Patents
Literature
465 results about "Computer virus" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
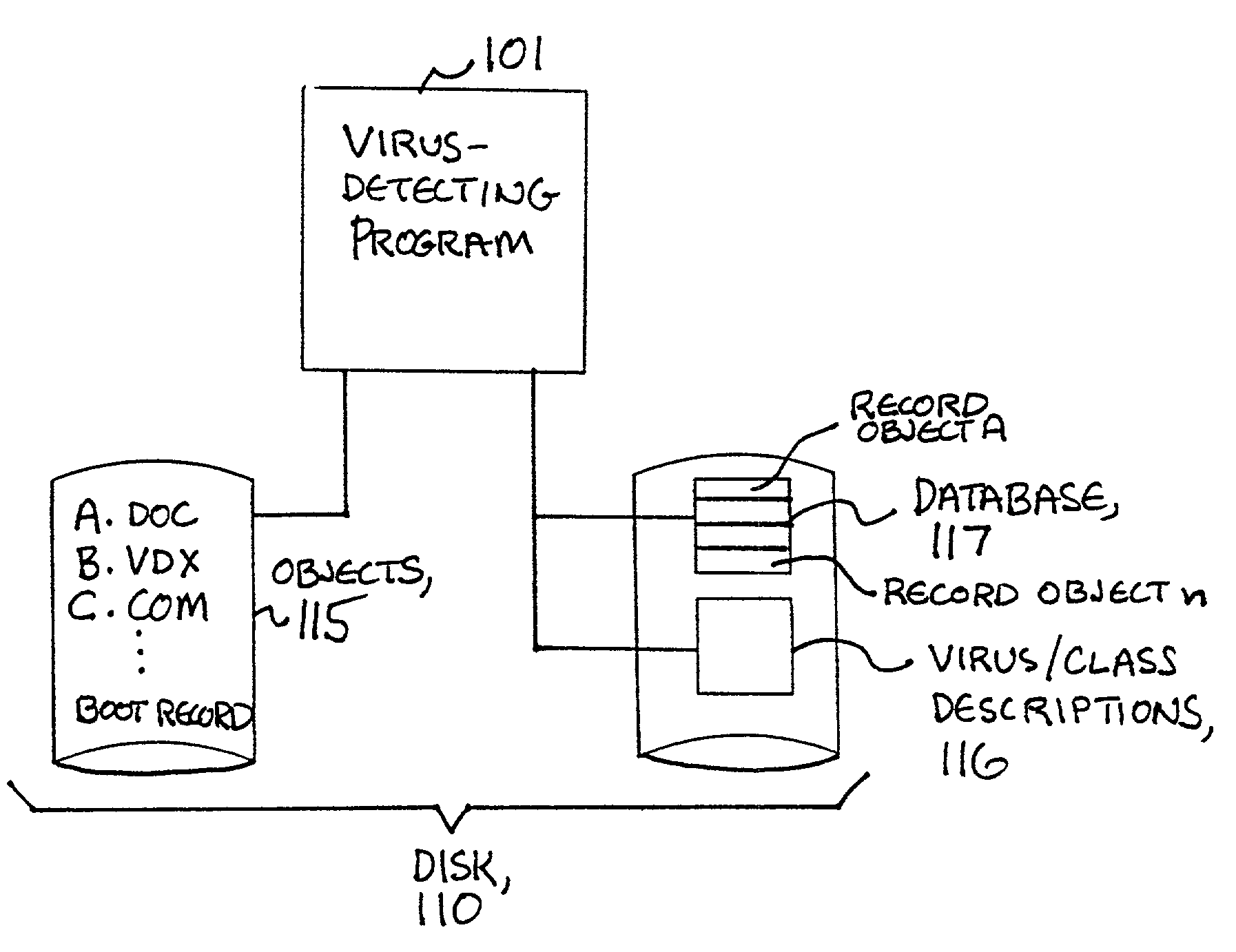
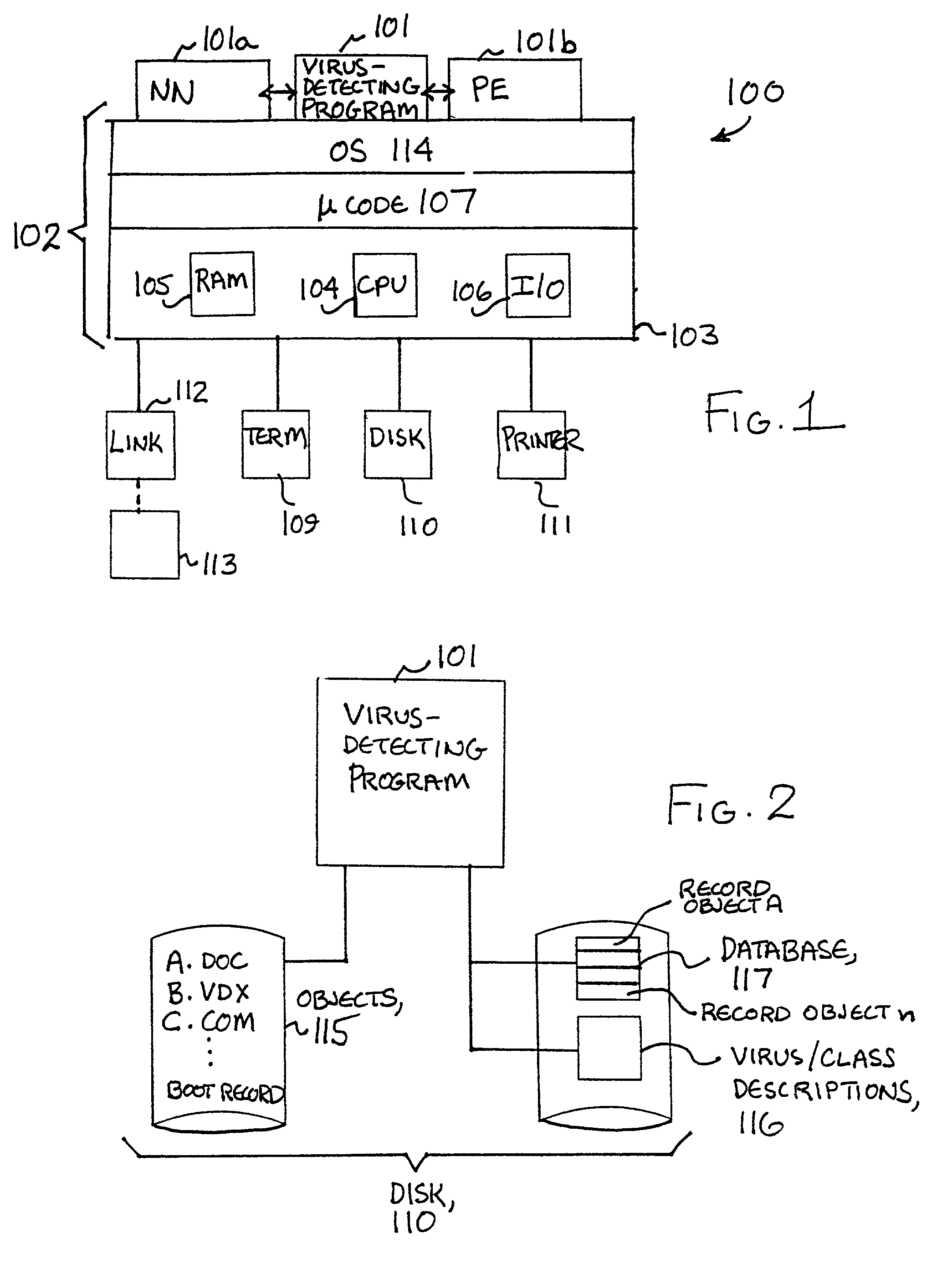
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. When this replication succeeds, the affected areas are then said to be "infected" with a computer virus.
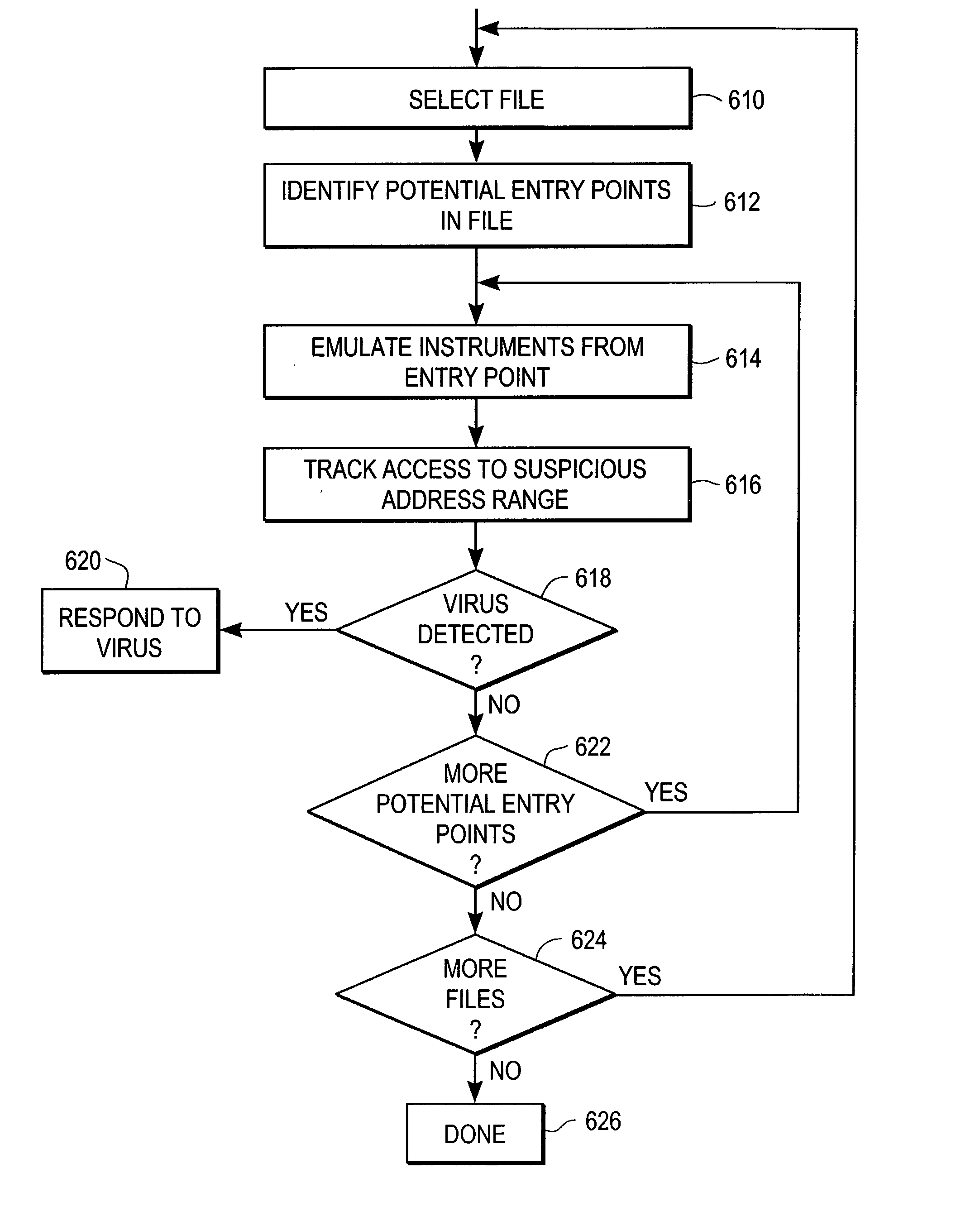
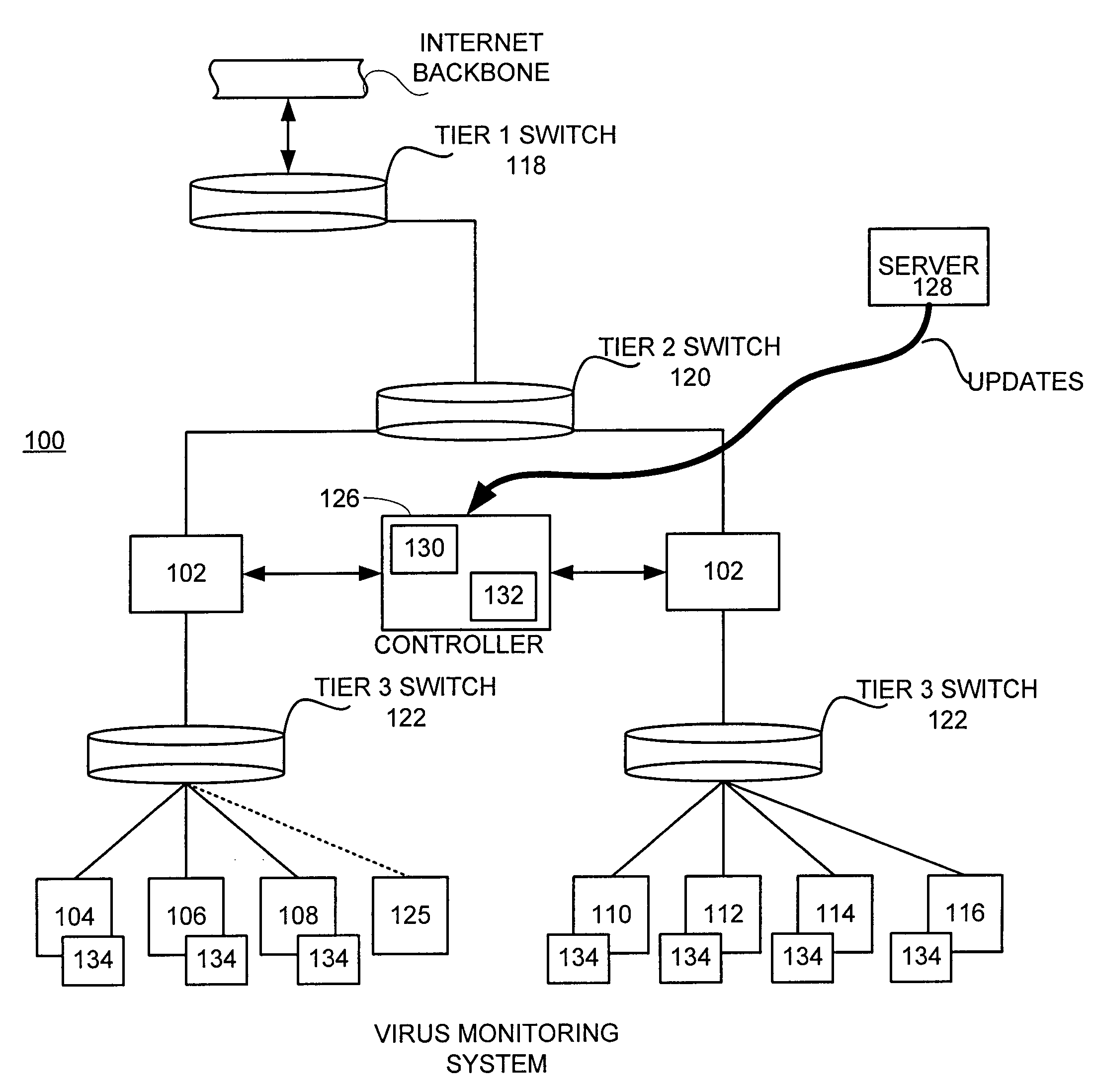
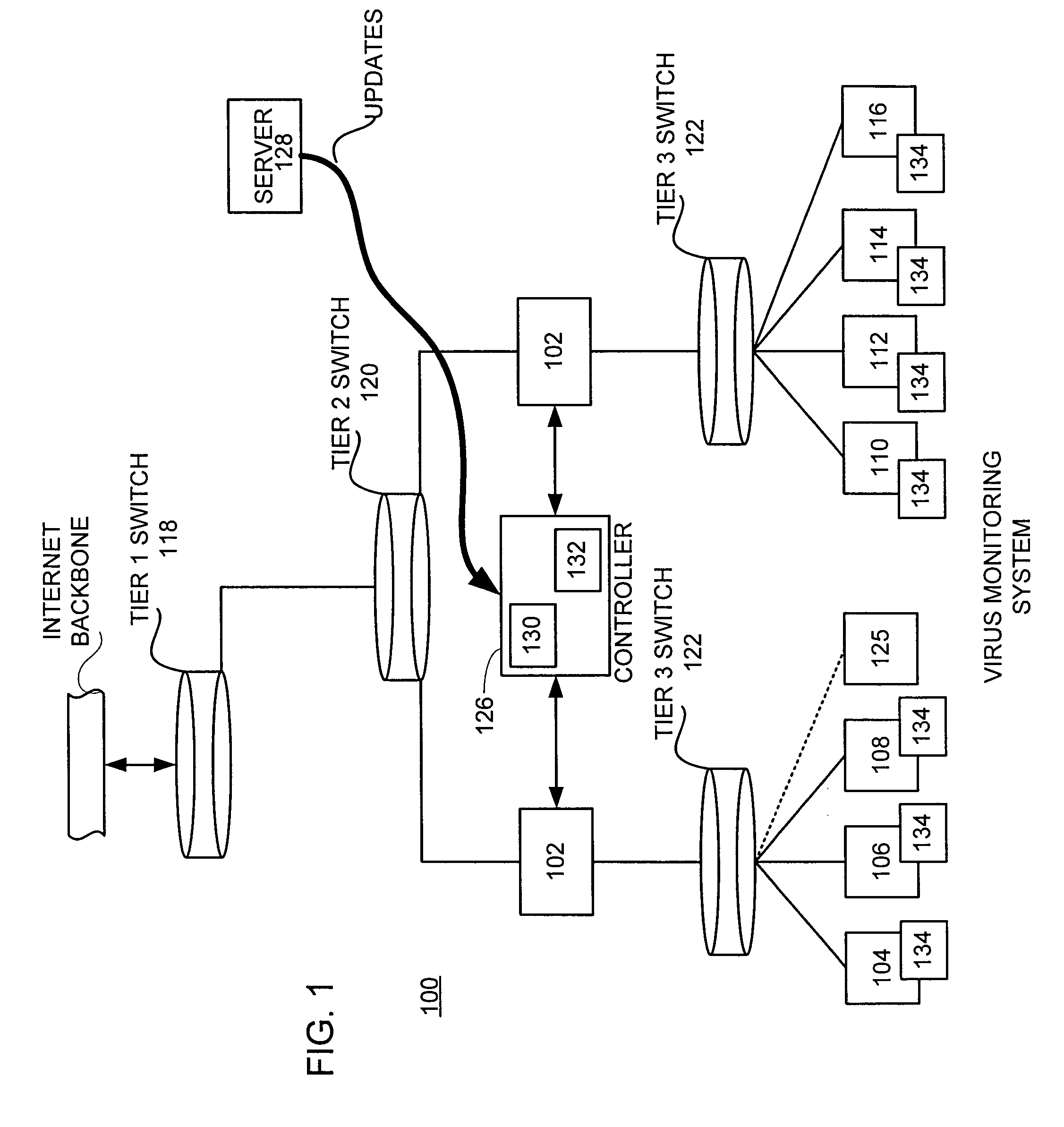
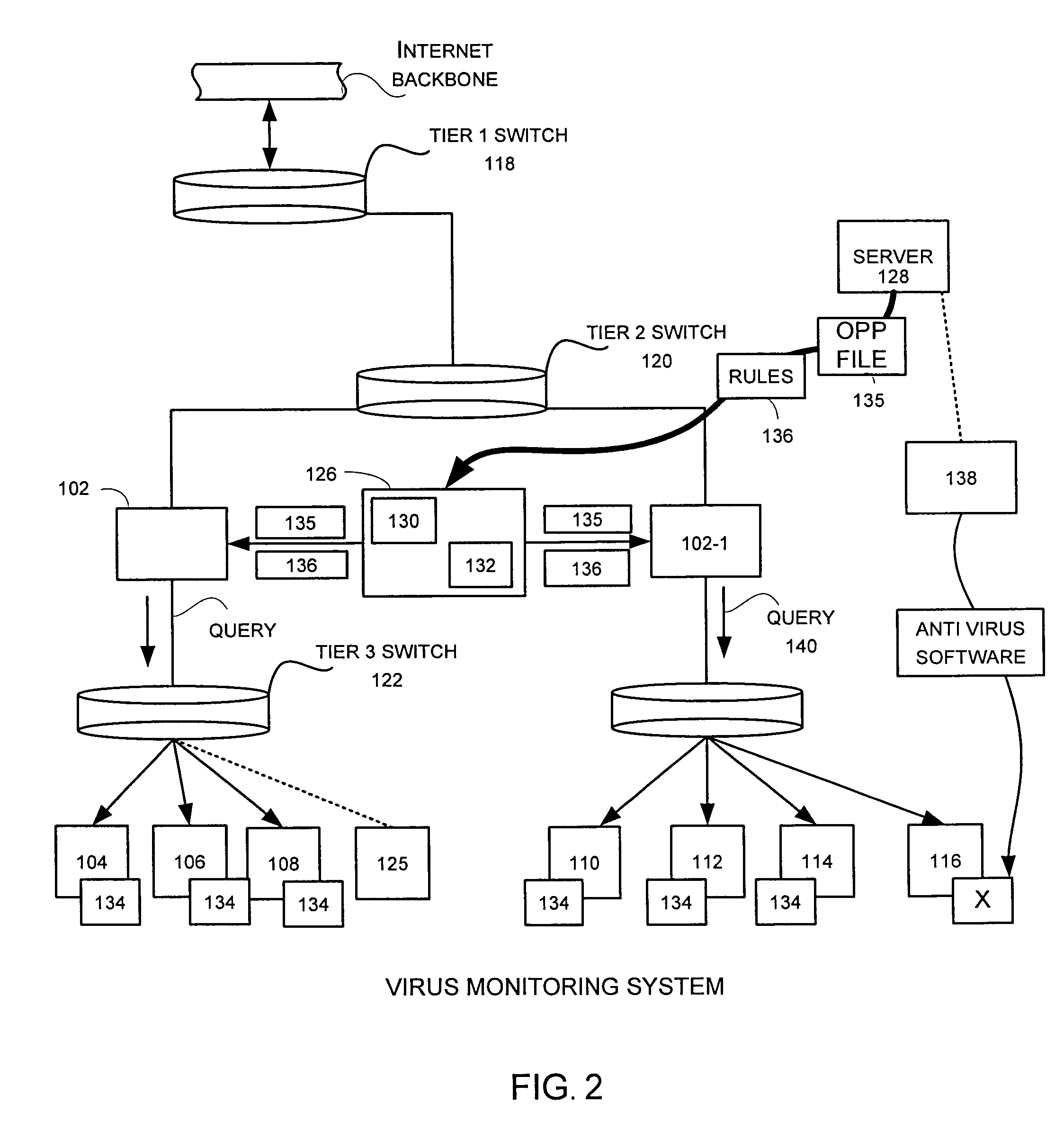
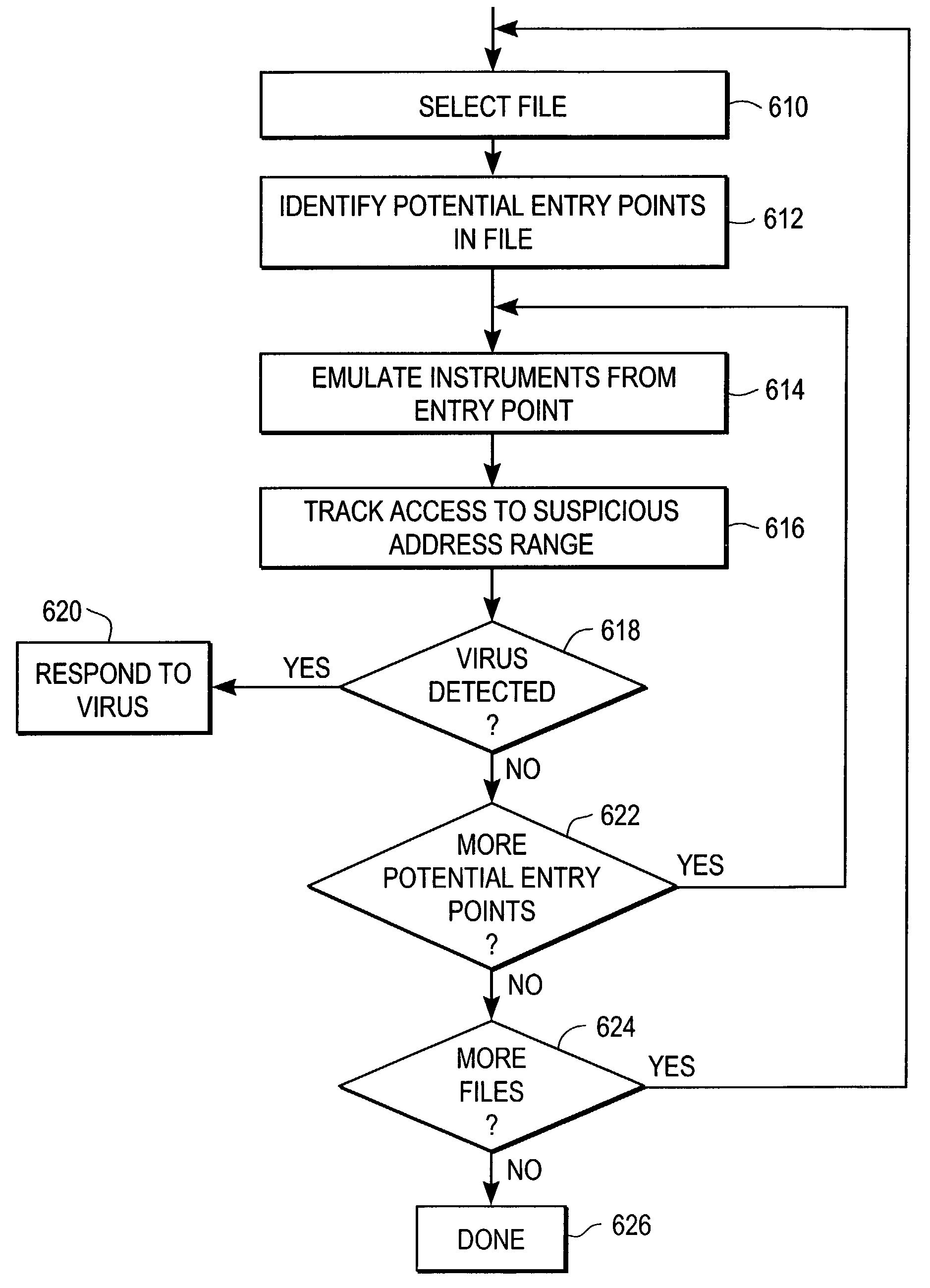
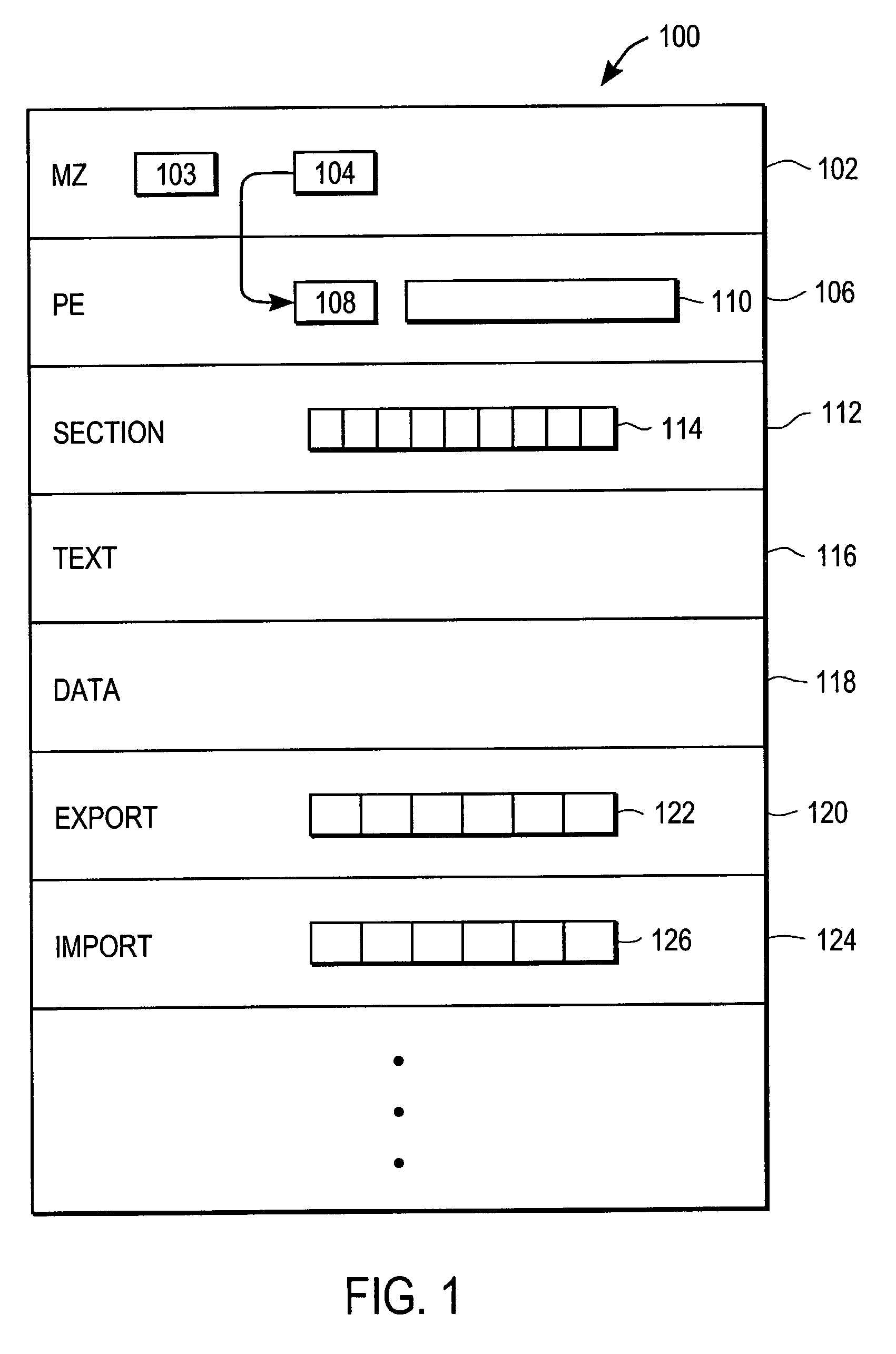
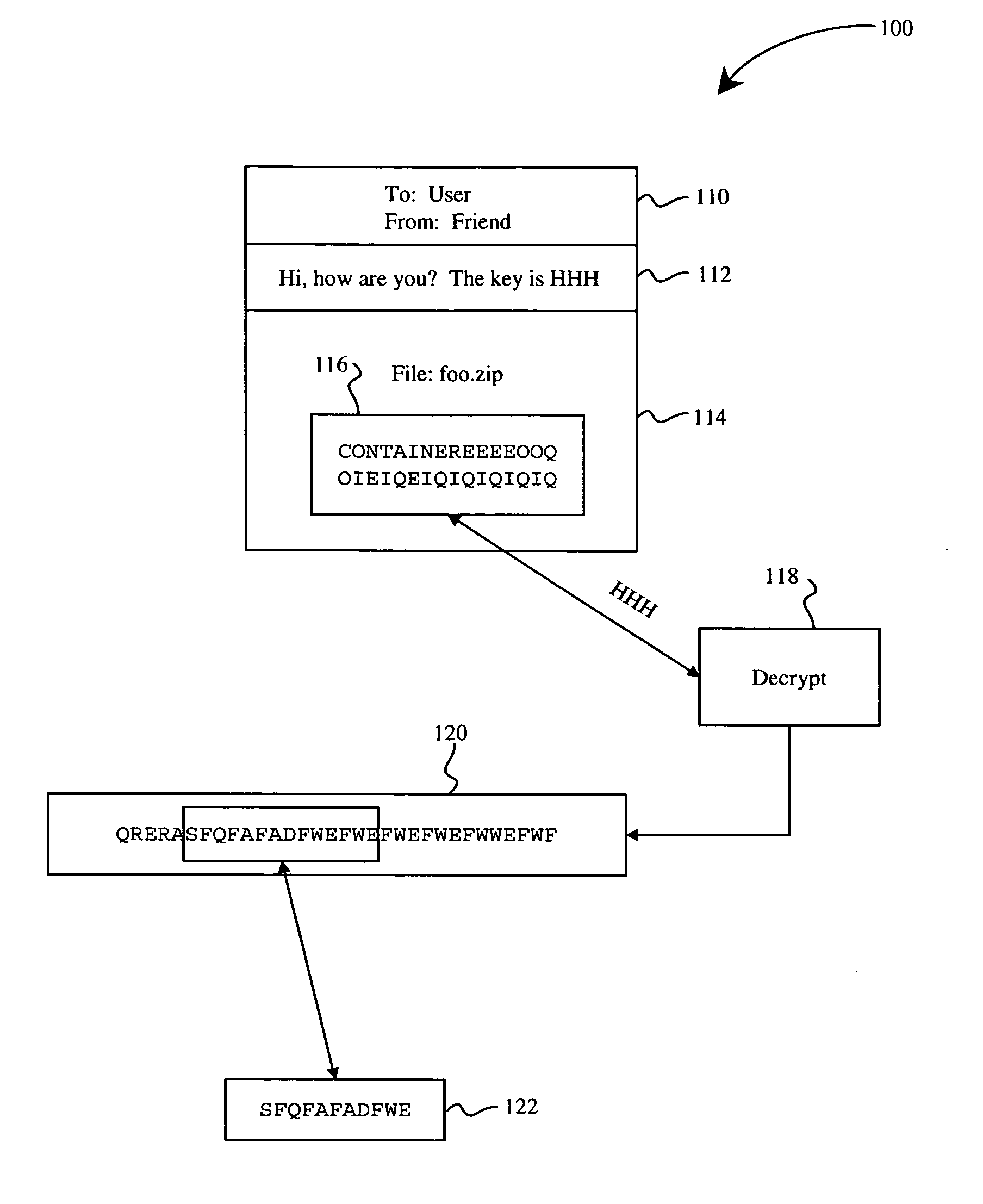
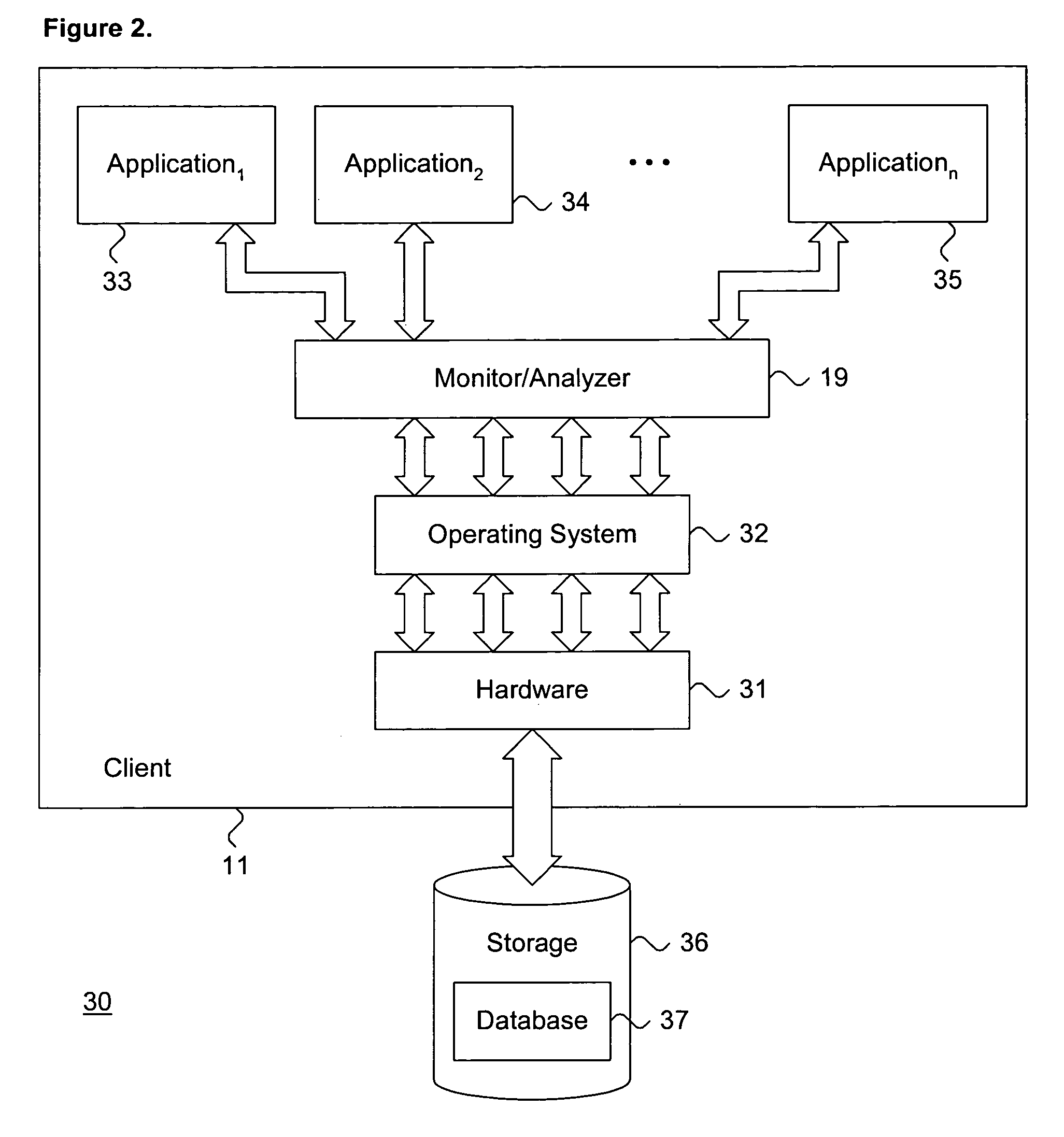
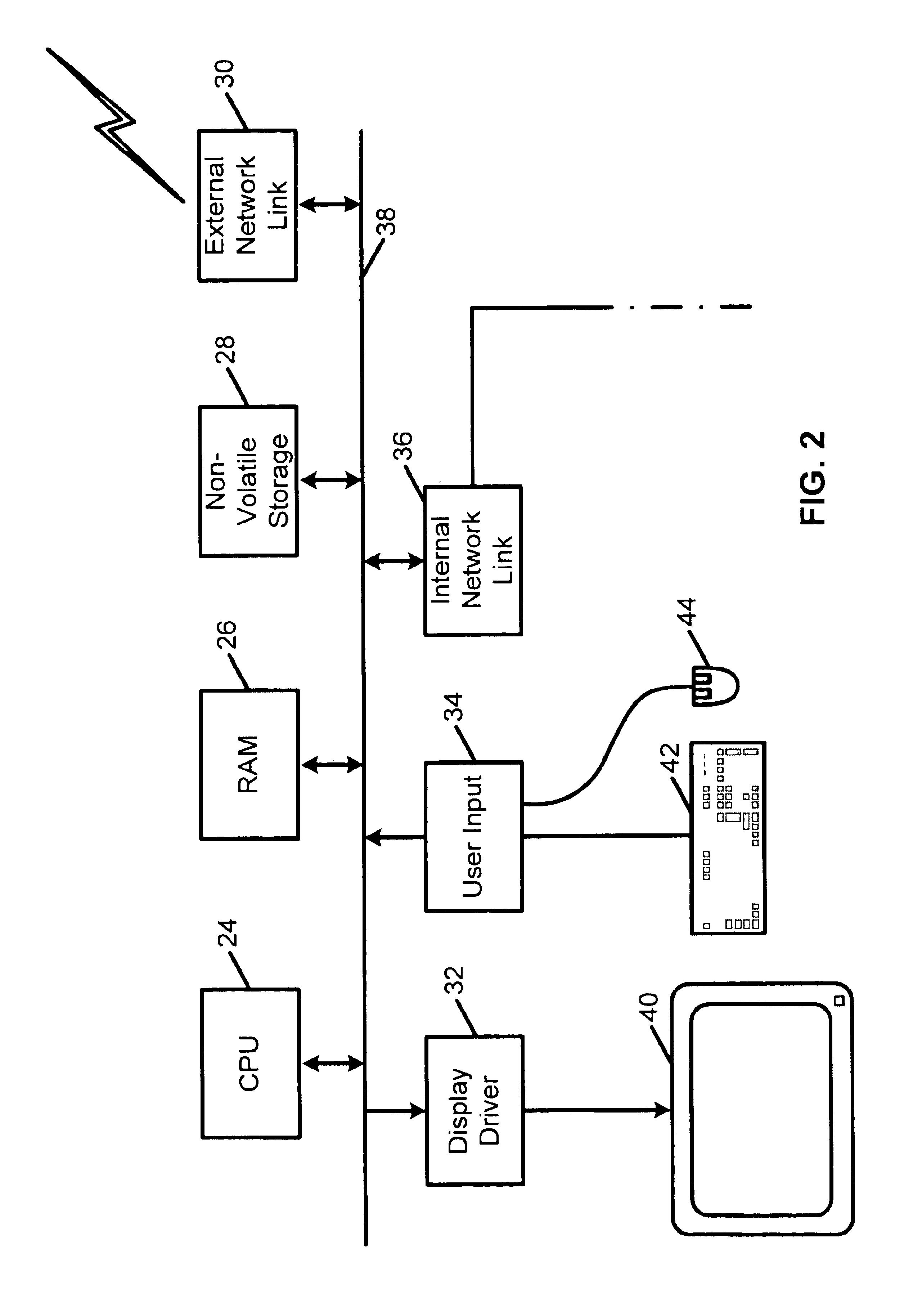
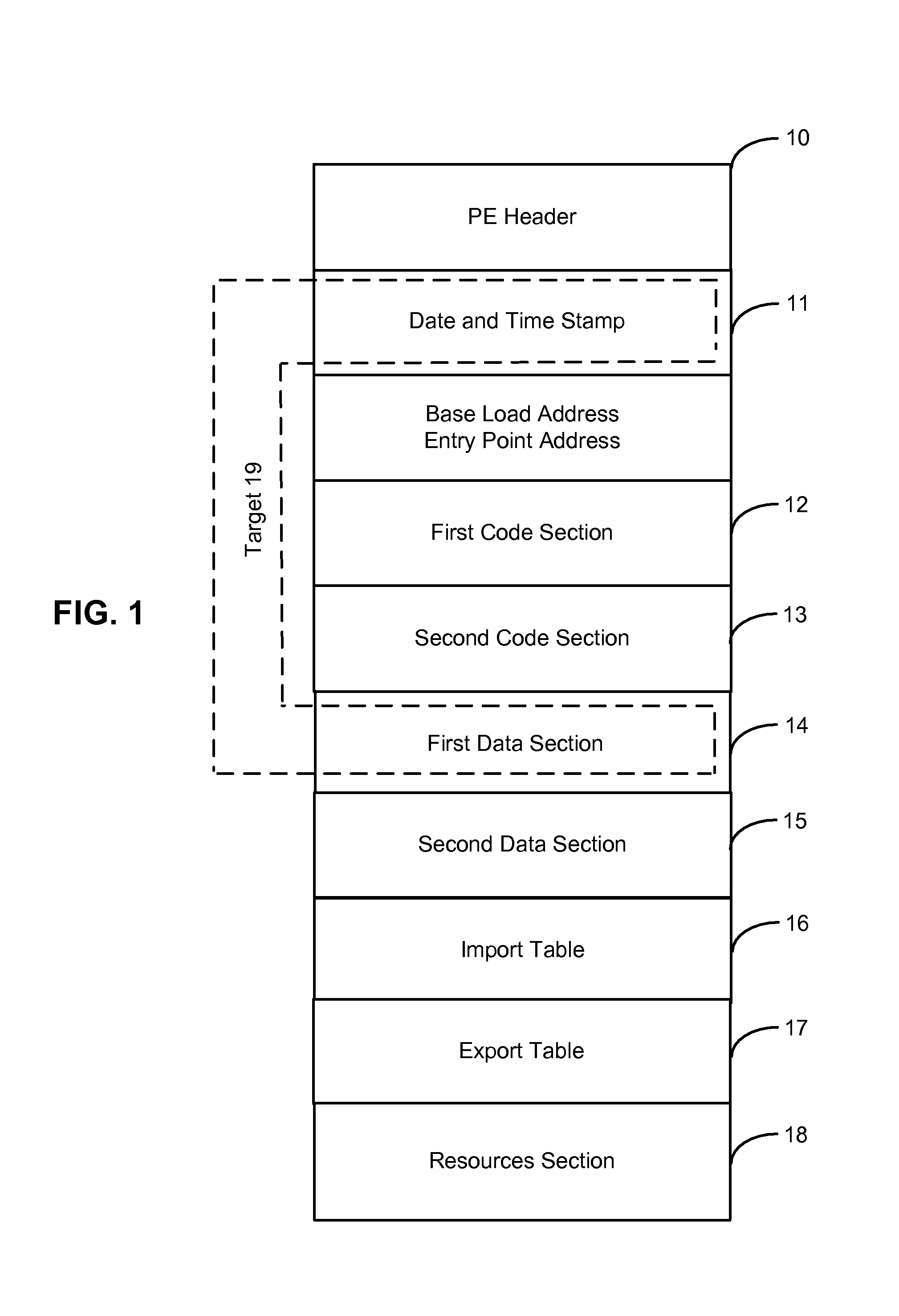
Heuristic detection of malicious computer code by page tracking
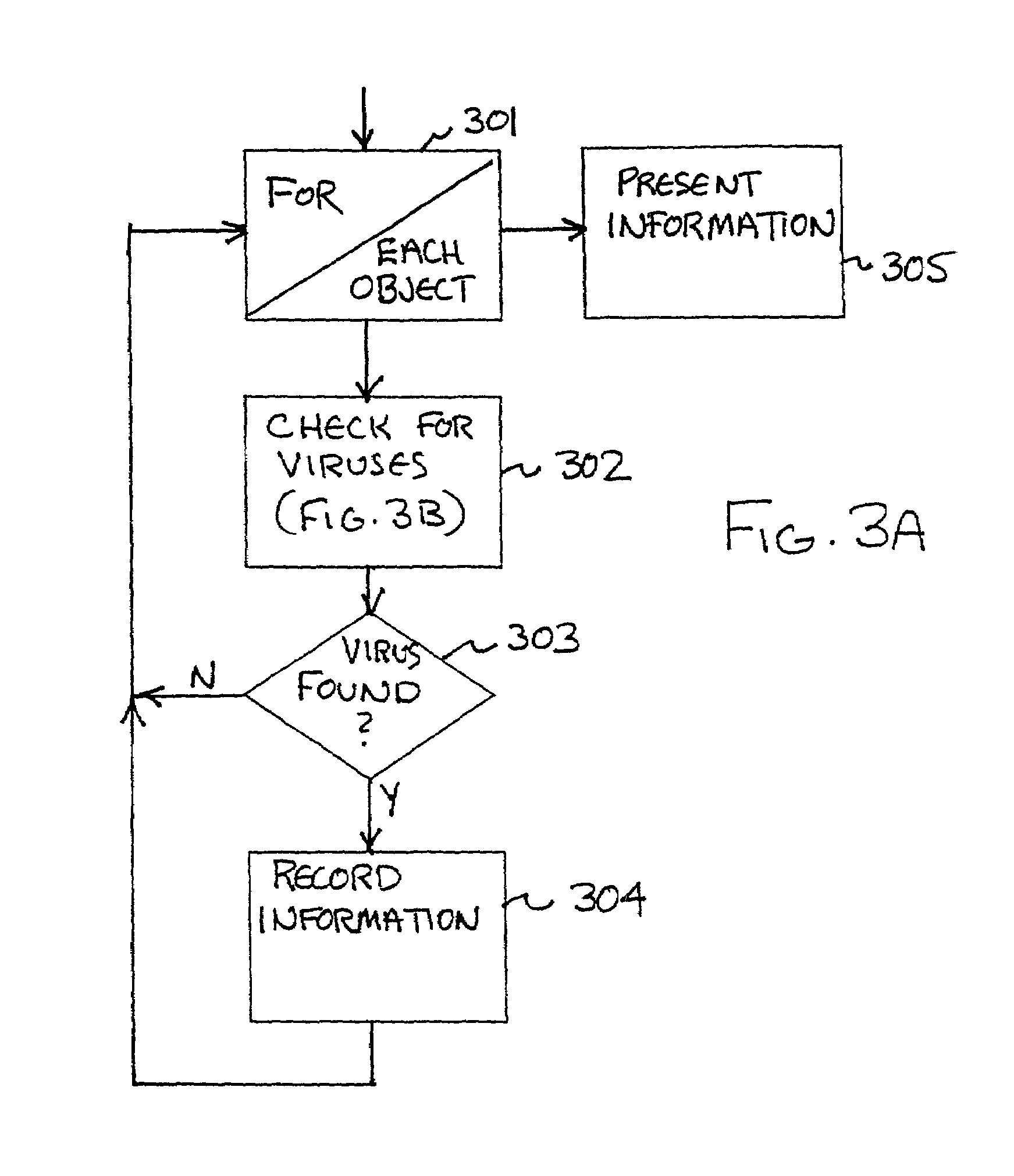
To detect a computer virus in a host file (100), an emulating module (414) emulates the host file (100) in a virtual machine (422) having a virtual memory (426). While emulating the host file (100), the system (400) tracks the host file's access of the virtual memory (426). Responsive to an access in a non-normal address range of the virtual memory (426) by the host file (100), a flag recording module (522) sets a flag. A virus reporting module (526) declares a potential virus based on whether the flag is set.
Owner:CA TECH INC
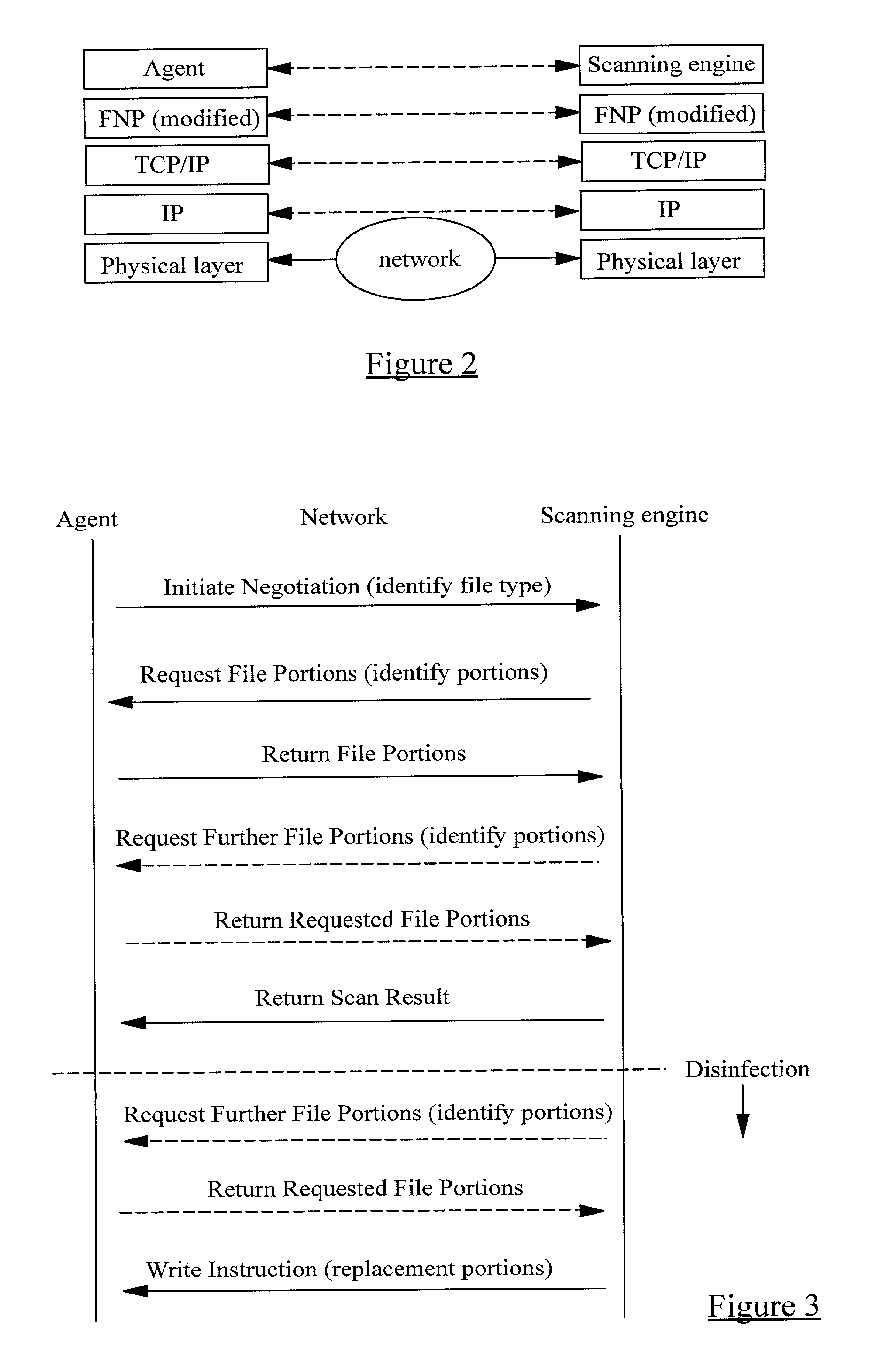
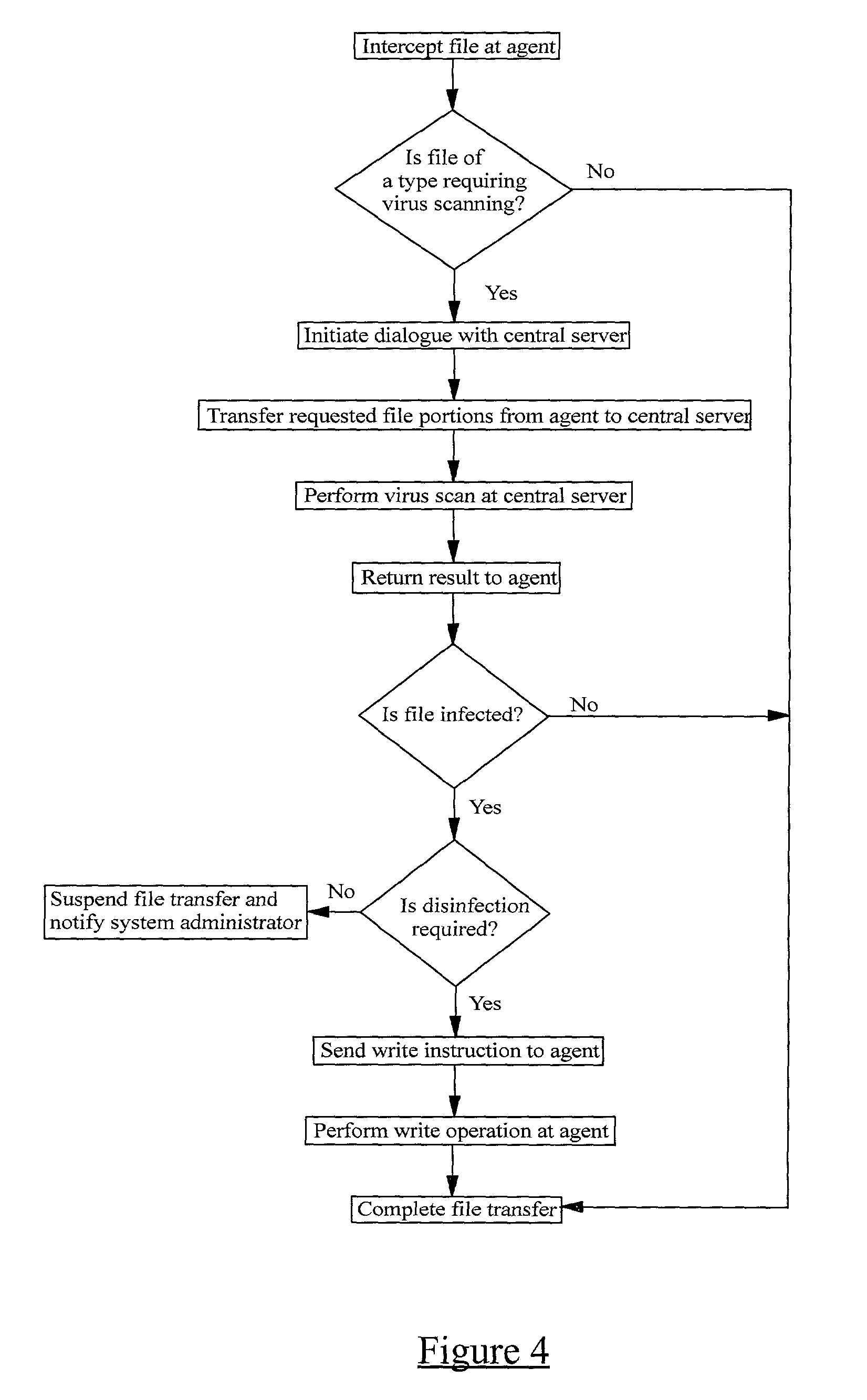
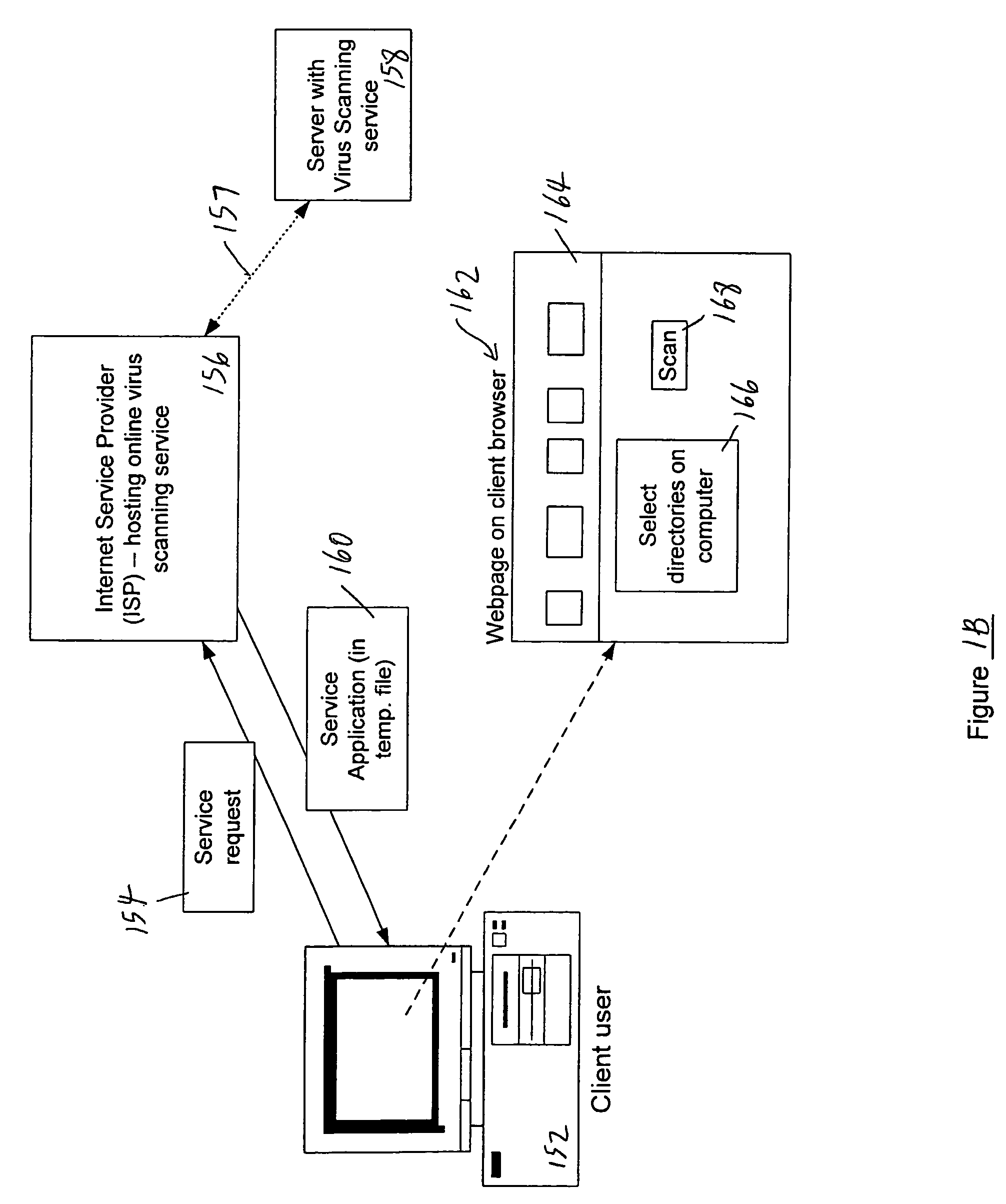
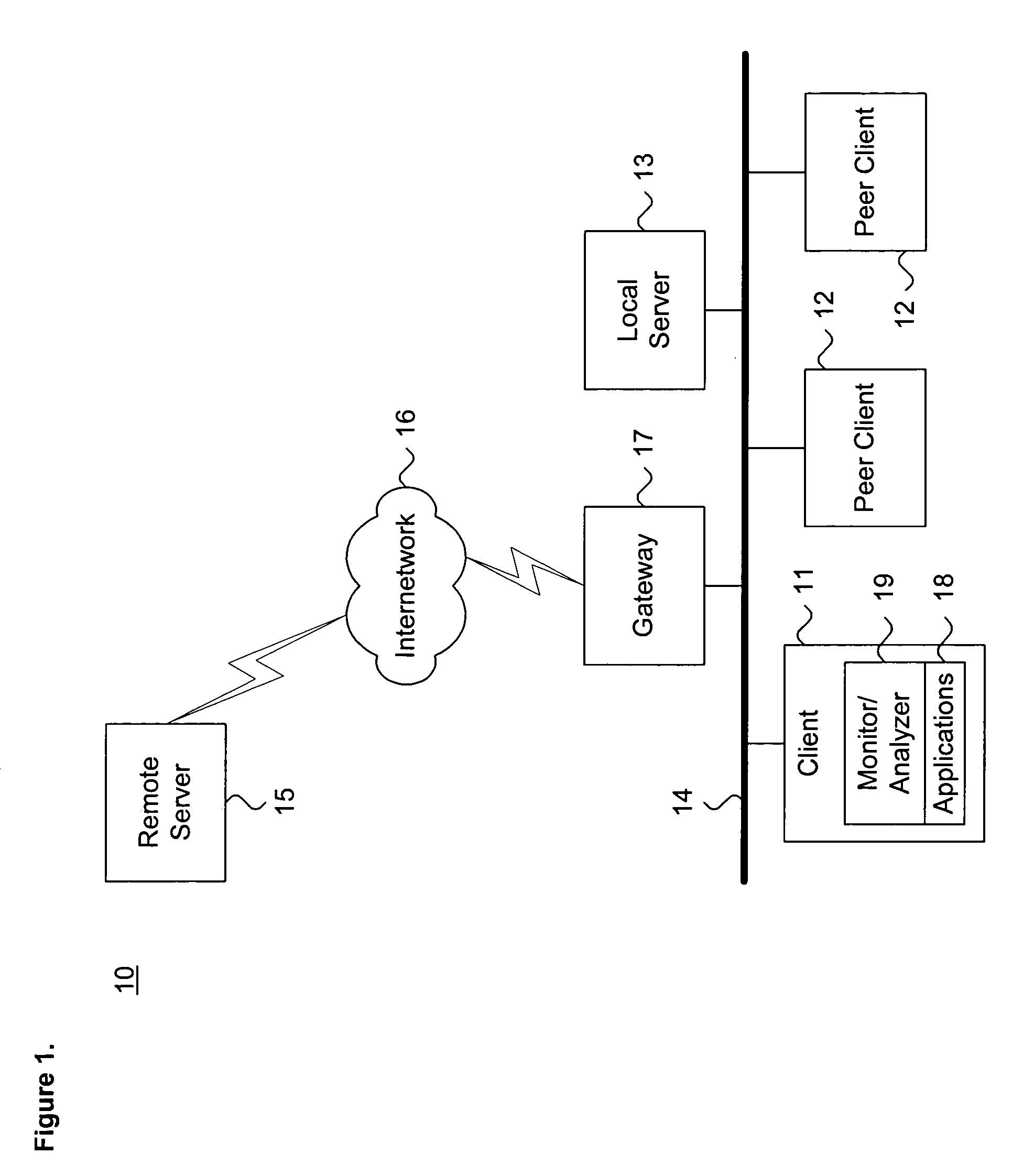
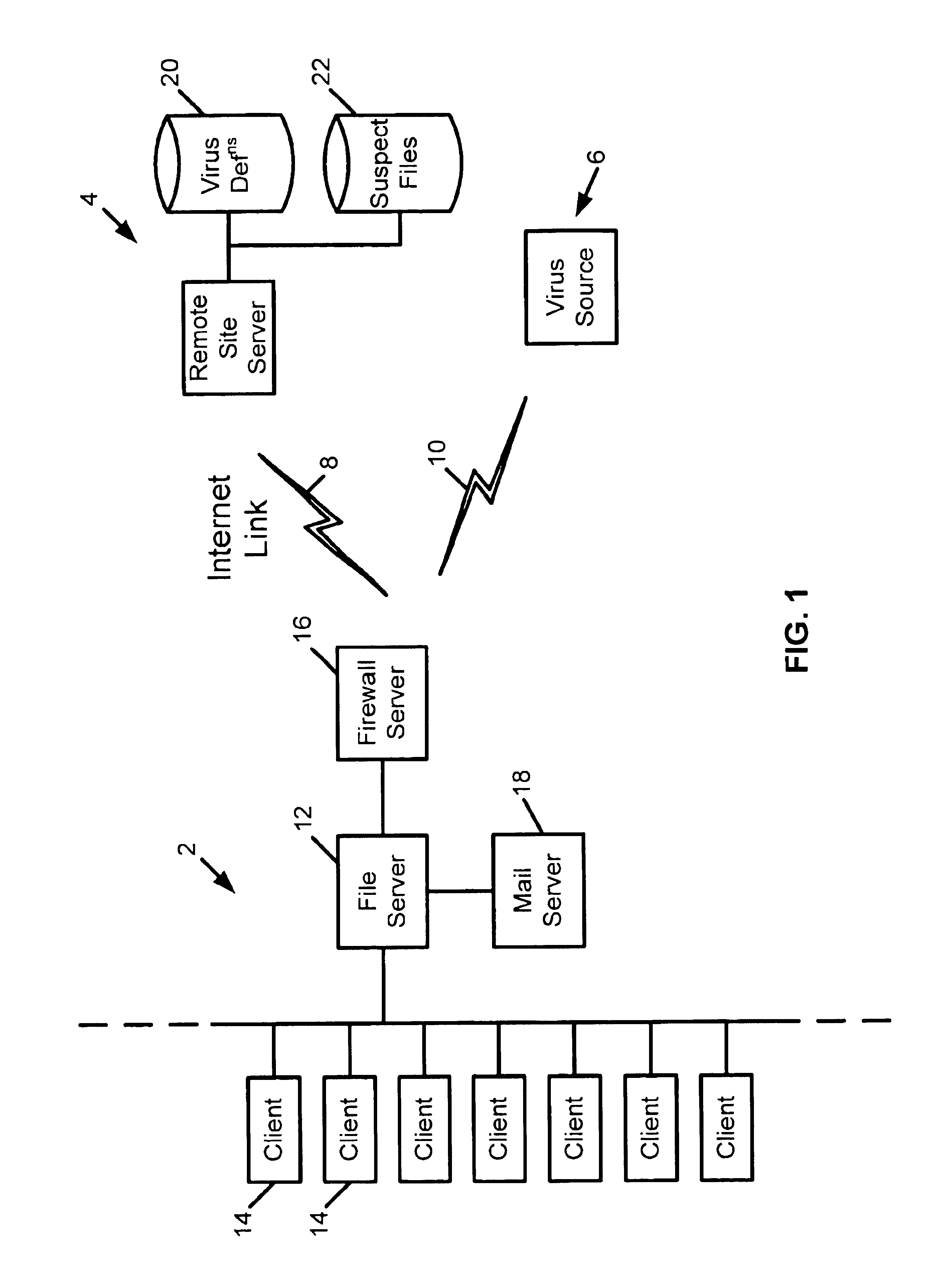
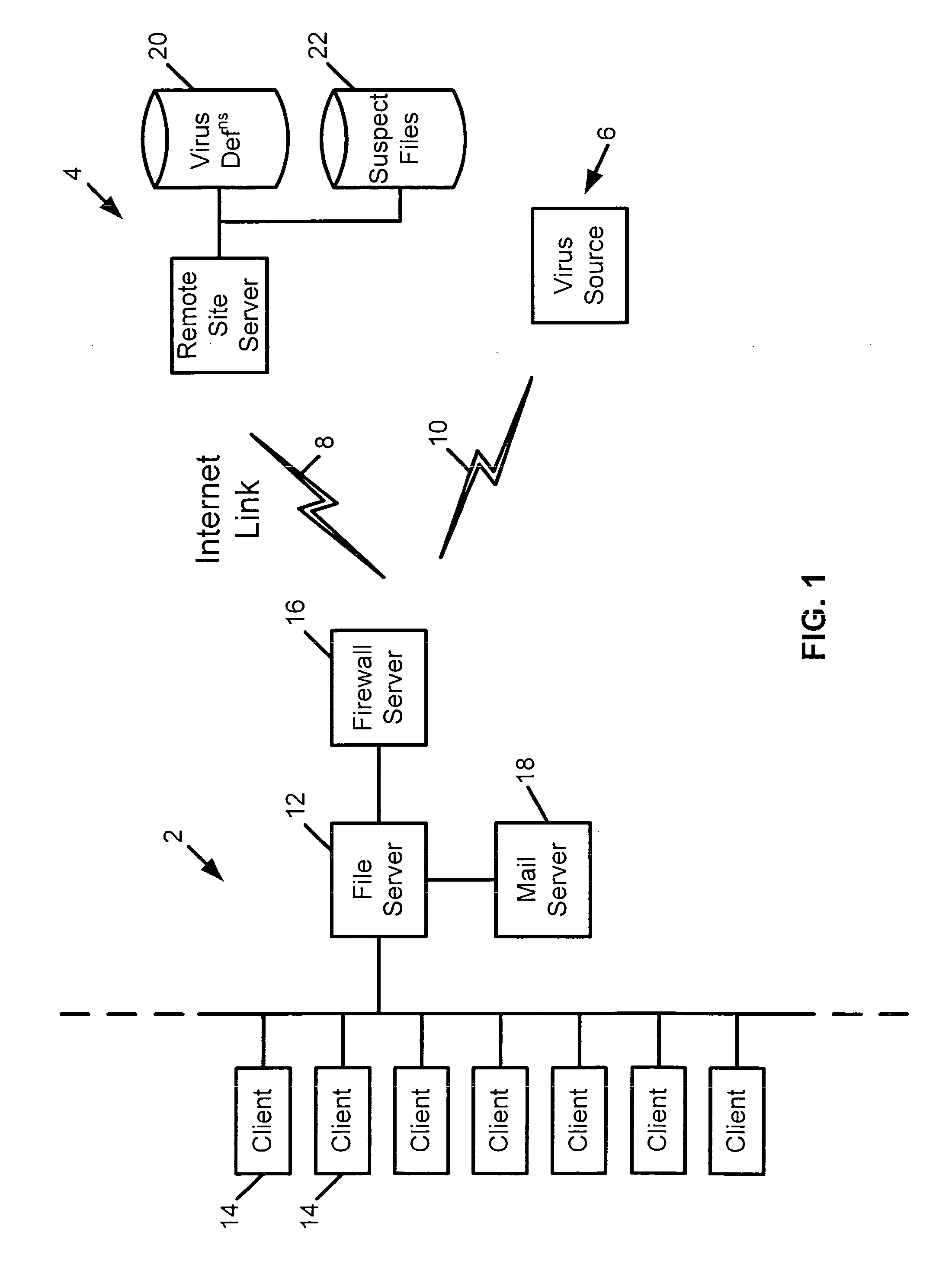
Remote computer virus scanning
InactiveUS20010005889A1Improve network securityLower the volumeMemory loss protectionDigital data processing detailsRemote computerVirus
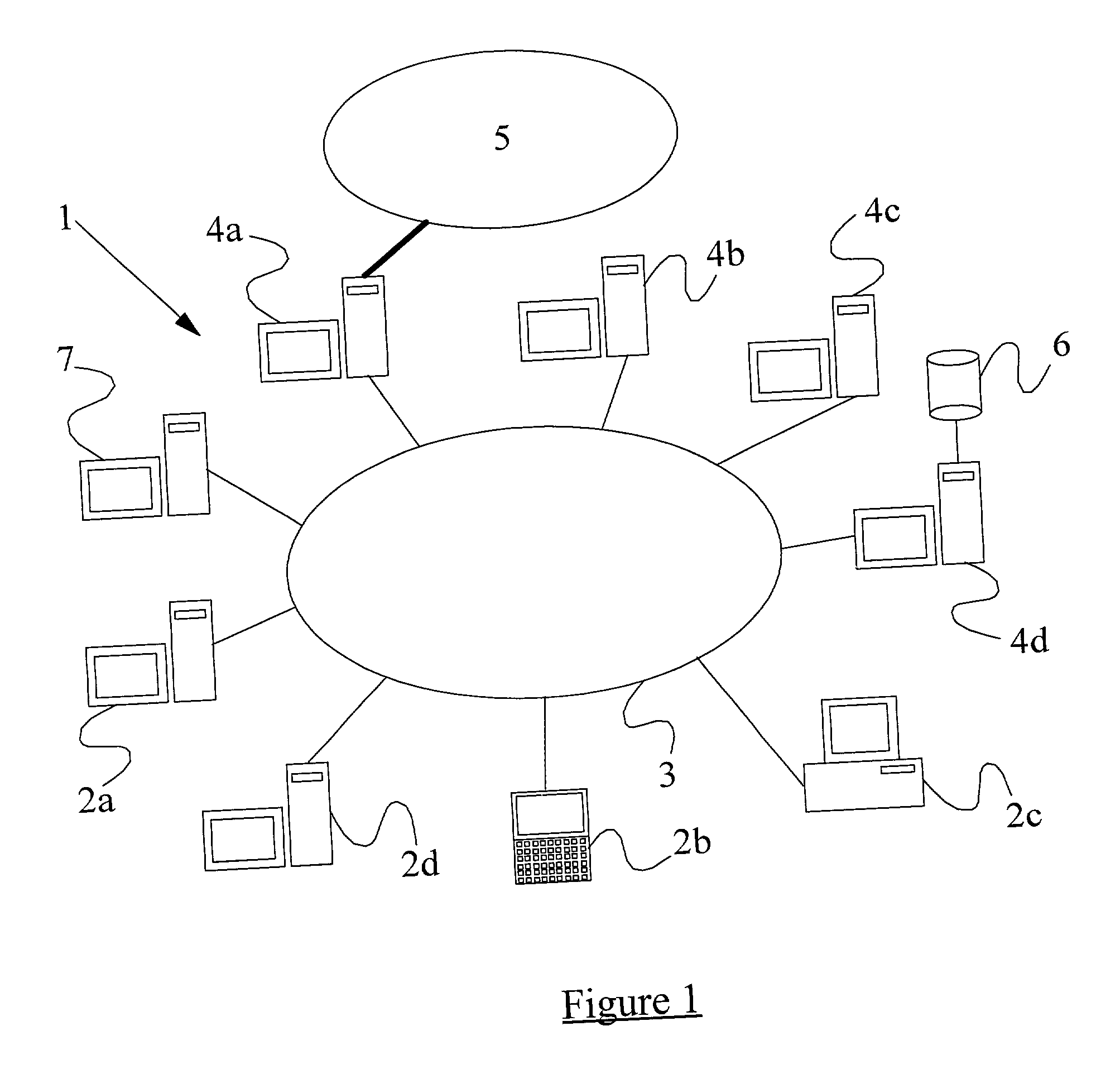
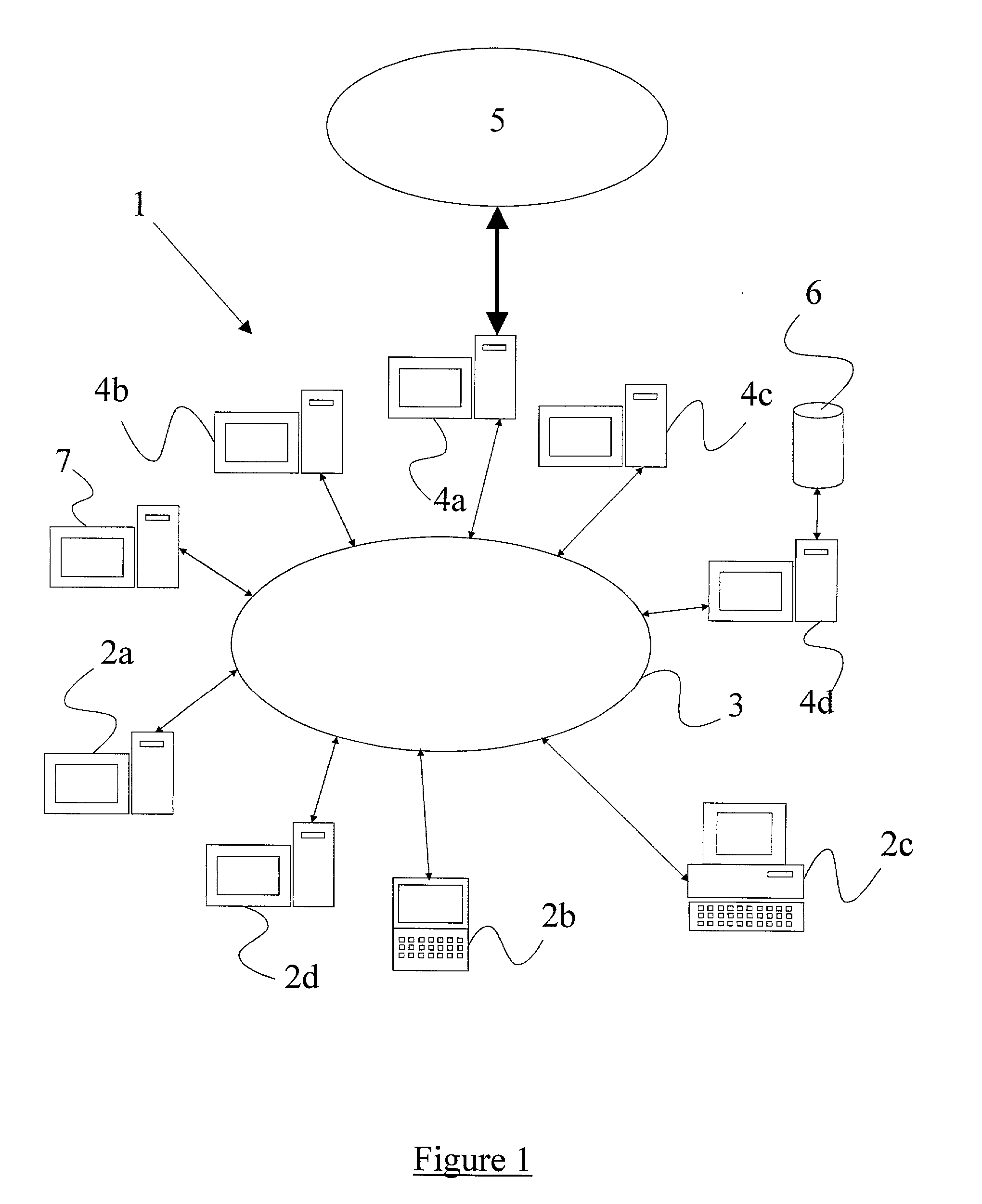
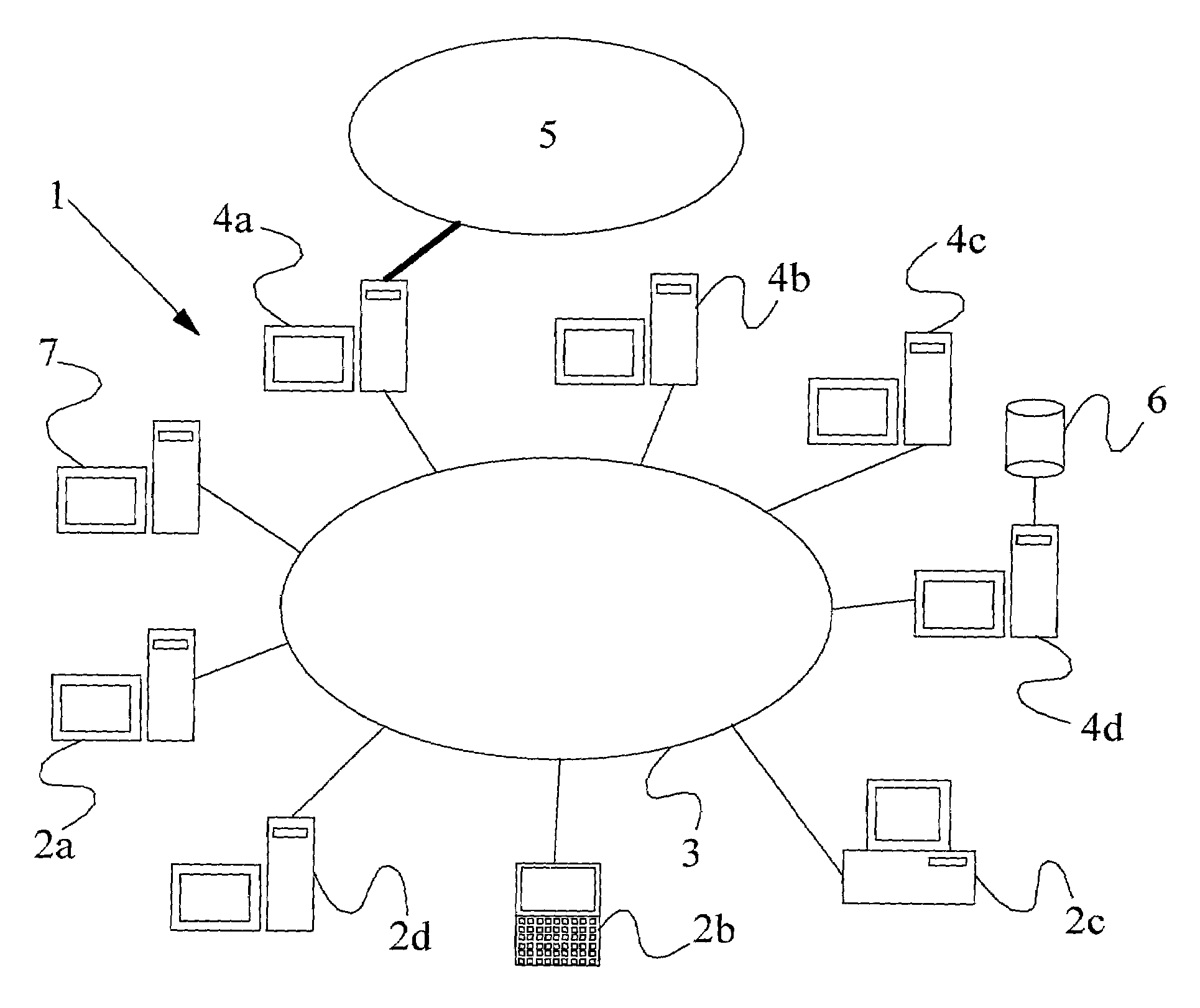
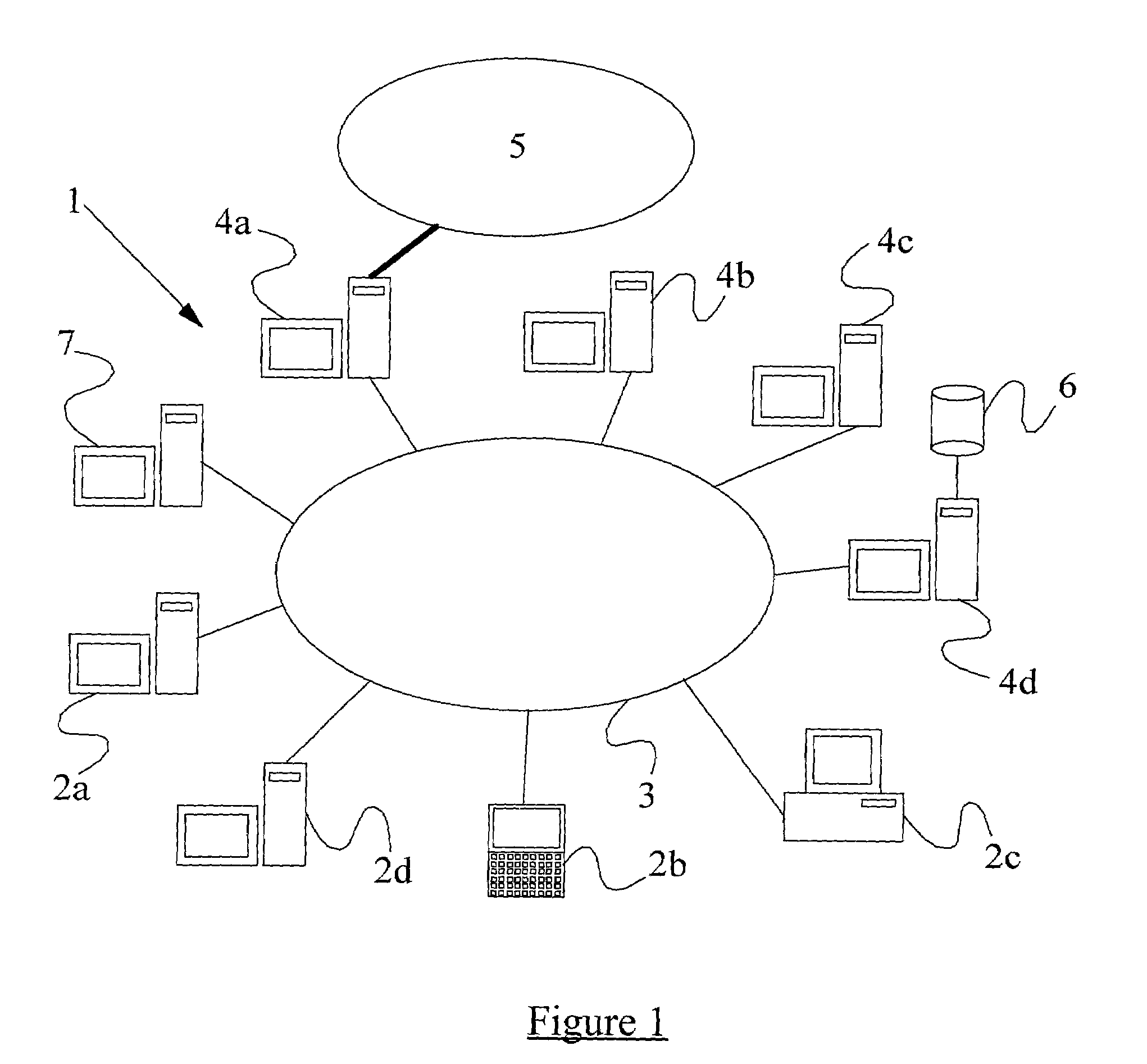
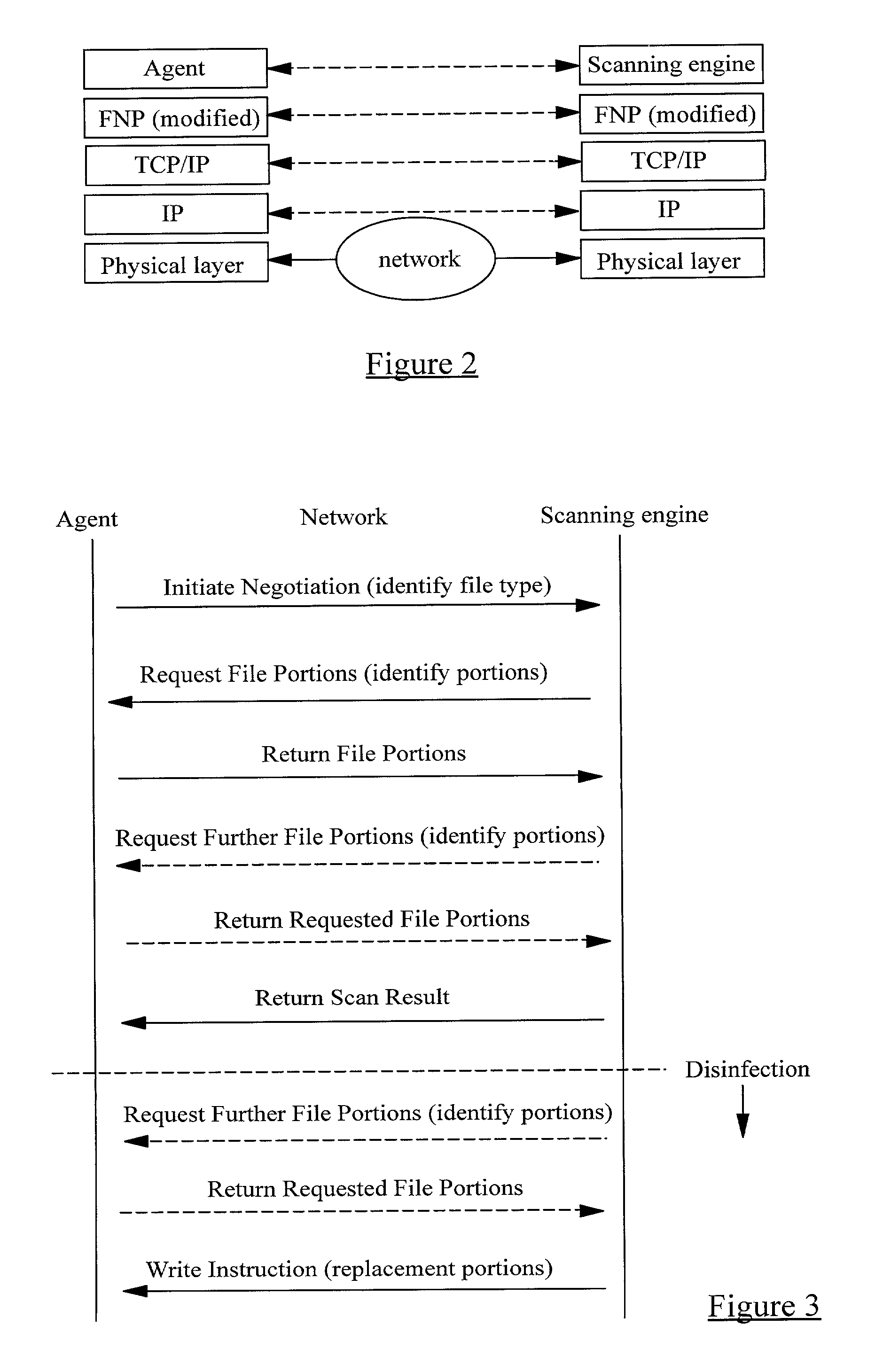
A method of scanning electronic files for computer viruses comprises identifying at a first node 4 of a computer network 1, electronic files which require to be scanned for computer viruses. The first node 4 initiates a dialogue with a second node 7 of the network 1, the second node comprising a virus scanning application. During the dialogue, the second node 7 identifies to the first node 4 one or more portions of the electronic file required by the virus scanning application. The first node 4 transfers the identified portions to the second node 7 which then carries out a virus scanning operation. The result of this operation is then returned to the first node 4.
Owner:F SECURE CORP
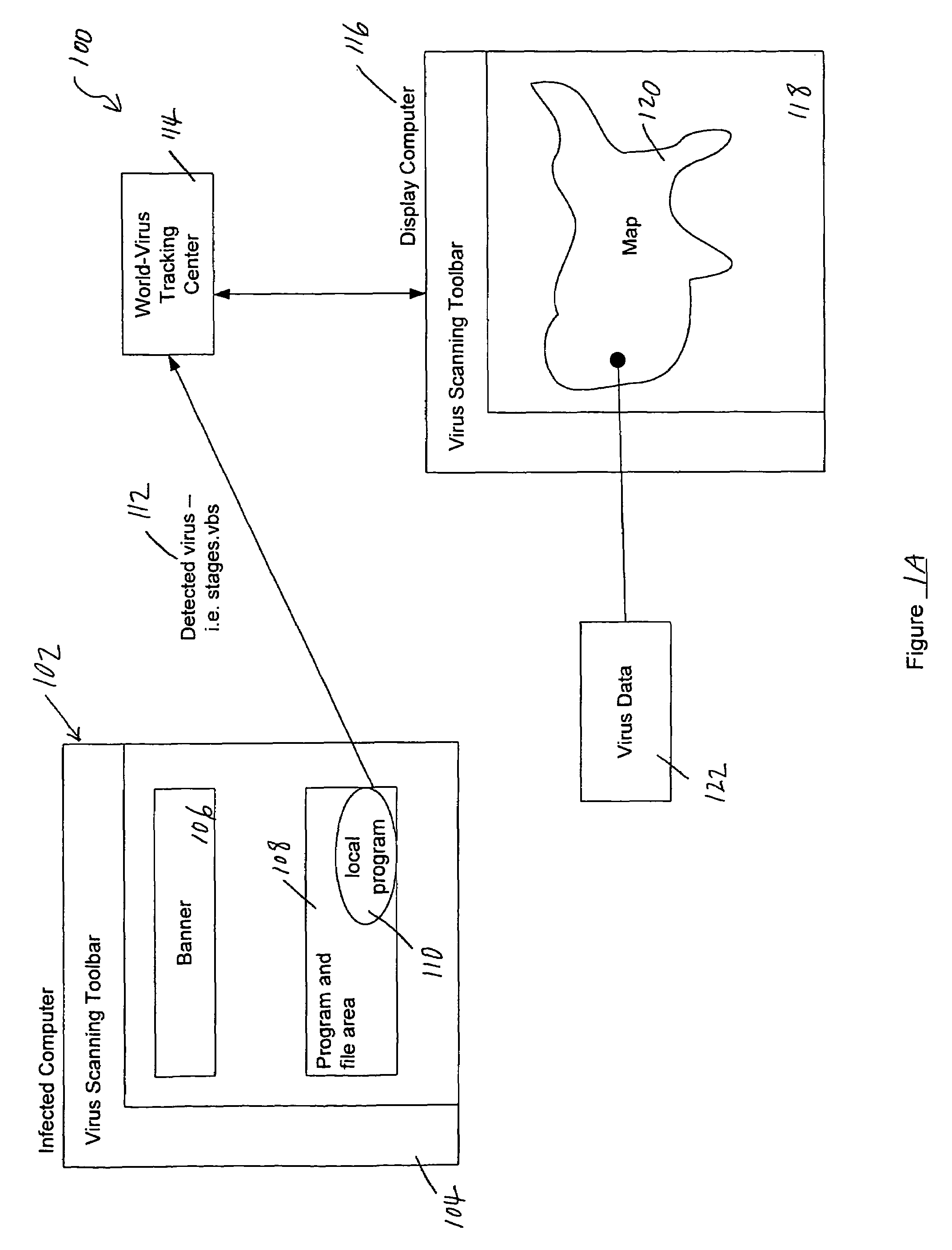
Tracking and reporting of computer virus information
An apparatus and method for providing real-time tracking of virus information as reported from various computers on a distributed computer network. Each client computer on the distributed network contacts an anti-virus scanning site. The site provides a small program or applet that resides in temporary memory of the client computer. The client-user invokes the scan with supplied pattern updates for detecting recent viruses. When the scan has been completed, the user is prompted to supply a country of origin. The name of the virus, its frequency of occurrence, and the country are forwarded as a virus scan log to a virus tracking server, which receives the virus information and thereafter stores it in a database server, which is used to further calculate virus trace display information. A tracking user contacts the virus tracking server and receives map information, which traces the virus activity. The maps show, according to user preference, the names of the viruses encountered in each country, and their frequencies of occurrence.
Owner:TREND MICRO INC
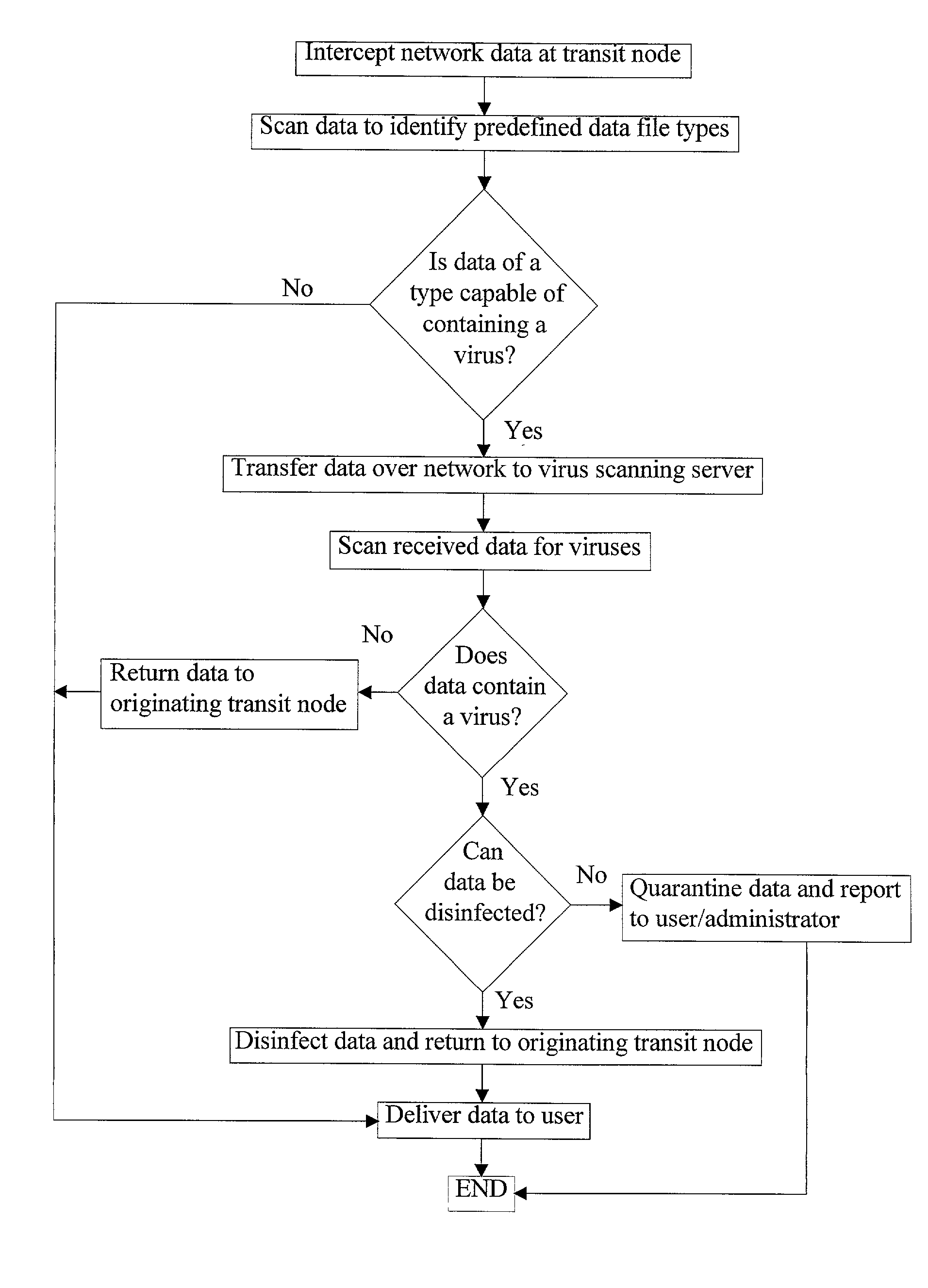
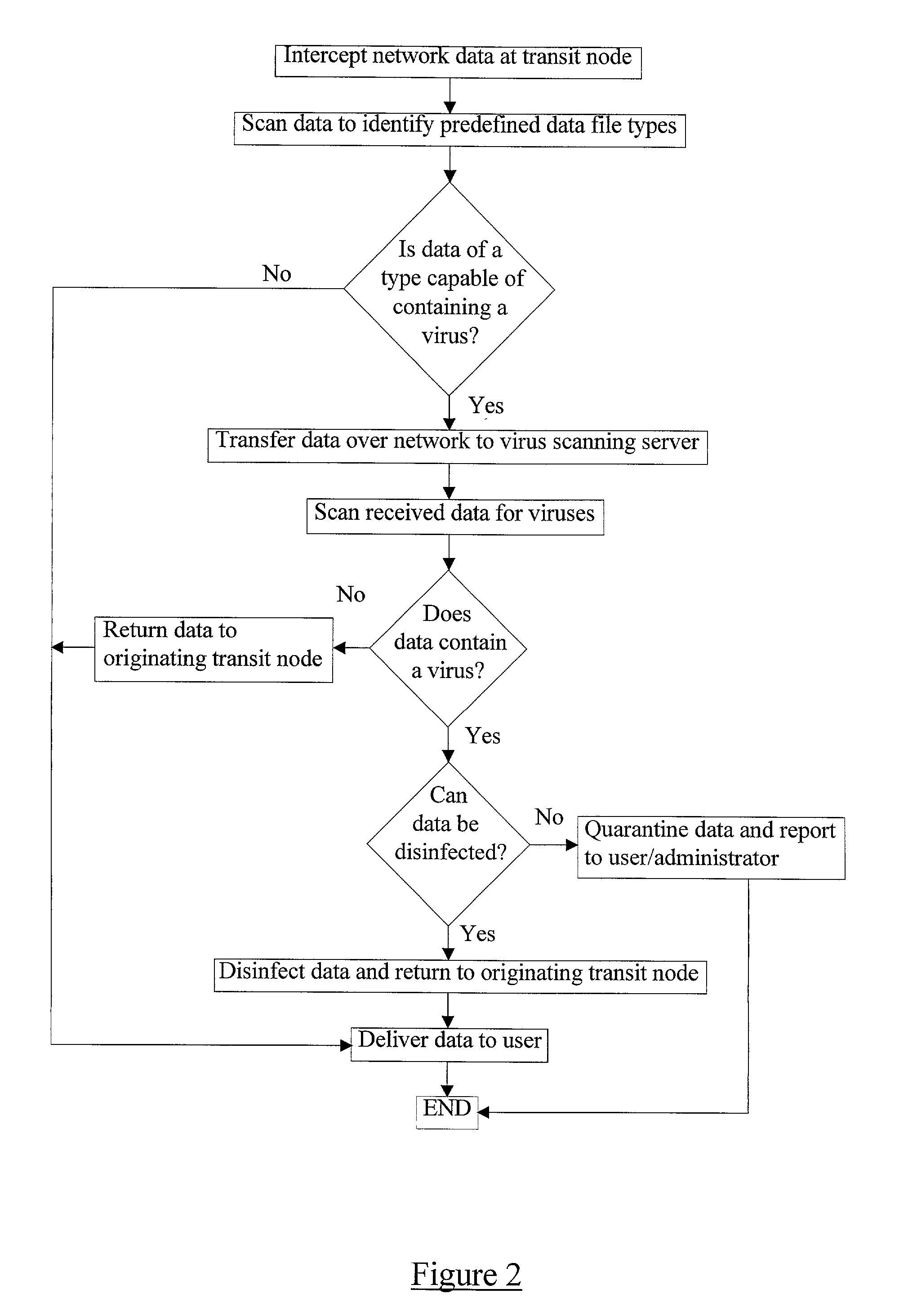
Distributed computer virus detection and scanning
InactiveUS20030191957A1Avoid the needEasy to identifyMemory loss protectionError detection/correctionVirus presentData transmission
A method of detecting viruses in a computer network 1 comprising intercepting data at at least one data transit node 4 of the network 1. The transit node 4 identifies which of the data is of a type capable of containing a virus and transfers the identified data to a virus scanning server 7 over the network 1. The identified data is received at the virus scanning server 7 which scans the data to identify viruses present therein. The server 7 subsequently acts in dependence upon the outcome of the virus scan.
Owner:F SECURE CORP
Inoculation of computing devices against a selected computer virus
ActiveUS7287278B2Avoid infectionMemory loss protectionUnauthorized memory use protectionComputer scienceVirus
In a distributed network having a number of server computers and associated client devices, method of creating an anti-computer virus agent is described. As a method, the inoculation is carried out by parsing a selected computer virus into a detection module that identifies a selected one of the client devices as a target client device, an infection module that causes the virus to infect those target client devices not infected by the selected virus, and a viral code payload module that infects the targeted client device modifying the infection module to infect those computers already infected by the selected virus; and incorporating inoculation viral code in the payload module that acts to prevent further infection by the selected virus.
Owner:TREND MICRO INC
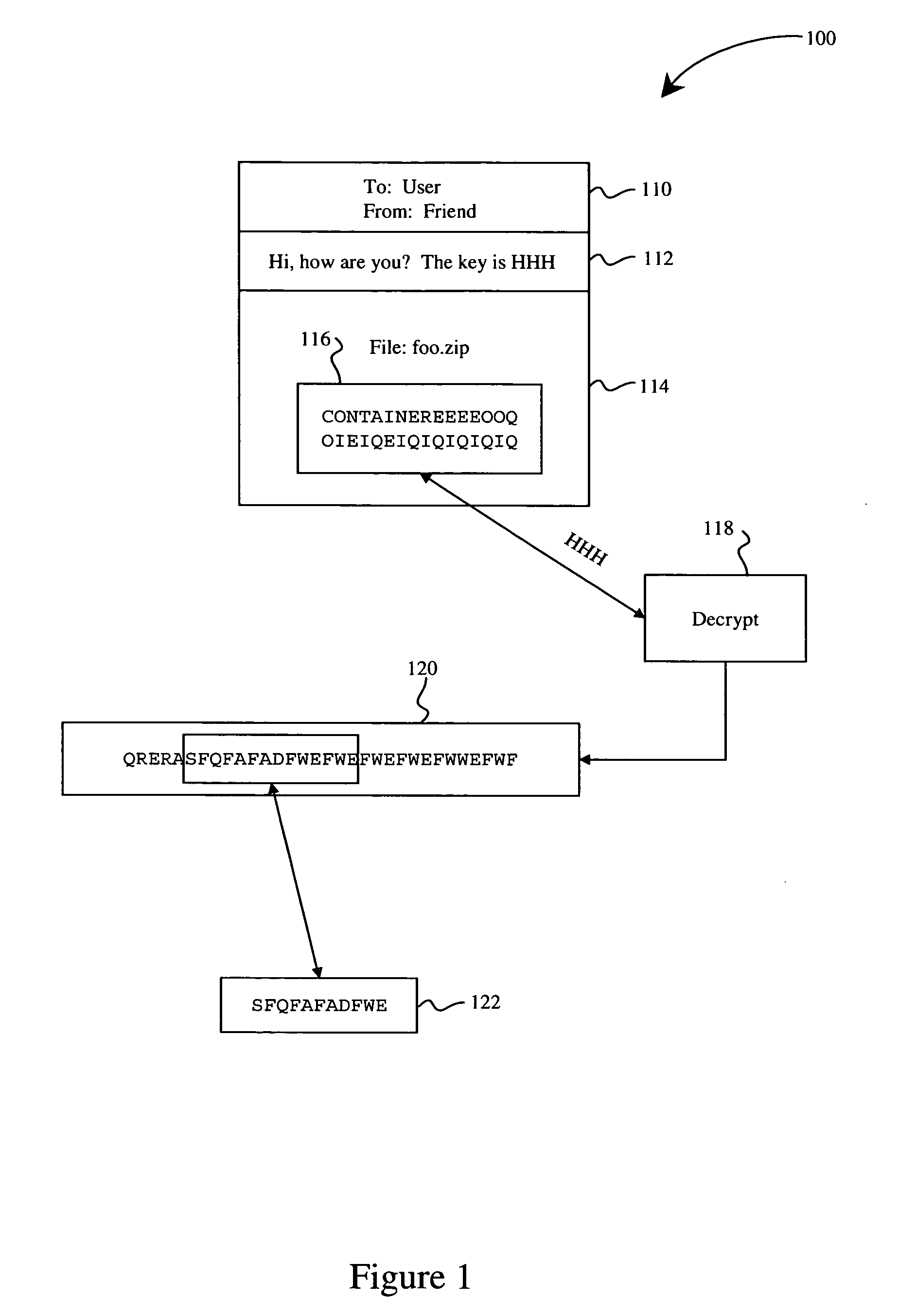
Heuristic detection of malicious computer code by page tracking
To detect a computer virus in a host file (100), an emulating module (414) emulates the host file (100) in a virtual machine (422) having a virtual memory (426). While emulating the host file (100), the system (400) tracks the host file's access of the virtual memory (426). Responsive to an access in a non-normal address range of the virtual memory (426) by the host file (100), a flag recording module (522) sets a flag. A virus reporting module (526) declares a potential virus based on whether the flag is set.
Owner:CA TECH INC
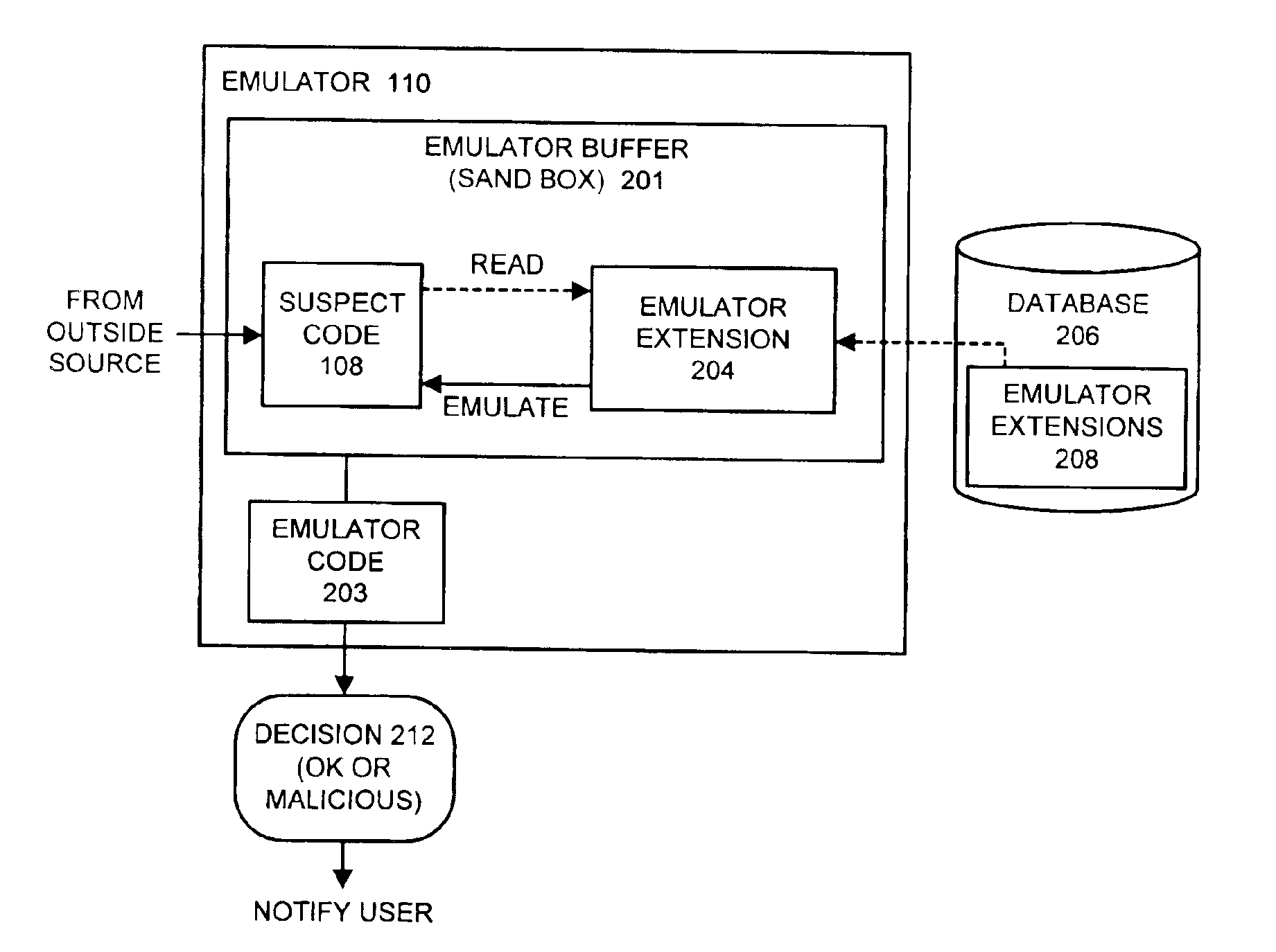
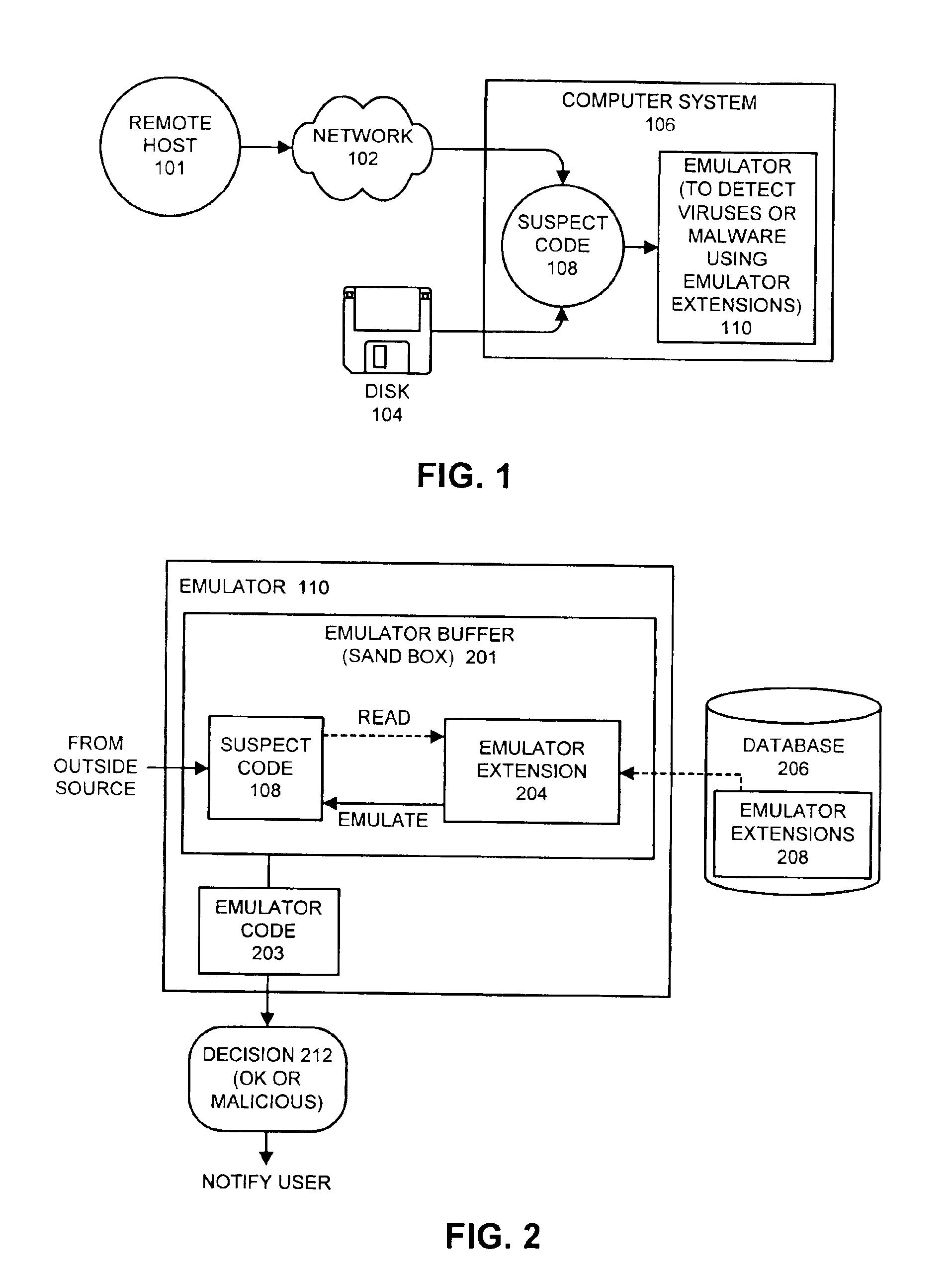
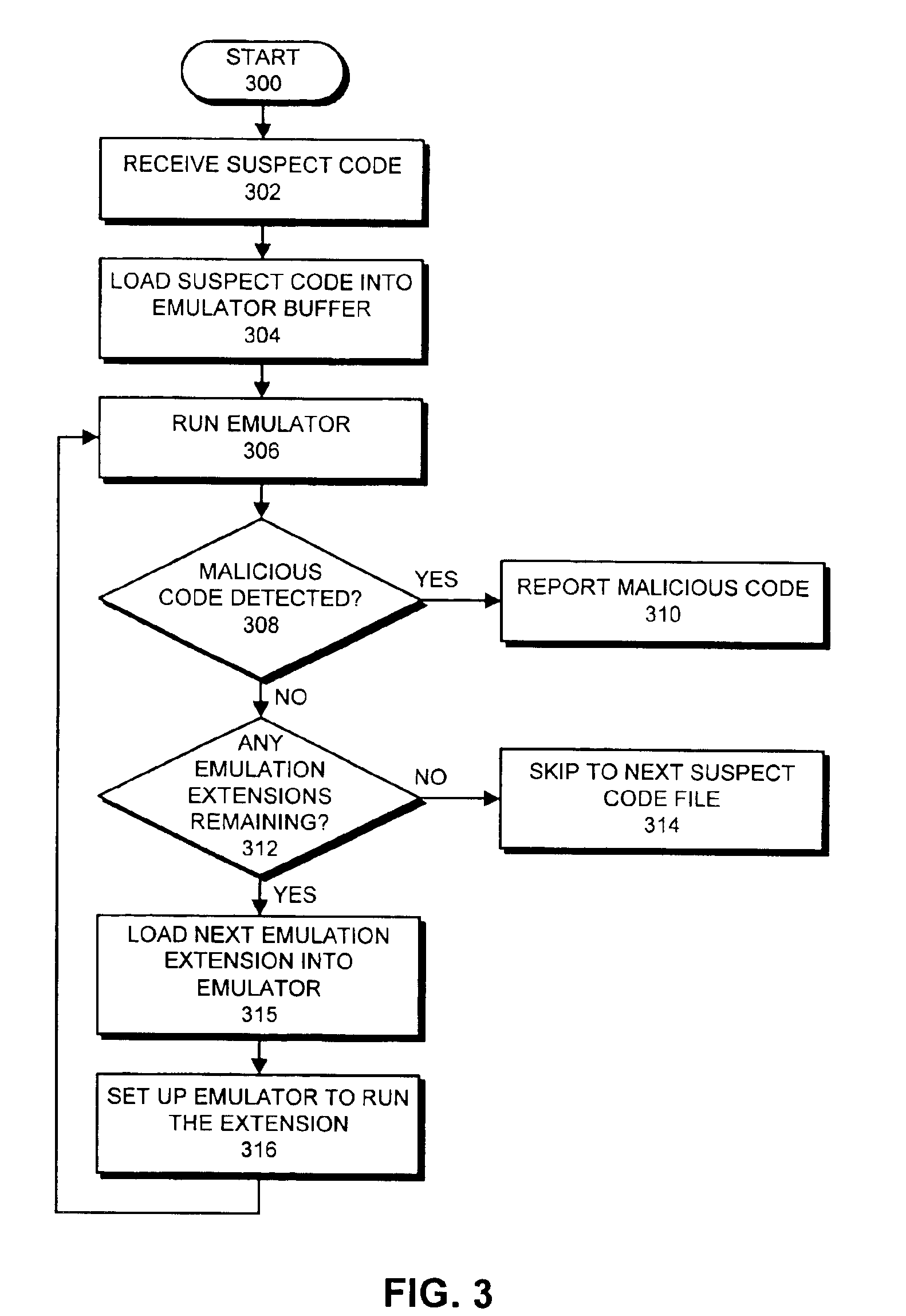
Detecting computer viruses or malicious software by patching instructions into an emulator
InactiveUS6907396B1High simulationPlatform integrity maintainanceTransmissionProgram instructionAnalog computer
One embodiment of the present invention provides a system for emulating computer viruses and / or malicious software that operates by patching additional program instructions into an emulator in order to aid in detecting a computer virus and / or malicious software within suspect code. During operation, the system loads a first emulator extension into the emulator. This first emulator extension includes program instructions that aid in the process of emulating the suspect code in order to detect a computer virus and / or malicious software. The system also loads the suspect code into an emulator buffer. Next, the system performs an emulation using the first emulator extension and the suspect code. This emulation is performed within an insulated environment in a computer system so that the computer system is insulated from malicious actions of the suspect code. During this emulation, the system determines whether the suspect code is likely to exhibit malicious behavior. In one embodiment of the present invention, loading the first emulator extension into the emulator involves loading the first emulator extension into the emulator buffer within the emulator. In this embodiment, performing the emulation involves emulating the program instructions that comprise the first emulator extension.
Owner:MCAFEE LLC
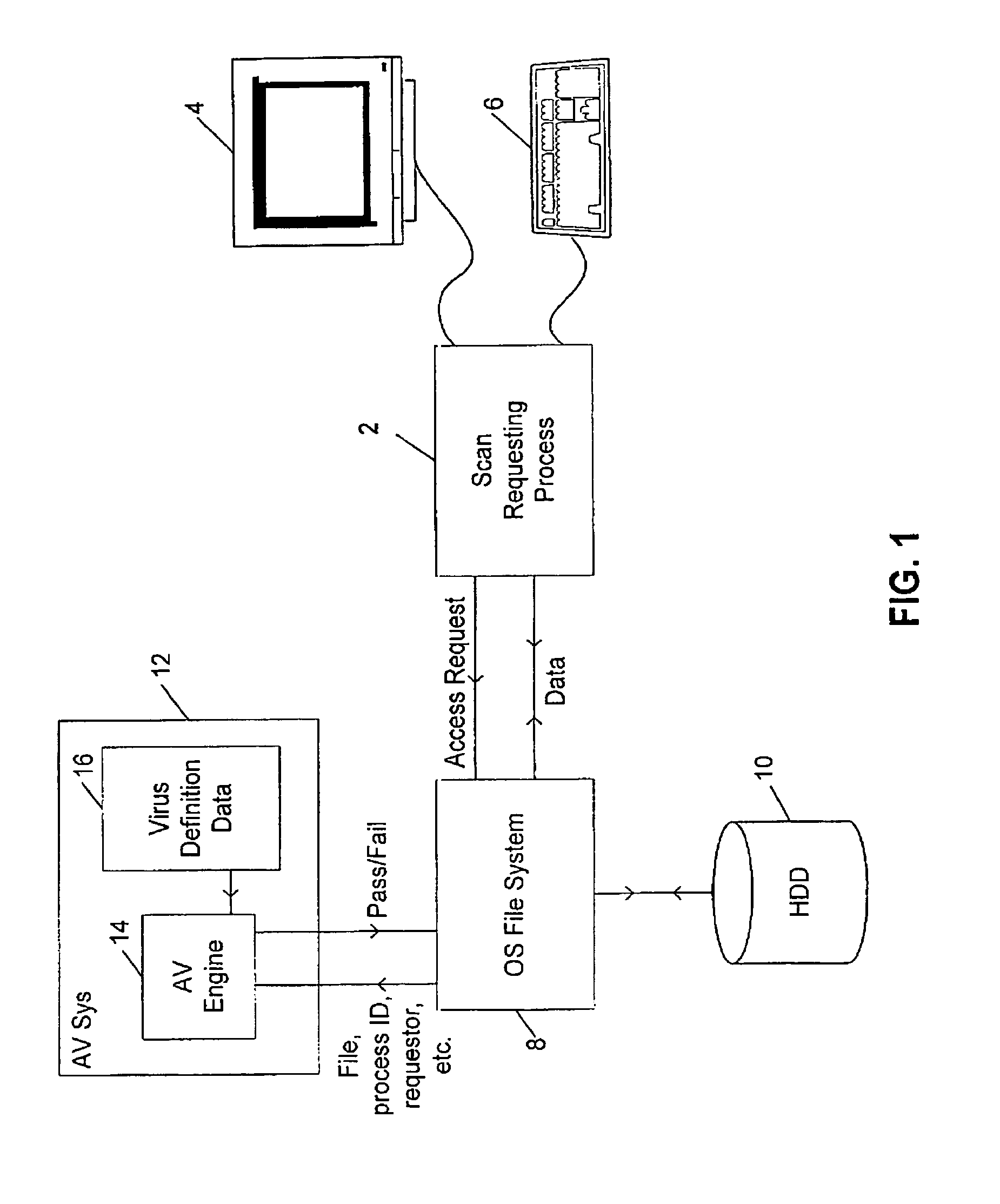
System and method for computer virus detection utilizing heuristic analysis
ActiveUS7231667B2Memory loss protectionUnauthorized memory use protectionChronological timeComputer engineering
A computer virus detection method includes compiling a list of heuristic events and a chronological order in which they occur, comparing the list of heuristic events and the chronological order with a defined list of heuristic events occurring in a defined chronological order and determining whether a computer virus is present based on a result of the comparing.
Owner:COMP ASSOC THINK INC
System and method for detecting computer virus
ActiveUS20060015747A1User identity/authority verificationUnauthorized memory use protectionComputer hardwareComputer science
A method is disclosed for detecting computer viruses. The method allows receipt of an electronic mail message that includes at least one encrypted attachment. The electronic mail message is examined in order to identify potential encryption codes. The encryption codes are used in order to attempt and decrypt the attachments. The attachments are expanded into one or more files. The files are then checked for the presence of computer viruses.
Owner:RED HAT
System and method for dynamically detecting computer viruses through associative behavioral analysis of runtime state
InactiveUS6973577B1Data processing applicationsMemory loss protectionApplication softwareMultiple applications
Owner:MCAFEE LLC
Remote computer virus scanning
InactiveUS7020895B2Lower the volumeImprove network securityMemory loss protectionDigital data processing detailsRemote computerVirus
A method of scanning electronic files for computer viruses comprises identifying at a first node 4 of a computer network 1, electronic files which require to be scanned for computer viruses. The first node 4 initiates a dialogue with a second node 7 of the network 1, the second node comprising a virus scanning application. During the dialogue, the second node 7 identifies to the first node 4 one or more portions of the electronic file required by the virus scanning application. The first node 4 transfers the identified portions to the second node 7 which then carries out a virus scanning operation. The result of this operation is then returned to the first node 4.
Owner:F SECURE CORP
Computer virus screening
InactiveUS6577920B1Effectively block transferEffectively block processingMemory loss protectionError detection/correctionViral infectionDatabase
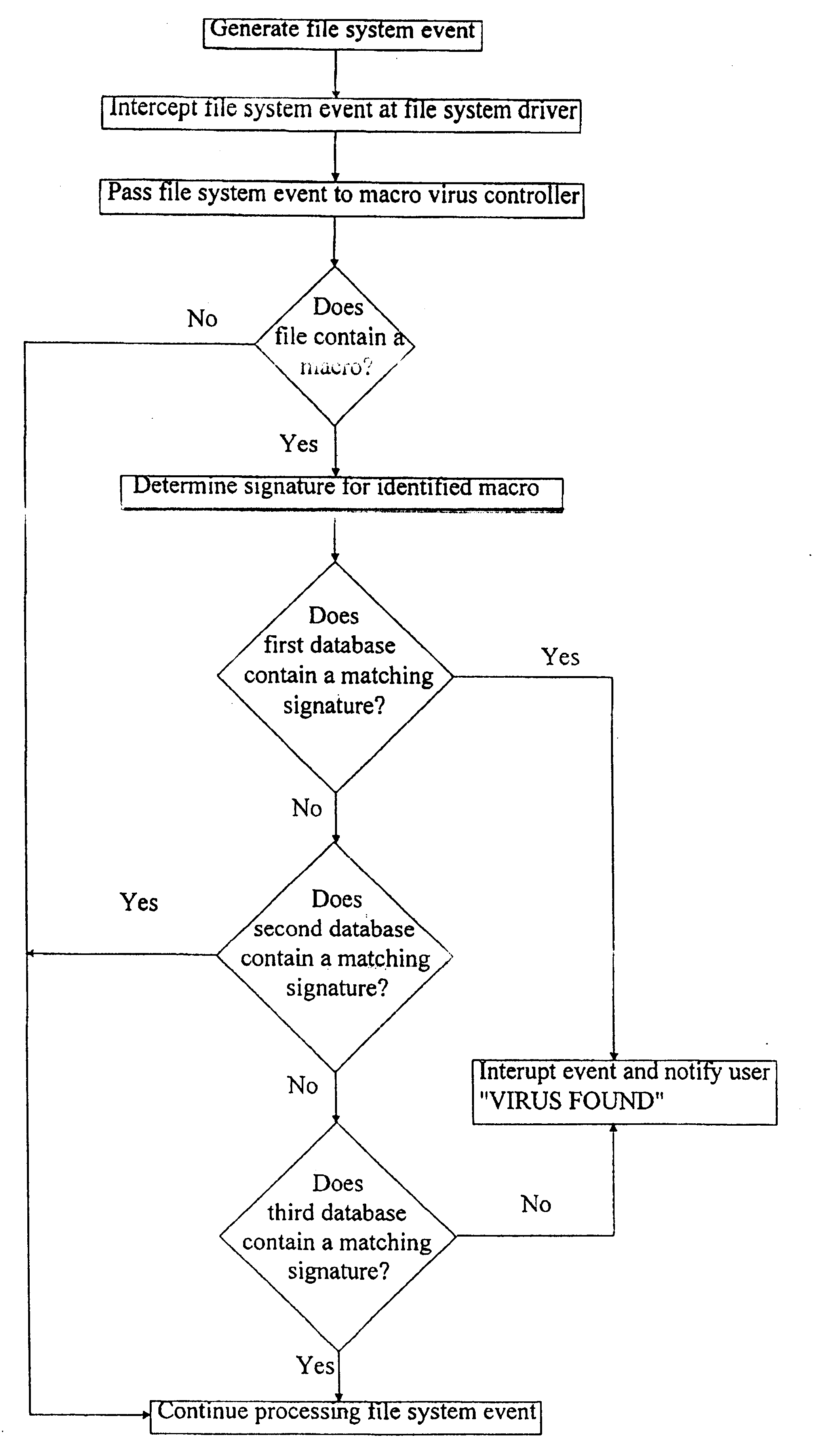
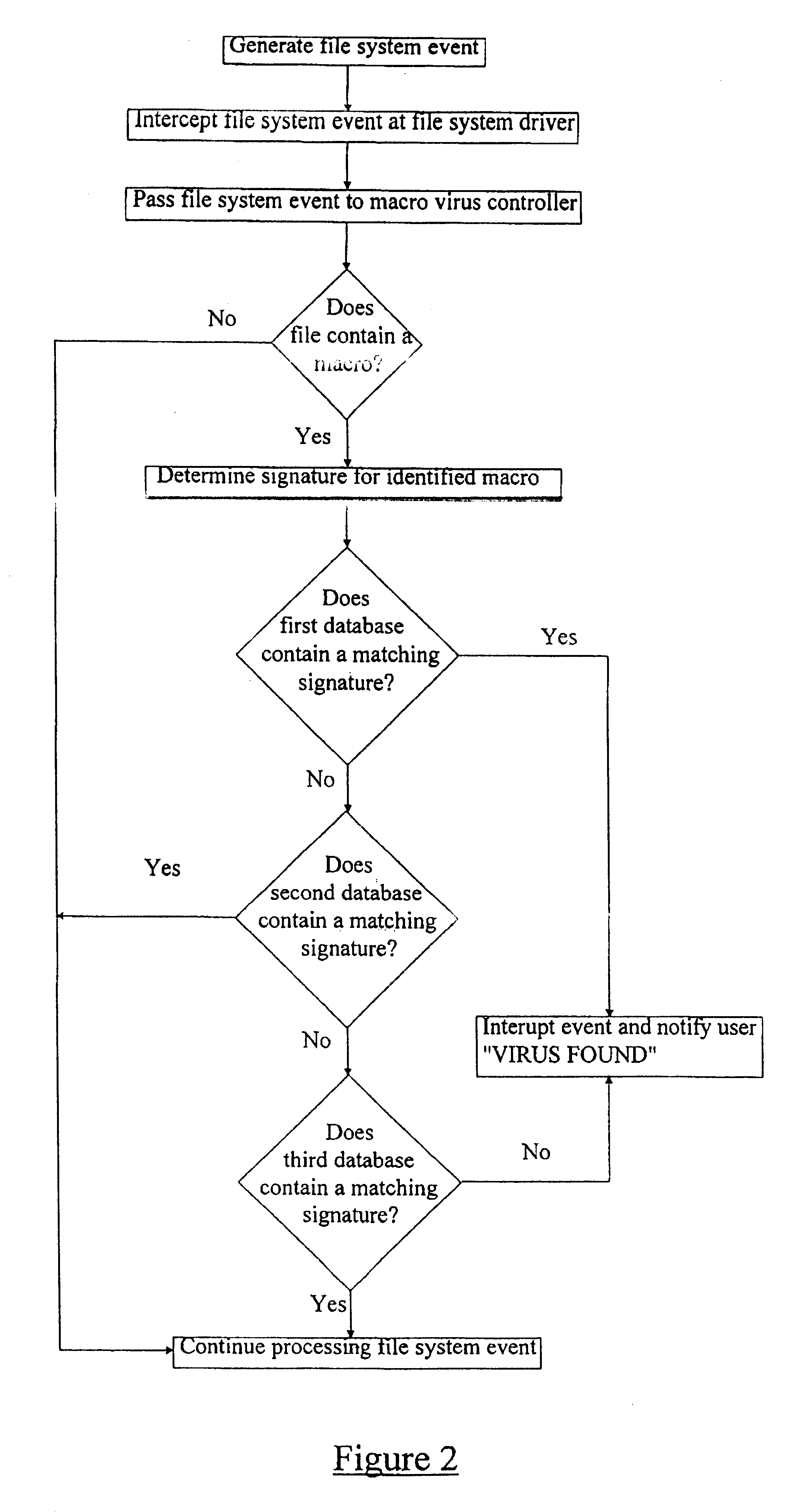
A method of screening a software file for viral infection comprising defining a first database of known macro virus signatures, a second database of known and certified commercial macro signatures, and a third database of known and certified local macro signatures. The file is scanned to determine whether or not the file contains a macro. If the file contains a macro, a signature for the macro is determined and screened against the signatures contained in said databases. A user is alerted in the event that the macro has a signature corresponding to a signature contained in said first database and / or in the event that the macro has a signature which does not correspond to a signature contained in either of the second and third databases.
Owner:F SECURE CORP
Pre-approval of computer files during a malware detection
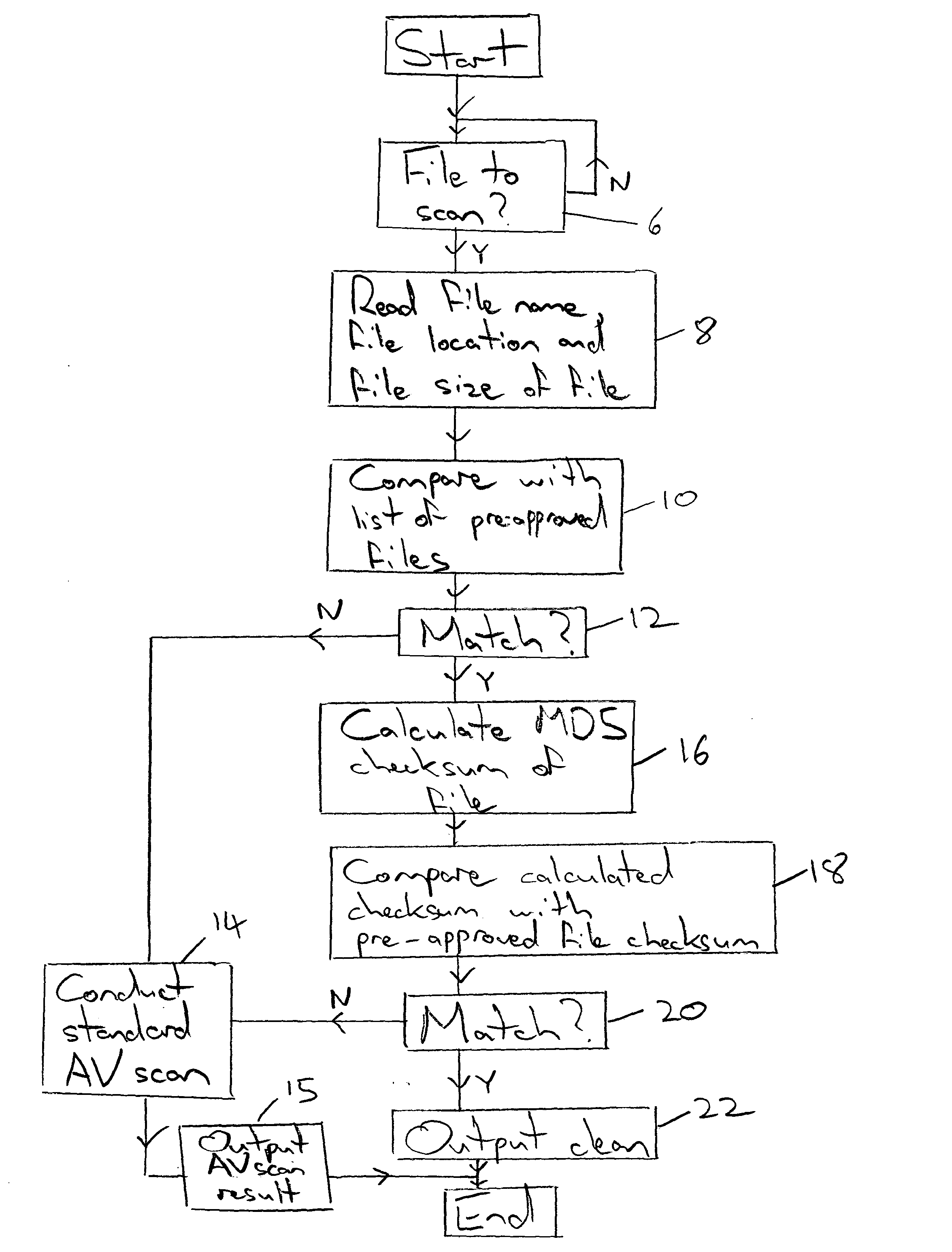
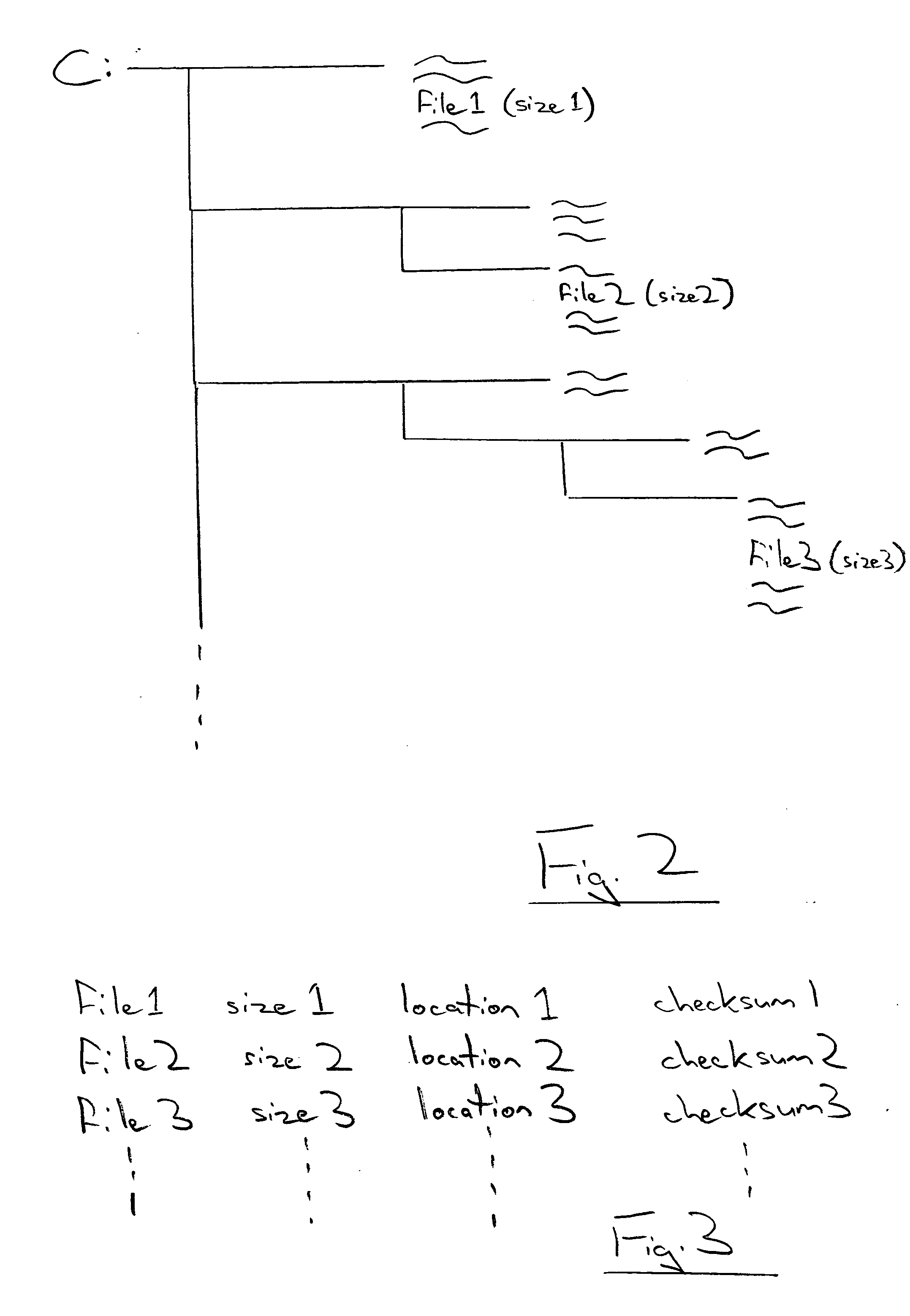
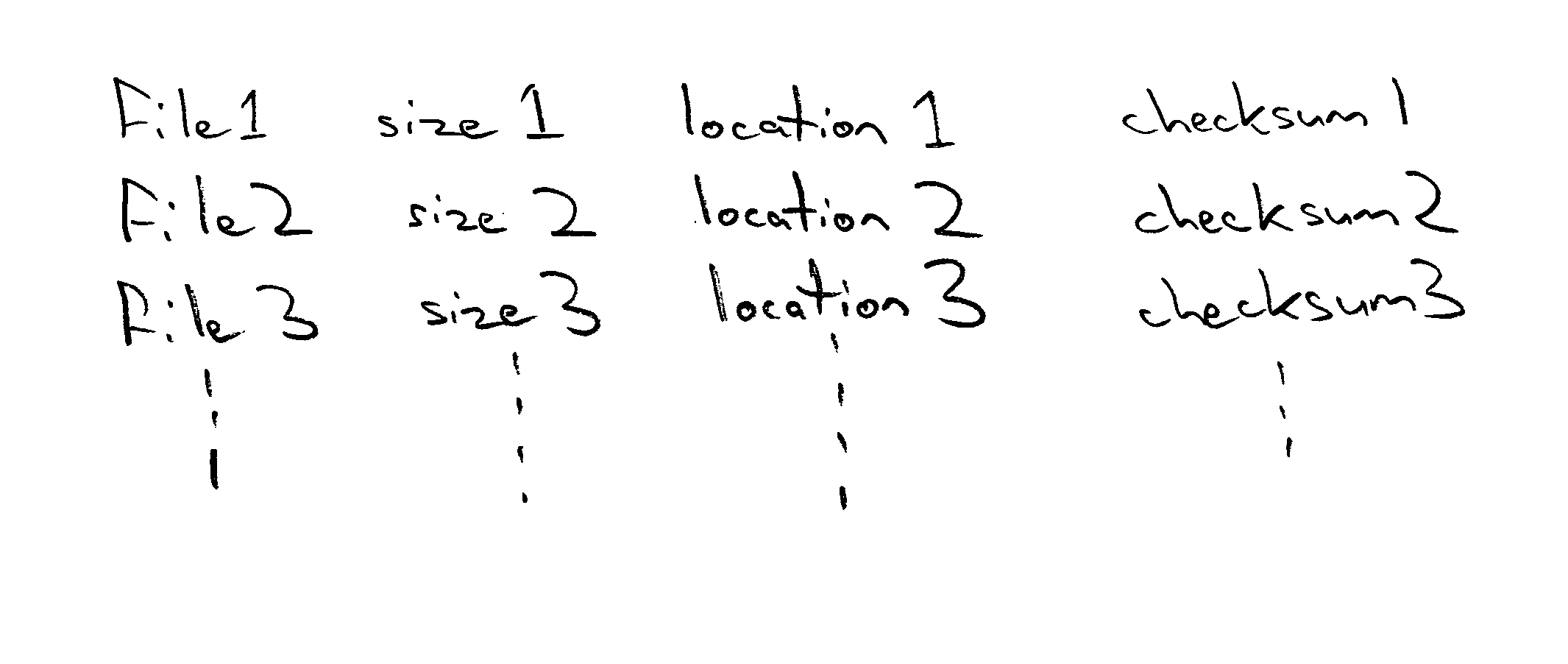
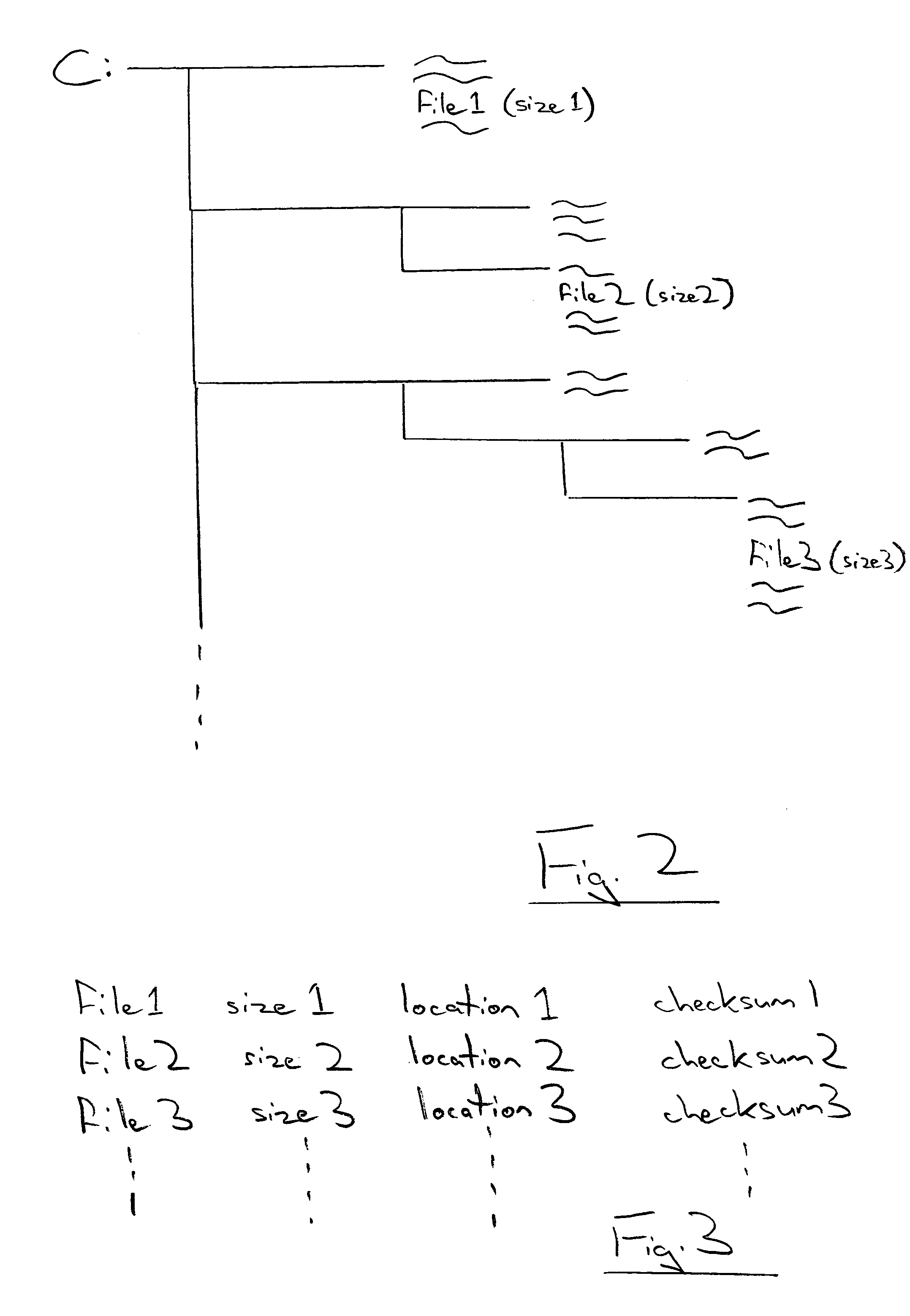
InactiveUS20050021994A1Addressing slow performanceEffectively ensureMemory loss protectionDigital data processing detailsChecksumFile size
A malware detection system seeking to identify computer viruses, worms, Trojans, banned files and the like acts to determine from the file name, file size and storage location of a computer file being tested, whether that computer file potentially matches a specific known malware free computer file stored within a list of such specific known malware free computer files. If a match occurs indicating that the candidate computer file is potentially the specific known malware free computer file, then this is confirmed by calculating a checksum of the candidate computer file and comparing this against a stored corresponding checksum of the specific known malware free computer file. If these checksums match, then the candidate computer file can be passed as clean without requiring further time consuming malware detection scanning.
Owner:MCAFEE INC
Computer virus detection
InactiveUS6886099B1Easy to detectUseful in detectionMemory loss protectionUnauthorized memory use protectionOutbreakComputer science
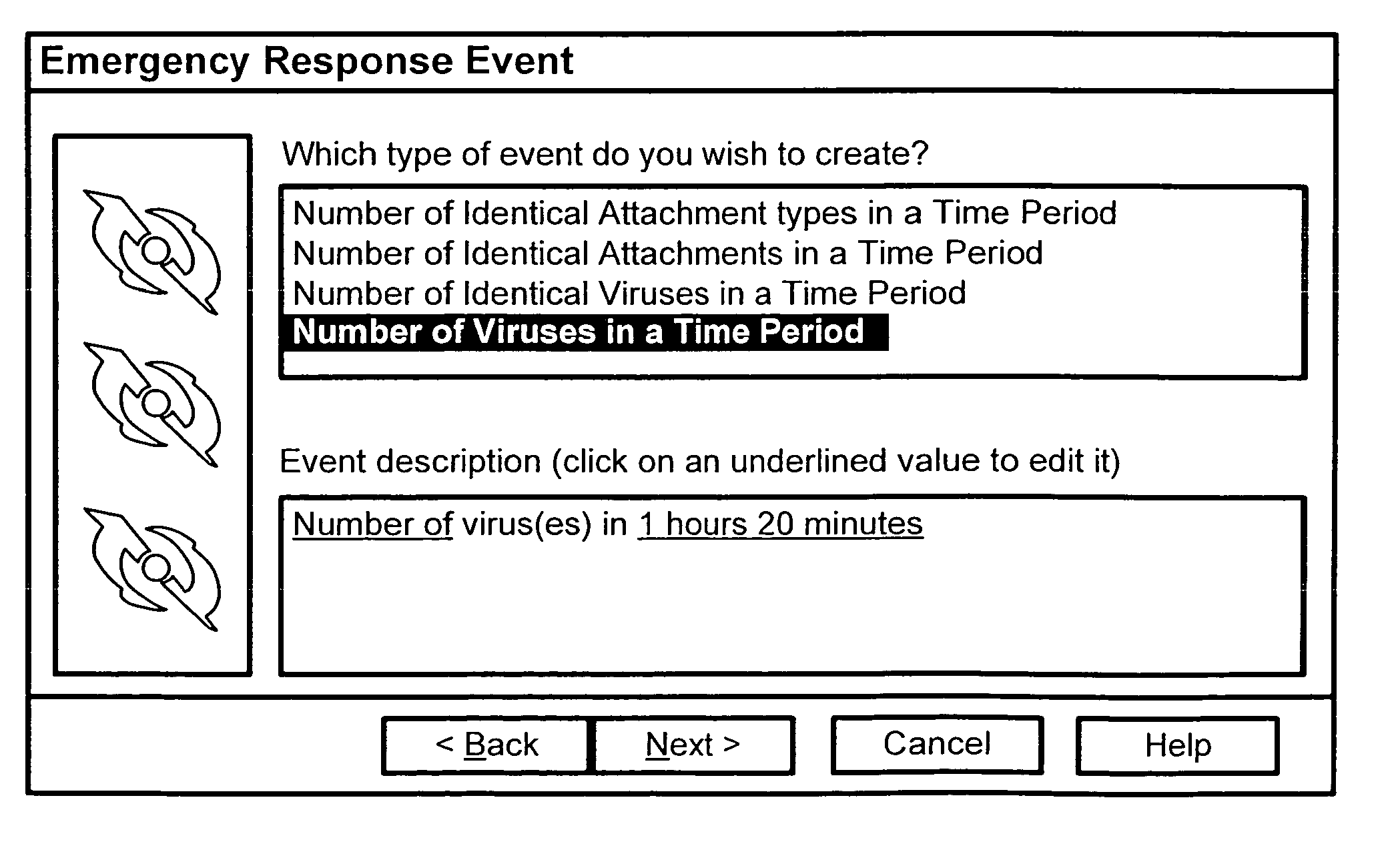
A computer virus outbreak is detected by comparing one or more measurement parameters determined over a measurement period against a threshold level. The measurement parameters can include a measurement of how many E-mail messages are sent having an identical file attachment, file type or simply in total. The threshold levels may be varied with the time of day and day of week as well as the tests applied.
Owner:MCAFEE LLC
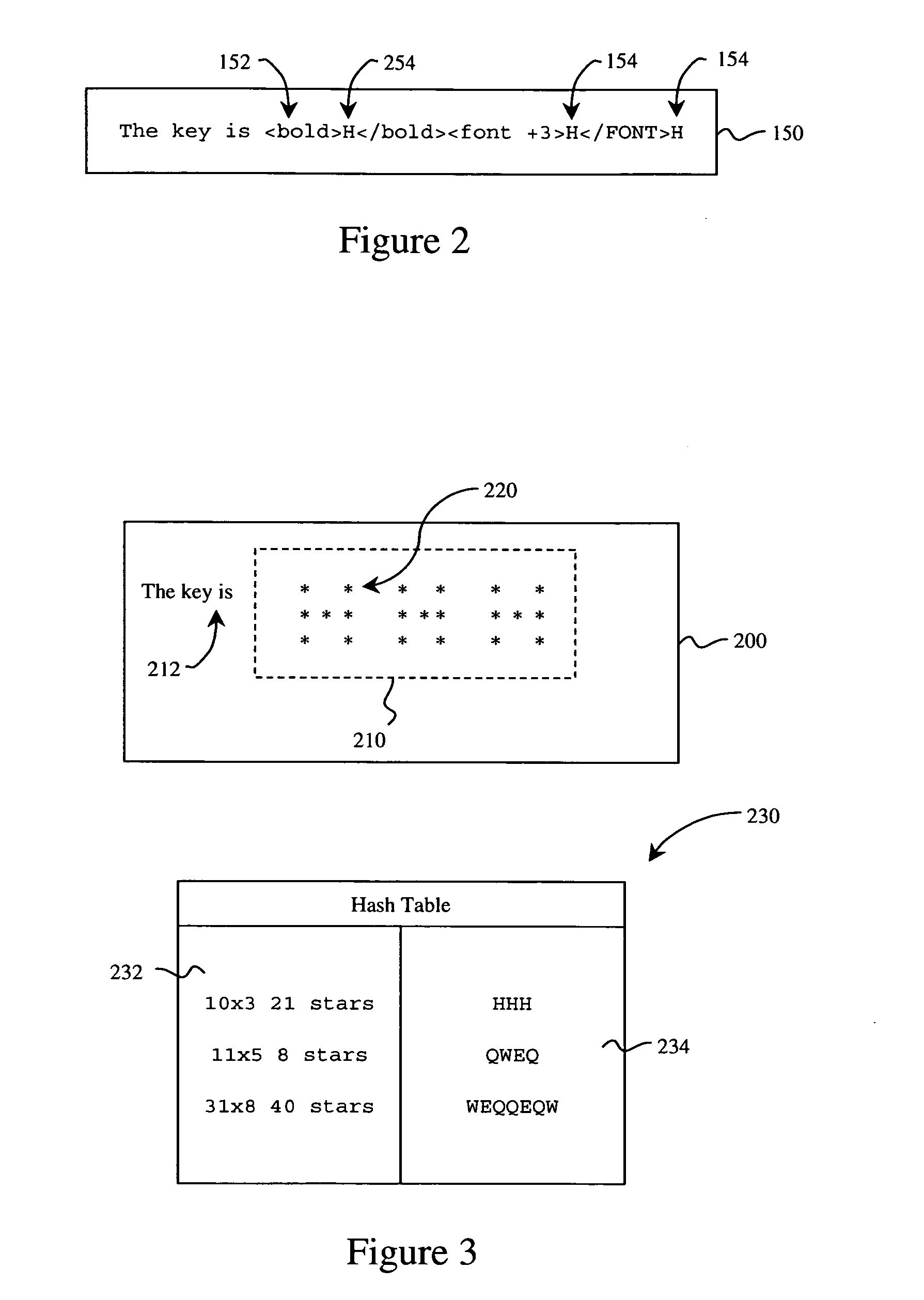
Histogram-based virus detection
InactiveUS6971019B1Easy to detectDigital data processing detailsUser identity/authority verificationCode moduleComputer science
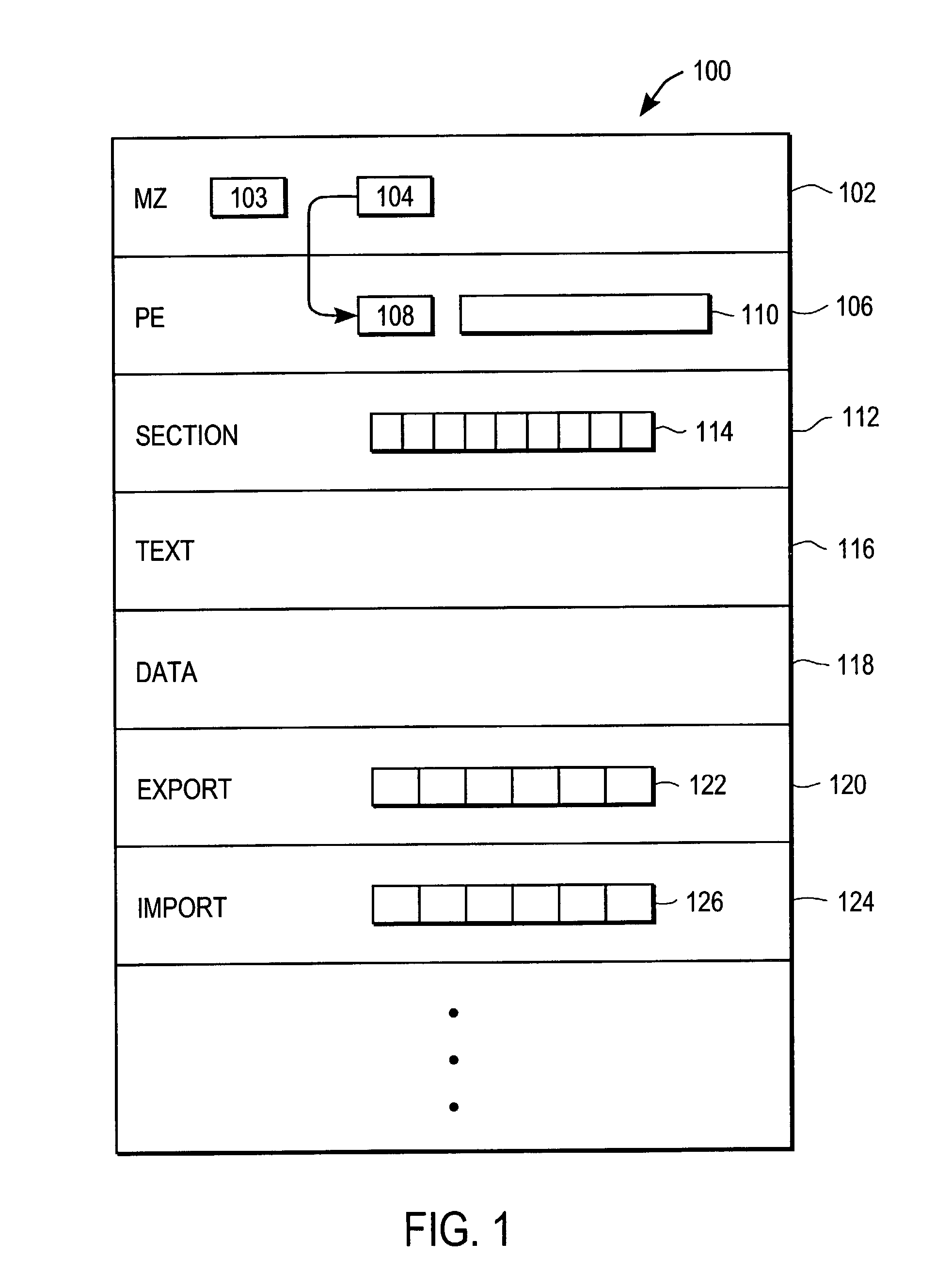
A virus detection system (VDS) (400) uses a histogram to detect the presence of a computer virus in a computer file. The VDS (400) has a P-code data (410) for holding P-code, a virus definition file (VDF) (412) for holding signature of known viruses, and an engine (414) for controlling the VDS. The engine (414) contains a P-code interpreter (418) for interpreting the P-code, a scanning module (424) for scanning regions of the file (100) for the virus signatures in the VDF (412), and an emulating module (426) for emulating instructions in the file. The emulating module (426) contains a histogram generation module (HGM) (436) for generating a histogram of characteristics of instructions emulated by the emulating module (426) and a histogram definition module (HDF) (438) for specifying the characteristics to be included in the generated histogram. The emulating module (426) uses the generated histogram (500) to determine how many of the instructions of the computer file (100) to emulate. The emulating module (426) emulates (712) instructions and the HGM (436) generates a histogram of the instructions until active instructions are note detected. When active instructions are not detected (714), a P-code module is executed (722) to analyze the histogram (500) and determine whether a the file (100) contains a virus. The P-code can also decide to extend (728) emulation. The HGM (436) is also used to detect (822) the presence of dummy loops during virus decryption.
Owner:CA TECH INC
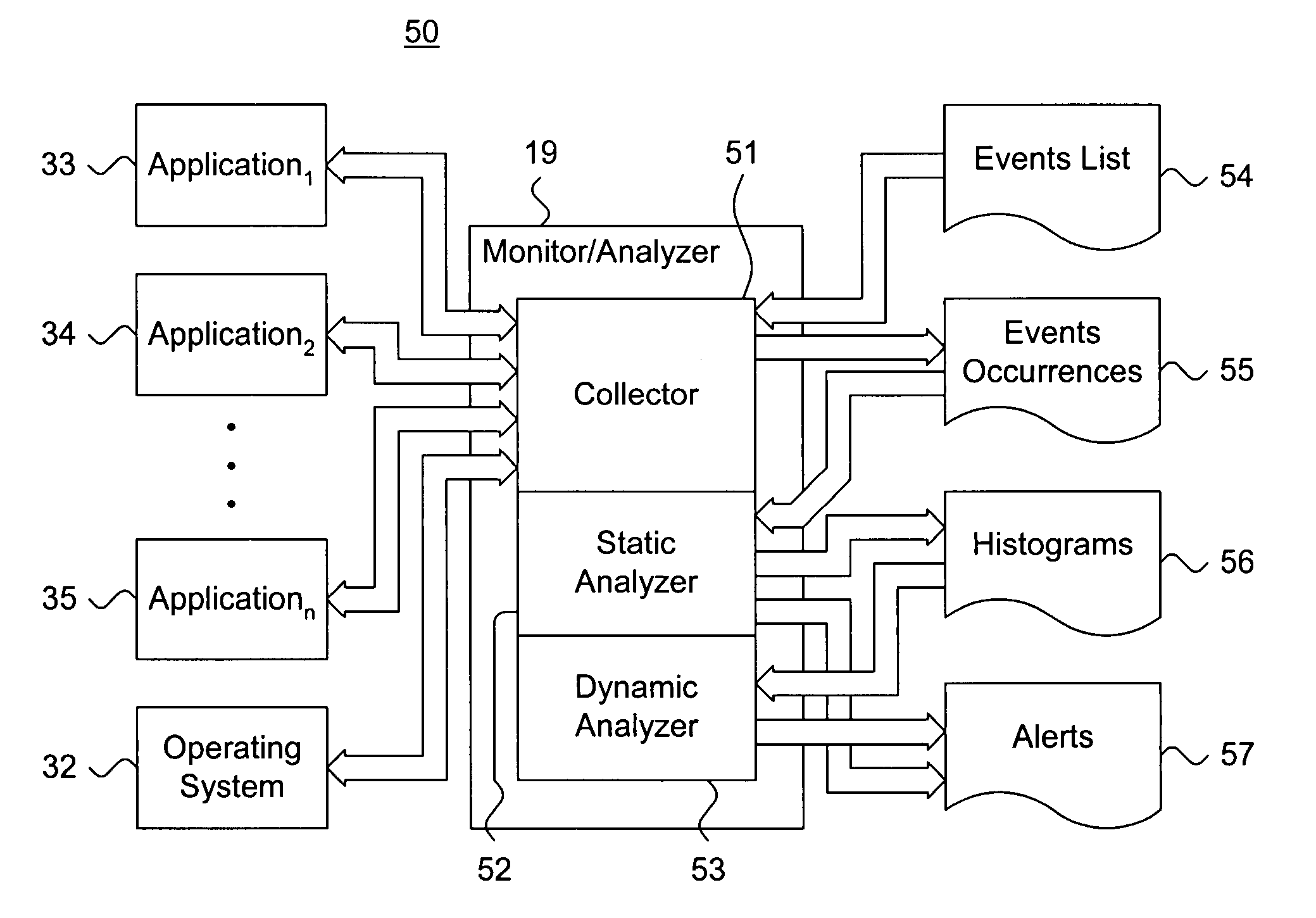
Computer security threat data collection and aggregation with user privacy protection
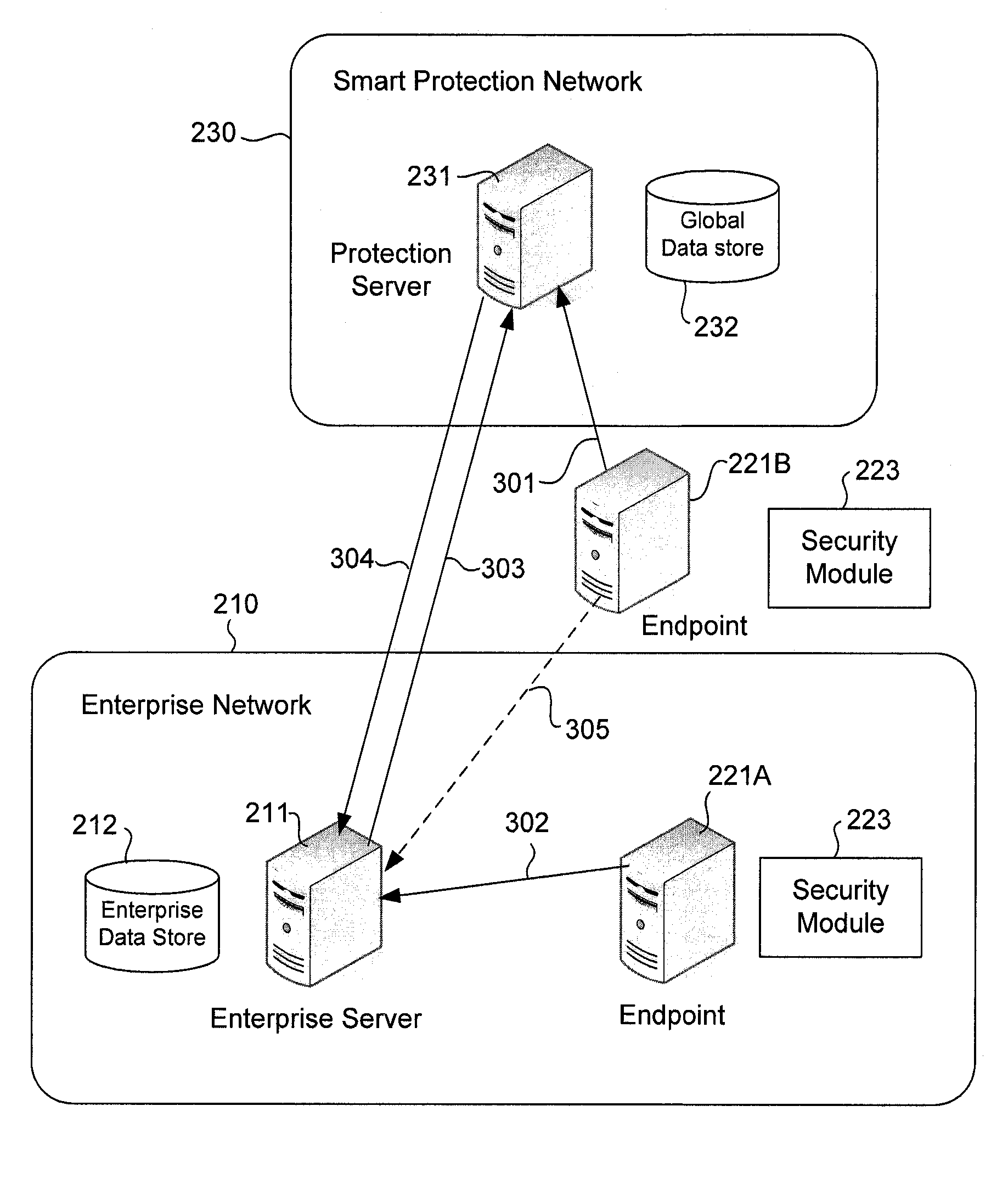
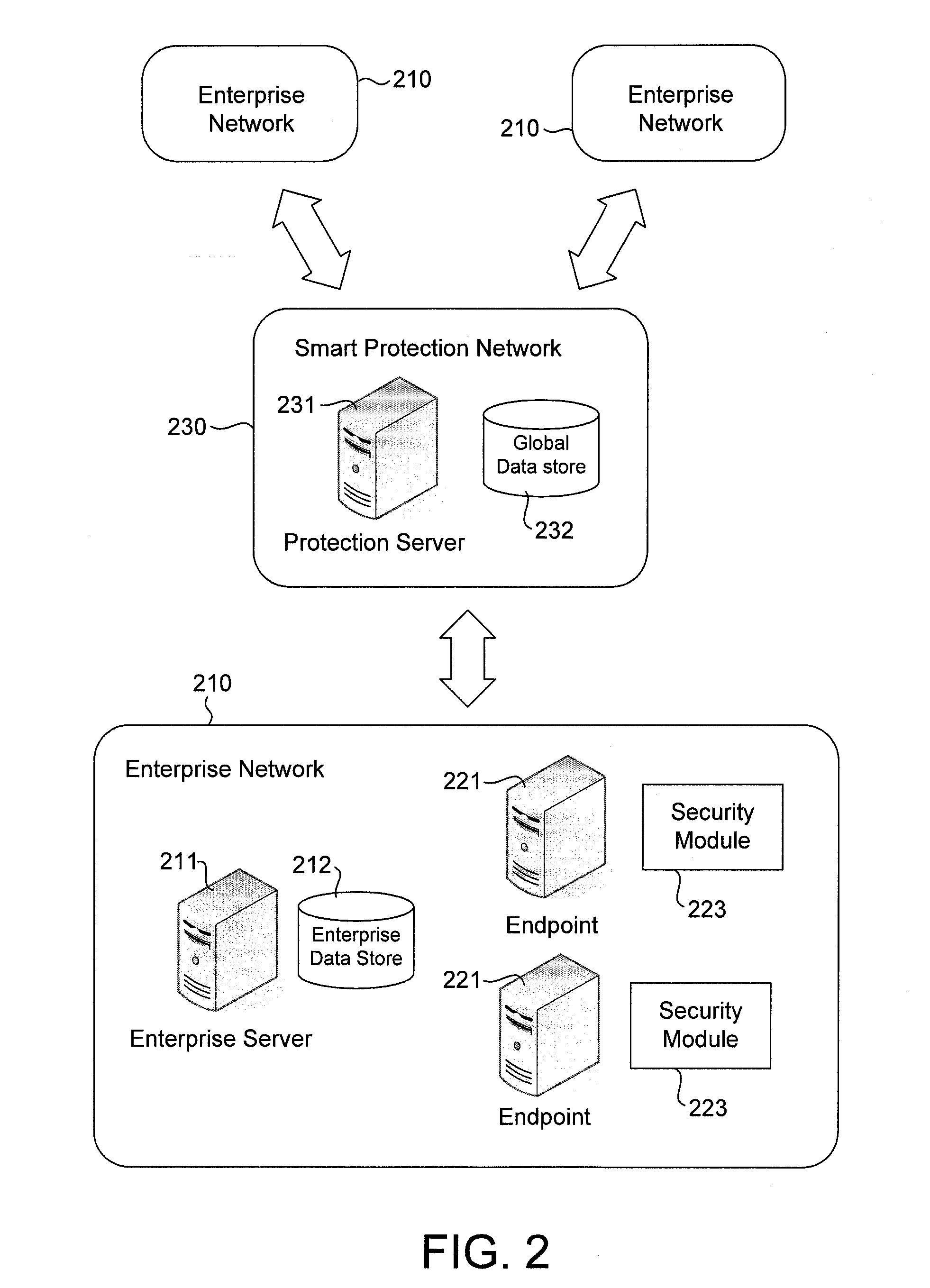
An endpoint computer in an enterprise network is configured to detect computer security threat events, such as presence of a computer virus. Upon detection of a threat event, the endpoint computer generates computer security threat data for the threat event. The threat data may include user identifiable data that can be used to identify a user in the enterprise network. The endpoint computer encrypts the user identifiable data prior to sending the threat data to a smart protection network or to an enterprise server where threat data from various enterprise networks are collected for analysis. The endpoint computer may also encrypt an identifier for the threat data and provide the encrypted identifier to the smart protection network and to an enterprise server in the enterprise network. The enterprise server may use the encrypted identifier to retrieve the threat data from the smart protection network to generate user-specific reports.
Owner:TREND MICRO INC
Pre-approval of computer files during a malware detection
InactiveUS7257842B2Abundant resourcesImpact speedMemory loss protectionDigital data processing detailsChecksumMalware
A malware detection system seeking to identify computer viruses, worms, Trojans, banned files and the like acts to determine from the file name, file size and storage location of a computer file being tested, whether that computer file potentially matches a specific known malware free computer file stored within a list of such specific known malware free computer files. If a match occurs indicating that the candidate computer file is potentially the specific known malware free computer file, then this is confirmed by calculating a checksum of the candidate computer file and comparing this against a stored corresponding checksum of the specific known malware free computer file. If these checksums match, then the candidate computer file can be passed as clean without requiring further time consuming malware detection scanning.
Owner:MCAFEE INC
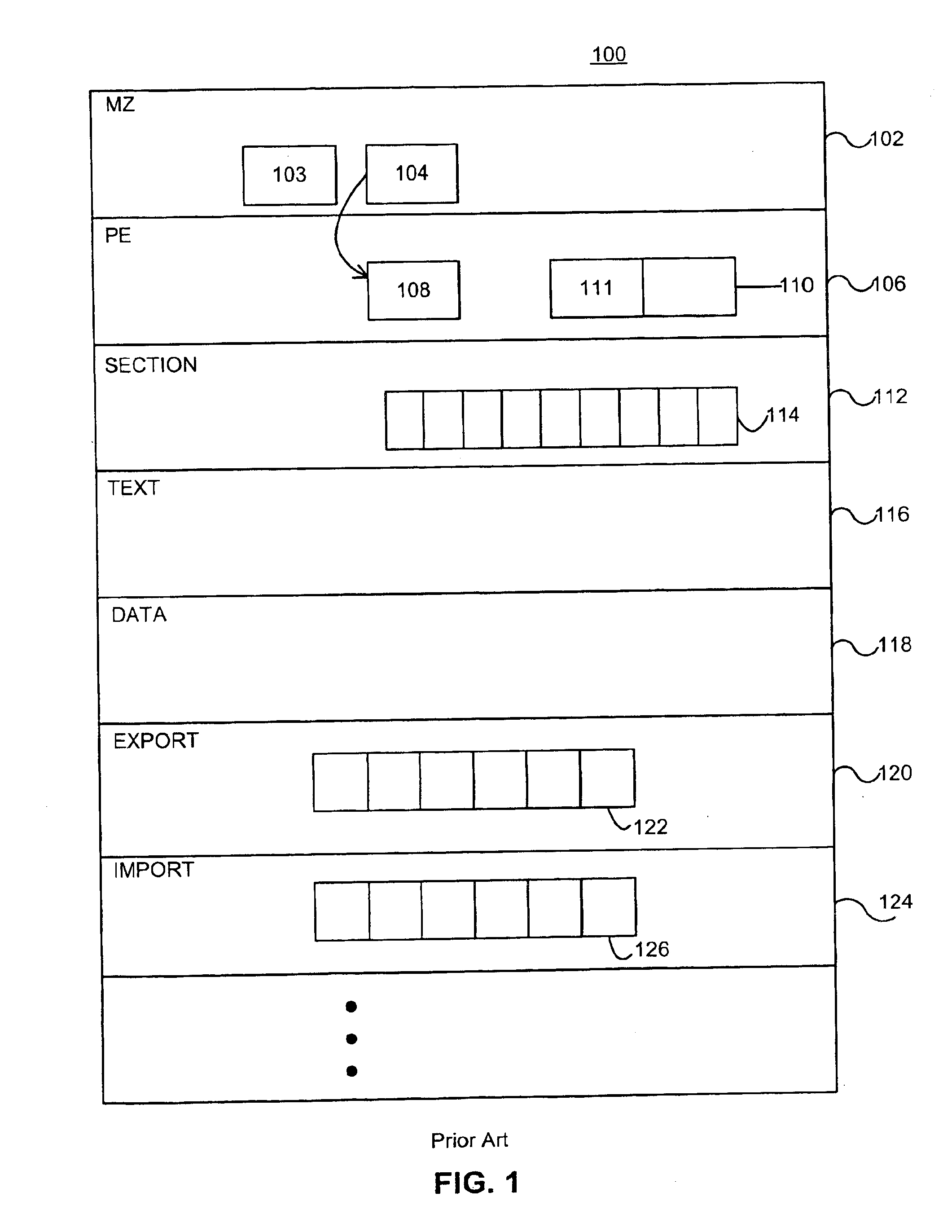
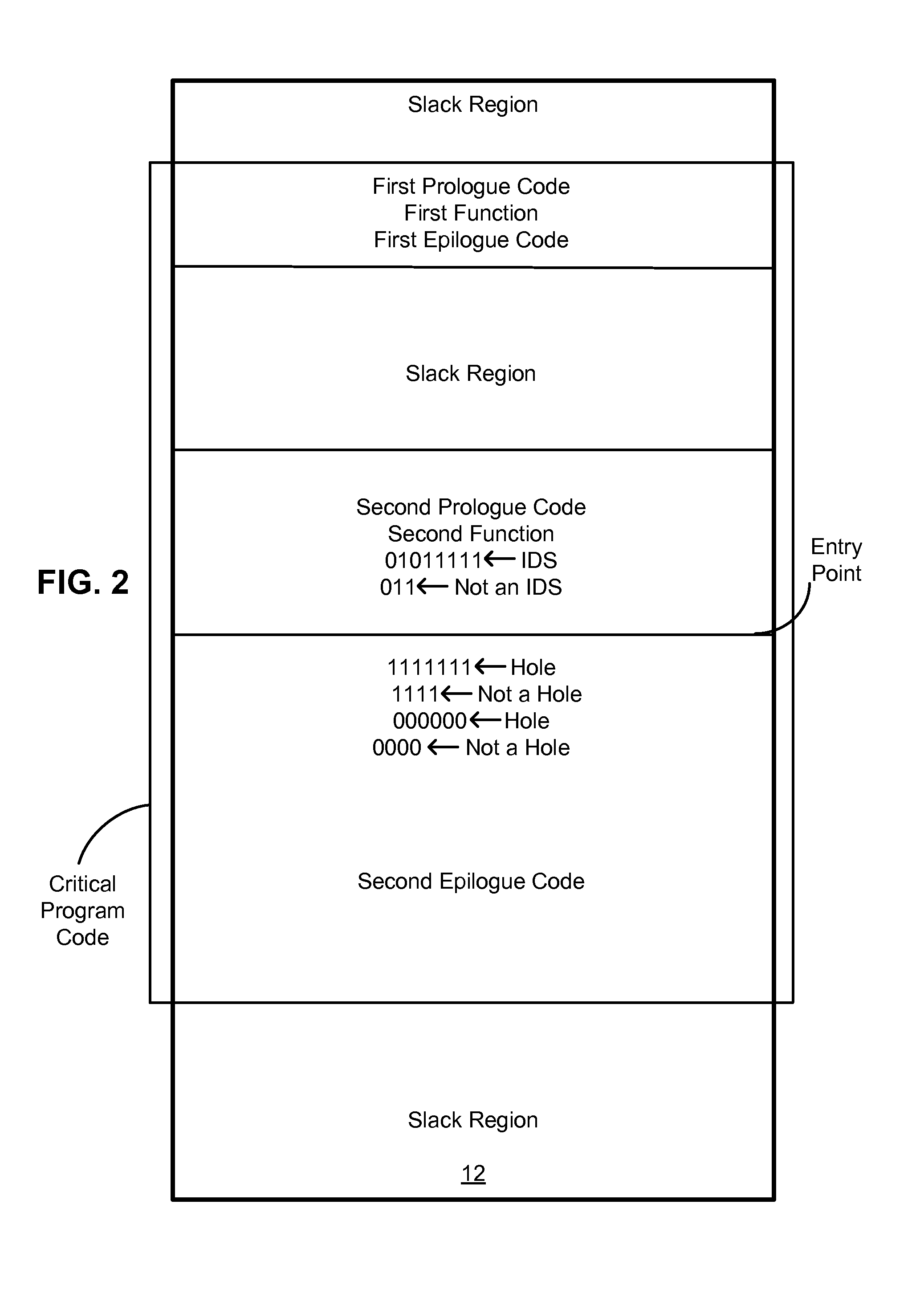
Heuristic detection of computer viruses
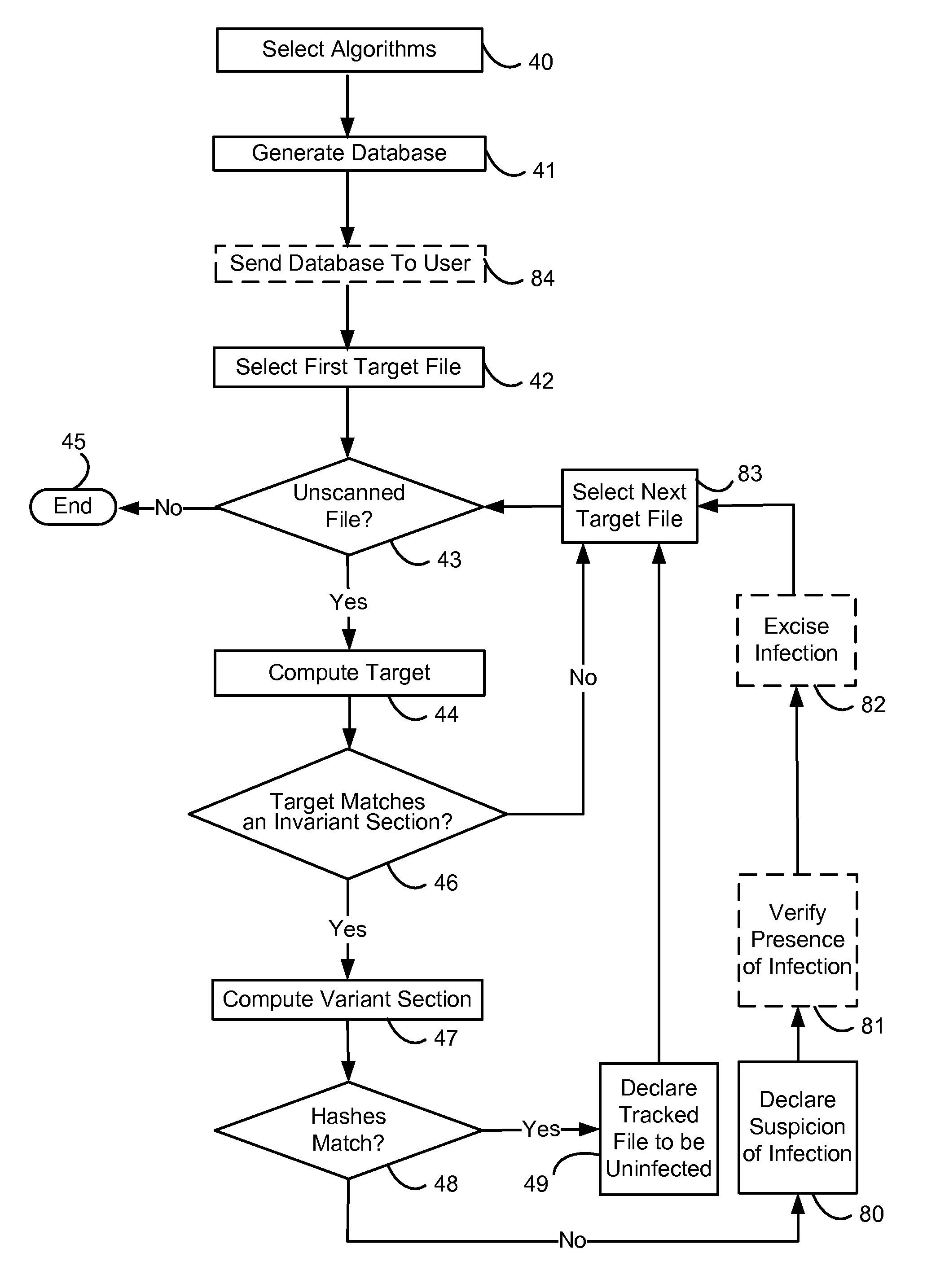
Computer-implemented methods, apparati, and computer-readable media for detecting the presence of viral infections in target files (10) located within a computer. The invention has broad applicability to a number of different platforms, including Windows. A preferred method for performing the invention comprises the steps of: scanning a target file (10) with an antivirus scanner, said scanning step including computing (44) a target section (19) corresponding to an invariant section of said target file (10); declaring the target file (10) to be a tracked file (10) when the target section (19) matches an invariant section in a database generated (41) from uninfected versions of the target files (10); for each tracked file (10), identifying (47) a variant section that is likely to be varied by a viral infection; comparing (48) the variant section in the tracked file (10) with the same variant section in the uninfected version of the tracked file (10) in said database; and declaring (80) a suspicion that a virus is present in the tracked file (10) when the two variant sections do not match.
Owner:NORTONLIFELOCK INC
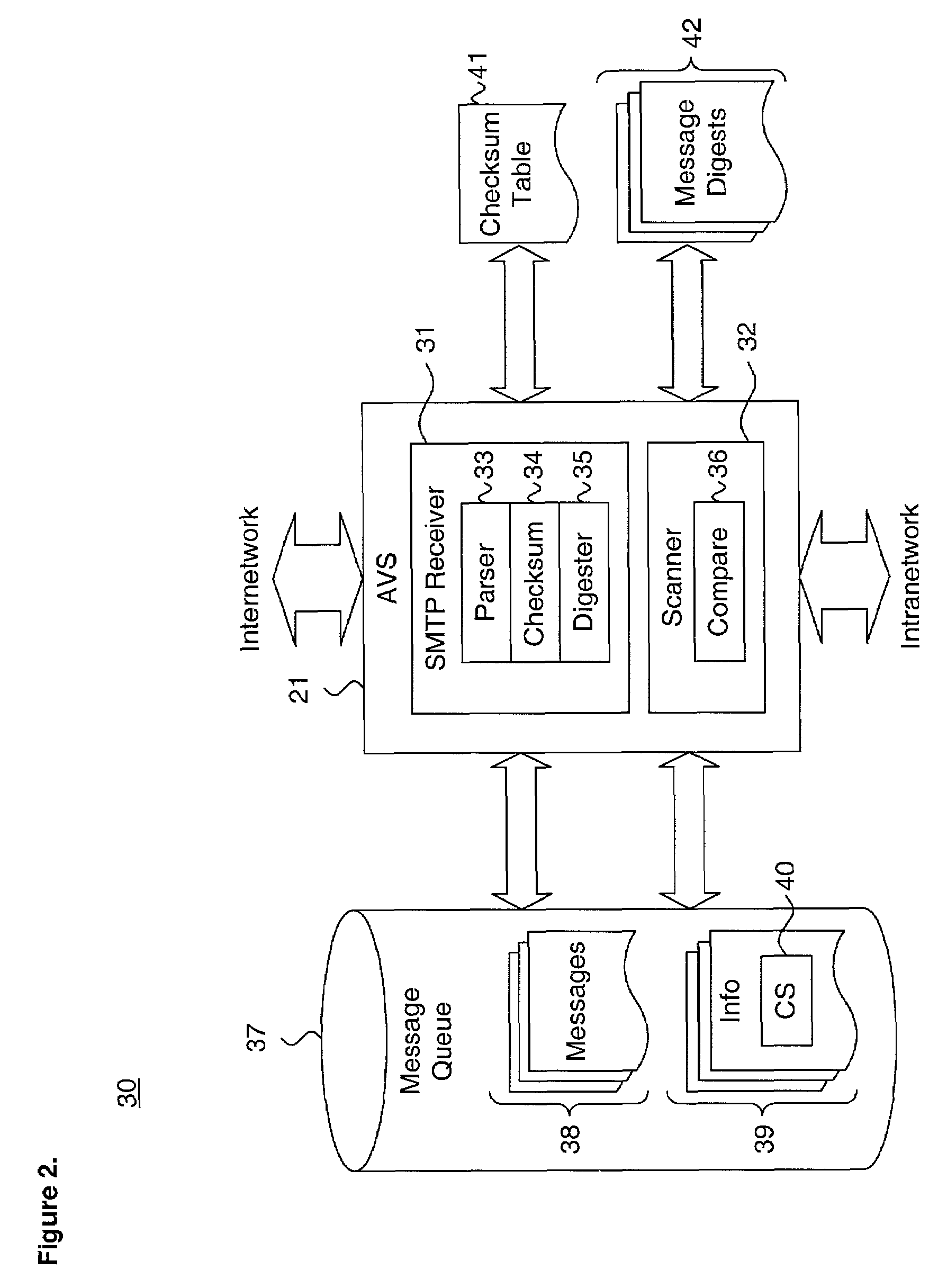
System and method for performing efficient computer virus scanning of transient messages using checksums in a distributed computing environment
ActiveUS6993660B1Efficient detectionMemory loss protectionUser identity/authority verificationDistributed Computing EnvironmentChecksum
A system and method for performing efficient computer virus scanning of transient messages using checksums in a distributed computing environment is described. An incoming message is intercepted at a network domain boundary. The incoming message includes a body storing message content. The message content is parsed from the body and a checksum is calculated over the parsed message content. The checksum is stored in an information file associated with the incoming message in a transient message store. The incoming message is scanned for a presence of at least one of a computer virus and malware to identify infected message contents. The checksum corresponding to each infected message content and an infection indicator is recorded.
Owner:MCAFEE LLC
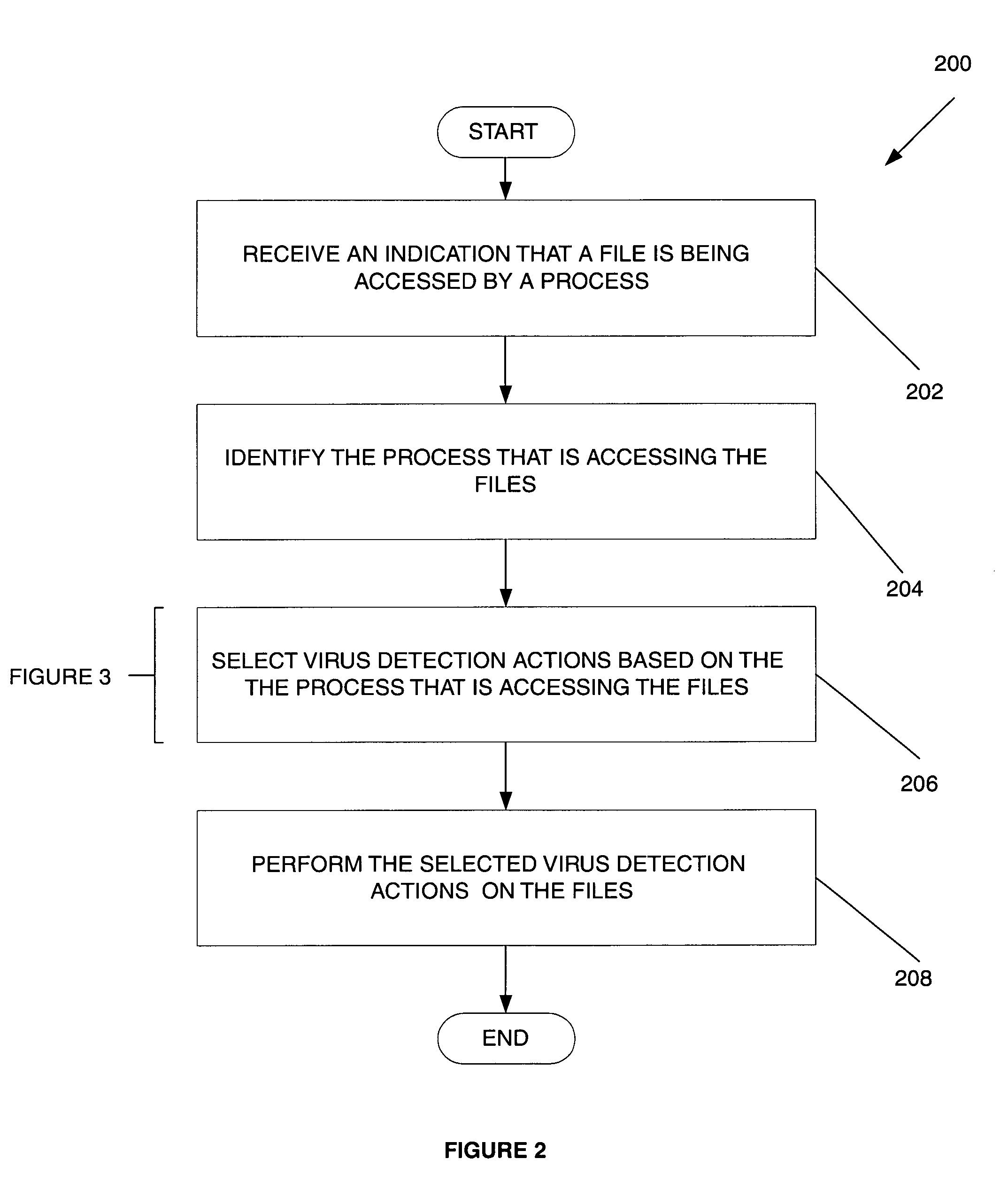
System, method and computer program product for process-based selection of virus detection actions
InactiveUS6973578B1Easy to useMemory loss protectionUnauthorized memory use protectionVirus detectionDatabase
A system, method and computer program product are provided for efficient on-access computer virus scanning of files. Initially, a process for accessing files is identified. Thereafter, virus detection actions are selected based at least in part on the process. The virus detection actions are then performed on the files.
Owner:MCAFEE LLC
Method of constructing data classifiers and classifiers constructed according to the method
InactiveUS6622134B1Efficient constructionAvoid trainingDigital computer detailsCharacter and pattern recognitionOvertrainingAlgorithm
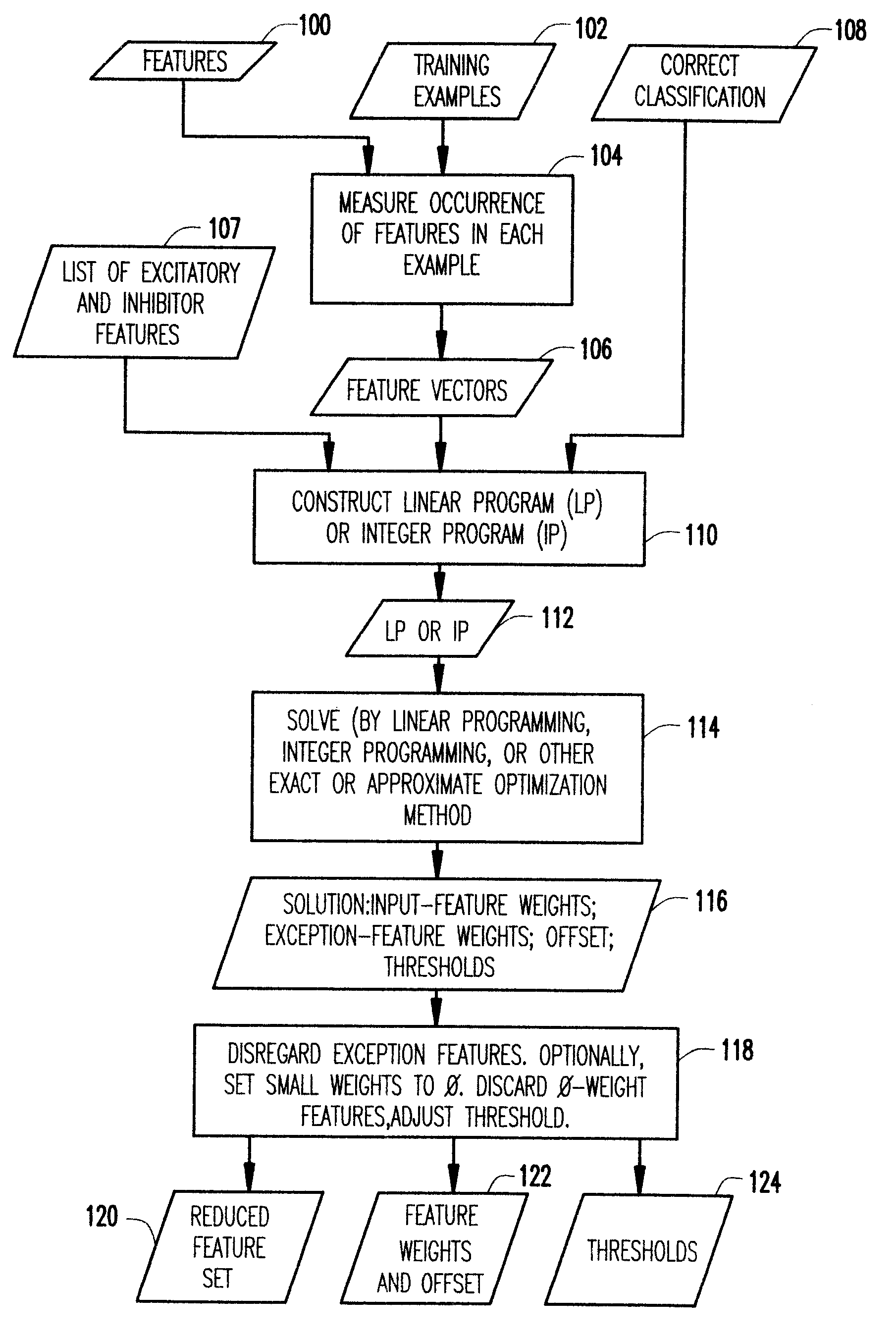
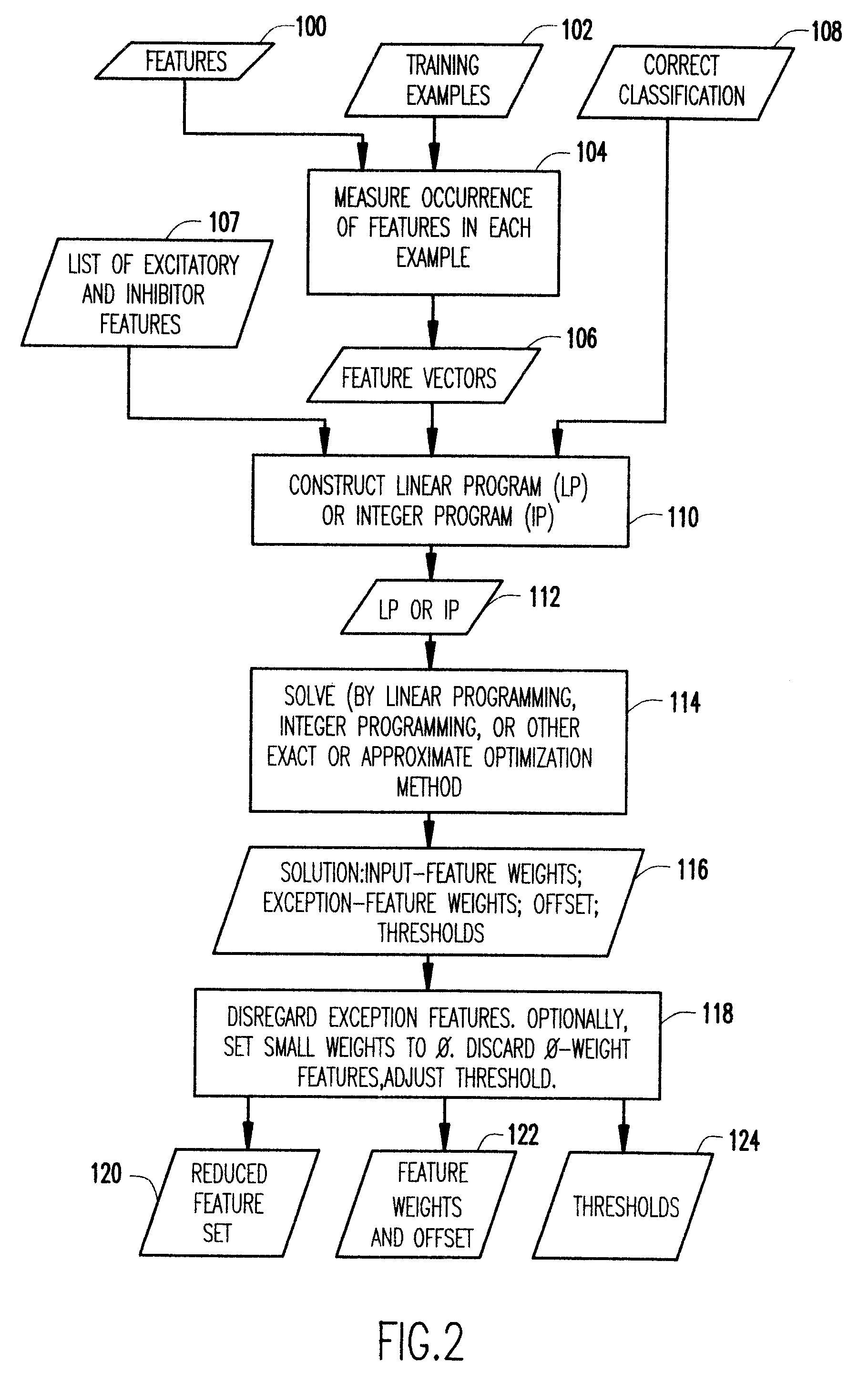
A method of constructing data classifiers in cases where the number of features is much larger than the number of training examples and it is critical to avoid overtraining, is particularly useful in recognizing computer objects containing or likely to contain a computer virus. The method provides a novel way of tolerating imperfectly classifiable data, of learning in time polynomial in the size of the input data, and of avoiding overtraining. Training is performed by constructing and solving a linear program (LP) or integer program (IP).
Owner:TREND MICRO INC
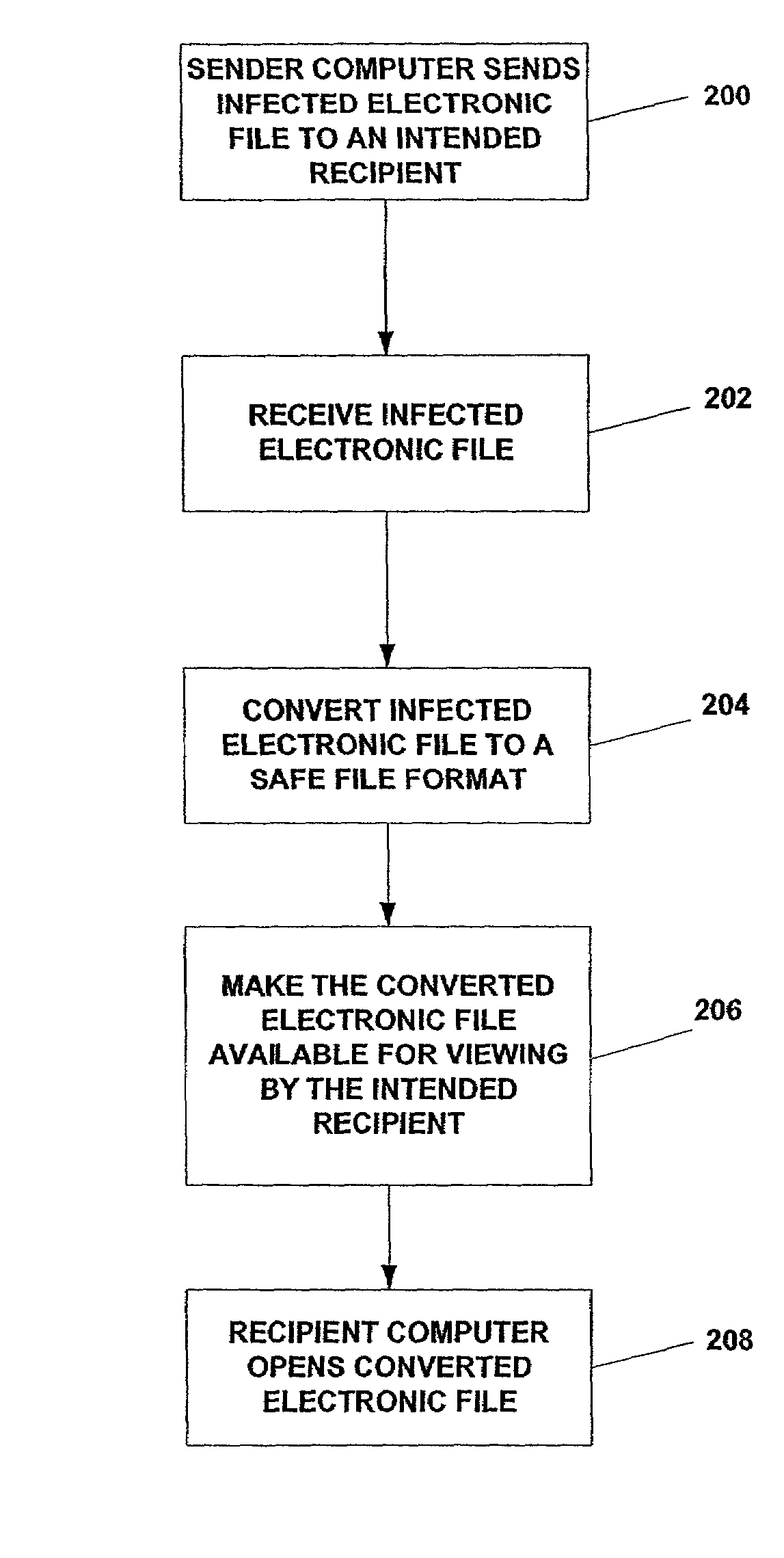
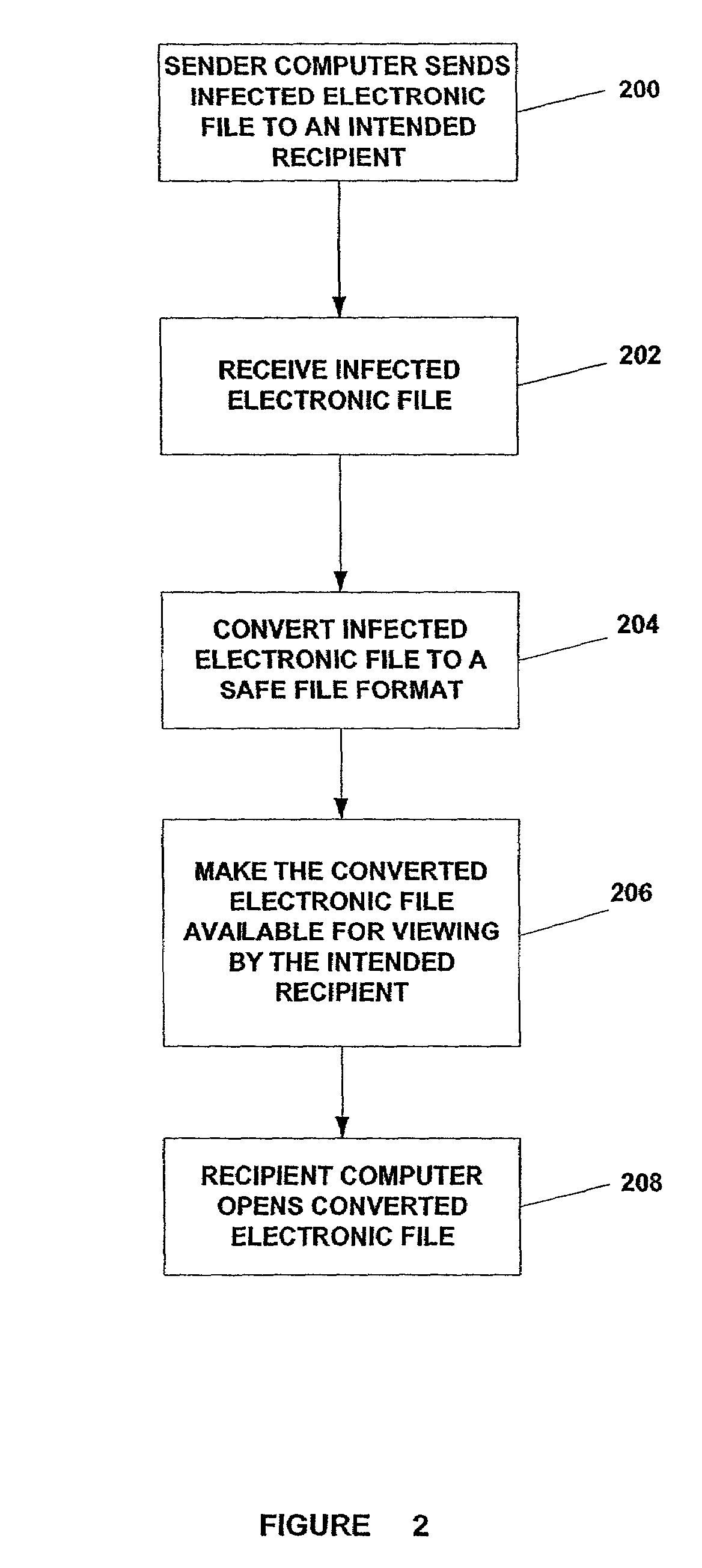
Systems and methods for making electronic files that have been converted to a safe format available for viewing by an intended recipient
System and methods of converting electronic files infected with a computer virus from a first format to a second, safe format and then making the converted electronic file available for viewing by the intended recipient.
Owner:MCAFEE LLC
Virus check device and system
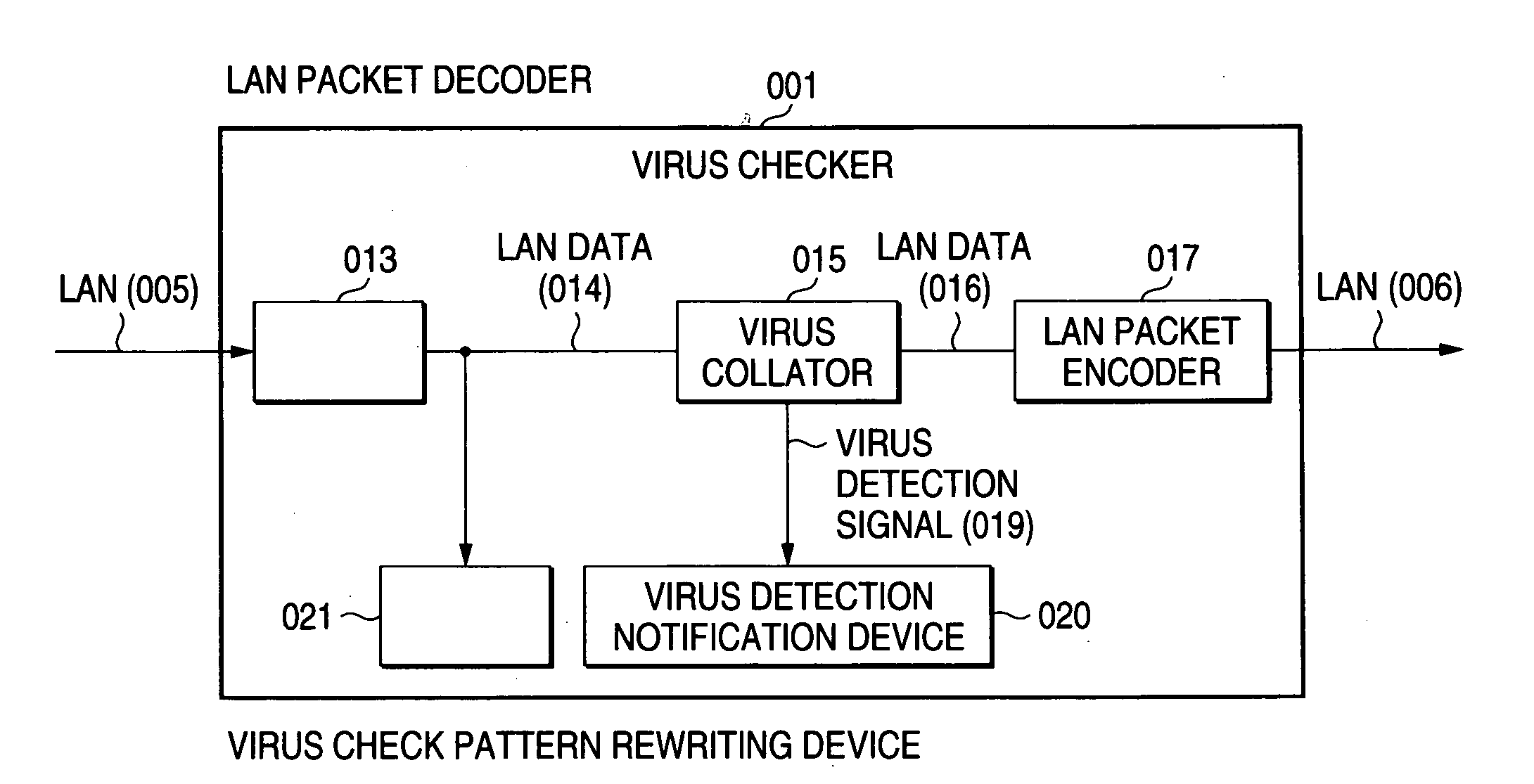
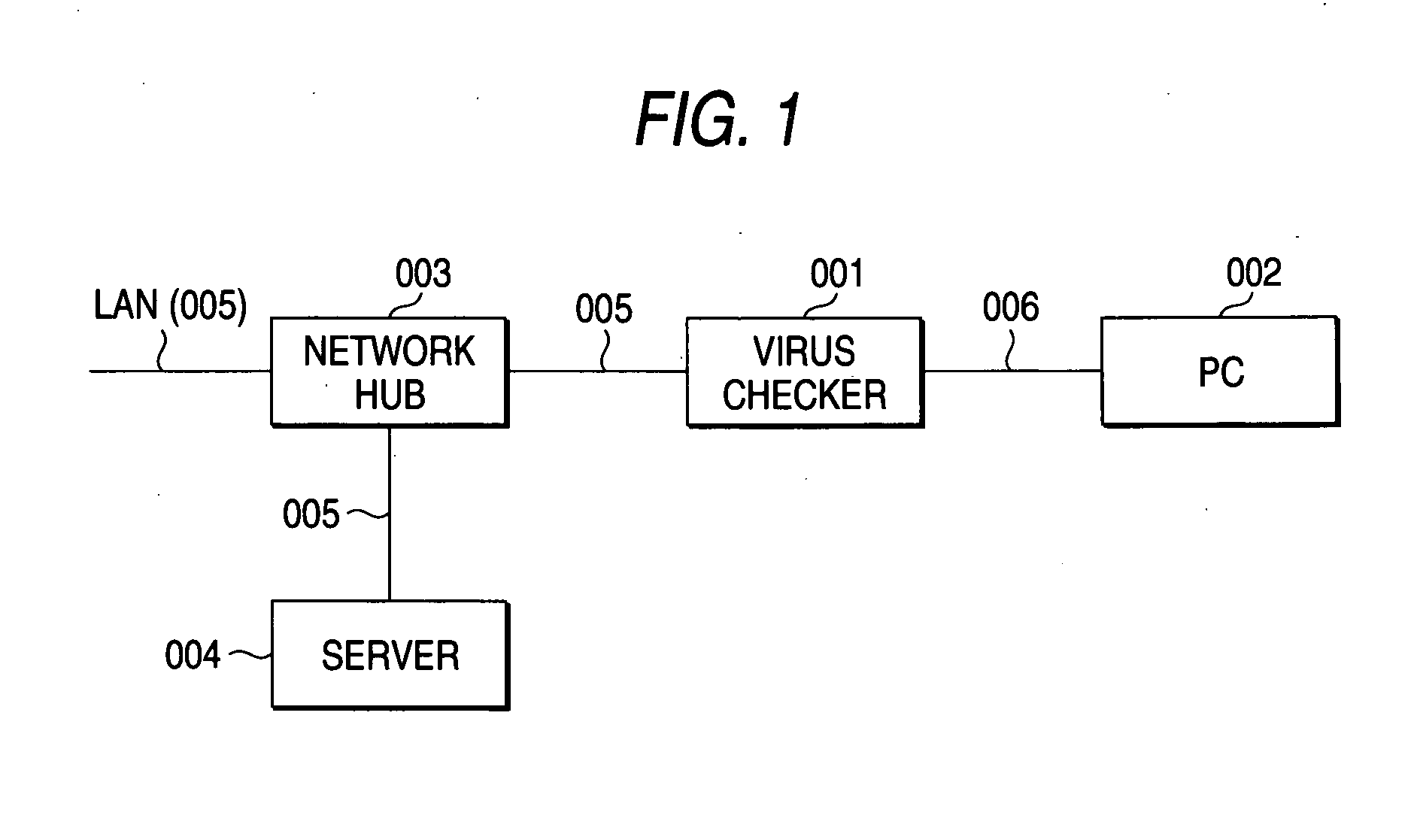
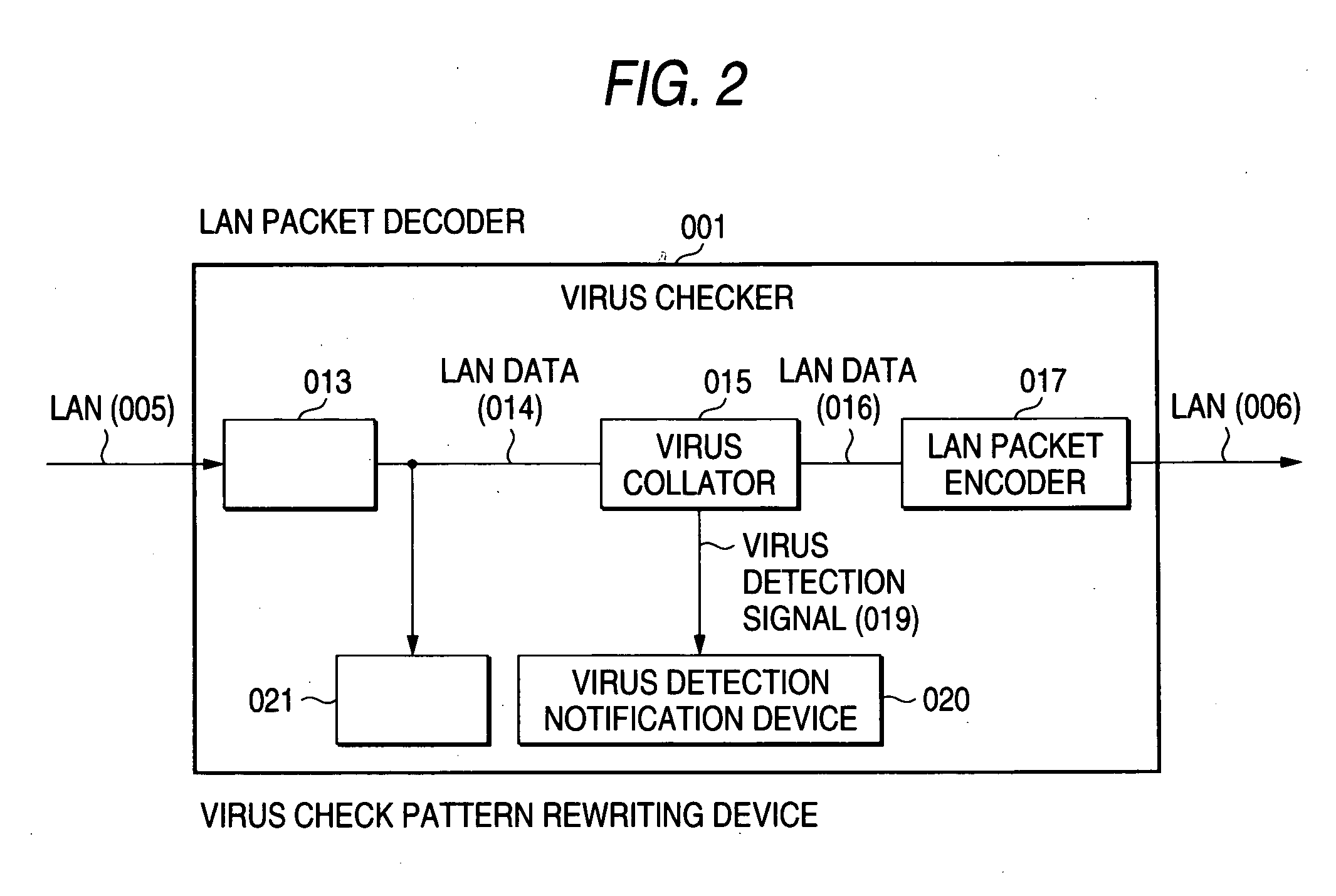
InactiveUS20060242686A1High speed machiningSimple processDigital data processing detailsError detection/correctionDigital dataInformation processing
The present invention detects a computer virus at high speed from digital data acquired through a network using hardware in virus monitoring. With the invention, in an information processing terminal 002 capable of communicating with other information processing apparatus through a communication network 005, a virus checking apparatus 001 constructed of a hardware circuit is disposed in the side of an input channel of the network 005 and a virus is checked from input data from the network 005 by the virus checking apparatus 001. In order to change a virus pattern collated with the input data by hardware, the hardware circuit is detachably mounted or a rewritable logic device is used in the hardware circuit. The virus pattern of the logic device can be rewritten by sending virus definition information of a server 004 or control data generated based on this information to the virus checking apparatus 001.
Owner:NAT INST OF ADVANCED IND SCI & TECH
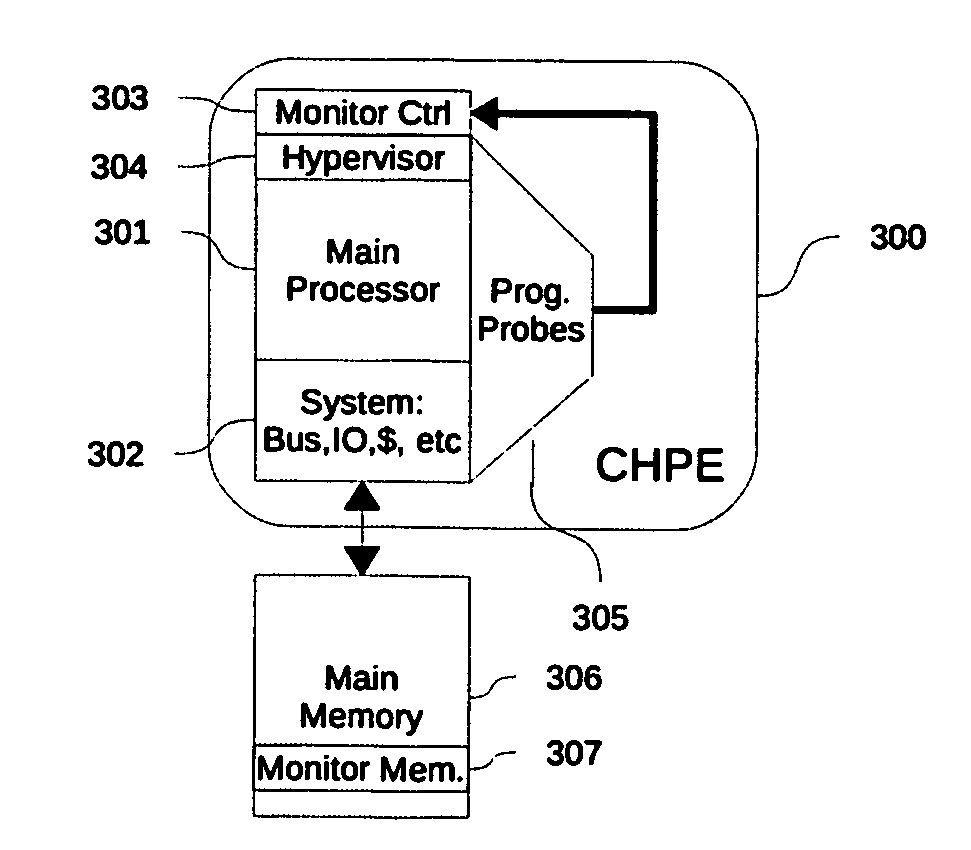
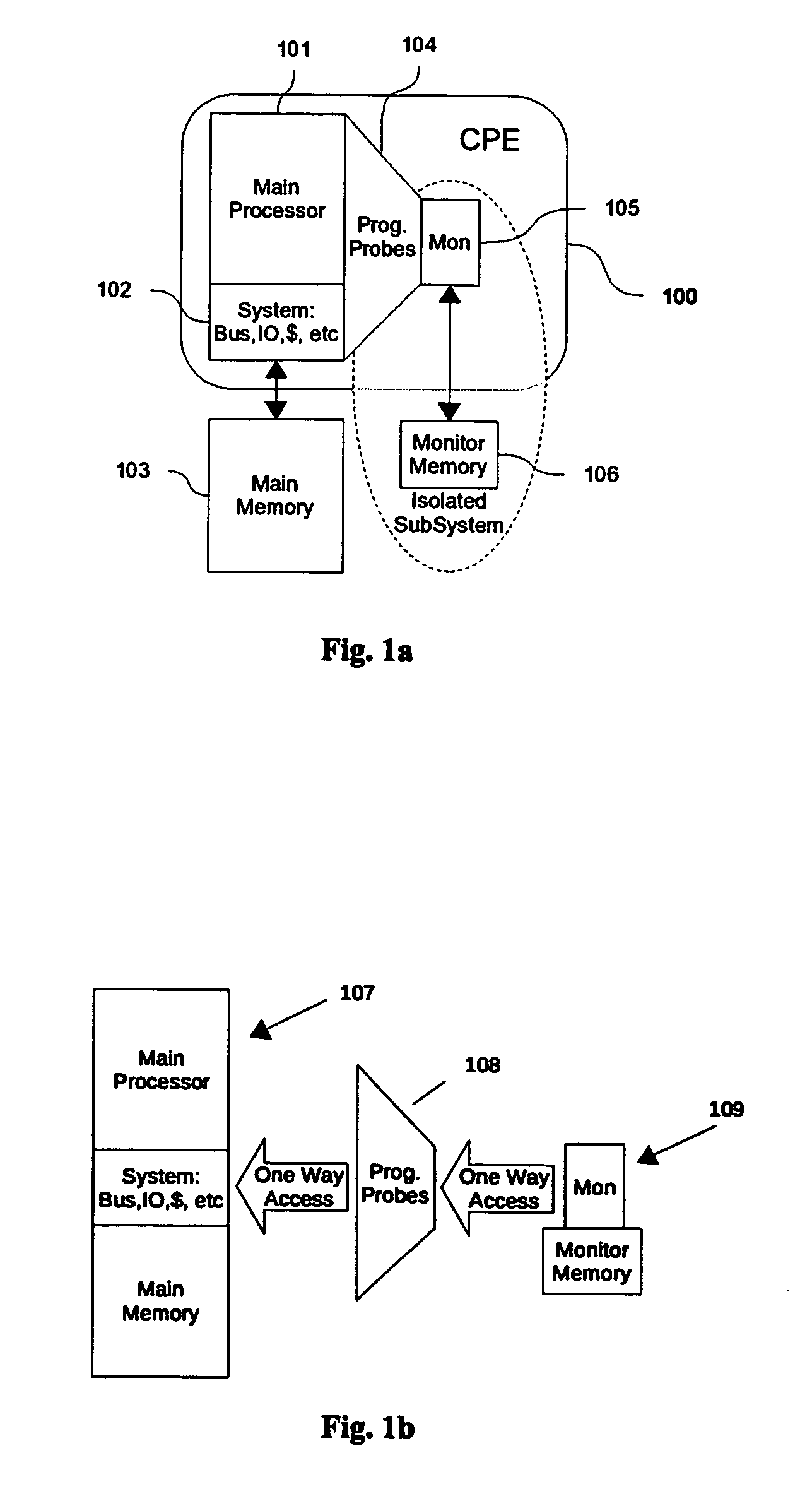
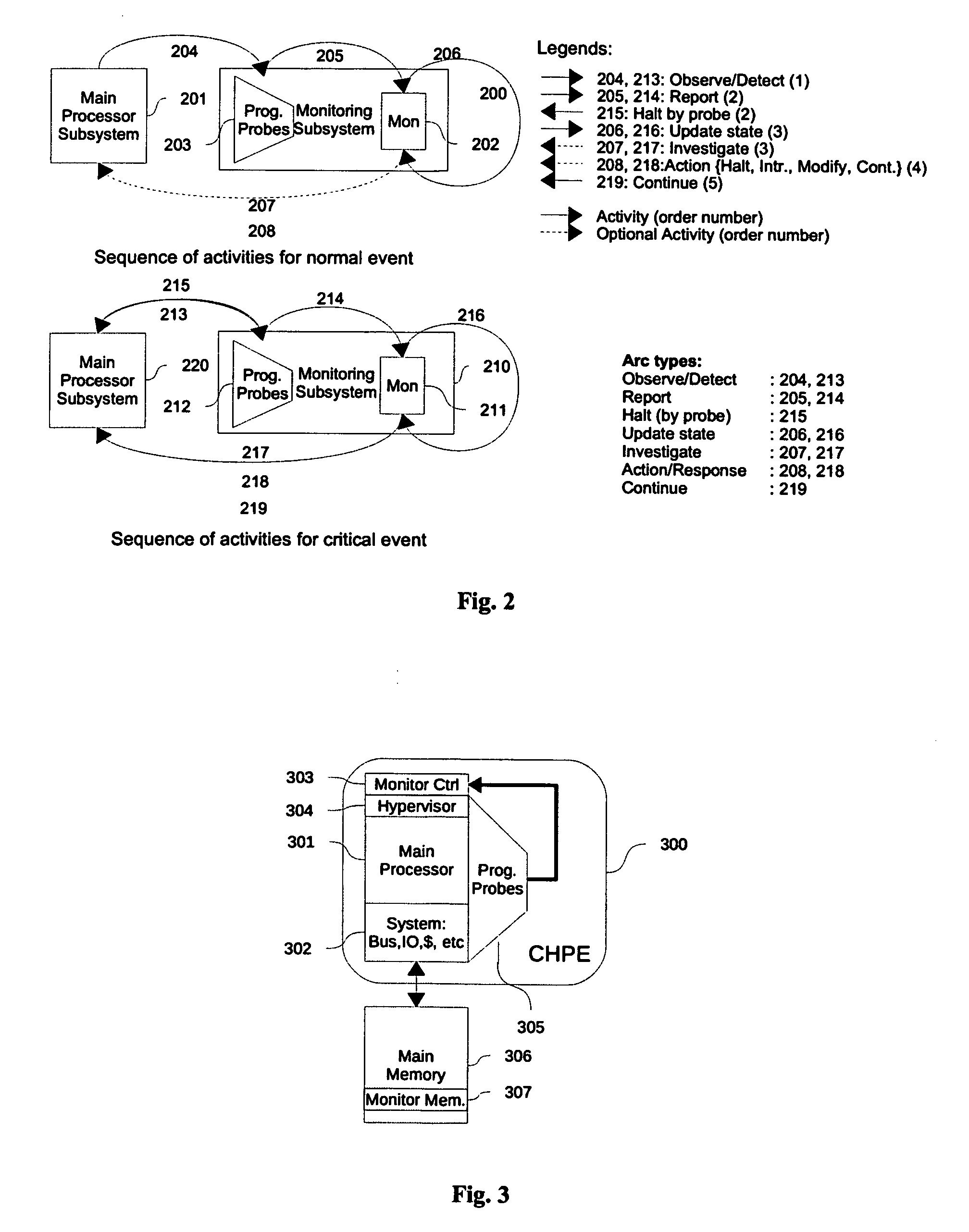
Cognizant engines: systems and methods for enabling program observability and controlability at instruction level granularity
ActiveUS20100107252A1Improve performanceEfficient powerMemory loss protectionError detection/correctionGranularityControllability
The present invention is directed to system for and methods of real time observing, monitoring, and detecting anomalies in programs' behavior at instruction level. The hardware assist design in this invention provides fine grained observability, and controllability. Fine grained observability provides unprecedented opportunity for detecting anomaly. Controllability provides a powerful tool for stopping anomaly, repairing the kernel and restoring the state of processing. The performance improvement over pure software approach is estimated to be many orders of magnitudes. This invention is also effective and efficient in detecting mutating computer viruses, where normal, signature based, virus detection is under performing.
Owner:MERTOGUNO SUKAMO
Method and apparatus for increasing virus detection speed using a database
InactiveUS6952776B1Simple technologyLess timeData processing applicationsUnauthorized memory use protectionVirus detectionComputer virus
A virus detection method for use in a computer system that contains at least one object that may potentially become infected with a computer virus. The method has steps of providing a database for storing information that is descriptive of a state of the object as it existed at a point in the past. For an object that is indicated as having a current state that is described by the stored information, another step programmatically examines the object for a presence of a computer virus while assuming that the current state of the object is the same as the state of the object as it existed at the point in the past. The the database stores additional information, beyond what is necessary to determine simply whether or not a particular object, such as a file, has changed. The additional information is employed to achieve a more rapid virus scan, even when the list of viruses being scanned for has changed since a previous scan.
Owner:TREND MICRO INC
Computer virus detection
InactiveUS7093293B1Easy to detectUseful in detectionMemory loss protectionUnauthorized memory use protectionOutbreakComputer science
A computer virus outbreak is detected by comparing one or more measurement parameters determined over a measurement period against a threshold level. The measurement parameters can include a measurement of how many E-mail messages are sent having an identical file attachment, file type or simply in total. The threshold levels may be varied with the time of day and day of week as well as the tests applied.
Owner:MCAFEE LLC
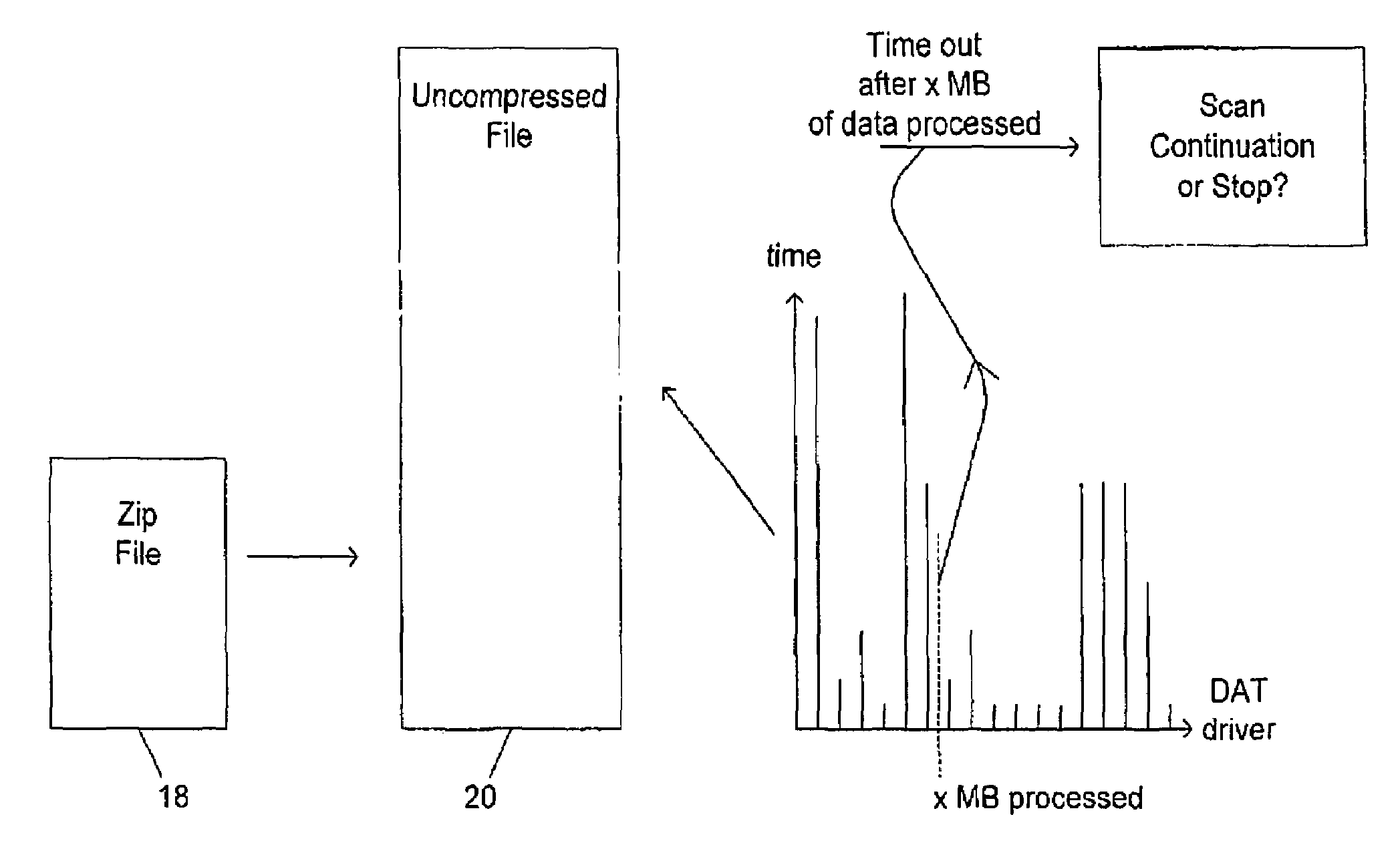
Providing break points in a malware scanning operation
InactiveUS6968461B1Increased complexityLow complexity valueMemory loss protectionUser identity/authority verificationMalwareData treatment
A computer virus scanning system is described in which during the scanning operation a measurement value indicative of the amount of data processing performed is calculated and this measurement value used to trigger breaks in the virus scanning operation. The triggered breaks can be used to perform a determination as to whether or not the virus scanning operations should be early terminated. One possibility is to measure the total size of the data processed during the virus scanning operation and calculate a ratio of this compared to the size of the computer file being virus scanned. If this calculated ratio exceeds a predetermined threshold, then virus scanning may be terminated. Another possibility is to associate a complexity value with each of a plurality of tests applied in the virus scanning operation. A total for these complexity values may be used to trigger the breaks and also to trigger early termination upon exceeding of respective threshold levels.
Owner:MCAFEE LLC
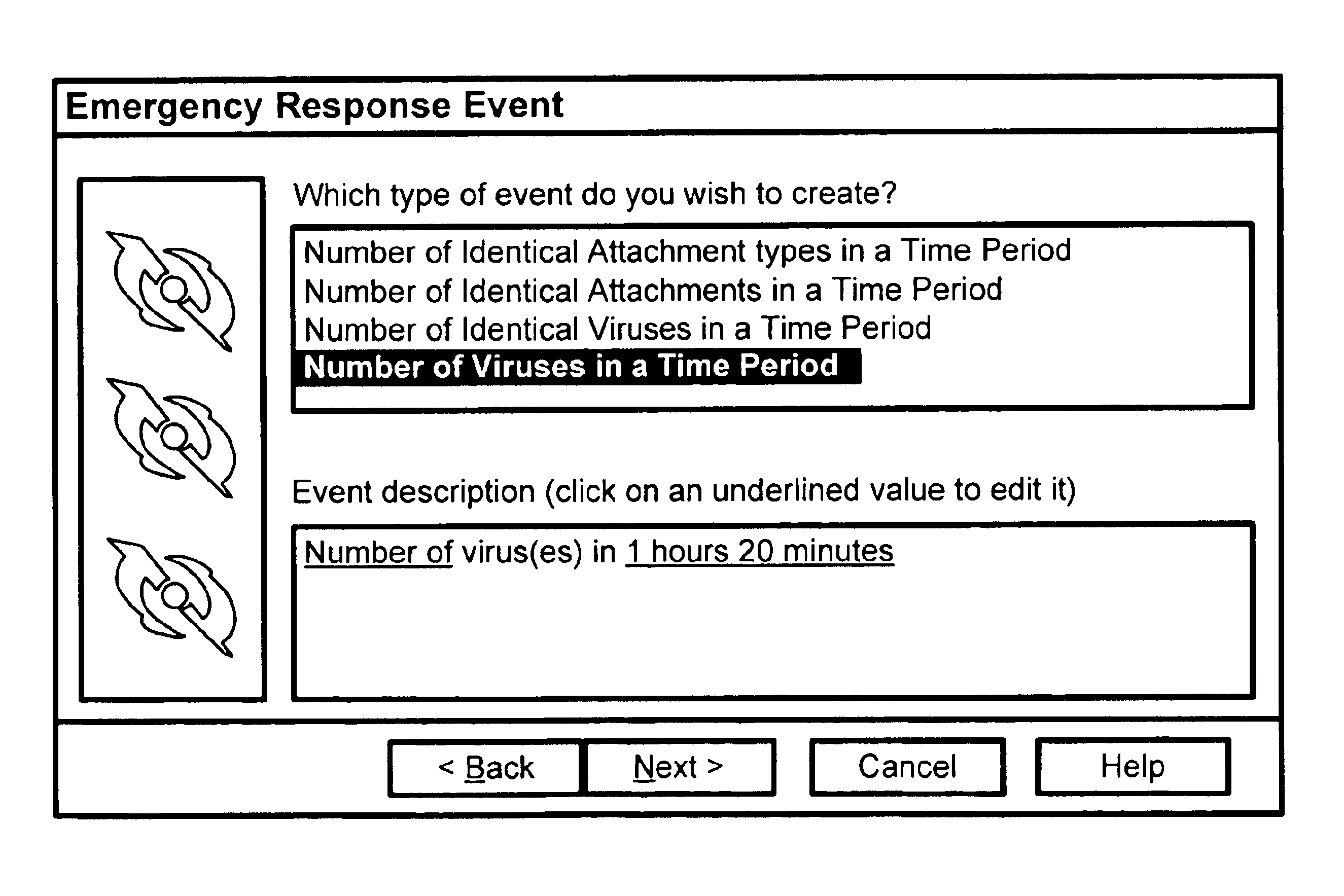
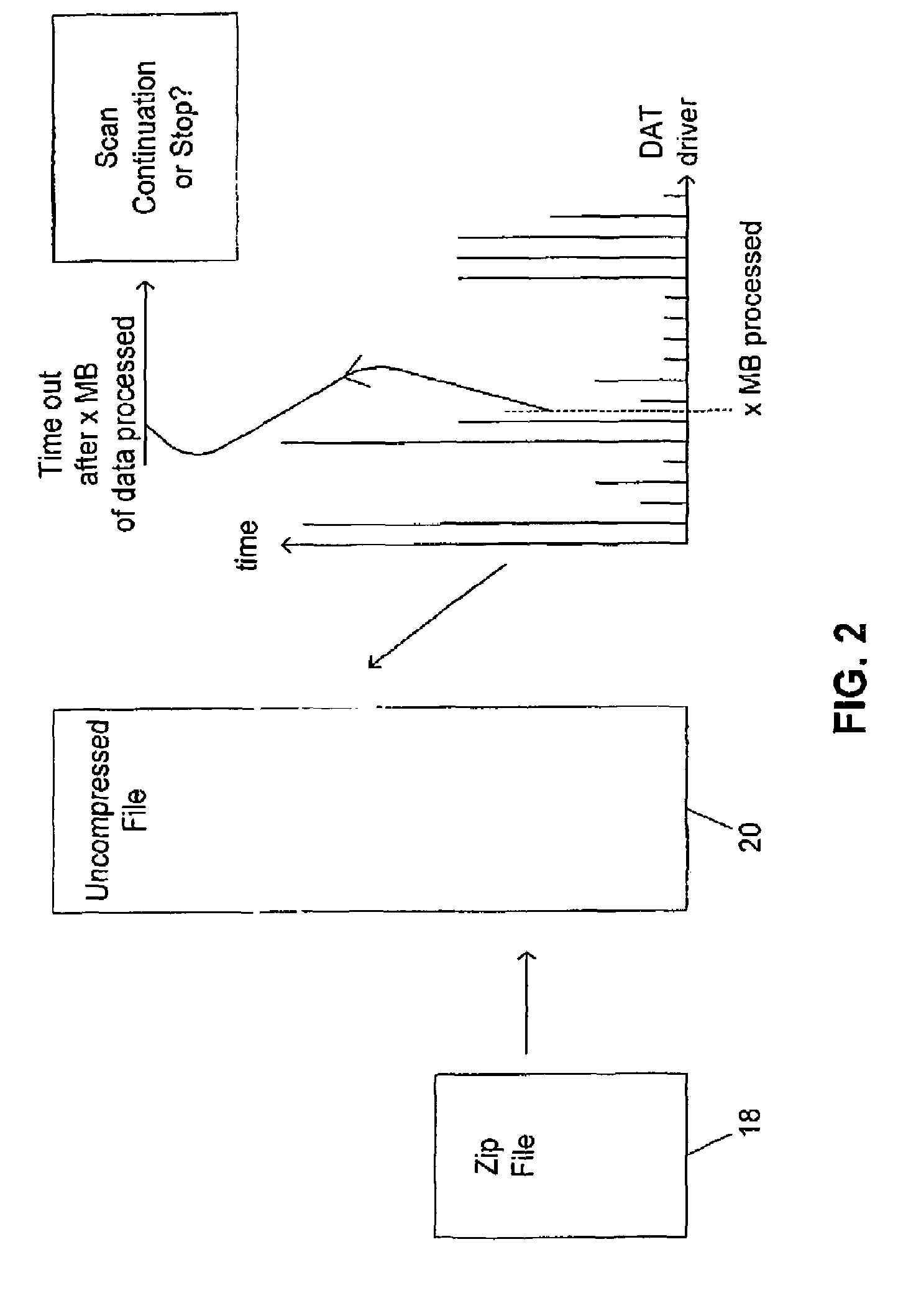
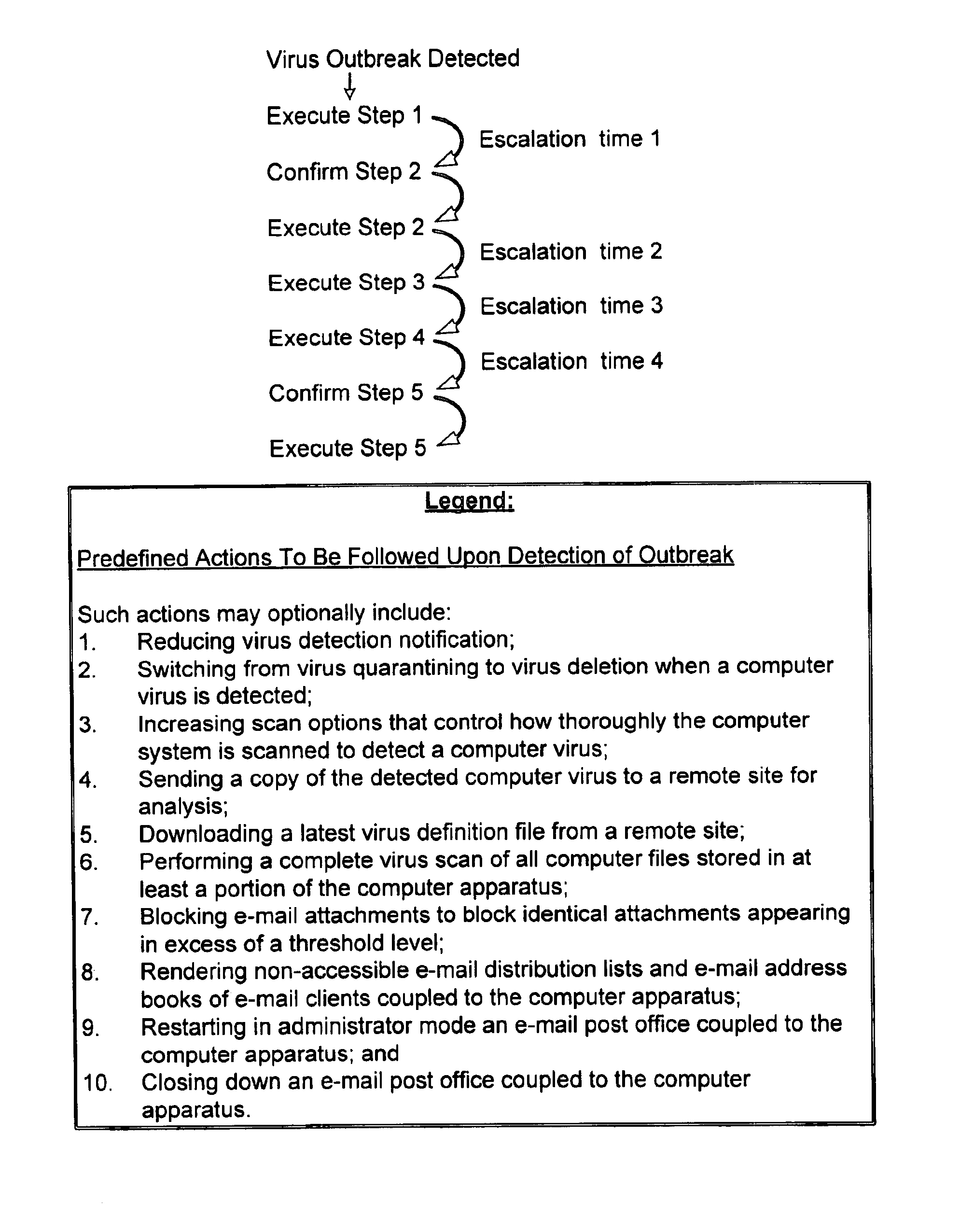
Response to a computer virus outbreak
InactiveUS6898715B1Light loadInhibit computer virus propagationMemory loss protectionUnauthorized memory use protectionAnti virusAddress book
When a computer virus outbreak is detected, a predefined sequence of steps are automatically or manually followed using rule definitions, that may include office hours, to invoke anti-virus counter-measures. The counter-measures can include reducing virus notification, increasing scanning options, blocking E-mail attachments, hiding E-mail address books and the like. The predetermined sequence of actions may be varied with the time of day and day of week.
Owner:MCAFEE LLC
Method and apparatus for the detection, notification, and elimination of certain computer viruses on a network using a promiscuous system as bait
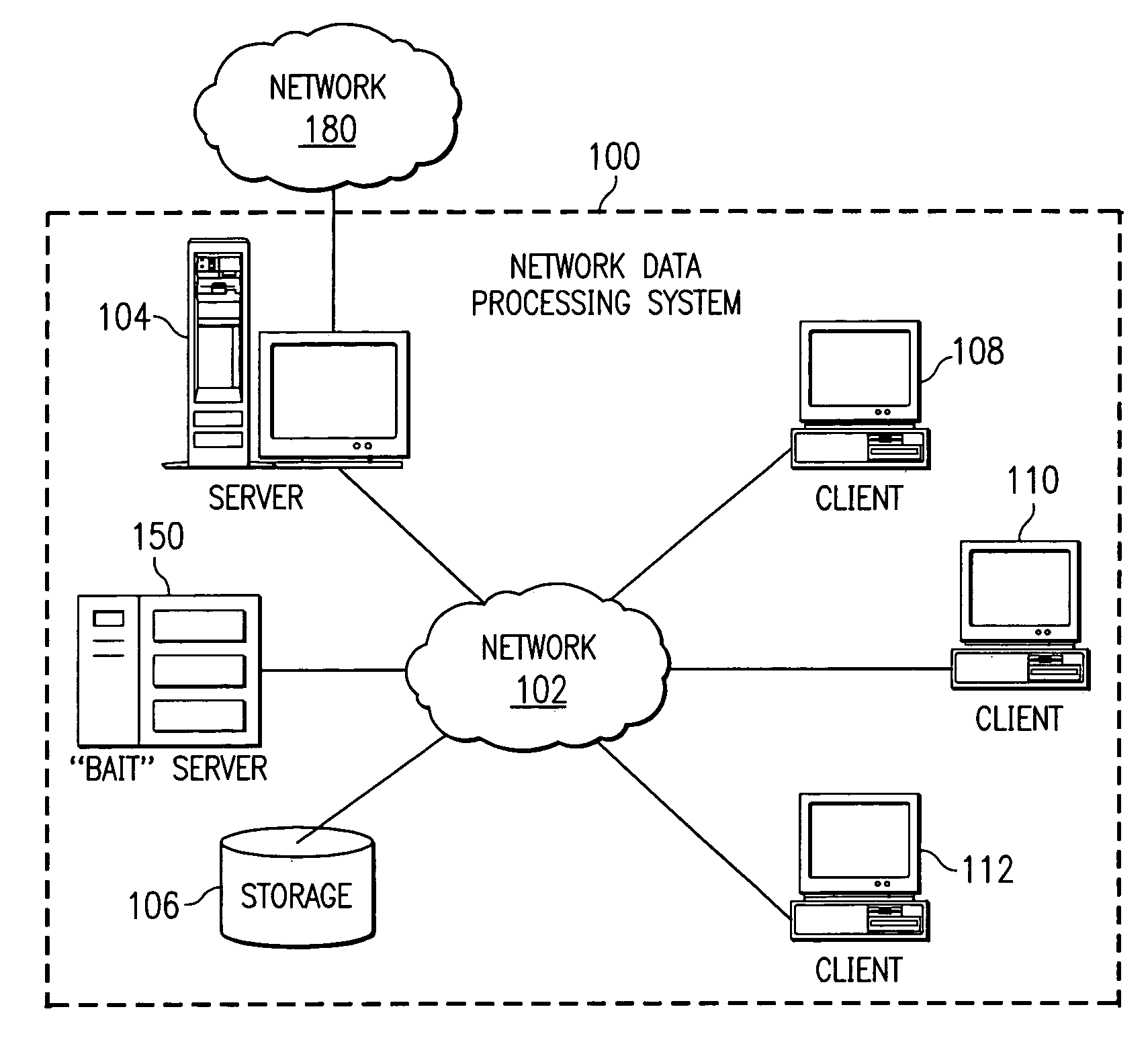
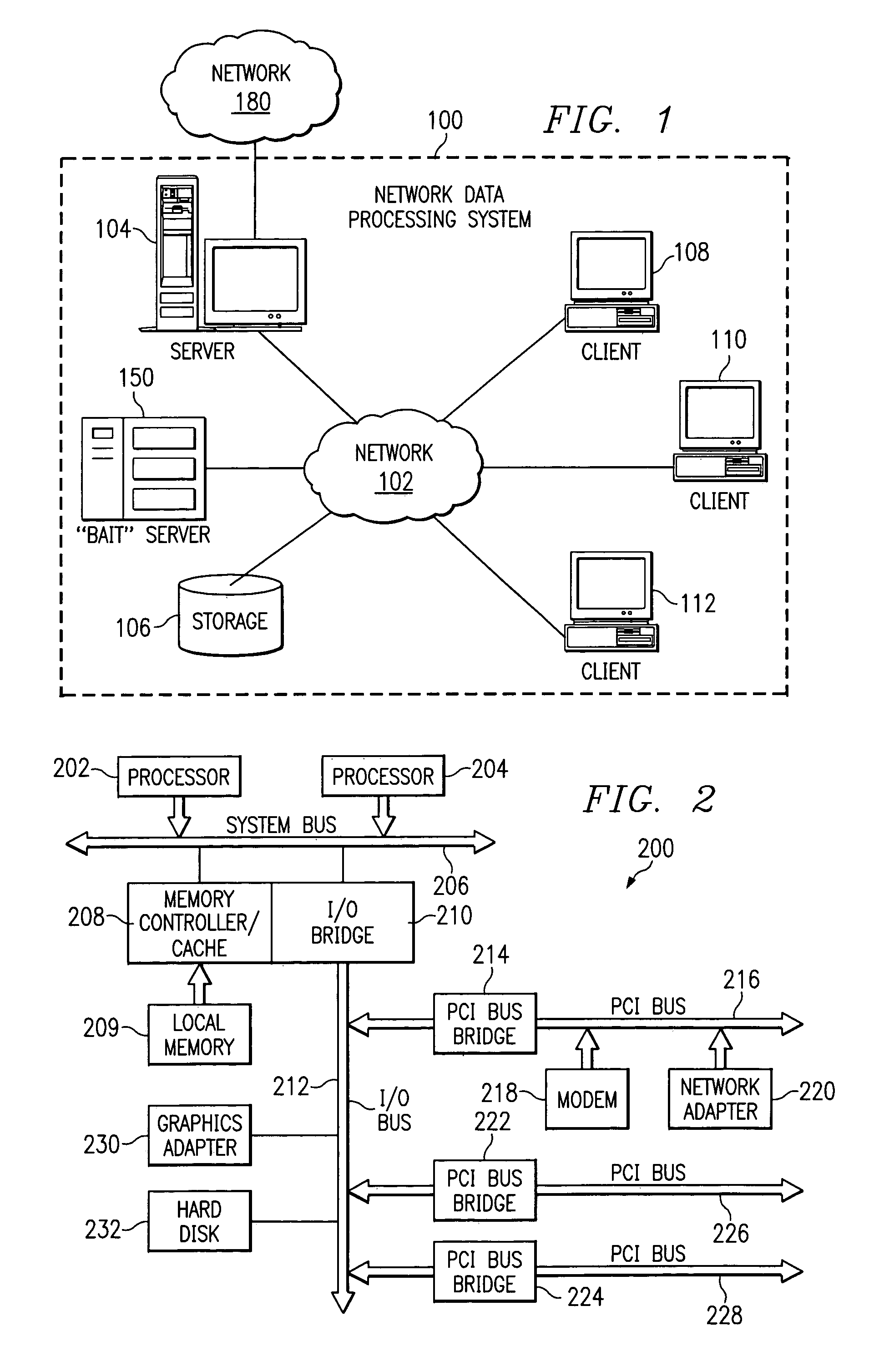
A method, computer program product, and network data processing system for identifying, locating, and deleting viruses is provided. In one embodiment, the network data processing system includes a local server, several client data processing systems, and a bait server. The address of the bait server is not published to the clients. Thus, any attempt to access the bait server would indicate the presence of a virus on the client attempting access. The bait server monitors itself and, responsive to an attempt from a client to access the bait server, broadcasts an indication that a virus attack is underway to all devices within the network. The bait server then ignores all further access requests by the offending client until it receives an indication that the offending client has been disinfected and directs the local server to disconnect the offending client(s) from the network. The bait server also notifies the local server and / or a network administrator of the problem and the identity of the offending client allowing appropriate action to be initiated to disinfect the offending client.
Owner:LENOVO PC INT
Anti-virus protection at a network gateway
InactiveUS20050120229A1Minimize exposureMemory loss protectionDigital data processing detailsAnti virusVirus
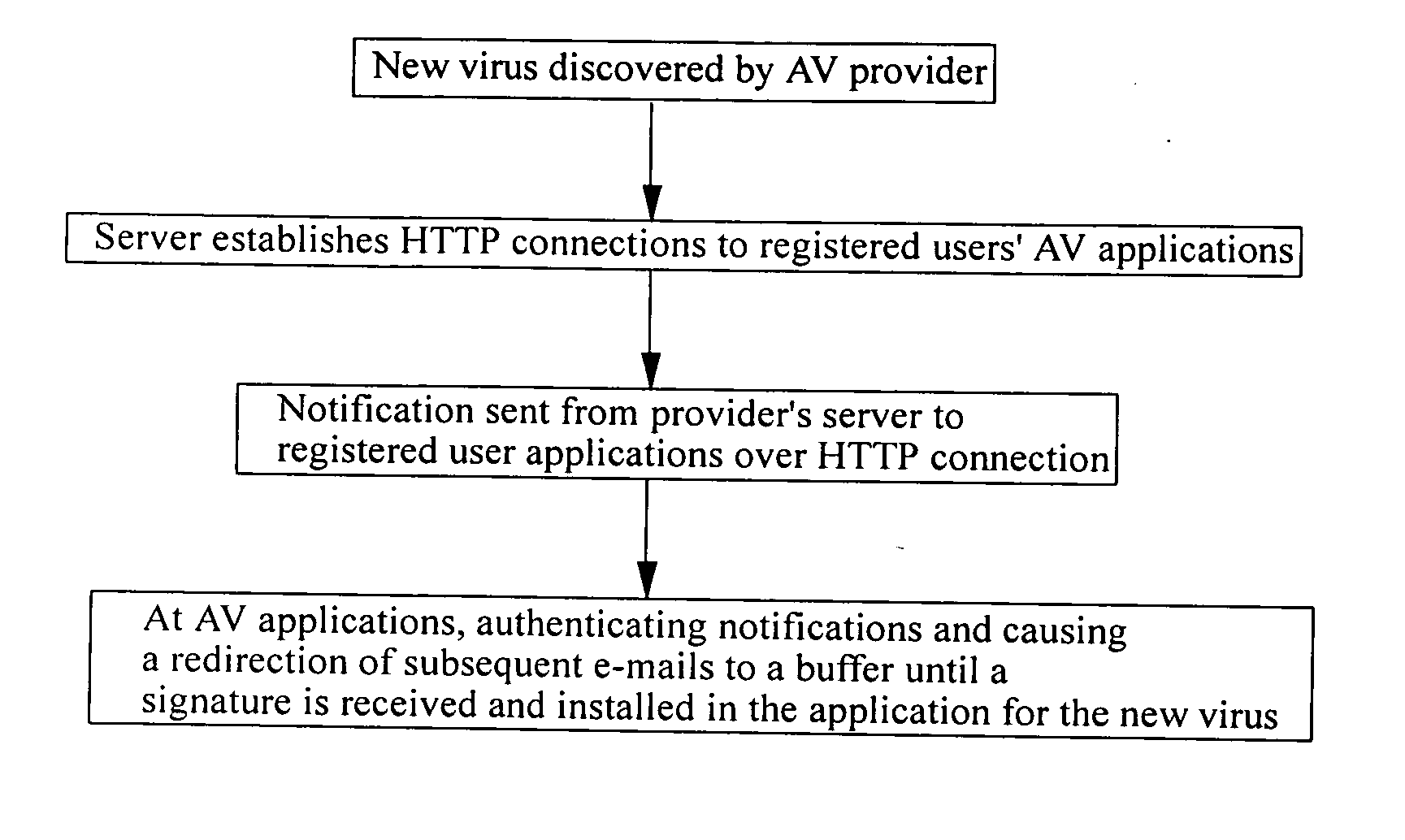
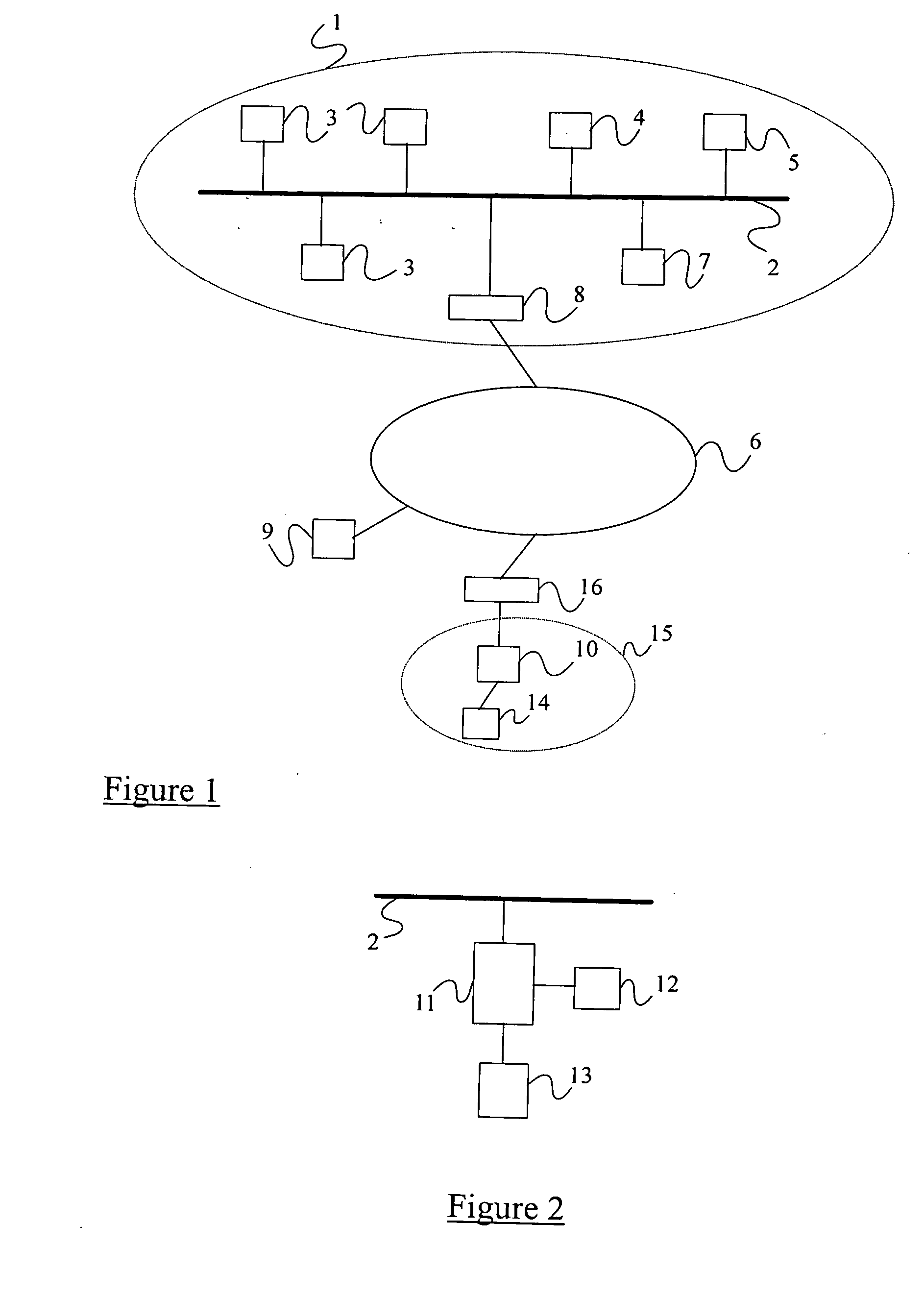
A method of preventing the infection of a computer network 1 by a computer virus, where that virus can be spread by e-mail traffic. The method comprises installing at an e-mail gateway 7 of the network an anti-virus application 12, which application scans at least incoming e-mail traffic for known viruses. In the event that a new virus is detected by the provider of the anti-virus application 12, a notification of this event is sent from the provider to the anti-virus-application 12. At the anti-virus application 12, receipt of said notification results in the diversion of incoming e-mails or their attachments to a buffer 13 for safe storage.
Owner:F SECURE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com