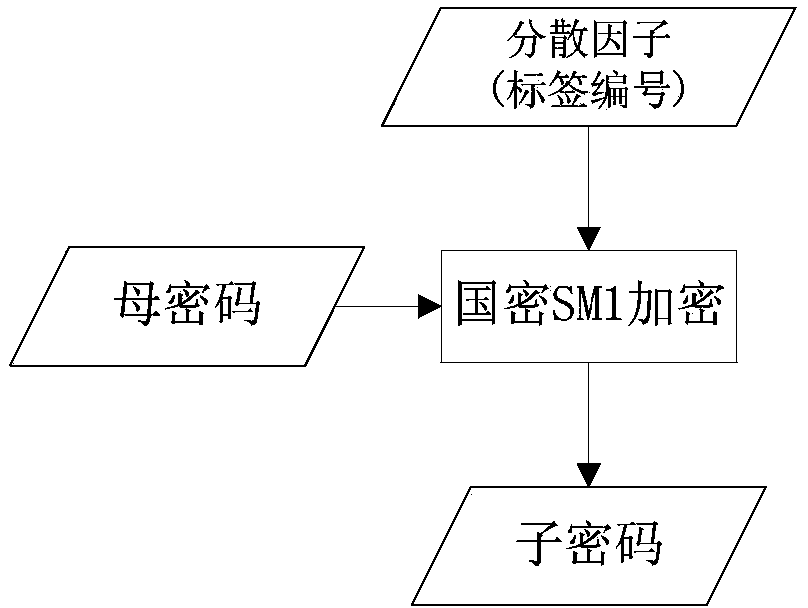
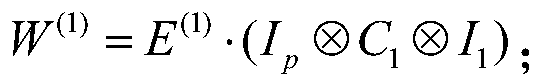Patents
Literature
60results about How to "Non-repudiation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
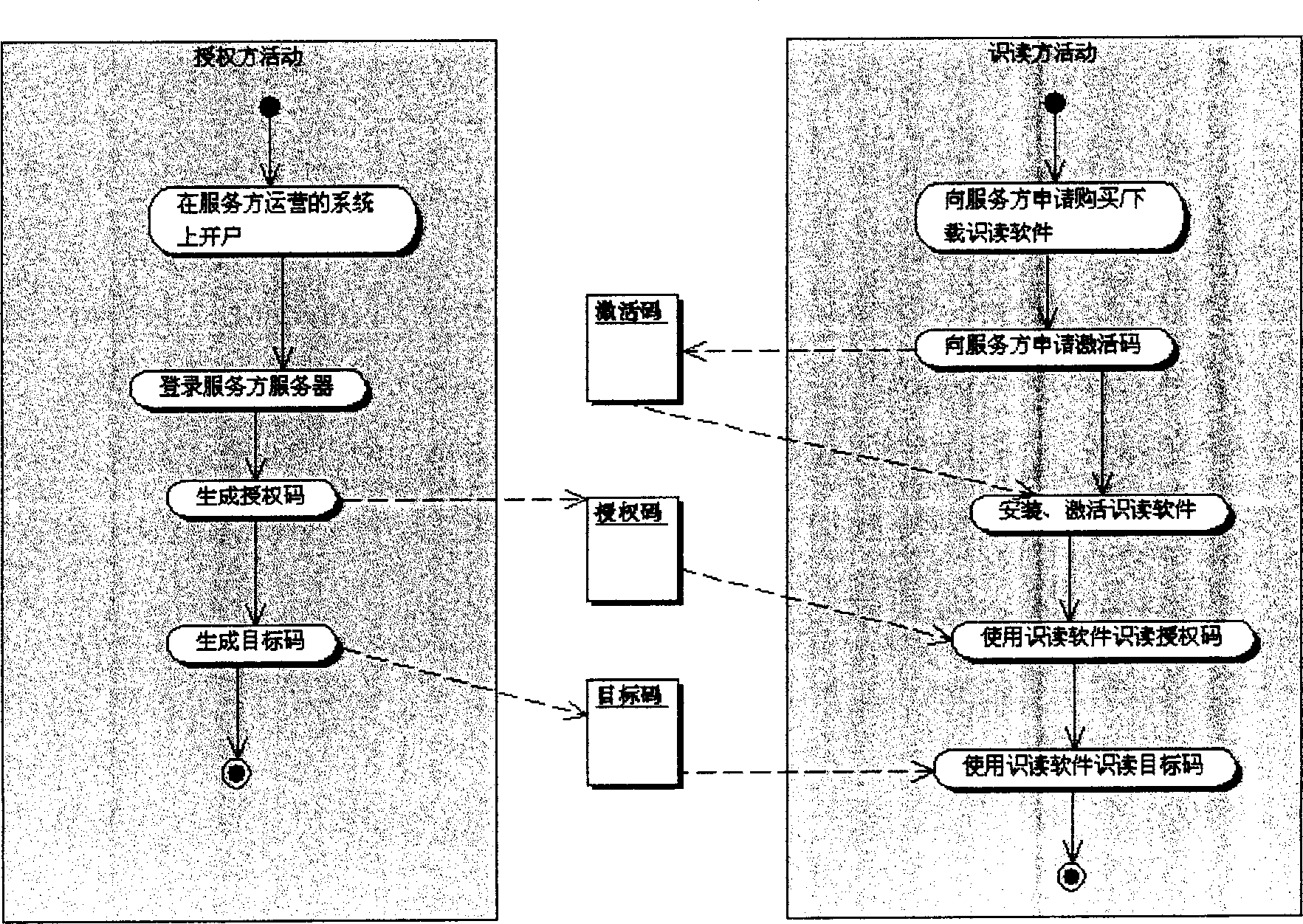
Method and system for identity verification of digital certificate based on TEE (Trusted Execution Environment)
ActiveCN105429760AEnsure true willEnsure that the identity verification process can reflect the true willUser identity/authority verificationPasswordPersonal identity verification
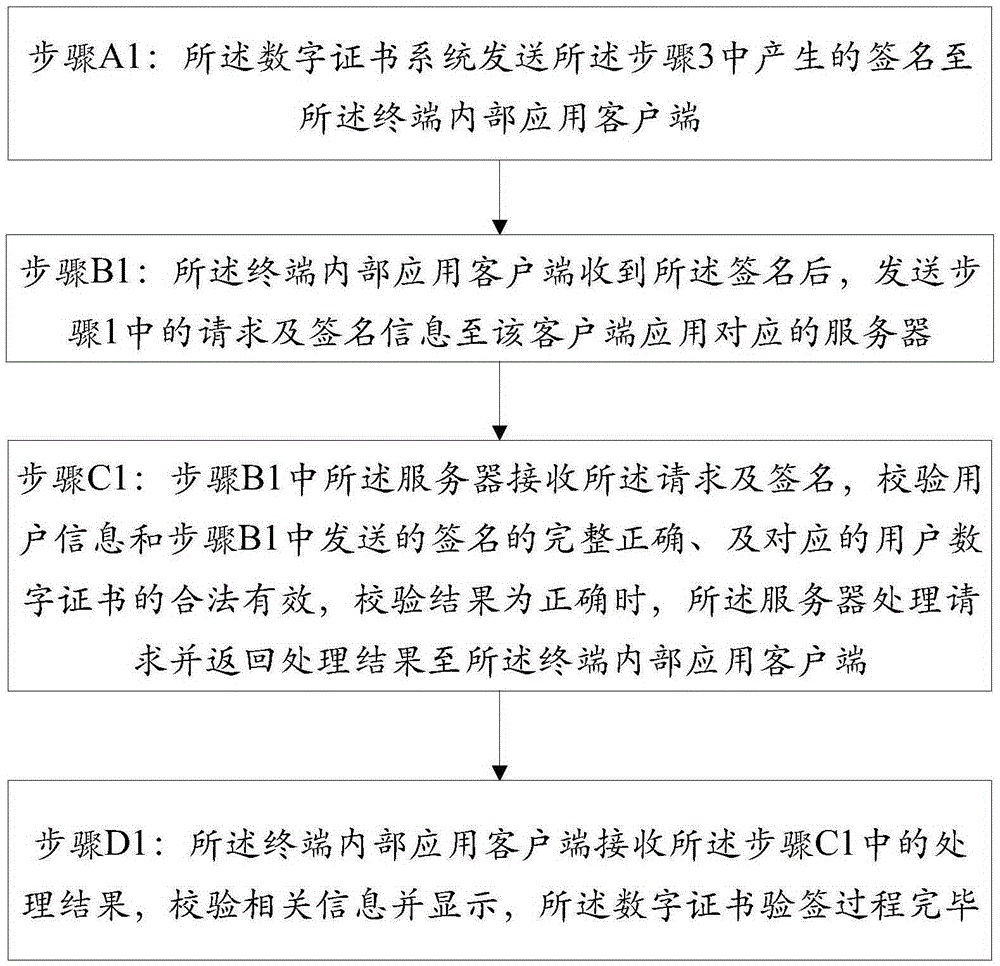
The invention discloses a method for identity verification of a digital certificate based on a TEE (Trusted Execution Environment). The method comprises pre-configuration of a digital certificate system through a terminal, a digital certificate signature process and a digital certificate signature verification process. The method is characterized in that the terminal is provided with the TEE; the digital certificate signature process is carried out on the terminal and is used for utilizing a private key of the digital certificate to sign for a user request; the digital certificate signature verification process is used for authenticating identity of a requested user, and the authentication method comprises verification of validity and effectiveness of the digital certificate and integrity and correctness of the signature, wherein the digital certificate signature process is carried out under the TEE; the sensitive information, such as a user key, identity information, biological characteristic information and password information, is stored through a secure storage module, so that the problems that the signature process is carried out in REE and the sensitive information of the user is stored under the REE environment to cause privacy disclosure and stolen hidden danger of property in the prior art are avoided.
Owner:神州融安数字科技(北京)有限公司
Official seal fake detection method and device based on network digital certificate and network lookup
InactiveCN104268742ANon-repudiationEliminate the role of forged documentsDigital data authenticationOffice automationPasswordDisplay device
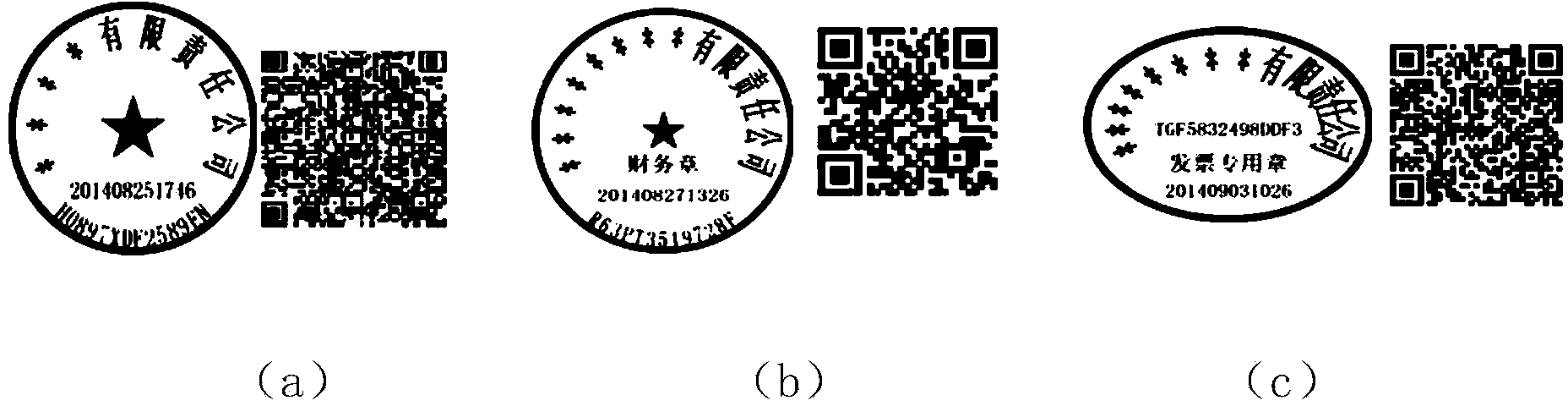
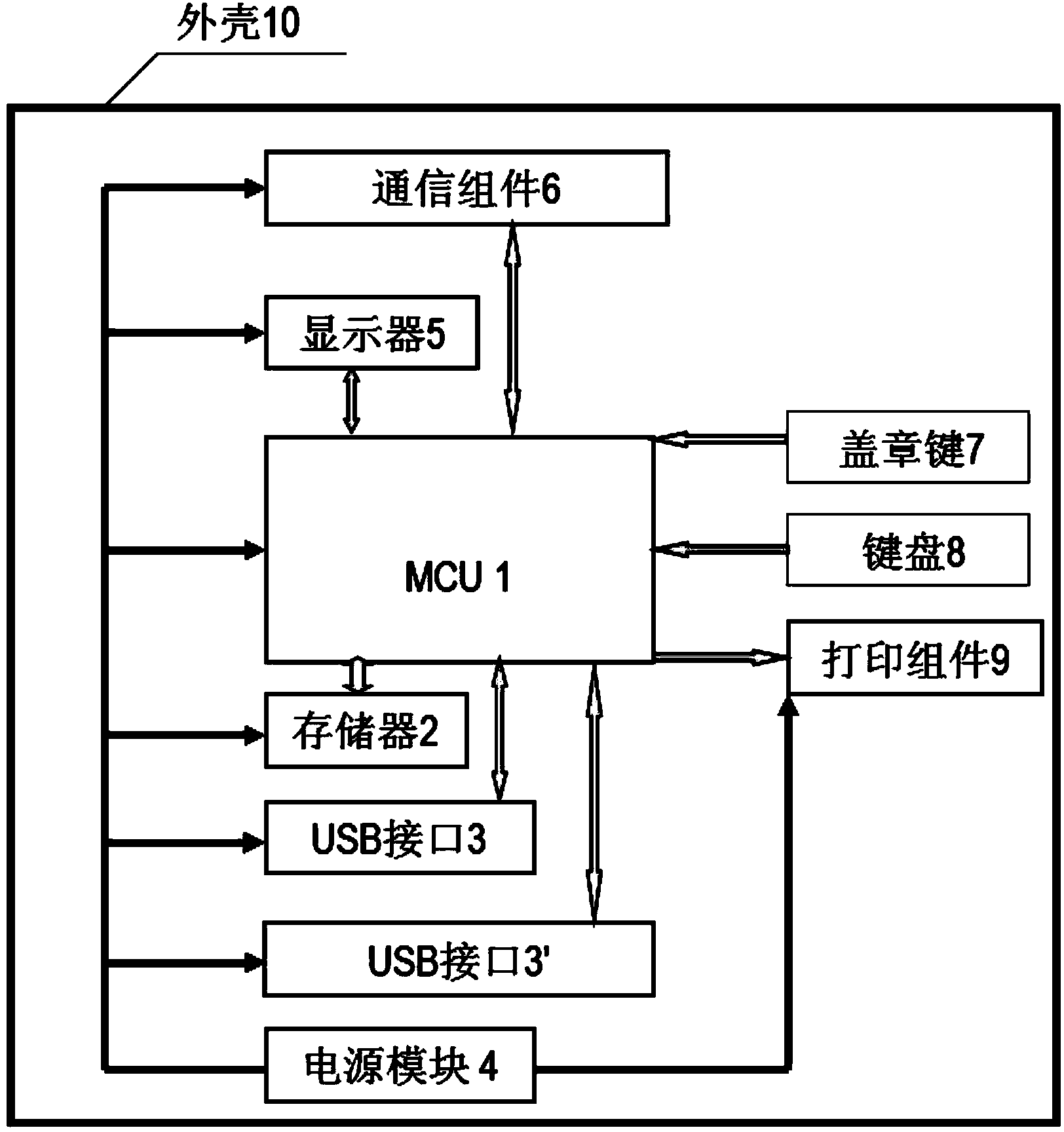
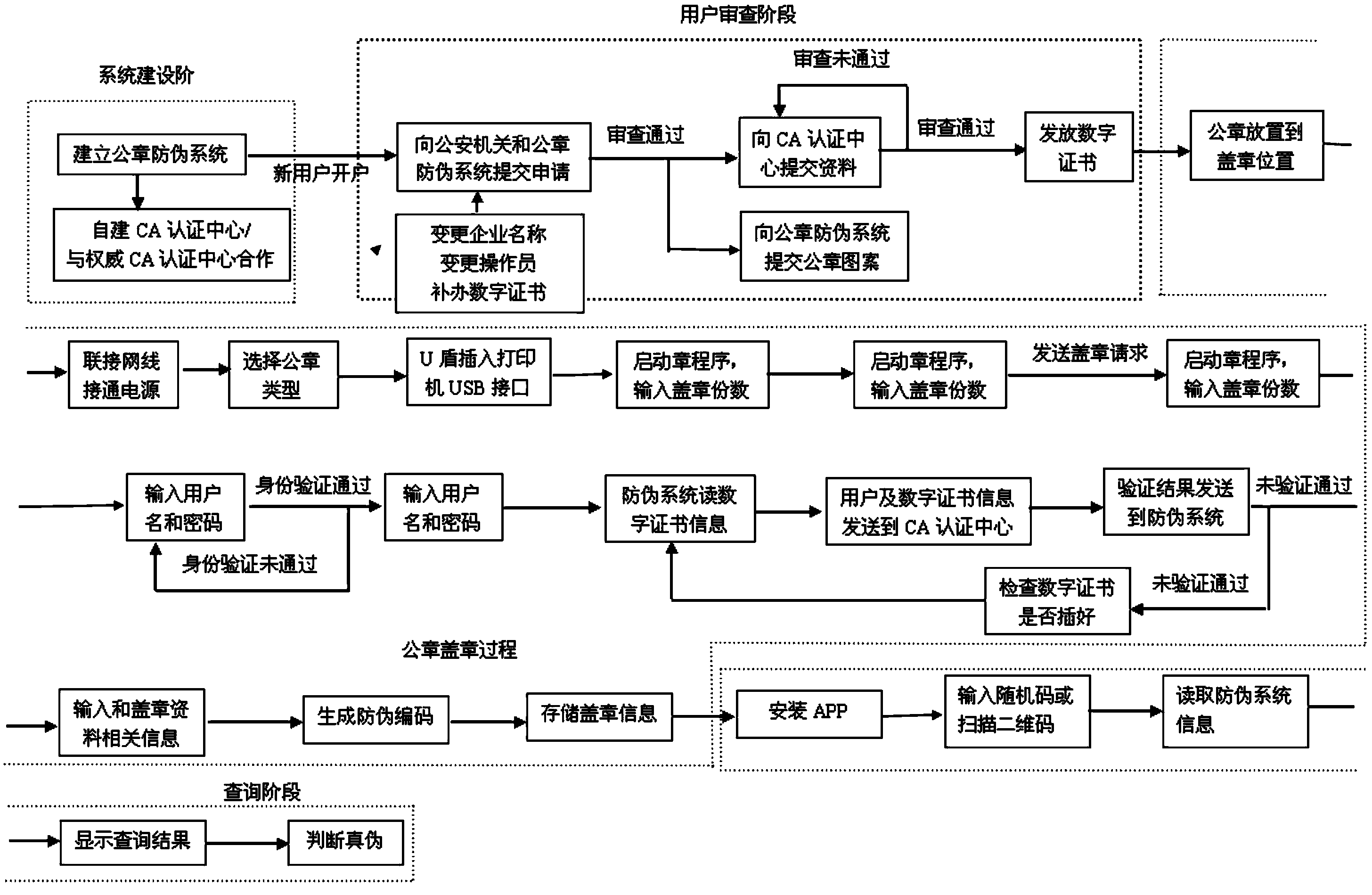
The invention discloses an official seal fake detection method and device based on a network digital certificate and network lookup. The device comprises an official seal printer connected with an official seal fake detection system. A central processing unit MCU in the official seal printer is connected with a communication assembly, a displayer, a printing assembly, a storage and a USB interface. A power module supplies power to the official seal printer. The official seal fake detection method comprises the steps that the official seal fake detection system is built for user inspection, the digital certificate is issued when a user passes identity authentication, the official seal printer prompts selection of official seal types, a USB intelligent card is plugged into the USB interface of the official seal printer, copies needing to be stamped, the user name and a password are input, the identity and validity of the digital certificate are verified, fake detection codes are generated in the official seal fake detection system randomly, the official seal printer displays an official seal pattern, the user selects the position of a two-dimension code, and the official seal printer prints an official seal. By means of the method, whether the official seal is true or false can be queried whenever and wherever, the official seal can be verified and queried whenever and wherever through mobile phone APPs, and hazards caused when false official seals or copied official seals are used are completely eradicated.
Owner:SHAANXI WANYU ELECTRONICS INFORMATION TECH CO LTD
Intelligent mobile terminal based collaborative transaction method and system
InactiveCN106157040AMaximize utilizationAccelerated asset circulationPre-payment schemesMarketingThird partyComputer terminal
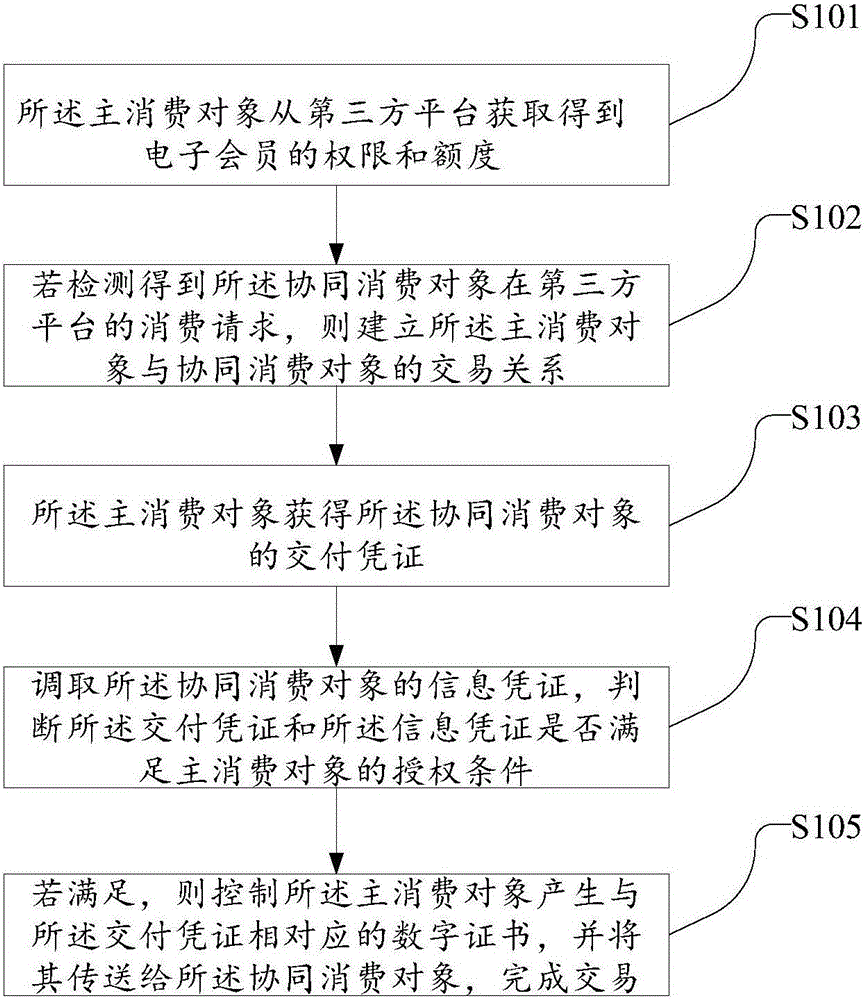
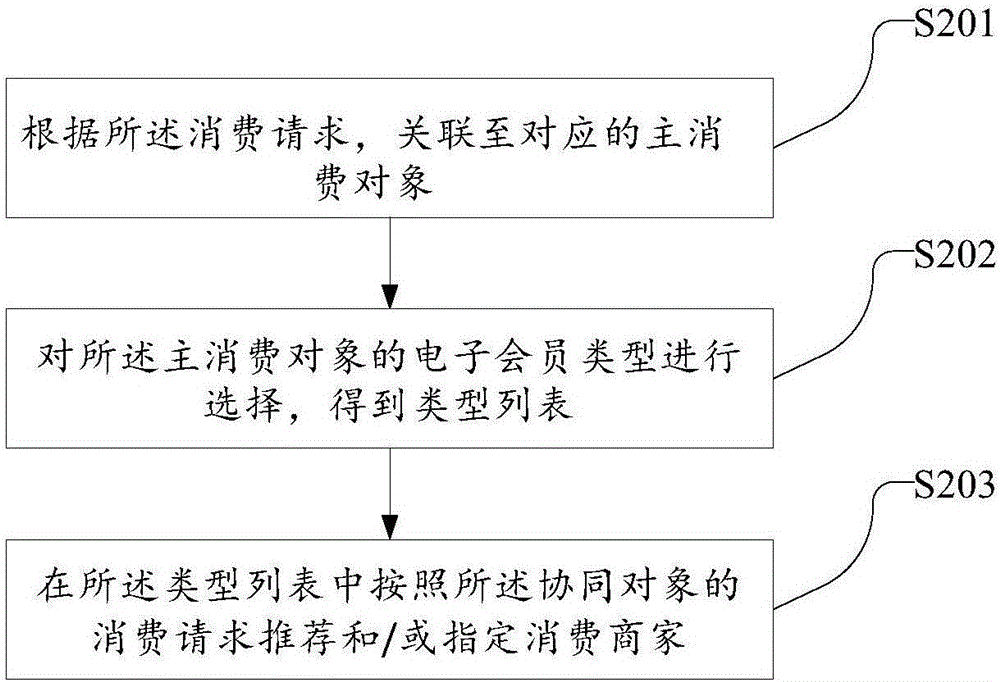
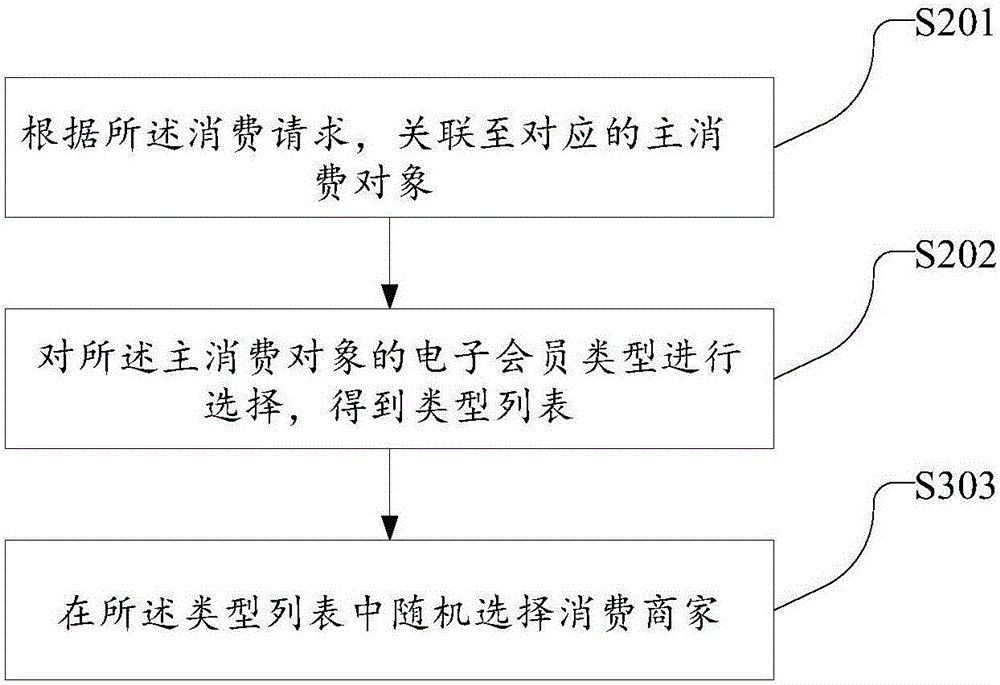
The invention discloses an intelligent mobile terminal based collaborative transaction method and system. The method includes: a main consumer acquiring permissions and limits to acquire an E-membership from a third-party platform; if consume requests of a collaborative consumer are detected to acquire, establishing transaction relationship of the main consumer and the collaborative consumer; the main consumer acquiring a delivery proof of the collaborative consumer; taking an information proof of the collaborative consumer and judging whether the delivery proof and the information proof meet permission conditions of the main consumer or not; if yes, controlling a digital certificate generated from the main consumer and corresponding to the delivery proof and transmitting the digital certificate to the collaborative consumer to complete transaction. With the method, personnel without electronic membership cards can also perform collaborative consumption as long as acquiring the limited permissions and limits, the purpose of partial transfer of the permissions and limits of the electronic memberships is achieved, prepaid asset corresponding to the limits can be used maximumly, and asset circulation is fastened.
Owner:詹博凯
Composition of encrypted two dimensional bar codes and application method therefor
InactiveCN1878057AImprove securityWith anti-counterfeiting functionKey distribution for secure communicationCoding/ciphering apparatusThe InternetInformation security
Owner:王向东
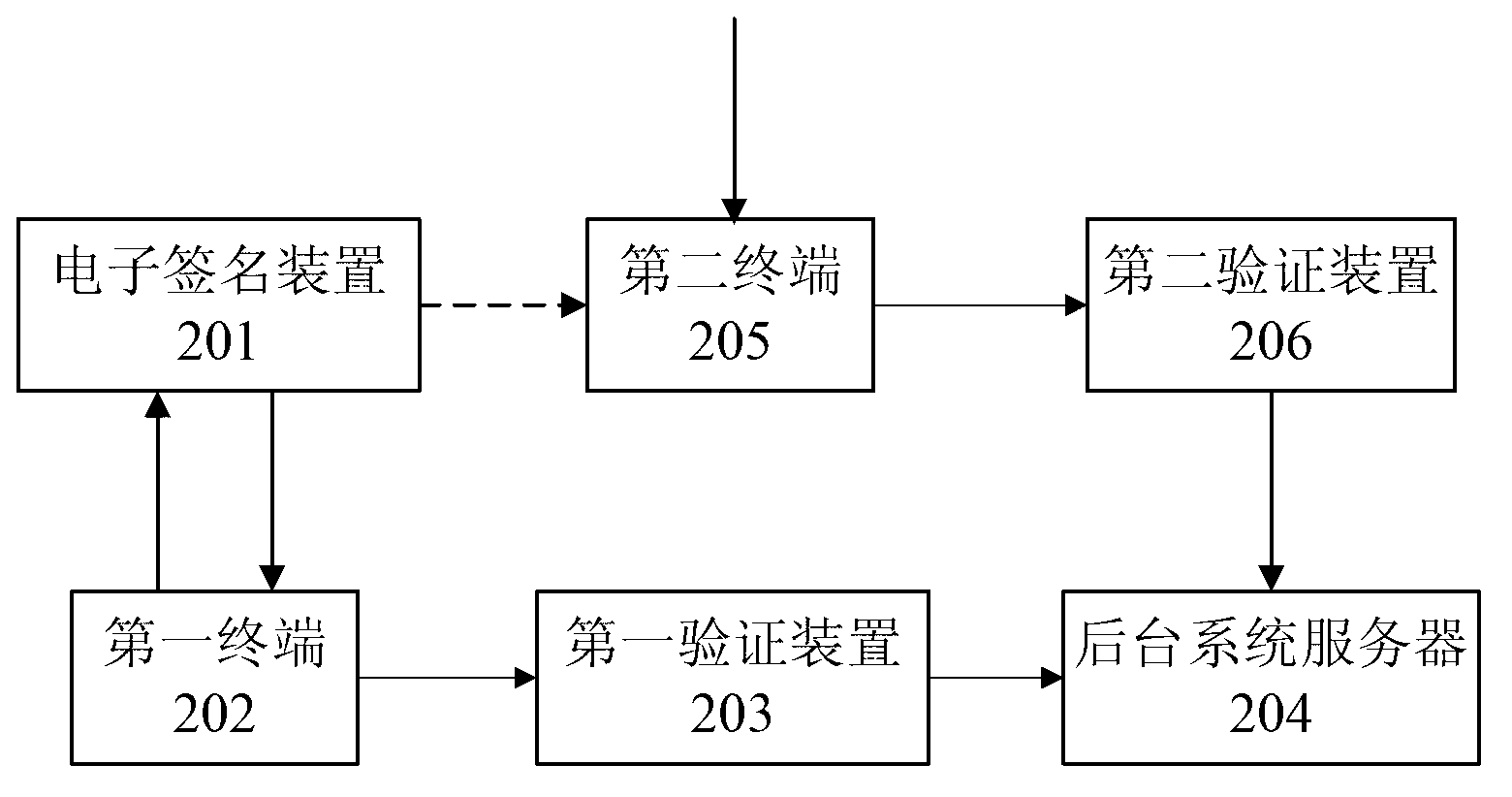
Information processing method and system
ActiveCN103220281AEnsure safetyWon't leakDigital data authenticationSecuring communicationInformation processingElectronic signature
The invention discloses an information processing method and system. The information processing method comprises the following steps that a first terminal transmits operation request information to an electronic signature device; the electronic signature device generates a combined code, generates a signature message according to the operation request information and the combined code, regulates the content of the combined code to obtain a first processing code, and transmits the first processing code and the signature message to the first terminal; the first terminal notifies a first verification device of verifying the signature message; if the verification passes, the first signature device notifies a server of preprocessing the operation request information; the server preprocesses the operation request information to obtain preprocessed information; the electronic signature device outputs a prompt message of the combined code; a second terminal takes the obtained combined code as a code to be verified; the second terminal notifies a second verification device of verifying the code to be verified; and if the verification passes, the second verification device triggers the server to respond a flow of the operation request information according to the preprocessed information.
Owner:TENDYRON CORP
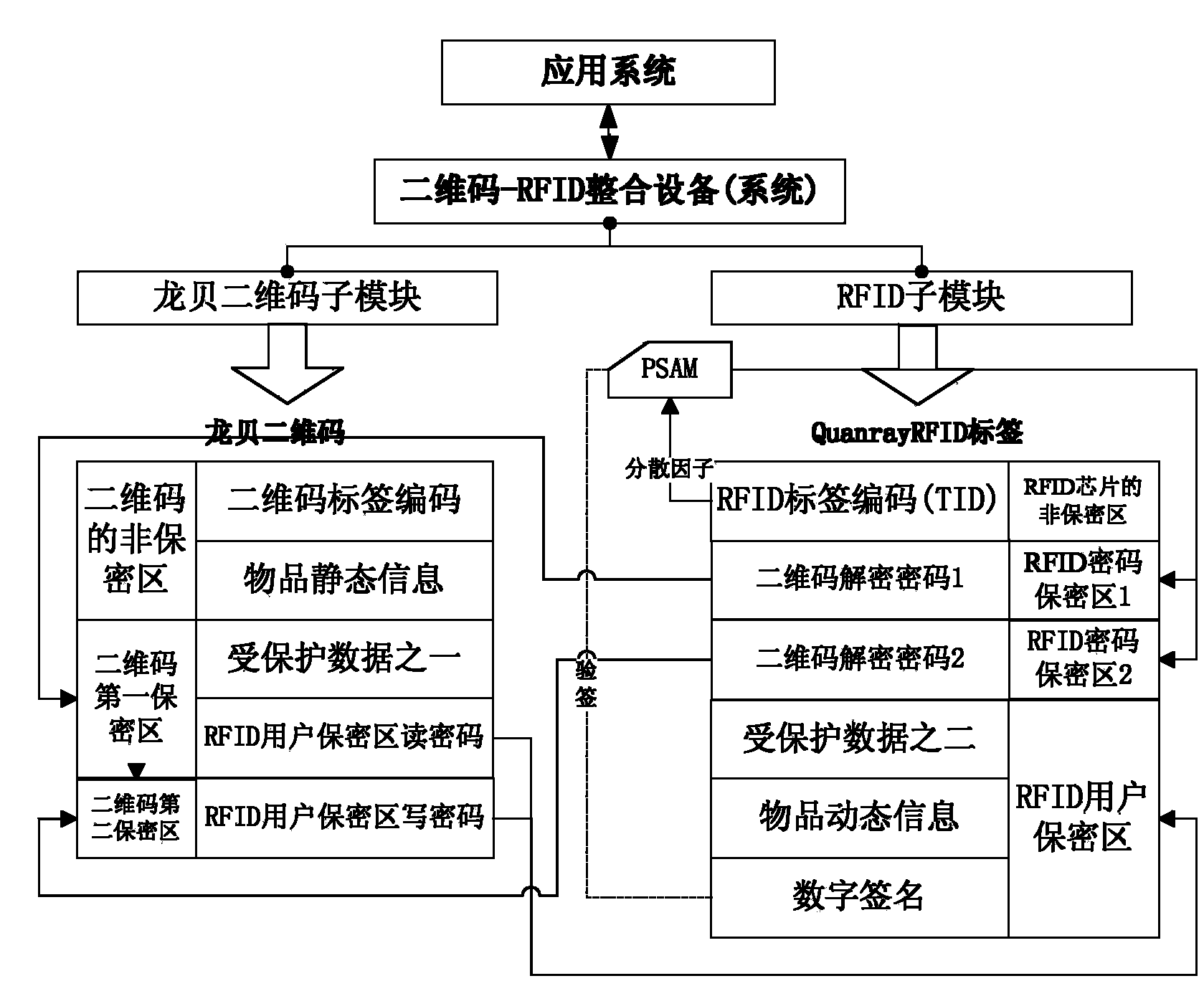
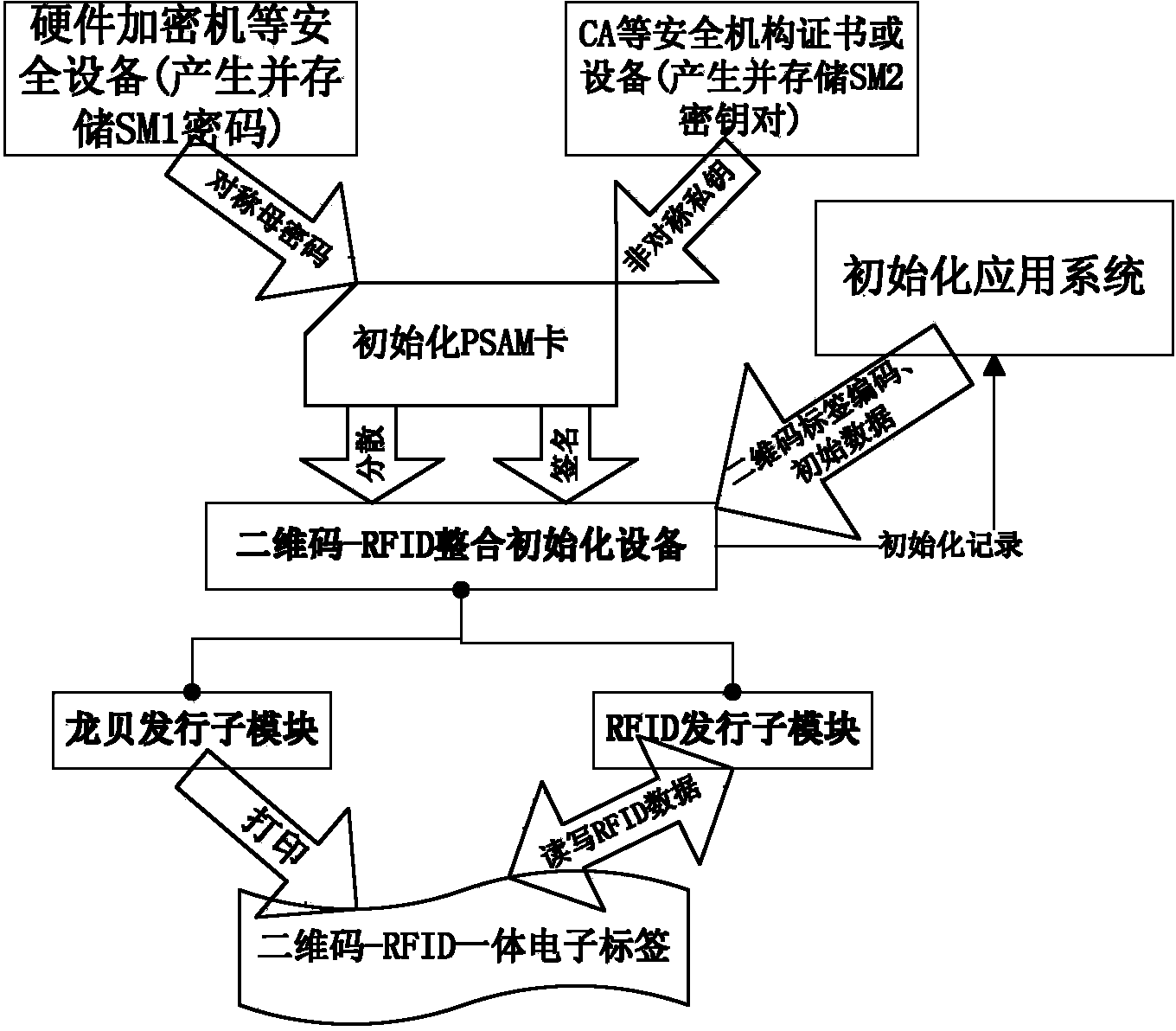
Anti-counterfeit label and anti-counterfeit method based on combination of two-dimension codes and RFID chips
ActiveCN104166871AAnti-counterfeiting advantageGood anti-counterfeiting featuresRecord carriers used with machinesDigital signaturePassword
The invention relates to an anti-counterfeit label based on the combination of two-dimension codes and RFID chips. The data area of the two-dimension codes and the data area of the RFID chips are respectively divided into a non-secrecy zone and a secrecy zone, each secrecy zone is divided into multiple secrecy zone bodies, two-dimension code label codes are stored in the non-secrecy zone of the two-dimension codes, and the secrecy zone of the two-dimension codes is divided into a first two-dimension code secrecy zone body for storing protected data needed by a user; RFID label codes are stored in the non-secrecy zone of the RFID chips, and the secrecy zone of the RFID chips is divided into the RFID user secrecy zone body and the RFID password secrecy zone body; in the verification process, access to the RFID password secrecy zone body is achieved firstly to obtain a decoding password of the two-dimension code secrecy zone body, the needed data are obtained from the two-dimension codes, the data, including a digital signature, of the RFID user secrecy zone body are read, the digital signature is regenerated, and two digital digests are verified to finally obtain a result whether to be true or counterfeit or a result whether to be legal or illegal. The defects of a traditional anti-counterfeit technology can be overcome well, and the anti-counterfeit label is difficult to counterfeit.
Owner:SHANGHAI QUANRAY ELECTRONICS
Information sequence building method and system thereof
InactiveCN108471379APublish flexiblePost beautifulData processing applicationsData switching networksCommunications systemComputer science
The invention provides an information sequence building method and a system thereof, and belongs to the information sequence building field. The system comprises a publishing platform and an instant communication system. The publishing platform is used for editing, storage, calculation, and statistics of published information, and is used to transmit the edited information to the instant communication system. The instant communication system is used for the information sequence building. By setting the sequence building information in a collective and unified way, and counting the sequence building information, the sequence building information can be counted in a better way, and information of participants can be queried, and at the same time, the defect of the traditional sequence building can be solved, and a good popularization value is provided.
Owner:广西中科万宏信息科技有限责任公司
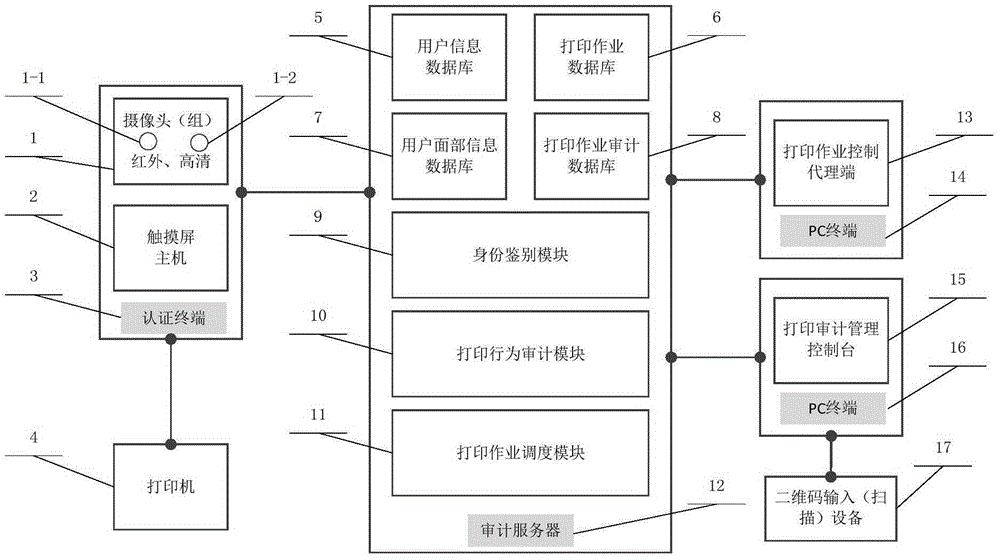
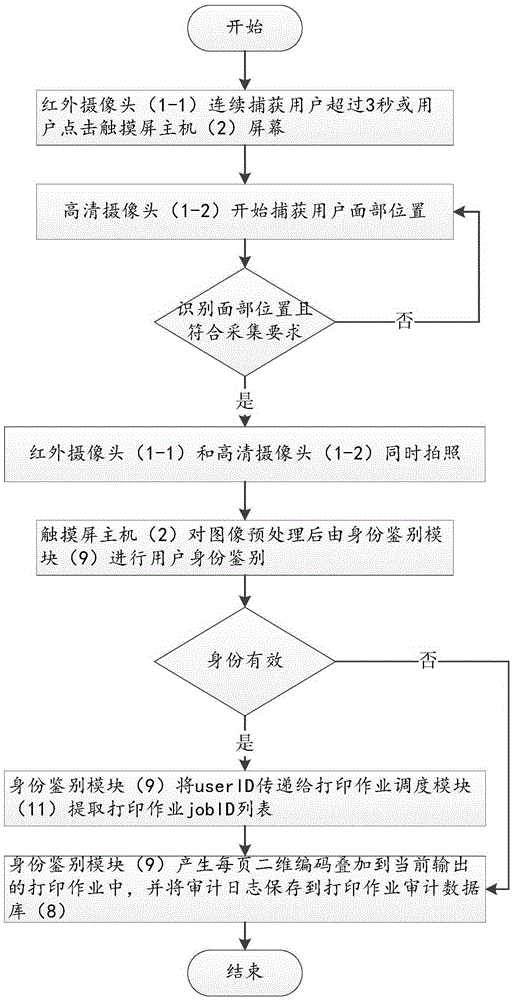
Facial recognition-based secure printing audition system
ActiveCN105426137ARealize real-name system auditReduce the risk of identity fraudDigital data authenticationDigital output to print unitsFacial recognition systemEthernet
The invention relates to a facial recognition-based secure printing audition system. The facial recognition-based secure printing audition system is connected with an identity authentication terminal, a printing audition server, a printer and a terminal computer through an Ethernet framework, and comprises an identity authentication module, a printing operation control module and a printing behavior audition module. The facial recognition-based secure printing audition system is used for decreasing the risk and threat caused by the operation of carrying out printing output by illegal users which pretends to be legal users in the sensitive carrier production process, realizing the printing identity authentication and behavior audition in a real-name system at a price as small as possible, decreasing the chances of unauthorized sensitive data output leakage of malicious users and tracing the faces of the real printing output personnel and the panorama photos of the operators, so as to ensure the security of the sensitive information and the reliable audition of the information.
Owner:AVICIT CO LTD
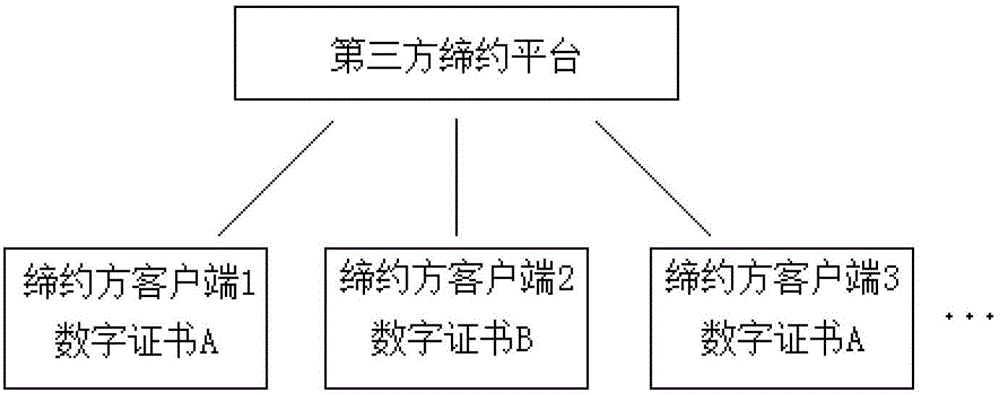
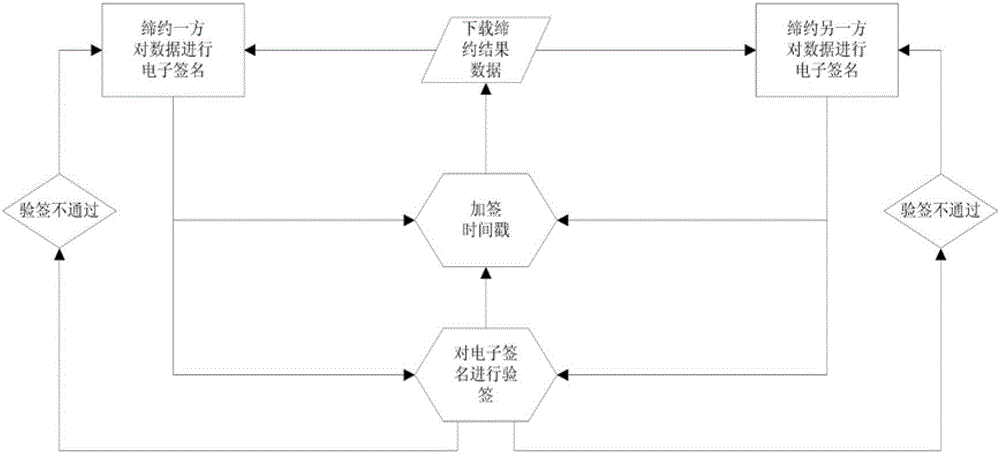
Third-party platform electronic contracting system based on electronic signature technology
ActiveCN102724042AGuaranteed complete and authentic certificationEnsure safetyUser identity/authority verificationThird partyTimestamp
A third-party platform electronic contracting system based on the electronic signature technology comprises contracting party client sides and a third-party contracting platform. Contracting parties hold the same or different digital certificates, and the third-party contracting platform is used for electronic contracting, can provide integrated verification and timestamps for different certificate chains, certificate states and certificate validity periods and guarantees accuracy and validity of mutual electronic contracting of the contracting parties held the same or different digital certificates issued by the CA (certification authority). The third-party platform electronic contracting system uses the electronic signature technology for decomposition, simulation, reconstruction, recombination and solidification of critical steps, critical factors and critical processes, so that technological holes of existing electronic contracting are made up, and accuracy and validity of electronic contracting are guaranteed.
Owner:江苏买卖网电子商务有限公司
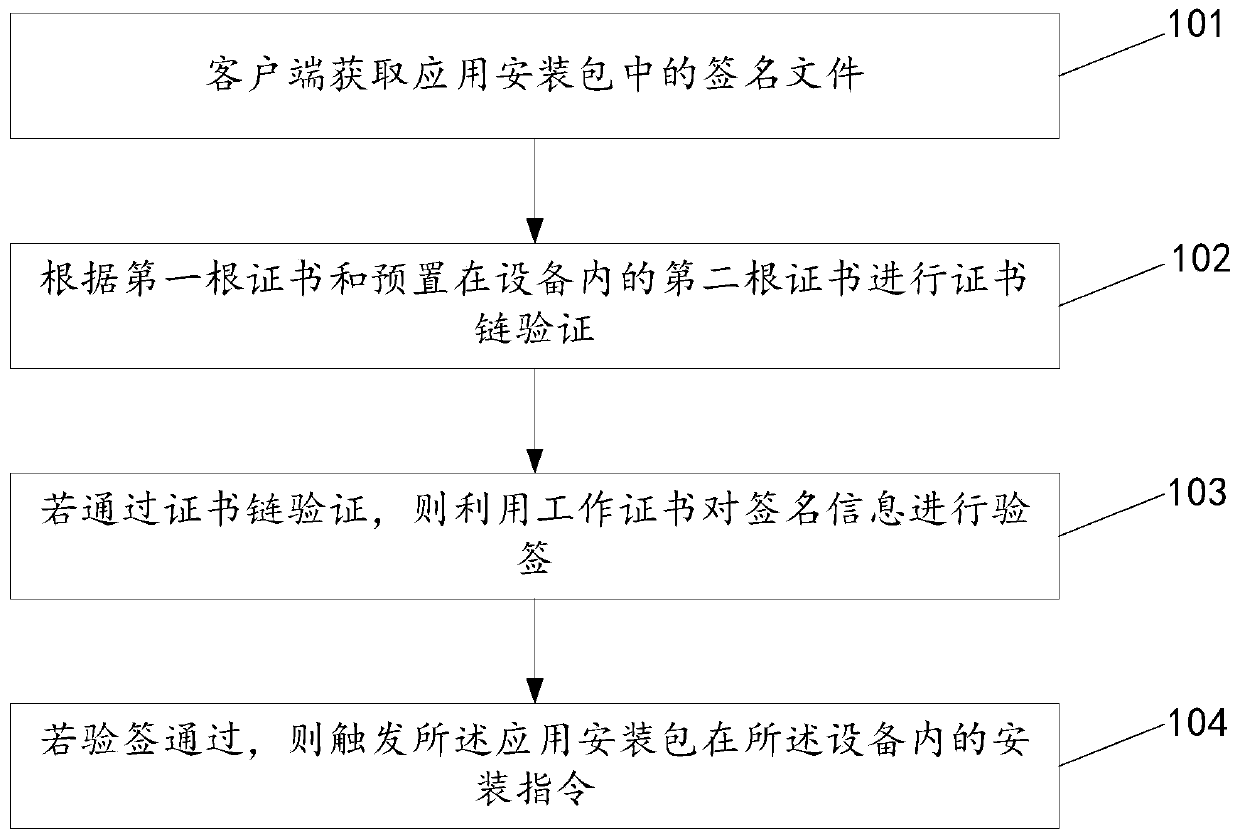
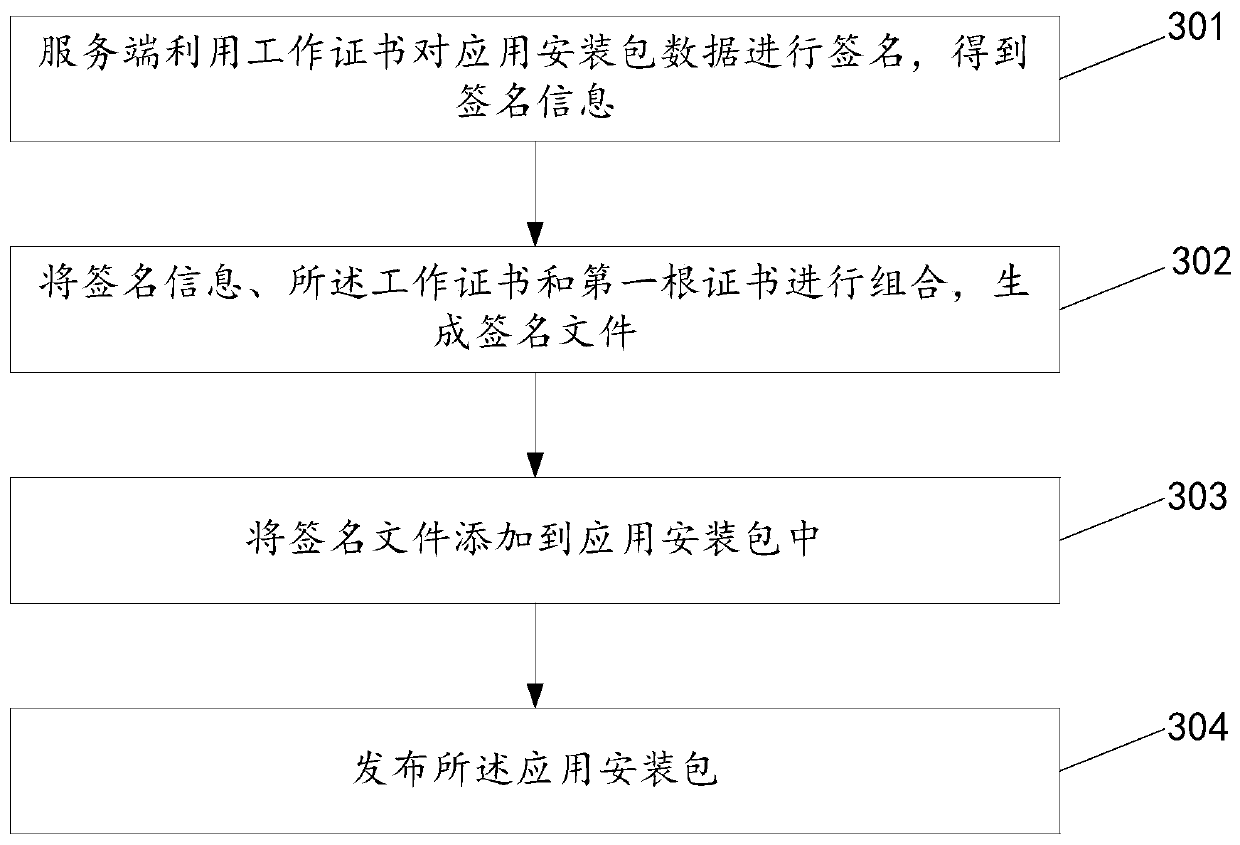
Security processing method, device and system for application installation
InactiveCN110362990ANon-repudiationFully combinedDigital data protectionRoot certificateSignature file
The invention discloses a security processing method, device and system for application installation, belongs to the field of application security, and aims to enhance security detection of equipmenton application installation and more effectively ensure equipment security. The method comprises the steps of: obtaining a signature file in an application installation package, wherein the signaturefile comprises signature information, a first root certificate and a working certificate; performing certificate chain verification according to the first root certificate and a second root certificate preset in the equipment; if the signature information passes the certificate chain verification, performing signature verification on the signature information by using the working certificate; andif the signature verification is passed, triggering an installation instruction of the application installation package in the device.
Owner:KOUBEI SHANGHAI INFORMATION TECH CO LTD
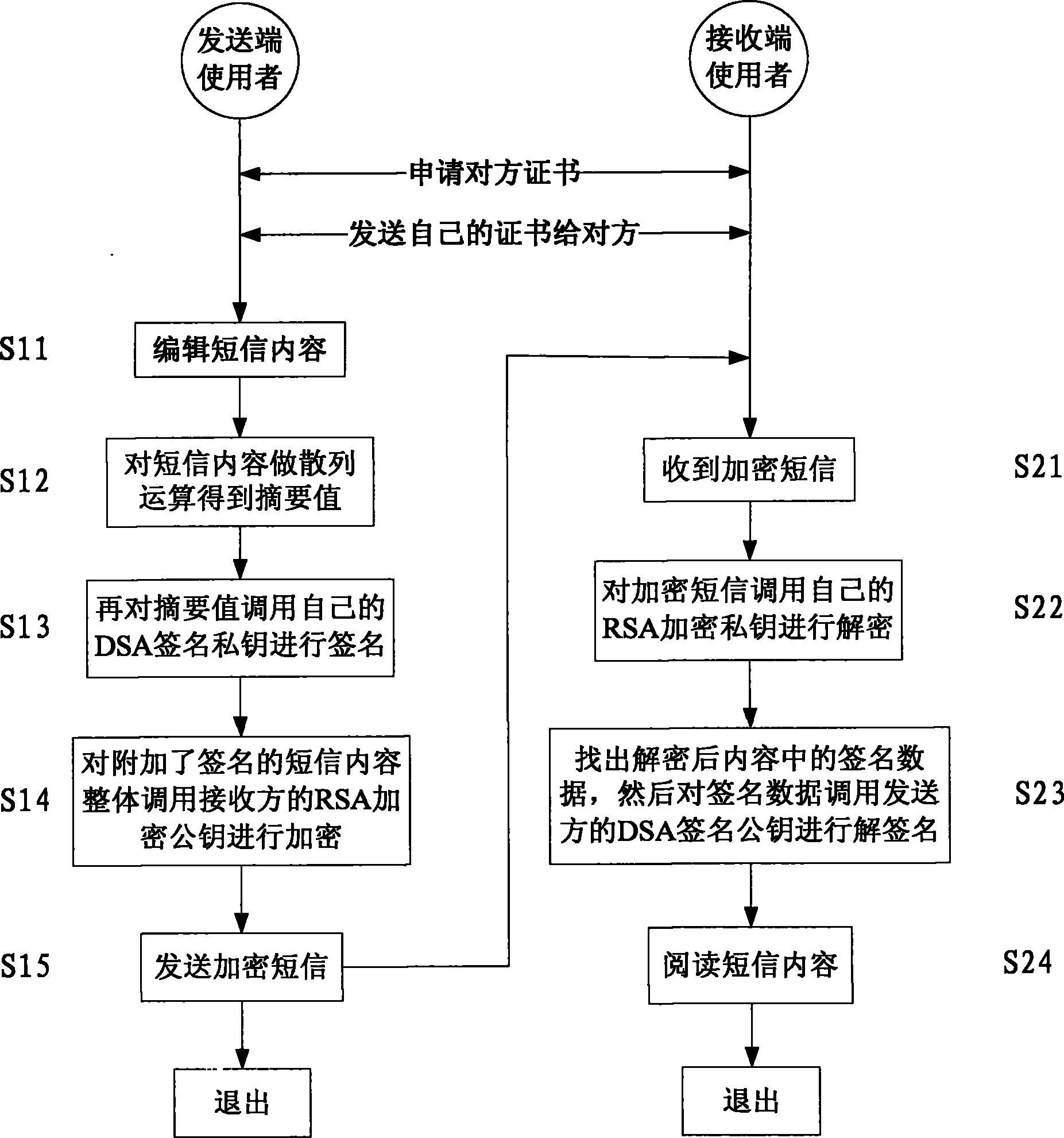
Mobile phone encrypted short message structure and method for transmitting and receiving mobile phone encrypted short message by applying same
InactiveCN102104844AFix security issuesNon-repudiationMessaging/mailboxes/announcementsSecurity arrangementShort Message ServiceDigital Signature Algorithm
The invention refers to a mobile phone encrypted short message structure and a method for transmitting and receiving a mobile phone encrypted short message by applying the structure. The method for transmitting and receiving the mobile phone encrypted short message comprises the steps of: a) enabling a sending terminal user to send an encrypted short message, which comprises the following steps of: S11) editing short message content; S12) obtaining an abstract value of the short message content; S13) applying a signature to the abstract value by utilizing a DSA (digital signature algorithm) encryption private key of the sending terminal user; S14) performing encryption on the signature and the short message content by utilizing a RSA (Rivest-Shamir-Adleman) encryption public key in a digit certificate of a receiving terminal user; and S15) sending the encrypted short message, wherein the encrypted short message structure is the special structure of the invention; and b) enabling the receiving terminal user to receive and read the encrypted short message, which comprises the following steps of: S21) enabling the receiving terminal user to receive the encrypted short message; S22) decrypting the encrypted short message by utilizing a RSA encryption private key of the receiving terminal user; and s24) reading the encrypted short message content.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Semi-quantum group signature method and system based on quantum walk
ActiveCN110166251AReduce demandEnsure safetyKey distribution for secure communicationUser identity/authority verificationInformation transmissionSecurity analysis
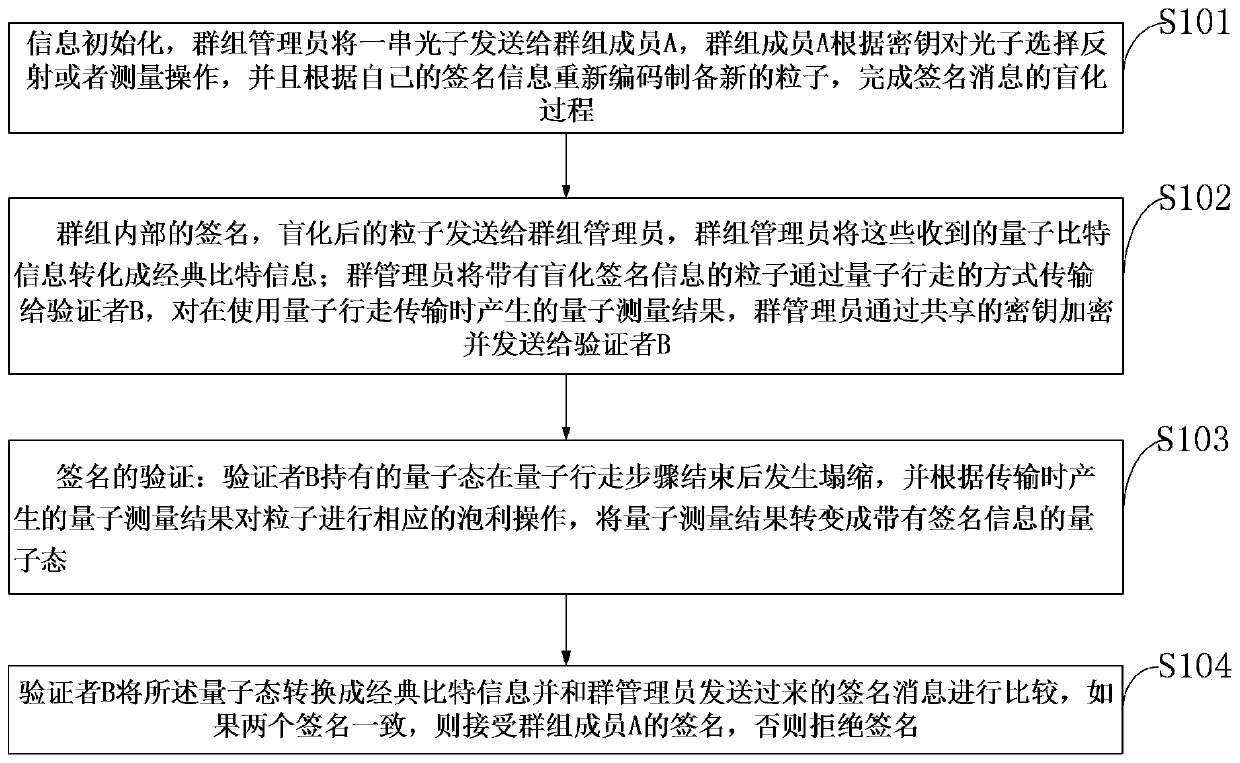
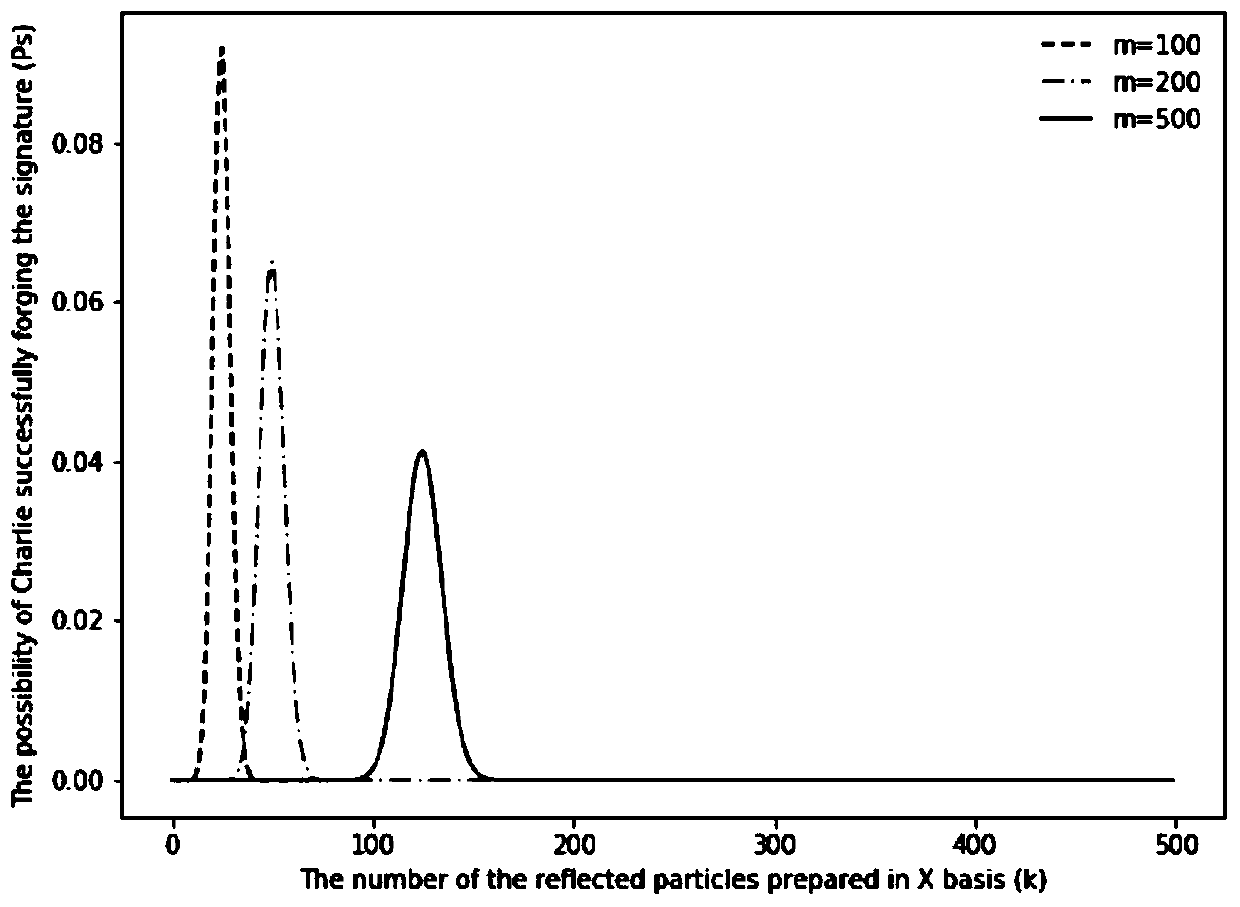
The invention belongs to the technical field of quantum communication, and discloses a semi-quantum group signature method and system based on quantum walk, and the method comprises the steps: carrying out the group internal communication through employing a semi-quantum communication mode; using a quantum walking-based mode to carry out communication outside a group, entangled particles being automatically generated in a walking process, and transmitting a communication message by adopting a quantum walking-based invisible transmission state; when the distributed information is signed by group members, performing blind processing on the message by using a certain coding rule, so that the blind information is not acquired by other group members and external potential attackers; and carrying out anti-repudiation, anti-denial, anti-forgery, interception retransmission attack and entanglement attack security analysis on the blind information. According to the method, single-photon-based information transmission is adopted for communication in the group, so that quantum preparation and detection are relatively easy, and the communication cost is greatly saved in the actual applicationprocess.
Owner:CHENGDU UNIV OF INFORMATION TECH
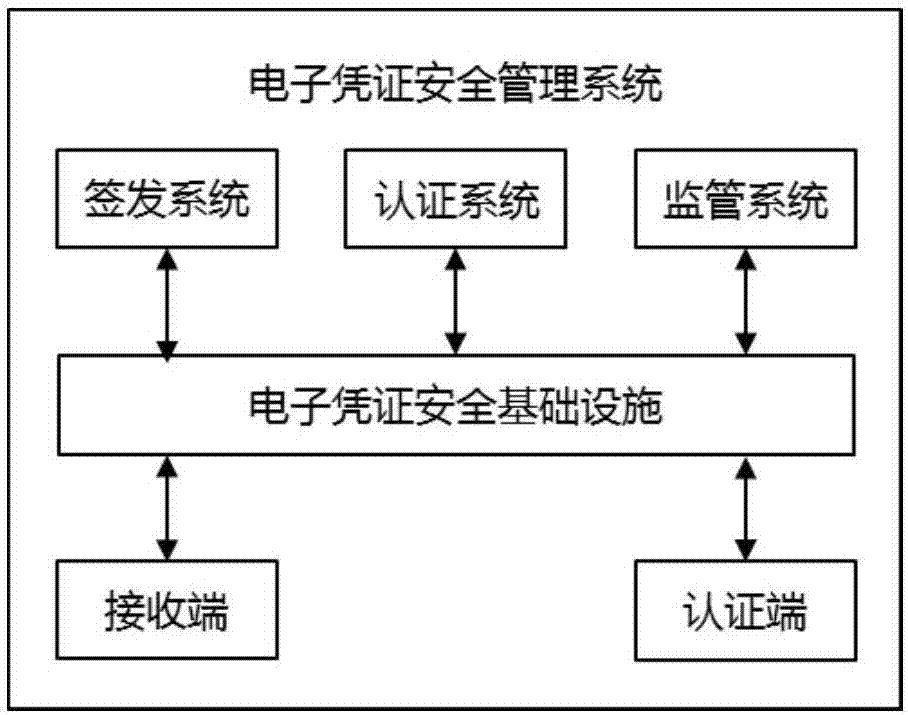
Electronic certificate security management method and system
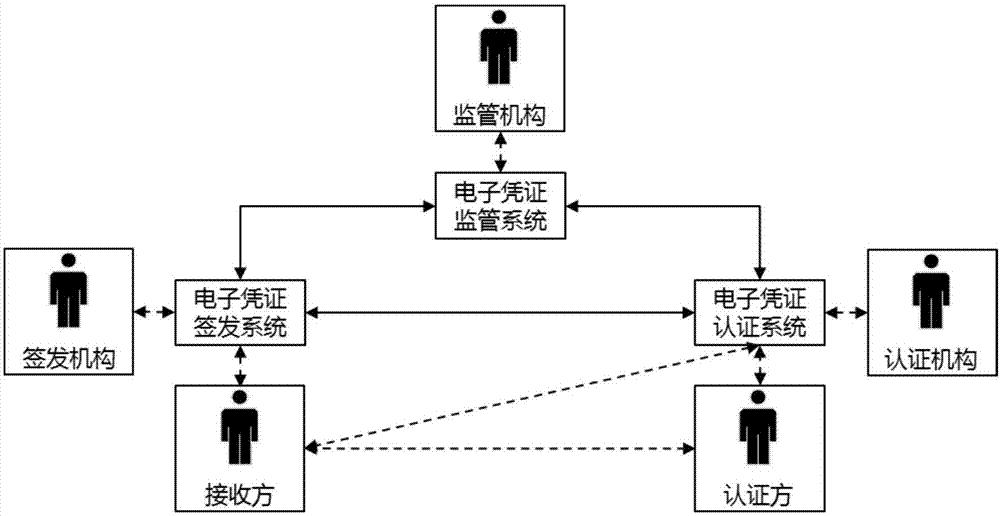
ActiveCN107277000ASolve the costFix security issuesTransmissionMarketingSecurity managementAuthentication
The invention discloses an electronic certificate security management method and system. The electronic certificate security management method comprises the following steps: issuing electronic certificate signing and issuing application; authenticating the receiving end, generating the electronic certificate, and issuing the electronic certificate and the signing and issuing information to the security basic module of electronic certificate; obtaining the electronic certificate and the electronic certificate signing and issuing results from the electronic certificate security basic module; issuing the electronic certificate authentication application to the electronic certificate security basic module; authenticating the receiving end by means of the electronic certificate security basic module, issuing the authentication confirmation information to the electronic certificate security basic module, and waiting for the receiver to confirm; confirming the authentication confirmation information by the receiving end; and obtaining the authentication results of the electronic certificate from the electronic certificate security basic module. By means of the scheme disclosed by the invention, the defects of the electronic certificate issuing, authentication and supervision platform in the prior art in the aspects of cost, safety and convenience can be solved.
Owner:北京明朝万达科技股份有限公司
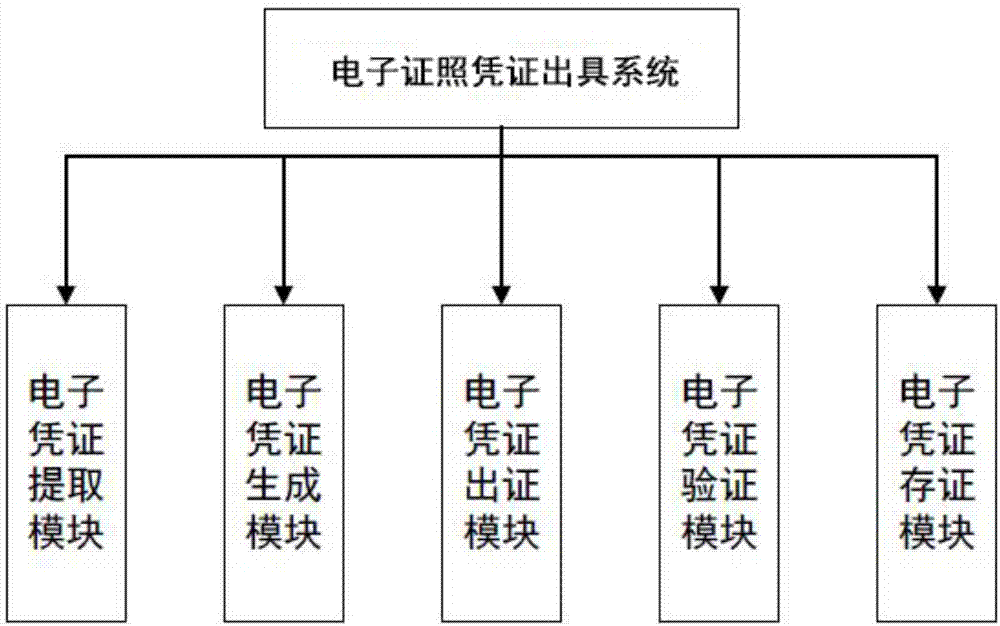
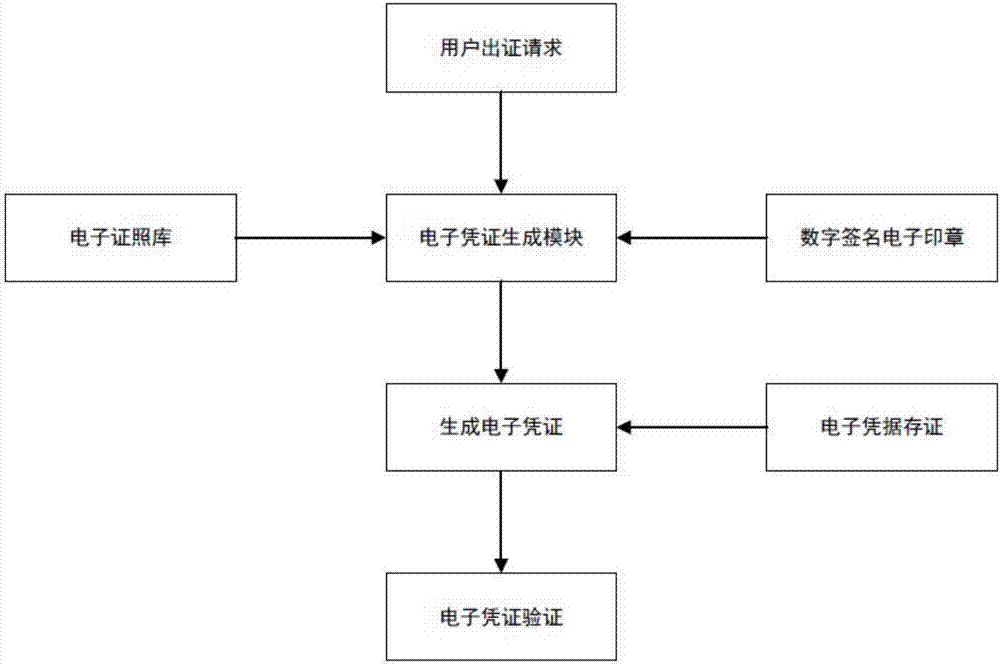
Electronic license certificate issuing system
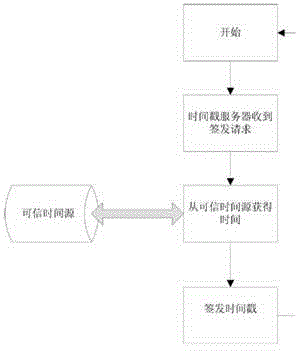
The invention discloses an electronic license certificate issuing system. The system comprises an electronic certificate generating module for extracting corresponding electronic certificate information from an electronic license library according to user information, license information and license application parameter in a certificate issuing request, thereby issuing the certificate by adding the user request information, the certificate issuing description information and the certificate issuing timestamp information which are related to the certificate issuing time; the system strengthens the certificate issuing information, and adds the user request information, the certificate issuing description information and the certificate issuing timestamp information on the license basic information; and meanwhile, the application of the electronic signature and the digital stamp ensures that the certificate issuing information is verifiable, traceable and non-reputation; a log record is preserved for each certificate issuing information, thereby facilitating the future query and verification.
Owner:合肥拓普网络系统工程有限责任公司
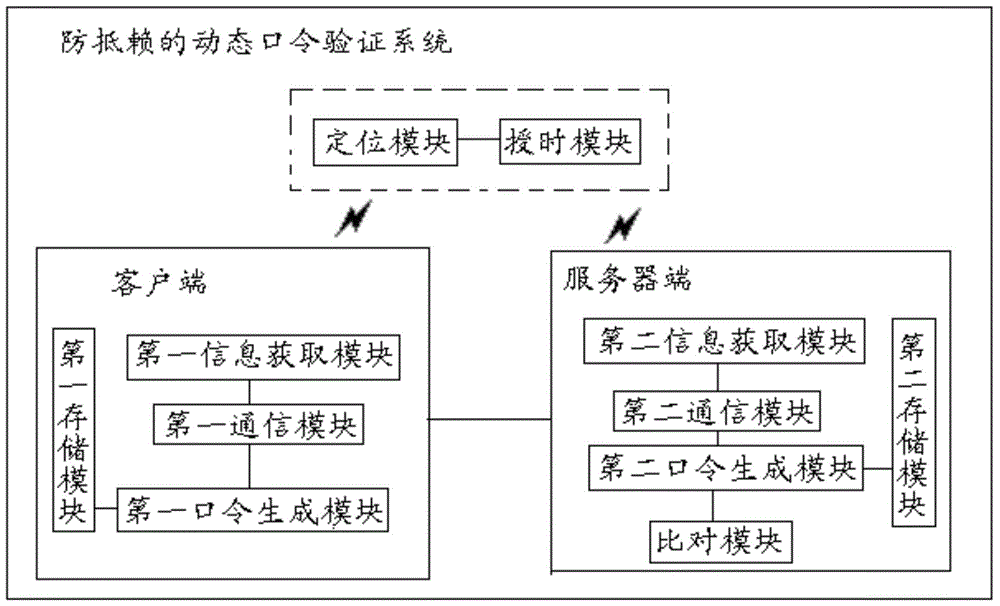
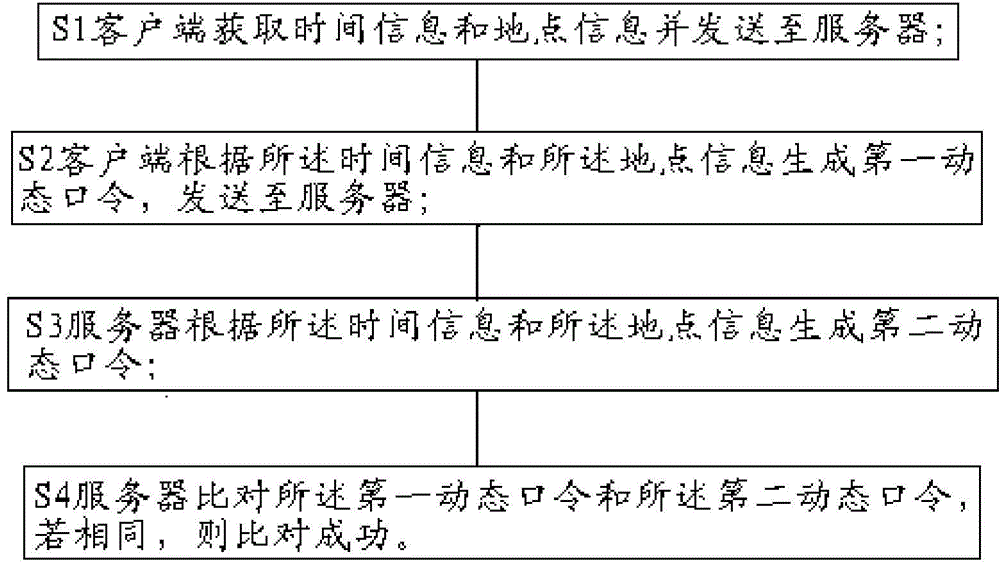
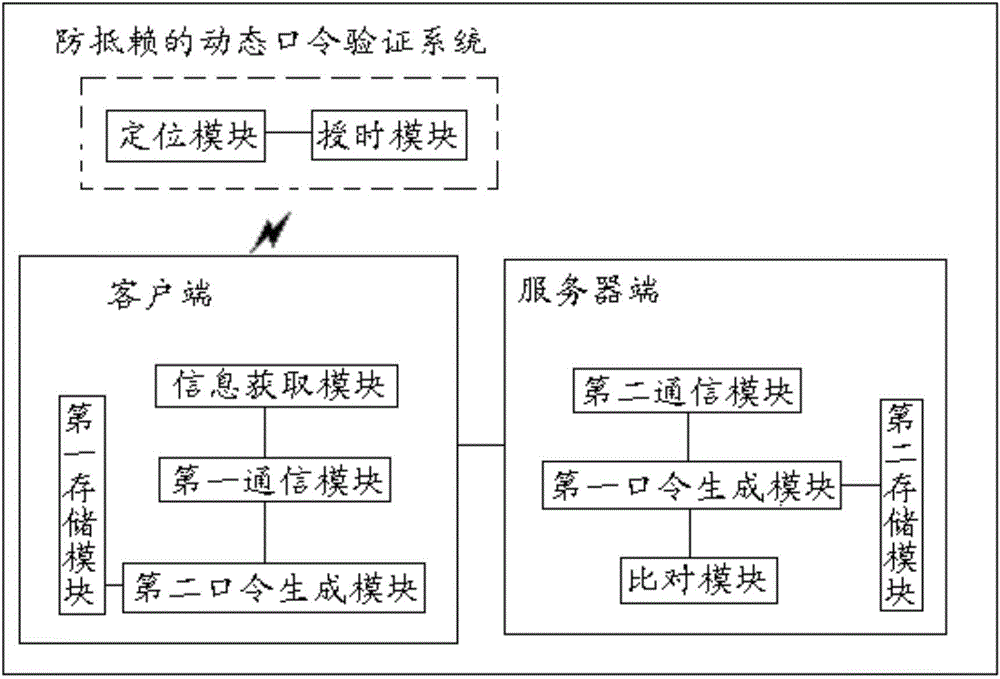
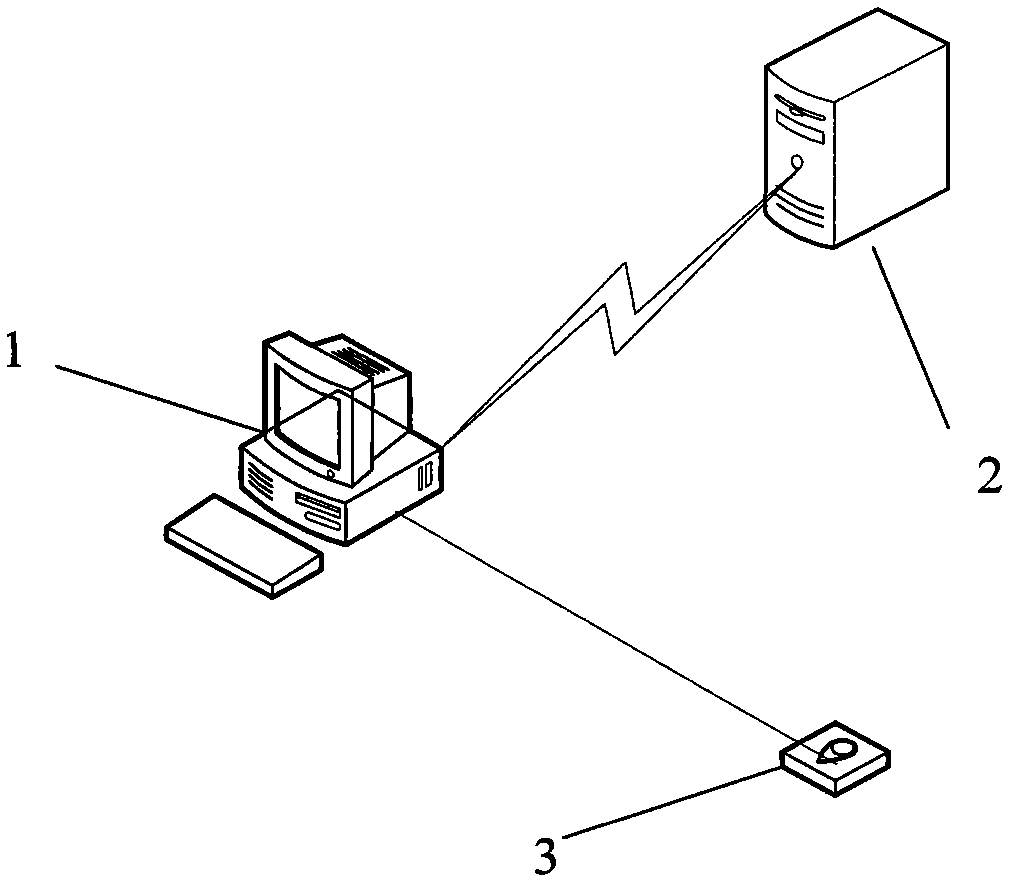
Anti-repudiation dynamic password generating method and dynamic password verification system
InactiveCN104683358ANon-repudiationUser identity/authority verificationSecurity arrangementTime informationPassword
The invention provides an anti-repudiation dynamic password generating method and an anti-repudiation dynamic password generating system. The method comprises the following steps that S1, a client acquires first time information and first place information by virtue of a positioning satellite and transmits an instruction to a server at the same time; S2, the server receives and executes the instruction and acquires second time information and second place information by virtue of the positioning satellite; S3, the client generates a first dynamic password according to the first time information and the first place information, and transmits the first dynamic password to the server; S4, the server generates a second dynamic password according to the second time information and the second place information; and S5, the server compares the first dynamic password with the second dynamic password, and if the first dynamic password is the same as the second dynamic password, the comparison is successful, and the verification is finished. According to the method provided by the invention, the current time and place of the client are acquired by the client and the server by virtue of a satellite, and the time information and the place information are used as key elements for generating dynamic passwords, so that the dynamic passwords have anti-repudiation properties.
Owner:SHANGHAI PEOPLENET SECURITY TECH
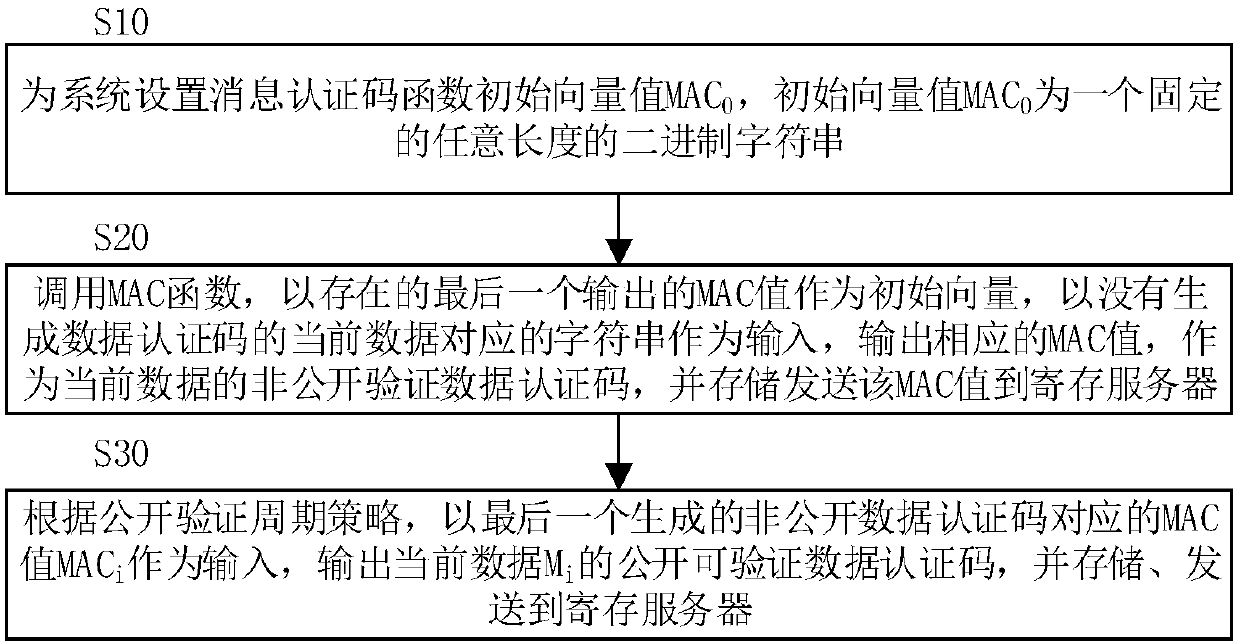
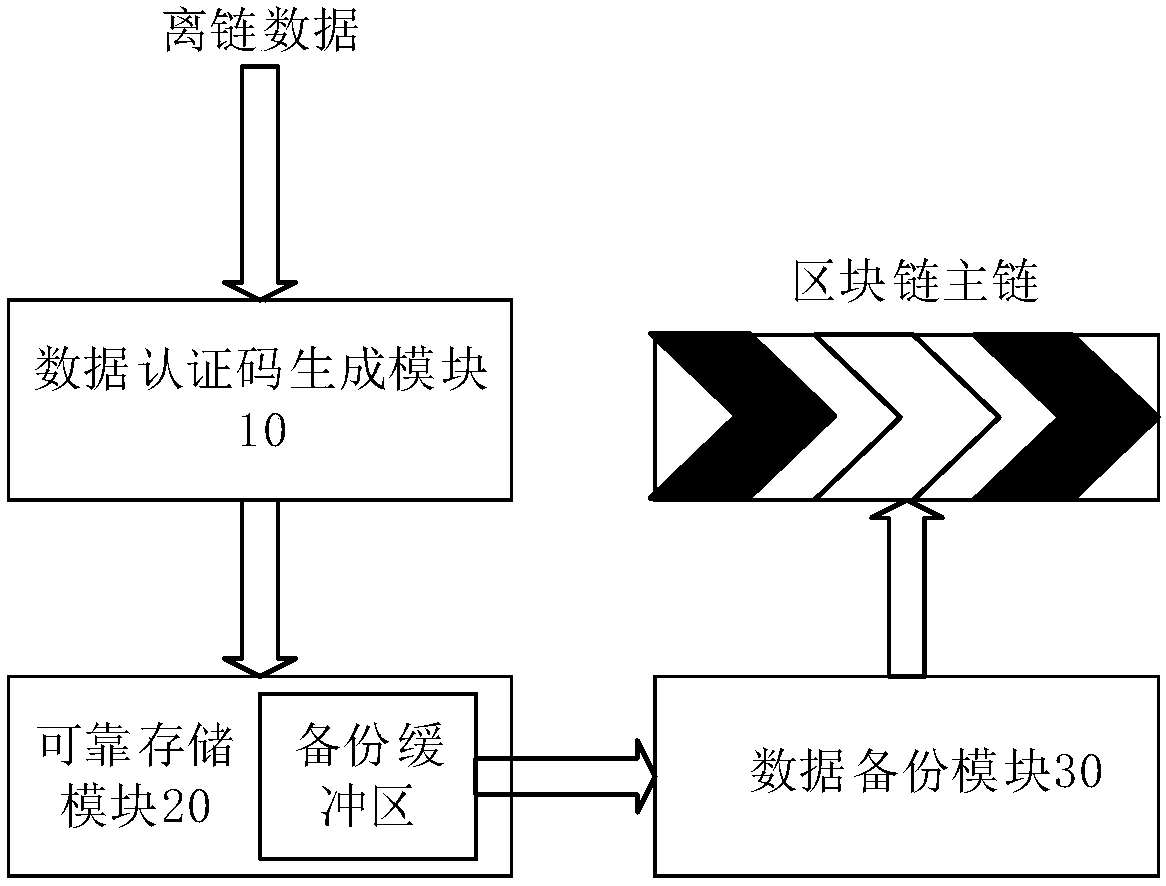
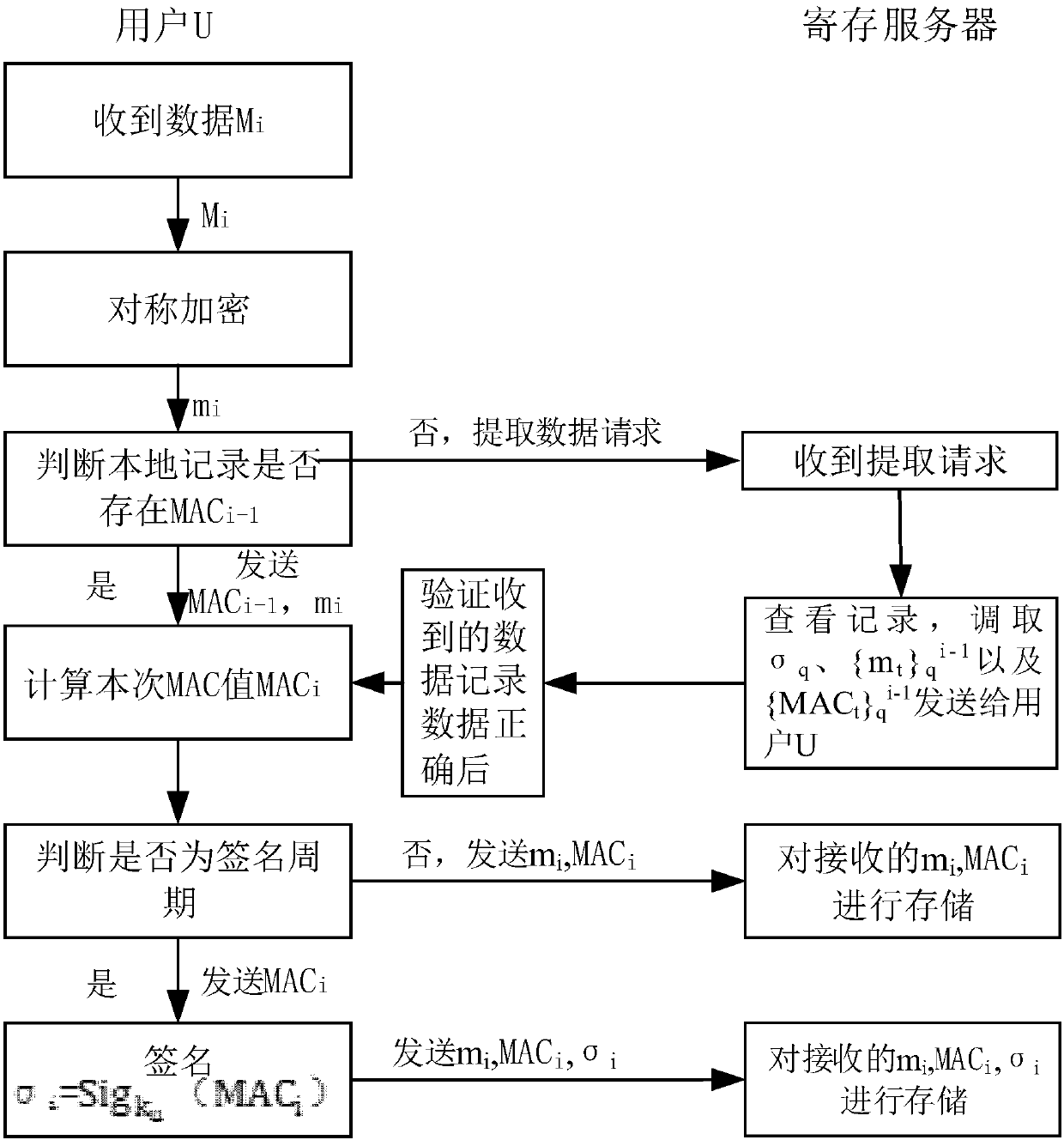
Generation method for data authentication code
ActiveCN107566360AReduce the risk of lossImprove reliabilityTransmissionComputer hardwareInitialization vector
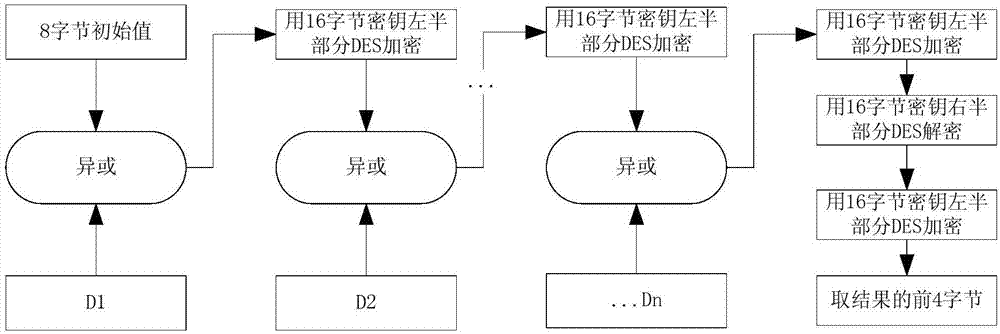
The invention discloses a generation method for a data authentication code. The method comprises the steps of setting a binary character string with a fixed random length as an initial vector value MAC0 of an MAC function; calling the MAC function, using a currently existing last output MAC value MACi-1 as an initial vector, using a character string corresponding to current data Mi of which the data authentication code is not generated as an input, outputting the corresponding MAC value MACi to serve as a non-public verification data authentication code of the current data Mi, and storing andsending the MAC value MACi to a register server; using the MAC value MACi corresponding to the last generated non-public verification data authentication code as the input according to a public verification period strategy, outputting a public verifiable data authentication code of the current data Mi, and storing and sending the code to the register server. According to the generation method provided by the invention, the generated data authentication code of the current data can authenticate all previous data, so that a data loss risk is reduced, reliability and security of data authentication are enhanced, and data authentication efficiency is improved.
Owner:北京中科锐链科技有限公司
Anti-repudiation dynamic password generating method and dynamic password verification system
InactiveCN104683355ANon-repudiationImprove securityUser identity/authority verificationTime informationPassword
The invention provides an anti-repudiation dynamic password generating method and an anti-repudiation dynamic password generating system. The method comprises the following steps that S1, a client acquires time information and place information and transmits the time information and the place information to a server; S2, the client generates a first dynamic password according to the time information and the place information, and transmits the first dynamic password to the server; S3, the server generates a second dynamic password according to the time information and the place information; and S4, the server compares the first dynamic password with the second dynamic password, and if the first dynamic password is the same as the second dynamic password, the comparison is successful. According to the method provided by the invention, the current time and place of the client are acquired by a satellite, and the time information and the place information are used as key elements for generating dynamic passwords, so that the dynamic passwords have anti-repudiation properties.
Owner:SHANGHAI PEOPLENET SECURITY TECH
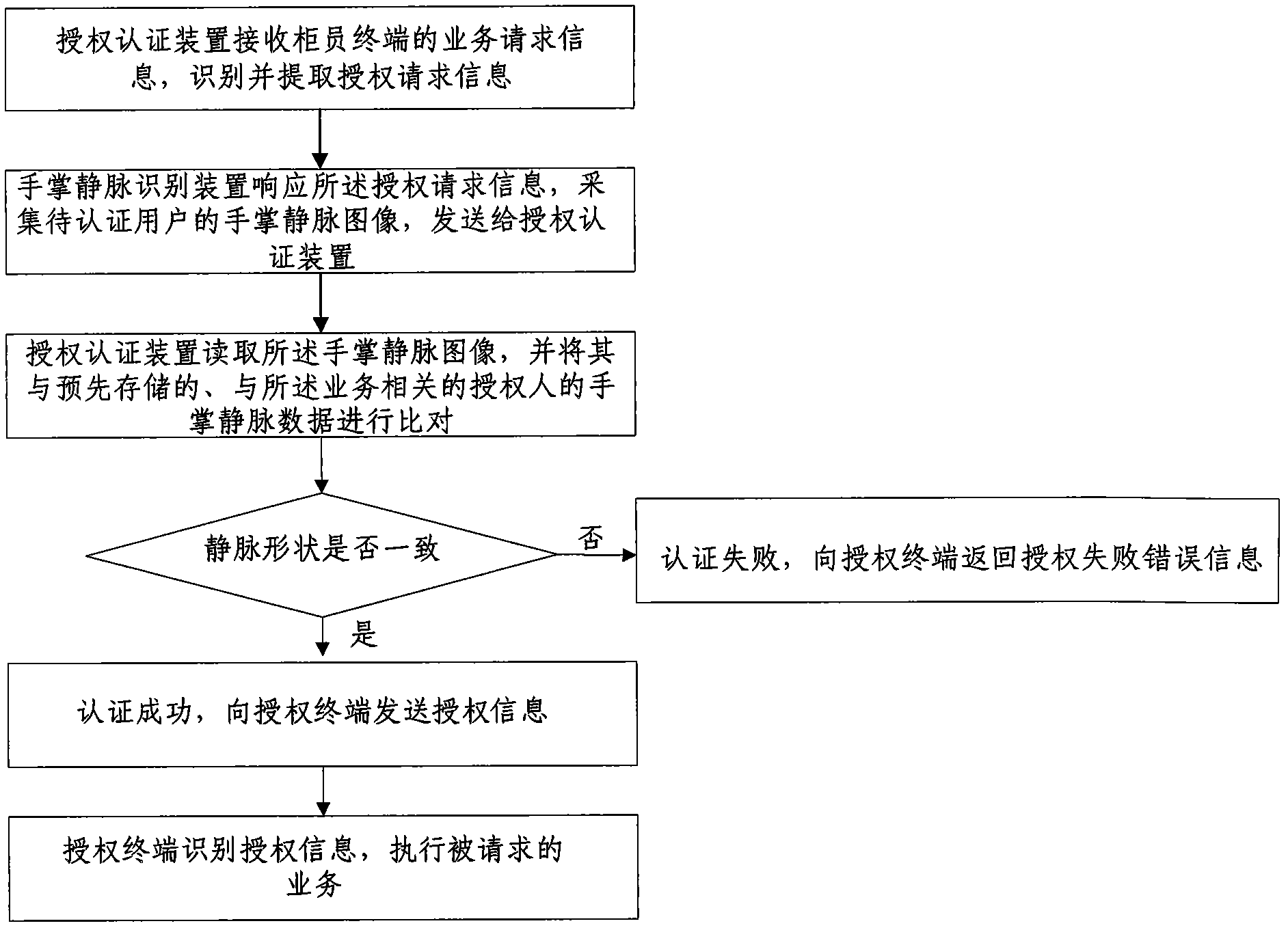
Palm vein authentication-based bank authorization and credit system and method
InactiveCN102075530APut an end to easy forgettingPrevent theftUser identity/authority verificationCredit systemIdentification device
The invention discloses a palm vein authentication-based bank authorization and credit system and a palm vein authentication-based bank authorization and credit method. The system comprises an authorized terminal, an authorized certification device and a palm vein identification device, wherein the authorized terminal sends service request information to the authorized certification device according to a bank service process requirement; the authorized certification device receives the service request information, identifies, extracts and sends authentication request information to the palm vein identification device, reads a palm vein image of a user to be certified, compares the palm vein image of the user to be certified with pre-stored palm vein data of an authorizer, and sends authorization information to the authorized terminal if the palm vein image of the user to be certified matches the pre-stored palm vein data of the authorizer; and the palm vein identification device responds to the authorization request information, acquires the palm vein image of the user to be certified, and processes and transmits the palm vein image to the authorized certification device. The system and the method stop the potential safety hazard in a conventional authorization and credit system, are simple in operation, have anti-denial performance and traceability because of the uniqueness and the non-replicability of palm vein information, do not need to perform any transformation on a conventional bank background service system, and can be integrated with other systems of a bank conveniently.
Owner:天公(山东)信息科技有限公司
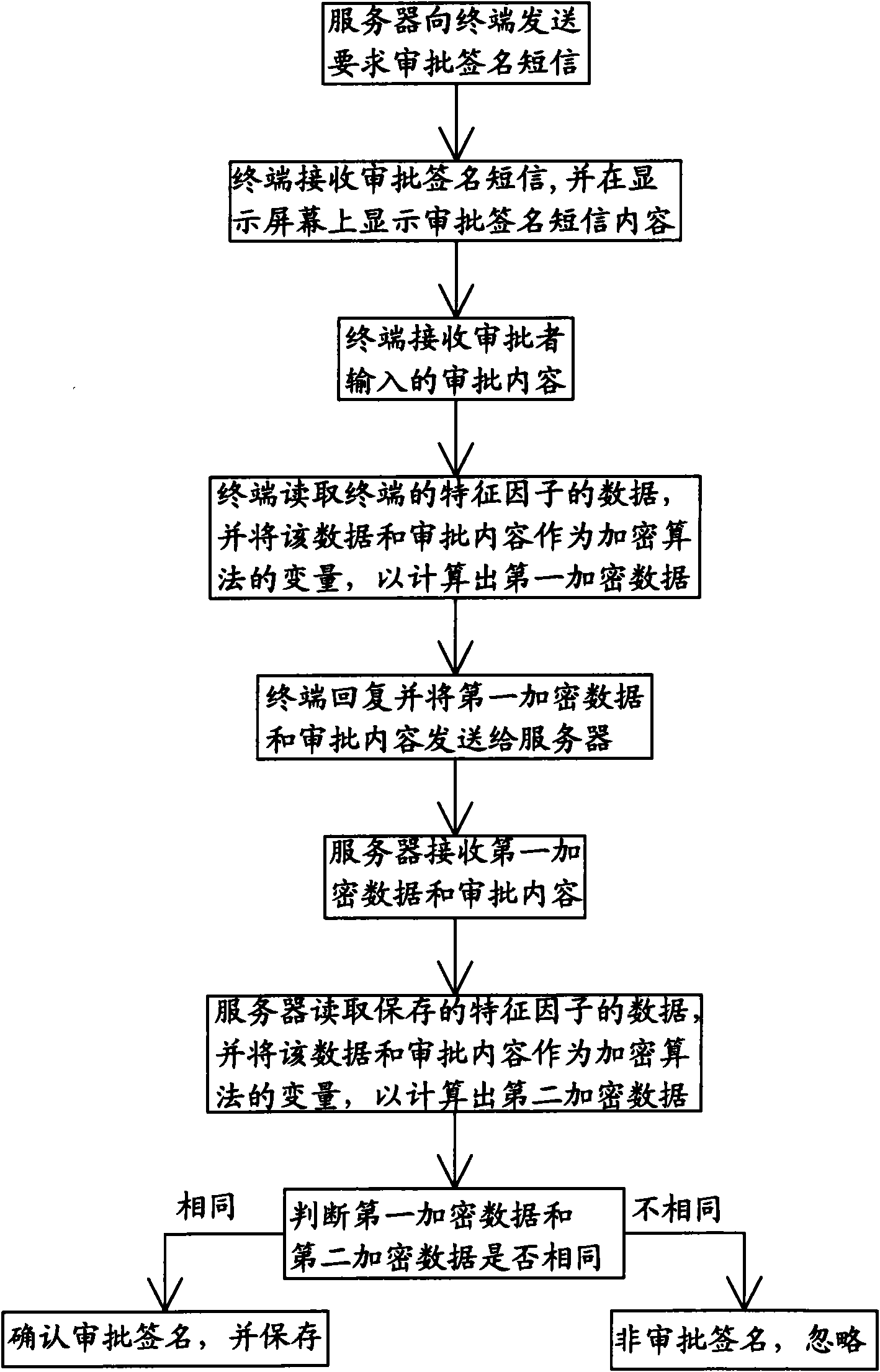
Method for mobile electronic signature
InactiveCN101605310AImprove securityAvoid confusionUser identity/authority verificationMessaging/mailboxes/announcementsMobile electronicsEncryption
The invention discloses a method for a mobile electronic signature. The method comprises the following steps that: a server sends a short message requesting an approval signature to a terminal; the terminal receives the approval signature short message and displays the content of the approval signature short message on a display screen; the terminal receives the approving content inputted by an approver; the terminal reads the data of the characteristic factor of the terminal, and works out the first encrypted data by taking the data and the approving content as variables of an encryption algorithm; the terminal answers and sends the first encrypted data and the approving content to the server; the server receives the first encrypted data and the approving content; the server reads the stored data of the characteristic factor, and works out the second encrypted data by taking the data and the approving content as variables of the encryption algorithm; and whether the first encrypted data and the second encrypted data are the same is judged, if so, the approval signature is confirmed and stored, otherwise the signature is the unapproved signature and neglected. The method has the advantages that the signature approver can give particular written instructions or assessments and examine the correctness of the approving content according to the content to be approved.
Owner:XIAMEN STELCOM INFORMATION & TECH
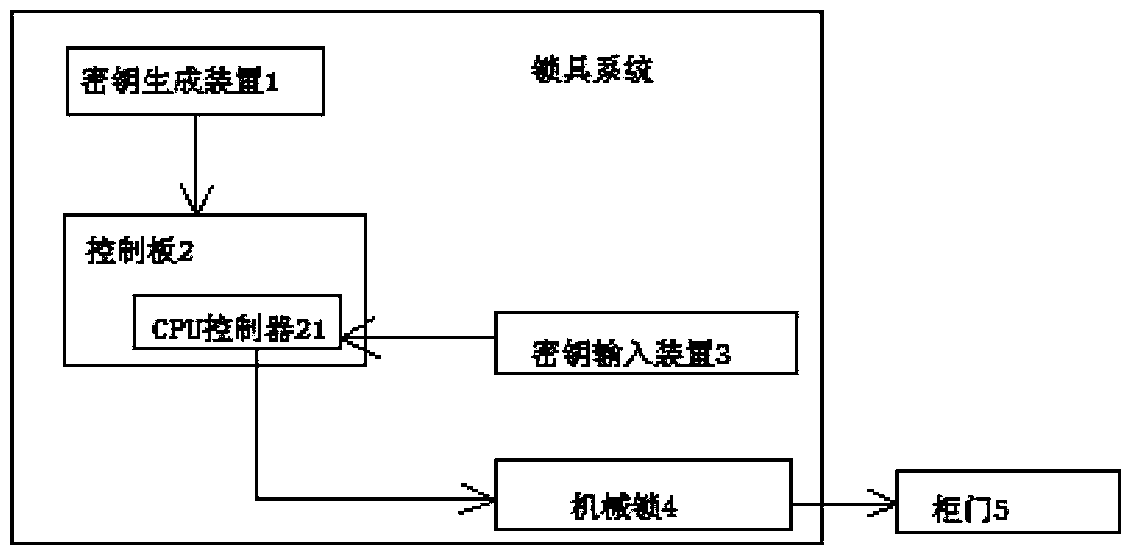
Mutual assistance type lock system adopting asymmetric encryption technology and control method of mutual assistance type lock system
InactiveCN103440695AAnti-crackingNon-repudiationIndividual entry/exit registersNon symmetricKey generation
The invention discloses a mutual assistance type lock system adopting an asymmetric encryption technology and a control method of the mutual assistance type lock system. The mutual assistance type lock system comprises a key generation device, a control panel, a key input device and one or more electromechanical locks, wherein the key generation device generates a locking key and an unlocking key in pairs; the control panel comprises a CPU (central processing unit) controller and an affiliated storage device thereof; the output end of the key input device is connected with the CPU controller; the CPU controller controls the electromechanical locks to be locked or unlocked; the electromechanical locks are arranged on various openable doors. According to the brand-new lock system provided by the invention, a set of lock can be locked and unlocked by one or more groups of different keys in pairs; in a pair of keys, one key is used for locking while the other key is used for unlocking, and a group comprises the two keys which are used in pairs; representation and carrier forms of the keys can be but not limited to cipher texts, bi-dimensional codes, keys, magnetic cards, IC (integrated circuit) cards and the like. By the flexible adoption of an asymmetric encryption algorithm, the mutual assistance type lock system has the characteristics of credibility, cracking prevention, repudiation prevention and the like and is safe and reliable.
Owner:吴俊杰
Timestamp-based transaction verification method
ActiveCN107301545AImprove securityImprove effectivenessKey distribution for secure communicationUser identity/authority verificationPaymentTimestamp
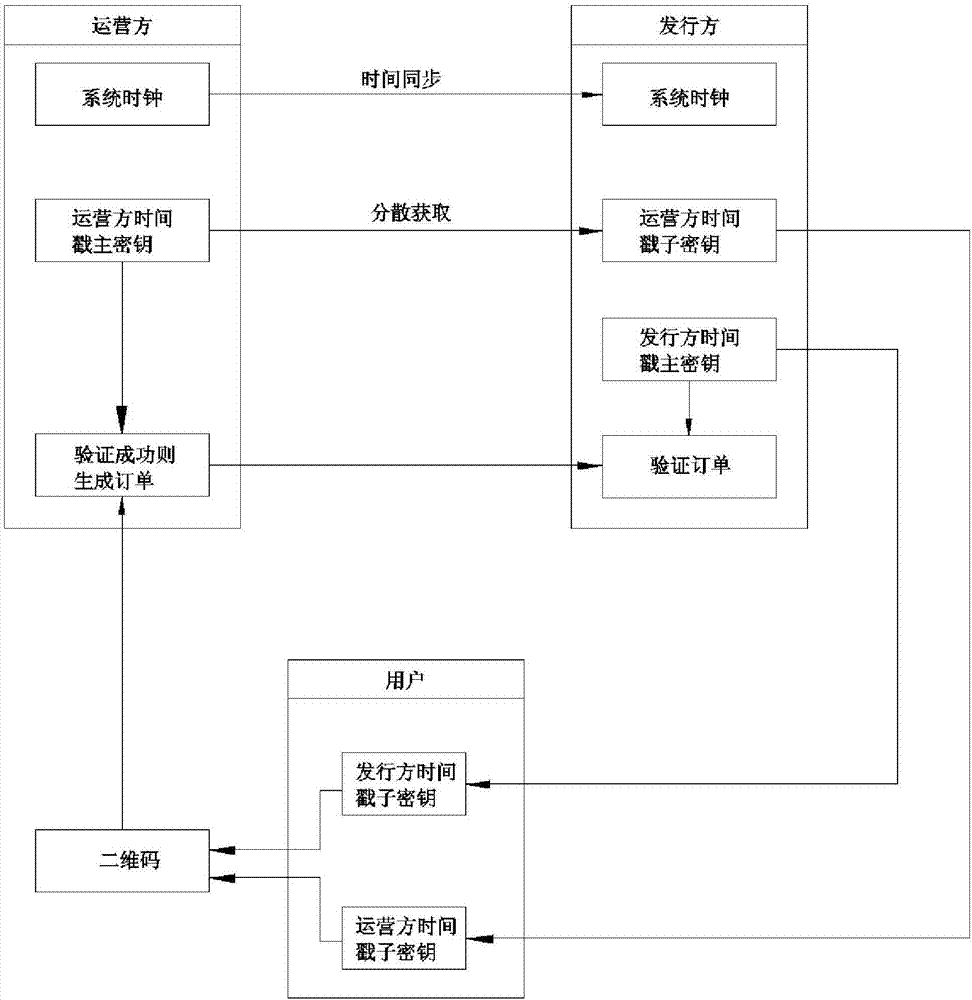
The invention discloses a timestamp-based transaction verification method. The method comprises the steps that a system is initialized, an issuer acquires a system clock from an operator to complete time synchronization, the operator generates an operator timestamp main key, and the issuer generates an issuer timestamp main key; operator timestamp sub-keys obtained after dispersion of the operator timestamp main key are released to the issuer, and a user acquires the operator timestamp sub-keys from the issuer and issuer timestamp sub-keys obtained after dispersion of the issuer timestamp main key; in the transaction process, the user performs operation to complete an order and submits the order to the operator, the order is dually encrypted with the operator timestamp sub-keys and the account issuer timestamp sub-keys; the operator verifies the order through the operator timestamp main key, and the order is submitted to the issuer after passing the verification; and the issuer verifies the order through an issuer timestamp, and payment is completed if the order passes the verification. Through the method, dual verification can be realized, and therefore the security and validity of payment verification are further improved.
Owner:广州羊城通有限公司
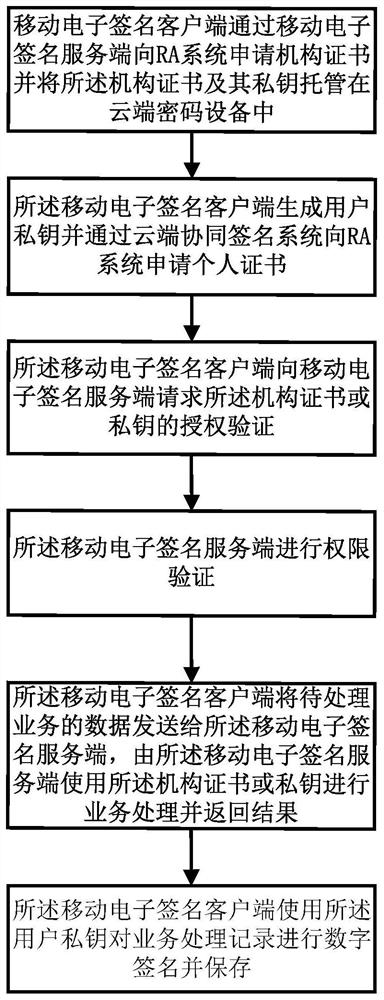
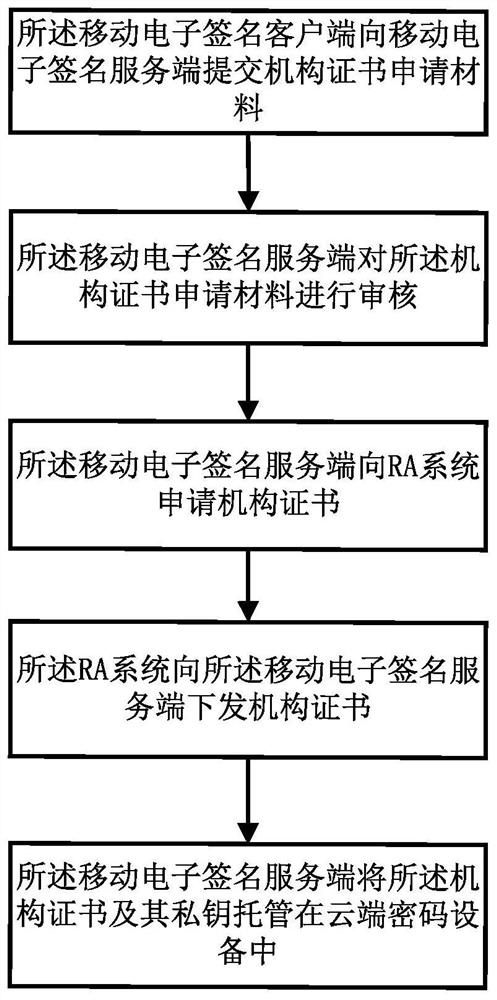
Mobile electronic signature-based trusteeship key use method and system, computer equipment and storage medium
InactiveCN113271207AEnsure safetyAvoid risk of lossKey distribution for secure communicationUser identity/authority verificationInternet privacyDigital signature
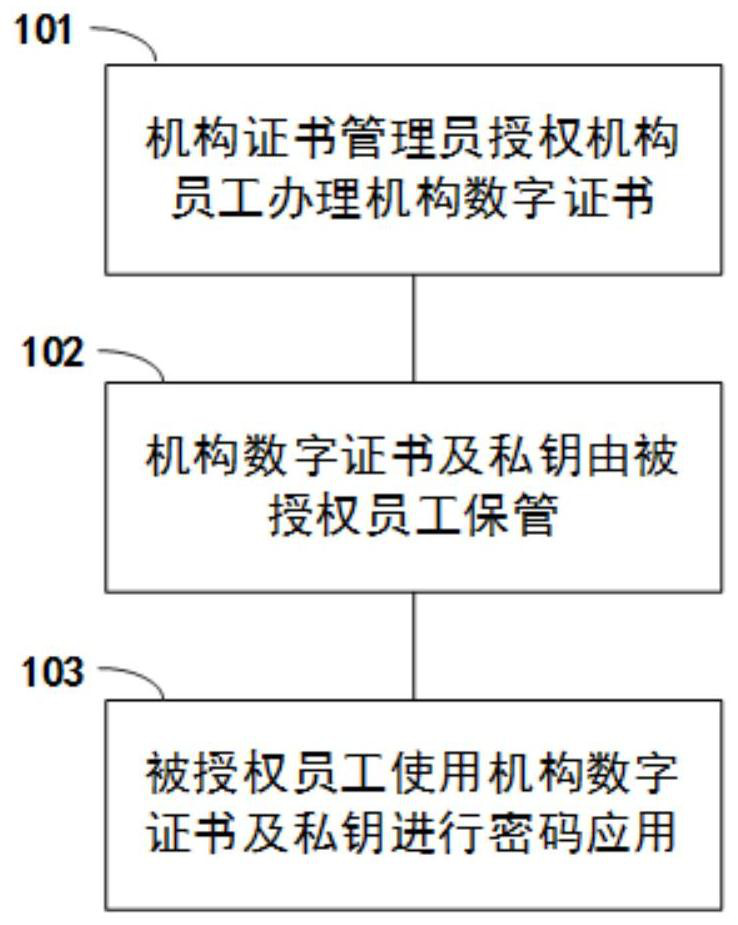
The invention relates to the technical field of PKI (Public Key Infrastructure), in particular to a mobile electronic signature-based trusteeship key use method and system, computer equipment and a storage medium. The method comprises the following steps: a mobile electronic signature client applies for an institution certificate, hosts the institution certificate and a private key in cloud password equipment, generates user private keys, dispersedly stores the user private keys in the mobile electronic signature client and a cloud collaborative signature system, and applies for a personal certificate; the mobile electronic signature client requests an institution certificate or a private key to authorize and verify; the mobile electronic signature server performs authority verification on the individual user, processes the service data by using an institution certificate or a private key, and returns a result; and the service processing record is digitally signed and stored by using the private key of the individual user. According to the method, the cloud password service technology is adopted to carry out centralized management on the secret keys, digital signature storage is carried out on log records while password services are provided for authorized users, and it is guaranteed that behaviors of the authorized users are not repudiated while the security of the private keys is guaranteed.
Owner:福建瑞术信息科技有限公司
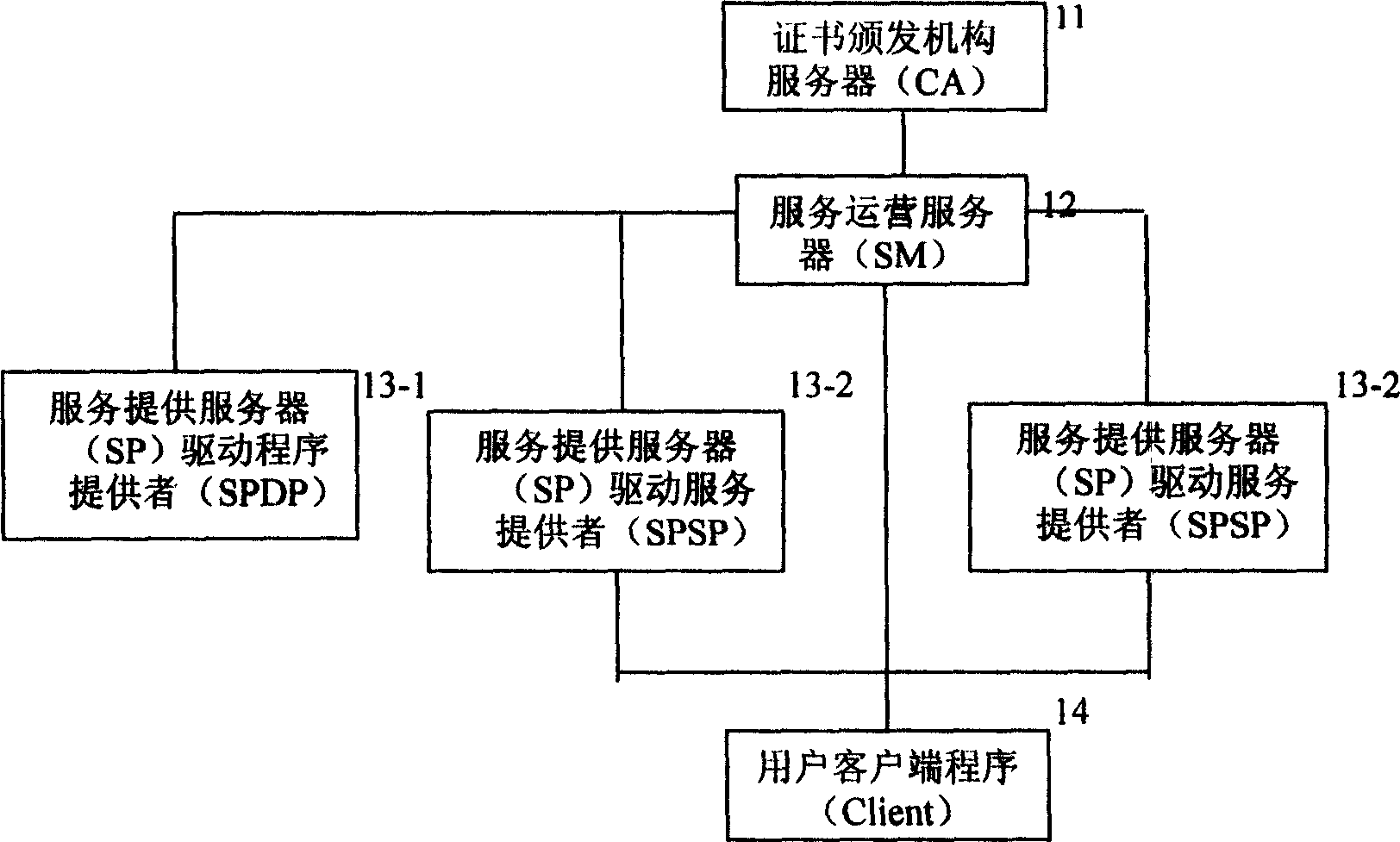
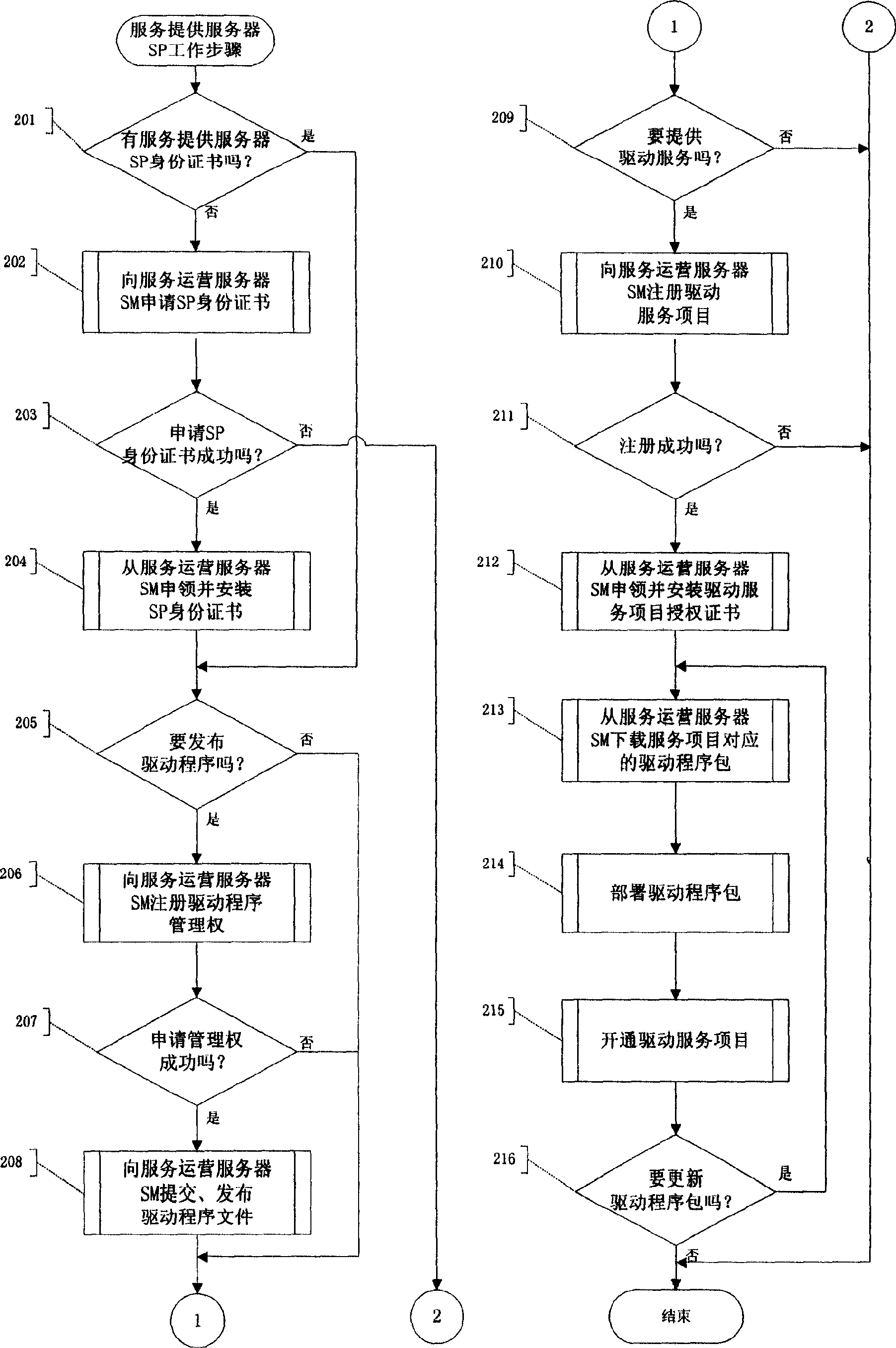
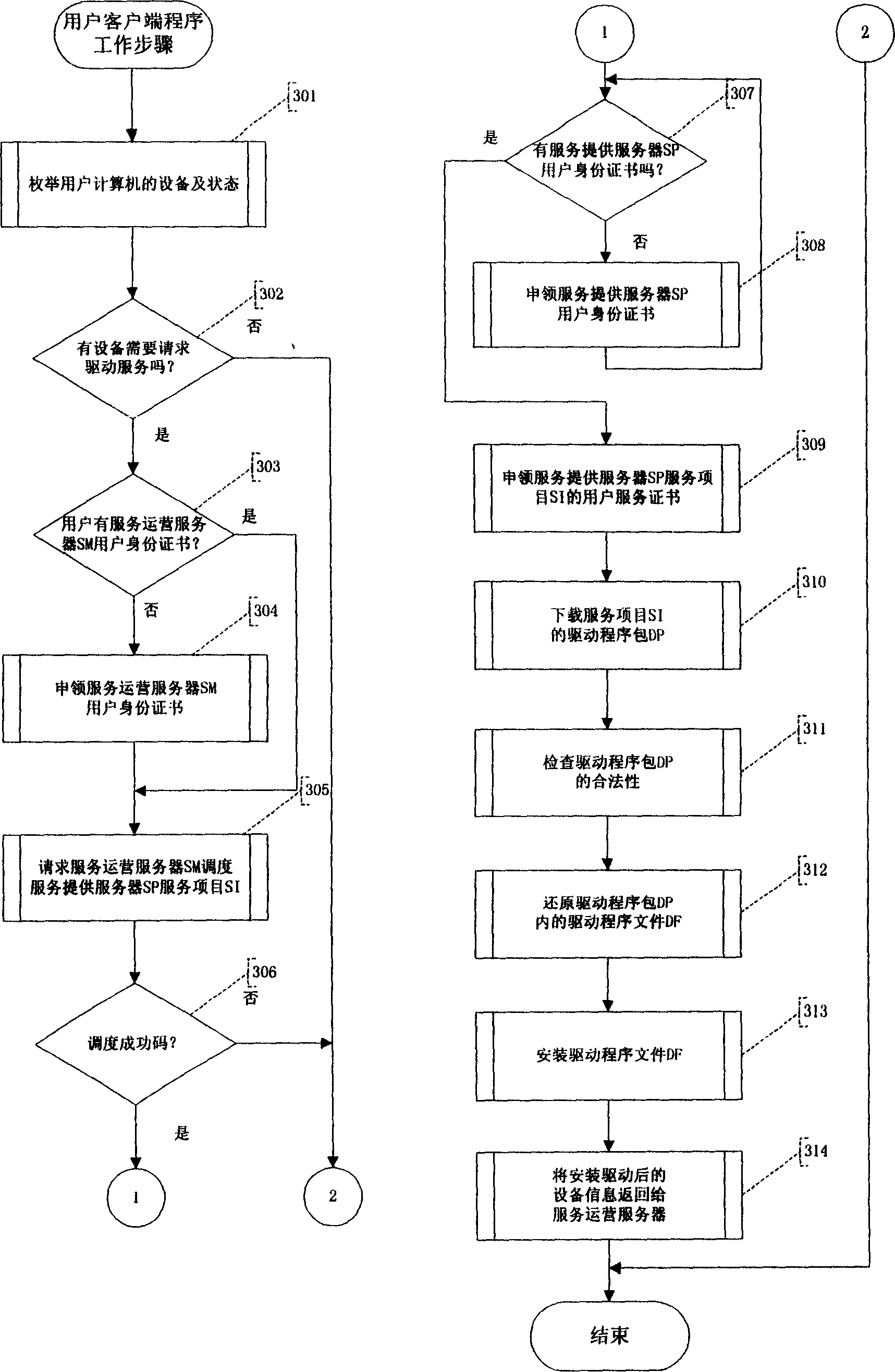
Method for implementing computer driving service security network system
InactiveCN1606270AAvoid complexityAvoid hidden dangersUser identity/authority verificationProgram loading/initiatingService provisionClient-side
This invention provides a realization method for a computer driving service safety network including: A driving service provider (SP) applies for a service providing identity certification (SPC) to an operation server(SM), the SP for providing driving programs (SPDP) provides the driving program (DF) to SM and examined by SM, the DF is issued by the service items SI. The SPSP registers a service of SI to SM. The user customer end program client gets the service of SI to ensure the true and legal driving program source.
Owner:耿健
Credit information synchronization method based on block chain and credit joint reward and punishment system
ActiveCN110727734ANon-repudiationImmutableFinanceDatabase distribution/replicationComputer networkThe Internet
The invention discloses a credit information synchronization method based on a block chain and a credit joint reward and punishment system, and relates to the technical field of the Internet. The method comprises: a first-level node receiving an information uploading request sent by a first user account, wherein the information uploading request comprises credit information; uploading the credit information to a block chain platform; when the credit information meets the chaining condition, storing the credit information to a block chain through a block chain platform; synchronizing the creditinformation to the second-level node through the block chain; and the first-level node synchronizing the credit information to each node in the system by using the decentralized block chain, so thatthe problem of inconsistent data of each level of nodes in the credit joint reward and punishment system is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
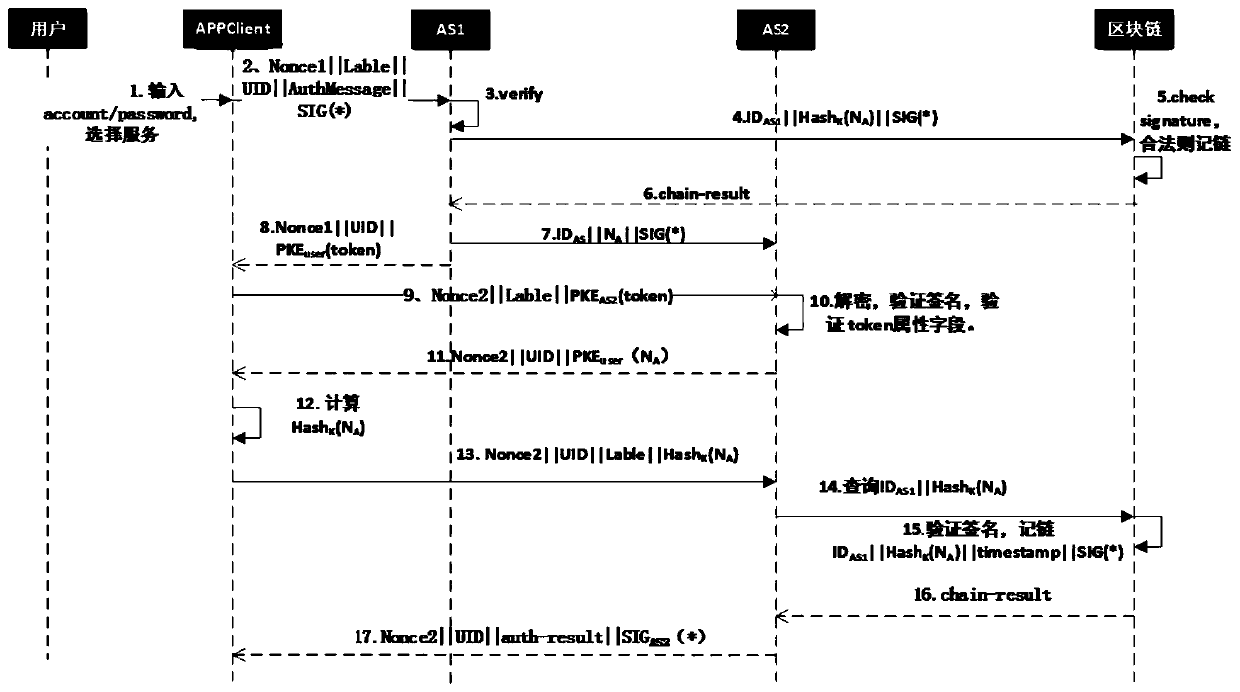
Cross-domain trust transfer method based on block chain
PendingCN111464535ALow costNo need to face the difficulty of managing multiple accountsTransmissionInternet privacyPassword
The invention relates to the technical field of block chains and discloses a cross-domain trust transmission method based on a block chain. After a user logs in an original application system and passes original domain authentication, a local domain authentication server issues an alliance token to the user, records an authentication certificate, sends a challenge value to an out-domain authentication server through a confidential channel according to a service demand selected by the user, and returns user successful authentication information. The user can autonomously select and access the out-of-domain application within a period of time. The out-of-domain authentication server performs secondary challenge response on the token held by the user and realizes cross-domain authentication in a block chain checking mode. Trust islands caused by different authentication mechanisms of independent trust systems are broken through, a trust transmission method based on the block chain is provided, endorsement of a central authority is not needed, and a user can log in other applications with the same or lower security level in the alliance only by registering and managing one account password.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
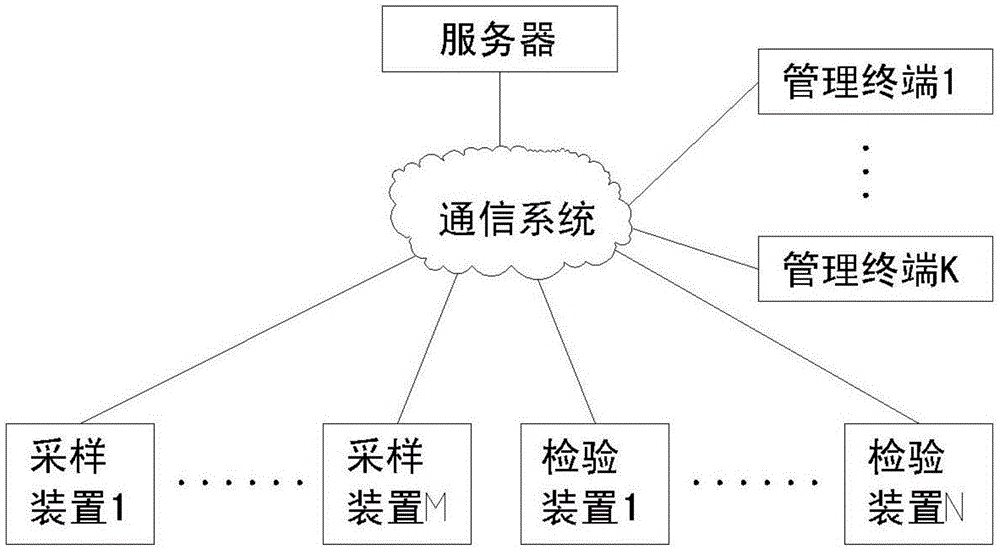
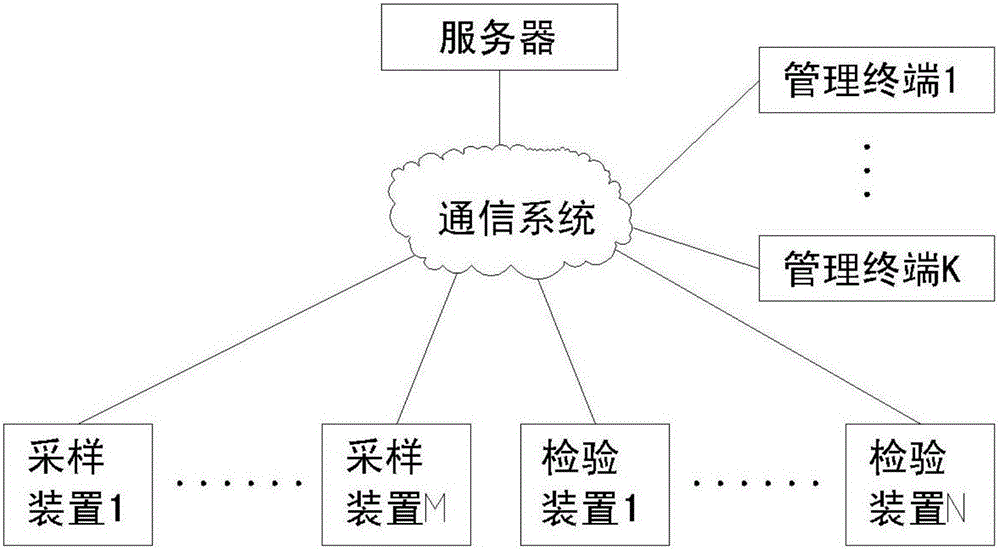
Anti-counterfeiting system and anti-counterfeiting method based on random anti-counterfeiting marks
InactiveCN104794624AUnforgeableNon-repudiationCo-operative working arrangementsCharacter and pattern recognitionThird partyCommunications system
The invention relates to an anti-counterfeiting system and an anti-counterfeiting method based on random anti-counterfeiting marks. The anti-counterfeiting system comprises a server, a sampling device and an inspection device which are connected to one another through a communication system. The anti-counterfeiting marks cannot be counterfeited; by the anti-counterfeiting method, a manufacturer cannot deny if the manufacture transmits the anti-counterfeiting marks to a server; the system can track all operations on the anti-counterfeiting marks; each anti-counterfeiting mark is associated with a corresponding user or a corresponding factory; all operation records and related information of all the anti-counterfeiting marks can be audited and consulted; the anti-counterfeiting system runs in the server by a third party; and when the third part follows rules severely, the anti-counterfeiting marks cannot be counterfeited or denied through the anti-counterfeiting system, and the anti-counterfeiting cost is low.
Owner:石立公
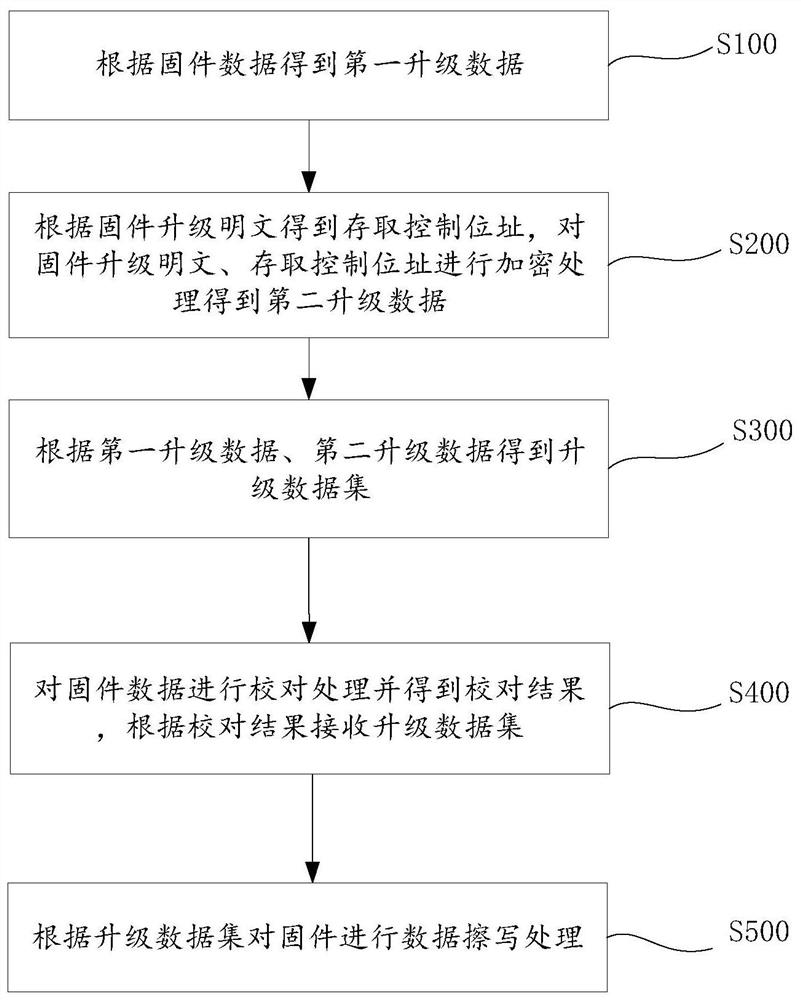
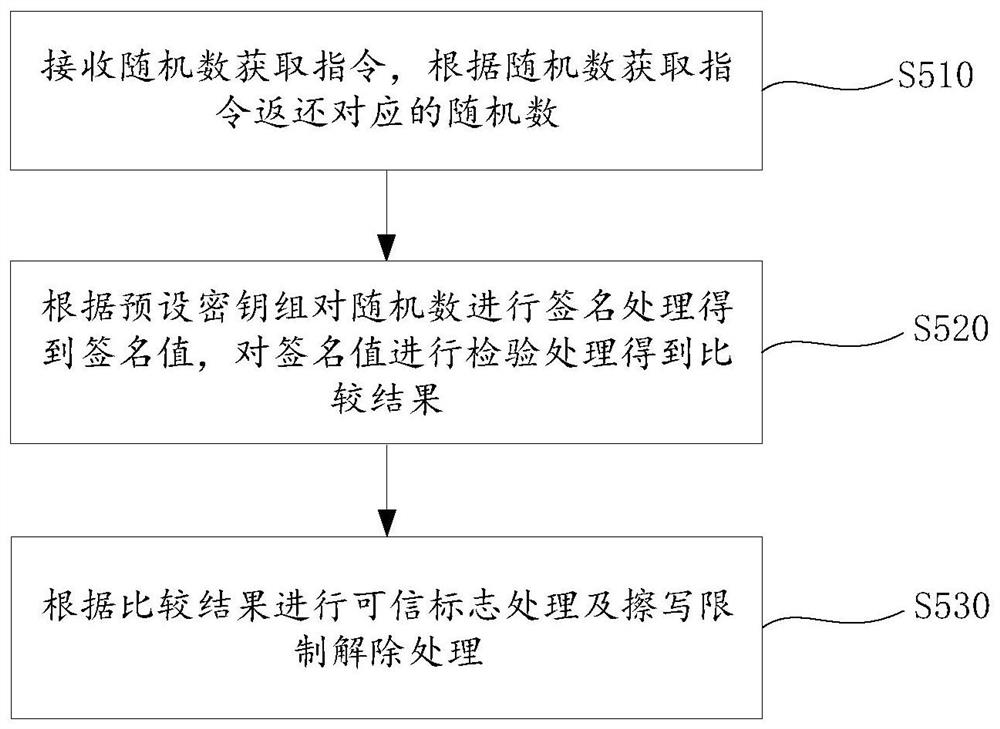
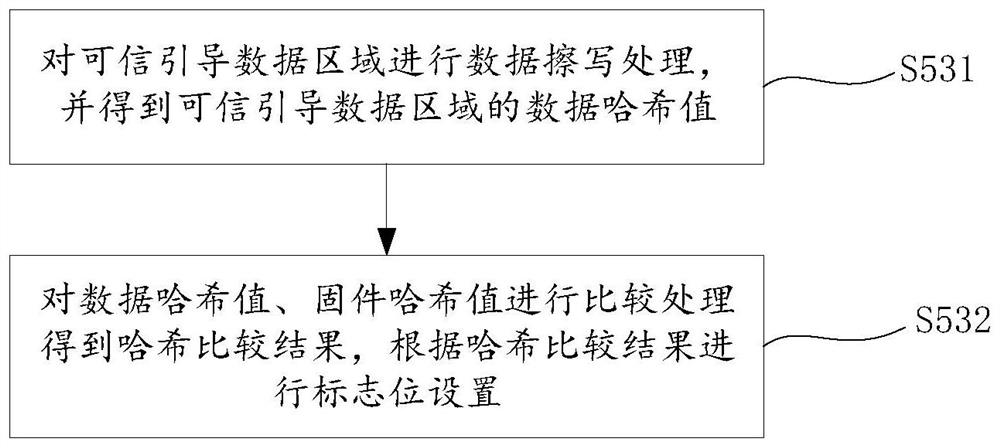
Security chip upgrading method and computer readable storage medium
PendingCN112417422AGuaranteed legal dataNon-repudiationDigital data authenticationSoftware deploymentPlaintextData set
The invention discloses a security chip upgrading method and a computer readable storage medium. The security chip upgrading method comprises the steps of obtaining first upgrading data according to firmware data; obtaining an access control address according to the firmware upgrading plaintext, and encrypting the firmware upgrading plaintext and the access control address to obtain second upgrading data; obtaining an upgrading data set according to the first upgrading data and the second upgrading data; performing proofreading processing on the firmware data to obtain a proofreading result, and receiving the upgrading data set according to the proofreading result; and performing data erasing and writing processing on firmware according to the upgrading data set. The firmware data can be proofread to obtain the proofread result, and the upgrade data set is received according to the proofread result to ensure that the received data set is legal data.
Owner:深圳市中易通安全芯科技有限公司
Random anti-counterfeiting mark-based anti-counterfeiting system and anti-counterfeiting method thereof
InactiveCN106066989AUnforgeableNon-repudiationCo-operative working arrangementsCharacter and pattern recognitionThird partyCommunications system
The invention relates to a random anti-counterfeiting mark-based anti-counterfeiting system and an anti-counterfeiting method thereof. The anti-counterfeiting system includes a server, sampling devices and inspection devices; the server, the sampling devices and the inspection devices are connected via a communication system. According to the system and method of the invention, used anti-counterfeiting marks are uncounterfeitable; with the support of the anti-counterfeiting method, once fabricators transmit the anti-counterfeiting marks to the server, the anti-counterfeiting marks cannot be denied; the system tracks and records all operations of the anti-counterfeiting marks; each anti-counterfeiting mark is associated with users / manufacturers; all operation records and related information thereof of all the anti-counterfeiting marks can be checked and verified; and the server is operated by a third party, and the third party strictly abides by rules. With the anti-counterfeiting system adopted, the anti-counterfeiting marks have uncounterfeitability and non-repudiation and are low in cost.
Owner:石立公
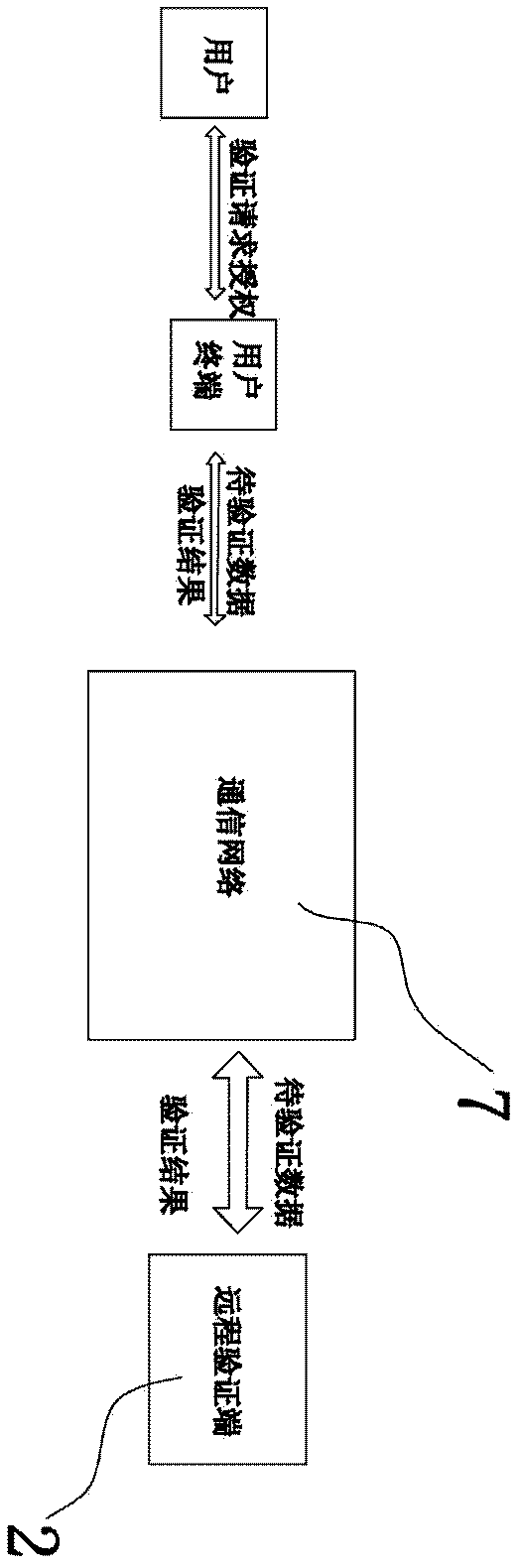
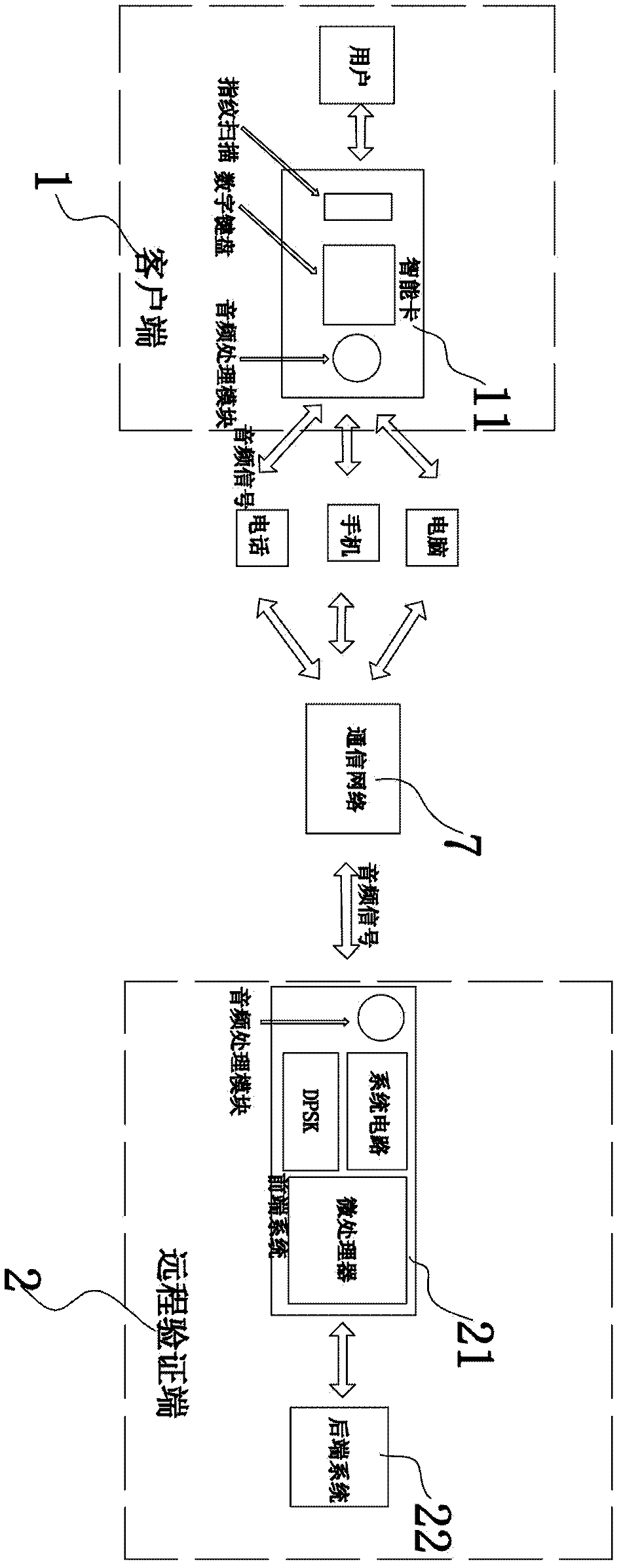
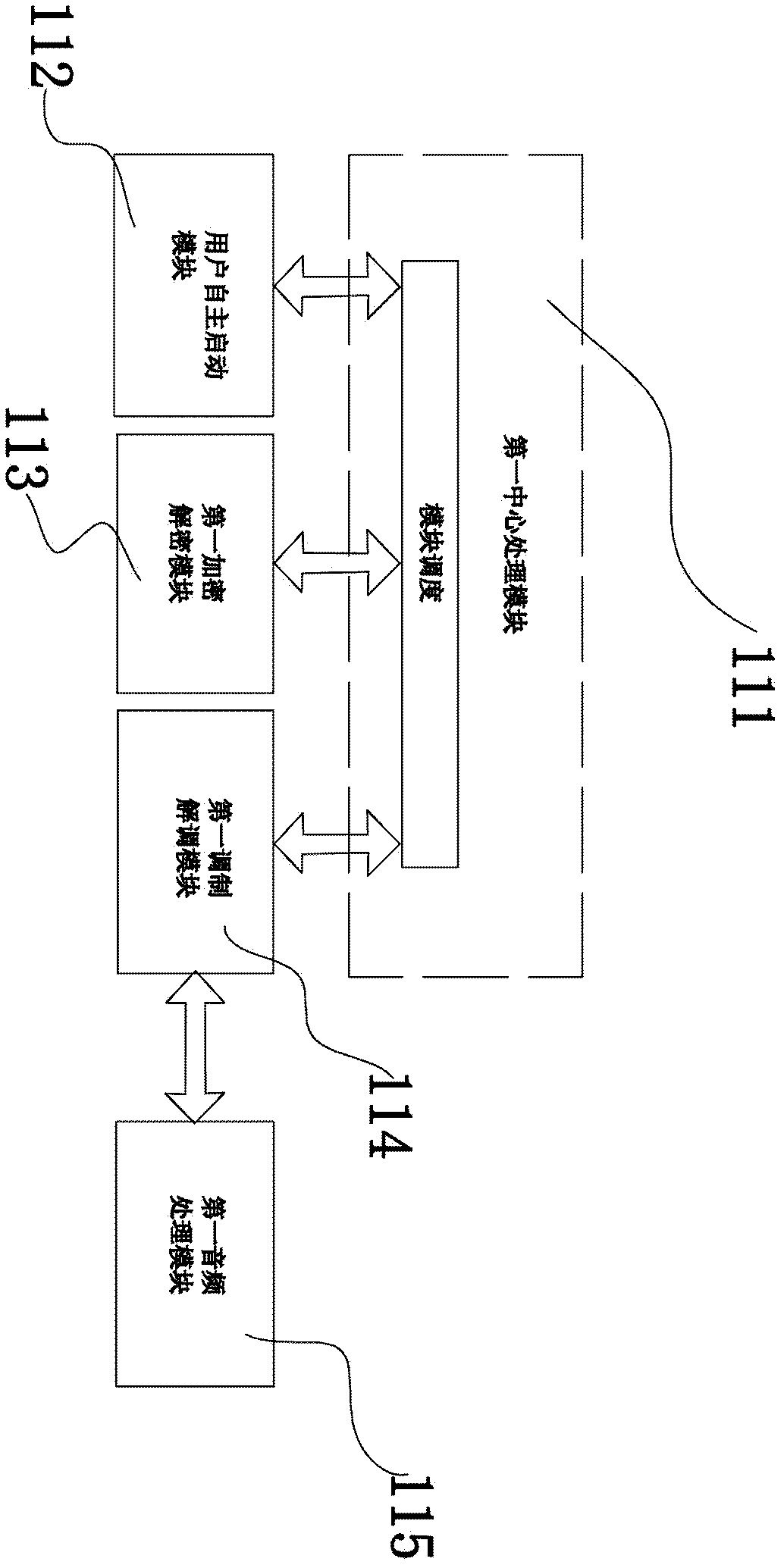
Pervasive-network-oriented remote identity authentication system and method
InactiveCN102412970BAchieve uniquenessImprove usabilityPublic key for secure communicationUser identity/authority verificationEnd systemComputer module
The invention discloses a pervasive-network-oriented remote identity authentication system and method. The system comprises a user terminal, a rear end system and a front end system connected with the rear end system, wherein an intelligent card is adopted in the user terminal, prestores with user certificate information, is paired with a private key and a public key and is used for issuing the public key to the rear end system in advance; the intelligent card mainly comprises a first central processing module, a user autonomous starting module, a first encrypting and deciphering module, a first modulating and demodulating module and a first audio processing module; the user autonomous starting module, the first encrypting and deciphering module and the first modulating and demodulating module are respectively and mutually communicated with the first central processing module; the first audio processing module and the first modulating and demodulating module are communicated with each other; and the front end system mainly comprises a second audio processing module, a second modulating and demodulating module, a first encrypting and deciphering module and a second central processing module. The pervasive-network-oriented remote identity authentication system and method disclosed by the invention have the advantages of low cost, simplicity for operation, high safety performance, strong universality and good reputation preventing property.
Owner:NINGBO JUHUAI ELECTRONICS TECH
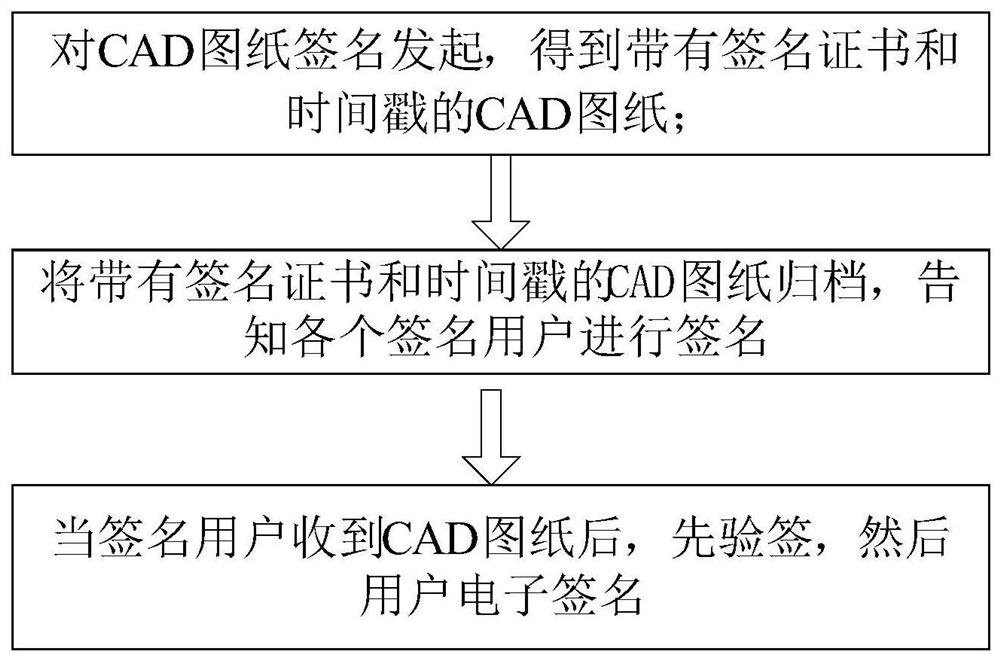
Multi-user electronic signature method for CAD drawing
PendingCN112052435AGuarantee authenticityIntegrityDatabase updatingDigital data protectionHandwritingTimestamp
The invention discloses a CAD drawing multi-user electronic signature method, which comprises the following steps: initiating CAD drawing signature to obtain a CAD drawing with a signature certificateand a timestamp; filing the CAD drawing with the signature certificate and the timestamp, and informing each signature user to sign; and after the signature user receives the CAD drawing, carrying out signature verification (judging whether the current drawing is tampered in a circulation process), and enabling the user to carry out electronic signature. According to the scheme of the invention,a plurality of signers can sign own electronic seals (signature handwriting) and signature timestamps at specified positions on a CAD drawing, and attach own signature certificates and timestamps to the drawing; multi-user signature is effective, and drawing information seen by a plurality of signature backbone persons before signature can be consistent; and the user can see the signer and the signing time on the signing list of the drawing and can also check the signer and the signing time through a visual method.
Owner:杭州尚尚签网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com