Composition of encrypted two dimensional bar codes and application method therefor
A technology of two-dimensional barcodes and application methods, which is applied to encoding/decoding devices and key distribution, and can solve the problems of inability to guarantee key and private information security, unsatisfactory application popularity, and restricted application range, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0166] Embodiment 1: Identity authentication: used for identity identification, including: identity documents, VIP cards, electronic invitations, shareholder cards, etc.
[0167] Specific application examples - electronic invitations:
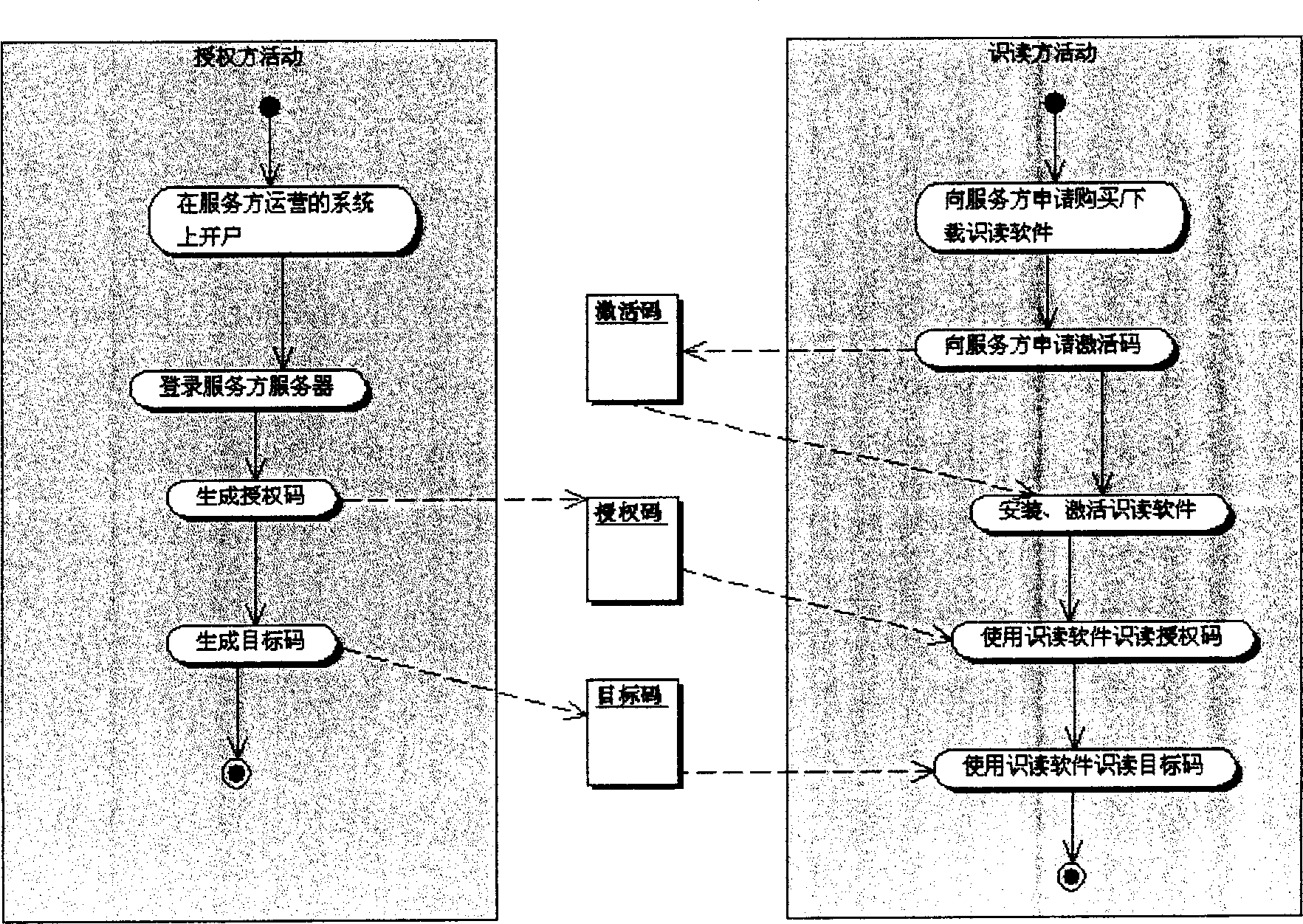
[0168] The exhibition organization, as the authorizing party, generates an object code for each invitee; the plain text content can be key information, such as room number, seat number, and identity information of the invitee. And specify the decryption password principle of this application, the decryption password can be a randomly generated password or the ID number of the invitee.
[0169] The exhibition organization will print the target code on the invitation and send it to each invitee in electronic or paper form.
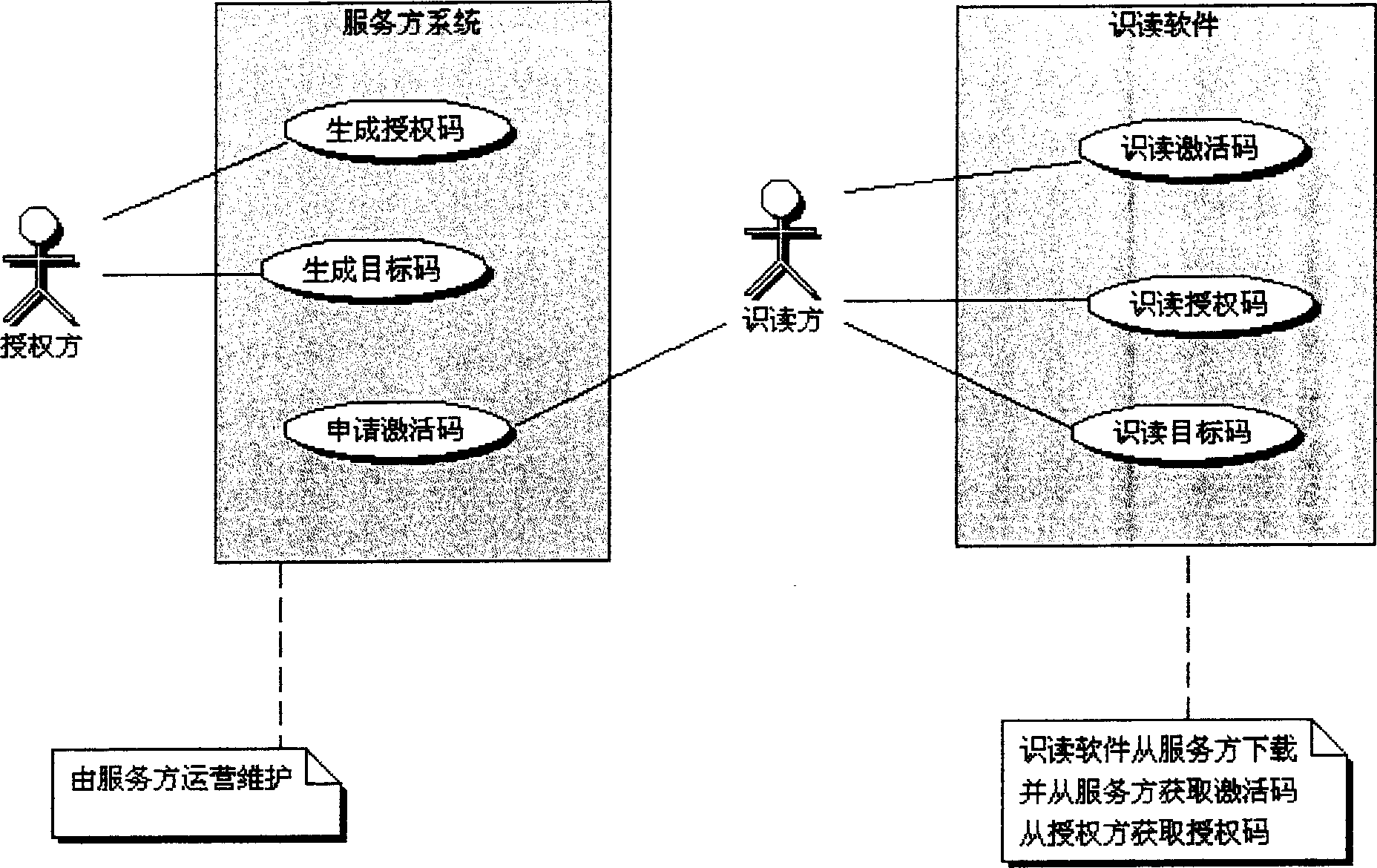
[0170] The exhibition organization sends the activation code and authorization code to the exhibition reception unit.
[0171] The exhibition reception unit installs the encrypted two-dimensional barcode reading software of t...
Embodiment 2
[0175] Embodiment 2: Electronic ticketing, for one-time use of valuable tickets and coupons. Including: performance ticketing, transportation ticketing, etc.
[0176] Specific application example - electronic ticket:
[0177] An airline sells civil aviation tickets online.
[0178] Internet users visit the ticketing website, order online, and complete the payment. After the website dynamically generates a target code, the content is the flight number, departure time, seat number, ticket price, identity of the purchaser, insurance amount, etc. information, the decryption password can be set by the user.
[0179] The airline, as the authorizing party, gives the activation code and authorization code to the company's check-in desk at the airport.
[0180] Install the reading software at the processing desk, use the activation code to activate, and use the authorization code to obtain the reading permission.
[0181] When the user takes the printed target code as a ticket and ...
Embodiment 3
[0183] Embodiment 3: Electronic lottery coupons, for electronic coupons that can be exchanged for physical objects / cash and generated online. Including: electronic lottery tickets, physical (or token) coupons issued by websites, and vouchers for receiving prizes in Internet games and entertainment, etc.
[0184] Specific application example-online lottery sales
[0185] A lottery sales organization opened online lottery sales.
[0186] Lottery players can place bets and purchases directly on the Internet, and each purchase request will instantly generate an encrypted two-dimensional barcode target code of the present invention. Information, players can decide whether to set a decryption password by themselves.
[0187] The lottery sales agency, as the authorized party, grants the activation code and the authorization code to each lottery prize redemption office. The redemption office uses the activation code to activate the reading software, and uses the authorization code ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com