Patents
Literature
1911 results about "Request–response" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
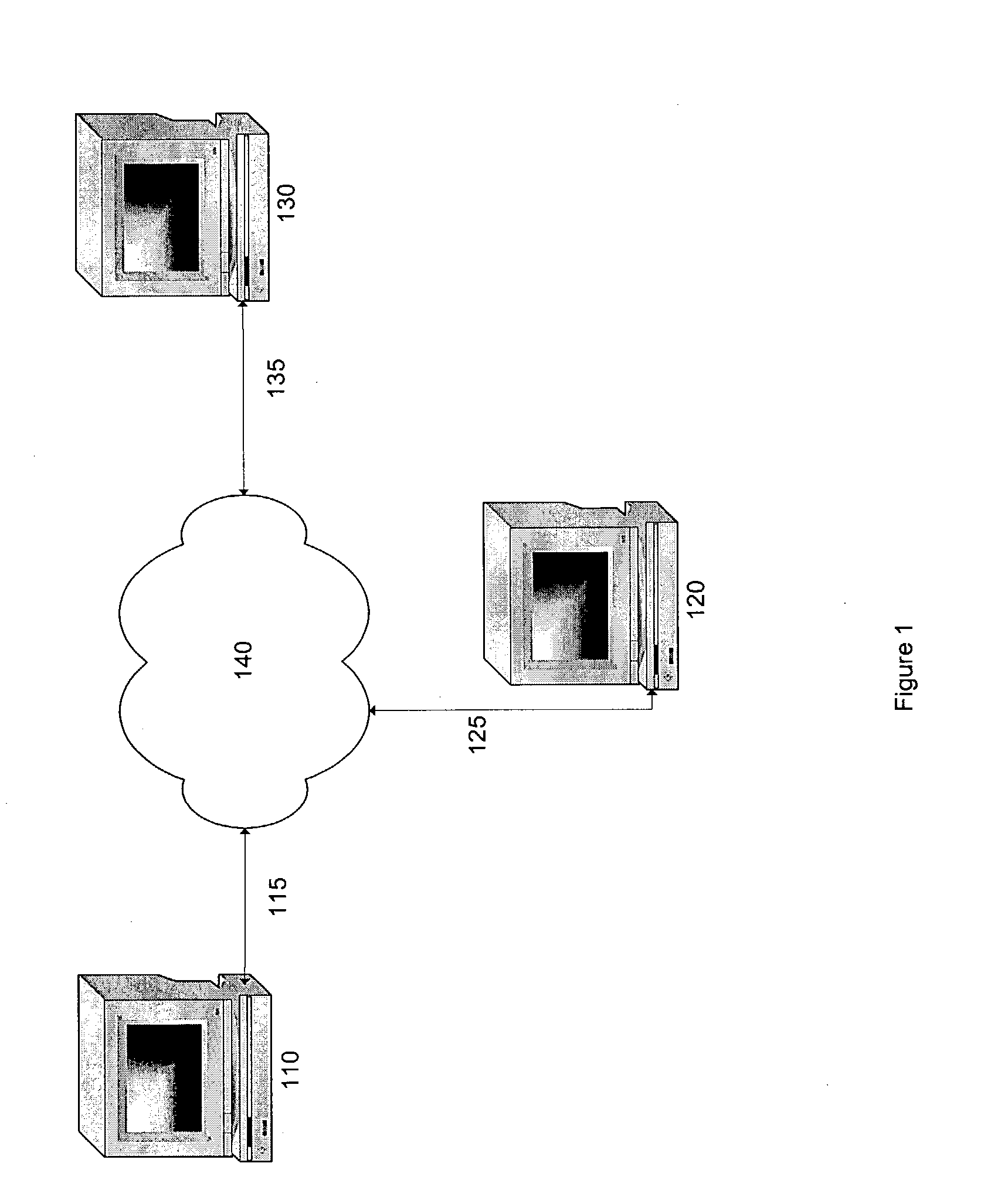
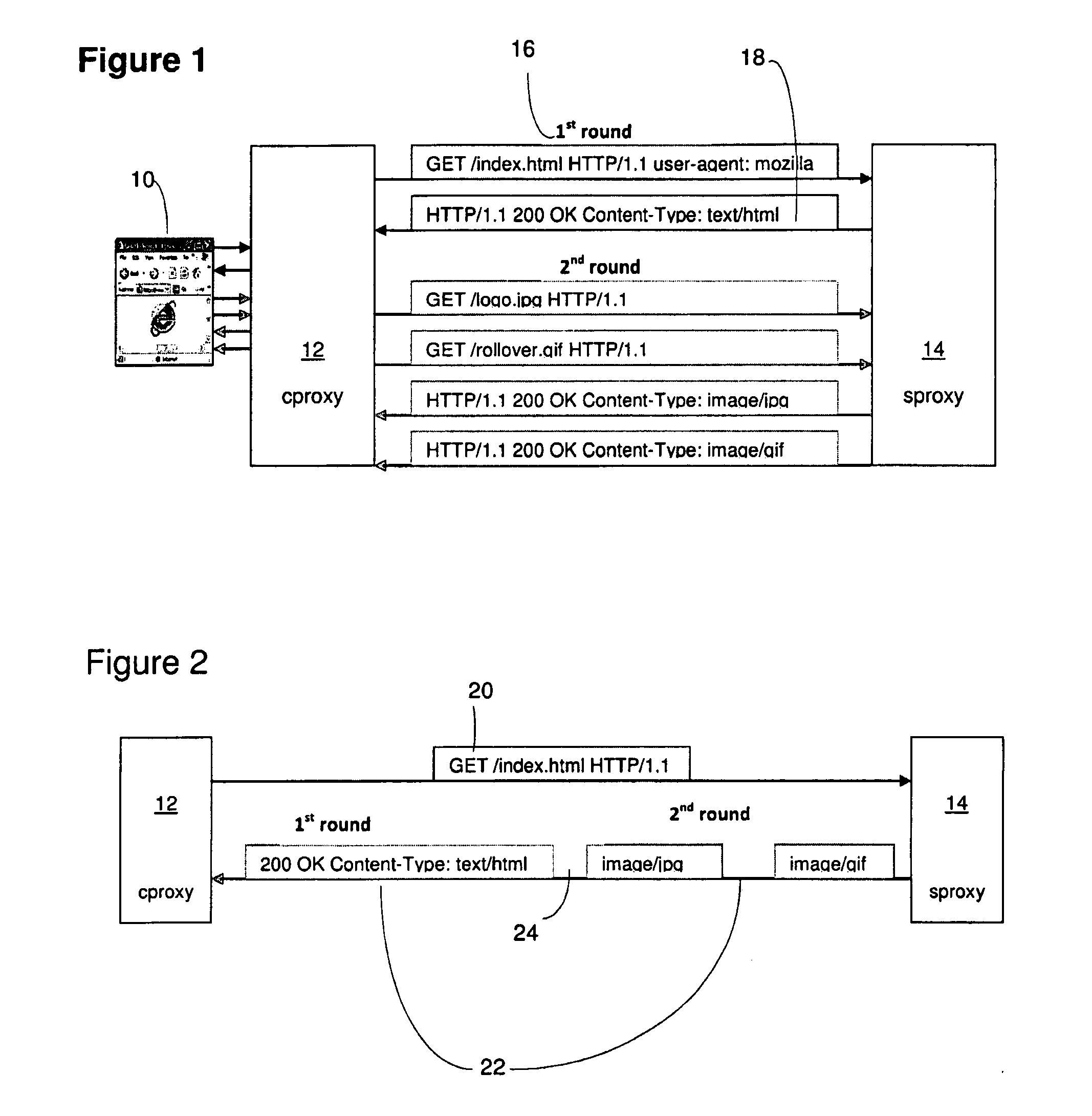
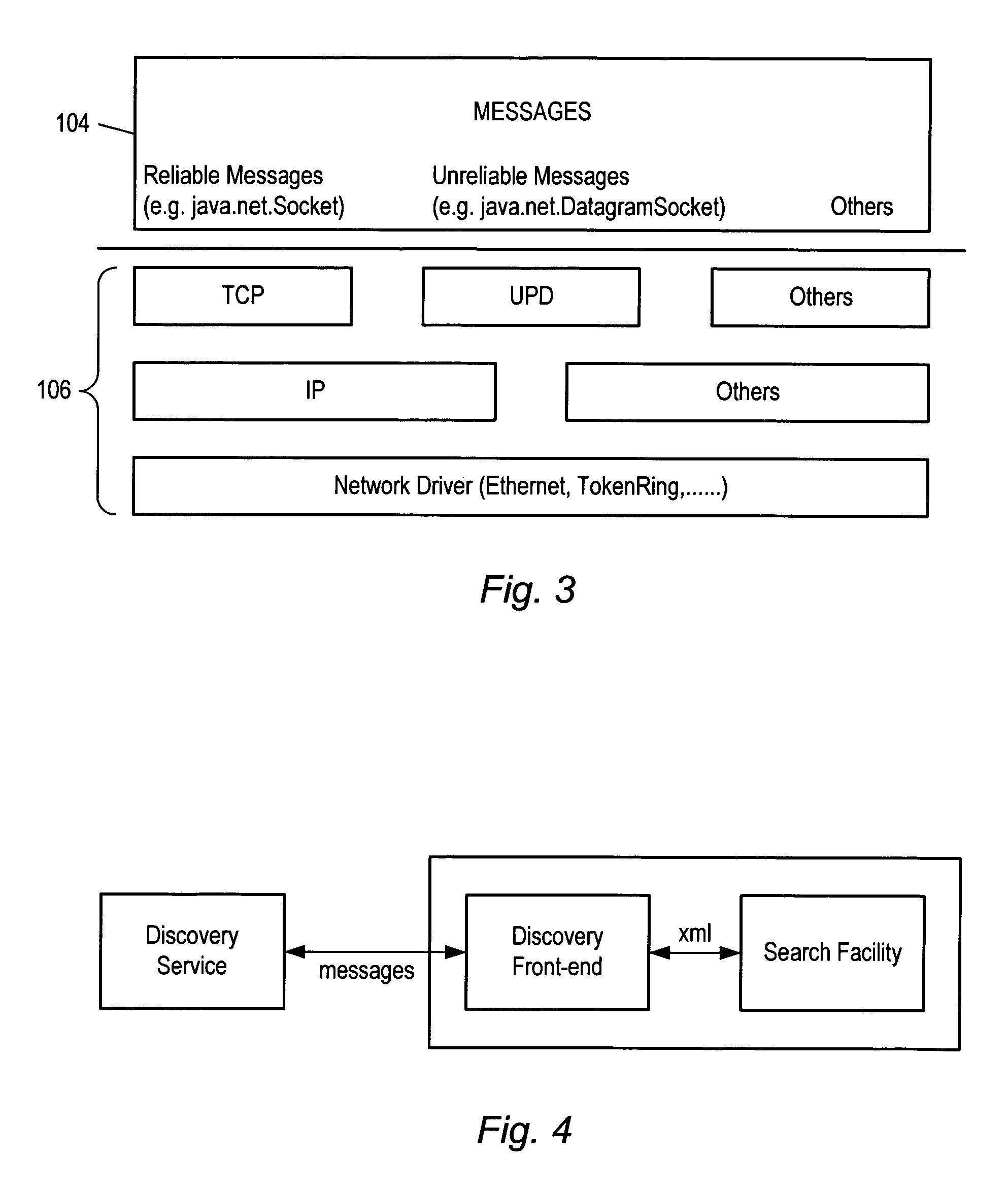
Request–response, or request–reply, is one of the basic methods computers use to communicate with each other, in which the first computer sends a request for some data and the second responds to the request. Usually, there is a series of such interchanges until the complete message is sent; browsing a web page is an example of request–response communication. Request–response can be seen as a telephone call, in which someone is called and they answer the call.
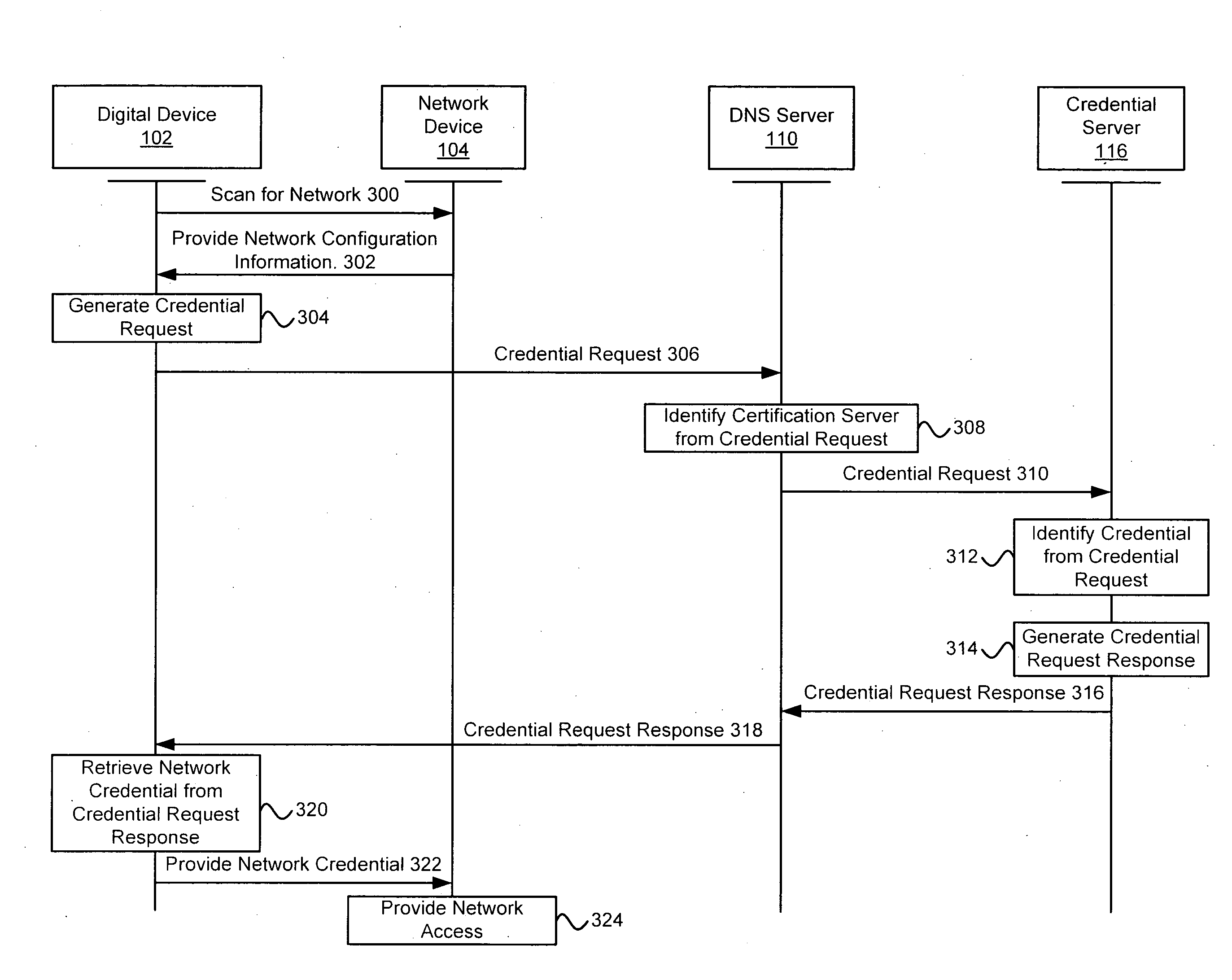
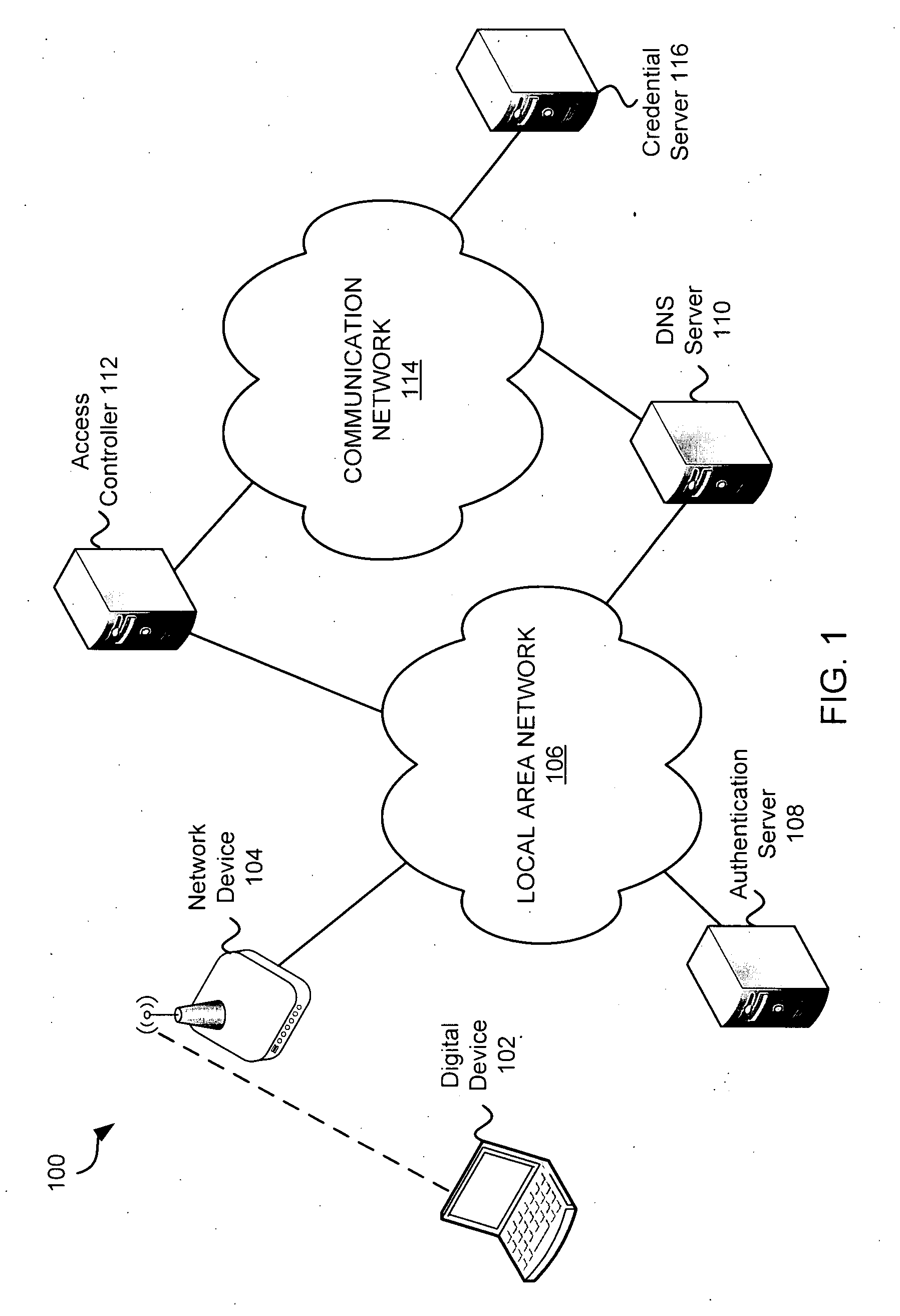
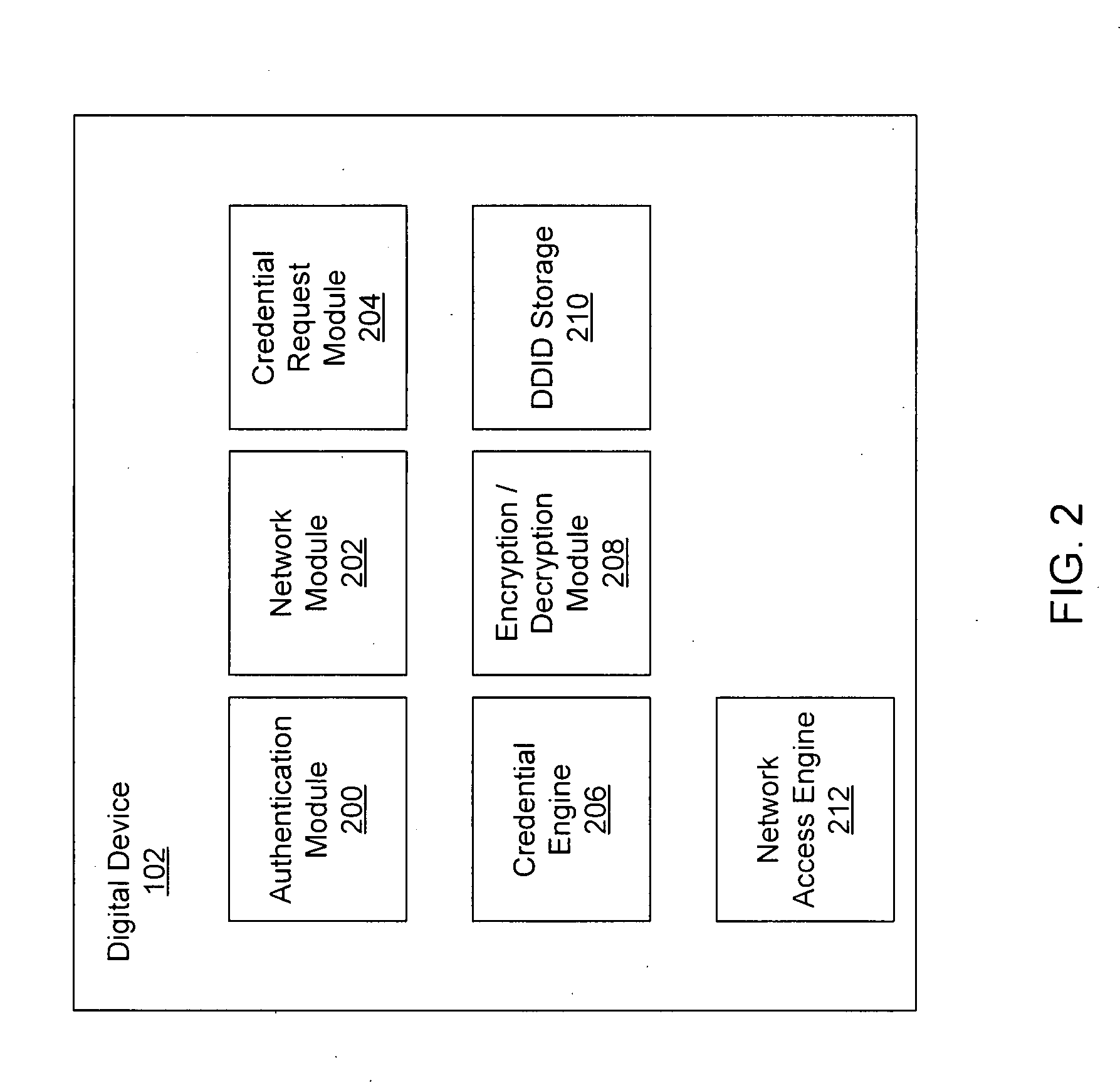
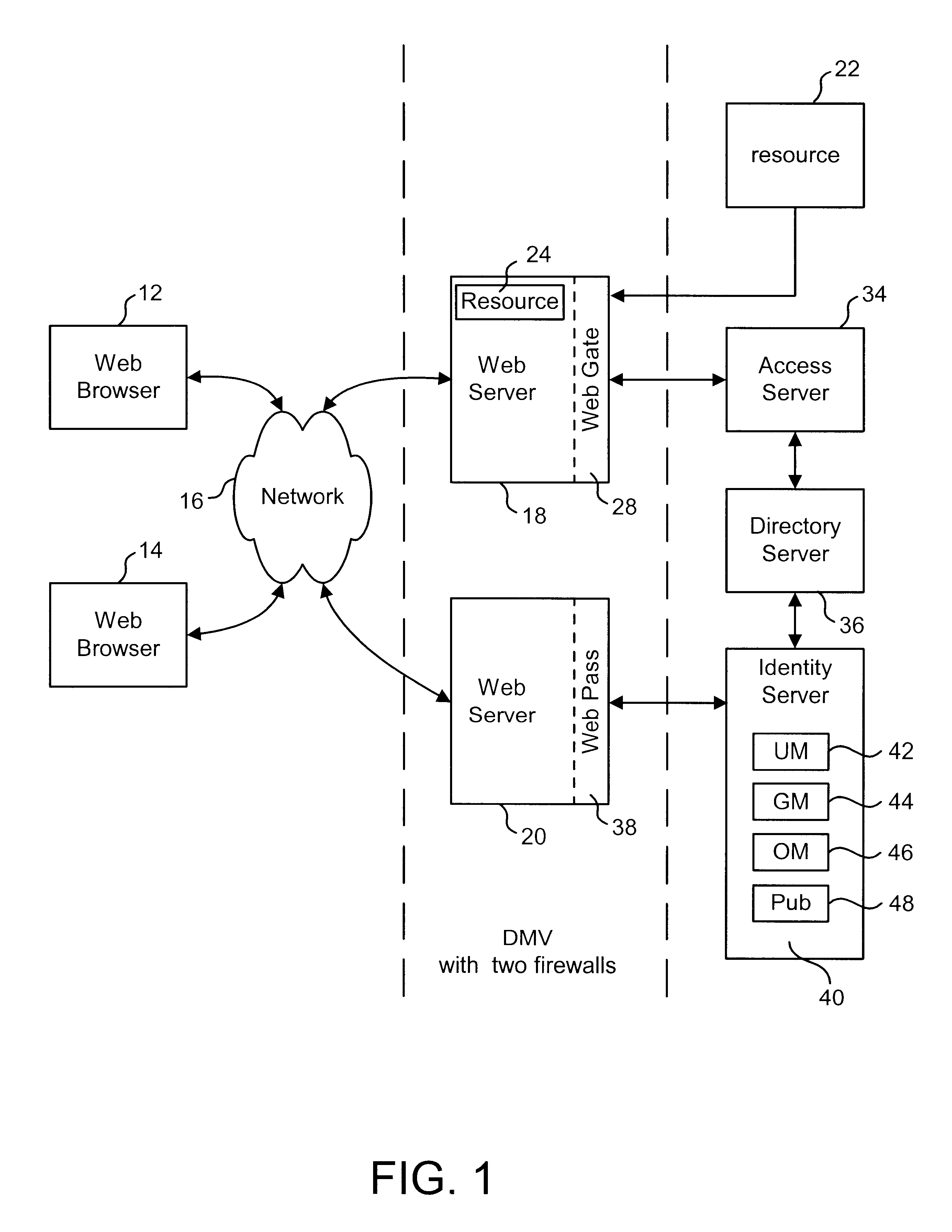
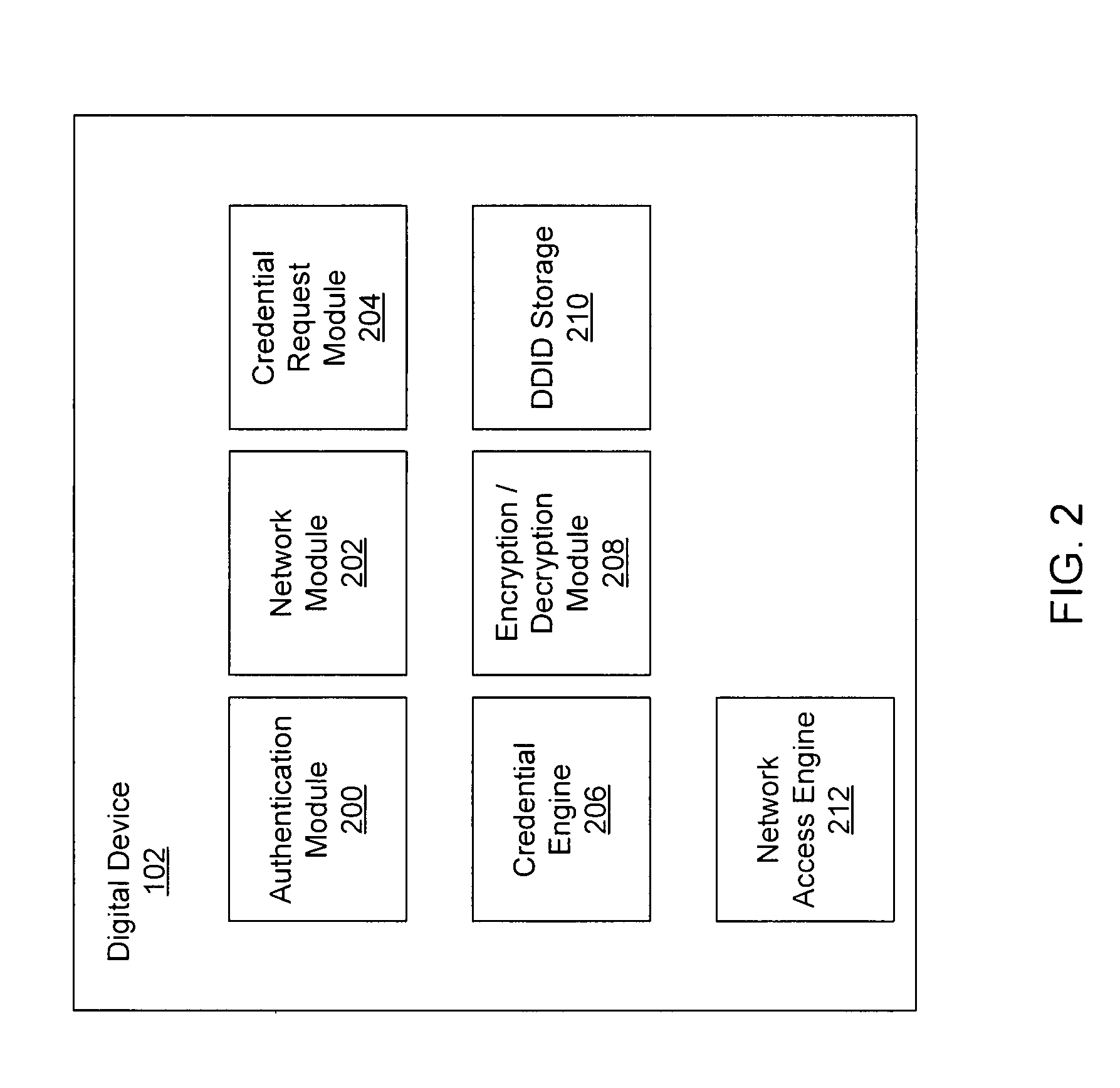
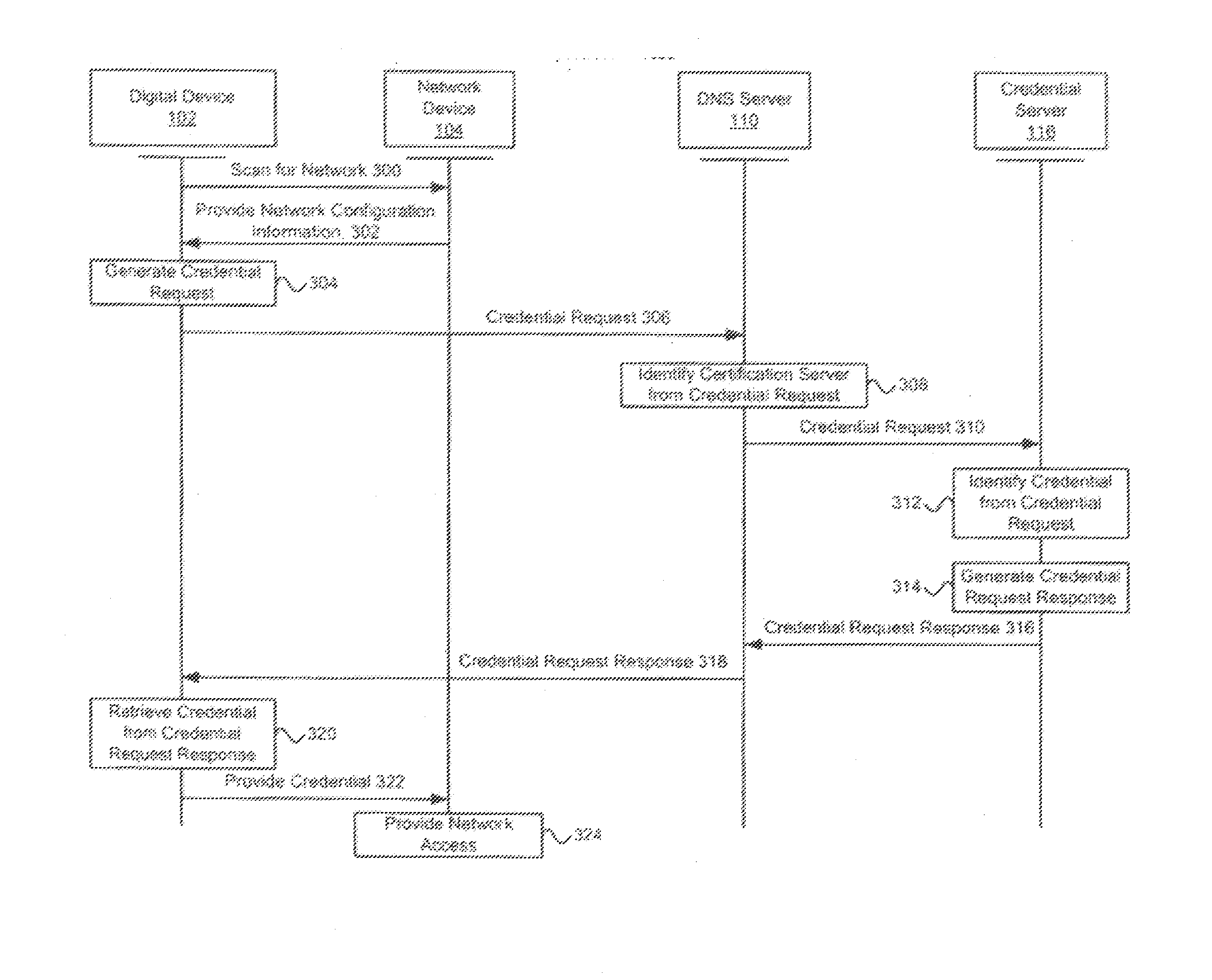
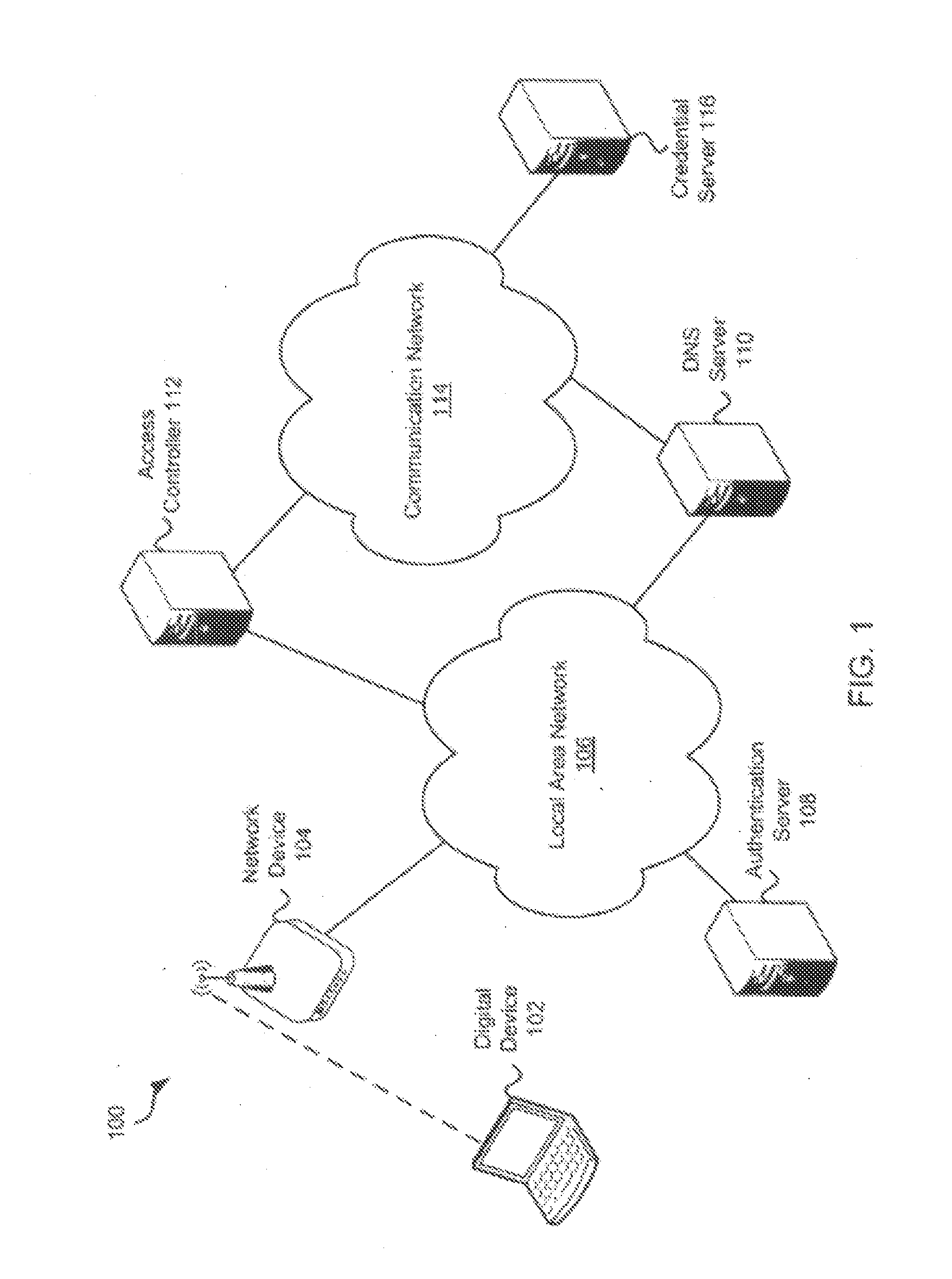
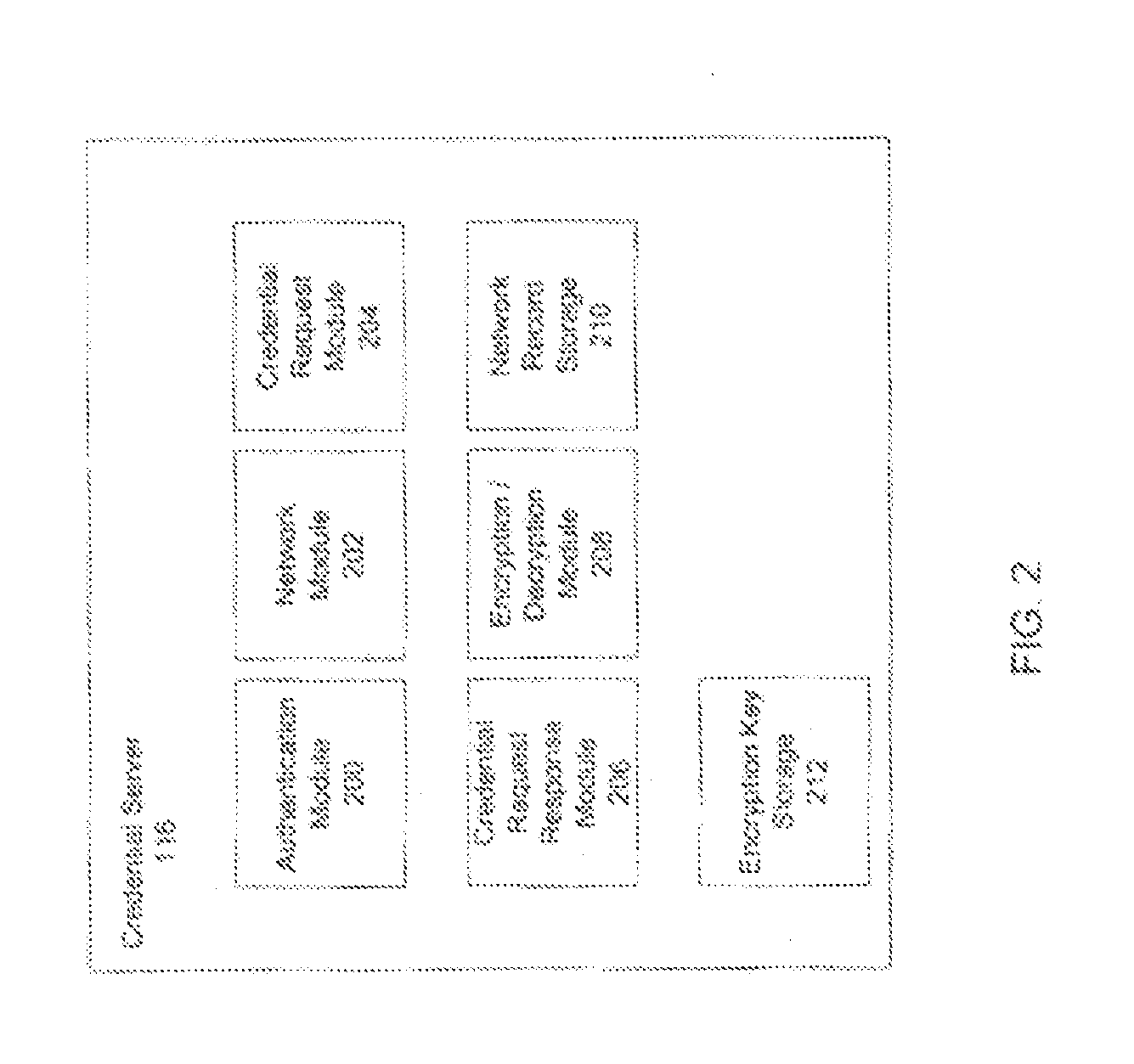
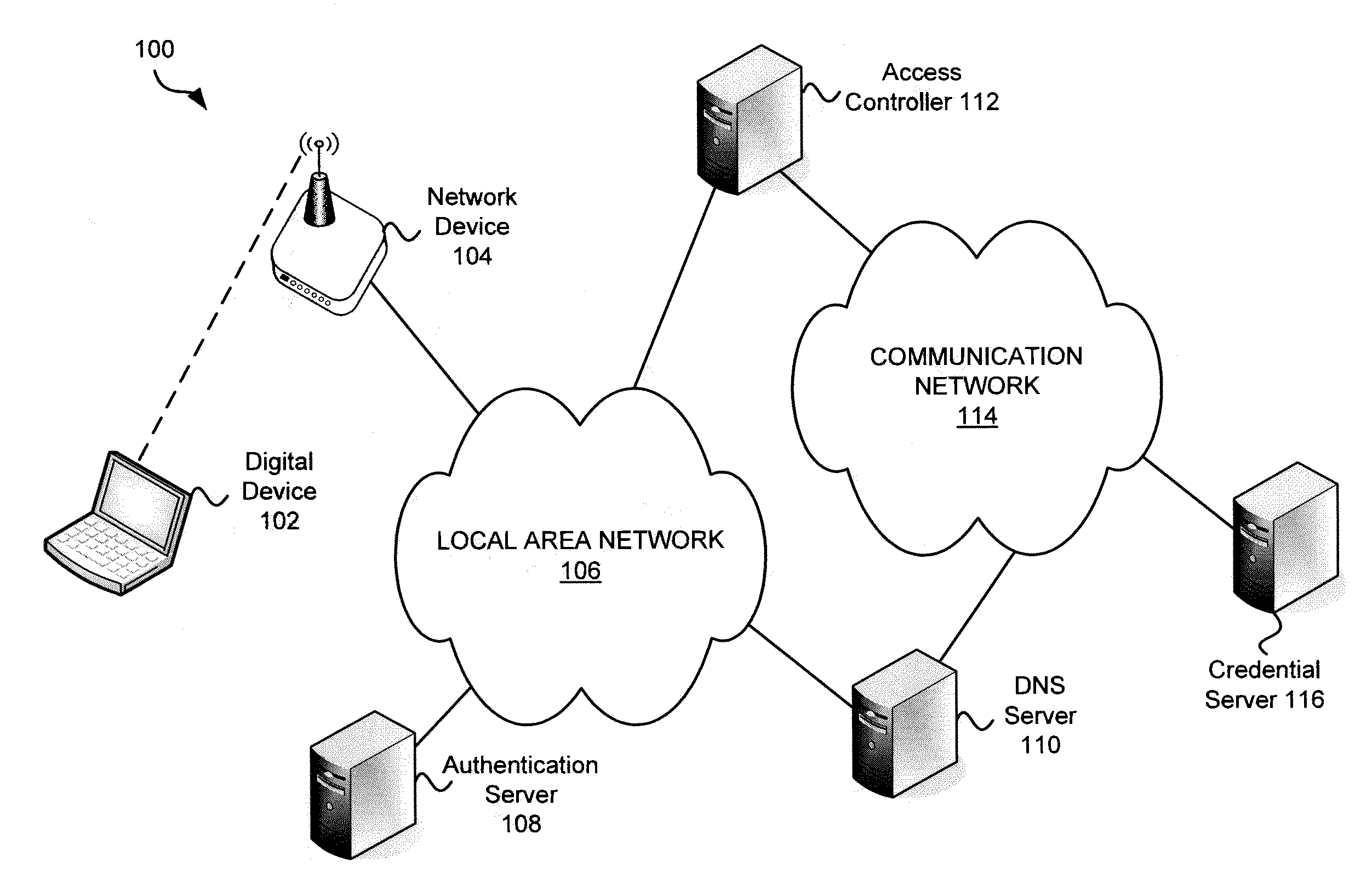
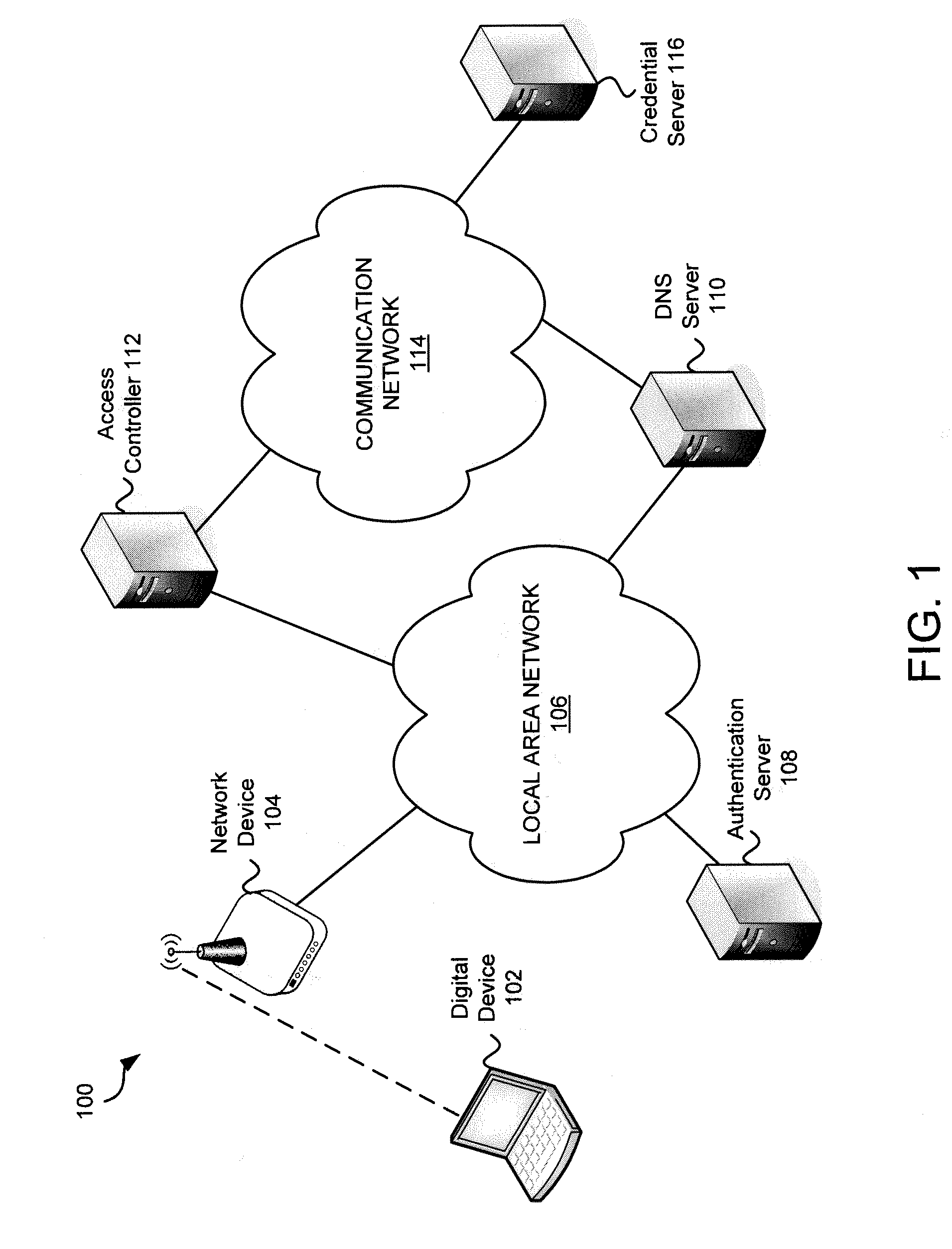
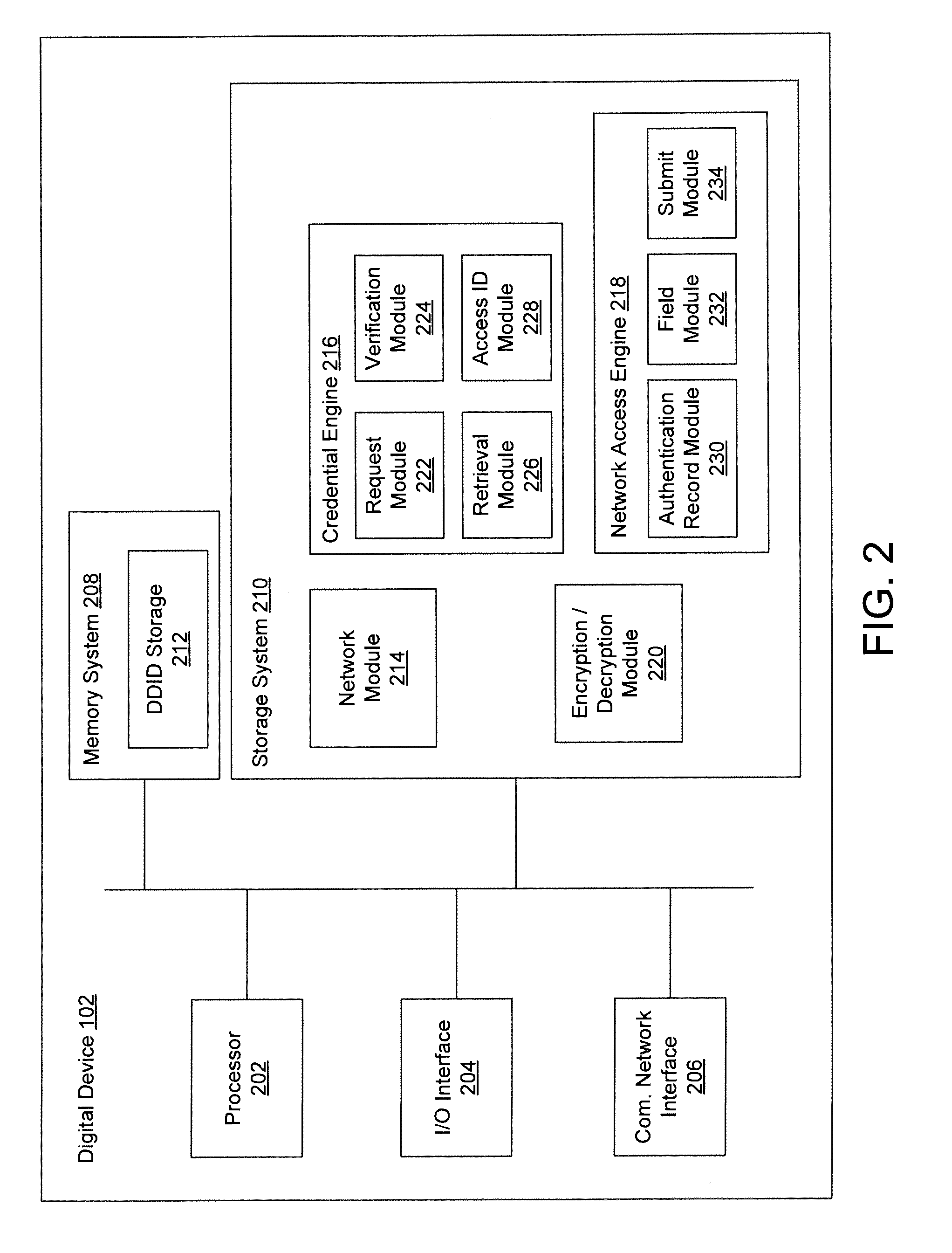
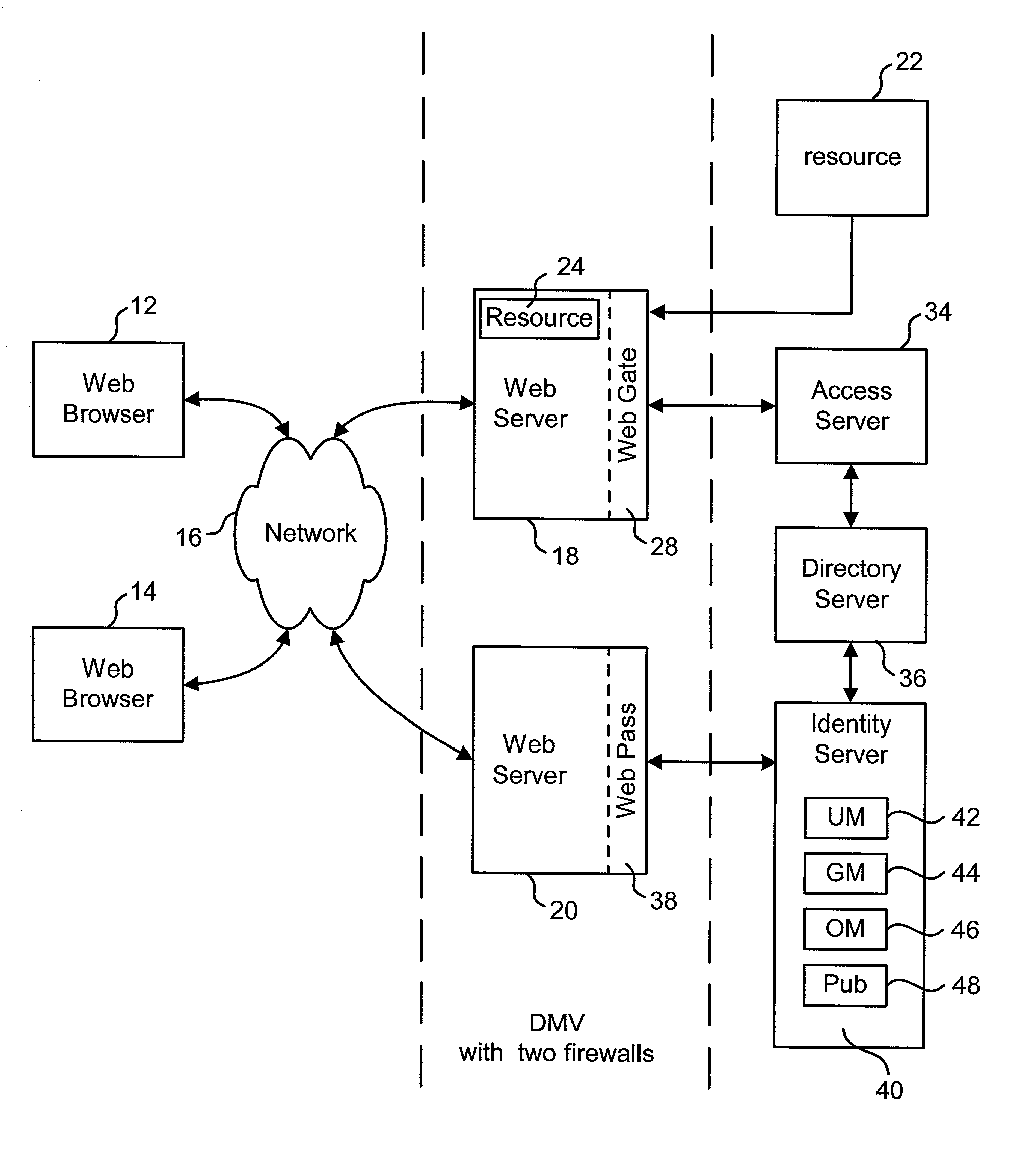
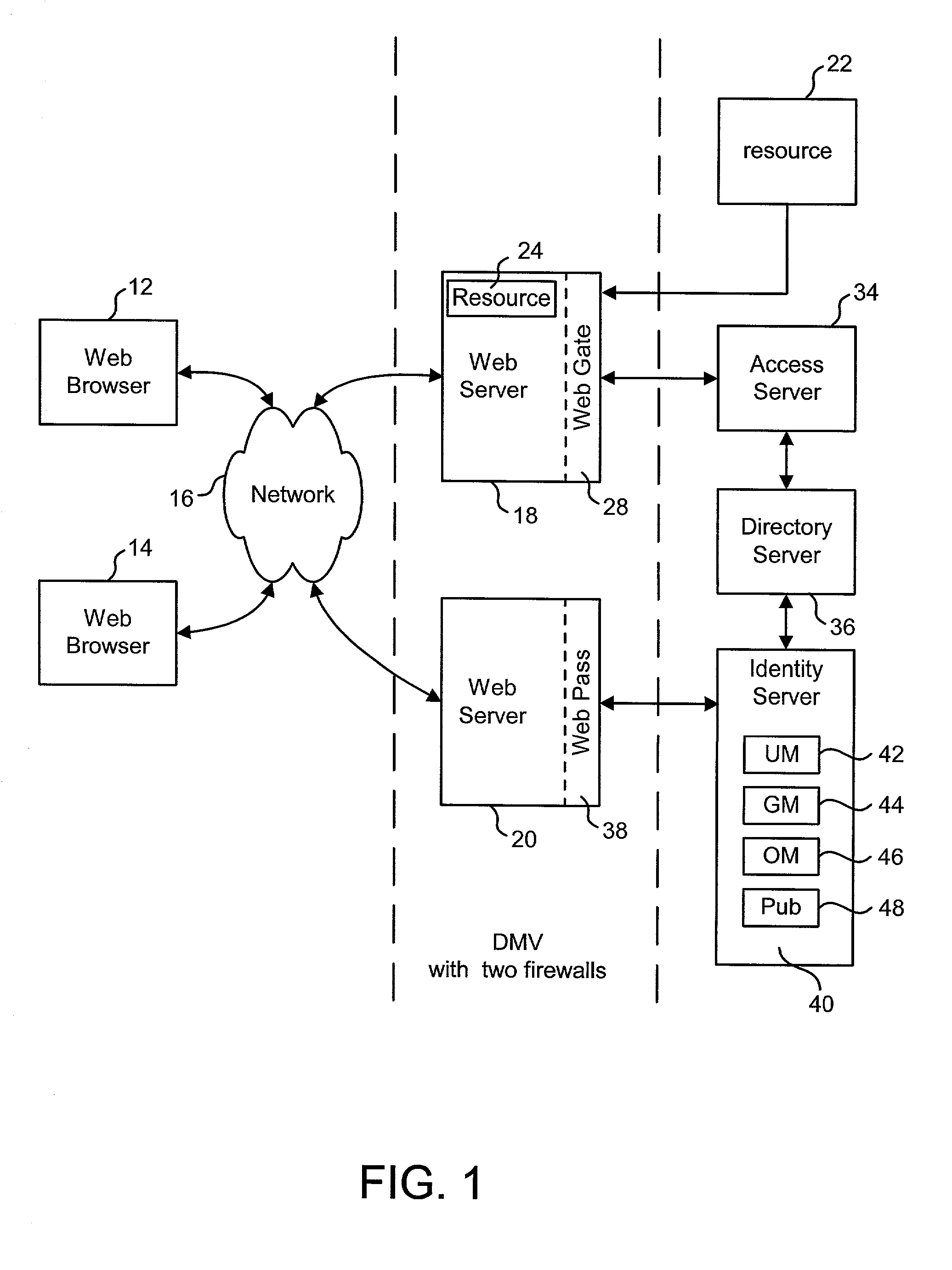
Systems and methods for acquiring network credentials
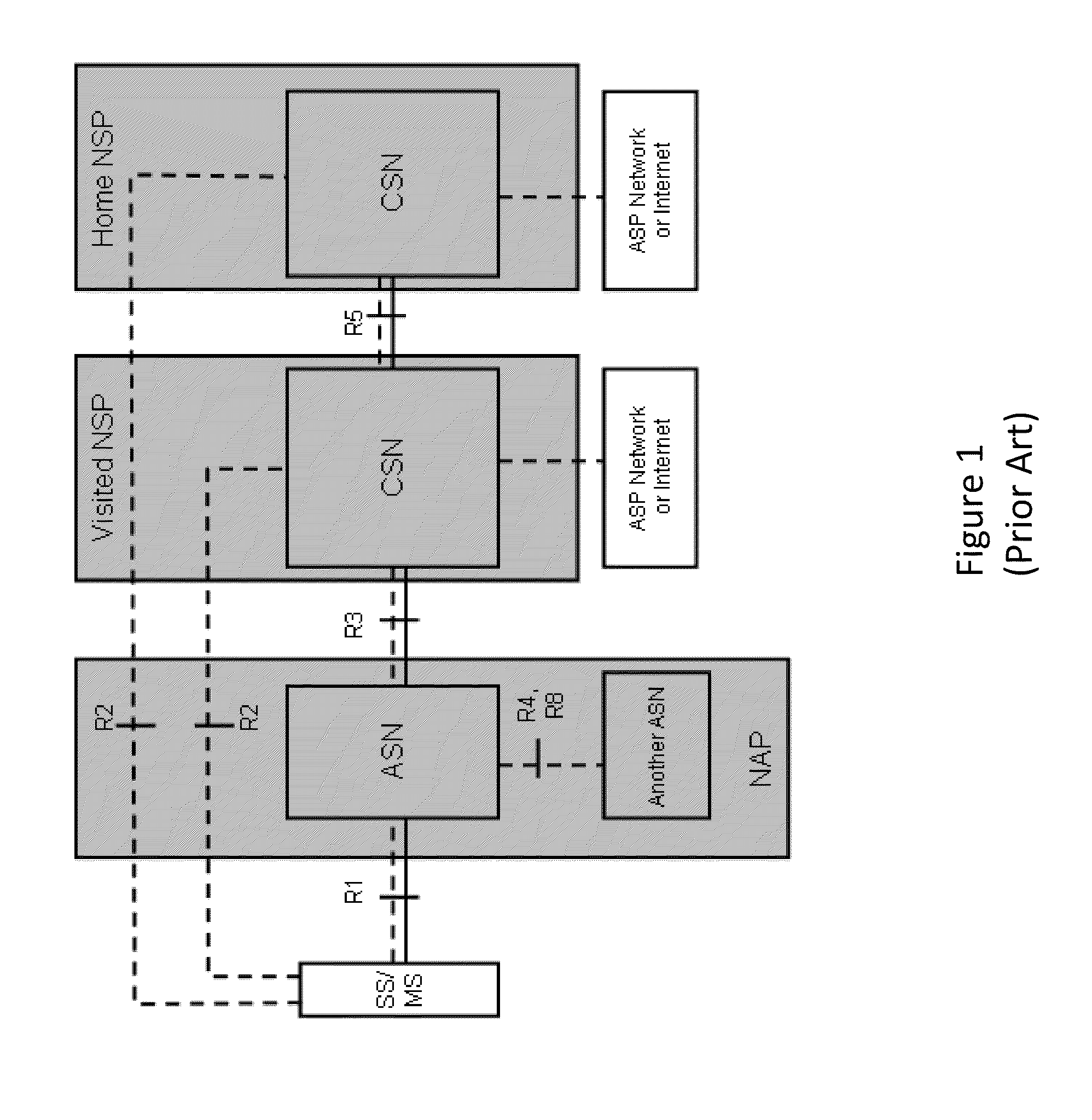
ActiveUS20080060066A1Digital data processing detailsAnalogue secracy/subscription systemsRequest–responseNetwork Access Device
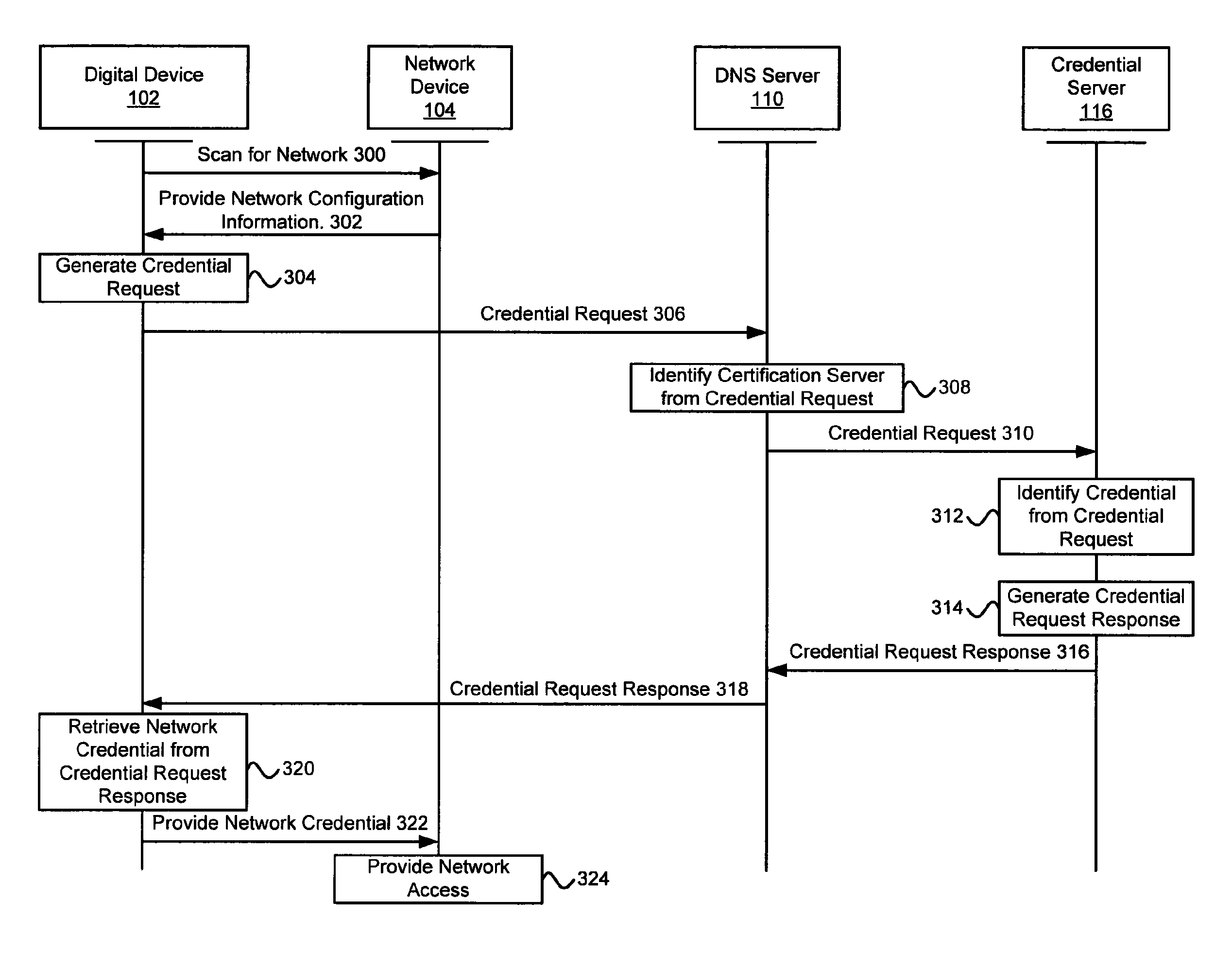
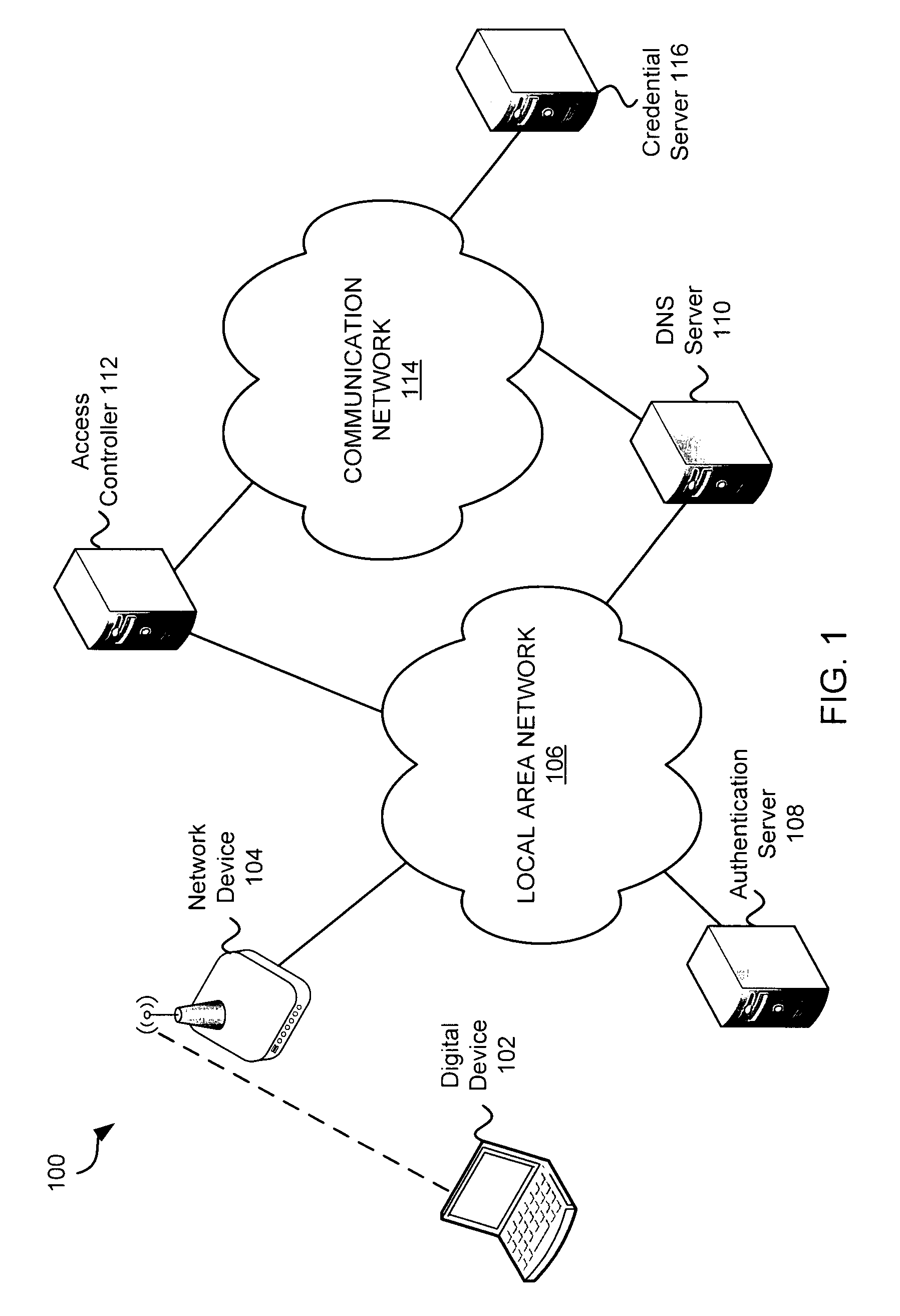
Exemplary methods and systems for acquiring network credentials for network access are described. The exemplary method comprises receiving network configuration information from a network device on a communication network, generating a credential request, transmitting the credential request to a credential server over a standard protocol of the network device, receiving the credential request response, and providing a network credential from the credential request response to the network device to access the communication network.
Owner:CHANNEL IP BV
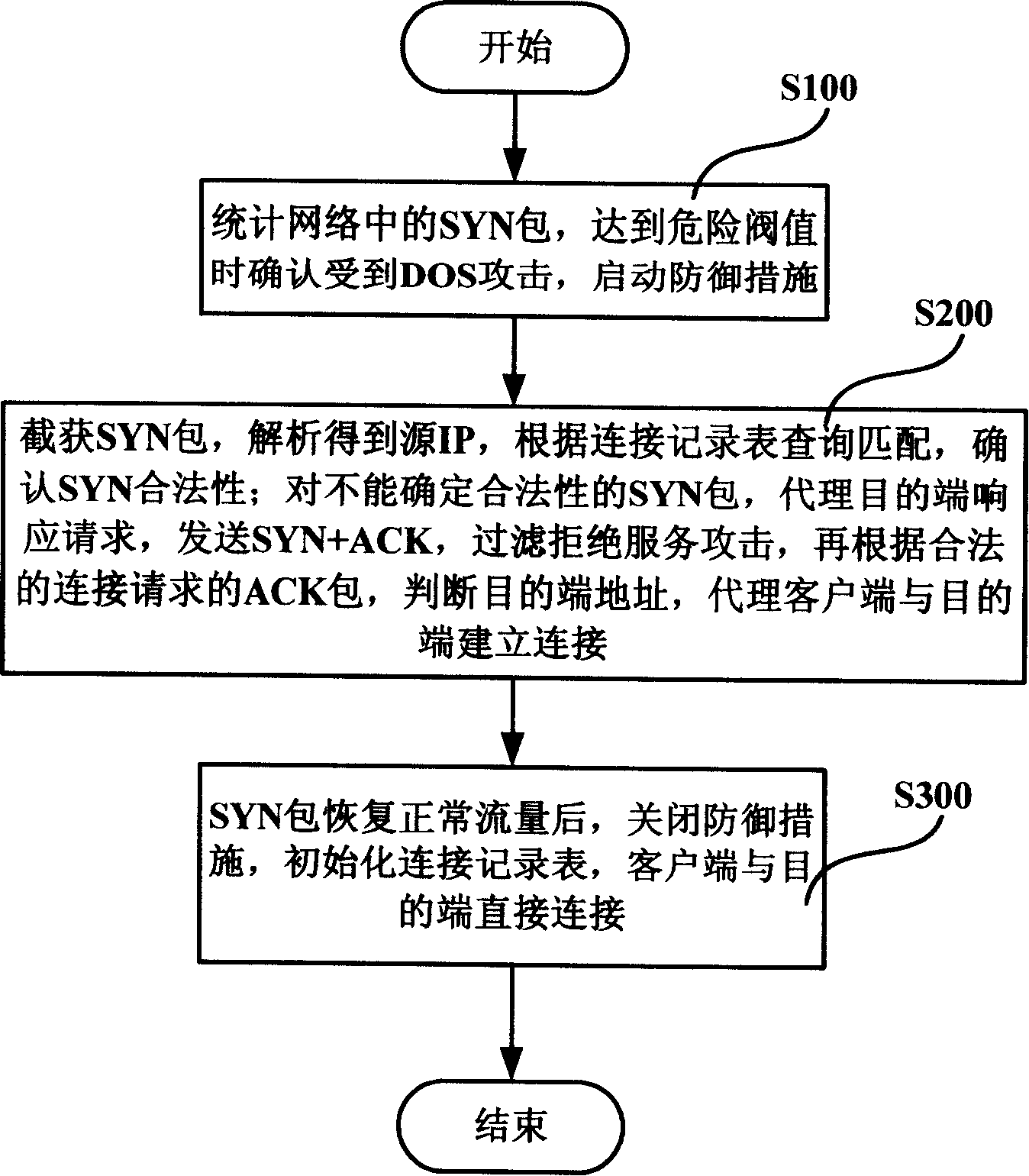
Preparing output XML based on selected programs and XML templates
Owner:ORACLE INT CORP
Systems and methods for acquiring network credentials
ActiveUS8191124B2Digital data processing detailsAnalogue secracy/subscription systemsRequest–responseNetwork Access Device
Exemplary methods and systems for acquiring network credentials for network access are described. The exemplary method includes receiving network configuration information from a network device on a communication network, generating a credential request, transmitting the credential request to a credential server over a standard protocol of the network device, receiving the credential request response, and providing a network credential from the credential request response to the network device to access the communication network.
Owner:CHANNEL IP BV
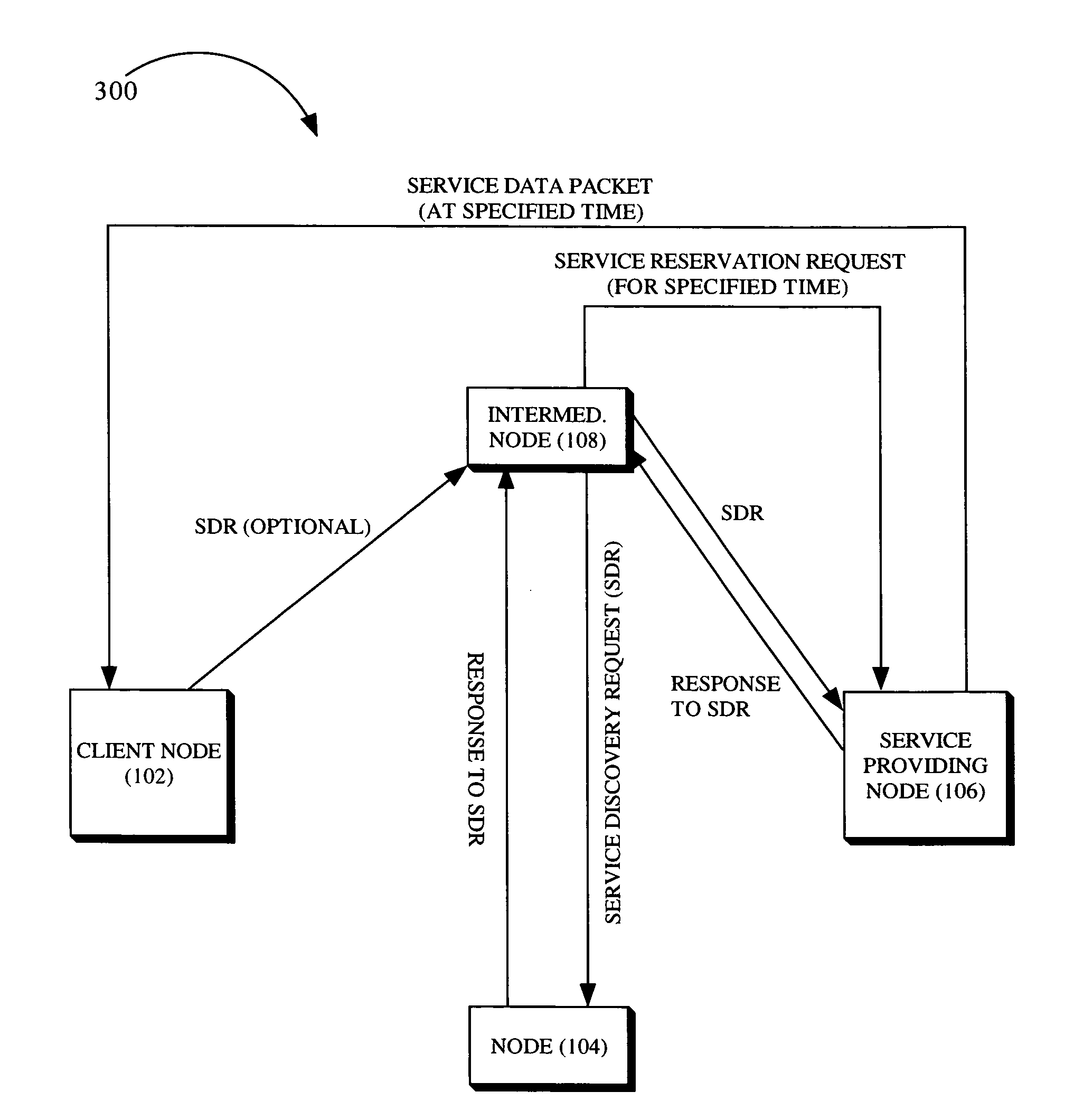
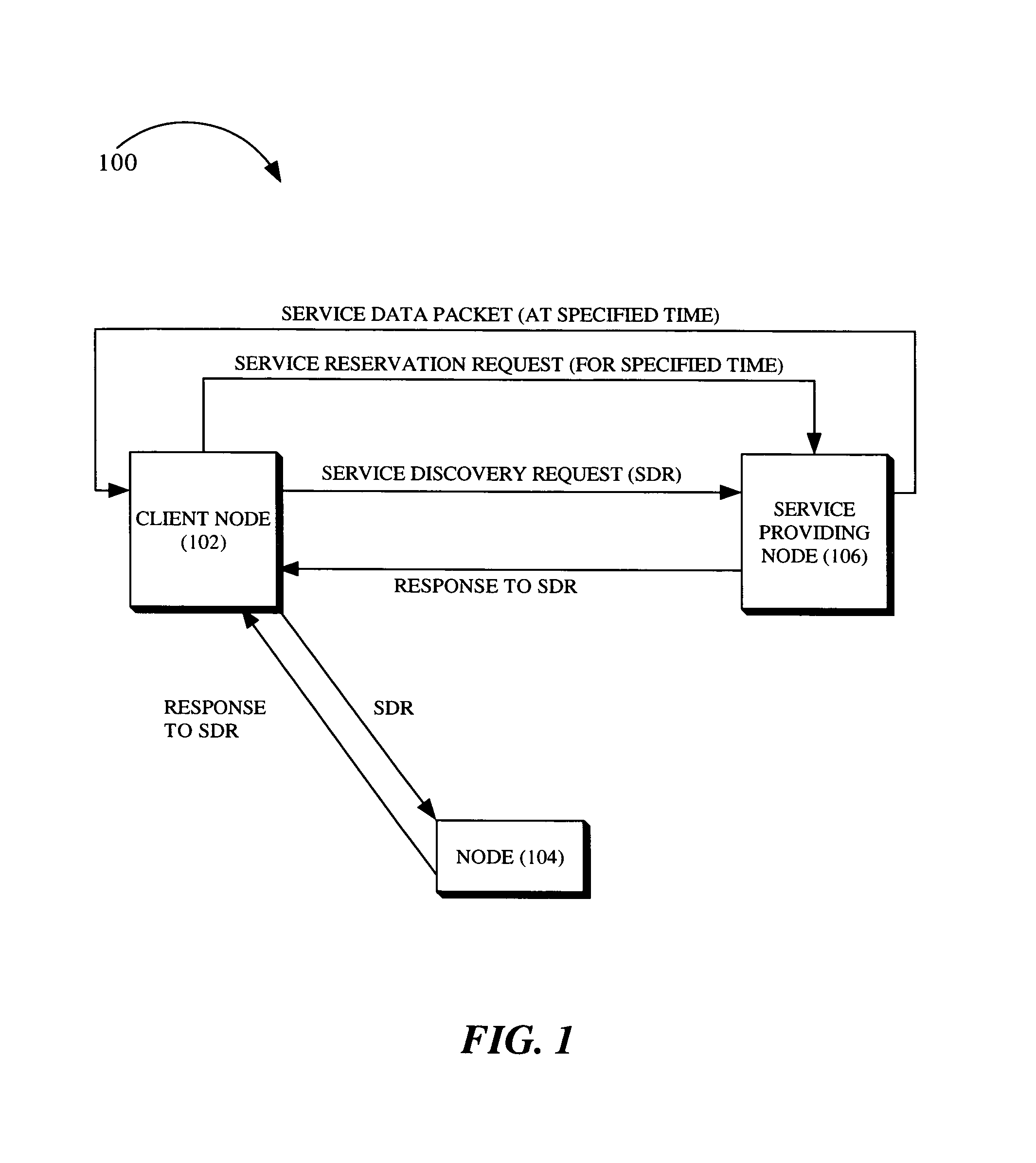
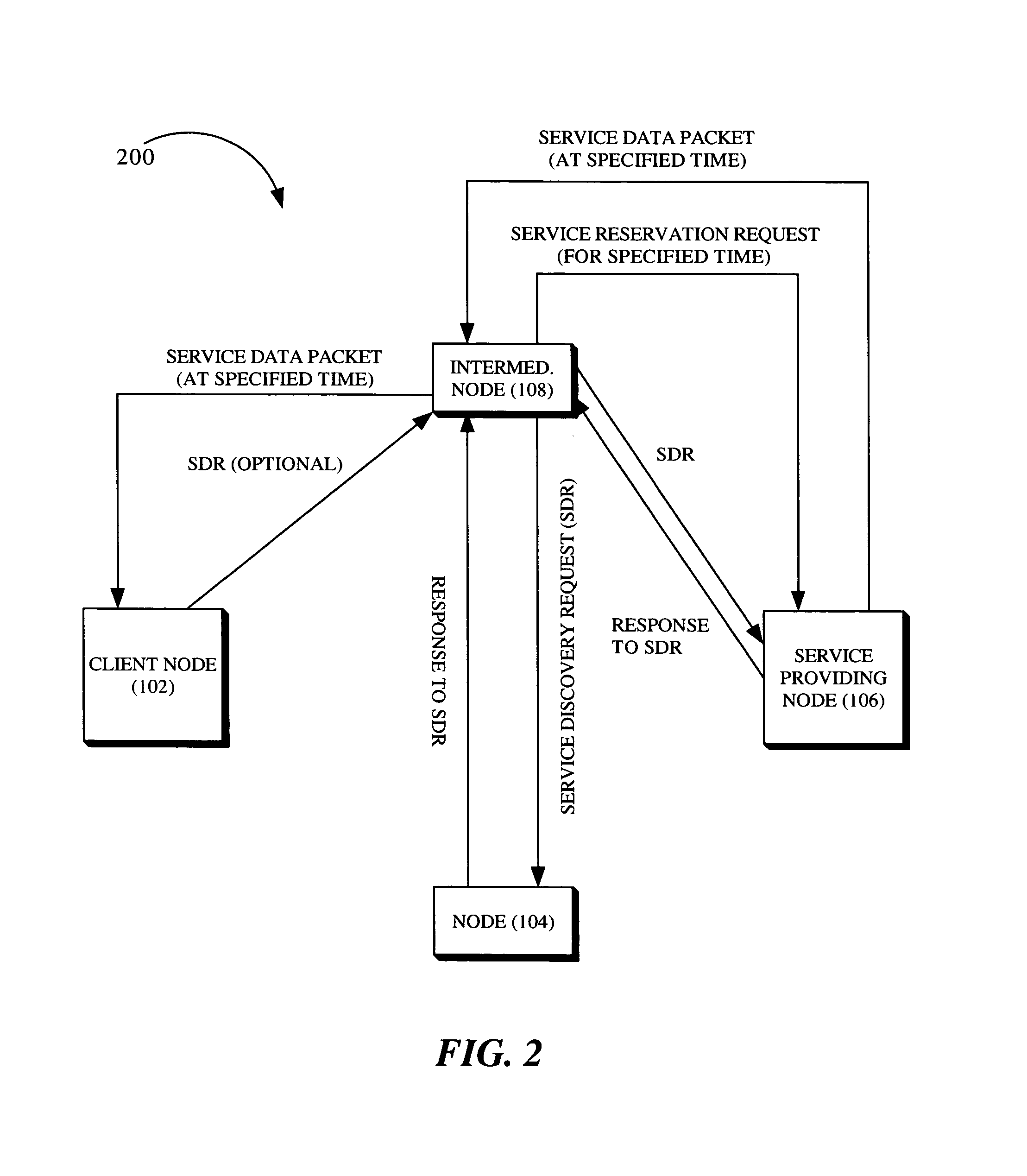
System and method for a priori scheduling of network services
InactiveUS8832302B1Service provisioningMultiple digital computer combinationsService provisionClient-side
The present invention is a method for providing services for a mobile ad hoc network, which includes receiving a service discovery request of a client node of the network. The method further includes directing the service discovery request to at least one node of the mobile ad hoc network. The method further includes receiving a service discovery request response from a node included in the at least one node, the response indicating that a service providing node is present within the network and is capable of providing the requested service. The method further includes determining a data transfer route for connecting the service providing node with the client node. The method further includes transmitting a service reservation request to the service providing node, wherein the service reservation request specifies a future time that a service is to be provided to the client node.
Owner:ROCKWELL COLINS
Systems and Methods for Obtaining Network Credentials
ActiveUS20110047603A1Digital data processing detailsNetwork topologiesDigital deviceRequest–response
Systems and methods for obtaining network credentials are disclosed. In some embodiments, a method comprises receiving, with a digital device, a network identifier from a network device, providing a first credential request including the network identifier to another digital device on a network, receiving a request for additional network information from the other digital device, providing a second credential request including additional network information to the other digital device, receiving a credential request response including network credentials from the other digital device, and providing the network credentials from the credential request response to a network device.
Owner:CHANNEL VENTURES GRP LLC
Service-oriented architecture and methods for direct invocation of services utilizing a service requestor invocation framework
InactiveUS20080140857A1Effective guidanceEfficient use ofData processing applicationsMultiple digital computer combinationsData processing systemDirect communication
A data processing system implementing a service-oriented architecture that efficiently provides for self-directed communications between service requesters and service providers. Service providers, operative to implement a predefined computing functions, are responsive to first service requests and operative to provide a first service responses. Service requesters executed remote from service providers are operative to provide second service requests and receive second service responses. A service invocation framework local to each service requester functions to convert between first and second service requests and first and second service responses and to establish direct invocation communications connection with a selected service provider for the exchange of first service requests responses. A service invocation manager provides configuration meta-data, upon dynamic request by a service invocation framework, to define the conversions and communications connection to be implemented by the service invocation framework with respect to a service provider.
Owner:PRIMITIVE LOGIC
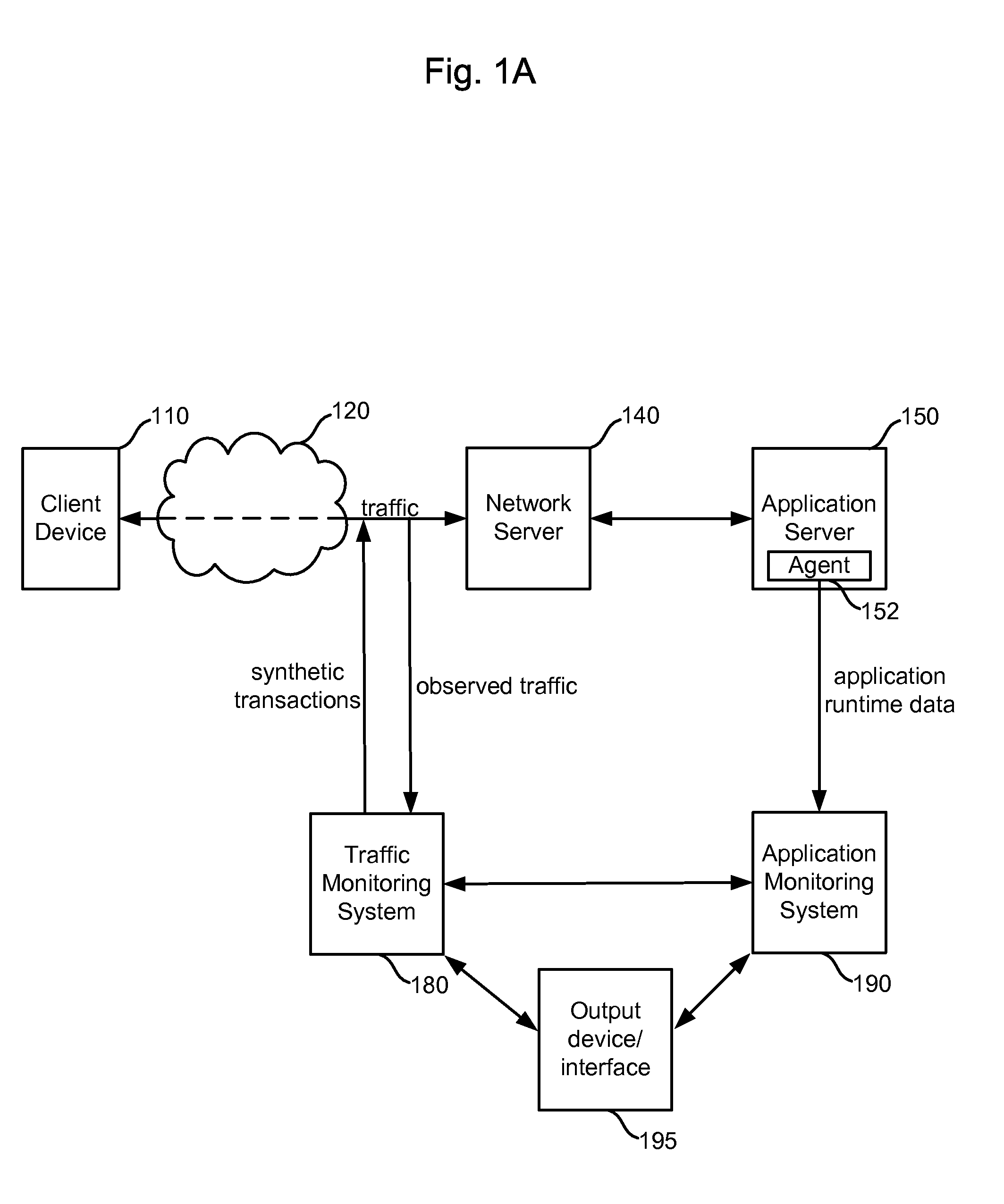
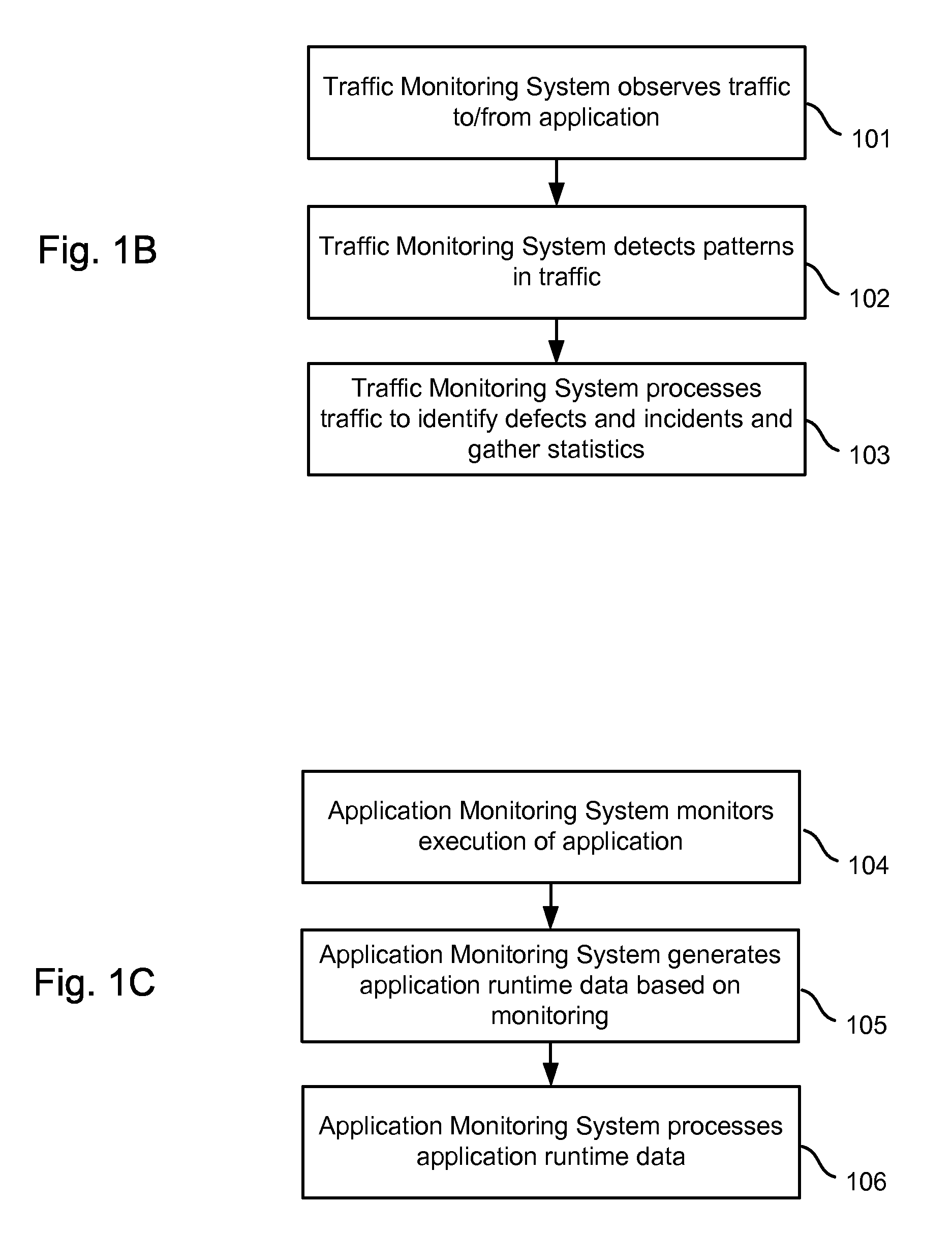
Integrating traffic monitoring data and application runtime data
ActiveUS20070266149A1Enhance capacity planningImprove rendering capabilitiesDigital computer detailsTransmissionTraffic capacityData information
Information is obtained from an application monitoring system which monitors the execution of an application and a traffic monitoring system which monitors traffic between clients and the application. The clients interact with the application to perform transactions or other tasks. Traffic monitoring data, such as information regarding defects and incidents, and application runtime data, such as traces of invoked application components, can be integrated in an output such as an interface to provide an enhanced understanding of system performance. Related traffic monitoring data and application runtime data can be linked by a request-response pair identifier associated with a request provided to the application and a response provided by the application.
Owner:CA TECH INC
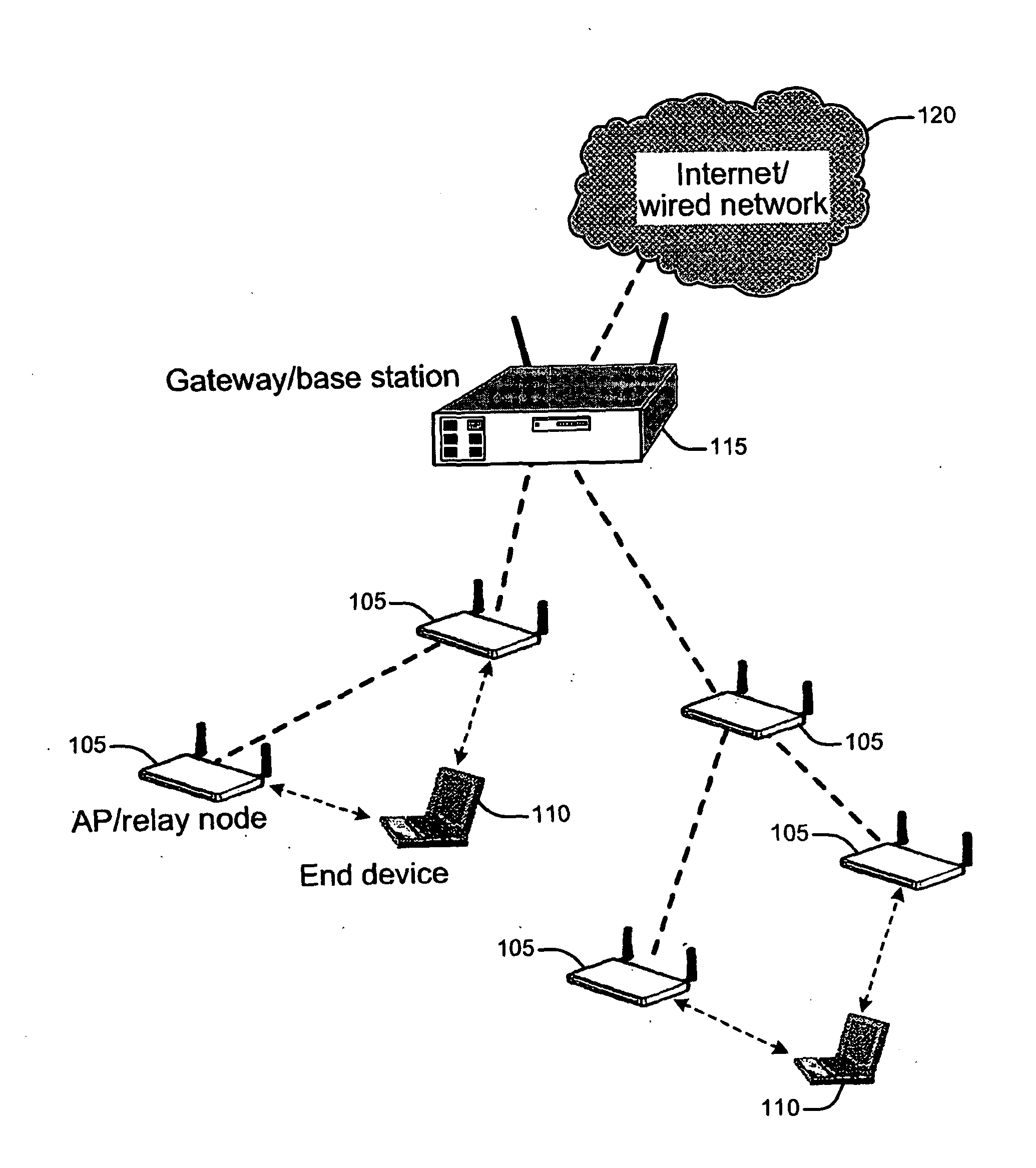
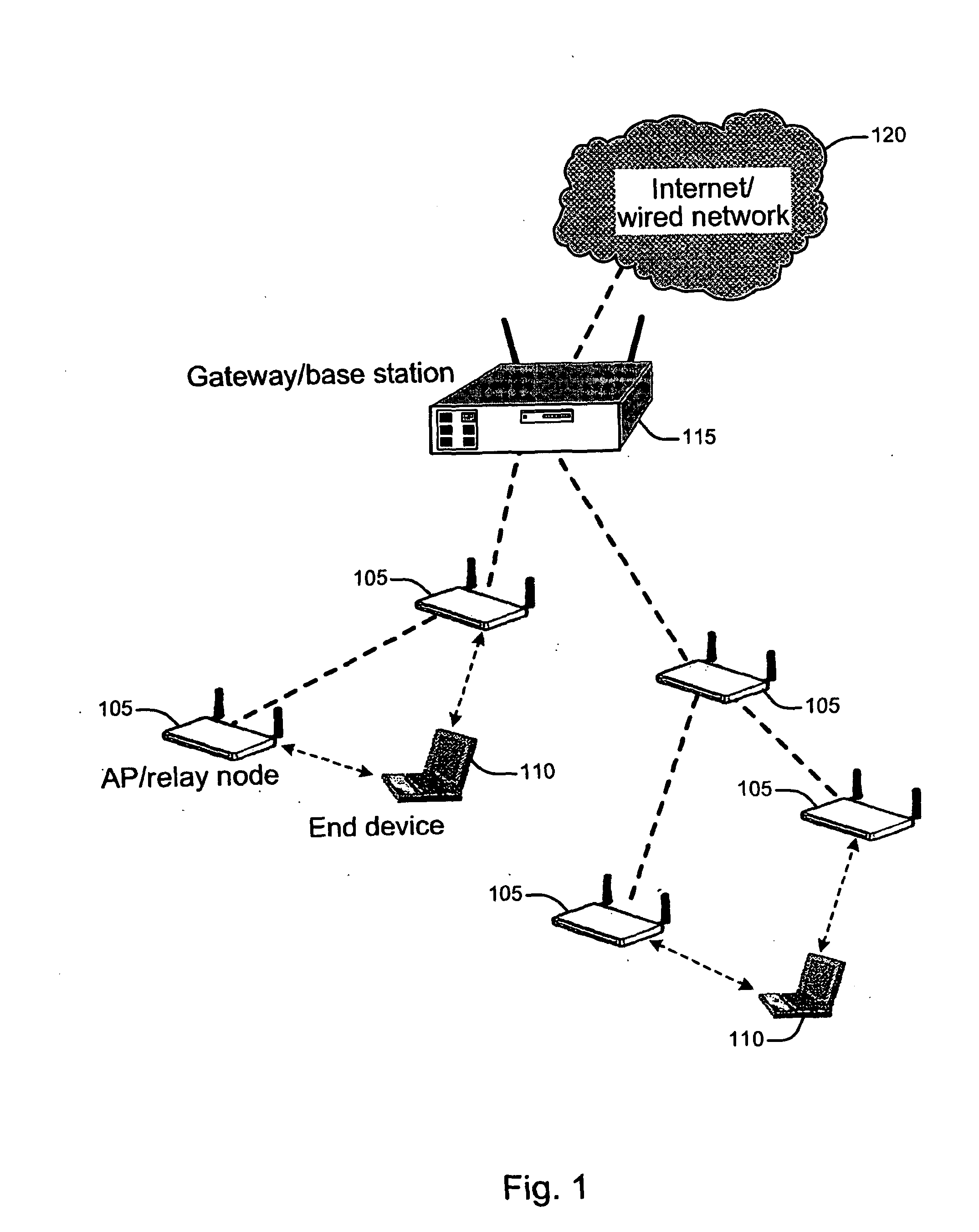
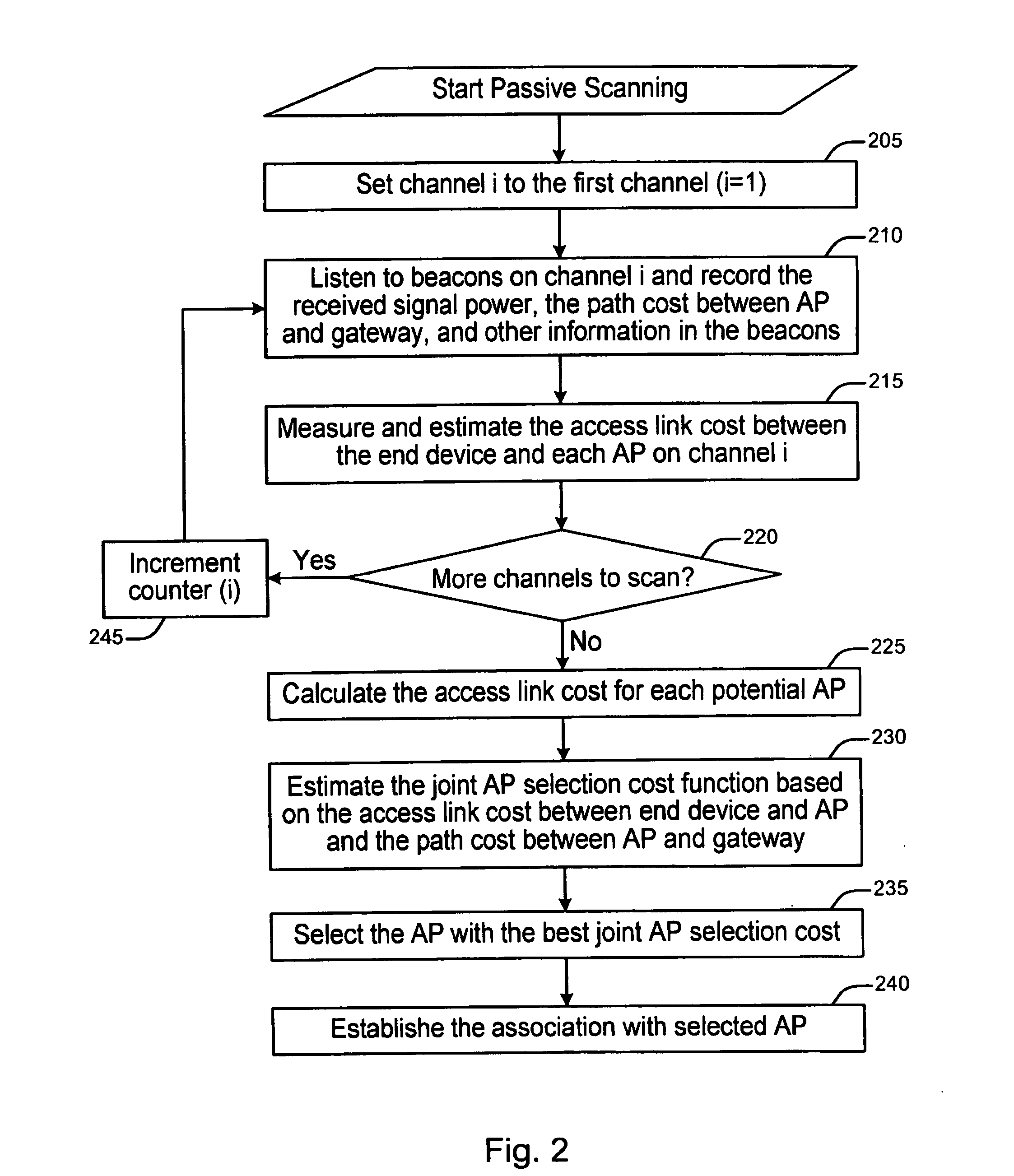
Method to select access point and relay node in multi-hop wireless networking
ActiveUS20100091669A1Quality improvementError preventionTransmission systemsTerminal equipmentRequest–response
A method and apparatus are described for selecting an access point in a wireless network, including initializing a channel index, recording a received signal power and information contained in one of a beacon message and a probe request response message, calculating an access link metric for each candidate access point, the access link metric being between an end device and each candidate access point on the channel indexed by the channel index responsive to the received signal power and information receiving a path metric between each candidate access point and a gateway, estimating a function using the access link metric and the path metric, selecting one of the candidate access points based on the function and establishing a connection with the selected access point. Also described is a method and apparatus for maintaining a connection with an access point.
Owner:THOMSON LICENSING SA
System and method for modeling and dynamically deploying services into a distributed networking architecture
InactiveUS20060029054A1Avoid disadvantagesMultiplex system selection arrangementsCircuit switching systemsHosting environmentNetwork architecture
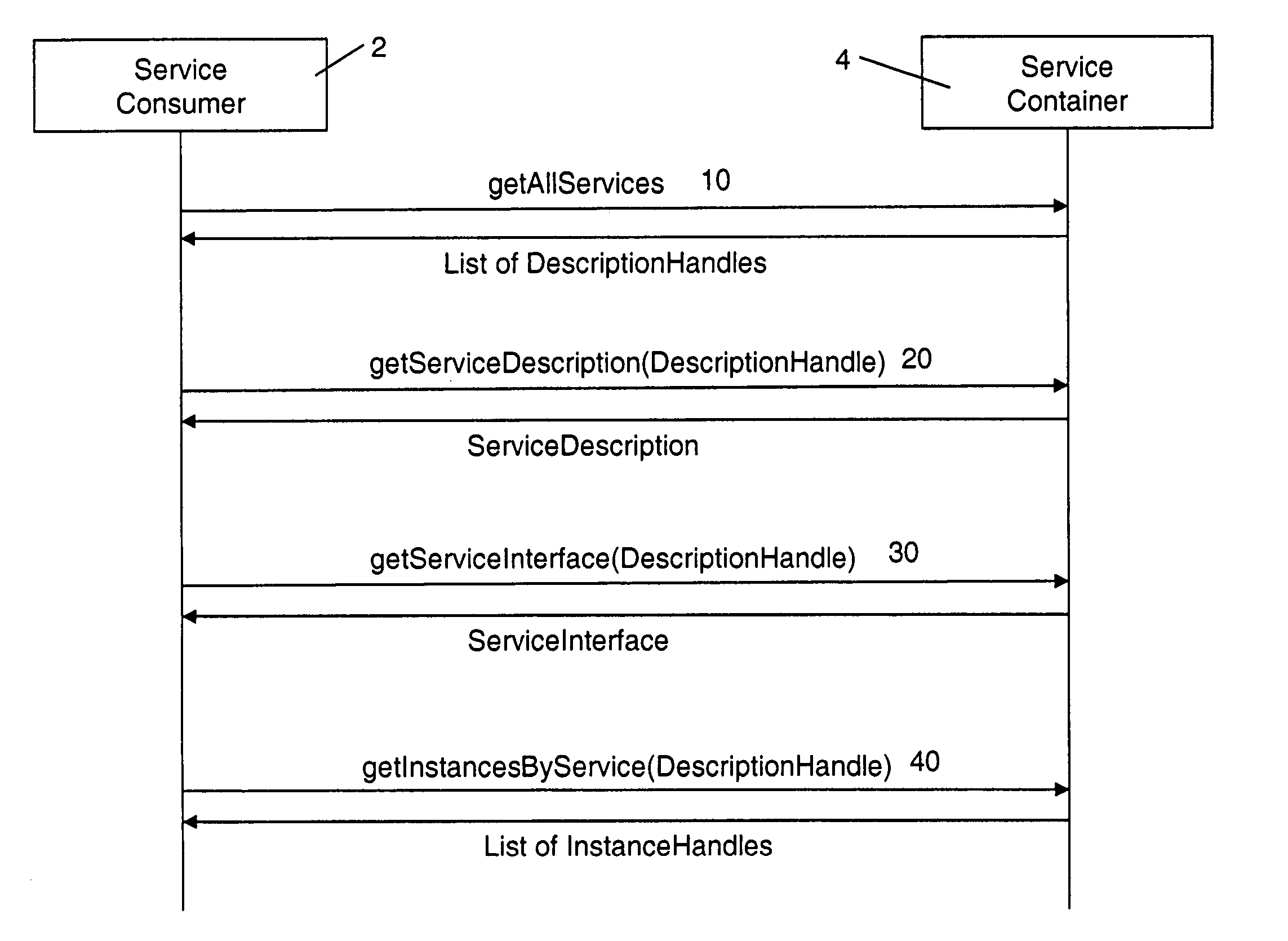
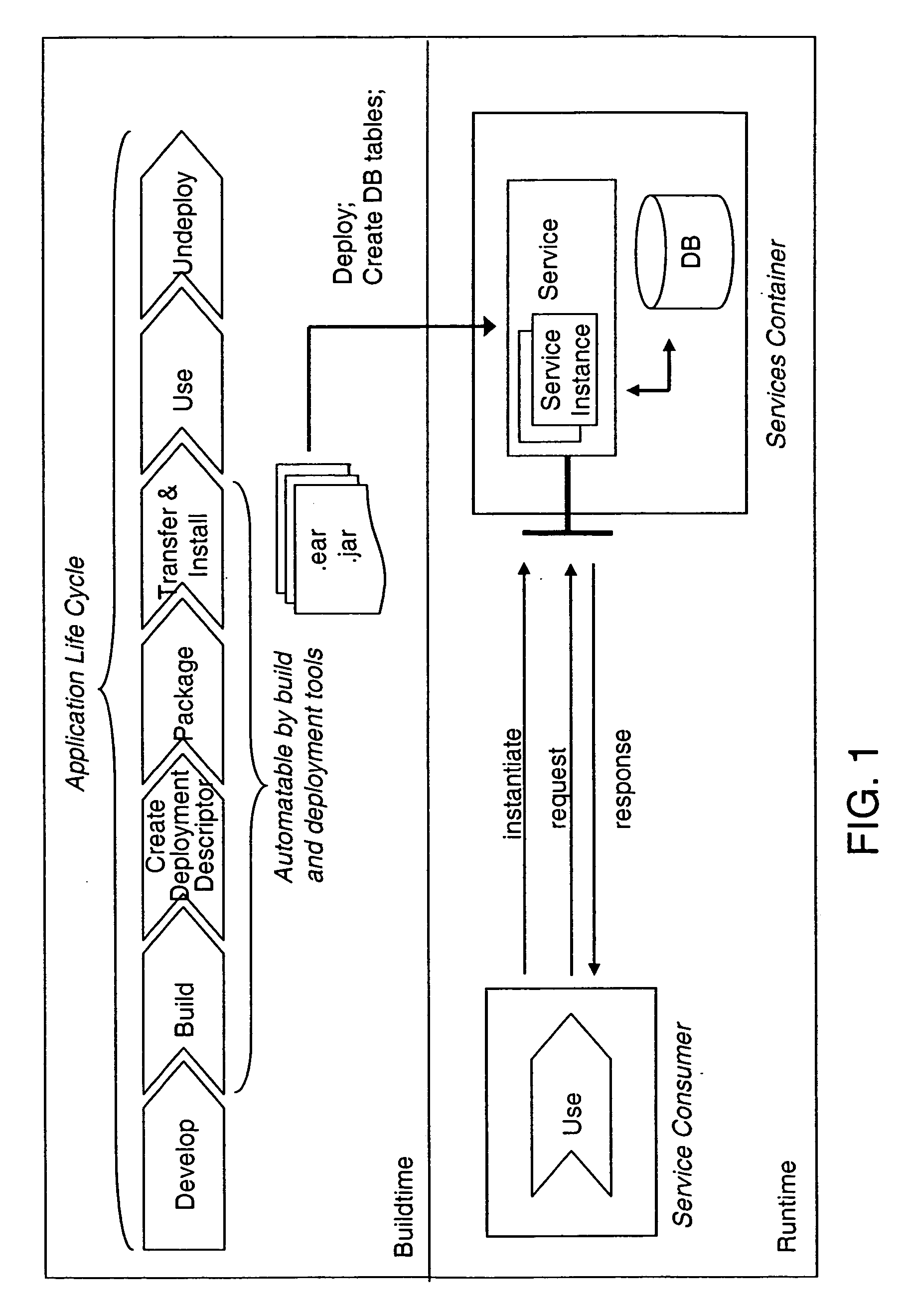
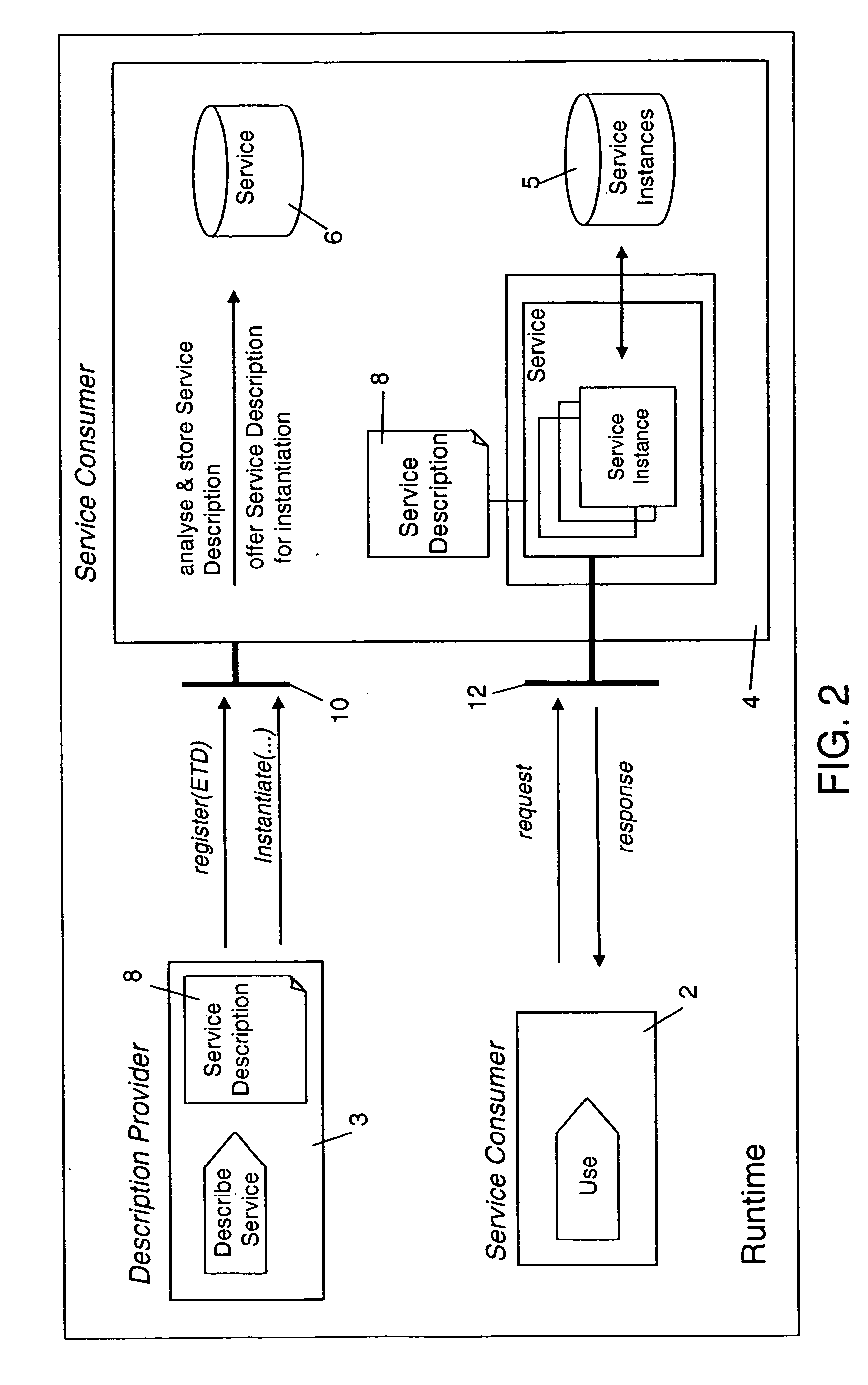
The present invention describes a new system and method for modeling and dynamically deploying services into a distributed networking architecture, especially in a service-oriented architecture. The service container being part of distributed networking architecture exposes its functionality as services. It provides a registration service for deploying service descriptions. Having created a new service description in any declarative description language (i.e. a description of a (stateful) service e.g. a stateful Web service), the description provider invokes the registration service at the service container that allows to register (i.e. deploy) that new service description during runtime without restarting service container. The service container is responsible to analyze and check the submitted new service description for validity, to store the service description and to make it available for interested services consumers for instantiation. If a new service has been successfully registered, a new service interface for accessing that new service is automatically created by the service container. Interested services consumers may query the hosting environment for the available services being hosted and to subsequently instantiate a new service. A service consumer may then invoke any exposed service operation on a given service instance which generally follows a request response pattern.
Owner:IBM CORP
System and method of executing and controlling workflow processes
ActiveUS20040153350A1Digital computer detailsMultiprogramming arrangementsSuccessful completionDocument preparation
A method of executing and controlling a workflow process includes a request-response control process for coordinating activities between a plurality of entities, whereby an entity creates and sends a message requesting execution of an activity and another entity receives, parses and responds to the request. The message includes activity-specific data and activity status data. The activity status data signifies, for example, whether a corresponding activity has been successfully performed (i.e., completed) or failed. Process information, including control logic for the workflow process, is specified in an at least one uncompiled document, which may include an extensible stylesheet and an extensible markup language document. A document type definition defines the structure of the document. The control logic may include serial, AND-parallel, OR-parallel, XOR-parallel, CON-parallel and iterative instructions and a definition of successful completion and / or failure for an activity according to the control logic. The control logic also specifies a forward transition for a completed activity and a backward transition for a failed activity. A parser processes the message according to the control logic for the workflow process and the document type definition. A compiled workflow engine and database are not required.
Owner:HANDYSOFT CORP
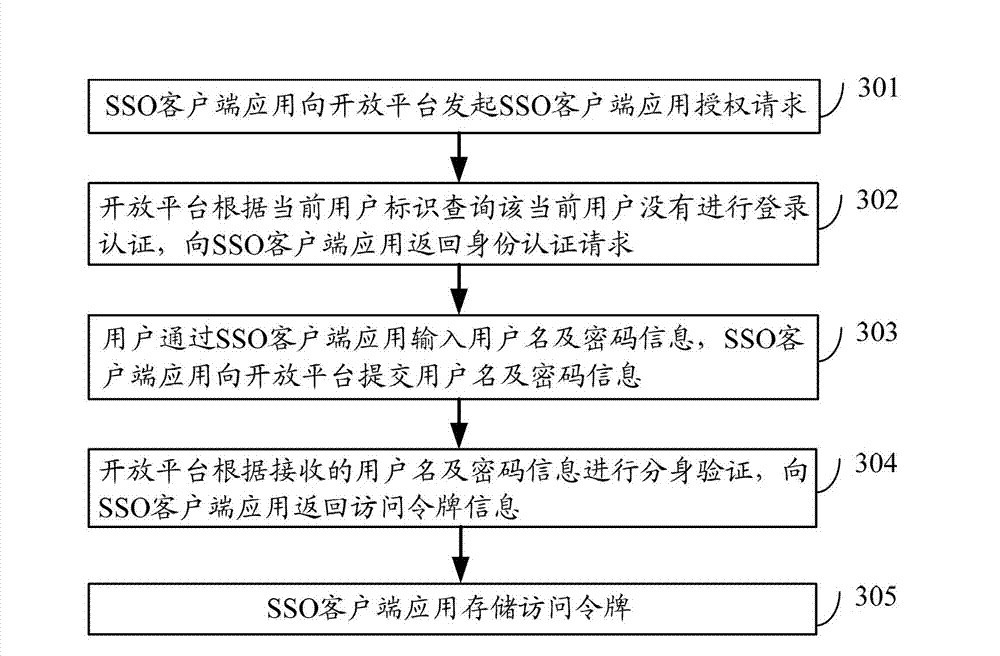
Method, device and system for implementing authorization of third-party application based on open platform
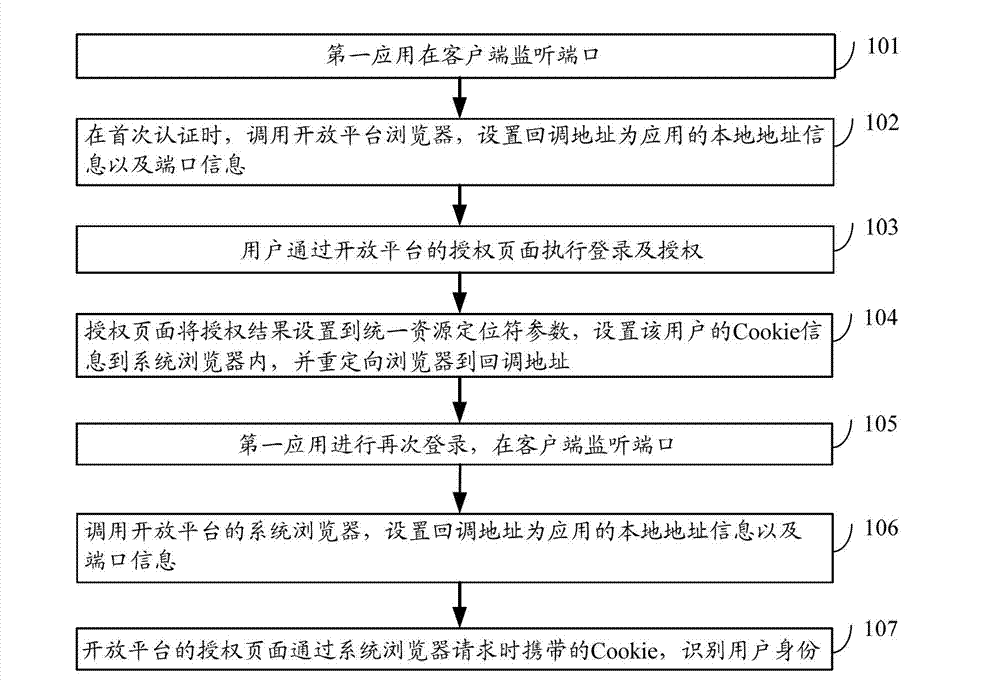
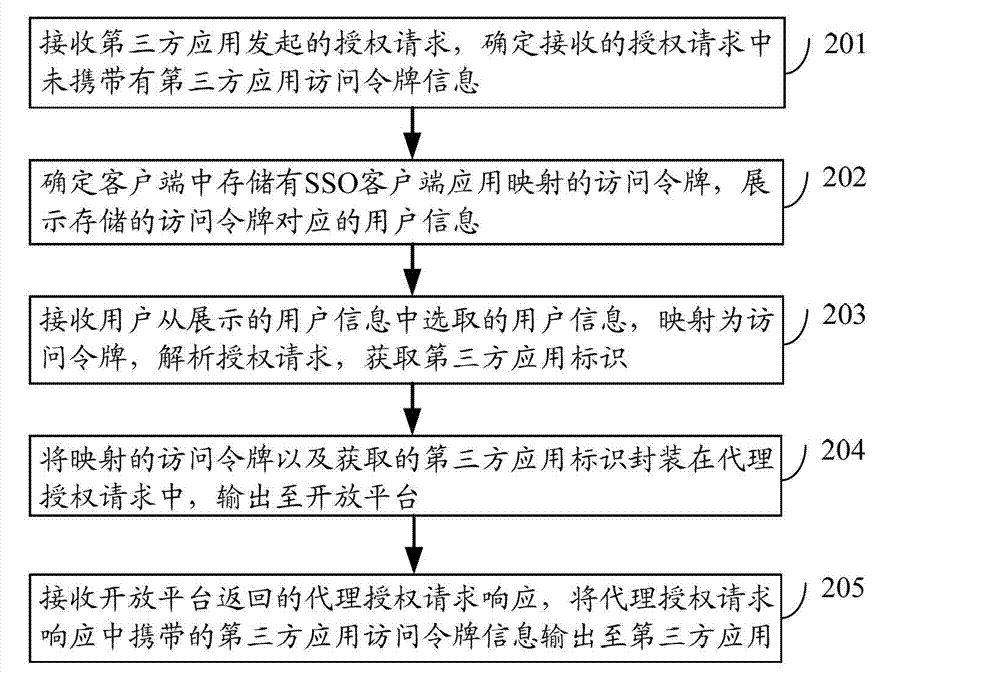
ActiveCN103051630AShorten the timeEasy to operateUser identity/authority verificationThird partyOpen platform
The invention discloses a method, a device and a system for implementing the authorization of a third-party application based on an open platform. The method comprises the following steps of: receiving an authorization request initiated by the third-party application, and determining that the received authorization request does not carry third-party application access token information; determining that an access token for single sign-on (SSO) client application mapping is stored in a client, and displaying user information corresponding to the stored access token; receiving user information which is selected from the displayed user information by a user, mapping the user information into the access token, analyzing the authorization request, and acquiring a third-party application identifier; packaging the mapped access token and the acquired third-party application identifier into an agent authorization request, and outputting the agent authorization request to the open platform; and receiving an agent authorization request response returned by the open platform, and outputting the third-party application access token information carried in the agent authorization request response to the third-party application. By the invention, application authorization efficiency can be improved.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
Systems and Methods for Identifying a Network
ActiveUS20100095359A1Digital data processing detailsMultiple digital computer combinationsDigital deviceRequest–response
Exemplary systems and methods for identifying a wireless network are provided. In exemplary embodiments, a method includes at least a digital device receiving network information associated with a network, generating an access identifier based on the network information, generating a credential request including the access identifier, providing the credential request to a credential server, receiving a credential request response from the credential server, the credential request response comprising network credentials to access the network, and providing the network credentials to a network device to access the network.
Owner:CHANNEL IP BV
System and method of executing and controlling workflow processes
ActiveUS7168077B2Digital computer detailsMultiprogramming arrangementsSuccessful completionExtensible markup
A method of executing and controlling a workflow process includes a request-response control process for coordinating activities between a plurality of entities, whereby an entity creates and sends a message requesting execution of an activity and another entity receives, parses and responds to the request. The message includes activity-specific data and activity status data. The activity status data signifies, for example, whether a corresponding activity has been successfully performed (i.e., completed) or failed. Process information, including control logic for the workflow process, is specified in an at least one uncompiled document, which may include an extensible stylesheet and an extensible markup language document. A document type definition defines the structure of the document. The control logic may include serial, AND-parallel, OR-parallel, XOR-parallel, CON-parallel and iterative instructions and a definition of successful completion and / or failure for an activity according to the control logic. The control logic also specifies a forward transition for a completed activity and a backward transition for a failed activity. A parser processes the message according to the control logic for the workflow process and the document type definition. A compiled workflow engine and database are not required.
Owner:HANDYSOFT CORP
Network based device for providing RFID middleware functionality
ActiveUS20070027966A1Thermometer detailsFrequency-division multiplex detailsData compressionApplication-oriented networks
Some embodiments of the present invention provide middleware functionality integrated into a module of a network device, such as a router or switch, that is configured to provide application-oriented network (“AON”) services. Some preferred implementations of the invention provide policy-based application services for RFID data, such as conditional routing, security (encryption, identification, authentication and authorization), data translation and / or transformation, data compression, data caching, etc. Some preferred implementations can interpret an application request and route to an appropriate network address of an RFID reader. Preferably, ALE (application-level event) aggregation and filtering can also be performed on behalf of the application. Some methods of the invention allow event data to be sent to applications (including but not limited to business applications) as request-response messages. Other methods of the invention allow event data to be sent to applications in the form of asynchronous notifications.
Owner:CISCO TECH INC
Between-load-and-vehicle communication system
InactiveUS20060193282A1High error rateReduce overheadError prevention/detection by using return channelNetwork traffic/resource managementTransaction managementTransaction service
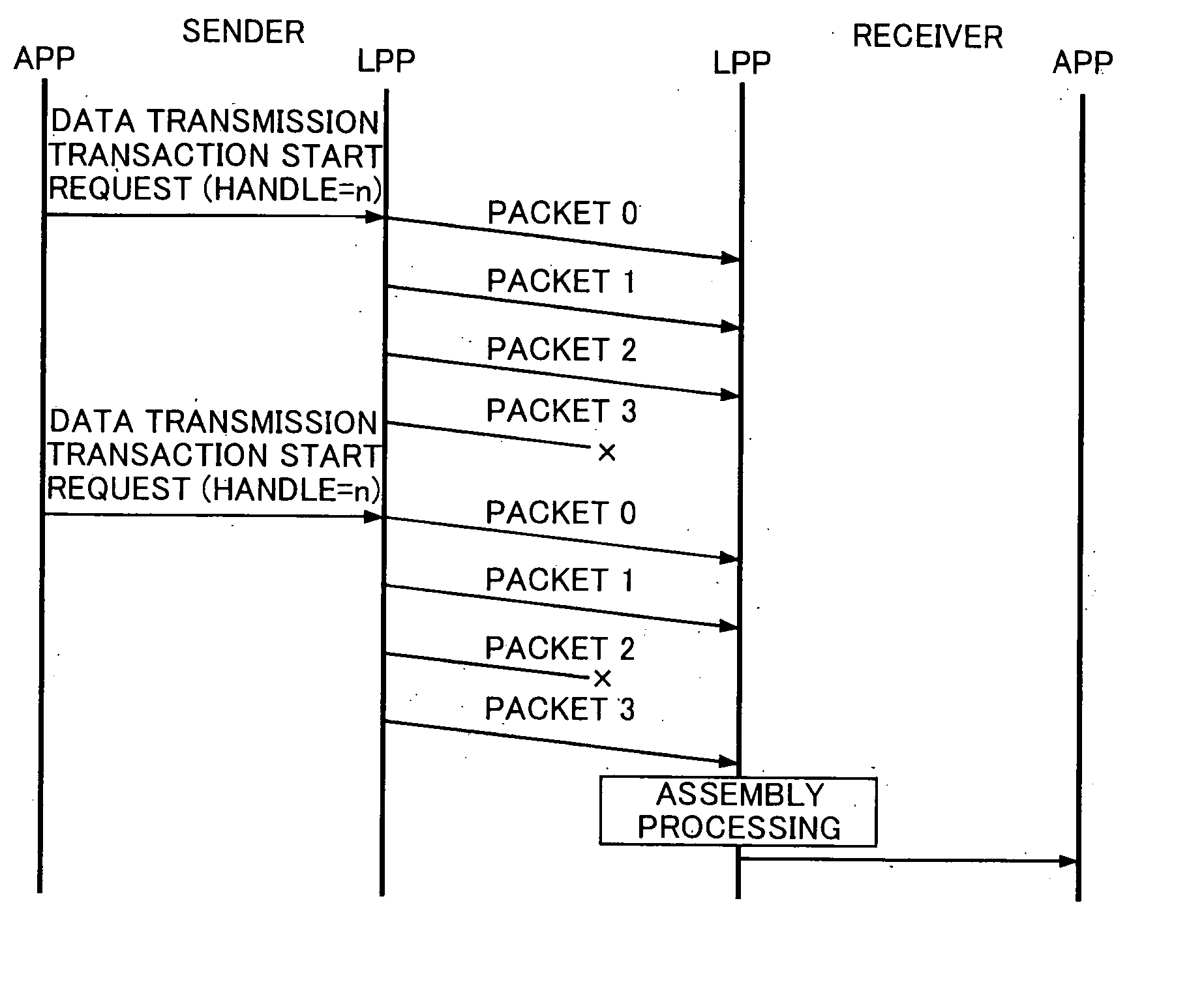
A roadside-to-vehicle communication system for providing a mobile station with application service by utilizing roadside-to-vehicle communication implemented between the mobile station that travels on a road and a base station system installed along the road provides non-network-type communication protocols that can implement diverse application services, even when the mobile station is moving. The roadside-to-vehicle communication system includes transfer service processing entities for implementing data transfer among applications and transaction management entities have undelivered data resenders, data send / receive for each message, and a message segmenter / assembler that provides unidirectional data transmission and request-response transaction services.
Owner:MITSUBISHI ELECTRIC CORP
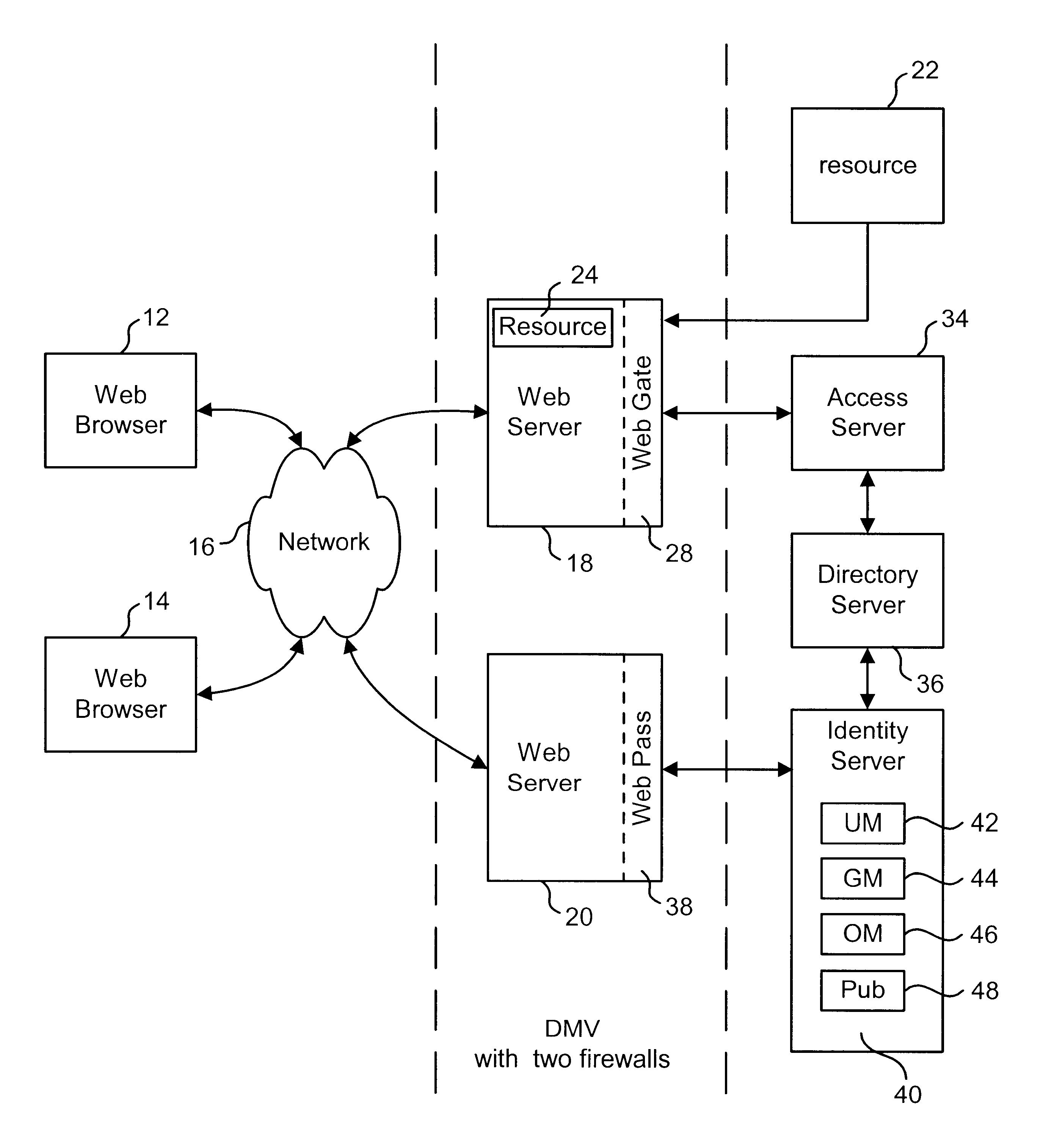
Preparing output XML based on selected programs and XML templates
An Identity System delivers customized request responses that integrate the results of multiple programs. The Identity System receives and translates a user request. The Identity Systems employs a program service to identify all the programs required to complete the request. The Identity System uses a XML data registry to retrieve a XML template and XSL stylesheet for each program. The Identity System executes all of the programs for the request and organizes their results into a single data structure, based on the templates for each program. The Identity System then applies attribute display characteristics to convert the data structure into a single Output XML. The Output XML can be provided directly to the user or receive further processing using the retrieved XSL stylesheets.
Owner:ORACLE INT CORP
Method and System for Interworking Between Two Different Networks
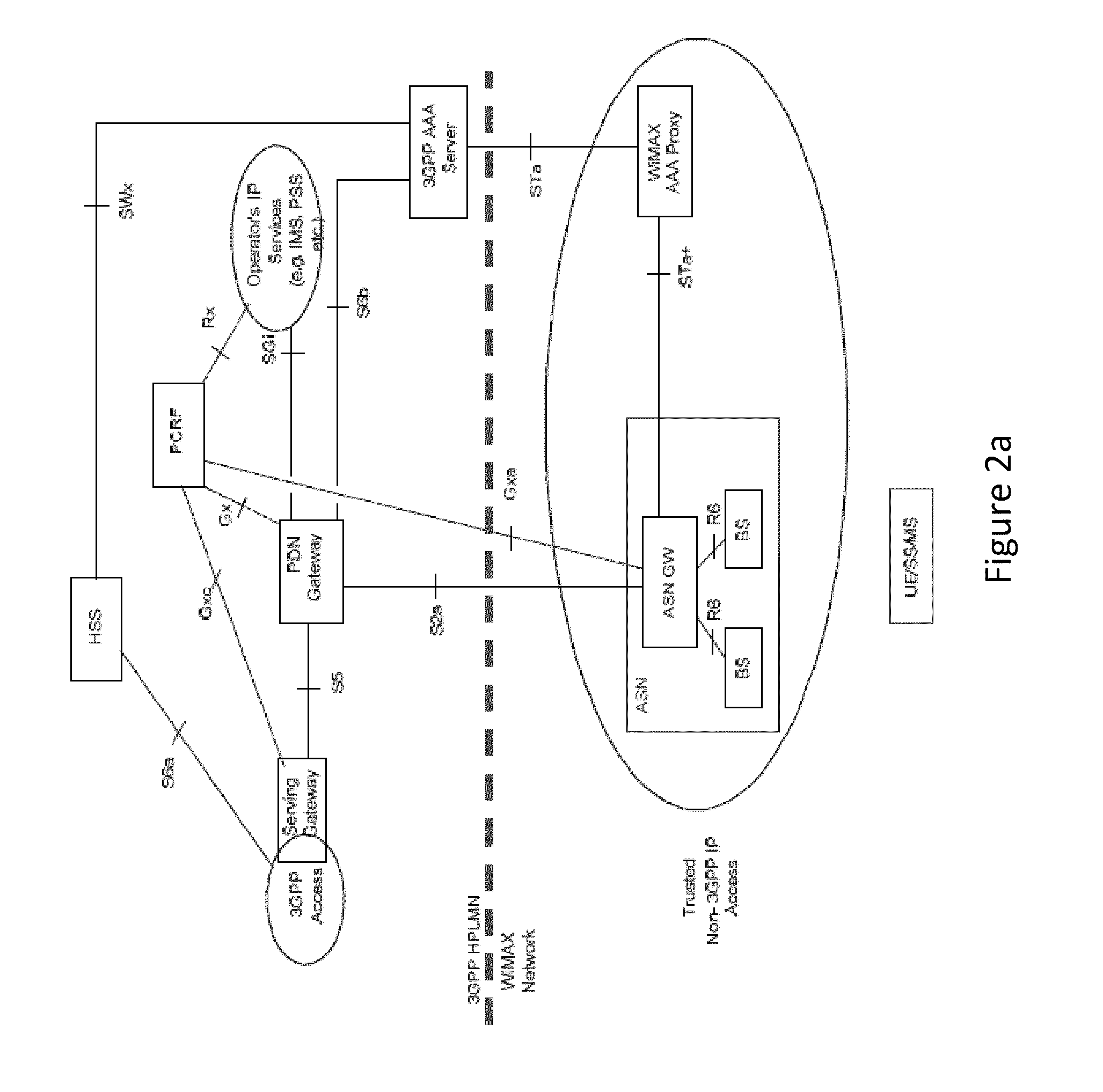
ActiveUS20100035578A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsHandoverRequest–response
Systems and methods for interworking between two different networks are presented. In one embodiment, a method for wireless communication includes requesting a network access from an access point of a first network, and transmitting an EAP authentication request from the access point to a user end. An EAP authentication request response is sent from the user end to the access point. The EAP authentication request response includes an attach type indicator that indicates to a gateway associated with the access point whether the attach request is an initial attachment or a handover from a second network.
Owner:FUTUREWEI TECH INC
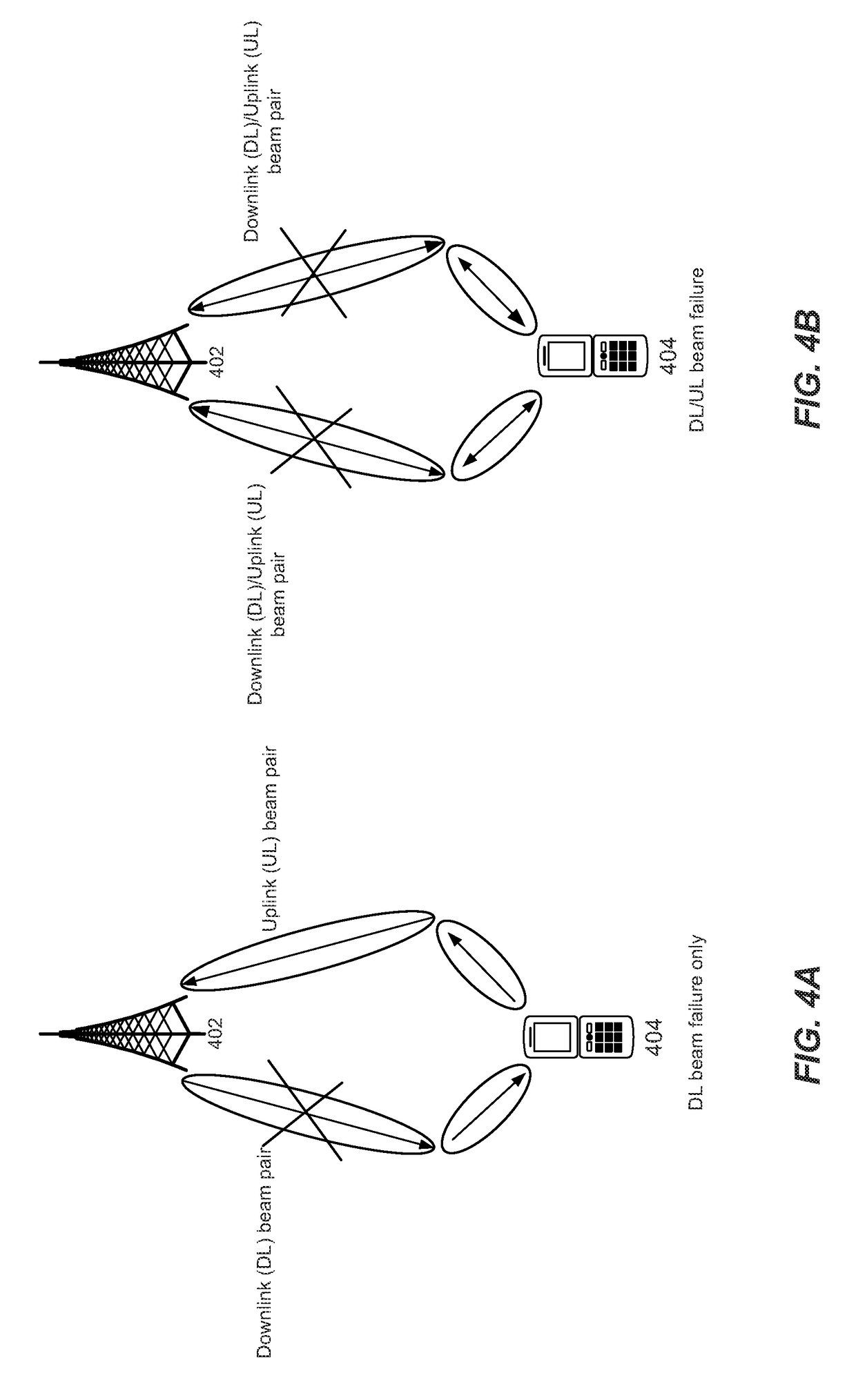
Method for response to beam failure recovery request
ActiveUS20180367374A1Well formedSynchronisation arrangementSignal allocationUser equipmentRequest–response
The disclosure relates to technology for beam failure recovery in user equipment. The user equipment sends a beam failure recovery request to the base station upon detection of a beam failure between the base station and the user equipment, and monitors one or more candidate beams in which to receive the beam failure recovery request response from the base station, based on an association between a beam failure recovery request response and a beam failure recovery request.
Owner:FUTUREWEI TECH INC
Monitoring asynchronous transactions within service oriented architecture
InactiveUS20090216874A1Well formedDigital computer detailsOffice automationUnique identifierMonitoring system
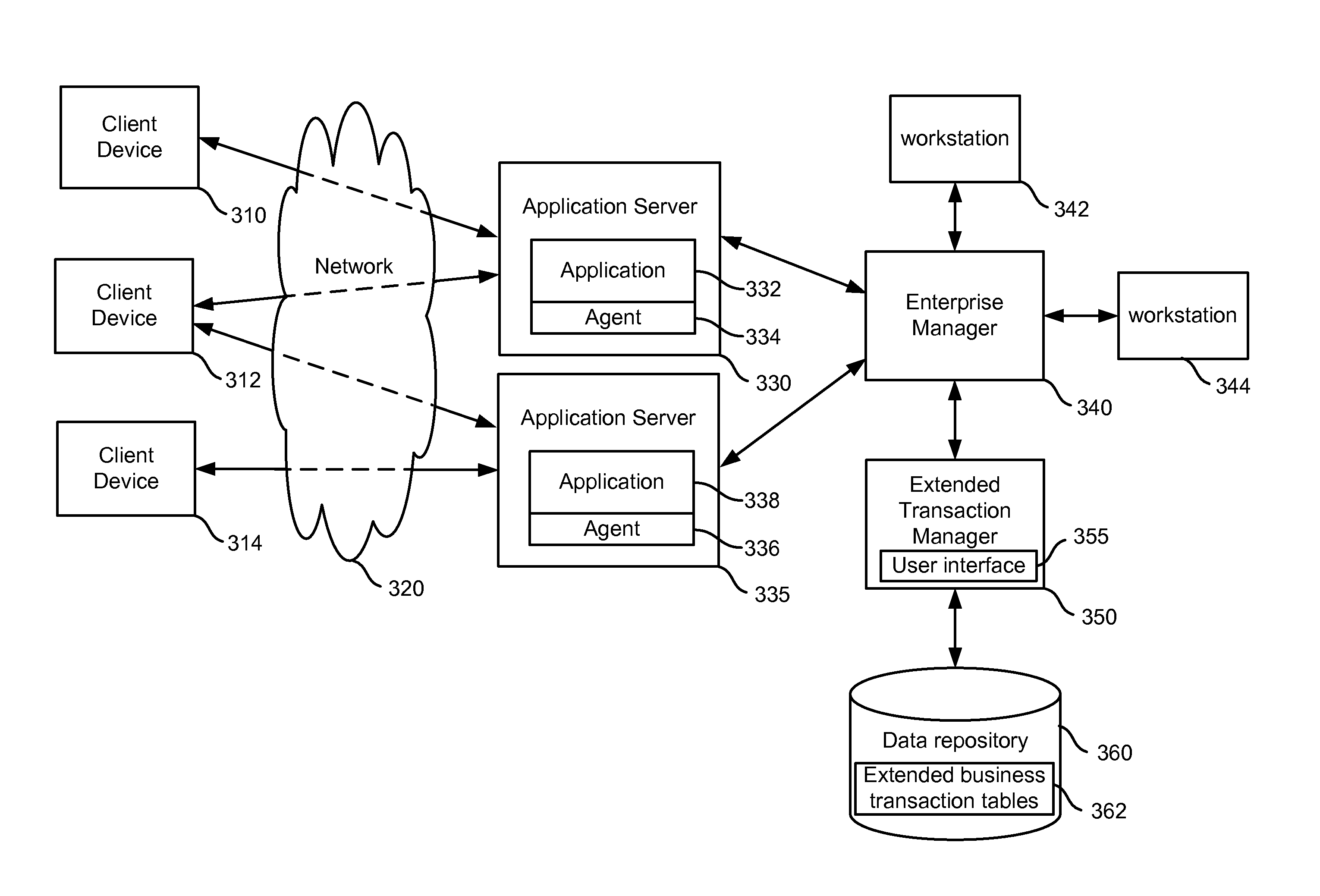
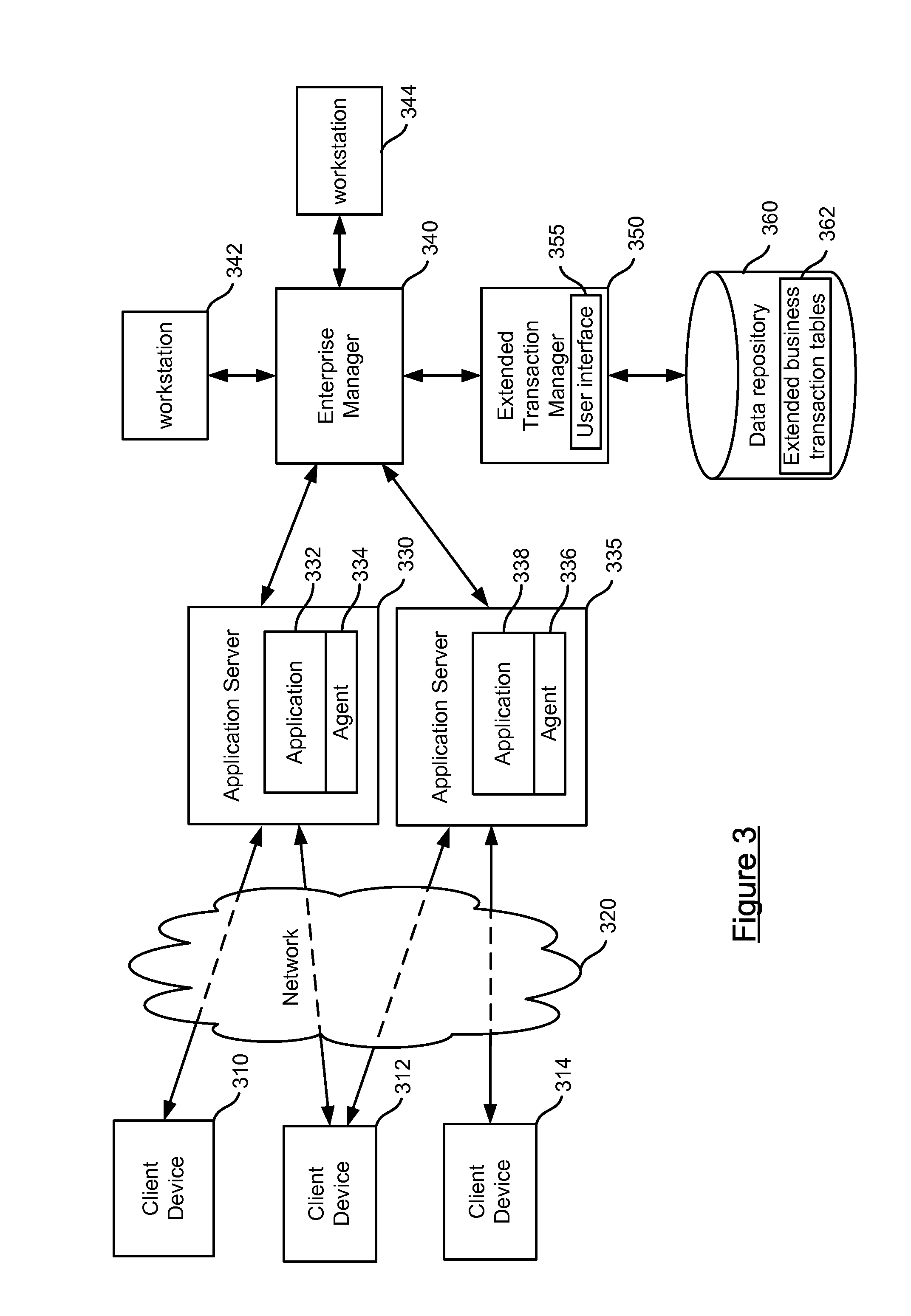
A monitoring system is used to monitor extended business transactions comprised of asynchronous messages. Each message may be a request or a response of an application transaction request-response pair and may be identified with a unique identifier. The unique identifier may be used to identify two or more asynchronous messages, where each extended business transaction may be associated with one or more unique identifiers to identify messages that comprise the business transaction. The extended business transactions are completed over an extended period of time and implemented over several different machines which may or may not be in communication with each other are monitored. Alerts are generated when messages of the extended business transaction do not satisfy a threshold or other criteria, such as a time period for occurring. A user interface or other mechanism may be used to configure the transactions and provide information regarding the status of the transactions and alerts generated for uncompleted portions of the transaction.
Owner:CA TECH INC
Methods and systems for routing messages through a communications network based on message content
InactiveUS7487262B2Information formatData switching by path configurationTelecommunications networkComputer science
A method and system for routing messages through a communications network based on the content of the message. The method of the present invention comprises providing a method for retrieving information through a telecommunications network comprising receiving, in a message data structure, a request message comprising a command; sending a query message to a content provider based on the command; receiving a query response message from the content provider comprising response information; and sending a request response message based on the response information.
Owner:AT&T MOBILITY II LLC
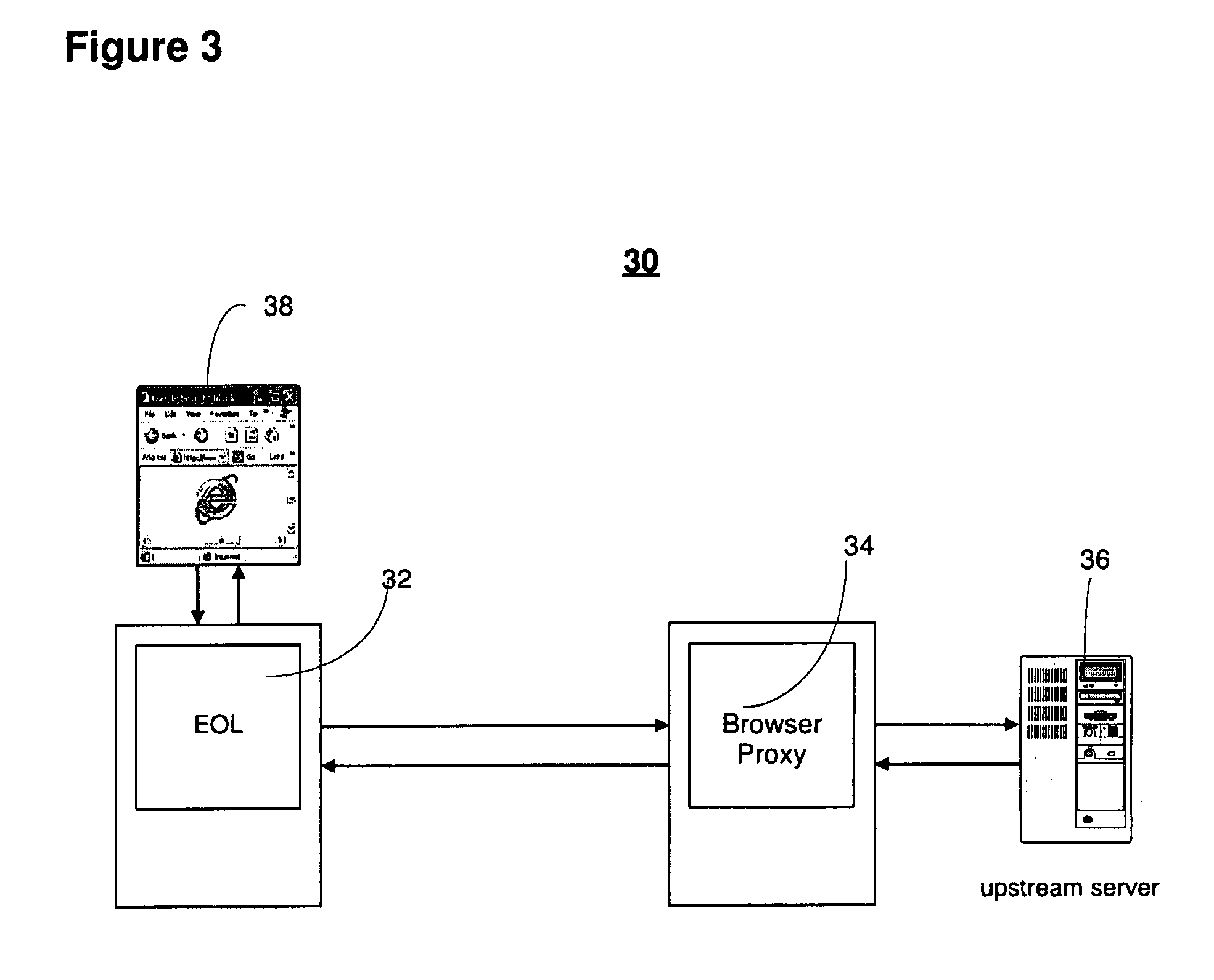
Content procurement architecture
InactiveUS20080155016A1Minimize response timeEnhance client interestMultiple digital computer combinationsTransmissionSchema for Object-Oriented XMLComputer science
There is provided an architecture (system and method) to accelerate web response time and to provide a level platform to meet the interests from both providers and users of content. The concept of user object is introduced to present user interests or disinterests. If a user's browser has already cached a particular provider object, then a corresponding user object indicates that the user is not interested in that object. Otherwise, a user can indicate his / her interests in objects specified either by a set of criteria or explicit description of objects. The web response is accelerated by generalization of the split-proxy architecture of content networking. The user is represented by the user proxy and browser proxy 34. Unlike the traditional content delivery architecture, the content procurement architecture pushes user interests close to the provider sites and minimizes the request-response time between the user proxy and the provider proxy. The request-response sequence is accelerated by pipelining and minimizing all unnecessary stop-and-wait actions.
Owner:IST INT
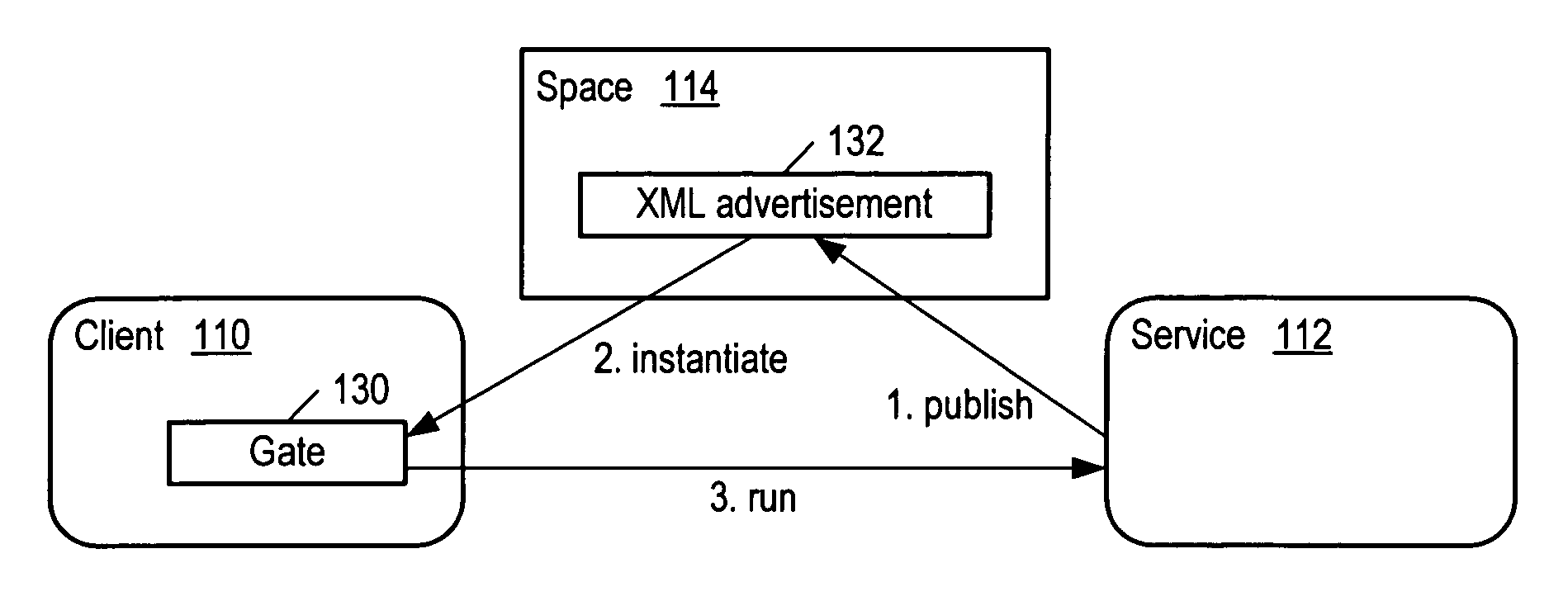
Messaging system using pairs of message gates in a distributed computing environment
InactiveUS7065574B1Verify correctnessVerify the correctness of the response messageResource allocationDigital computer detailsDistributed Computing EnvironmentClient-side
Various embodiments of message gate pairs are described. A message gate pair may provide a mechanism for communicating requests from clients to services and response from services to clients. A message gate pair may be used to create a secure atomic bi-directional message channel for request-response message passing. The distributed computing environment may employ a message transport in which a message gate exists on both the client and the service. The two gates may work together to provide a secure and reliable message channel. Client and service gates may perform the actual sending and receiving of the messages from the client to the service using a protocol specified in a service advertisement. The message gates may provide a level of abstraction between a client and a service. A client may reference a service through a message gate instead of referencing the service directly. Messages gates may allow clients and services to exchange messages in a secure and reliable fashion over any suitable message transport (e.g. HTTP). For a client, a message gate may represent the authority to use some or all of a service's capabilities. Each capability may be expressed in terms of a message that may be sent to the service. Each such message may be sent through a client message gate that may verify the correctness of the message. The message may be received by a service message gate that may authenticate the message and verify its correctness.
Owner:ORACLE INT CORP
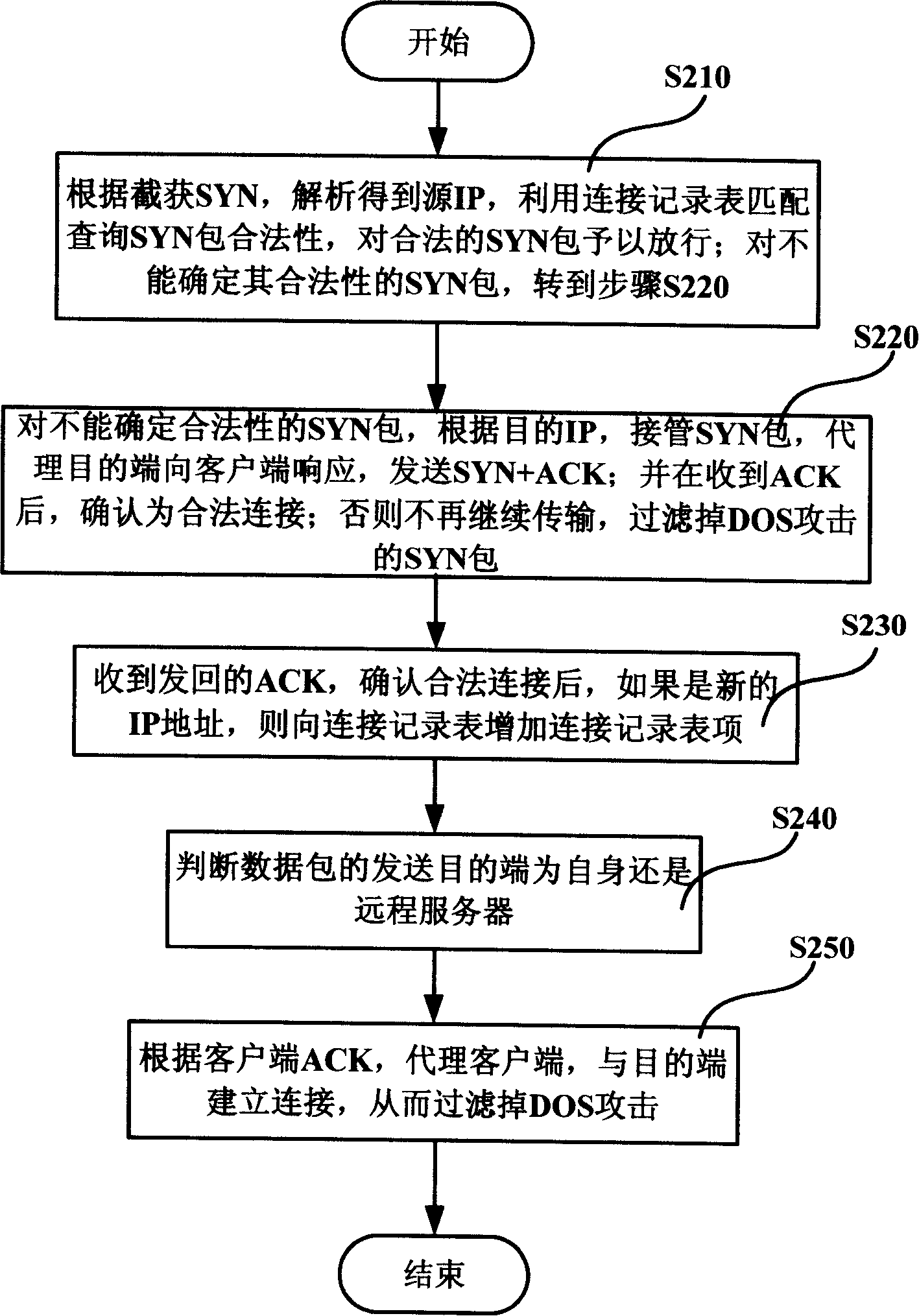
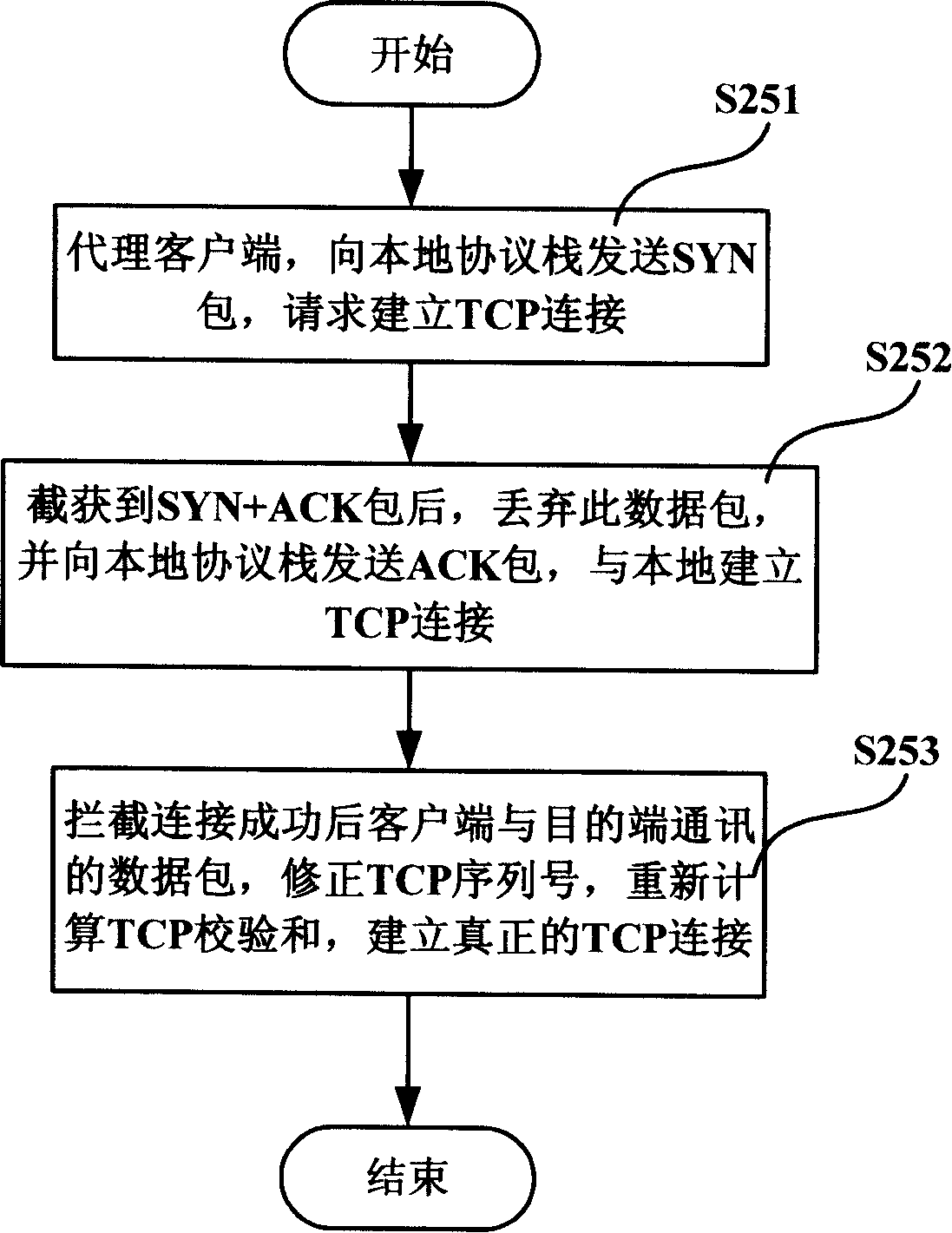
Refused service attack protection method, network system and proxy server
ActiveCN101175013AEasy to integrateEasy maintenanceData switching networksSecuring communicationNetworked systemClient-side
The invention discloses a refusing service attacks protection method, a network system and a proxy server. Through intercepting a connection request packet, the invention obtains the source address of the connection request packet through the analysis and queries the legality of the matching connection request packet. To the connection request packet which cannot determine the legality, an agent objective end responses to the requests of clients, filters out the refusing service attacks and judges the address of the objective end according to the legal connection request response packet. The connection between the agent objective end and the objective end is constructed to realize the refusing service attacks protection. The invention can finish the integrated protection of local and remote servers.
Owner:FORTINET
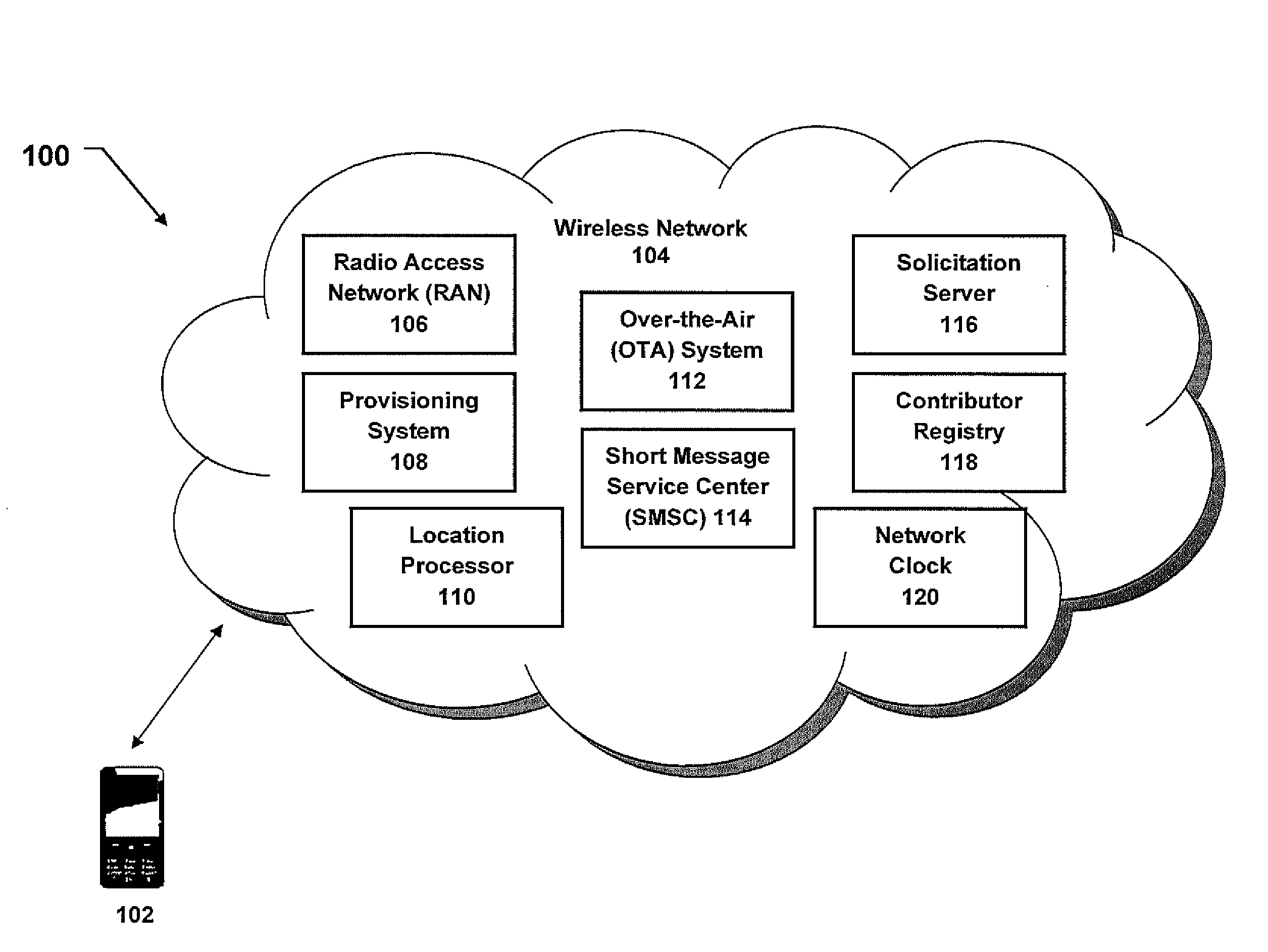
Location and Time Specific Mobile Participation Platform
ActiveUS20110143776A1Facilitate solicitationEasy to collectPower managementResourcesThird partyDevice type
A mobile participation platform enables a wireless network operator or third party to solicit response data related to a specific time and location specific event by signaling multiple mobile device users that meet predefined qualifications. The qualifications include presence at the specific location at the specific time, and may include other characteristics, such as prior consent to receive solicitations, and particular device type or data collection functionality. The platform locates mobile devices that may qualify for participation, and generates and transmits a solicitation. Mobile devices receiving the solicitation may activate a participation client to acknowledge the solicitation and to contribute by submitting the requested response data, which may include photos, text, sensor data, audio, video and the like. The qualifications are verified, the response data is validated, and anonymity and privacy are maintained by associating the mobile device and other pertinent non-identifying information with an encrypted identifier.
Owner:AT&T INTPROP I L P
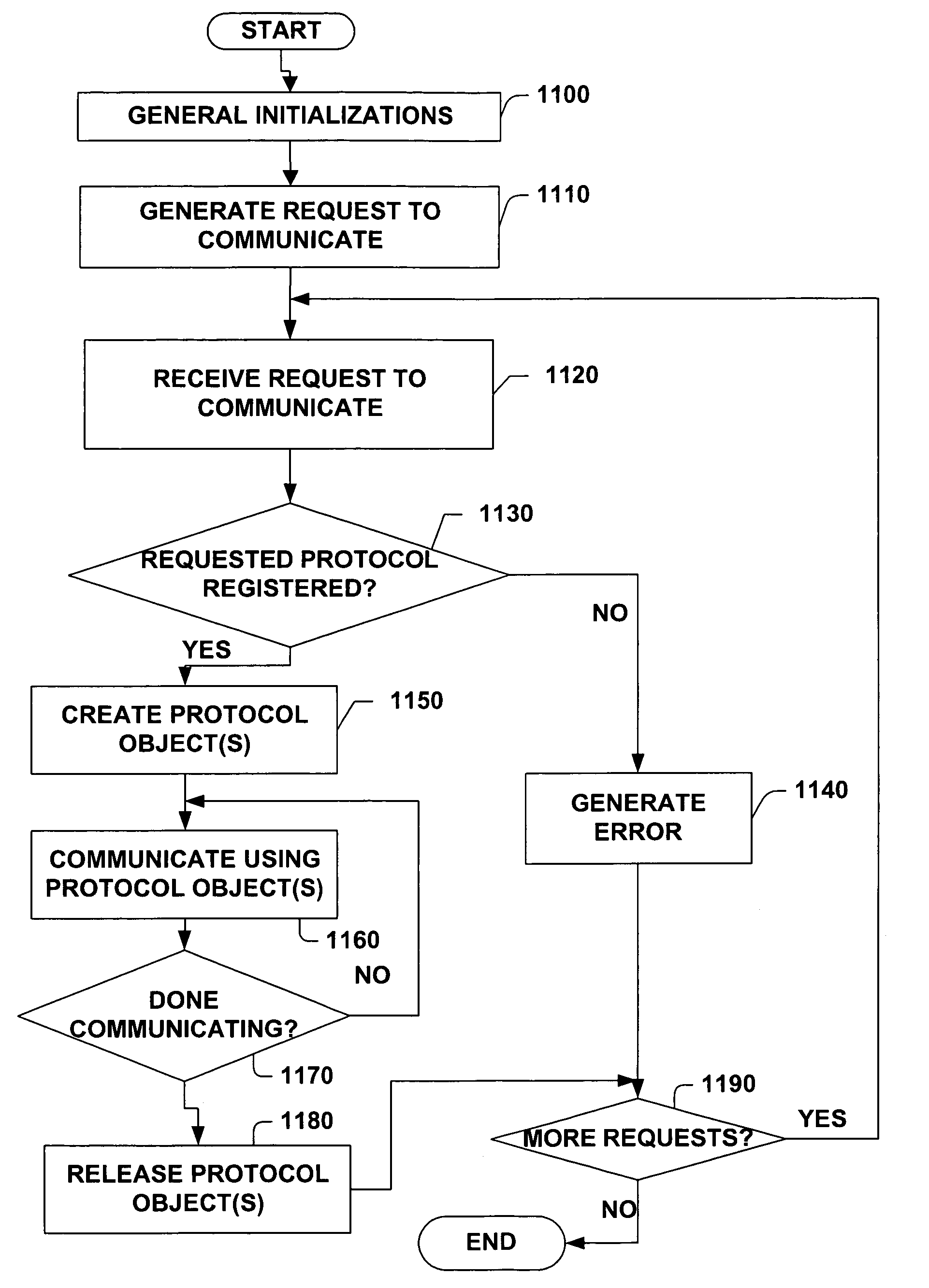
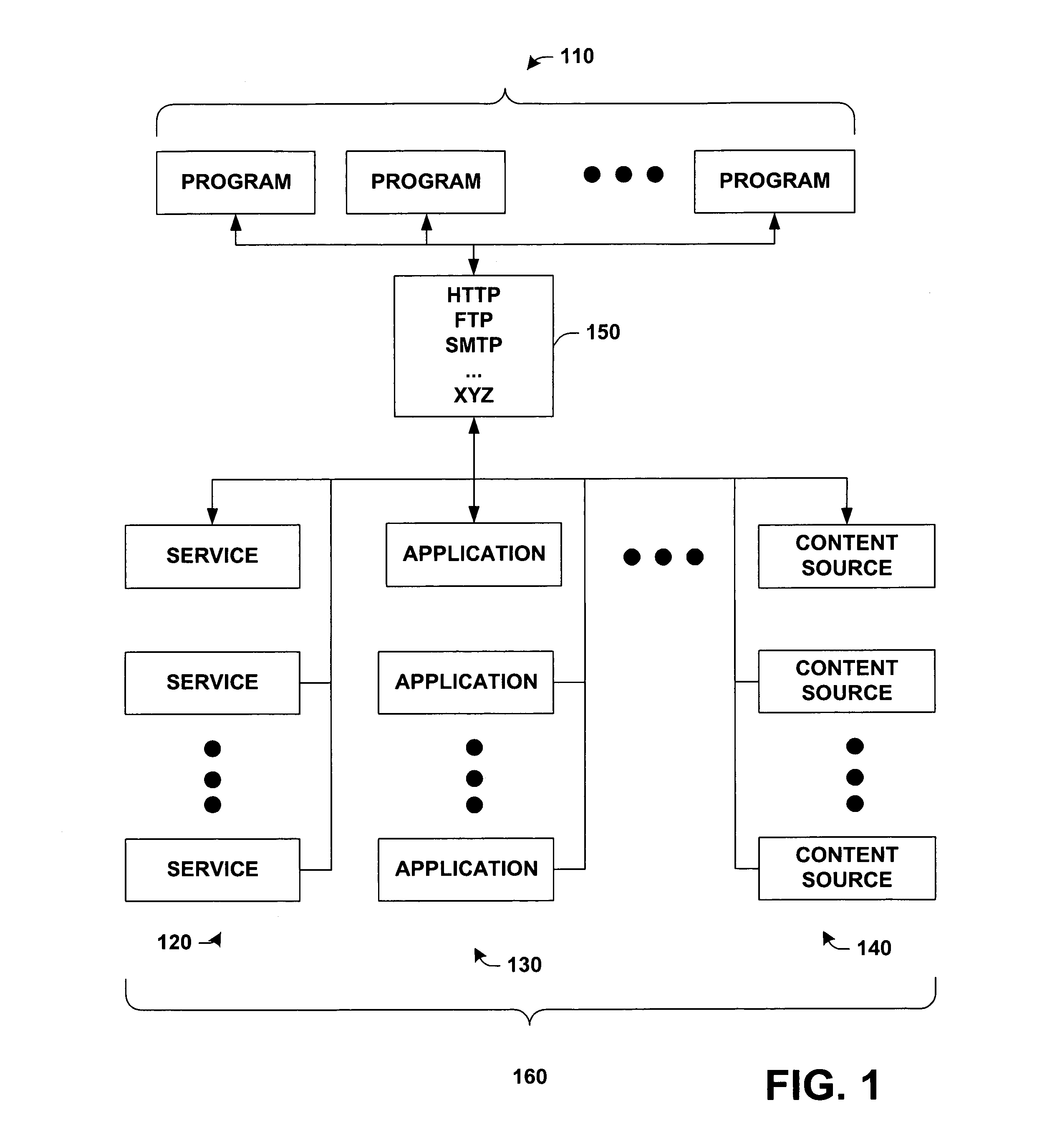
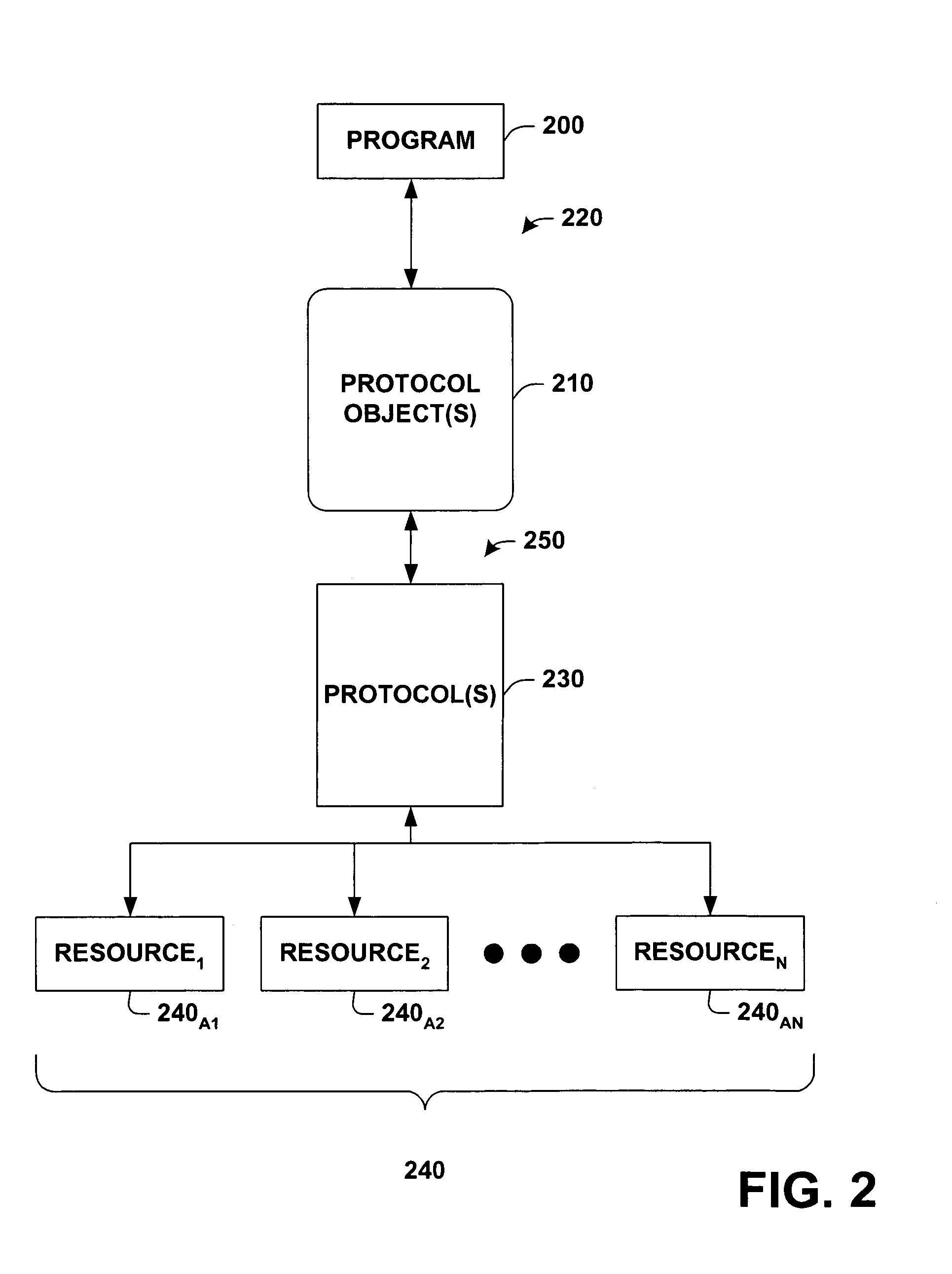
Protocol agnostic request response pattern
InactiveUS6996833B1Enhanced interactionFacilitates receiving and sending messageMultiprogramming arrangementsMultiple digital computer combinationsNetworking protocolProtocol processing
A system and method for facilitating communications over a protocol is provided. The system includes a class factory that holds identifiers associated with determining which, if any, registered protocol object creator should be employed to create a protocol object. The protocol object implements an abstract network protocol base class. The protocol object is employed to abstract details of communicating over a protocol and to provide a byte stream interface to communications occurring over the protocol, while removing protocol specific code from an application program. The method includes creating an instance of a protocol object from a source of registered protocol handlers based on a request to communicate over a protocol and using a base class API to communicate over the protocol through the protocol object.
Owner:MICROSOFT TECH LICENSING LLC
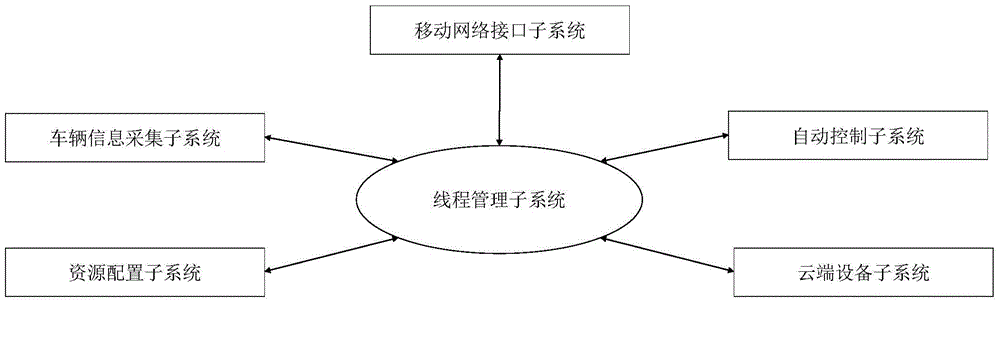
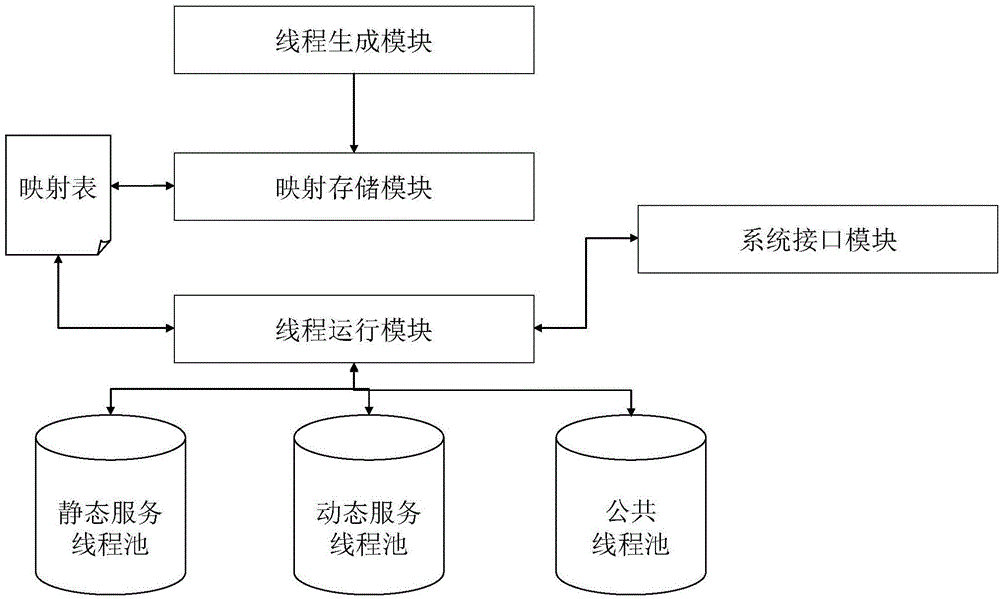
Cloud-computing-based parking lot management system
ActiveCN104408967AIn line with the operating rulesSatisfy needs such as preferencesTicket-issuing apparatusIndication of parksing free spacesAutomatic controlData platform
The invention provides a cloud-computing-based parking lot management system which comprises a vehicle information collecting subsystem, a thread management subsystem, a resource allocation subsystem, a cloud equipment subsystem, a mobile network interface subsystem and an automatic control subsystem. The could-computing-based parking lot management system can realize interaction with an intelligent cellphone client side, a cloud computing platform is taken as a processing architecture, a big data platform is taken as an information basis, resource distribution, data processing and request response are performed on the basis of service threads, efficient distribution and reasonable utilization of resources are realized by dividing static and dynamic service threads, own running laws of a parking lot are fully met, and high instantaneity requirements on service in the process of traveling can be met. The cloud-computing-based parking lot management system is supportive of a series of intelligent application scenes like parking space vacancy prediction inquiry, parking space optimized selection, incoming and outgoing path planning, vehicle collecting navigation and mobile payment of parking fee.
Owner:浙江中南机电智能科技有限公司
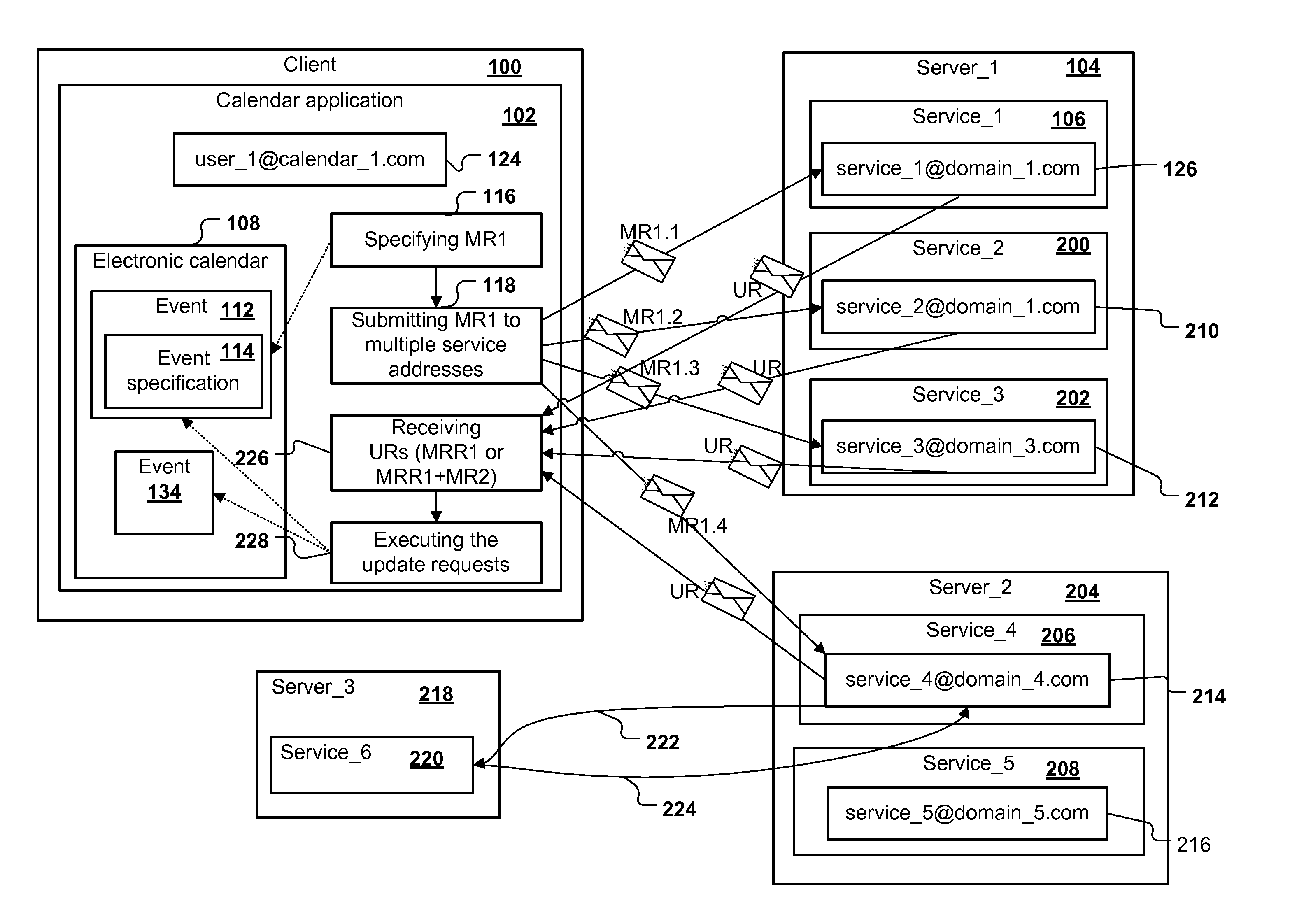
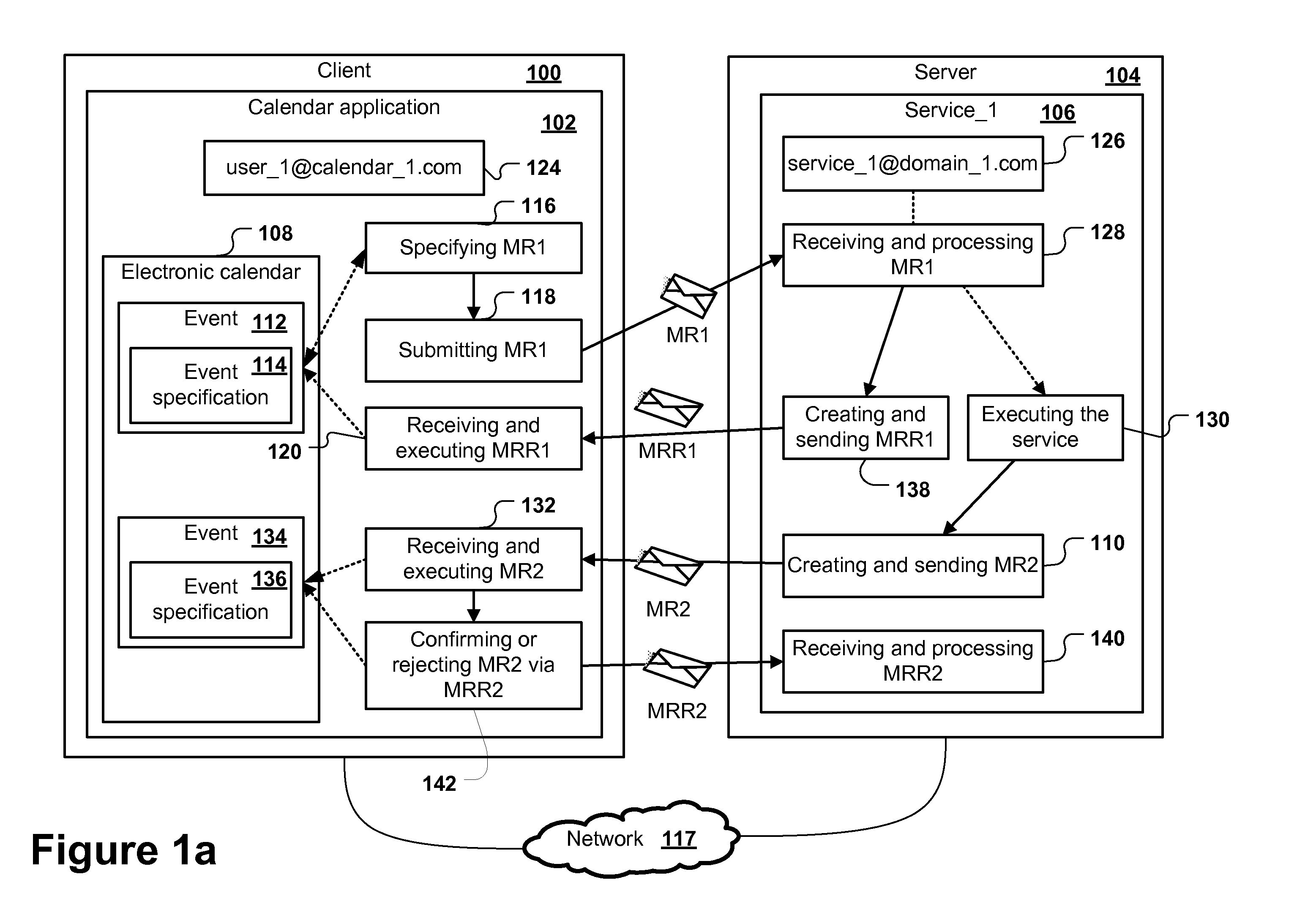
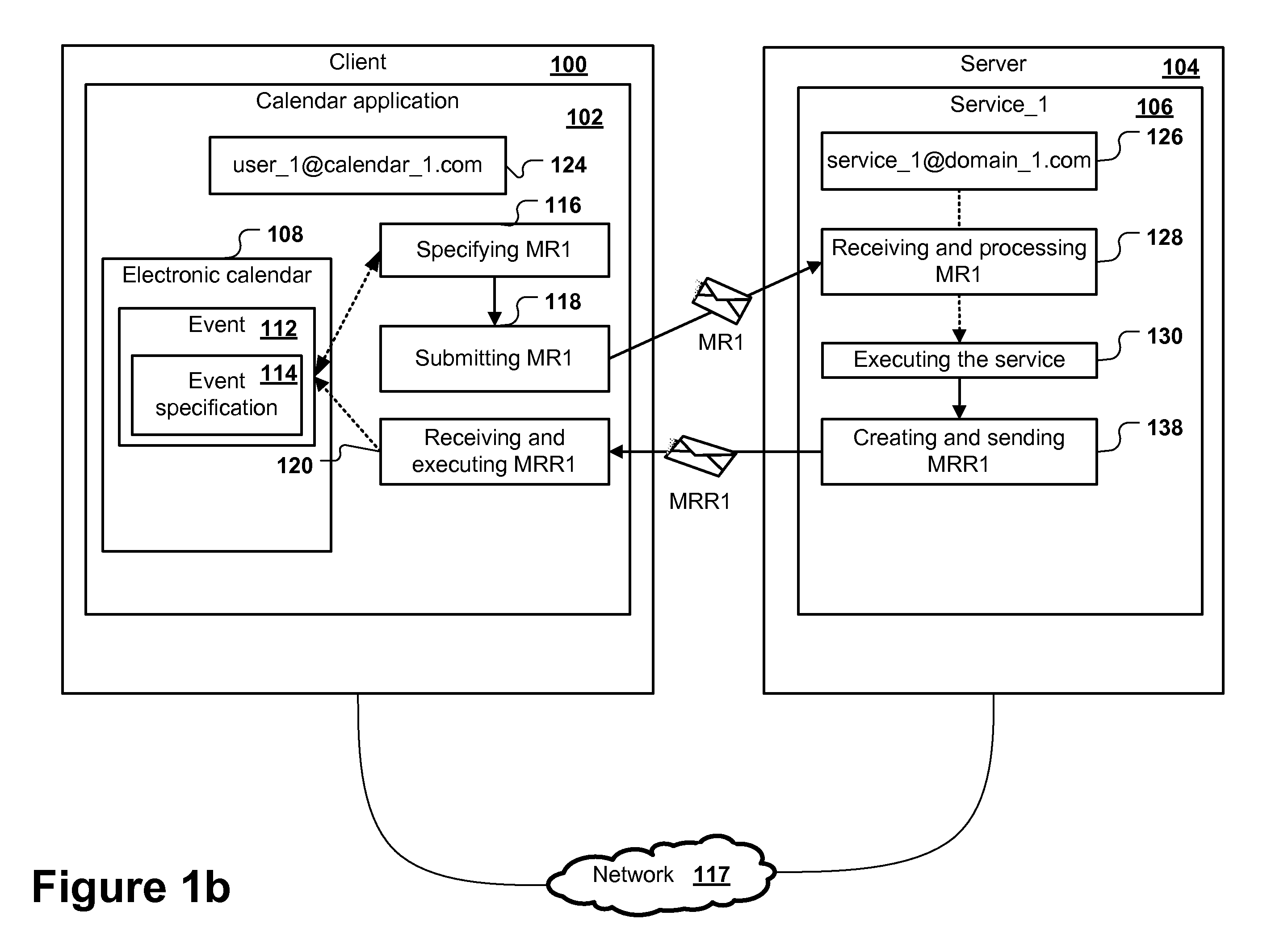
Computer implemented method for integrating services in a calendar application via meeting request e-mails
ActiveUS20110125545A1Reduce in quantityReducing possible sourceInput/output for user-computer interactionFinanceElectronic mailDatabase
The invention relates to a method for integrating services in a calendar application via the meeting request functionality of calendar programs comprising:initiating one or multiple services, wherein the initiation may involve the transmission of calendar event information from the calendar application to the service, the service requests being sent as meeting request e-mails to one or more service e-mail addresses, each service e-mail address representing a service,receiving the update requests generated by the one or multiple services, the update requests being meeting request response e-mails or one or multiple second meeting request e-mailsprocessing the received update requests, andupdating the calendar application.
Owner:SAG
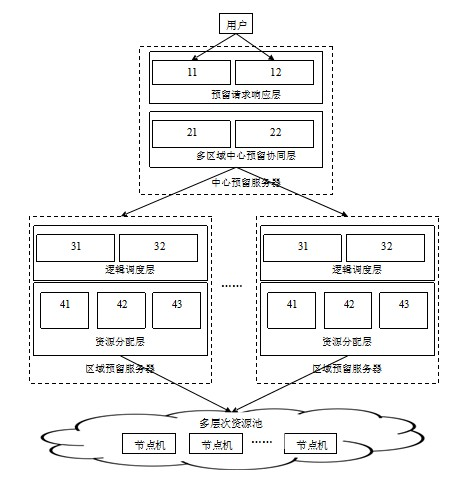
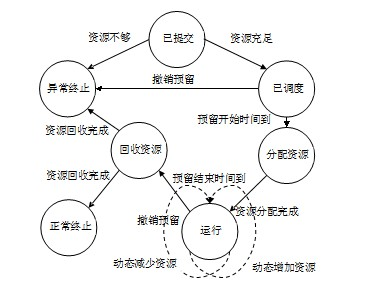
Layered resource reservation system under cloud computing environment
InactiveCN102014159ARealize dynamic deploymentOptimized reservationTransmissionResource poolMutual influence
The invention discloses a layered resource reservation system under a cloud computing environment. The system consists of a center reservation server, an area reservation server and a multi-level resource pool, wherein the center reservation server comprises a reservation request response layer and a multi-area center reservation collaborative layer; the reservation request response layer is responsible for sending a resource reservation request and accessing reserved resources; the multi-area center reservation collaborative layer is responsible for receiving the resource reservation request of the center reservation server; the area reservation server is divided into a logic scheduling layer and a resource distributing layer; the logic scheduling layer is responsible for receiving a resource reservation subrequest and distributing resources logically; the resource distributing layer is responsible for executing resource distribution and recovery; and the multi-level resource pool comprises a plurality of computing nodes which can be scheduled. The layered resource reservation system can adapt to the dynamic properties of a cloud computing platform and cloud computing application, thus eliminating mutual influences of various cloud computing applications due to resource competition, and guaranting the normal and stable operations of applications and services.
Owner:HUAZHONG UNIV OF SCI & TECH
Information processing apparatus, information processing method, and information processing program
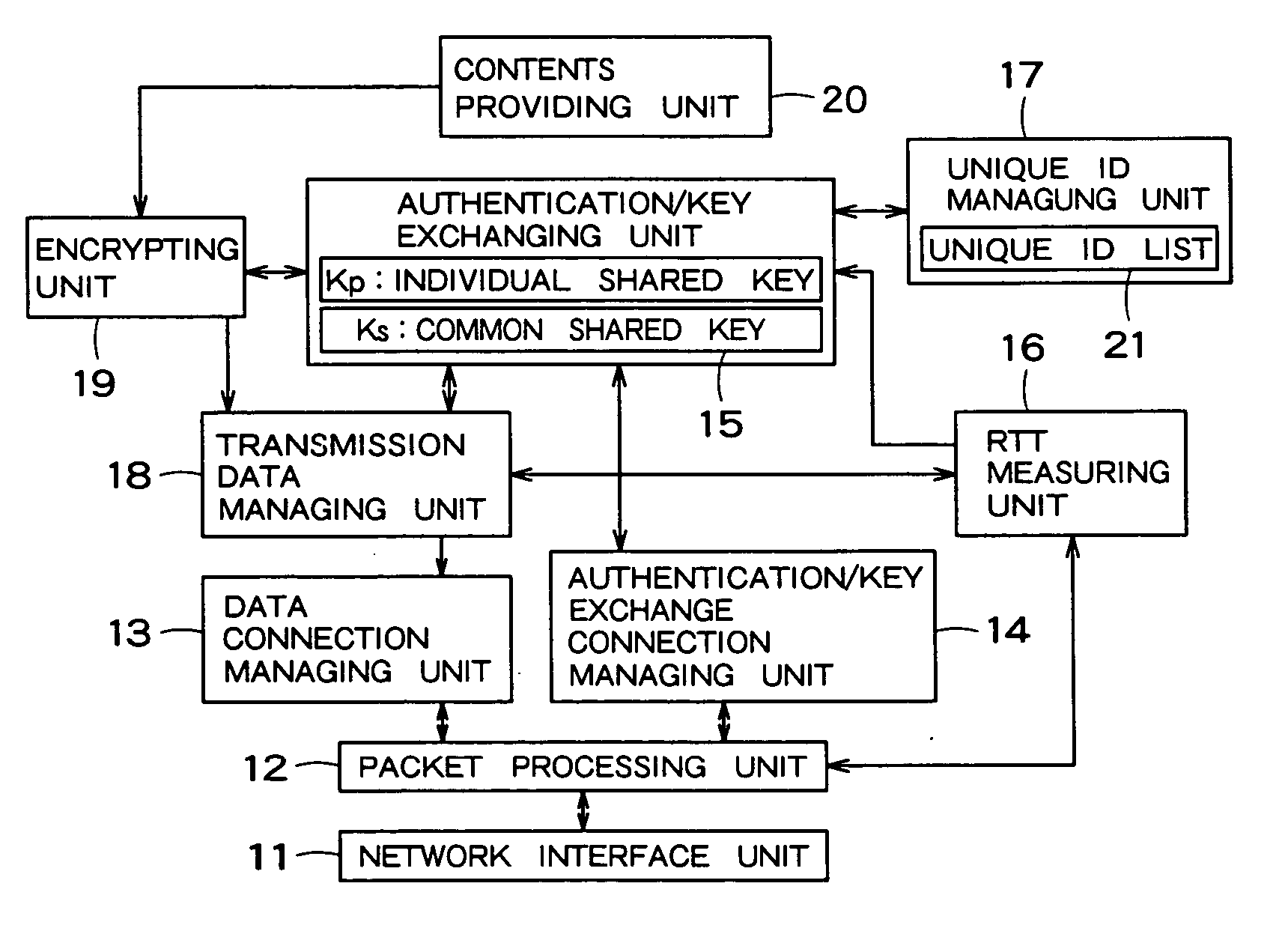
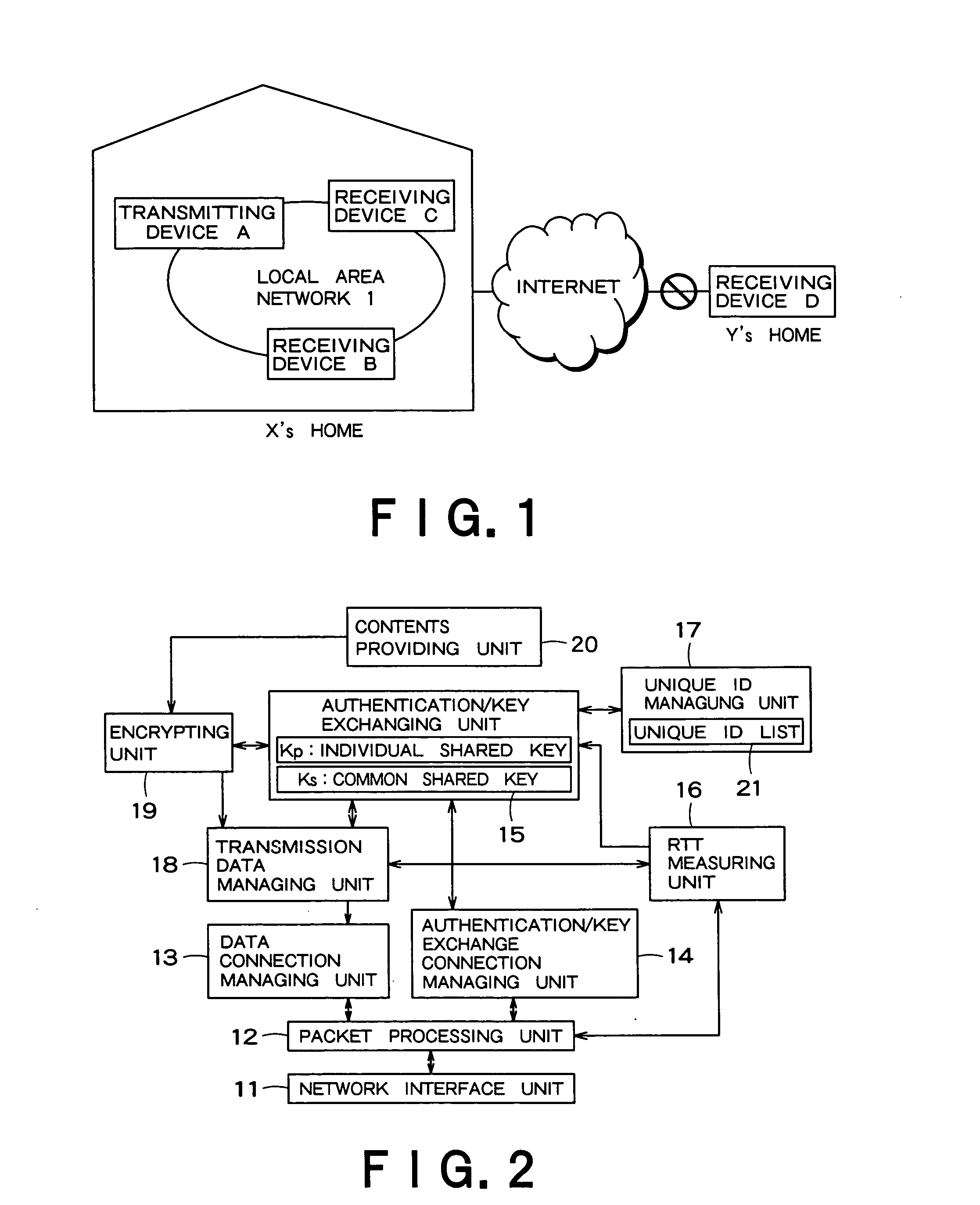
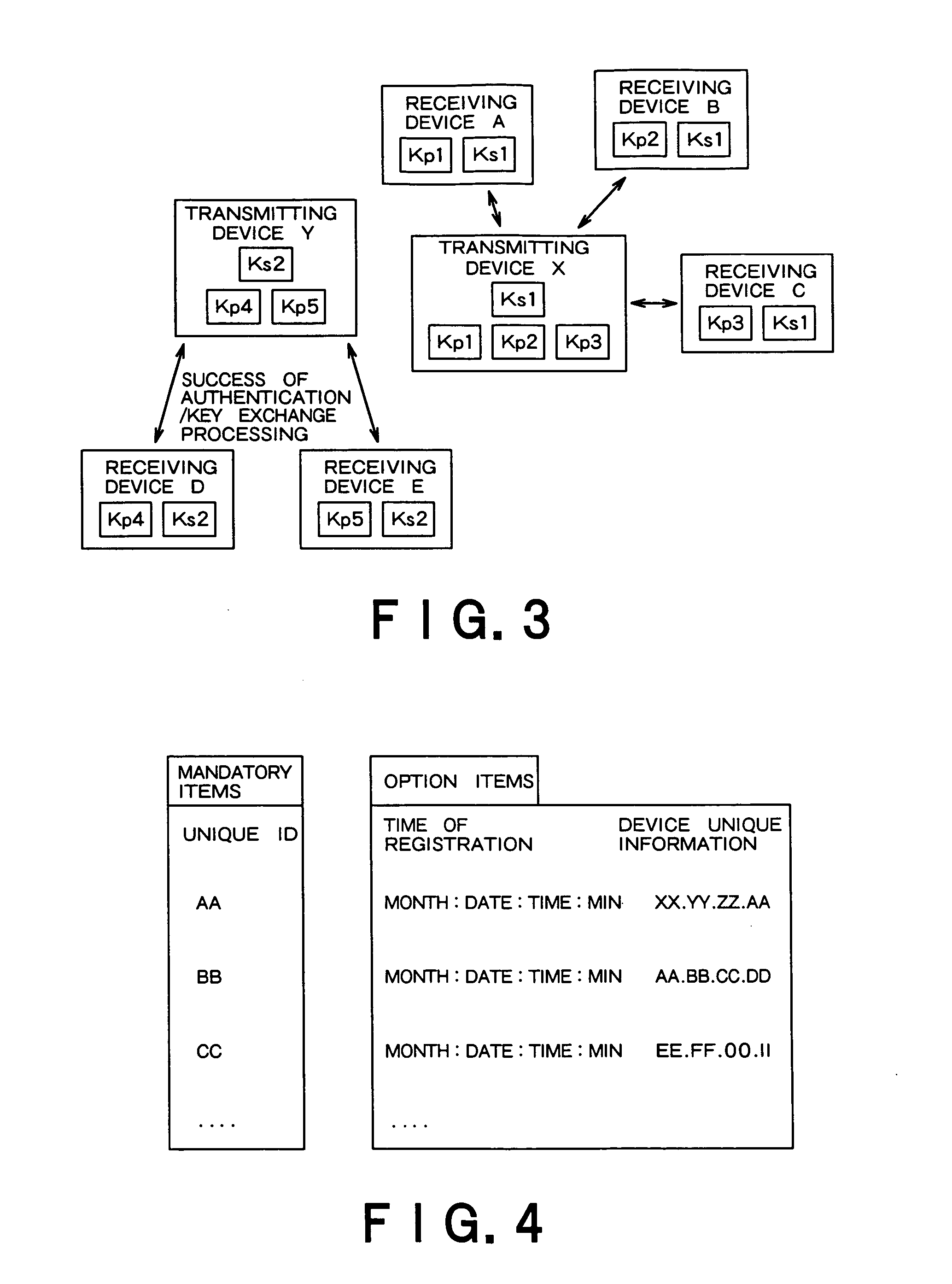
ActiveUS20050259824A1Easy to useReliably prevent illegal useDigital data authenticationSecret communicationComputer hardwareKey exchange
An information processing apparatus has an authentication / key exchange unit, a round trip time measuring unit, a common key transmitter, a contents transmitter and a contents transmitter. The round trip time measuring unit sends a round trip time measuring request generated to the communication apparatus through the first communication connection to measure the round trip time, and check whether the measured round trip time is within a predetermined time and whether a transmitting source of the round trip request response is the communication apparatus sharing the first key. The common key transmitter encrypts a second key used for contents transmission by using the first key and transmits the encrypted second key through the first communication connection when the round trip time measuring unit succeeds in the checking. The contents transmitter encrypts the contents requested by the communication apparatus by using the second key and sends the encrypted contents to the communication apparatus through the second communication connection.
Owner:KK TOSHIBA
Storage medium control unit, data storage device, data storage system, method, and control program
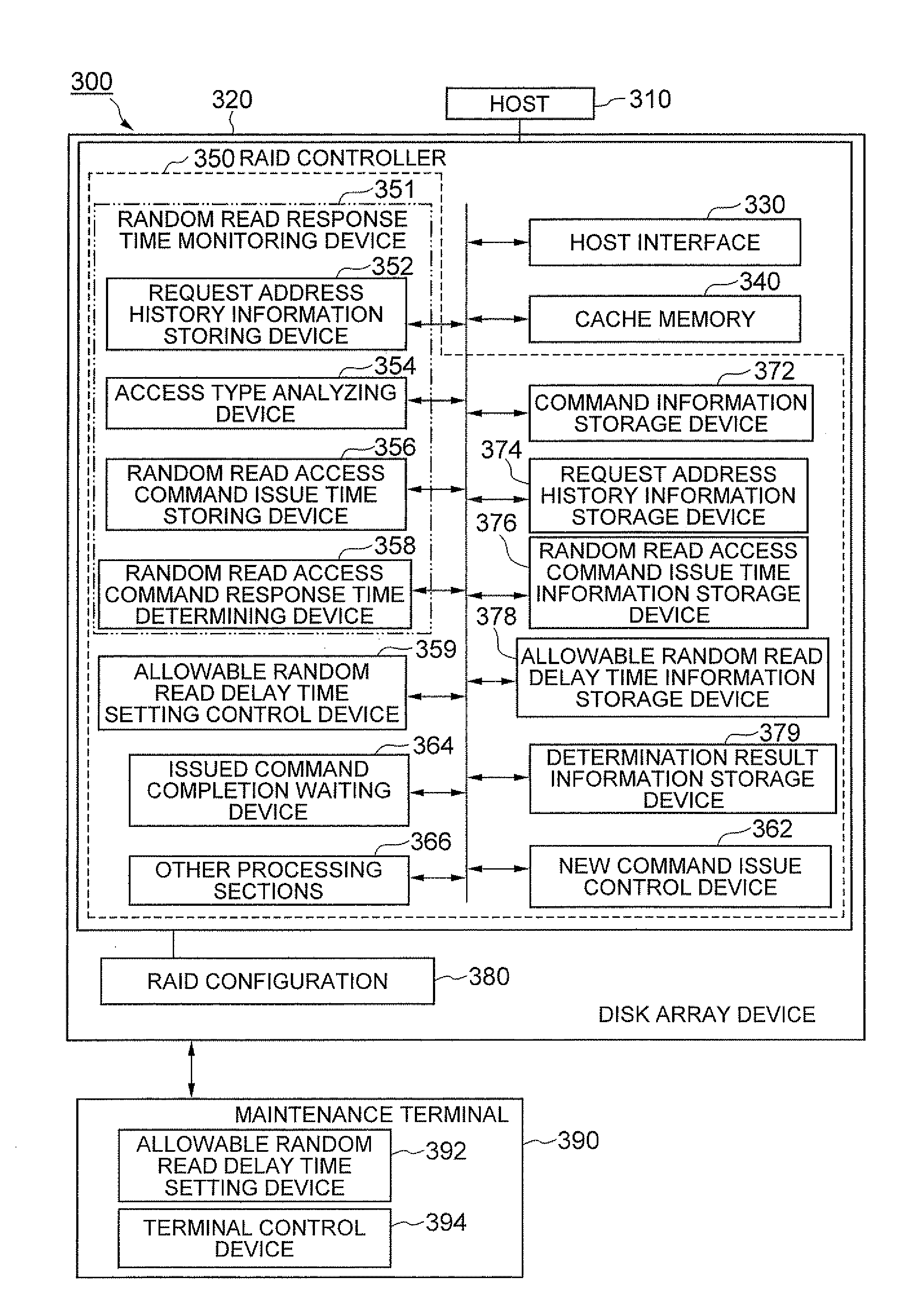
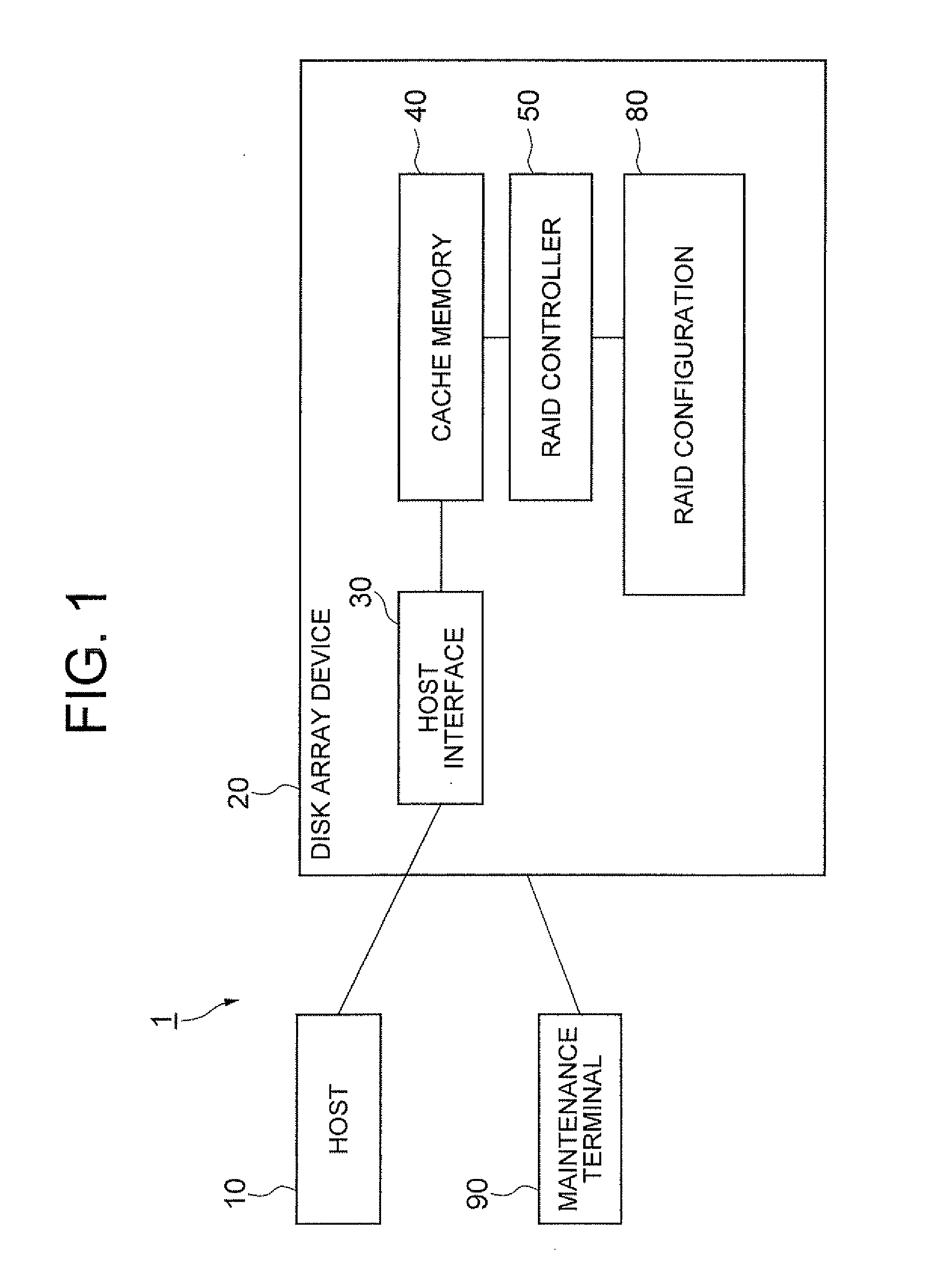
InactiveUS20080282031A1Improve processing speedAvoid residueMemory adressing/allocation/relocationUnauthorized memory use protectionMedia controlsDelayed time
To prevent random access commands from remaining even in the case of mixed sequential and random accesses. A storage medium control unit is used in a data storage device adapted to perform processing on a data storage medium based on multiple requests including sequential access requests and random access requests. The storage medium control unit includes: request response delay monitoring device for monitoring the presence of delay in response to the requests based on whether or not the response time for each request exceeds a certain allowable delay time; and request control device for preventing the rearrangement processing of the sequential access requests and controlling the processing of the requests to be performed in a certain request order at the allowable delay time if exceeded.
Owner:NEC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com