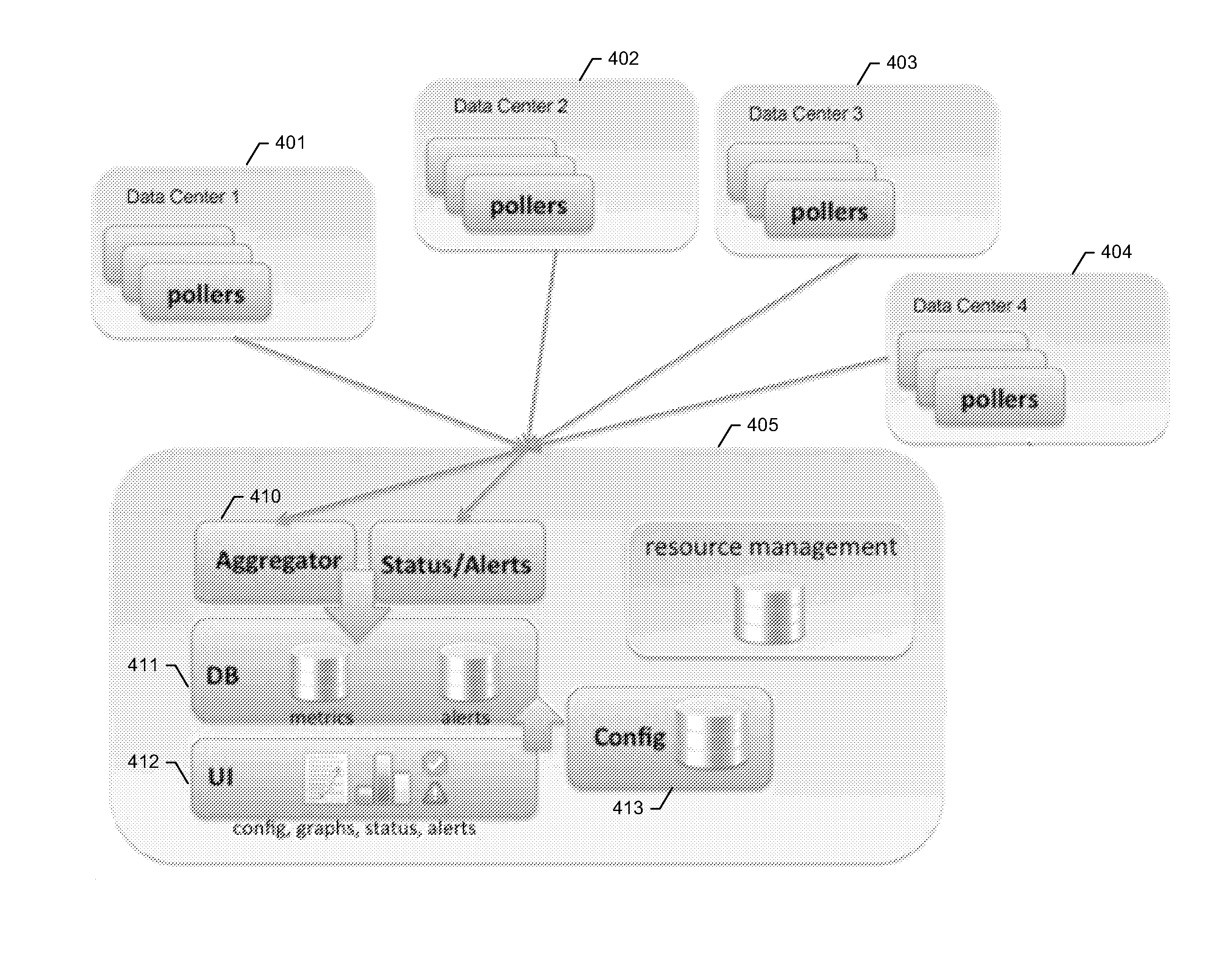Patents
Literature
179 results about "Web traffic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
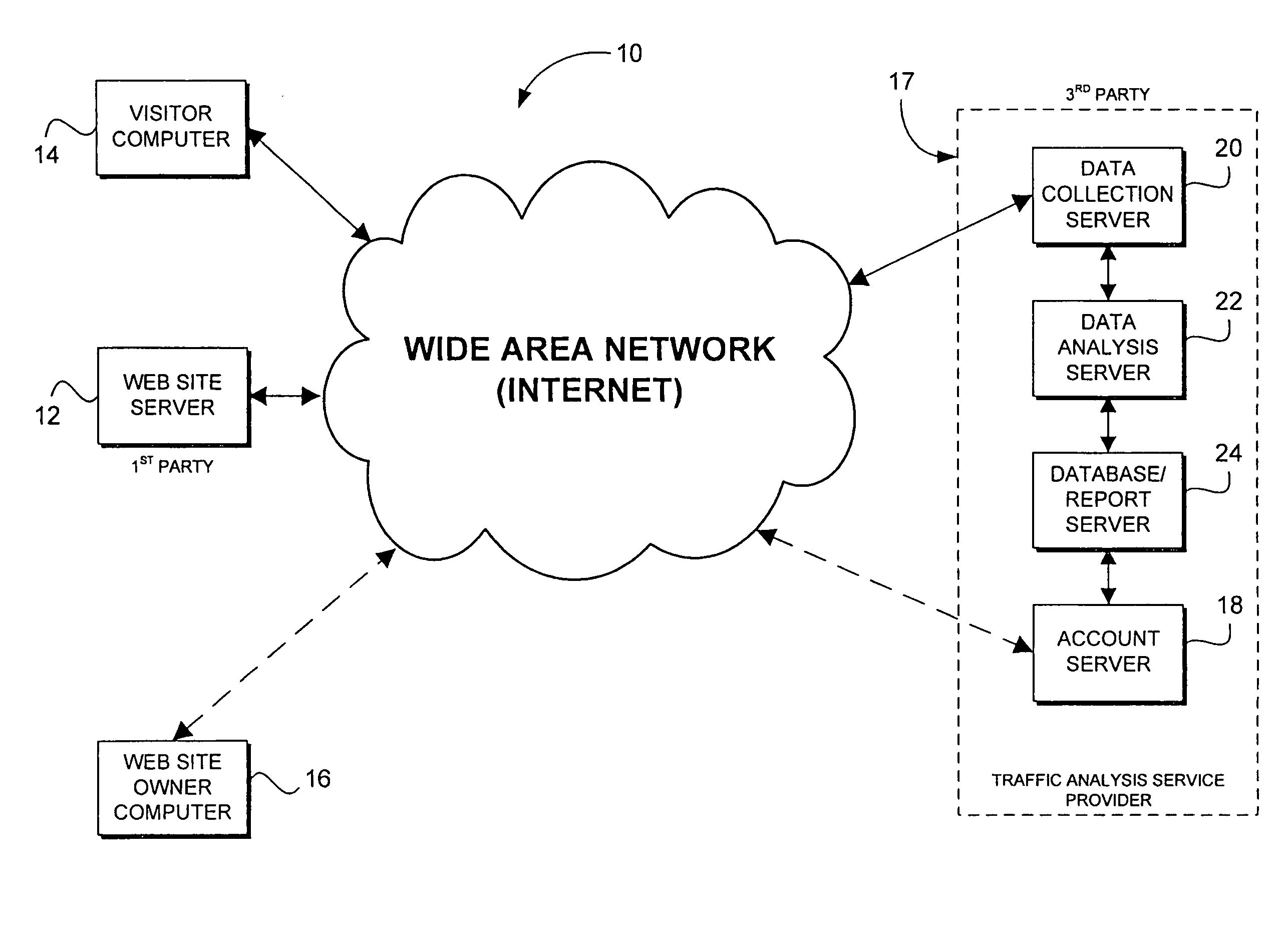
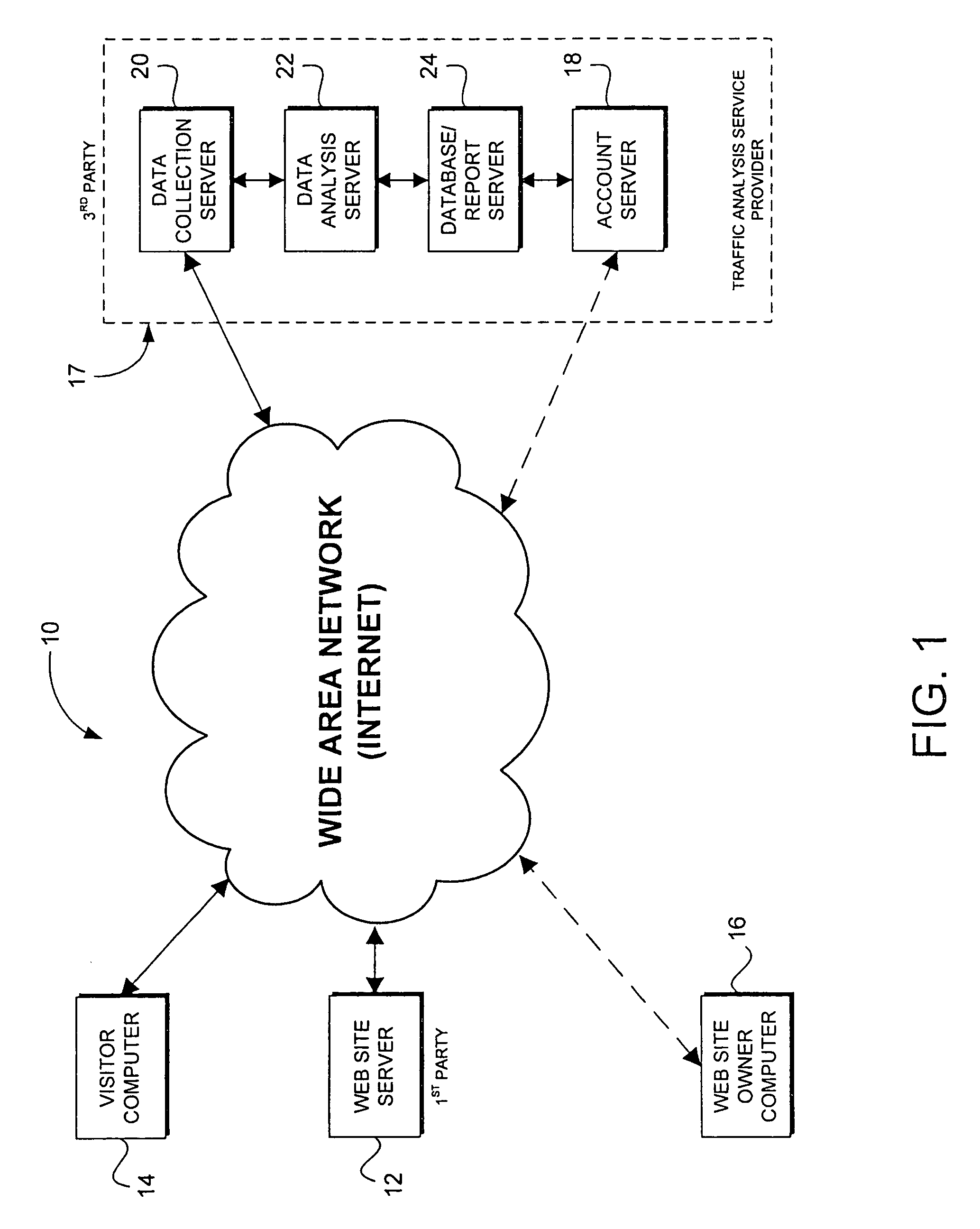
Web traffic is the amount of data sent and received by visitors to a website. This necessarily does not include the traffic generated by bots. Since the mid-1990s, web traffic has been the largest portion of Internet traffic. This is determined by the number of visitors and the number of pages they visit. Sites monitor the incoming and outgoing traffic to see which parts or pages of their site are popular and if there are any apparent trends, such as one specific page being viewed mostly by people in a particular country. There are many ways to monitor this traffic and the gathered data is used to help structure sites, highlight security problems or indicate a potential lack of bandwidth.
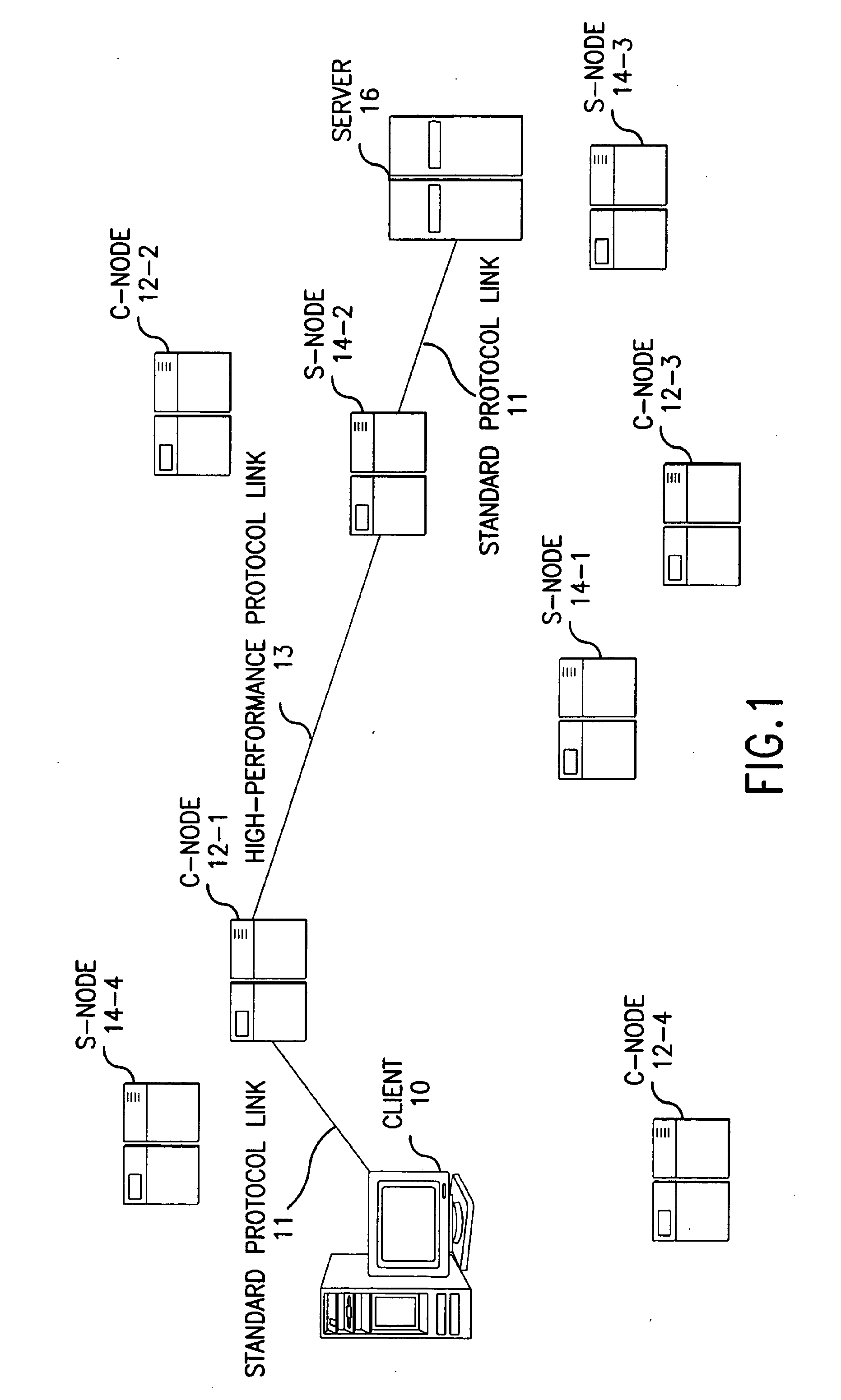
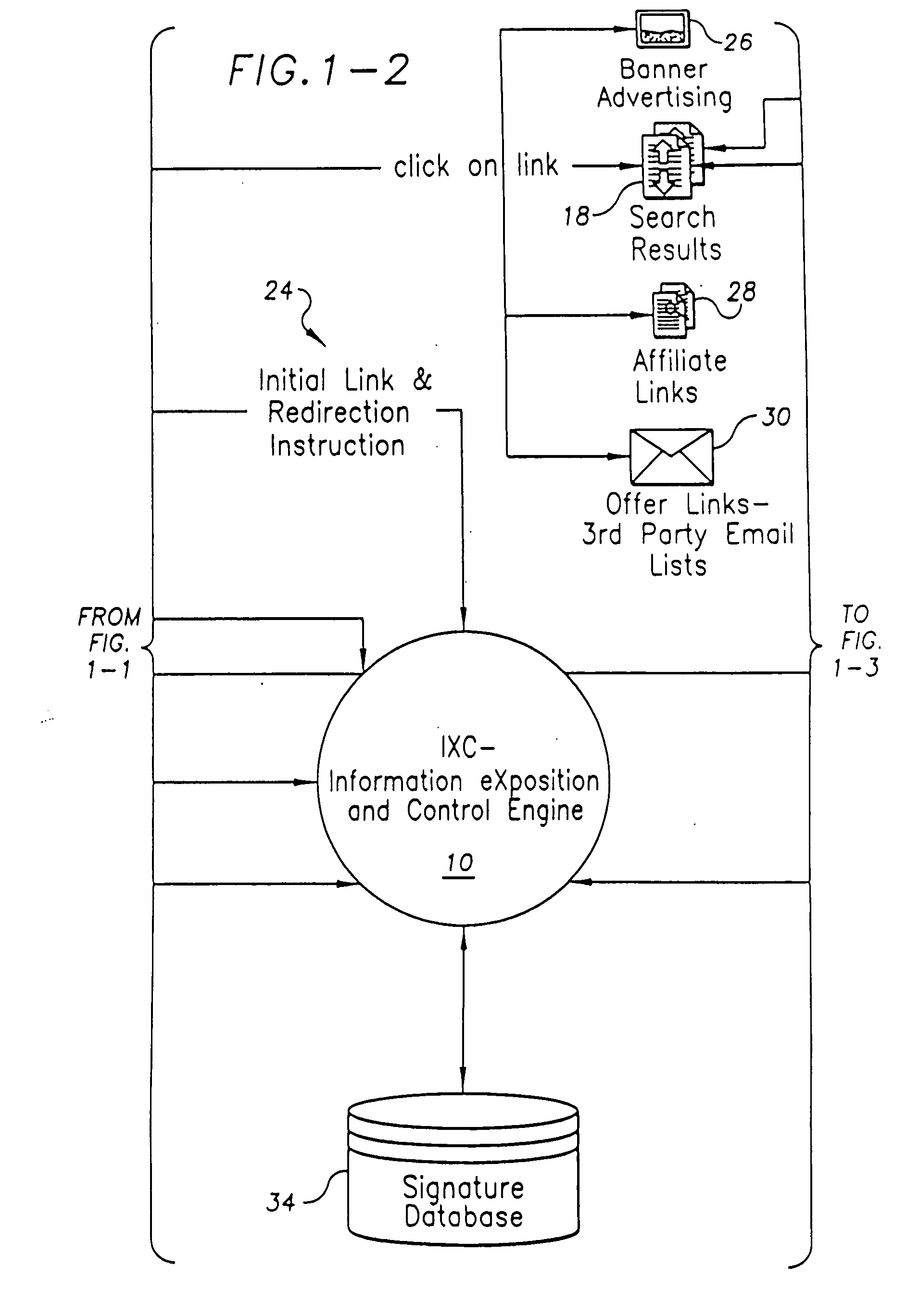
Method for high-performance delivery of web content
InactiveUS20050044270A1Improve performanceReduce deliveryDigital computer detailsData switching networksWeb serviceWeb cache
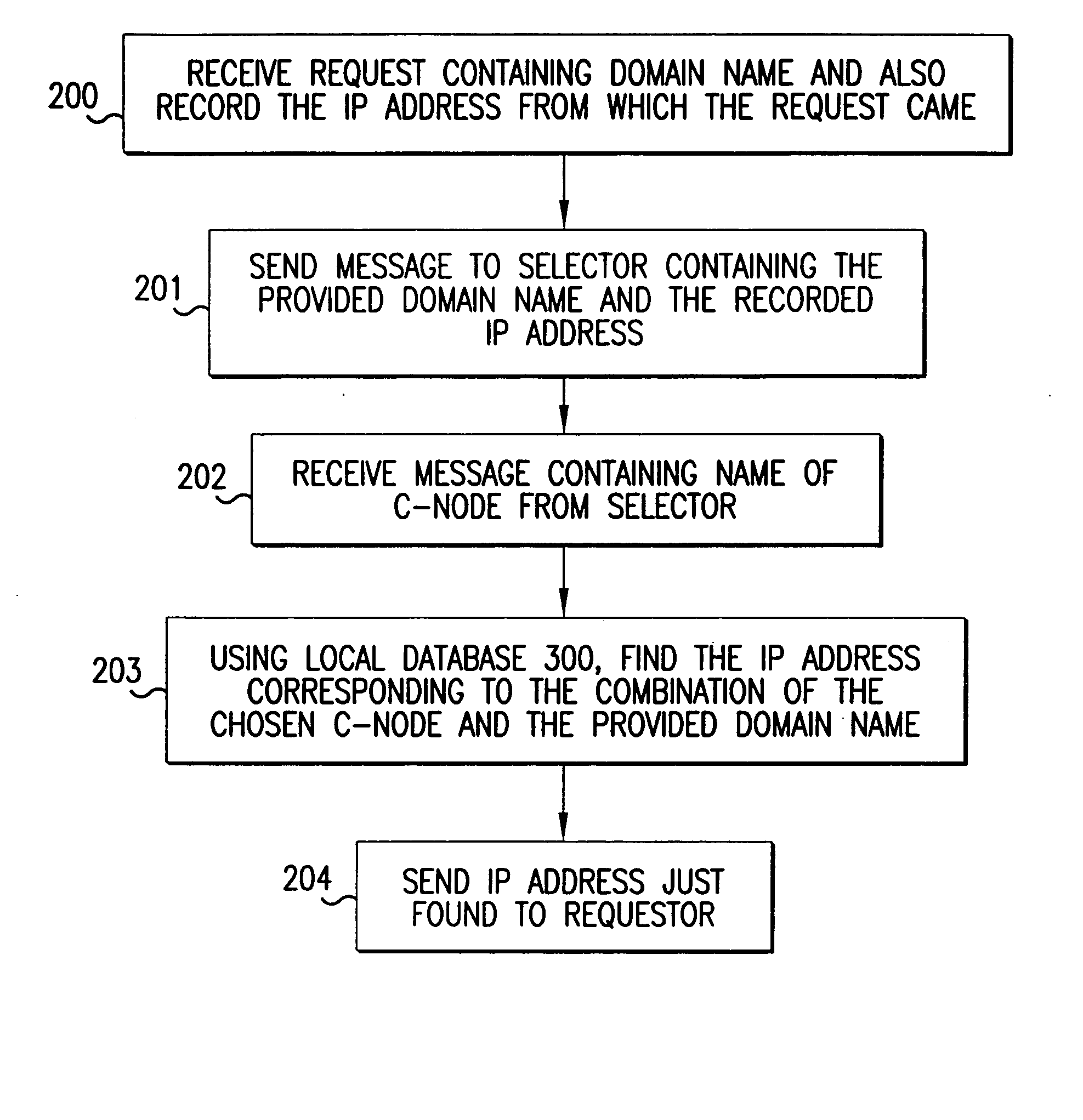
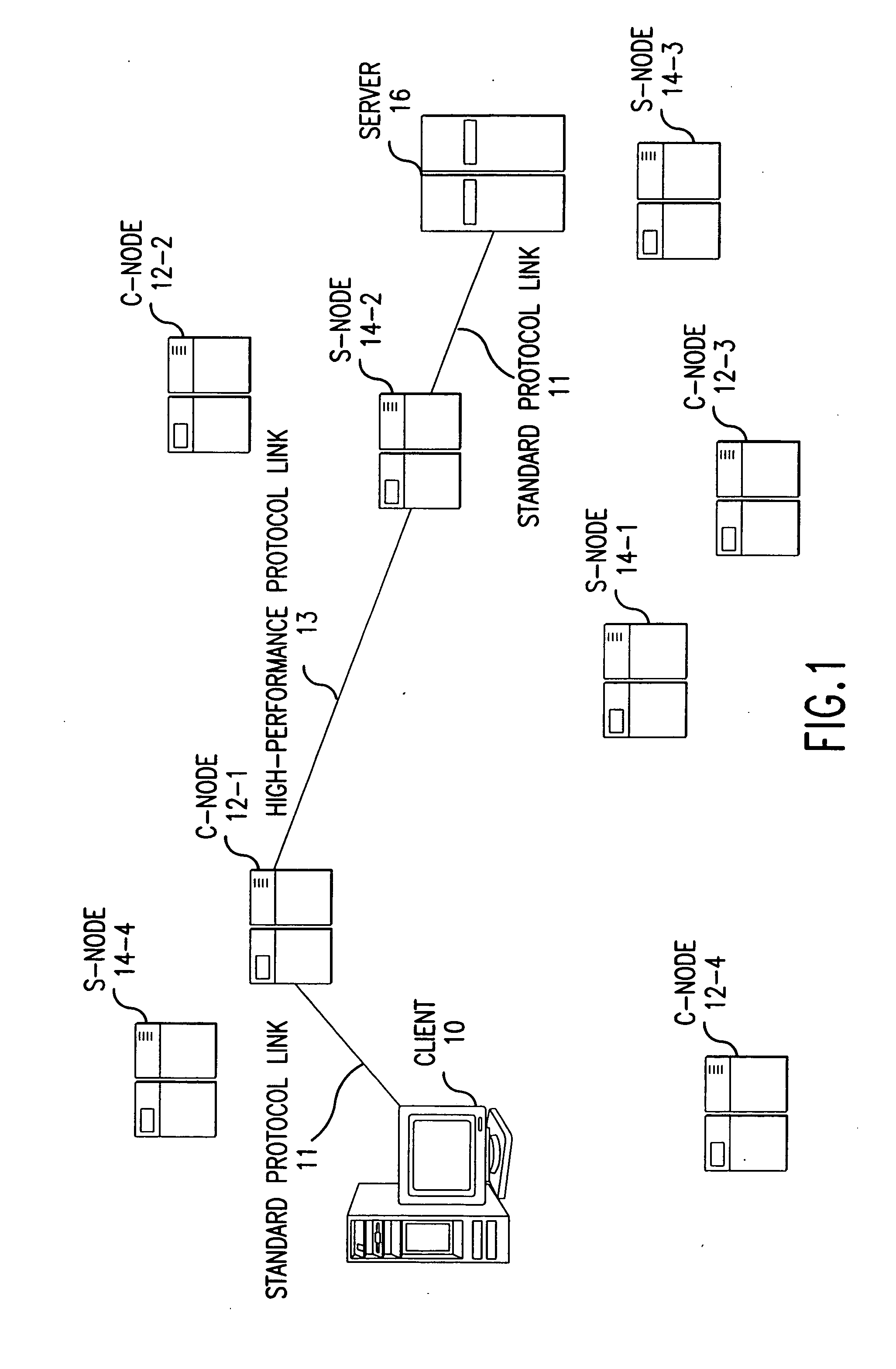
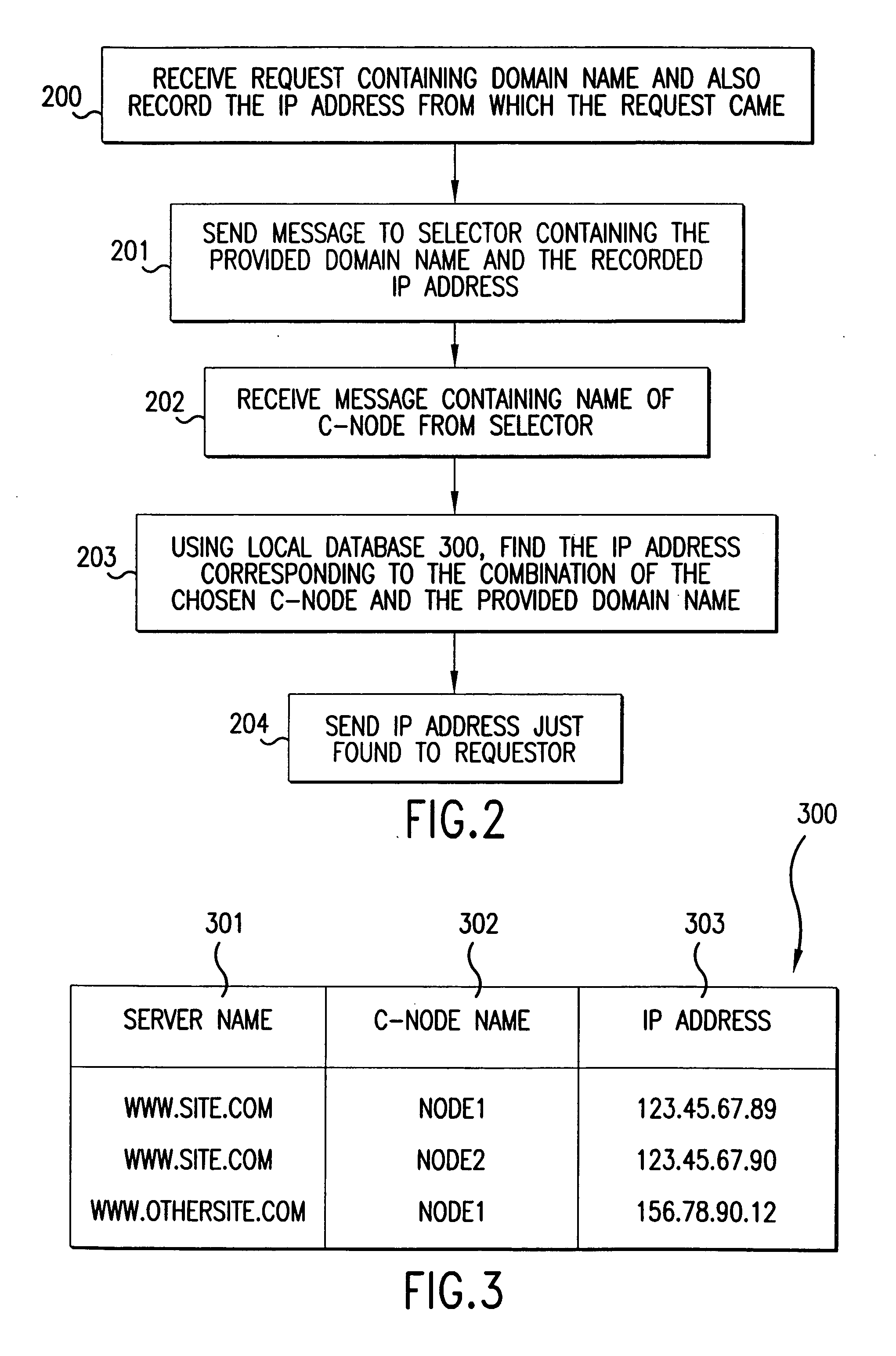
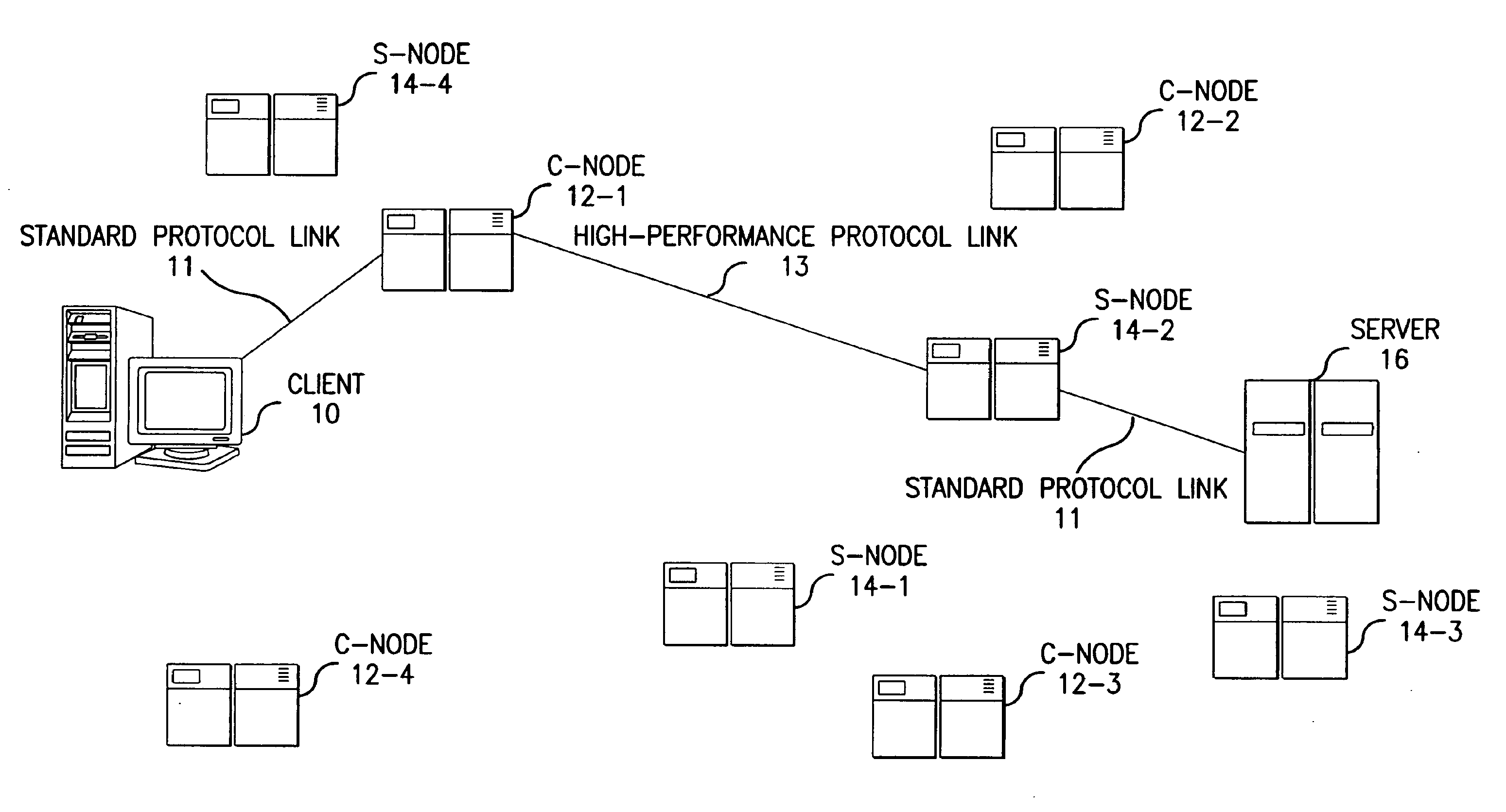
The present invention provides a method and apparatus for increasing the performance of world-wide-web traffic over the Internet. A distributed network of specialized nodes of two types is dispersed around the Internet. A web client's requests are directed to a node of the first type chosen to be close to the client, and the client communicates with this node using a standard protocol such as HTTP. This first node receives the request, and communicates the request to a node of the second type chosen to be close to the request's ultimate destination (e.g., a web server capable of generating a response to the request.) The first node communicates the request to the second node using a different, specialized, protocol that has been designed for improved performance and specifically to reduce traffic volume and to reduce latency. The second node receives communication from the first node using this specialized protocol, converts it back to a standard protocol such as HTTP, and forwards the request to the destination computer or server. Responses from the destination to the client take the corresponding reverse route, and also are carried over a specialized protocol between the two nodes. In addition, these nodes can employ other techniques such as web caches that avoid or improve some communication steps. Thus, specialized, proprietary, or complex protocols and techniques can be quickly deployed to enhance web performance without requiring significant changes to the clients or servers.
Owner:AKAMAI TECH INC
Method for high-performance delivery of web content
InactiveUS20070050522A1Improve performanceReduce deliveryMultiple digital computer combinationsData switching networksWeb serviceWeb cache
The present invention provides a method and apparatus for increasing the performance of world-wide-web traffic over the Internet. A distributed network of specialized nodes of two types is dispersed around the Internet. A web client's requests are directed to a node of the first type chosen to be close to the client, and the client communicates with this node using a standard protocol such as HTTP. This first node receives the request, and communicates the request to a node of the second type chosen to be close to the request's ultimate destination (e.g., a web server capable of generating a response to the request.) The first node communicates the request to the second node using a different, specialized, protocol that has been designed for improved performance and specifically to reduce traffic volume and to reduce latency. The second node receives communication from the first node using this specialized protocol, converts it back to a standard protocol such as HTTP, and forwards the request to the destination computer or server. Responses from the destination to the client take the corresponding reverse route, and also are carried over a specialized protocol between the two nodes. In addition, these nodes can employ other techniques such as web caches that avoid or improve some communication steps. Thus, specialized, proprietary, or complex protocols and techniques can be quickly deployed to enhance web performance without requiring significant changes to the clients or servers.
Owner:AKAMAI TECH INC
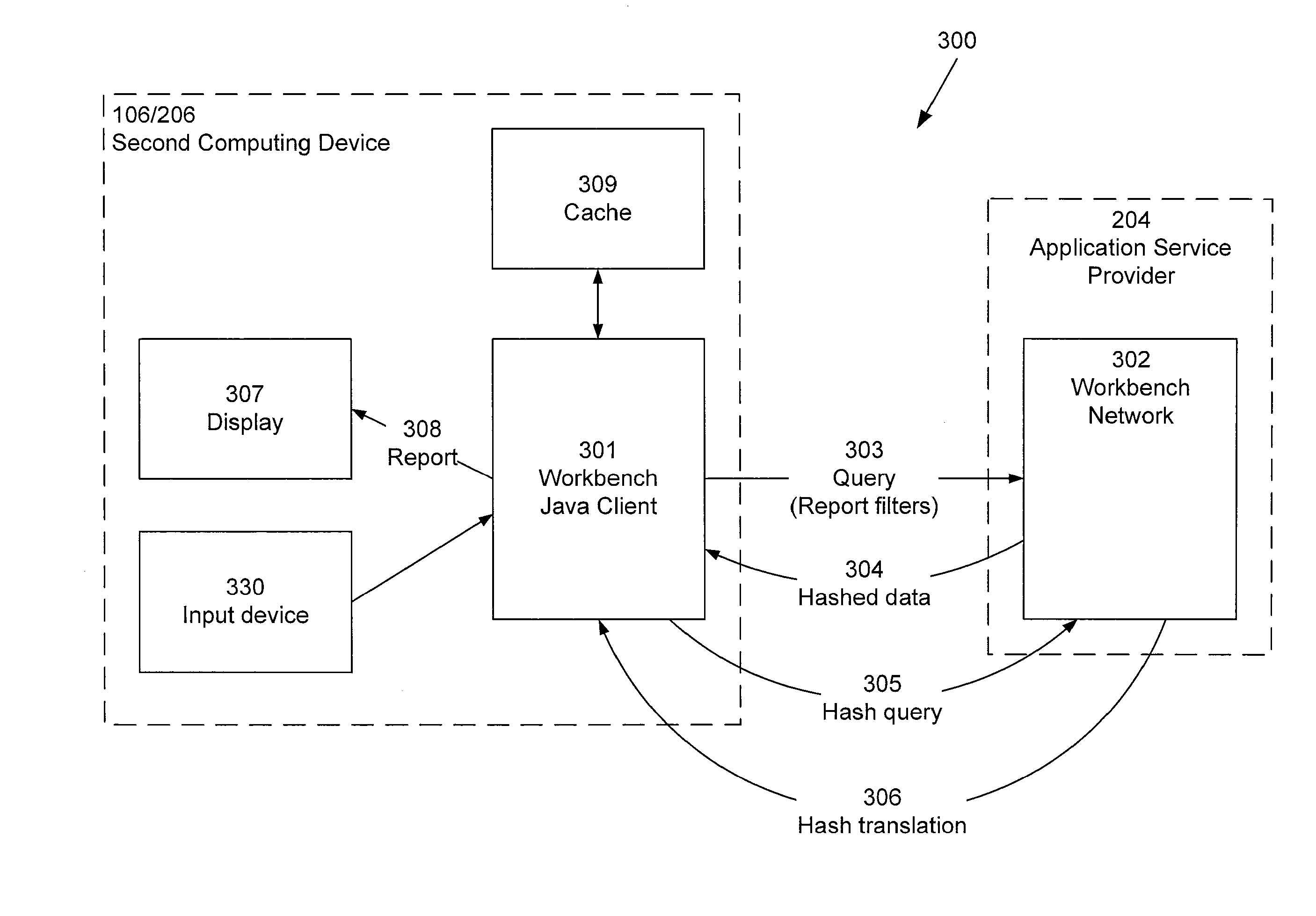
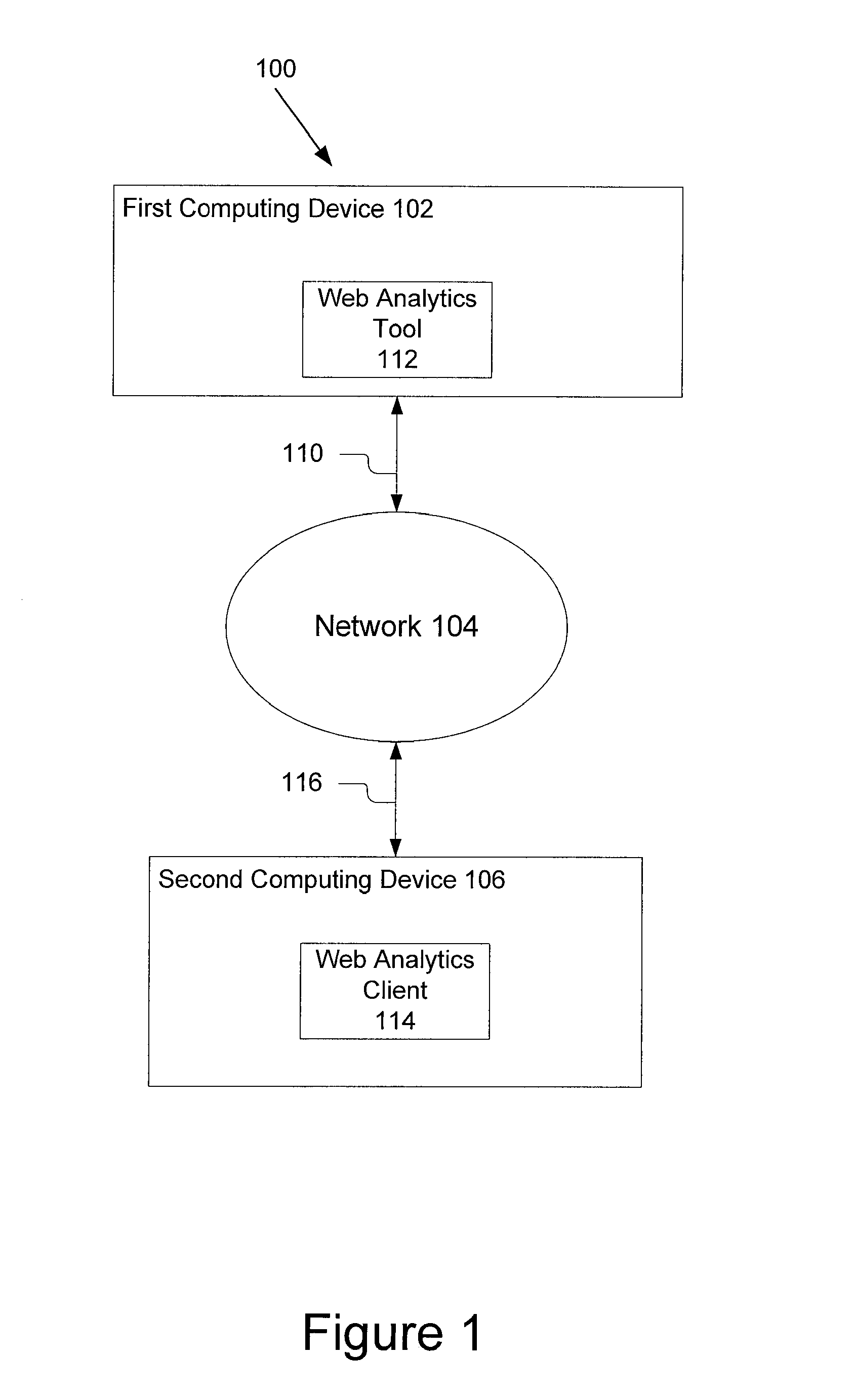
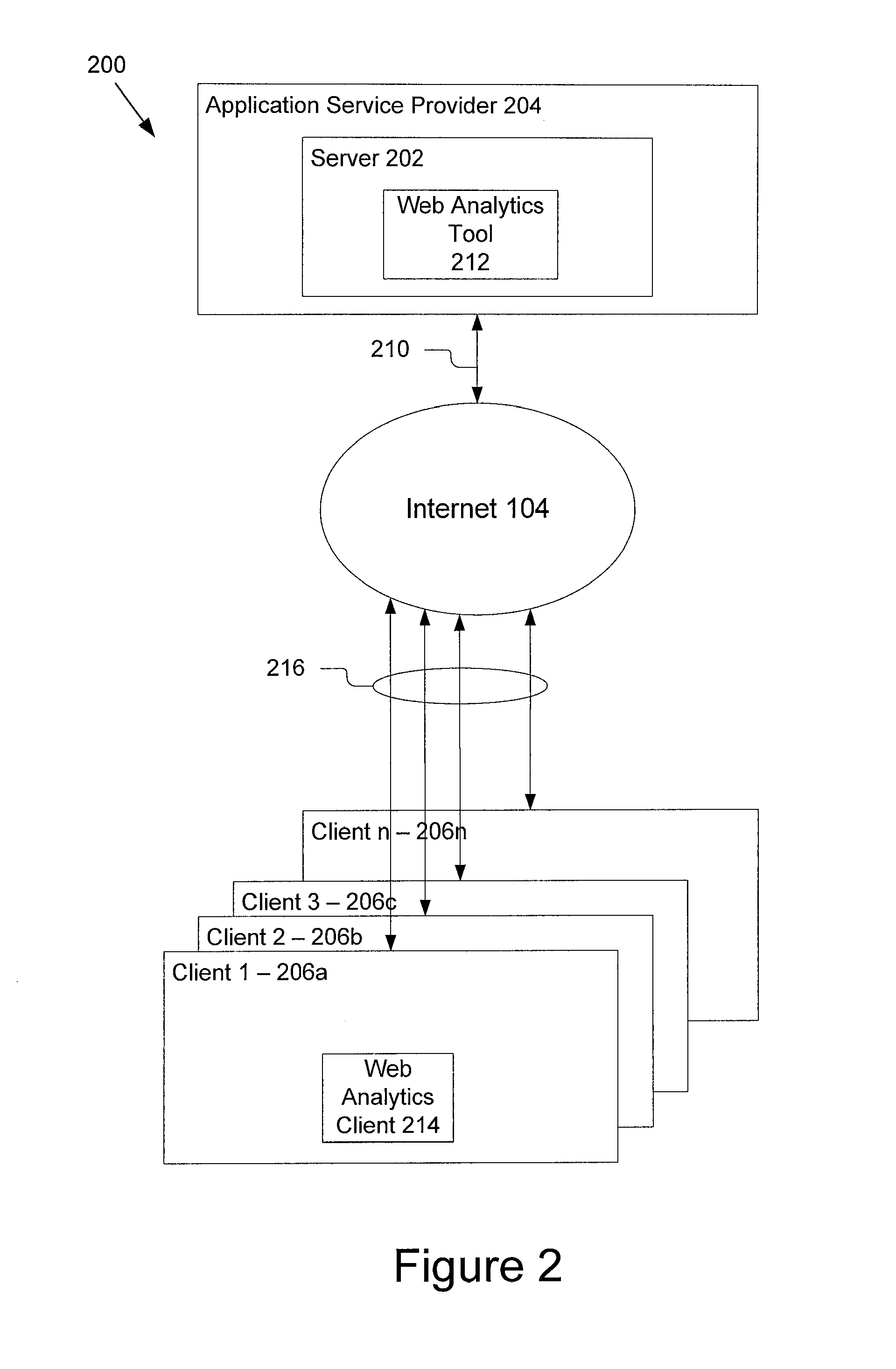
Asp for web analytics including a real-time segmentation workbench
ActiveUS20070011304A1Function increaseReal-time accessDigital computer detailsMarketingService provisionWeb analytics
An application service provider system for retrieving and displaying web analytic data, or segmentation workbench, comprises a server and several client computing devices. The server includes a web analytics tool. Each of the clients preferably includes a web analytics client for communication with the server. The application service provider system is architecture allows web analytics service to be provided to users with an application service provider where the web traffic information for different users can be segregated and share a single server while communicating with different clients of different user companies. The present invention also includes a number of methods for retrieving and presenting web analytics data
Owner:ADOBE INC
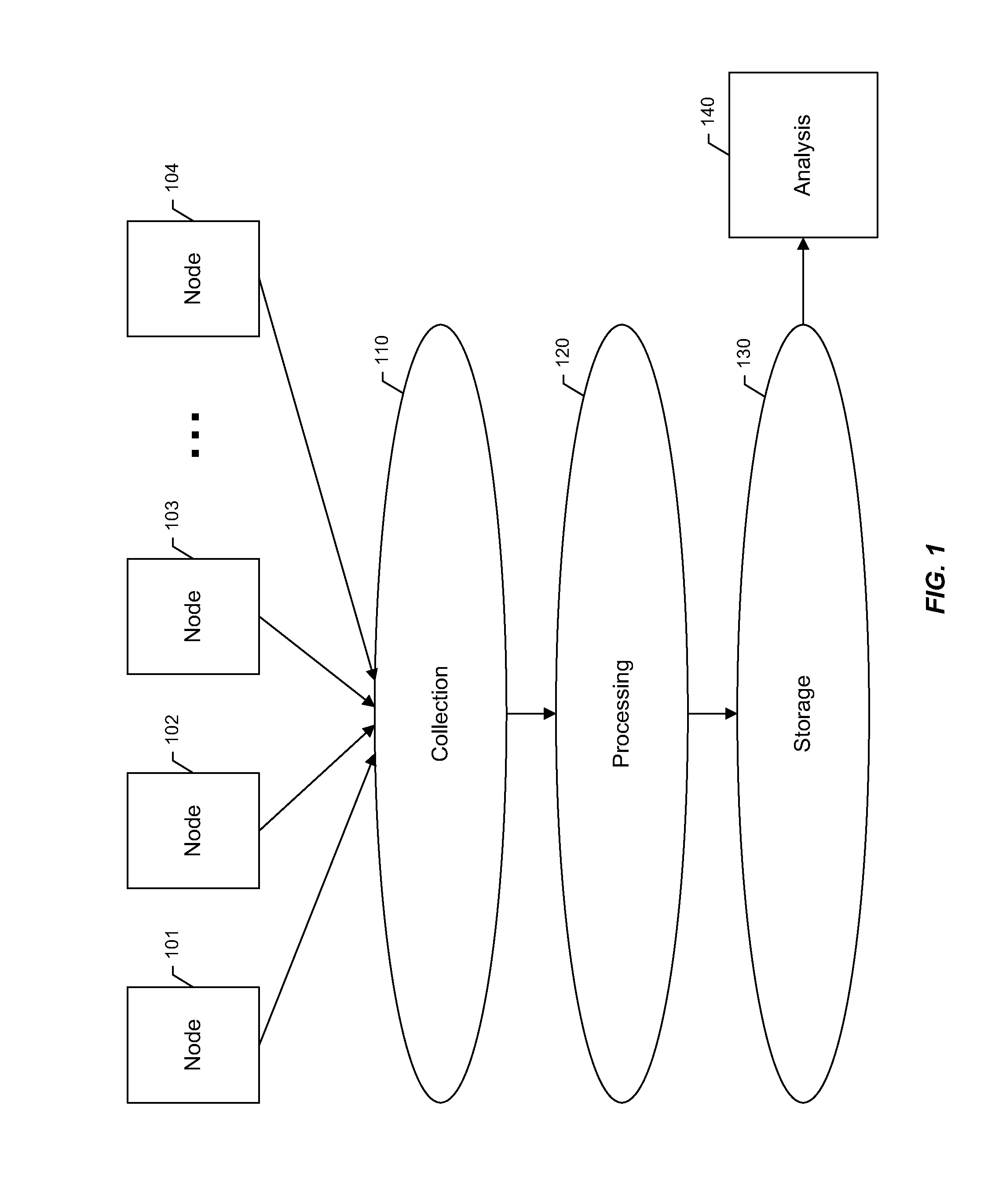
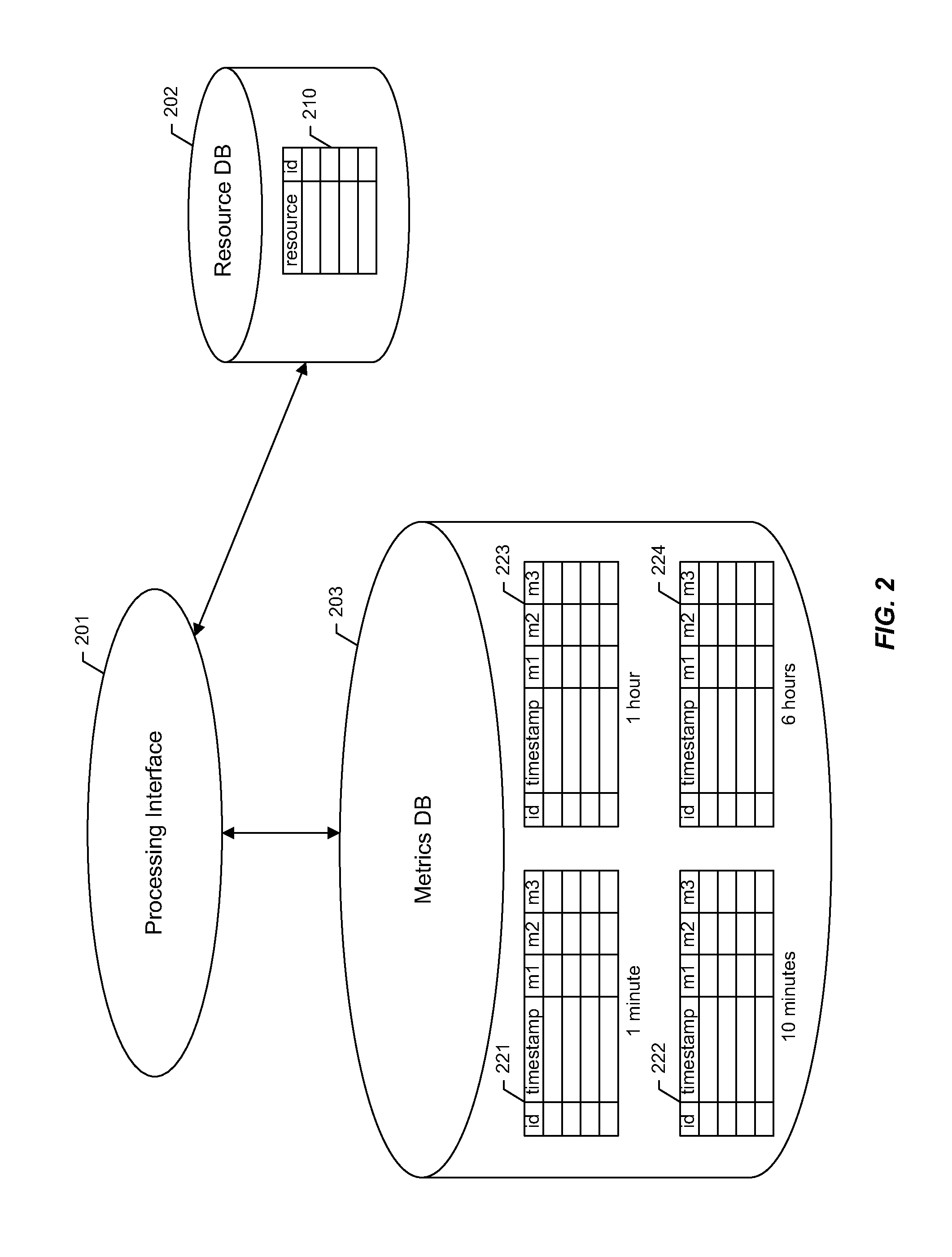
Time series storage for large-scale monitoring system
InactiveUS20110153603A1Efficient storageDigital data information retrievalDigital data processing detailsRetention periodInternet traffic
Methods and apparatus are described for collecting and storing large volumes of time series data. For example, such data may comprise metrics gathered from one or more large-scale computing clusters over time. Data are gathered from resources which define aspects of interest in the clusters, such as nodes serving web traffic. The time series data are aggregated into sampling intervals, which measure data points from a resource at successive periods of time. These data points are organized in a database according to the resource and sampling interval. Profiles may also be used to further organize data by the types of metrics gathered. Data are kept in the database during a retention period, after which they may be purged. Each sampling interval may define a different retention period, allowing operating records to stretch far back in time while respecting storage constraints.
Owner:OATH INC
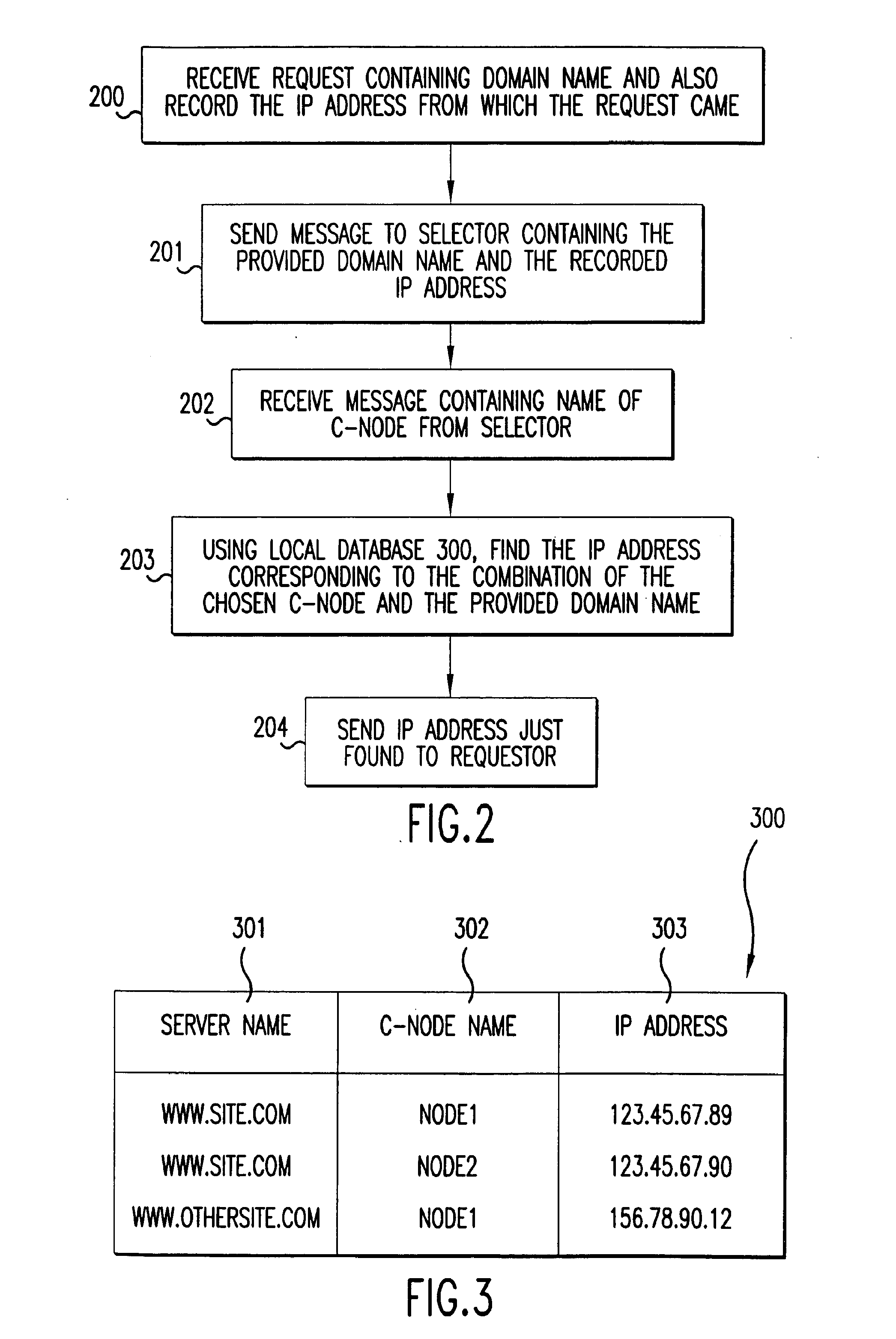
Existent Domain Name DNS Traffic Capture and Analysis
ActiveUS20100257266A1Accurate ratingAccurate pictureAdvertisementsMultiple digital computer combinationsDomain nameTraffic capacity
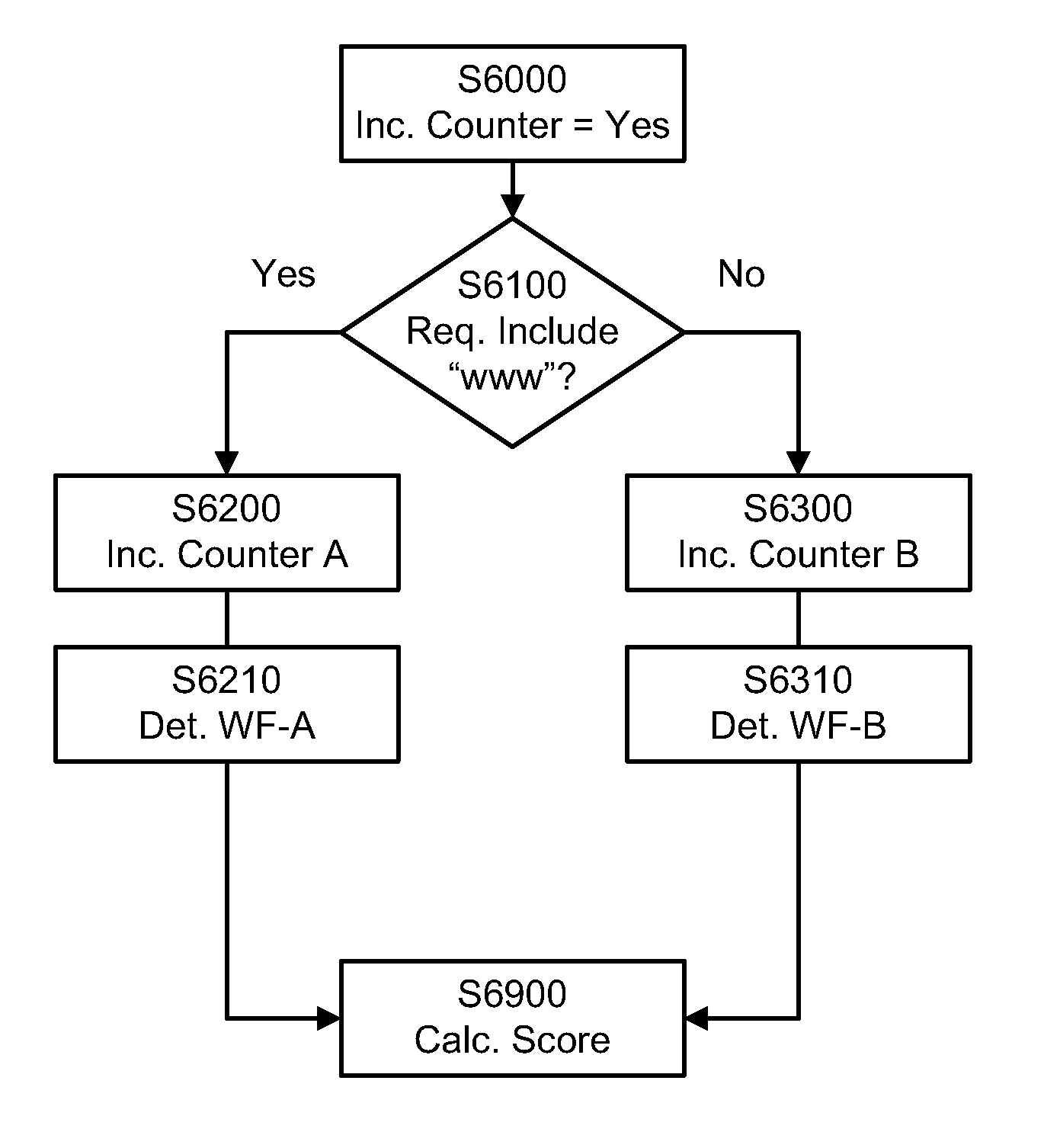
Systems and methods for scoring a domain web traffic based on DNS traffic requests received at an authoritative name server to resolve the domain name. A request to resolve the domain name is received at an authoritative name server. A counter, such as a server counter or a hit counter, for the domain name is incremented based on the received request. A score, such as a domain traffic score or a domain rank, is calculated based upon a count of the counter. Calculating the score may also include applying a weighting factor to the counters based on information about a requesting set of resolvers and other domains / websites that may be linking and driving traffic to the domain whose traffic score is being calculated. Examples of relevant set of resolvers information may include location, traffic levels, traffic type and architecture of the set of resolvers.
Owner:VERISIGN
Method and system for redirecting web page requests on a TCP/IP network
InactiveUS6438125B1Data switching by path configurationMultiple digital computer combinationsTraffic capacityIp address
A method and system for redirecting web page requests on a TCP / IP network is described. The method may be performed by a web traffic monitor that intercepts at least a portion of web-based traffic from a client / subscriber on a network. Based on a predetermined criterion, the web traffic monitor either responds to the client / subscriber with an action other than that which was intended by the user or relays the traffic to the destination originally intended by the user. The predetermined criterion may be chosen from, among others, a time period that has elapsed since the last web page request issued from the client / subscriber, a particular IP destination address requested by the client / subscriber, or the client / subscriber's IP address. Once the predetermined criterion is met, the traffic monitor acts appropriately by, for example, substituting a replacement web page for the web page requested by the client / subscriber. Appropriate methods of returning the replacement web page to the client / subscriber include, but are not limited to, returning the replacement web page: (1) without ever returning the intended web page; (2) for only a predetermined period of time; or (3) in a secondary browser window that pops on top of the intended web page, which is returned in a primary browser window.
Owner:RPX CLEARINGHOUSE
System and method of securing networks against applications threats
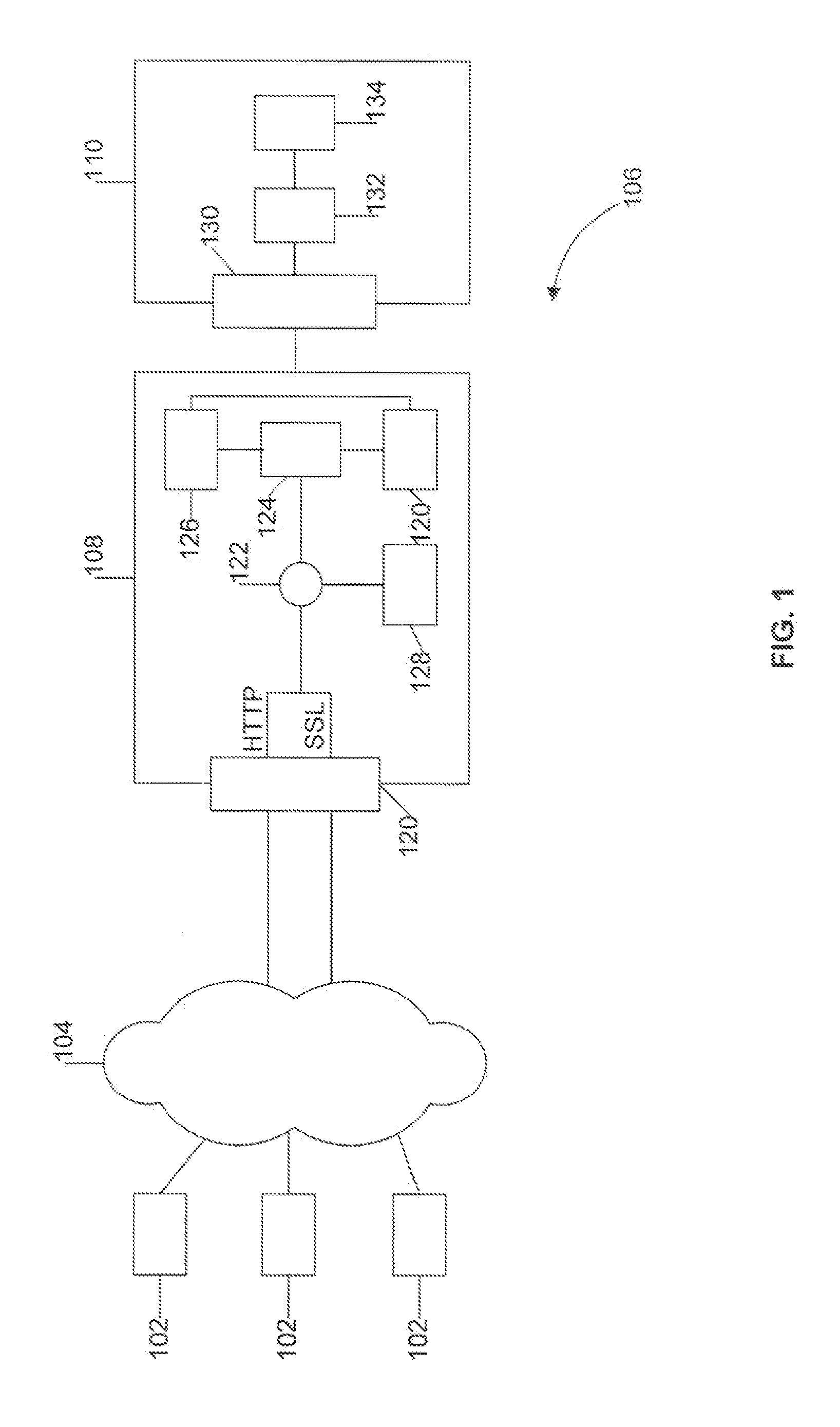
InactiveUS20080047009A1Easy to deployMinimal impactMemory loss protectionError detection/correctionWeb applicationInternet privacy
A system and method for protection of Web based applications are described. A Web application security system is included within a computer network to monitor traffic received from a wide area network, such as the Internet, and determine if there is a threat to the Web application. The Web application security system monitors web traffic in a non-inline configuration and identifies any anomalous traffic against a profile that identifies acceptable behavior of a user of the application. Any anomalous traffic is analyzed and appropriate protective action is taken to secure the Web application against an attack.
Owner:TRUSTWAVE HOLDINGS
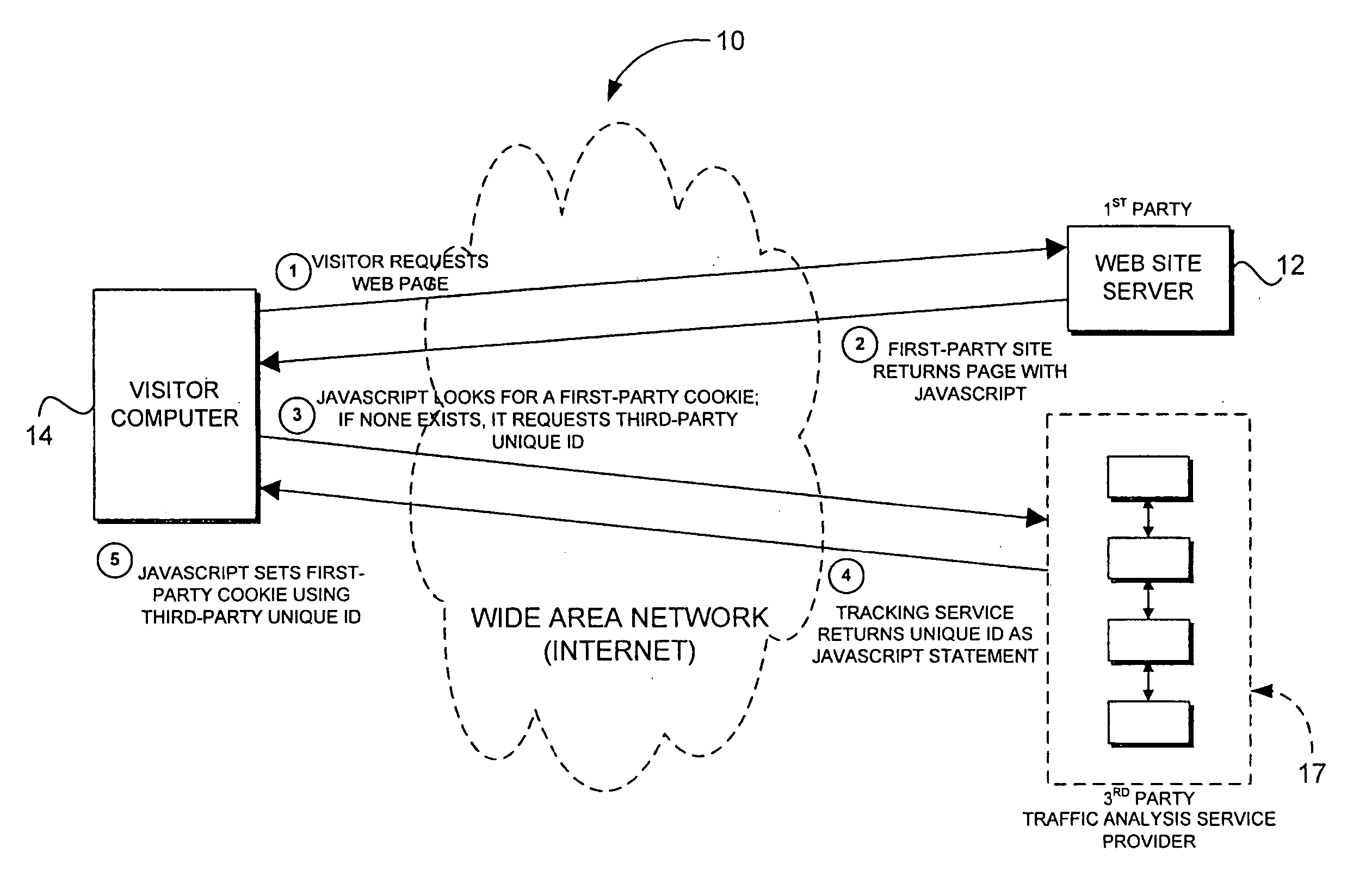
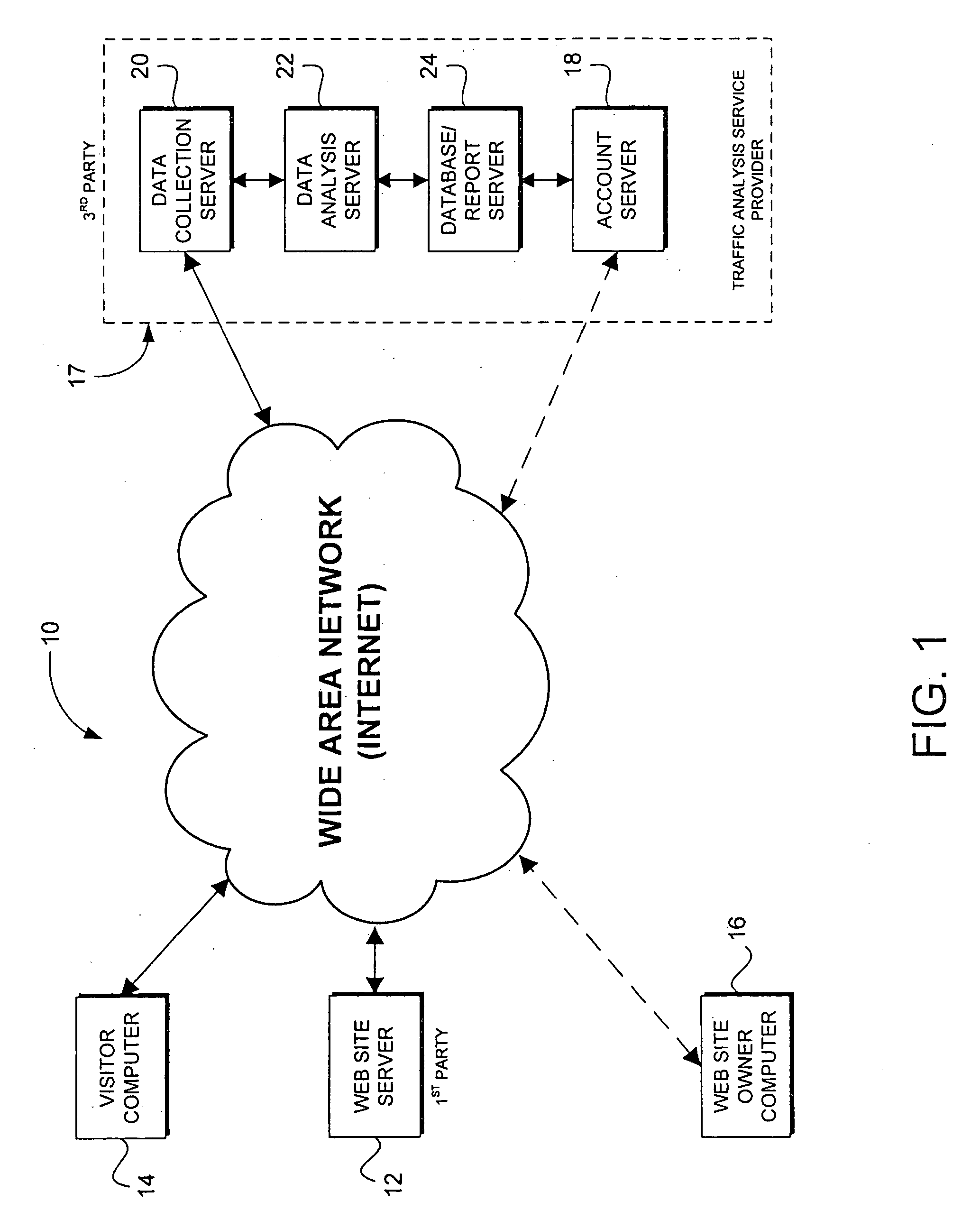
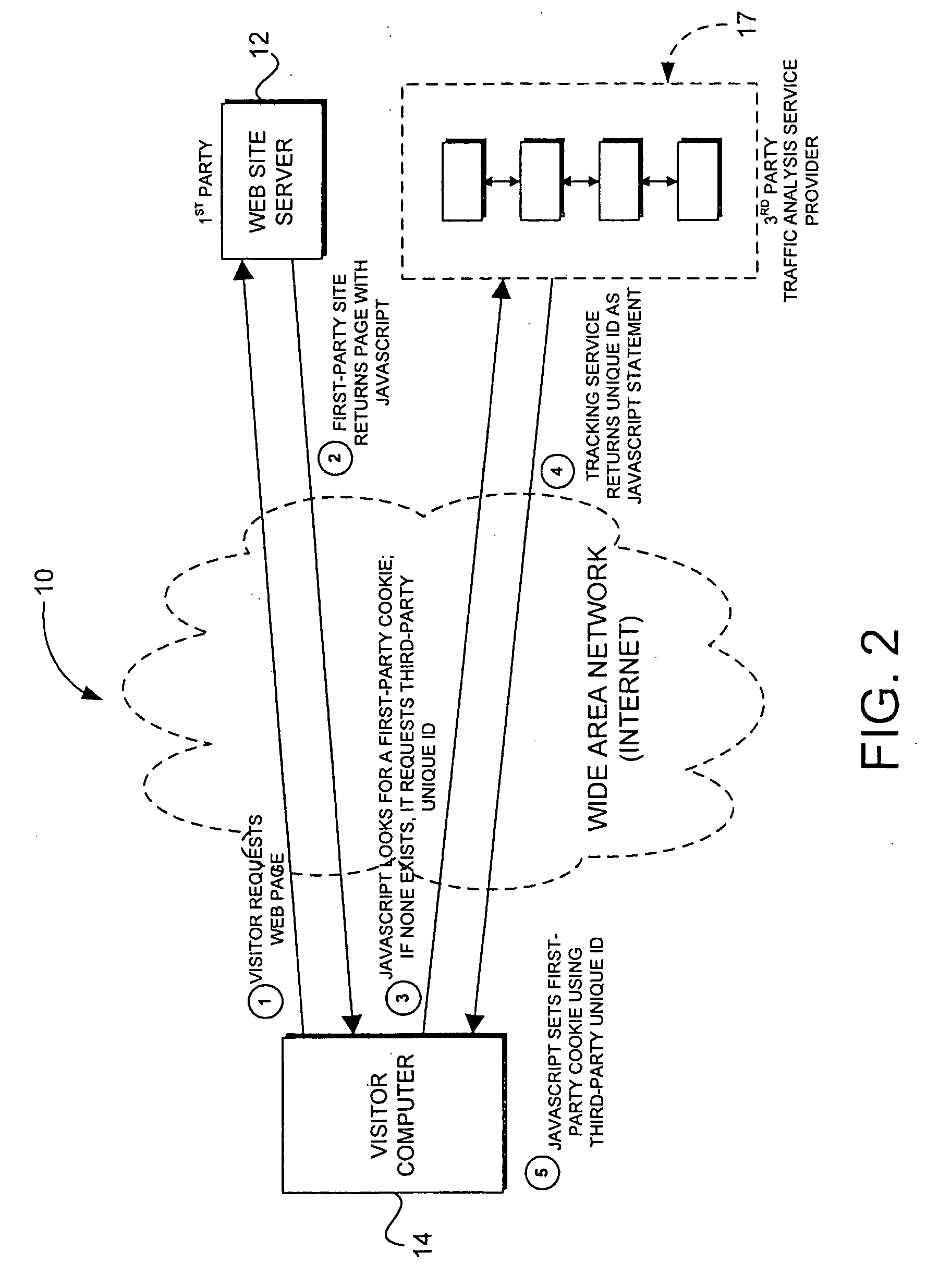
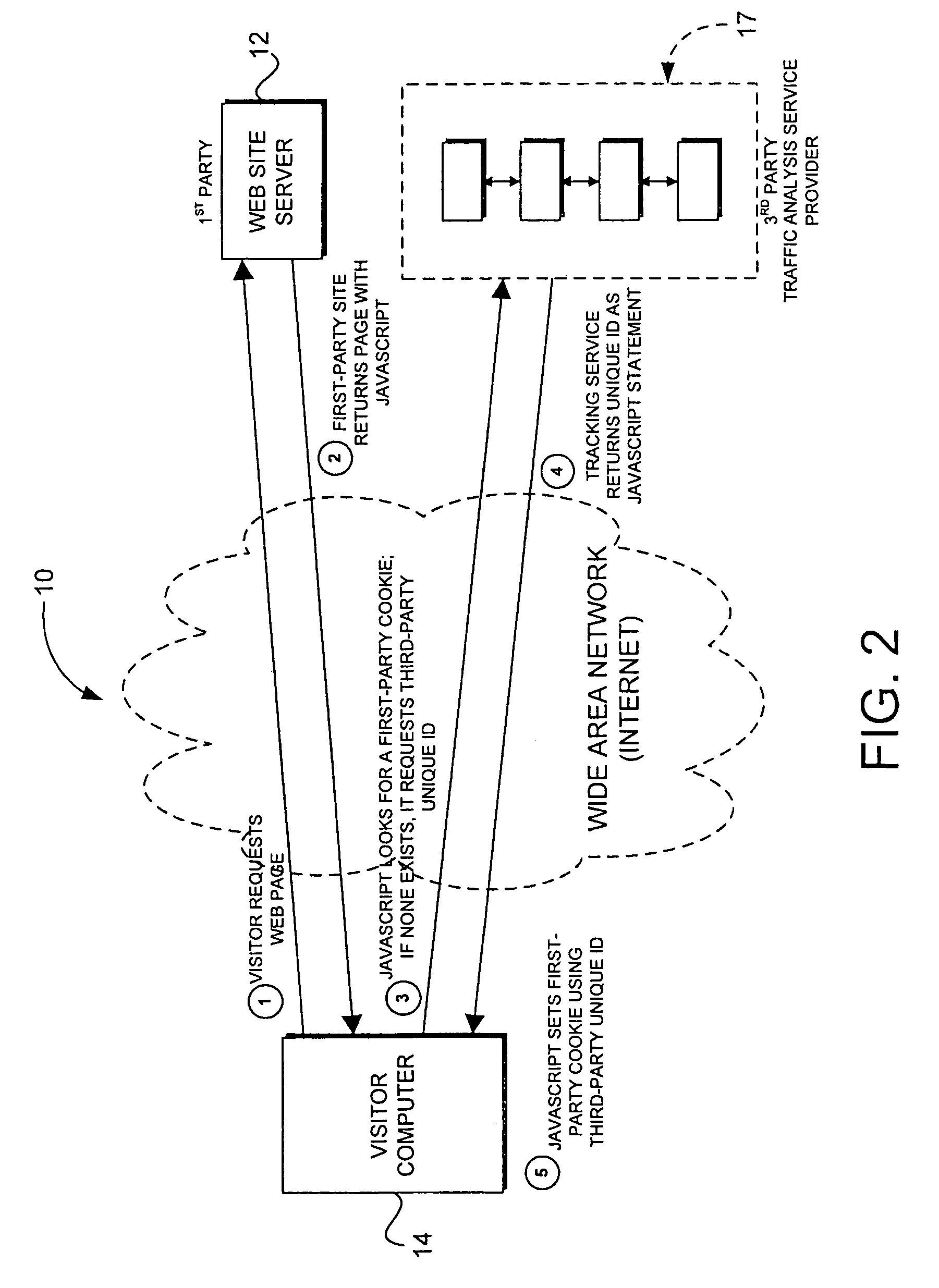
First-party cookie for tracking web traffic
ActiveUS20060265495A1Improve accuracyAccuracy suffersMultiple digital computer combinationsTransmissionThird partyWeb site
Web traffic reporting methods that rely upon third-party cookies suffer in accuracy when those tracking cookies are frequently refused by web users or deleted once they have been accepted. The invention described herein circumvents this problem by employing first-party cookies instead. This is accomplished by a client-side script that maintains the first-party cookie (as placed by the web site in question) and sends a site-maintained visitor ID to a tracking service for analysis. The effect is to improve the accuracy of traffic statistics that rely on that cookie.
Owner:ORACLE INT CORP
Method for cross-domain tracking of web site traffic
ActiveUS8131861B2Improve accuracyAccuracy suffersMultiple digital computer combinationsTransmissionWeb siteThird party
Web traffic reporting methods that rely upon third-party cookies suffer in accuracy when those tracking cookies are frequently refused by web users or deleted once they have been accepted. The invention described herein circumvents this problem by employing first-party cookies instead. This is accomplished by a client-side script that maintains the first-party cookie (as placed by the web site in question) and sends a site-maintained visitor ID to a tracking service for analysis. The effect is to improve the accuracy of traffic statistics that rely on that cookie.
Owner:ORACLE INT CORP
Method and system for providing Web browsing through a firewall in a peer to peer network
InactiveUS20050229243A1User identity/authority verificationUnauthorized memory use protectionData packWeb browser
A method and system for providing a computer running a Web browser HTTP access to a peer server located behind a firewall in a peer-to-peer network is described. The method and system first include providing the peer-to-peer network with a proxy server. The peer server then registers an outbound socket connection with the proxy server. In response to the proxy server receiving an HTTP request to access the peer server from the web browser, the HTTP request is translated into a request packet and the request packet is sent to the peer server. In response to the peer server receiving the request packet, the peer server translates the request packet back into the HTTP request and then responds to the request, thereby enabling generic web traffic to flow.
Owner:IKORONGO TECH
Dynamic-content web crawling through traffic monitoring
InactiveUS20040128285A1Avoid custom time-consume integrationEasy to solveData processing applicationsWeb data indexingTraffic capacityUniform resource locator
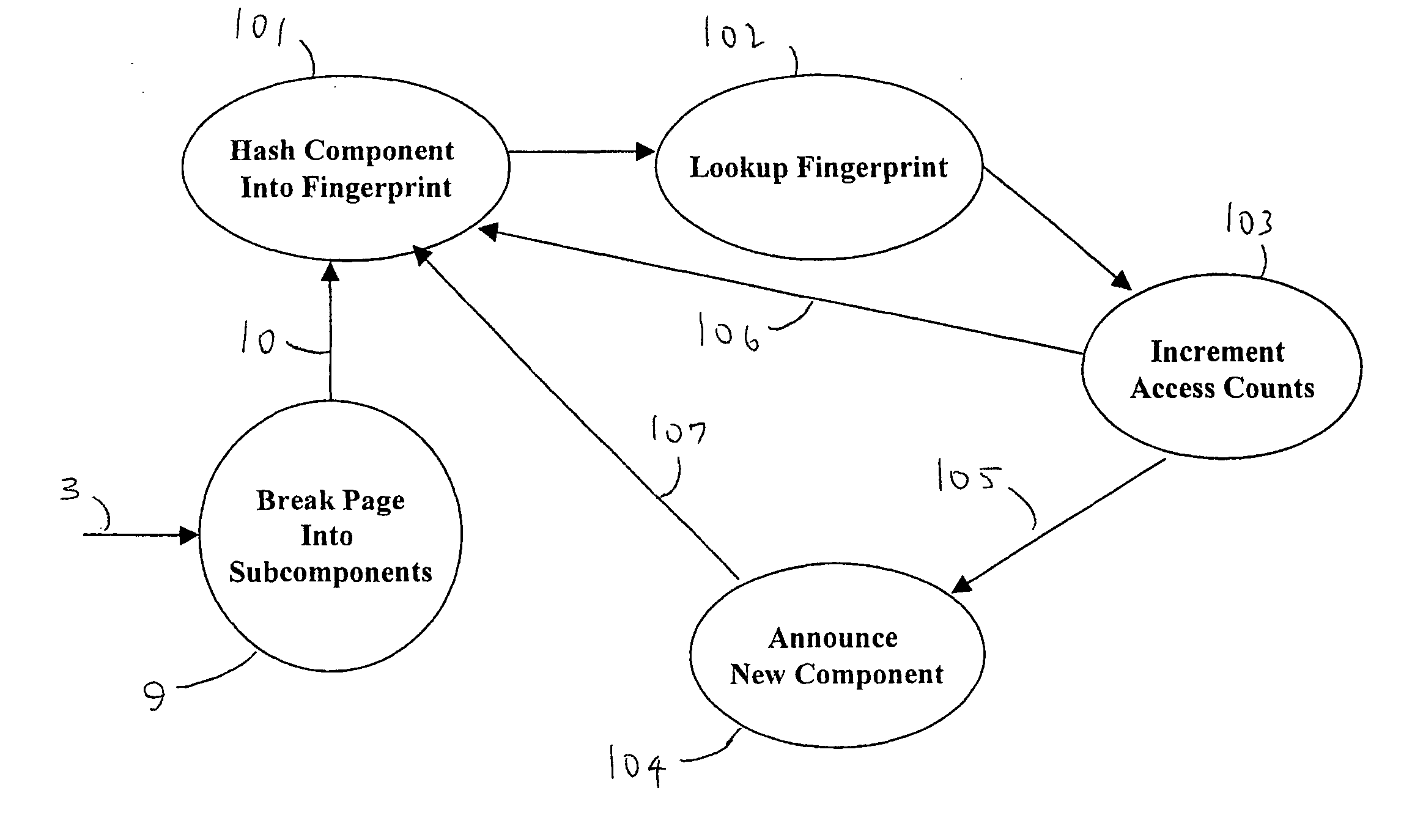
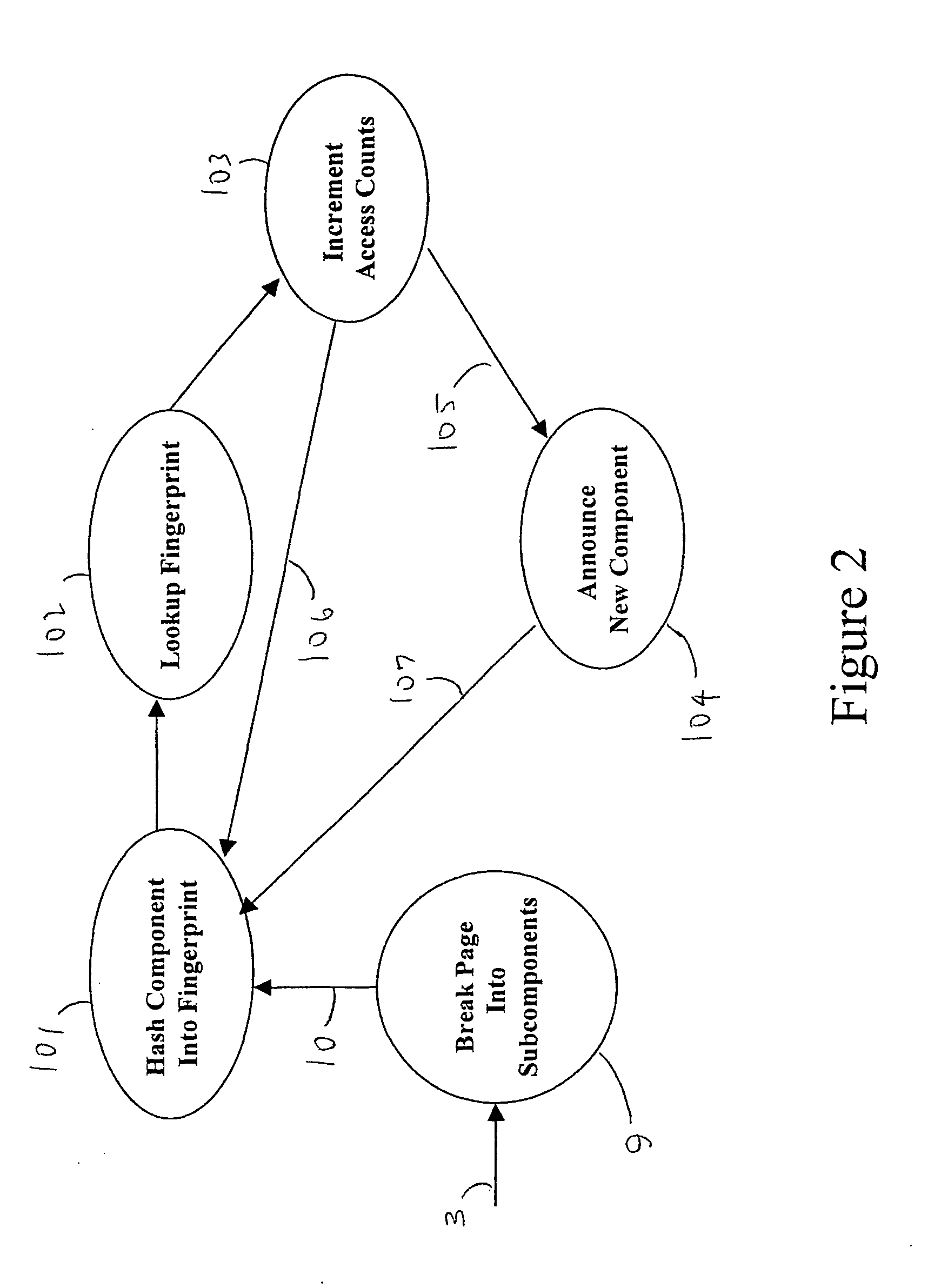
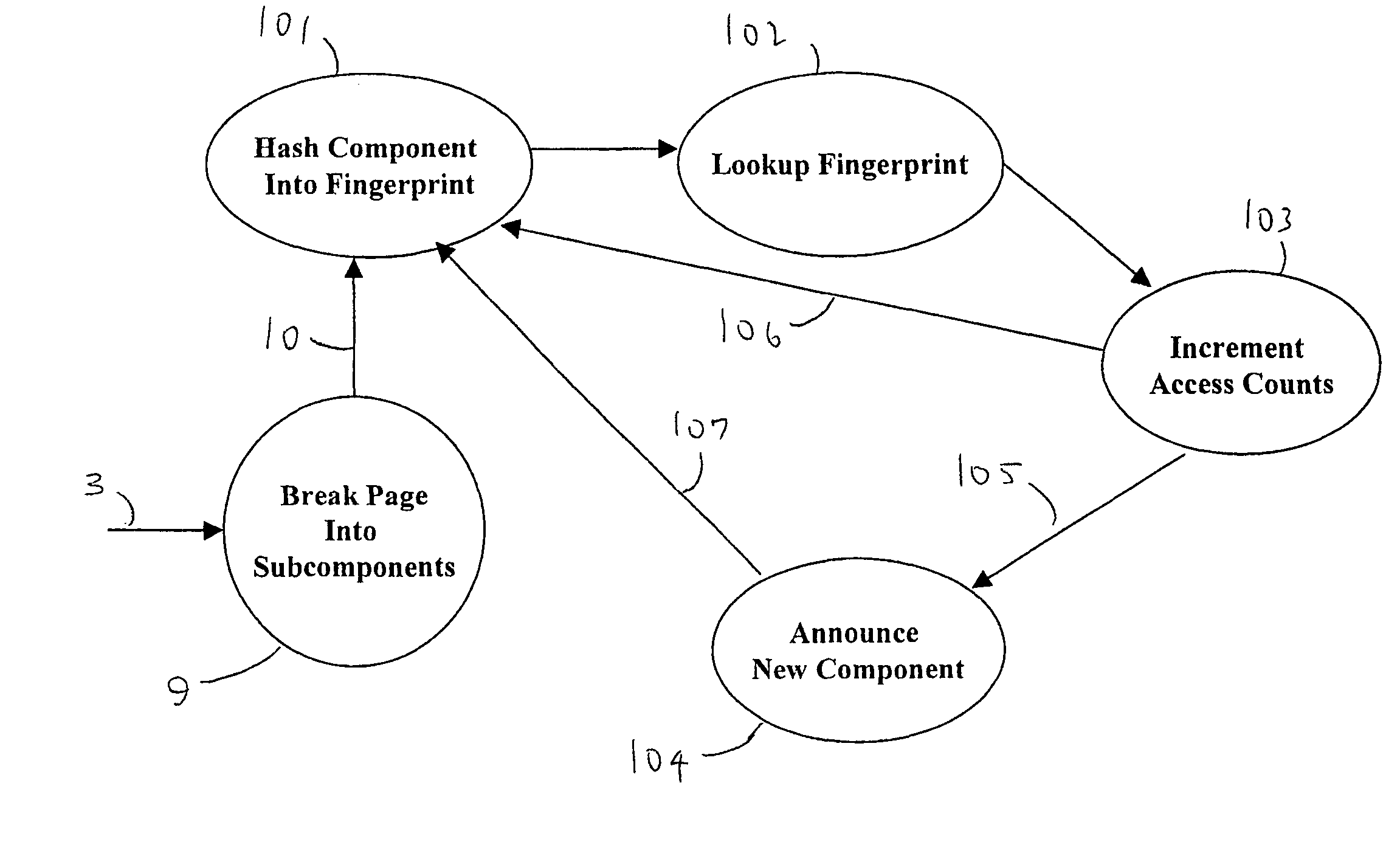
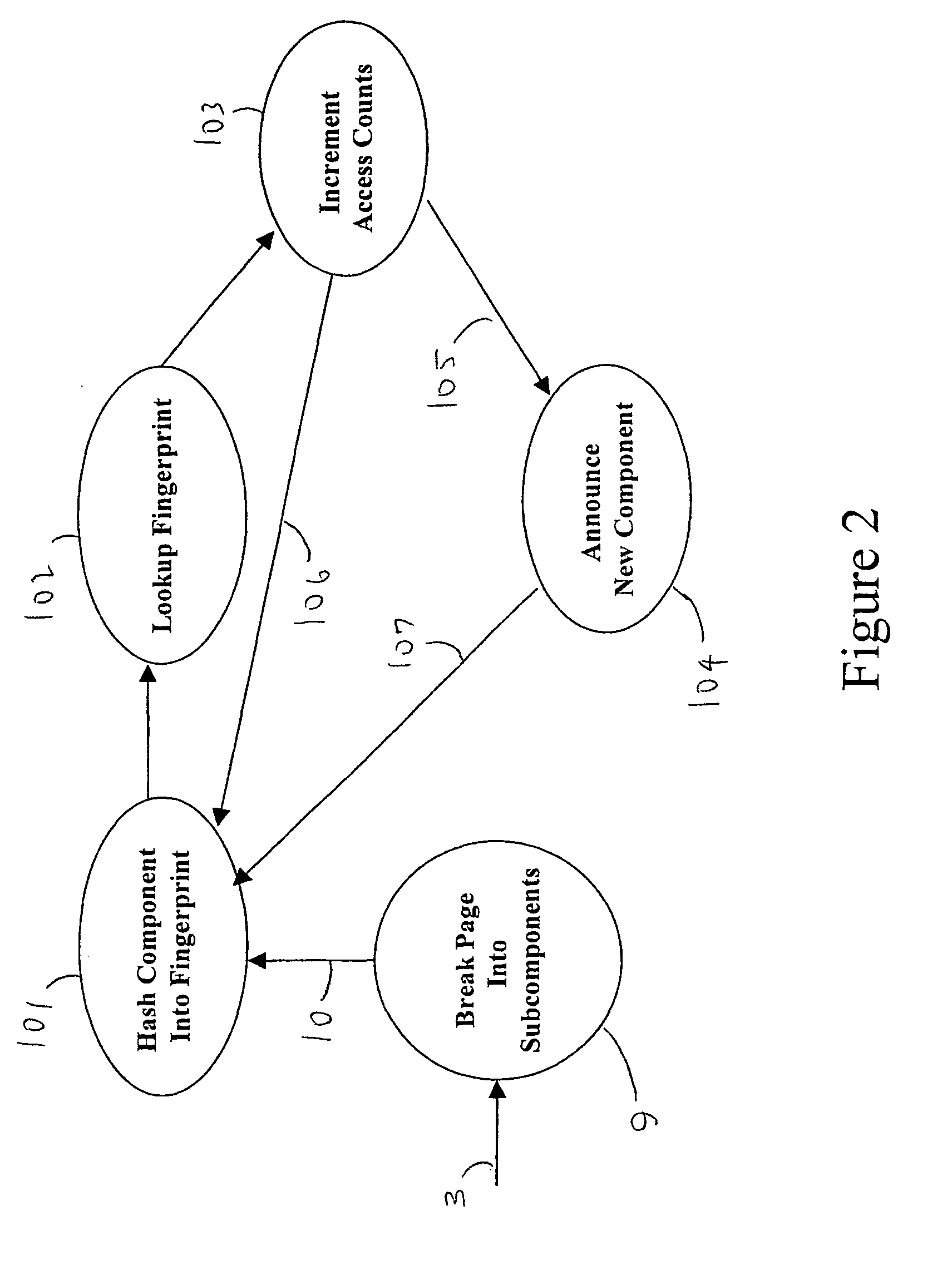
A dynamic-content web crawler is disclosed. These New Crawlers (NCs) are located at points between the server and user, and monitor content from said points, for example by proxying the web traffic or sniffing the traffic as it goes by. Web page content is recursively parsed into subcomponents. Sub-components are fingerpinted with a cyclic redundancy check code or other loss-full compression in order to be able to detect recurrence of the sub-component in subsequent pages. Those sub-components which persist in the web traffic, as measured by the frequency NCs (6) are defined as having substantive content of interest to data-mining applications. Where a substantive content sub-component is added to or removed from a web page, then this change is significant and is sent to a duplication filter (11) so that if multiple NCs (6) detect a change in a web page only one announcement of the changed URL will be broadcast to data-mining applications (8). The NC (6) identifies substantive content sub-components which repeatably are part of a page pointed to by a URL. Provision is also made for limiting monitoring to pages having a flag authorizing discovery of the page by a monitor.
Owner:RESOURCE CONSORTIUM LTD LLC
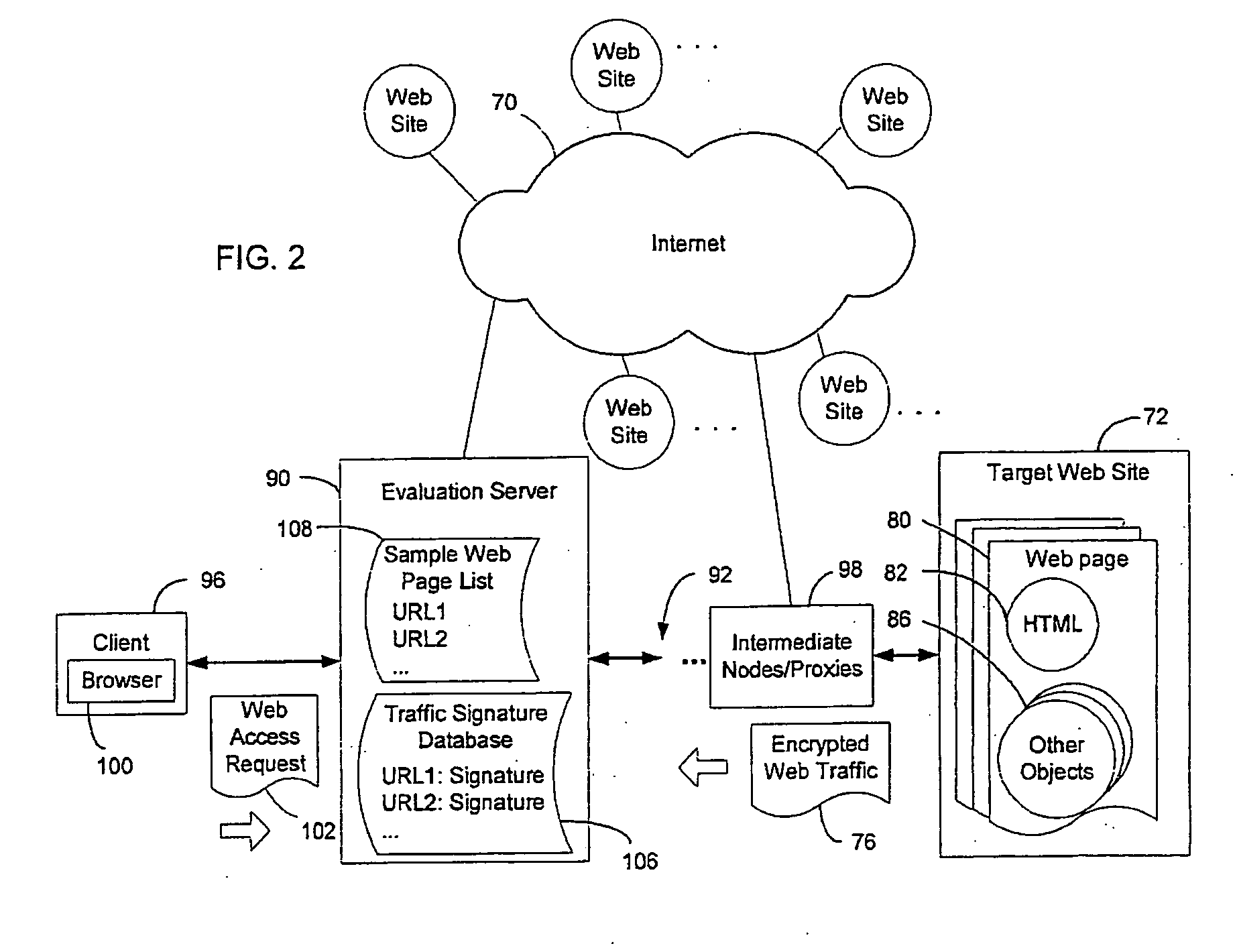
System and method for evaluating and enhancing source anonymity for encrypted web traffic
InactiveUS20060059091A1Reduce uniquenessDifficult to identifyComputer security arrangementsSecuring communicationWeb siteCountermeasure
A system and method is provided for evaluating the effectiveness of data encryption for hiding the identity of the source of Web traffic. A signature is constructed from encrypted Web traffic for a Web page sent by a target Web site, and the signature is compared with archived traffic signatures obtained by accessing various Web pages of interest in advance. If the signature of the detected encrypted Web traffic matches a stored traffic signature beyond a pre-set statistical threshold, a positive match is found, and the source of the traffic is identified. Countermeasures for reducing the reliability of source identification based on traffic signature matching are provided.
Owner:MICROSOFT TECH LICENSING LLC
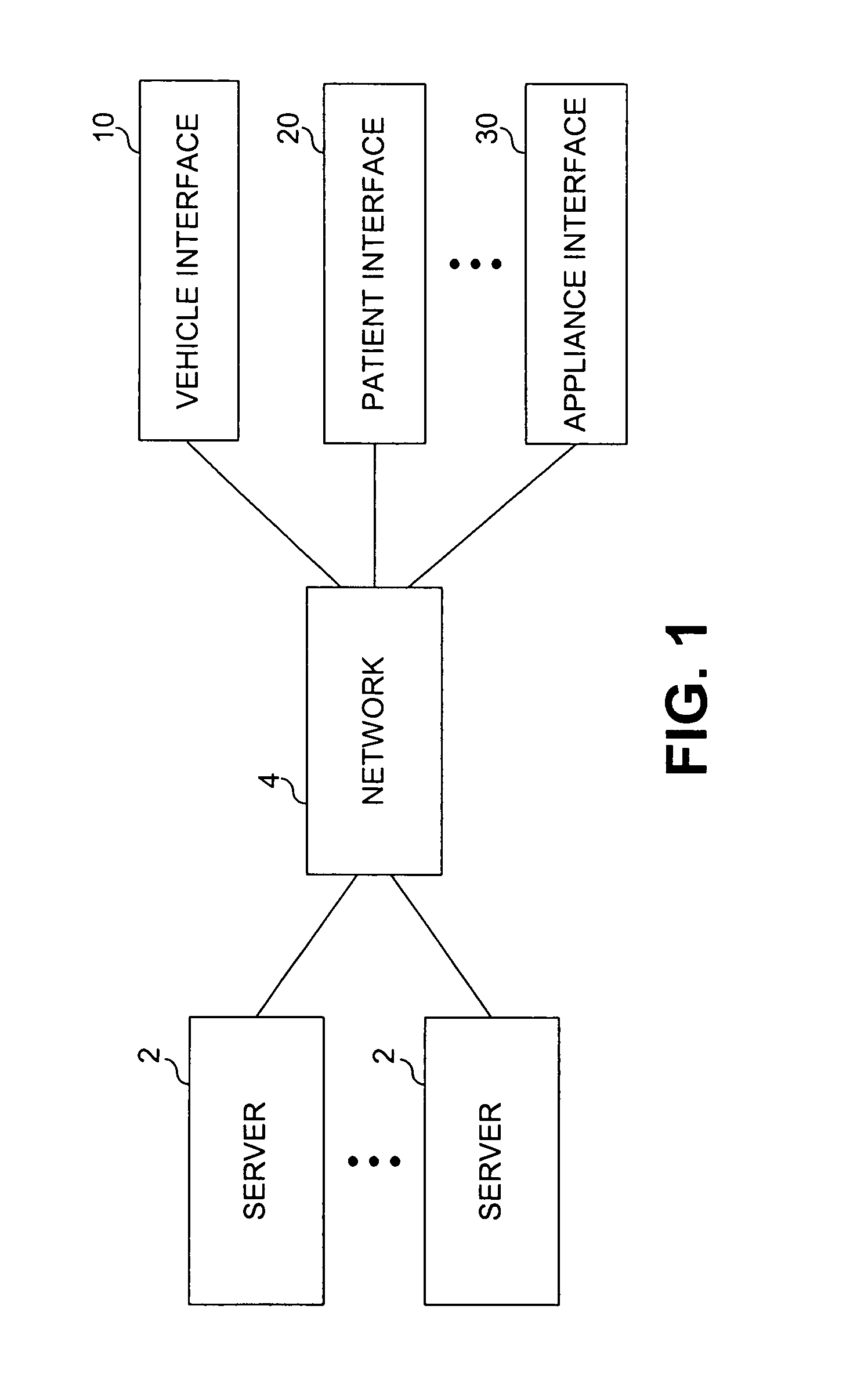
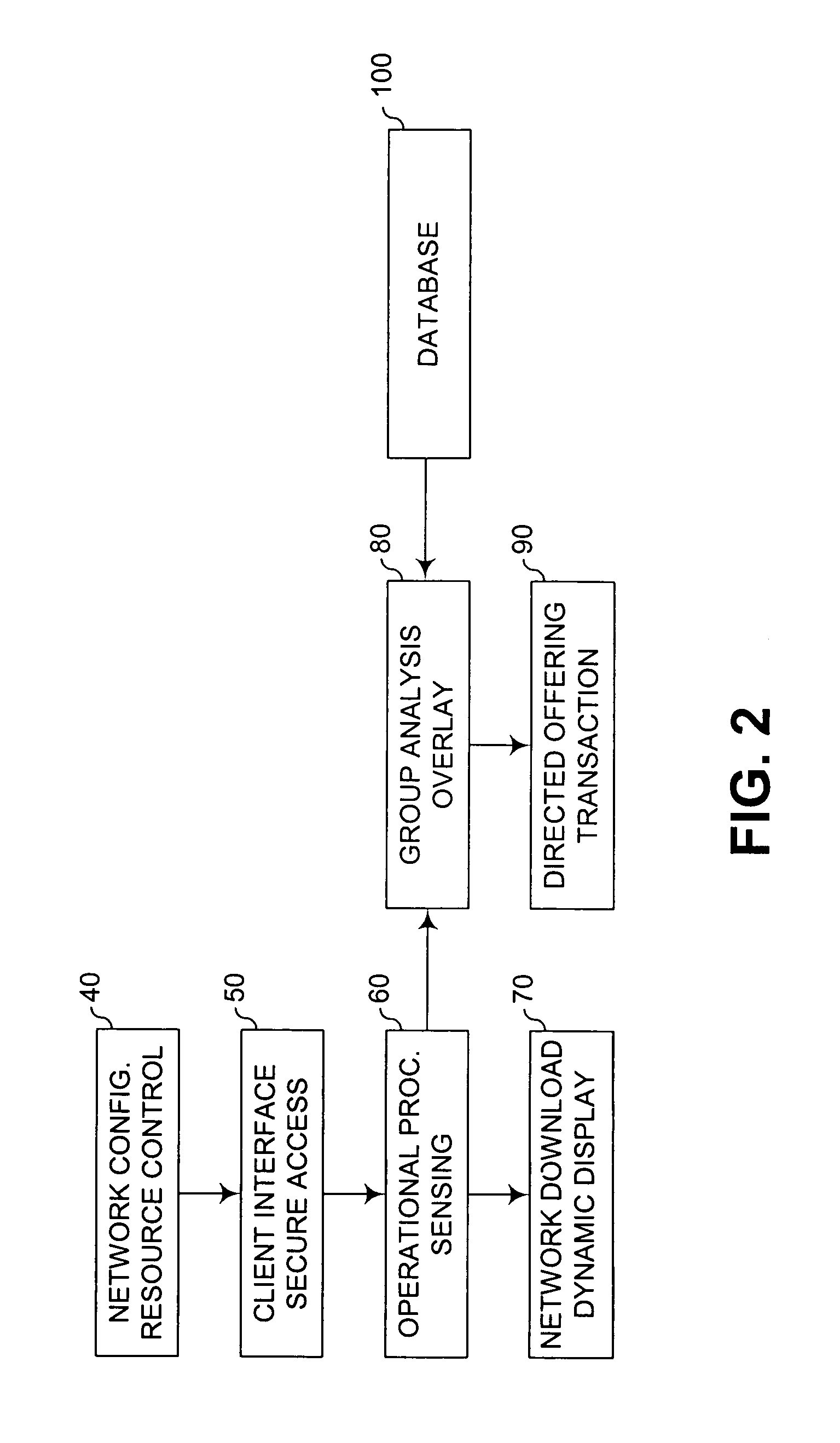
Adaptive direct transaction for network client group
Internet-based software and associated database provide group analysis overlay to monitor client-server web traffic and provide direct marketing to client group. Client car, patient, office or school sensor and interface provides overlay attribute for database comparison to classify usage pattern, location, timing, or family for targeted messaging for enhanced service from server source. Database group registry tracks client classification and provides adaptive context mapping according to set attribute relative to targeted on-line transaction.
Owner:FERNANDEZ & ASSOCS +1
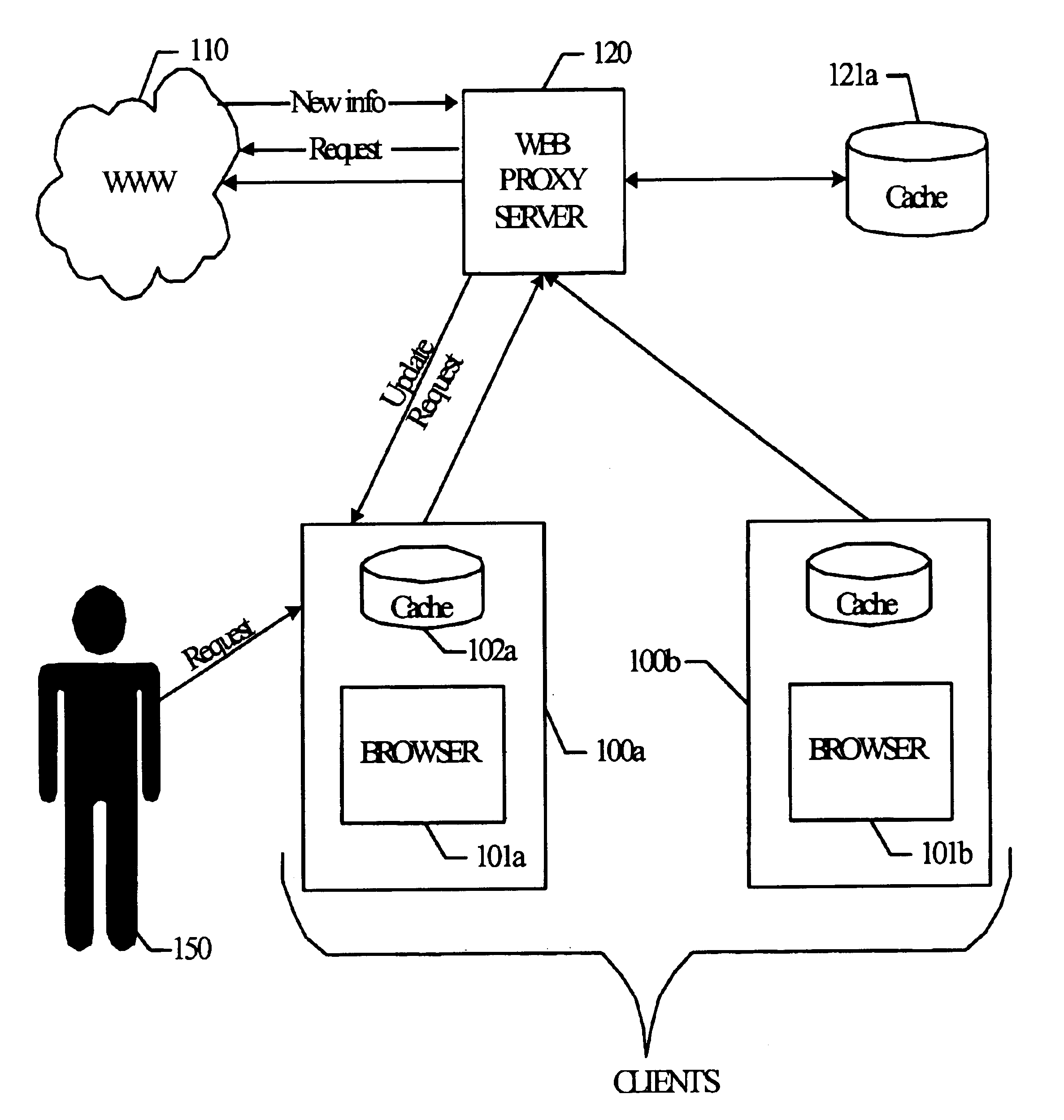
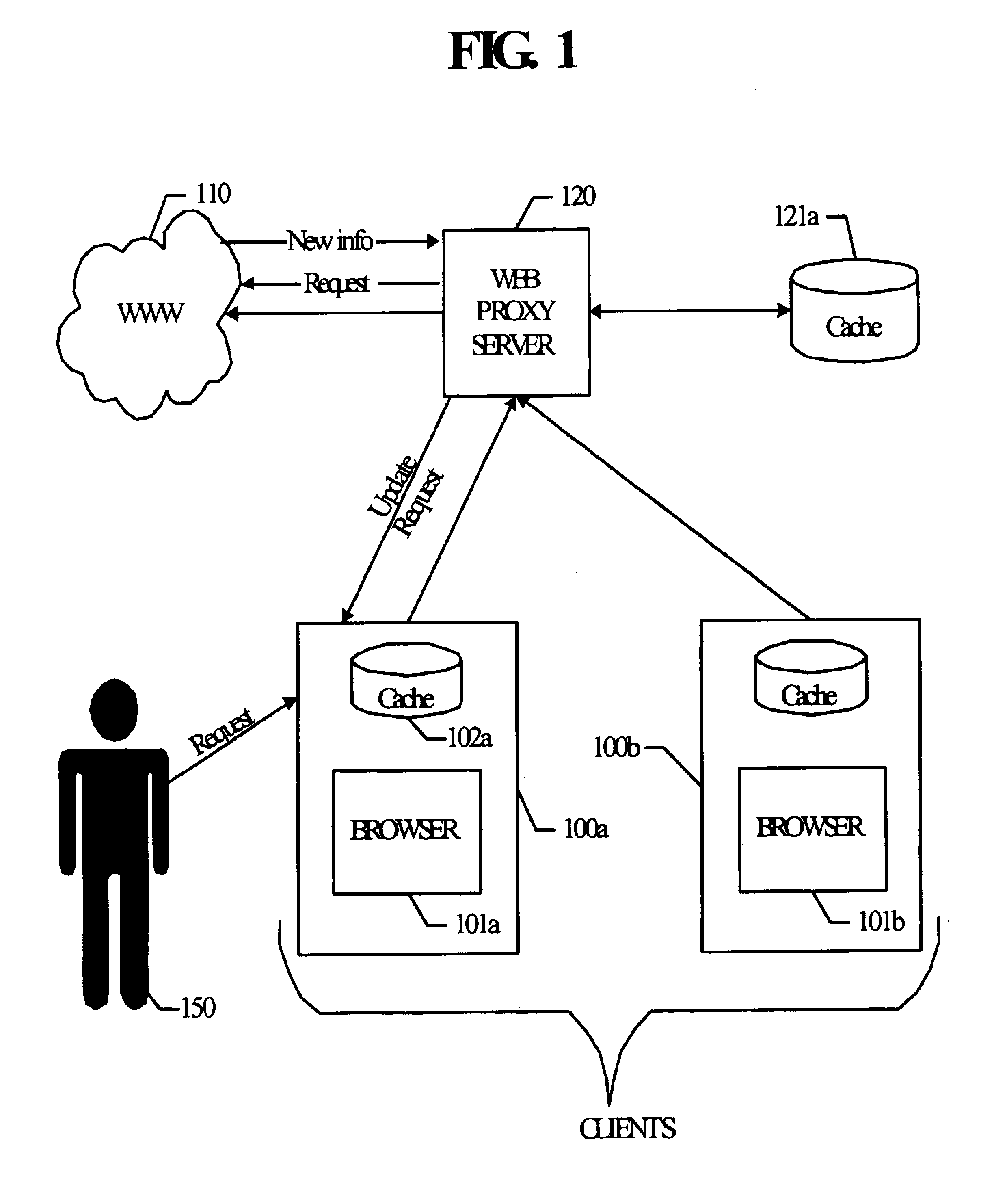
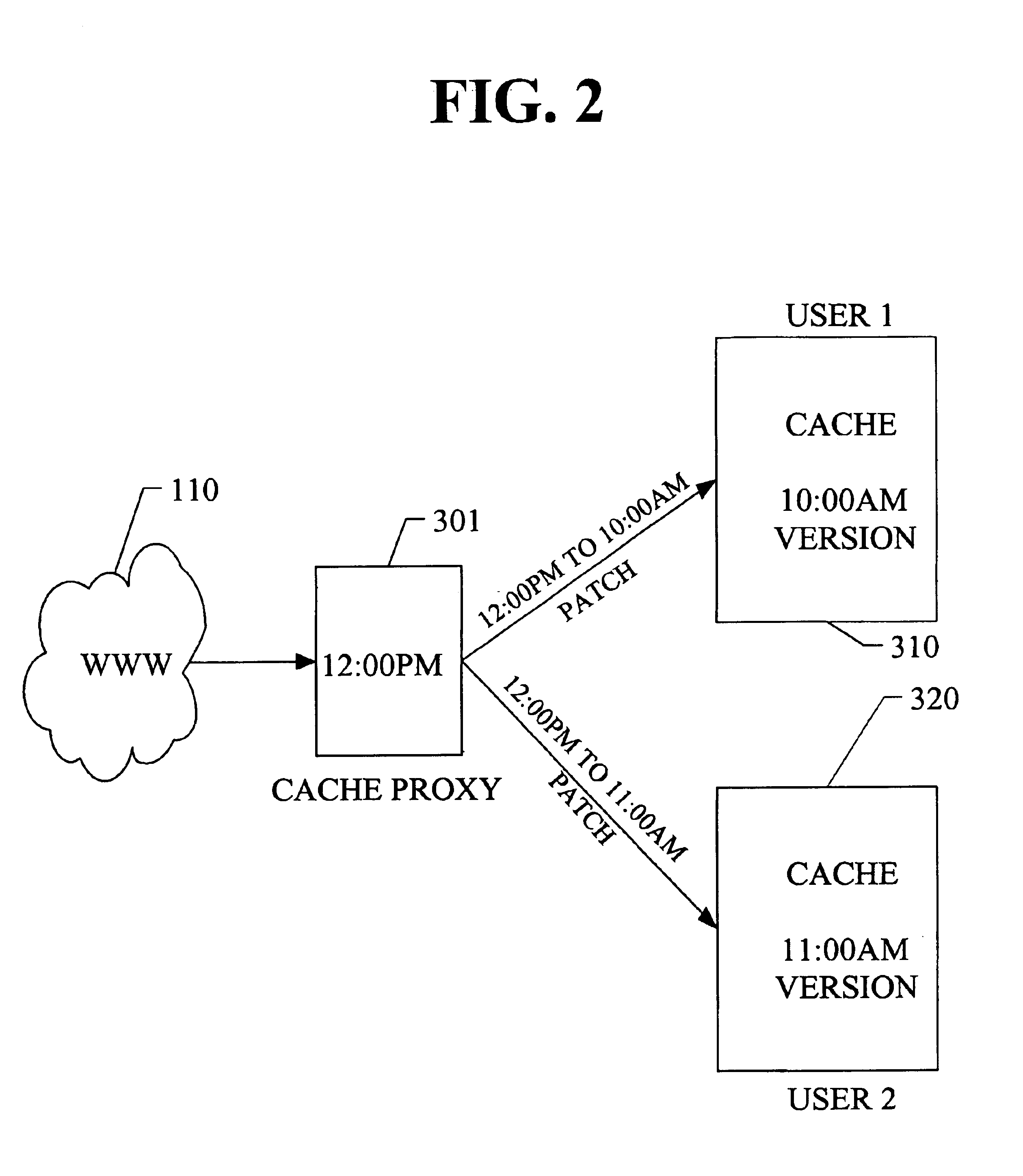
System and method for patch enabled data transmissions
InactiveUS6912591B2Reduce needImprove bandwidth usageDigital data information retrievalMultiple digital computer combinationsTraffic capacityData set
A system and method relating to techniques to efficiently update data transmissions, and more particularly to a system and method for using patch enabling Web traffic or Web Internet transmissions, using existing infrastructure so that “difference” information can be sent to an application rather than a complete updated data set, therefore increasing the effective bandwidth along the transmission medium / channel. A proxy server tracks previous versions of content being sent to various clients. In the case where this is new data to the requesting client, then the proxy server sends back the most recent version of this data to the client. If the requested data is an updated version of something already stored in cache on the client side (i.e., data already known to be sent to the client), then the proxy server runs a differencing algorithm and generates a binary patch file identifying steps to perform to update the information. If there is no version of the requested information already on server side and client side, then the entire information packet is sent to the client. Both the server and client must be “patch-enabled”.
Owner:LEIDOS
Systems and methods for associating social media systems and web pages
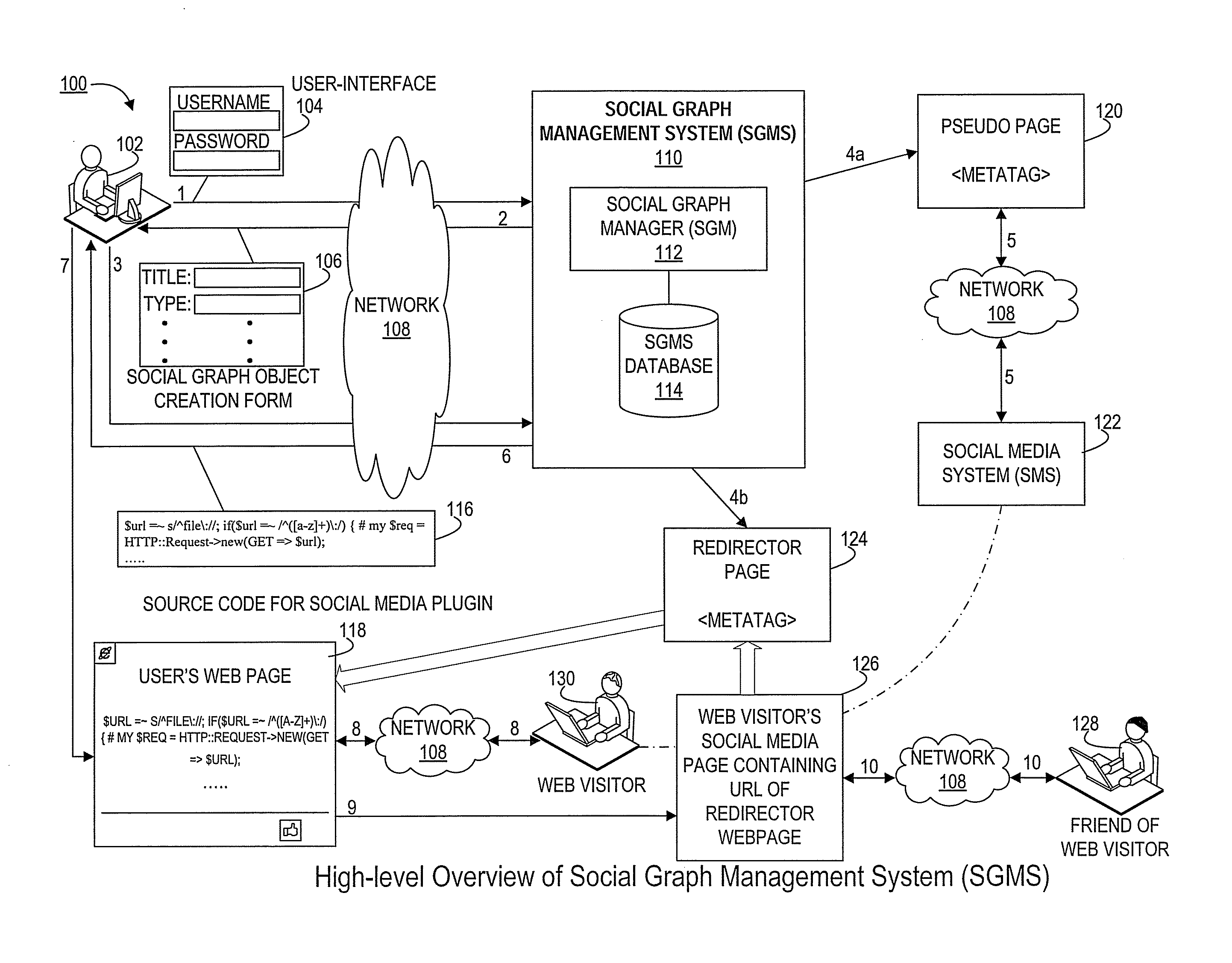
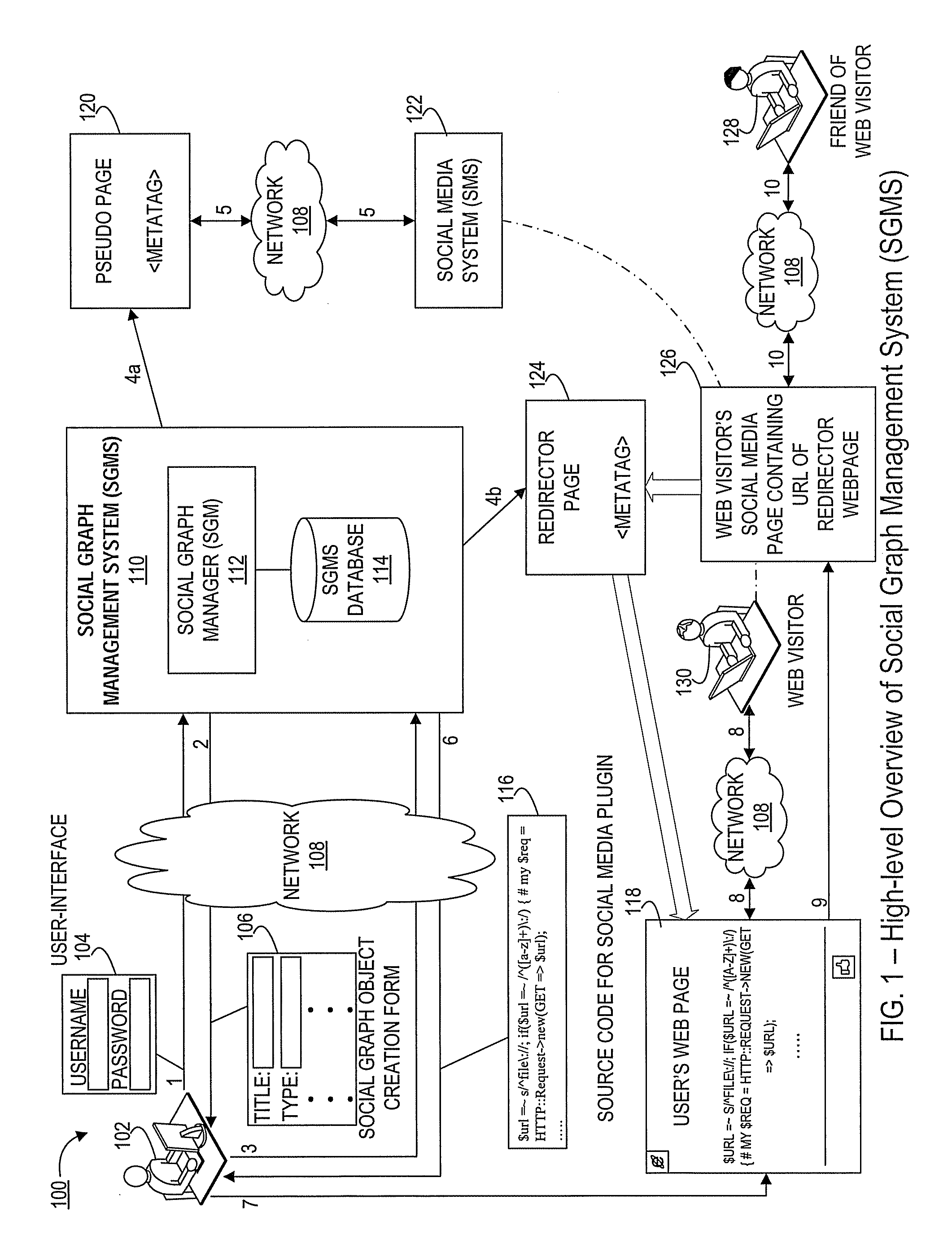
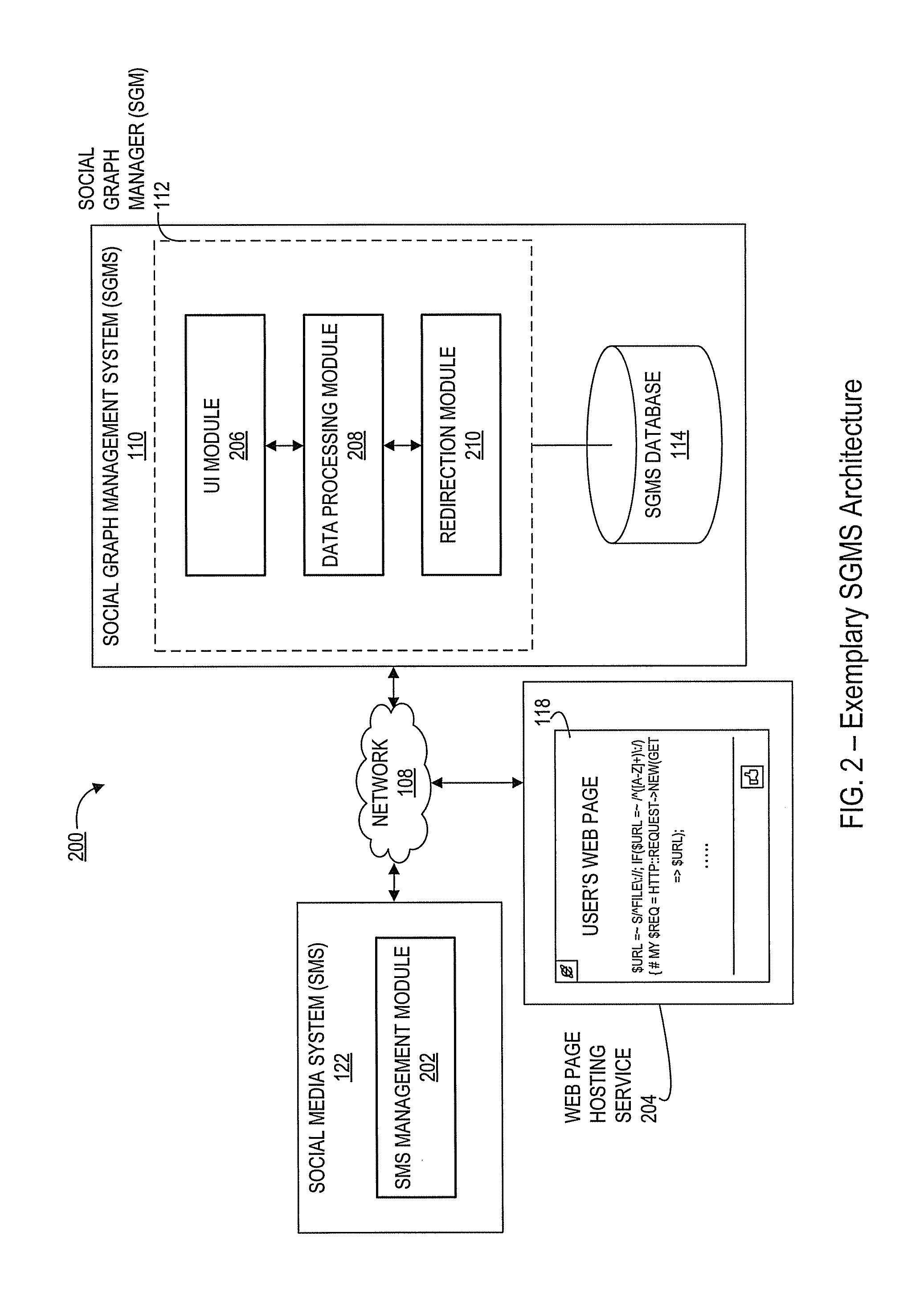
InactiveUS20120011432A1Promote associationEasy accessData switching networksMarketingSocial mediaSocial graph
Systems and methods for the creation and management of electronic associations between social media systems and web pages. Such associations promote greater interactions between web page visitors and users of social media pages. A social graph management system (SGMS) receives information related to a web page, and creates associations between the web page and social media pages. A process of creating such associations involves configuration of social media software for insertion into the web page. Furthermore, creating associations also involves creation of an intermediary page (and related data structures) by the SGMS in order to direct traffic between the web page and social media pages. User activity in the web page is tracked in addition to web traffic arriving at the intermediary page at subsequent times for computation of various analytics.
Owner:ORACLE INT CORP
Techniques for optimizing propagation of multiple types of data
Systems and approaches are provided to reduce power usage of a computing device connected to a third generation (3G), 3G+, or fourth generation (4G) mobile network. A computing device can be configured for concurrent transmission of a first type of data, such as VoIP or VoLTE data, and a second type of data, such as web traffic or file download data, yet remain optimized for low power usage. The quality of service (Qos) for VoIP or VoLTE is not affected by these systems and techniques while changes to the computing device's data throughput capacity can be minimized for transmission of the second type of data. These techniques can be directed or managed by the computing device or the network in various embodiments.
Owner:AMAZON TECH INC
Method and apparatus for generating a sale offer to selected individuals over electronic network systems
InactiveUS7243082B1No costSignificant trafficFinanceBuying/selling/leasing transactionsWeb siteSystems design
A method and apparatus are provided for generating a sale offer over an electronic network (such as the Internet). The method and apparatus may be used with a commercial sale system designed to increase the revenue income of Web site by offering, at a substantially discounted or virtually free basis, one or more goods and / or services to visitors of the Web site. According to the features of the invention, the seller (who may be the owner or co-owner of the Web site) transmits a sale offer on the Web site for a high quality good or service, wherein the good or service can be purchased for free or a cost near to zero. The seller may make the offer visible and available to a number of perspective buyers, who are connected at that very moment to the Web site. According to an additional aspect of the invention, the sale offer may be available for only a very limited amount of time (e.g., one or more minutes) and may be offered at random or unpredictable times on the Web site in order to increase Web traffic to the site.
Owner:TRIUMVIRATE SYST LLC
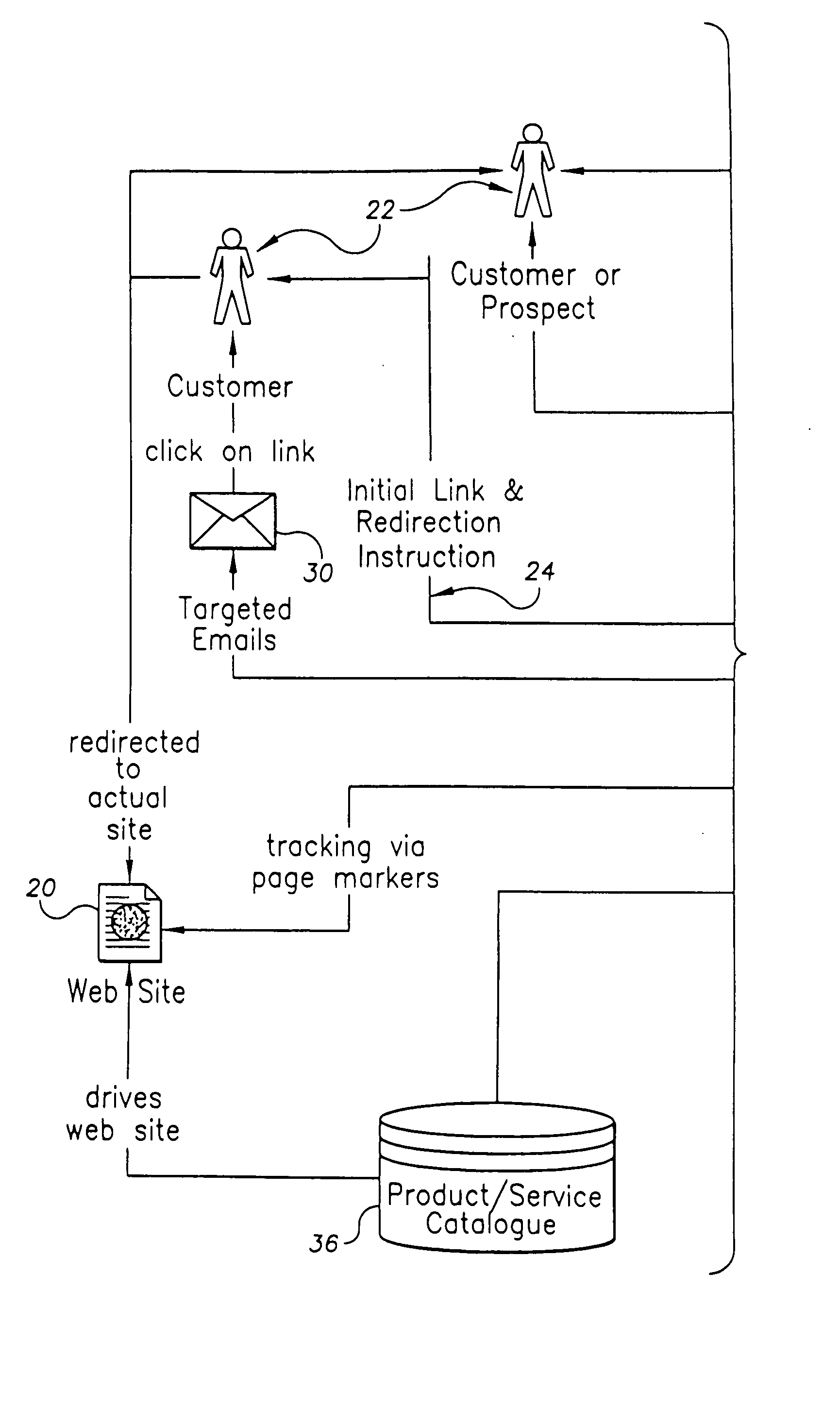
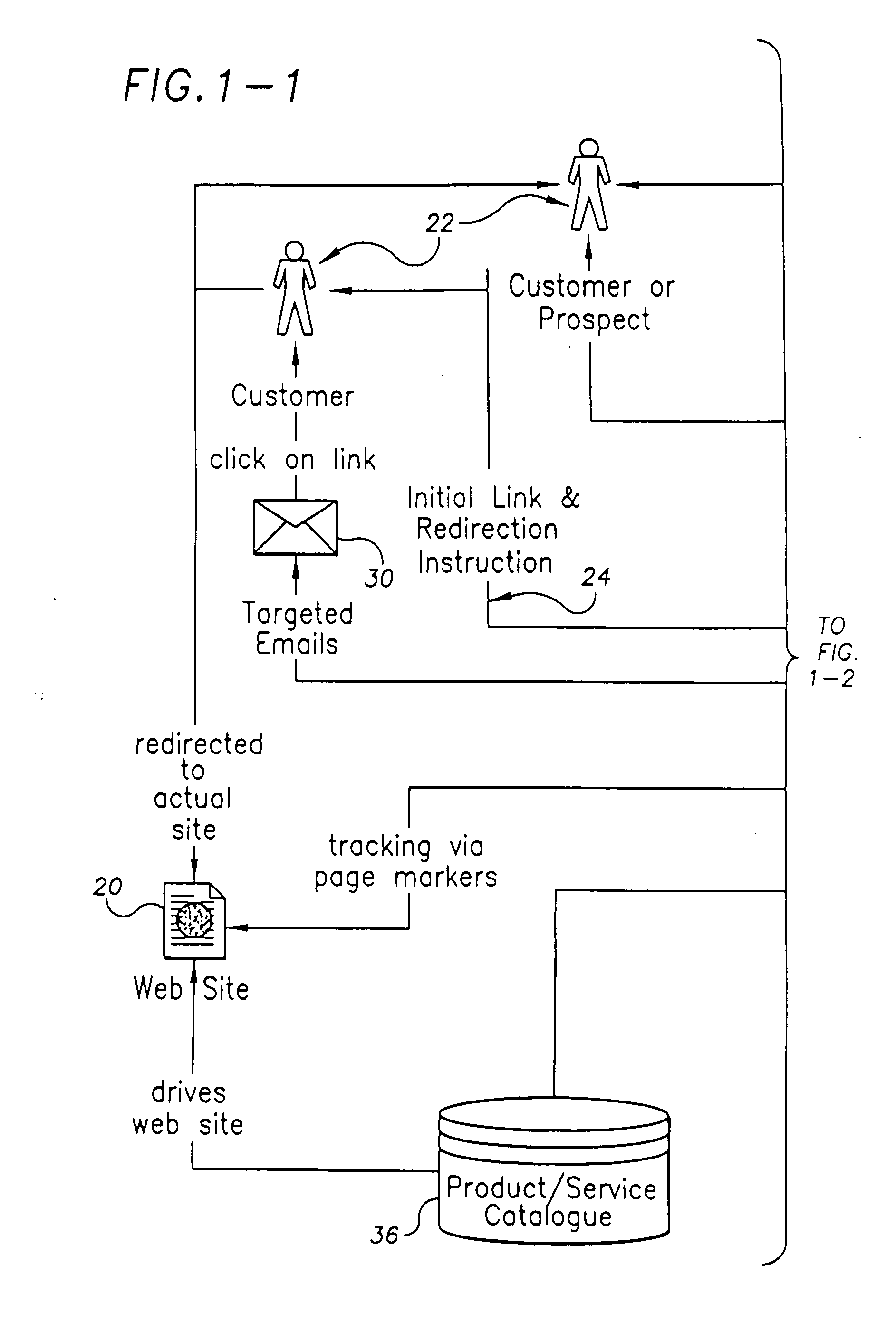
Method and system for enhanced Web page delivery and visitor tracking
InactiveUS20060248452A1Enhancing web page deliveryReduce deliveryWebsite content managementMarketingWeb siteWeb traffic
A system for and method of enhancing web page delivery and visitor tracking. The invention provides the ability to control redirection of Web traffic of humans. It can identify visitors to a Web page, track their movements, log critical information, and analyze the Web traffic in order to judge the success in driving quality traffic to some known goal on a Web site, such as a sale. The system tracks visitors via use of redirection with an image tag. The invention can also use unique image marker references to prevent browsers from accessing cached images.
Owner:THRYV INC
Cluster-based visualization of user traffic on an internet site
InactiveUS7454705B2Significant to useData processing applicationsDigital data processing detailsTraffic capacityWeb traffic
Visualizing Internet web traffic is disclosed. In one embodiment, a number of windows are displayed, corresponding to a number of clusters into which users have been partitioned based on similar web browsing behavior. The windows are ordered from the cluster having the greatest number of users to the cluster having the least number of users. Each window has one or more rows, where each row corresponds to a user within the cluster. Each row has an ordered number of visible units, such as blocks, where each block corresponds to a web page visited by the user. The blocks can be color coded by the type of web page they represent. In one embodiment, the corresponding cluster models for the clusters are alternatively displayed in the windows.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic-content web crawling through traffic monitoring
InactiveUS7143088B2Avoid custom time-consume integrationEasy to solveData processing applicationsWeb data indexingTraffic capacityApplication software
A dynamic-content web crawler is disclosed. These New Crawlers (NCs) are located at points between the server and user, and monitor content from said points, for example by proxying the web traffic or sniffing the traffic as it goes by. Web page content is recursively parsed into subcomponents. Sub-components are fingerpinted with a cyclic redundancy check code or other loss-full compression in order to be able to detect recurrence of the sub-component in subsequent pages. Those sub-components which persist in the web traffic, as measured by the frequency NCs (6) are defined as having substantive content of interest to data-mining applications. Where a substantive content sub-component is added to or removed from a web page, then this change is significant and is sent to a duplication filter (11) so that if multiple NCs (6) detect a change in a web page only one announcement of the changed URL will be broadcast to data-mining applications (8). The NC (6) identifies substantive content sub-components which repeatably are part of a page pointed to by a URL. Provision is also made for limiting monitoring to pages having a flag authorizing discovery of the page by a monitor.
Owner:RESOURCE CONSORTIUM LTD LLC
Network Monitoring System And Method
InactiveUS20080104231A1Multiple digital computer combinationsTransmissionNetwork conditionsTime-Consuming
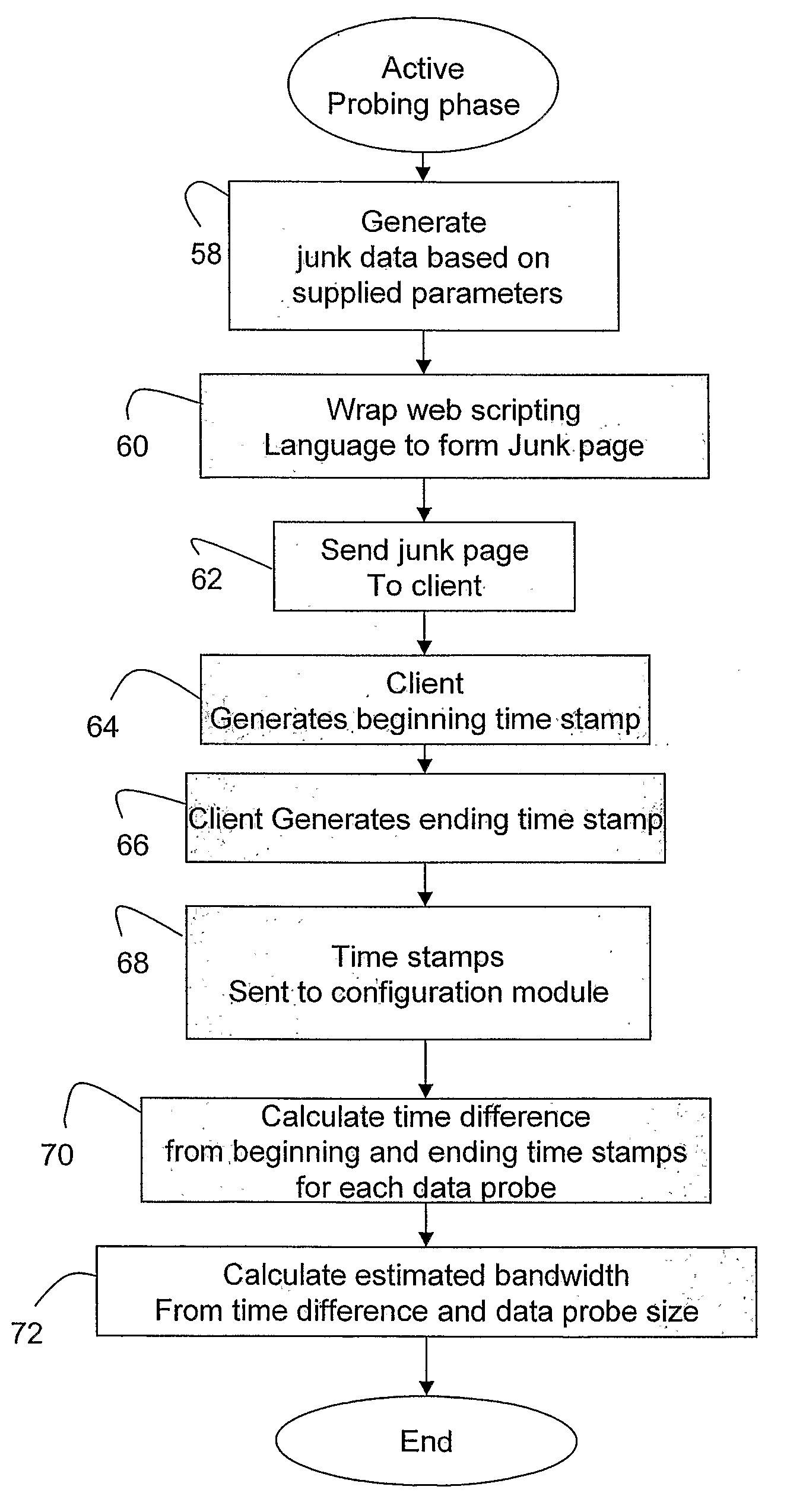
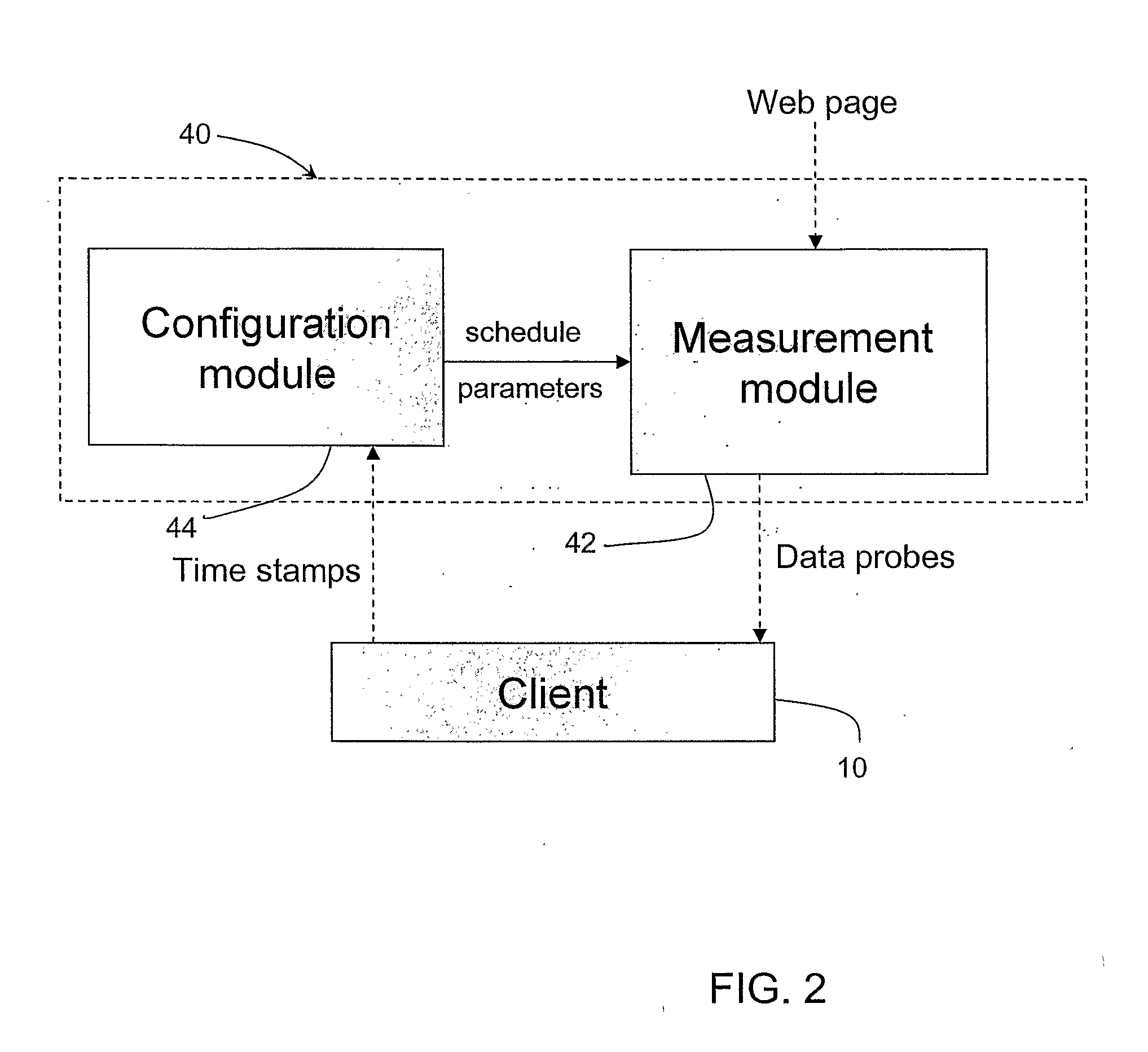
A method for monitoring a wireless channel or wireless network. Preferably, the method and system monitors a web-based network. Active data probing is used to estimate bandwidth availability when no a-priori knowledge of the current channel or network condition is available, and passive monitoring is used to track ongoing web traffic in estimating the current bandwidth available. Data probes are selected that are dynamically customized based on application requirements and the network variability observed in view of a balancing between accuracy of the bandwidth estimation and the potential overhead in terms of time consumed and additional traffic used. In this way, under specified limits of overhead, the active probing attempts to achieve best-effort network bandwidth estimation, and the passive monitoring tracks ongoing web traffic in estimating the current bandwidth available.
Owner:RGT UNIV OF CALIFORNIA
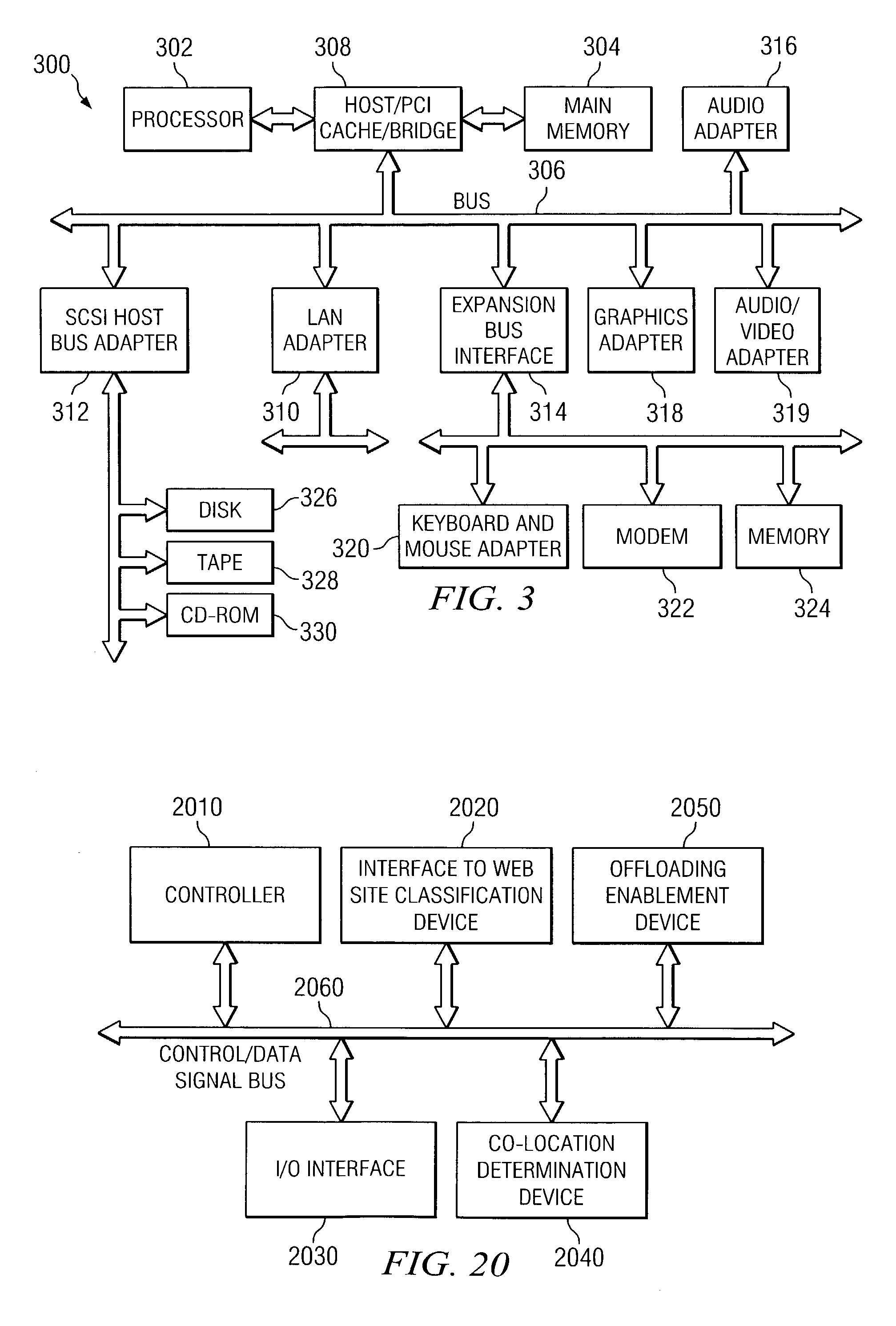
Apparatus and methods for co-location and offloading of web site traffic based on traffic pattern recognition
Apparatus and methods for identifying traffic patterns to web sites based on templates that characterize the arrival of traffic to the web sites are provided. Based on these templates, determinations are made as to which web sites should be co-located so as to optimize resource allocation. Specifically, web sites whose templates are complimentary, i.e. a first web site having a peak in arrival traffic at time t1 and a second web site that has a trough in arrival traffic at time t1, are designated as being candidates for co-location. In addition, the present invention uses the templates identified for the traffic patterns of web sites to determine thresholds for offloading traffic to other servers. These thresholds include a first threshold at which offloading should be performed, a second threshold that takes into consideration the lead time needed to begin offloading, and a third threshold that takes into consideration a lag time needed to stop all offloading of traffic to the other servers.
Owner:INT BUSINESS MASCH CORP
Method and apparatus for generating a sale offer over an electronic network system
A method and apparatus are provided for generating a sale offer over an electronic network (such as the Internet). The method and apparatus may be used with a commercial sale system designed to increase the revenue income of Web site by offering, at a substantially discounted or virtually free basis, one more goods and / or services to visitors of the Web site. According to the features of the invention, the seller (who may be the owner or co-owner of the Web site) transmits a sale offer on the Web site for a high quality good or service, wherein the good or service can be purchased for free or a cost near to zero. The seller may make the offer visible and available to a number of perspective buyers, who are connected at that very moment to the Web site. According to an additional aspect of the invention, the sale offer may be available for only a very limited amount of time (e.g., one or more minutes) and may be offered at random or unpredictable times on the Web site in order to increase Web traffic to the site.
Owner:TRIUMVIRATE SYST LLC
Web VPN
ActiveUS20120023570A1Computer security arrangementsMultiple digital computer combinationsWeb browserWeb service
Web-based VPN system and corresponding service. The inventive web VPN system / service could be accessed by the users using only a conventional web browser without the need to install any specialized VPN client software on the user terminal, as it is the case with conventional VPN systems. User's terminal could be a user's desktop computer, notebook or a mobile device, such as a cell prone or a PDA, or any other computing platform what so ever, used by the user to access various network resources, such as web pages. One aspect is a web VPN service that encrypts, using, for example, SSL encryption, all web traffic going between the user's terminal and the Internet. System comprises a VPN server / proxy and an associated web server accessible by the user via a communication network, such as Internet. The web server associated with the VPN server / proxy communicates with the latter and enables the user to access and use the functionality provided by the private VPN server / proxy by means of a conventional web browser installed on the user's terminal.
Owner:AURA SUB LLC
Apparatus for analyzing traffic
An apparatus for analyzing traffic is provided. The apparatus may precisely identify and analyze web traffic through 5 tuple-, HTTP-, and request / response pair-based packet analysis by monitoring the correlation between sessions.
Owner:ELECTRONICS & TELECOMM RES INST
Method & system for enhanced web page delivery
InactiveUS7260774B2Reduce deliveryMultiple digital computer combinationsWebsite content managementVisibilityWeb site
A system for and method of enhancing web page delivery. The invention provides the ability to control redirection of Web traffic of humans and search engine spiders. It can differentiate between these types of visitors to a Web page, track their movements, log critical information, and analyze the Web traffic in order to judge the success in driving quality traffic to some known goal on a Web site, such as a sale. The system may generate dynamically optimized web pages targeted to specific search engines, in order to optimize the search engine ranking and visibility of a Web site, such as an online marketer's Web site.
Owner:THRYV INC
Direct Tracking of Keywords to Ads/Text
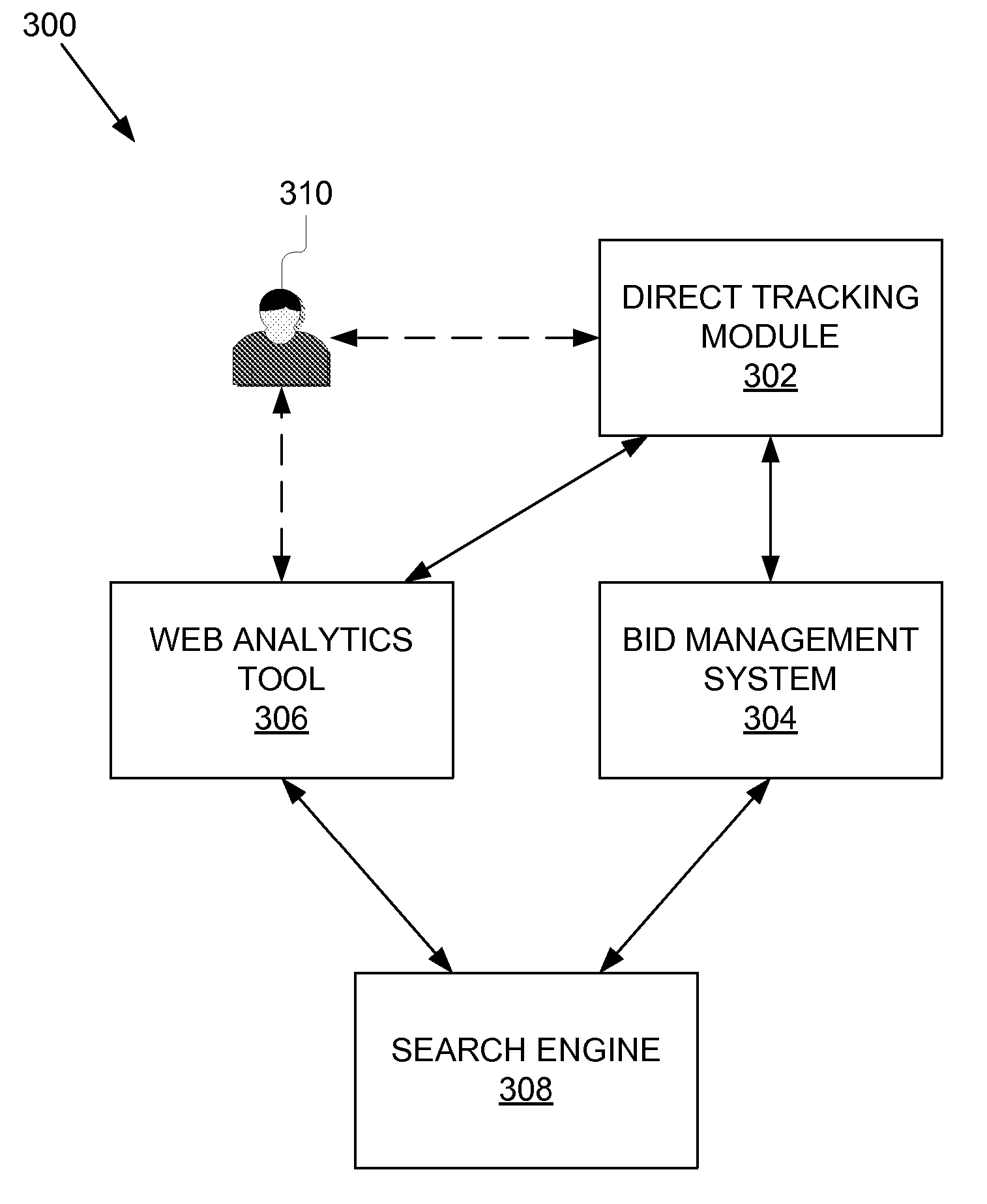
ActiveUS20070100811A1Reduce uncertaintyOvercomes deficiencyFinanceWebsite content managementPresent dayWeb analytics
The present invention overcomes the deficiencies and limitations of the prior art by providing a direct tracking module for keywords. In one embodiment, the system comprises a direct tracking module, a bid management system, a web analytics tool and a search engine. The direct tracking module interfaces with the bid management system to provide user interfaces for reviewing data about specific keyword and ads / text pairs. The direct tracking module uses unique codes to provide specific information about which combination of keyword and text generated specific Web traffic, such as traffic that generated a sale. This is particularly advantageous because the keyword / text pairs that generate a large number of sales can be reused to generate future traffic. Similarly, keyword / text pairs that do not generate Web traffic can be eliminated from the words that are purchased by the advertiser. Thus, the present invention greatly reduces the uncertainty presently provided by keyword purchasing schemes offered by present-day search engines. The present invention also includes a novel method for the direct tracking of keywords to ads / text.
Owner:ADOBE INC
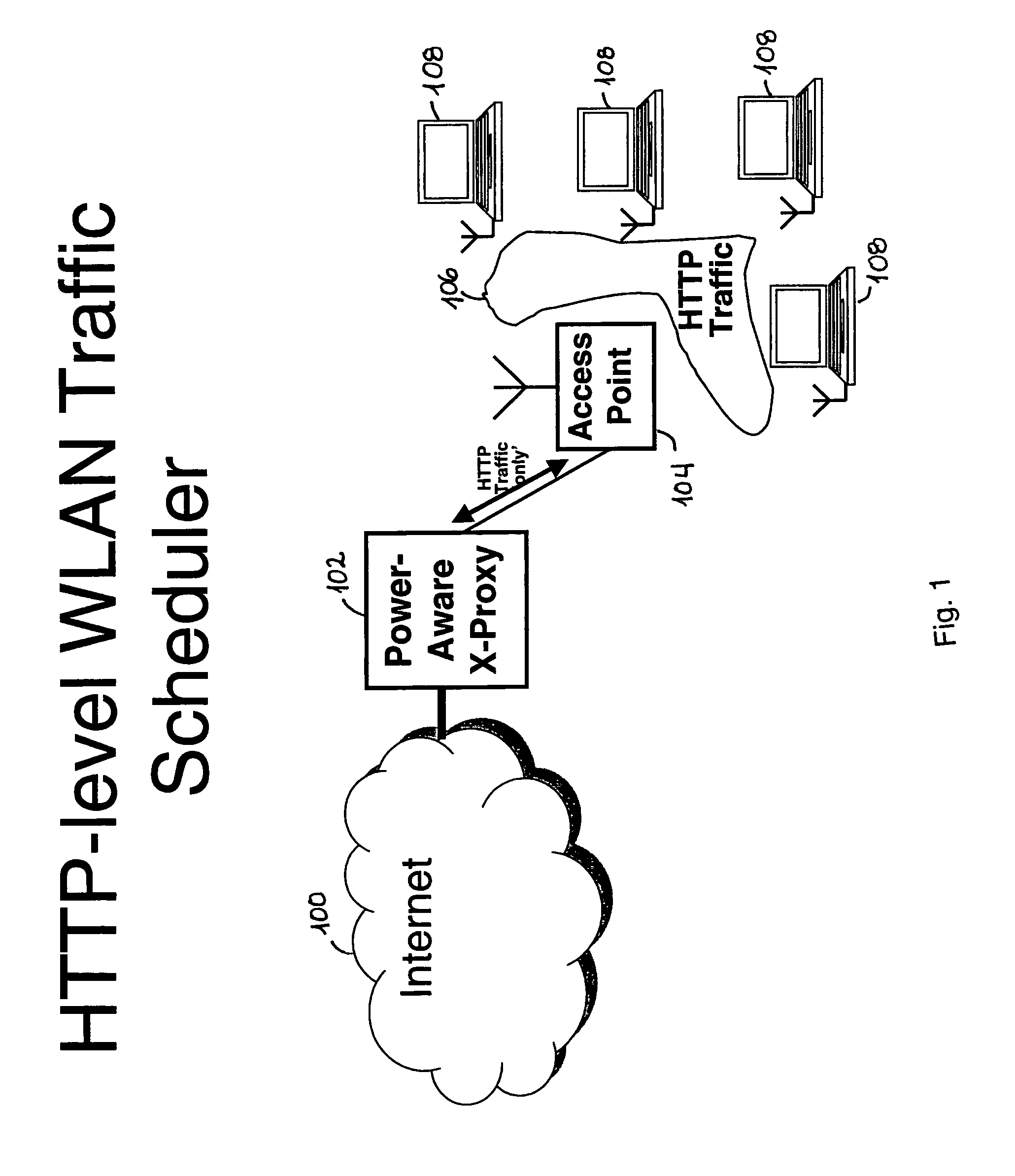
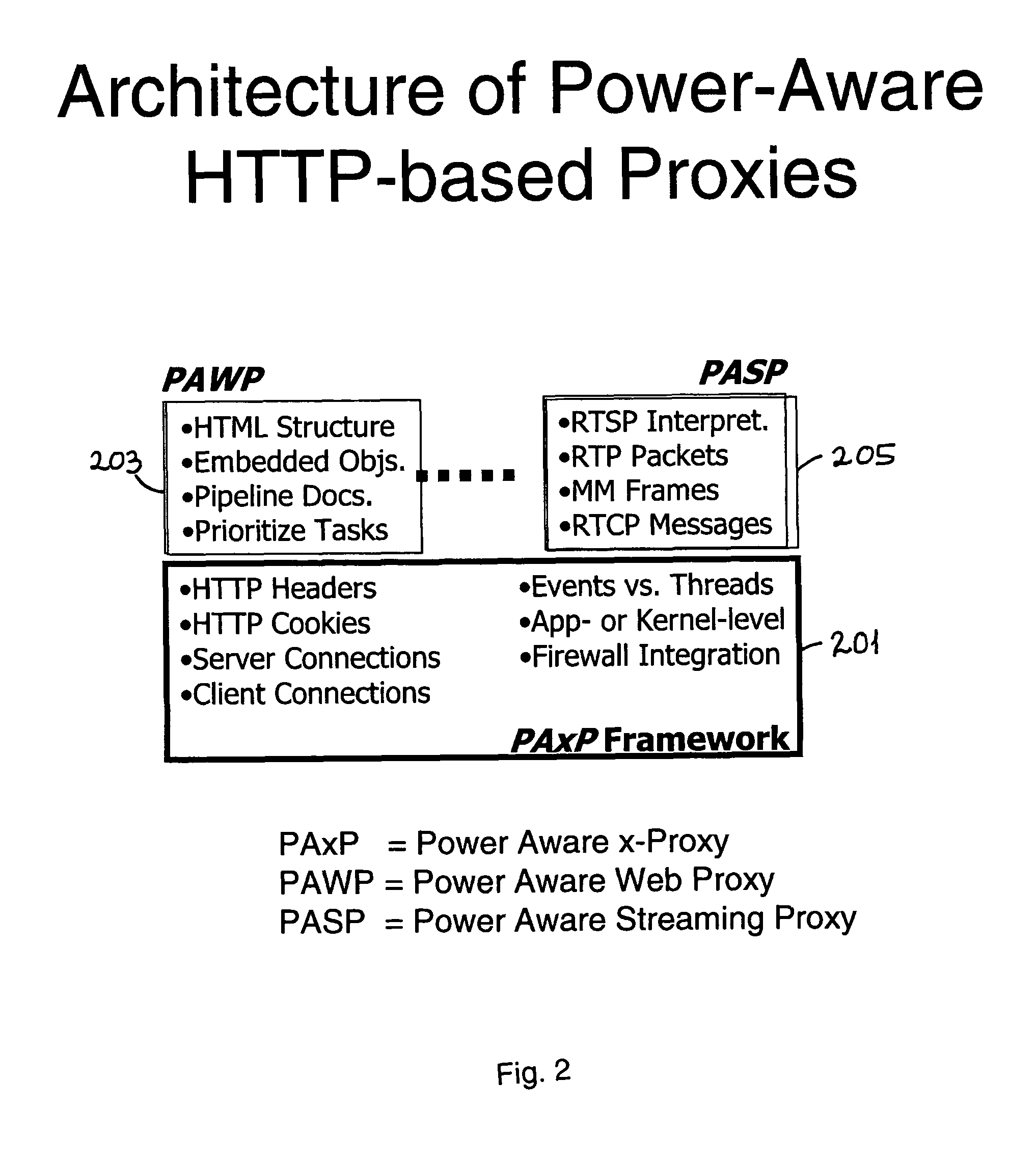
Method and apparatus for scheduling wireless LAN traffic
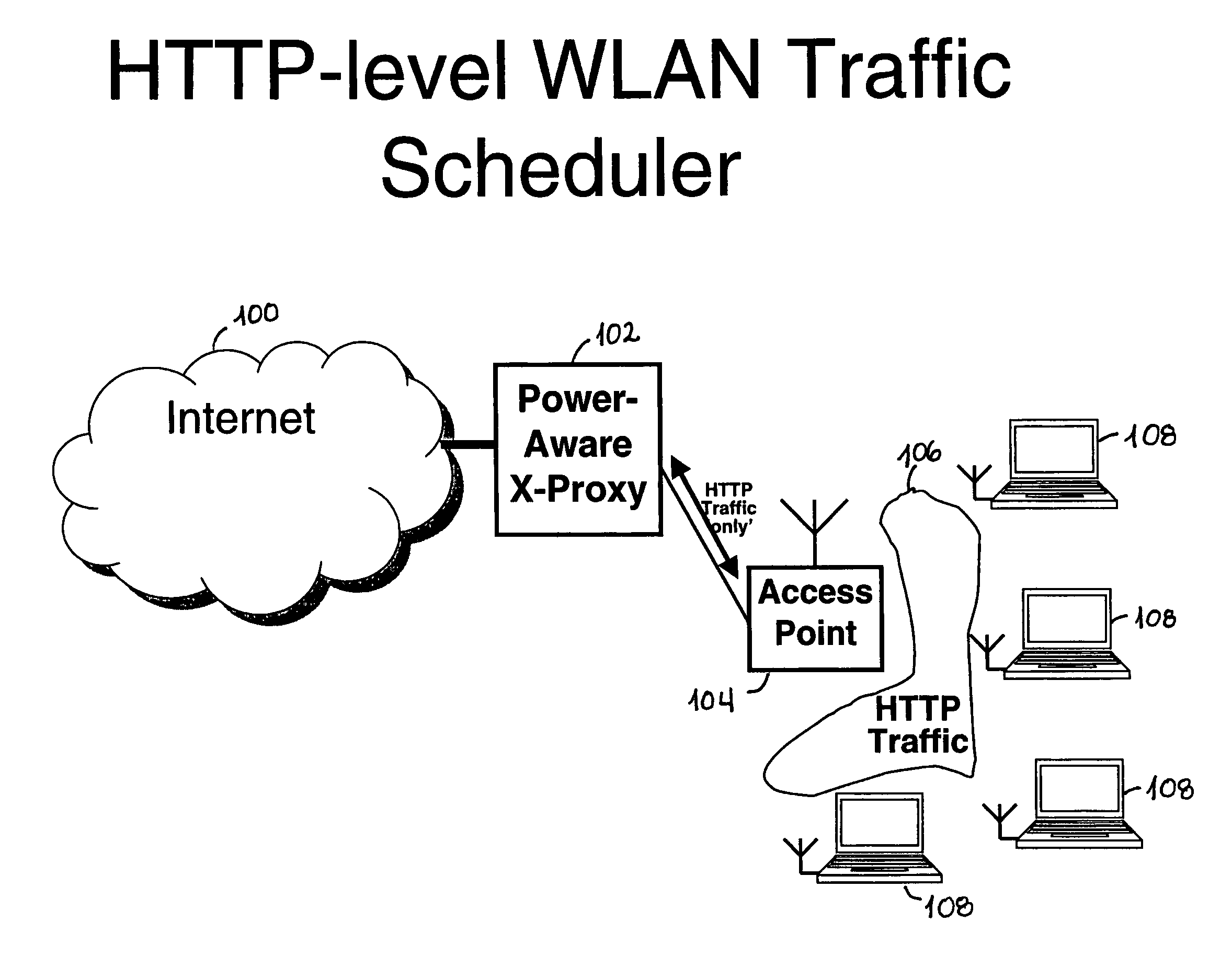
To conserve energy, components in mobile devices normally have to transition less frequently between “active” and “sleep” modes, and to sleep for longer intervals. In accordance with at least one presently preferred embodiment of the present invention, there is broadly contemplated herein an approach to reduce energy consumption by using HTTP proxies to shape incoming WLAN traffic. Proxies contemplated herein use techniques specific to the HTTP payload to compensate for any negative impact that shaping may have. Thus, there is described herein the architecture of a “PowerAware Streaming Proxy” (PASP), built on a PowerAware x-Proxy (PAxP) framework. PASP preferably uses RTSP / RTP semantics to effectively schedule media streams across the WLAN. Herein, PASP is compared with PAWP, which is a PAxP extension for web traffic, and problem areas are identified.
Owner:LENOVO PC INT
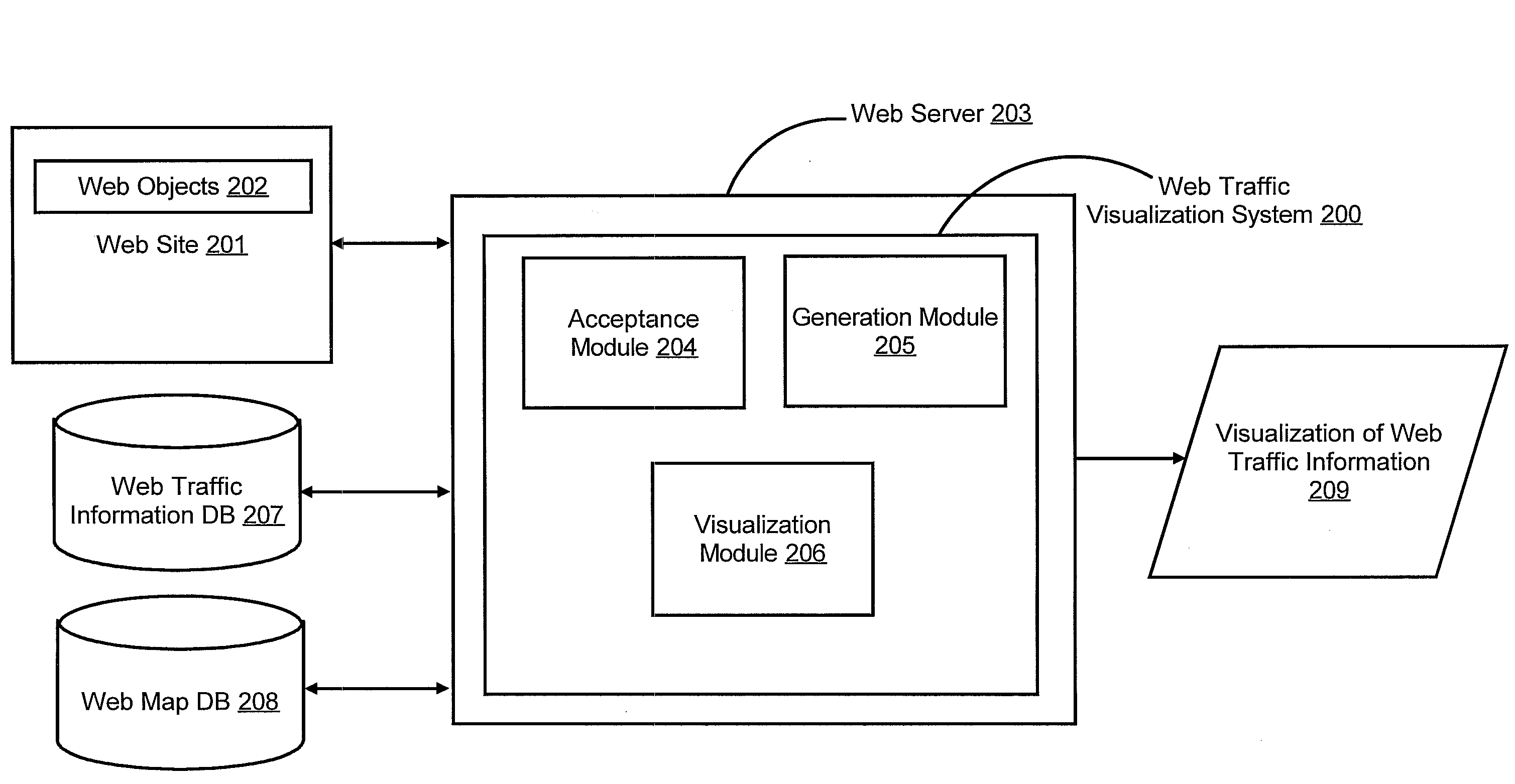
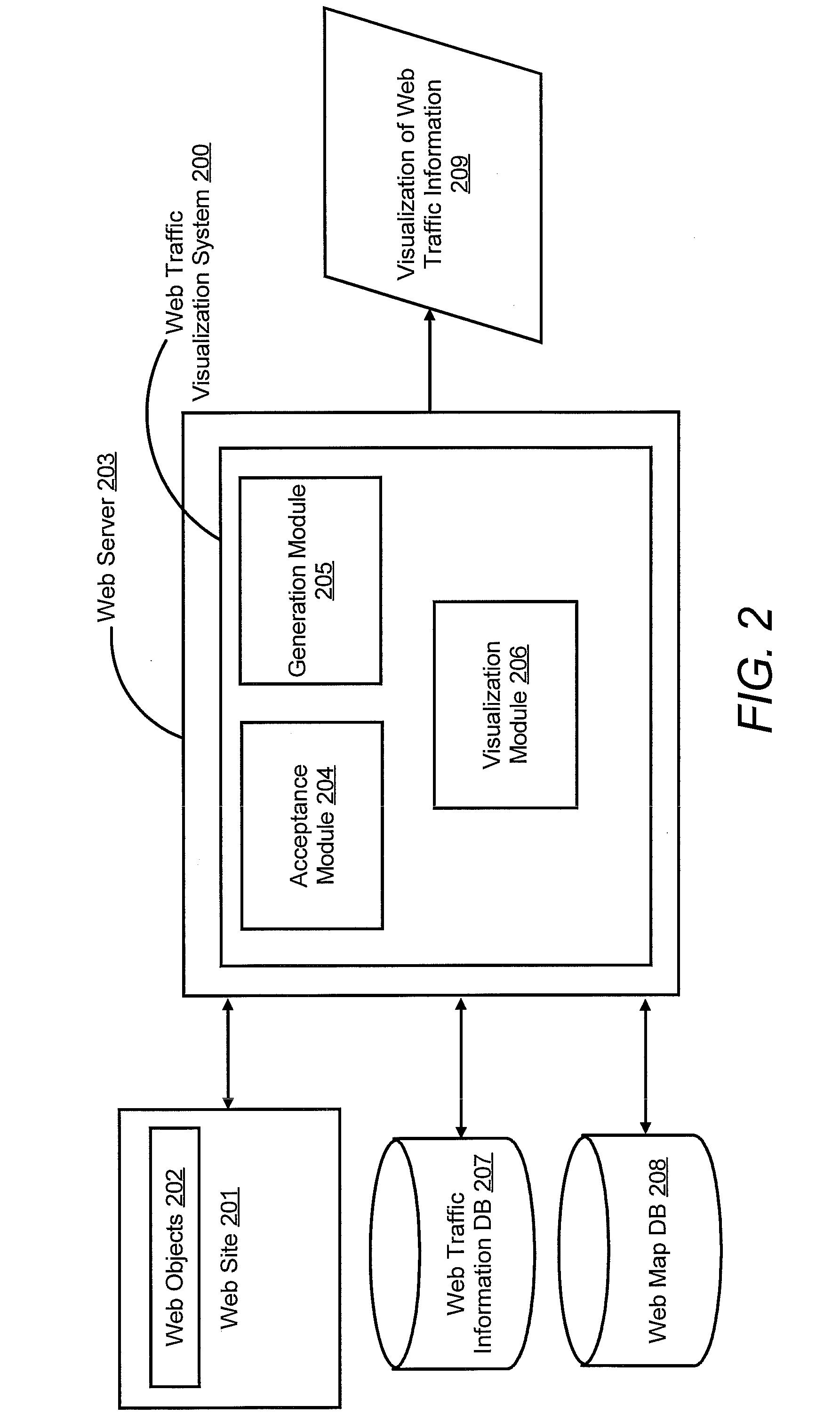
Traffic visualization across web maps
ActiveUS20110055710A1Input/output for user-computer interactionDigital computer detailsWeb siteInternet traffic
A web traffic visualization system includes a generation module configured to generate a web map. The web map includes web objects and links connecting the web objects, where the web objects are for a web site. The web traffic visualization system also includes an acceptance module configured to assign a unique ID to a visitor of the web site and receive a visitor action performed by the visitor on a web object in the web site tagged with the unique ID. The web traffic visualization system is further configured to include a visualization module configured to generate and display the visitor action on the web map in response to receiving the visitor action tagged with the unique ID.
Owner:ACCENTURE GLOBAL SERVICES LTD
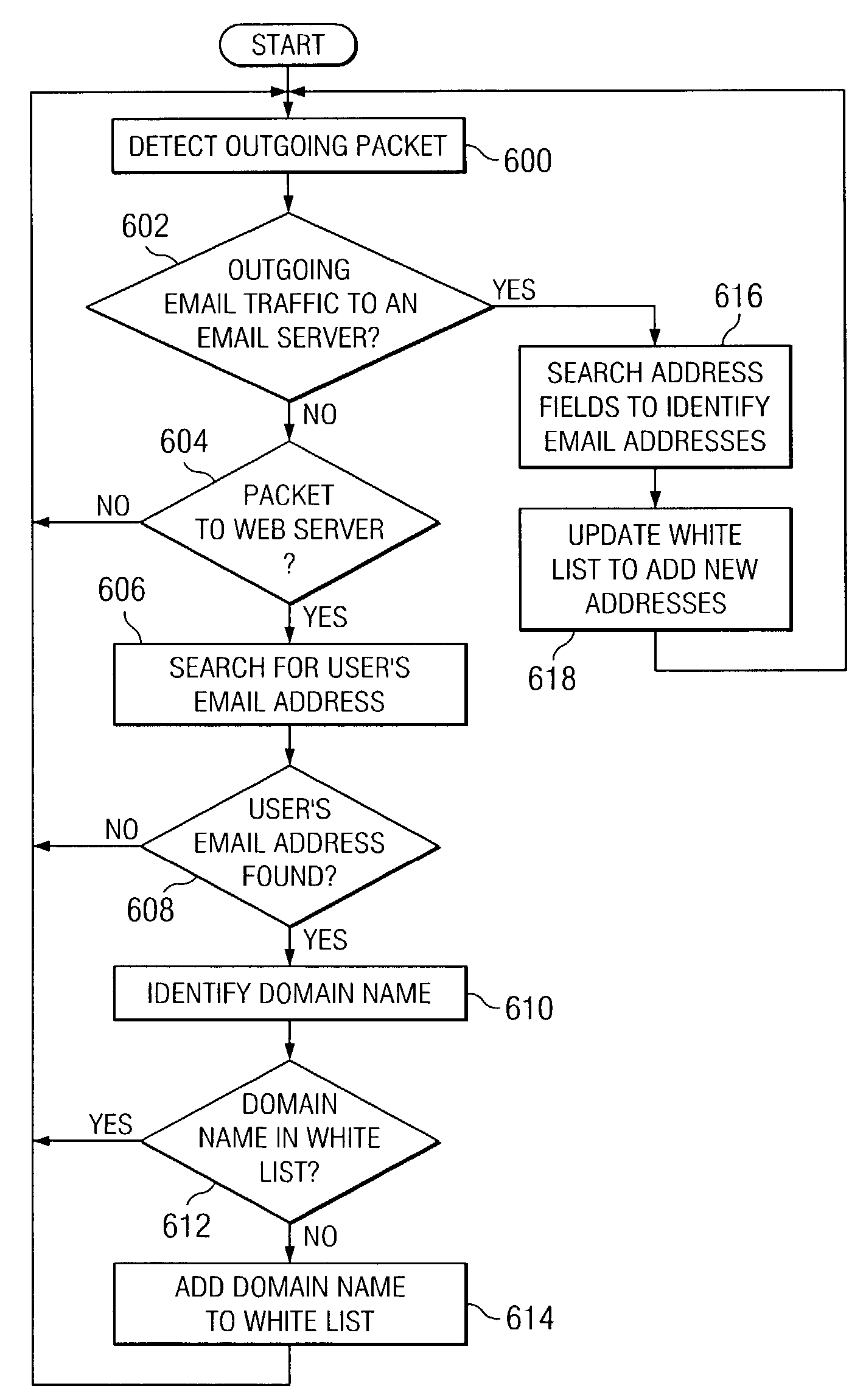
Method for managing email messages
ActiveUS7454467B2Data switching by path configurationMultiple digital computer combinationsDomain nameData pack
A method, apparatus, and computer instructions for managing email messages. Outgoing packets are monitored. The outgoing packets are parsed for outgoing email messages. An identification of recipients in packets for outgoing email messages is made. A list of email addresses is updated with email addresses for the identified recipients, wherein the list of email addresses is used to accept incoming email messages. The outgoing packets also are parsed to identify Web traffic containing a user email address. A domain name of the destination is identified for Web traffic containing the user email address. The list of email messages is updated with this domain name. Incoming email messages are screened to see if the domain name is present in the email address of the sender in determining whether to accepted the email messages.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com