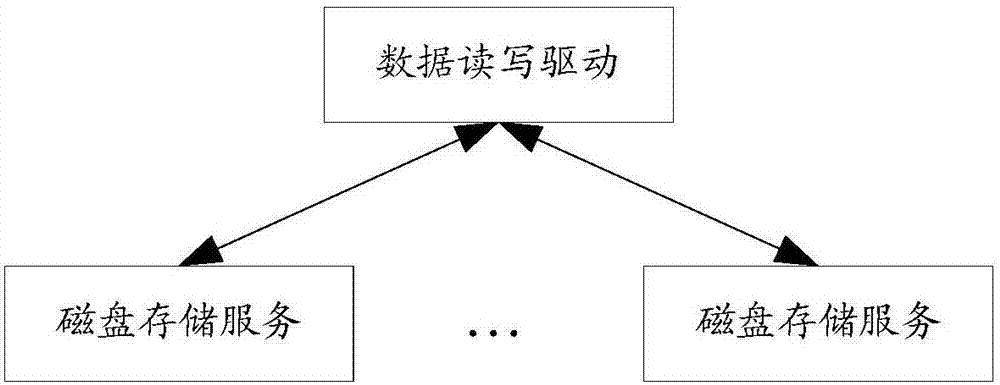
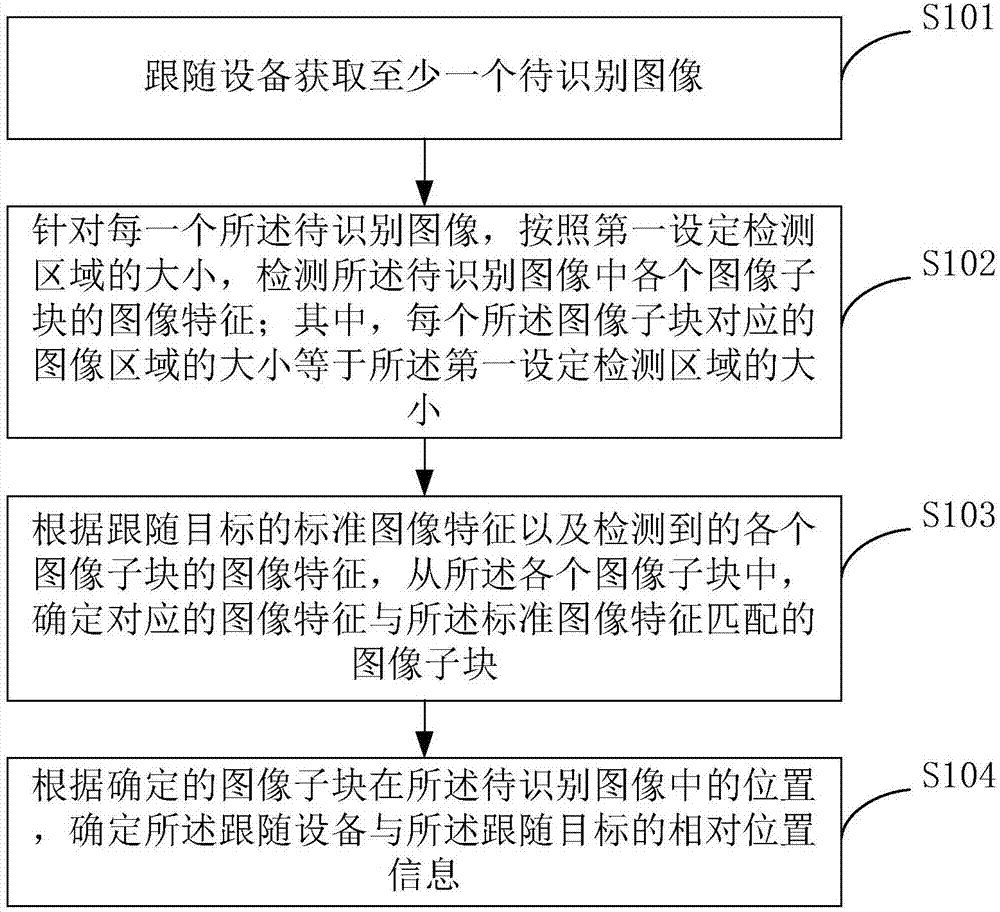
Patents
Literature
580results about How to "Reduce the risk of loss" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for storing mass of small files on basis of master-slave distributed file system
ActiveCN103020315ATo achieve fault toleranceSolve the problem when storing a large number of small filesSpecial data processing applicationsDistributed File SystemData file
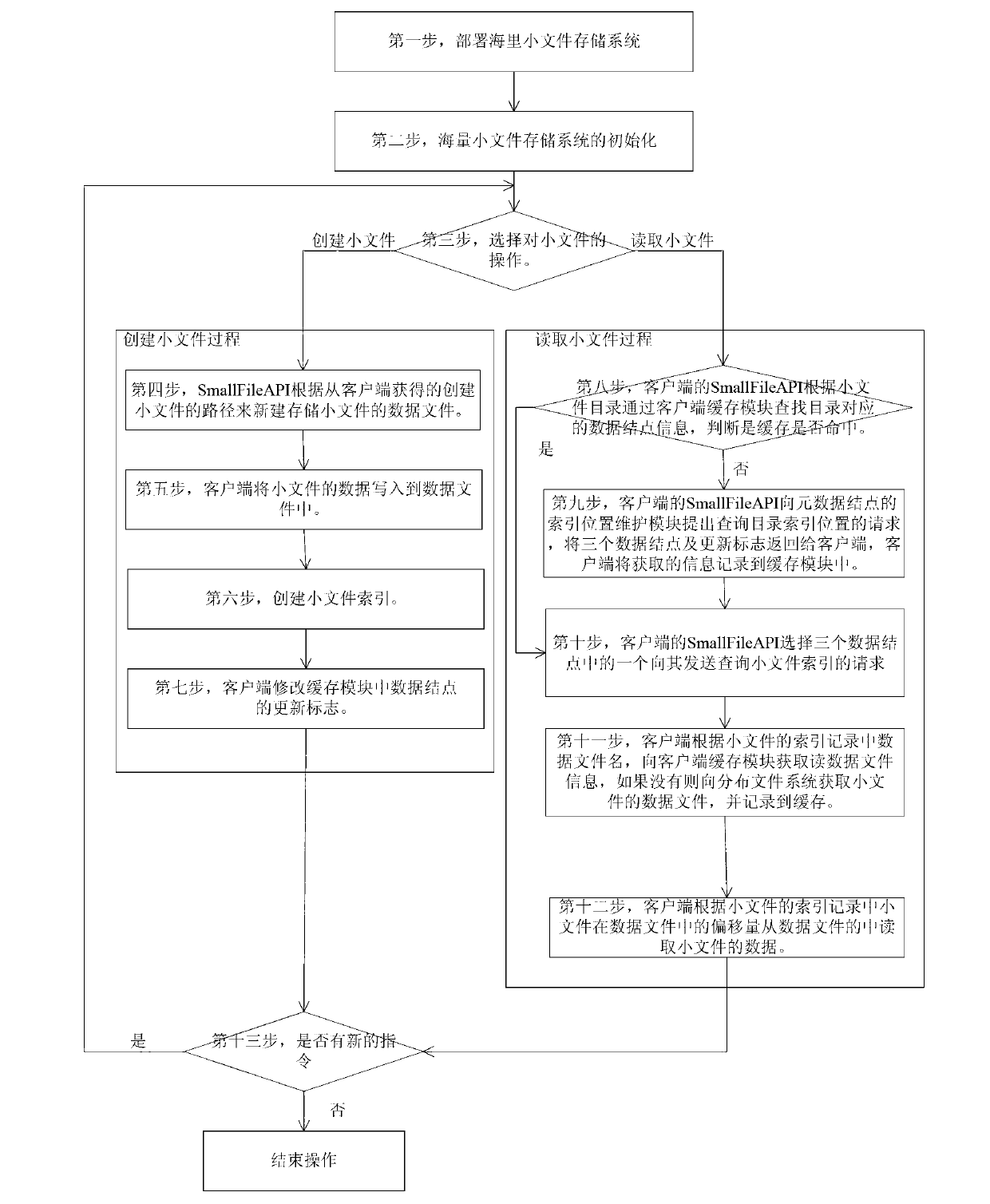
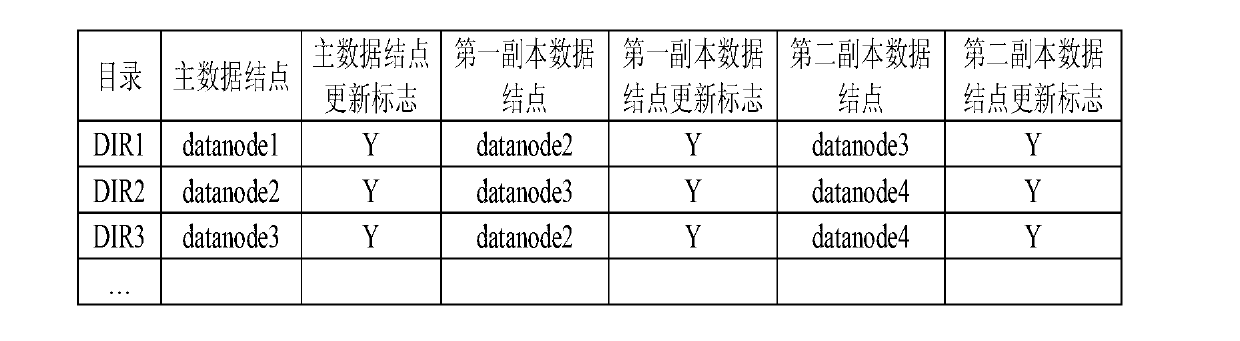
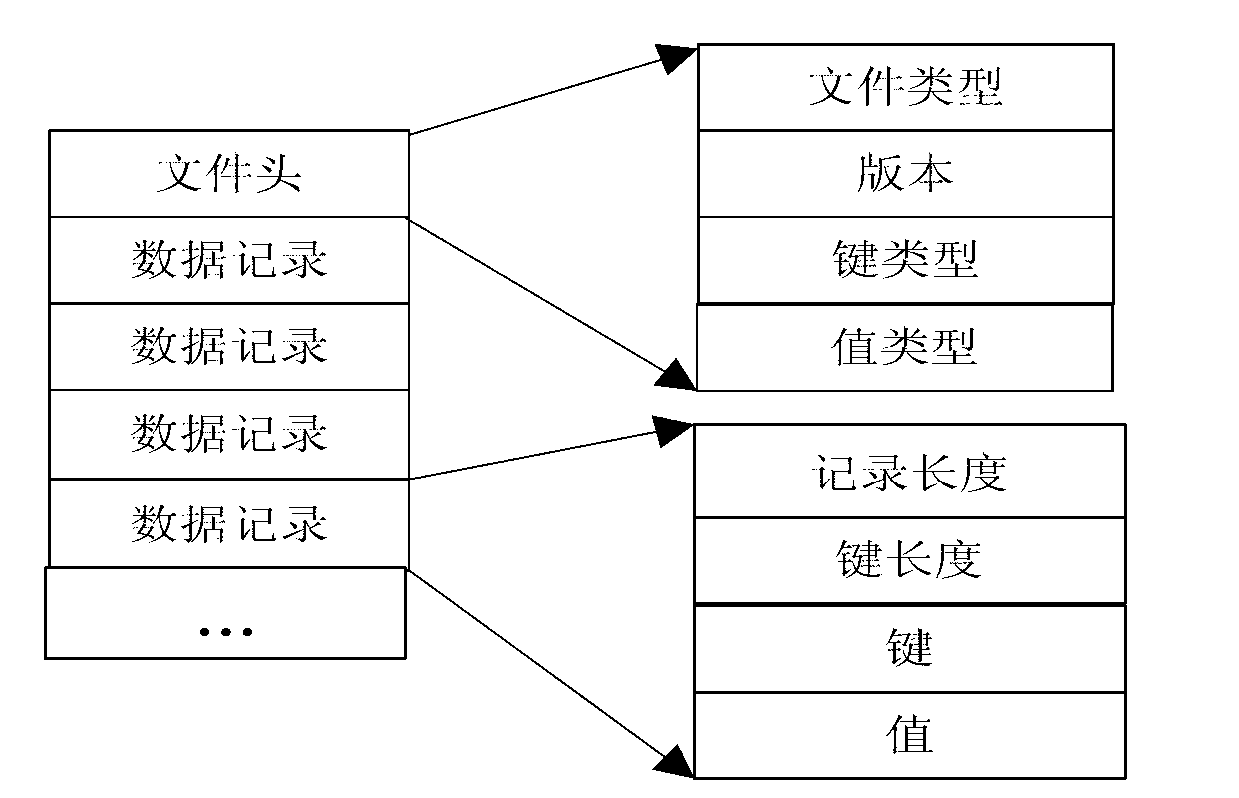
The invention discloses a method for storing a mass of small files on the basis of a master-slave distributed file system, and aims to solve the problem about storing the mass small files in the master-slave distributed file system. The technical scheme includes that the method includes that a mass small file storage system is deployed and initialized, and then small files are created and read by a SmallFileAPI (small file-application program interface) of a client side according to a command received from a keyboard. When the small files are created by a system, the SmallFileAPI creates data files of the small files according to small file paths obtained from the client side, writes in small file data and simultaneously creates small file indexes at data nodes; when the small files are read by the system, data node information corresponding to a parent directory is acquired according to the small file paths, an index request is transmitted to any of the data nodes, and finally the small file data are read from the data files according to index information. By the aid of the method, the problem about mass of storage metadata of the mass of small files is solved, writing efficiency of the mass small file storage system is improved, and reliability of the system is guaranteed.
Owner:NAT UNIV OF DEFENSE TECH
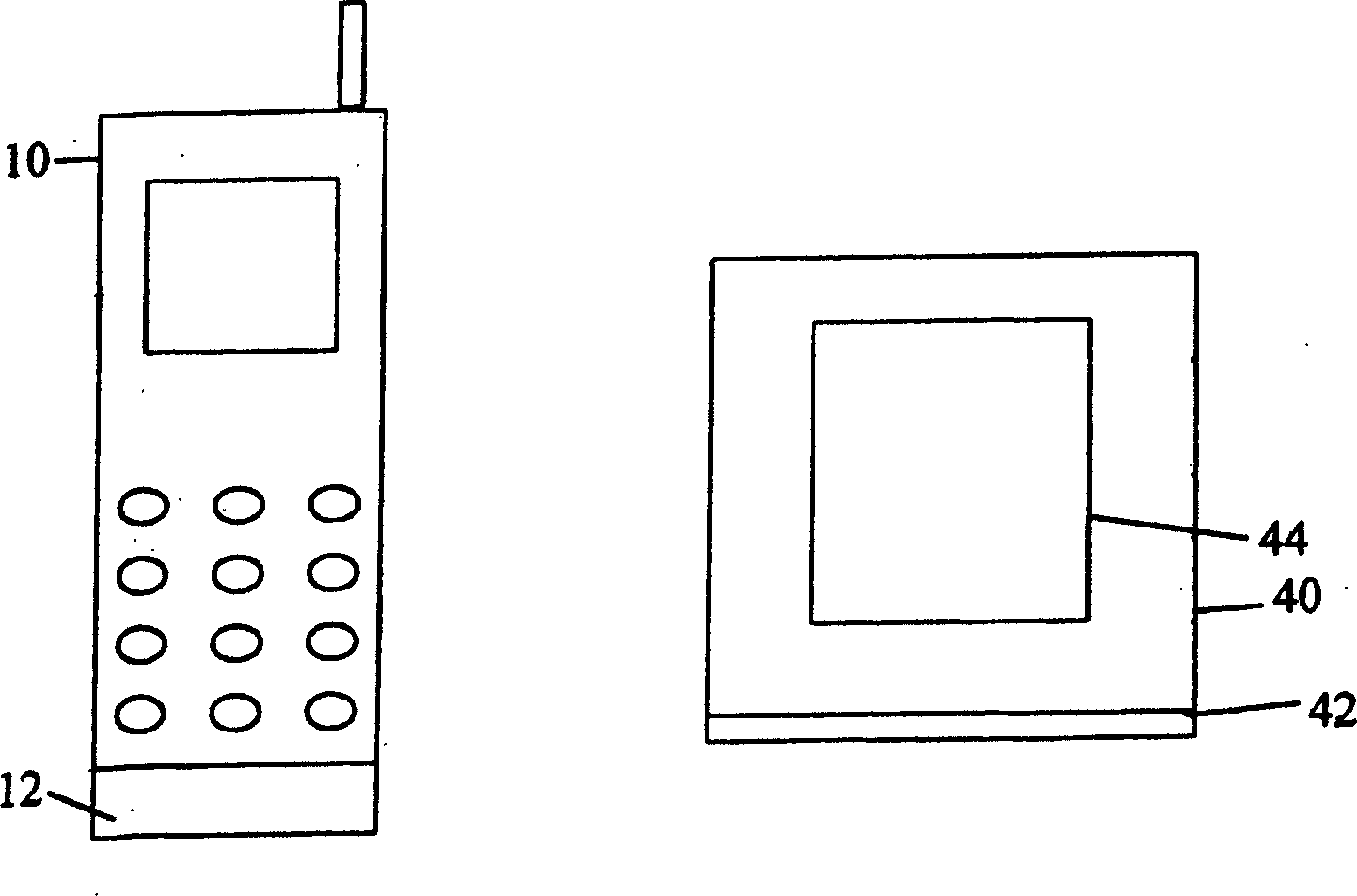
Active miss prevention system and method for handheld device
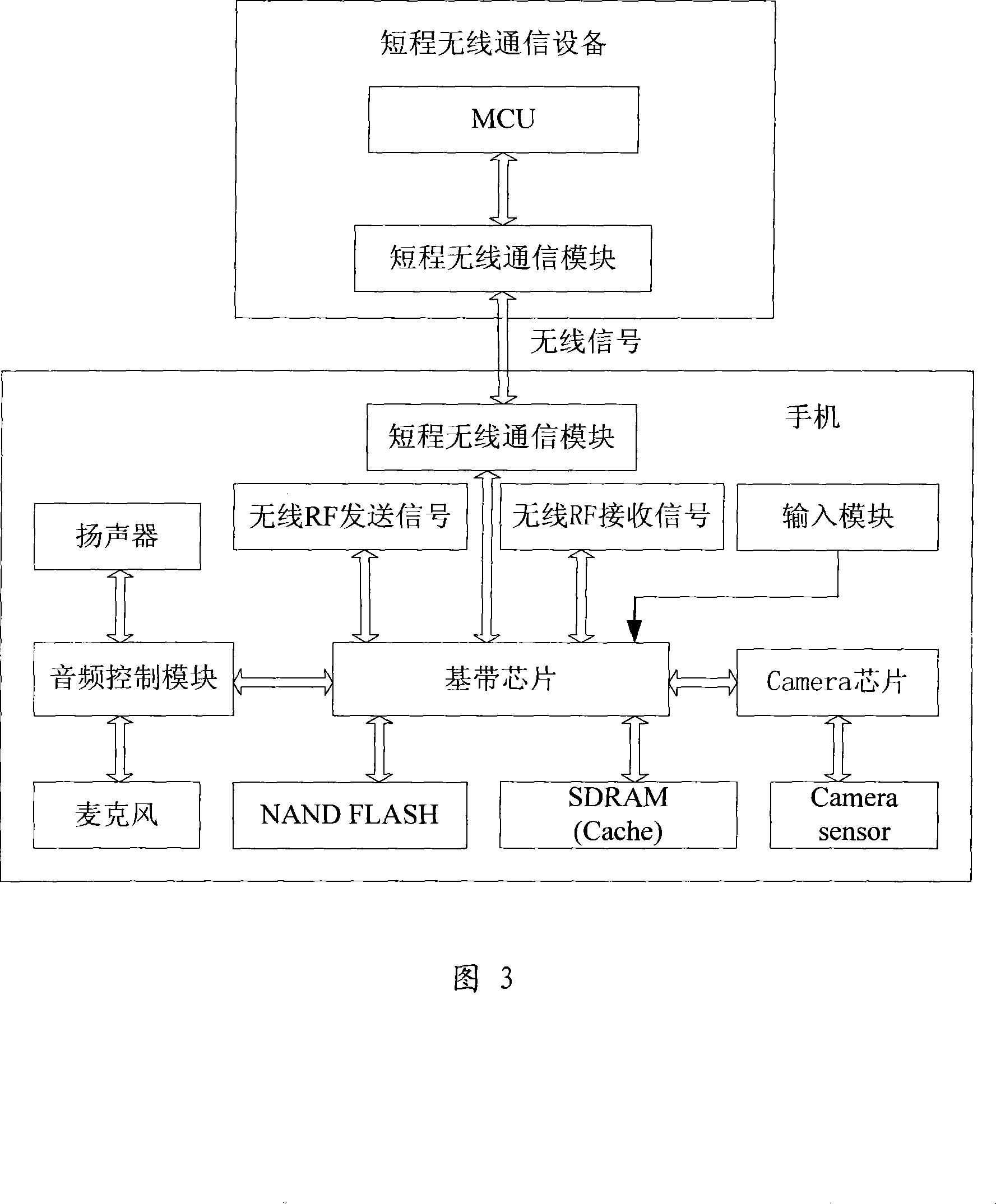
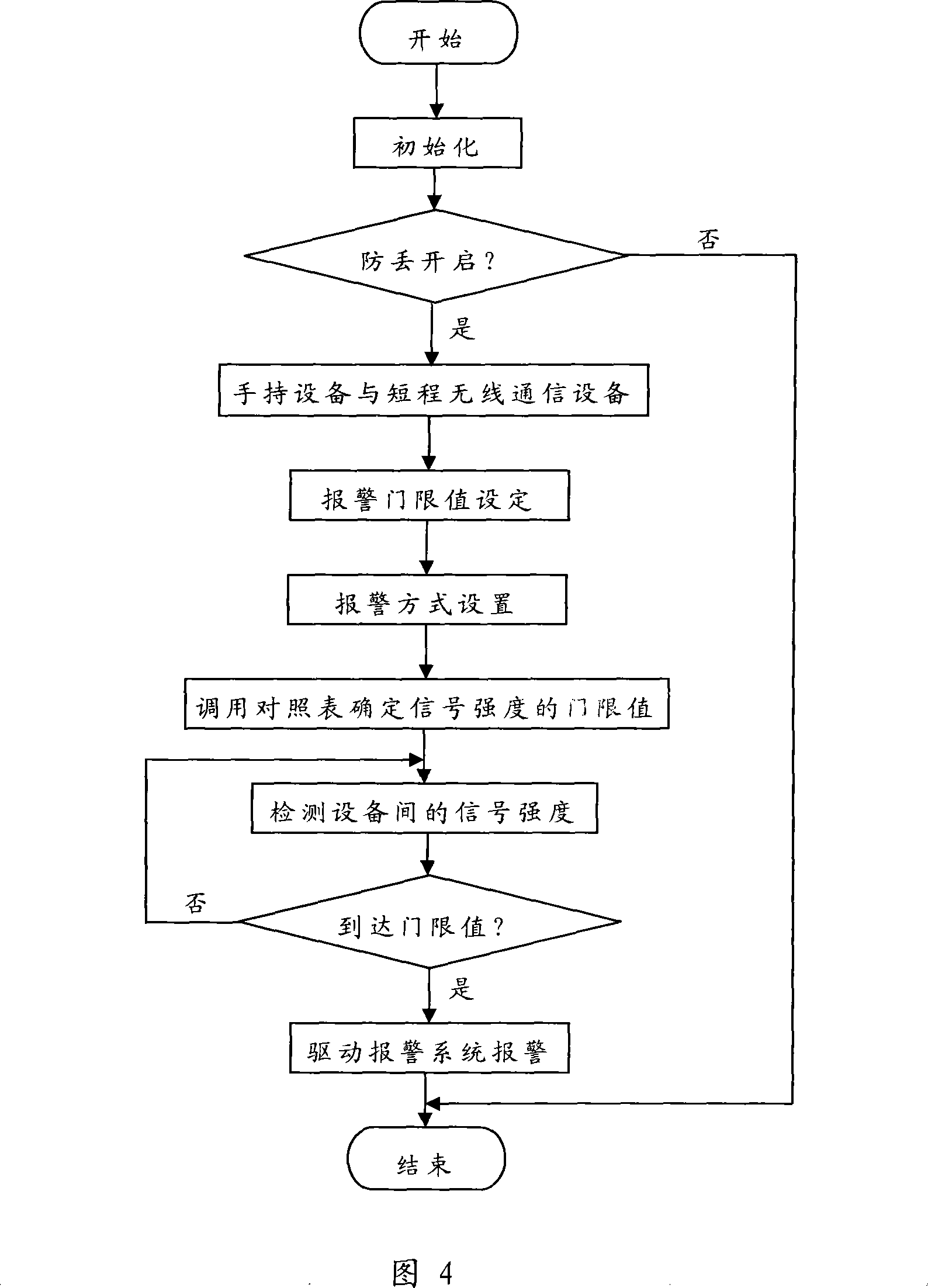
InactiveCN101237479AAvoid lossReduce the risk of lossTransmissionTelephone set constructionsShortest distanceBluetooth
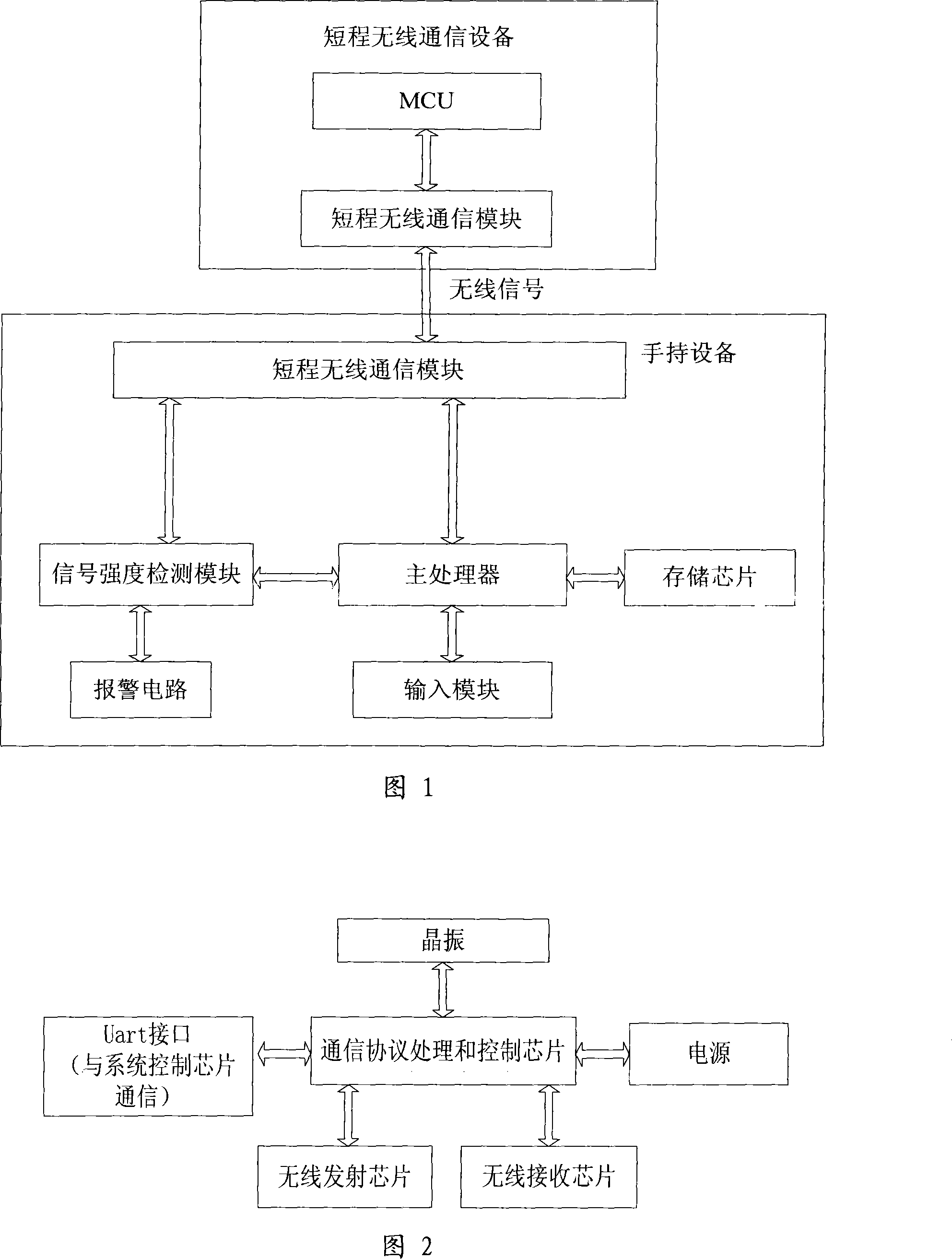
The invention discloses an active anti-loss system and an anti-loss method for a handheld device, comprising a handheld device and a short-distance wireless communication device for communicating with the handheld device, wherein the handheld device or the short-distance wireless communication device output an alarm when detecting that the signal intensity in between reaches a set threshold value, so that when moving away from the short-distance wireless communication device, the handheld device output an alarm to remind an owner of the loss of the handheld device. The method conducts real time detection of the distance between the handheld device and the short-distance communication device such as a Bluetooth device, an infrared device, etc. and actively outputs an alarm when the distance goes beyond a threshold value to remind the owner to prevent the handheld device from being lost, thereby reducing the risks of losing the handheld device. The active anti-loss method can not only prevent the handheld device from being stolen, but also prevent the handheld device from being stolen due to the carelessness of the owner.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
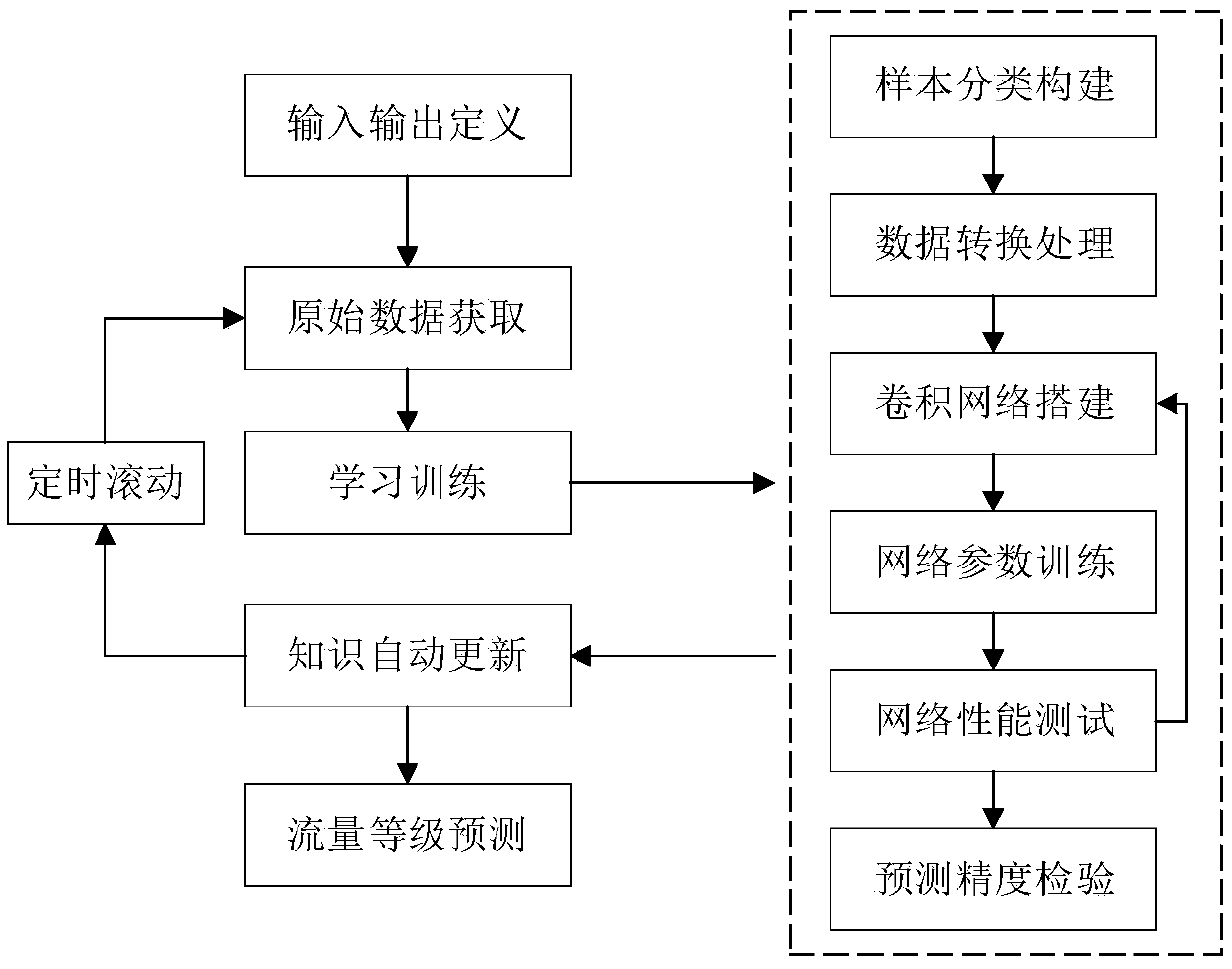
Flow rate level prediction method based on convolutional neural network deep learning
ActiveCN108875161AReduce the risk of lossStrong dependenceClimate change adaptationDesign optimisation/simulationData setNerve network
The invention provides a flow rate level prediction method based on convolutional neural network deep learning. The method comprises the following steps that: selecting an impact factor which is potentially related to the inflow flow rate of a reservoir as an input set; carrying out sample set classification and original input dataset construction; carrying out standardized processing on the original input dataset in the sample set; building a multilayer convolutional neural network; taking mean square error minimization as a loss function to determine prediction accuracy; carrying out networkparameter training; carrying out network performance testing; checking prediction accuracy; carrying out the rolling learning training on model parameters; automatically saving a learning training achievement, and automatically updating the knowledge record of a real-time library; and through a network model, carrying out calculation to obtain a final flow rate level prediction result. By use ofthe method, low-layer characteristics are combined to form high-layer characteristic fusion, so that an objective can be subjected to advanced abstract description, a data input pattern and a spatialand temporal distribution rule can be found through automatic learning, and therefore, the method can be effectively applied to the field of drainage basin water regimen forecasting.
Owner:CHANGJIANG SURVEY PLANNING DESIGN & RES
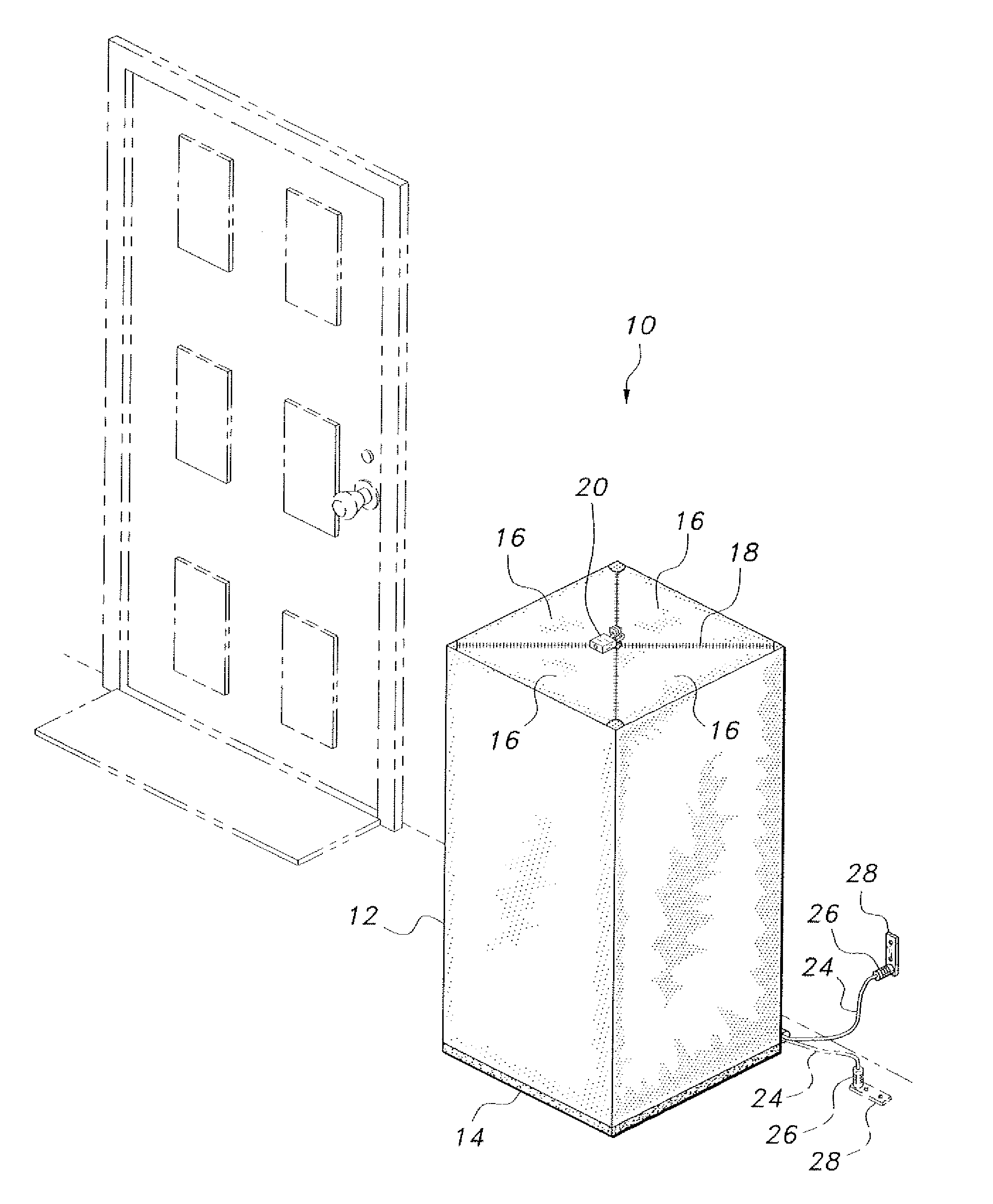
Security receptacle for packages
The security receptacle for packages provides protection for delivered packages and parcels. The receptacle is fabricated from a flexible, weather-resistant, cut-resistant material capable of expanding to accommodate variously sized packages. A lockable, zippered top is provided to securely close the receptacle. The bottom of the receptacle is adapted to accommodate a cable lock to secure the container to a stationary object. A facility is provided to store the receptacle when not in use,
Owner:GOOSE CREEK LLC
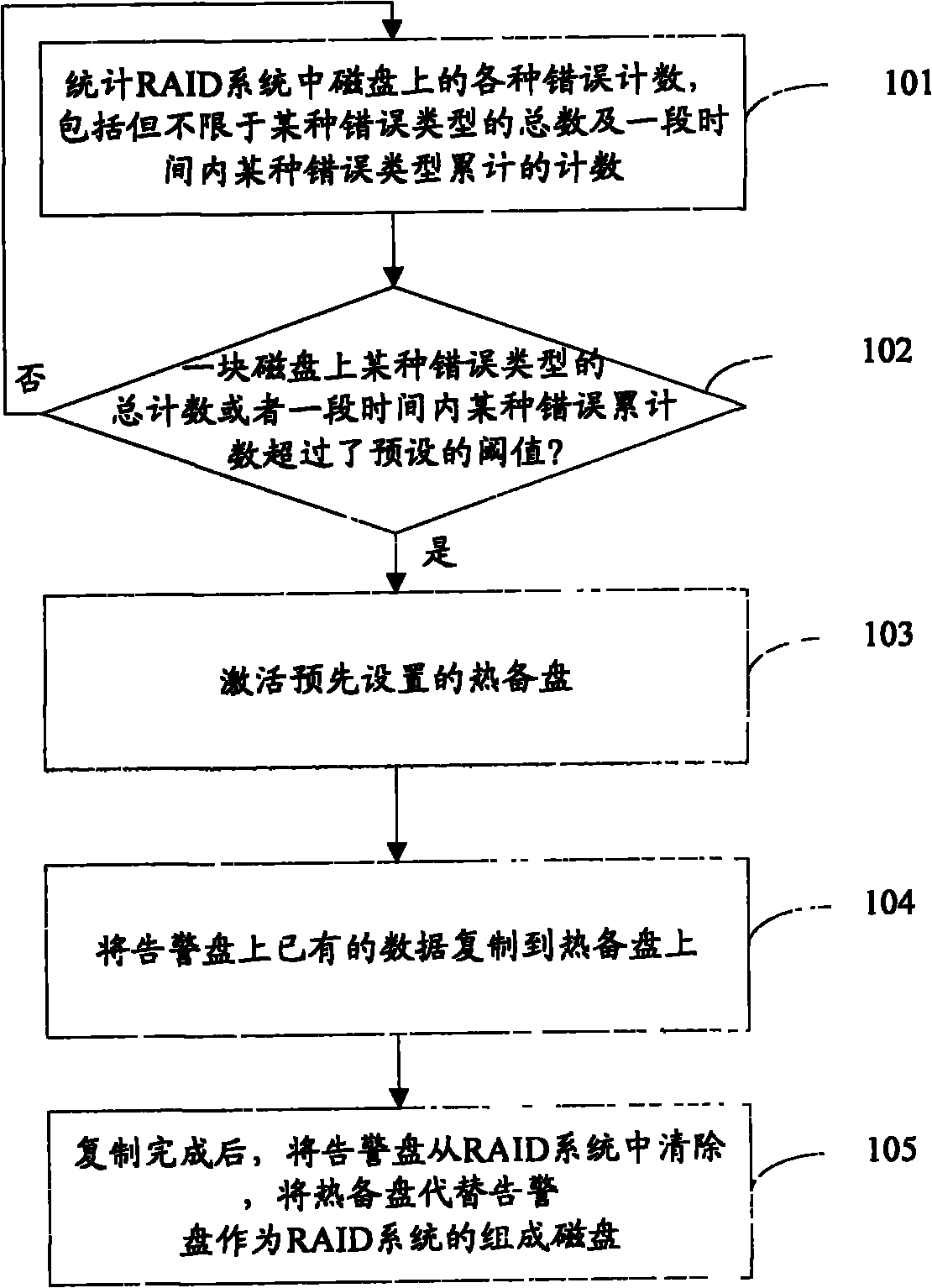
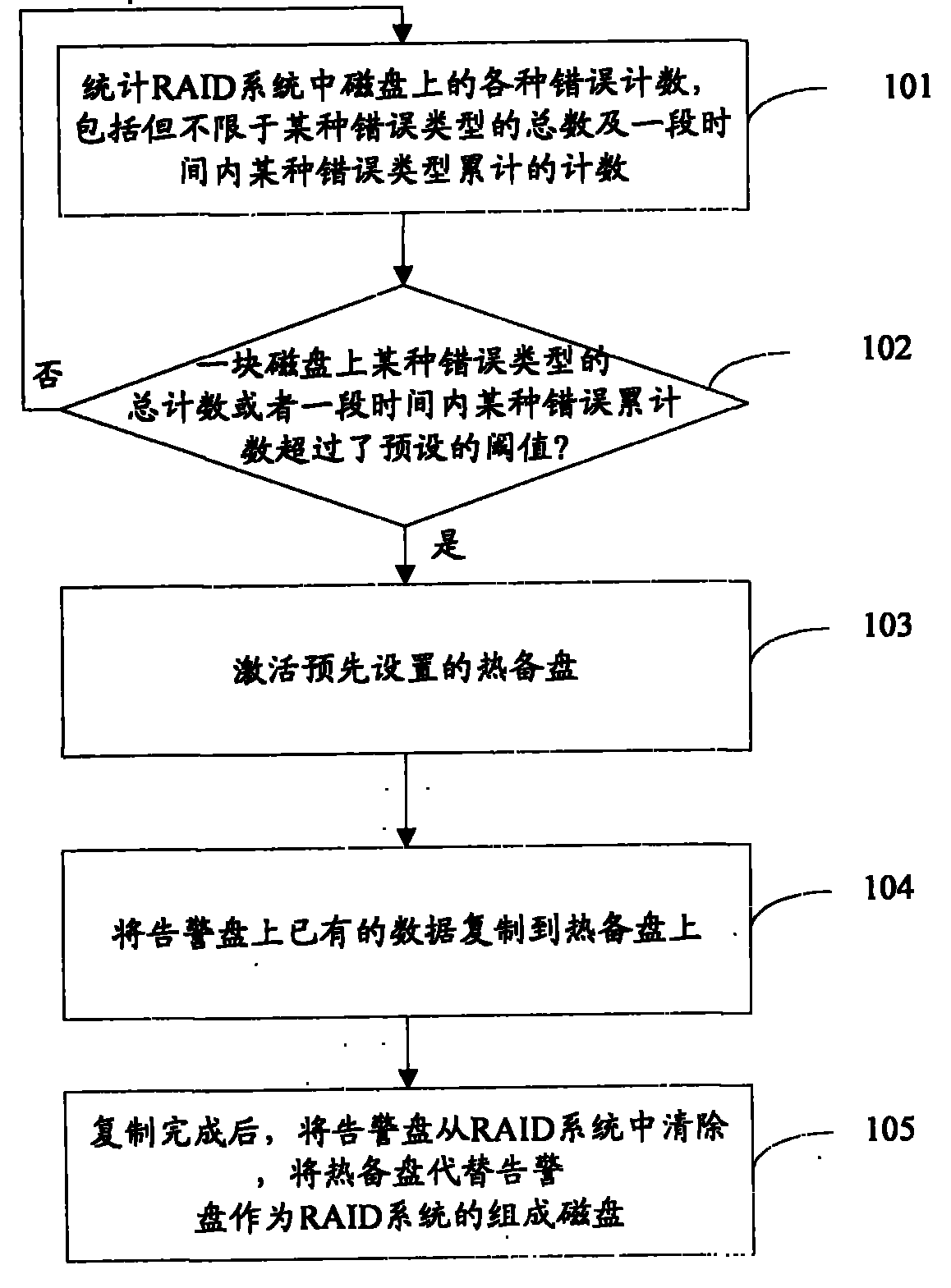
Improved disk array reconstruction method
ActiveCN102012847AReduce the risk of lossShorten the timeInput/output to record carriersRedundant data error correctionRAIDReconstruction method
The invention provides a disk array reconstruction method. The improved disk array reconstruction method comprises the following steps of: A, counting error counts in disks in a redundant array of independent disks (RAID) system; B, judging whether the error count in one disk of the RAID system exceeds a preset threshold value or not, if so, executing a step C, otherwise returning to the step a; C, setting the disk as a warning disk, activating a preset hot spare disk and replicating existing data in the warning disk into the hot spare disk; and D, after the replication, deleting the warning disk from the RAID system and substituting the hot spare disk for the error disk as the component disk of the RAID system. In the scheme, the risk of data loss in the reconstruction process can be effectively reduced and the reconstruction process is accelerated.
Owner:UNITED INFORMATION TECH +1
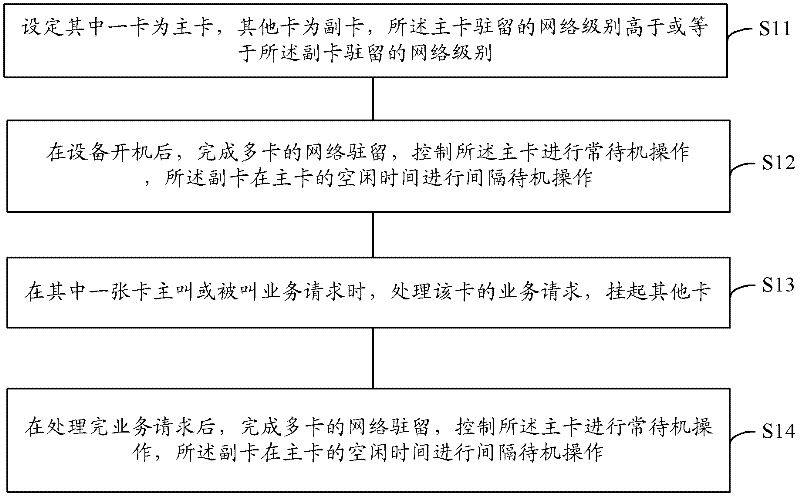
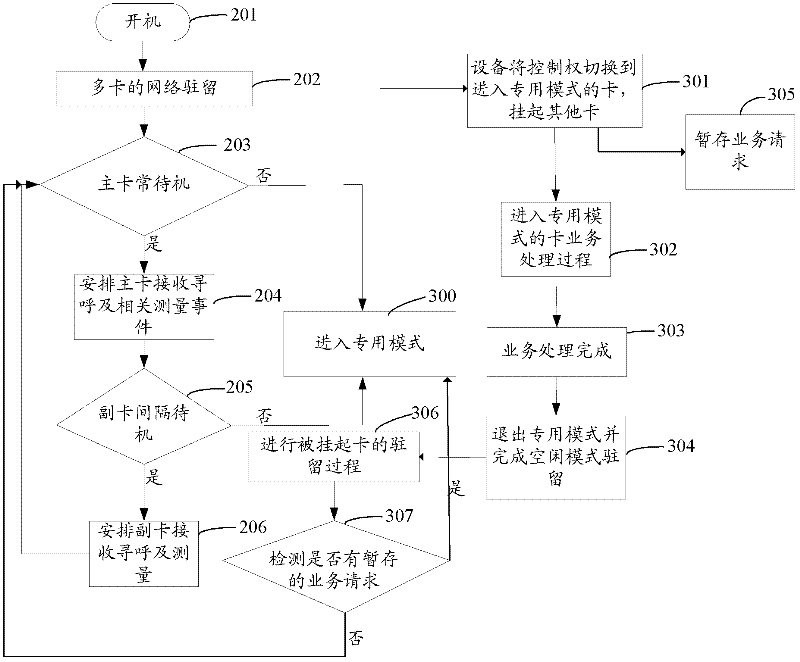
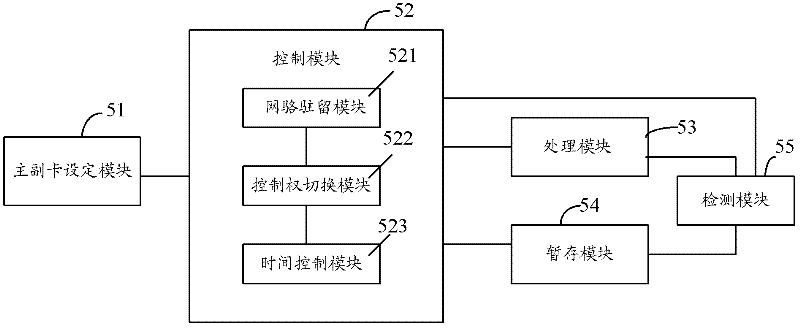
Mobile terminal equipment and multi-card dispatching method and device thereof
InactiveCN102244941AReduce consumptionReduce switching delayWireless communicationComputer hardwareResidence
The invention discloses mobile terminal equipment and a dispatching method and device thereof. The multi-card dispatching method comprises the following steps of: setting one card as a main card and other cards as secondary cards, wherein the level of a network resident by the main card is higher than or equal to that of a network resident by the secondary cards; after starting the equipment, completing network residences of the plurality of cards, controlling the main card to perform normal standby operation and controlling the secondary cards to perform interval standby operation at the idle time of the main card; when one card calls or is called by a service request, processing the service request of the card and hanging on other cards; and, after processing the service request, completing the network residences of the plurality of cards, controlling the main card to perform the normal standby operation and controlling the auxiliary cards to perform the interval standby operation at the idle time of the main card. According to the technical scheme, the power consumption and the risk in losing called paging can be reduced.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
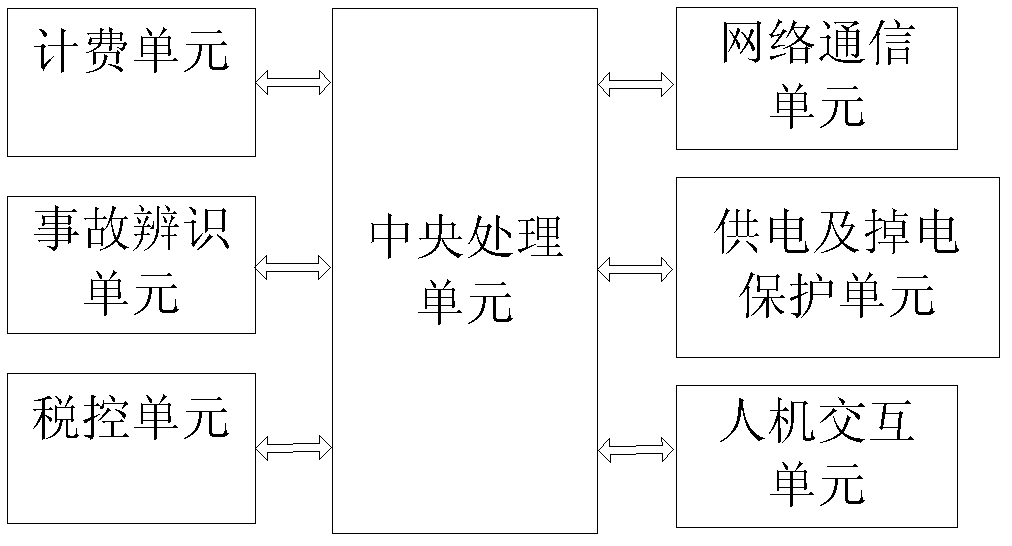
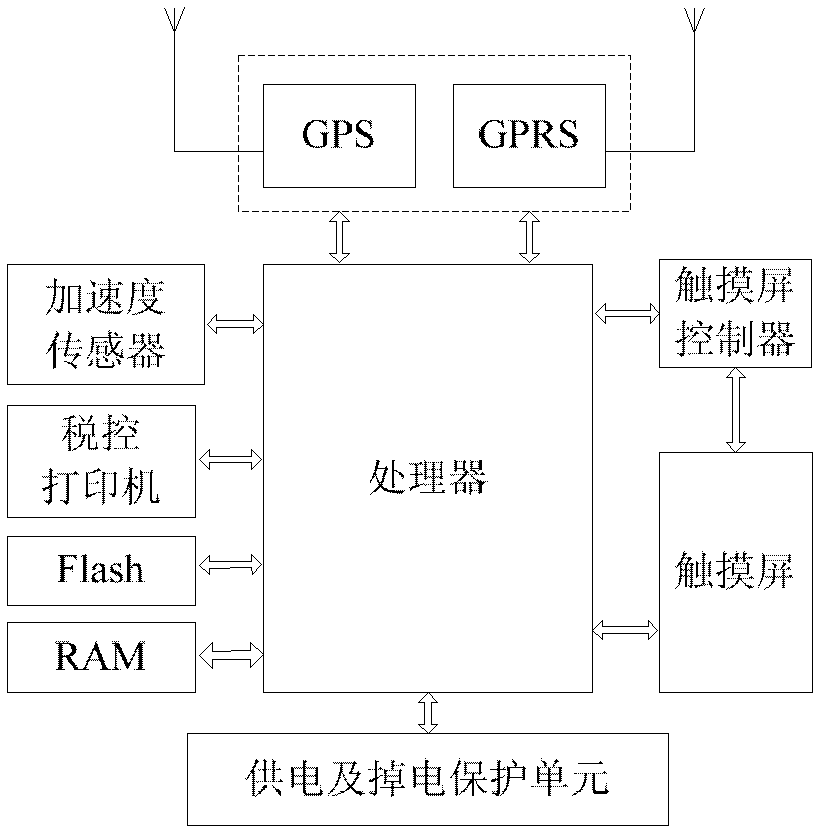
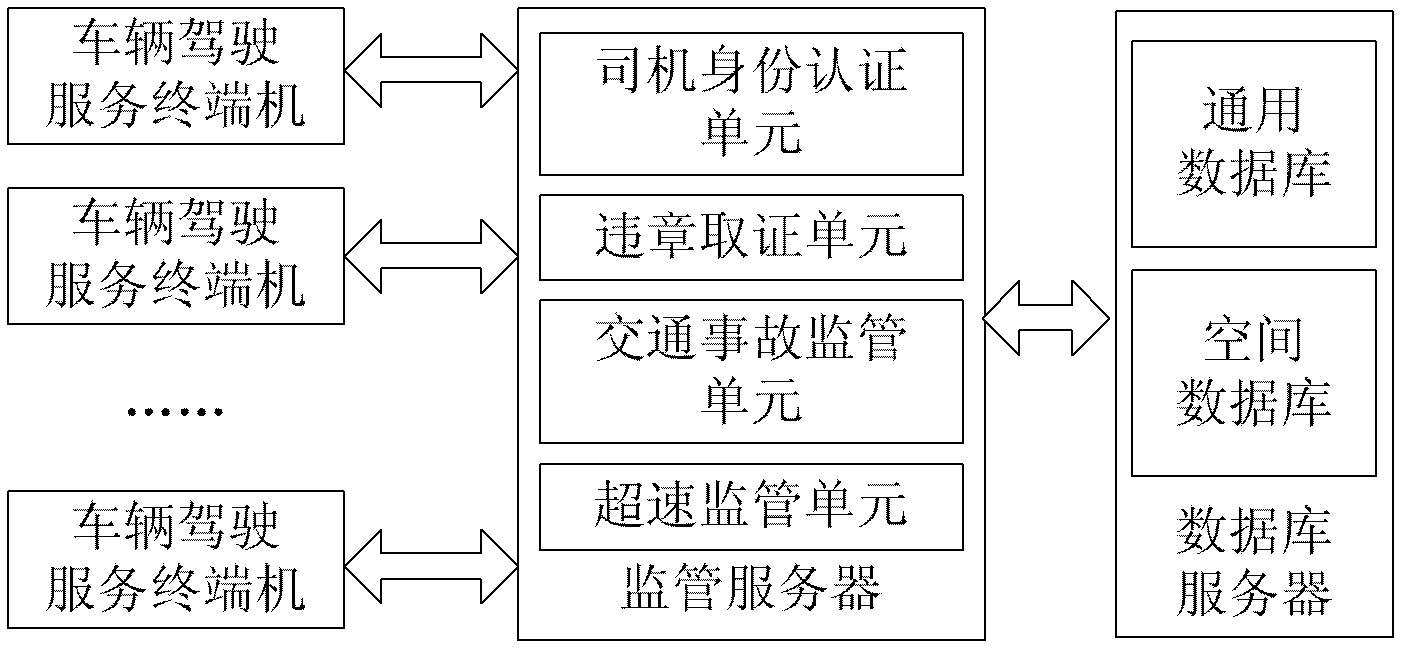
Vehicle driving service terminal system and working method thereof
ActiveCN102354405ASolve the difficult problem of determining the liability for violationsRealize acquisitionTicket-issuing apparatusRegistering/indicating working of vehiclesEngineeringVehicle driving
The invention relates to a vehicle driving service terminal system comprising a vehicle driving service terminal, a supervision server and a database server, wherein the supervision server is in communication connection with the vehicle driving service terminal and the database server. The vehicle driving service terminal can be used for collecting vehicle moving status information and storing the vehicle moving status information through a far end without being connected with a vehicle body; vehicle travel tracks and driver information are bound and stored in a far-end server, thereby reducing risk of data loss and further solving the problem that violation liability in vehicle driving services is difficult to determine; the vehicle driving service terminal is connected with the supervision server so that real-time supervision of vehicle over-speed behavior is realized; serious traffic accidents can be identified in a condition that the vehicle driving service terminal is not connected with the vehicle body by using an accident identification method based on an acceleration and GPS (Global Position System) technology; and furthermore, by using a billing method of an 'equidistant interval' sample based on the GPS technology, a billing error caused by disturbance of a GPS signal is effectively decreased and accurate billing is realized.
Owner:马龙泉
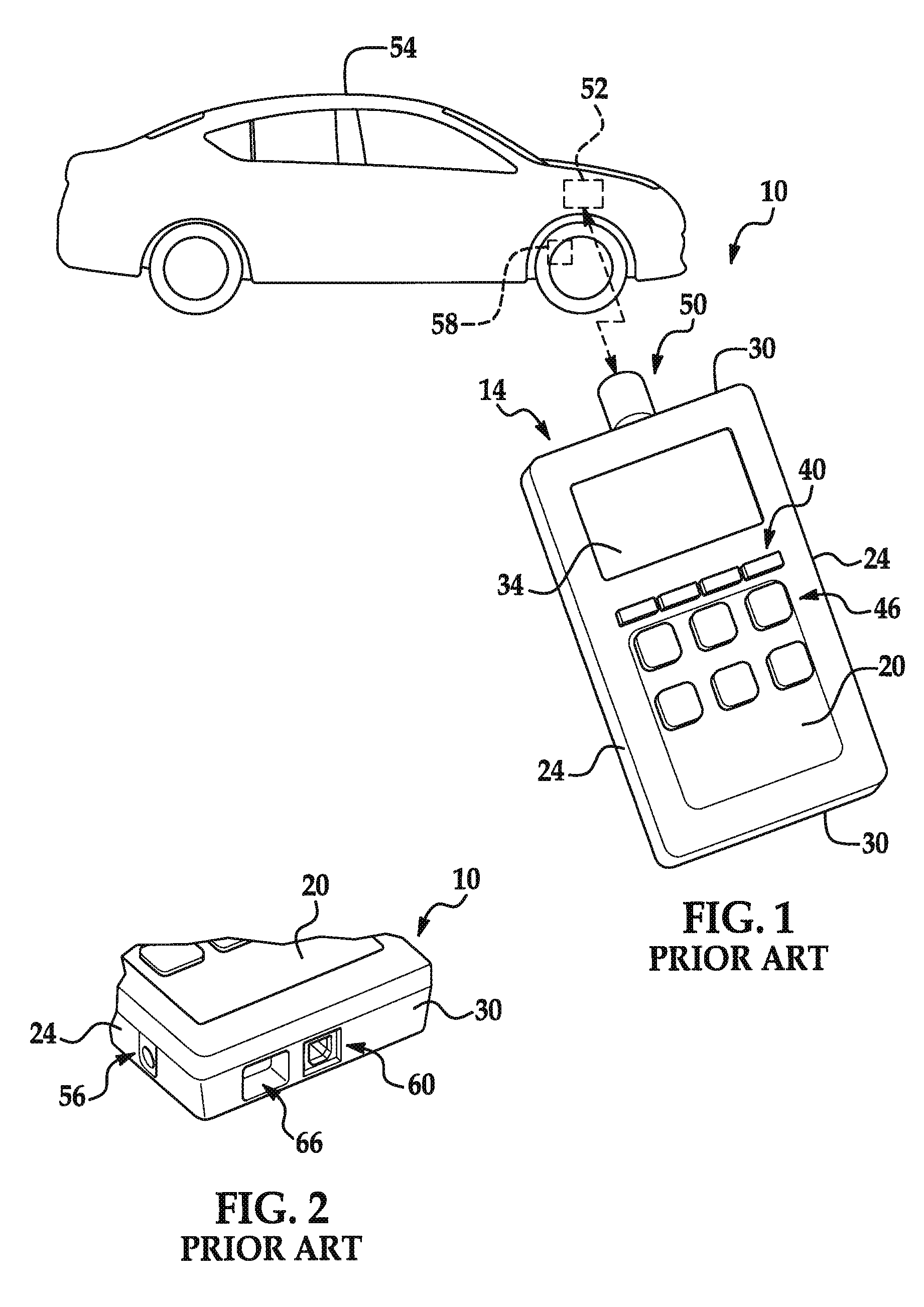
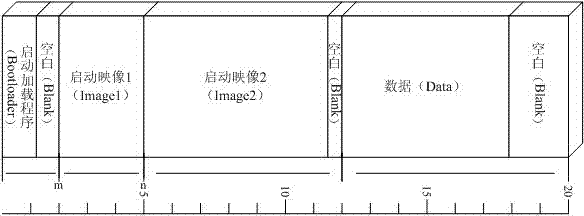
Universal tire pressure monitoring system tool and methods
ActiveUS9050862B2Reduce the risk of lossVehicle testingRegistering/indicating working of vehiclesElectronic communicationOptical scanners
Disclosed herein is an improved universal TPMS tool. According to one aspect of the tool, the tool can include a housing and a processor and a memory storage device positioned within the housing. The tool can optionally include a key pad positioned on the housing in communication with the processor for input of commands from a user, an electronic communication port positioned on the housing in communication with the processor, and an antenna for transmission and receipt of electronic information from the plurality of TPMS tire sensors. The tool can also include an optical scanner for reading indicia connected to the vehicle.
Owner:ATEQ CORP
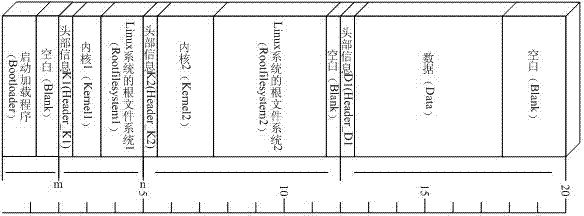
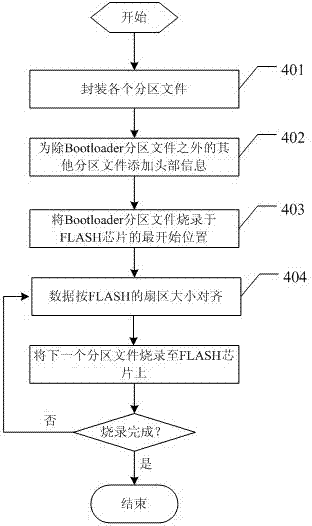
Data partition storage method and system boot method of embedded system
ActiveCN102693283AAvoid the risk of not being able to locate partitionsEasy to useProgram loading/initiatingSpecial data processing applicationsFile systemCentralized management
The invention provides a data partition storage method and a system boot method of an embedded system, wherein the data partition storage method comprises the following steps: packaging each partition files including a Bootloader partition file, one or two Image partition files containing kernels and root file systems, and other user data partition files; respectively adding header information to all the partition files except the Bootloader partition file, the header information being used for identifying attributes of a current partition file; and writing each partition files into a FLASH chip in a sector alignment manner. In embodiments according to the invention, a centralized partition table dose not need to be set, not requiring implementation of centralized management, thereby, enabling simple and convenient use and improved safety, avoiding a risk of incapability of positioning each partition after the centralized partition table being damaged; functions of each partition are independent from each other, rendering no effect on each other, thereby, reducing data loss risk; partition data is organized in a compact manner, which enables the system to be more concise.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
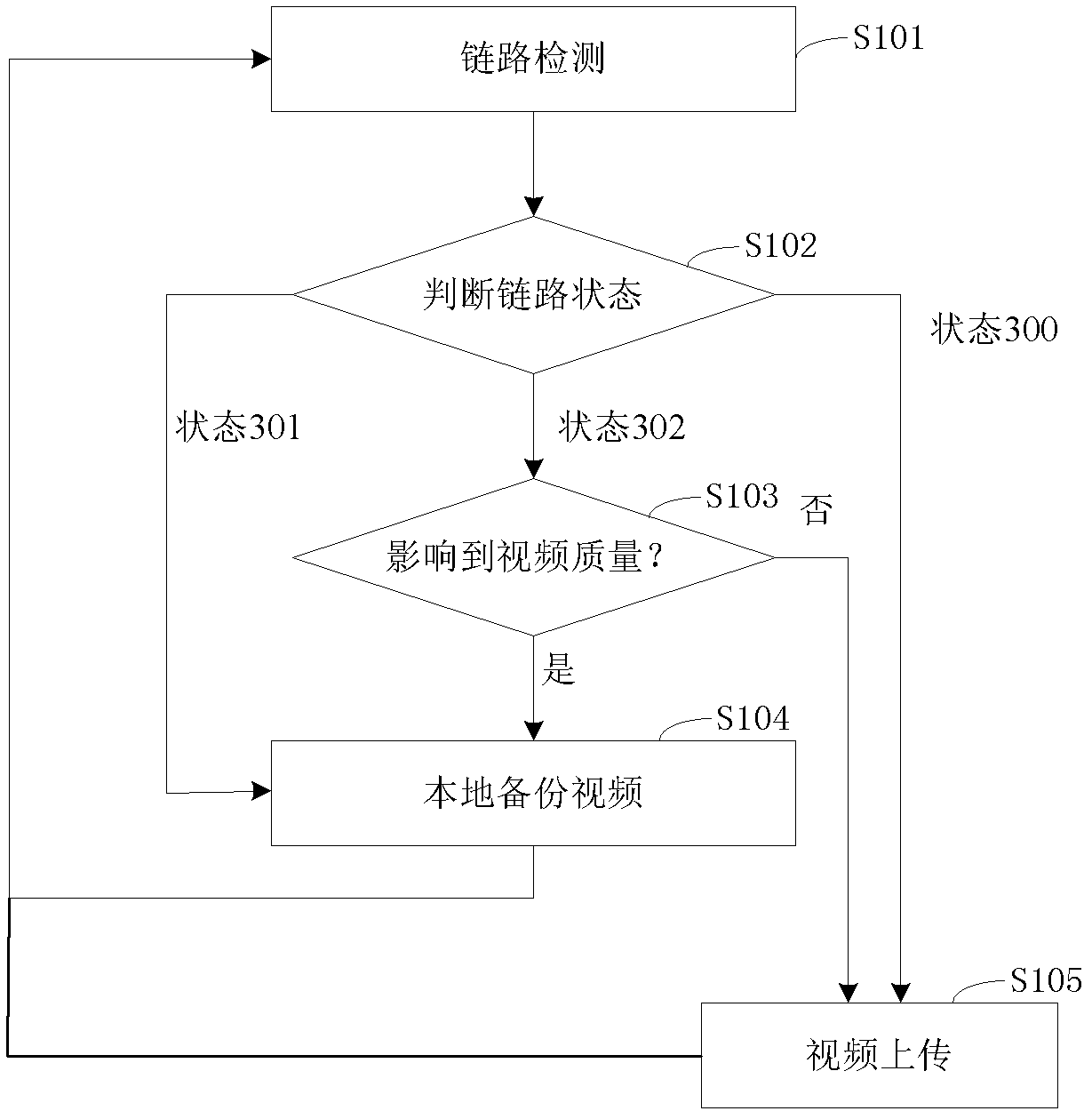
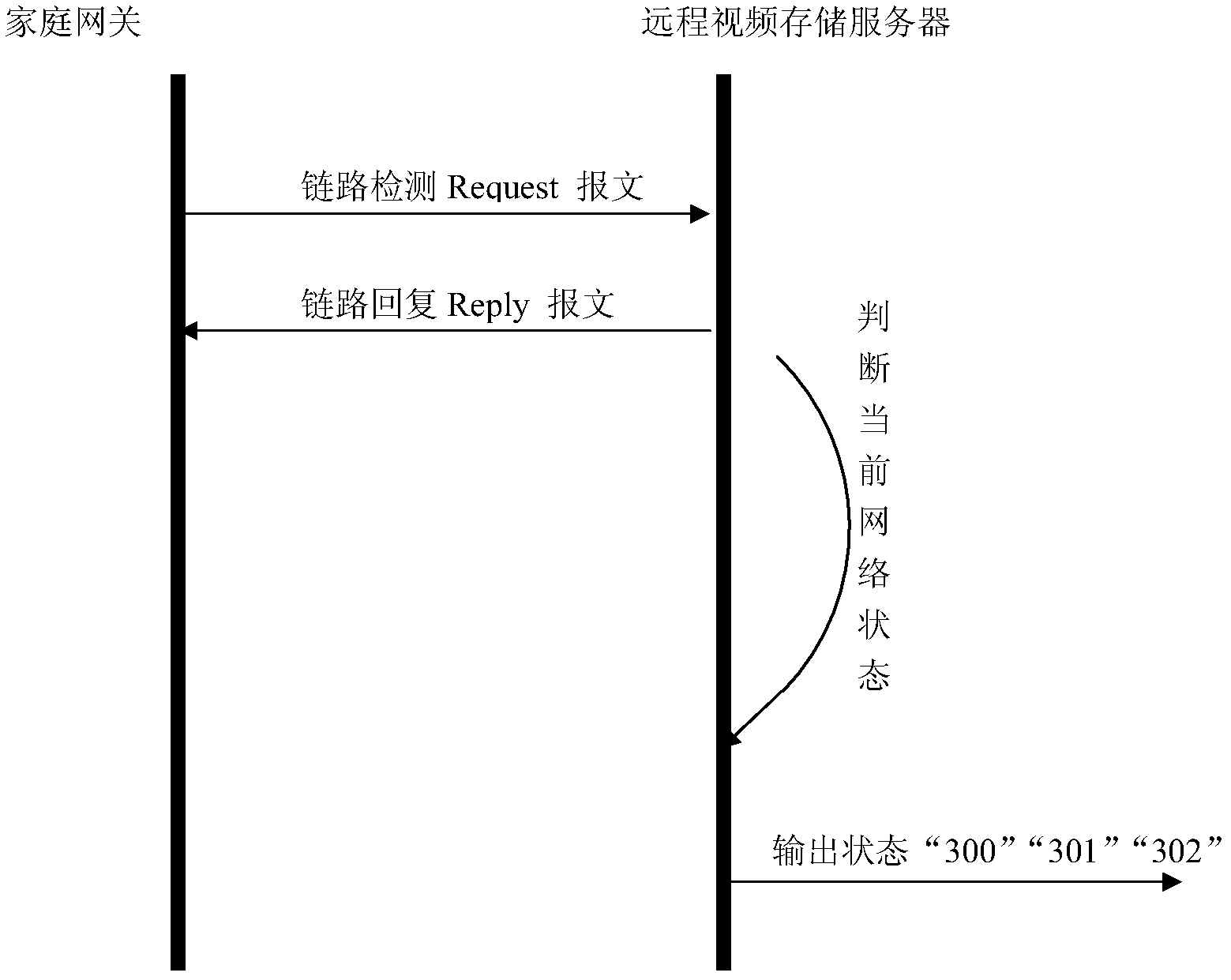
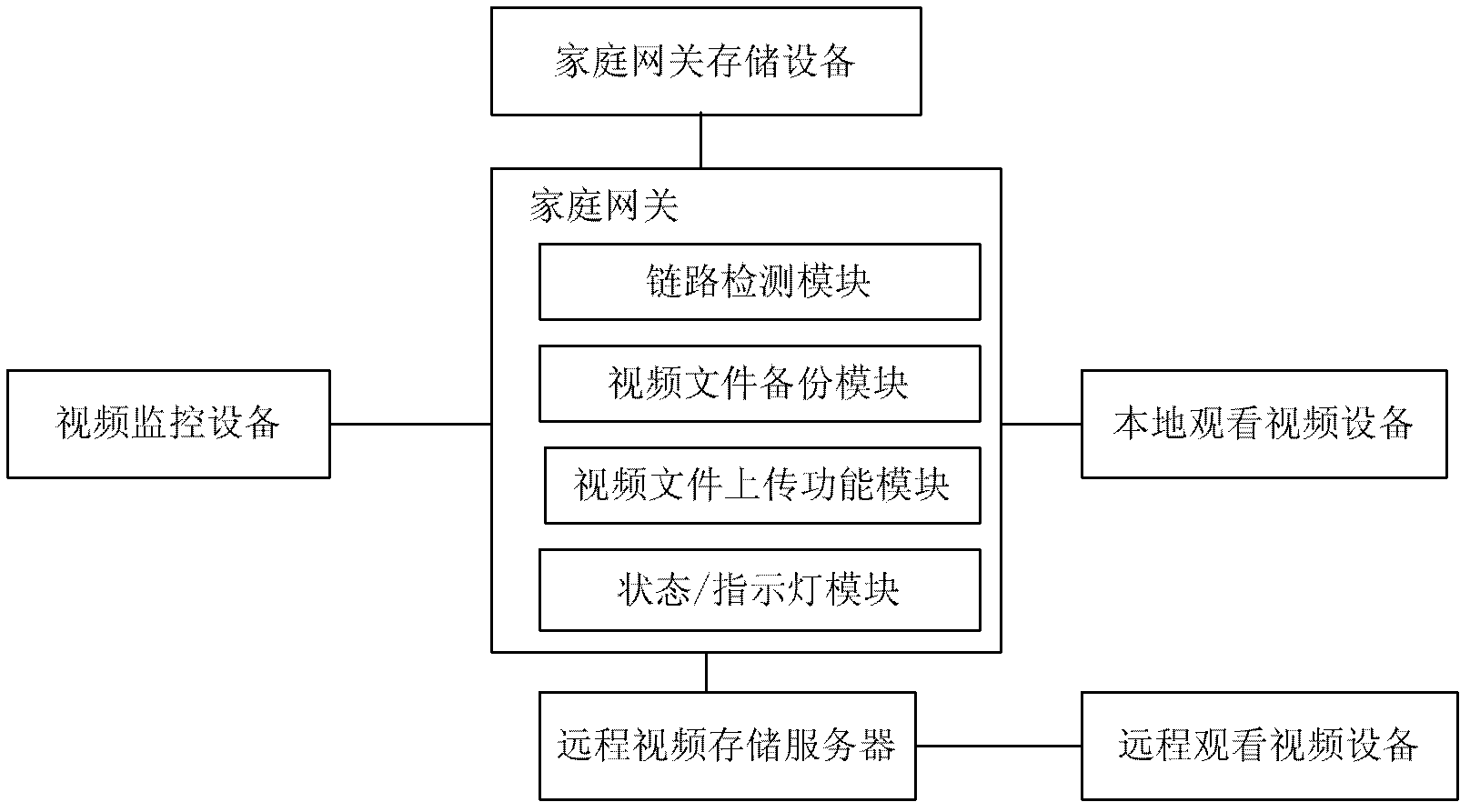
Video backup method and system based on security and protection home gateway
InactiveCN103024326AIntegrity guaranteedAvoid lossTelevision system detailsColor television detailsVideo storageData loss
The invention discloses a video backup method and system based on a security and protection home gateway. The video backup method comprises the following steps that: the home gateway of a network video system periodically sends a link detection report to a server and judges whether a current network state is normal or not according to a link reply report responded by the server; if the current network state is normal, the home gateway uploads current video data of the network video system to the server; and if the current network state is abnormal, the home gateway stores the current video data of the network video system to a local storage space of the home gateway. The video backup method and system provided by the invention solve the problem that a home gateway monitoring video cannot be stored into a long-distance video storage server when the long-distance video storage server or a network is abnormal in the prior art through a local data backup mechanism when the network is abnormal, so that the integrity of video data can be effectively ensured, and the risk of losing the video data can be reduced.
Owner:ZTE CORP
Method, system and equipment for storing video data in video monitoring system
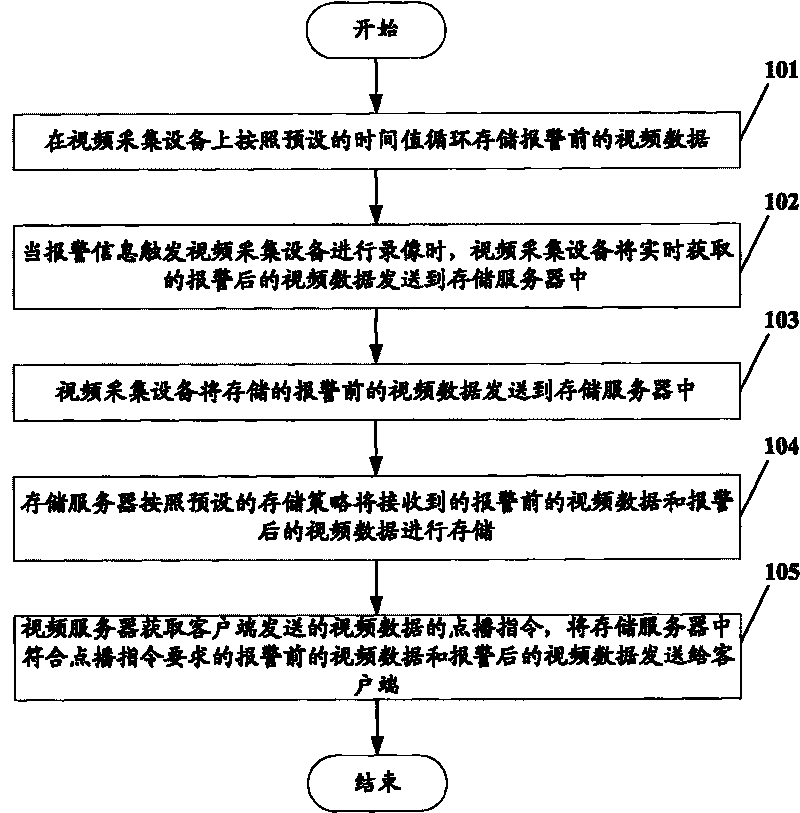
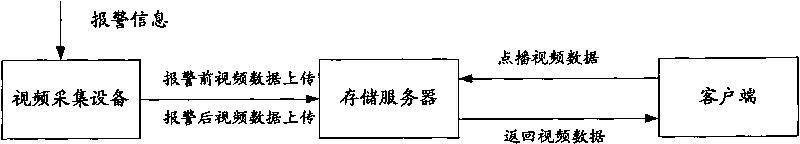
InactiveCN101753938AReduce the risk of lossEasy to manageTelevision system detailsColor television detailsVideo monitoringMonitoring system
The present invention discloses a method, a system and equipment for storing video data in a video monitoring system, which belongs to the technical field of video monitoring. The method comprises the following steps: video data before alarming is circularly stored according to preset time value on video collecting equipment; when alarming information contacts the video collecting equipment to record, video data after alarming which is timely gained is transmitted into a storing server by the video collecting equipment, and the stored video data before alarming is transmitted to a storing server by the video collecting equipment; and the video data before alarming and the video data after alarming which are received are stored to single storing modules by the storing server according to the preset storing strategy. Therefore, video data stored in the monitoring system can be convenient for clients to manage.
Owner:VIMICRO CORP
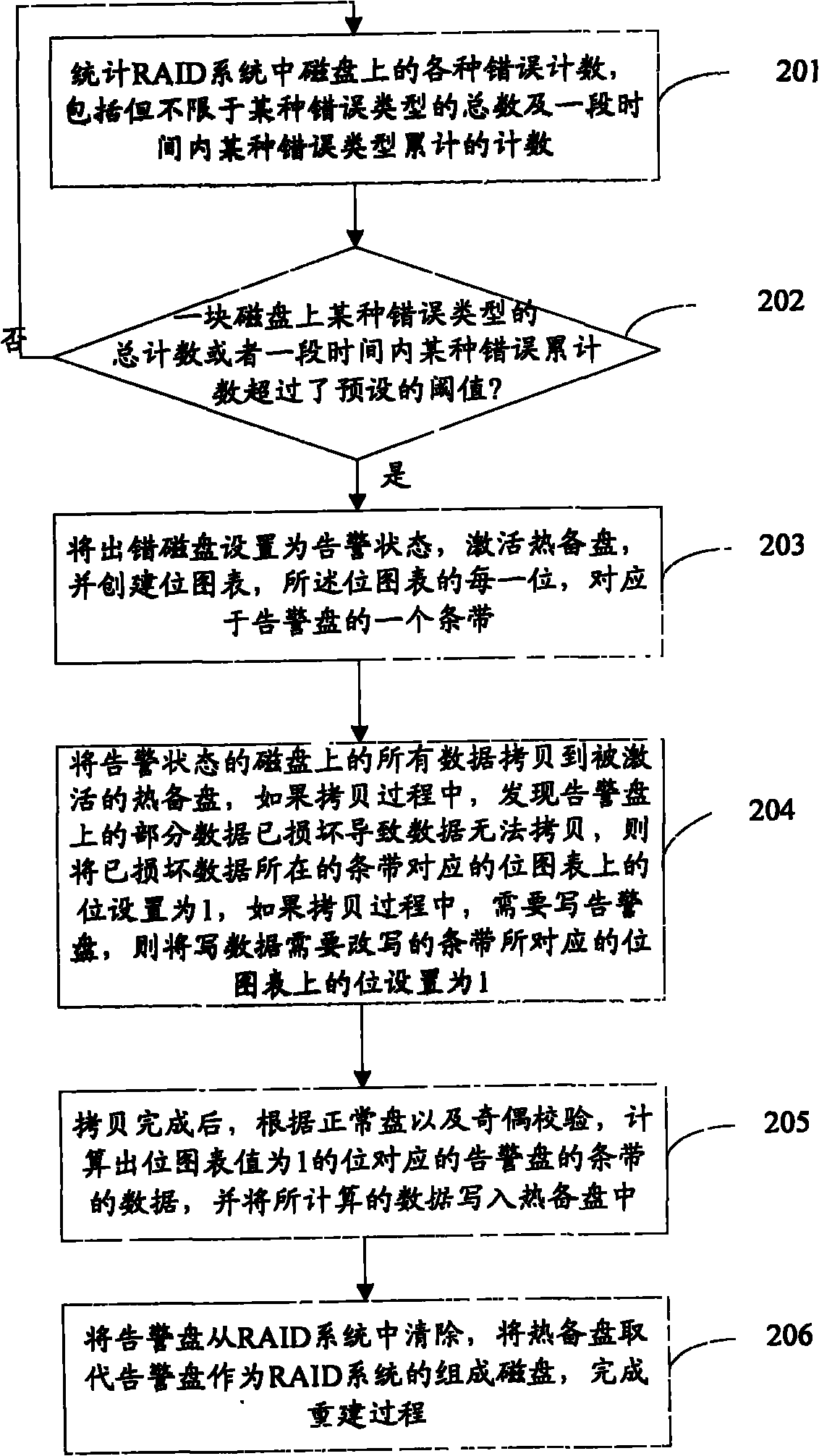
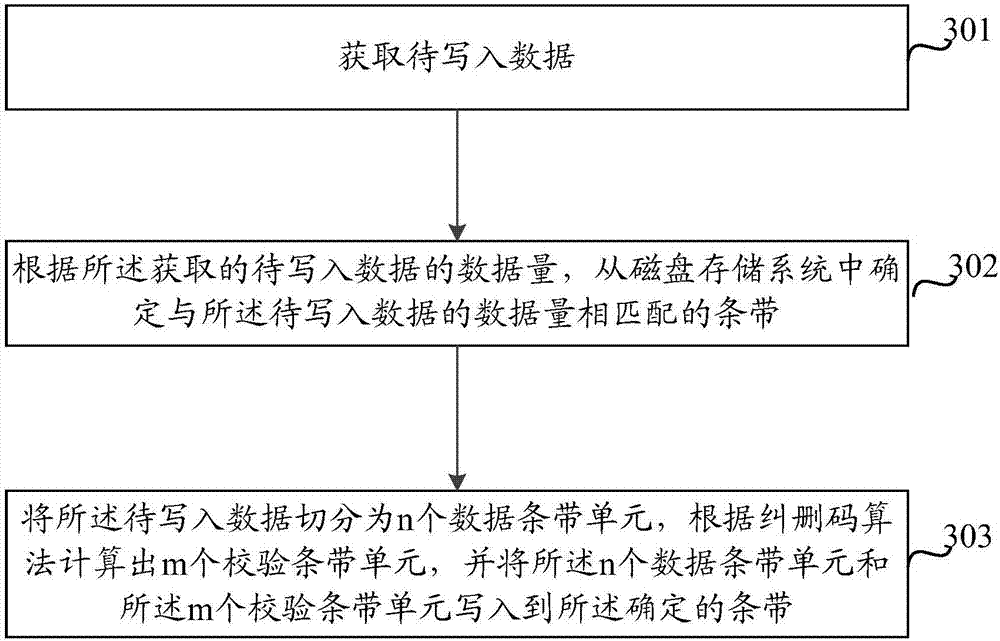
Method and device for writing data into
ActiveCN107273048ALow data write latencyReduce riskInput/output to record carriersRedundant data error correctionComputer architectureData set
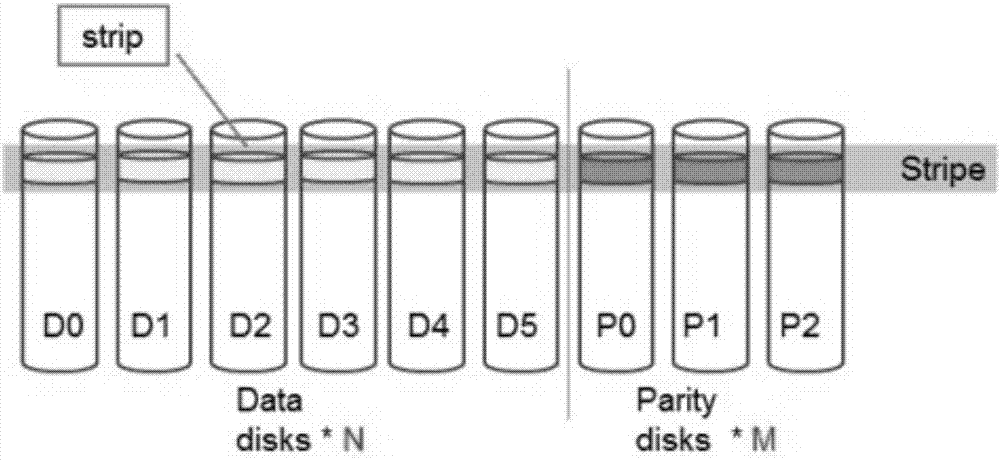
The invention discloses a method and device for writing data into. The method includes obtaining of the data to be written into, a strip matched with the volume of the obtained data to be written into is determined from a disk storage system according to the volume of the obtained data to be written into, wherein the disk storage system includes multiple strips different in depth, each strip includes n data strip units and m verification strip units, the data to be written into is divided into n data strip units, the m verification strip units are calculated out through an erasure code algorithm, and the n data strip units and the m verification strip units are written into the determined strip. According to the volume of the data to be written into, the strip of the suitable depth is selected, the data to be written into is written into the selected strip through the erasure code algorithm, and the effects that the throughput is improved by selecting the strip with the large depth when the volume of the data is large, and when the volume of the data is small, the strip with small depth is selected, so that the risks of delayed writing and data losing are reduced.
Owner:ZHEJIANG DAHUA TECH CO LTD
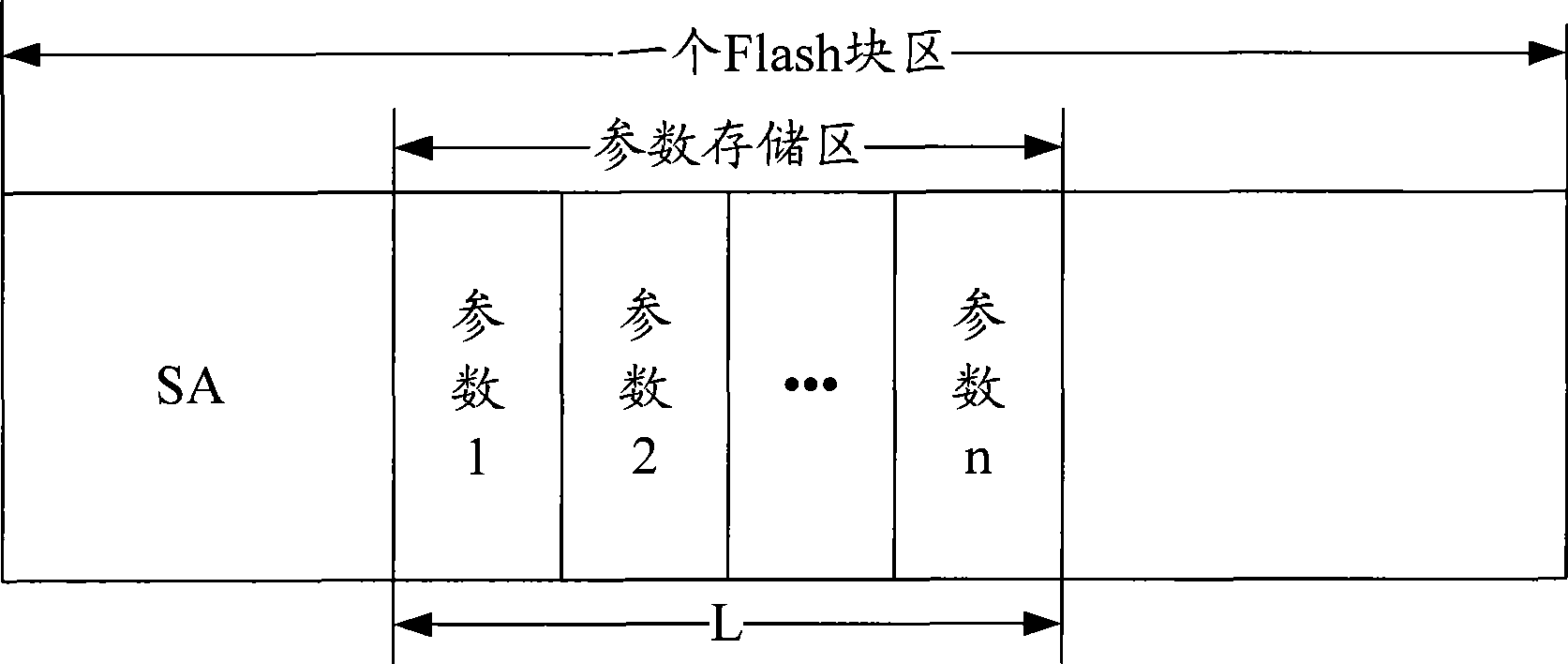
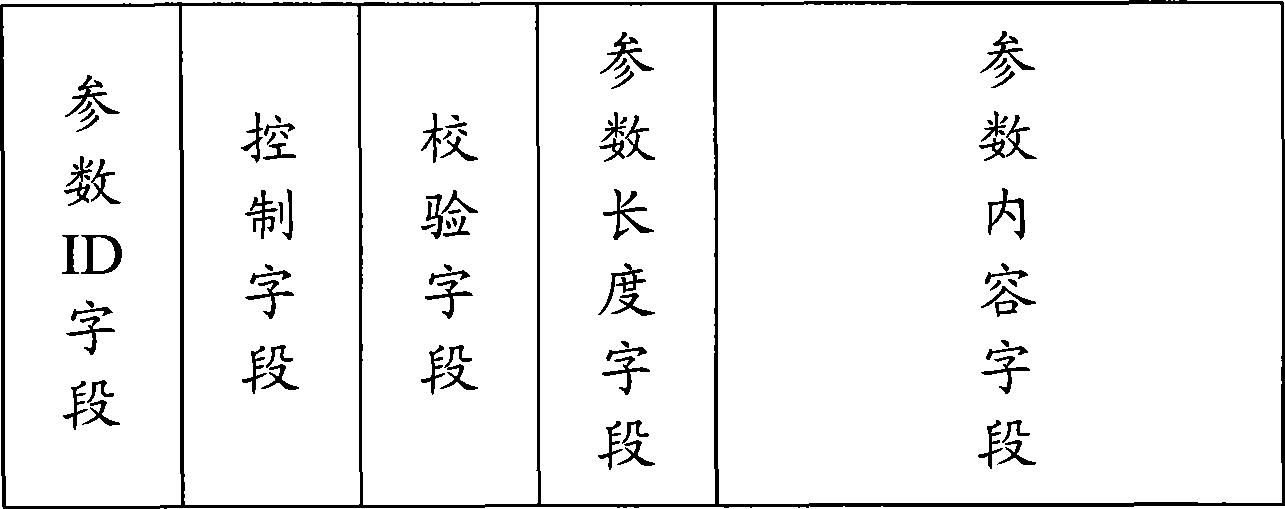
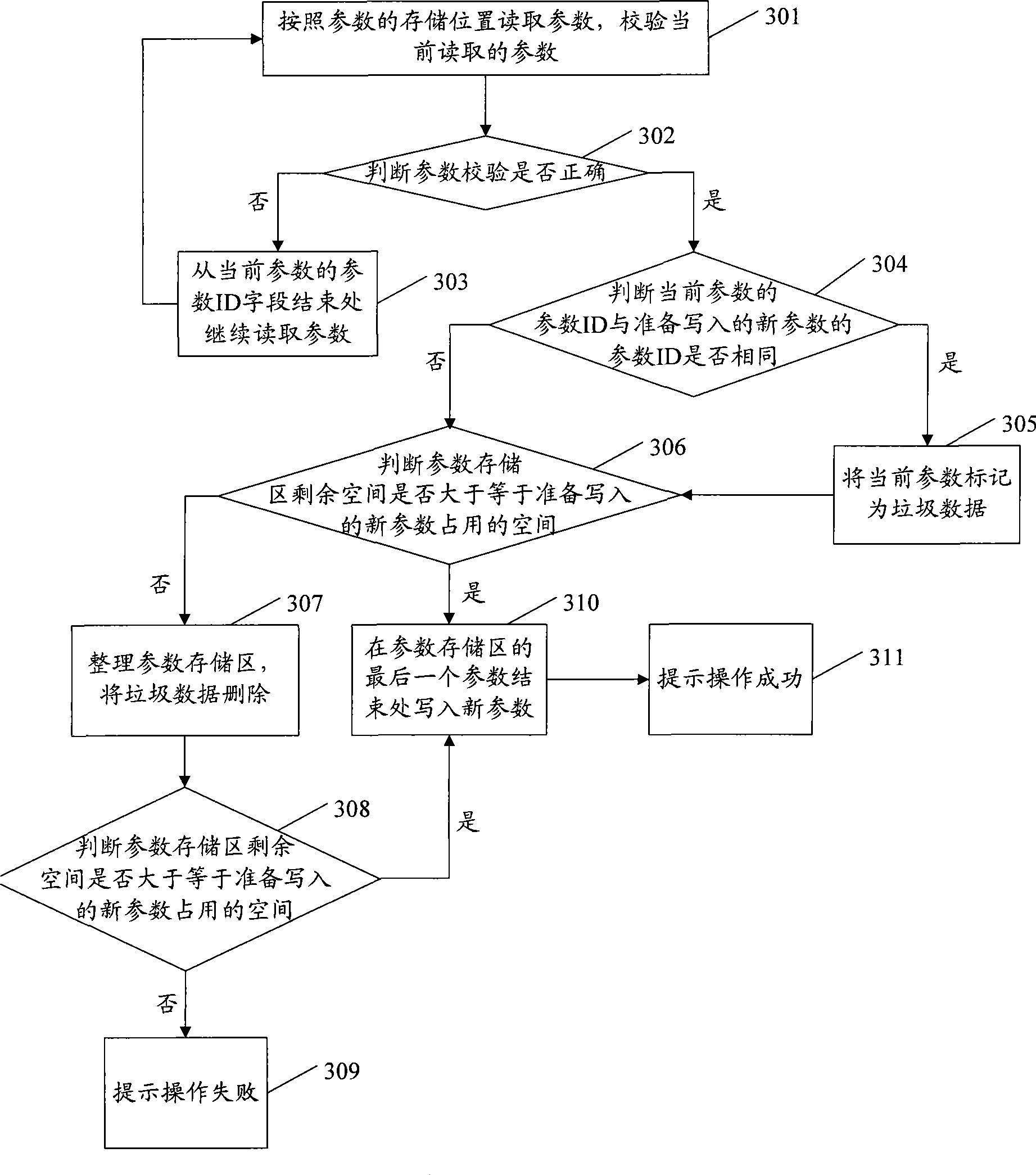
Parameter management method and system based on embedded type equipment flash memory
ActiveCN101436158AIncrease profitSave Flash spaceMemory adressing/allocation/relocationManagement systemUtilization rate
The invention discloses a parameter management method based on an embedded type equipment flash memory. The method comprises the following steps: according to a fixed format, parameters are encapsulated to obtain parameter data blocks; the parameter data blocks are sequentially stored in a parameter storage region; according to a parameter ID of a new parameter which is prepared to read, whether a parameter containing the same parameter ID exists in the parameter storage region is retrieved; if existing, the current parameter is marked as trash data; whether the residual space in the parameter storage region can contain the new parameter is judged; if not existing, whether the residual space in the parameter storage region can contain the new parameter is directly judged; and when the residual space in the parameter storage region can contain the new parameter, the new parameter is read in the finishing position of the last parameter in the parameter storage region. The invention also discloses a parameter management system based on the embedded type equipment flash memory; and the method and the system can improve the utilization rate of the space of the flash memory, prolong the service life of the flash memory and improve the safety in reading or modifying the parameters.
Owner:ZTE CORP
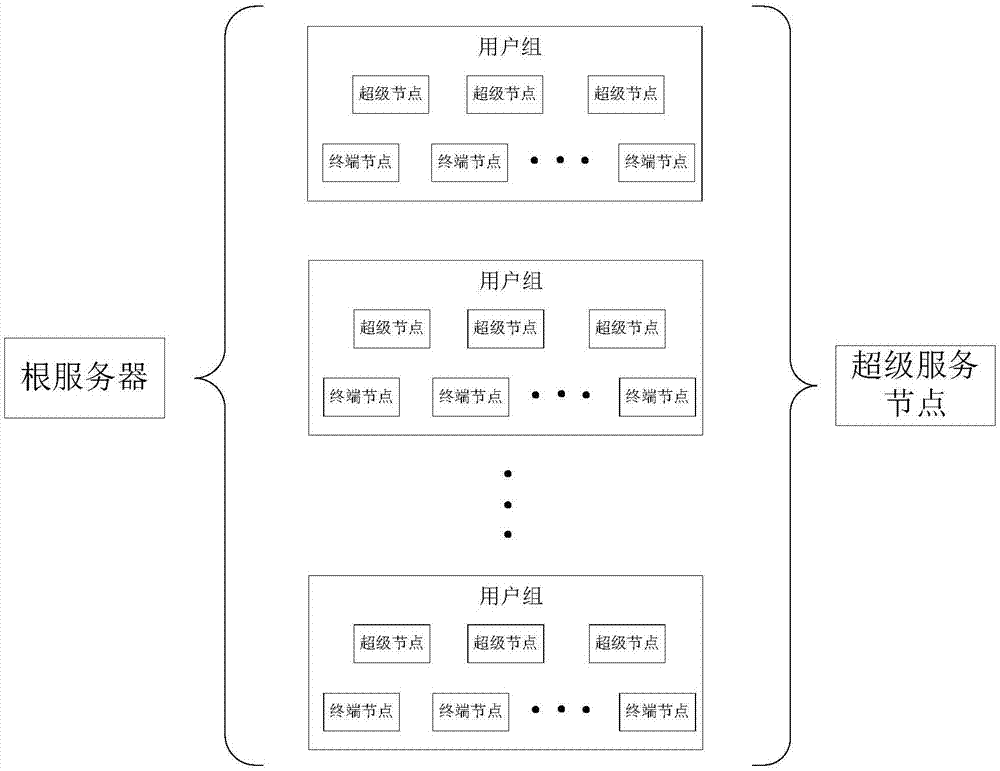
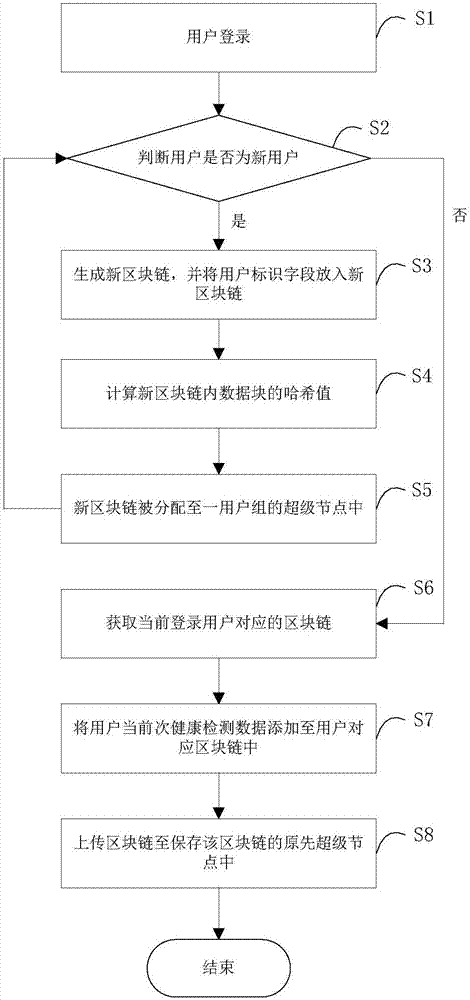
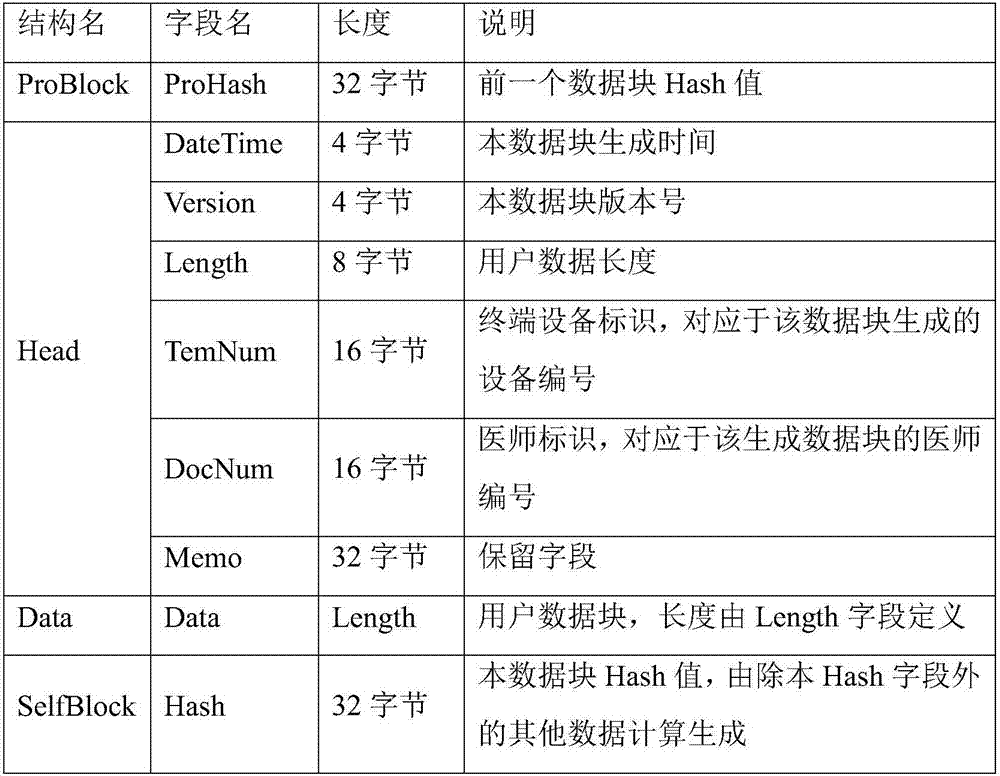
Block chain technology-based health detection data management system and method
ActiveCN106951185AReduce the risk of lossReduce management costsInput/output to record carriersRedundant data error correctionTerminal equipmentData management
The invention relates to the field of data management and discloses a block chain technology-based health detection data management system. The system comprises a plurality of terminal nodes, a plurality of super nodes, at least one user group and a root node server, wherein each terminal node corresponds to a service terminal device for bearing user health detection; the service terminal device is used for generating health detection data and caching the health detection data; the user group includes at least one super node; the root node server is used for converting the terminal nodes to the super nodes according to running time of the terminal nodes and system resource abundance degree, and establishing the user group; and the root node server is also used for synchronizing the health detection data stored between the super nodes in the user group. The invention also discloses a block chain technology-based health detection data management method. According to the block chain technology-based health detection data management system and the block chain technology-based health detection data management method, the safety, completeness and reliability of the user health detection data which are stored in a distributed system for a long time can be effectively guaranteed.
Owner:哈尔滨爱宁智慧科技有限公司
Distributed file indexing system and method based on block chain and cloud storage server
ActiveCN110399338AIncrease redundancyImprove securityFile access structuresFile metadata searchingResource utilizationSmart contract
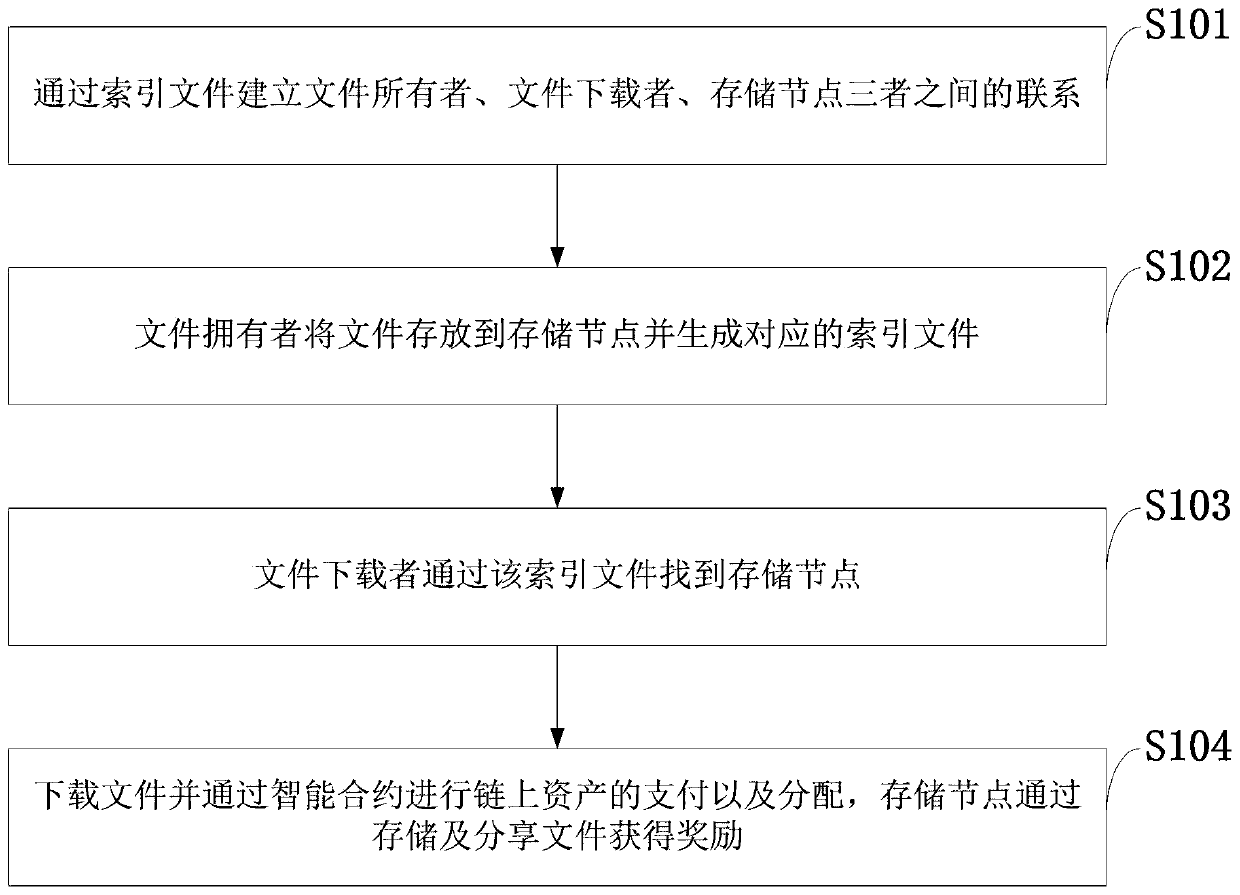
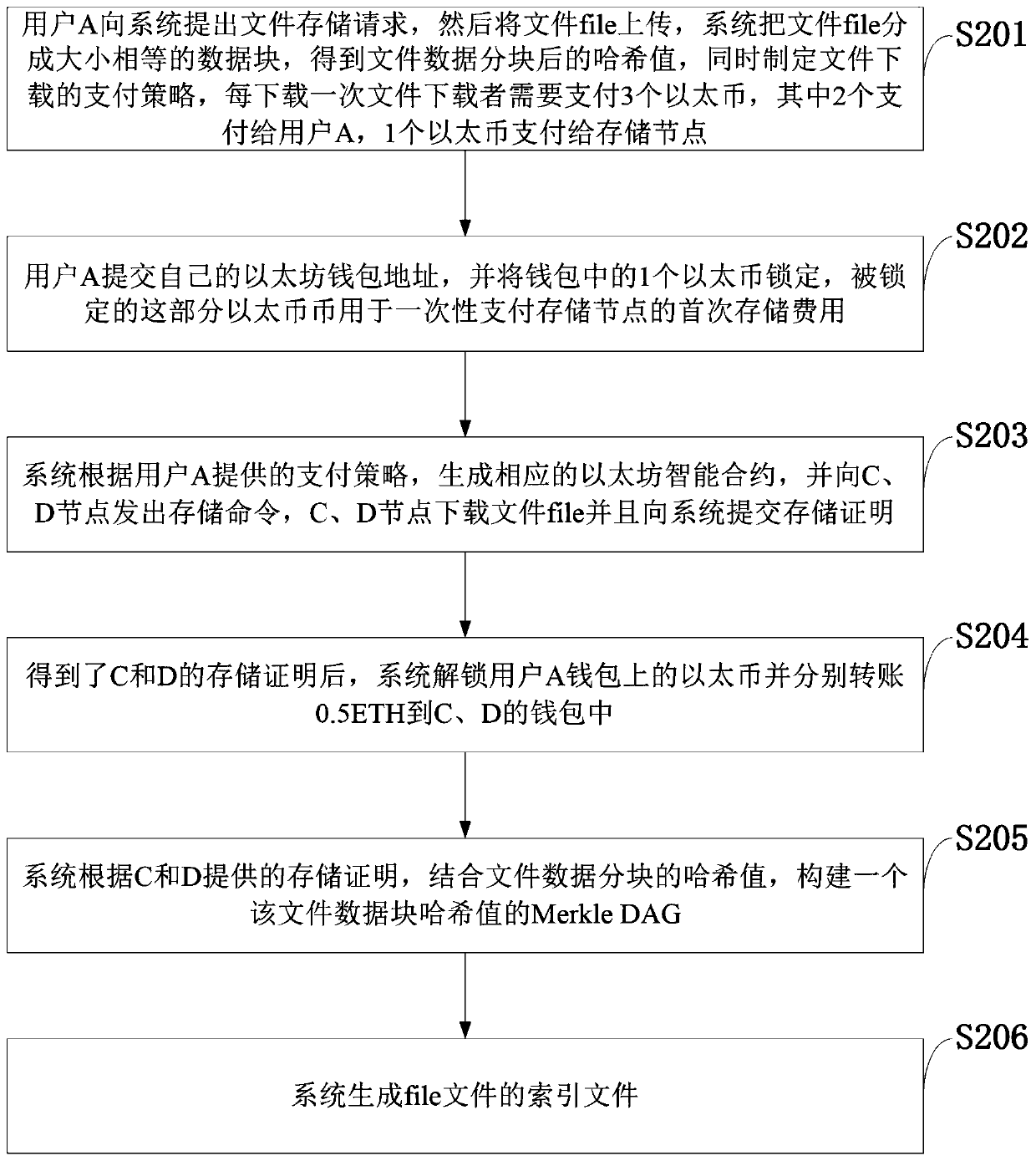
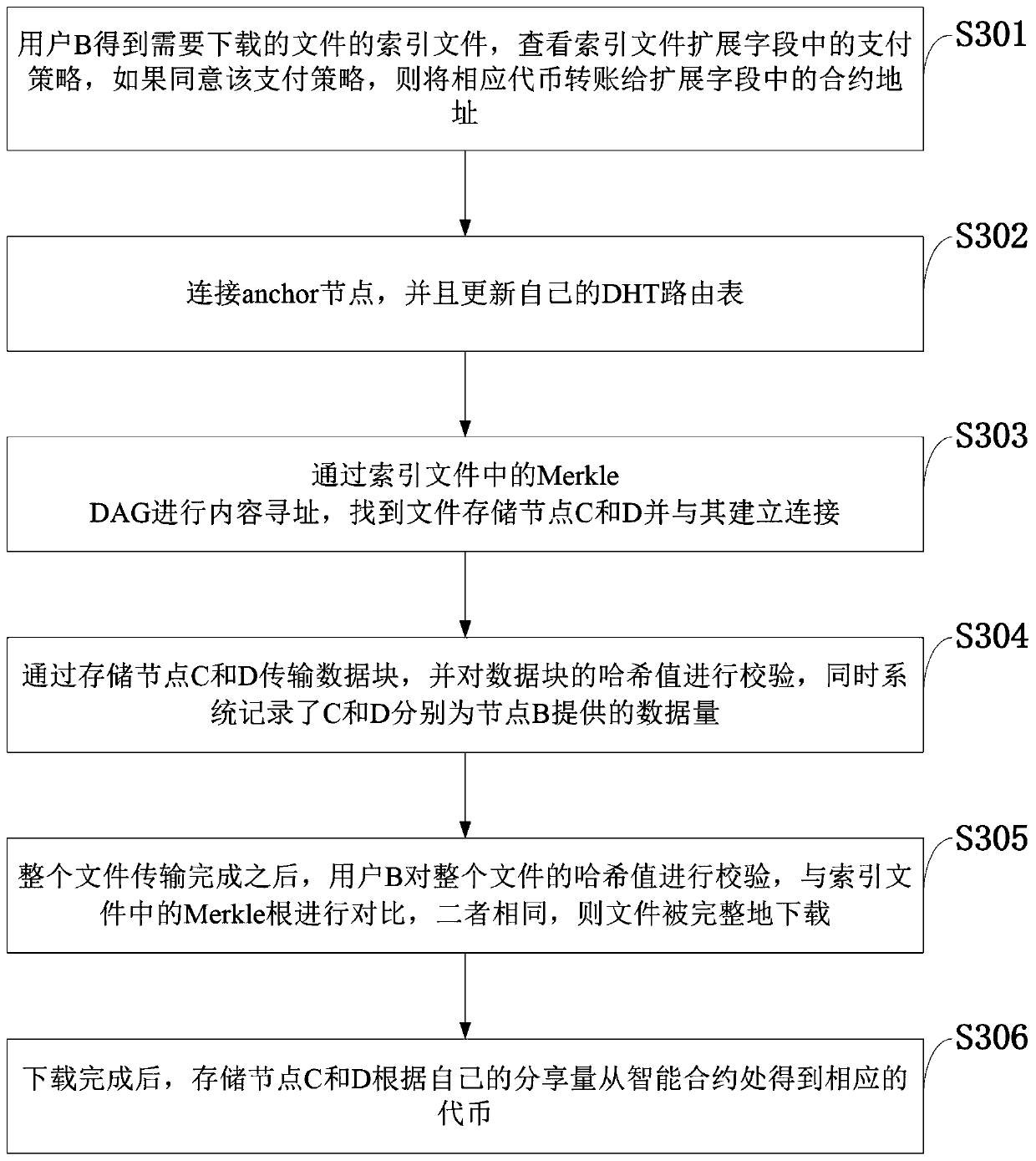
The invention belongs to the technical field of file distributed storage and distributed indexing. The invention discloses a distributed file indexing system and method based on a block chain and a cloud storage server. A relationship among the file owner, the file downloader and the storage node is established through the index file; and a file owner stores a file in a storage node and generatesa corresponding index file, a file downloader finds the storage node through the index file, downloads the file and pays and distributes assets on a chain through an intelligent contract, and the storage node obtains awards through file storage and sharing. According to the invention, a centralized inquiry server can be omitted, the file sharing fairness is guaranteed through the intelligent contract, and the resource utilization rate is greatly increased; and meanwhile, the block chain network and the storage network are decoupled, the block chain network does not directly store data, only MerkleDAG containing the file hash value is stored, mutual cooperation is achieved, and the practicability is improved.
Owner:XIDIAN UNIV +1
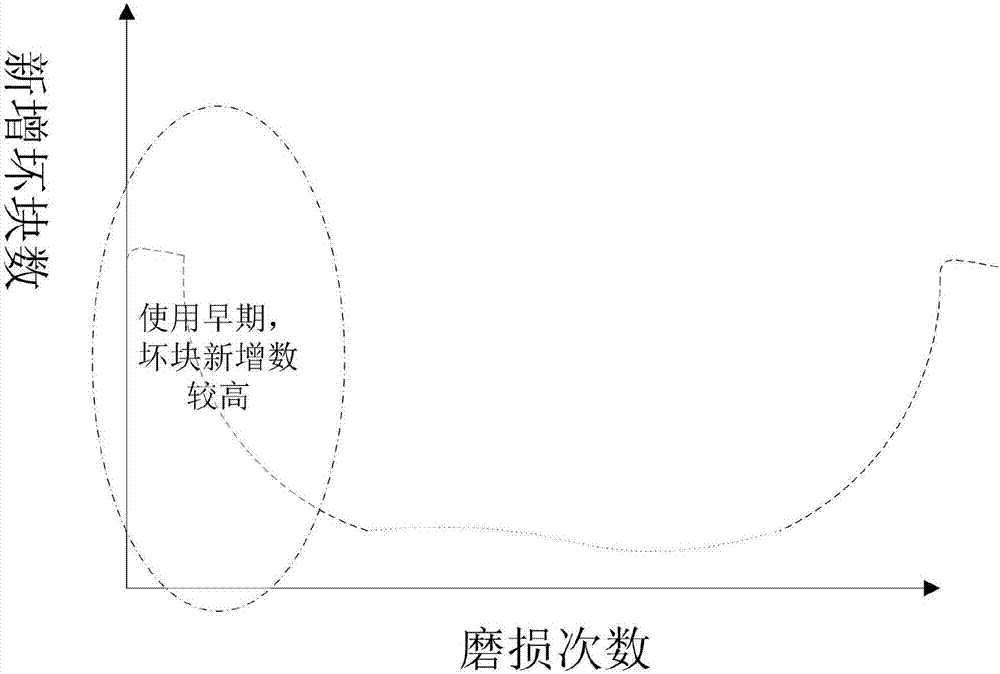
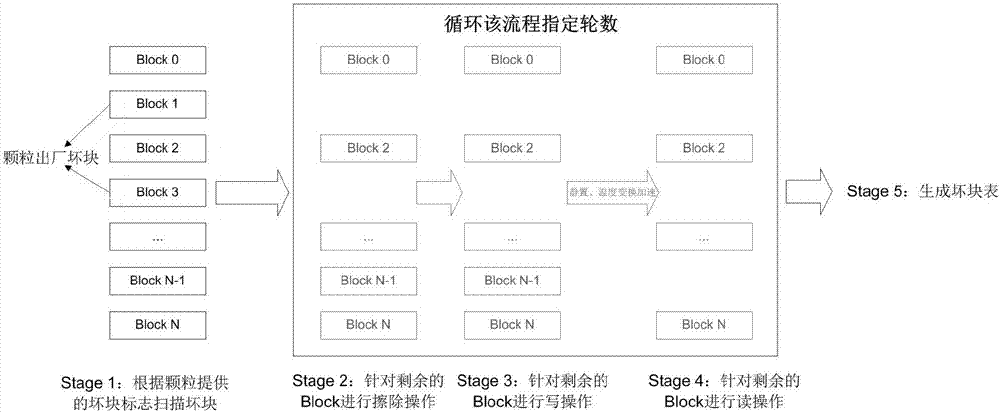
Method for identifying bad blocks of solid state disk
ActiveCN106981315ABad block reductionReduce the risk of lossStatic storageSolid-state driveData loss
The invention discloses a method for identifying bad blocks of a solid state disk. The method is characterized in that bad block aging check operation is added to the solid state disk; in the bad block aging check operation, initial bad block marks of a storage chip are scanned, an initial bad block table is established, and specified round check operation is added to a storage unit of the solid state disk; in the check operation, the bad block table is read, and all normal blocks are subjected to erasure operation, writing operation, reading operation and operation of checking the number of bit errors in each block according to information in the bad block table; and when the erasure operation fails, the writing operation fails or it is checked in each round that the number of the bit errors in the blocks exceeds a preset error correction threshold, the blocks are marked as the bad blocks, and bad block information is added to the bad block table. The easily damaged blocks of the solid state disk in an early stage of use are exposed and identified in advance, so that the bad block probability during use of users is reduced and the risk of user data loss is effectively lowered.
Owner:RAMAXEL TECH SHENZHEN
Mobile terminal and combined terminal device
ActiveCN104717330ARemove black borderKeep the feelTelephone set constructionsEngineeringTerminal server
Owner:ZHEJIANG GEELY HLDG GRP CO LTD +1
Terminal login system and method
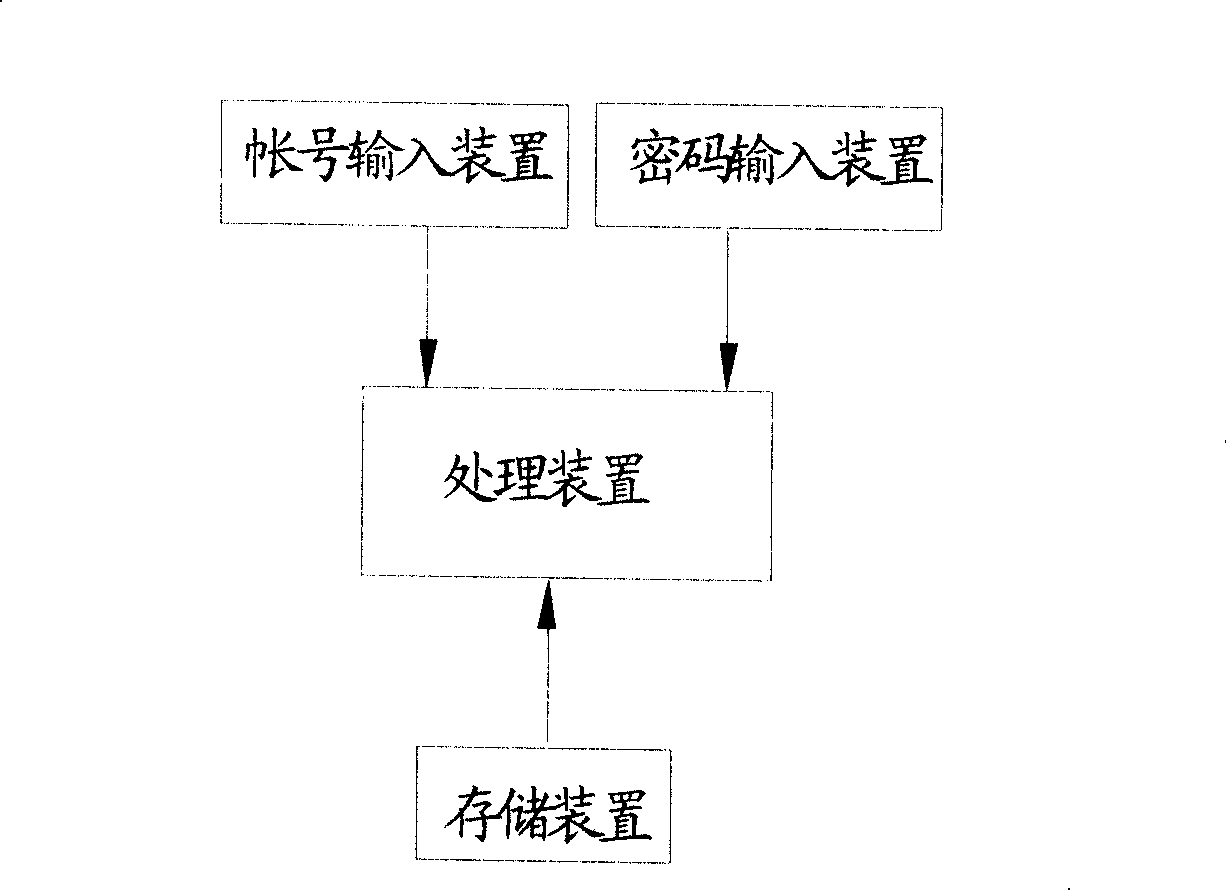
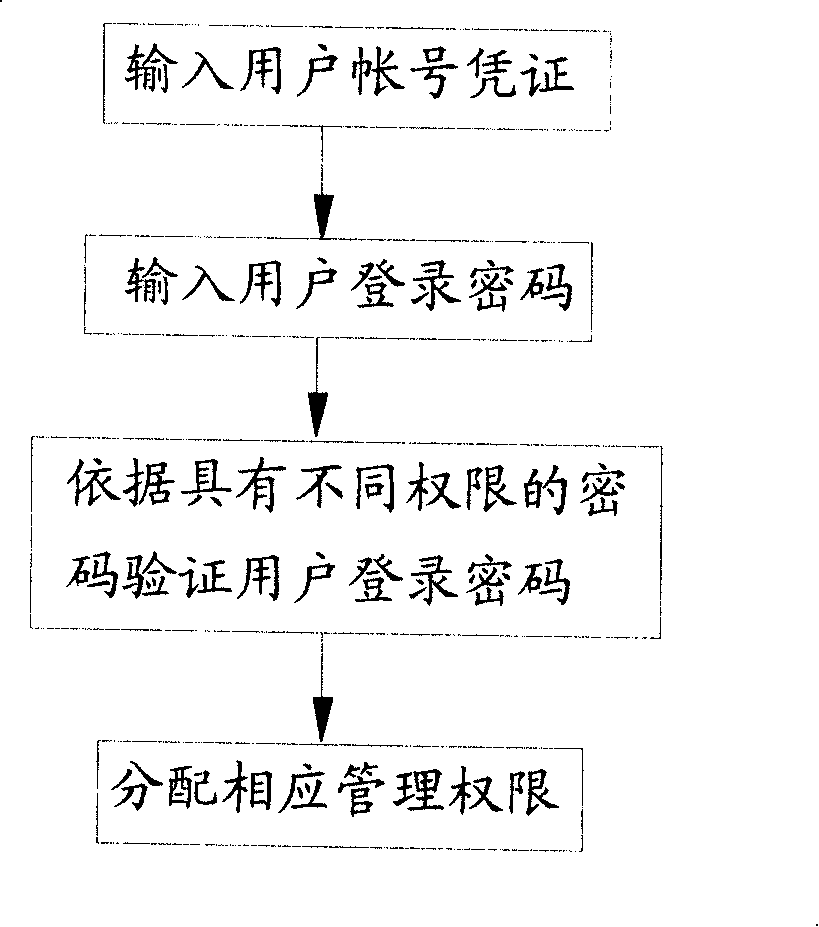
InactiveCN101183468AReduce risk of loss of administrative privilegesReduce customer lossComplete banking machinesAcutation objectsPasswordCipher
The invention relates to a system and a method for terminal password login; wherein the method comprises that the following steps: input the account voucher; input the login password of user; verify the login password of the user according to at least two preset passwords with different administrative authorities; assign the authorities to the user. With the method of setting at least two passwords with different administrative authorities in the terminal password login system, the invention has the advantages that the user can acquire the corresponding administrative authority by inputting different passwords according to the actual operating situation; thus the prior risk of losing all the administrative authorities caused by the stealing of the password is reduced and the loss of the user is also reduced.
Owner:杨文烈
Safe storage system and method for off-chain data of block chain
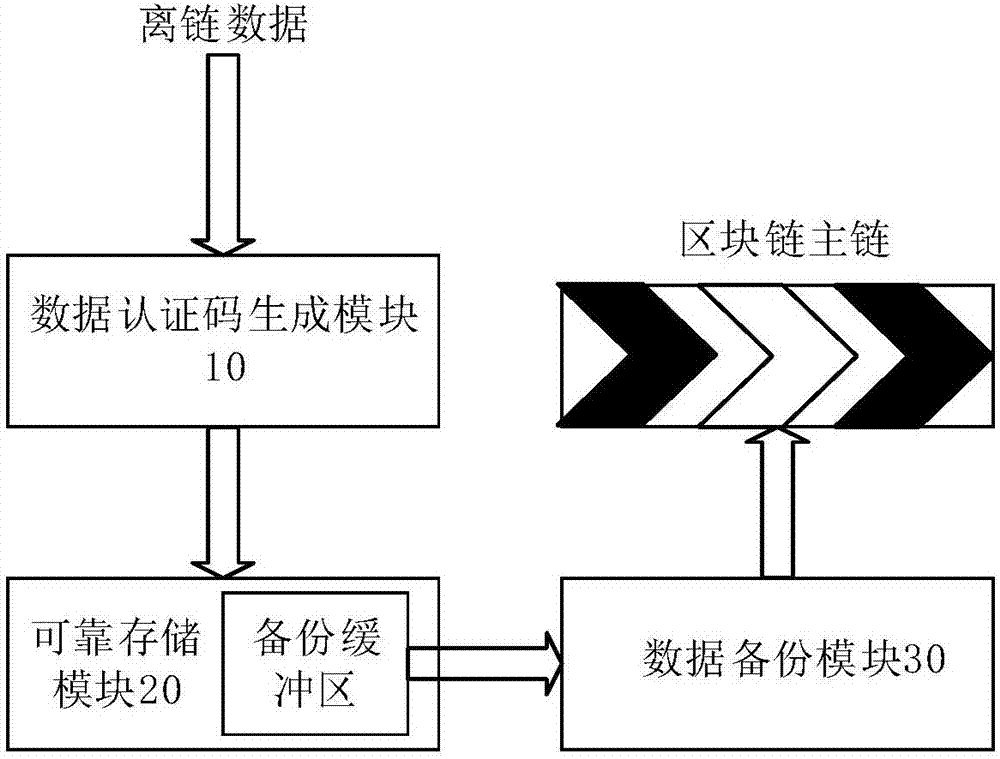
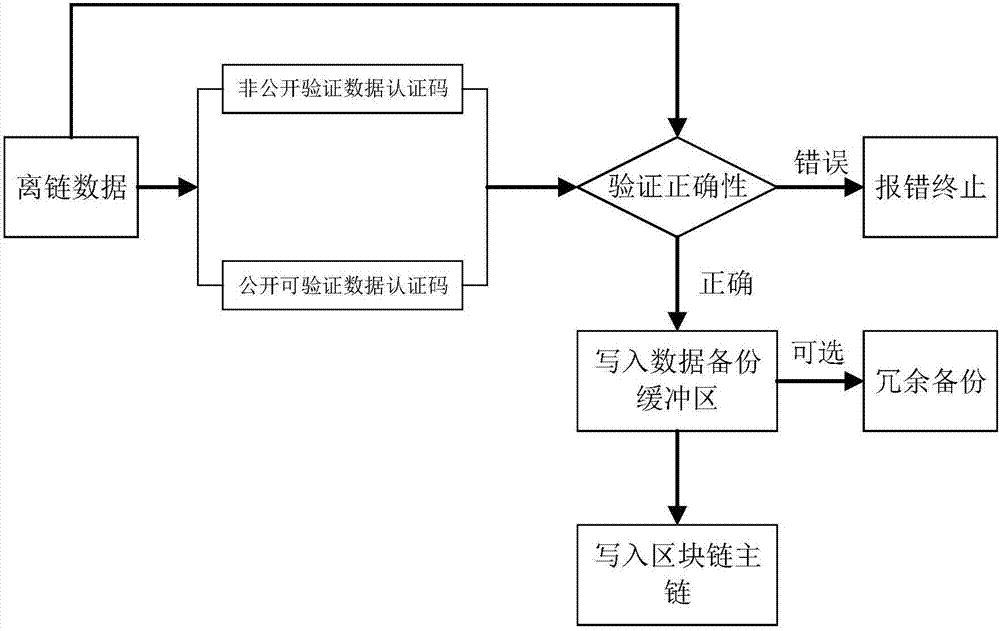
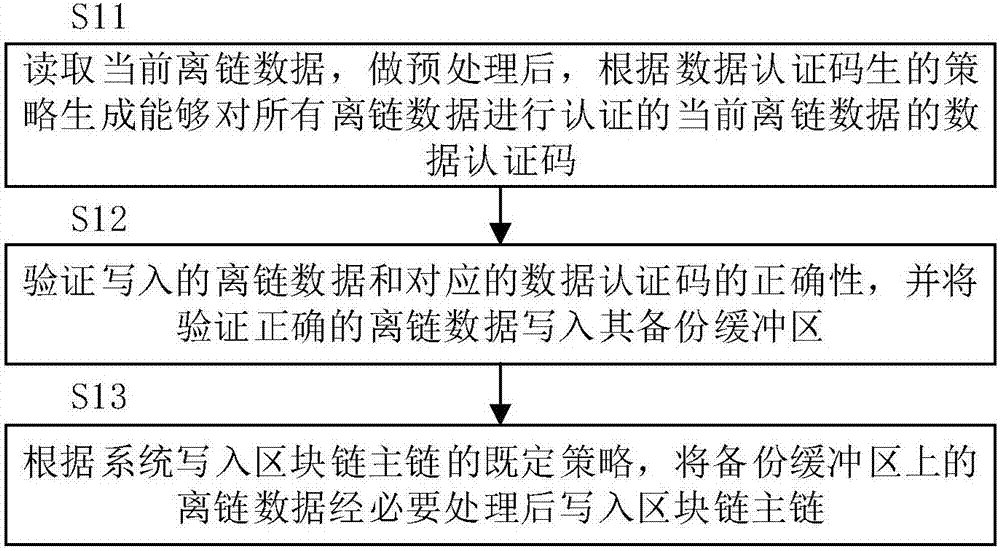
ActiveCN107480559AReduce the risk of lossGuaranteed correctnessKey distribution for secure communicationUser identity/authority verificationThird partyData loss
The invention discloses a safe storage system and method for off-chain data of a block chain. The method comprises the steps of reading current off-chain data, and after preprocessing, generating a data authentication code of the current off-chain data according to a policy for generating data authentication codes, wherein the data authentication code can be used for authenticating all off-chain data; verifying the correctness of written off-chain data and the corresponding data authentication code, and writing the off-chain data which is authenticated successfully into a backup buffer area; according to a set policy for writing data into a main chain of the block chain by the system, writing the processed off-chain data on the backup buffer area into the main chain of the block chain. According to the safe storage system and method for the off-chain data of the block chain, by introducing reliable storage of a third party, the loss problem of the off-chain data is solved; by utilizing the characteristic that the data authentication code of the current off-chain data can be used for authenticating all the off-chain data, the loss risk of the off-chain data can be further reduced, the reliability and security of a block chain branching technique are improved, and meanwhile the authentication speed is increased.
Owner:北京中科锐链科技有限公司
Network information security protection system based on Internet
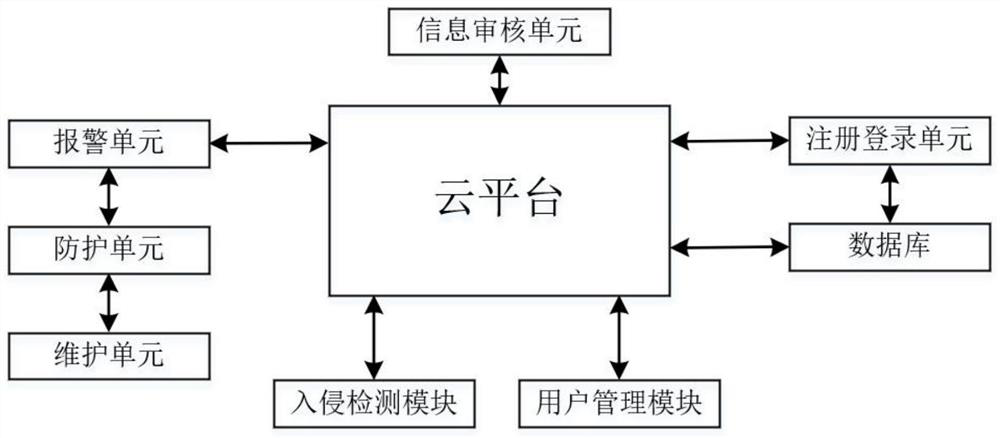
InactiveCN112187792AImprove securityReduce the risk of lossPlatform integrity maintainanceTransmissionThe InternetInformation security
The invention discloses a network information security protection system based on the Internet. The network information security protection system comprises a cloud platform, a registration and loginunit, a database, an information auditing unit, an intrusion detection module, a user management module, an alarm unit and a protection unit. The method comprises the following steps: detecting systemdata through an intrusion detection module, acquiring illegal access times, virus type quantity and vulnerability quantity of a system, acquiring a system intrusion coefficient Y through a formula, and comparing the system intrusion coefficient Y with an intrusion coefficient threshold value: if the system intrusion coefficient Y is less than or equal to the intrusion coefficient threshold value,judging that intrusion does not exist in the system; generating a system security signal and sending the system security signal to the cloud platform; if the system intrusion coefficient Y is greaterthan the intrusion coefficient threshold, judging that intrusion exists in the system, generating a system danger signal and sending the system danger signal to an alarm unit. After the system is detected, viruses are eliminated before data loss of the system, so that the data security is improved, and the risk of data loss is reduced.
Owner:安徽思珀特信息科技有限公司
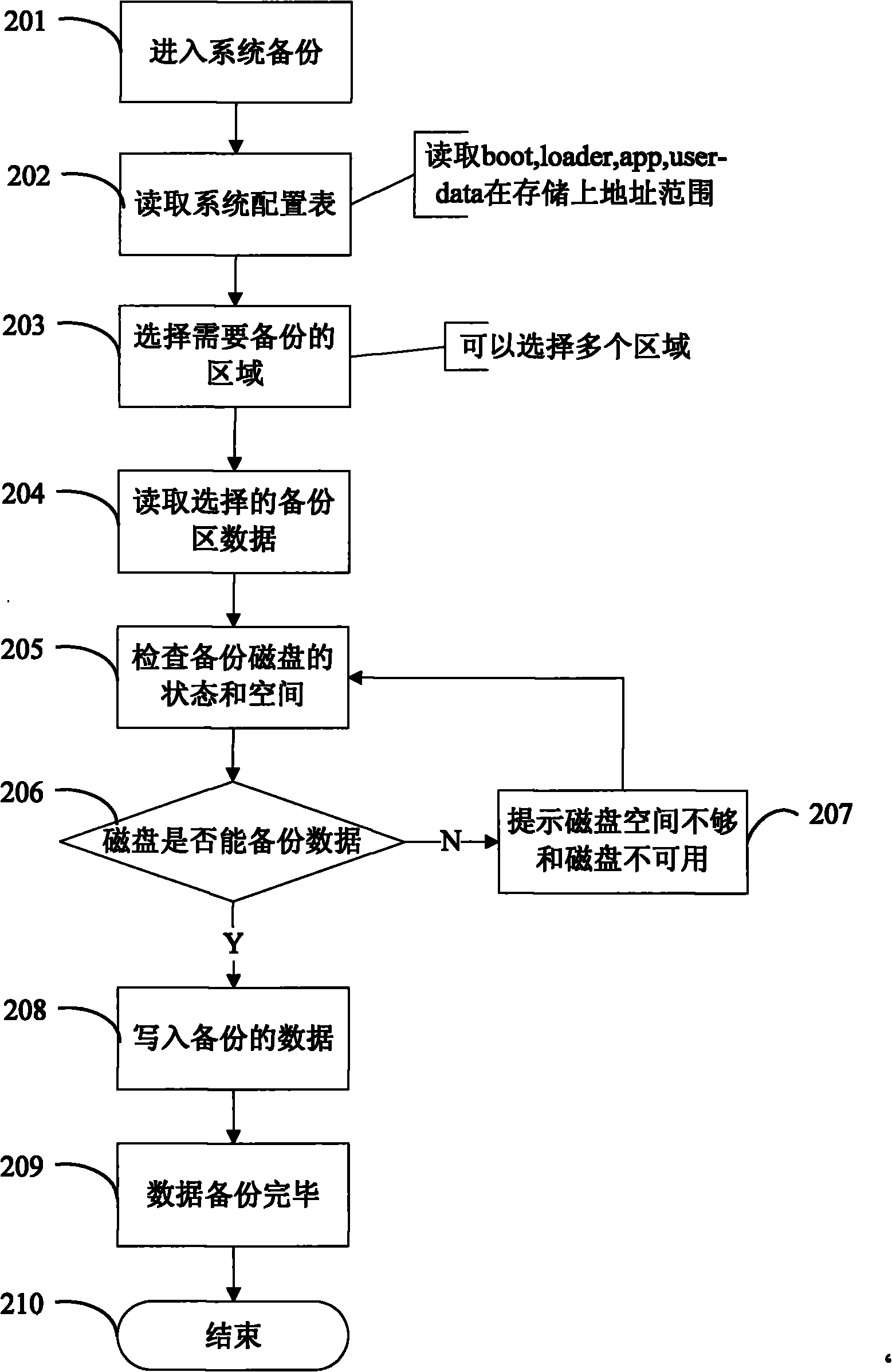
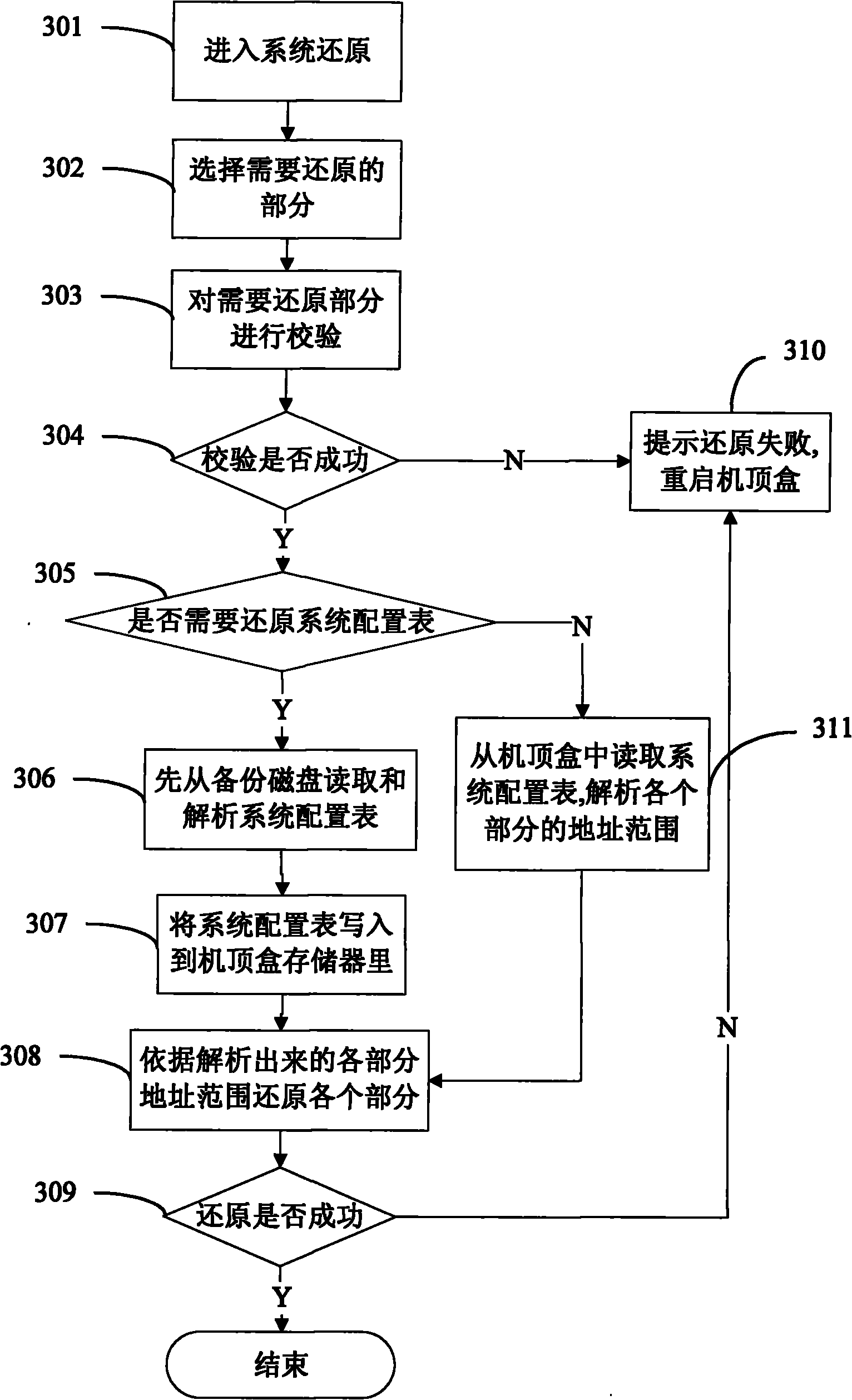
Backup and restore method for DTV receiving terminal software system
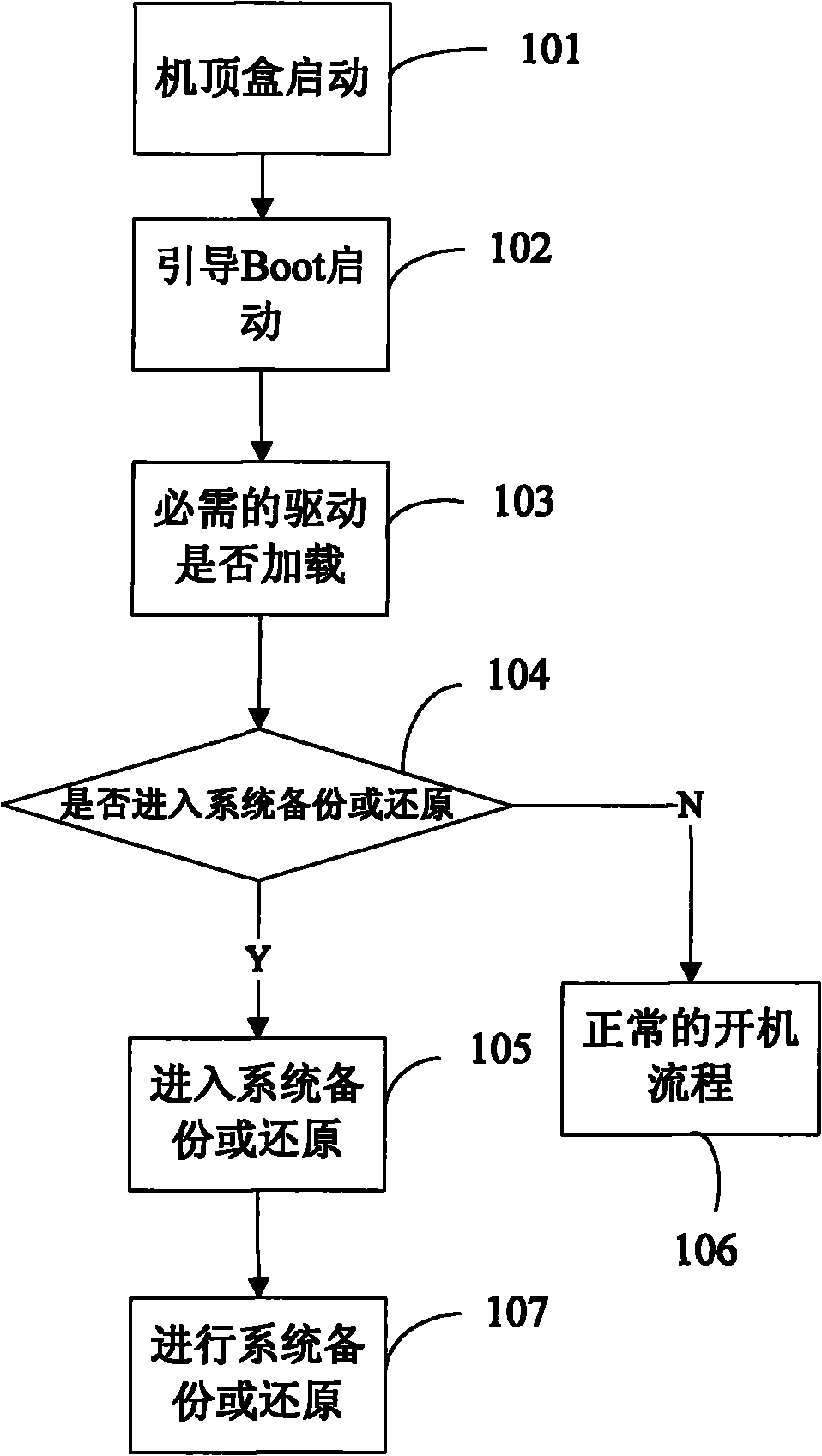
InactiveCN101771804AFunctionalReduce the risk of lossTelevision system detailsColor television detailsDigital televisionExternal storage
The invention discloses a backup and restore method for a DTV receiving terminal software system; wherein after the DTV receiving terminal guides a boot to normally start and load divers, a backup system is selected and entered, the user parameters or DTV receiving terminal software are stored in an external memory storage as backup through a backup system of the DTV receiving terminal; after the DTV receiving terminal guides the boot to normally start and the basic drivers are loaded, the DTV receiving terminal is connected with the external memory storage, a restore system is selected and entered, the loss data or system is restored through the restore system of the DTV receiving terminal. The DTV receiving terminal has backup or restore function, and accordingly reduces the data loss hazard.
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD
Operation behavior monitoring method, mobile terminal and computer readable storage medium
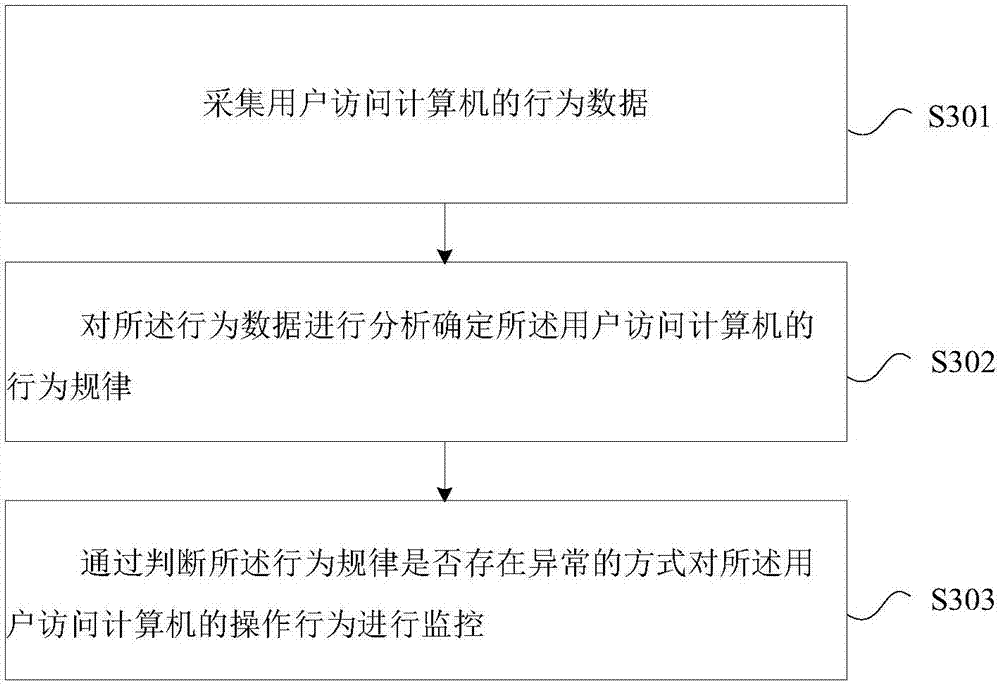
InactiveCN107977303ASolve problems with a high risk of lossReduce the risk of lossHardware monitoringOperational behaviorData loss
The invention discloses an operation behavior monitoring method. According to the method, behavior data of a user accessing a computer is collected; the behavior data is analyzed to determine the behavior law of the user accessing the computer; and the operation behavior of the user accessing the computer is monitored by means of judging whether the behavior law is abnormal. The invention furthermore discloses a mobile terminal and a computer readable storage medium. Through the method, the mobile terminal and the computer readable storage medium, the problem that in the prior art, an abnormaloperation behavior of the user accessing the computer cannot be monitored, and consequently the risk of data loss is high is solved; and through monitoring of the behavior of the user accessing the computer, the abnormal behavior of the user can be discovered in real time, and the risk of data loss is lowered.
Owner:NUBIA TECHNOLOGY CO LTD
A library seat management system based on the visual Internet of Things
ActiveCN109902628AWill not cause occupationEasy to readCharacter and pattern recognitionResourcesStart timeComputer science
The invention discloses a library seat management system based on a visual Internet of Things. The system comprises a reader identity authentication module which realizes reader identity authentication on a seat through face recognition; a reader real-time posture detection module which is used for detecting the posture of the reader and judging whether the reader leaves the seat or not; And an overtime reminding module which is used for starting timing when the reader leaves the seat, and sending a reminder to the reader and / or an administrator when the leaving time exceeds a threshold value.The system can automatically identify whether readers leave the seats or not, automatically start timing when it is detected that the readers leave the seats, and achieve the function of reminding the readers to return to the seats or notifying workers to recycle the seats according to preset conditions, so that the problems that at present, the seat distribution and management modes of a libraryare unreasonable, and the seats are occupied for a long time are solved.
Owner:GUANGZHOU UNIVERSITY
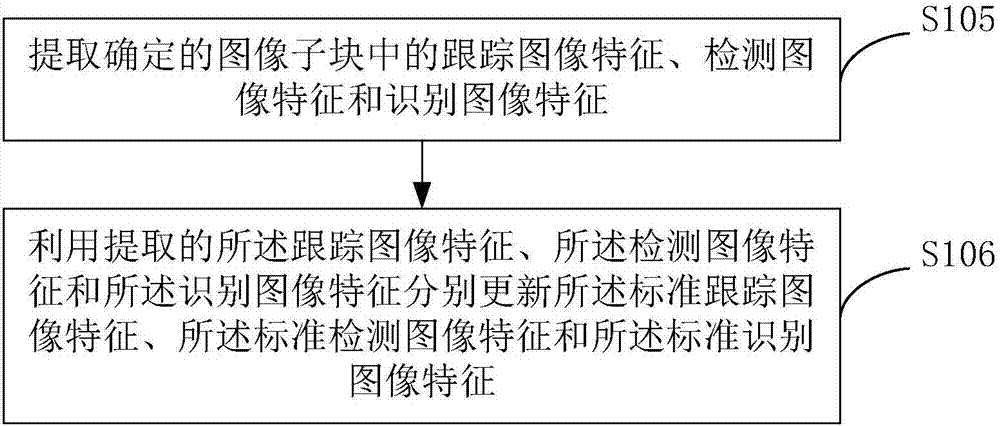
Blockchain data sharing encryption and decryption method, equipment, and storage medium
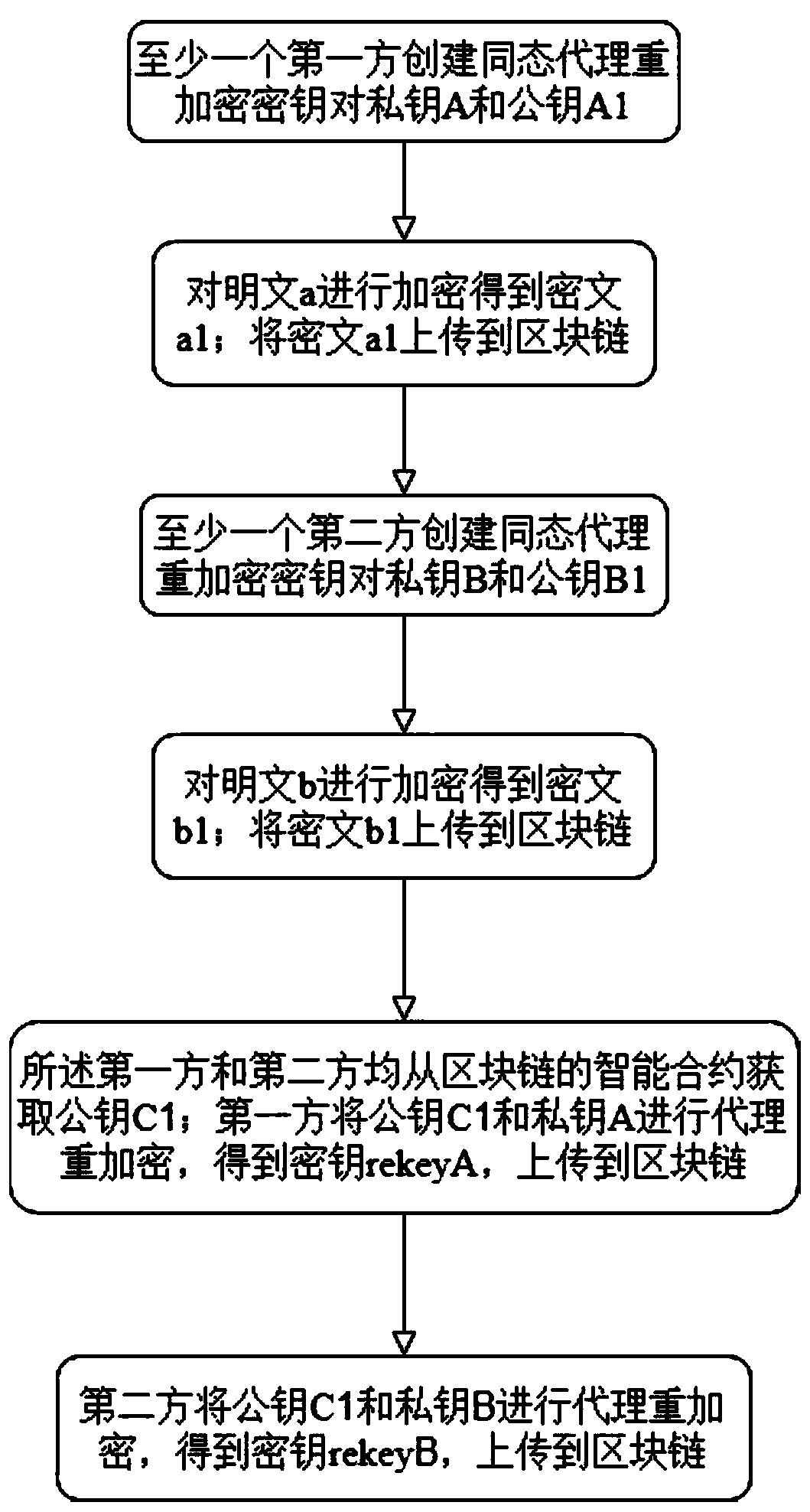
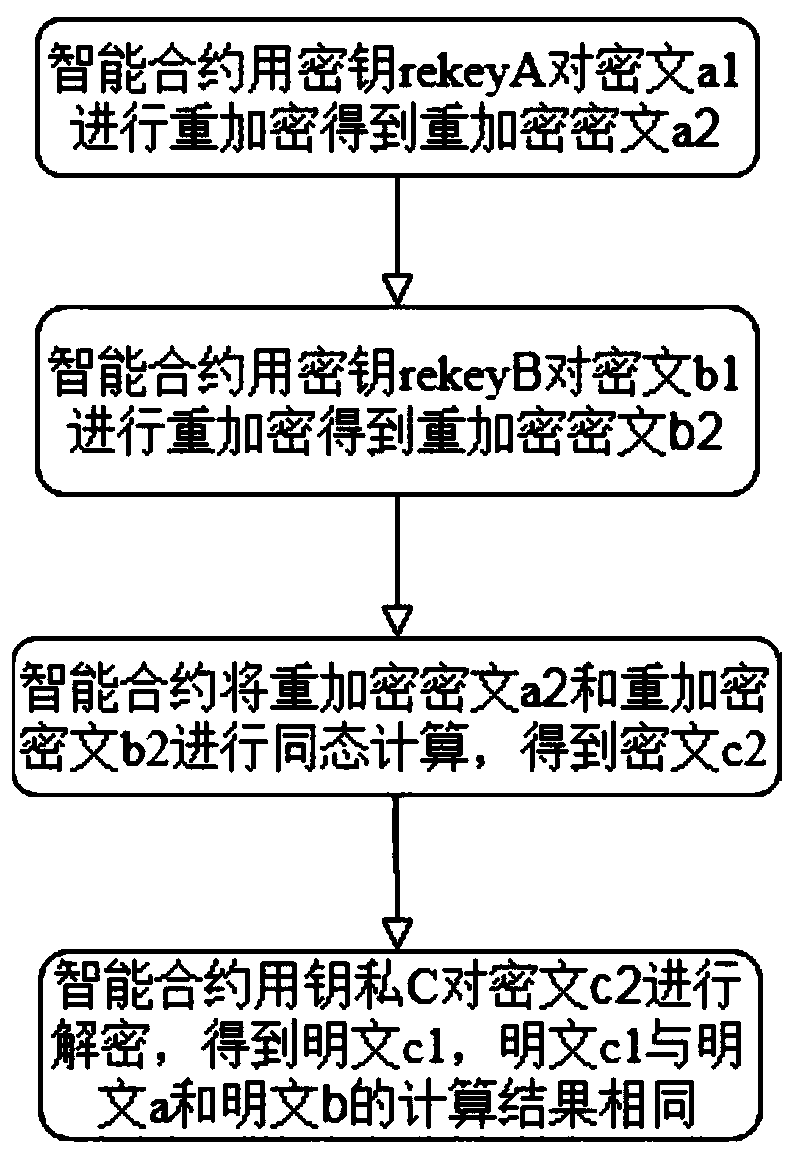
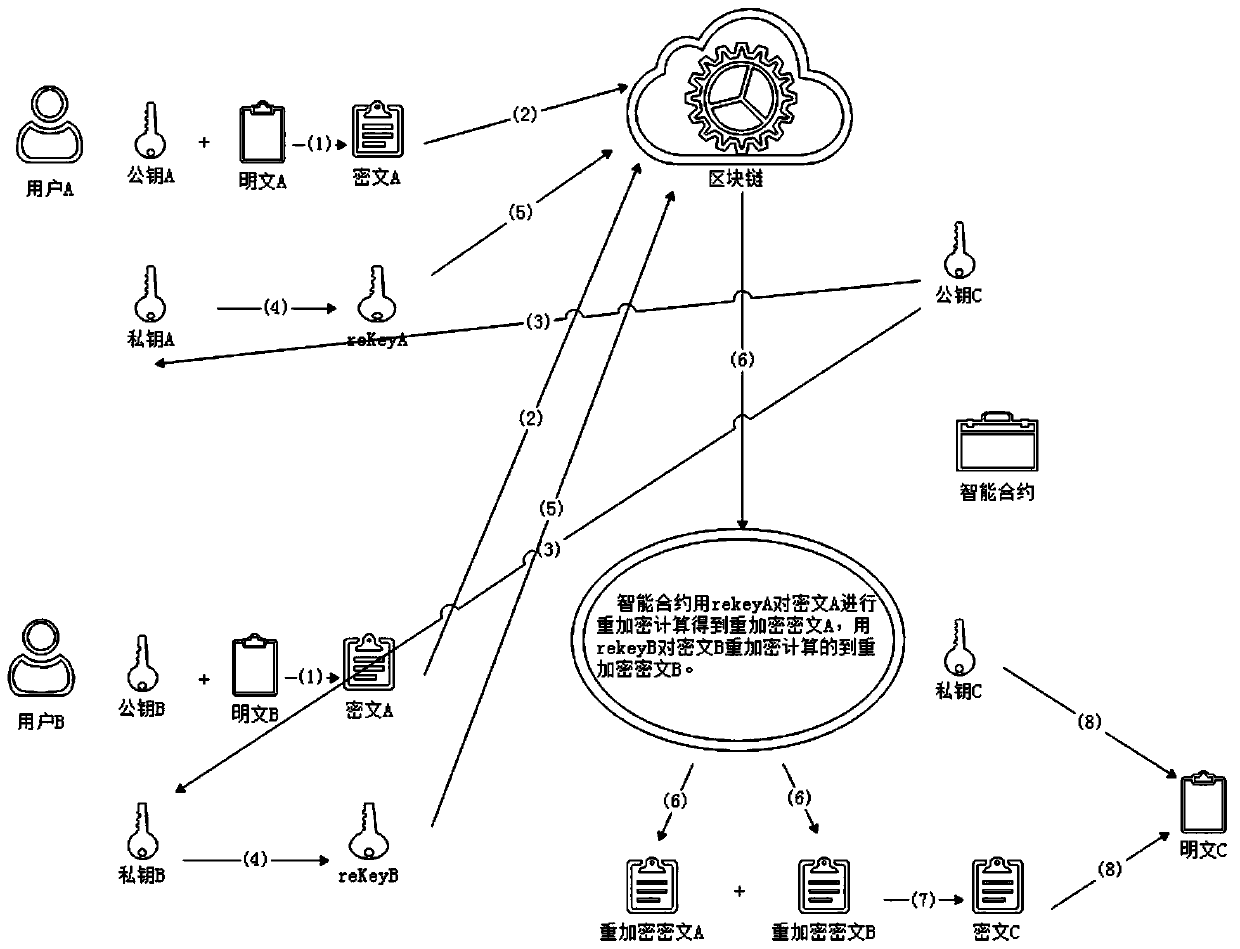
ActiveCN111385301AReduce interaction processImprove operational efficiencyCommunication with homomorphic encryptionPlaintextCiphertext
The invention discloses a blockchain data sharing encryption and decryption method, equipment and a storage medium, which belong to the technical field of blockchains. The blockchain data sharing encryption and decryption method comprises the steps of: creating a homomorphic proxy re-encryption key pair private key A and public key A1 by at least one first party; encrypting a plaintext a to obtaina ciphertext a1; uploading the ciphertext a1 to a blockchain; creating a homomorphic proxy re-encryption key pair private key B and public key B1 by at least one second party; encrypting a plaintextb to obtain a ciphertext b1; uploading the ciphertext b1 to the blockchain; acquiring a public key C1 from an intelligent contract of the blockchain by the first party and the second party; performingproxy re-encryption on the public key C1 and the private key A to obtain a secret key rekey A by the first party, and uploading the secret key rekey A to the blockchain; and performing proxy re-encryption on the public key C1 and the private key B to obtain a secret key rekey B by the second party, and uploading the secret key rekey B to the blockchain, wherein the intelligent contract creates akey pair private C and public key C1 through homomorphic encryption. The blockchain data sharing encryption and decryption method solves the homomorphic problem of conducting safety calculation basedon private data of the blockchain, reduces the interaction process between users and the blockchain and between the users, moves some operations under the chain to the chain, and makes calculation more credible.
Owner:湖南智慧政务区块链科技有限公司
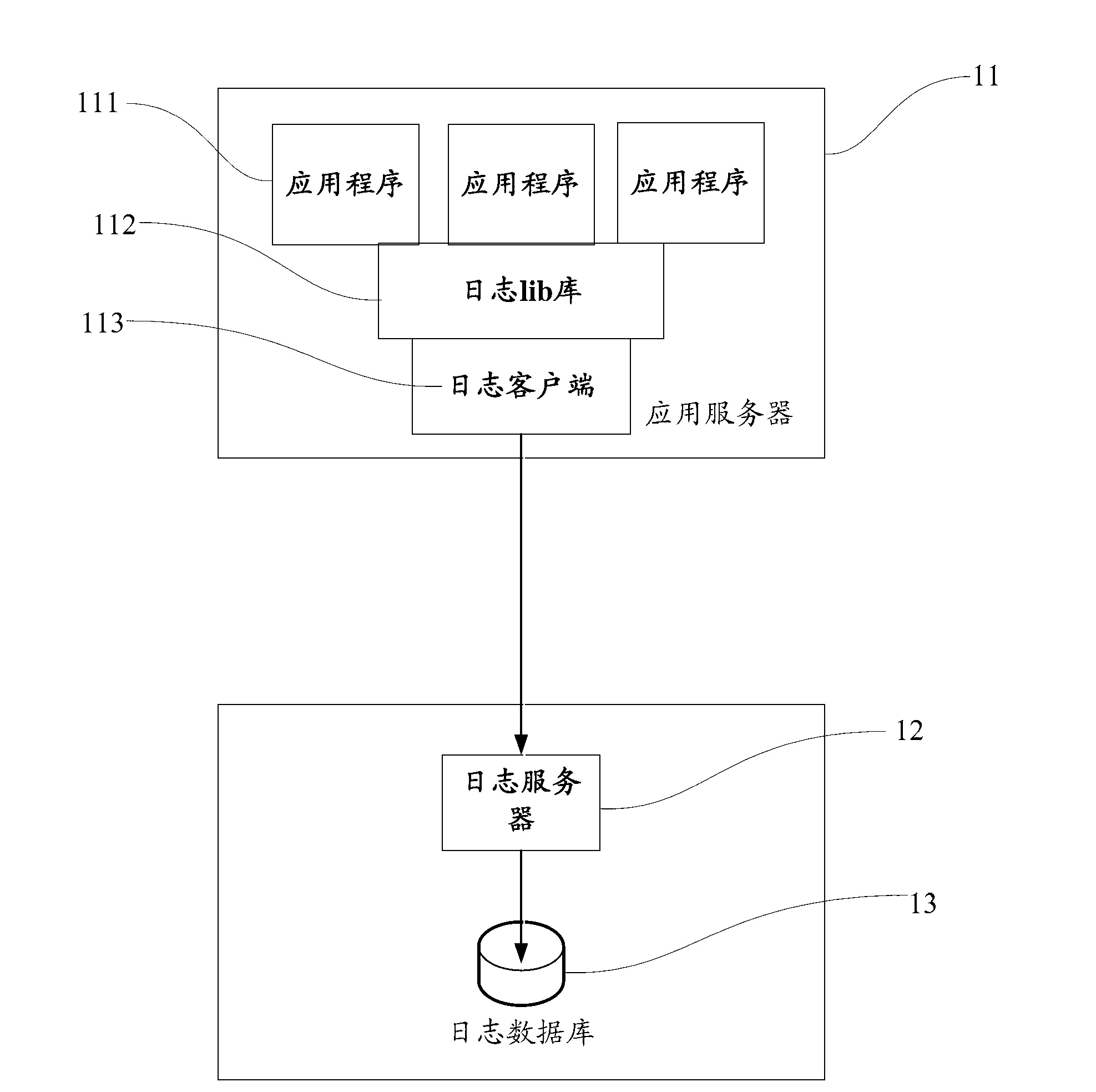
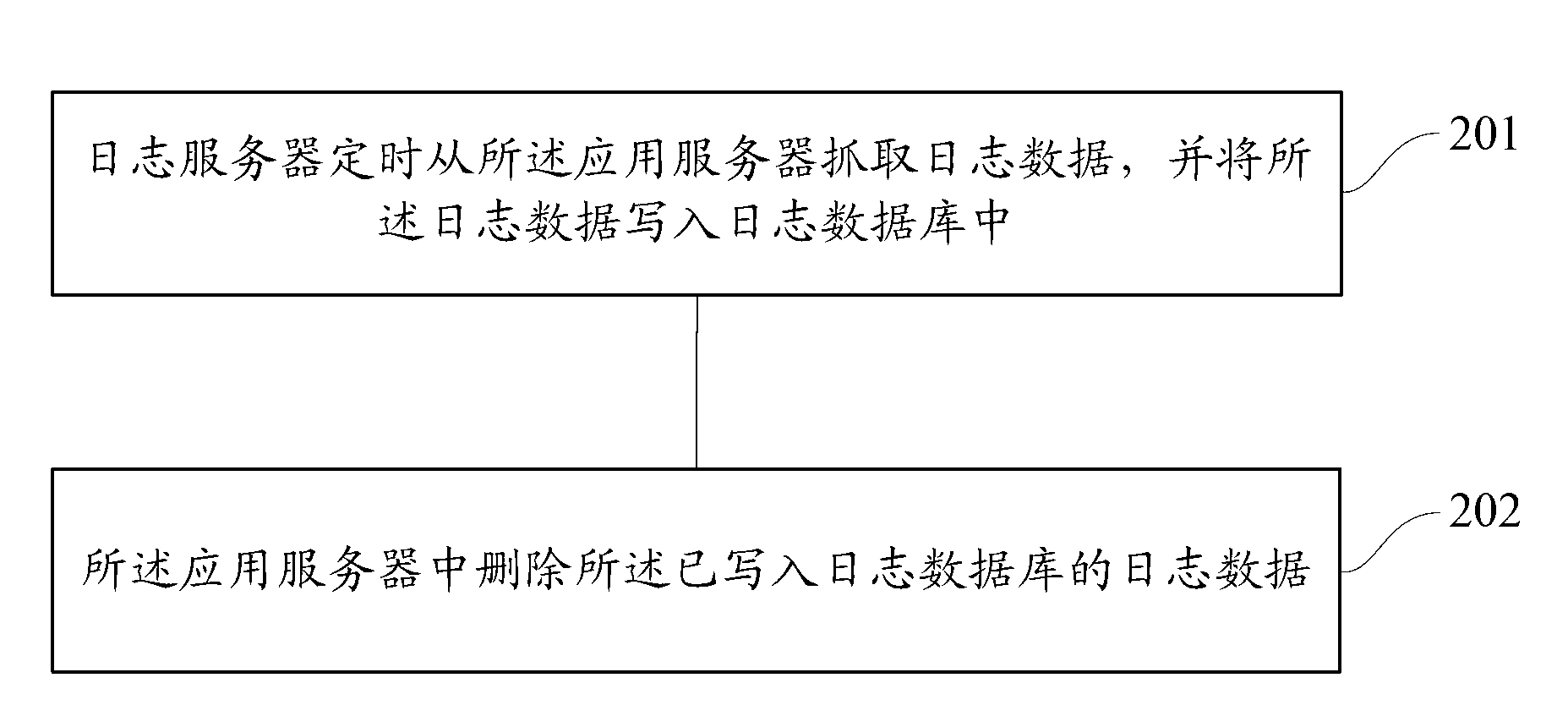
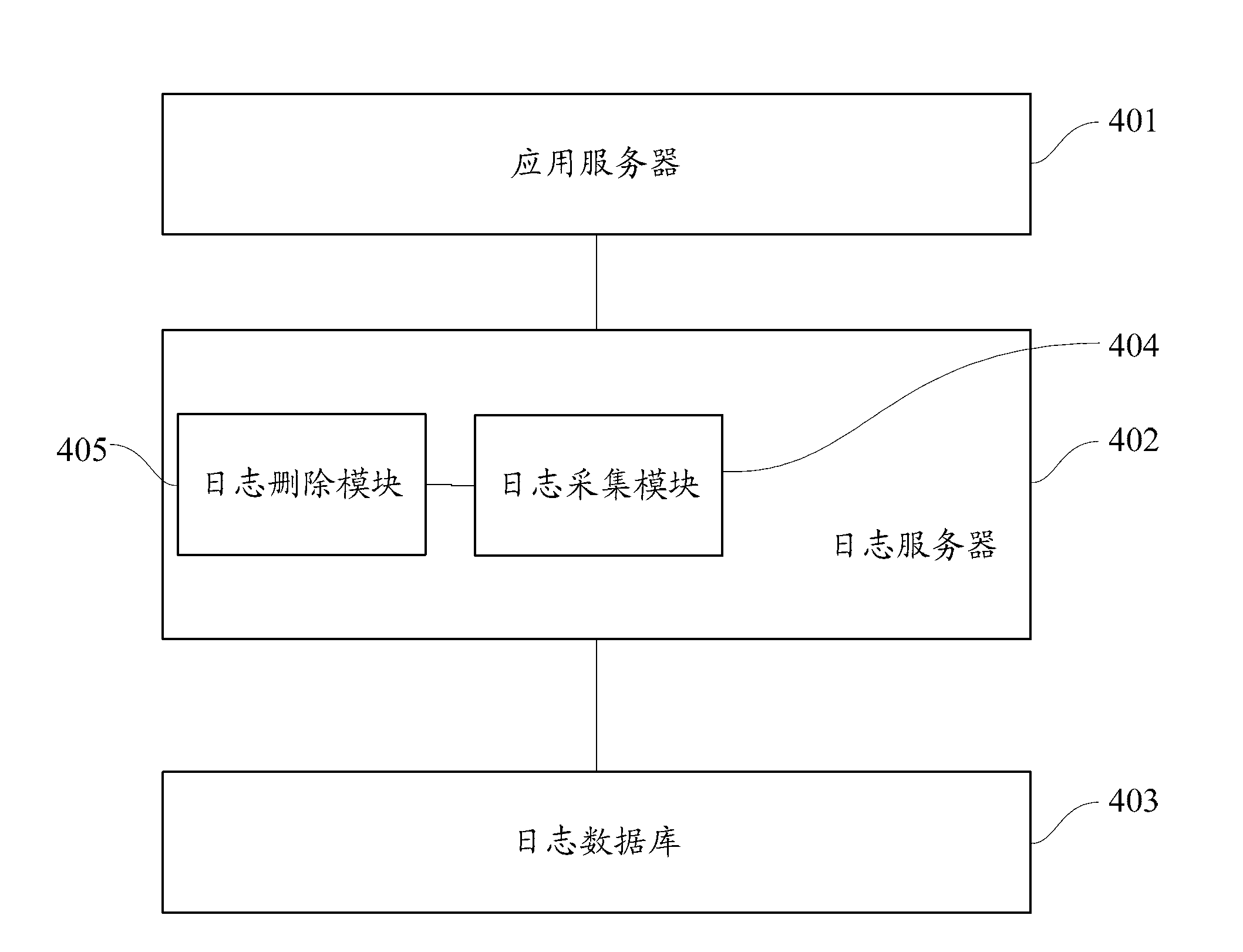
Method and system of log data transmission
ActiveCN102937931ASolve the lossReduce the risk of lossHardware monitoringSpecial data processing applicationsApplication serverData transmission
The invention discloses a method and a system of log data transmission. The log data transmission relates to a process of transmitting log data generated by an application server to a log server, the log server comprises a log database, or, the log server is connected with the log database. The method includes that the log server captures the log data from the application server at regular time and writes the log data into the log database, and the log data which is written into the log database is deleted from the application server. The method and the system of the log data transmission can reduce risks of data loss and storage redundancy.
Owner:BEIJING QIHOO TECH CO LTD +1
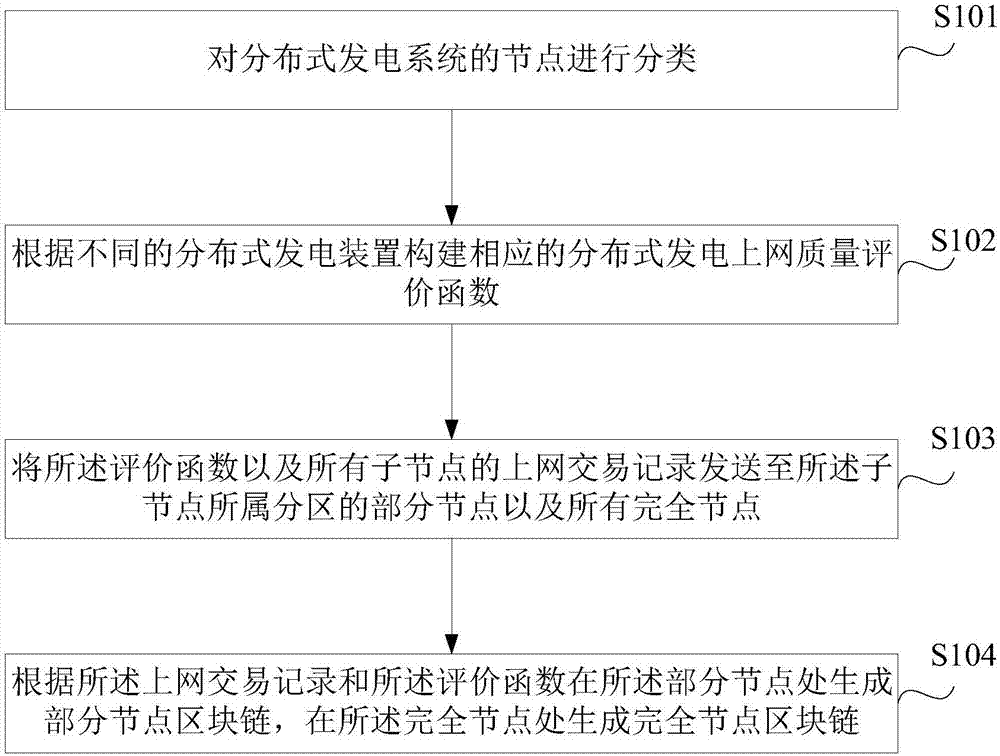
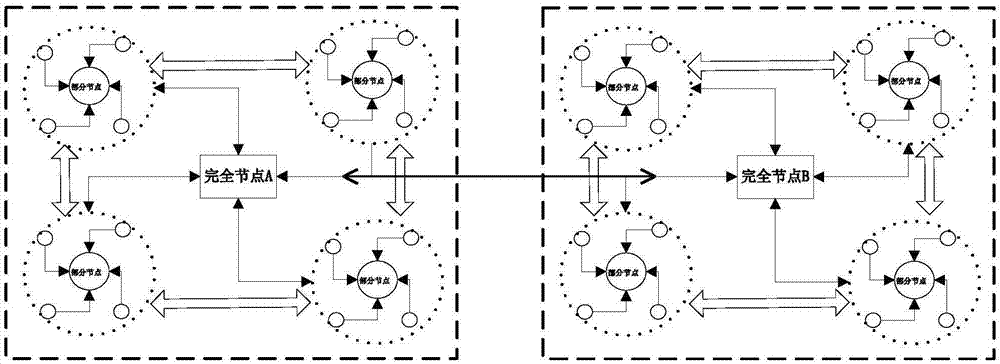
Block chain technology-based distributed power generation quality evaluation method and apparatus
ActiveCN107301501AReduce the risk of lossGuaranteed to be tamper-proofResourcesSpecial data processing applicationsData informationData loss
The invention discloses a block chain technology-based distributed power generation quality evaluation method and apparatus. The method comprises the steps of firstly classifying nodes of a distributed power generation system into sub-nodes, partial nodes and complete nodes; and secondly, sending online transaction records and evaluation functions of the sub-nodes to the subordinate partial nodes and all the complete nodes, and performing storage in a block chain mode. Compared with the prior art, the method has the advantages that the distributed power generation evaluation functions and transaction information data of the nodes are sent to the partial nodes and all the complete nodes of a region where the nodes are located; random hashing is performed at the partial nodes and the complete nodes; the distributed power generation related data information is added with time stamps; and block packaging is performed to generate a block chain of the complete nodes and a block chain of the partial nodes. Therefore, the data loss risk can be lowered, the data is ensured not to be tampered, and the cost of a database framework is properly reduced.
Owner:BEIJING HUITONG JINCAI INFORMATION TECH +3
Method for preventing loss of data and movable data memory
InactiveCN101694778AAvoid lossReduce the risk of lossMemory loss protectionDigital storageParallel computingData memory
The invention discloses a method for preventing loss of data and a movable data memory. The movable data memory is a data memory and is characterized by including a first data memory and a second data memory, wherein the first data memory and the second data memory are connected into a combined data memory through a mutually matched data interface; the first data memory is simultaneously providedwith a USB male port and a USB female port; the second data memory is provided with the USB male port; and the USB male port of the second data memory is inserted in the USB female port of the first data memory to consequently form a combined data memory. The method and the data memory effectively solve the problem that the easy loss of U disks causes the loss of data and are characterized by simple structure, convenient use and the like.
Owner:卢林发
Method for location of following target and following device
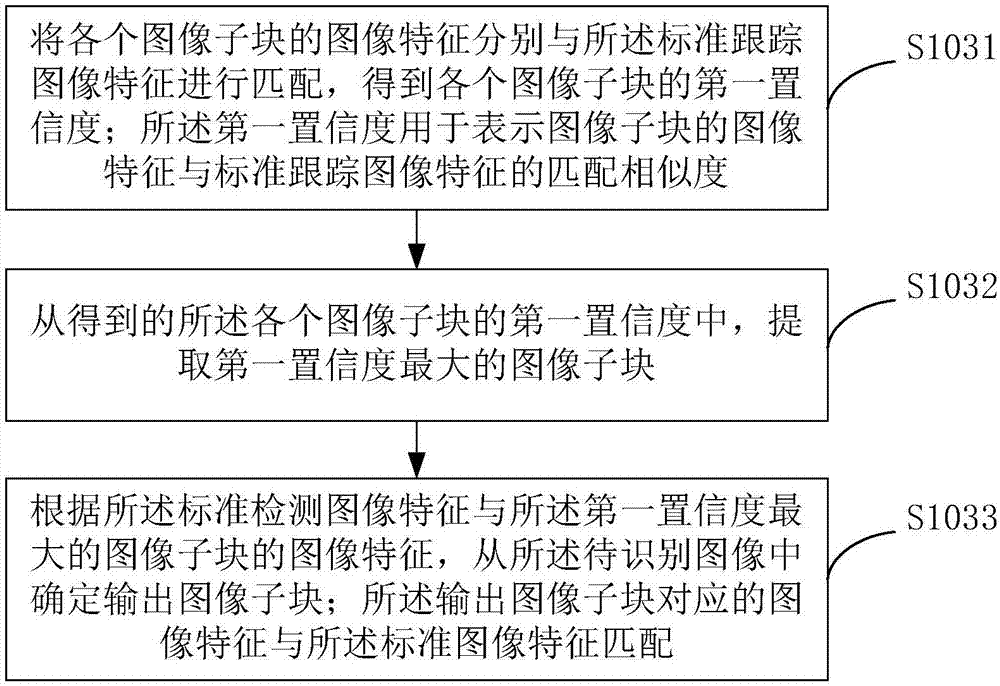
ActiveCN107292907AReduce the risk of lossPrecise positioningImage analysisTarget-seeking controlImaging FeatureVisual perception
The present invention provides a method for location of following target and a following device. An image to be identified is obtained based on vision, image subblocks corresponding to image areas at each position in the image to be identified is subjected to image feature matching through standard image features, an image subblock having image features matching the standard image features is determined, and the relative position information of a following device and a following target is determined according to the position information of the image subblock in the image to be identified. A mode of the relative position information of the location following device of an image to be identified and the following target based on the vision is not easy to be interfered by a surrounding environment, the location precision is high, the following device is ensured to accurately track the following target, the following device does not need real-time observation and maintenance by users, and therefore the problems are avoided that user operation is complex, the time consumption is long and the like, the utilization efficiency of user tripping time is improved, and the risk of loss of a luggage box is greatly reduced.
Owner:LINGDONG TECH BEIJING CO LTD
Data security device
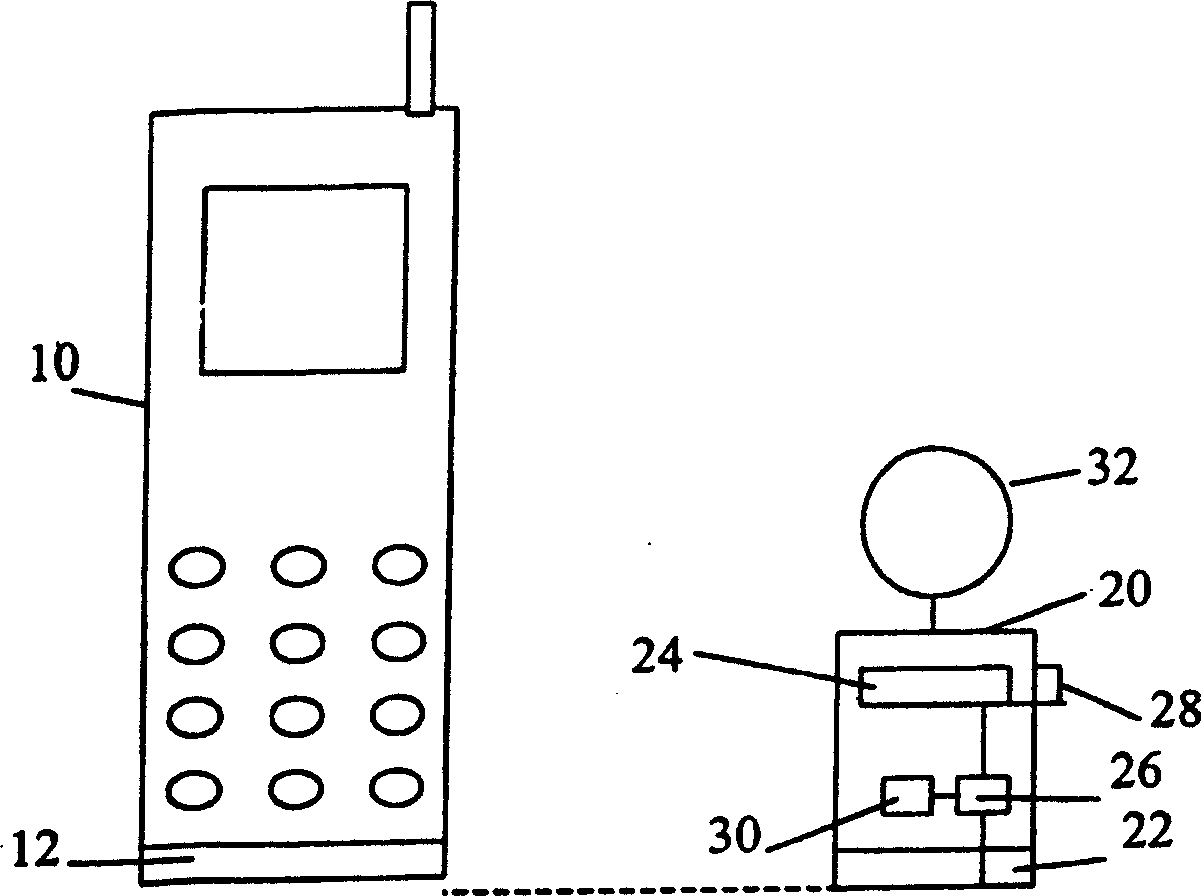
InactiveCN1547863AAvoid the need for manual backupsReduce the risk of lossUnauthorised/fraudulent call preventionInternal/peripheral component protectionTime segmentCommunication link
A method of safeguarding against loss of data stored in a portable data storage device or loss of the data storage device itself is described. A user-carried backup device having memory and a wireless communication link for communicating with the portable data storage device is provided. The backup device and the portable data storage device communicate periodically or quasi-continuously over the wireless communication link and may backup data entered into the portable data storage device and check for removal of the portable data storage device. An alarm is activated to alert a user to loss of the portable data storage device if the portable data storage device is out of range of communication for a predetermined period.
Owner:DATA TRANSFER & COMM
Online packing machine
ActiveCN105857699AEasy to passReduce the risk of lossPackaging automatic controlPackaging fruits/vegetablesAutomatic controlBreakage rate
The invention discloses an online packing machine which comprises a content conveying device and a filling box conveying device, wherein a content inlet and a content outlet are formed in the content conveying device; the content outlet is located above the filling box conveying device; the content conveying device is arranged as a power conveying device; the filling box conveying device is arranged as the power conveying device with an adjustable inclined angle; a running control device is arranged on the filling box conveying device; the content conveying device and the filling box conveying device are both arranged as conveyer belt conveying devices; a transition device is arranged at the content outlet; the running control device is arranged as a control switch or an automatic control device; the control switch or the automatic control device is used for controlling the filling box conveying device to work or stop. According to the online packing machine, the labor intensity can be relieved, the number of operators can be reduced, the production efficiency is high, the content breakage rate is low, and the online packing machine is suitable for different sizes of fruits and vegetables.
Owner:MAF RODA MACHINERY YANTAI CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com