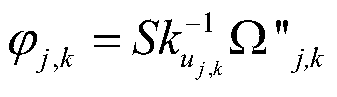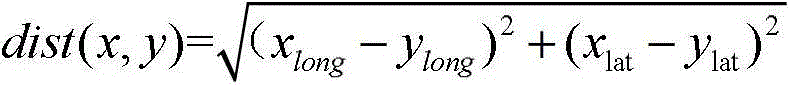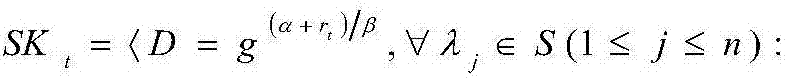Patents
Literature
268 results about "Mobile cloud" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
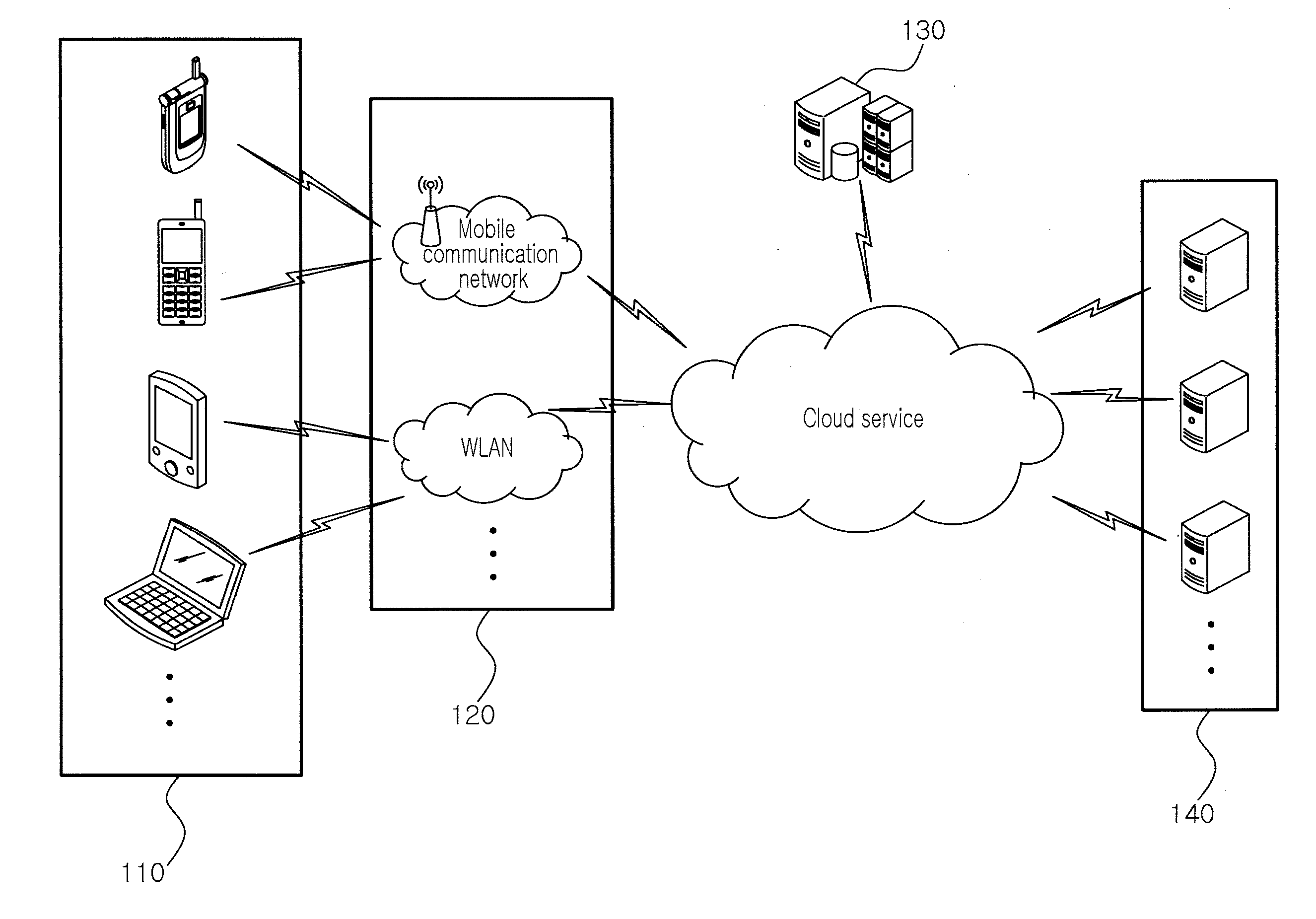
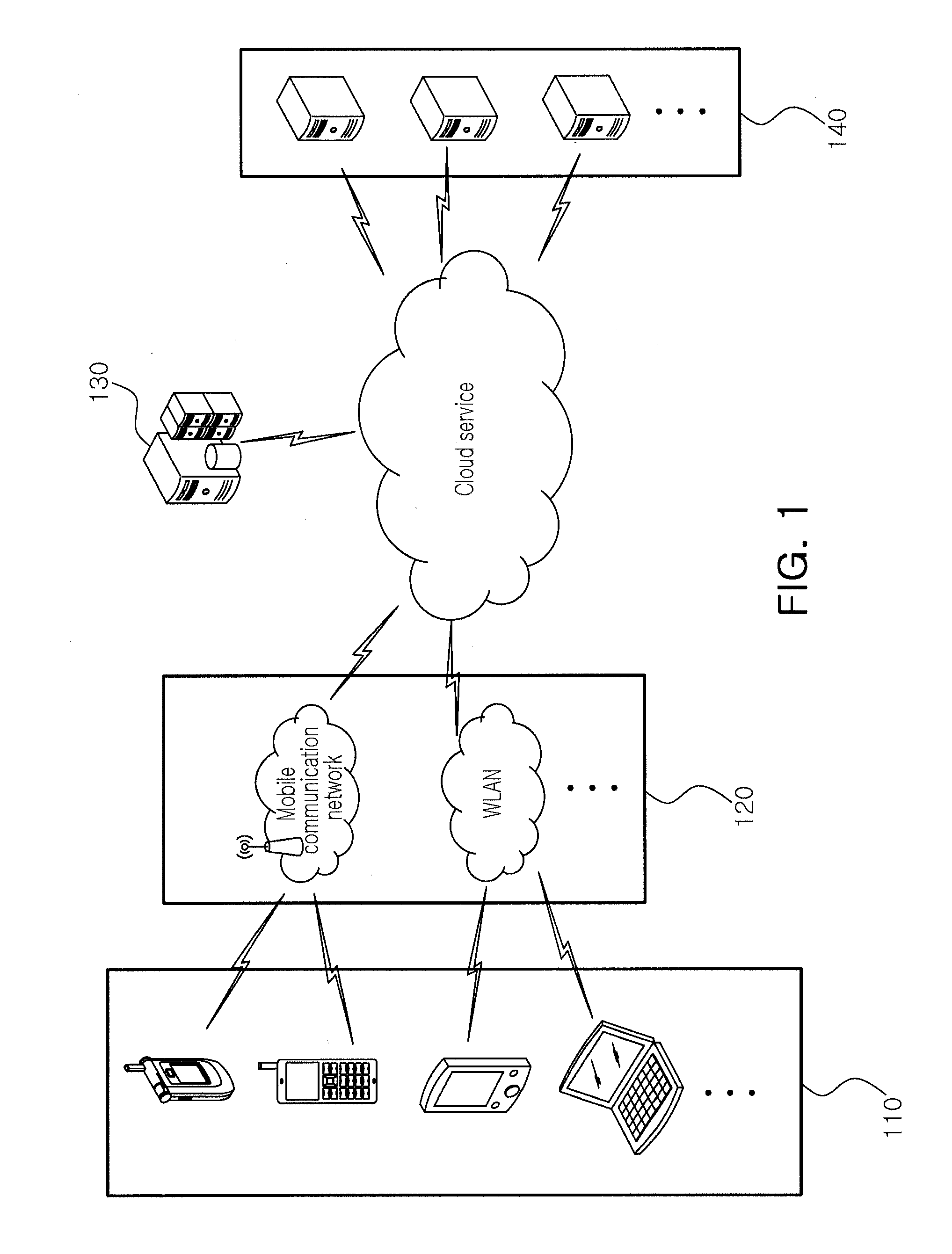
Mobile terminal for providing mobile cloud service and operation method thereof
InactiveUS20110093567A1Easy to solveMultiple digital computer combinationsProgram controlMobile cloudComputer terminal
A mobile terminal for using a mobile cloud service and an operation method of the mobile terminal are disclosed. The mobile terminal accessible to a mobile cloud server, including: a mobile cloud terminal platform accessing the mobile cloud server to acquire a cloud application, and providing a mobile cloud service by using the acquired cloud application; a local terminal platform executing a local application installed in the mobile terminal; and an operating system (OS) selectively driving one of the mobile cloud terminal platforms and the local platform according to a user set environment.
Owner:ELECTRONICS & TELECOMM RES INST
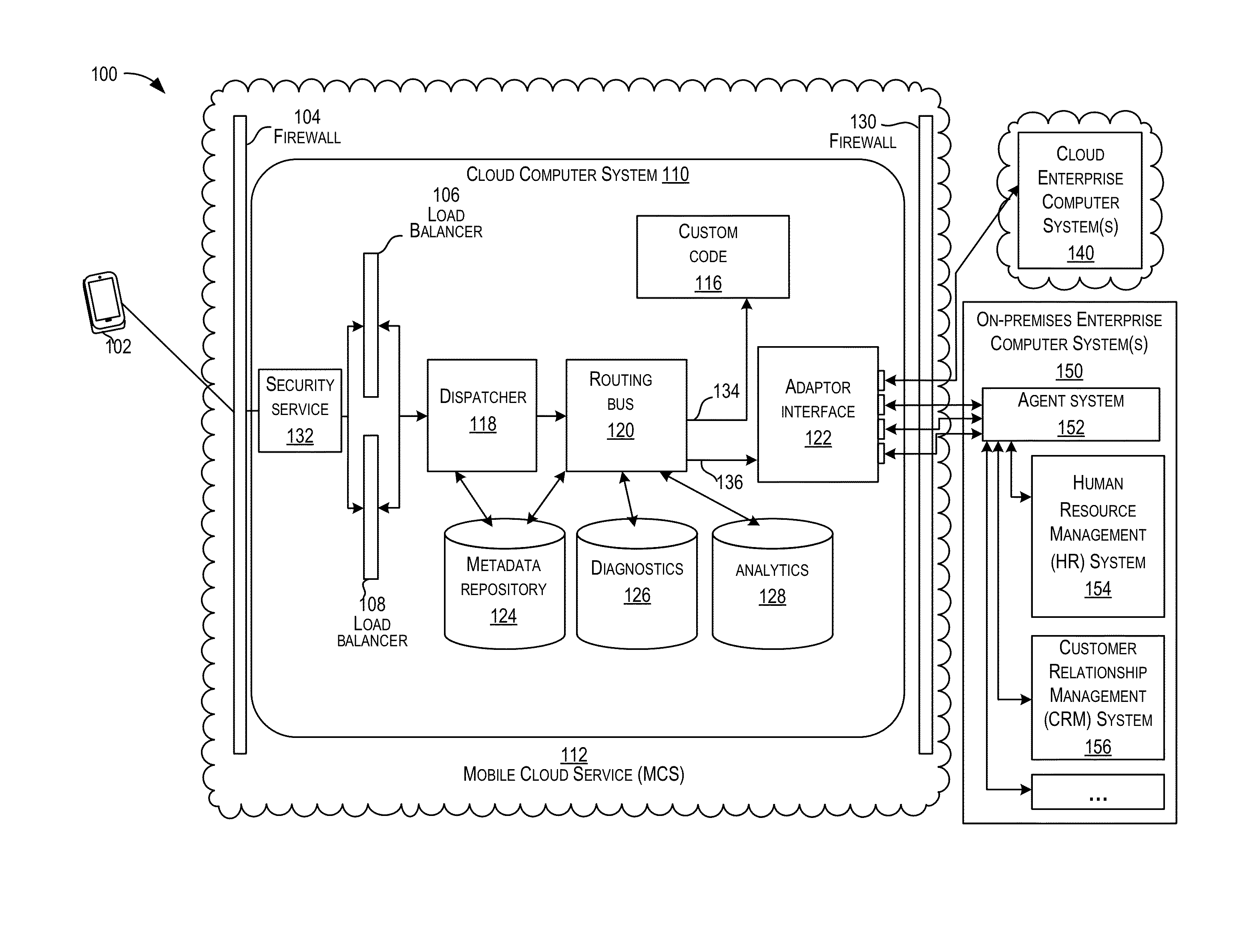
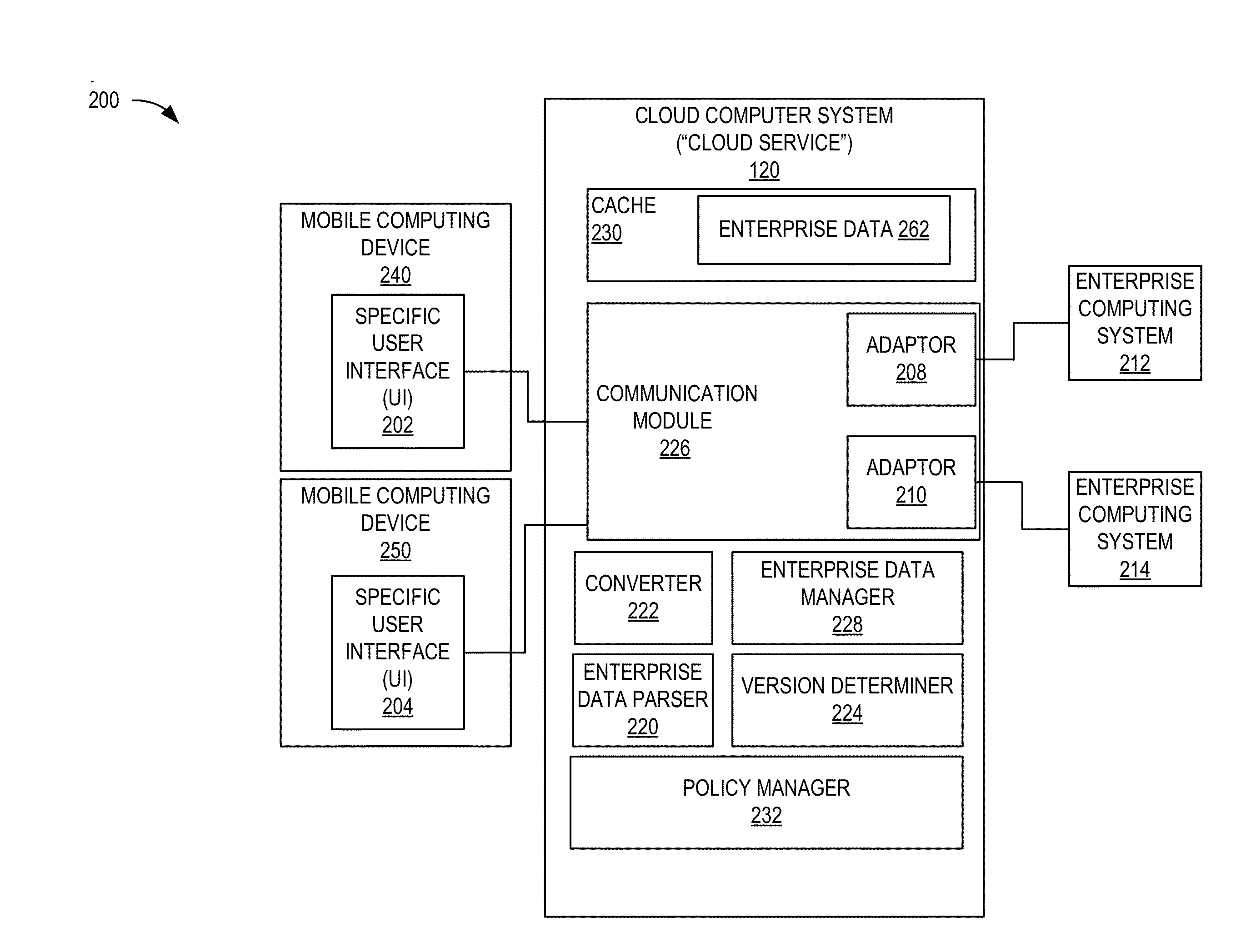
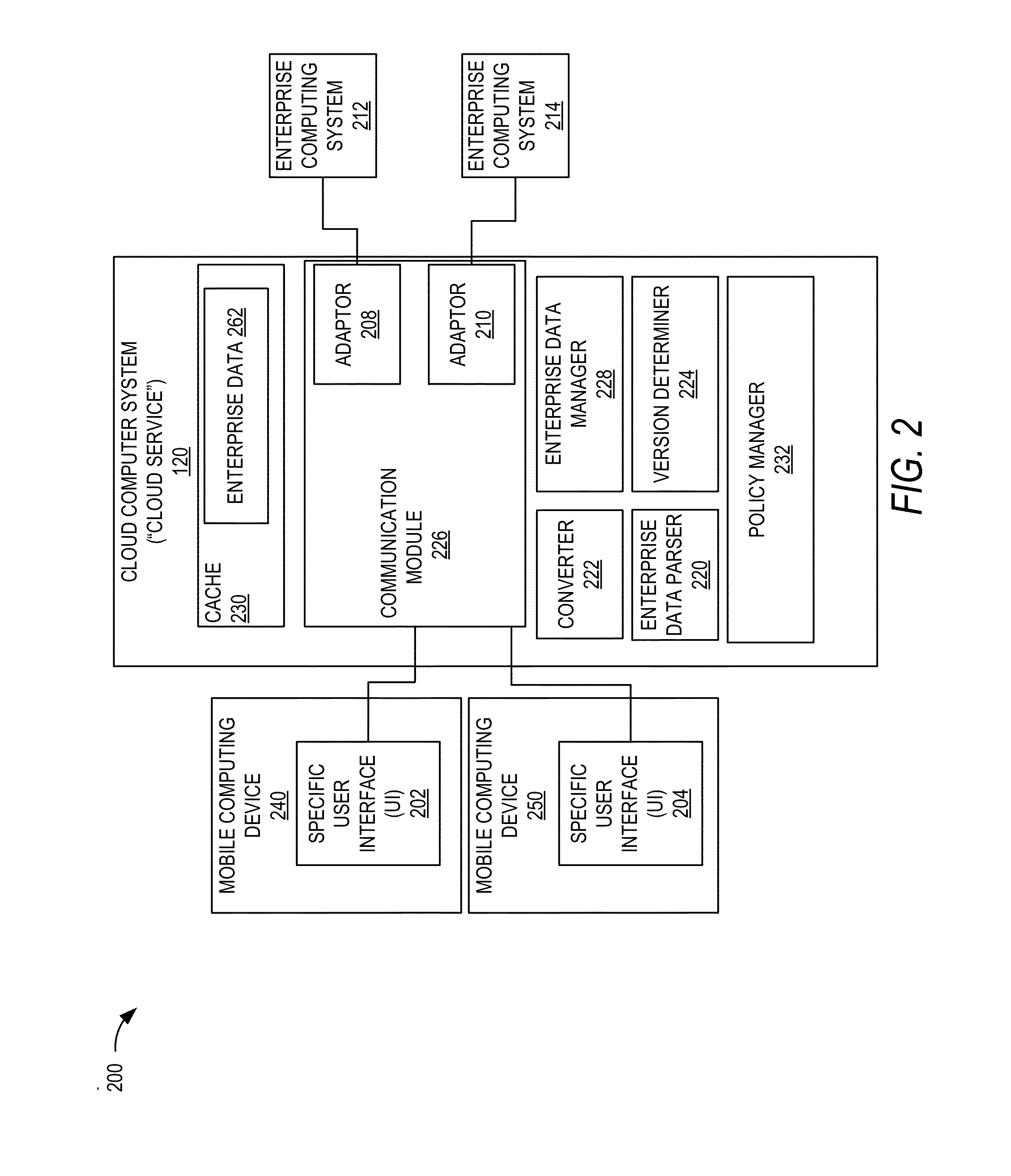
Mobile cloud service architecture
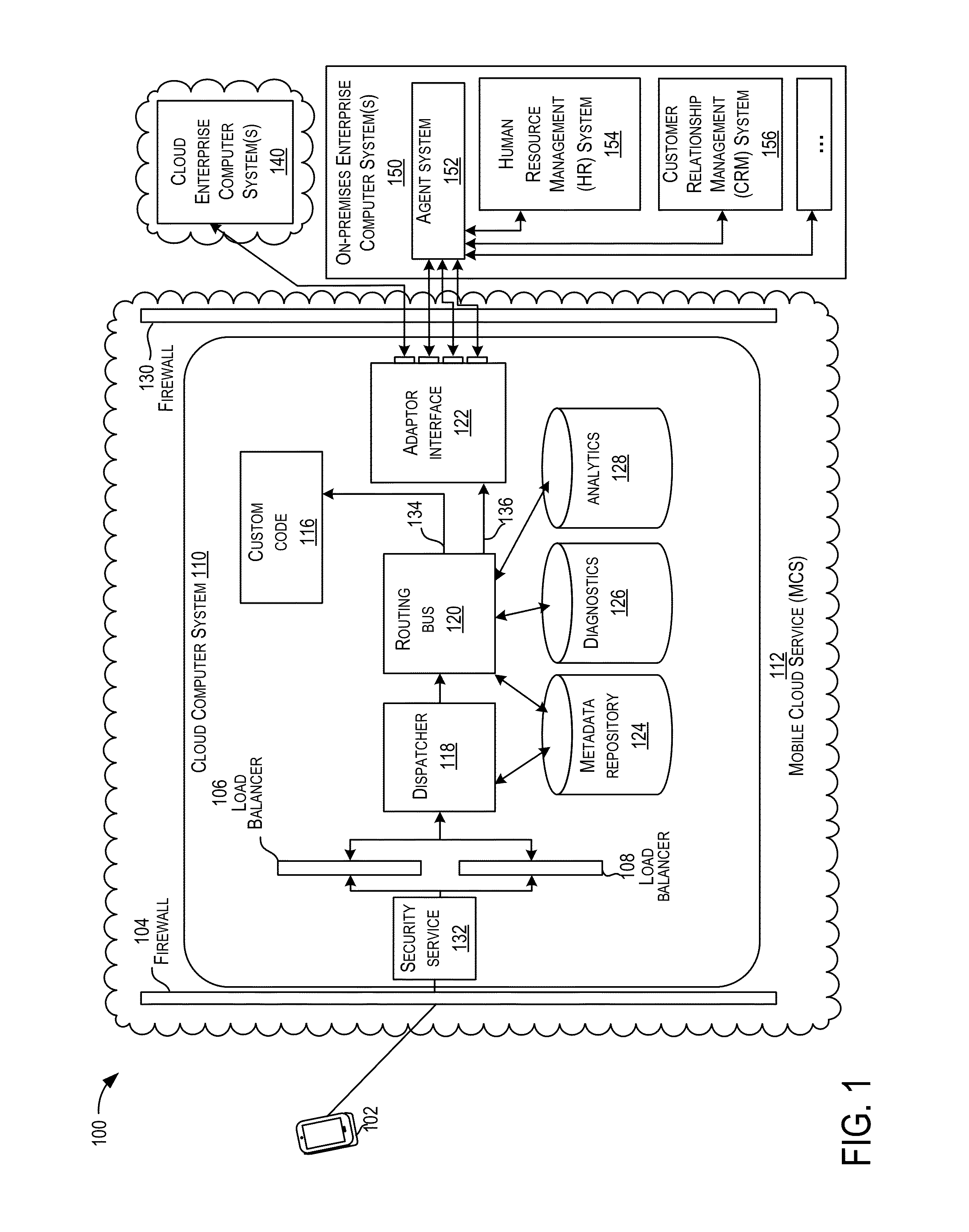
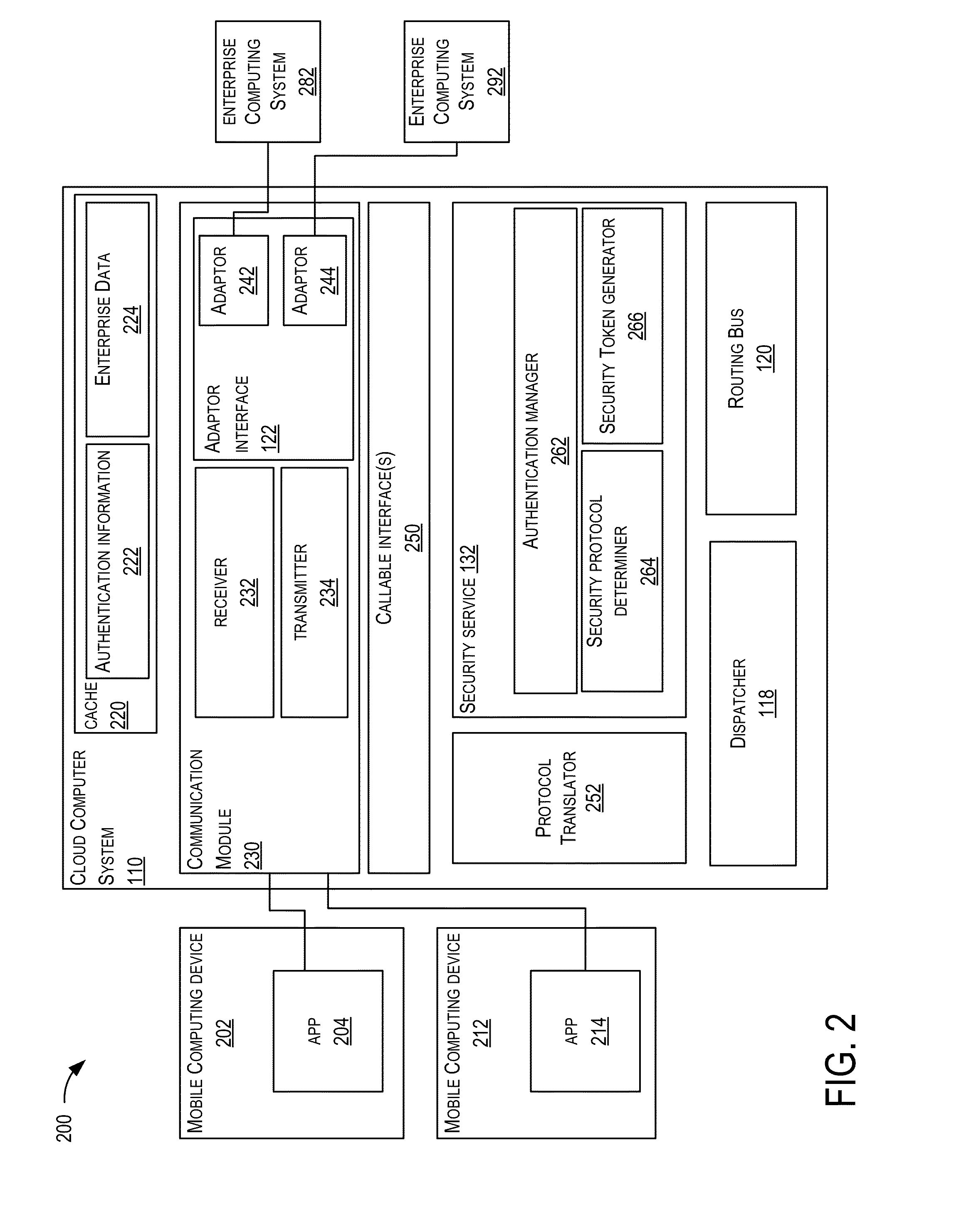
ActiveUS20150229638A1Facilitate communicationDigital data processing detailsInformation formatMobile cloudBusiness enterprise
Techniques are described for implementing a cloud computer system to facilitate communication between a computing device (e.g., a mobile computing device) and enterprise computer systems. In certain embodiments, the cloud computer system may receive, from a computing device, a request for a service provided by an enterprise computer system. The cloud computer system may determine security authentication of a user for the requested service. A security protocol may be determined for a requested enterprise computer system and a security token may be generated for the request according to the determined security protocol. The request may be sent to the requested enterprise computer system. In some embodiments, security authentication for a request to an enterprise computer system may be determined based on previous authentication. The cloud computer system may be configured to communicate with several different enterprise computer systems according to their supported protocols (e.g., communication protocol and / or security protocol).
Owner:ORACLE INT CORP
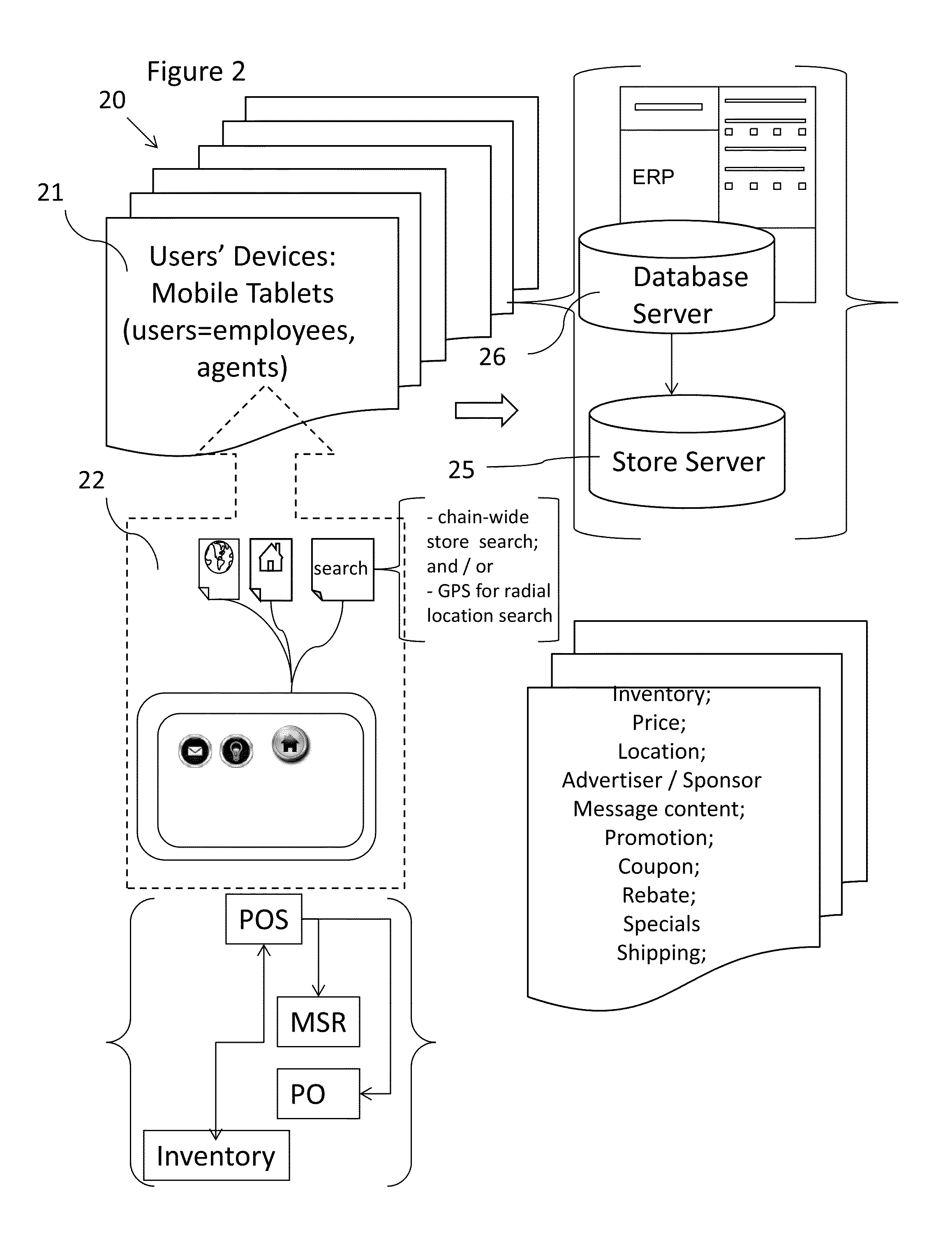
Store mobile cloud application system for inventory management and customer order fulfillment and method for retail establishment
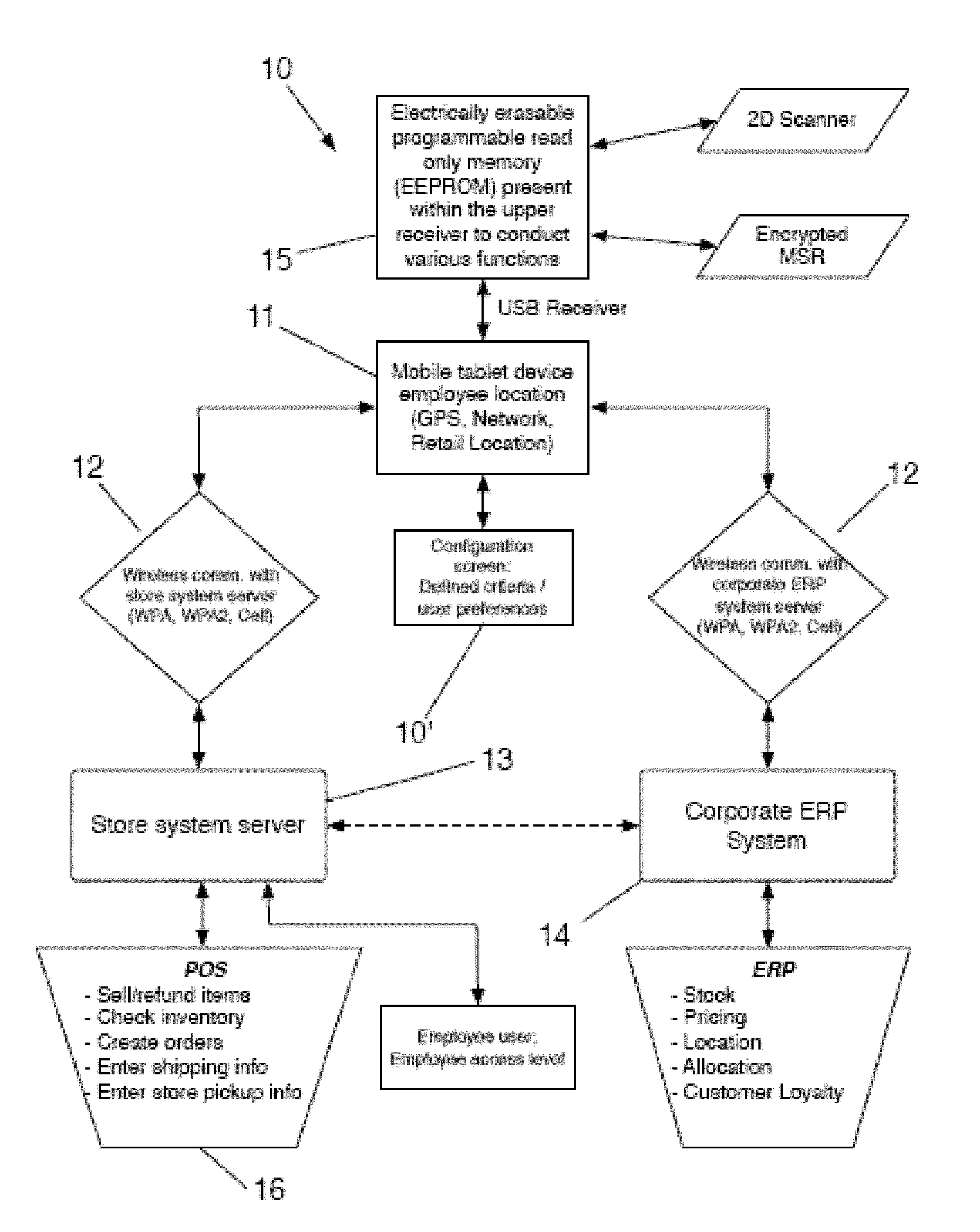
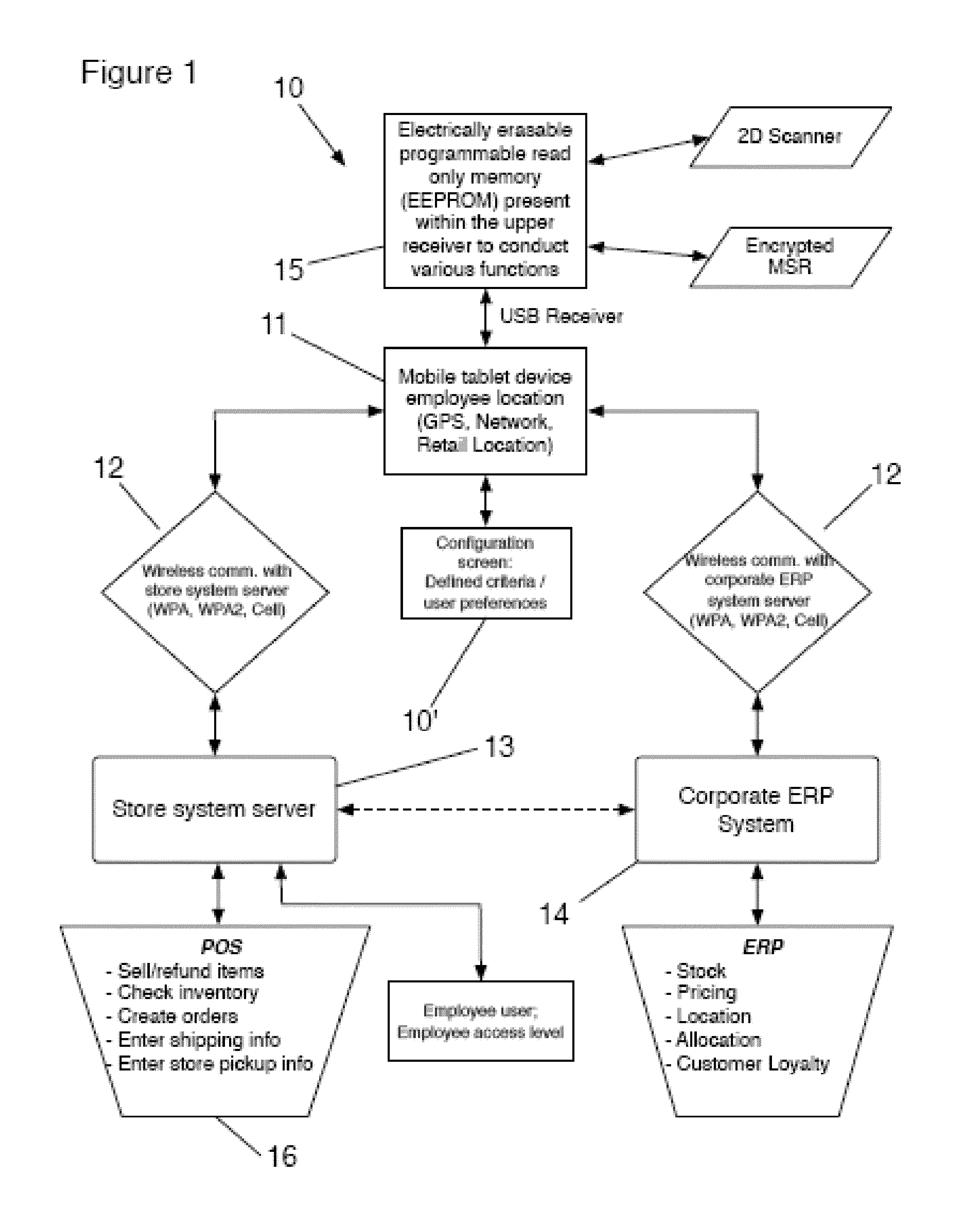
ActiveUS20140249947A1Improved sale environmentImprove the environmentHand manipulated computer devicesPayment architectureOrder fulfillmentMobile cloud
A store mobile cloud application system executes a retail store purchasing system having plurality of barcode scanners and scan guns integrated with a mobile tablet device carried by employees. The mobile tablet device is rotatably attached to a base housing directly below it connected by a base mount universal receiver with rotatable coupling. The Main PCB has an EEPROM controlling operations of the USB devices including the scanner and an MSR. The mobile tablet device has mobile applications which allow wireless communication with a POS store systems server and the corporate ERP system, and also commands the EEPROM. Scanned data involving a product to be purchased is received by the mobile tablet device and sent wirelessly to the POS store systems server to obtain product data. The allocation of inventory sold, but not available in the store, are processed real-time through the corporate ERP system and available for review chain-wide.
Owner:RETAIL TECH
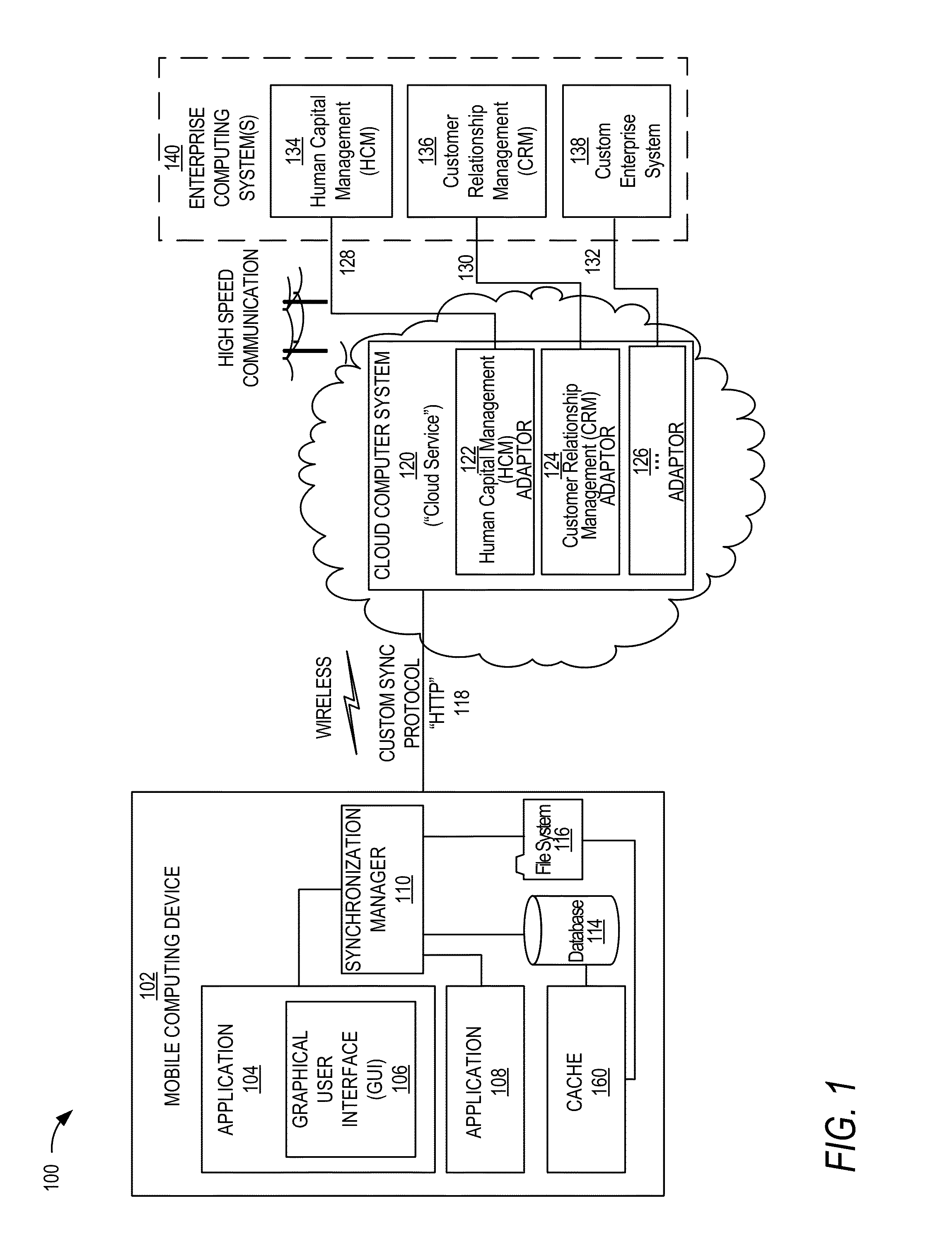
Infrastructure for synchronization of mobile device with mobile cloud service
ActiveUS20150278245A1Good synchronizationEasy to identifyDigital data information retrievalDigital data processing detailsHuman resource managementMobile cloud
Techniques are described for implementing a cloud computer system (e.g., “a cloud service”) for facilitating the synchronization of enterprise data between mobile computing devices and enterprise computing systems (e.g., human resource management systems, business management systems, or the like). The cloud service may convert enterprise data received from different enterprise computing systems to a format that can be managed and updated easily by mobile computing devices. The converted format may enable distinct information to be easily identified. The enterprise data may be associated with policy information and version information to manage synchronization of the enterprise data. In some embodiments, the cloud service may manage synchronization with mobile computing devices based on classification of a communication connection the mobile computing devices have to a wireless network. The communication connection may be used to determine a manner for synchronizing enterprise data between the mobile computing devices and the cloud computer system.
Owner:ORACLE INT CORP
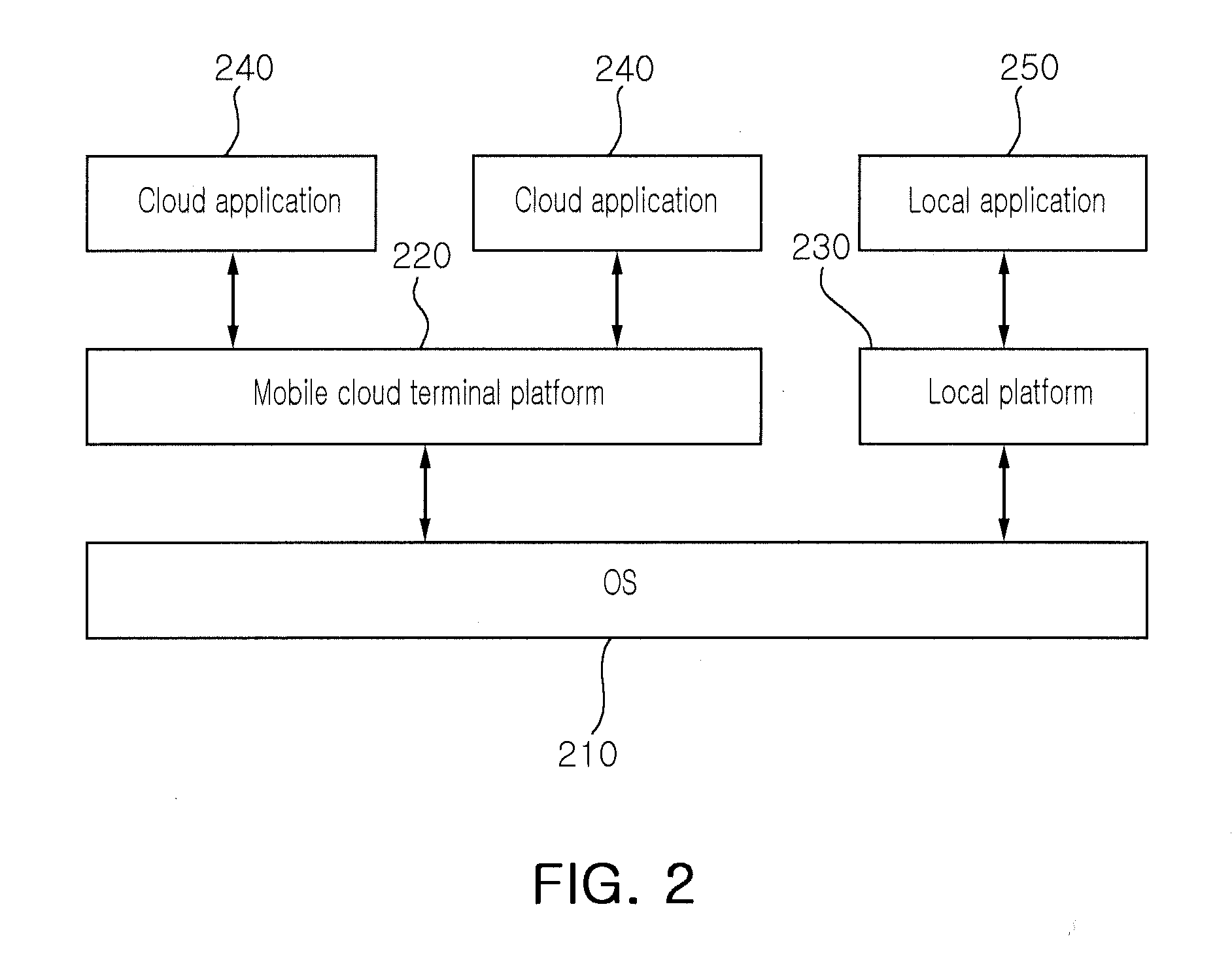
Mobile terminal device inlcuding mobile cloud platform
InactiveUS20100248698A1Special service for subscribersMultiple digital computer combinationsVirtualizationMobile cloud
Provided is a mobile terminal device including a mobile cloud platform. The mobile cloud platform includes a mobile cloud platform layer, a mobile cloud application layer, and a mobile cloud service layer. The mobile cloud platform layer virtualizes resources provided from the mobile terminal device. The mobile cloud application layer provides a service requested by a user to the user through a virtual mobile terminal user interface. The mobile cloud service layer provides the requested service constantly regardless of a change of mobile terminal environment. The mobile terminal device forms a mobile cloud together with other mobile terminal devices. Each of the mobile terminal devices includes a mobile cloud platform.
Owner:ELECTRONICS & TELECOMM RES INST
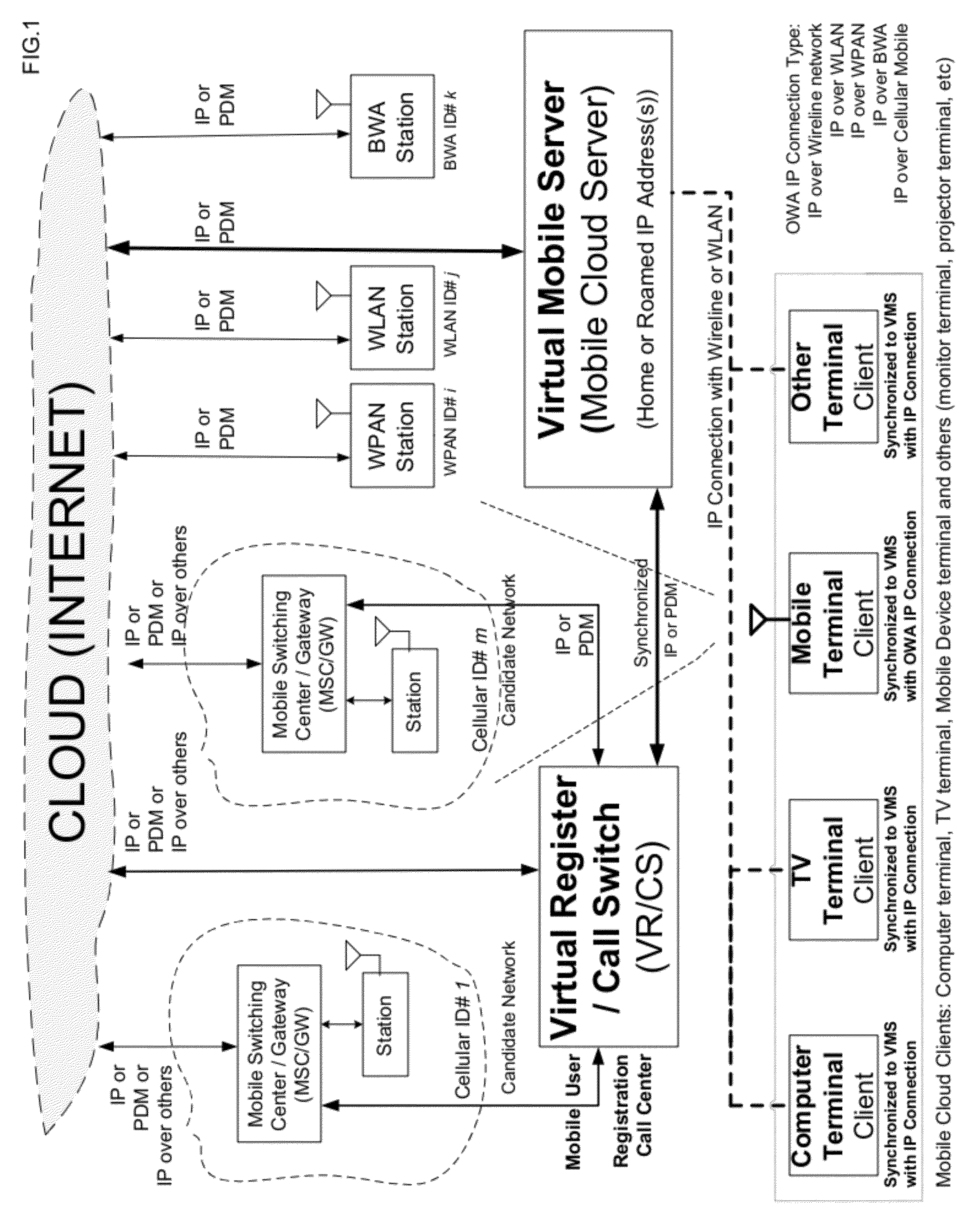
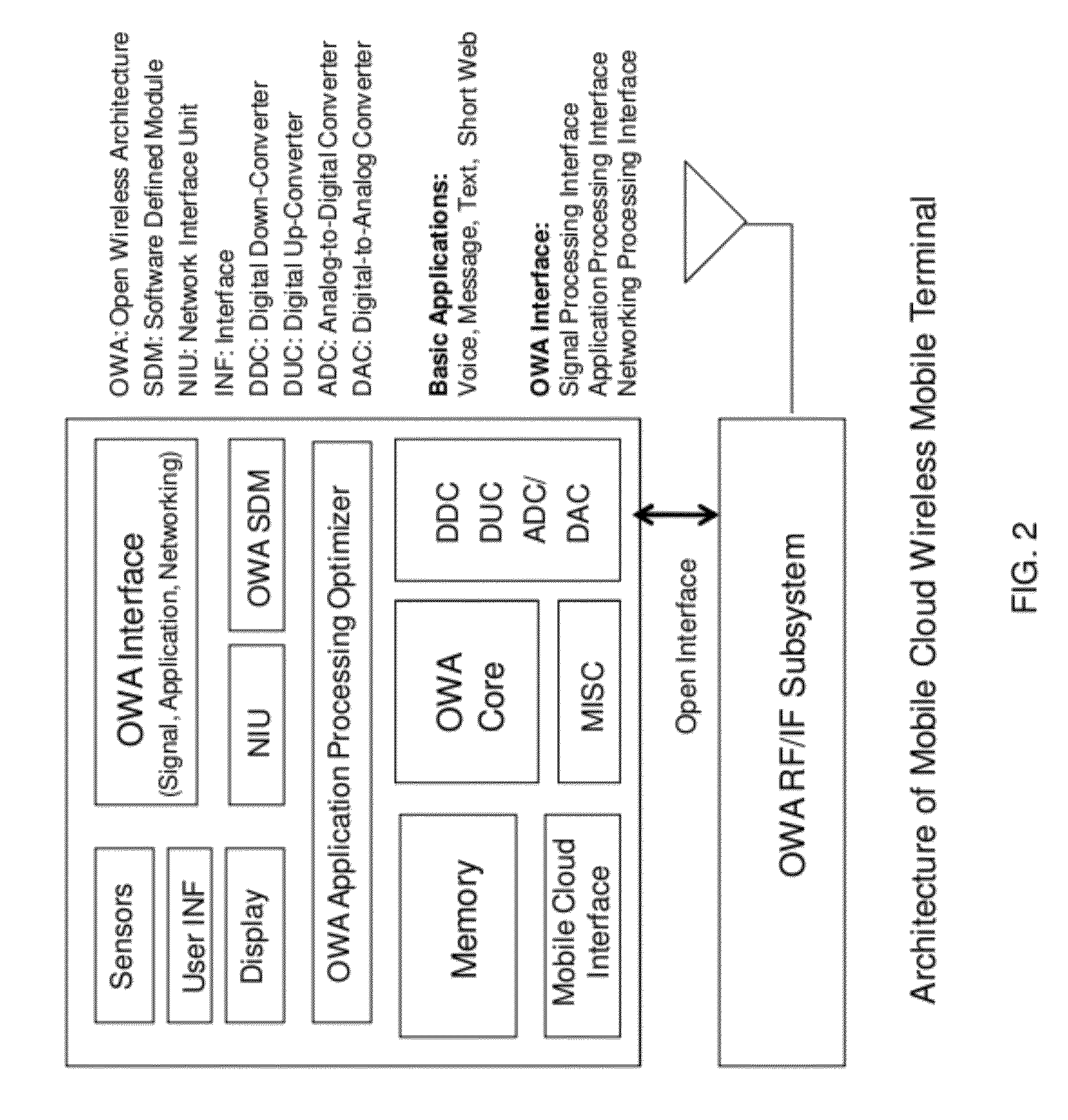
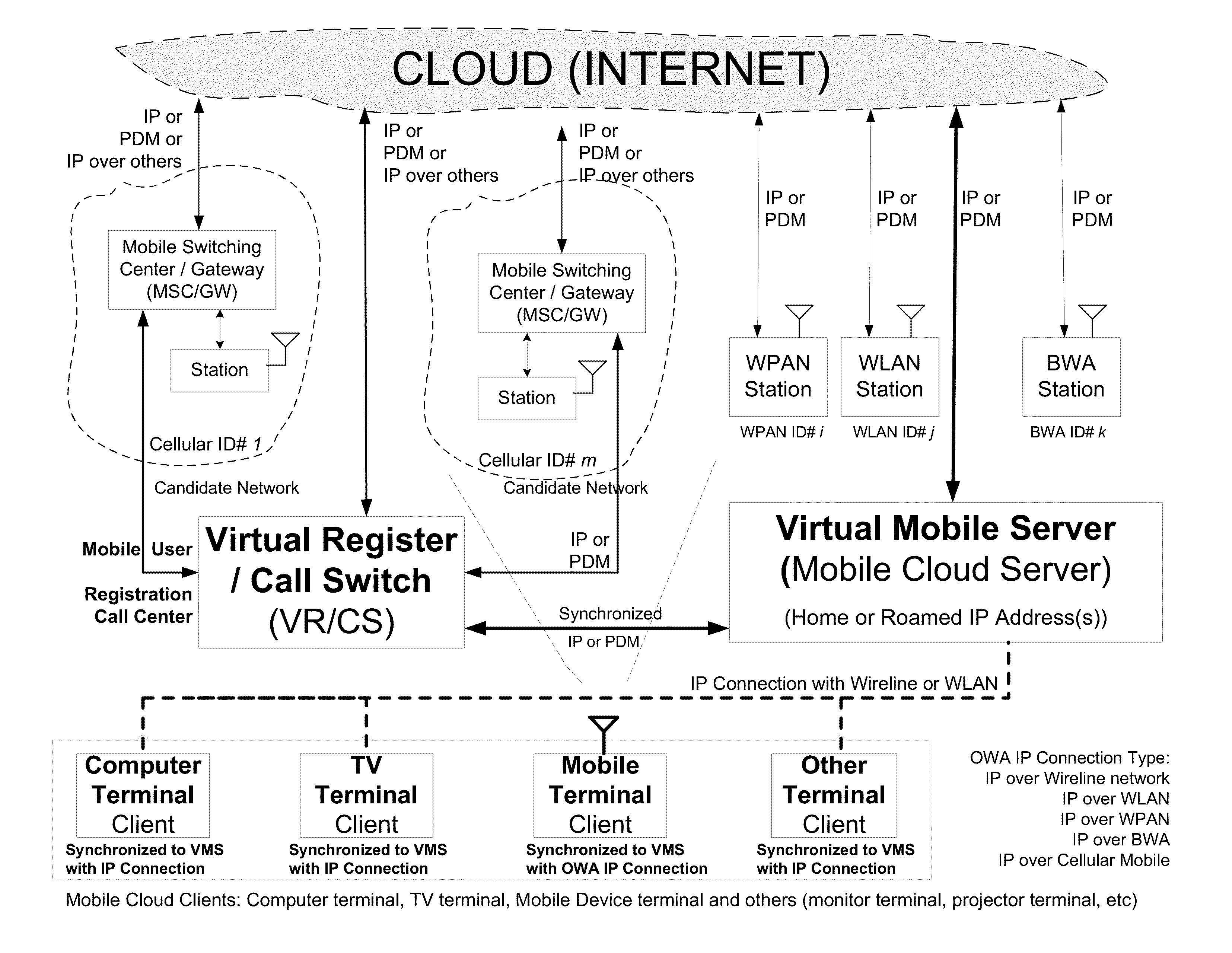
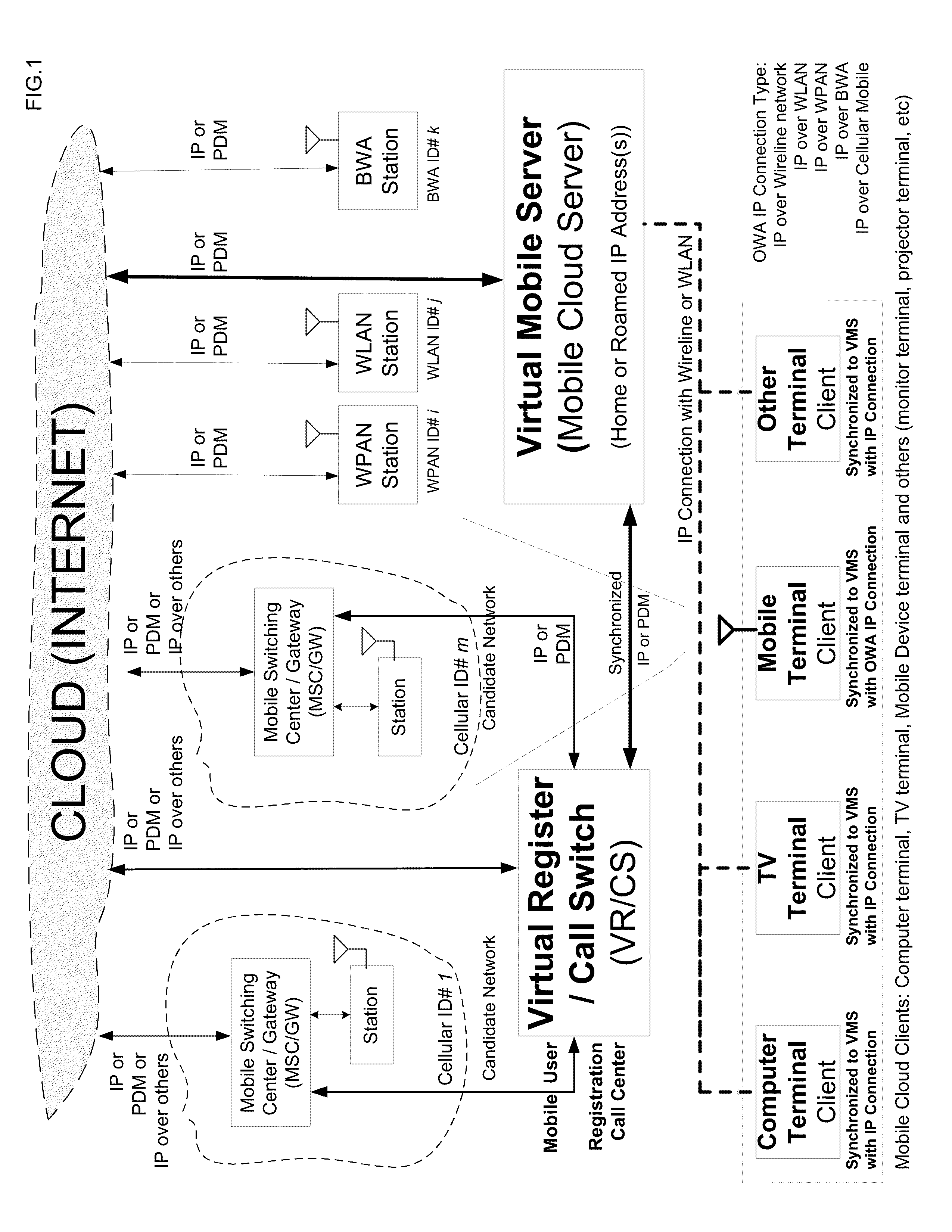
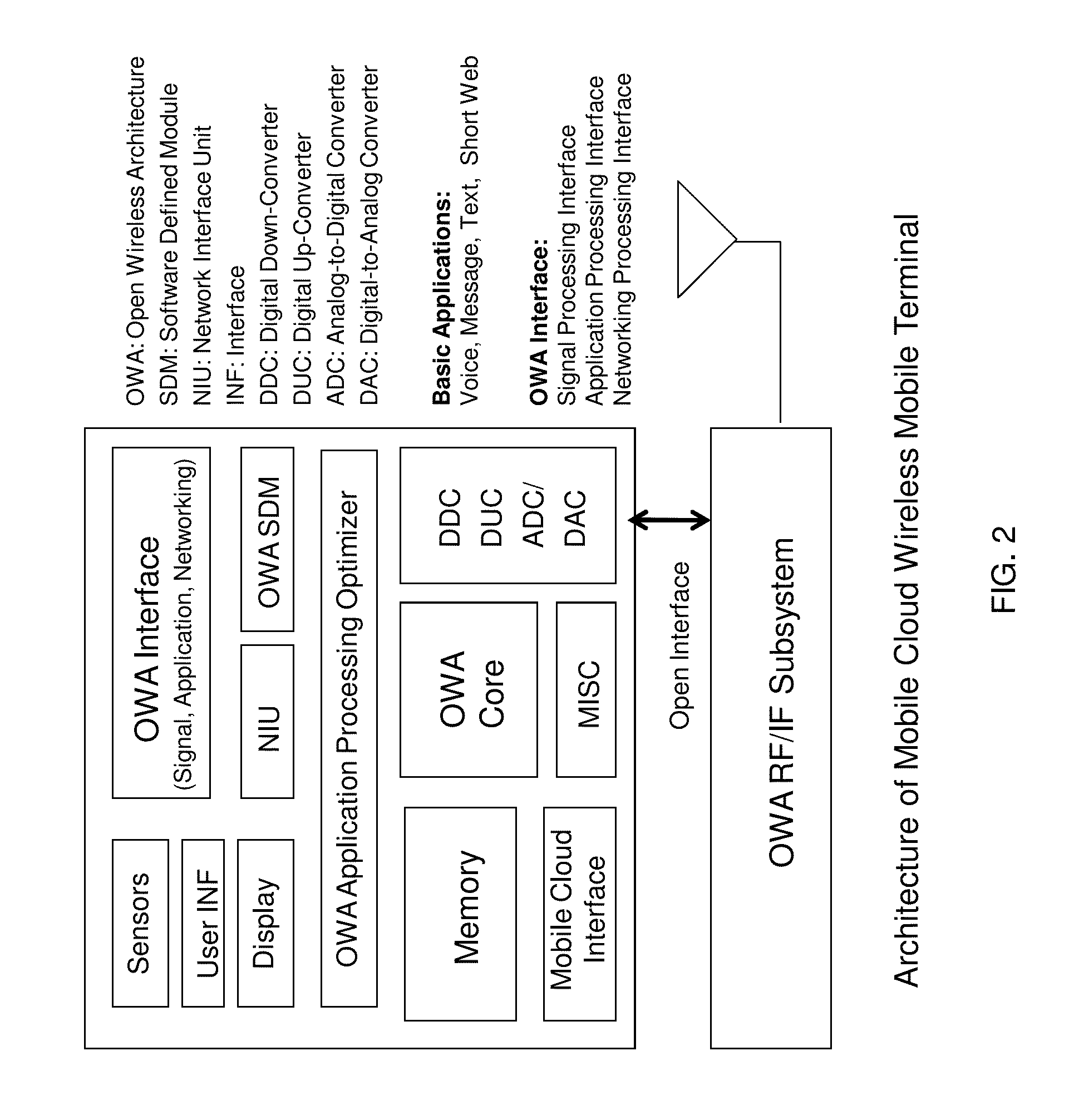
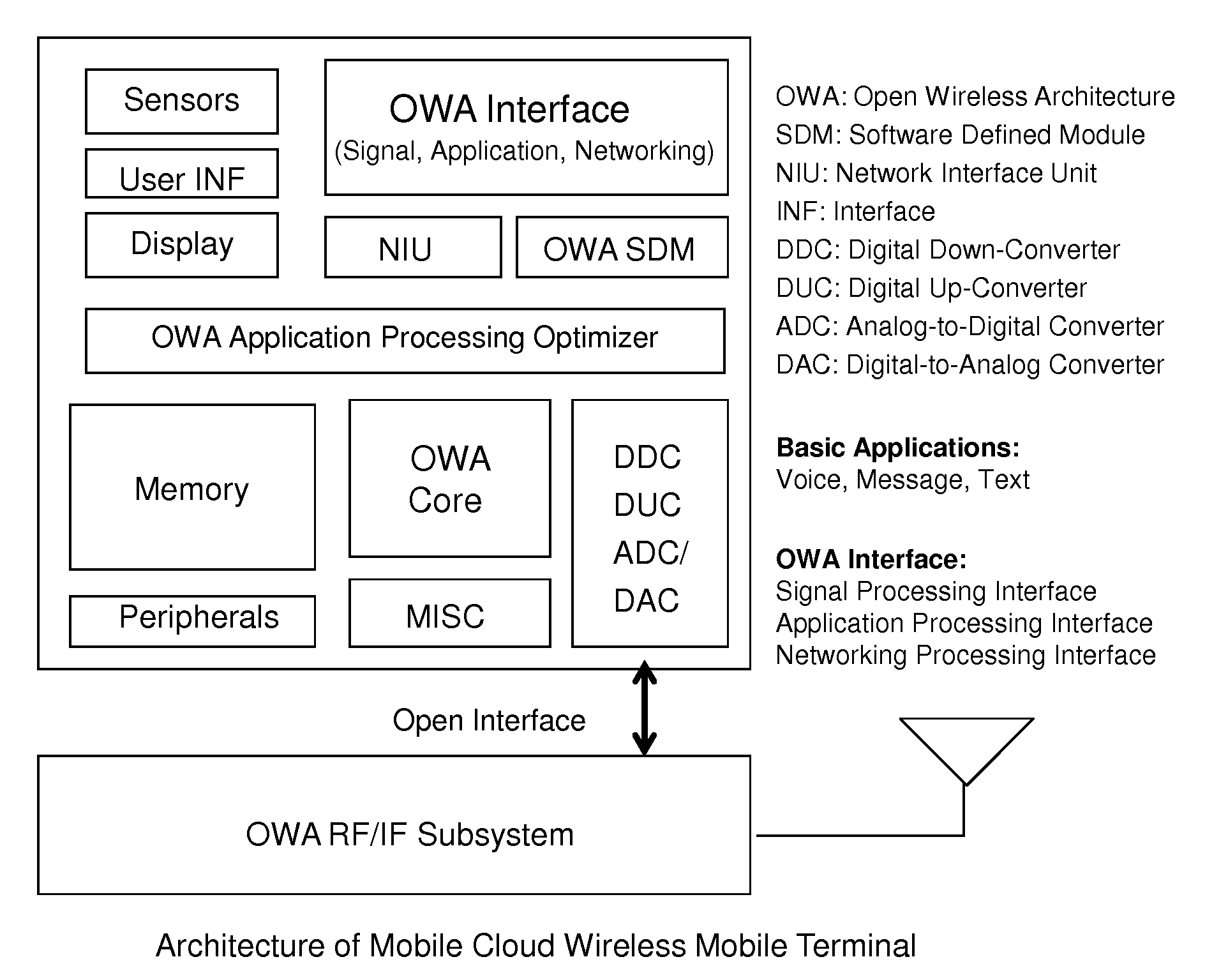
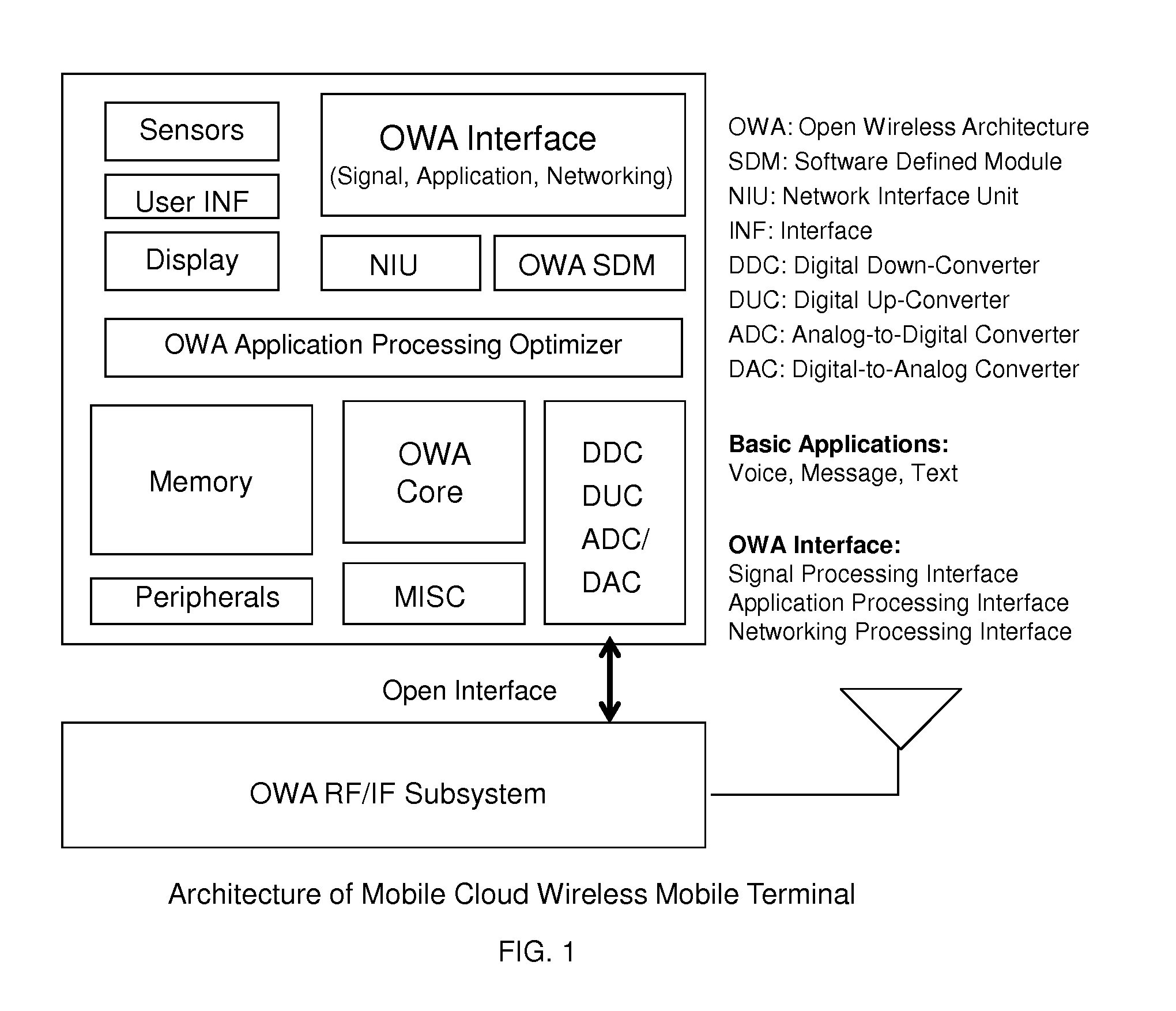
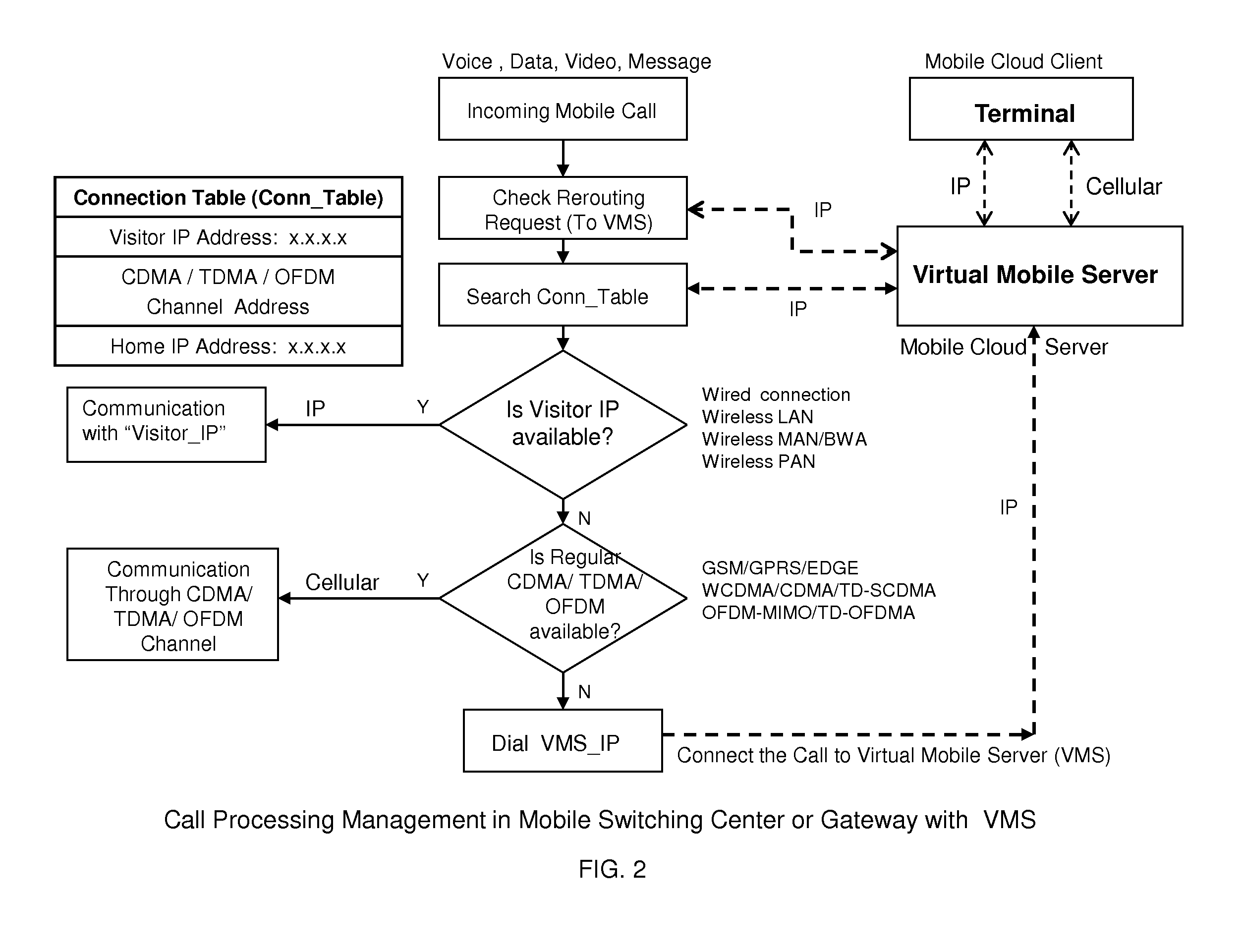
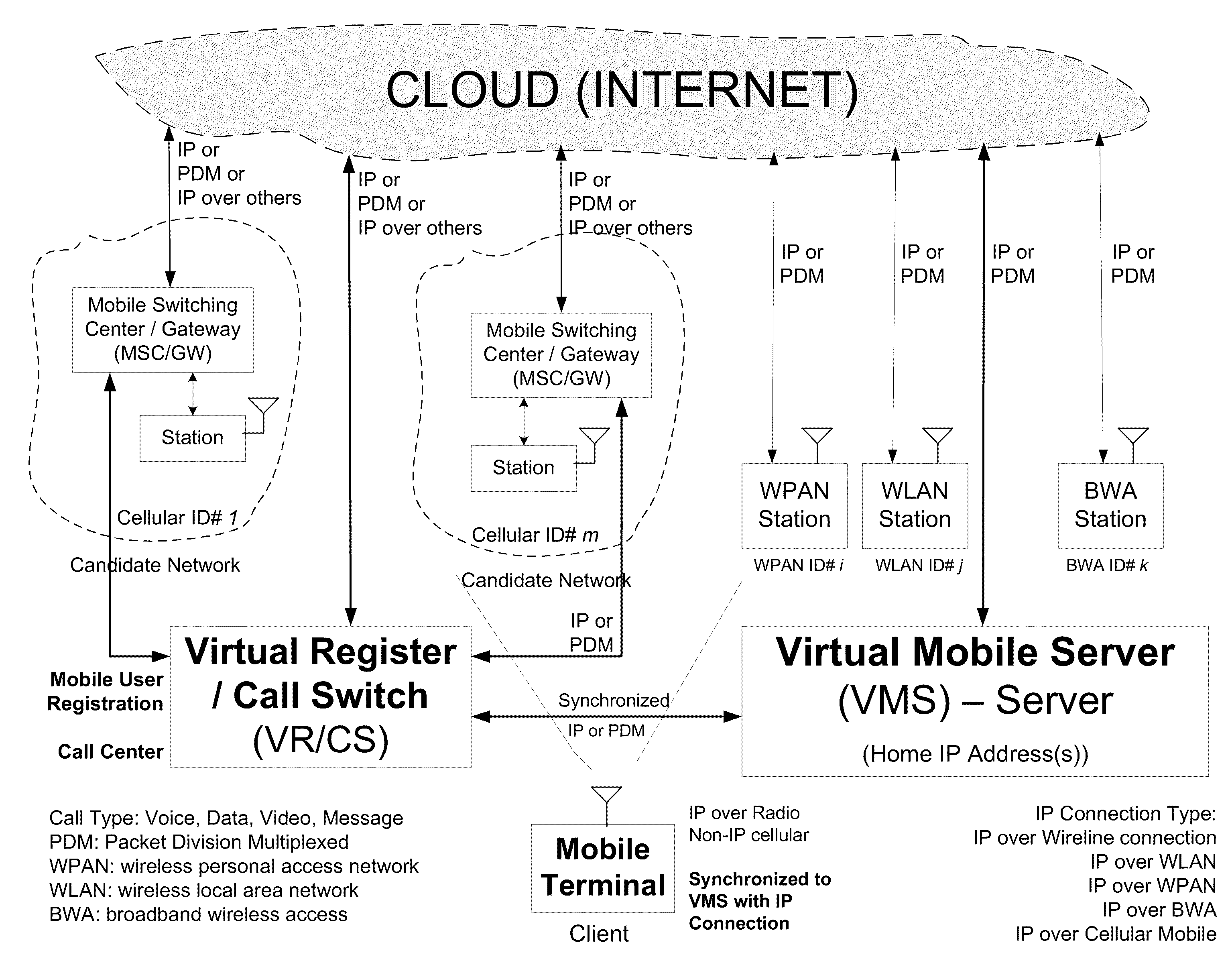
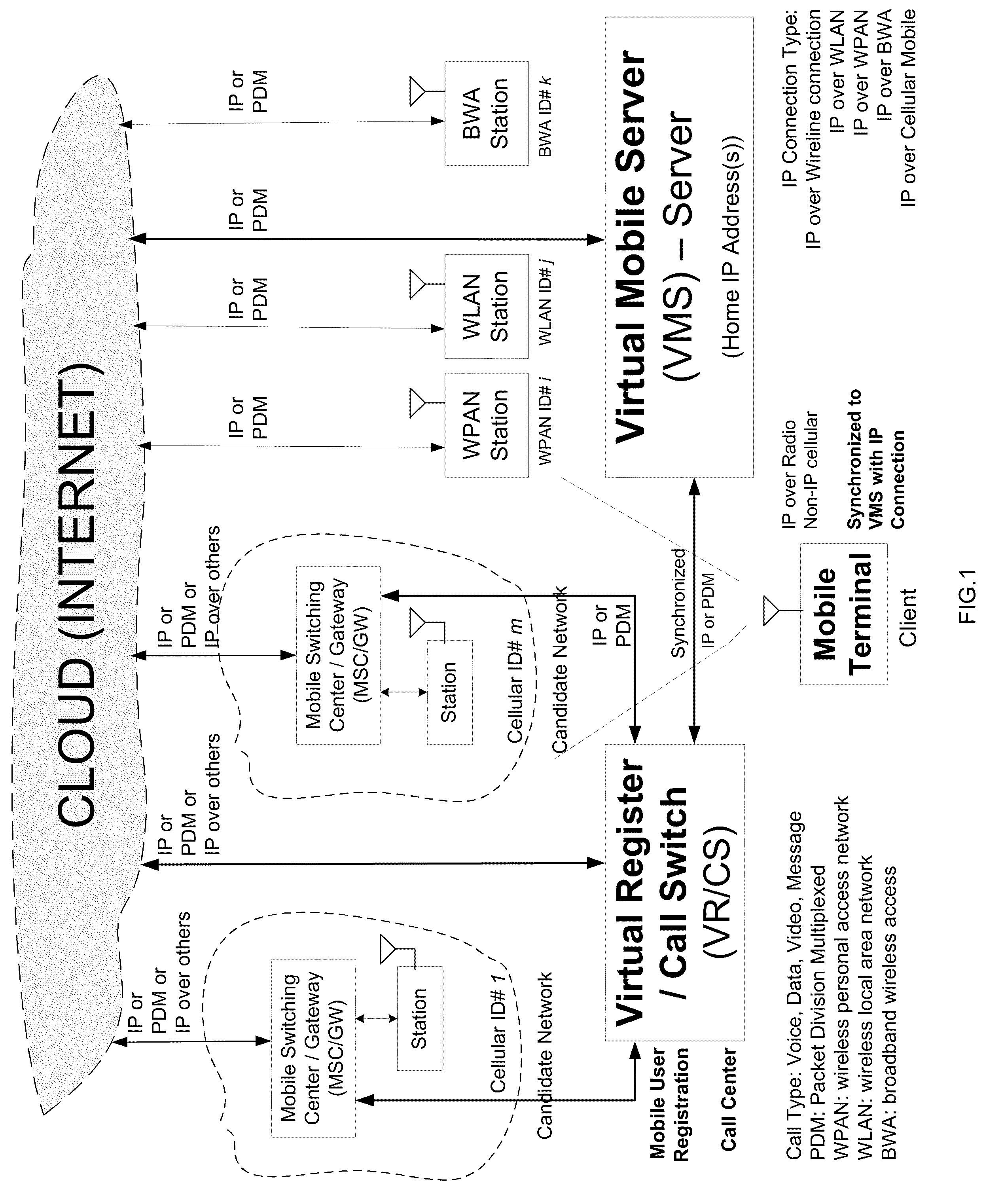
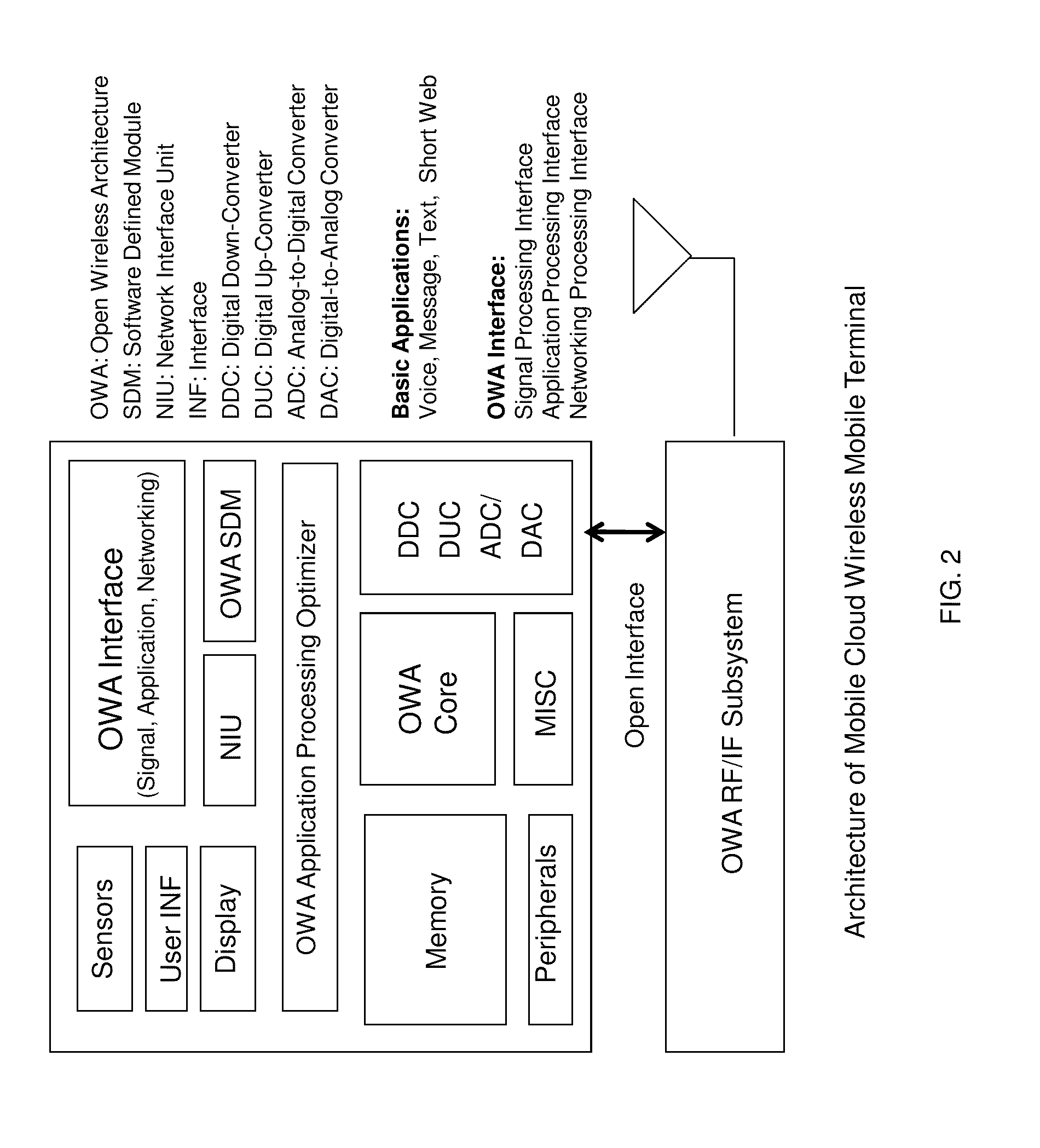
Open wireless architecture (OWA) mobile cloud infrastructure and method
InactiveUS20120296963A1Spectrum efficiency is improvedOptimize network resourcesNetwork topologiesWireless commuication servicesWireless transmissionFrequency spectrum
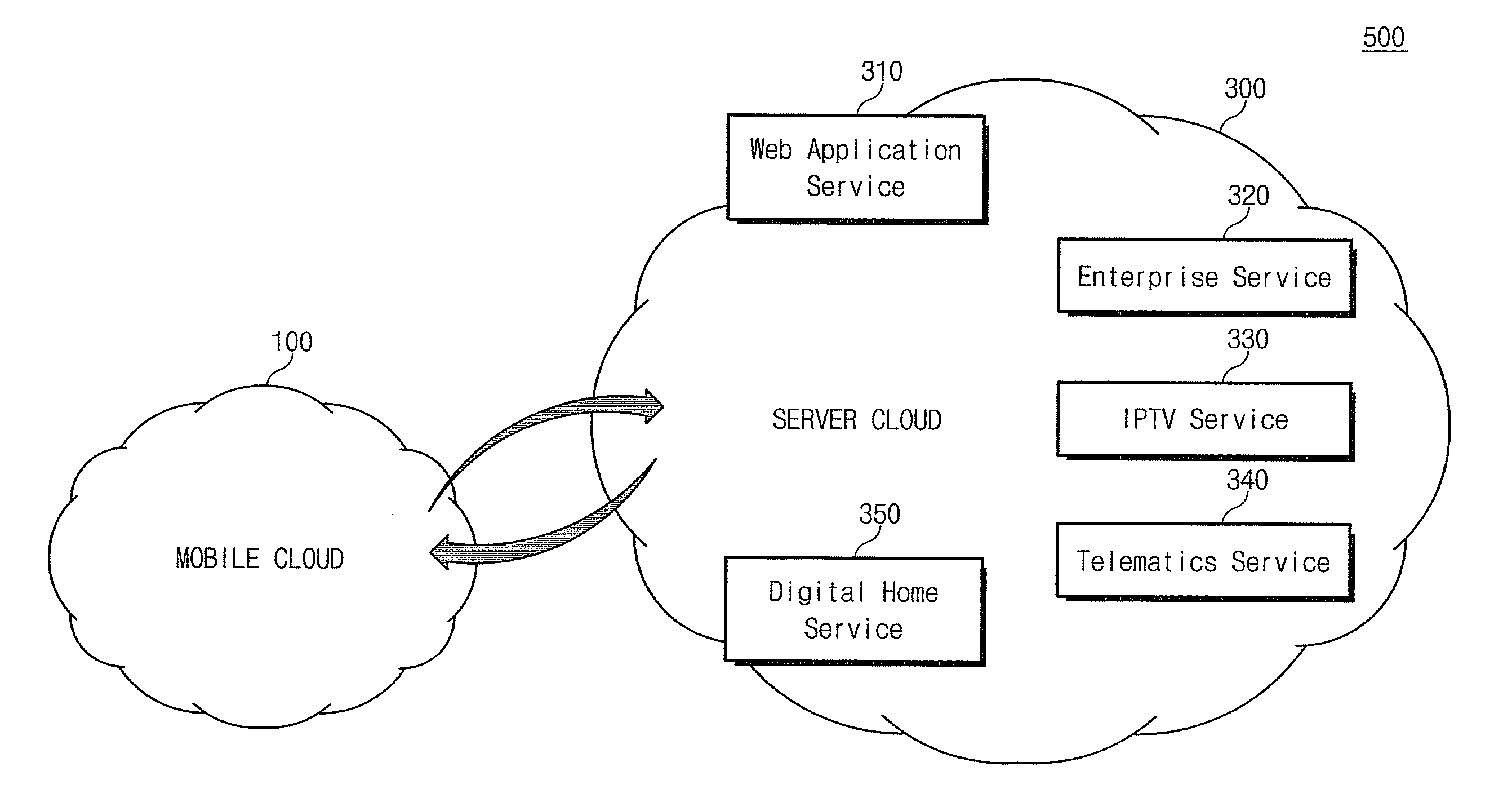
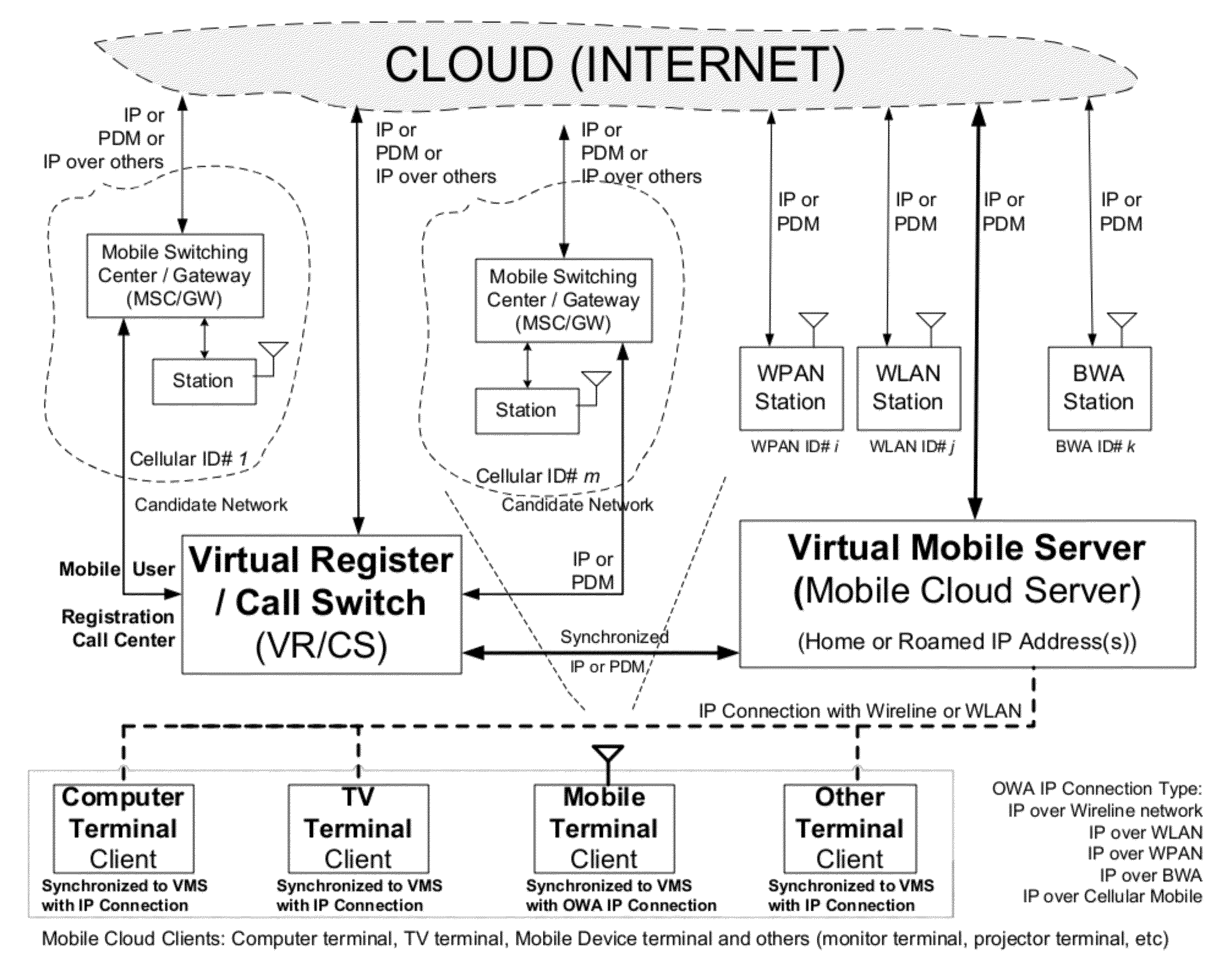
A future mobile terminal converging multiple wireless transmission technologies by utilizing a cost-effective and spectrum-efficient mobile cloud solution by introducing Virtual Mobile Server (VMS) and Virtual Register and Call Switch (VR / CS) systems and methods based on the innovative open wireless architecture (OWA) technology platform, and the mobile terminal extended to other mobile cloud clients including computer terminal and television terminal fully synchronized through the VMS.
Owner:PALO ALTO RES
Open wireless architecture (OWA) mobile cloud infrastructure and method
ActiveUS20150229713A1Spectrum efficiency is improvedOptimize network resourcesPower managementNetwork traffic/resource managementWireless transmissionFrequency spectrum
An advanced mobile terminal converging multiple wireless transmission technologies by utilizing a cost-effective and spectrum-efficient mobile cloud solution by introducing Virtual Mobile Server (VMS) and Virtual Register and Call Switch (VR / CS) systems and methods based on the innovative open wireless architecture (OWA) technology platform, and the mobile terminal shared with other mobile cloud clients including computer terminal and television terminal fully synchronized through the VMS for the integrated smart home and smart office platform for the enterprise mobility solutions between home and enterprise.
Owner:PALO ALTO RES
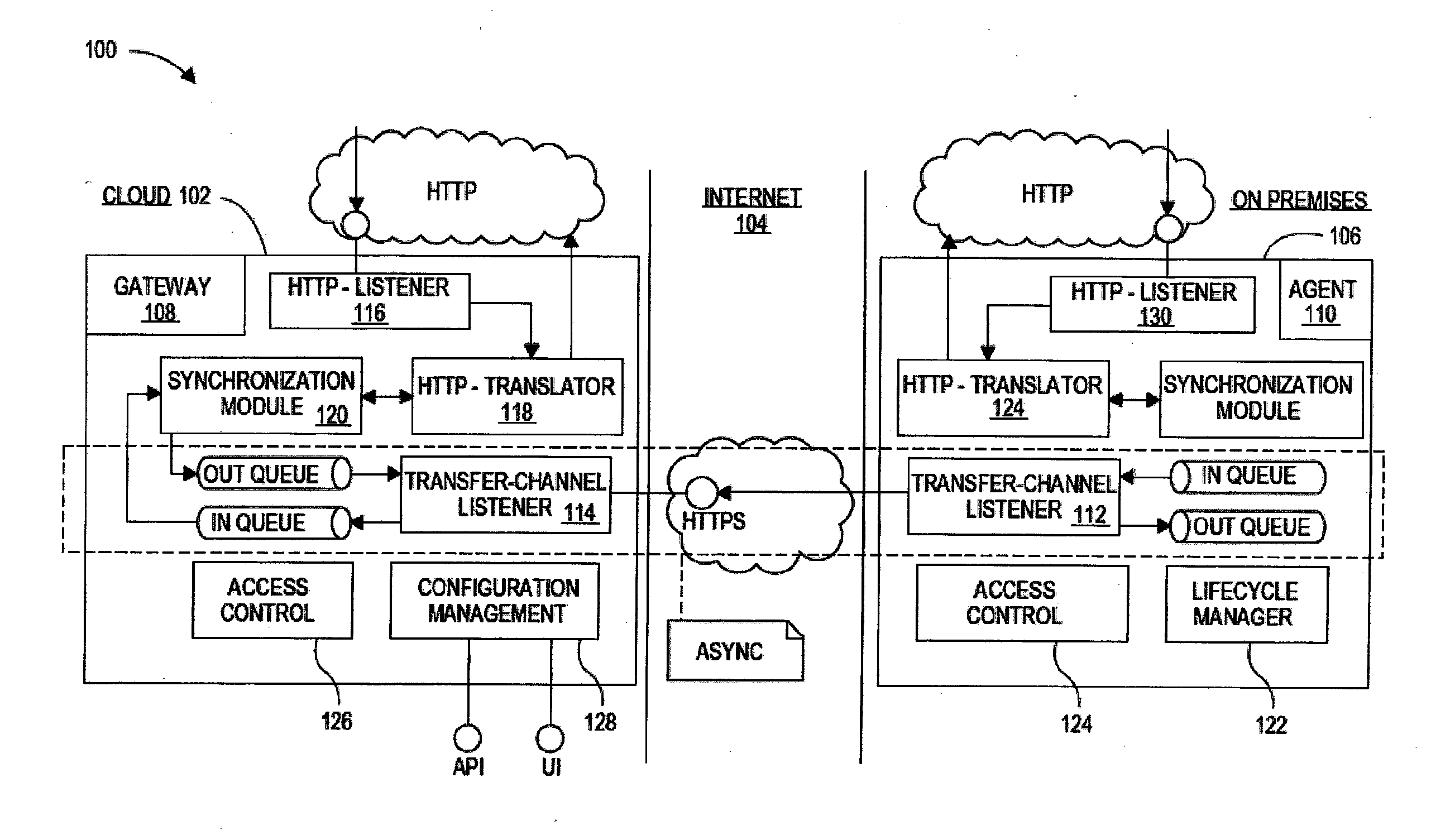
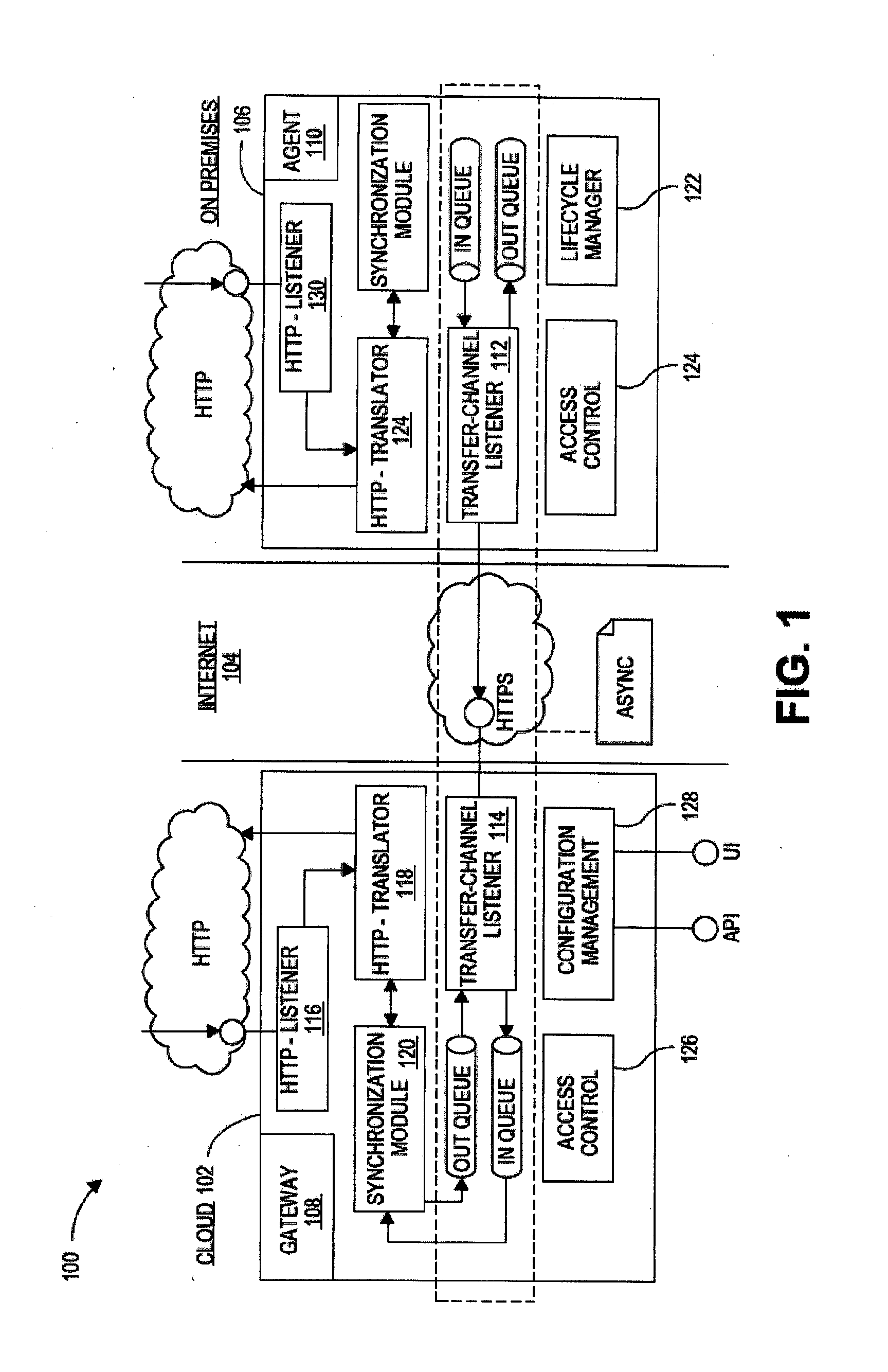
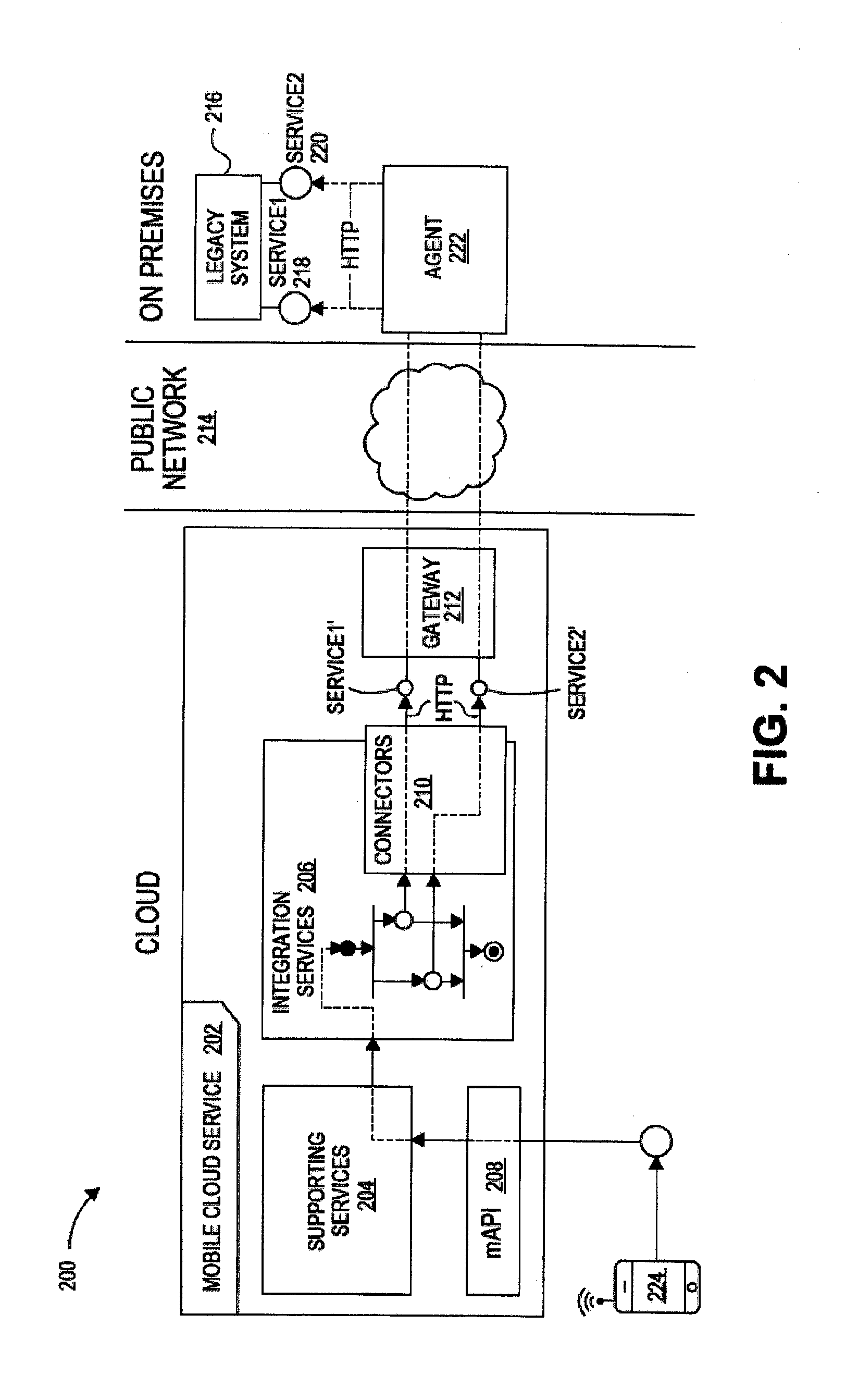
On-premises agent for mobile cloud service
Systems, devices, and methods are disclosed for an agent device within a company's network firewall to initiate an HTTP connection with a cloud-based gateway and then upgrade the connection to a WebSockets protocol in order to have an interactive session. Over this interactive session, a mobile device, which connects to the cloud-based intermediary, can request data from servers inside the company's firewalls. Because the firewall is traversed using HTTP protocols (with WebSockets), it can be as safe as letting employees browse the web from inside the company's network.
Owner:ORACLE INT CORP
Mobile cloud architecture based on open wireless architecture (OWA) platform
InactiveUS20100238840A1Simple system implementationMaximize system performanceSpecial service provision for substationMultiplex system selection arrangementsMobile cloudReal-time computing
A simplified future mobile terminal system converging multiple wireless transmission technologies by utilizing a cost-effective and spectrum-efficient mobile cloud solution based on the innovative virtual mobile server system of the open wireless architecture (OWA) platform.
Owner:PALO ALTO RES
Open wireless architecture (OWA) mobile cloud infrastructure and method
ActiveUS20110176528A1Spectrum efficiency is improvedOptimize network resourcesNetwork topologiesWireless network protocolsWireless transmissionFrequency spectrum
A future mobile terminal converging multiple wireless transmission technologies by utilizing a cost-effective and spectrum-efficient mobile cloud solution by introducing the Virtual Mobile Server (VMS) and Virtual Register and Call Switch (VR / CS) systems and methods based on the innovative open wireless architecture (OWA) technology platform.
Owner:LU WEI +3
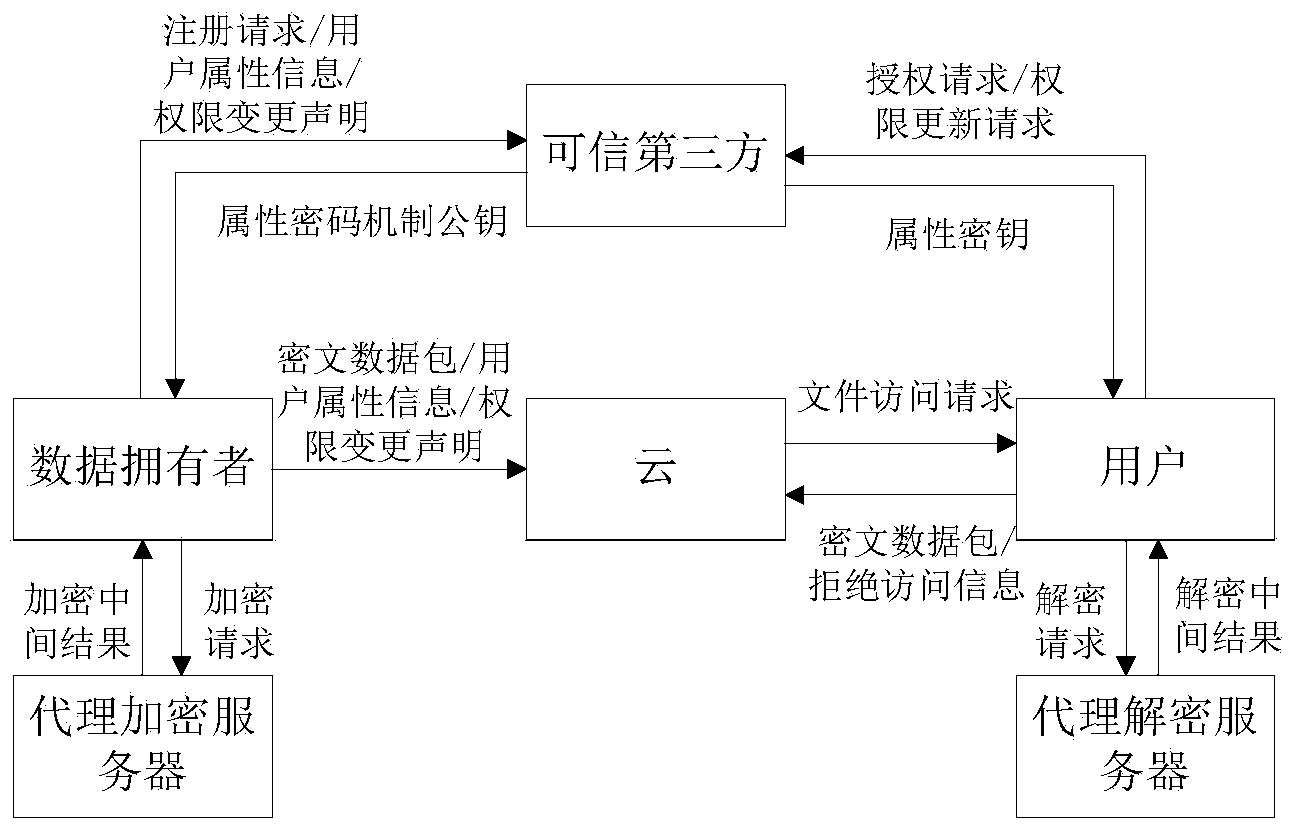
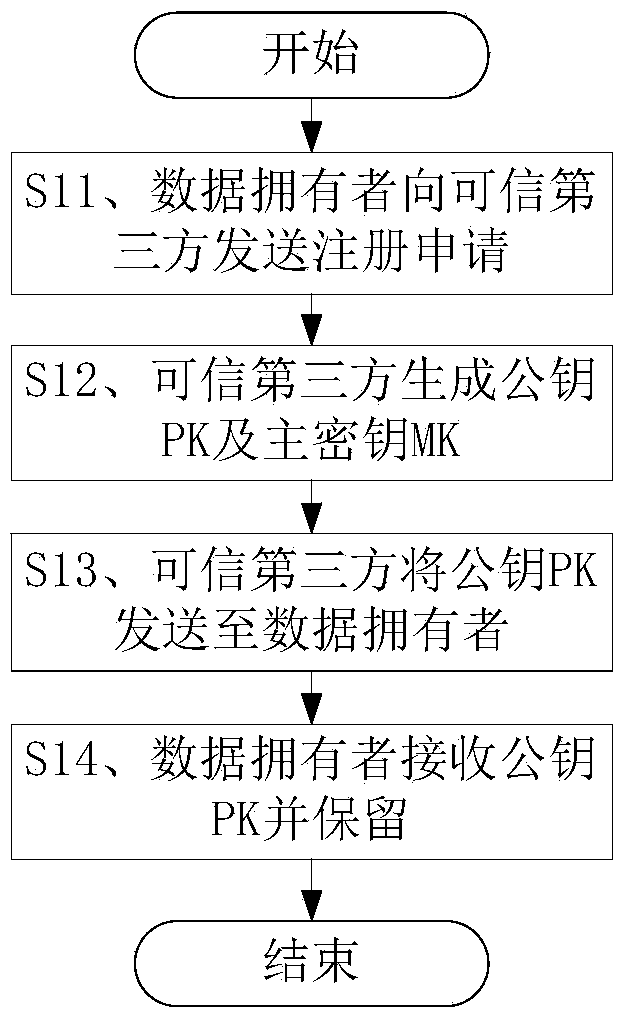
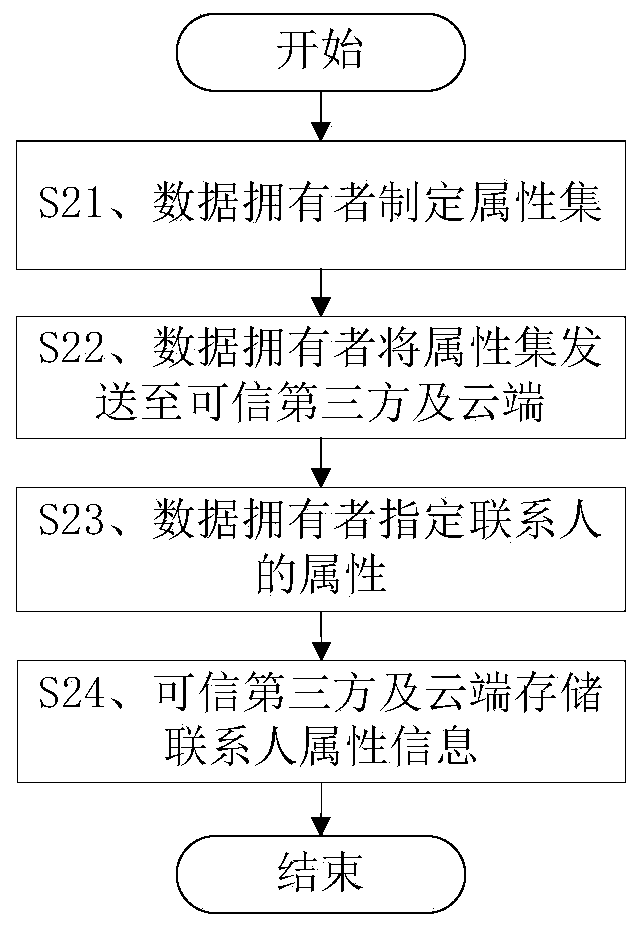
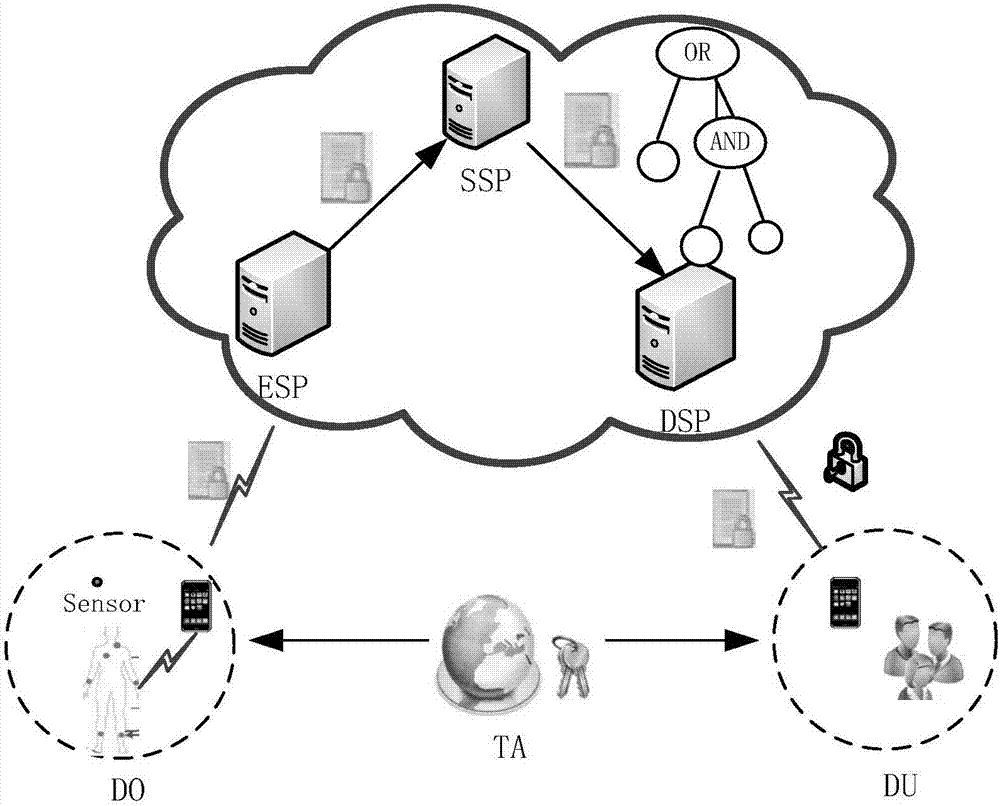
Method for safely sharing mobile cloud storage light-level data
The invention discloses a method for safely sharing mobile cloud storage light-level data. The method comprises the steps that an attribute set is registered in a credible third party by a data owner, the attribute set is assigned to a user by the data owner, the user is authorized by the credible third party through an attribute code mechanism according to the attribute set of the user, so that an attribute key is generated, when the data owner uses a mobile side to share a file, the file is firstly encrypted through a symmetric cryptography mechanism, a symmetric key is encrypted through a proxy encryption server by the utilization of an attribute key mechanism, a file ciphertext and a key ciphertext are sent to a cloud side, after the file ciphertext and the key ciphertext are read from the cloud side by the user, the attribute code mechanism is used by a proxy decryption server to decrypt the file, an authority limit alteration statement is sent to the credible third party and the cloud side by the data owner, and judgments are made by the credible third party and the cloud side, so that authority limits of the user are increased or deleted. According to the method for safely sharing the mobile cloud storage light-level data, the data can be safely shared on the mobile side on the conditions that electric quantity and computing power are limited.
Owner:HUAZHONG UNIV OF SCI & TECH
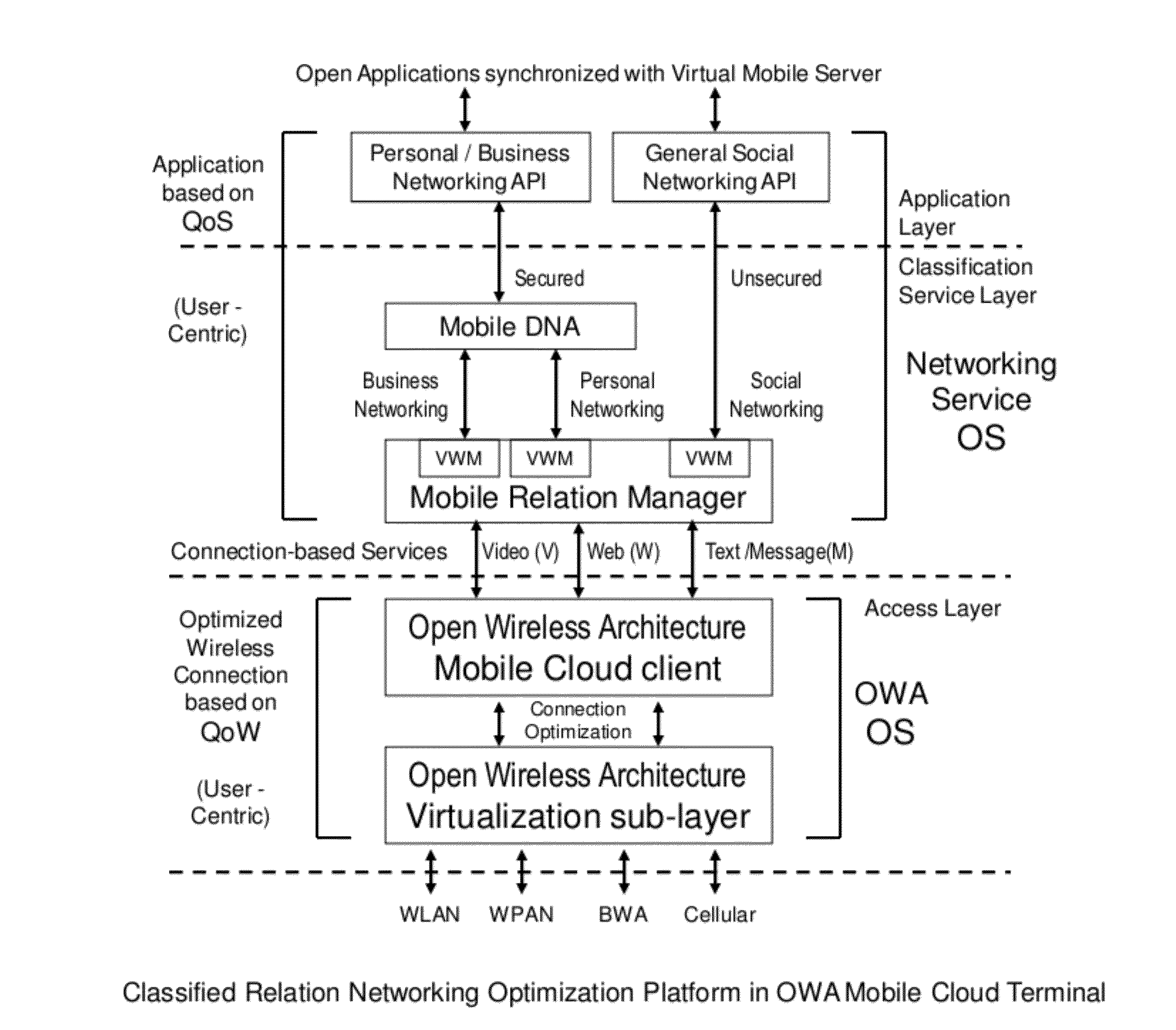
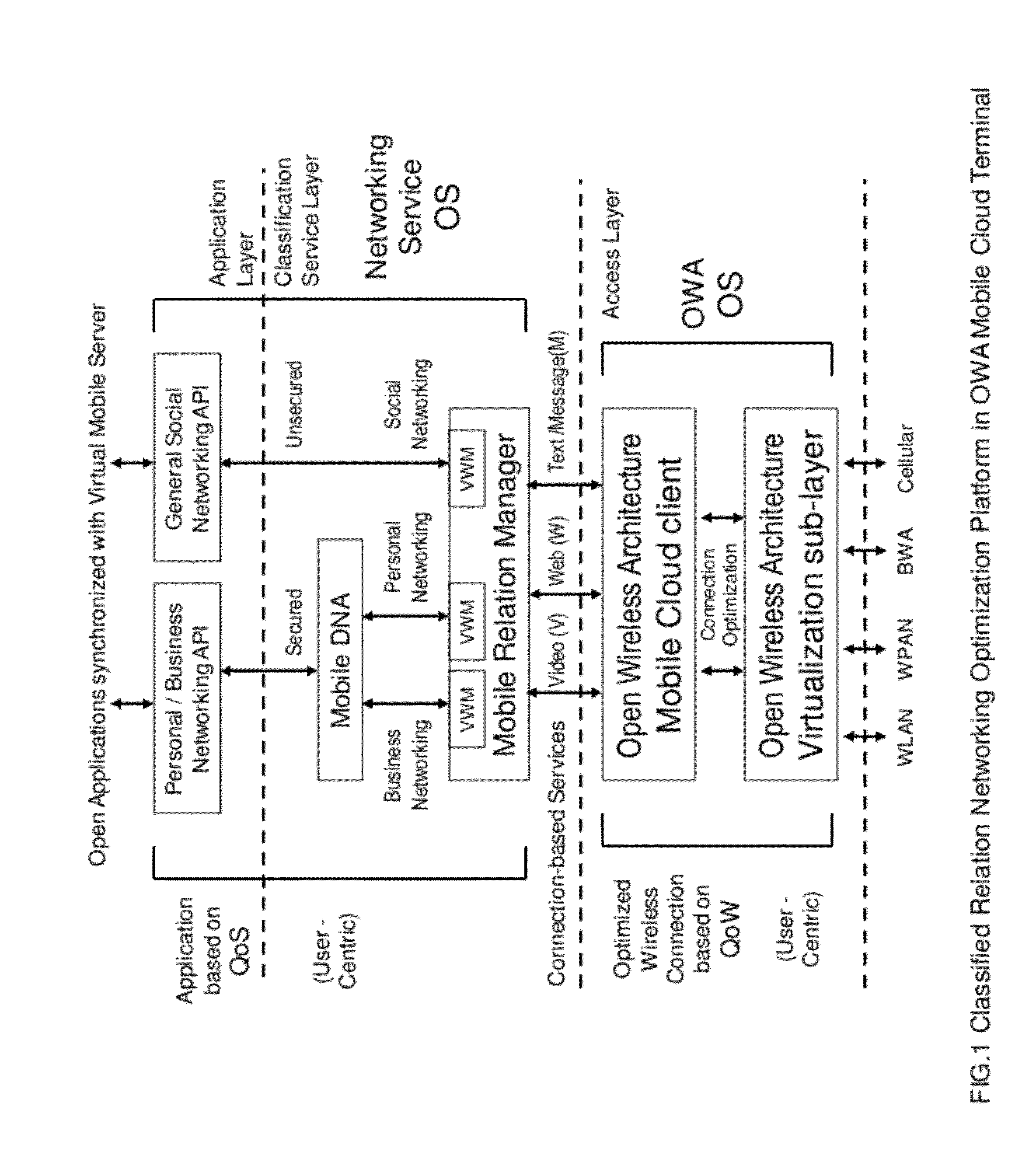
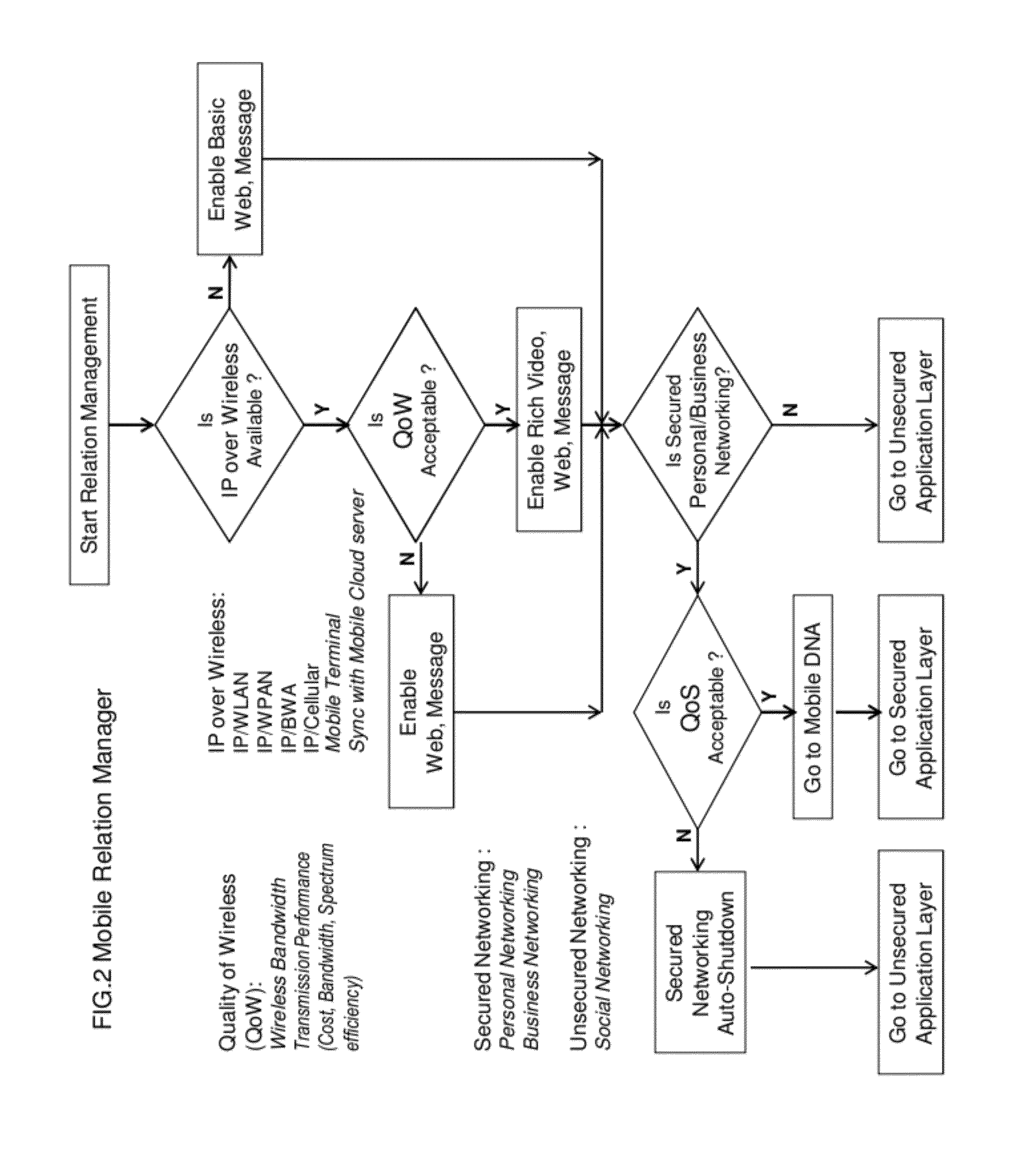
Classified relation networking optimization platform in open wireless architecture (OWA) mobile cloud terminal device
ActiveUS20120224694A1Error preventionFrequency-division multiplex detailsMobile businessMobile cloud
A fully user-centric mobile relation networking management of business networking, personal networking and social networking for mobile terminal device with networking services adaptively and intelligently optimized by converged wireless connections based on open wireless architecture (OWA) mobile cloud infrastructure with QoW (Quality of Wireless connection) control through OWA Operating System (OS) to enable highly secured relation networking for mobile business and personal networking users.
Owner:PALO ALTO RES
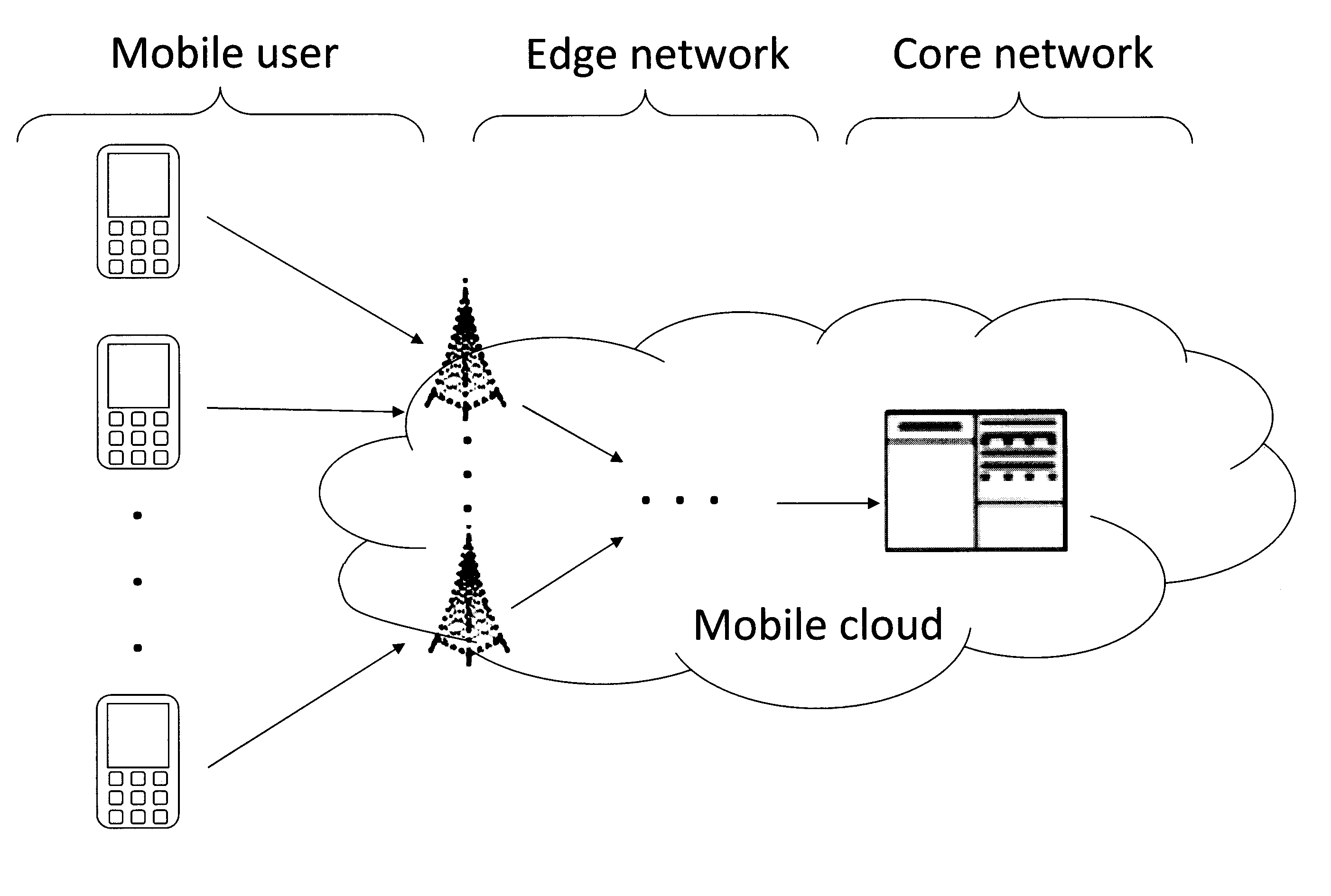
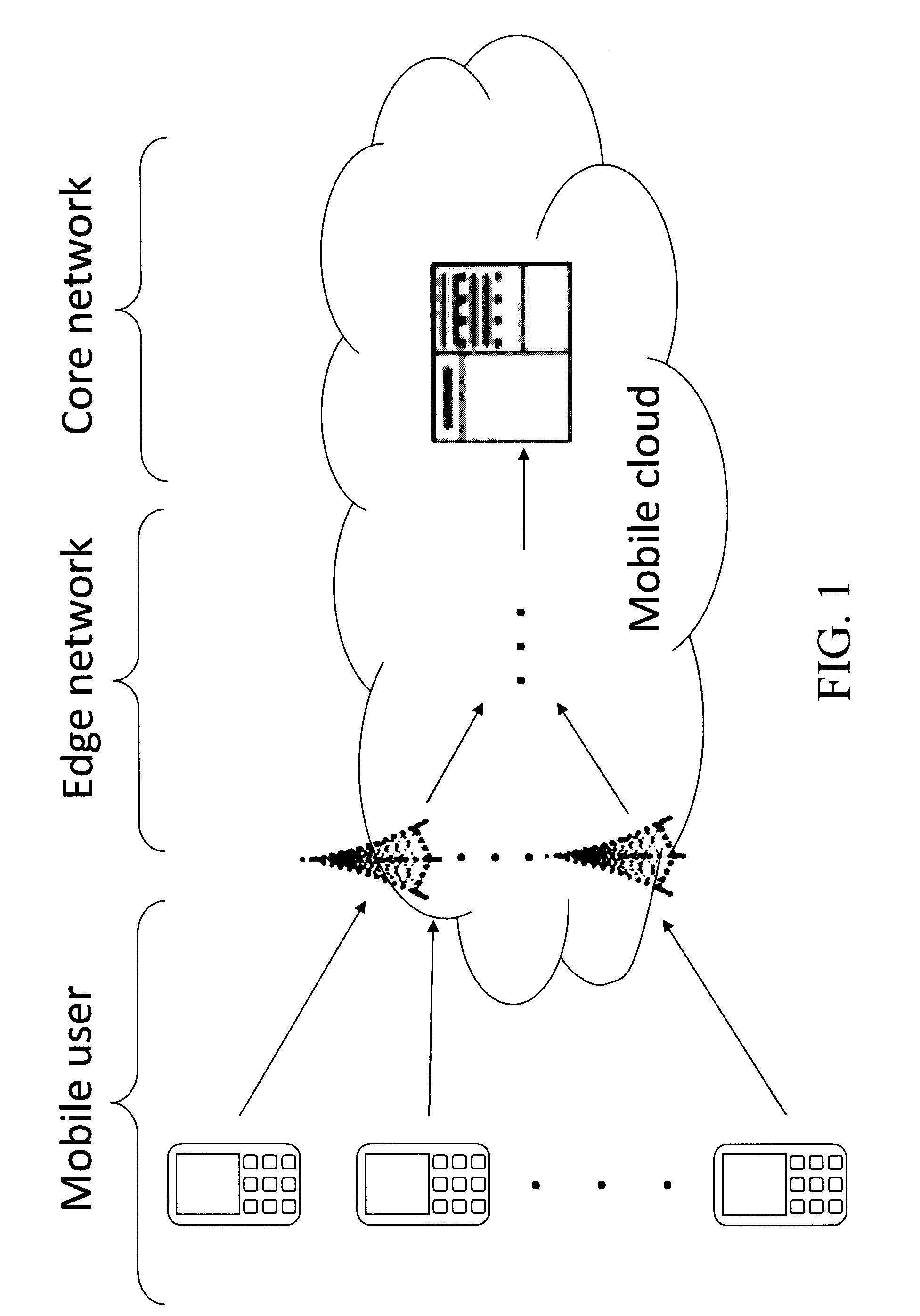
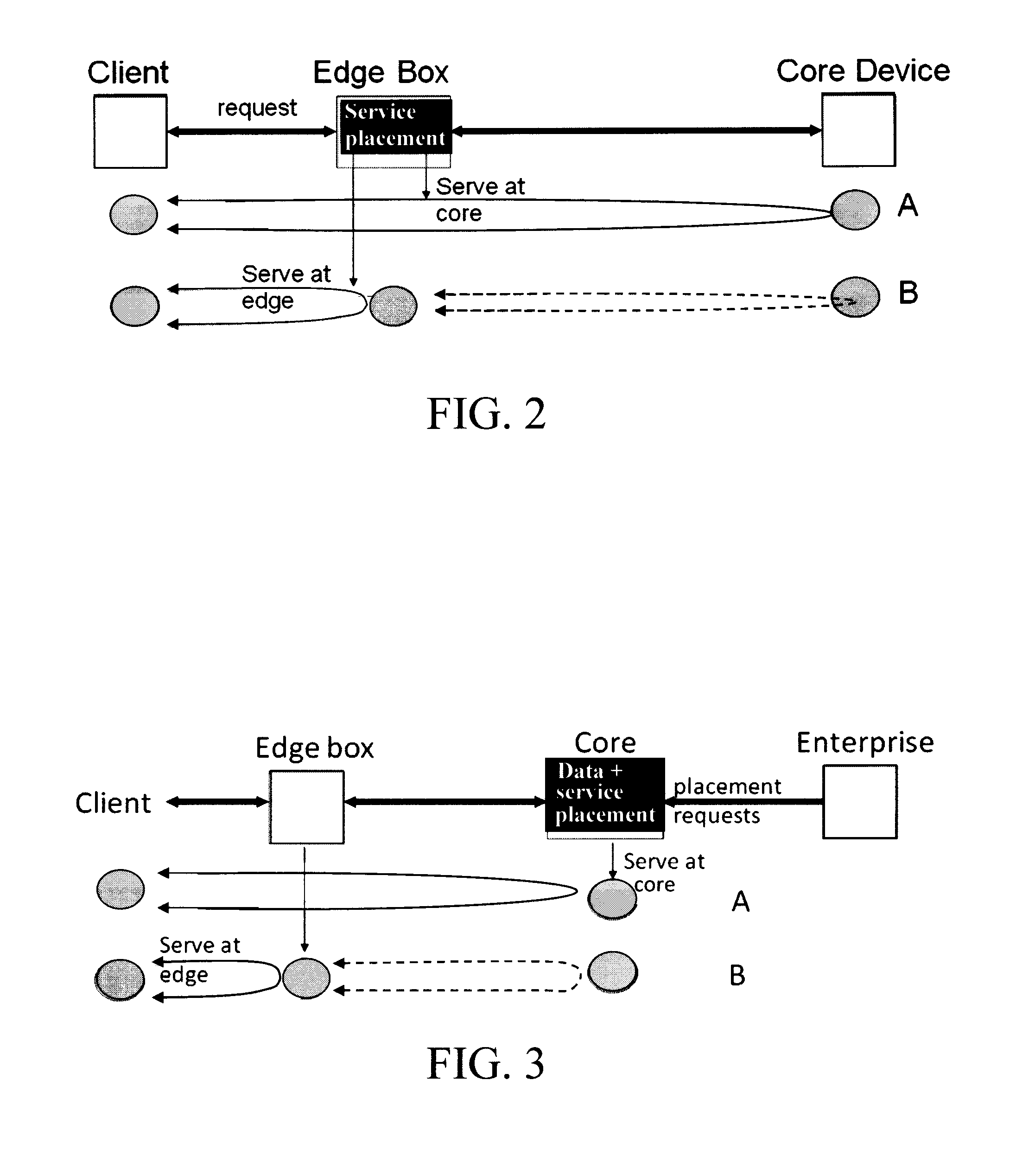
Techniques for Mobility-Aware Dynamic Service Placement in Mobile Clouds
Techniques to adaptively launch / replace applications and services on edge devices in a cellular infrastructure and / or adaptively place content and computation at the edge devices based on logic at the network core are provided. In one aspect, a method for dynamic placement of applications in a cellular network mobile cloud is provided which includes the steps of: (a) obtaining: (i) a model of the cellular network, (ii) a model of user mobility patterns in the cellular network, and (iii) a model of a profile of the applications; (b) upon receipt of requests from users for the applications, obtaining runtime states at edge servers in the mobile cloud; and (c) upon obtaining the runtime states at the edge servers, placing the requests among the edge servers and a core server in the mobile cloud based on the models obtained in step (a) and the runtime states obtained in step (b).
Owner:IBM CORP
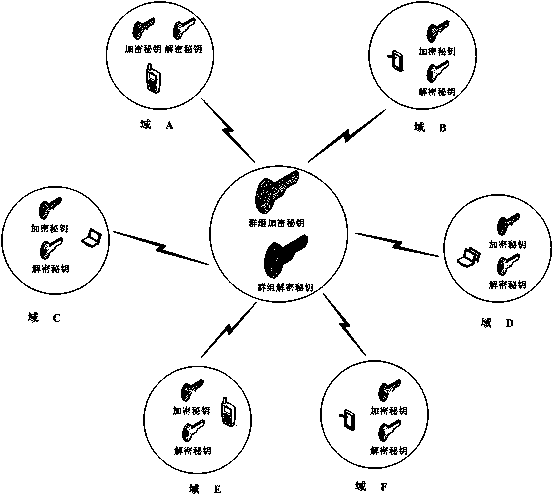
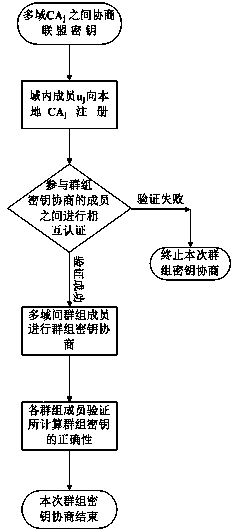
Multi-inter-domain asymmetric group key agreement protocol method in mobile cloud computing environment
ActiveCN104660415AWide distributionNetwork heterogeneityKey distribution for secure communicationUser identity/authority verificationMobile cloudConfidentiality
The invention discloses a multi-inter-domain asymmetric group key agreement protocol method under the mobile cloud computing network environment. The method comprises the following steps: adopting a bilinear mapping technology and a blind secret key technology to realize a short signature mechanism between a domain secret key management center and a domain terminal; using a short signature technology to realize a multi-inter-domain group key agreement authentication mechanism of terminals distributed in different domains, and further realize asymmetric group key agreement of the terminals distributed in multiple domains. The protocol method disclosed by the invention has the anonymity and the authentication, supports dynamic group key updating of nodes, and realizes the security of forward confidentiality and backward confidentiality of the group keys; on the hypothesis of the Diffe-Hellman bilinear computing problem, the security of the protocol is proved; the computing and communication energy consumption of the protocol is low; the method is good in flexibility, security and practicability, and suitable for cross-domain group key agreement of the terminals distributed in the multiple domains under the mobile cloud computing network environment.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
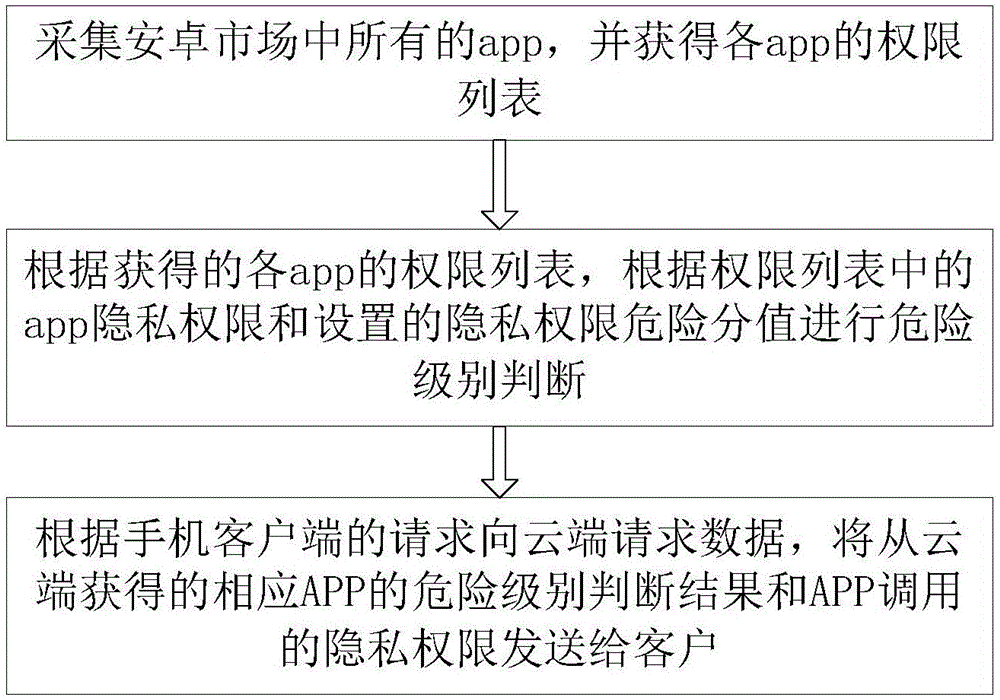
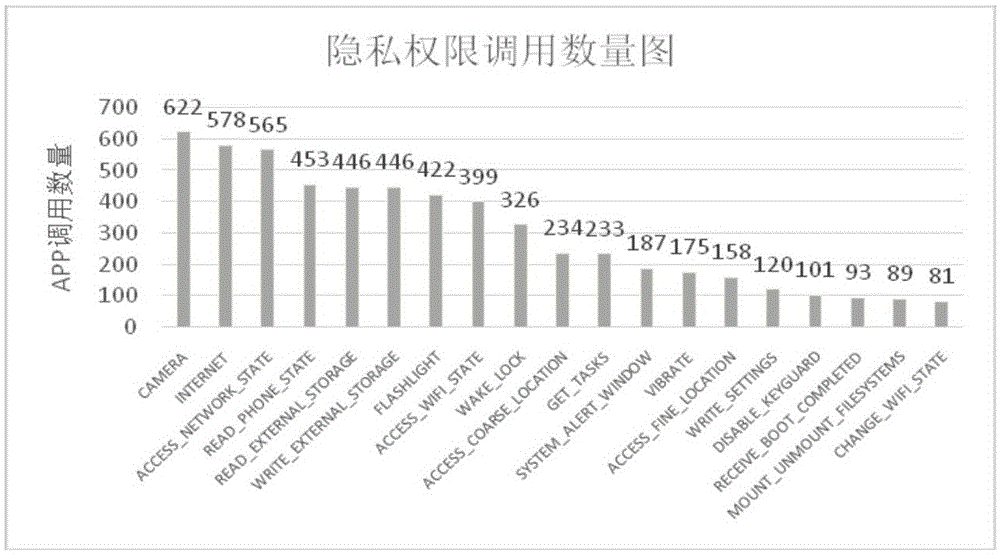
Android platform App risk assessment method based on mobile cloud computing and Android platform App risk assessment device based on mobile cloud computing
InactiveCN105117544AReduce the risk of privacy breachesTransmissionSpecial data processing applicationsMobile cloudInternet privacy
The invention discloses an Android platform App (Application) risk assessment method based on mobile cloud computing and an Android platform App risk assessment device based on the mobile cloud computing. The method comprises the following steps of: collecting all Apps in an Android market, and obtaining a permission list of each App; uploading data of the obtained permission list to the cloud; performing risk grade judgment according to the App privacy permission in the permission list and the set privacy permission risk mark in accordance with the obtained permission list of each App; and requesting data to the cloud according to the request of a mobile phone client, and sending the corresponding App risk grade judgment result obtained from the cloud and the privacy permission called by the App to a customer. The method and the device have the advantages that the permission characteristics of mass Apps are subjected to similar App population characteristic analysis; the dynamic minimum permission set of a certain population is defined; then, the malicious tendency of Android application software is detected by a similarity calculation method; a feasible and effective App assessment method is provided for a user; and the user privacy leakage risk is effectively reduced.
Owner:武汉市教云慧智信息技术有限公司
Electric power system resource integration method based on mobile cloud computing
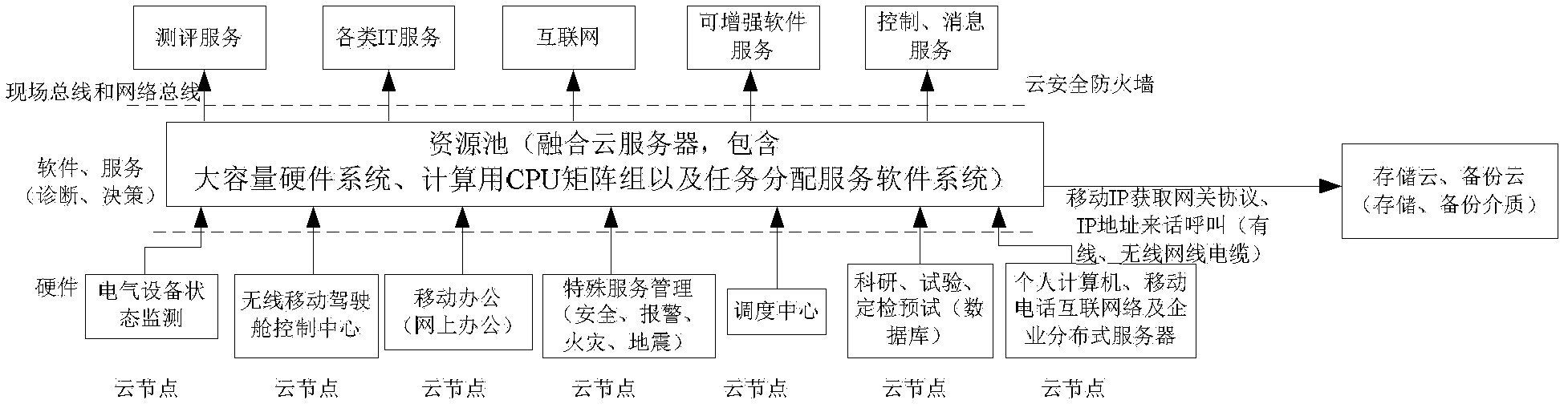
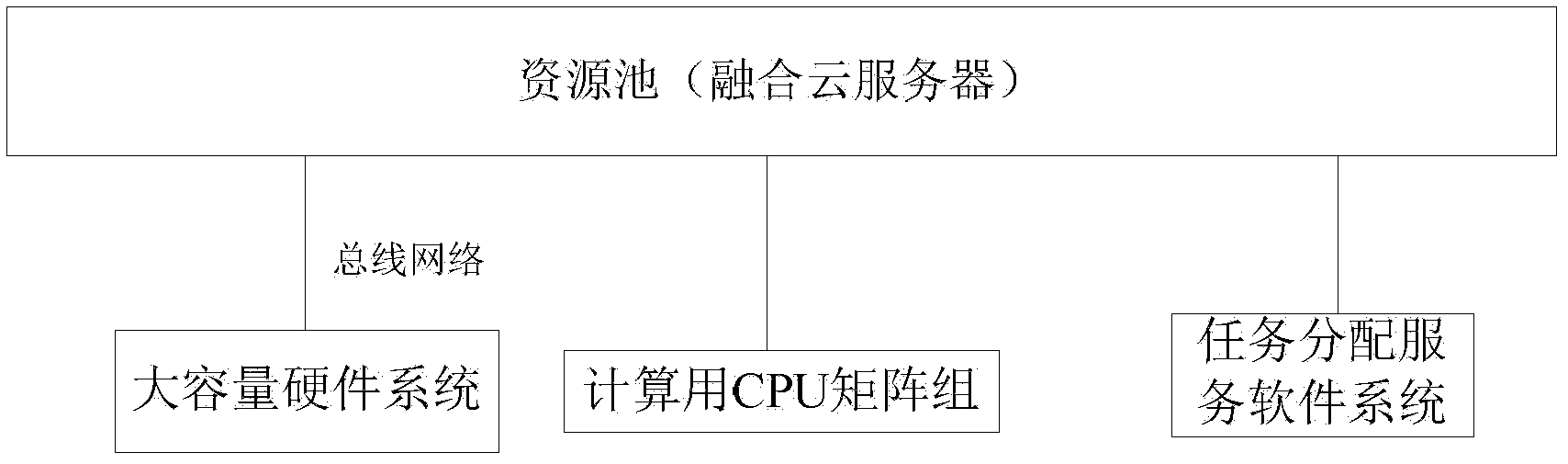
ActiveCN102664951AReduce construction costsImprove resource utilizationData switching networksResource poolMobile cloud
Disclosed is an electric power system resource integration method based on mobile cloud computing. The electric power system resource integration method includes that an electrical device condition monitoring module, a wireless mobile control cabin control center module, a mobile working module, a special service management module, a dispatching center module, a scientific research module, an experiment module, a scheduled maintenance pre-experiment module, a personal computer module, an electronic book module, a mobile phone internet module, and an enterprise distributed type server module in the whole power grid system are connected into a distributed type cloud internet through a resource pool (fusion cloud server). The method which integrates internal resources of the electric power system based on the mobile cloud computing mode has the advantages of being low in construction cost, and high in resource utilization rate, preventing recycle, being high in popularization, and the like.
Owner:YUN NAN ELECTRIC TEST & RES INST GRP CO LTD ELECTRIC INST +1
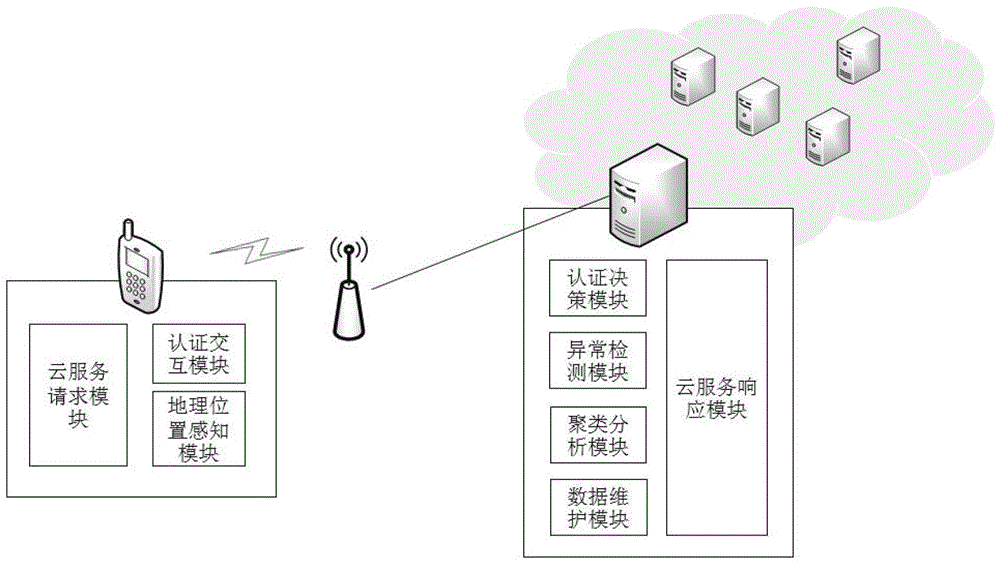
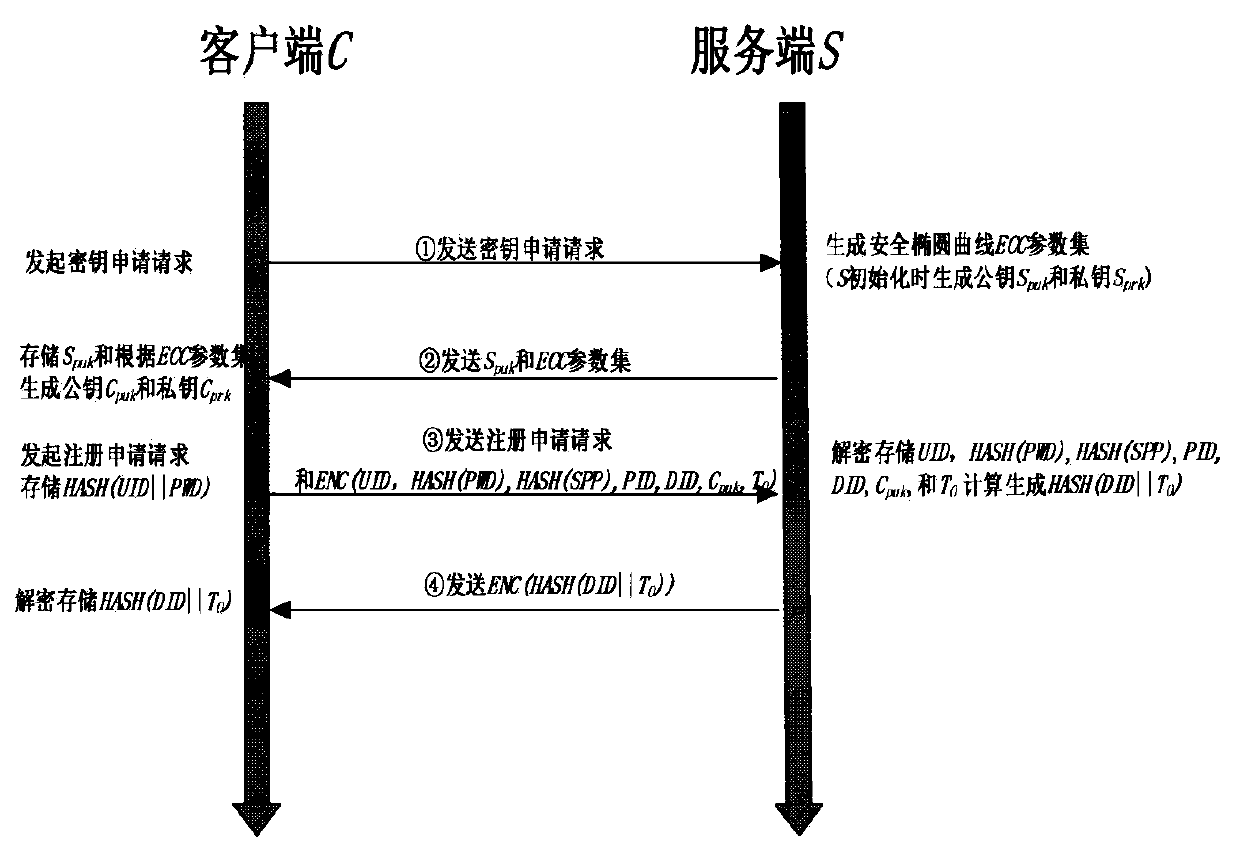
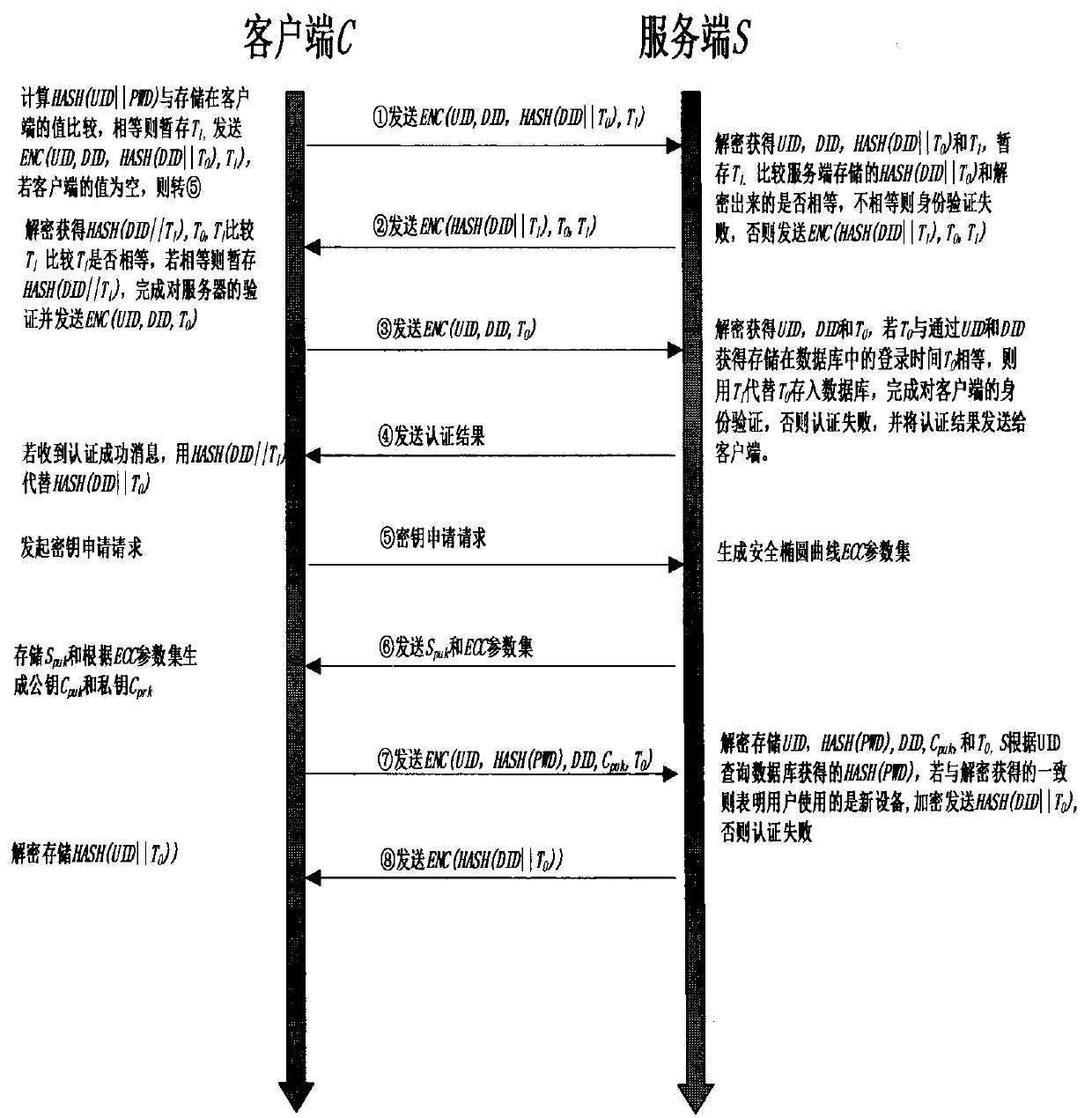
Dynamic authentication method of client side suitable for mobile cloud
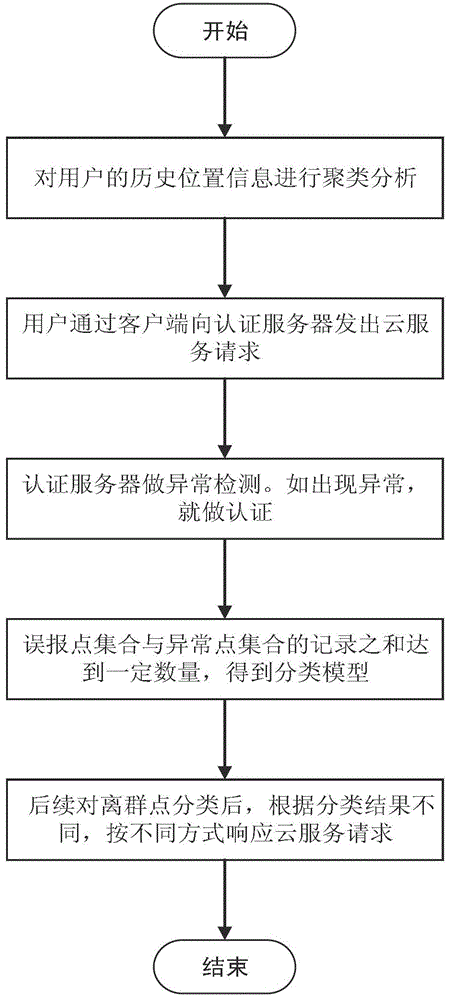
InactiveCN103338188AHigh precisionAvoid risk of lossUser identity/authority verificationMobile cloudOutlier
The invention discloses a dynamic authentication method of a client side suitable for a mobile cloud. The method comprises the following steps: 1) conducting cluster analysis of historical location information of a user; 2) sending a cloud service request / requests to an authentication server through the client side by the user; 3) confirming a cluster A to which the current location information of the client side corresponds by the authentication server, if the ratio of the number of data points in the cluster A to a sum is less than a threshold value t, deciding that the current location information is an outlier and conducting authentication, if the authentication is passed, recording the current location information in a misinformation point collection and responding to the request, otherwise, refusing the request, and recording the current location information in an outlier collection; 4) if the sum of the recorded misinformation point collection and the recorded outlier collection is greater than a threshold value L, marking and combining the sum to be used as a training data of classification to obtain a classification model; and 5) as for subsequent cloud service requests of the user, utilizing the classification model to conduct classification for outliers to respond to the cloud service request. The method improves the data security and account security of the user.
Owner:PEKING UNIV
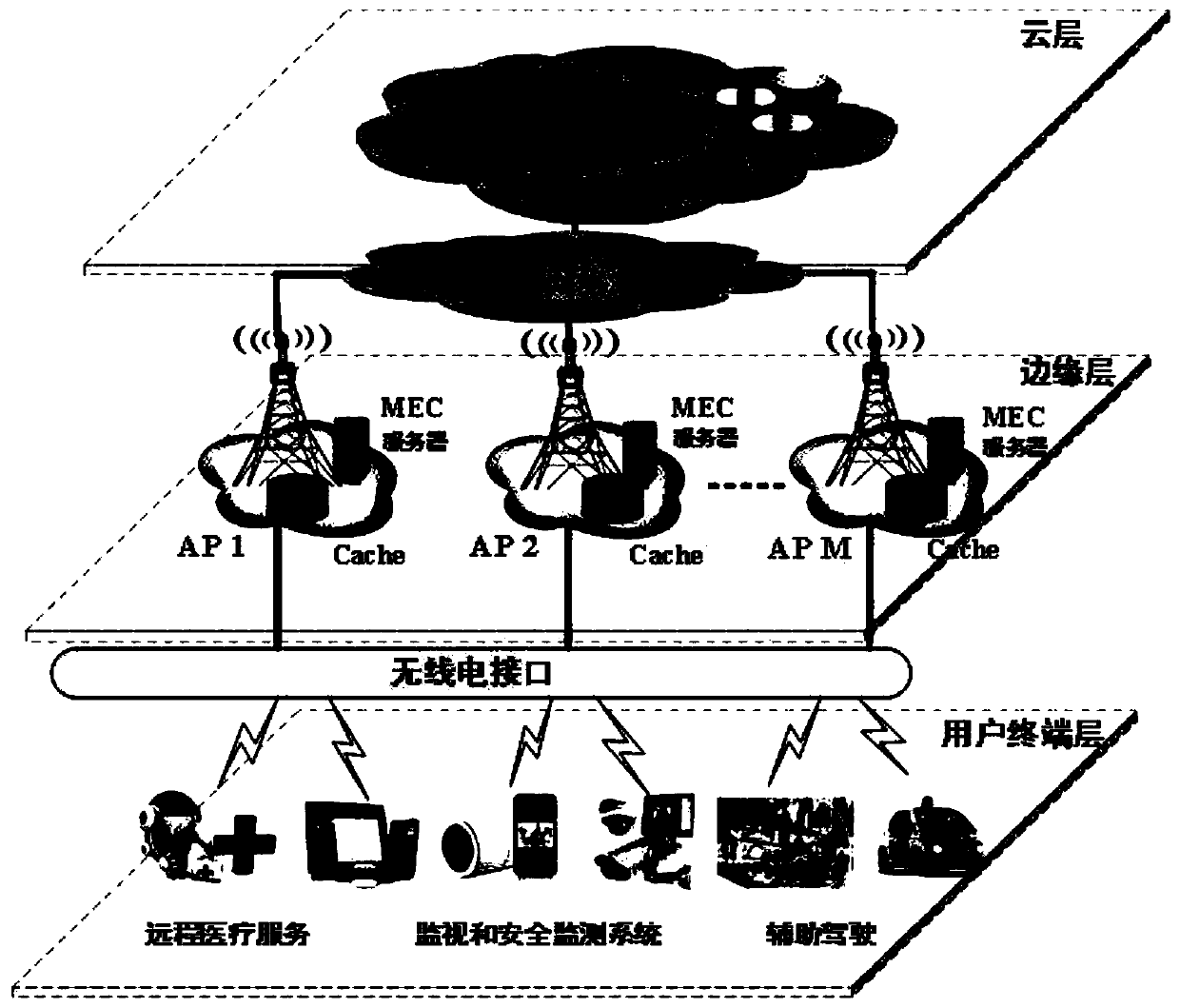
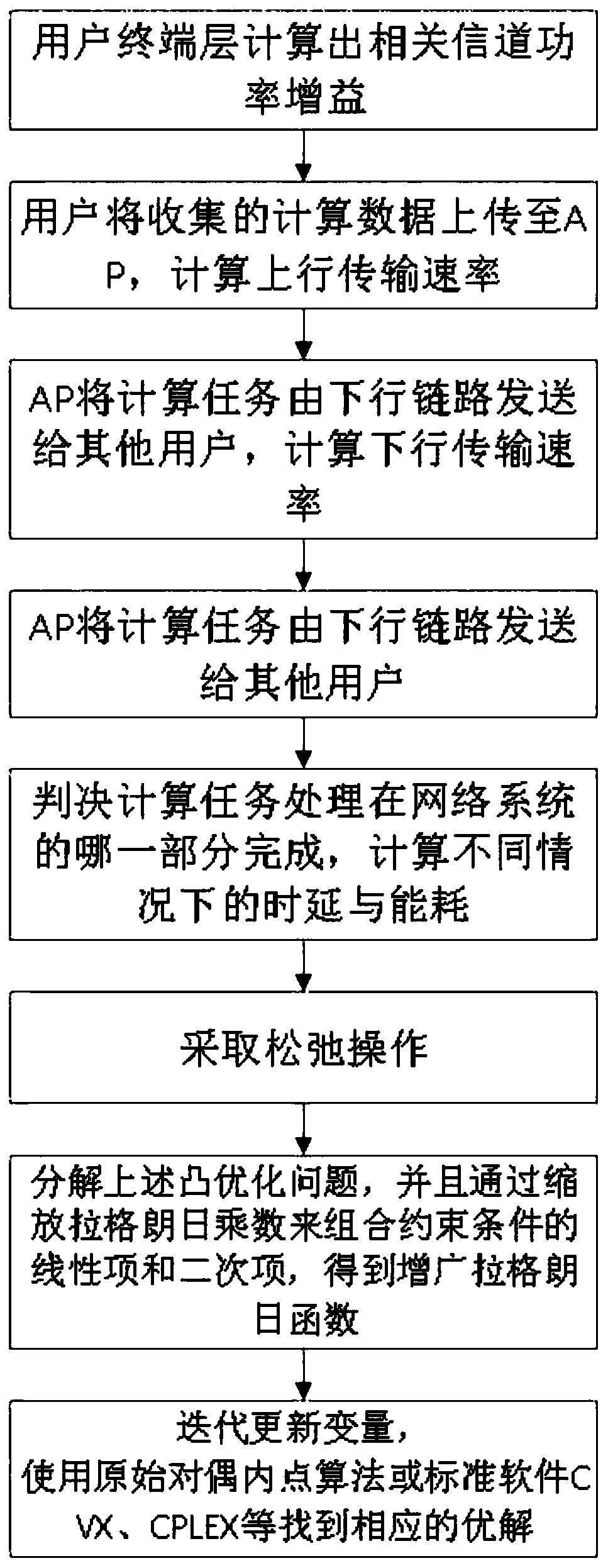
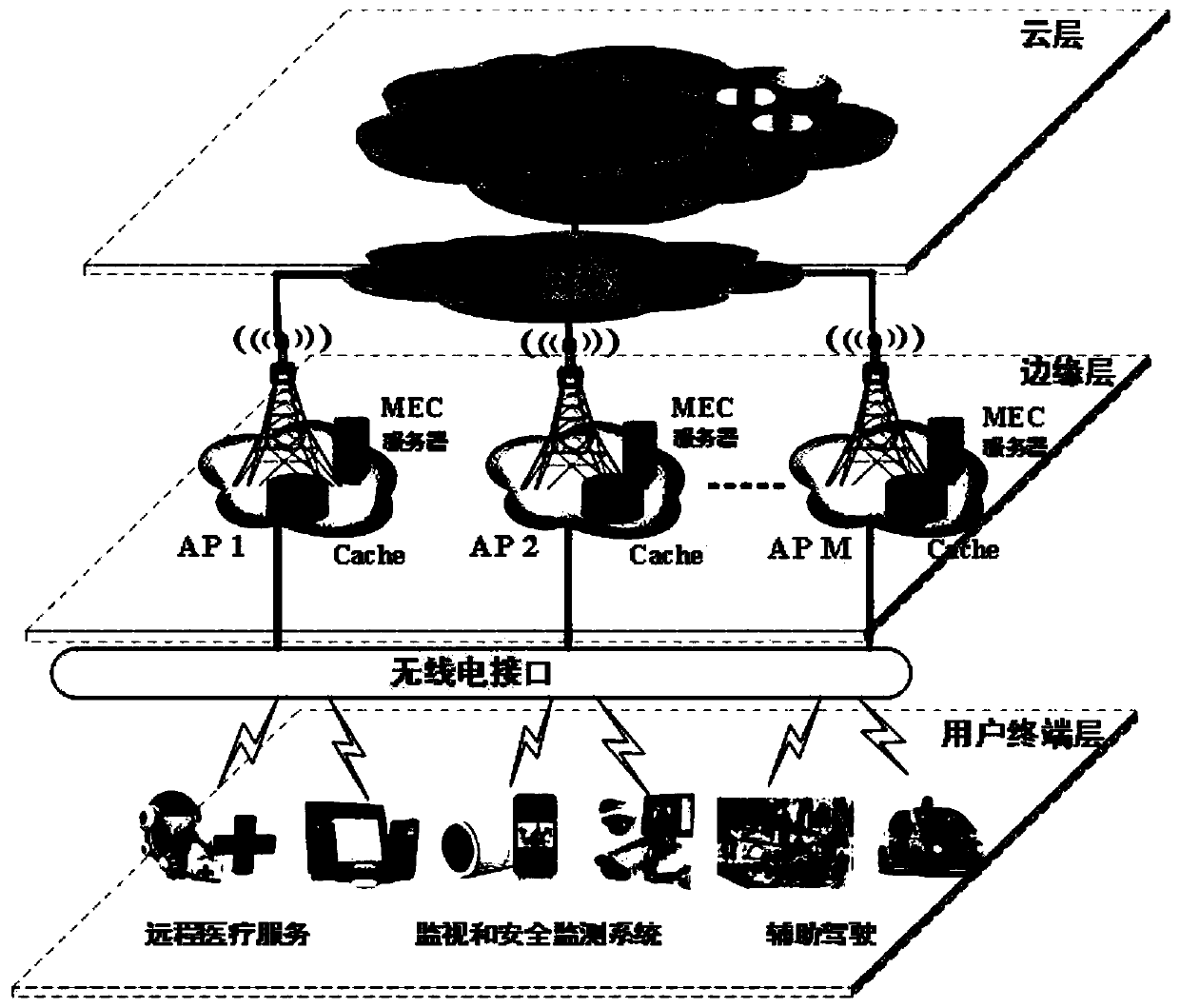
Task unloading and data caching method for hybrid mobile cloud/edge computing
PendingCN110018834APowerful computing cacheTake advantage ofResource allocationEnergy efficient computingChannel powerComputer architecture
The invention discloses a task unloading and data caching method for hybrid mobile cloud / edge computing, and belongs to the technical field of decision optimization and multi-user resource allocation.The method comprises the following steps: 1) calculating channel power gain; 2) uploading the calculation data to an AP, and calculating uplink and downlink transmission rates; 3) judging which partof the user of the user terminal layer, the MEC server of the edge layer or the cloud server in the cloud layer the task processing is completed, and calculating task processing time delay and energyconsumption which are completed according to corresponding conditions after judging; 4) obtaining a minimization optimization problem of the task processing process delay; 5) copying a local variableand storing the local variable in the MEC server; 6) using an alternating direction multiplier method to obtain an augmented Lagrangian function, and 7) performing iteratively updating to obtain a final expression form of the optimized objective function, and finding out the minimization of the task processing process delay. The method satisfies the energy consumption of the user, and minimizes the total user delay while constraining the storage and calculation capability of the AP.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
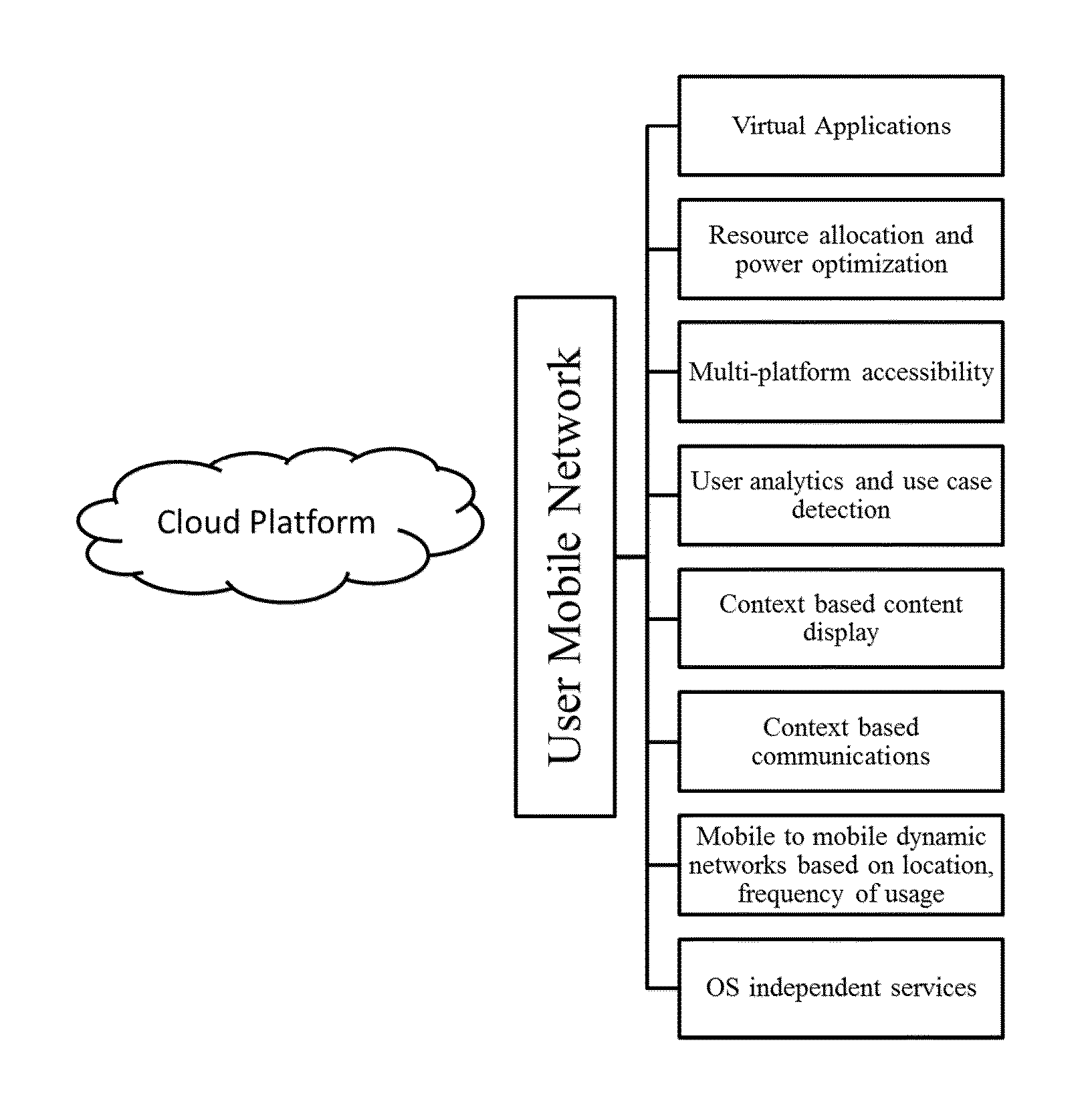
System and method for context based user intent sensing and content or application delivery on mobile devices
InactiveUS20130178241A1Substation equipmentMobile application execution environmentsMobile cloudTemporal context
The embodiments of the present system includes a mobile device with a native or installed mobile application that communicates with a cloud platform for context based content delivery to the mobile terminal device. The mobile cloud platform includes a mobile cloud virtualization layer, a mobile cloud content delivery layer and a mobile cloud network layer. The mobile cloud virtualization layer functions as a storage and process center. It allocates resources for native applications and other user information storage, content storage for static services, content storage for dynamic services and runs application processes for mobile users independent of the mobile platform. The mobile cloud content delivery layer runs a context-adaptive engine that delivers service provider content to a mobile platform based on space-time context of the user. The mobile cloud network layer forms dynamic local networks as well as high frequency usage networks with other mobile terminal devices based on the user analytical data.
Owner:INSET INC
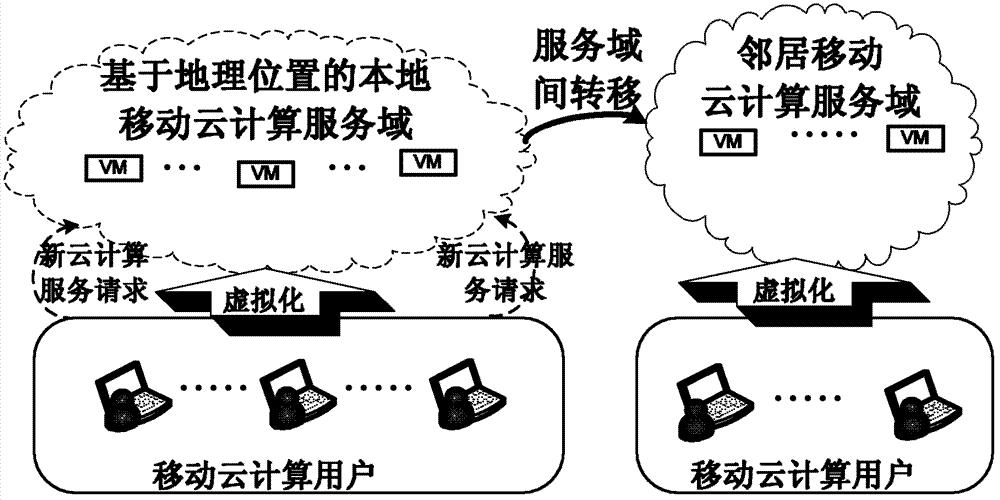
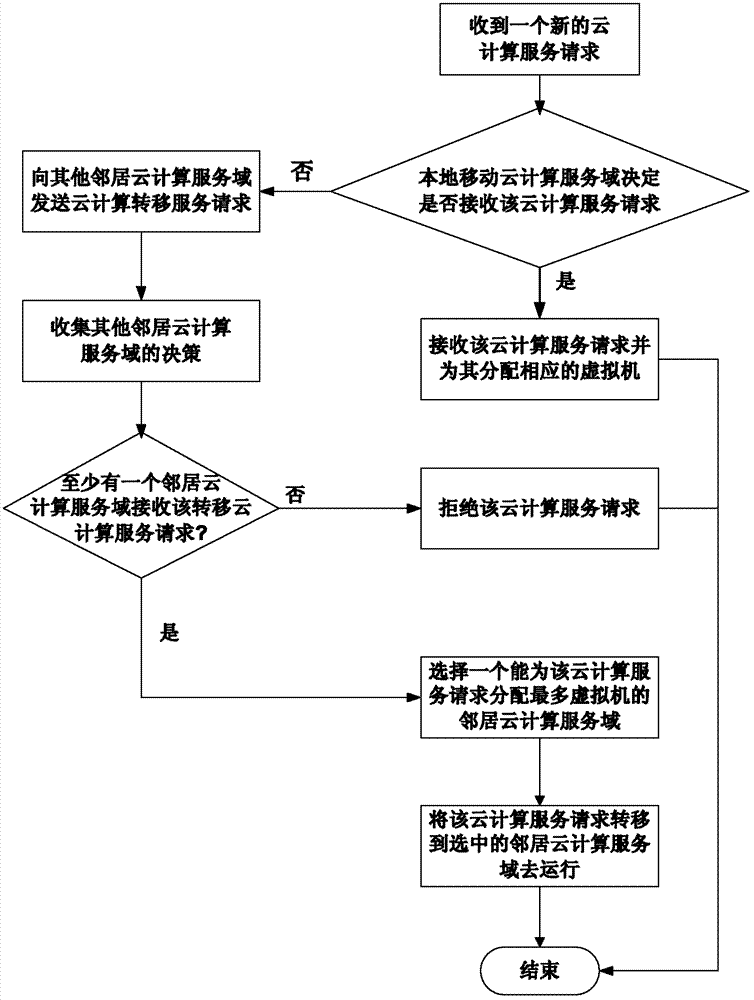
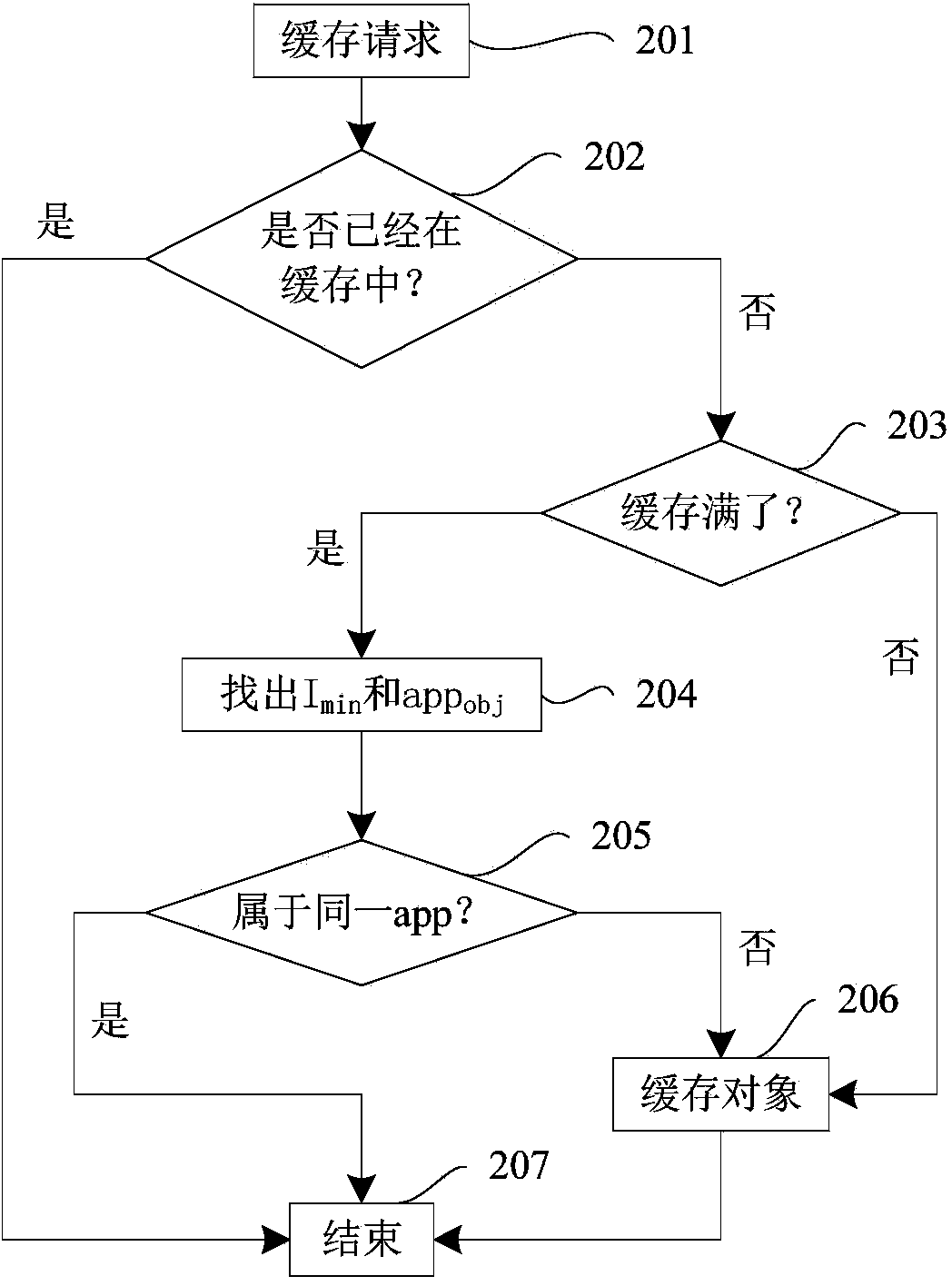
Mobile cloud computing resource optimal allocation method
InactiveCN102857548AImprove resource utilizationImprove system yieldTransmissionService domainMobile cloud
The invention provides a mobile cloud computing resource optimal allocation method which comprises the following steps of: establishing a transfer implementation method between different service domains of cloud computing as a cloud computing resource allocation model of a mobile cloud computing system; analyzing the system long-term income of a mobile cloud computing service domain while considering the condition of transferring the cloud computing service between different cloud computing service domains by taking a mobile terminal and a mobile cloud computing service domain as a whole so as to obtain the best cloud computing resource allocation scheme between different mobile cloud computing service domains; and finally deciding to receive, transfer or reject a service request of the mobile terminal in the local cloud computing service domain. The method provided by the invention increases the system income of a cloud computing network and the customer satisfaction (or user QoE (quality of experience)) of a mobile cloud computing user on the basis of considering the benefits of the cloud computing service domain as well as the benefits of the mobile cloud computing user.
Owner:梁宏斌
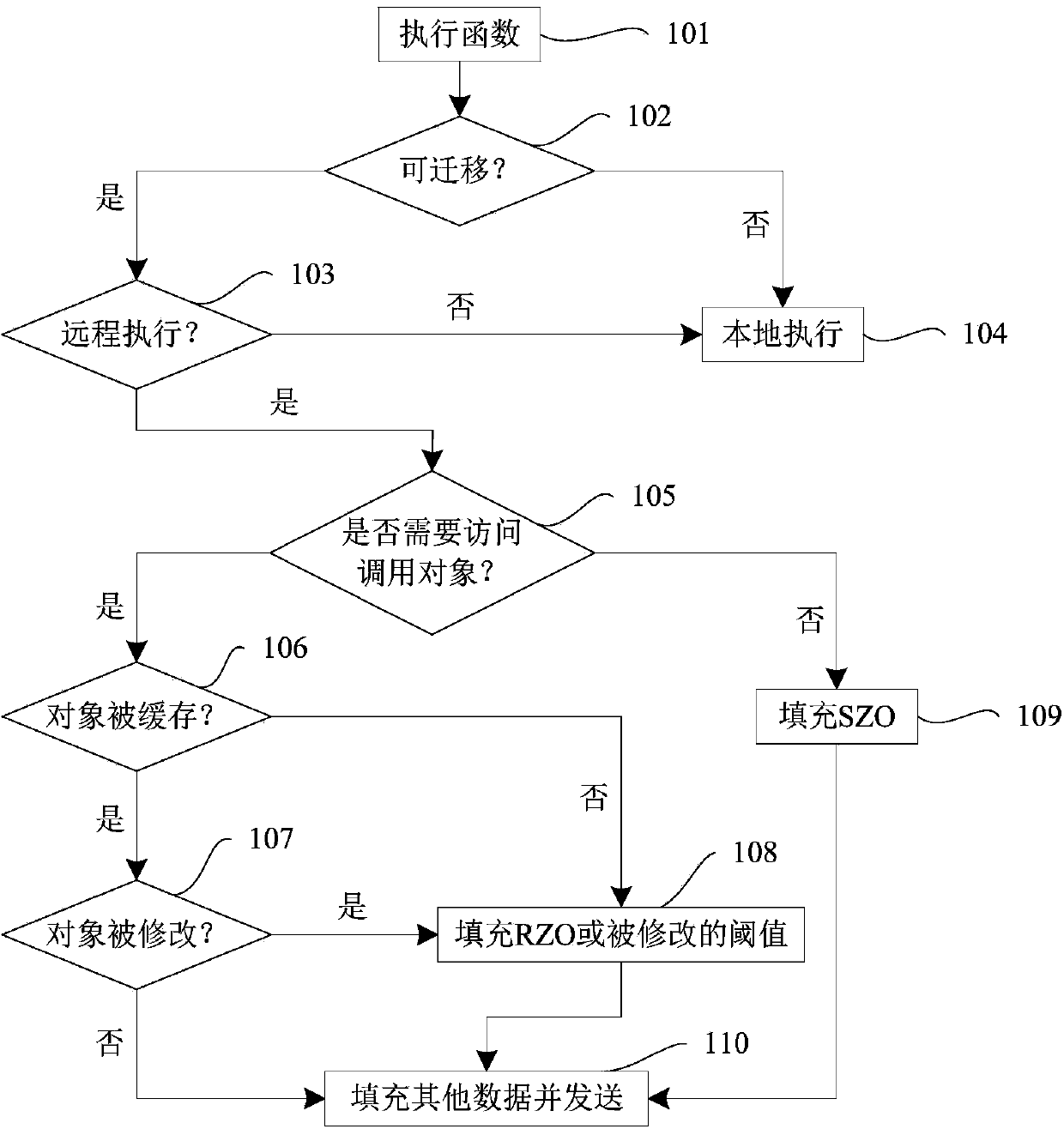
Method and system for migrating mobile cloud computing
InactiveCN104202373AComputational resources are not neglectedSave transmission resourcesTransmissionMobile cloudMobile end
The invention discloses a method and a system for migrating mobile cloud computing. The method and the system are used for migrating calculated load at a mobile end to a cloud server end. The method for migrating the mobile cloud computing comprises the steps of migration judgment and energy consumption comparison, wherein the step of migration judgment is used for judging whether a function needing to be implemented at the mobile end can be migrated to the cloud server end for implementation; the step of energy consumption comparison is used for comparing the time and energy consumption of an executive function migrated to the cloud server end required for implementation at the cloud server end with the time and energy consumption of an executive function migrated to the cloud server end required for implementation at the mobile end, and migrating the function implemented by the cloud serer end with shorter required time and smaller energy consumption to the cloud server end for implementation. The invention provides a light weight mobile cloud computing migration decision frame model, and the function for computing the consumed time and energy in the program implemented at the mobile end is migrated to the cloud server end for implementation.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Mobile cloud and end internet of Things system and method adopting same
ActiveCN102637291AAchieve immediacyAchieve precisionData processing applicationsSubstation equipmentMobile cloudInterconnection
The invention provides a mobile cloud and end internet of Things system which is characterized by comprising a detected client mobile user end, and a medicine center cloud end, wherein the medicine center cloud end receives data coming from the detected client mobile user end, packs and re-files filed data into different specialist physician reception modules; and the different specialist physician reception modules send data to different doctor mobile user ends. According to another technical scheme, the invention provides a classified treatment information generating method. According to the system and the method, three carriers: the client mobile user end, the medicine center cloud end and the doctor mobile user ends are used for constructing and assisting the current conventional electronic health medical system by establishing and managing a strong online database based on wireless communication network tele-interconnection of a mobile, online interaction of a Web page module, and a virtual cloud server technology, thus truly realizing instantaneity, precision, efficiency, stability, fidelity and safety of internet of Things medicine.
Owner:ZHONGSHAN HOSPITAL FUDAN UNIV +1
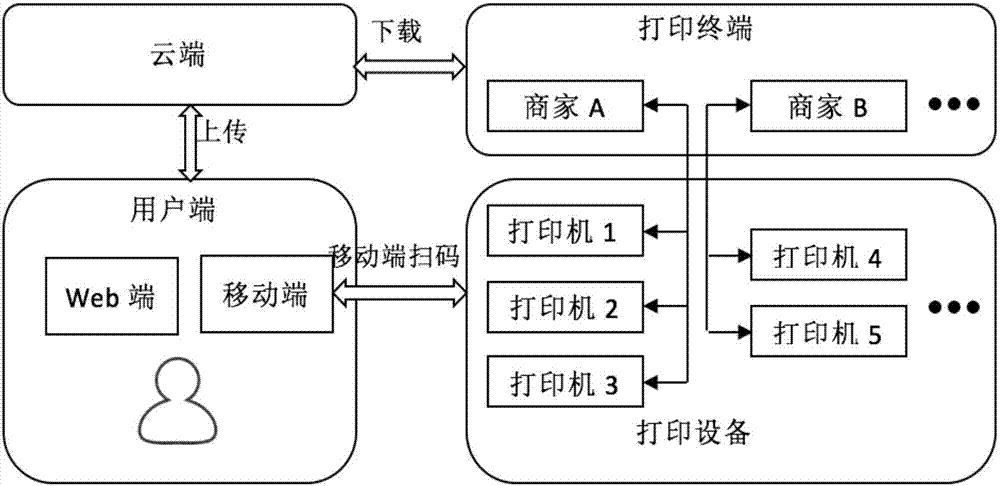
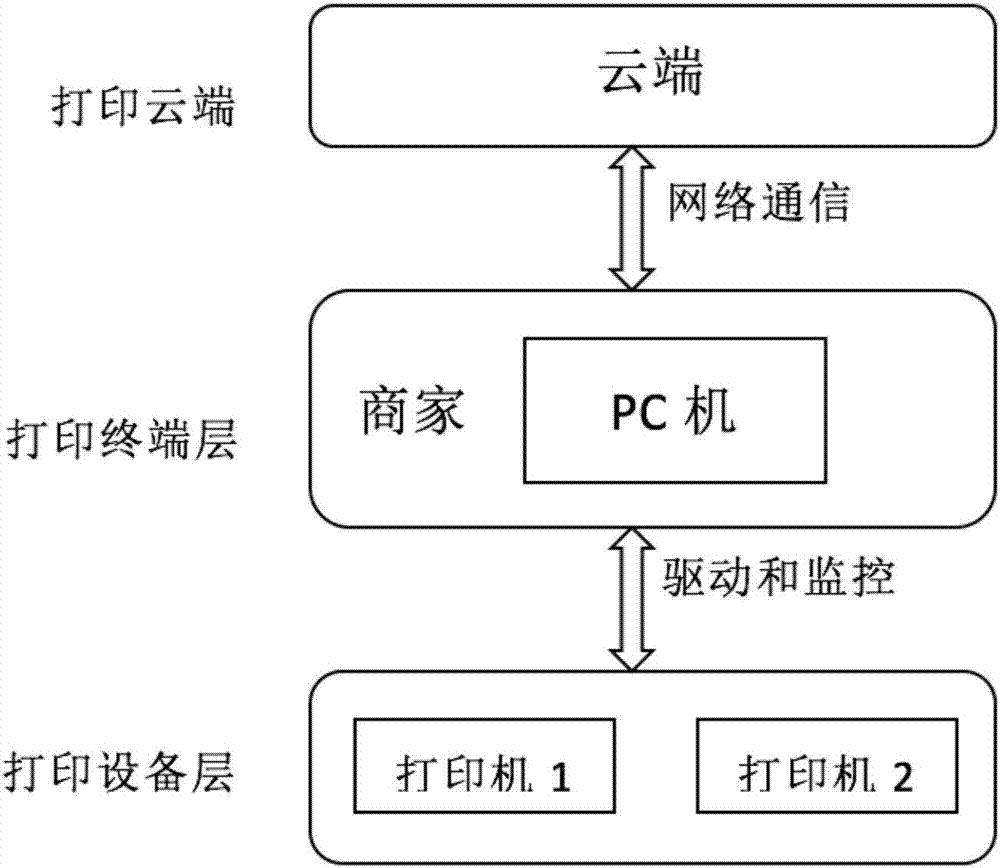
Mobile cloud printing method and system
InactiveCN106951198AMake the most of your printing capabilitiesFull supervision of printingDigital output to print unitsMobile cloudComputer terminal
The invention discloses a mobile cloud printing method and system and belongs to the field of cloud printing. The system comprises a mobile terminal, a printing terminal and a cloud terminal, wherein the printing terminal registers a printer connected with the printing terminal at the cloud terminal, and a cloud printer recognition two-dimensional code is obtained and pasted to the body of the printer; during printing, the mobile terminal uploads printing parameters and a document to the cloud terminal, the two-dimensional code on the body of the selected printer is scanned, and ID of the selected printer is acquired and uploaded to the cloud terminal; the cloud terminal makes a printing task after receiving the ID of the printer, and the printing task is added into a task queue of the printer, wherein the printing task contains the printing parameters and the document; and the printing terminal makes a real-time request to the cloud terminal to acquire the task queue of the printer connected with the printing terminal, and the printer is driven to complete the printing task. Meanwhile, the mobile cloud printing method is also realized through the technical scheme. According to the technical scheme, the printer is selected by scanning the two-dimensional code, and therefore a user can complete printing and taking immediately after arrival; printing of the document is monitored in the whole process, so that the privacy security of printed files is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Multi-authority ciphertext-policy attribute-based encryption method
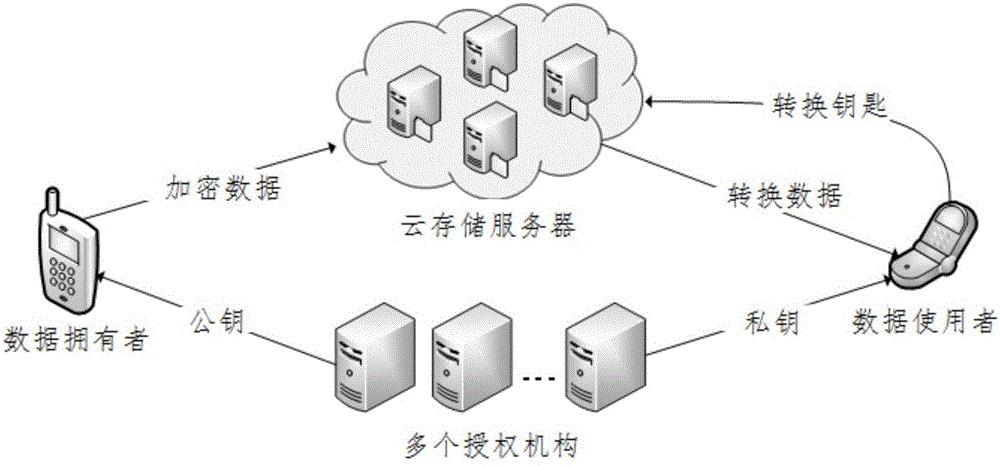
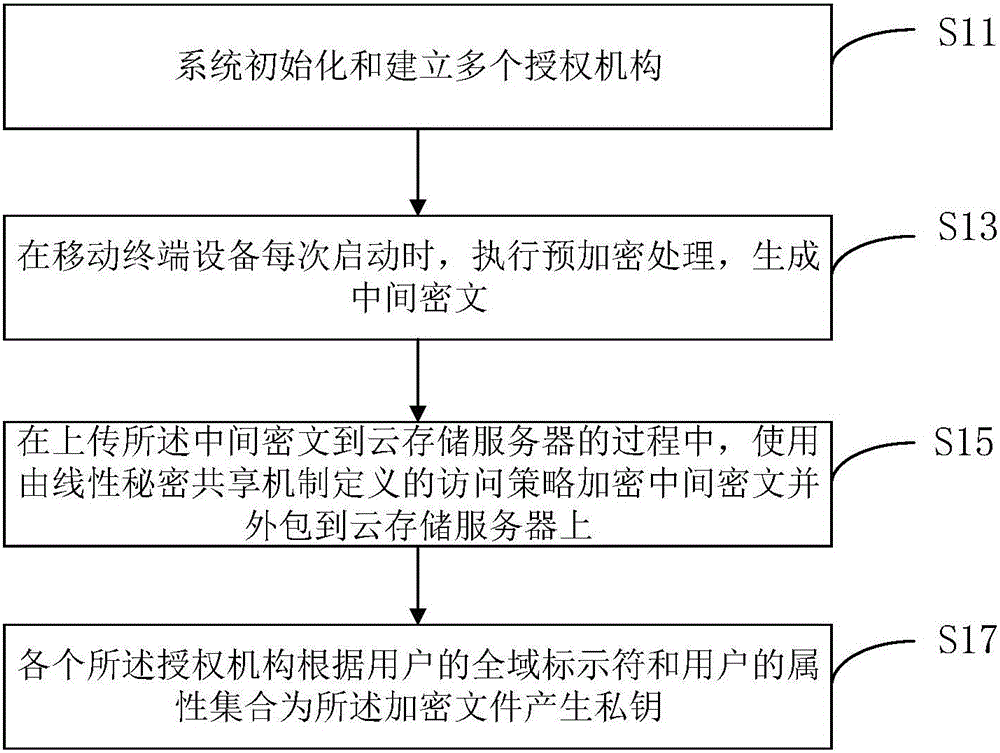
ActiveCN106230590AEnsure safetyImprove battery lifeKey distribution for secure communicationPublic key for secure communicationAttribute-based encryptionMobile cloud
The invention discloses a multi-authority ciphertext-policy attribute-based encryption method. The method includes following steps: step 1, performing system initialization and establishing a plurality of authorities; step 2, before each starting of a mobile terminal device, executing pre-encryption treatment, and generating an intermediate ciphertext; step 3, in a process of uploading the intermediate ciphertext to a cloud storage server, encrypting the intermediate ciphertext by employing an access policy defined by a linear secret sharing mechanism, and outsourcing the intermediate ciphertext to the cloud storage server; and step 4, generating a private key for an encryption file according to global identifiers of users and an attribute set of the users by each authority. According to the method, aiming at the mobile cloud storage environment, on the premise of guaranteeing the data security, a lot of pairing operations are pre-processed in advance by employing the encryption pre-processing technology so that the calculation cost of online encryption is minimum; and by employing the secret key transformation technology and decryption outsourcing, a lot of pairing operations are outsourced to the cloud storage server so that the decryption calculation cost of the mobile terminal is reduced.
Owner:ANHUI UNIVERSITY
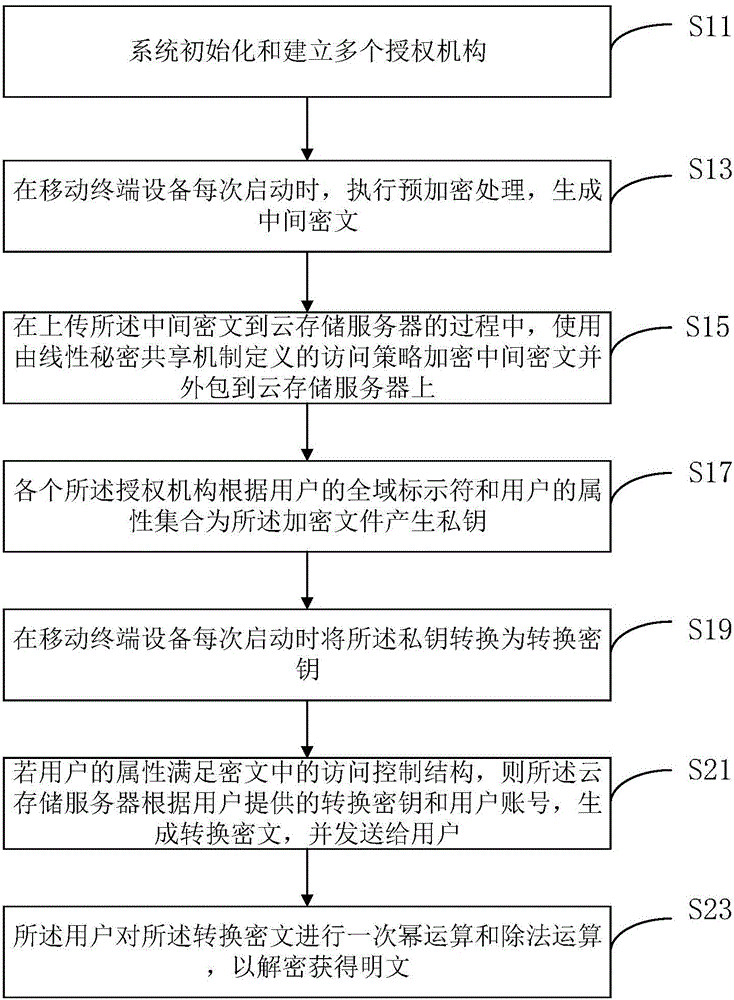
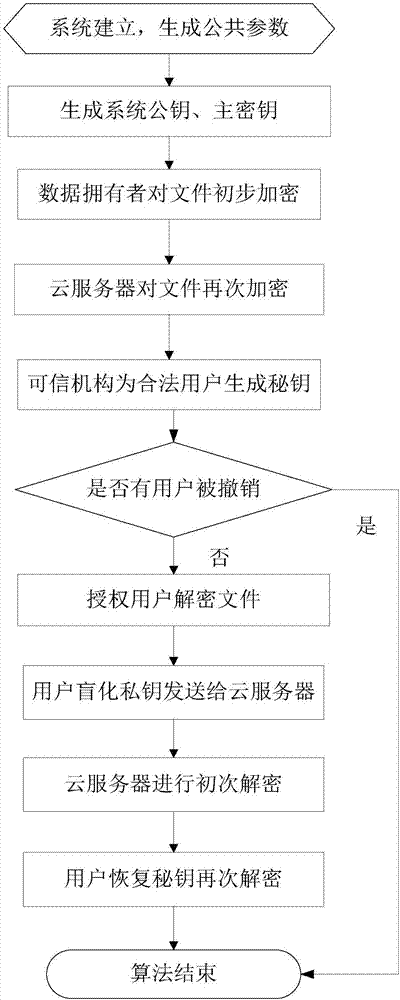
Outsourcing encryption and decryption CP-ABE method capable of achieving user revocation
InactiveCN107359986AFunction increasePerfect rights management functionKey distribution for secure communicationPlaintextMobile cloud
The invention discloses an outsourcing encryption and decryption CP-ABE method capable of achieving user revocation, and relates to the technical field of data encryption and decryption in a mobile cloud environment. The method further achieves the outsourcing encryption operation on the basis of conventional outsourcing attribute encryption, and reduces the encryption calculation cost of a local client. The method achieves the access control of fine granularity of a file on a cloud server, simplifies the secret key management operation for a user, and achieves the revocation of the access authority of an unauthorized user. When the user is revoked, a legal user does not need to update a secret key, and alleviates the burden of an authorization mechanism. The local user just needs to carry out the simple XOR operation to update a cryptograph. The security proof indicates that the method provided by the invention has the non-adaptive selection plaintext safety under a common dual linear group model. The performance analysis indicates that the method reduces the encryption calculation cost of mobile equipment more effectively, can achieve the revocation of an illegal user efficiently, and achieves the control of the access authority of the user effectively.
Owner:JINAN UNIVERSITY
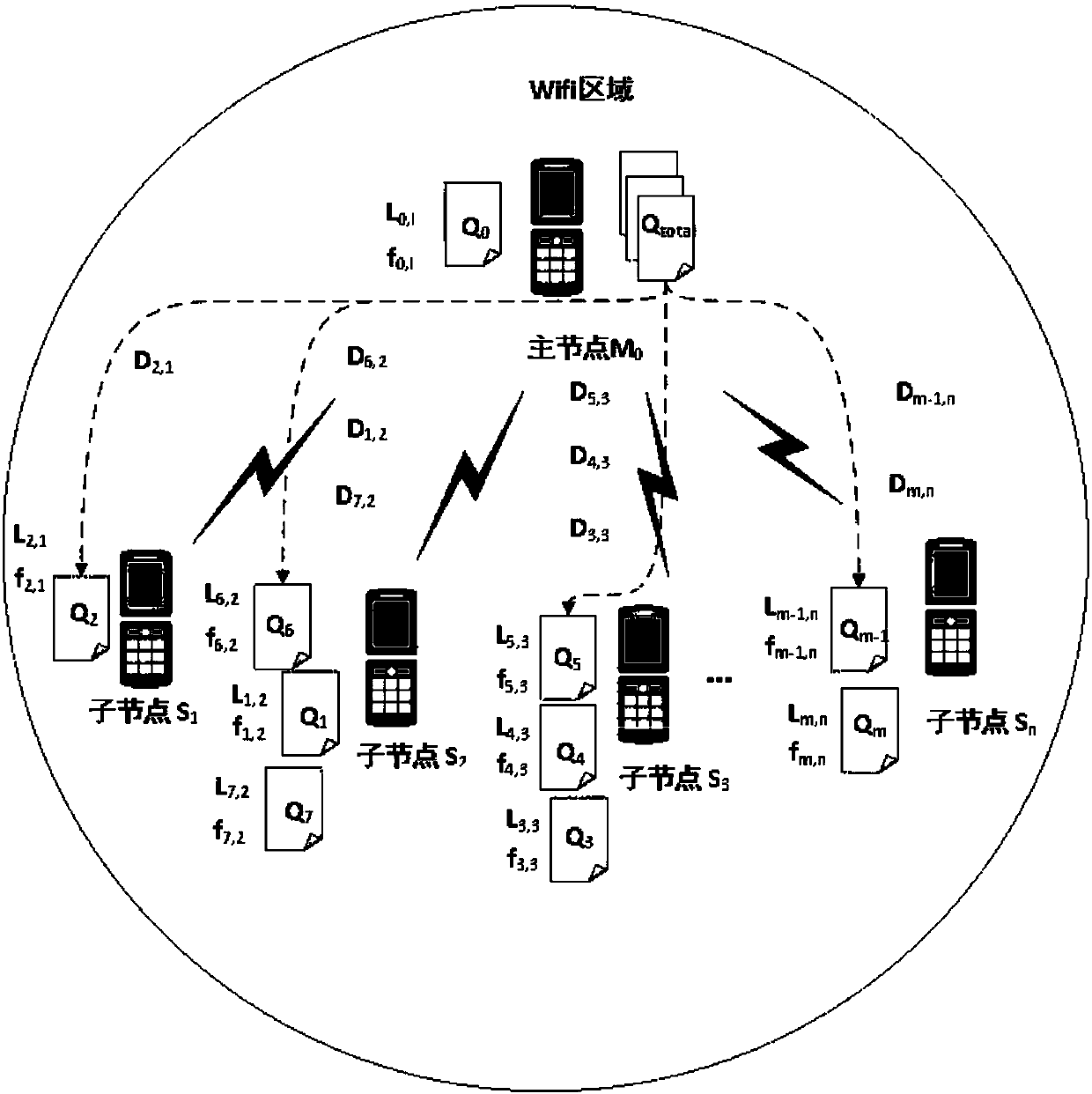
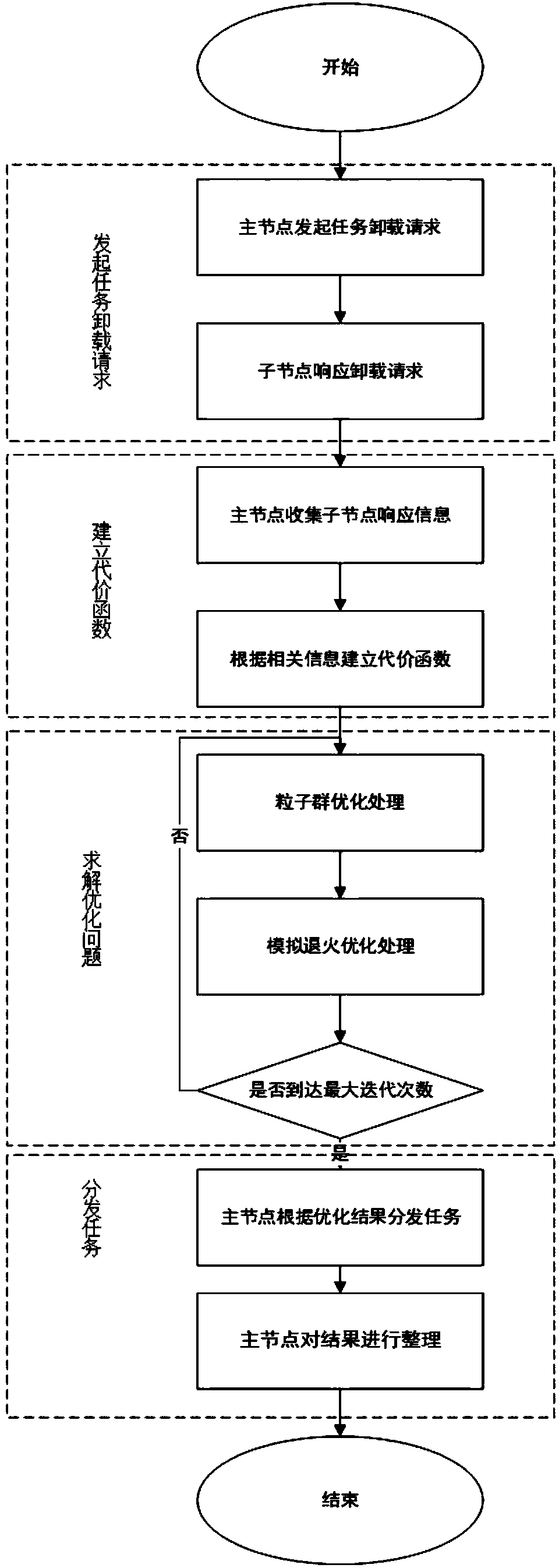
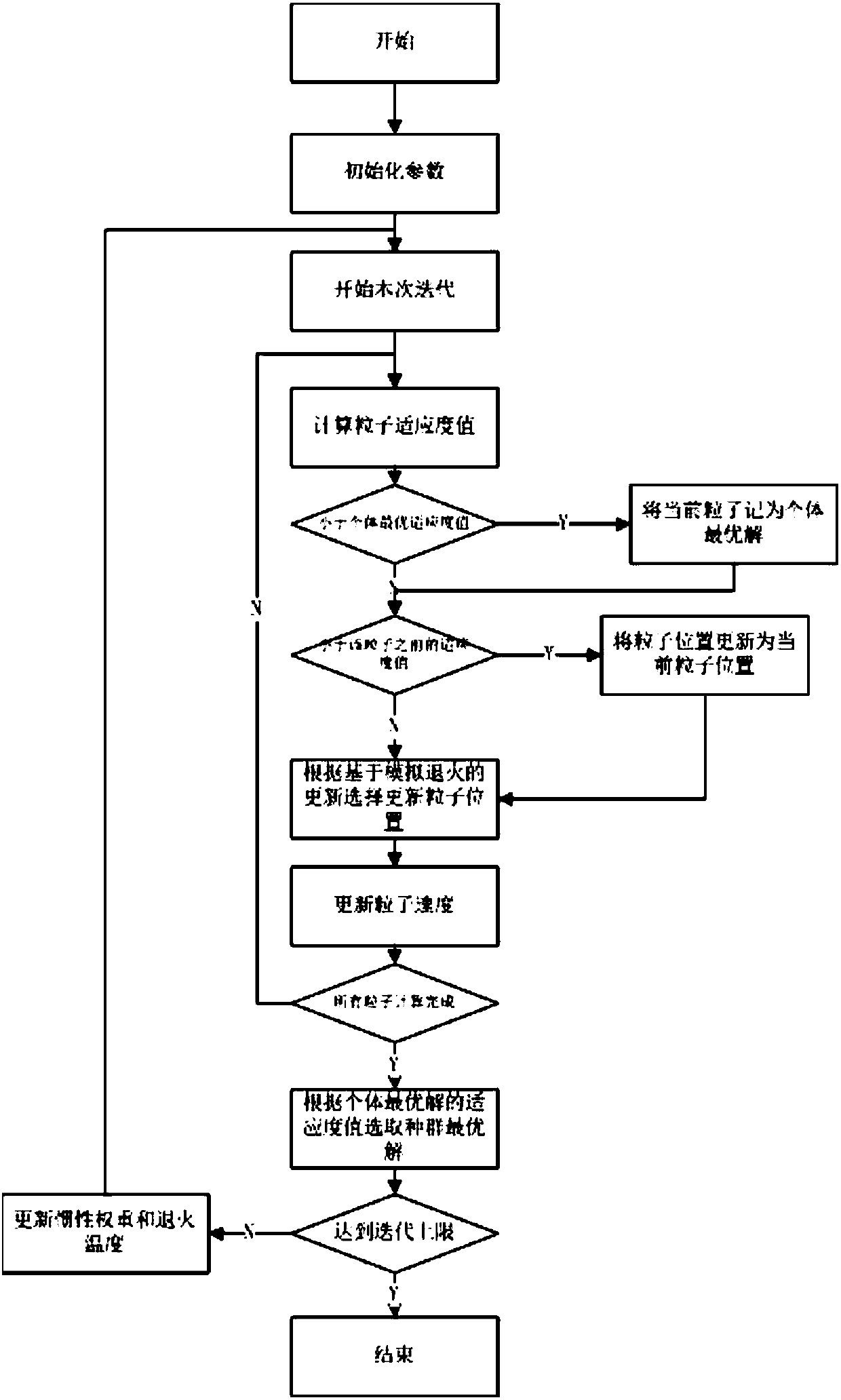
Task allocation method based on particle swarm and simulated annealing optimization in mobile cloud
ActiveCN107766135AEfficient sharingProgram initiation/switchingResource allocationRelevant informationMobile cloud
The invention provides a task allocation method based on a particle swarm and simulated annealing optimization in mobile cloud. Multiple mobile nodes are involved in the allocation method. The mobilenodes form a self-organized network in a wireless mode and share computing resources under the condition that no basic network facilities are available. The task allocation method comprises the four stages that (1) a task uninstalling request is initiated, wherein when a complicated computing task exists on a main node and the main node does not have sufficient computing resources for processing the task, the main node sends the task uninstalling request to slave nodes; (2) a cost function is established, wherein the main node generates a task uninstalling cost function according to remainingcomputing resource information of the slave nodes and relevant information needed for processing the complicated computing task; (3) an optimization problem is solved, wherein a task allocation algorithm based on the particle swarm and simulated annealing optimization is executed, and a task allocation result is obtained; and (4) the task is allocated, wherein the main node allocates the computingtask to all the slave nodes according to the optimization result.
Owner:SOUTHEAST UNIV
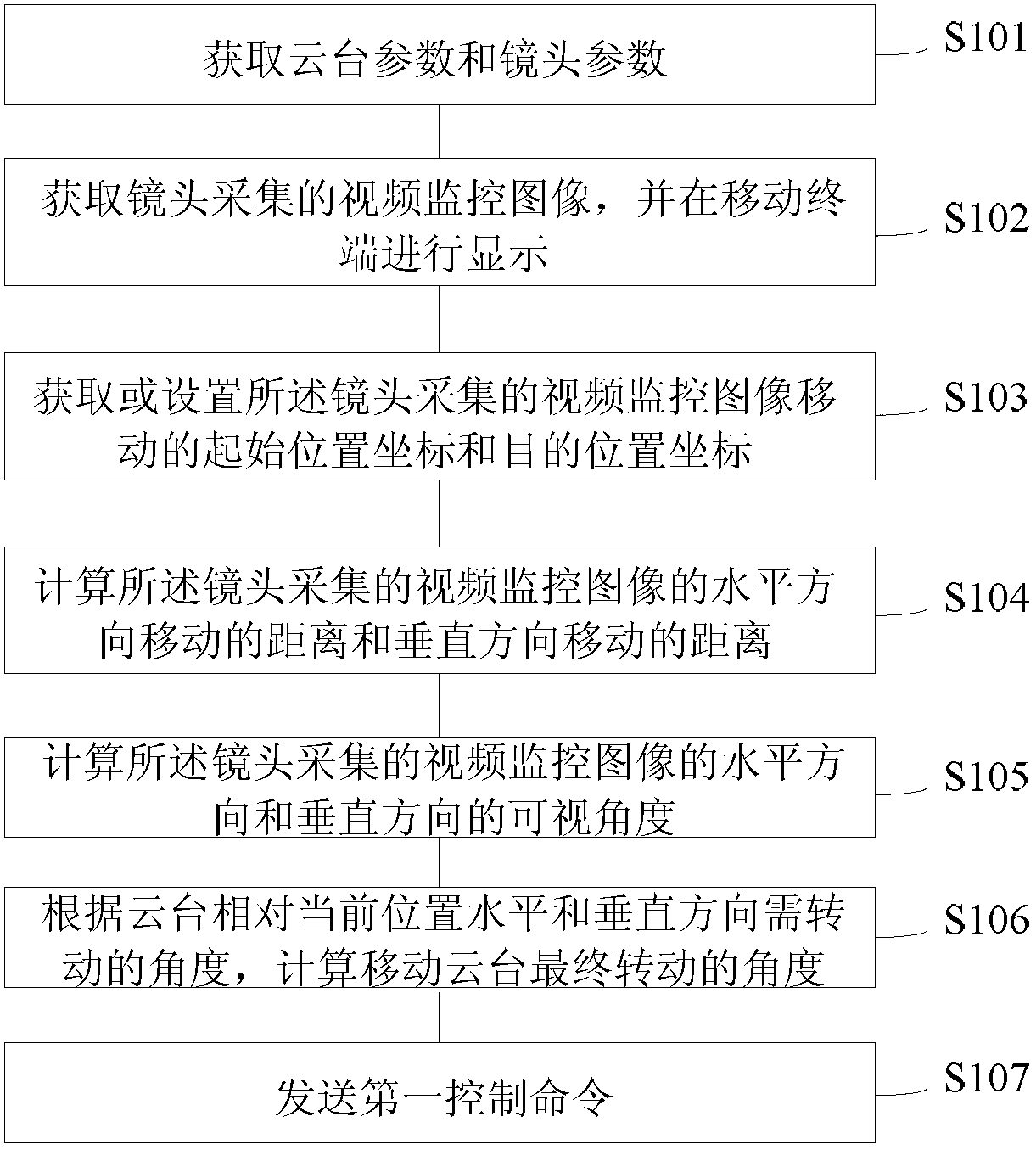
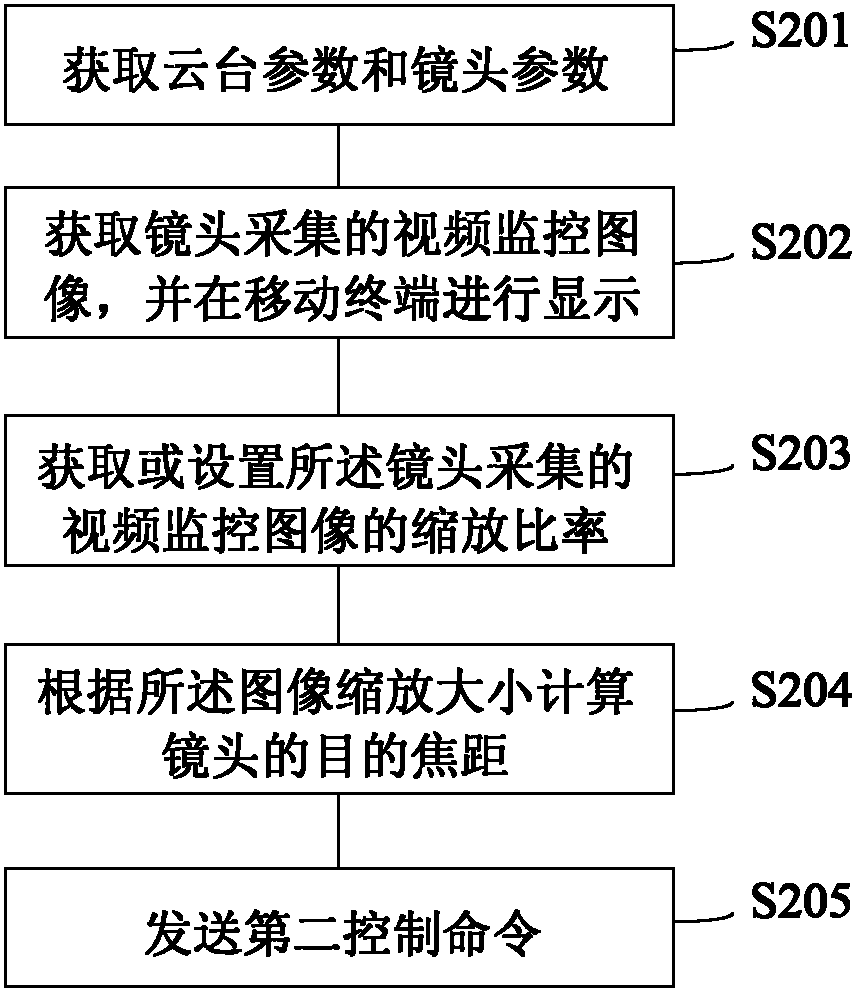
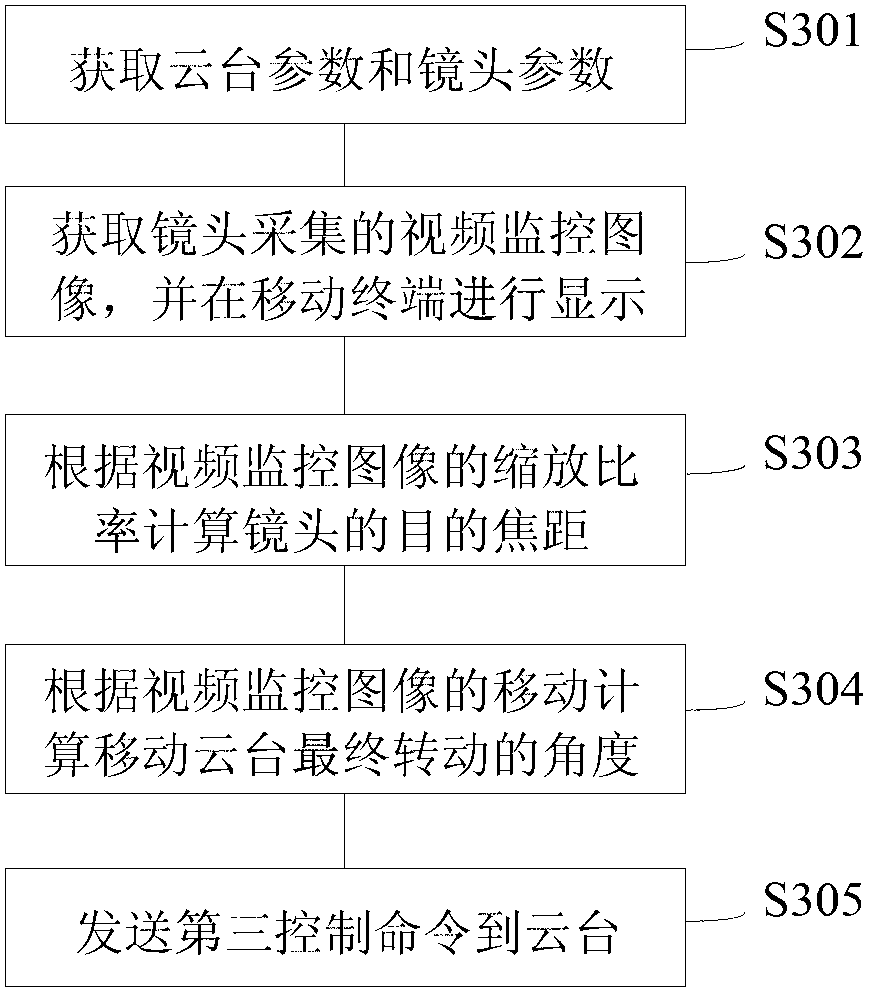
Video monitoring cloud platform controlling method and device
InactiveCN103108170AEasy to controlExactly one moveTelevision system detailsColor television detailsEmbedded systemMobile cloud
The invention discloses a video monitoring cloud platform controlling method and a device and belongs to the field of video monitoring. The video monitoring cloud platform controlling method and the device can obtain cloud platform parameters and lens parameters through a mobile terminal and displays video monitoring images collected by a lens in the mobile terminal. Required rotation angles of the mobile platform and target focal length of the lens are calculated on the mobile terminal based on settings of a user and then a control order is sent to control rotation of a cloud platform or contraction of the lens. With the video monitoring cloud platform controlling method and the device, a monitoring client terminal can visually control the cloud platform so that the lens can accurately be moved to a designated position once or contracted to a required size.
Owner:深圳市云宙多媒体技术有限公司
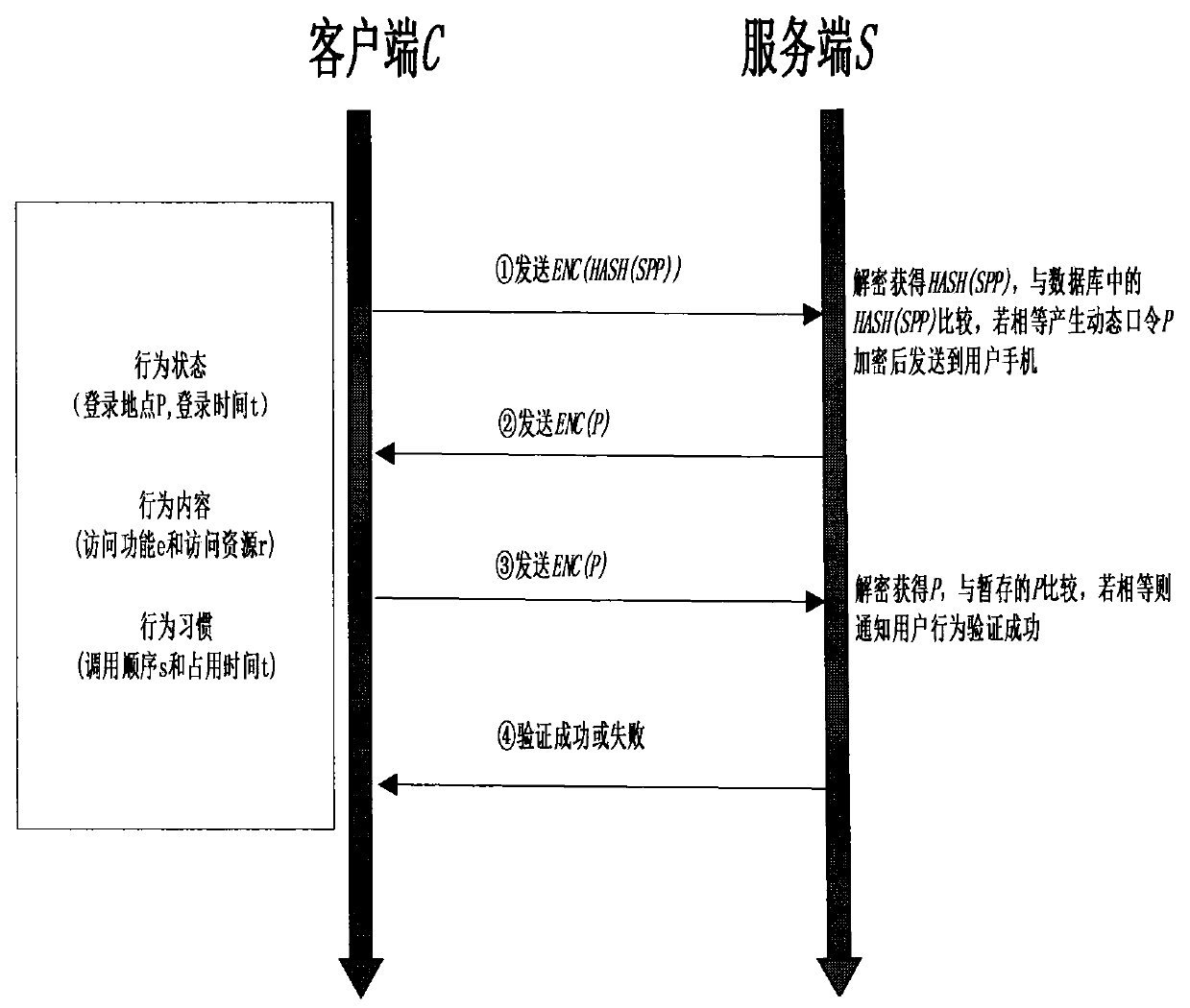
OTP and user behavior-based certification and authorization method in mobile cloud computing environment
InactiveCN105099690ASolve the problem of not being able to resist decimal attacksEnsure credibleUser identity/authority verificationMobile cloudClient-side
The present invention discloses an OTP and user behavior-based certification and authorization method in a mobile cloud computing environment. The method is characterized in that various intelligent mobile terminals available for users are enabled to be accessed to the cloud service via a wireless network in the mobile cloud computing environment and the bidirectional identity authentication between a client and a server is realized through improving the one-time password (OTP) technology. In this way, the safety and the reliability of the identity authentication process are improved. Meanwhile, according to the specific behavior habits of a user accessed to the cloud service, the features of historical behavior data of the user are analyzed and extracted based on the data mining technology. In this way, a knowledge database of the normal behavior patterns of the user is formed. When the user behaves abnormally or suspiciously, the identity of the user is authenticated again. Only when the user passes the identity authentication process, the corresponding service is authorized for the user. Therefore, the illegal operation of others is avoided, and the information security of the user is fully ensured.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
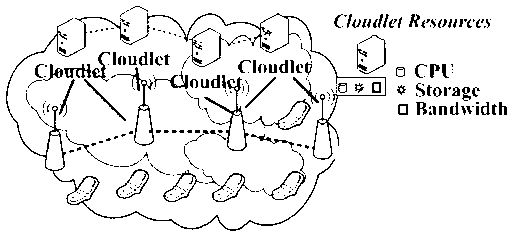
Multi-dimensional resource pricing method in mobile cloud computing environment based on bilateral market
ActiveCN103218737AAchieve optimal configurationEvenly distributedEnergy efficient ICTMarketingMobile cloudResource pricing
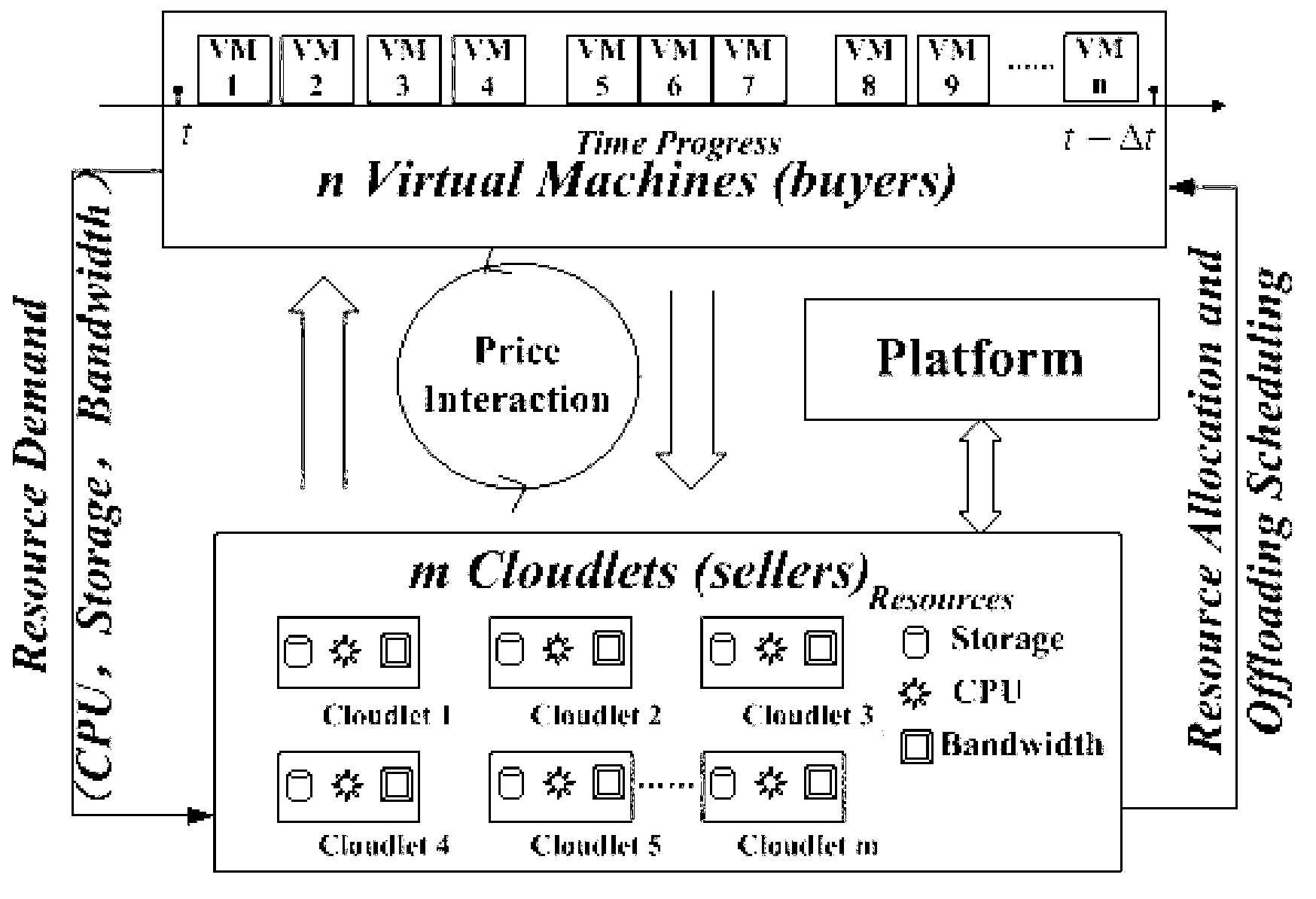
The invention discloses a multi-dimensional resource pricing method in a mobile cloud computing environment based on a bilateral market. The method runs in the mobile cloud computing environment, the method involves two groups of participants in the mobile cloud computing environment, one group of participants are Cloudlets which have resources, and the other group of participants are VMs which request the resources. The VMs are regarded as a buyer in a bilateral market economic model, the Cloudlets are regarded as a seller, and the two sides complete allocation of the resources through a price interactive mechanism, unloading execution of an application request from the VMs to the Cloudlets is completed, and energy consumption of the mobile equipment is reduced. The price interactive mechanism in the method is based on a bilateral market game and is designed through combination of a punishment pricing mechanism and a balanced utility discount, the multi-dimensional resources of the application request of a mobile user can be reasonably distributed and dispatched on a plurality of Cloudlets, and therefore system benefits of a mobile cloud are maximized.
Owner:HUNAN UNIV
Mobile cloud environment context awareness computing migration method
The invention relates to a mobile cloud environment context awareness computing migration method. The method includes the following steps that: a design pattern supporting computing dynamic migration in an application is provided; an evaluation model is put forward, so that optimal cloud resources can be automatically selected for computing migration based on the context of a mobile device; and a framework for supporting the above design model and the evaluation model is realized. The method of the invention can be flexibly applied to a complex and changeable mobile cloud environment. Compared with a traditional migration method, the method of the invention can greatly improve the performance of the mobile device and user experience and enhance the endurance of the mobile device.
Owner:FUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com