Patents
Literature
1033 results about "Standard protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
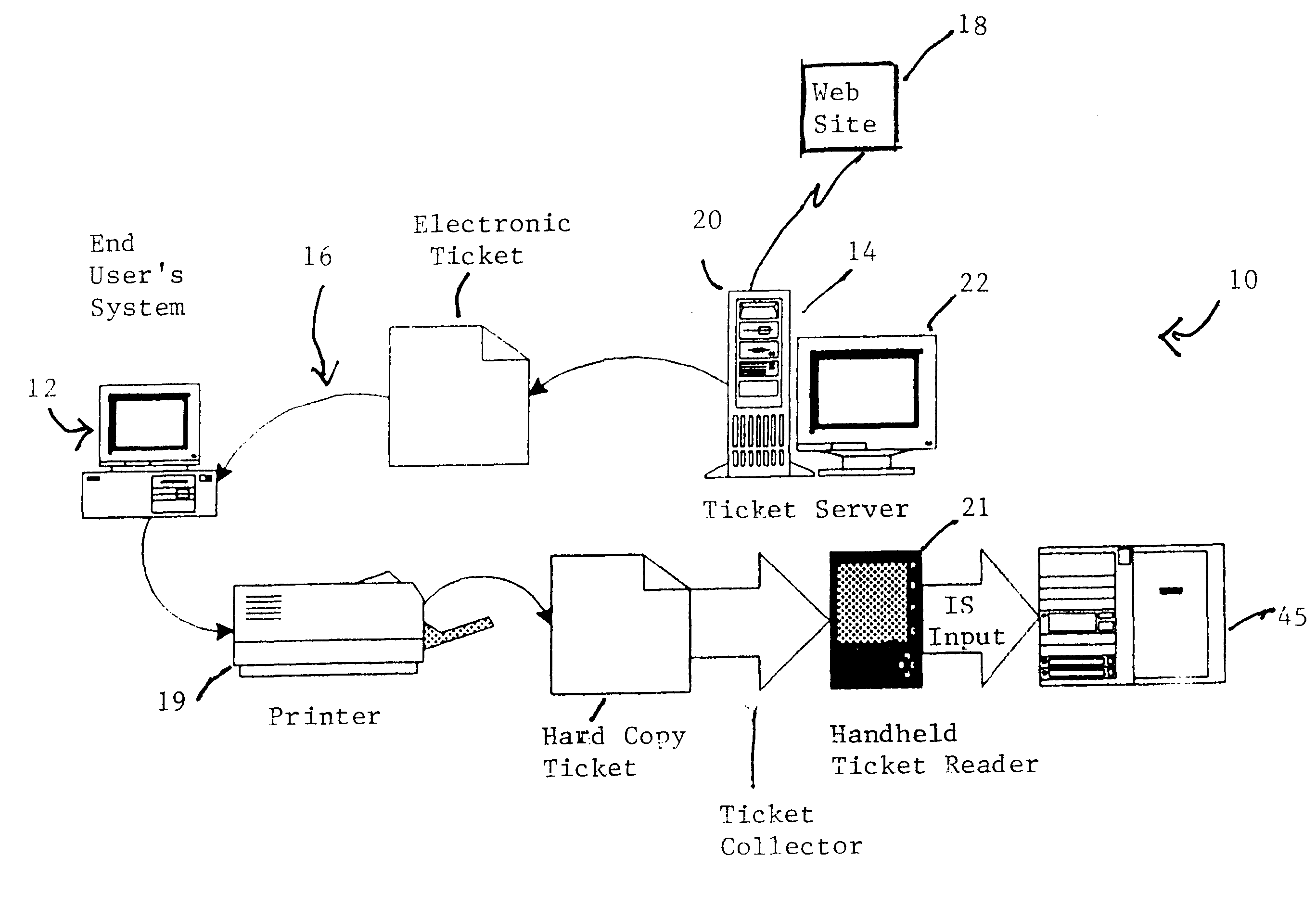
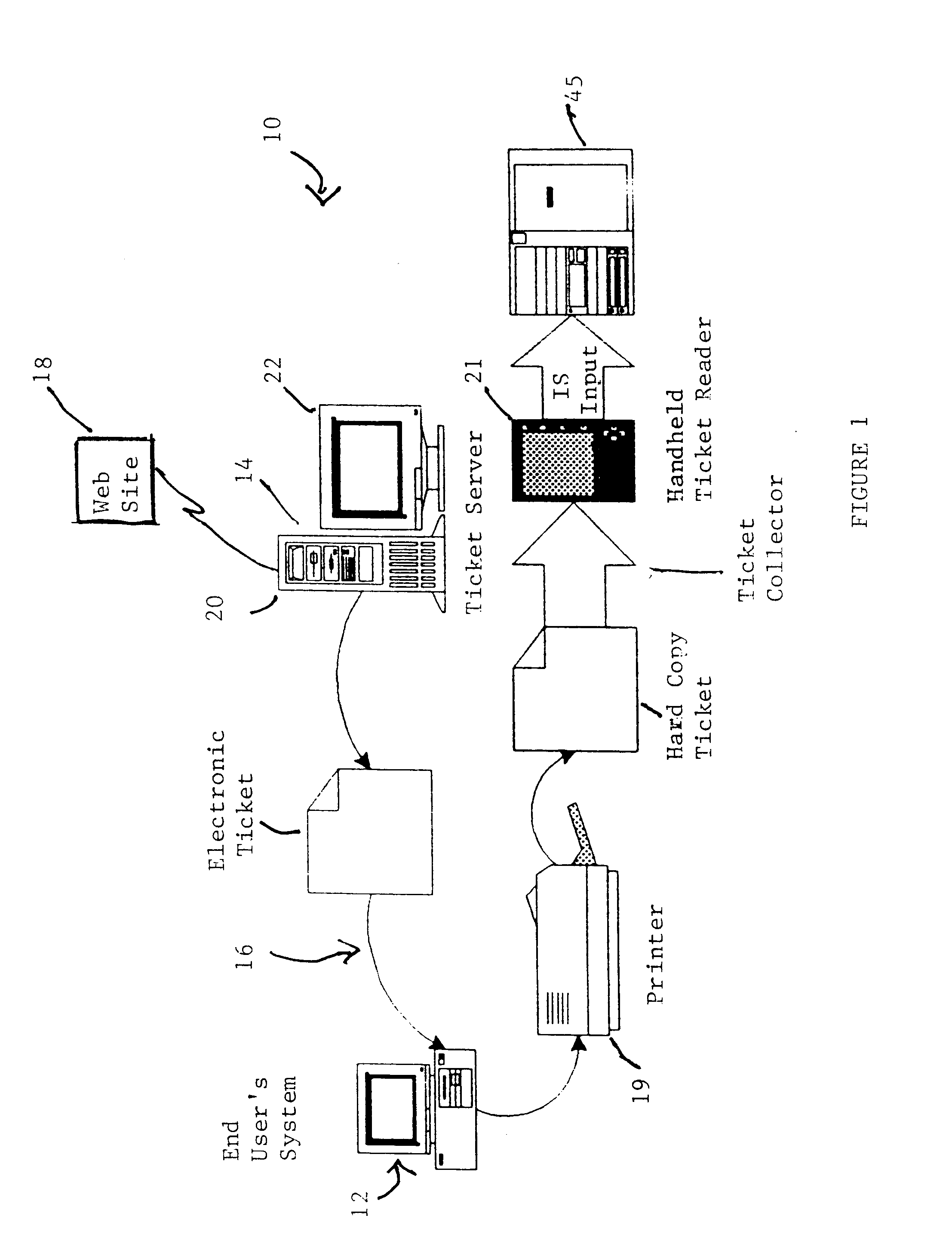
Cryptographic encoded ticket issuing and collection system for remote purchasers
InactiveUS6223166B1Prevent ticket fraudTicket-issuing apparatusElectrical apparatusCollection systemInformation networks
A cryptographic encoded, ticket issuing and collection system for real-time purchase of tickets by purchasers at remote user stations in an information network that includes a plurality of remote user stations coupled to a server in an information network, e.g., the Internet, for purchase of services, products, or tickets to an event. An operator of the remote user station selects a ticket for purchase to an event using standard protocols of information network. An electronic ticket is transmitted to the operator and includes a cypher code created using a public key cryptography system. The operator displays the electronic ticket for verification purposes and proceeds to print out the ticket at the station. The ticket is presented to a ticket collector whereupon the ticket is scanned by a portable terminal for decoding the cypher code using a public key reloaded into the terminal by the producers of the event. The decoded cypher code is compared against the event description stored in the portable terminal and if equal, the ticket is accepted for admission to the event. The ticket information is stored in the portable terminal and subsequently uploaded to the information system to check for duplicate tickets.
Owner:IBM CORP
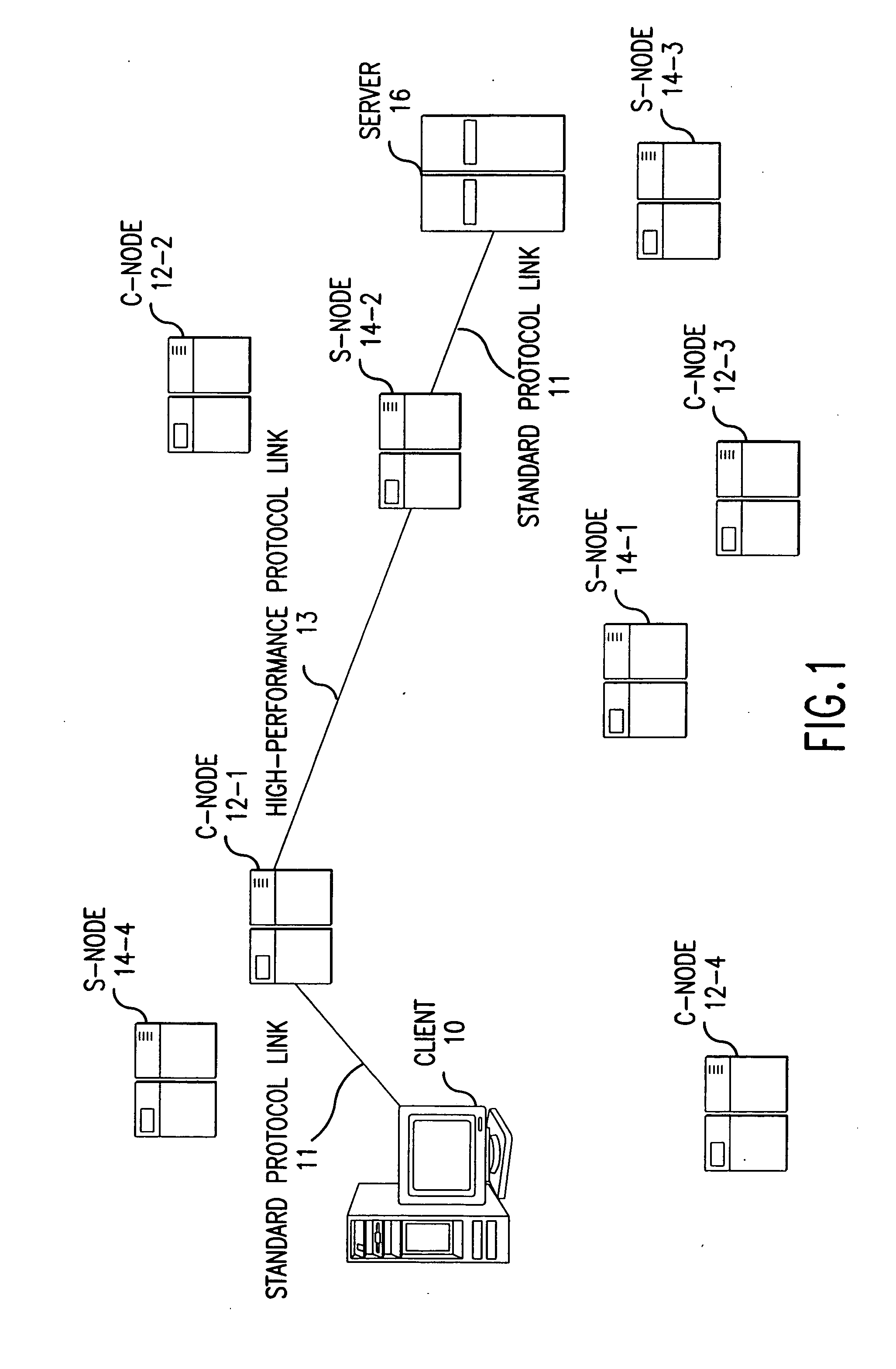
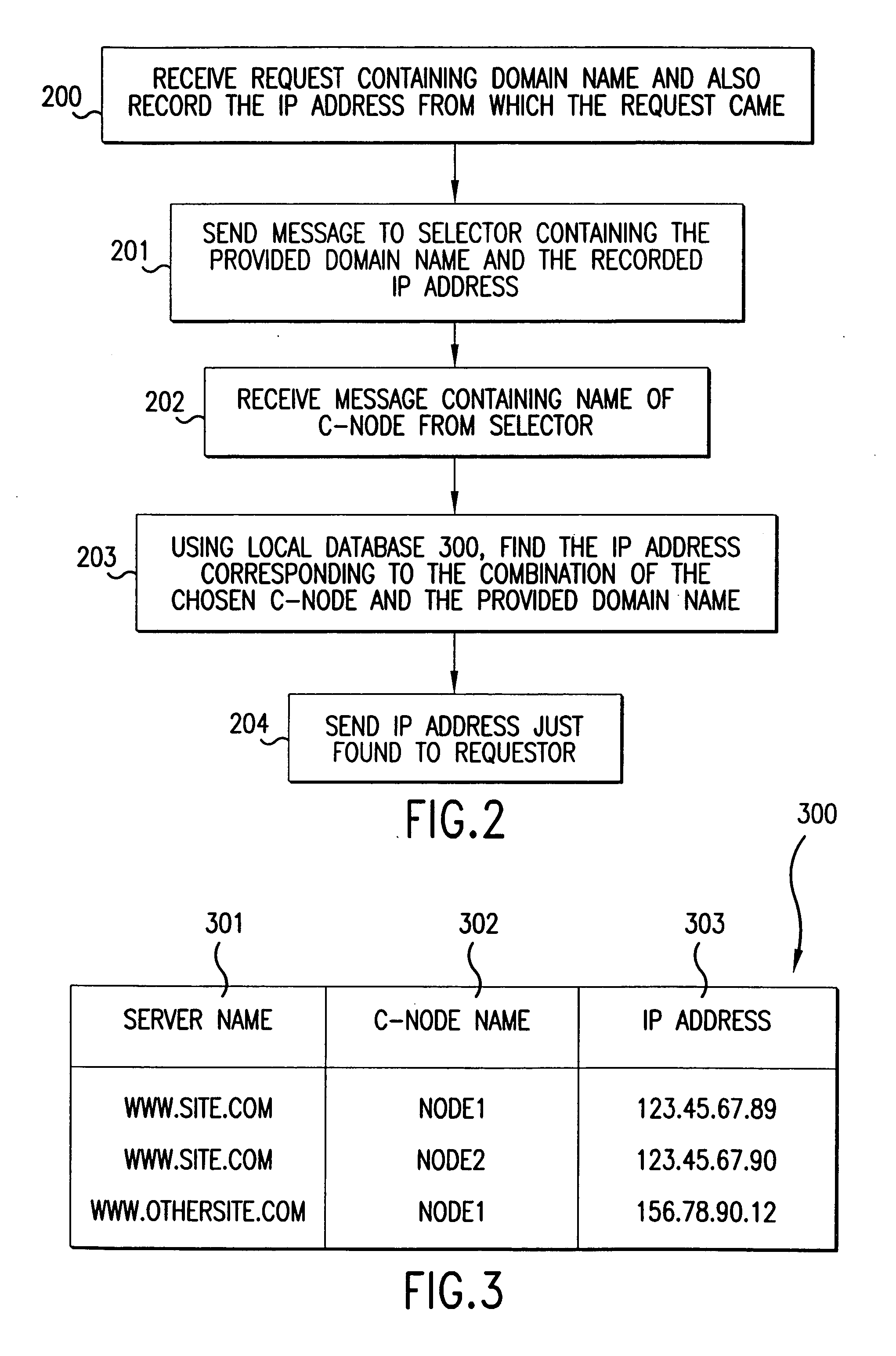
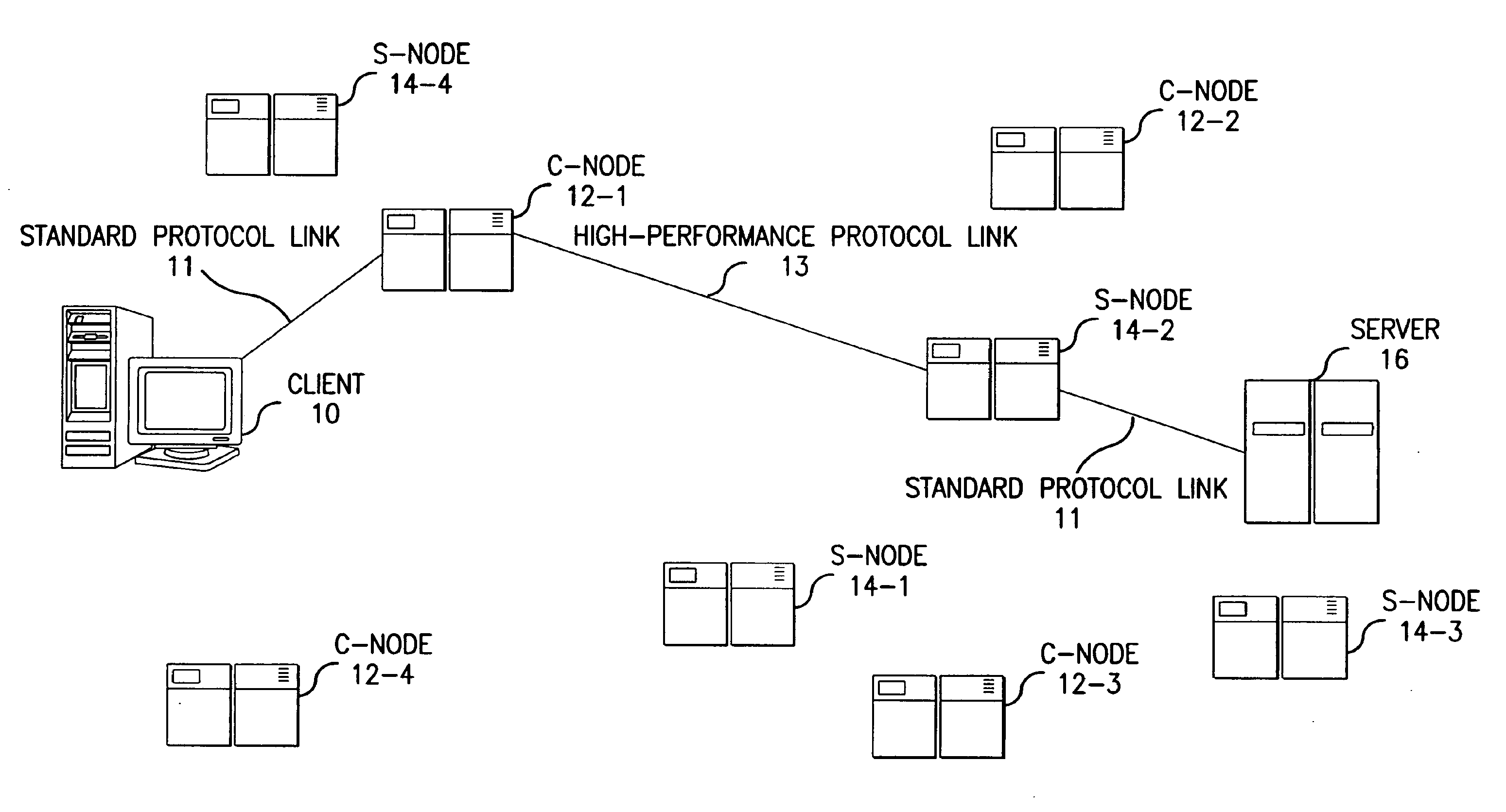
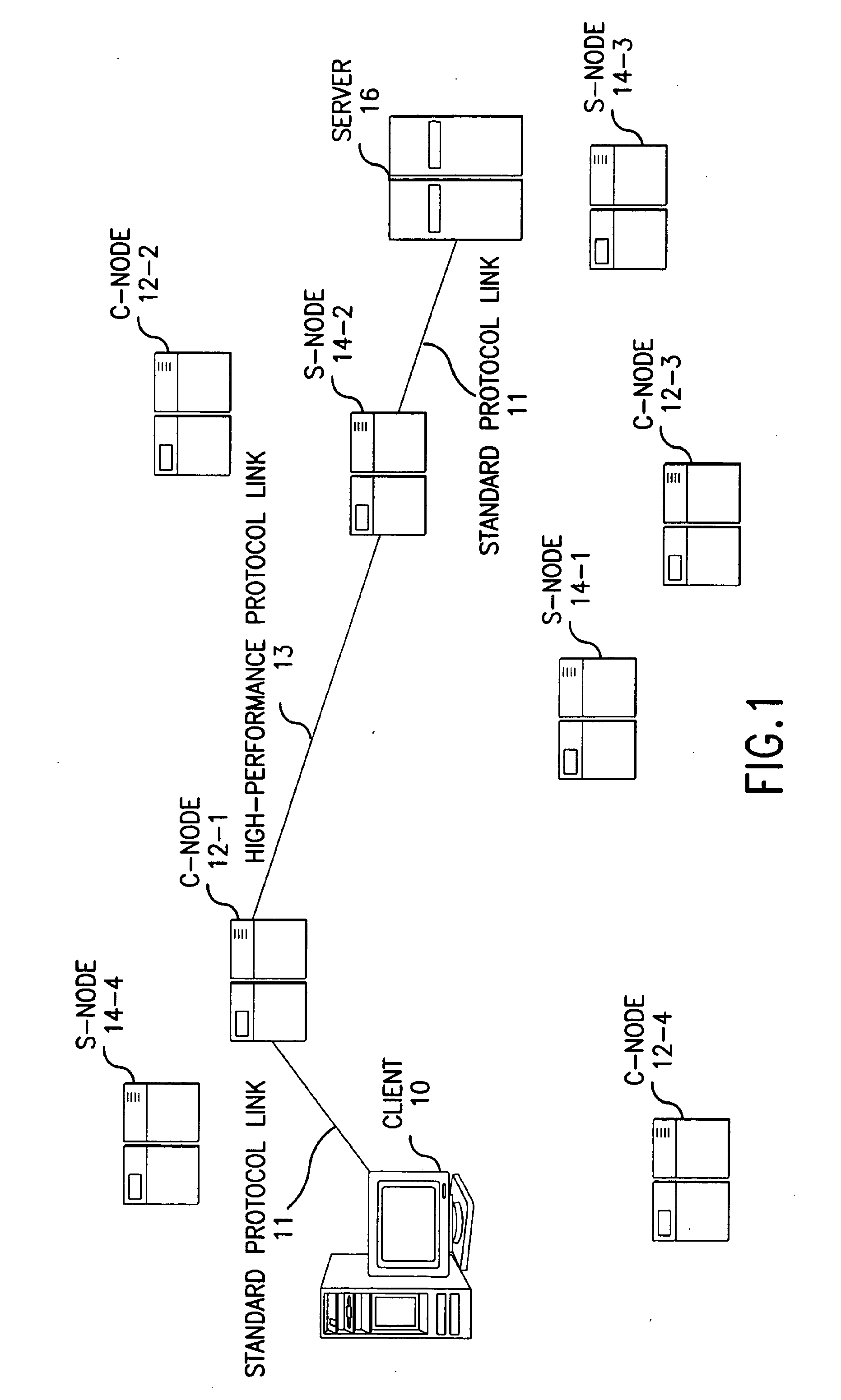
Method for high-performance delivery of web content
InactiveUS20050044270A1Improve performanceReduce deliveryDigital computer detailsData switching networksWeb serviceWeb cache
The present invention provides a method and apparatus for increasing the performance of world-wide-web traffic over the Internet. A distributed network of specialized nodes of two types is dispersed around the Internet. A web client's requests are directed to a node of the first type chosen to be close to the client, and the client communicates with this node using a standard protocol such as HTTP. This first node receives the request, and communicates the request to a node of the second type chosen to be close to the request's ultimate destination (e.g., a web server capable of generating a response to the request.) The first node communicates the request to the second node using a different, specialized, protocol that has been designed for improved performance and specifically to reduce traffic volume and to reduce latency. The second node receives communication from the first node using this specialized protocol, converts it back to a standard protocol such as HTTP, and forwards the request to the destination computer or server. Responses from the destination to the client take the corresponding reverse route, and also are carried over a specialized protocol between the two nodes. In addition, these nodes can employ other techniques such as web caches that avoid or improve some communication steps. Thus, specialized, proprietary, or complex protocols and techniques can be quickly deployed to enhance web performance without requiring significant changes to the clients or servers.
Owner:AKAMAI TECH INC
Method for high-performance delivery of web content
InactiveUS20070050522A1Improve performanceReduce deliveryMultiple digital computer combinationsData switching networksWeb serviceWeb cache
The present invention provides a method and apparatus for increasing the performance of world-wide-web traffic over the Internet. A distributed network of specialized nodes of two types is dispersed around the Internet. A web client's requests are directed to a node of the first type chosen to be close to the client, and the client communicates with this node using a standard protocol such as HTTP. This first node receives the request, and communicates the request to a node of the second type chosen to be close to the request's ultimate destination (e.g., a web server capable of generating a response to the request.) The first node communicates the request to the second node using a different, specialized, protocol that has been designed for improved performance and specifically to reduce traffic volume and to reduce latency. The second node receives communication from the first node using this specialized protocol, converts it back to a standard protocol such as HTTP, and forwards the request to the destination computer or server. Responses from the destination to the client take the corresponding reverse route, and also are carried over a specialized protocol between the two nodes. In addition, these nodes can employ other techniques such as web caches that avoid or improve some communication steps. Thus, specialized, proprietary, or complex protocols and techniques can be quickly deployed to enhance web performance without requiring significant changes to the clients or servers.
Owner:AKAMAI TECH INC
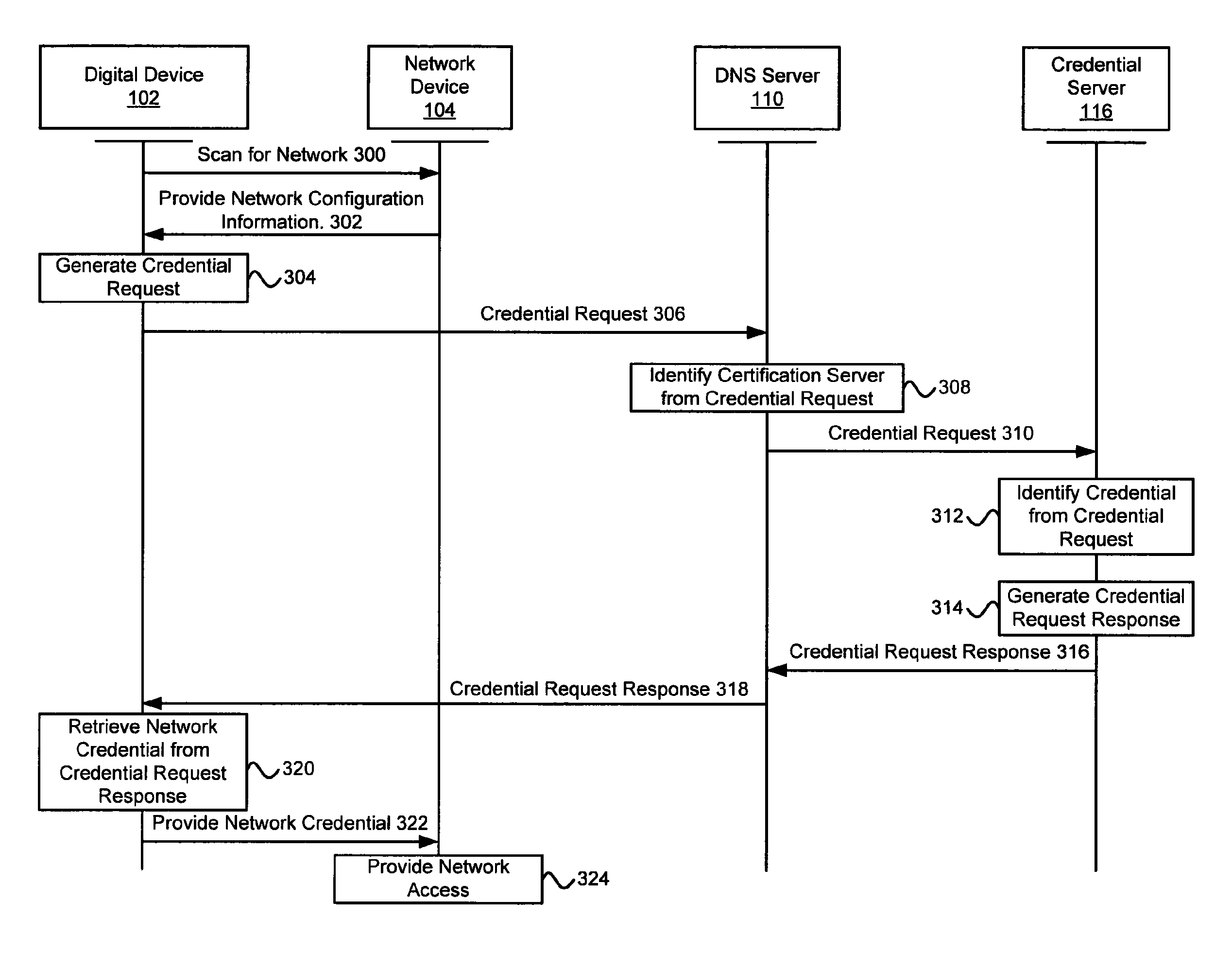
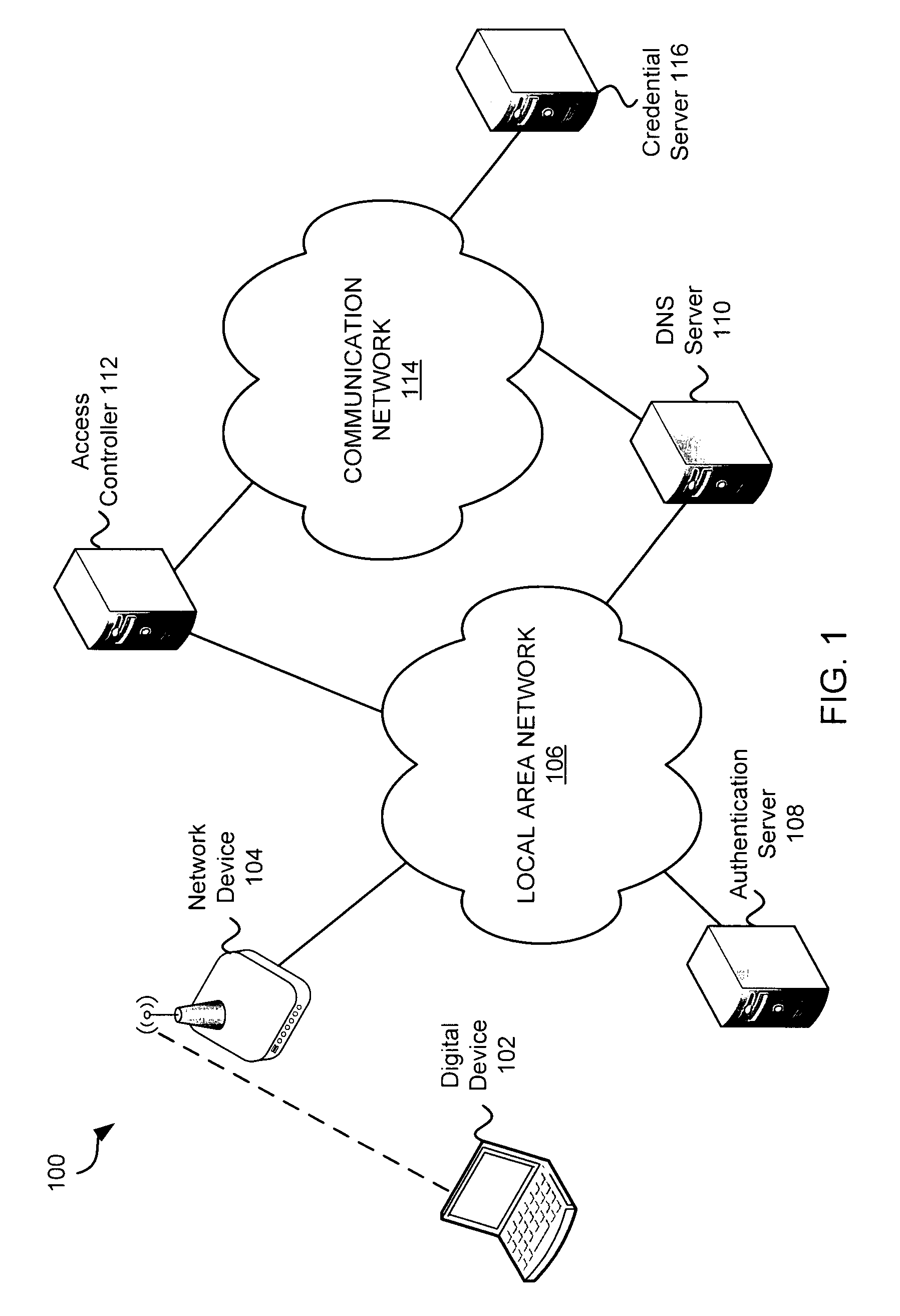
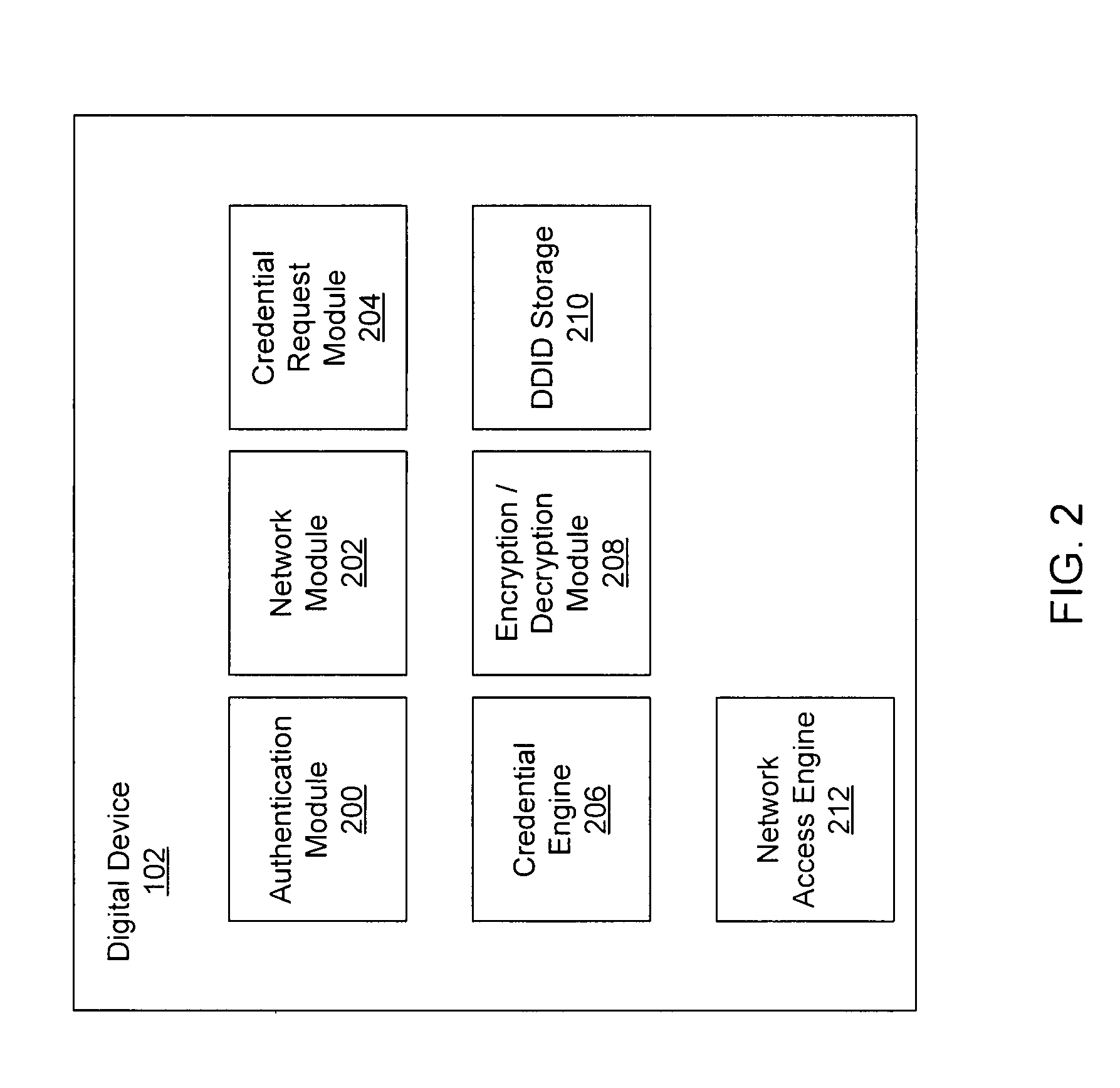
Systems and methods for acquiring network credentials
ActiveUS20080060066A1Digital data processing detailsAnalogue secracy/subscription systemsRequest–responseNetwork Access Device
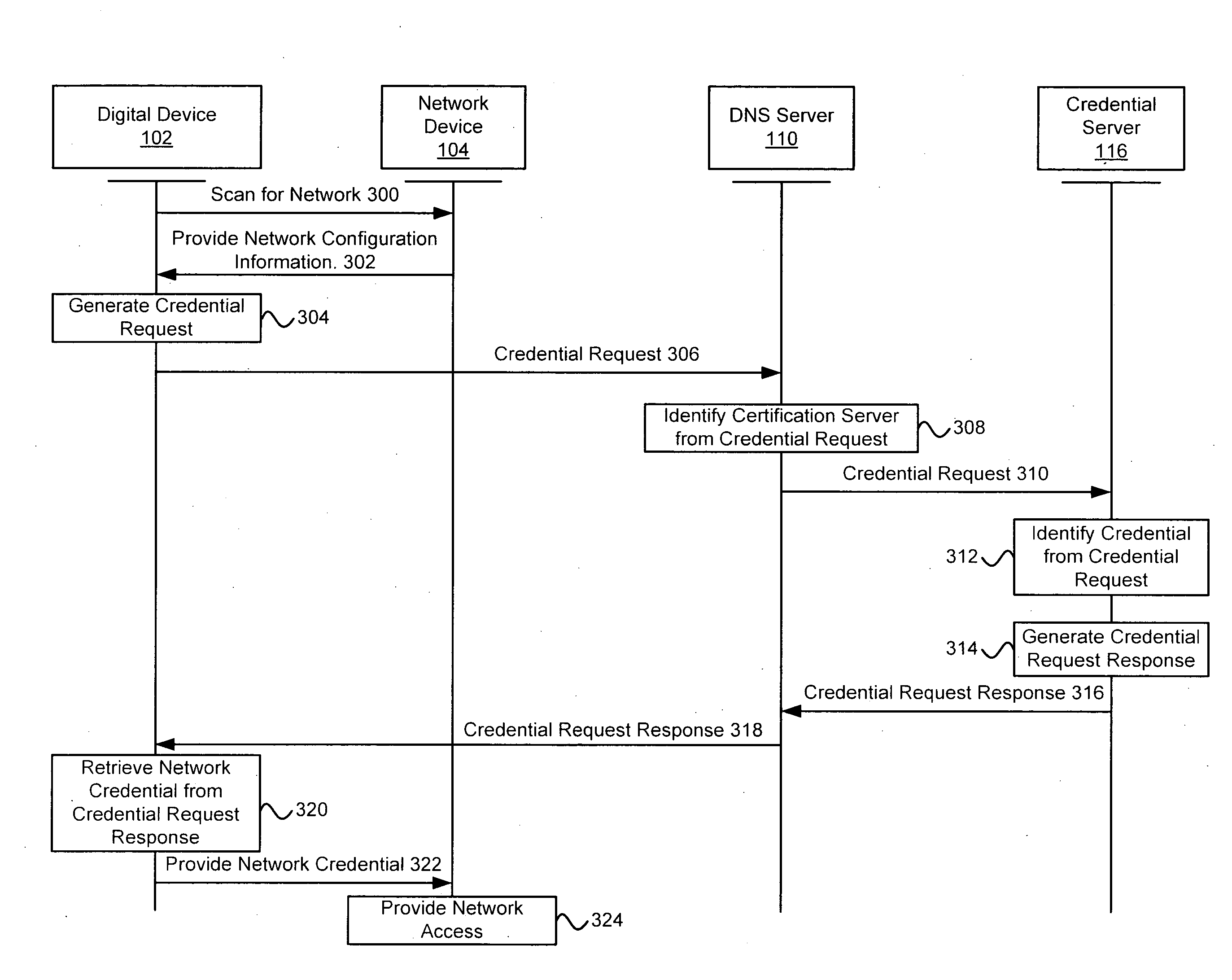
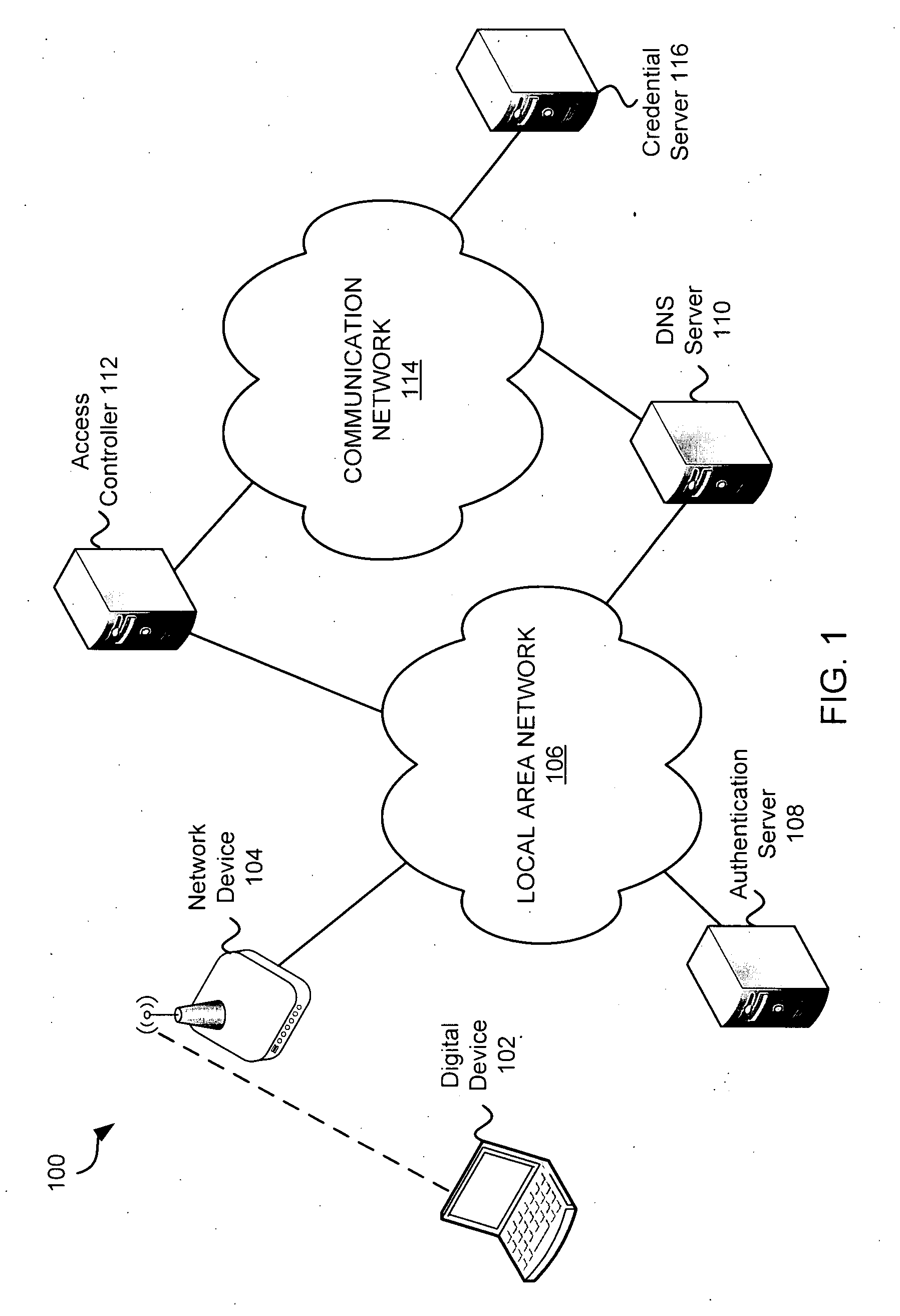
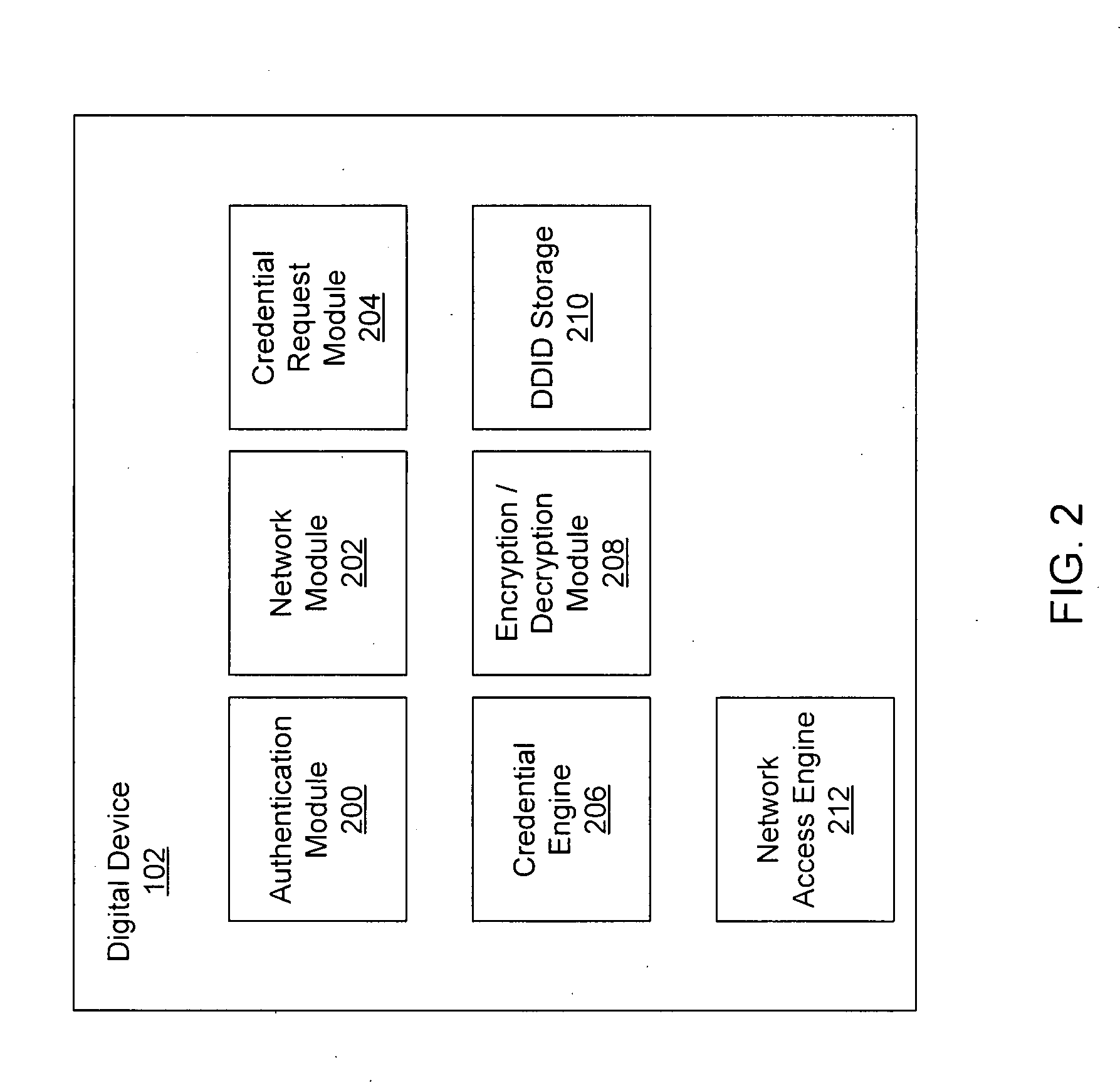
Exemplary methods and systems for acquiring network credentials for network access are described. The exemplary method comprises receiving network configuration information from a network device on a communication network, generating a credential request, transmitting the credential request to a credential server over a standard protocol of the network device, receiving the credential request response, and providing a network credential from the credential request response to the network device to access the communication network.
Owner:CHANNEL IP BV
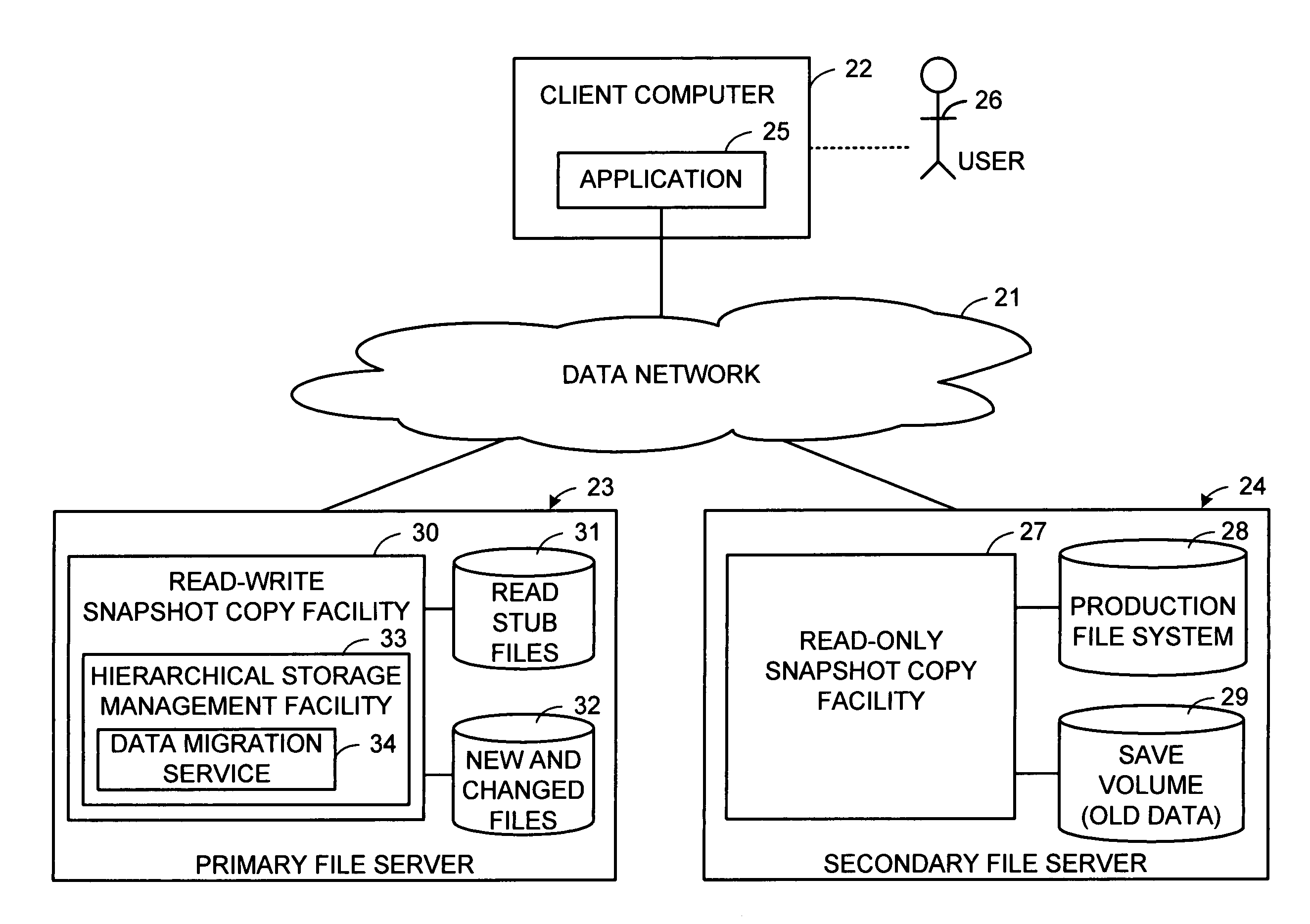
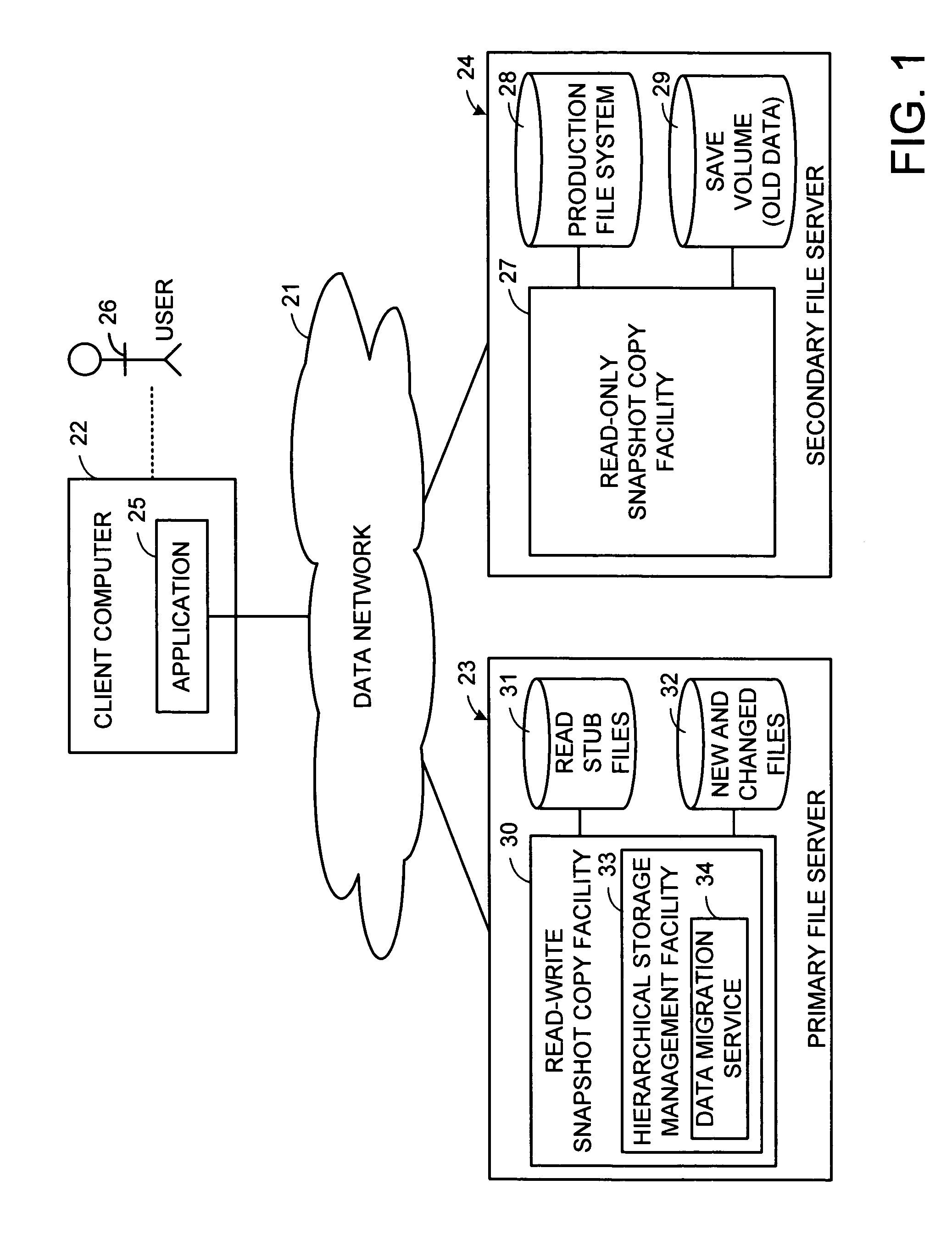
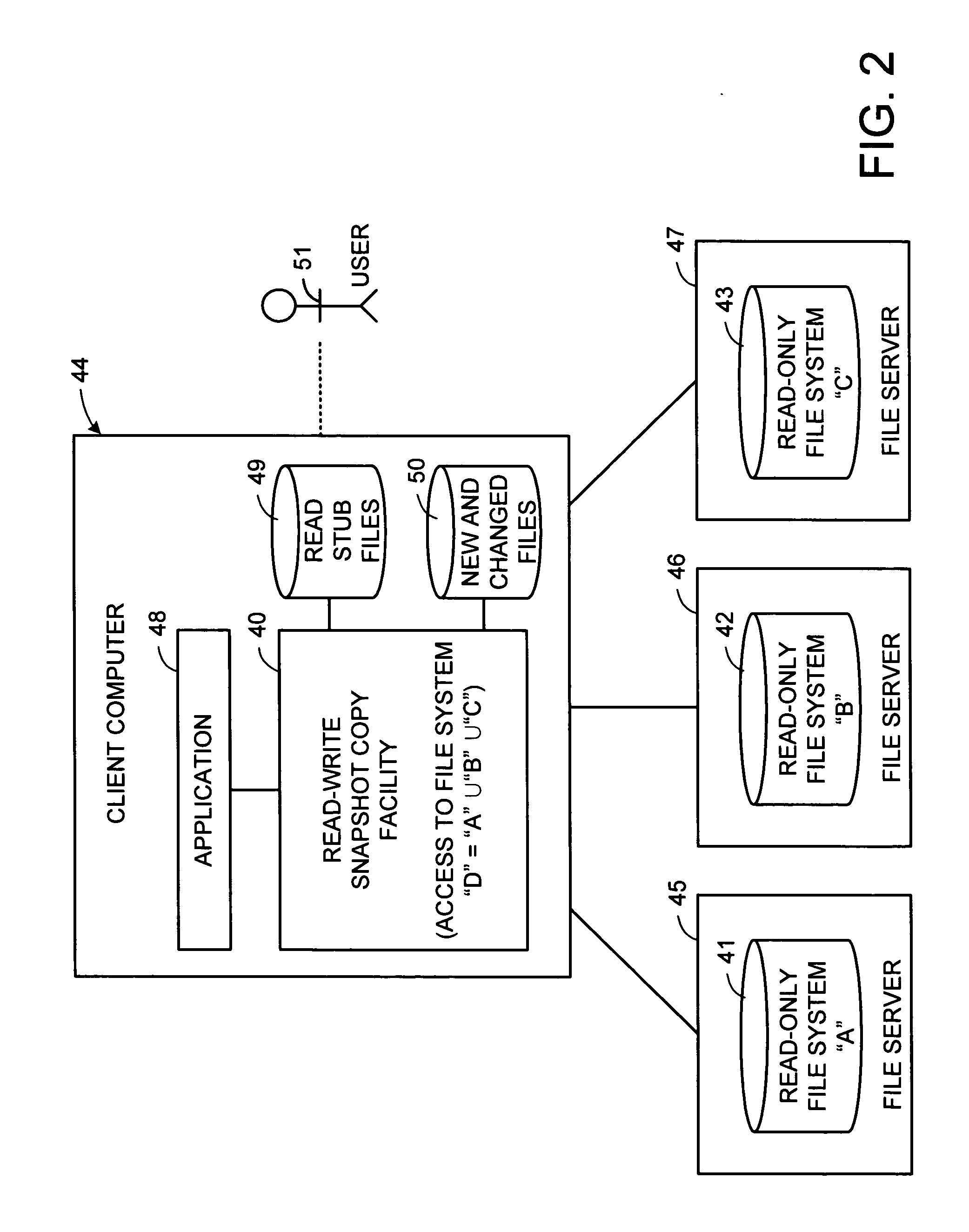
Distributed open writable snapshot copy facility using file migration policies
ActiveUS20060212481A1Data processing applicationsDigital data processing detailsFile systemHeterogeneous network
A read-write snapshot copy facility is constructed from a hierarchical storage management facility. The read-write snapshot copy file system initially comprises stub files pointing to the files in a read-only snapshot copy file system. When an application writes to a file in the read-write snapshot copy, the read-write snapshot copy facility migrates a copy of the file to replace the stub file, and then writes to the migrated file. Because the read-write snapshot copy facility references the files in the read-only snapshot file system in a network namespace using standard protocols such as NFS or CIFS, the read-write snapshot copy facility permits referencing of distributed read-only snapshot file systems in an open (heterogeneous) network environment, and the read-write snapshot copy is scalable by linking the read-write snapshot copy facility to multiple file servers containing read-only snapshot file systems.
Owner:EMC IP HLDG CO LLC
Systems and methods for acquiring network credentials
ActiveUS8191124B2Digital data processing detailsAnalogue secracy/subscription systemsRequest–responseNetwork Access Device
Exemplary methods and systems for acquiring network credentials for network access are described. The exemplary method includes receiving network configuration information from a network device on a communication network, generating a credential request, transmitting the credential request to a credential server over a standard protocol of the network device, receiving the credential request response, and providing a network credential from the credential request response to the network device to access the communication network.
Owner:CHANNEL IP BV
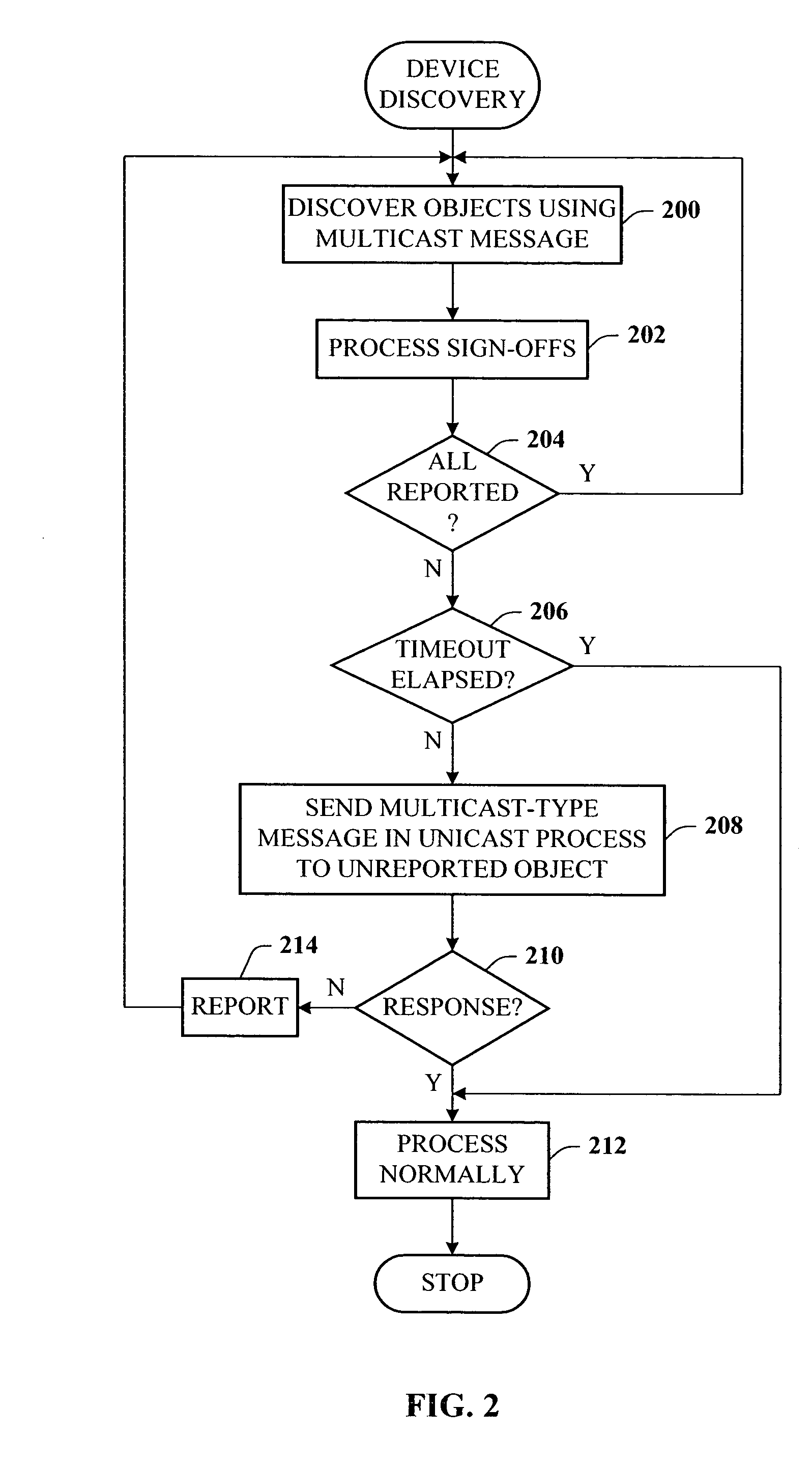
Presence tracking for datagram based protocols with search
InactiveUS20050108331A1Reduce network trafficEasy searchMultiple digital computer combinationsSecuring communicationClient-sideBroadcast multicast
A presence tracking architecture for datagram-based protocols. A client application seeking to know the presence or lack thereof of a device and / or service utilizes a standard protocol in a non-intuitive way to trigger notification of the device and / or service before any associated timeout expires. At first presence, a multicast message is broadcast to notify all devices. Subsequently, on-demand notification may be requested by a client application by sending directly (e.g., in unicast) to the device before its timeout has expired a message that is normally only sent in multicast. If capable, the device can then respond normally with a unicast message indicating it is on-line. If the response is not received, the device and / or service is determined to be off-line.
Owner:MICROSOFT TECH LICENSING LLC
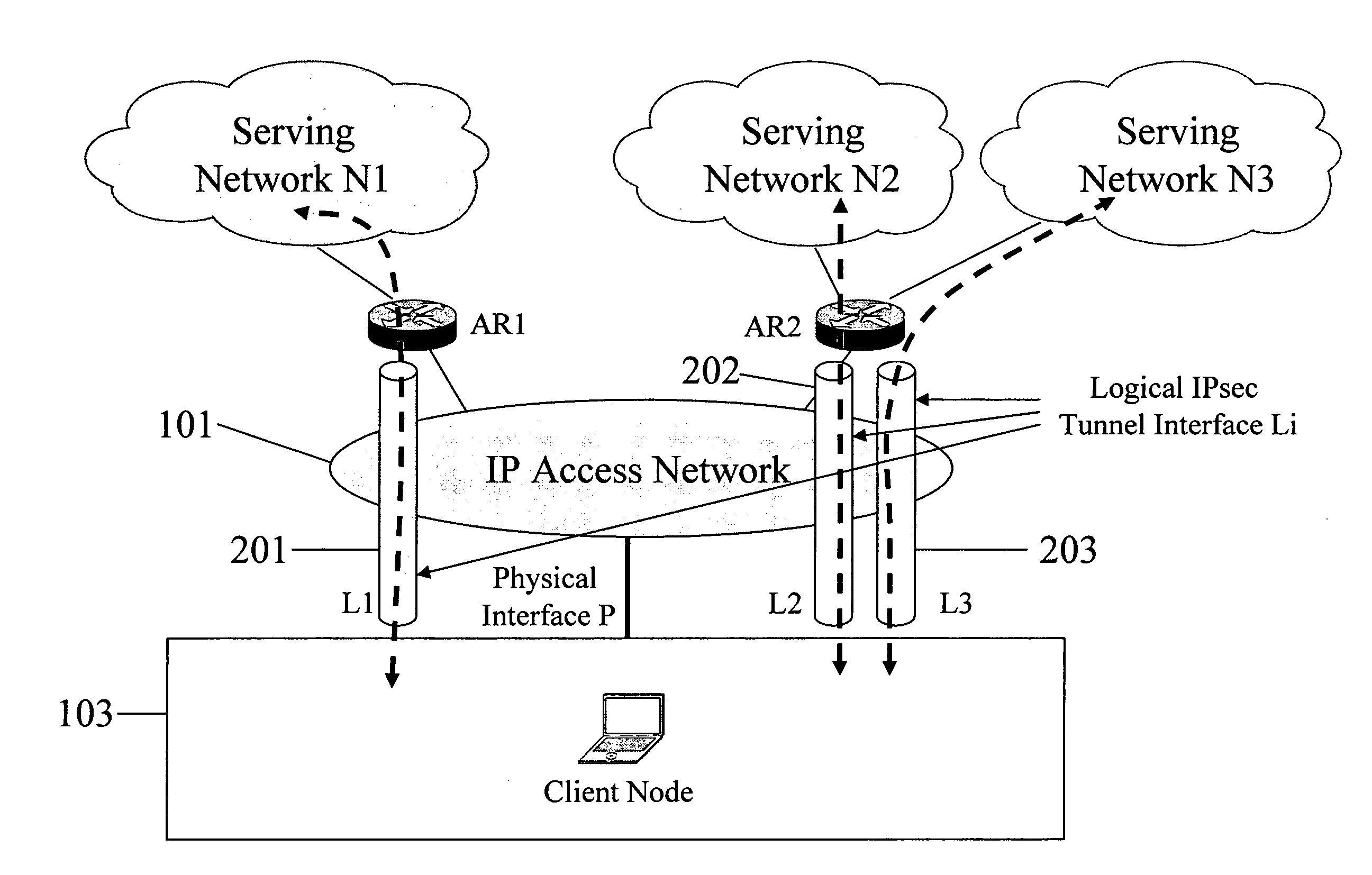
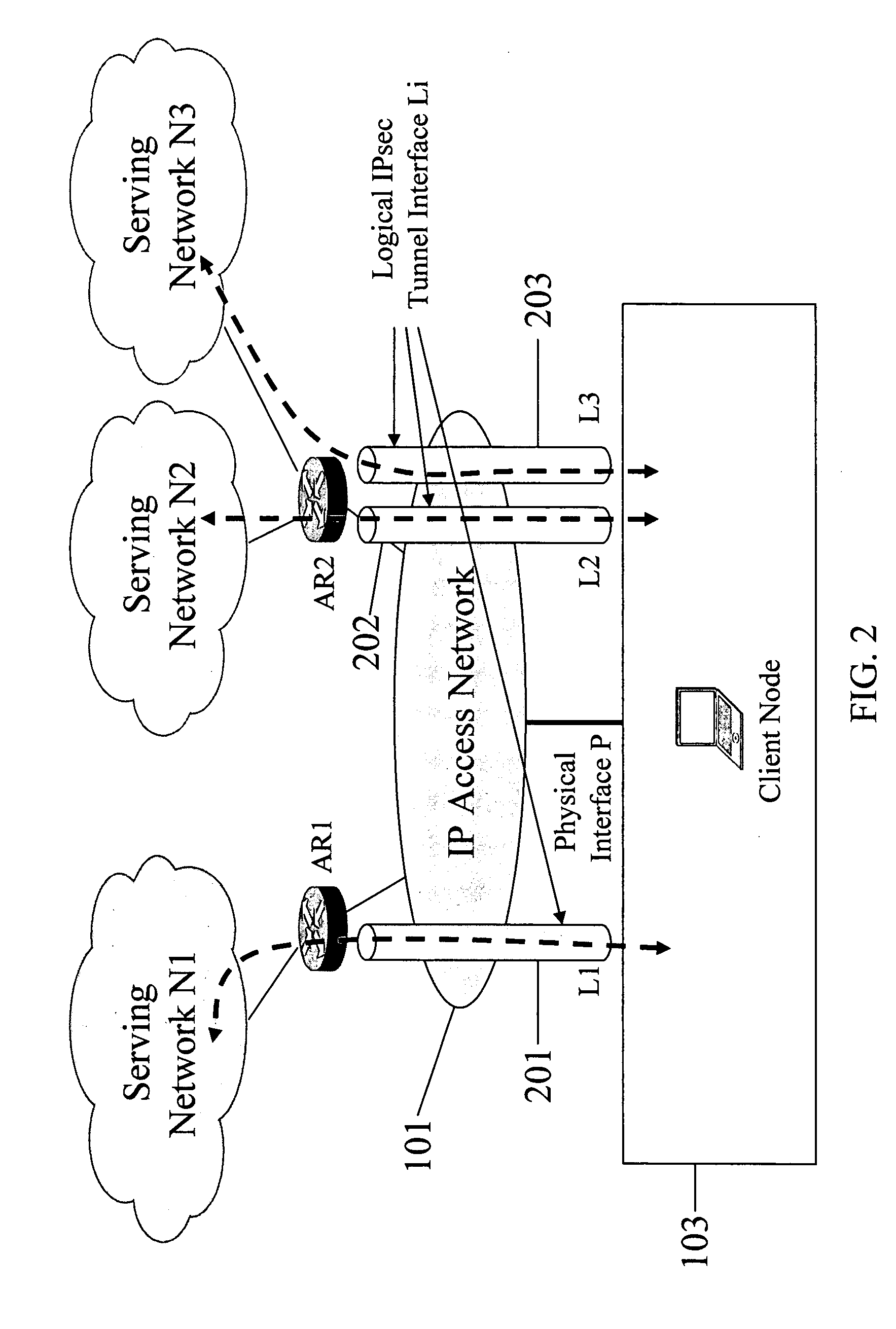
Serving network selection and multihoming using IP access network
InactiveUS20050165953A1Simple methodAssess restrictionMultiple digital computer combinationsAccess networkClient-side
In some illustrative embodiments, an IP-layer based network selection and multihoming method is provided that enables a flexible and secure dynamic selection of one or more serving networks for use by a client node. The method is independent of any link-layer technology. A serving network can be an ISP network, a NAP network exchange facility, a VLAN, or the like. Network information is advertised to a client node, the client node is authenticated and authorized for use of an access router, and a secure tunnel is established between the client node and the access router. The method can be implemented by using standard protocols, and can work over any existing or future link-layer technologies that are able to carry IP datagrams, without any modification.
Owner:TELCORDIA TECHNOLOGIES INC +2
Method and system for configuration and download in a restricted architecture network
ActiveUS20060010438A1Avoids complication and difficultySimplify writingDigital computer detailsData resettingExtensibilityData file
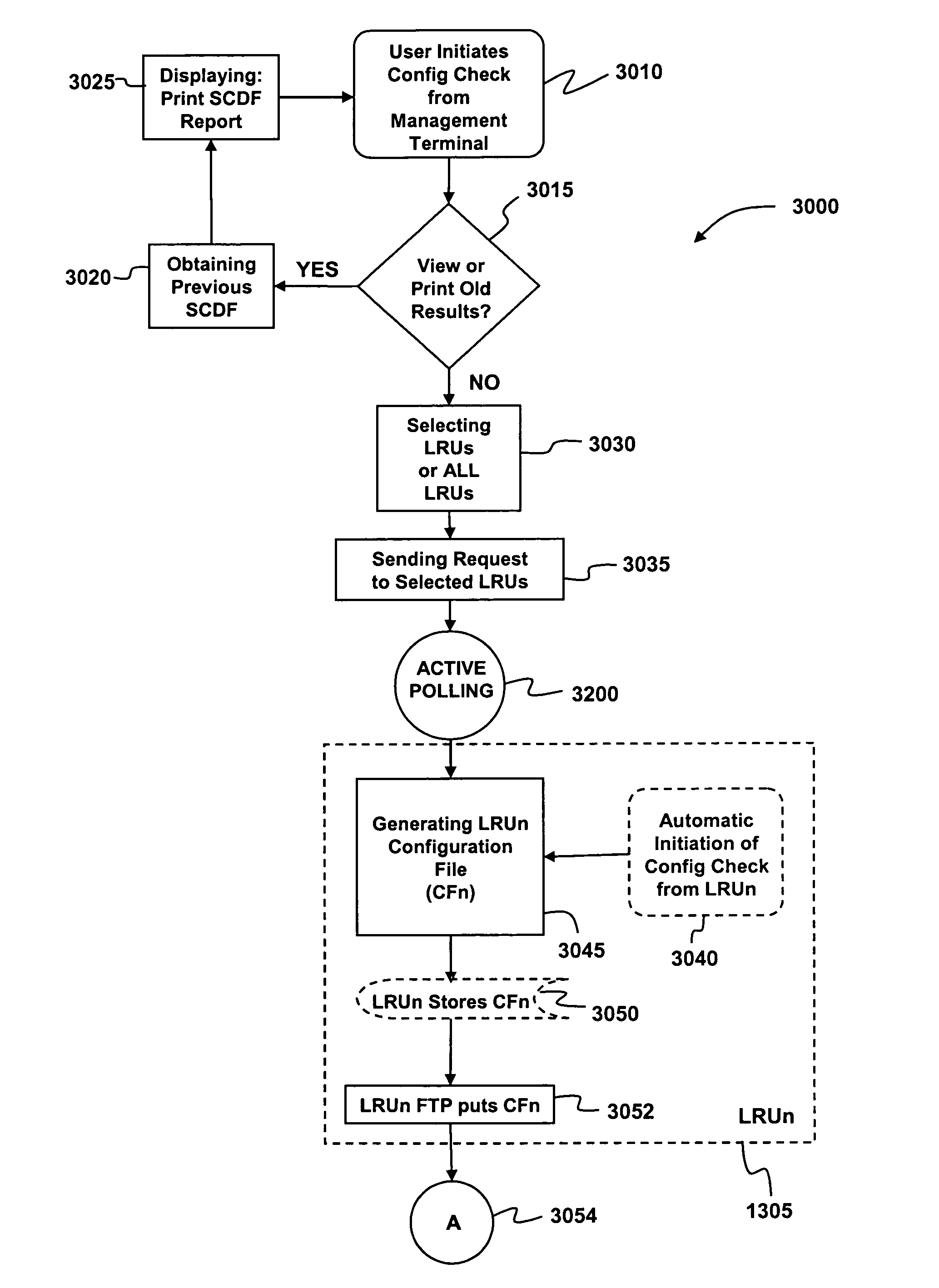
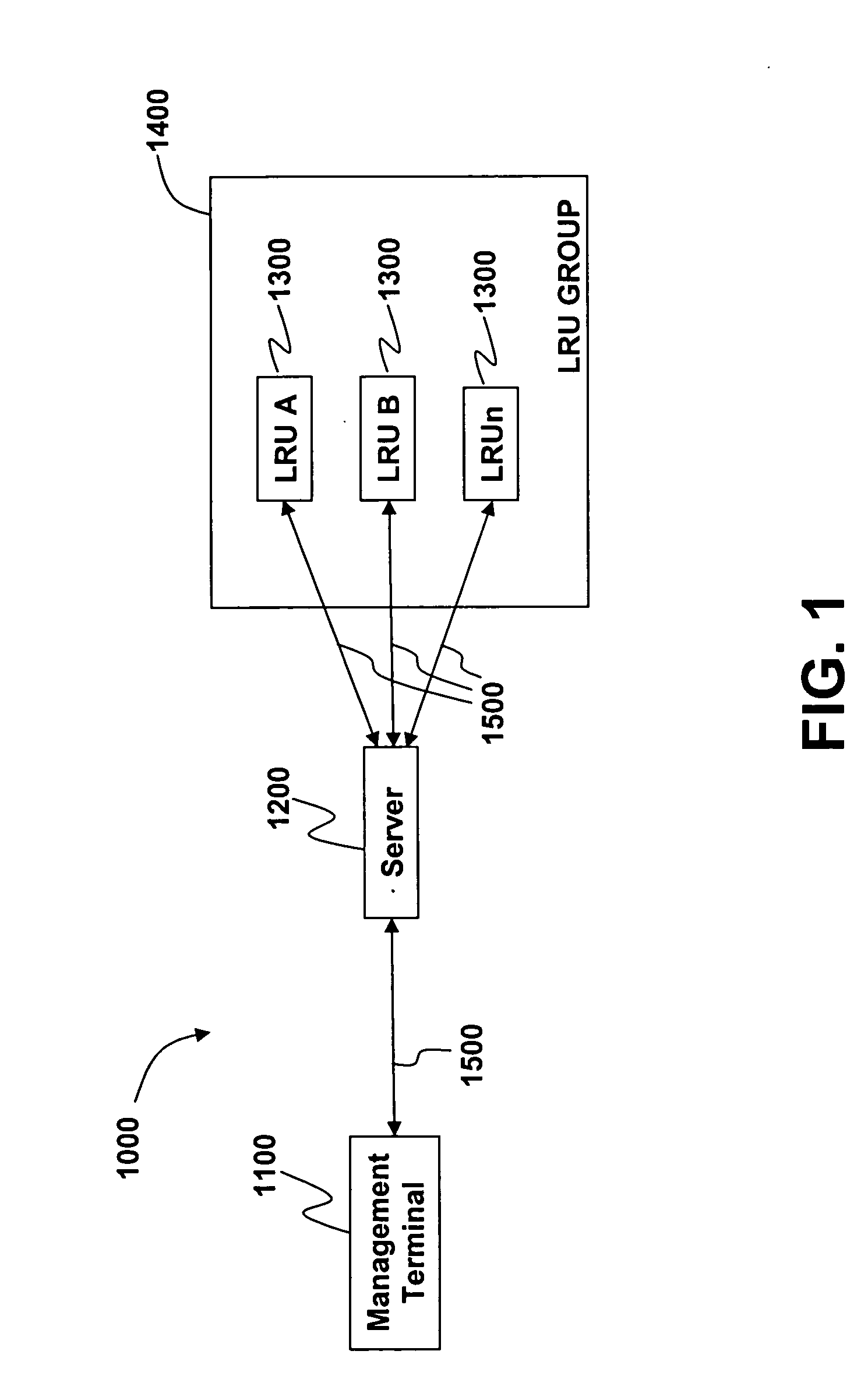
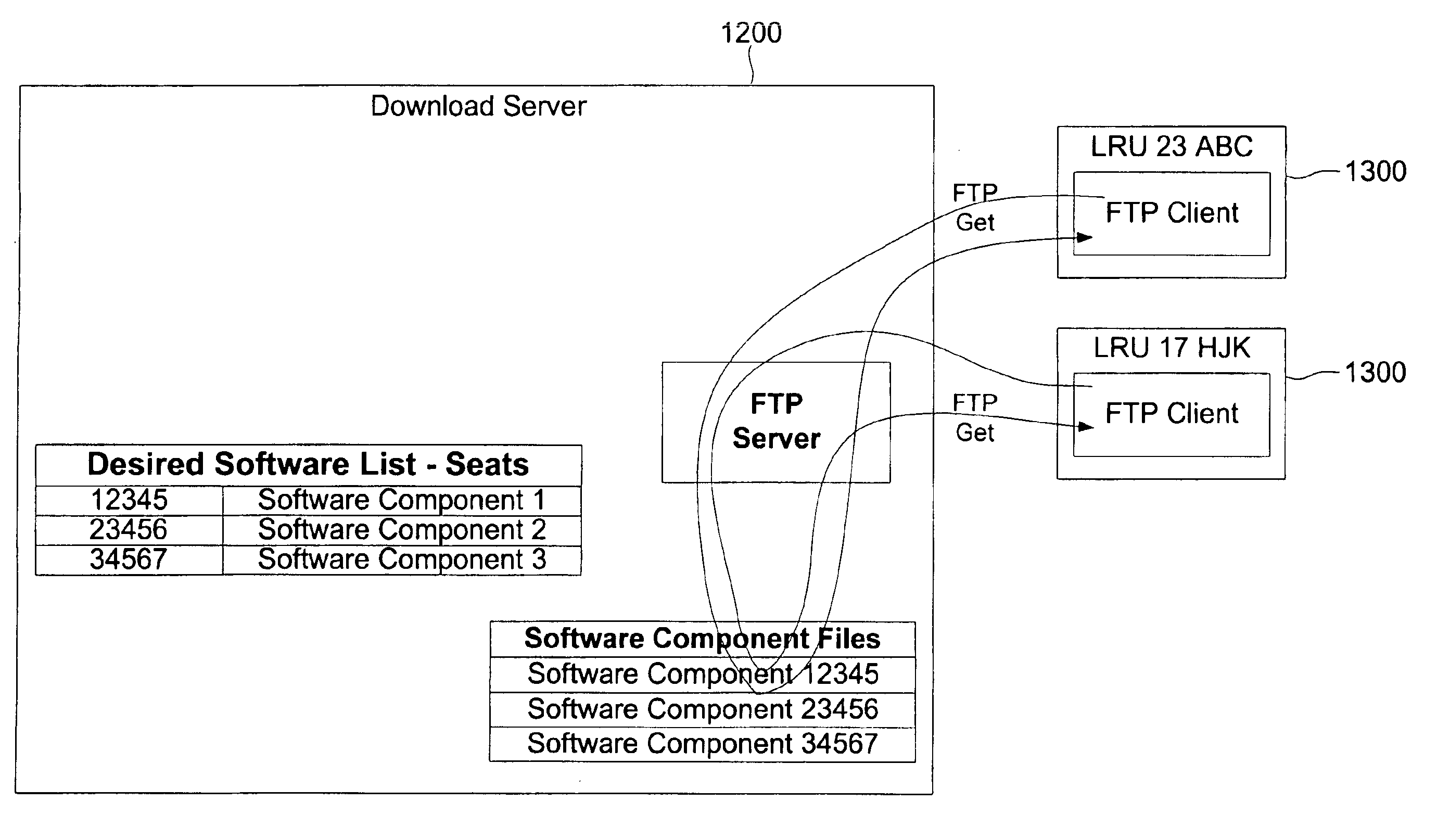
A method and system are provided for updating software configurations of line-replaceable unit (LRU) computers in a restricted architecture network such as an in-flight entertainment system (IFES). Operating in an efficient and parallel manner, each of the LRUs independently creates an individual configuration file that identifies current software components. Each of the LRUs transmits its respective configuration file to a configuration server either automatically upon startup or manually upon request. The configuration server updates a system configuration data file with the current configuration files received from the individual LRUs. In a downloading method, a download server sends a list of desired software components to the LRUs. Each of the LRUs independently and simultaneously transfer (download) the needed software from the download server. The LRU independently requests the download server to download the needed software components. To improve scalability and reliability, the file transfers utilize standard protocols, such as FTP.
Owner:THALES AVIONICS INC
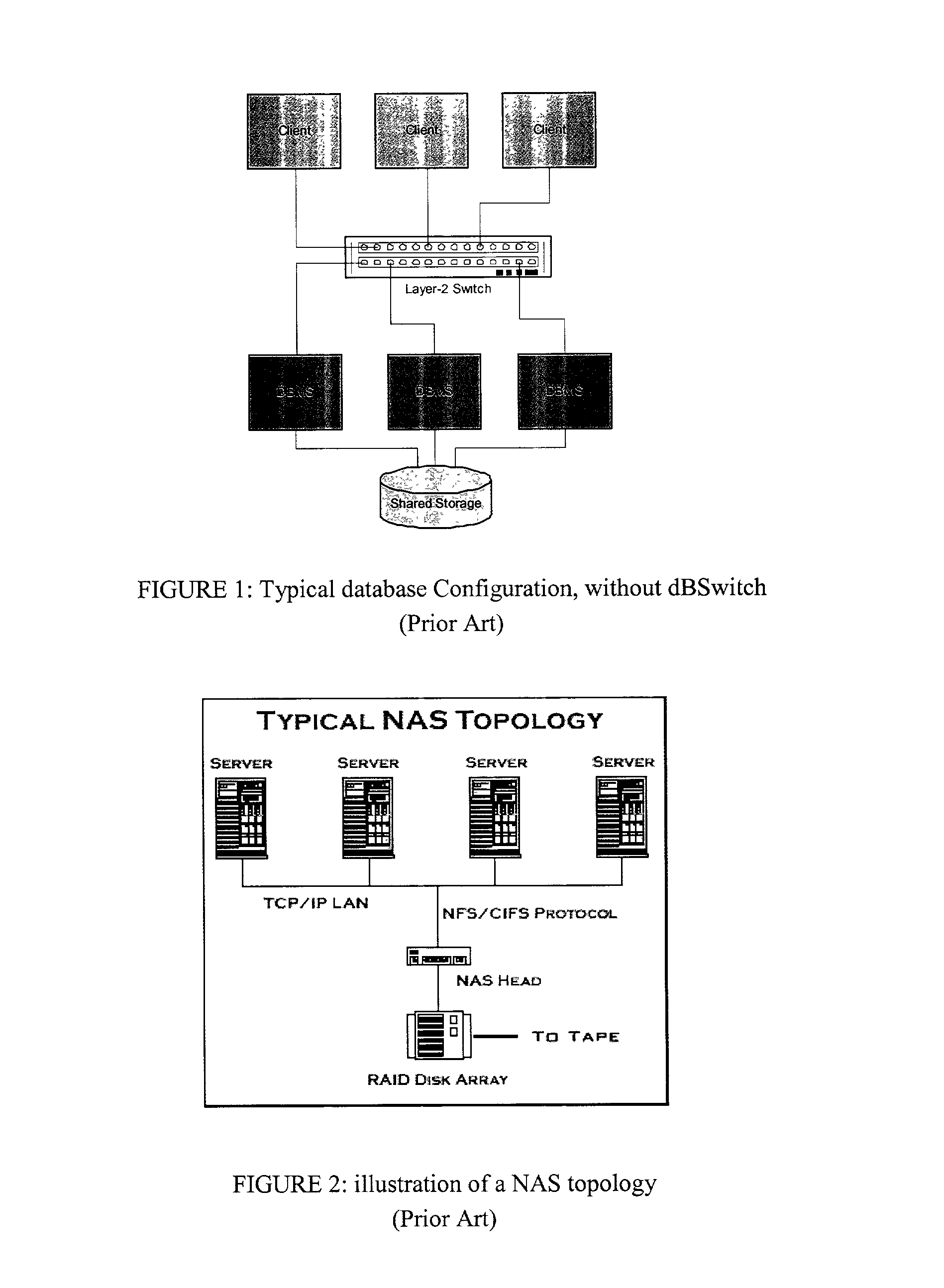
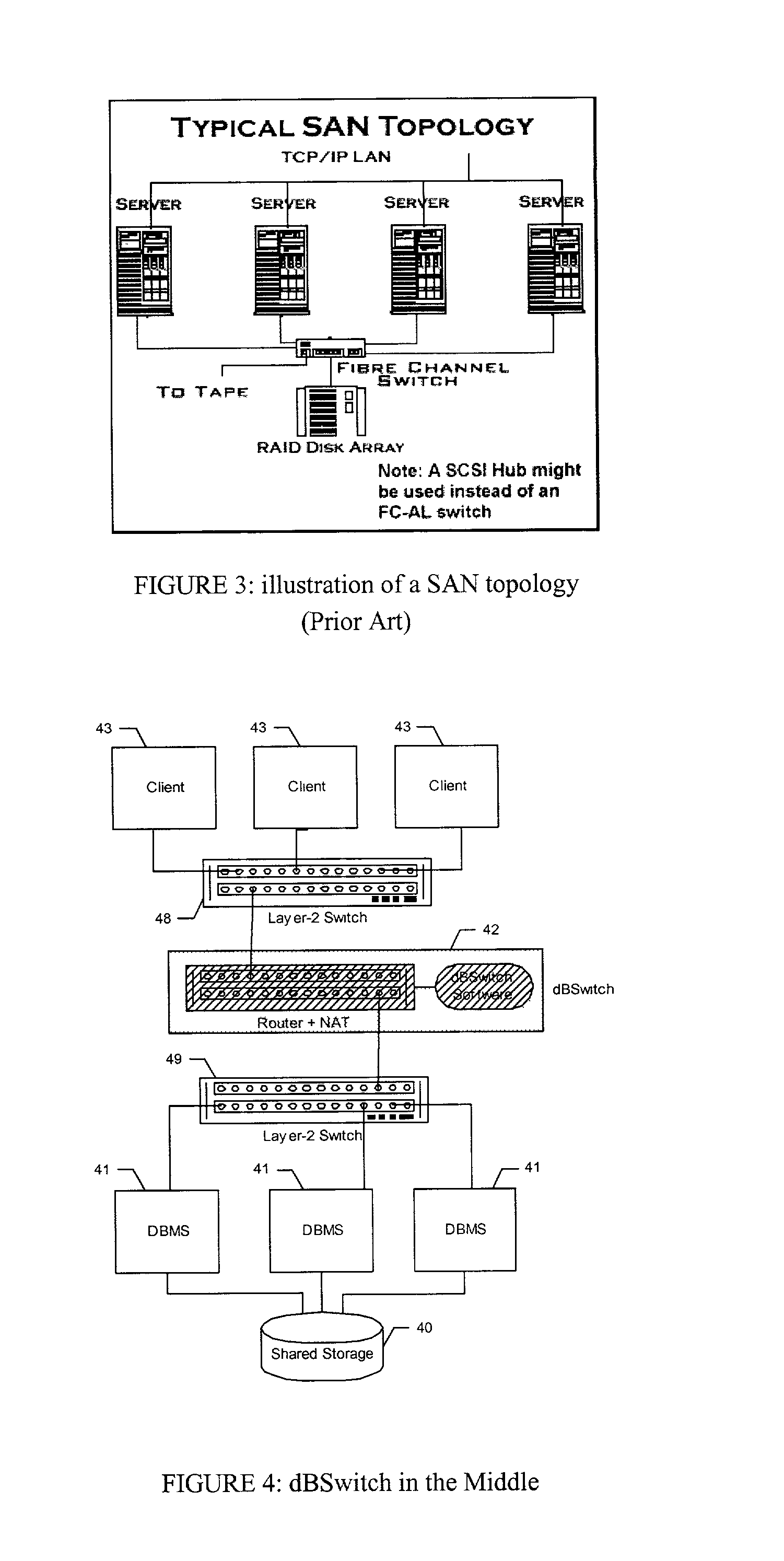
Database Switch enabling a database area network
InactiveUS20030154236A1Multiple digital computer combinationsTransmissionArea networkApplication software
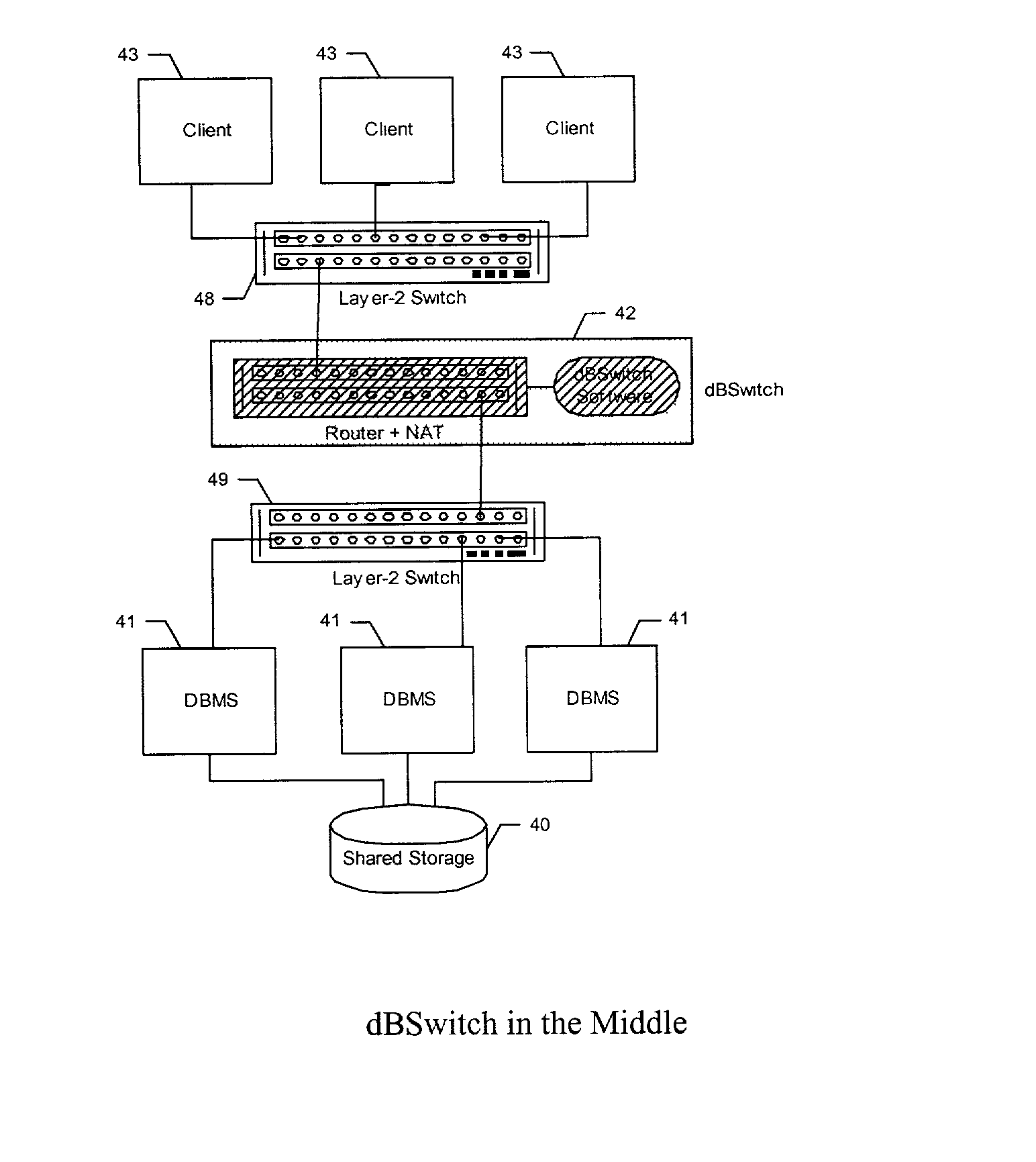
A method and system for improving utilization of the typical DBMS client-server configuration is provided. Specifically, the present invention can include a Database Switch (dBSwitch) situated between the applications and database servers in a network, capable of dynamically and transparently connecting applications to databases using standard database servers and standard protocols. The Database Switch appliance performs this database routing in real time, with high bandwidth and negligible latency. The Database Switch enables the formation of a Database Area Network (DAN) architecture, which promotes database virtualization by integrating the database servers, the shared storage, and the interconnecting network, making them appear to be one large, scalable database server. This DAN architecture yields high utilization, high availability, scalability on demand, simplified management and security, in a shared and heterogeneous application environment.
Owner:DAR SHAUL +3
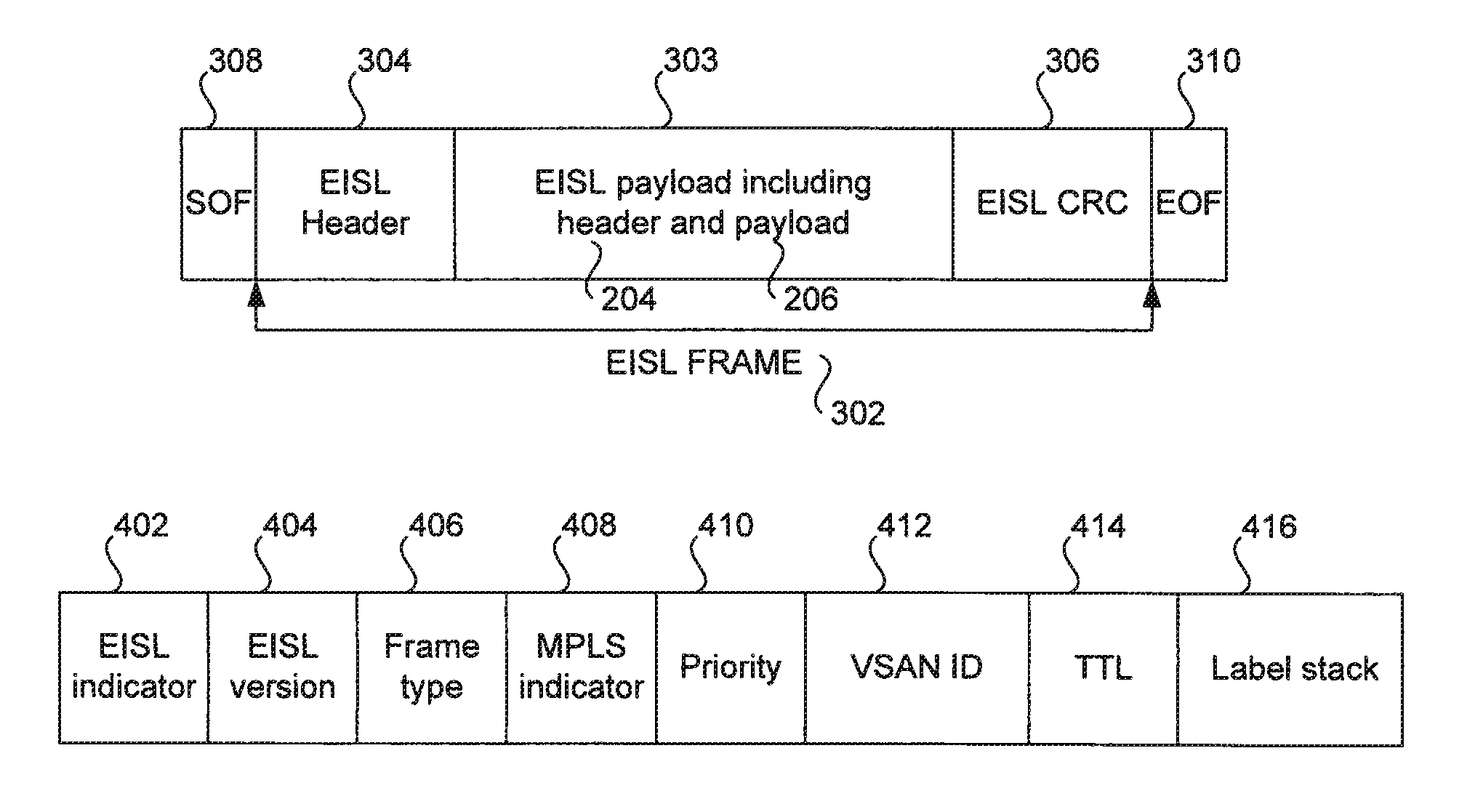
Methods and apparatus for encapsulating a frame for transmission in a storage area network
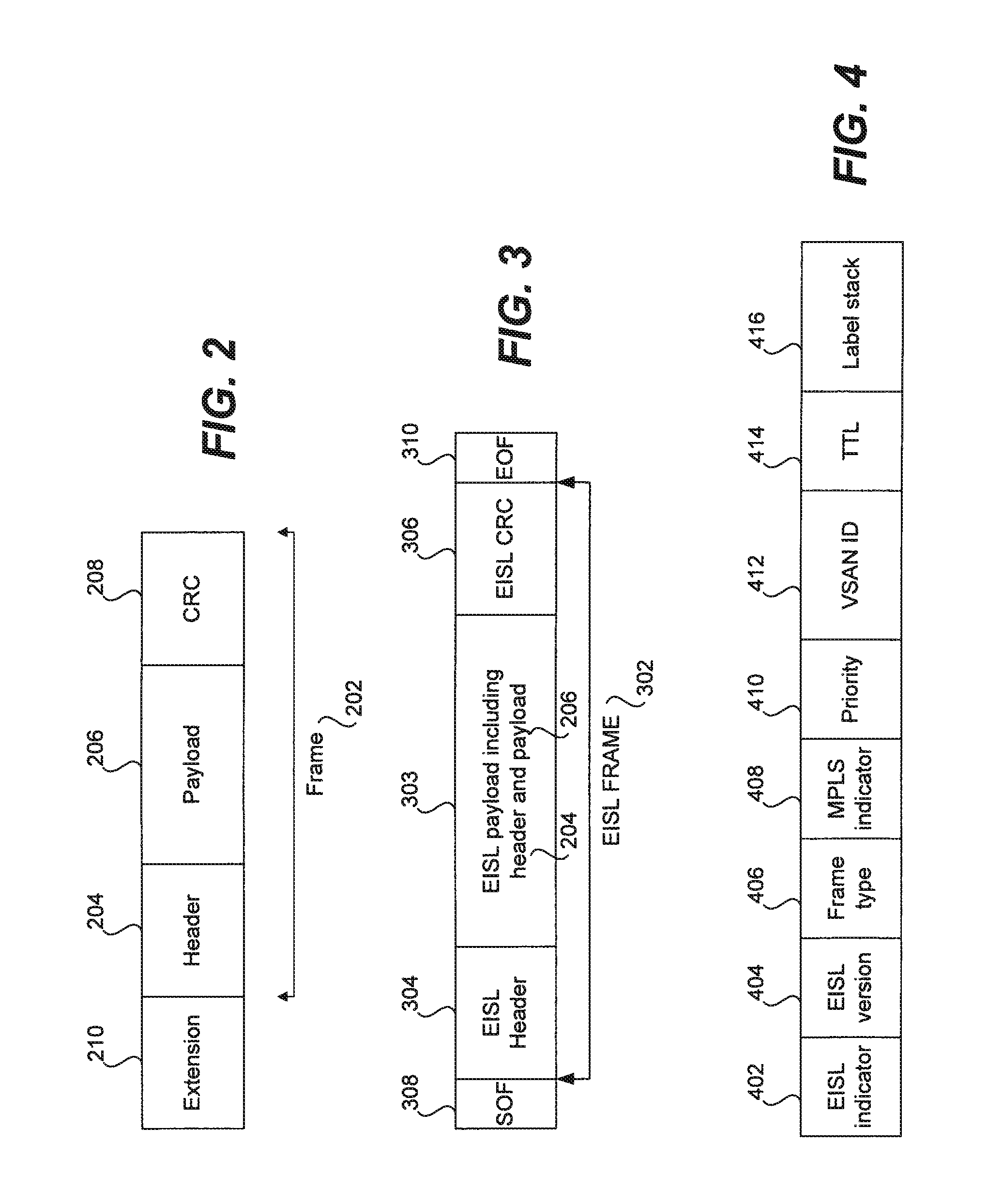
Methods and apparatus for encapsulating a packet or frame for transmission in a storage area network are disclosed. A packet or frame compatible with a standard protocol employed in the storage area network is received or generated. The packet or frame is then encapsulated with a virtual storage area network identifier. The packet or frame may further be encapsulated with at least one of a TTL value, MPLS information, and a type of traffic to be carried by the packet or frame. For instance, the type of traffic to be carried by the packet or frame may include Ethernet, Fibre Channel, and Infiniband. Once encapsulated, the encapsulated packet or frame is sent over the storage area network. For instance, the encapsulated packet or frame may be generated as well as transmitted by a switch over an inter-switch link in the storage area network.
Owner:CISCO TECH INC
USB Autorun Device
InactiveUS20110010470A1No costly mass memoryReduce manufacturing costInternal/peripheral component protectionDigital data authenticationMass storageMicrocontroller
A portable, application-specific USB autorun device, following connection to a computer terminal, automatically initialises or presents itself as a known type of device and then automatically sends to the terminal a sequence of data complying with a standard protocol, that sequence of data automatically causing content to be accessed or a task to be initiated. The device (i) includes a standardised USB module that includes a USB microcontroller, the standardised module being designed to be attached to or embedded in multiple types of different, application specific packages but (ii) excludes mass memory storage for applications or end-user data.
Owner:ARKEYTYP IP LTD
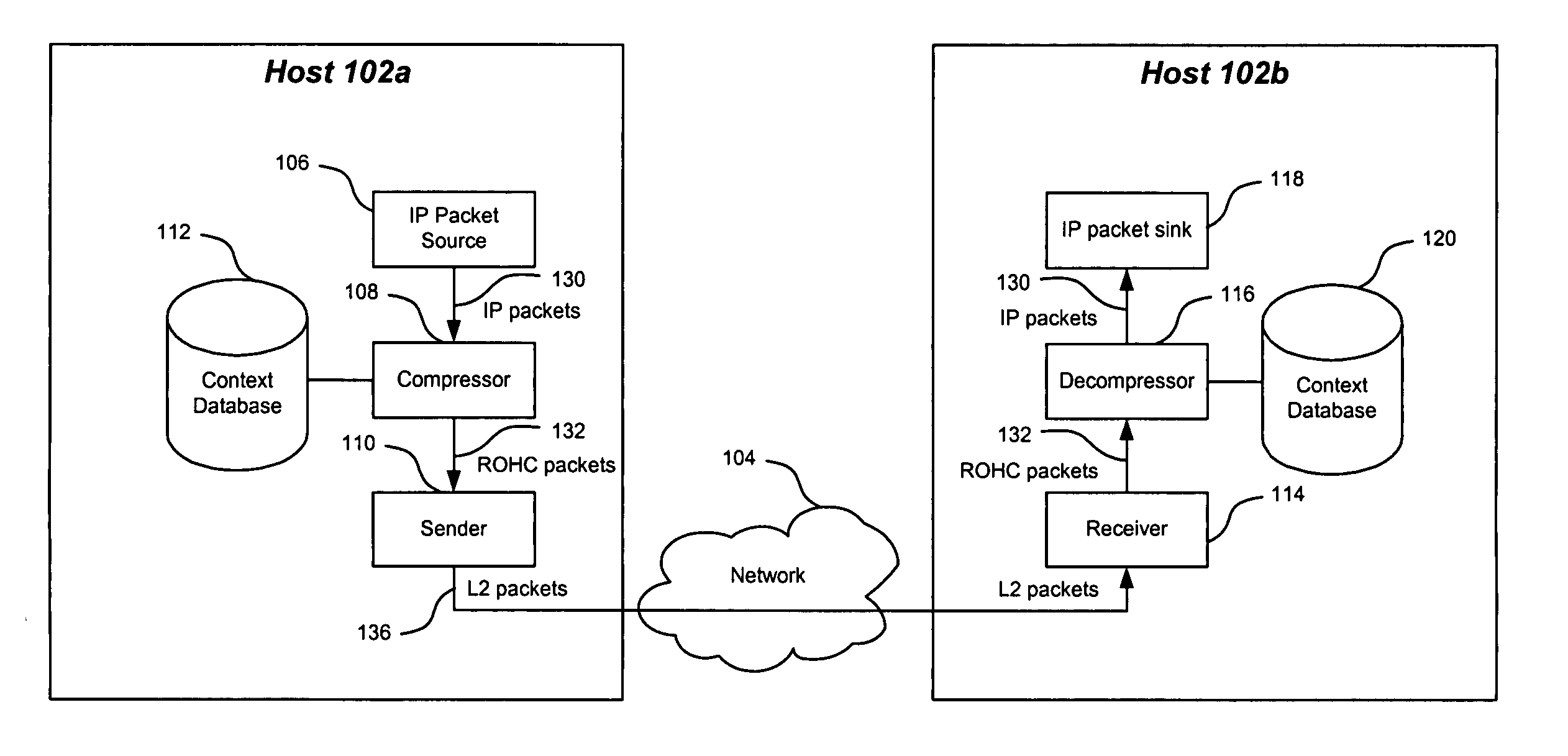
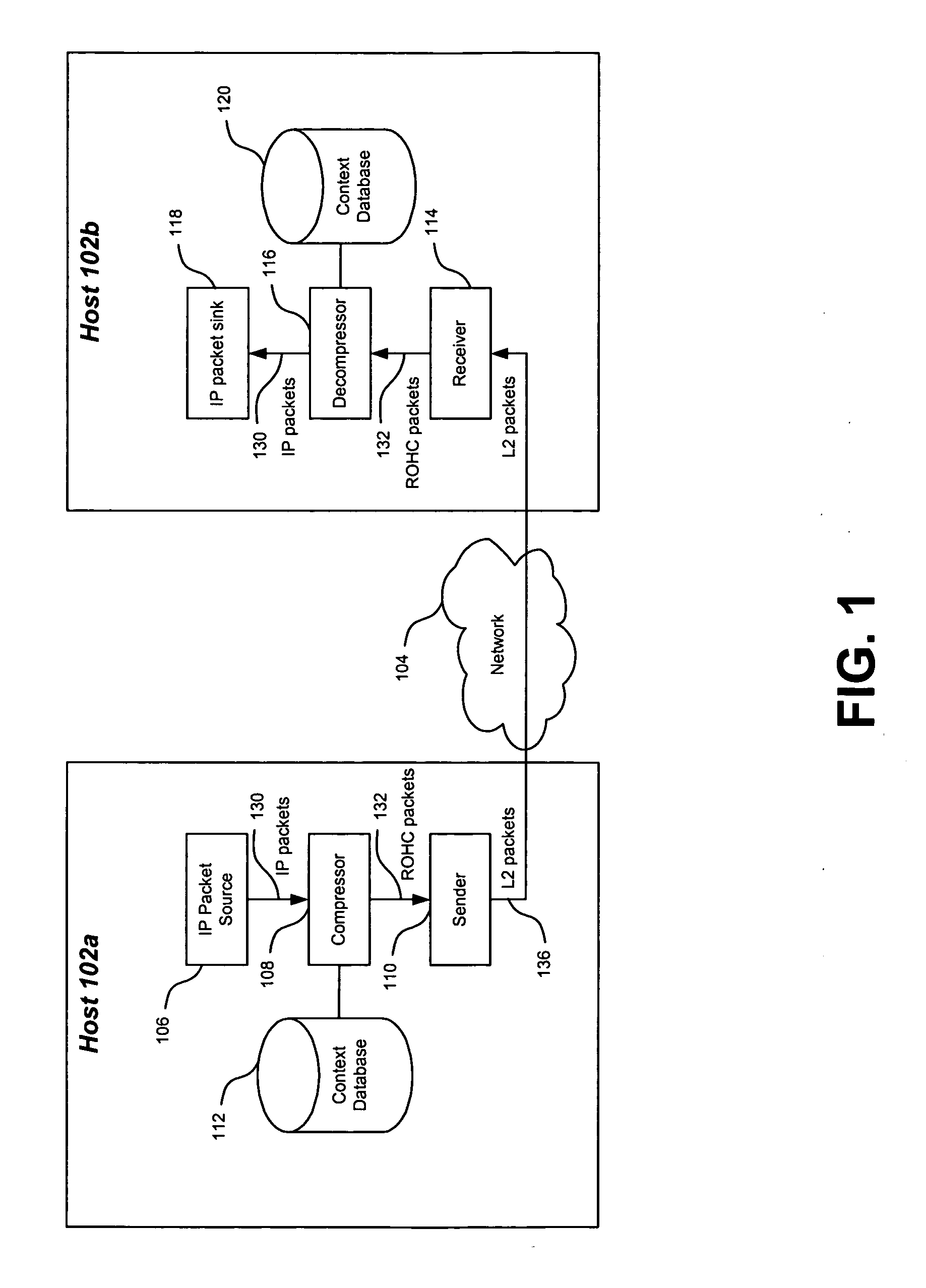
Method and system for header compression
ActiveUS20050160184A1Reduce digitsSpecial service provision for substationData switching by path configurationReliable multicastRobust Header Compression
A compression context for a plurality of packets is established with a receiving device. Each of these packets is associated with one or more reliable multicast protocols, such as the Layered Coding Transform (LCT) protocol, the Asynchronous Layered Coding (ALC) protocol, the FLUTE protocol, the MUPPET protocol, and the NACK-Oriented Reliable Multicast (NORM) protocol. Upon establishment of the compression context, a compressed packet is generated for one of the plurality of packets and transmitted to the receiving device. The compressed packet has a reduced number of bits in its header. Upon receipt, the receiving device decompresses the compressed packet based on the compression context.
Owner:III HLDG 3
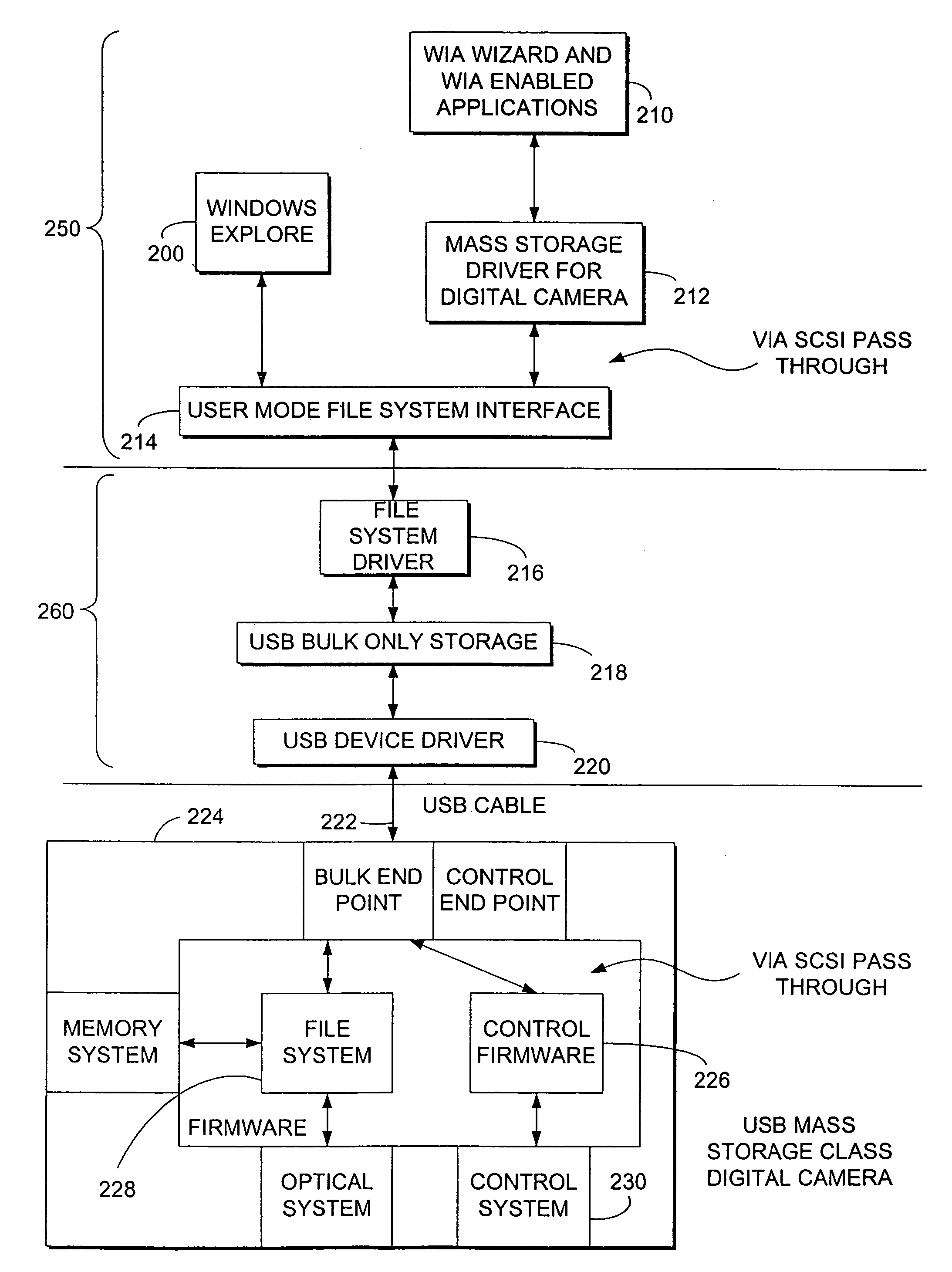
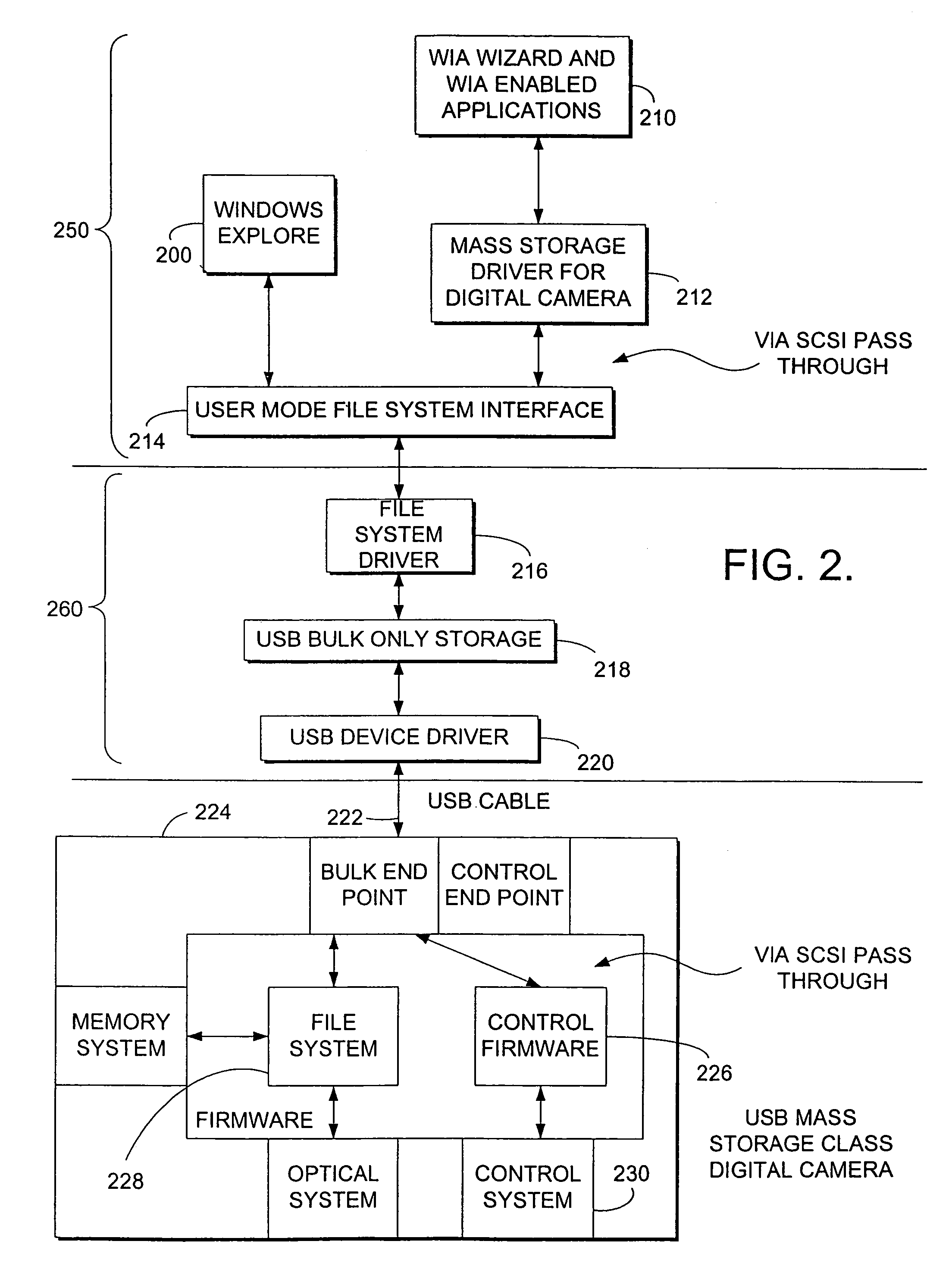
System and method for controlling mass storage class digital imaging devices
InactiveUS7246179B2Input/output processes for data processingPictoral communicationMass storageDigital imaging
A method is provided for controlling a Mass Storage Class Digital Imaging Device using a SCSI pass through protocol. The protocol is based on industry standard SCSI protocol with modifications and extensions to allow transparent communication over a medium and is referred to as SCSI Pass Through (SPT). This protocol defines a set of commands that are initiated in a computer. The commands also include and extend industry standard Picture Transfer Protocol and are targeted for application and execution in a Mass Storage Class Digital Imaging Device. The invention includes the definition of data buffers in the form of data structures that can be used for packaging, passing, and receiving information related to the digital imaging device. The protocol is applicable to communication mediums that can be utilized in connecting any digital storage device to a computing device.
Owner:MICROSOFT TECH LICENSING LLC
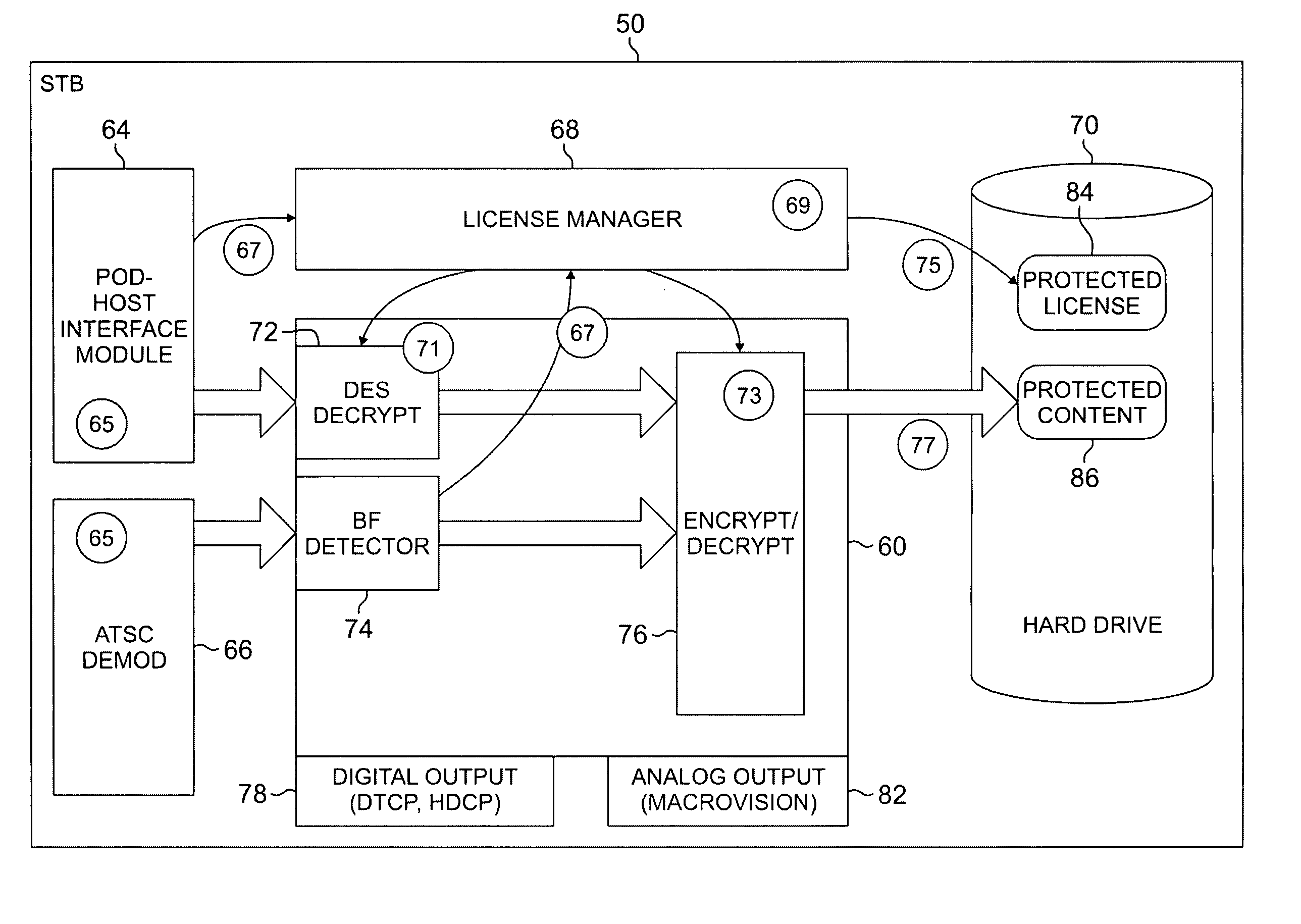
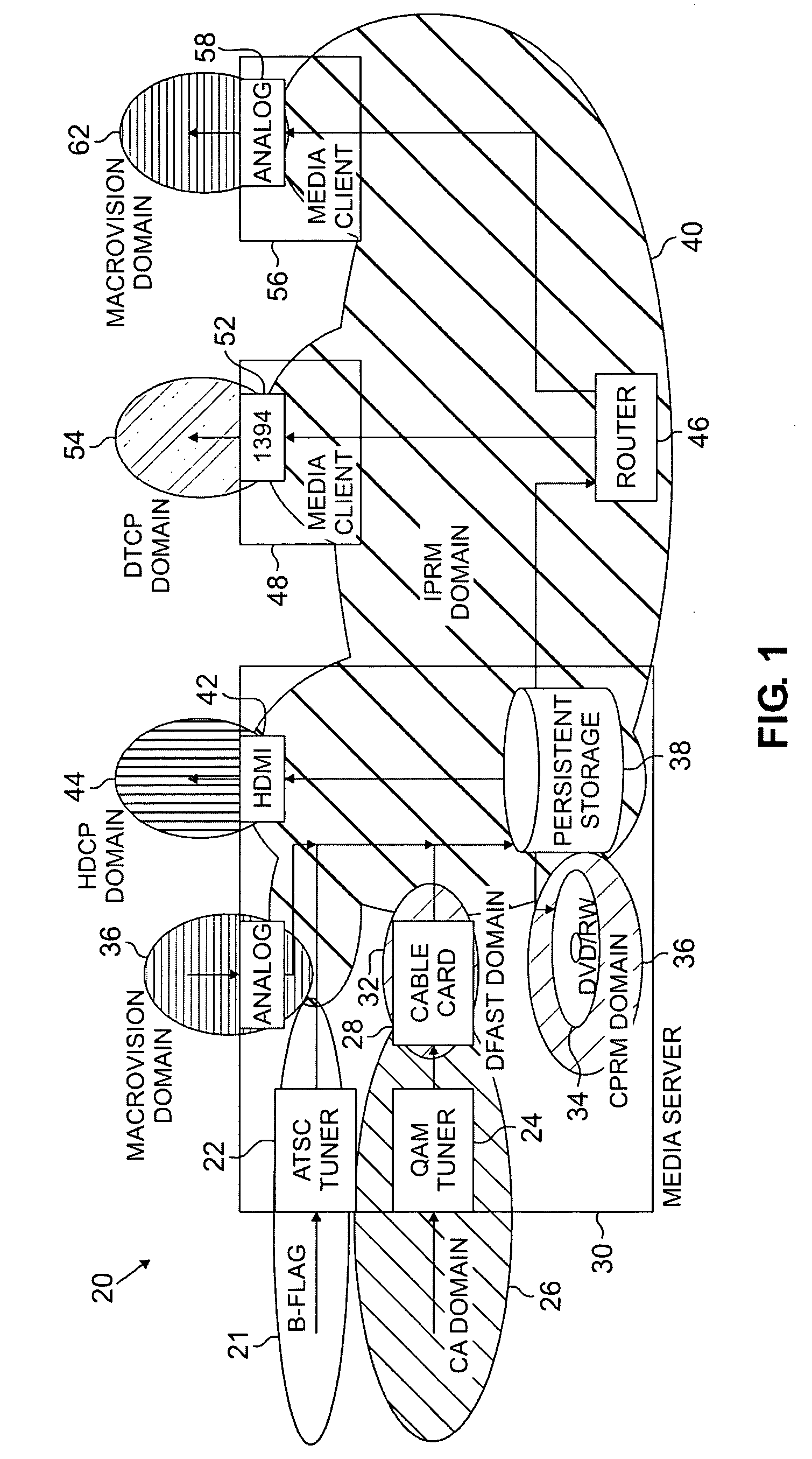
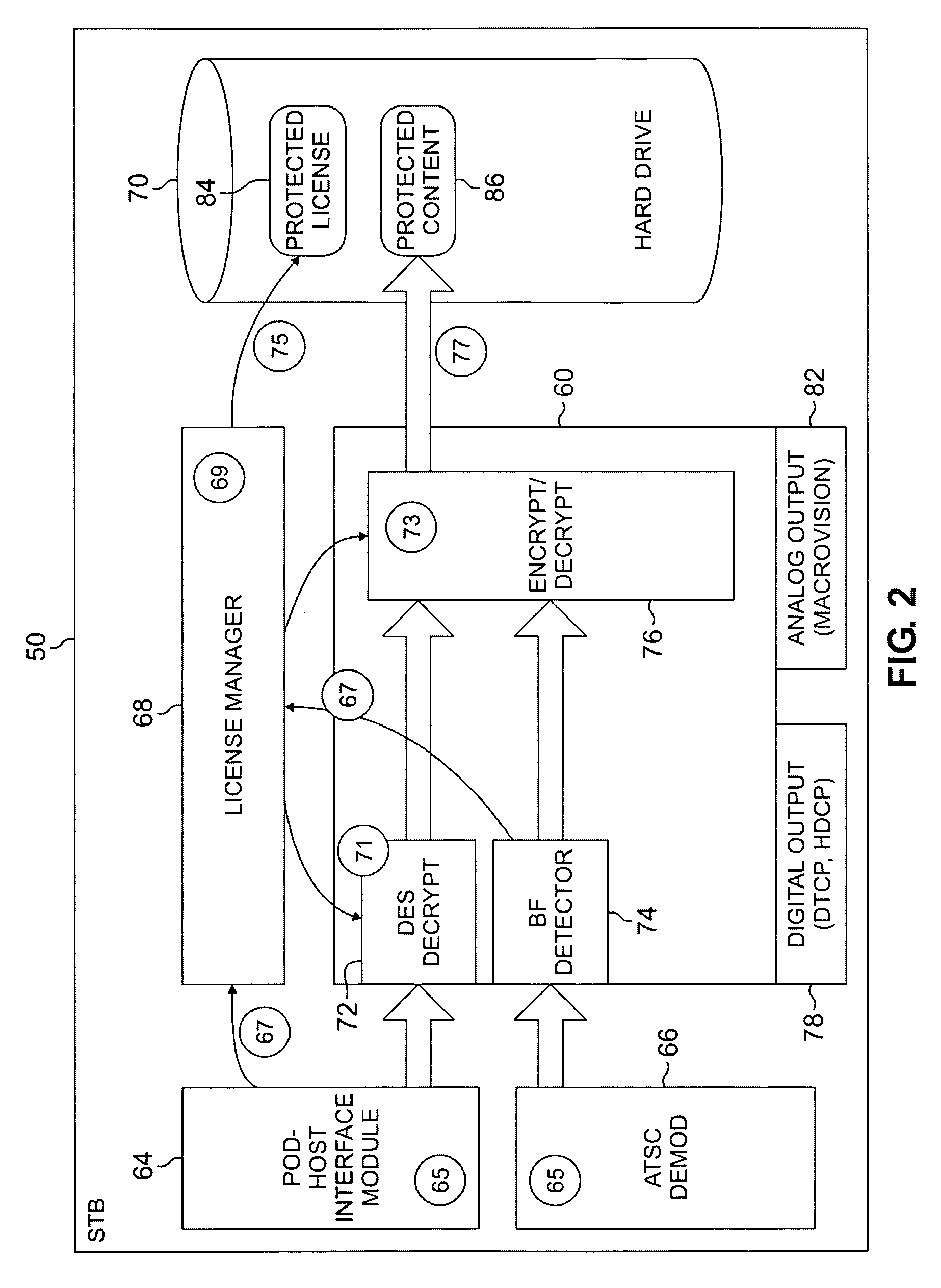
Digital rights management for local recording and home network distribution
The systems disclosed here provide a complete standards-based end-to-end scalable system for storage, delivery and in-home distribution of digital content over IP networks using standard protocols such as Real-time Transport Protocol (“RTP”) or IP-encapsulated MPEG-2 Transport Stream, or traditional MPEG-2 networks. Mechanisms are provided for receiving content from one security domain, re-encrypting that content uniquely for a receiving device, persistently storing that content, and playing back that content at a later time to and within another security domain. The systems also provide the ability to stream the persistently-stored content from the initial receiving device to another device that has been authenticated as part of a, e.g., home network. This allows a media server, e.g., a dual-tuner set-top box (“STB”) with hard drive, to deliver recorded content to any TV in the house by streaming to media clients such as STBs.
Owner:GOOGLE TECH HLDG LLC
Portable digital video camera configured for remote image acquisition control and viewing
ActiveUS20140049636A1Easy to editEasy to catchTelevision system detailsTransmission systemsDigital videoWireless Application Protocol
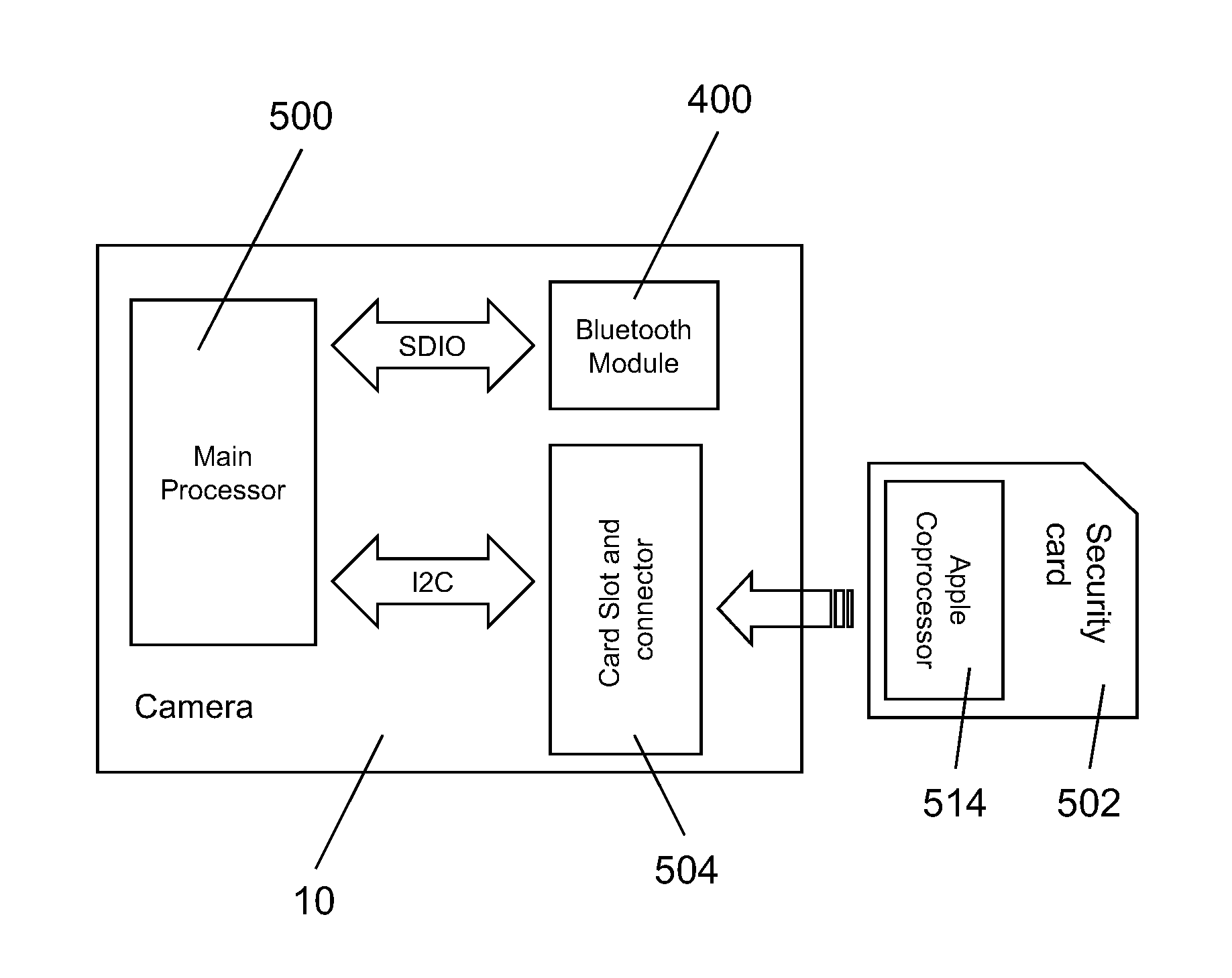
A wearable digital video camera (10) is equipped with wireless connection protocol and global navigation and location positioning system technology to provide remote image acquisition control and viewing. The Bluetooth® packet-based open wireless technology standard protocol (400) is preferred for use in providing control signals or streaming data to the digital video camera and for accessing image content stored on or streaming from the digital video camera. The GPS technology (402) is preferred for use in tracking of the location of the digital video camera as it records image information. A rotating mount (300) with a locking member (330) on the camera housing (22) allows adjustment of the pointing angle of the wearable digital video camera when it is attached to a mounting surface.
Owner:CONTOUR IP HLDG
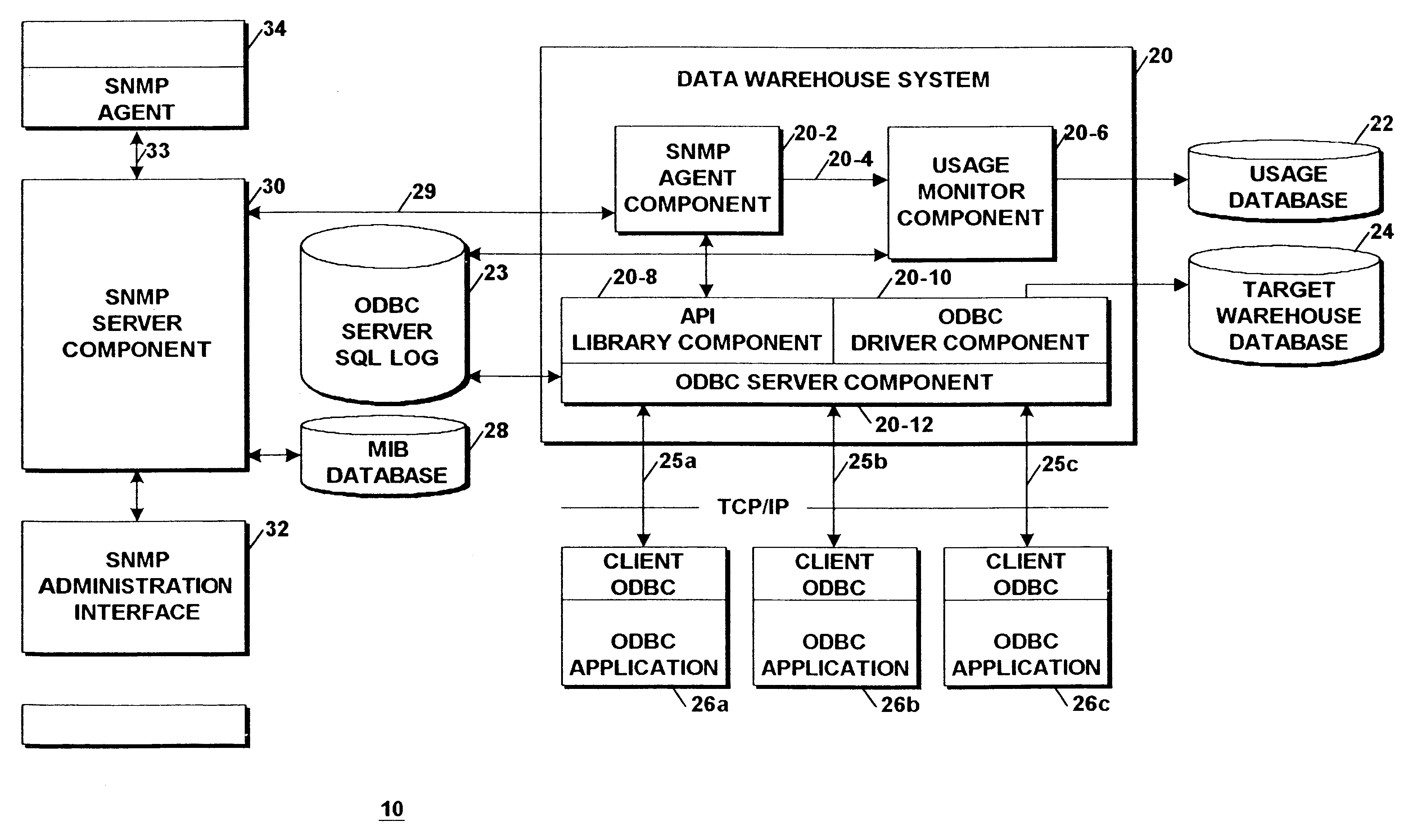
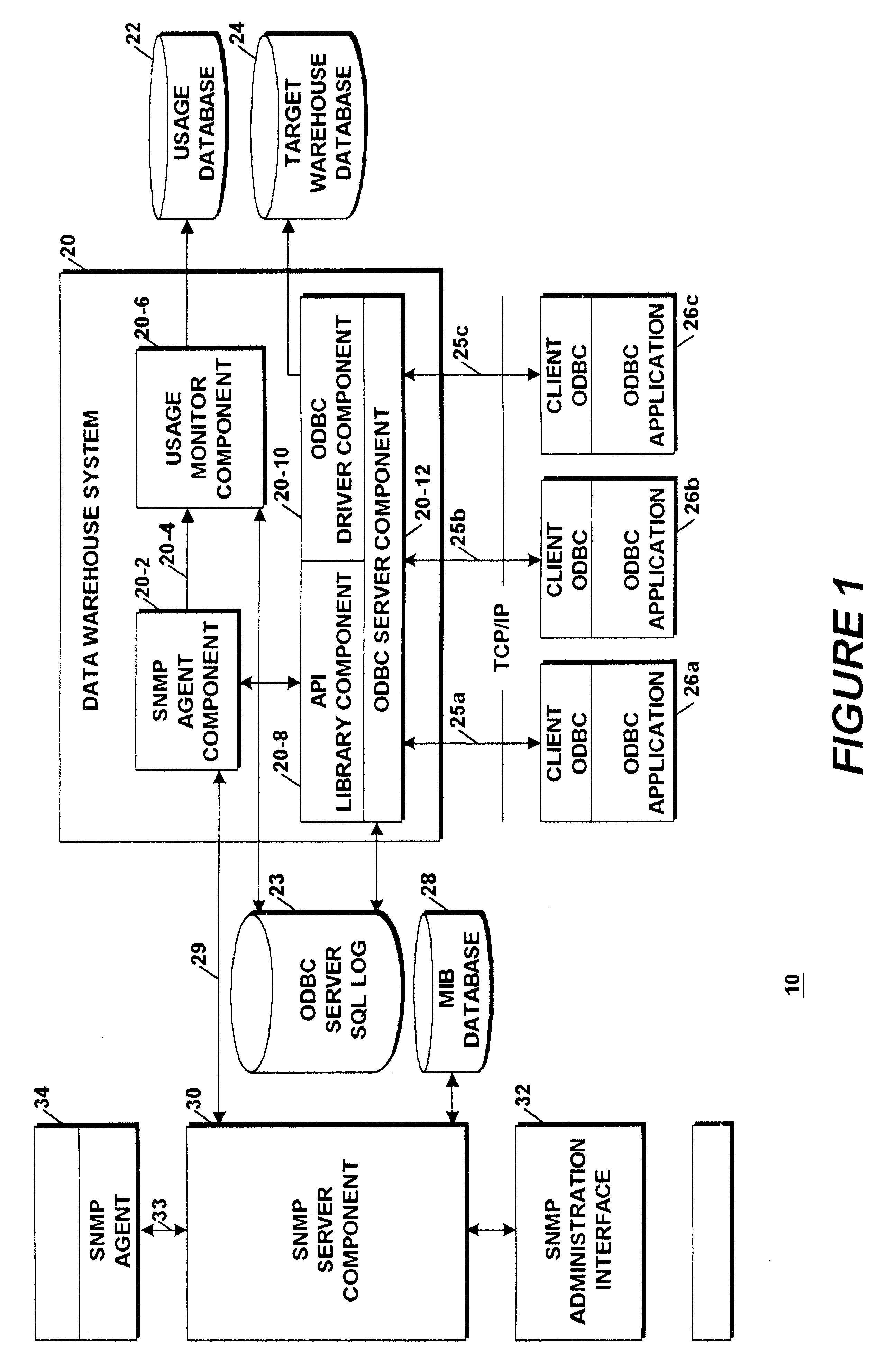
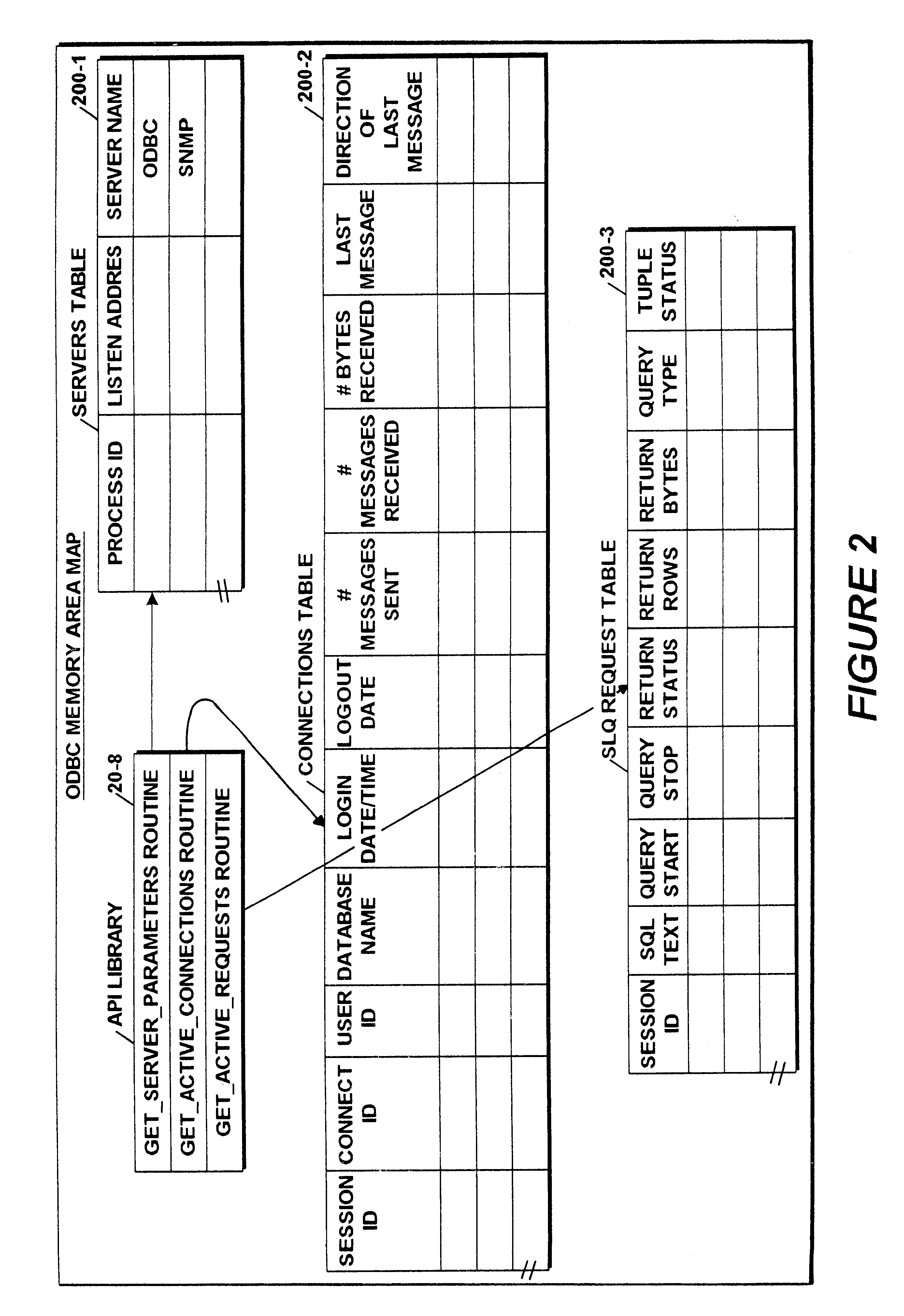
Application programming interface for monitoring data warehouse activity occurring through a client/server open database connectivity interface
InactiveUS6363391B1Simple processData processing applicationsDigital computer detailsData connectionData warehouse
An Application Programming Interface (API) provides interoperability between different monitoring and administrative components of a data warehouse system that utilizes different standard protocols. One of the protocols is the well known data connectivity protocol, Open Database Connectivity (ODBC) that defines a standard interface between applications and data sources. A second one of the protocols is the well known network management protocol, Simple Network Management Protocol (SNMP) that defines a standard interface between an agent component and a network management system. The API provides a facility that enables the different components to access user and connection information maintained by an ODBC server component derived from servicing client system application SQL queries made by system users.
Owner:BULL HN INFORMATION SYST INC
Method and system for network connection chain traceback using network flow data
InactiveUS20150256555A1Improve good performanceMemory loss protectionError detection/correctionTraffic capacityNetwork connection
Disclosed are provided a method and a system for network connection chain traceback by using network flow data in order to trace an attack source site for cyber hacking attacks that goes by way of various sites without addition of new equipment of a network or modification a standard protocol when the cyber hacking attack occurs in the Internet and an internal network.
Owner:ELECTRONICS & TELECOMM RES INST
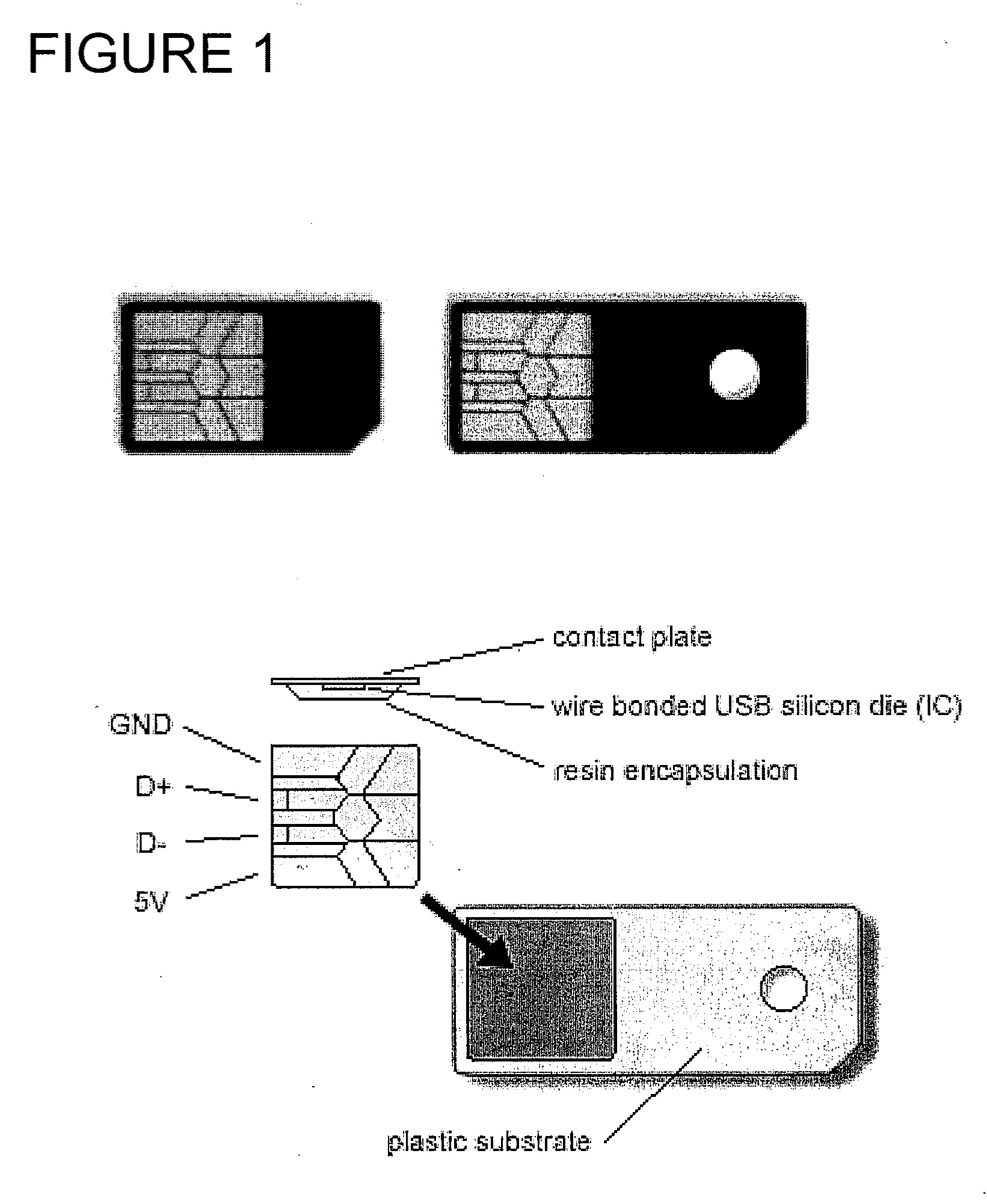
Method and apparatus for activating a computer system in response to a stimulus from a universal serial bus peripheral
InactiveUS6622178B1Power supply for data processingInput/output processes for data processingElectricityComputerized system
A method and apparatus for activating a computer system in response to a stimulus from a universal serial bus (USB) peripheral provides a mechanism for powering up a computer system or restoring it from a suspended mode of operation. The apparatus includes a controllable power supply and a non-standard protocol using the USB wire connections, to provide a method for polling the peripheral to determine if activity has occurred which a host computer system should use to trigger activation.
Owner:GOOGLE LLC
Method and system for configuration and download in a restricted architecture network
InactiveUS6973479B2Avoid complicationsAvoid difficultyMultiple digital computer combinationsProgram loading/initiatingExtensibilityData file
A method and system are provided for updating software configurations of line-replaceable unit (LRU) computers in a restricted architecture network such as an in-flight entertainment system (IFES). Operating in an efficient and parallel manner, each of the LRUs independently creates an individual configuration file that identifies current software components. Each of the LRUs transmits its respective configuration file to a configuration server either automatically upon startup or manually upon request. The configuration server updates a system configuration data file with the current configuration files received from the individual LRUs. In a downloading method, a download server sends a list of desired software components to the LRUs. Each of the LRUs independently and simultaneously transfer (download) the needed software from the download server. The LRU independently requests the download server to download the needed software components. To improve scalability and reliability, the file transfers utilize standard protocols, such as FTP.
Owner:THALES AVIONICS INC
System for securely communicating amongst client computer systems
InactiveUS6973477B1Protect normal transmissionEasy to integrateMultiple digital computer combinationsAutomatic exchangesOperational systemModem device
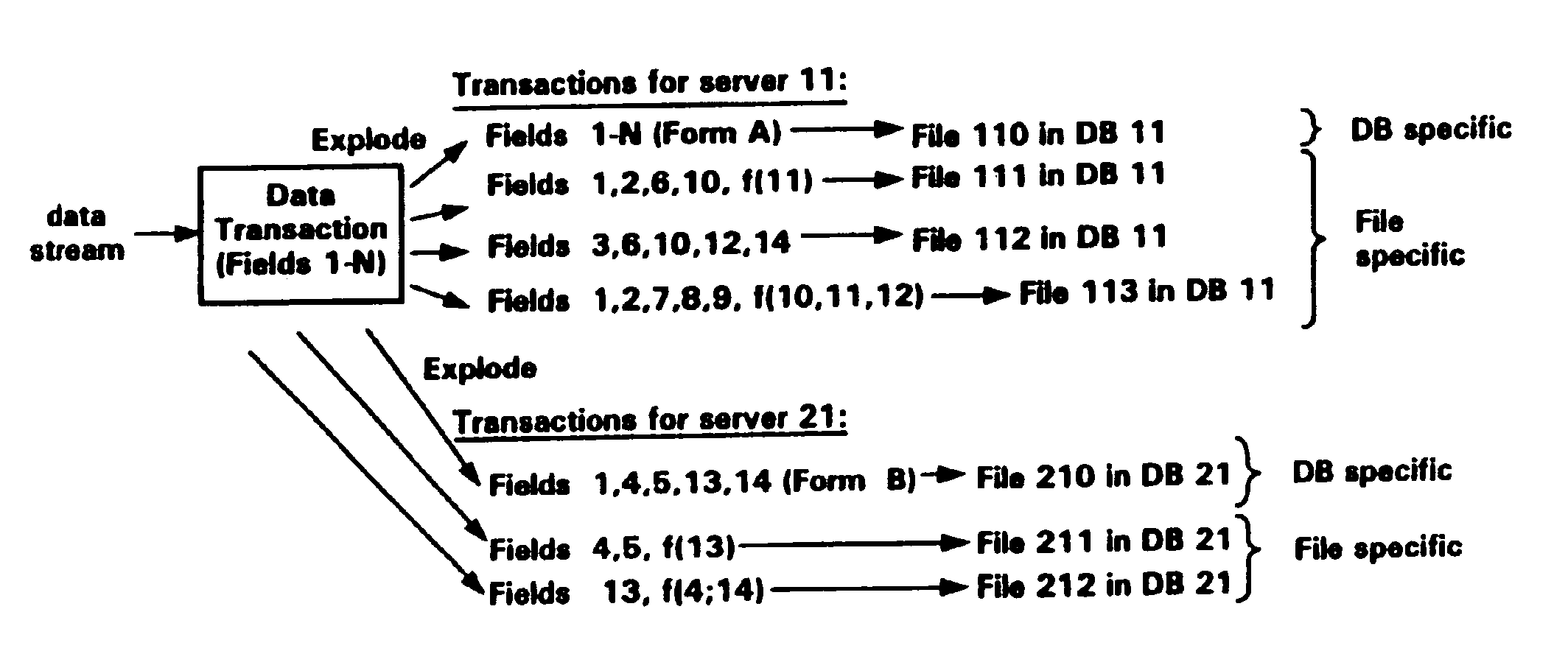
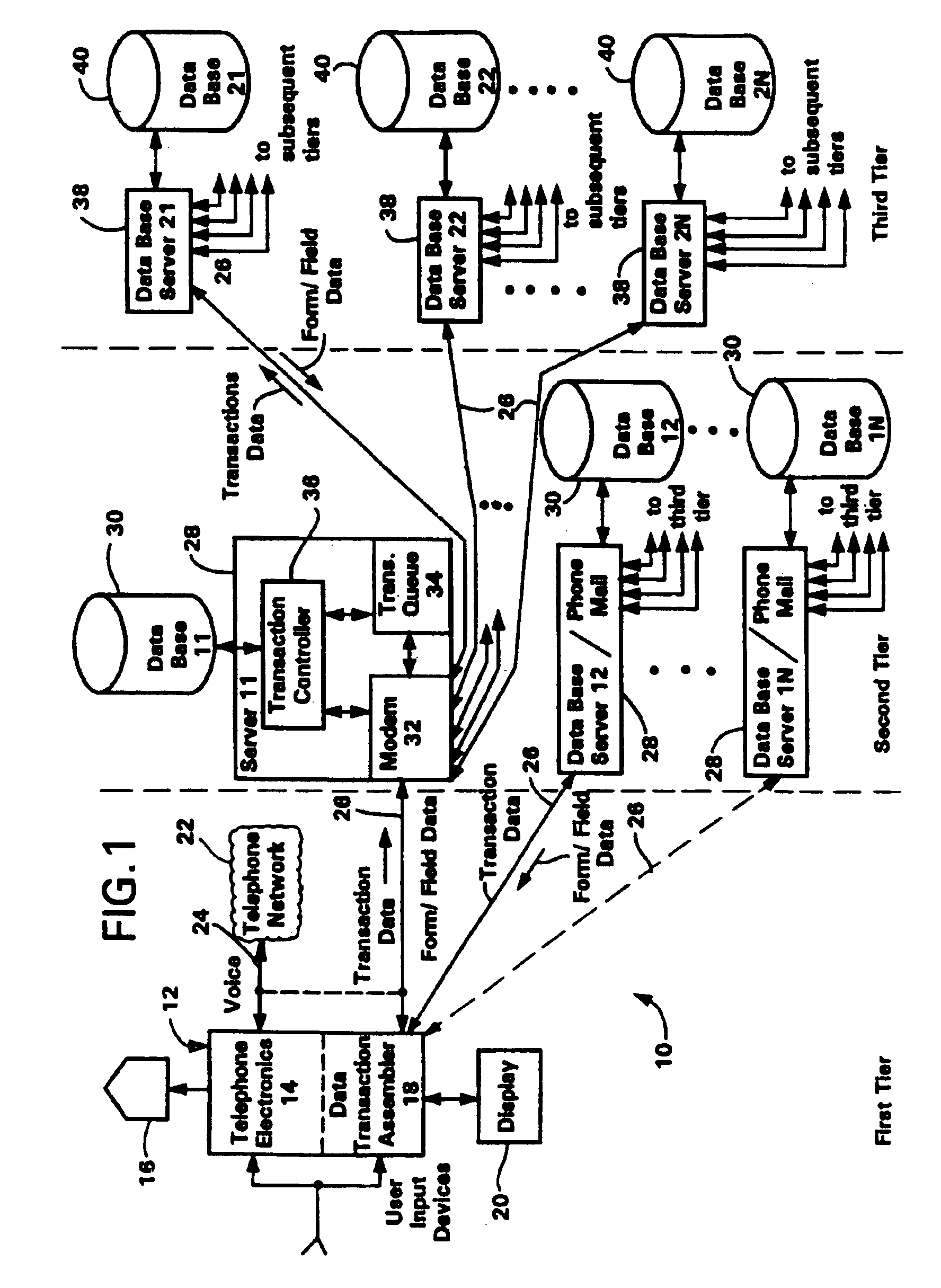
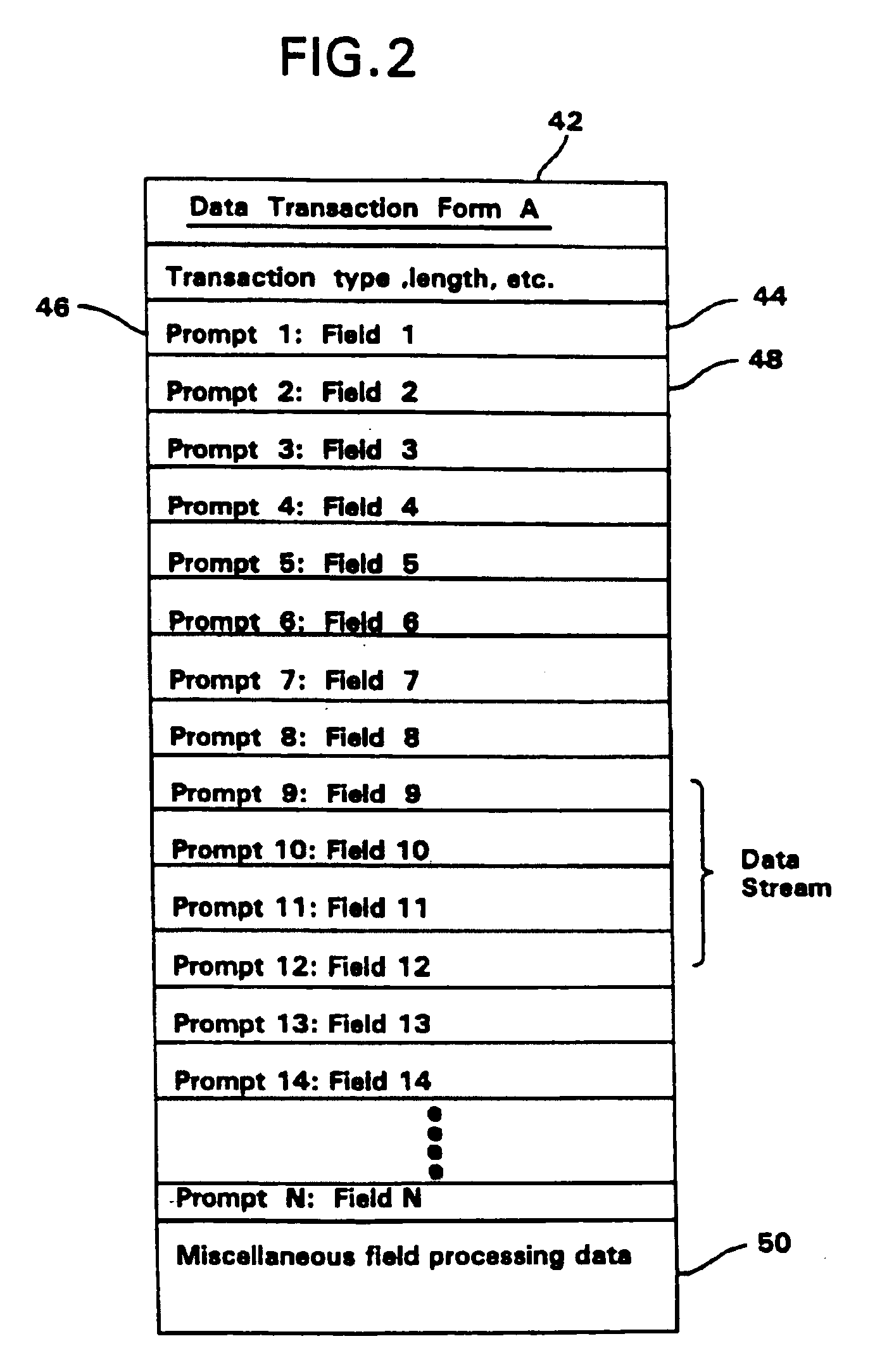
A data transaction processing system in which transaction data is entered by the user in response to prompts in a template which is tailored to each user application. The template and entered data are accumulated into data transactions that are immediately transmitted upon completion to an external database server for processing and storage. The data transaction is received via standard protocols at the database server which, depending upon the application, stores the entire data transaction, explodes the data transaction to produce ancillary records which are then stored, and / or forwards the data transaction or some or all of the ancillary records to other database servers for updating other databases associated with those database servers. In response to requests from the transaction entry device, the database server may return data streams for use in completing the fields in the data transaction or in presenting a menu on the display which was read in from the database server or a remote phone mail system. The transaction entry device is integrated with a telephone and is accessed via a touch screen, an optional keyboard, a magnetic card reader, voice entry, a modem, and the like.A plurality of such database servers under the control of broad operations system server (BOSS) software and a plurality of form-driven client computing devices are provided to create an open platform system for receiving and transmitting transaction data to or from the client devices, other applications and databases. Advantageously, a locator server computer serves to retrieve IP address numbers, PSTN numbers and other network identification information for use in identifying and locating, e.g., an originating user and a destination client device. A robust security and authentication scheme along with robust storage protects the transmission of sensitive or confidential data.
Owner:CYBERFONE TECH
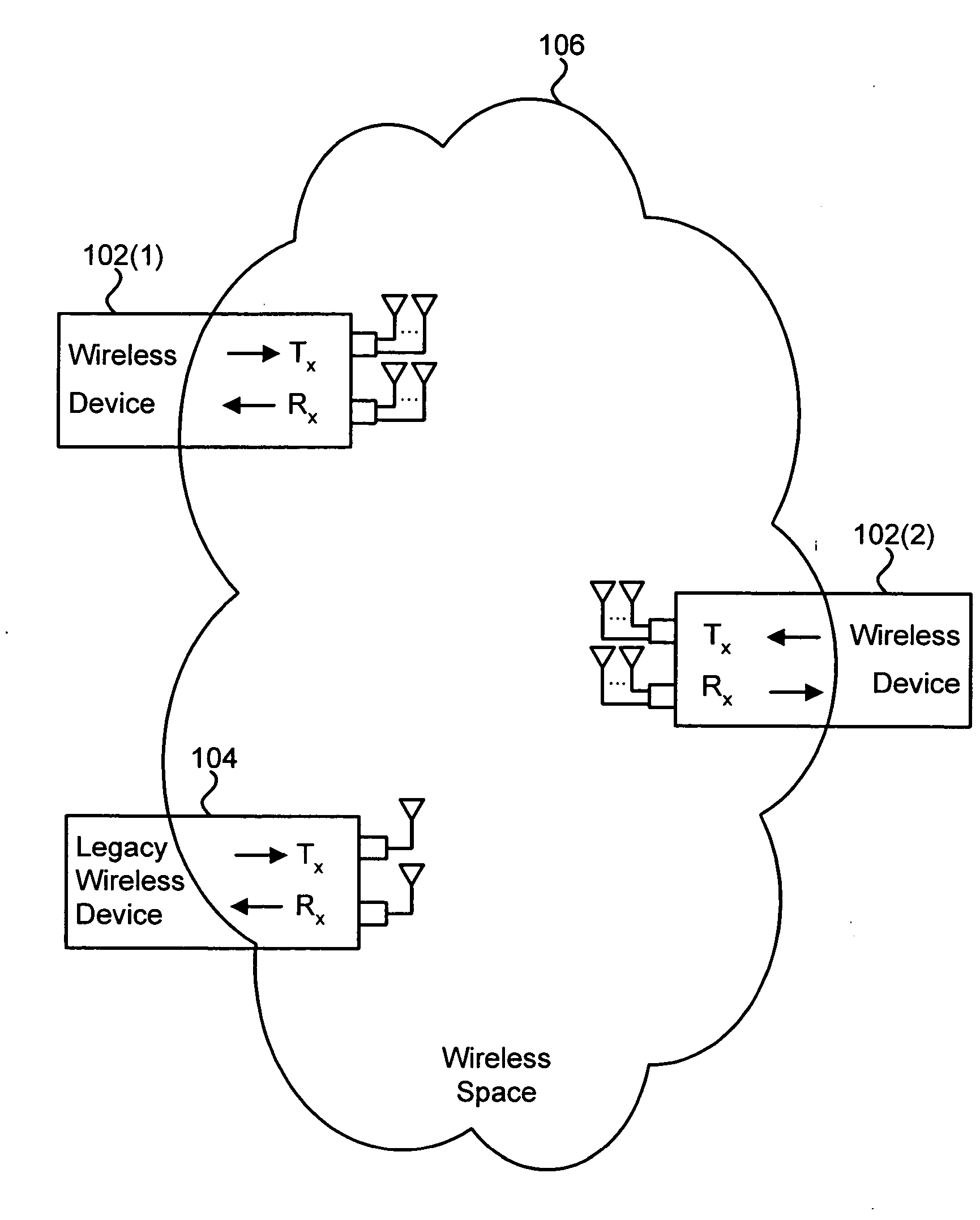
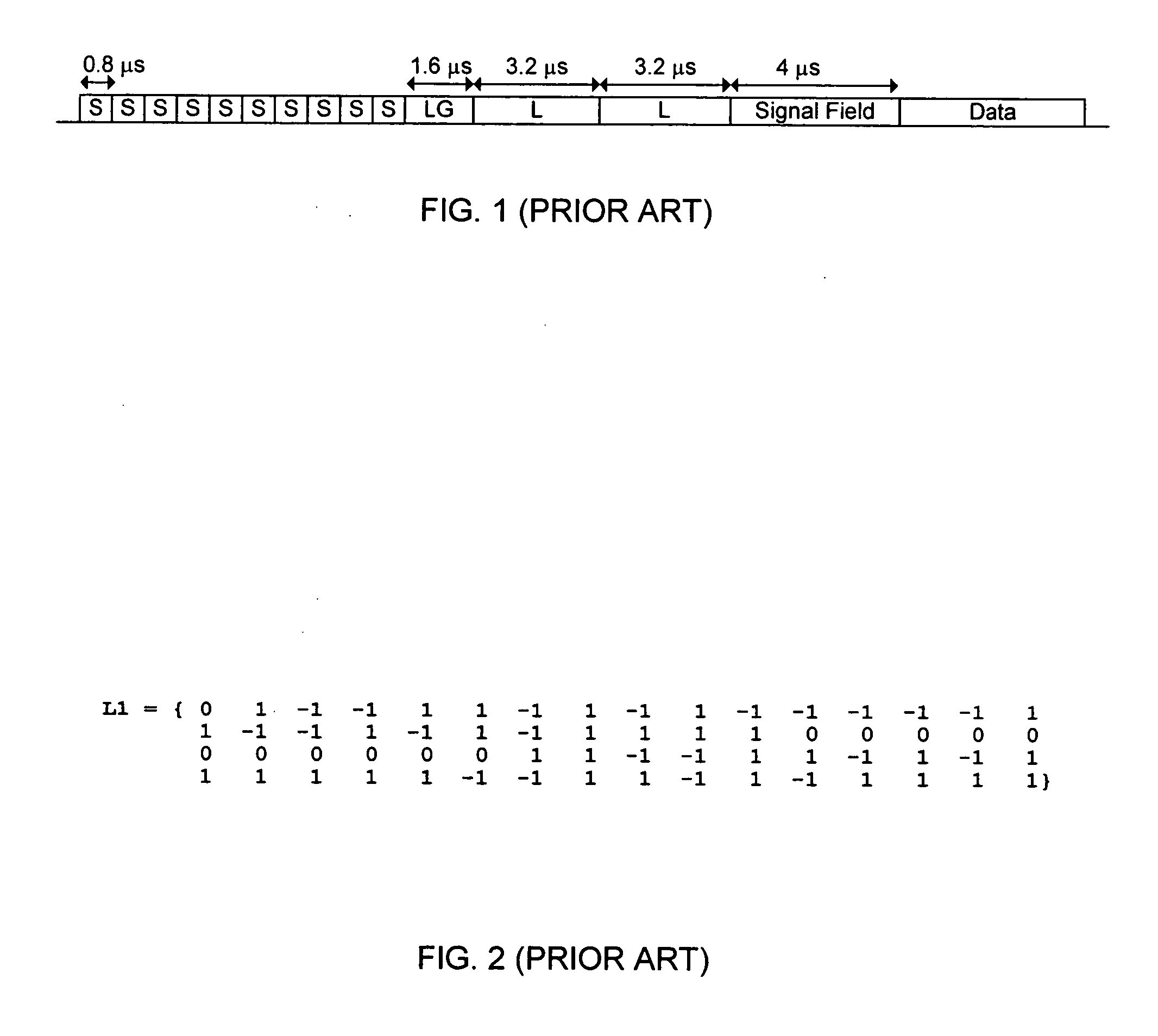
Wireless messaging preambles allowing for beamforming and legacy device coexistence
ActiveUS20060193340A1Modulated-carrier systemsNetwork traffic/resource managementMessage passingMixed mode
A modified preamble is used by extended devices that operate in mixed mode environments and green field environments, to accommodate beamforming of transmissions. In one process, an extended wireless device processes data for transmission of that data as a packet, wherein the extended wireless device is a device configured to communicate using a standard protocol understood by each node device and an extended protocol not understood by legacy node devices. If the packet is to be directed at an extended device, the extended wireless device sends a preamble of that packet that is usable in an extended mode at extended devices and usable at a receiving legacy device to determine that the receiving legacy device is not the destination of data to follow the preamble. Once the receiving legacy device is expected to be deferring the network, the extended wireless device can beamform its signal or otherwise vary from the legacy protocol in communications with extended devices.
Owner:QUALCOMM INC
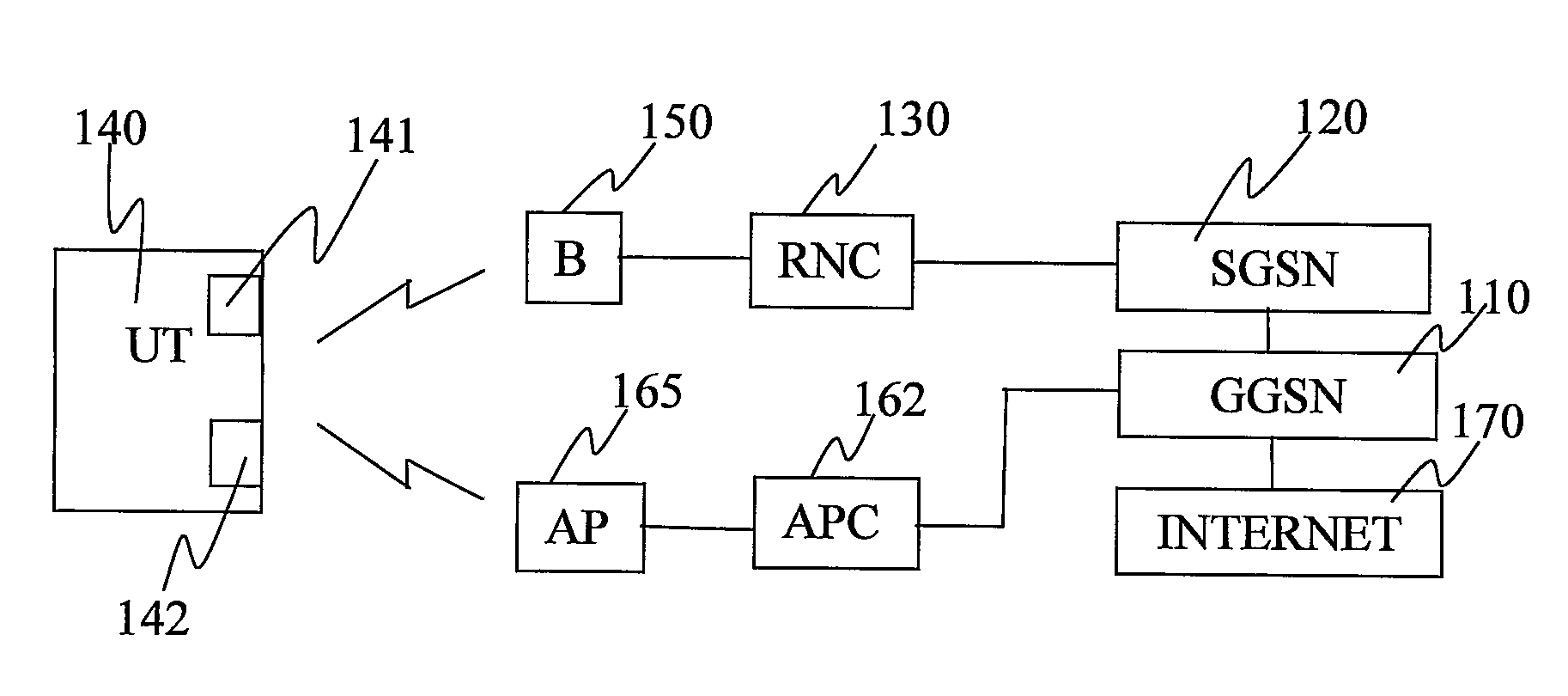
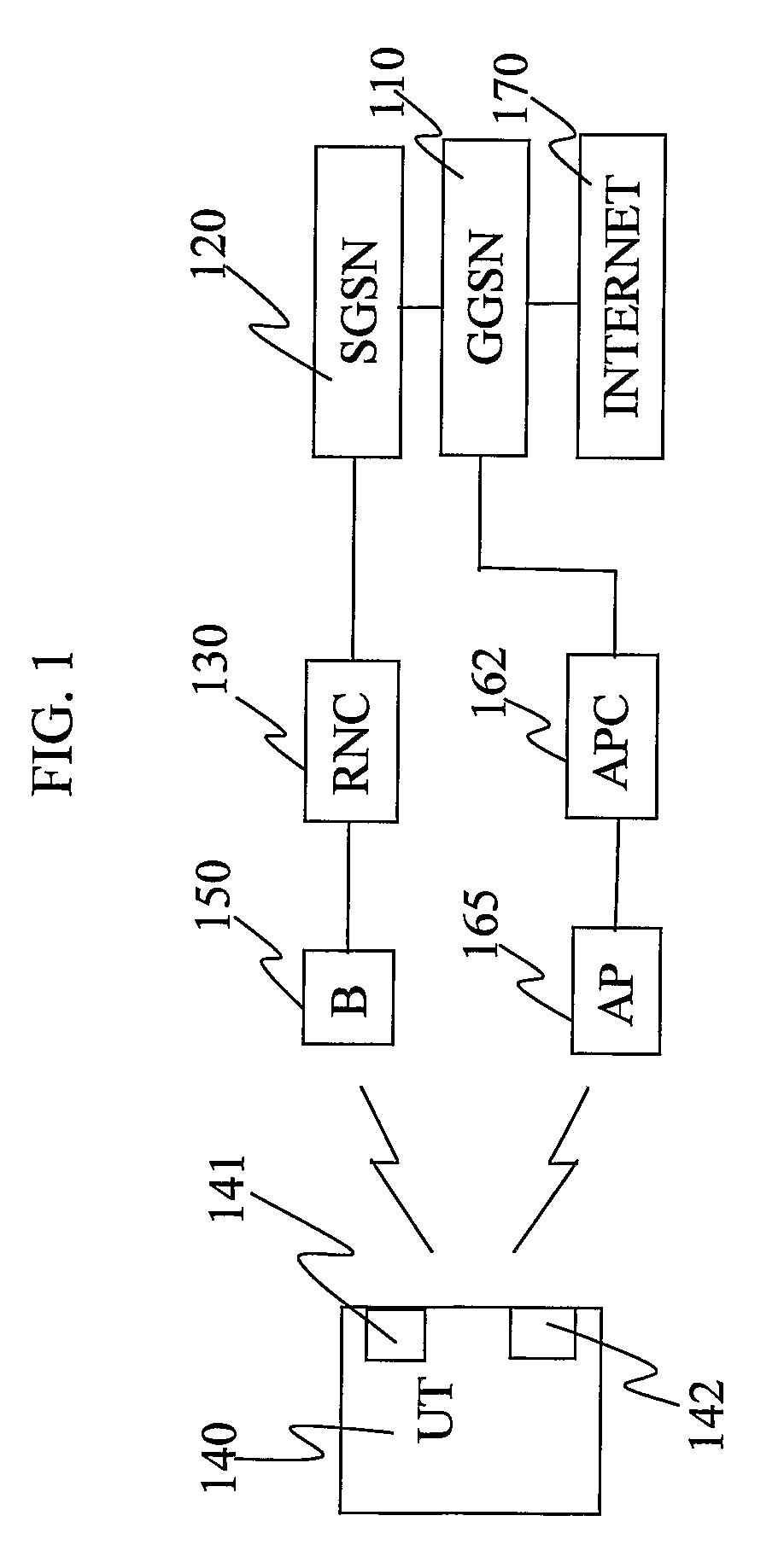
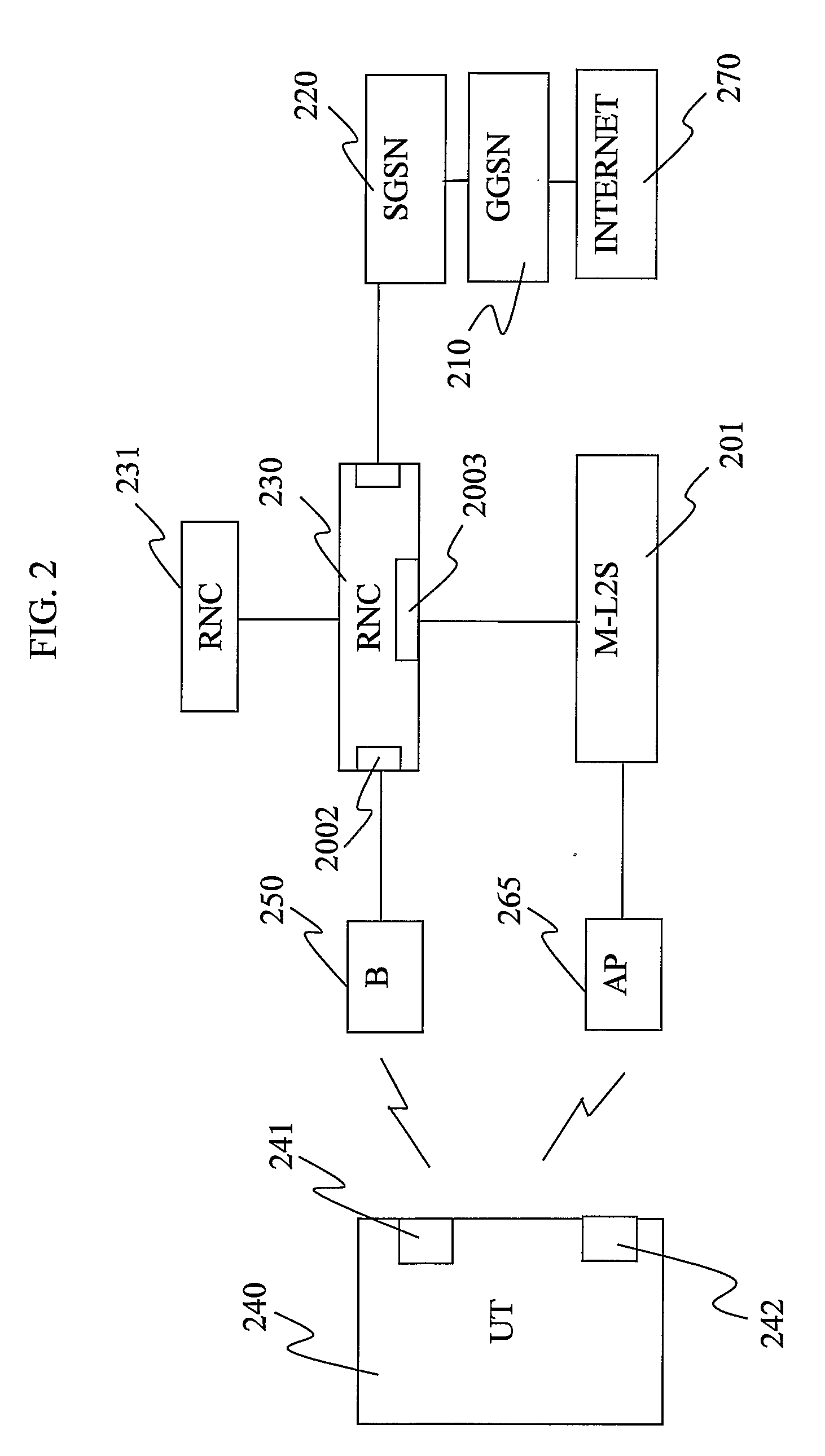
Internetworking of Cellular Radio Networks and Wireless Data Networks
ActiveUS20090131053A1Reduce overall network signallingReduce riskRadio/inductive link selection arrangementsWireless commuication servicesAccess networkCellular radio
The invention provides a method, to be used by a RNC (230), for assisting a handover of a data session from a first routing path, associated with a first access network, to an alternative routing path, associated with an alternative access network, wherein data is routed over said first access network to a UT (240) by binding a session identifier to a first routing identifier, wherein said session identifier and said first routing identifier are defined in accordance with a standard protocol routing scheme of said first access network, the method comprising the following steps: —receiving a capability message uniquely identifying said UT (240) according to a standard protocol routing scheme of said first access network and according to an alternative standard protocol routing scheme of said alternative access network, —creating an alternative routing identifier for said session complying with the standard protocol routing scheme of said alternative access network and associating said alternative routing identifier with said UT (240), and, —associating said session identifier with said alternative routing identifier. The invention also provides an RNC (230), a UT (240), software and software media for realising the invention.
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method for fast, reliable byte stream transport
ActiveUS7305486B2Easy to operateMaintaining % API compliance with TCPError prevention/detection by using return channelTransmission systemsData streamByte
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
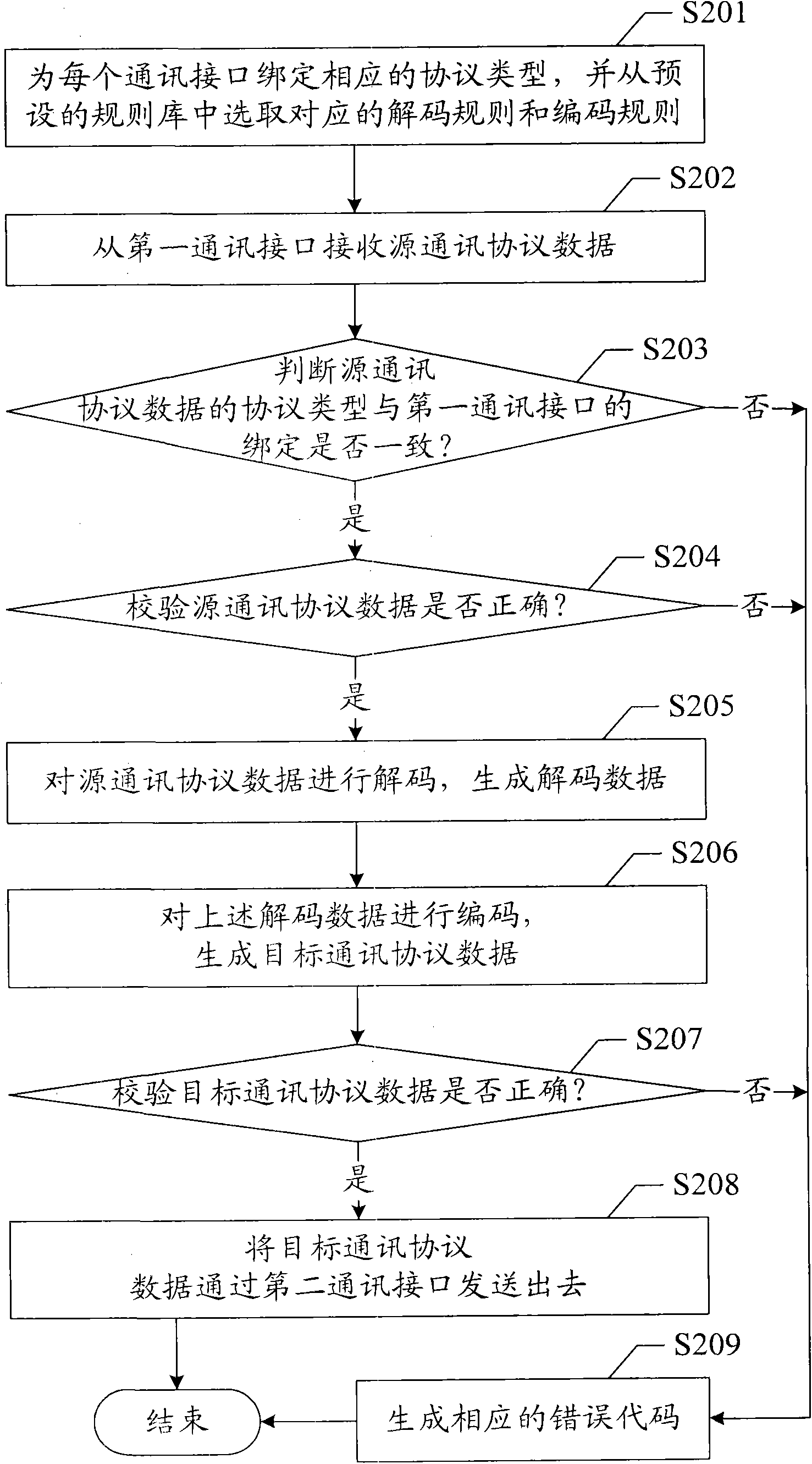
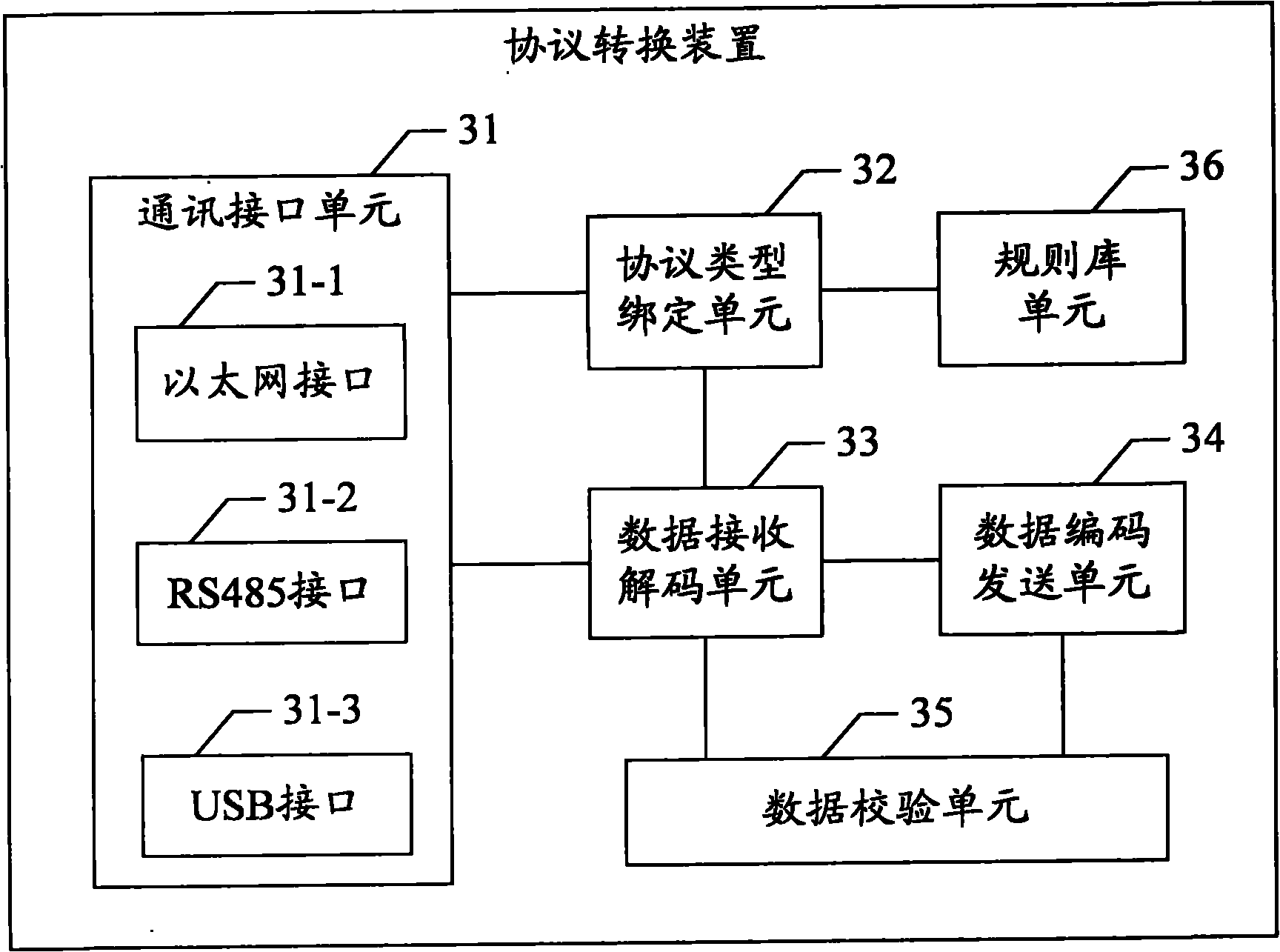
Protocol conversion method and device
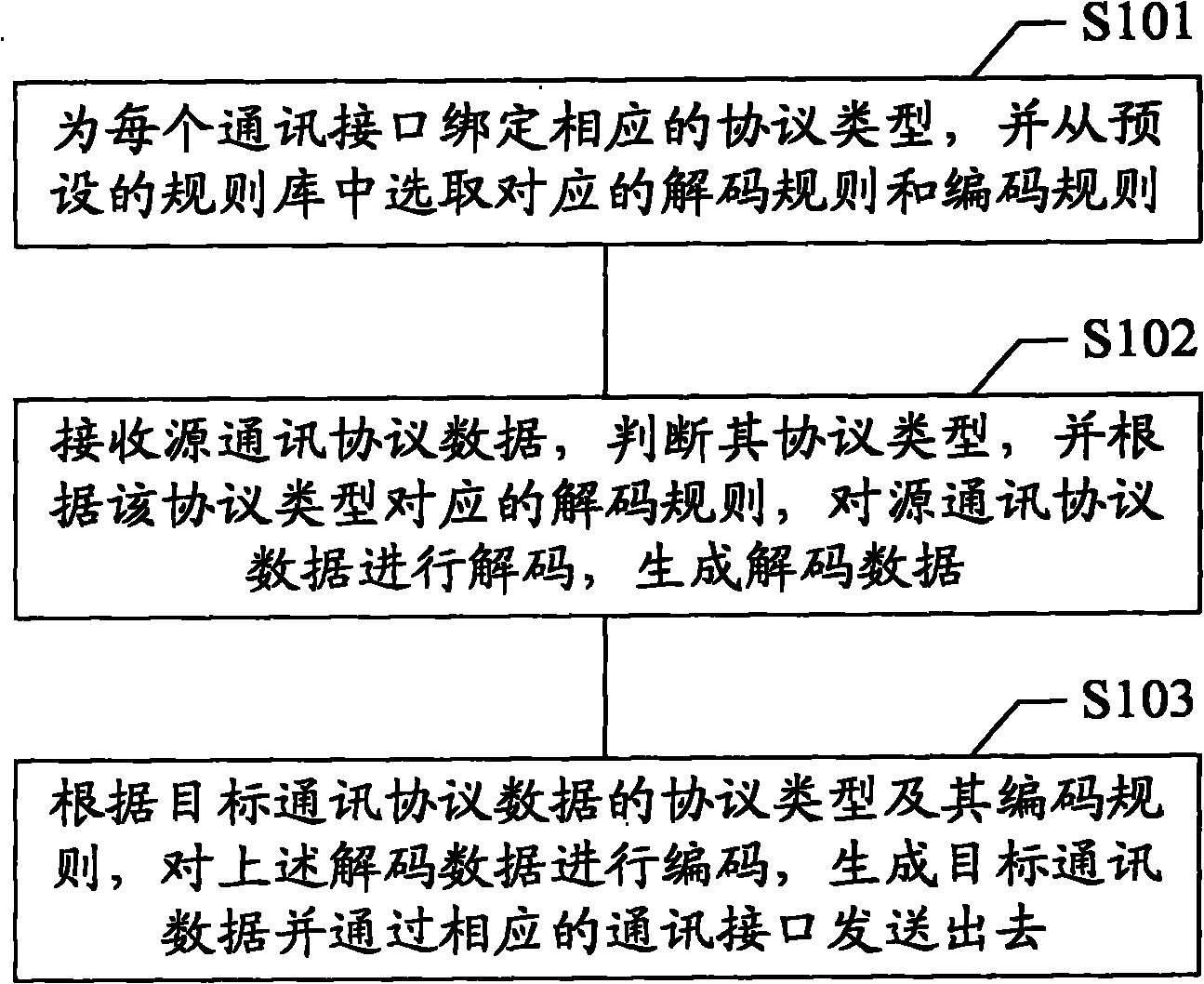
The invention provides a protocol conversion method and device. The protocol conversion device at least comprises a first communication interface and a second communication interface. The protocol conversion method comprises the following steps: binding corresponding protocol types for the communication interfaces, and selecting corresponding decoding and encoding rules from a preset rule base; receiving source communication protocol data from a first communication interface, judging the protocol type of the source communication protocol data, and decoding the source communication protocol data to generate decoded data; and encoding the decoded data to generate target communication data, and sending out the target communication data through a second communication interface. The method and the device in the invention have the advantages that the types of source communication protocols and target communication protocols are unrestricted, thus realizing data conversion for a plurality of the existing standard protocols and manufacturer custom protocols, and solving the problems such as single product function and worse reusability as a result that only specific protocols can be converted in the prior art.
Owner:BEIJING TELLHOW INTELLIGENT ENG CO LTD
Network visible inter-logical router links
InactiveUS20070140235A1Reduce in quantityProvide efficiencyData switching by path configurationNetwork connectionsVisibilityDatapath
A scheme for allowing logical routers to achieve data path efficiency and still maintain network visible virtual links is provided by allowing logical routers in the same physical router to share routing information using standard protocols in place of proprietary route leaking, and by analyzing received data packets to determine if they are tandem data packets or terminating data packets. Tandem data packets are routed directly to egress ports with a single pass through the switch fabric to achieve efficiency, while the TTL value of the packet is decremented twice to maintain the external appearance of the separation of the logical routers. Terminating data packets are routed to other logical routers over virtual links to allow network visibility of the inter-logical router links.
Owner:AVAYA HLDG
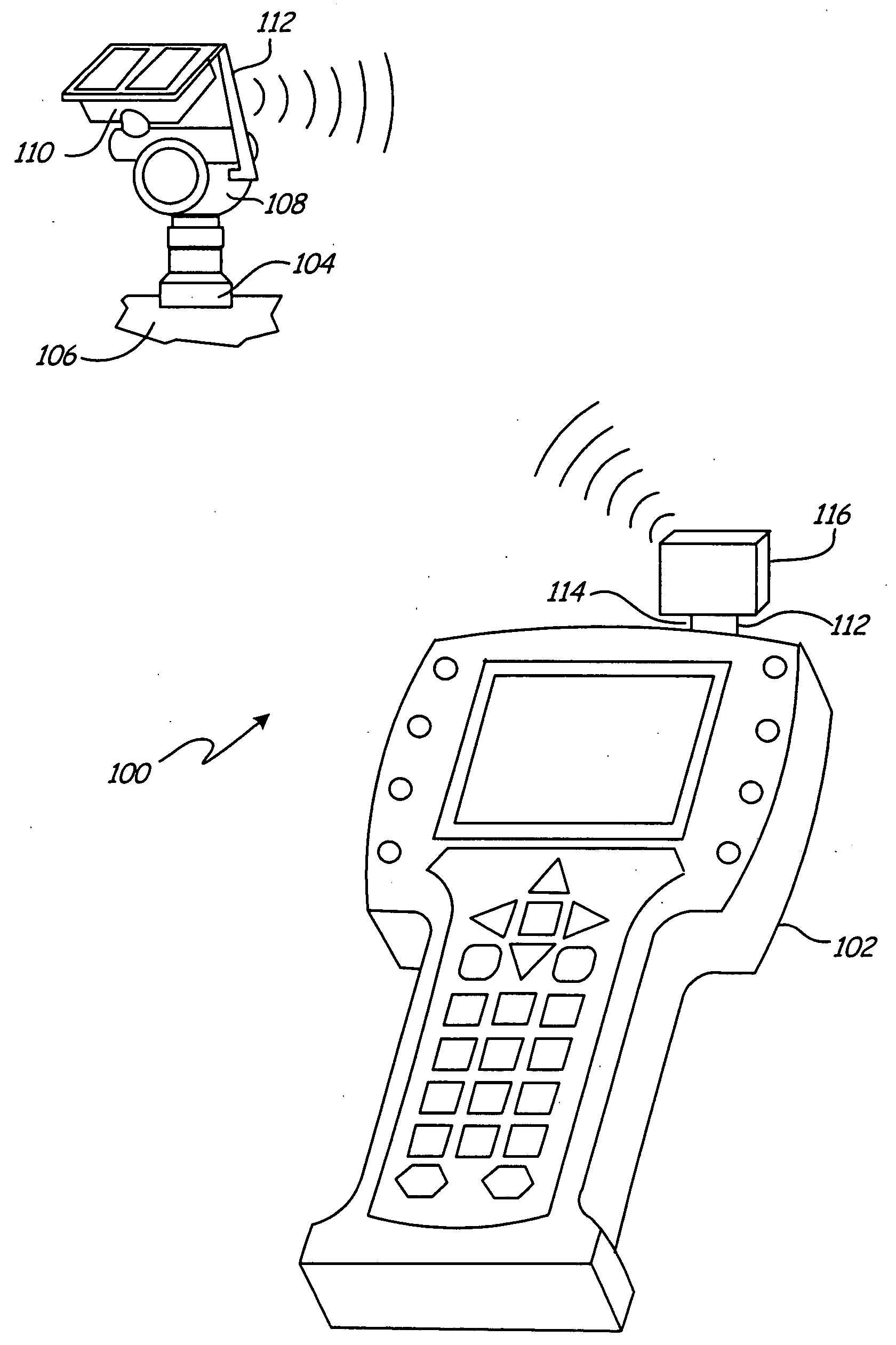
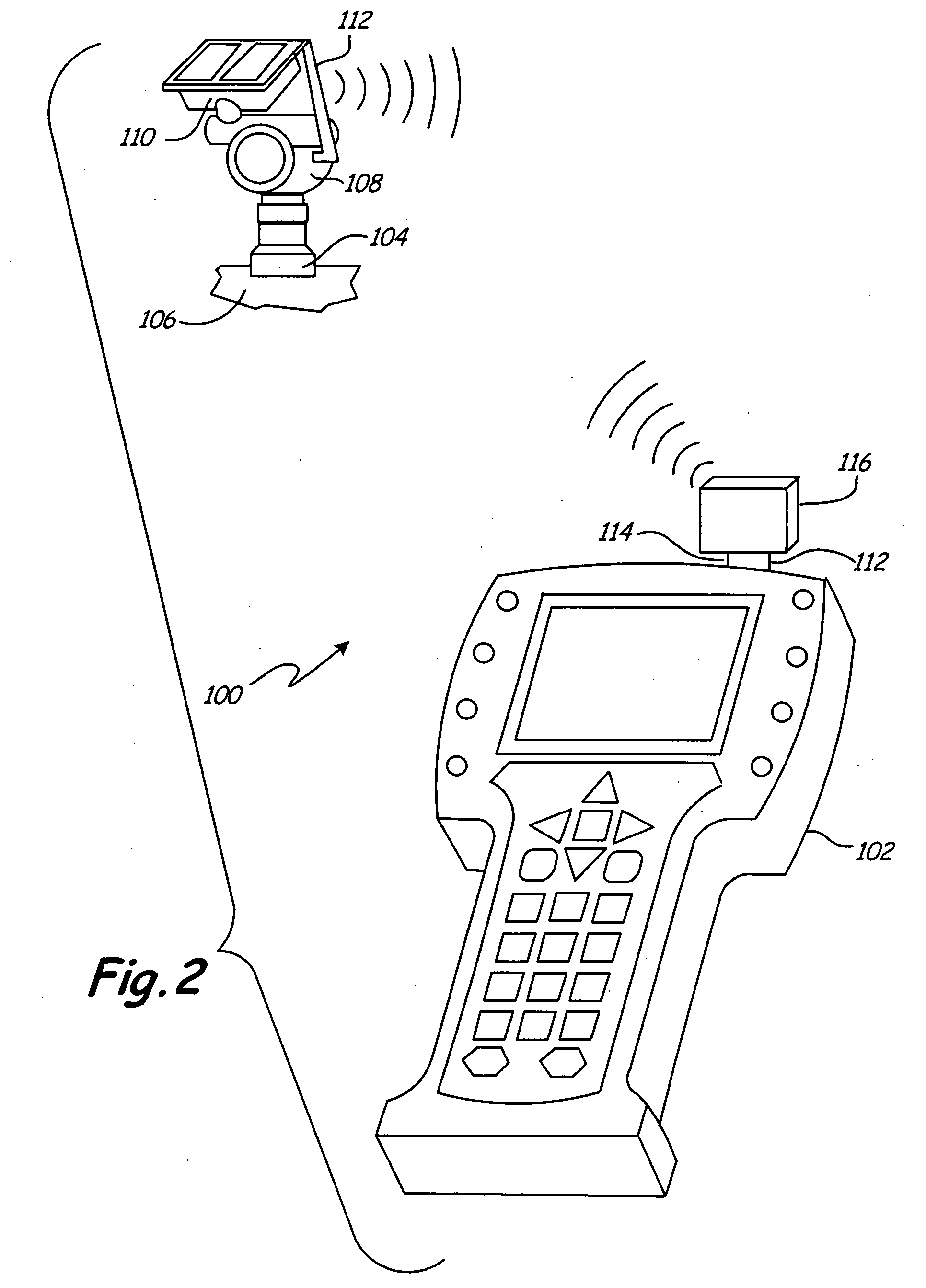
Wireless process communication adapter for handheld field maintenance tool
A wireless process communication adapter is provided. The adapter includes a plurality of plugs that are coupleable to a handheld field maintenance tool. A loop communication module is operably coupled to the plurality of plugs. The loop communication module is configured to communicate digitally in accordance with a process loop communication standard protocol. A controller is coupled to the loop communication module, and is configured to transform at least one message received from the loop communication module to at least one corresponding wireless protocol packet. A wireless communication module is coupled to the controller and configured to receive the at least one corresponding wireless protocol packet and generate a wireless signal based upon the at least one wireless protocol packet.
Owner:FISHER-ROSEMOUNT SYST INC
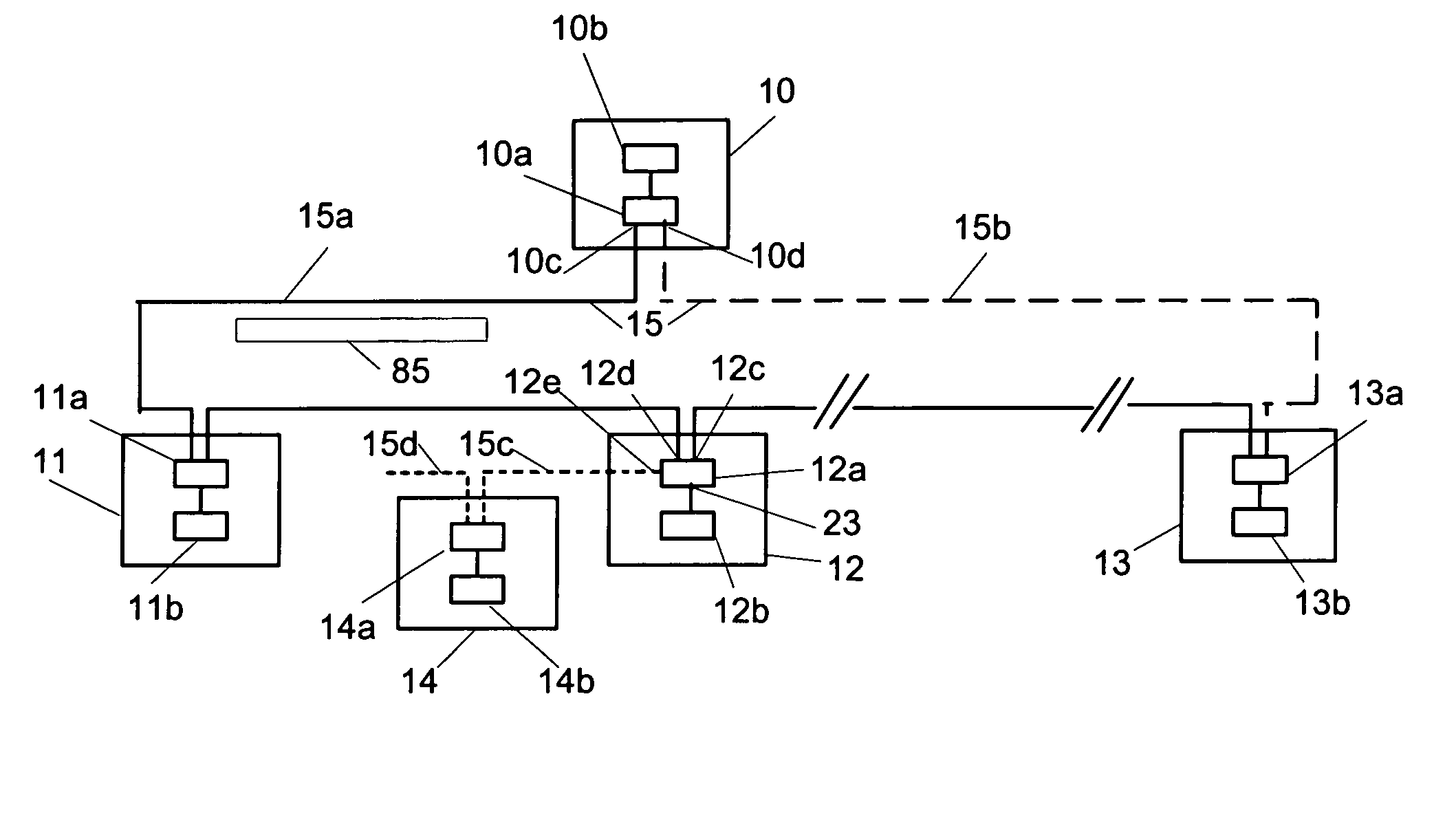
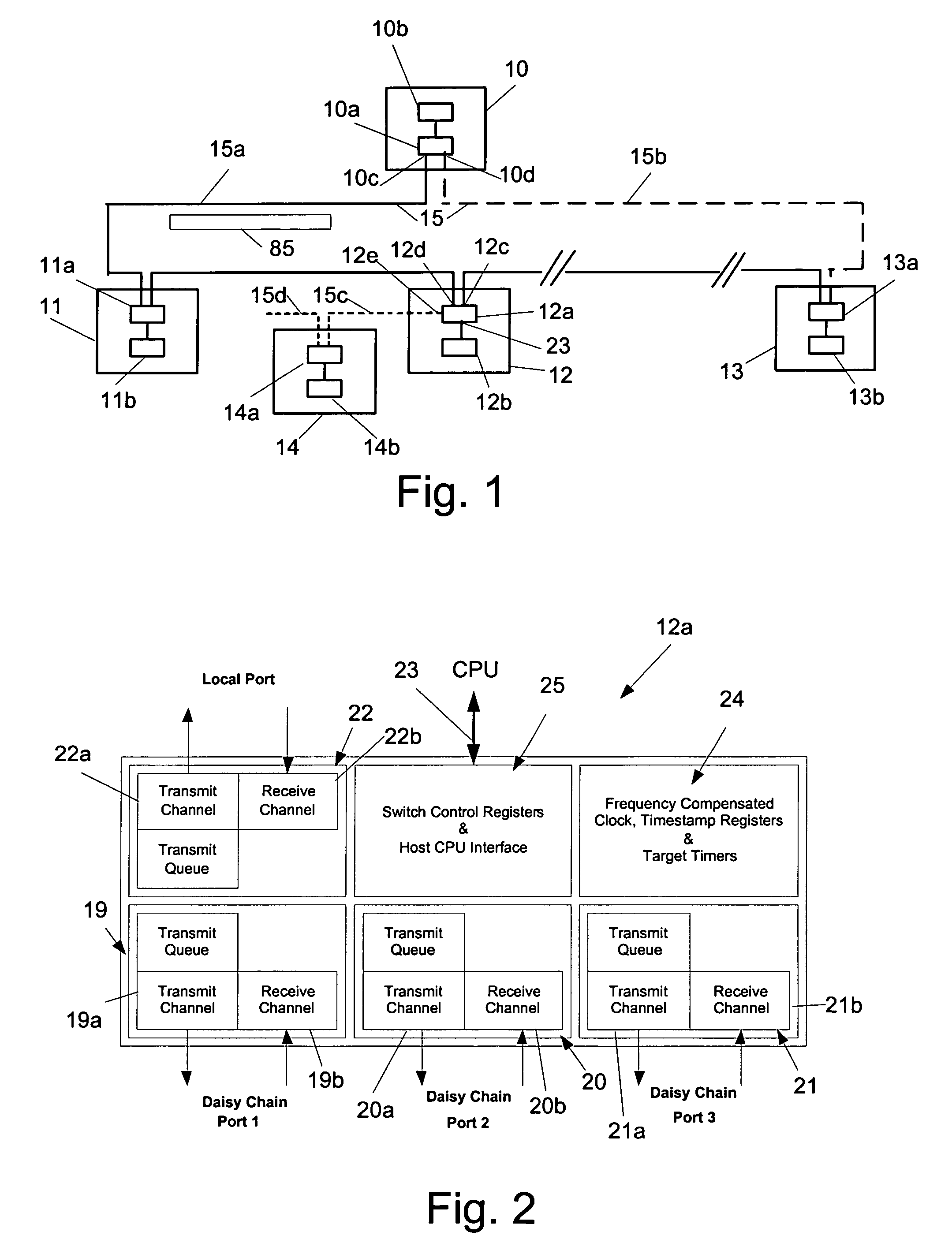
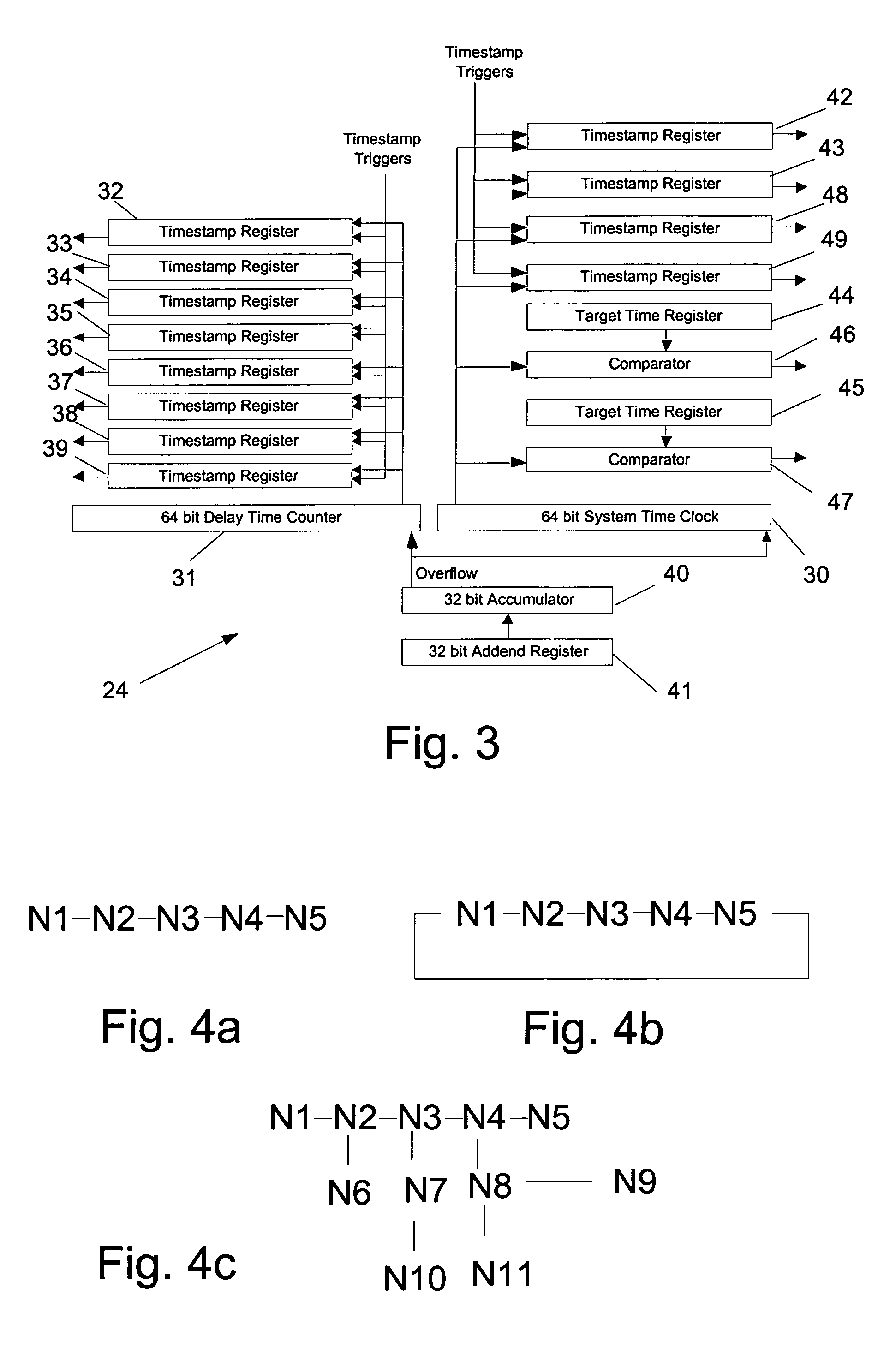
Time synchronization, deterministic data delivery and redundancy for cascaded nodes on full duplex ethernet networks
ActiveUS7649912B2Simple systemAccurate accountingTime-division multiplexGenerating/distributing signalsData synchronizationTimestamp
Owner:ROCKWELL AUTOMATION TECH
Region-wide messaging system and methods including validation of transactions
InactiveUS6882708B1The method is simple and reliableMultiplex system selection arrangementsInterconnection arrangementsComputer networkEngineering
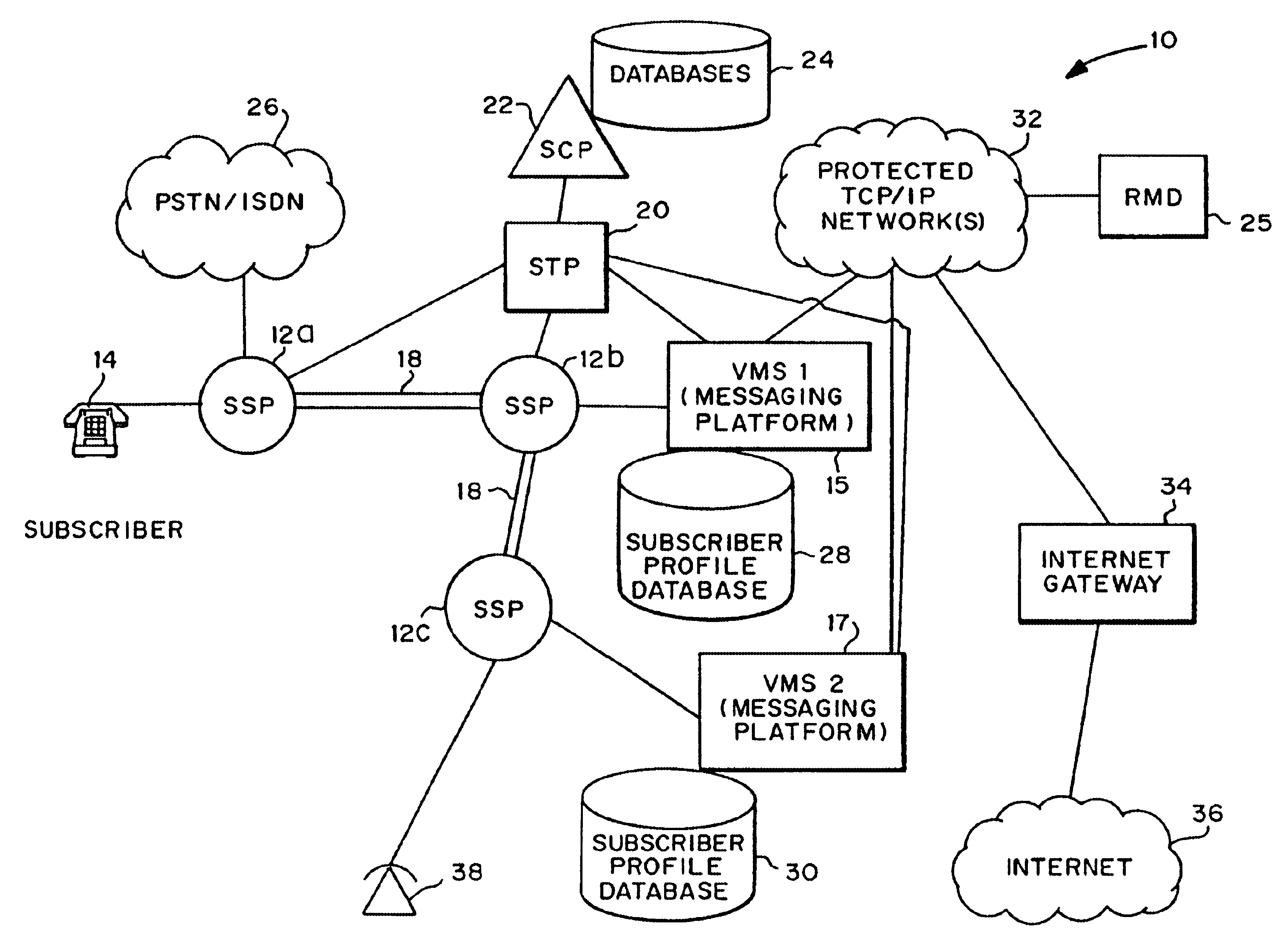
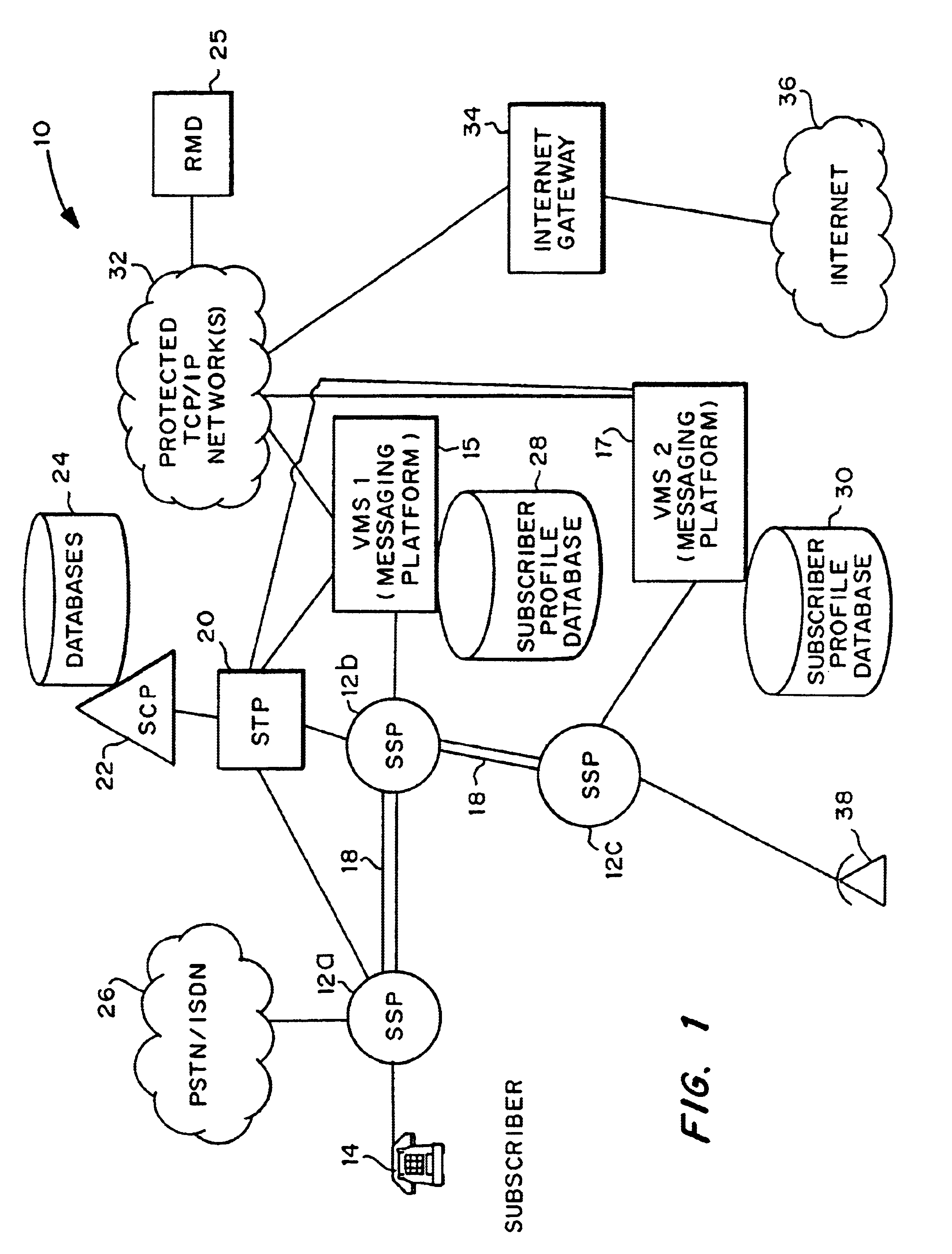
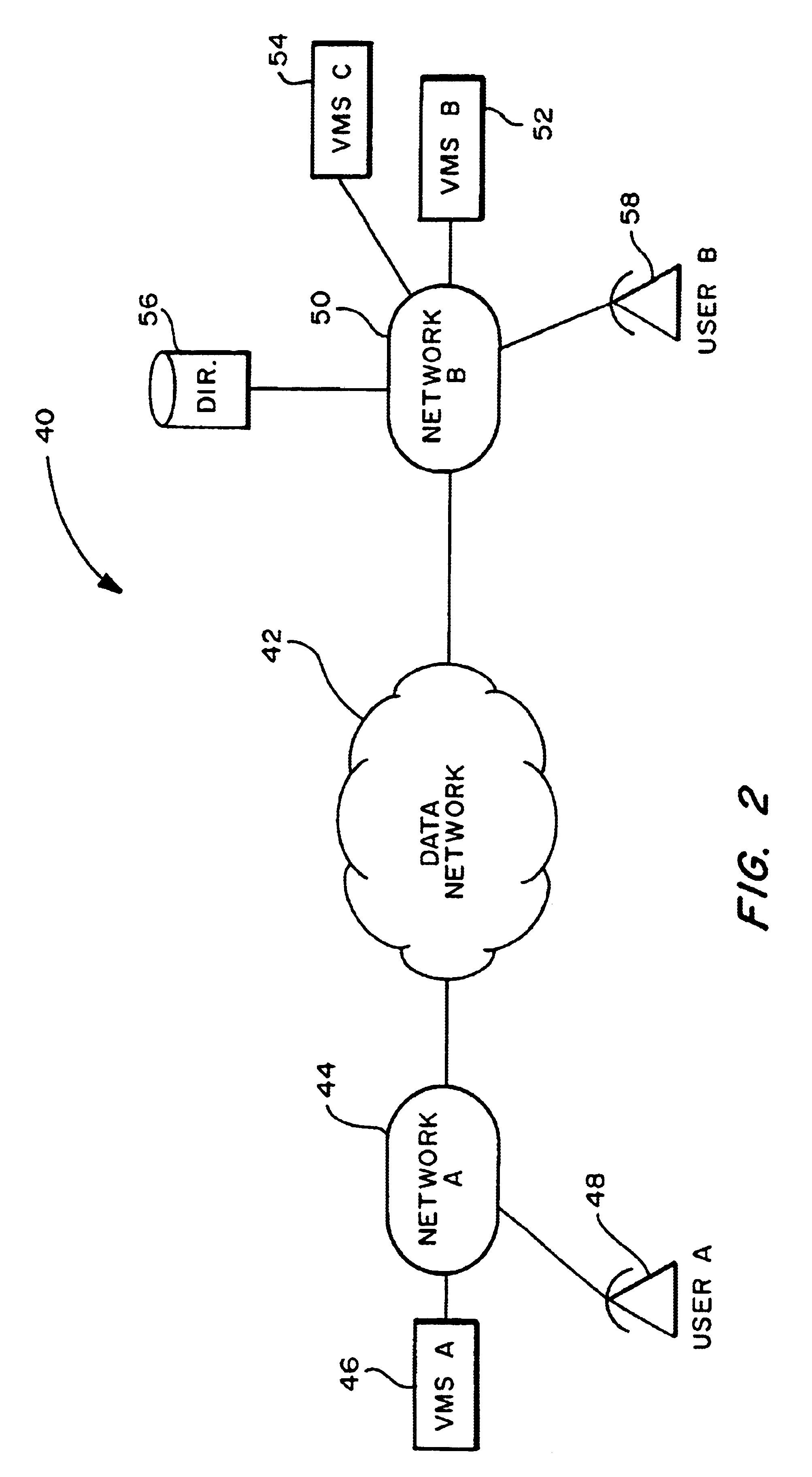
Methods and systems are disclosed that allow for the exchange of voice mail messages between different VMSs of different service providers and / or in different networks by the transmission of such messages through a data network using a standard protocol of the data network. Methods and systems also are disclosed that validate message transactions among subscribers receiving regional messaging services over the PSTN. The subscribers are located in different geographic areas and may be provided their voice, facsimile or data messaging services by different companies. The present invention validates passing messages (data) among customers of potentially different companies located in different areas by assessing the validity of the transaction in light of a number of conditions, including applicable regulatory or business conditions.
Owner:BELLSOUTH INTPROP COR
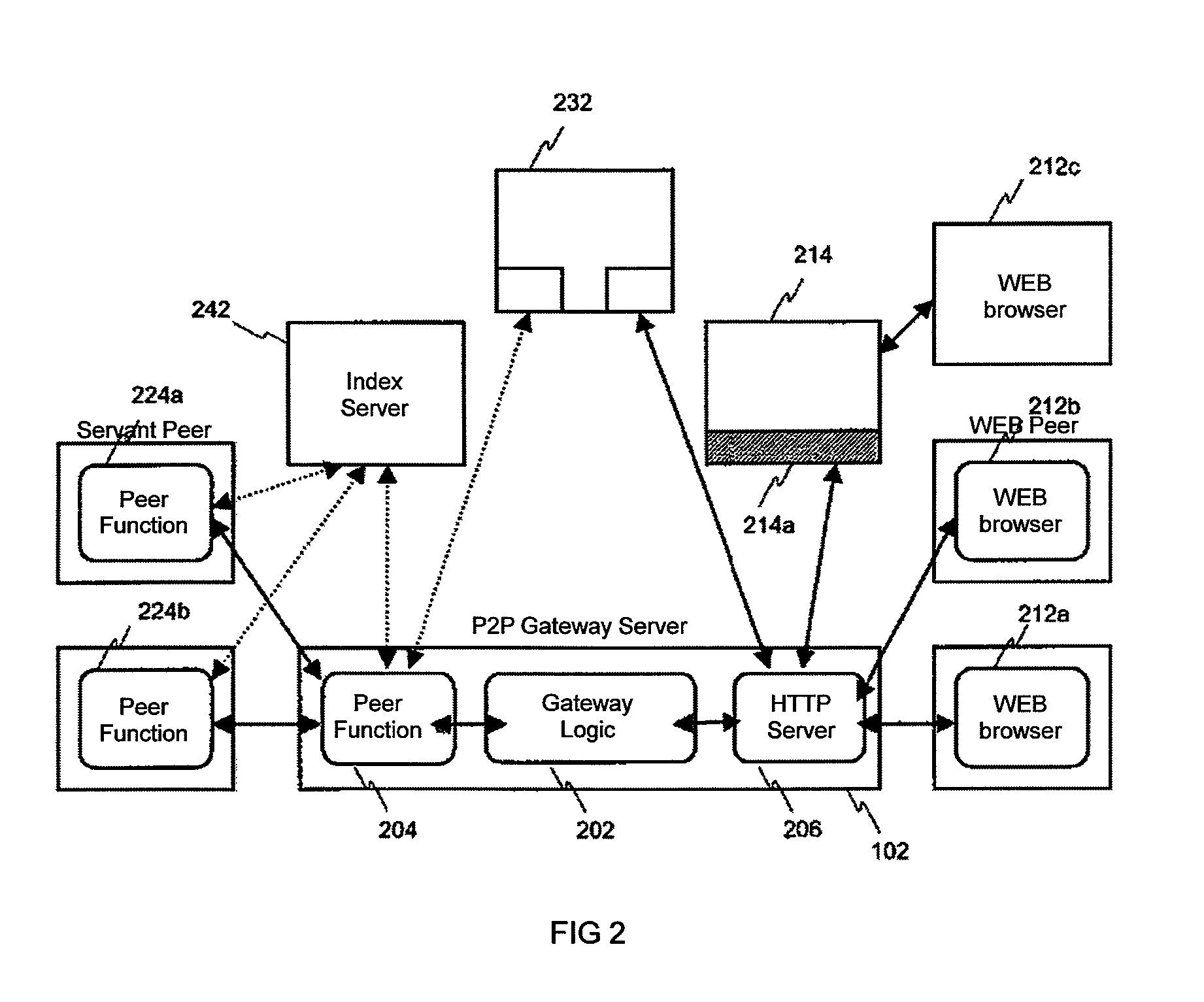
Method and apparatus for peer-to-peer access
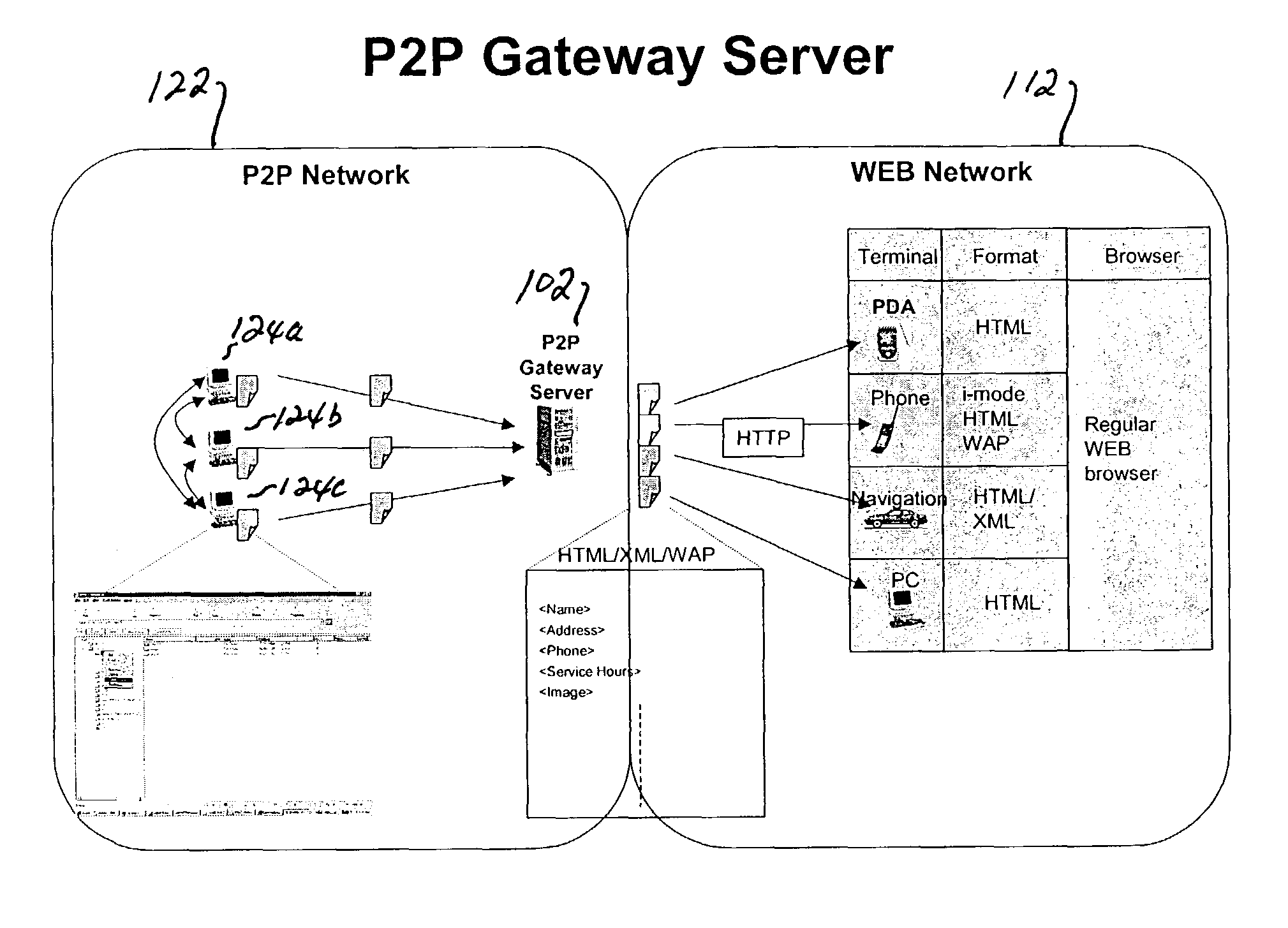
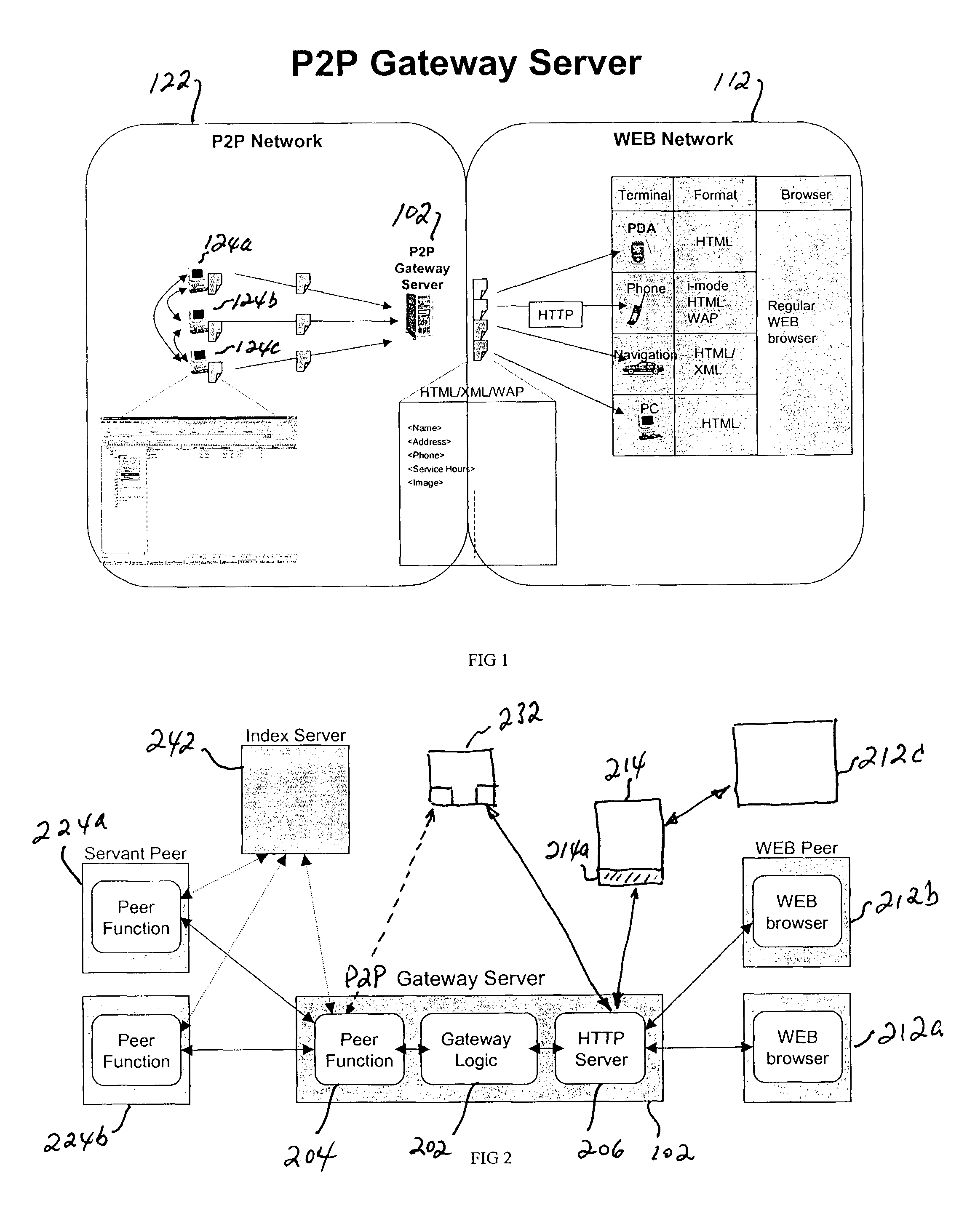
In a specific embodiment of the invention, a peer-to-peer interfacing device is described. The particular embodiment of the invention facilitates access by a Web browser, allowing a Web user to benefit from the access capability of a peer-to-peer network, such as file sharing. The interfacing device can communicate using a standard protocol (e.g., HTML), thus allowing the Web user to access the peer-to-peer network with a conventional Web browser. The interfacing device can interact on the peer-to-peer network side, and thus appears to the peer-to-peer network as a peer machine.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com