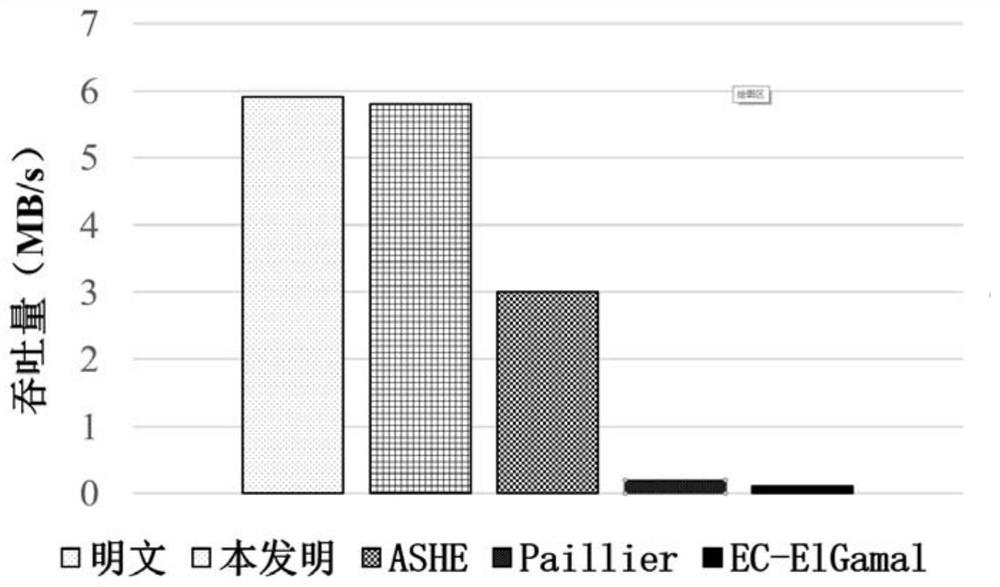
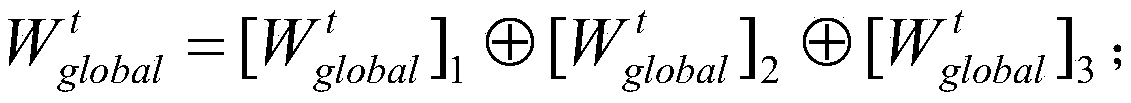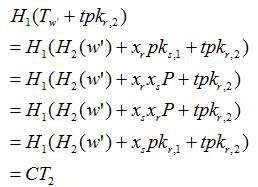Patents
Literature
60results about How to "Enable secure sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
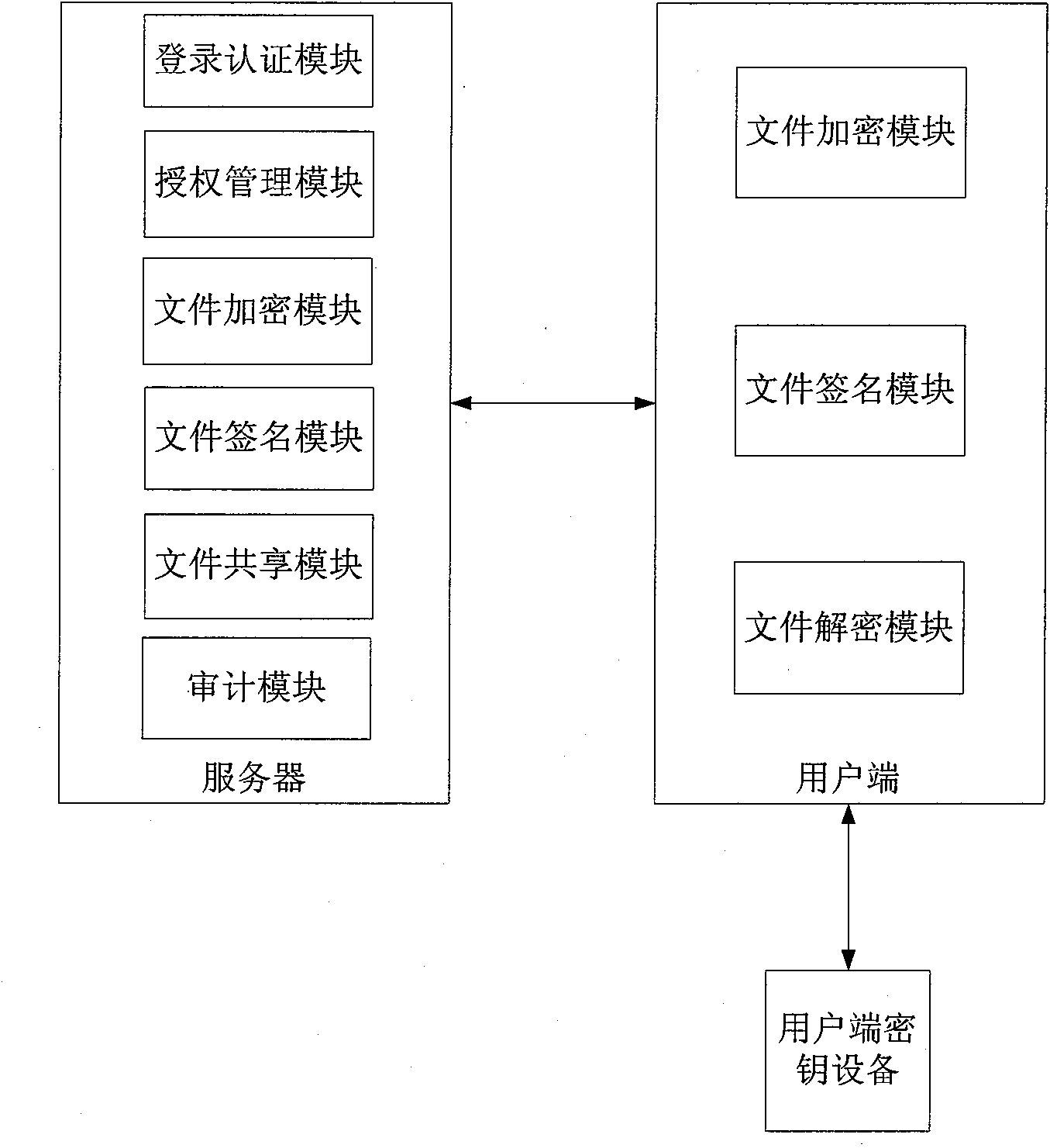
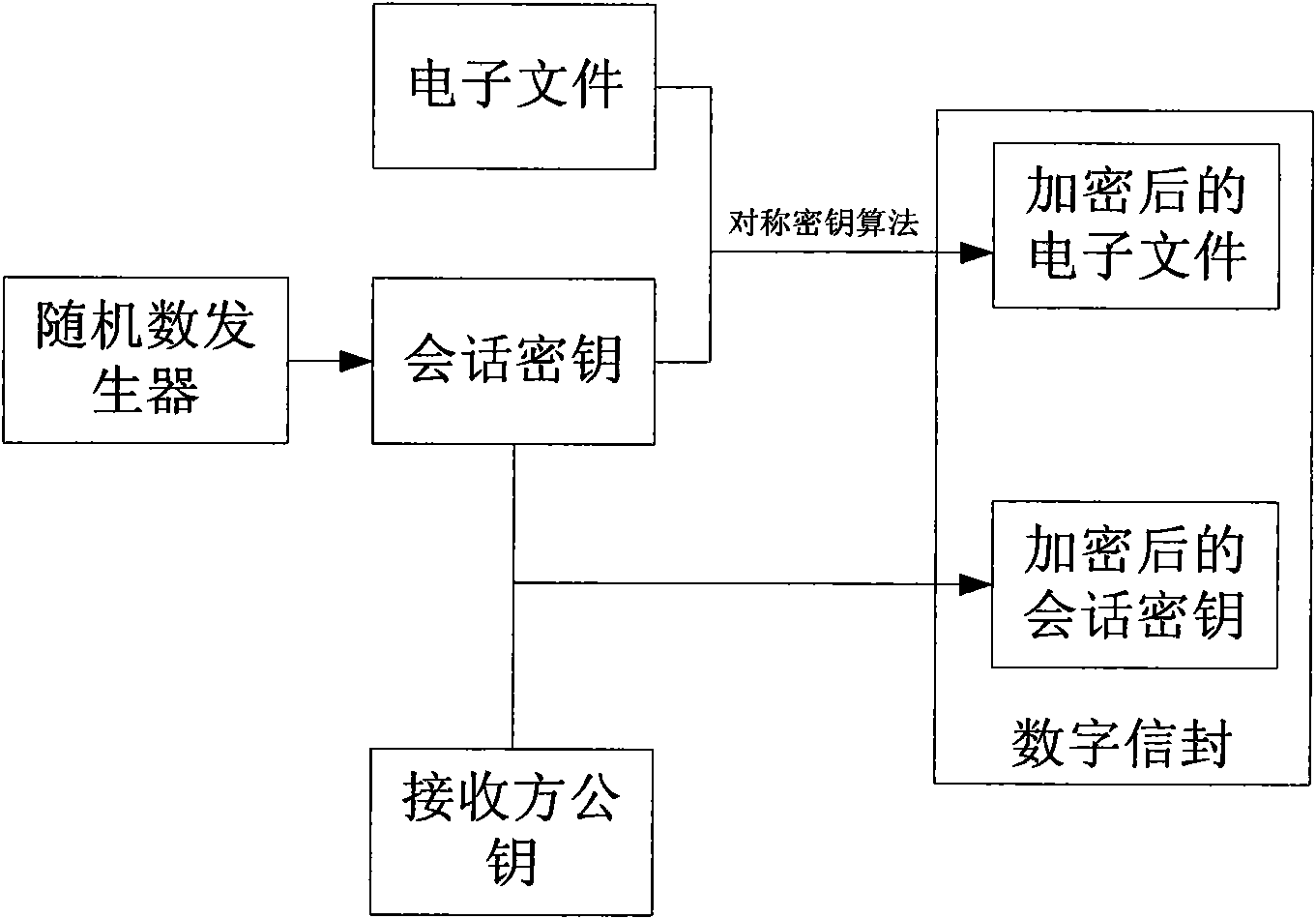
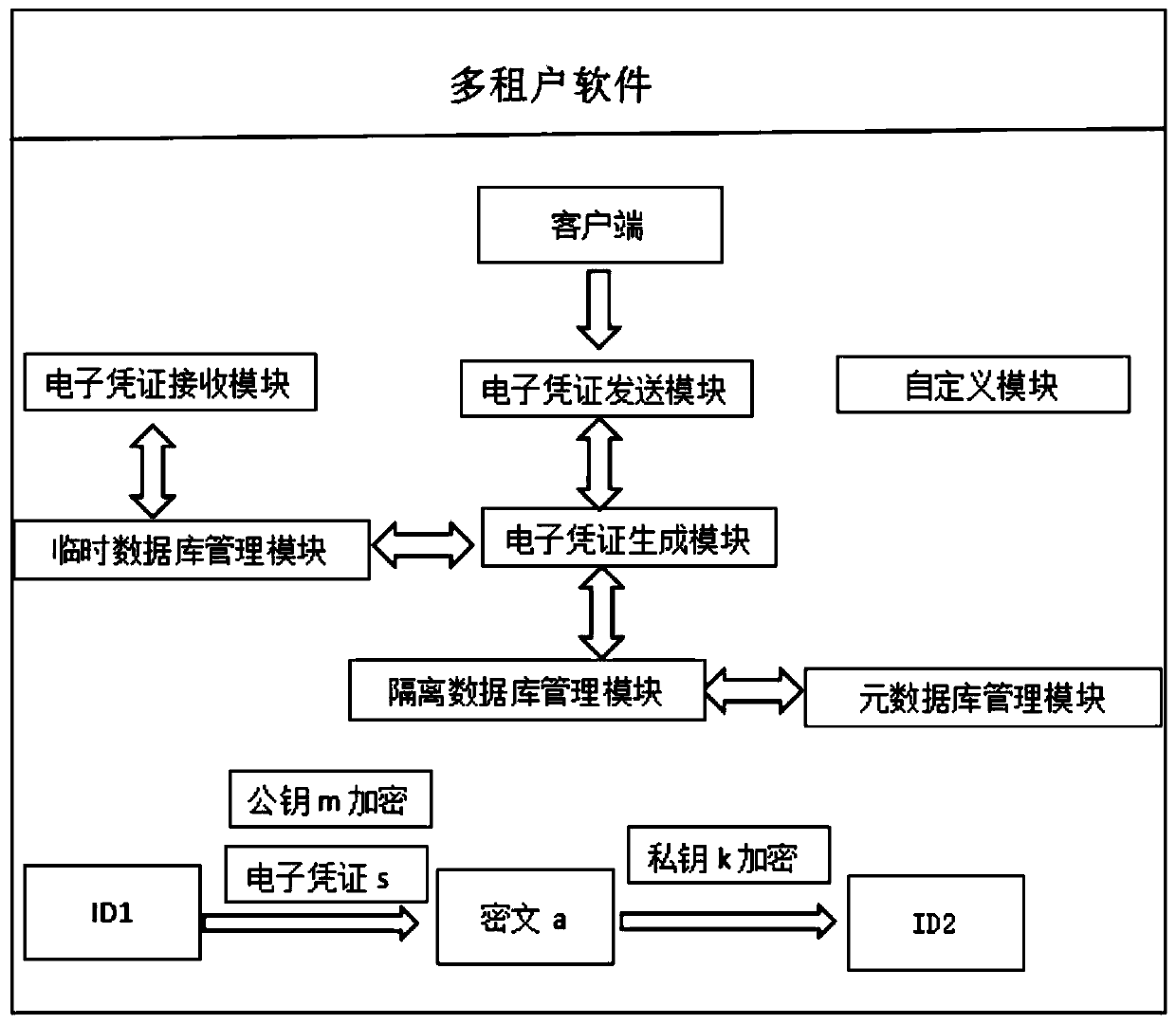
Electronic document safe sharing system and method thereof
InactiveCN101989984AGuarantee authenticitySafe storagePublic key for secure communicationUser identity/authority verificationClient-sideSafe storage
The invention discloses an electronic document safe sharing system which can realize safe storage and fully sharing of secret document. The electronic document safe sharing system comprises a document encrypting module and a document decrypting module; wherein the document encrypting module utilizes a session key to symmetrically encrypt electronic document data, receiver identification (public key) is utilized to asymmetrically encrypt the session key, and finally the encrypted symmetric key and encrypted electronic document data are packed into a digital envelop; and the document decrypting module utilizes an own private key to decrypt the digital envelop. The electronic document safe sharing method of the invention takes CPK combined public key or CPK compound public key technology as the basis, flexible digital signature and secret key exchange capacity thereof are utilized, and a confidential document management system which is from a server to a client, contains information storage and transmission to each use link and is integrated with document data encryption, access control, authorization management, dynamic key exchange and process audit trail into a whole is constructed.
Owner:BEIJING E HENXEN AUTHENTICATION TECH +1
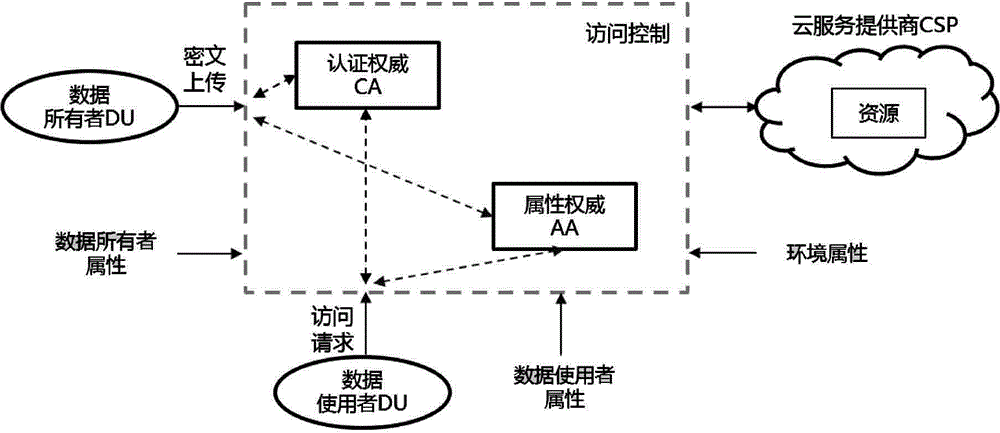
Method for cloud data confidentiality protection and access control
InactiveCN104378386AEnsure safetyEnable secure sharingTransmissionAttribute-based encryptionCloud service provider
The invention discloses a method for cloud data confidentiality protection and access control. The method includes the specific implementation processes: adopting a symmetric cryptosystem correlation algorithm for realizing encryption of sensitive data, and storing the data in a cloud server in an encrypted form; and adopting a ciphertext-policy attribute-based encryption mechanism to realize protection of a data encryption key. An encrypted access policy can be formulated by a data owner as required, and only the data user satisfying conditions of the access policy can access to the encrypted sensitive data by decryption. Compared with the prior art, the method has the advantages that security of the data in a cloud storage system under the open environment is guaranteed under the premise that a cloud server provider is untrusted, security sharing of the sensitive data is realized, and huge computation overhead brought to the data owner by key distribution and data management can be reduced.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
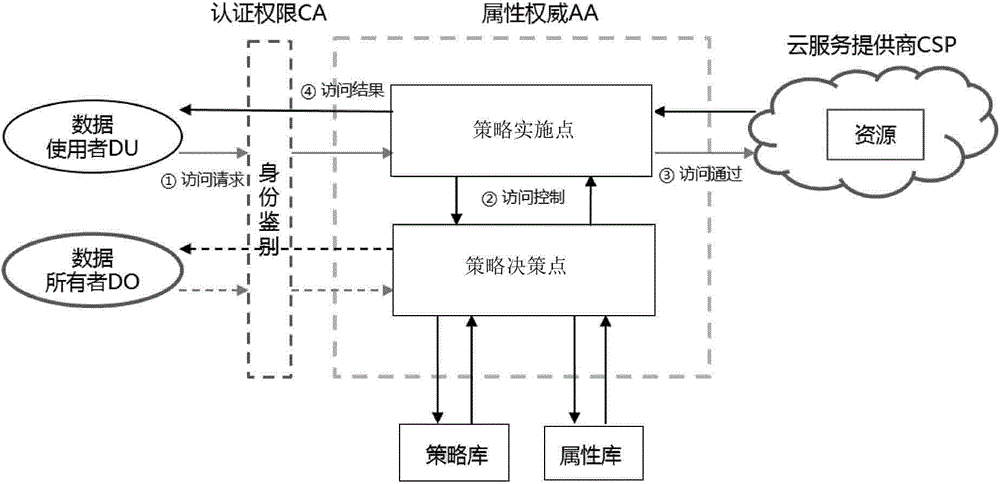
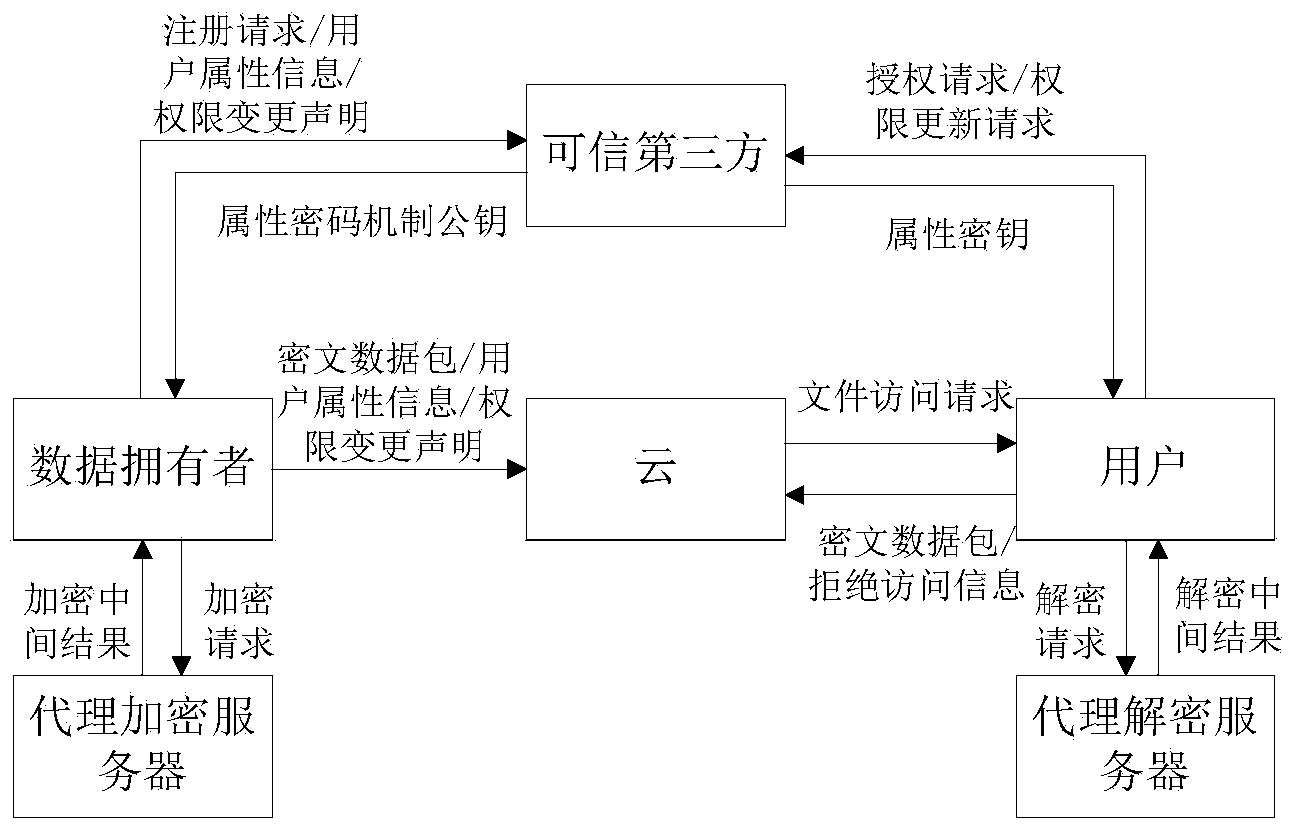
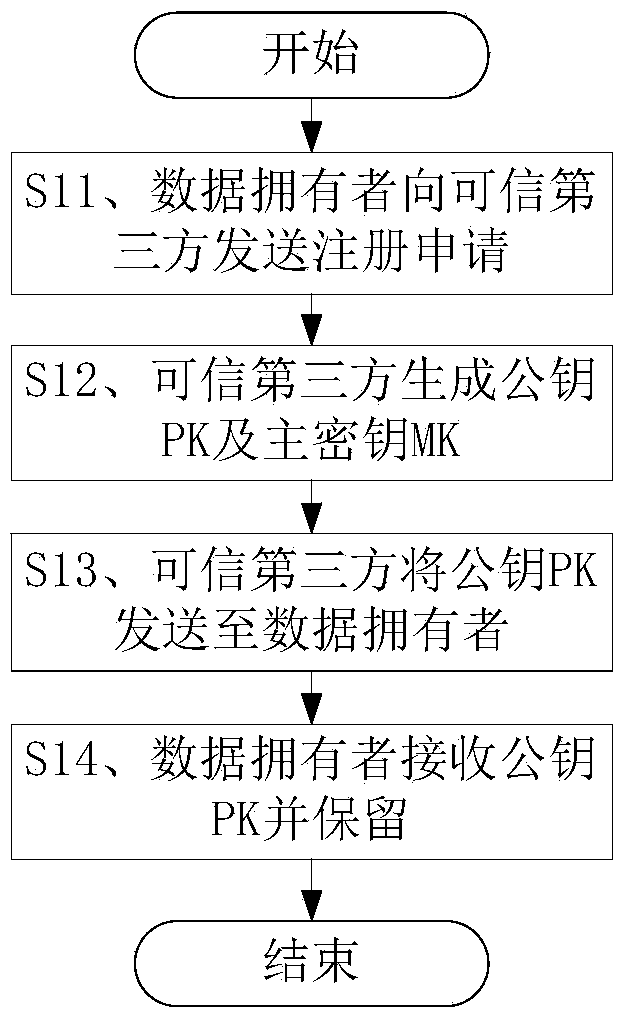
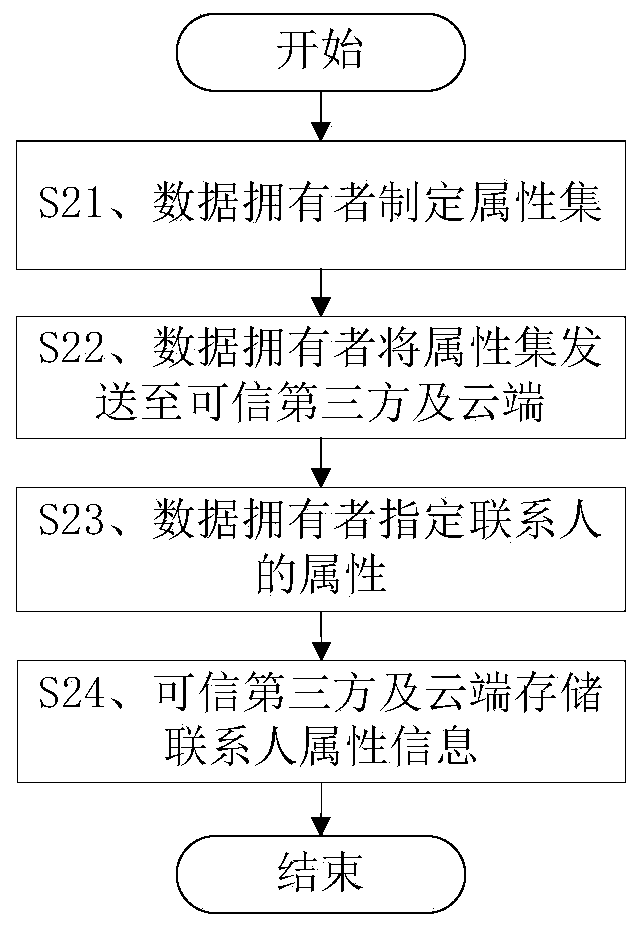
Method for safely sharing mobile cloud storage light-level data
The invention discloses a method for safely sharing mobile cloud storage light-level data. The method comprises the steps that an attribute set is registered in a credible third party by a data owner, the attribute set is assigned to a user by the data owner, the user is authorized by the credible third party through an attribute code mechanism according to the attribute set of the user, so that an attribute key is generated, when the data owner uses a mobile side to share a file, the file is firstly encrypted through a symmetric cryptography mechanism, a symmetric key is encrypted through a proxy encryption server by the utilization of an attribute key mechanism, a file ciphertext and a key ciphertext are sent to a cloud side, after the file ciphertext and the key ciphertext are read from the cloud side by the user, the attribute code mechanism is used by a proxy decryption server to decrypt the file, an authority limit alteration statement is sent to the credible third party and the cloud side by the data owner, and judgments are made by the credible third party and the cloud side, so that authority limits of the user are increased or deleted. According to the method for safely sharing the mobile cloud storage light-level data, the data can be safely shared on the mobile side on the conditions that electric quantity and computing power are limited.
Owner:HUAZHONG UNIV OF SCI & TECH
Data storage and sharing system
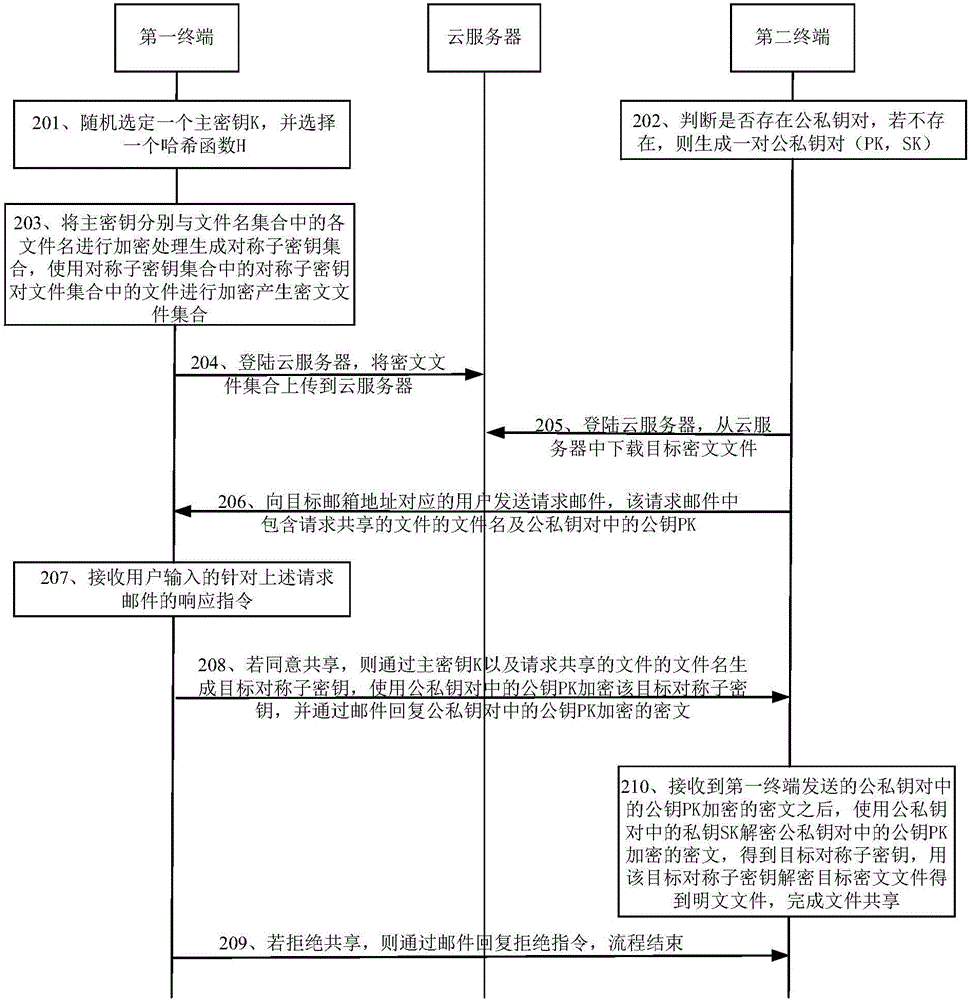
ActiveCN106453612AImplement secure cloud storageEnable secure sharingData switching networksPlaintextCiphertext
The invention discloses a data storage and sharing system, comprising a first terminal, a cloud server and a second terminal, wherein the first terminal is used for encrypting main keys and file names to generate a symmetrical sub-key set, then encrypting files to be encrypted by using symmetrical sub-keys to generate an encrypted file set, and uploading the encrypted file set; the second terminal is used for downloading a target encrypted file from the cloud server, and sending a requested mail to a target mail address; the first terminal is further used for, when a user agrees with sharing files, sending the encrypted target symmetrical sub-keys to the second terminal via a mail, and when the user does not agree with sharing, replying a rejection instruction via a mail; and the second terminal is further used for, after receiving the encrypted target symmetrical sub-keys, decrypting the encrypted target symmetrical sub-keys to obtain the target symmetrical sub-keys, and decrypting the target encrypted file by using the target symmetrical sub-keys to obtain a decrypted file, thus completing file sharing. The system can improve the data storage and sharing security.
Owner:HUAZHONG UNIV OF SCI & TECH
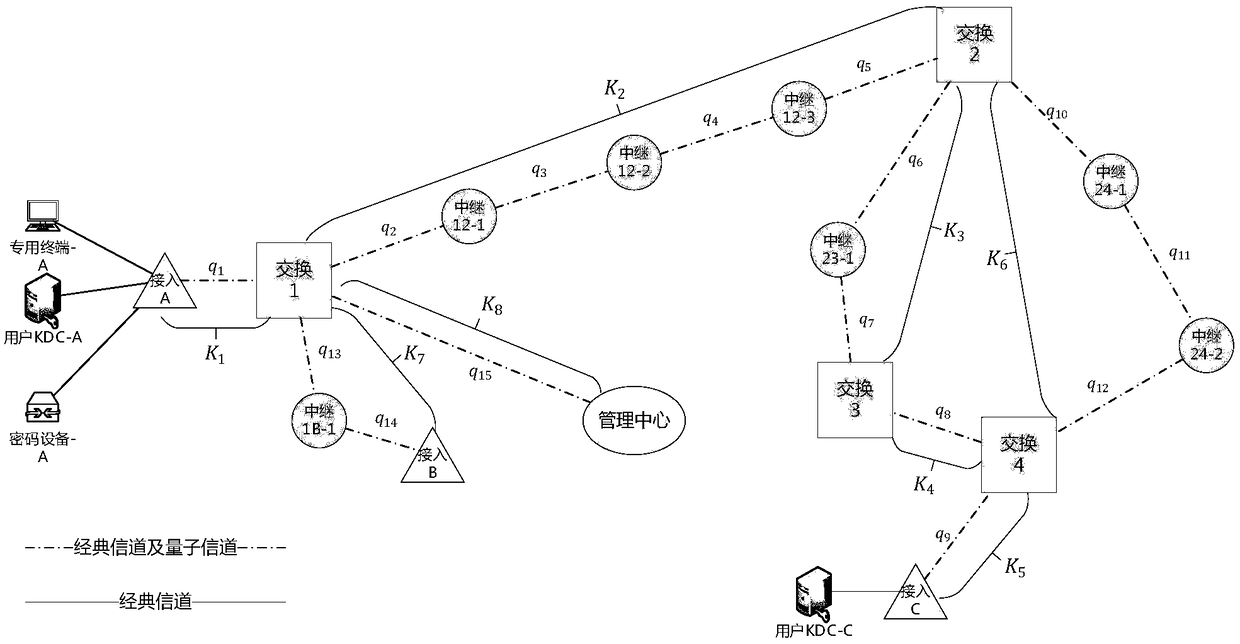
Quantum secret communication network system based on quantum key distribution technology, and application thereof
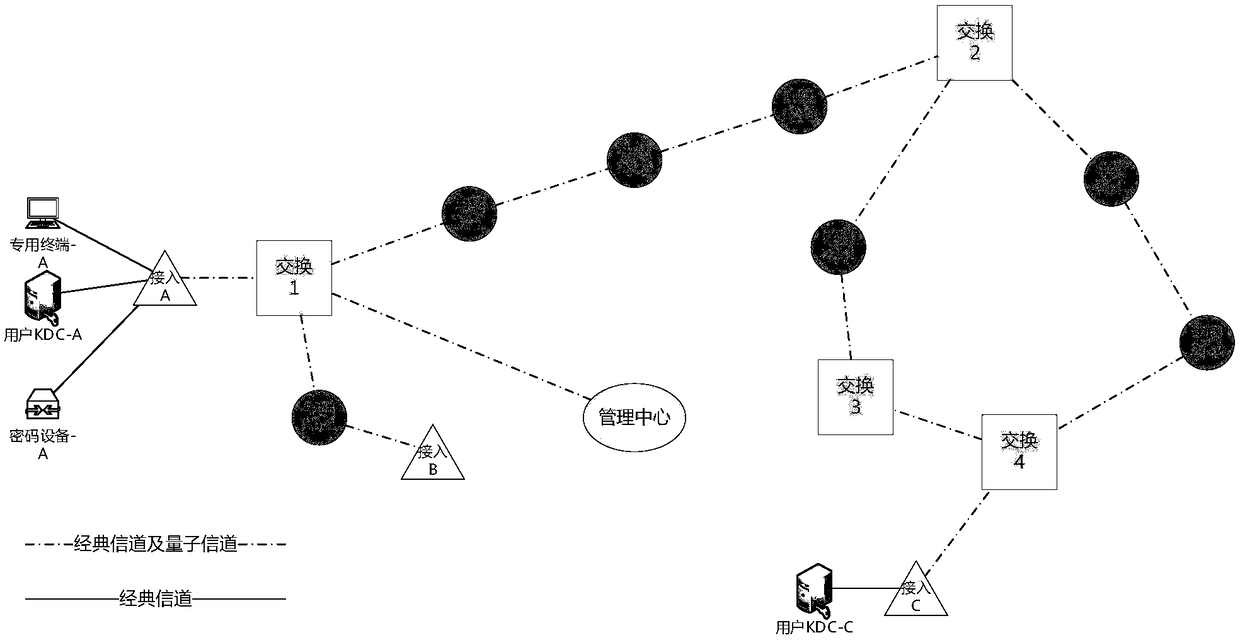
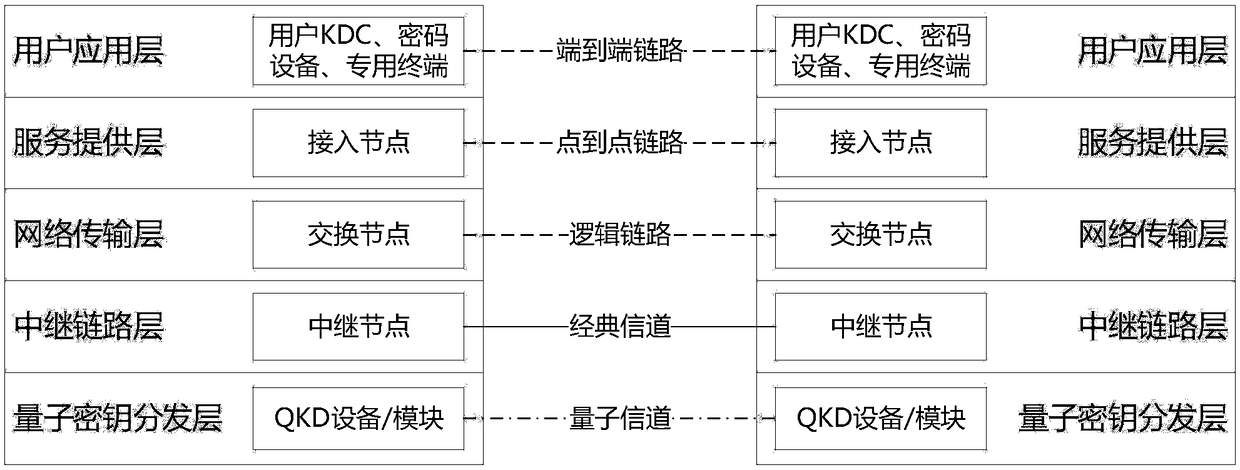
PendingCN109302288AAvoid attackImprove transmission securityKey distribution for secure communicationService provisionSingle point
The invention discloses a quantum secret communication network system based on quantum key distribution technology, and an application thereof. The quantum secret communication network system physically comprises an access node, a switching node and a relay node, the nodes are respectively connected by using classic channels and quantum channels, wherein the classic channel for quantum key distribution performs communication in a non-IP mode; and the network system is logically divided into a quantum key distribution layer, a relay link layer, a network transmission layer, a service provisionlayer and a user application layer from bottom to top. The quantum secret communication network system disclosed by the invention overcomes the single point failure problem caused by a centralized routing server in the existing network; and the quantum secret communication network system disclosed by the invention communicates the classic channel for quantum key distribution in the non-IP mode, thereby effectively avoiding the network attacks for the TCP / IP technology, and the communication protection based on a quantum key is used as a basic function to further enhance the transmission security of the classic channel.
Owner:中共中央办公厅电子科技学院 +1
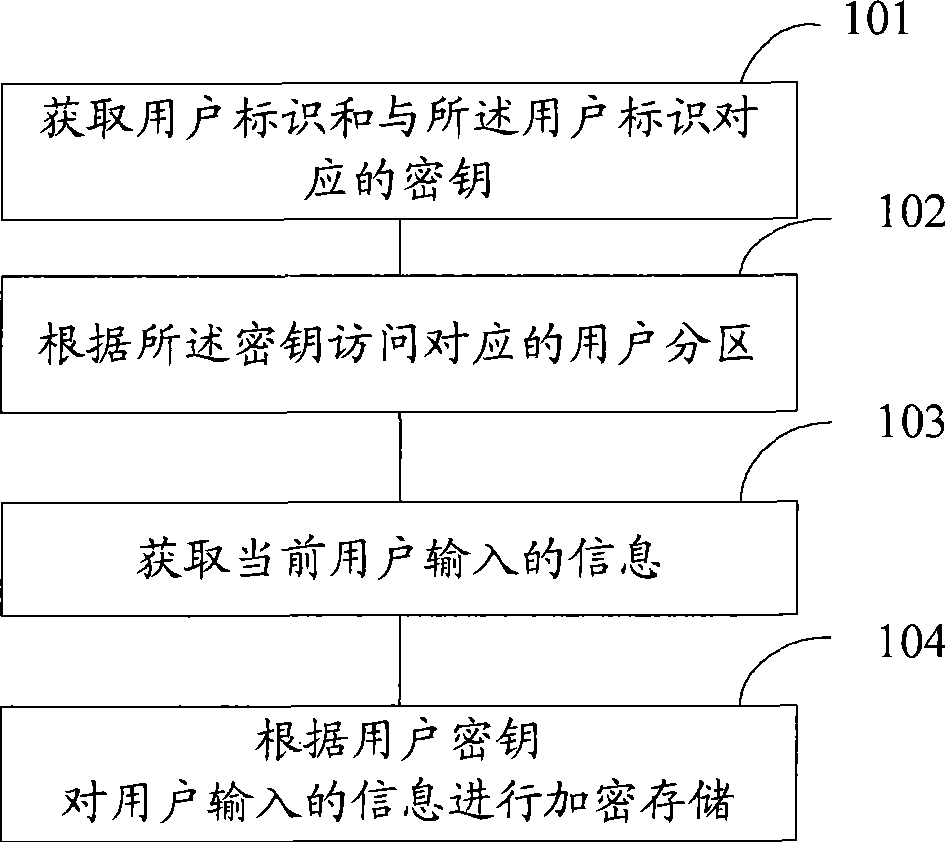
Memory encryption method, apparatus and system
InactiveCN101488110AEnable secure sharingSafety protectionUnauthorized memory use protectionComputer hardwareEncryption
The embodiment of the invention discloses an encryption storage method and comprises the steps as follows: a user identification and a key corresponding to the user identification are obtained; and a user partition corresponding to the user identification is accessed with the key. The embodiment of the invention also provides a corresponding encryption storage device. Different users of the same storage device own respective different keys, and each key only can decrypt a corresponding encryption partition, so that the technical proposal of the invention can carry out safer protection towards a storage medium. Different keys are used for realizing the safety share of different users for different encryption partitions on the same medium.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
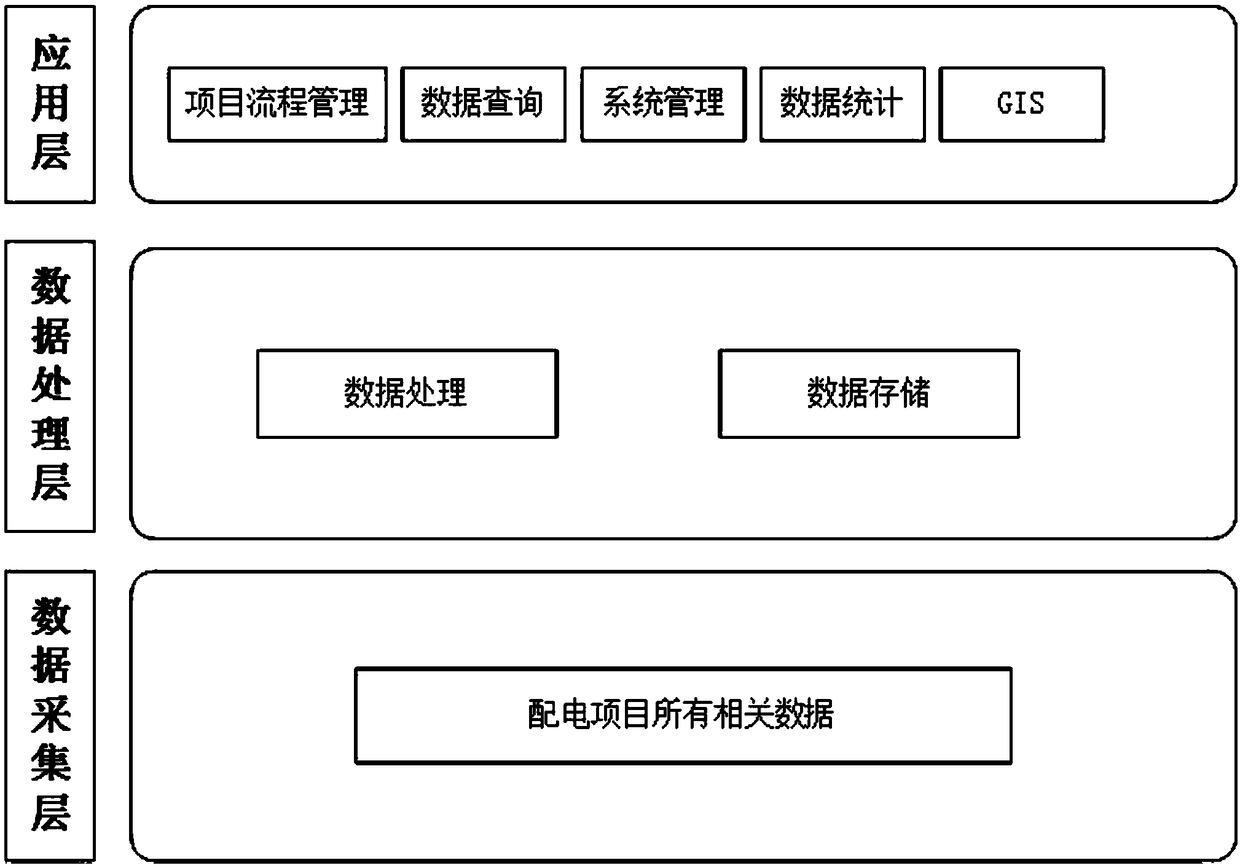
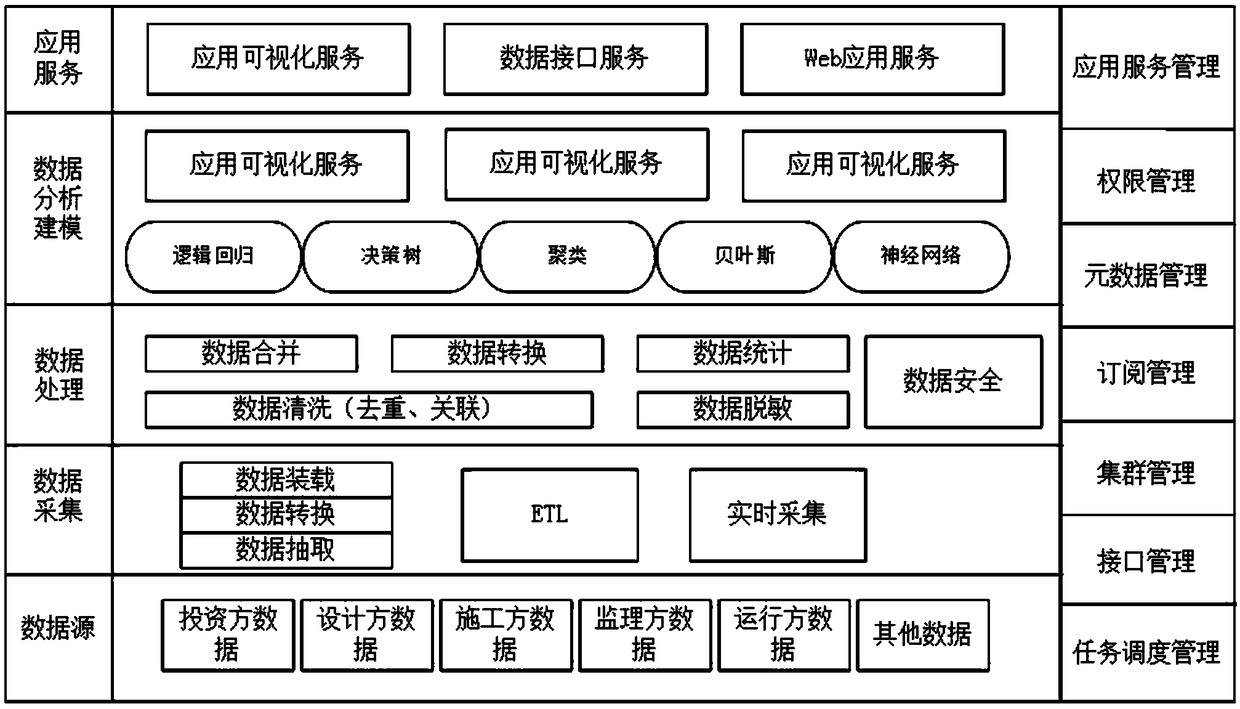
Distribution engineering construction intelligent integrated management system
ActiveCN109492991AEfficiently promote the construction processEnable secure sharingDatabase management systemsOffice automationData acquisitionIntelligent management
The invention discloses a distribution engineering construction intelligent integrated management system, which comprises a data acquisition layer, a data processing and storage layer and an application layer. Among them, the data acquisition layer collects the data of the units involved in the power distribution project; data processing and storage layer is responsible for data cleaning, conversion, storage and storage; the application layer is the intelligent management software of distribution project. The invention designs a scientific, safe and efficient distribution project management system combined with a big data cloud platform, which can intelligently overall manage each project participant in a distribution project construction, realize the construction information safety sharing of each participant, and efficiently promote the project construction process.
Owner:SOUTH CHINA UNIV OF TECH +1
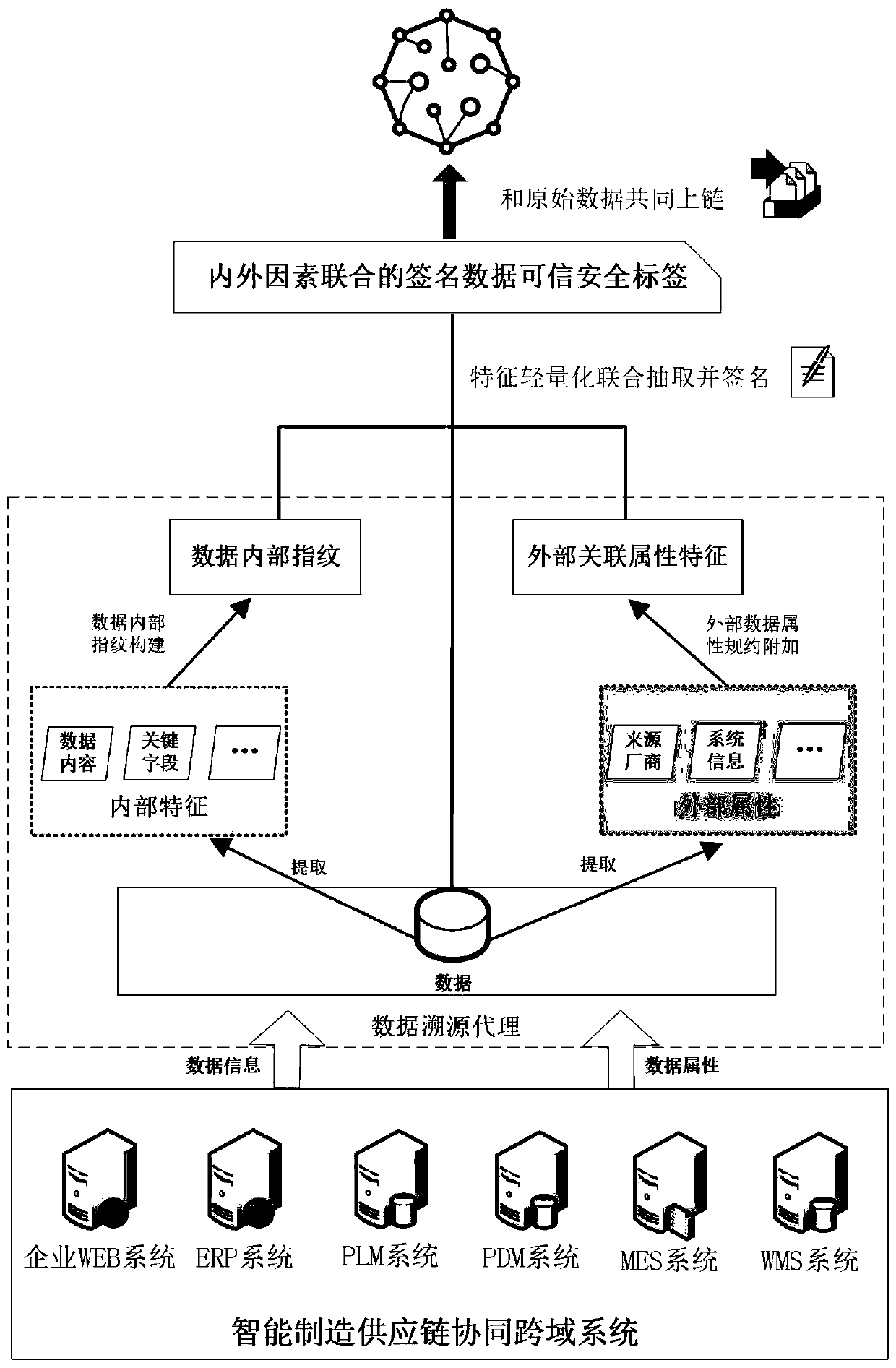
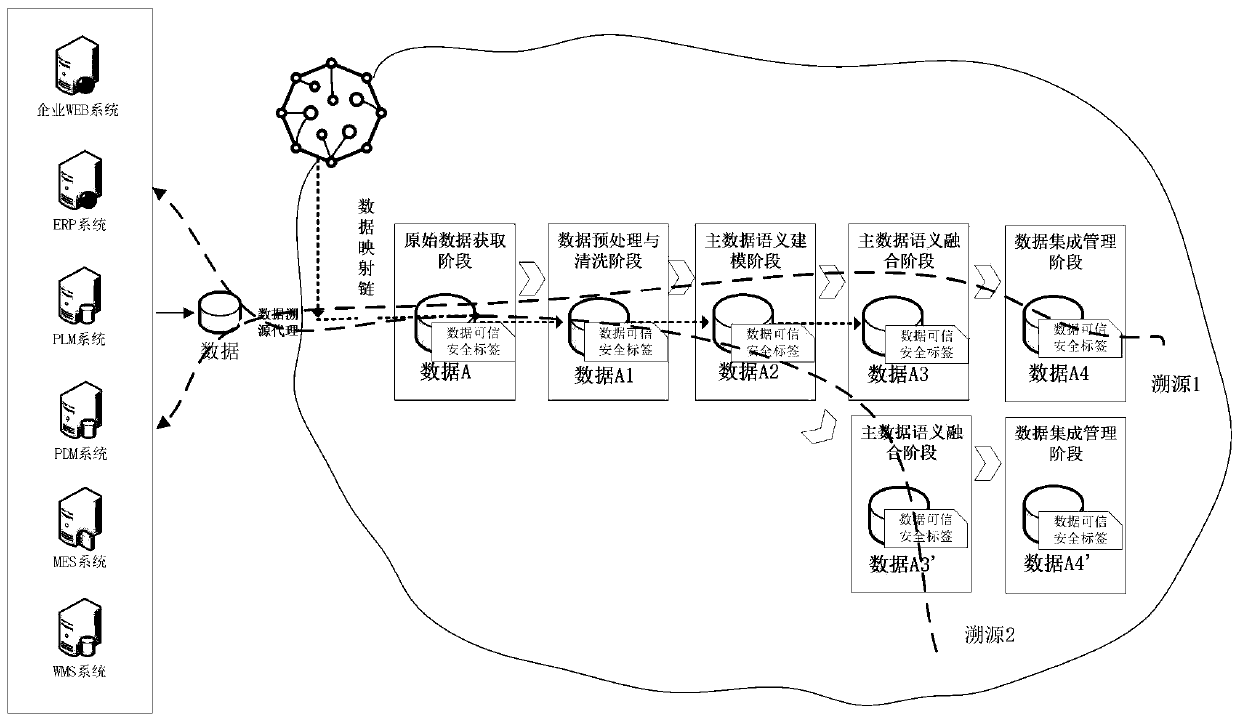
Manufacturing industry cross-domain heterogeneous data identity construction and tracing method based on block chain
ActiveCN110084070AUniqueness guaranteedGuaranteed to be tamper-proofFinanceDigital data protectionChain systemFingerprint
The invention provides a manufacturing industry cross-domain heterogeneous data identity construction and tracing method based on a block chain. The method comprises the steps that firstly, a data tracing proxy is preset in the multi-data processing stage of an intelligent manufacturing industry supply chain collaborative cross-domain system, and data interaction with the block chain system is achieved through the proxy; a data tracing proxy extracts data internal fingerprints which can be shared and are written into a database of each enterprise, a lightweight elliptic curve feature extraction algorithm is designed by combining external association attribute features of the data, internal and external cause joint features are further extracted and signed, and a data credible security label combining internal and external factors is constructed. Secondly, an intelligent contract is called, in the multi-data processing stage of the supply chain cooperative cross-domain system, a recordis generated and stored in a data mapping logic chain in a block chain, a multi-party consensus mechanism based on the block chain and a tamper-proof characteristic are combined with the automation capability of an intelligent contract in the block chain, and multi-scale and multi-data processing stage data identity chain tracing is realized.
Owner:INST OF INFORMATION ENG CAS
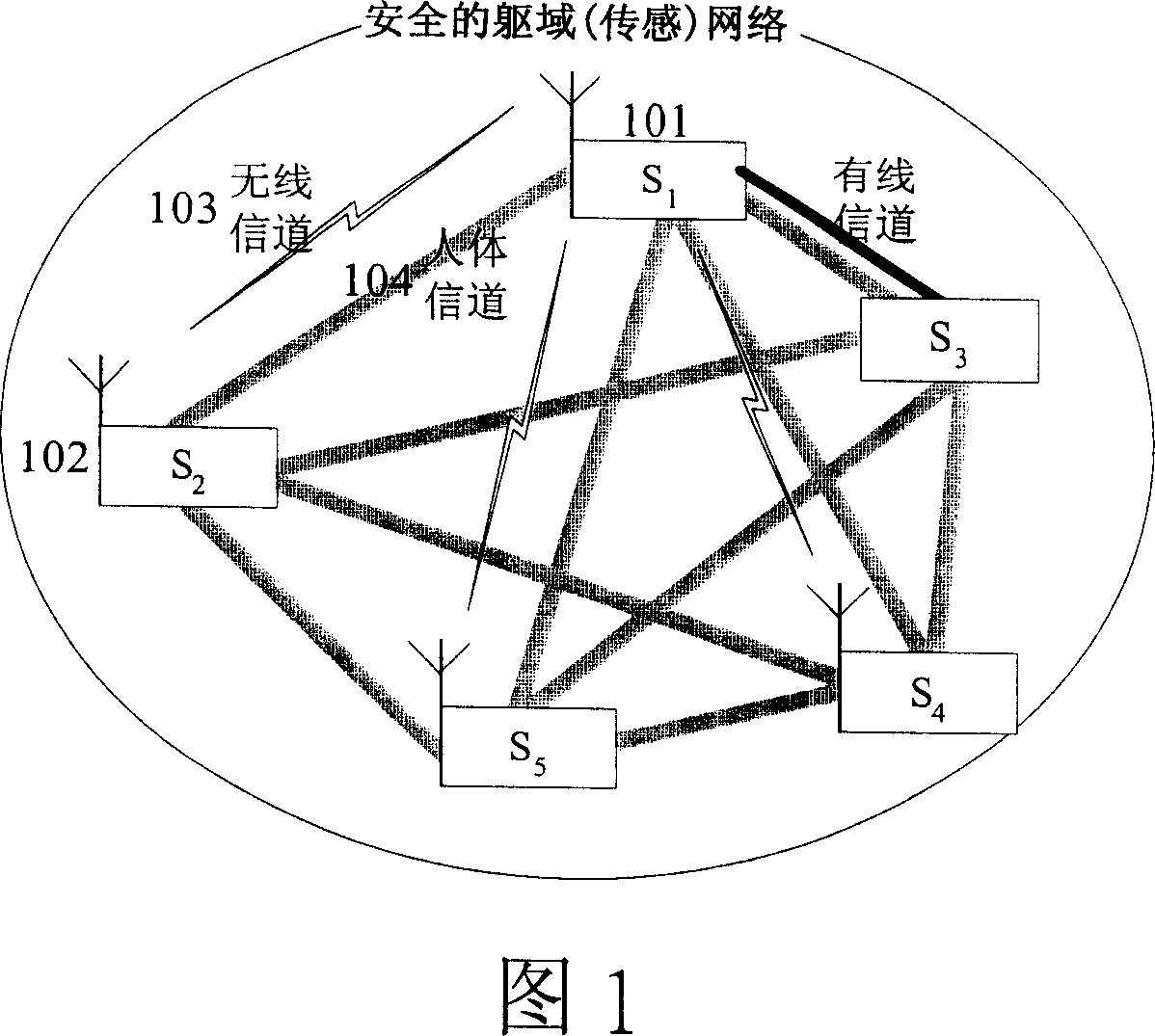
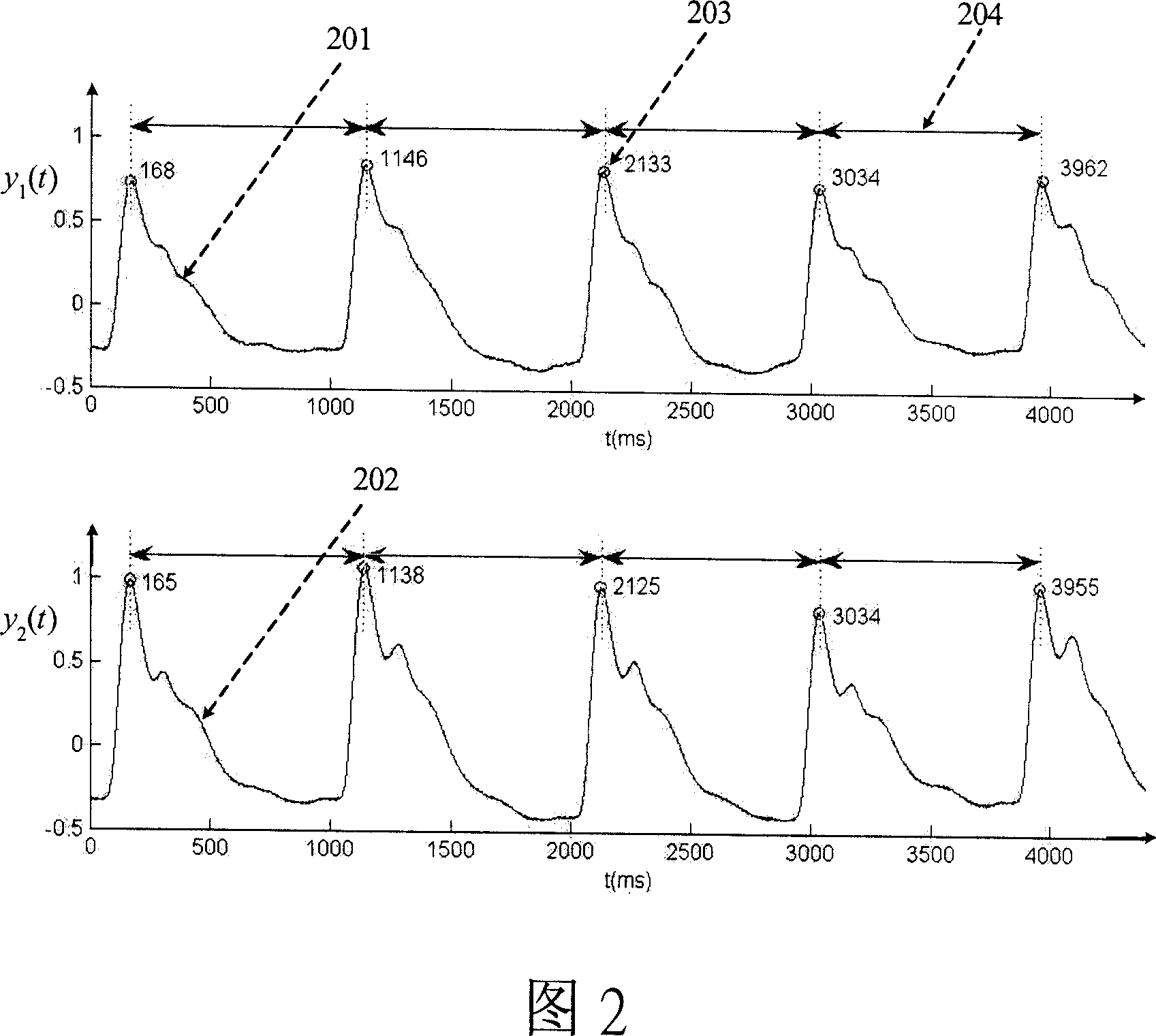
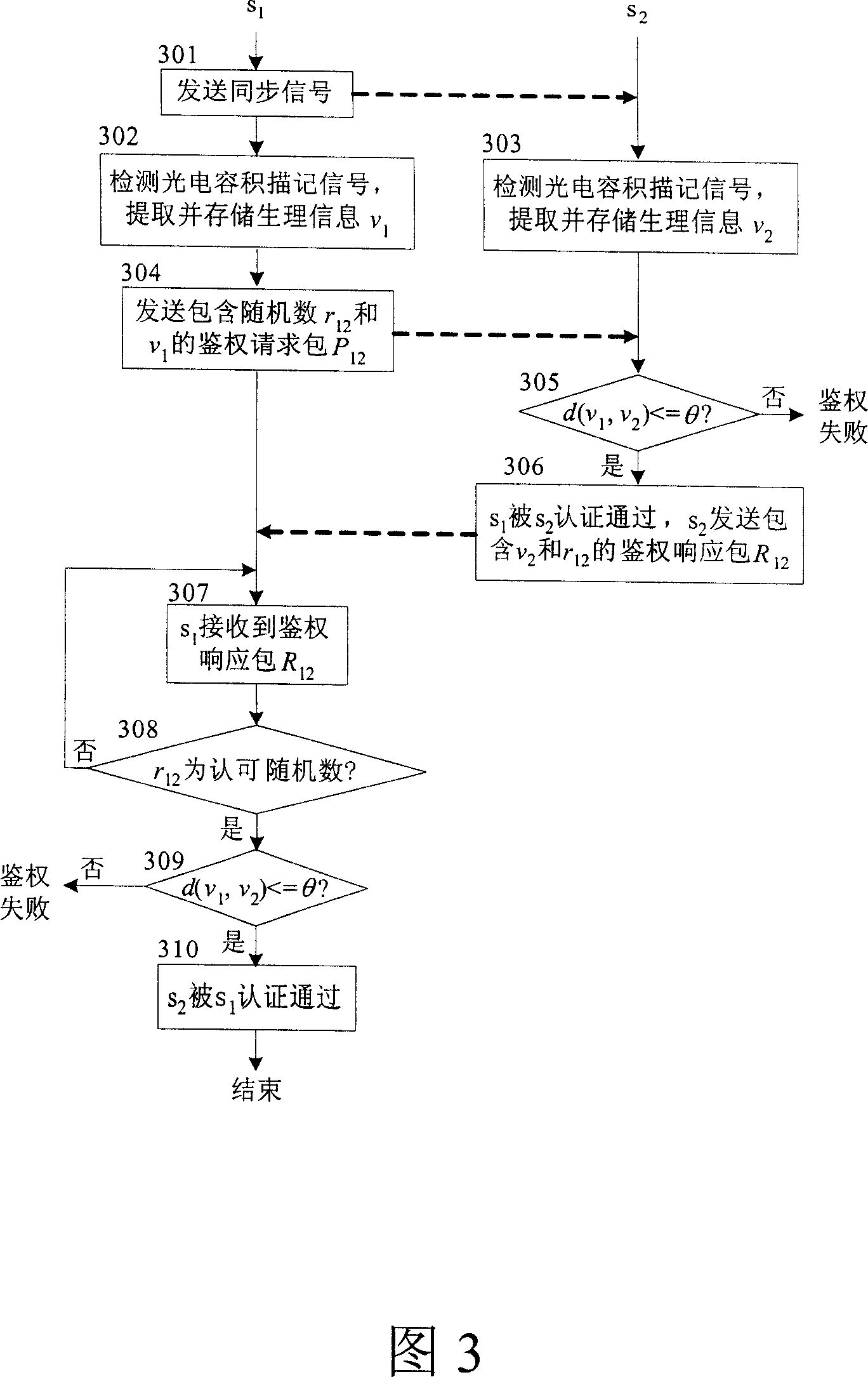
Entity capability discrimination and key managing method for body (sensor) network
InactiveCN101047497AReduce system loadImprove securitySecuring communicationHuman bodyBiomedical sensors
An entity right-certification and cipher key managing method used on body network includes using body sensor network or body area network formed by biomedical transducer self-organization as basic network to obtain and process as well as transmit biomedical information for realizing real time remote monitor on human-body physiological state and utilizing human body channel connected to said biomedical transducer in multiple way for realizing high efficiency of entity right- certification and cipher key management.
Owner:THE CHINESE UNIVERSITY OF HONG KONG
Data hiding query security sharing system and method based on multi-party security computing
ActiveCN112367170AEnsure safetyIncrease security risksKey distribution for secure communicationEngineeringInformation security
The invention relates to the technical field of big data technologies and cryptology, in particular to a data hiding query security sharing system and method based on multi-party security computing. The invention provides a data hiding query security sharing system and method based on multi-party security computing. The system comprises a DH key interaction module, a user key information hiding interaction module, a user core data hiding interaction module and a user core data security sharing module. A new thought is provided for breaking a current inter-institution data barrier, a new schemeis provided for inter-institution data safety sharing, it is ensured that user identity information cannot be decrypted by other third parties through a key dynamic dual encryption technology and a secret sharing algorithm, and information safety sharing that institution core data cannot be delivered out of a database is achieved. Not only is safety of user information ensured, but also safety ofdata assets of a financial institution is ensured.
Owner:SICHUAN XW BANK CO LTD
Realization method and system for community-based educational resource sharing service interface
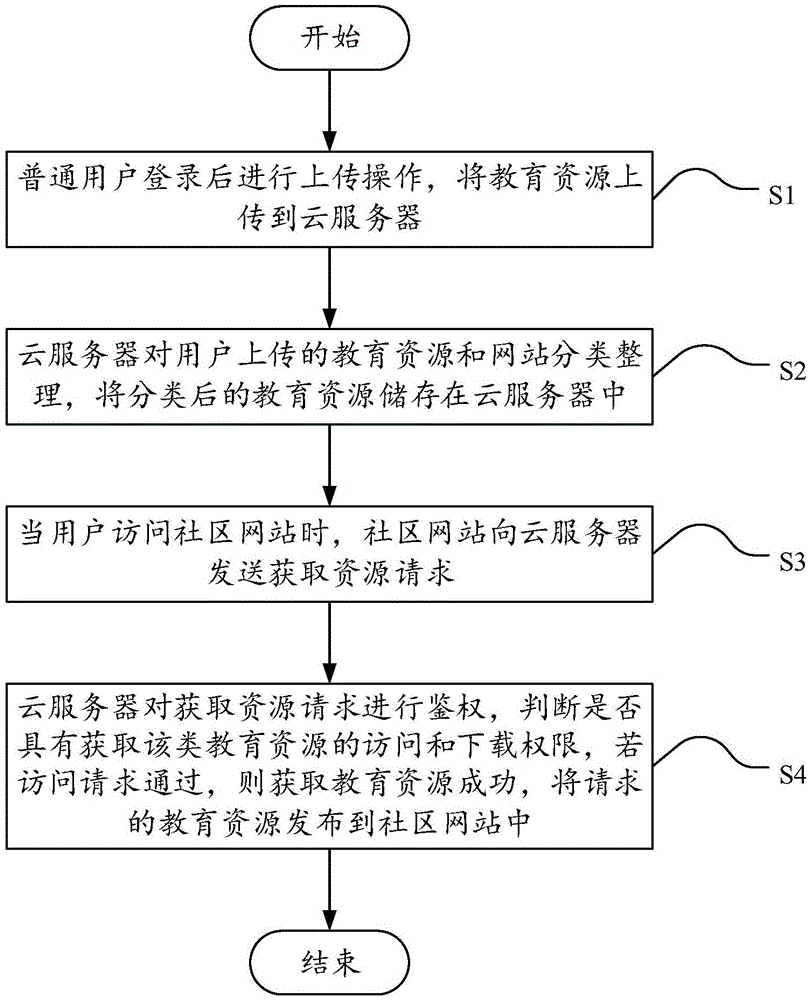
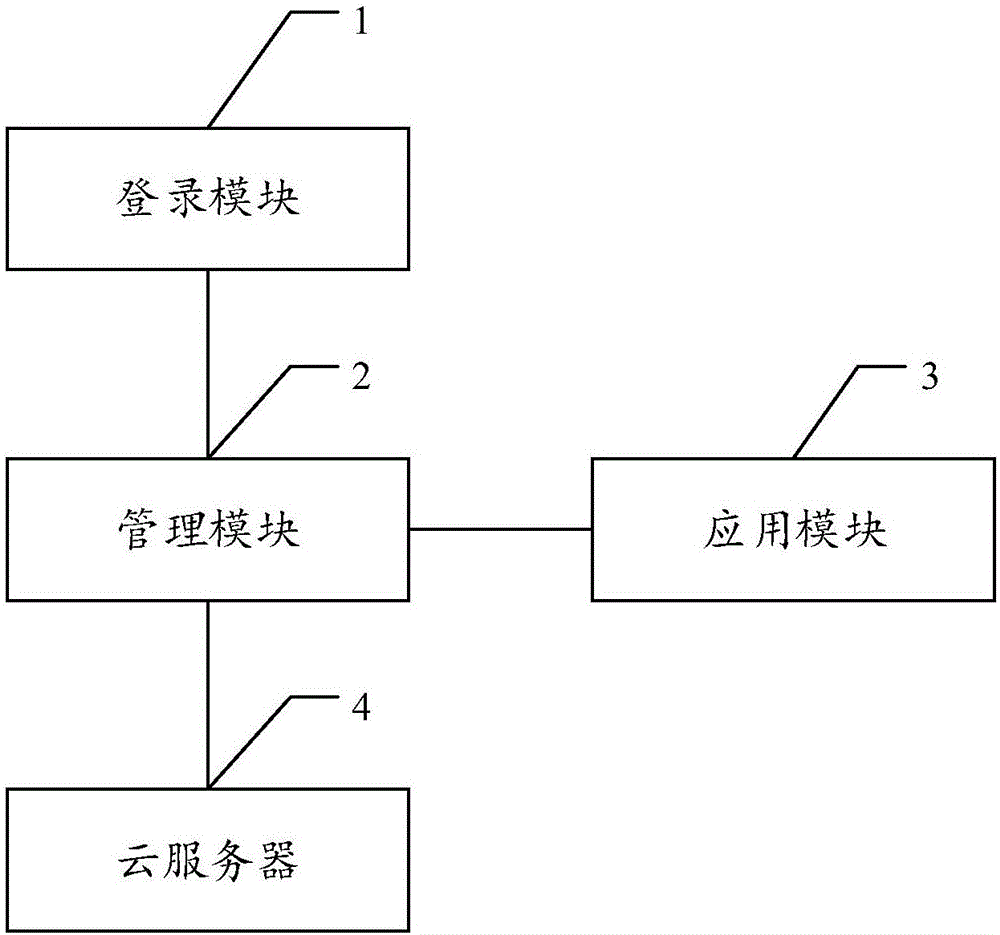
InactiveCN106790555AImprove securityEnable secure sharingData processing applicationsTransmissionCommunity basedWorld Wide Web
The embodiment of the invention discloses a realization method and system for a community-based educational resource sharing service interface. The method comprises the steps that general users log in a cloud server and then carry out uploading operation, thereby uploading educational resources to the cloud server; the cloud server classifies the educational resources and websites uploaded by the users and stores the classified educational resources to the cloud server; when a user accesses a community website, the community website sends a resource obtaining request to the cloud server; and the cloud server authenticates the resource obtaining request, judges whether the user has access and downloading authority for obtaining the educational resources or not, if the access request is authenticated successfully, the educational resources are obtained successfully, and the requested educational resources are issued to the community website. According to the embodiment of the invention, the resources are uniformly stored through cloud computing, the community resources are shared securely, the educational resources are shared, the repeated resources are reduced, the space is saved, and moreover, the storage and sharing security of the educational resources is improved.
Owner:SUN YAT SEN UNIV
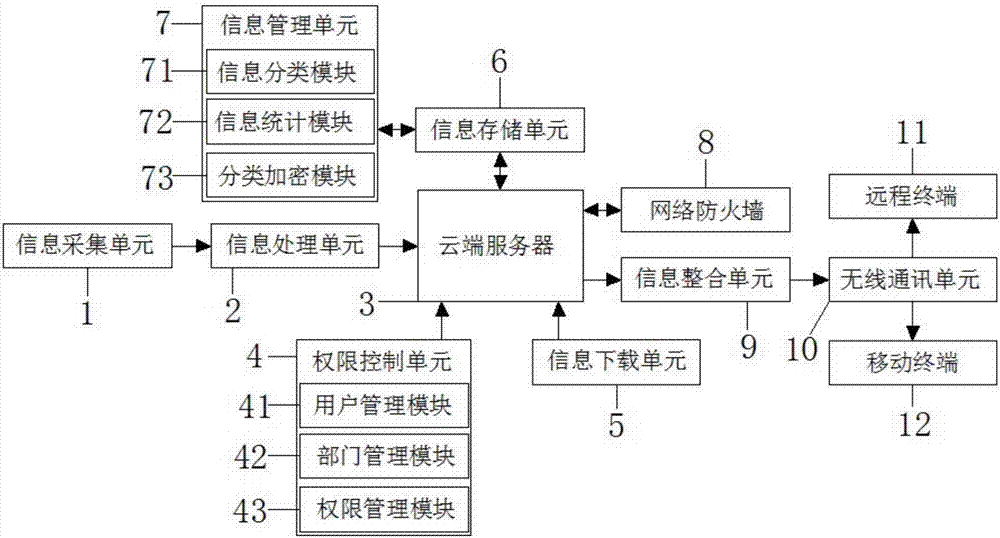
Information management cloud sharing system
InactiveCN107172014AAchieve sharingEnable secure sharingTransmissionInformation processingData information
The invention discloses an information management cloud sharing system in the technical field of information management. The information management cloud sharing system comprises an information acquisition unit, an information processing unit, a cloud server, an authority control unit, an information downloading unit, an information storage unit, an information management unit, a network firewall, an information integration unit, a wireless communication unit, a remote terminal and a mobile terminal. The information management cloud sharing system realizes safe sharing of information and guarantees information safety; as different authorities are set for different users through the authority setting, the user of each authority only can share the information within the user authority, a user with a common authority cannot share high-level data information; and as a manager also can carry out wireless data distribution, information sharing is realized, and the system safety performance is improved.
Owner:QILU UNIV OF TECH
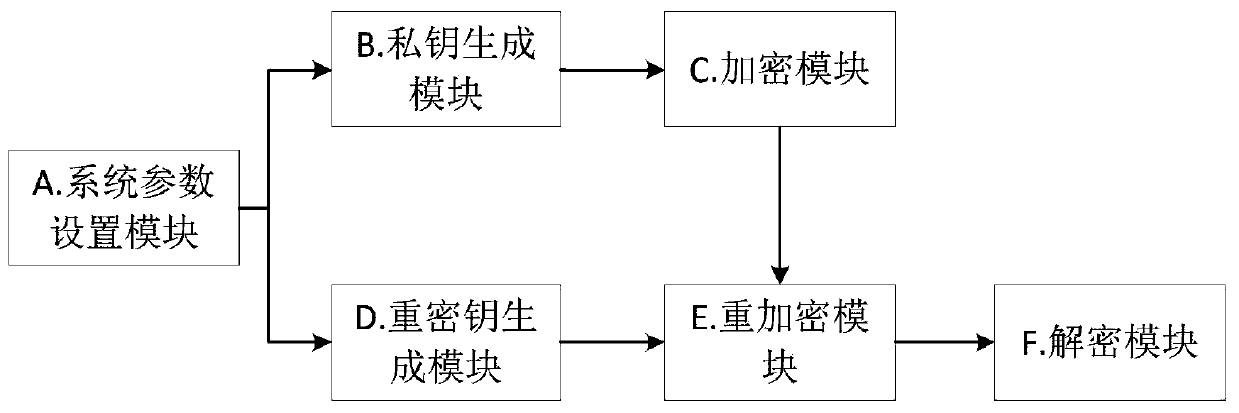
Attribute-based anti-collusion attack proxy re-encryption method
ActiveCN110635909AGuaranteed safe sharingEnable secure sharingKey distribution for secure communicationMultiple keys/algorithms usageAccess structureReusability
The invention provides an attribute-based anti-collusion attack proxy re-encryption method, which relates to the technical field of data encryption, and comprises a system parameter setting module forinputting a security parameter 1<n> and generating a system public parameter params and a main private key MSK; a private key generation module for inputting params and MSK into an attribute list L to generate a private key SK<L> and a corresponding public key PK<L>; an encryption module for inputting params, L, PK<L>, an access structure (W, rho) and a message M, wherein the algorithm returns ciphertext; a re-key generation module for inputting params, attribute lists L1, l2 and the secret key of the attribute list L1, wherein the algorithm returns the re-encryption secret key shown in the description; a re-encryption module for inputting the params, a new access structure (W', rho') and the ciphertext corresponding to the attribute list L1, wherein the algorithm returns the ciphertext corresponding to the re-encrypted L2; and a decryption module for inputting the params, the ciphertext C<L> and the private key SK<L>, wherein the algorithm returns a message M or a terminator T upsidedown. The proxy re-encryption method has the characteristics of quantum attack resistance, unidirectionality, reusability and collusion attack resistance.
Owner:HUAIBEI NORMAL UNIVERSITY
Device authentication method, device access method and device
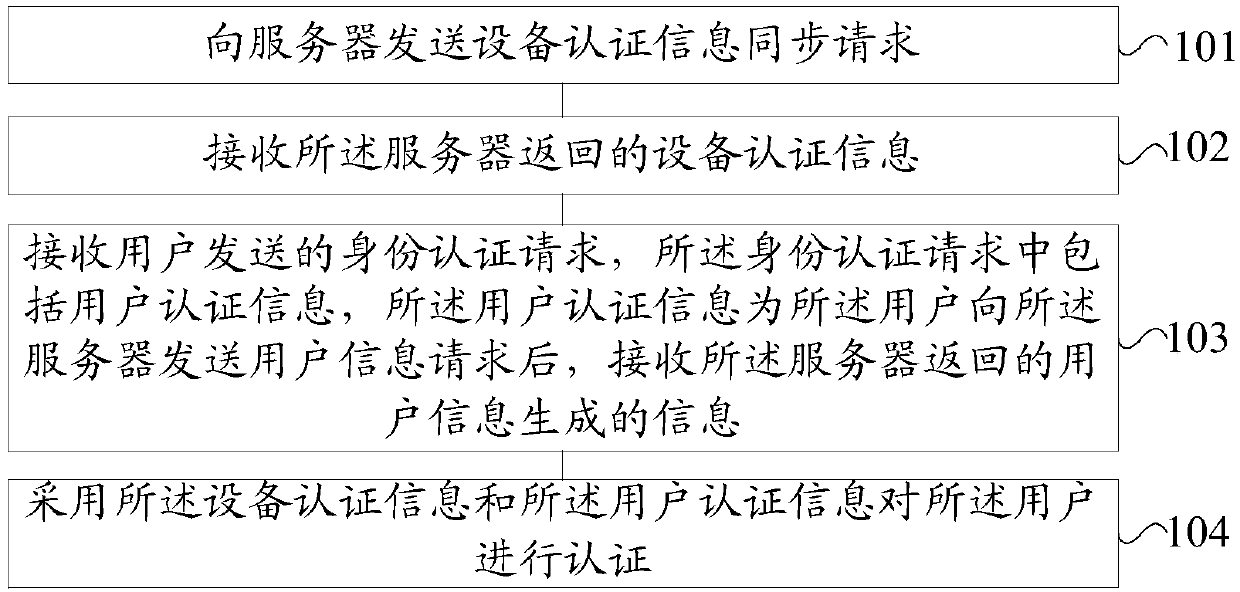
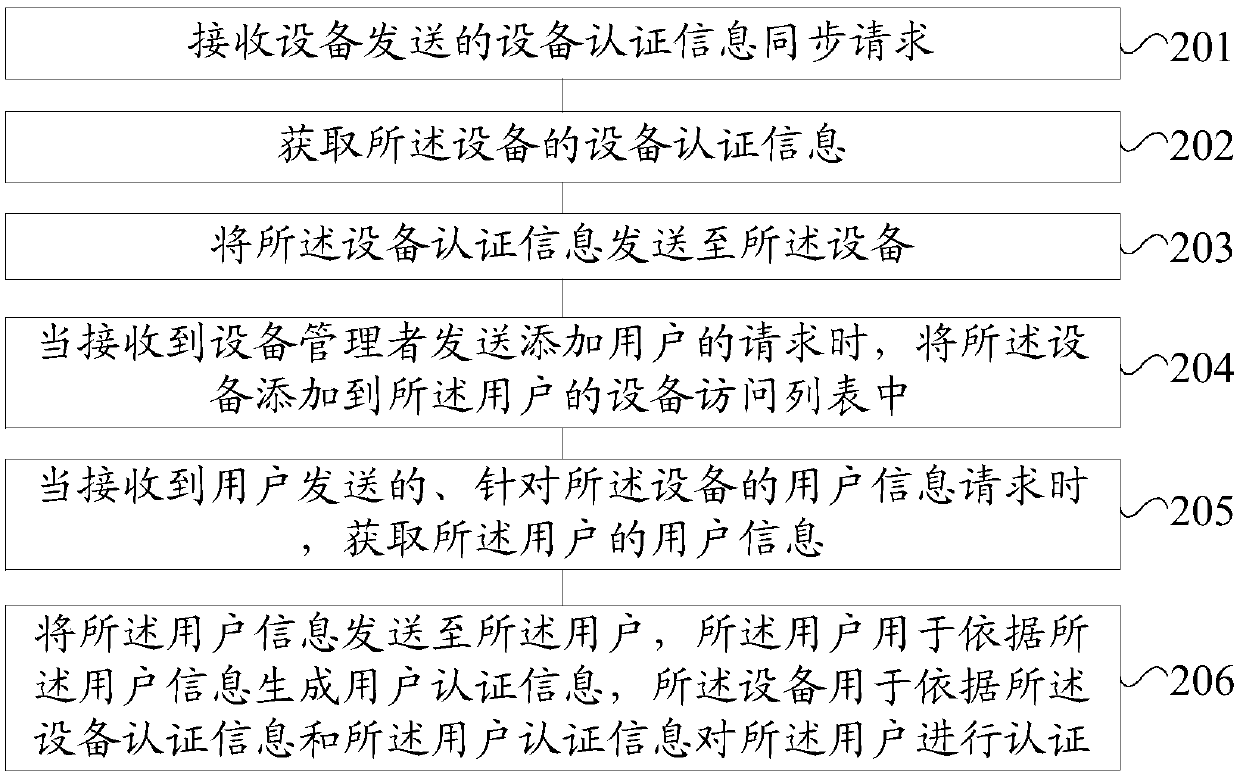
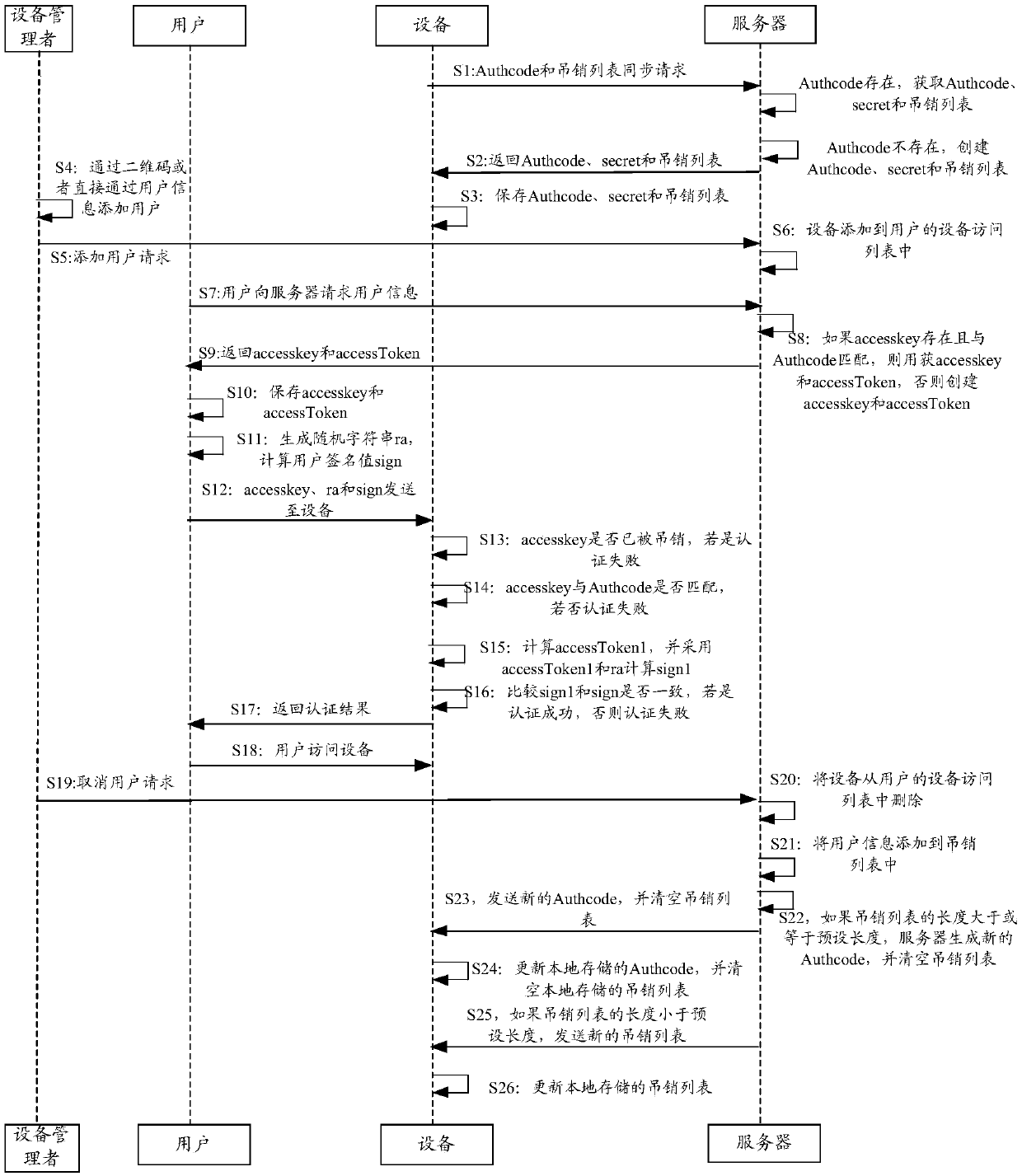
ActiveCN110753023AAvoid the problem of security holes without identity authenticationEnable secure sharingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAccess methodThe Internet
The embodiment of the invention provides an equipment authentication method and device and an equipment access method and device. The equipment authentication method comprises the steps that an equipment authentication information synchronization request is sent to a server; receiving equipment authentication information returned by the server; receiving an identity authentication request sent bya user, the identity authentication request comprising user authentication information, the user authentication information being information generated by receiving user information returned by the server after the user sends a user information request to the server; and authenticating the user by adopting the equipment authentication information and the user authentication information. Accordingto the embodiment of the invention, the method comprises the steps: carrying out the processing, the equipment synchronizes the equipment authentication information; the user is authenticated by adopting the equipment authentication information and the user authentication information, and the equipment accepts the access of the local area network user after the authentication succeeds, so that theproblem of safety holes caused by not performing identity authentication on the local area network user can be avoided, and the identity authentication of the equipment to the user and the safety sharing of the Internet of Things equipment are realized.
Owner:ALIBABA GRP HLDG LTD
Distributed computing method and system based on block chain
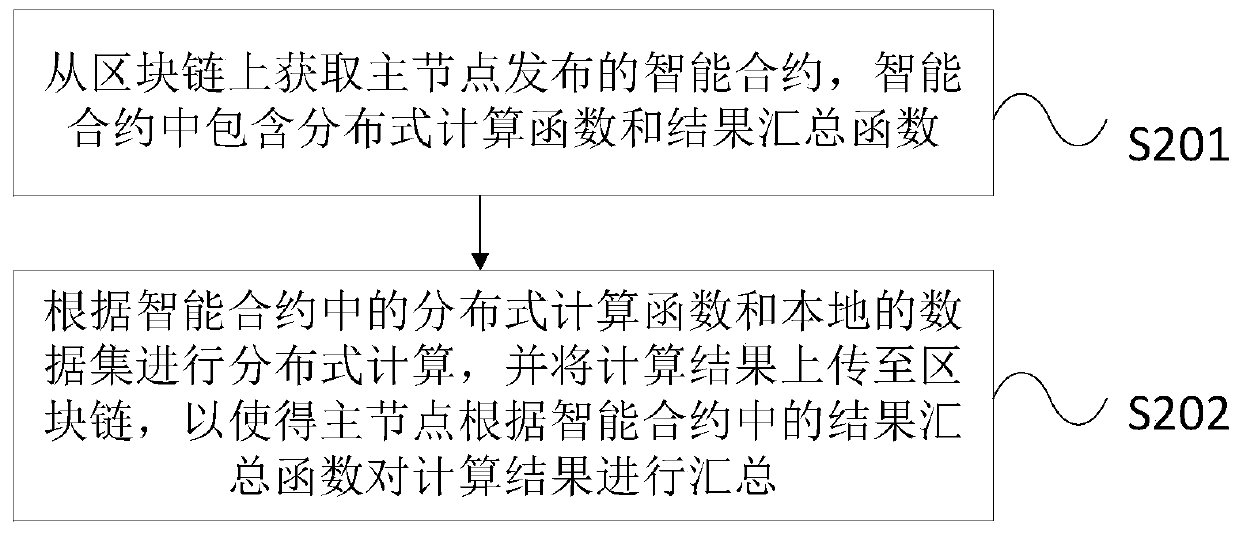
ActiveCN110245514AEnable secure sharingPrevent leakageDigital data protectionTransmissionSmart contractLarge scale data
The embodiment of the invention provides a distributed computing method and system based on a block chain. A main node in the block chain compiles an intelligent contract according to the calculation requirement of the main node and releases the intelligent contract to the block chain, so the slave nodes in the block chain are enabled to carry out distributed computing based on the local computing resources and the distributed calculation function in the intelligent contract; and finally, the master node summarizes calculation results of all the slave nodes according to a result summarizing function in the smart contract. According to the method and the system, redesign and improvement are carried out on the basis of the existing block chain system, and the transaction process of the whole block chain is converted into a distributed computing framework, so that the safe sharing of data can be effectively realized while large-scale data is computed in a distributed manner, the safety of the data is ensured, and the data is prevented from being leaked.
Owner:TSINGHUA UNIV
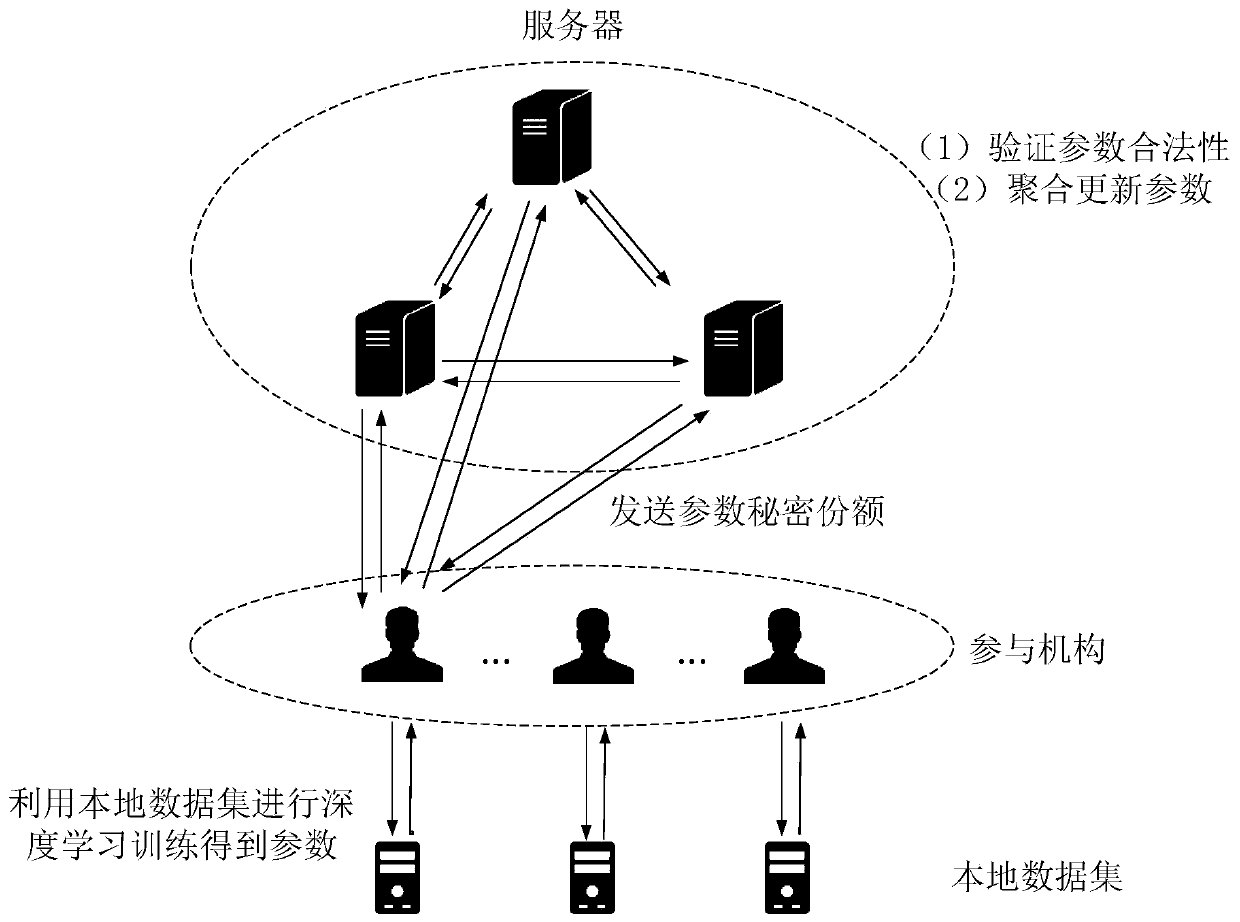
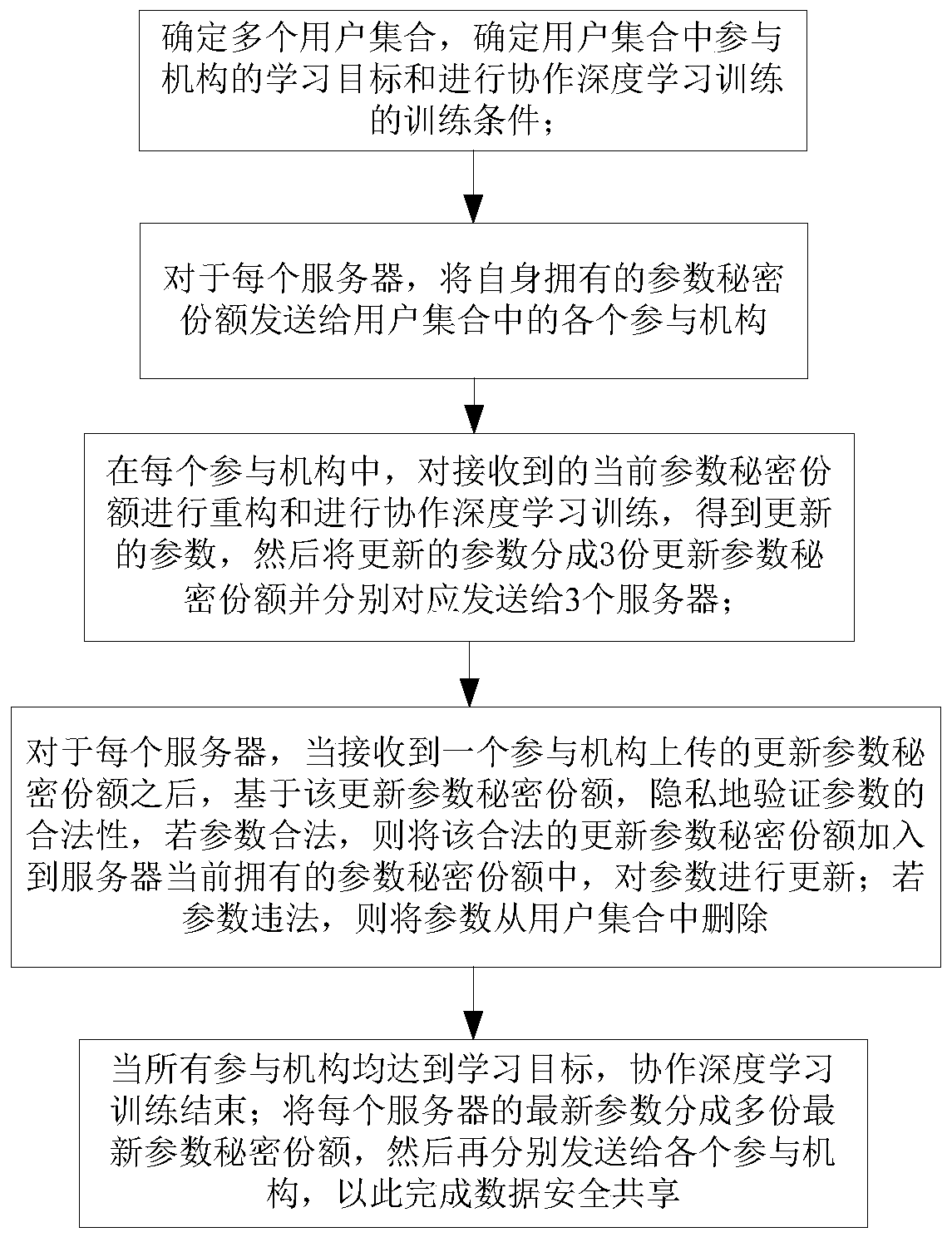
Data security sharing method, storage medium and computing equipment
PendingCN111243698AEnable secure sharingPrivacy protectionMedical data miningPatient-specific dataComputer networkSecret share
The invention discloses a data security sharing method, a storage medium and computing equipment. The method comprises the following steps: firstly, determining a plurality of user sets and learning targets and training conditions of participating mechanisms in the user sets; dividing parameters of each server into current parameter secret shares and sending the current parameter secret shares tothe participating mechanisms; reconstructing, by the participating mechanism, the current parameter secret share and performs cooperative deep learning training, dividing the obtained updated parameters into updated parameter secret shares and sending the updated parameter secret shares to the server; verifying, by the server, whether the parameters are legal or not according to the updated parameter secret shares, and if yes, adding the updated parameter secret shares into the parameter secret shares currently owned by the server; and when all participation mechanisms reach the learning target, dividing the latest parameters of each server into latest parameter secret shares, and then sending the latest parameter secret shares to the participating mechanisms, thereby completing data security sharing. According to the invention, the parameter security can be ensured while the privacy is protected, and the data security sharing among different participating mechanisms is realized.
Owner:JINAN UNIVERSITY
Manufacturing industry staff information management method and system, electronic device and storage medium
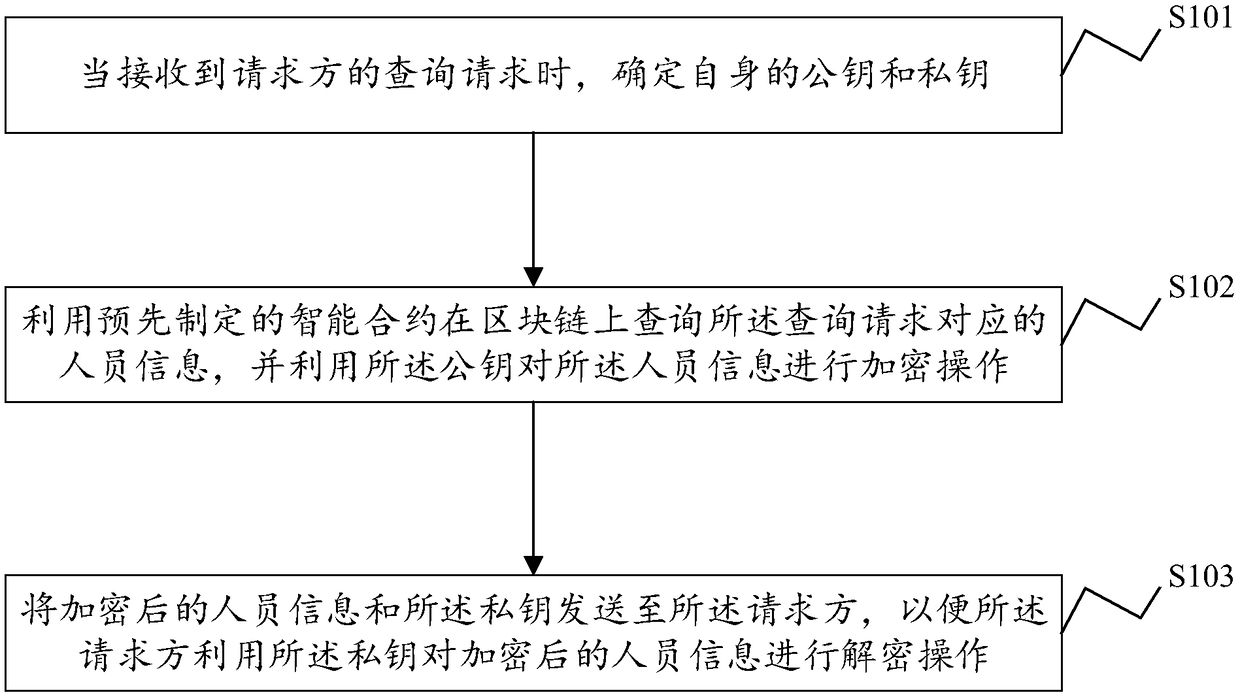
ActiveCN109194628APrevent leakageProtect interestsKey distribution for secure communicationUser identity/authority verificationCommon keyResource information
The present invention discloses a manufacturing industry staff information management method and system, an electronic device and a storage medium. The method comprise the steps of: when a query request of a requester is received, determining public keys and private keys itself; employing a pre-established smart contract to inquire staff information corresponding to the query request on a blockchain, and employing the public keys to perform encryption operation for the staff information; and sending the encrypted staff information and the private information to the requester to allow the requester to employ the private keys to perform decryption operation of the encrypted staff information. The manufacturing industry staff information management method employs the blockchain technology tostore the manufacturing industry staff information, each blockchain node device has the public keys and the private keys corresponding to itself, and the features of the blockchain decentration and the asymmetric encryption are employed to allow the staff information not be easily leaked so as to achieve the safety sharing of the human resource information while guaranteeing the enterprise benefit.
Owner:GUANGDONG UNIV OF TECH
Encryption method for multiple color images based on complete ternary tree structure
InactiveCN106846232AEnable secure sharingEffective against statistical attacksImage data processing detailsKnown-plaintext attackEncryption system
The invention relates to the technical fields of information security and optical information processing and provides a new image encryption method. Through the method, multiple password attacks such as known-plaintext attacks and chosen-plaintext attacks can be effectively resisted. Besides, the method has strong abilities in resisting violent attacks, statistical attacks, noise attacks, shear attacks, etc. The adopted technical scheme is an encryption method for multiple color images based on a complete ternary tree structure. According to the method, in an encryption system based on the complete ternary tree structure, encryption modules serve as branch nodes and root nodes of a complete ternary tree, three color channels of the color images serve as leaf nodes connected with the branch nodes, different color images correspond to different encryption paths and master keys, and therefore different decryption paths are available. The method is mainly applied to information security and optical information processing.
Owner:TIANJIN UNIV
Cross-network security data sharing method and system based on block chain
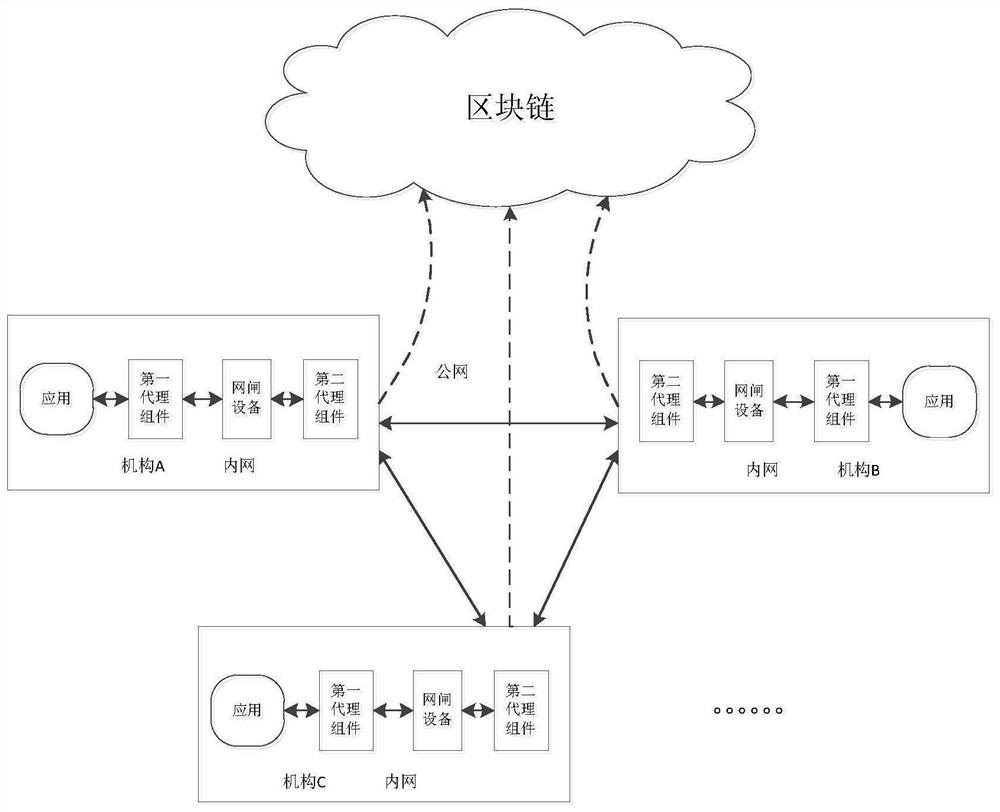
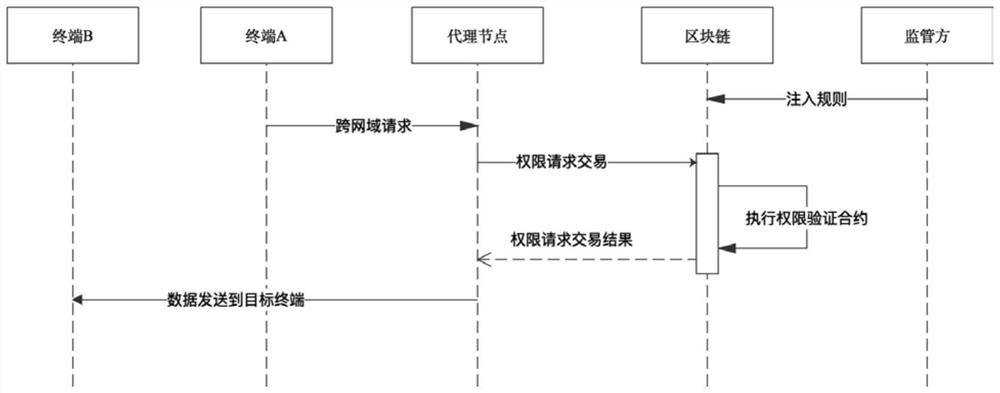
ActiveCN112738239AGuaranteed credibilityGuaranteed traceabilityTransmissionInformation transmissionEngineering
The invention relates to a cross-network security data sharing method and system based on a block chain in an information transmission technology. The cross-network security data sharing method specifically comprises the following steps: enabling a block chain to receive a cross-domain request transaction to an intranet of an institution sent by a request application end proxy node; verifying whether the cross-domain request transaction conforms to a loaded verification rule or not, and sending a verification result to a request application end proxy node; if the verification result is yes, receiving meta-information of shared data sent by the application end proxy node to the intranet receiving end proxy node in a cross-network manner; storing the cross-domain request transaction and the meta-information to generate a new block; wherein the block link receives cross-domain request transactions and meta-information which are from the Internet application end agent node or the intranet application end agent node and send data to the intranet. Cross-gatekeeper data sharing records are stored through a block chain, rule verification is automatically executed through an intelligent contract, cross-domain safe sharing of automatic data is achieved in cooperation with a cross-network communication agent, the real-time performance is high, and the efficiency is high.
Owner:HANGZHOU QULIAN TECH CO LTD
Data processing method and device based on block chain, equipment and storage medium
PendingCN112804218AImprove efficiencyImprove securitySecuring communicationMedical reportsTerminal equipmentEngineering
The embodiment of the invention discloses a data processing method and device based on a block chain, equipment and a storage medium. The method comprises the steps of receiving an acquisition request of a first medical institution for medical data of a target user; reading an authorization record about the medical data of the target user from the first block chain network according to the acquisition request; verifying whether the first medical institution has the authority of acquiring the medical data of the target user according to the authorization record; if the first medical institution does not have the authority, refusing to send the medical data of the target user to a terminal device corresponding to the first medical institution; and if the first medical institution has the authority, reading the medical data of the target user from the second block chain network, and sending the medical data of the target user to a terminal device corresponding to the first medical institution. By adopting the method and the device, the medical data of the target user can be safely shared among multiple medical institutions, the method and the device are suitable for the field of smart medical treatment, and construction of a smart city can be further promoted.
Owner:深圳平安智慧医健科技有限公司
Regional government affair collaborative office system based on block chain and multi-tenant technology
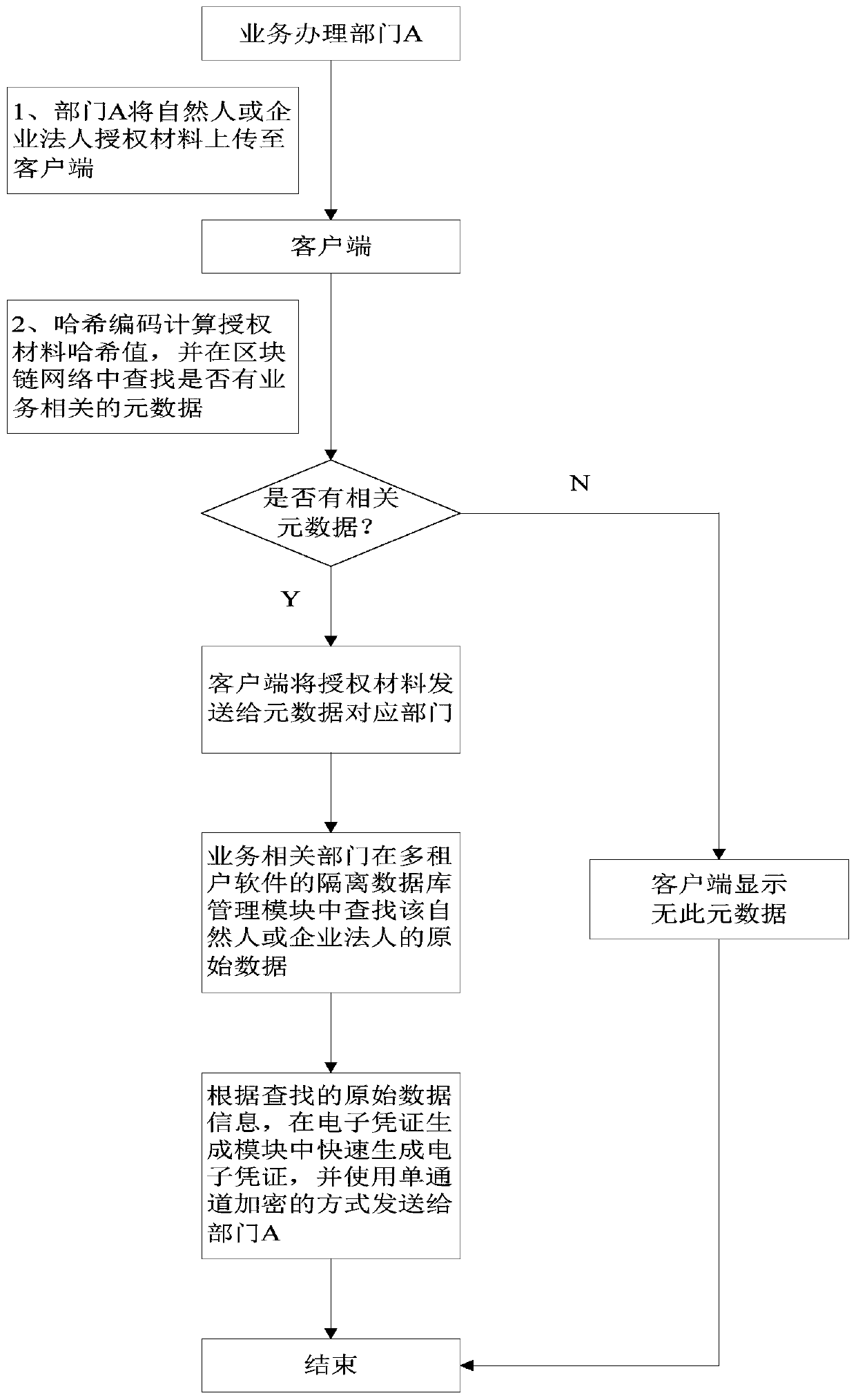
InactiveCN109784864ARealize collaborative officeEnable secure sharingOffice automationTimestampOriginal data
The invention relates to a regional government affair collaborative office system based on a block chain and a multi-tenant technology, and belongs to the field of electronic government affairs. The method comprises: on a platform of a constructed government affair collaborative office system, government departments use the same multi-tenant software to isolate original data of a natural person oran enterprise legal person, and metadata is uploaded to a block chain network; And the department A submits authorization materials of the natural person or the enterprise legal person through the client of the block chain network, and automatically searches metadata information in the block chain network. If metadata information related to services exists, the authorization materials are sent todepartments corresponding to the metadata, the departments send electronic certificates to the department A in a single-channel encryption mode in multi-tenant software, and the block chain network records electronic certificate codes, timestamps, IDs and authorization material Hash values. By combining the block chain and the multi-tenant technology, data isolation of all departments of the government and collaborative office of government departments are achieved, and government affair service efficiency is improved.
Owner:山西创时代数智创新研究院有限公司
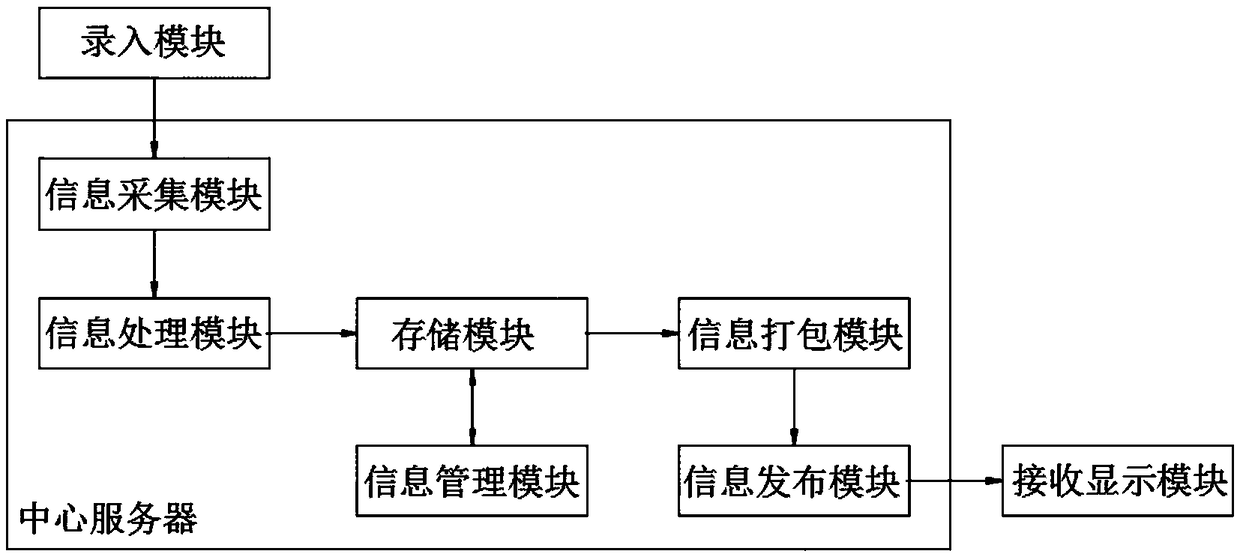
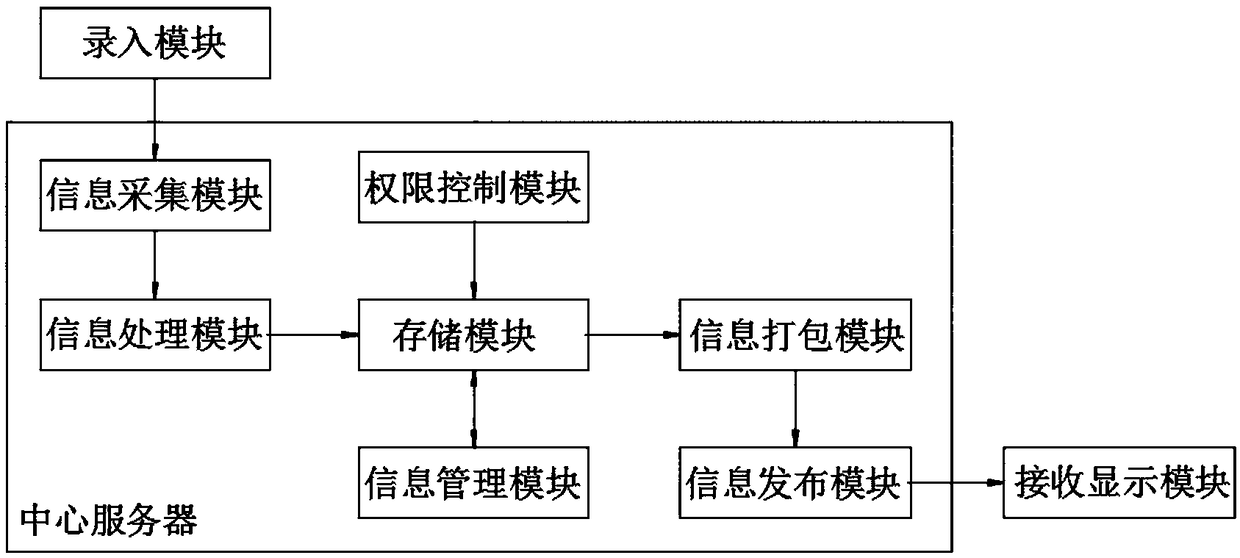
IoT-based information sharing system
InactiveCN108833422AEnable secure sharingEnsure information securityTransmissionAuthority controlInternet of Things
The invention discloses an IoT-based information sharing system comprising an input module, a central server and a receiving display module. The input module establishes a communication connection with the central server for processing and storing information. The central server establishes a communication connection with the receiving display module for displaying information. The input module isused for inputting information. The central server includes an information acquisition module, an information processing module, a storage module, an information management module, an authority control module, an information packaging module, and an information release module. The storage module and the information management module achieve a network interactive connection with each other. The IoT-based information sharing system realizes secure information sharing, ensures information security, and allocates different authorities to different users by authority setting. User with certain authorities can only obtain the information within the authorities of the users and users with common authorities cannot obtain high-level data information. The IoT-based information sharing system can fast share information and is very convenient.
Owner:WUXI NANLIGONG TECH DEV
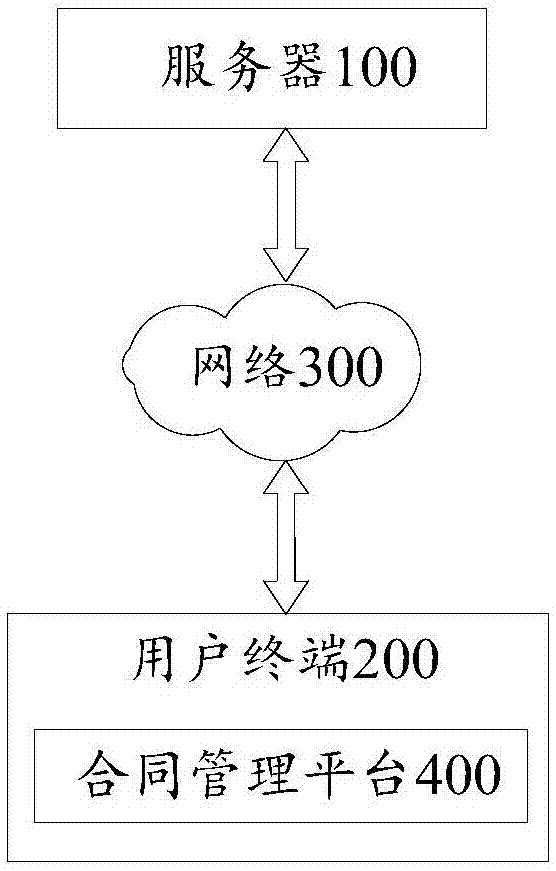
Contract management method and server
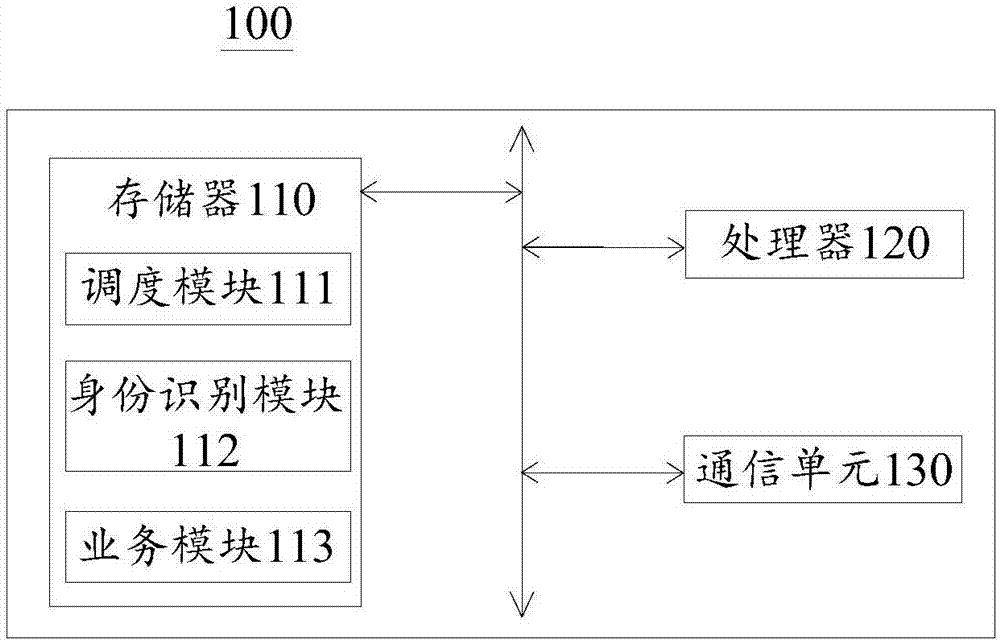
InactiveCN107579990ARealize online managementEnable secure sharingTransmissionAuthorizationComputer science
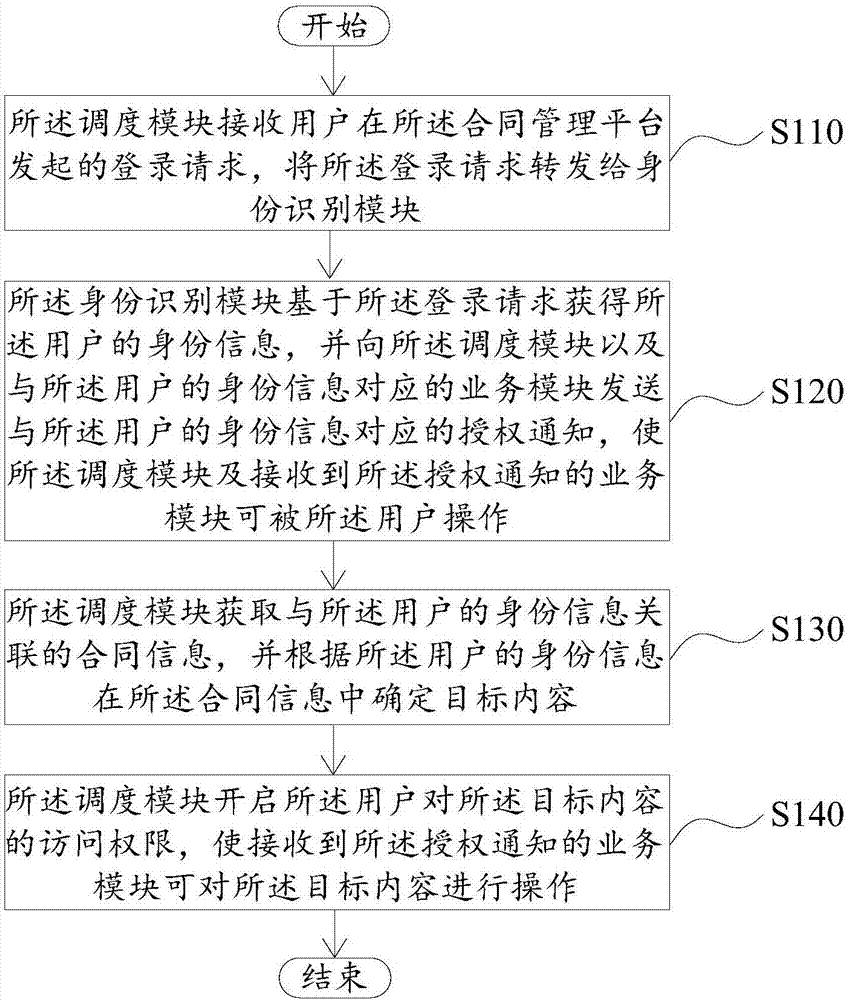
The invention provides a contract management method and a server. The method is applied to the server, and the server provides a contact management platform and comprises a scheduling module, an identity identification module and at least one service module. The method comprises the steps that the scheduling module receives a login request initiated by a user on the contact management platform andforwards the login request to the identity identification module; the identity identification module acquires identity information of the user on the basis of the login request and sends an authorization notification corresponding to the identity information of the user to the scheduling module and the service module corresponding to the identity information of the user to enable the scheduling module and the service module receiving the authorization notification to be capable of being operated by the user; the scheduling module acquires contact information associated with the identity information of the user to determine target content; and the scheduling module enables an access permission of the user on the target content to enable the service module receiving the authorization notification to be capable of operating the target content.
Owner:北京华云智汇科技有限公司
Data trusted security sharing system and method based on block chain technology
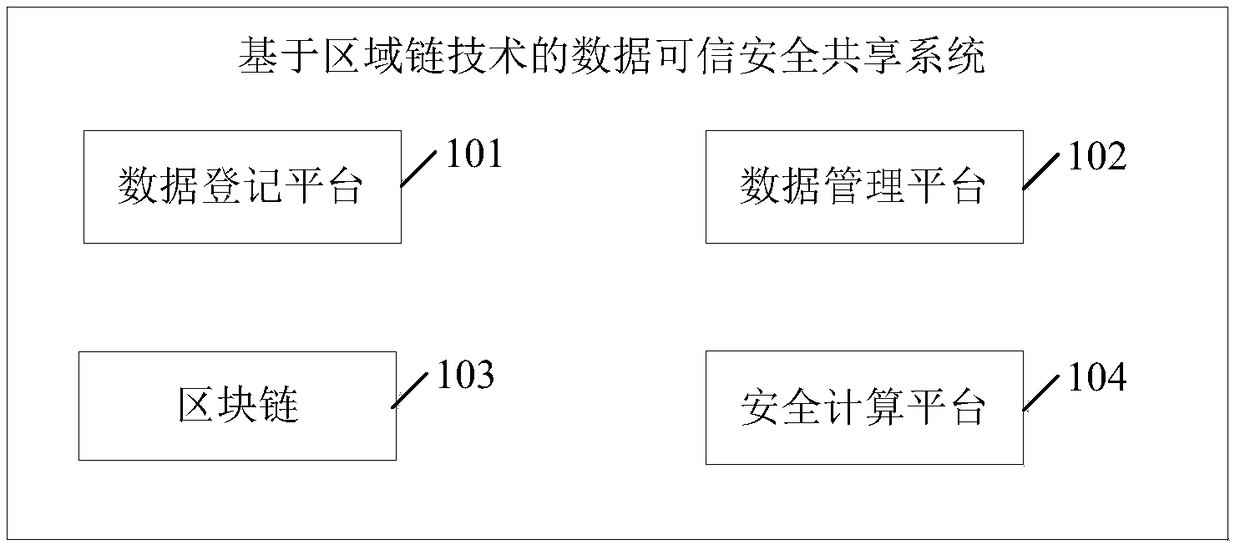
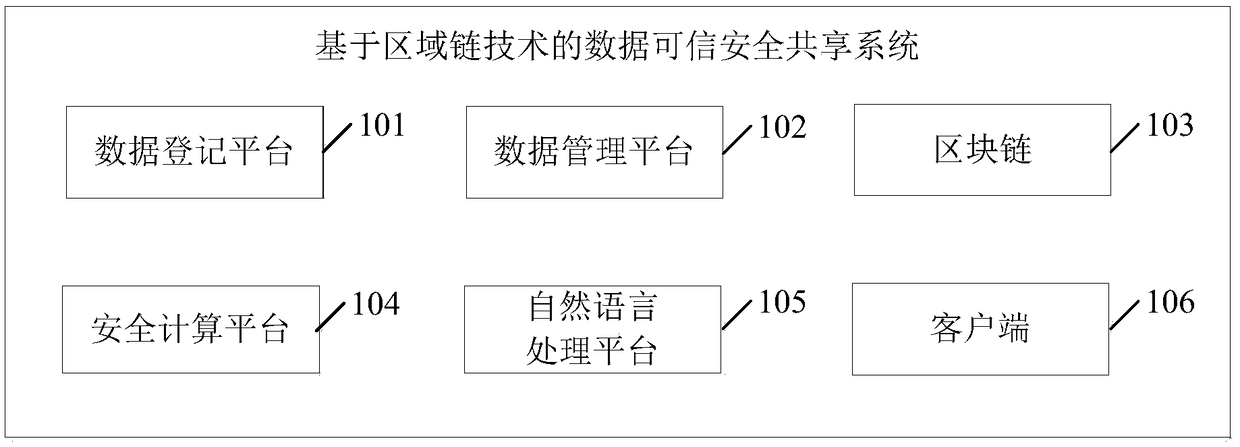
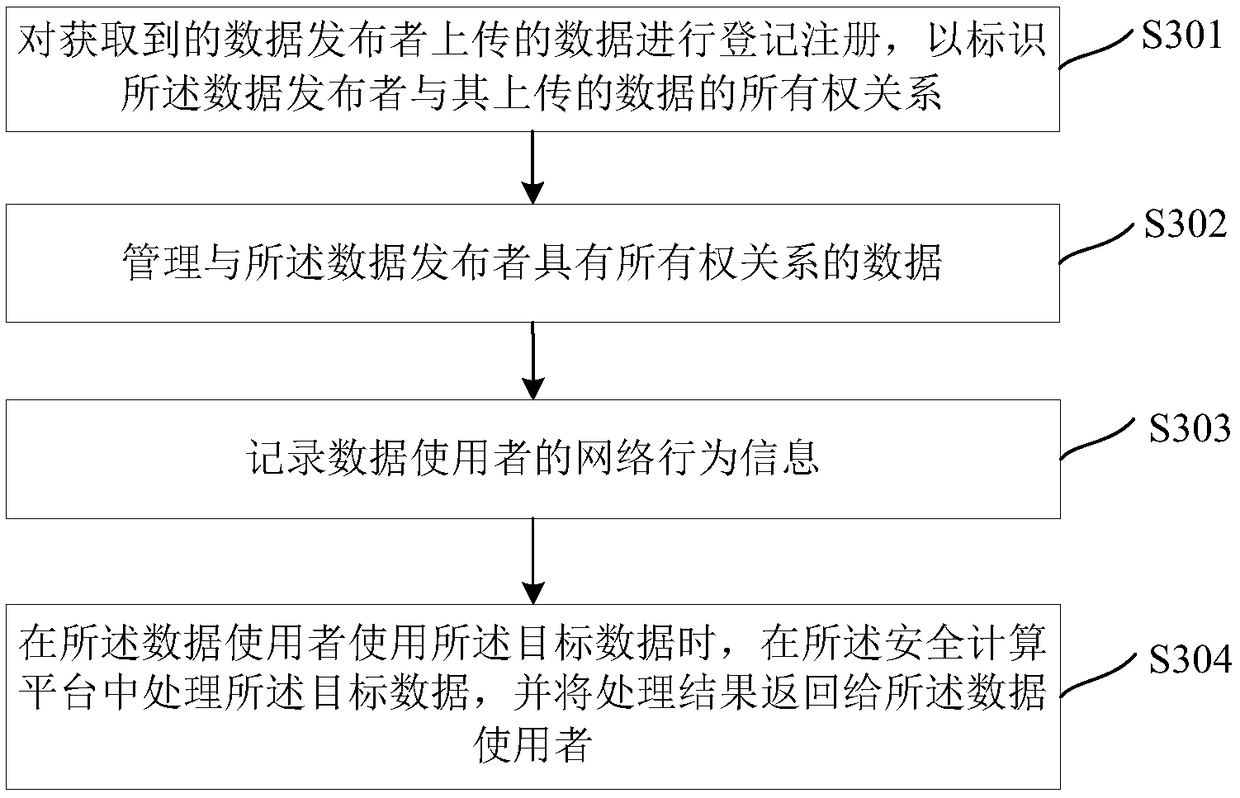
The present application discloses a data trusted security sharing system and method based on area chain technology. The system comprises a data registration platform, a data management platform, a security computing platform and a block chain. The data registration platform registers the data uploaded by the data publisher uniformly, which realizes the protection of data ownership in the process of data circulation. The data management platform manages the data which has the ownership relation with the data publisher, and effectively guarantees the data publisher's ownership to the data. In the data flow, the block chain records the network behavior information of the data users, monitors the network behavior, and ensures the data involved in the network behavior to be true and reliable. When the data user uses the target data, the target data is processed in the secure computing platform, and the processing result is returned to the data user, so as to realize the separation of the data ownership and the use right, avoid the data user to contact the data, and ensure the safety and controllability of the data circulation process.
Owner:TSINGHUA UNIV
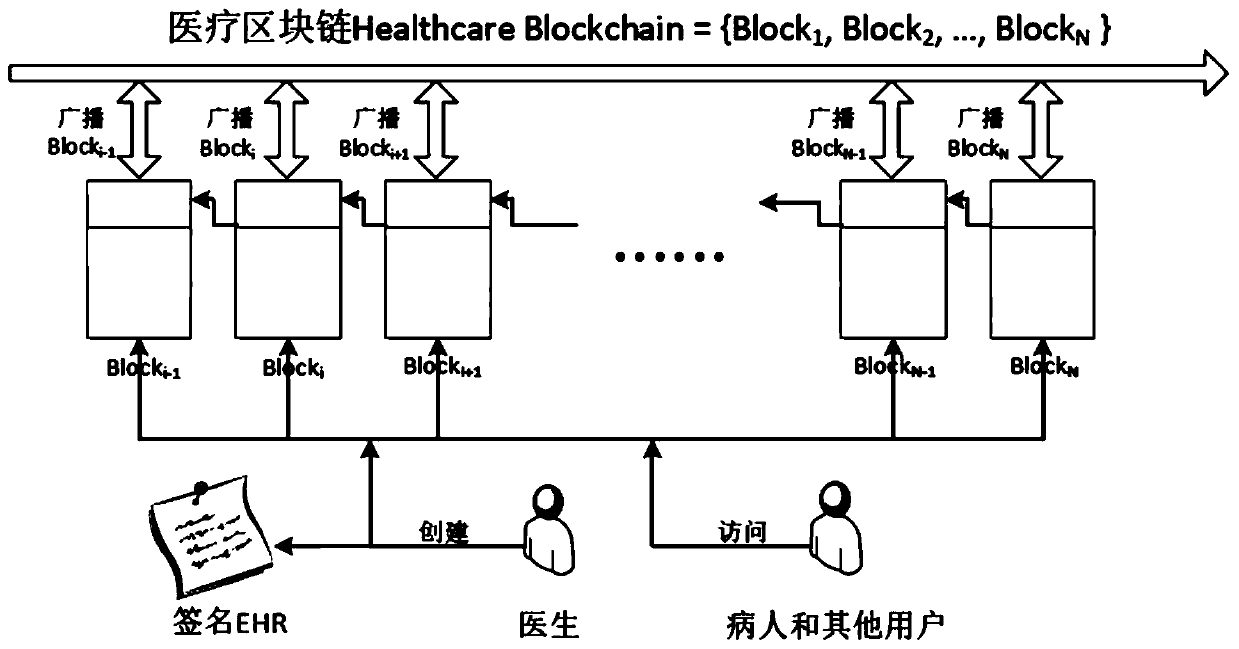
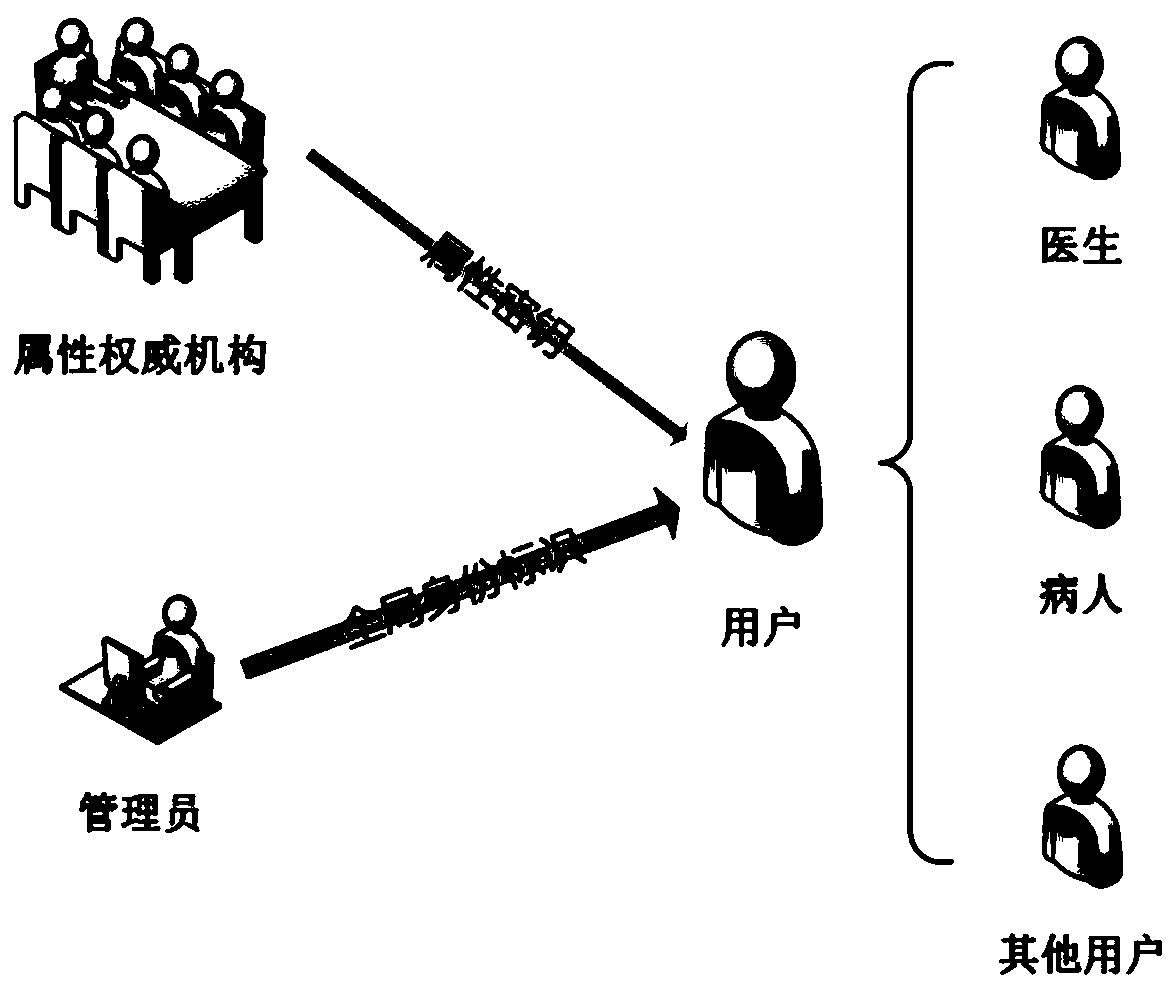
Blockchain medical data management method based on distributed attribute signature and system
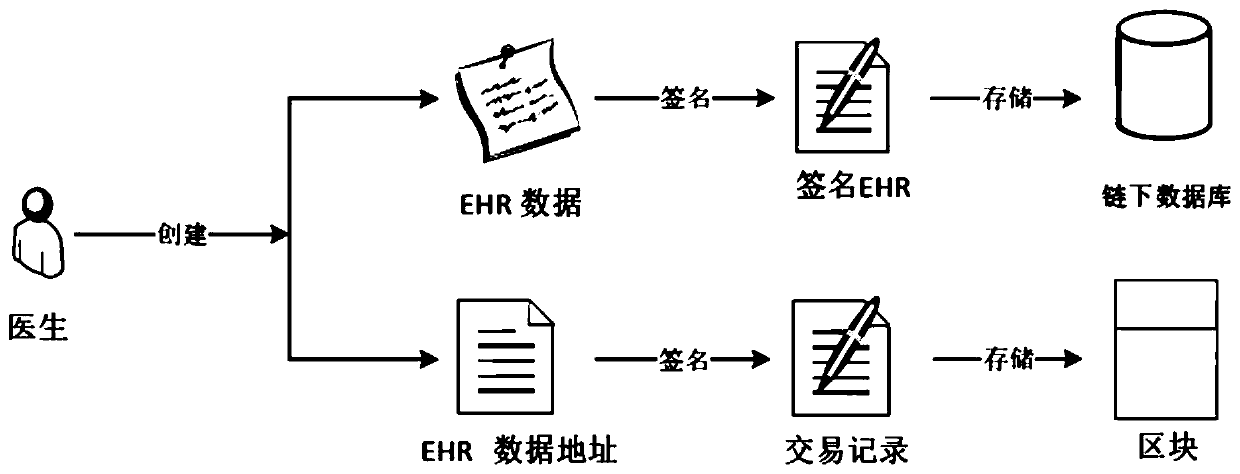
ActiveCN109979550AAttribute validationDo not reveal identityDigital data protectionPatient-specific dataHash functionFinancial transaction
The invention discloses a blockchain medical data management method based on distributed attribute signature and a system. The method comprises the following steps of S1, generating a global parameterof the distributed attribute signature and selecting a Hash function; S2, producing a signature secret key and a verification secret key which correspond with each attribute by each attribute authority mechanism; S3, generating a signature secret key set which corresponds with the global identity identification and the attribute set of a user by the user; S4, after generating EHR data by the user, storing the signature in an off-chain database, performing address signature on the HER data, and issuing the address signature in the blockchain; and S5, firstly verifying the signature attribute of the address which is stored in an on-line transaction by the user, and finding the EHR in the off-chain database through the address and verifying the attribute of a data signature person. The blockchain medical data management method and the system have advantages of protecting identity information of the signature person, realizing EHR data safe sharing over different CDO systems, and settlinga problem of blockchain storage capacity limitation through an on-chain and off-chain coordinated storage mode.
Owner:INST OF INFORMATION ENG CAS
Lightweight searchable encryption method and device based on elliptic curve
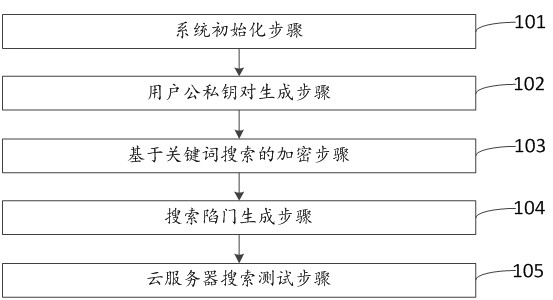
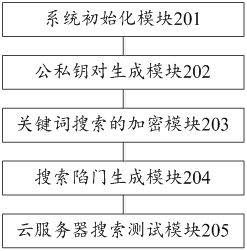
ActiveCN112560075AEnable secure sharingGuaranteed confidentialityDigital data protectionComputations using residue arithmeticOriginal dataCloud data
The invention provides a lightweight searchable encryption method and device based on an elliptic curve. The method comprises the following steps: a system initialization step; a user public and private key pair generation step; an encryption step based on keyword search; encrypting the original data file by using a universal public key encryption technology; a search trap door generating step; and a cloud server search testing step. According to the keyword guessing attack resistant lightweight searchable encryption method, an elliptic curve cryptographic algorithm is utilized, and the requirements on calculation and storage expenditure are relatively low, so that the keyword guessing attack resistant lightweight searchable encryption method has a lightweight characteristic, can be widelyapplied to various mobile intelligent terminal platforms with limited hardware resources, and has a keyword guessing resistance characteristic; therefore, the server cannot guess the keywords queriedby the user, and the information security of the cloud data is effectively guaranteed.
Owner:SOUTHWEST PETROLEUM UNIV
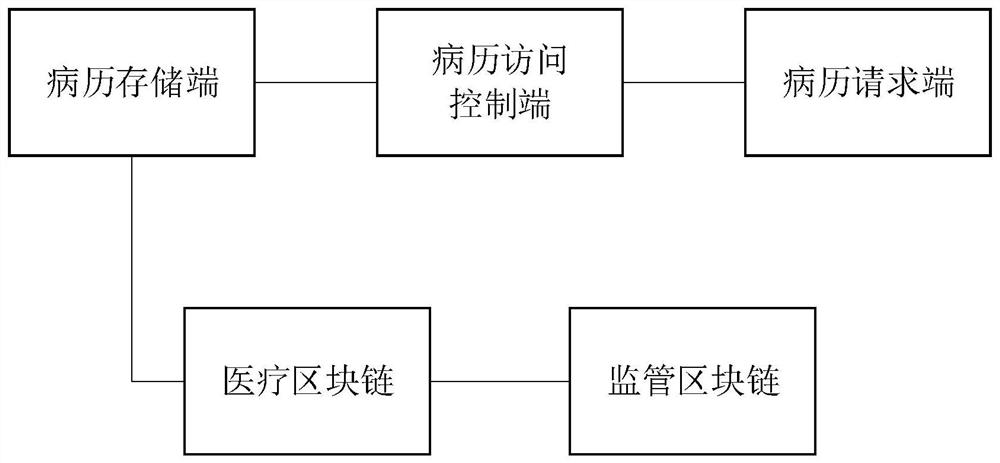
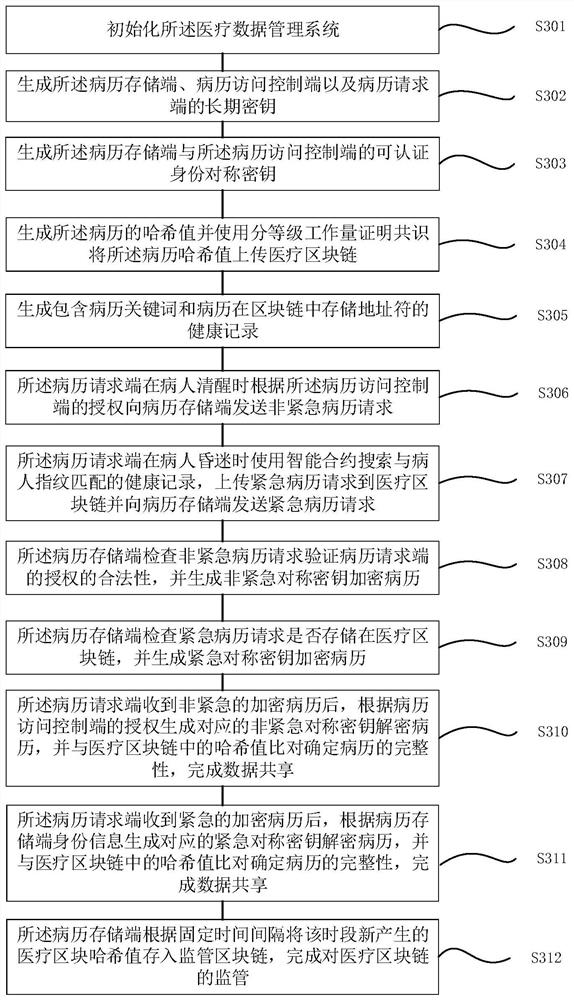
Medical data management system based on double block chains and patient authorized medical record sharing method
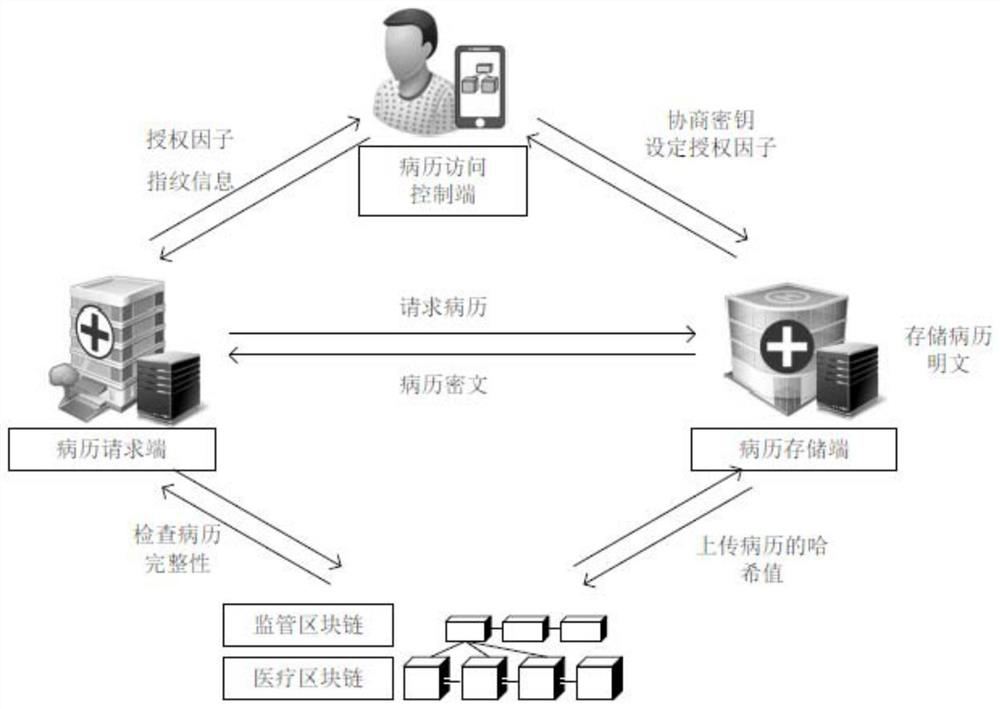
PendingCN113764060ADefend against attackAvoid the risk of medical disputesDatabase distribution/replicationDigital data protectionMedical emergencyIn patient
The invention discloses a medical data management system based on double block chains and a patient authorized medical record sharing method, and relates to the technical field of authenticated key negotiation algorithms. The medical data management system comprises a medical block chain, a supervision block chain, a medical record storage end, a medical record access control endfor sending medical record access authorization to a medical record request end and calling an intelligent contract to store health records containing medical record keywords, and a medical record request end which is used for acquiring active authorization and requesting data from the medical record storage end when the patient is awake and calling the intelligent contract to search the health record matched with the fingerprint of the patient when the patient is coma so as to request data from the medical record storage end. According to the system and the method, a graded workload proof consensus mechanism is adopted, the speed of generating the new block is changed according to the emergency degree of the transaction, a double-chain structure is used for supervising the data on the chain, and privately mining attacks are effectively resisted.
Owner:ANHUI NORMAL UNIV
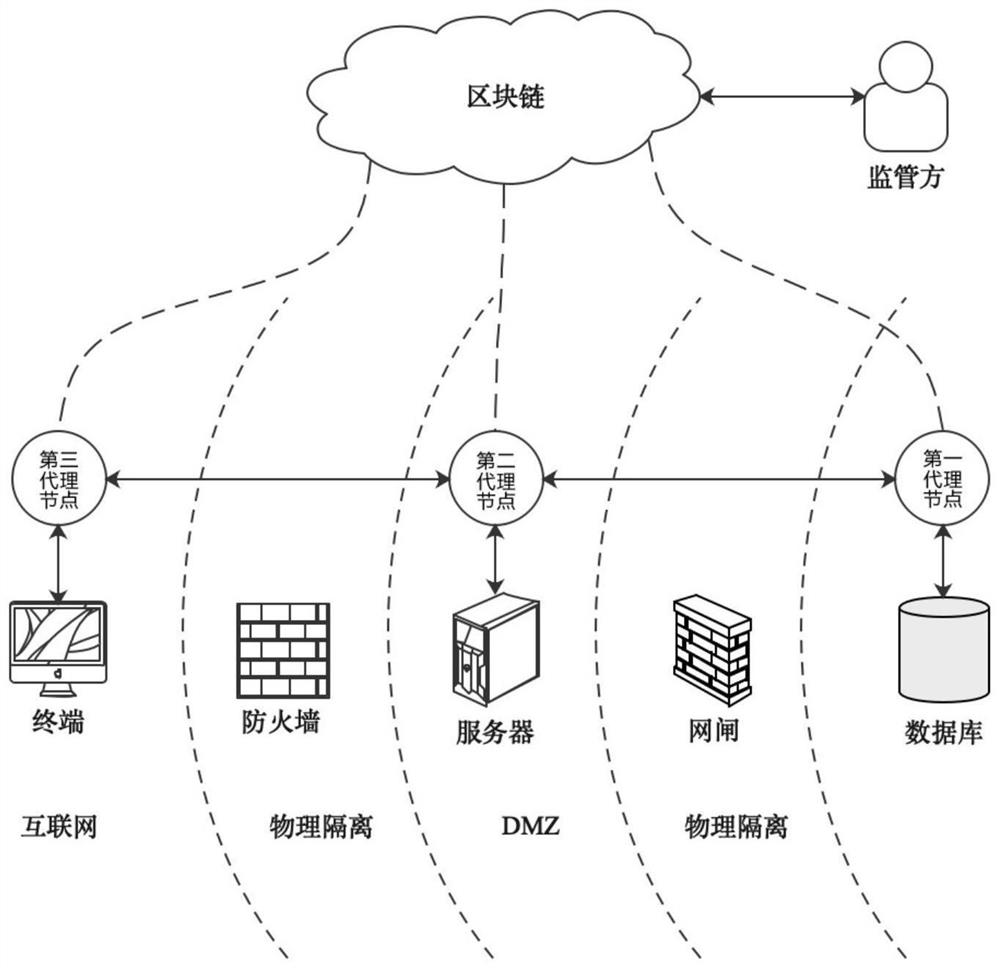
A data security sharing exchange method and data security sharing exchange platform system
The invention provides a data safety sharing and exchanging method and system. The system comprises a block chain infrastructure, a block chain storage library, an access agent subsystem and a request agent subsystem. The data safety sharing and exchanging method comprises the steps that the access agent subsystem receives description information of first target data, and publishes the description information to the block chain storage library; the request agent subsystem chooses description information of second target data from the description information, generates a data authority request and publishes the data authority request to the block chain storage library; the access agent subsystem obtains the data authority request, replies to the data authority request, and publishes authority reply information to the block chain storage library; the request agent subsystem obtains the authority reply information and judges whether the authority reply succeeds or not, and if yes, the request agent subsystem publishes a data access request of the second target data to the block chain storage library; the access agent subsystem obtains the data access request of the second target data from the block chain storage library, and provides the second target data for a data demand party corresponding to the request agent subsystem.
Owner:北京明朝万达科技股份有限公司
Method for realizing ecological environment space big data integration and sharing
InactiveCN110647673AAccurate classificationGrab directlyData processing applicationsGeneral water supply conservationEnvironmental resource managementEcological environment
The invention discloses a method for realizing ecological environment space big data integration and sharing. The invention relates to the technical field of ecological environment protection. Water quality environment monitoring information, atmospheric environment monitoring information, soil environment monitoring information, ecological environment pollution source information, ecological garbage monitoring and processing information, ecological garbage treatment information and ecological garbage pollution information are collected in different time periods and different places; the method comprises the following steps: acquiring information of a user, storing the information at a source end through grammar mapping and field mapping, capturing target information in a manner of inputting retrieval information, and generating associated information at the same time, so that the user acquires required information at the moment, the problem of safely sharing environmental informationresources is solved, and the acquired information is stored and shared in different time periods and different places.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Privacy protection efficient aggregation and access control method for power grid data
PendingCN112668039AEnable secure sharingReduce dependenceData processing applicationsDigital data protectionCiphertextData access control
The invention discloses a privacy protection efficient aggregation and access control method for power grid data, which comprises the following steps of: generating all n key sequences required in a fixed time period, dividing data generated in the time period into n independent data blocks according to time slices, and calculating a data aggregation abstract of each database; encrypting all the data blocks in the time period by a secret key to generate an encrypted file, sending the encrypted file to a cloud server to be stored, and then obtaining a ciphertext according to the request of a data user and the access permission; and performing aggregation and decryption operation on the ciphertext by using the key set issued by the intelligent terminal to obtain a plaintext aggregation result of the power grid data. According to the method, low-delay query can be supported for power grid data which is huge in volume, high in generation speed and low in value density. The computing power of the edge intelligent terminal is fully utilized, dependence on the cloud server is reduced, and safe sharing of power grid data is achieved through fine-grained data access control.
Owner:STATE GRID INFO TELECOM GREAT POWER SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com