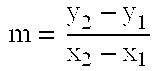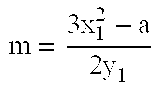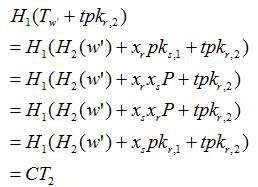Patents
Literature
72 results about "Elliptic curve cryptographic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
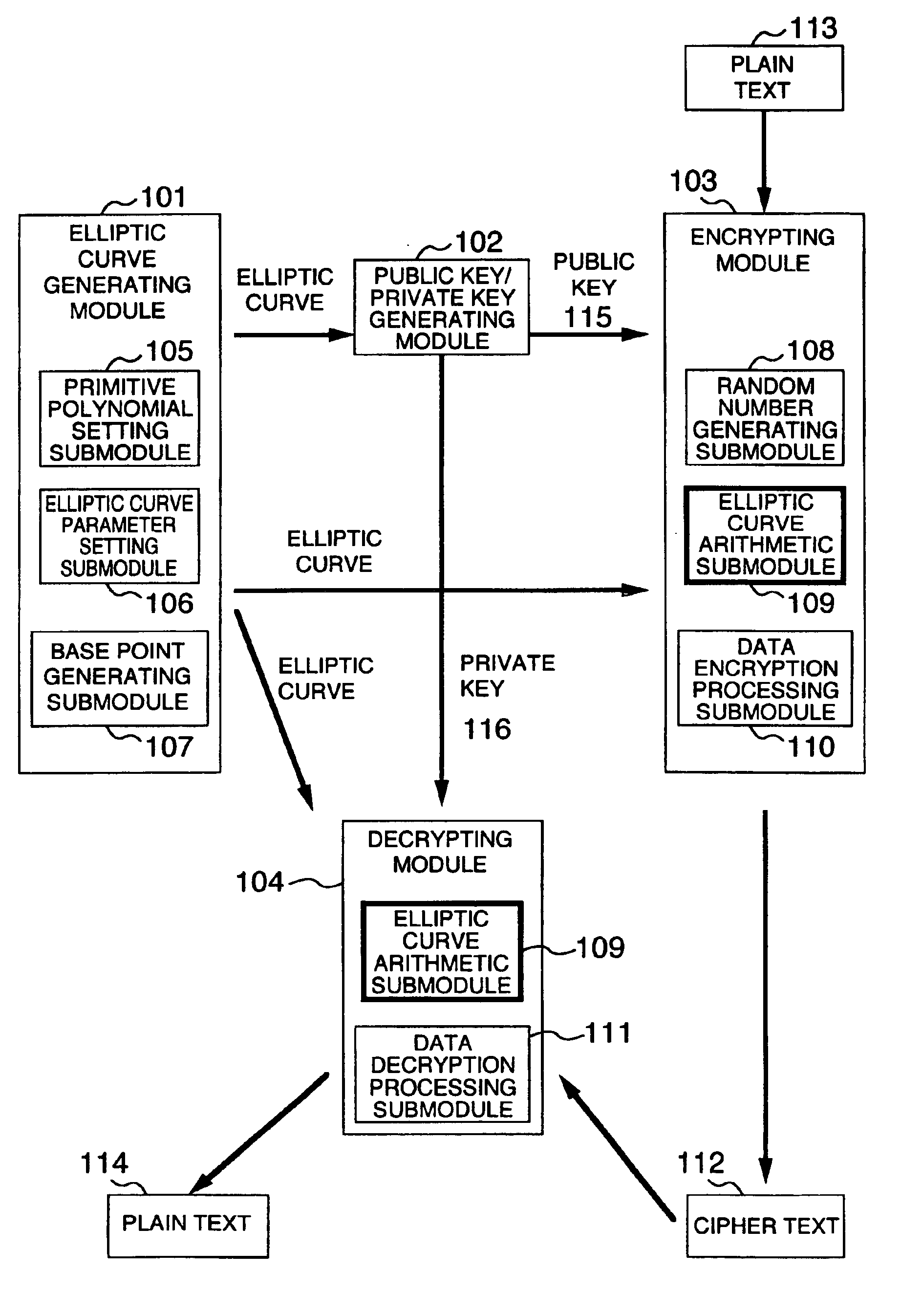
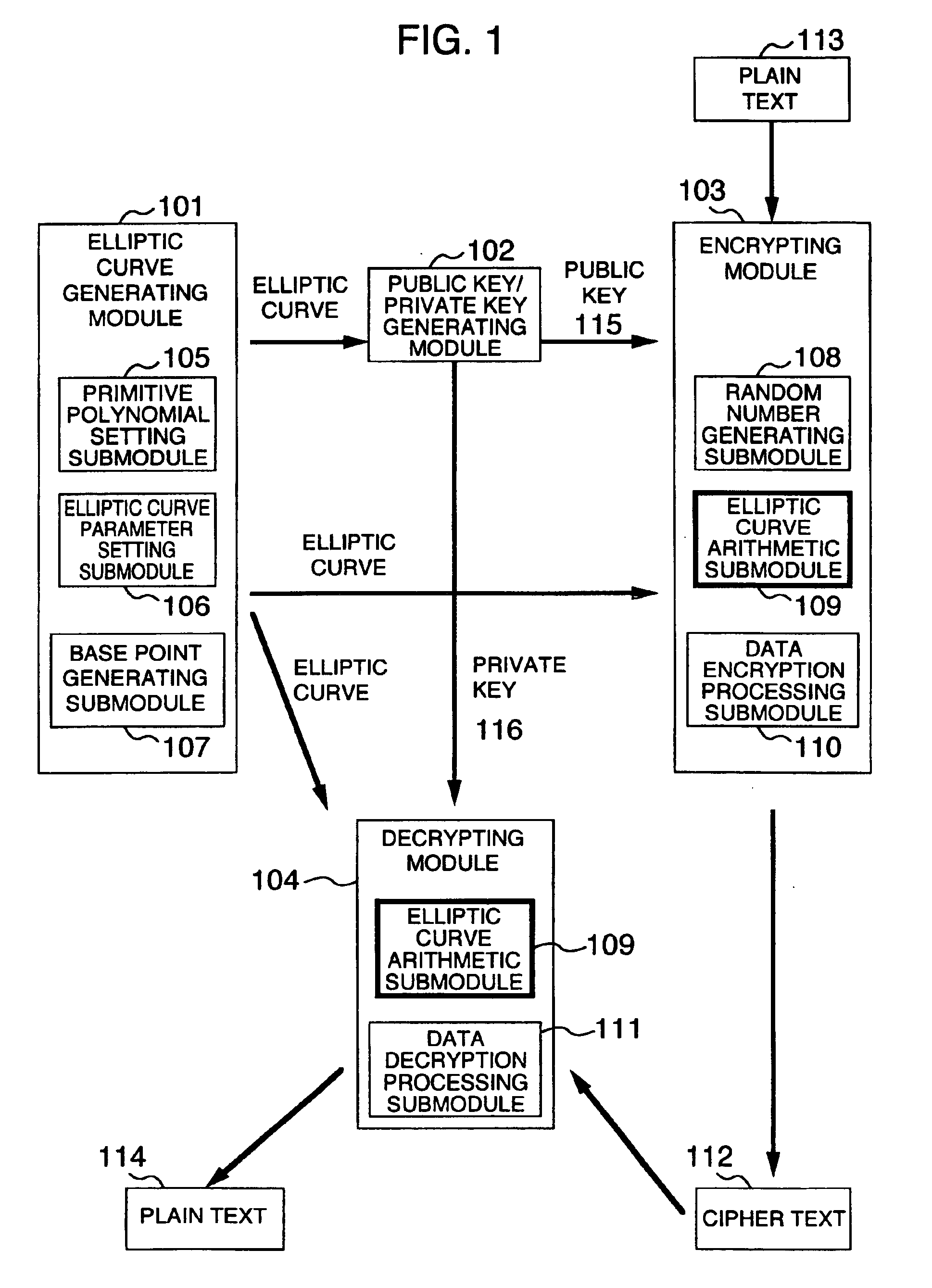
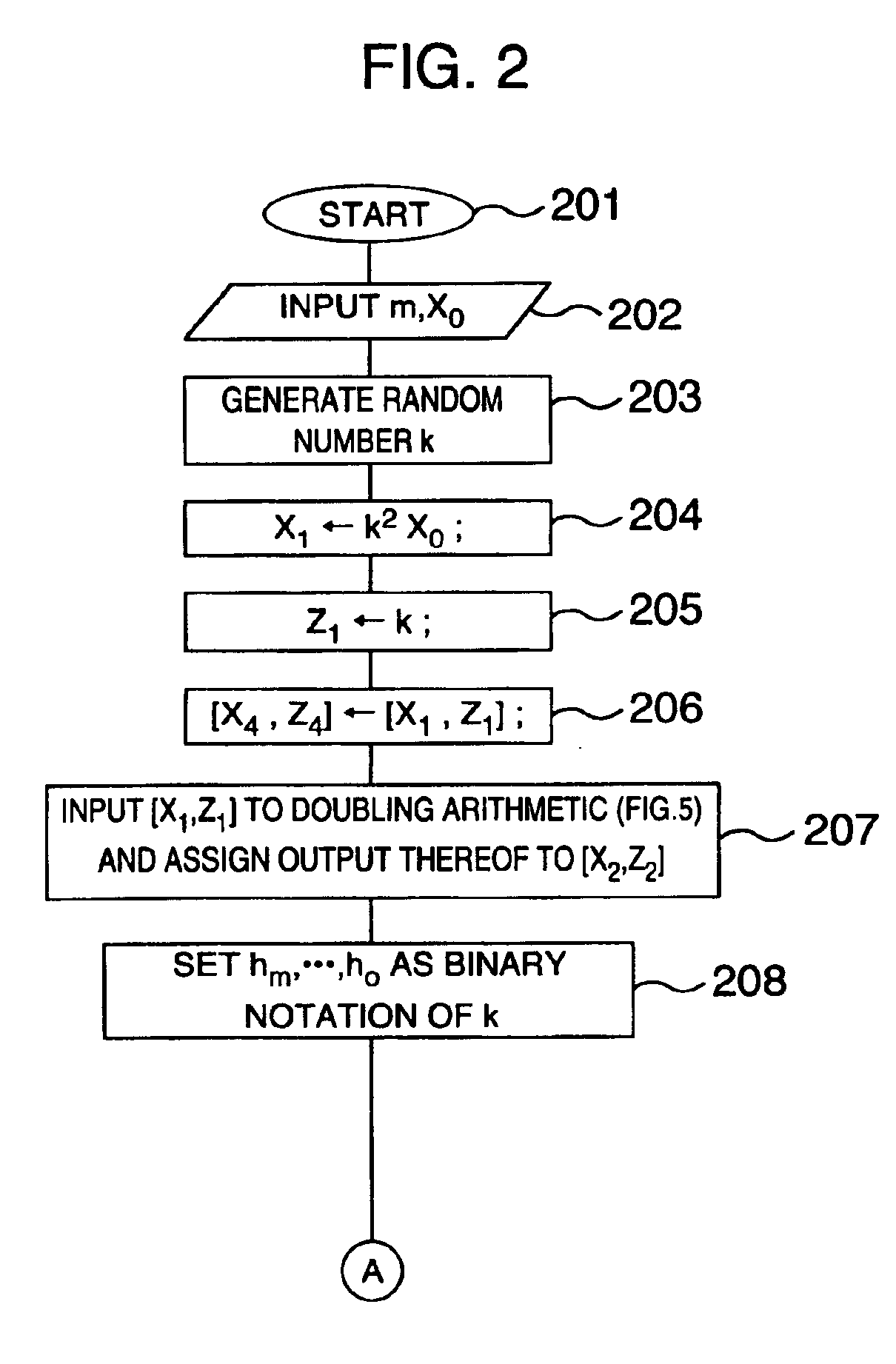
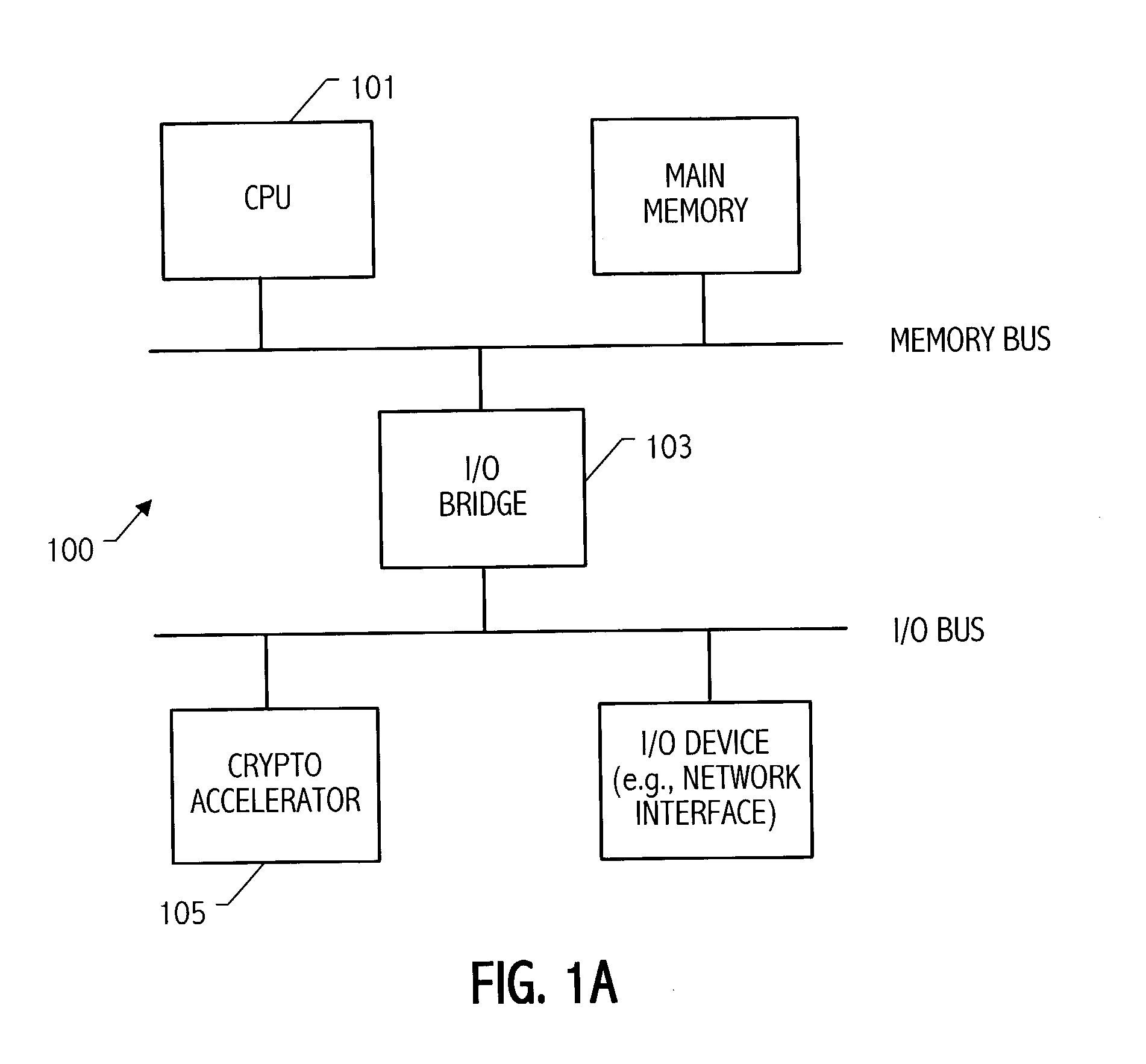
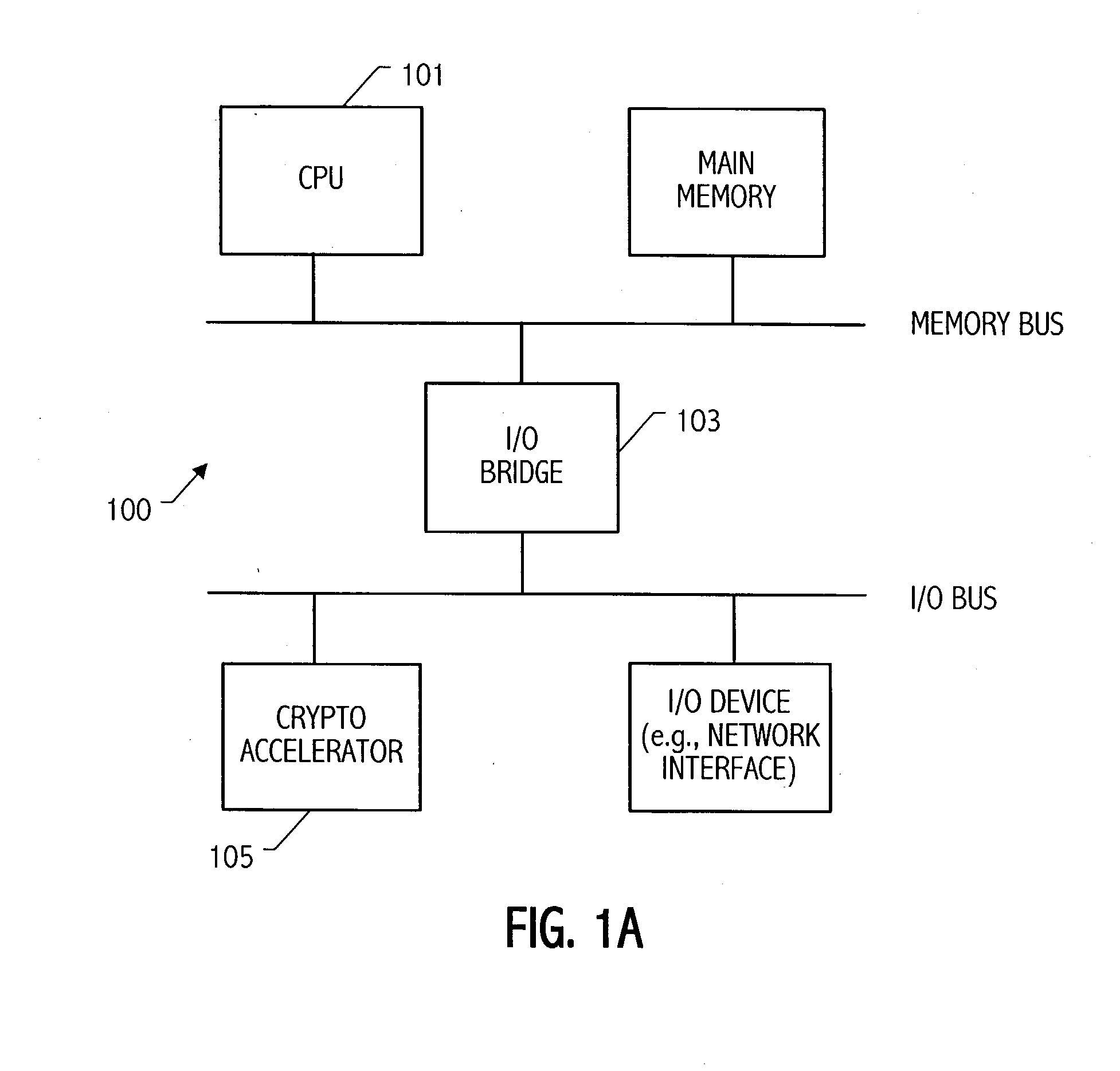
Method and apparatus for elliptic curve cryptography and recording medium therefore
InactiveUS6876745B1Prevent leakageRandom number generatorsPublic key for secure communicationComputer hardwarePower analysis
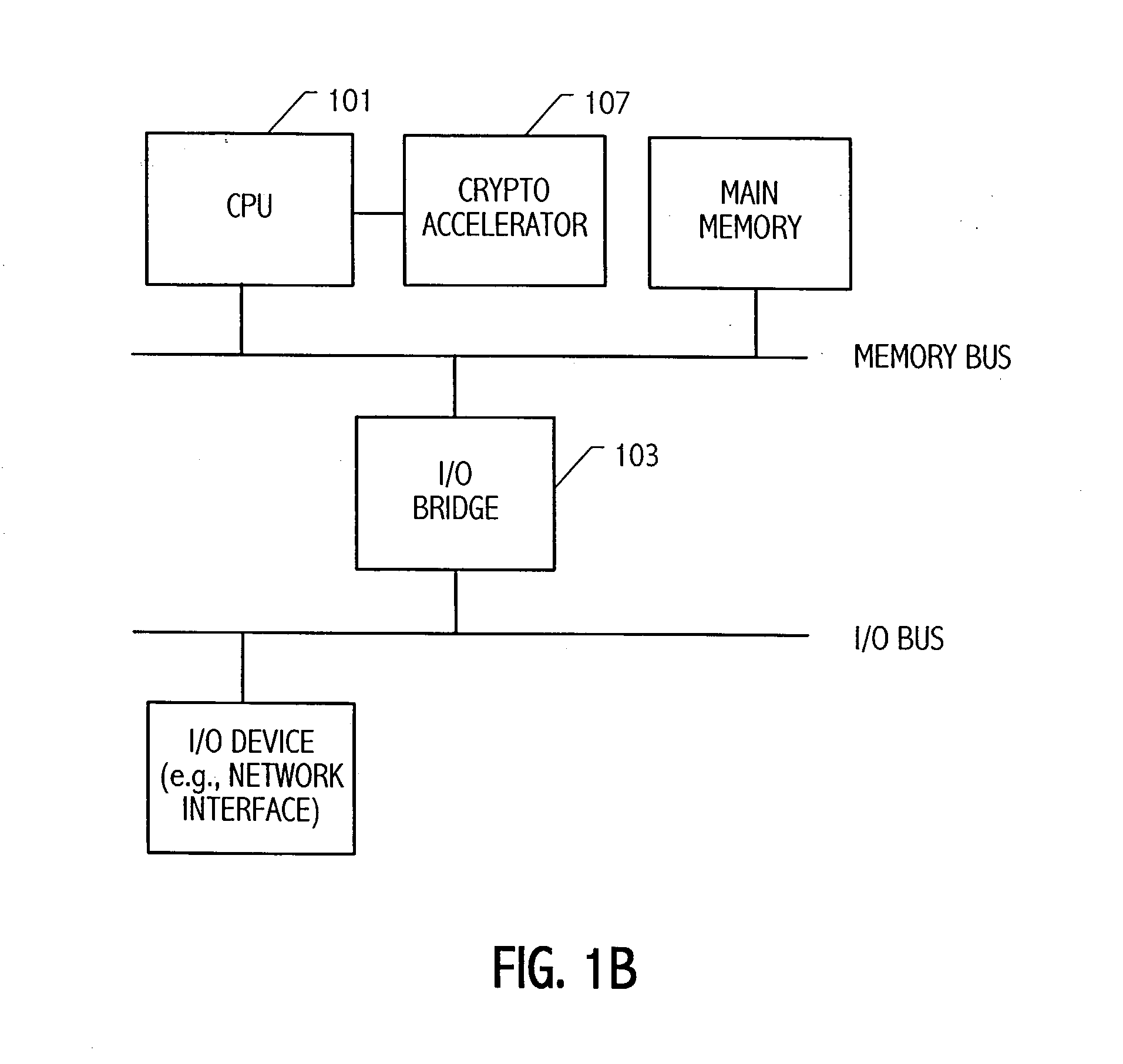
A method and an apparatus capable of realizing at a high speed an elliptic curve cryptography in a finite field of characteristic 2, in which the elliptic curve is given by y2+xy=x3+ax2+b (b≠0) and an elliptic curve cryptography method which can protect private key information against leaking from deviation information of processing time to thereby defend a cipher text against a timing attack and a differential power analysis attack are provided. To this end, an arithmetic process for executing scalar multiplication arithmetic d(x, y) a constant number of times per bit of the private key d is adopted. Further, for the scalar multiplication d(x, y), a random number k is generated upon transformation of the affine coordinates (x, y) to the projective coordinates for thereby effectuating the transformation (x, y)→[kx, ky, k] or alternatively (x, y)→[k2x, k3y, k]. Thus, object for the arithmetic is varied by the random number (k).
Owner:HITACHI LTD
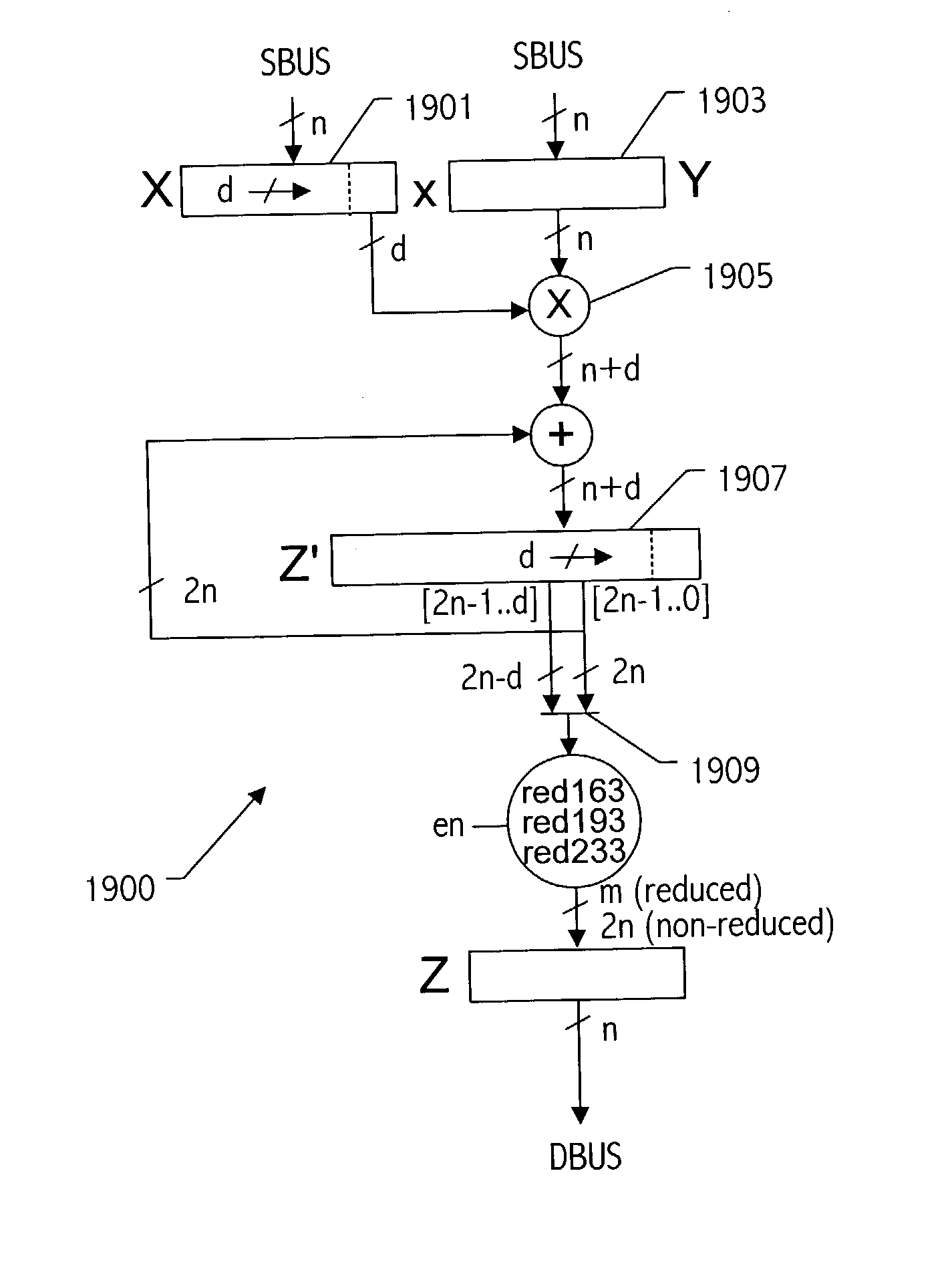
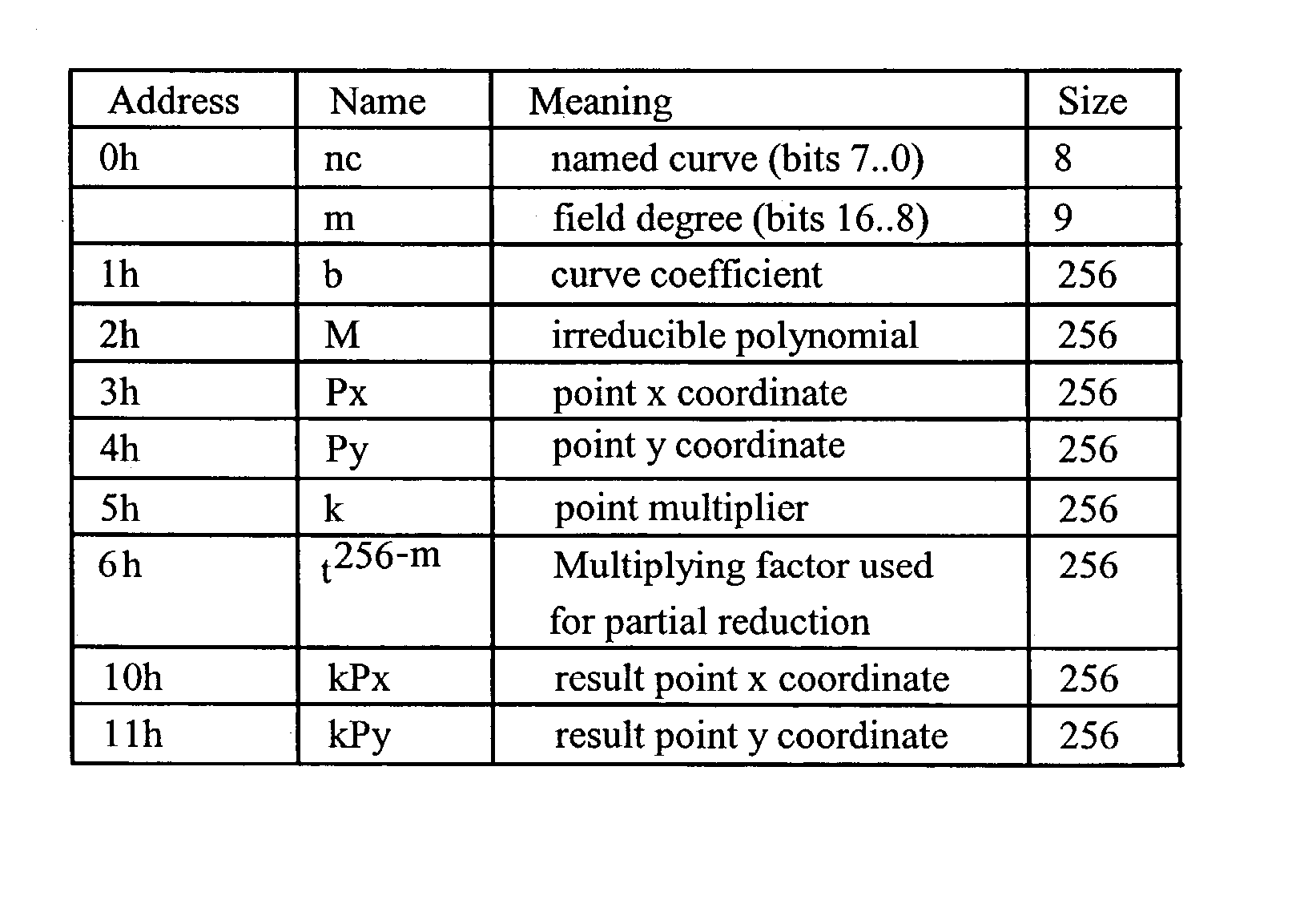
Generic implementations of ellipitic curve cryptography using partial reduction
ActiveUS20030208518A1Digital computer detailsComputations using residue arithmeticBinary multiplierOperand
A reduction operation is utilized in an arithmetic operation on two binary polynomials X(t) and Y(t) over GF(2), where an irreducible polynomial Mm(t)=t<m>+am-1t<m-1>+am-2t<m-2>+ . . . +a1t+a0, where the coefficients as are equal to either 1 or 0, and m is a field degree. The reduction operation includes partially reducing a result of the arithmetic operation on the two binary polynomials to produce a congruent polynomial of degree less than a chosen integer n, with m<=n. The partial reduction includes using a polynomial M'=(Mm(t)-t<m>)*t<n-m>, or a polynomial M''=Mm(t)*t<n-m >as part of reducing the result to the degree less than n and greater than or equal to m. The integer n can be the data path width of an arithmetic unit performing the arithmetic operation, a multiple of a digit size of a multiplier performing the arithmetic operation, a word size of a storage location, such as a register, or a maximum operand size of a functional unit in which the arithmetic operation is performed.
Owner:ORACLE INT CORP
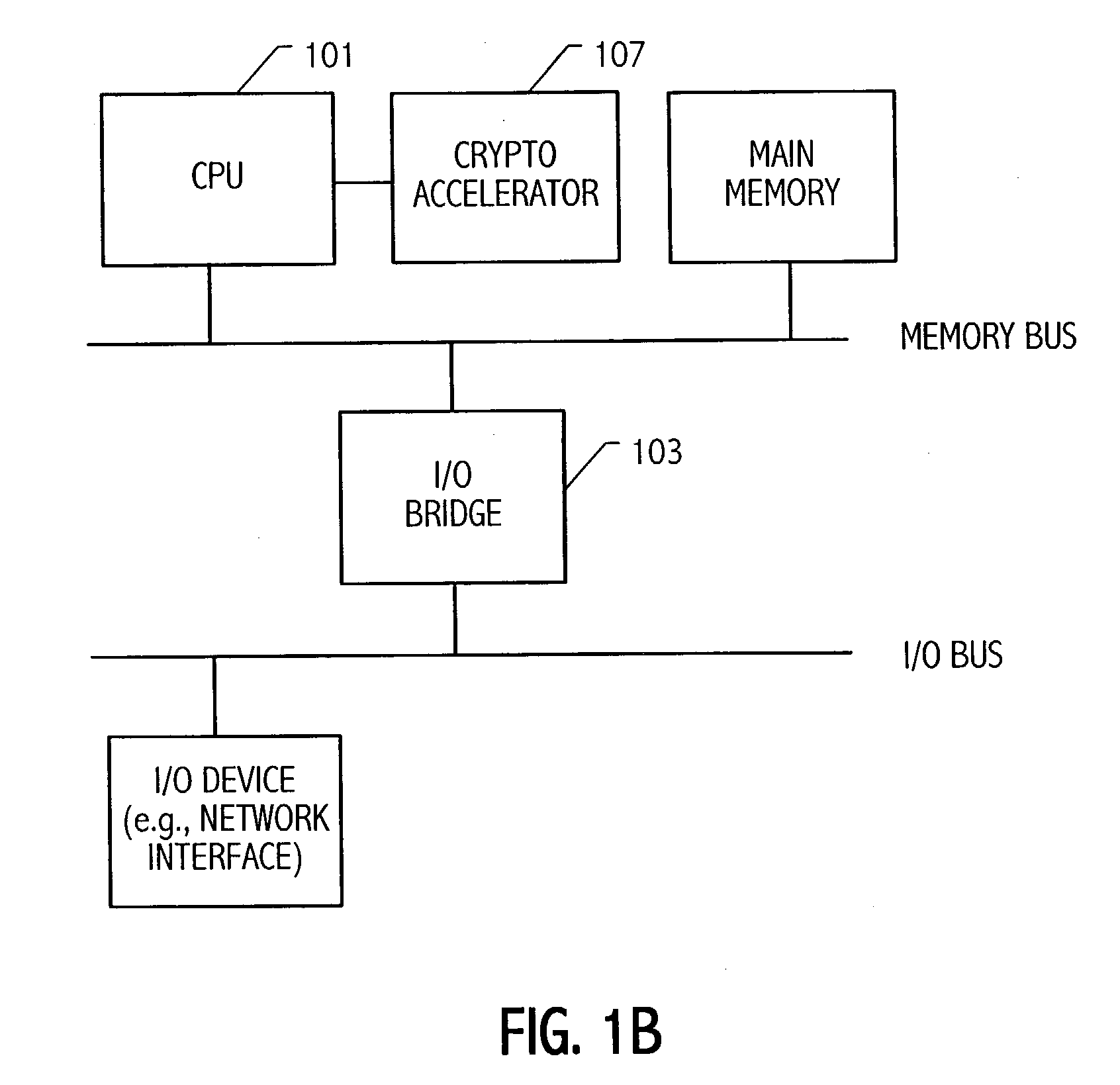
Hardware accelerator for elliptic curve cryptography
ActiveUS20030206629A1Public key for secure communicationDigital computer detailsEllipseElliptic curve cryptography
An elliptic curve processing apparatus that performs operations on elliptic curves specified over binary polynomial fields includes a functional unit that has a digit serial multiplier with a digit size of at least two bits. The elliptic curve processing apparatus performs reduction for respective generic curves using arbitrary irreducible polynomials, which correspond to respective ones of the generic curves. The elliptic curve processing apparatus may include hardwired reduction circuits in the functional unit for use with respective named curves. A storage location in the elliptic curve processing apparatus may be used to specify whether an operation is for one of the named curves or for one of the generic curves. The elliptic curve processing apparatus responds to an arithmetic instruction to utilize a respective one of the hardwired reduction circuits for reduction for respective named curves and a multiplier circuit for reduction for a plurality of generic curves, the multiplier coupled to perform reduction for respective generic curves using arbitrary irreducible polynomials, the arbitrary irreducible polynomials corresponding to respective ones of the generic curves. The elliptic curve processing apparatus operable on elliptic curves specified over binary polynomial fields performs a conditional branch according to whether a curve being processed is a generic curve or a named curve.
Owner:SUN MICROSYSTEMS INC
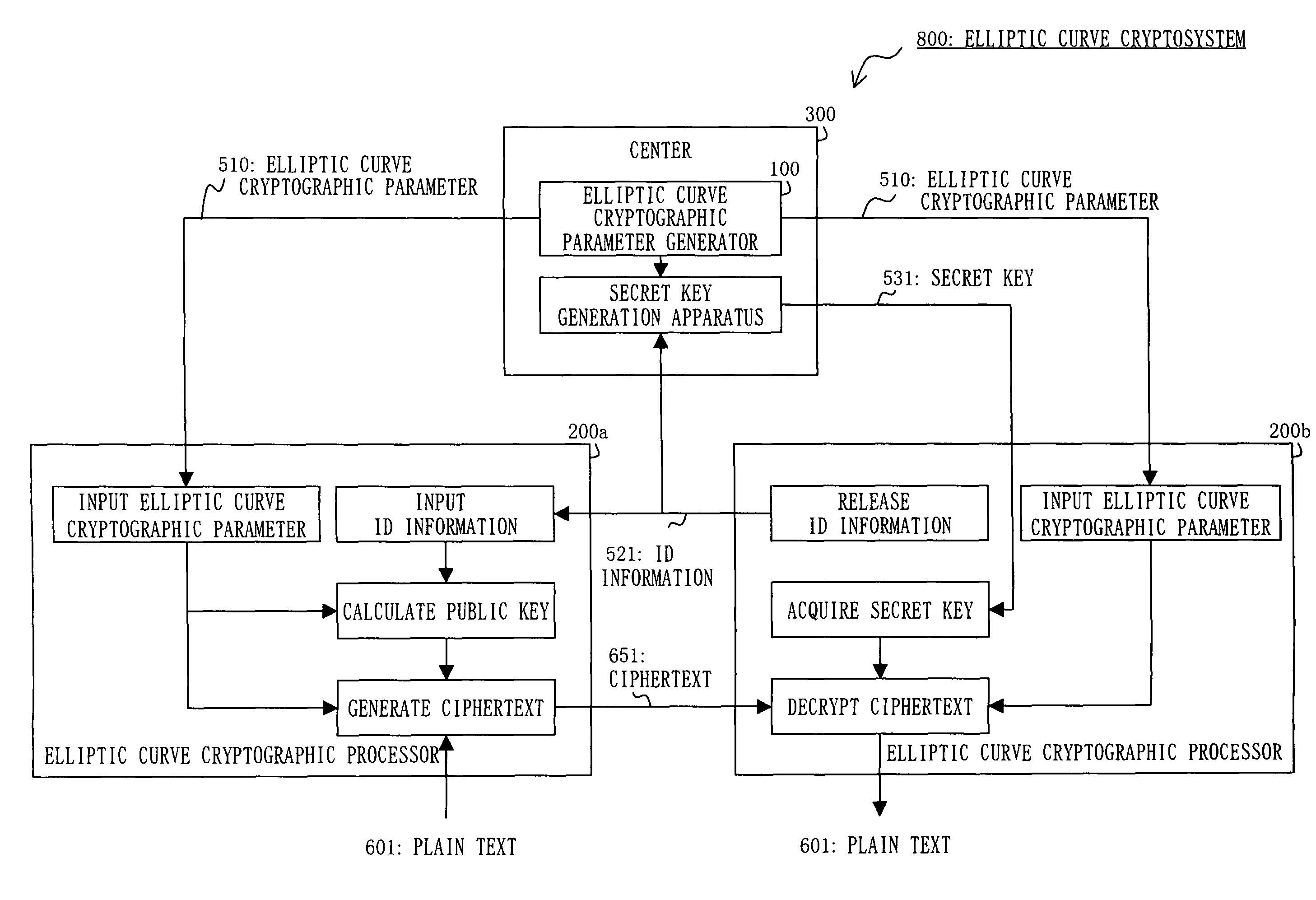
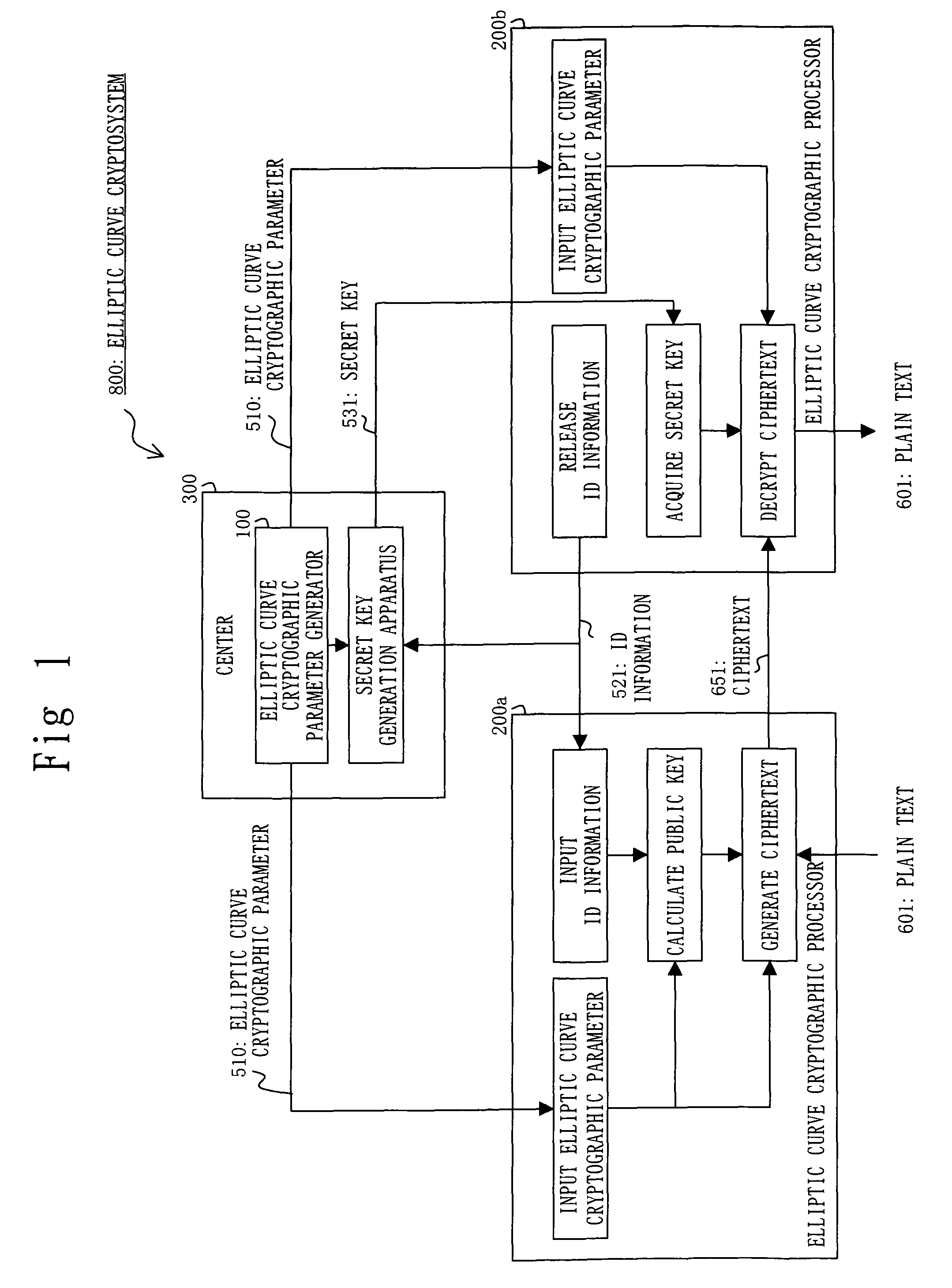
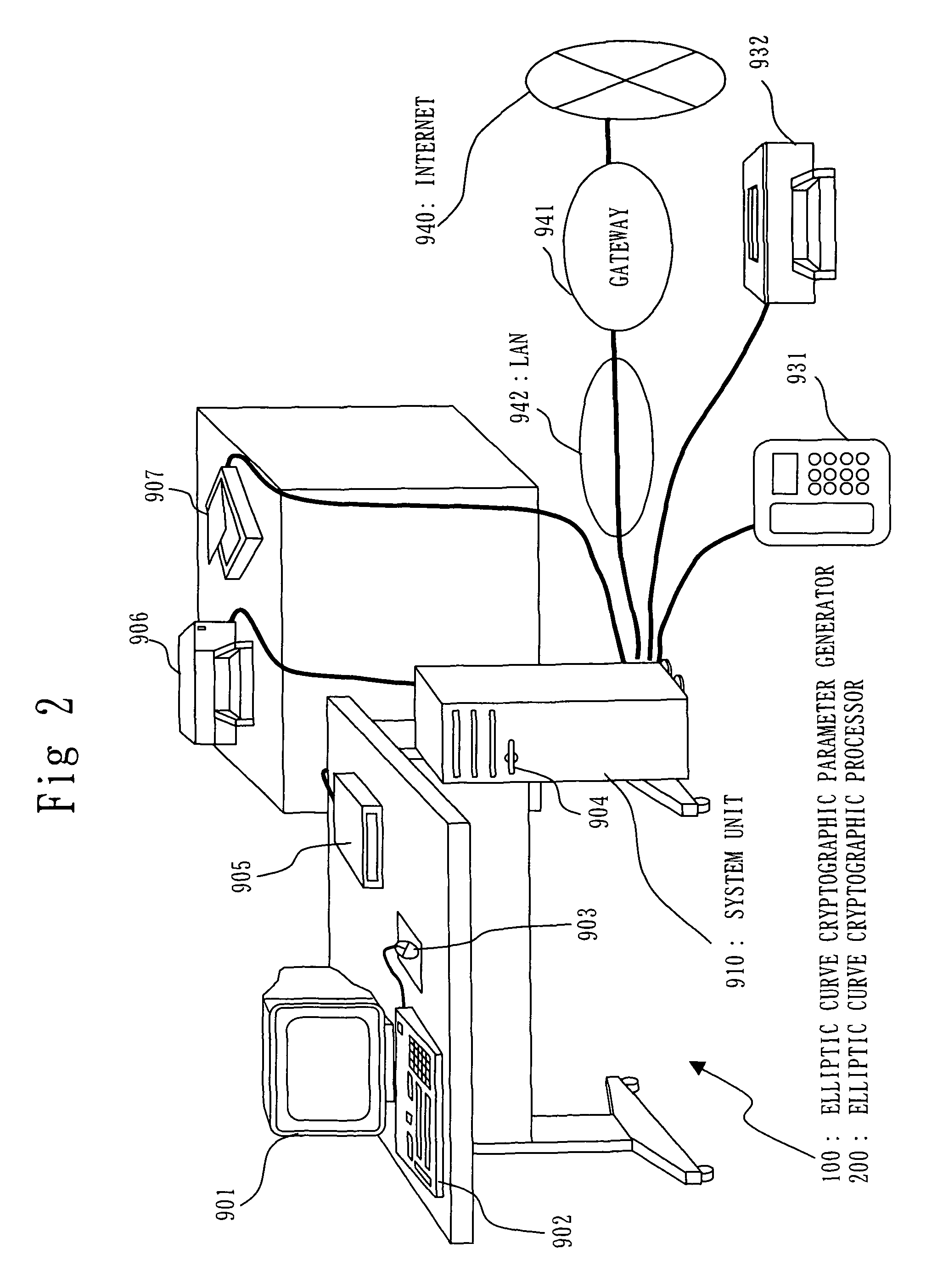
Apparatus for Generating Elliptic Curve Cryptographic Parameter, Apparatus for Processing Elliptic Curve Cryptograph, Program for Generating Elliptic Curve Cryptographic Parameter, and Program for Processing Elliptic Cryptograph
ActiveUS20090285386A1Easy to changePublic key for secure communicationDigital data processing detailsPairing computationElliptic curve cryptographic
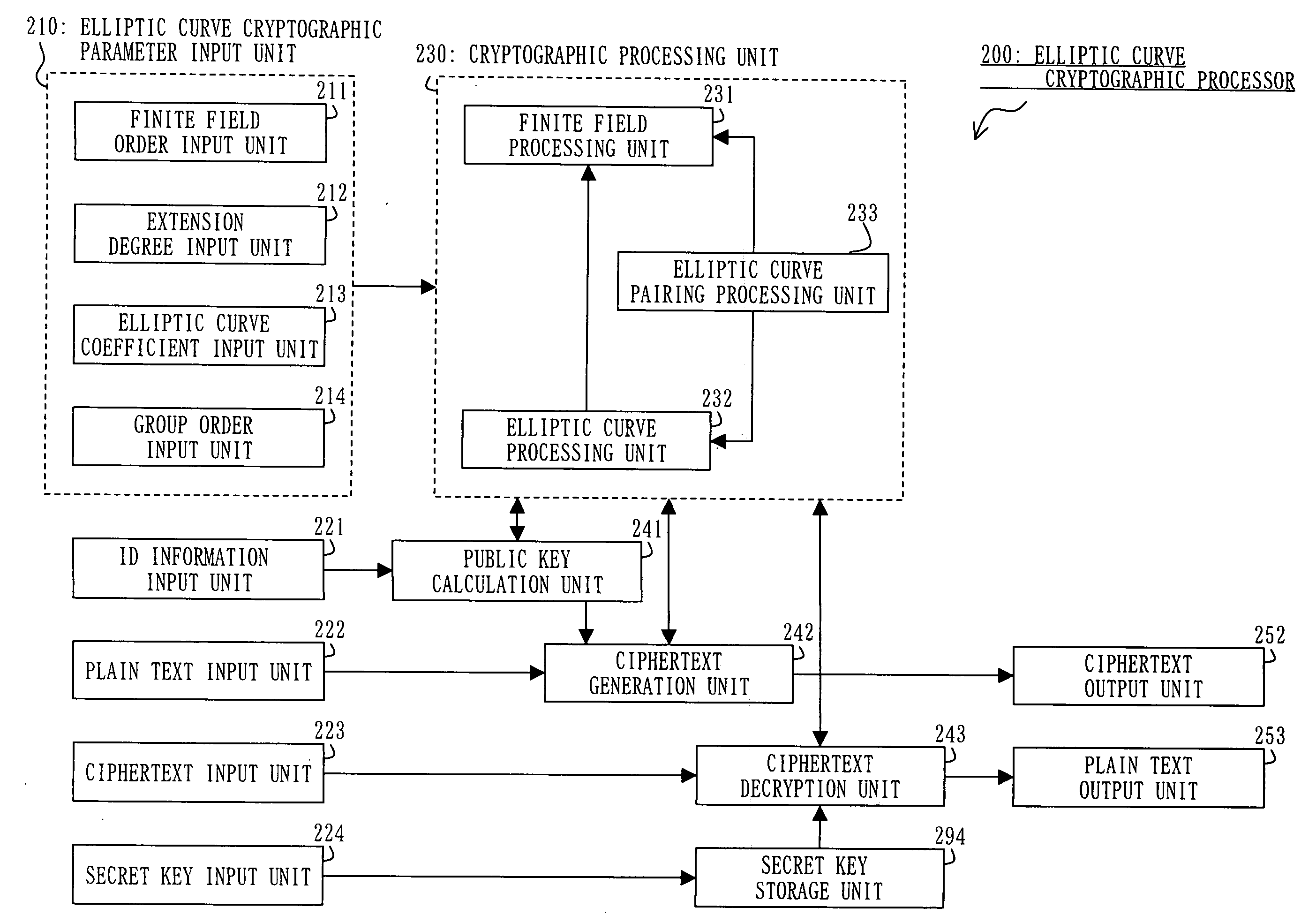
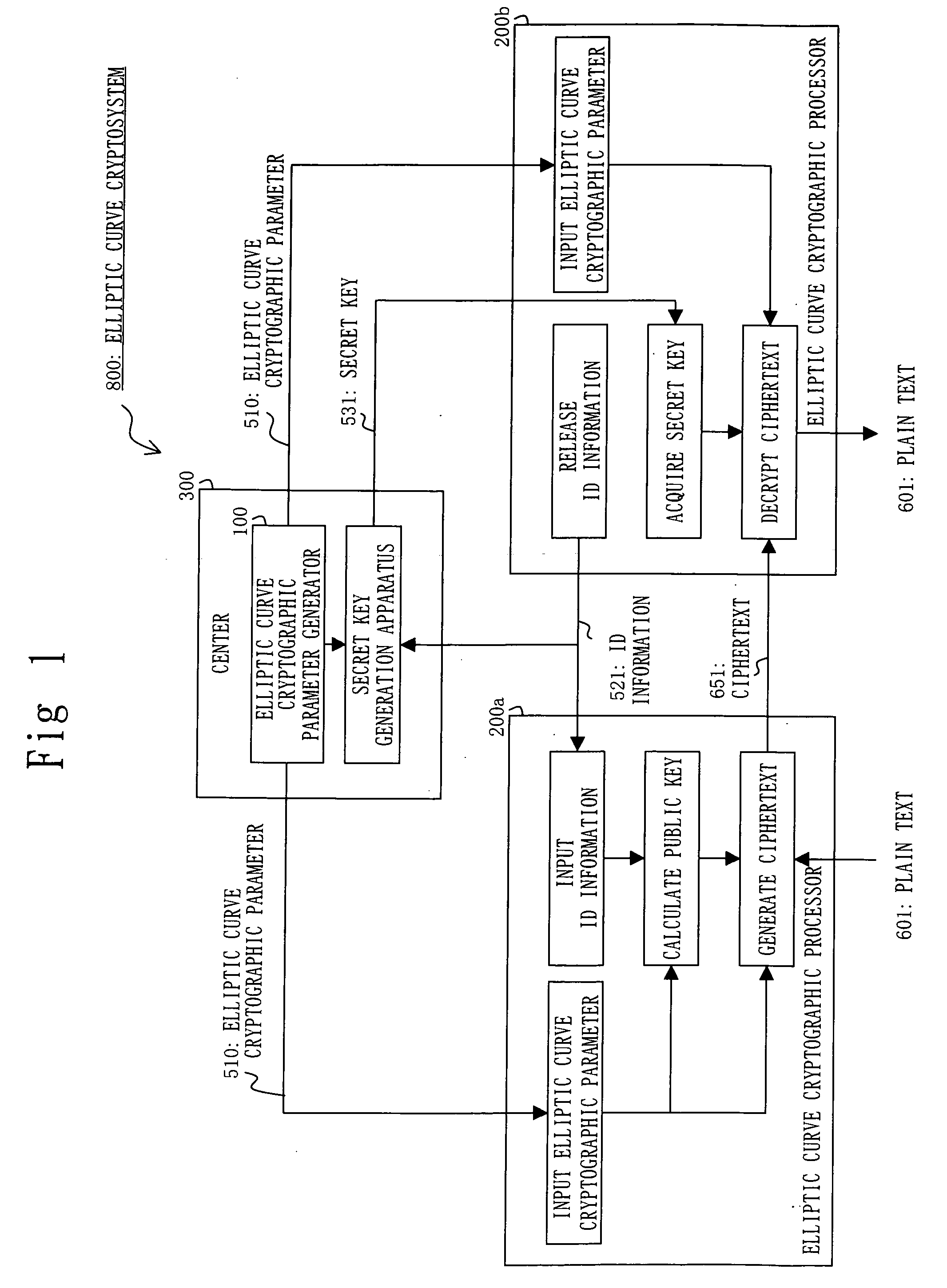
A prime number generation unit 110 generates an integer r having a form suitable for fast elliptic curve pairing computation, by using a processing device (S302 to S303). The prime number generation unit 110 judges whether the integer r is a prime number or not, by using the processing device (S304). When the integer r is a prime number, the prime number generation unit 110 judges whether the prime number r is a group order capable of easily changing the level of security or not, by using the processing device (S305). Thereby, it is possible to generate an elliptic curve parameter which is settable to an elliptic curve cryptographic processor that performs elliptic curve pairing computation using an algorithm capable of performing fast computation even by using a processing device with low computational capacity and which is capable of easily changing the level of security.
Owner:MITSUBISHI ELECTRIC CORP
Hash functions using elliptic curve cryptography
InactiveUS20100166174A1Finite divisionUser identity/authority verificationDigital computer detailsComputer hardwareHash function
The hash functions using elliptic curve cryptography are hash functions that are produced using both an elliptic curve and a twist of the elliptic curve. Hash points are assigned values that either correspond to points on the elliptic curve or to points on the twist, depending upon whether the scalar value of the corresponding message block produces a quadratic residue or a quadratic non-residue when substituted as the x-value into the elliptic curve equation. The corresponding hash point x-coordinates are concatenated to form the hash bit string. The hash points may be doubled, and the hash functions may be applied to multimedia data by applying a media compression method to the message data before computing the hash points.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
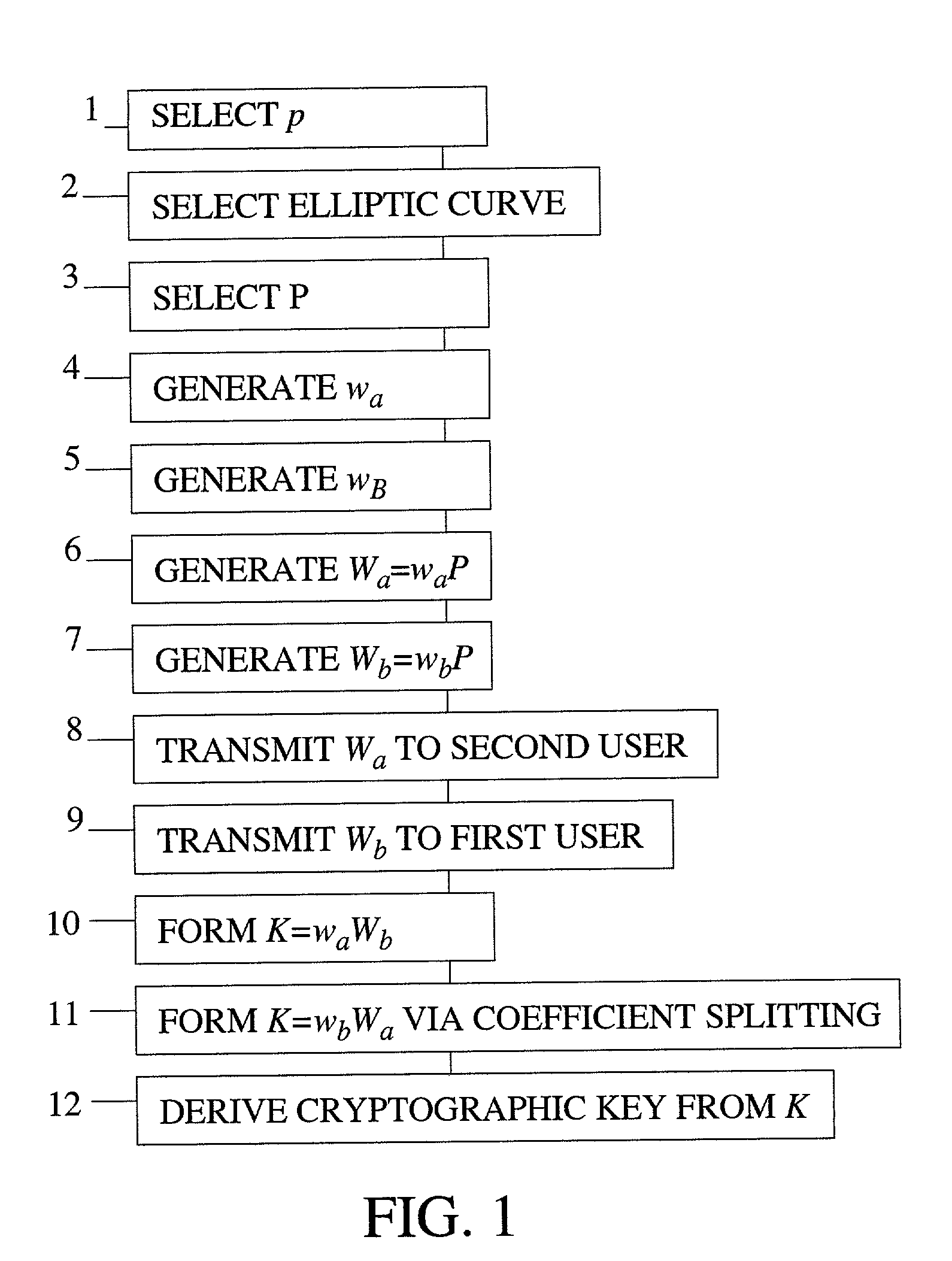
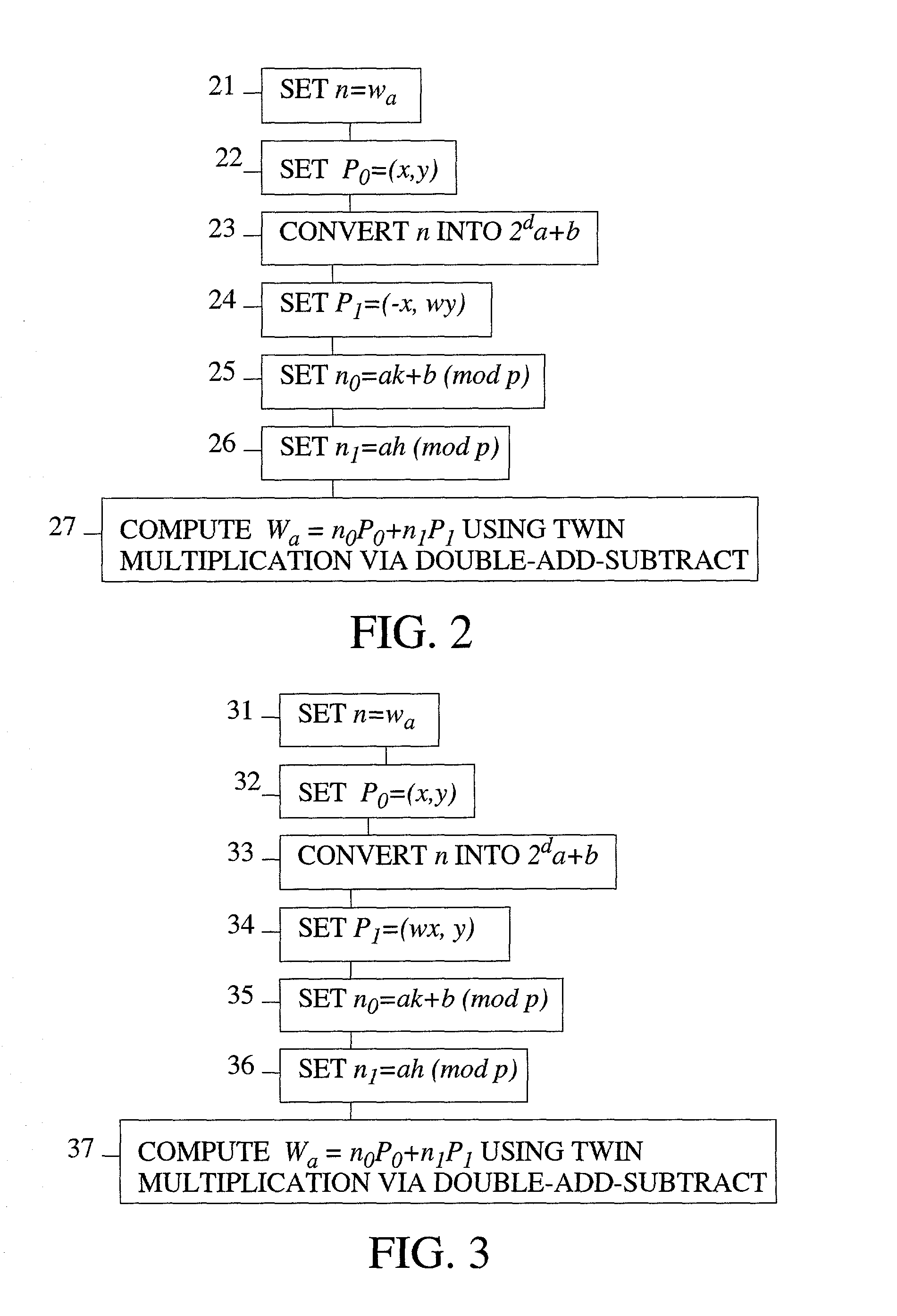
Method of elliptic curve cryptographic key agreement using coefficient splitting
ActiveUS7062044B1Public key for secure communicationSecret communicationComputer securityElliptic curve cryptographic
A method of generating a cryptographic key in an authenticated manner using coefficient splitting. Select a prime number p and an elliptic curve of either a first class or a second class. Select a point P. The first user generates ra, wa, and Ra=raP and Wa=waP via coefficient splitting. The second user generates rb, wb, and Rb=rbP and Wb=wbP via coefficient splitting. After the users have exchanged the points Ra, Wa, Rb, Wb, the first user generates ca, ga, and caWb, and gaRb via coefficient splitting, and the second user generates cb, gb, and cbWa and gbRa via coefficient splitting. Each user then sums the corresponding results to form K and derives the cryptographic key from K in the same user-definable manner. An unauthenticated key exchange method is also presented.
Owner:NATIONAL SECURITY AGENCY
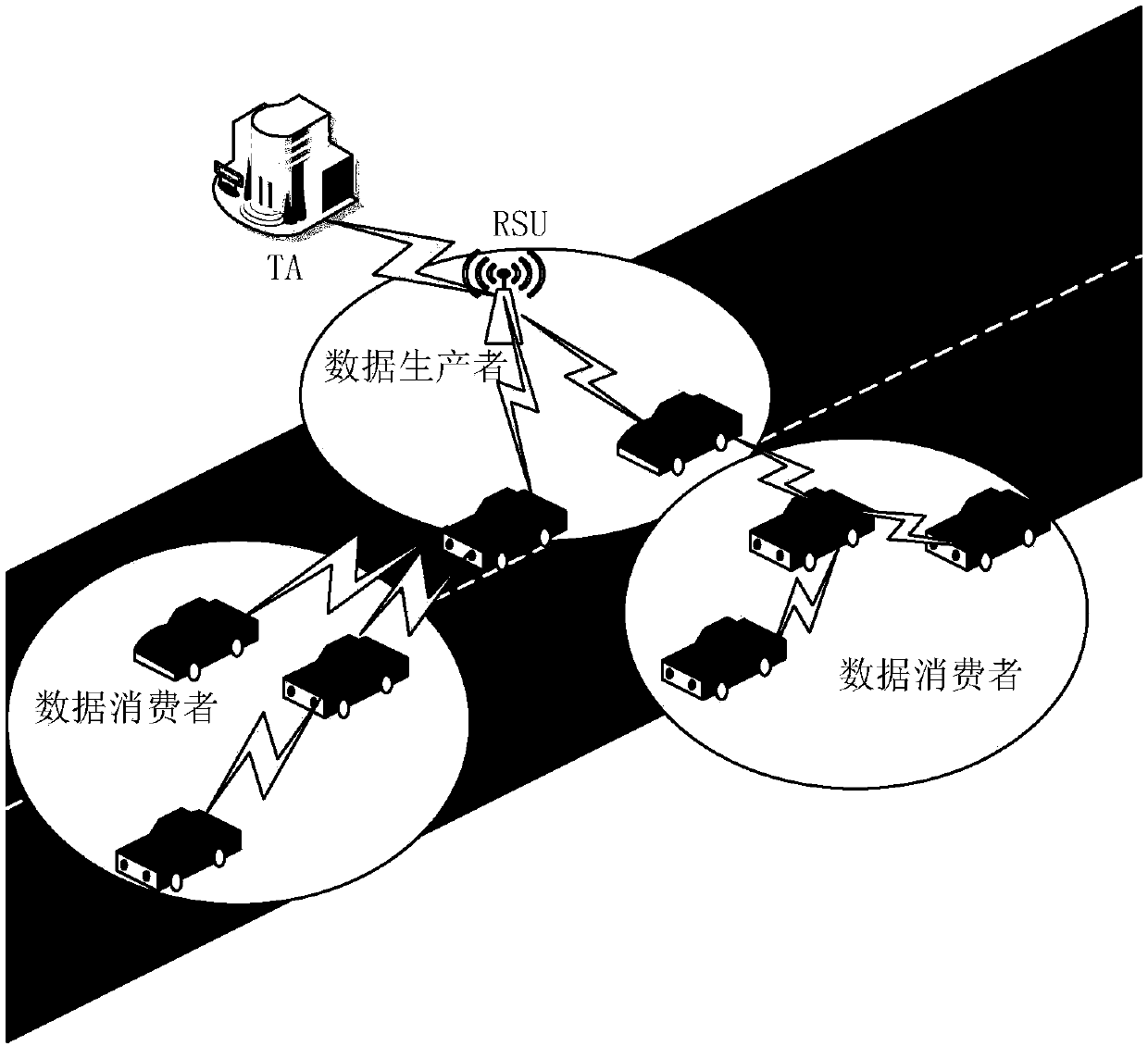
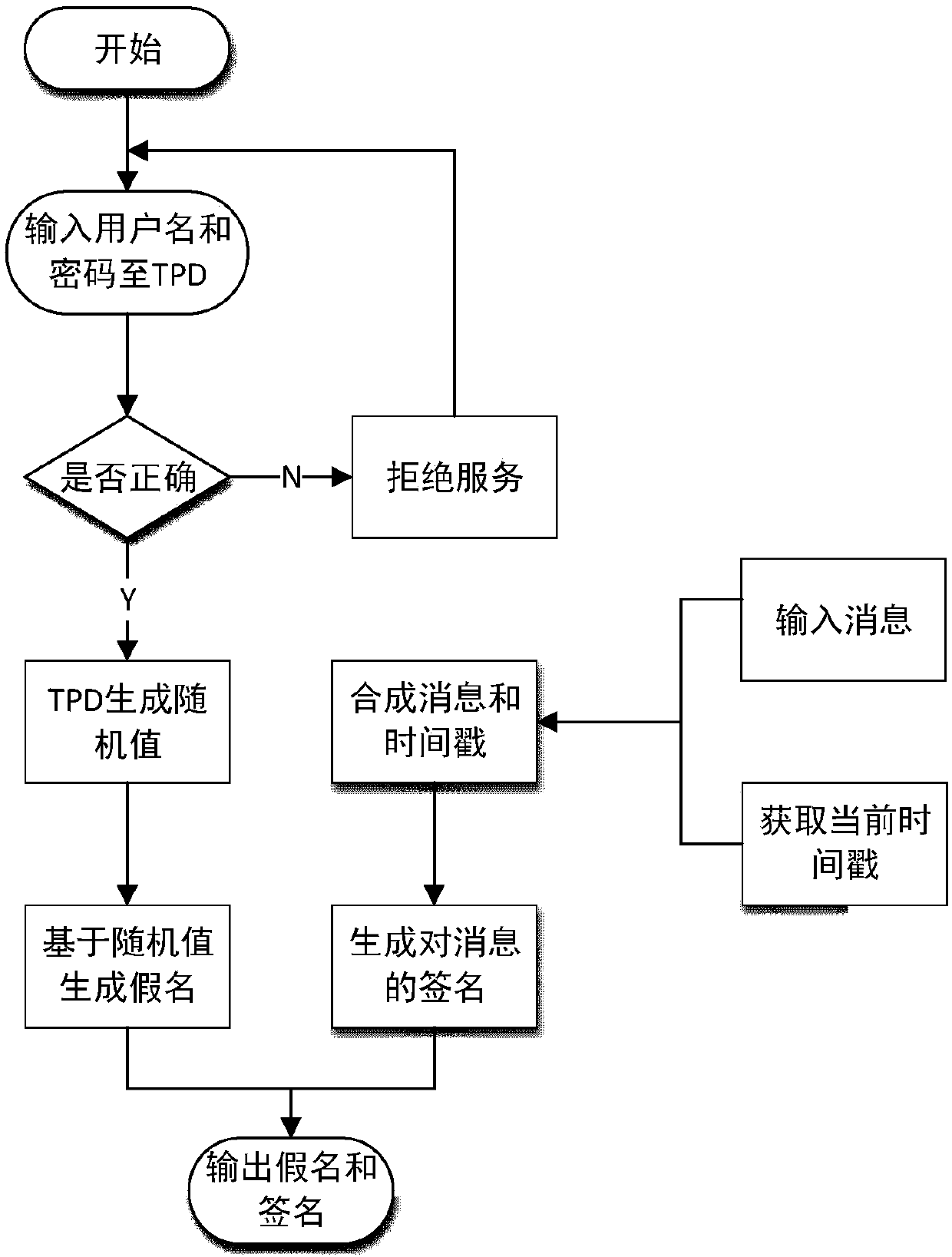
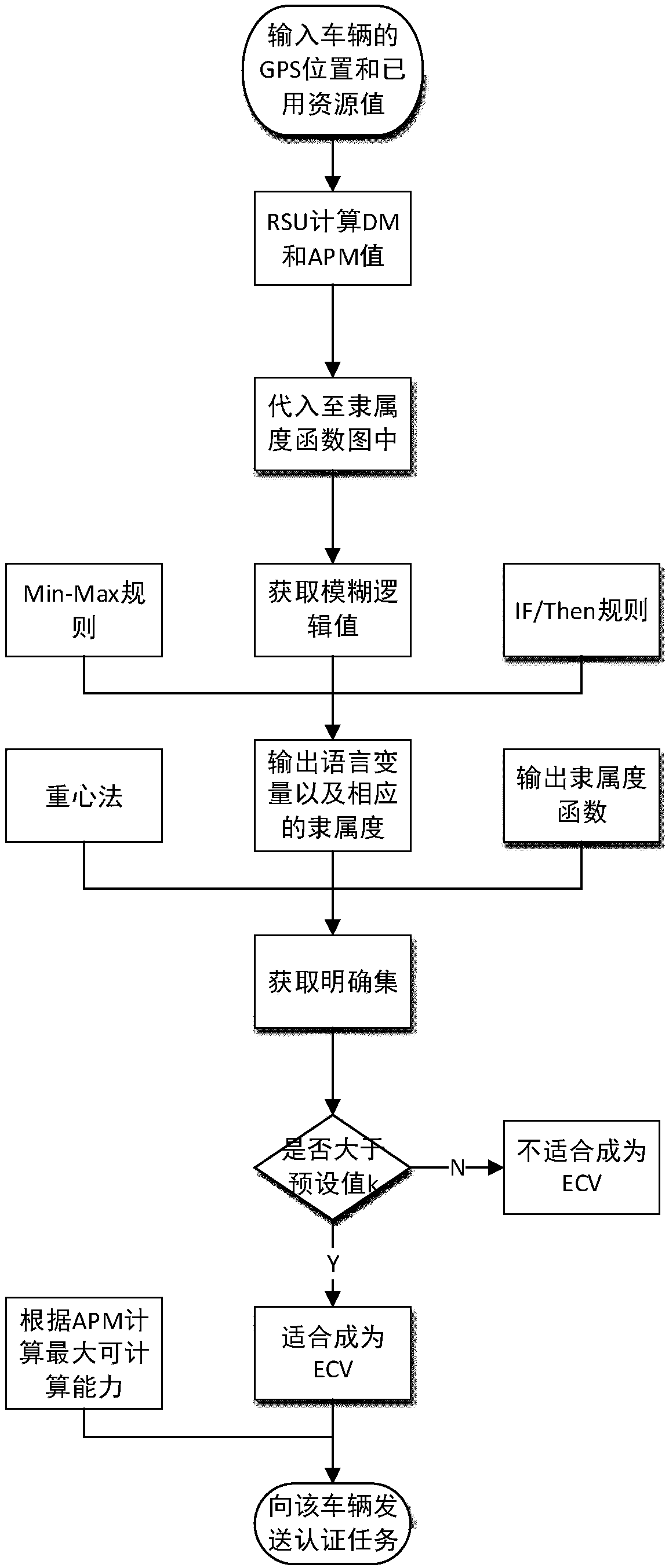
Efficient message authentication method for vehicular ad hoc network based on edge computing
ActiveCN107634837AReduce overheadLow message authentication redundancyKey distribution for secure communicationPublic key for secure communicationLocal optimumEdge computing
The invention discloses an efficient message authentication method for a vehicular ad hoc network based on edge computing, which comprises the steps of system initialization of participating entitiesof the Internet of vehicles, wherein the step comprises two processes such as parameter generation and vehicle pseudonym and signature generation; and (2) message authentication of an RSU (Roadside Unit) and a vehicle, wherein the step comprises four processes such that the RSU elects an edge computing vehicle (ECV), the ECV executes a task, the RSU checks an authentication result of the ECV and vehicle message authentication is performed. The signing portion of the invention adopts an elliptic curve cryptography based operation, thereby enabling the computation and transmission overhead to below; further the ECV is elected according to a fuzzy logic control theory to achieve local optimal election; the ECV is set to help the RSU to achieve quick and accurate message signature authentication; and the RSU reduces the redundant authentication of the whole system to the maximum extent through broadcasting the authentication result, and the operating efficiency of the whole vehicular ad hoc network is improved.
Owner:ANHUI UNIVERSITY
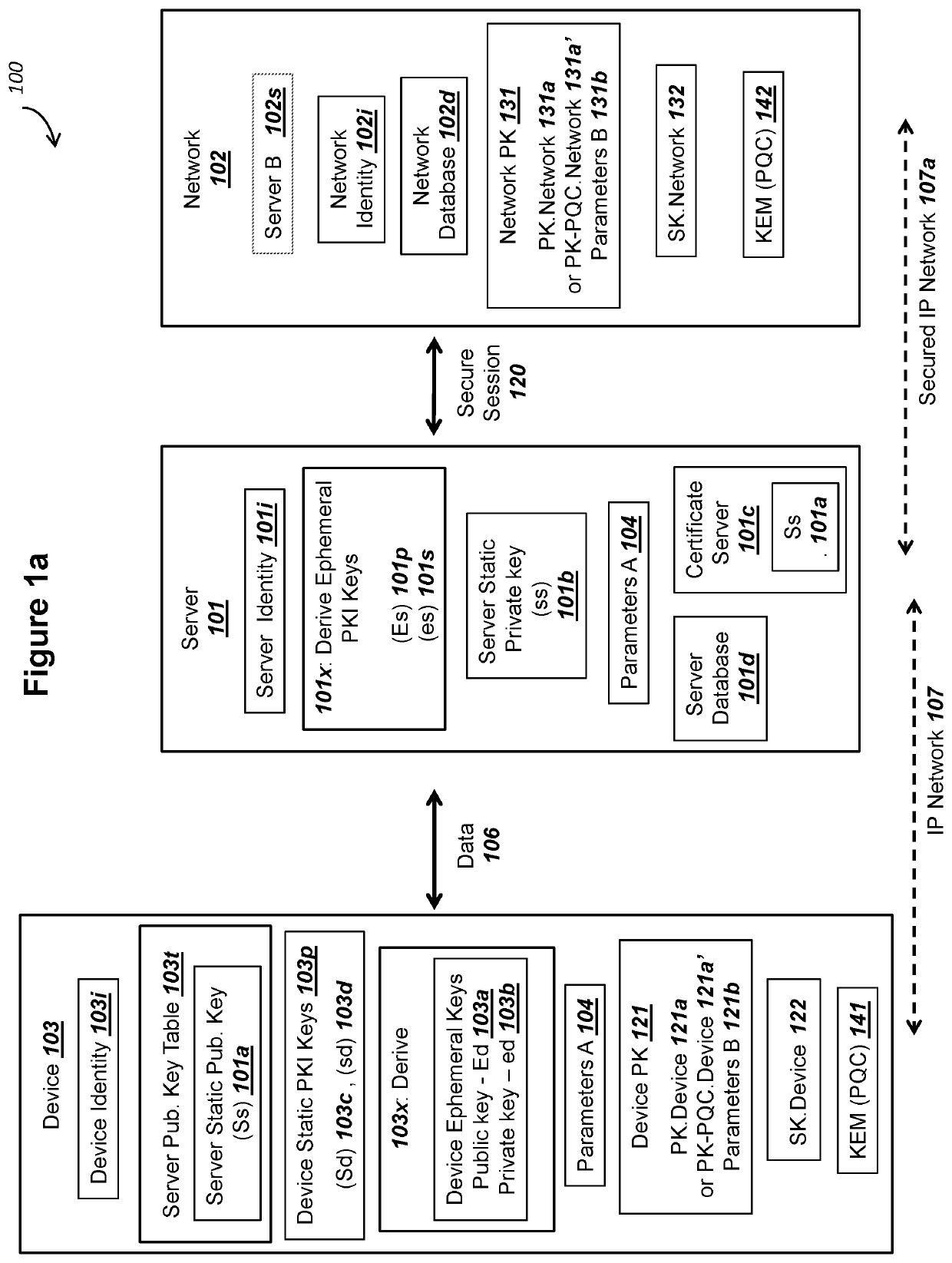
Public key exchange with authenticated ecdhe and security against quantum computers
ActiveUS20200280436A1Solve insufficient capacityQuantum computersKey distribution for secure communicationKey exchangeKey (cryptography)
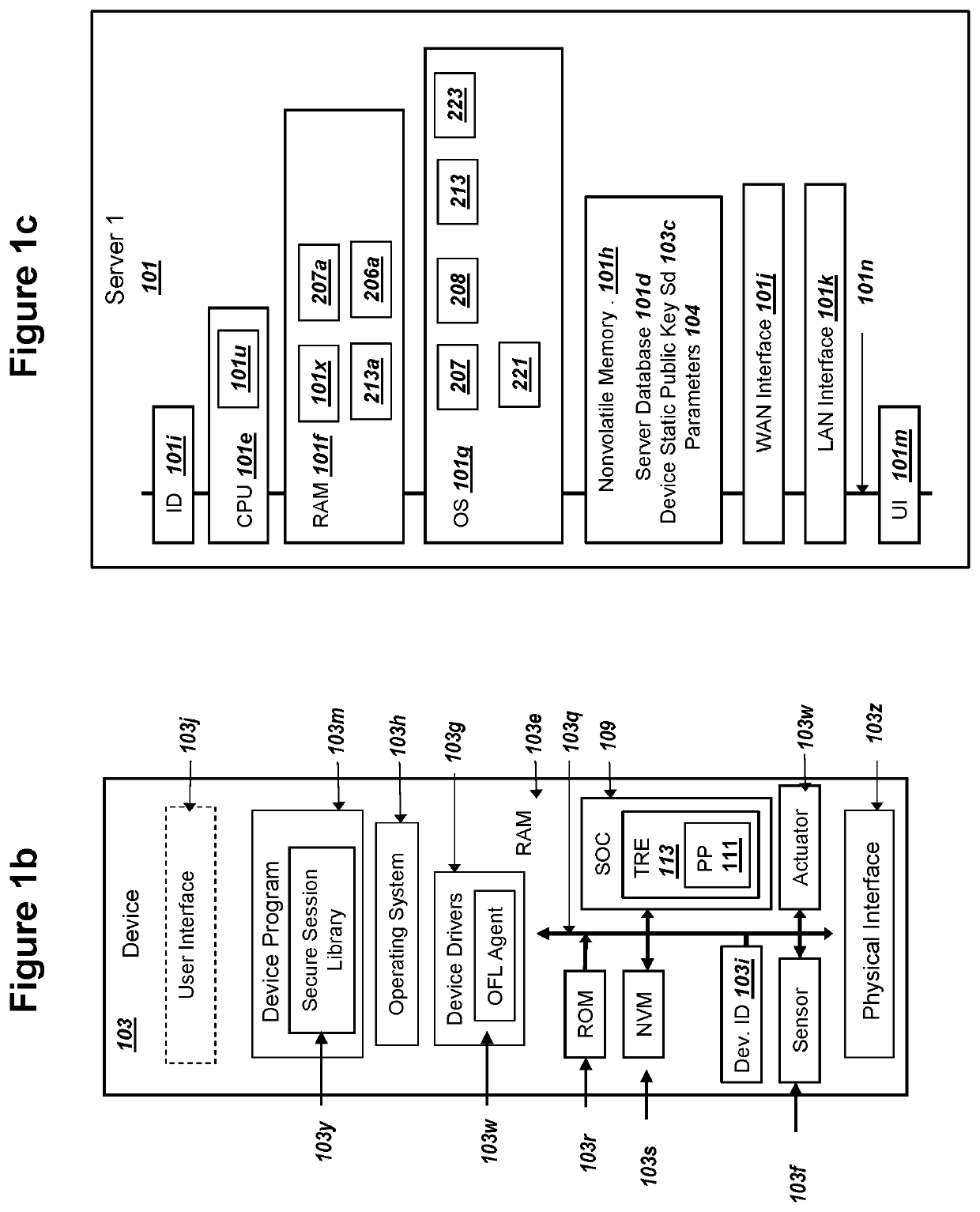
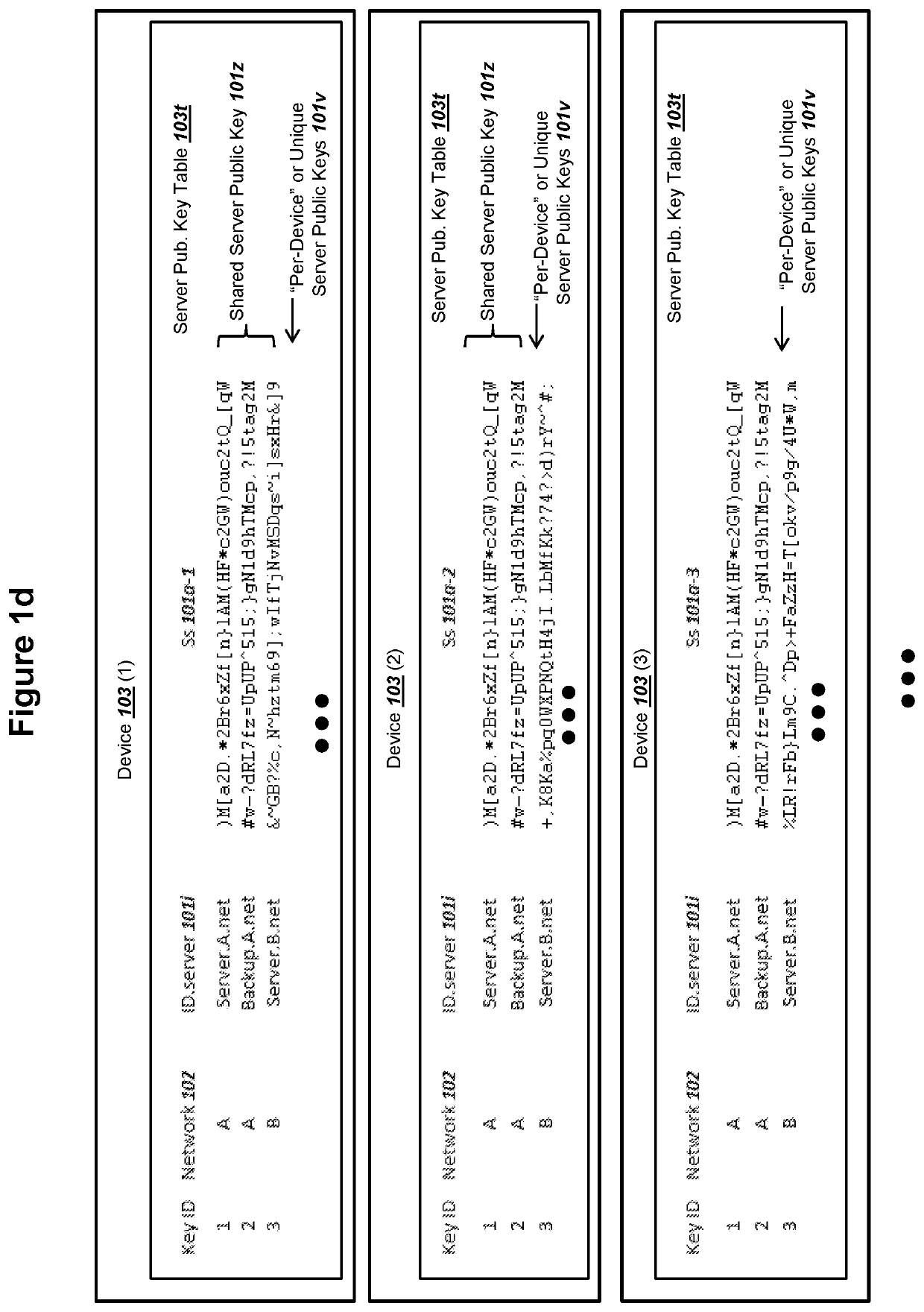
Elliptic Curve Cryptography (ECC) can provide security against quantum computers that could feasibly determine private keys from public keys. A server communicating with a device can store and use PKI keys comprising server private key ss, device public key Sd, and device ephemeral public key Ed. The device can store and use the corresponding PKI keys, such as server public key Ss. The key use can support all of (i) mutual authentication, (ii) forward secrecy, and (iii) shared secret key exchange. The server and the device can conduct an ECDHE key exchange with the PKI keys to mutually derive a symmetric ciphering key K1. The device can encrypt a device public key PK.Device with K1 and send to the server as a first ciphertext. The server can encrypt a server public key PK.Network with at least K1 and send to the device as a second ciphertext.
Owner:IOT & M2M TECH LLC
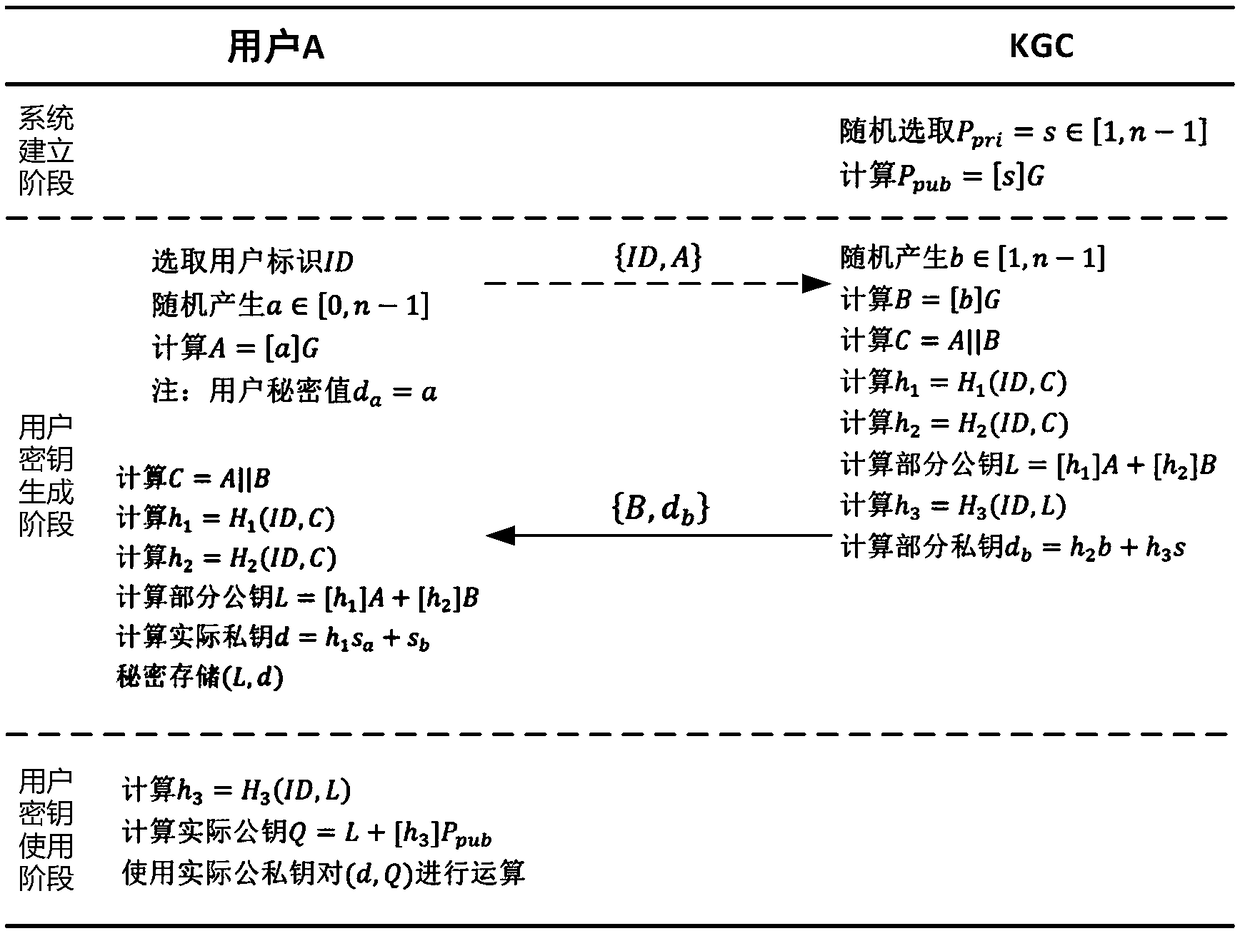
An implementation method of certificateless public key cryptosystem based on elliptic curve
ActiveCN108989053AAvoid managementAvoid using effectsPublic key for secure communicationUser identity/authority verificationPublic key cryptosystemKey generation
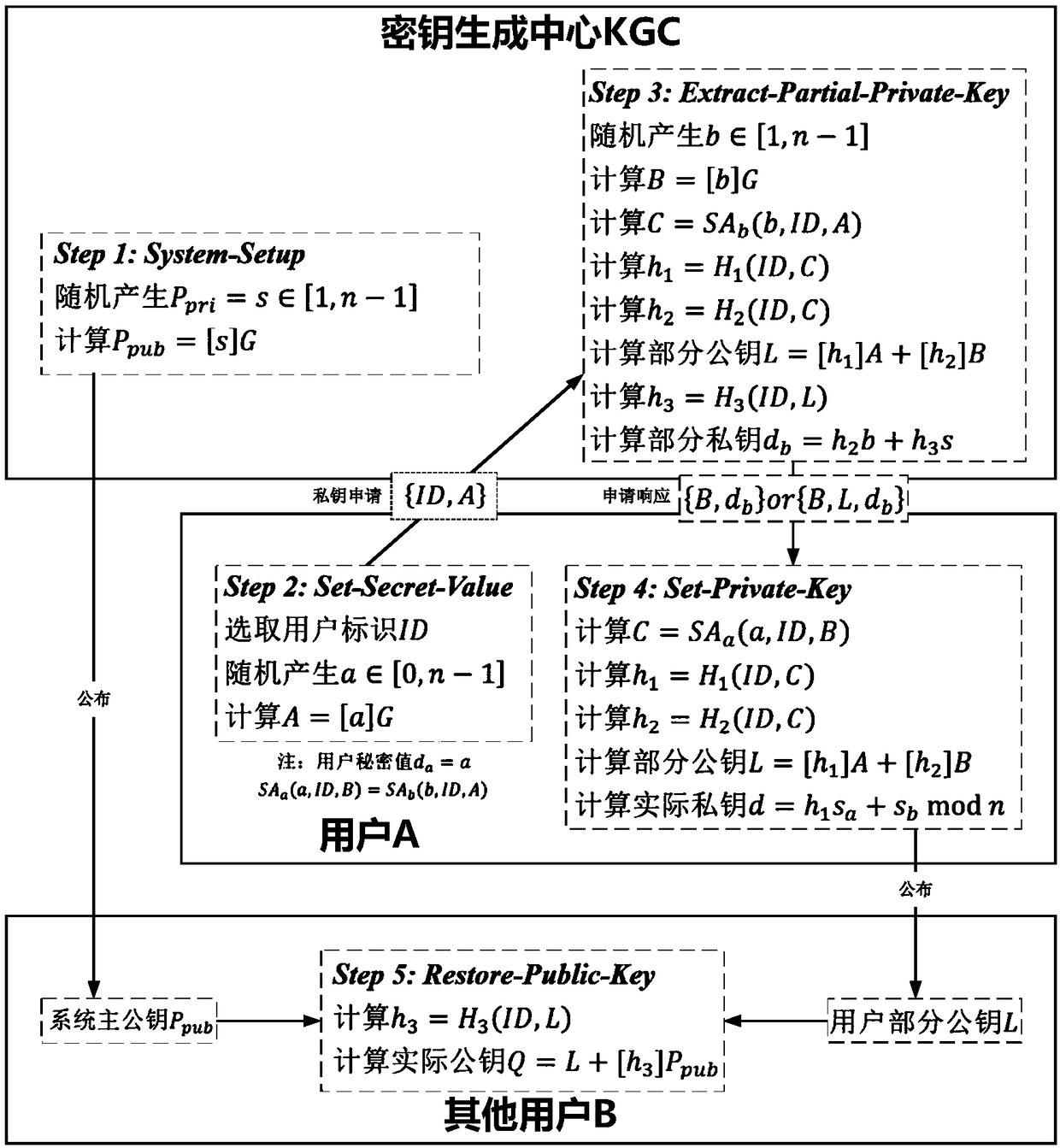
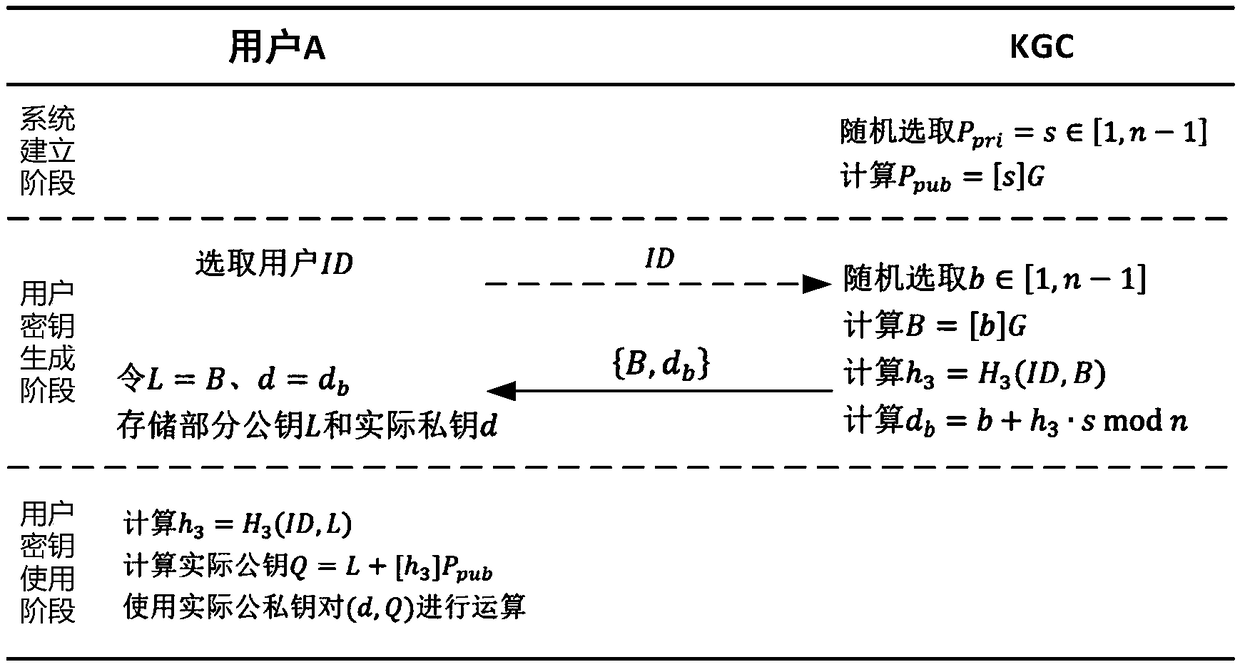
The invention discloses an implementation method of a certificateless public key cryptosystem based on an elliptic curve, which is used for solving the problems of system establishment, user key generation and use under the certificateless cryptosystem. In the present invention, the key generation center determines system parameters and publishes them. Then, the user submits an application to thekey generation center based on the randomly selected secret value, and the key generation center randomly generates a user partial private key based on the system master private key and the application information and returns the user partial private key, and finally the user calculates the actual private key and the partial public key based on the partial private key. In use, other users first get the actual public key based on the user identity and partial public key restoration, and then calculate according to the standard cryptographic algorithm. The invention effectively avoids the use problem of the certificate, can realize the binding of the user identification and the public key, and ensures that only the user can know the private key. The invention has the characteristics of highcomputational efficiency, strong security and the like, and can be applied to various standard elliptic curve cryptographic algorithms without changing the algorithm logic.
Owner:武汉珈港科技有限公司
Elliptic curve-based message authentication code
InactiveUS20100169658A1Finite divisionUser identity/authority verificationElliptic curve discrete logarithm problemComputer hardware
The elliptic curve-based message authentication code is a computational method for improving the security of existing message authentication code (MAC) generating methods through the use of elliptic curve cryptography. Particularly, the message authentication codes and elliptic curve cryptography are based on an elliptic curve discrete logarithm problem, which is well known in mathematics to be a computationally hard problem.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
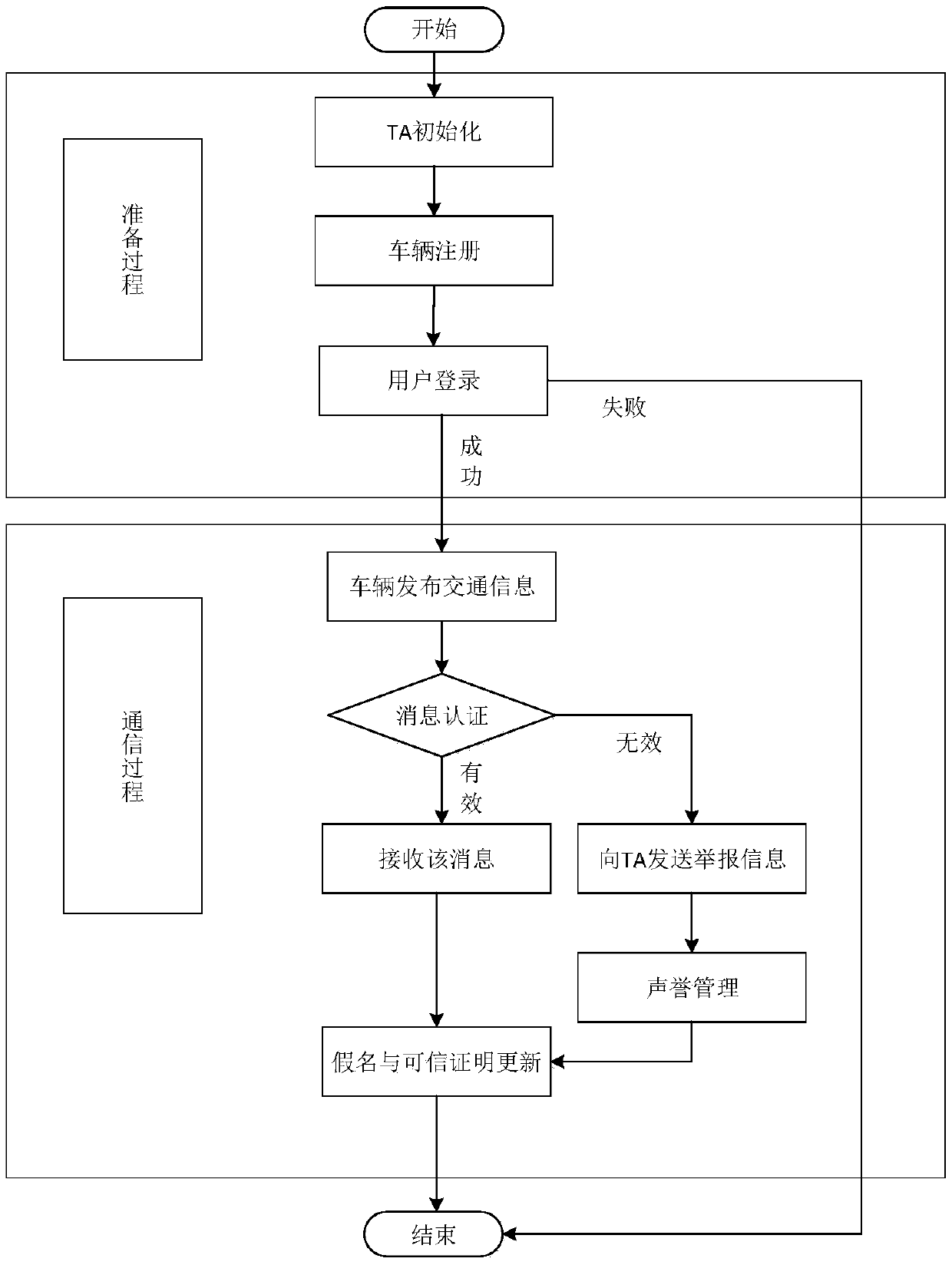
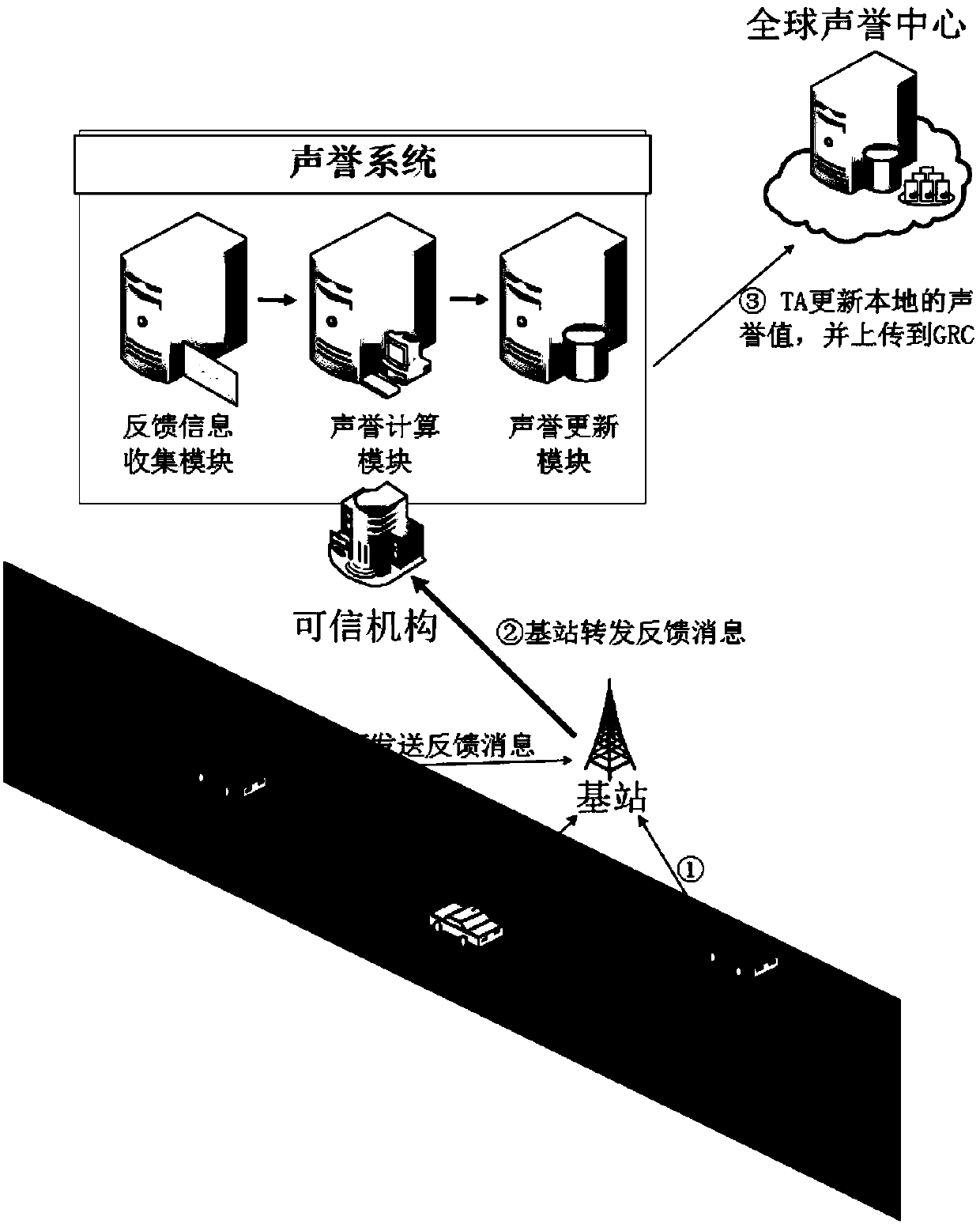
A fast message authentication method for 5G vehicle networking based on reputation system
ActiveCN109005542AImprove reliabilityImprove message authentication efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMessage authentication codeElliptic curve cryptography
The invention discloses a 5G vehicle networking fast message authentication method based on a reputation system, which comprises the steps of TA initialization, vehicle registration, user login, vehicle publishing traffic information, message authentication, reputation management, updating of pseudonym and trustworthiness certification and the like. The invention uses a reputation system to improve the reliability of messages, because vehicles with reputations below the threshold cannot obtain from the TA the trustworthy proof required to participate in the communication, the 5G vehicle networking communication model in the invention is no longer limited to the mandatory assumption that the roadside base station is completely trusted or has been fully deployed, only the 5G base station isneeded to assist in transmitting the message in the vehicle networking, in addition, the signature part in the invention adopts the operation based on the elliptic curve cryptography and supports thebatch authentication of the message, so the calculation is low in transmission cost and the overall message authentication efficiency is higher.
Owner:ANHUI UNIVERSITY
Apparatus for generating elliptic curve cryptographic parameter, apparatus for processing elliptic curve cryptograph, program for generating elliptic curve cryptographic parameter, and program for processing elliptic curve cryptograph
ActiveUS8111826B2Easy to changeDigital data processing detailsPublic key for secure communicationPairing computationComputer science
A prime number generation unit 110 generates an integer r having a form suitable for fast elliptic curve pairing computation, by using a processing device (S302 to S303). The prime number generation unit 110 judges whether the integer r is a prime number or not, by using the processing device (S304). When the integer r is a prime number, the prime number generation unit 110 judges whether the prime number r is a group order capable of easily changing the level of security or not, by using the processing device (S305). Thereby, it is possible to generate an elliptic curve parameter which is settable to an elliptic curve cryptographic processor that performs elliptic curve pairing computation using an algorithm capable of performing fast computation even by using a processing device with low computational capacity and which is capable of easily changing the level of security.
Owner:MITSUBISHI ELECTRIC CORP
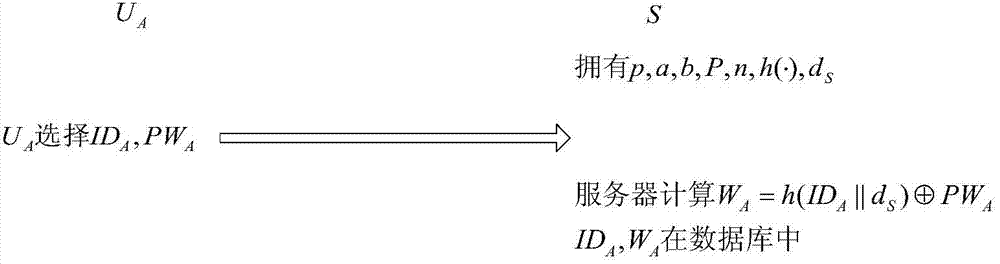
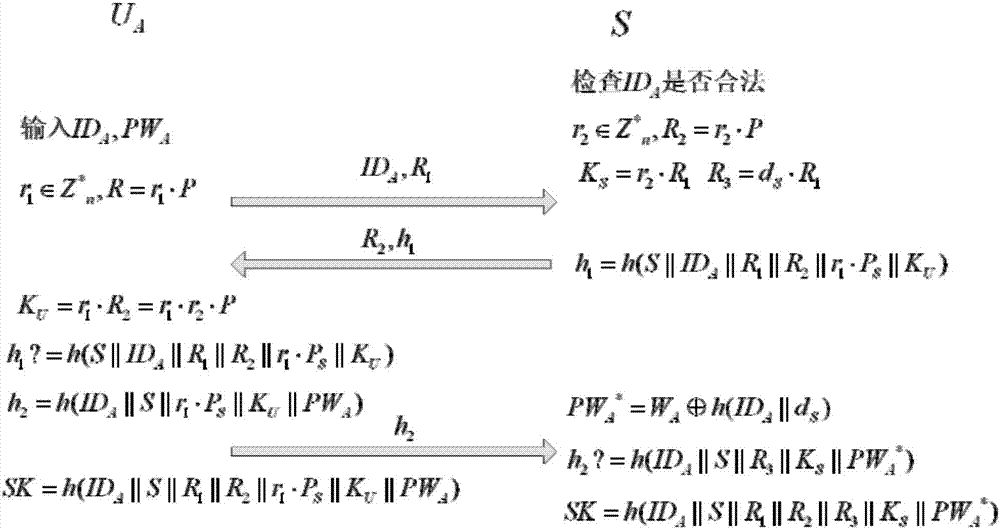
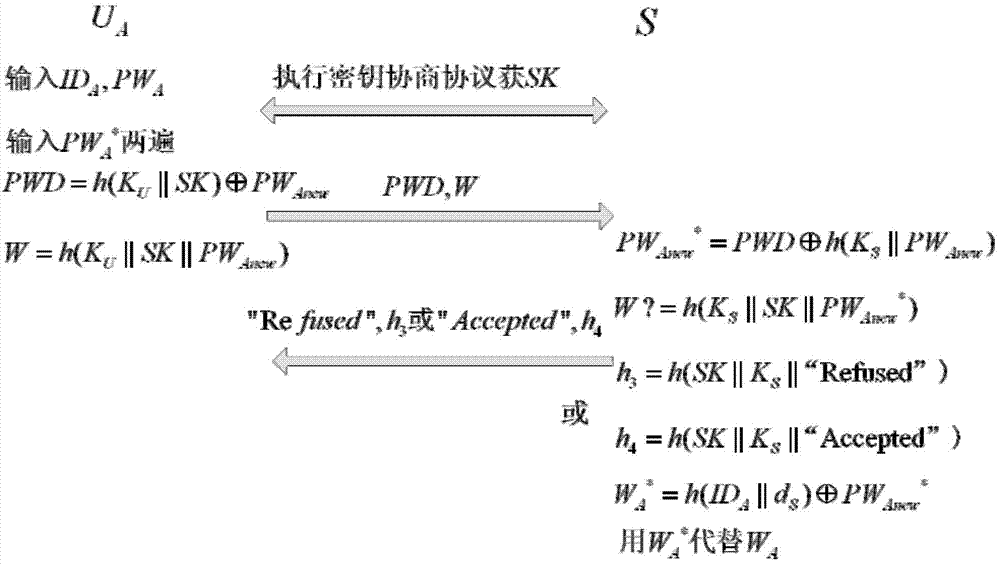
Remote protocol authentication method based on passwords
ActiveCN103905437ADefense against replay attacksResistant to Guessing AttacksUser identity/authority verificationPasswordSession key
The invention relates to a remote protocol authentication method based on passwords. The method is characterized in that the method is achieved on the basis of the elliptic curve cryptographic algorithm, and the method includes the following steps that 1, in a system initialization sub-protocol, a user and a server negotiate elliptic curve cryptosystem parameters which need to be used in subsequent authentication; 2, a new user UA performs registration through a user registration sub-protocol and selects an identity label and a user password PWA; 3, when the user UA wants to login a system to perform session key negotiation, firstly the user UA inputs the identity label IDA and the user password PWA, then double-way authentication is conducted between the user UA and the server and secret keys used in subsequent communication are negotiated through identity authentication and a key negotiation sub-protocol.
Owner:HARBIN ENG UNIV
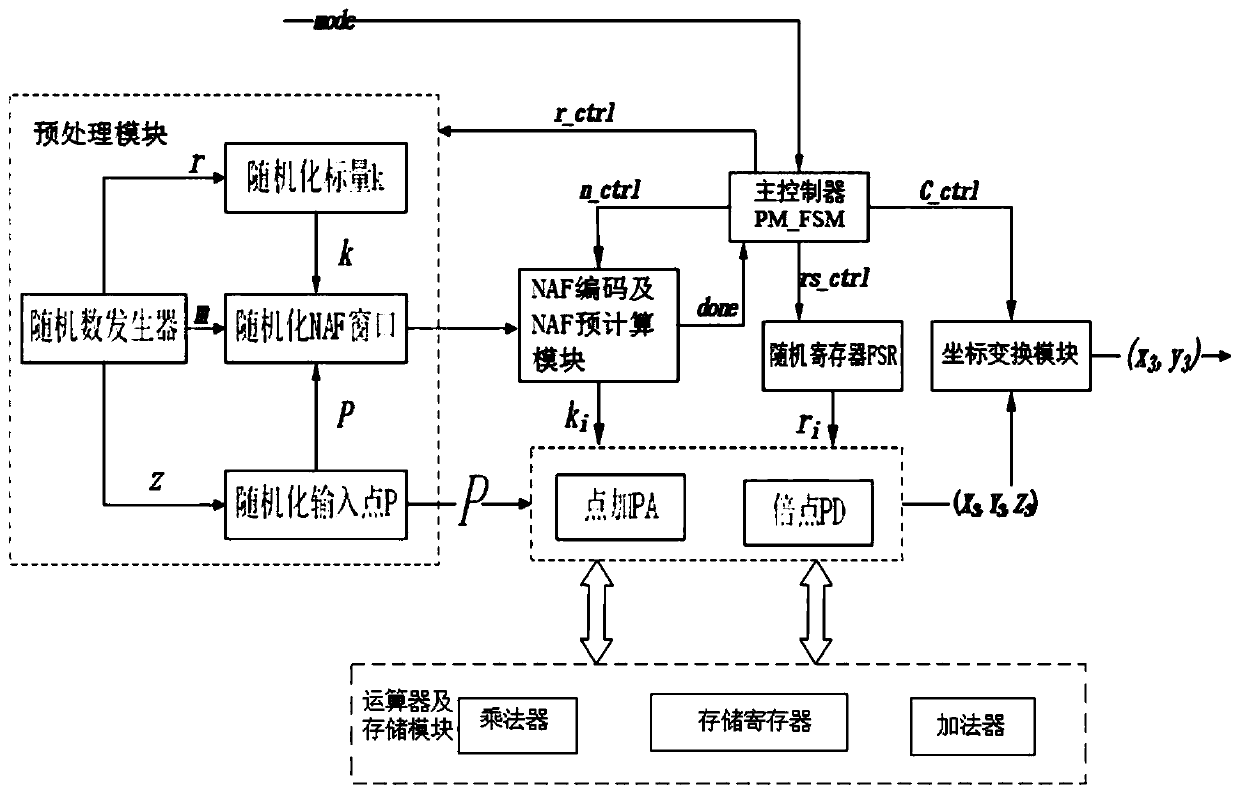
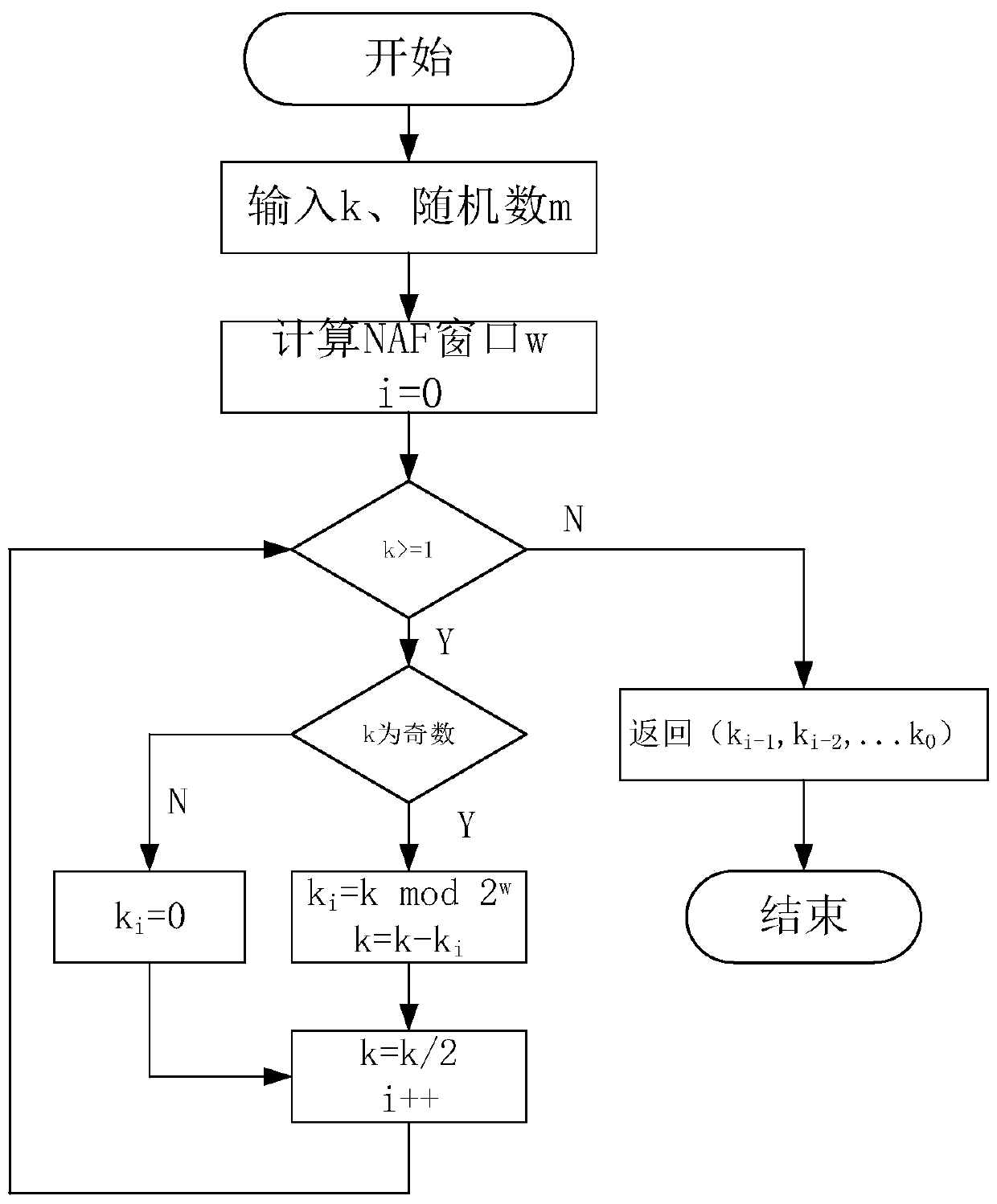
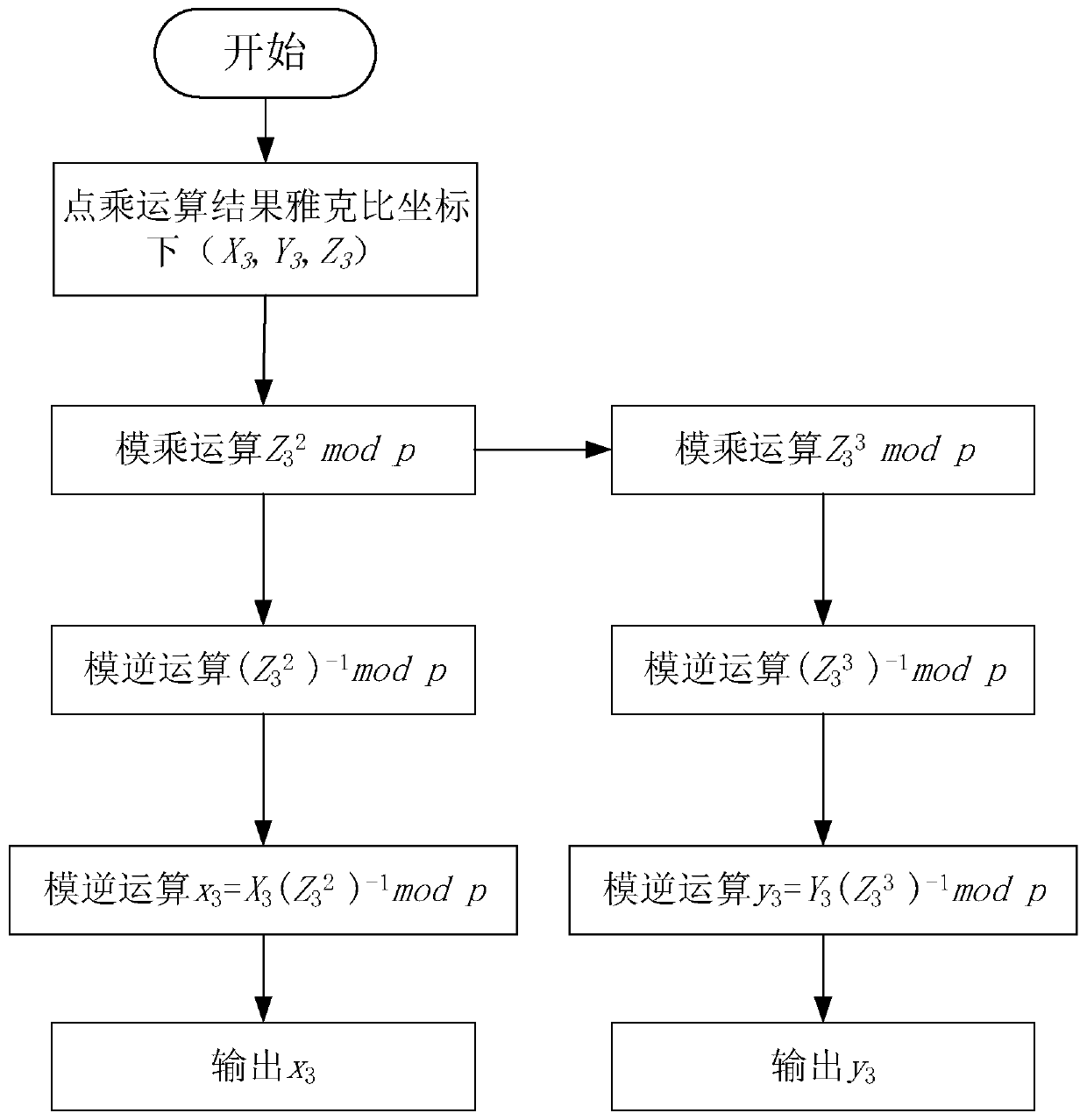
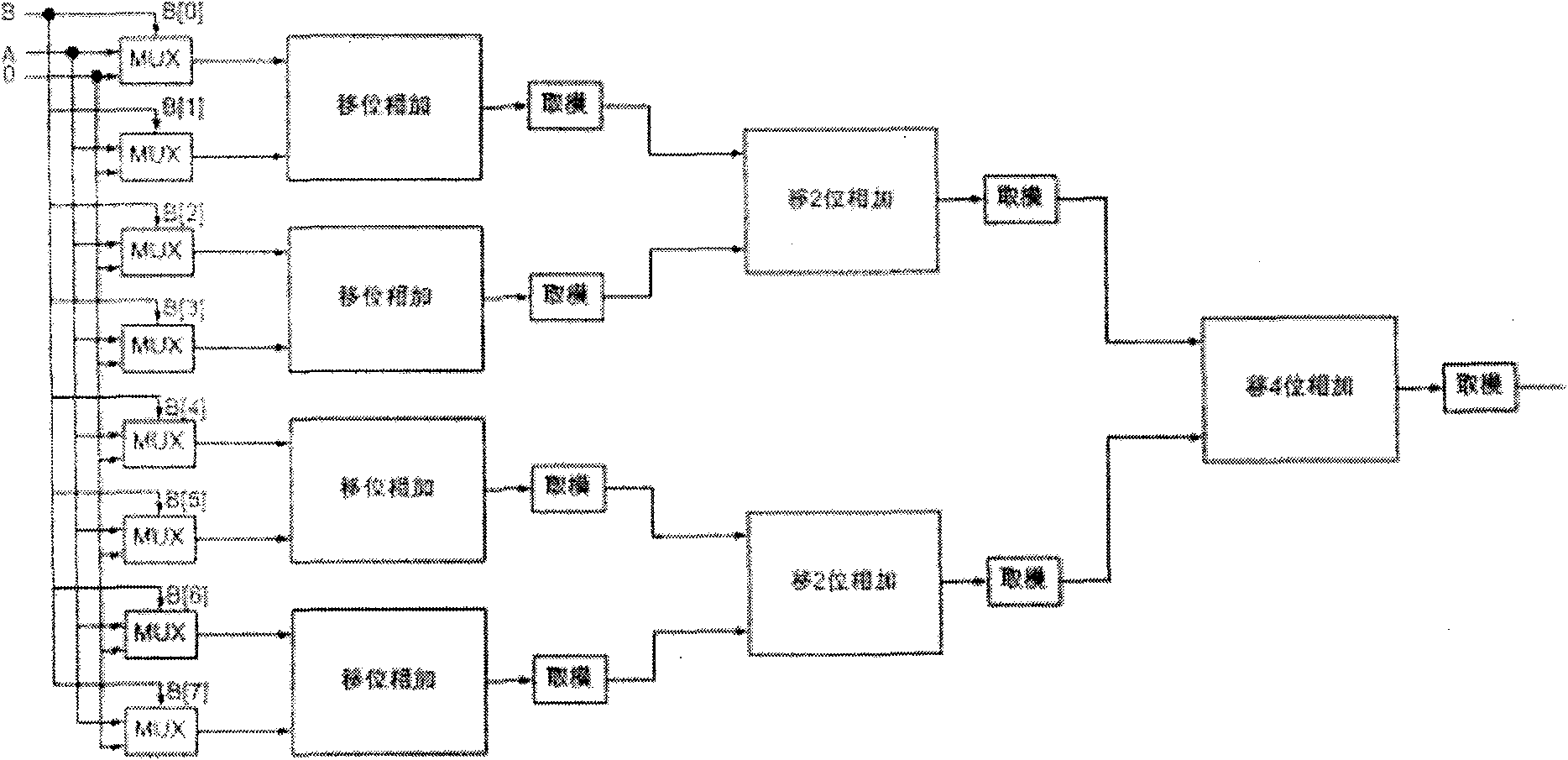
Side channel attack resistant SM2 dot product architecture based on algorithm layer and operation method thereof
ActiveCN110611559AImprove securityImprove resource utilizationPublic key for secure communicationCryptographic attack countermeasuresShift registerResource utilization
The invention discloses a side channel attack resistant SM2 dot product architecture based on an algorithm layer and an operation method thereof, and the scalar value of each dot product operation israndomized by randomizing an NAF window value, so that base point coordinates participated in each calculation are different to resist differential power consumption analysis attacks; through introducing a random shift register, redundant operation is added in a point addition and multiple point iteration process; therefore, the relation between the point doubling point operation times and the secret key is eliminated, simple power consumption analysis SPA, differential power consumption analysis DPA, high-order differential power consumption attack HO _ DPA and template attack are resisted, and pseudo operation operation is introduced into point doubling and point doubling, so that the purpose of balancing power consumption is achieved. According to the method, the problem that an existing SM2 point multiplication algorithm cannot effectively defend against various side channel attacks is solved, higher safety is achieved, other cryptographic operations under an elliptic curve cryptographic system are considered, and the resource utilization rate is increased.
Owner:GUANGDONG UNIV OF TECH
High-performance superscalar elliptic curve cryptographic processor chip
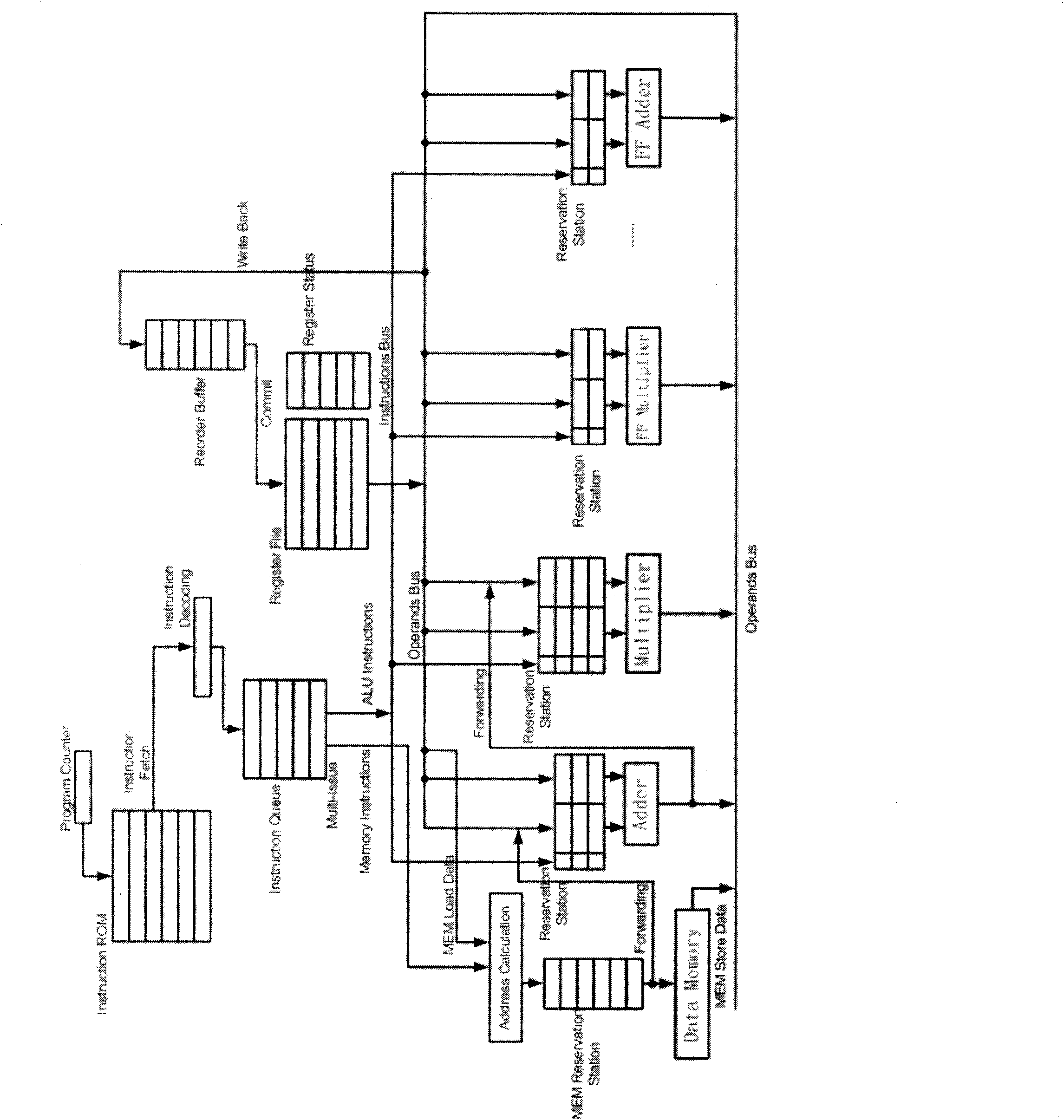
ActiveCN102682232AFast operationEasy programmingPlatform integrity maintainanceComputer hardwareFinite field arithmetic
The invention designs a high-performance superscalar elliptic curve cryptographic processor chip shown as in the figure and relates to the technical fields of information security, encryption and decryption and chips. The chip designed by the invnetion adopts the modern processor superscalar technology,fully utilizes an instruction set to double the operational performance; a high-speed finite field multiplier greatly improves the computational efficiency, and properly solves the performance bottleneck of an elliptic curve cryptographic processor; the instruction set including the finite field arithmetic operation supported by the processor not only ensures that an elliptical curve cryptographic algorithm is more convenient to realize, but also makes necessary preparation for the future standardization; and the chip has a wide application prospect in the fields requiring information security, such as finance, communication and national defense.
Owner:赛芯半导体技术(北京)有限公司
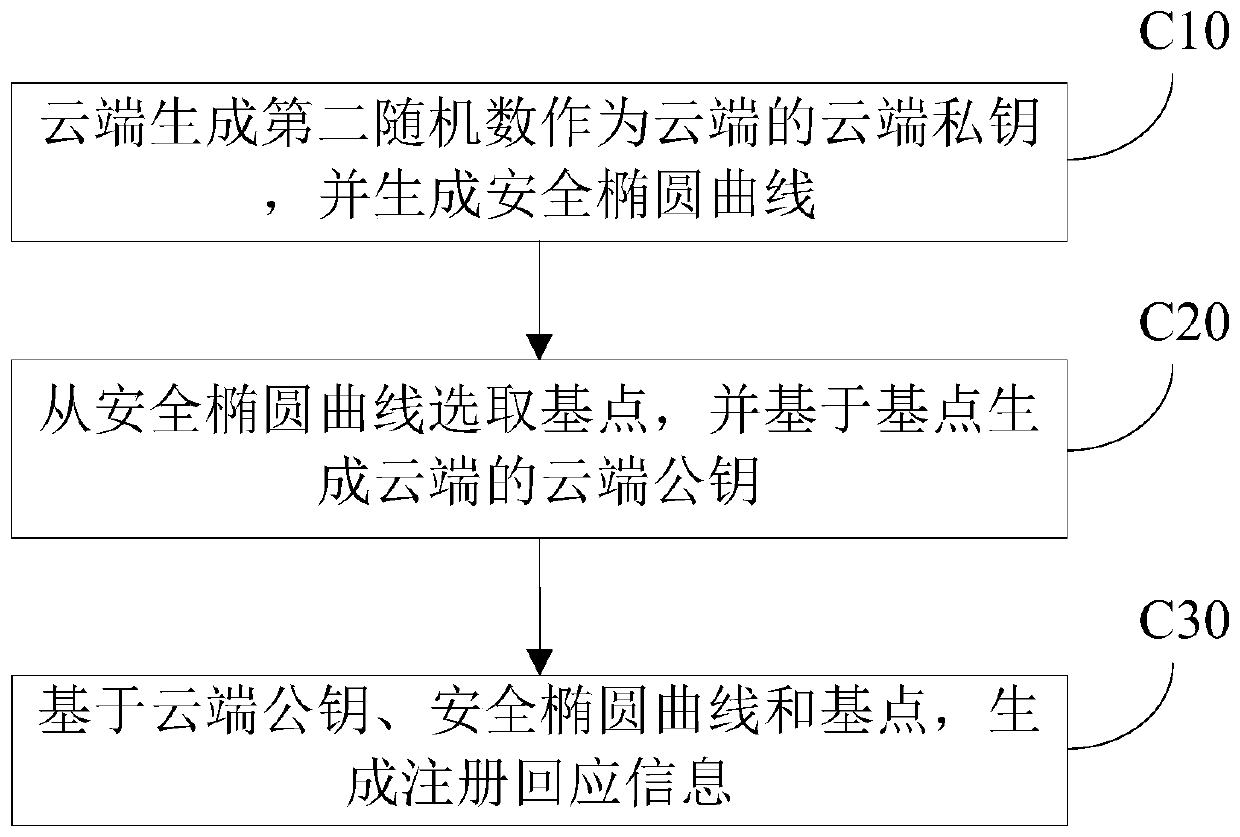
Data security authentication method between cloud and edge node
ActiveCN111294352ASmall sizeSmall system parametersKey distribution for secure communicationPublic key for secure communicationKey sizeTimestamp
The invention provides a data security authentication method between a cloud and an edge node, and the method provides a bidirectional identity authentication protocol between the edge node and the cloud, can guarantee the authenticity and effectiveness of the identities of the cloud and the edge node, prevents malicious attacks from permeating into a core network, and greatly guarantees the industrial Internet security. According to the method, an elliptic curve cryptographic algorithm is introduced to encrypt key data in an authentication process; the algorithm key size, the system parameters and the storage space are relatively small; operation speed is high, the highest safety intensity per bit is realized; the method is suitable for an authentication environment of edge computing nodes with limited computing resources and storage resources. According to the method, the data plaintext transmission leakage risk is avoided, the replay attack is avoided through the timestamp, the hashiterative operation of the one-time password authentication protocol is simplified, compared with the original authentication protocol, the security is higher, the operation efficiency is also improved, and the authentication security requirement can be met under the environment that the edge node resources are limited.
Owner:国家工业信息安全发展研究中心
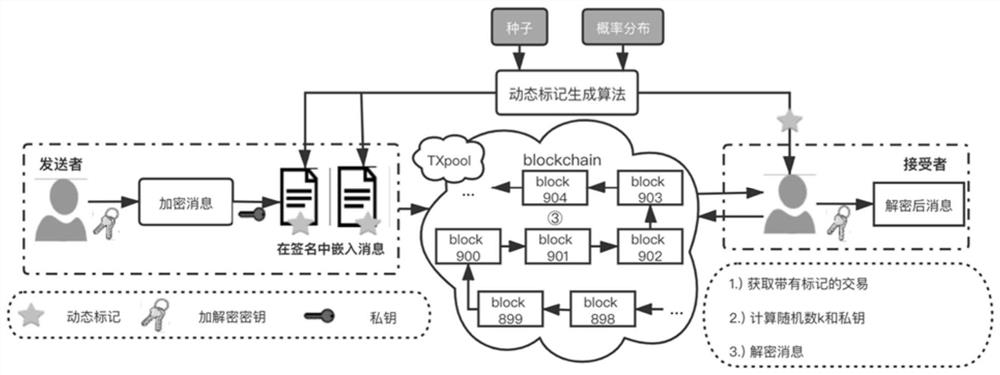
Block chain hidden information transmission method and system based on dynamic marking
PendingCN112070496ATamper resistantNo changes involvedDigital data protectionPayment protocolsKey (cryptography)Algorithm
The invention relates to a block chain hidden information transmission method and system based on dynamic marking. The method comprises the following steps: counting data true probability distributionof an OP_RETURN field of a block chain protocol; generating a dynamic mark according to the negotiated seed and the data real probability distribution of the OP_RETURN field; and enabling the sendernode to fill the dynamic marks into the OP_RETURN fields of the two transactions, performing digital signature by adopting an elliptic curve cryptographic algorithm, and sending the two signed transactions to the block chain; enabling the receiver node to identify the two transactions according to the dynamic marks, performing elliptic curve cryptography algorithm random number leakage attack on digital signatures of the two transactions, calculating used random factors, deducing a private key, namely an encoded encrypted message, decoding the encrypted message and decrypting the encrypted message by using a secret key negotiated with the sender node. According to the invention, the undetectability and tracking resistance of the channel can be realized, the strong robustness is satisfied,and the risk of user privacy exposure is greatly reduced.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
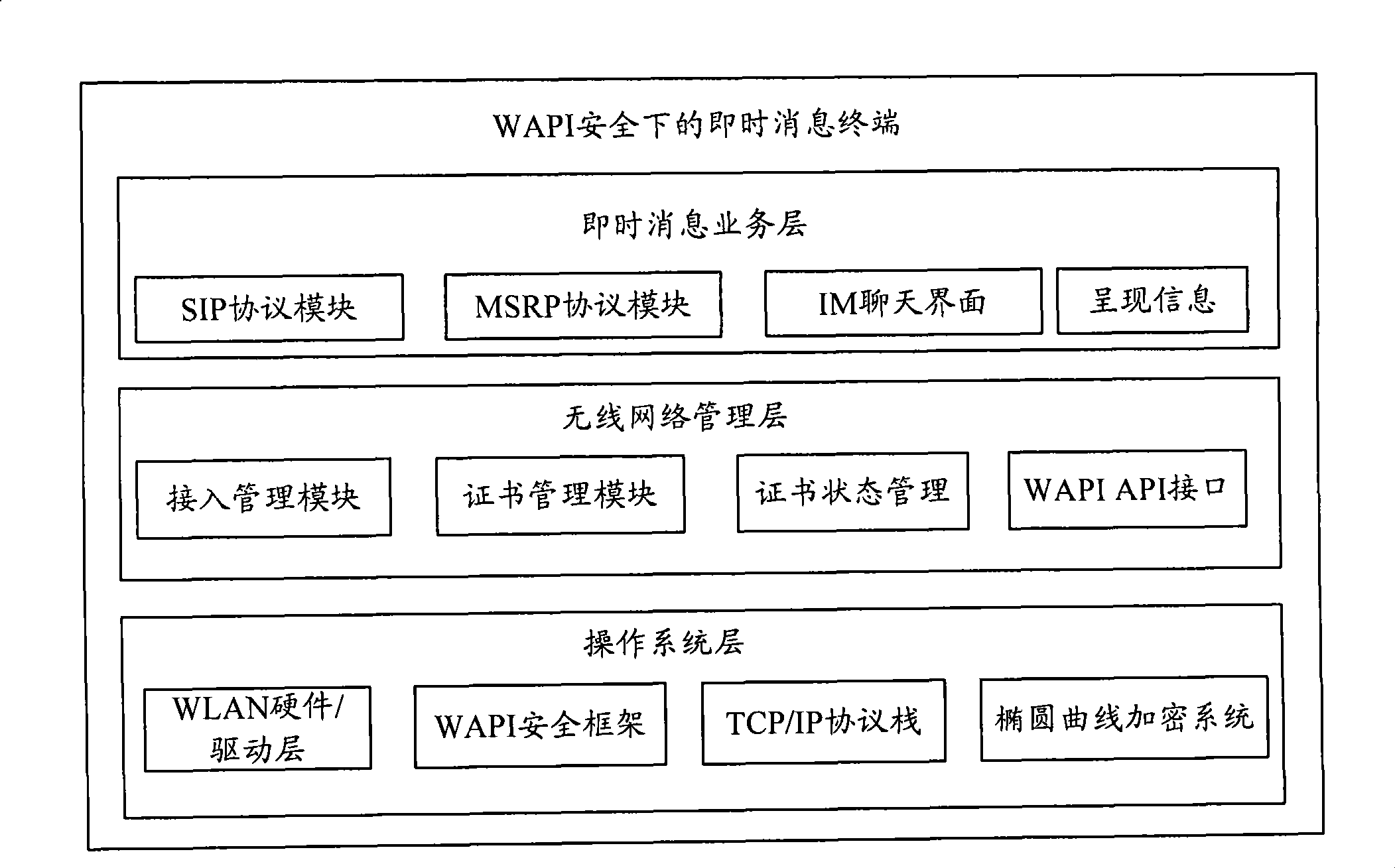
Instant message transmitting method, system and WAPI terminal
The invention discloses a transmission method, a system and a WAPI terminal for instant messages; wherein the method comprises: after a first WAPI terminal and a second WAPI terminal are accessed to an IMS core network, the first WAPI terminal carries out Hash operation to the sent instant message to get a first operation result; the first WAPI terminal uses a private key and elliptic curve cryptographic algorithm to encrypt the first operation result to obtain a second operation result; the first WAPI terminal sends the unencrypted instant messages and the second operation result to the second WAPI terminal. The adoption of the invention can provide an anti-tamper, non-repudiation and safe instant message communication mechanism.
Owner:ZTE CORP
Method for generic-point parallel elliptic curve scalar multiplication
InactiveUS20140105381A1Increases speed and efficiencySpeed up scalar multiplicationDigital data processing detailsSecret communicationEllipseParallel computing
The method for generic-point parallel elliptic curve scalar multiplication replaces the pre-computation overhead of conventional elliptic curve scalar multiplication by post-computations that can be parallelized. This greatly increases the speed and efficiency of scalar multiplication performed in elliptic curve cryptography. According to the method, when scalar multiplication is required, the scalar integer is partitioned into a plurality of partitions, and calculations in each partition are performed simultaneously or in parallel on separate processors using conventional binary protocols. The bit size of each partition is adjusted to balance the load between the processors, i.e., so that each processor performs substantially the same number of point operations. The resulting calculations from each partition are accumulated or summed to produce the point that is the product of the scalar multiplication.
Owner:UMM AL QURA UNIVERISTY +1
Block chain key recovery method and device
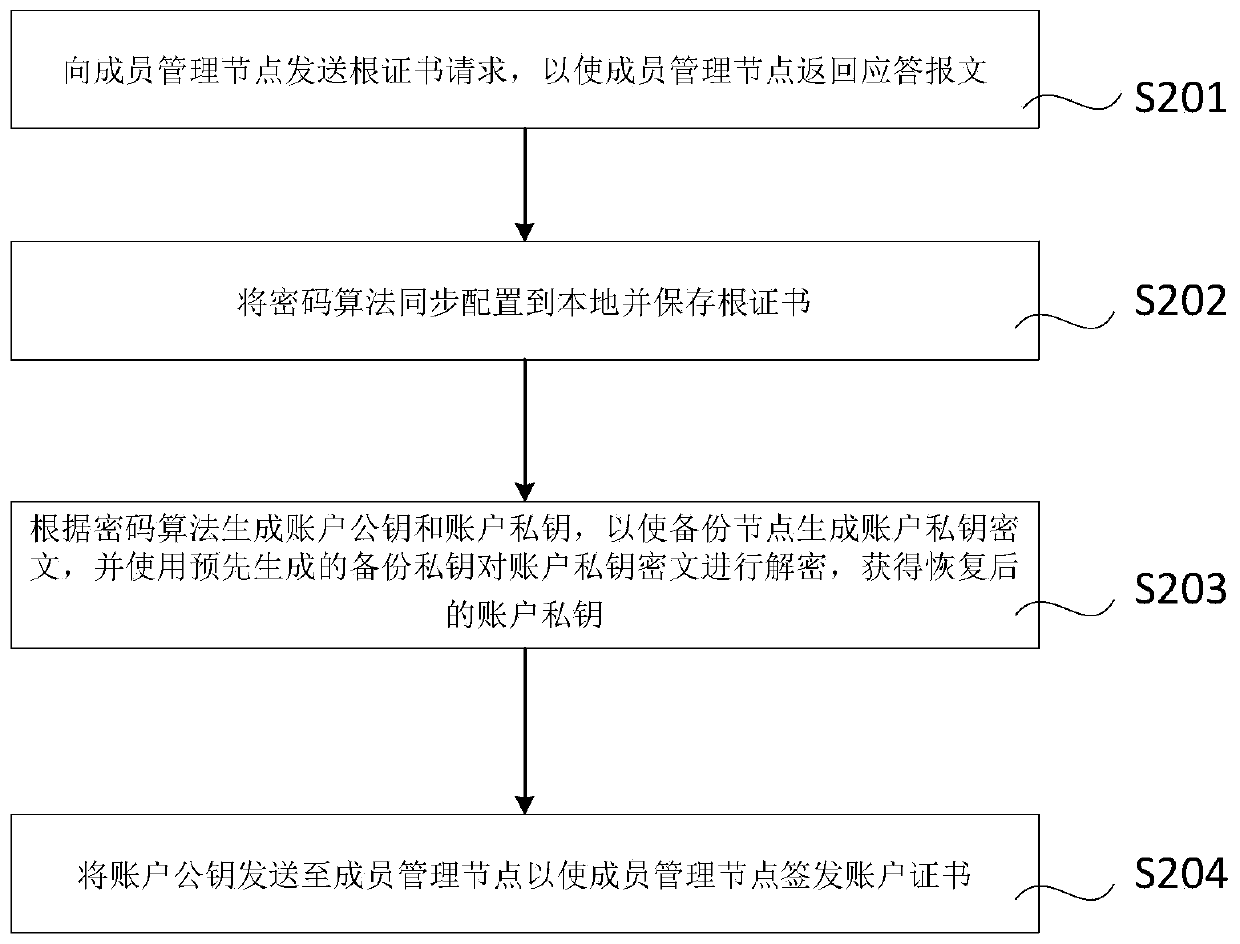
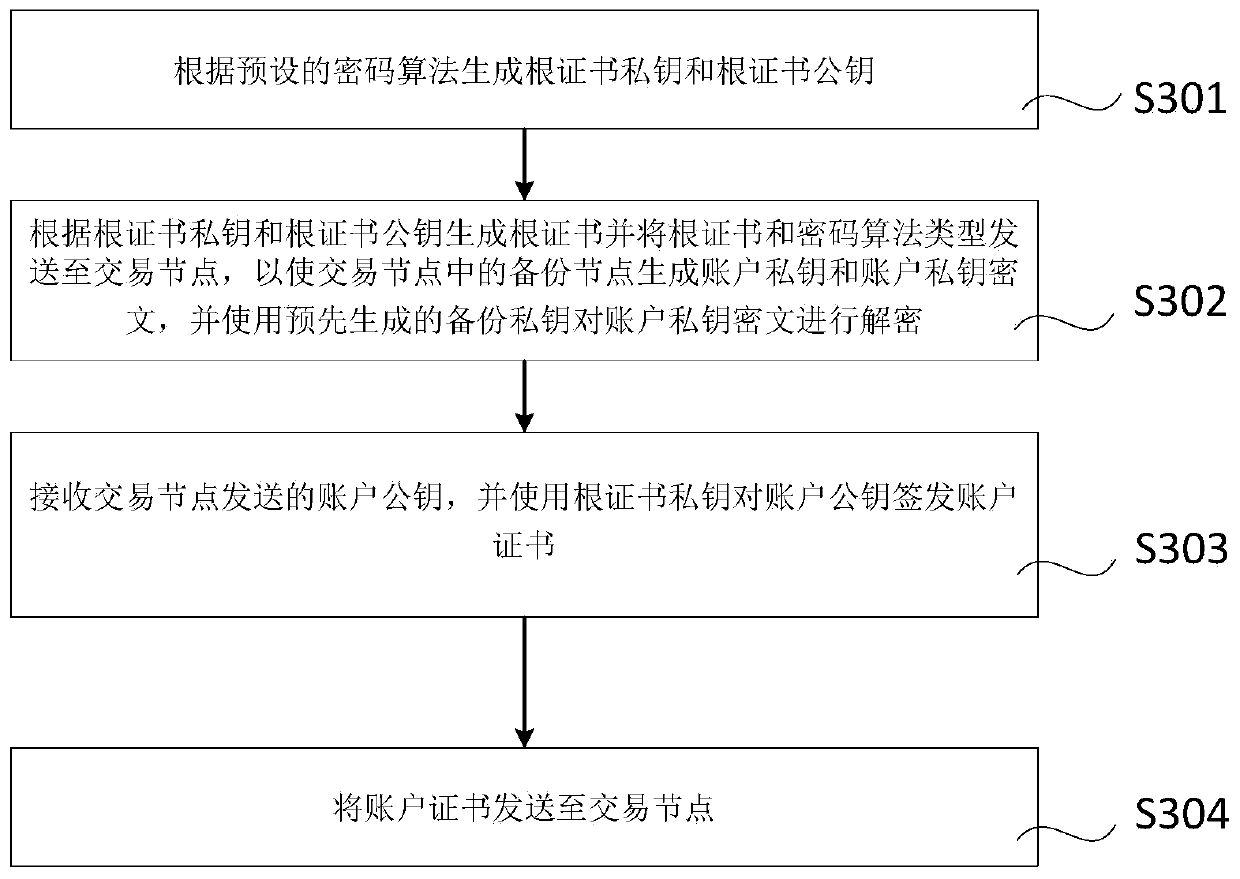
ActiveCN111339199ASolve the problem that blockchain transactions cannot be performedDatabase distribution/replicationDigital data protectionComputer networkCiphertext
The invention provides a blockchain key recovery method and device. The method comprises the steps of generating a backup private key according to a help private key obtained from a first help node; obtaining an account private key ciphertext backed up in the member management node in advance, and decrypting the account private key ciphertext by using the backup private key to obtain a recovered account private key, wherein the first help node is a transaction node in the blockchain. The public and private key addition homomorphic principle of the elliptic curve cryptographic algorithm is utilized, elliptic curve point addition operation is carried out on the help public and private key to generate the backup public and private key pair used for encrypting and decrypting the account private key, and therefore backup and recovery of the account private key are achieved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
A cryptosystem and digital signature method
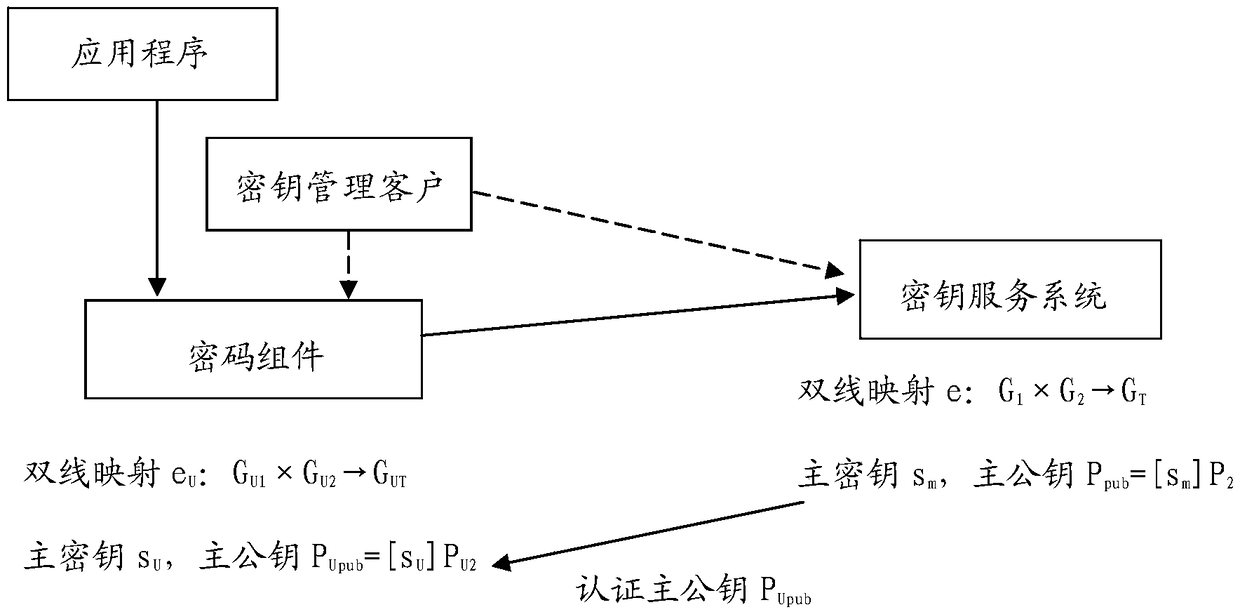
ActiveCN108989054AKey distribution for secure communicationPublic key for secure communicationDigital signatureCryptosystem
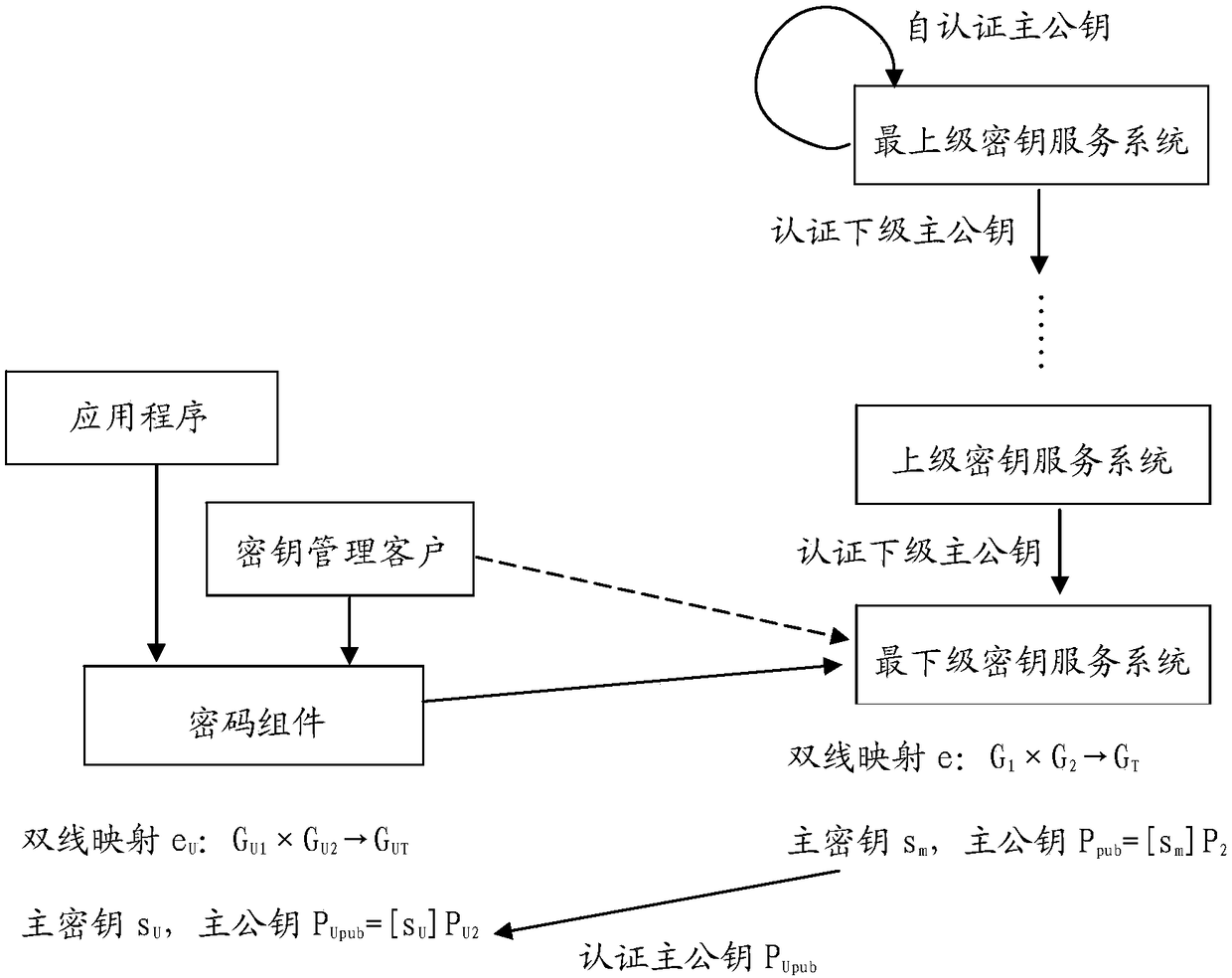
The invention relates to a cryptographic system and a digital signature method. The cryptographic system comprises a key service system and a cryptographic component. The key service system has a master key sm adopting bilinear mapping cryptography. The cryptographic component has the master keys sU, PU1, PU2 and PUpub= [sU] PU2 adopting bilinear mapping cryptographic operation, where PU1 and PU2are the generators of bilinear mapping groups GU1 and GU2 of the cryptographic component, respectively. The key service system digitally signs the data including the user's identity information U, PUpub and key restriction information of the cryptographic component by using the master key sm to generate the authentication data CU of the PUpub. The cryptographic component uses the key sU to digitally sign the data by using the identification cryptographic algorithm or the elliptic curve cryptographic algorithm, and the signed data contains the CU. After verifying the validity of the CU, the signature verifier verifies the digital signature of the data by using PU1, PU2 and PUpub.
Owner:WUHAN UNIV OF TECH
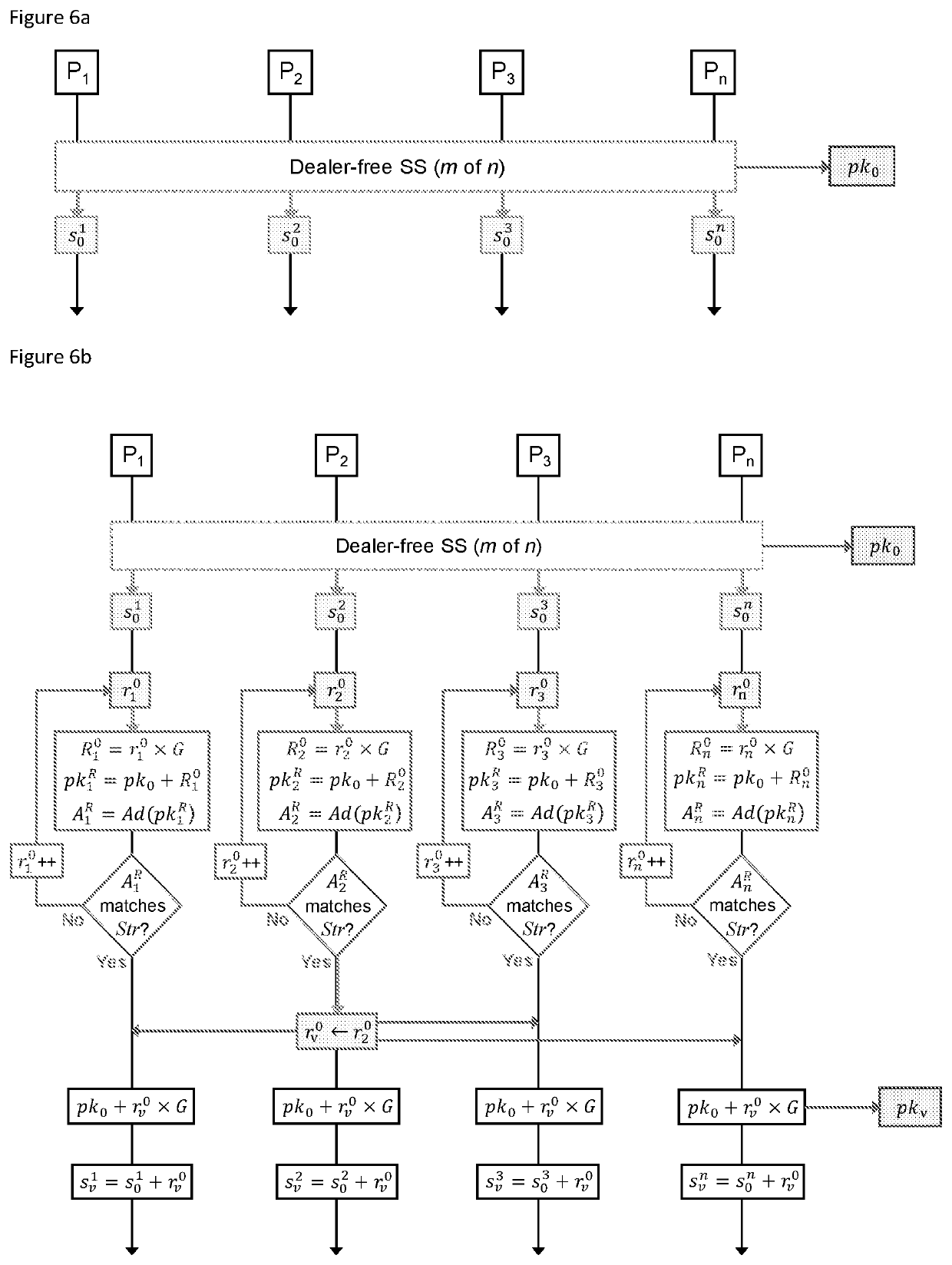
Computer-implemented systems and methods for performing computational tasks across a group operating in a trust-less or dealer-free manner
ActiveUS20210075600A1Easy to operateKey distribution for secure communicationMultiple keys/algorithms usageKey (cryptography)Theoretical computer science
The invention relates to secure determination of a solution (S) to a computational task by a dealer-free threshold signature group. Access to a resource or reward is offered in exchange for the solution. The method enables individuals in said group to work together in a trust-less, or dealer-free manner. To achieve this, individuals generate their own key pair and use their public key to establish with the group an initial shared public key that they can all use, in parallel, to find a solution to the task. Their own private keys remain secret and, therefore, the collaboration is trust¬less, and operates efficiently, because a verified shared public key is created using the initial shared public key that was used when a solution is found and verified. The resource or reward can be secured by the verified shared public key. Because the private keys of each participant were used in the determination of the initial shared public key that lead to the solution then participants must then collaborate to unlock the resource or reward because the corresponding shared private key can only be generated by all participants or a pre-agreed threshold of participants. Efficiency is achievable by using an initial shared public key and calculating with the group a verified shared public key after the solution has been found. The invention enables the task to be trust-less by using the homomorphic properties of elliptic curve cryptography when applying Shamir's secret sharing scheme. The inventive concept resides in the secure, trust-less and efficient way in which a group can collaborate. The invention can be agnostic to the task.
Owner:NCHAIN LICENSING AG
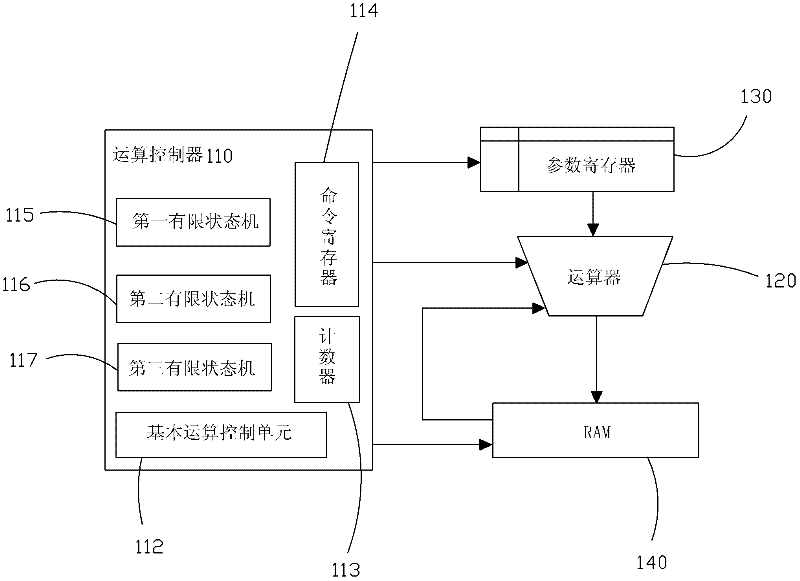
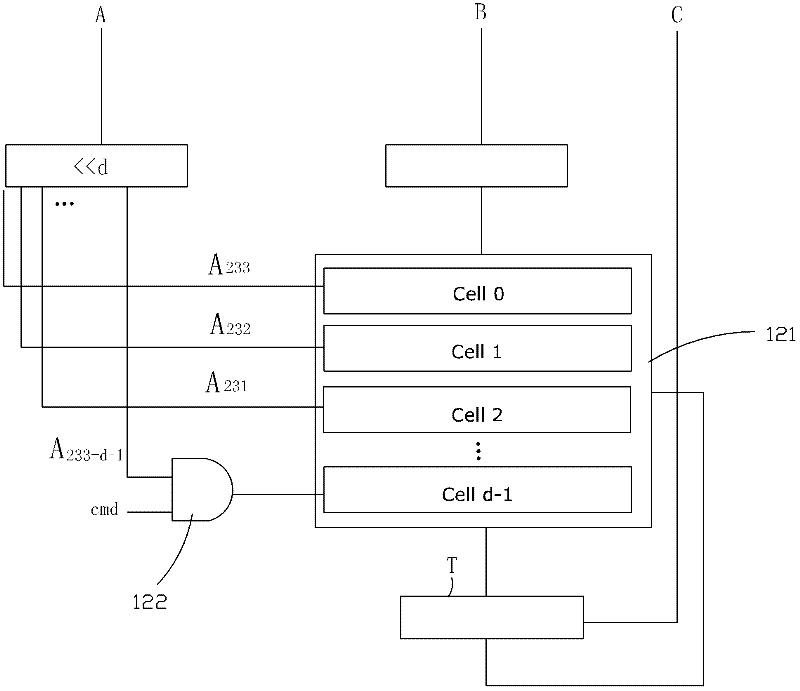
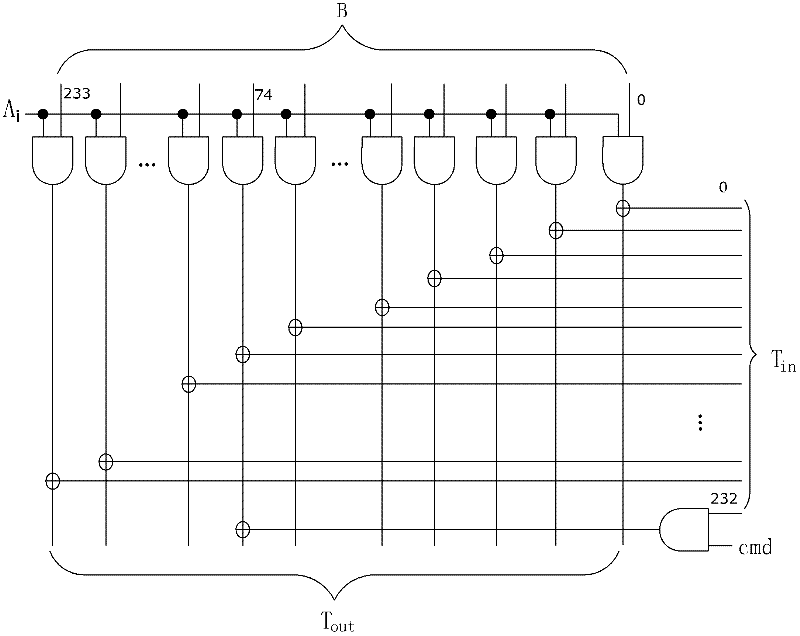
Elliptic curve cryptographic coprocessor
ActiveCN102412965ASimple structureReduce volumeUser identity/authority verificationCoprocessorControl signal
The invention provides an elliptic curve cryptographic coprocessor, comprising an arithmetic controller, an arithmetic device, a parameter register and a RAM (Random-Access Memory), wherein the arithmetic controller is respectively in electrical connection with the arithmetic device, the parameter register and the RAM, and is used for elliptic curve point multiplication and generating a control signal for the arithmetic device to finish modular addition and modular multiplication on a base field; the arithmetic device is respectively in electrical connection with the parameter register and the RAM, and is used for modular addition and modular multiplication on the base field; the parameter register is used for storing parameters of an elliptic curve equation and pre-computing the parameters; and the RAM is used for receiving the data transmitted from the outside and storing the computation result, and exchanging data with the outside. The elliptic curve cryptographic coprocessor has simple interface manners; the computation speed is increased greatly by means of a state machine; the elliptic curve point multiplication process is optimized, intermediate variables are reduced, and consequently, the number of registers is reduced; and a modular addition and modular multiplication circuit on the base field is reused to the greatest extent, so that the circuit area is reduced.
Owner:SHENZHEN DECARD SMART CARD TECH
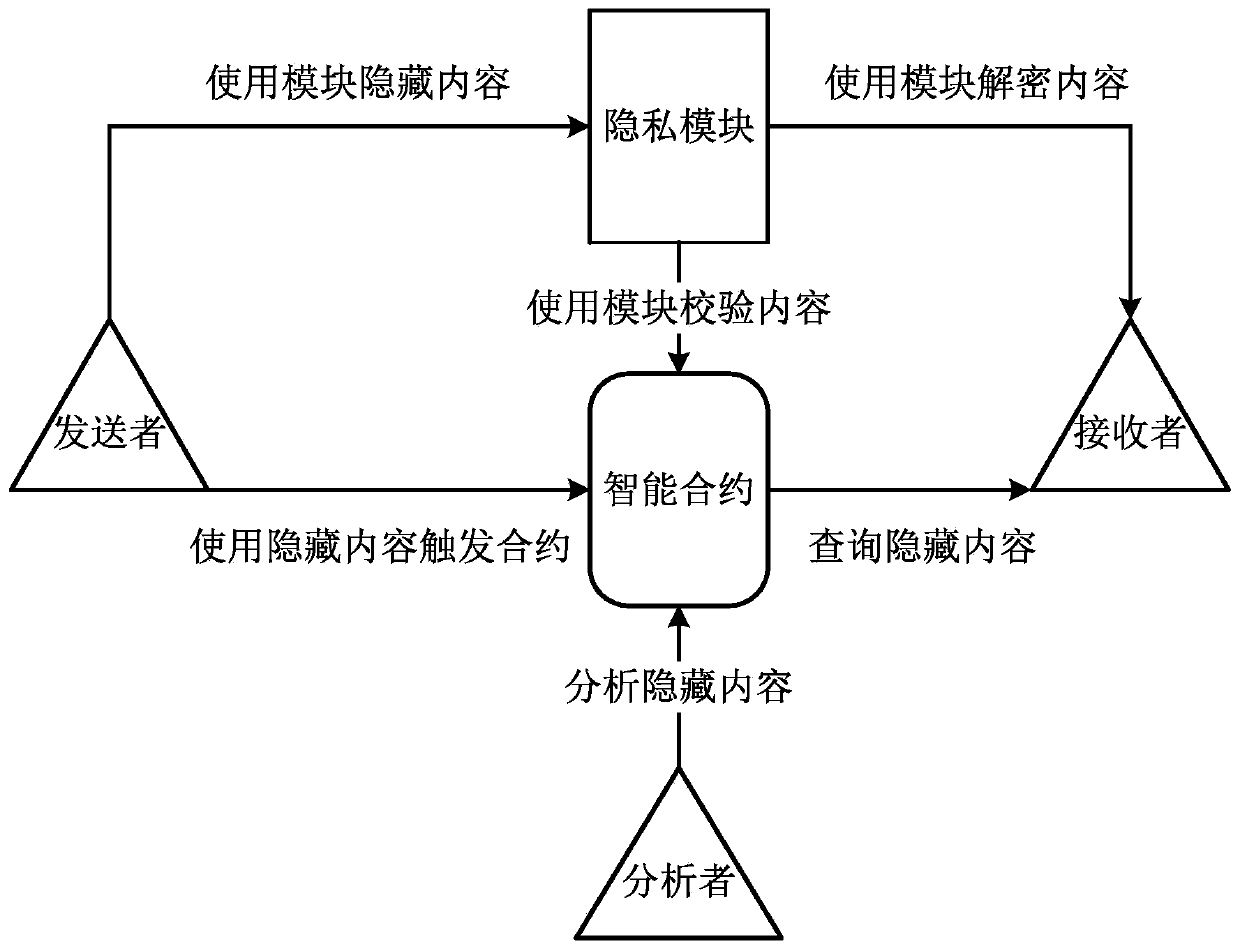
Privacy protection method and device based on blockchain smart contract
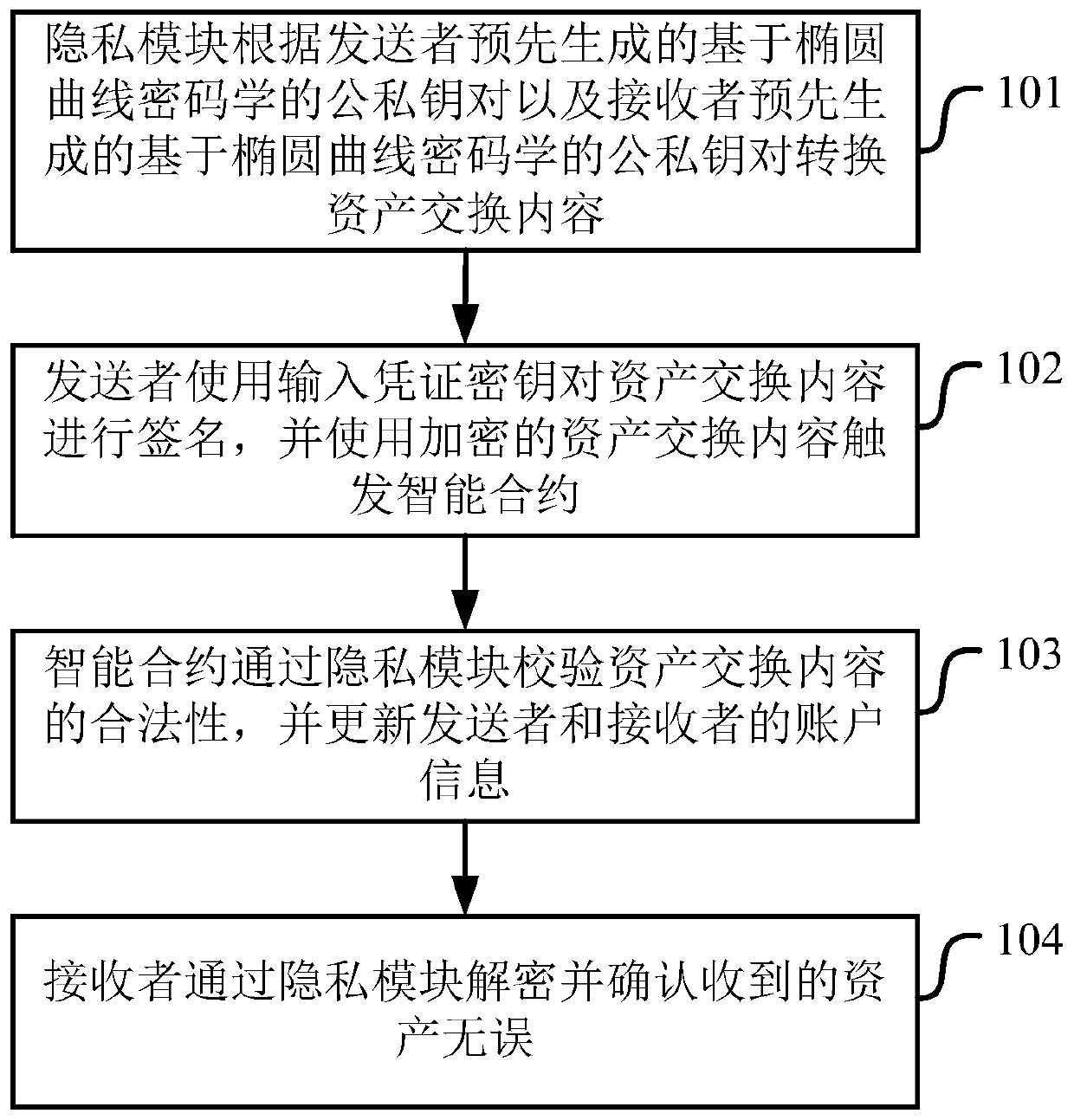
PendingCN111277415AQuick proofQuick verificationPublic key for secure communicationUser identity/authority verificationKey (cryptography)Privacy protection
The invention discloses a privacy protection method and device based on a blockchain smart contract. The method comprises the steps that a privacy module converts asset exchange content according to apublic and private key pair based on elliptic curve cryptography and pre-generated by a sender and a public and private key pair based on elliptic curve cryptography and pre-generated by a receiver;the sender signs the asset exchange content by using the input voucher key, and triggers an intelligent contract by using the encrypted asset exchange content; the smart contract verifies the legalityof the asset exchange content through the privacy module, and updates the account information of the sender and the receiver; and the receiver decrypts and confirms that the received assets are correct through the privacy module. By adopting the scheme, the identity information and the asset exchange content information can be completely hidden, the asset transfer process does not need interaction between two parties, and the certification and verification processes are quick and can be completed within milliseconds.
Owner:BUBI BEIJING NETWORK TECH CO LTD
Digital signature system based on shared knowledge
InactiveUS20060153367A1Facilitating adoptionEasy to usePublic key for secure communicationSecret communicationDigital signatureDeterministic function
A method in a digital signature system includes providing a public key of a first party to a second party for later verification of a digital signature. The method includes: identifying domain parameters of an elliptic curve, including a generating point; transforming the generating point into a second generating point as a deterministic function of shared knowledge; and generating the public key as a deterministic function of a private key and the domain parameters, in which the second generating point is substituted for the identified generating point. The public key and private key constitute a public-private key pair of elliptic curve cryptography. A digital signature is generated as a function of the private key and the domain parameters, in which the second generating point again is substituted for the initial generating point identified. The shared knowledge is known to and shared between the first party and the second party.
Owner:FIRST DATA
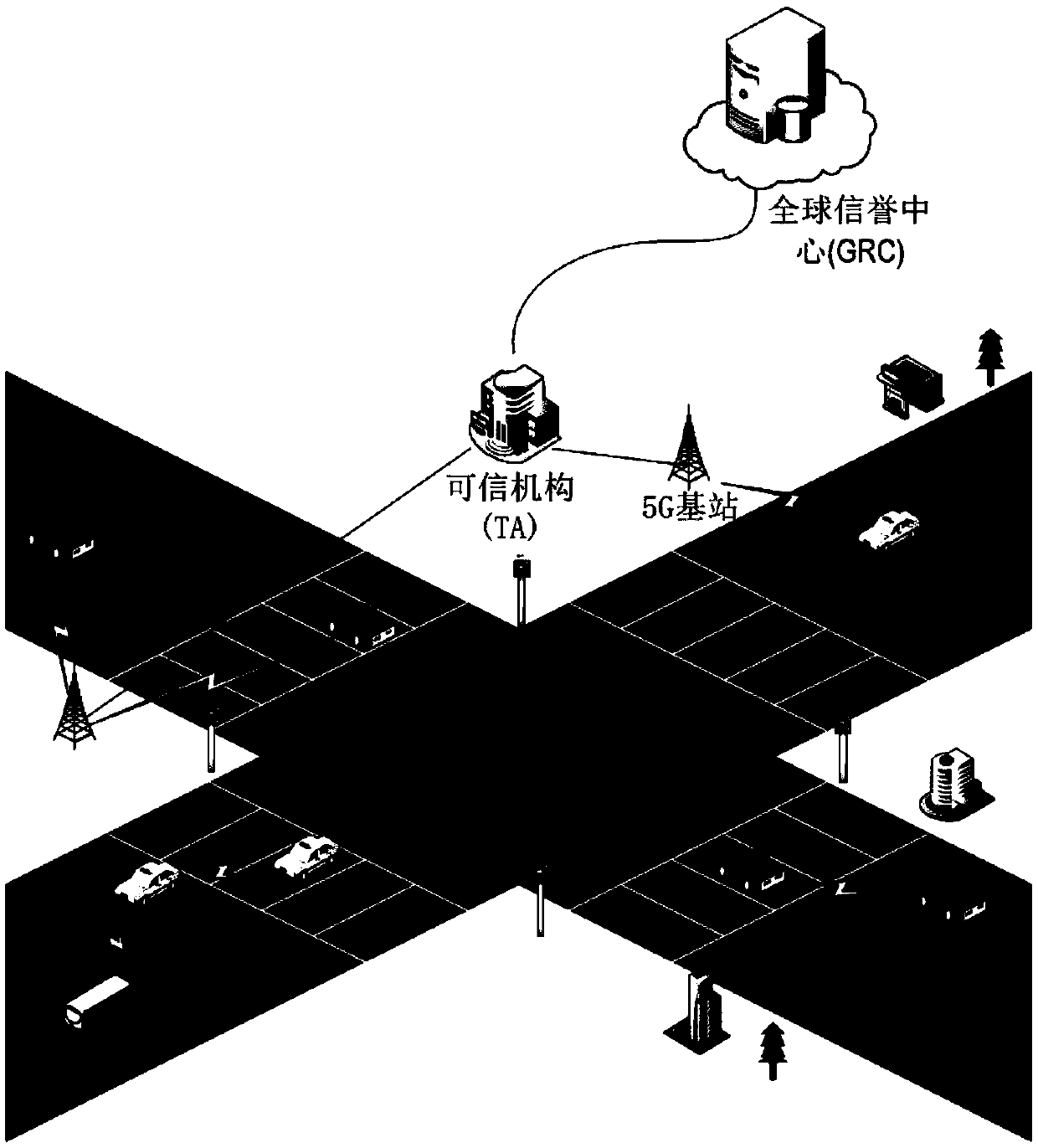
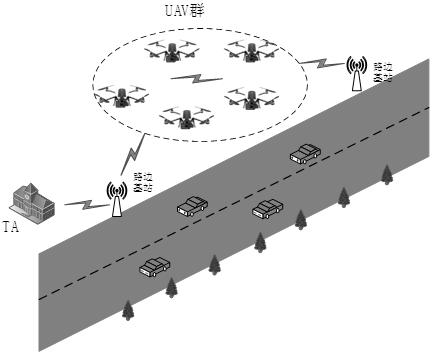
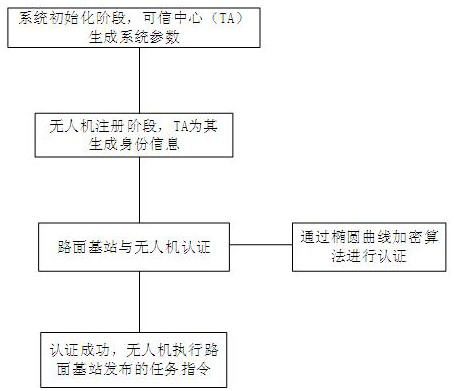
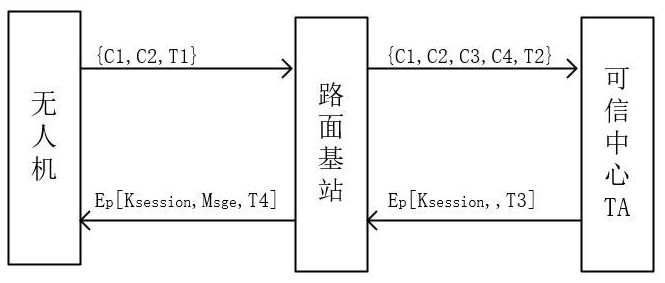
Elliptic curve encryption-based unmanned aerial vehicle and base station communication identity authentication method
ActiveCN112073964AReduce latencyGuaranteed impenetrabilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesElliptic curve discrete logarithm problemCommunications security
The invention aims to design an elliptic curve encryption-based unmanned aerial vehicle and base station communication identity authentication method, which comprises the following steps that: in an initialization stage of a system, a trusted center generates system parameters and broadcasts the system parameters to an unmanned aerial vehicle network; each unmanned aerial vehicle in the unmanned aerial vehicle group is authenticated and registered by the trusted center; the pavement base station and the unmanned aerial vehicle initiate an authentication request; and after successful authentication, the pavement base station sends an instruction packet to the unmanned aerial vehicle, and the unmanned aerial vehicle receives the instruction and executes an instruction task. The authentication method is mainly based on the elliptic curve cryptography theory, and based on the elliptic curve discrete logarithm problem (ECDLP), it is guaranteed that communication data are difficult to crack;the flow of identity authentication between the unmanned aerial vehicle and the pavement base station effectively protects the communication security of the pavement base station and the unmanned aerial vehicle, ensures the identity privacy of the pavement base station and the unmanned aerial vehicle, can effectively prevent replay attacks and man-in-the-middle attacks, prevents the unmanned aerial vehicle from executing malicious tasks due to malicious attacks, and ensures the communication security of the unmanned aerial vehicle.
Owner:HENAN UNIVERSITY
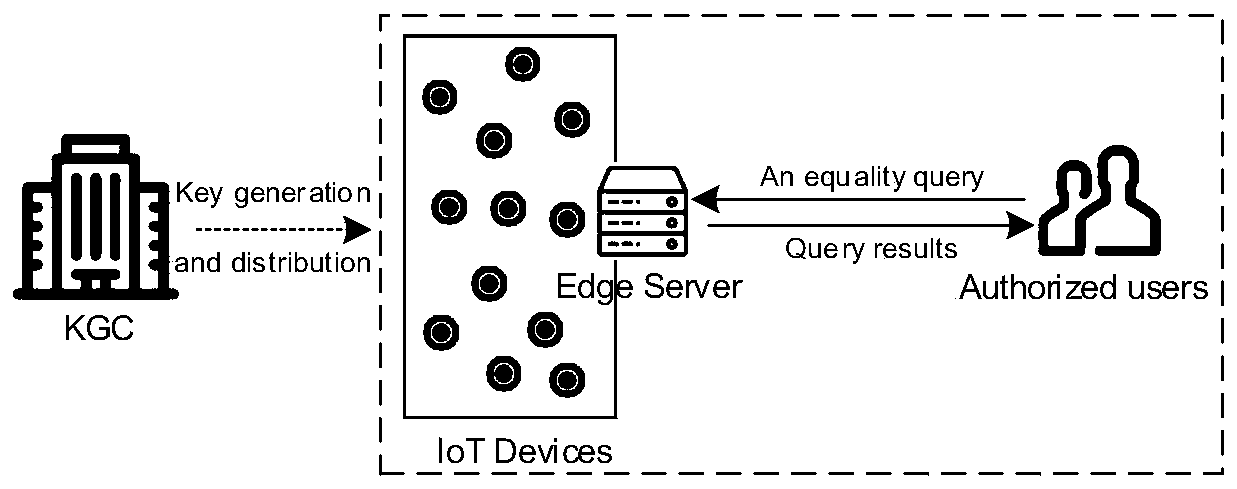
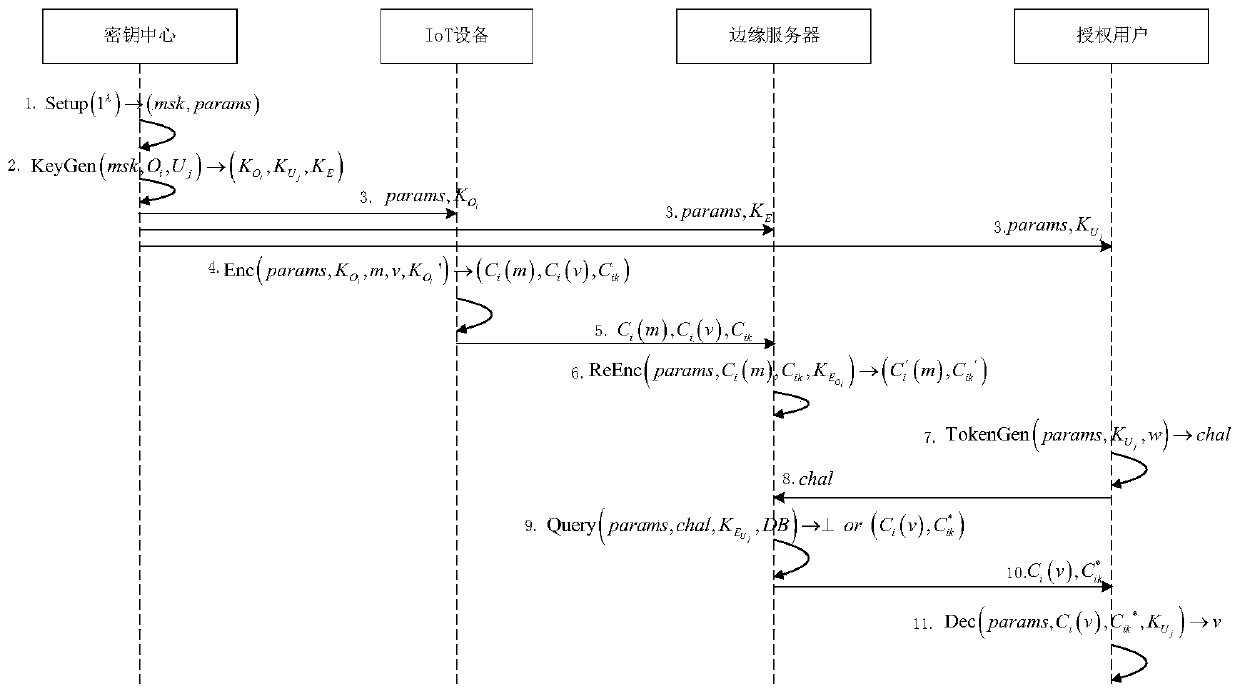
Equivalent query method for lightweight privacy protection
ActiveCN110933026AGuaranteed privacyEfficient constructionPublic key for secure communicationKey (cryptography)Edge server
The invention relates to an equivalent query method for lightweight privacy protection, which comprises four roles, namely a key center, IoT equipment, an edge server and an authorized user. The secret key center executes initialization operation, public parameters are disclosed, and a main secret key is stored by the secret key center; the secret key center executes a secret key generation operation, generates a secret key and distributes the secret key to other roles; the IoT equipment encrypts own data and then outsources the encrypted data to the edge server; the edge server re-encrypts the data and then stores the data; the authorized user sends a query request to the edge server; the edge server returns a query result in response to the query request; and finally, the authorized userdecrypts the query result returned by the server to obtain plaintext data. According to the method, proxy re-encryption is realized based on elliptic curve cryptography, and an efficient and safe query scheme in edge computing is effectively constructed. Compared with the prior art, the privacy of outsourcing data can be guaranteed, meanwhile, the calculation expenditure in the encryption and decryption process is reduced, and the method is more suitable for edge equipment with weak calculation and storage capacity.
Owner:NORTHEASTERN UNIV
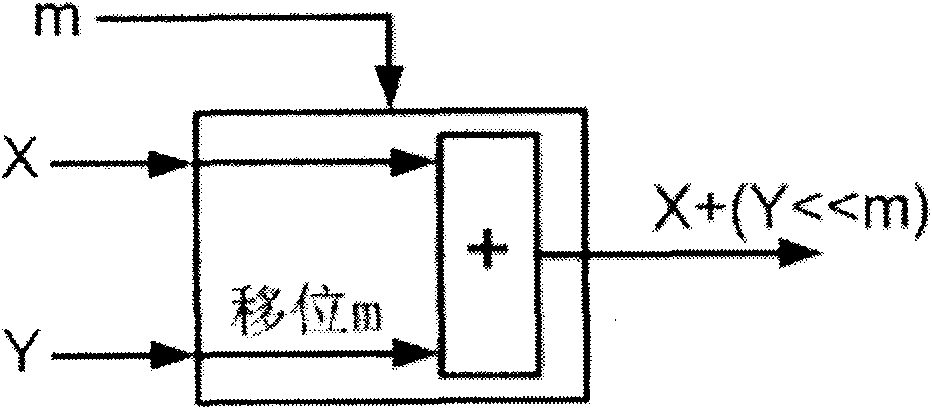
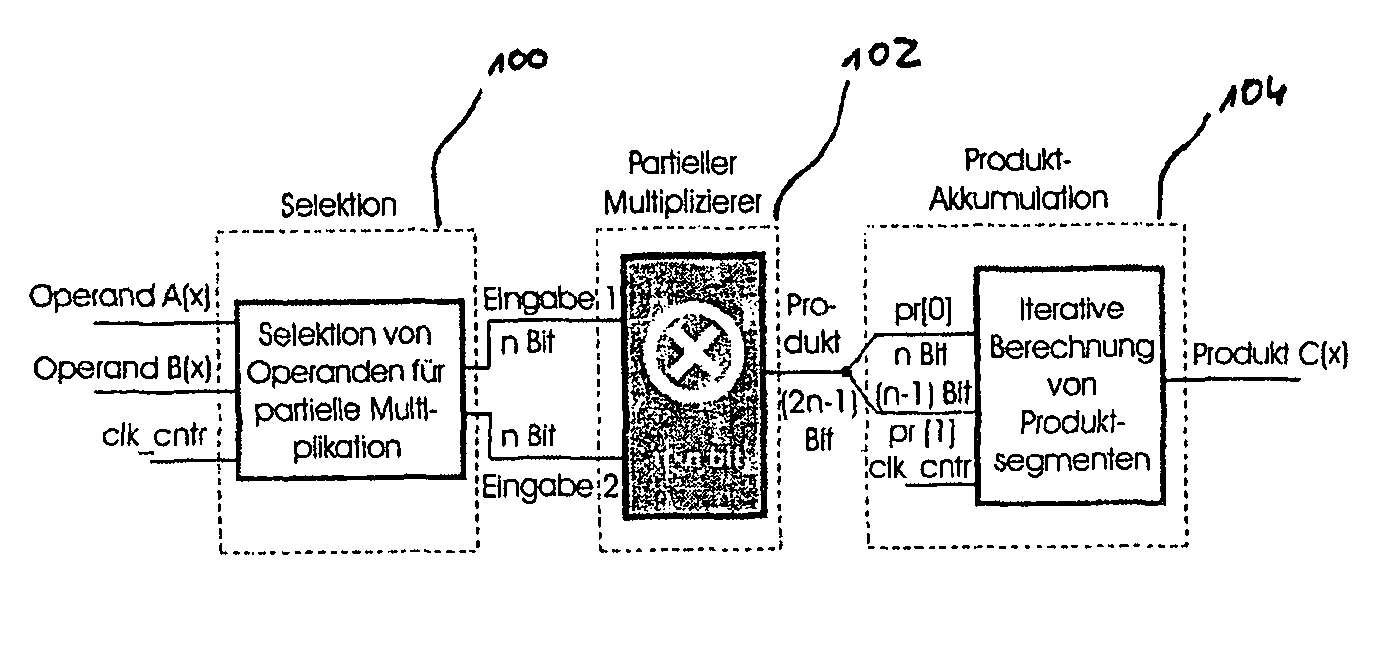
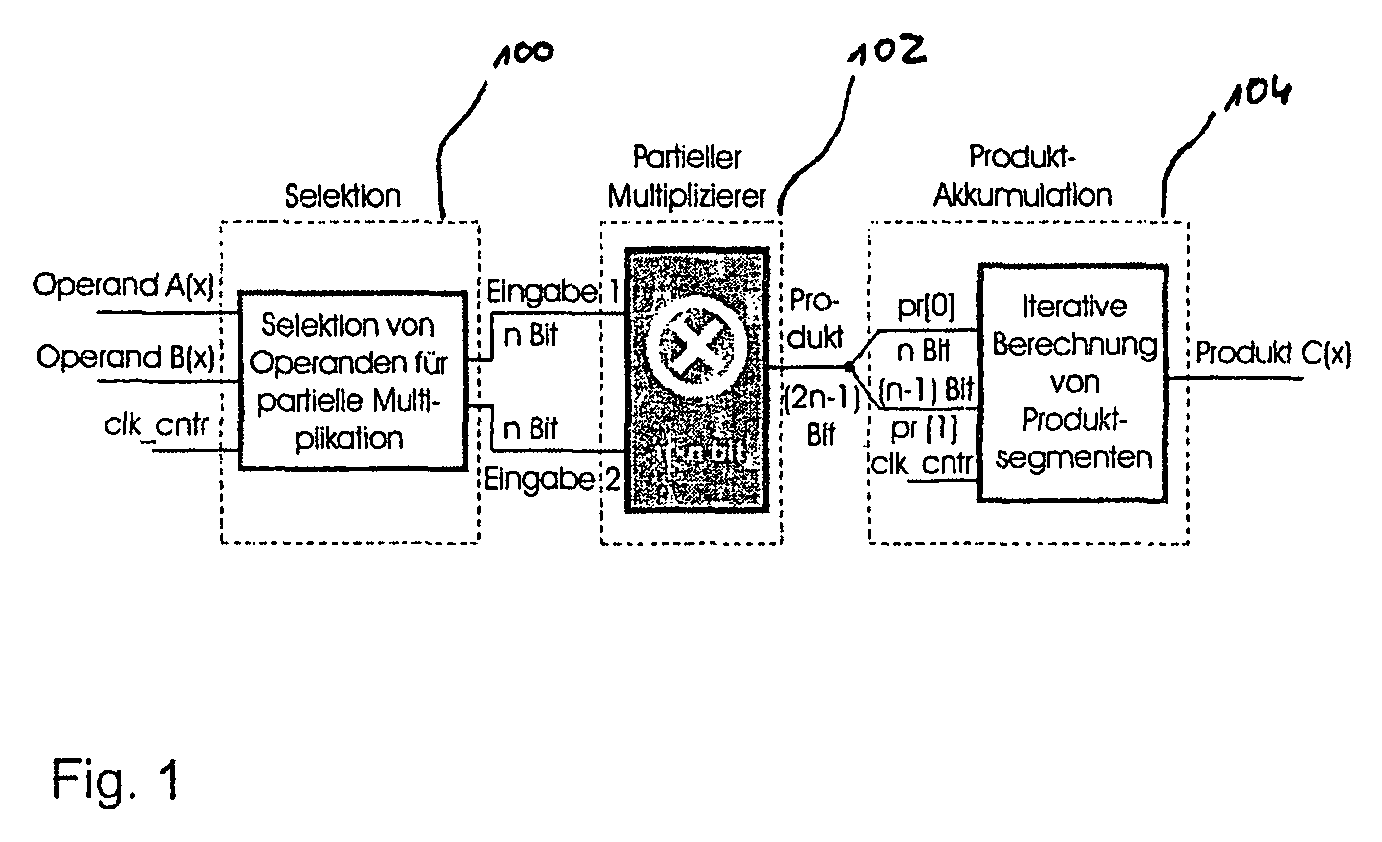
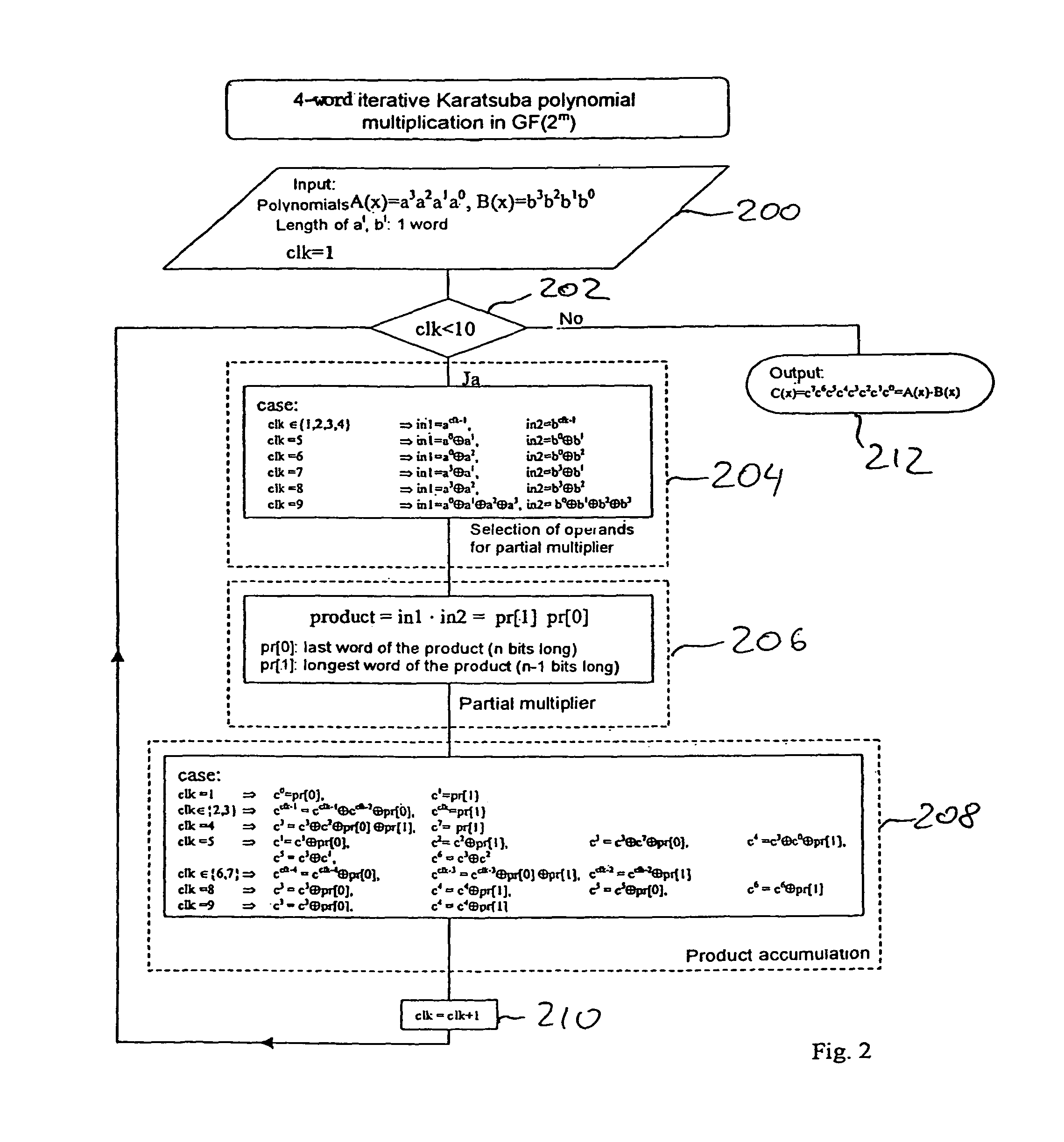
Method and apparatus for calculating a polynomial multiplication, in particular for elliptic curve cryptography
ActiveUS8477935B2Easy to operateEnergy efficient ICTPublic key for secure communicationComputer hardwareEnergy consumption
Safeguarding communication channels is required in particular in wireless networks. The use of encryption mechanisms in the form of software is limited by the required calculation and energy capacities of mobile terminals. Costs are of significance when using hardware solutions for cryptographic operations. The present invention provides an approach which simultaneously tackles all those points. It concerns a hardware accelerator for polynomial multiplication in extended Galois fields (GF), wherein the per se known Karatsuba method is iteratively applied in accordance with the invention. When using the invention the area requirement can be reduced for example from 6.2 mm2 to 2.1 mm2. The solution according to the invention also reduces the energy consumption in comparison with solutions in accordance with the state of the art by 30%.
Owner:IHP GMBH - INNOVATIONS FOR HIGH PERFORMANCE MICROELECTRONICS INST FOR INNOVATIVE MIKROLEKEKTRONIK
Lightweight searchable encryption method and device based on elliptic curve
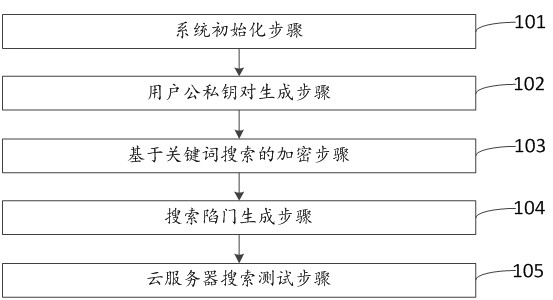
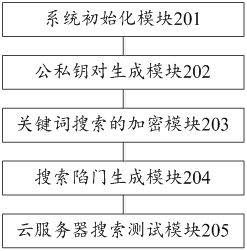
ActiveCN112560075AEnable secure sharingGuaranteed confidentialityDigital data protectionComputations using residue arithmeticOriginal dataCloud data
The invention provides a lightweight searchable encryption method and device based on an elliptic curve. The method comprises the following steps: a system initialization step; a user public and private key pair generation step; an encryption step based on keyword search; encrypting the original data file by using a universal public key encryption technology; a search trap door generating step; and a cloud server search testing step. According to the keyword guessing attack resistant lightweight searchable encryption method, an elliptic curve cryptographic algorithm is utilized, and the requirements on calculation and storage expenditure are relatively low, so that the keyword guessing attack resistant lightweight searchable encryption method has a lightweight characteristic, can be widelyapplied to various mobile intelligent terminal platforms with limited hardware resources, and has a keyword guessing resistance characteristic; therefore, the server cannot guess the keywords queriedby the user, and the information security of the cloud data is effectively guaranteed.
Owner:SOUTHWEST PETROLEUM UNIV
Cooperative spectrum sensing location privacy protection method based on blockchain
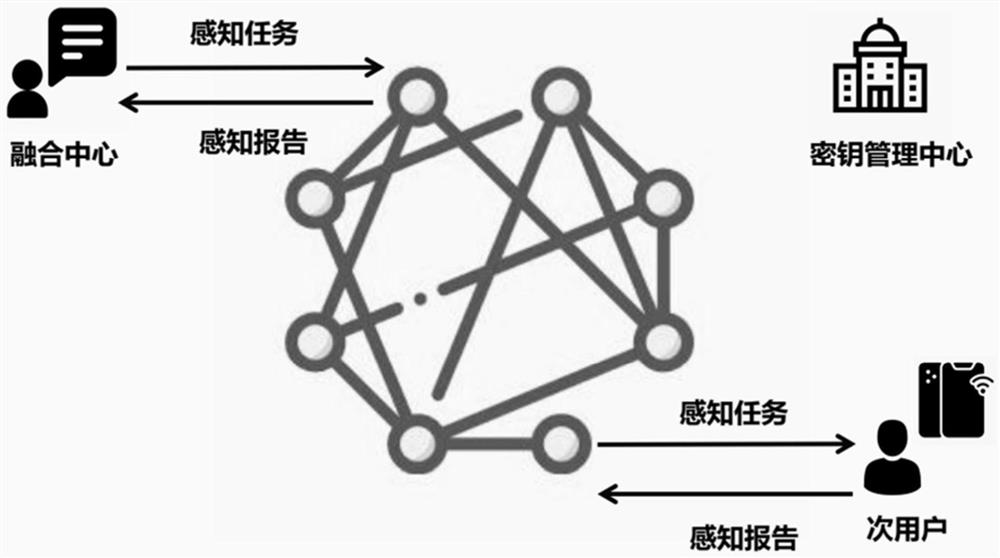
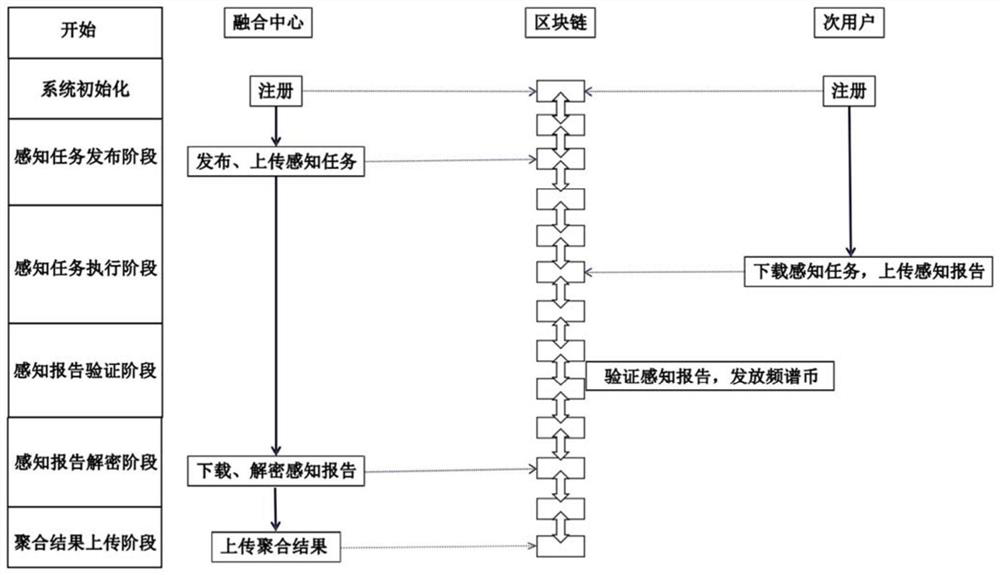
ActiveCN113079140AProtection securityPrevent theftKey distribution for secure communicationPublic key for secure communicationFusion centerTimestamp
The invention discloses a cooperative spectrum sensing location privacy protection method based on a blockchain, which utilizes the anonymity of the blockchain to enable a secondary user to anonymously upload a sensing report to the blockchain, avoids the relevance between the sensing report and the secondary user, prevents a fusion center from associating the sensing report with the secondary user during decryption, and protects the security of the sensing report in the fusion process. The secondary user encrypts and signs the sensing report by using the elliptic curve cryptography technology, so that the sensing report is prevented from being stolen and tampered in the transmission process, and the confidentiality and integrity of the sensing report in the transmission process are ensured. According to the method, the sensing report is prevented from being replayed in the transmission process by using the timestamp, and the timeliness of the sensing report in the transmission process is ensured. According to the method, the automatic verification characteristic of a smart contract is utilized, and the smart contract, instead of the fusion center, automatically verifies the digital signature of the sensing report, so that the calculation overhead of the fusion center is reduced.
Owner:FUJIAN NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com