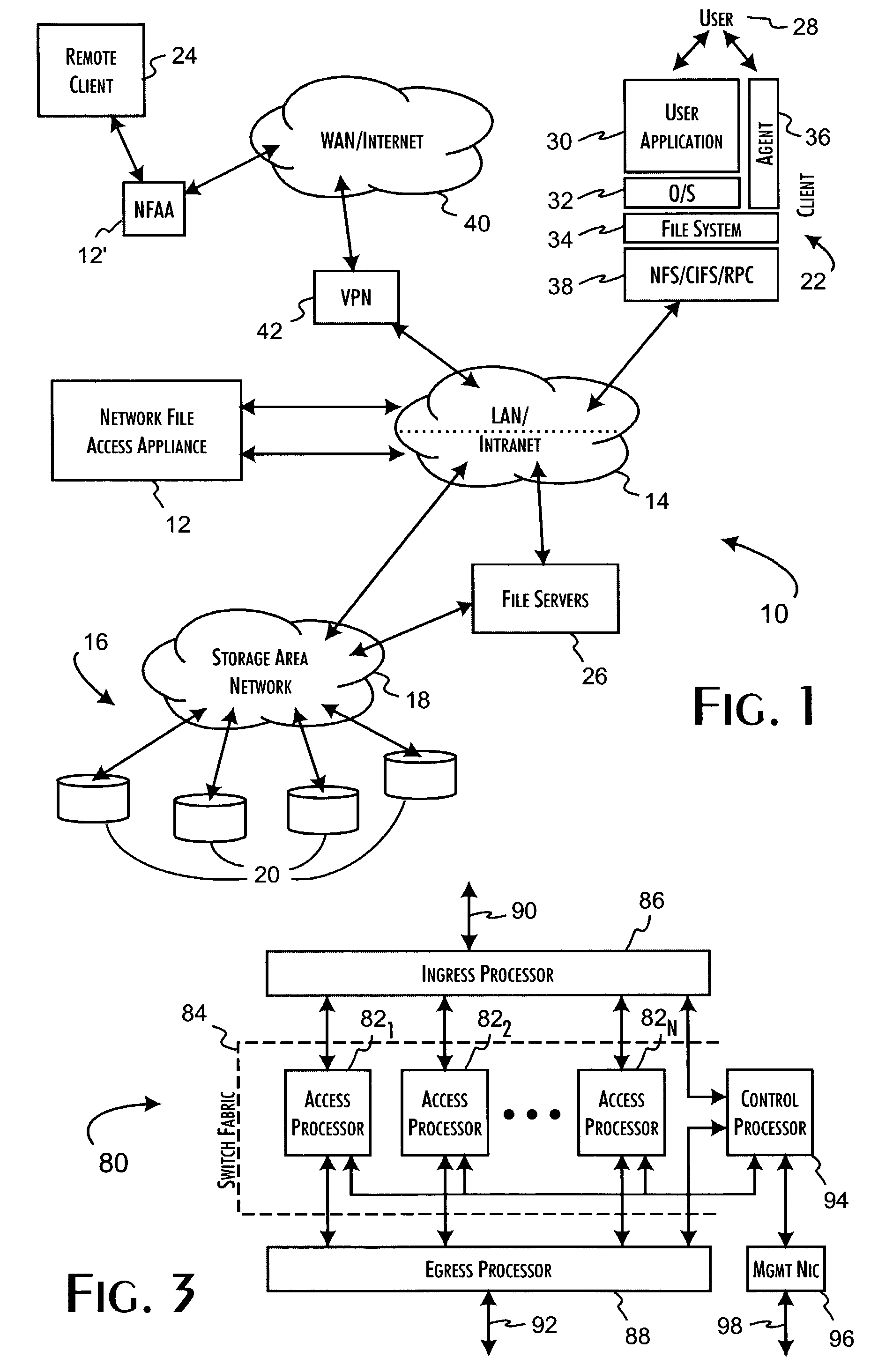
Logical access block processing protocol for transparent secure file storage
InactiveUS7334124B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationComputer hardwareDigital signature
Network data files are secure through the operation of an infrastructure gateway-based network file access appliance. Network file data, corresponding to network pocket payload data, are further reduced to a sequence of data blocks that are secured through any combination of block encryption, compression, and digital signatures. File meta-data, including encryption, compression and block-level digital signatures are persistently stored with the file data, either in-band in the file as stored or out-of-band key as a separately stored file or file policy record. File meta-data is recovered with accesses of the file data to support bidirectional encryption and compression and to detect tampering with the file data by comparison against block-level digital signatures.
Owner:THALES ESECURITY INC
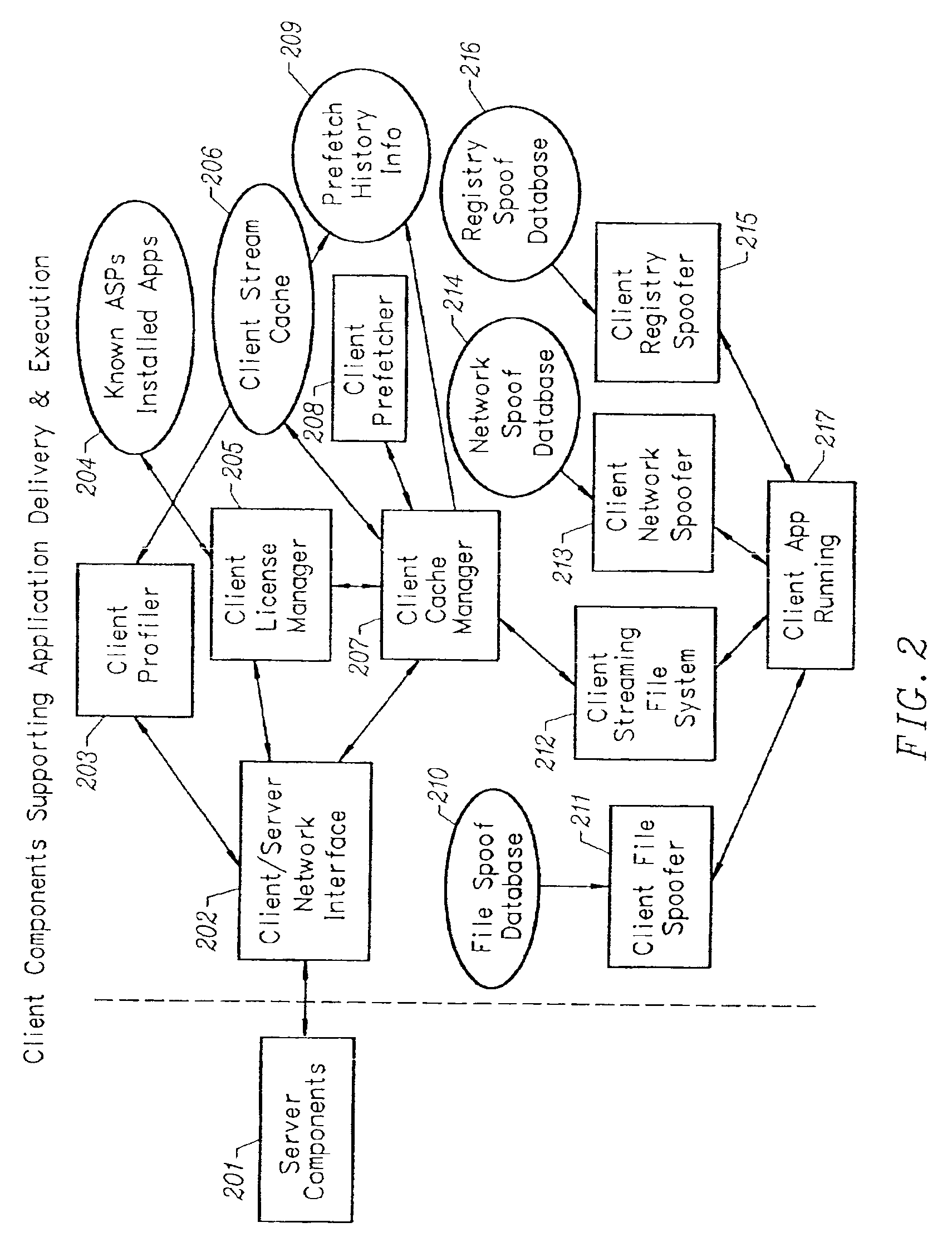
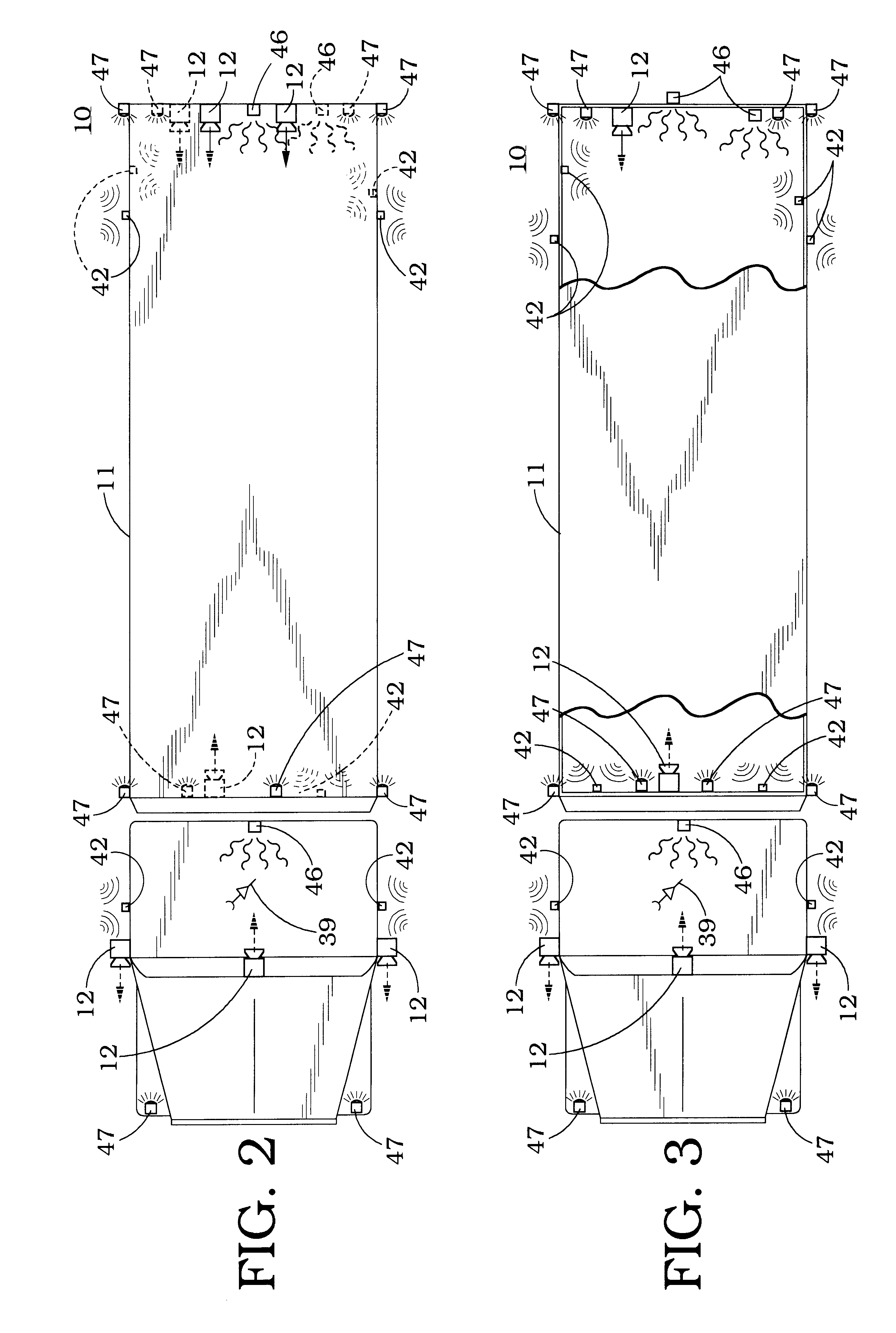
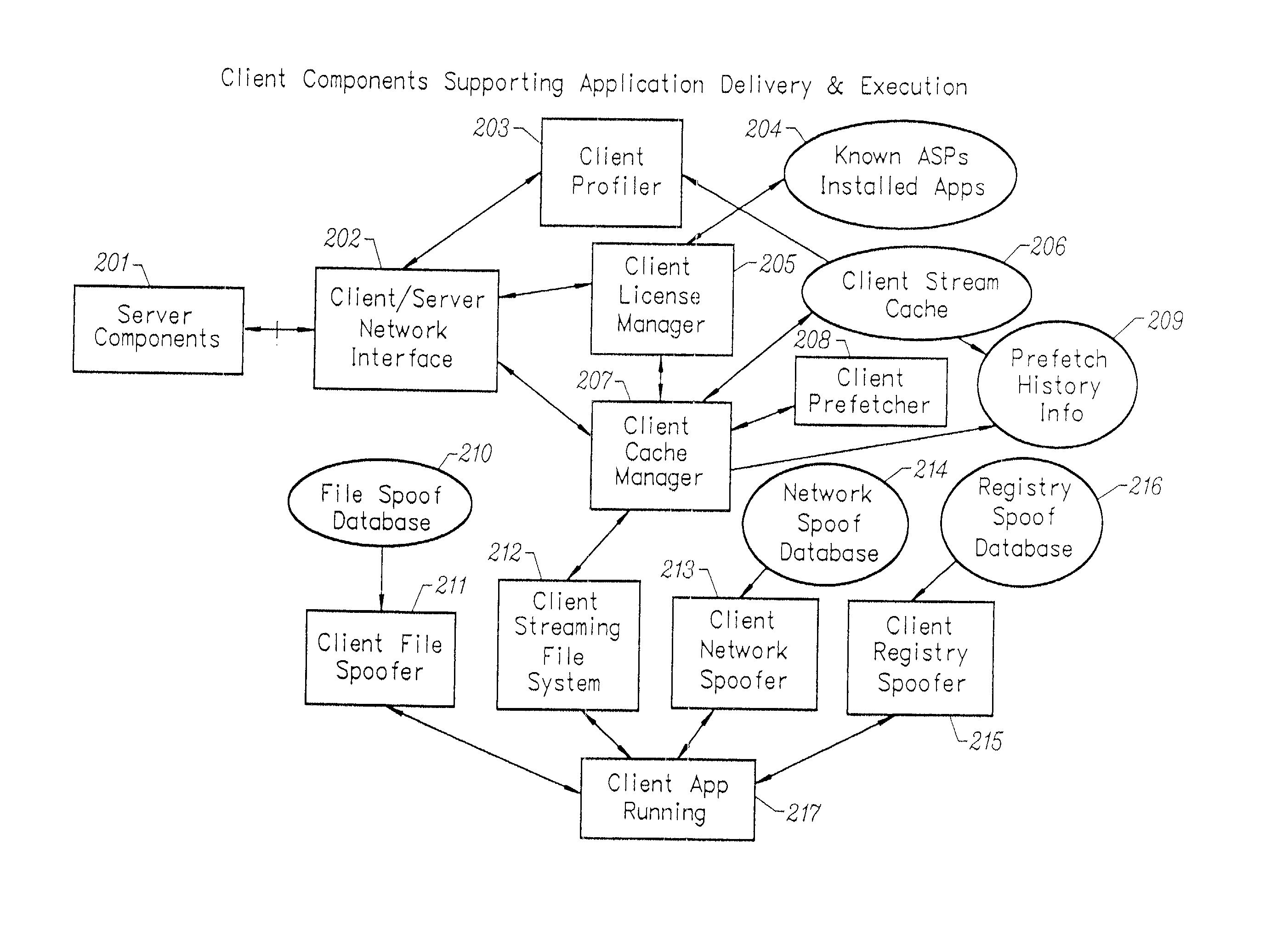
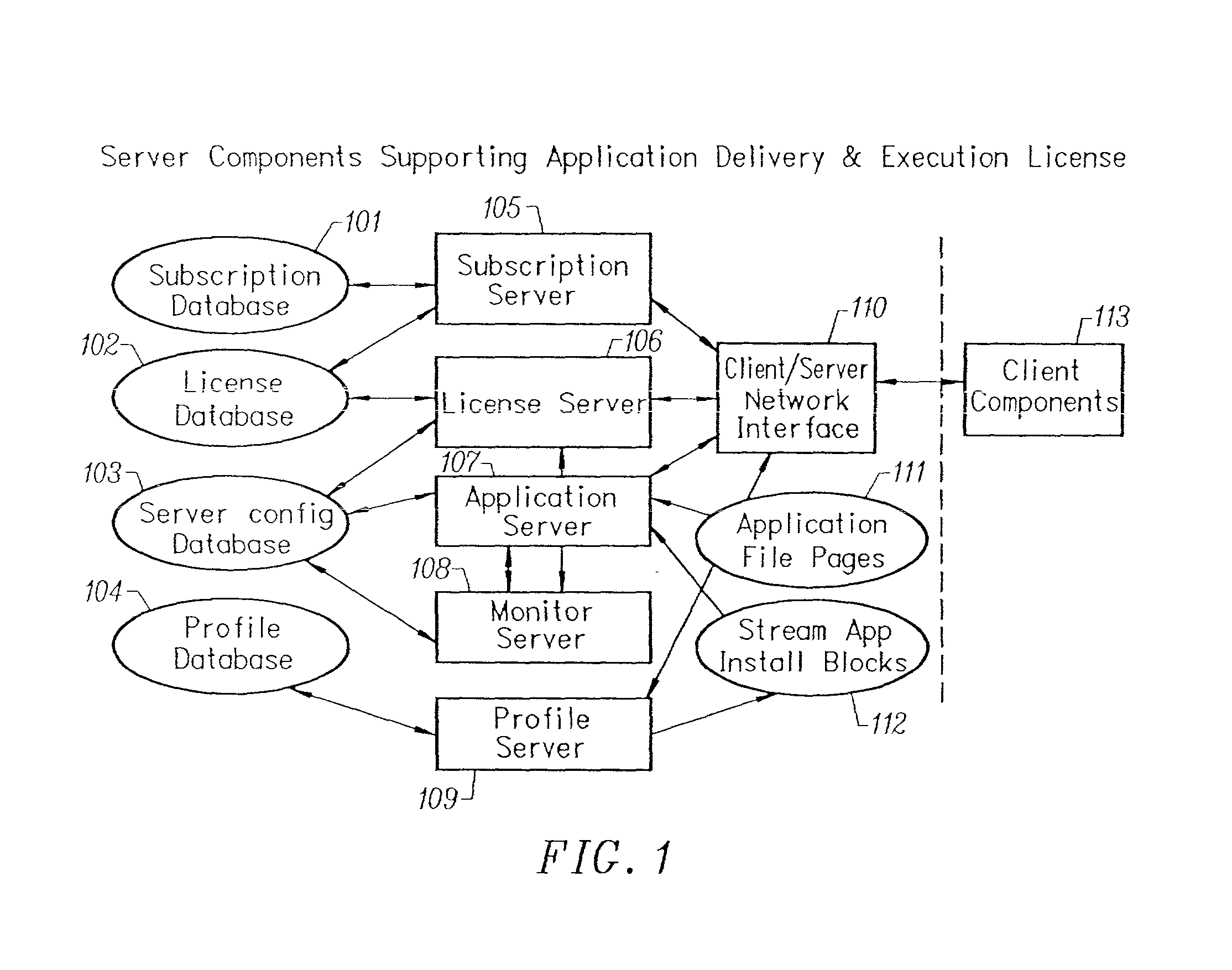
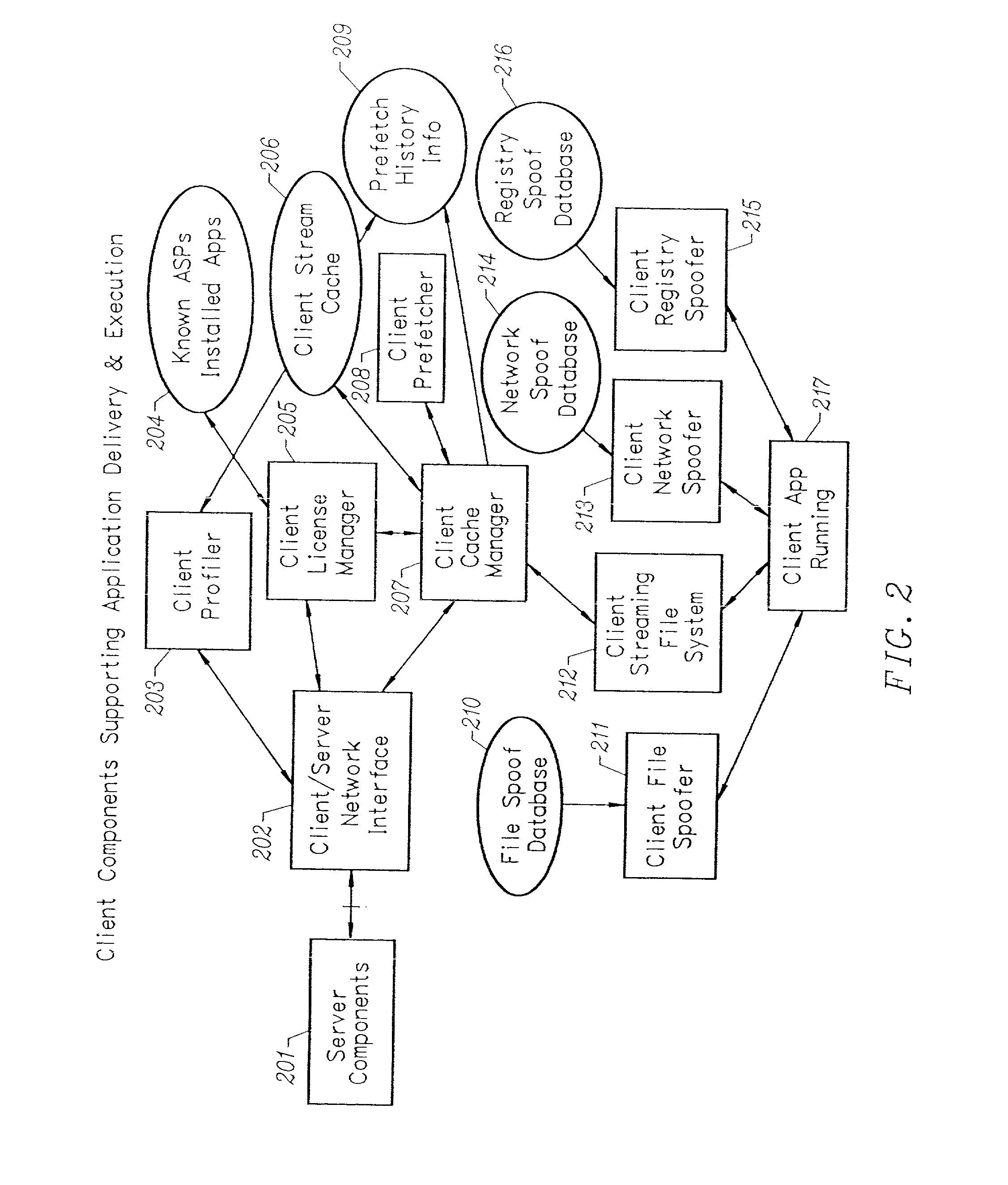
Client-side performance optimization system for streamed applications
InactiveUS6959320B2Efficiently stream and executeEasily integrates into client system 's operating systemMultiple digital computer combinationsProgram loading/initiatingApplication serverData file
An client-side performance optimization system for streamed applications provides several approaches for fulfilling client-side application code and data file requests for streamed applications. A streaming file system or file driver is installed on the client system that receives and fulfills application code and data requests from a persistent cache or the streaming application server. The client or the server can initiate the prefetching of application code and data to improve interactive application performance. A client-to-client communication mechanism allows local application customization to travel from one client machine to another without involving server communication. Applications are patched or upgraded via a change in the root directory for that application. The client can be notified of application upgrades by the server which can be marked as mandatory, in which case the client will force the application to be upgraded. The server broadcasts an application program's code and data and any client that is interested in that particular application program stores the broadcasted code and data for later use.
Owner:NUMECENT HLDG
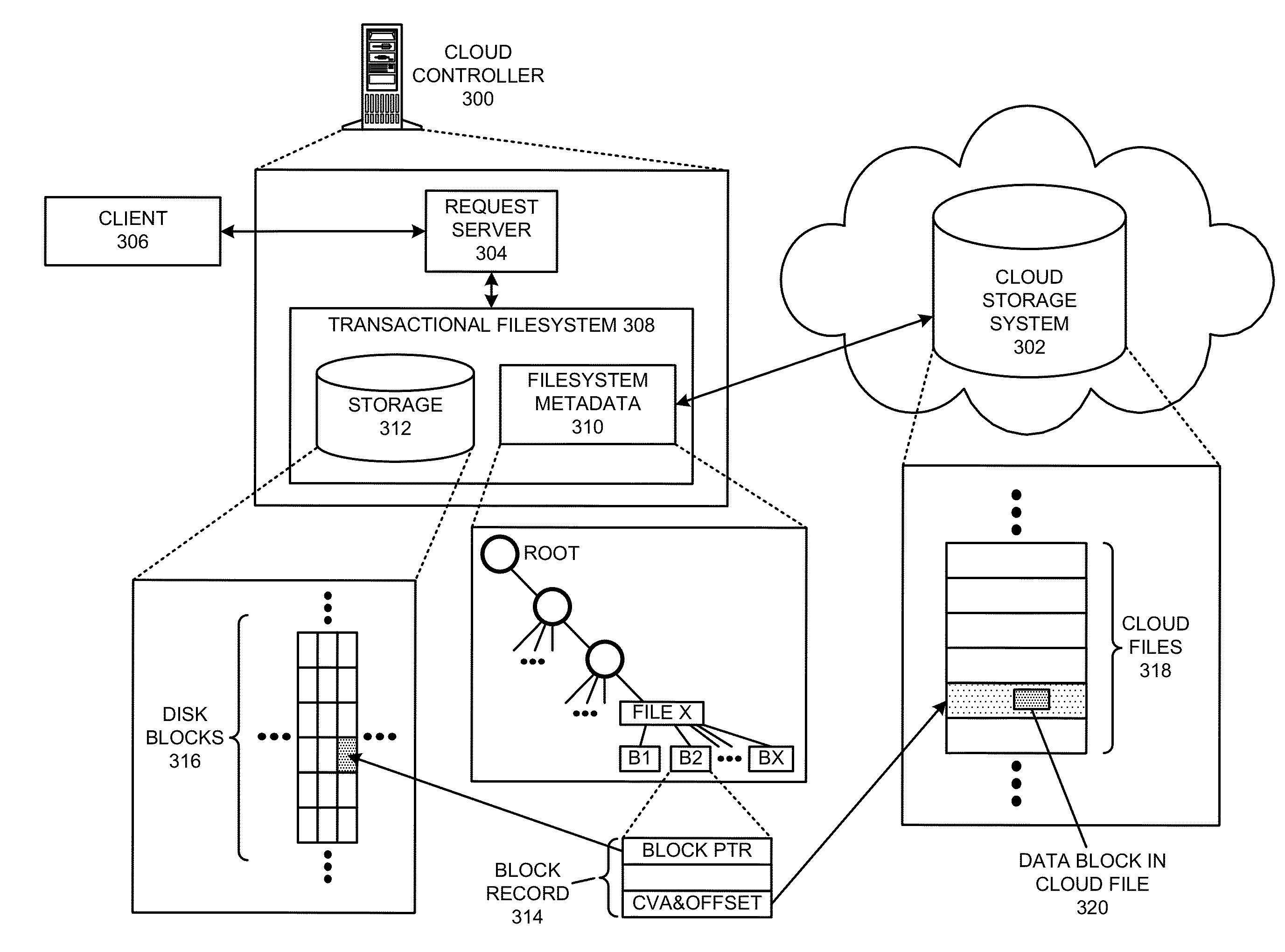
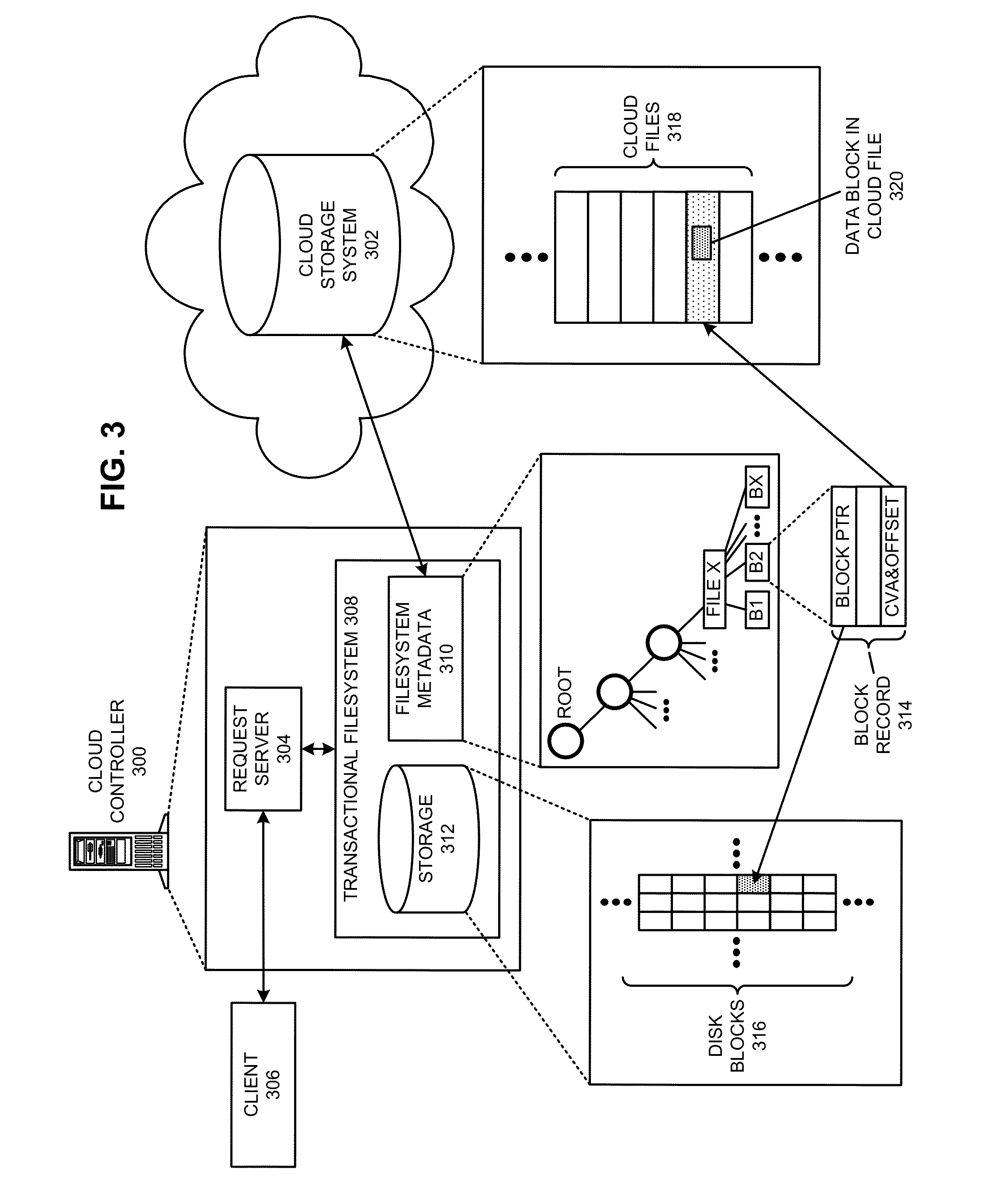
Executing a cloud command for a distributed filesystem
ActiveUS20140006354A1Reduce administrative burdenReduce overheadDigital data information retrievalDigital data processing detailsDistributed File SystemFile system
The disclosed embodiments disclose techniques for executing a cloud command for a distributed filesystem. Two or more cloud controllers collectively manage distributed filesystem data that is stored in one or more cloud storage systems; the cloud controllers ensure data consistency for the stored data, and each cloud controller caches portions of the distributed filesystem. During operation, a cloud controller presents a distributed-filesystem-specific capability to a client system as a file in the distributed filesystem (e.g., using a file abstraction). Upon receiving a request from the client system to access and / or operate upon this file, the client controller executes an associated cloud command. More specifically, the cloud controller initiates a specially-defined operation that accesses additional functionality for the distributed filesystem that exceeds the scope of individual reads and writes to a typical data file.
Owner:PANZURA LLC
Generating and matching hashes of multimedia content
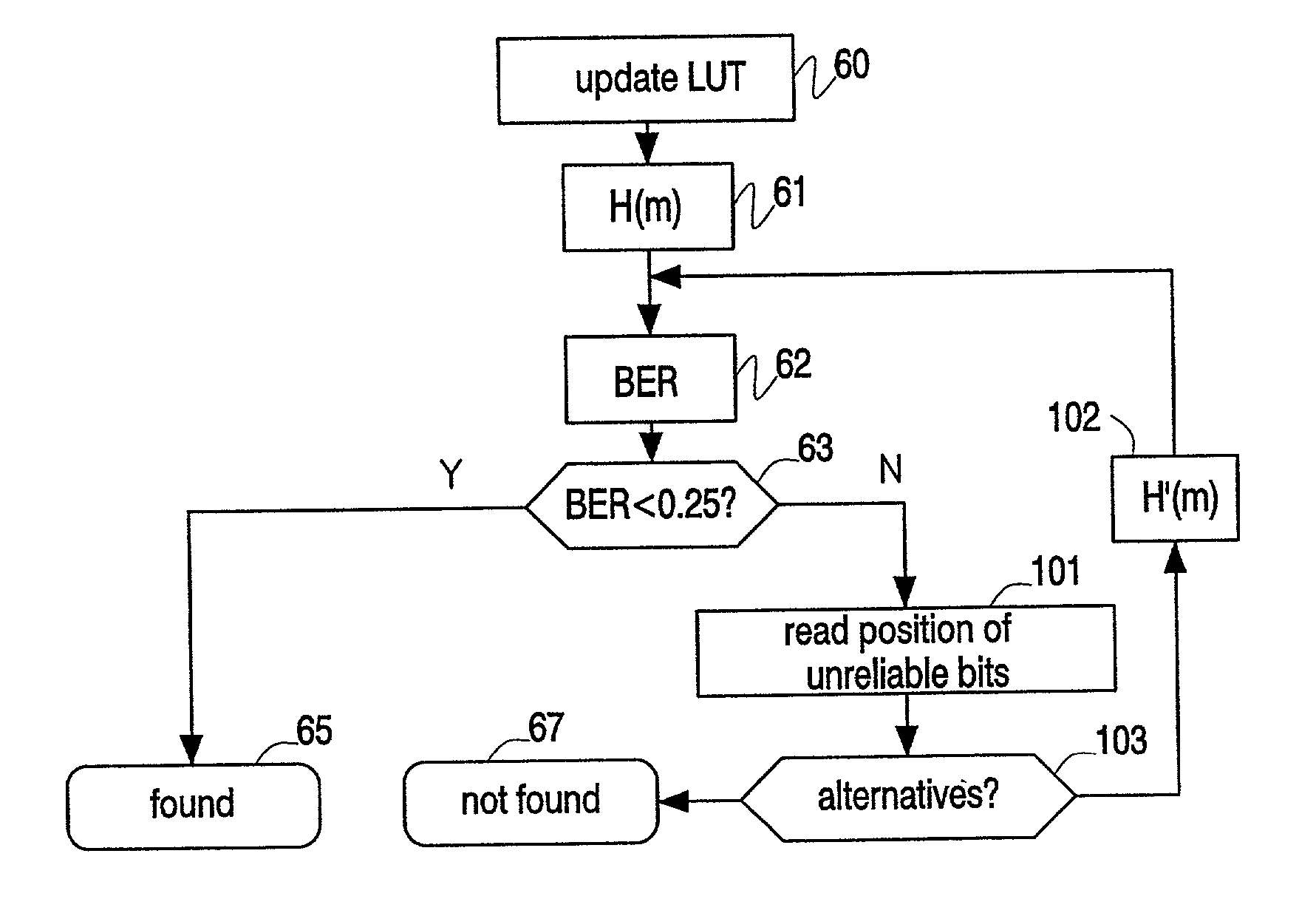
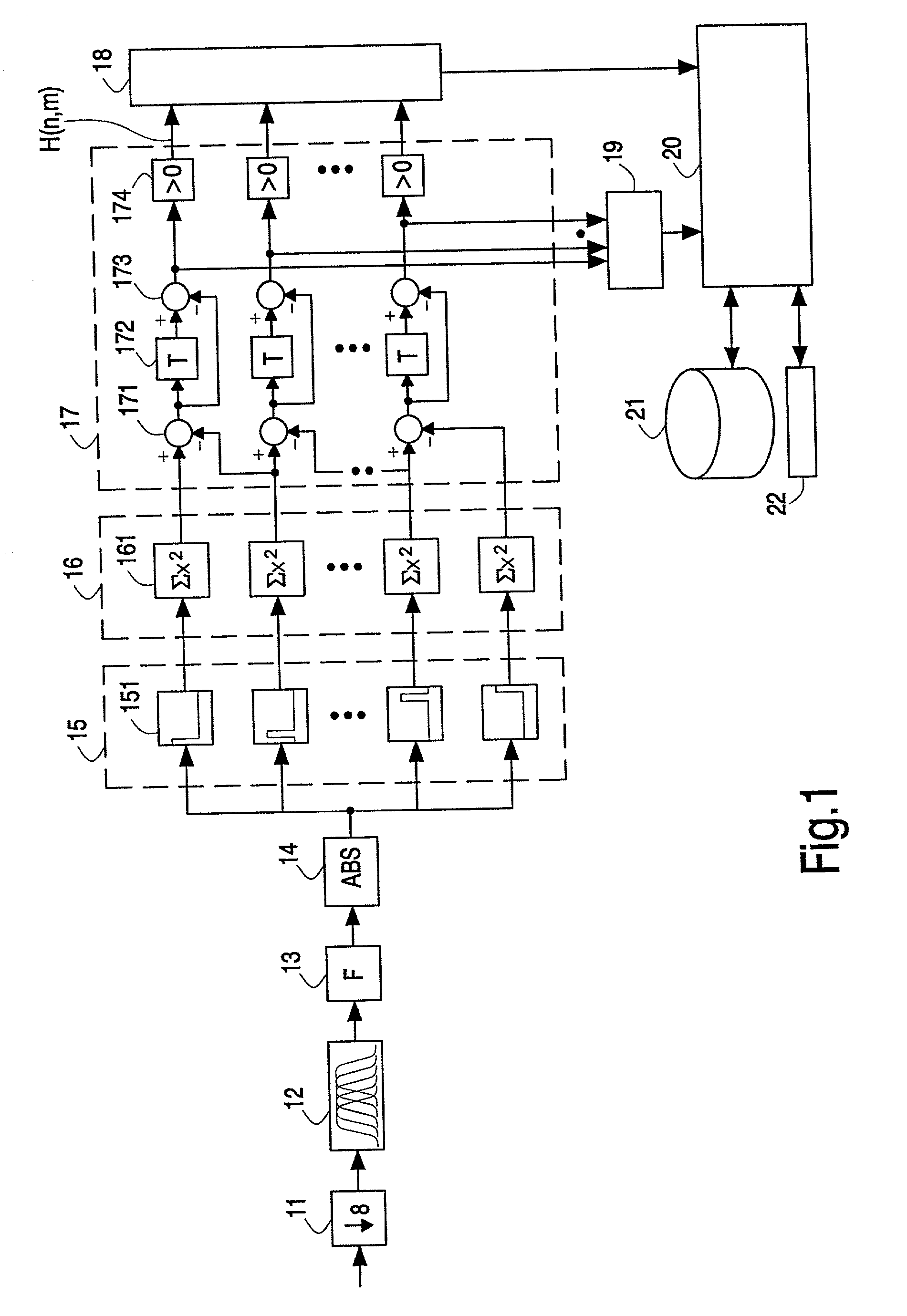
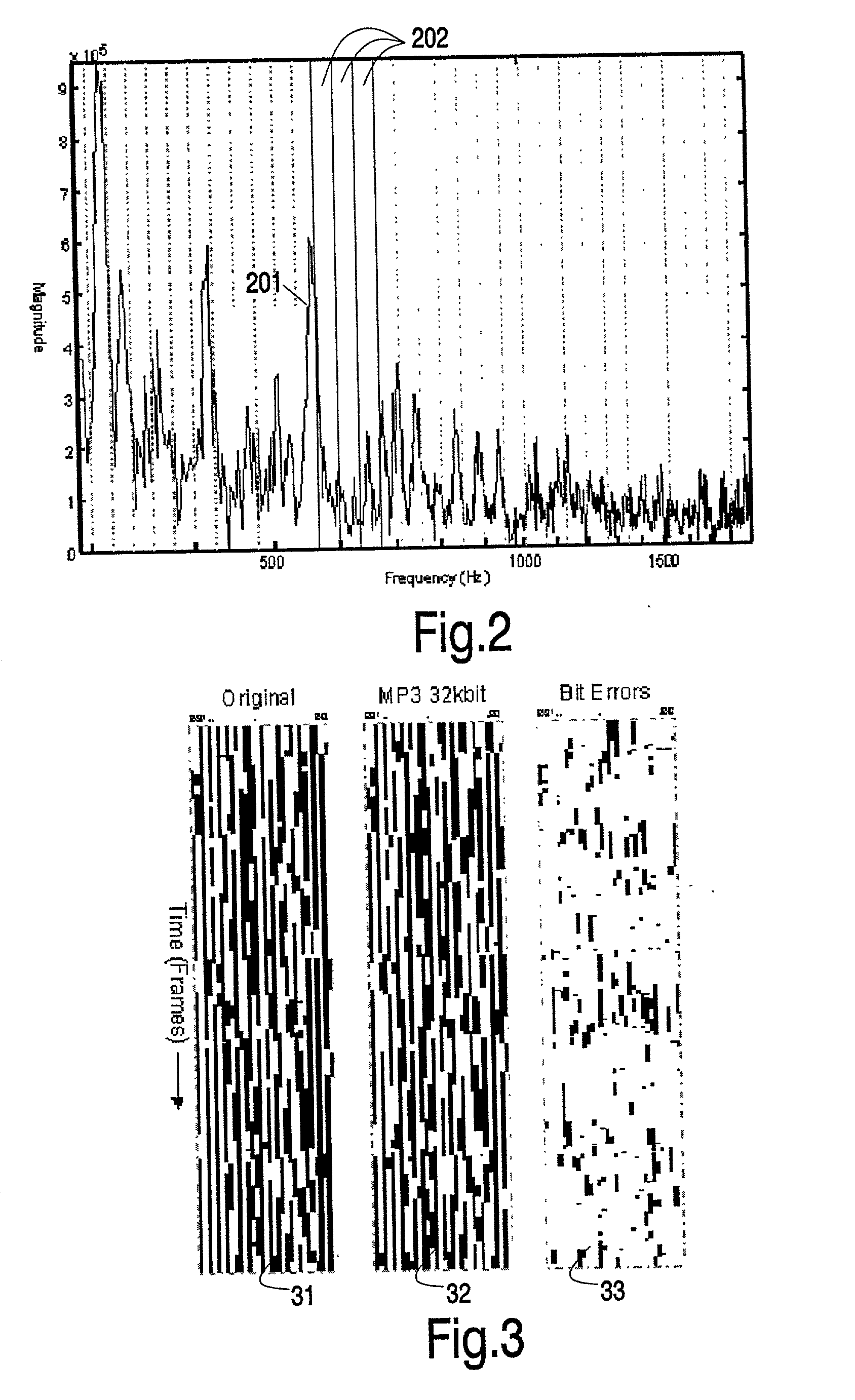
ActiveUS20020178410A1RobustRobust hashingElectrophonic musical instrumentsCode conversionFrequency spectrumAlgorithm
Hashes are short summaries or signatures of data files which can be used to identify the file. Hashing multimedia content (audio, video, images) is difficult because the hash of original content and processed (e.g. compressed) content may differ significantly. The disclosed method generates robust hashes for multimedia content, for example, audio clips. The audio clip is divided (12) into successive (preferably overlapping) frames. For each frame, the frequency spectrum is divided (15) into bands. A robust property of each band (e.g. energy) is computed (16) and represented (17) by a respective hash bit. An audio clip is thus represented by a concatenation of binary hash words, one for each frame. To identify a possibly compressed audio signal, a block of hash words derived therefrom is matched by a computer (20) with a large database (21). Such matching strategies are also disclosed. In an advantageous embodiment, the extraction process also provides information (19) as to which of the hash bits are the least reliable. Flipping these bits considerably improves the speed and performance of the matching process.
Owner:GRACENOTE
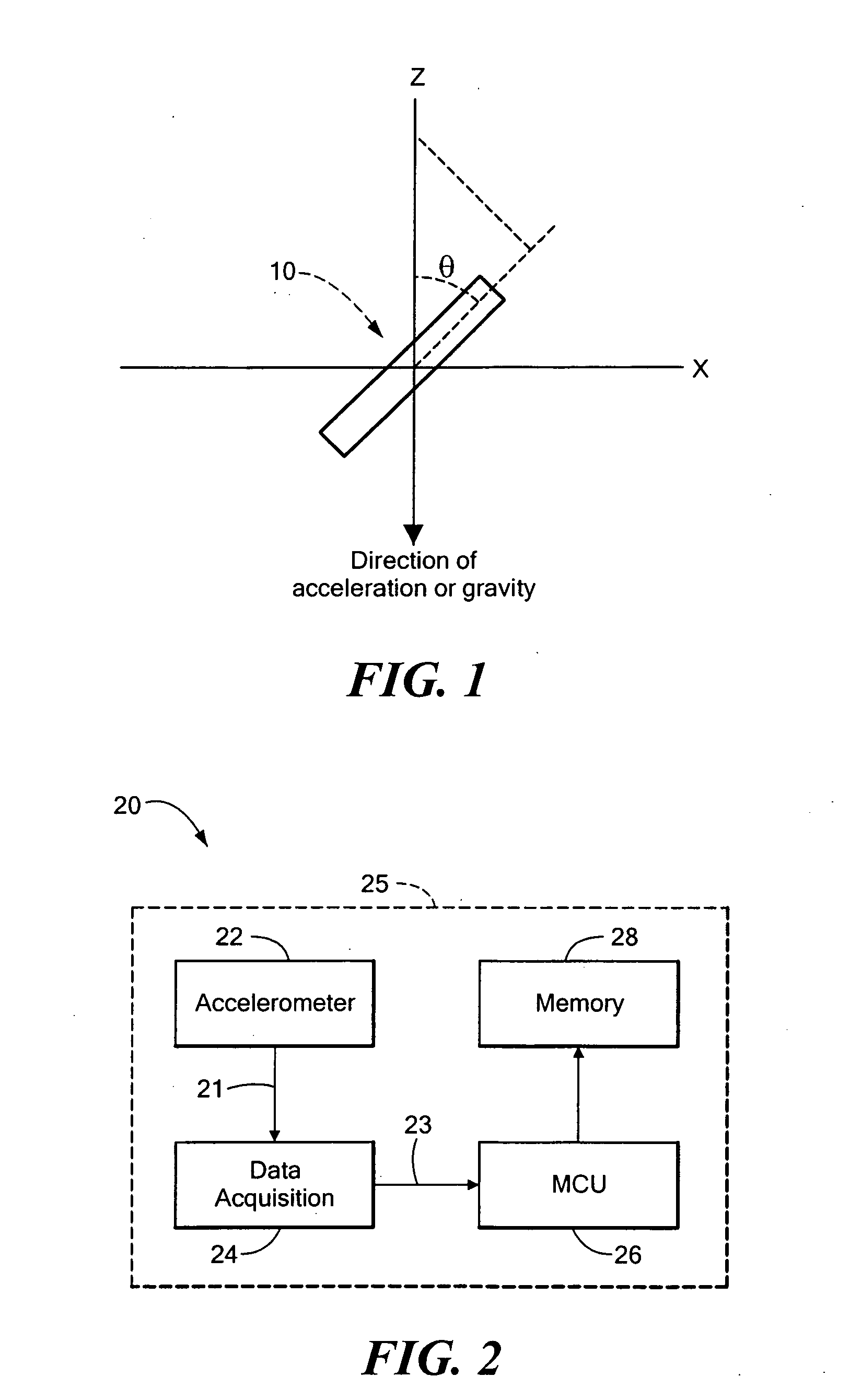
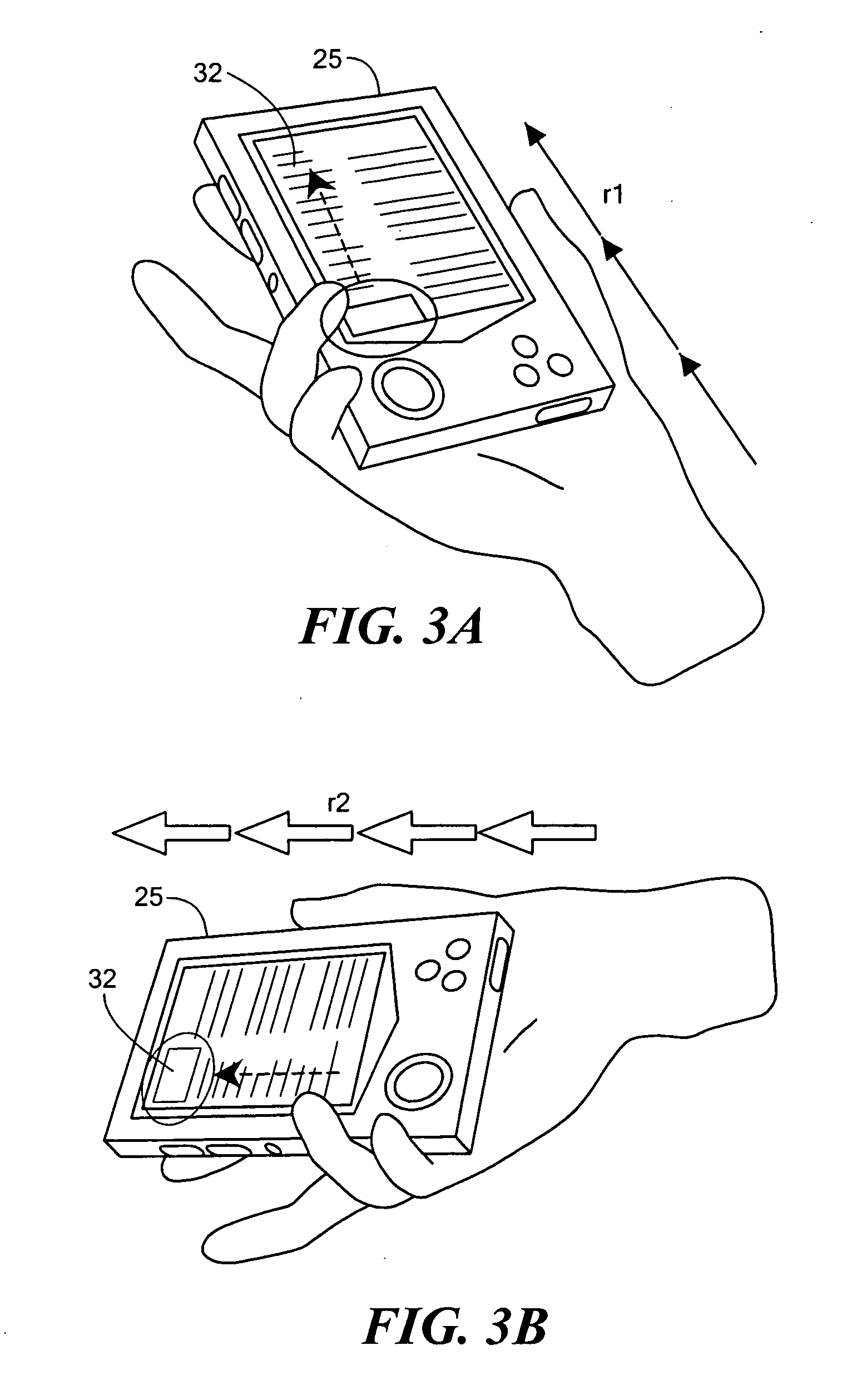
Air-writing and motion sensing input for portable devices
The use of motion sensing to perform sophisticated command control and data input into a portable device is disclosed. A motion sensor is embedded or fixedly attached to a portable device to measure movement, motion or tilt of the device in one-, two- or three-dimensions when the portable device is used to air-write or make gestures. The use of full motion information such as rate of change of motion or tilt angle to perform functions and commands is also disclosed. In addition, the use of air-writing to input search criteria and filter schemes for portable devices to manage, search, and sort through various data, files, and information is disclosed.
Owner:MEMSIC
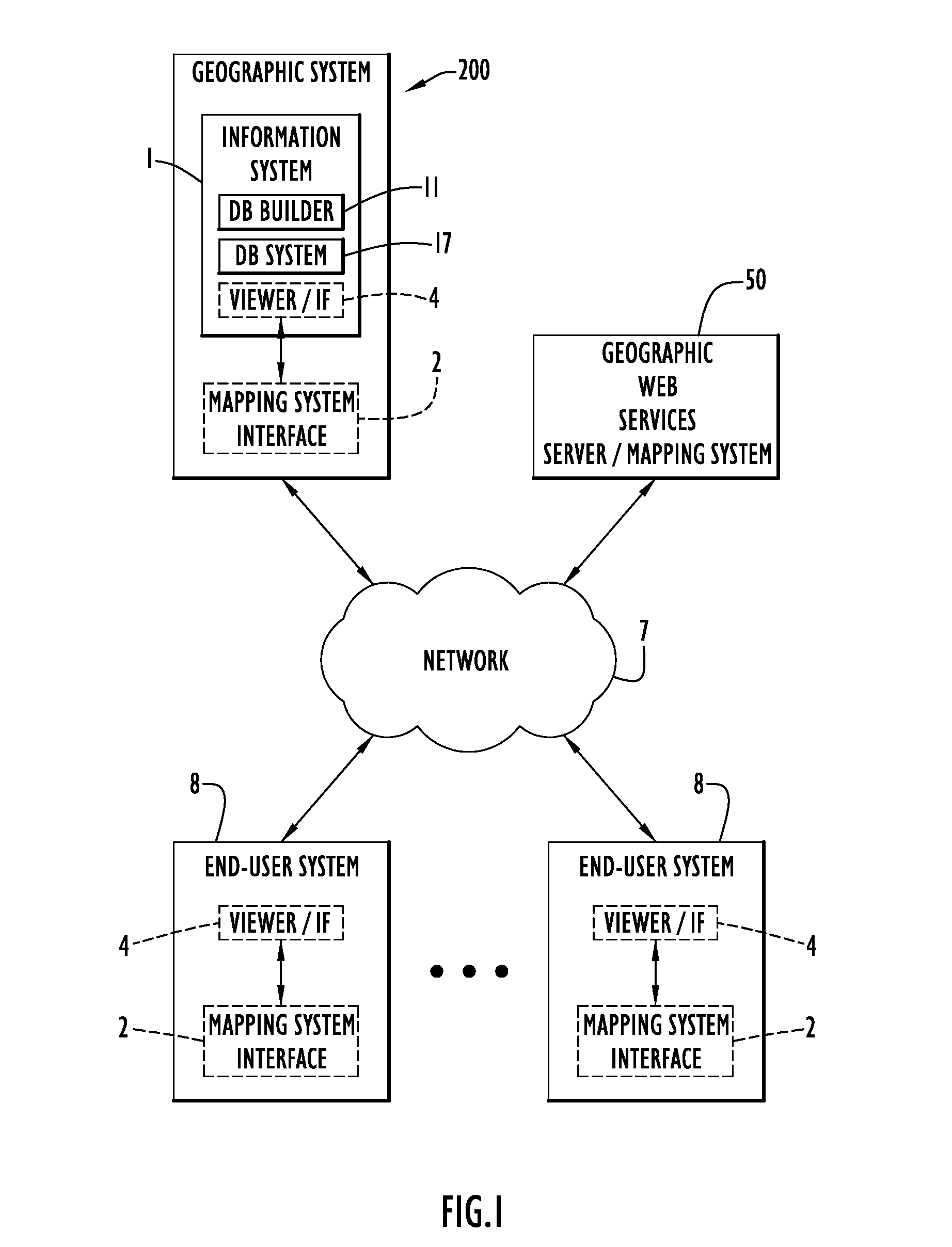
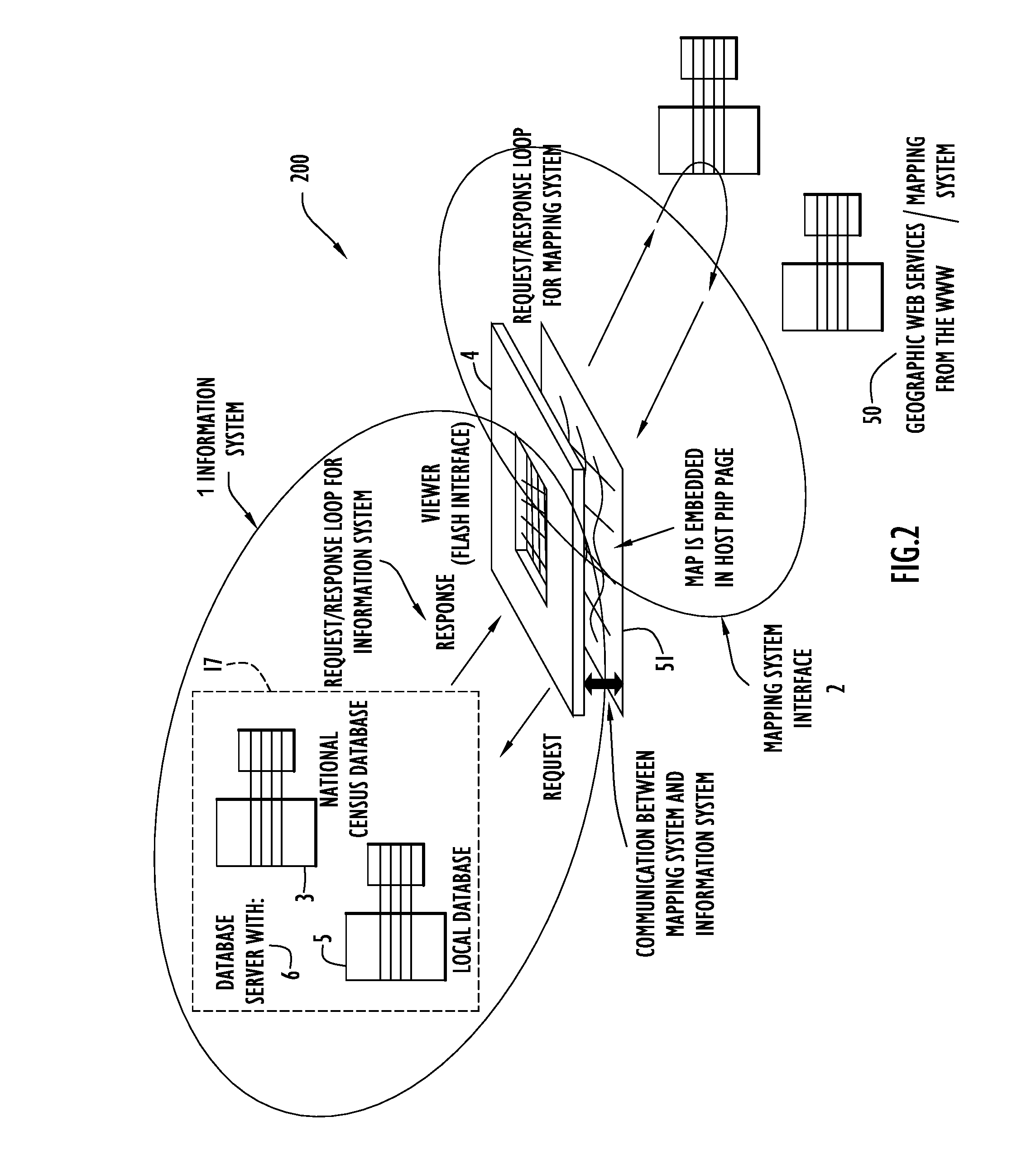
System and Method of Overlaying and Integrating Data with Geographic Mapping Applications
InactiveUS20080059889A1Comprehensive geographic breadthComprehensive detailDigital data processing detailsRadio transmissionRelational databaseTopic analysis
Owner:PARKER CHERYL +1
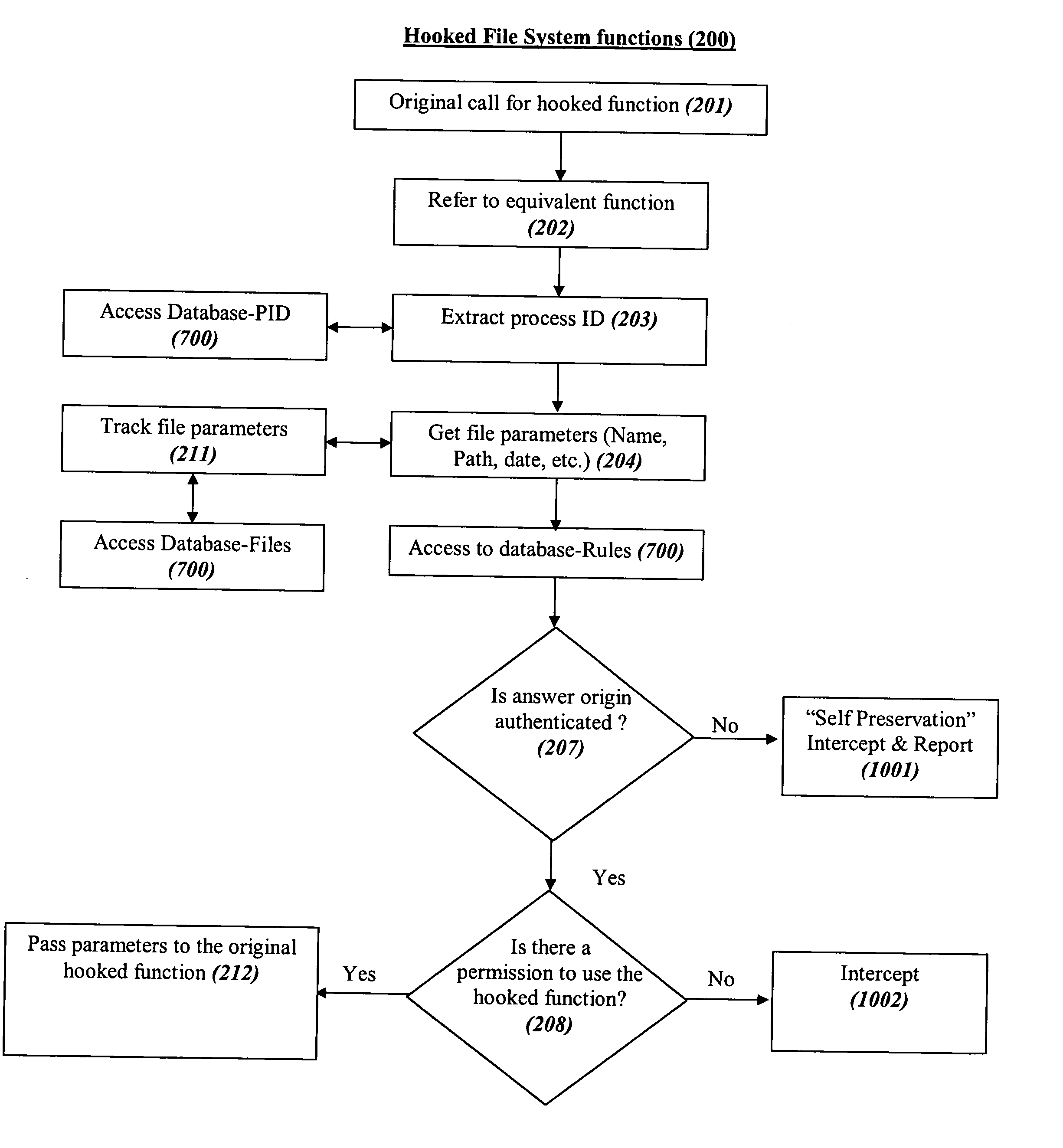
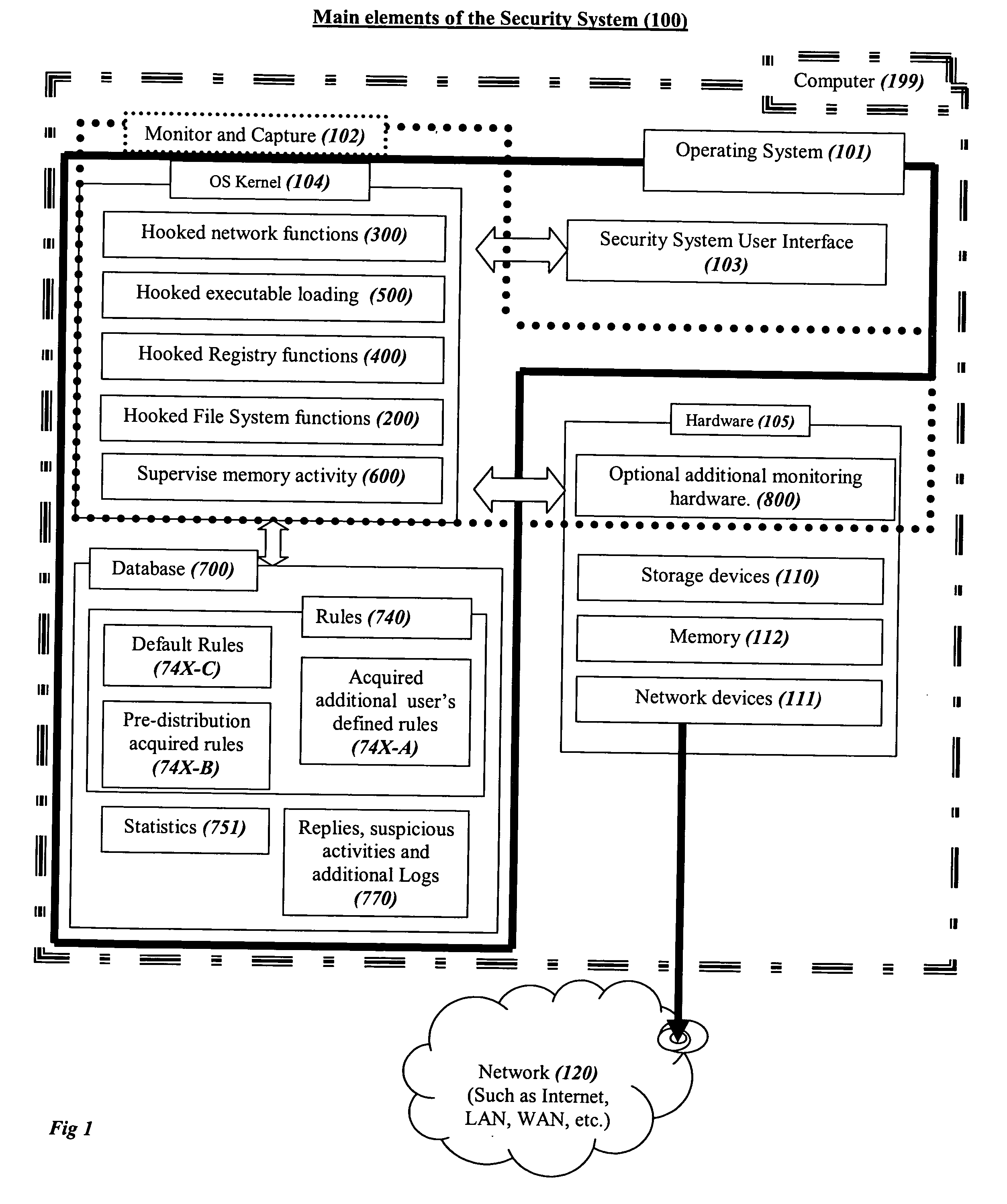
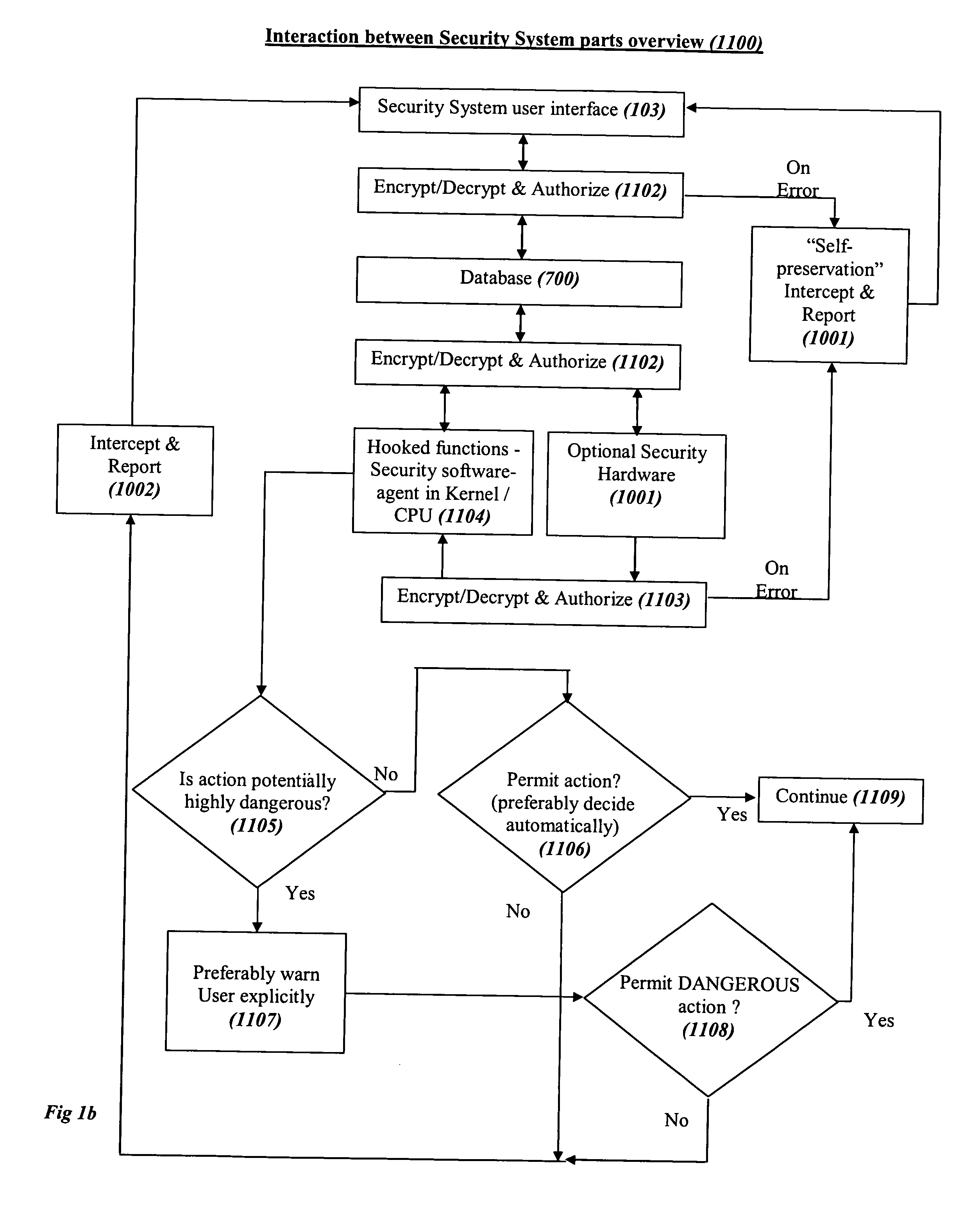
System and method for comprehensive general electric protection for computers against malicious programs that may steal information and/or cause damages
ActiveUS20050120242A1Reduce chanceDigital data processing detailsMultiple digital computer combinationsFree accessOperational system
In the prior art of computer security by default programs are allowed to do whatever they like to other programs or to their data files or to critical files of the operating system, which is as absurd as letting a guest in a hotel bother other guests as he pleases, steal their property or copy it or destroy it, or have free access to the hotel's management resources. The present concept is based on automatic segregation between programs. This is preferably done by creating automatically an unlimited number of Virtual Environments (VEs) with virtual sharing of resources, so that the programs in each VE think that they are alone on the computer, and (unless explicitly allowed by the user) any changes that they think they made in virtually shared resources are in reality only made in their own VE, while the user preferably has an integrated view of the computer.
Owner:BARHON MAYER BATYA
Methods and systems for selectively displaying advertisements
InactiveUS7136871B2Promote maximizationTelevision system detailsAdvertisementsComputer moduleMetadata
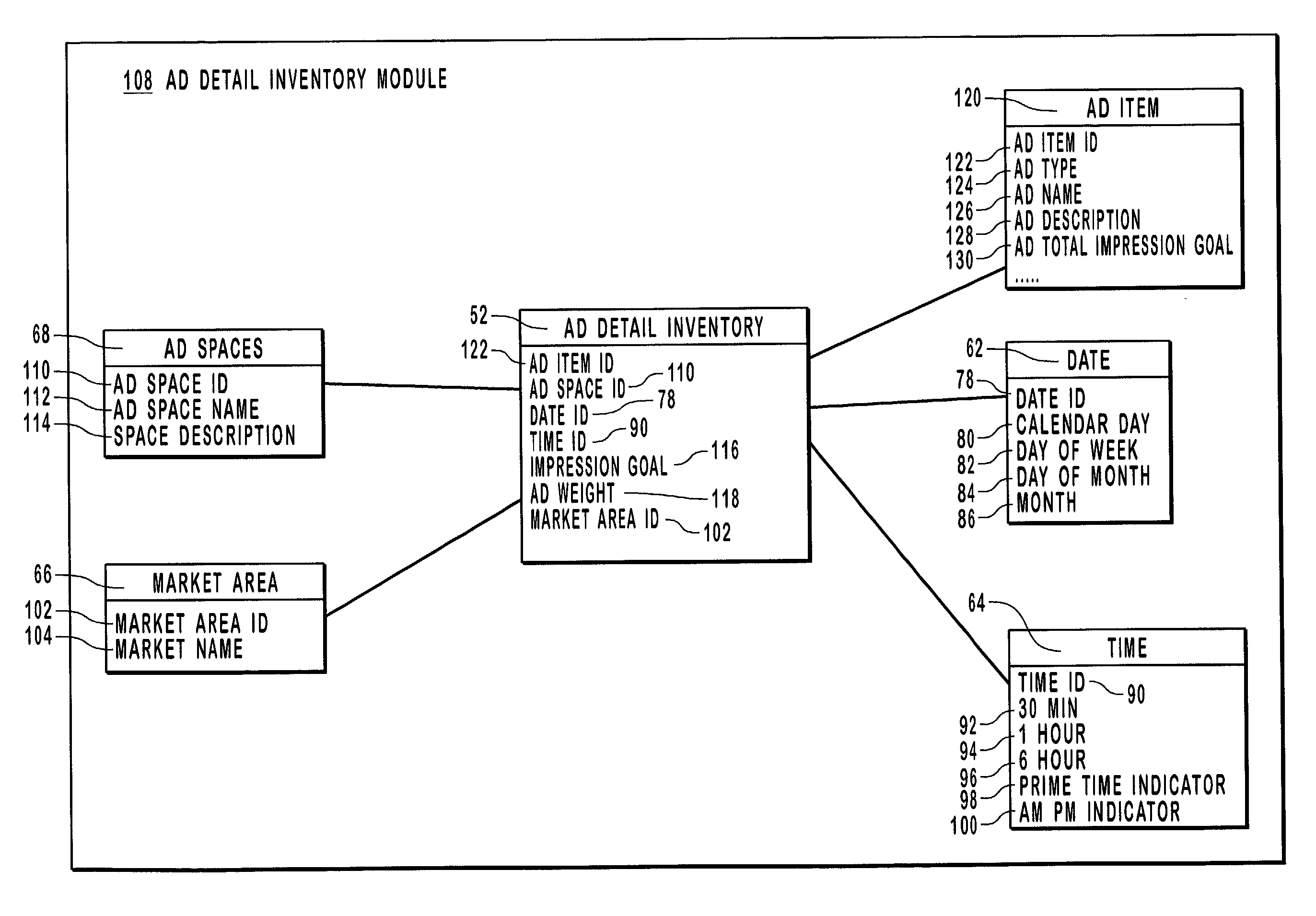
A system, including a planning module, a control module and a receiver module, configured to schedule display of one or more advertising impressions of available advertising inventory. The planning module enables scheduling a requested quantity of advertising impressions in accordance with target criteria. Further, the planning module enables selecting an advertising impression goal for advertisement, assigning an advertising type and defining a weight for the advertisements. The control module receives the schedule, the advertising type and the defined weights and generates one or more metadata files that contain target criteria, advertising type and weights for the advertisements. The one or more metadata files, with the advertisements, are delivered to the receiver module that is configured to define a display frequency for the advertisements based upon one or more of the metadata files. The receiver module selectively displays advertisement content associated with the advertisements to achieve the advertising impression goal.
Owner:ZHIGU HLDG
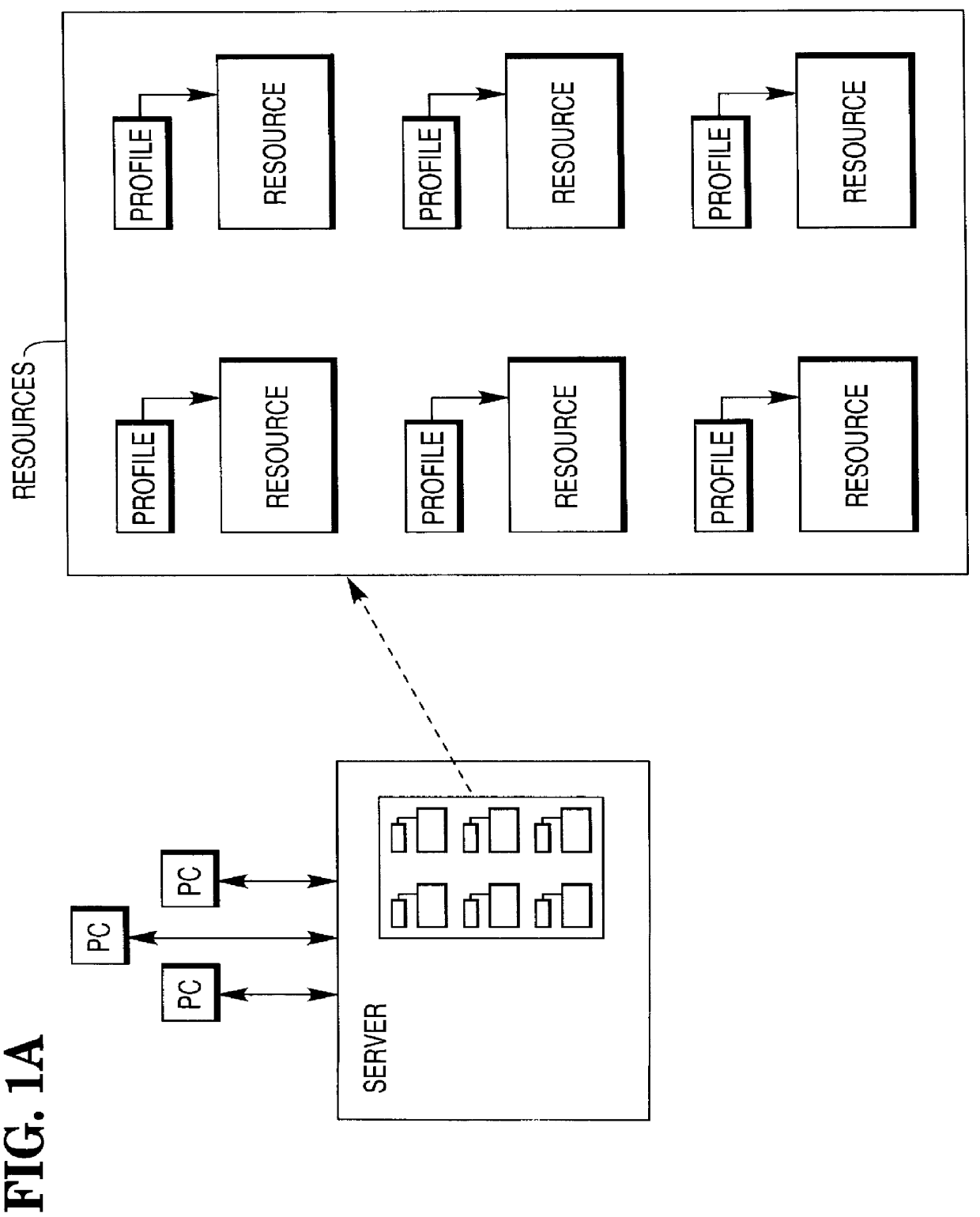
Computer system for management of resources
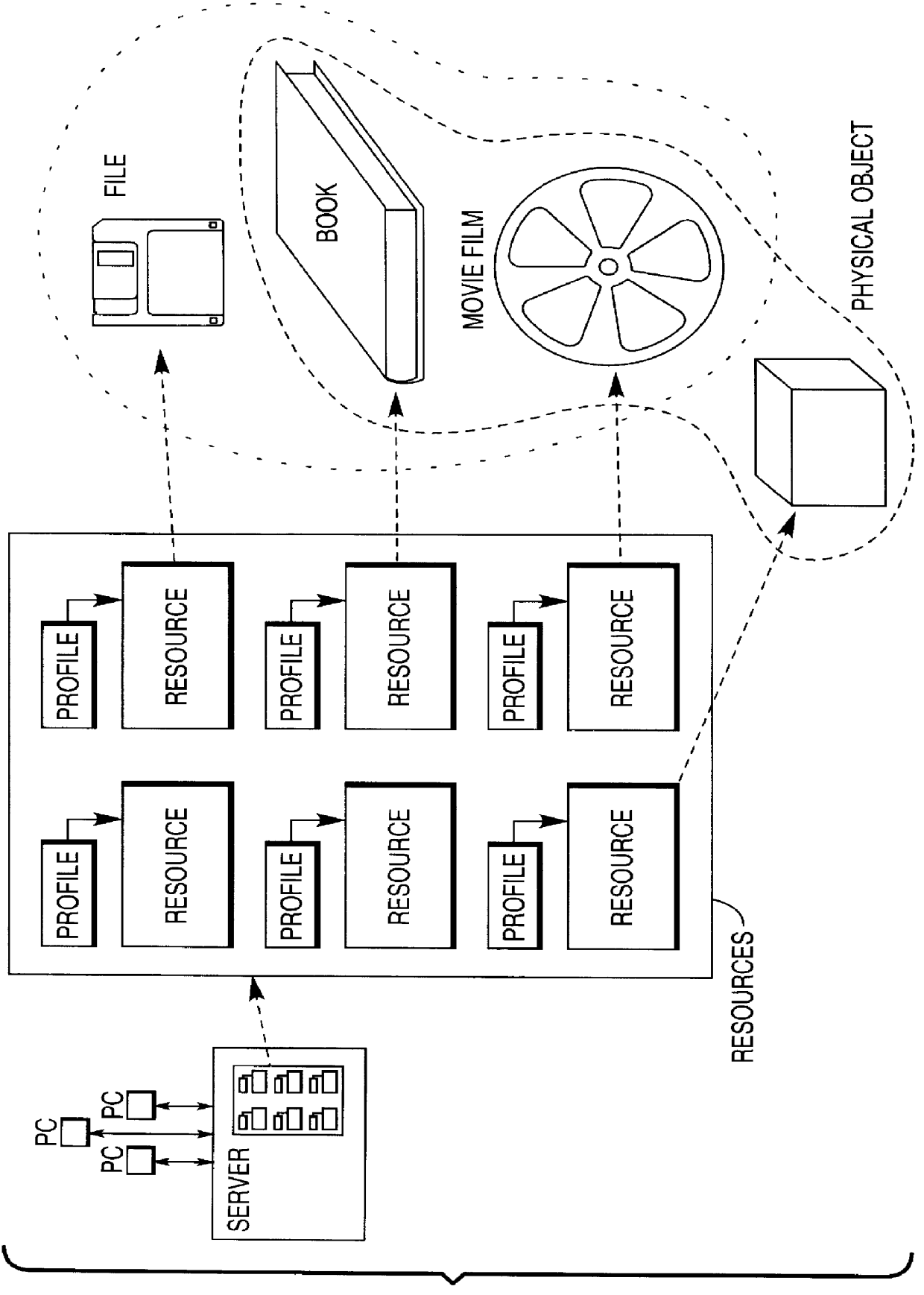
InactiveUS6026403ADigital data information retrievalMultiple digital computer combinationsGraphicsData file
The invention concerns a system for managing resources, which can take the form of (a) computer-compatible information, such as data files and programs, and (b) non-computer-compatible information, as data contained on microfiche, and (c) physical objects. The resources are located at graphically diverse sites. The invention contains a descriptive profile for each resource, and allows any user to search all profiles, and to search the profiles according to "fields" (a database term), such as by location of the resources, or by category of the resources. The user can order delivery of a selected resource, and the system causes delivery of the resource to be executed, irrespective of the form (eg, physical object) of the resource. The invention allows a provider of a new resource to limit access to the resource, by identifying users who are authorized to obtain access to the resource. Non-authorized users cannot obtain access to the profiles of these resources.
Owner:NCR CORP
Secure, vehicle mounted, surveillance system
InactiveUS6211907B1Allow accessRegistering/indicating working of vehiclesAnti-theft devicesTransceiverData file
A novel system for gathering, analyzing and storing information for the purpose of motor vehicle theft and vandalism investigations. An on board secure vehicle mounted surveillance system, that can monitor the vehicle for brief or extended periods of time that can operate whether the vehicle is on or off, having a video camera for generating video signals of an incident proximate the vehicle, having an audio device for monitoring events proximate the vehicle, motion sensor to activate the system and lights activated by the system to illuminate the area viewed by the camera. The video signals are digitized into a synchronized data file, carrying a unique vehicle identification and a time indicator with other input data occurring on or about the vehicle such as audio recordings and the like. The file is encrypted and stored on a large capacity, code accessible device or transmitted, via a transceiver, real time to authorities and / or an off vehicle storage site. Once written, the encrypted file cannot be altered or corrupted, decrypted without the encryption key, or accessed without the access authorization code. The stored data file can be down loaded to be used as evidence.
Owner:EVICAM INT
Virtual desktop manager system and method
The present invention comprises a method and computer implemented system for presenting multiple virtual desktops on a display of a computer system. A “pager” window is displayed on a desktop (either real or virtual) which comprises multiple subpanes, each of which contains a scaled virtual desktop having dimensions that are proportional to, but less than the dimensions of a corresponding virtual desktop. Each scaled virtual desktop provides a representation of the corresponding full-size virtual desktop that would display one or more application windows whose content may optionally be replaced by the icon designating the application program or data file displayed therein, for sake of visual clarity. The present invention also provides a mechanism for varying the background image of virtual desktop, and thus, of each scaled virtual desktop pane, in addition to a number of enhancements to the user interface for controlling the virtual desktop environment including transparency hiding of the pager window, constant aspect ratio scaling of the pager window, mouse desktop changing with corner exclusion, display and interaction with window lists, individual pop up menus for windows, starting desktop selection, a method for moving windows between virtual desktops, a method to override virtual desktop behaviors, a method for placing child windows on the same desktop as the parent window, notification of desktop changes, tracking topmost application on other desktops, sticky monitors, and API remote control.
Owner:THOMPSON JEFFREY W +4
Client-side performance optimization system for streamed applications
InactiveUS20020091763A1Improve application performanceMultiple digital computer combinationsProgram loading/initiatingData fileApplication software
An client-side performance optimization system for streamed applications provides several approaches for fulfilling client-side application code and data file requests for streamed applications. A streaming file system or file driver is installed on the client system that receives and fulfills application code and data requests from a persistent cache or the streaming application server. The client or the server can initiate the prefetching of application code and data to improve interactive application performance. A client-to-client communication mechanism allows local application customization to travel from one client machine to another without involving server communication. Applications are patched or upgraded via a change in the root directory for that application. The client can be notified of application upgrades by the server which can be marked as mandatory, in which case the client will force the application to be upgraded. The server broadcasts an application program's code and data and any client that is interested in that particular application program stores the broadcasted code and data for later use.
Owner:NUMECENT HLDG
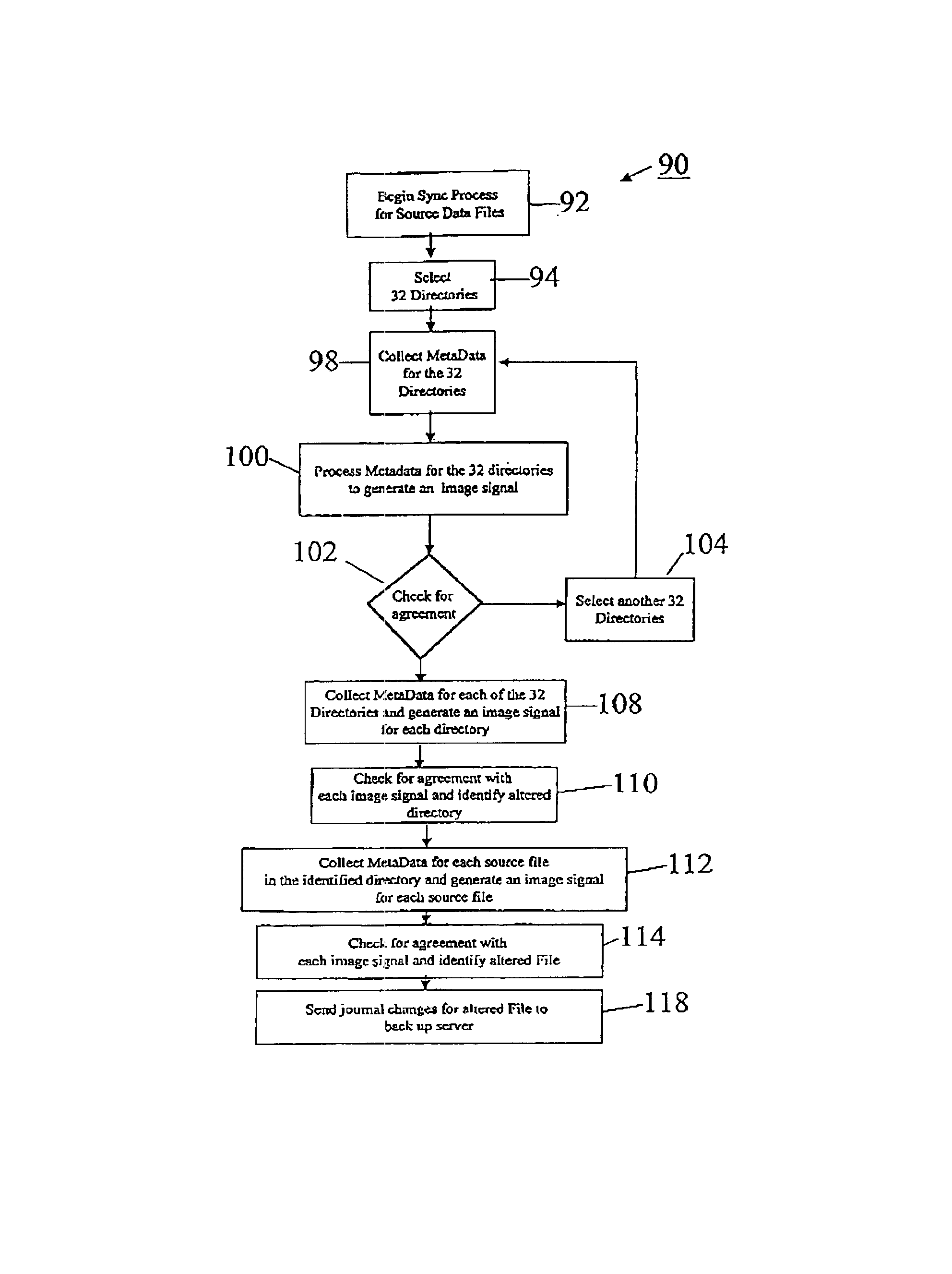
Systems and methods for backing up data files
InactiveUS6847984B1Provide integrityReduce demandData processing applicationsError detection/correctionBaseline dataData file
The invention provides systems and methods for continuous back up of data stored on a computer network. To this end the systems of the invention include a synchronization process that replicates selected source data files data stored on the network and to create a corresponding set of replicated data files, called the target data files, that are stored on a back up server. This synchronization process builds a baseline data structure of target data files. In parallel to this synchronization process, the system includes a dynamic replication process that includes a plurality of agents, each of which monitors a portion of the source data files to detect and capture, at the byte-level, changes to the source data files. Each agent may record the changes to a respective journal file, and as the dynamic replication process detects that the journal files contain data, the journal files are transferred or copied to the back up server so that the captured changes can be written to the appropriate ones of the target data files.
Owner:KEEPITSAFE INC
Method and storage and manipulation of storage system metrics
InactiveUS7082441B1Promote generationEasy accessData processing applicationsError detection/correctionData operationsData description
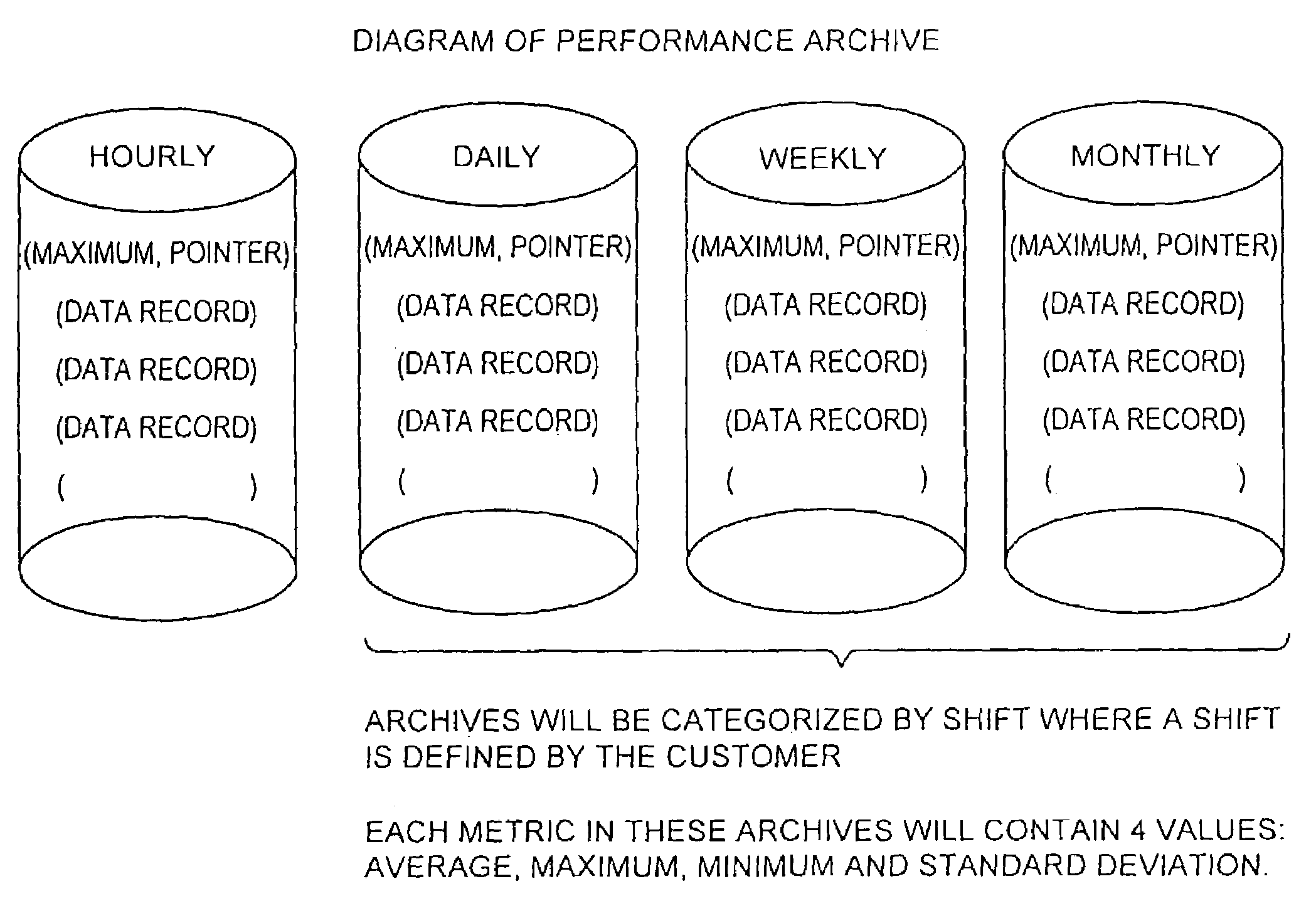
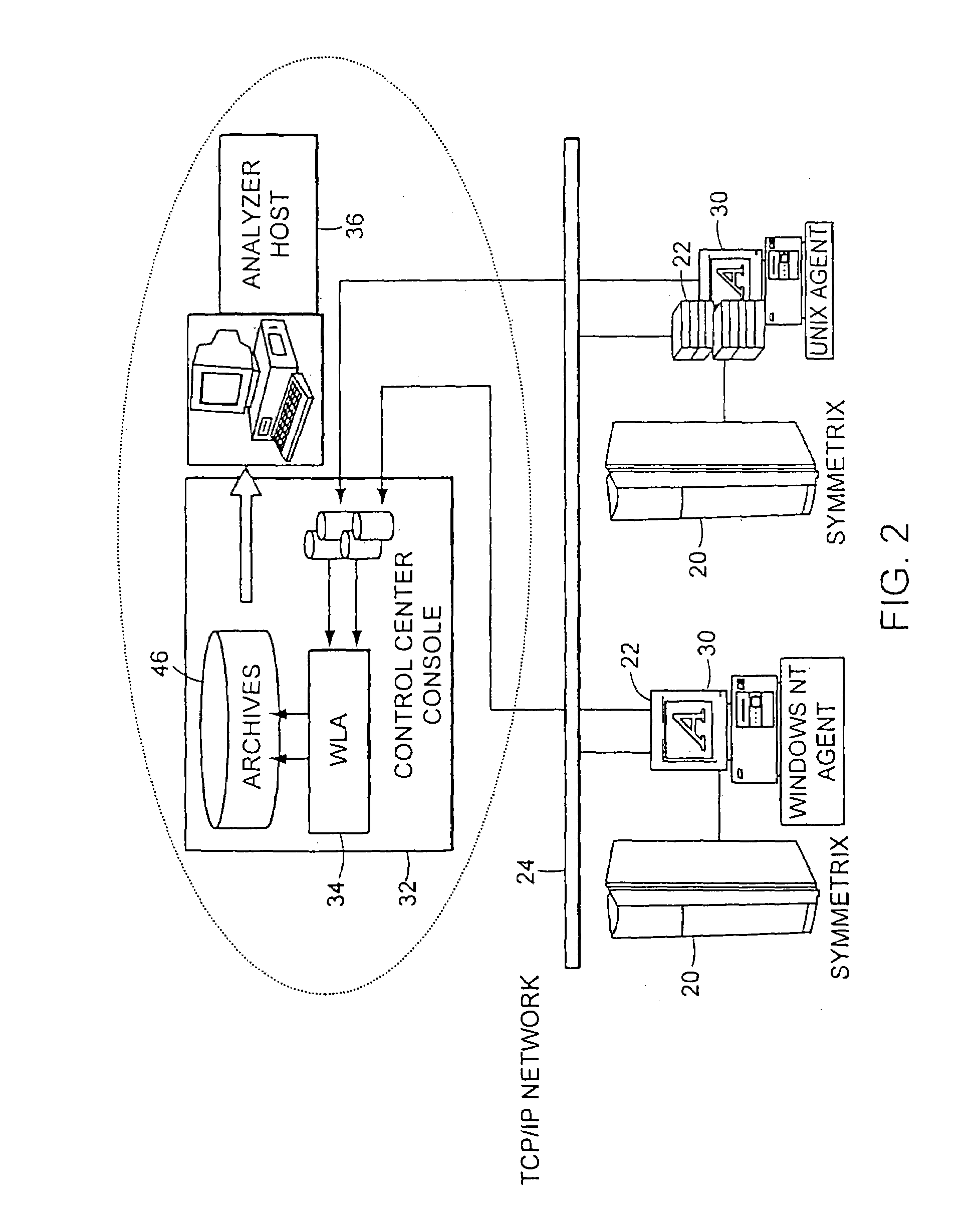
A method for storage and manipulation of storage system metrics incorporates a self-describing format wherein each data file includes a header block that contains the description and order of the periodic data. The header block is followed by a data block in which the data items are presented in the order that they appear in the data description block for that category. Two types of data are managed, including Base Metrics and Derived Metrics. Base Metrics are metrics that appear in the data file sent by an agent. Derived Metrics are computed based on a set of functions that derive new metrics from the base metrics as well as from previously defined derived metrics. A subset of the data block or file describes the configuration of the storage system at the time that the data file was created. Thus the data file contains a header section that in addition to describing the metrics also describes the configuration. A performance view component a user interface that facilitates access to the archives, and data manipulation effecting enhanced performance analysis, workload characterization and capacity planning. The performance view component facilitates generation of factory and user defined views of monitored metrics / parameters. Metrics from a storage system can be correlated using the performance view features, and parameters across machines can be correlated as well. System configuration(s) can be viewed and changed via the performance view user interface.
Owner:EMC IP HLDG CO LLC
Shape-based geometry engine to perform smoothing and other layout beautification operations
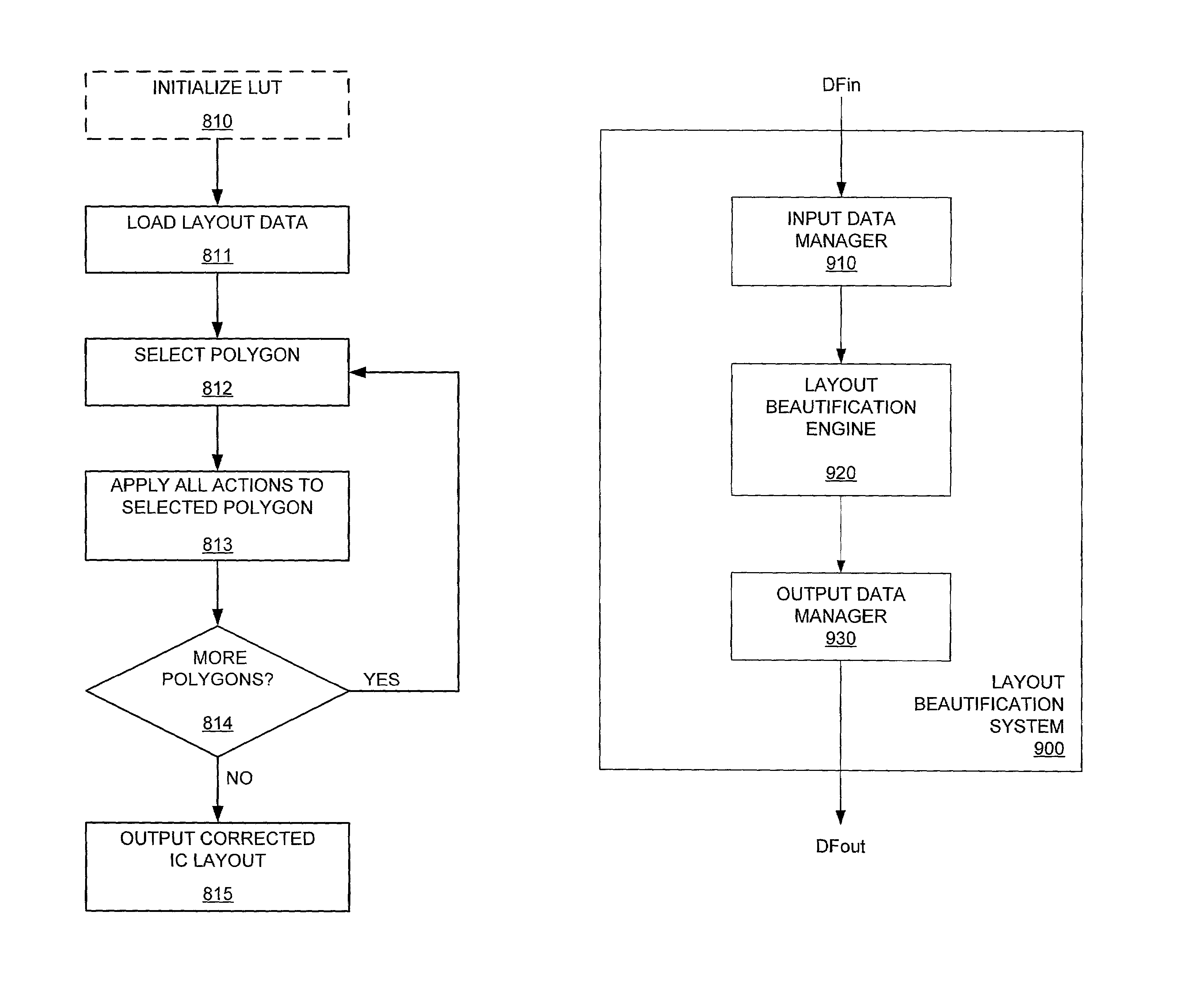
ActiveUS7159197B2Efficient executionData be eliminatedOriginals for photomechanical treatmentComputer aided designData fileEngineering
A shape-based layout beautification operation can be performed on an IC layout to correct layout imperfections. A shape is described by edges (and vertices) related according to specified properties. Each shape can be configured to match specific layout imperfection types. Corrective actions can then be associated with the shapes, advantageously enabling efficient formulation and precise application of those corrective actions. Corrective actions can include absolute, adaptive, or replacement-type modifications to the detected layout imperfections. A concurrent processing methodology can be used to minimize processing overhead during layout beautification, and the actions can also be incorporated into a lookup table to further reduce runtime. A layout beautification system can also be connected to a network across which shapes, actions, and IC layout data files can be accessed and retrieved.
Owner:SYNOPSYS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com