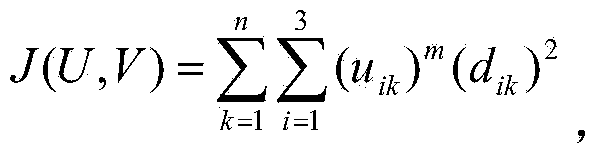Patents
Literature
862 results about "Behavior monitoring" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
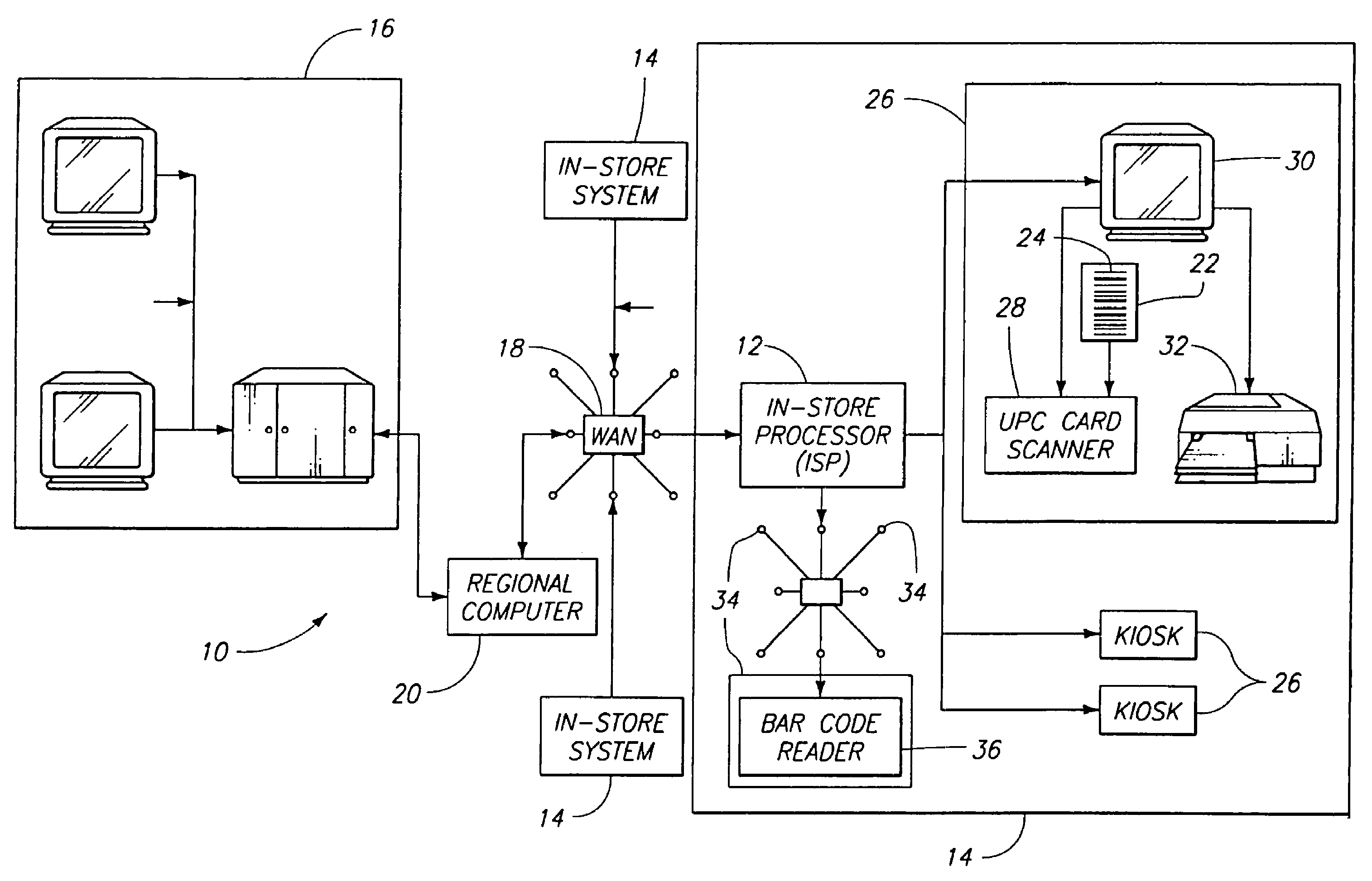
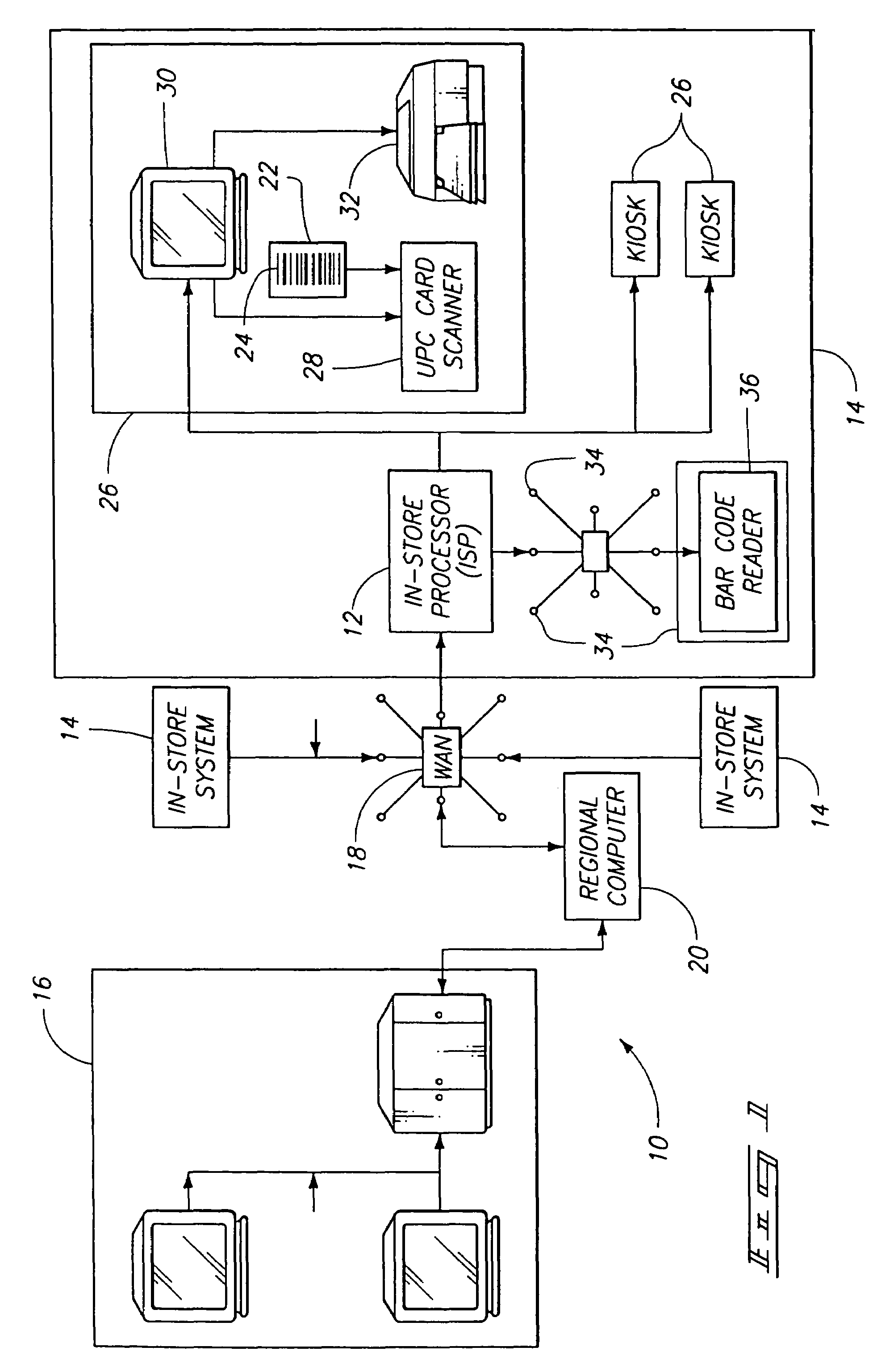
Targeted marketing and purchase behavior monitoring system
A system for presenting customized special offers to customers, the special offers including targeted offers to a customer selected from a plurality of customers, and for collecting purchasing behavior information concerning the customers, the system comprising a computer including a database containing customer account information providing information specific to a particular customer account; the at computer also including a database containing special offers including a targeted offer which is to be made to selected customer accounts on the basis of targeted offer targeting parameters; a plurality of customer cards, each customer card having machine readable card information indicating at least identification of the card with a particular customer account; a customer interface in communication with the computer to transfer data therebetween; the customer interface having a card reader for reading machine readable card information from the customer card; the computer including means for generating a customized customer offer list available to that particular customer account which includes the special offer; an offer communicator for communicating the customer offer list to the customer for which it is generated; a check-out at which the customer presents purchased item information indicating items being purchased by the customer; the check-out including a card reader for reading the customer card; the computer including means for sending information from the customized customer offer list to the check-out; the computer further including means for collecting customer purchase information which is indicative of items being purchased by the customer via the check-out; the computer still further including means for editing the customer account information to reflect items purchased by the customer.
Owner:CATALINA MARKETING CORP
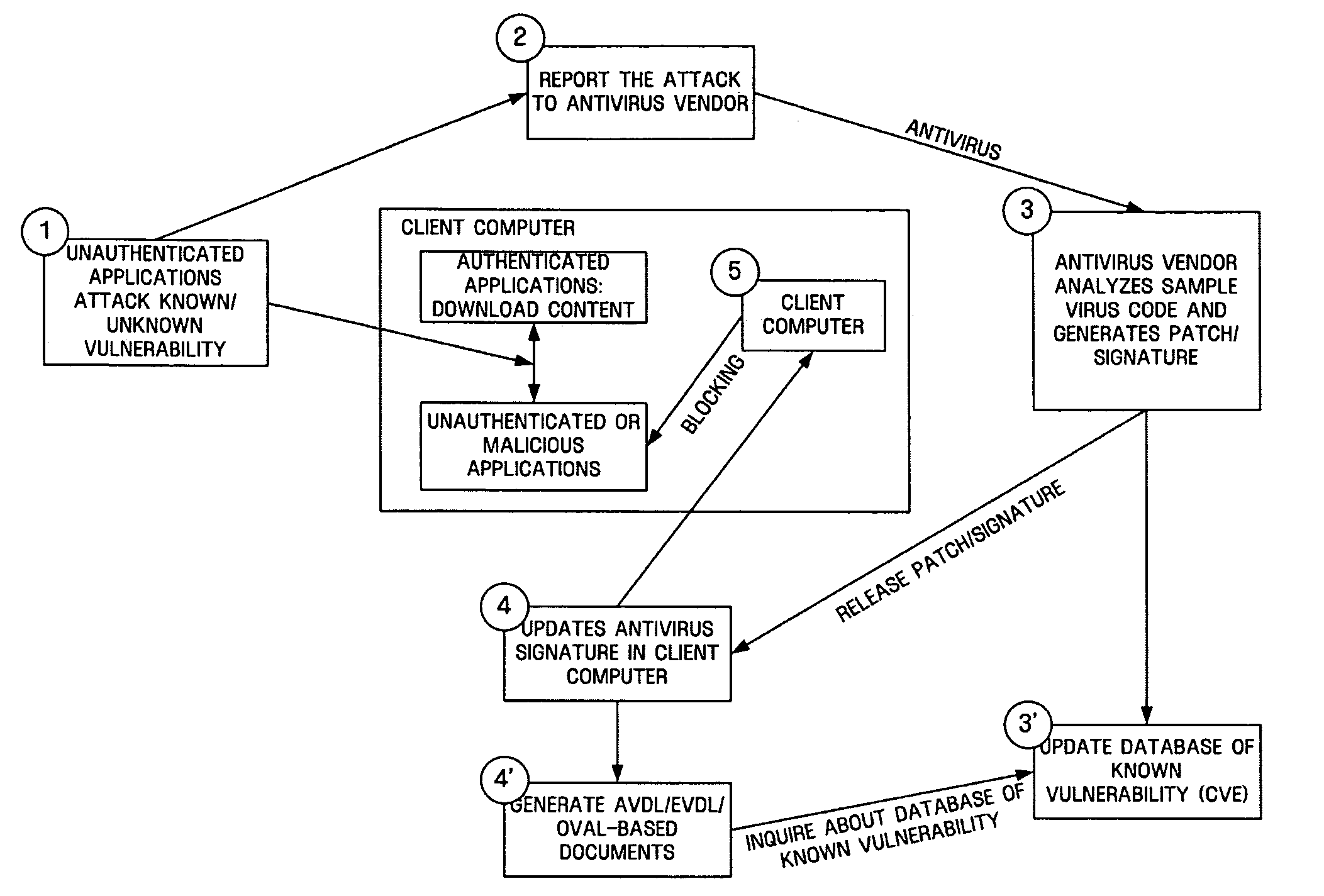
Driver Behavior Monitoring
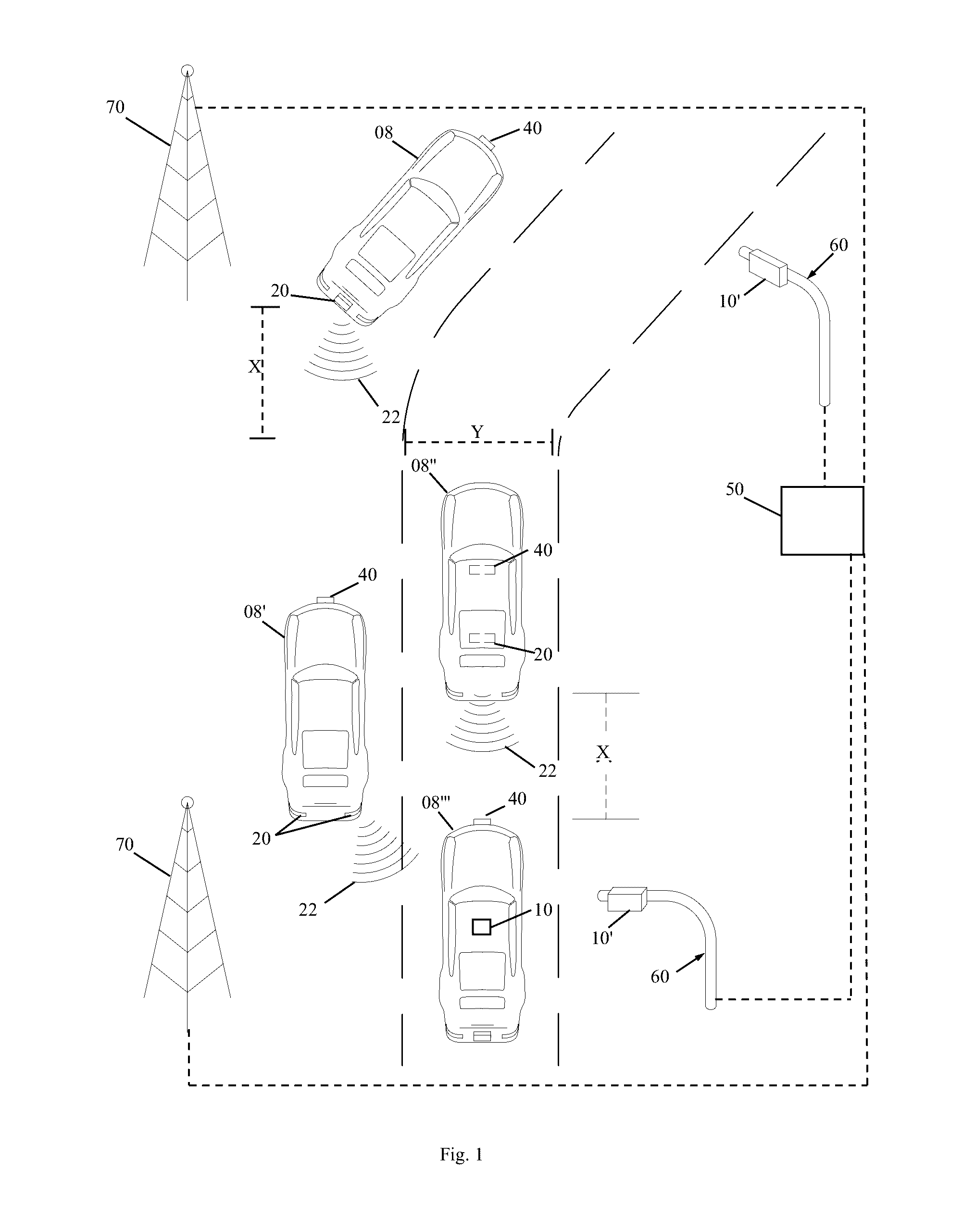
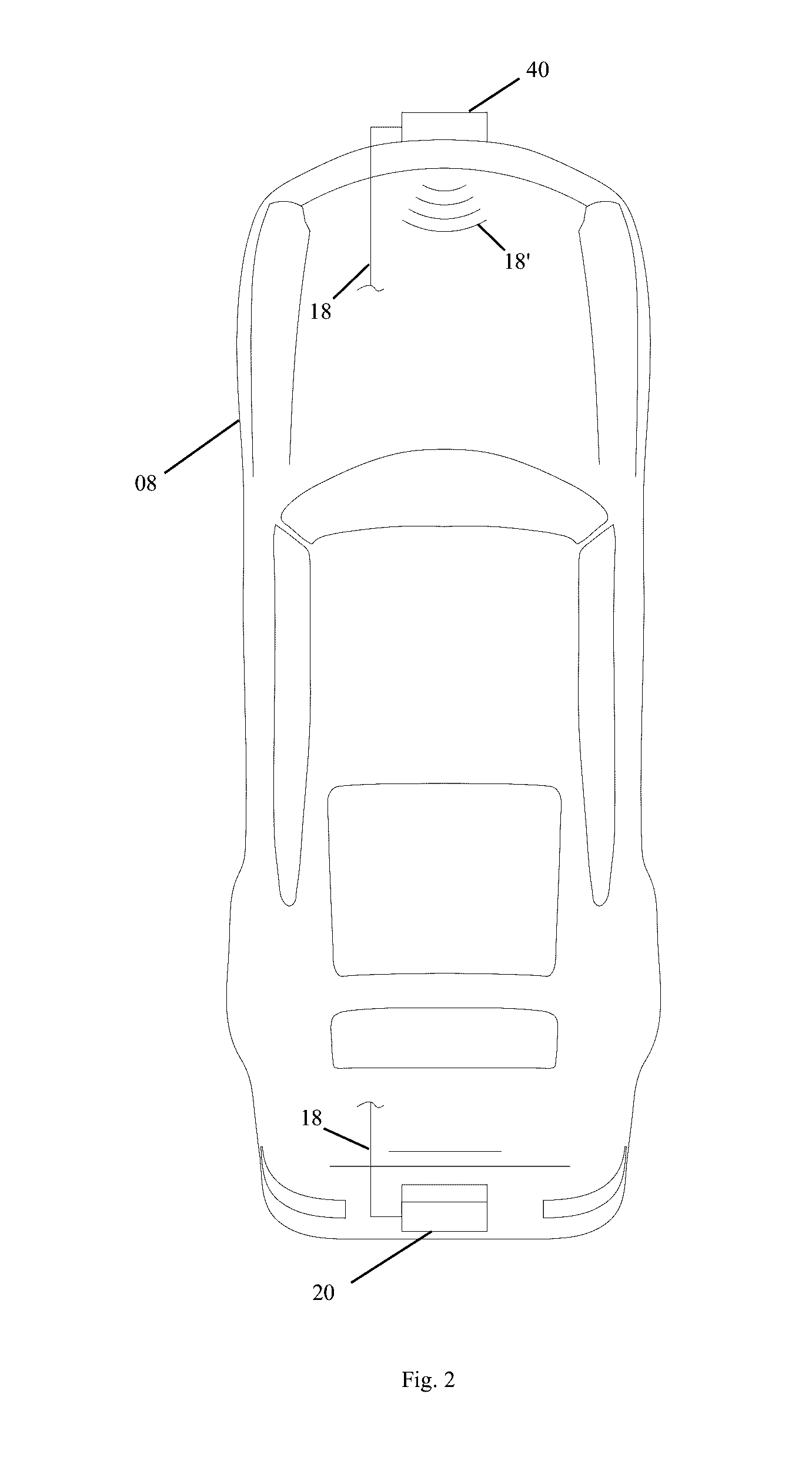
ActiveUS20170024938A1Instruments for road network navigationRegistering/indicating working of vehiclesDriver/operatorEvent data
Exemplary embodiments of the present invention are directed to a system for monitoring, recording, and analyzing driver activity. An exemplary system comprises a sensor module configured to receive data from one or more sensors that measure acceleration or deceleration associated with a vehicle. A stop detection module is configured to receive the sensor module data, process the sensor module data, and determine an abrupt acceleration or deceleration event. A location module is configured to retrieve the location of the vehicle simultaneous with an abrupt acceleration or deceleration event. The system stores the location of the abrupt acceleration or deceleration event in an event record in an event database.
Owner:LINDSAY JOHN
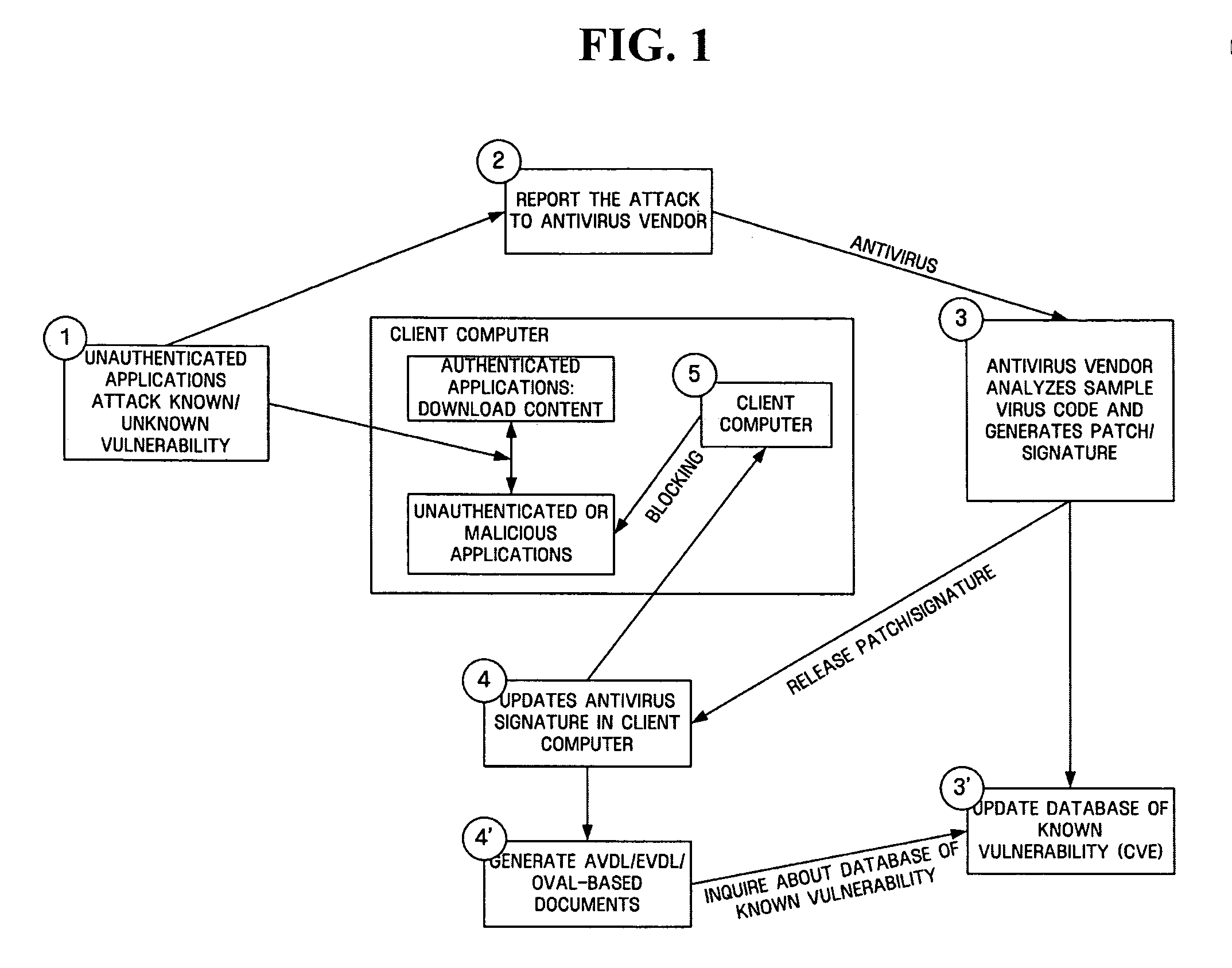
System and method for automatically analyzing, detecting and classifying malicious program behavior
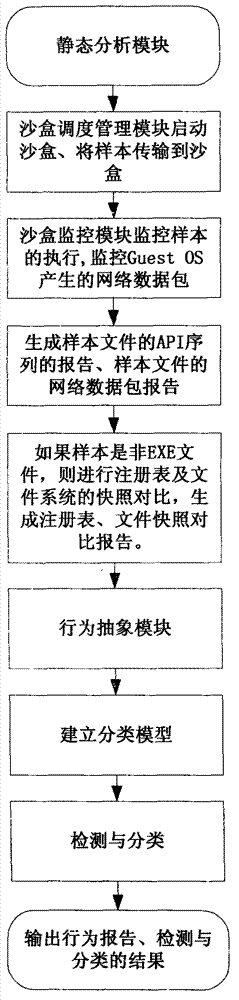
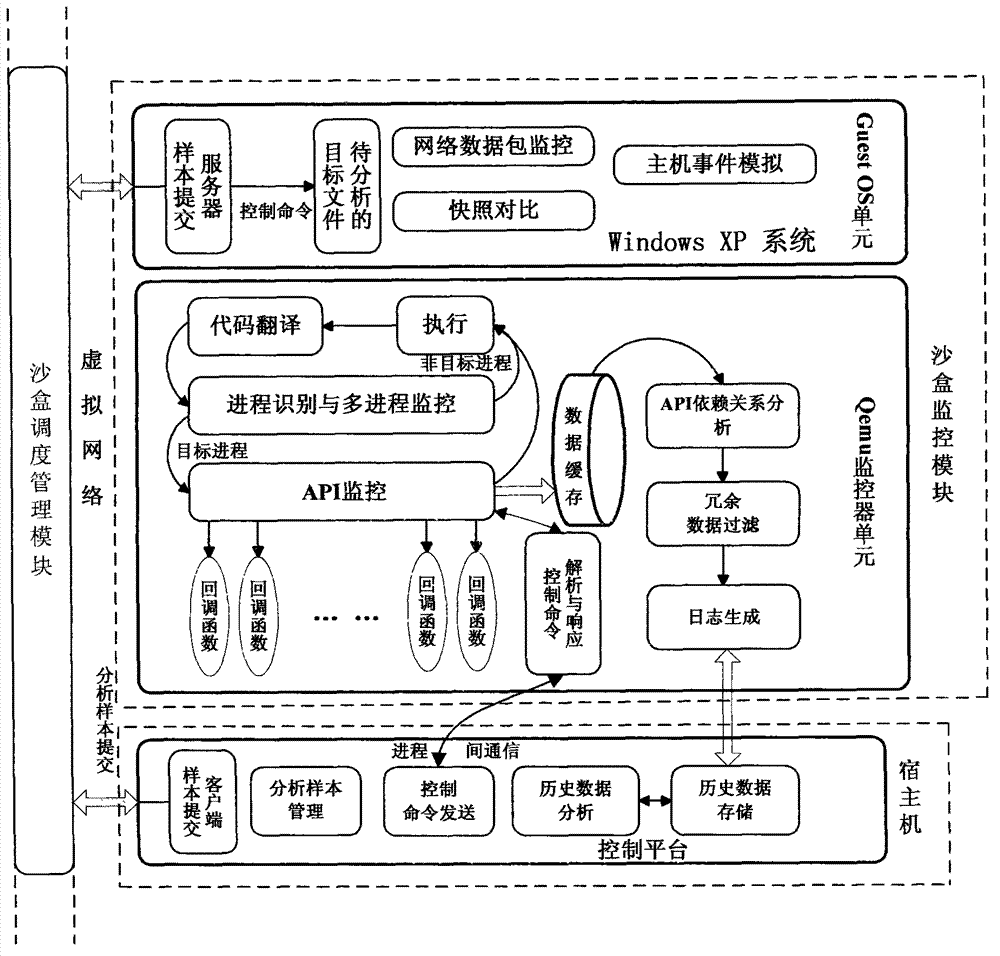
ActiveCN102930210ACause damageOvercome shortcomings such as inability to perform adequatelyPlatform integrity maintainanceSpecial data processing applicationsDomain nameNetwork behavior
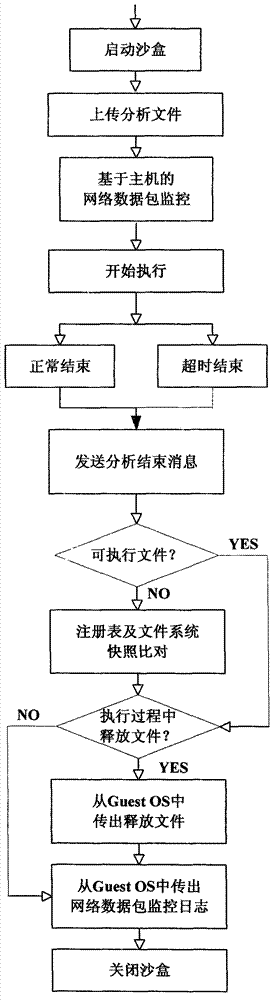
The invention discloses a system and a method for automatically analyzing, detecting and classifying a malicious program behavior. The system comprises a static analysis module, a sandbox dispatching management module, a sandbox monitoring module, a behavior abstraction module and a detection and classification module. Compared with the prior art, the system has the advantages that 1, the system is based on a behavior monitoring technology in an instruction set simulation environment; and 2, a virtual Internet is established in a sandbox through means of environment configuration, server program modification and the like, and a common network service is simulated, so that operations such as domain name server (DNS) resolution, http access, file download, Email login and mailing initiated by a malicious program can be successfully executed, the malicious program is inveigled to generate a malicious network behavior, the network behaviors are prevented from damaging a host machine and a real network, and the defects that the malicious program network behavior cannot be fully expressed during dynamic behavior analysis of a malicious program and the like are overcome.
Owner:JIANGSU JINLING TECH GRP CORP
ATM secure authentication and pre-alarming method based on face recognition
ActiveCN101266704AEnsure safetyGuaranteed privacyCharacter and pattern recognitionAlarmsComputer networkAcquisition apparatus
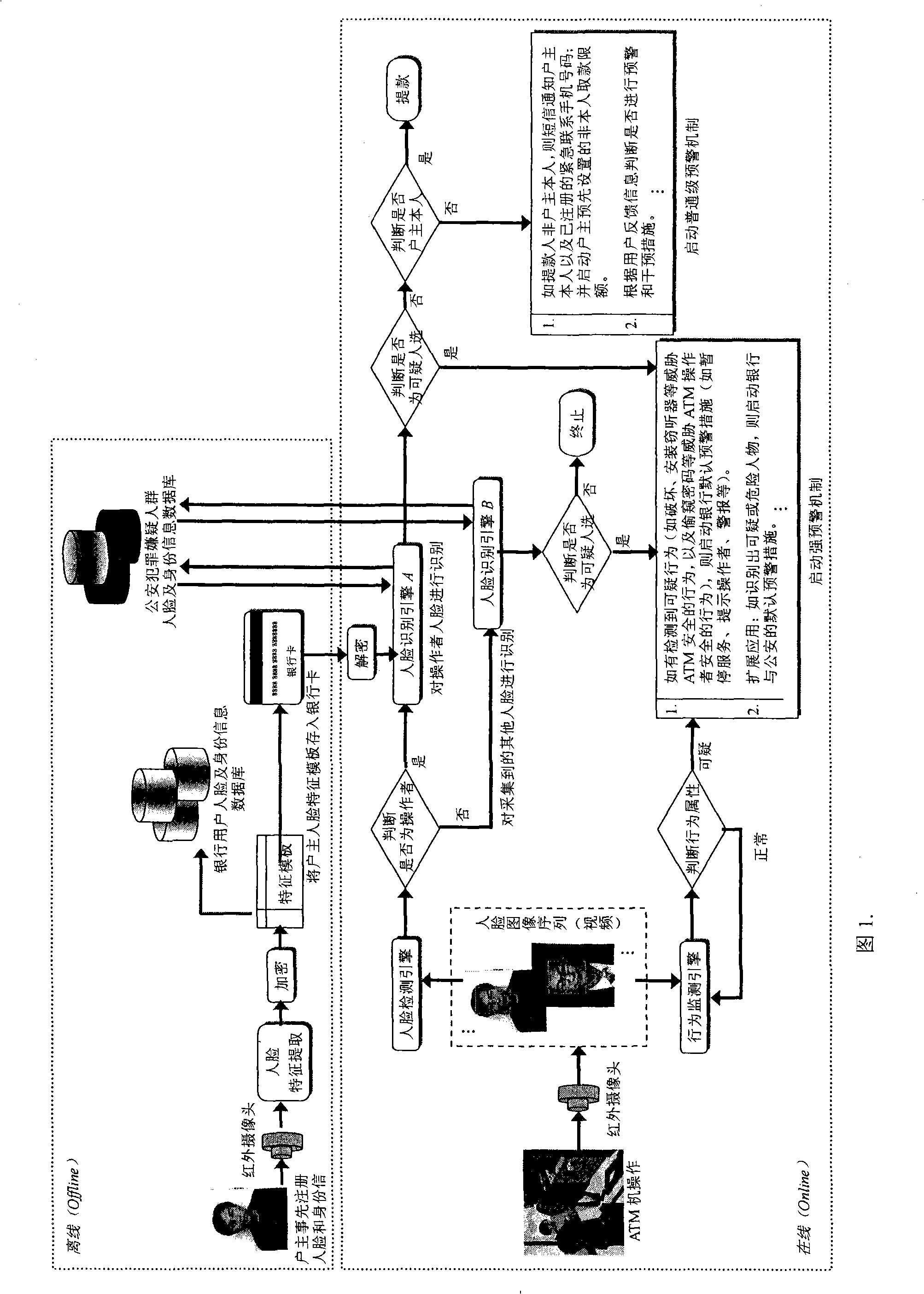
The invention discloses an ATM security certificate and a pre-warning method based on face recognition. The invention introduces face recognition and video detection into the applications of ATM and bank card business for the first time, which can obviously improve the security of ATM financial system, effectively reduce and overawe various ATM fraud and criminal activities. The complete system operation process in the method of the invention is: firstly, registering the face information of a holder at a service window which arranges an infrared face acquisition equipment or with the registration by the users themselves on ATM in bank, and saving the encrypted face information to a bank database and a bank card. Then, determining whether the ATM operator to be recognized is the holder of the bank card or not through verifying the user's identity by a face recognition engine; determining and recognizing whether existing behaviors that threaten ATM and the users though a behavior monitoring engine; and determining whether to trigger corresponding pre-warning mechanism or not according to the recognition result. The invention can extend to the applications of bank book business, public security monitoring and pursuing escaped criminals, etc.
Owner:哈尔滨维科智能系统有限公司
Classroom behavior monitoring system and method based on face and voice recognition
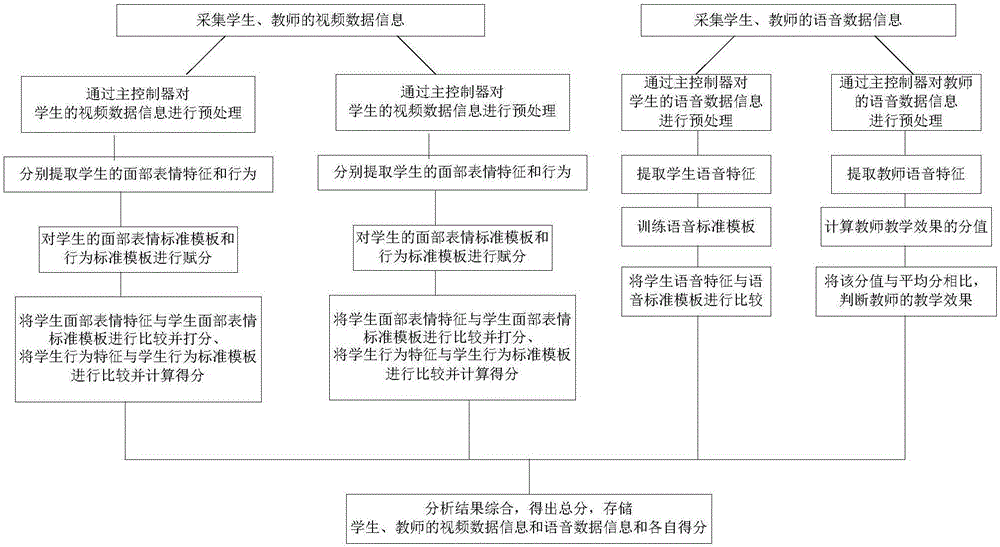
ActiveCN106851216AImprove developmentImprove learning effectSpeech analysisClosed circuit television systemsFacial expressionSpeech sound
Owner:SHANDONG NORMAL UNIV
Method and system for tracking and behavioral monitoring of multiple objects moving through multiple fields-of-view
InactiveUS20050265582A1Image enhancementTelevision system detailsComputer graphics (images)Radiology
A computerized method of video analysis that includes receiving several series of video frames generated by a number of image sensors. Each image sensor has a field-of-view. The image sensors monitor a portion of a monitored environment. The computerized method also includes concurrently tracking, independent of calibration, multiple objects within the monitored environment as the objects move between fields-of-view, at least two of which overlap, and multiple objects within one field-of-view. The tracking is based on the plurality of received series of video frames
Owner:INTELLIVID
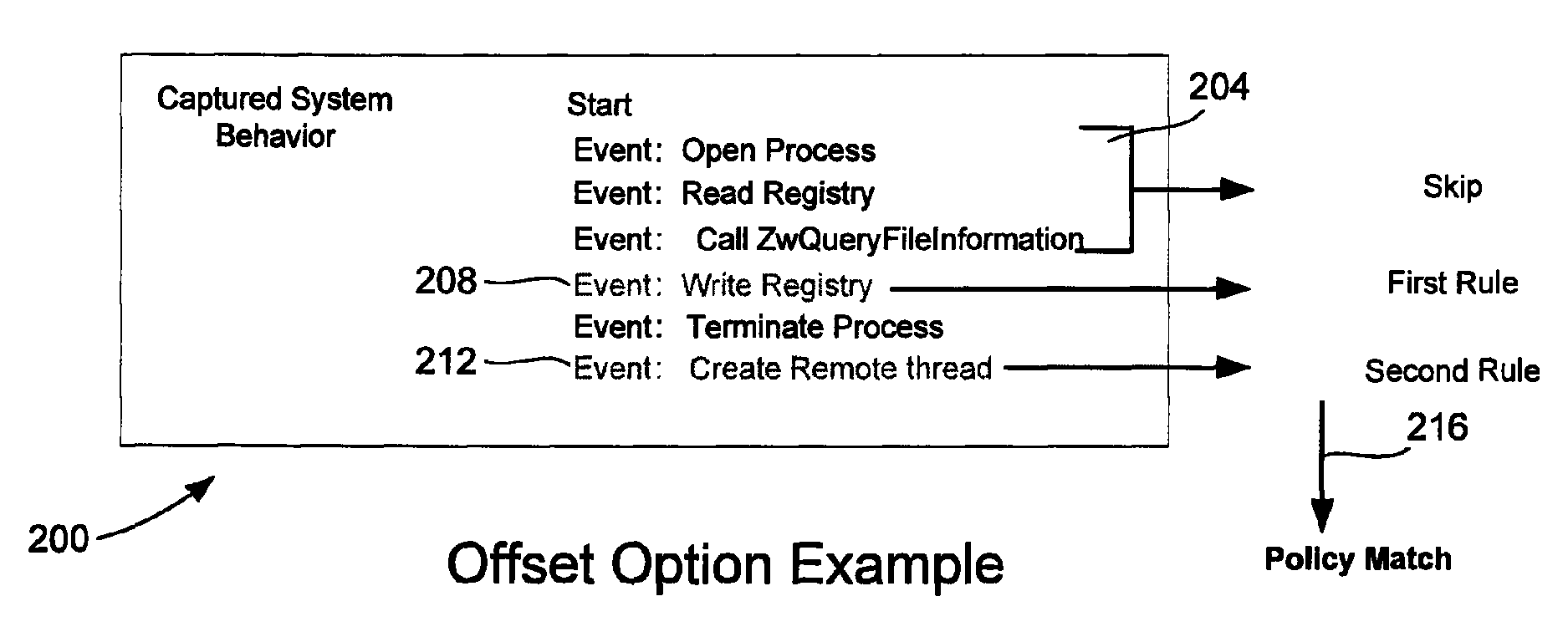
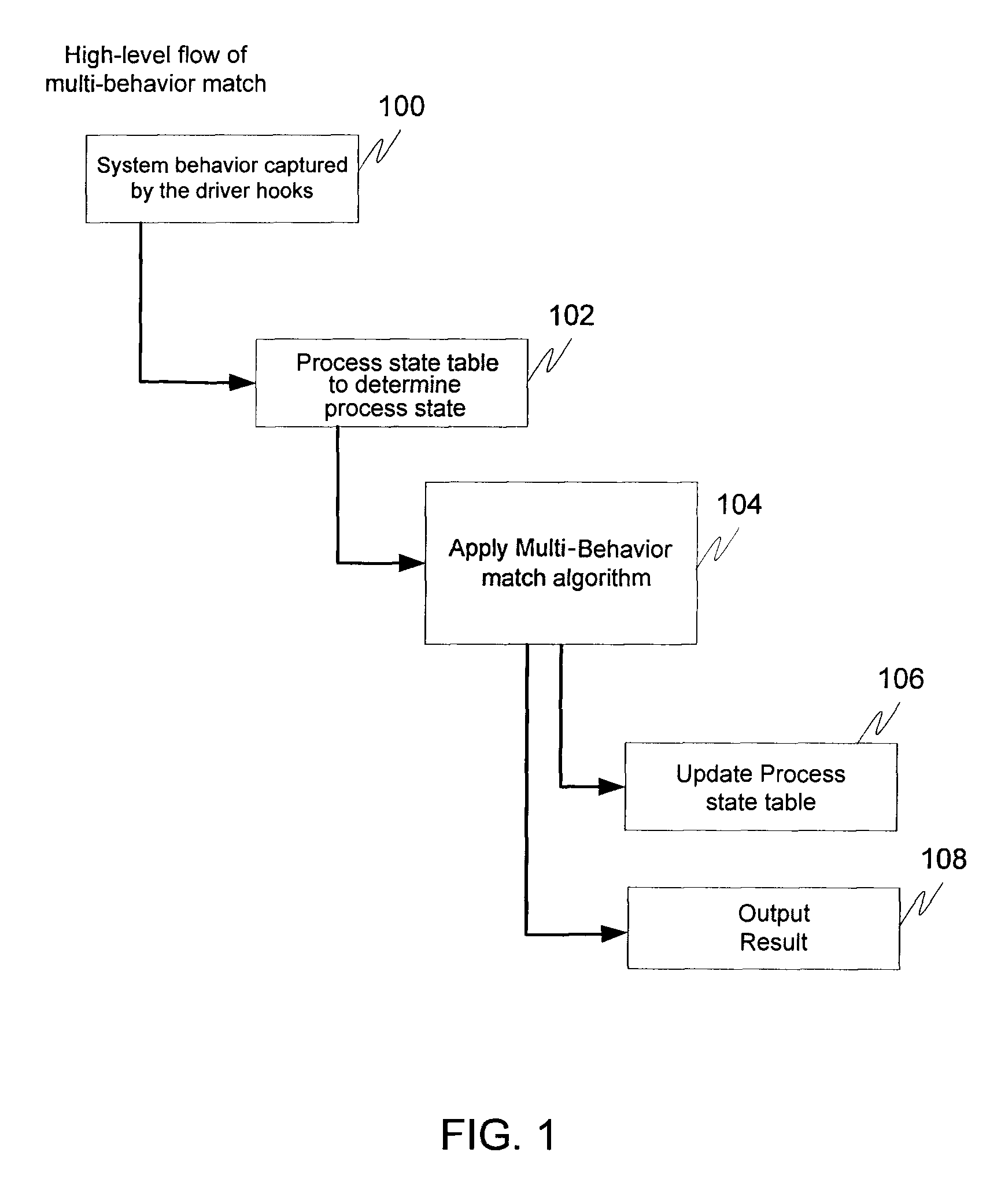
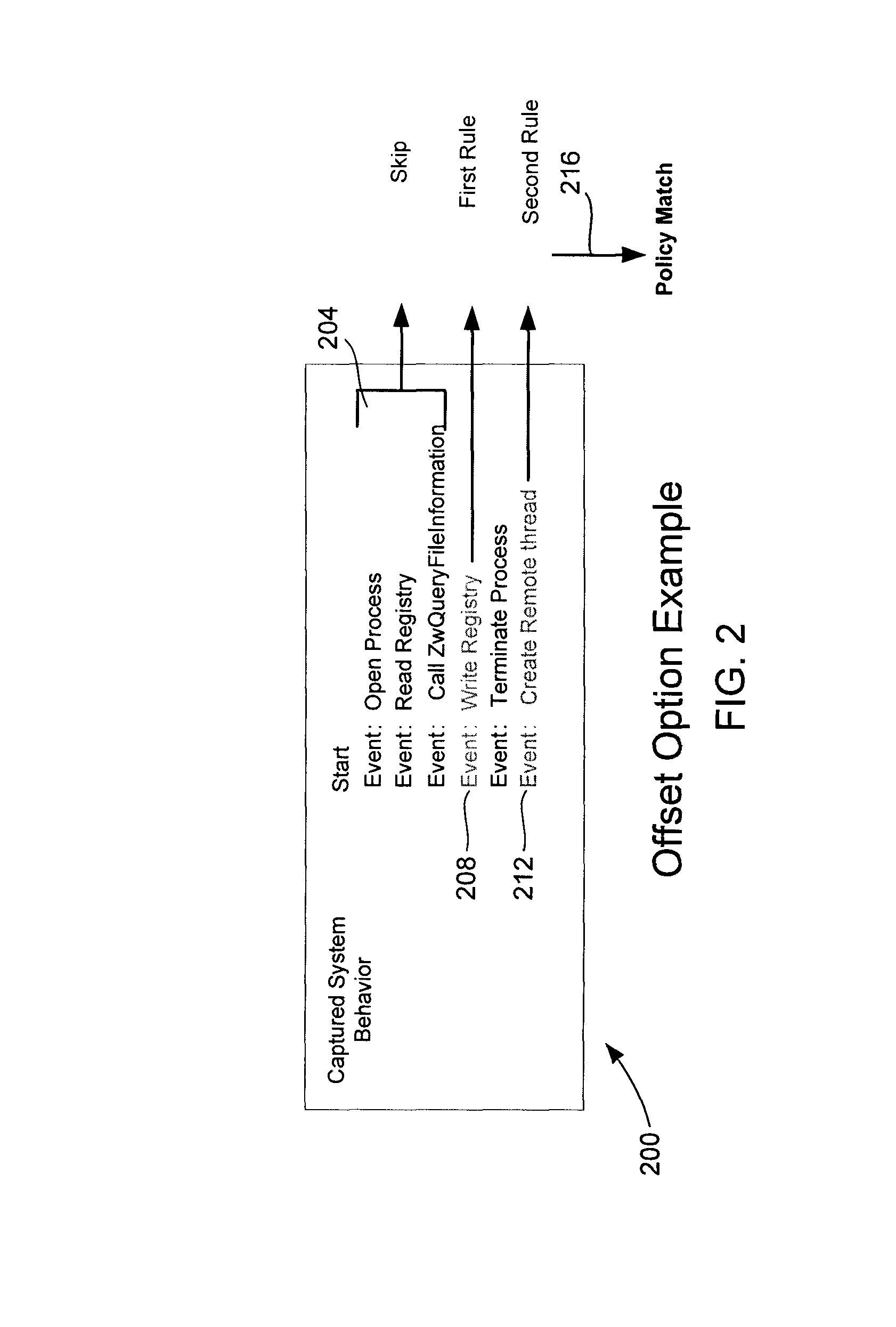
Multi-behavior policy matching for malware detection
ActiveUS8370931B1Avoid problemsPreventing inefficient searchMemory loss protectionDigital data processing detailsComputerized systemMalware
Multi-behavior matching in a computer system is performed in order to identify suspicious sequences of activities. System behavior is captured using driver hooks. A behavior monitoring system determines the process to which the system behavior belongs by processing a table. This includes using the process ID and thread ID of the system behavior as lookups into the table. A multi-behavior matching algorithm is applied to determine if there is any matching suspicious behavior by matching sets of rules (a policy) to system events caused by a particular process. A state machine is used to keep track of matching policies. Options to the rules and policies (such as “offset,”“depth,”“distance,”“within,”“ordered” and “occurrence / interval”) are used to refine when a rule or policy is allowed to produce a positive match, reducing false positives.
Owner:TREND MICRO INC
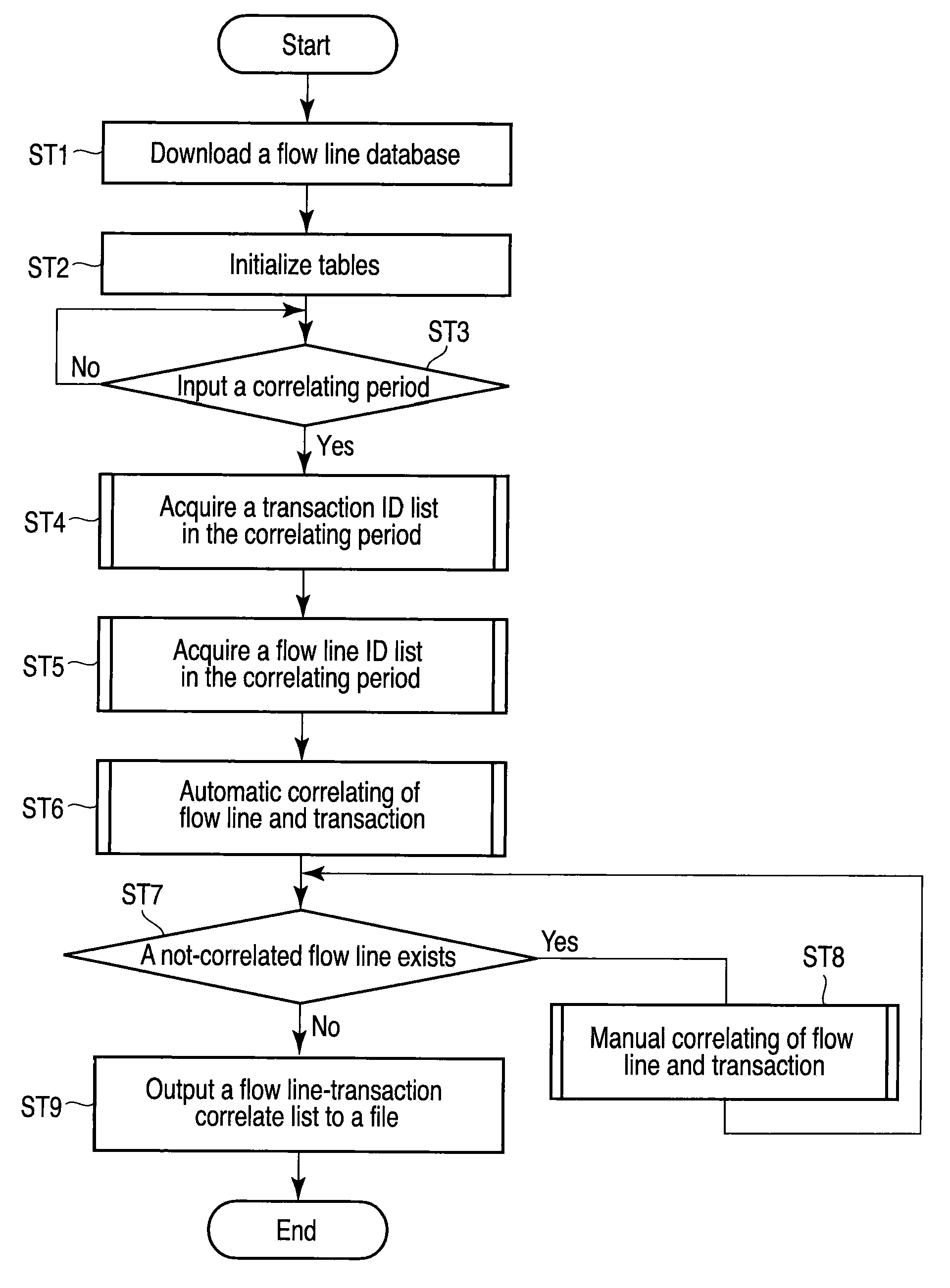
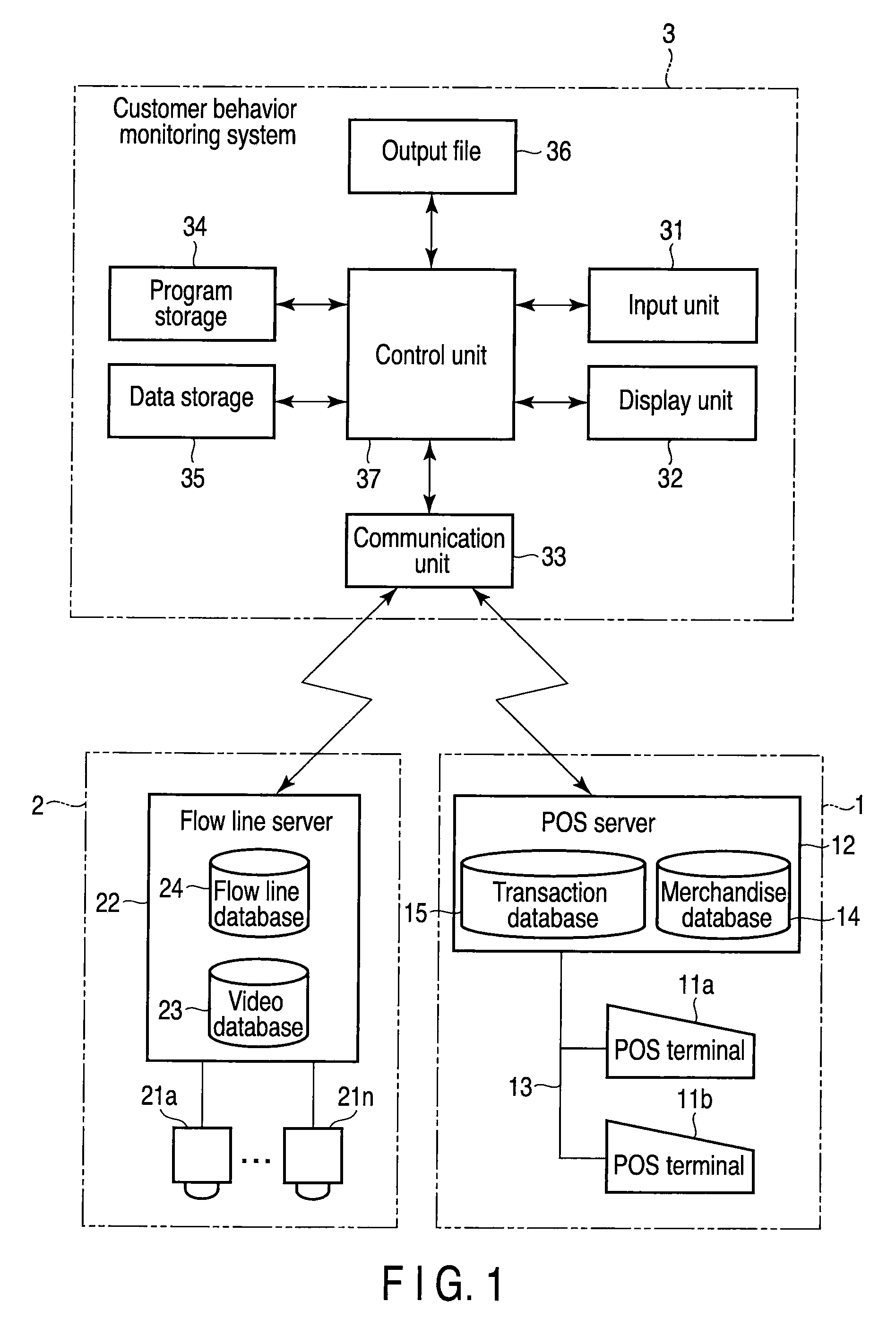
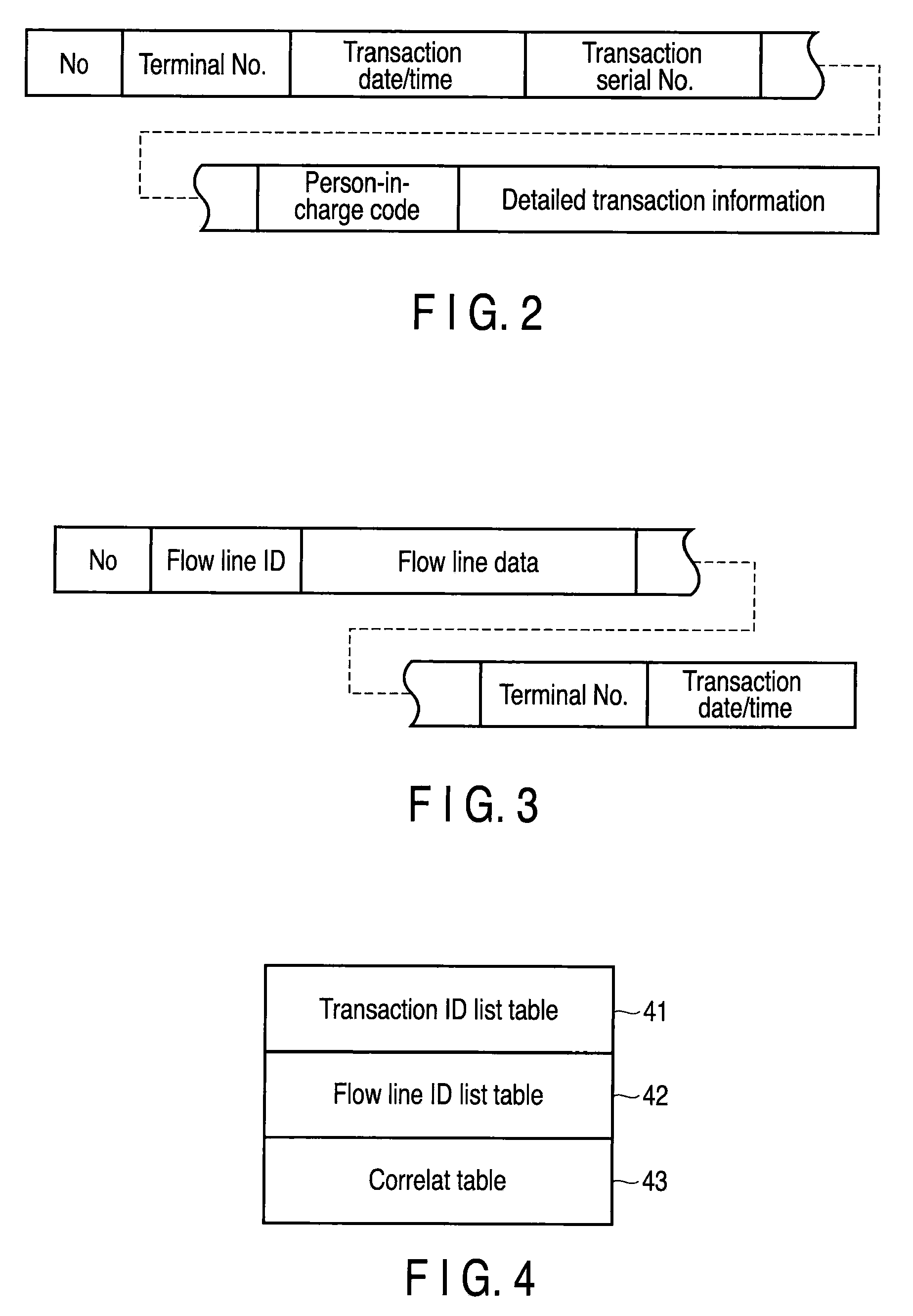
Customer behavior monitoring system, method, and program
A flow line storage stores flow line data of each customer obtained by tracking a behavior of each customer in a store, by adding time data on an estimated time of payment made by each customer. A transaction data storage stores transaction data for each customer including records of items purchased by each customer, by adding time data on an estimated time of payment made by each customer. A combination unit determines a combination in which a difference between time data is minimum, for each piece of flow line data stored in the flow line storage and each piece of transaction data stored in the transaction data storage. A correlating unit correlates the flow line data and transaction data combined by the combination unit.
Owner:TOSHIBA TEC KK
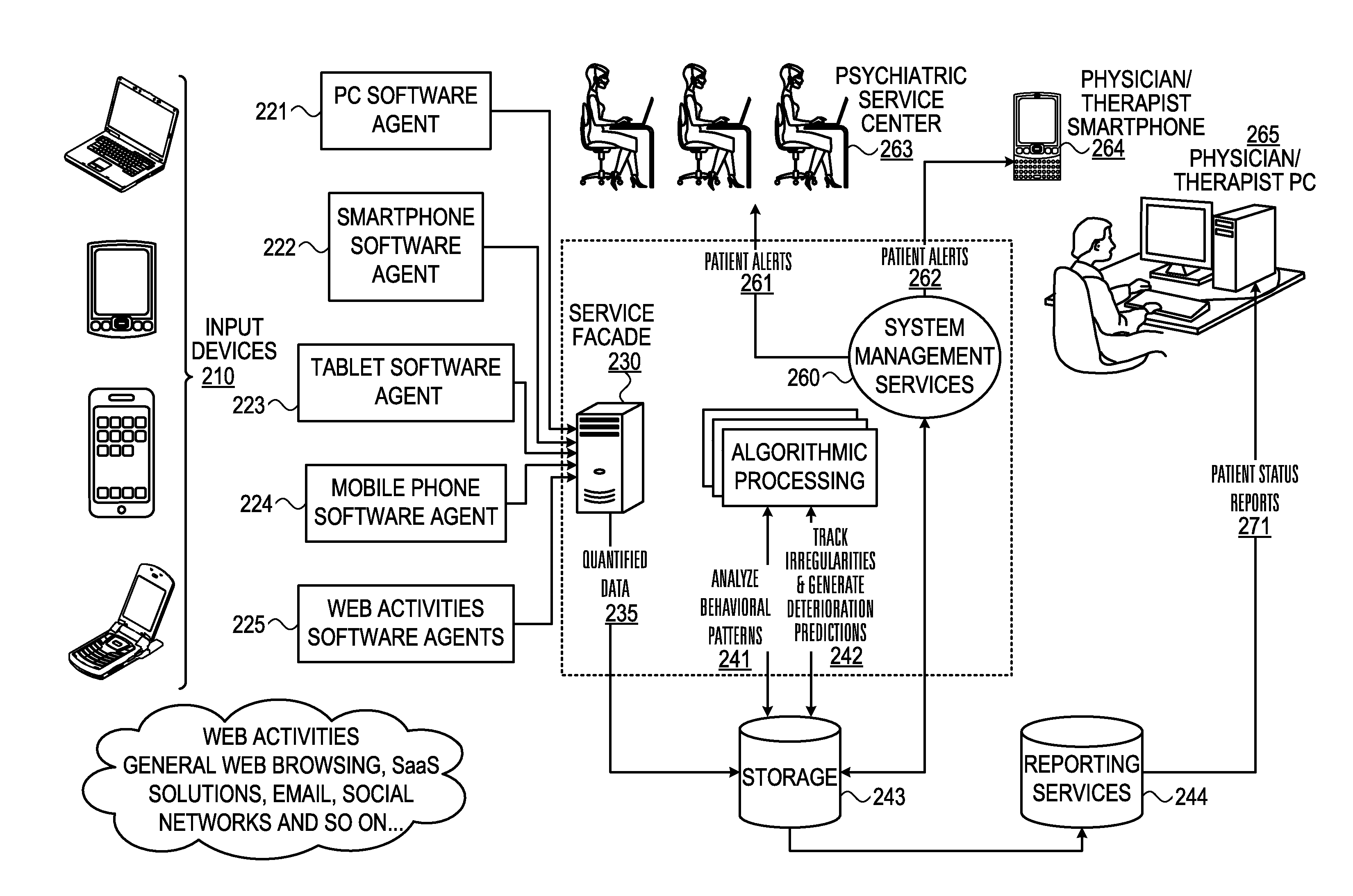
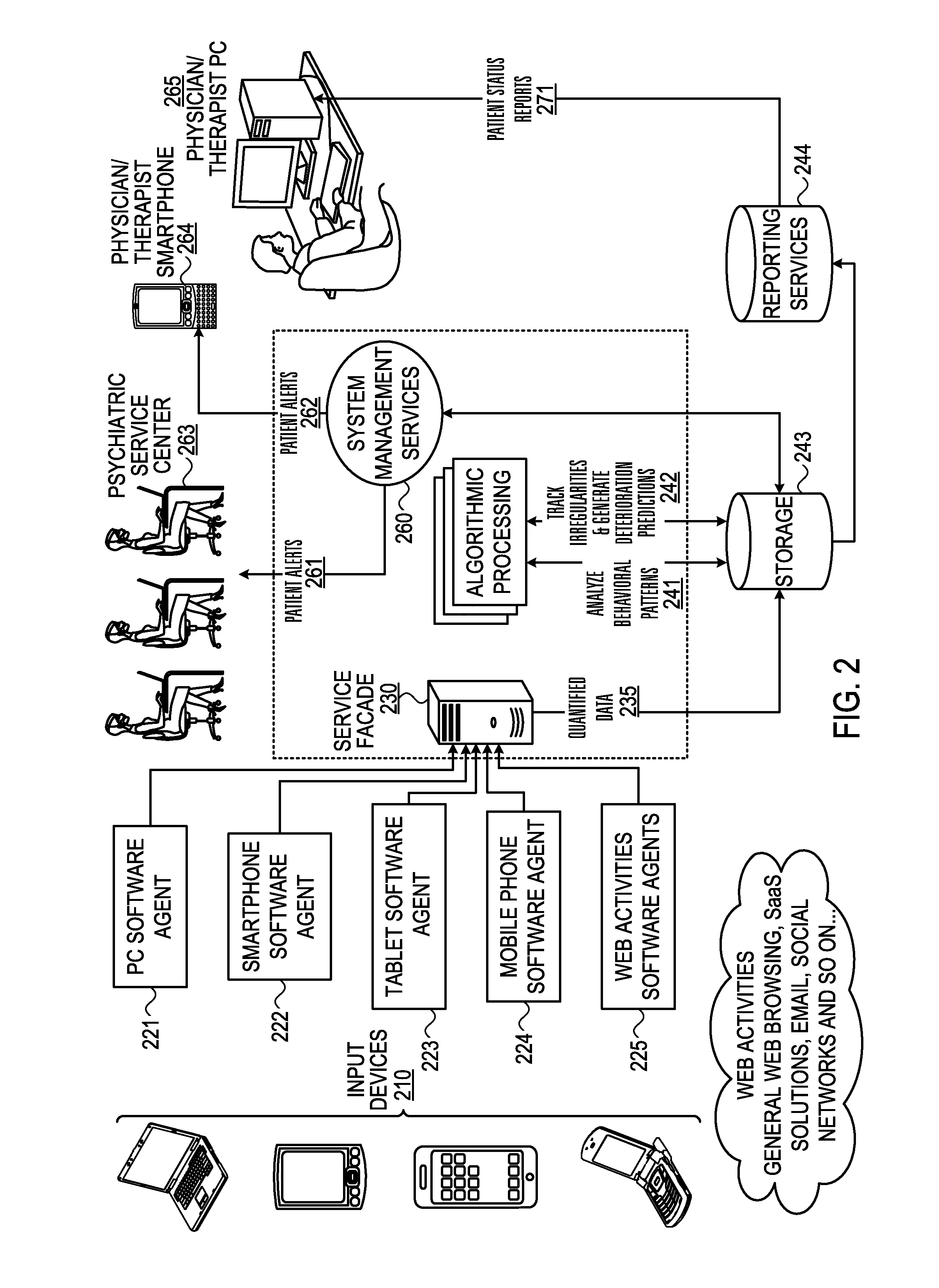
Mental health digital behavior monitoring support system and method
InactiveUS20130297536A1Digital computer detailsMedical automated diagnosisTablet computerSupporting system
A system and method for monitoring a user's mental health tor and collect data concerning. The user's use of electronic devices is tracked, such as usage of his mobile phone, tablet and his web activity. The invention “learns” each patient's unique behavioral patterns to be used as a “base line” representing the steady state (chronic phase) of the patient. The algorithmic processing unit detects any irregularities in a patient's behavioral patterns and produces a deterioration prediction. If it is determined that a threshold is exceeded, an alert is sent to a health professional.
Owner:ALMOSNI BERNIE +1
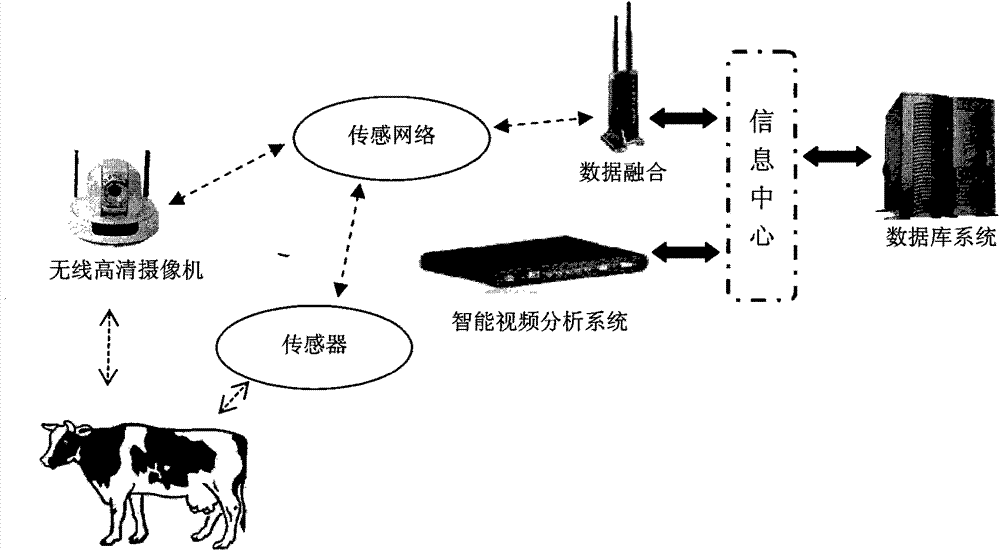
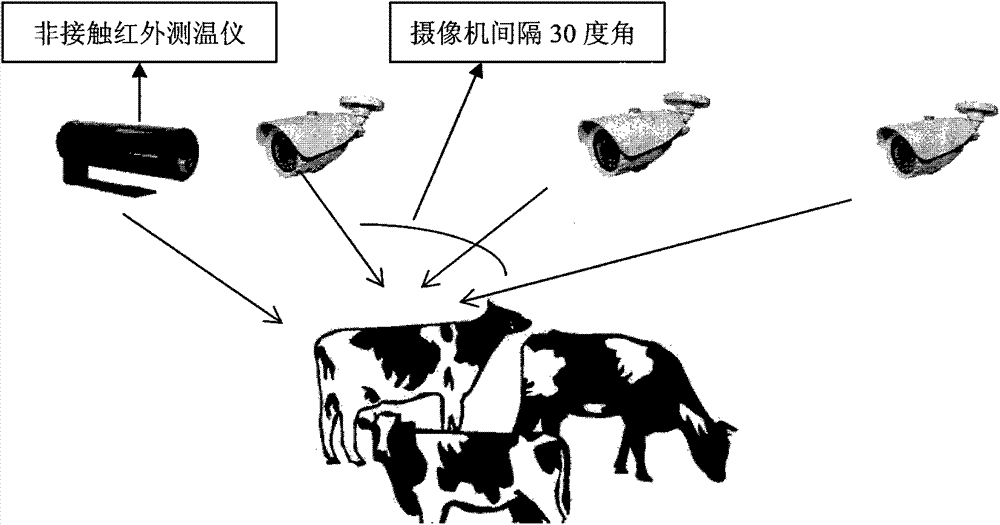
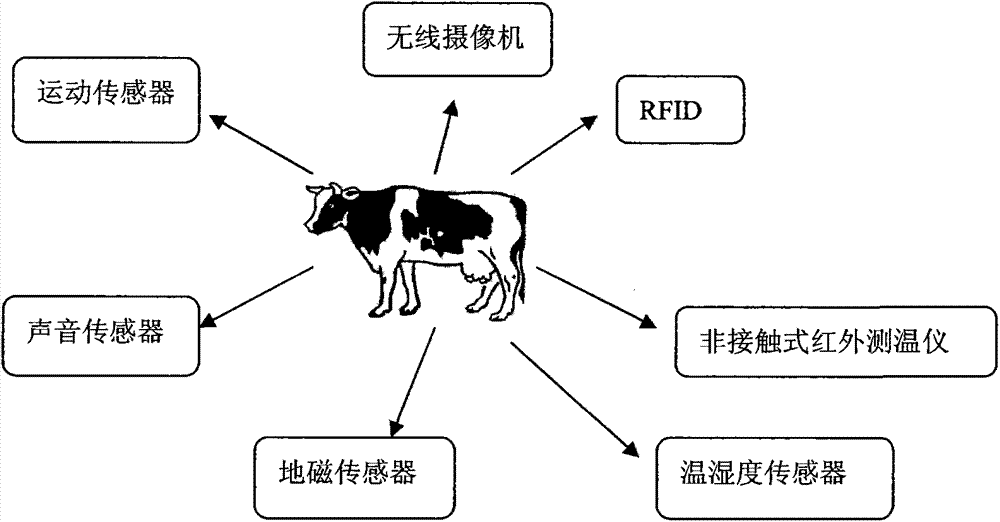
Intelligent livestock behavior monitoring system based on internet of things and computer vision
InactiveCN103488148AMeasurement devicesProgramme total factory controlVideo monitoringSoftware system
The invention discloses an intelligent livestock behavior monitoring system. According to the system, the aim that monitoring and analysis are carried out on livestock behaviors on a real farming scene by fusing the internet of things and the computer vision technology is achieved for the first time, a video monitoring and sensor network hardware and software system based on the WiFi technology is constructed for the first time, the problems that a traditional cable is high in installation cost, long in consumed time and hard to expand are solved, the monitoring and analysis on the behaviors of dairy cows on the real farming scene is achieved by fusing the internet of things and the computer vision technology, and the monitoring and analysis on several kinds of daily behaviors, such as ingestion, drinking, rumination, excretion, exercise, rest and exploration are achieved. Meanwhile, occurrences of abnormal events are monitored, and the alarm is automatically given on the abnormal behaviors.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
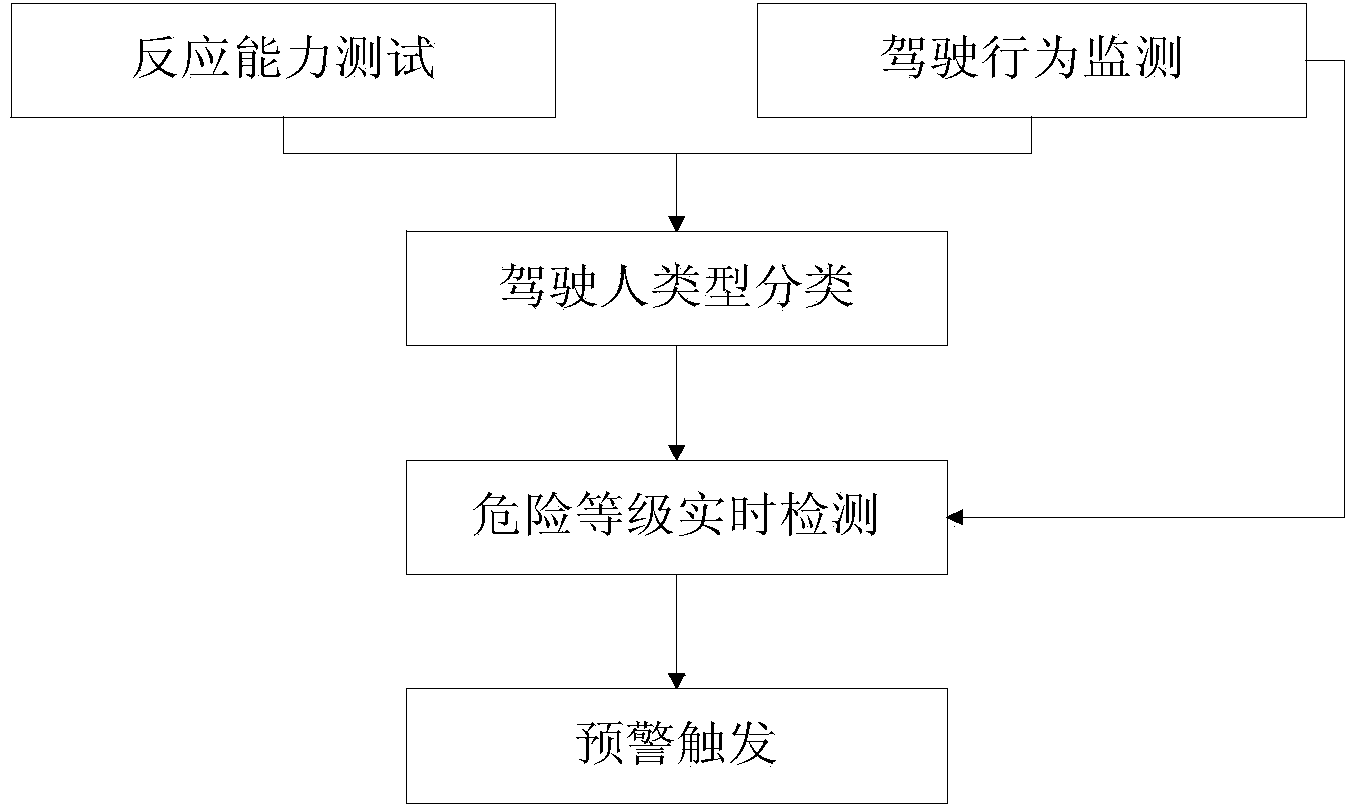
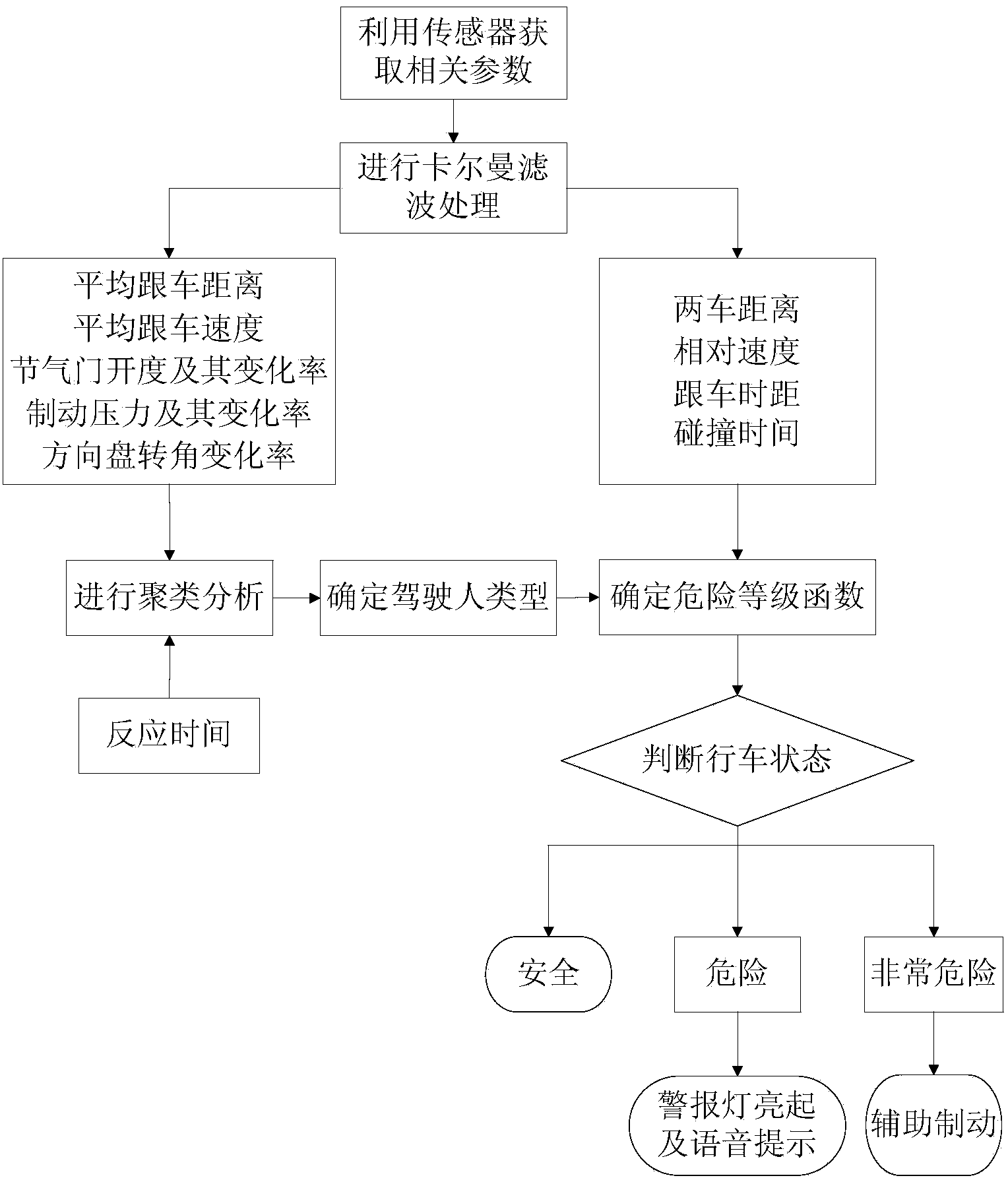
Rear-end collision pre-warning method based on driver types
InactiveCN103531042AAvoid the impact of rear-end warningImprove detection accuracyDetection of traffic movementAnti-collision systemsRear-end collisionReaction time test
The invention discloses a rear-end collision pre-warning method based on driver types, and aims to solve the problem that the pre-warning accuracy is reduced due to no consideration of driving habits of different types of drivers in the prior art. The rear-end collision pre-warning method comprises the steps as follows: 1, an emergency reaction ability test: reaction time of a tested driver is tested by a reaction time tester; 2, driving behavior monitoring: corresponding sensors are respectively utilized to acquire operation parameters of the tested driver, a distance between the tested vehicle and a vehicle ahead and a relative speed; 3, classification of driver types: according to emergency reaction ability test data and driving behavior monitoring data of the tested driver, an unsupervised cluster analysis method is adopted to determine the driver type on the basis of a preset reaction capacity classification rule and a driving style membership grade function; 4, real-time danger level detection: a danger level judgment equation suitable for the driver type of the tested driver is selected to judge current driving danger level of the tested vehicle; and 5, pre-warning triggering.
Owner:JILIN UNIV
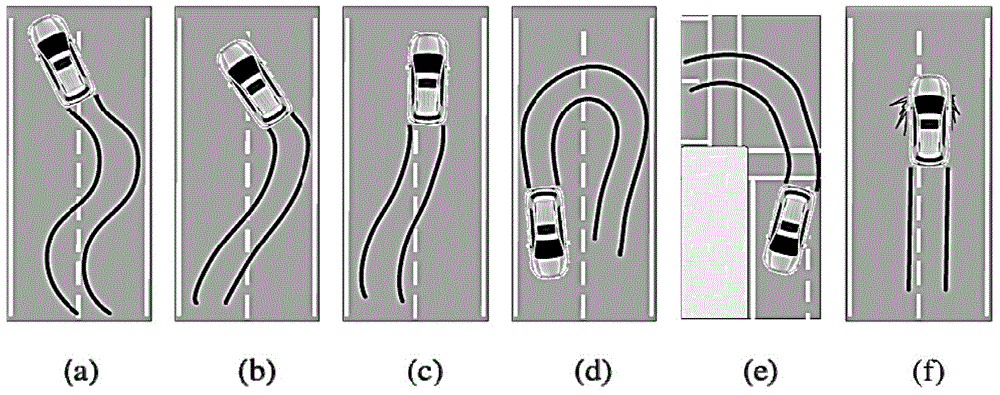
Aberrant driving behavior monitoring and recognizing method and system based on smart mobile terminal
InactiveCN104463244ACharacter and pattern recognitionSignalling/lighting devicesSimulationEngineering
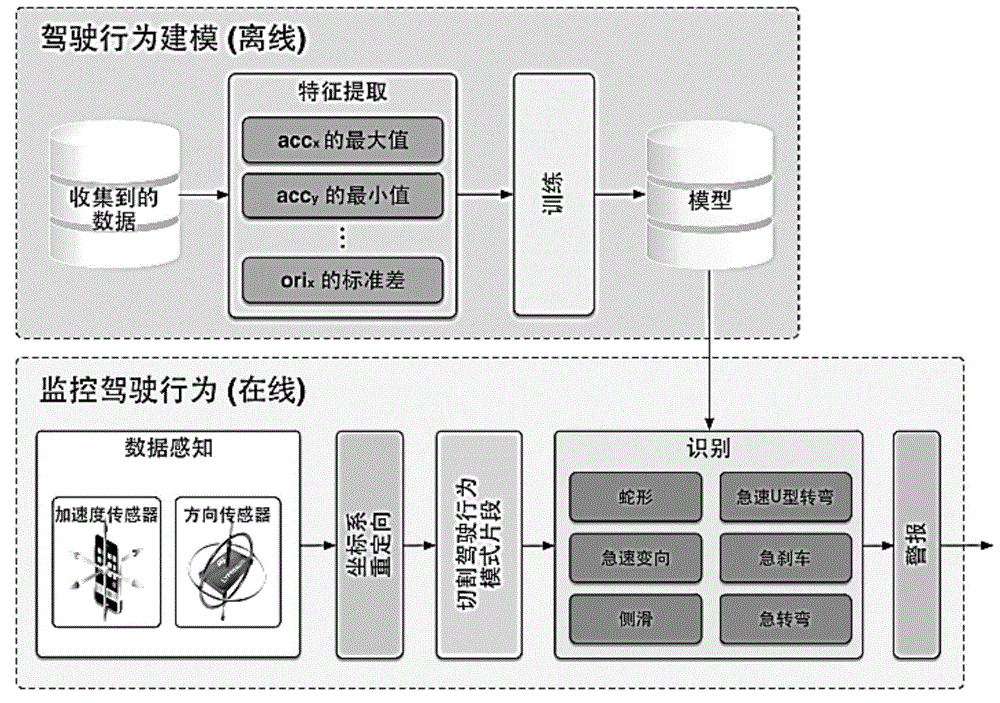
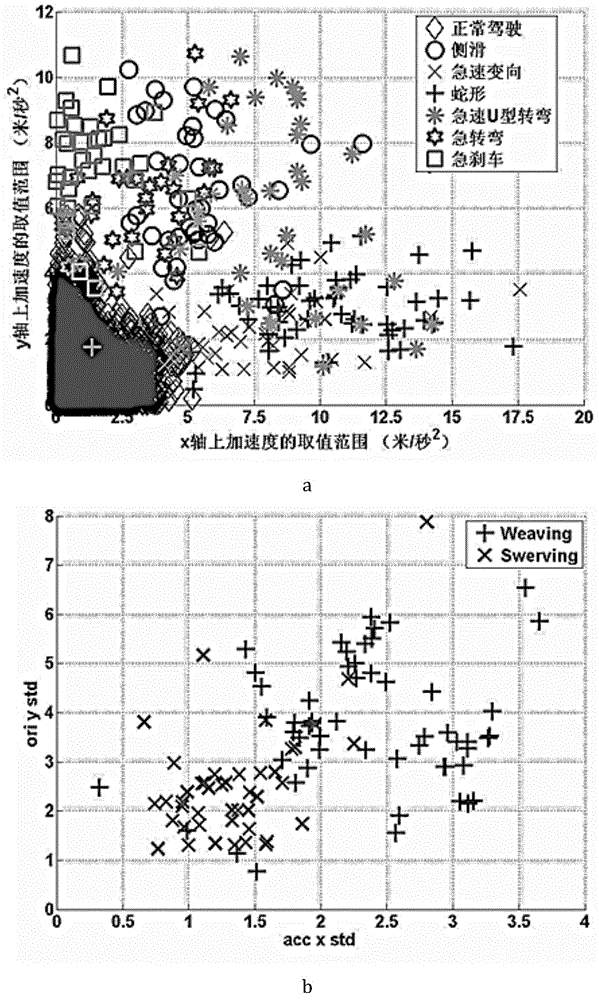
Disclosed are an aberrant driving behavior monitoring and recognizing method and system based on a smart mobile terminal. Data are collected from a sensor, characteristic value data are extracted, then a characteristic value is trained through a machine learning method, a classifier model is set up, a driving behavior pattern is intercepted in the real-time monitoring process, and six kinds of aberrant driving behaviors are judged. Sidewinding driving, rapid turning, sideslipping, rapid U turning, sudden turning and sudden braking in the aberrant driving behaviors can be fast detected through the sensor of a smart phone. An experimental result shows that the mean total precision of the specific types of the aberrant driving behaviors recognized by the system is 96.20 percent.
Owner:SHANGHAI JIAO TONG UNIV
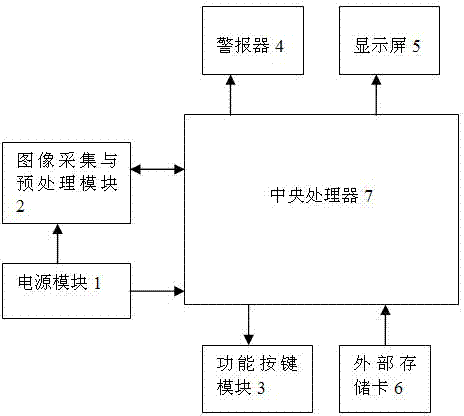
Driver's driving behavior monitoring device and monitoring method based on video detection
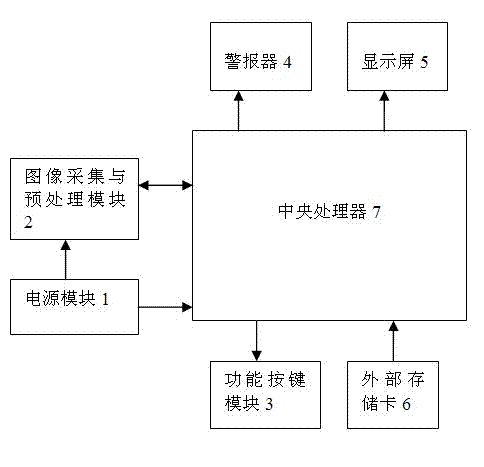
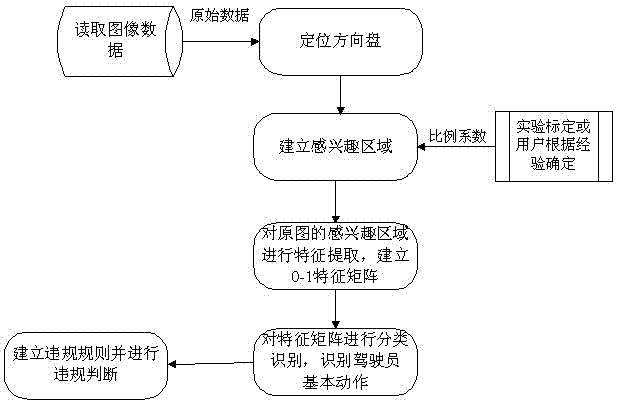
InactiveCN102263937AAvoid traffic accidentsSimple calculationCharacter and pattern recognitionClosed circuit television systemsDriver/operatorBehavior monitoring
The invention provides a driver's driving behavior monitoring device and a monitoring method based on video detection. The monitoring device comprises an image acquisition and preprocessing module, a function button module, an alarm, a display screen, an external storage card, a power module and a central processor. The monitoring method comprises the following steps: the equipment performs a self-test, and the central processor configures an internal register of the image acquisition and preprocessing module; the image acquisition and preprocessing module takes charge of acquiring image dataand preprocessing image analog signals; the format of the preprocessed data is converted by the central processor; the driver's driving behavior is recognized based on video detection; and if the driver's driving behavior is judged as an illegal behavior, the alarm generates a corresponding warning, and the corresponding illegal picture is stored in the external storage card for later checking and tracking. Through the driver's driving behavior monitoring device and monitoring method, whether a driver has an illegal behavior during driving can be effectively monitored, a warning is given about the illegal behavior, and traffic accidents caused by illegal operations of the driver can be effectively avoided.
Owner:SOUTH CHINA UNIV OF TECH +1
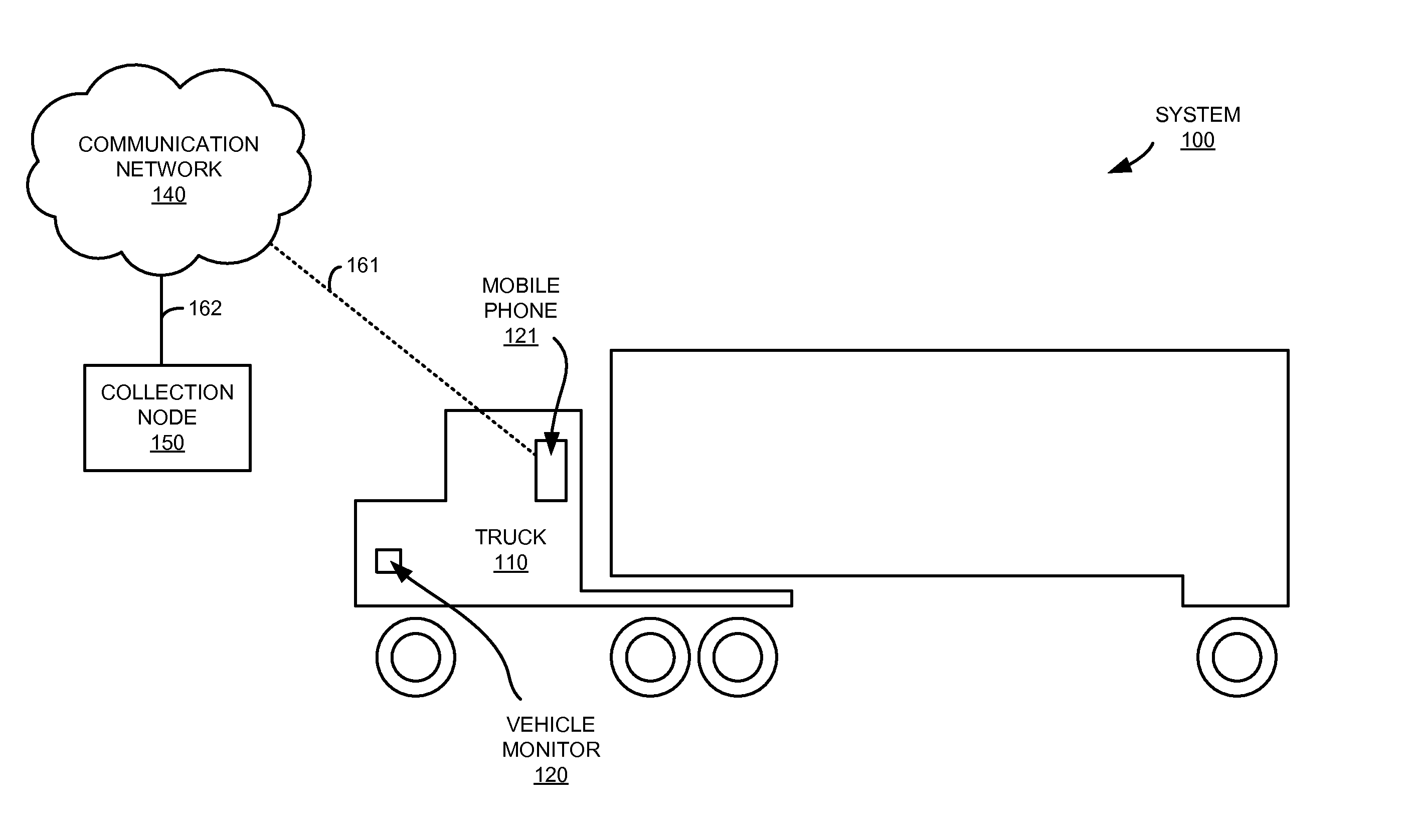
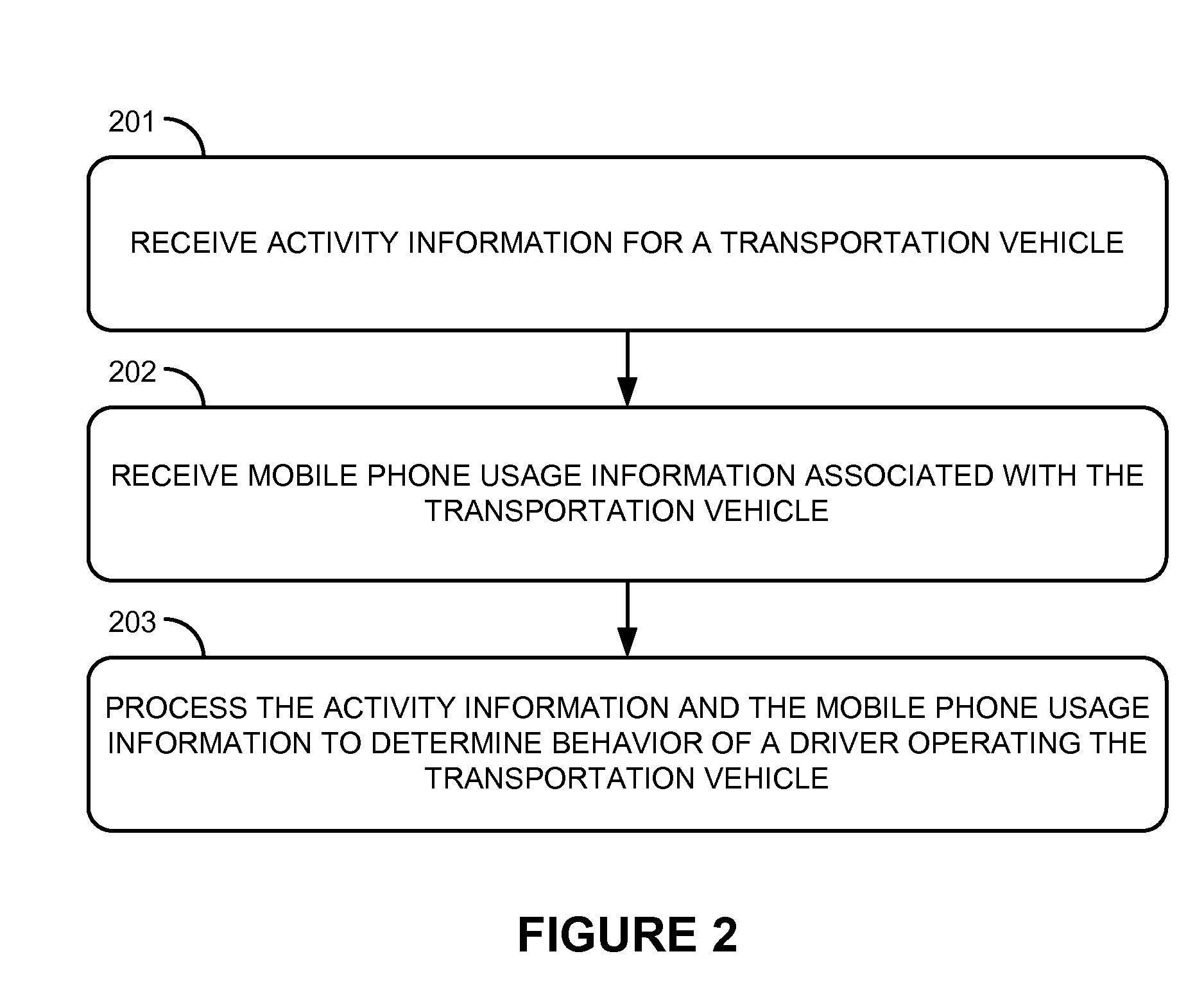
Vehicle driver behavior monitoring and correlation
InactiveUS20110281564A1Registering/indicating working of vehiclesSpecial service for subscribersDriver/operatorMonitoring system
What is disclosed are various methods of operating vehicle monitoring systems. One example method includes receiving activity information for a transportation vehicle, receiving mobile phone usage information associated with the transportation vehicle, and processing the activity information and the mobile phone usage information to determine behavior of a driver operating the transportation vehicle. The method could also include, in some examples, processing the activity information and the mobile phone usage information to identify the driver operating the transportation vehicle. Other example methods include processing motion data of a vehicle associated with the vehicle monitoring system to determine a route of the vehicle, processing the route to subdivide the route into a plurality of segments based upon the motion data, and determining if the vehicle was exceeding speed limits associated with any of the plurality of segments and reporting speeding information to a driver of the vehicle.
Owner:GEOFORCE
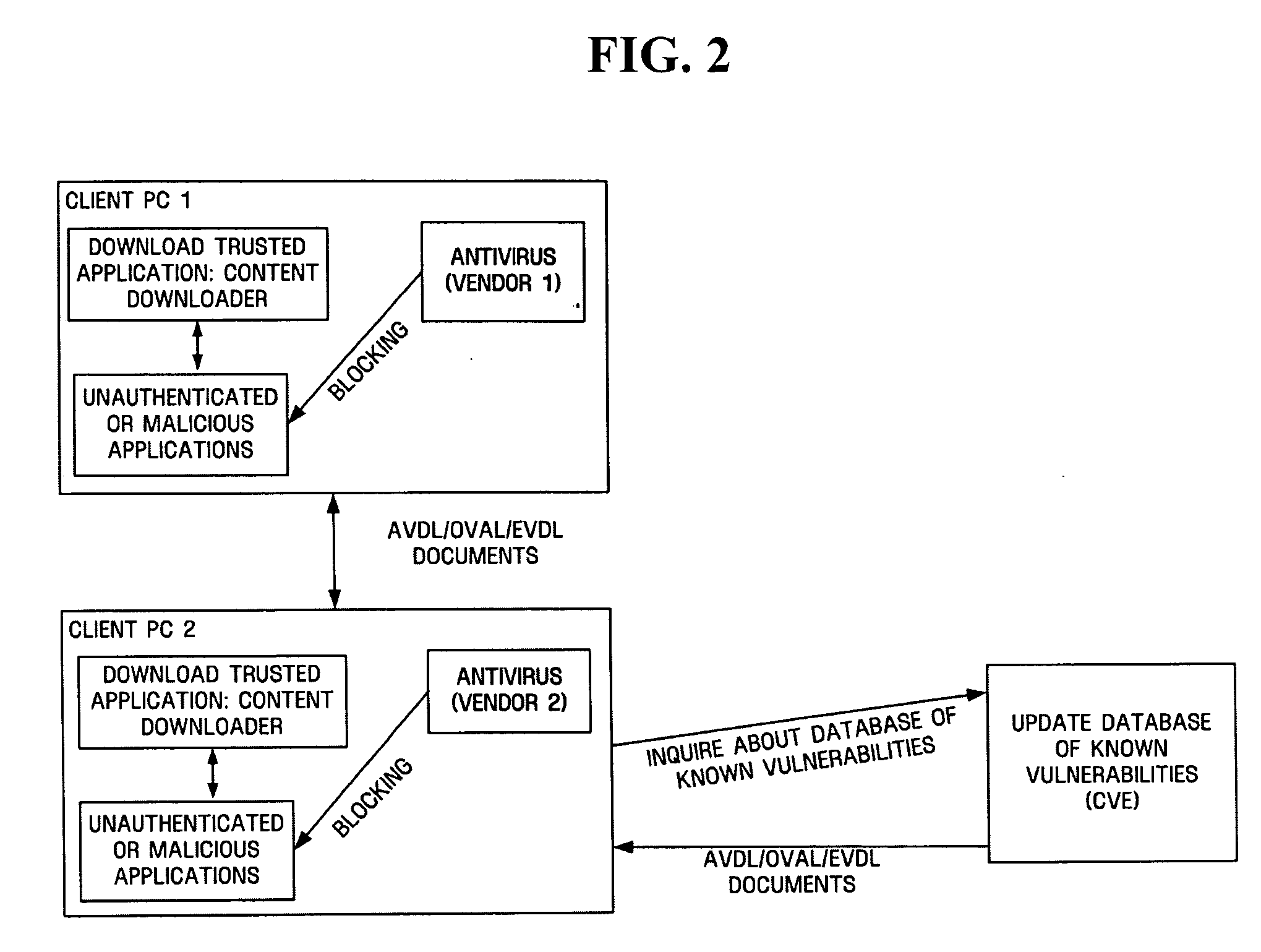
Apparatus and method for using information on malicious application behaviors among devices
InactiveUS20070192866A1Memory loss protectionError detection/correctionPaper documentDocument preparation
A device for using information on malicious application behaviors is provided. The device includes a capability-monitoring unit that monitors application capabilities, a behavior-monitoring unit that monitors application behaviors, an mBDL-generating unit that generates a document in a formal language specifying the application capabilities and the application behaviors, and a controlling unit that controls execution of application using the formal language.
Owner:SAMSUNG ELECTRONICS CO LTD
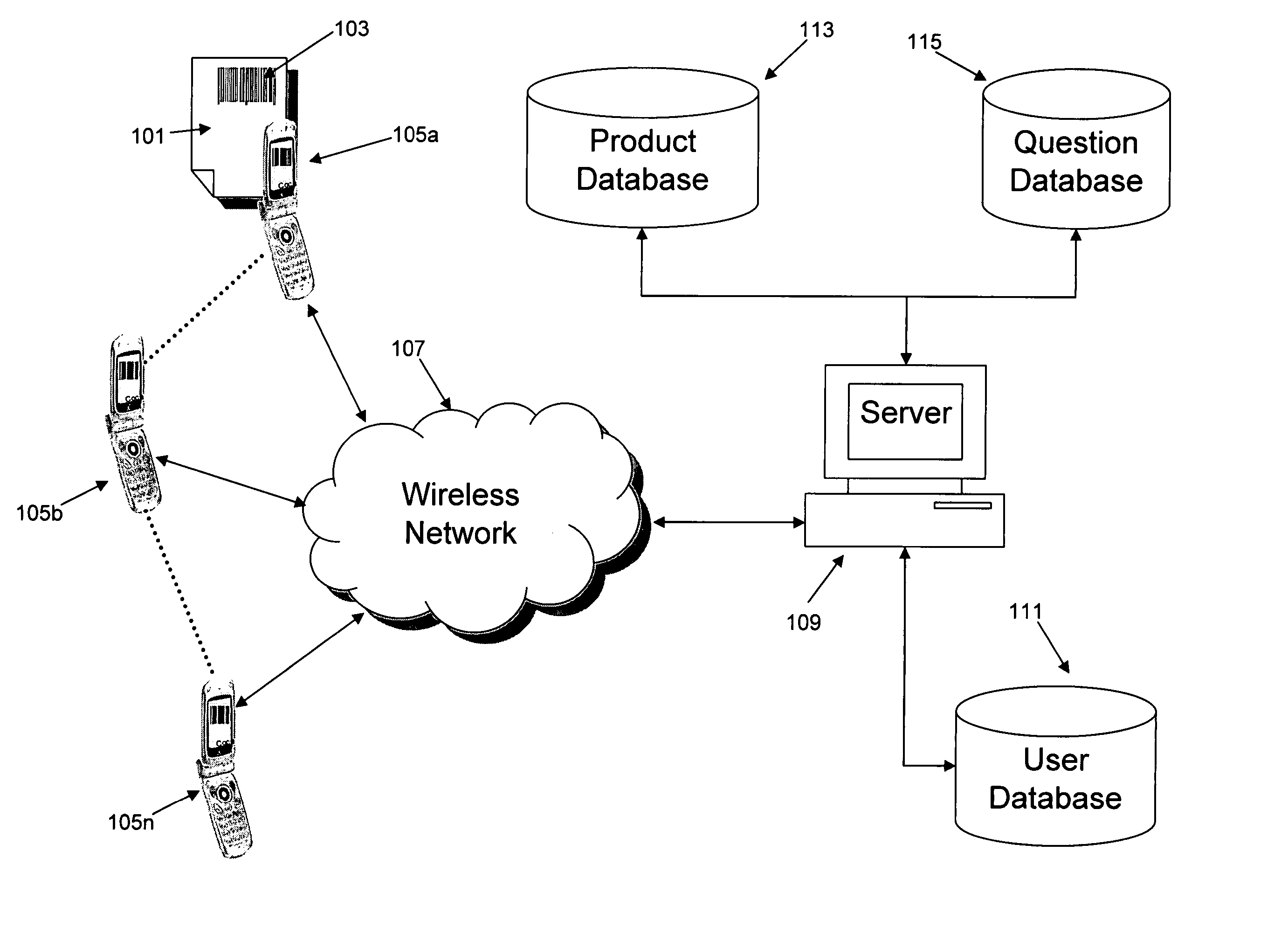
Real-time behavior monitoring system
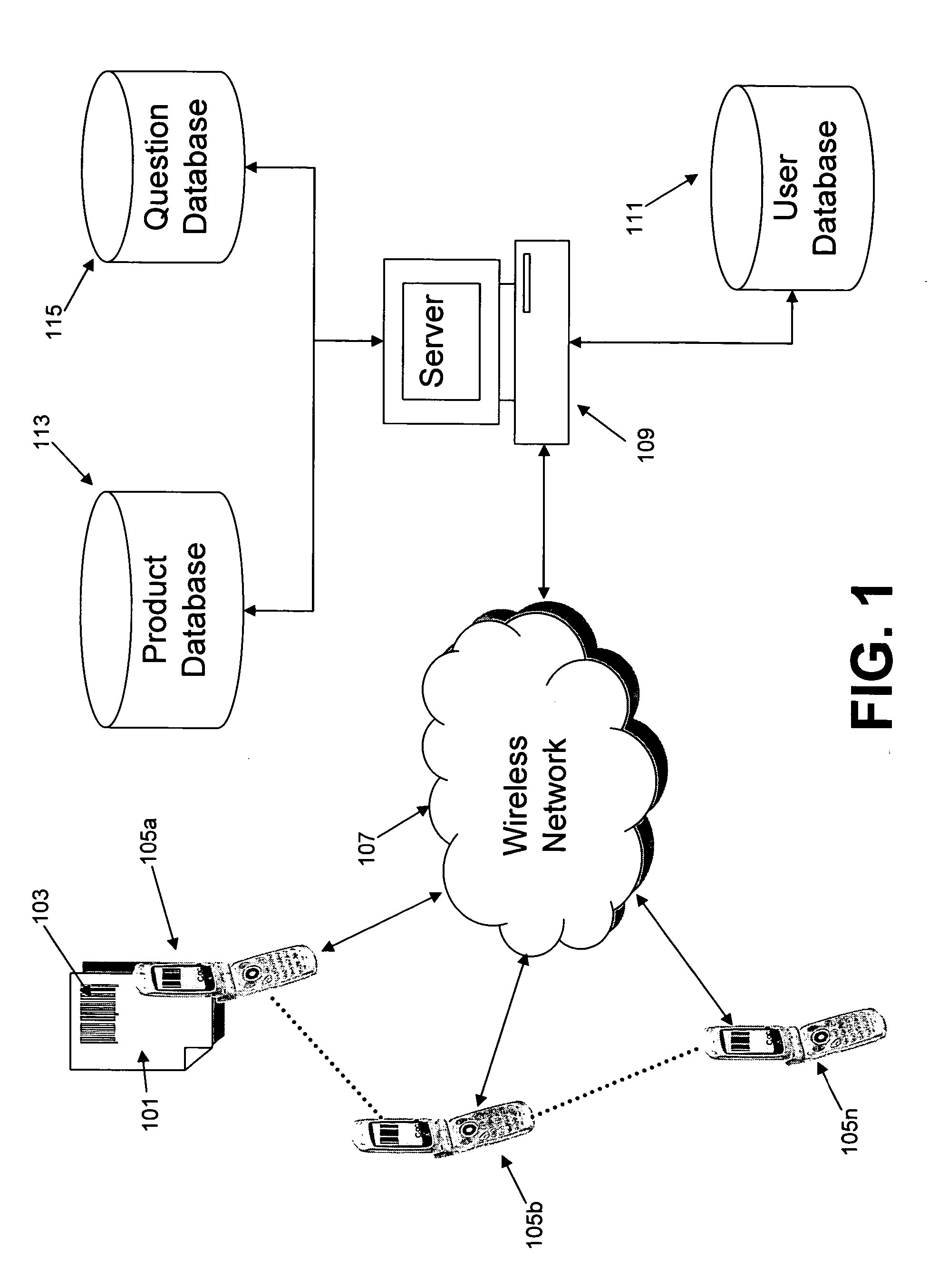
InactiveUS20050246196A1Encourage participationMarket predictionsSpecial data processing applicationsBarcodeMobile device
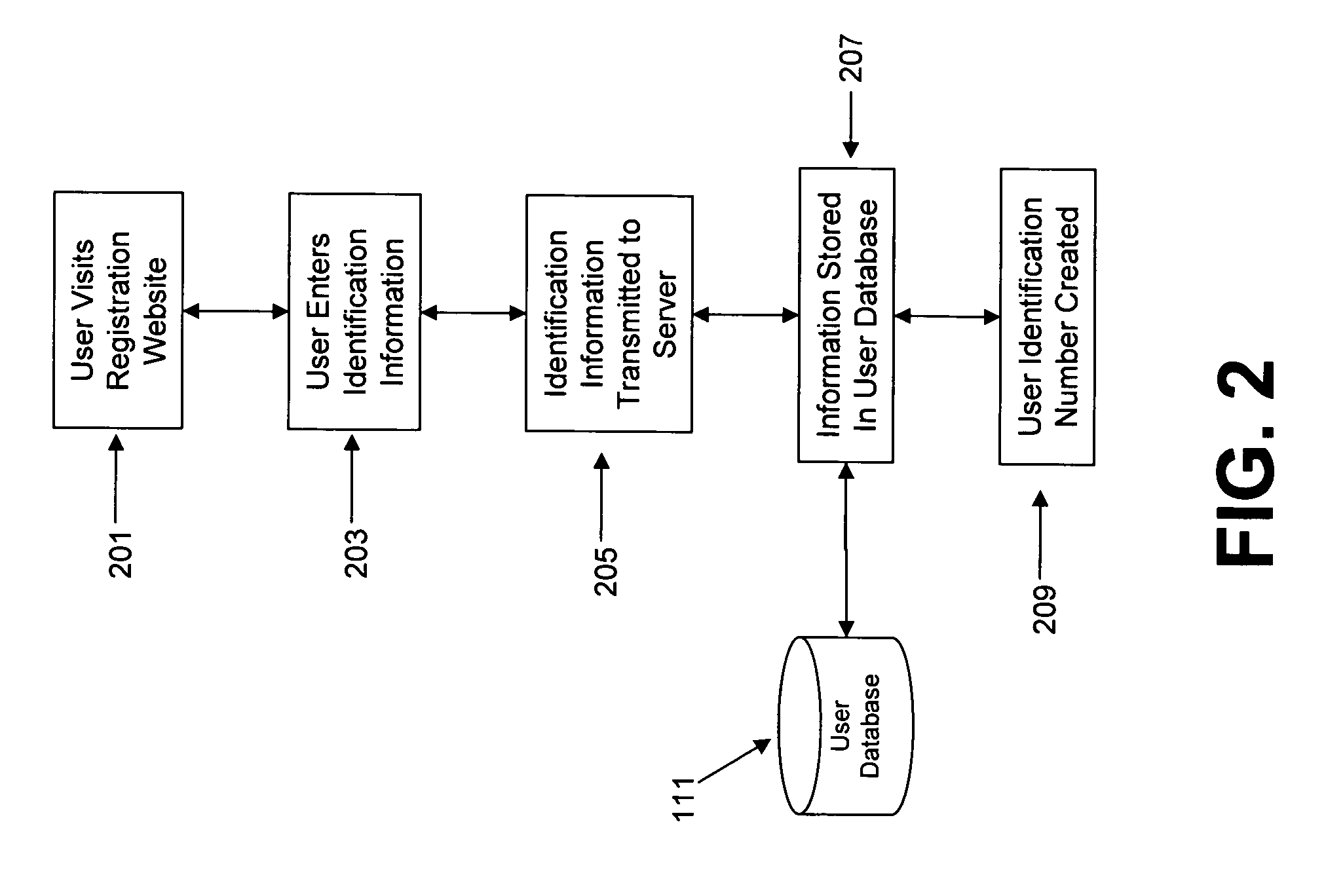
The present invention discloses a behavior monitoring system and method for tracking users' consumer behavior in real-time. Each participant of the system is equipped with a mobile device capable of decoding barcodes. Every time a participant makes a purchase, they scan the barcode located on the product and answer preliminary questions about the product. This information is then sent to a server via a wireless network and stored in a user database. The participant is then prompted with a series of more specific questions once the scanned barcode has been identified using a product database. The answers to the additional questions are also stored in the user database.
Owner:SCANBUY
Process exception list updating in a malware behavior monitoring program
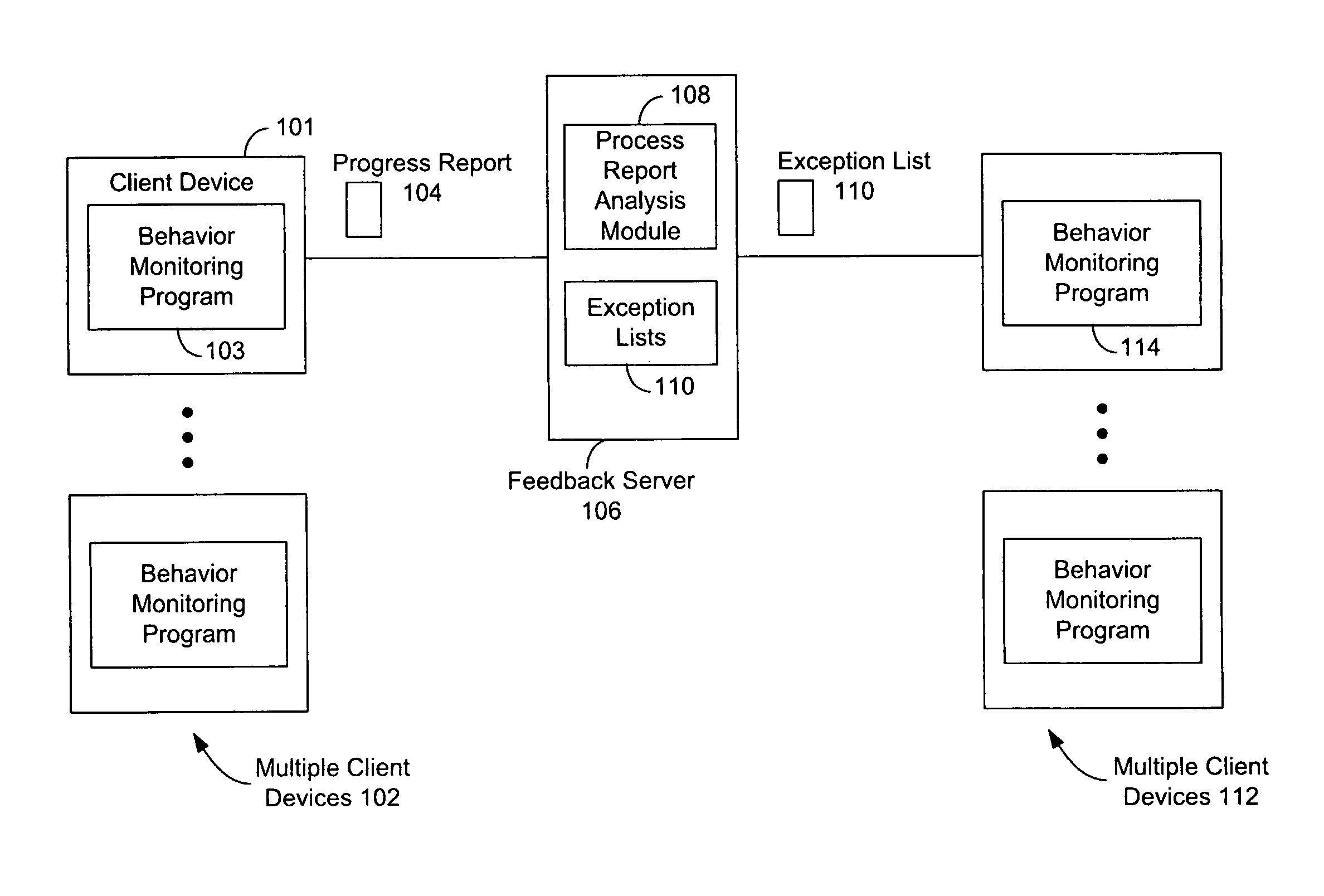
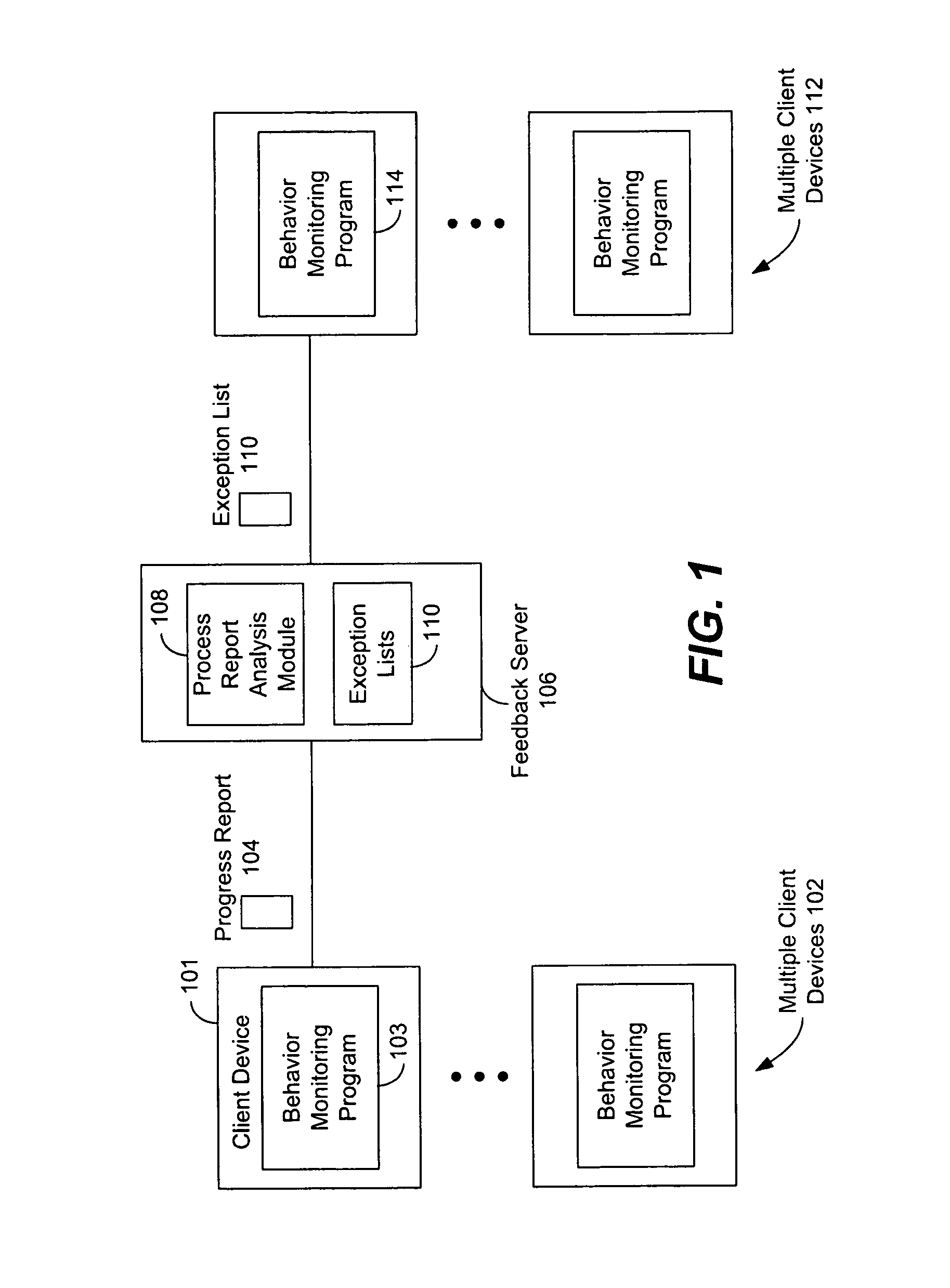
ActiveUS8220054B1Promote generationMemory loss protectionUnauthorized memory use protectionReport evaluationService provision
Generating an exception list by a service provider for use in behavior monitoring programs for malware detection is described. A feedback server controlled by a malware prevention service provider receives client process reports from client devices owned by the service provider's customers and others using the provider's behavior monitoring software. The process reports contain data on processes that were evaluated (on the client device) as being processes that require a significant amount of CPU resources (i.e., above a certain threshold) to monitor and that have previously executed on the client device and were considered safe or non-harmful to the device. The feedback server receives the process reports and creates a statistics summary report, which is used by the service provider in evaluating whether to include the processes in the provider's official exception list which is distributed to its customers for use in their behavior monitoring programs. While creating the process reports on the client devices, the devices are able to temporarily address issues caused by processes taking up too much of the behavior monitor's CPU usage by including the process on exception list only for that client. The final decision as to whether the process will be on the final or official exception list is made by the service provider.
Owner:TREND MICRO INC
Driving behavior monitoring method, device and system based on automobile data recorder
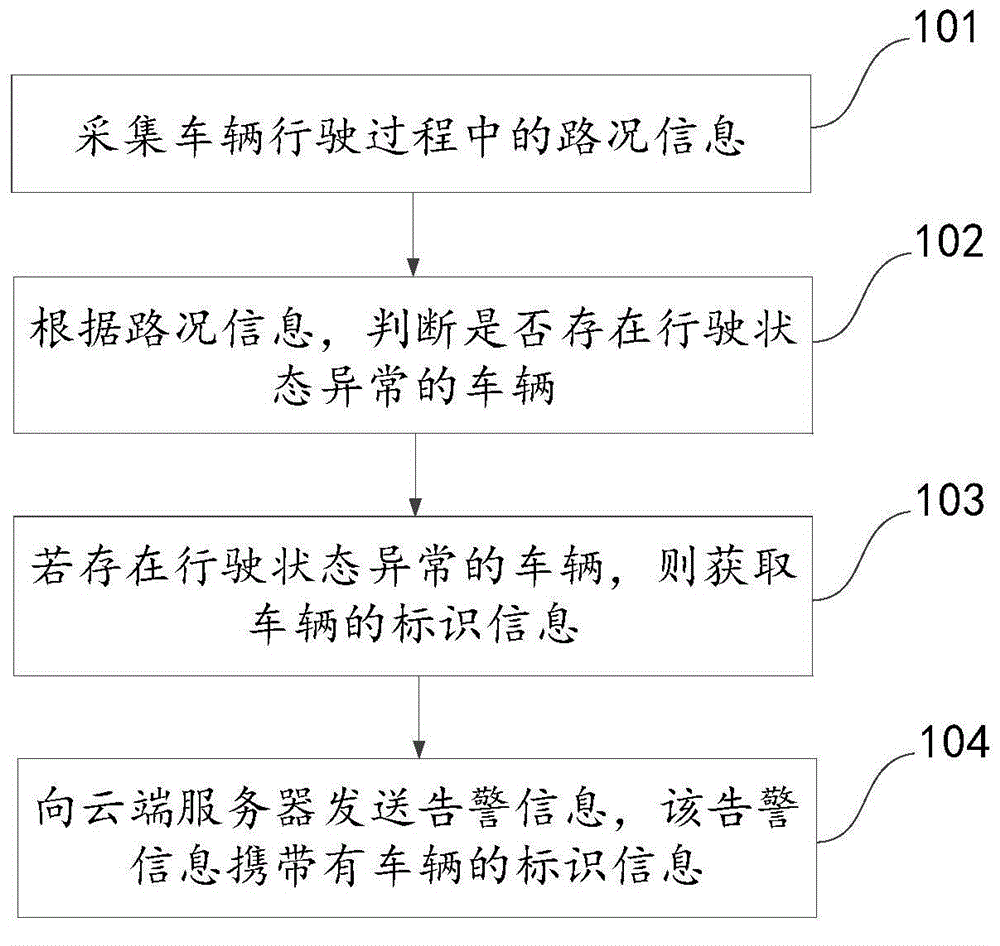
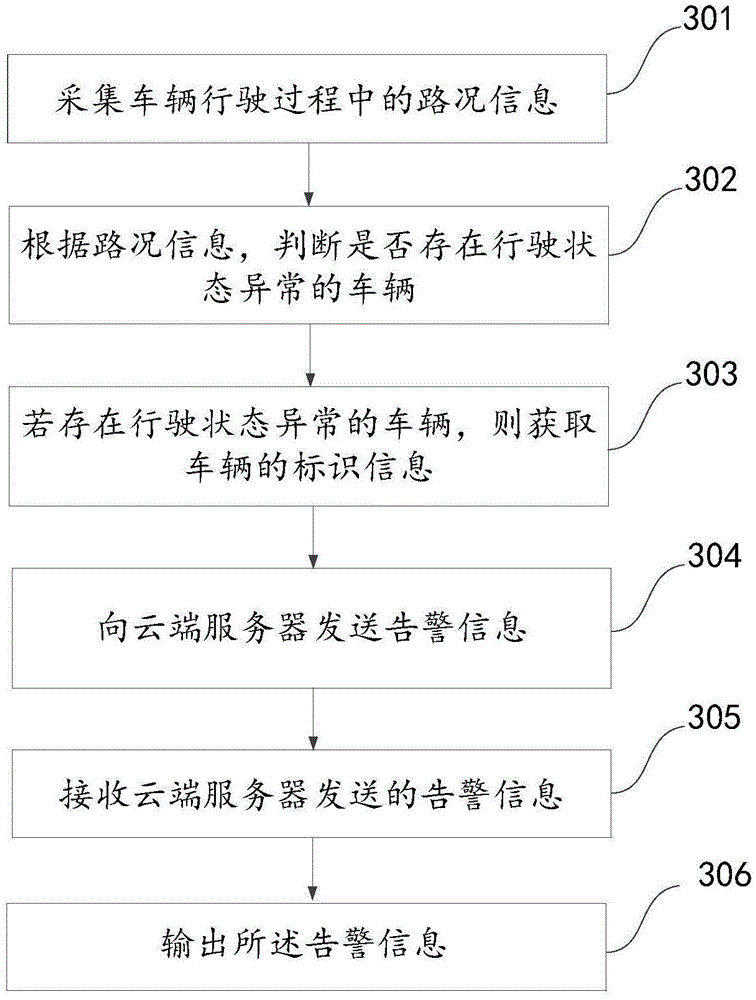
ActiveCN104882001AImprove securityRegistering/indicating working of vehiclesDetection of traffic movementEngineeringVehicle driving
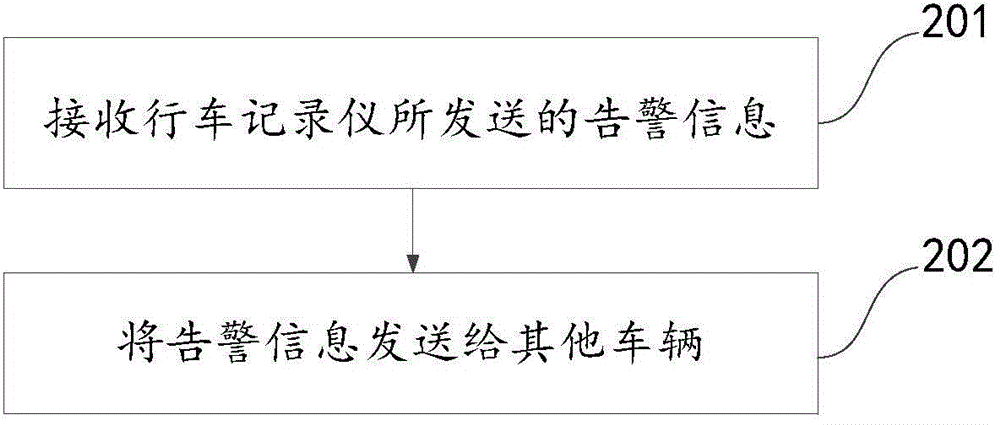
The invention discloses a driving behavior monitoring method, device and system based on an automobile data recorder and relates to the technical field of vehicle-mounted communication. By the adoption of the driving behavior monitoring method, device and system, a vehicle driving behavior can be monitored effectively through the automobile data recorder, and a driver can be assisted in judging or selecting the vehicle driving behavior. According to the main technical scheme, the road condition during vehicle traveling is acquired; whether a vehicle in an abnormal traveling state exists or not is judged; if yes, the identification information of the vehicle is obtained; warning information containing the identification information of the vehicle is sent to a cloud side server so that the warning information containing the vehicle identification information can be sent to other vehicles through the cloud side server. The driving behavior monitoring method, device and system are mainly used for monitoring vehicle driving behaviors by means of the automobile data recorder.
Owner:北京鸿享技术服务有限公司
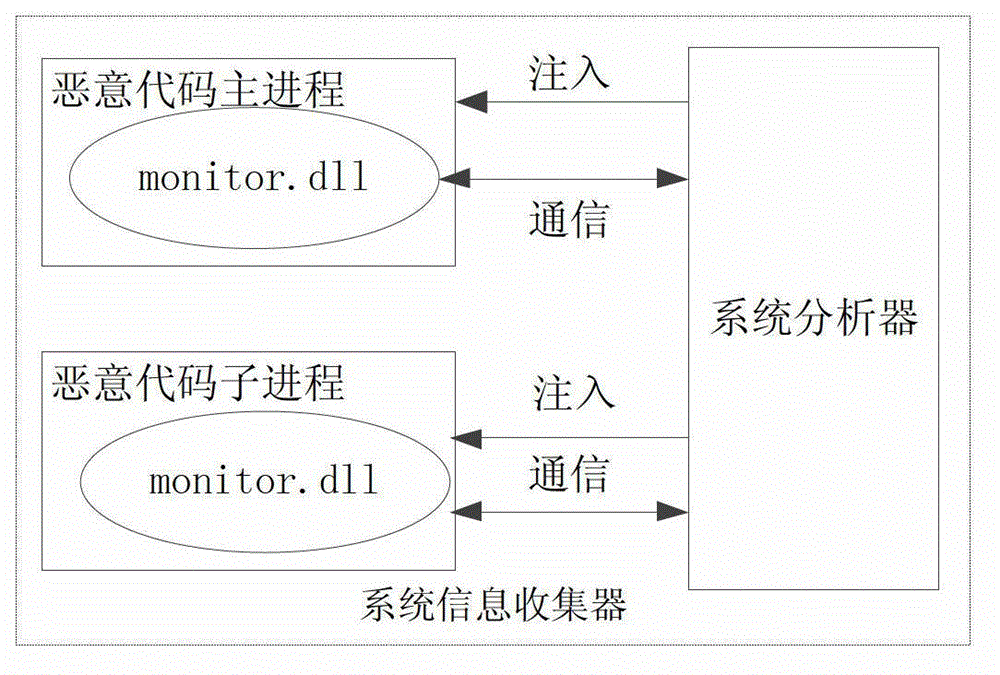
Automatic analyzing system and method for dynamic action of malicious program
InactiveCN101154258AImprove efficiencyImprove operational efficiencyPlatform integrity maintainanceBehavioral analyticsExecution unit
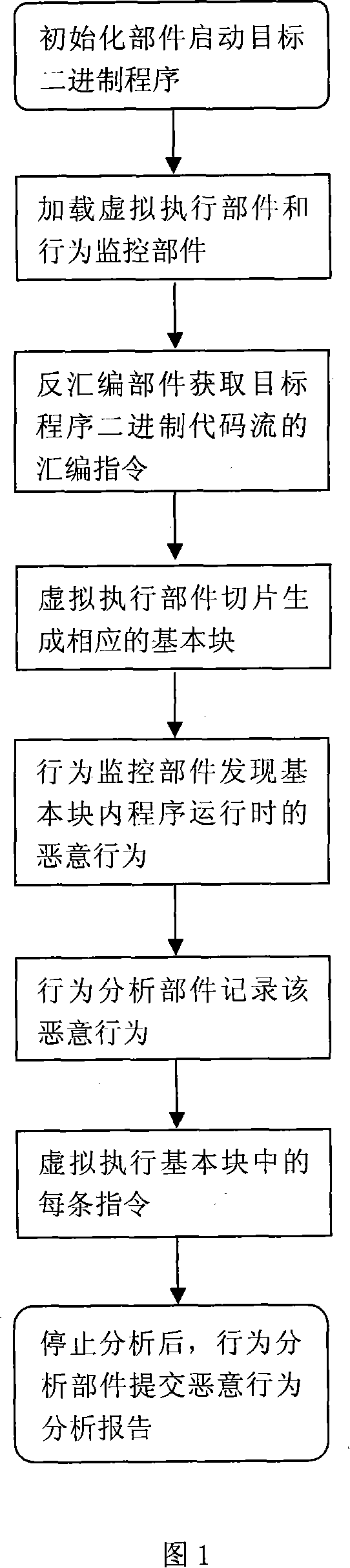
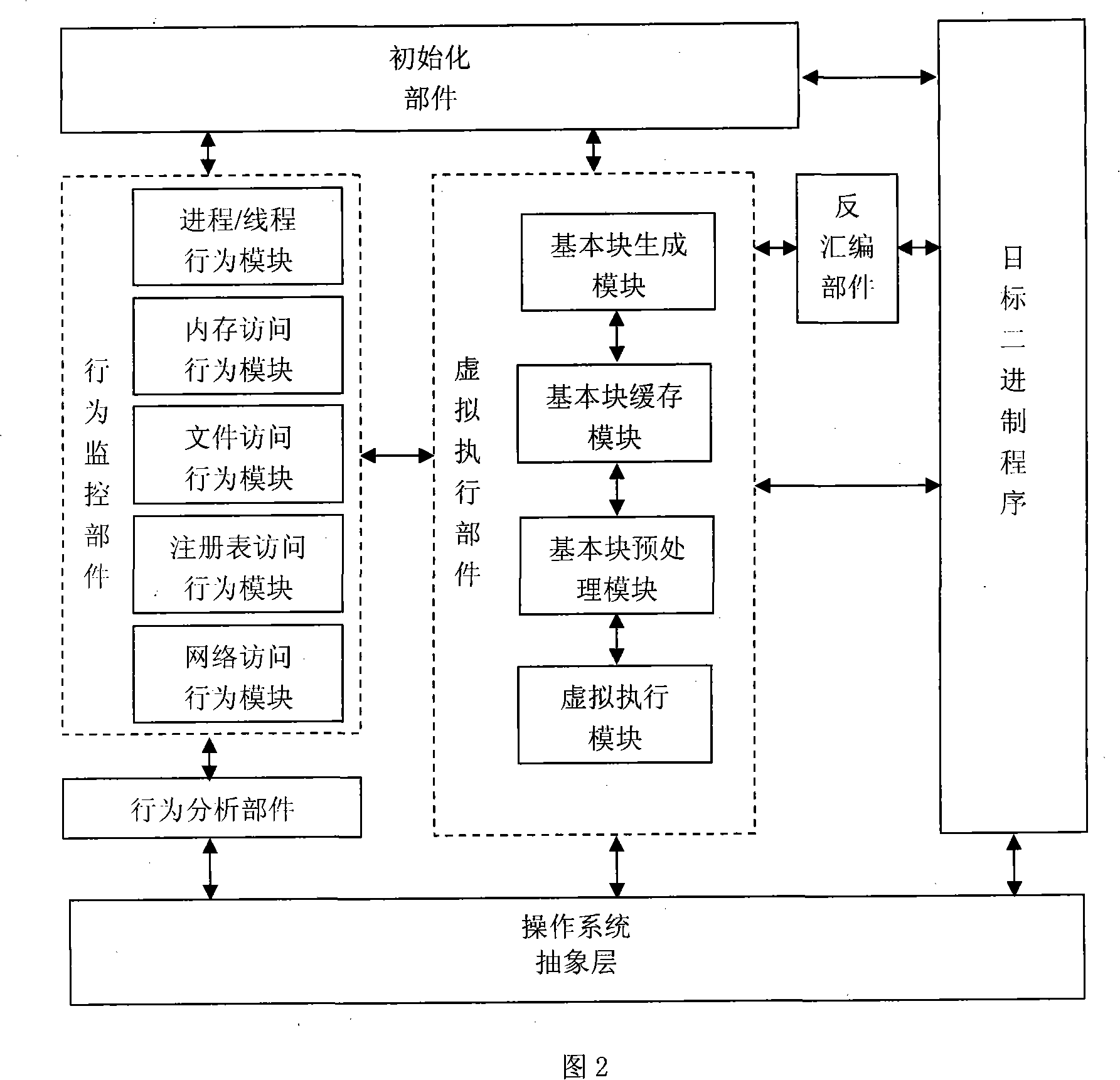
The invention relates to an automatic analysis system and a method of malice binary program dynamic behavior. The system consists of an initialization unit, a virtual execution unit, a disassembling unit, a behavior monitoring unit and a behavior analysis unit. The method is that: the initialization unit activates a monitored program, and the virtual execution unit and the behavior monitoring unit are then loaded; the disassembling unit acquires the assembler instruction of the binary code flow of an object program, the virtual execution unit slices and generates a corresponding basic block, and the behavior monitoring unit judges whether the basic block contains any malice behavior defined by a rule base; if the basic block does contain a malice behavior, the behavior monitoring unit can transfer the command to the behavior analysis unit and record the malice behavior; after being returned, each instruction in the basic block can be virtually executed; the behavior analysis unit puts forward a malice behavior analysis report after the program execution quits or a user stops the analysis process forcibly. The invention enables complete control and analysis of malice program running behavior in a virtual environment and a detailed report can provide effective buckler aiming at the malice program.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Comprehensive video monitoring system of intelligent traffic
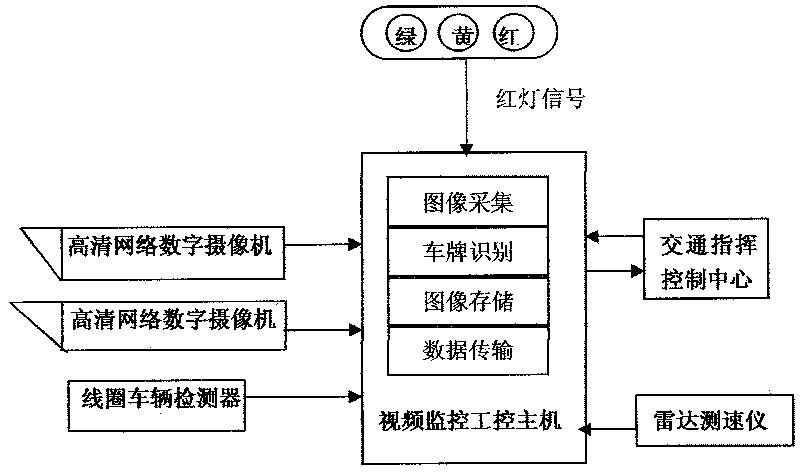
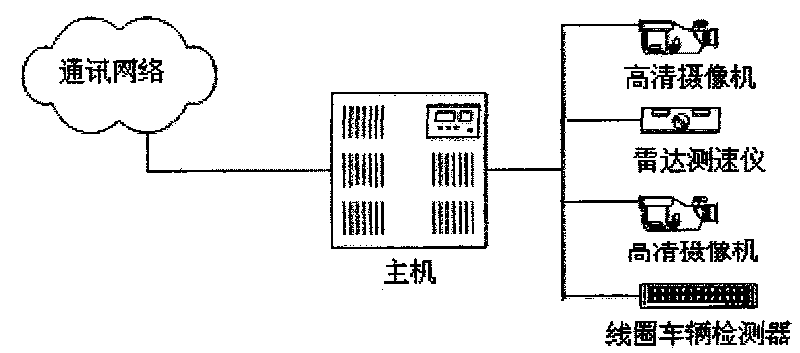
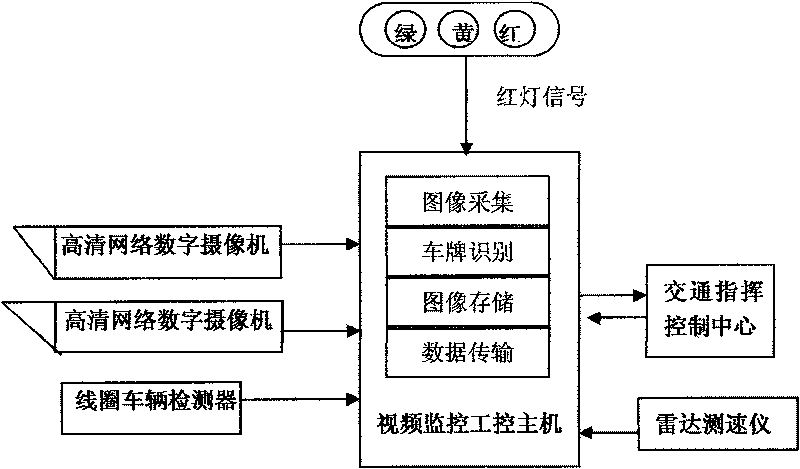
ActiveCN101692310AImprove anti-interference abilityLow costDetection of traffic movementClosed circuit television systemsLicense numberEmbedded technology
The invention provides a comprehensive video monitoring system of intelligent traffic, belonging to the field of intelligent traffic and electronic police. The monitoring system comprises at least one high-definition digital web camera, a video-monitoring industrial control host, a loop vehicle detector and / or a radar device and a high-definition intelligent traffic behavior monitoring unit. The intelligent system is capable of integrating various intelligent traffic monitoring behaviors as a whole, that is, fulfilling the functions of multilane illegal activity monitoring, license number recognition and traffic data acquisition on a single machine at the same time, and conducting detection, analysis and evidence collection on various illegal activities by using the Linux-based embedded technology in combination with the watchdog technology and the network management function. The monitoring system based on the invention has the advantages of high stability, low mistaking and missing rate and high anti-interference capacity, and the monitoring system can effectively filter the interference caused by bicycles, passersby and light; and the monitoring system has flexible, customized monitoring modes, thereby meeting the monitoring requirements under complex environment.
Owner:DERUISHI BEIJING TECH DEV
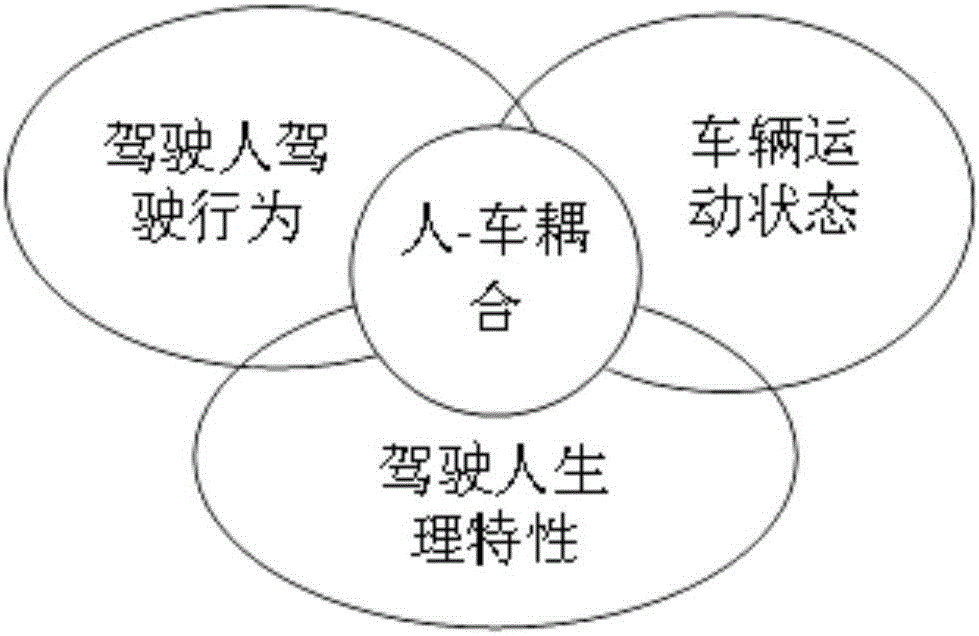
Driver-vehicle coupling-safe driving behavior monitoring and early warning system and method
InactiveCN106781581AImprove timelinessImprove accuracyAnti-collision systemsSignalling/lighting devicesRisk levelEarly warning system
The invention relates to a driver-vehicle coupling-safe driving behavior monitoring and early warning system and method and belongs to the vehicle active safe driving field. The system includes a vehicle-mounted monitoring and early warning sub-system, a vehicle-mounted satellite positioning monitoring subsystem, a wireless communication subsystem, a big data driving behavior analysis subsystem and a nearby vehicle communication subsystem. According to the method, the driving behaviors of a driver and the postures of a vehicle are monitored in real time; relevant data are collected and preprocessed; big data and cloud computing analysis means are adopted to perform driver's physiological characteristic and vehicle state coupled analysis; and a vehicle-mounted early warning module is started when an early warning requirement is satisfied, and different modes of risk early warning are carried out according to different risk levels. According to the driver-vehicle coupling-safe driving behavior monitoring and early warning system and method of the invention, coupled analysis is performed based on the behaviors of the driver and the postures of the vehicle, so that dangerous behaviors can be accurately analyzed out, and early warning can be performed, and therefore, the timeliness of abnormal driving behavior early warning can be improved; and early warning can be divided into in-vehicle early warning and Internet of Vehicles-based inter-vehicle early warning, and therefore, traffic accidents can be effectively prevented.
Owner:SHENZHEN POLYTECHNIC
Intelligent wearable terminal based child behavior monitoring and developing method and system
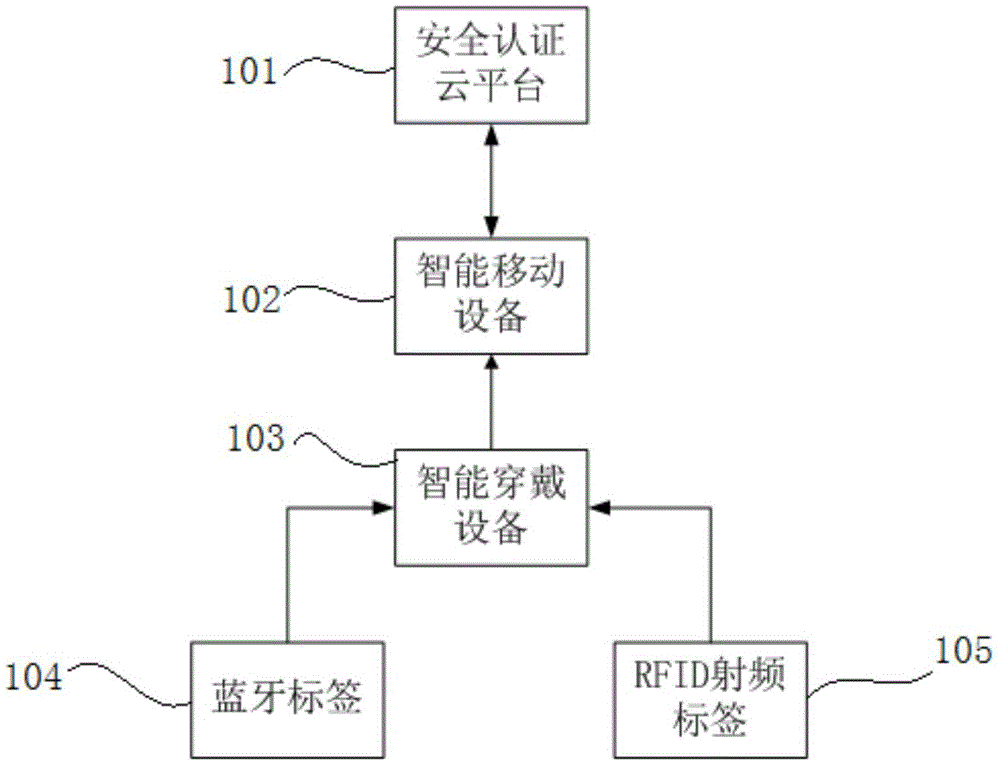
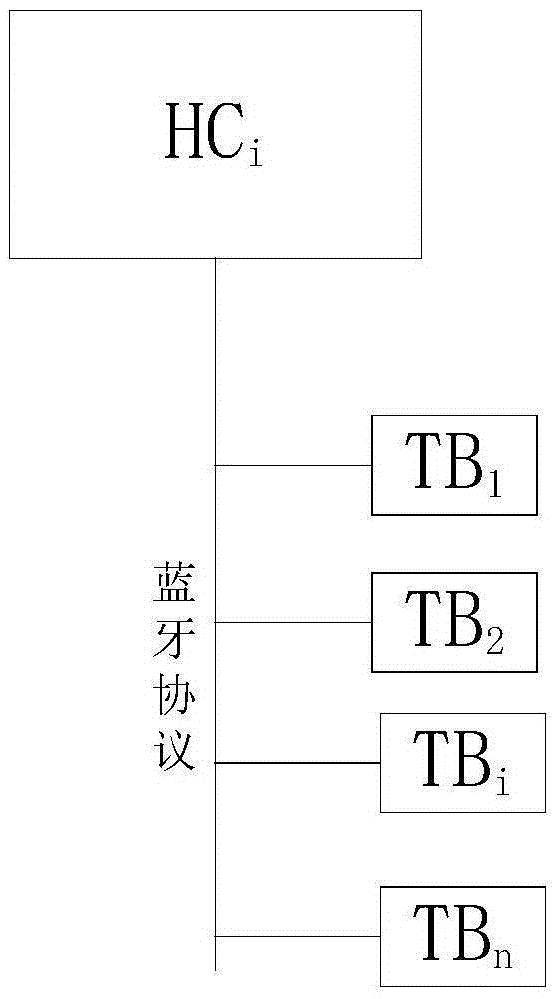
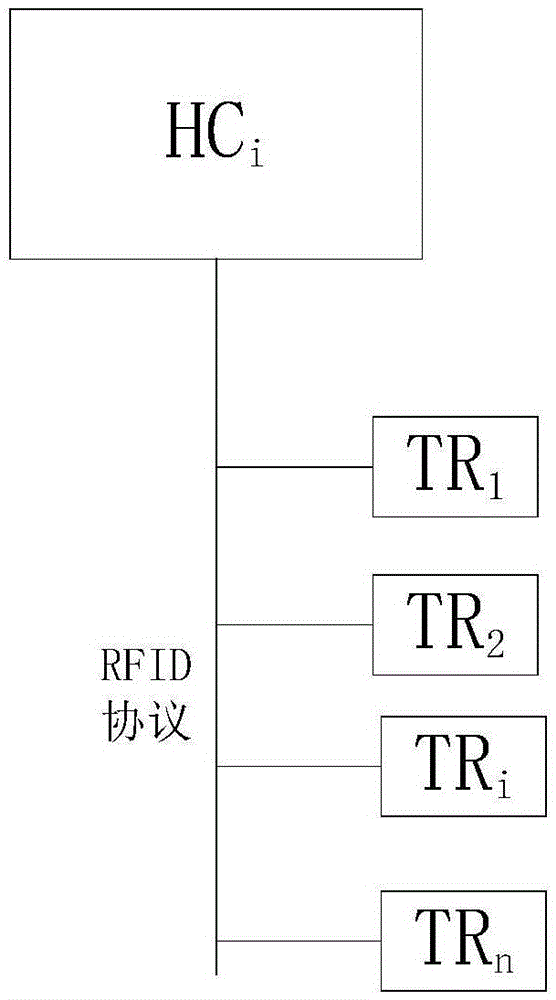
InactiveCN105608654AAchieve recordIncrease the database of dynamic behavior habitsCo-operative working arrangementsOffice automationWi-FiData information
The present invention discloses an intelligent wearable terminal based child behavior monitoring and developing system and method. The system comprises an intelligent wearable device, a Bluetooth tag, an RFID radio-frequency tag, an intelligent mobile device, a security authentication cloud platform and a data cloud platform. The method comprises: based on a position relationship, establishing a Bluetooth tag based on a Bluetooth Ad Hoc network, and a radio-frequency tag, and according to the Bluetooth tag and the radio-frequency tag, monitoring a behavior of a child wearing an intelligent wearable terminal; uploading a monitoring result to a cloud-end server; establishing a classifiable dynamic behavior habit database according to child basic data information and child daily behavior data; and comparing child behavior data in the dynamic behavior habit database with behavior data in a preset standard behavior database, and outputting early-warning and prompting information. According to the method and system disclosed by the present invention, by integrating technologies such as Bluetooth, RFID and Wi-fi, child behavior monitoring and development are implemented.
Owner:刘国正
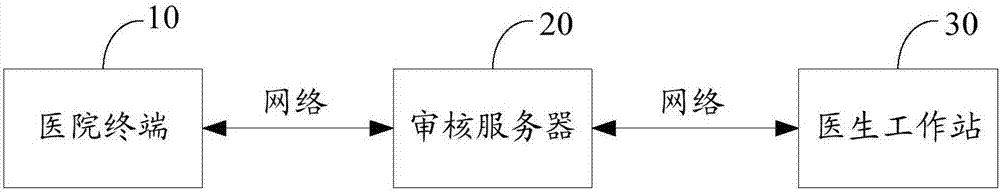
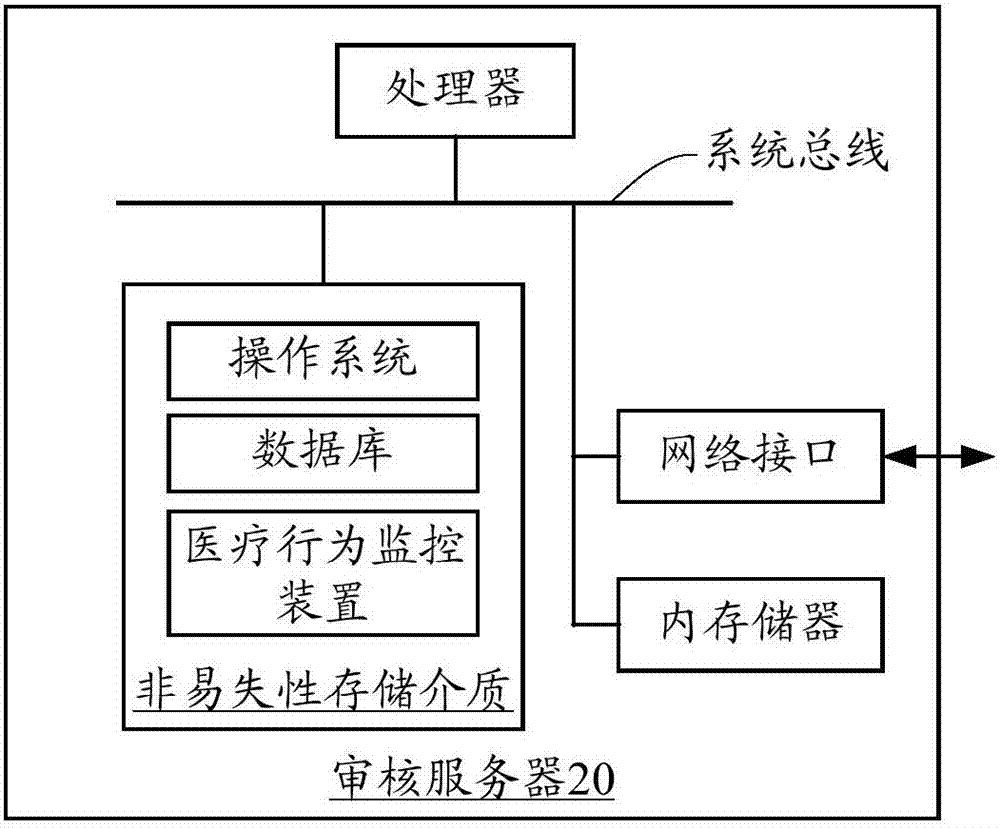
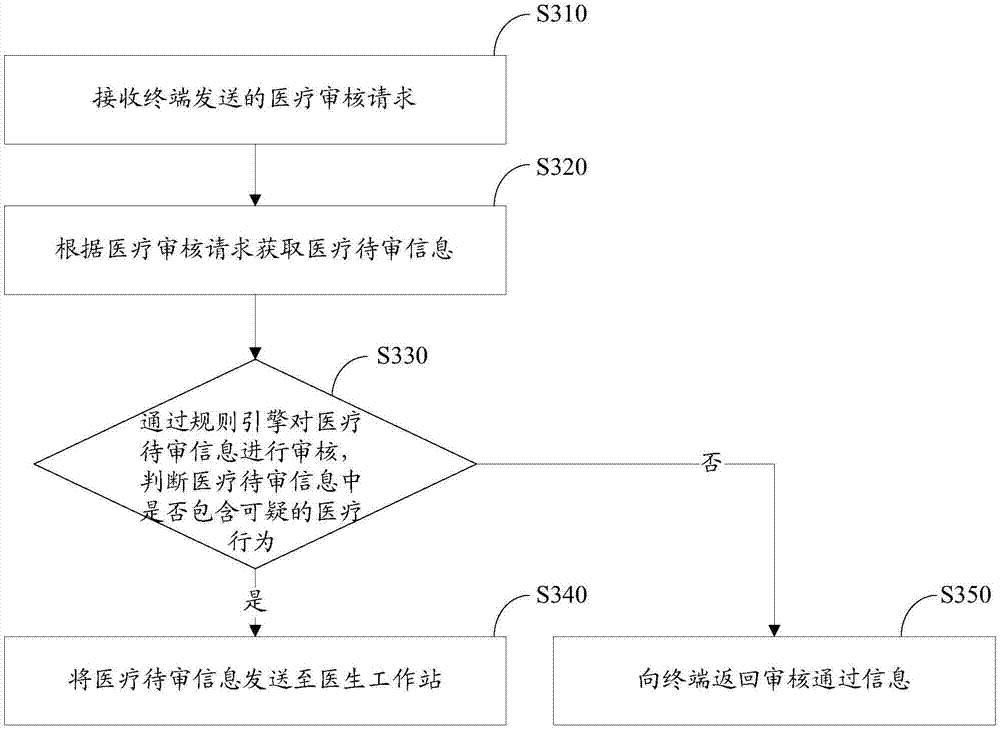
Medical behavior monitoring method and device
ActiveCN107133438AComprehensive detectionAccurate detectionSpecial data processing applicationsMedical adviceWorkstation
The invention relates to a medical behavior monitoring method and device. The method comprises the following steps that a medical check request sent by a terminal is received, wherein the medical check request comprises a check-in check request, a medical advice check request and a fee check request; to-be-checked medical information is acquired according to the medical check request; the to-be-checked medical information is checked through a rule engine, and whether the to-be-checked medical information contains suspicious medical behaviors or not is judged, wherein the rule engine is obtained through compiling on the basis of check conditions of the to-be-checked medical information; if the to-be-checked medical information contains the suspicious medical behaviors, the to-be-checked medical information is sent to a doctor working station. The medical behavior monitoring method and device can comprehensively and accurately detect the suspicious medical behaviors, insurance fraud behaviors can be effectively prevented, and the public interest loss can be reduced.
Owner:PING AN MEDICAL & HEALTHCARE MANAGEMENT CO LTD
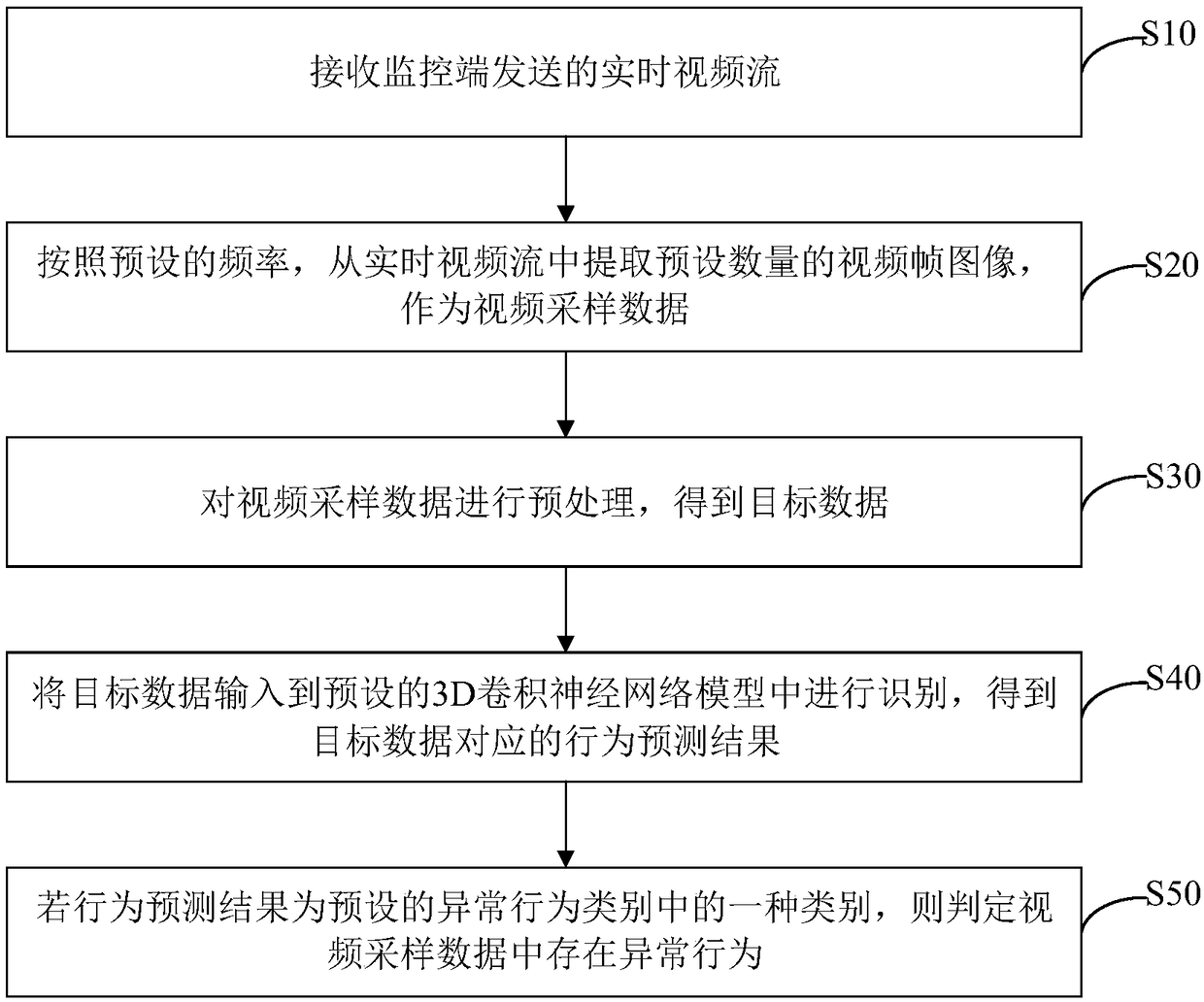
Abnormal behavior monitoring method, apparatus, computer device, and storage medium
PendingCN109241946AIncrease the level of automationImprove monitoring efficiencyImage enhancementImage analysisBehavior monitoringConvolution
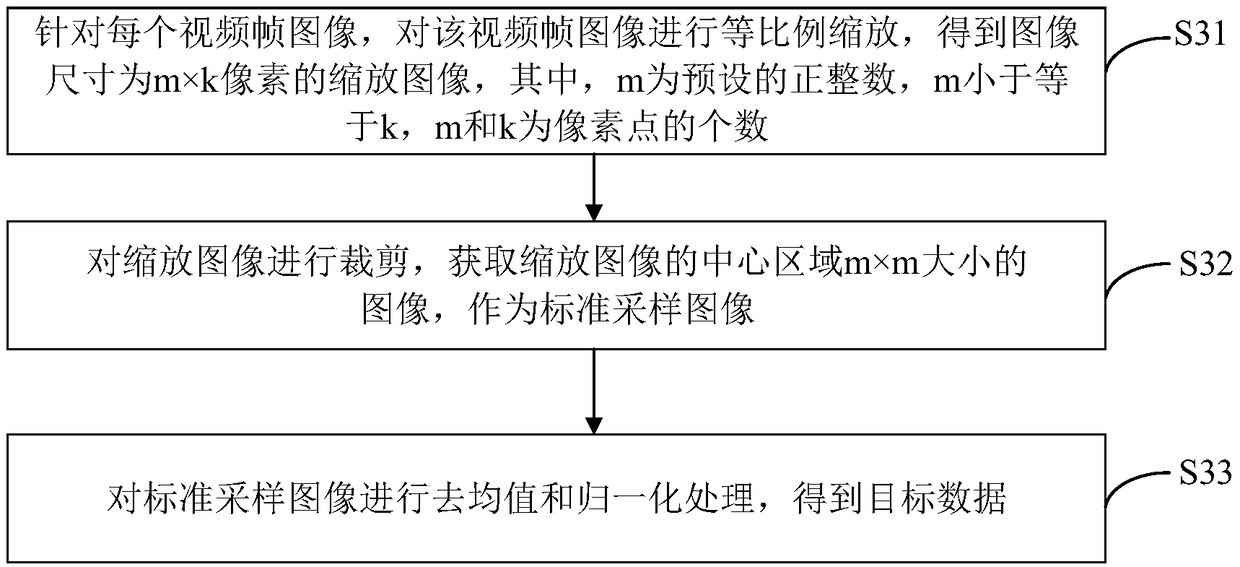
An abnormal behavior monitoring method, apparatus, computer device, and storage medium are disclosed. The method comprises: receiving a real-time video stream sent by a monitoring end, and extractinga preset number of video frame images from the video frame images according to a preset frequency as video sample data, thus avoiding network congestion and low processing efficiency caused by real-time video streams with large amount of data from being used directly, which improves the stability and timeliness of abnormal behavior monitoring, At that same time, the video sample data is preprocessed to obtain target data, and then the target data is input into the preset 3D convolutional neural network model for recognition, and the recognition result is compared with the preset abnormal behavior category, When the recognition result is one of the preset abnormal behavior categories, it is determined that the abnormal behavior is included in the video sampling data, so that the abnormal behavior in the video sampling data is automatically recognized by the 3D convolutional neural network model, and the automation and efficiency of the abnormal behavior monitoring are ensured.
Owner:PING AN TECH (SHENZHEN) CO LTD
Abnormal behavior monitoring processing method and device, computer device and storage medium
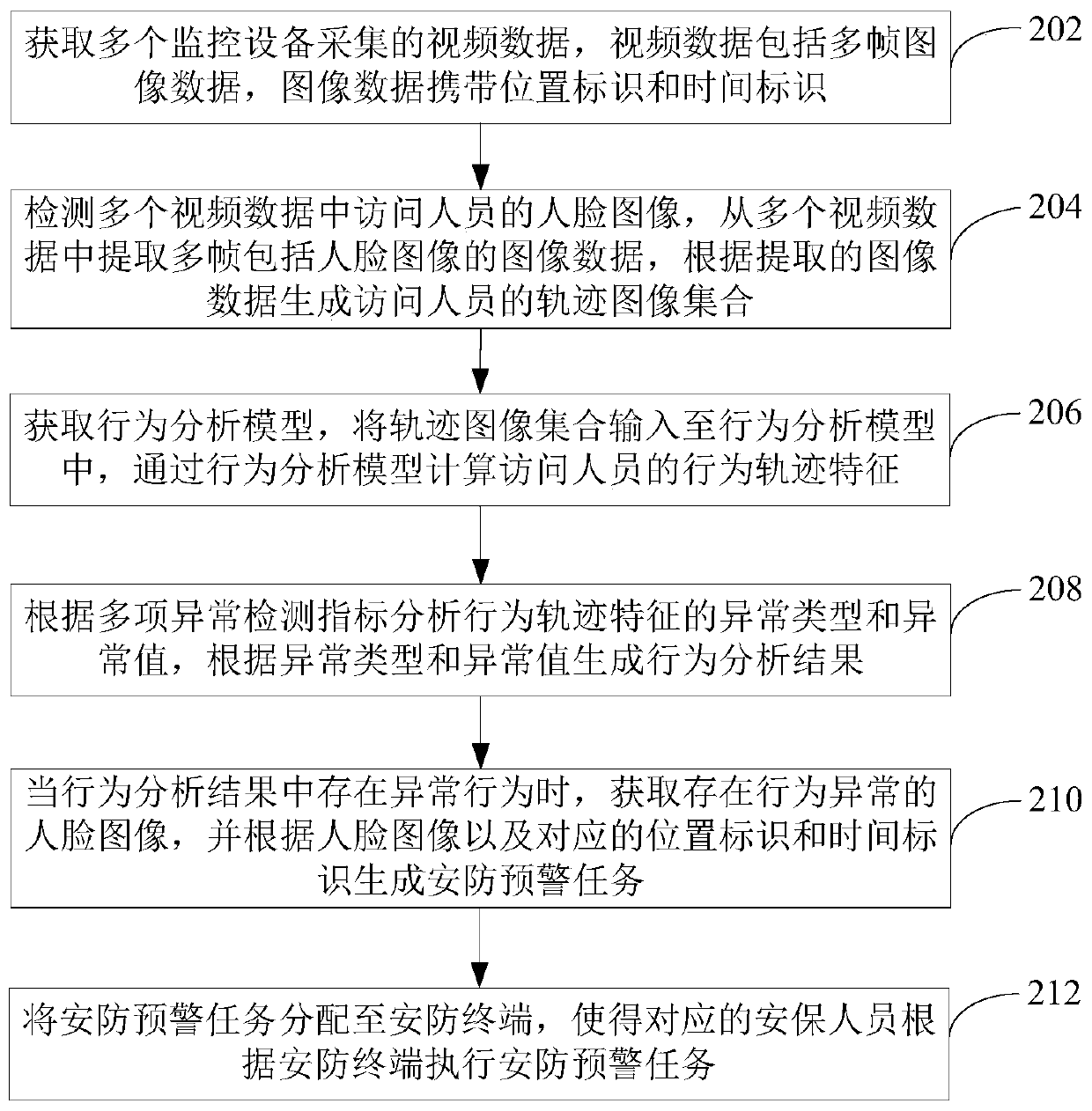
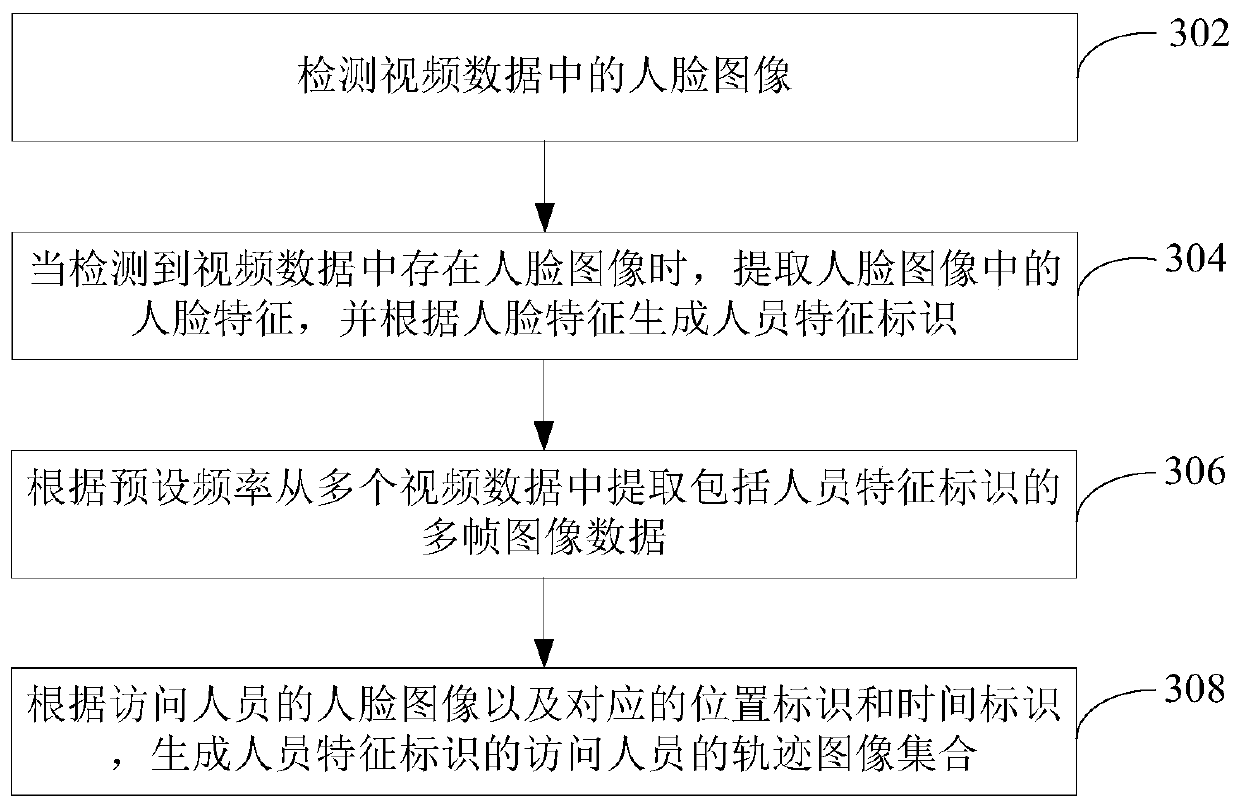
InactiveCN110443109AEasy to handleTimely and effective executionData processing applicationsCharacter and pattern recognitionBehavioral analyticsAnomaly detection
The invention relates to an abnormal behavior monitoring processing method, and the method comprises the steps: obtaining video data collected by a plurality of pieces of monitoring equipment, detecting a face image of a visitor in the plurality of pieces of video data, extracting a plurality of frames of image data comprising the face image from the plurality of pieces of video data, and generating a track image set corresponding to the visitor; calculating behavior track characteristics of the track image set through a behavior analysis model, analyzing abnormal types and abnormal values ofthe behavior track characteristics according to the plurality of abnormal detection indexes, and generating a behavior analysis result; when an abnormal behavior exists in the behavior analysis result, obtaining a face image with the abnormal behavior, and generating a security and protection early warning task according to the face image and the corresponding position identifier and time identifier; distributing the security and protection early warning task to the security and protection terminal so that the corresponding security personnel can execute the security and protection early warning task according to the security and protection terminal. By adopting the method, the abnormal behaviors of the visitors can be accurately and effectively identified so as to improve the abnormal monitoring efficiency of the park.
Owner:WANYI TECH
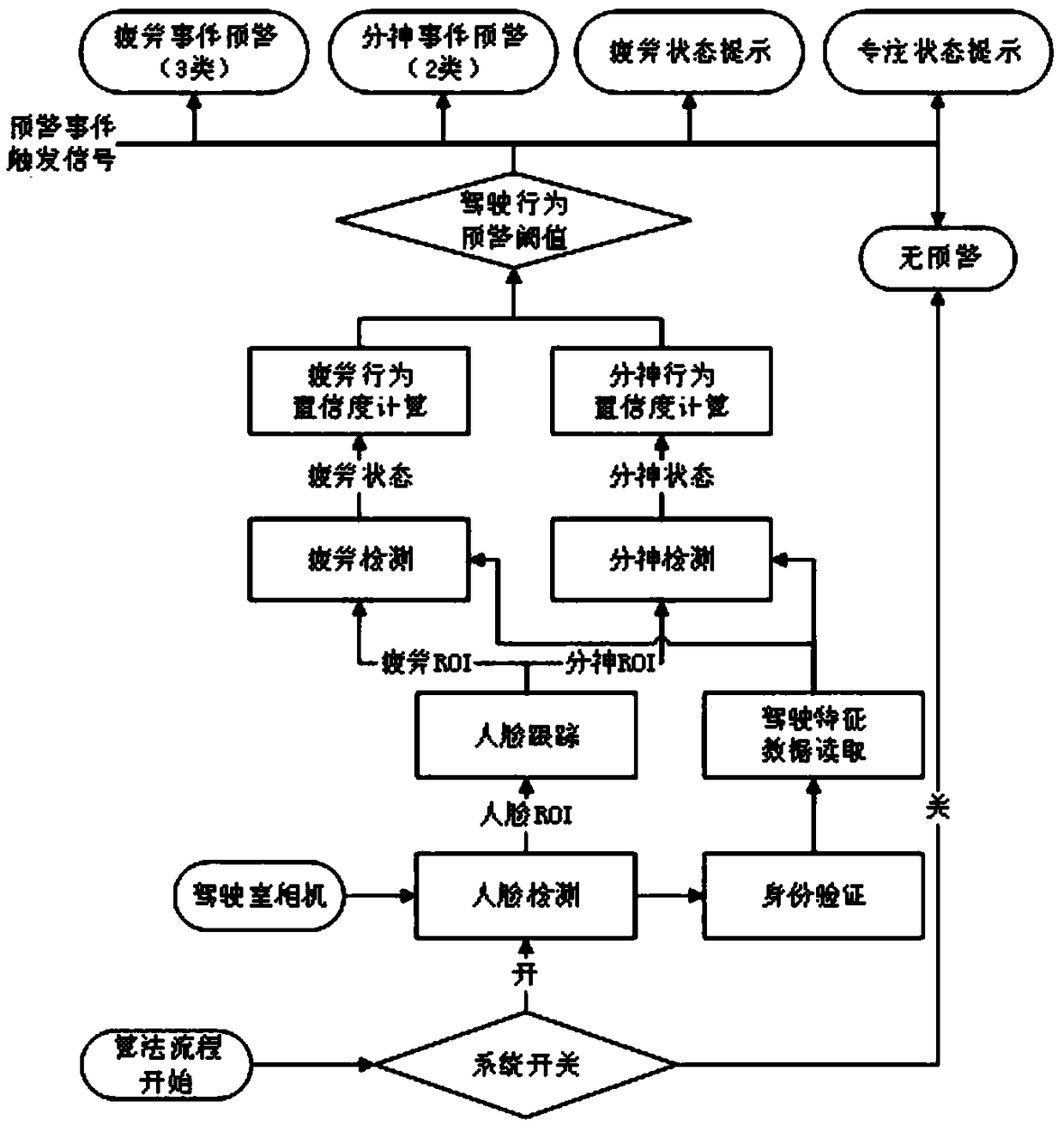
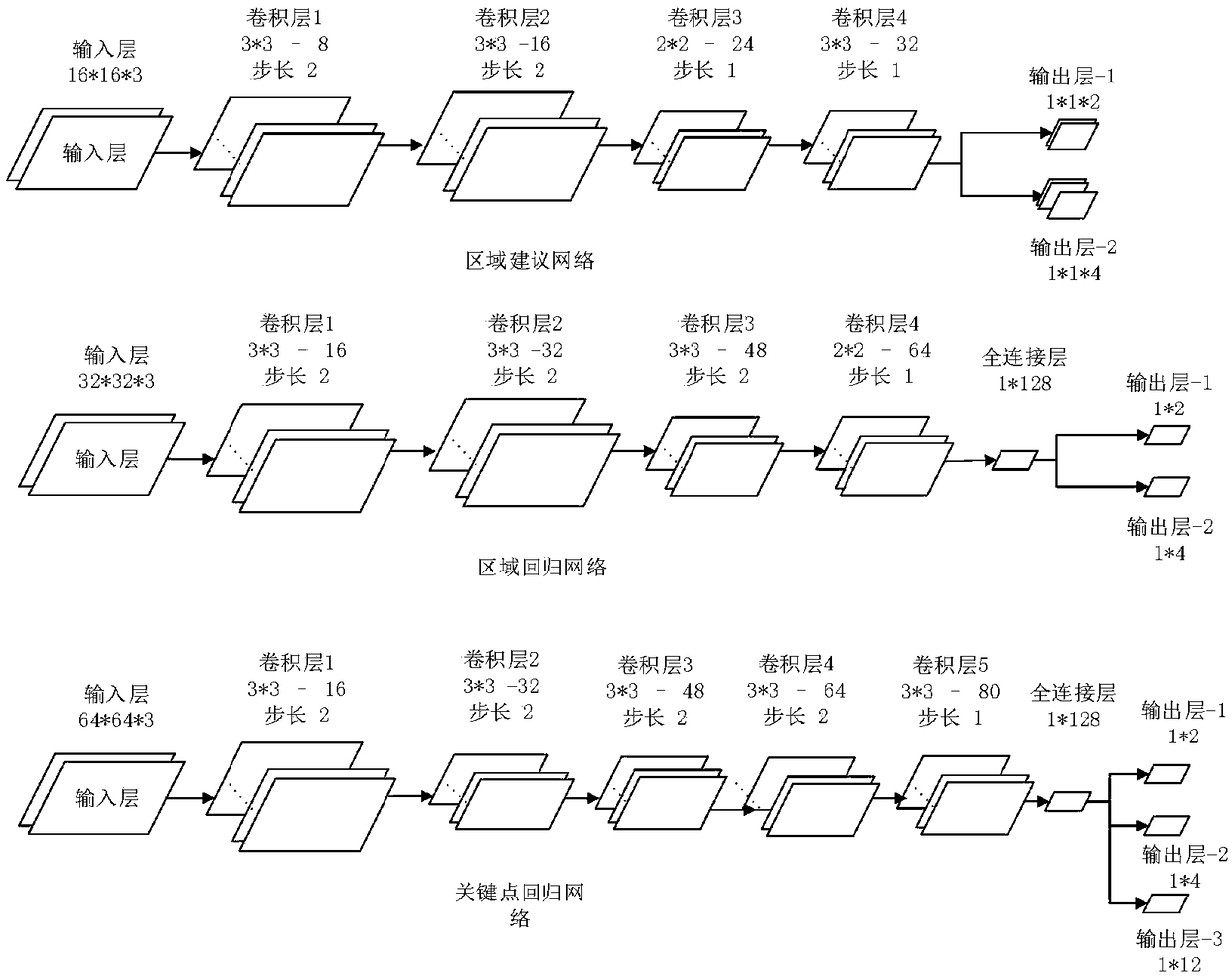
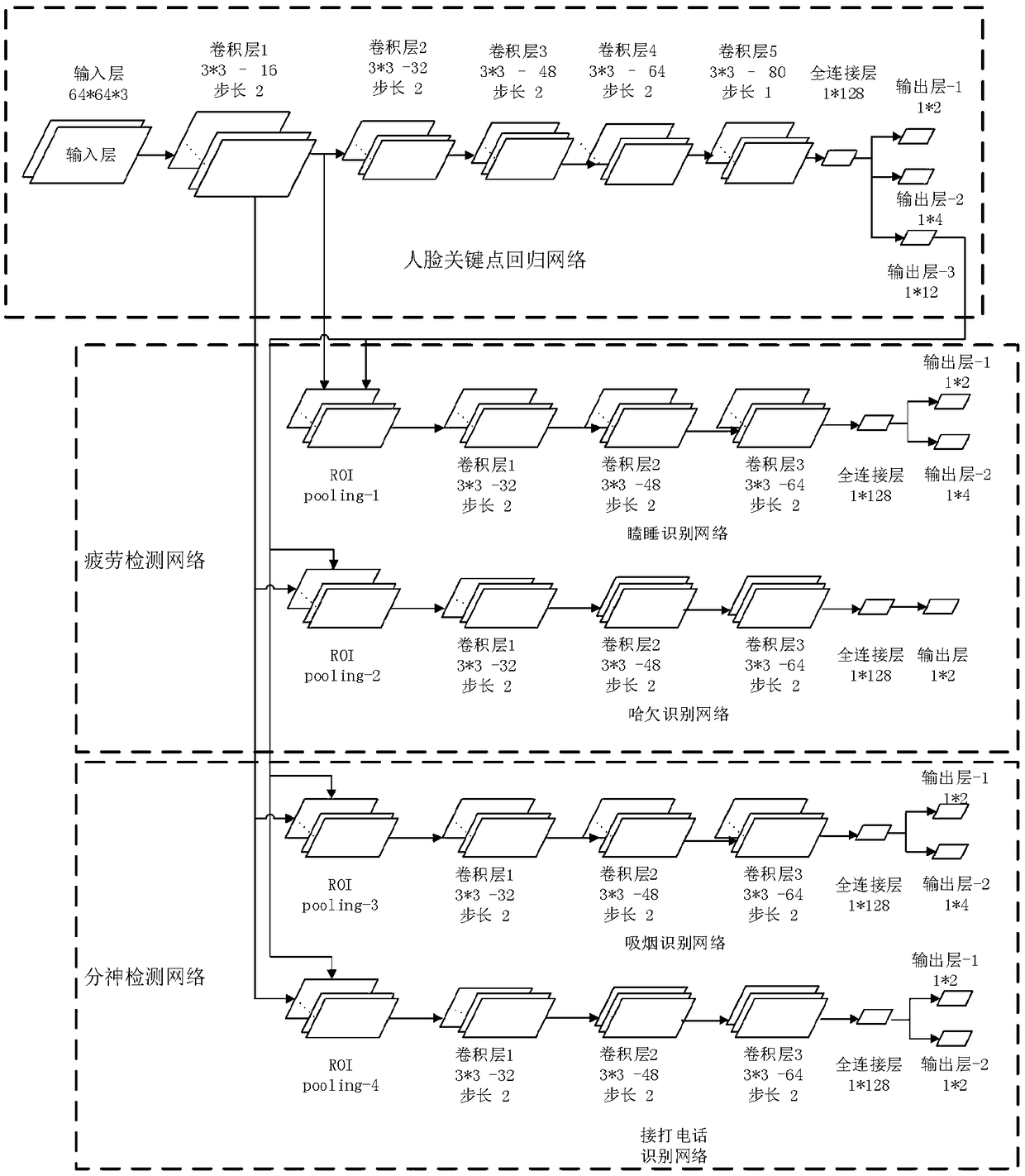
Vision-based driving behavior detecting method
ActiveCN108960065AWide range of early warning applicationsImprove effectivenessCharacter and pattern recognitionControl devicesFace detectionDistraction
The invention provides a vision-based driving behavior detecting method. The method comprises: collecting a cab image, extracting face information, carrying out face detection and identity verification by using a deep convolutional neural network, and outputting a face key point position and a face feature map; on the basis of the outputted face key point position and face feature map, carrying out fatigue driving application detection and distracting driving application detection; and determining a fatigue state and distraction state of a driver based on fatigue driving and distracting driving application detection results, sending out fatigue early-warning and distracting early-warning signals, warning a driving fatigue behavior and driving distraction behavior early, and determining anddisplaying a driving fatigue level and a driving concentration level. According to the invention, the driver behavior monitoring system is perfected; the fatigue driving behaviors like drowsiness, yawning, and head lowering and distracting driving behaviors like call receiving and calling and smoking during the driving process are analyzed intelligently; and behavior prompting is carried out.
Owner:ZHEJIANG LEAPMOTOR TECH CO LTD
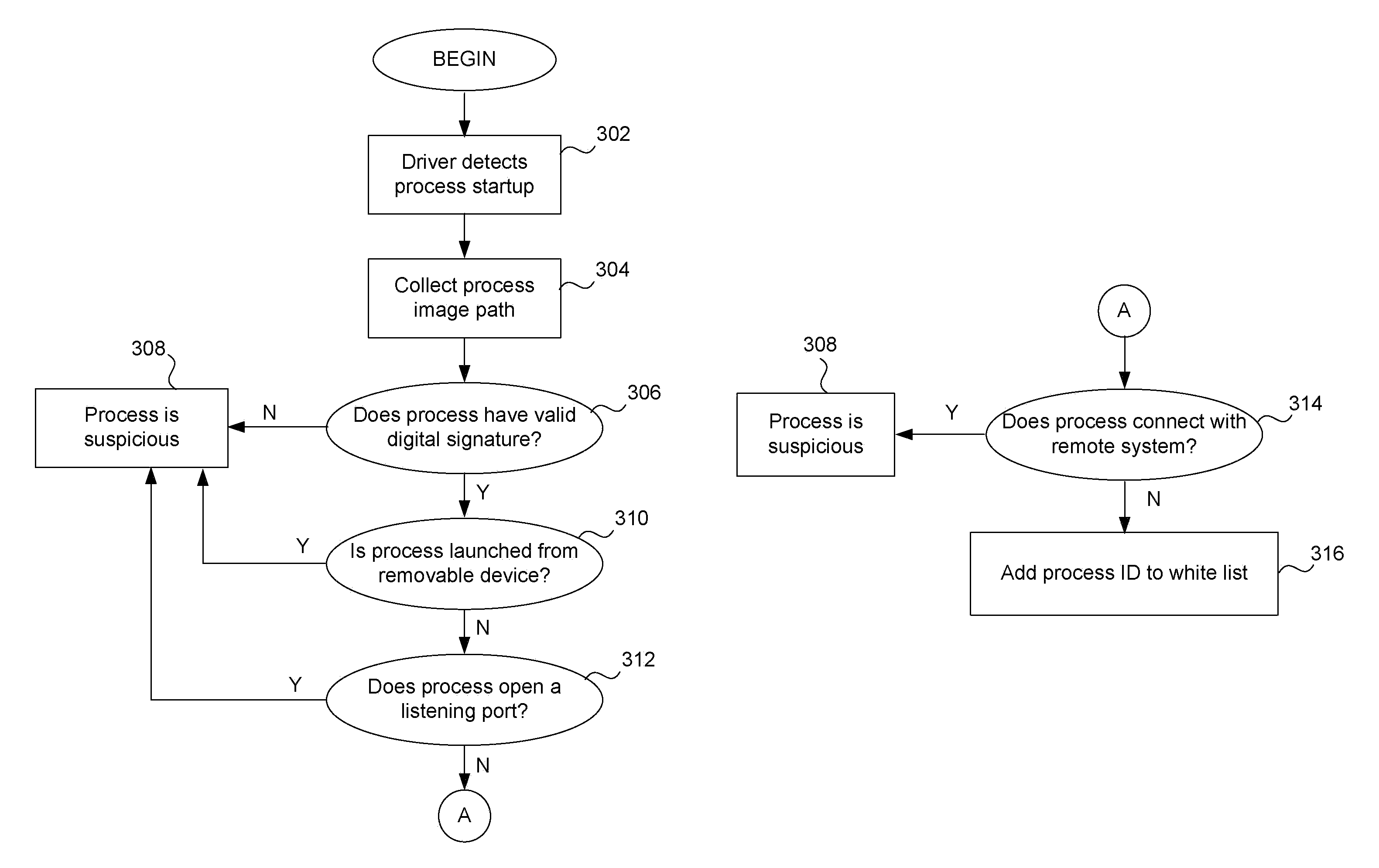
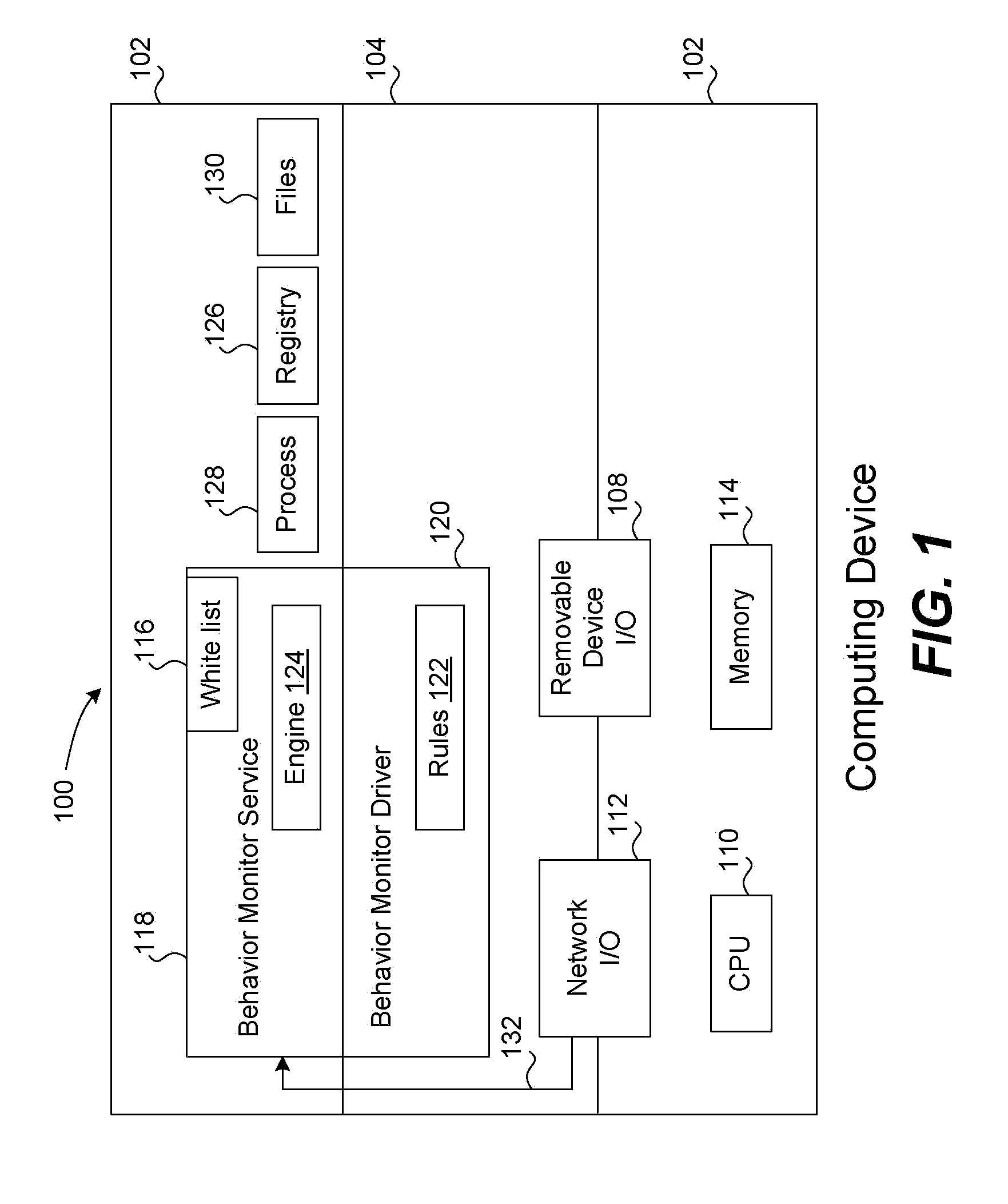
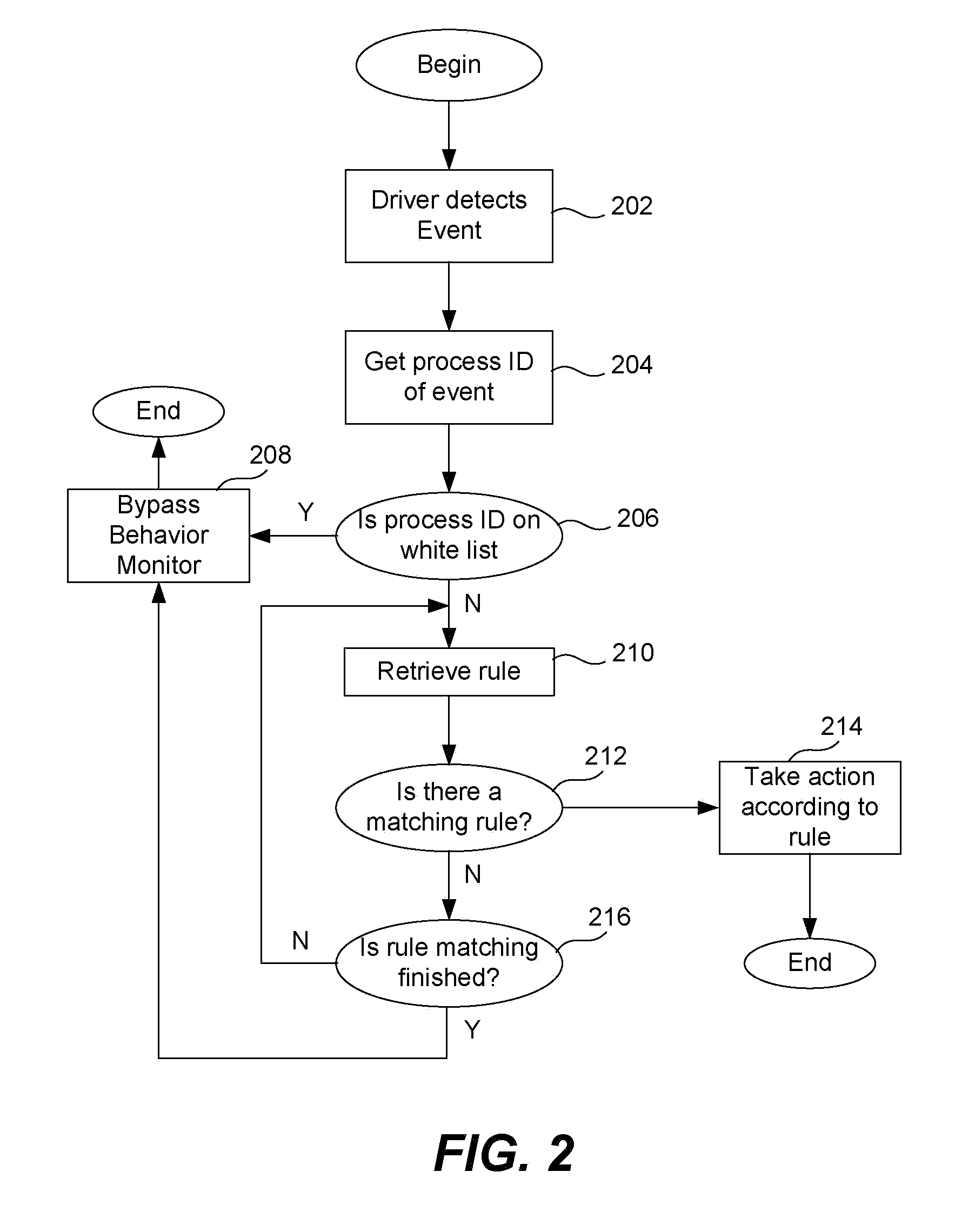
White list creation in behavior monitoring system
ActiveUS8161552B1Memory loss protectionDigital data processing detailsDigital signatureMonitoring system
A white list (or exception list) for a behavior monitoring system for detecting unknown malware on a computing device is maintained automatically without human intervention. A white list contains process IDs and other data relating to processes that are determined to be (or very likely be) free of malware. If a process is on this list, the rule matching operations of a conventional behavior monitor are not performed, thereby saving processing resources on the computing device. When a process start up is detected, the behavior monitor performs a series of checks or tests. If the process has all valid digital signatures and is not launched from a removable storage device (such as a USB key) and is not enabled to make any inbound or outbound connections, it is eligible for being on the white list. The white list is also automatically maintained by removing process IDs for processes that have terminated or which attempt to make a new outbound or inbound connection, such as a TCP / UDP connection. Scheduled integrity checks on the white list are also performed by examining the process stack for each process to ensure that there are no abnormal files in the process stack.
Owner:TREND MICRO INC
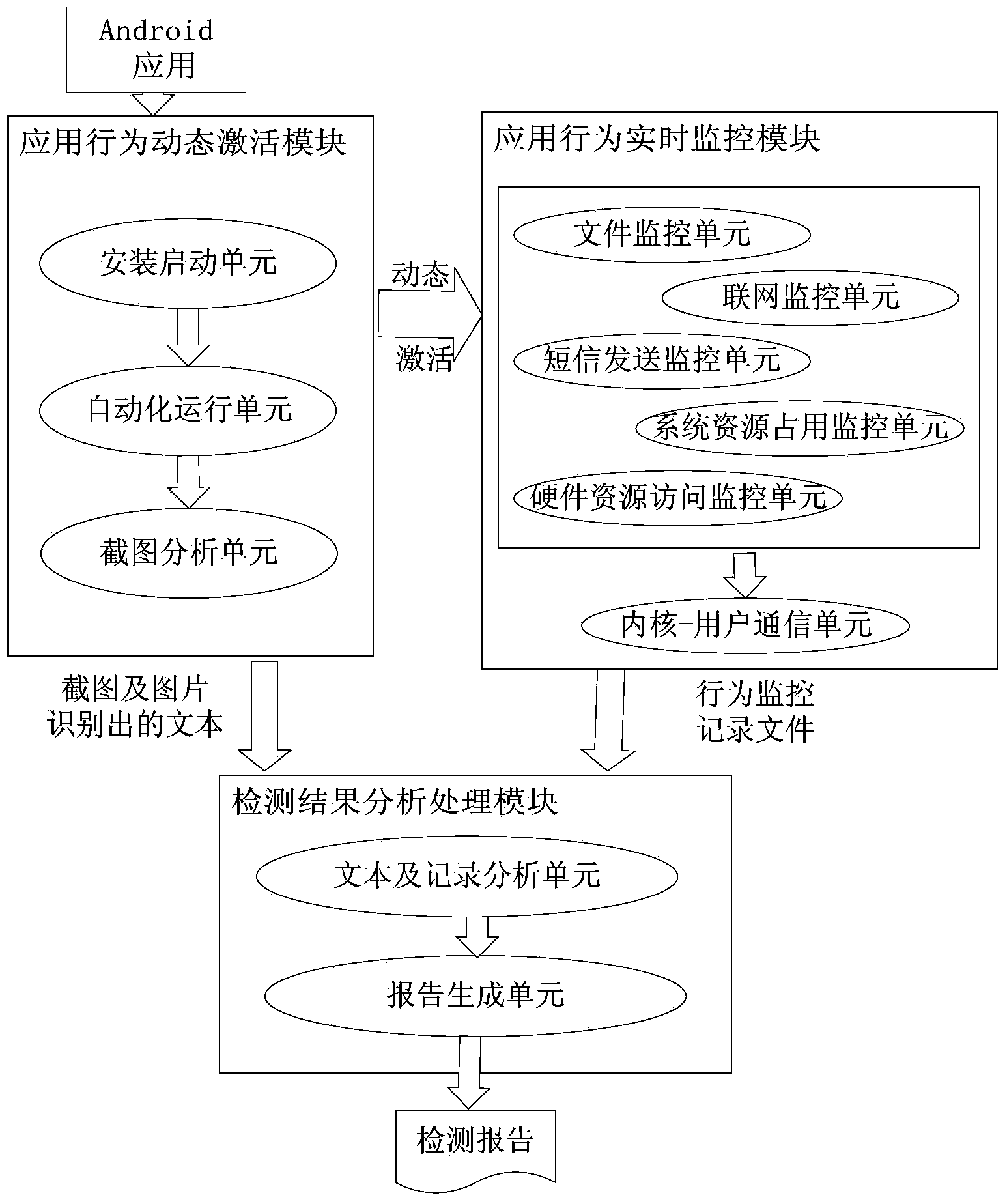
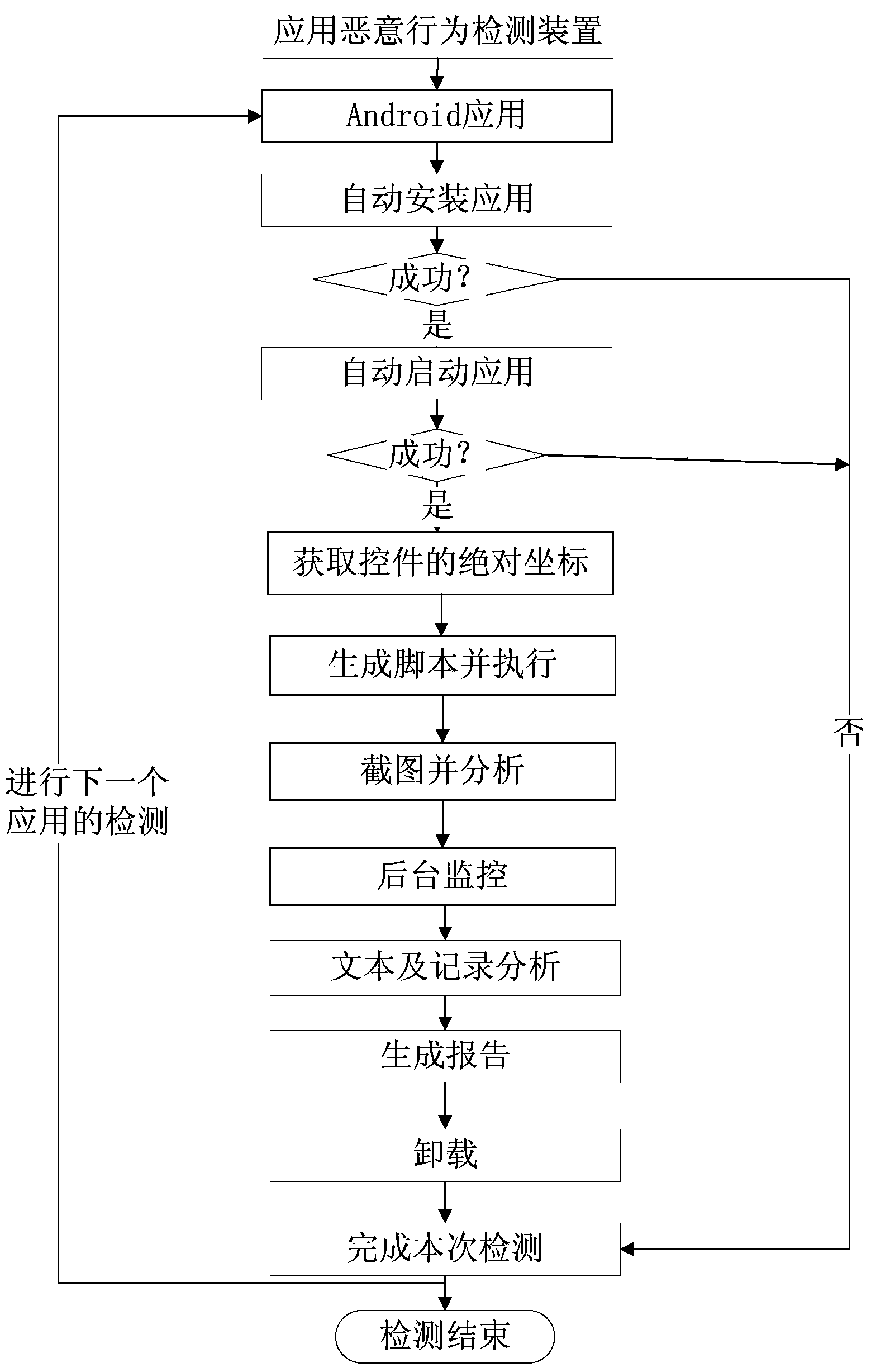
Android malicious code detection device and method based on dynamic activation and behavior monitoring
InactiveCN104182688ARealize the detection of full functional coverageEnsure comprehensivenessPlatform integrity maintainanceTraffic capacityNetwork connection
Disclosed is an android malicious code detection device and method based on dynamic activation and behavior monitoring. According to the device, behaviors of a cellphone terminal automatically installing and starting an application to be detected and automatically activating the application are controlled; meanwhile, during the whole running process of the application, information of the cellphone terminal, such as file access, short message sending, network connection, traffic, system resource usage and hardware resource access, is monitored in real time, malicious behaviors of malicious codes are detected, a detection report is generated and provided for a user, and behaviors of the application under detection are dynamically detected. The device comprises an application behavior dynamic activation module, an application behavior real-time monitoring module and a detection result analysis module. The device and the method have the innovative advantages that all control and interface operations are achieved for the application by a software interaction technology, all application behaviors are dynamically activated, all-function automatic monitoring and detection is achieved for the application on the premise of finishing self-functions, and detection can be comprehensive and complete.
Owner:BEIJING SOFTSEC TECH
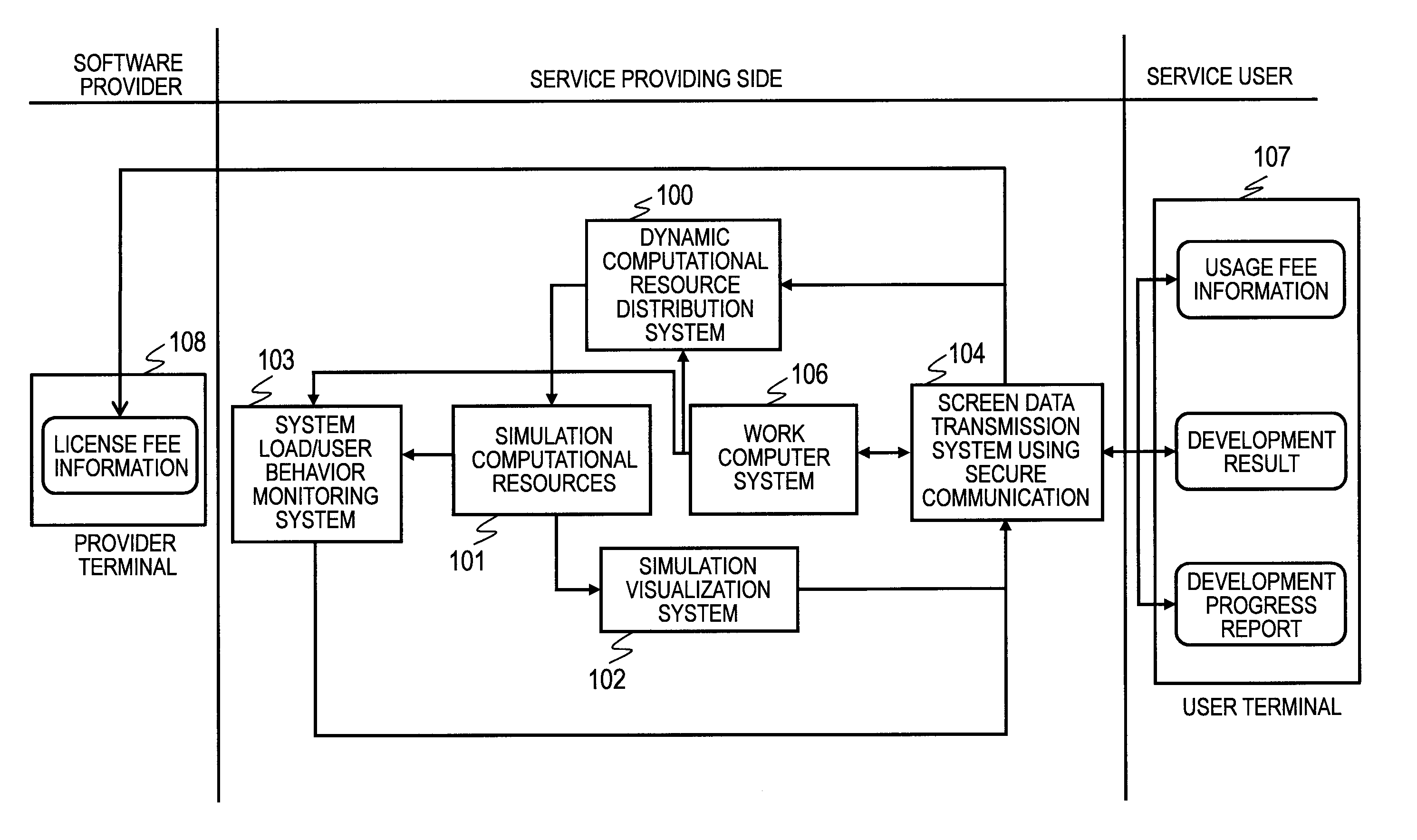
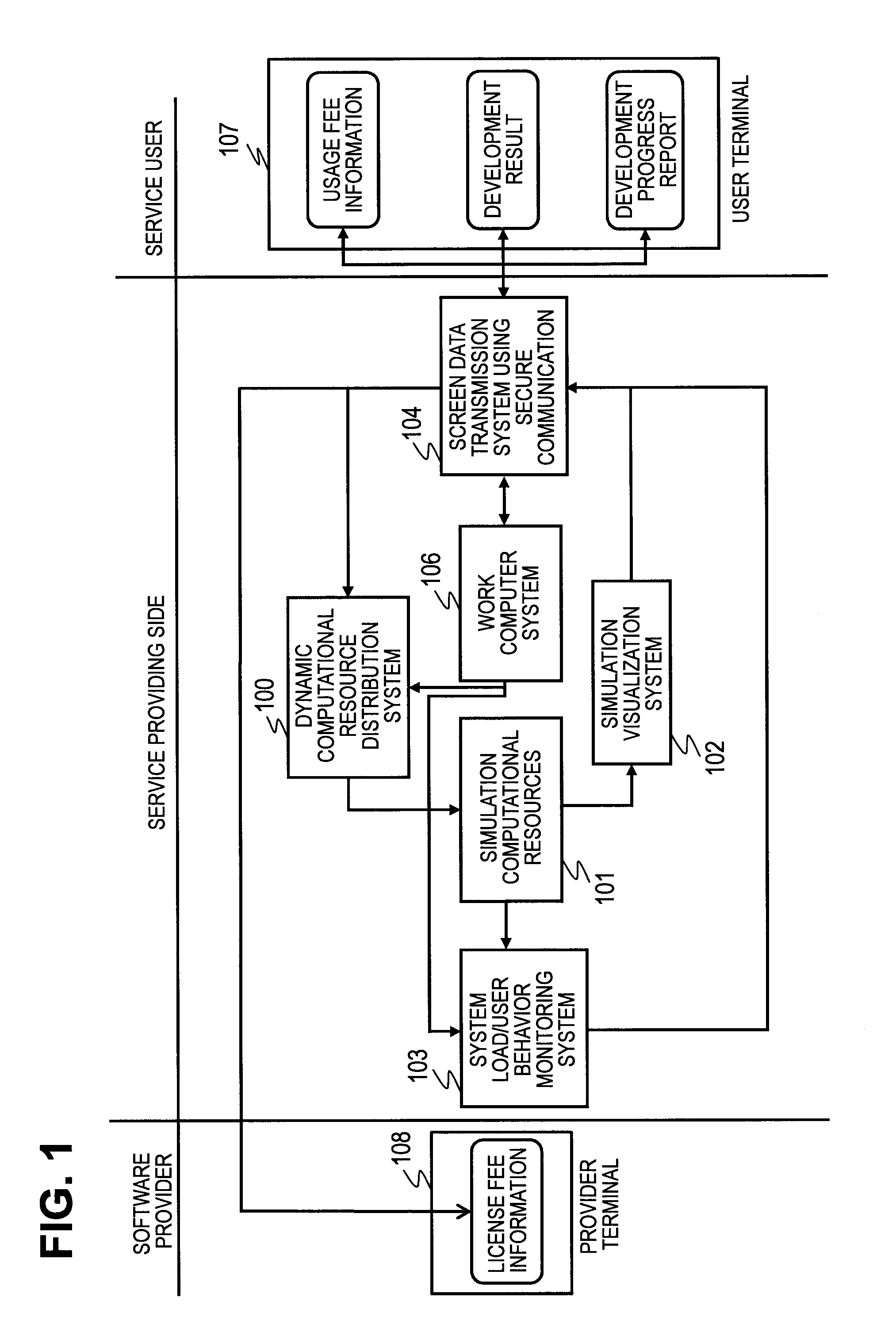
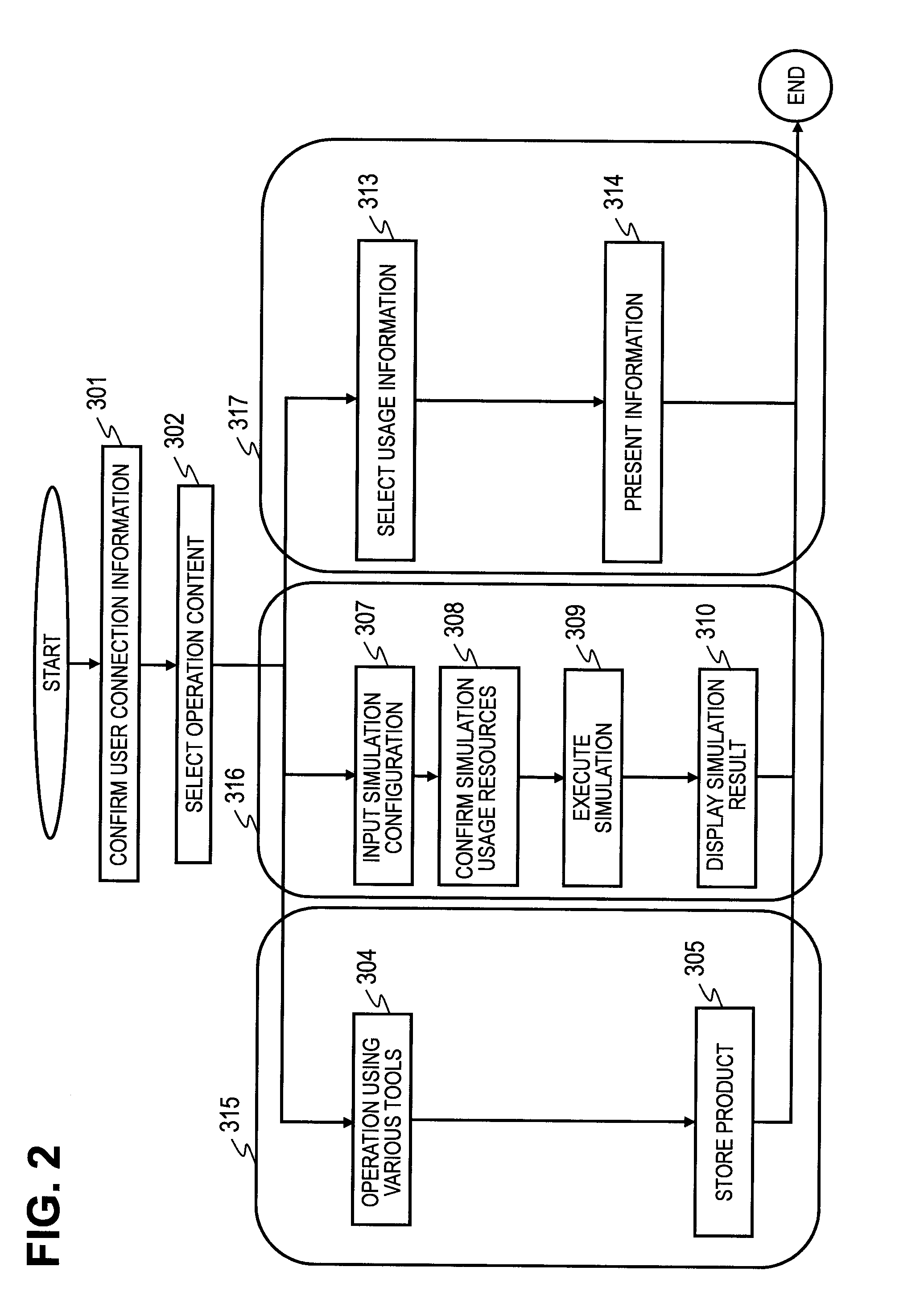
Computer System, Program, and Method for Assigning Computational Resource to be Used in Simulation
InactiveUS20120123764A1Easy to shareExecute quick and accurateError detection/correctionSpecial data processing applicationsComputerized systemDistribution system
The cost necessary for introducing and maintaining a development environment that includes multiple simulators is suppressed, and a sharing of designing information is promoted, to make parameter adjustment of simulators easy. Provided is a service that unifies development environment on a computer provided with: a working computer system that can guarantee that there is no leaking of designing files; a user behavior monitoring system that collects utilization history of simulators or software, for each of the users, and selects development process of each of the users from the collected information; and a dynamic computational-resource distribution system that can conduct an automatic optimization of a complex simulation configuration, from information collected by the aforementioned user behavior monitoring system.
Owner:HITACHI LTD
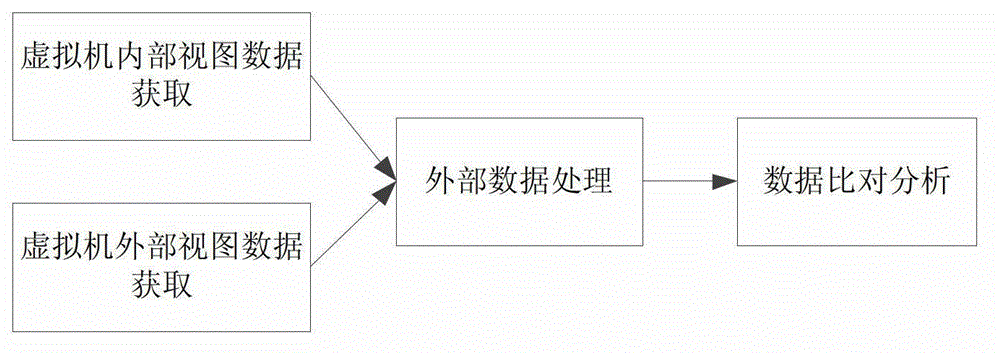
Detection method and system for cross comparison of malicious code of interior and exterior view based on virtual machine
ActiveCN102750475AImprove detection accuracyRealize multi-point monitoringComputer security arrangementsSoftware simulation/interpretation/emulationView basedOriginal report
The invention provides a detection method and system for cross comparison of malicious codes of an interior and exterior view based on a virtual machine.The method comprises the following steps that: a virtual machine controller starts a virtual machine detector, sends malicious codes of an analysis catalogue to the virtual machine detector and controls the virtual machine detector; the virtual machine detector monitors the memory change of the virtual machine while running the malicious codes, records the running trace, forms an original report, and then sends the report to a comprehensive analyzer after the original report generation is finished; and the comprehensive analyzer comprehensively analyzes the relation of behavior event attribute elements and behavior text relation of the malicious sequence behavior recorded by the reports to analyze the malicious behaviors of changing the malicious codes. The method and system can acquire operation behaviors of a virtual machine system by adopting a real-time multi-view dynamic behavior monitoring mode.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com