Patents
Literature
185 results about "Analog computer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An analog computer or analogue computer is a type of computer that uses the continuously changeable aspects of physical phenomena such as electrical, mechanical, or hydraulic quantities to model the problem being solved. In contrast, digital computers represent varying quantities symbolically and by discrete values of both time and amplitude.
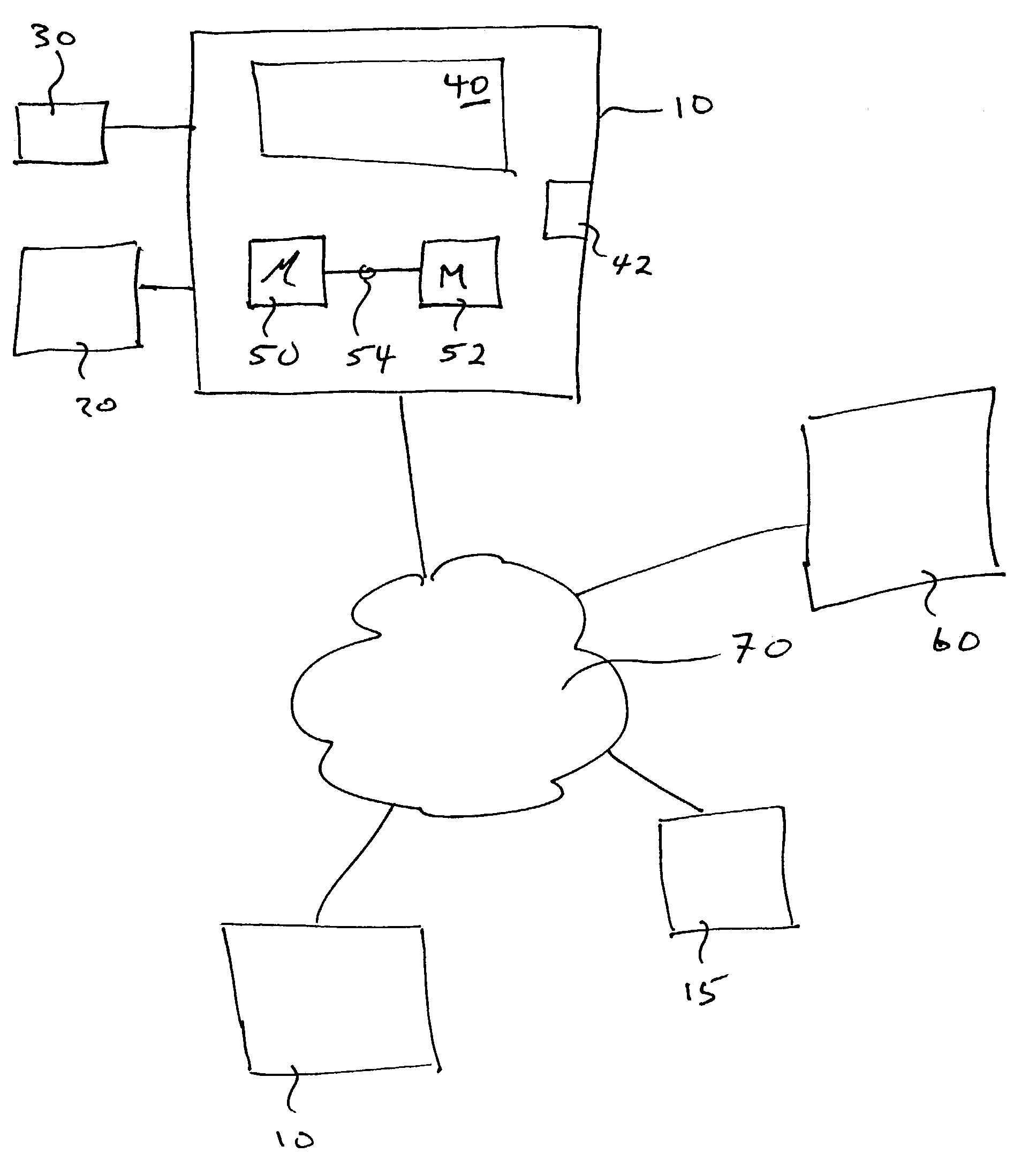
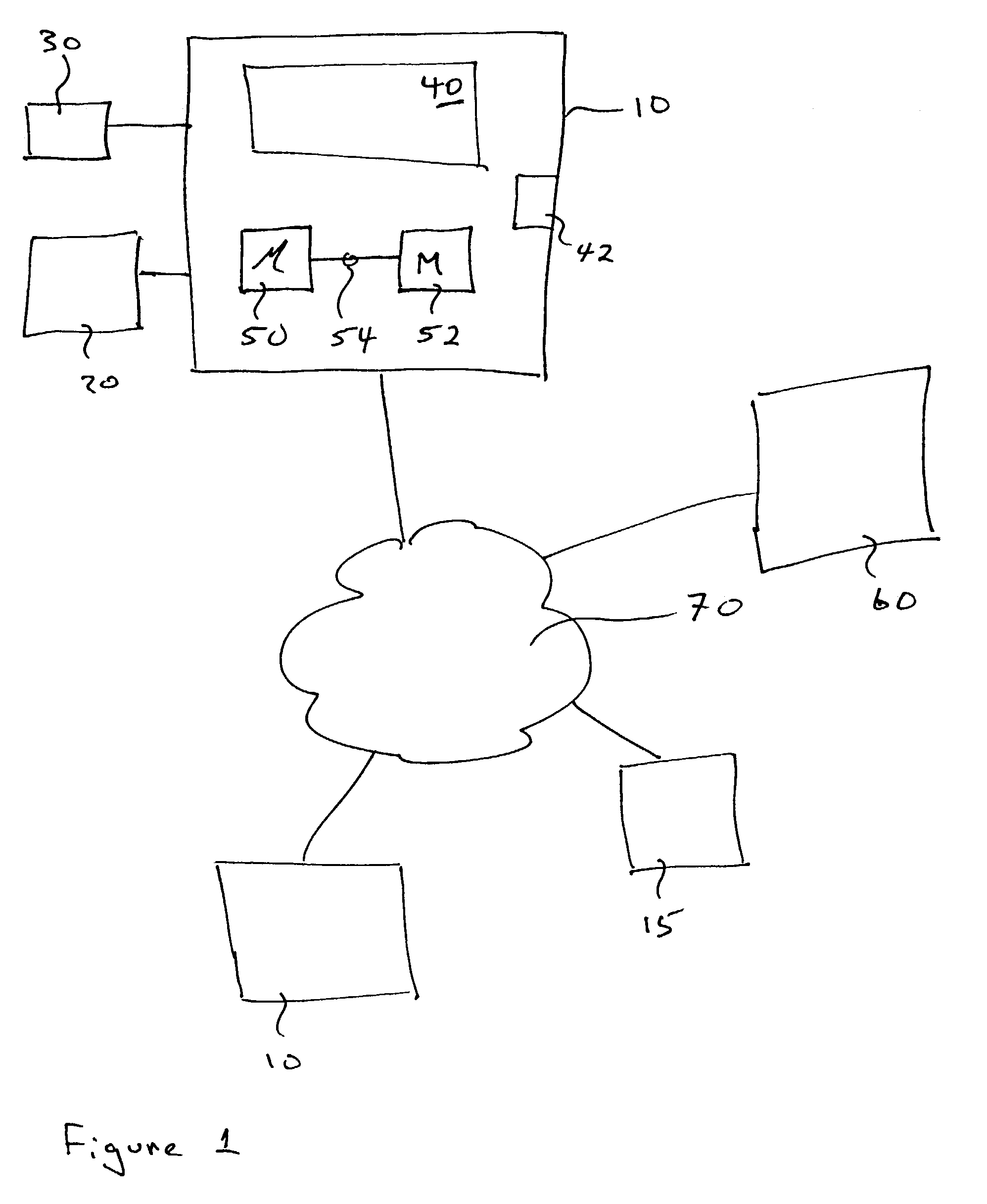
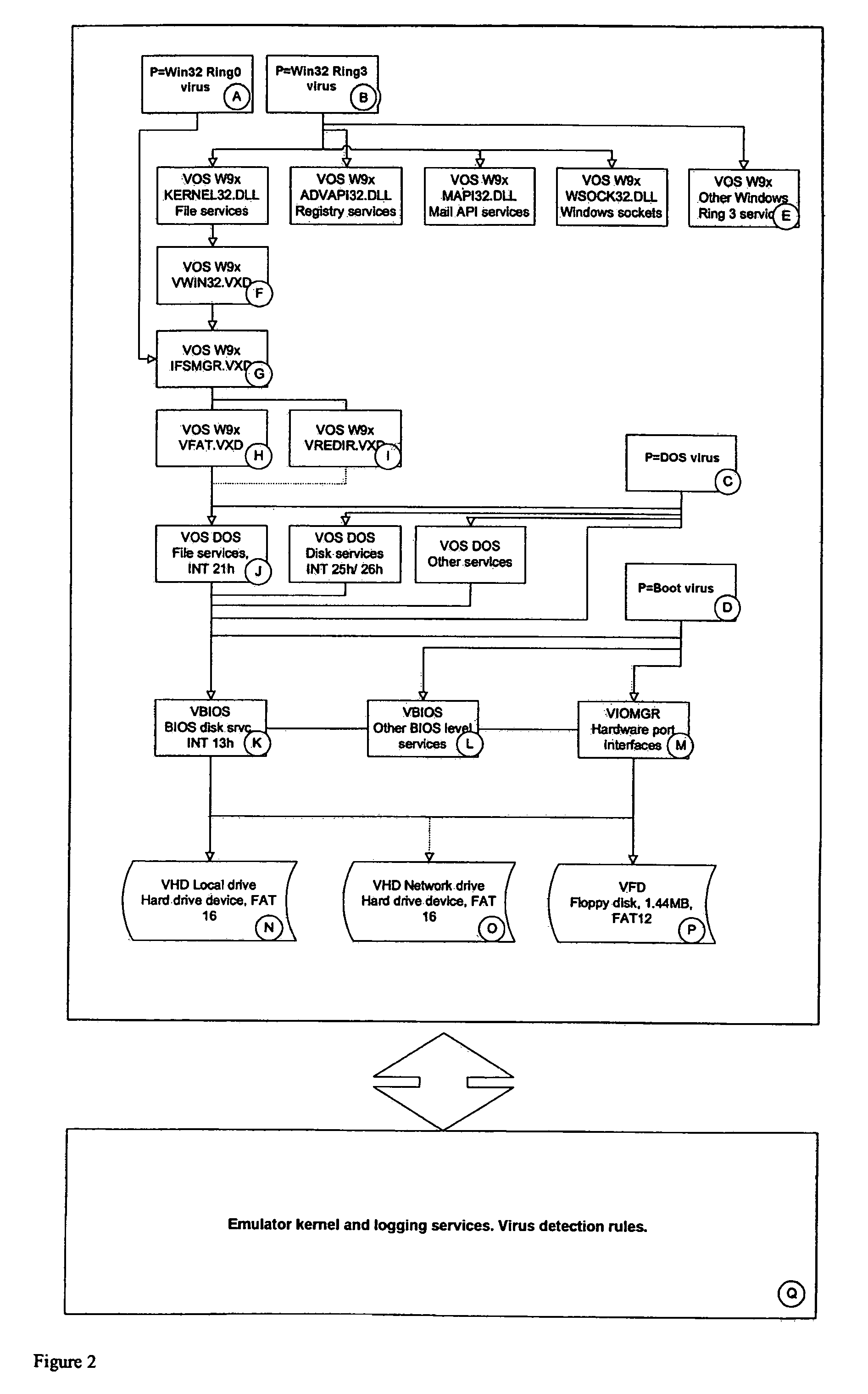
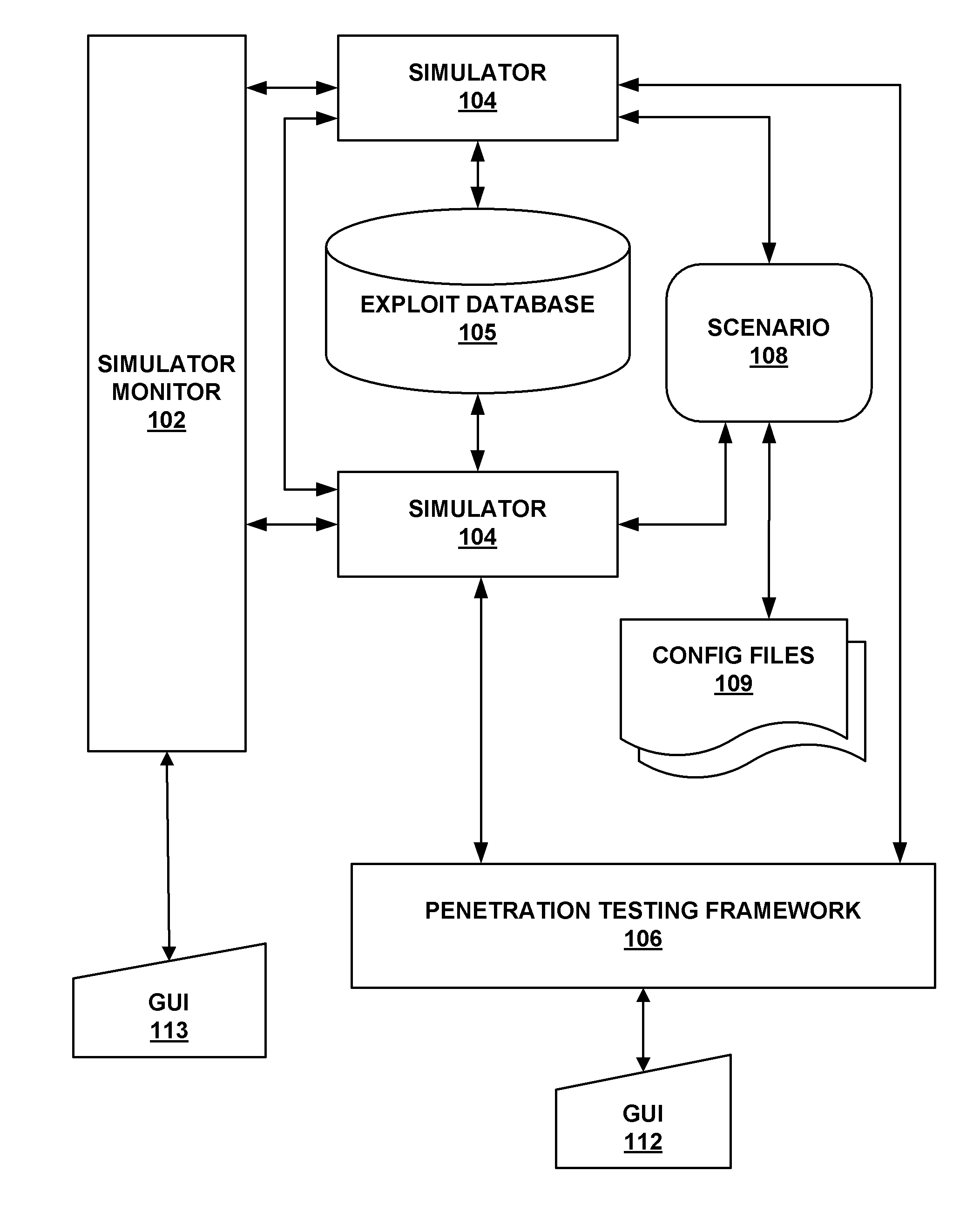
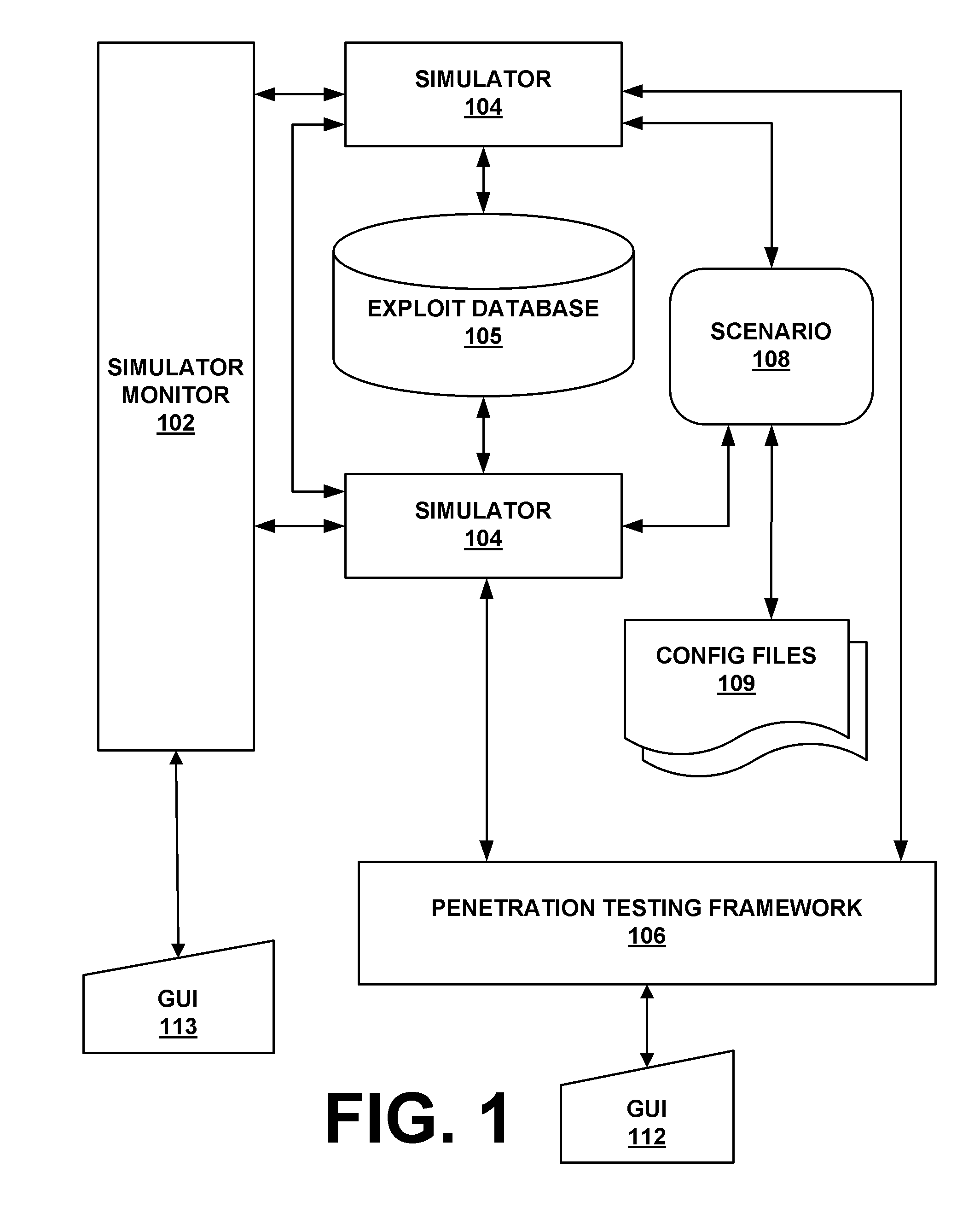
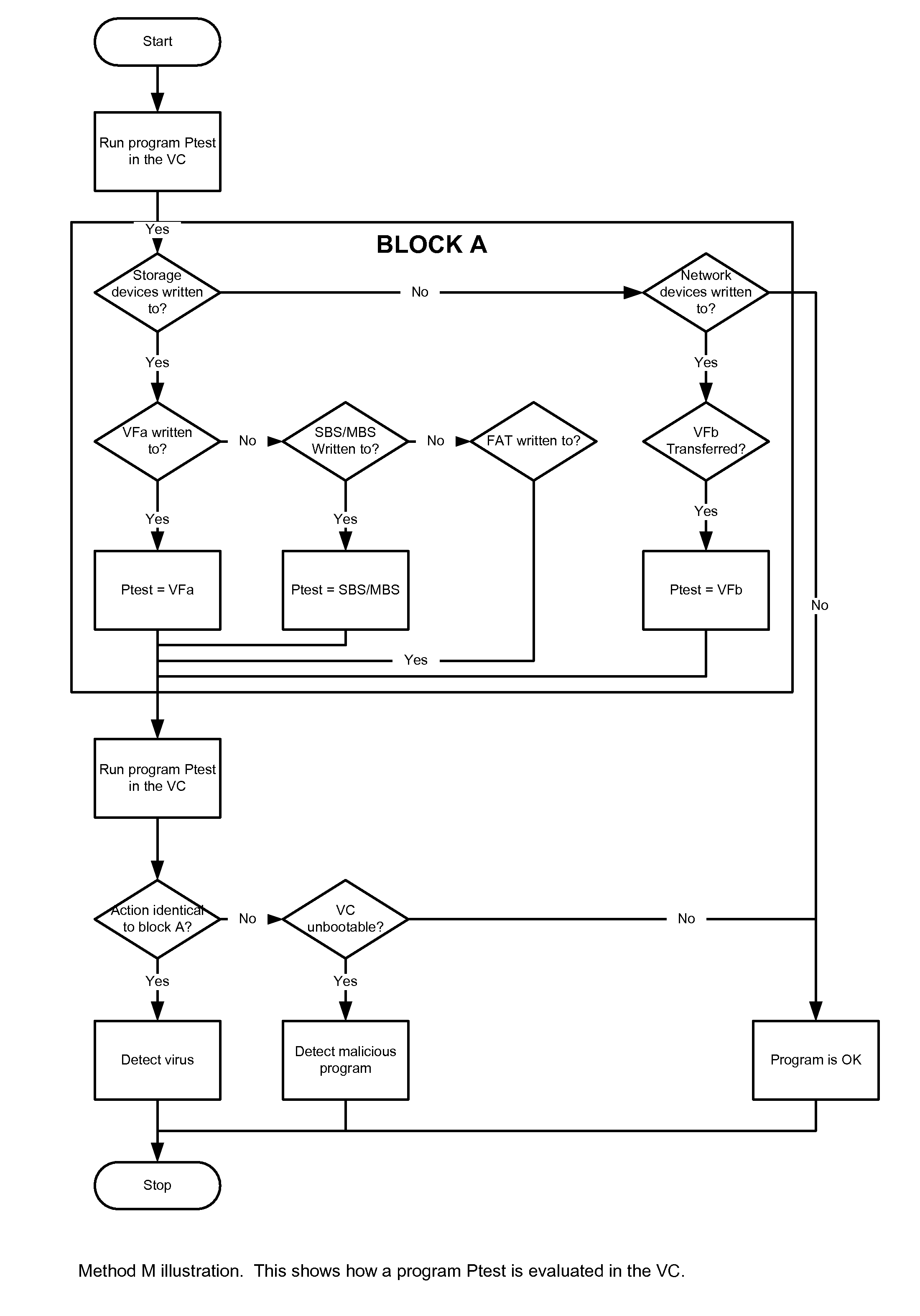
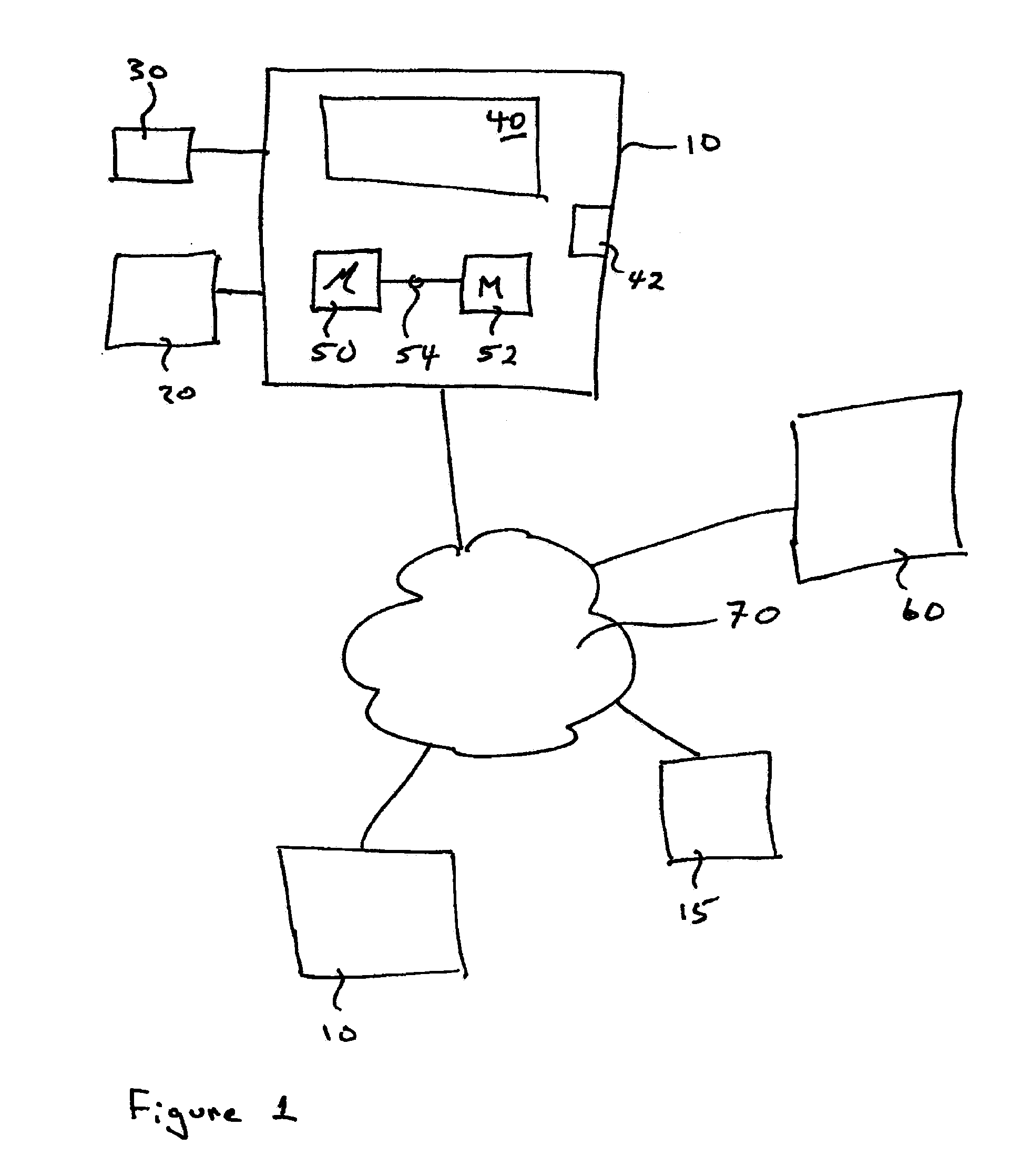
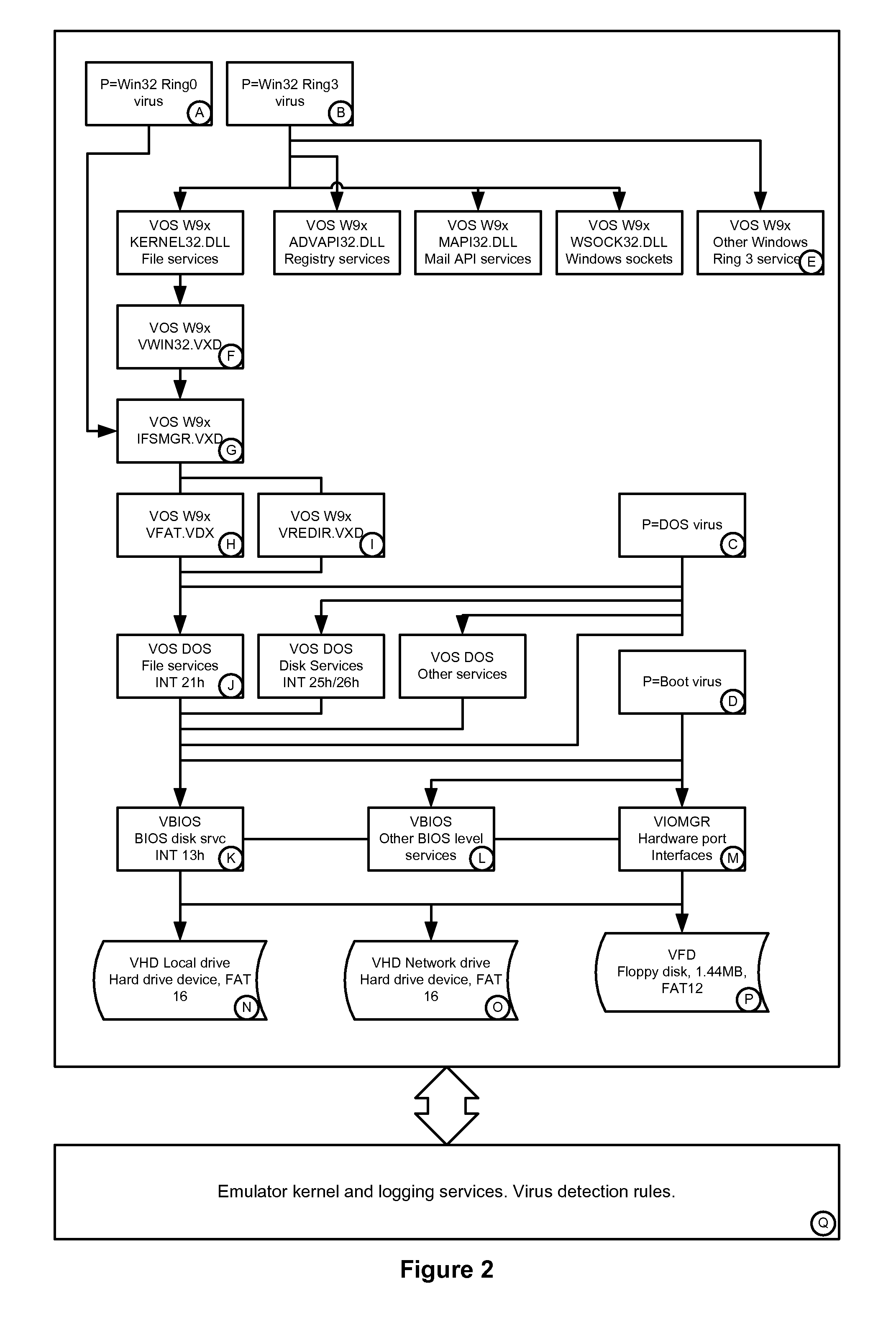
Simulated computer system for monitoring of software performance
InactiveUS7356736B2Reduce riskMemory loss protectionError detection/correctionVery low riskOperational system
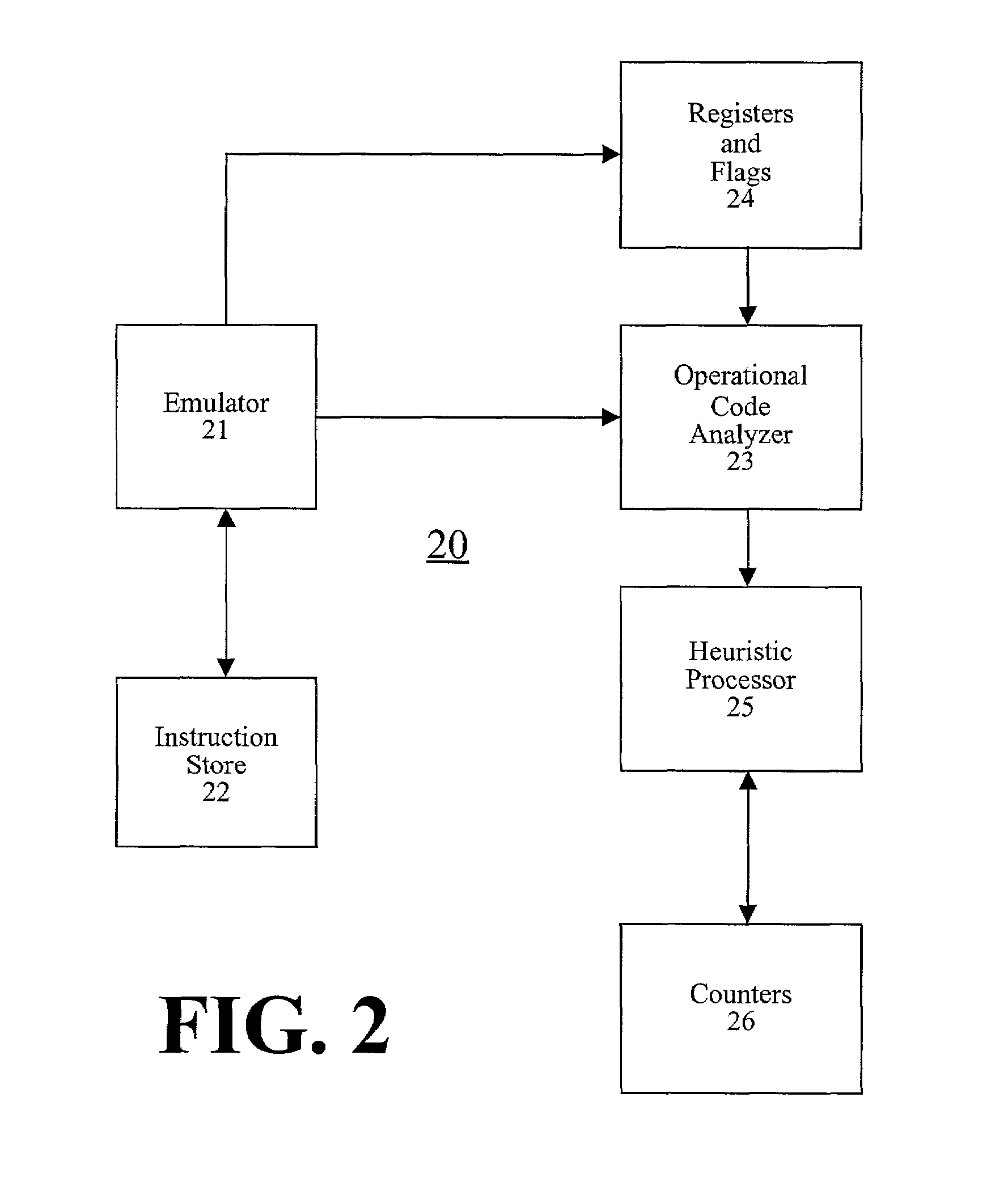
A system S is defined which is capable of simulating a computer (virtual computer, VC) for the purpose of software performance monitoring. The system is implemented as a set of software modules (SM) that can be exchanged to change the behavior of the VC. The VC is driven by a CPU emulator, and can run any operating system (virtual operating system, VOS) that is supported by the available SM's. The system is designed to log accesses to system resources and the nature of these accesses. The system is particularly useful for determining whether an executable or file contains an unknown virus, with a very low risk of false positives. Detected viruses include encrypted, polymorphic, metamorphic and other virus types.
Owner:CA TECH INC
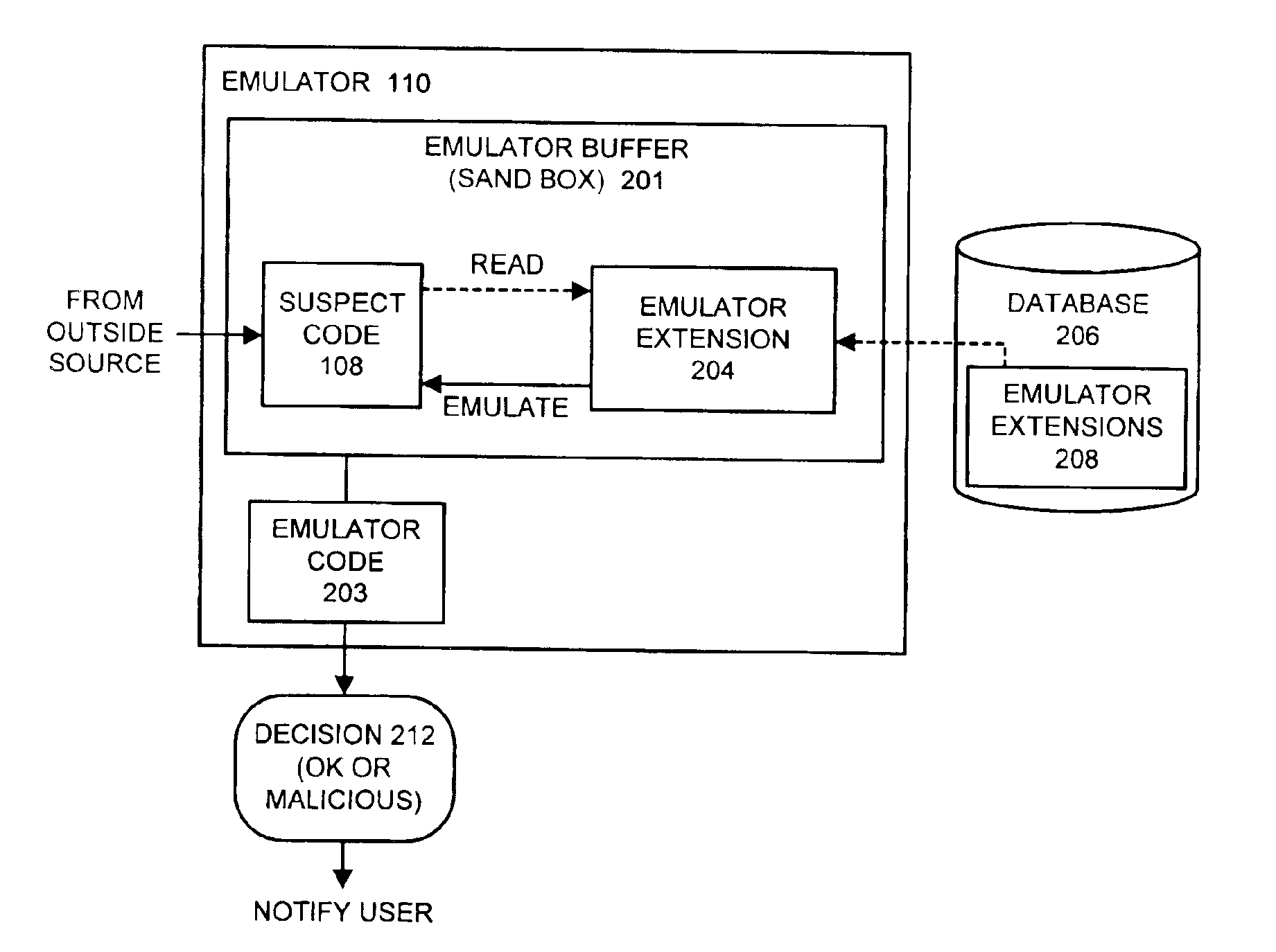
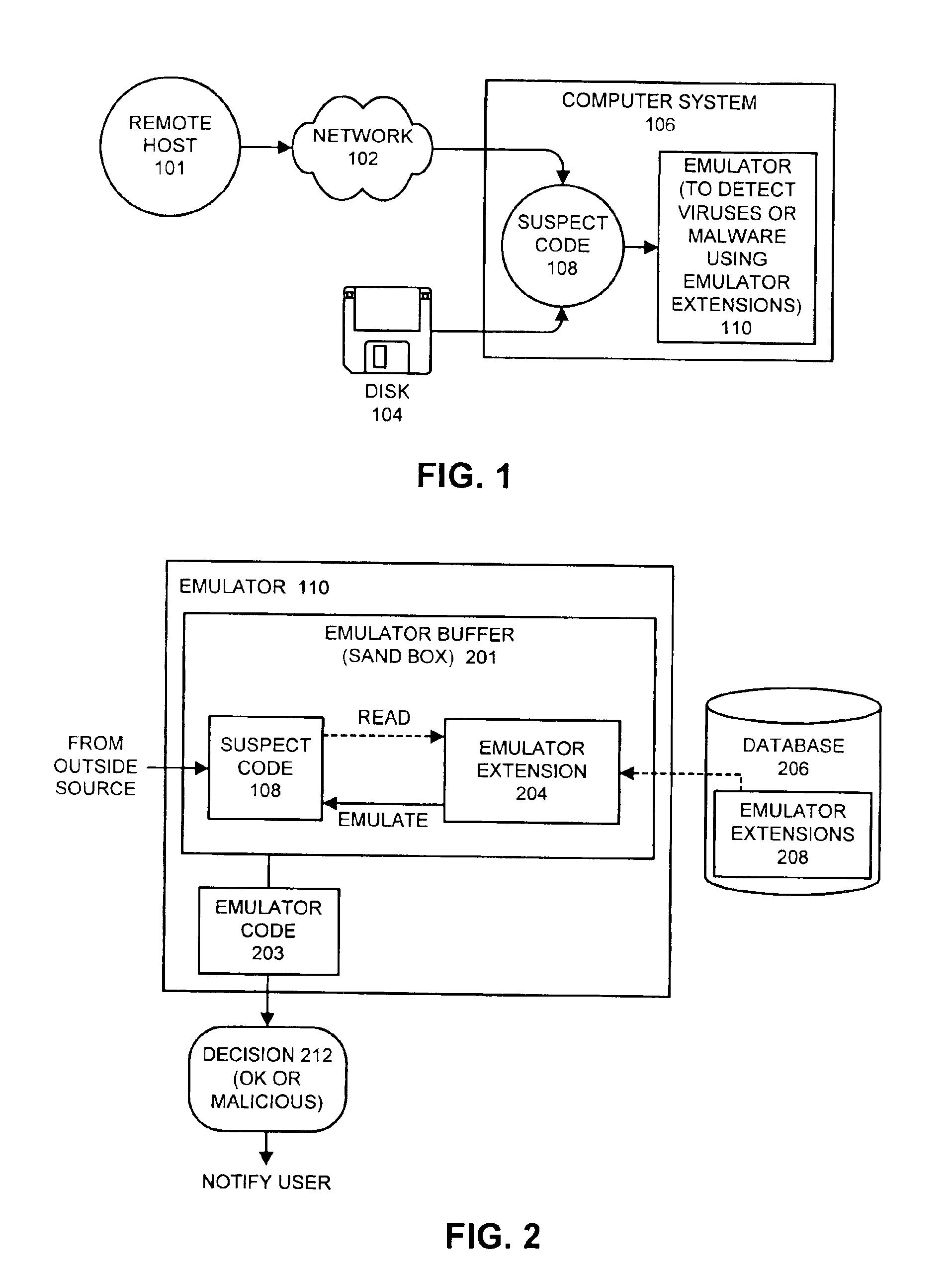
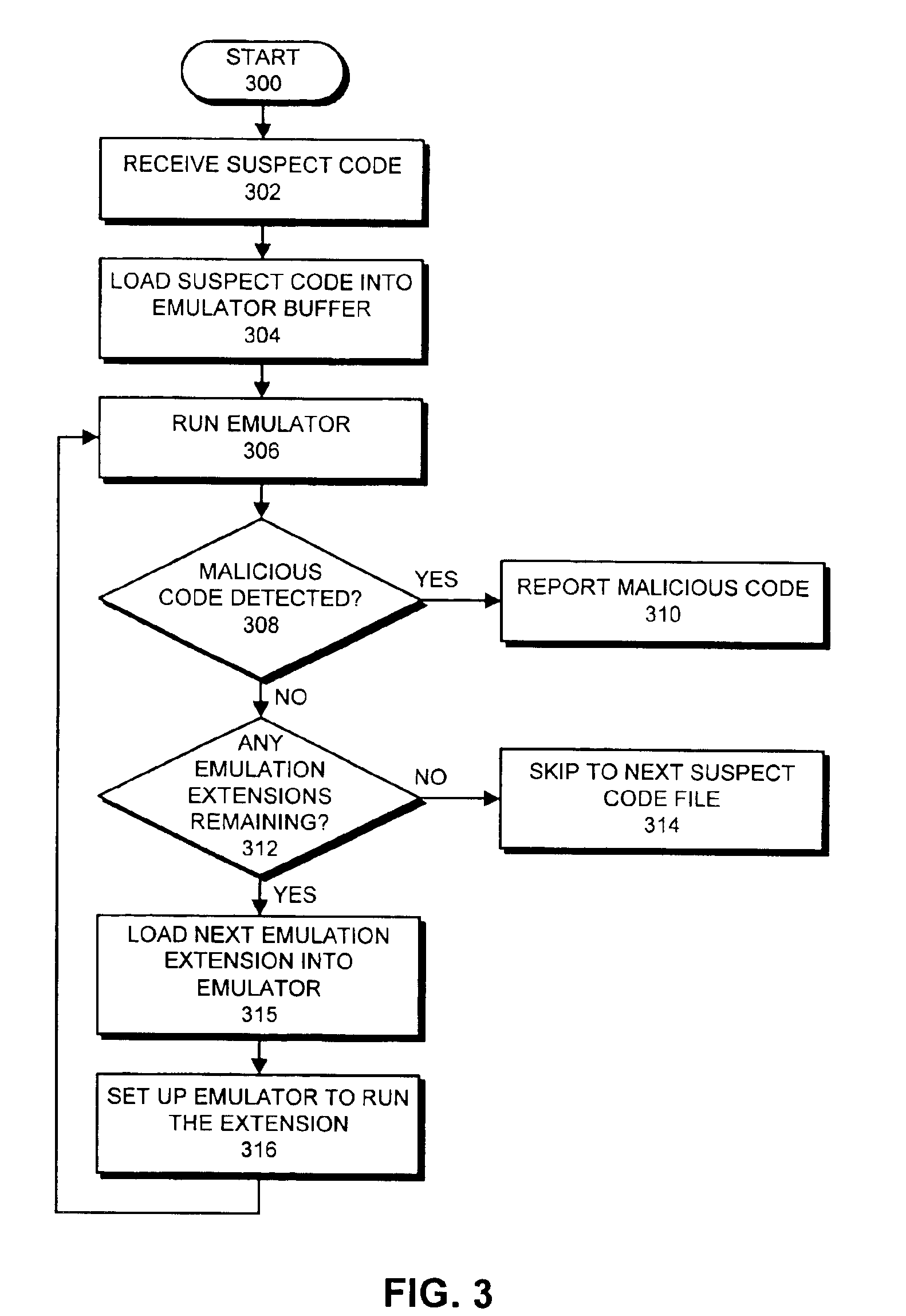
Detecting computer viruses or malicious software by patching instructions into an emulator
InactiveUS6907396B1High simulationPlatform integrity maintainanceTransmissionProgram instructionAnalog computer
One embodiment of the present invention provides a system for emulating computer viruses and / or malicious software that operates by patching additional program instructions into an emulator in order to aid in detecting a computer virus and / or malicious software within suspect code. During operation, the system loads a first emulator extension into the emulator. This first emulator extension includes program instructions that aid in the process of emulating the suspect code in order to detect a computer virus and / or malicious software. The system also loads the suspect code into an emulator buffer. Next, the system performs an emulation using the first emulator extension and the suspect code. This emulation is performed within an insulated environment in a computer system so that the computer system is insulated from malicious actions of the suspect code. During this emulation, the system determines whether the suspect code is likely to exhibit malicious behavior. In one embodiment of the present invention, loading the first emulator extension into the emulator involves loading the first emulator extension into the emulator buffer within the emulator. In this embodiment, performing the emulation involves emulating the program instructions that comprise the first emulator extension.
Owner:MCAFEE LLC
Interactive quest game
A gaming system and method of game play is provided wherein the gaming is earned out within a themed physical play space comprising an existing or specially configured entertainment facility or play structure. The game utilizes electronically identifiable objects, such as colored balls, shaped objects, cards, bands, tags and / or the like, to provide an interactive game play experience generally simulative of a computer adventure game experience. Play participants are challenged to work and cooperate with other play participants to find identified objects, clues or other information and to use the objects, clues or information to solve various puzzles or problems that present encumbrances inhibiting players' advancement in the game. Optionally, each play participant possesses a unique RFID band, card or the like, that electronically identifies the play participant and enables the play system to award and track points or other rewards to successful play participants individually or working with other play participants as a team. The game in accordance with the invention provides the intellectual challenge and excitement of a computer adventure game, but with tangible interactives, physical challenges, and social interaction.
Owner:MQ GAMING
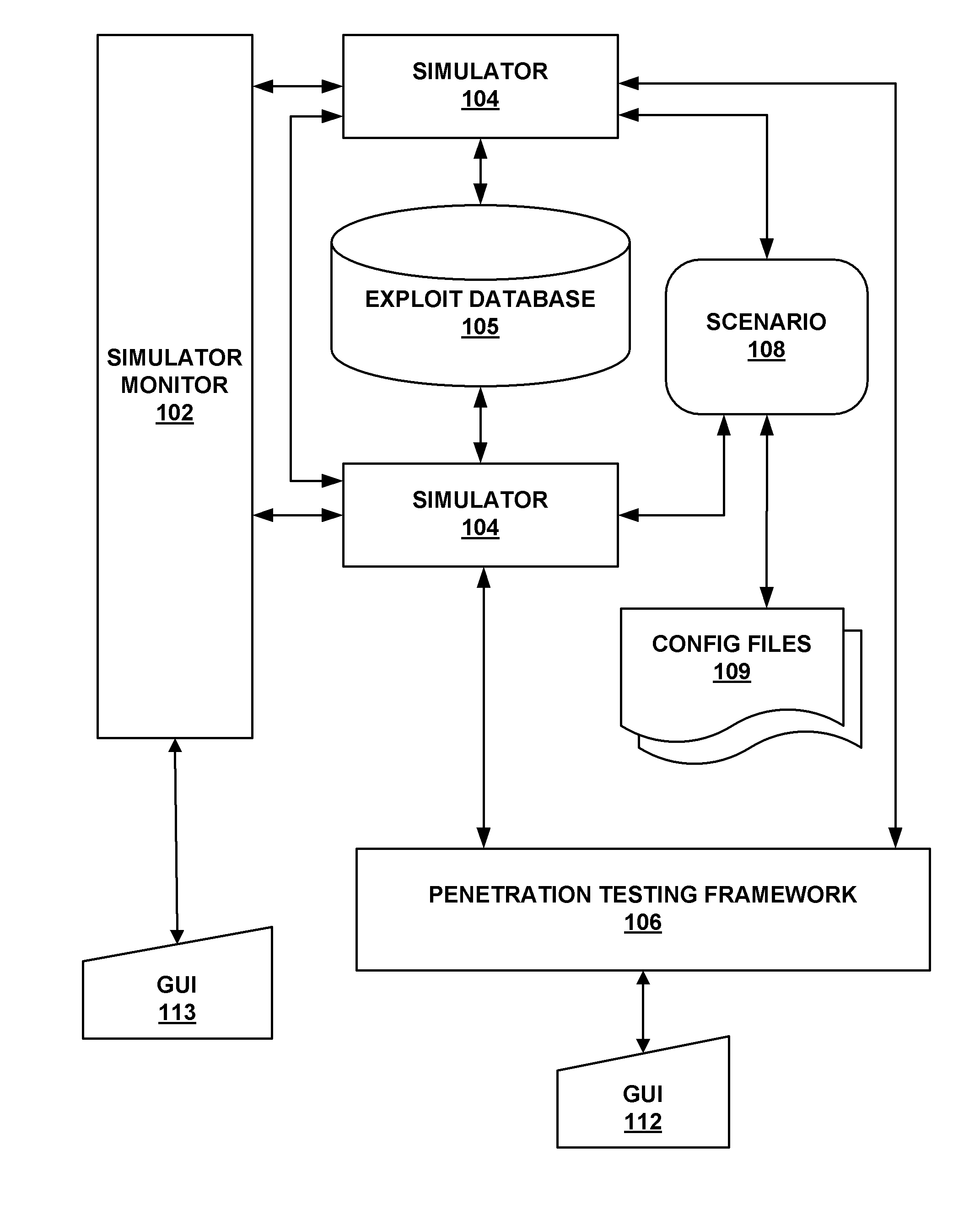
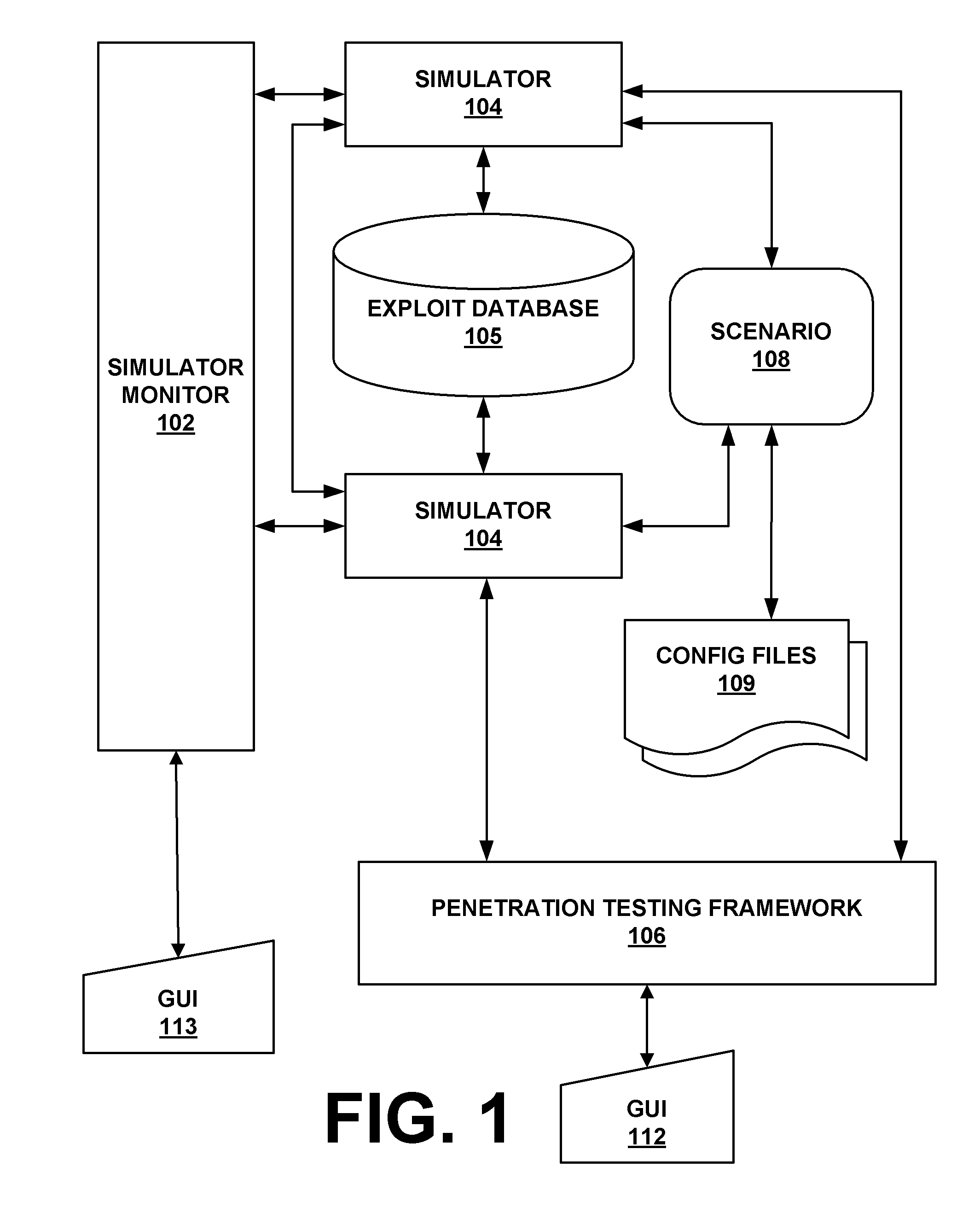
System and method for simulating computer network attacks
ActiveUS20090007270A1Memory loss protectionError detection/correctionOperational systemNetwork agent
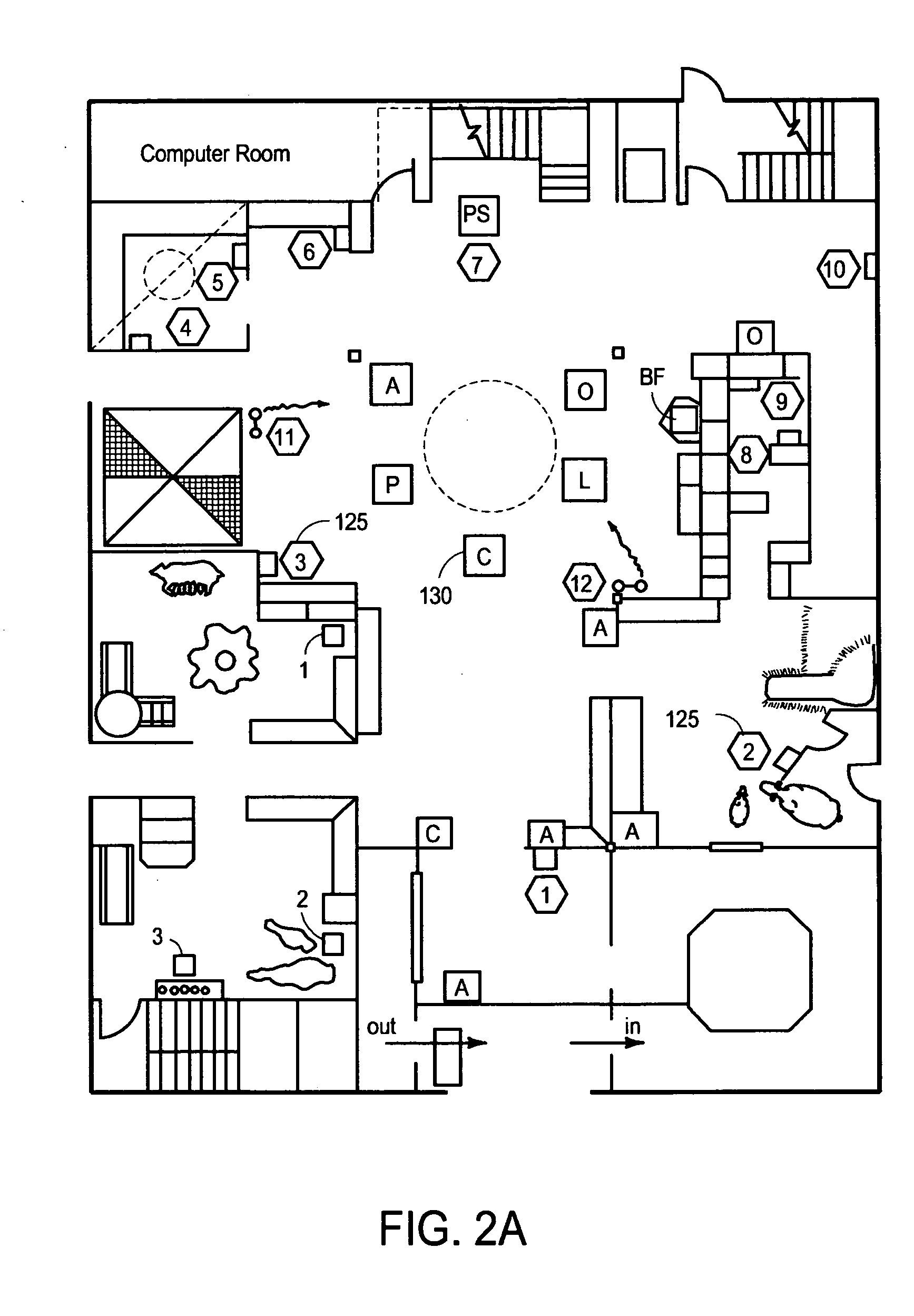
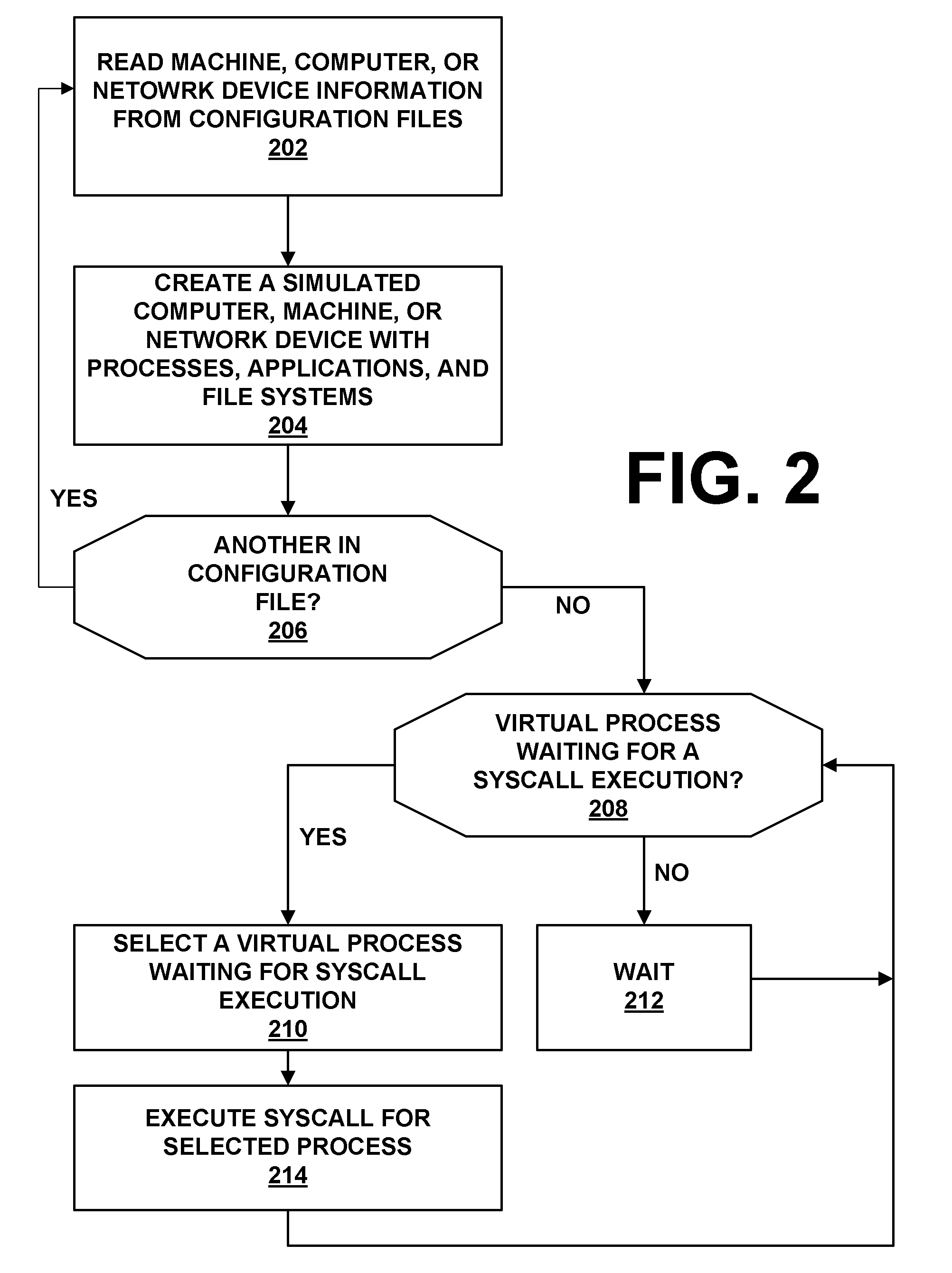
The present invention provides a system and method for providing computer network attack simulation. The method includes the steps of: receiving a network configuration and setup description; simulating the network configuration based on the received network configuration; receiving at least one confirmed vulnerability of at least one computer, machine, or network device in the simulated network; receiving a method for compromising the confirmed vulnerability of the at least one computer, machine, or network device; and virtually installing a network agent on the at least one computer, machine, or network device, wherein the network agent allows a penetration tester to execute arbitrary operating system calls on the at least one computer, machine, or network device.
Owner:FORTRA LLC
Machine-implementable project finance analysis and negotiating tool software, method and system
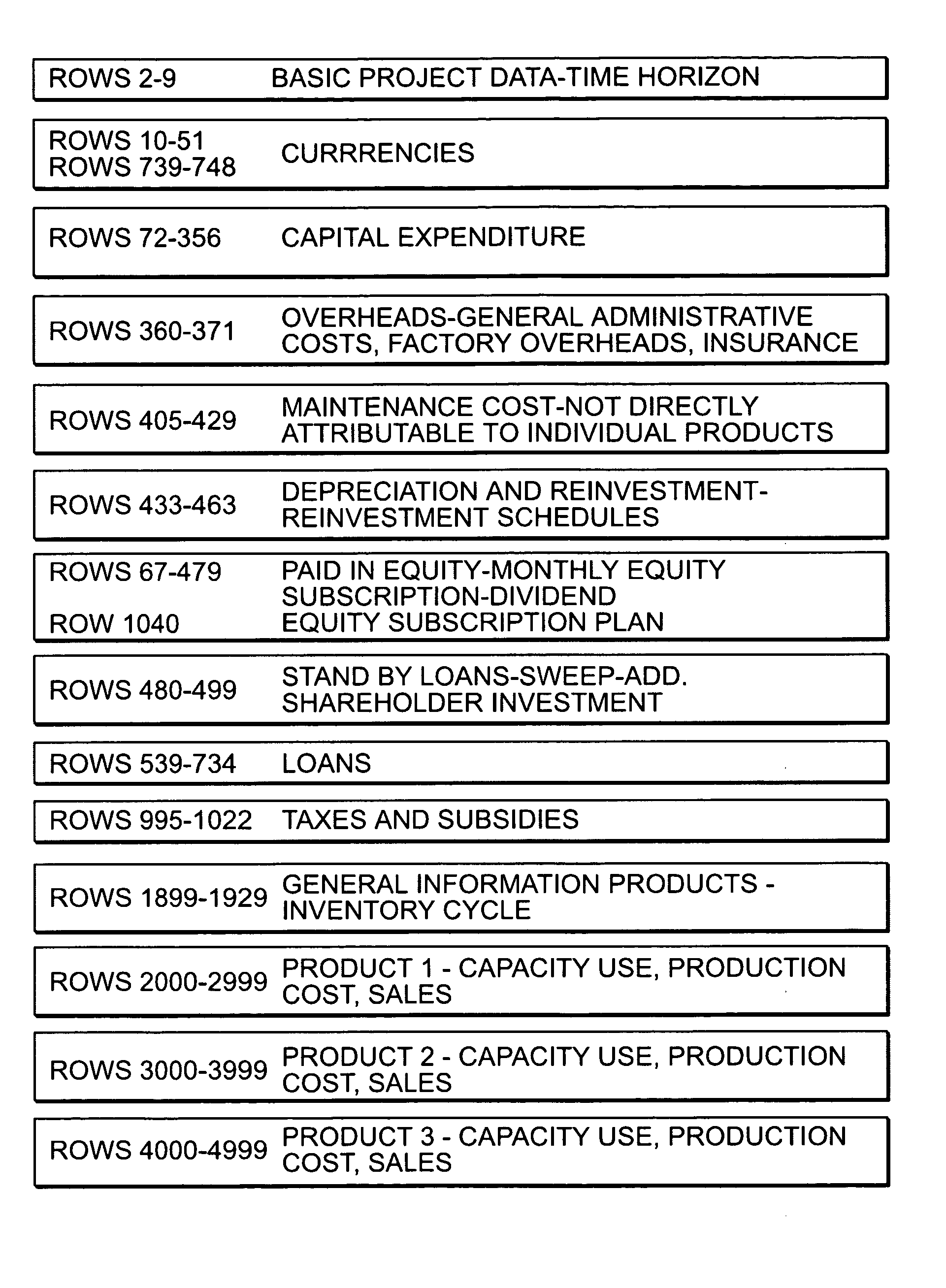
A financial simulation computer program product and method to create a project preparation, negotiating, and testing environment using standard project finance tools. A computer usable medium having computer-readable program code is embodied in a medium for generating financial statements, financial data, charts, graphs and reports using the standard project finance tools. The product and method allow automatically generated or manual entry of and editing of capital expenditure time series for multiple contracts in multiple capital expenditure categories. Limited recourse including debt service reserve accounts, stand-by loans and risk-sharing with suppliers and off-takers is taken into account. A desired financing time horizon is selected for each loan. For each loan the user can either manually enter disbursements or select a capital expenditure category and finance a percentage of the category. A loan disbursement time series is automatically generated. A loan disbursement times series is optionally generated independently of changes in capital expenditures and exchange rates based upon an earlier automatically generated loan disbursement time series.
Owner:MAESTLE WILFRIED A
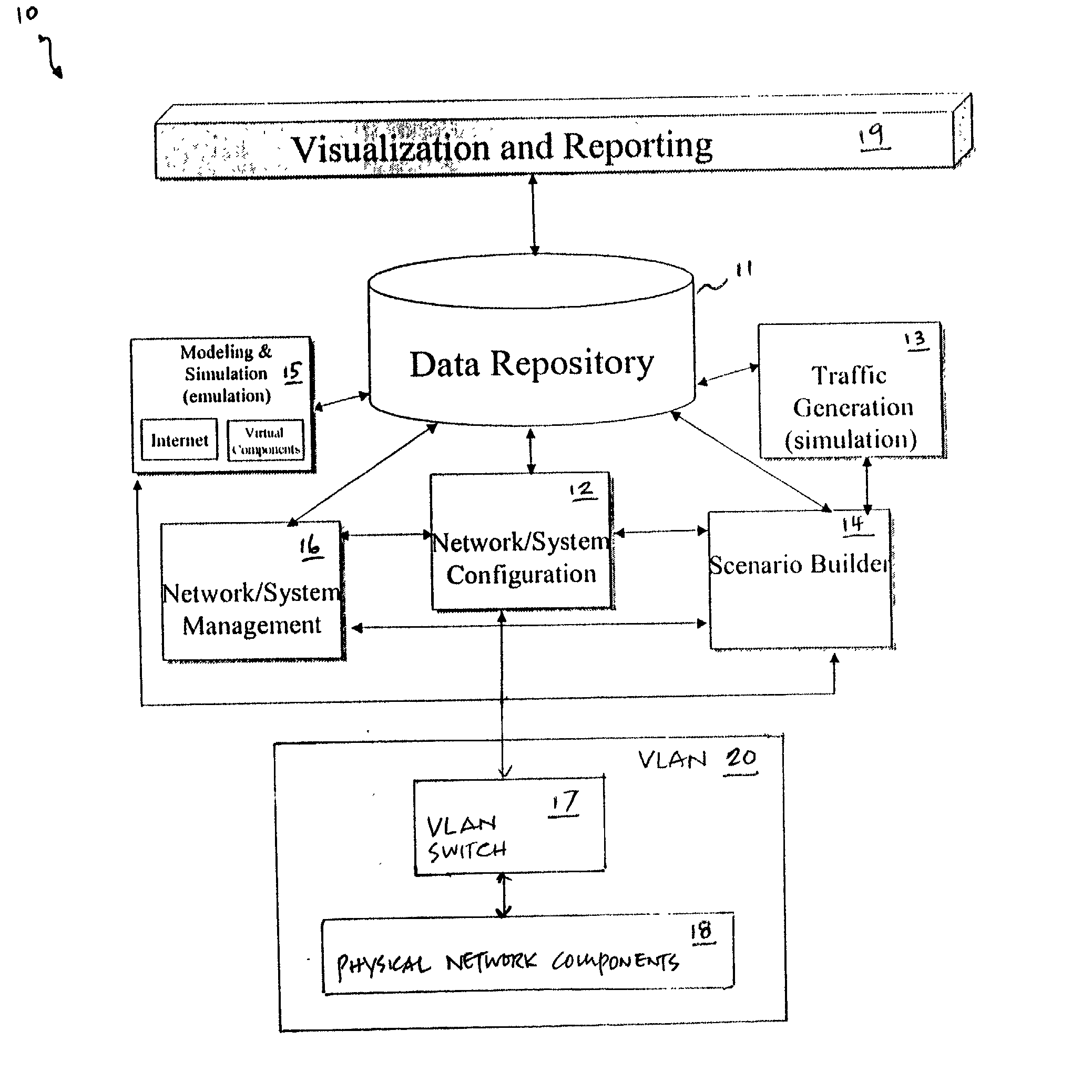
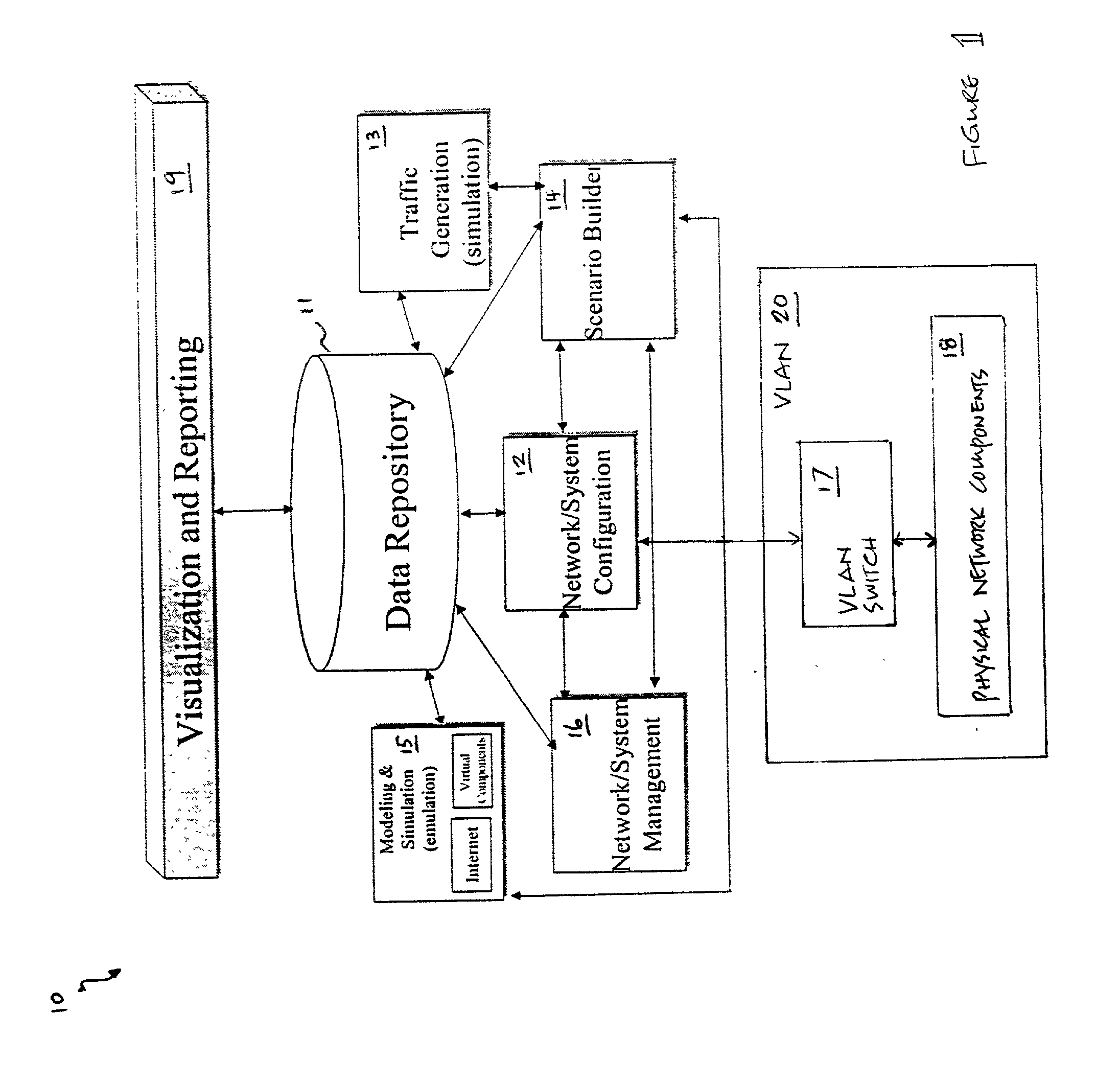
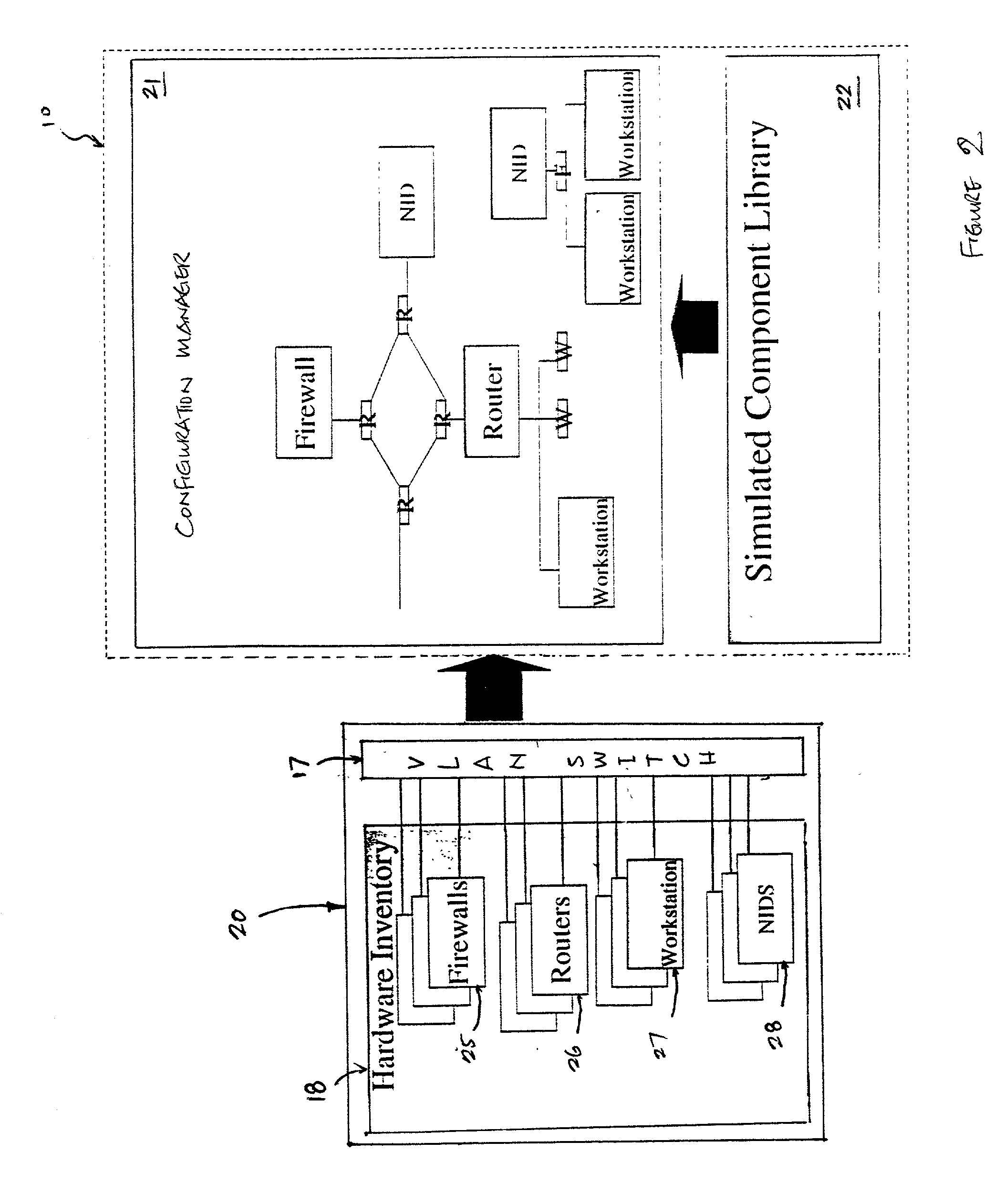
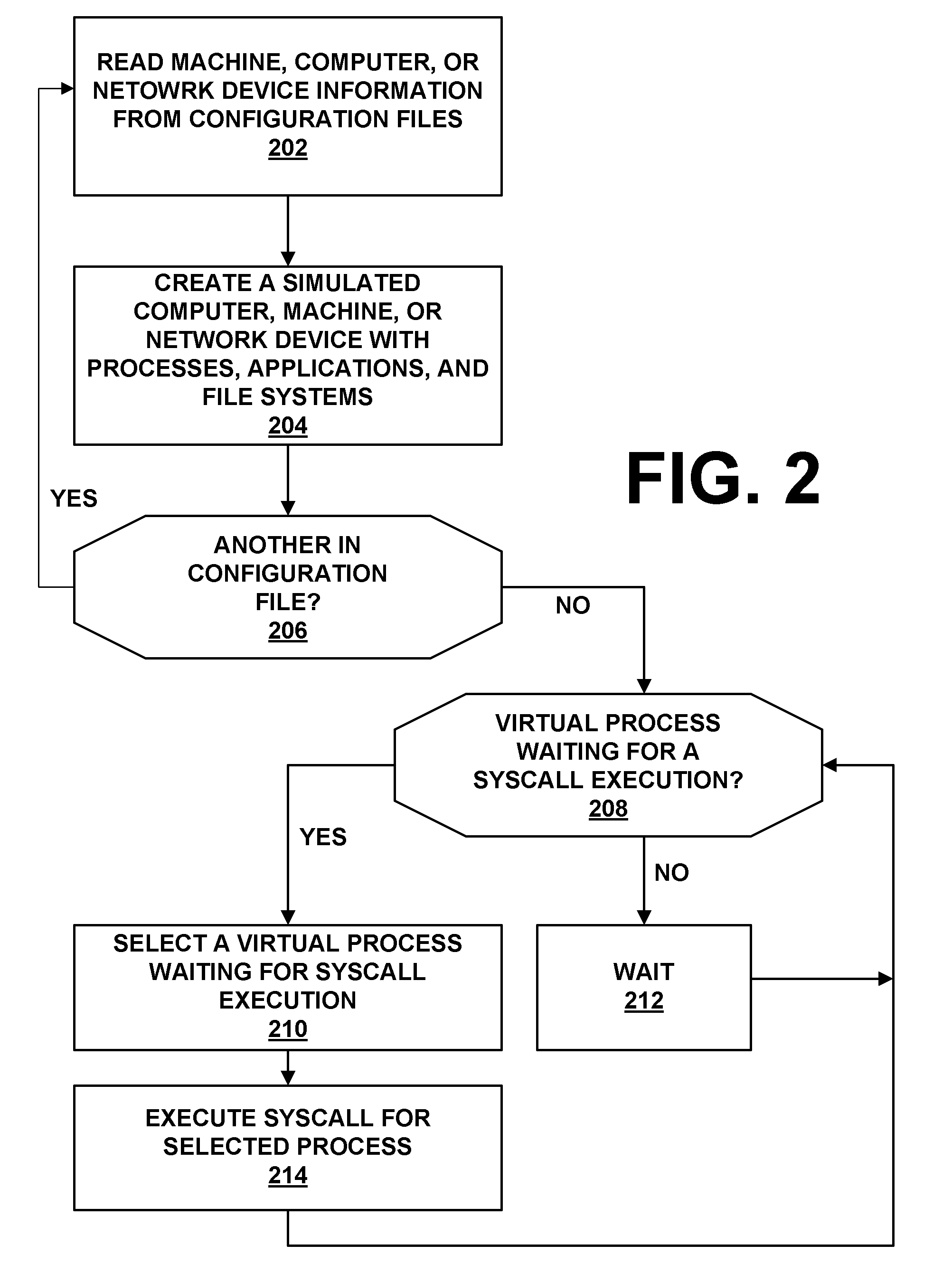
Method and system for simulating computer networks to facilitate testing of computer network security
InactiveUS20030212908A1Memory loss protectionUnauthorized memory use protectionAnalog computerReal-time testing
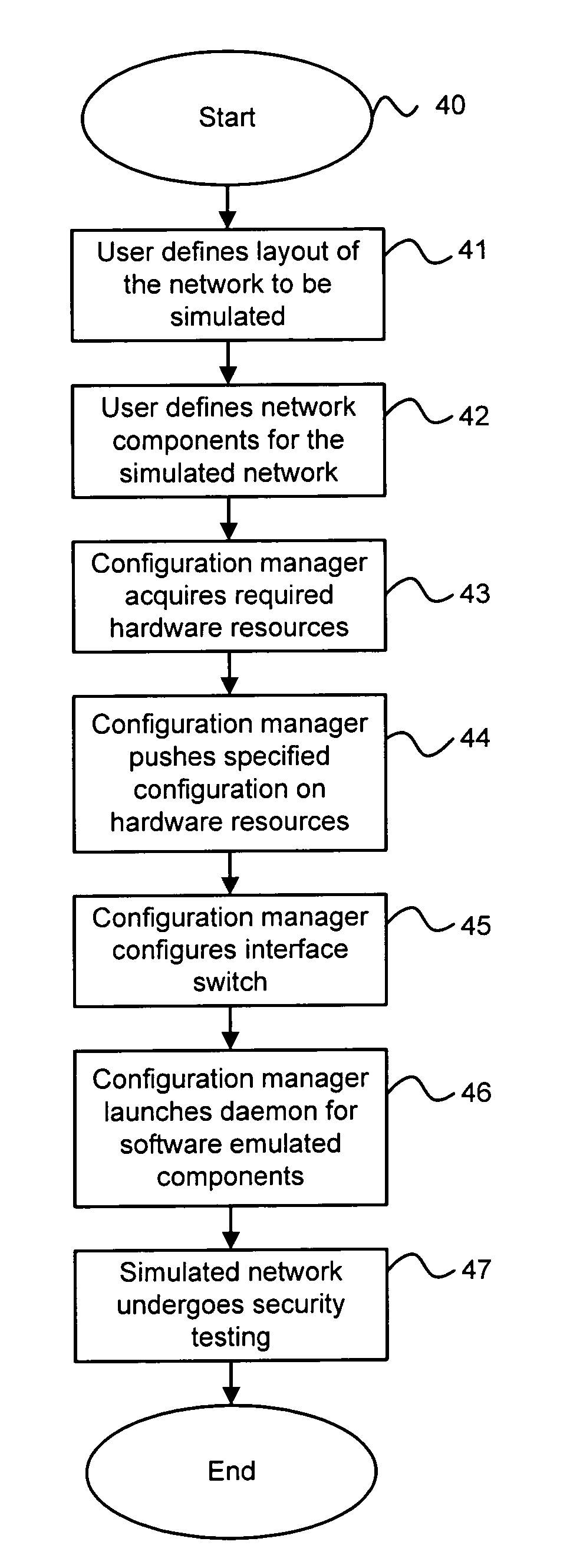
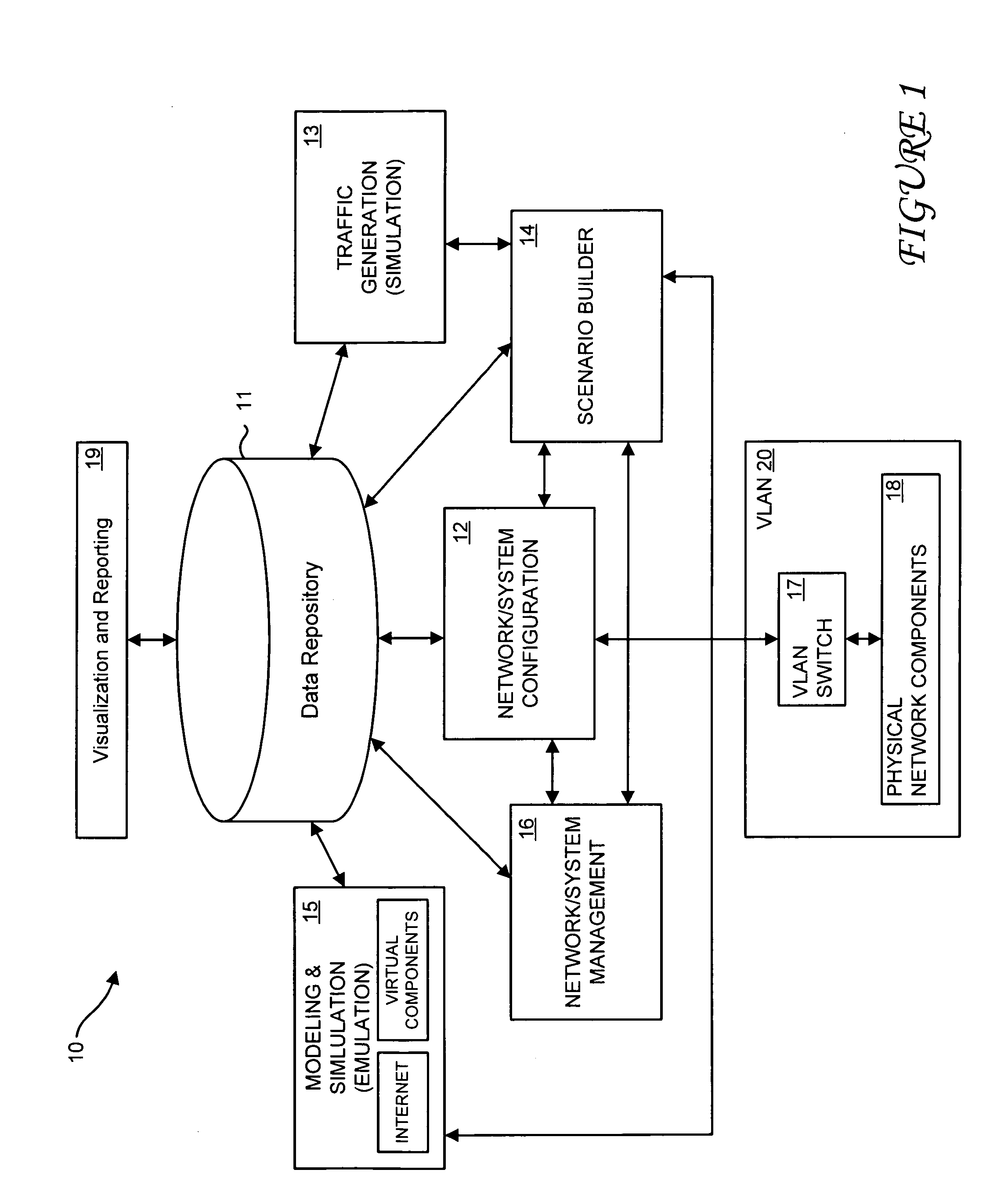
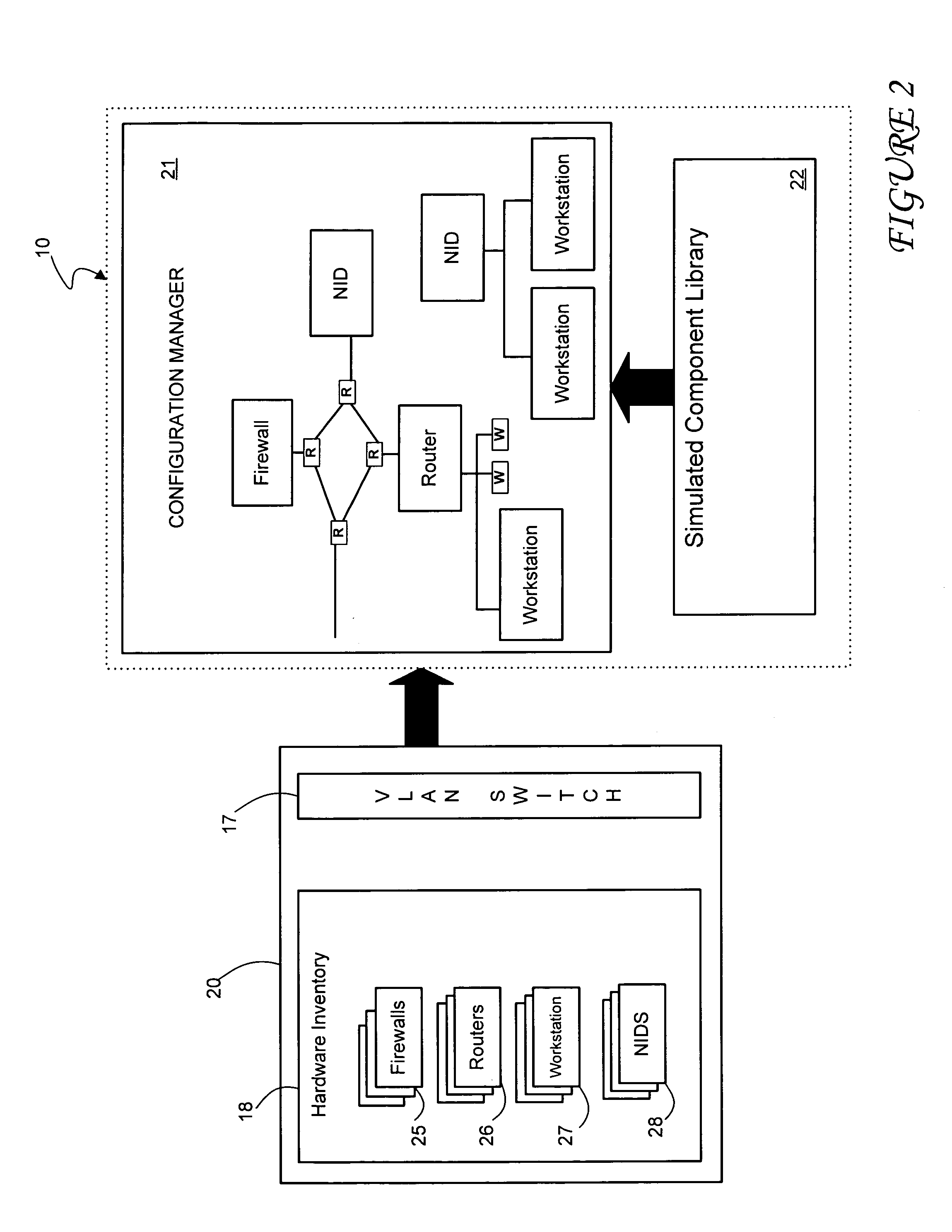
A method and system for simulating computer networks and computer network components to test computer network security is disclosed. A user specifies a desired configuration of a simulated computer network by using a configuration manager. The user also defines all the network components within the simulated computer network by specifying whether a component should be provided in hardware or should be simulated via software. Upon receiving the above-mentioned information from the user, the configuration manager acquires the required hardware resources from a hardware inventory. The configuration manager utilizes an interface switch that connects the hardware in the hardware inventory to produce the desired network layout. Next, the specified configuration for each of the network components is pushed into the acquired hardware resources. Computer network components to be simulated with software are subsequently initialized by the configuration manager. At this point, the user can use the simulated computer network for real-time testing of network security.
Owner:LOCKHEED MARTIN CORP
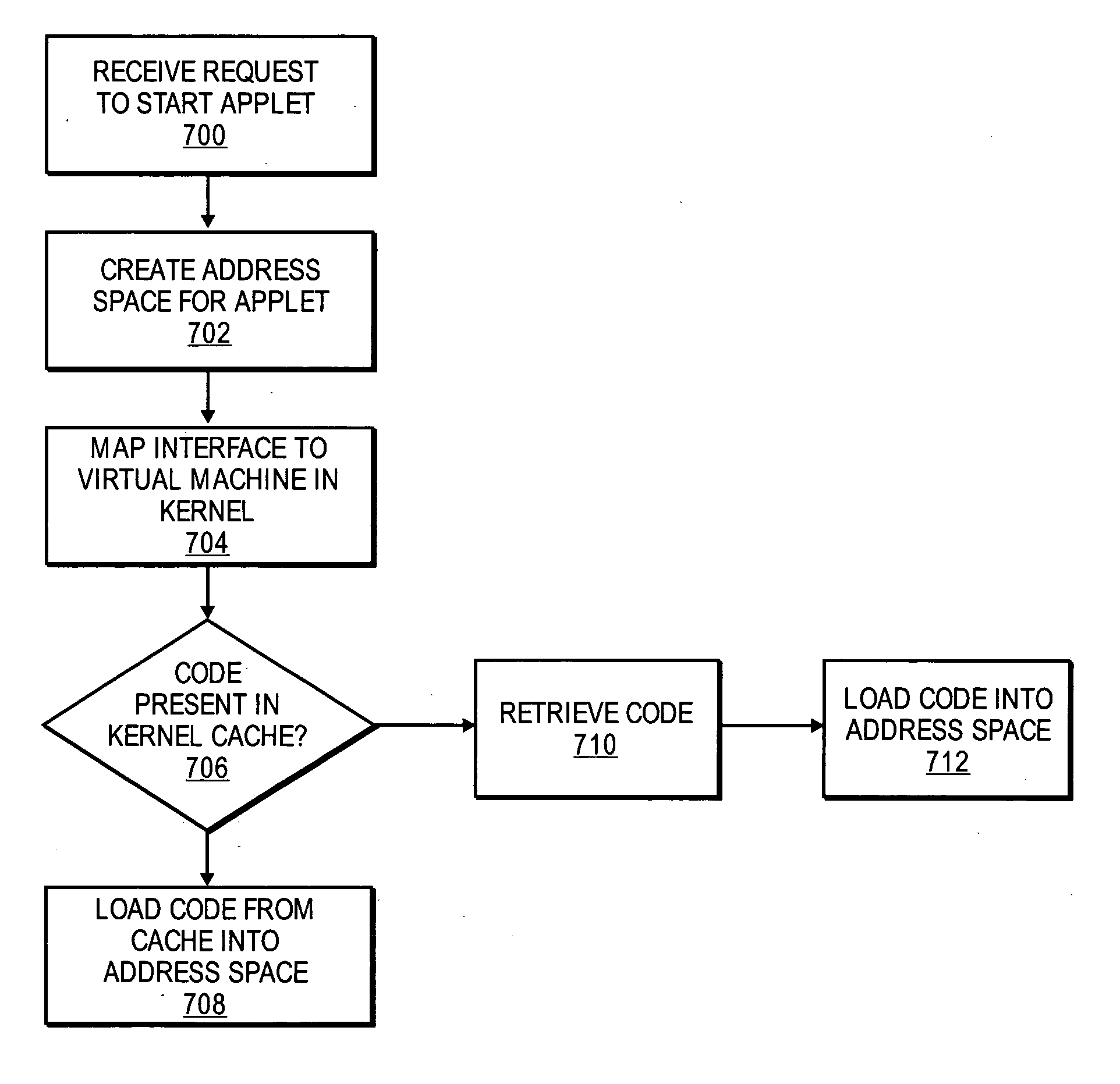
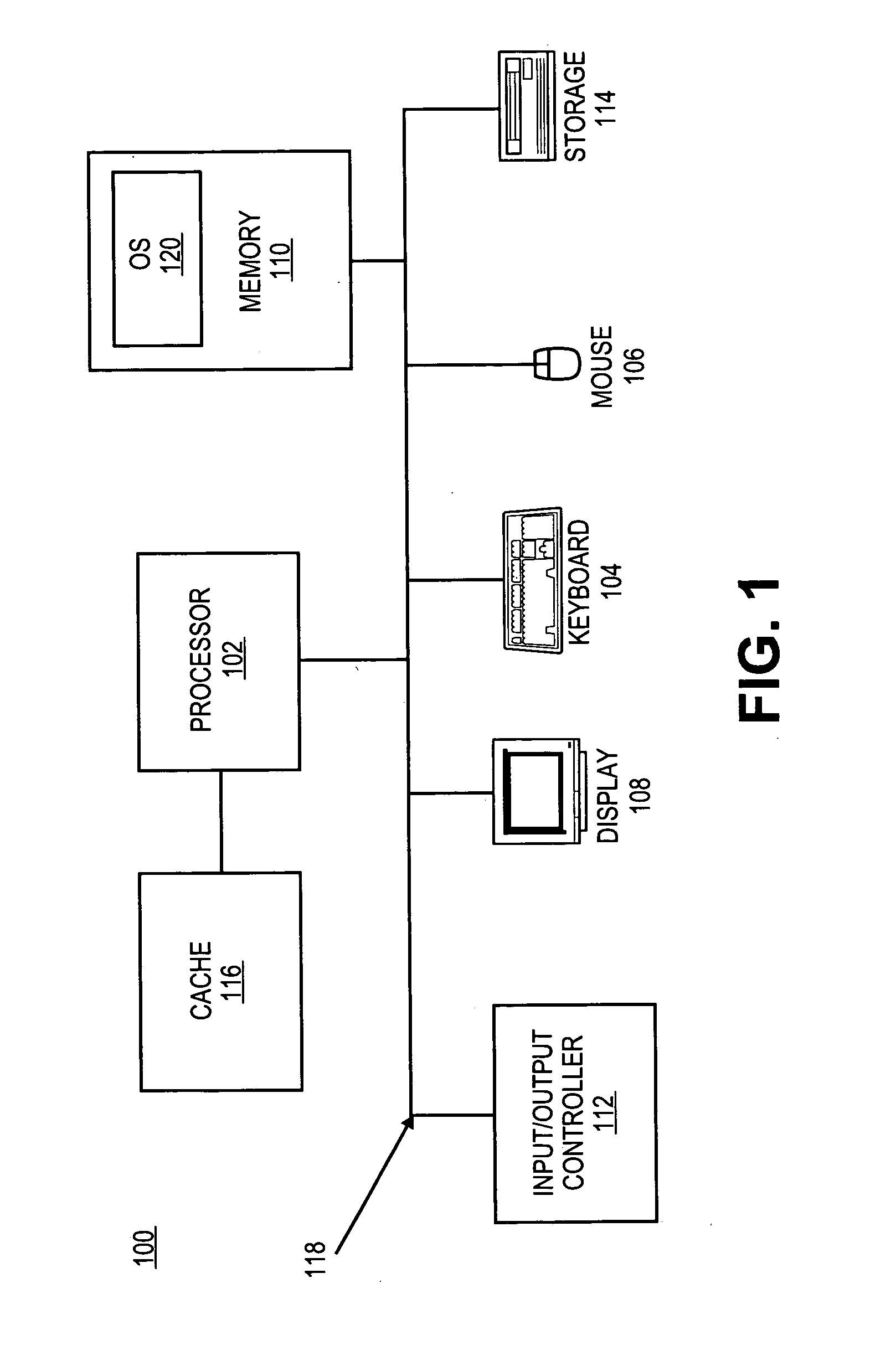
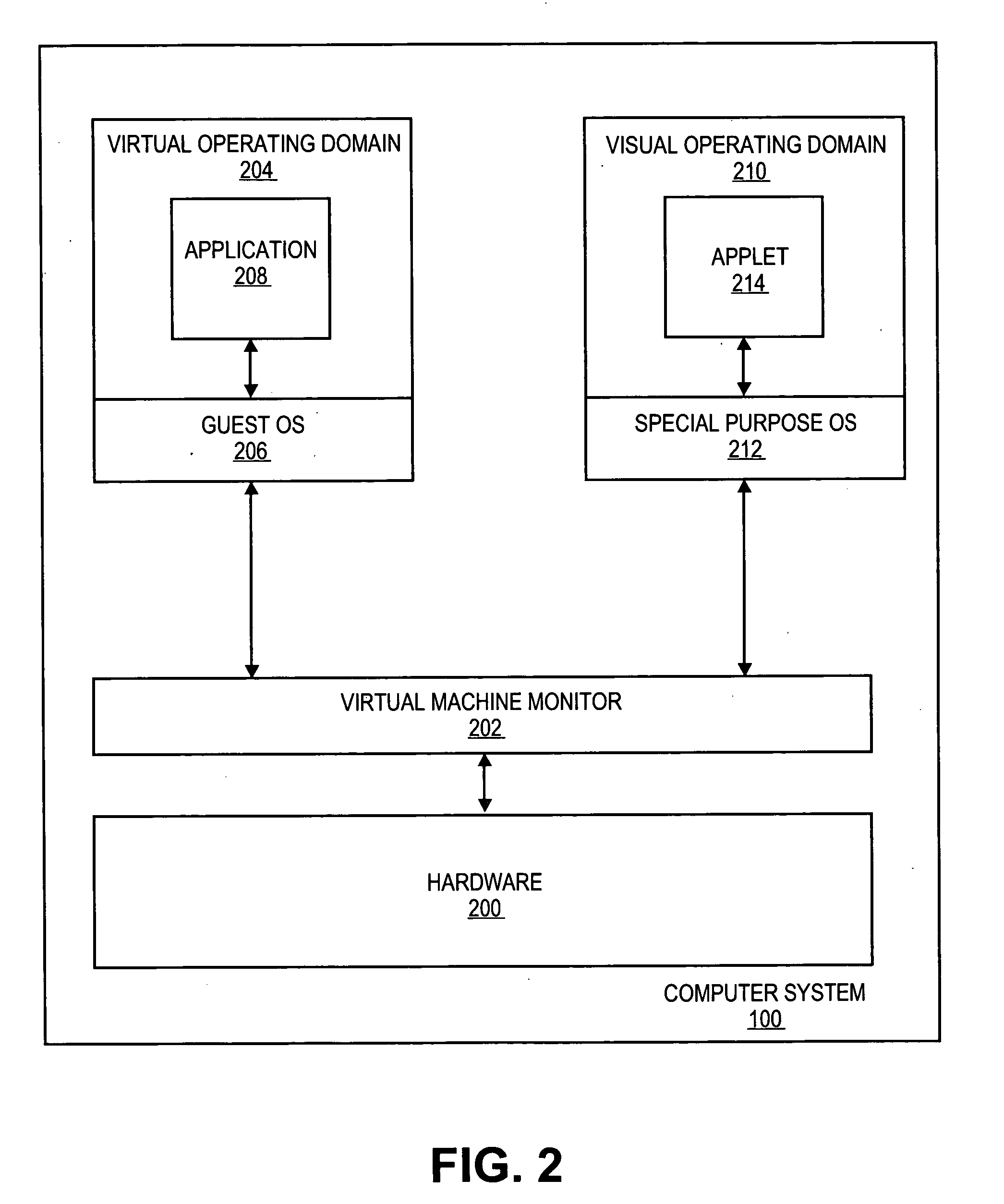
Purpose domain for in-kernel virtual machine for low overhead startup and low resource usage
ActiveUS20070169024A1Software simulation/interpretation/emulationMemory systemsOperational systemAnalog computer
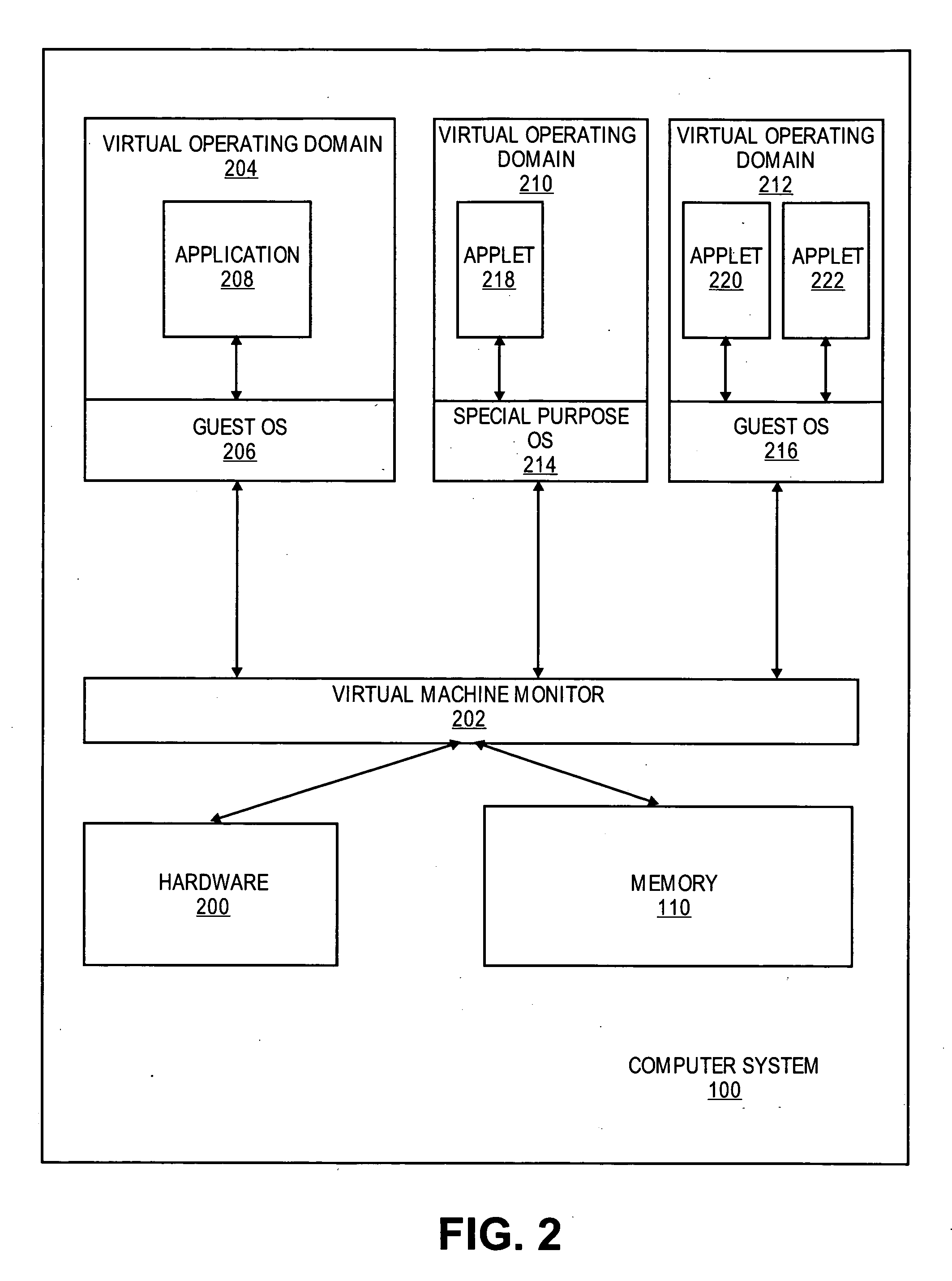
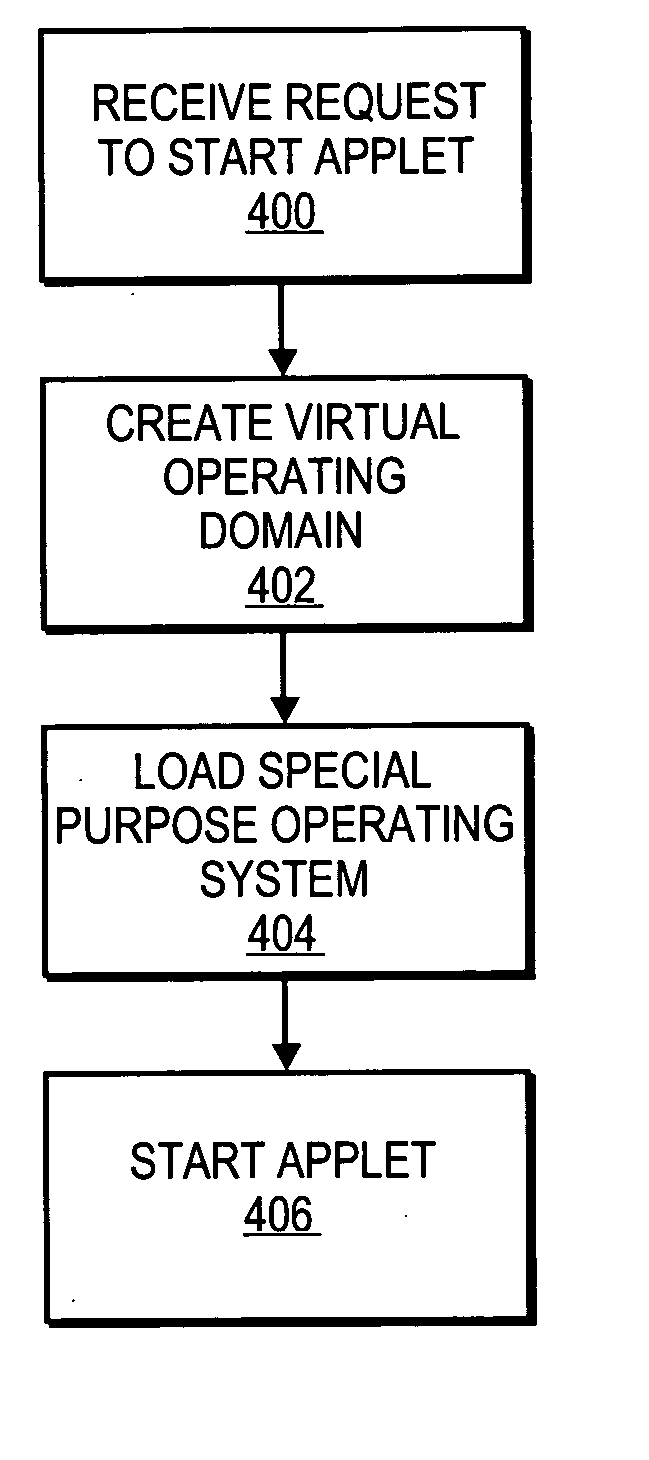
Embodiments of the present invention provide an architecture for securely and efficiently executing byte code generated from a general programming language. In particular, a computer system is divided into a hierarchy comprising multiple types of virtual machines. A thin layer of software, known as a virtual machine monitor, virtualizes the hardware of the computer system and emulates the hardware of the computer system to form a first type of virtual machine. This first type of virtual machine implements a virtual operating domain that allows running its own operating system. Within a virtual operating domain, a byte code interpreter may further implement a second type of virtual machine that executes byte code generated from a program written in a general purpose programming language. The byte code interpreter is incorporated into the operating system running in the virtual operating domain. The byte code interpreter implementing the virtual machine that executes byte code may be divided into a kernel component and one or more user level components. The kernel component of the virtual machine is integrated into the operating system kernel. The user level component provides support for execution of an applet and couples the applet to the operating system. In addition, an operating system running in a virtual operating domain may be configured as a special purpose operating system that is optimized for the functions of a particular byte code interpreter.
Owner:RED HAT
Emulating A Computer Run Time Environment
InactiveUS20090282139A1Multiple digital computer combinationsSoftware simulation/interpretation/emulationOperational systemCode Translation
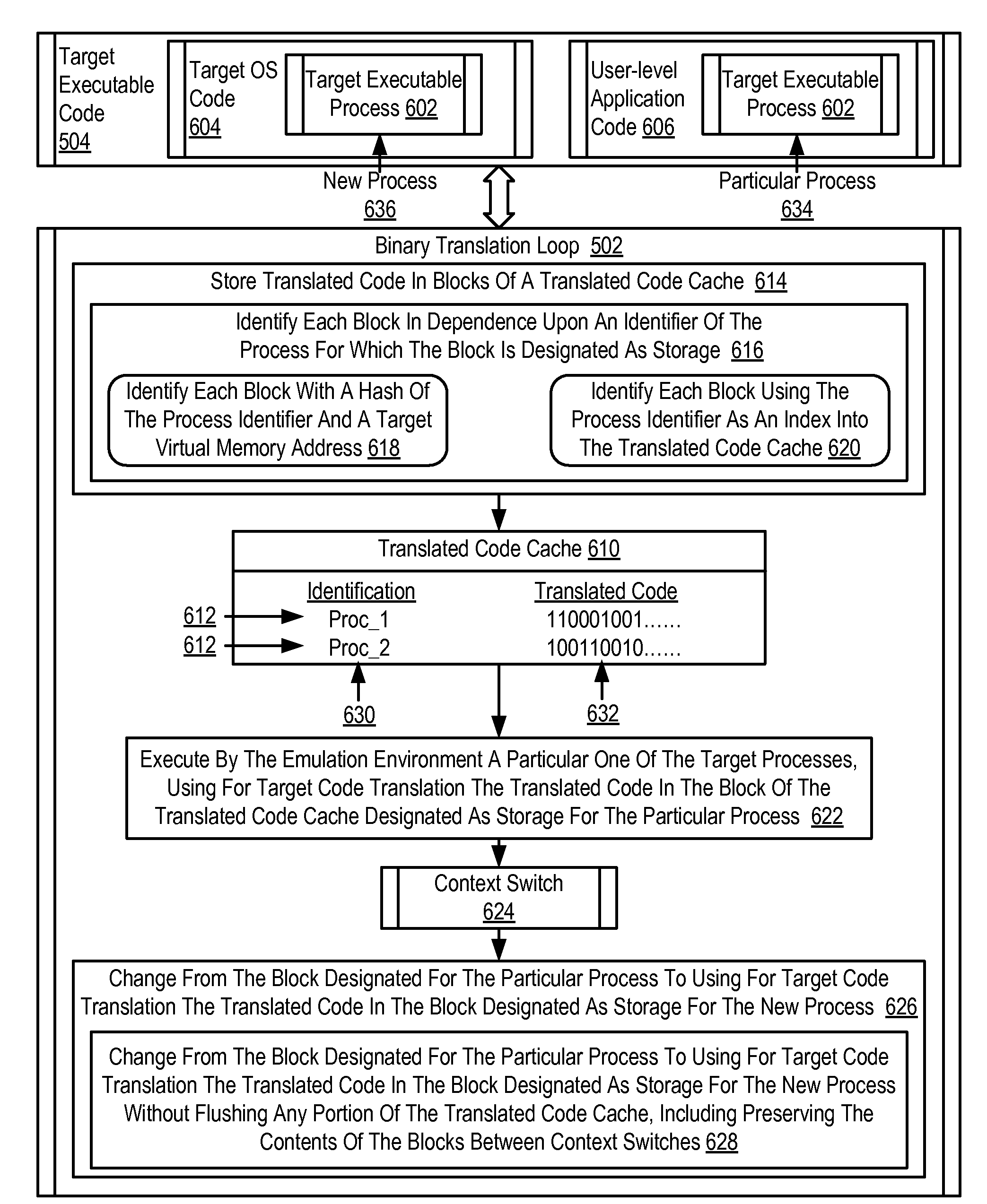
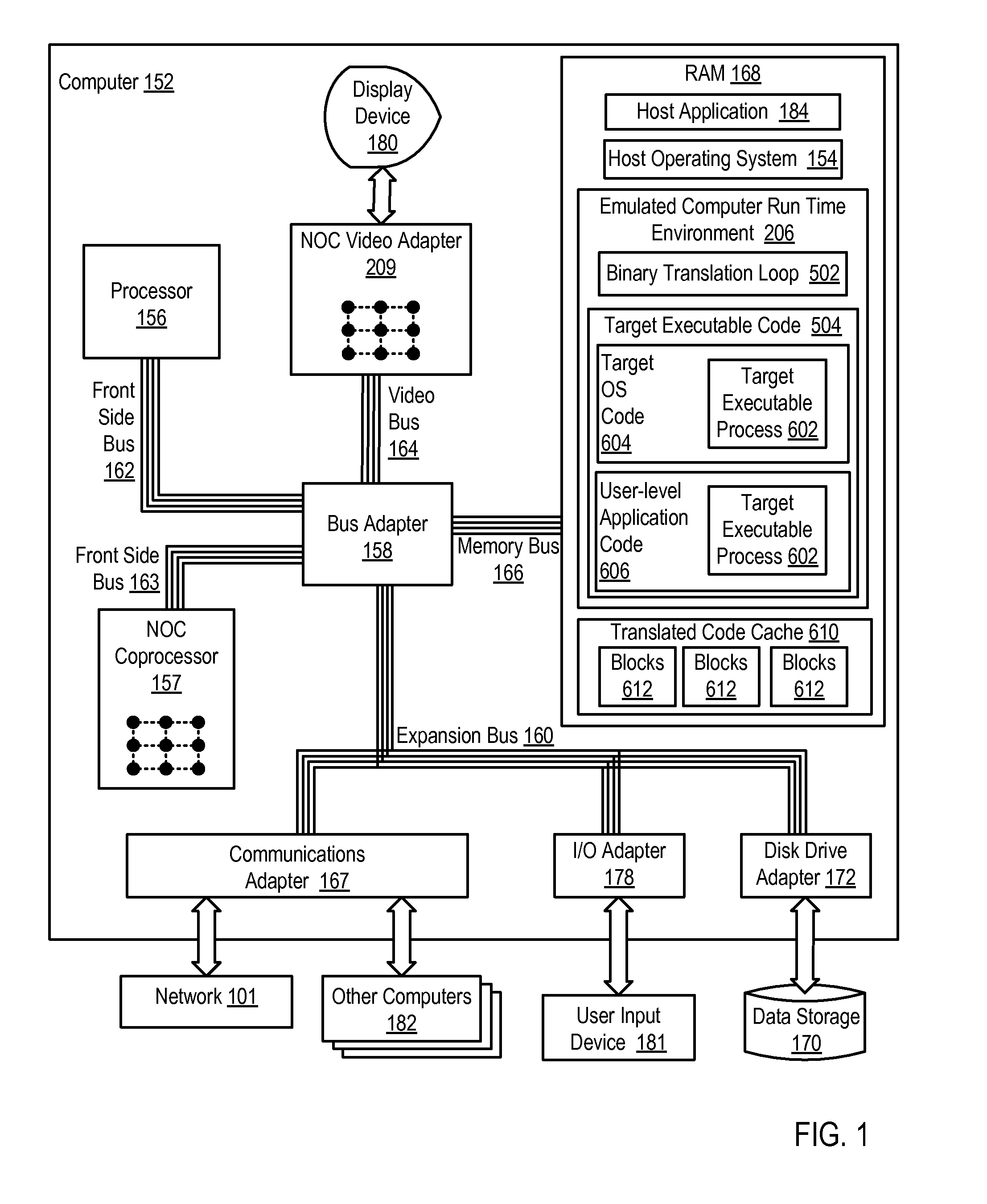
Emulating a computer run time environment including: storing translated code in blocks of a translated code cache, each block of the translated code cache designated for storage of translated code for a separate one of the target executable processes, including identifying each block in dependence upon an identifier of the process for which the block is designated as storage; executing by the emulation environment a particular one of the target executable processes, using for target code translation the translated code in the block of the translated code cache designated as storage for the particular process; and upon encountering a context switch by the target operating system to execution of a new target executable process, changing from the block designated for the particular process to using for target code translation the translated code in the block of the translated code cache designated as storage for the new target executable process.
Owner:IBM CORP
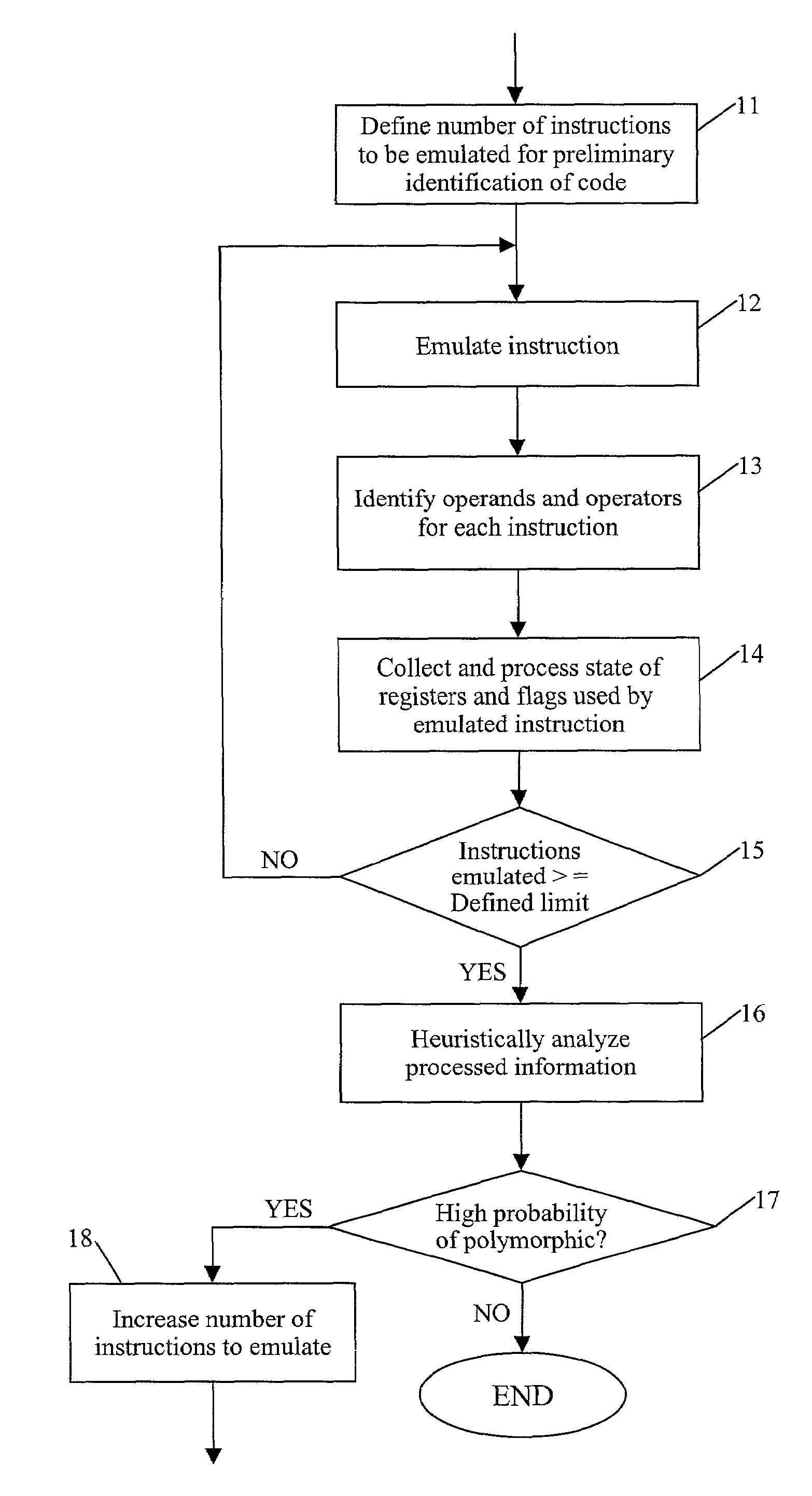
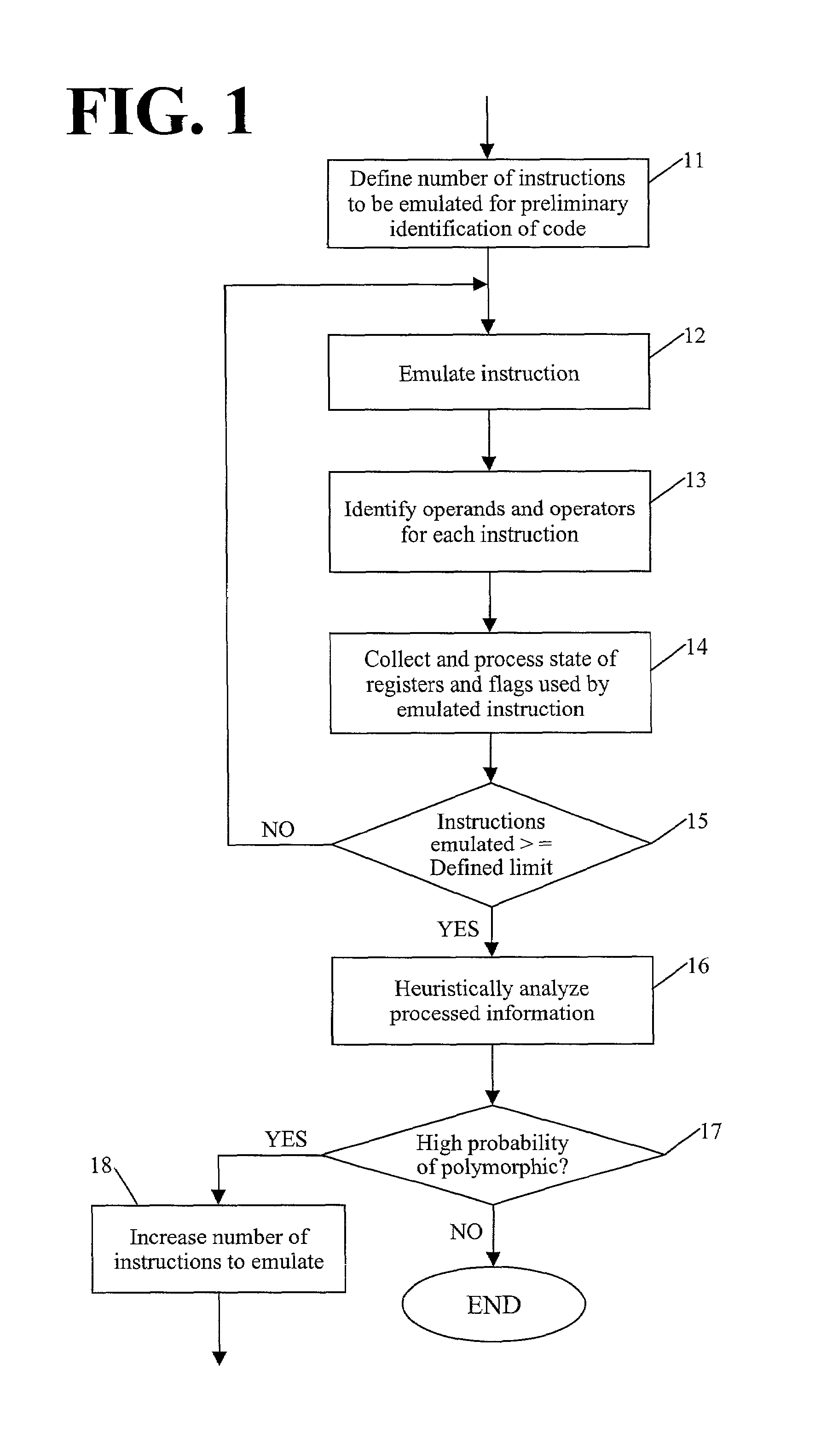
Detection of polymorphic virus code using dataflow analysis
A method and apparatus for detecting polymorphic viral code in a computer program is provided. The apparatus comprises an emulator, an operational code analyzer and an heuristic analyzer. The emulator emulates a selected number of instructions of the computer program. The operational code analyzer collects and stores information corresponding to operands and operators used in the instructions and the state of registers / flags after each emulated instruction execution. The heuristic analyzer determines a probability that the computer program contains viral code based on an heuristic analysis of register / flag state information supplied by the operational code analyzer.
Owner:COMP ASSOC THINK INC
Purpose domain for low overhead virtual machines
InactiveUS20070169005A1Multiprogramming arrangementsSoftware simulation/interpretation/emulationOperational systemAnalog computer
Embodiments of the present invention provide an architecture for securely and efficiently executing byte code generated from a general programming language. In particular, a computer system is divided into a hierarchy comprising multiple types of virtual machines. A thin layer of software, known as a virtual machine monitor, virtualizes the hardware of the computer system and emulates the hardware of the computer system to form a first type of virtual machine. This first type of virtual machine implements a virtual operating domain that allows running its own operating system. Within a virtual operating domain, a byte code interpreter may further implement a second type of virtual machine that executes byte code generated from a program written in a general purpose programming language. The byte code interpreter is incorporated into the operating system running in the virtual operating domain. In addition, an operating system running in a virtual operating domain may be configured as a special purpose operating system that is optimized for the functions of a particular byte code interpreter.
Owner:RED HAT
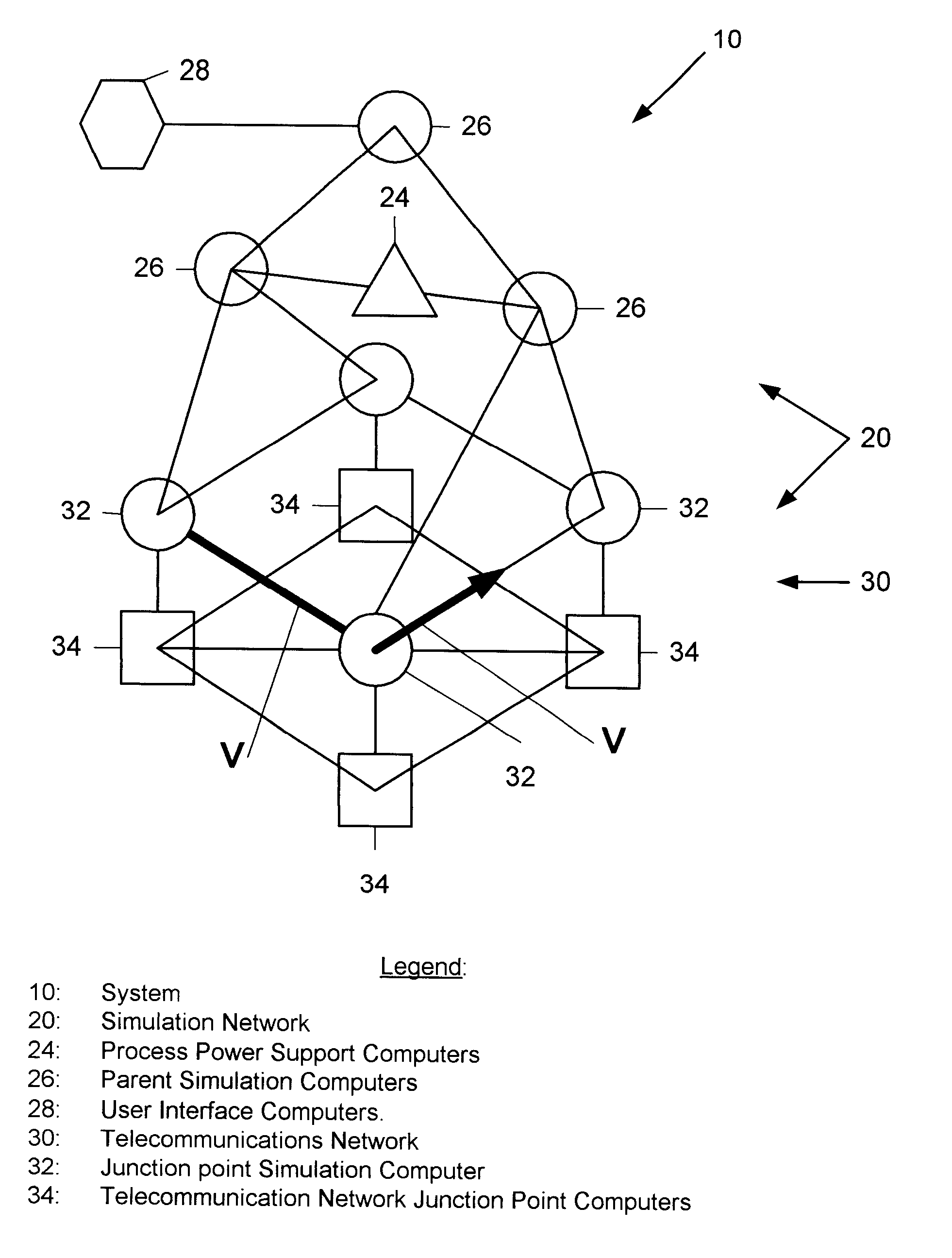
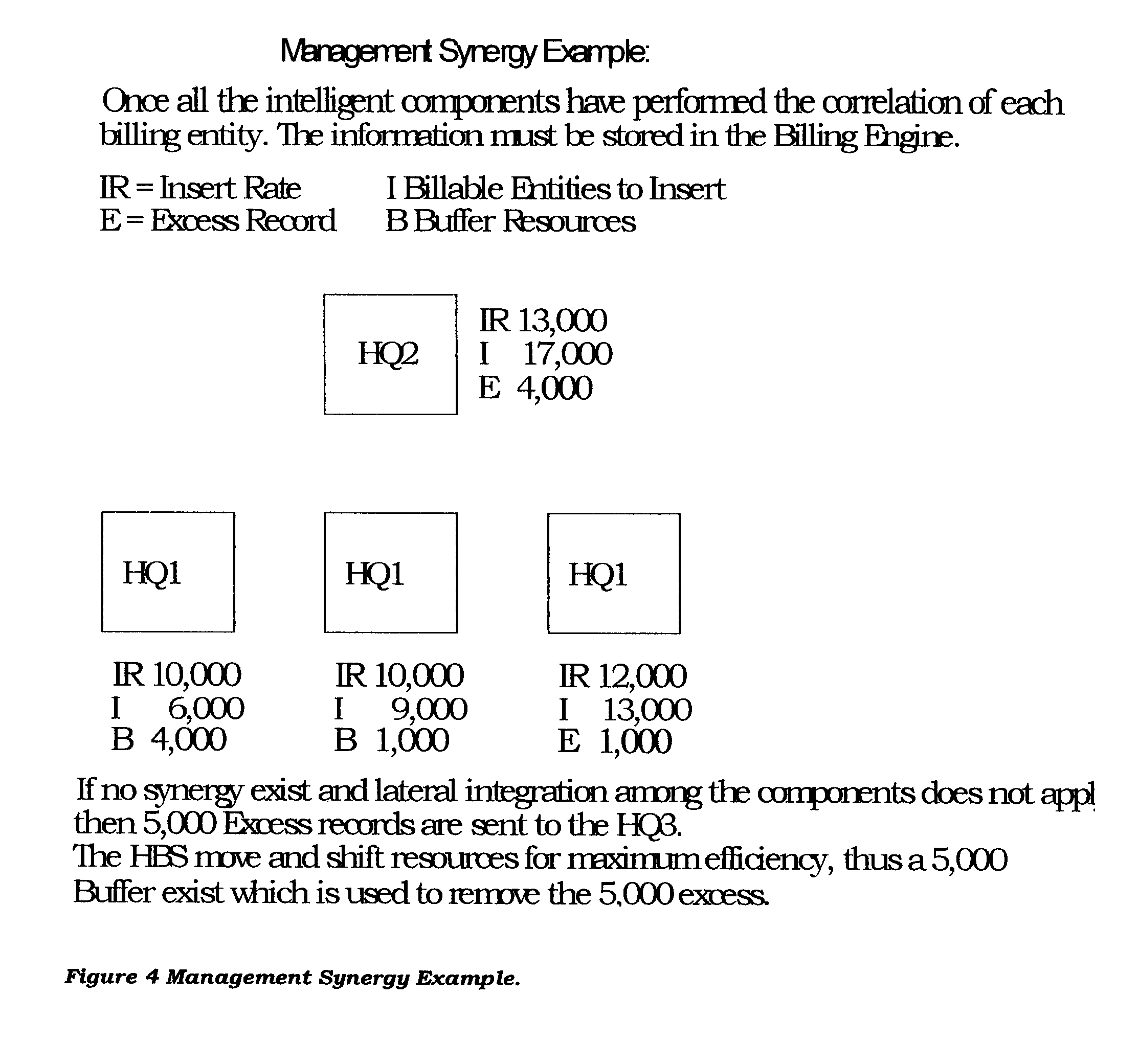
Parallel computer network and method for telecommunications network simulation to route calls and continuously estimate call billing in real time
InactiveUS6614893B1Use minimizedPower maximizationMultiplex system selection arrangementsInterconnection arrangementsTelecommunications networkAnalog computer
A telecommunications call routing and billing computer system includes a telecommunications network including a junction point including a call routing switching device, and including two call routing links meeting at the junction point and in communication with each other through the call routing switching device; and a call routing simulation network including a junction point simulation computer located at the junction point and in communication with the call routing switching device and the two call routing links. A method of placing a call through such a telecommunications network includes the steps of: placing one junction point simulation computer at each telecommunications network call junction point; for each call placed with the telecommunications network, plotting a call routing vector through the simulation network with forward chaining through the junction point simulation computers; and sending routing vector information back through the simulation network with rearward chaining to direct the call along a parallel routing vector through the telecommunications network. The method preferably includes the additional steps of: monitoring buffer levels of telecommunications network junction point computers with the simulation computer at each junction point; and using the buffer level information to shunt calls from telecommunications network junction point computers having smaller buffers to those having larger buffers.
Owner:PAIZ RICHARD S
System and method for simulating computer network attacks
The present invention provides a system and method for providing computer network attack simulation. The method includes the steps of: receiving a network configuration and setup description; simulating the network configuration based on the received network configuration; receiving at least one confirmed vulnerability of at least one computer, machine, or network device in the simulated network; receiving a method for compromising the confirmed vulnerability of the at least one computer, machine, or network device; and virtually installing a network agent on the at least one computer, machine, or network device, wherein the network agent allows a penetration tester to execute arbitrary operating system calls on the at least one computer, machine, or network device.
Owner:FORTRA LLC
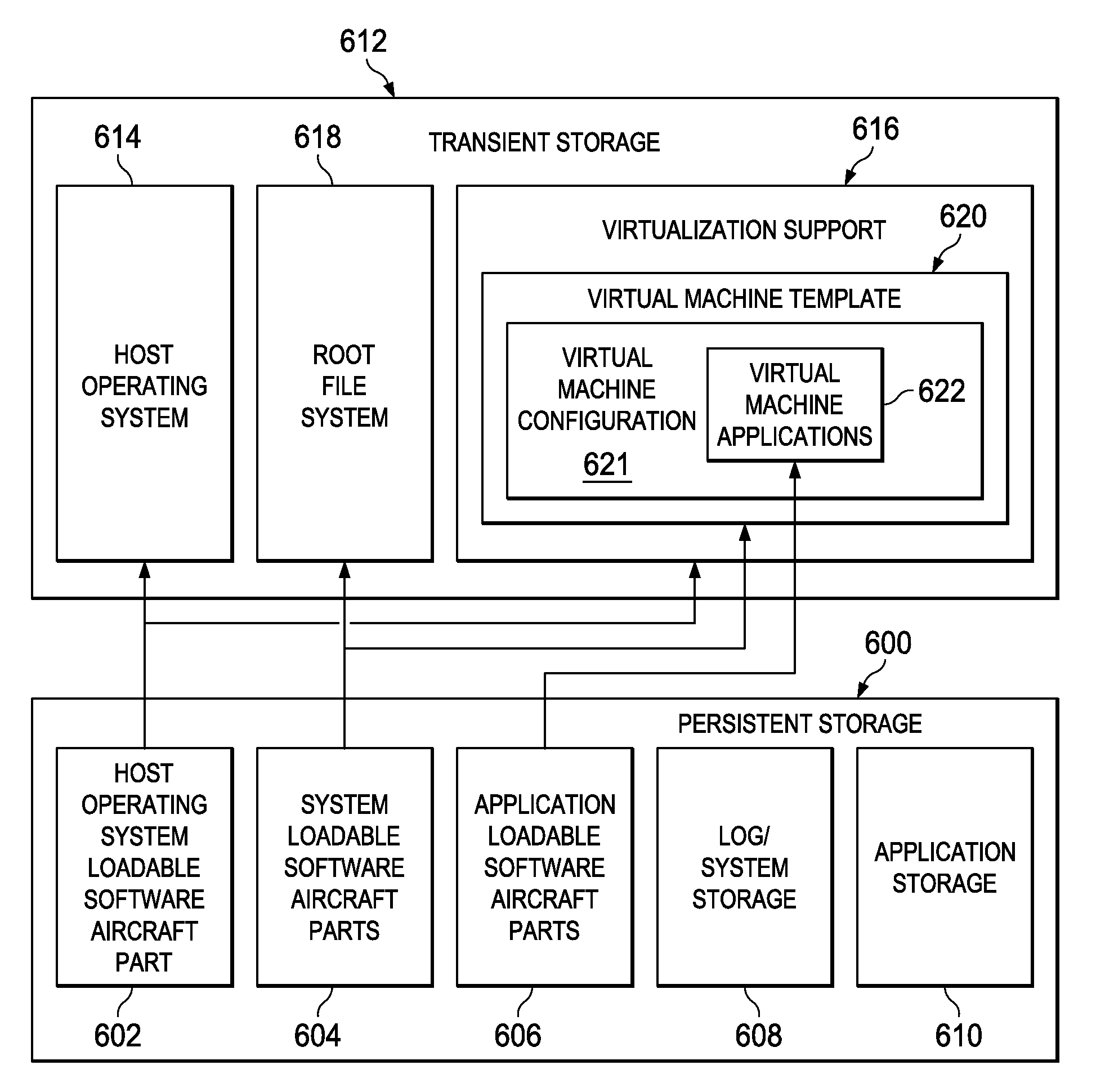
Virtual Machines for Aircraft Network Data Processing Systems
InactiveUS20130031543A1Aircraft health monitoring devicesSoftware simulation/interpretation/emulationData processing systemOperational system
A method and apparatus are provided for operating a network data processing system on an aircraft. A number of operations are performed in a virtual machine on the aircraft. The virtual machine runs on a processor unit in the network data processing system on the aircraft to create a simulated computer environment. The virtual machine accesses resources of the processor unit for performing the number of operations using a host operating system on the processor unit. A current state of the aircraft is identified by the network data processing system. Running of the virtual machine is managed based on the current state of the aircraft and a policy for managing the virtual machine for different states of the aircraft.
Owner:THE BOEING CO
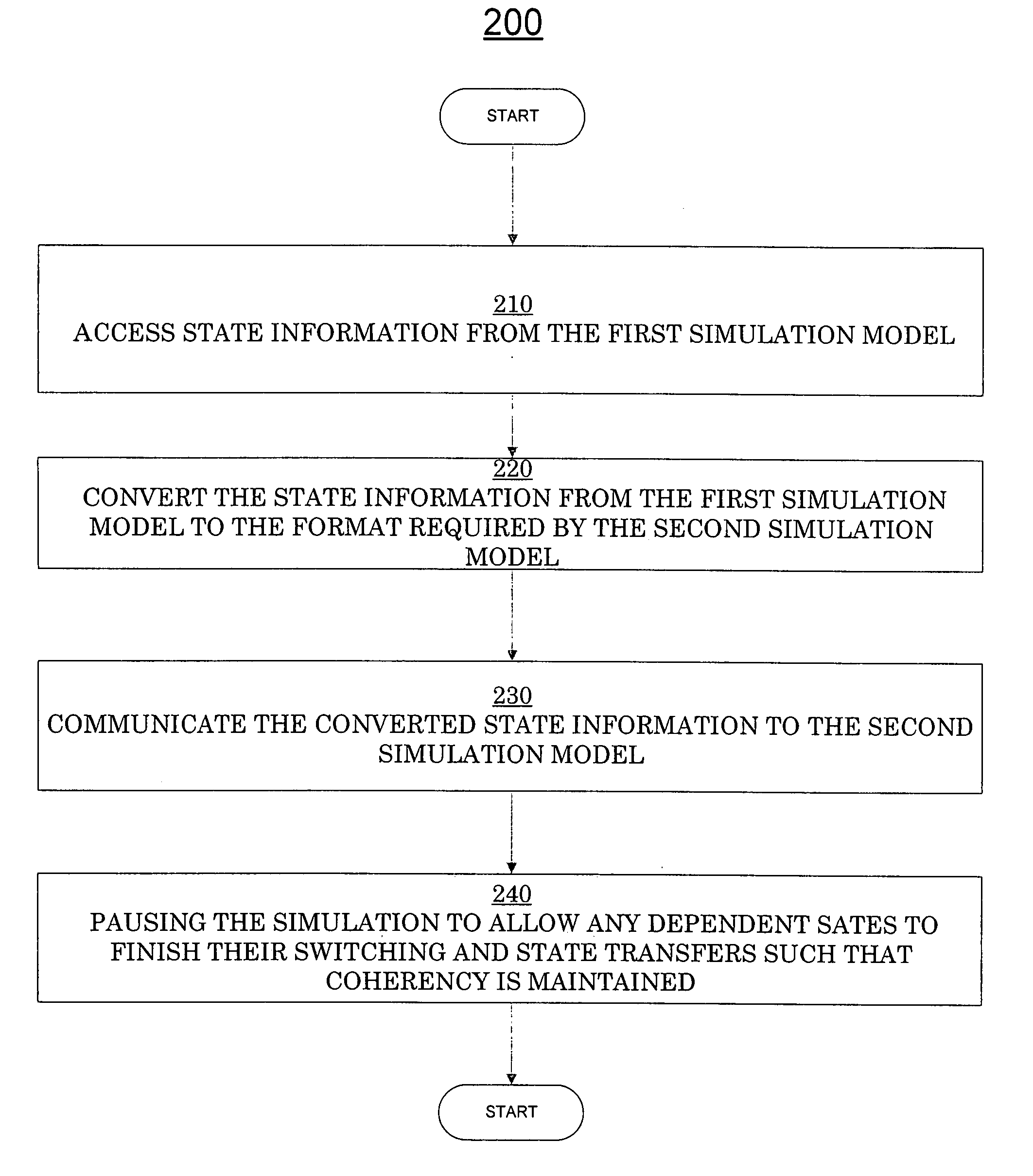
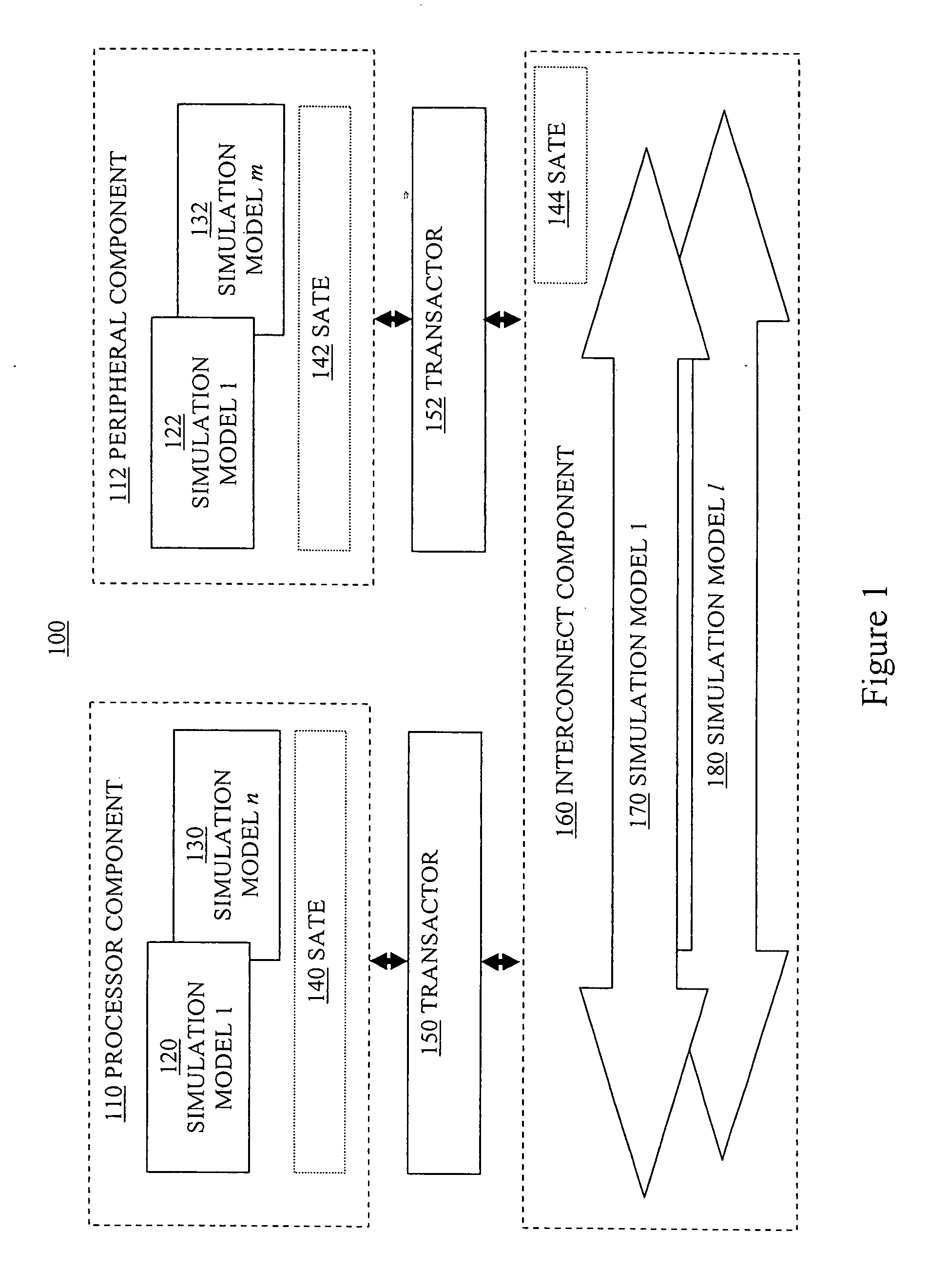
Run-time switching for simulation with dynamic run-time accuracy adjustment
ActiveUS20070192079A1Satisfies needError detection/correctionDesign optimisation/simulationComputational scienceTemporal information
Systems and methods for run-time switching for simulation with dynamic run-time accuracy adjustment. In one embodiment, a computer implemented method performs a simulation of a computer instruction executing on a simulated hardware design by a first simulation model, wherein the first simulation model provides first timing information of the simulation. The first timing information is stored to a computer usable media. A pending subsequent simulation of the instruction is detected. Responsive to the presence of the first timing information in the computer usable media, the computer instruction is simulated by a second simulation model, wherein the second simulation model provides less accurate second timing information of the simulation than the first simulation model. The simulation run time information is updated for the subsequent simulation with the first timing information.
Owner:SYNOPSYS INC
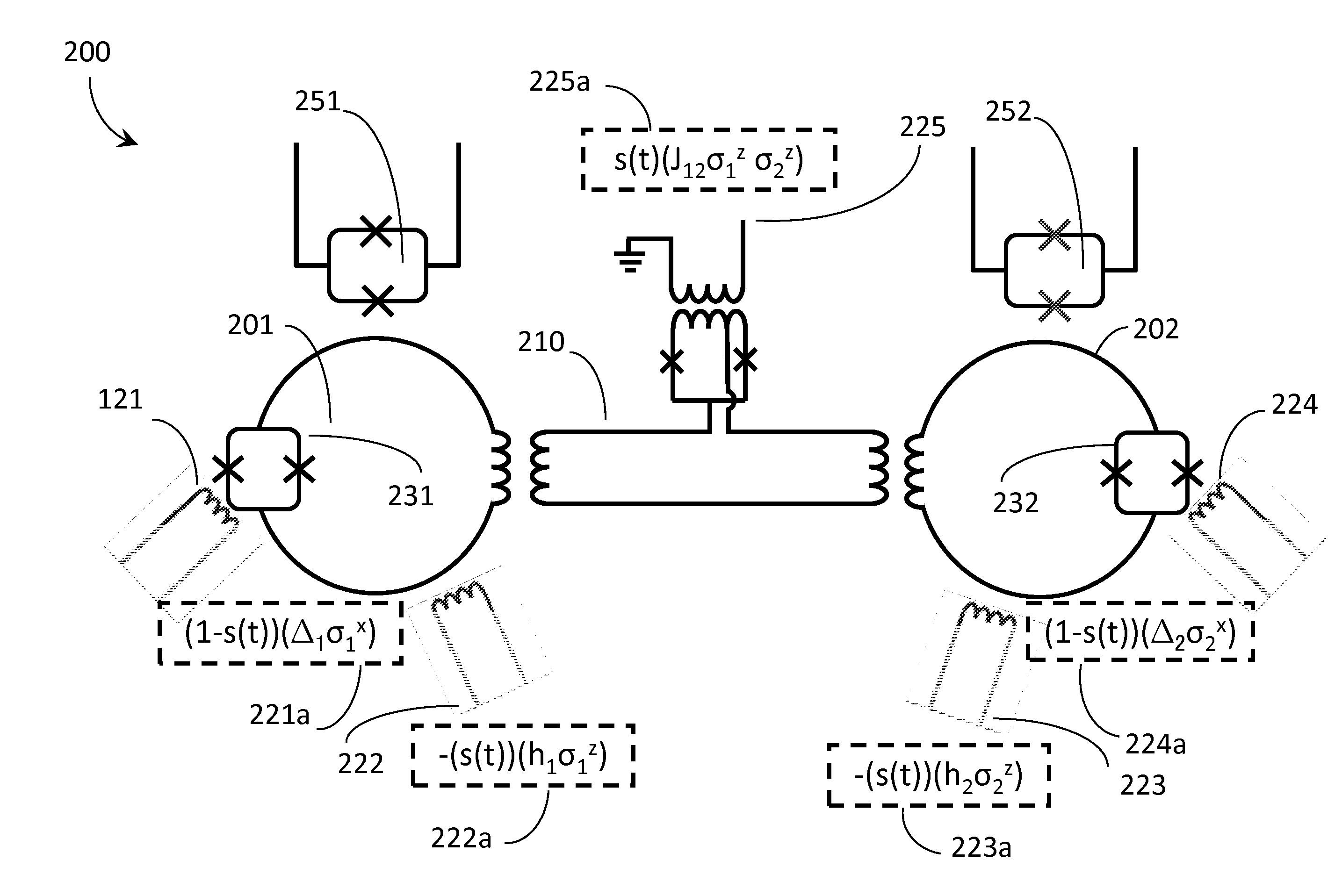
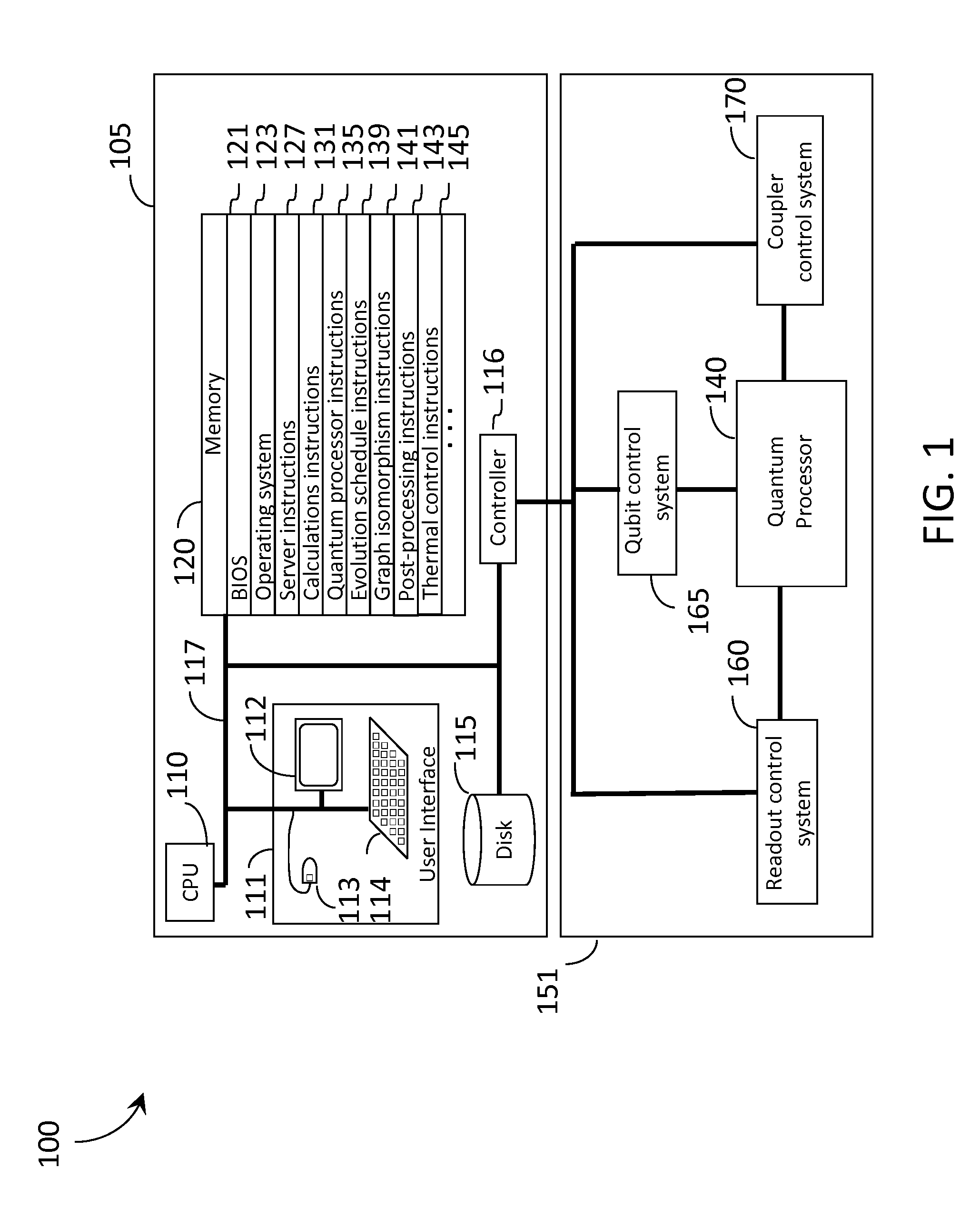
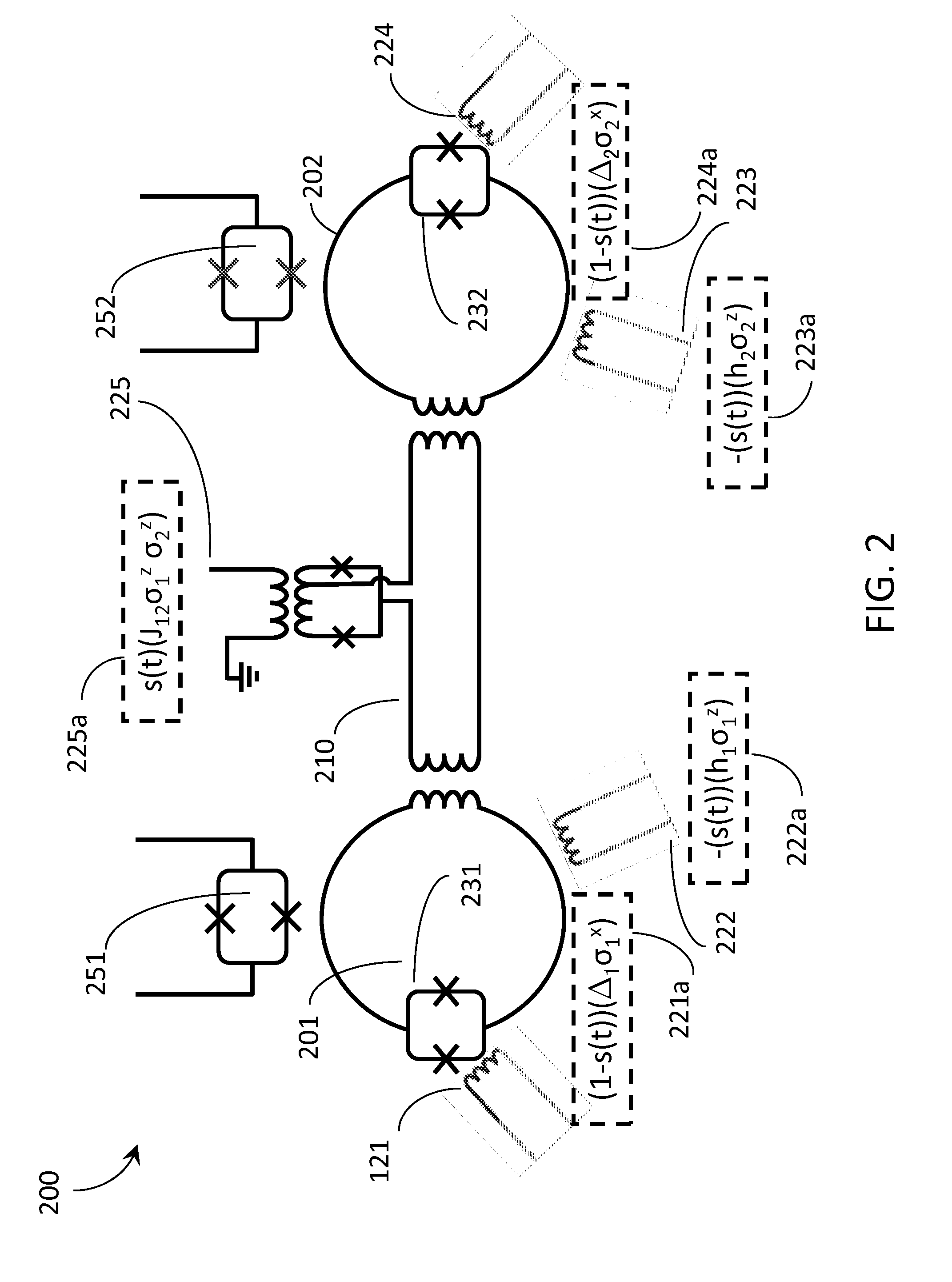
Systems and methods employing new evolution schedules in an analog computer with applications to determining isomorphic graphs and post-processing solutions
ActiveUS20150363708A1Quantum computersArchitecture with single central processing unitAnalog processorAnalog computer
A second problem Hamiltonian may replace a first problem Hamiltonian during evolution of an analog processor (e.g., quantum processor) during a first iteration in solving a first problem. This may be repeated during a second, or further successive iterations on the first problem, following re-initialization of the analog processor. An analog processor may evolve under a first non-monotonic evolution schedule during a first iteration, and second non-monotonic evolution schedule under second, or additional non-monotonic evolution schedule under even further iterations. A first graph and second graph may each be processed to extract final states versus a plurality of evolution schedules, and a determination made as to whether the first graph is isomorphic with respect to the second graph. An analog processor may evolve by decreasing a temperature of, and a set of quantum fluctuations, within the analog processor until the analog processor reaches a state preferred by a problem Hamiltonian.
Owner:D WAVE SYSTEMS INC
Method for Reading and Writing Data Wirelessly from Simulated Munitions
InactiveUS20090053678A1Ammunition projectilesMultiplex system selection arrangementsElectricityTransceiver
A weapon simulation system includes a simulated weapon and simulated munition, with the simulated weapon being in electrical communication with a primary simulation computer and an instructor computing station. The simulated munition includes an RFID tag installed therein, with the RFID tag having information about the particular simulated munition. When the simulated munition is placed in an insert in the simulated weapon, an RFID transceiver in the simulated weapon will read the information from the RFID tag using an antenna, and further transmit the identification information of the simulated munition to a weapon controller. The weapon controller is further in electrical communication with a primary simulation computer generating a simulation, which is in electrical communication with an instructor computer.
Owner:MEGGITT TRAINING SYST
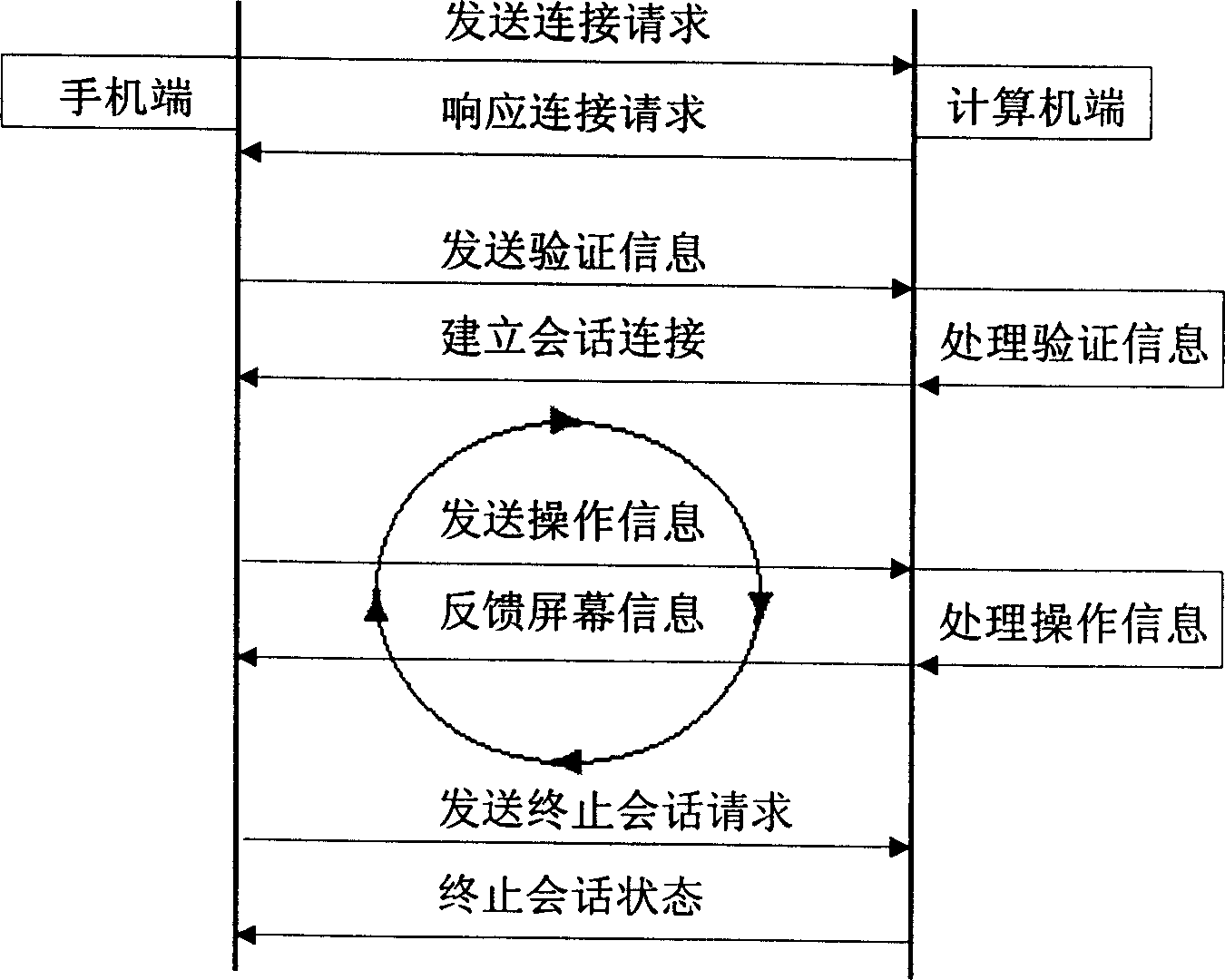
Method for remote controlling computer based on intelligent mobile phone platform
InactiveCN1867012ASolve insufficient bandwidthSolve the difficulty of slow computing speedTelephonic communicationRadio/inductive link selection arrangementsAnalog computerRemote control
The invention relates to a method for controlling computer, based on intelligent mobile phone remote access, belonging to the mobile information managing technique. Wherein, it comprises: the mobile phone terminal uses WAP communication network protocol to connect the computer; the computer validates the user identity and accesses into the computer; the computer generates the local screen image and uses slicing algorithm to generate the image matched with the size of mobile phone screen; then sending the generated screen image via compression to the mobile phone; the mobile phone receives and decompresses the screen image to display it on the mobile phone screen; the mobile phone via simulating the computer operation realizes remote control on the computer. The invention can use mobile phone to control the computer remotely, while it can use the same interface and operation as local computer.
Owner:北京千锋互联科技有限公司
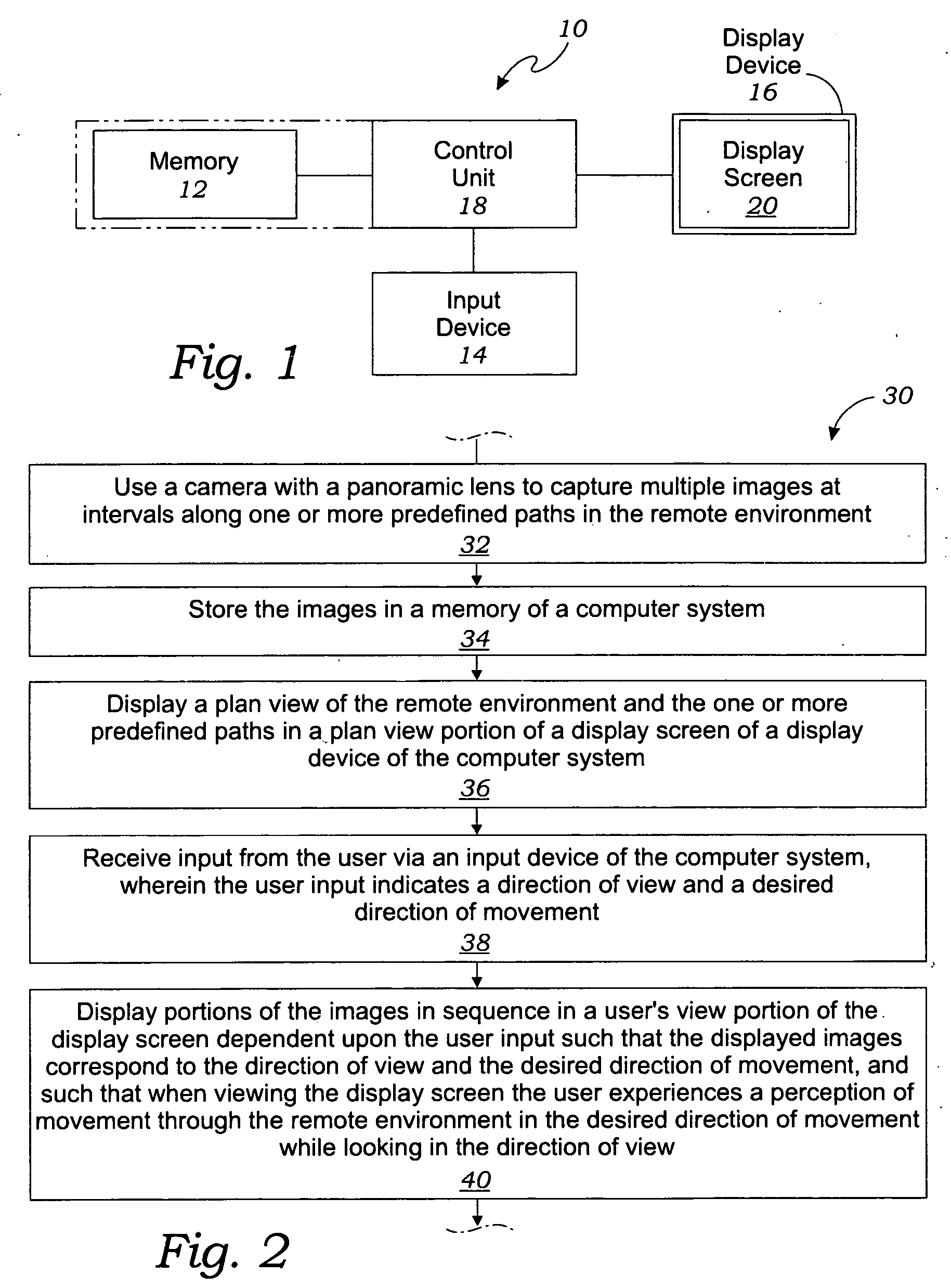
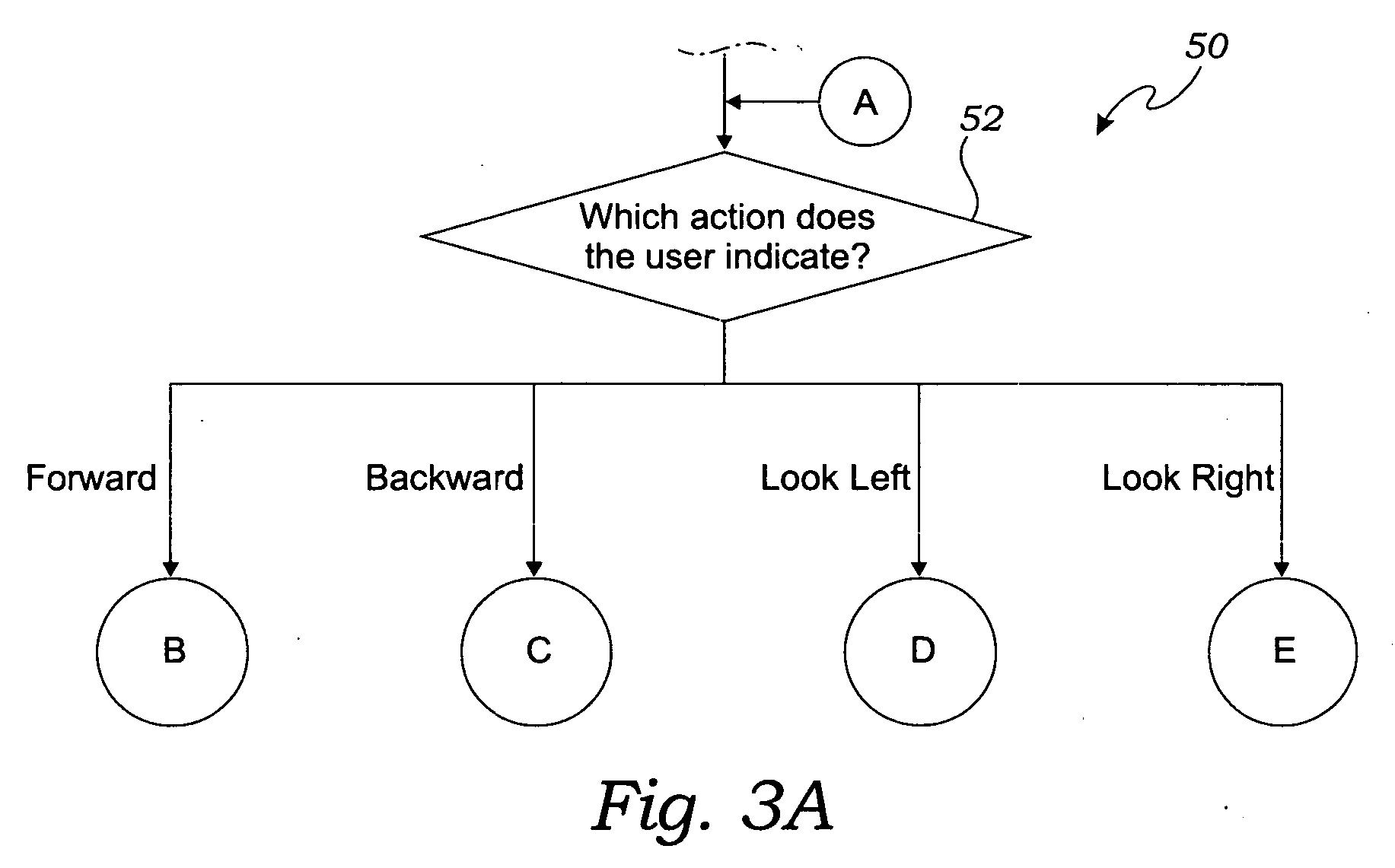
Methods for simulating movement of a computer user through a remote environment
Methods are disclosed for simulating movement of a user through a remote environment. In one embodiment, a camera is provided having a panoramic lens. The camera is used to capture multiple 360 degree panoramic images at intervals along at least one predefined path in the remote environment. A computer system is provided having a memory, a display device with a display screen, and an input device. The images are stored in the memory of the computer system. A plan view of the remote environment and the at least one predefined path are displayed in a plan view portion of the display screen. User input is received via the input device, wherein the user input is indicative of a direction of view and a desired direction of movement. Portions of the images are displayed in sequence in a user's view portion of the display screen dependent upon the user input.
Owner:MILLER JACOB JAMES
Method and system for simulating computer networks to facilitate testing of computer network security
InactiveUS7379857B2Error preventionFrequency-division multiplex detailsAnalog computerReal-time testing
A method and system for simulating computer networks and computer network components to test computer network security is disclosed. A user specifies a desired configuration of a simulated computer network by using a configuration manager. The user also defines all the network components within the simulated computer network by specifying whether a component should be provided in hardware or should be simulated via software. Upon receiving the above-mentioned information from the user, the configuration manager acquires the required hardware resources from a hardware inventory. The configuration manager utilizes an interface switch that connects the hardware in the hardware inventory to produce the desired network layout. Next, the specified configuration for each of the network components is pushed into the acquired hardware resources. Computer network components to be simulated with software are subsequently initialized by the configuration manager. At this point, the user can use the simulated computer network for real-time testing of network security.
Owner:LOCKHEED MARTIN CORP
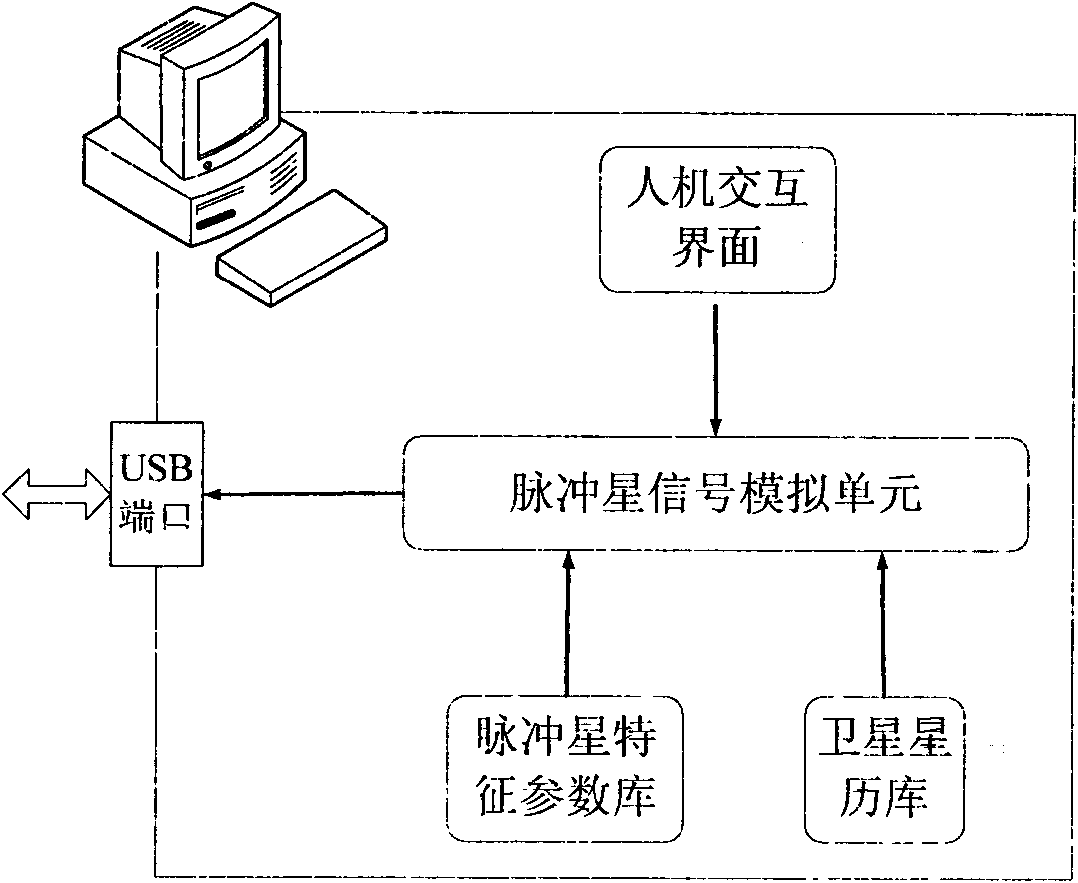
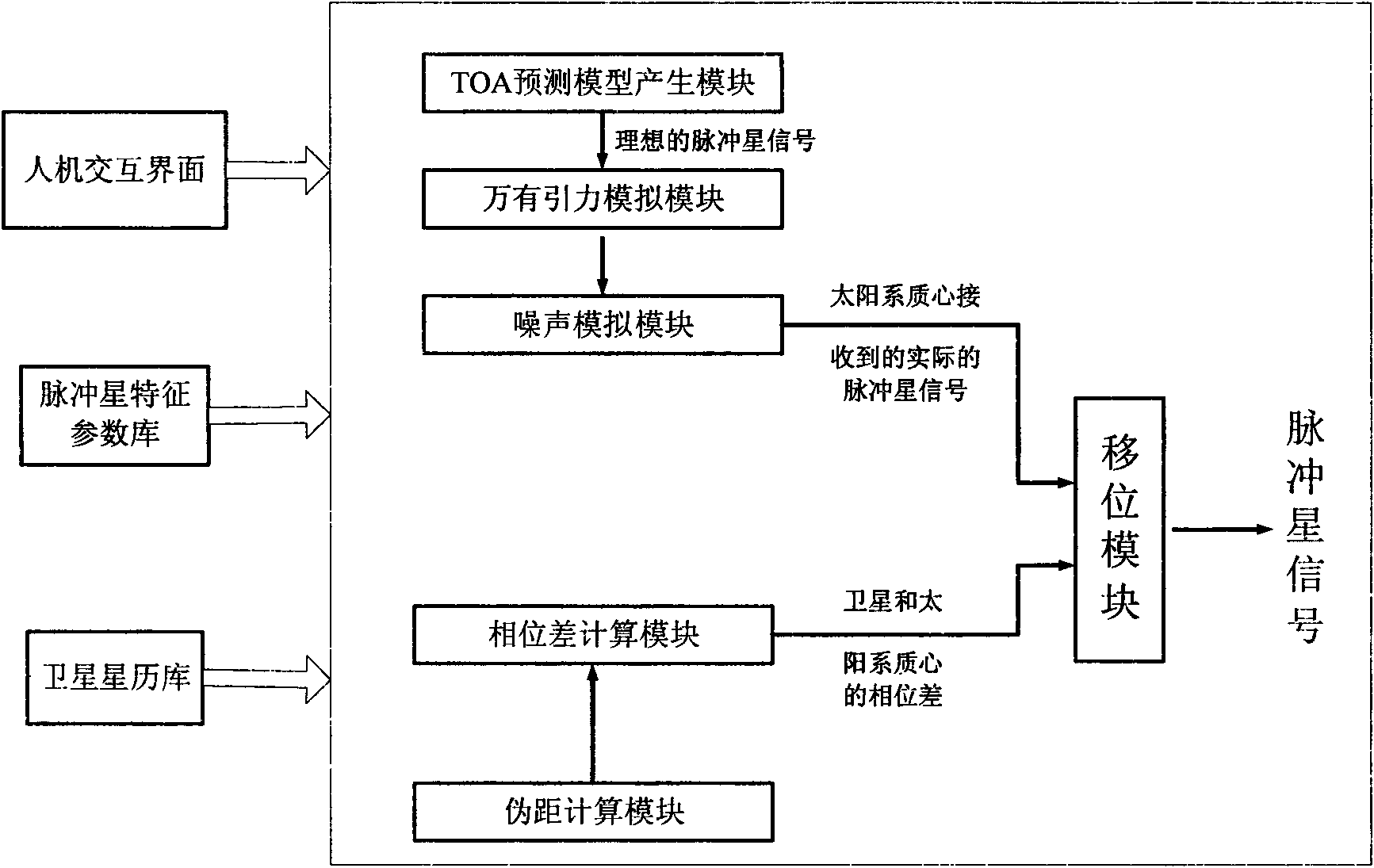
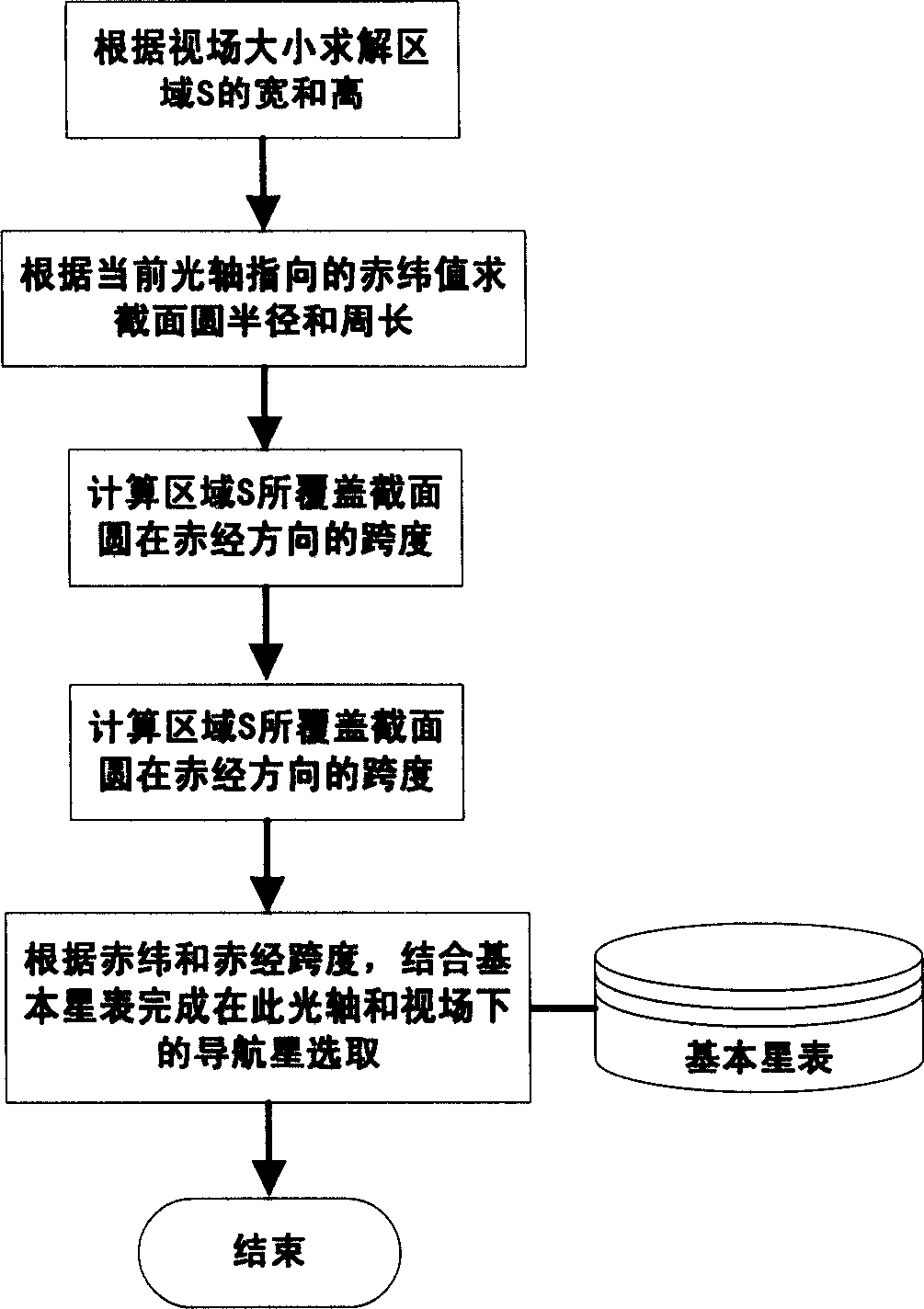
Pulsar signal simulator
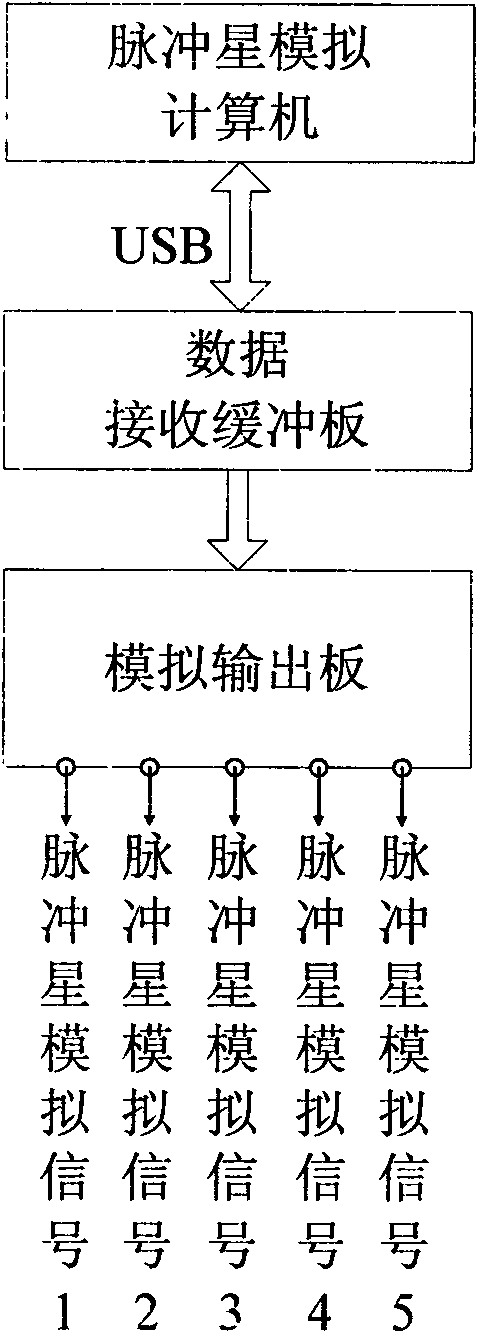
InactiveCN101603831AFlexible designEasy to implementNavigation by astronomical meansAnalog computerInteraction interface
The invention discloses a pulsar signal simulator mainly solving the problem that X-ray pulsar signals only can be obtained by a satellite carrying X-ray detector at present. The system mainly comprises a pulsar analog computer, a data receiving buffer board and an analog signal output board, wherein, the pulsar analog computer stimulates user input according to human-computer interaction interface, extracts information in a pulsar characteristic parameter library and a satellite ephemeris library, generates pulsar data received in the satellite operation process, and transmits the pulsar data to the data receiving buffer board via a data port; the data receiving buffer board puts received data into a cache and transmits the data to an analog output board if needed; the analog output board converts the received digital signal into an analog signal so as to stimulate and generate X-ray pulsar signals. The invention can stimulate the pulsar signal received in the satellite operation process, has flexible arrangement and wide application range, and can be used for proving the X-ray pulsar navigation theory method and researching engineering technology.
Owner:XIDIAN UNIV
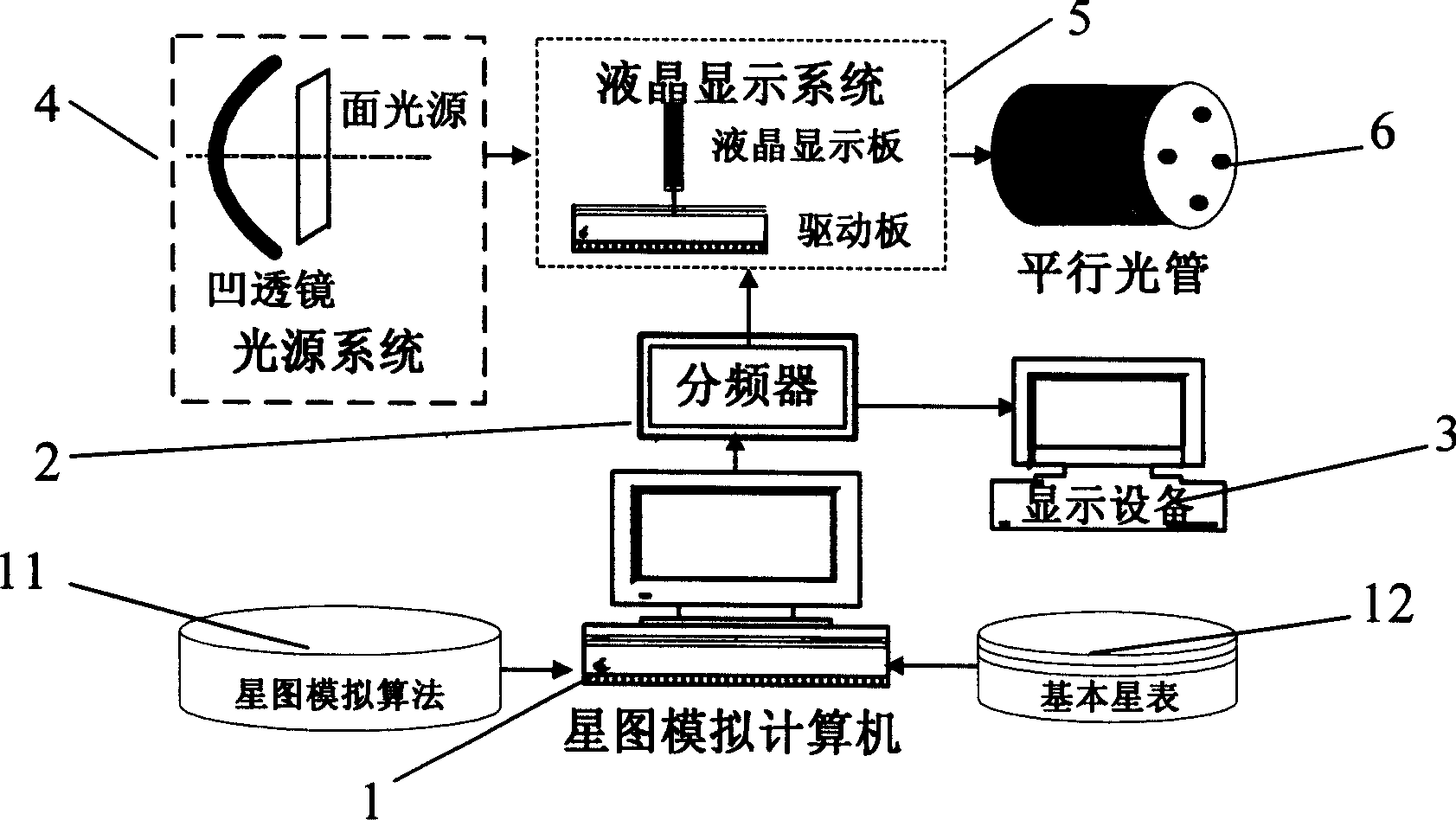
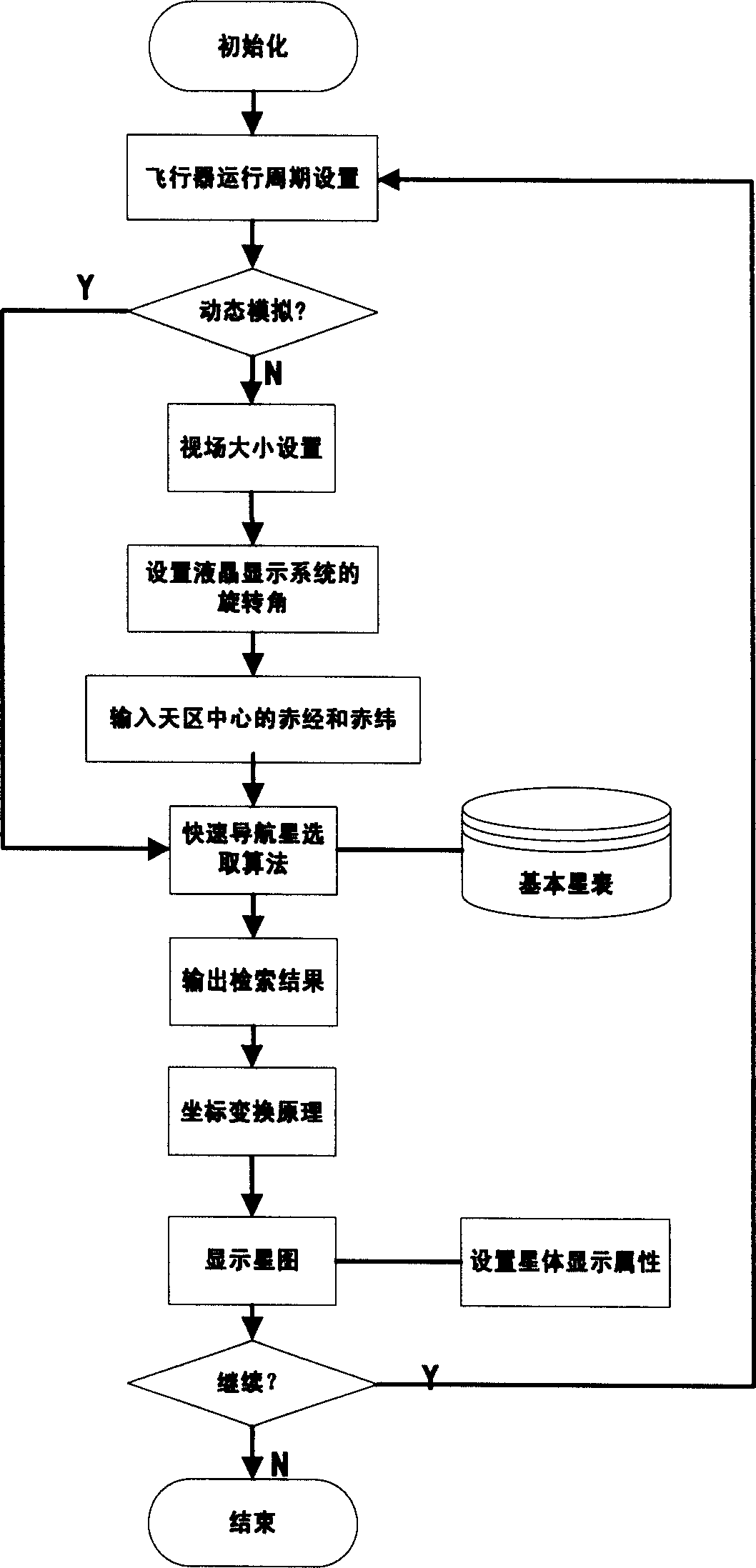
High precision low cost starlight simulator
ActiveCN1912547AOvercome precisionOvercome speedInstruments for comonautical navigationCosmonautic vehicle trackingVisual field lossFixed stars
A starlight simulator with high accuracy consists of light source system formed by concave lens and surface light source, star atlas analog computer being set with star atlas analog algorithm and basic star table for calculating out mapping positions of each navigation star on liquid crystal display system, frequency divider for dividing said mapping positions to different units, display unit for carrying out directly viewing display, liquid crystal display system for displaying distribution of fixed star, parallel light tube being used to set liquid crystal display system on its focal plane and being used to simulate parallel star light of infinite truly under specific visual field and shaft.
Owner:BEIHANG UNIV
Simulated computer system for monitoring of software performance
InactiveUS20080201129A1Reduce riskMemory loss protectionError detection/correctionVery low riskOperational system
A system S is defined which is capable of simulating a computer (virtual computer, VC) for the purpose of software performance monitoring. The system is implemented as a set of software modules (SM) that can be exchanged to change the behavior of the VC. The VC is driven by a CPU emulator, and can run any operating system (virtual operating system, VOS) that is supported by the available SM's. The system is designed to log accesses to system resources and the nature of these accesses. The system is particularly useful for determining whether an executable or file contains an unknown virus, with a very low risk of false positives. Detected viruses include encrypted, polymorphic, metamorphic and other virus types.
Owner:CA TECH INC
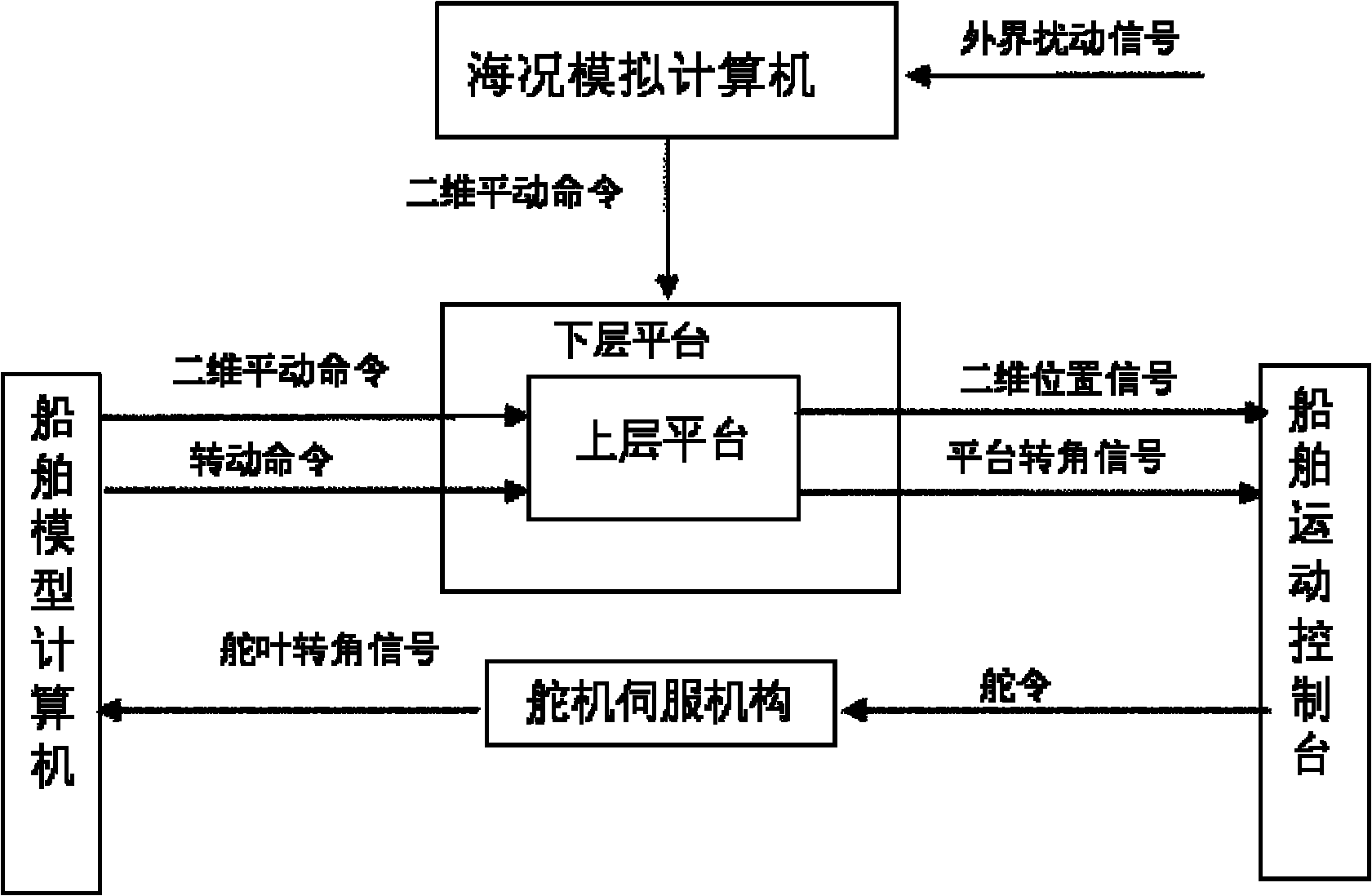
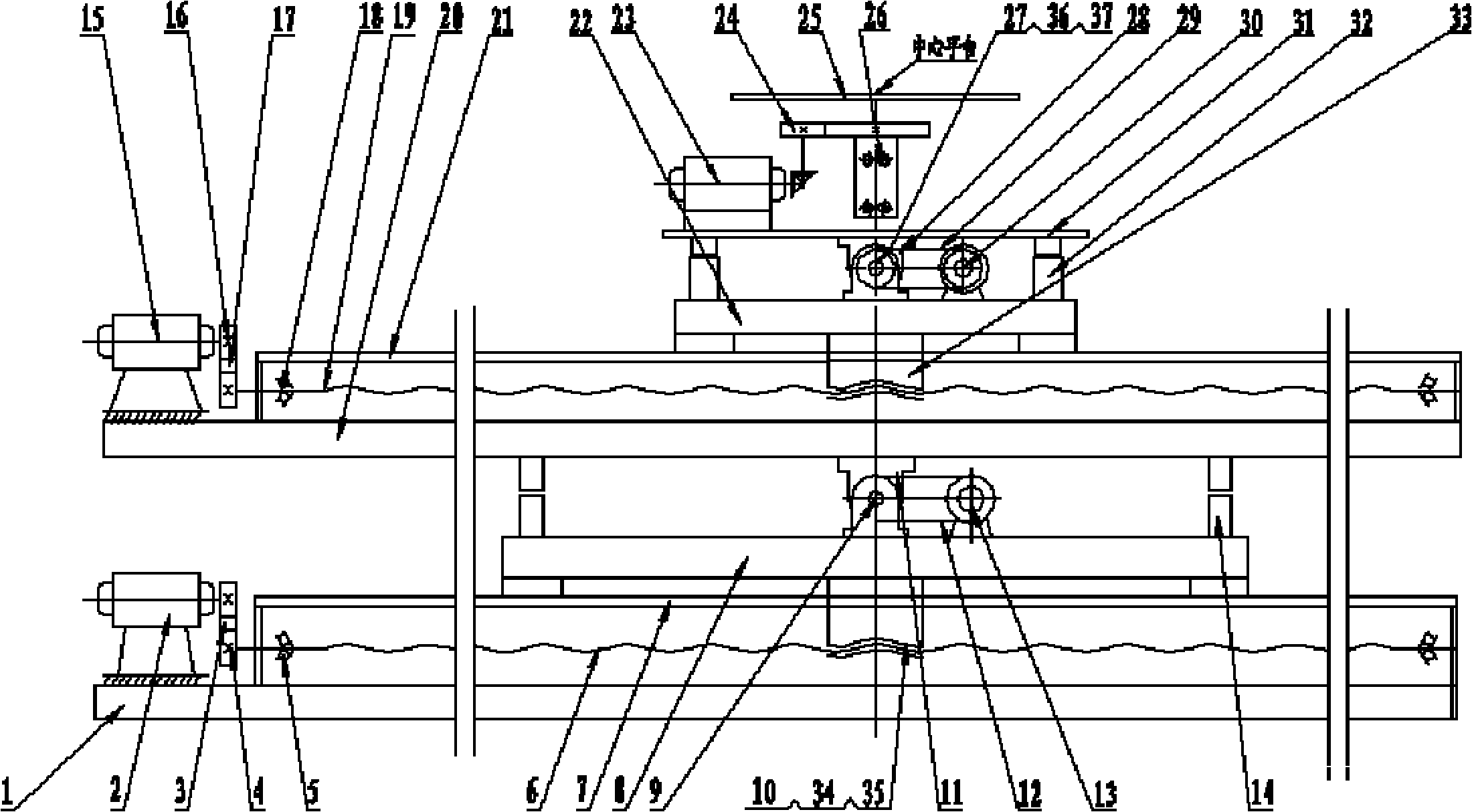
Ship position motion test platform
InactiveCN102074144AAchieving Dynamic PositioningRealize half-physical simulation experimentCosmonautic condition simulationsSimulatorsAnalog computerRelative motion
The invention relates to a ship position motion test platform, which comprises upper and lower layers which make two-dimensional translation, wherein the upper and lower layers are controlled by a motion lock to make relative motion, and a position sensor, a compass and a global positioning system (GPS) are installed on a central platform; a sea condition simulation computer receives current sea conditions input by a keyboard, calculates and simulates the impact of external interference on a ship position and sends a two-dimensional translation command to control the lower layer to be used for simulating the sea conditions, and a ship motion console issues corresponding control commands to a rudder and a side thruster according to the detected ship position; and a ship model computer receives the commands issued by the ship motion console, obtains the current rubber angle and the position of a ship under the action of the side thruster by calculation, issues the two-dimensional translation commands to control the upper layer to move relative to the lower layer, issues rotating commands to control the central platform to rotate, and simulates the deflection of the ship under the action of the side thruster at the current rudder angle. In the ship position motion test platform, the ship parameters and the sea conditions can be arbitrarily set to realize the semi-physical simulation test of the dynamic positioning and automatic berthing or unberthing of the ship.
Owner:DALIAN MARITIME UNIVERSITY +1
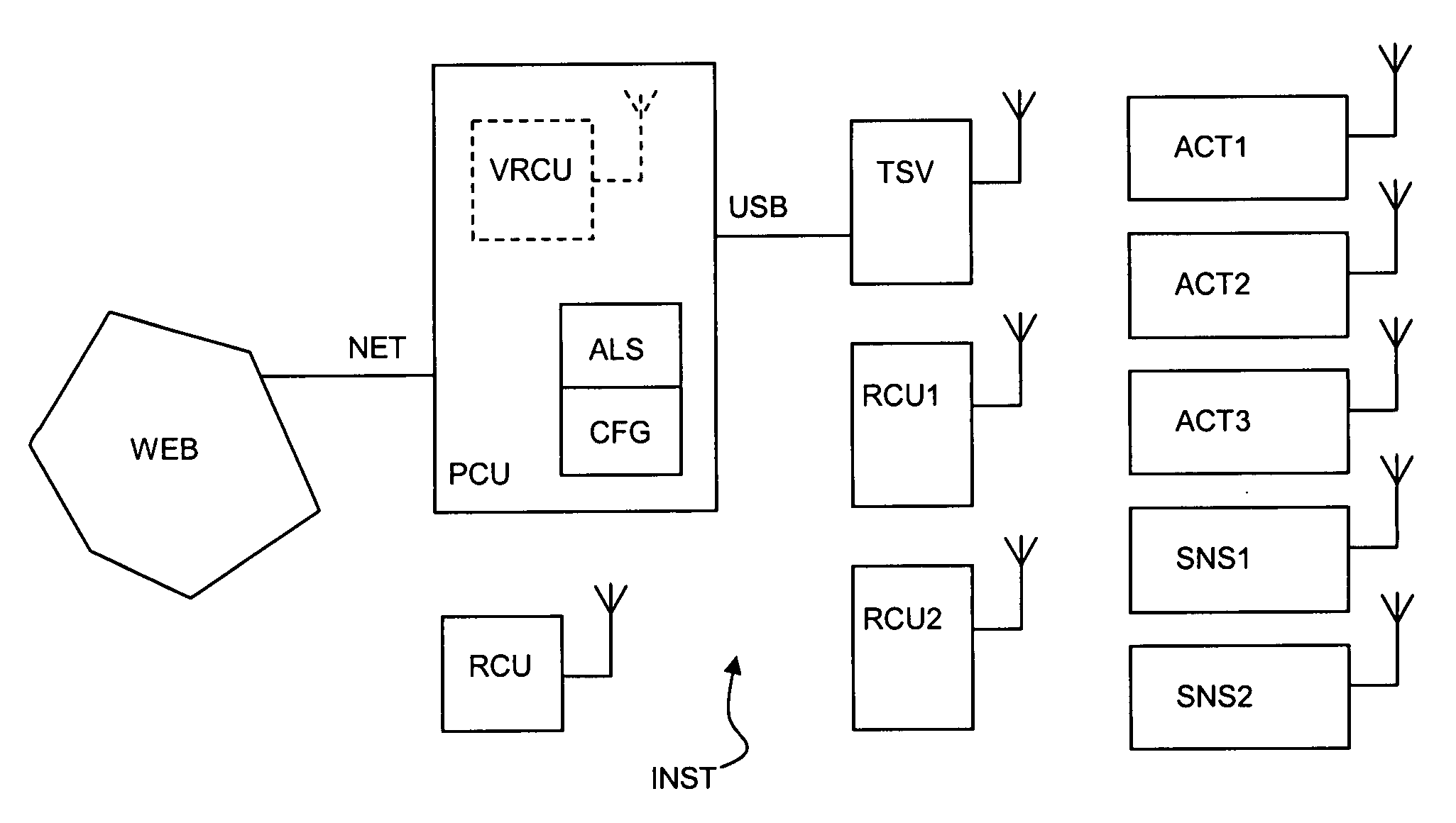
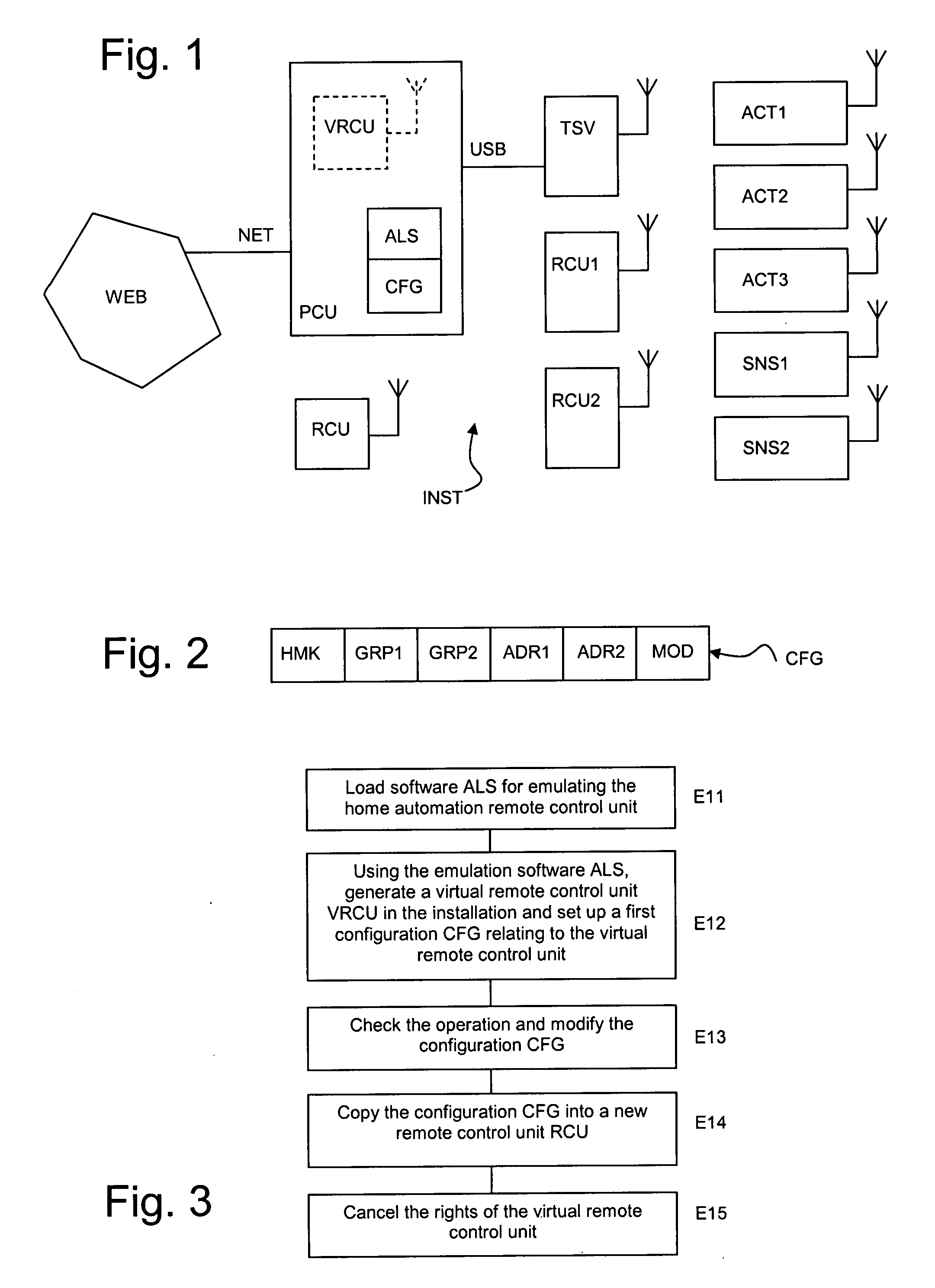
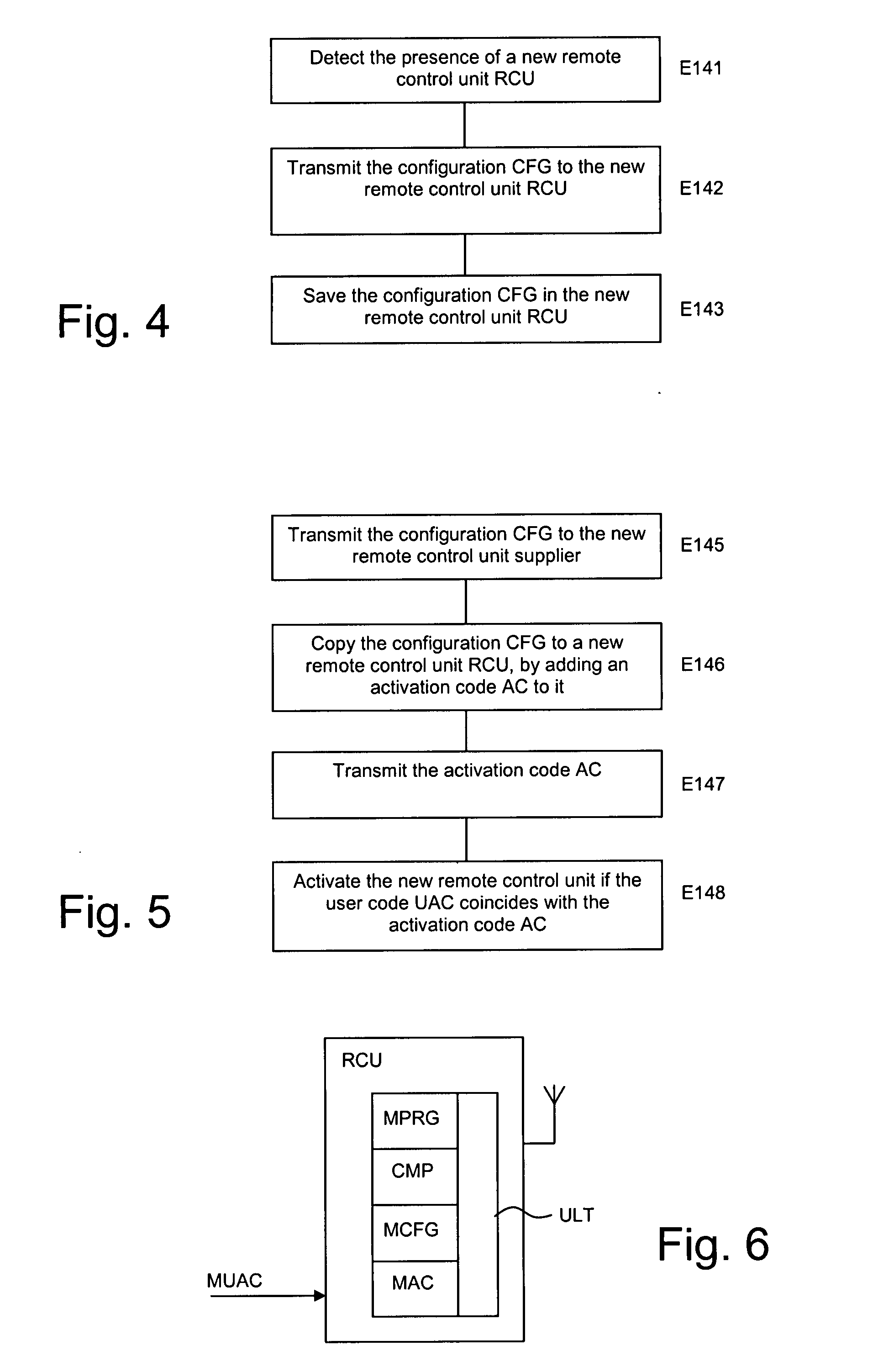
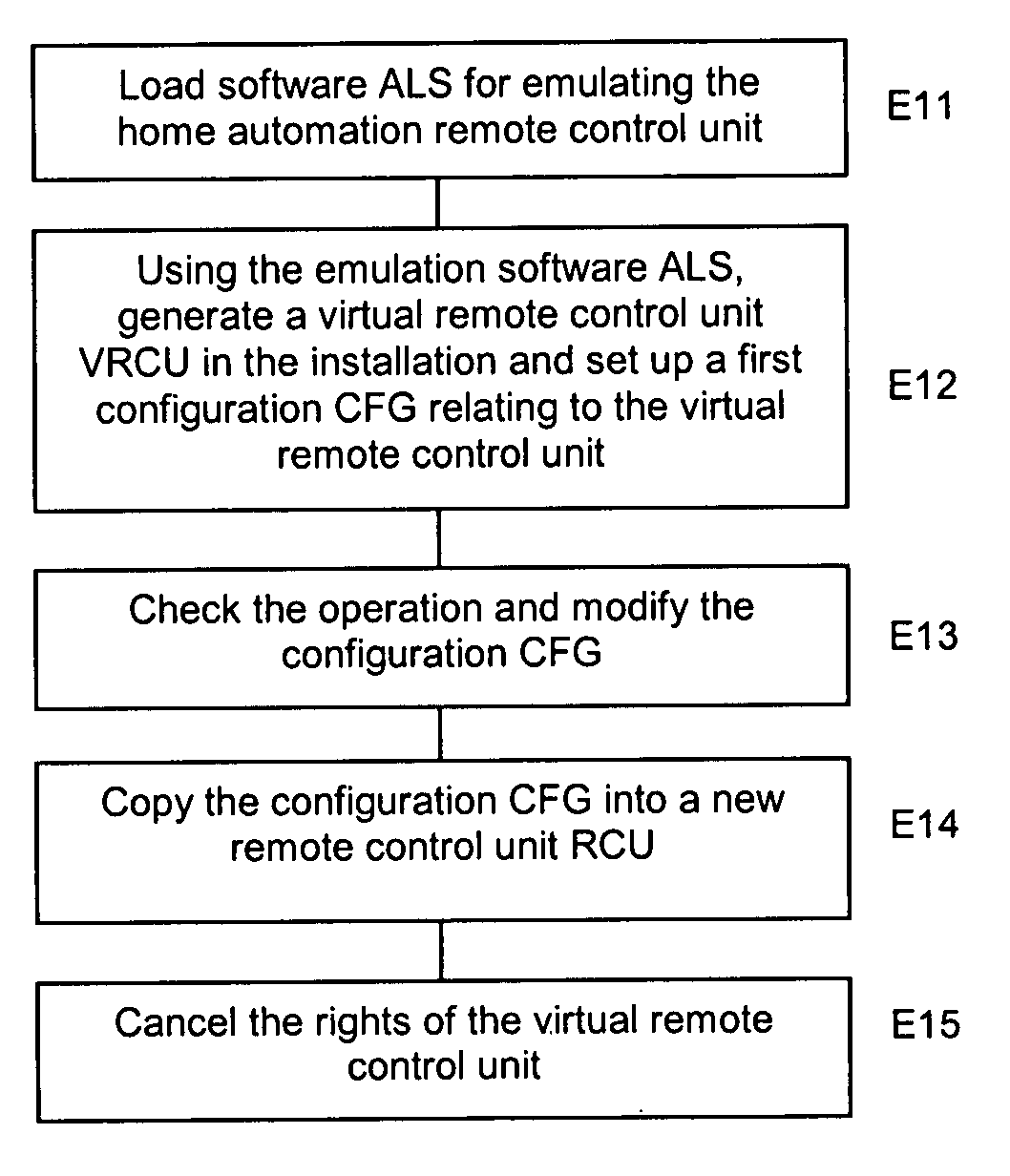
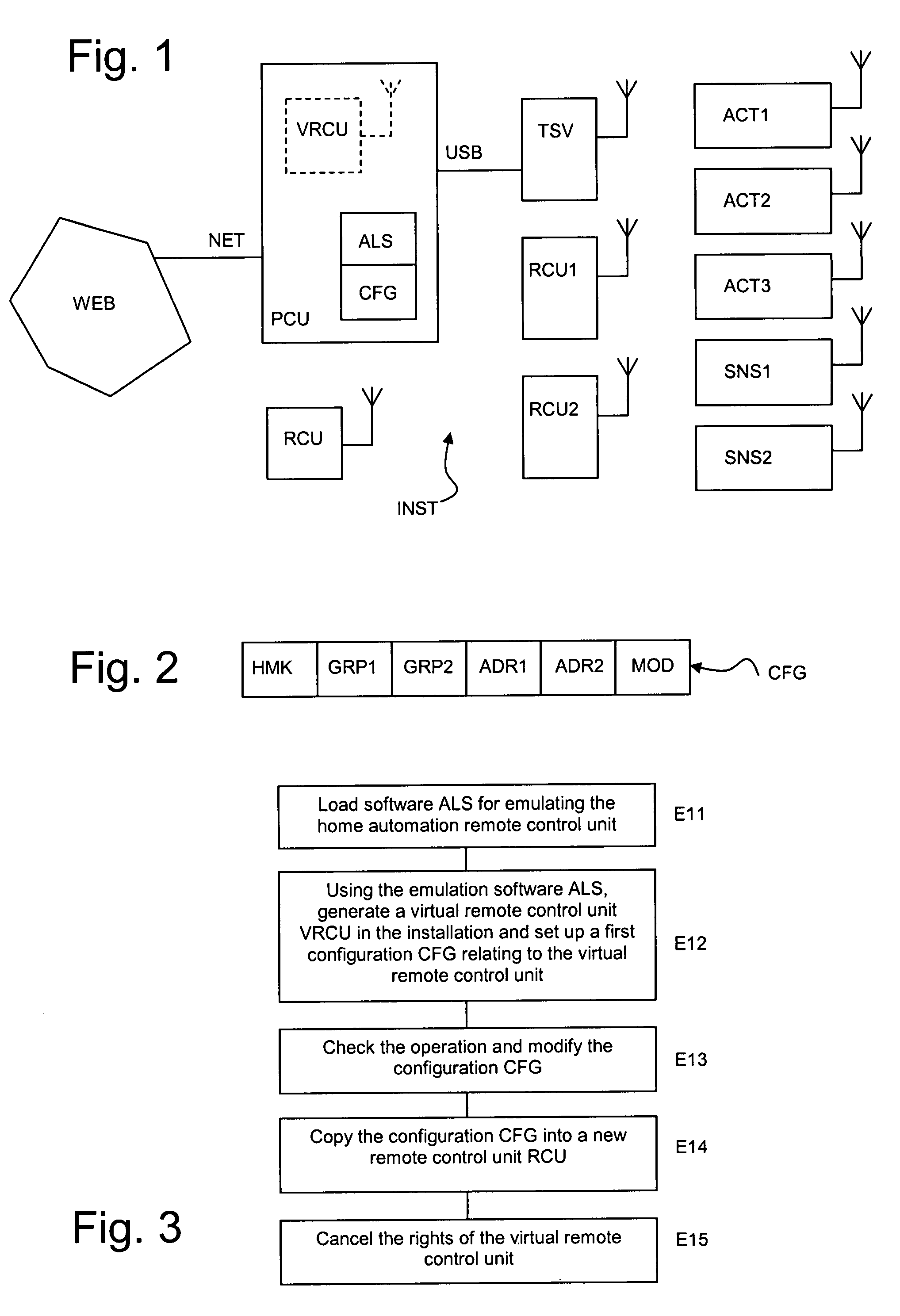
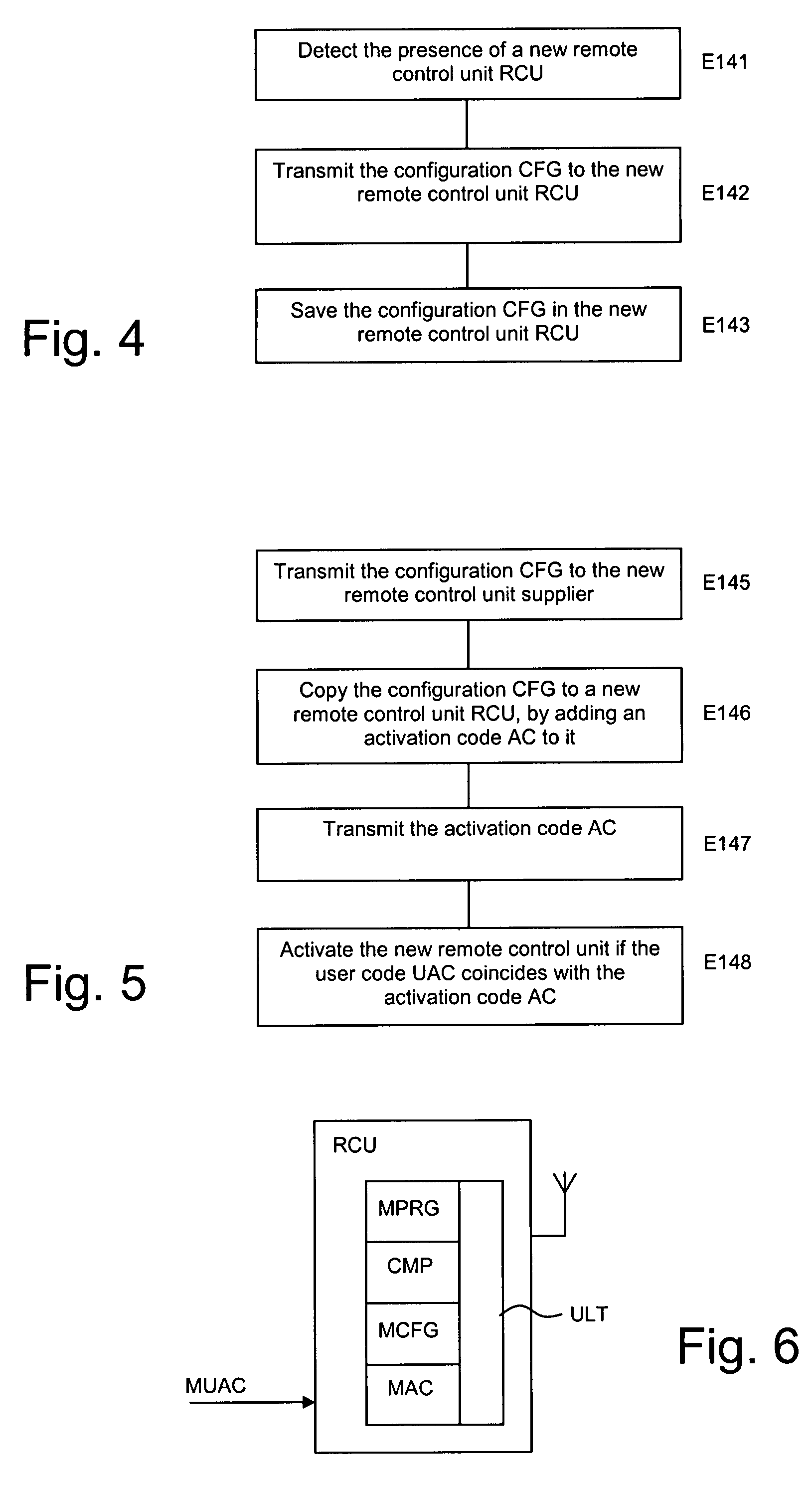
Method of testing and installing a home automation remote control unit
InactiveUS20070260331A1Easy to installOvercomes drawbackTelevision system detailsElectric signal transmission systemsAnalog computerRemote control
A method of testing and installing a remote control unit (RCU) for controlling elements (ACT1, ACT2, ACT3) of a home automation network, intended for managing the security or heat or light comfort in a building, comprising the use of software (ALS) emulating the remote control unit in a computer (PCU) to define a virtual remote control unit (VRCU), and the configuring of the virtual remote control unit to enable the elements of the network to be controlled, wherein sending rights are assigned to the virtual remote control unit at the time of that configuration and wherein the cancellation of these sending rights results at least from a step for copying the configuration (CFG) of the virtual remote control unit in the remote control unit.
Owner:SOMFY SAS
Method of testing and installing a home automation remote control unit
InactiveUS7860679B2Easy to installTelevision system detailsElectric signal transmission systemsAnalog computerRemote control
A method of testing and installing a remote control unit (RCU) for controlling elements (ACT1, ACT2, ACT3) of a home automation network, intended for managing the security or heat or light comfort in a building, comprising the use of software (ALS) emulating the remote control unit in a computer (PCU) to define a virtual remote control unit (VRCU), and the configuring of the virtual remote control unit to enable the elements of the network to be controlled, wherein sending rights are assigned to the virtual remote control unit at the time of that configuration and wherein the cancellation of these sending rights results at least from a step for copying the configuration (CFG) of the virtual remote control unit in the remote control unit.
Owner:SOMFY SAS
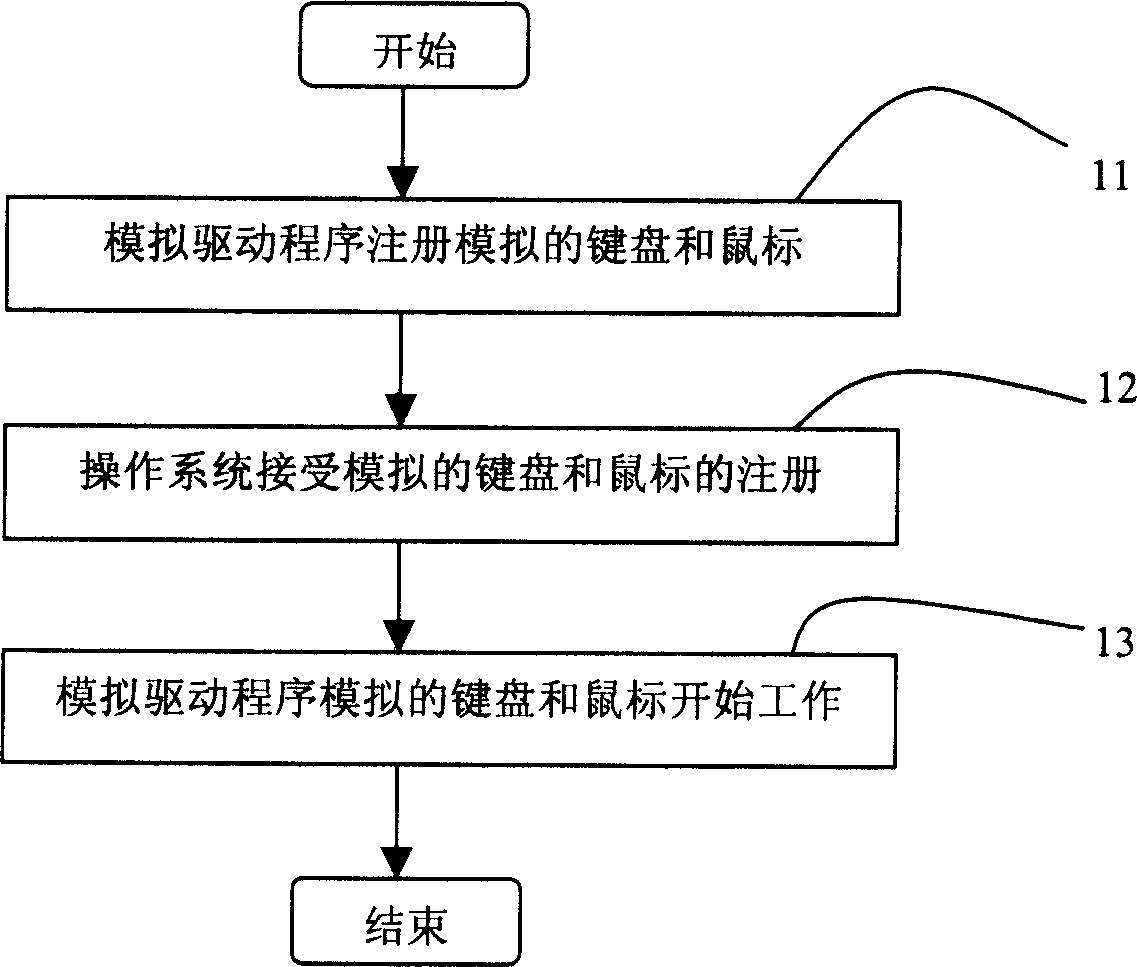
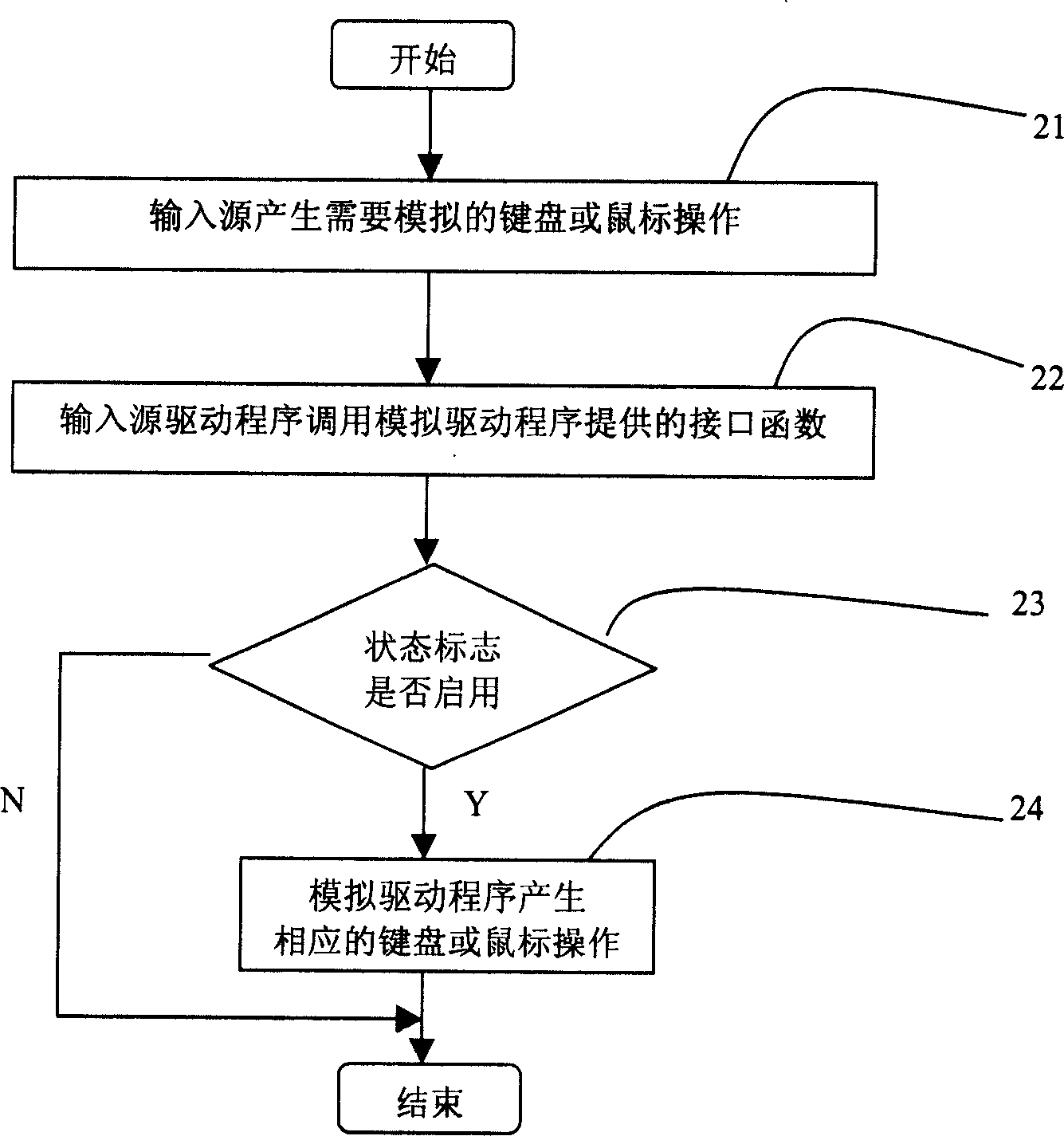
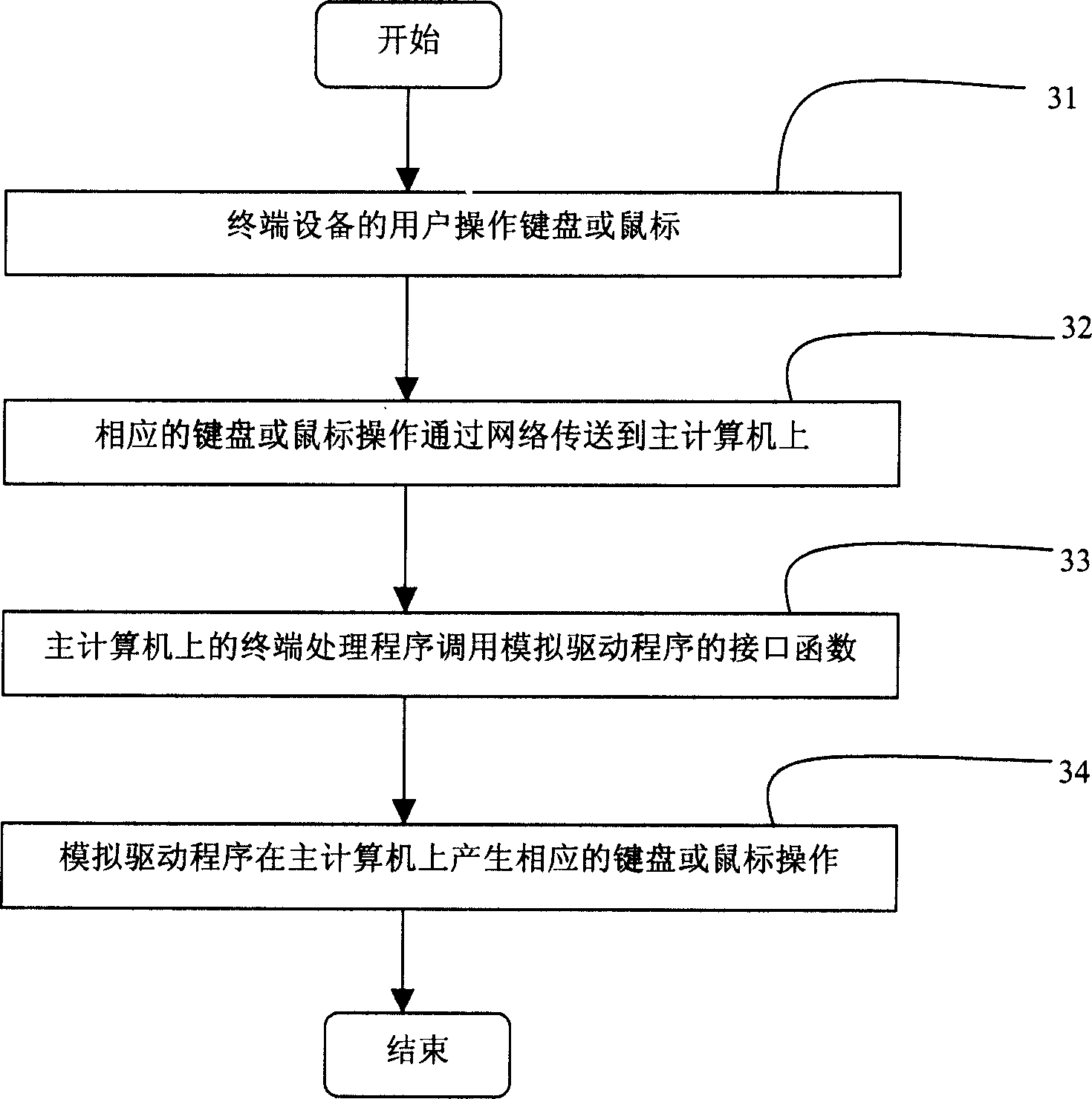
Method for simulating computer keyboard or mouse operation
InactiveCN1591336AReduce dependencyIncrease flexibilitySoftware simulation/interpretation/emulationInput/output processes for data processingAnalog computerComputerized system
The present invention discloses a method for simulating computer keyboard or mouse operation. It is characterized by that in the computer system a simulation drive program for simulating keyboard or mouse operation is set, and at least an input source equipment capable of simulating keyboard or mouse operation is defined, and a correspondent equipment drive program is set, and the described simulation drive program and the described equipment drive program can be called firstly when the system is started and resided in the computer system, so that when the keyboard or mouse simulation operation data correspondent to input of input source equipment are obtained by said equipment drive program and said simulation operation data are transferred into simulation drive program, the simulation drive program can utilize described simulation operation data to produce operation for simulating keyboard or mouse.
Owner:LENOVO (BEIJING) CO LTD
Simulation system for multi-node process control systems
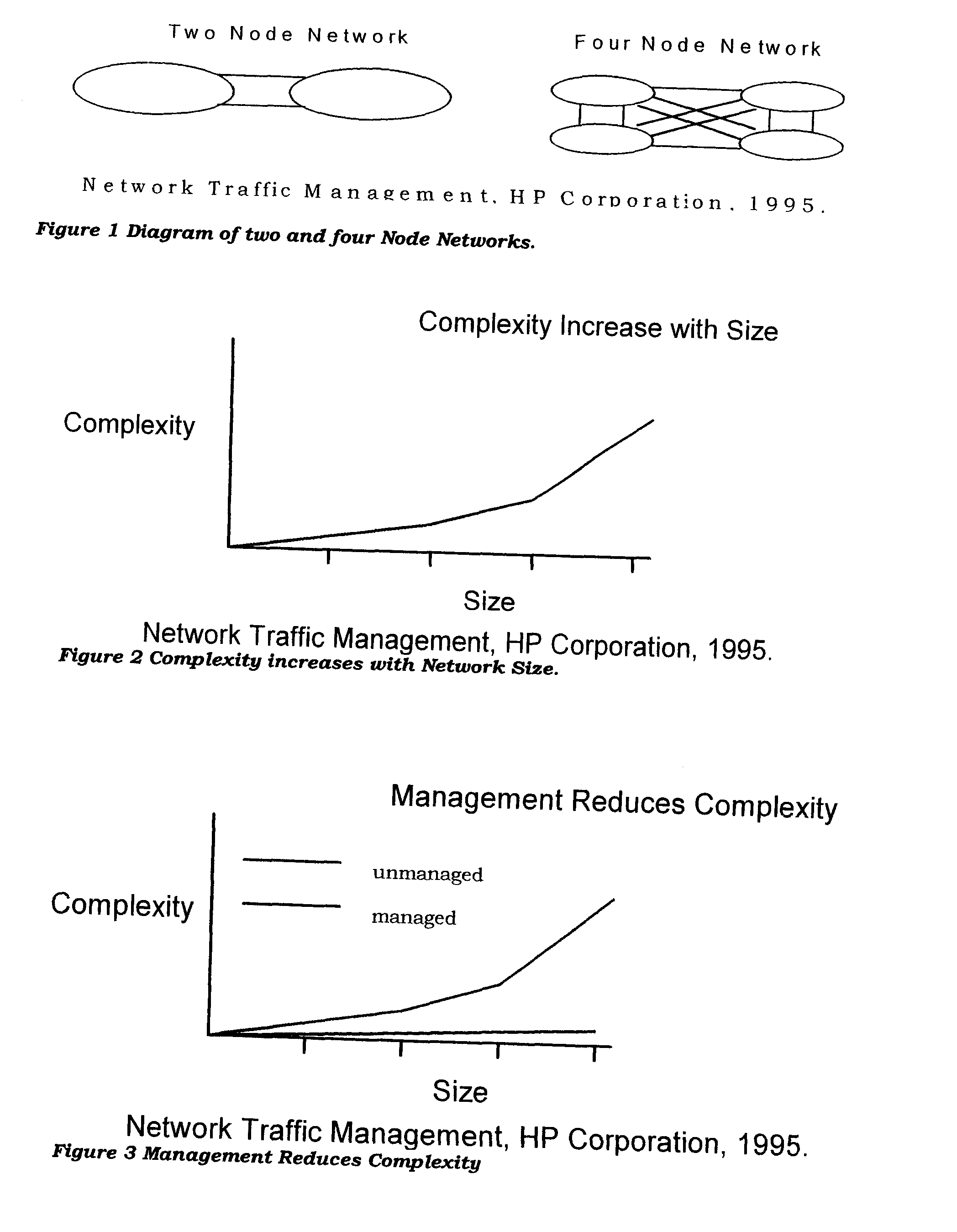
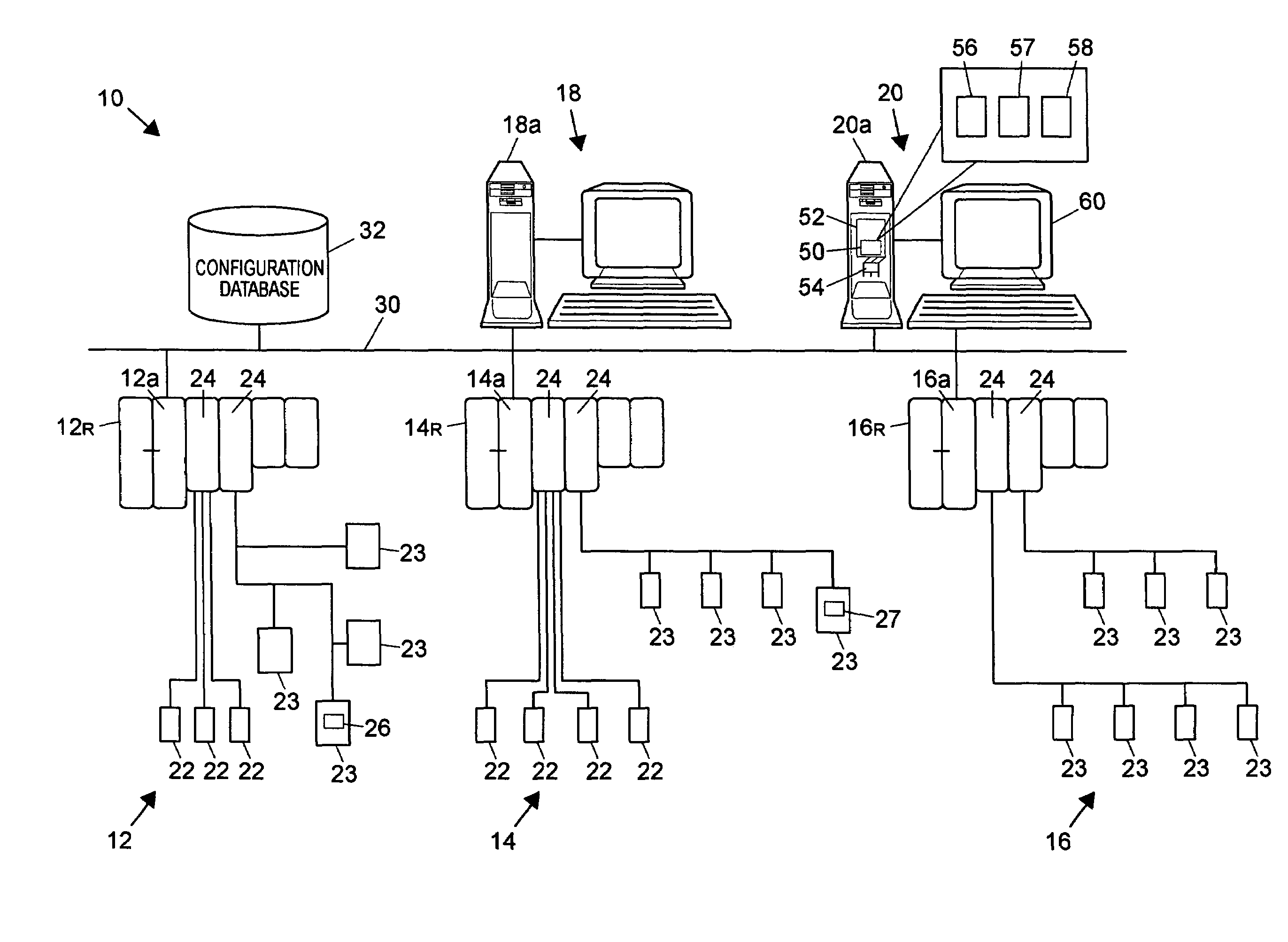
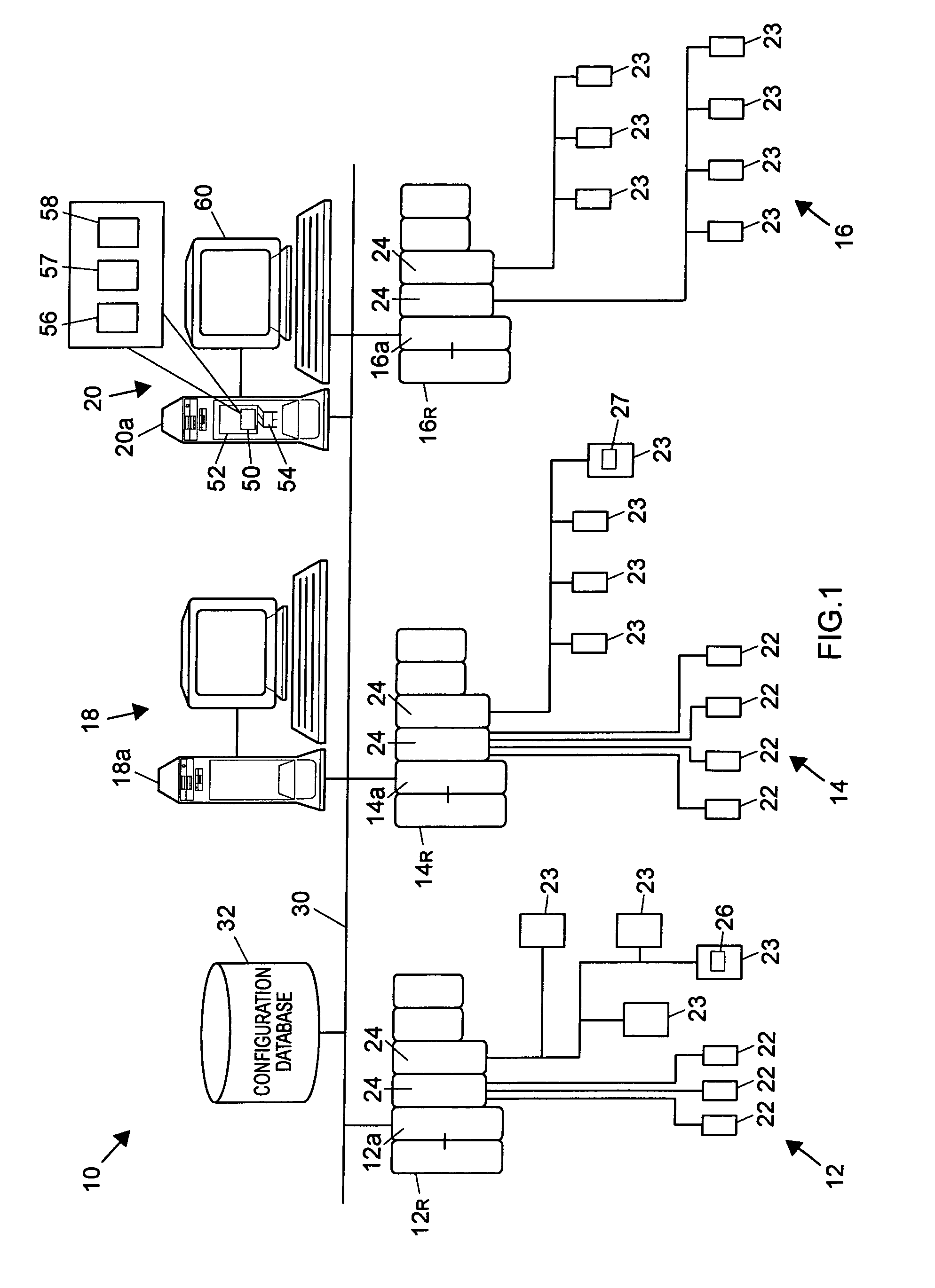
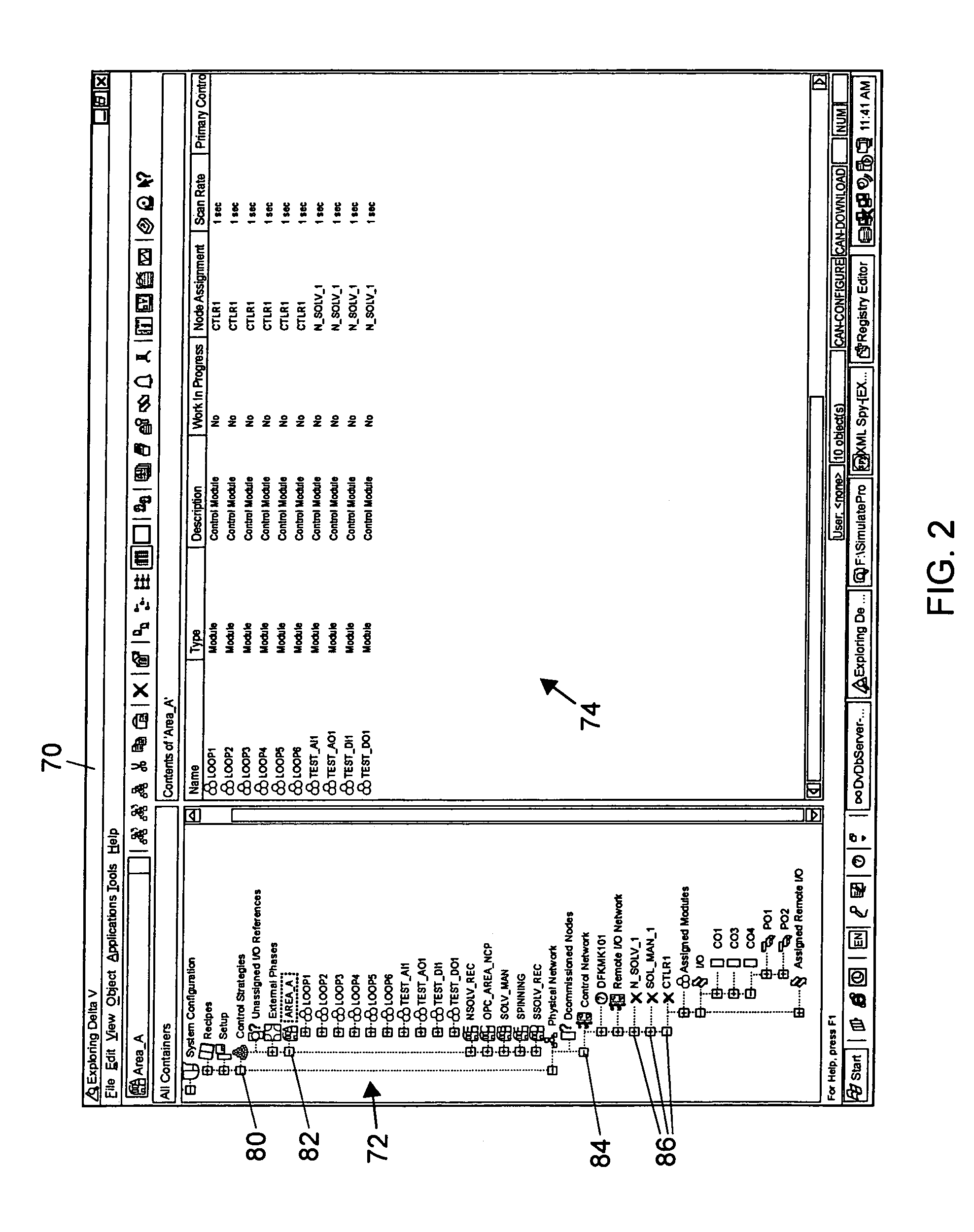
A simulation system attaches to a configuration database for one or more fully configured nodes of a process control system and copies the modules within those nodes into one or more simulation computers as simulation modules. The simulation system includes an algorithm that automatically creates a reference parameter module for each of the copied nodes that stores a reference parameter for each of the inputs, outputs or other references to signals external to the nodes. In the case of the Fieldbus function blocks, the simulation system automatically creates a function block within the simulation workstation in the protocol of the controller node which mimics the operation of the Fieldbus function block, and then creates the simulation system having those mimicked Fieldbus function blocks operating as if they had originally been configured to be in the controller being simulated, instead of within a field device external to the controller.
Owner:FISHER-ROSEMOUNT SYST INC
Testing method and system for simulating real operation environment of computer network application program
InactiveCN106844220APrecise positioningSoftware testing/debuggingData switching networksAnalog computerApplication software
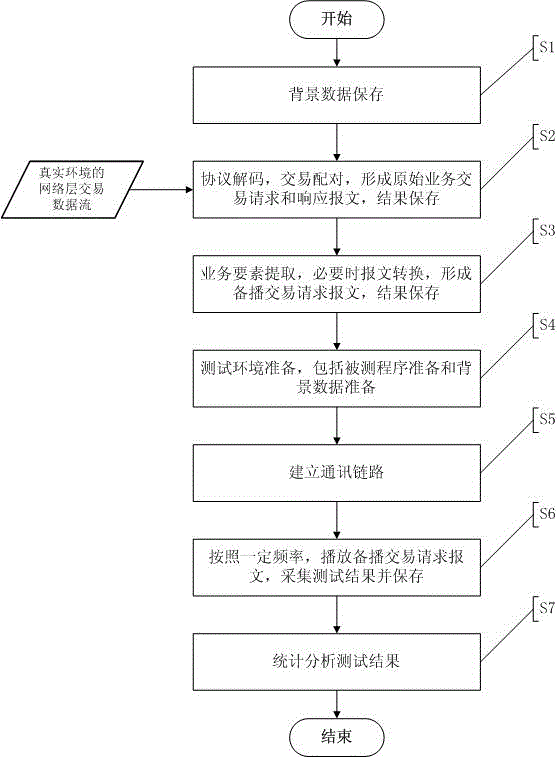
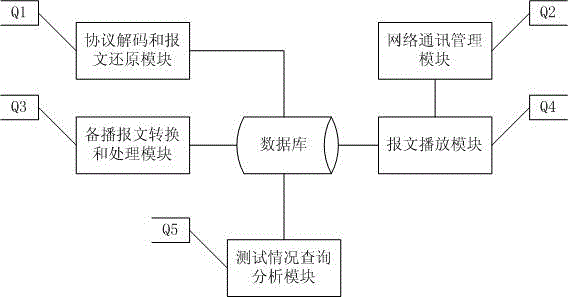
The invention provides a testing method and system for simulating a real operation environment of a computer network application program to solve the problem or overcome the shortcoming of large difference between a testing scene and an actual operation scene in the testing process of a current computer application program. The method includes the steps: storing real business transaction messages recorded from an actual production environment in a database according to actual business occurrence order after network protocol decoding and request response message pairing; storing background database information in starting and finishing of recording; performing adaptive transformation on the stored transaction messages according to a certain transformation rule; simulating the real operation environment for the transformed transaction messages according to the recording time sequence and the recording background data; replaying request messages; checking whether the tested program is correctly processed or not according to recording response messages; determining the quality and the performance of the tested program.
Owner:北京融信易安信息技术有限公司
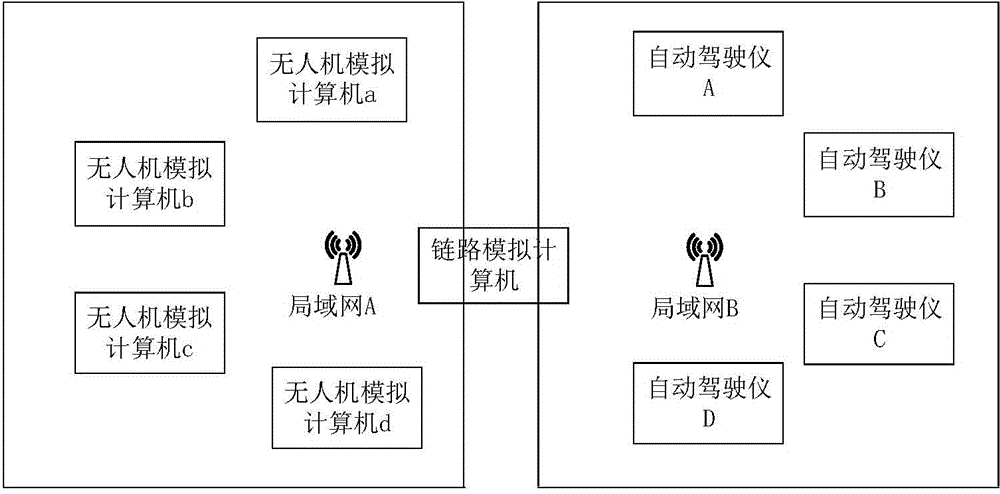
Real-time simulation experiment system of multi-unmanned plane distributed synergetic hardware in loop
ActiveCN104880961AMake up for the defects of large actual deviationReduce experiment costSimulator controlReal-time simulationSoftware emulation
The invention relates to a real-time simulation experiment system of multi-unmanned plane distributed synergetic hardware in a loop, and belongs to the technical field of cooperative control of multiple autonomous bodies. A link analog computer and n unmanned plane analog computers are in the same local network A, the link analog computer can intercommunicate with any one of the n unmanned plane analog computer, at the same time, the n unmanned plane analog computers can intercommunicate, the link analog computer and n automatic pilots are in the other local network B, and the link analog computer can intercommunicate with any one of the n automatic pilots. The unmanned plane analog computers and the automatic pilots are in one-to-one correspondence; and each automatic pilot adopts a distributed control mode to control the corresponding unmanned plane analog computer. The real-time simulation experiment system of the multi-unmanned plane distributed synergetic hardware in the loop uses mature commercial flight simulator software to simulate unmanned planes, reduces experiment cost and complexity, and can obtain simulation precision as high as possible, and the automatic pilots in the simulation loop can make up for a defect of large deviation of pure software simulation from engineering practice.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
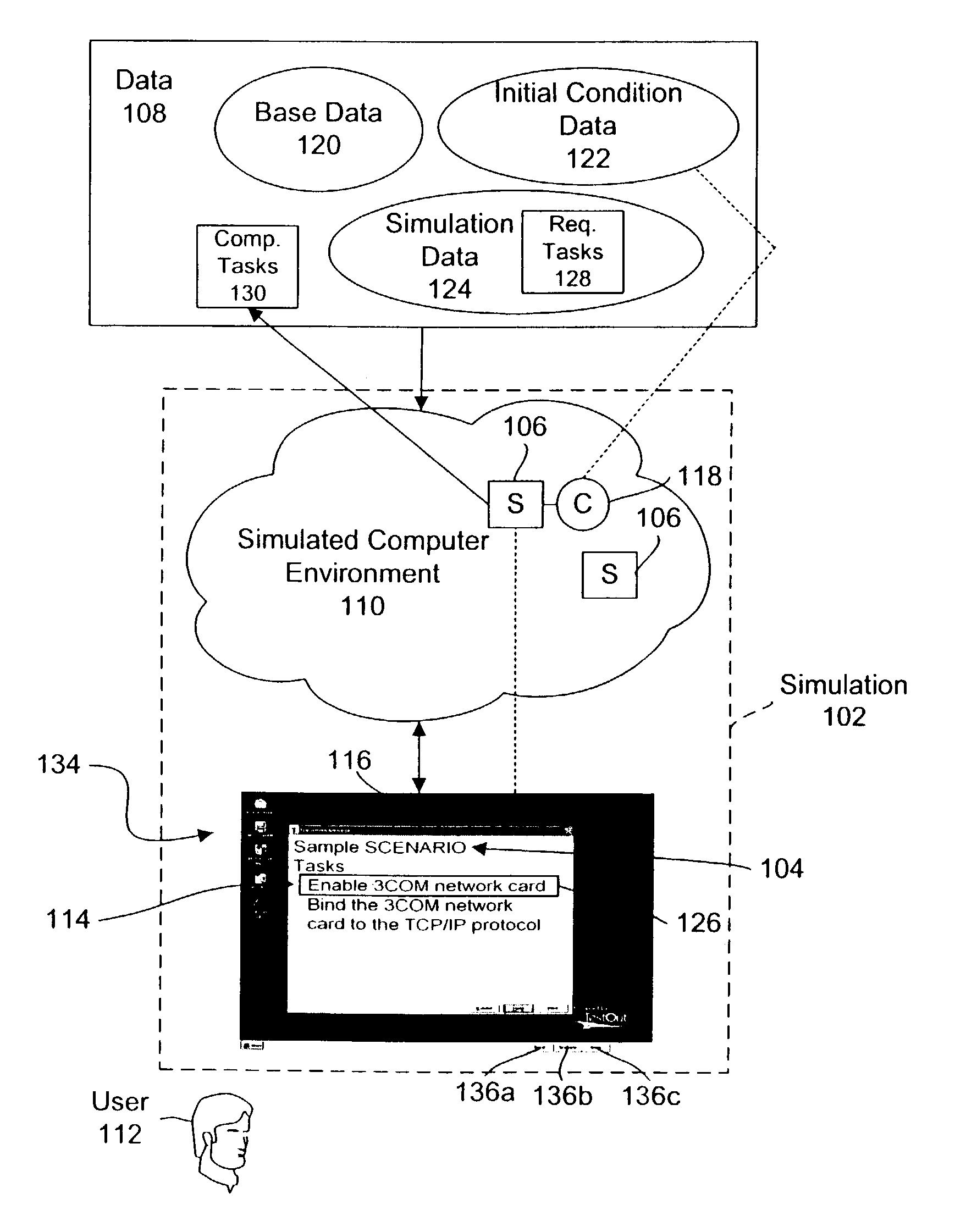
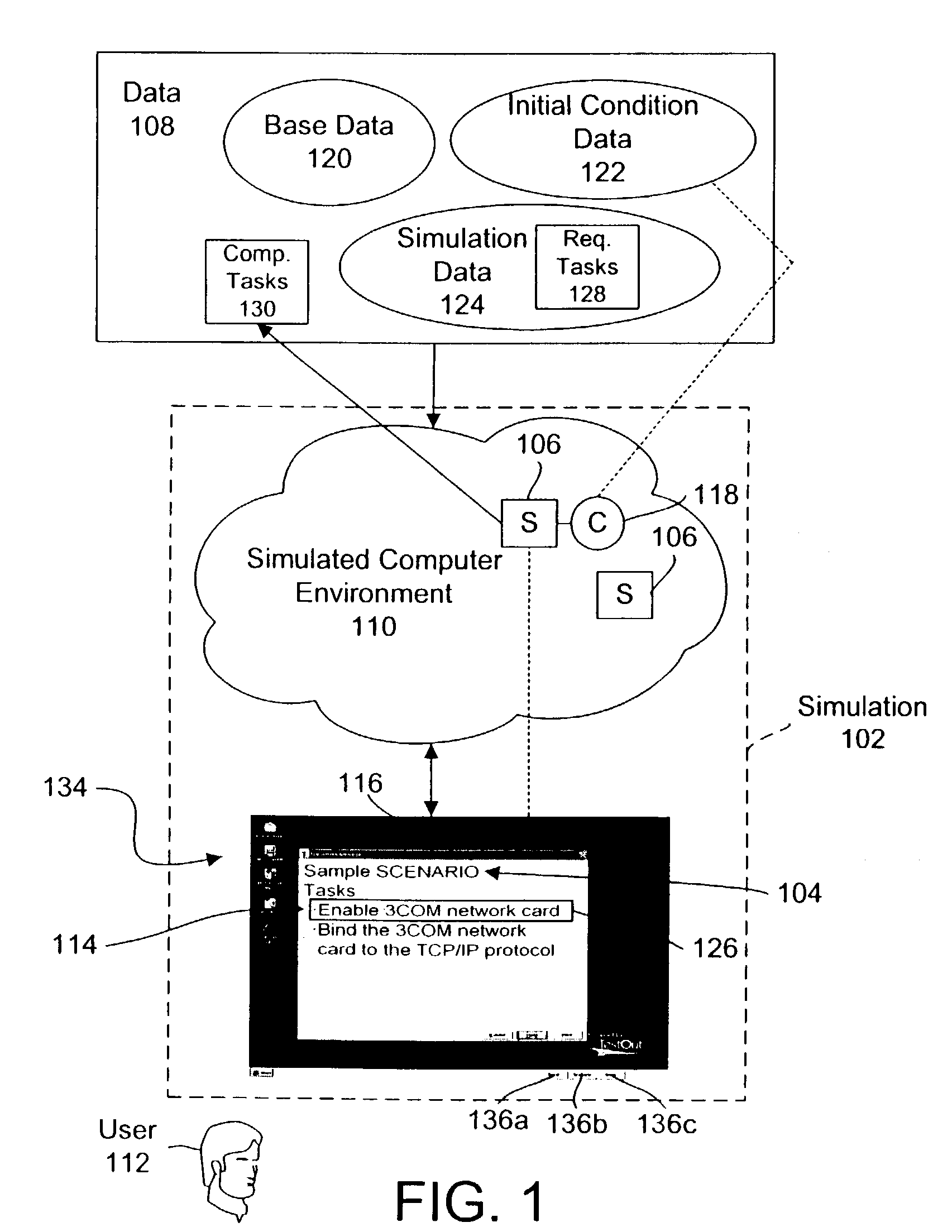
System and method for simulating a computer environment and evaluating a user's performance within a simulation
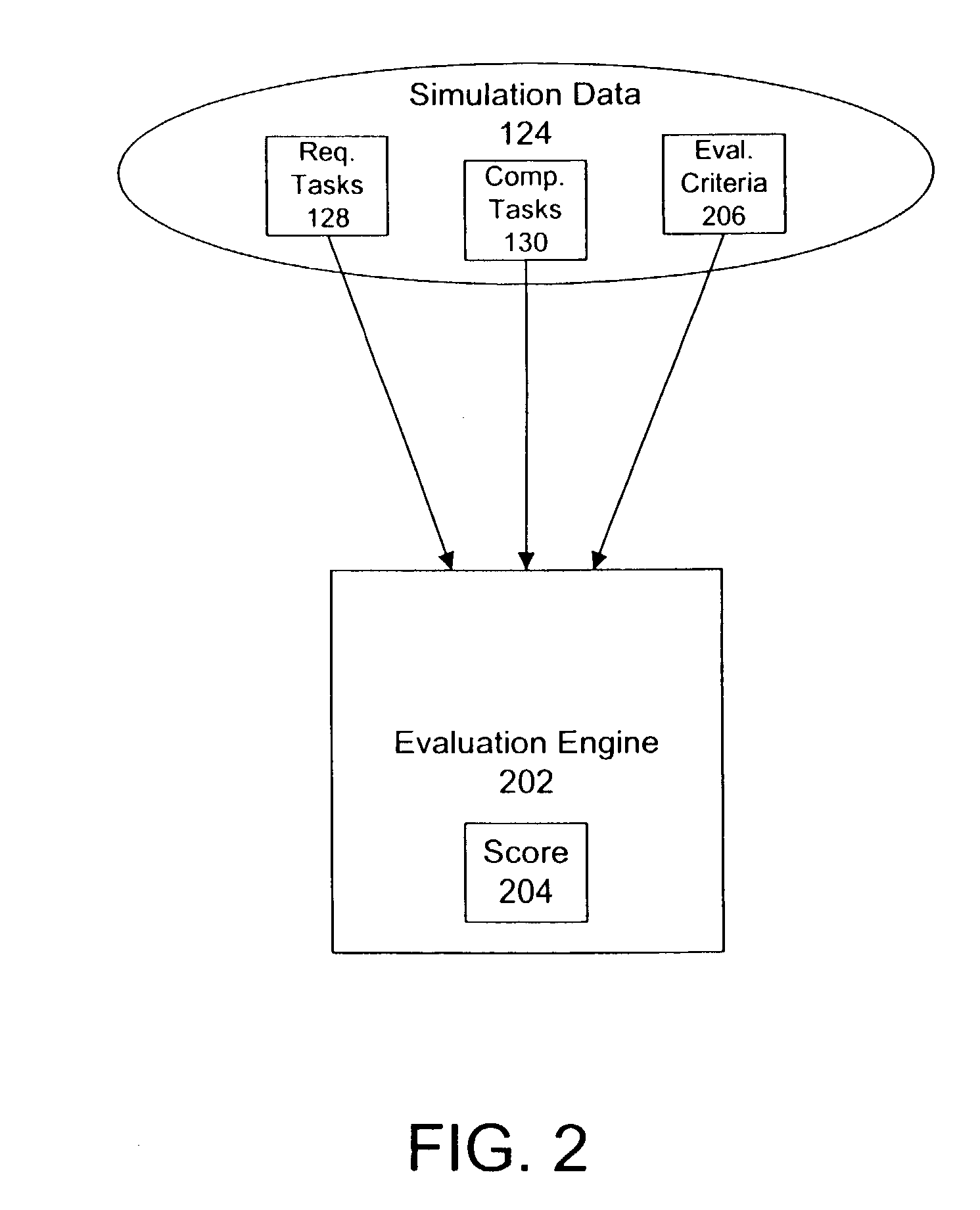
InactiveUS7089172B2Error detection/correctionSpecific program execution arrangementsAnalog computerSimulation based
A system and method is provided for simulating a computer environment and evaluating a user's performance within a simulation which uses the computer environment. The method reads base data which defines a simulated component within a simulated computer environment. Initial condition data may also be read to modify a simulated component. The simulated computer environment is represented by executing one or more simulators to simulate actual software modules. A simulation is presented to a user. The simulation includes a scenario and a set of tasks to be completed. As the user interacts with the simulators, tasks completed by the user are recorded. Finally, the set of completed tasks are evaluated to determine a user's performance within the simulation. The system and method allows a simulation author to automatically define a set of possible tasks for a simulation by performing the desired tasks in the simulated computer environment. The system and method provides a robust evaluation process for simulations. Partial scores, weighted scores, partially weighted scores, and binary scores are provided, as well as rescoring of simulations and simulation-based exam question seeding.
Owner:TESTOUT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com