Automatic analyzing system and method for dynamic action of malicious program
A technology for automatic analysis and malicious programs, which is applied in the field of system security and network security, and automatic analysis system for dynamic behavior of malicious programs. Effects on Performance and Operational Efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
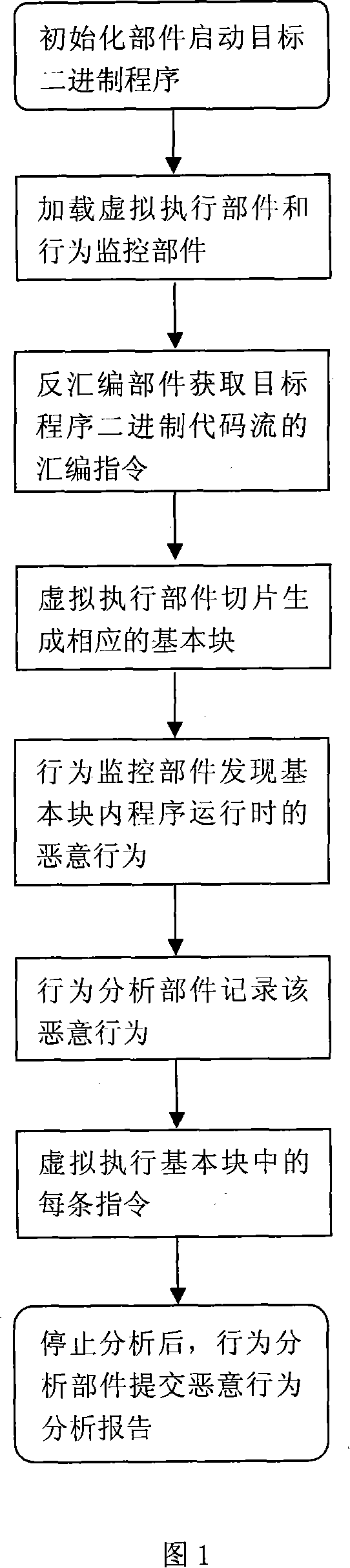
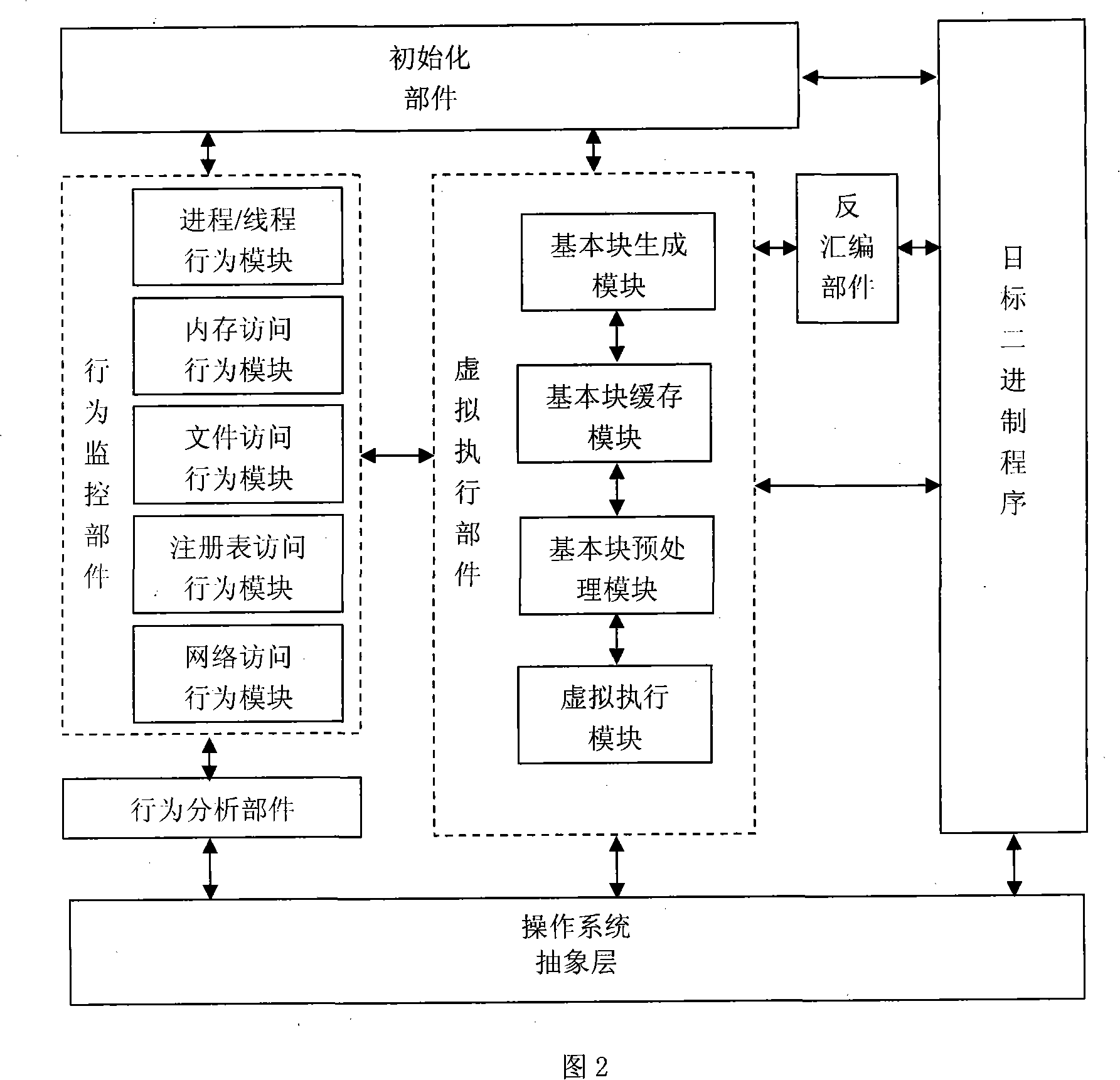
[0025] Referring to Fig. 1, the initialization component of the malicious program dynamic behavior automatic analysis system first starts the unknown binary program to be analyzed, and will also load the virtual execution component and the behavior monitoring component at the same time. The virtual execution unit will be loaded into the process space of the target binary program, so as to effectively control the execution of the target binary program code flow. The behavior monitoring component contains the default security behavior rule library, and users can also access the interface to process these rules, and support the addition, deletion and modification of rules.
[0026] After the initialization is completed, the binary program enters the execution state. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com