Patents
Literature
10344results about How to "Easy to solve" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
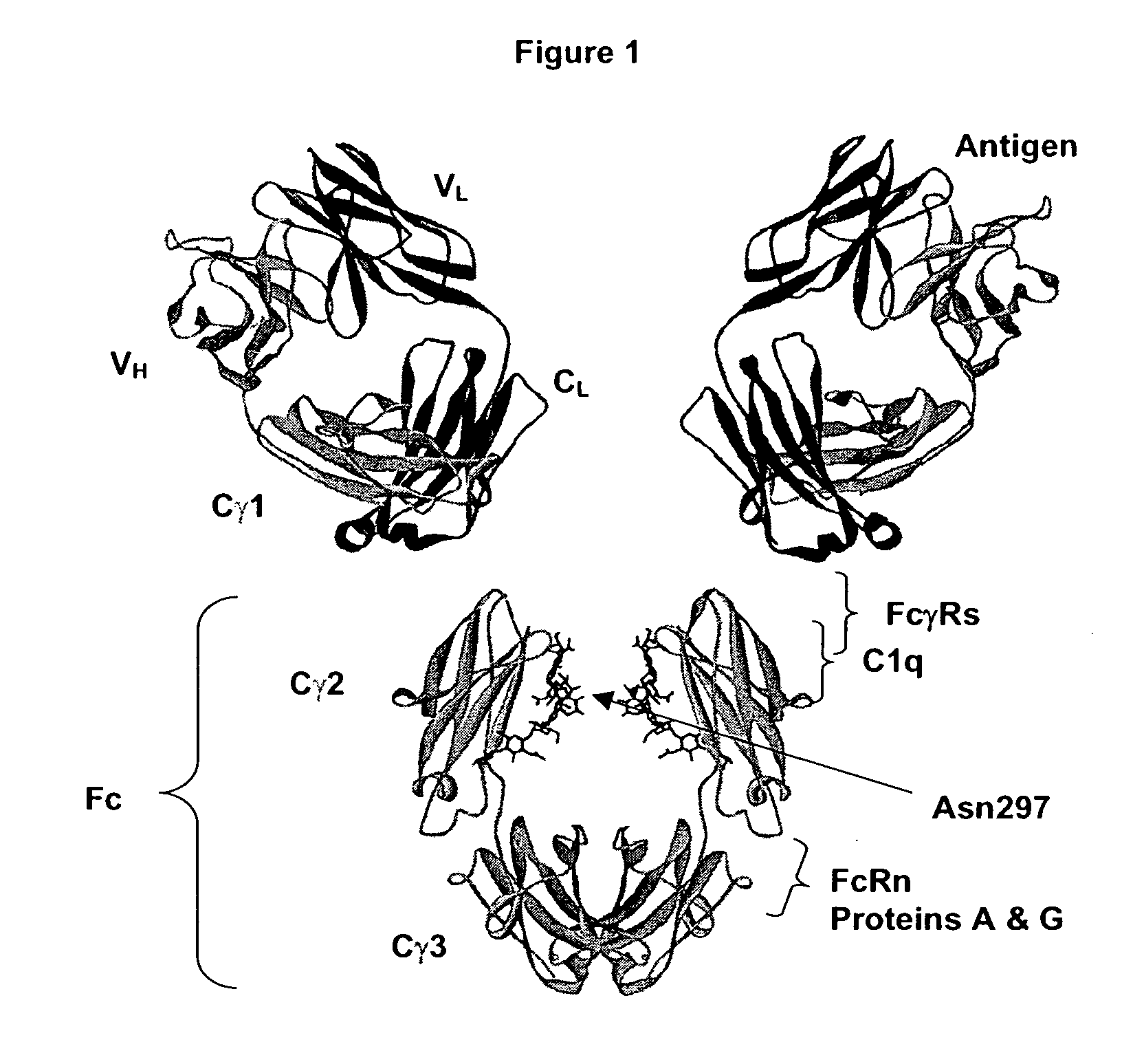
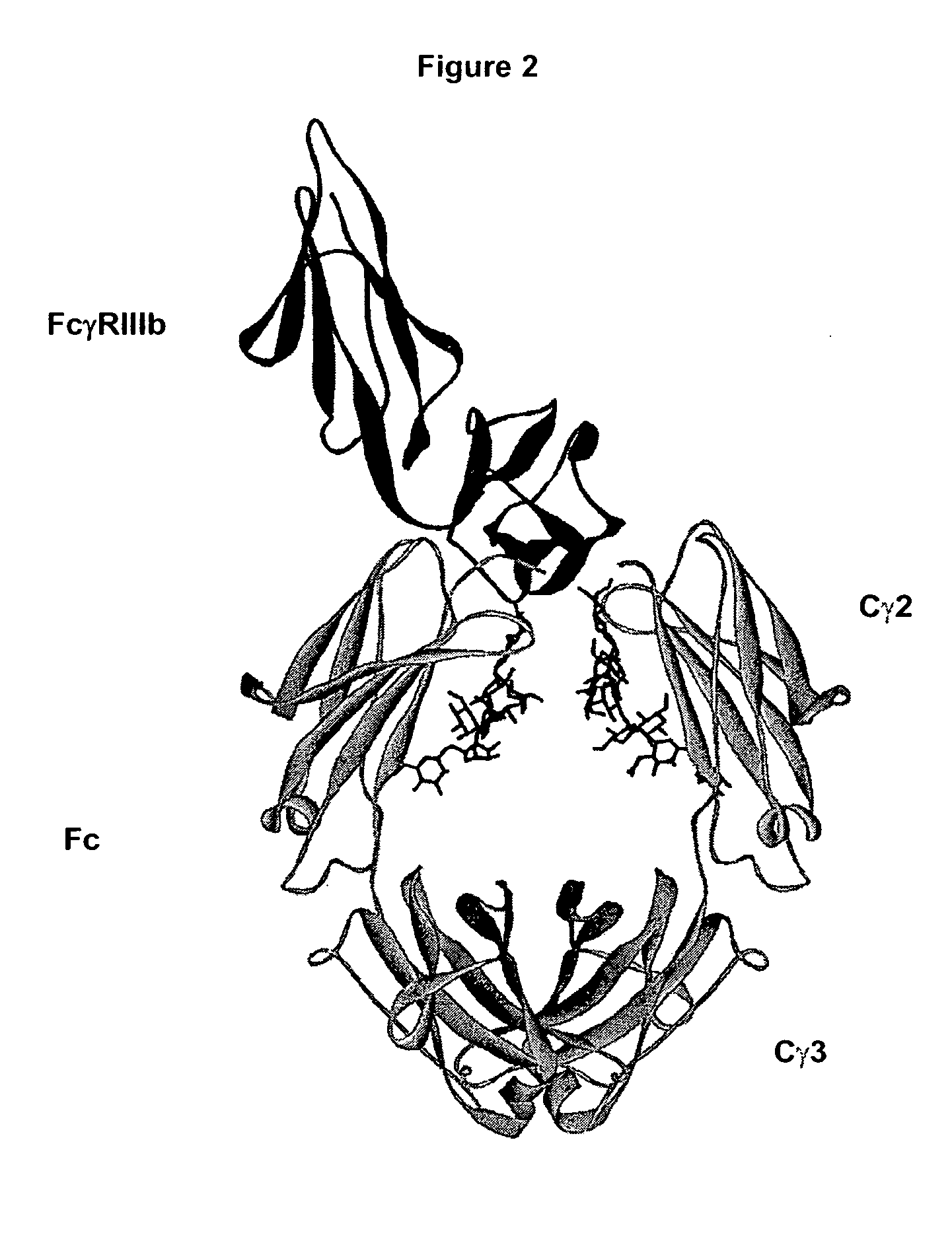
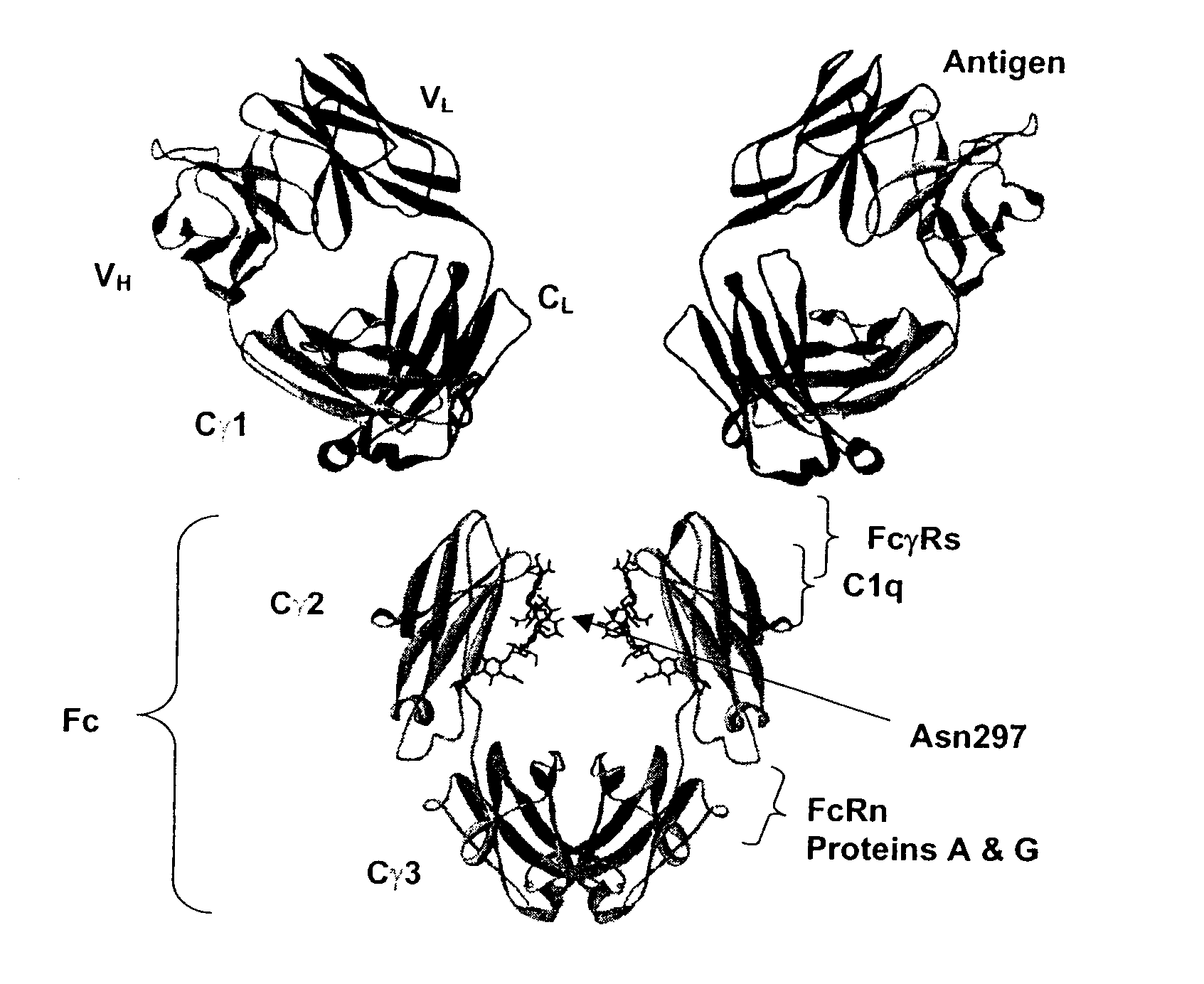
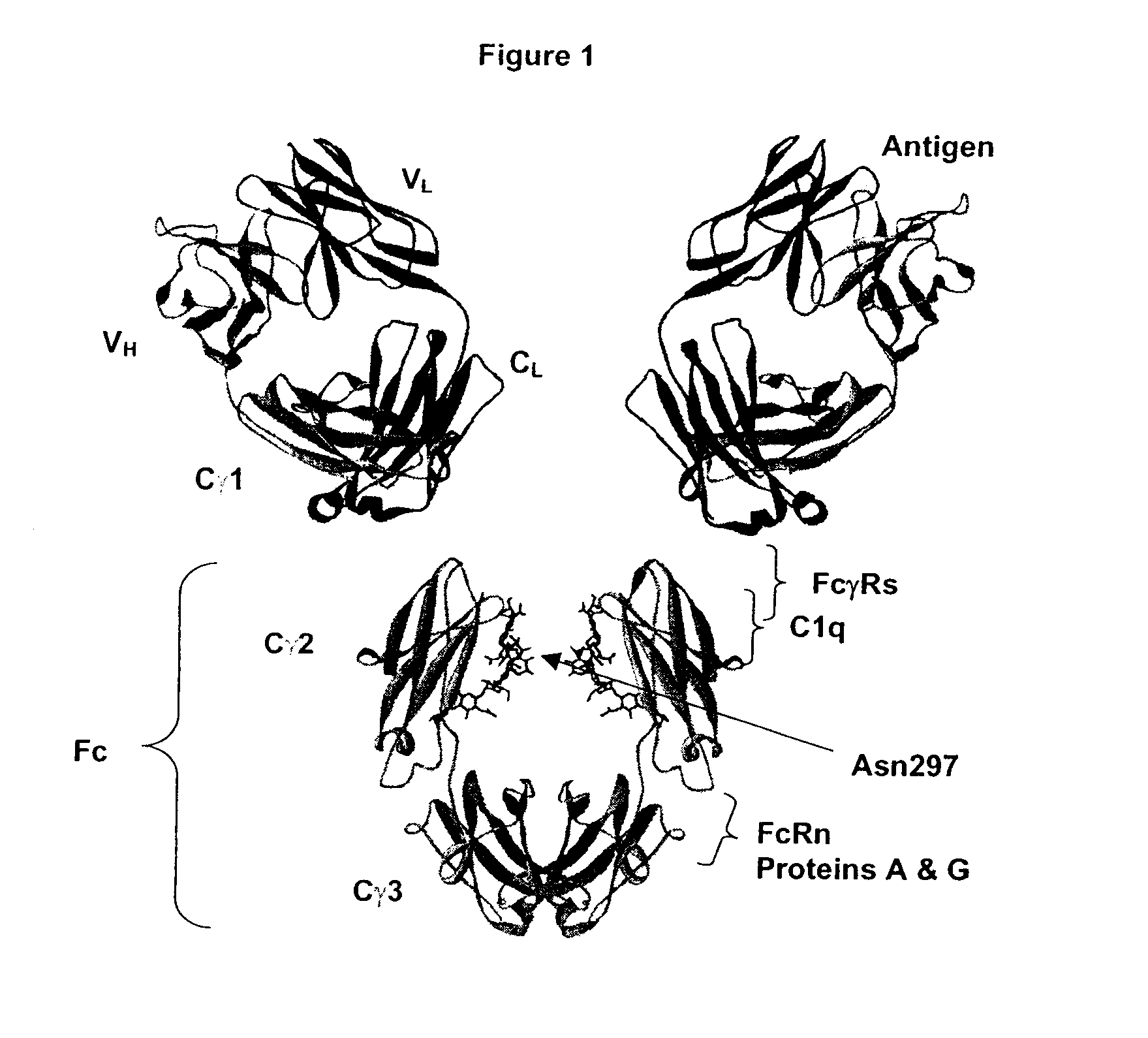
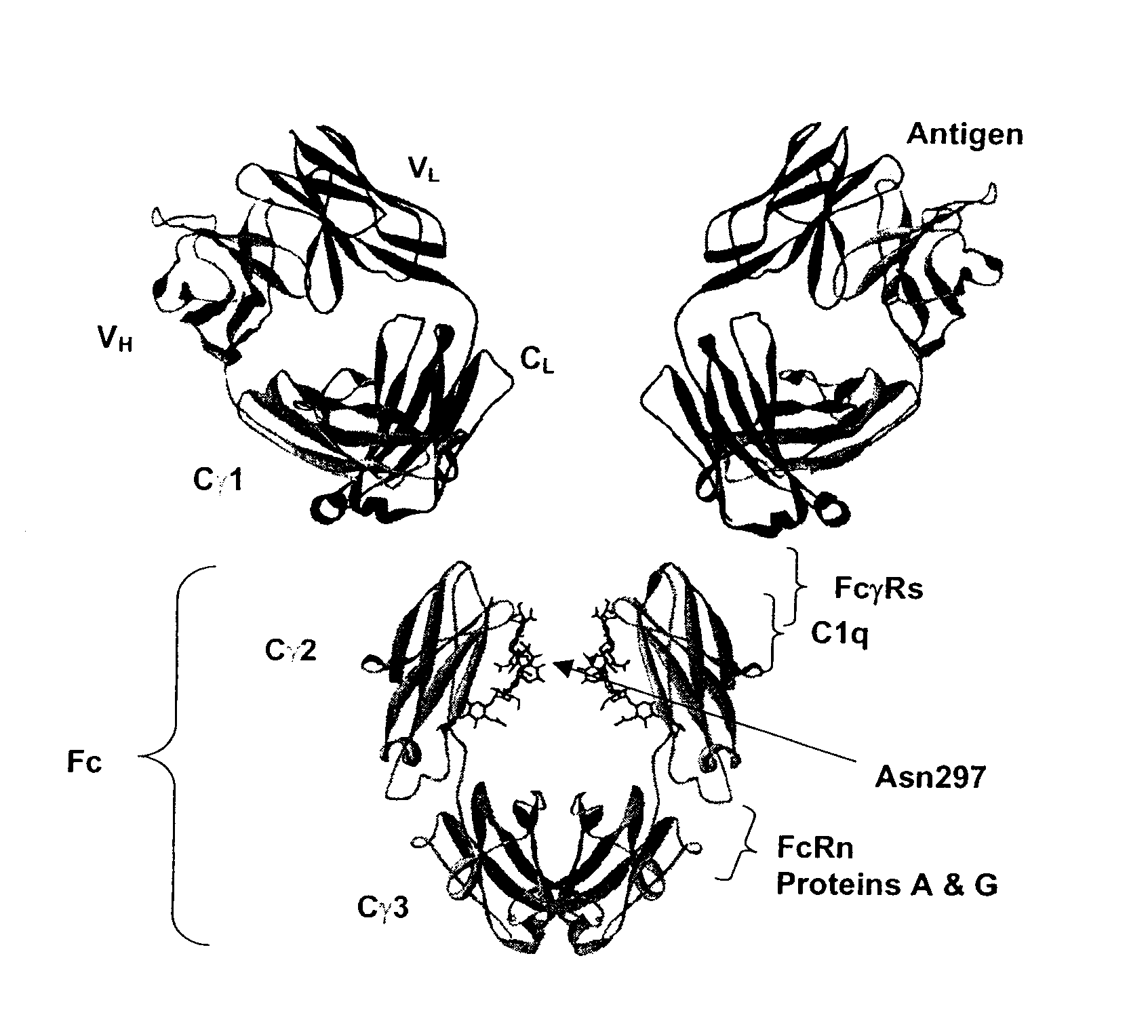
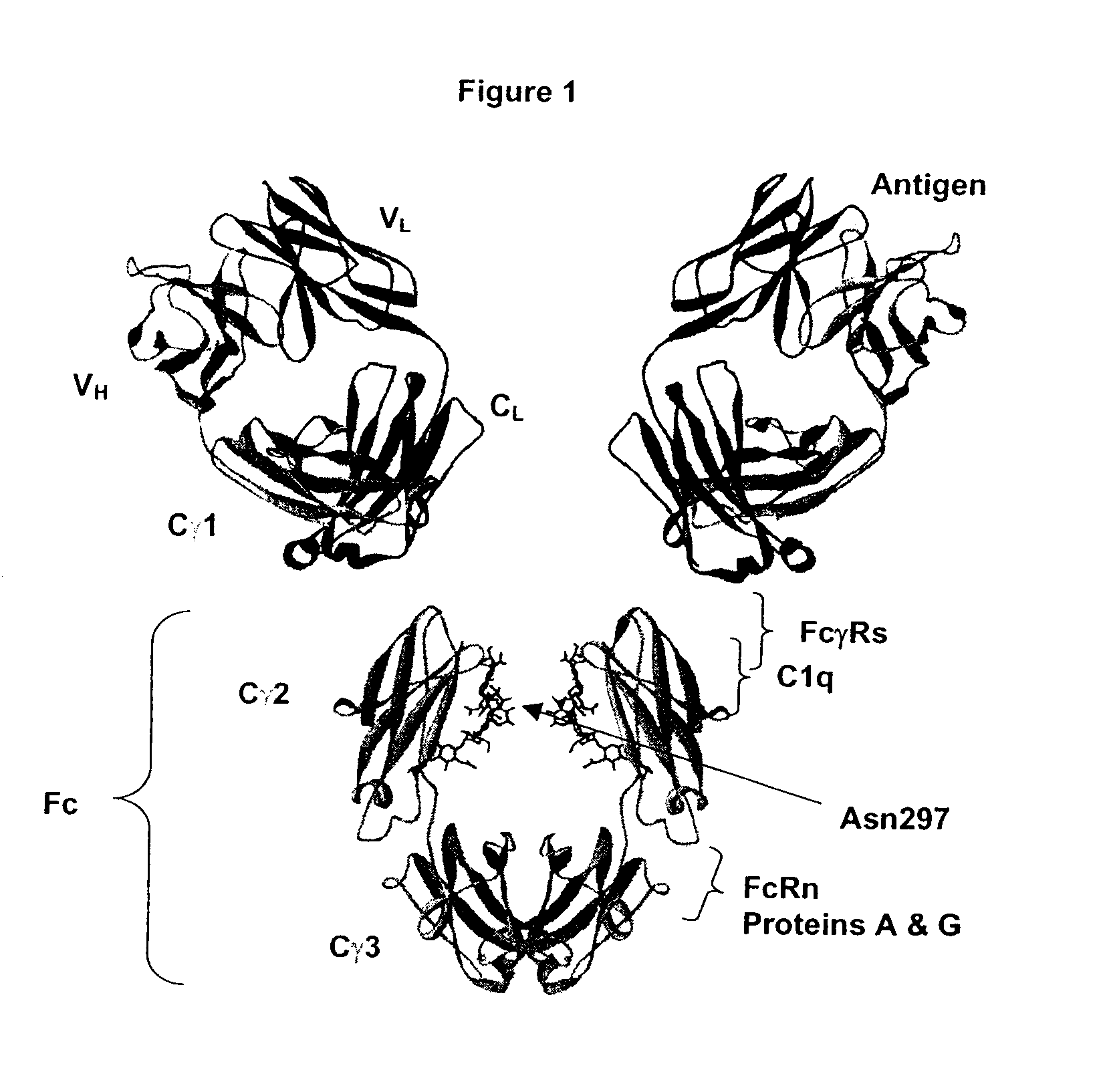
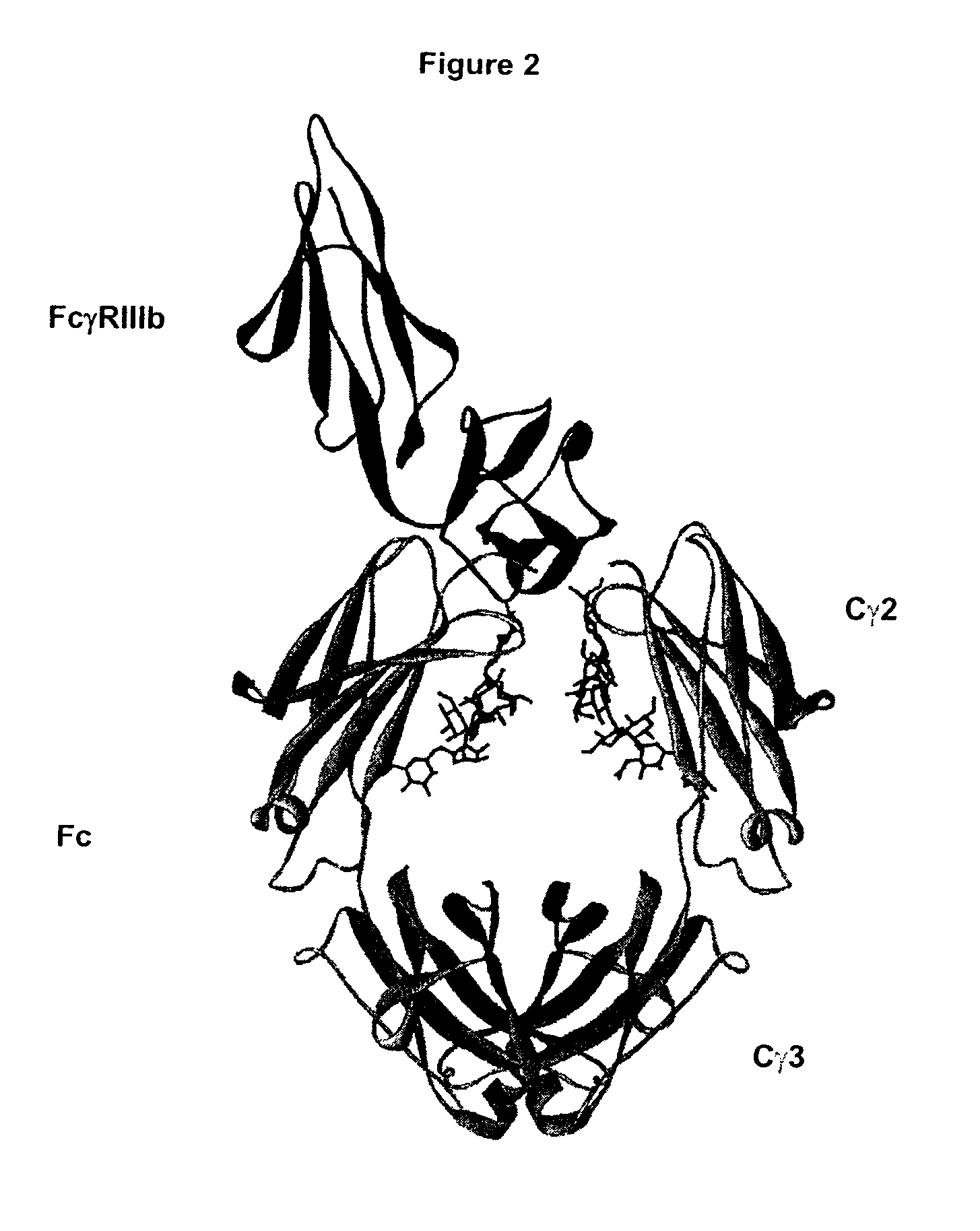
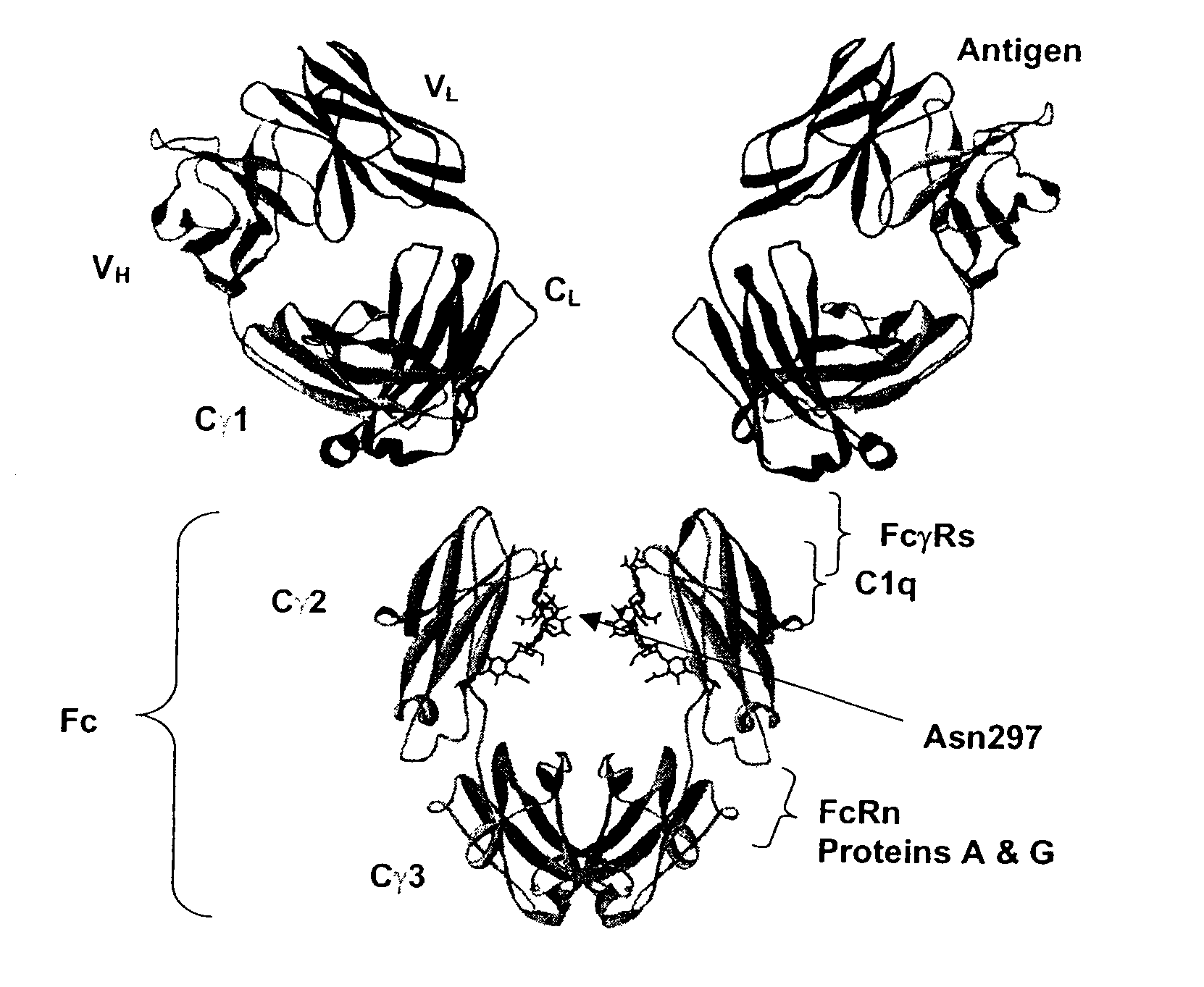
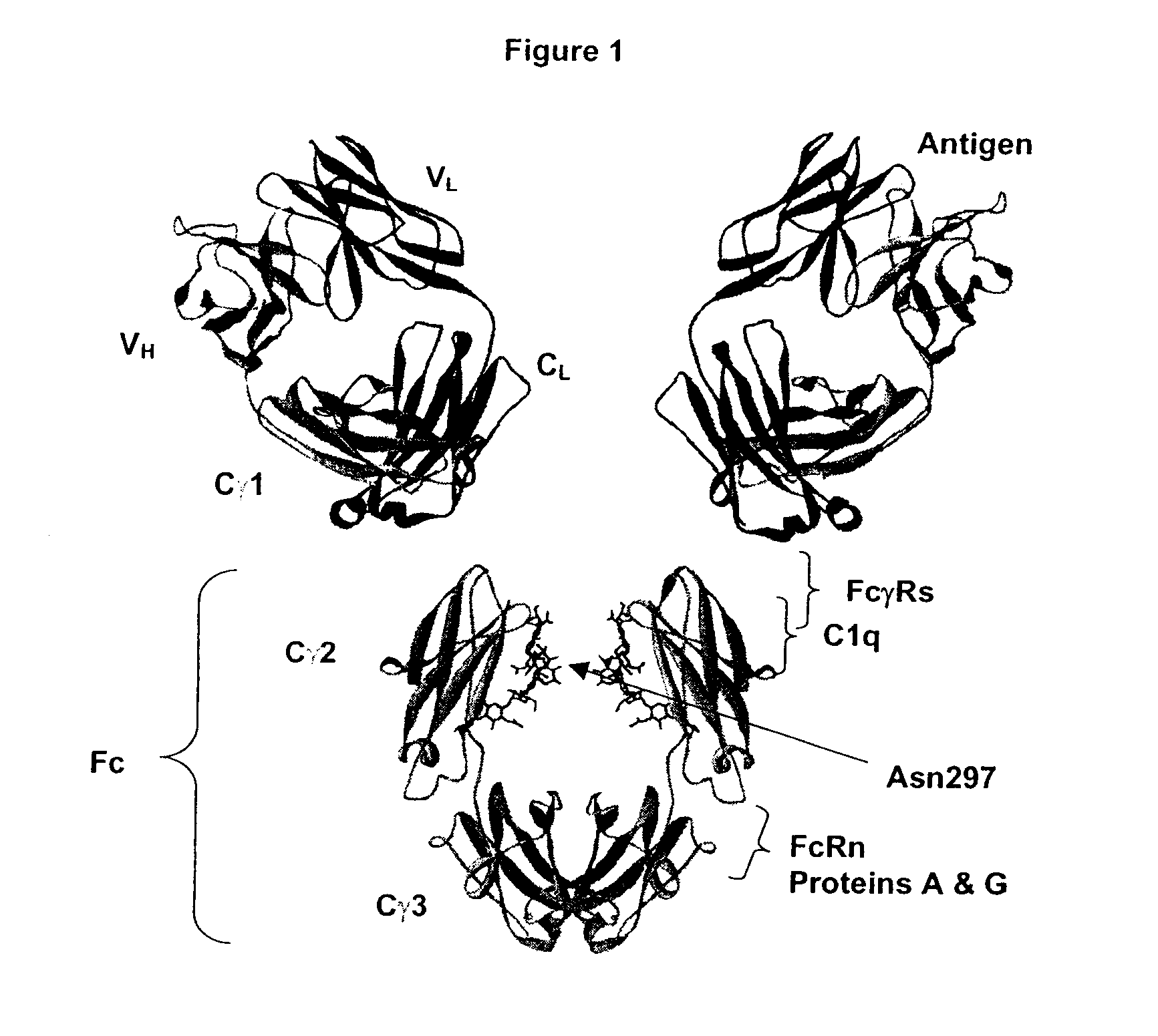
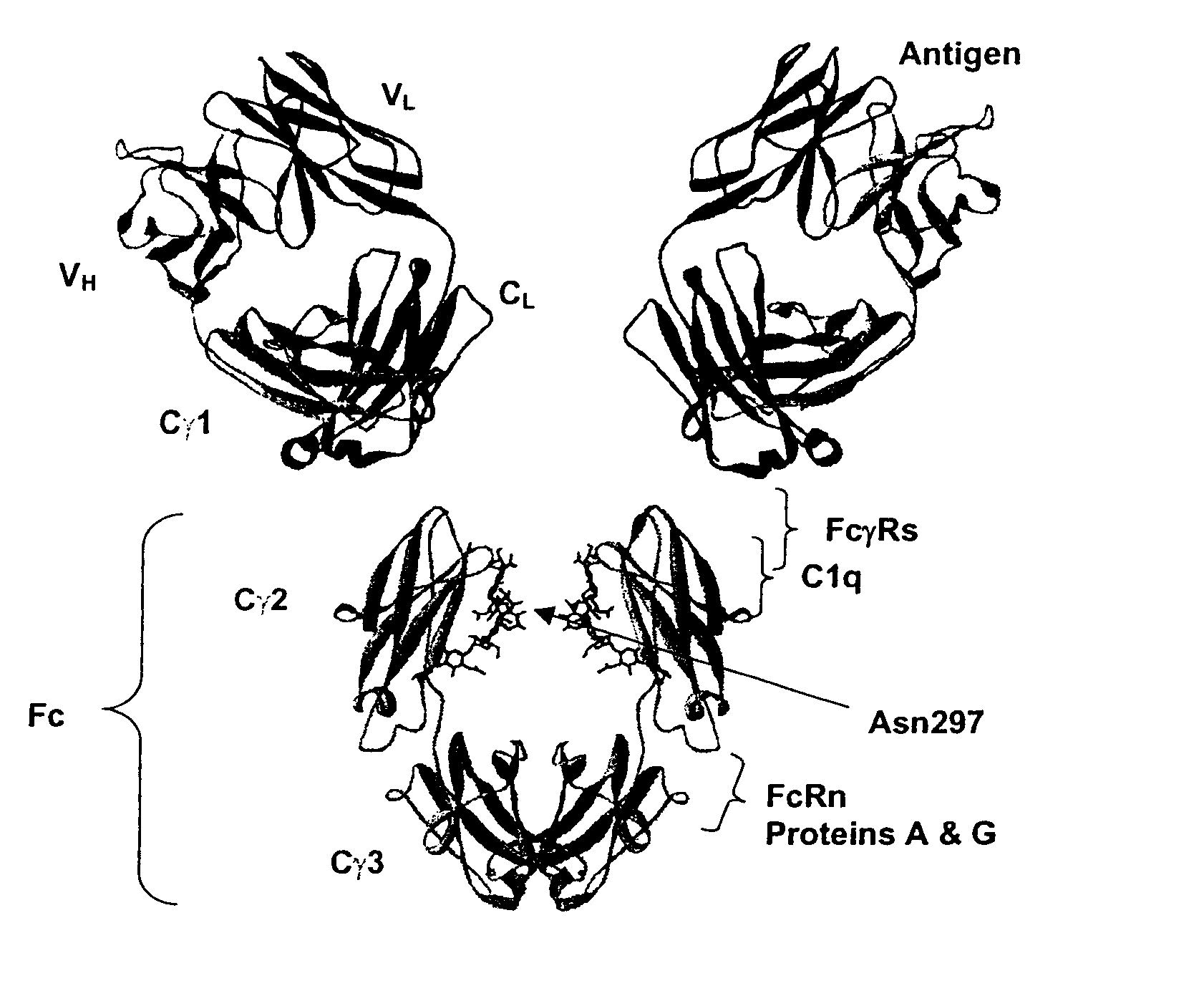
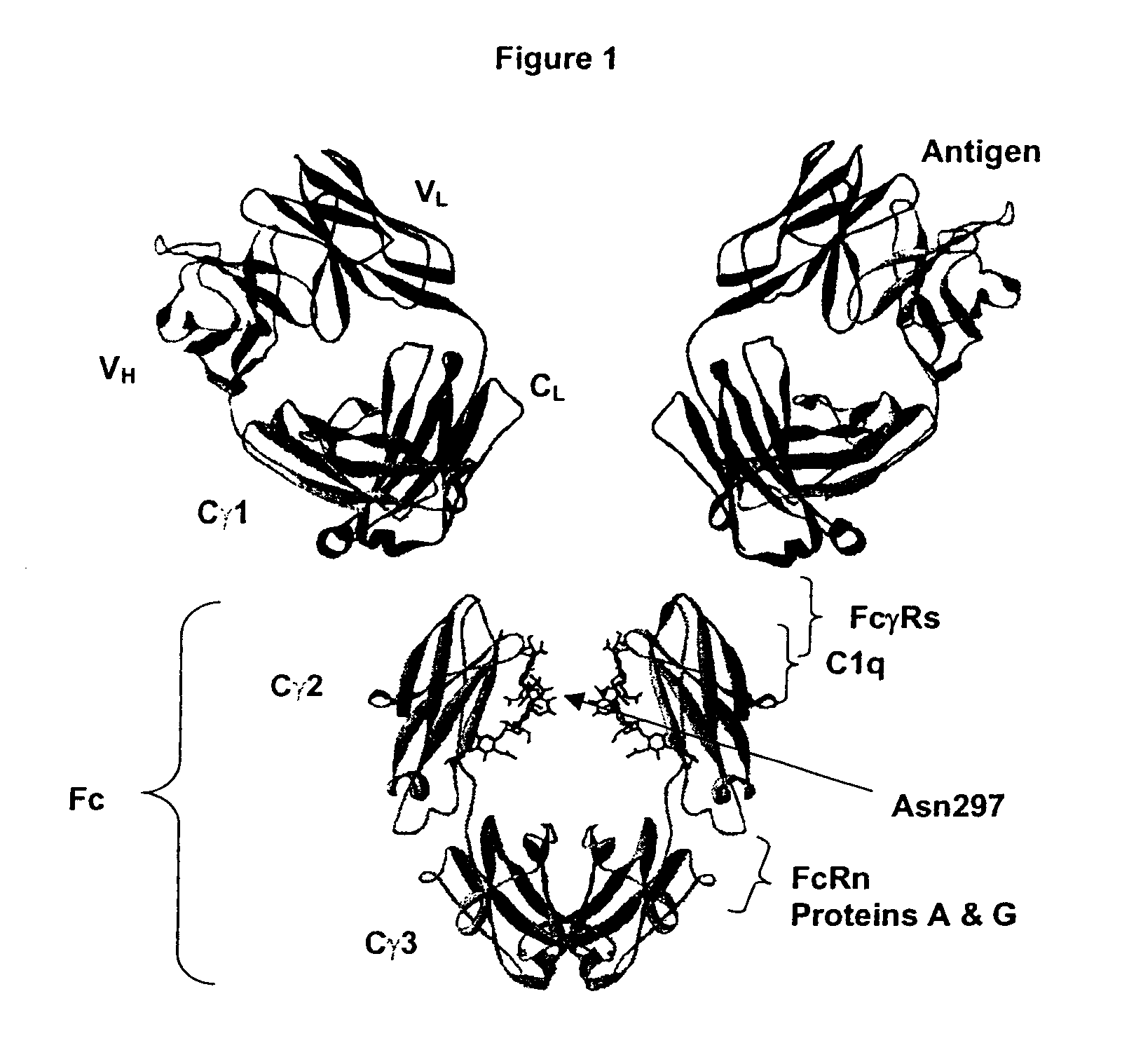
Optimized Fc variants
ActiveUS20060024298A1Weak affinityFunction increaseAntibody ingredientsImmunoglobulinsChemistryBiochemistry
Owner:XENCOR
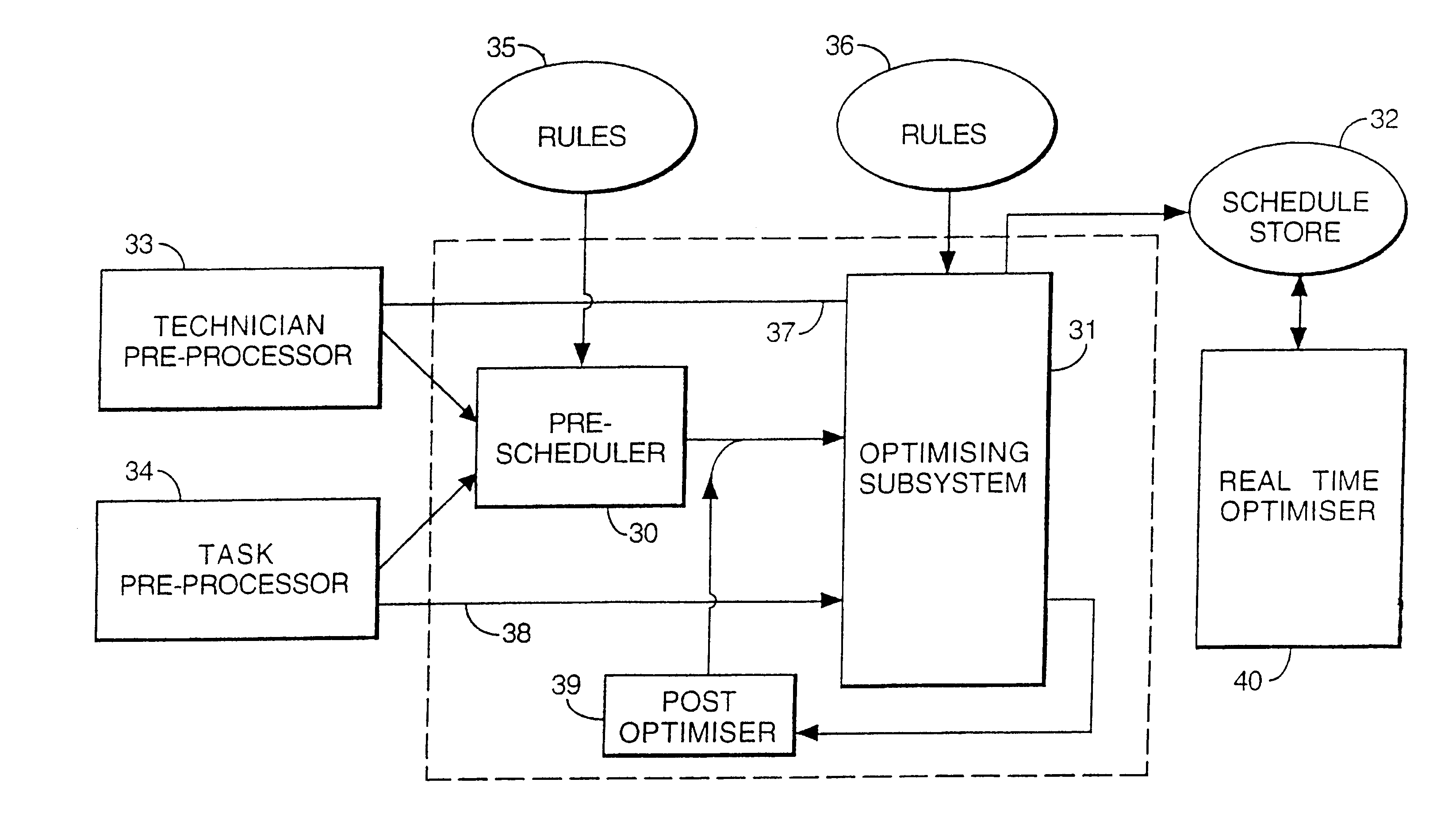
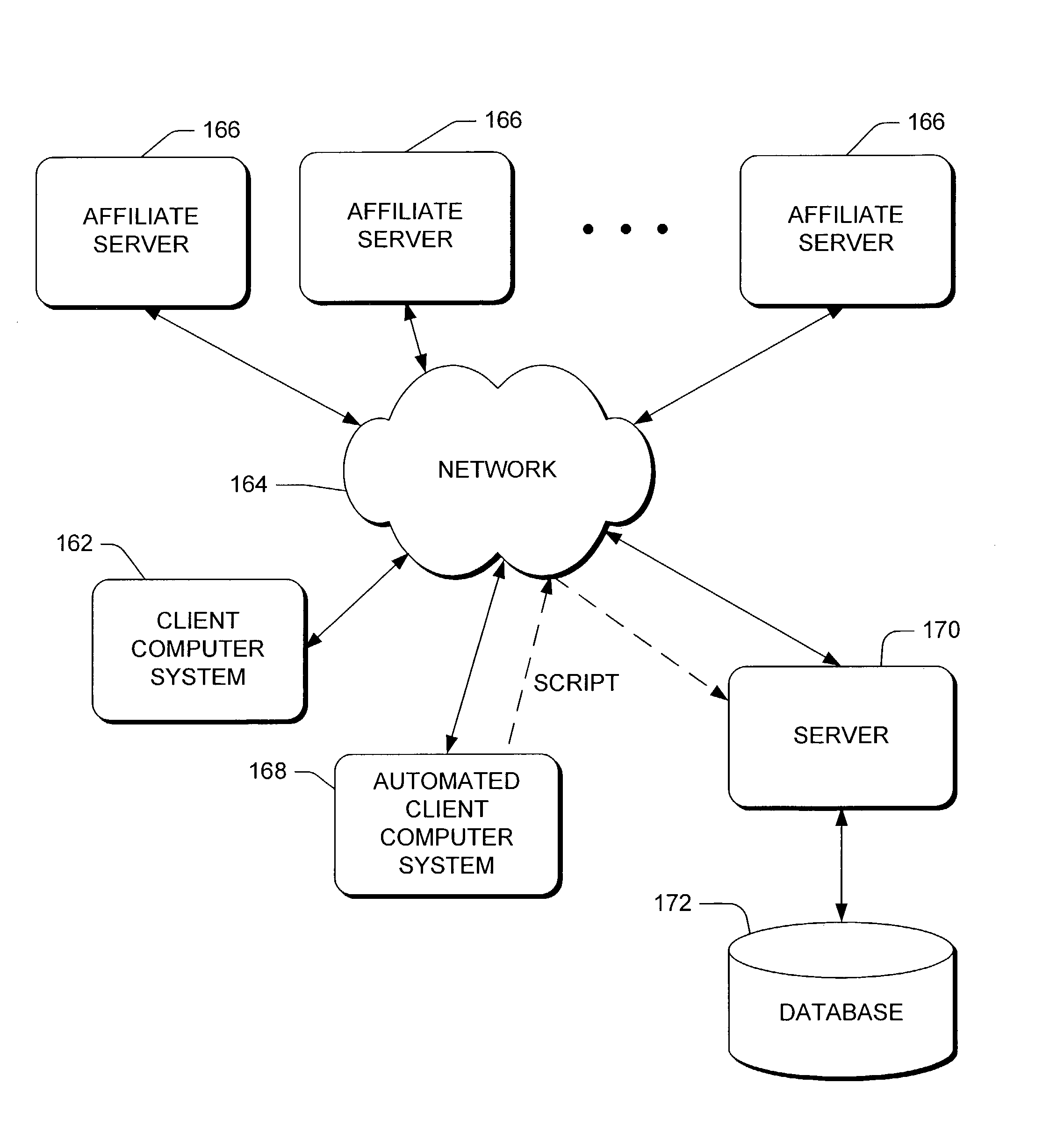
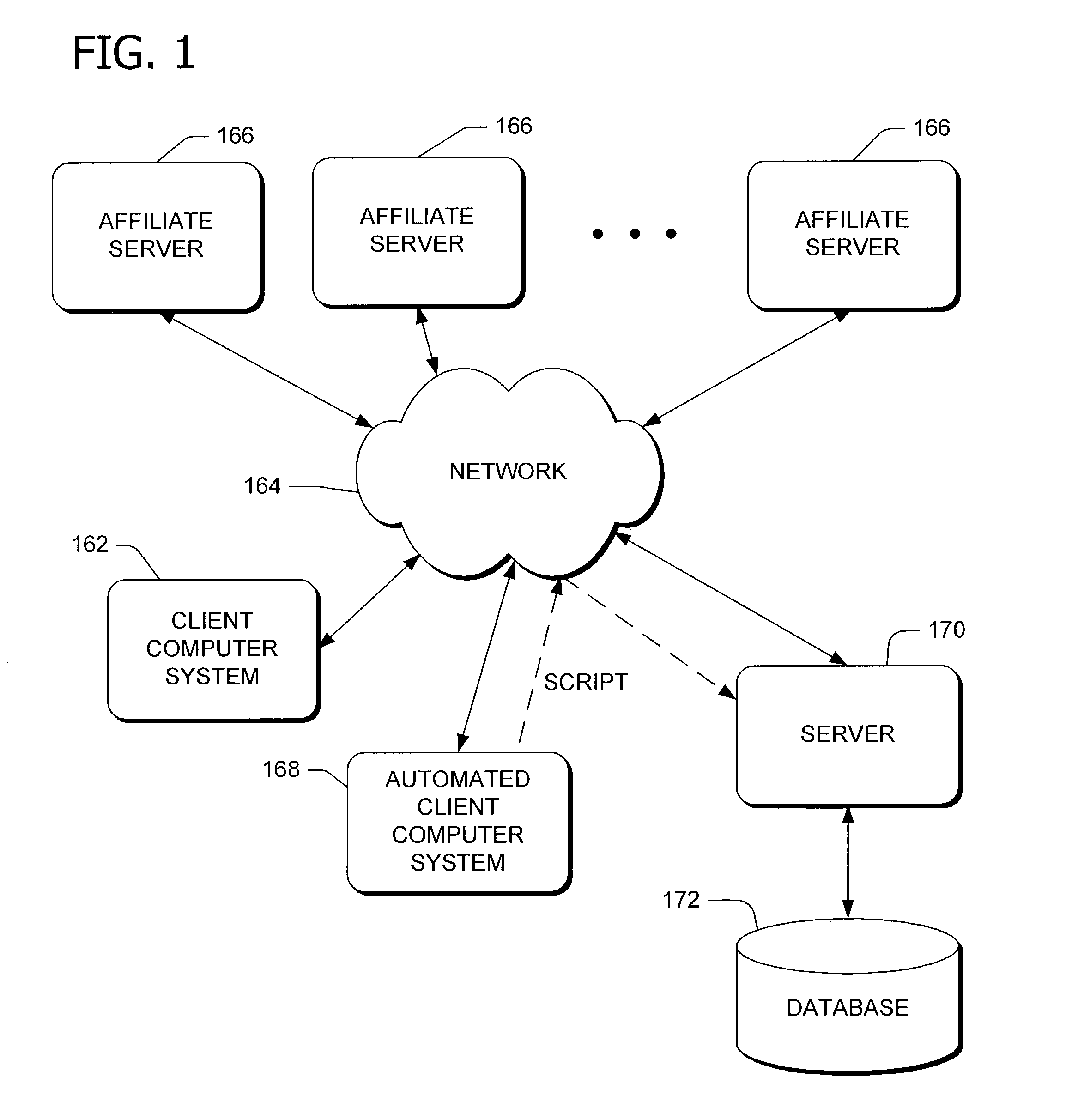
Method and apparatus for resource allocation when schedule changes are incorporated in real time
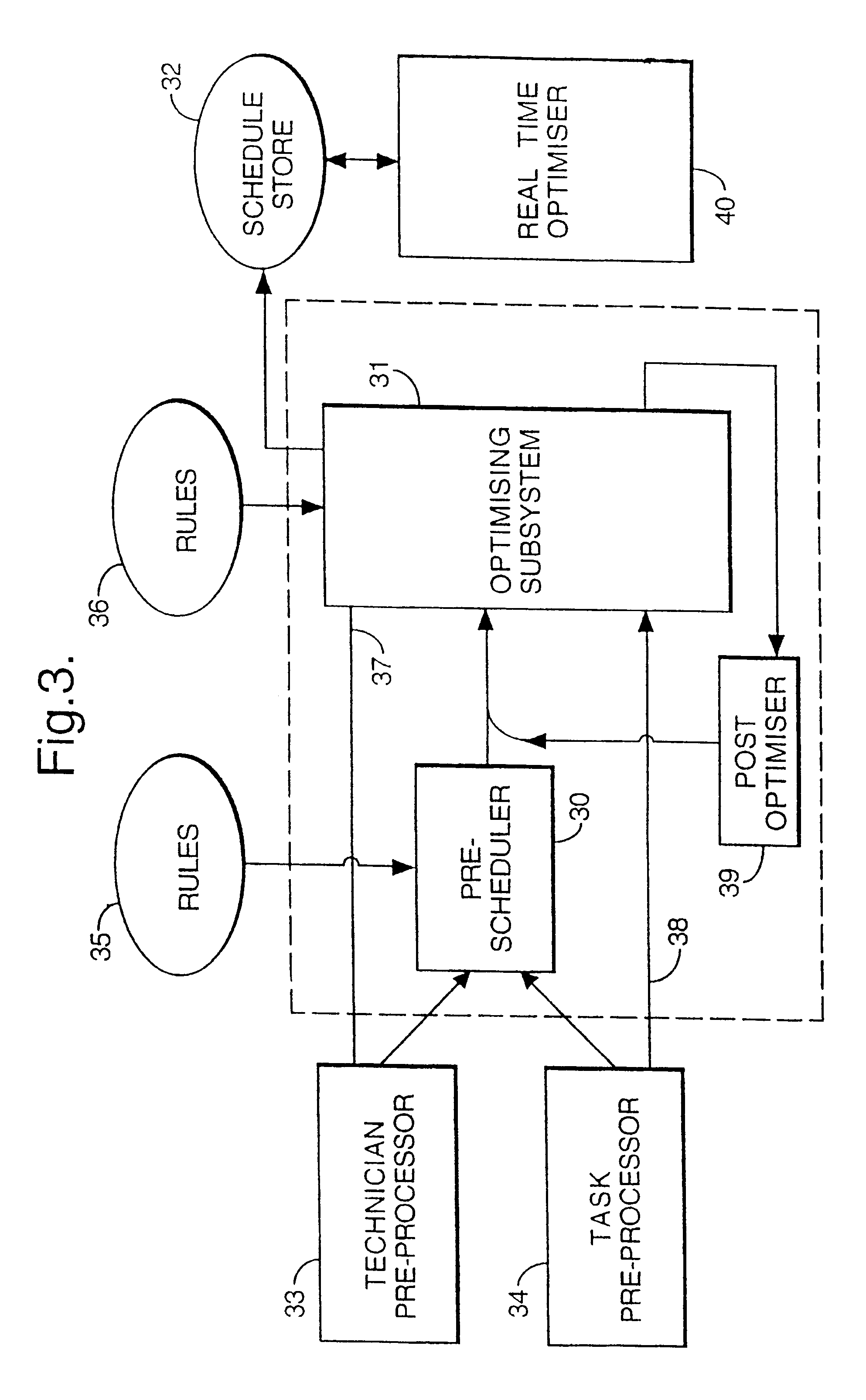
InactiveUS6578005B1Improve distributionEasy to solveResourcesSpecial data processing applicationsTime scheduleRule-based system
A plurality of resources, typically service operatives, are allocated to a plurality of tasks by a method in which initial information relating to the tasks to be allocated and the resources available to perform the tasks is provided. An initial series of schedules is first generated allocating resources to the tasks, and then modifying the individual schedule of at least one resource in response to updated information. Changes to individual schedules may be made in response to such updated information independently of the schedule generation. The initial, series of schedules may be generated in a two-stage process in which a rule-based system allocates tasks selected as being difficult to allocate (e.g., because they are linked to other tasks). then a stochastic (non-systematic) search system compiles the rest of the schedule. Periodically, the stochastic system may be interrupted to allow a further rule-based system to analyze the schedules created thus far, and fix the best ones in the schedule, so that the stochastic system can then concentrate on improving the remaining schedules. In order to allow the system to handle rapid changes in the requirements for tasks and the resources, on a scale faster than the time required to generate the schedules, a schedule modification system is arranged to make changes in the short term in between schedule updates delivered by the schedule generation system.
Owner:TRIMBLE MRM
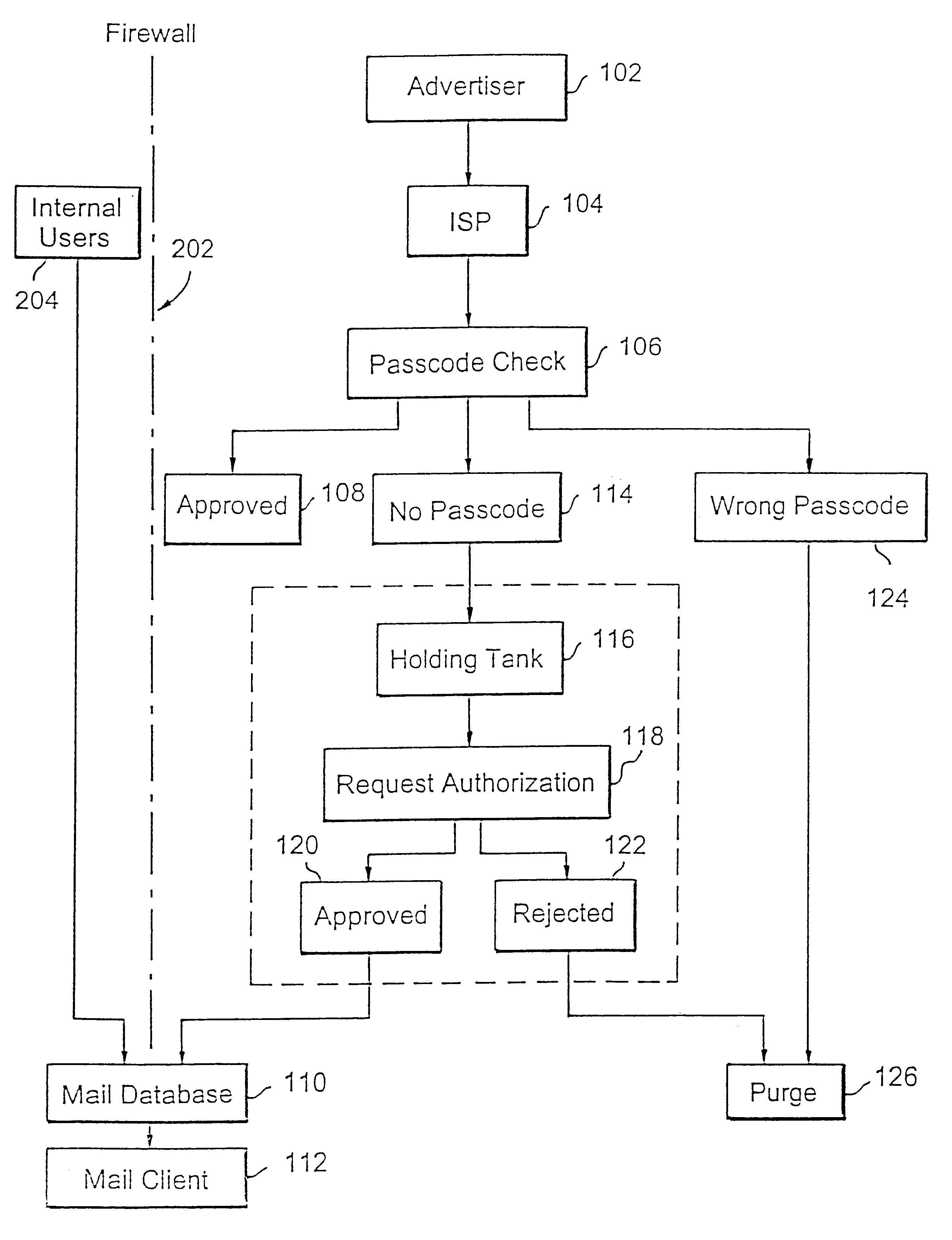
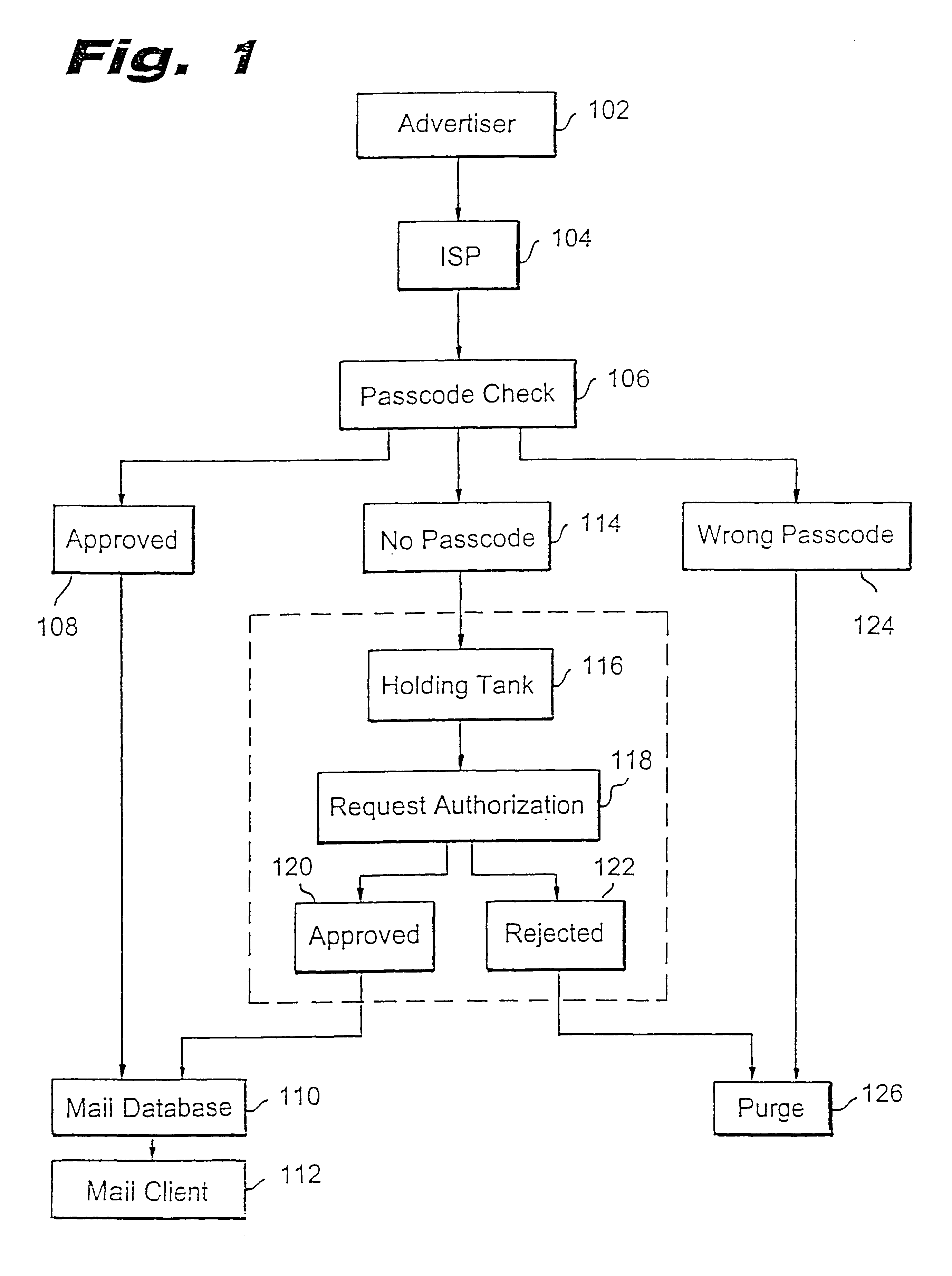
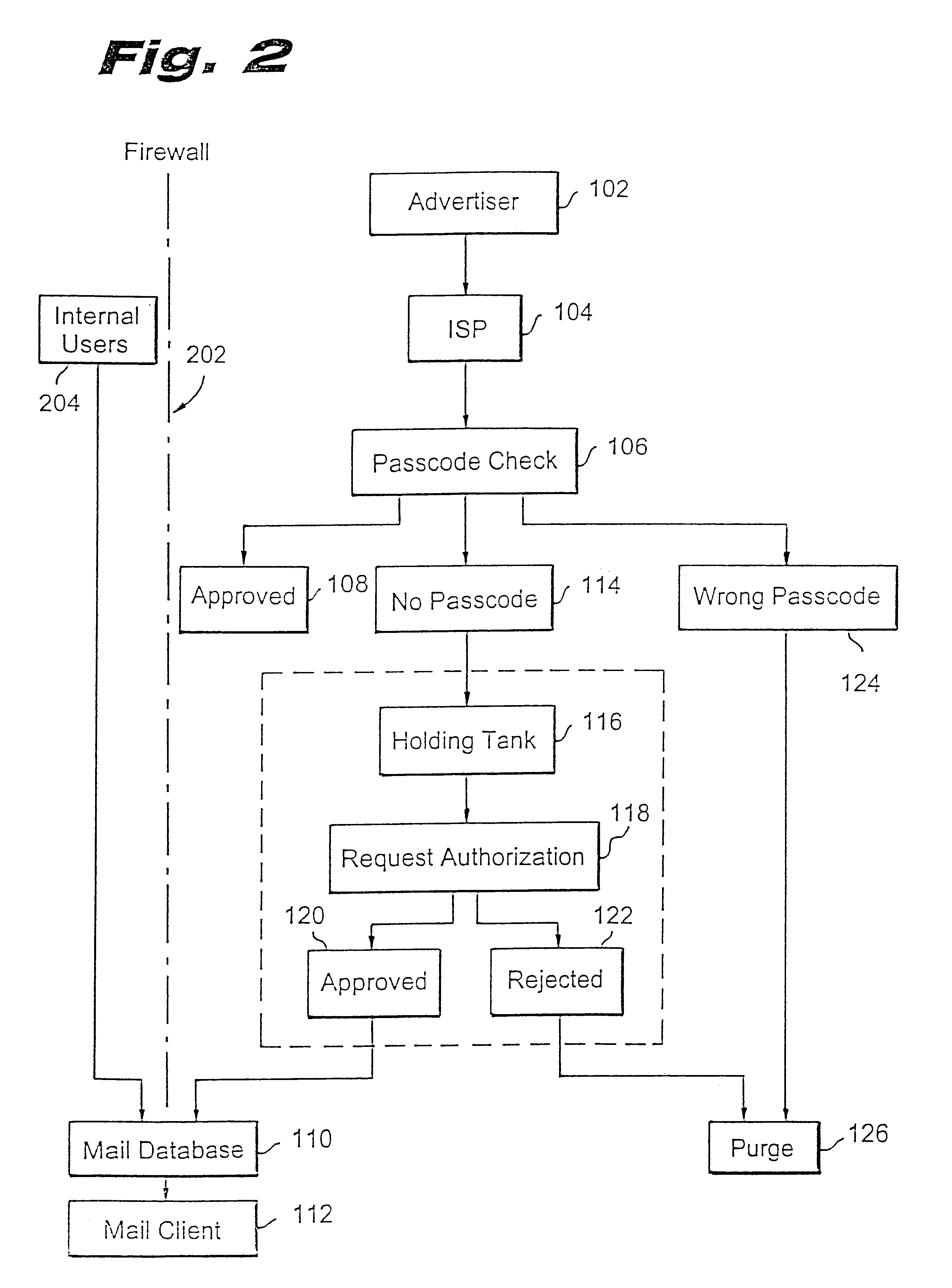
Method for blocking all unwanted e-mail (SPAM) using a header-based password
InactiveUS6266692B1Easy to sendEasy to solveOffice automationData switching networksEmail addressPassword
A method for blocking and / or filtering electronic mail. Selected senders are provided with a valid passcode associated with an e-mail address. When an e-mail is received at a mail server node, a field in a header of the e-mail is checked for a valid passcode associated with the destination e-mail address. If a valid passcode is detected, the e-mail is automatically sent to a receiver at the e-mail address. If an incorrect passcode is detected, the e-mail is automatically deleted at the server node and does not reach the receiver. If there is no passcode in the e-mail header, the e-mail is held temporarily, until the receiver approves to receive the e-mail. If the receiver rejects the e-mail, the e-mail is deleted. The present invention includes an additional capability for the senders of e-mails to request a passcode associated with a specific e-mail address in a lookup directory, before sending an e-mail to that address. Furthermore, the present invention enables firewall servers to block incoming e-mails only if they are received from the public Internet, thereby allowing all internal e-mails to reach the receiver without having to include valid passcodes.
Owner:TREND MICRO INC
Packet Sampling Flow-Based Detection of Network Intrusions
InactiveUS20050210533A1Accurate and reliable methodEnhanced wide-area IDS solutionMemory loss protectionDigital data processing detailsTraffic volumeClient-side
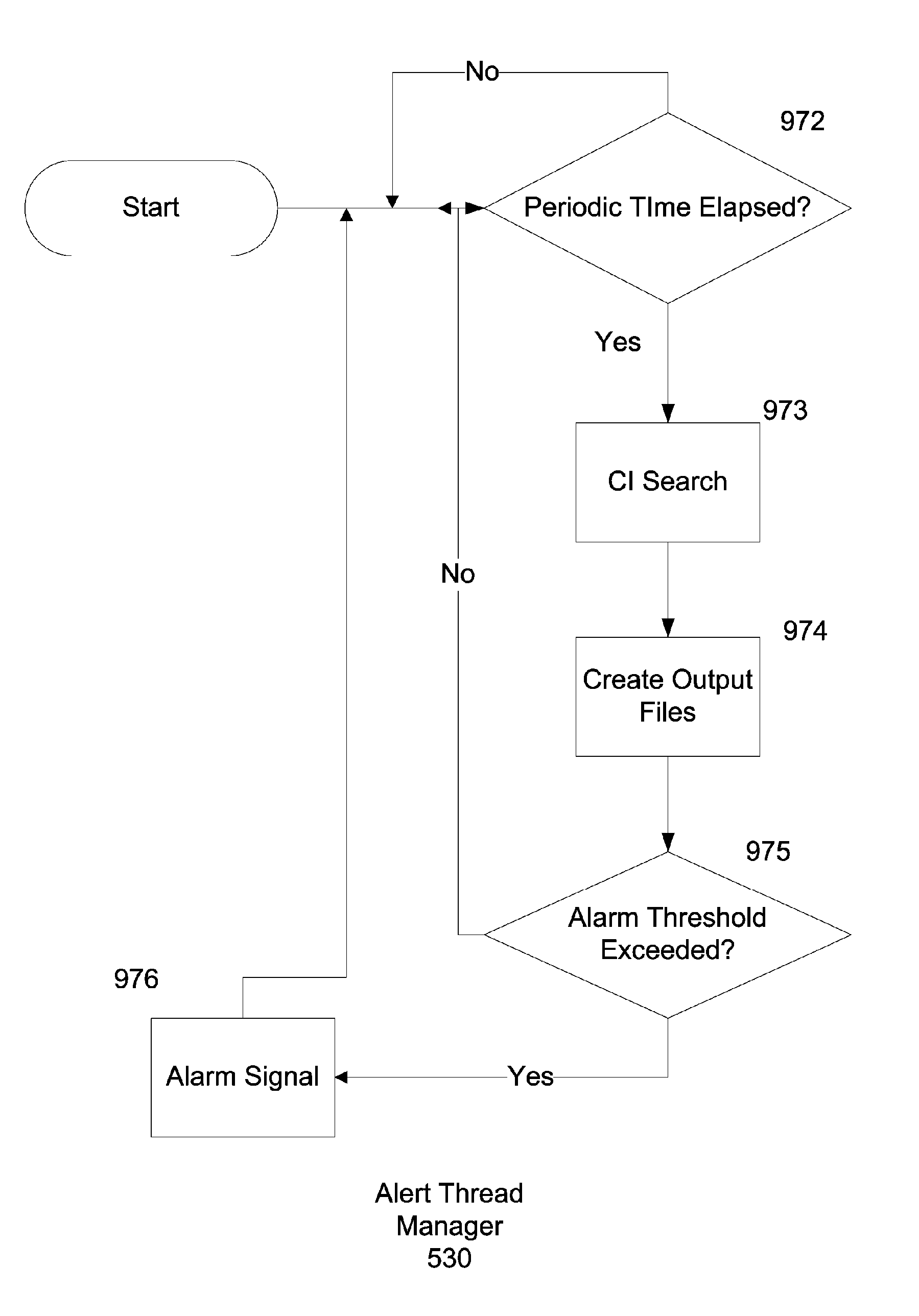
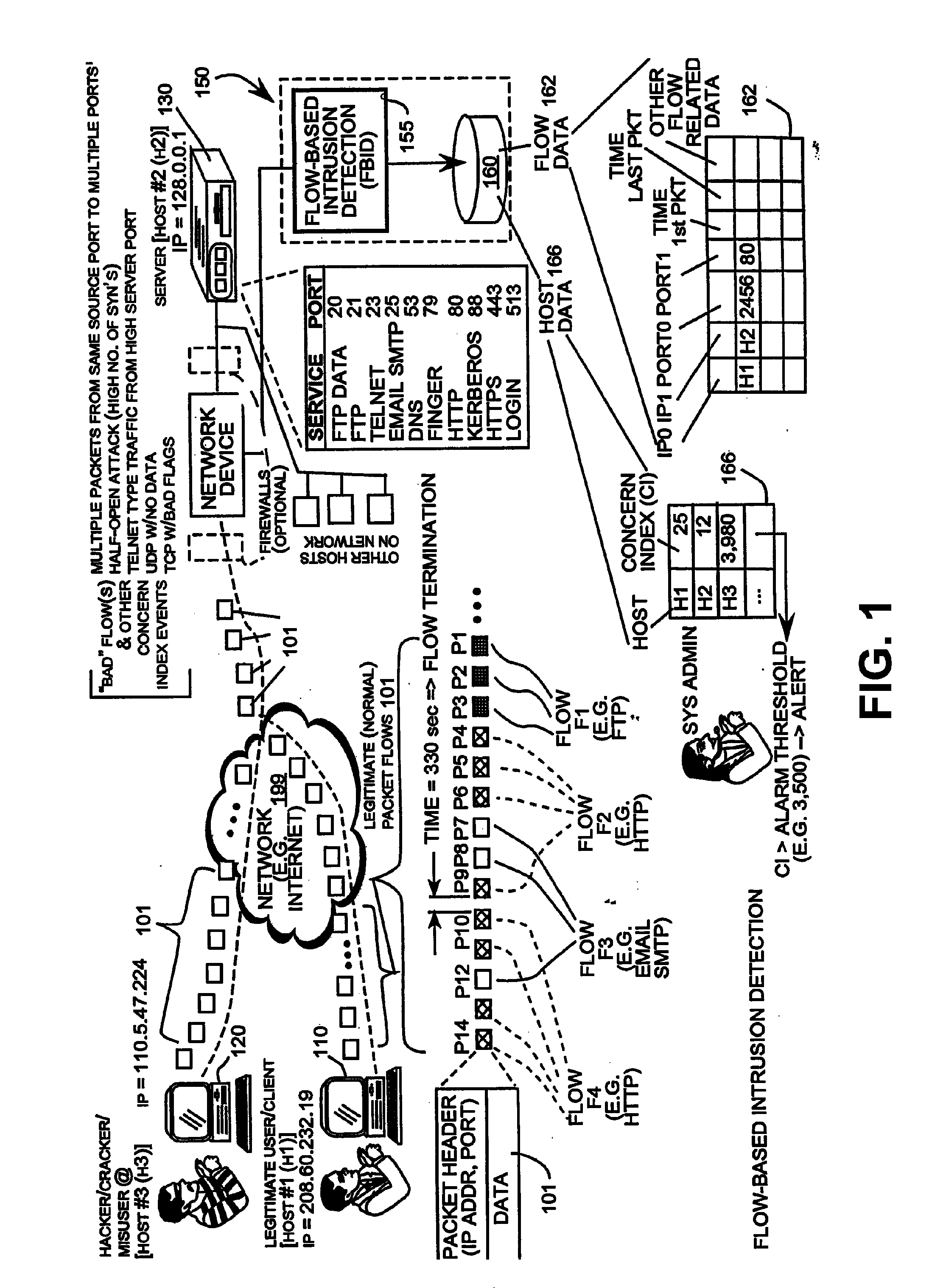
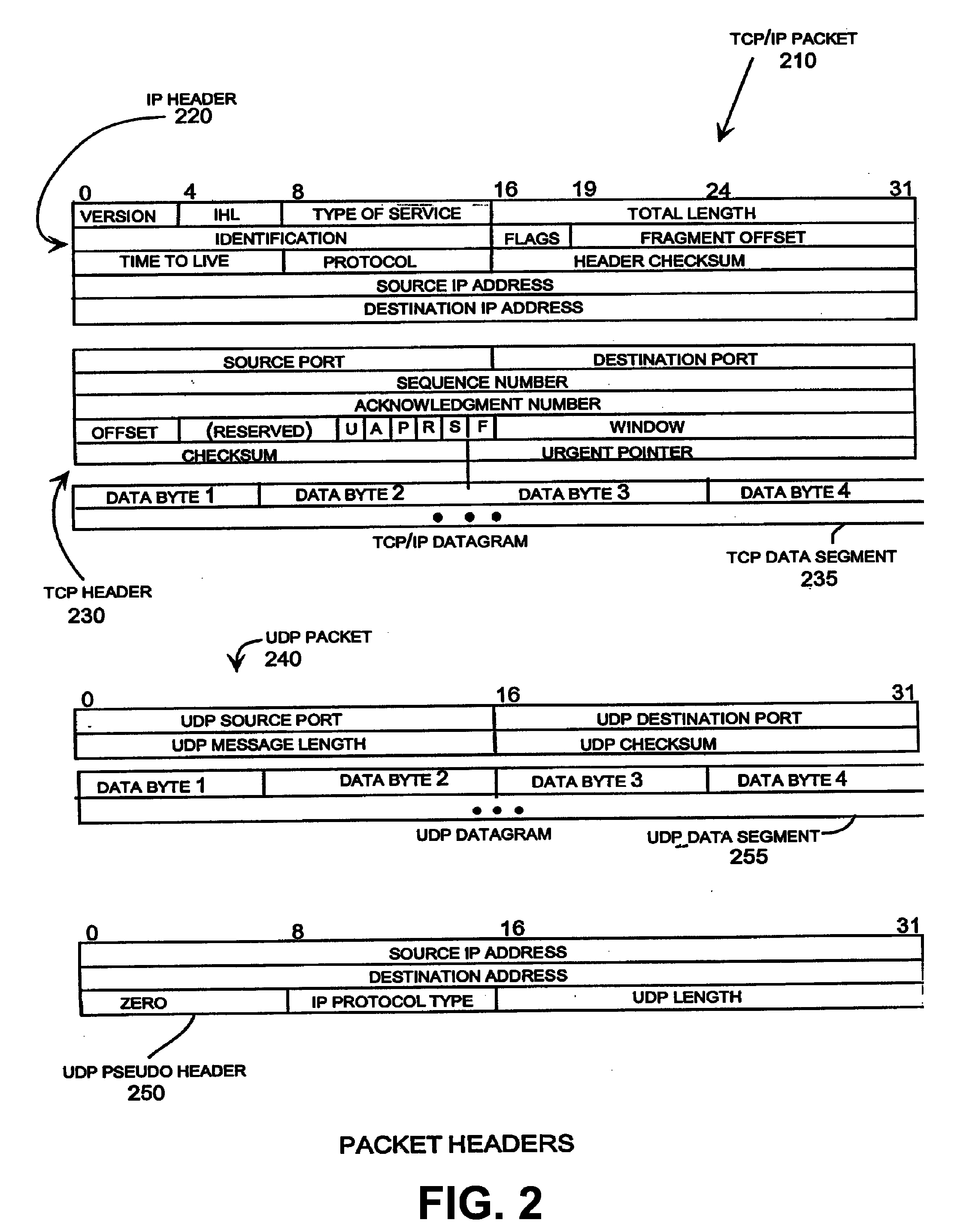
A flow-based intrusion detection system for detecting intrusions in computer communication networks. Data packets representing communications between hosts in a computer-to-computer communication network are processed and assigned to various client / server flows. Statistics are collected for each flow. Then, the flow statistics are analyzed to determine if the flow appears to be legitimate traffic or possible suspicious activity. A concern index value is assigned to each flow that appears suspicious. By assigning a value to each flow that appears suspicious and adding that value to the total concern index of the responsible host, it is possible to identify hosts that are engaged in intrusion activity. When the concern index value of a host exceeds a preset alarm value, an alert is issued and appropriate action can be taken.
Owner:CISCO TECH INC
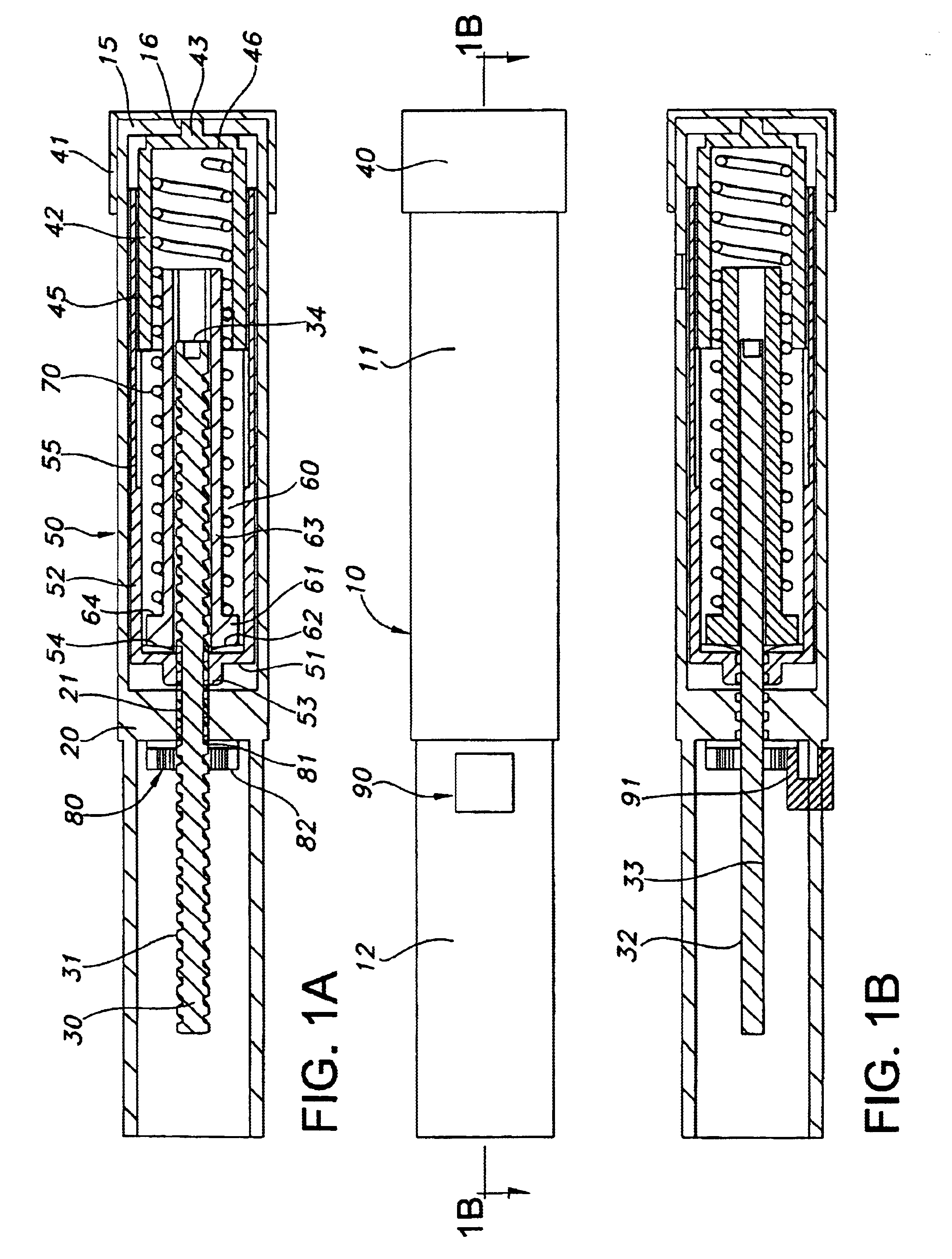
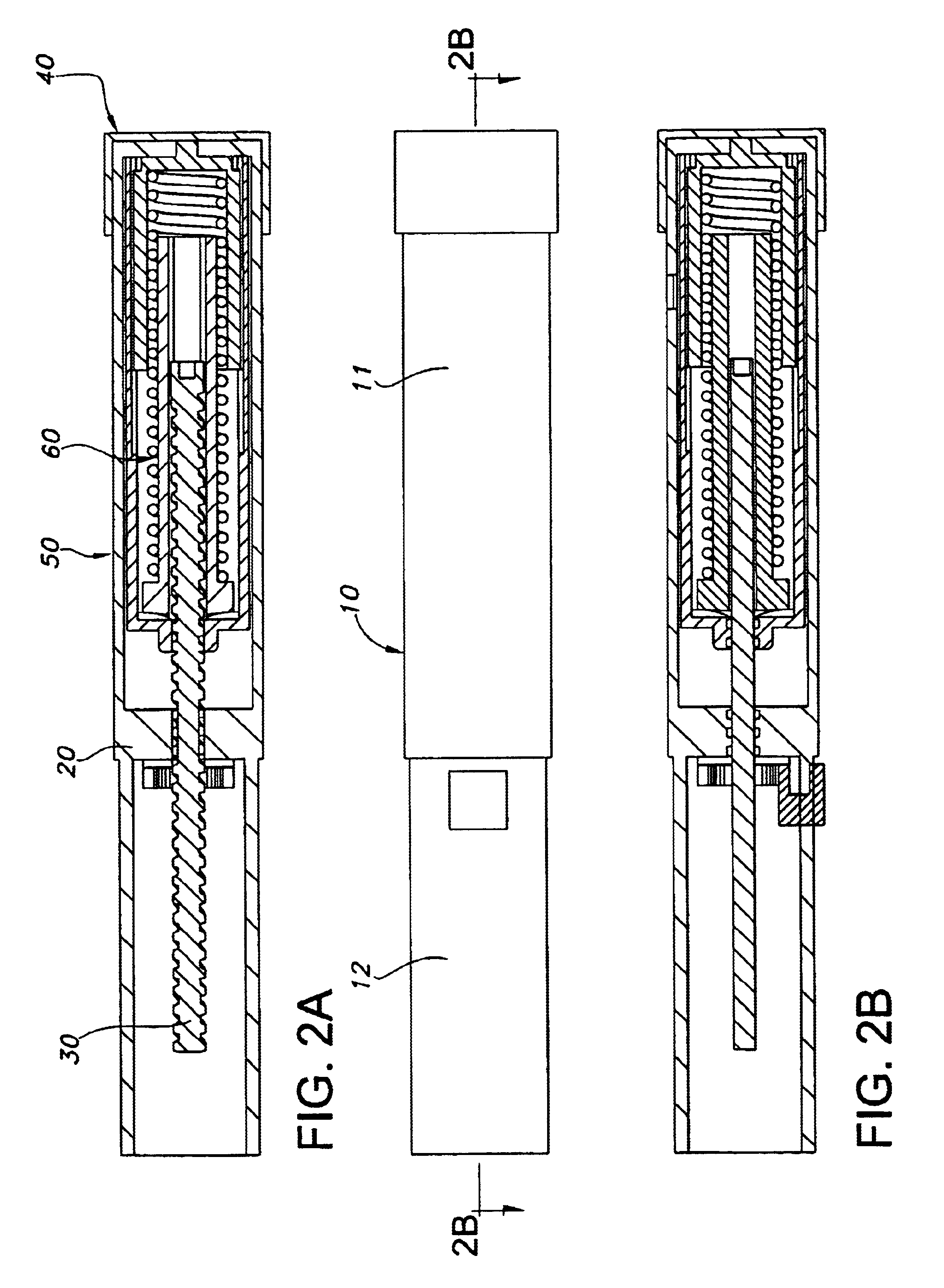
Automatic injection device with reset feature
InactiveUS6899699B2Solve the lack of resistanceEasy to solveAmpoule syringesAutomatic syringesInjection deviceBiomedical engineering
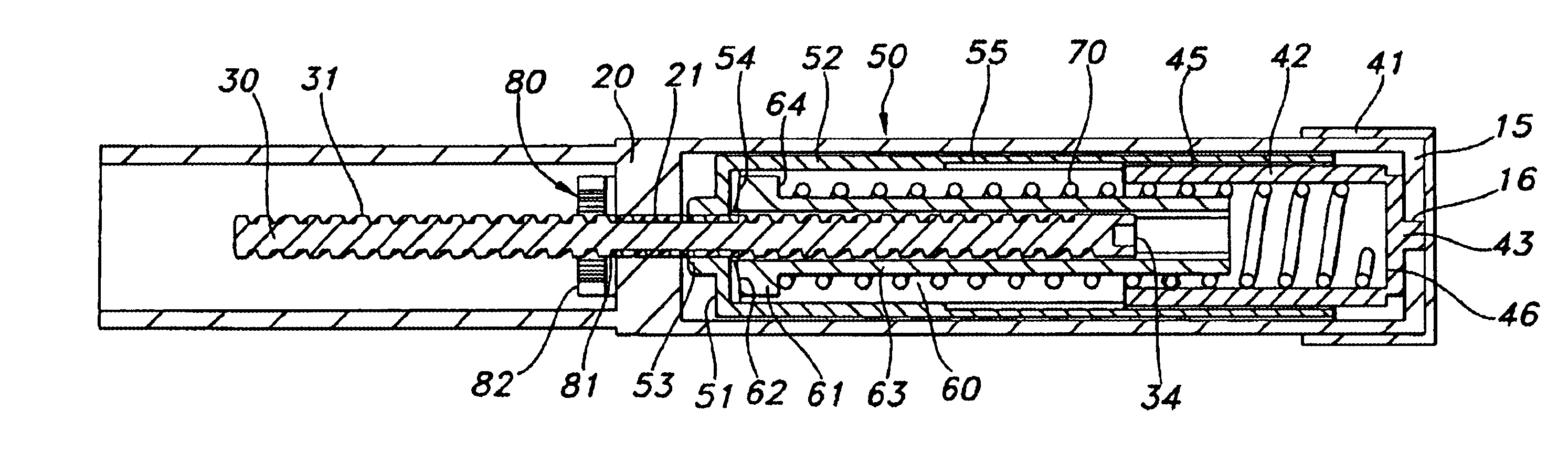
The present invention relates to a dose setting and expelling device comprising a drive member and a dose setting mechanism which simultaneously sets a given dose and stores the energy necessary for a subsequently driving the drive member in order to expel a dose of medicine from an injection device. According to the invention the dose setting mechanism allows adjustment in both directions, such that a given set dose can be reduced or cancelled by reversing the input motion, typically by rotating a setting member backwardly, this in contrast to the known devices which either requires an additional release mechanism or which cannot be reversed at all.
Owner:NOVO NORDISK AS
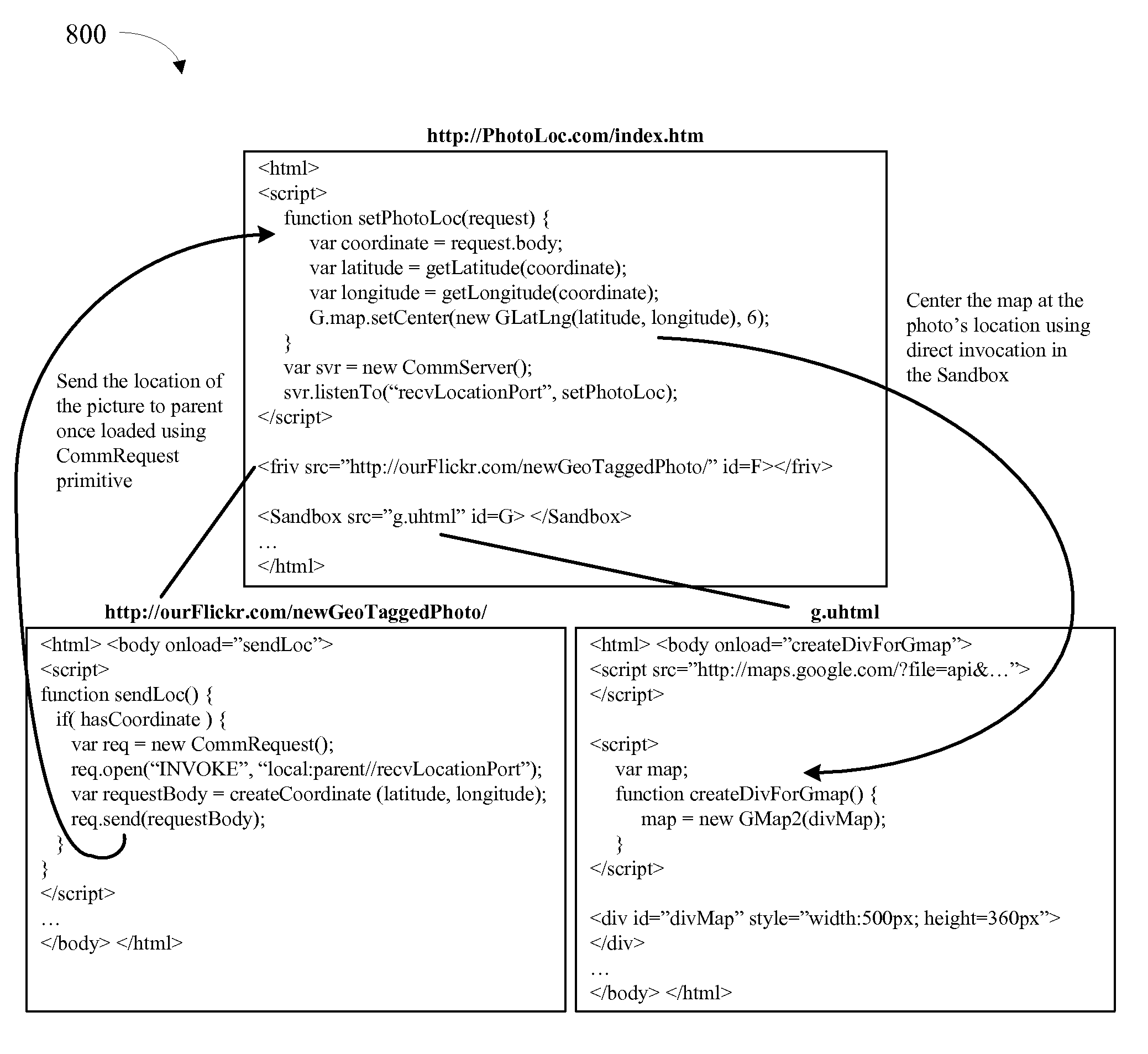
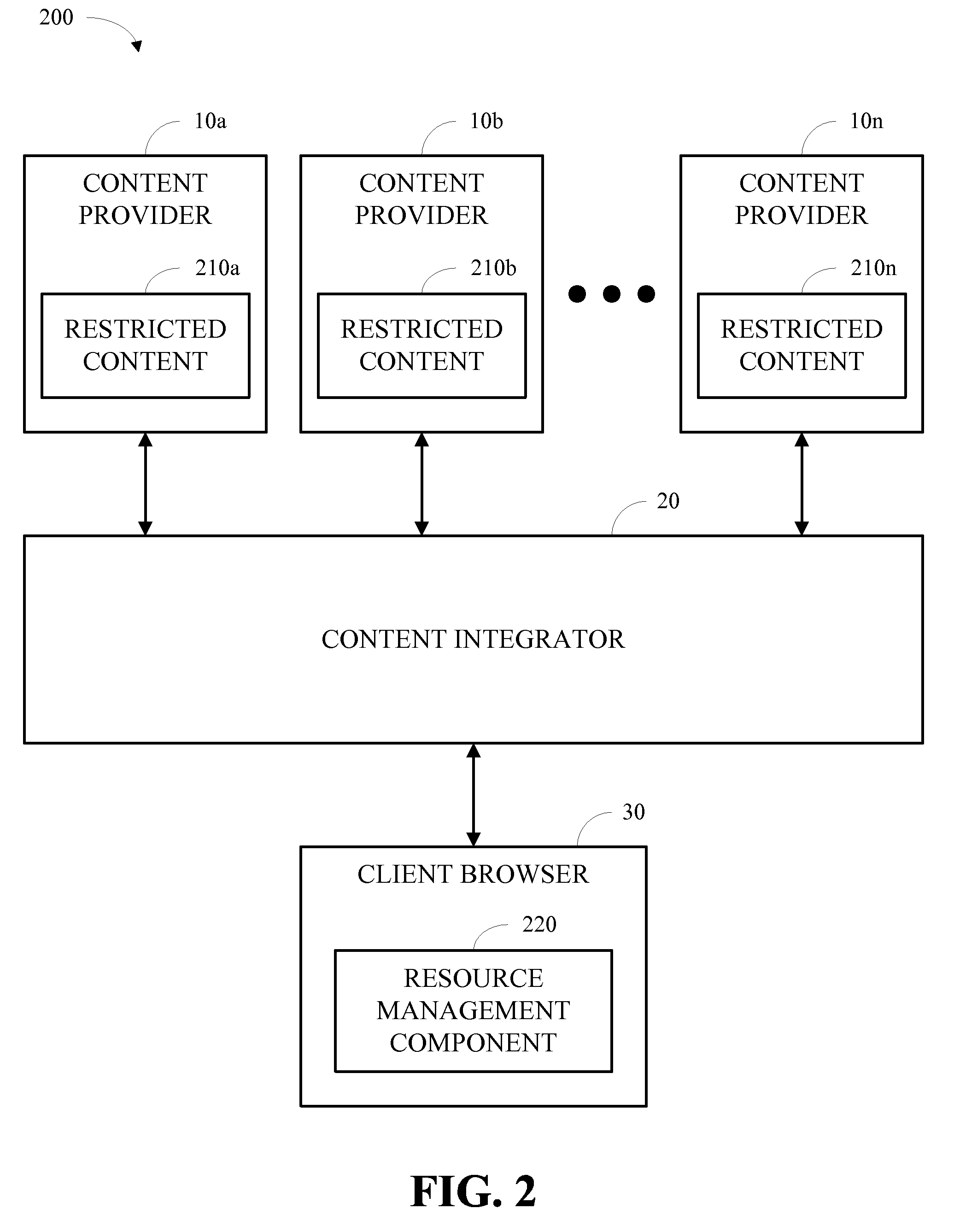
Protection and communication abstractions for web browsers
ActiveUS20080313648A1Facilitate asymmetric level of trustAvoid attackPlatform integrity maintainanceTransmissionWeb browserResource management
Systems and methodologies for accessing resources associated with a Web-based application in accordance with one or more embodiments disclosed herein may include a browser that obtains at least first resources from a first domain and second resources from a second domain and a resource management component that facilitates controlled communication between the first resources and the second resources and prevents the first resources and the second resources from accessing other resources that the first resources and the second resources are not permitted to access. The resource management component may be further operable to contain restricted services in a sandbox containment structure and / or to isolate access-controlled resources in a service instance. In addition, the resource management component may be operable to facilitate the flexible display of resources from disparate domains and / or controlled communication therebetween.
Owner:MICROSOFT TECH LICENSING LLC
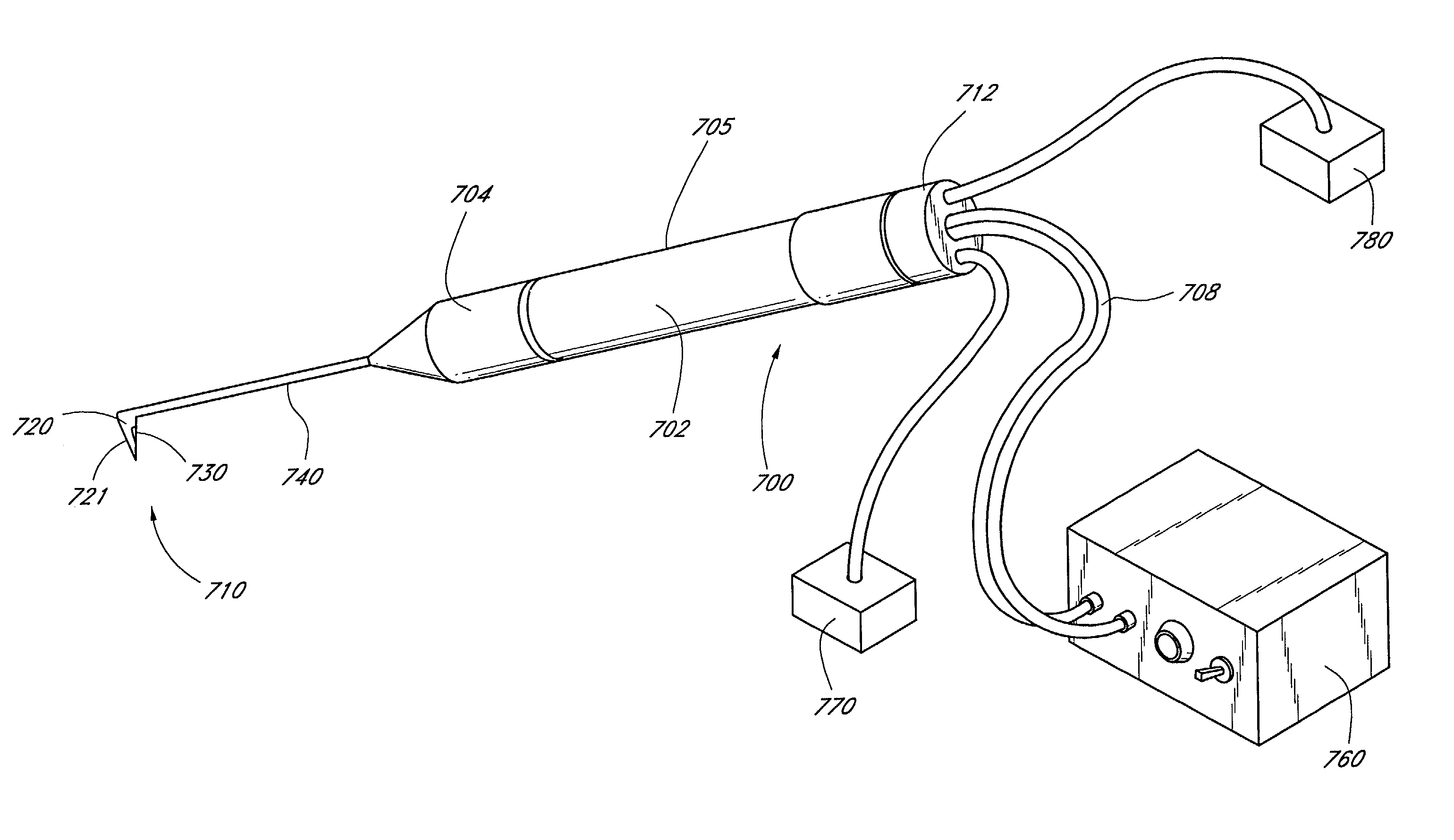
Minimally invasive glaucoma surgical instrument and method
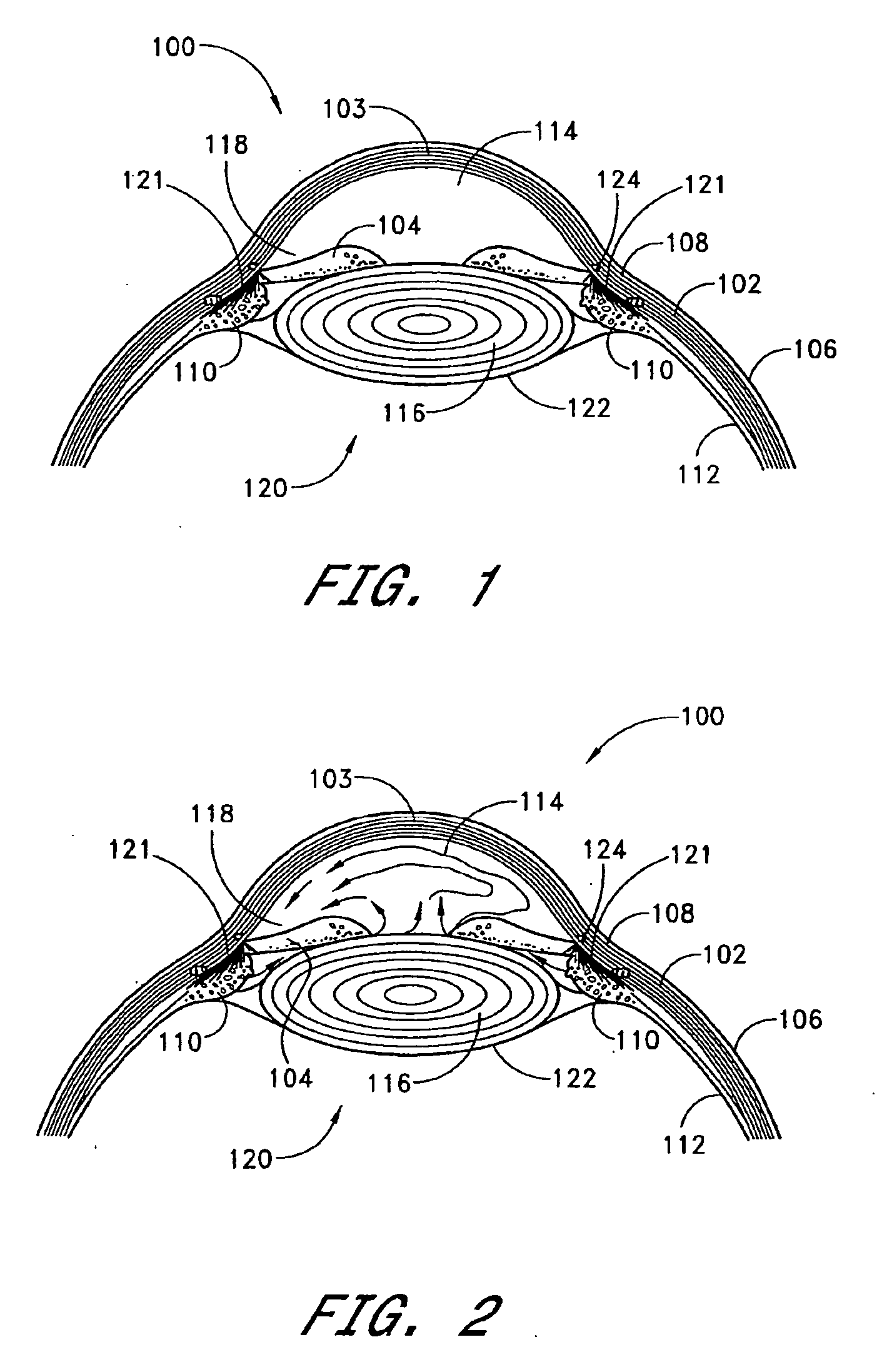
InactiveUS6979328B2Easy to solveEasy accessSurgical needlesDiagnostic recording/measuringSchlemm's canalSurgical instrumentation
A surgical instrument and methods for the treatment of glaucoma are provided. The instrument uses either cauterization, a laser to ablate, sonic or ultrasonic energy to emulsify, or mechanical cutting of a portion of the trabecular meshwork. The instrument may also be provided with irrigation, aspiration, and a footplate. The footplate is used to enter Schlemm's canal, serves as a guide, and also protects Schlemm's canal.
Owner:RGT UNIV OF CALIFORNIA
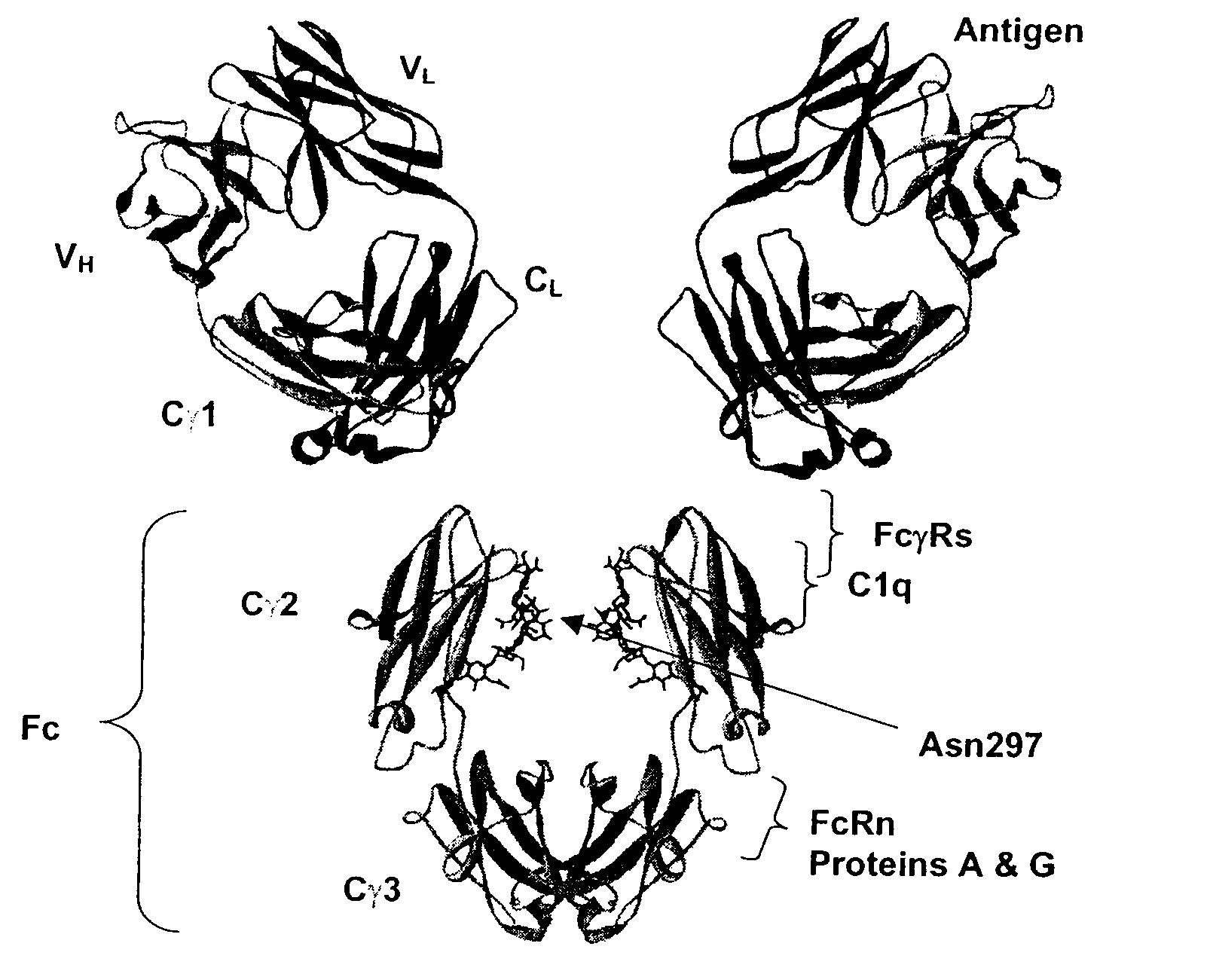
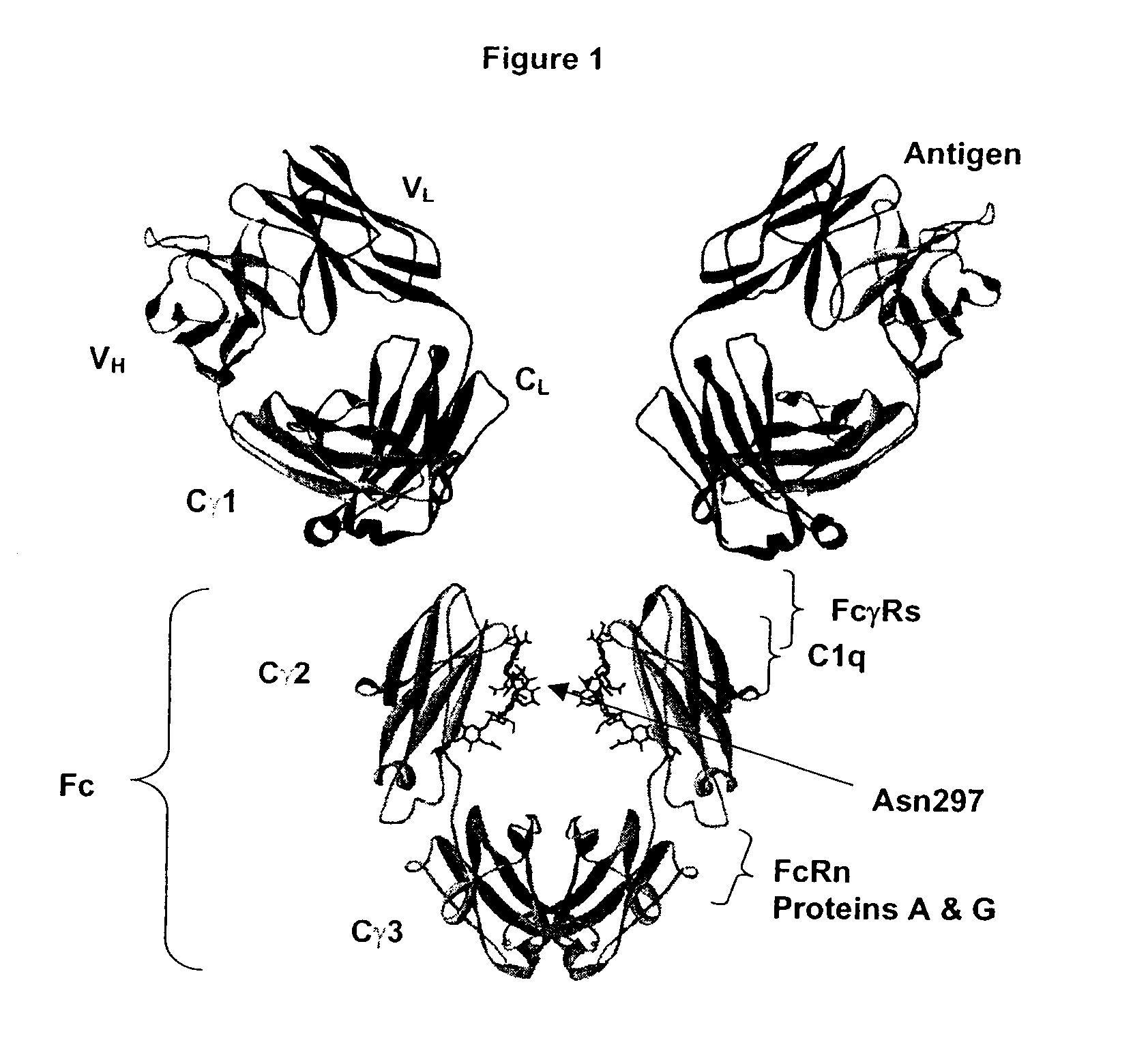
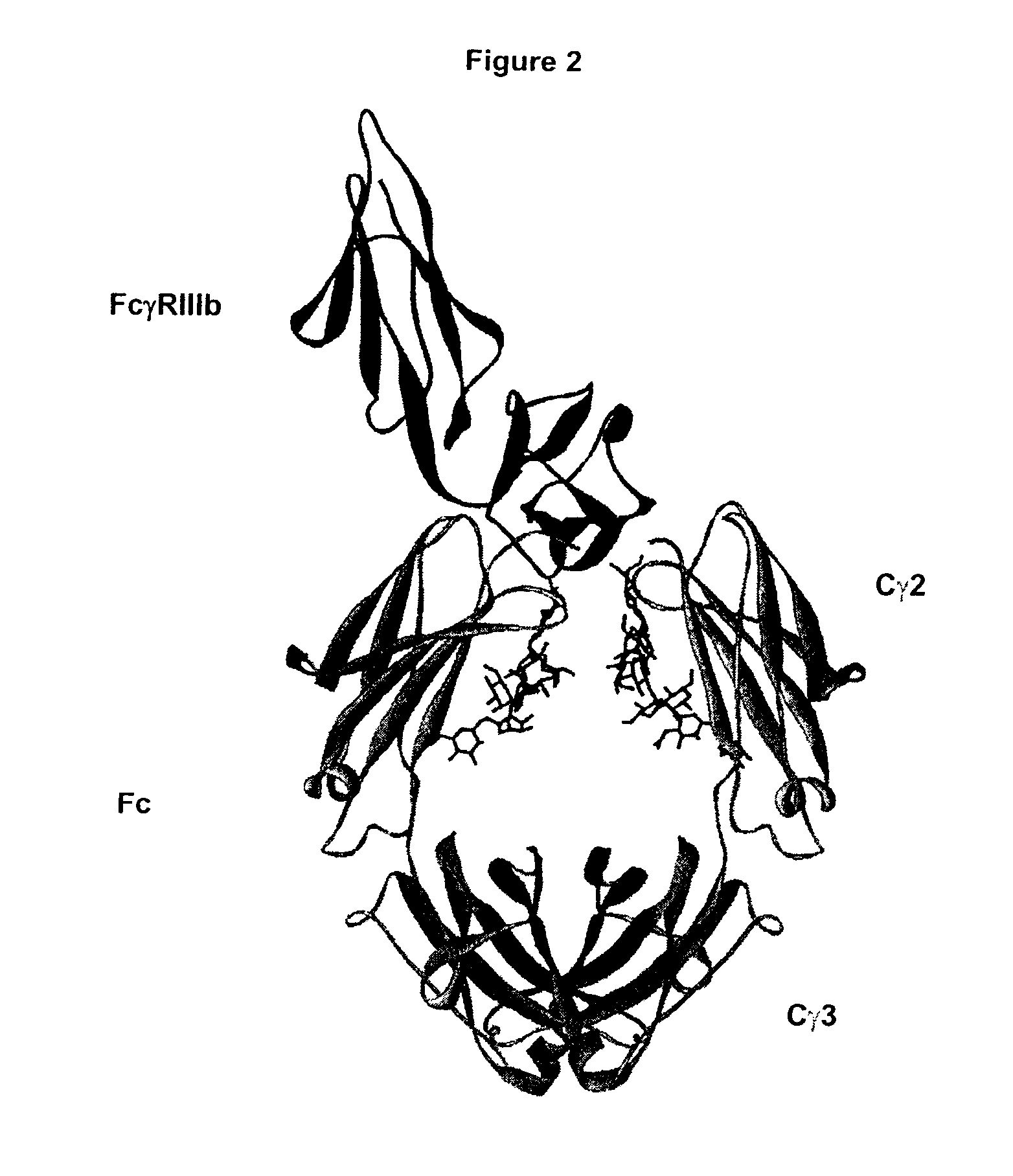
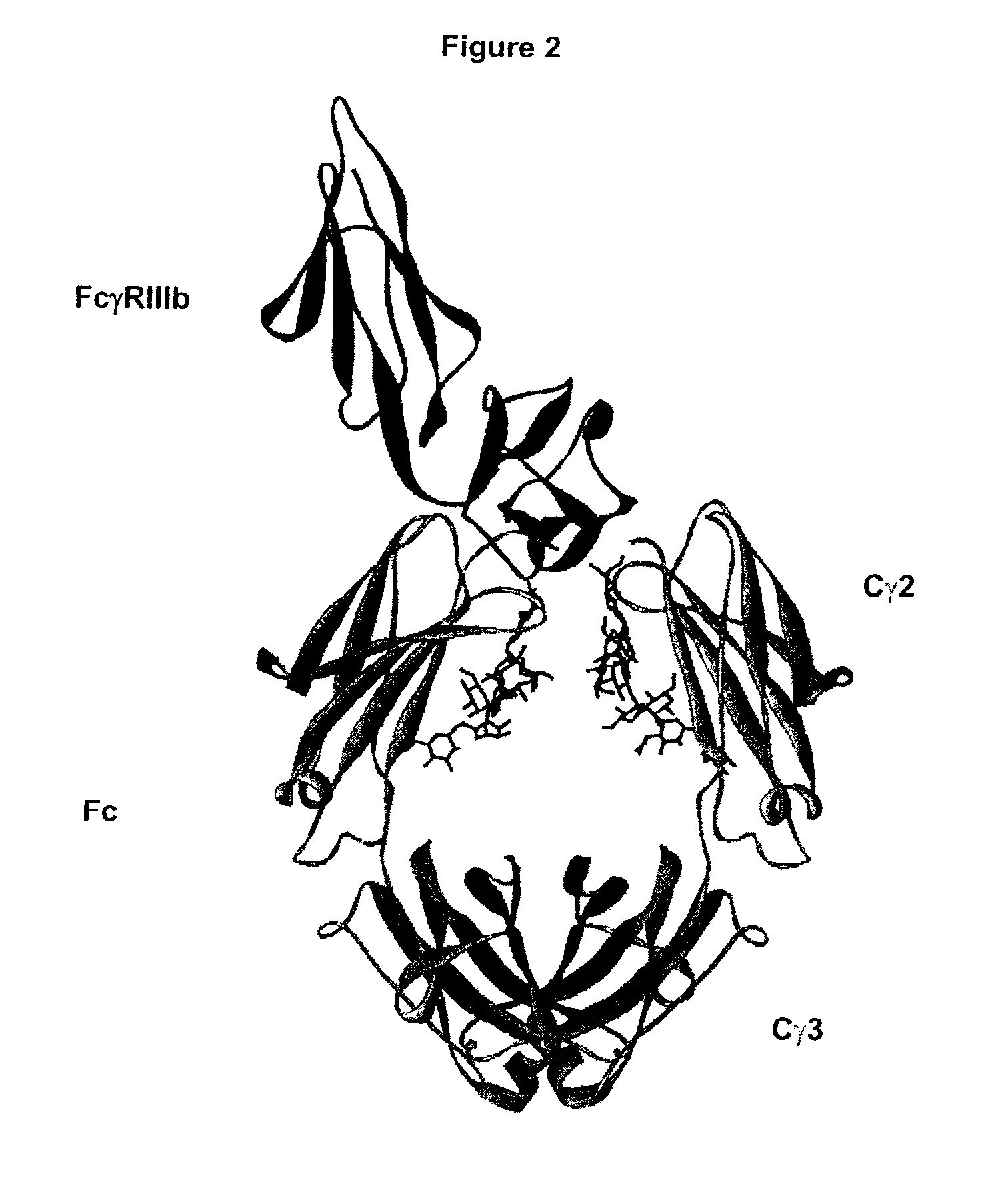
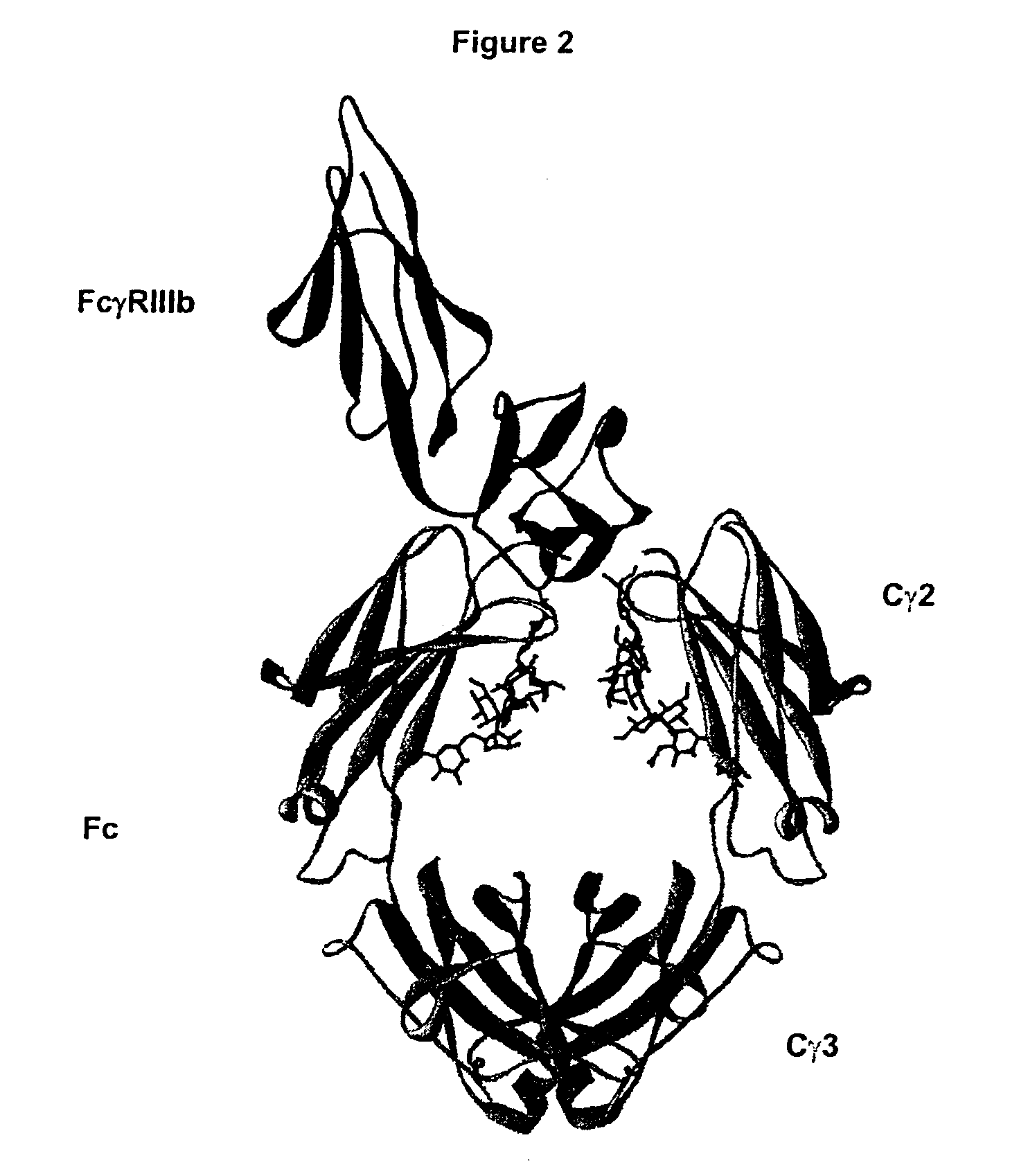
Fc Variants Having Increased Affinity for FcyRIIb
ActiveUS20070231329A1Weak affinityFunction increaseImmunoglobulins against cell receptors/antigens/surface-determinantsAntibody ingredientsChemistry
Owner:XENCOR
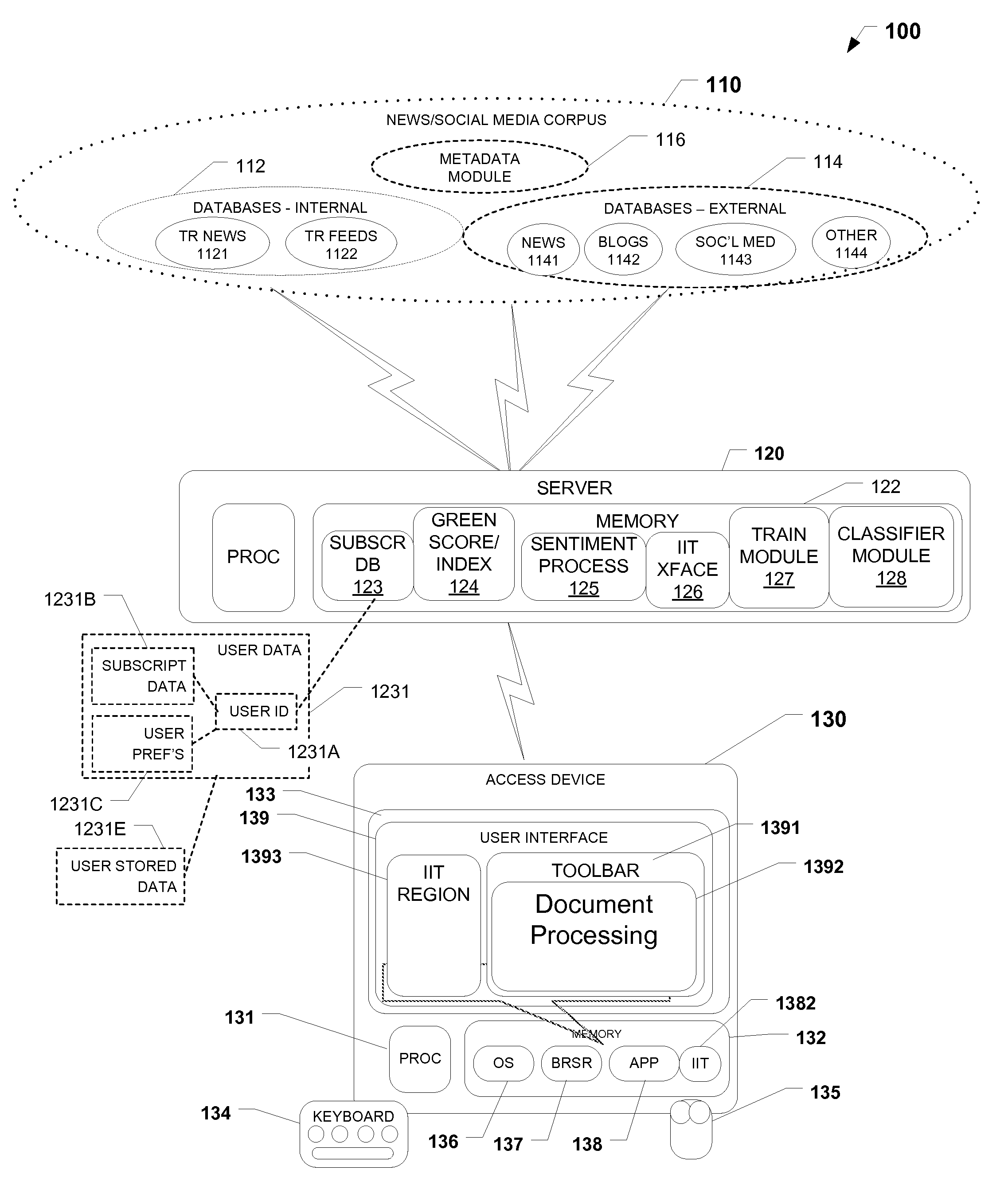
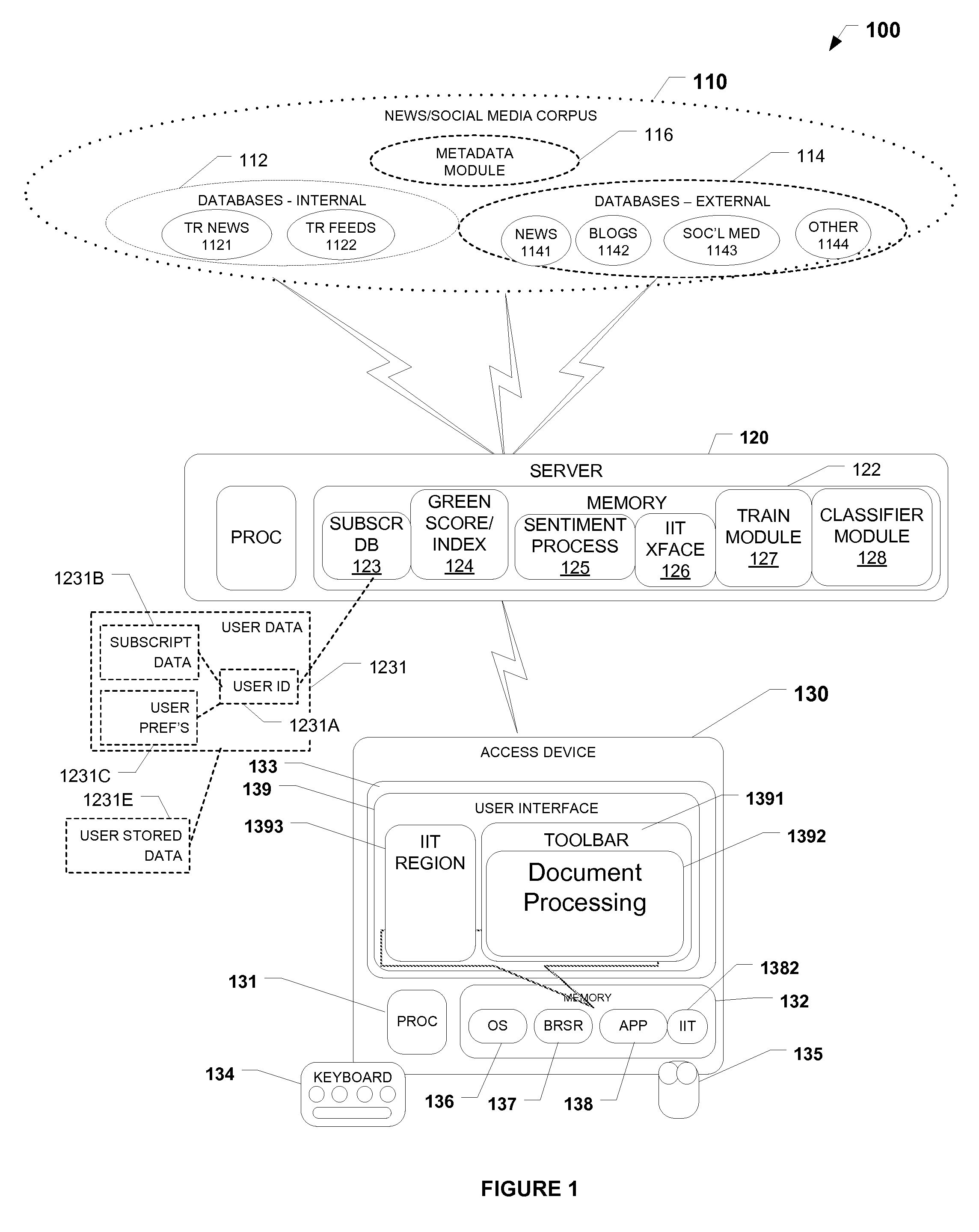
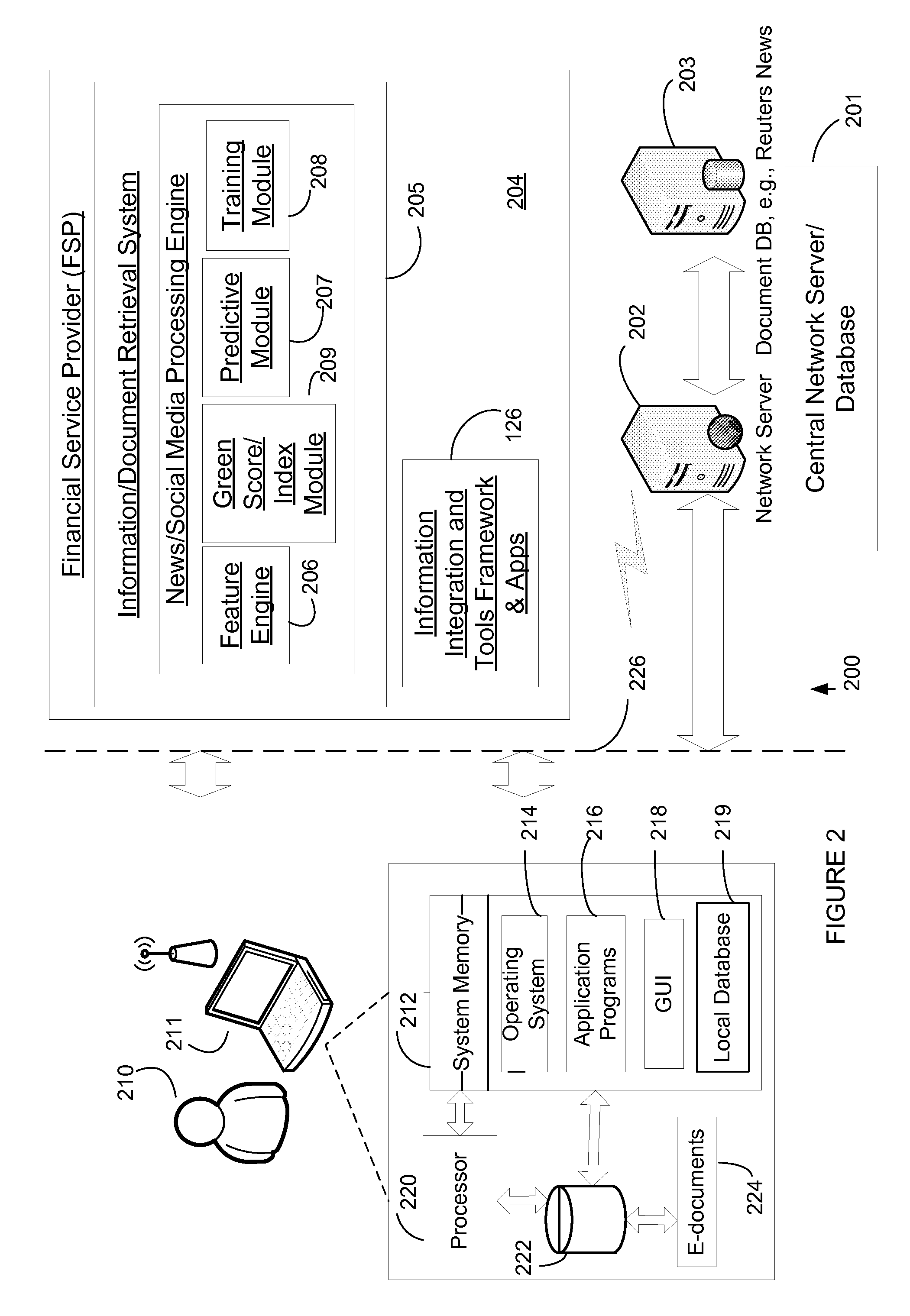
Methods and systems for generating composite index using social media sourced data and sentiment analysis
PendingUS20120296845A1Profound effectEnhance contentFinanceSemantic analysisFinancial securityData science
The present invention provides a News / Media Analytics System (NMAS) adapted to automatically process and “read” news stories and content from blogs, twitter, and other social media sources, represented by news / media corpus, in as close to real-time as possible. Quantitative analysis, techniques or mathematics, such as green scoring / composite module and sentiment processing module are processed to arrive at green scores, green certification, and / or model the value of financial securities, including generating a composite environmental or green index. The NMAS automatically processes news stories, filings, new / social media and other content and applies one or more models against the content to determine green scoring and / or anticipate behavior of stock price and other investment vehicles. The NMAS leverages traditional and, especially, social media resources to provide a sentiment-based solution that expands the scope of conventional tools for creating a socially aware composite index.
Owner:REFINITIV US ORG LLC
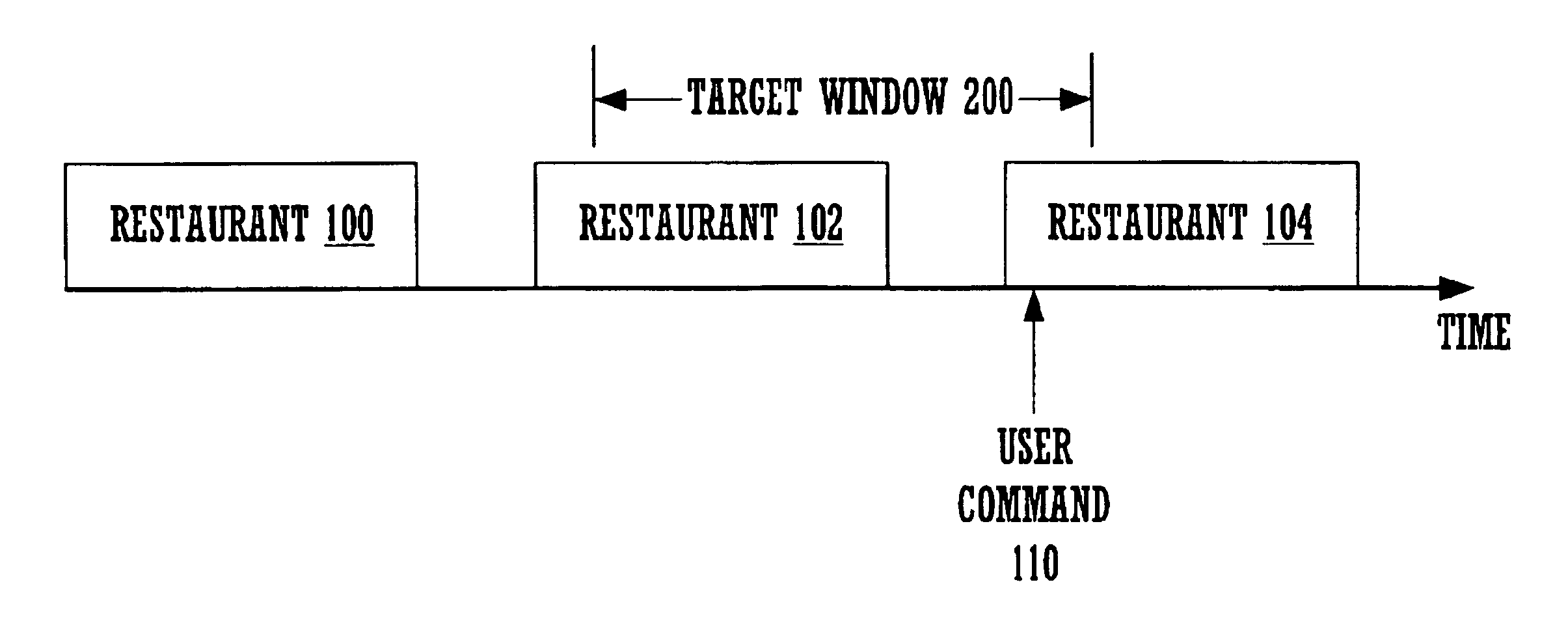
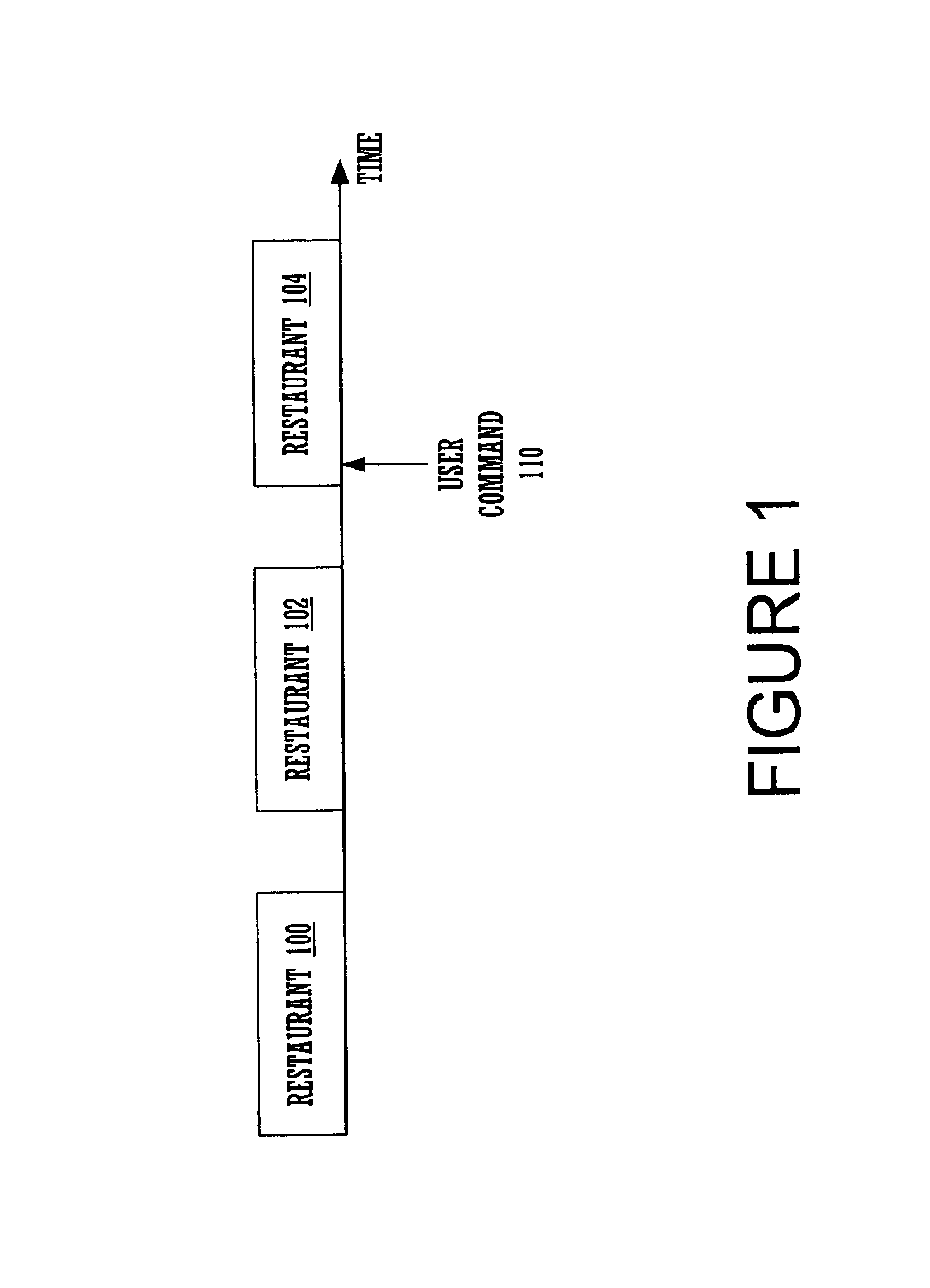
Handling of speech recognition in a declarative markup language
InactiveUS6941268B2Reliably and simply determiningEasy to solveAutomatic exchangesSpeech recognitionSpeech applicationsApplication software
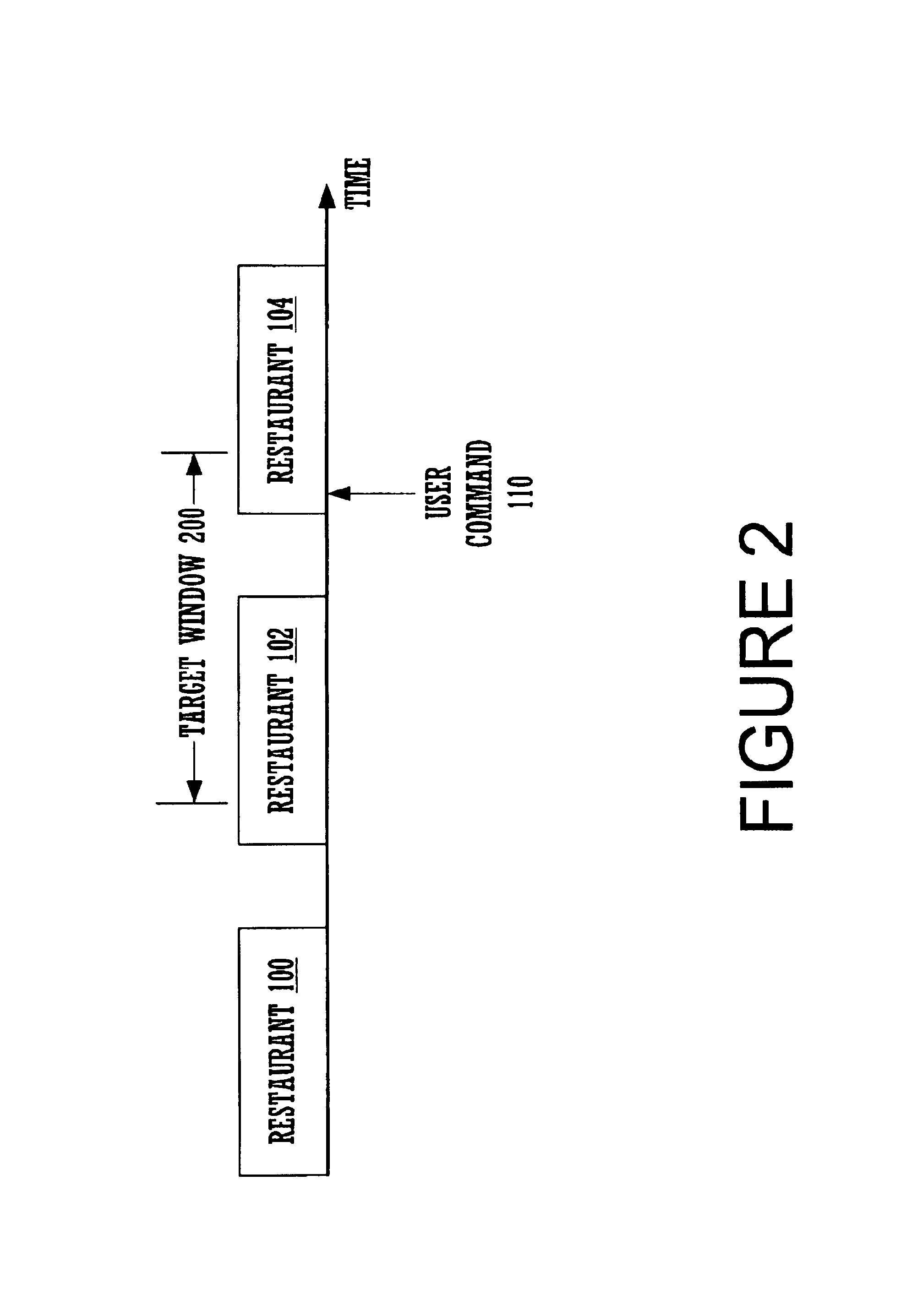
Declarative markup languages for speech applications such as VoiceXML are becoming more prevalent programming modalities for describing speech applications. Present declarative markup languages for speech applications model the running speech application as a state machine with the program specifying the transitions amongst the states. These languages can be extended to support a marker-semantic to more easily solve several problems that are otherwise not easily solved. In one embodiment, a partially overlapping target window is implemented using a mark semantic. Other uses include measurement of user listening time, detection and avoidance of errors, and better resumption of playback after a false barge in.
Owner:MICROSOFT TECH LICENSING LLC
Minimally invasive glaucoma surgical instrument and method
InactiveUS20060106370A1Easy accessEasy to solveLaser surgeryDiagnosticsSchlemm's canalMinimally invasive glaucoma surgery
Apparatuses and methods for the treatment of glaucoma are provided. The instrument uses either cauterization, a laser to ablate, sonic or ultrasonic energy to emulsify, or mechanical cutting of a portion of the trabecular meshwork. The instrument may also be provided with irrigation, aspiration, and a footplate. The footplate is used to enter Schlemm's canal, serves as a guide, and also protects Schlemm's canal.
Owner:RGT UNIV OF CALIFORNIA
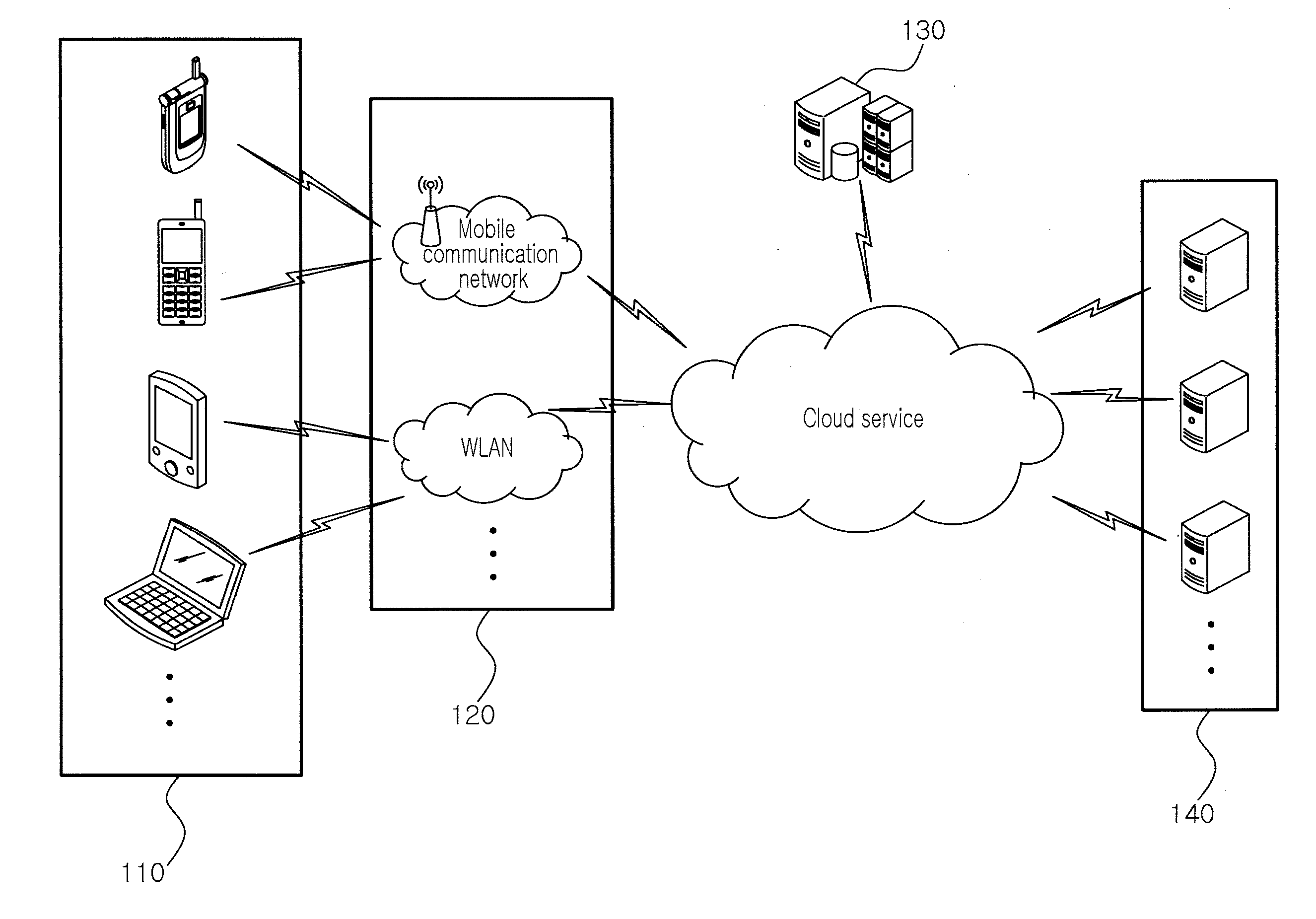
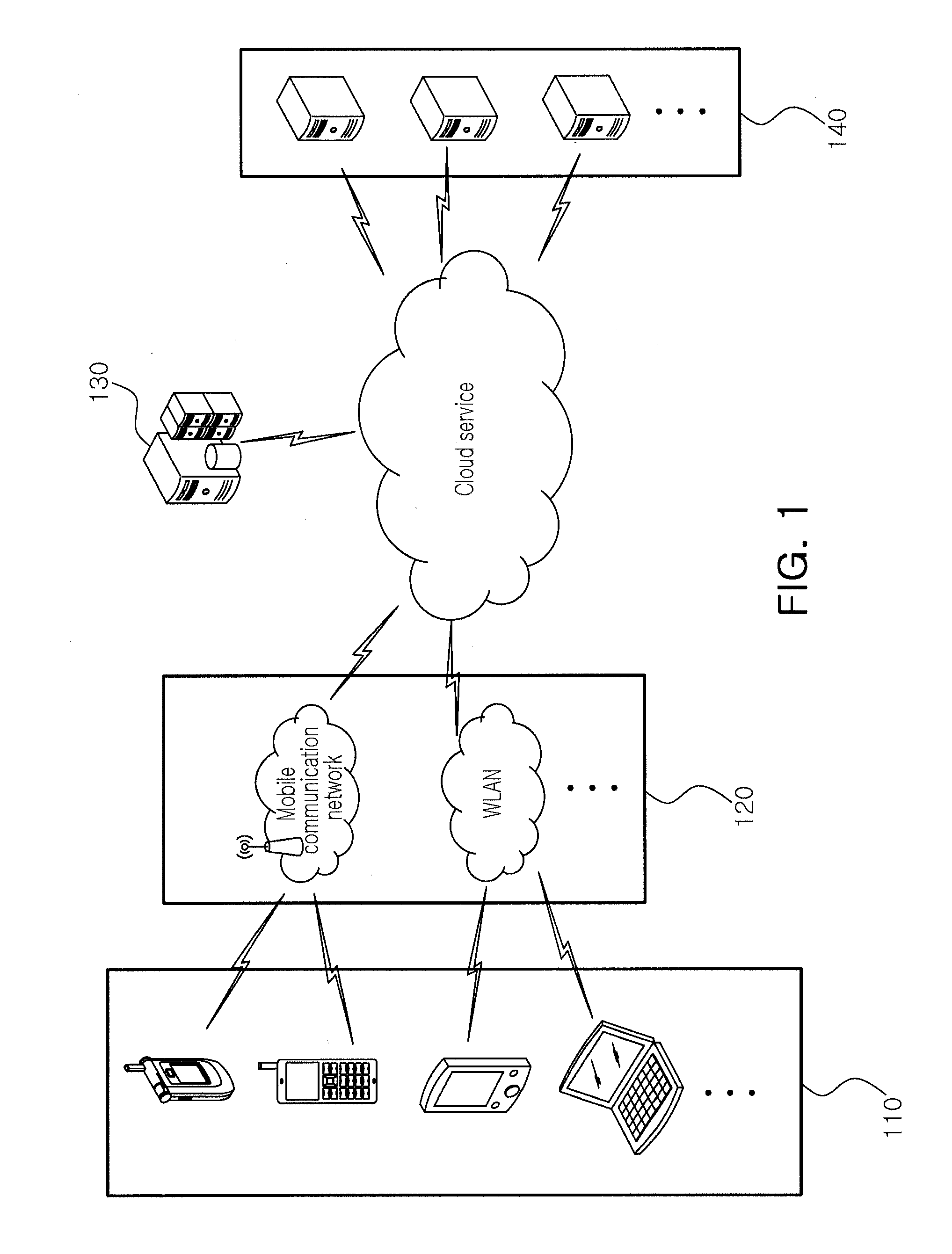
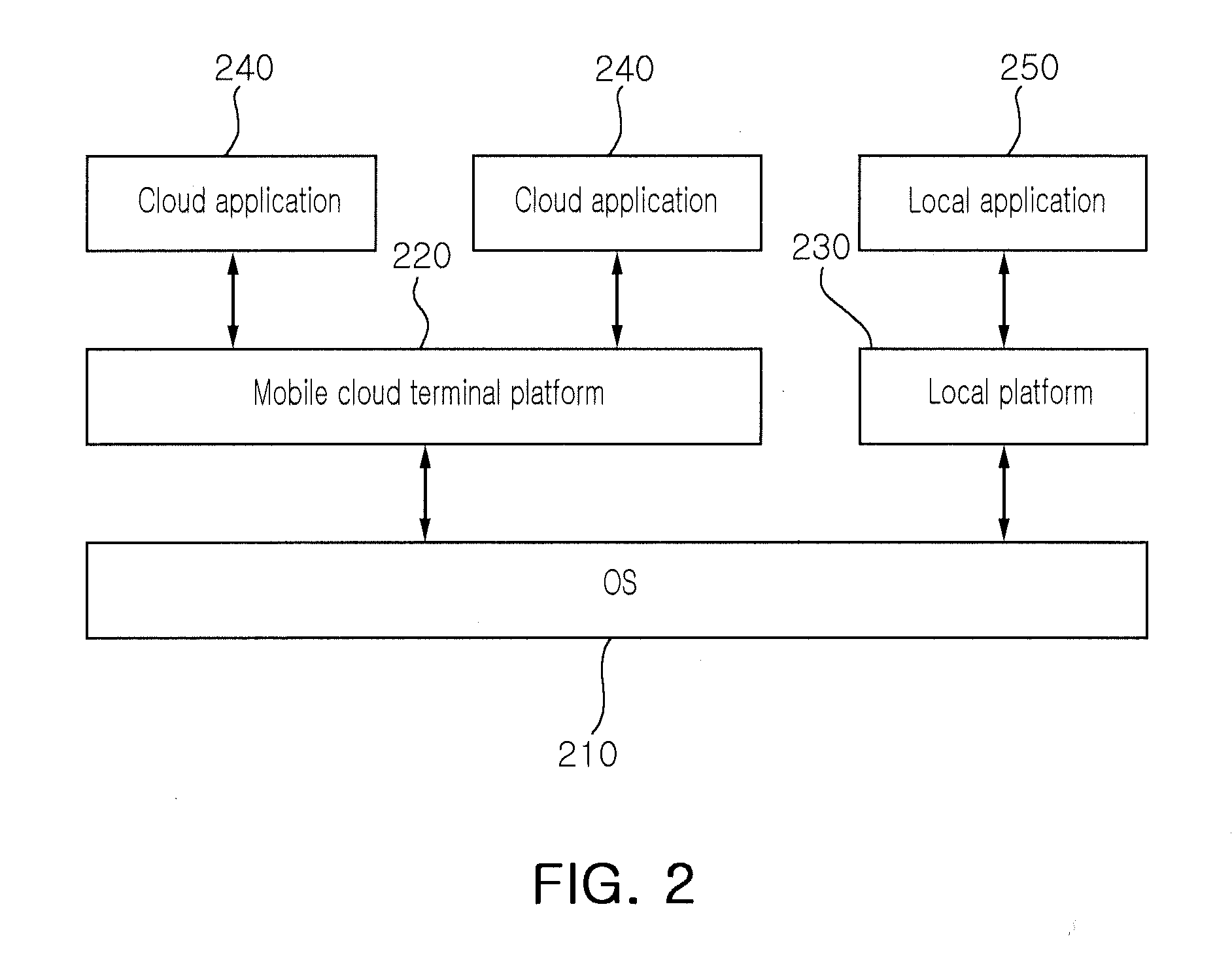
Mobile terminal for providing mobile cloud service and operation method thereof
InactiveUS20110093567A1Easy to solveMultiple digital computer combinationsProgram controlMobile cloudComputer terminal
A mobile terminal for using a mobile cloud service and an operation method of the mobile terminal are disclosed. The mobile terminal accessible to a mobile cloud server, including: a mobile cloud terminal platform accessing the mobile cloud server to acquire a cloud application, and providing a mobile cloud service by using the acquired cloud application; a local terminal platform executing a local application installed in the mobile terminal; and an operating system (OS) selectively driving one of the mobile cloud terminal platforms and the local platform according to a user set environment.
Owner:ELECTRONICS & TELECOMM RES INST
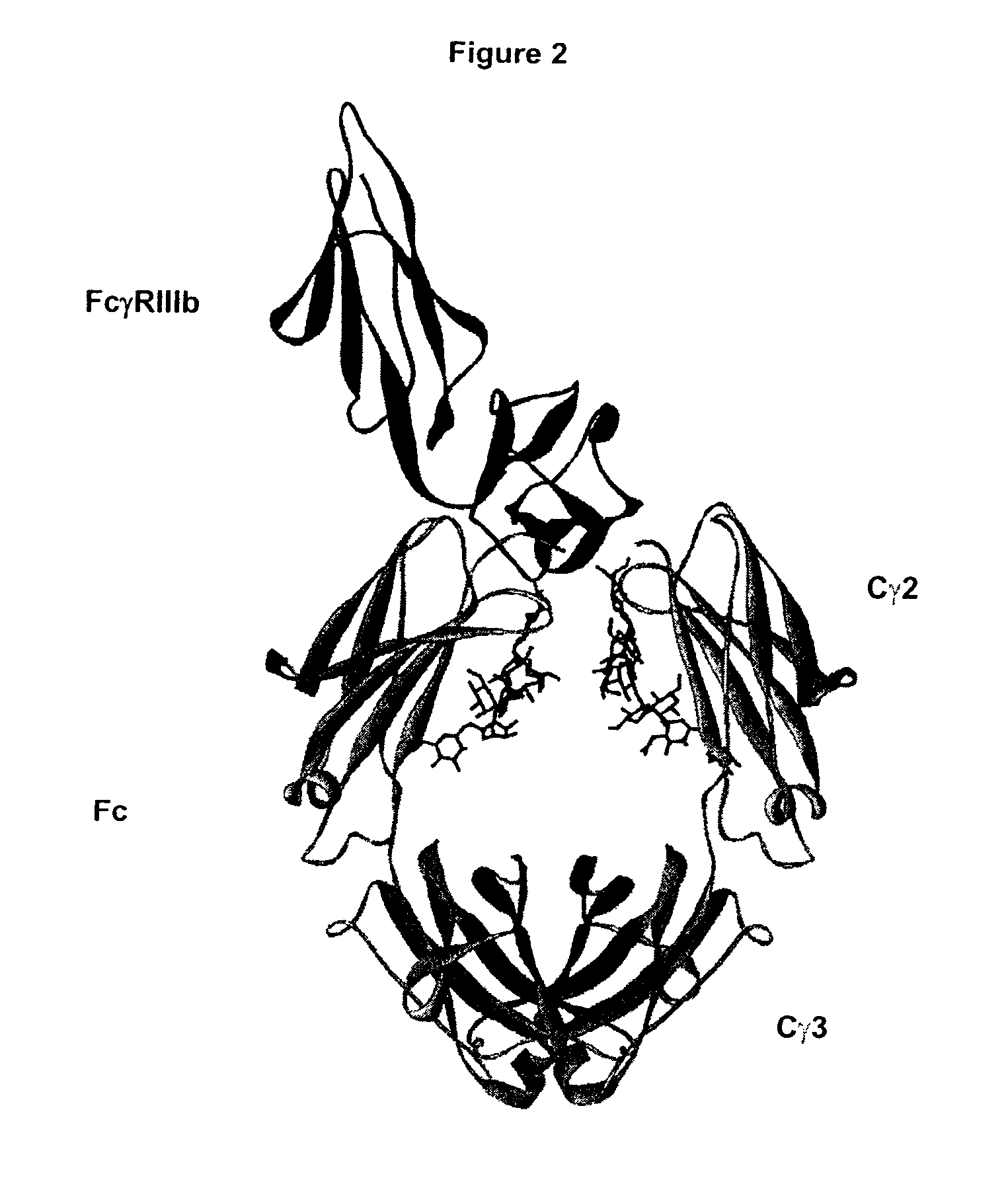
Fc Variants Having Decreased Affinity for FcyRllla
InactiveUS20070237767A1Weak affinityFunction increaseImmunoglobulins against animals/humansAntibody ingredientsChemistry
Owner:XENCOR INC
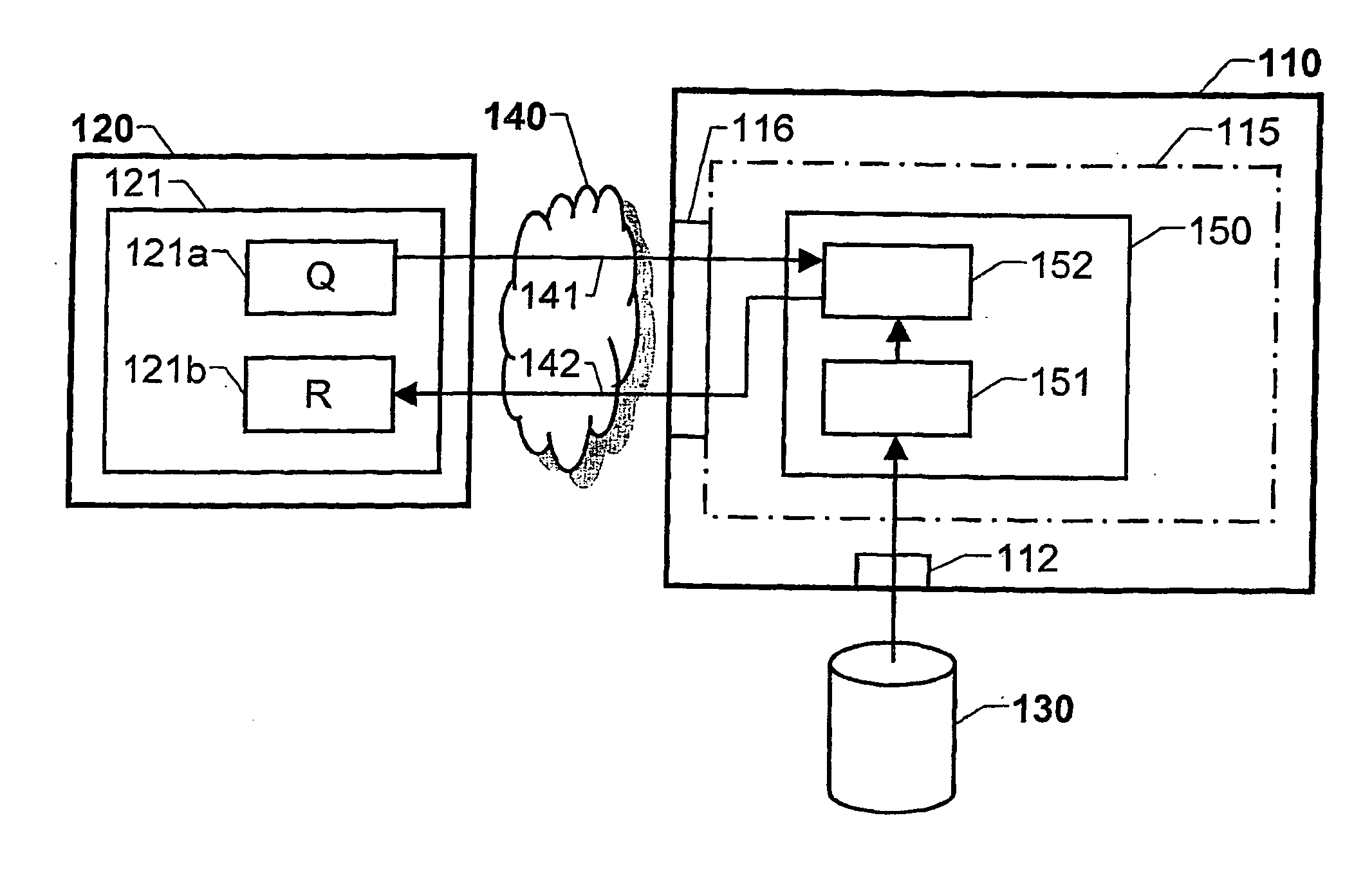
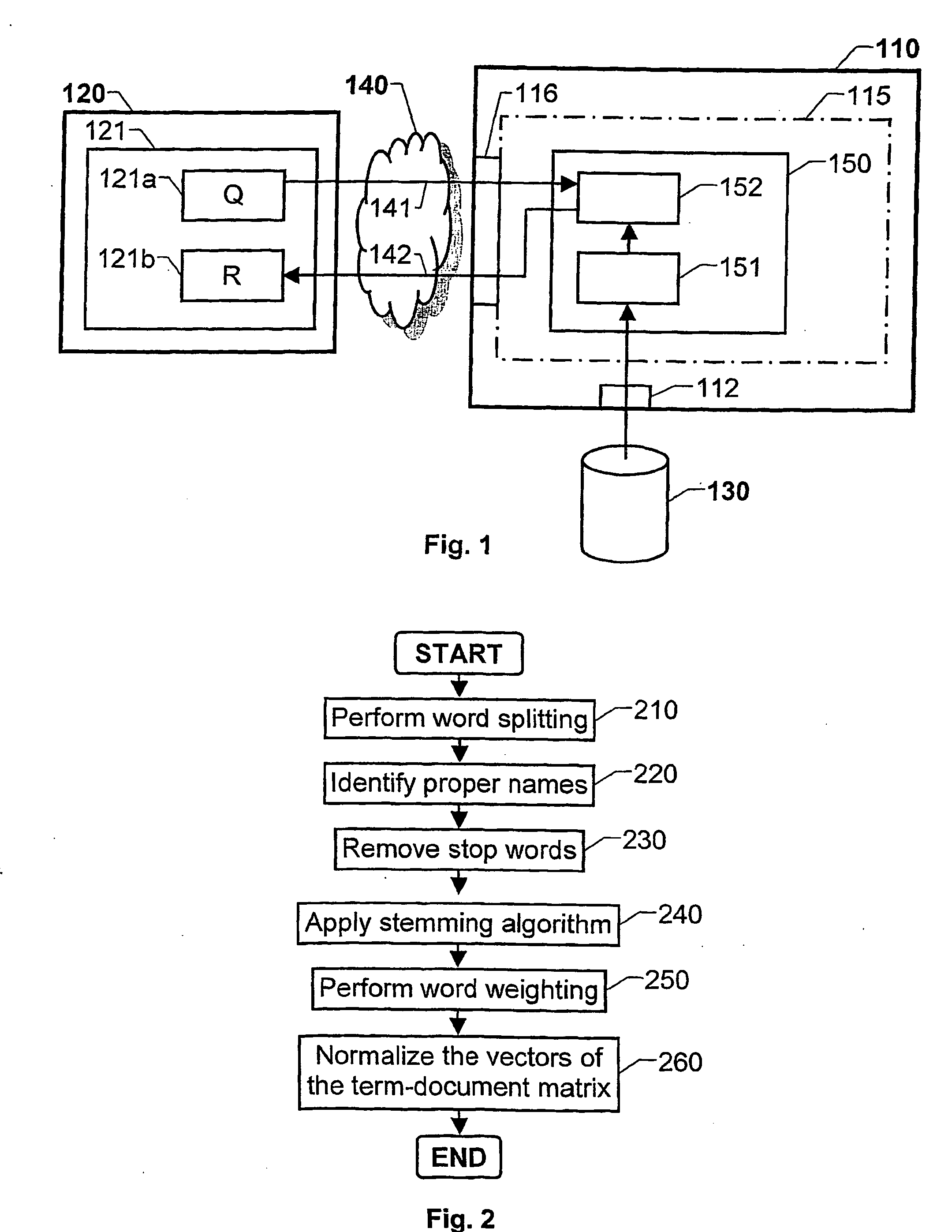
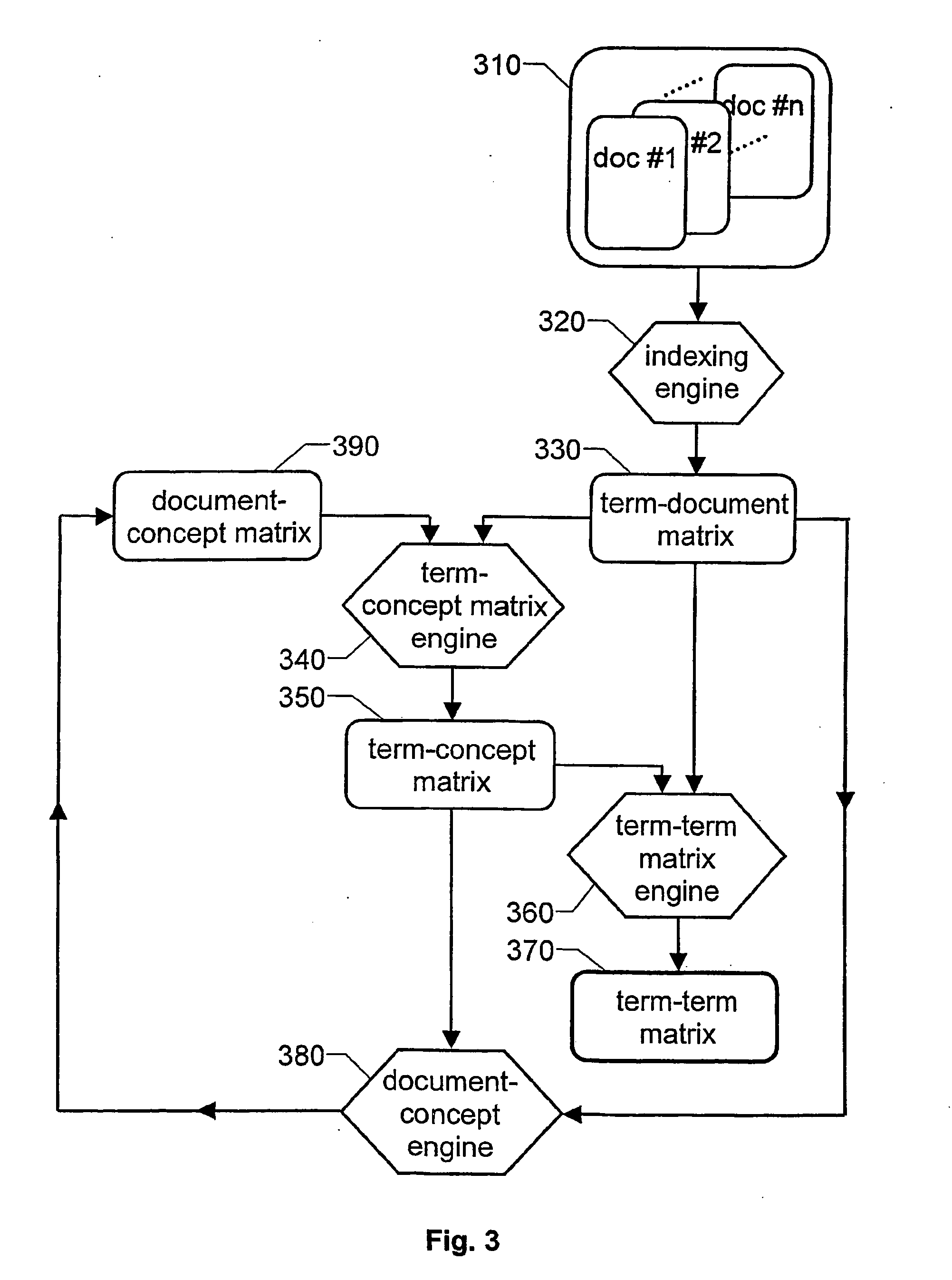
Information data retrieval, where the data is organized in terms, documents and document corpora
ActiveUS20050149494A1Easy to solveEasy to FeedbackDigital data processing detailsObject oriented databasesPaper documentDocument preparation
The invention relates to improved solutions for information retrieval, wherein the information is represented by digitized text data. This data is further presumed to be organized in terms (431-438), documents and document corpora, where each document contains at least one term (431-438) and each document corpus contains at least one document. Based on a concept vector (420-424), which conceptually classifies the contents of each document, a term-to-concept vector is generated for each term (431-438) in the document corpus. The term-to-concept vector describes a relationship between the term (431) and each of the concept vectors (420-424). On basis of the term-to-concept vectors for the document corpus, a term-term matrix is generated which describes a term-to-term relationship between all the terms (431-438) in the document corpus. The term-term matrix may then be processed and used for retrieving information from the document corpus, such as the fact that a first term (431) is related to a second term (436).
Owner:ELUCIDON GROUP
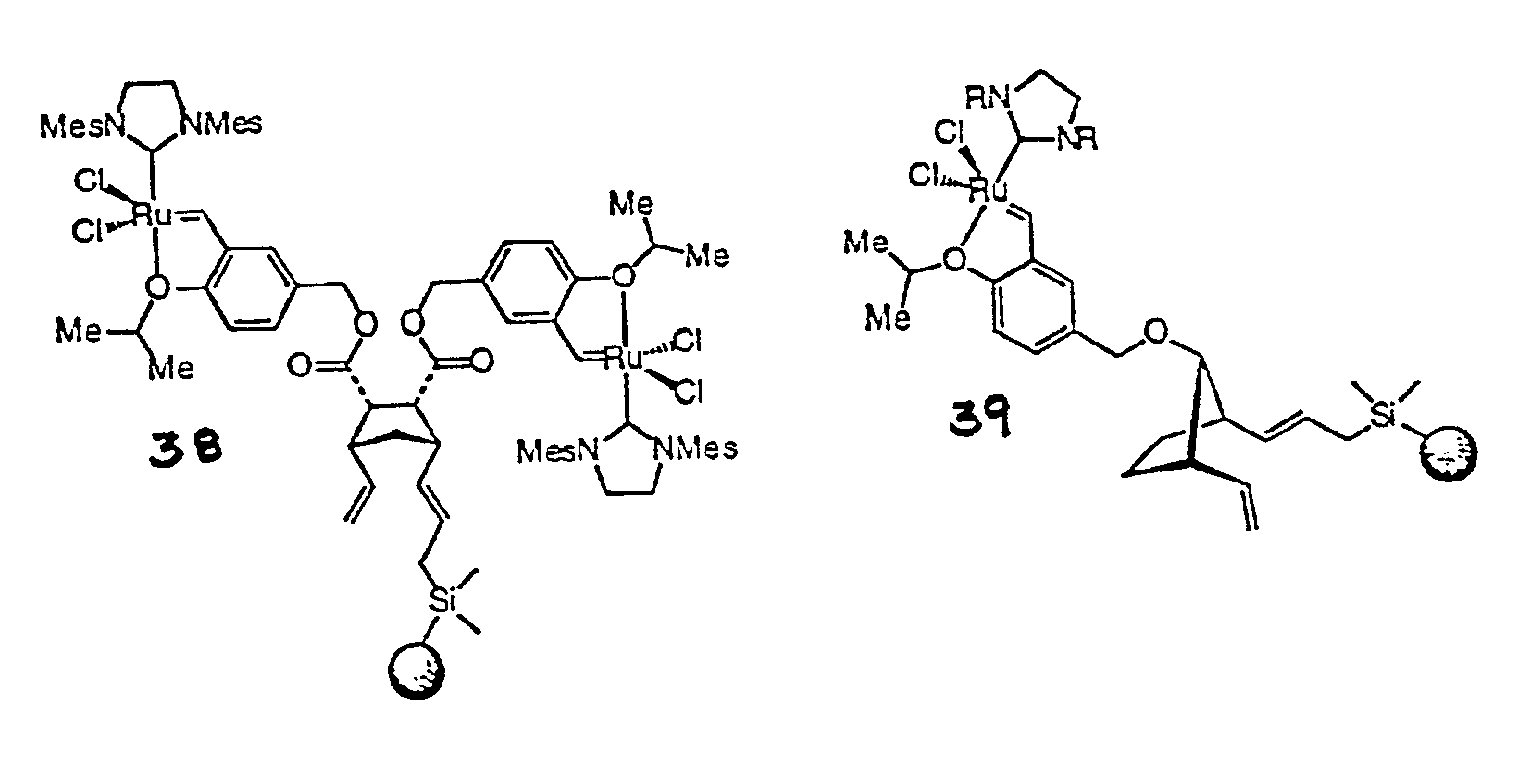
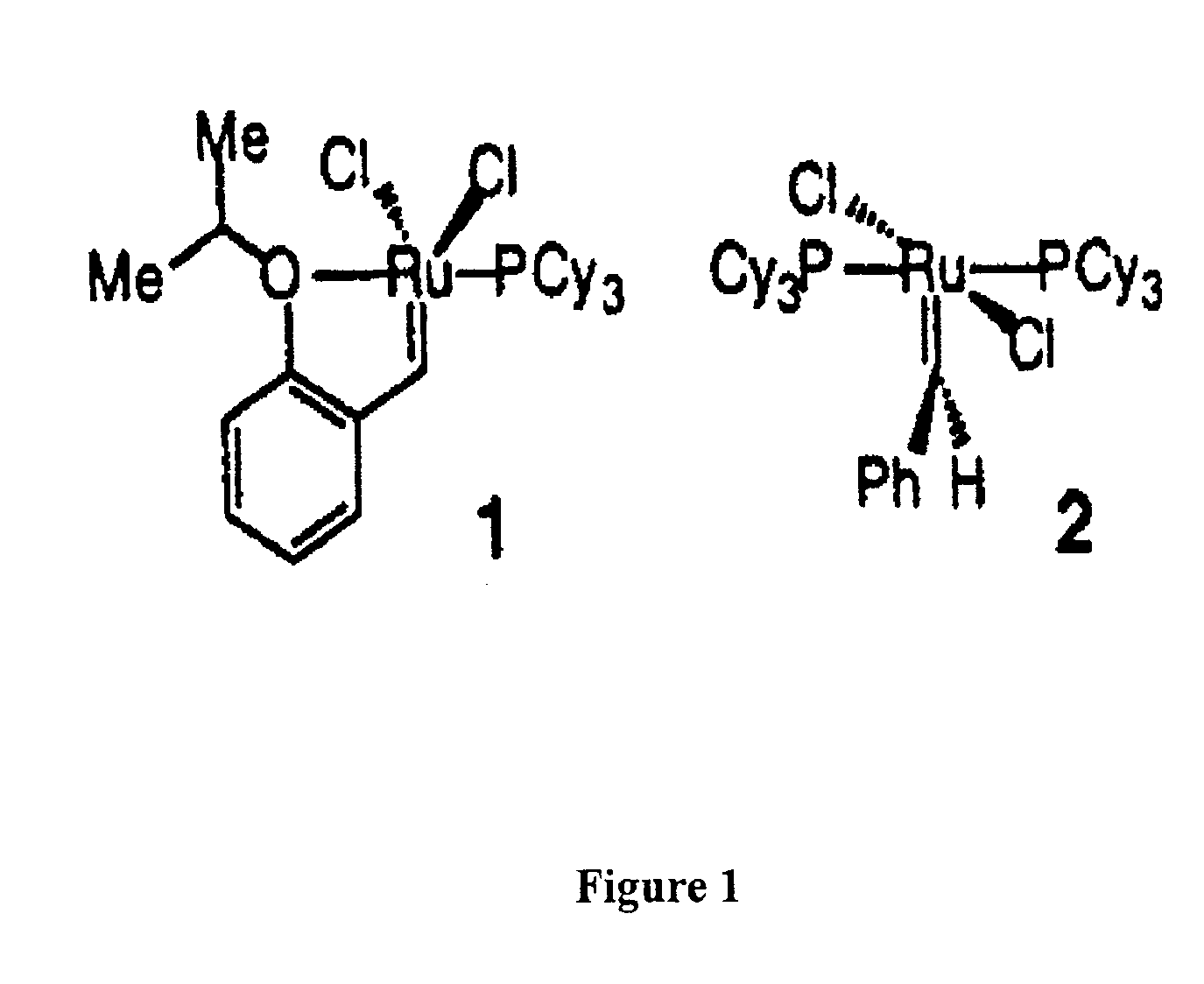
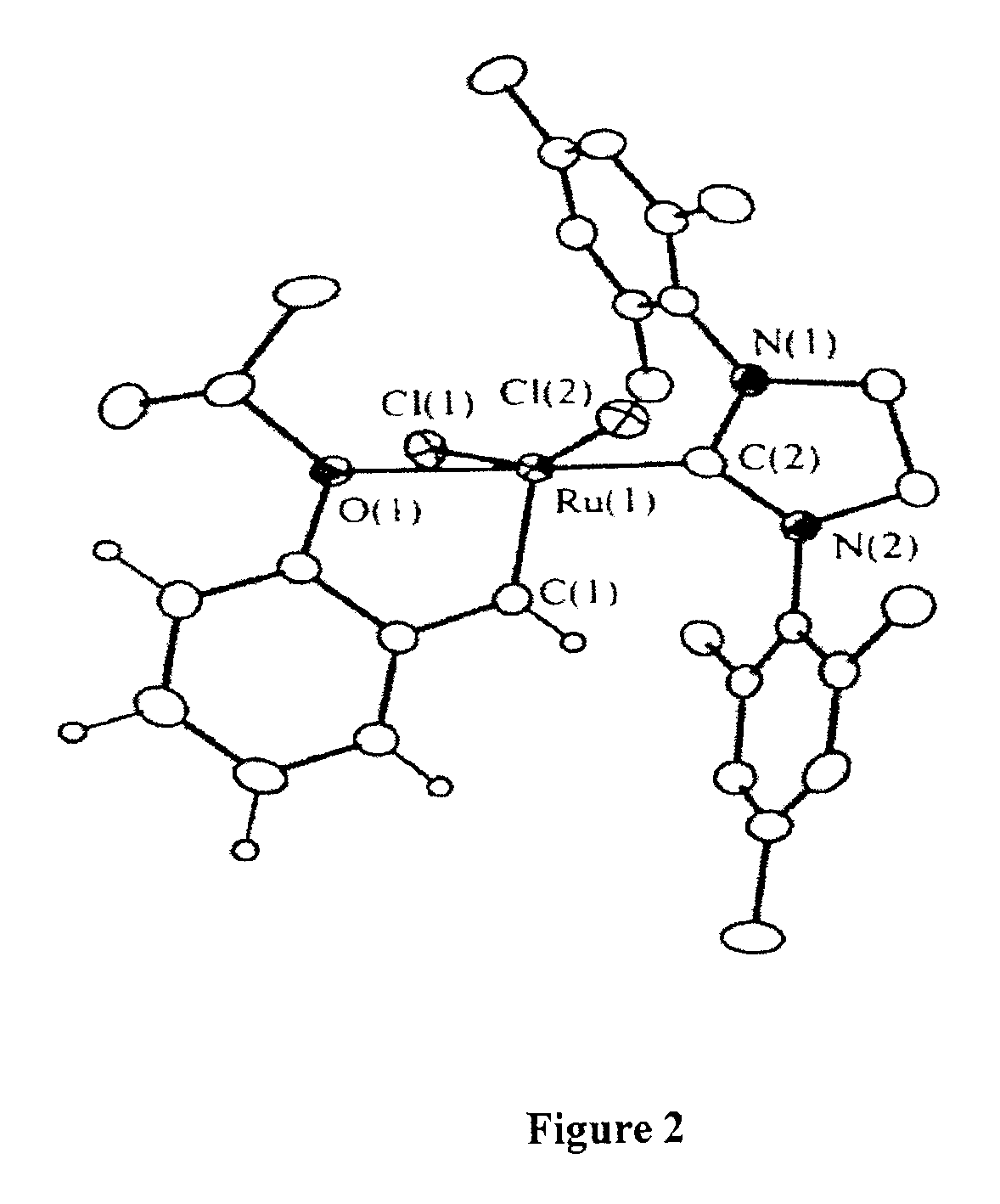
Recyclable metathesis catalysts
ActiveUS6921735B2Highly efficient mannerReadily isolableOrganic chemistry methodsCarboxylic acid esters preparationEtherCoordination complex
Highly active, recoverable and recyclable transition metal-based metathesis catalysts and their organometallic complexes including dendrimeric complexes are disclosed, including a Ru complex bearing a 1,3-dimesityl-4,5-dihydroimidazol-2-ylidene and styrenyl ether ligand. The heterocyclic ligand significantly enhances the catalytic activity, and the styrenyl ether allows for the easy recovery of the Ru complex. Derivatized catalysts capable of being immobilized on substrate surfaces are also disclosed. The present catalysts can be used to catalyze ring-closing metathesis (RCM), ring-opening (ROM) and cross metatheses (CM) reactions, and promote the efficient formation of various trisubstituted olefins at ambient temperature in high yield.
Owner:BOSTON COLLEGE
Speech enhancement techniques on the power spectrum
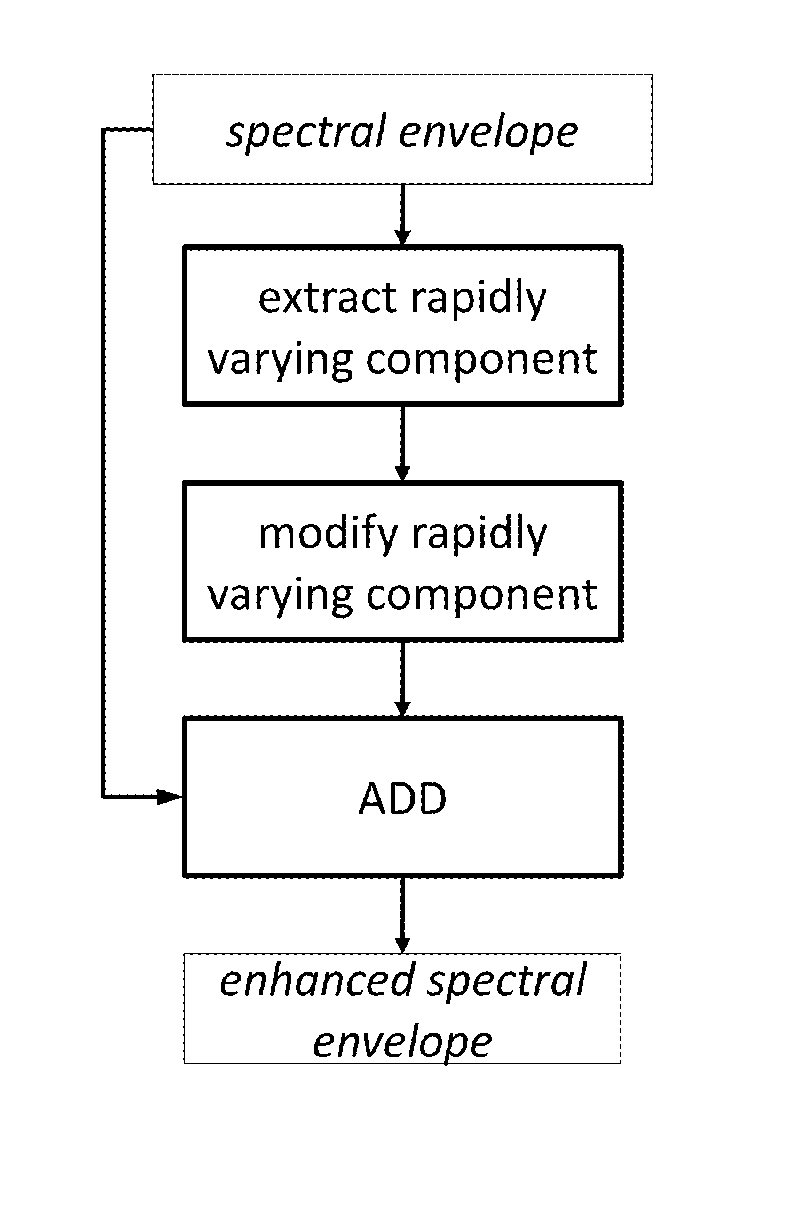
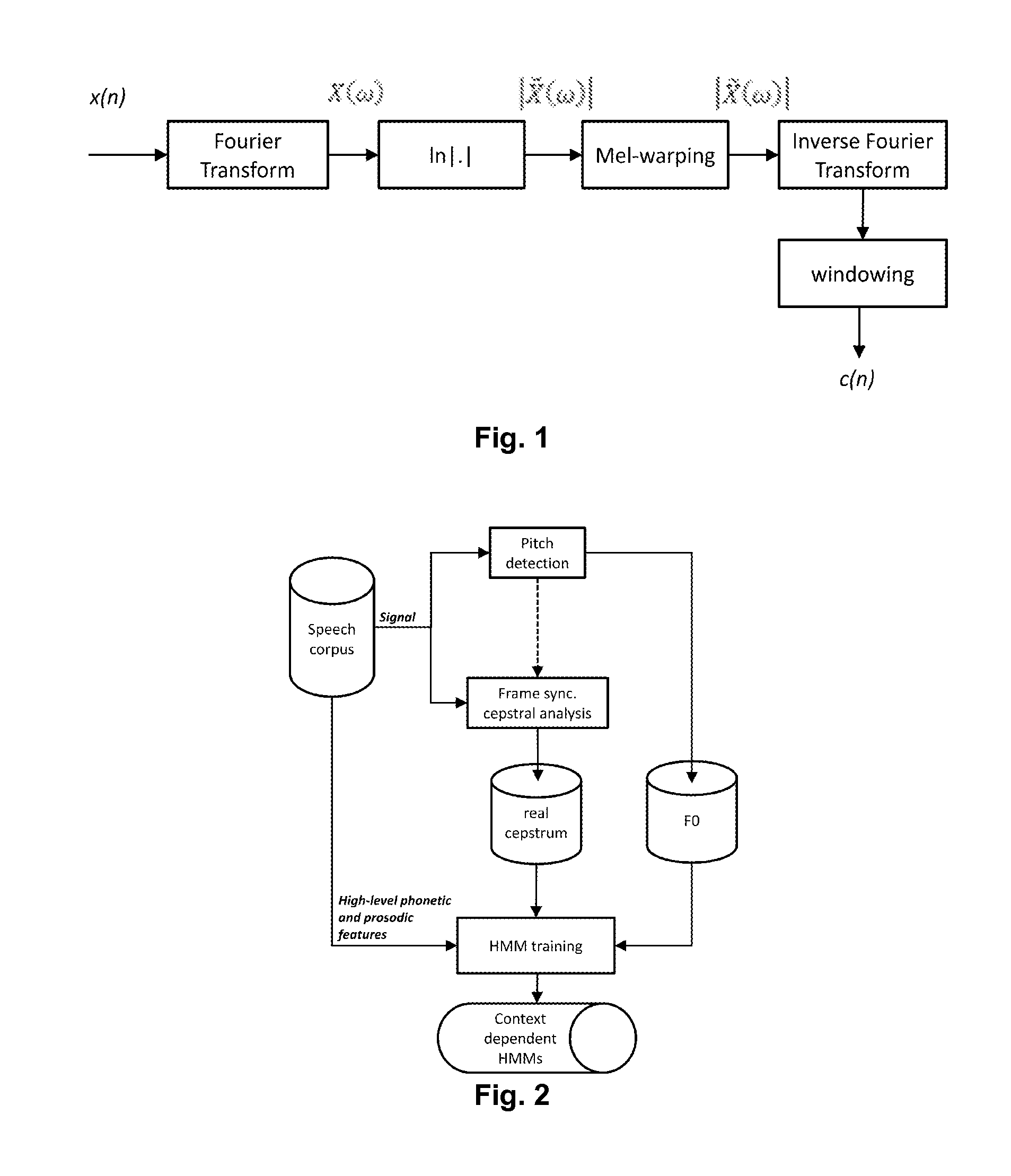
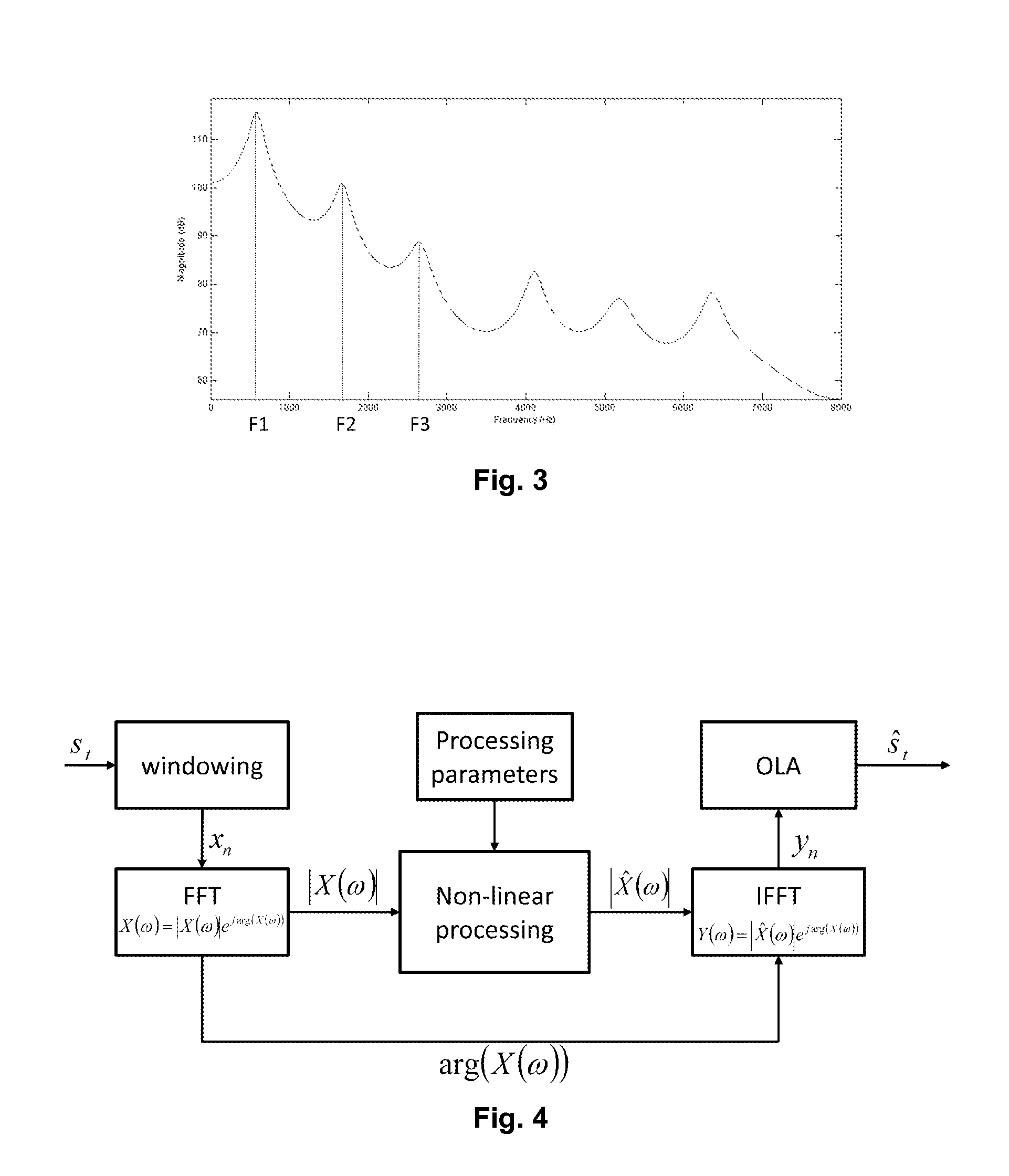
The method provides a spectral speech description to be used for synthesis of a speech utterance, where at least one spectral envelope input representation is received. In one solution the improvement is made by manipulation an extremum, i.e. a peak or a valley, in the rapidly varying component of the spectral envelope representation. The rapidly varying component of the spectral envelope representation is manipulated to sharpen and / or accentuate extrema after which it is merged back with the slowly varying component or the spectral envelope input representation to create an enhanced spectral envelope final representation. In other solutions a complex spectrum envelope final representation is created with phase information derived from one of the group delay representation of a real spectral envelope input representation corresponding to a short-time speech signal and a transformed phase component of the discrete complex frequency domain input representation corresponding to the speech utterance.
Owner:CERENCE OPERATING CO
Fc Variants Having Decreased Affinity for FcyRlla
InactiveUS20070243188A1Weak affinityFunction increaseImmunoglobulins against animals/humansAntibody ingredientsChemistry
Owner:XENCOR INC
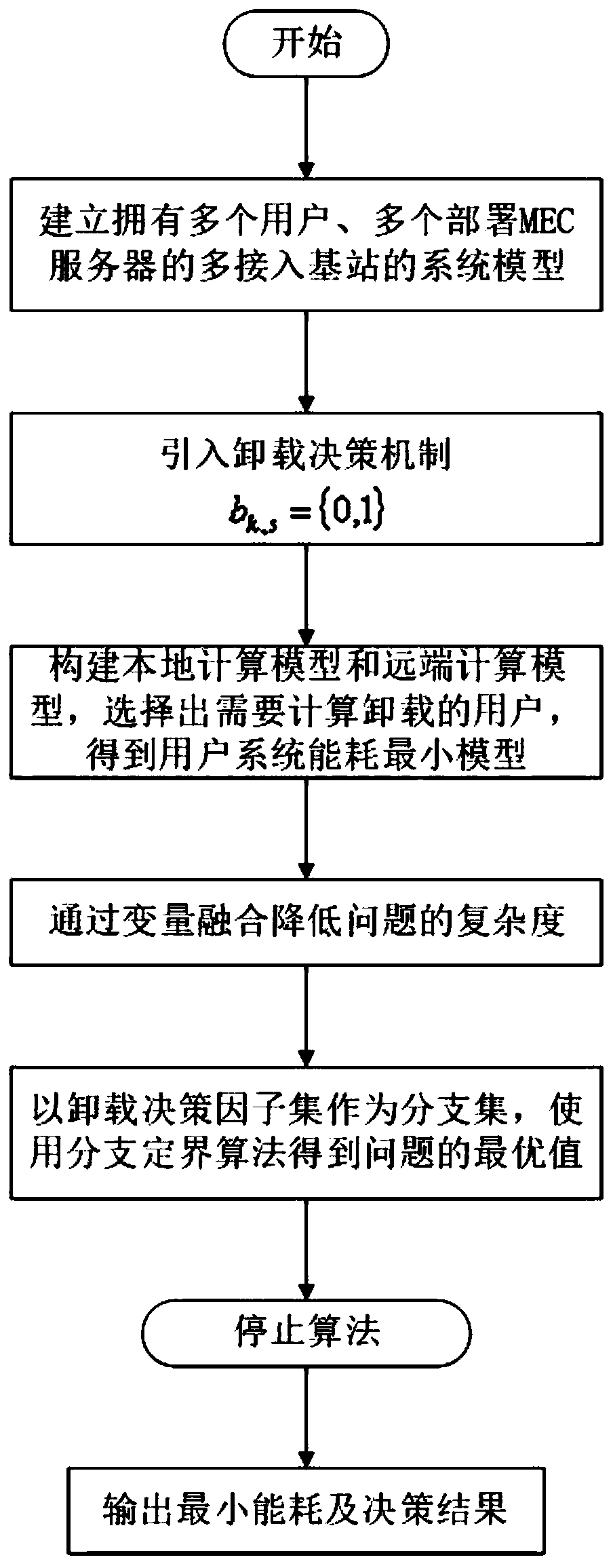
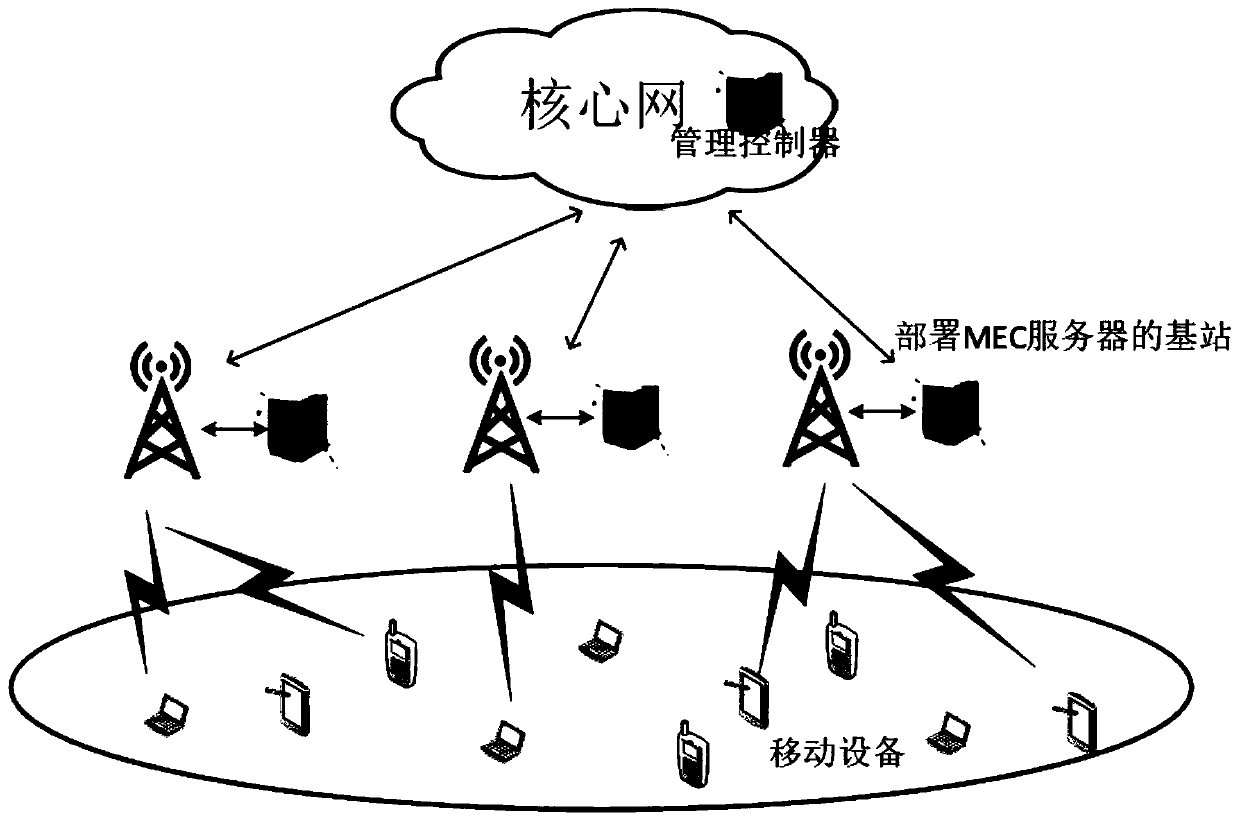
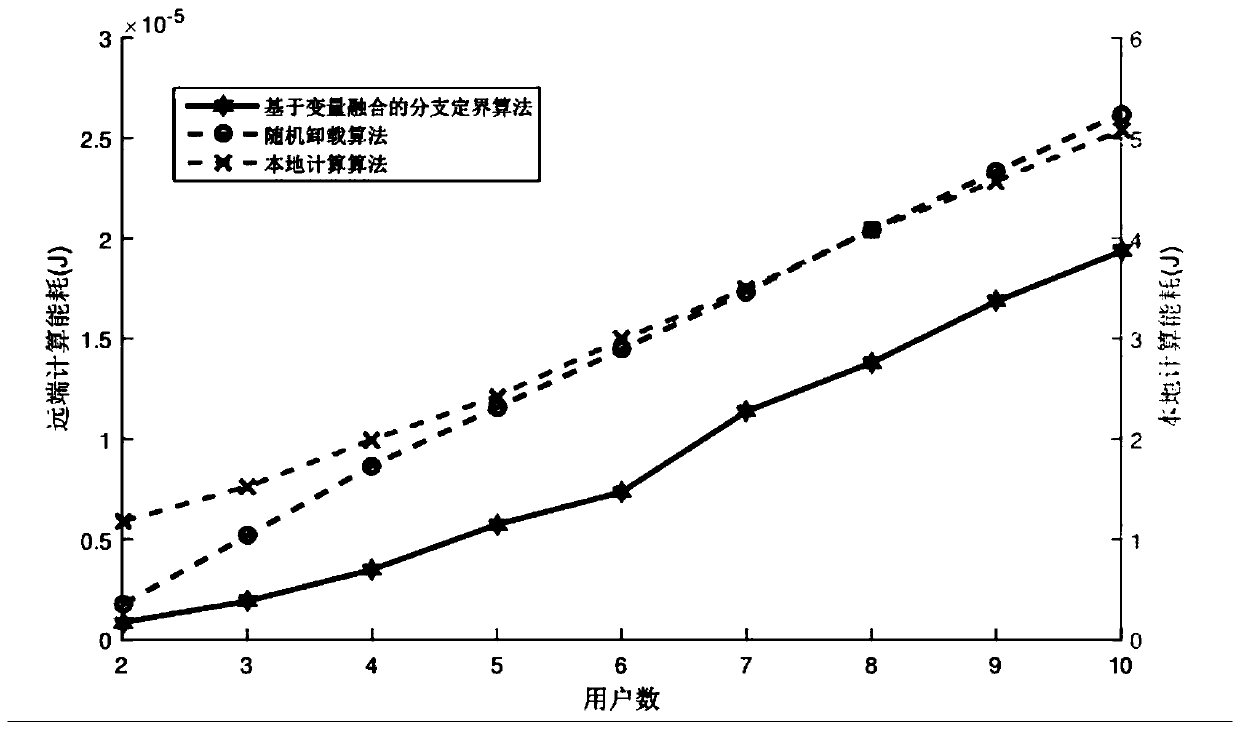
A joint optimization method for task unloading and resource allocation in a mobile edge computing network
ActiveCN109814951AFull restorationUniversalService provisioningProgram loading/initiatingDecision takingWireless resource allocation
The invention discloses a joint optimization method for task unloading and resource allocation in a mobile edge computing network, which comprises the following steps of 1, establishing an OFDMA (Orthogonal Frequency Division Multiple Access)-based multi-MEC (Mobile Edge Computing) base station and a multi-user scene model, wherein the MEC base station supports the multi-user access; 2, introducing an unloading decision mechanism; Meanwhile, constructing a local calculation model and a remote calculation model, selecting a user needing to perform calculation unloading, and establishing a calculation task unloading and resource allocation scheme based on minimum energy consumption under the condition of meeting the time delay constraint according to the conditions; 3, carrying out variablefusion on three mutually constrained optimization variables, namely an unloading decision variable, a wireless resource distribution variable and a computing resource distribution variable, so as to simplify the problem; and 4, obtaining an unloading decision and a resource allocation result which enable the total energy consumption of the user in the MEC system to be minimum through a branch andbound algorithm. The method has the advantage that the energy consumption of the system can be effectively reduced on the premise that strict time delay limitation is guaranteed.
Owner:NANJING UNIV OF POSTS & TELECOMM
Fc Variants Having Increased Affinity for FcyRl
InactiveUS20070237765A1Weak affinityFunction increaseImmunoglobulins against animals/humansAntibody ingredientsChemistry
Owner:XENCOR INC
Prevention of unauthorized scripts
ActiveUS7606915B1Improved script preventionEasy to solveDigital data processing detailsMultiple digital computer combinationsComputer hardwareCorrect response
Methods and system of preventing unauthorized scripting. The invention includes providing one or more tests to a user for distinguishing the user from a machine when the user requests access to the server. By storing information on a correct solution to the test in a block of data and sending the block of data together with the test, the invention provides stateless operation. Moreover, maintaining a database of previously used correct responses prevents replay attacks. The invention also includes providing combinations of alternative tests, such as visually altered textual character strings, audible character strings, and computational puzzles. Other aspects of the invention are directed to computer-readable media for use with the methods and system.
Owner:MICROSOFT TECH LICENSING LLC
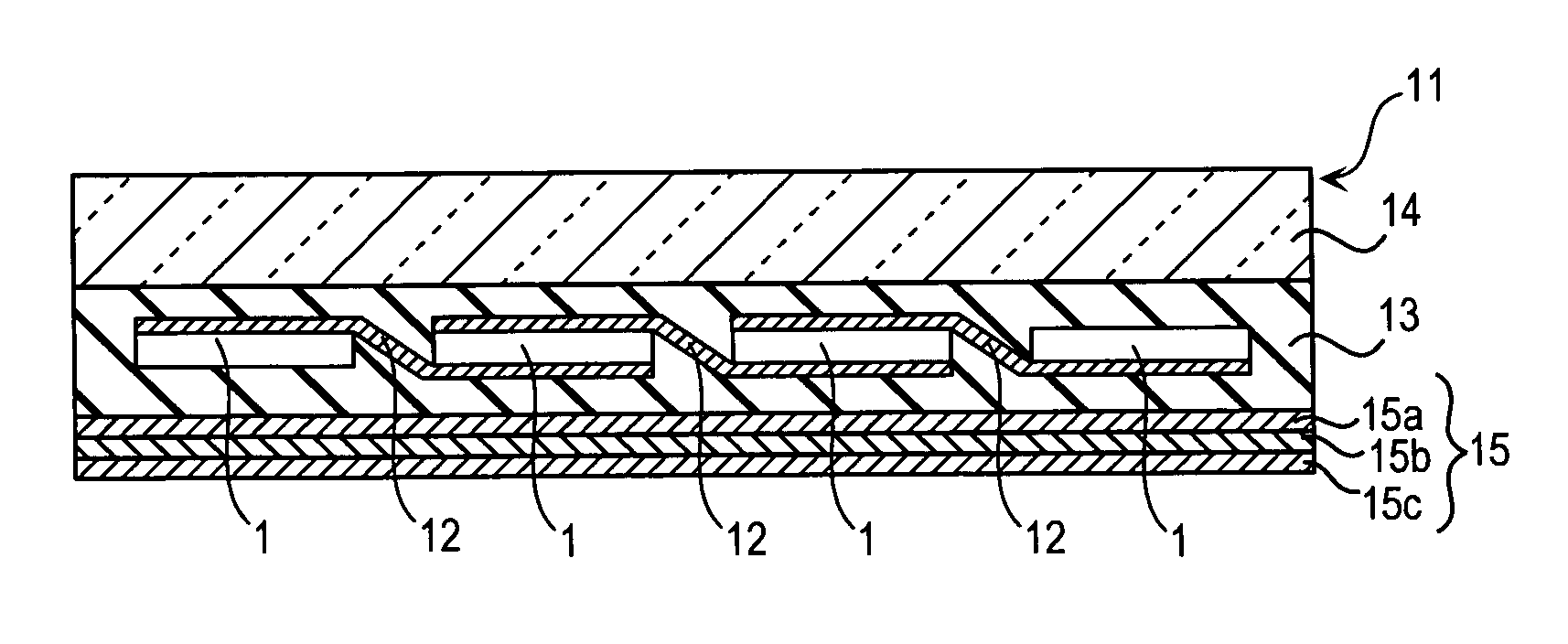
Solar cell module
InactiveUS20050199279A1Easy to solveImprove moisture resistancePV power plantsPhotovoltaic energy generationVitrificationSilver paste
A solar cell module of the present invention was made to improve adhesion between electrodes, which is formed with thermosetting resin containing silver paste, of a solar cell element and connecting tabs coated with lead (Pb) free solder. To achieve this purpose, the solar cell module is comprised of a front surface member, a rear surface protective member, a plurality of solar cell elements provided between the front surface member and the rear surface protective member, and connecting tabs for electrically connecting the solar cell elements to each other through electrodes with the use of lead free solder. The electrodes of the solar cell elements are made of silver paste containing thermosetting resin and silver powder. The thermosetting resin contains epoxy resin at volume ratio of 70% or more having a glass transition rate of 80° C. to 200° C. measured by a TMA method. The connecting tabs coated with lead free solder are soldered to the electrodes.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
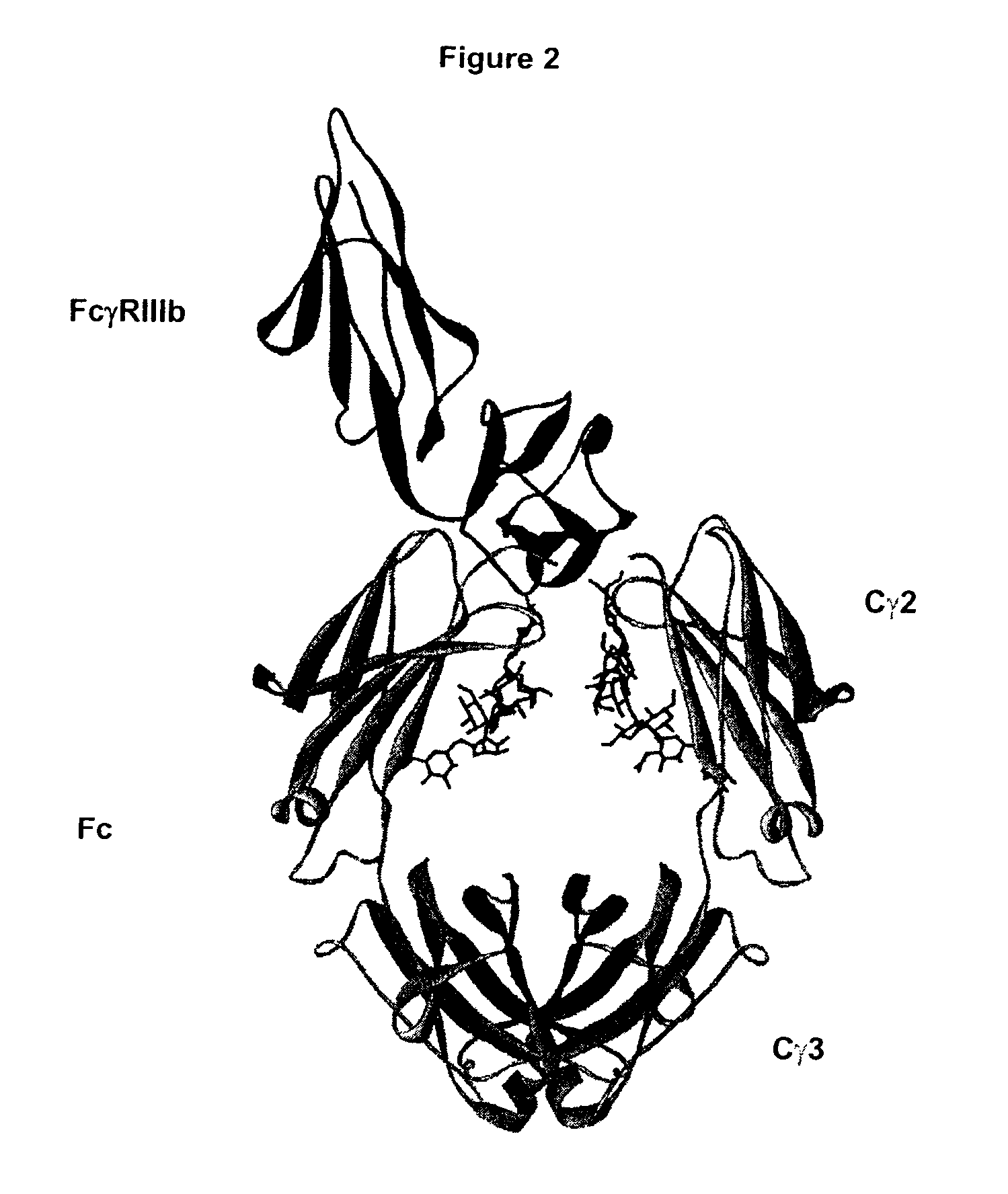
Fc Variants Having Increased Affinity for FcyRllla
InactiveUS20070237766A1Weak affinityFunction increaseImmunoglobulins against animals/humansAntibody ingredientsChemistry
Owner:XENCOR INC
Fc Variants with Increased Affinity for FcyRIIC
InactiveUS20080057056A1Weak affinityFunction increaseSugar derivativesImmunoglobulins against cell receptors/antigens/surface-determinantsChemistryBiochemistry
Owner:XENCOR INC
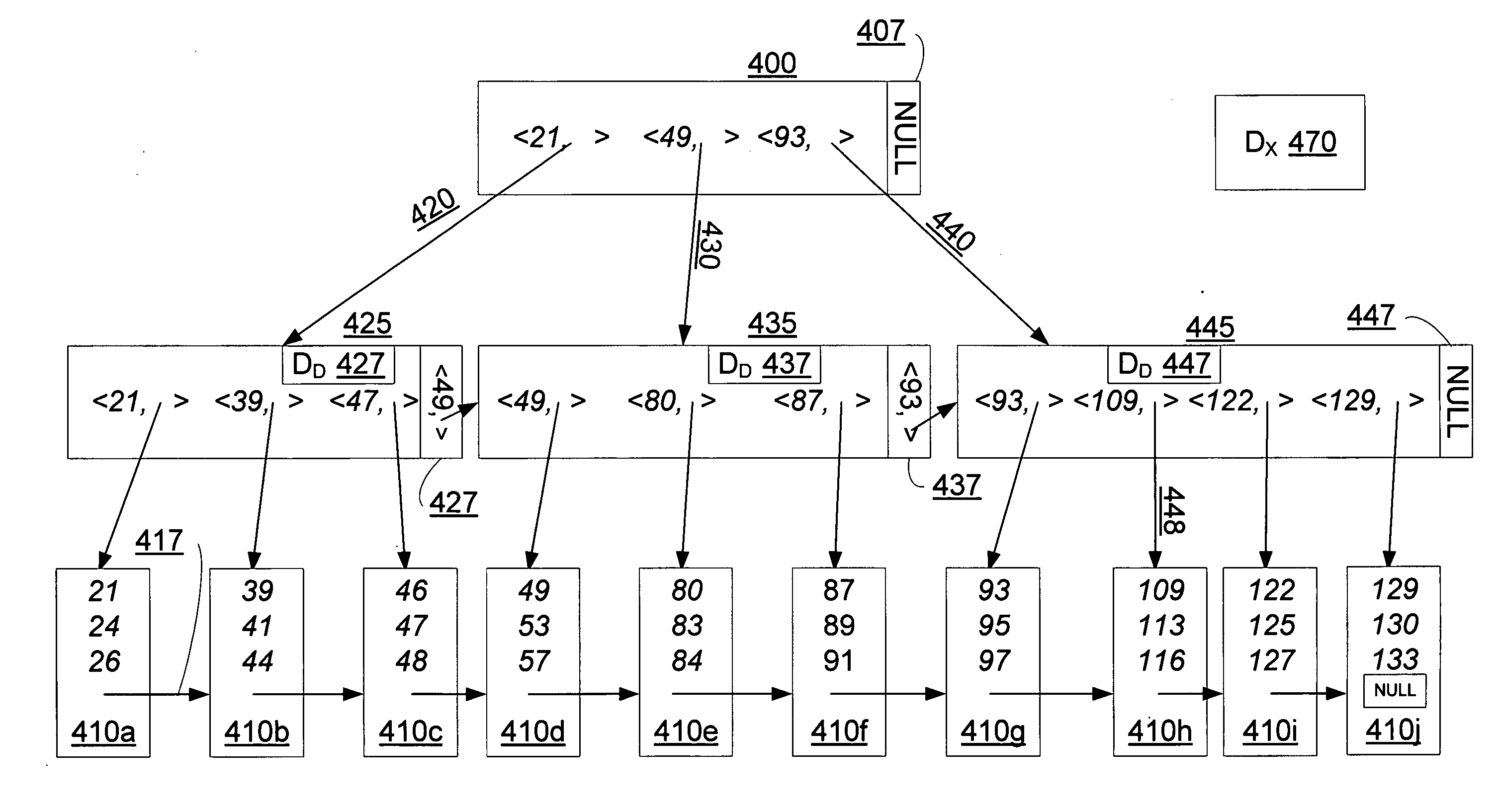
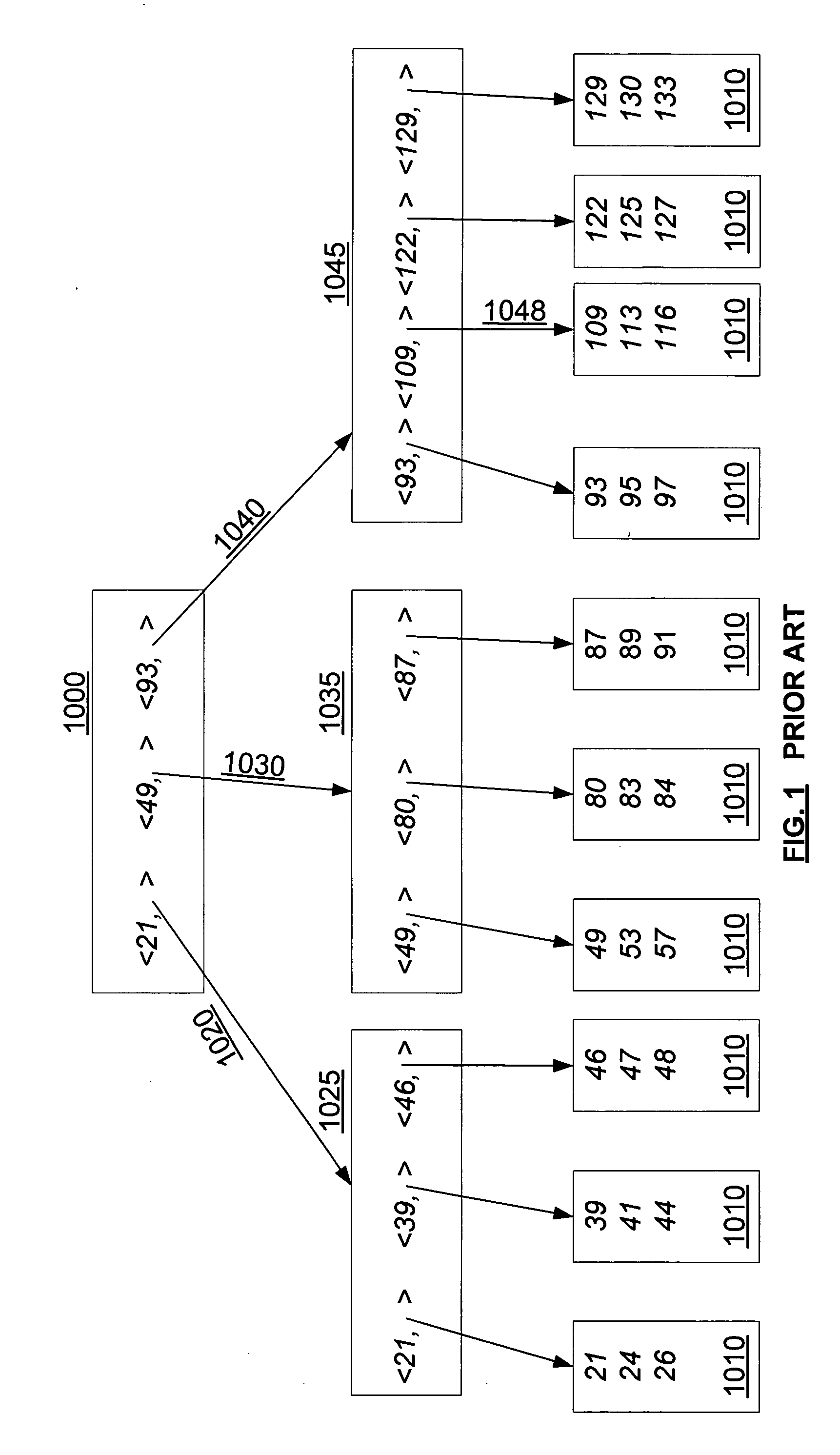
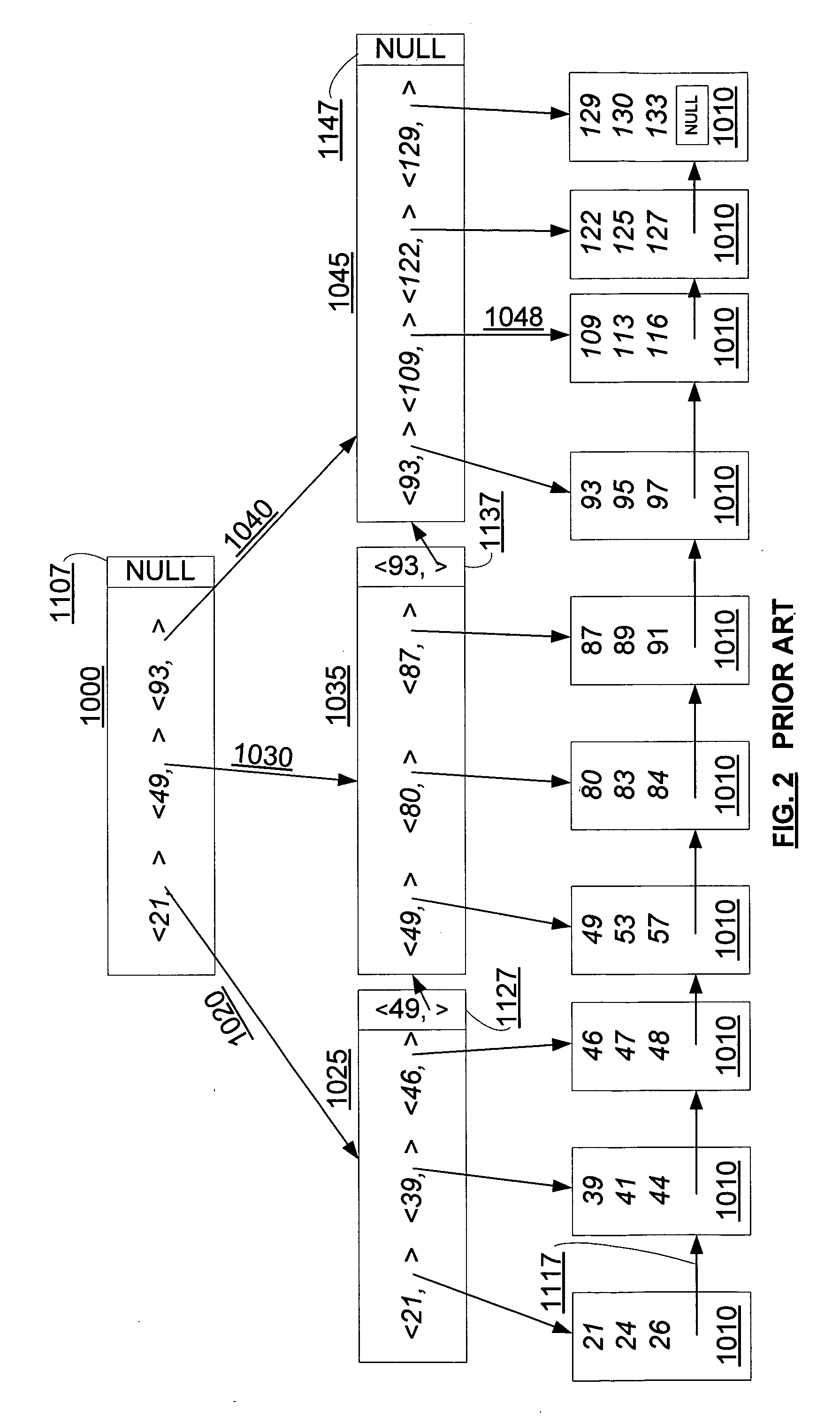
Concurrency control for B-trees with node deletion
InactiveUS20050171960A1Highly concurrent access of dataEasy to solveData processing applicationsDigital data information retrievalConcurrency controlTree (data structure)
A data structure, added to a modified form of the Blink-tree data structure, tracks delete states for nodes. The index delete state (DX) indicates whether it is safe to directly access an index node without re-traversing the B-tree. The DX state is maintained globally, outside of the tree structure. The data delete state (DD) indicates whether it is safe to post an index term for a new leaf node. A DD state is maintained in each level 1 node for its leaf nodes. Delete states indicate whether a specific node has not been deleted, or whether it may have been deleted. Delete states are used to remove the necessity for atomic node splits and chains of latches for deletes, while not requiring retraversal. This property of not requiring a retraversal is exploited to simplify the tree modification operations.
Owner:MICROSOFT TECH LICENSING LLC
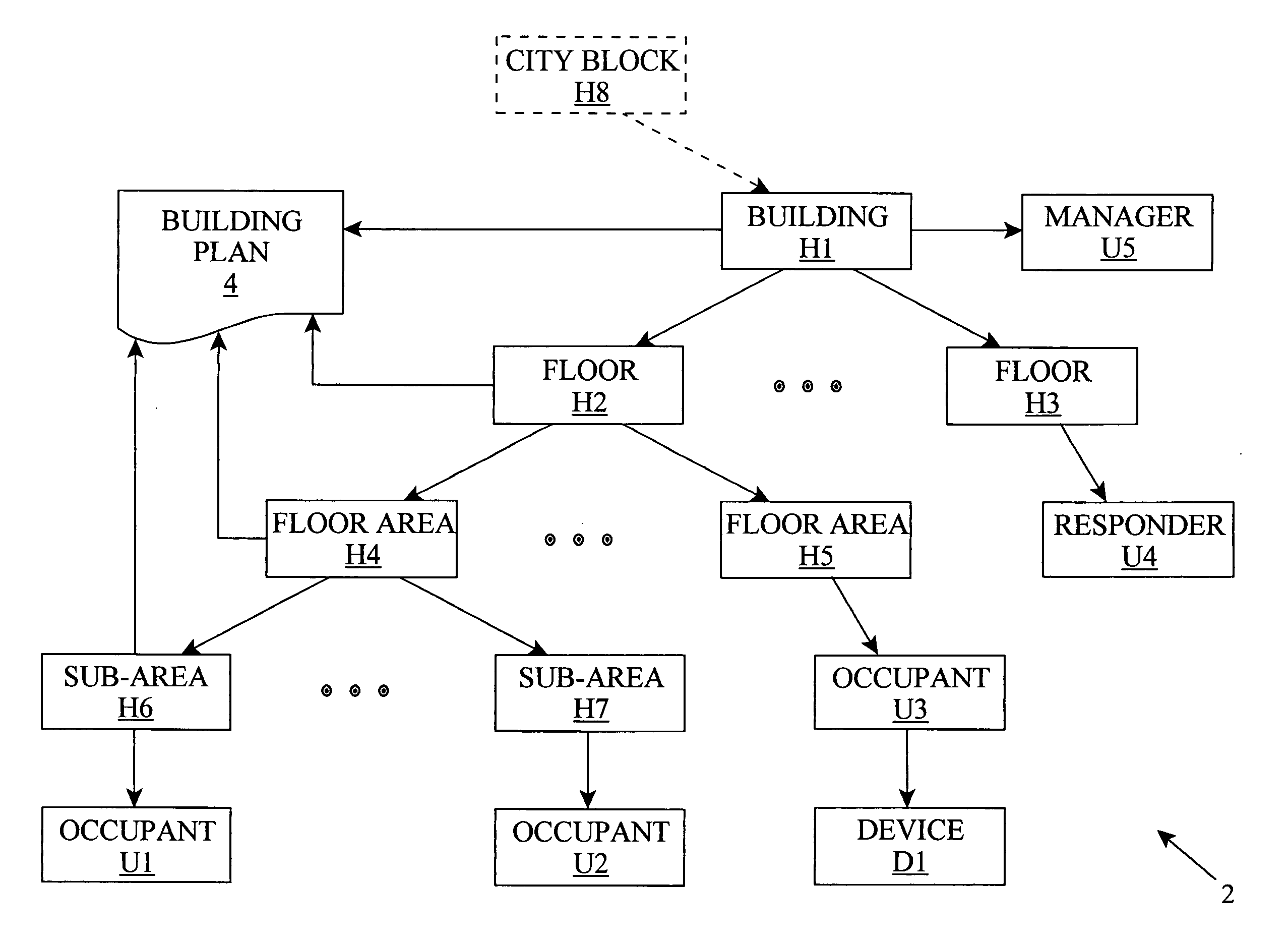
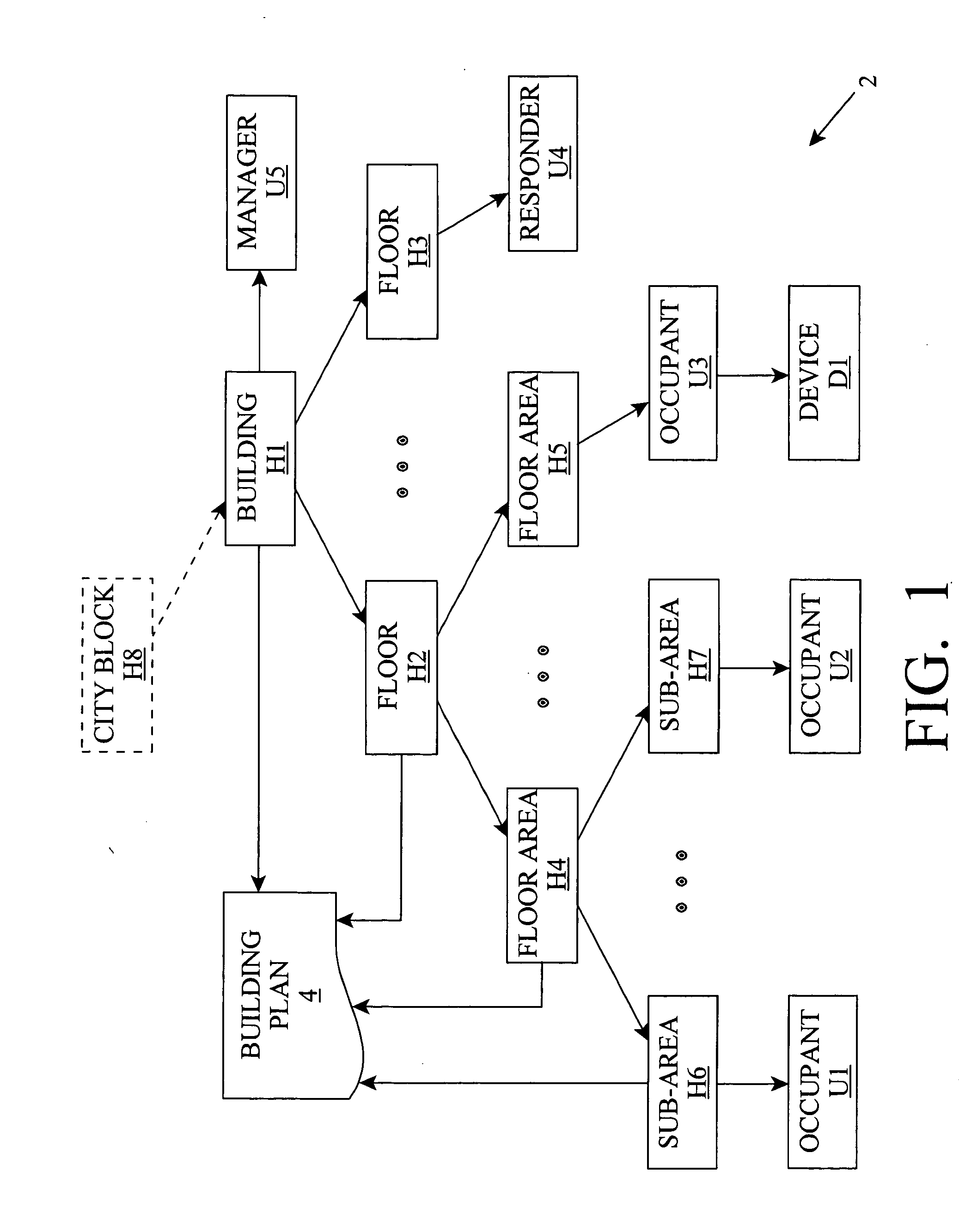
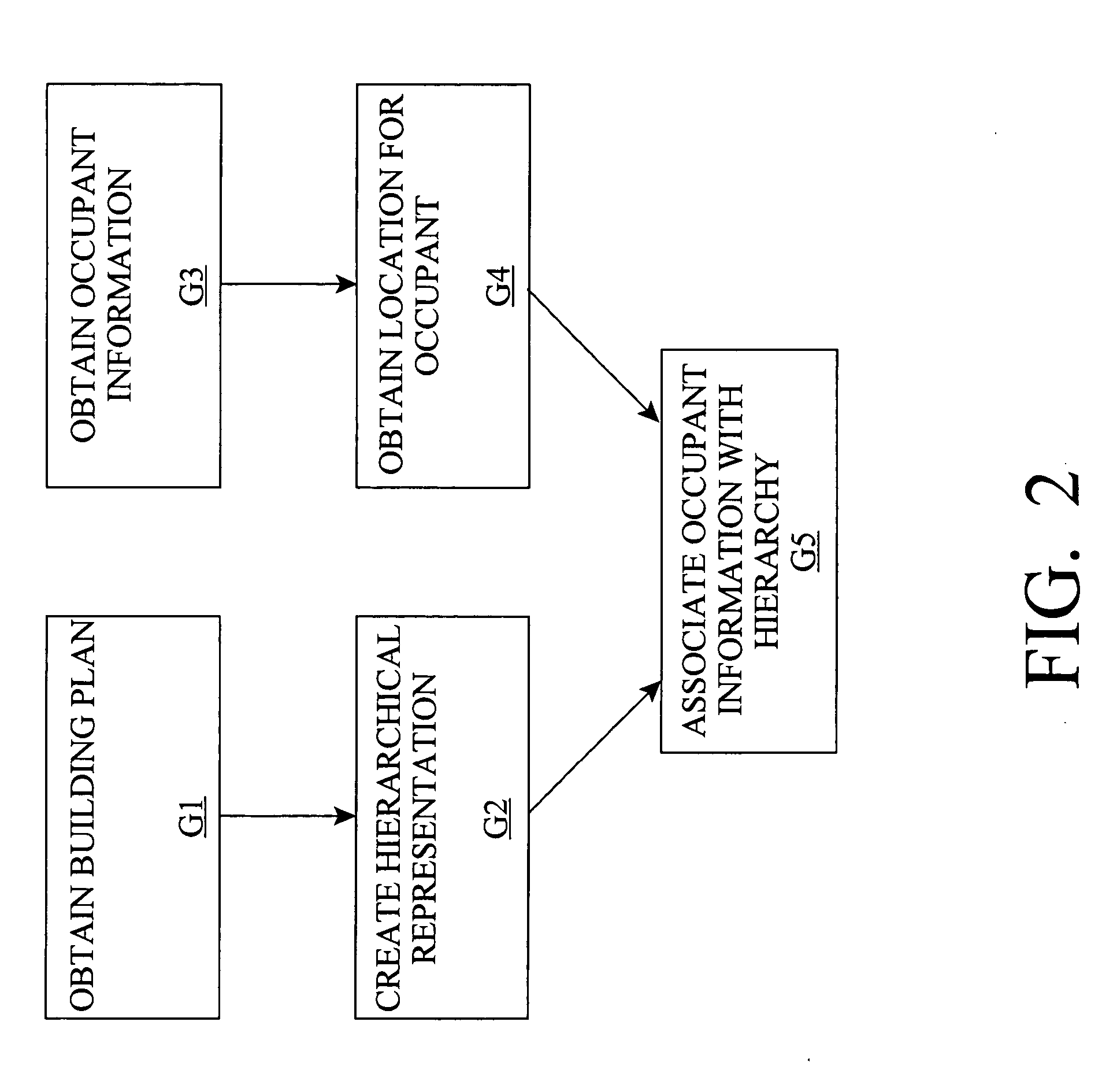
Managing an occupant of a structure during an emergency event
InactiveUS20050190053A1Increase contactEasy to manageSignalling system detailsVisible signalling systemsComputer scienceTwo-way communication
An occupant management method, system, and program product that associate occupant information with information about a physical area. For example, the invention can generate a hierarchical representation of a physical area such as a building or the like. The hierarchical representation is used to manage occupants of the physical area. For example, contact information for occupants can be maintained and associated with a physical location, and / or directions can be provided from a starting point to a designated destination point. The hierarchical representation can be used to facilitate two-way communication between an occupant and an emergency responder during an emergency event. Further, a response plan can be defined for an emergency event and implemented when the emergency event is identified.
Owner:DIONE DIEGANE
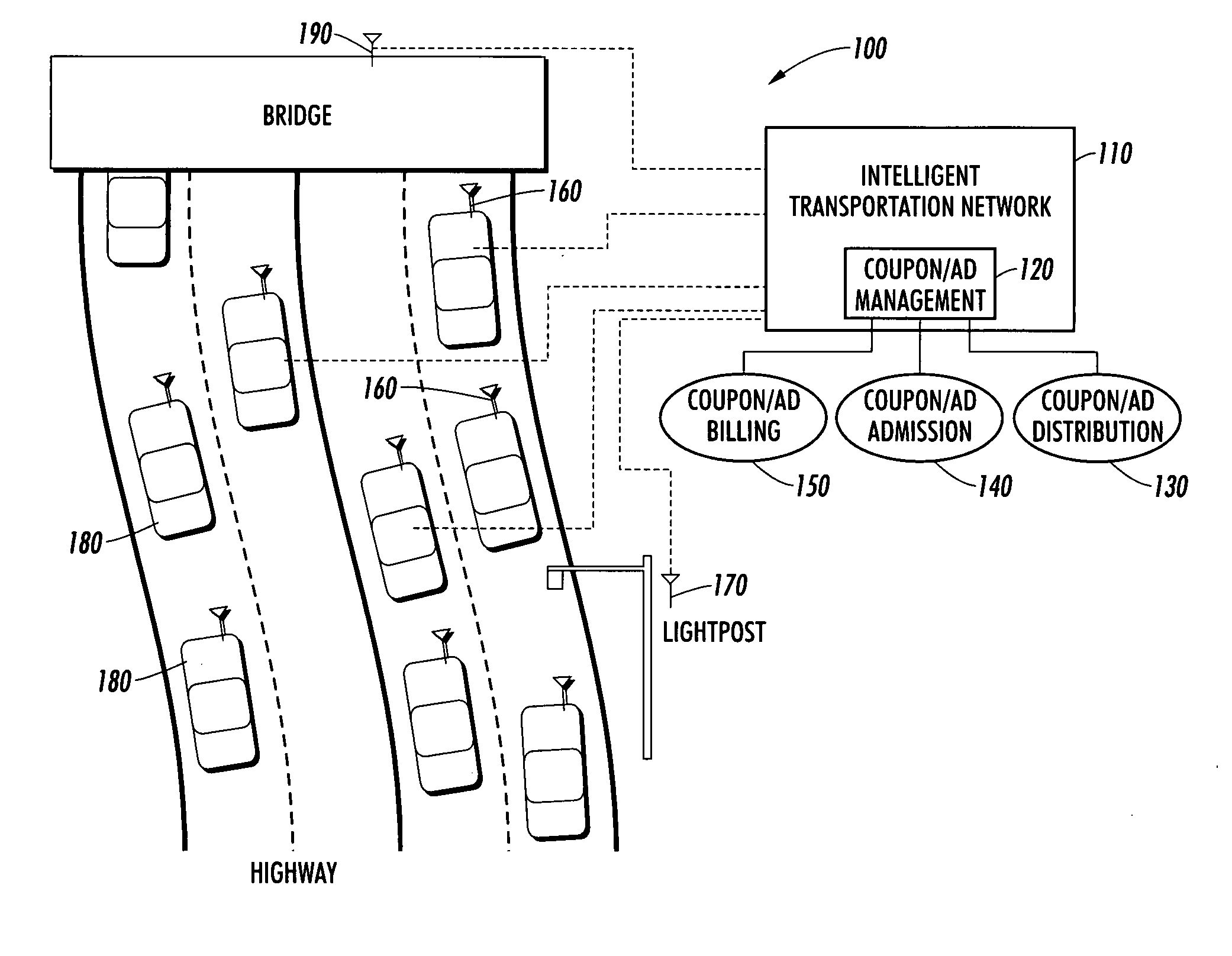
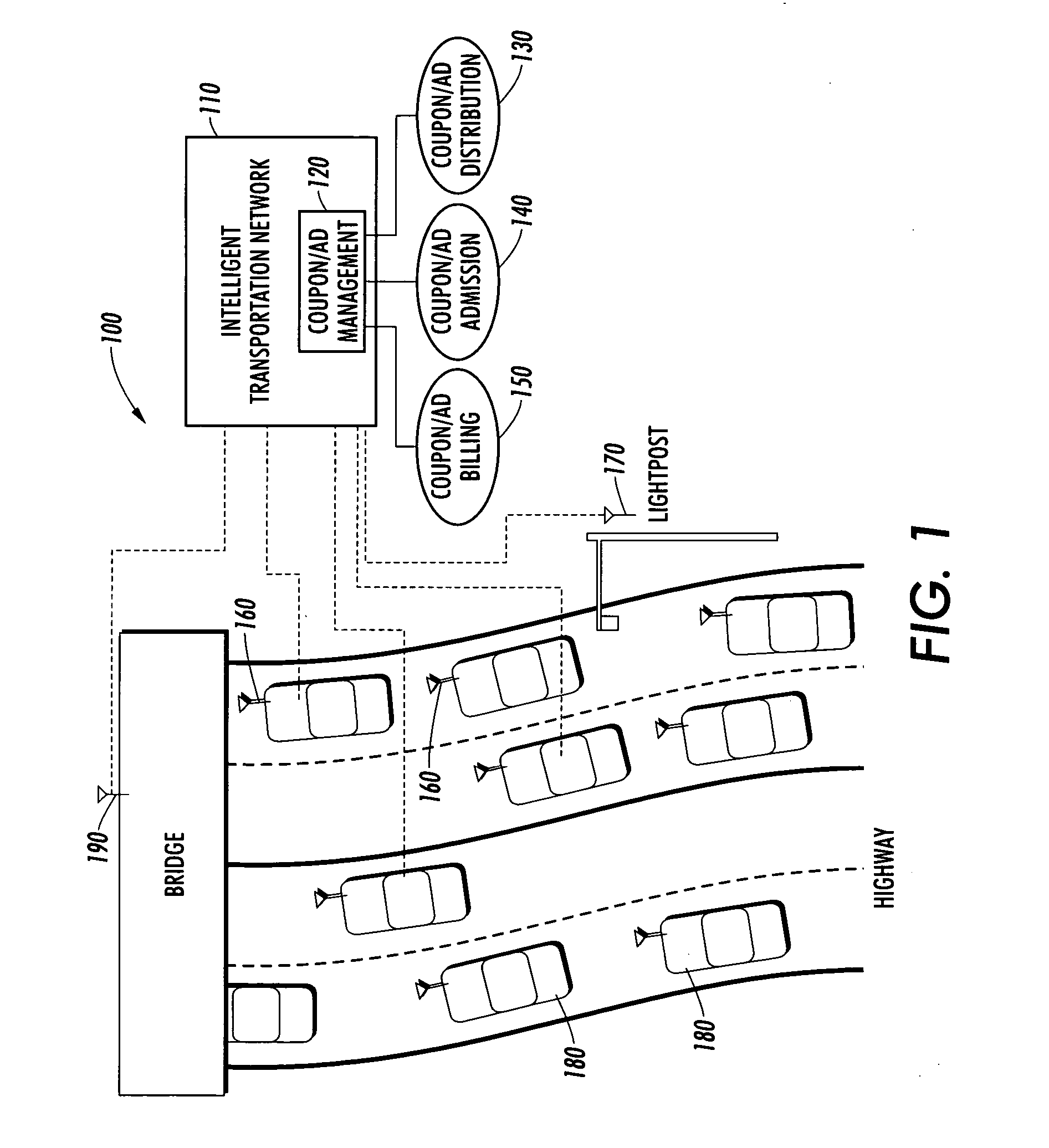
Vehicle network advertising system
InactiveUS20070061057A1Easy to solveOptimize architectureNetwork traffic/resource managementVehicle position/course/altitude controlContext recognitionWorld Wide Web
An architecture for context-aware advertisement and delivery among mobile communication devices over a communication network, in which the architecture is stored and executed as an application for use by network devices. The architecture includes a navigation module, which provides map data vehicles on the network and a context recognition module, which interprets data provided by sensors within the vehicle. Advertising data is received by a data reception module. A configuration module determines presentation slot availability. The value and content of the authenticated advertisement is verified by the advertisement management module; selected advertisements are presented to the vehicle user.
Owner:PALO ALTO RES CENT INC
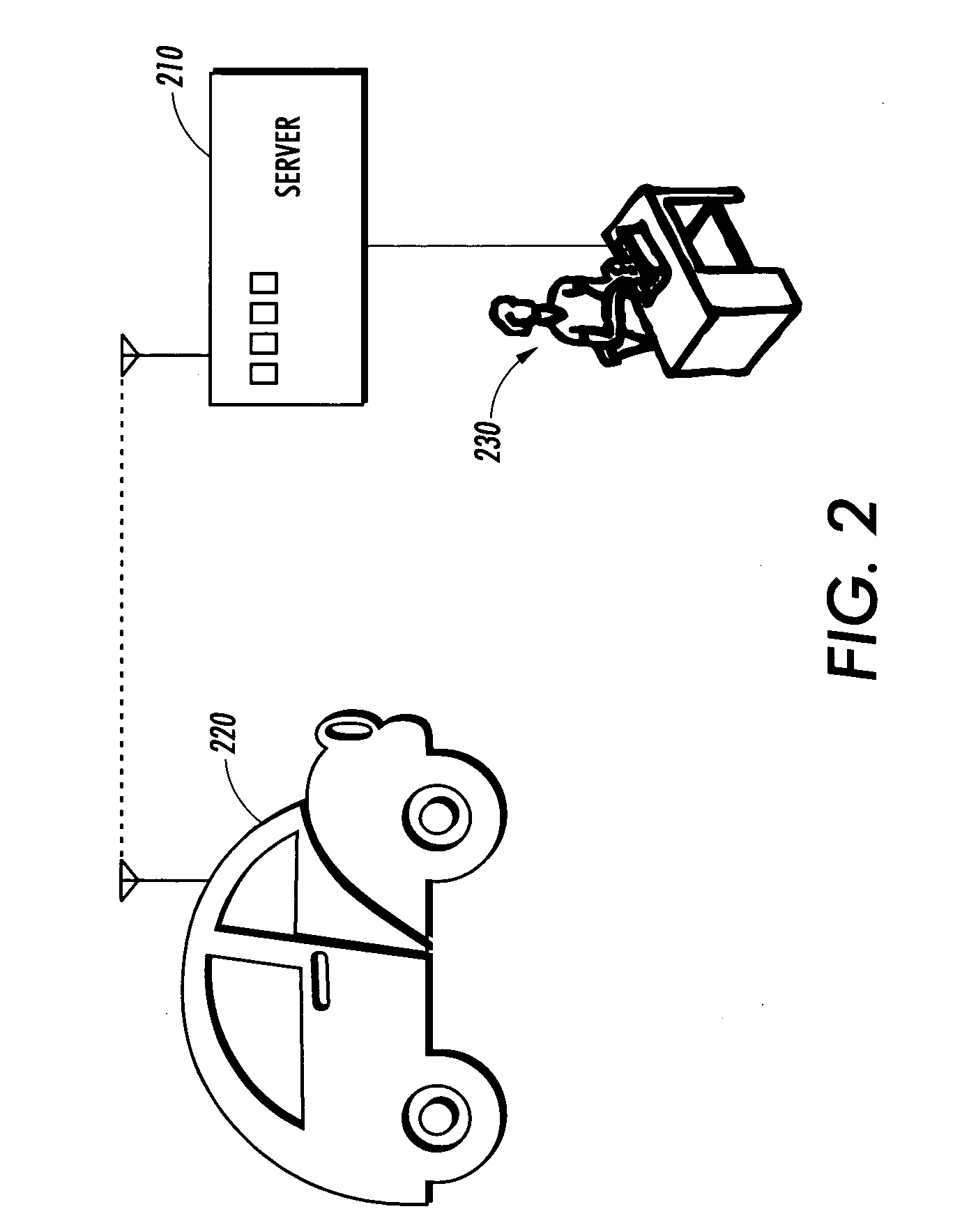
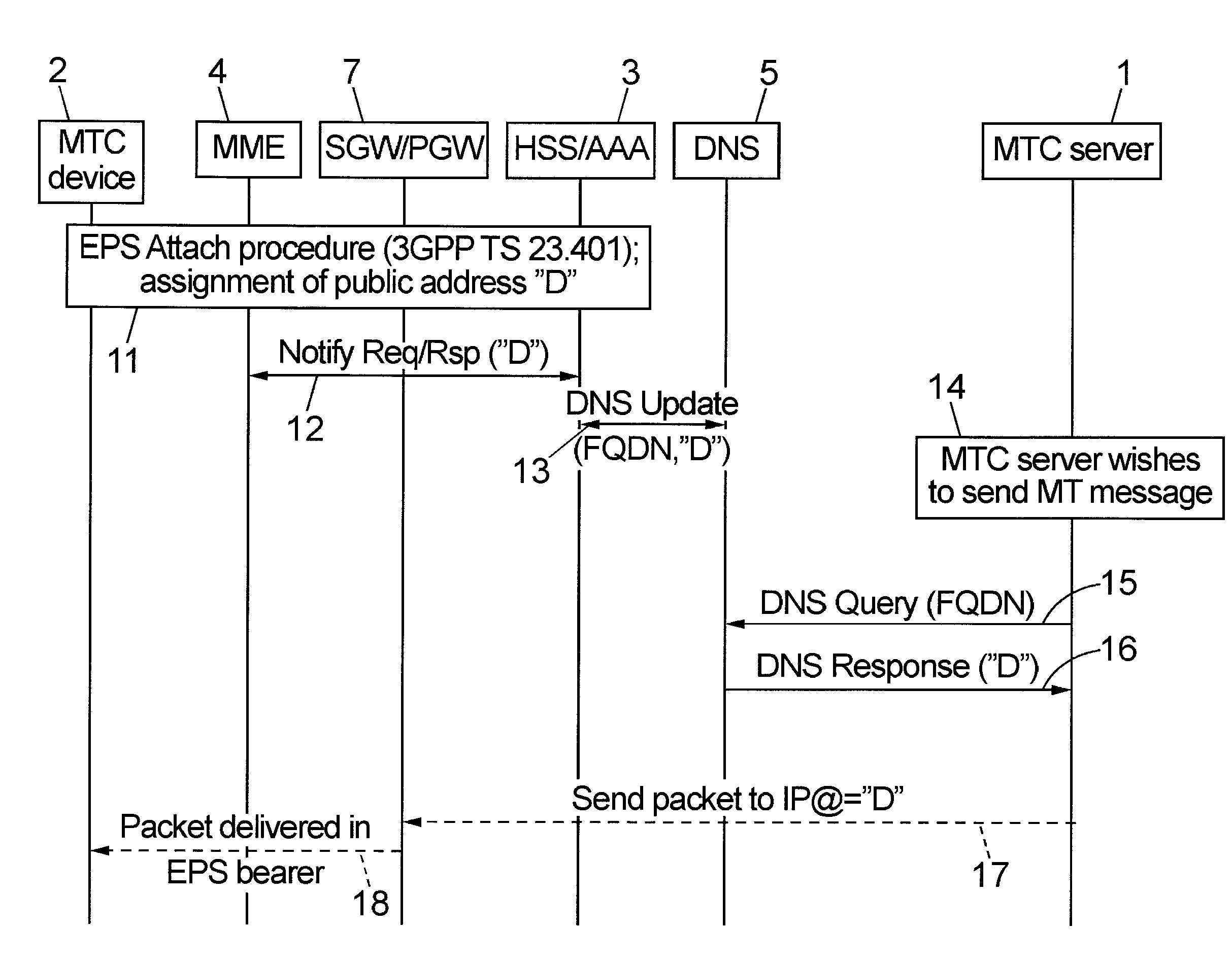
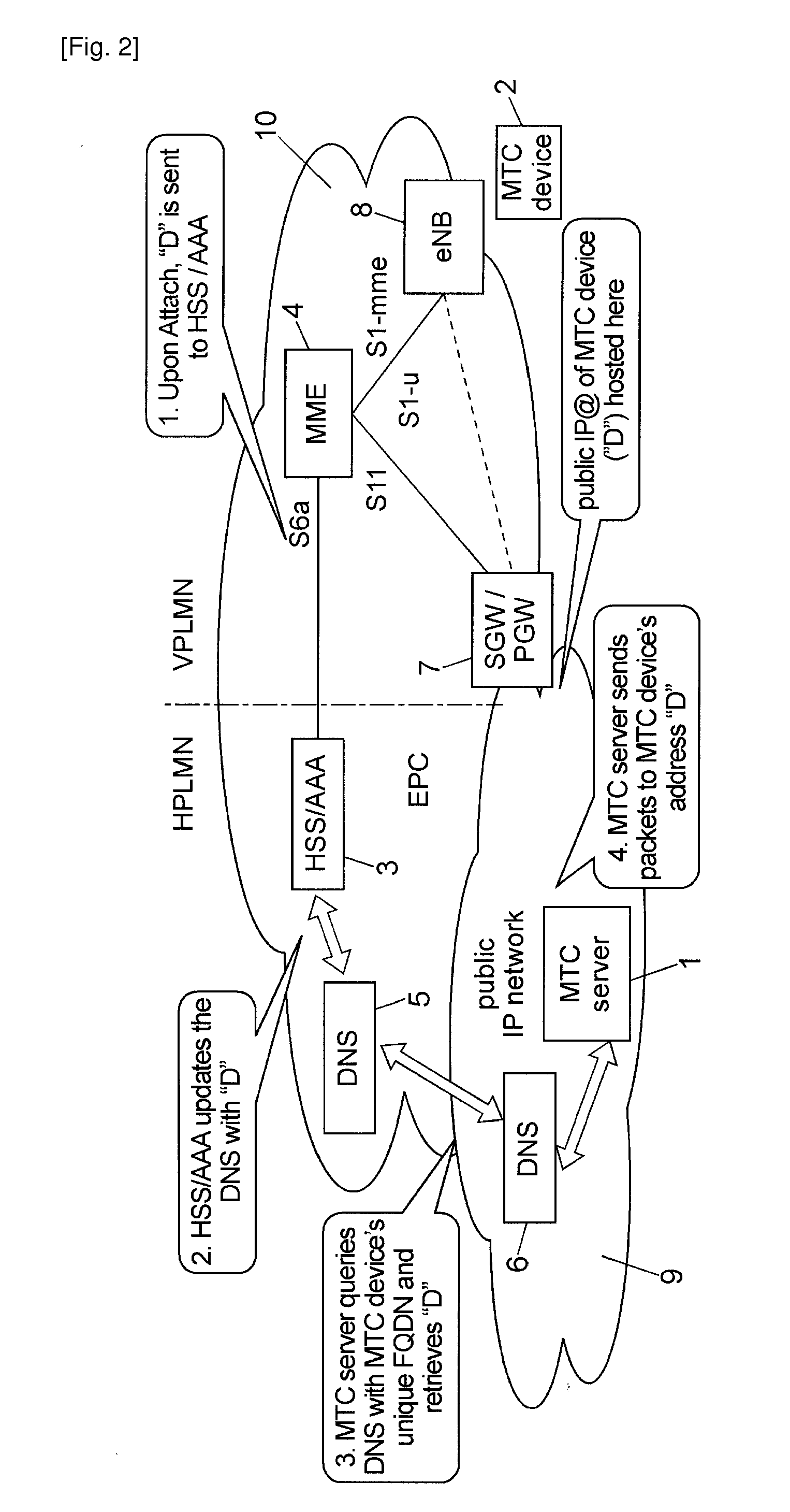
Mobile Terminated Communication Method and Related Devices
ActiveUS20120224516A1Good conditionAvoid complex processConnection managementData switching by path configurationIp addressUnique identifier
Method for allowing a mobile terminated communication to a destination device (2) through at least one mobile communication network (10) from a source entity (1) located in a public IP address network (9). The method comprises: a subscriber server (3) of the mobile communication network receiving an IP address (“D”) of the destination device from a node (4) of the mobile communication network, and the subscriber server updating a DNS record containing a static unique identifier of the destination device stored in an authoritative DNS server (5) reachable via the public IP address network, with said destination device IP address.
Owner:LG ELECTRONICS INC
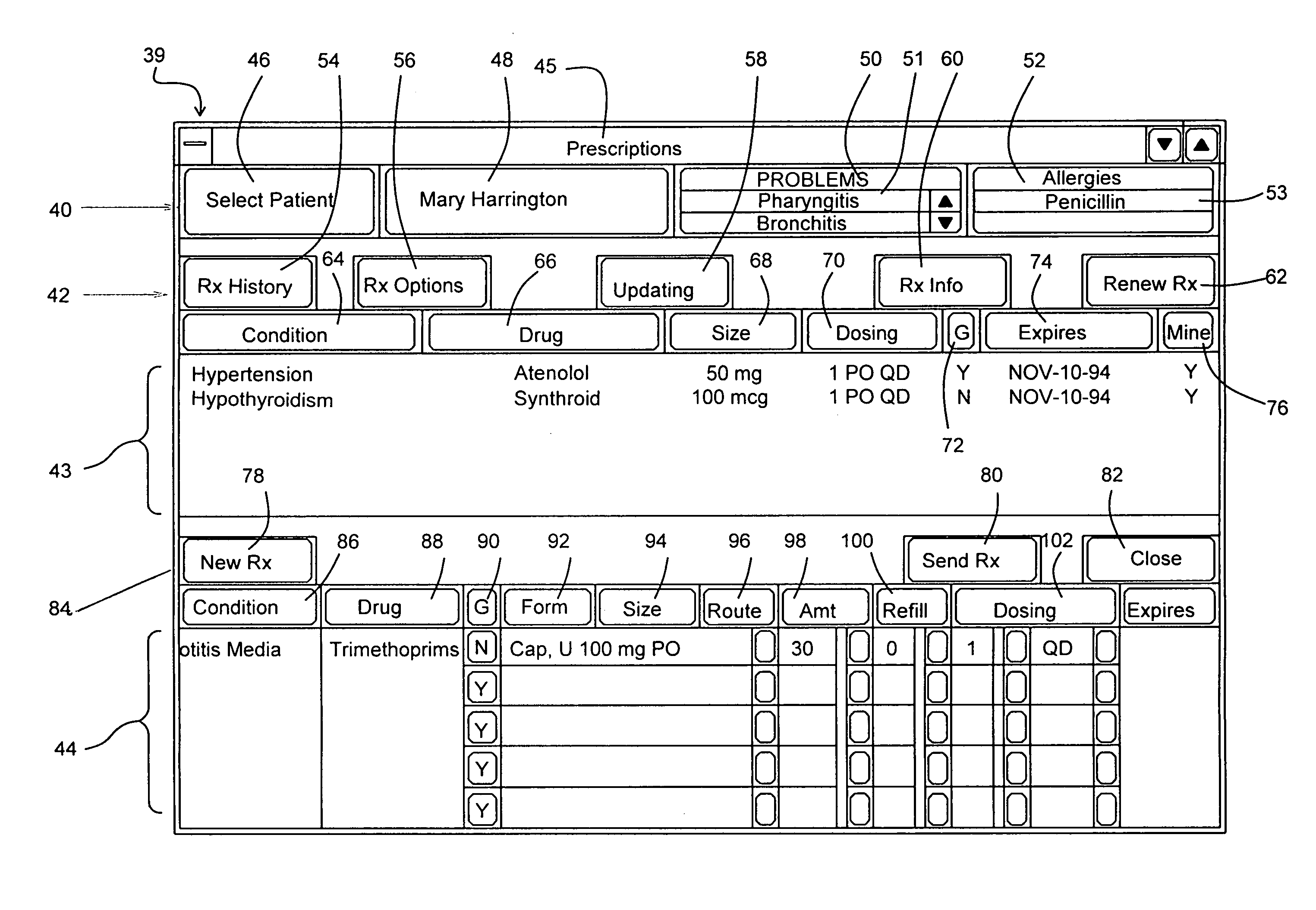
Prescription management system
InactiveUS7072840B1Easy to solveQuality improvementMedical data miningFinanceSoftware systemDrug identification
A prescription creation software system implemented on a computer is provided. The prescription creation software system includes a prescription creation screen display to allow the data capture of information including, patient-identifying data, prescribed drug identification data and drug quantification data. The prescription creation software system additionally provides a prescriber with drug formulary information identifying at least one drug as a patient's drug formulary preference, prior to completion of the prescription.
Owner:CYBEAR
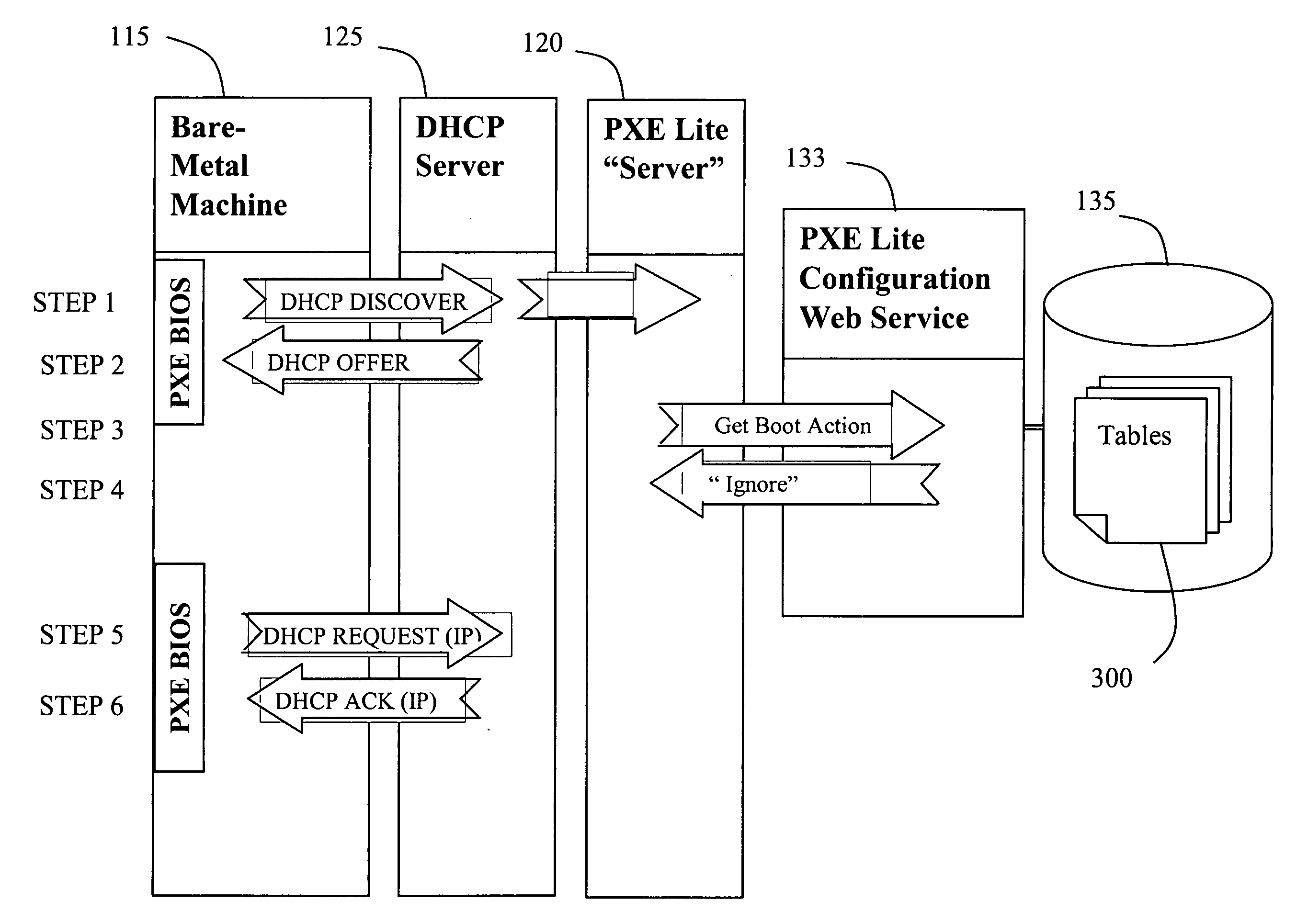
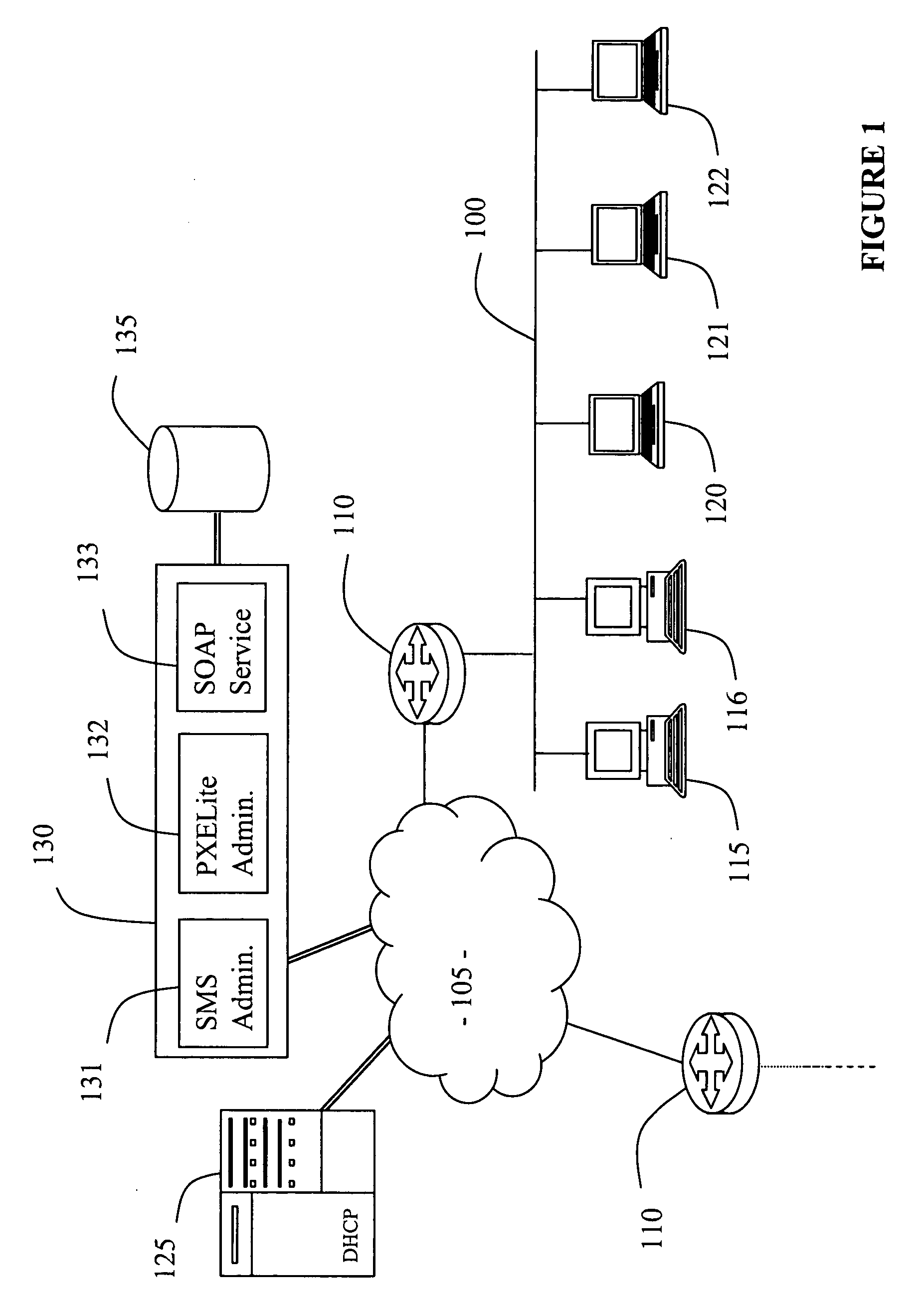
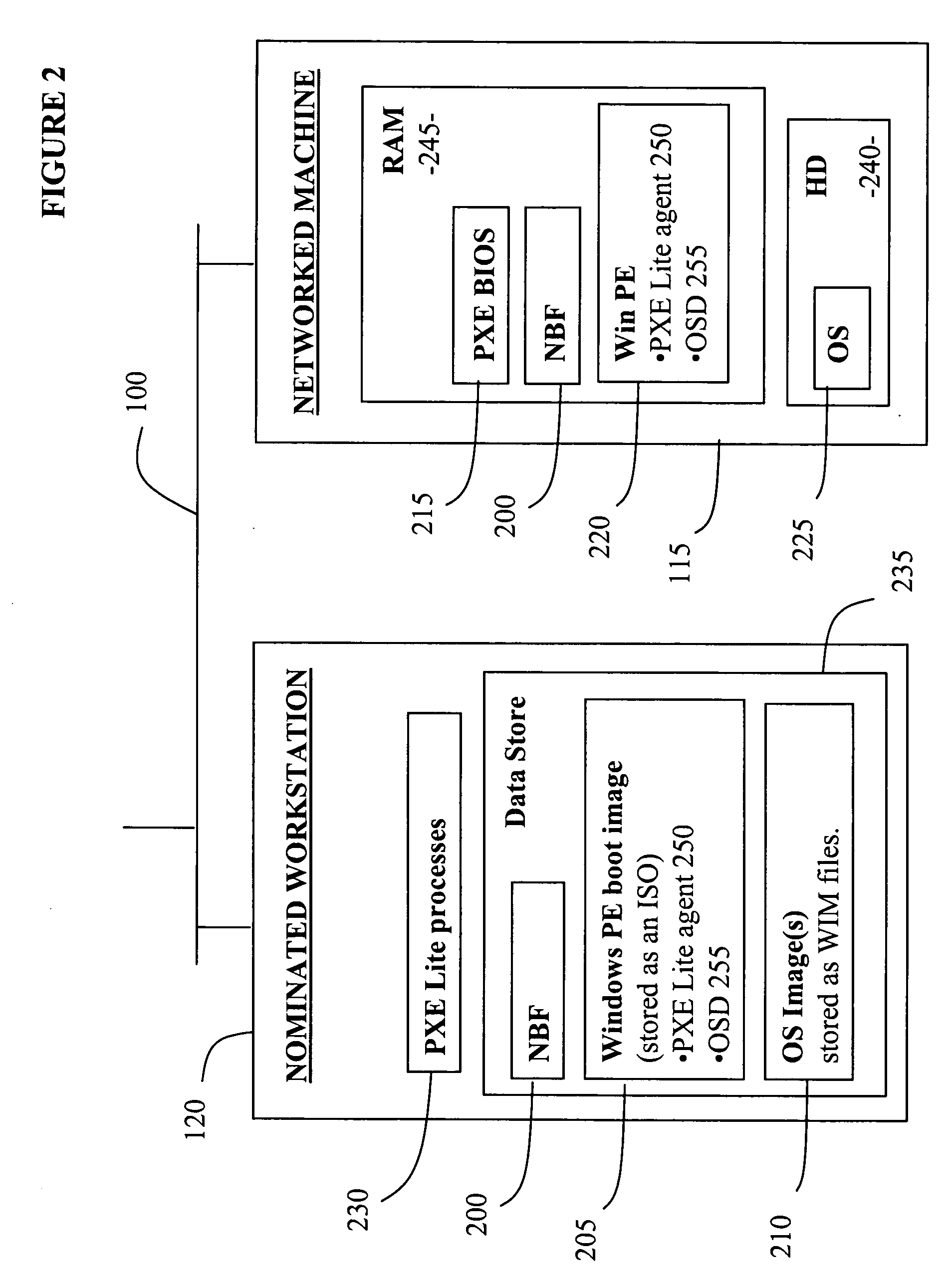
Network booting apparatus and method
ActiveUS20080155245A1Avoid problemsEasy to solveDigital computer detailsProgram controlOperational systemNetwork booting
An operating system deployment arrangement provides a database connected to a network for use in monitoring the boot status of machines connected to sub-networks of the network. A workstation connected to a sub-network is adapted to act as a server for a pre-installation environment to machines newly connecting to the sub-network or at the same geographical location. The workstation carries a program for detecting boot initiation messages broadcast on the sub-network and for progressing booting of newly connecting machines in accordance with boot action data held by the database. In particular, the workstation also sends a software agent and operating system deployment processes to a newly connected machine and the agent takes over progression of the booting process from the workstation. The data held in the database for any one machine is updated as booting progresses. Flexibility is provided both in administration of the boot action data held in the database and by means of user interaction software loaded to a newly connected machine in the course of booting.
Owner:1E LTD
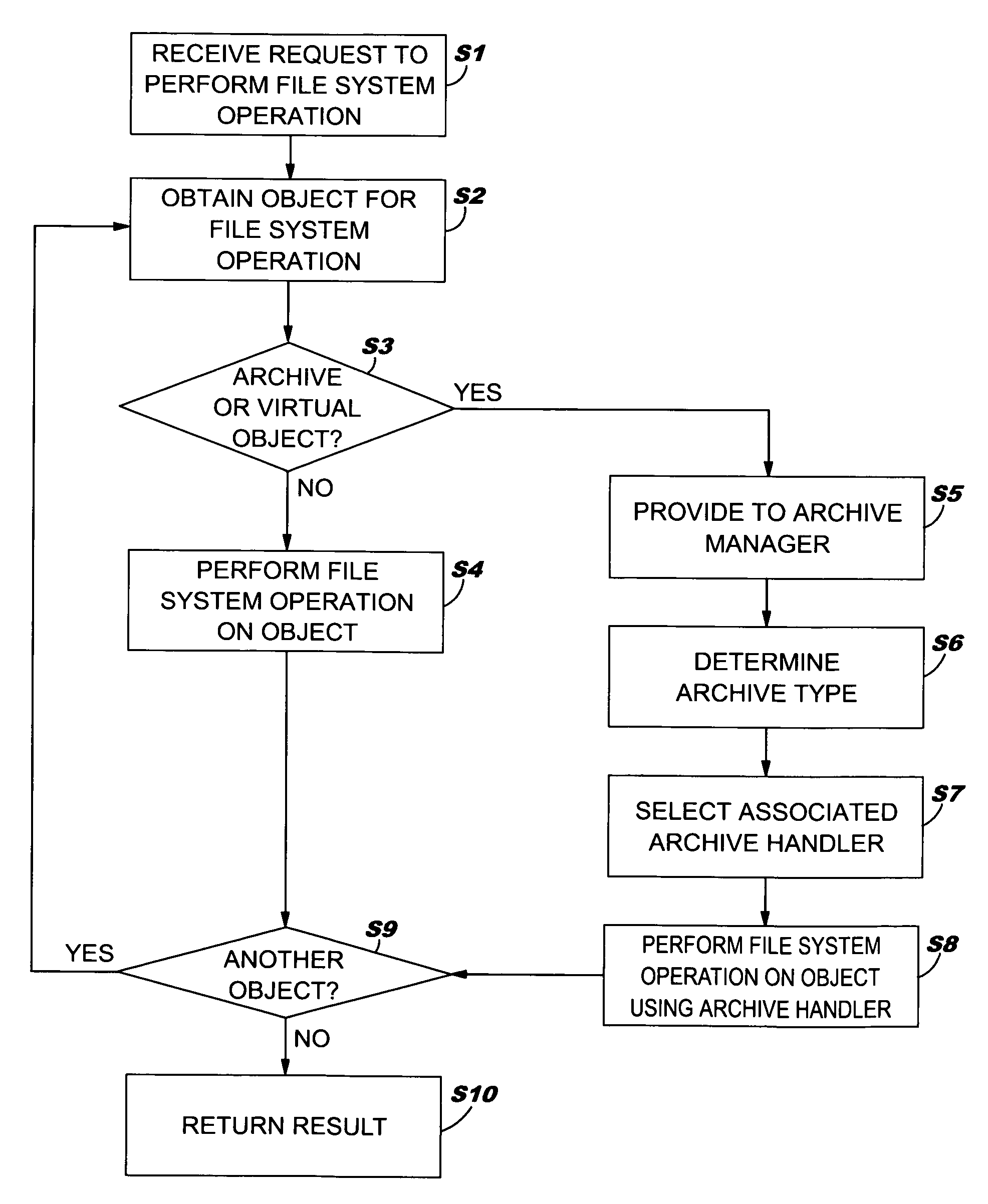
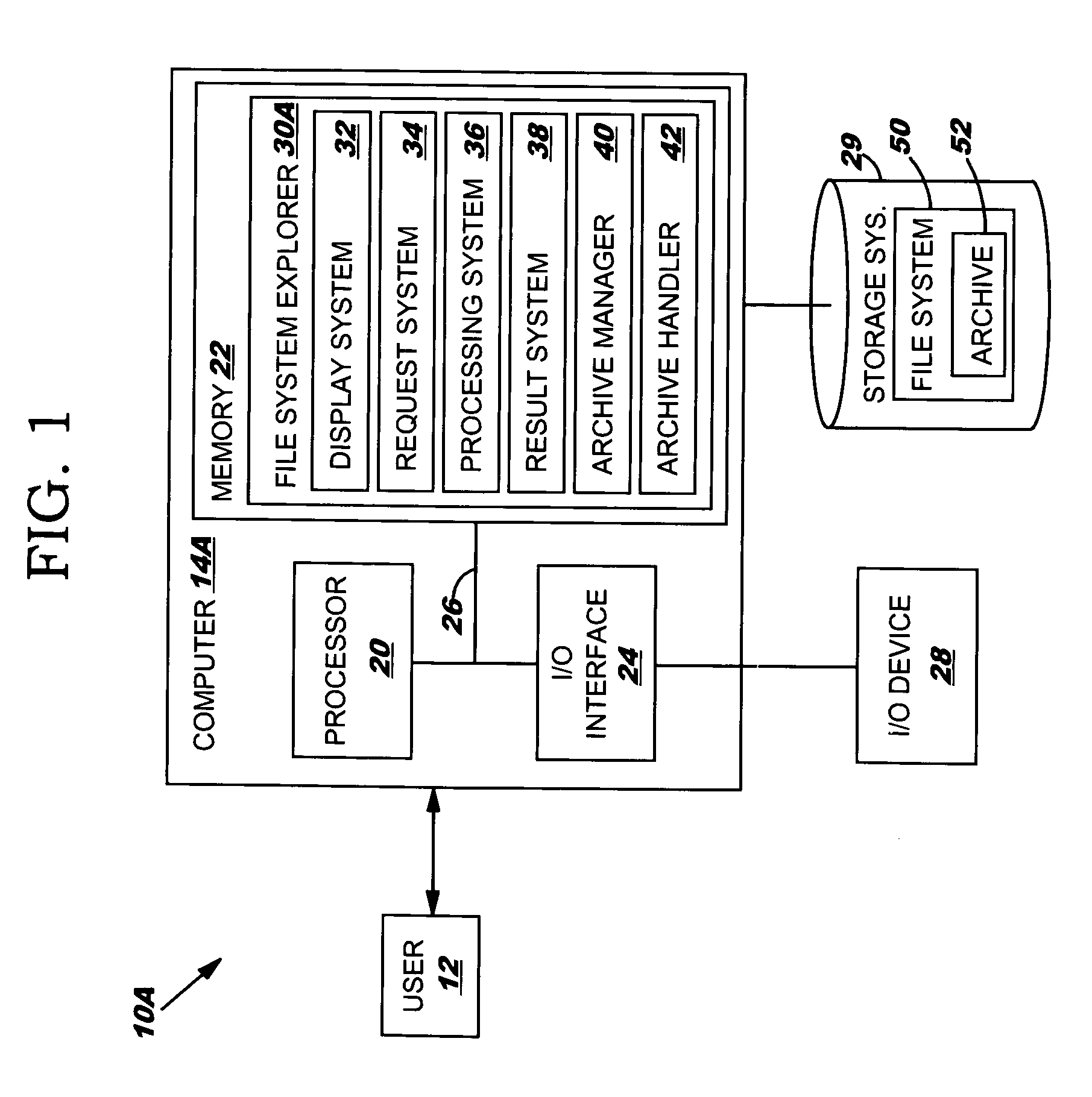
Method, system and program product for managing a file system that includes an archive
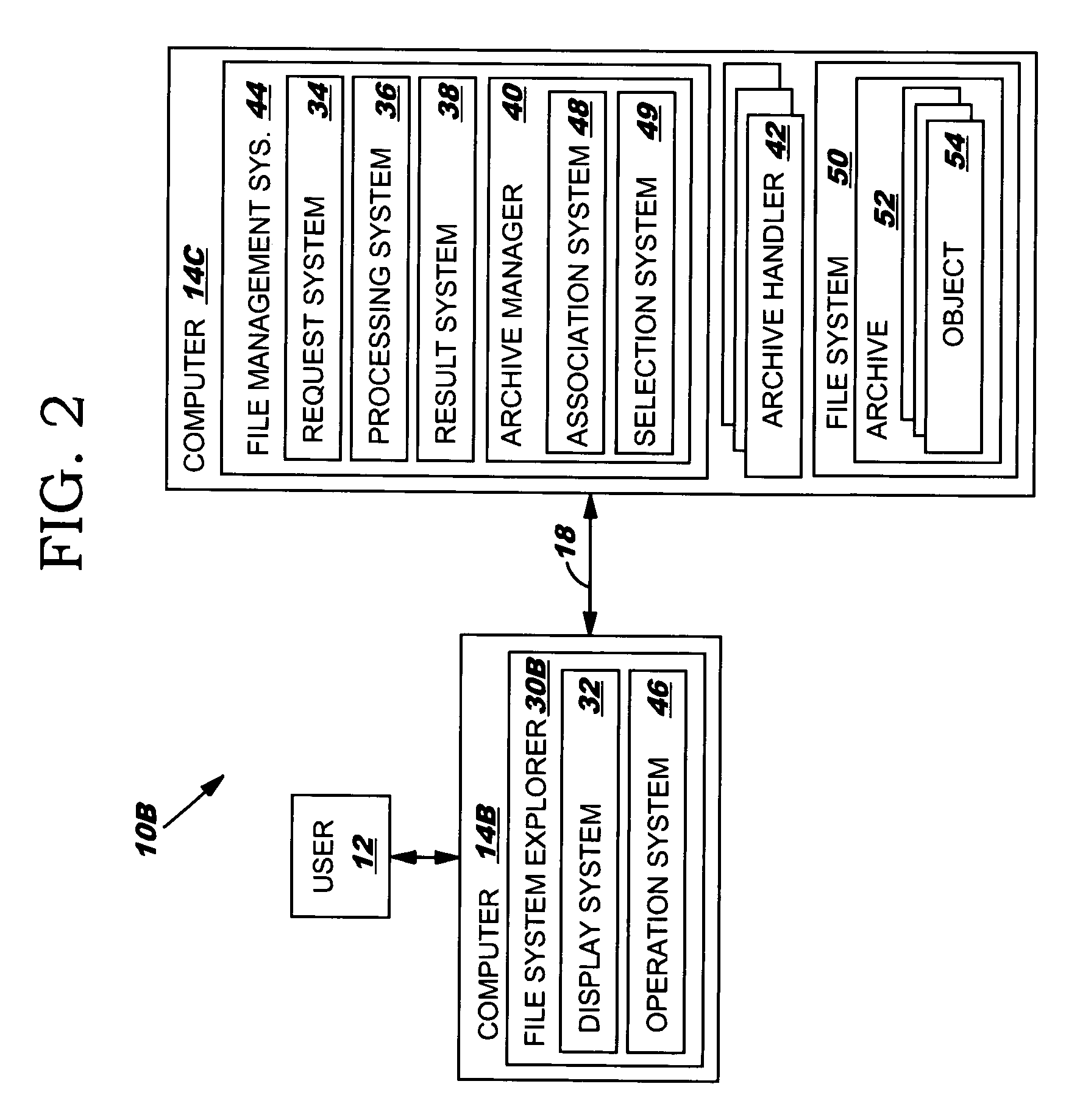
ActiveUS7730035B2Enables local performanceEasy to solveDigital data processing detailsSpecial data processing applicationsFile systemDatabase
An improved solution for managing a file system that includes an archive is provided. In particular, a request for a file system operation can be received and performed on an object that is stored in an archive. The file system operation can be received from a first computer and performed on the object on a second computer. Further, an archive manager can be included that manages an extensible set of archive handlers. In this case, each archive handler can implement a set of file system operations for archives of a particular archive type.
Owner:TWITTER INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com