Patents
Literature
37results about How to "Tamper-resistant" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
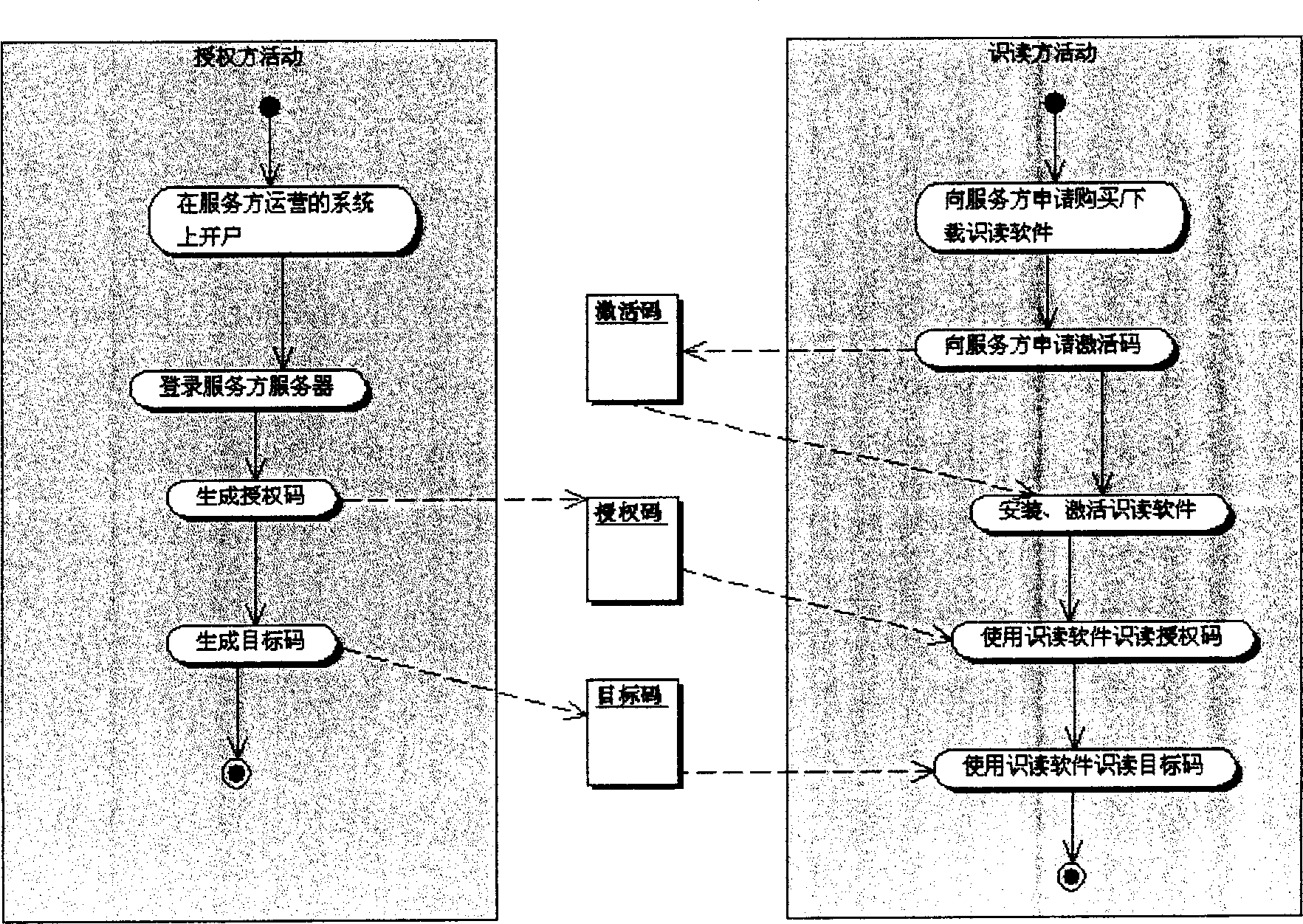
Security label which is optically read by terahertz radiation
InactiveUS20060231625A1Tamper resistantOther printing matterPaper-money testing devicesInternet privacyTerahertz radiation
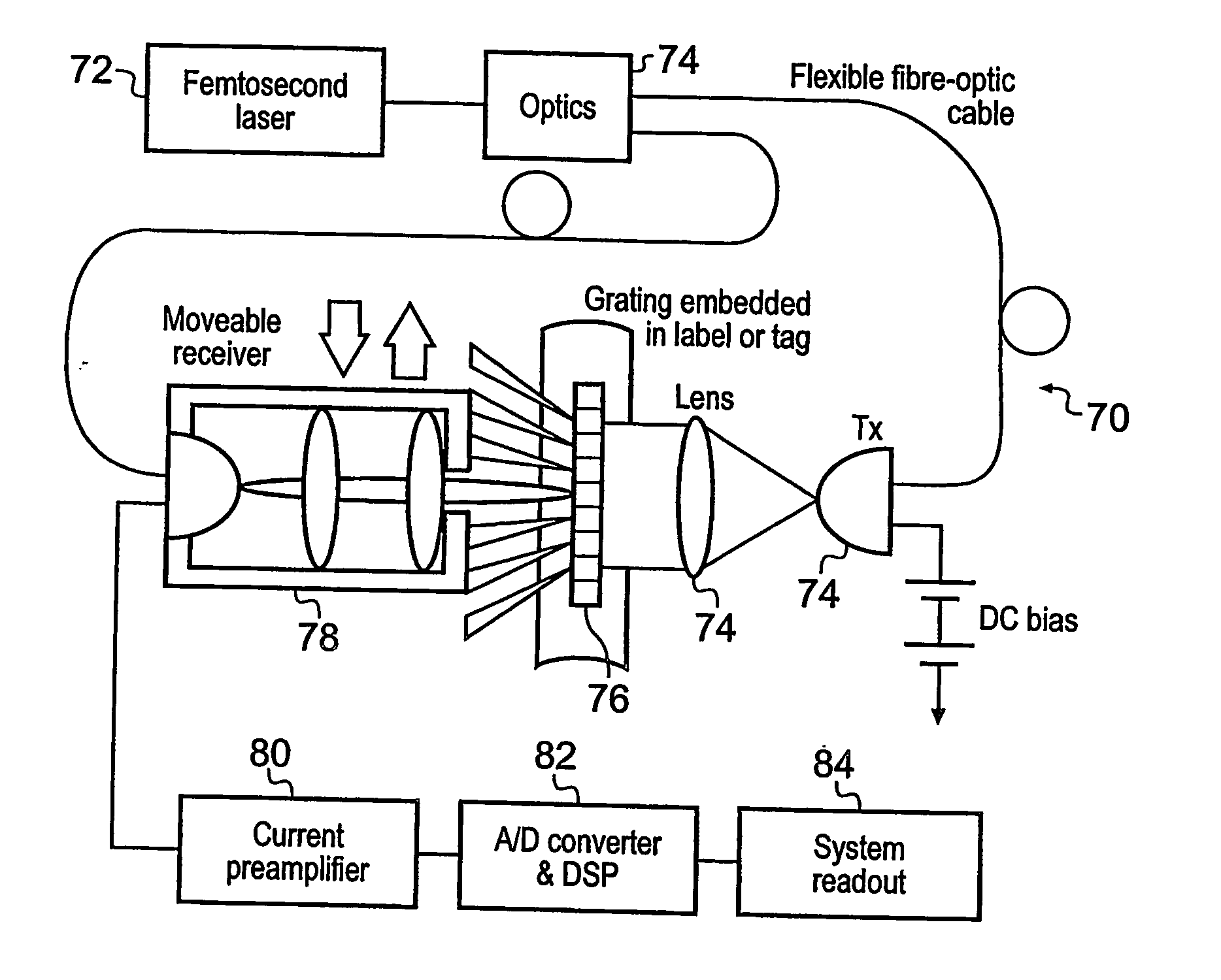
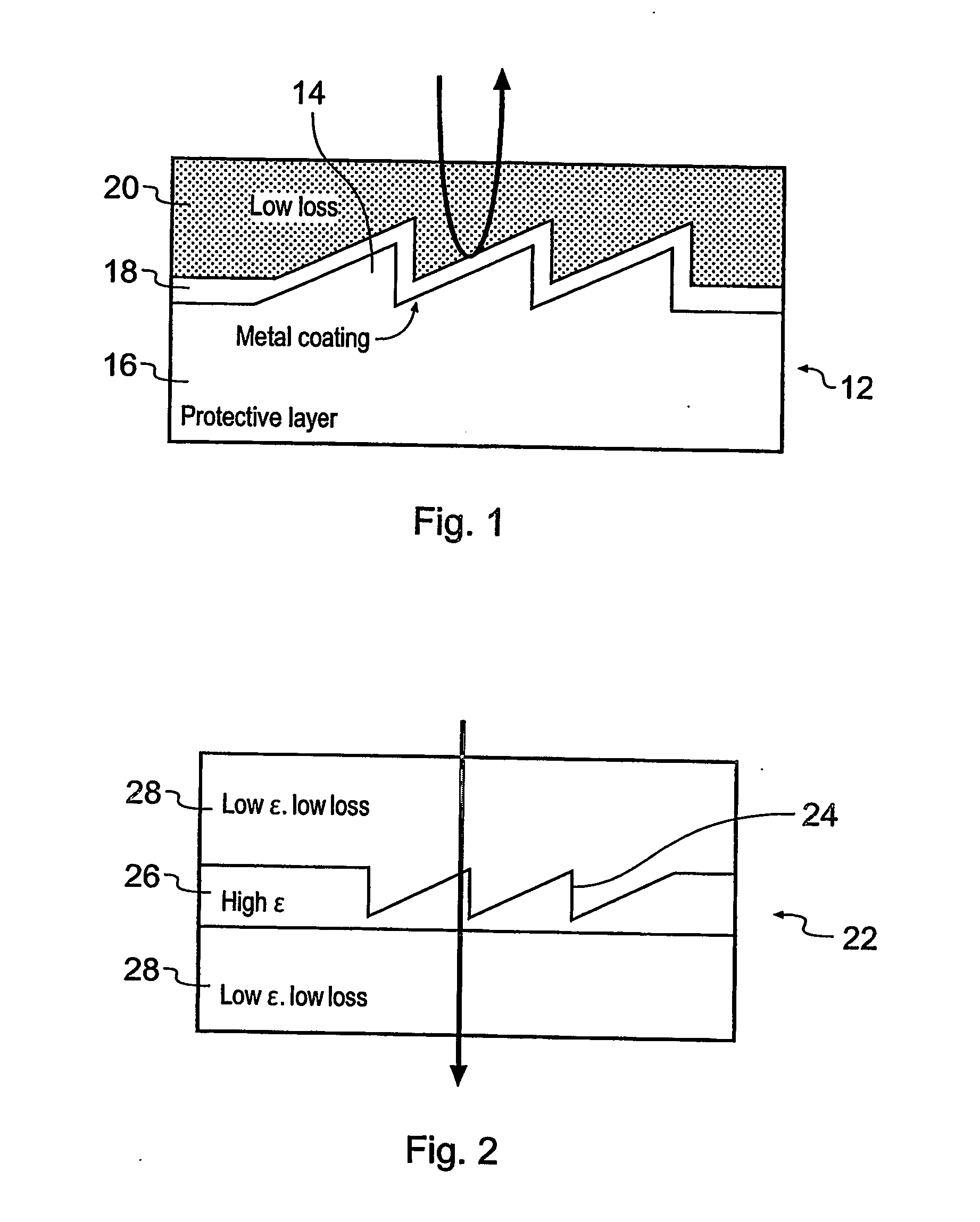
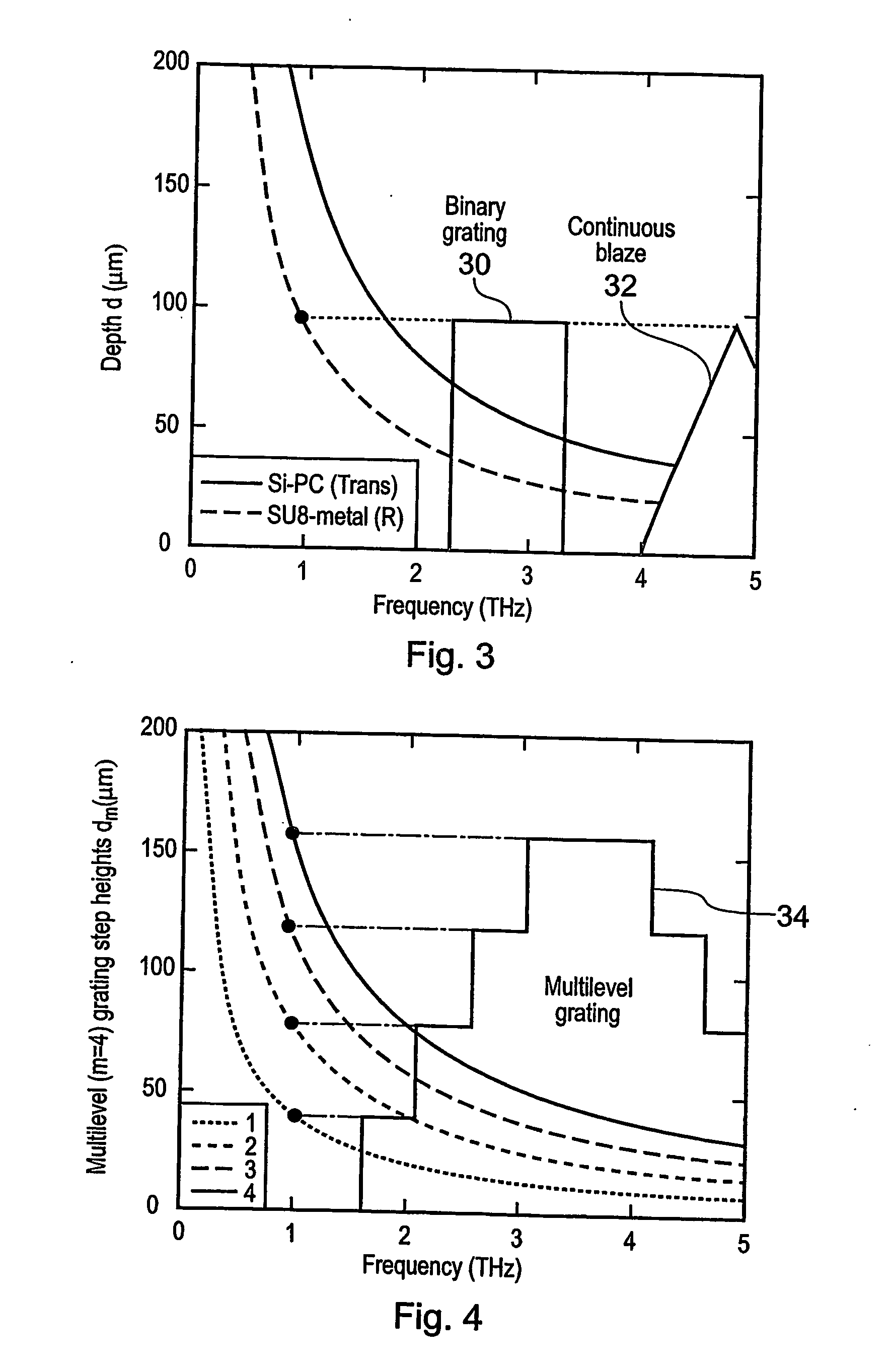
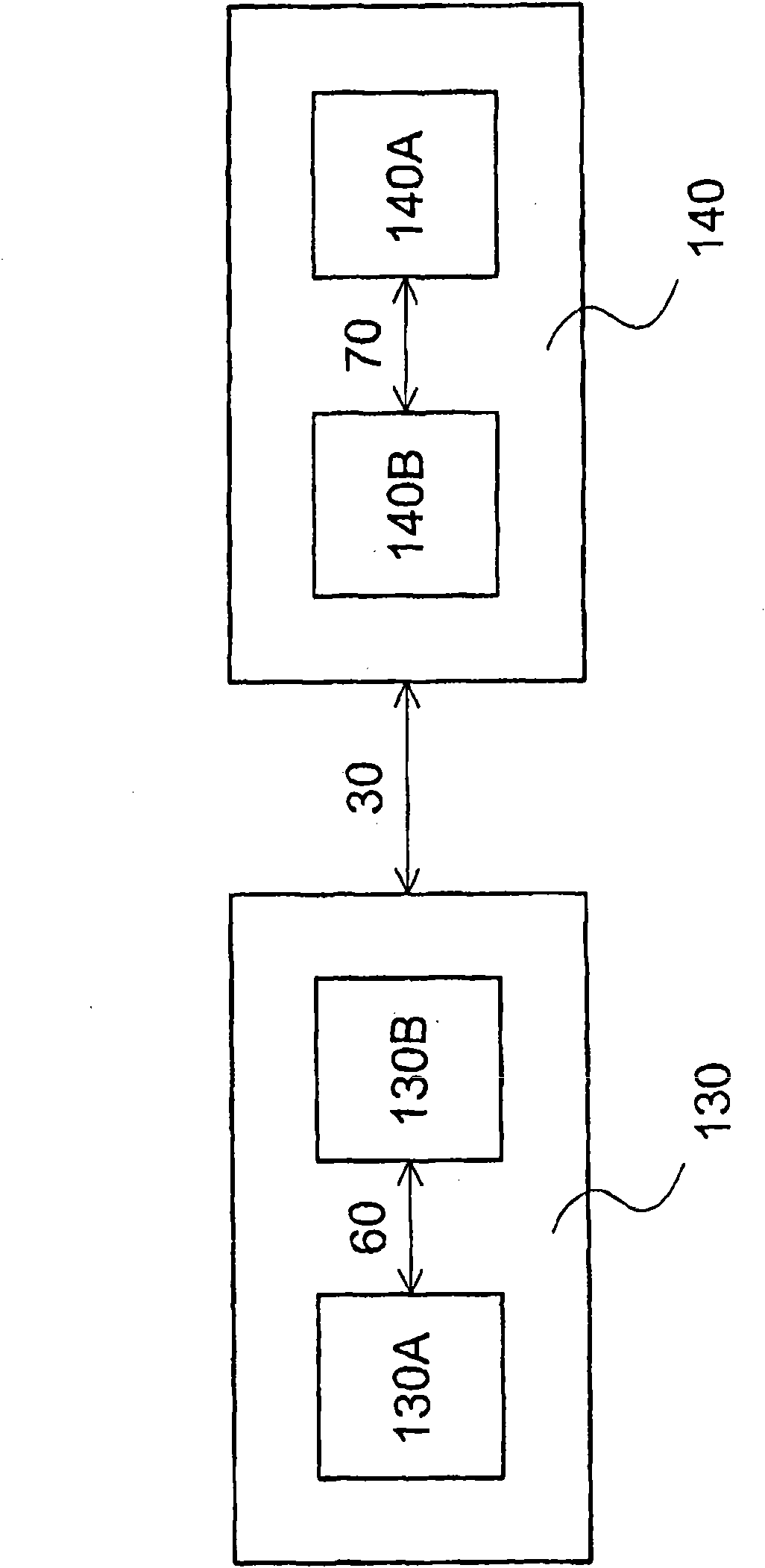
The present invention relates to security label (12) for securing or authenticating goods or services or a security document. Currently radio frequency ID cards, having an inductive loop and a microchip containing security information, are used. However, such RF ID cards are expensive to manufacture. Therefore it is proposed to use a security label or document (12) including a terahertz image or tag (14, 15, 76) which may beta hologram. Security information can then be read by reflection or transmission of terahertz radiation which is not visible to the unaided eye. The terahertz image or tag may be covered by a material (66, 68) opaque to visible light, but transparent or transmissive of terahertz wavelengths, making it difficult for potential fraudsters to investigate the terahertz image. A method of making such a security label or document, a security or authentication method and system using terahertz radiation are also disclosed.
Owner:THE UNIV COURT OF THE UNIV OF GLASGOW
Devices and Methods Useful for Authorizing Purchases Associated with a Vehicle
InactiveUS20090045978A1Easy to installStrong adhesionDetection of traffic movementBuying/selling/leasing transactionsEngineeringEmbedded system
Disclosed are various devices useful as components of a system for authorizing purchases associated with a vehicle that are generally simple to install, operate and maintain and are generally resistant to abuse. Devices disclosed include theft-resistant vehicular identification tags, sealed identification tag reader and variable range tag-readers.
Owner:GASNGO R&D LTD
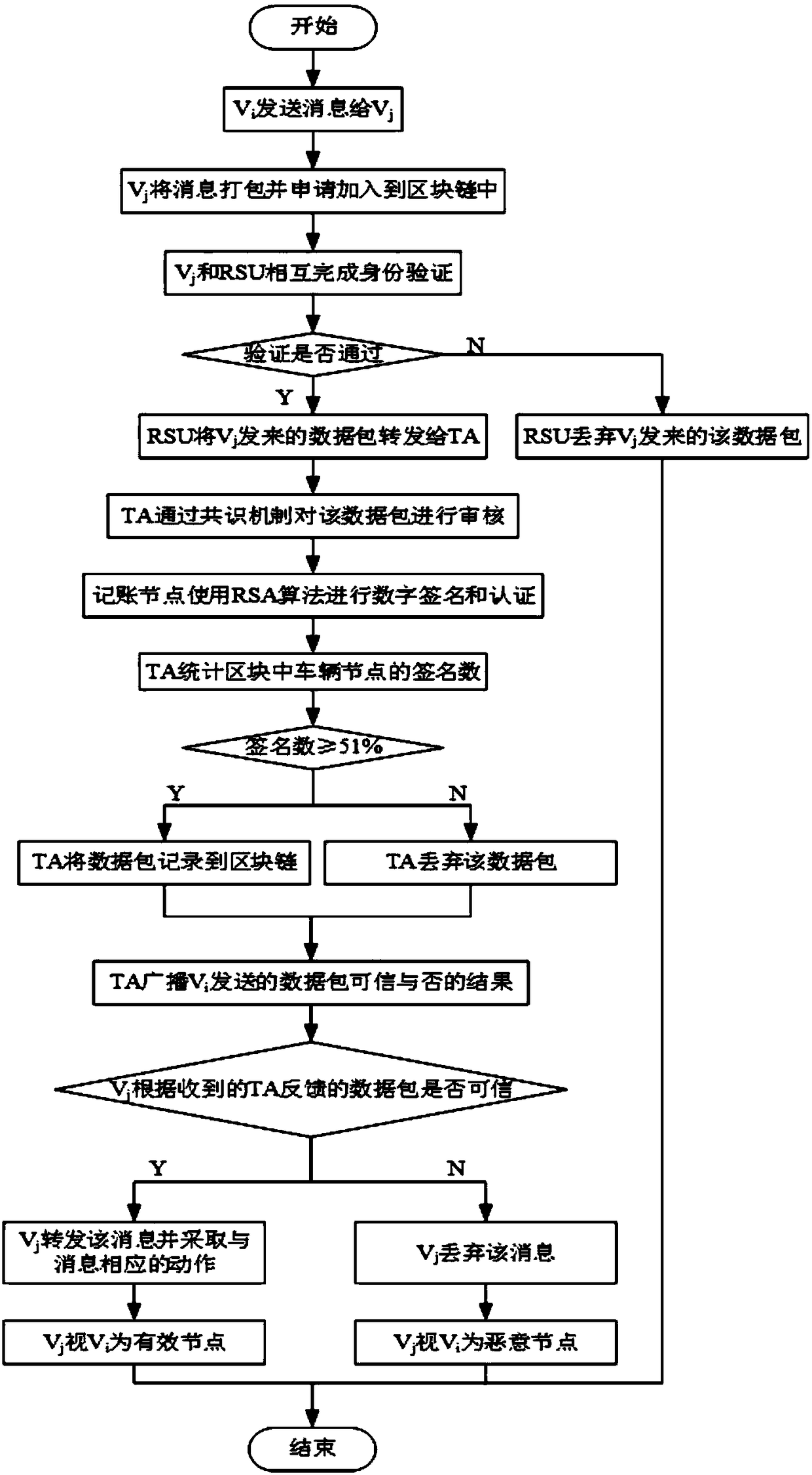
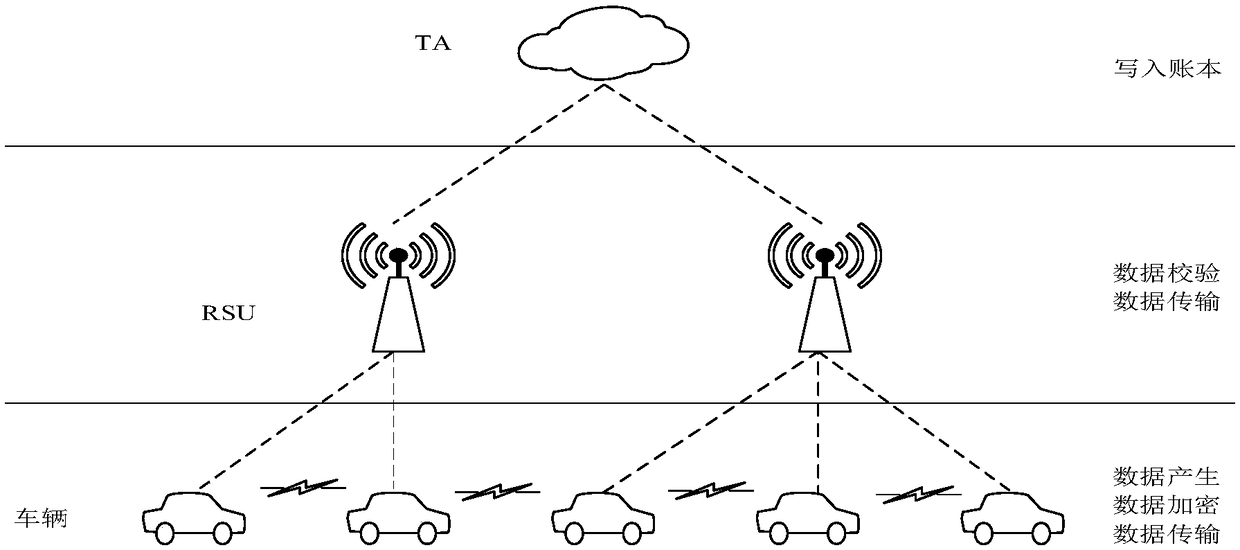
Internet of vehicles malicious node detection system and method for integrated block chain consensus mechanism
ActiveCN109462836AEfficient and accurate detectionNot easy to tamper withParticular environment based servicesVehicle wireless communication serviceDigital signatureThe Internet
The invention discloses an Internet of vehicles malicious node detection system and method for an integrated block chain consensus mechanism. Messages sent by a vehicle sending node Vi and identity information of a vehicle sending node Vi are packaged into a request authentication data packet to be sent to RSU via any vehicle receiving node Vj; after receiving the data packet, the RSU performs mutual identity authentication with the Vj; if the mutual identity authentication is passed, the RSU forwards the received data packet sent by the Vj to a TA; according to the traceability of a databaserecorded by a block chain, digital signature and information authentication are performed by using a RSA algorithm; the consensus mechanism is used for detecting whether the vehicle node is a malicious node through combining with the current state of the vehicle node. According to the method, the characteristic that the data recorded by the block chain is not easy to tamper is used, the maliciousvehicle in the Internet of vehicles can be efficiently and accurately detected, meanwhile, the problems of decentralized management and privacy protection of the Internet of vehicles also can be solved, and thus the problem that in the Internet of vehicles, the detection accuracy of the malicious node is low is solved, and the network overhead is effectively reduced.
Owner:CHANGAN UNIV
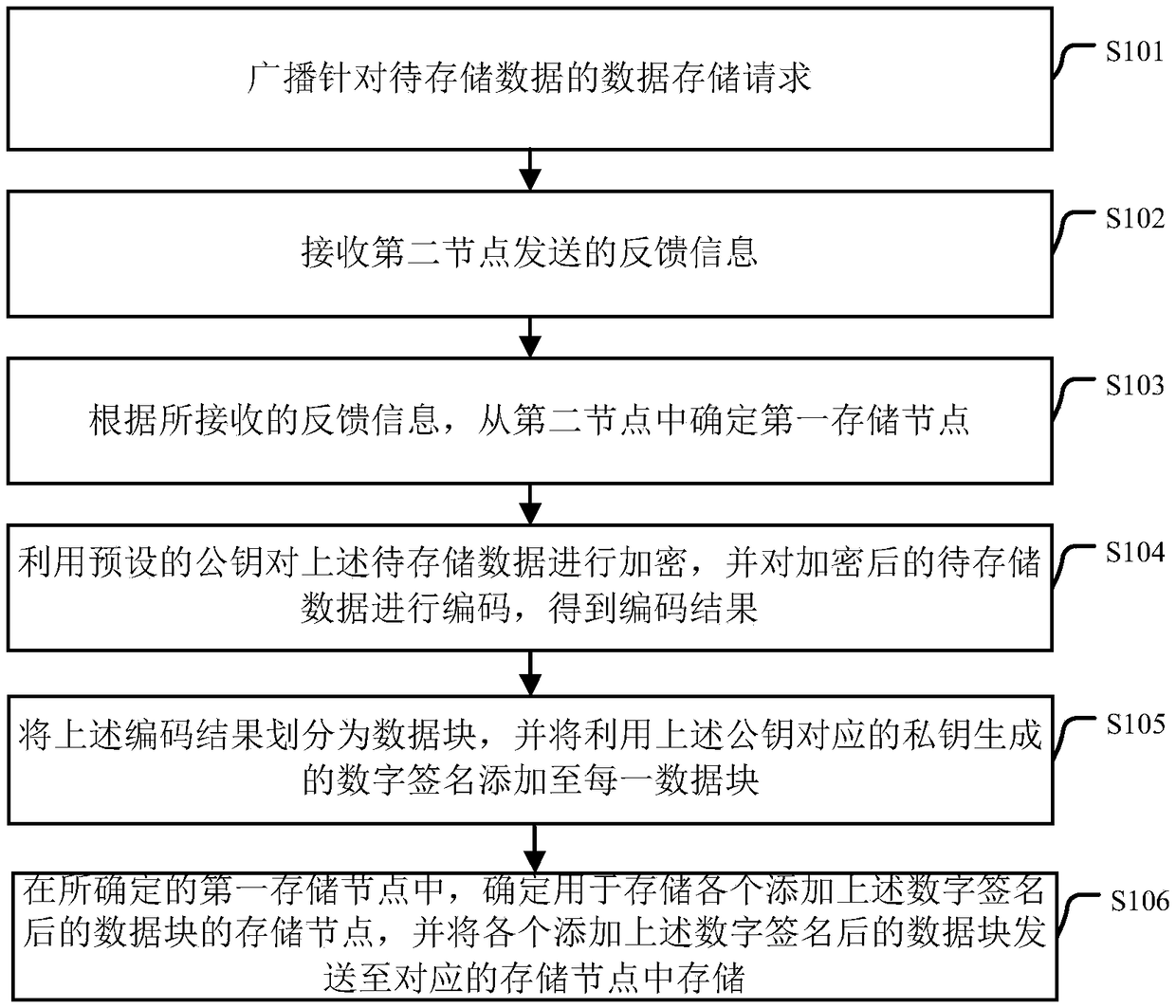
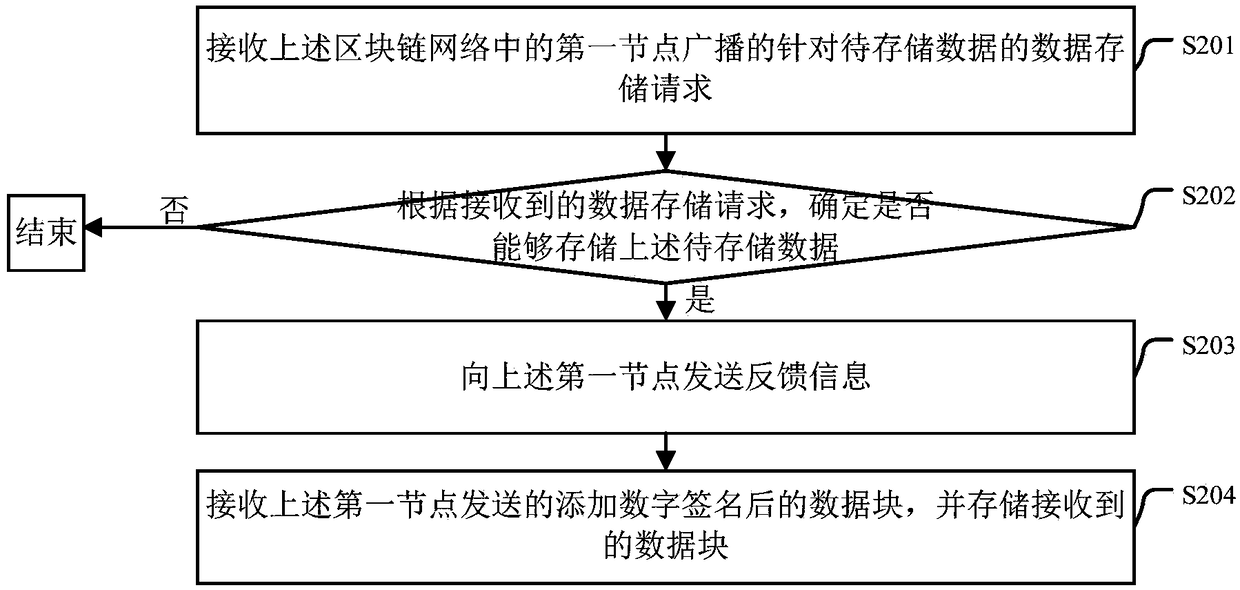
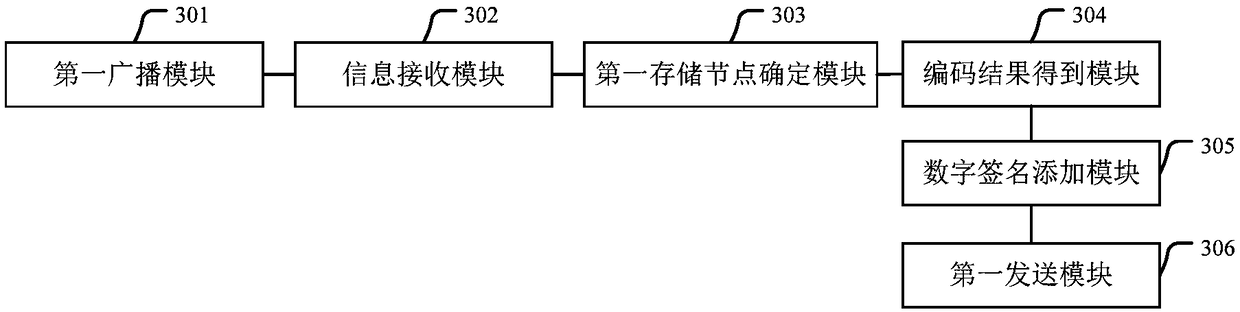
Data storage method and apparatus
InactiveCN109302495AImprove securityTamper-resistantUser identity/authority verificationComputer securityStorage security
The embodiment of the invention provides a data storage method and apparatus. The method comprises the following steps: determining a first storage node from a second node according to received feedback information corresponding to a data storage request sent by the second node for broadcast, encrypting to-be-stored data by using a preset public key, and encoding the encrypted to-be-stored data toobtain an encoding result; dividing the encoding result into data blocks, and adding a digital signature generated by using a private key corresponding to the public key to each data block; and determining a storage node of each data block with the added digital signature, and sending the data block to the determined storage node for storage. By application of the scheme provided by the embodiment of the invention , the data storage security can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Composition of encrypted two dimensional bar codes and application method therefor
InactiveCN1878057AImprove securityWith anti-counterfeiting functionKey distribution for secure communicationCoding/ciphering apparatusThe InternetInformation security
Owner:王向东
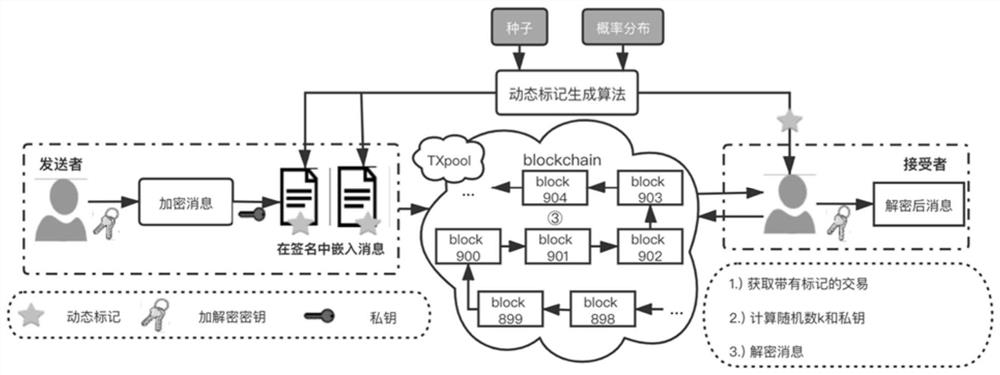
Block chain hidden information transmission method and system based on dynamic marking
PendingCN112070496ATamper resistantNo changes involvedDigital data protectionPayment protocolsKey (cryptography)Algorithm
The invention relates to a block chain hidden information transmission method and system based on dynamic marking. The method comprises the following steps: counting data true probability distributionof an OP_RETURN field of a block chain protocol; generating a dynamic mark according to the negotiated seed and the data real probability distribution of the OP_RETURN field; and enabling the sendernode to fill the dynamic marks into the OP_RETURN fields of the two transactions, performing digital signature by adopting an elliptic curve cryptographic algorithm, and sending the two signed transactions to the block chain; enabling the receiver node to identify the two transactions according to the dynamic marks, performing elliptic curve cryptography algorithm random number leakage attack on digital signatures of the two transactions, calculating used random factors, deducing a private key, namely an encoded encrypted message, decoding the encrypted message and decrypting the encrypted message by using a secret key negotiated with the sender node. According to the invention, the undetectability and tracking resistance of the channel can be realized, the strong robustness is satisfied,and the risk of user privacy exposure is greatly reduced.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Use, provision, customization and billing of services for mobile users through distinct electronic apparatuses
InactiveCN101543099AWith processing functionTamper-resistantAssess restrictionDigital data authenticationComputer terminalMobile telephony
An office electronic apparatus is associated to an apparatus card and is able to use or provide a service by means of identification information; the identification information allows billing of the use or provision of the service. A mobile telephone terminal is associated to a subscriber card storing subscriber identification information. According to the method of the present invention, at least the subscriber identification information and preferably also subscriber authentication information are transferred from the mobile telephone terminal to an office electronic apparatus when the said mobile telephone terminal is in proximity of the office electronic apparatus, the transferred information is stored into the apparatus card of the office electronic apparatus, and the service is autonomously used or provided by the office electronic apparatus by means of the transferred information.
Owner:TELECOM ITALIA SPA
Devices and methods useful for authorizing purchases associated with a vehicle
InactiveUS7907058B2Easy to installSimple to retrofitBuying/selling/leasing transactionsBurglar alarm by hand-portable articles removalEmbedded system
Various devices are useful as components of a system for authorizing purchases associated with a vehicle that are generally simple to install, operate and maintain and are generally resistant to abuse. The devices include theft-resistant vehicular identification tags, sealed identification tag reader and variable range tag-readers.
Owner:GASNGO R&D LTD
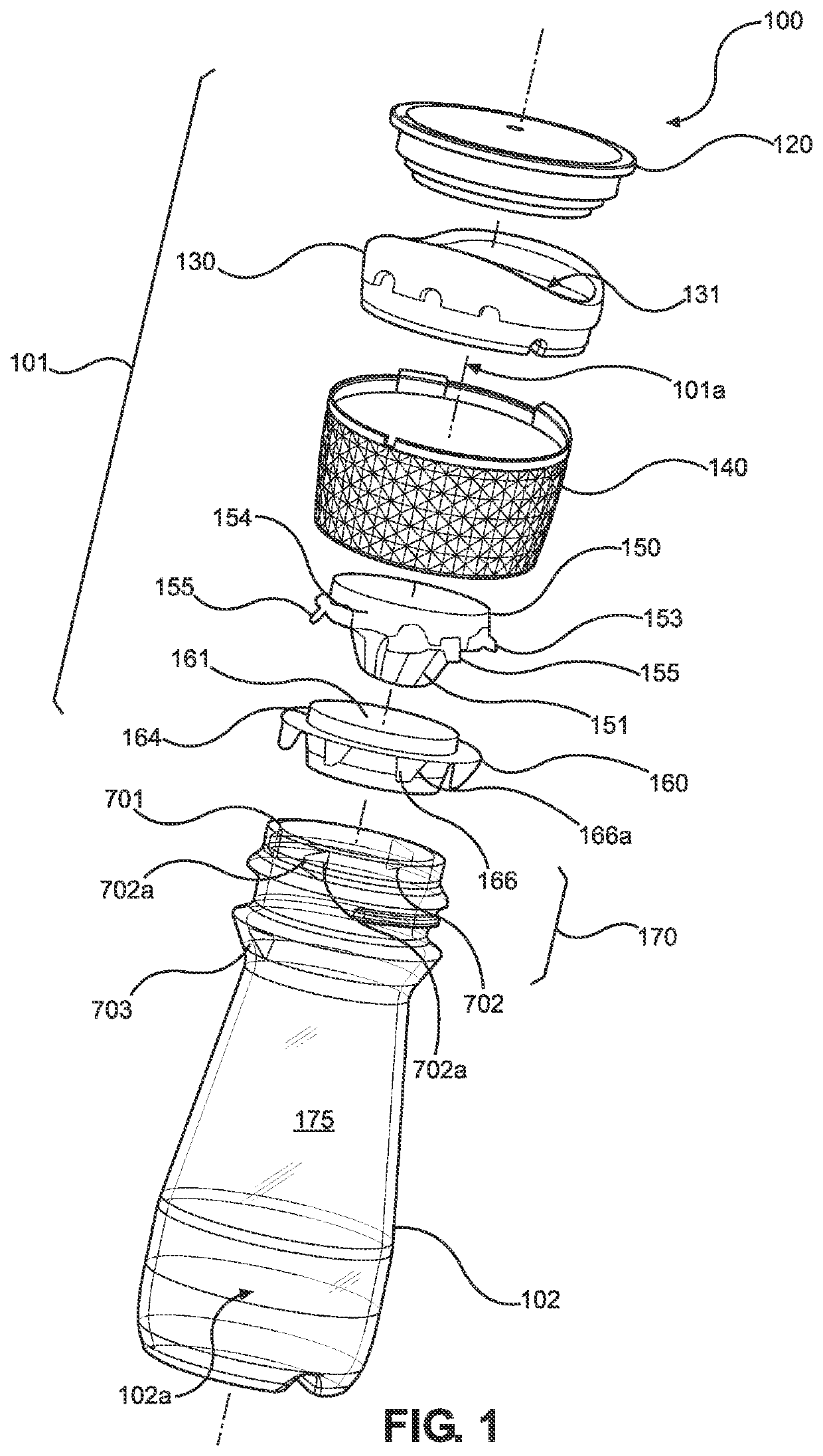
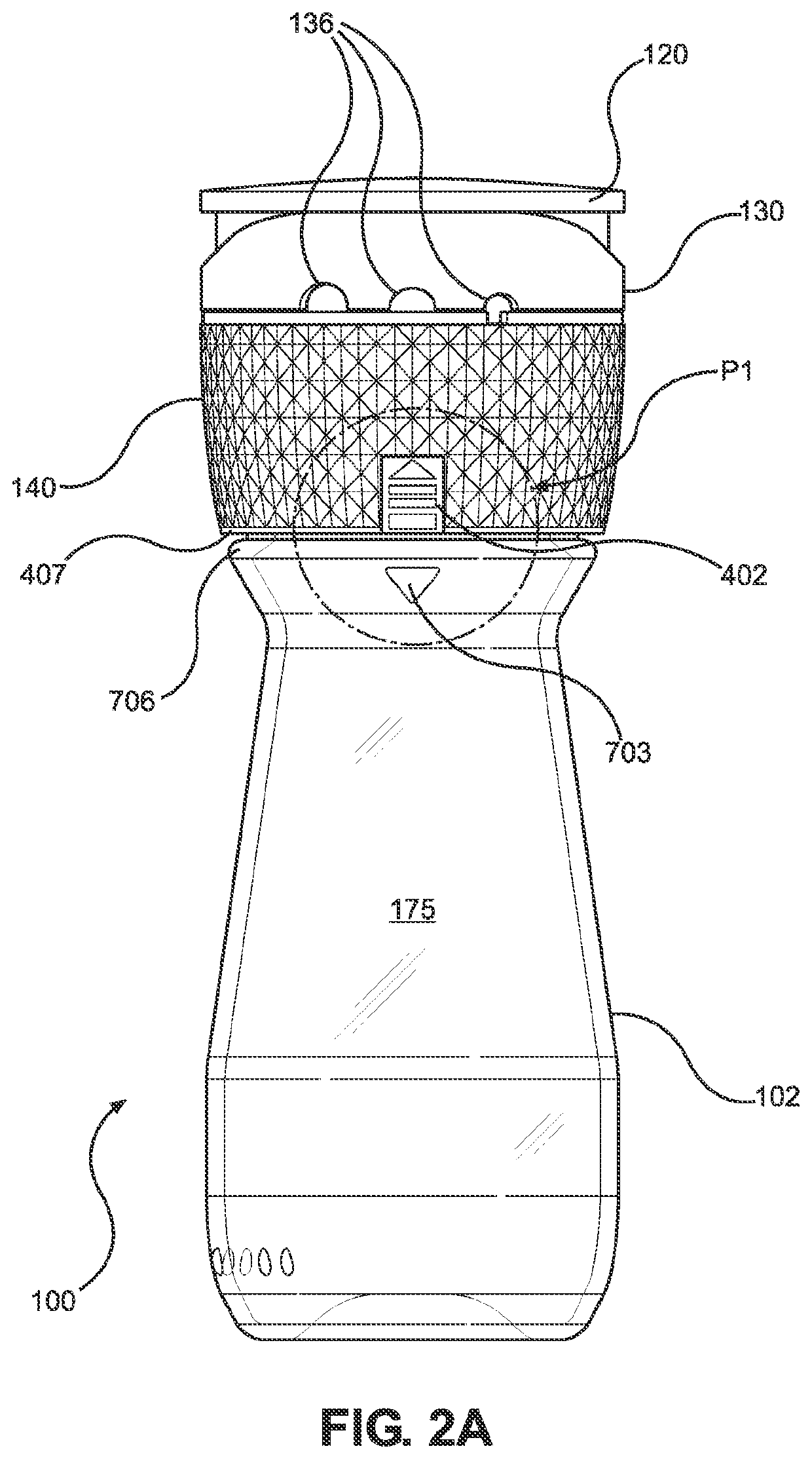
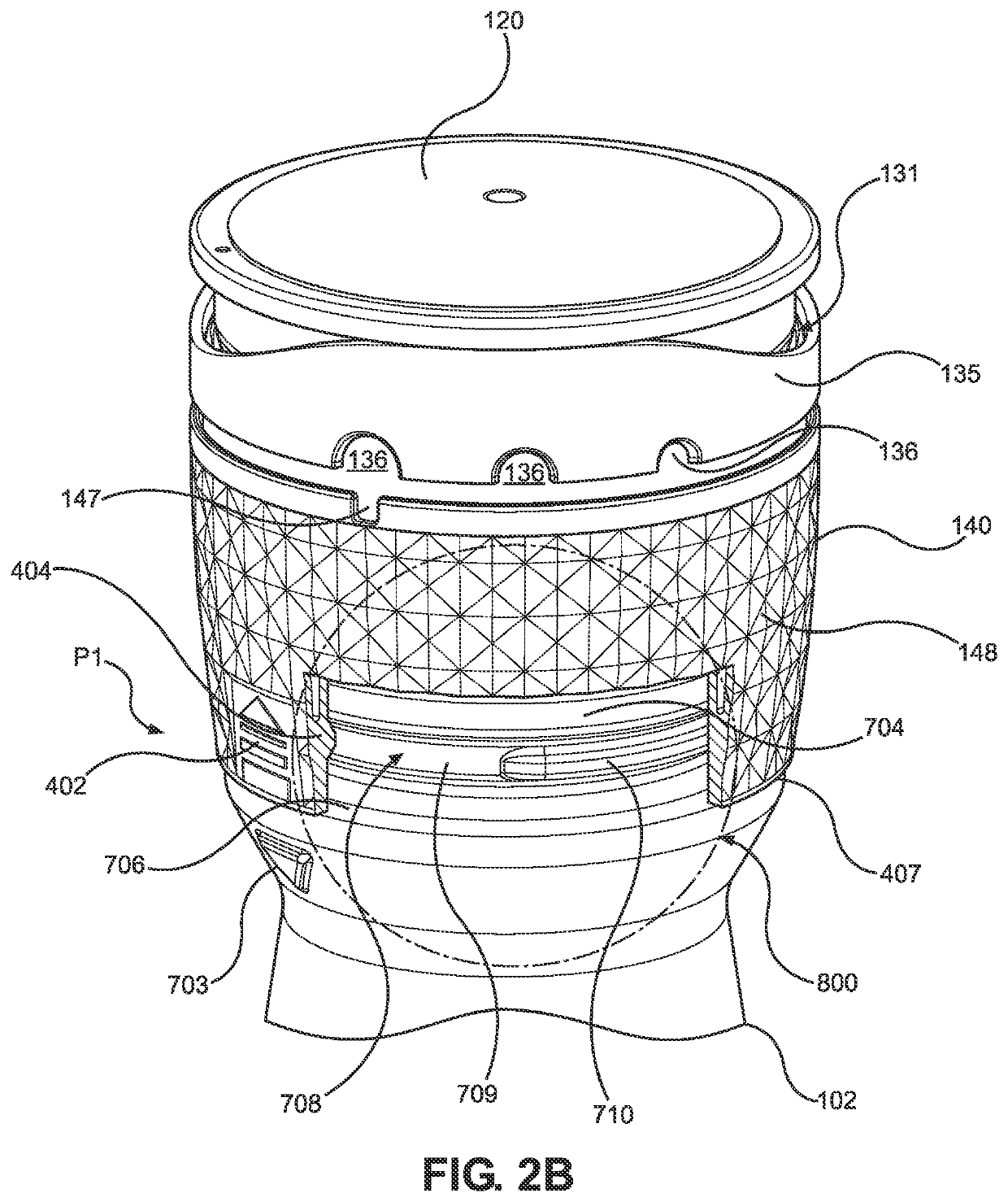
Grinder device
PendingUS20220248906A1Facilitates easy and secure removal/attachment of the capEncourages recyclabilityCoffee millsSpice millsEngineeringMechanical engineering
A grinder device is provided. The grinder device may include a container, a cap assembly configured to be friction-fit to the container such that the cap assembly is removably lockable to the container, and a grinding mill disposed within the cap assembly to perform a grinding operation of condiment disposed in the container. The grinding mill may include a movable grinder portion and a fixed grinder portion that are rotatable relative to each other, and the fixed grinder portion is engagable with the container to permit relative rotation between the cap assembly and the container.
Owner:MCCORMICK & CO INC
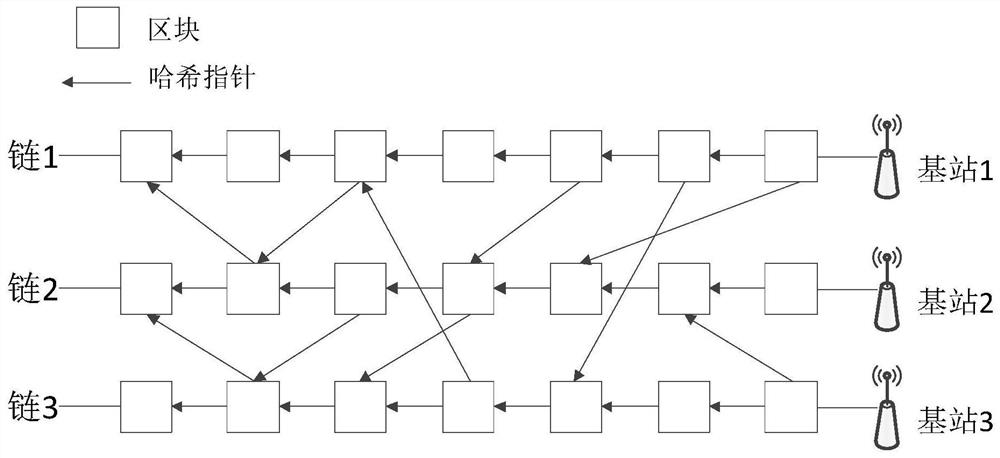
Thermal coal inbound acceptance method for thermal power enterprise on the basis of blockchain
InactiveCN110070659AWith anti-cracking functionLow costIndividual entry/exit registersResourcesQuality controlCoal
The invention relates to a thermal coal inbound acceptance method for a thermal power enterprise on the basis of a blockchain. The technical scheme of the method is that collected data is packaged toobtain a new blockchain block to serve as the data fingerprint of a current coal inbound process, and the data fingerprint is added into the blockchain of a blockchain system for a subsequent thermalpower enterprise to carry out the query backtracking work of any batch of coal quality control information at any time. A blockchain technology is adopted to store the collected data, the basic structure of the bottom layer of the blockchain is a linear linked list which is formed by connecting "blocks" in series, a subsequent block needs to record the Hash value of a previous block while data isrecorded, and all blocks are combined to form the blockchain. Therefore, the blockchain forms a total account book which is convenient in verification and is unchangeable, a situation that data is maliciously tampered in any node can be identified, and the data can be automatically recovered to a state before tampering through the data of other nodes.
Owner:CENT CHINA BRANCH OF CHINA DATANG CORP SCI & TECH RES INST CO LTD
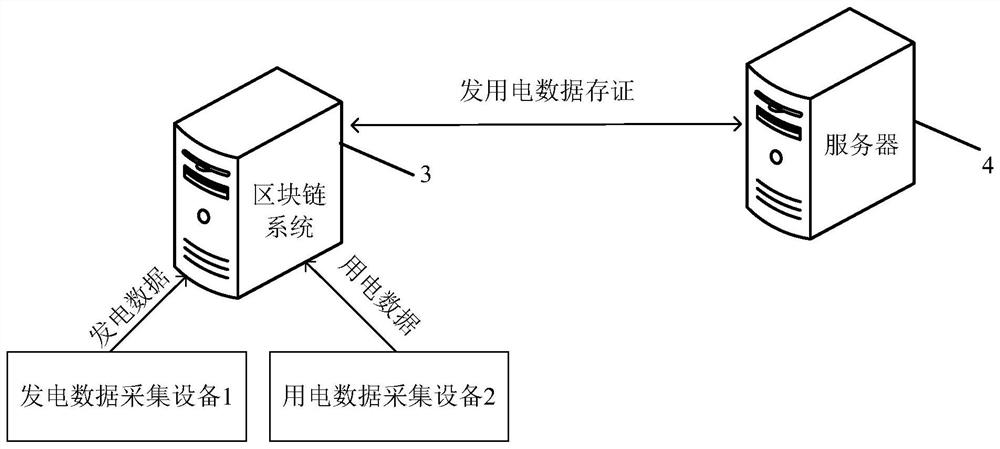
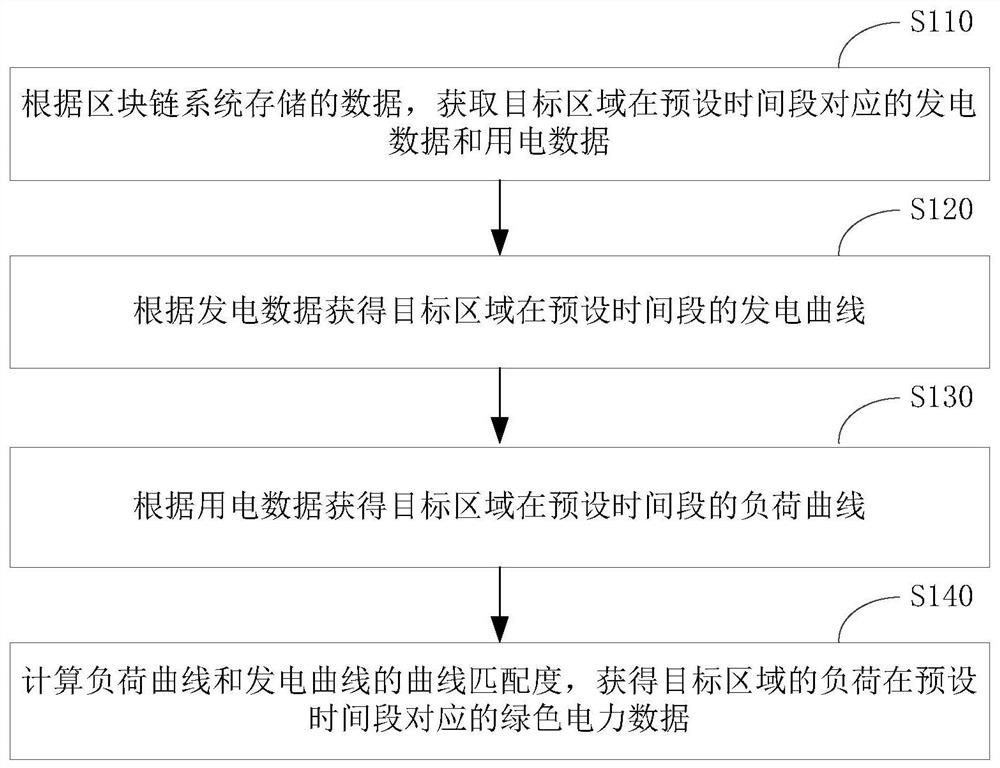
Green electricity source tracing method and device based on block chain
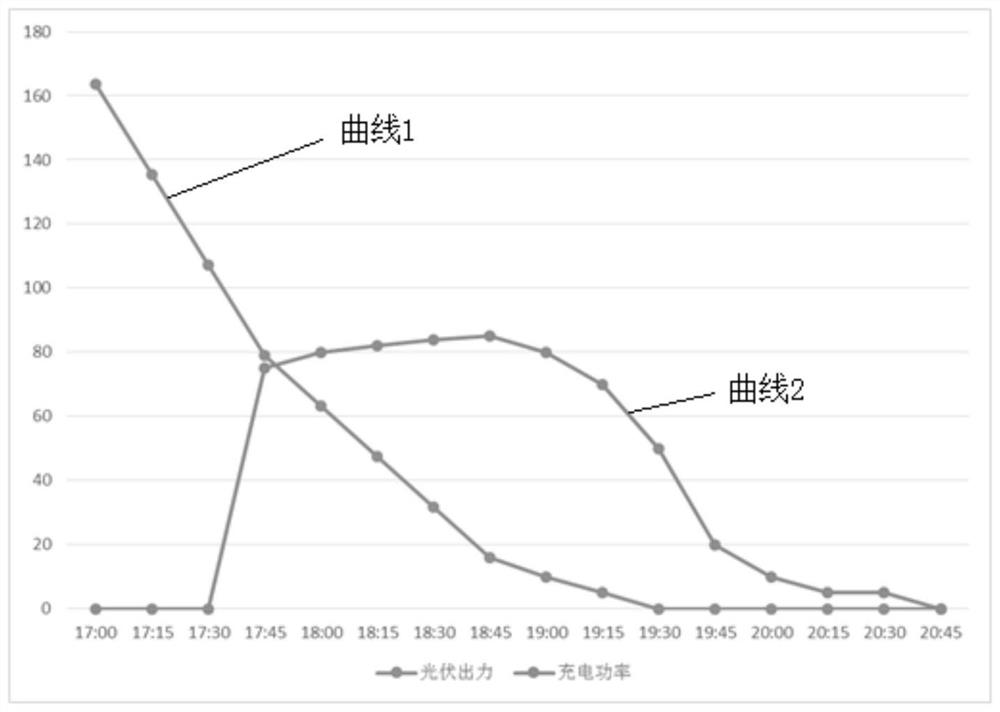
PendingCN113010605APut an end to the possibilityTamper-resistantDatabase distribution/replicationDigital data protectionPower usageData store
The invention provides a block chain-based green electricity source tracing method and device. The method comprises the steps: enabling a data collection device to carry out the digital signature of collected power generation data and power utilization data, and uploading the data to a block chain, and enabling a server to obtain the corresponding power generation data and power utilization data of a target region in a preset time period based on the data stored in a block chain system, drawing a power generation curve by using the power generation data, and drawing a load curve by using the power consumption data; and then, calculating a curve matching degree of the load curve and the power generation curve, and obtaining green power data corresponding to the load of the target region in a preset time period. According to the above process, the scheme can accurately measure the green power data in the power consumption data, such as the green power ratio and the green power, and provides a data basis for effectively measuring the contribution of the user to low carbon emission reduction. Moreover, according to the scheme, the possibility of manually modifying the data is avoided, so that the data has a tamper-proof characteristic, and the obtained green power data has a traceable characteristic.
Owner:合肥零碳技术有限公司
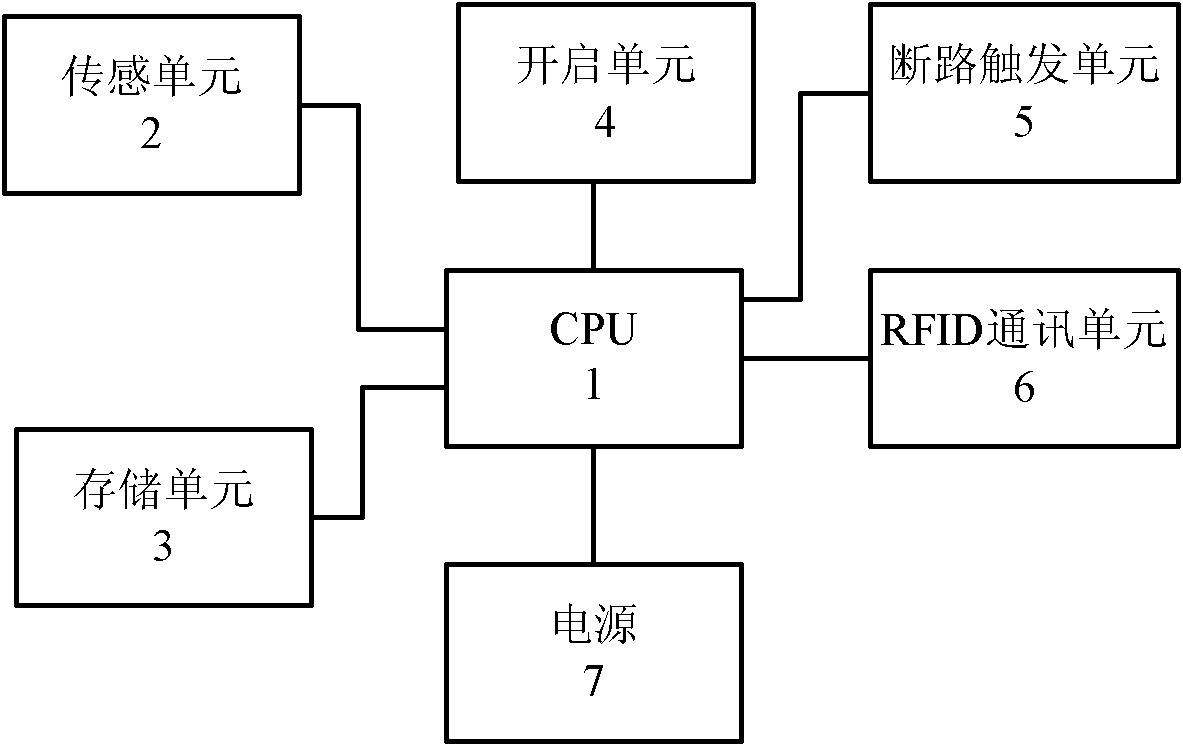
One-time tamper-proof RFID temperature and humidity recording and transmitting device for cold-chain logistics
InactiveCN103257595ATamper-resistantImprove securityElectric signal transmission systemsRecording measured valuesCold chainTamper resistance
The invention relates to a one-time tamper-proof RFID temperature and humidity recording and transmitting device for cold-chain logistics. The one-time tamper-proof RFID temperature and humidity recording and transmitting device for the cold-chain logistics comprises a CPU, a sensing unit, a storage unit, an opening unit, an open circuit trigger unit, a RFID communication unit and a power supply. The CPU is respectively connected with the sensing unit, the storage unit, the opening unit, the open circuit trigger unit, the RFID communication unit and the power supply. When the opening unit is opened, the CPU controls the sensing unit to begin to gather temperature and humidity information, wherein the temperature and humidity information is stored through the storage unit, the CPU detects and judges whether open circuit signals sent by the open circuit trigger unit are received or not in real time, if the open circuit signals are received, the CPU controls the sensing unit to stop gathering the temperature and humidity information, and meanwhile controls the RFID communication unit to be opened to send previously-gathered temperature and humidity data to an upper computer, and if the open circuit signals are not received, the CPU continues to detect whether the open circuit signals are received or not. Compared with the prior art, the one-time tamper-proof RFID temperature and humidity recording and transmitting device for the cold-chain logistics has the advantages that the temperature and humidity data can be automatically gathered, temperature and humidity data are objective, accurate and tamper-proof, and data gathering safety can be improved.
Owner:SHANGHAI YISHI ELECTRONICS INFORMATION
IOT equipment behavior credibility supervision method based on block chain
ActiveCN113115315AGuarantee authenticityPrevent crashSecurity arrangementSecuring communicationProtection mechanismNetwork architecture
The invention provides an IOT equipment behavior credibility supervision method based on a block chain, which is based on the block chain and the Internet of Things technology and is applied to the field of the Internet of Things. Aiming at the problem that a large amount of equipment lacks an effective security protection mechanism and is prone to attack to make untrusted behaviors in the Internet of Things industry at present, an IOT equipment supervision and management network architecture based on a block chain is designed, Internet of Things nodes are supervised by using a block chain technology, the nodes making untrusted behaviors are found and processed, and the security of the Internet of Things equipment is effectively improved. The method specifically comprises the steps that a block chain is deployed on an Internet of Things platform, a verification node on the chain generates a comprehensive reputation value for a common node according to data generated when the common node works by using algorithms such as deep learning and a neural network, and the comprehensive reputation value of each node is judged by using an artificial intelligence algorithm; and untrusted behaviors generated by the nodes whose reputation value is judged to be lower than the set reputation value threshold are reported, and support is provided for subsequent corresponding management and control operations.
Owner:QINGDAO UNIV OF SCI & TECH
Data symmetric encryption method for dual-plaintext transmission
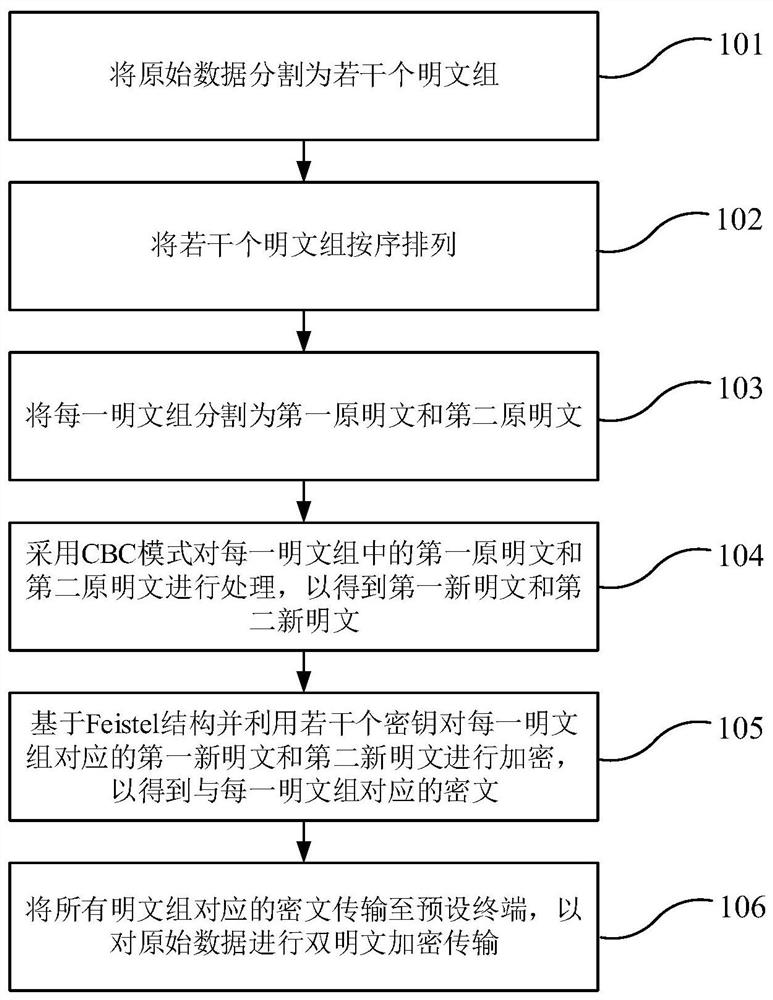
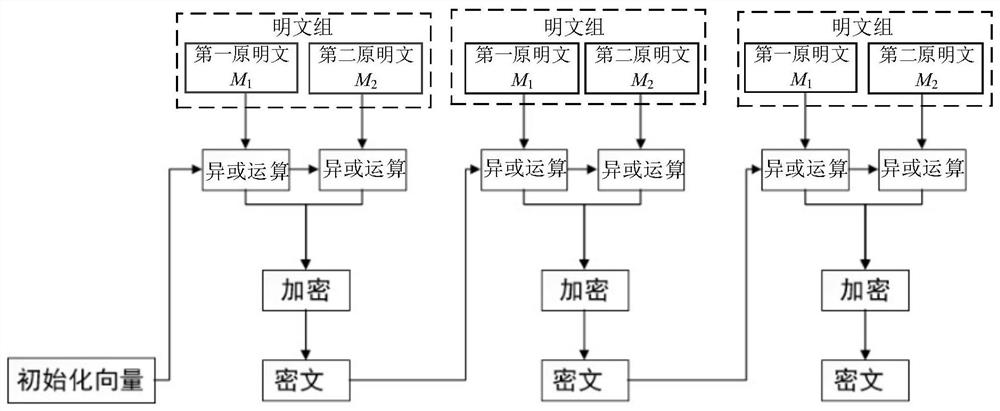
ActiveCN112866288APracticalEfficient encrypted transmissionEncryption apparatus with shift registers/memoriesPlaintextAlgorithm
The invention discloses a data symmetric encryption method for dual-plaintext transmission. The method comprises the following steps: dividing original data into a plurality of plaintext groups; arranging the plurality of plaintext groups in sequence; dividing each plaintext group into a first original plaintext and a second original plaintext; processing the first original plaintext and the second original plaintext in each plaintext group by adopting a CBC mode to obtain a first new plaintext and a second new plaintext; encrypting the first new plaintext and the second new plaintext corresponding to each plaintext group by using a plurality of keys based on a Feistel structure to obtain a ciphertext corresponding to each plaintext group; and transmitting the ciphertexts corresponding to all the plaintext groups to a preset terminal so as to perform dual-plaintext encryption transmission on the original data. Based on the three-wheel Feistel structure, dual-plaintext encryption transmission can be carried out on the original data with the dual-plaintext feature, feasibility is achieved, and the safety in the original data transmission process can be enhanced.
Owner:上海汉枫电子科技有限公司
Large-scale instrument sharing experiment execution credibility discrimination method
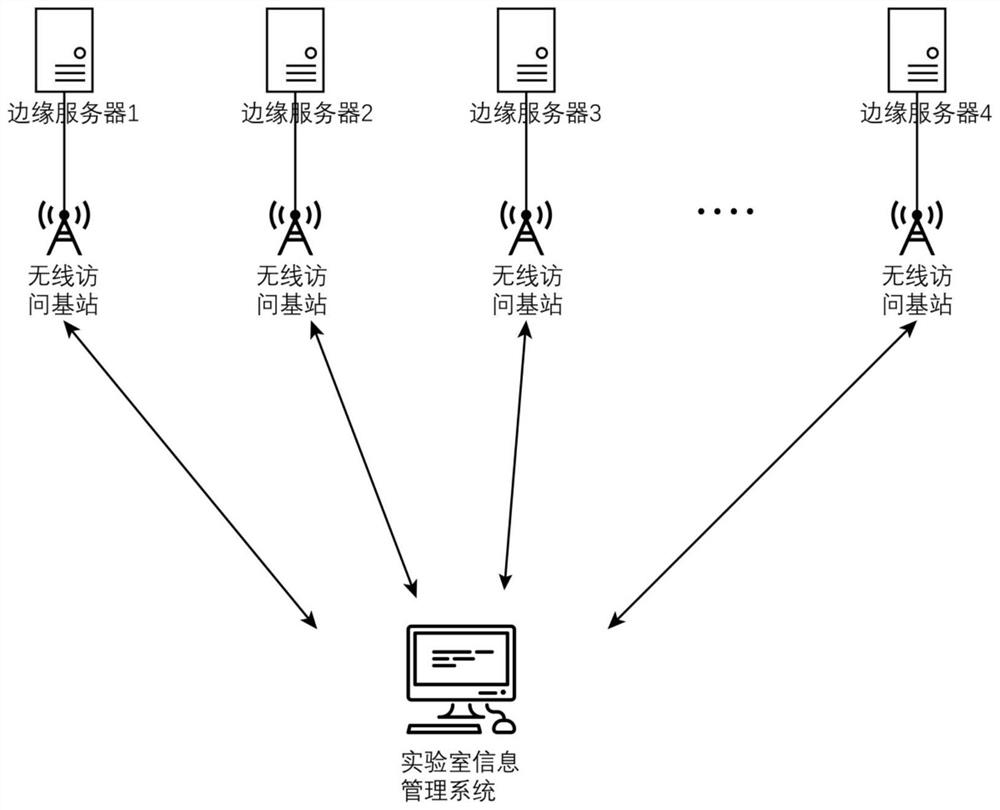
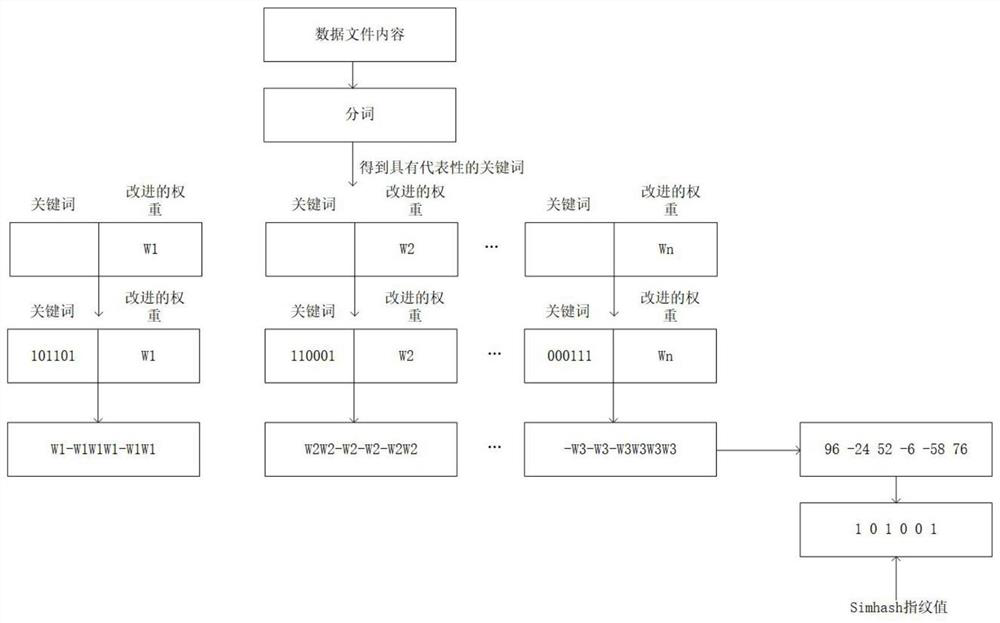
PendingCN114154476AUnique timestamp featureReflect usageDatabase distribution/replicationCharacter and pattern recognitionData fileEngineering
The invention discloses a method for judging the execution credibility of a shared experiment of a large instrument. The method comprises the following steps: (1) acquiring experiments and related sample data files which can be performed by all current large instruments, and establishing a data sample set; (2) uploading a data recording file obtained by direct connection with the large instrument to a laboratory information management system, and preprocessing the data recording file through an MEC; (3) transmitting the processed data record file to a block chain, and creating a data slice; and (4) a worker obtains the data recording file from the block chain through the secret key, compares the extracted data recording file with the sample data file in the data sample set by using a Simhash algorithm in pattern recognition, and judges the authenticity of experimental data. According to the method, the shared use data condition of the large instrument equipment can be obtained, so that whether the instrument equipment is actually used or not can be better judged. It is directly proved that the predetermined experiment of the shared instrument is real.
Owner:HANGZHOU DIANZI UNIV
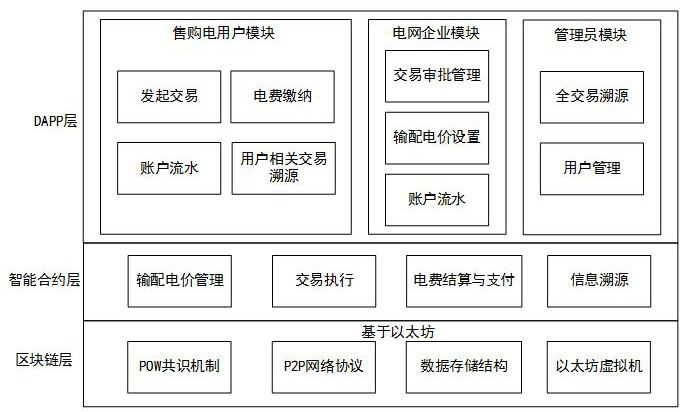
Medium and long term electricity transaction method and system based on smart contract
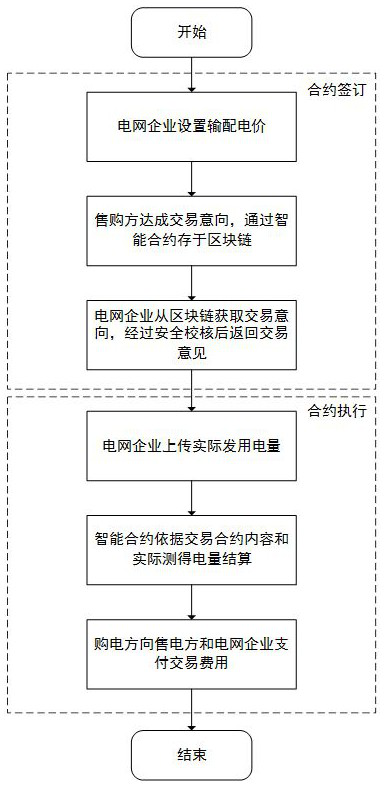
InactiveCN113971611AReduce the cost of trustTamper-resistantFinanceDigital data protectionComputer networkBusiness enterprise
The invention discloses a medium and long term power transaction method and system based on a smart contract, and belongs to the field of distributed power transaction, and the method comprises the steps: S1, a power grid enterprise sets a power transmission and distribution price, and uploads the power transmission and distribution price to a block chain; S2, after the electricity seller and the electricity purchaser reach a transaction intention, an intelligent contract is called to obtain the power transmission and distribution price from the block chain to draw up a medium and long term transaction contract and the transaction contract is stored to the block chain through the smart contract; S3, the power grid enterprise calls an intelligent contract to obtain a transaction contract from the block chain and performs security check and when the security check result is that the transaction is approved, contract signing succeeds; S4, the power grid enterprise uploads the measured transaction electric quantity of the seller and the buyer to the block chain through the smart contract for electric quantity settlement; and S5, the electricity purchaser sends the settled transaction fee to the smart contract account so that the smart contract account can distribute the transaction fee, and contract execution is completed. According to the invention, the problems of low cross-department data processing efficiency and difficulty in transaction information tracing and supervision in medium and long-term power transactions can be solved.
Owner:HUAZHONG UNIV OF SCI & TECH +2
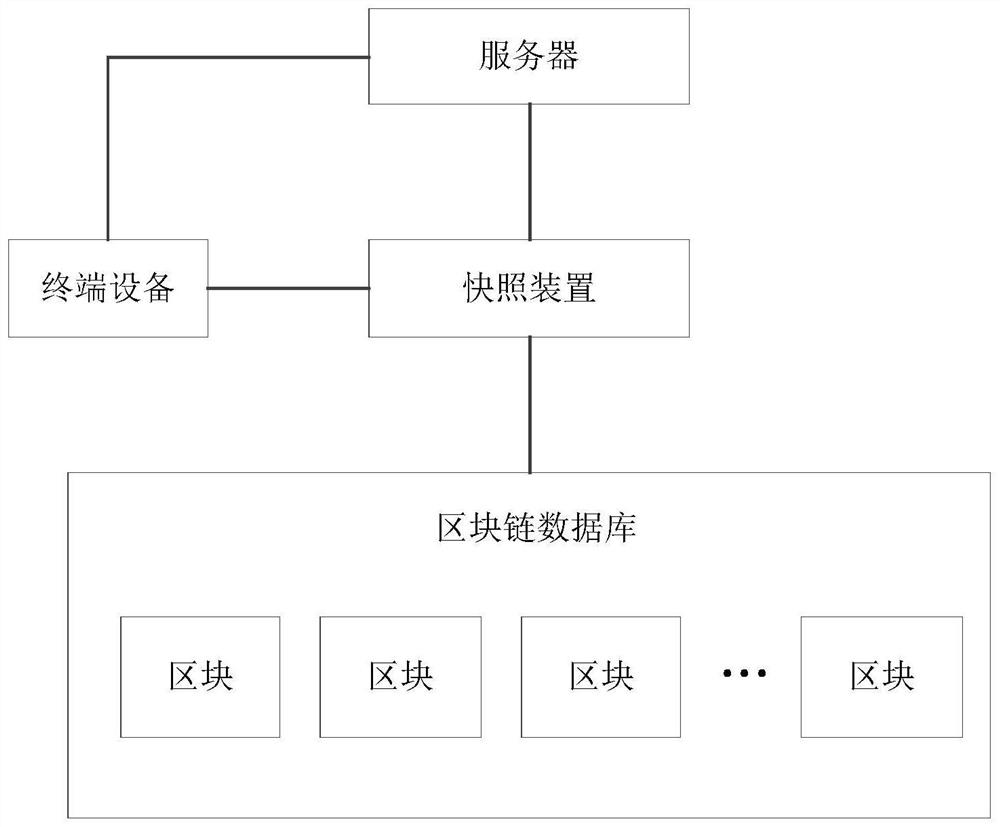
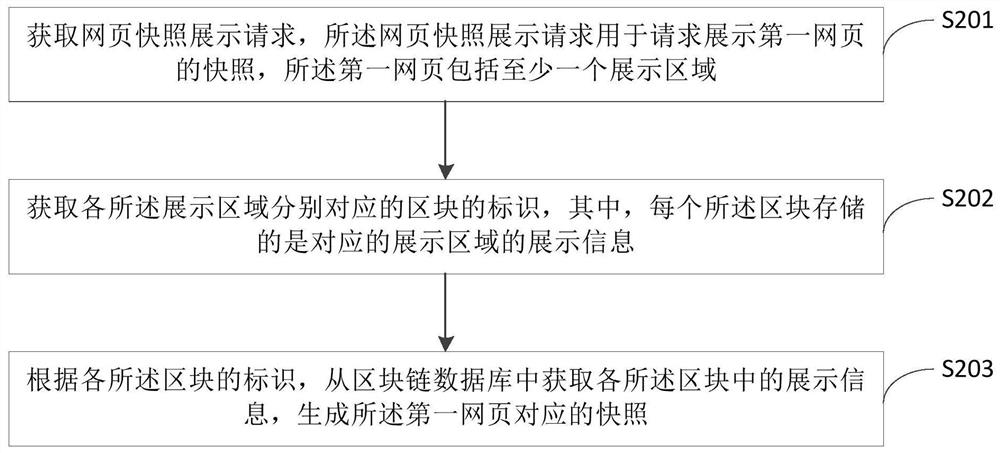
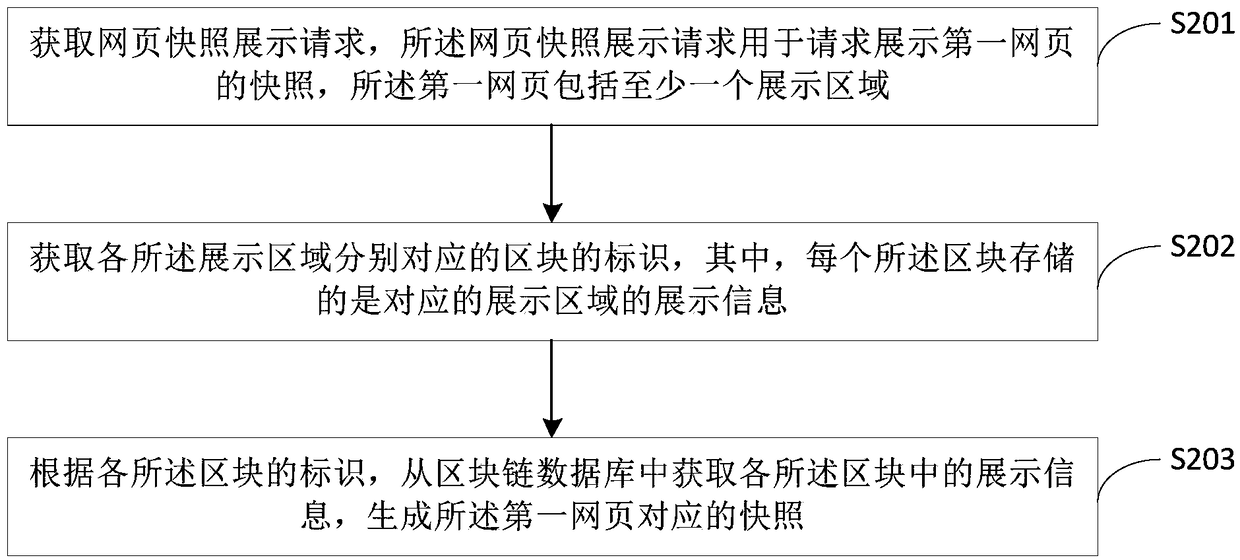
Method and device for generating webpage snapshot
The embodiment of the invention provides a method and device for generating a web page snapshot. The method comprises the steps of obtaining a web page snapshot presentation request, wherein the web page snapshot presentation request is for requesting the presentation of a snapshot of a first web page, and the first web page includes at least one display area; obtaining the identification of the blocks corresponding to each display area, obtaining the display information in each block from the block chain database according to the identification of each block, and generating a snapshot corresponding to the first web page. As a block chain technology is adopted to store the web pages in different regions, the generated web page snapshots are tamper-proof, and the authenticity of the web page snapshots is ensured. Furthermore, the method also reduces the waste of storage resources and improves the performance of the snapshot generation system.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Photo file management method and system based on block chain technology
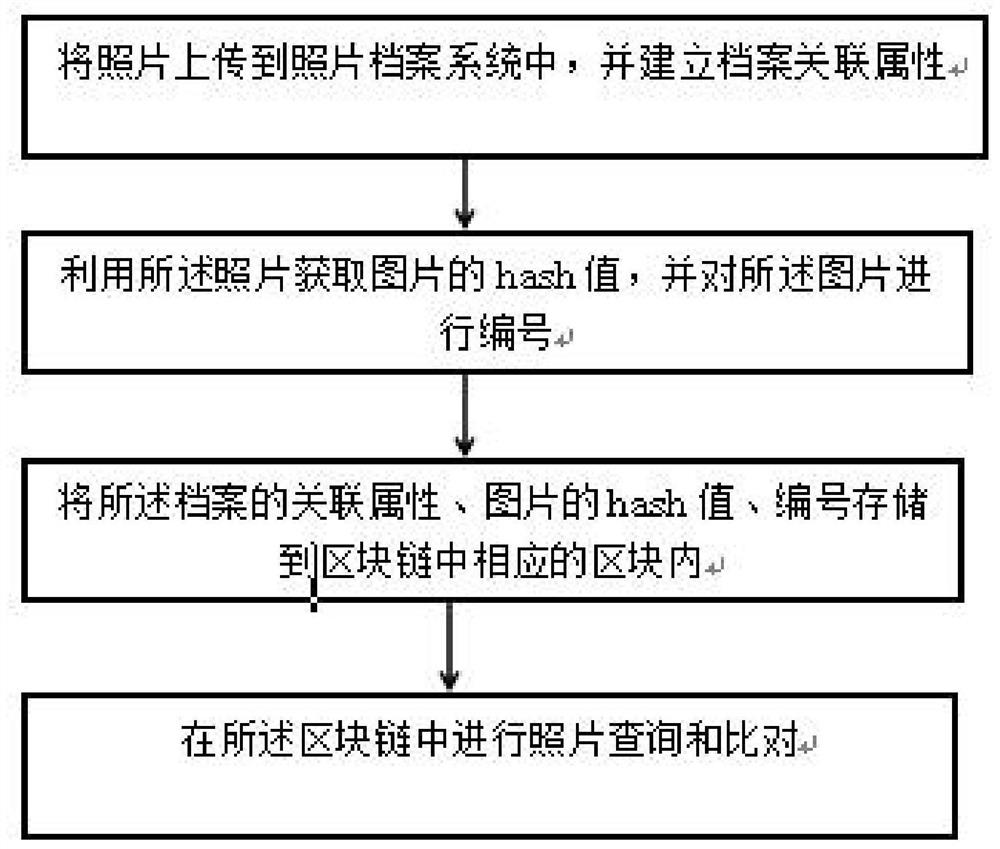
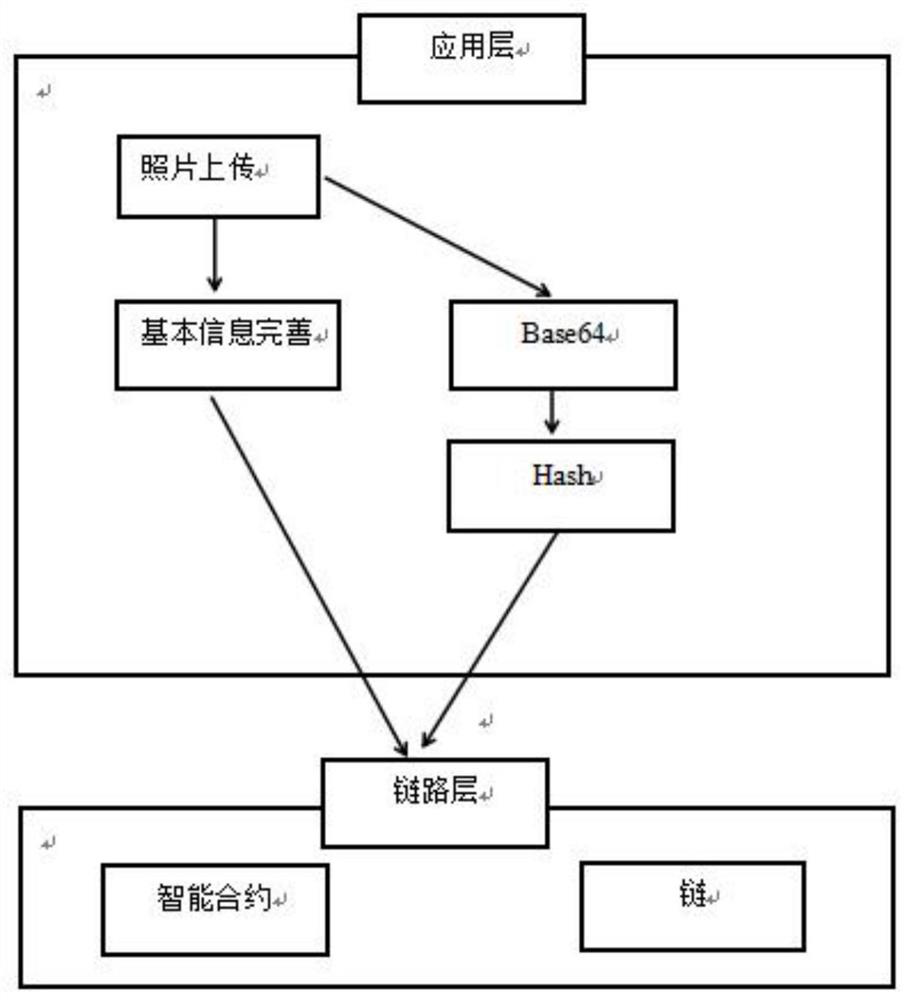
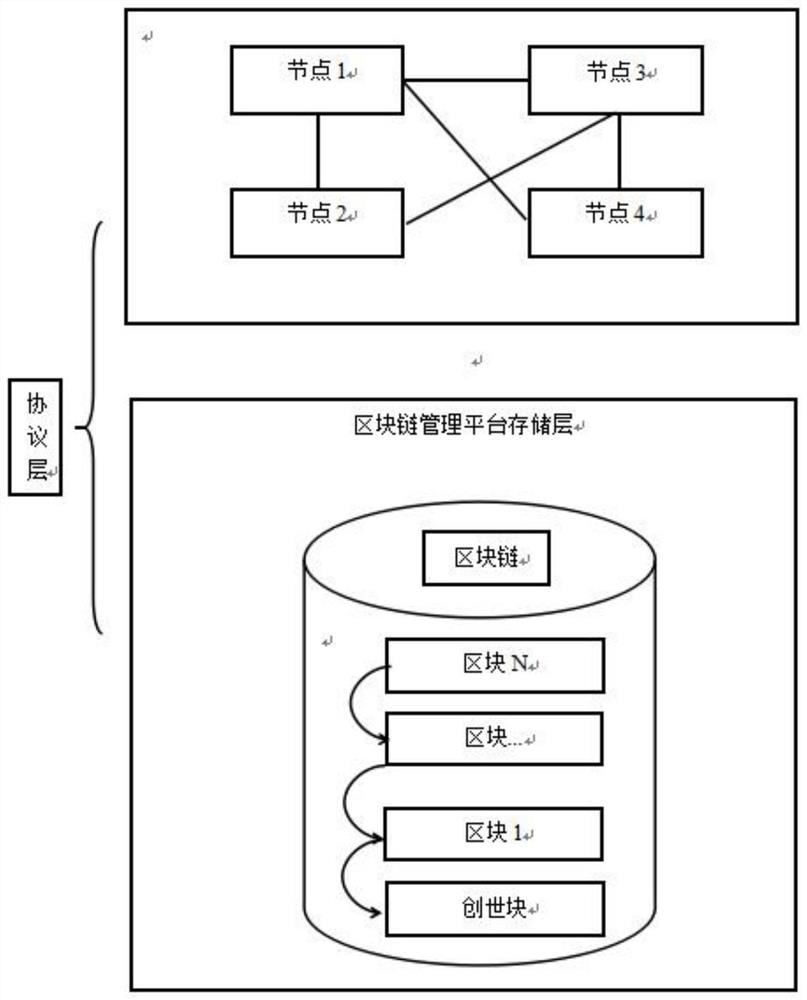
InactiveCN112632305ARealize functionTamper-resistantStill image data indexingStill image data queryingFile systemEngineering
A photo file management method based on a block chain technology comprises the following steps: uploading photos to a photo file system, and establishing file association attributes; obtaining a hash value of the photo, and numbering the photo; storing the associated attributes of the file, the hash value of the photo and the number into a corresponding block in a block chain; and carrying out photo query and comparison in the block chain. A photo file management system based on a block chain technology comprises a photo file acquisition system; a processing system, which is used for establishing photo file association attributes, acquiring hash values of the photos and numbering the photos; a block chain storage system, which is used for storing associated attributes of photo files and hash values and numbers of photos; and a query and comparison system. According to the invention, a decentralized blockchain platform is adopted to replace a traditional centralized data storage mode, and the storage has a tamper-proof capability. Meanwhile, the functions of storing and comparing the photo files are realized based on the block chain technology.
Owner:ANHUI UNIVERSITY
Method and device for generating web page snapshot
ActiveCN109325160ATamper-resistantGuarantee authenticityFinanceWeb data indexingTamper resistanceWeb page
The embodiment of the invention provides a method and device for generating a web page snapshot. The method comprises the steps of obtaining a web page snapshot presentation request, wherein the web page snapshot presentation request is for requesting the presentation of a snapshot of a first web page, and the first web page includes at least one display area; obtaining the identification of the blocks corresponding to each display area, obtaining the display information in each block from the block chain database according to the identification of each block, and generating a snapshot corresponding to the first web page. As a block chain technology is adopted to store the web pages in different regions, the generated web page snapshots are tamper-proof, and the authenticity of the web page snapshots is ensured. Furthermore, the method also reduces the waste of storage resources and improves the performance of the snapshot generation system.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
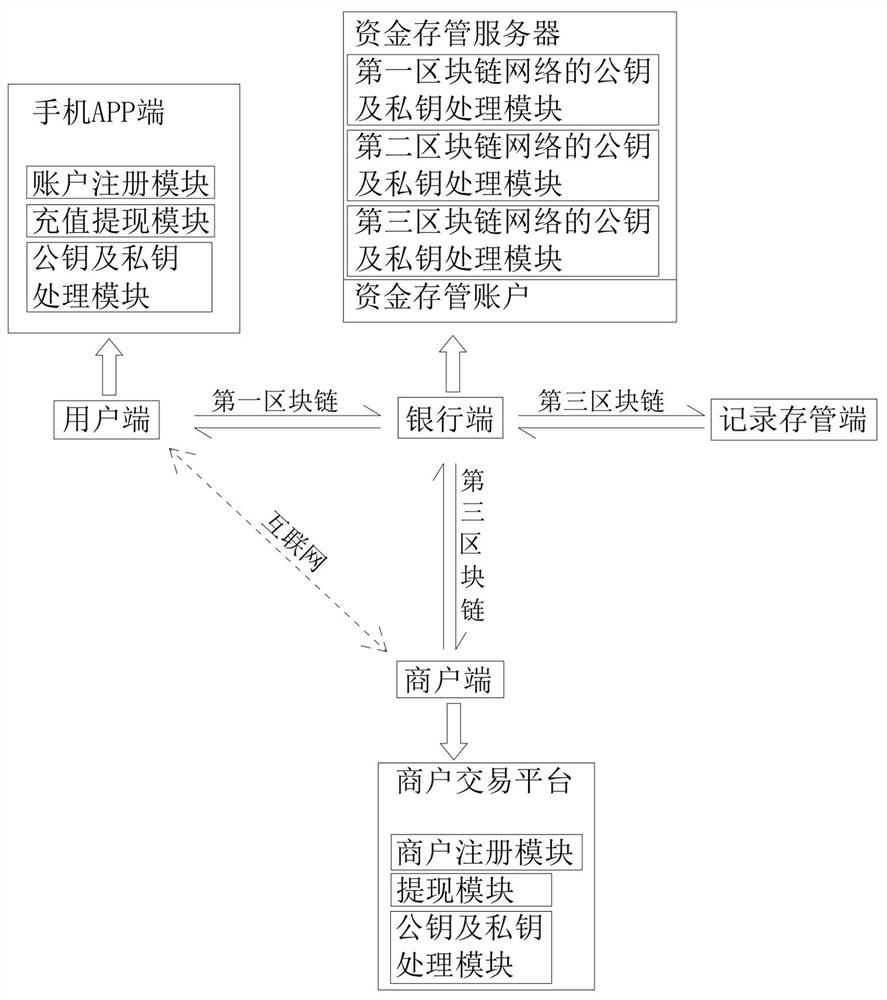
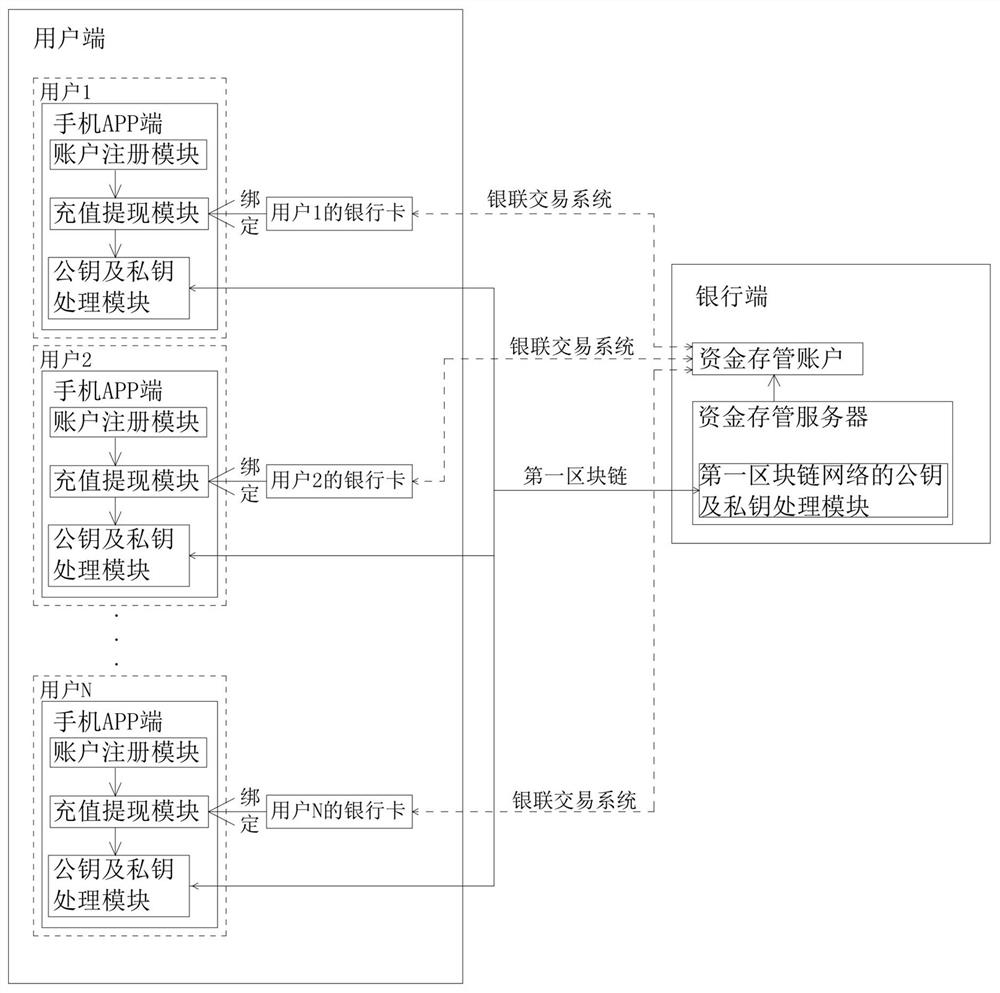
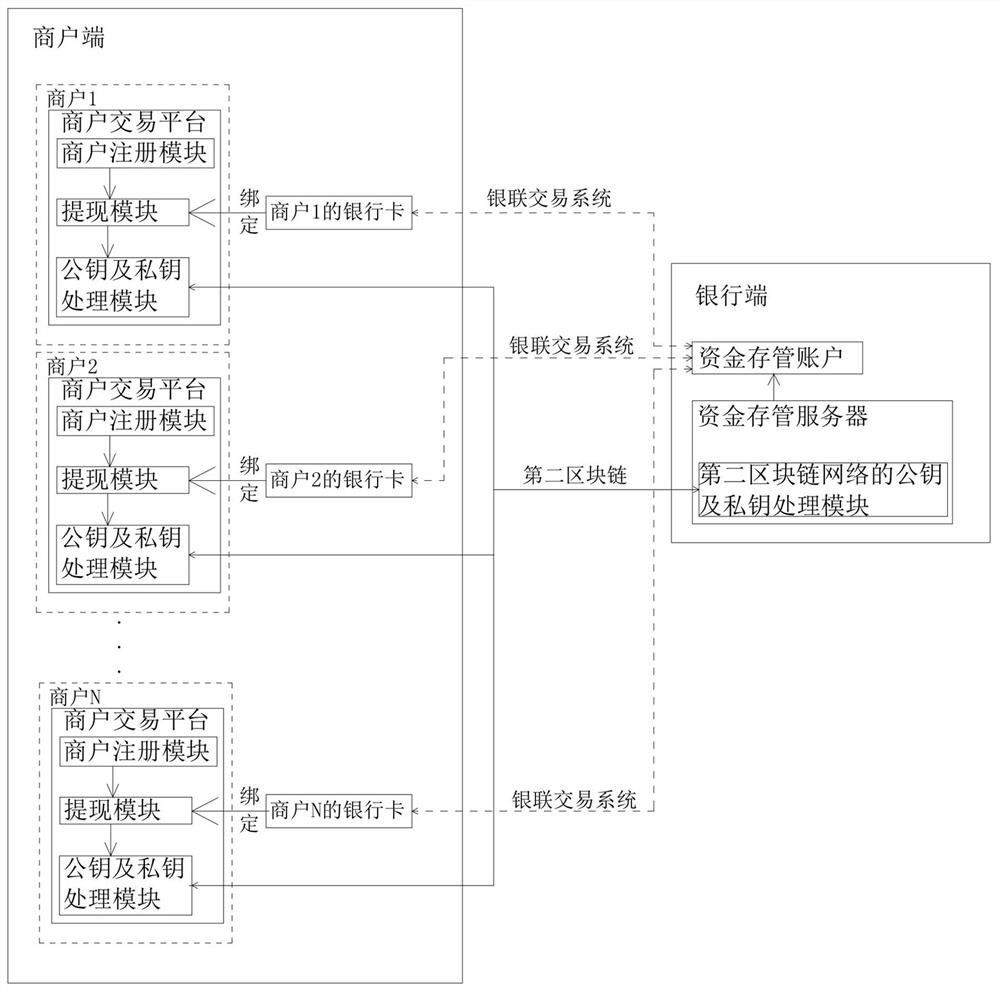
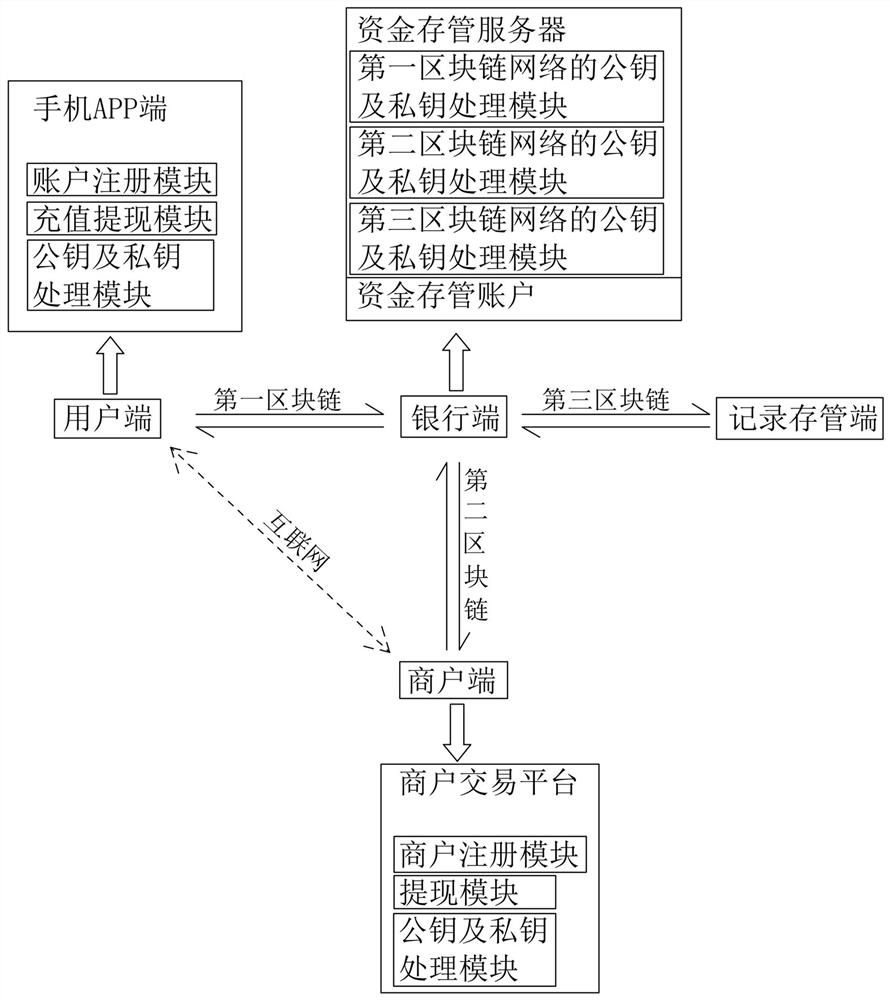
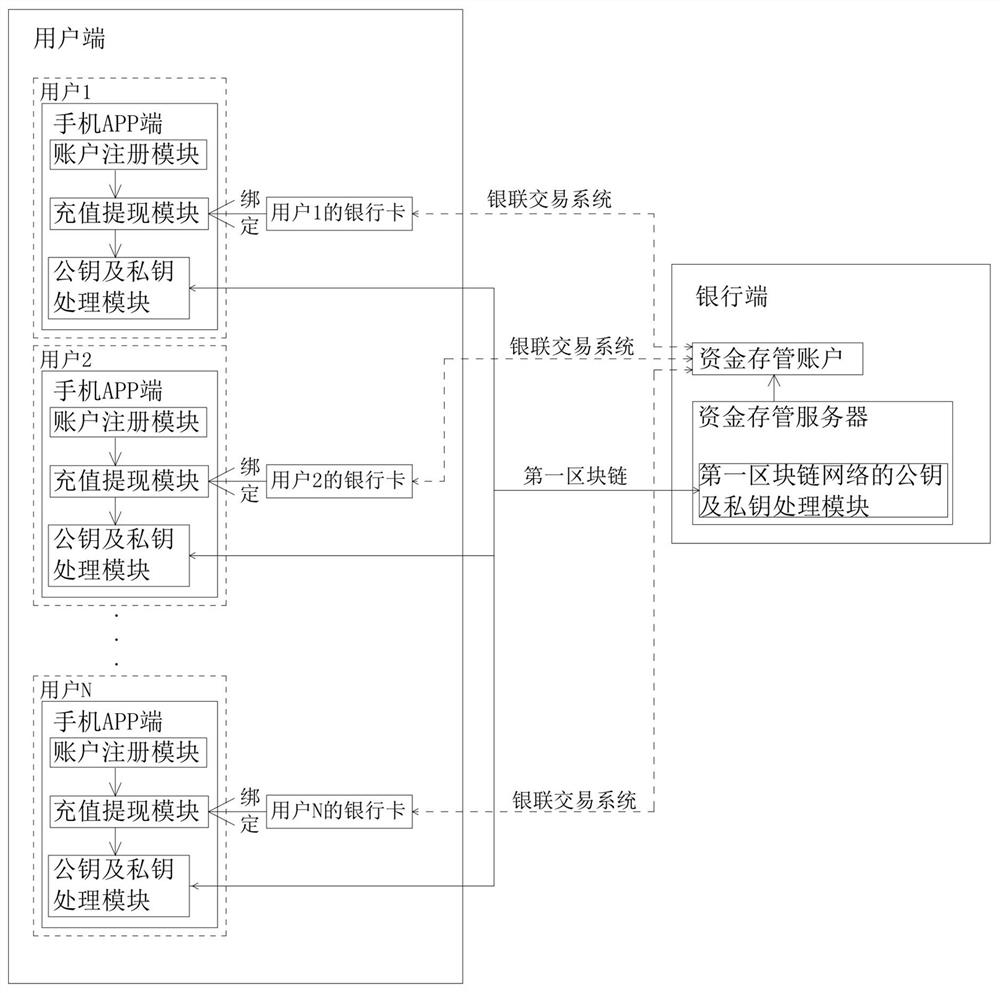
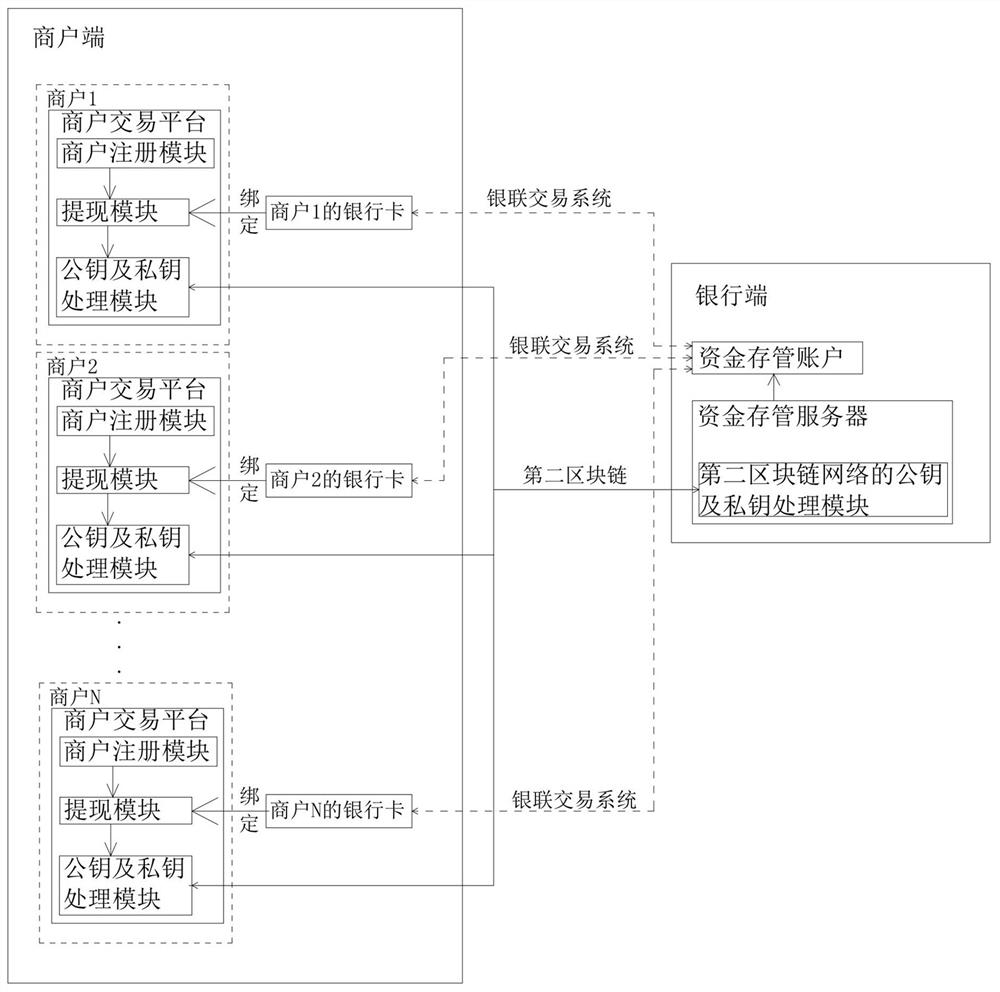
Fund account compliance processing system and implementation method
ActiveCN113240507ARealize unified storageImprove stability and securityFinanceDigital data protectionThe InternetFinancial transaction
The invention relates to the technical field of fund deposit and transaction, in particular to a fund account compliance processing system, which comprises a user side, a bank side, a merchant side and a record deposit side, and is characterized in that a first block chain network is arranged between the user side and the bank side, a second block chain network is arranged between the bank side and the merchant side, a third block chain network is arranged between the bank side and the record deposit side, and the user side and the merchant side are in internet data communication. According to the invention, unified deposit of funds can be achieved, supervision compliance is improved, and safety and stability of user or merchant fund exchange are improved.
Owner:绿漫科技有限公司
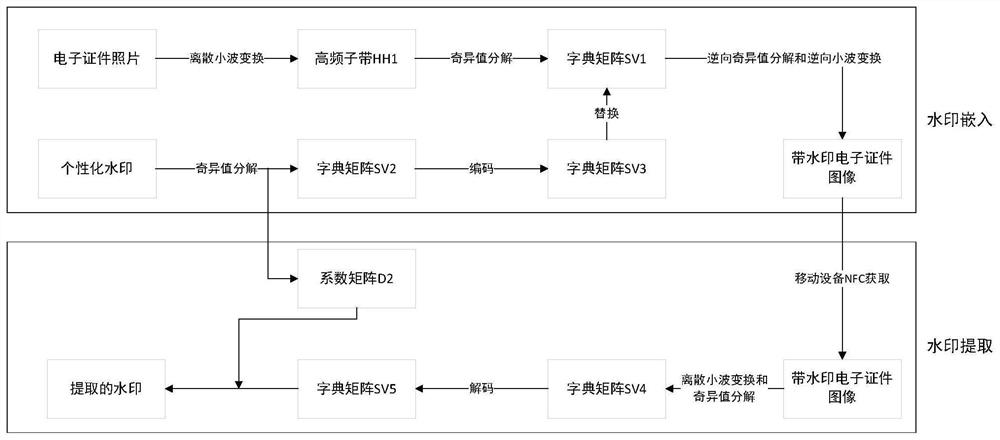
Personalized information embedding and authentication method for electronic documents for mobile devices
ActiveCN110782383BTamper-resistantAdaptableImage data processing detailsElectronic documentPersonalization
The present invention provides a method for embedding and authenticating personalized information of an electronic certificate for a mobile device, comprising the following steps: step S10, encoding an image of an electronic certificate and a personalized watermark image; step S20, embedding the watermark and generating a personalized watermark The electronic certificate image is sent to the user's mobile device; step S30, the electronic certificate image to be detected on the user's mobile device is obtained and decoded, and the personalized watermark image is regenerated, and identification and authentication are performed. The present invention can effectively embed personalized watermark information without changing the overall visual recognition of the electronic certificate image, and complete watermark extraction and authentication through mobile devices.
Owner:TRAFFIC MANAGEMENT RES INST OF THE MIN OF PUBLIC SECURITY
A capital account compliance processing system and implementation method
ActiveCN113240507BRealize unified storageImprove stability and securityFinanceDigital data protectionThe InternetFinancial transaction
The invention relates to the technical field of fund depository and transaction, in particular to a fund account compliance processing system, comprising a user end, a bank end, a merchant end and a record depository end, and a first block is set between the user end and the bank end Chain network, a second blockchain network is set between the bank end and the merchant end, a third blockchain network is set between the bank end and the record depository end, and Internet data communication is between the user end and the merchant end, the present invention can Realize the unified custody of funds, improve regulatory compliance, and the security and stability of user or merchant fund exchange.
Owner:绿漫科技有限公司
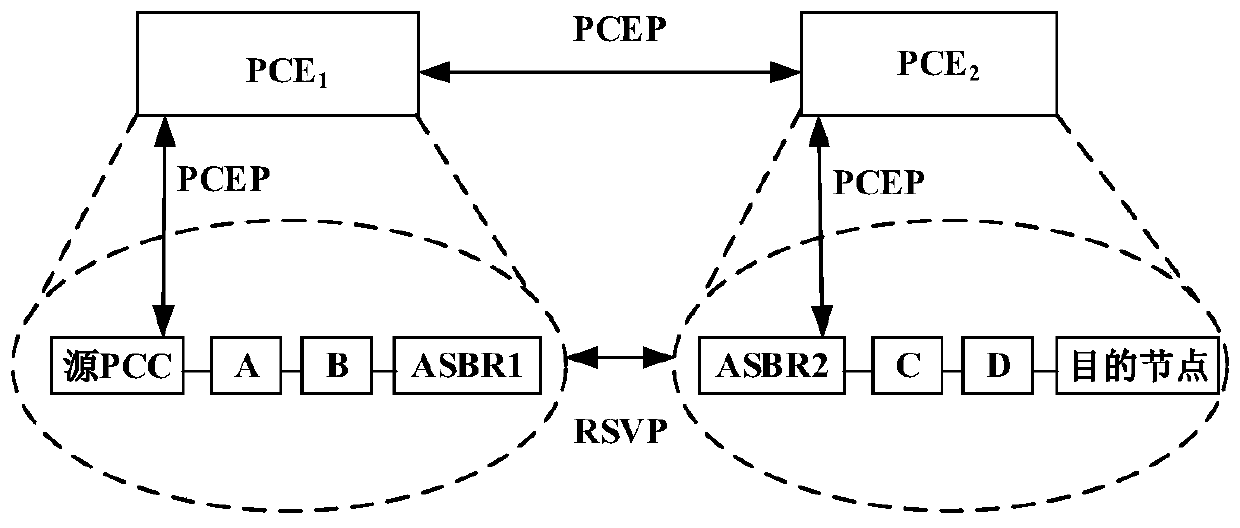
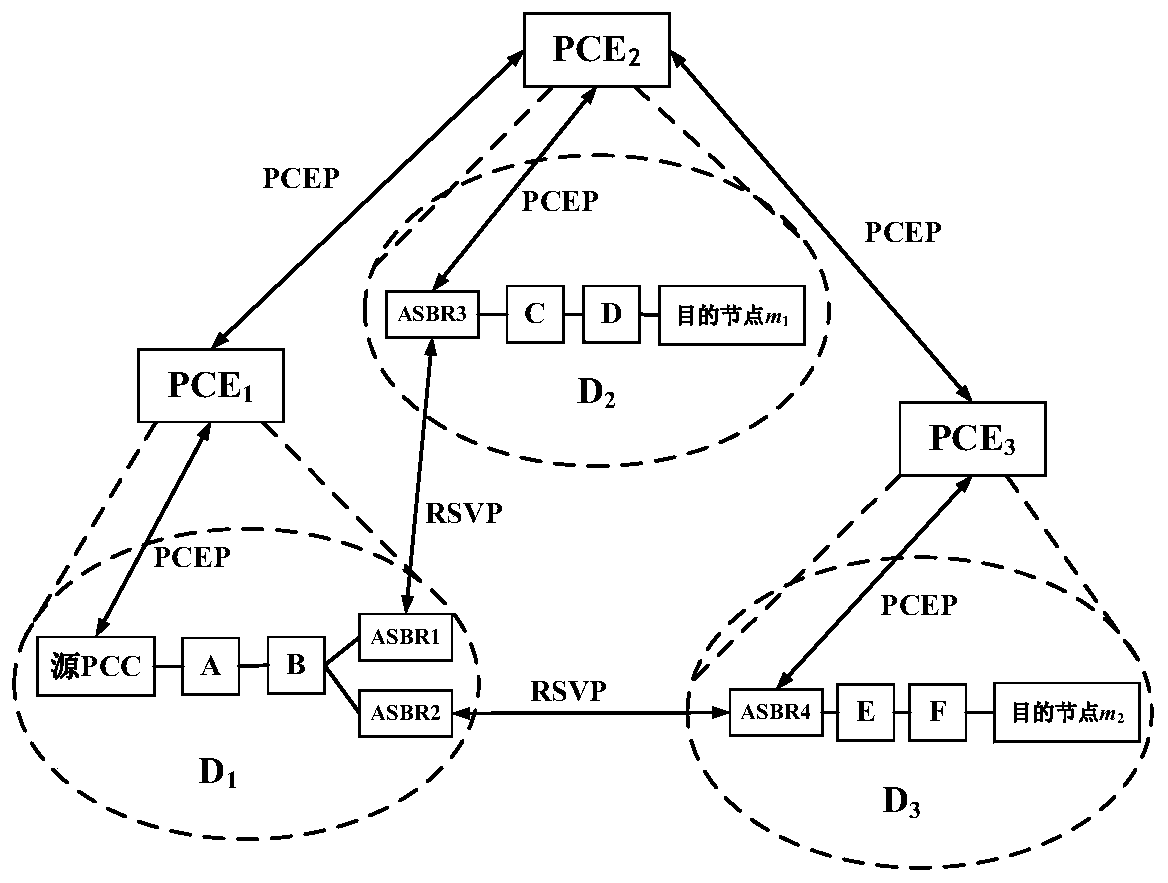
A system and method for establishing a secure optical tree in a multi-domain optical network based on distributed PCE
ActiveCN111030934BTamper resistantEnsure safetyMultiplex system selection arrangementsKey distribution for secure communicationEngineeringRouting algorithm
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Activity rewarding method and device based on block chain and storage medium
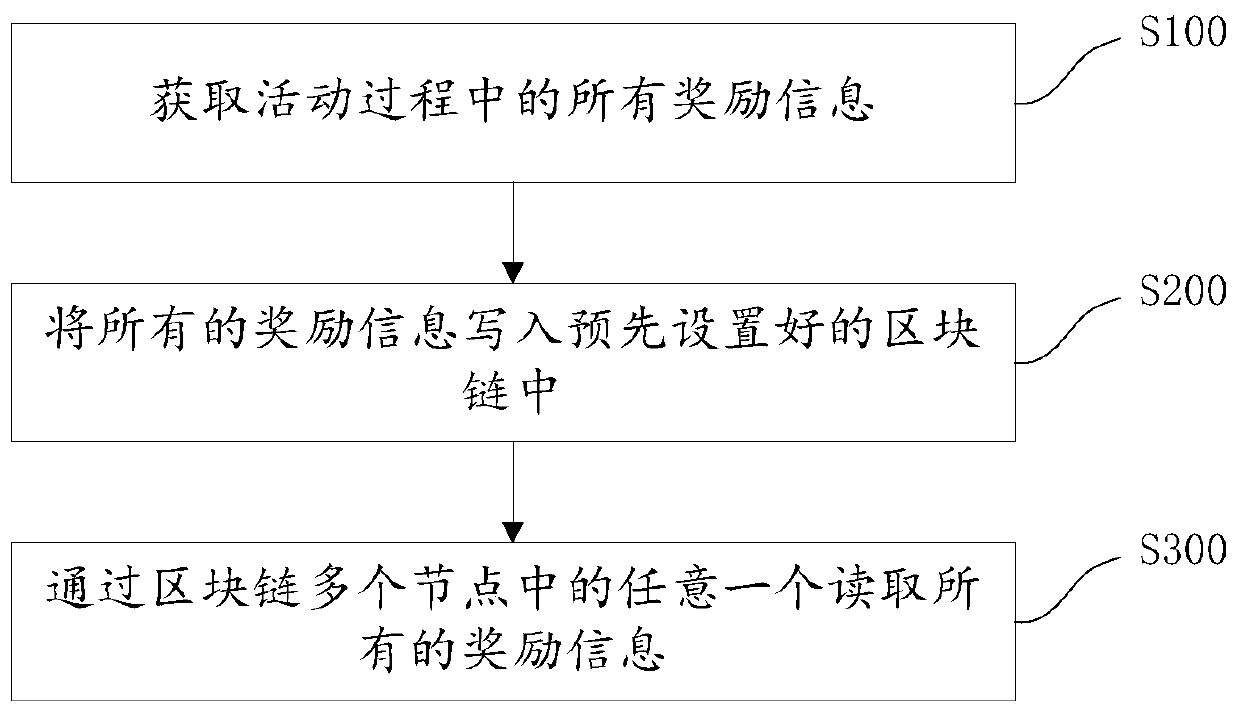
PendingCN111008860ACircumstances to prevent tamperingImprove recognitionDiscounts/incentivesDigital data protectionSoftware engineeringReal-time computing
The invention relates to the technical field of block chains, in particular to an activity rewarding method and device based on a block chain and a storage medium, and aims to solve the problem that award information of lottery activities published by merchants through interconnection is easily tampered. The activity rewarding method comprises the steps: obtaining all rewarding information in an activity process, wherein the activity comprises a lottery drawing activity, and the rewarding information comprises award-winning consumer information; writing all the rewarding information into a preset block chain; and reading all the rewarding information through any one of a plurality of nodes of the block chain. According to the activity rewarding method, the situation that the rewarding information generated in the activity process is tampered can be effectively prevented based on the tamper-proof characteristic of the block chain.
Owner:浪潮云洲工业互联网有限公司
Method, device and equipment for sending operation state information of rented equipment
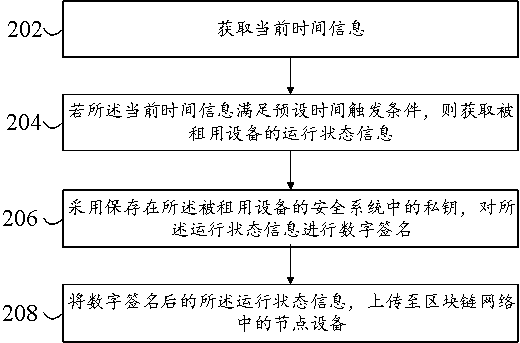
InactiveCN111400769AImprove securityImprove reliabilityDigital data protectionBuying/selling/leasing transactionsComputer networkDigital signature
The embodiment of the invention discloses a method, device and equipment for sending operation state information of rented equipment. The scheme is that when current time information meets a preset time triggering condition, the rented equipment can adopt a private key stored in a security system of the rented equipment to perform digital signature on operation state information of the rented equipment; and the digitally signed running state information is uploaded to node equipment in a blockchain network.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
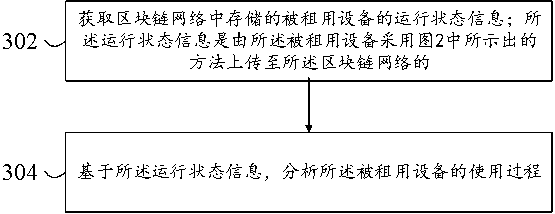
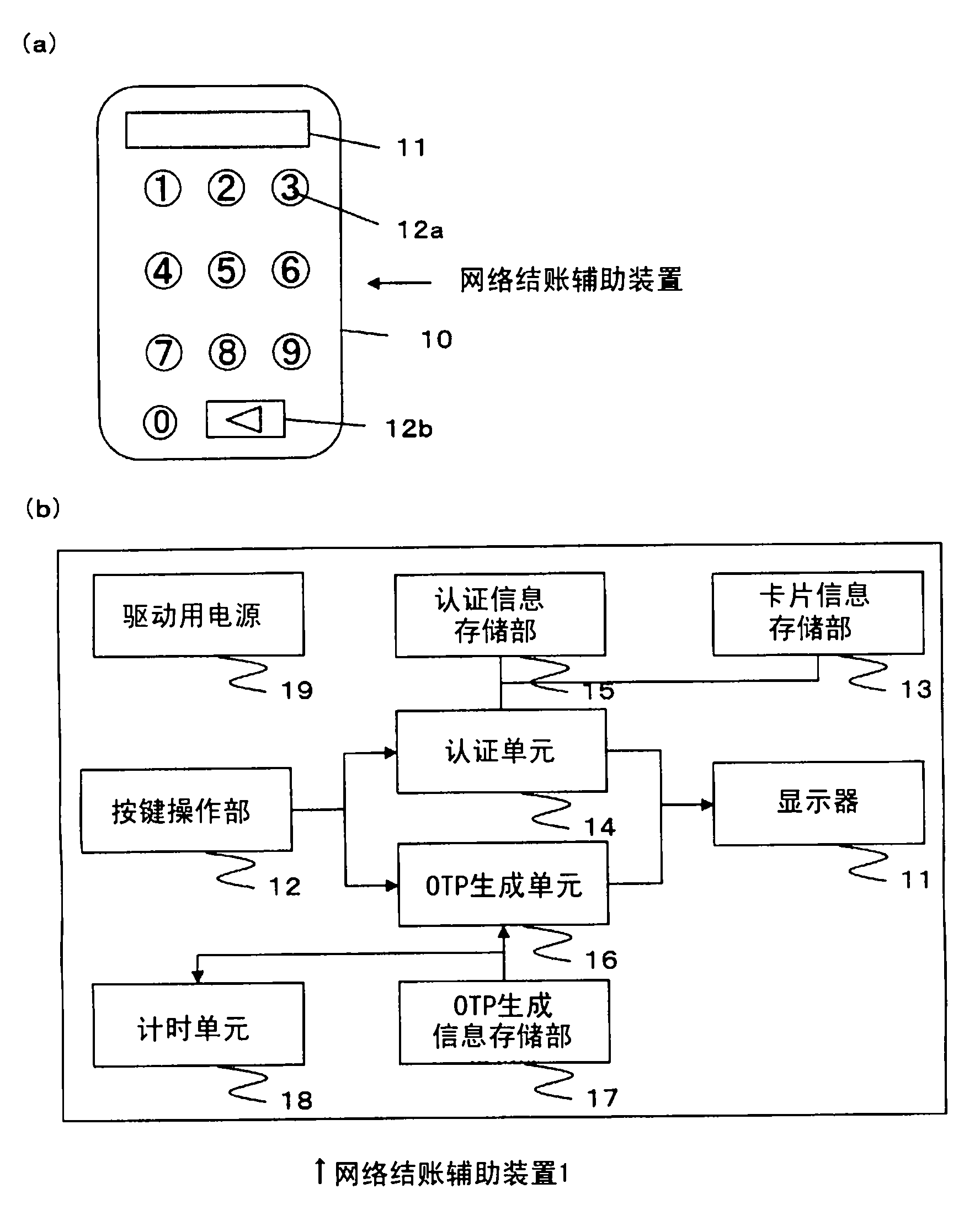
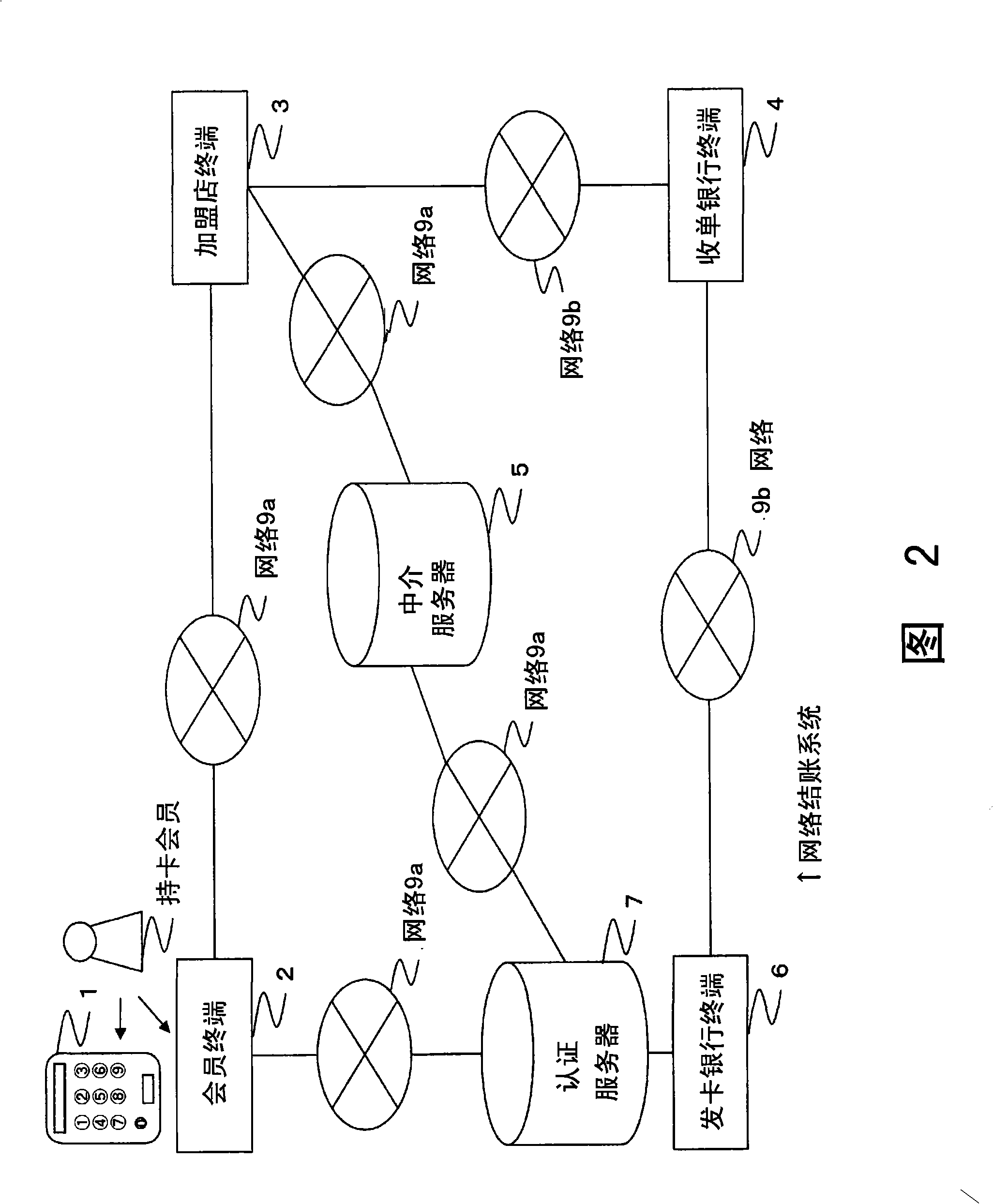
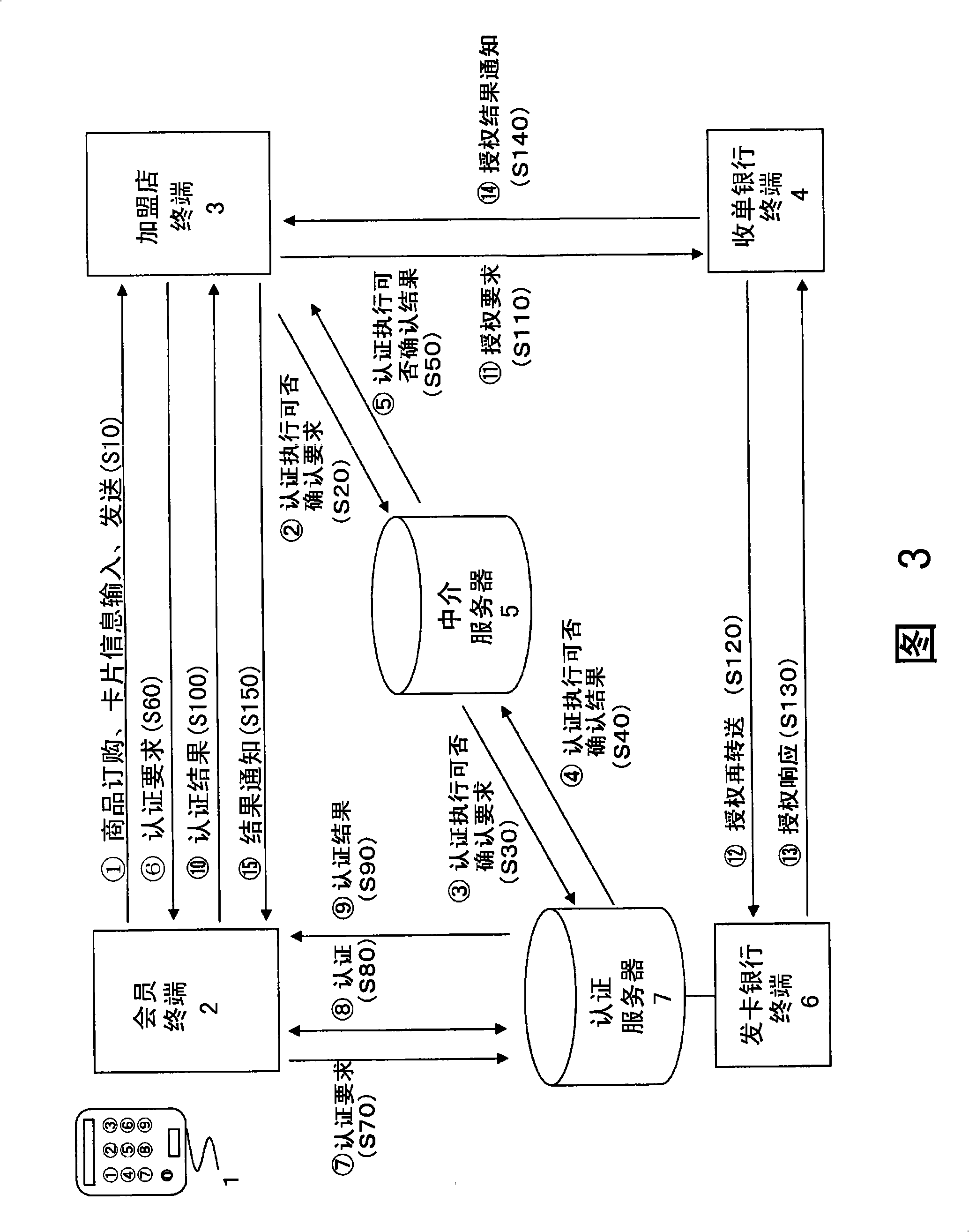
Net settlement assisting device
ActiveCN101496024BImprove stealthEasy to useDigital data authenticationCoding/ciphering apparatusDisplay deviceOne-time password
[PROBLEMS] A net settlement assisting device free of danger of eavesdropping and false alteration of a card number and a password and enabling more secure net business transaction. [MEANS FOR SOLVING PROBLEMS] A net settlement assisting device comprises a display (11), a card information storage section (13) where card information on a card contractor is so stored in advance as to be prevented from being read from outside, an authentication information storage section (15) where authentication information on the contractor is so stored in advance as to prevented from being read from outside, an OTP creation information storage section (17) where OTP creation information is stored in advance as to be prevented from being read from outside, a numeric keypad (12a), authenticating means (14) for authenticating the operator on the basis of the information inputted by means of the numeric keypad (12a) and displaying the card information on the display (11), and OTP creating means (16) for creating a one-time password according to the OTP creation information after the card information is displayed and displaying the one-time password on the display (11). The contractor is authenticated with the one-time password, thereby enabling a net transaction.
Owner:JAPAN CREDIT BUREAU
A security method, system and terminal using blockchain-based digital currency
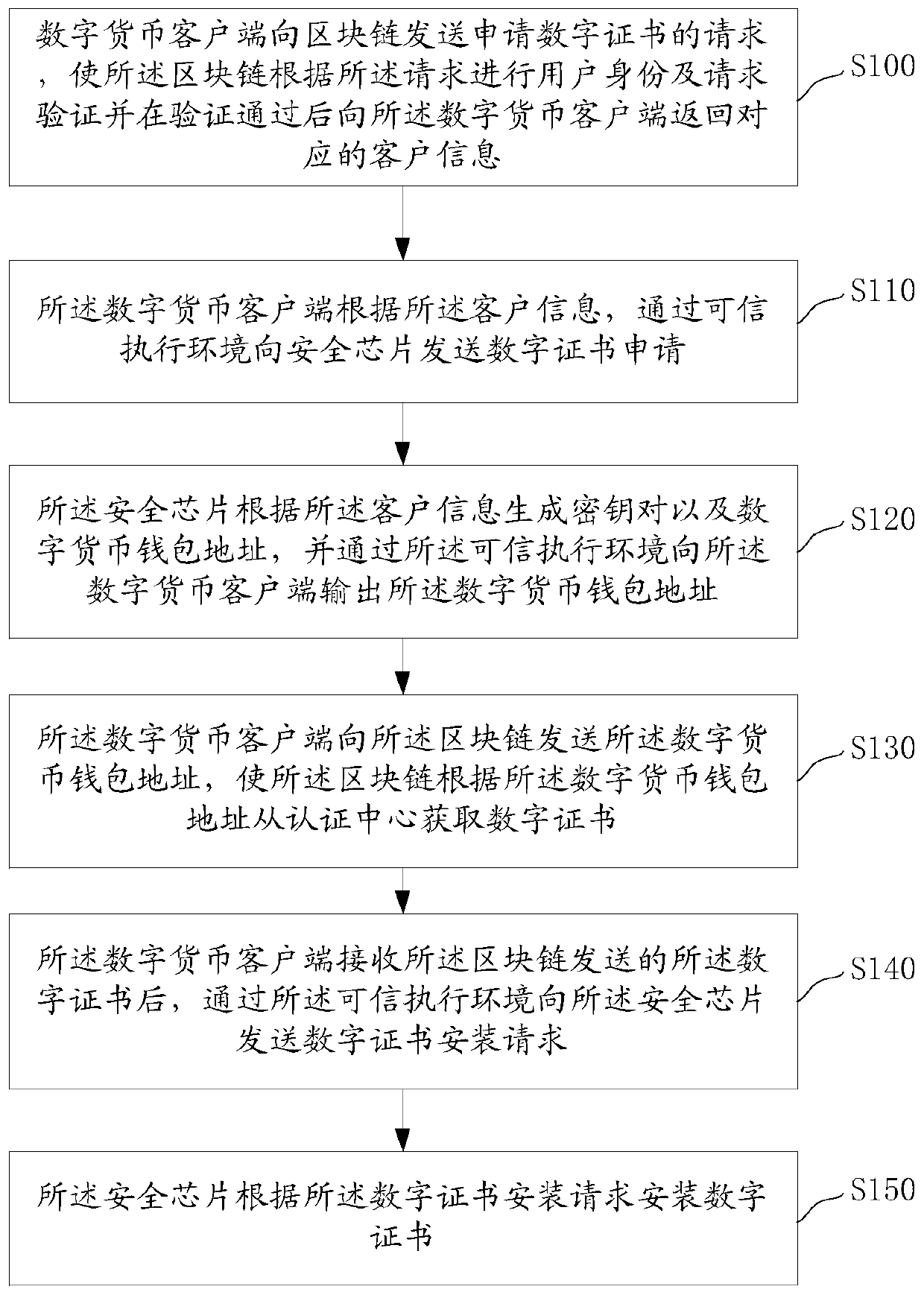
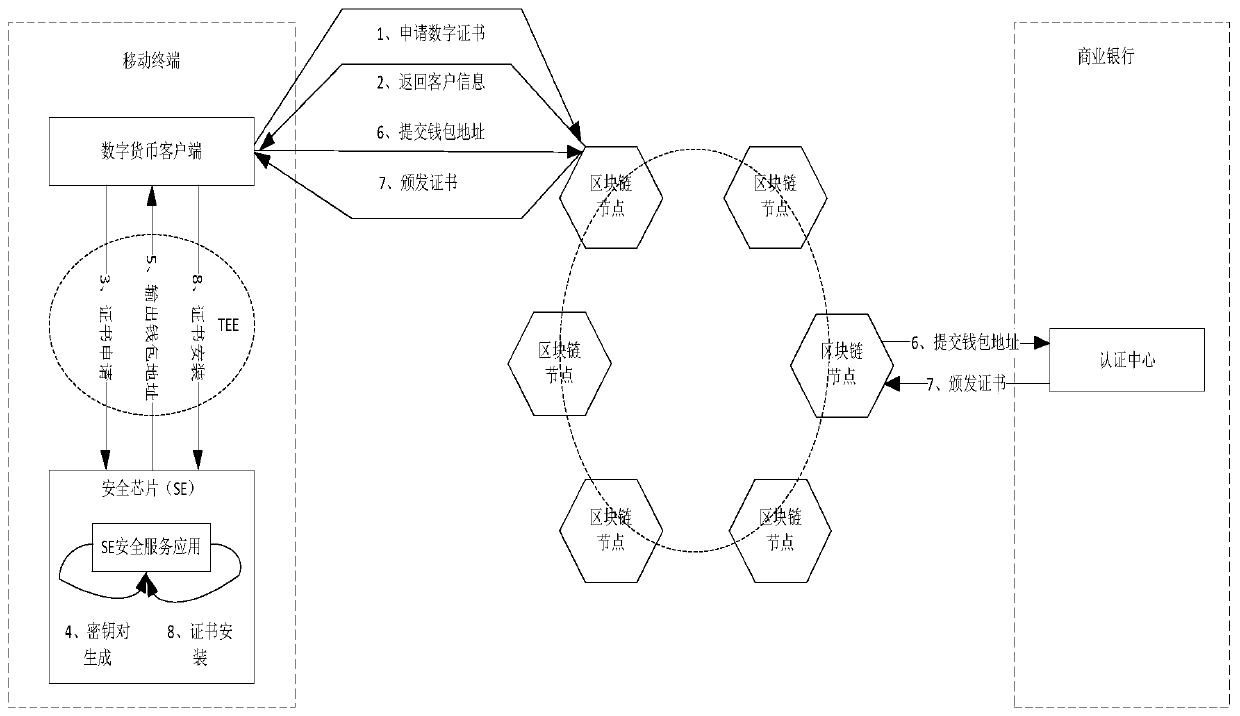
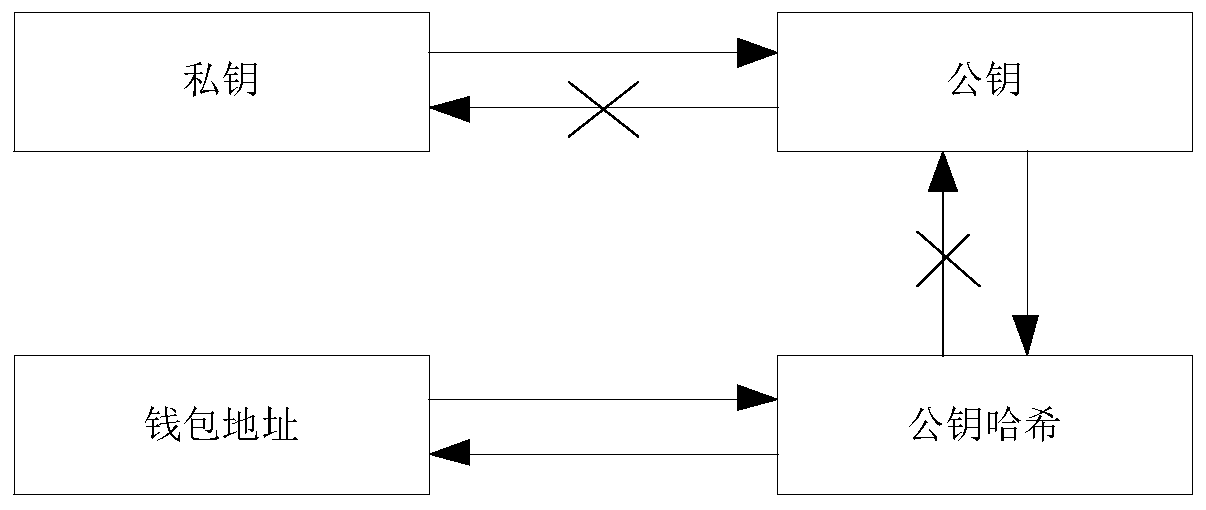
ActiveCN106850200BWith security encryption functionImprove securityKey distribution for secure communicationPublic key for secure communicationDigital currencyComputer network
The invention discloses a method and system for using digital currencies based on a block chain as well as a terminal. The method comprises the following steps: a digital currency client sends a request for applying a digital certificate to a block chain, and receives the corresponding customer information returned by the block chain after identity and request verification; a digital certificate application is sent to a security chip through a trusted execution environment according to the customer information; the security chip generates a key pair and a digital currency wallet address according to the customer information, and outputs the digital currency wallet address to the digital currency client through the trusted execution environment; the digital currency client sends the digital currency wallet address to the block chain to ensure that the block chain acquires the digital certificate from the authentication center according to the digital currency wallet address; and the digital currency client receives the digital certificate sent by the block chain, and sends a digital certificate installation request to the security chip through the trusted execution environment to ensure that the security chip is provided with the digital certificate. Thereby, the security of the block chain digital currency wallet can be increased through the security chip and the trusted execution environment.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院 +1
Multi-domain optical network security optical tree establishing system and method based on distributed PCE
ActiveCN111030934ATamper resistantEnsure safetyMultiplex system selection arrangementsKey distribution for secure communicationEngineeringRouting algorithm
The invention discloses a multi-domain optical network security optical tree establishing system and method based on distributed PCE. In a distributed PCE architecture, a trust model, a multicast routing algorithm, a GKMS-DA key management scheme and multiple security mechanisms are fused to ensure stable establishment of a security optical tree. Compared with a typical layered PCE-based protocol,the protocol has better performance in the aspects of network connection blocking rate, multicast tree establishment time and data packet delivery rate in a malicious environment.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Method of transferring broadcast related information from a portable terminal to a nearby broadcast receiver
InactiveCN101536374AImprove securityTamper resistantBroadcast system return channelsBroadcast characteristics identification/recognitionUser PrivilegeBroadcasting
A home electronic apparatus is able to receive a broadcasted communication service and to enjoy it by means of rights information; the rights information allows billing for the enjoyment. A mobile telephone terminal is associated to a subscriber card storing subscriber rights information. According to the method of the present invention, at least the subscriber rights information is transferred from the mobile telephone terminal to the home electronic apparatus when the mobile telephone terminal is in proximity of the home electronic apparatus, the transferred information is stored into the home electronic apparatus, and the broadcasted communication service is received and enjoyed by means of the transferred information.
Owner:TELECOM ITALIA SPA
Reversible tamper-proof data encryption and decryption method based on encryption and digest algorithms
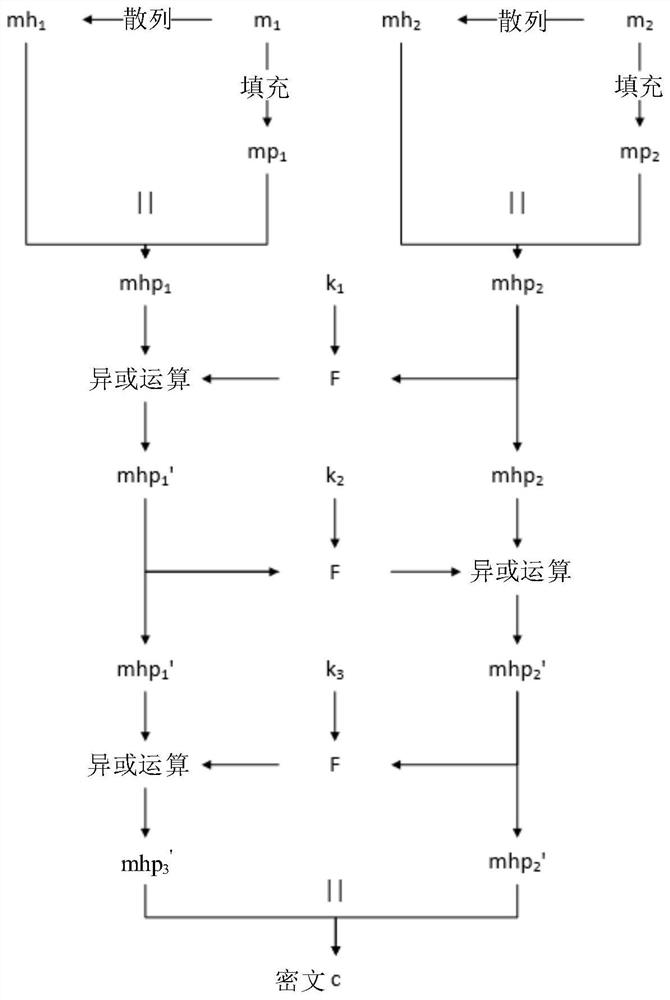
InactiveCN109347622AImprove securityReversibleMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesPlaintextTamper resistance
The invention discloses a reversible tamper-proof data encryption and decryption method based on encryption and digest algorithms. Main components for the method are as follows: two devices used for data encryption and decryption on a network. According to the method, the discreteness of the MD5 and the reversibility of the DES are combined, so that the safety of an encrypted ciphertext in a network transmission process is increased, and the ciphertext is prevented from being tampered and then transmitted after the ciphertext is tampered in the network transmission process, namely the tamper-proof performance is achieved; and meanwhile, after the ciphertext is received by a correct terminal, the ciphertext is decrypted to obtain plaintext data, namely the reversibility is achieved.
Owner:ZHEJIANG WANPENG EDUCATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com