Patents
Literature
7479 results about "Payload" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Payload is the carrying capacity of an aircraft or launch vehicle, usually measured in terms of weight. Depending on the nature of the flight or mission, the payload of a vehicle may include cargo, passengers, flight crew, munitions, scientific instruments or experiments, or other equipment. Extra fuel, when optionally carried, is also considered part of the payload. In a commercial context (i.e., an airline or air freight carrier), payload may refer only to revenue-generating cargo or paying passengers.
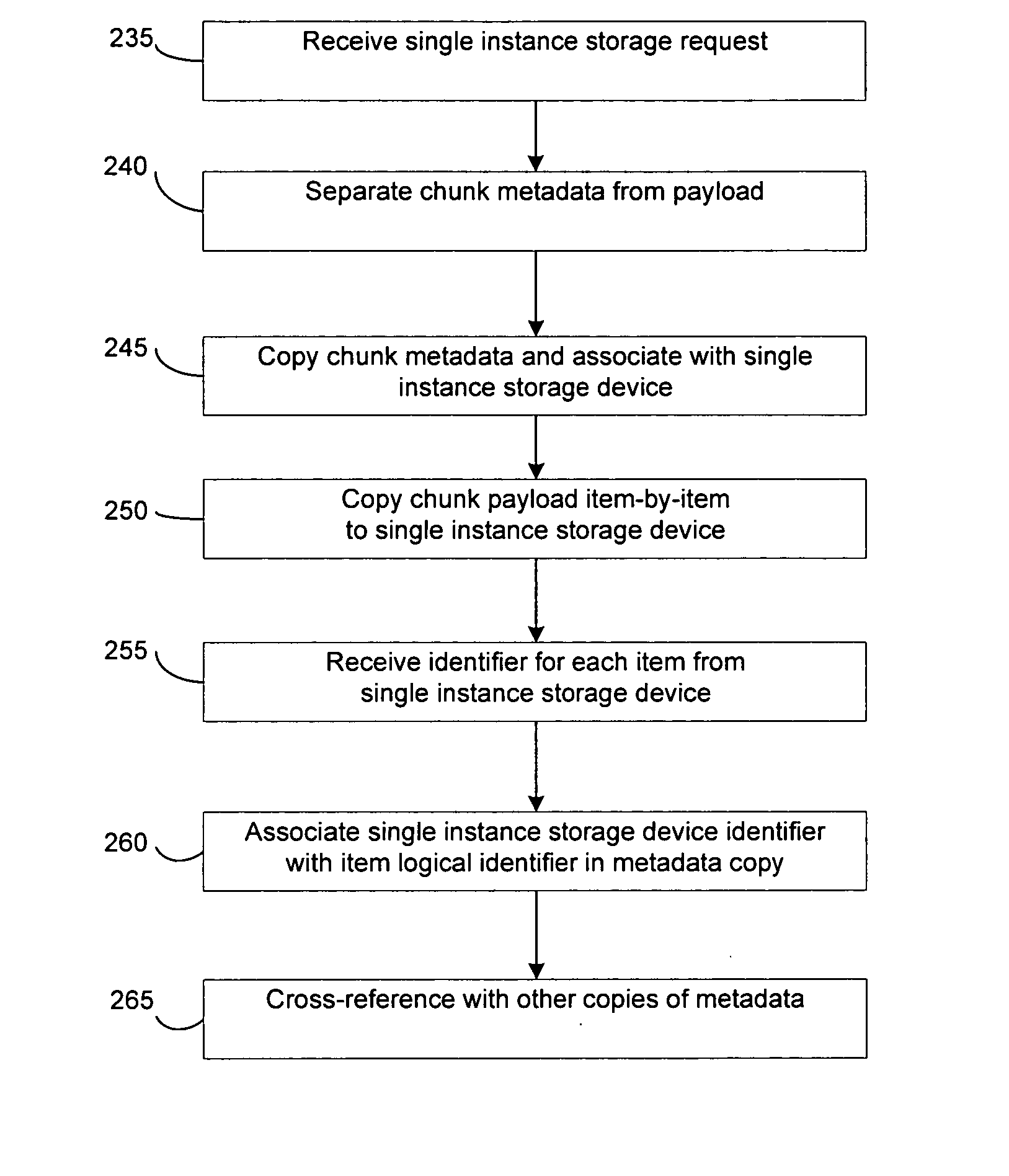
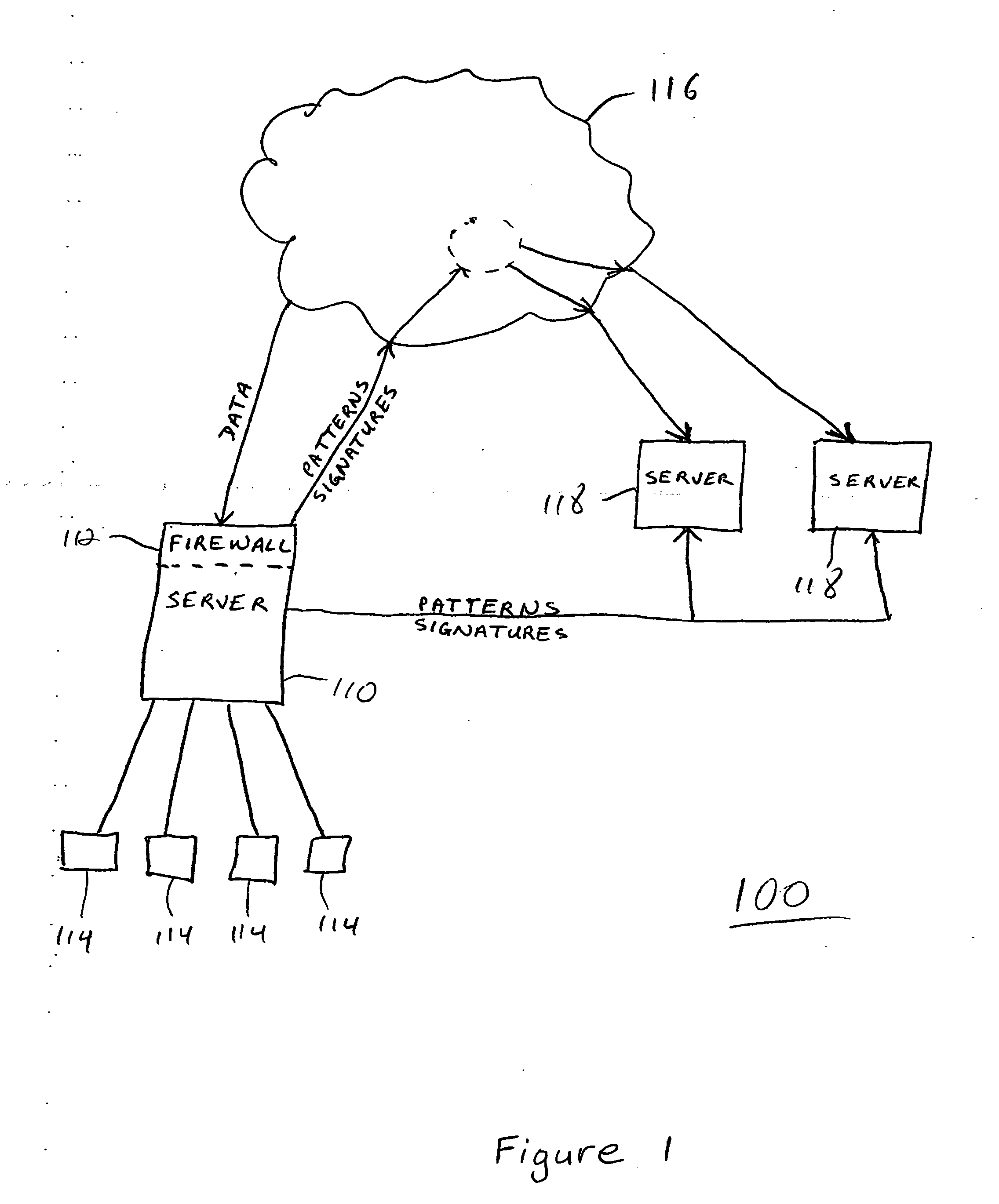
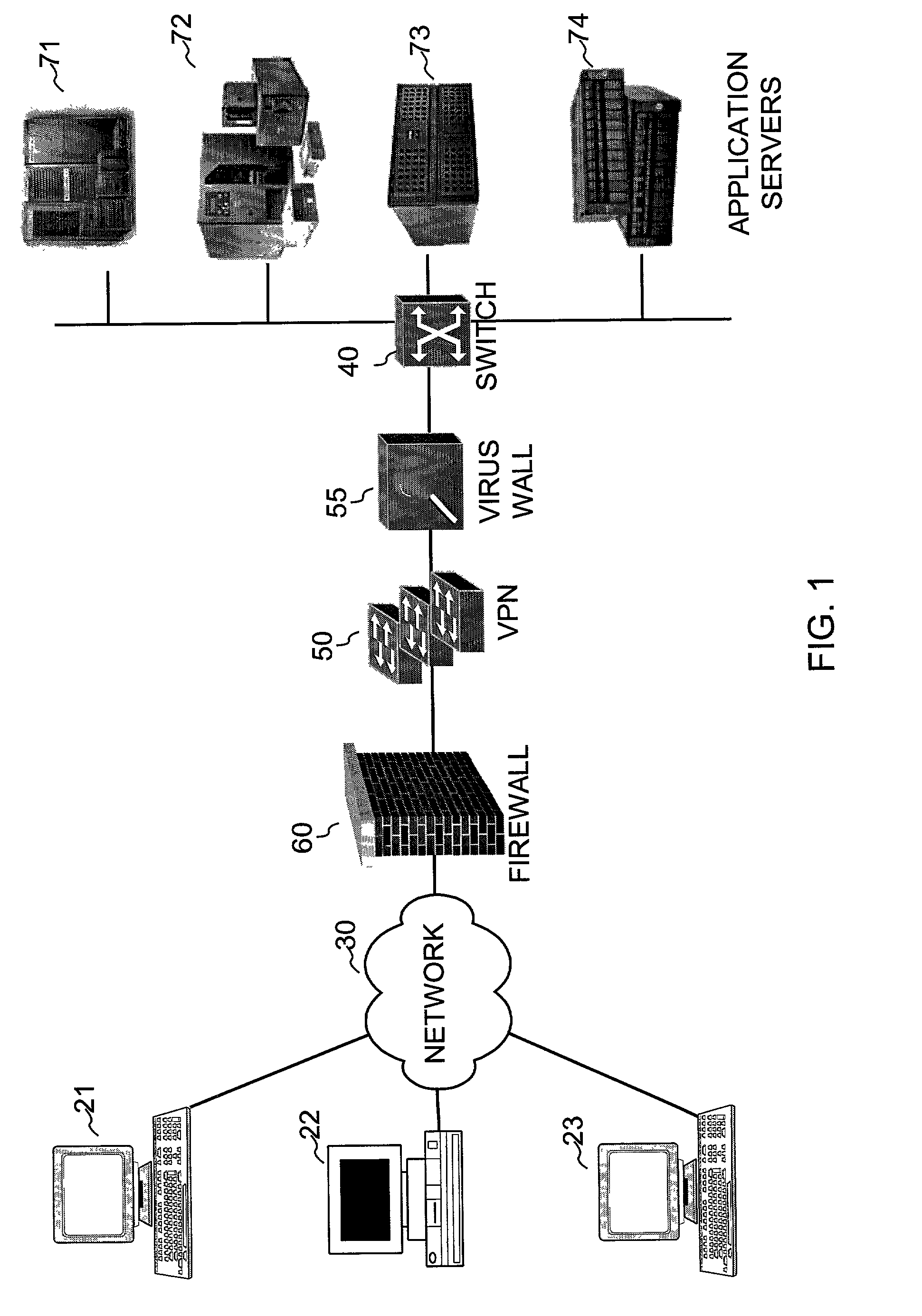
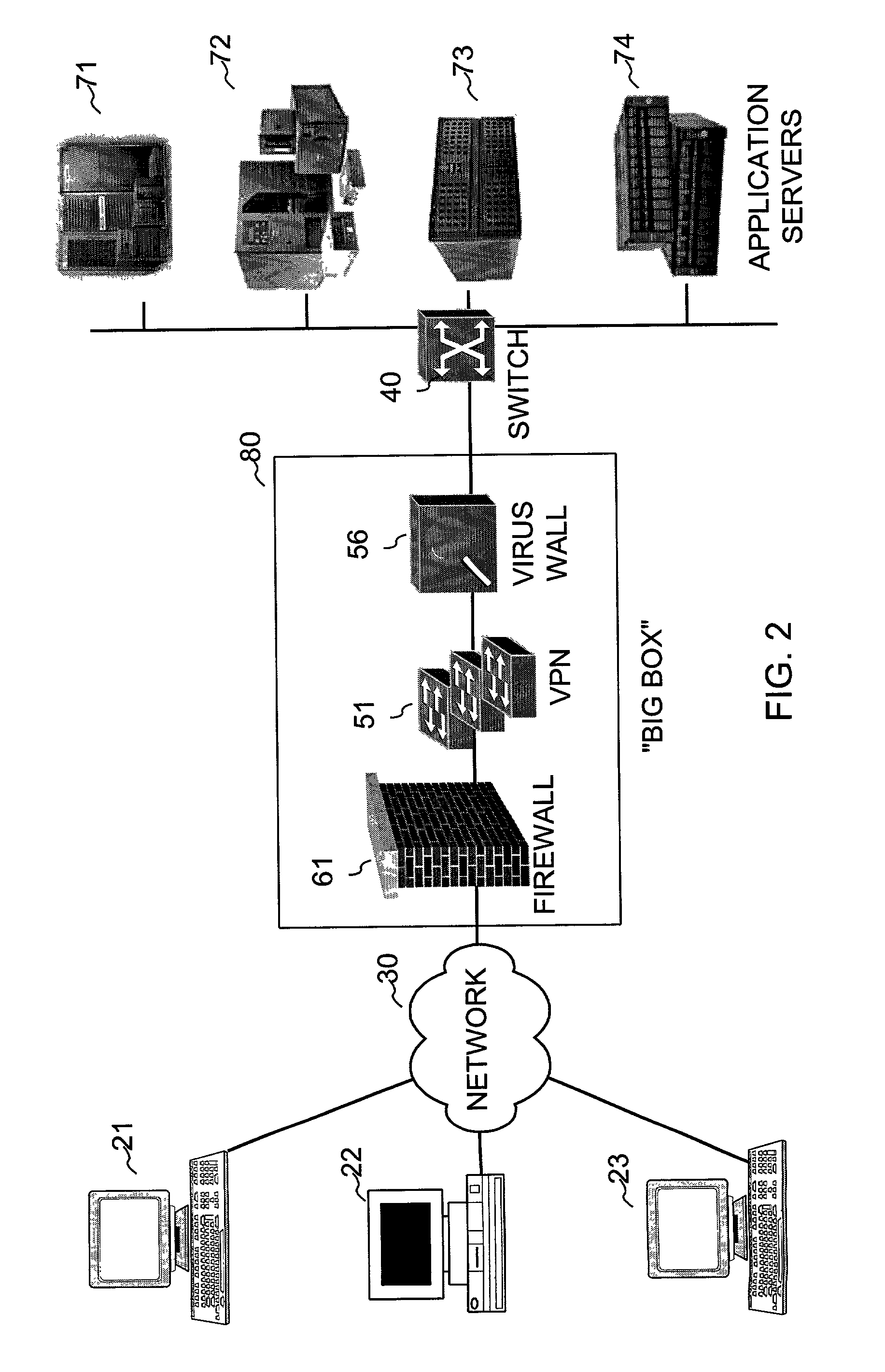
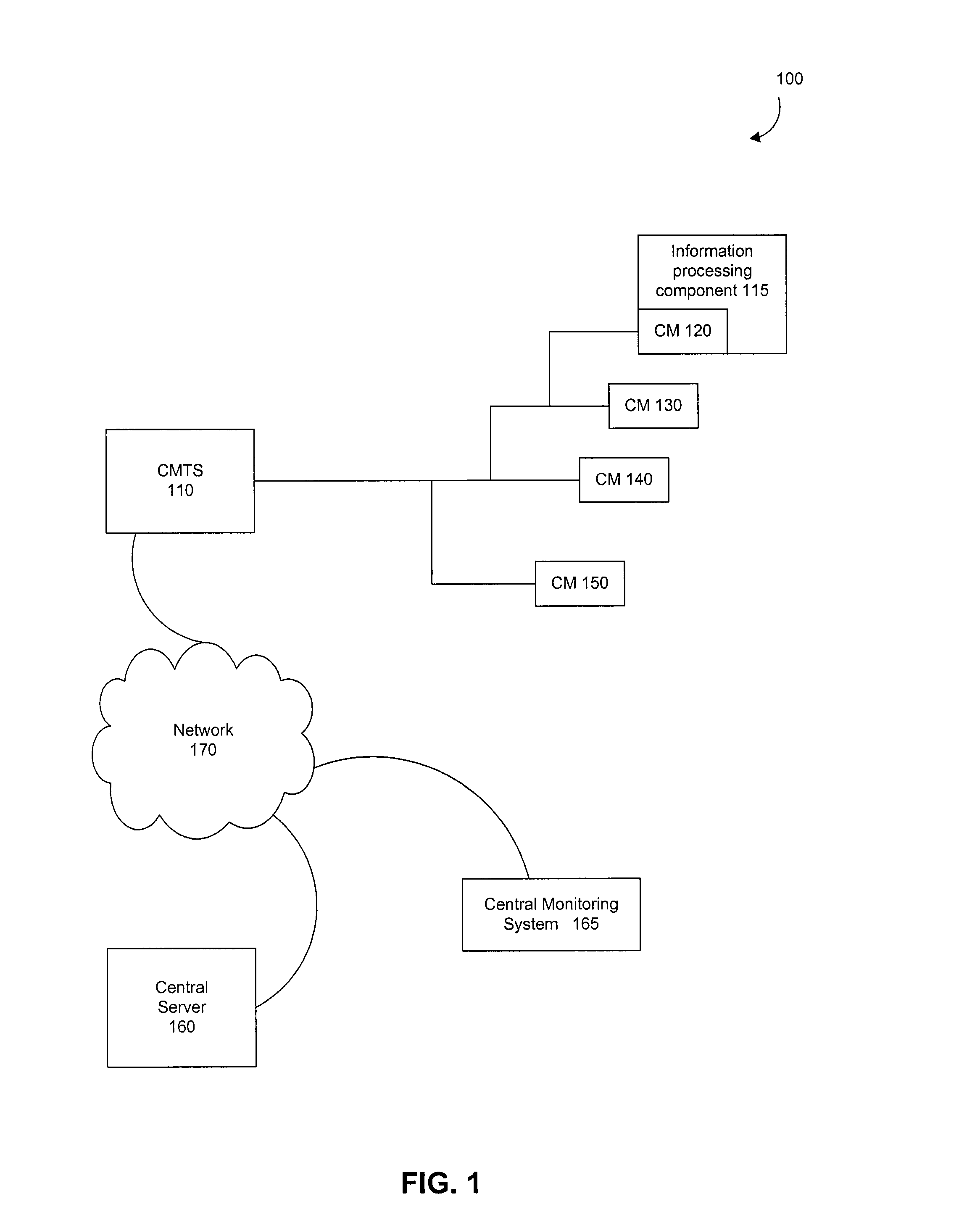
System and method to support single instance storage operations
Systems and methods for single instance storage operations are provided. Systems constructed in accordance with the principals of the present invention may process data containing a payload and associated metadata. Often, chunks of data are copied to traditional archive storage wherein some or all of the chunk, including the payload and associated metadata are copied to the physical archive storage medium. In some embodiments, chunks of data are designated for storage in single instance storage devices. The system may remove the encapsulation from the chunk and may copy the chunk payload to a single instance storage device. The single instance storage device may return a signature or other identifier for items copied from the chunk payload. The metadata associated with the chunk may be maintained in separate storage and may track the association between the logical identifiers and the signatures for the individual items of the chunk payload which may be generated by the single instance storage device.
Owner:COMMVAULT SYST INC
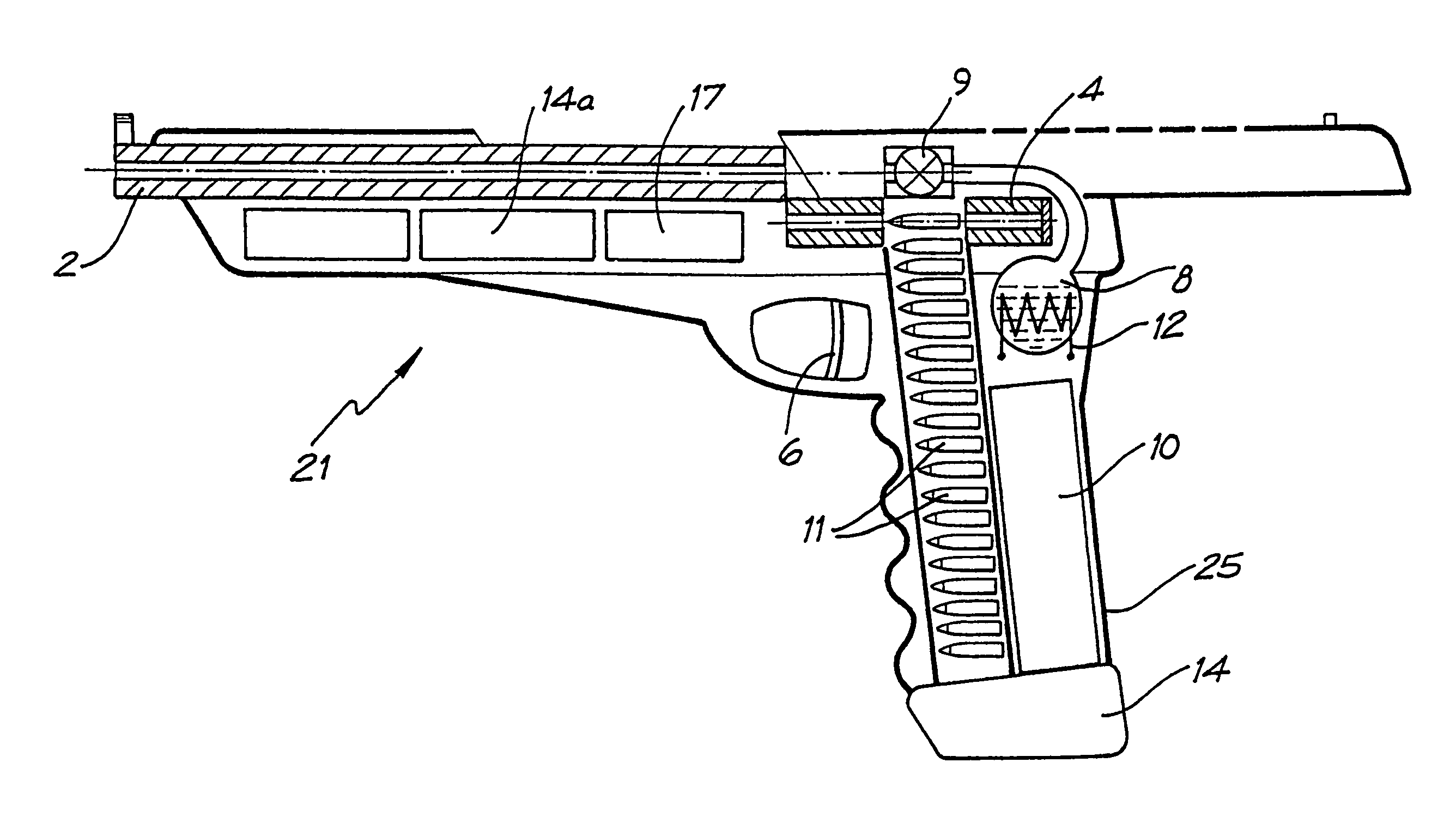
Projectile firing device using liquified gas propellant
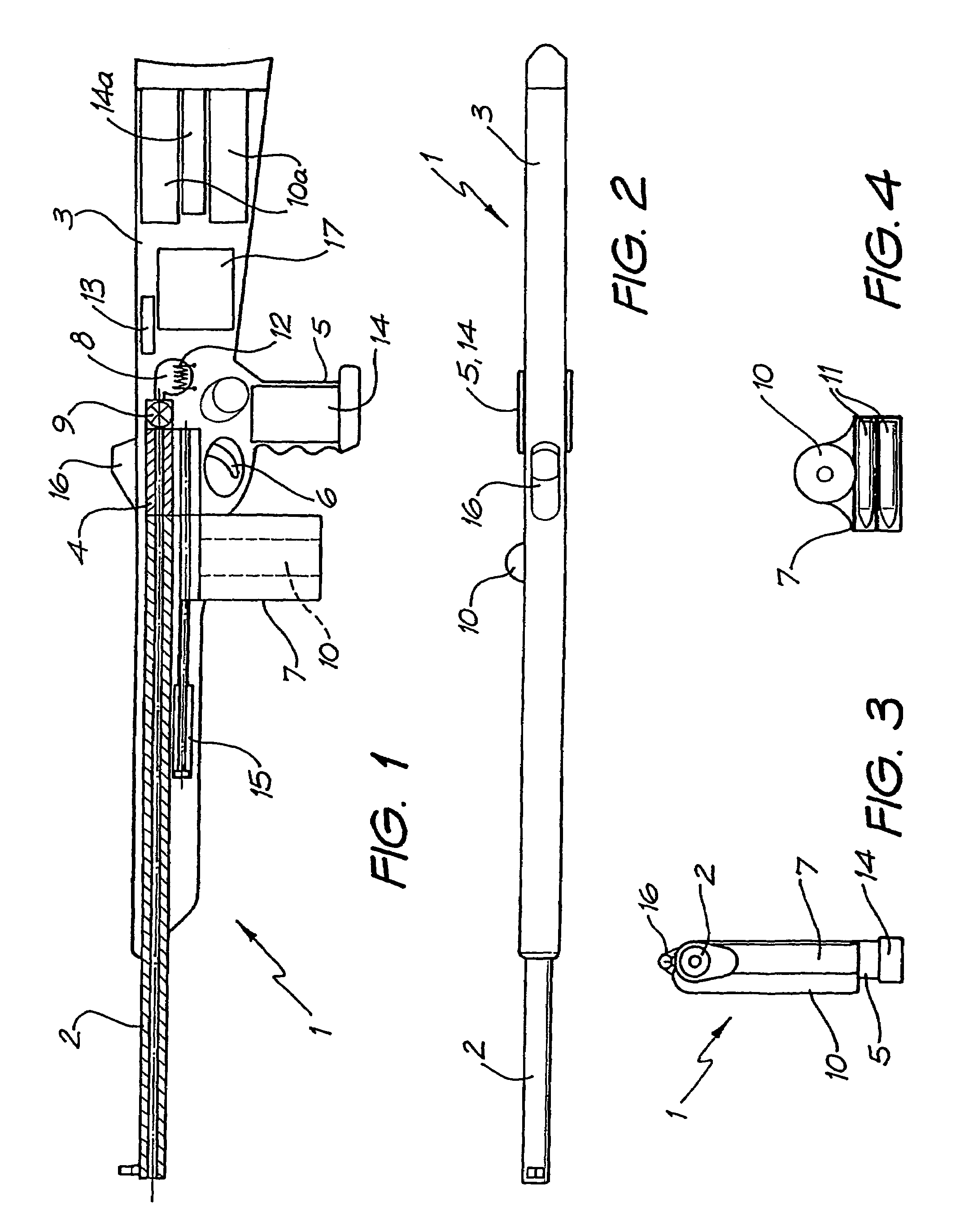
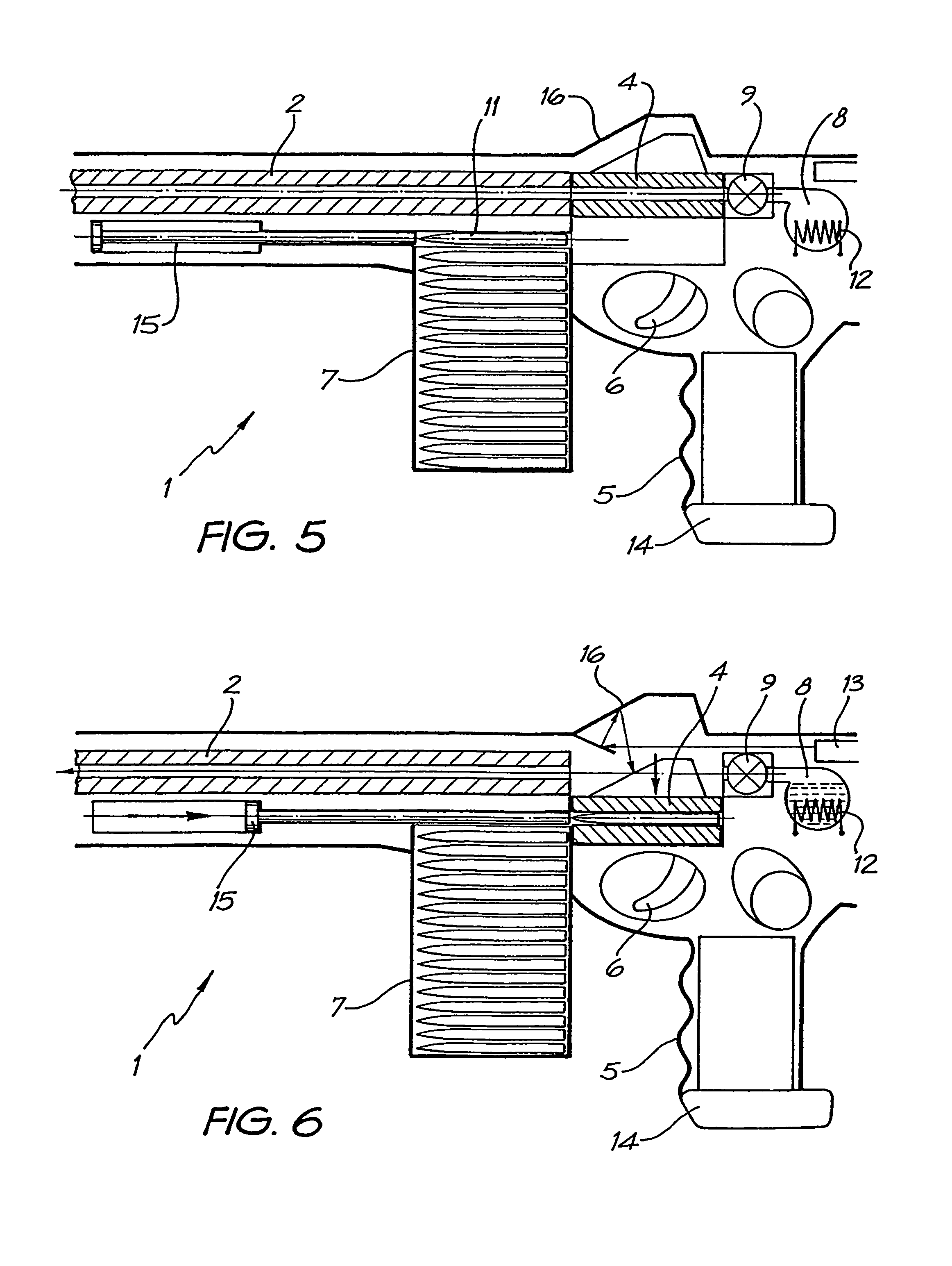
Rifle (1) comprises barrel (2) and loading means (15) for introducing a projectile from magazine (7) into breech (4). The projectile is propelled by a compressed gas propellant initially stored as a liquid in canister (10). The liquid is heated to a super critical state in chamber (8) by heating element (12) to induce a phase change such that the liquid becomes a highly dense gas. The phase change from liquid to gas provides the energy required to expel the projectile at high velocity from rifle (1), regardless of the ambient temperature. The propellant is preferably CO2 which is heated to 31.06° C. Rifle (1) produces minimal noise and no heat signature, making it suitable for military and stealth purposes. A pistol and launchers for grenades or mortar bombs are also disclosed. Another version can launch low earth orbit satellites or payloads.
Owner:POLY SYST PTY LTD
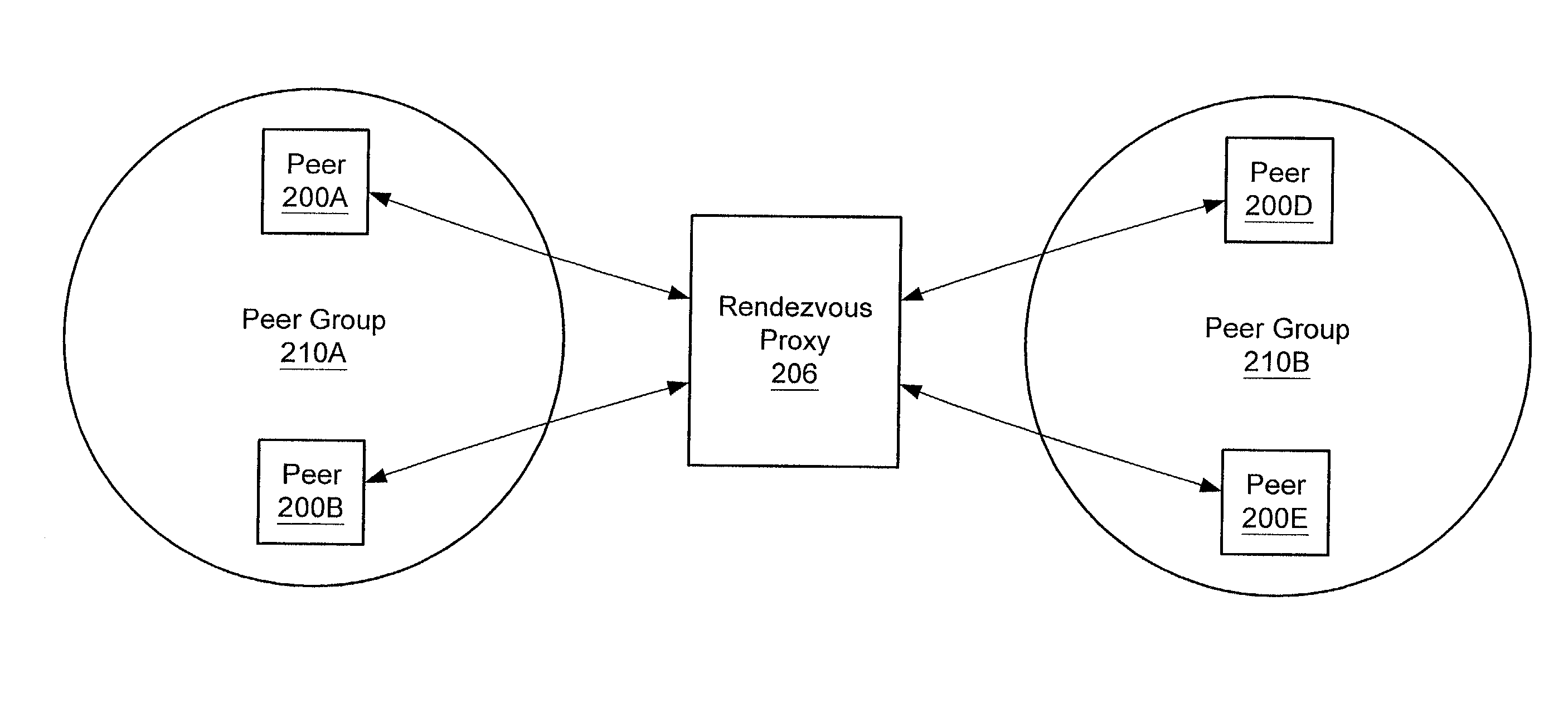
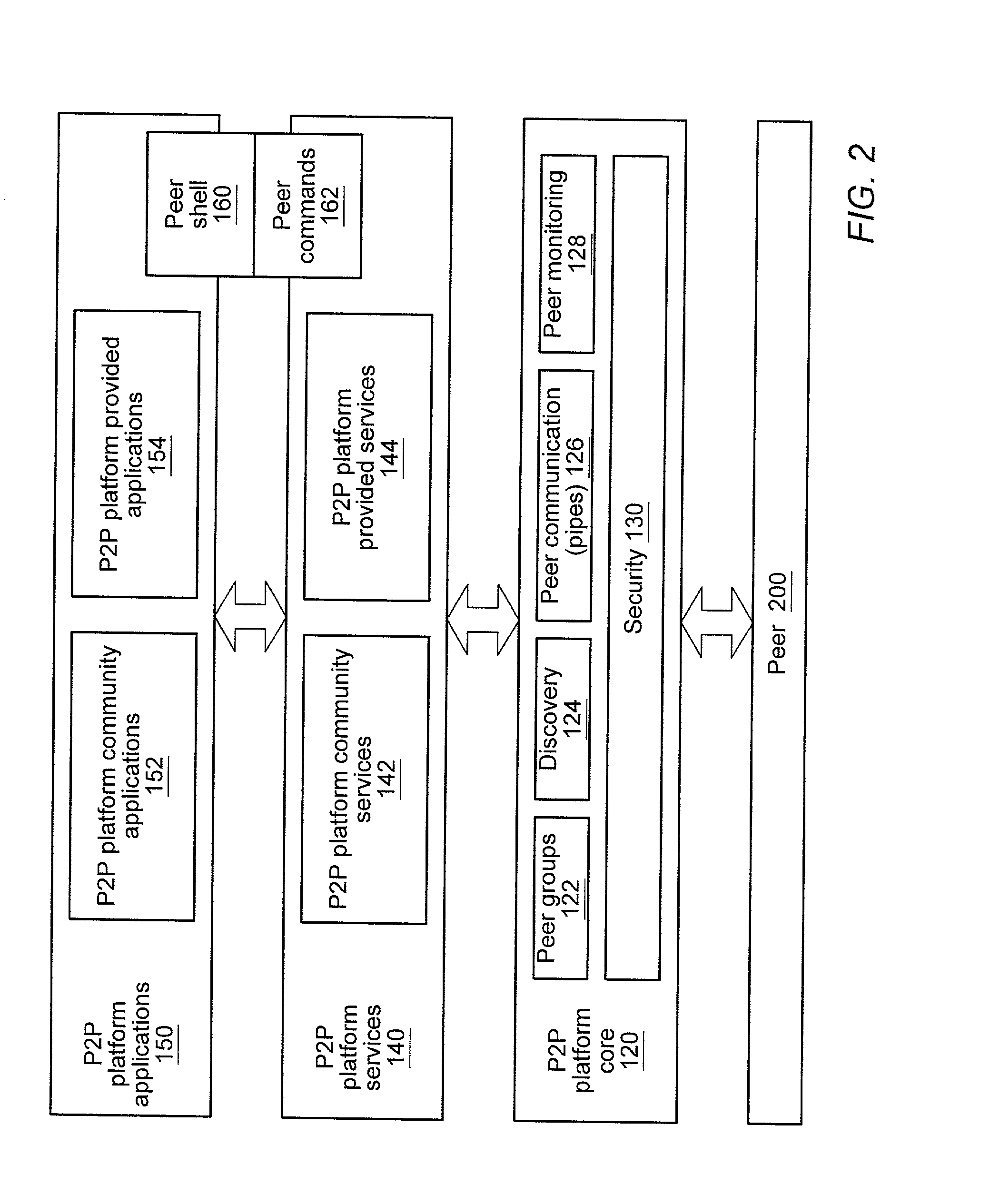
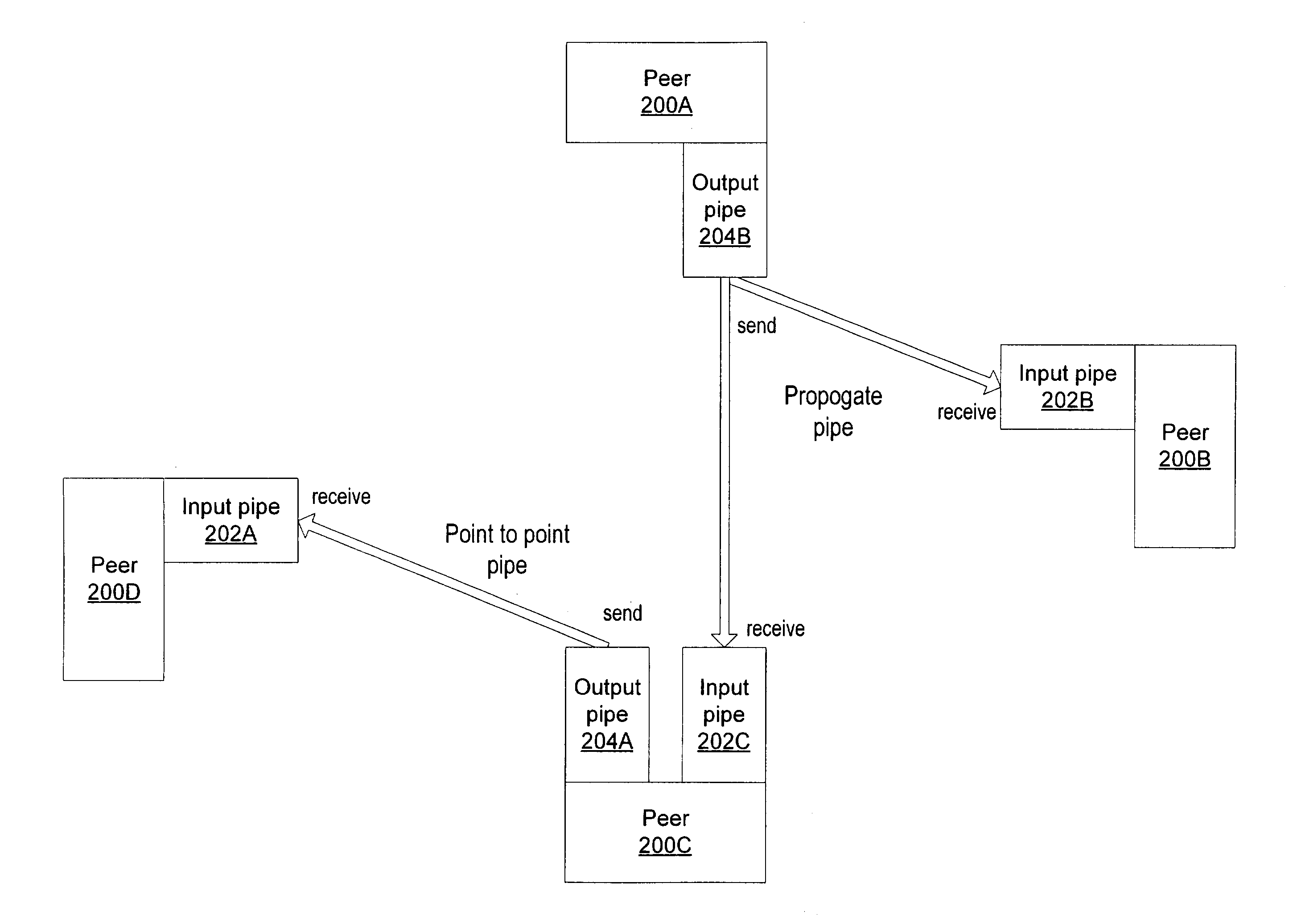
Relay peers for extending peer availability in a peer-to-peer networking environment
ActiveUS20020143855A1Multiprogramming arrangementsMultiple digital computer combinationsDistributed computingPeer-to-peer
A system and method for allowing peers to exchange messages with other peers independently of their network location in a peer-to-peer environment. Messages may be transparently routed, potentially traversing partitions (e.g. firewalls and NATs), and using different protocols to reach the destination peers. In one embodiment, any peer node may serve as a relay peer that allows peers inside a partition to have a presence outside the partition and provides a mechanism for peers outside partitions to discover and communicate with peers inside the partitions. In one embodiment, a relay peer may maintain information on routes to other peers and assist in relaying messages to other peers. In one embodiment, any peer may query a relay peer for route information. In one embodiment, messages may include routing information as part of their payloads.
Owner:ORACLE INT CORP
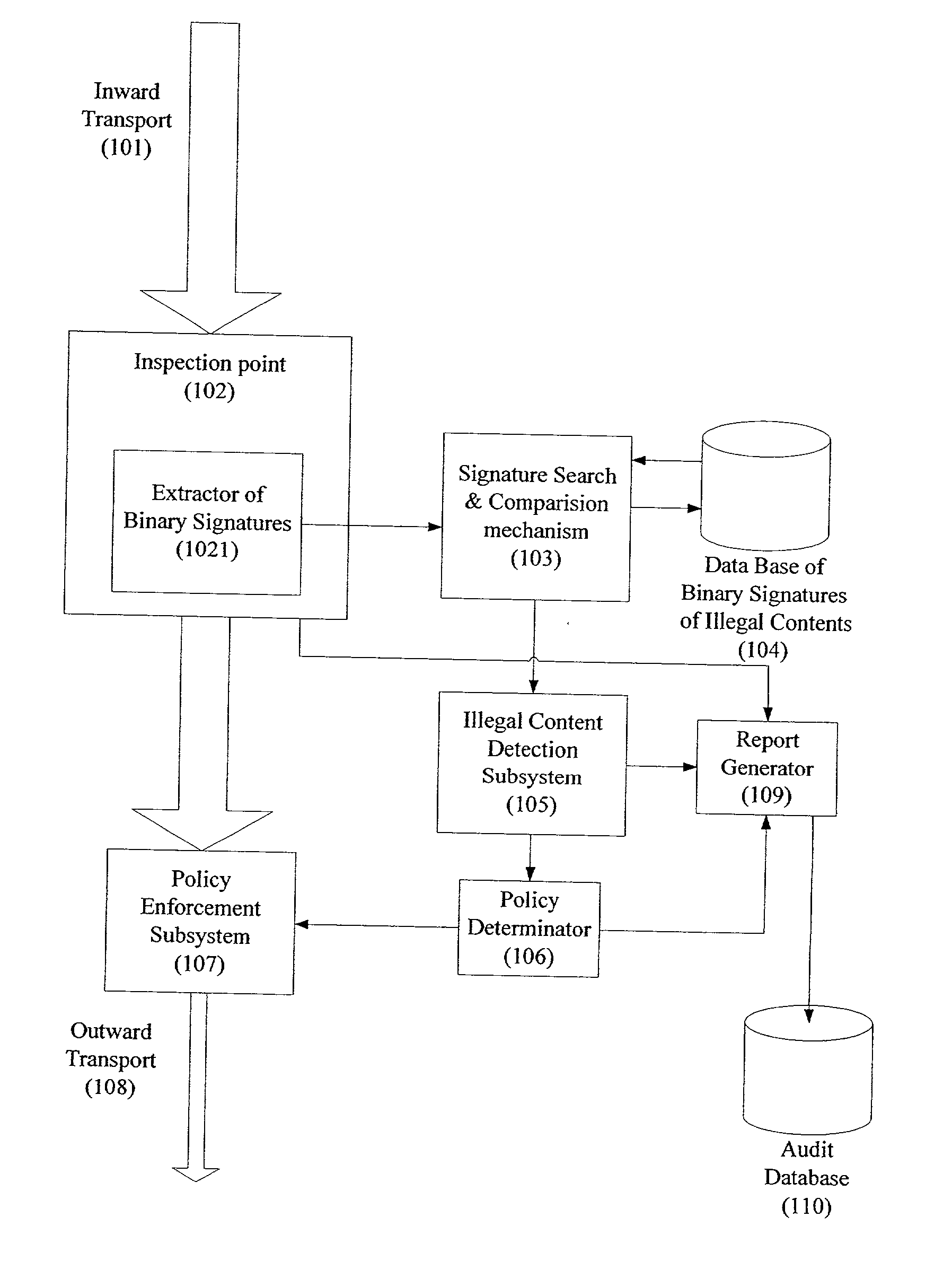
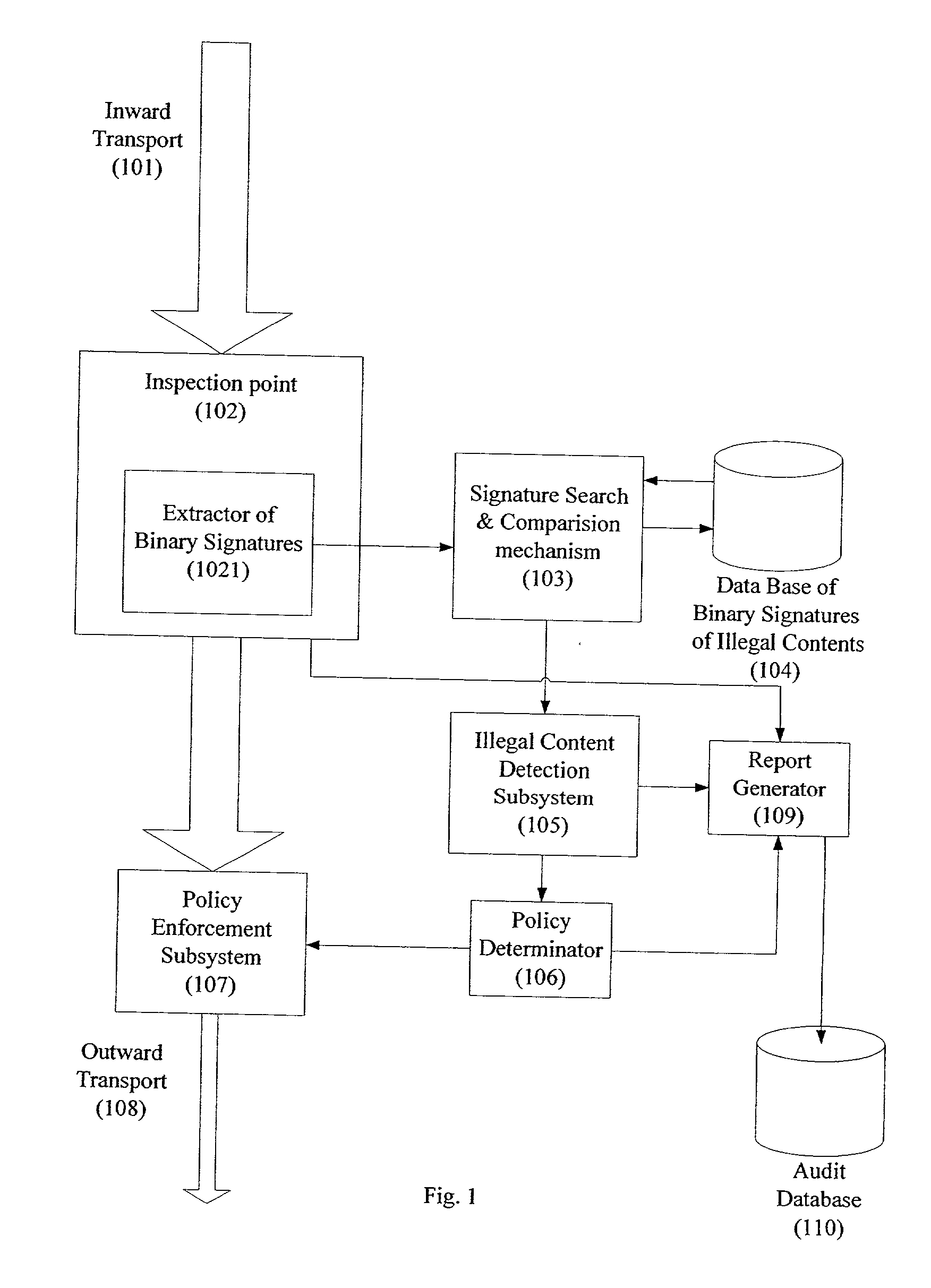
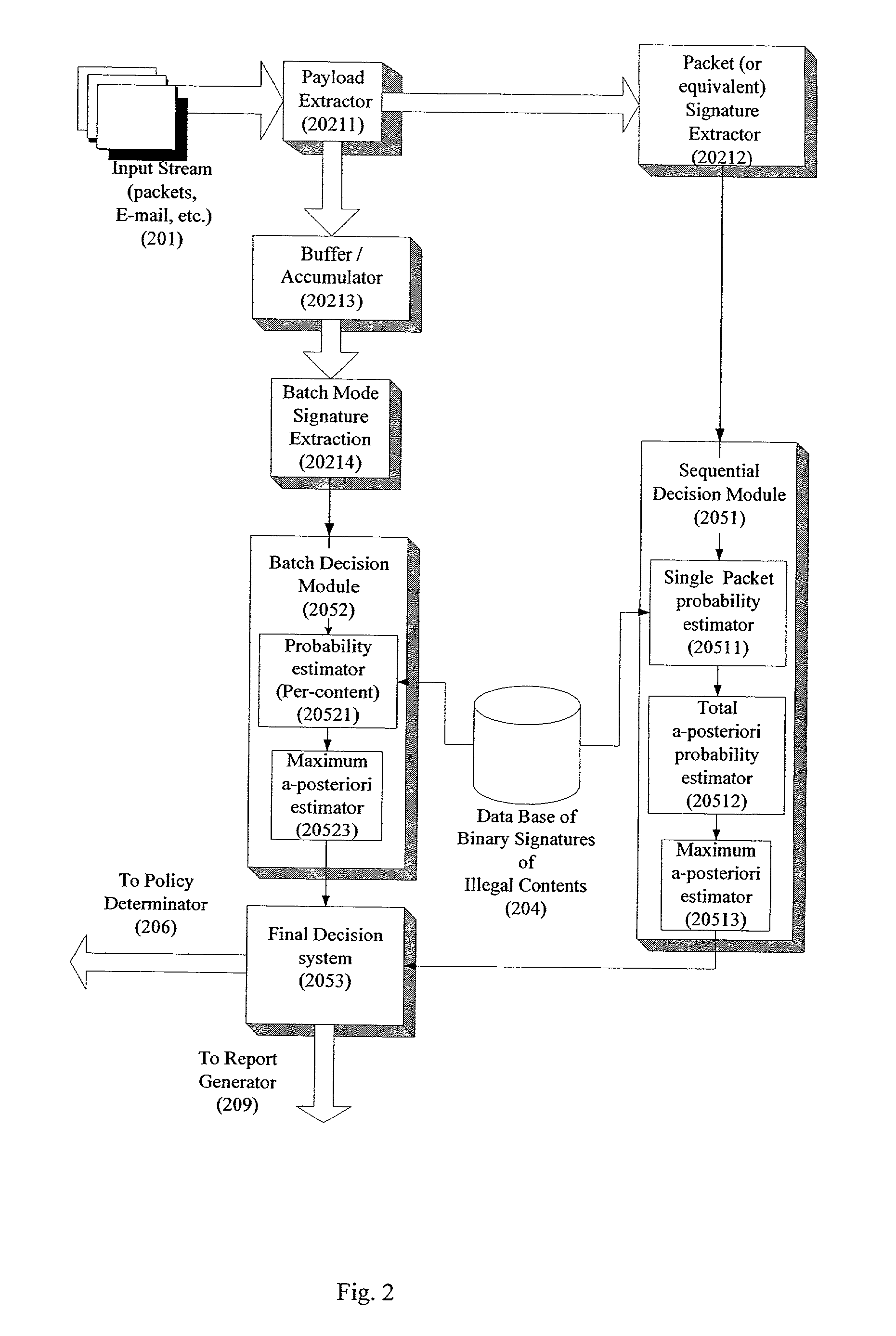
System and method for monitoring unauthorized transport of digital content
ActiveUS20020129140A1Reduce decreaseAttenuation bandwidthMemory loss protectionError detection/correctionDigital contentNumber content
A system for network content monitoring and control, comprising: a transport data monitor, connectable to a point in a network, for monitoring data being transported past said point, a signature extractor, associated with said transport data monitor, for extracting a derivation of said data, said derivation being indicative of content of said payload, a database of preobtained signatures of content whose movements it is desired to monitor, and a comparator for comparing said derivation with said preobtained signatures, thereby to determine whether said payload comprises any of said content whose movements it is desired to monitor. The monitoring result may be used in bandwidth control on the network to restrict transport of the content it is desired to control.
Owner:FORCEPOINT LLC
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS7093239B1Memory loss protectionDigital data processing detailsTheoretical computer scienceComputerized system
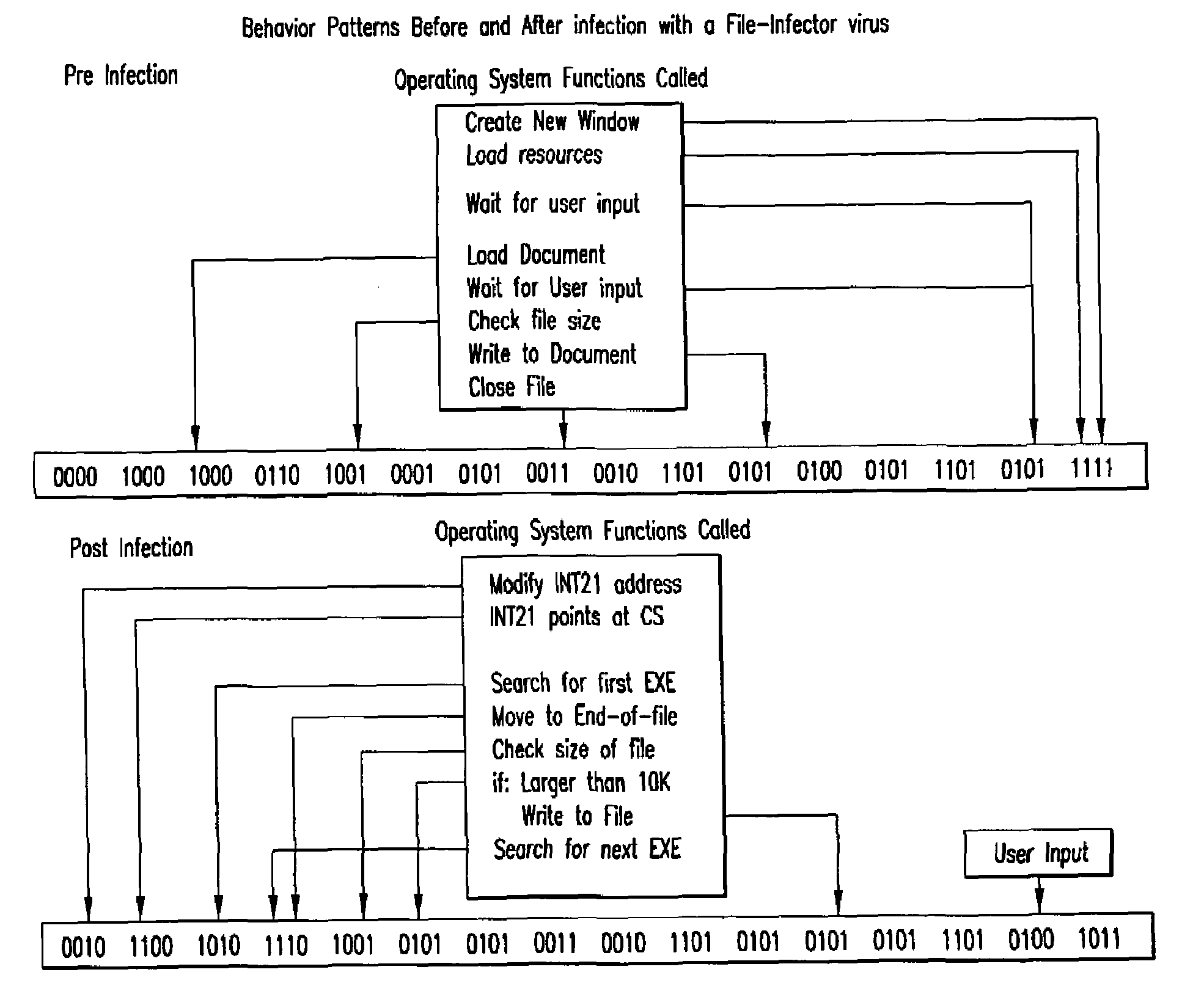
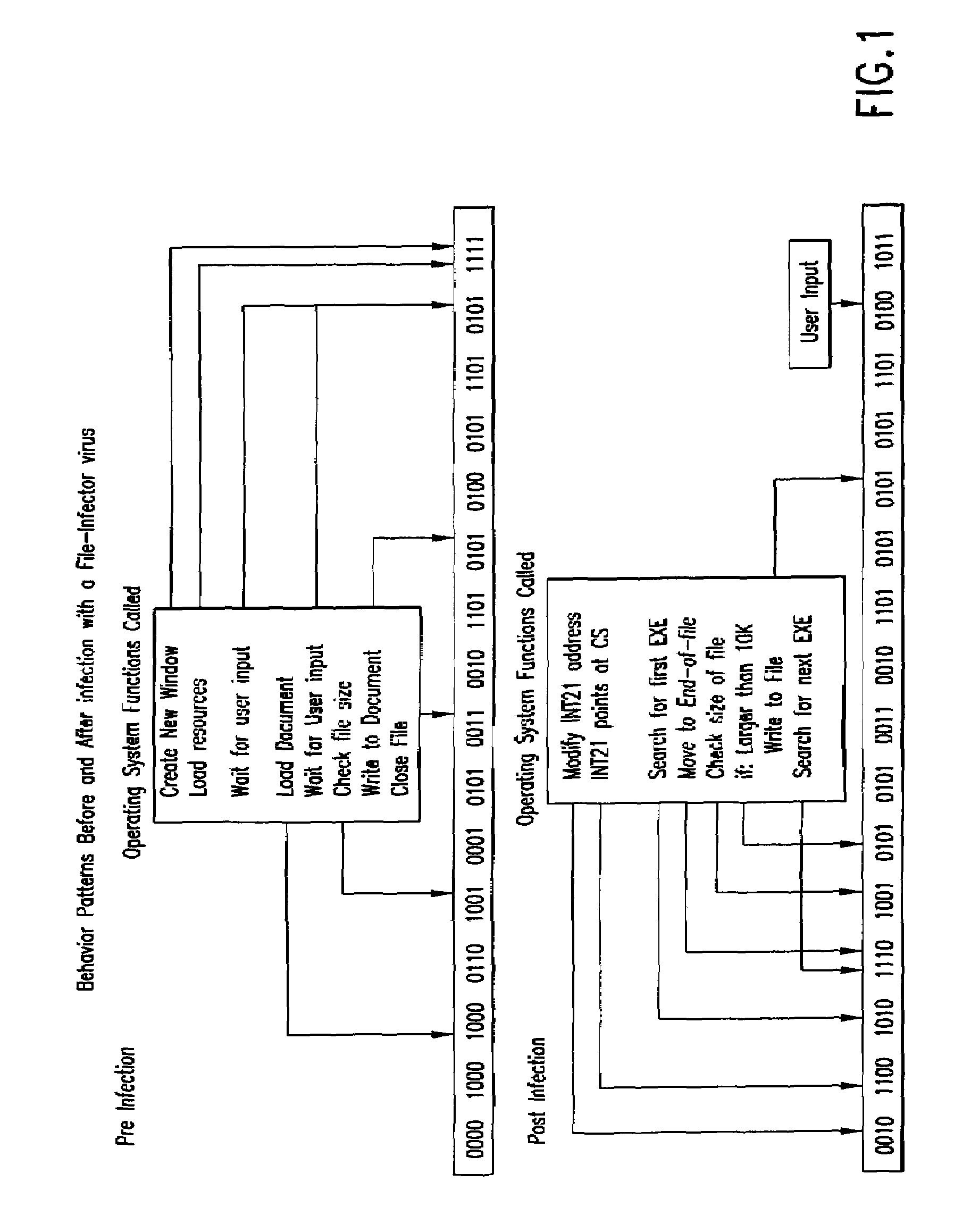
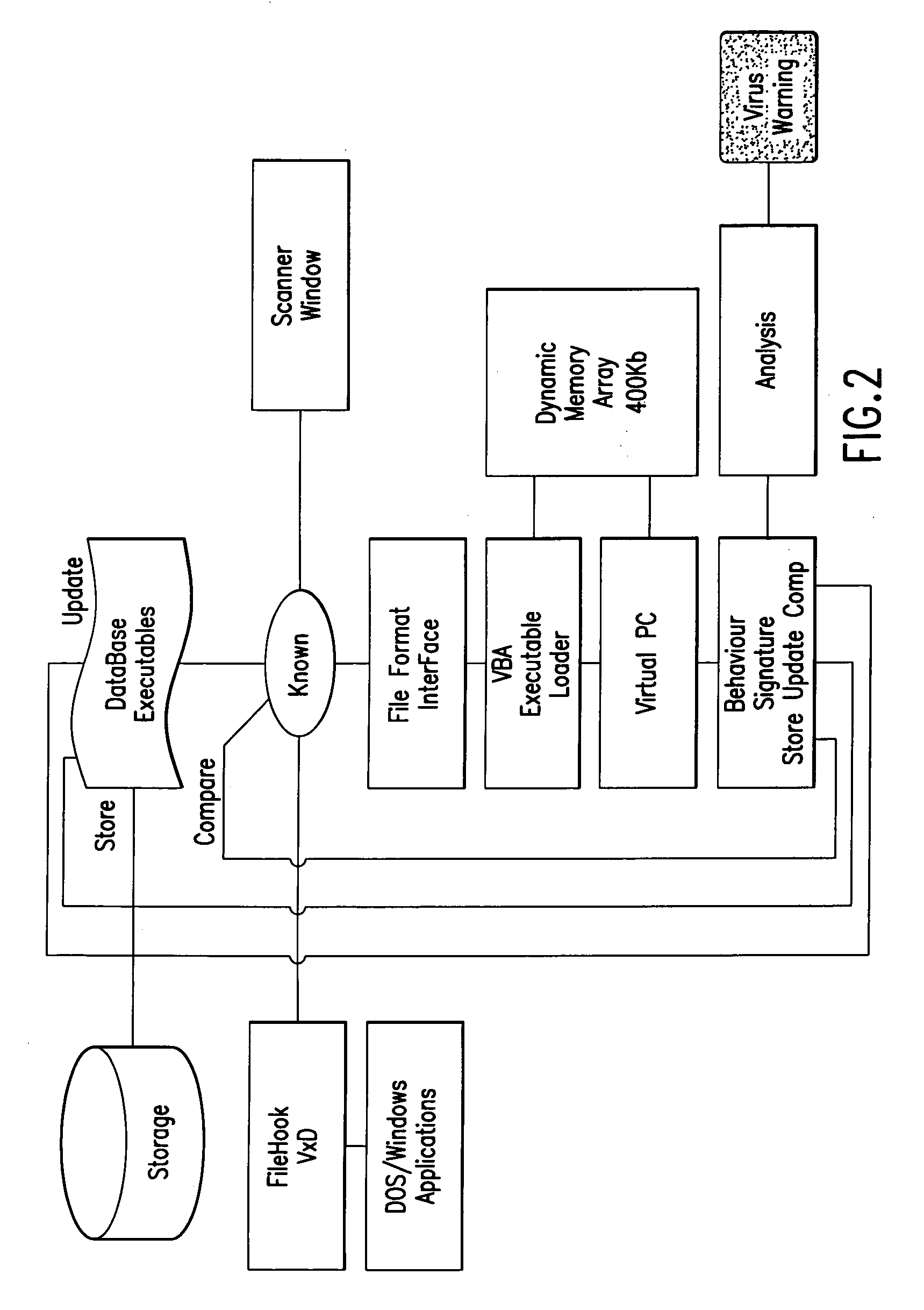
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
Selective and renewable encryption for secure distribution of video on-demand
InactiveUS6415031B1Two-way working systemsSelective content distributionDigital videoServer replication
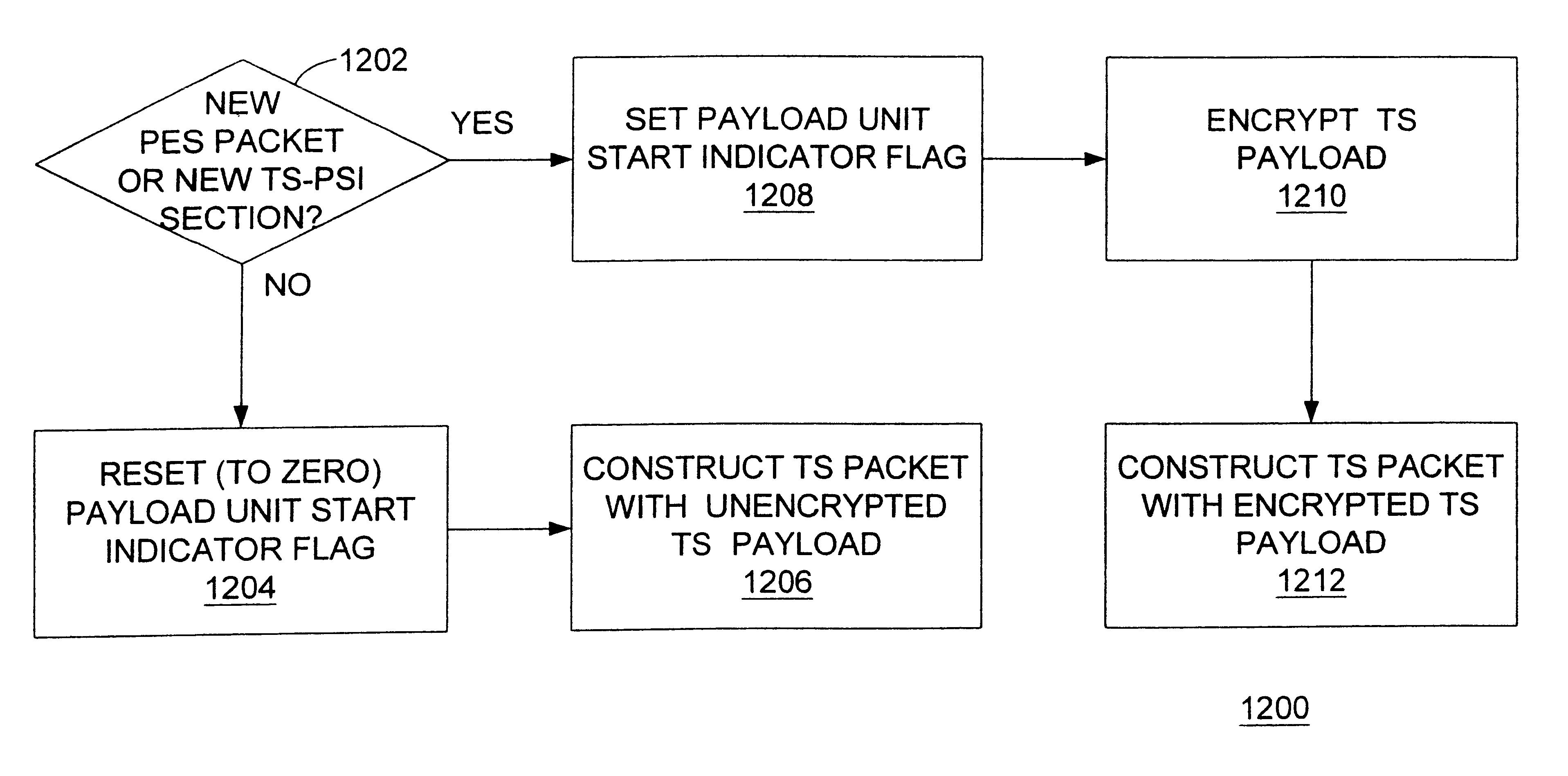
Selective encryption is provided in a process which includes: determining whether a predetermined criterion is satisfied; setting a selective encryption status field if the predetermined criterion is satisfied; and encrypting an unencrypted payload to generate an encrypted payload, and constructing a packet with the encrypted payload, if the predetermined criterion is satisfied. The predetermined criterion may be one of several criteria, each of which reduce the required amount of encryption and decryption while maintaining a high level of security. Renewable encryption is provided in a process which includes: copying a first encrypted digital video program from a remote server to a video source; decrypting the first encrypted digital video program using a first key to generate an unencrypted digital video program; encrypting the unencrypted digital video program using a second key to generate a second encrypted digital video program; transmitting the second encrypted digital video program from the video source to the remote server; and deleting the first encrypted digital video program from the remote server.
Owner:COMCAST IP HLDG I
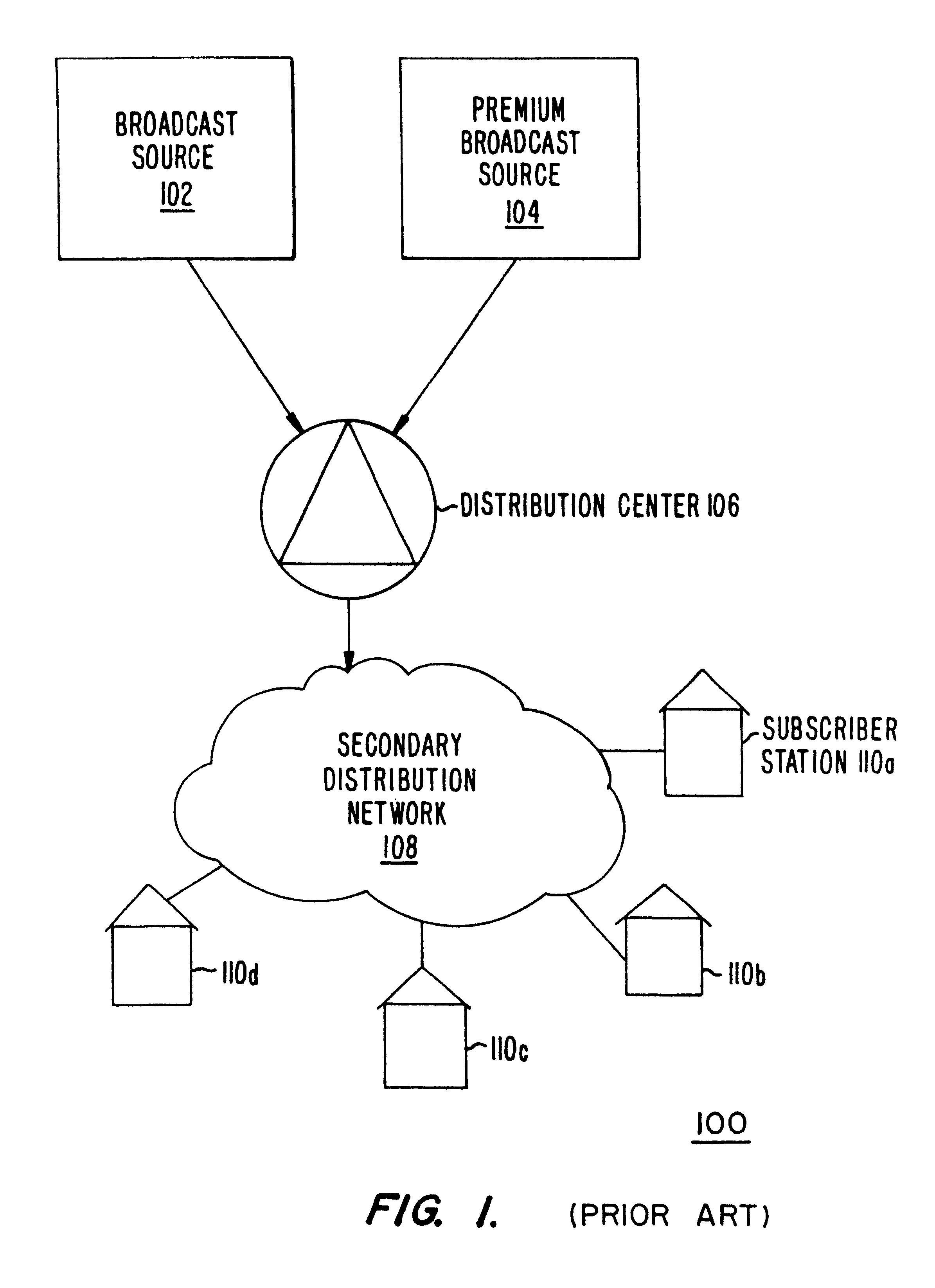
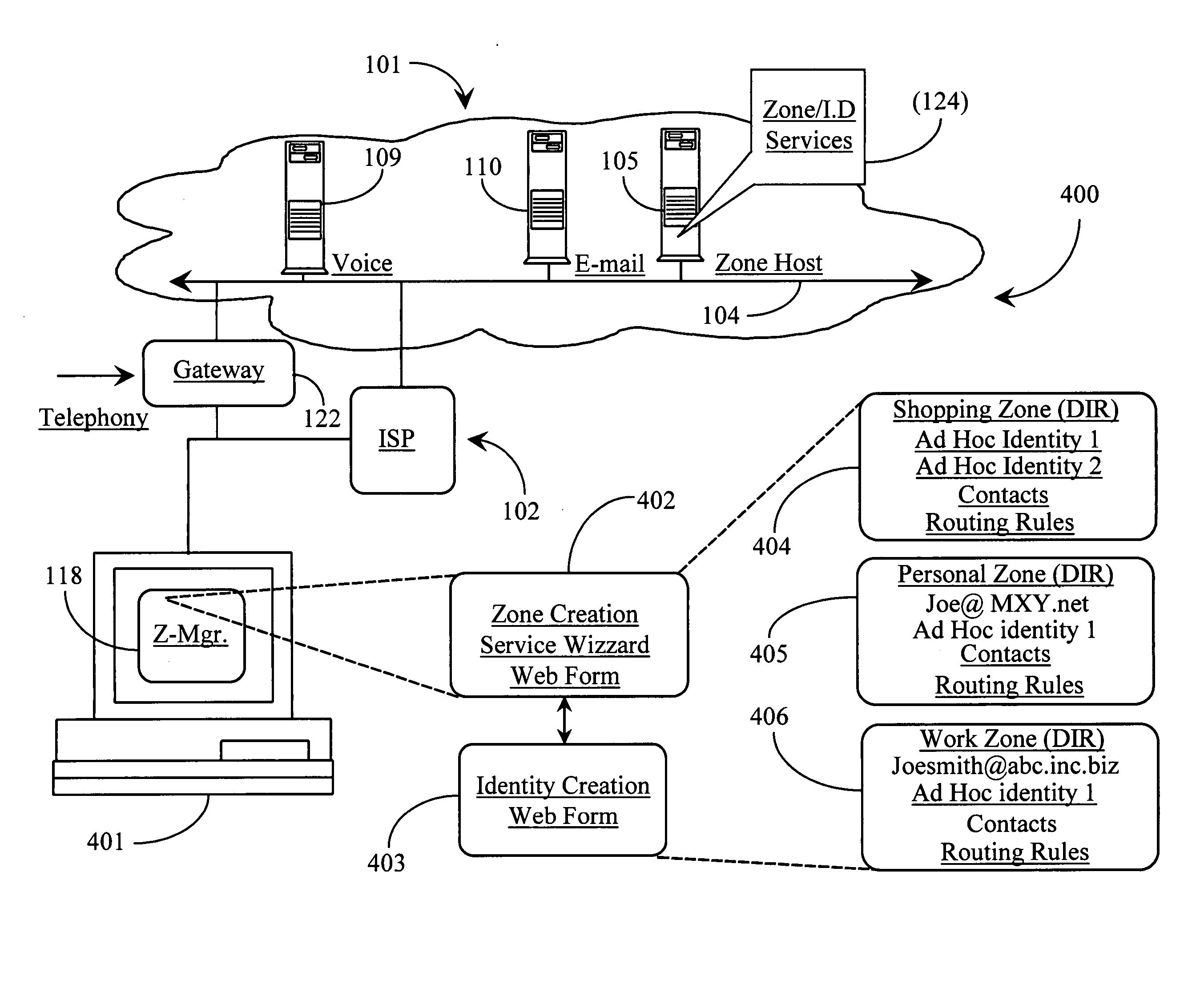
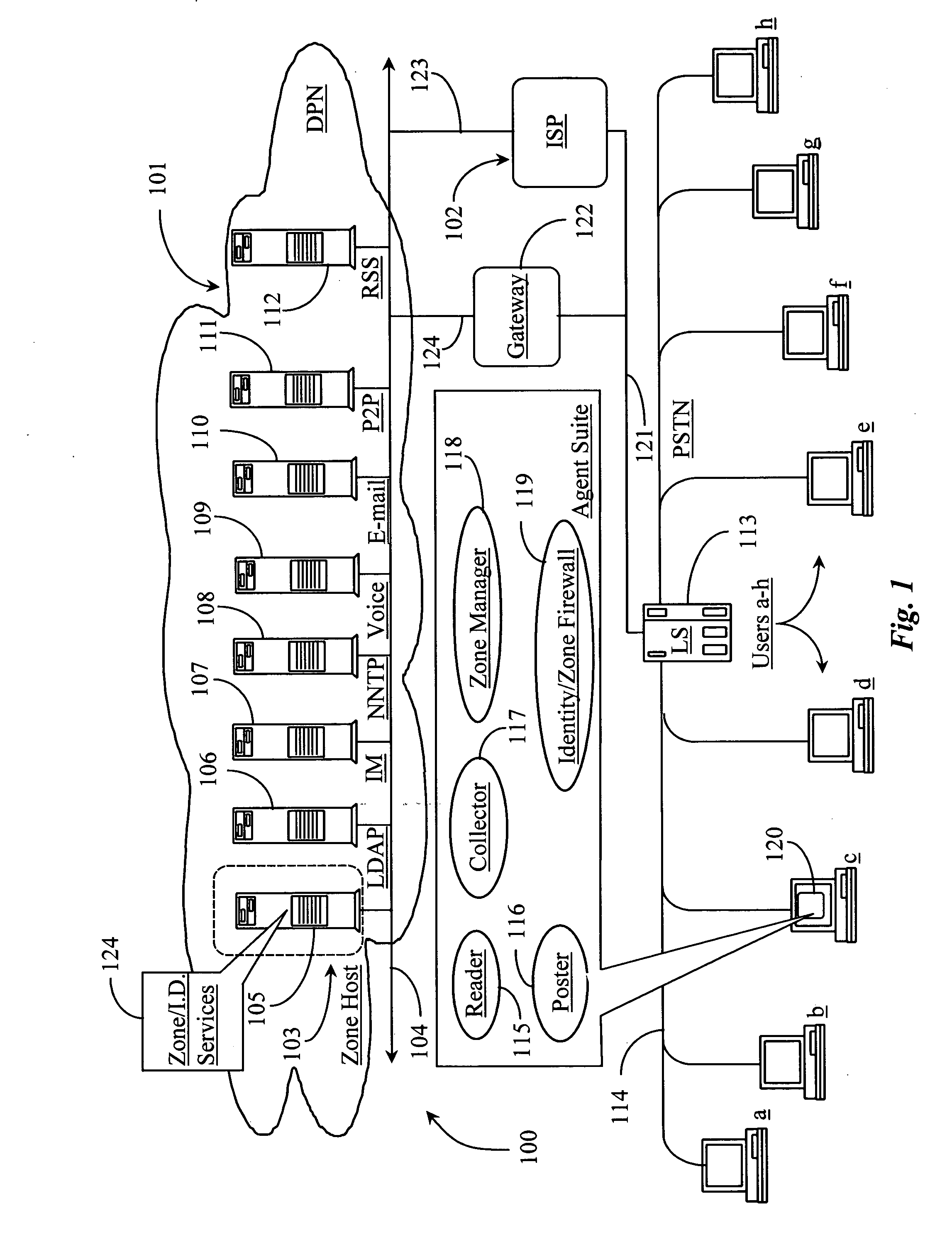
Methods and apparatus for identifying and facilitating a social interaction structure over a data packet network
ActiveUS20050198299A1Operation be completeServices signallingMultiple digital computer combinationsComputer networkSoftware suite
A software suite for managing the publishing and consumption of information and payload data across one or more transport protocols supported by a data-packet-network includes a posting application for publishing the information and payload data, and a consuming application for accessing and consuming the information and payload data. In a preferred embodiment the posting application enables posting of information that is consumable separately from the payload data wherein the information richly describes the payload data including provision of instructions for sampling the payload data before consuming the payload data.
Owner:FORTE INTERNET SOFTWARE
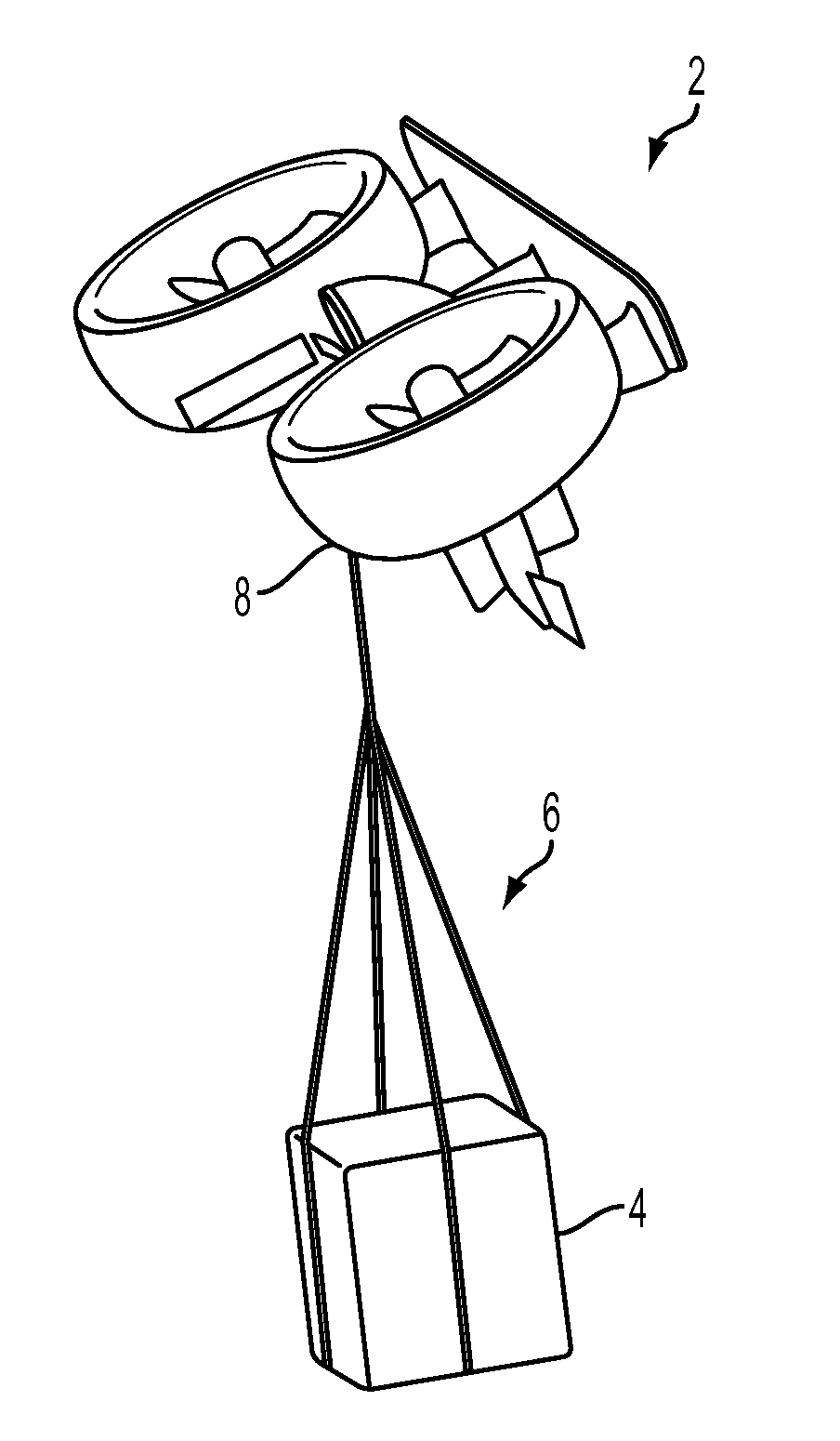
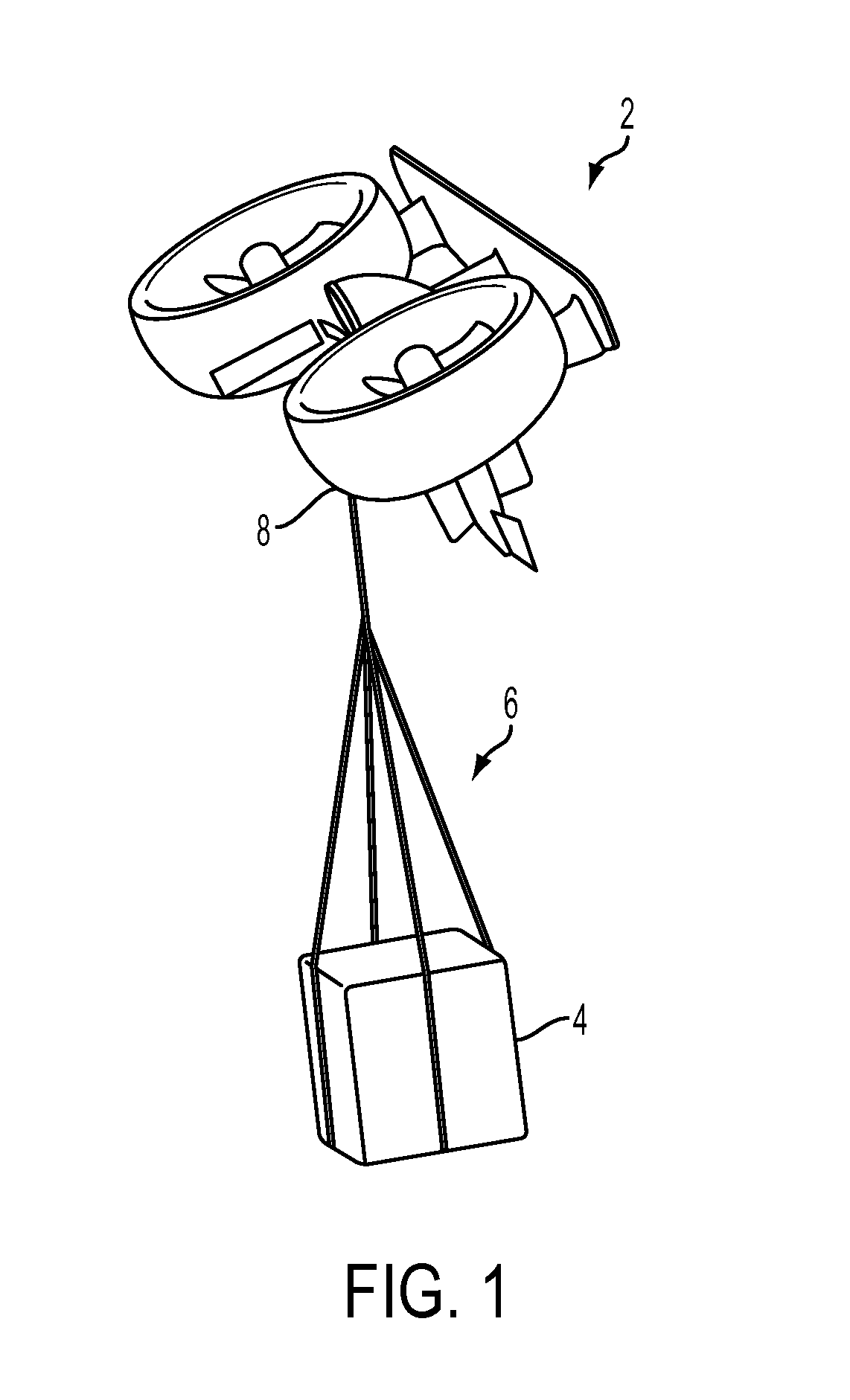
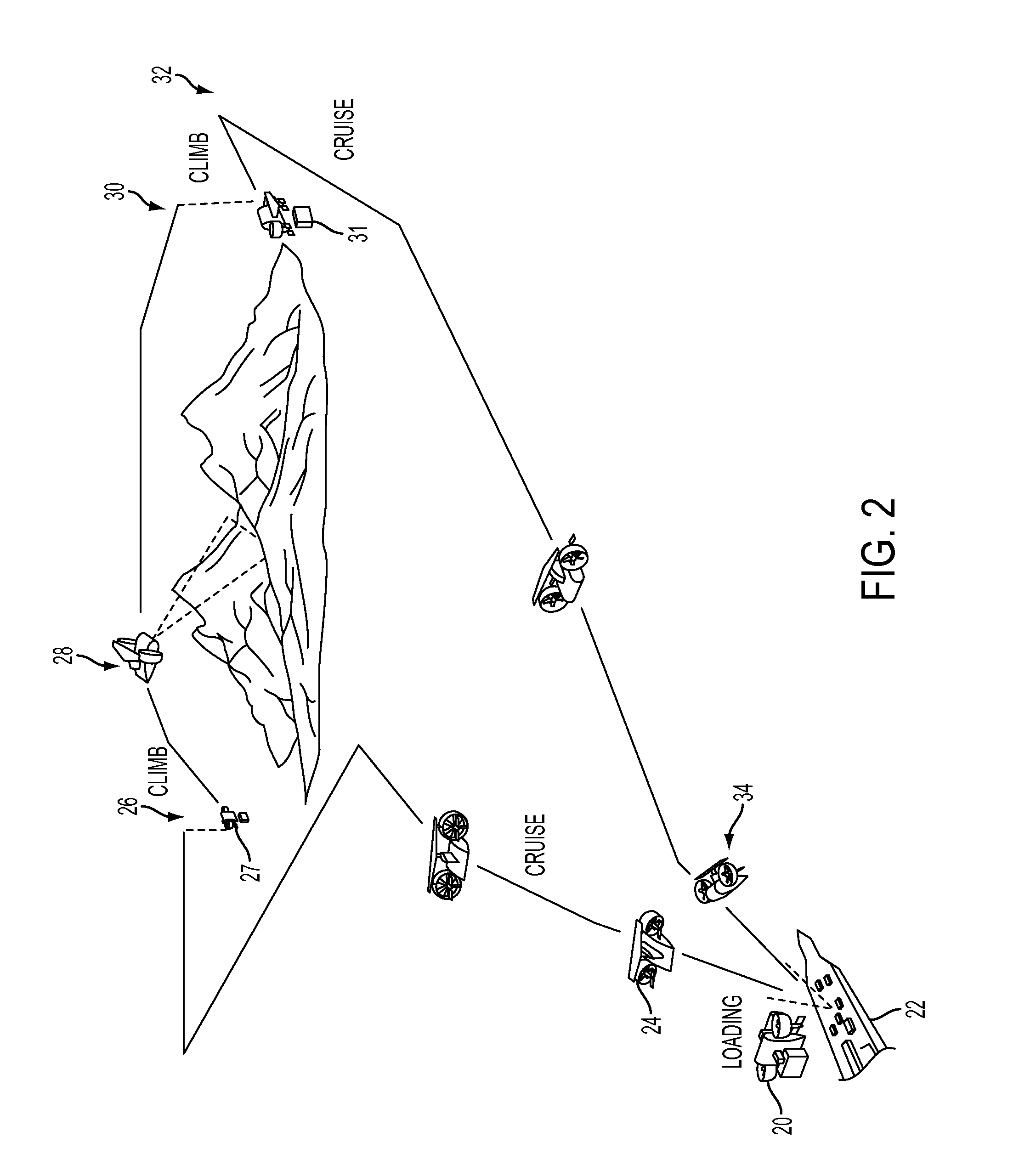
Tethered aerial system for data gathering
InactiveUS20130233964A1Increase horizontal rangeExtending flight spaceTethered aircraftActuated automaticallyLevel flightFlight vehicle
A tethered unmanned aerial vehicle (“UAV”) may be outfitted with a sensor payload for data gathering. The tethered UAV may be tethered to a ground station for constricting the flight space of the UAV while also providing the option for power delivery and / or bidirectional communications. The tethered UAV's flight path may be extended by introducing one or more secondary UAVs that cooperate to extend the horizontal flight path of a primary UAV. The ground station, which may be coupled with the tethered aerial vehicle, may comprise a listening switch configured to determine a condition of the tether such that the supply of power to the tether may be terminated when tether damage or a tether severance is detected.
Owner:AURORA FLIGHT SCI CORP
Systems and methods for providing stuctured policy expressions to represent unstructured data in a network appliance
ActiveUS20080225748A1Efficient configurationEfficient processingData switching by path configurationTraffic capacityData stream
Owner:CITRIX SYST INC
Systems and methods for non-traditional payment
The present invention includes systems and methods for facilitating transactions using non-traditional devices. A method of the present invention includes the steps of forming a transaction request at a non-traditional device, and communicating the transaction request to a reader. In one embodiment, the non-traditional device may be configured with a transponder or other RF operable device. In another embodiment, the non-traditional device may be configured with an RFID protocol, such as a protocol in ISO 8583 format. In yet another embodiment, the non-traditional device may be configured to facilitate transactions using a random number, an authentication tag, a counter, or an encrypted payload.
Owner:CHARTOLEAUX +1
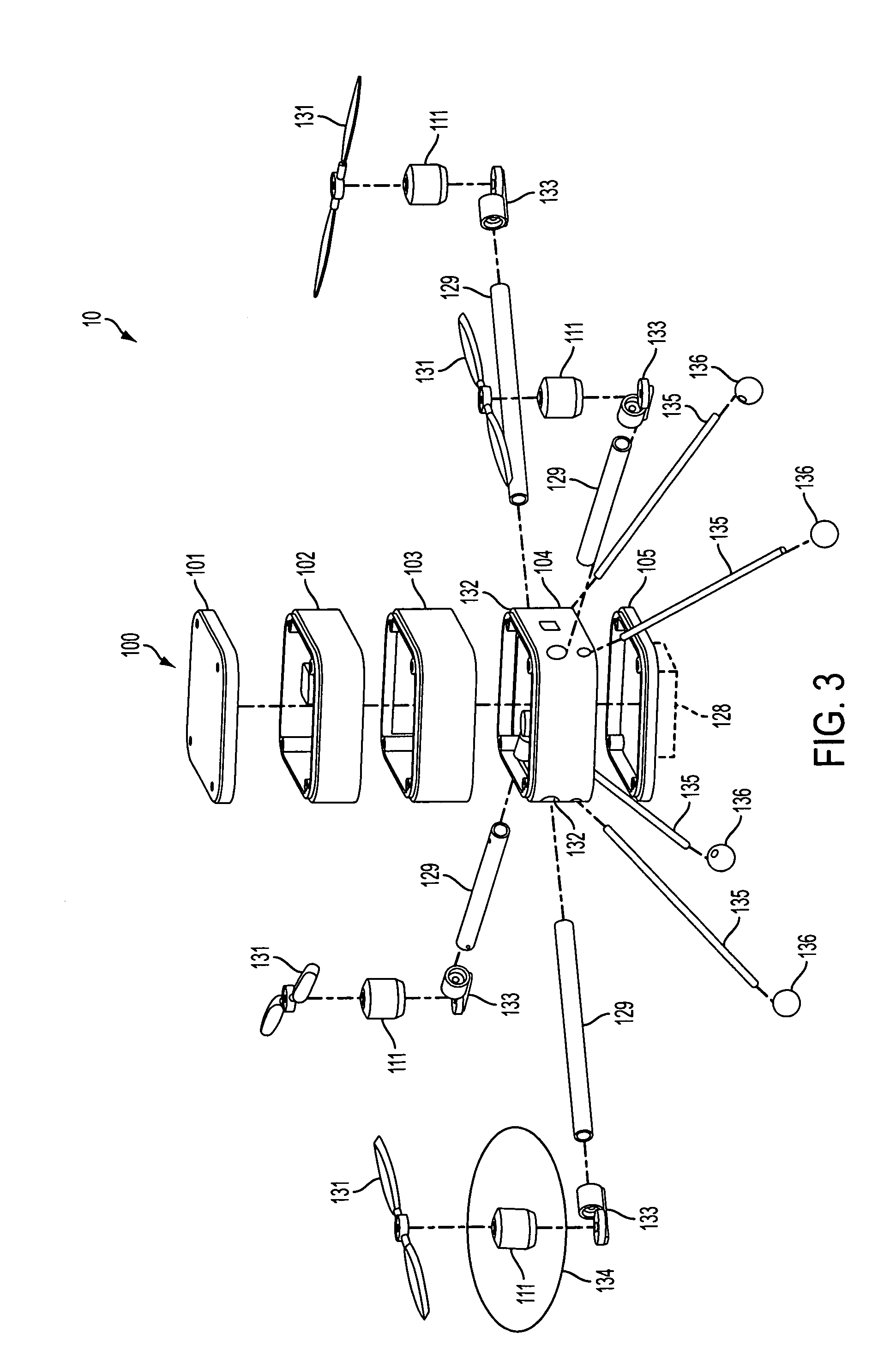
Helicopter with multi-rotors and wireless capability
InactiveUS20120083945A1Simple flightSimple usageAutonomous decision making processUnmanned aerial vehiclesNavigation systemFuselage
The present invention relates to a helicopter having a modular airframe, with multiple layers which can be connected easily, the layers which house the electronics (autopilot and navigation systems), batteries, and payload (including camera system) of the helicopter. The helicopter has four, six, and eight rotors, which can be easily changed via removing one module of the airframe. In one embodiment, the airframe has a vertical stacked appearance, and in another embodiment, a domed shape (where several of the layers are stacked internally). In one embodiment, there is a combination landing gear and camera mount. The helicopter allows for simple flight and usage by remote control, and non-remote control, users.
Owner:GEOTECH ENVIRONMENTAL EQUIP
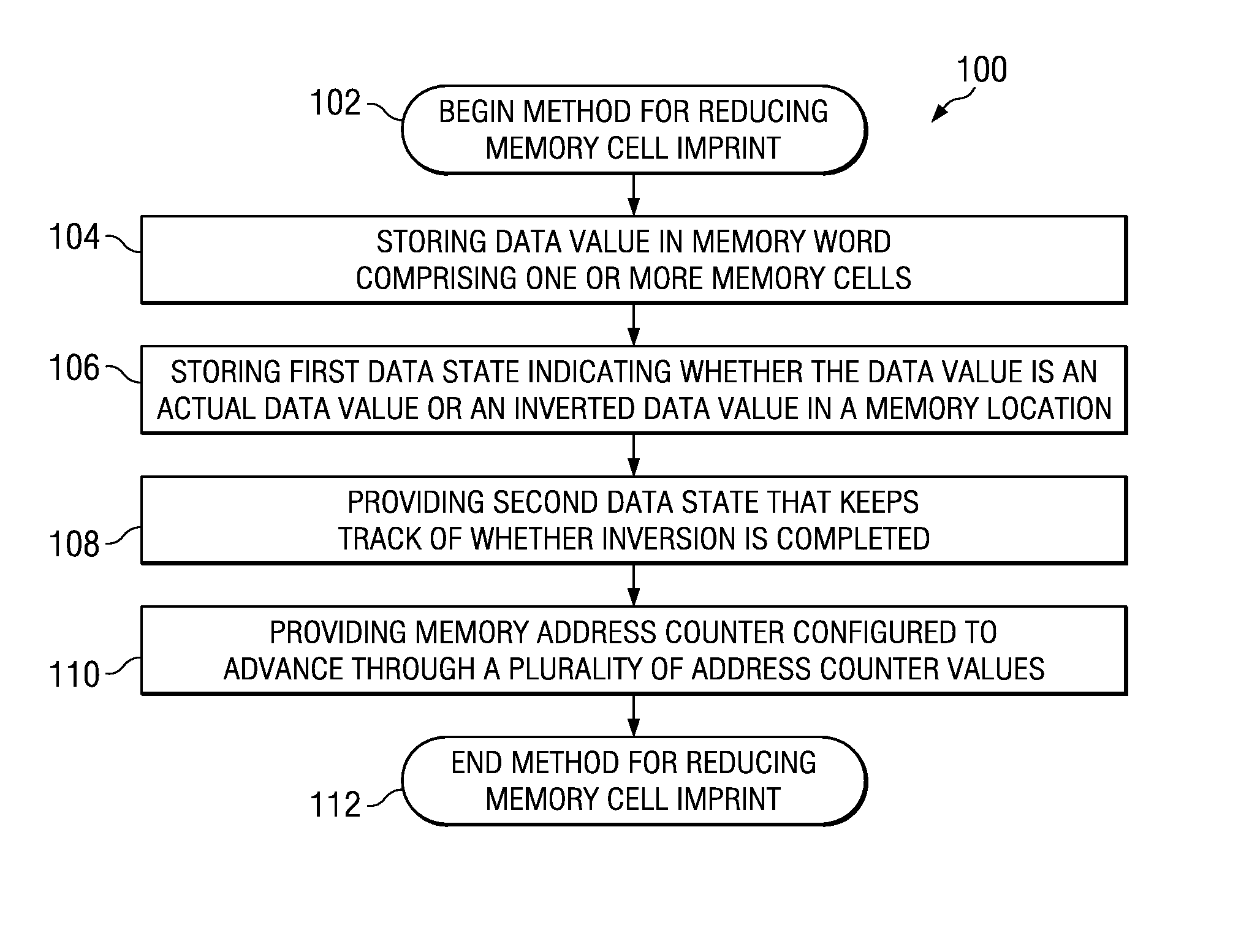
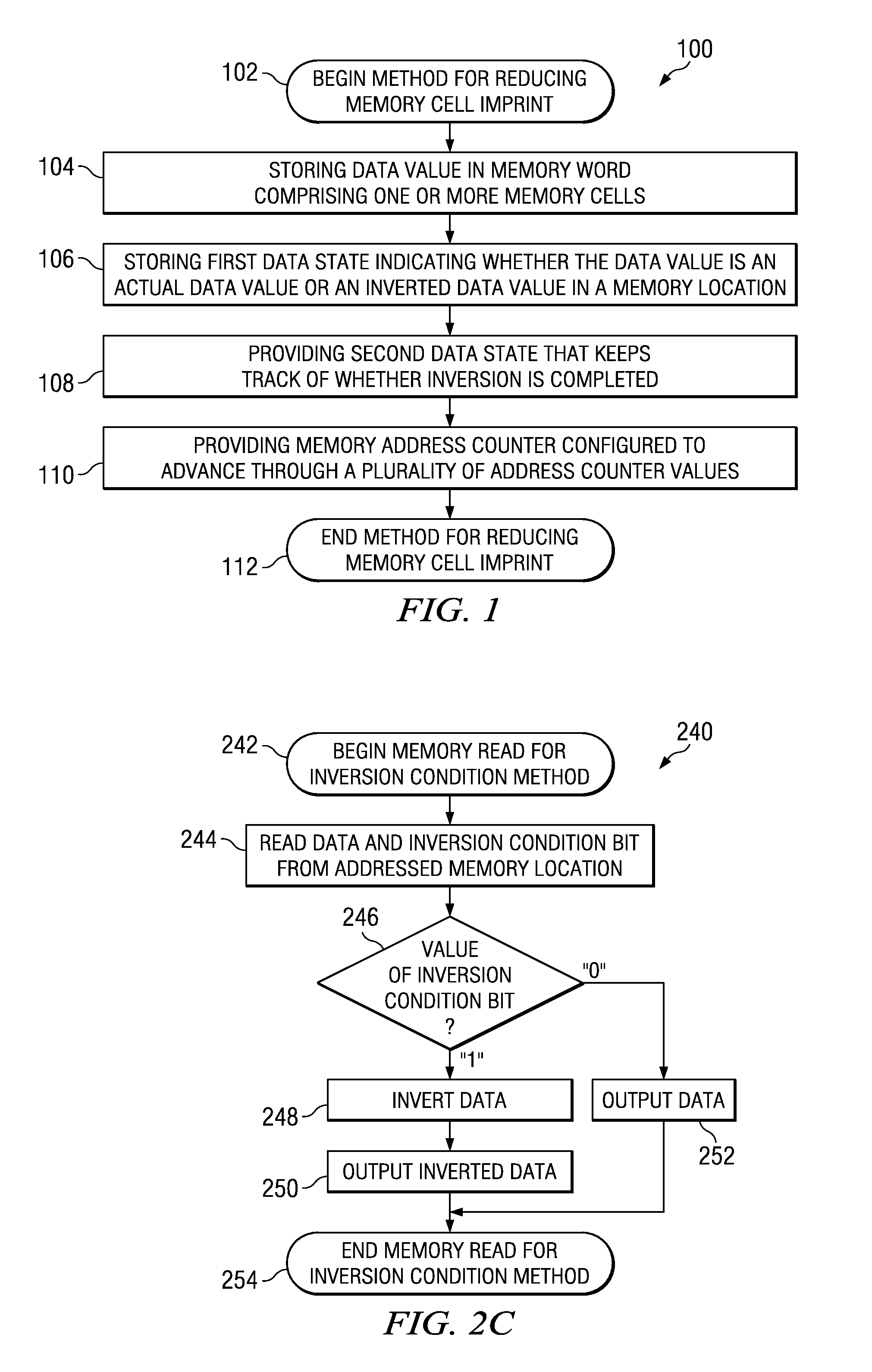
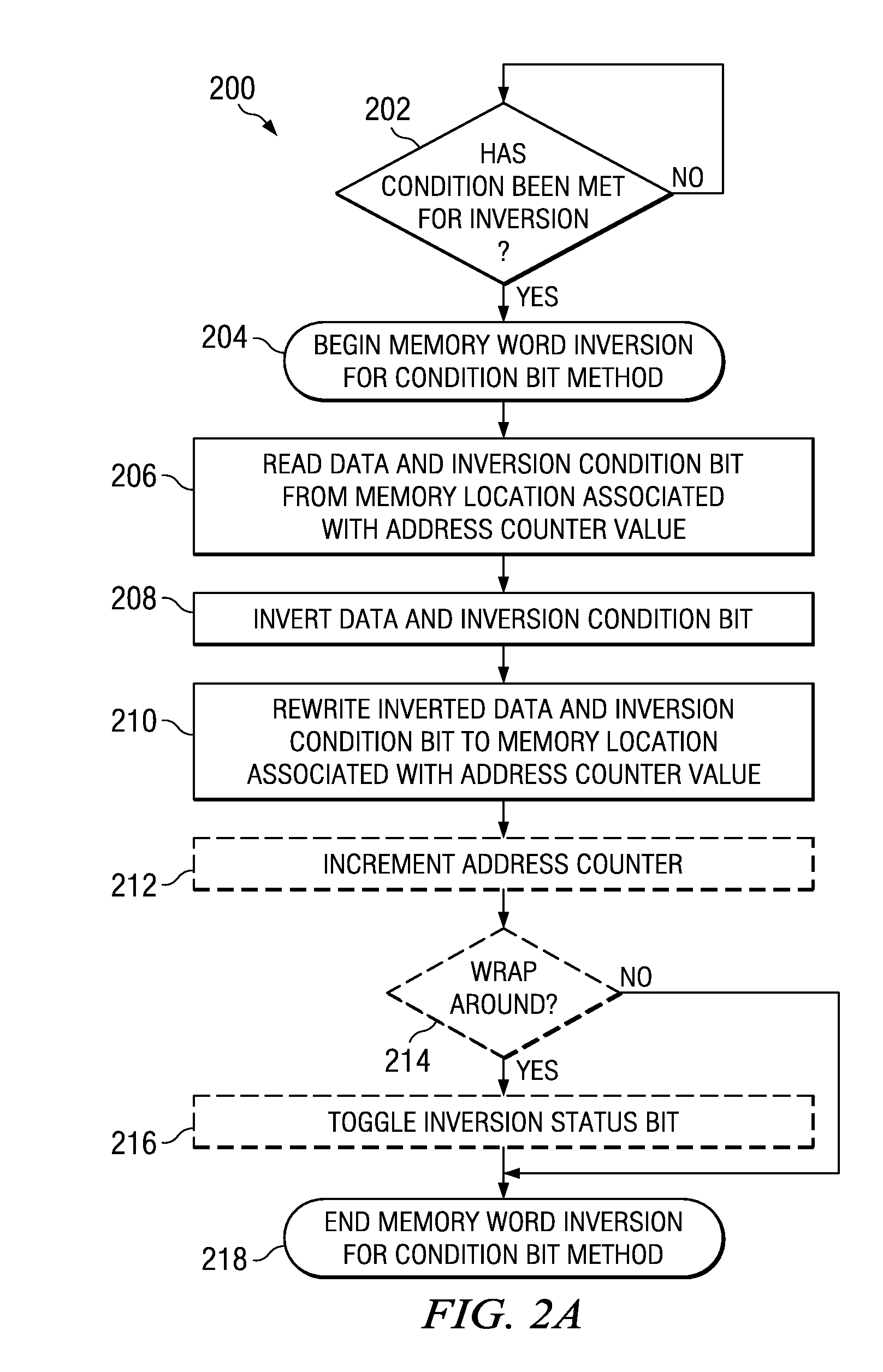
Technique for memory imprint reliability improvement
One embodiment of the present invention relates to a method of reducing imprint of a memory cell. The method comprises adding an inversion condition bit operably associated with one or more memory cells storing a memory word. The inversion condition bit indicates whether the memory word represents an actual payload or an inversion of the actual payload. The inversion condition bit and memory word are selectively toggled by a control circuitry. Inversion is performed by reading the inversion condition bit and memory word and rewriting the memory word back to the one or more memory cells in an inverted or non-inverted state, depending on an inversion condition bit. The inversion condition bit is then written to the inversion status bit value. The memory address is incremented, and the inversion status data state is toggled once the address counter addresses the entire memory array. Other methods and circuits are also disclosed.
Owner:TEXAS INSTR INC
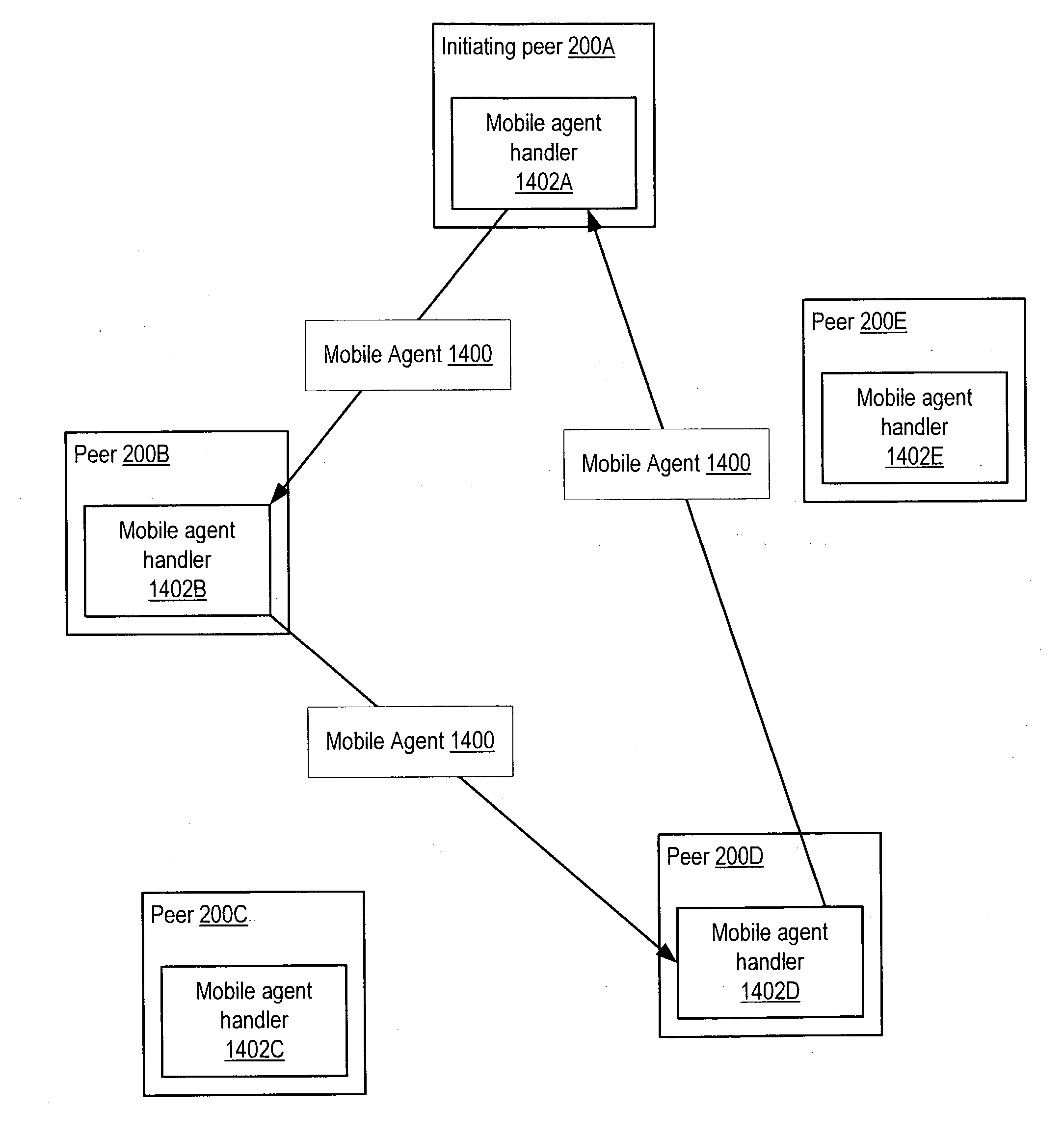
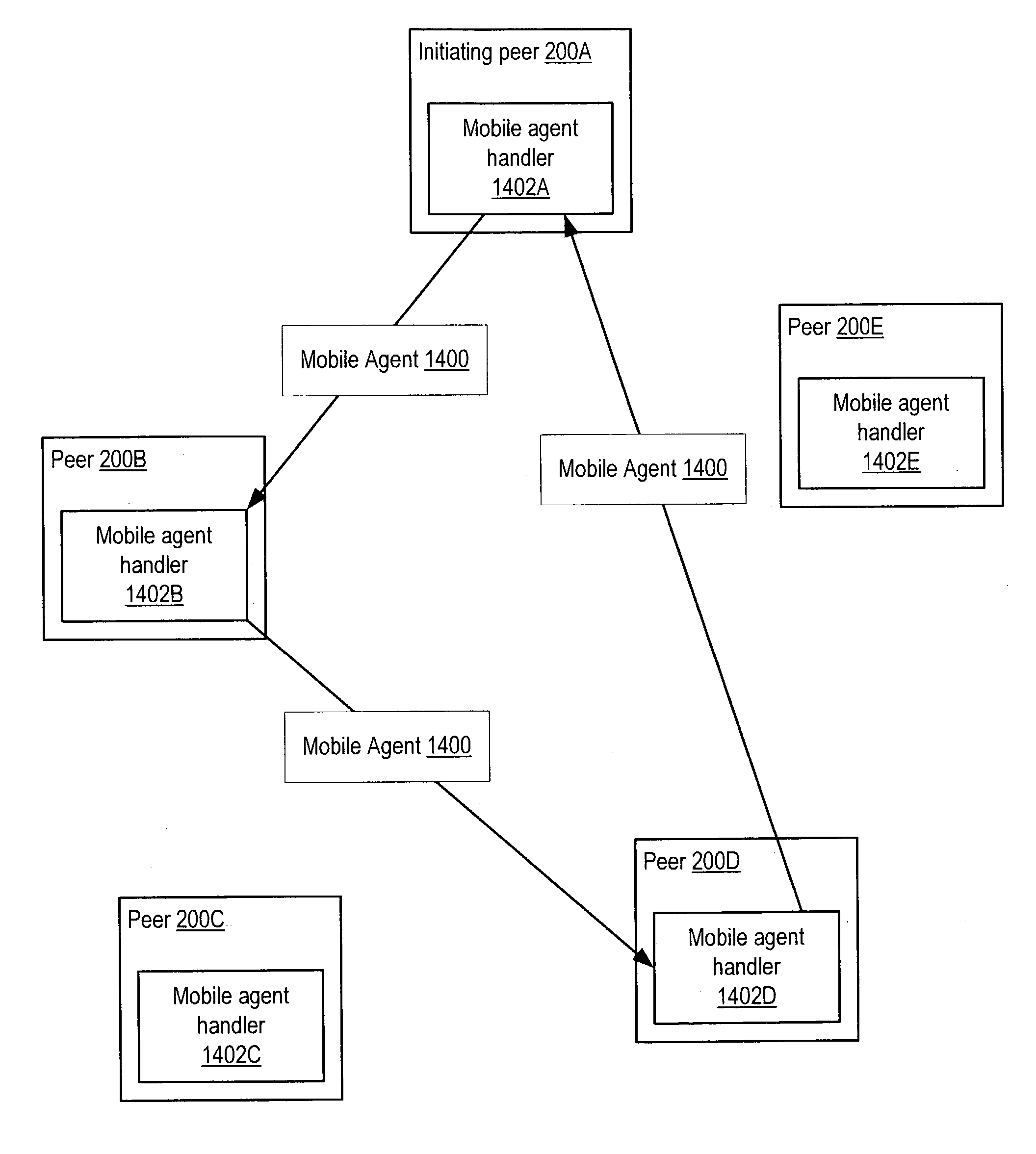
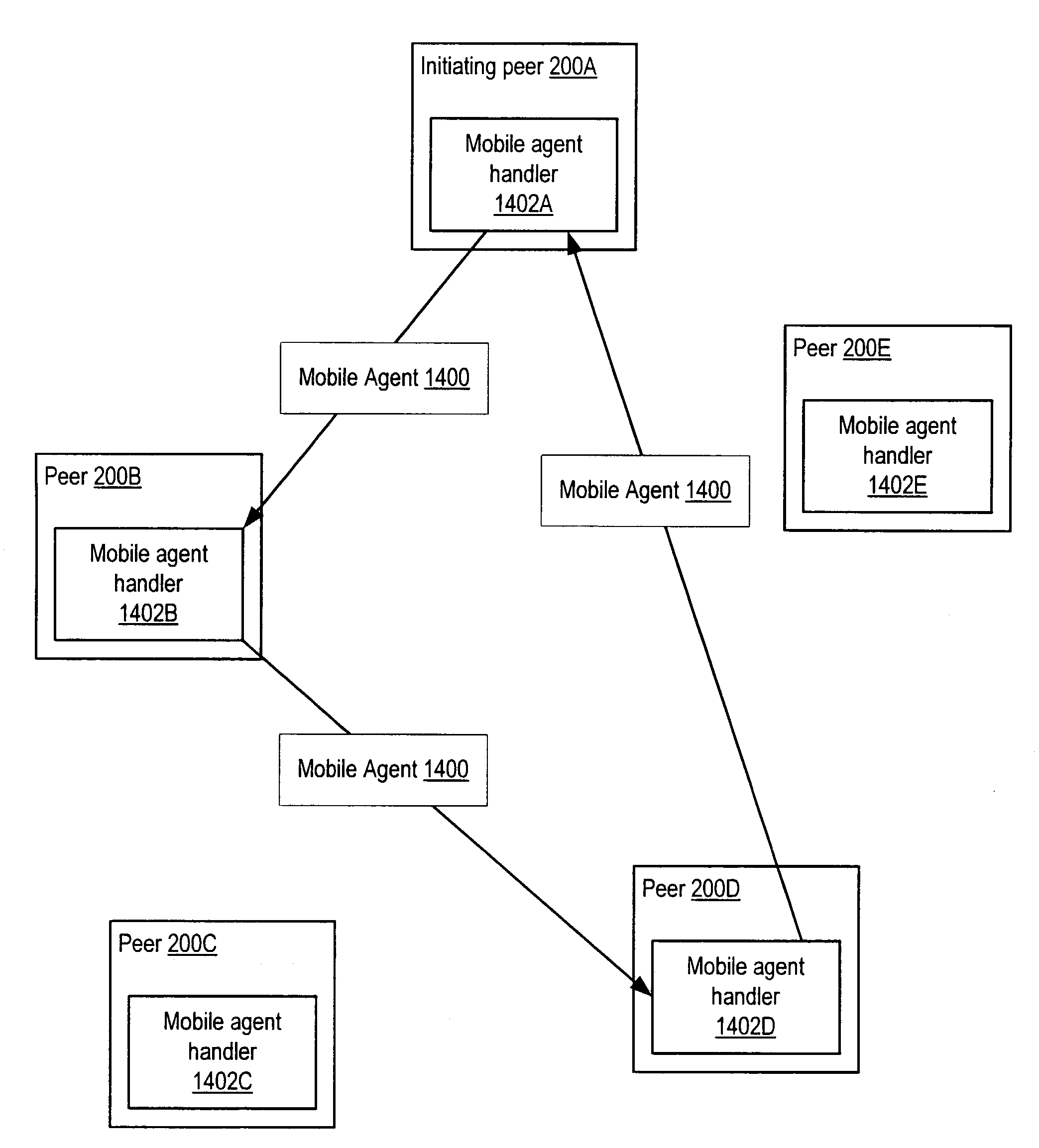
Managing distribution of content using mobile agents in peer-topeer networks
Embodiments of a system and method for using mobile agents for managing distribution of content in peer-to-peer networks. An initiating peer node may launch a mobile agent including an itinerary of a group of peer nodes configured to receive and share content from a distributor. The mobile agent may visit the peer nodes on the itinerary to search for and collect information on distributor content stored on the visited peer nodes. The mobile agent may return the payload to the initiating peer node after completing the itinerary. In one embodiment, the mobile agent may include authentication information, and each visited peer node may access the authentication information to verify the mobile agent as authorized by the distributor. The initiating peer node may examine the information provided by the mobile agent to detect unauthorized copies of the distributor content.
Owner:ORACLE INT CORP
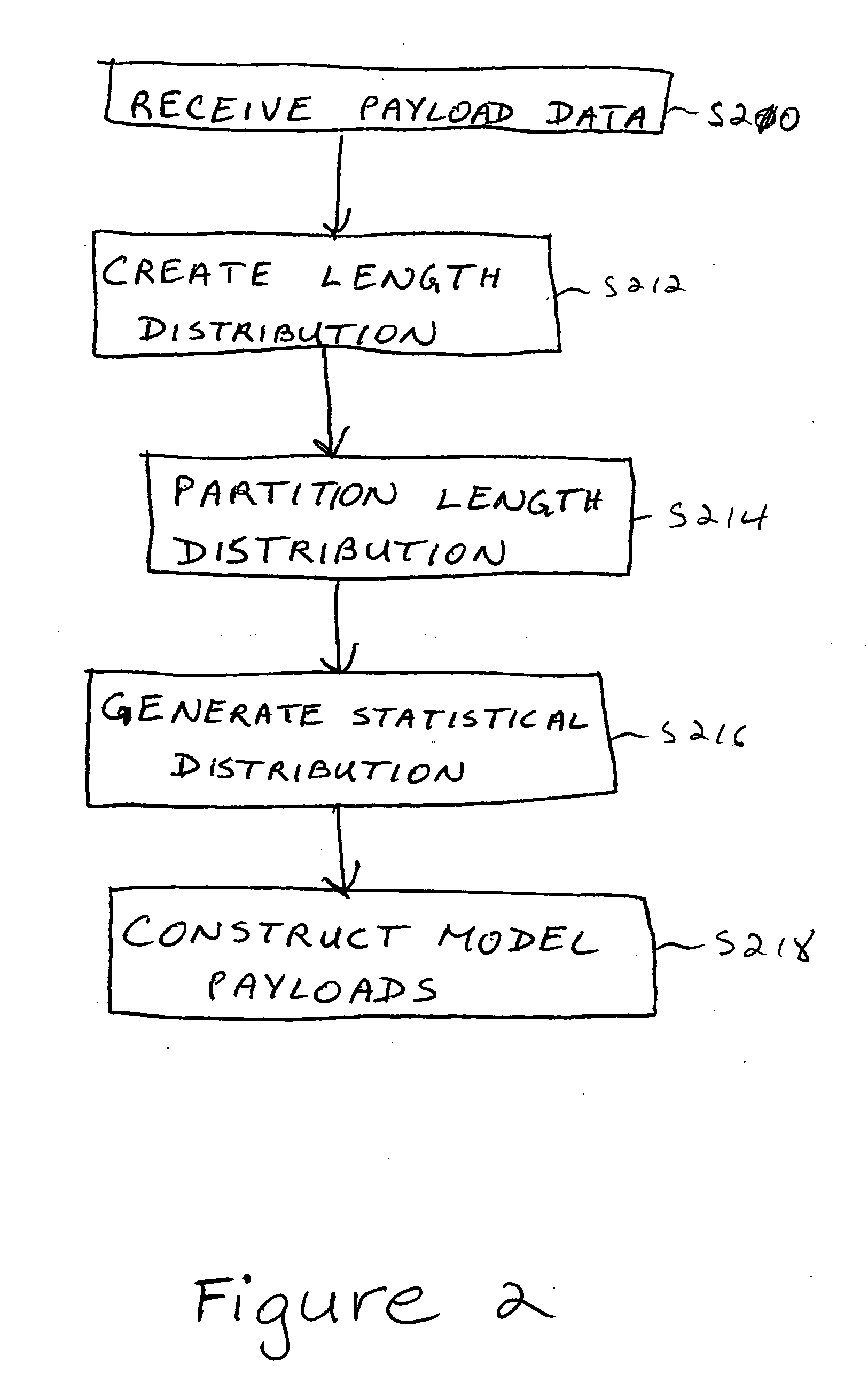
Apparatus method and medium for tracing the origin of network transmissions using n-gram distribution of data
ActiveUS20050265331A1Unauthorized memory use protectionTime-division multiplexWeb transportReal-time computing
A method, apparatus, and medium are provided for tracing the origin of network transmissions. Connection records are maintained at computer system for storing source and destination addresses. The connection records also maintain a statistical distribution of data corresponding to the data payload being transmitted. The statistical distribution can be compared to that of the connection records in order to identify the sender. The location of the sender can subsequently be determined from the source address stored in the connection record. The process can be repeated multiple times until the location of the original sender has been traced.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Autonomous Payload Parsing Management System and Structure for an Unmanned Aerial Vehicle
InactiveUS20110084162A1Improve versatilityIncrease in sizeStatic/dynamic balance measurementRemote controlled aircraftManagement systemControl logic
An unmanned aerial vehicle (UAV) for making partial deliveries of cargo provisions includes a UAV having one or more ducted fans and a structural interconnect connecting the one or more fans to a cargo pod. The cargo pod has an outer aerodynamic shell and one or more internal drive systems for modifying a relative position of one or more cargo provisions contained within the cargo pod. Control logic is configured to, after delivery of a partial portion of the cargo provisions contained within the cargo pod, vary a position of at least a portion of the remaining cargo provisions to maintain a substantially same center of gravity of the UAV relative to a center of gravity prior to delivery of the partial portion. Other center of gravity compensation mechanisms may also be controlled by the control logic to aid in maintaining the center of gravity of the UAV.
Owner:HONEYWELL INT INC
Managing distribution of content using mobile agents in peer-topeer networks
Embodiments of a system and method for using mobile agents for managing distribution of content in peer-to-peer networks. An initiating peer node may launch a mobile agent including an itinerary of a group of peer nodes configured to receive and share content from a distributor. The mobile agent may visit the peer nodes on the itinerary to search for and collect information on distributor content stored on the visited peer nodes. The mobile agent may return the payload to the initiating peer node after completing the itinerary. In one embodiment, the mobile agent may include authentication information, and each visited peer node may access the authentication information to verify the mobile agent as authorized by the distributor. The initiating peer node may examine the information provided by the mobile agent to detect unauthorized copies of the distributor content.
Owner:ORACLE INT CORP
Collaborative content coherence using mobile agents in peer-to-peer networks
ActiveUS20040088646A1Data processing applicationsMultiple digital computer combinationsDocumentationDistributed computing
Embodiments of a system and method for using mobile agents for collaborative content control in peer-to-peer networks. A peer may launch a mobile agent including an itinerary of peers to be visited and indications of one or more documents that the peers are collaboratively editing. The mobile agent may visit peers indicated by the itinerary to collect version information for the document(s). The mobile agent may return the version information to the initiating peer, which may coordinate each of the document(s) on the peer to a most recent version in accordance with the version information provided by the mobile agent. Visited peers may use the payload to determine if their version of the document(s) are up to date and, if not, may add a version update request to the payload. The initiating peer may send the most recent version information to peers that added version update requests to the payload.
Owner:ORACLE INT CORP
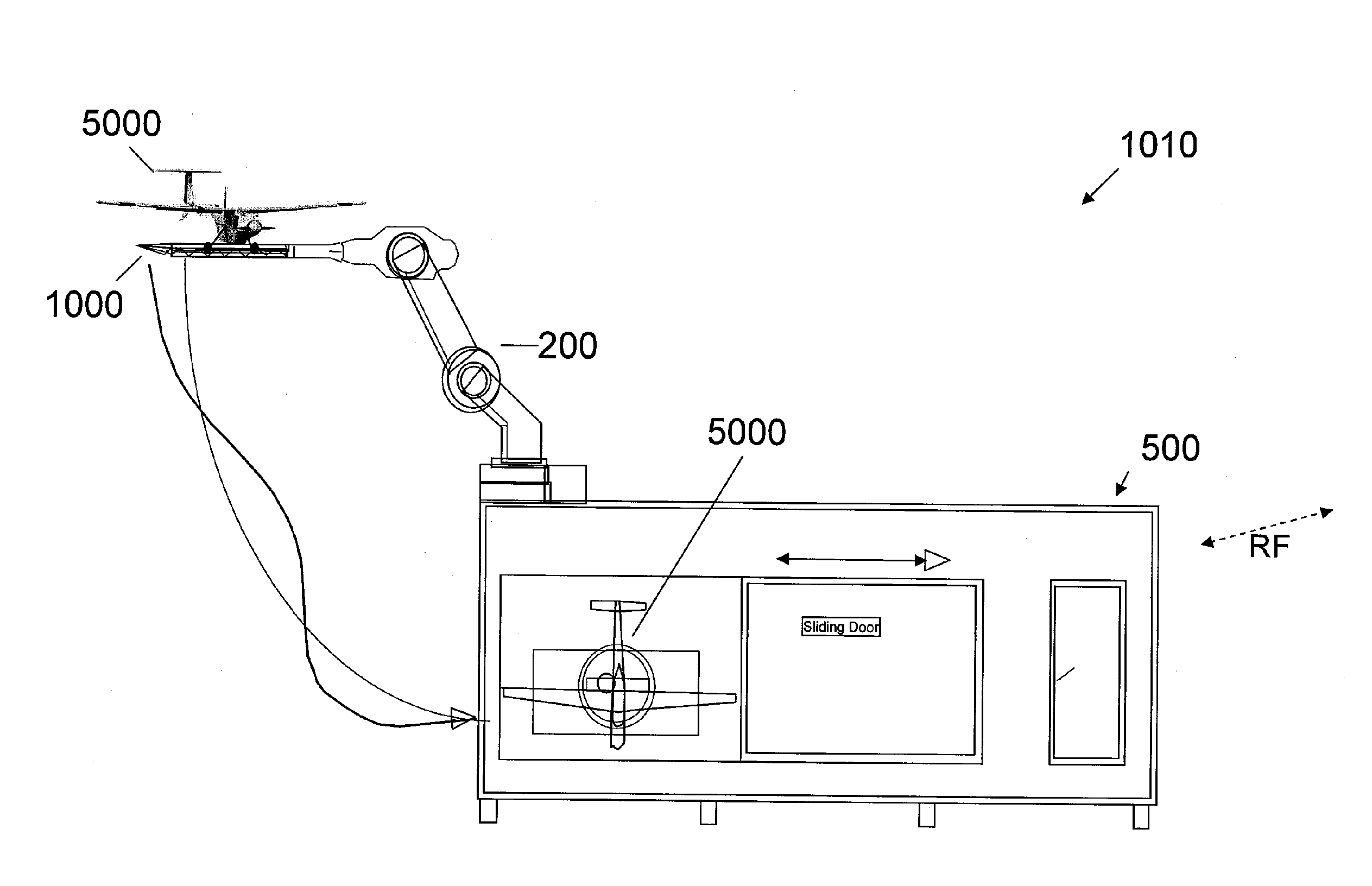
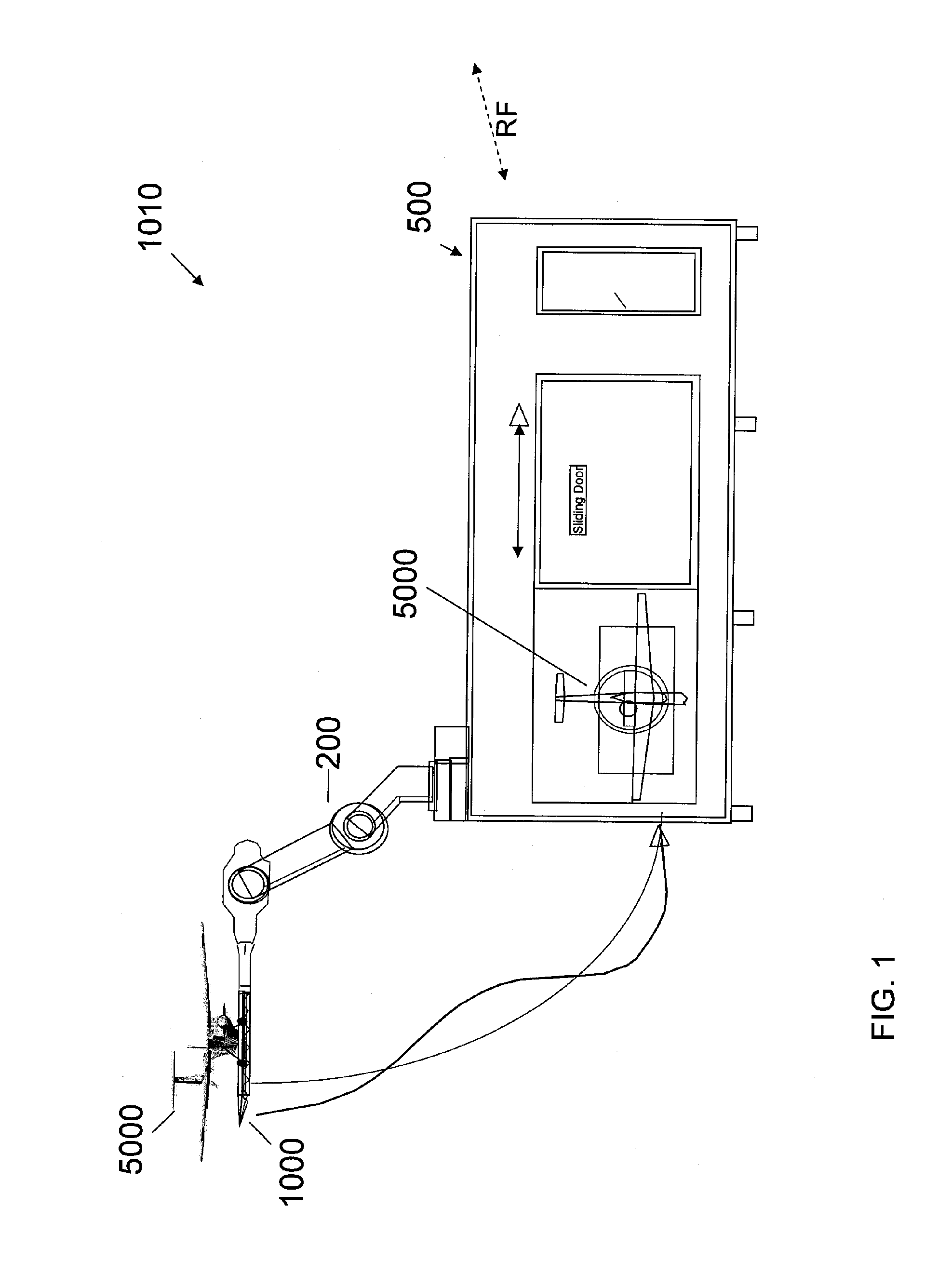
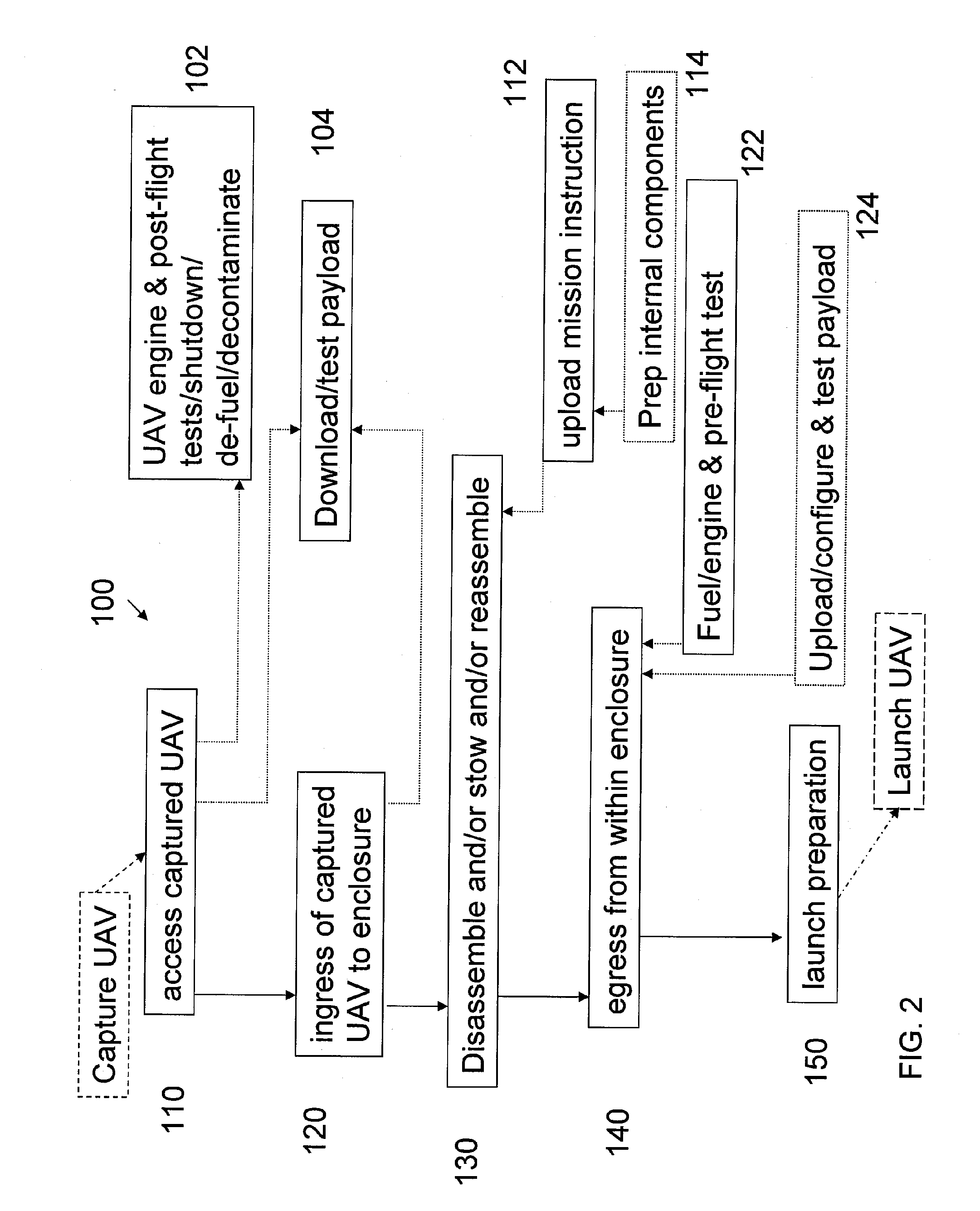
Autonomous Environmental Control System and Method For Post-Capture and Pre-Launch Management of an Unmanned Air Vehicle
An embodiment of the invention is directed to a system for controlling and managing a small unmanned air vehicle (UAV) between capture and launch of the UAV. The system includes an enclosure that provides environmental protection and isolation for multiple small UAVs in assembled and / or partially disassembled states. Control and management of the UAVs includes reorientation of a captured UAV from a landing platform and secure hand-off to the enclosure, decontamination, de-fueling, ingress to the enclosure, downloading of mission payload, UAV disassembly, stowage, retrieval and reassembly of the UAV, mission uploading, egress of the UAV from the enclosure, fueling, engine testing and launch readiness. An exemplary system includes two or more robots controlled by a multiple robot controller for autonomously carrying out the functions described above. A modular, compact, portable and autonomous system of UAV control and management is described.
Owner:LOCKHEED MARTIN CORP
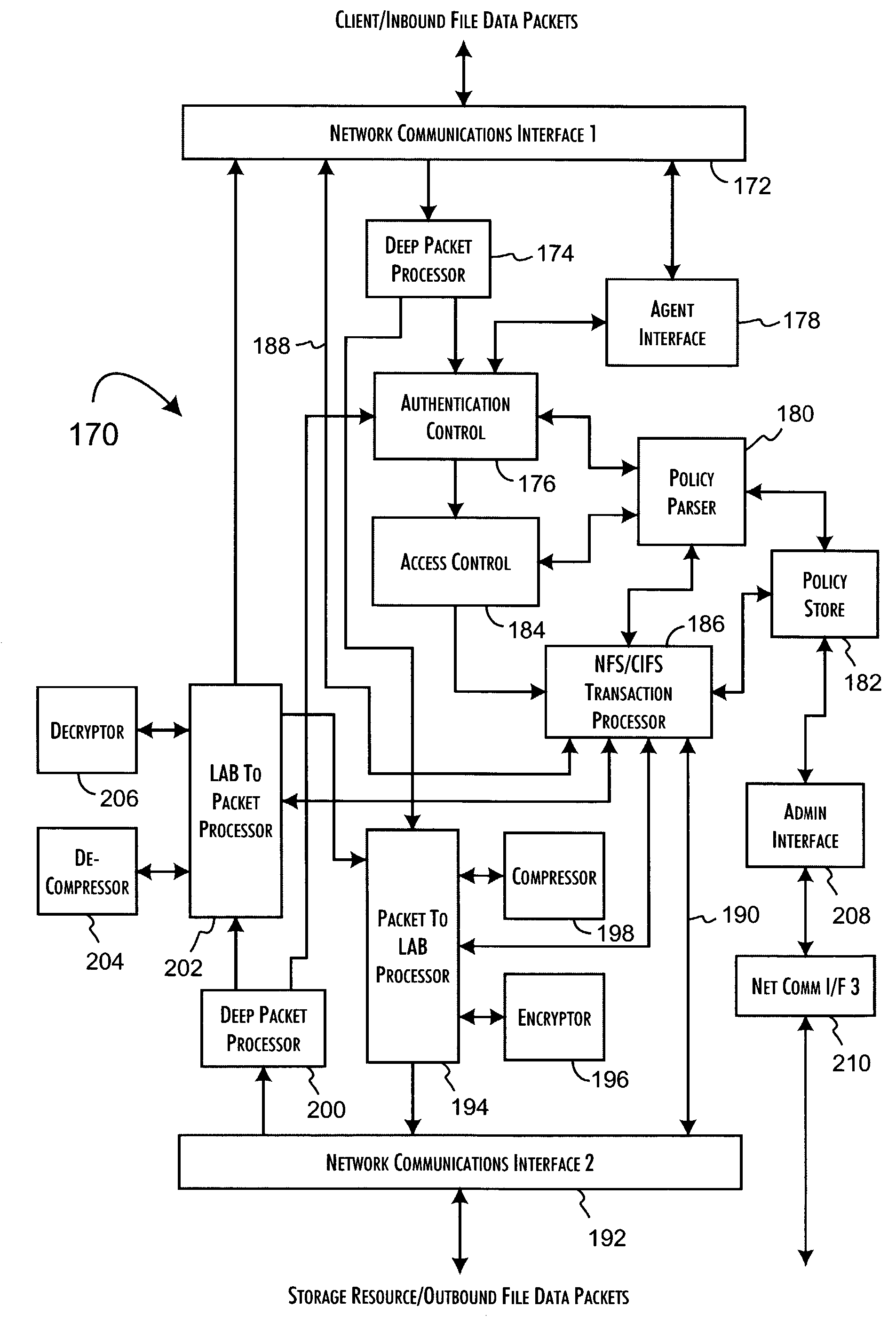
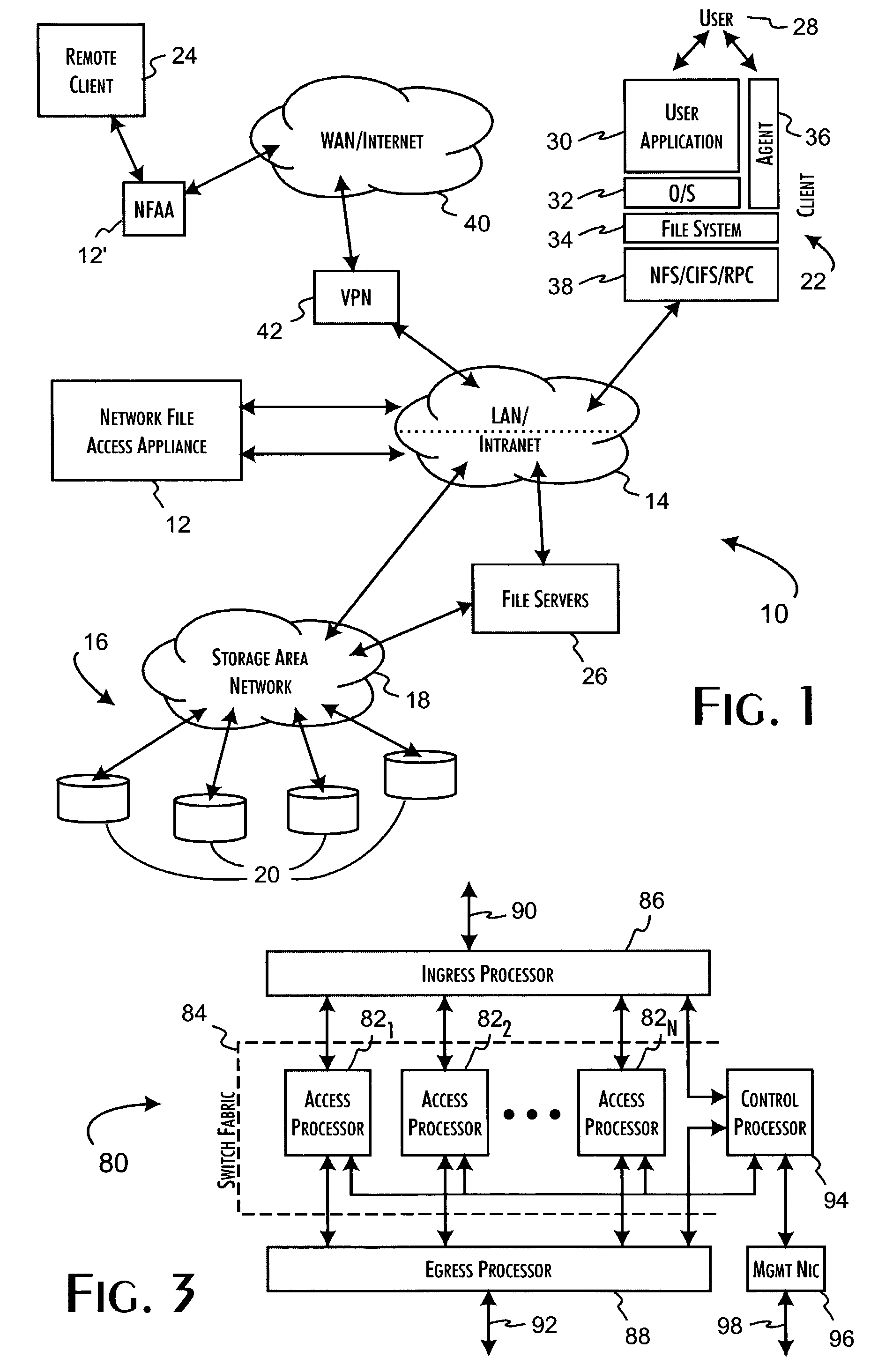
Logical access block processing protocol for transparent secure file storage
InactiveUS7334124B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationComputer hardwareDigital signature
Network data files are secure through the operation of an infrastructure gateway-based network file access appliance. Network file data, corresponding to network pocket payload data, are further reduced to a sequence of data blocks that are secured through any combination of block encryption, compression, and digital signatures. File meta-data, including encryption, compression and block-level digital signatures are persistently stored with the file data, either in-band in the file as stored or out-of-band key as a separately stored file or file policy record. File meta-data is recovered with accesses of the file data to support bidirectional encryption and compression and to detect tampering with the file data by comparison against block-level digital signatures.
Owner:THALES ESECURITY INC
Materials-handling system using autonomous transfer and transport vehicles
Methods and apparatus for selecting and combining items in an outbound container through the use of autonomous vehicles, each of which includes means for automatically loading and unloading a payload, to perform both transfer and transport functions in moving containers of items within a workspace via a network of roadways. Under computer control, said autonomous vehicles transfer and transport case containers of item units between incoming receiving stations, intermediate storage locations, and outgoing order-assembly stations where entire containers or individual item units are combined in the outbound container.
Owner:SYMBOTIC LLC
Inoculation of computing devices against a selected computer virus
ActiveUS7287278B2Avoid infectionMemory loss protectionUnauthorized memory use protectionComputer scienceVirus
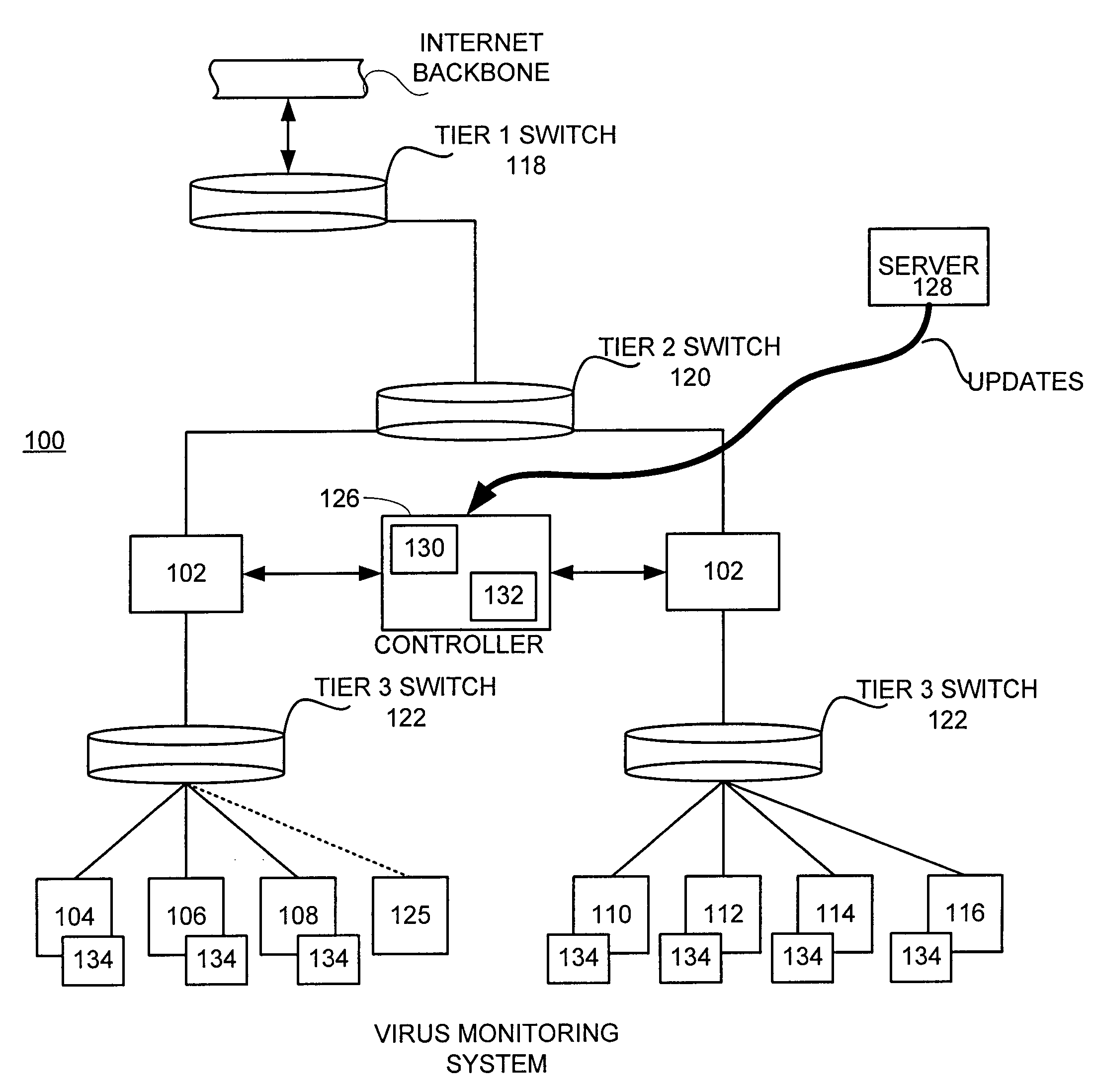
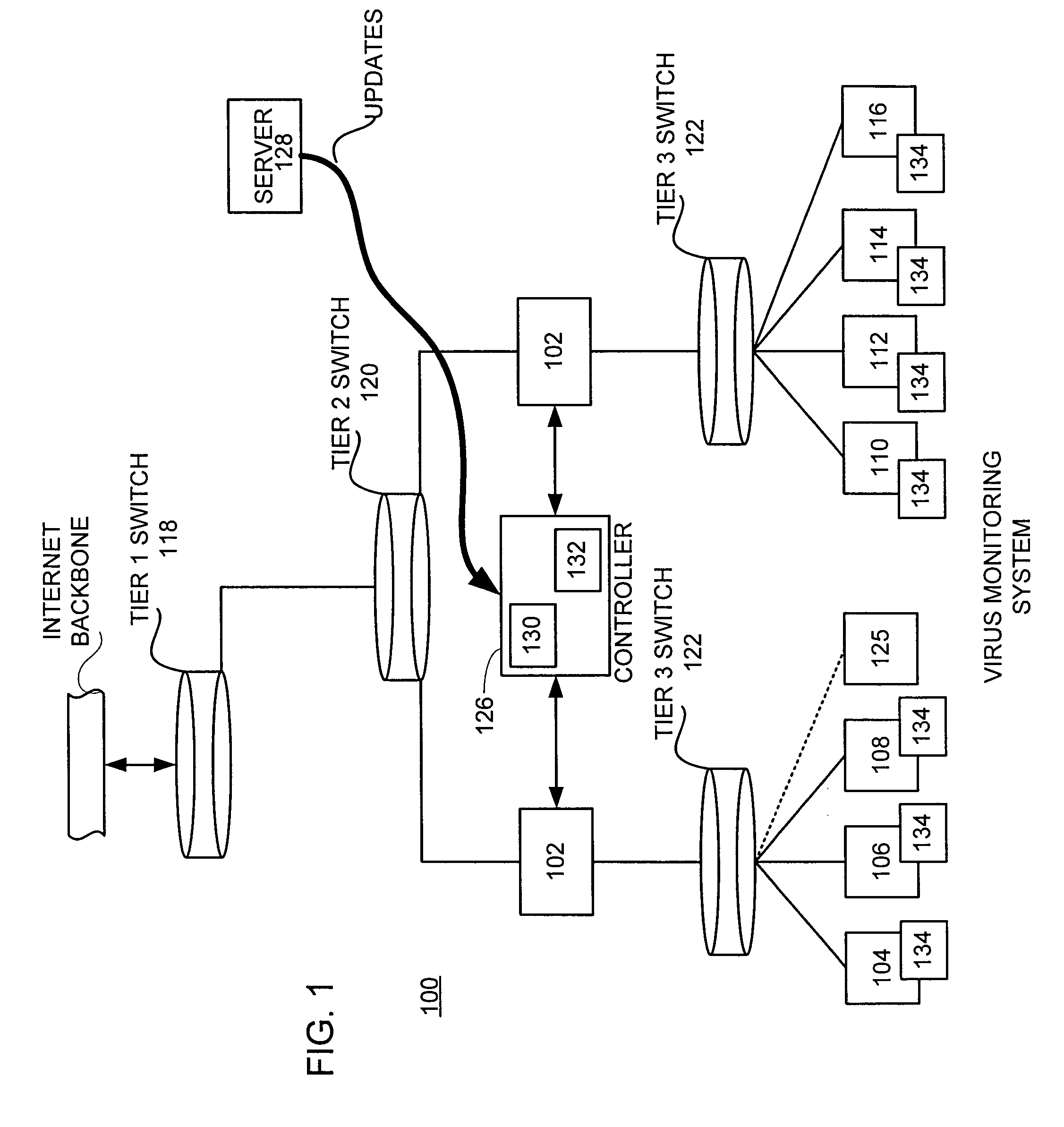
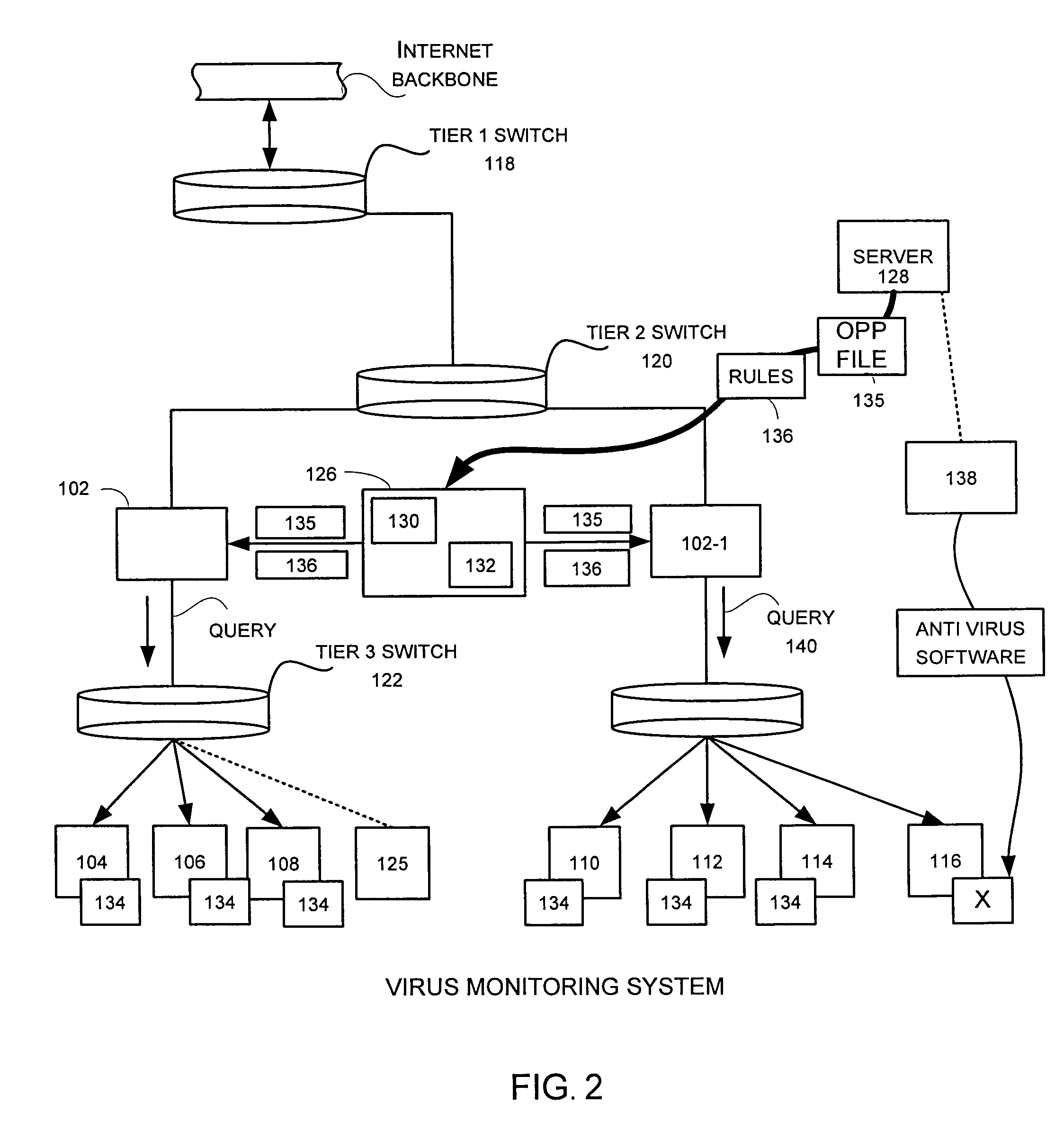
In a distributed network having a number of server computers and associated client devices, method of creating an anti-computer virus agent is described. As a method, the inoculation is carried out by parsing a selected computer virus into a detection module that identifies a selected one of the client devices as a target client device, an infection module that causes the virus to infect those target client devices not infected by the selected virus, and a viral code payload module that infects the targeted client device modifying the infection module to infect those computers already infected by the selected virus; and incorporating inoculation viral code in the payload module that acts to prevent further infection by the selected virus.
Owner:TREND MICRO INC
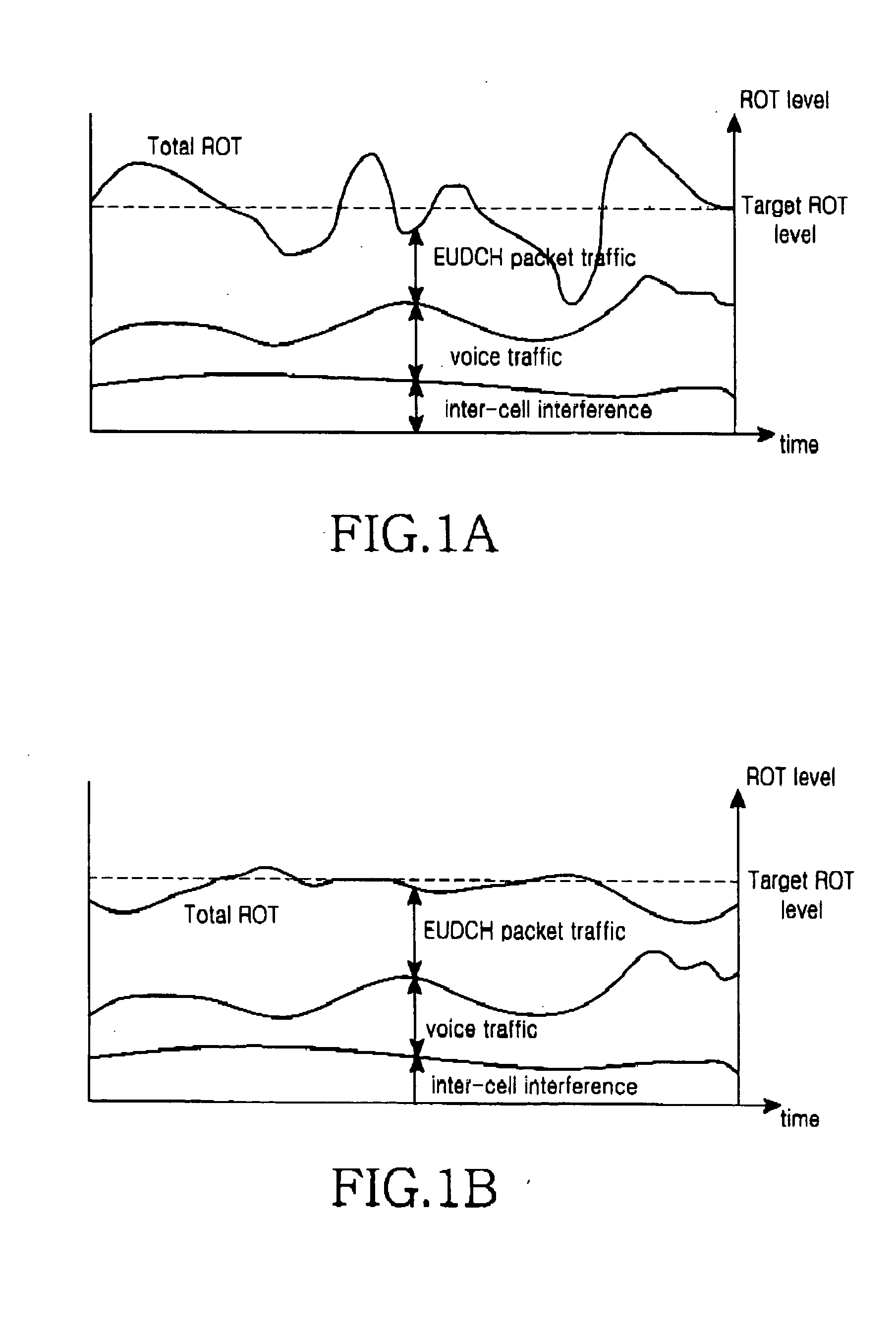
Method and apparatus for scheduling assignment of uplink packet transmission in mobile telecommunication system
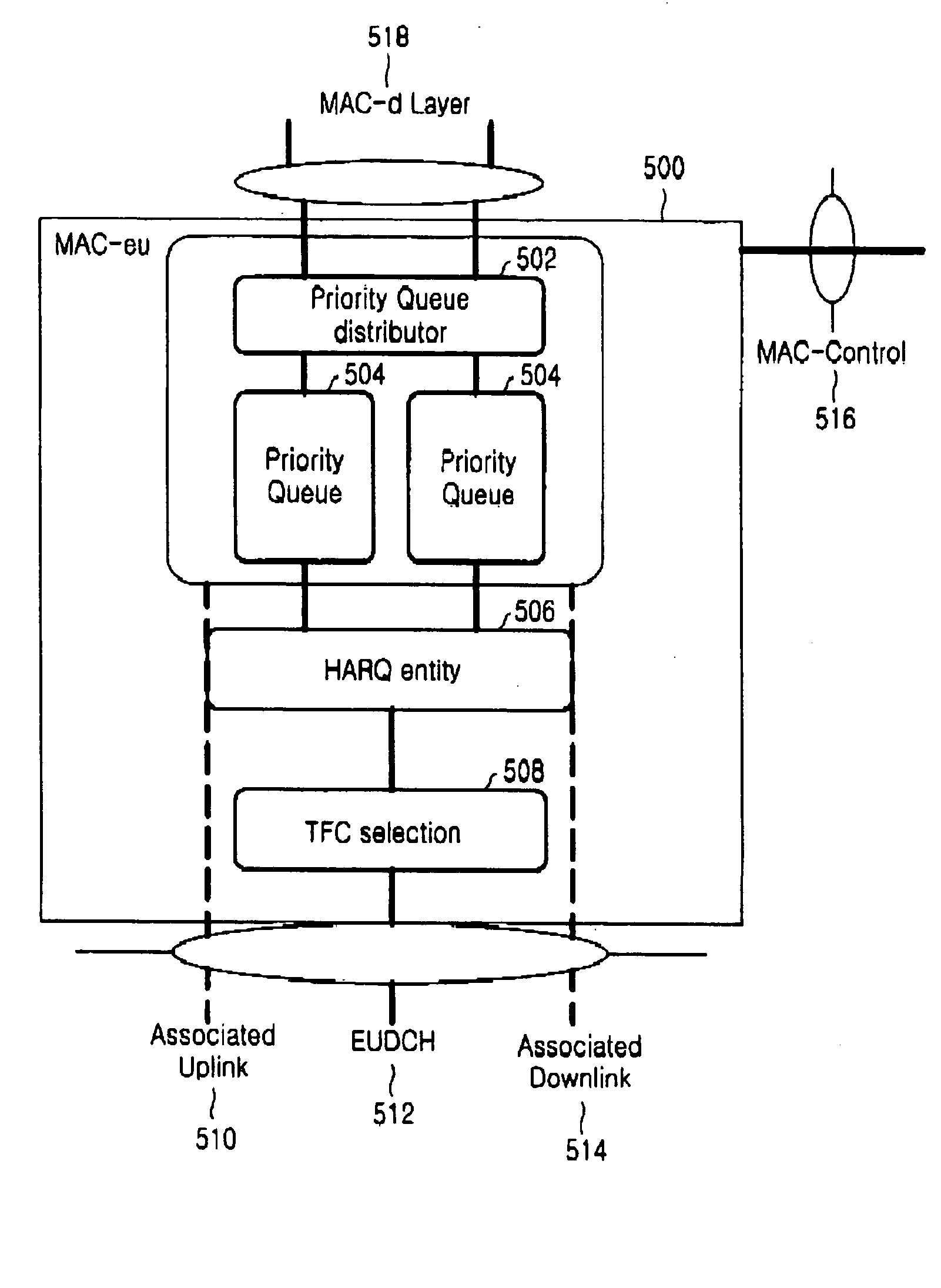
ActiveUS20050047416A1Easy to useNetwork traffic/resource managementNetwork topologiesMobile communication systemsData storing
A method and an apparatus for reporting a buffer status of a buffer storing packet data to be transmitted by a user equipment for a scheduling assignment of an uplink packet data service in a mobile communication system supporting the uplink packet data service are disclosed. A user equipment stores packet data having a priority corresponding to a plurality of priority queues having inherent priorities and relating to at least one service, and transmits buffer status information containing queue identifiers of the priority queues and buffer payload information representing an amount of the packet data stored in the priority queues. Herein, the user equipment inserts the buffer status information into a header part of a protocol data unit for the uplink packet data service, inserts the packet data into a payload part of the protocol data unit, and then transmits the protocol data unit.
Owner:SAMSUNG ELECTRONICS CO LTD
Wide area network using internet with quality of service
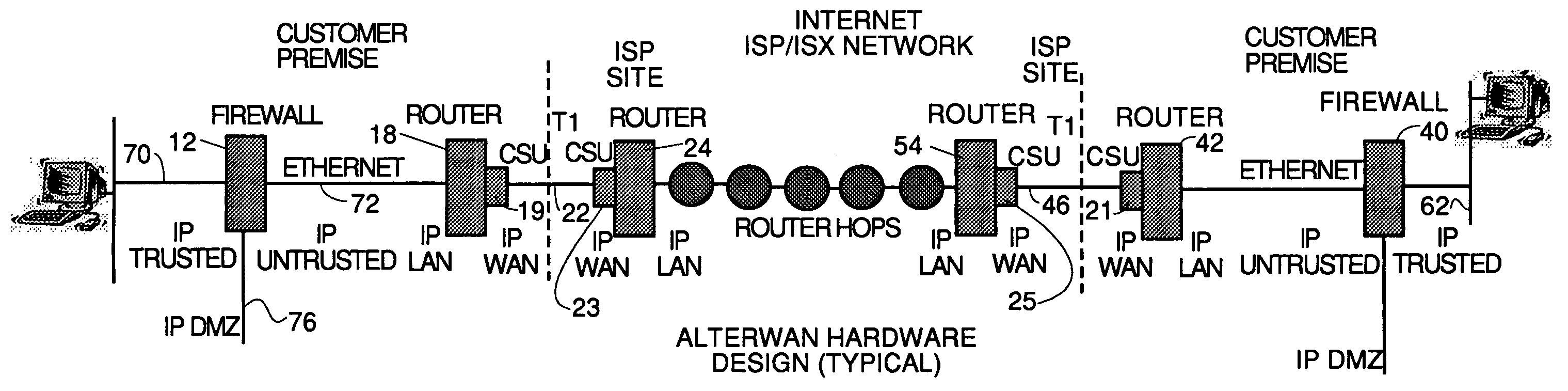
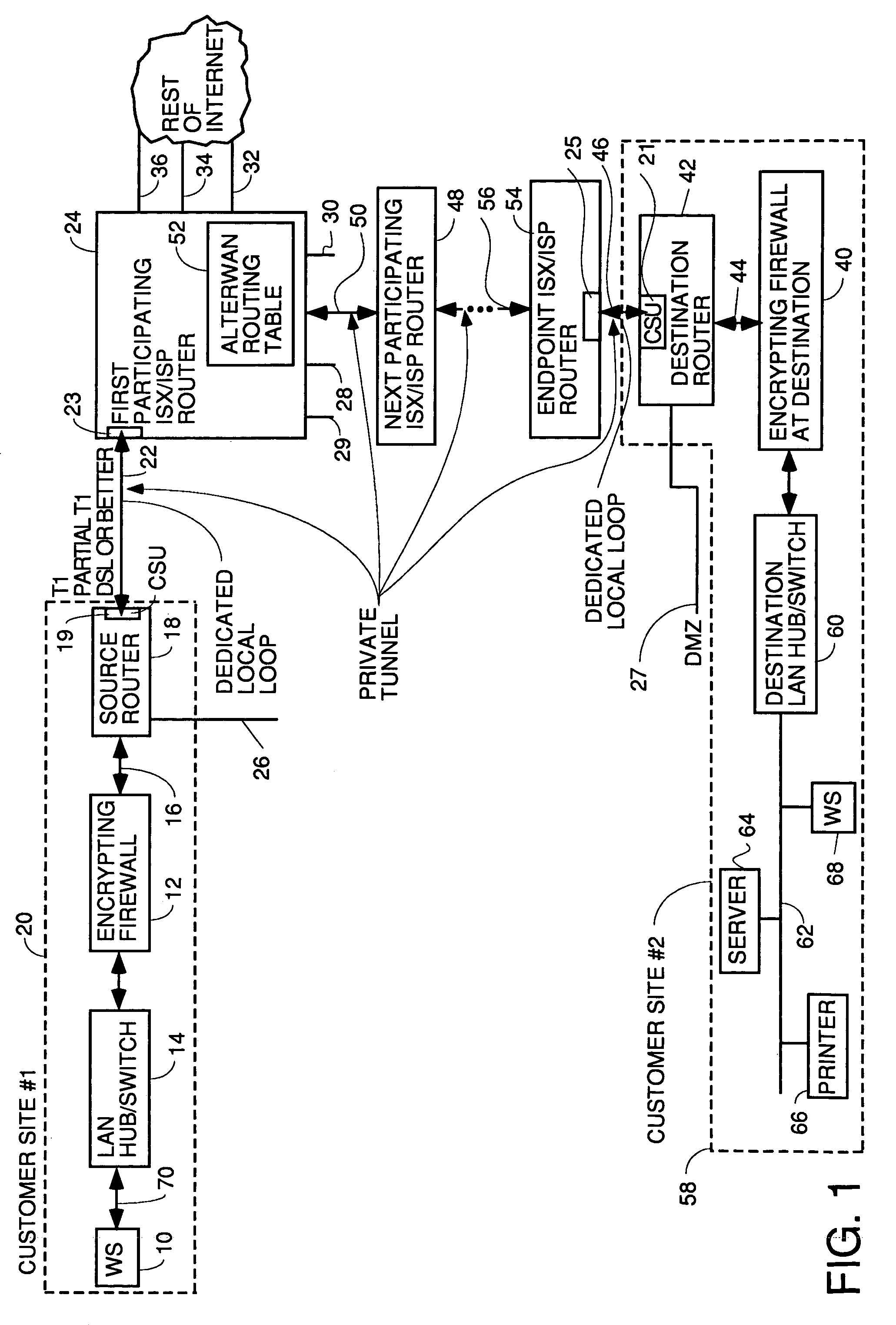
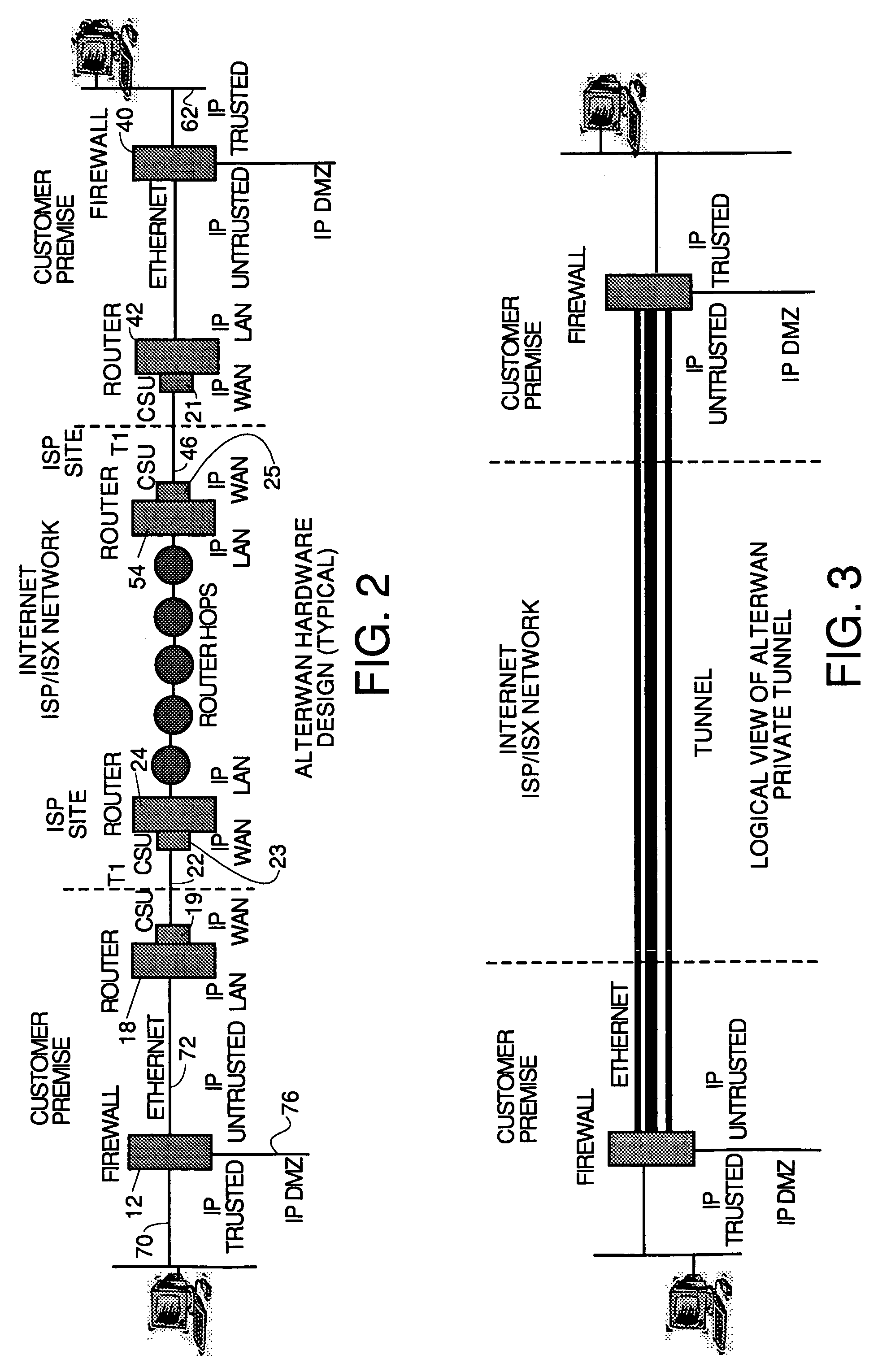
InactiveUS7111163B1Reduces monthly costQuality improvementDigital data processing detailsMultiple digital computer combinationsQuality of serviceTTEthernet
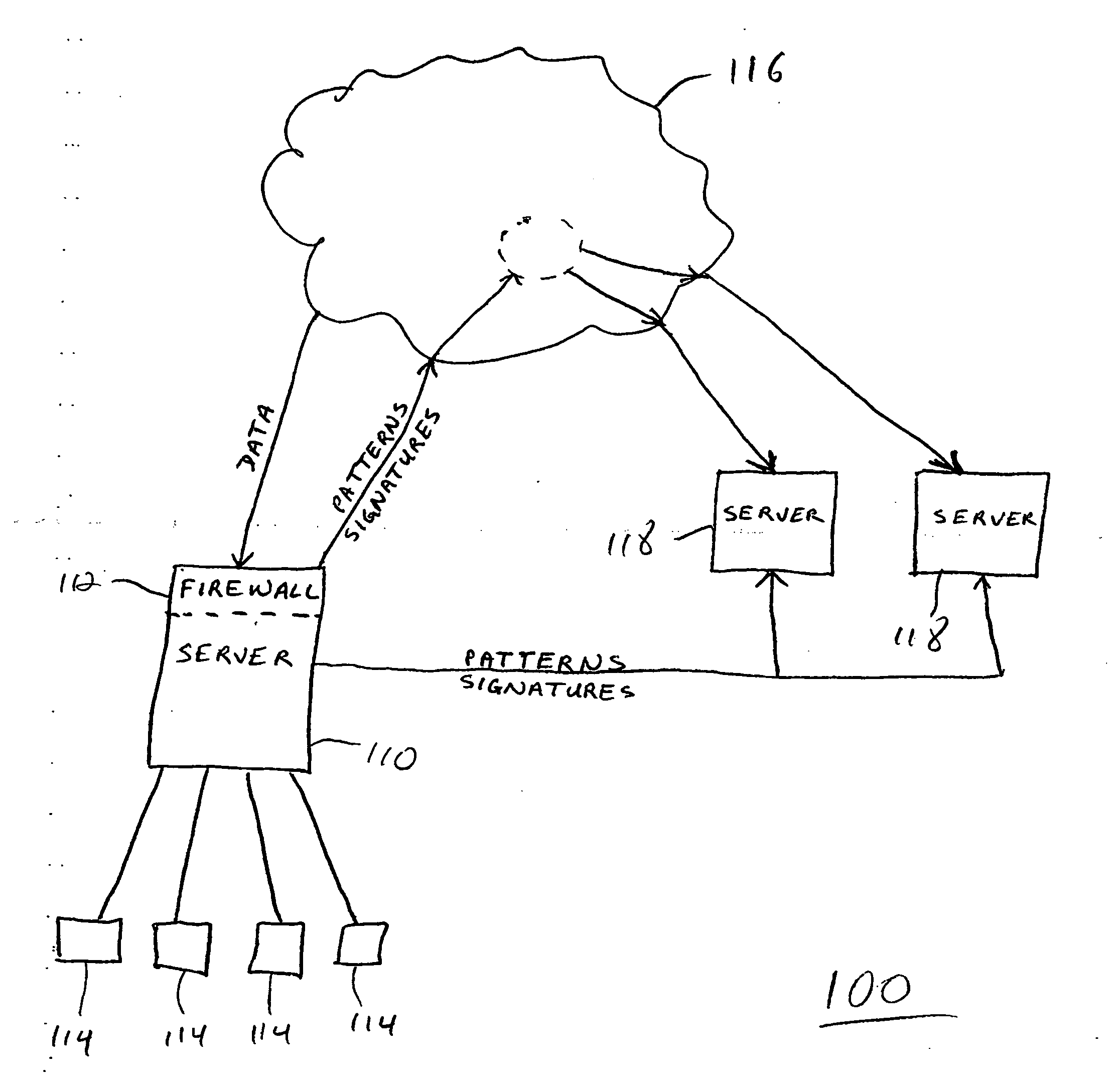
A wide area network using the internet as a backbone utilizing specially selected ISX / ISP providers whose routers route AlterWAN packets of said wide area network along private tunnels through the internet comprised of high bandwidth, low hop-count data paths. Firewalls are provided at each end of each private tunnel which recognize IP packets addressed to devices at the other end of the tunnel and encapsulate these packets in other IP packets which have a header which includes as the destination address, the IP address of the untrusted side of the firewall at the other end of the tunnel. The payload sections of these packets are the original IP packets and are encrypted and decrypted at both ends of the private tunnel using the same encryption algorithm using the same key or keys.
Owner:ALTERWAN
Peer trust evaluation using mobile agents in peer-to-peer networks
ActiveUS20040088369A1Digital data processing detailsMultiple digital computer combinationsPeer-to-peerRegion of interest
Embodiments of a system and method for using mobile agents to gather trust information for evaluating trust in peer-to-peer networks. A peer node may launch a mobile agent on a network including an itinerary of peer nodes to be visited by the mobile agent and an indication of an area of interest. The mobile agent may determine if a visited peer node stores trust evaluations for other peer nodes as providers of codats relevant to the area of interest and, if so, the trust evaluations may be stored as payload data in the mobile agent. After completing the itinerary, the mobile agent may return the payload to the initiating peer node. The initiating peer node may use the trust evaluations collected by the mobile agent in determining or adjusting trust evaluations for peer nodes as providers of codats relevant to the area of interest.
Owner:ORACLE INT CORP
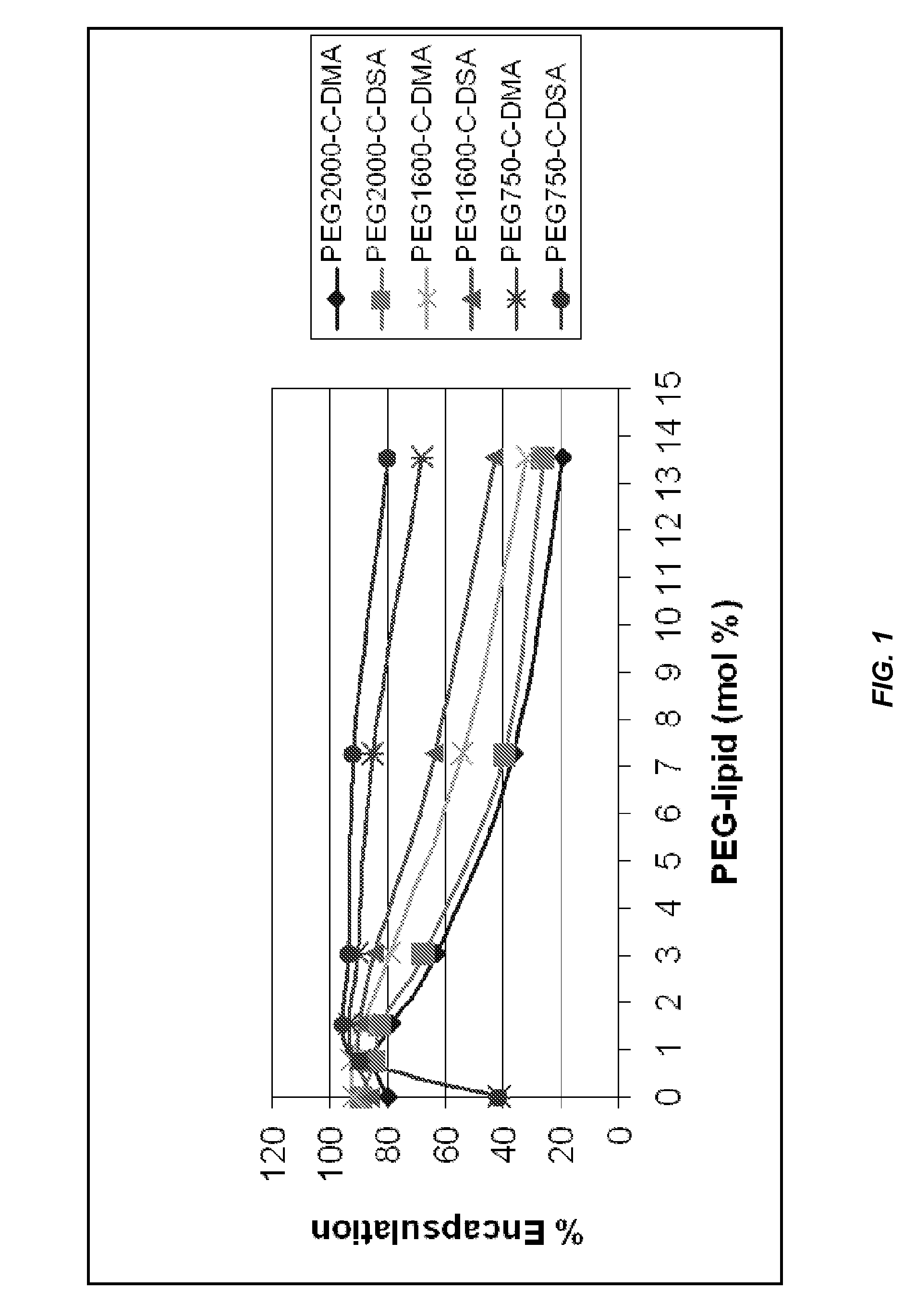
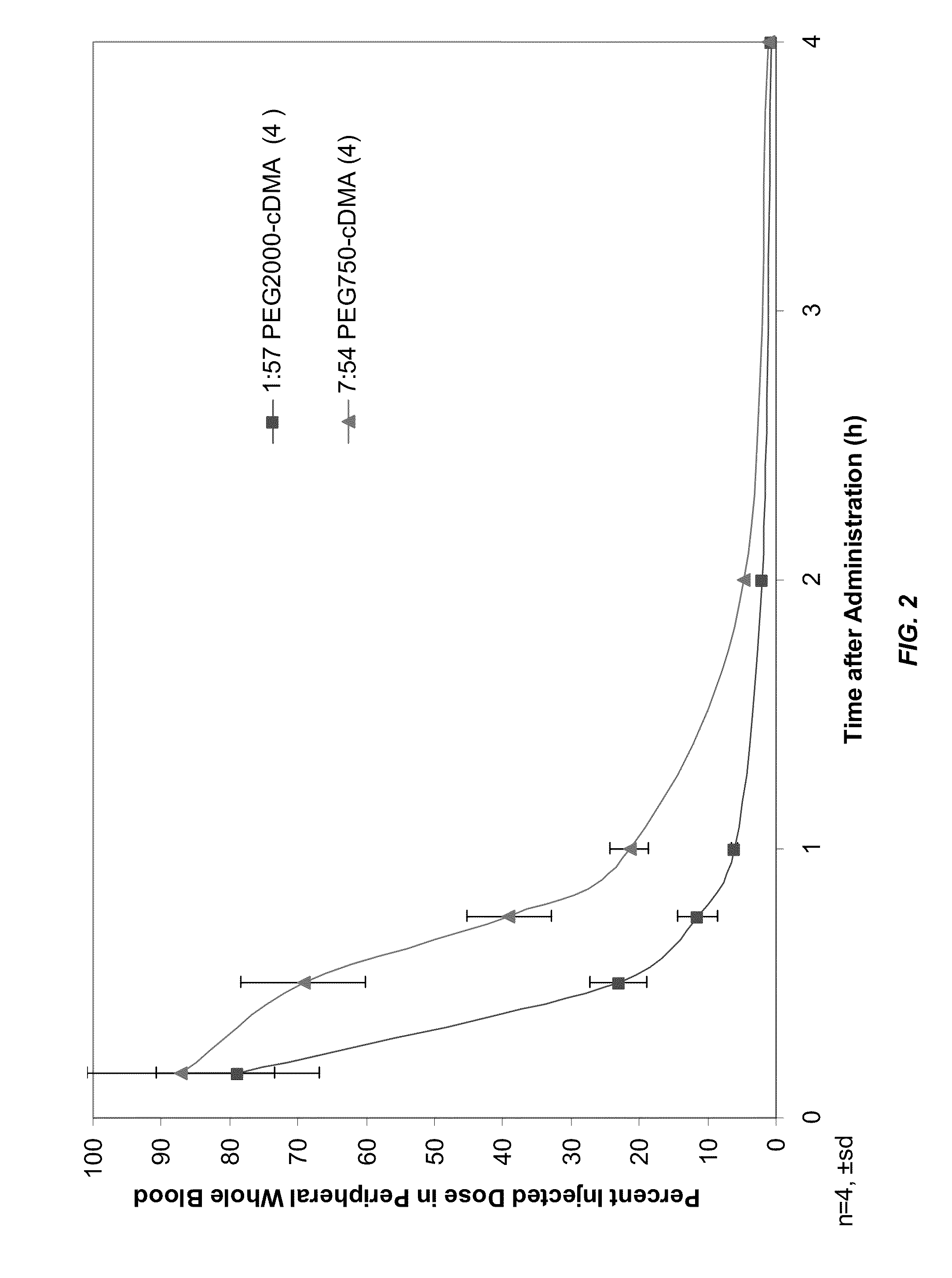
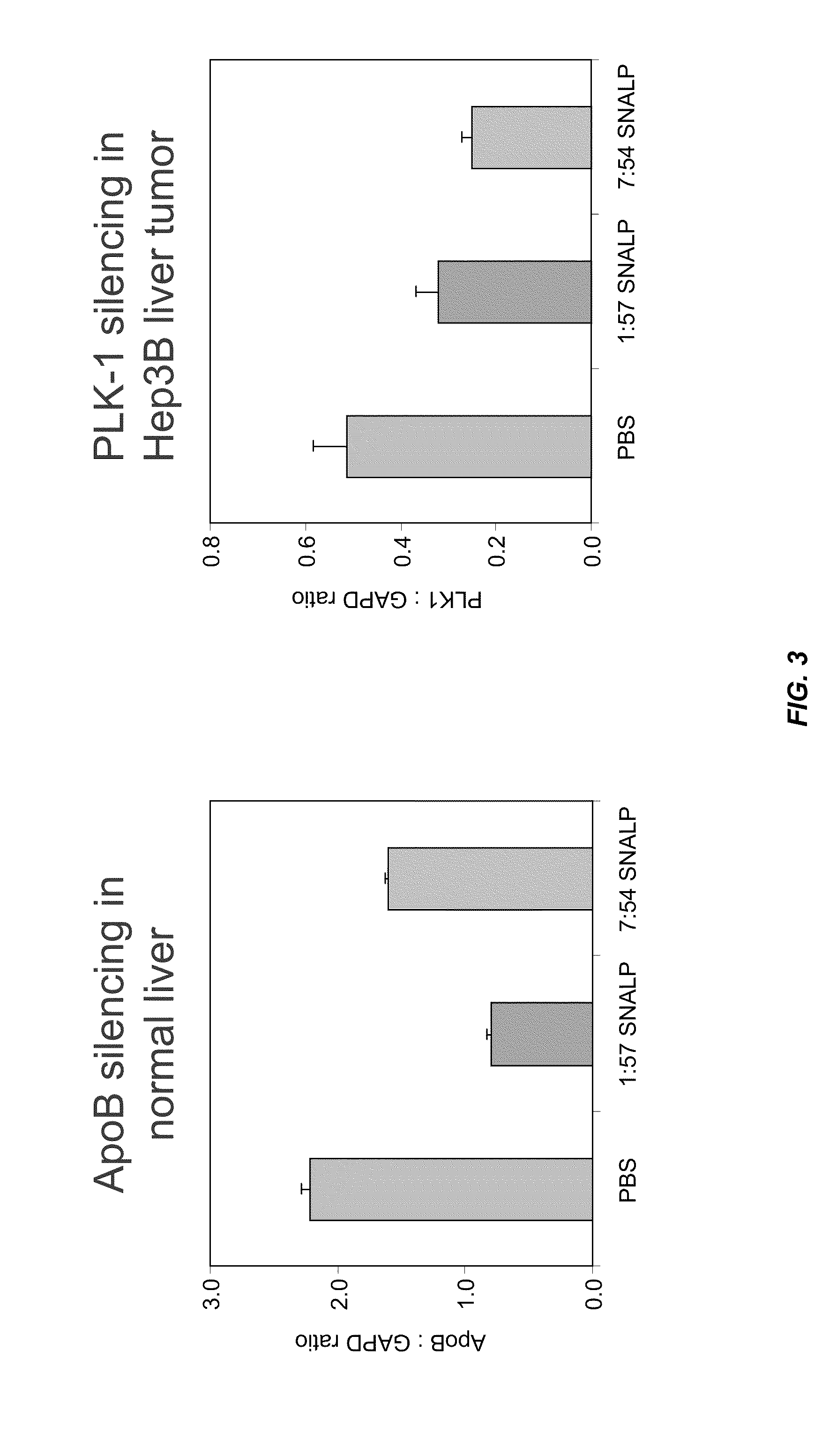
Lipid formulations for nucleic acid delivery
ActiveUS8283333B2Improve effectivenessHigh activityOrganic active ingredientsSugar derivativesLipid particleActive agent
The present invention provides novel, serum-stable lipid particles comprising one or more active agents or therapeutic agents, methods of making the lipid particles, and methods of delivering and / or administering the lipid particles. More particularly, the present invention provides serum-stable nucleic acid-lipid particles (SNALP) comprising a nucleic acid (e.g., one or more interfering RNA molecules), methods of making the SNALP, and methods of delivering and / or administering the SNALP (e.g., for the treatment of cancer). In particular embodiments, the present invention provides tumor-directed lipid particles that preferentially target solid tumors. The tumor-directed formulations of the present invention are capable of preferentially delivering a payload such as a nucleic acid to cells of solid tumors compared to non-cancerous cells.
Owner:ARBUTUS BIOPHARMA CORPORAT ION
Systems and methods for packet distribution
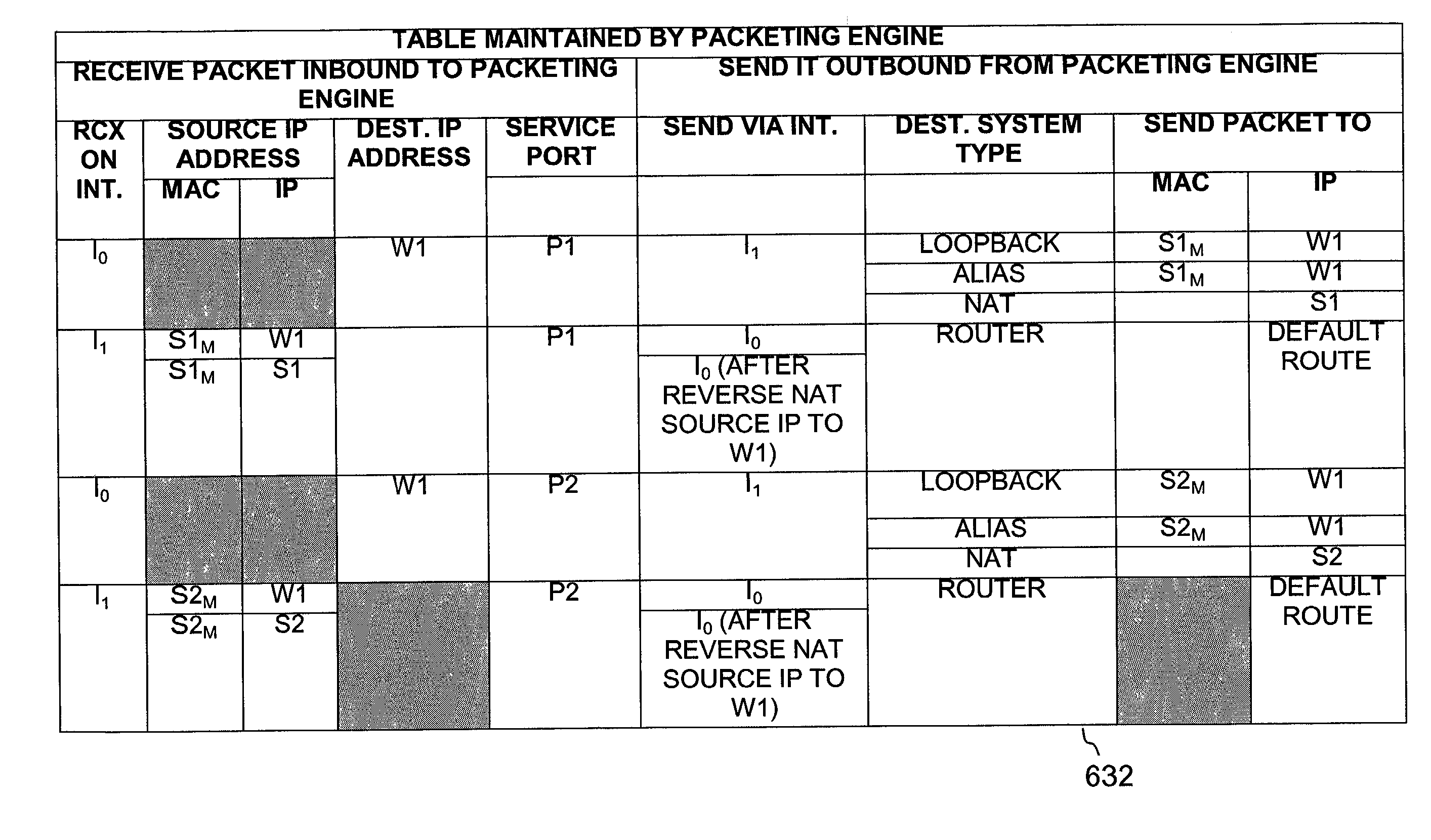
InactiveUS20020038339A1Multiple digital computer combinationsProgram controlNetwork applicationPayload
Embodiments of the present invention relate to methods and systems of managing delivery of data to network applications. In an embodiment, a delivery packet including a service address and a payload is received. A plurality of network applications associated with the service address of the data packet are identified. The plurality of network applications associated with the service address include a first network application and a second network application, where the first network application is different from the second network application. At least the payload of the data packet is sent to the first network application and the second network application.
Owner:SPONTANEOUS NETWORKS
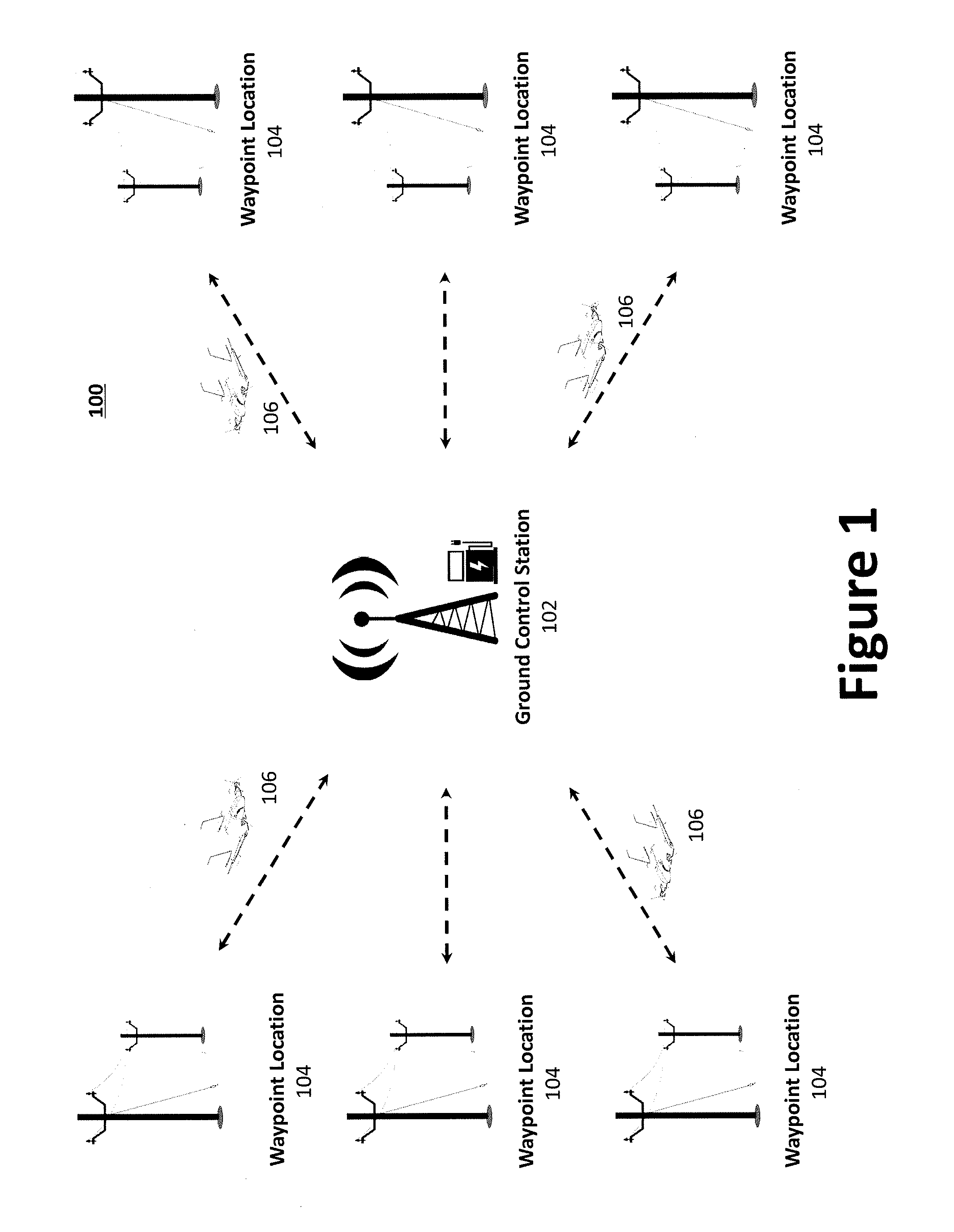
Aerial system and vehicle for continuous operation
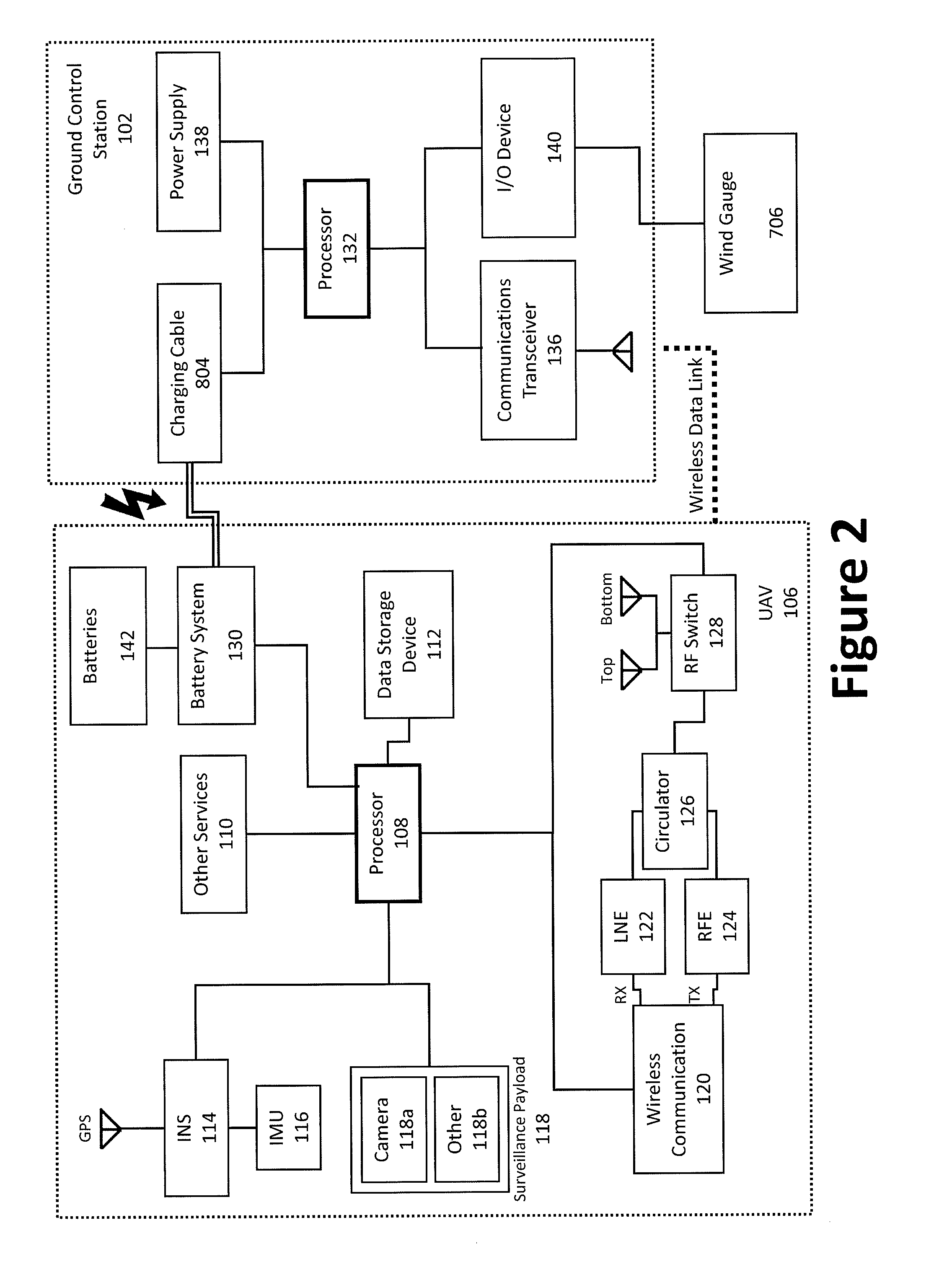
ActiveUS20160137311A1Analogue computers for vehiclesArrester hooksContinuous operationSurveillance data
An aerial vehicle system for gathering data may comprise a Waypoint Location, wherein the Waypoint Location comprises an arresting cable; a Ground Control Station, wherein the Ground Control Station comprises a charging cable; and an aerial vehicle, wherein the aerial vehicle comprises an onboard battery, a capturing hook and a sensor payload for generating surveillance data. The aerial vehicle may be configured to autonomously travel between the Waypoint Location and the Ground Control Station. The aerial vehicle may be configured to couple with the arresting cable via the capturing hook. The aerial vehicle may be configured to electronically couple with the charging cable via the capturing hook to facilitate charging the aerial vehicle's onboard battery.
Owner:AURORA FLIGHT SCI CORP
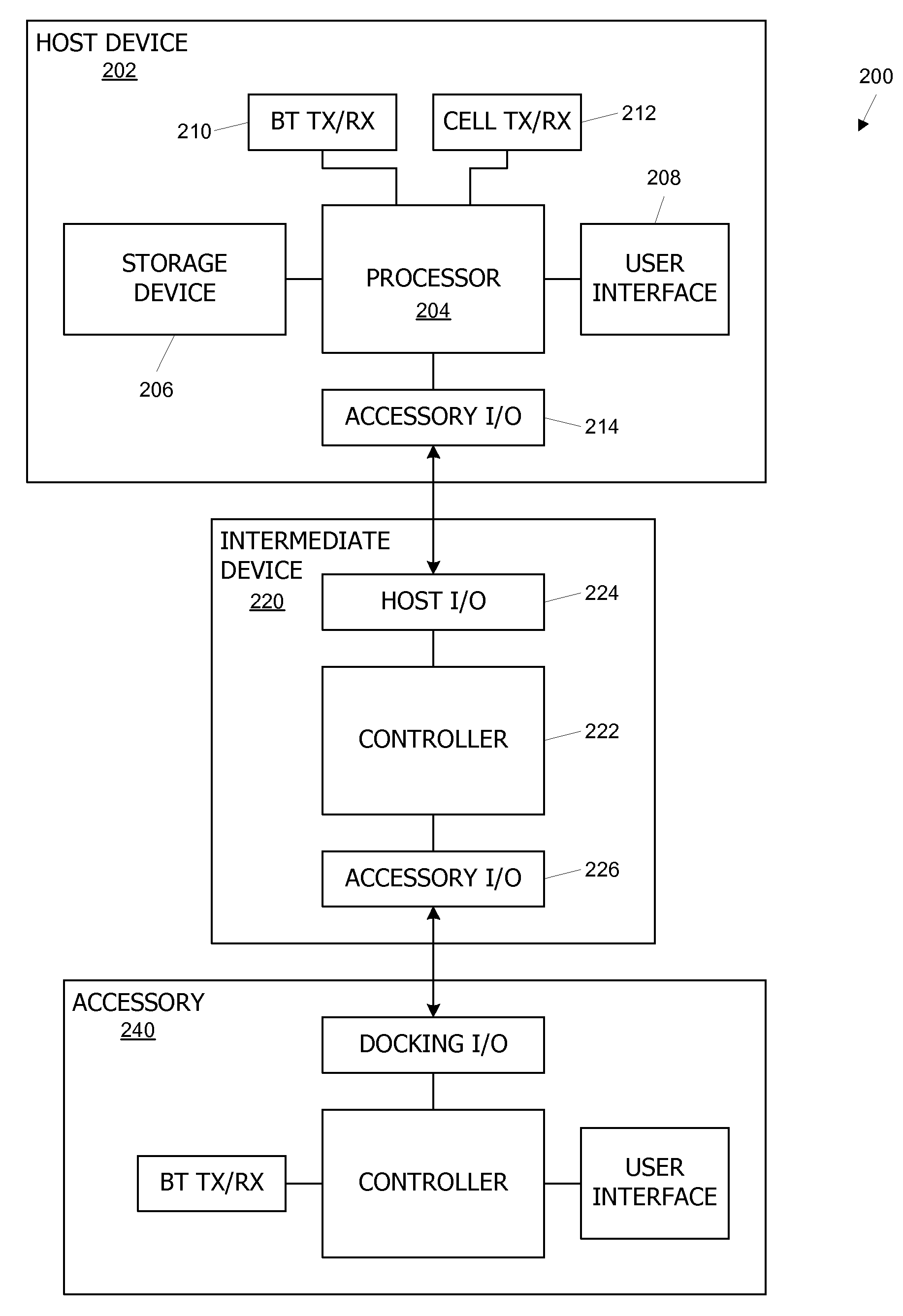
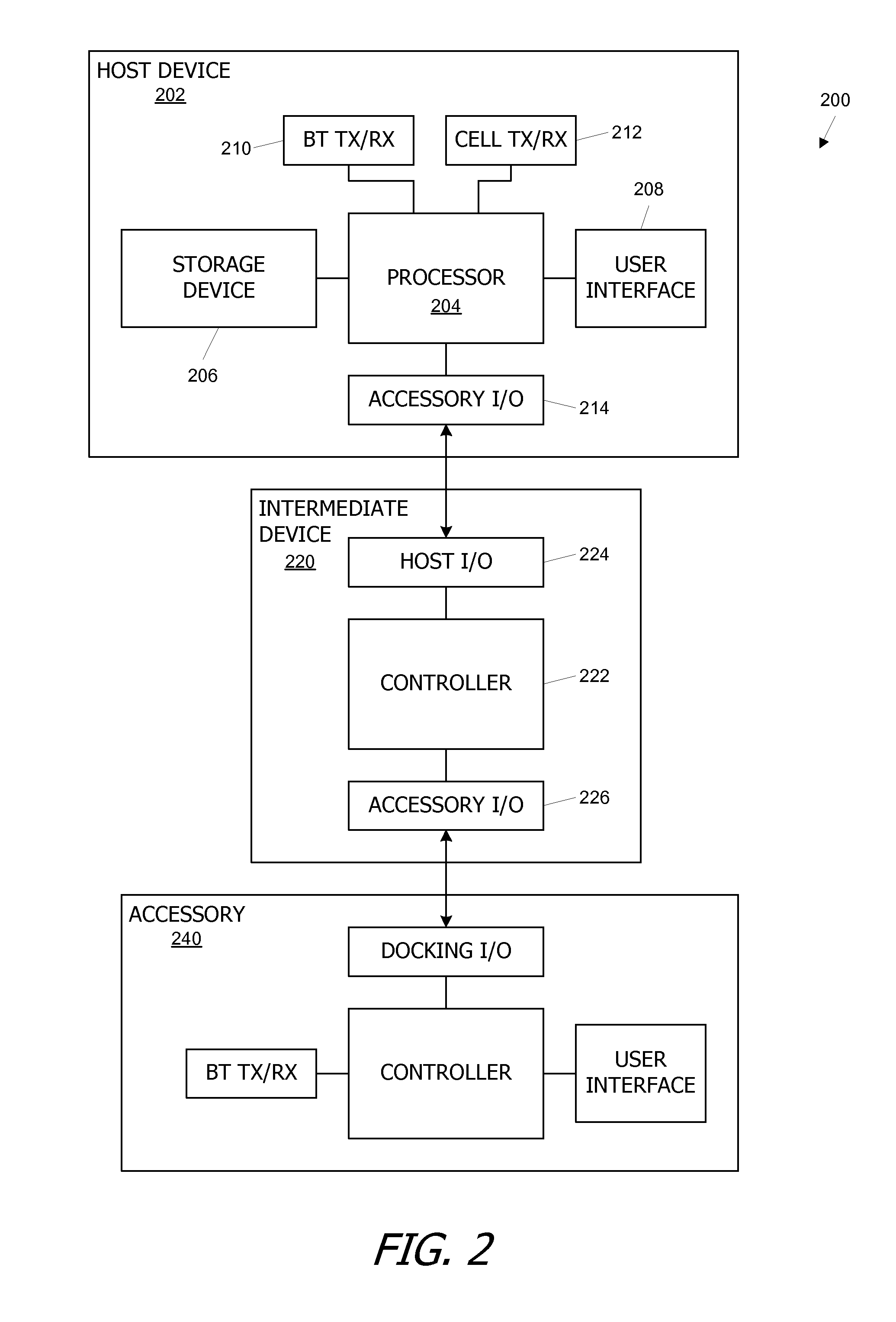
Communication between a host device and an accessory via an intermediate device
A host device and an accessory exchange information (e.g., commands and data) via an intermediate device. The host device and accessory can each connect to the intermediate device through a direct wired path and can exchange commands and data with the intermediate device. The host device and the accessory can also “tunnel” information to each other through the intermediate device, by packaging the tunneled information as a payload of a command recognizable by the intermediate device; the intermediate device can repackage and forward the payload. In some embodiments, the tunneled information relates to configuring a wireless link (e.g., a Bluetooth pairing) between the host device and the accessory.
Owner:APPLE INC
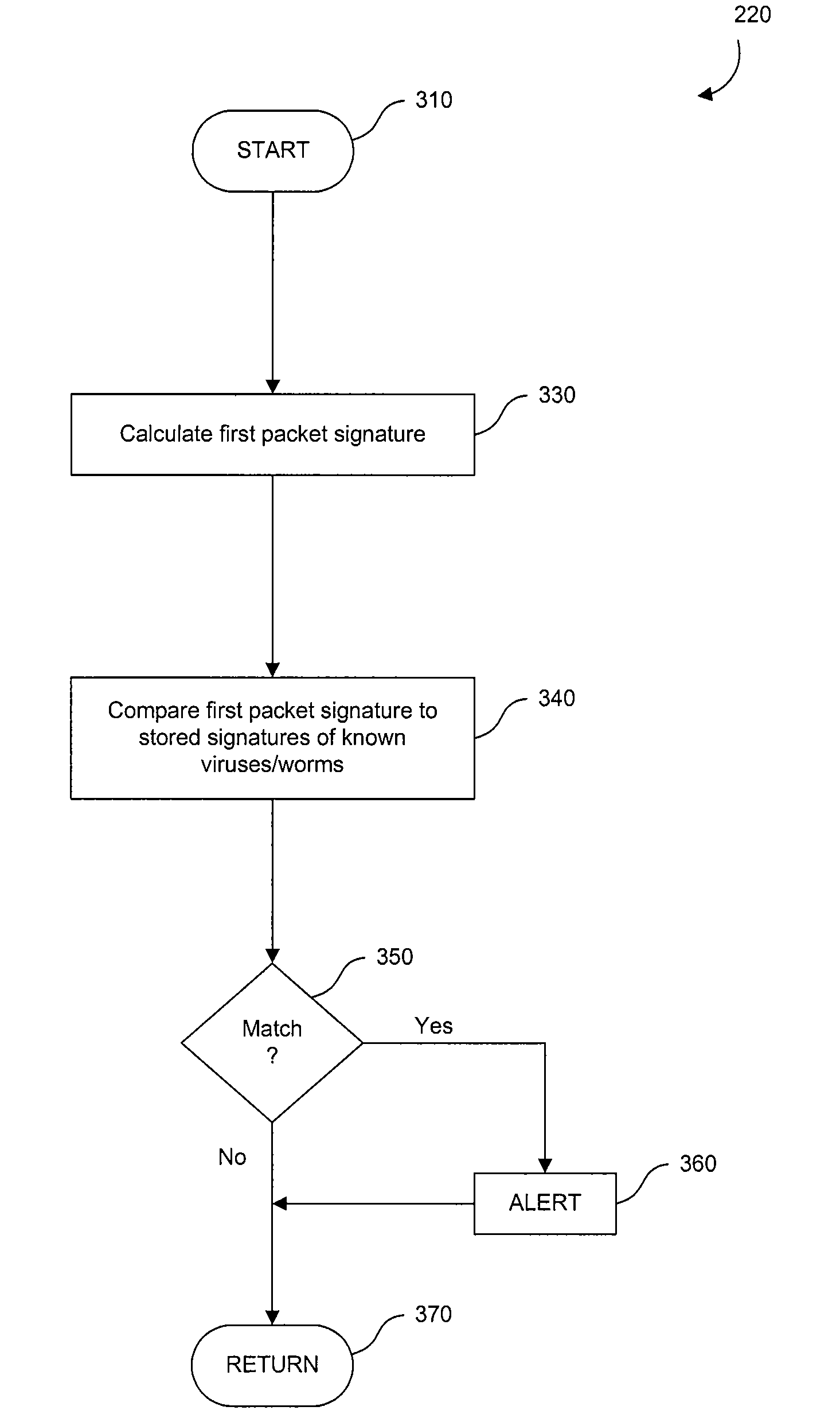
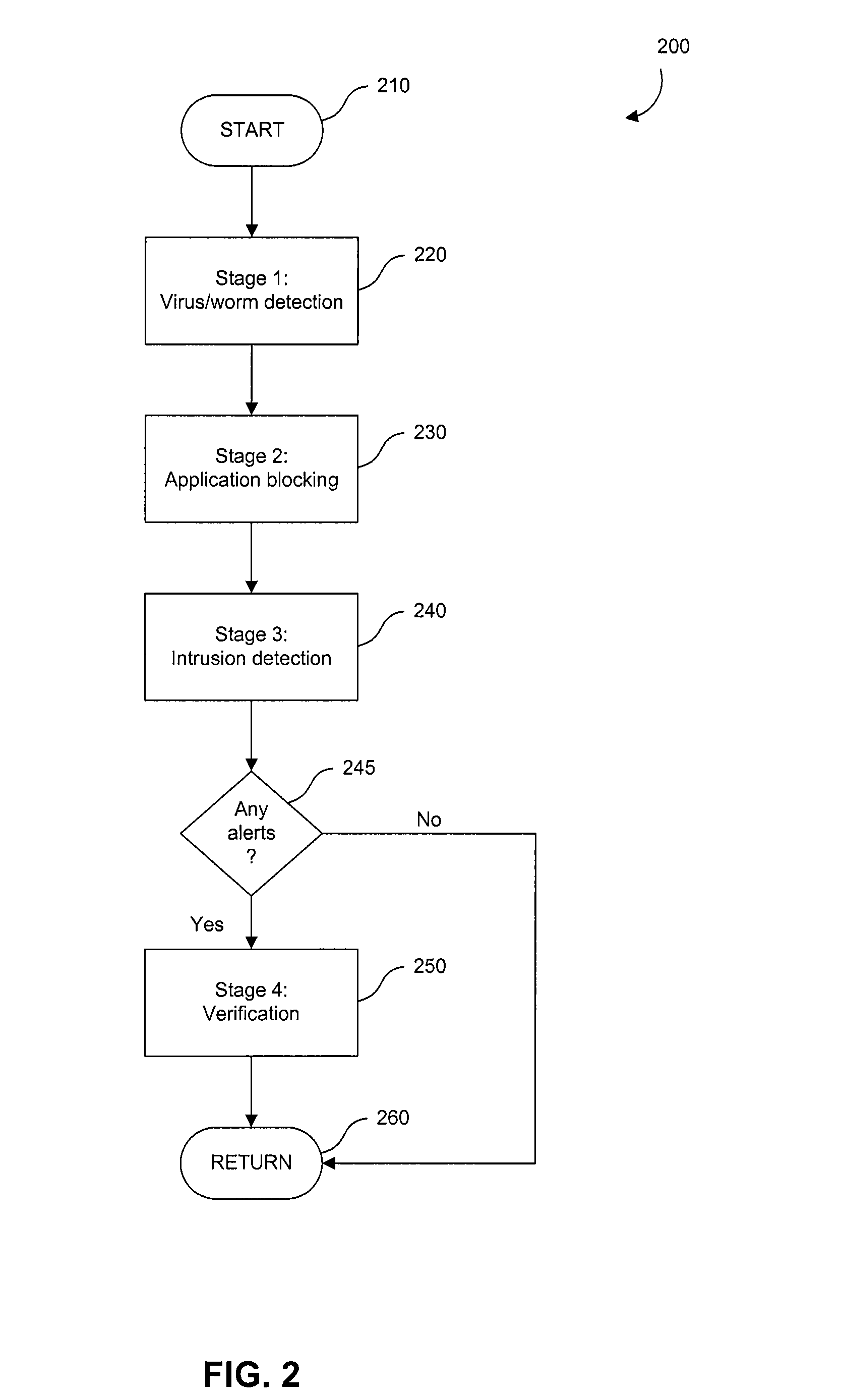
Multi-Stage Deep Packet Inspection for Lightweight Devices
InactiveUS20080313738A1Memory loss protectionError detection/correctionInformation processingThree stage
A system and method for the multi-stage analysis of incoming packets. Three stages are used, each of which addresses a particular category of threat by examining the headers and / or payload of each packet (“deep packet inspection”). The first stage detects incoming viruses or worms. The second stage detects malicious applications. The third stage detects attempts at intrusion. These three stages operate in sequence, but in alternative embodiments of the invention, they may be applied in a different order. These three stages are followed by a fourth stage that acts as a verification stage. If any of the first three stages detects a possible attack, then the packet or packets that have been flagged are routed to a central verification facility. In an embodiment of the invention, the verification facility is a server, coupled with a database. Here, suspect packets are compared to entries in the database to more comprehensively determine whether or not the packets represent an attempt to subvert the information processing system.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Collaborative content coherence using mobile agents in peer-to-peer networks
ActiveUS7328243B2Data processing applicationsMultiple digital computer combinationsDocumentationDistributed computing
A mobile agent may be provided for collaborative content control in peer-to-peer networks. A peer may launch a mobile agent including an itinerary of peers to be visited and indications of one or more documents that the peers are collaboratively editing. The mobile agent may visit peers indicated by the itinerary to collect version information for the document(s). The mobile agent may return the version information to the initiating peer, which may coordinate each of the document(s) on the peer to a most recent version in accordance with the version information provided by the mobile agent. Visited peers may use the payload to determine if their version of the document(s) are up to date and, if not, may add a version update request to the payload. The initiating peer may send the most recent version information to peers that added version update requests to the payload.
Owner:ORACLE INT CORP
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com