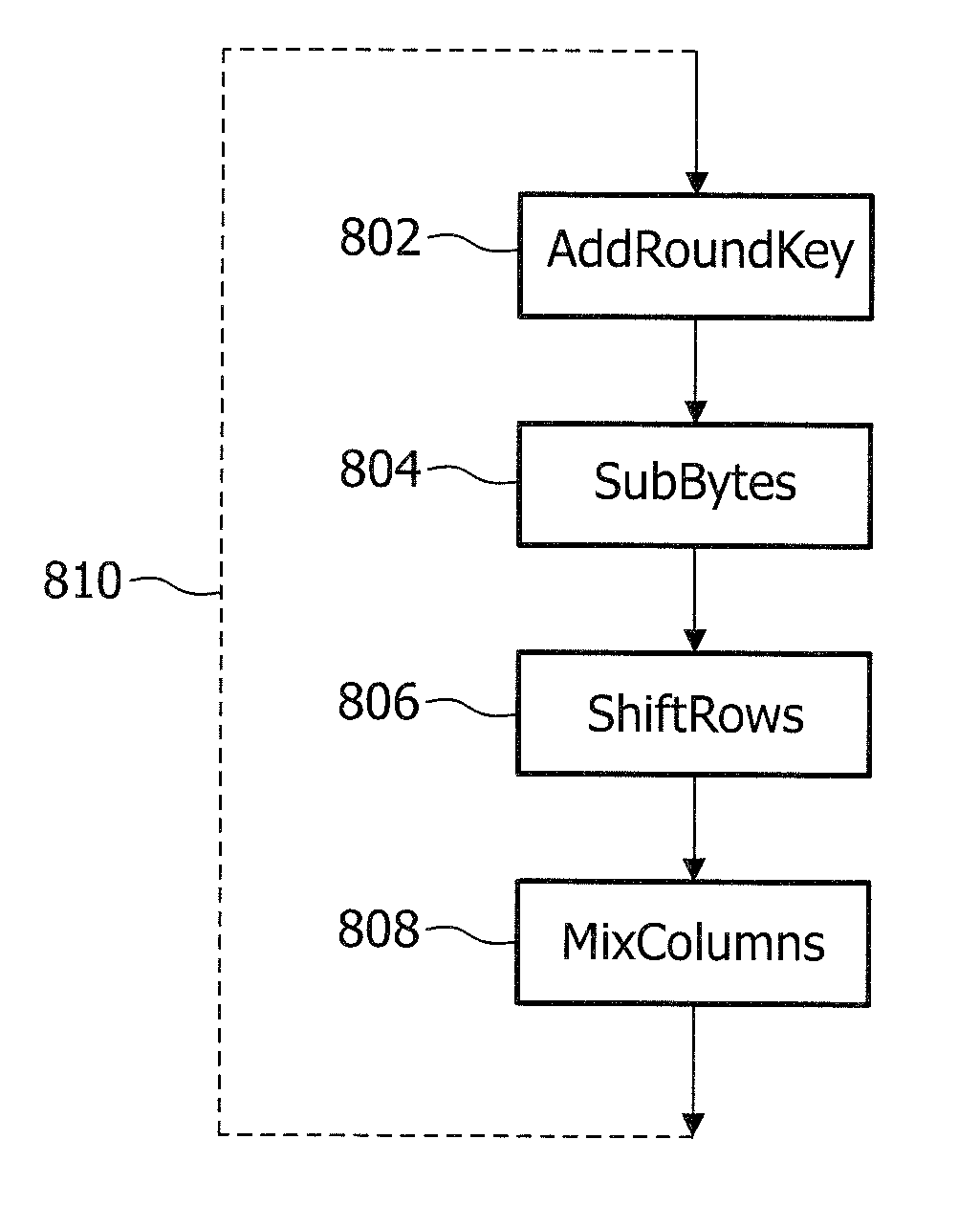
Patents
Literature
609 results about "Basic block" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
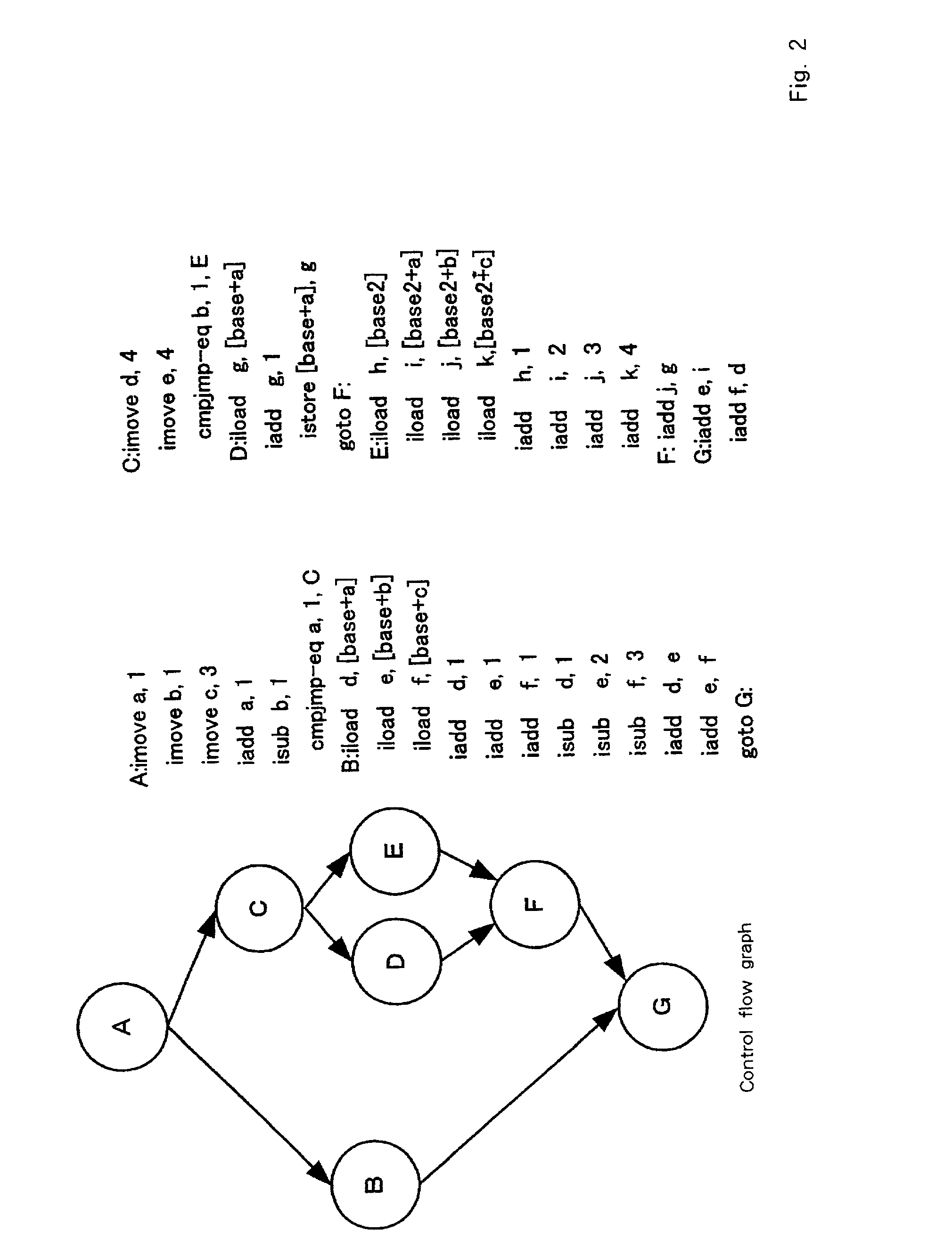
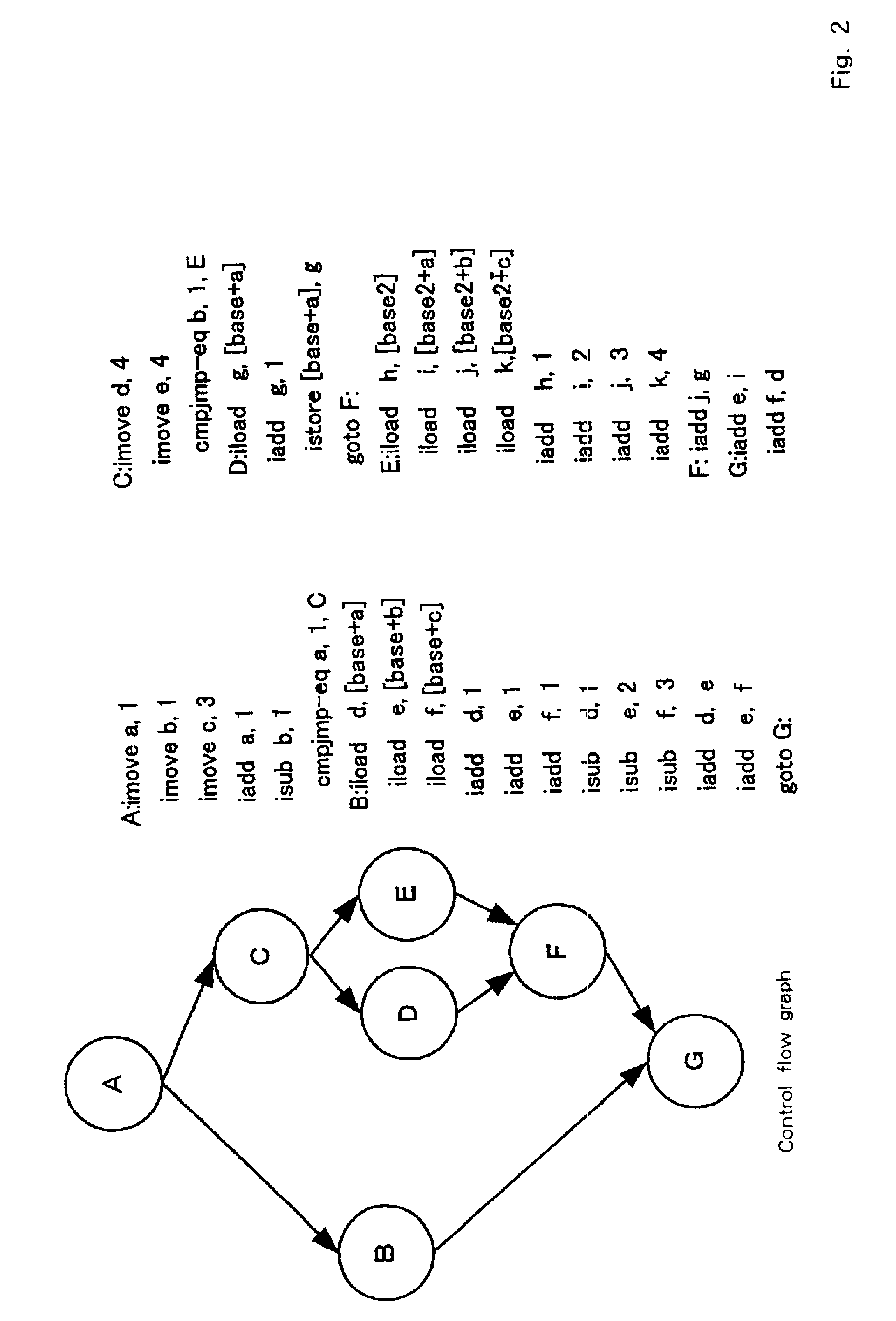
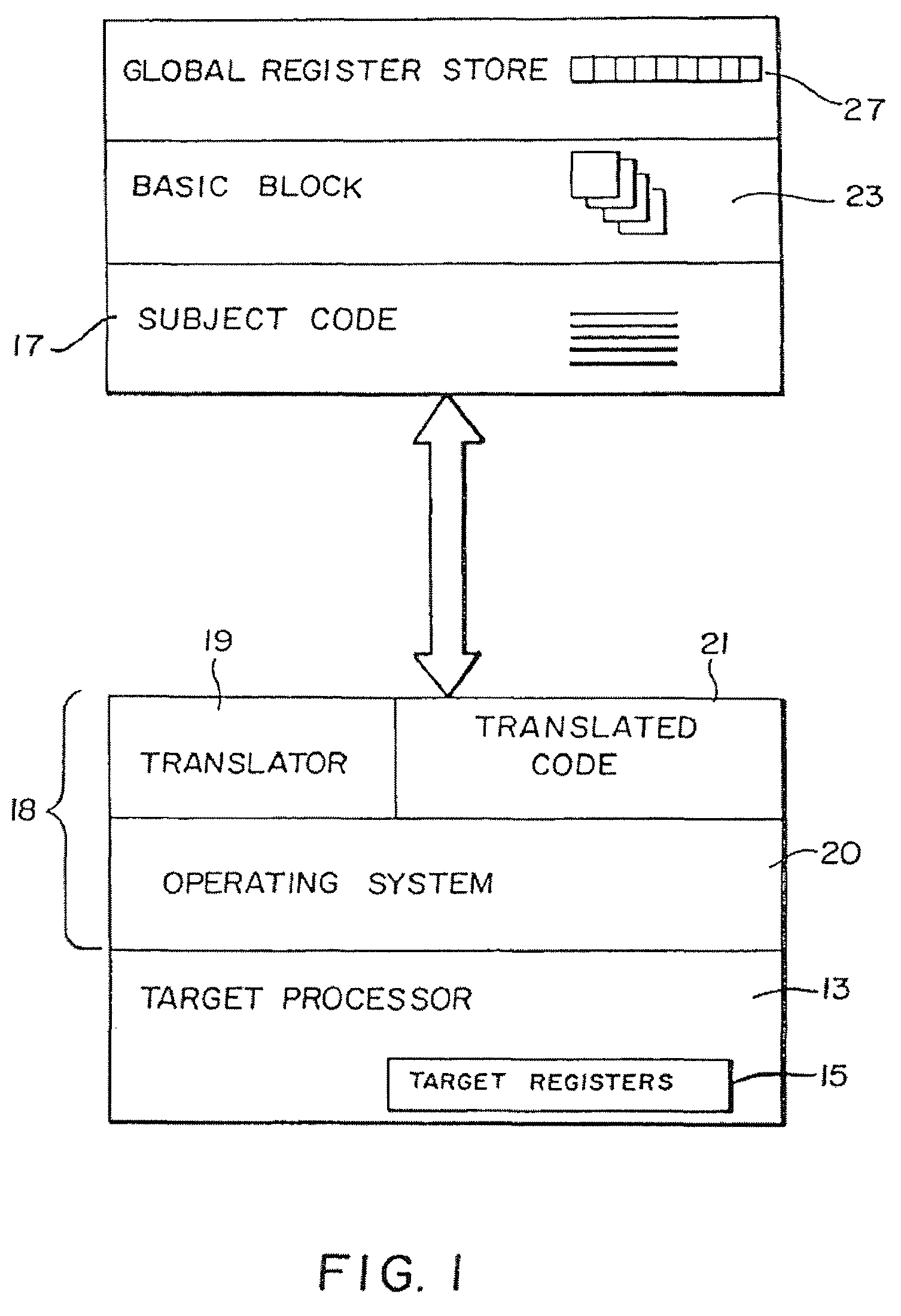
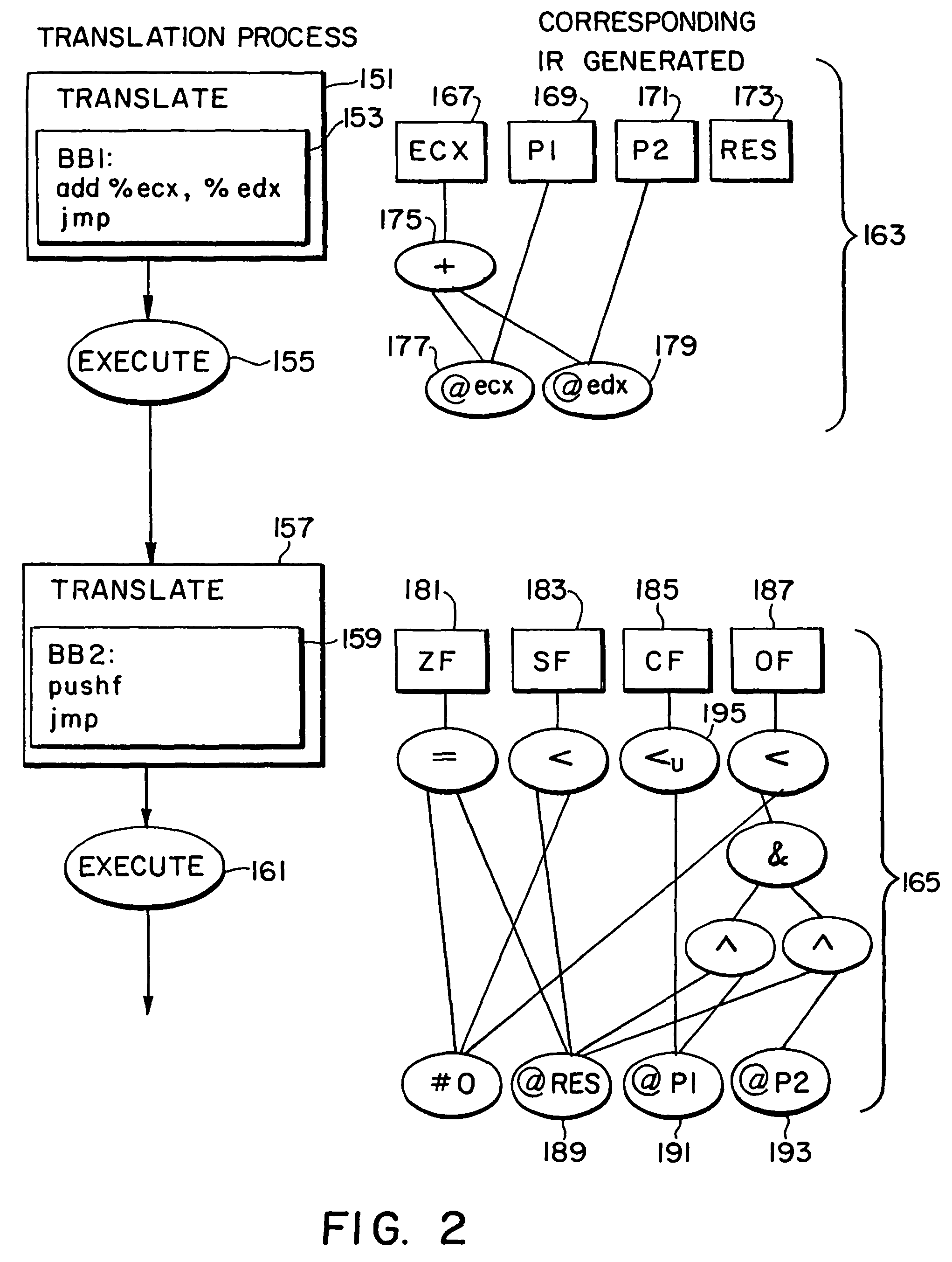
In compiler construction, a basic block is a straight-line code sequence with no branches in except to the entry and no branches out except at the exit. This restricted form makes a basic block highly amenable to analysis. Compilers usually decompose programs into their basic blocks as a first step in the analysis process. Basic blocks form the vertices or nodes in a control flow graph.
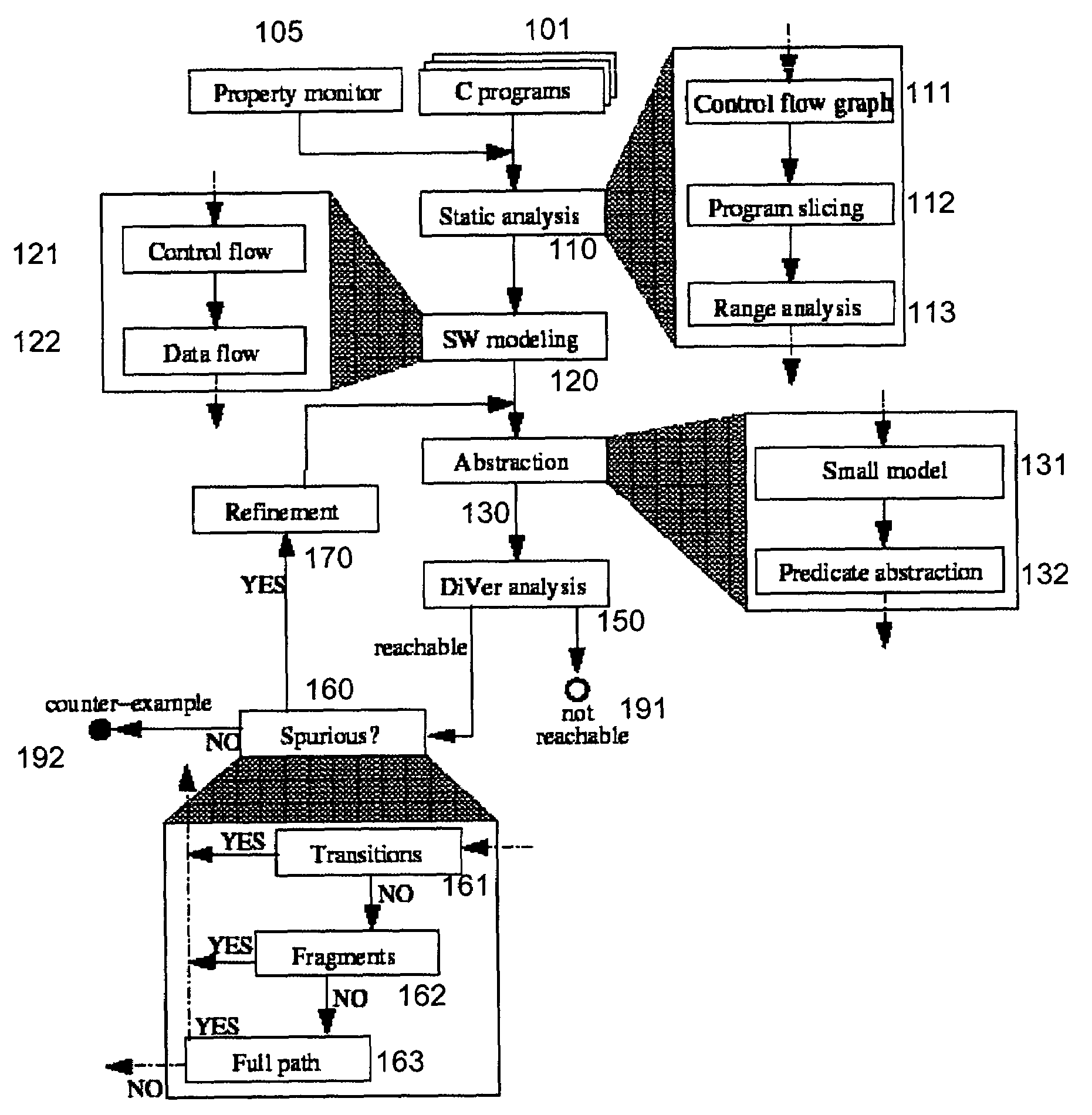
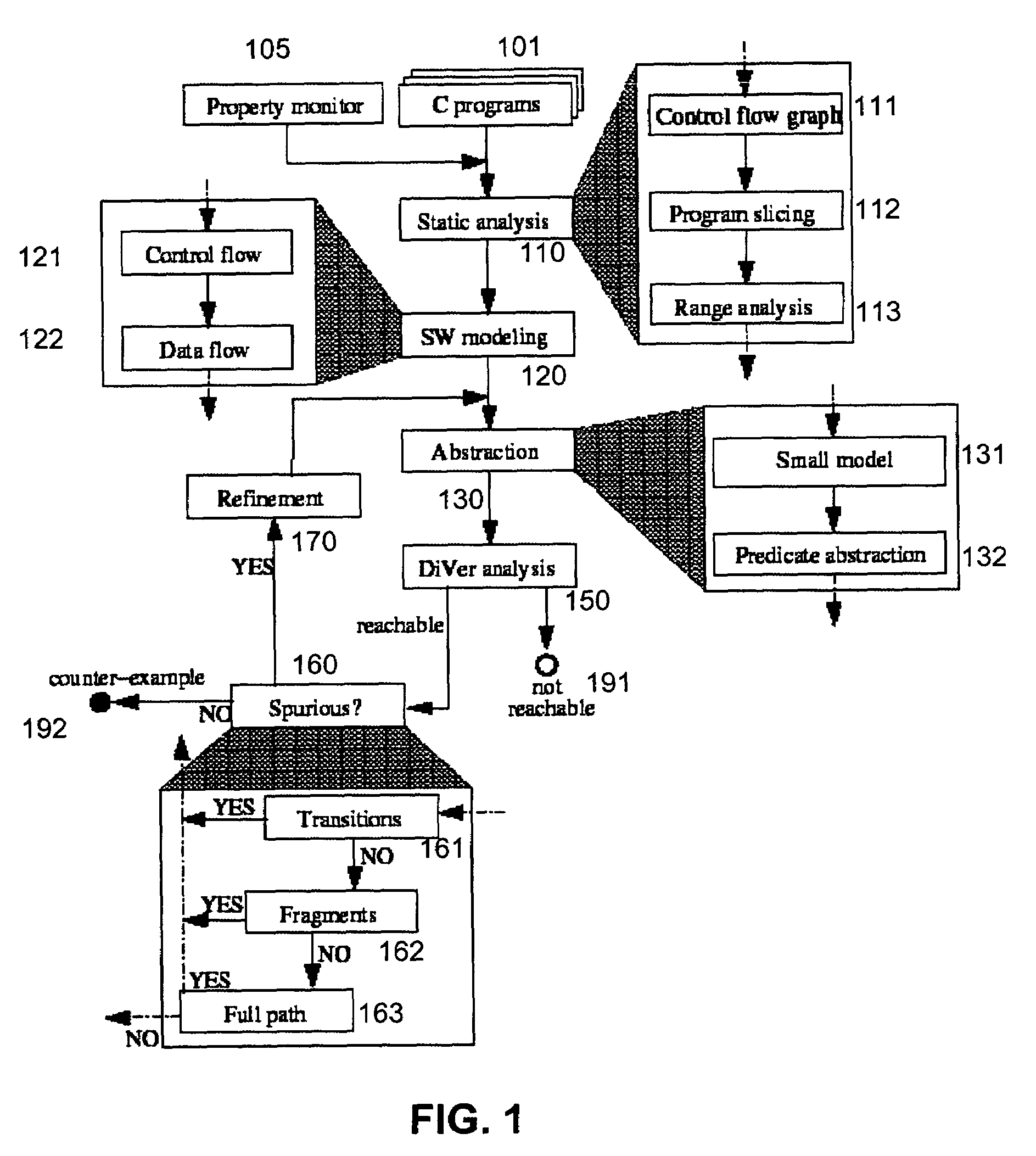
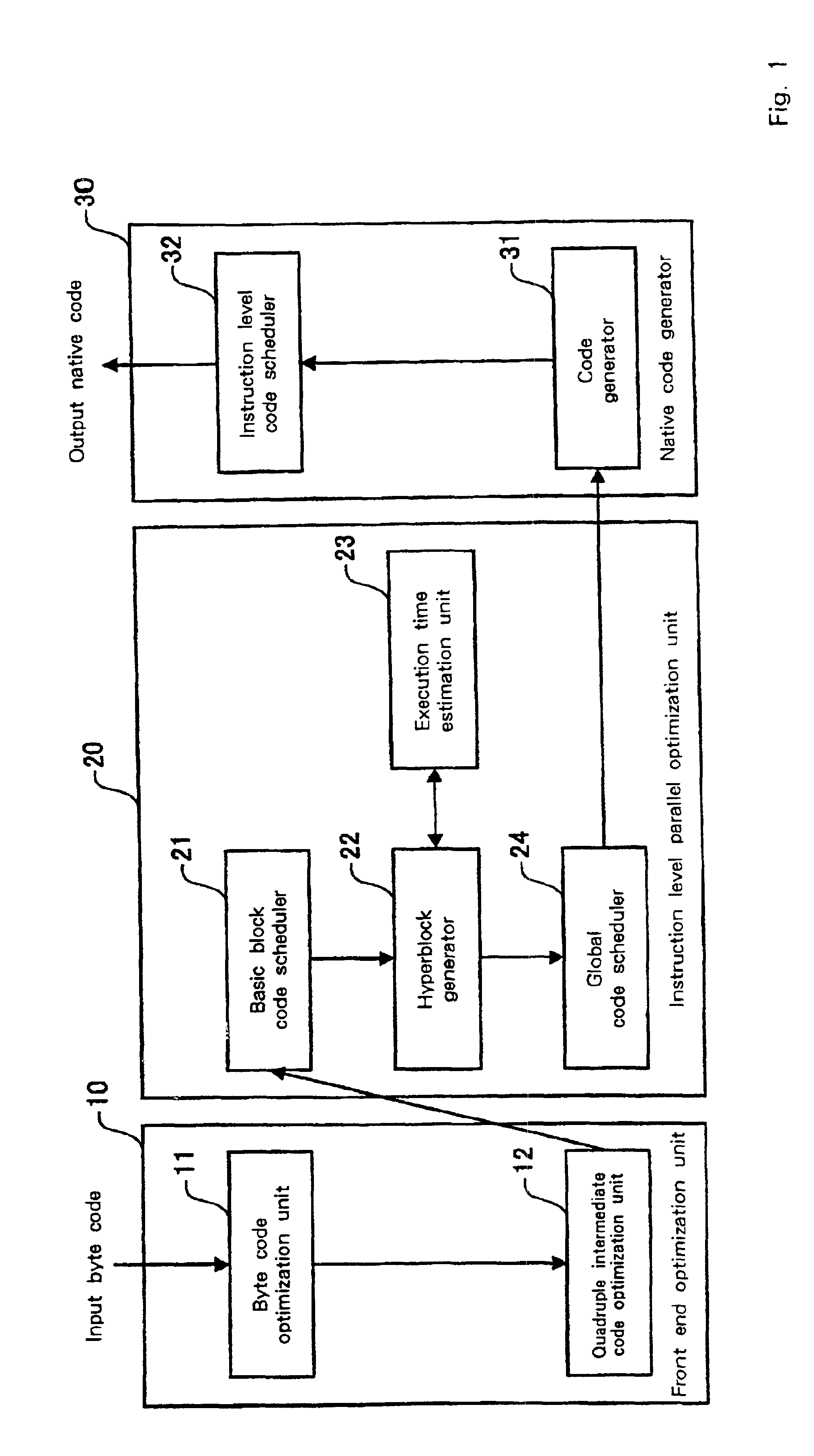
System and method for modeling, abstraction, and analysis of software
ActiveUS7346486B2Improve verification efficiencyImprove translationError detection/correctionComputation using non-denominational number representationBasic blockSoftware
A system and method is disclosed for formal verification of software programs that advantageously translates the software, which can have bounded recursion, into a Boolean representation comprised of basic blocks and which applies SAT-based model checking to the Boolean representation.
Owner:NEC CORP
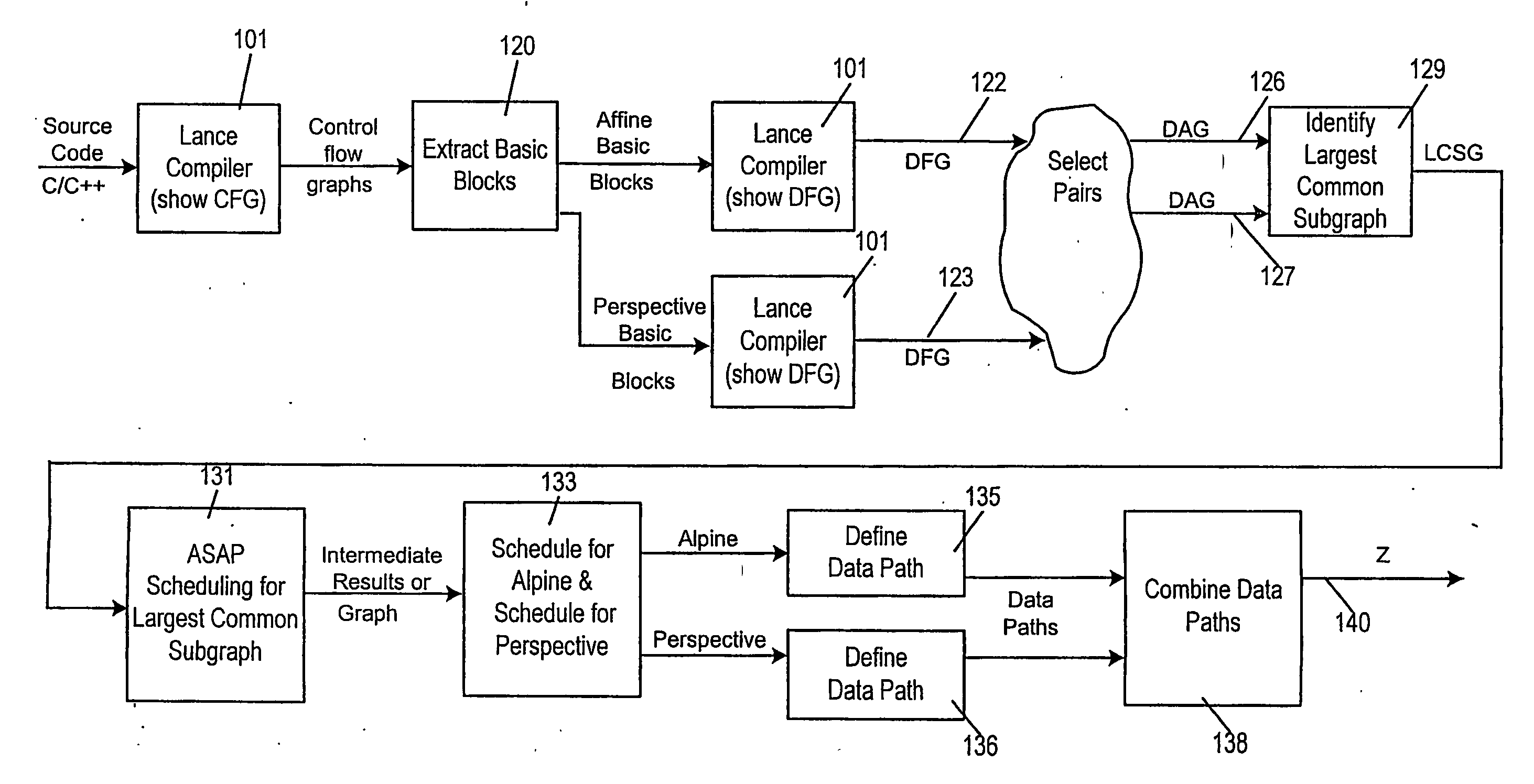
Reconfigurable processing
ActiveUS20070198971A1Reduce signal delayReduce areaEnergy efficient ICTSoftware engineeringPathPingComputer architecture
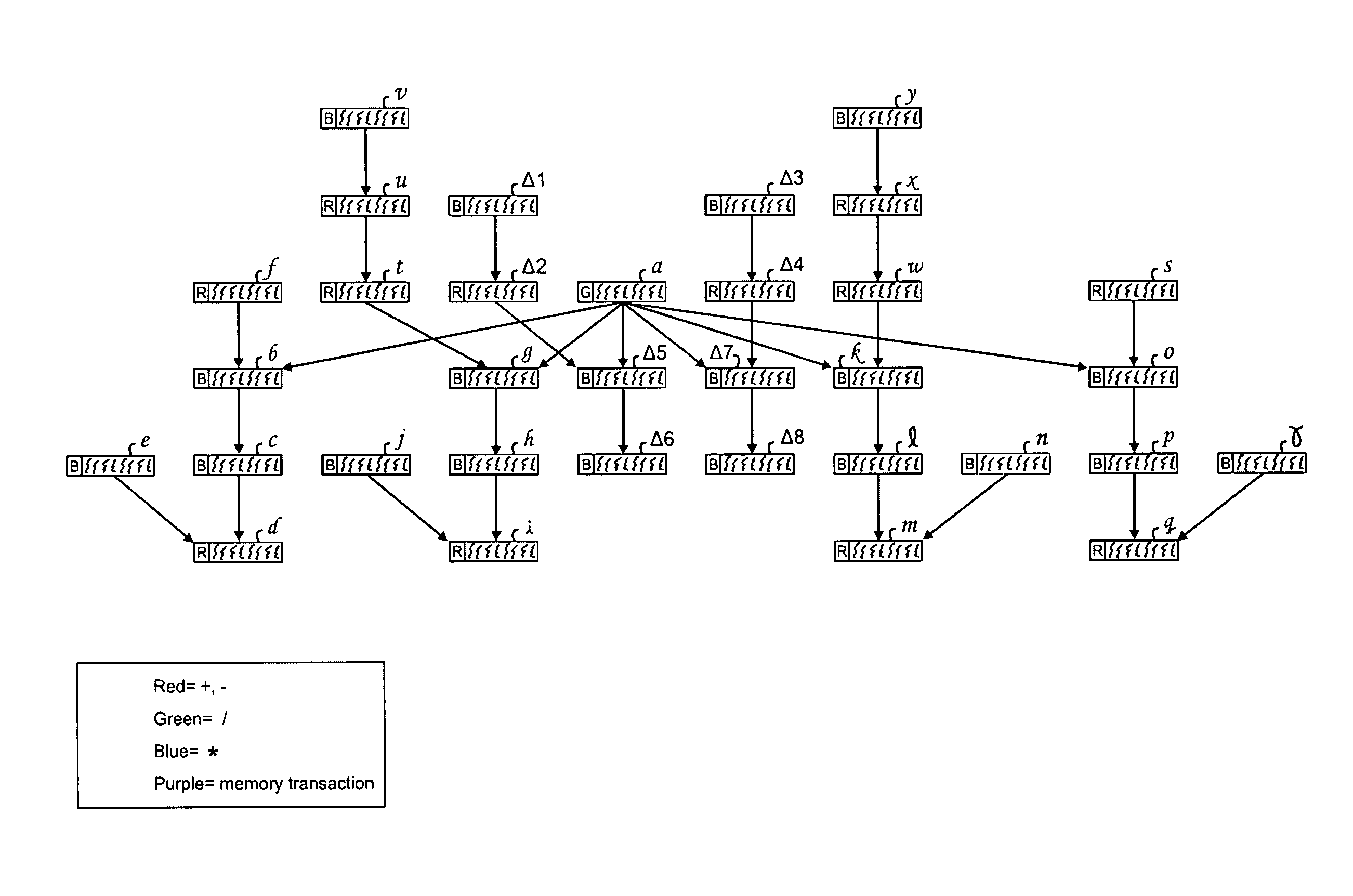
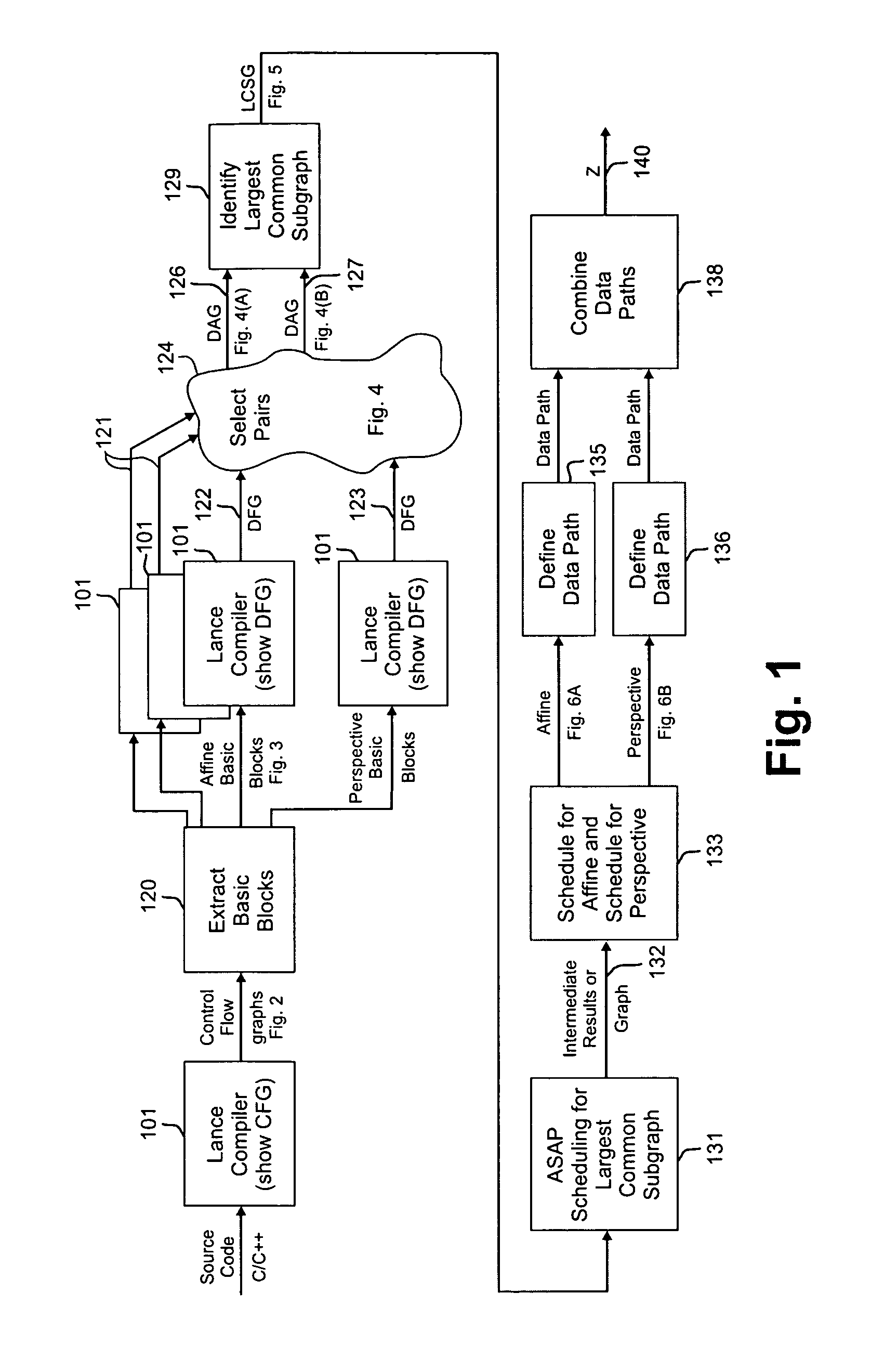
A method of producing a reconfigurable circuit device for running a computer program of moderate complexity such as multimedia processing. Code for the application is compiled into Control Flow Graphs representing distinct parts of the application to be run. From those Control Flow Graphs are extracted basic blocks. The basic blocks are converted to Data Flow Graphs by a compiler utility. From two or more Data Flow Graphs, a largest common subgraph is determined. The largest common subgraph is ASAP scheduled and substituted back into the Data Flow Graphs which also have been scheduled. The separate Data Flow Graphs containing the scheduled largest common subgraph are converted to data paths that are then combined to form code for operating the application. The largest common subgraph is effected in hardware that is shared among the parts of the application from which the Data Flow Graphs were developed. Scheduling of the overall code is effected for sequencing, providing fastest run times and the code is implemented in hardware by partitioning and placement of processing elements on a chip and design of the connective fabric for the design elements.
Owner:ARIZONA STATE UNIVERSITY
Semiconductor device
ActiveUS20110175646A1Suppress power consumptionPrevent degradationTransistorPower reduction in field effect transistorsProgrammable logic deviceLow leakage
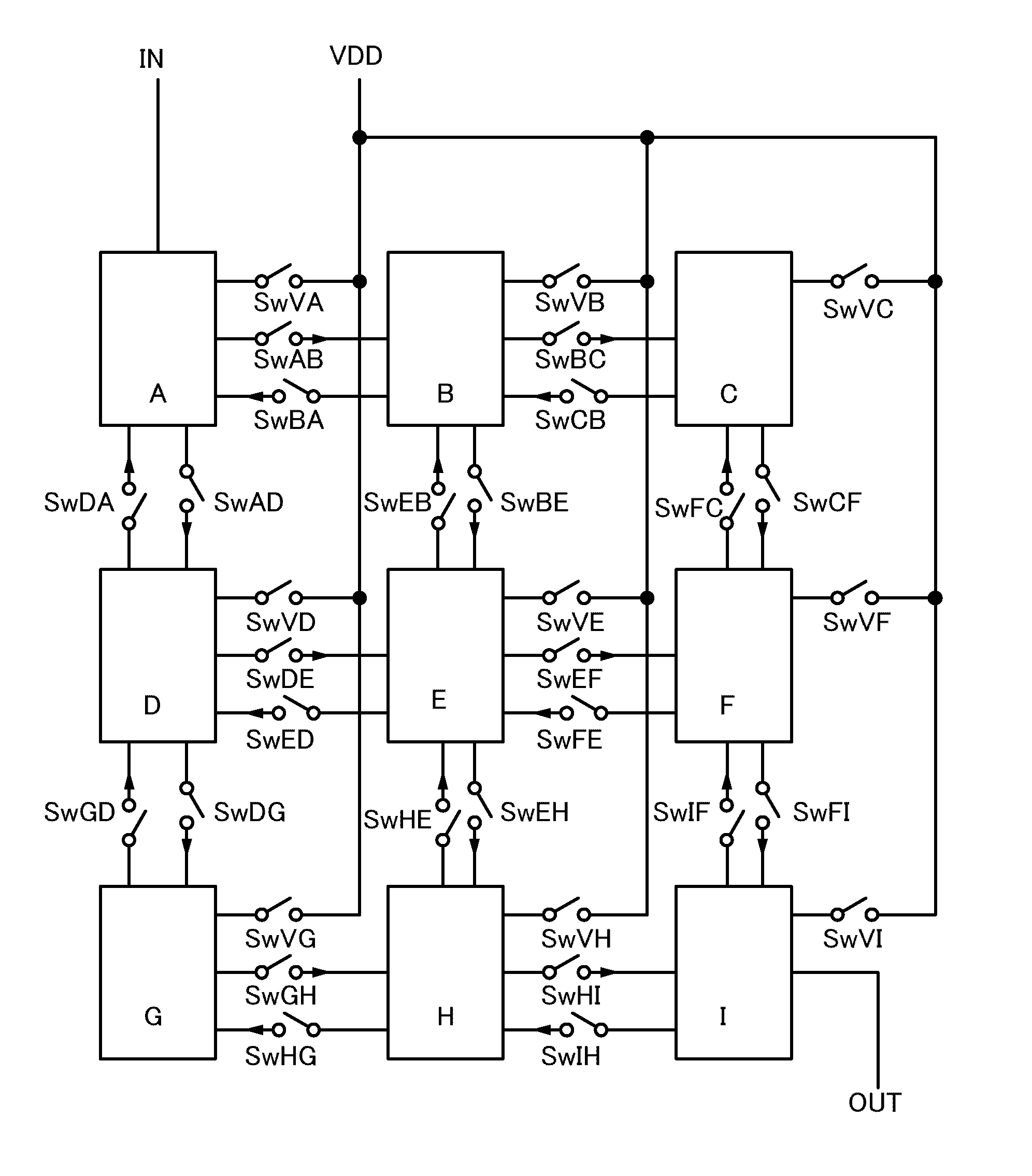
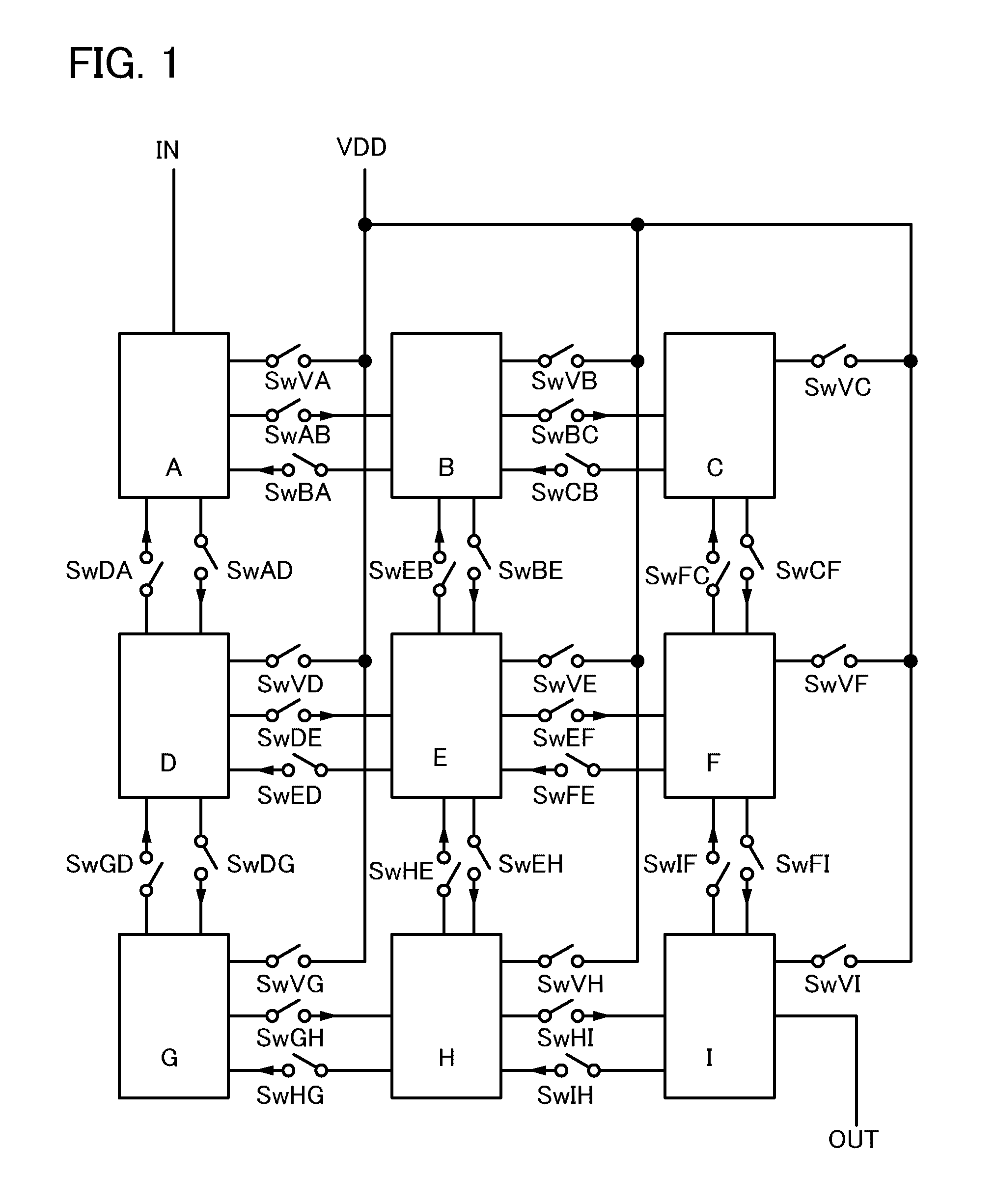
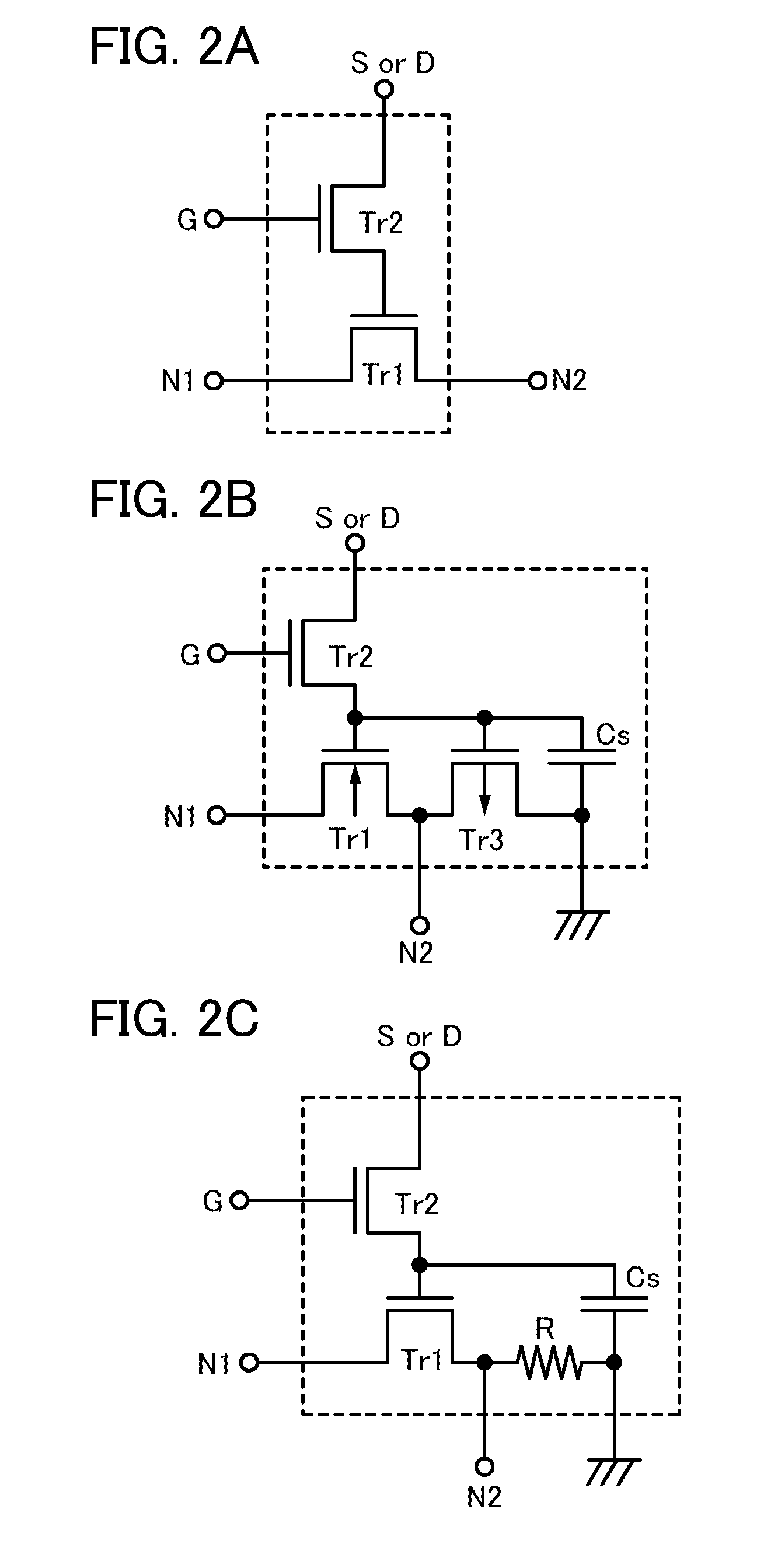
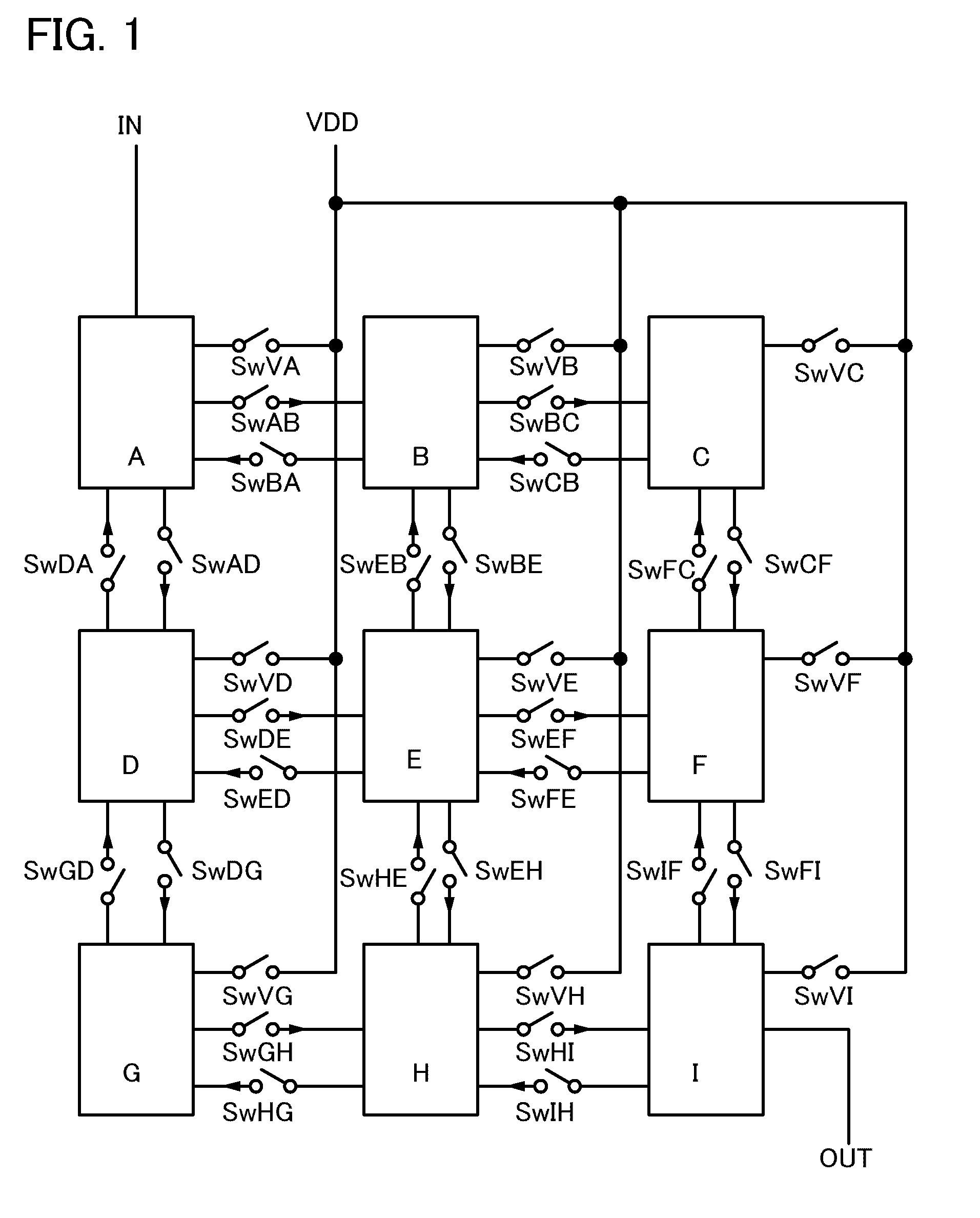
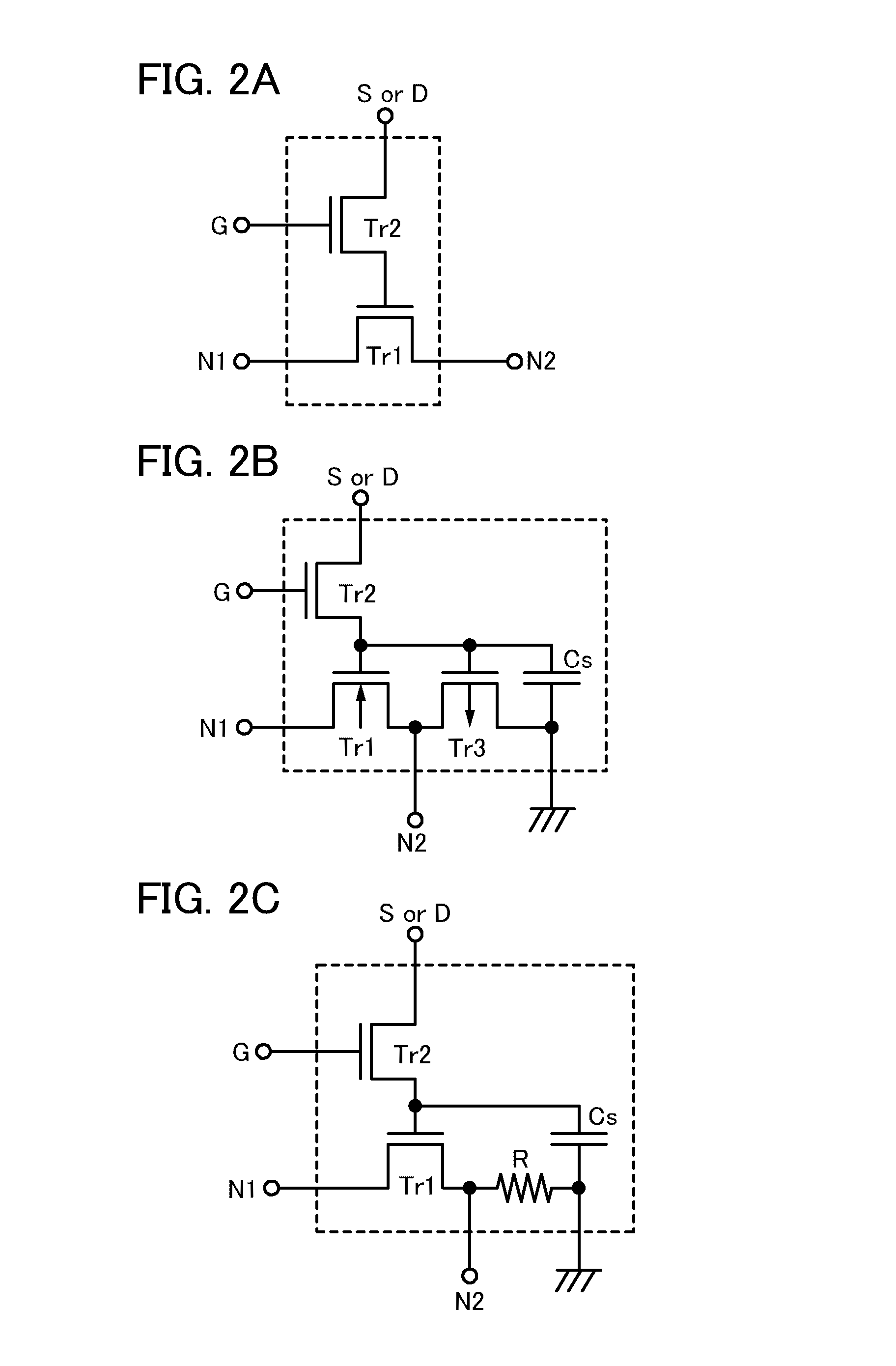
It is an object to provide a semiconductor device in which power consumption can be reduced. It is another object to provide a highly reliable semiconductor device using a programming cell, such as a programmable logic device (PLD). In accordance with a change in a configuration of connections between basic blocks, power supply voltage furnishing to the basic blocks is changed. That is, when the structure of connections between the basic blocks is such that a basic block does not contribute to a circuit, the supply of the power supply voltage to this basic block is stopped. Further, the supply of the power supply voltage to the basic blocks is controlled using a programming cell formed using a field effect transistor whose channel formation region is formed using an oxide semiconductor, the field effect transistor having extremely low off-state current or extremely low leakage current.
Owner:SEMICON ENERGY LAB CO LTD
Method and system for software instruction level tracing in a data processing system
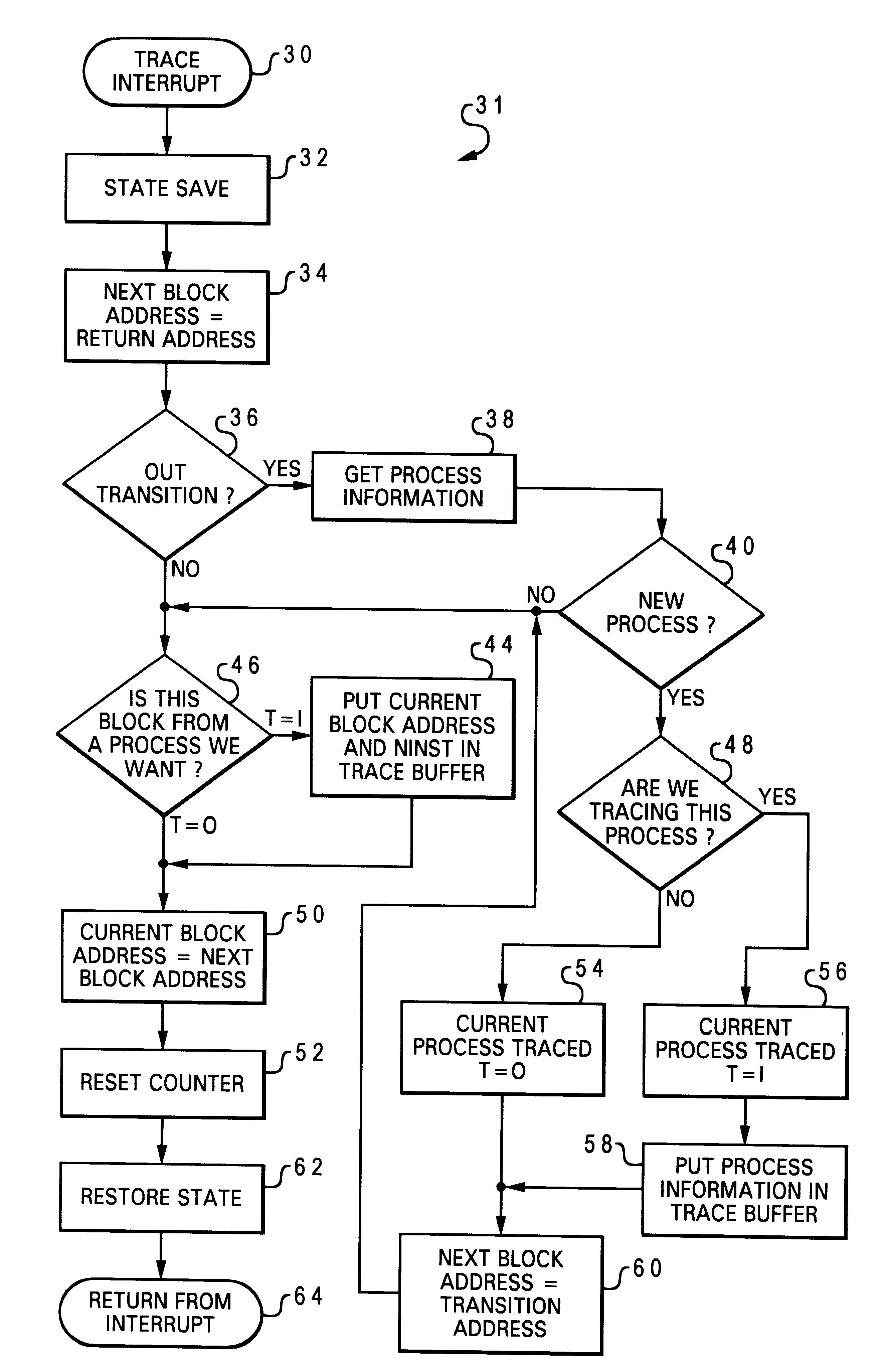
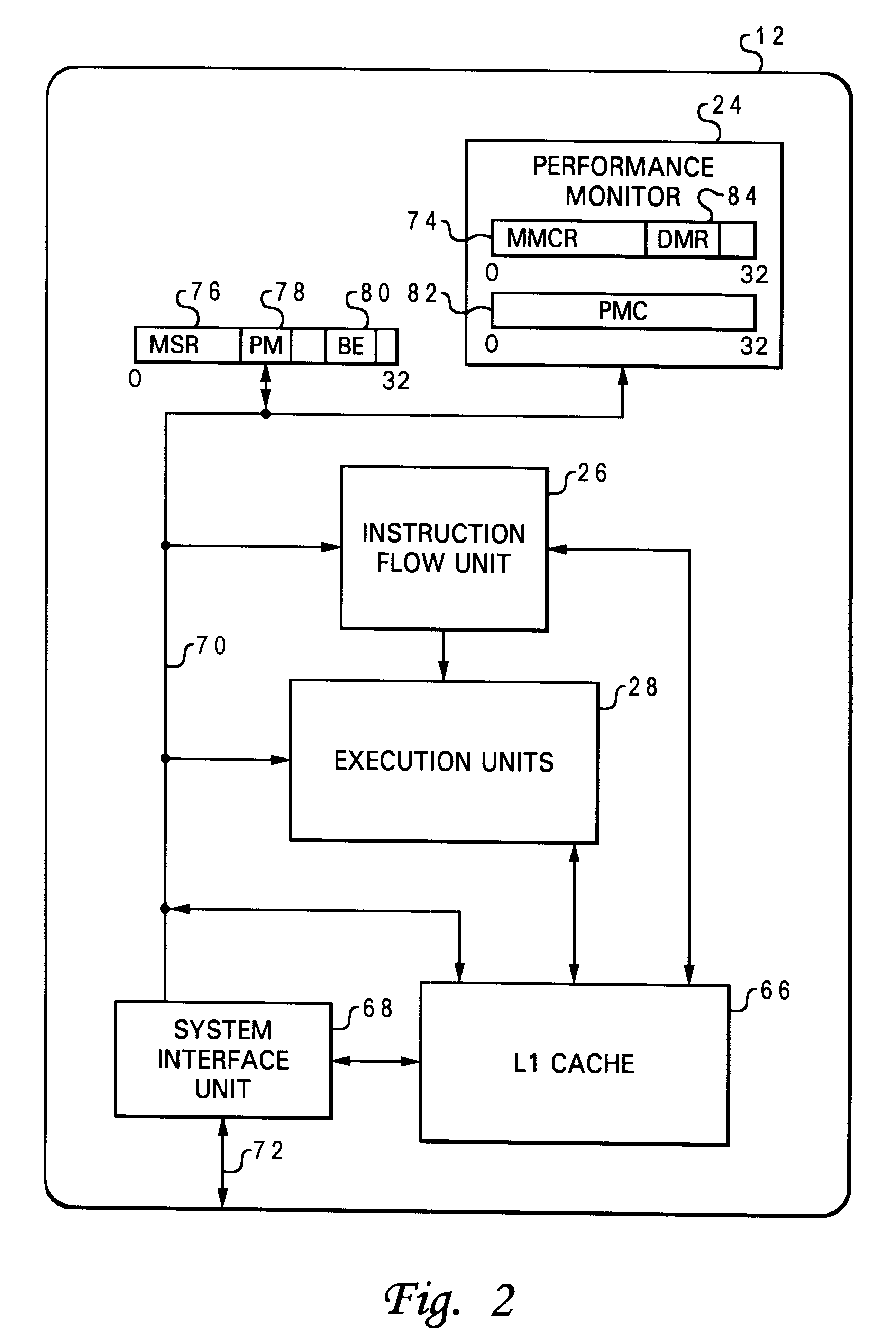
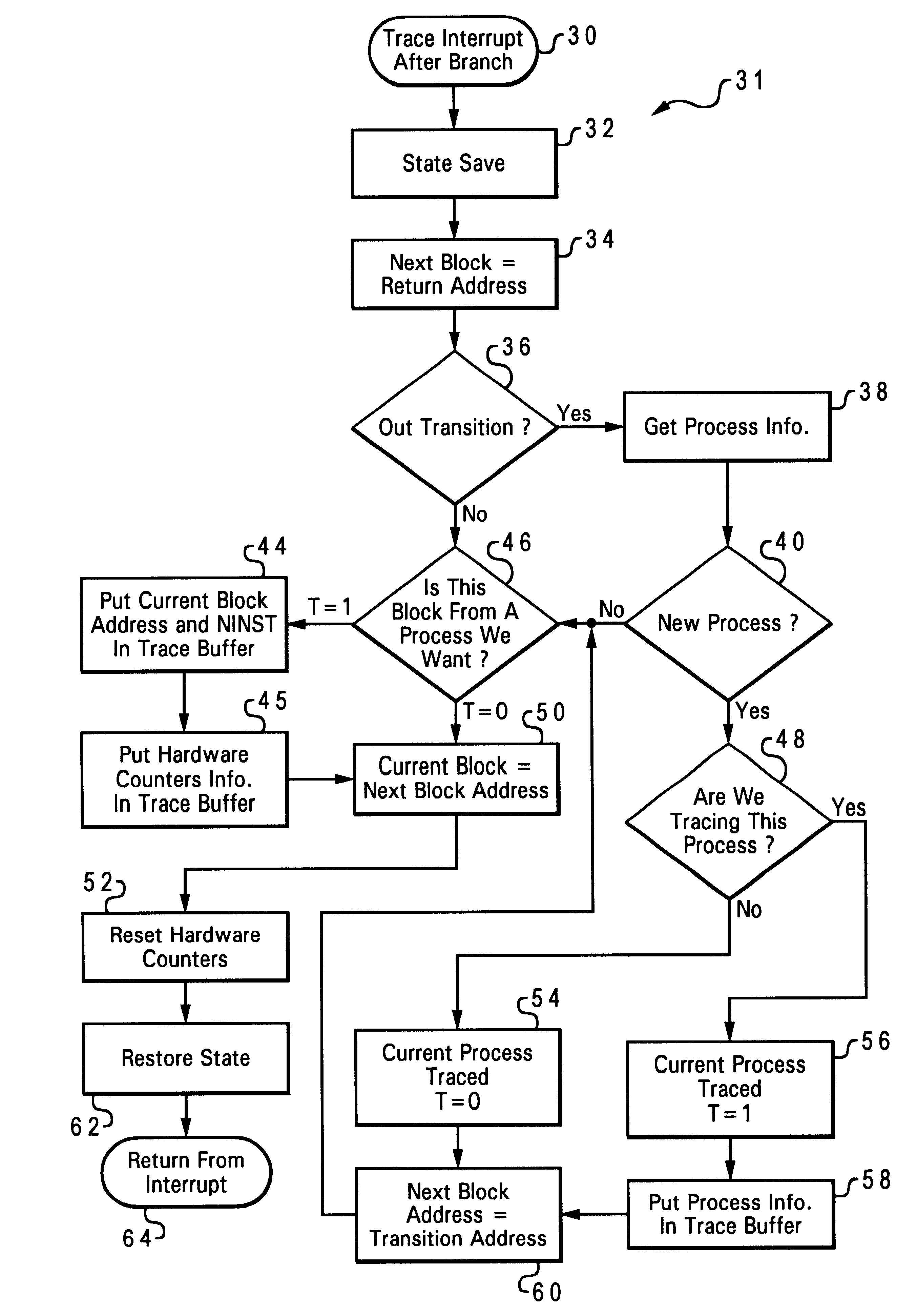
A method and system within a data processing system are disclosed for directly accessing code during a process by taking a trace by way of using an interruption. According to the present invention, the processor is programmed to generate a trace interrupt after each branch, or at the end of each basic block from the current process. This allows generation of exactly the same number of interruptions as would be produced by an instrumentation approach but without having to know where the basic blocks are in advance. By programming the performance monitor feature to count instructions, the exact size of each basic block is known. At each interrupt, the address of the beginning of the next basic block is saved which is the address where the interruption came from. Tracing information for the previous basic block including its address and its size (the current value of a counter) is created. If the current process is a process to be traced, the tracing information is stored in a trace buffer, the counter is reset to zero returning back to the process from the interrupt.
Owner:IBM CORP
Using padded instructions in a block-oriented cache
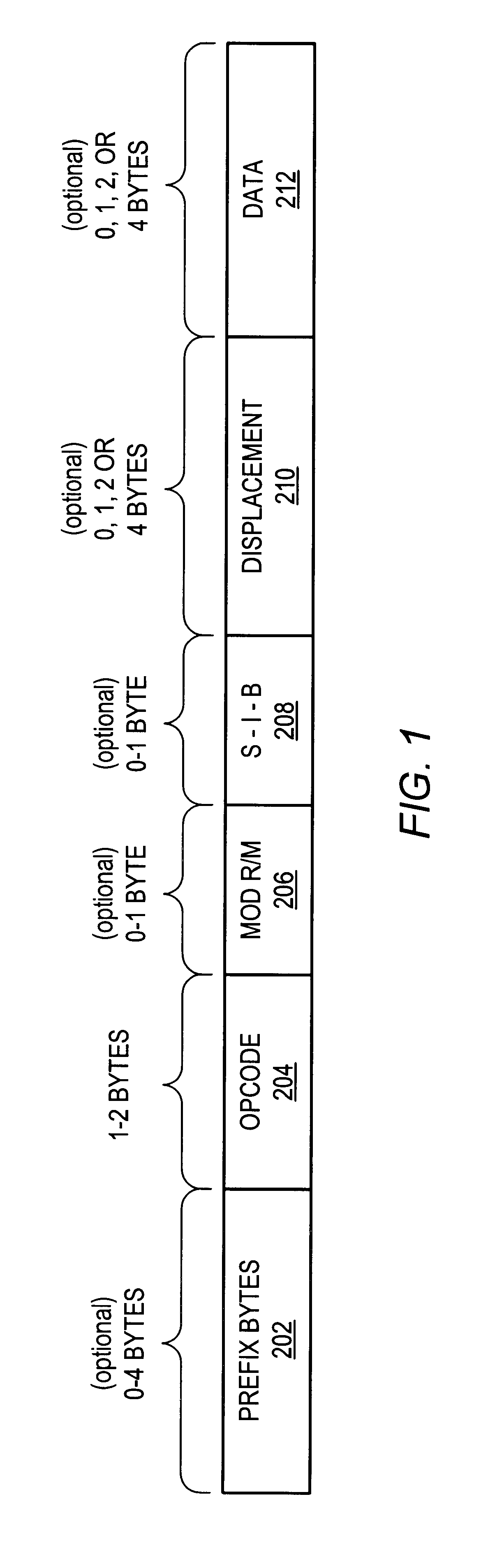
InactiveUS6339822B1Memory architecture accessing/allocationInstruction analysisComputerized systemVariable length
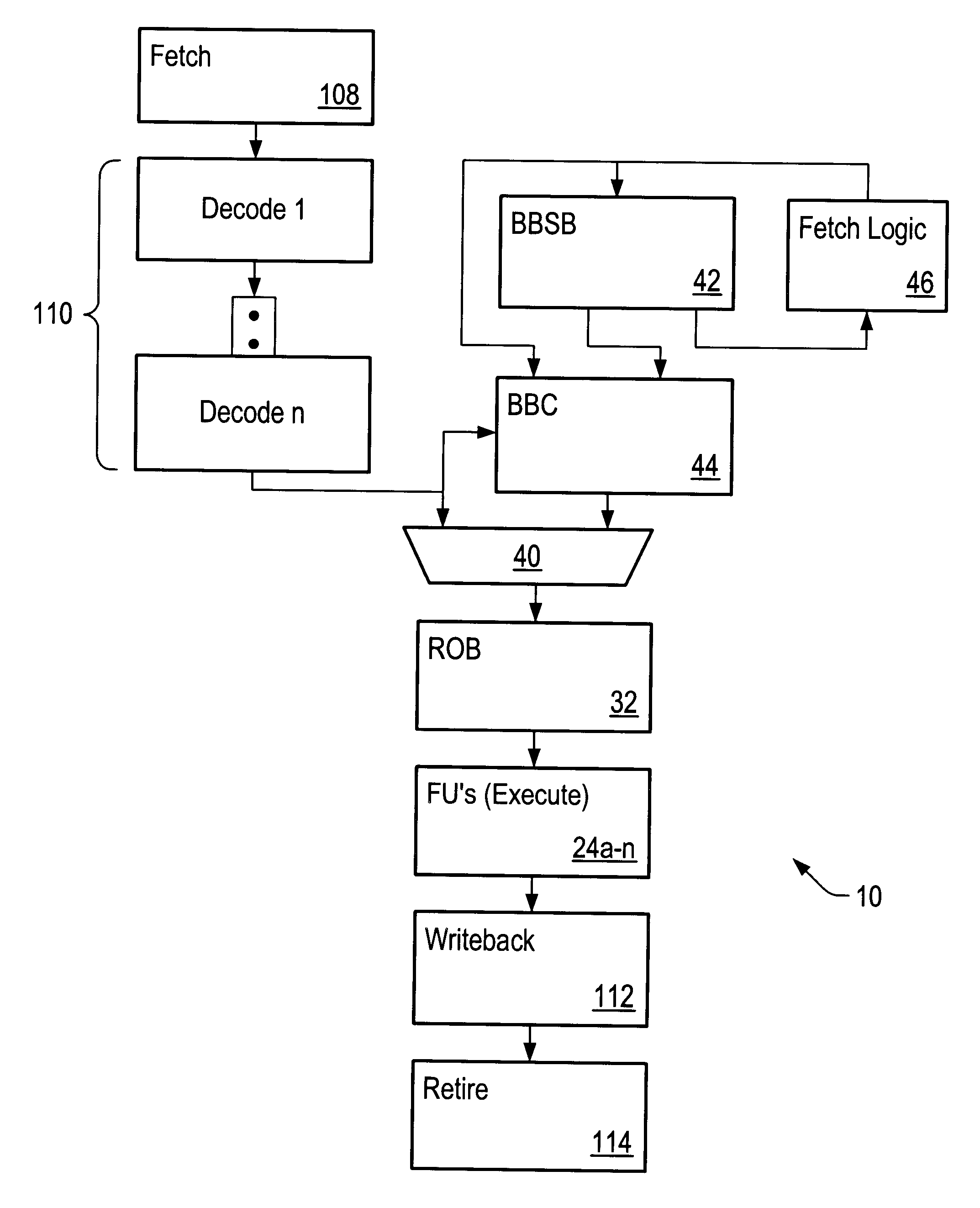
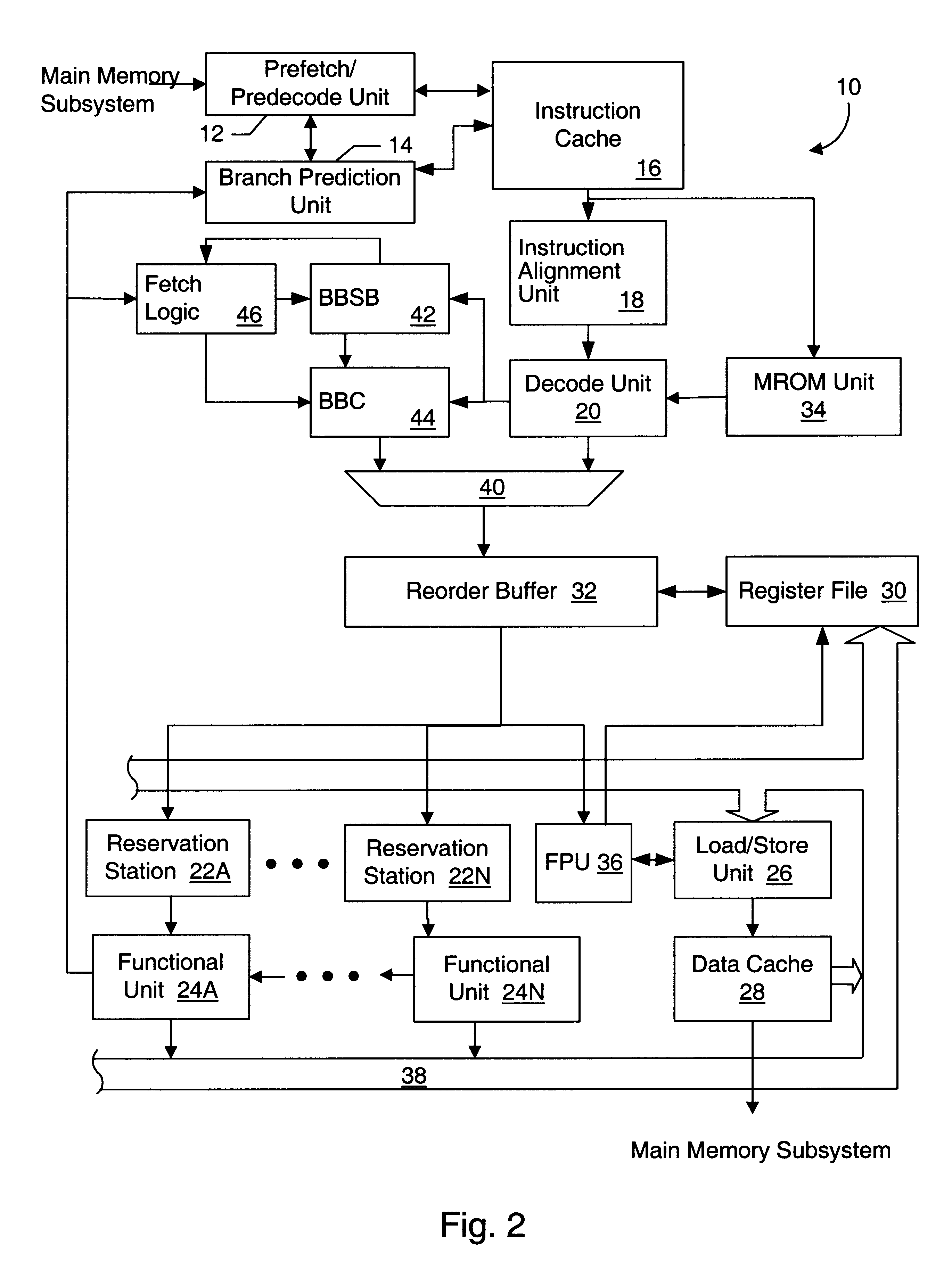
A microprocessor configured to cache basic blocks of instructions is disclosed. The microprocessor may comprise decoding logic, a basic block cache, and a branch prediction unit. The decoding logic is coupled to receive and decode variable-length instructions into padded instructions that have one of a predetermined number of predetermined lengths. The decoding logic is further configured to form basic blocks of instructions from the padded and decoded instructions. Basic blocks are natural divisions in instruction streams resulting from branch instructions. The start of a basic block is a target of a branch, and the end is another branch instruction. The basic block cache is configured to store the basic blocks in a plurality of storage locations, wherein each storage location is configured to store an address tag, a link bit, and at least a portion of one basic block. The link bit indicates whether the basic block stored in said storage location extends into another storage location. The branch prediction unit has a branch prediction array storing branch prediction information corresponding to each storage location within the basic block cache. A computer system and method for operating are also disclosed.
Owner:GLOBALFOUNDRIES INC
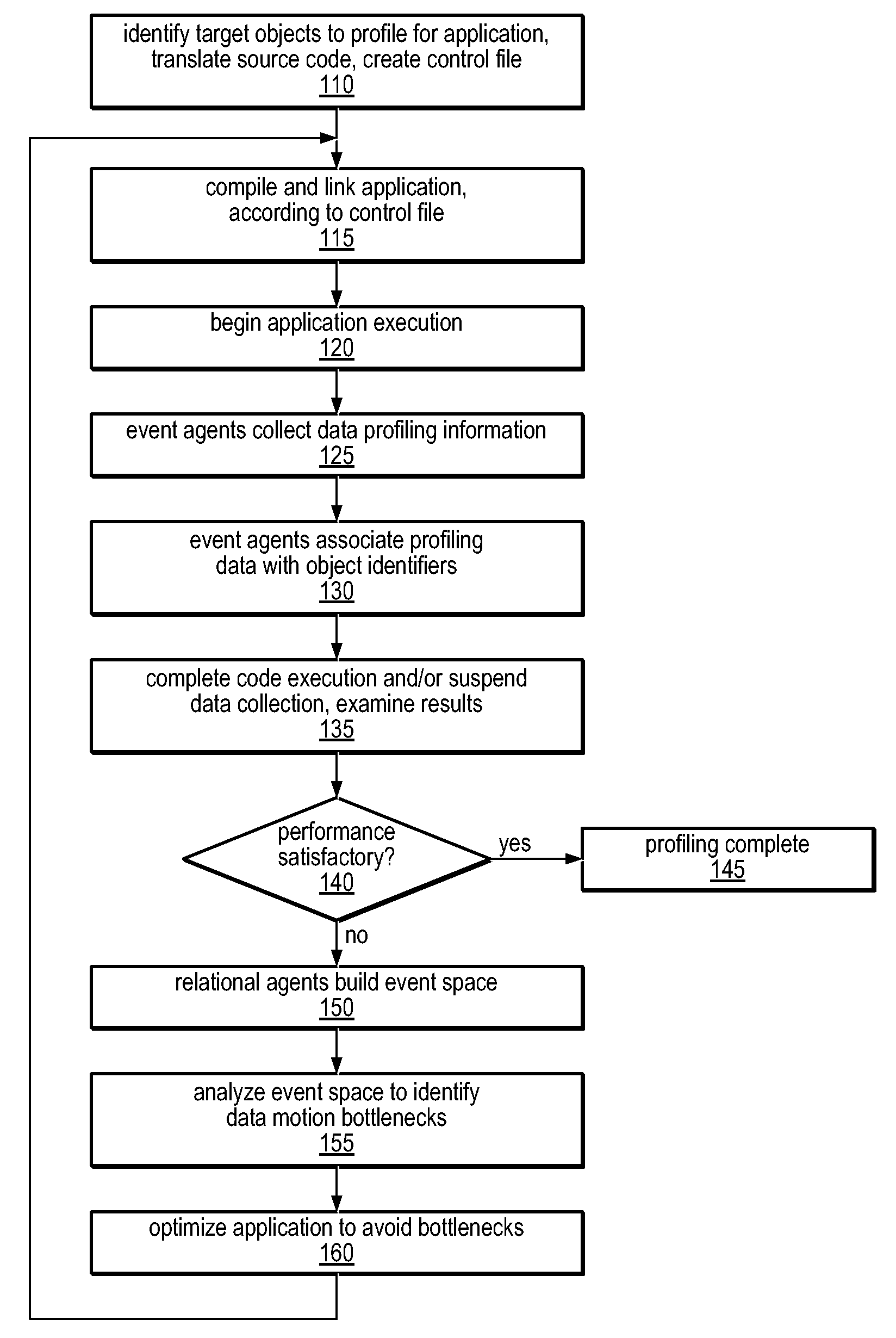
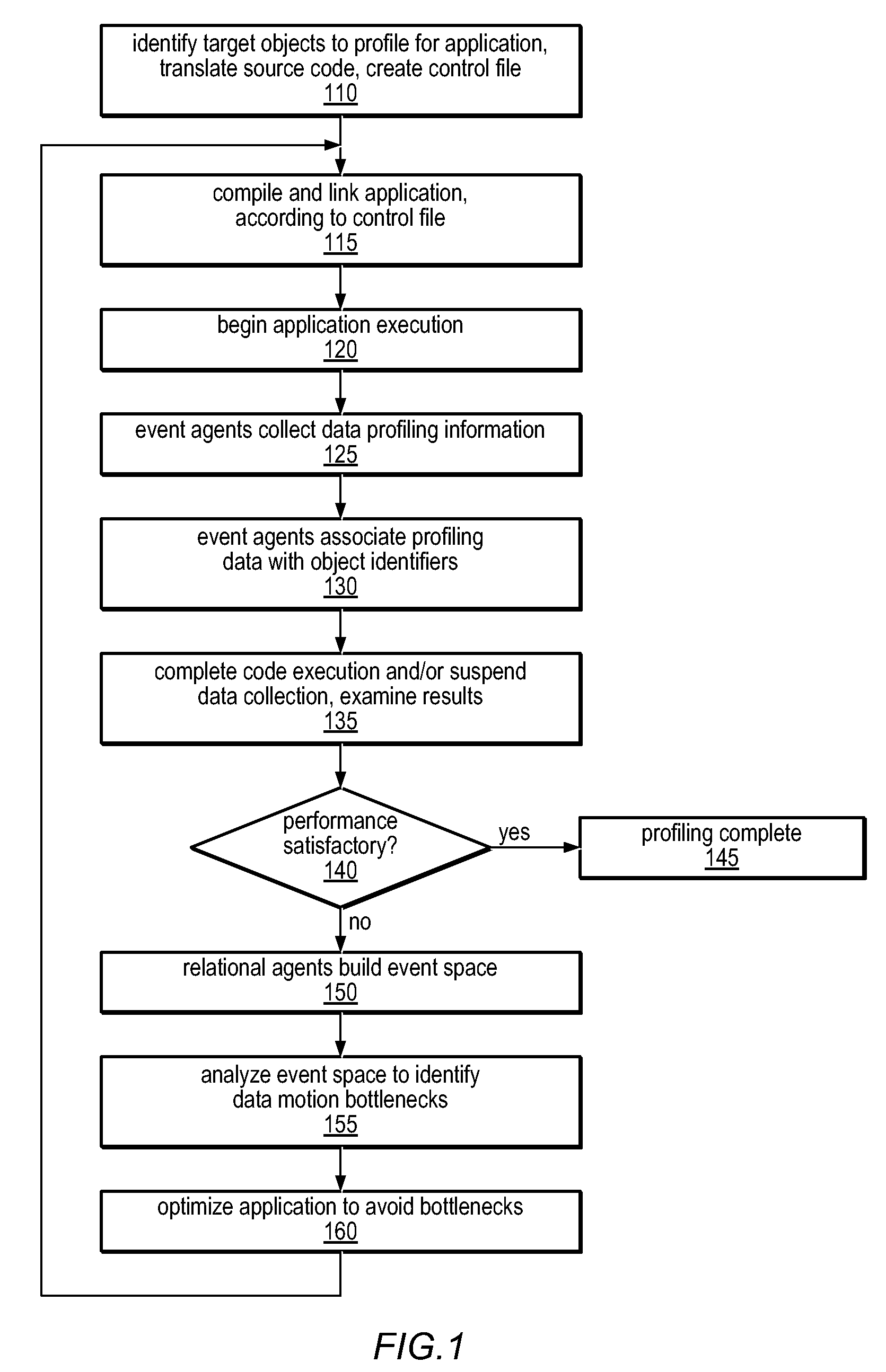
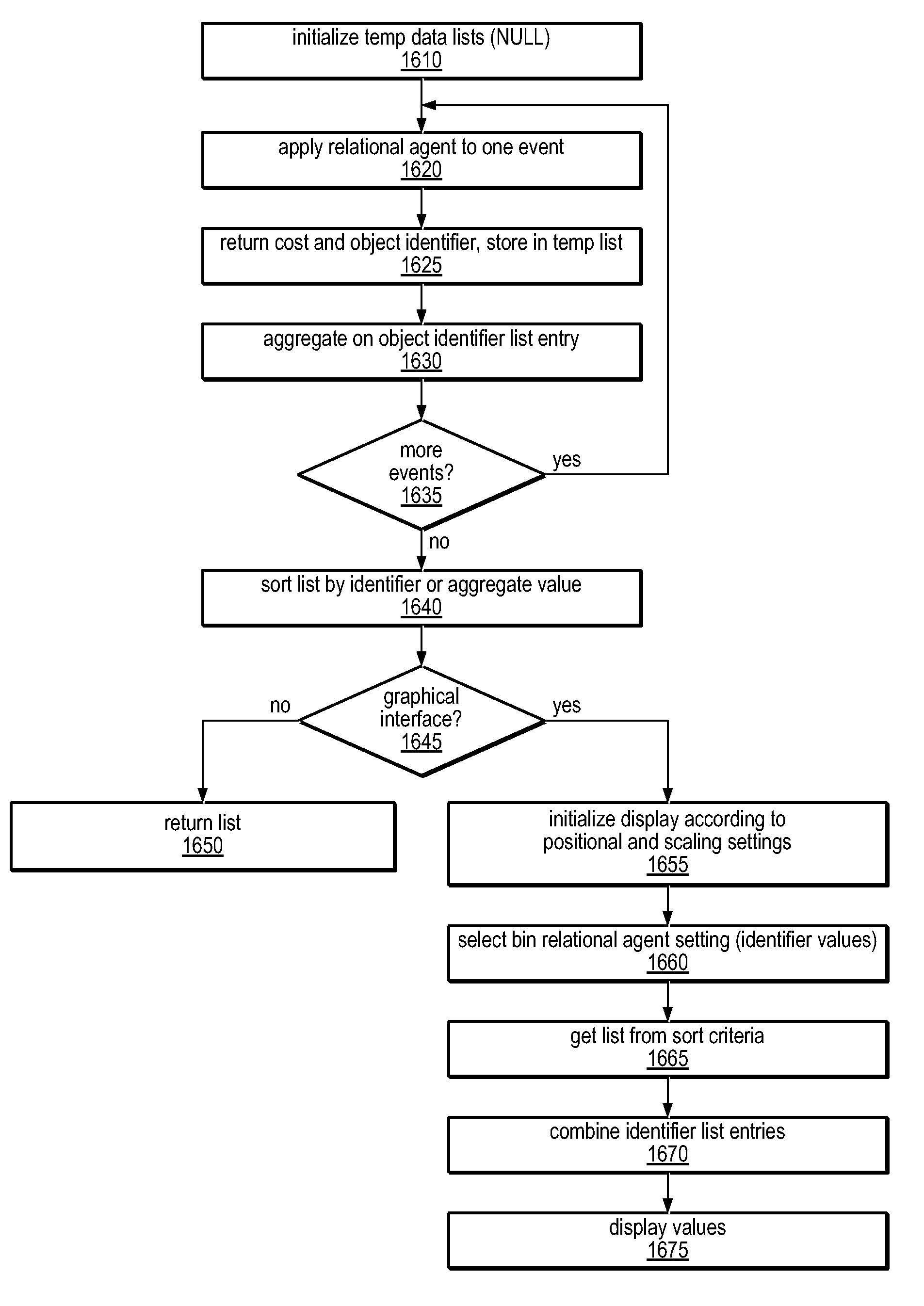
Method and Apparatus for Computing User-Specified Cost Metrics in a Data Space Profiler
ActiveUS20080127149A1Software engineeringSpecific program execution arrangementsCost metricData space
A system and method for profiling a software application may include means for defining a custom cost metric that includes a cost metric identifier and a cost function. The cost function may apply a mathematical formula to data extracted from an event set to calculate a respective cost metric value for each of one or more events in the event set. The data extracted from the event set may include one or more respective profiling object identifiers and one or more other respective costs associated with each of the one or more events. A cost associated with an event in the event space may be associated with a function or basic block of instructions. The cost function may include a distribution formula for attributing at least a portion of the cost associated with a function or basic block to each of the instructions comprising the function or basic block.
Owner:ORACLE INT CORP
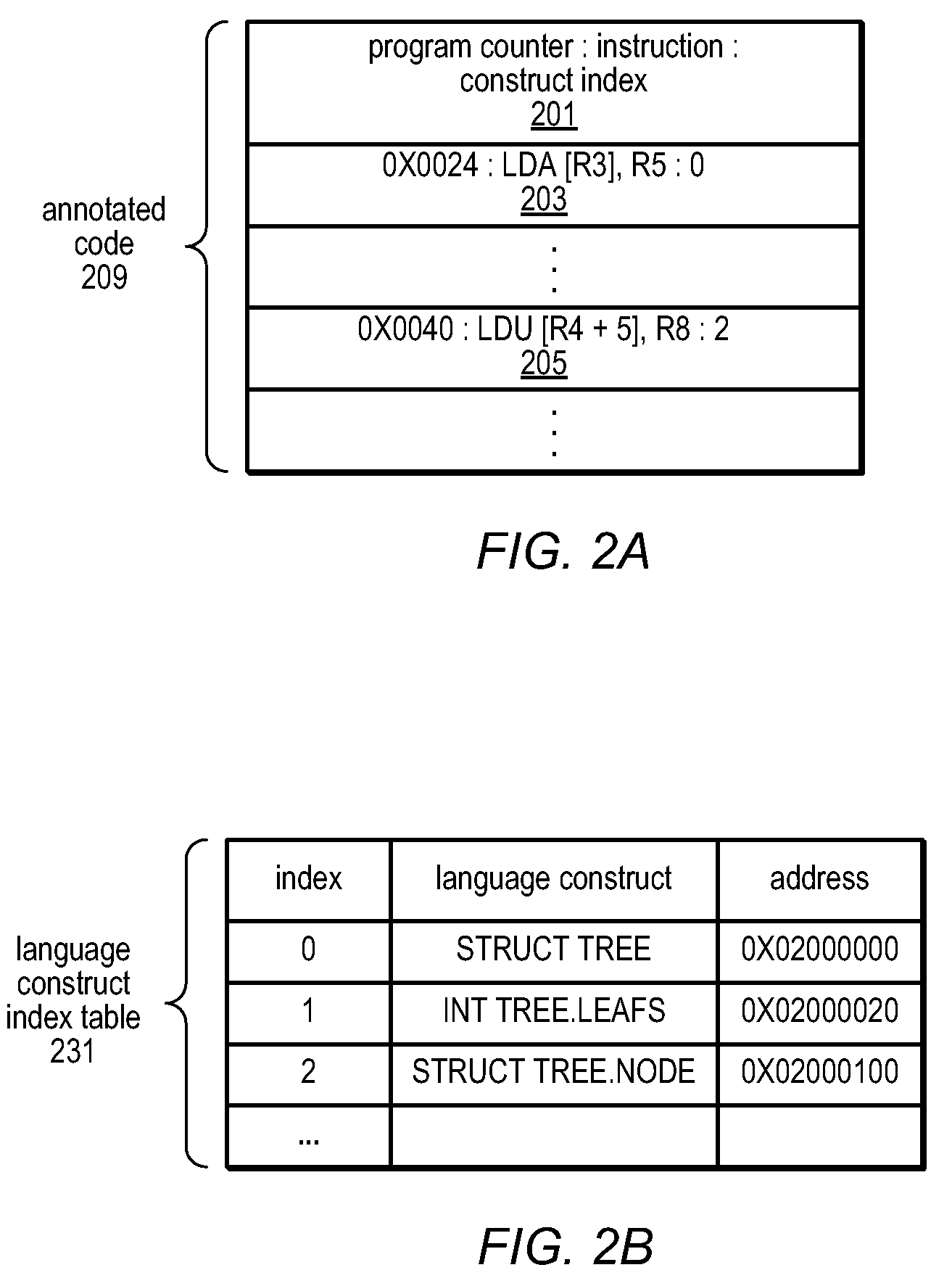
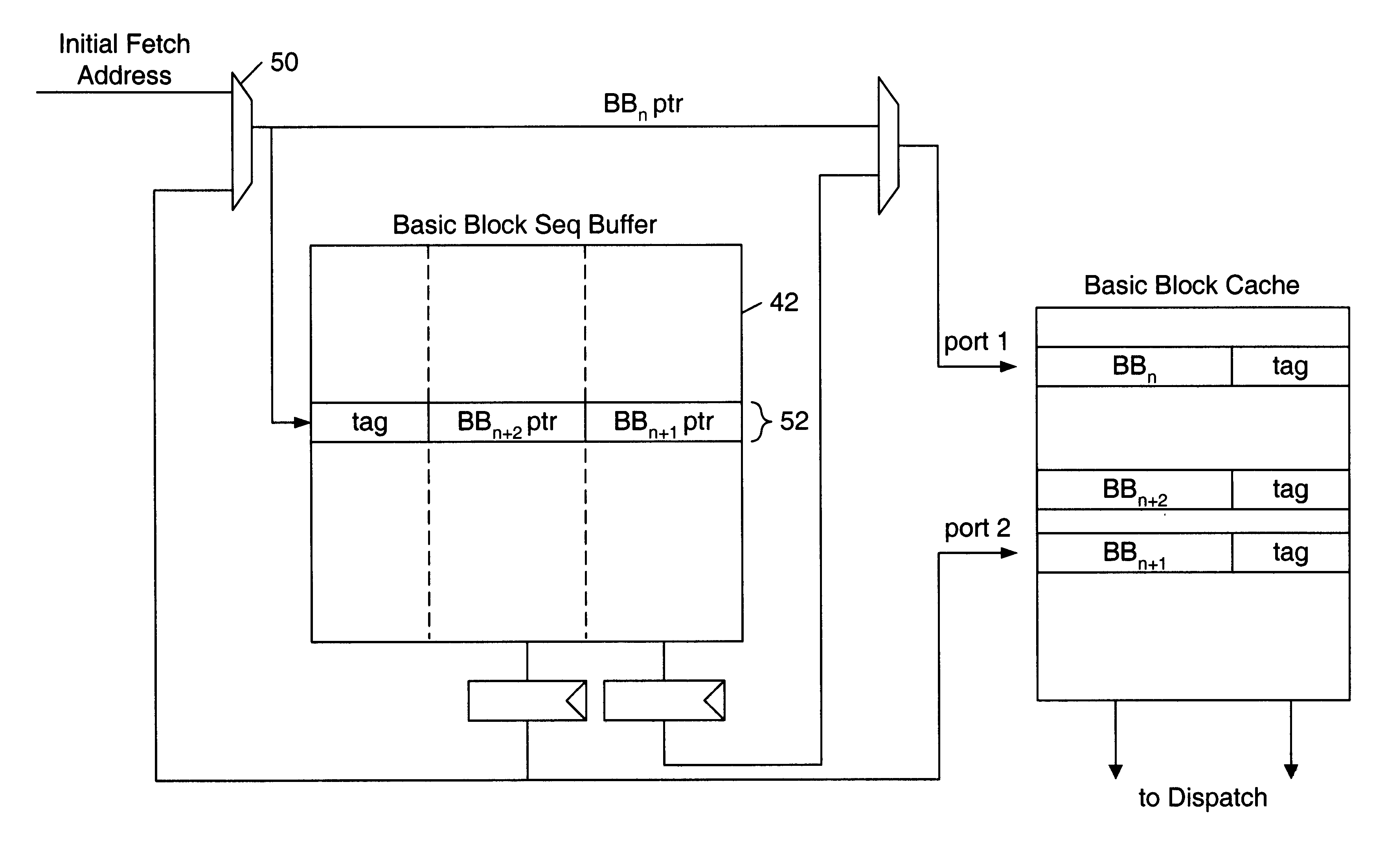
Basic block oriented trace cache utilizing a basic block sequence buffer to indicate program order of cached basic blocks
A cache memory configured to access stored instructions according to basic blocks is disclosed. Basic blocks are natural divisions in instruction streams resulting from branch instructions. The start of a basic block is a target of a branch, and the end is another branch instruction. A microprocessor configured to use a basic block oriented cache may comprise a basic block cache and a basic block sequence buffer. The basic block cache may have a plurality of storage locations configured to store basic blocks. The basic block sequence buffer also has a plurality of storage locations, each configured to store a block sequence entry. The block sequence entry may comprise an address tag and one or more basic block pointers. The address tag corresponds to the fetch address of a particular basic block, and the pointers point to basic blocks that follow the particular basic block in a predicted order. A system using the microprocessor and a method for caching instructions in a block oriented manner rather than conventional power-of-two memory blocks are also disclosed.
Owner:GLOBALFOUNDRIES INC
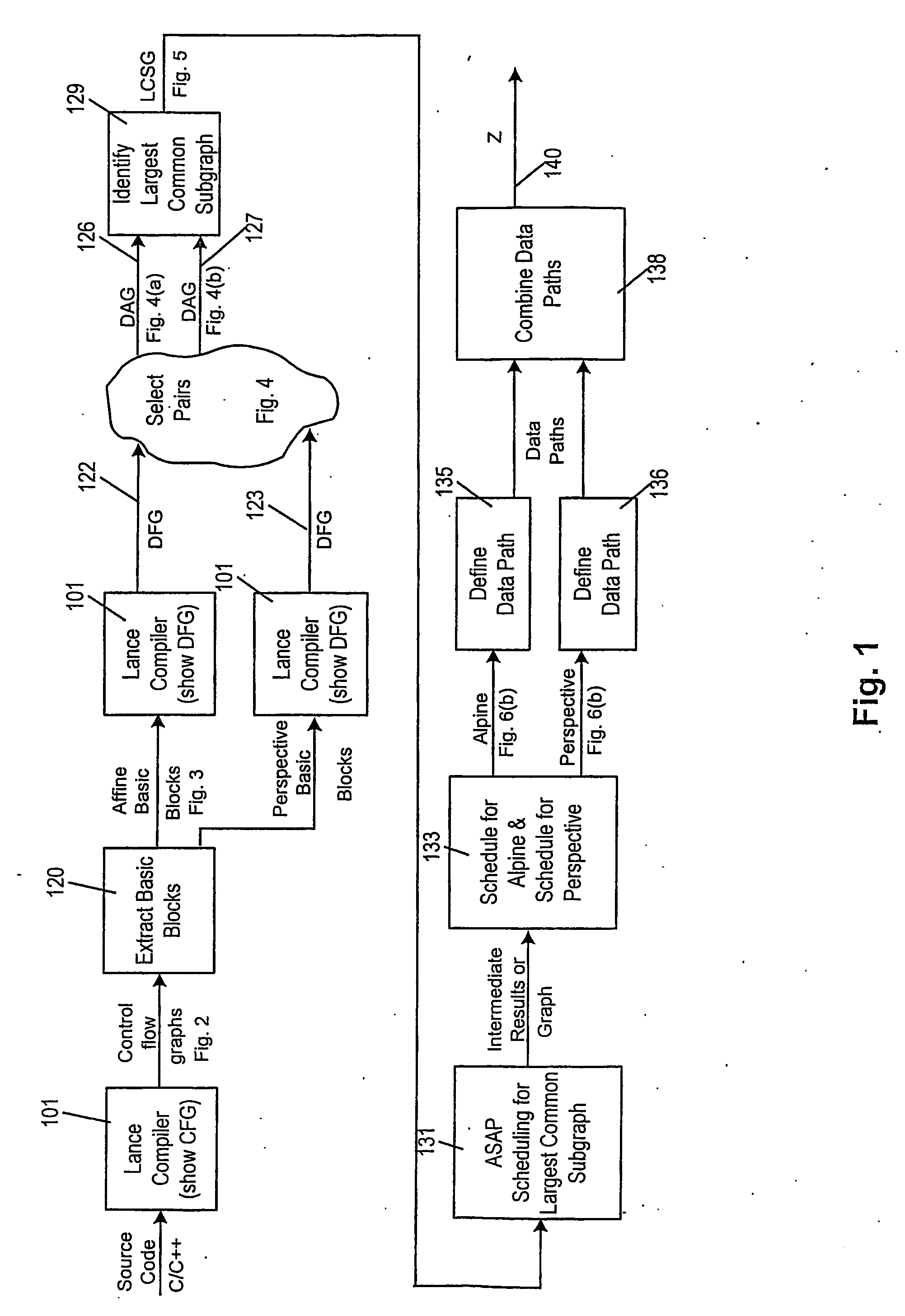
Reconfigurable processing
ActiveUS8281297B2Reduce the amount requiredQuick switchEnergy efficient ICTSoftware engineeringControl flowProcessing element
A method of producing a reconfigurable circuit device for running a computer program of moderate complexity such as multimedia processing. Code for the application is compiled into Control Flow Graphs representing distinct parts of the application to be run. From those Control Flow Graphs are extracted basic blocks. The basic blocks are converted to Data Flow Graphs by a compiler utility. From two or more Data Flow Graphs, a largest common subgraph is determined. The largest common subgraph is ASAP scheduled and substituted back into the Data Flow Graphs which also have been scheduled. The separate Data Flow Graphs containing the scheduled largest common subgraph are converted to data paths that are then combined to form code for operating the application. The largest common subgraph is effected in hardware that is shared among the parts of the application from which the Data Flow Graphs were developed. Scheduling of the overall code is effected for sequencing, providing fastest run times and the code is implemented in hardware by partitioning and placement of processing elements on a chip and design of the connective fabric for the design elements.
Owner:ARIZONA STATE UNIVERSITY
Method and apparatus for accurate profiling of computer programs
InactiveUS6934935B1Precise maintenanceHardware monitoringMultiprogramming arrangementsGraphicsOperational system
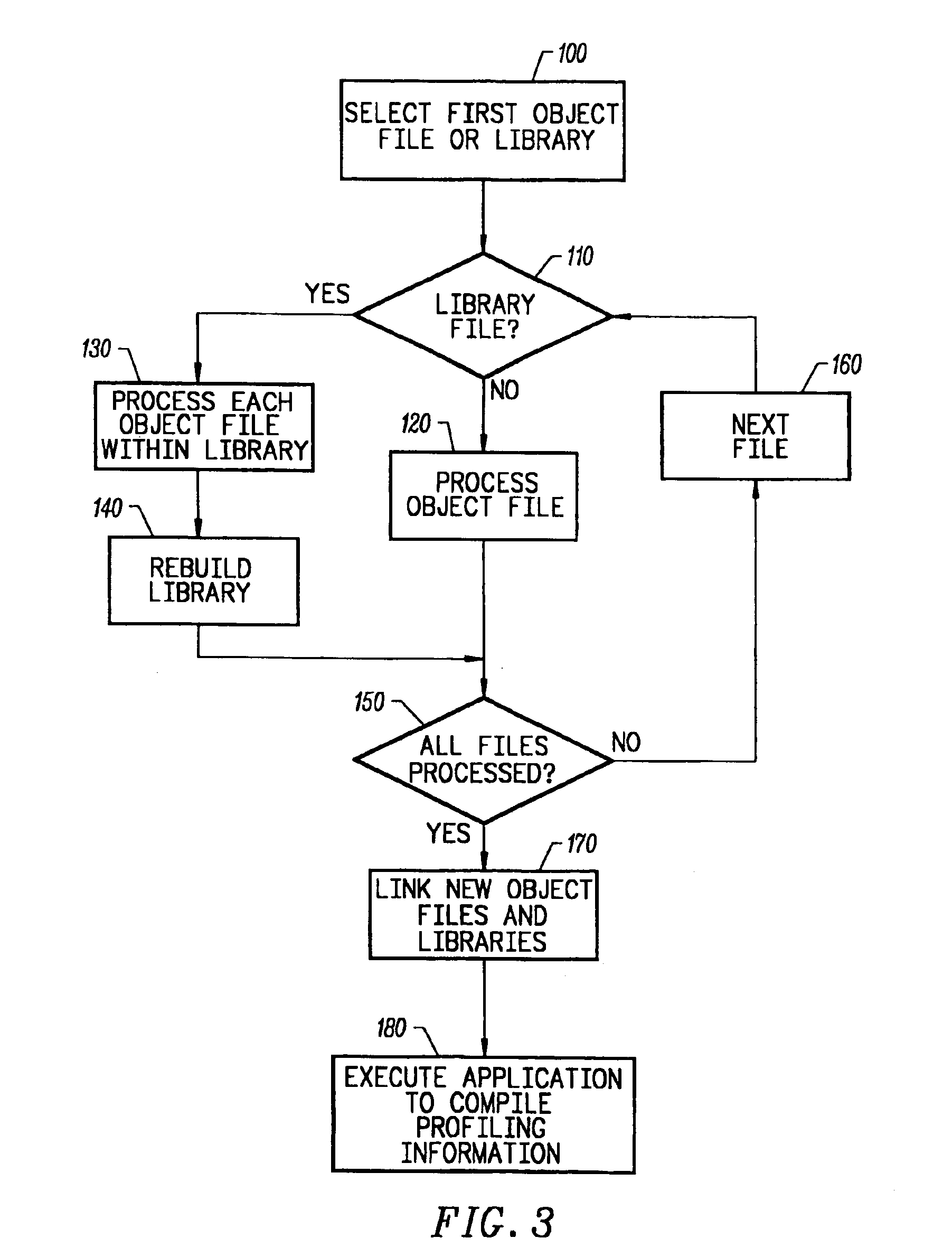
An object code expansion profiler equips a program for execution profiling by preprocessing the object code files of the program so as to add profiling monitoring code to the beginning of all or substantially all functions. The preprocessing includes, for each function, the steps of grouping the function's instructions into basic blocks, counting the number of cycles required to execute the instructions of the basic block, and inserting special monitoring code with the basic block. The special monitoring code is executed each time the basic block is executed, and updates the profiling information to reflect the number of cycles required to execute the basic block. Special handling is provided for profiling calls to the Operating System (OS). The resultant profiling information is converted into a call graph image most useful for human users. For each arc in the graph connecting a calling-function / parent-node to a called-function / child node, the displayed arc image has a width logarithmically proportional to the self+descendants time for the called function.
Owner:IBM CORP
Program optimization method, and compiler using the same
InactiveUS20020095666A1Short processing timeEfficient executionSoftware engineeringDigital computer detailsSource codeBasic block
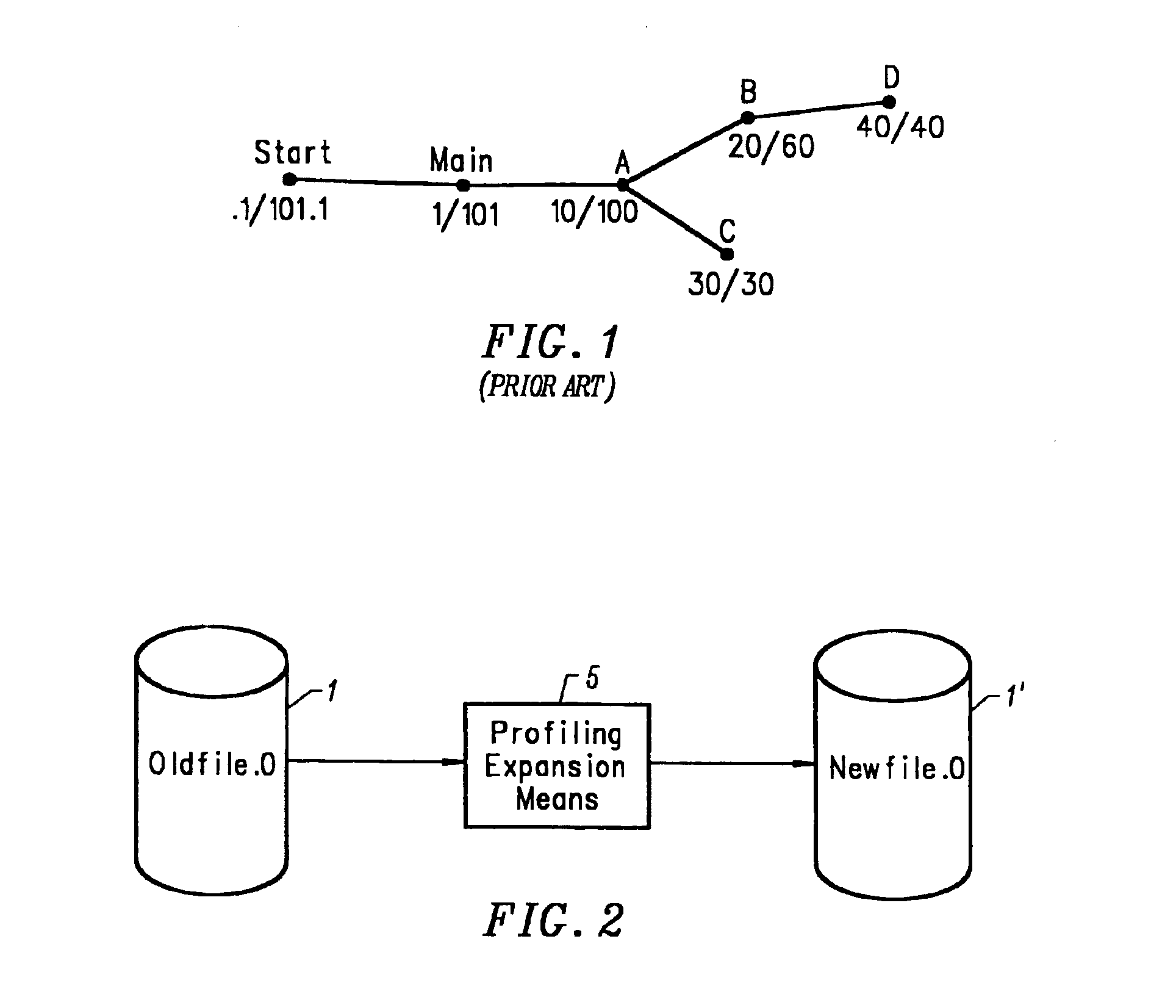
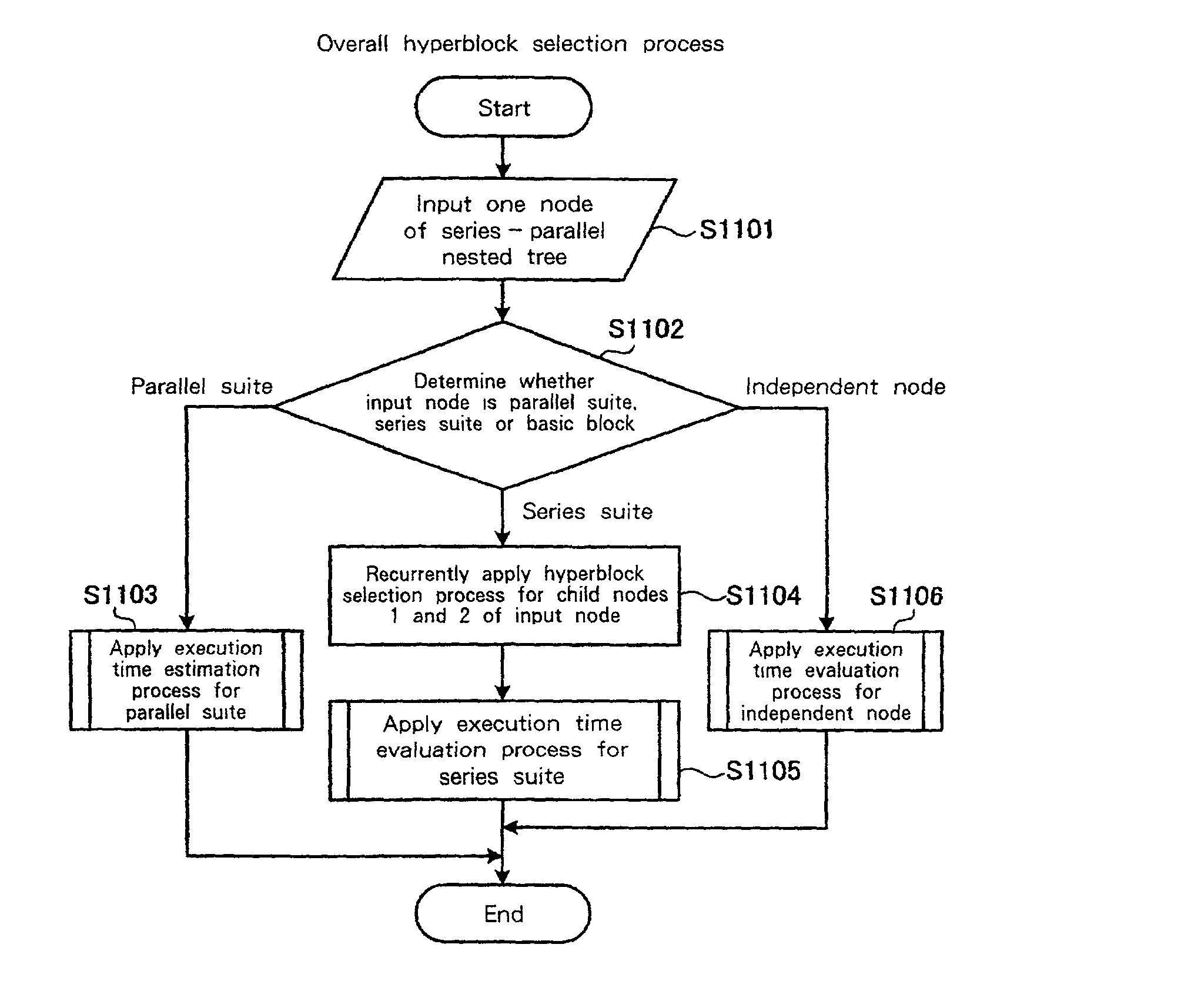
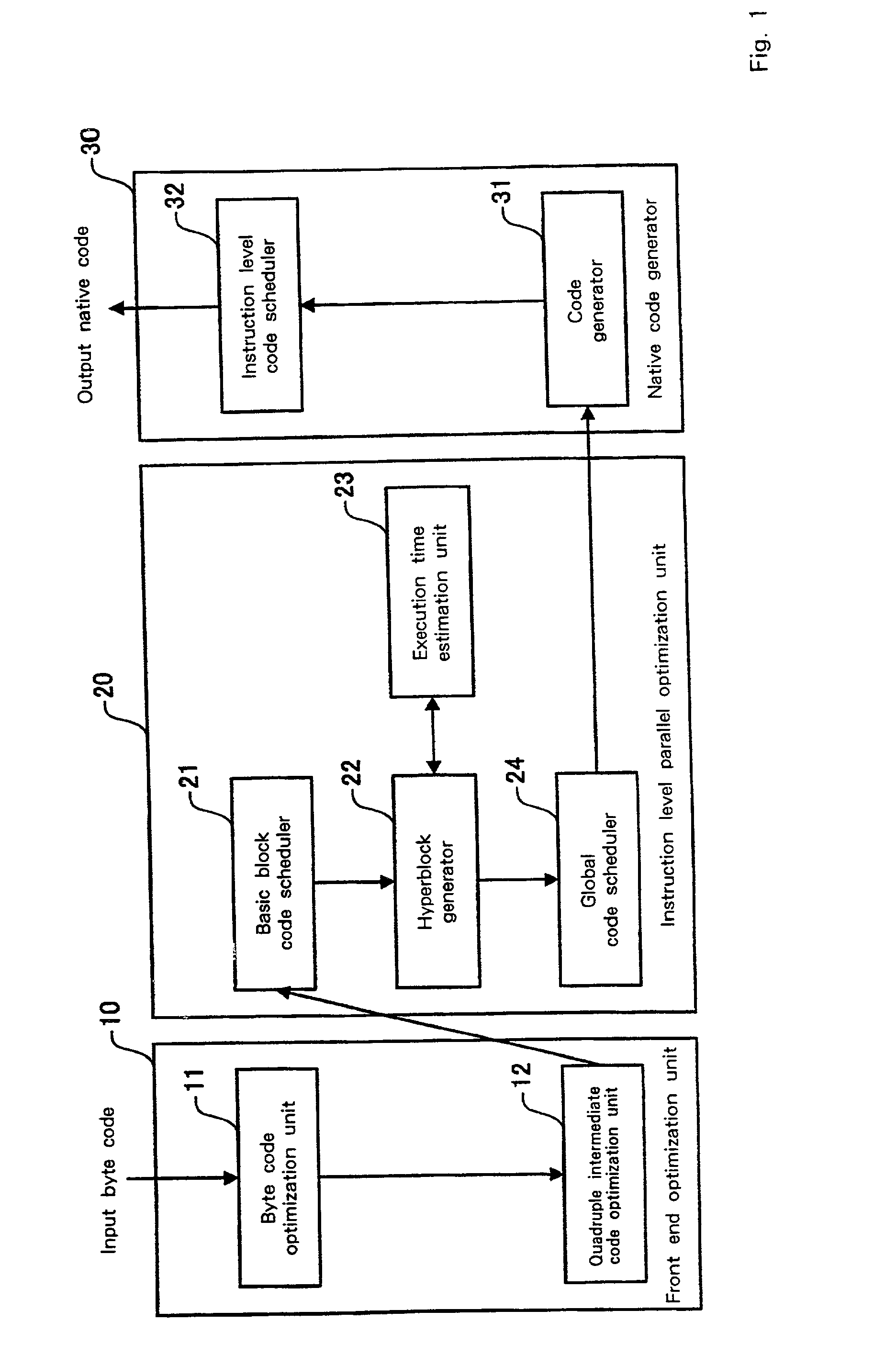
An optimization method and apparatus for converting source code for a program written in a programming language into machine language and for optimizing the program includes employing a basic block as a unit to estimate an execution time for the program to be processed, generating a nested tree that represents the connections of the basic blocks using a nesting structure, when a conditional branch is accompanied by a node in the nested tree, employing the execution time estimated by using the basic blocks as units to obtain an execution time at the node of the program when a conditional branching portion of a program is directly executed and when the conditional branching portion is executed in parallel, and defining the node as a parallel execution area group when the execution time required for the parallel execution is shorter or dividing multiple child nodes of the nodes into multiple parallel execution areas when the execution time for the conditional branching portion is shorter.
Owner:IBM CORP
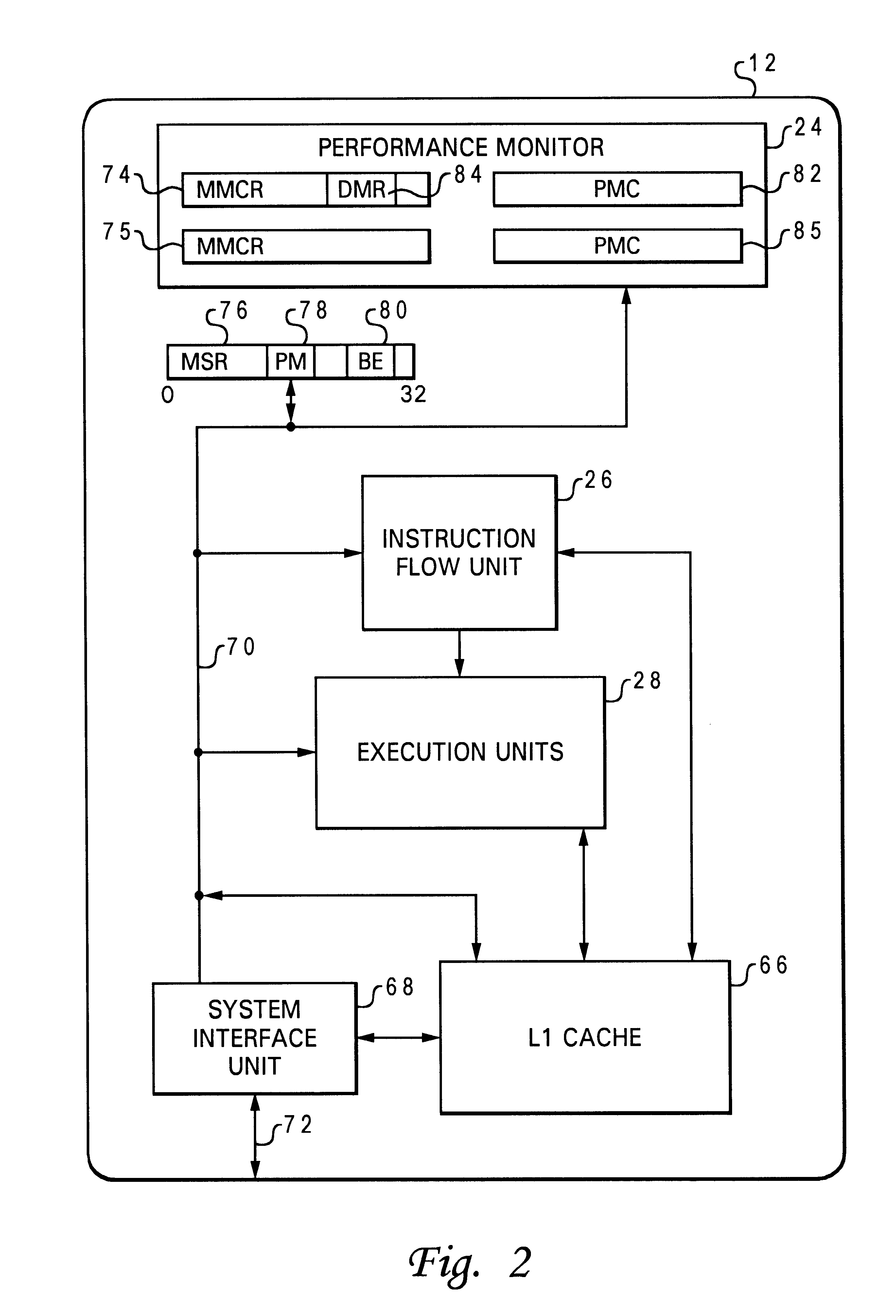
System for tracing hardware counters utilizing programmed performance monitor to generate trace interrupt after each branch instruction or at the end of each code basic block
A method and system within a data processing system or information handling system are disclosed for counting various events from a running program (hereafter called a process) by taking a trace by way of using an interruption. According to the present invention, a performance monitor feature within a data processing system is programmed to generate a trace interrupt after each branch instruction, or at the end of each basic block of code from a currently running program or process. By programming monitor mode control registers within the performance monitor feature, one or more counters are programmed to count various events happening on the data processing system thereby creating tracing information. If the current process is a process to be traced, the tracing information is stored in a trace buffer for post-processing analysis, the counters are reset to zero returning back to the process from the interrupt.
Owner:IBM CORP
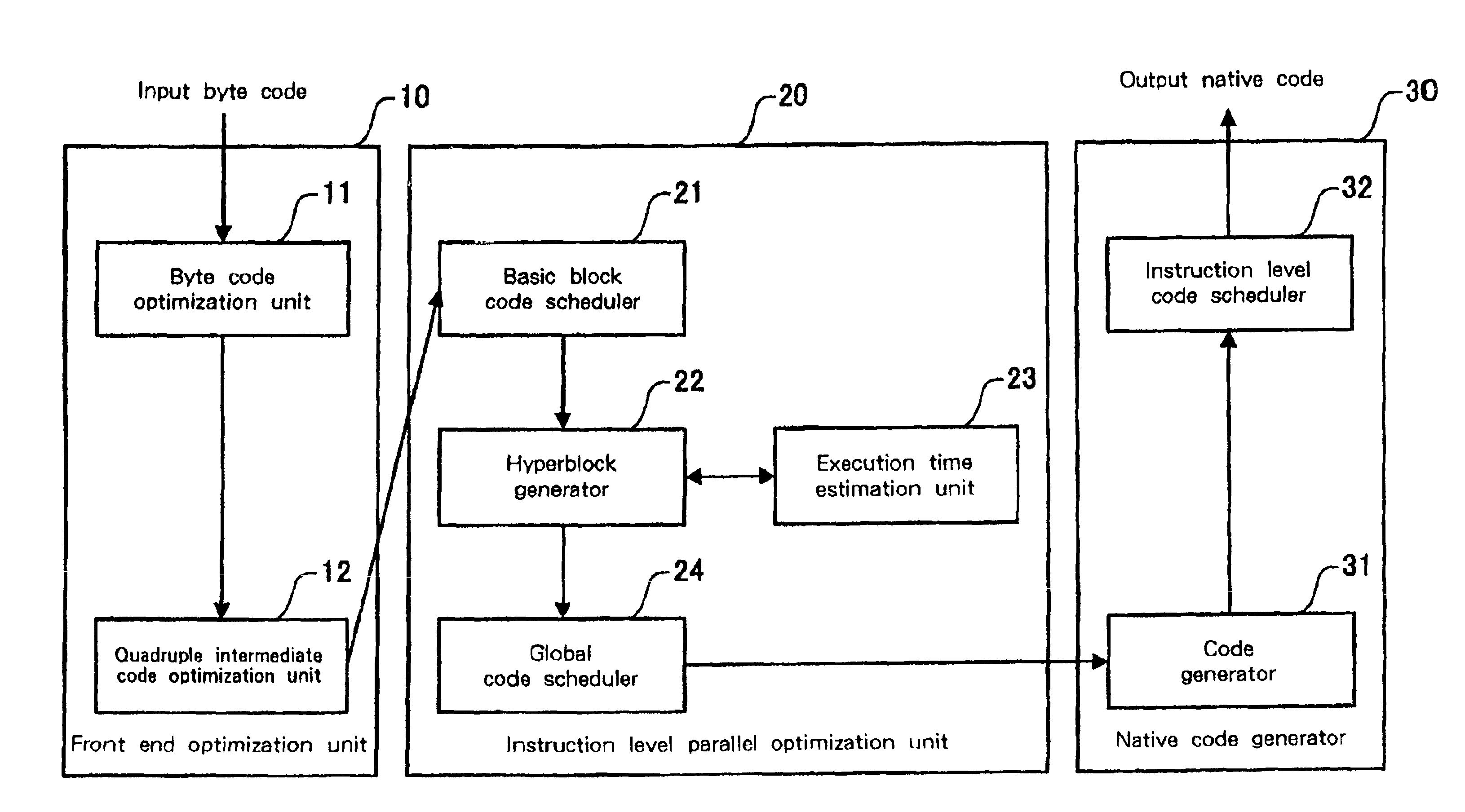
Fast just-in-time (JIT) scheduler
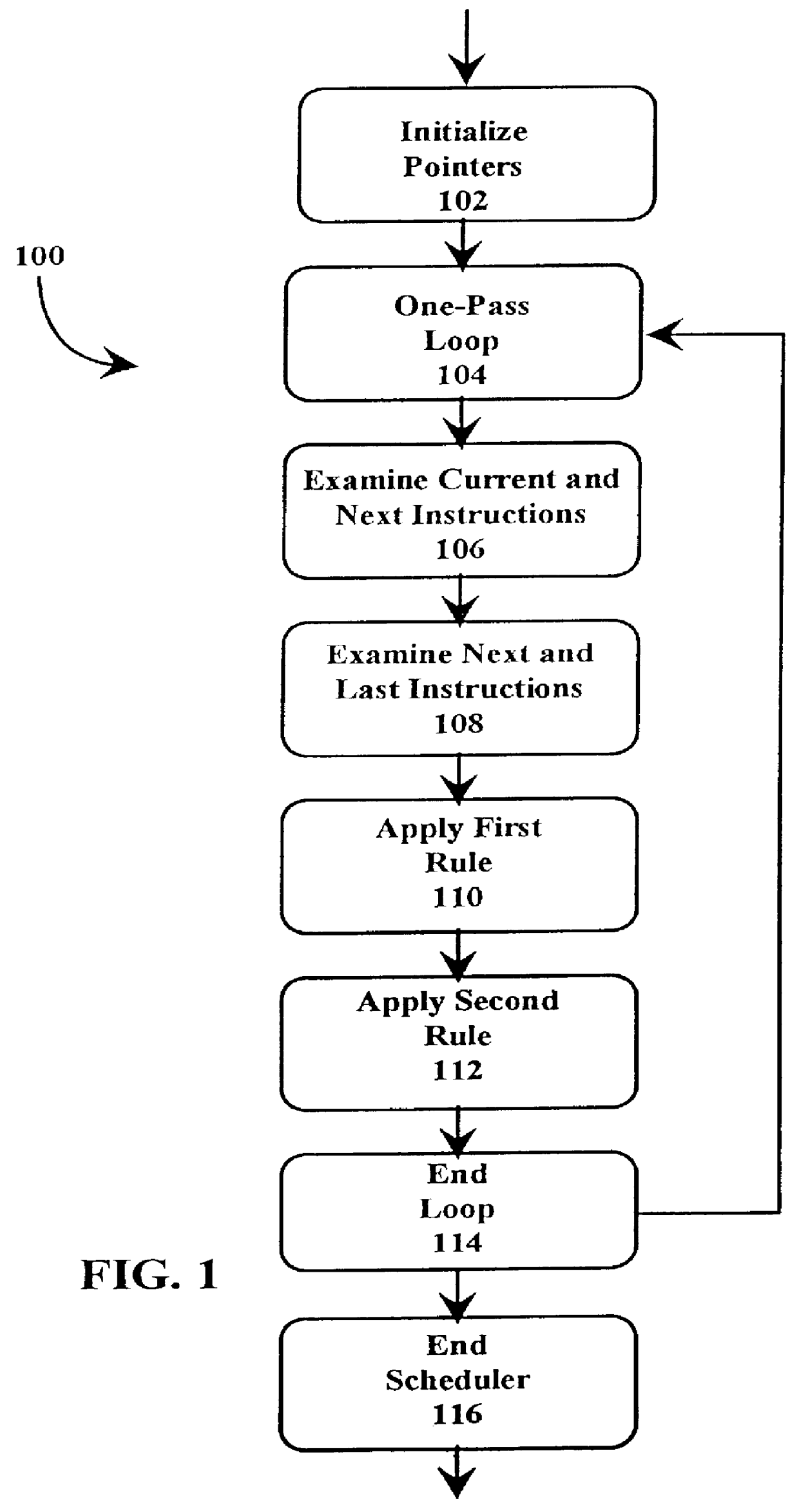
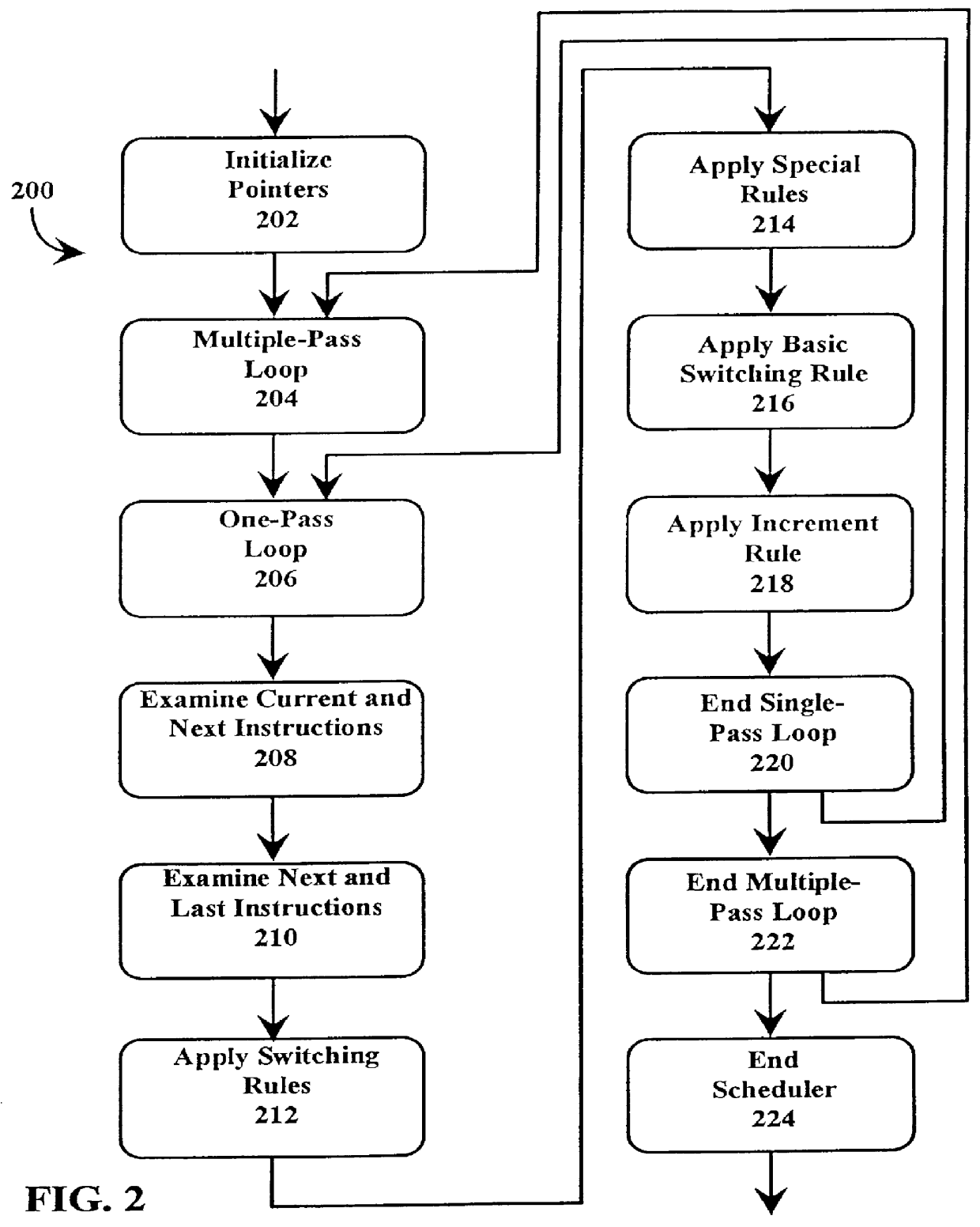
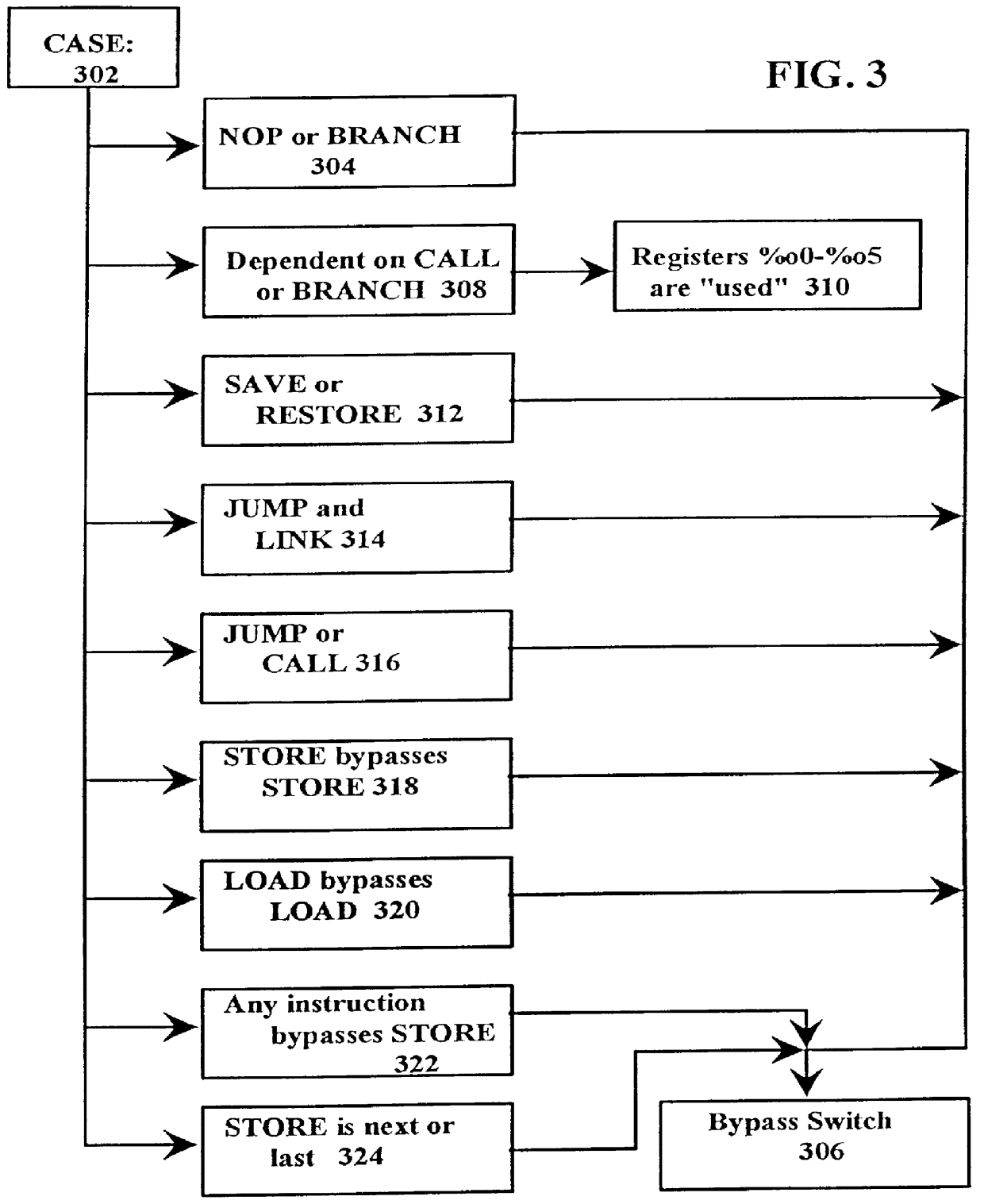
A just-in-time (JIT) compiler typically generates code from bytecodes that have a sequence of assembly instructions forming a "template". It has been discovered that a just-in-time (JIT) compiler generates a small number, approximately 2.3, assembly instructions per bytecode. It has also been discovered that, within a template, the assembly instructions are almost always dependent on the next assembly instruction. The absence of a dependence between instructions of different templates is exploited to increase the size of issue groups using scheduling. A fast method for scheduling program instructions is useful in just-in-time (JIT) compilers. Scheduling of instructions is generally useful for just-in-time (JIT) compilers that are targeted to in-order superscalar processors because the code generated by the JIT compilers is often sequential in nature. The disclosed fast scheduling method has a complexity, and therefore an execution time, that is proportional to the number of instructions in an instruction block (N complexity), a substantial improvement in comparison to the N2 complexity of conventional compiler schedulers. The described fast scheduler advantageously reorders instructions with a single pass, or few passes, through a basic instruction block while a conventional compiler scheduler such as the DAG scheduler must iterate over an instruction basic block many times. A fast scheduler operates using an analysis of a sliding window of three instructions, applying two rules within the three instruction window to determine when to reorder instructions. The analysis includes acquiring the opcodes and operands of each instruction in the three instruction window, and determining register usage and definition of the operands of each instruction with respect to the other instructions within the window. The rules are applied to determine ordering of the instructions within the window.
Owner:ORACLE INT CORP
Semiconductor device
ActiveUS8547753B2Improve versatilityReduce designPower reduction in field effect transistorsTransistorProgrammable logic deviceHemt circuits
Owner:SEMICON ENERGY LAB CO LTD
Systems, methods and computer program products for string analysis with security labels for vulnerability detection
InactiveUS7530107B1Suppress false detectionDetailed analysisMemory loss protectionError detection/correctionLocation detectionPre-condition
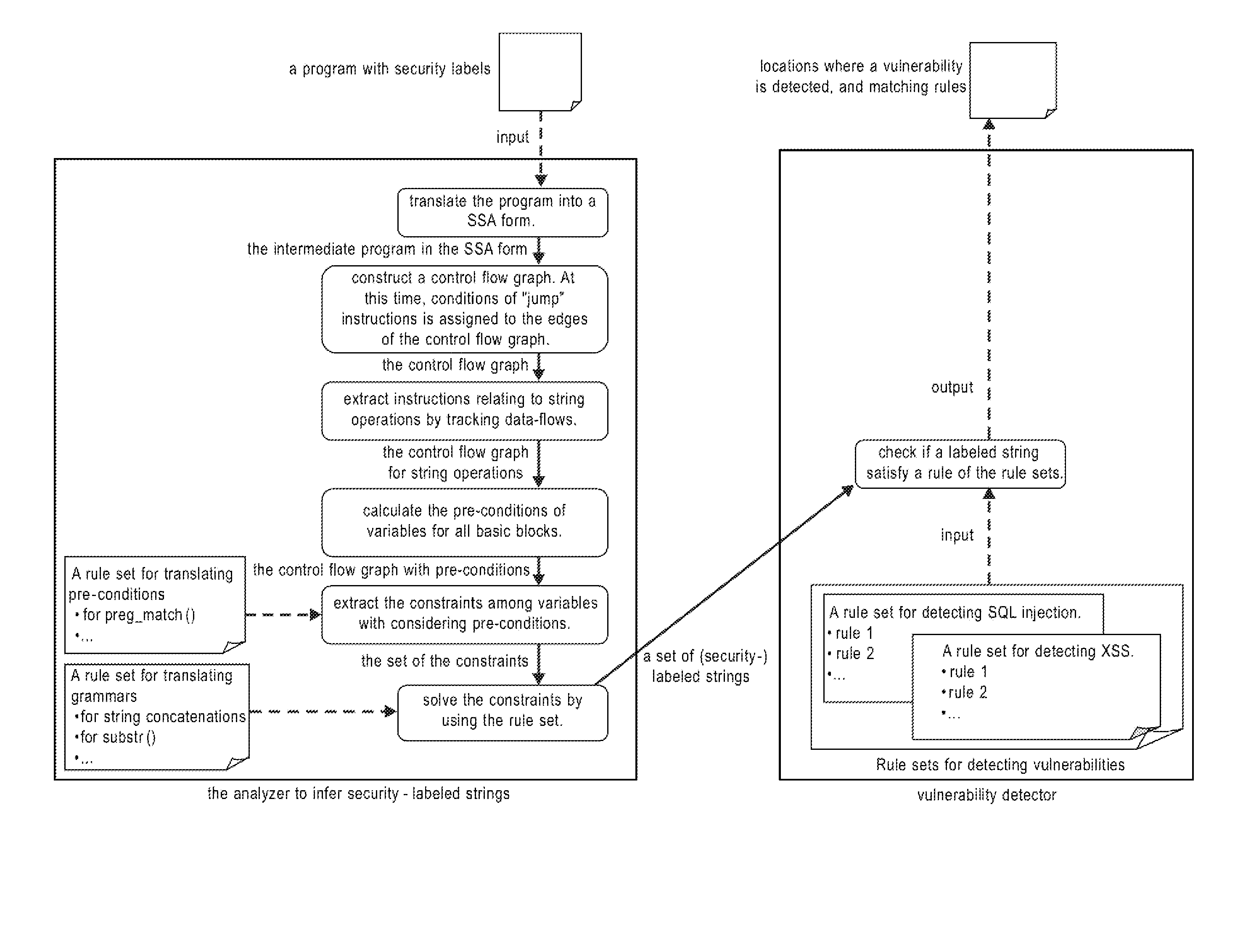
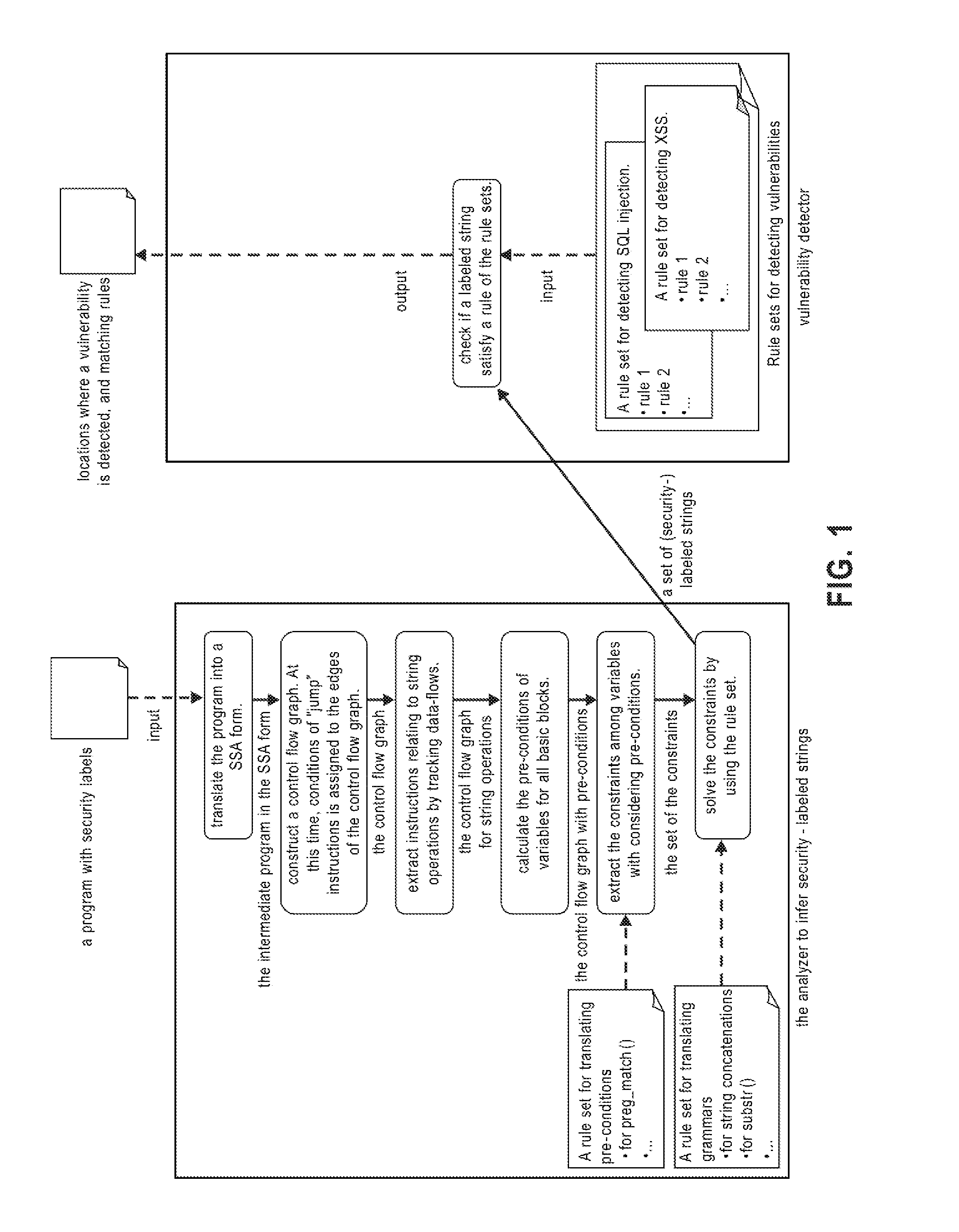
Systems, methods and computer program products for string analysis with security labels for vulnerability detection. Exemplary embodiments include a method in a computer system configured to analyze security-labeled strings and to detect vulnerability, the method including receiving a program with security labels, translating the program into a static single assignment form, constructing a control flow graph having basic blocks as nodes, extracting instructions relating to string functions and object variables, calculating pre-conditions of variables for the basic blocks, extracting constraints among the variables subject to a rule set for translating pre-conditions, solving the constraints and obtaining a set of strings that he object variables form as a context-free grammar to obtain a set of security-labeled strings, checking if the set of security-labeled strings satisfies a rule of the rule set for translating pre-conditions and identifying locations in the program where a vulnerability is detected.
Owner:IBM CORP
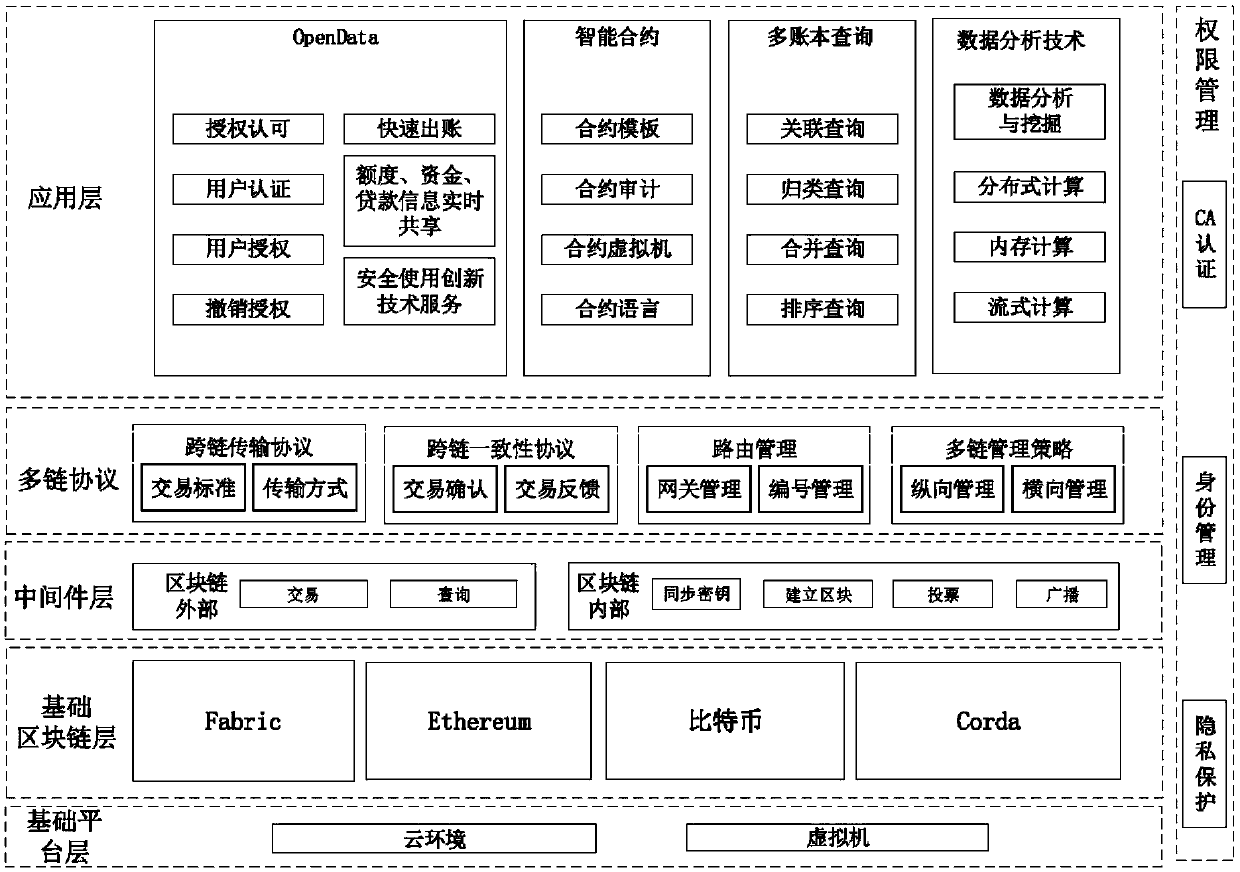
System architecture for cross-block-chain open data sharing under heterogeneous multi-chain architecture
ActiveCN108876370ASolve interconnection problemsQuality improvementPayment protocolsTransmission protocolOpen data
The invention provides a system architecture for cross-block-chain open data sharing under a heterogeneous multi-chain architecture. The system architecture comprises (1) an application layer, including an OpenData module, an intelligent contract module, a multi-account-book query module and a data analysis module; (2) a multi-chain protocol, including a cross-chain transmission protocol applied to a transaction standard and a transmission mode, a cross consistency protocol applied to transaction confirmation and transaction feedback, a heterogeneous block chain cross-chain data communicationand transaction protocol, routing management applied to gateway management and number management, and a multi-chain management strategy applied to longitudinal management and transverse management; (3) a middleware layer applied to transactions and query outside block chains and synchronous keys inside the block chains for establishing blocks and achieving voting and broadcast functions; (4) a basic block chain layer, including Fabric, Ethereum, Bitcoin and Corda; and (5) a basic platform layer based on a cloud environment and a virtual machine. The system architecture helps a user to securelyshare data and service provided by a third party, and the problem of "data splitting" is solved.
Owner:BEIHANG UNIV
Program optimization method, and compiler using the same
InactiveUS6817013B2Short processing timeEfficient executionSoftware engineeringDigital computer detailsBasic blockSource code
An optimization method and apparatus for converting source code for a program written in a programming language into machine language. The program includes a basic block as a unit to estimate an execution time for the program to be processed, generating a nested tree that represents the connections of the basic blocks using a nesting structure, when a conditional branch is accompanied by a node in the nested tree, employing the execution time estimated by using the basic blocks as units to obtain an execution time at the node of the program when a conditional branching portion of a program is directly executed and when the conditional branching portion is executed in parallel, and defining the node as a parallel execution area group when the execution time required for the parallel execution is shorter or dividing multiple child nodes of the nodes into multiple parallel execution areas.
Owner:INT BUSINESS MASCH CORP
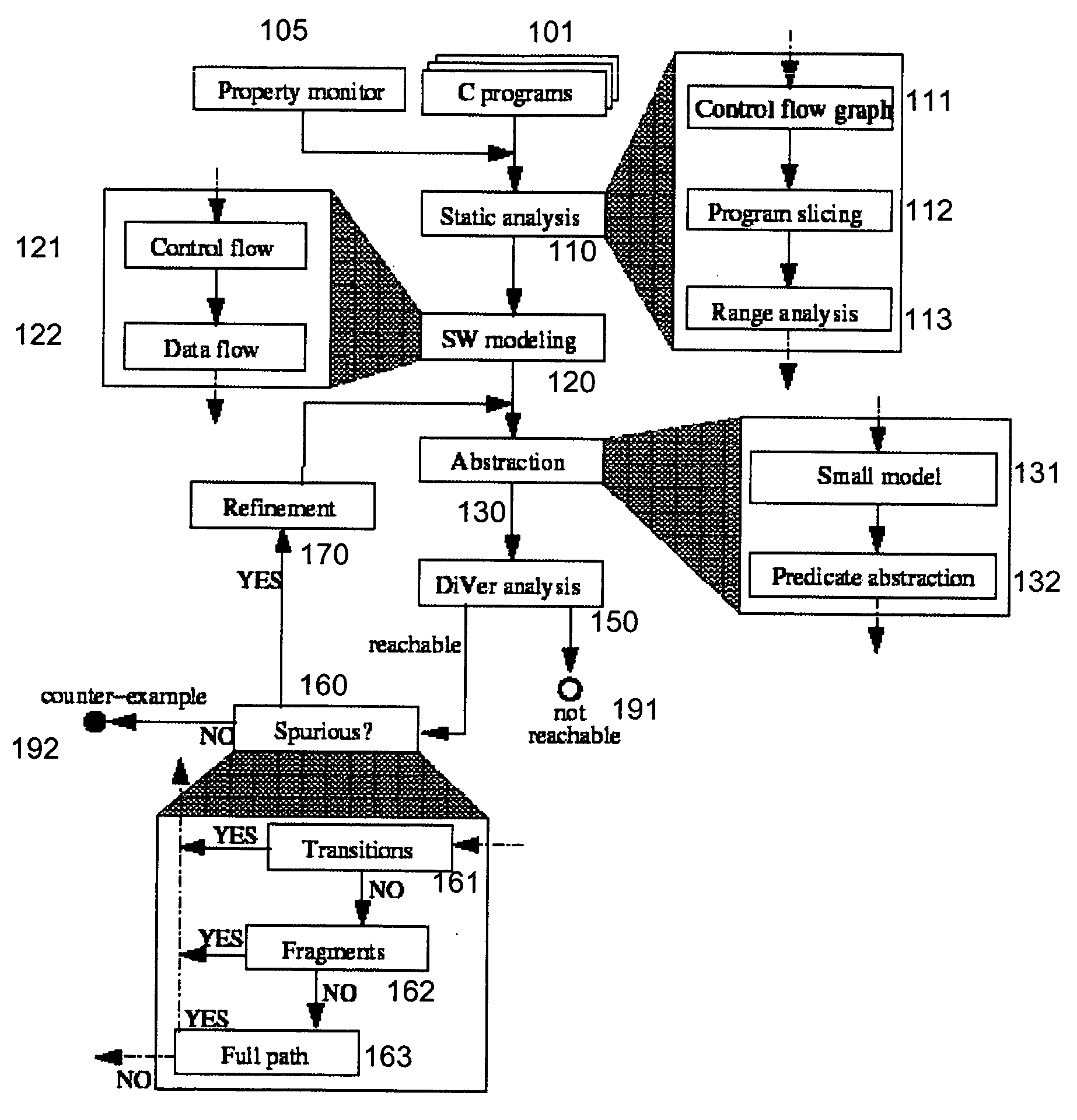
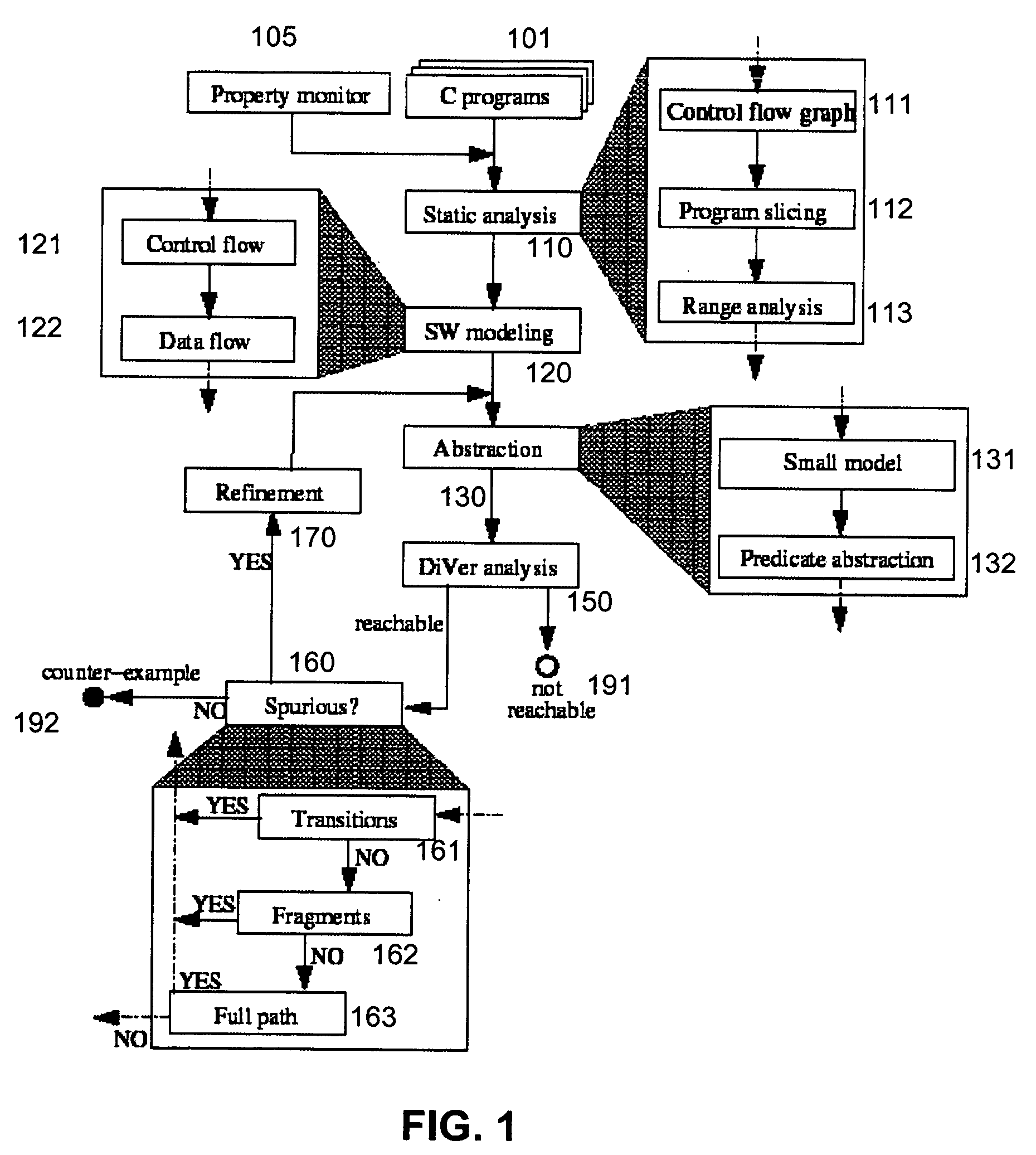
System and method for modeling, abstraction, and analysis of software
ActiveUS20050166167A1Improve verification efficiencyImprove translationError detection/correctionComputation using non-denominational number representationBasic blockSoftware
A system and method is disclosed for formal verification of software programs that advantageously translates the software, which can have bounded recursion, into a Boolean representation comprised of basic blocks and which applies SAT-based model checking to the Boolean representation.
Owner:NEC CORP
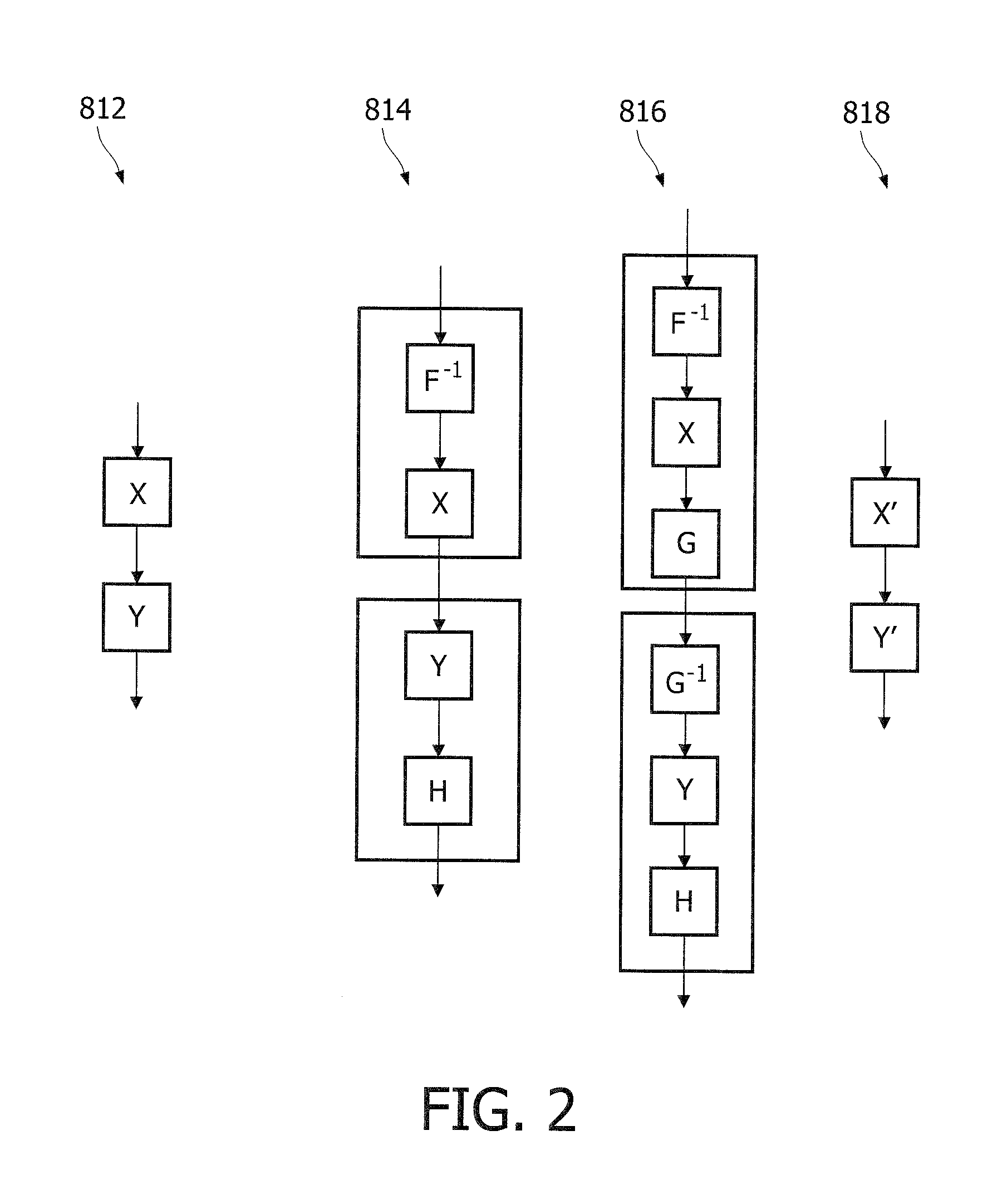
White-box cryptographic system with input dependent encodings
ActiveUS20120002807A1Simplified brokenImprove propertiesSecret communicationCryptographic attack countermeasuresComputer hardwareData encoding
A white-box cryptographic system is presented wherein at least one of its internal values is represented using an input dependent encoding. The system comprises a network of a plurality of basic blocks arranged for collectively performing a cryptographic operation. An encoder is arranged for encoding output data of a first one of the plurality of basic blocks into an encoder-output according to a selected one of a plurality of encoding schemes, said selection depending on an input-message to the system. A compensator is arranged for recoding intermediate data to compensate for the effect of the encoding according to a selected one of a plurality of recoding schemes. Using variable encodings instead of fixed encodings complicates reverse engineering the white-box cryptographic system.
Owner:IRDETO ACCESS
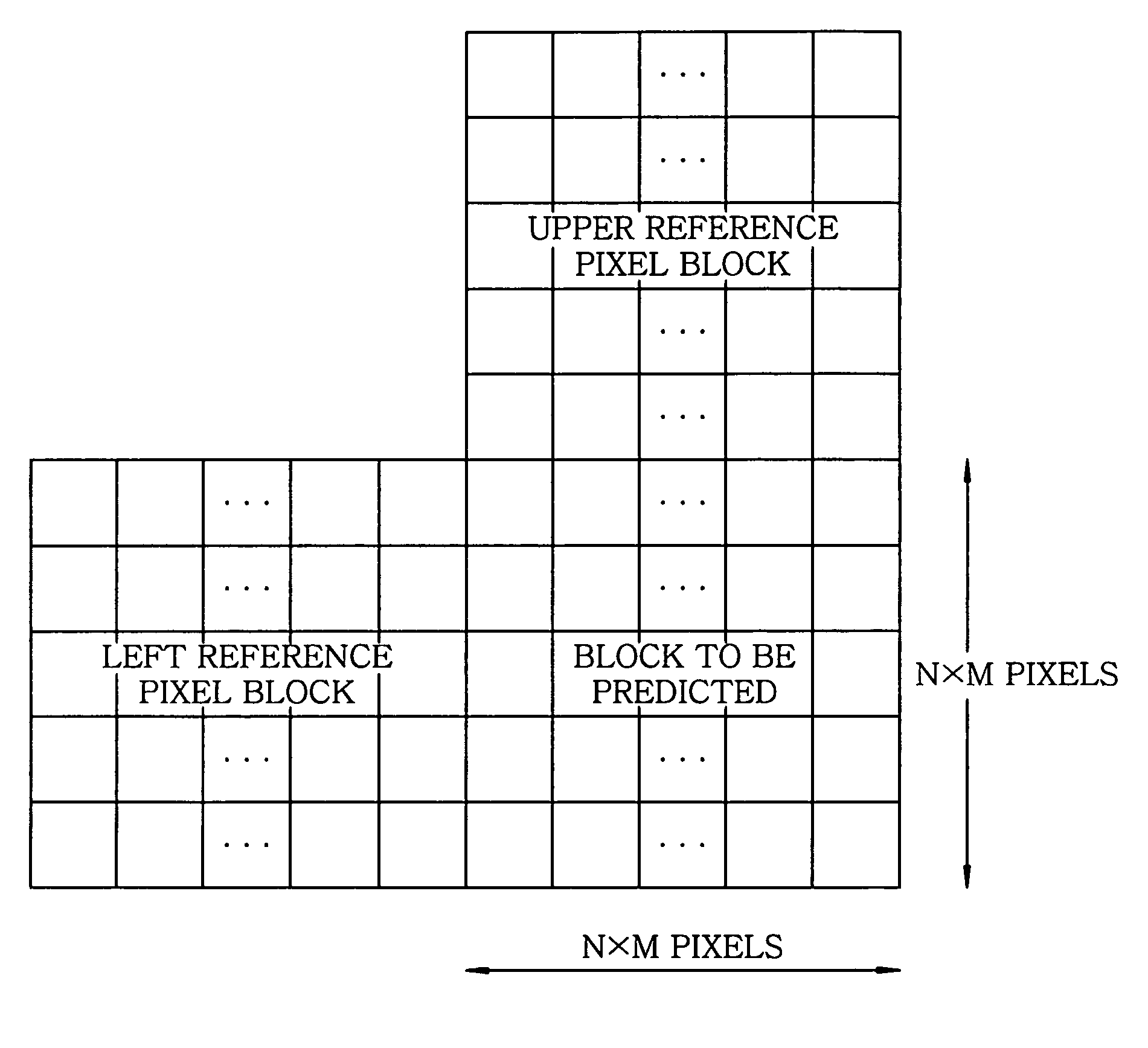
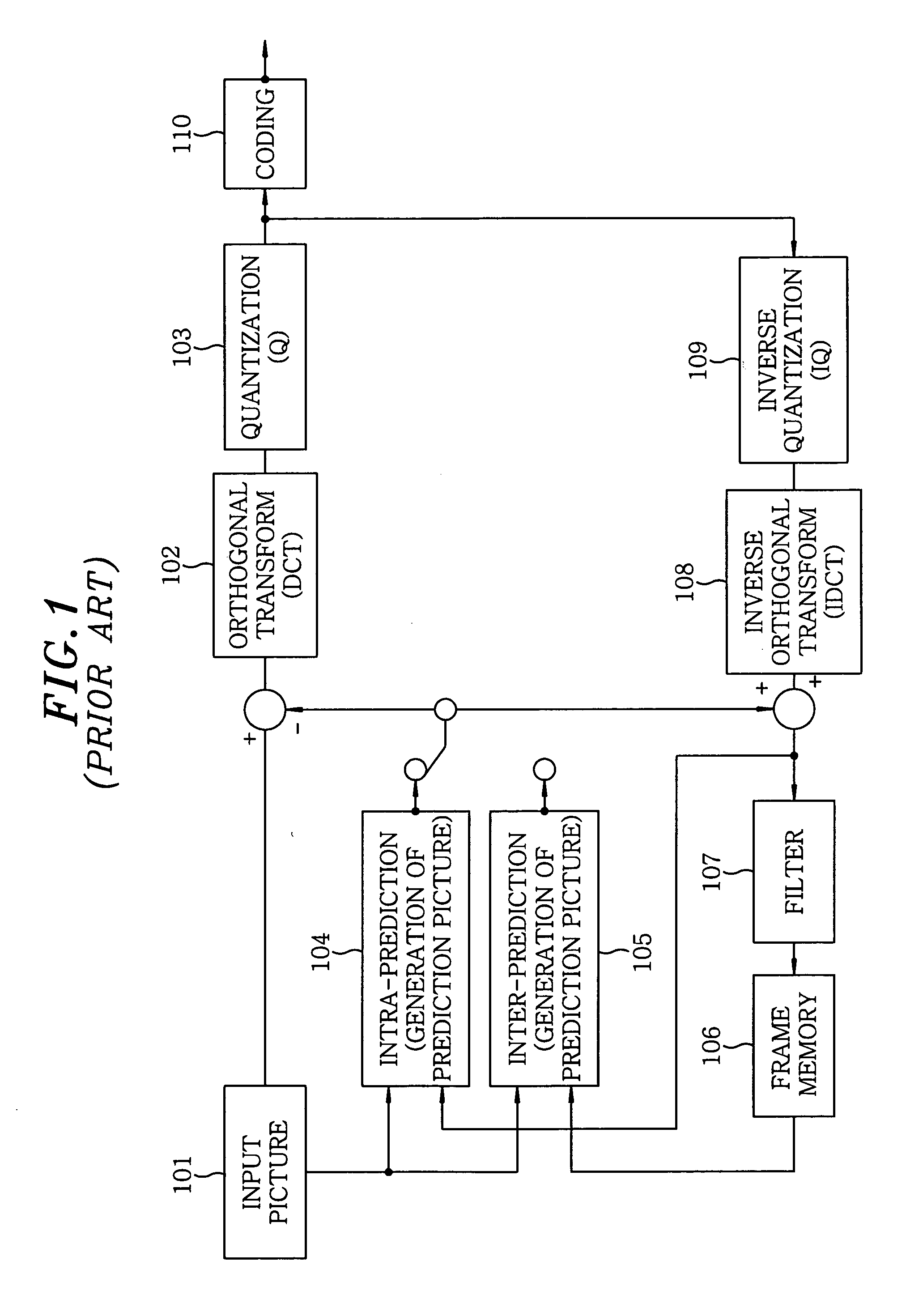
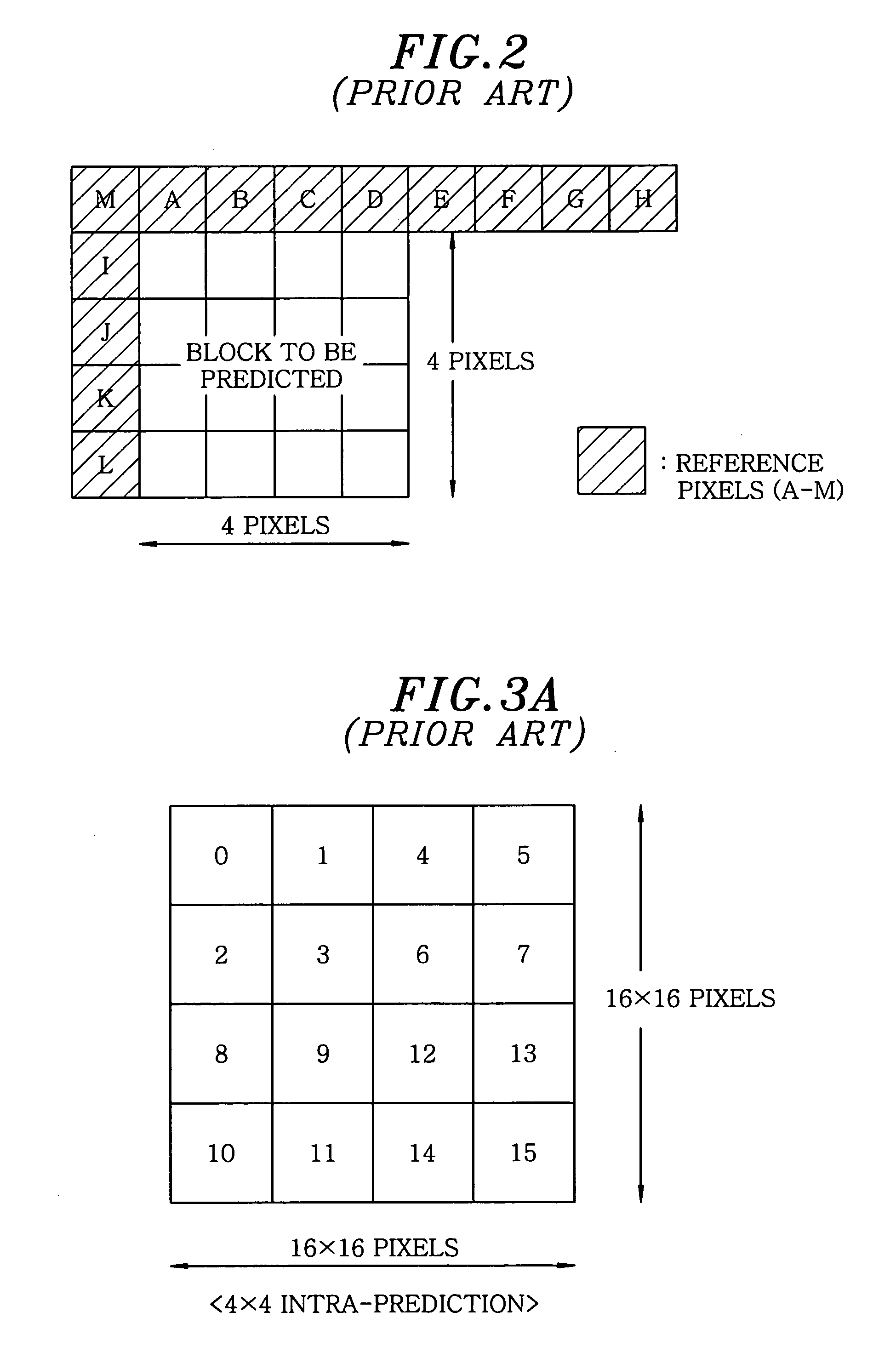
Moving picture coding apparatus
InactiveUS20100177821A1Good prediction accuracyImprove accuracyColor television with pulse code modulationColor television with bandwidth reductionComputer visionBasic block
A moving picture coding apparatus divides a picture into basic blocks and generates a prediction image of a block to be predicted in a basic block by using adjacent pixels in reference pixel blocks adjacent to the block to be predicted as reference pixels to perform predictive coding of a moving picture. When some of the reference pixels are not available, pixel values of the reference pixels that are not available are calculated based on pixels in the reference pixel blocks. The prediction image of the block to be predicted is generated by using the calculated pixel values instead of the reference pixels that are not available.
Owner:KOKUSA ELECTRIC CO LTD
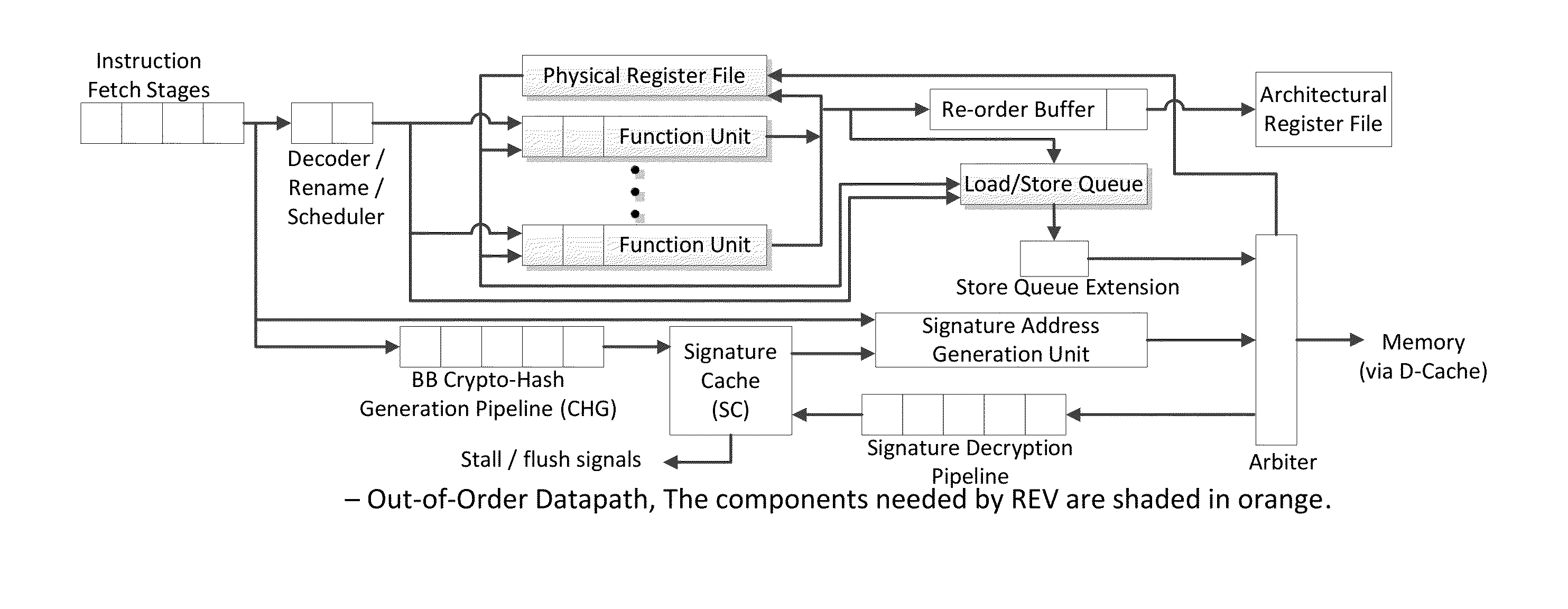
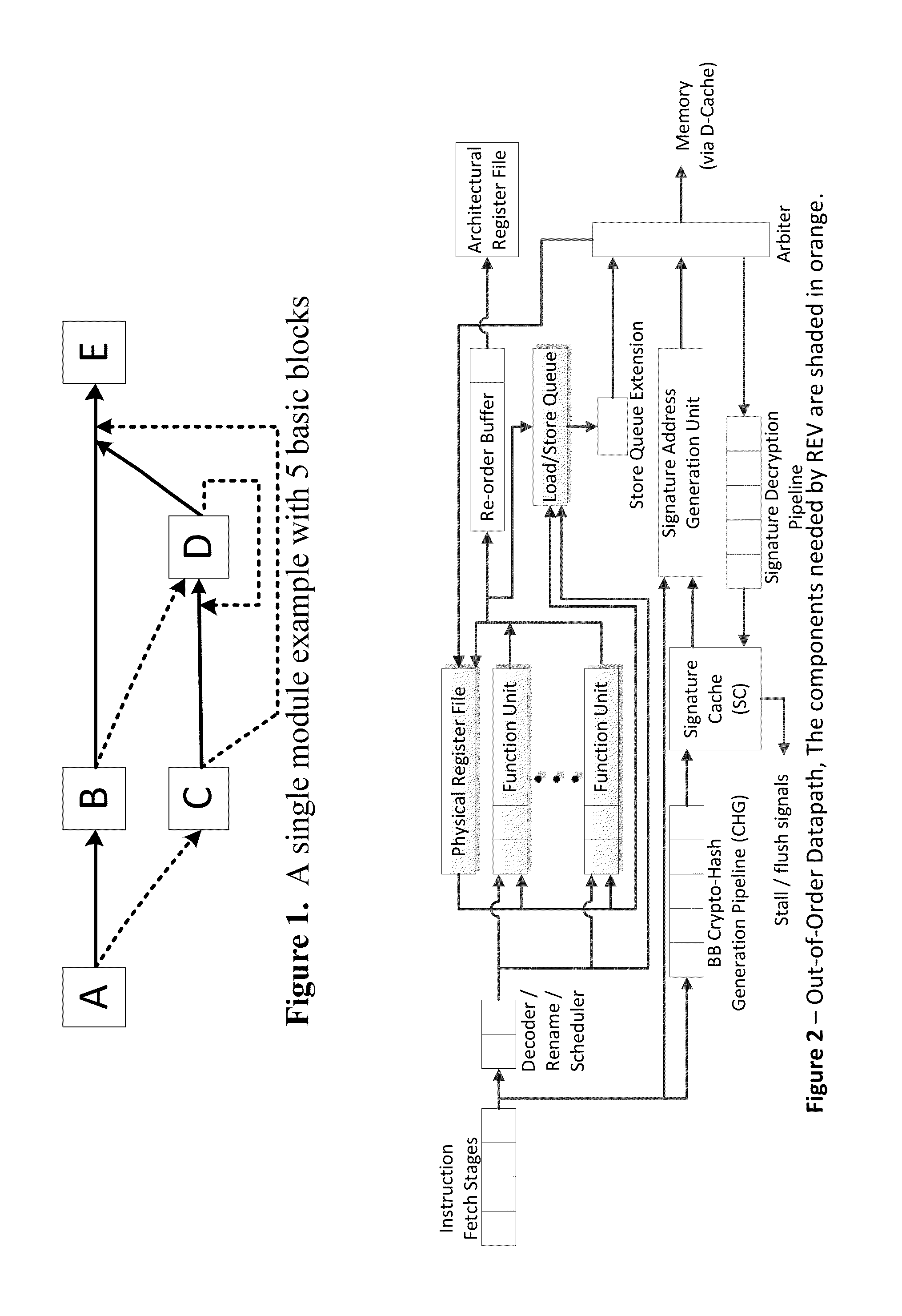
Continuous run-time validation of program execution: a practical approach
ActiveUS20140082327A1Easy to modifyGuaranteed CompatibilityError detection/correctionDigital computer detailsControl flowReal time validation
Trustworthy systems require that code be validated as genuine. Most systems implement this requirement prior to execution by matching a cryptographic hash of the binary file against a reference hash value, leaving the code vulnerable to run time compromises, such as code injection, return and jump-oriented programming, and illegal linking of the code to compromised library functions. The Run-time Execution Validator (REV) validates, as the program executes, the control flow path and instructions executed along the control flow path. REV uses a signature cache integrated into the processor pipeline to perform live validation of executions, at basic block boundaries, and ensures that changes to the program state are not made by the instructions within a basic block until the control flow path into the basic block and the instructions within the basic block are both validated.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
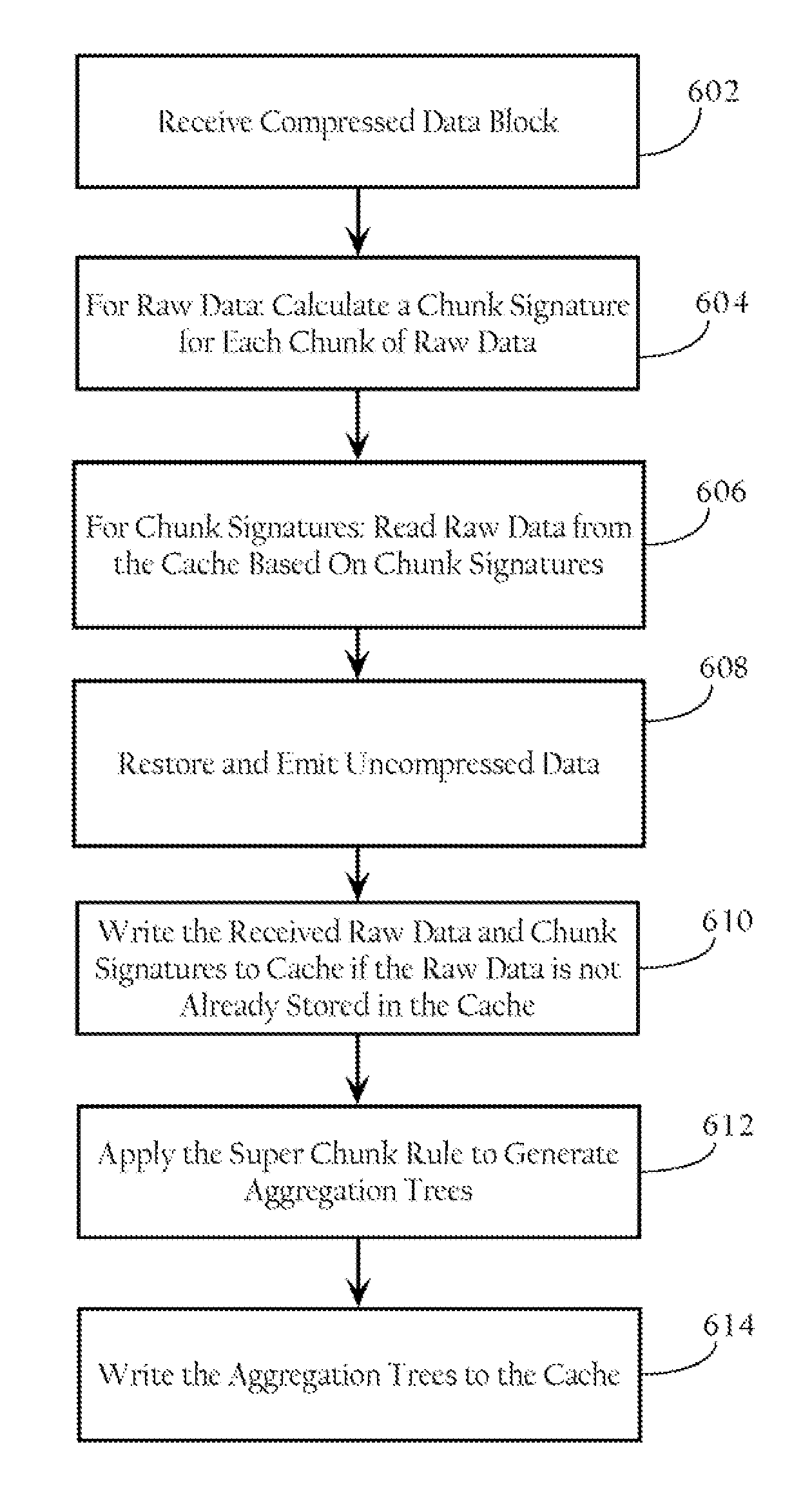
Redundancy elimination by aggregation of multiple chunks
A data redundancy elimination system. In particular implementations, a method includes storing in a memory one or more aggregation trees, each aggregation tree comprising one or more base chunk nodes and one or more super chunk nodes, wherein each base chunk node comprises a chunk signature and corresponding raw data, and wherein super chunk nodes correspond to child base chunk nodes and include a chunk signature; receiving a data block; dividing the data block into a plurality of base chunks, each base chunk having a degree value characterizing the occurrence probability of the base chunk; computing chunk signatures for the plurality of base chunks; applying a super chunk rule to contiguous sequences of base chunks of the plurality of base chunks to create one or more aggregation trees, wherein the super chunk rule aggregates base chunks based on the respective occurrence probabilities of the base chunks; identifying one or more nodes in the one or more created aggregation trees that match corresponding nodes of the aggregation trees in the memory; compressing the received data block based on the identified nodes; and conditionally adding the one or more created aggregation trees to the memory.
Owner:CISCO TECH INC
Set of blocks for construction game
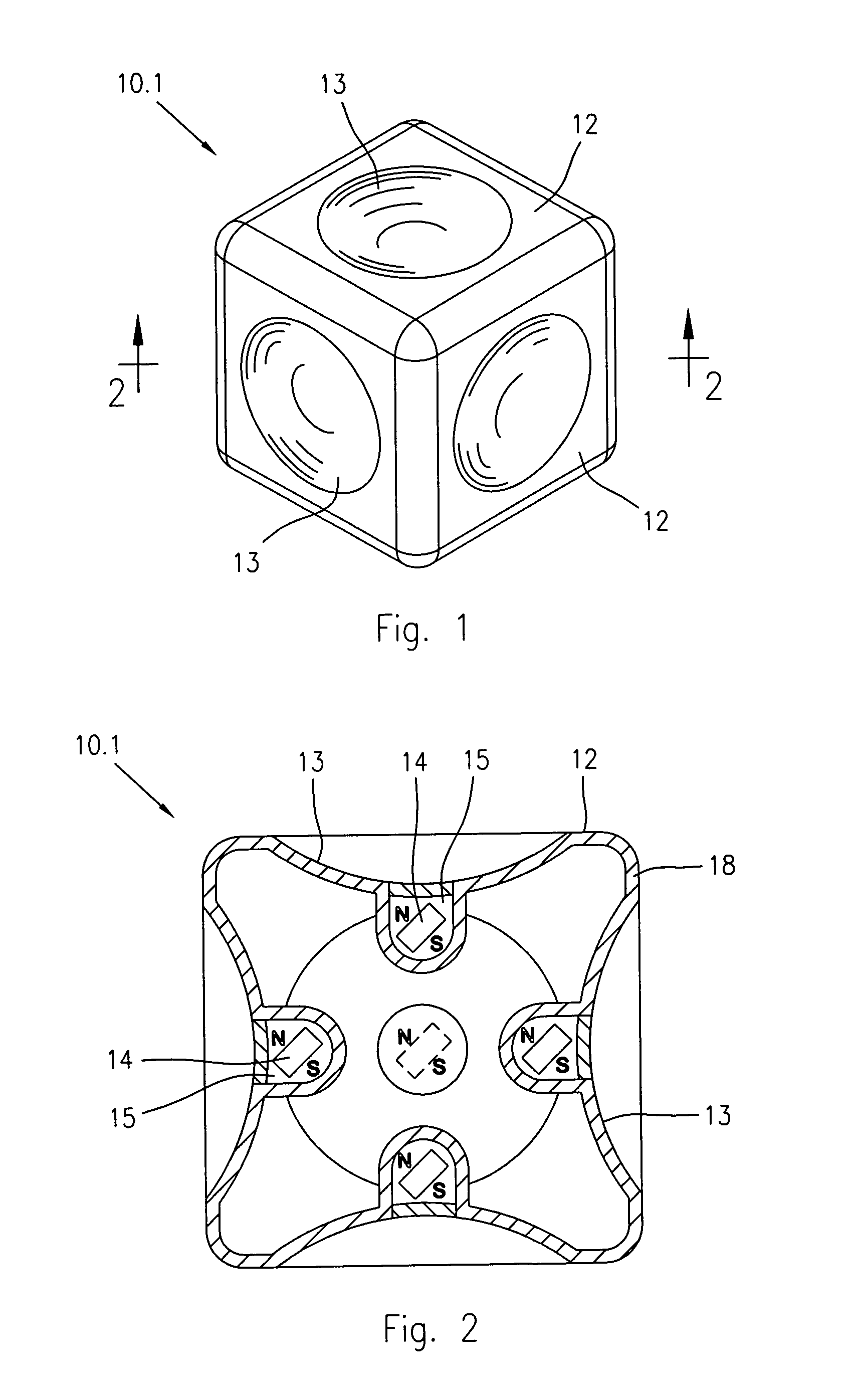
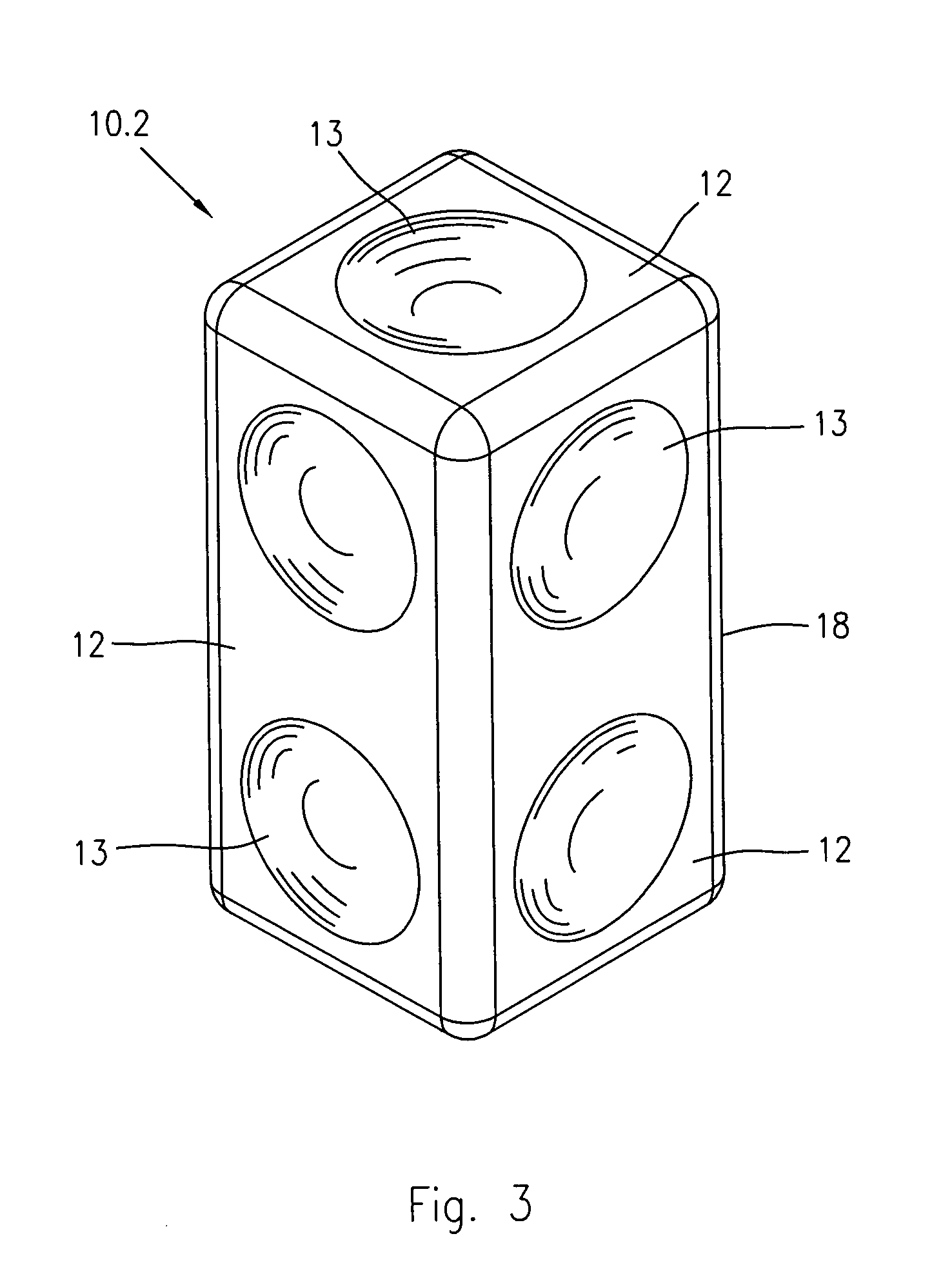
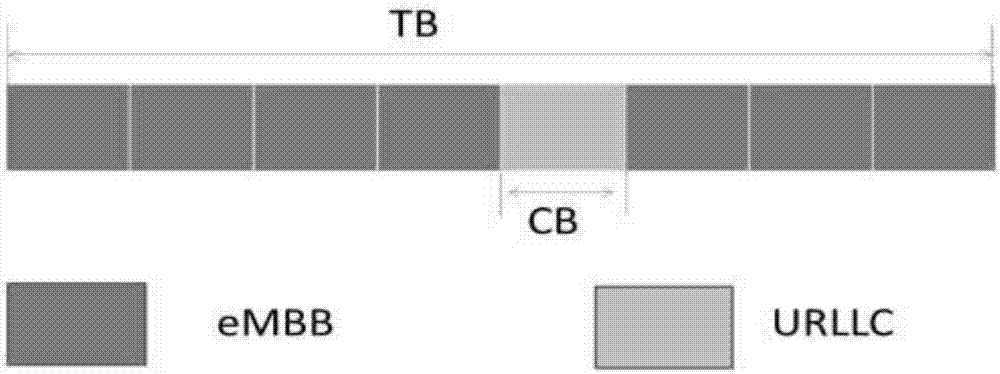
InactiveUS20100120322A1Facilitated magnetic anchorageUtmost freedom and versatilityToysCouplingEngineering
A set of blocks for constructing game assemblies for children includes basic block members (10) and complementary block members (11) that can be magnetically anchored and assembled each other; each basic block member (10) has a hollow body (18) including lateral faces having flat and / or shaped coupling surfaces. In turn, the complementary block members (11) include a hollow body (16) having lateral coupling surfaces matching with the coupling surfaces of the basic block members (10). Magnetic elements (14, 20) are fixedly or movably positioned in each basic and complementary block member (10, 11) to enable the anchorage and the assembling of the block members (10, 11) during the construction of the game. The block members (10, 11) have dimensions suitable to be easily gripped with the hands by a children, and may be provided with differently coloured surfaces to offer different tactile, visual and sound sensations during the game.
Owner:VICENTELLI CLAUDIO
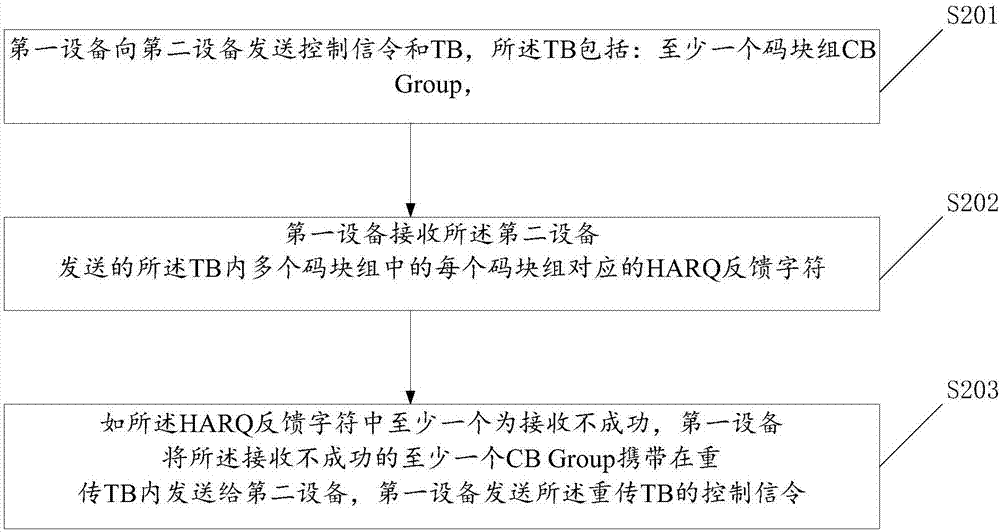
Code block retransmission method and device
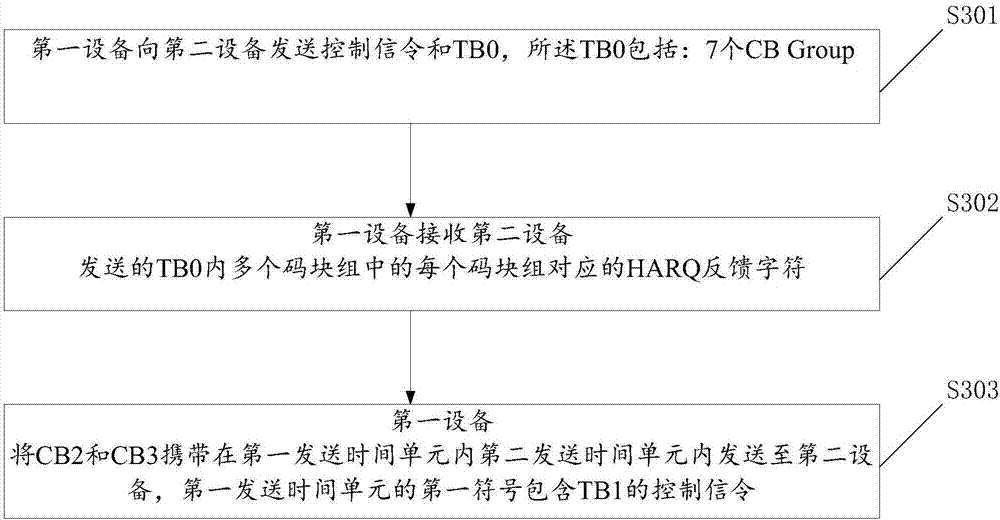
InactiveCN106888074AImprove efficiencyError prevention/detection by using return channelCoding blockComputer hardware
The present invention provides a code block retransmission method. The method comprises the steps of sending a control signaling and a transmission block (TB) from a first device to a second device, wherein the TB comprises at least one code block group (CB Group), and the CB Group is a transmission basic block of the transmission block; receiving a HARQ feedback character corresponding to each code block group of all the plurality of code block groups contained in the TB sent from the second device by the first device; if at least one HARQ feedback character is not successfully received, loading the at least one non-successfully received CB Group in a retransmitted TB by the first device and sending the retransmitted TB to the second device; and sending the control signaling of the retransmitted TB by the first device. The control signaling of the retransmitted TB is used for indicating the second device to identify the at least one CB Group. The technical scheme of the invention has the advantage of high efficiency.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
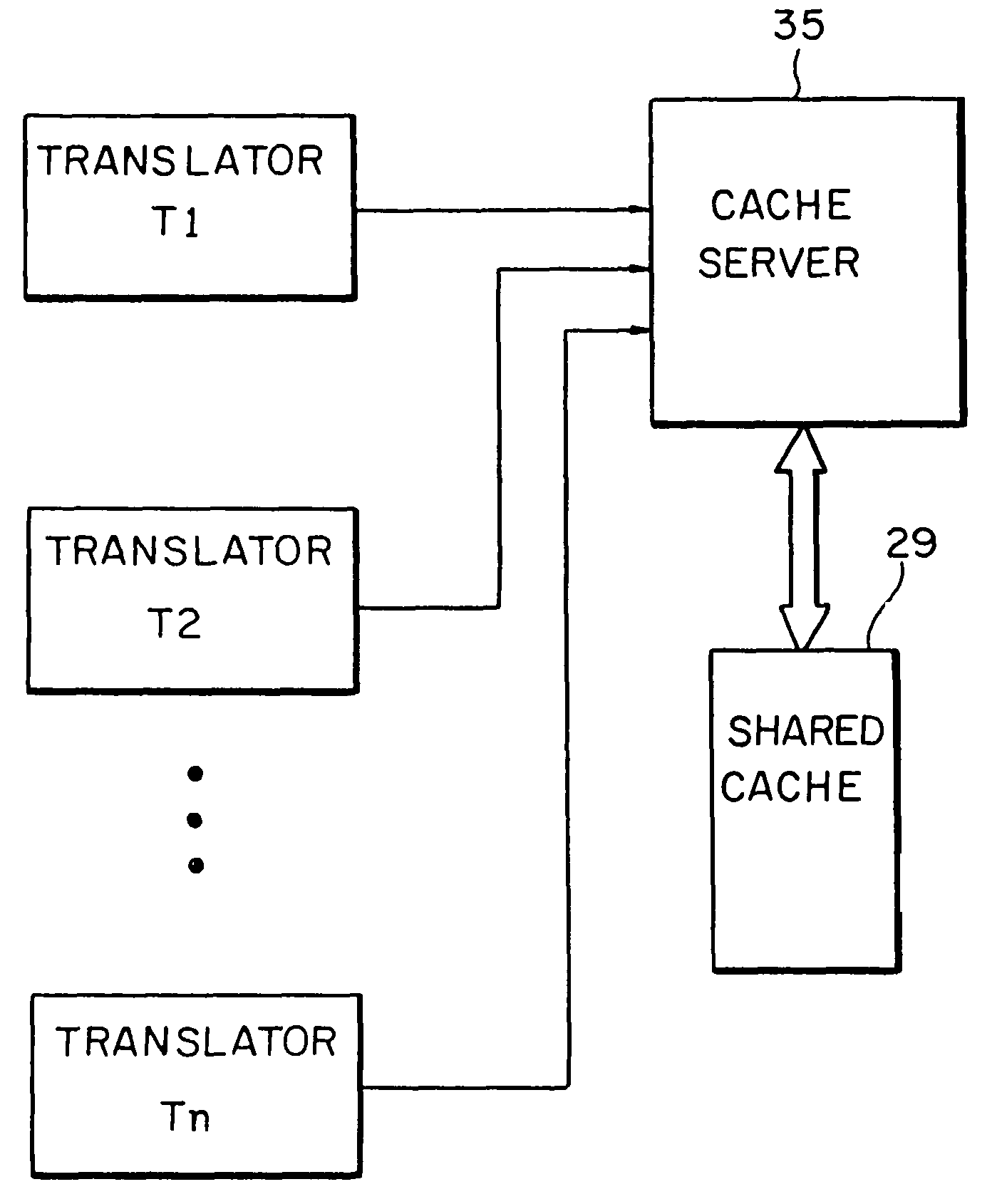
Shared code caching for program code conversion
ActiveUS7805710B2General purpose stored program computerProgram loading/initiatingCode TranslationObject code
Subject program code is translated to target code in basic block units at run-time in a process wherein translation of basic blocks is interleaved with execution of those translations. A shared code cache mechanism is added to persistently store subject code translations, such that a translator may reuse translations that were generated and / or optimized by earlier translator instances.
Owner:IBM CORP
Method and apparatus for computing user-specified cost metrics in a data space profiler
A system and method for profiling a software application may include means for defining a custom cost metric that includes a cost metric identifier and a cost function. The cost function may apply a mathematical formula to data extracted from an event set to calculate a respective cost metric value for each of one or more events in the event set. The data extracted from the event set may include one or more respective profiling object identifiers and one or more other respective costs associated with each of the one or more events. A cost associated with an event in the event space may be associated with a function or basic block of instructions. The cost function may include a distribution formula for attributing at least a portion of the cost associated with a function or basic block to each of the instructions comprising the function or basic block.
Owner:ORACLE INT CORP
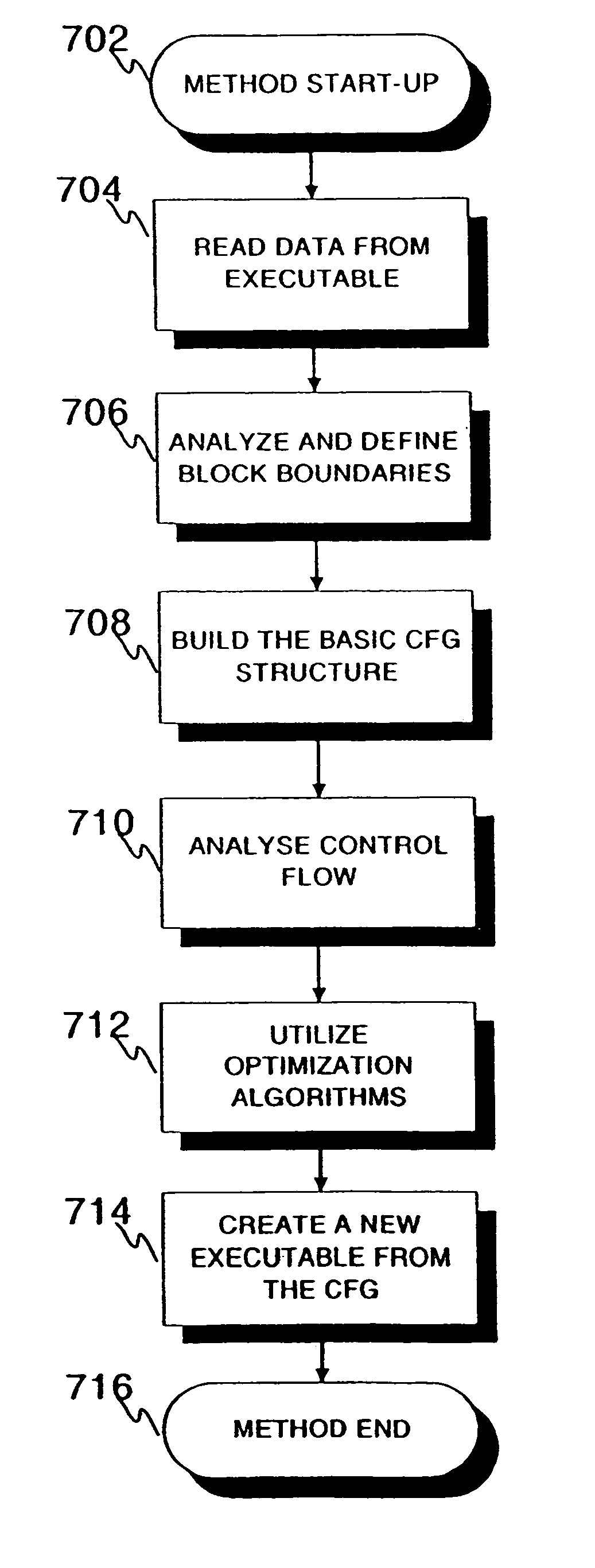
Constructing control flows graphs of binary executable programs at post-link time
InactiveUS7207038B2Clarifies overall structureReduce memory usageSoftware engineeringSoftware simulation/interpretation/emulationControl flowBasic block
A method and a system for constructing a control flow graph (CFG, 106) from an executable computer program (104). The solution detects data intermixed with instructions and instruction set changes. The method includes the steps of defining block leader types specifying basic block boundaries in the program (104), building a CFG structure (106) according to the basic blocks found in the program, and adding control flow and addressing information to the CFG (106) by propagating through the basic blocks and internals thereof. The CFG (106) may be then optimised (108) and a compacted executable (112) created as a result.
Owner:NOKIA CORP
Automatic analyzing system and method for dynamic action of malicious program
InactiveCN101154258AImprove efficiencyImprove operational efficiencyPlatform integrity maintainanceBehavioral analyticsExecution unit
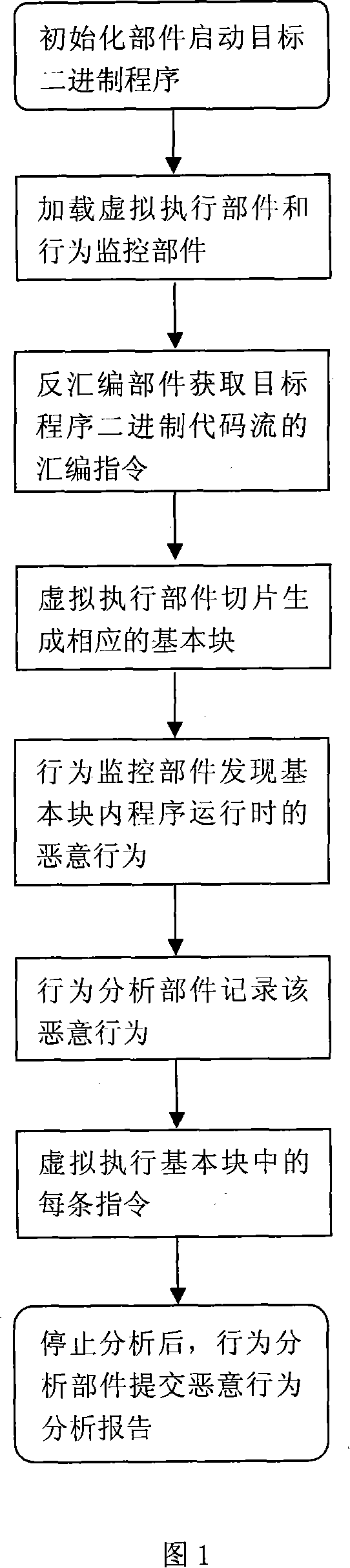
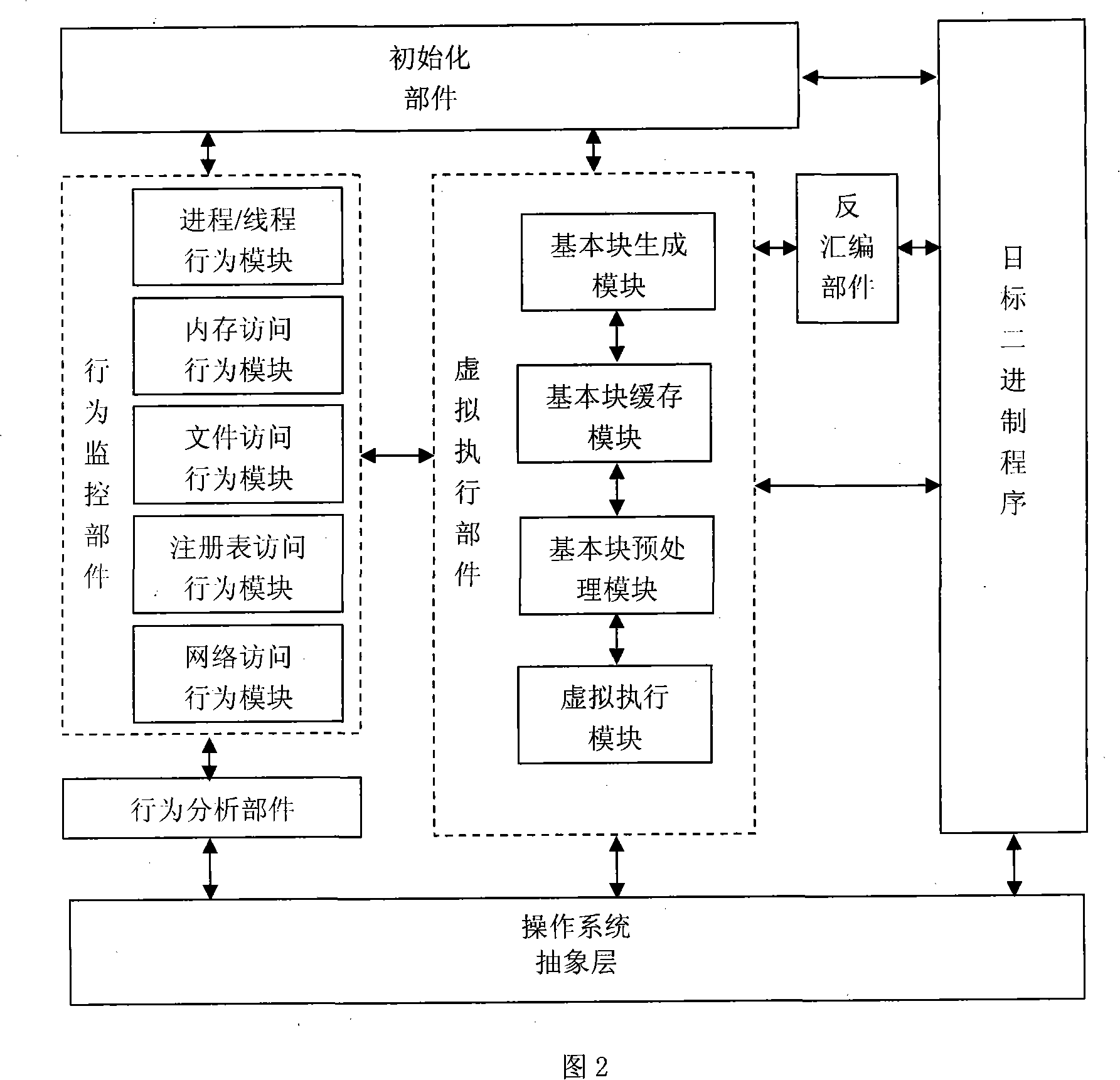
The invention relates to an automatic analysis system and a method of malice binary program dynamic behavior. The system consists of an initialization unit, a virtual execution unit, a disassembling unit, a behavior monitoring unit and a behavior analysis unit. The method is that: the initialization unit activates a monitored program, and the virtual execution unit and the behavior monitoring unit are then loaded; the disassembling unit acquires the assembler instruction of the binary code flow of an object program, the virtual execution unit slices and generates a corresponding basic block, and the behavior monitoring unit judges whether the basic block contains any malice behavior defined by a rule base; if the basic block does contain a malice behavior, the behavior monitoring unit can transfer the command to the behavior analysis unit and record the malice behavior; after being returned, each instruction in the basic block can be virtually executed; the behavior analysis unit puts forward a malice behavior analysis report after the program execution quits or a user stops the analysis process forcibly. The invention enables complete control and analysis of malice program running behavior in a virtual environment and a detailed report can provide effective buckler aiming at the malice program.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Application code integrity check during virtual machine runtime
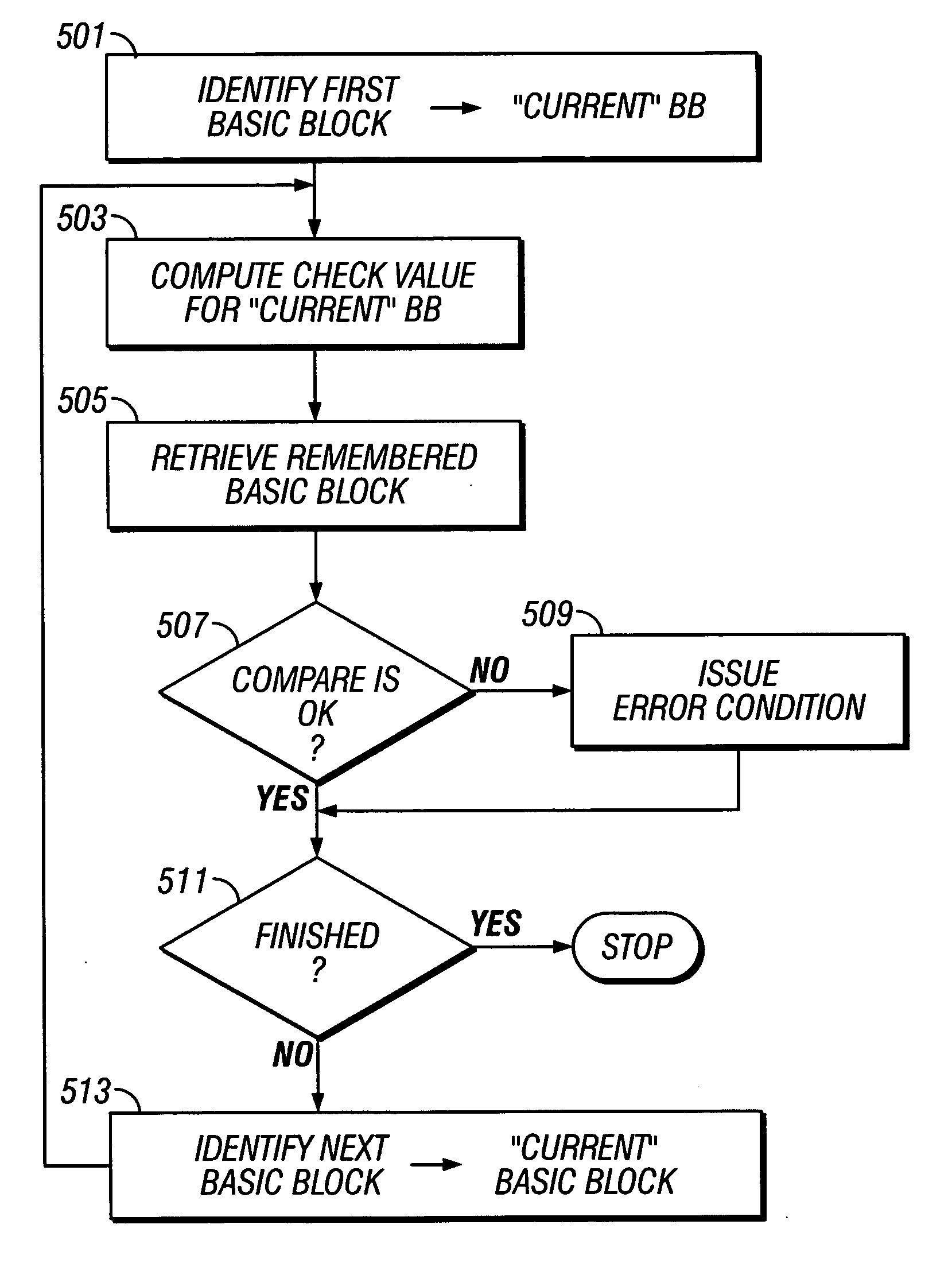
Protecting an application of a multi-application smart card against unauthorized manipulations. A system and method for guarding against unauthorized modifications includes partitioning the application into a plurality of basic blocks. Basic blocks are programming atomic units that have one entry point and one exit point and comprises a set of data units. For each basic block a check value associated with a basic block is computed wherein the check value is a function of the data units of the basic block. This check value is some how remembered and later recalled and checked either during execution of the corresponding basic block of the application program or prior to execution of the application program. During or prior to execution of the basic block the re-computed check value is verified to be the same as the remembered check value. If not, an error condition is indicated and a corrective action may be taken.
Owner:AXALTO INC
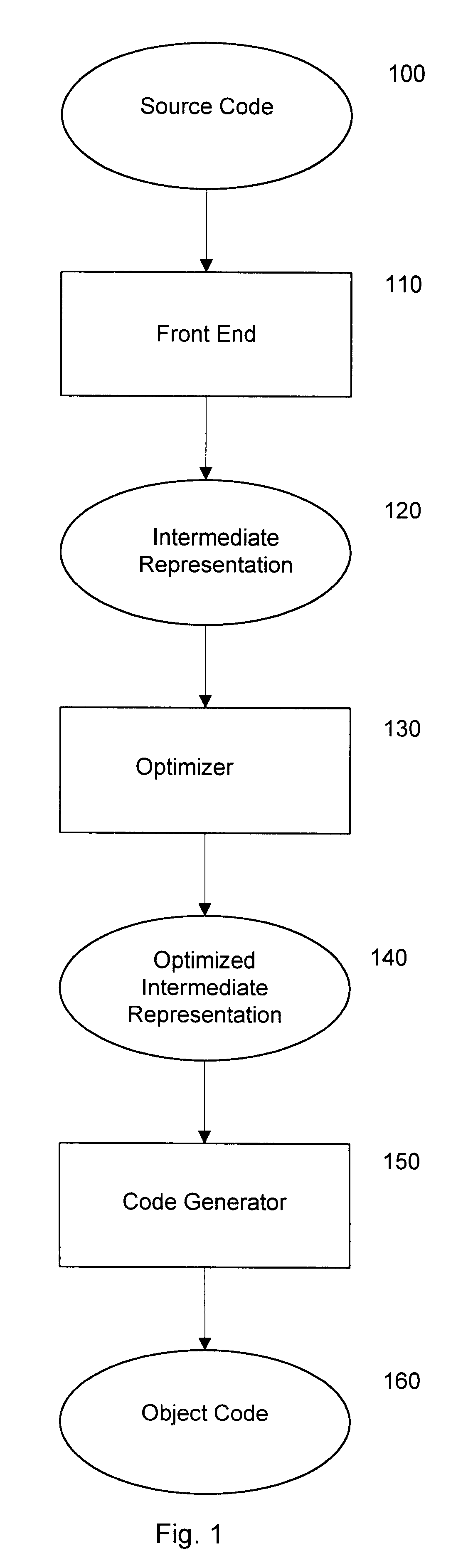
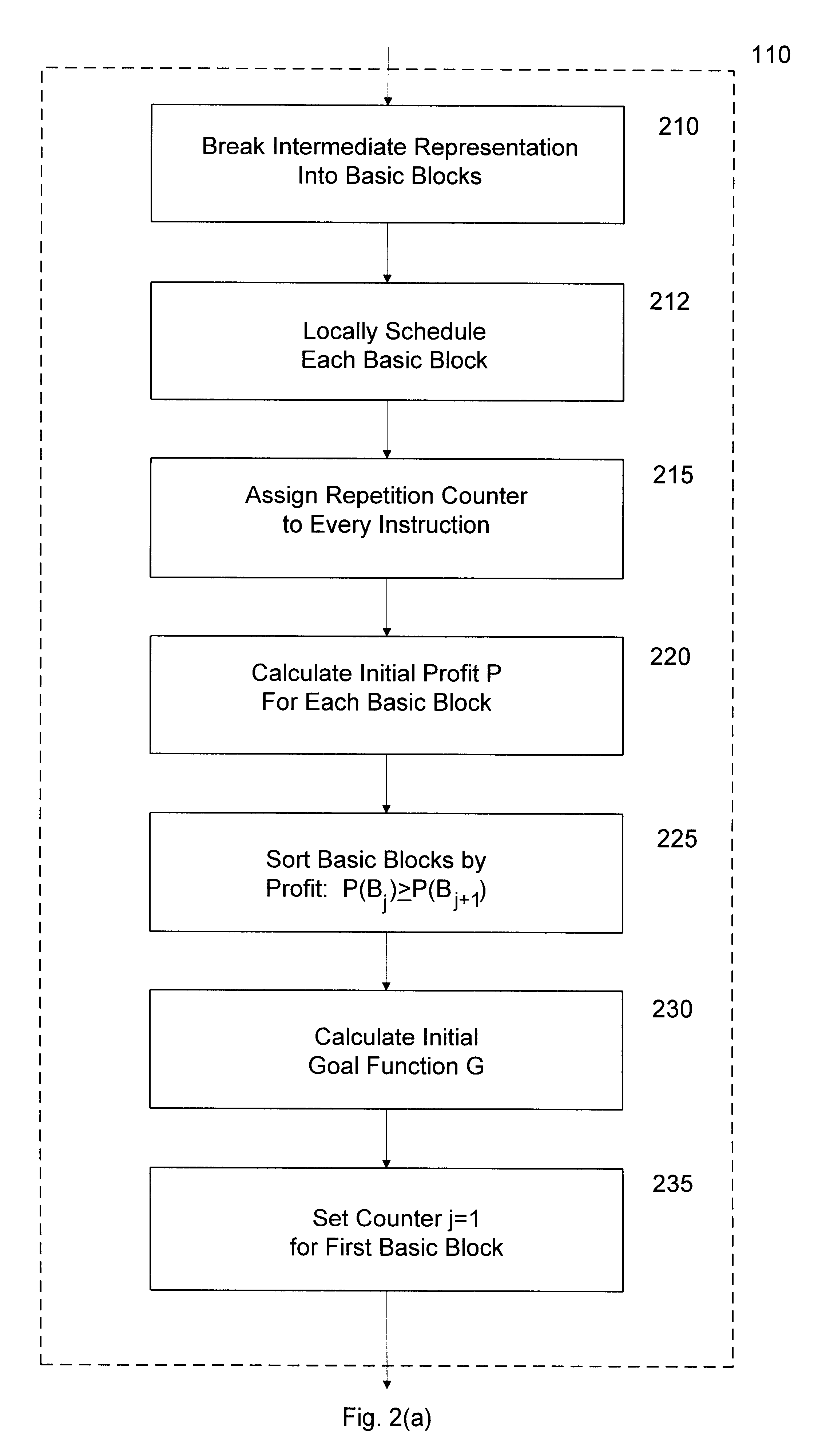
Profile driven code motion and scheduling
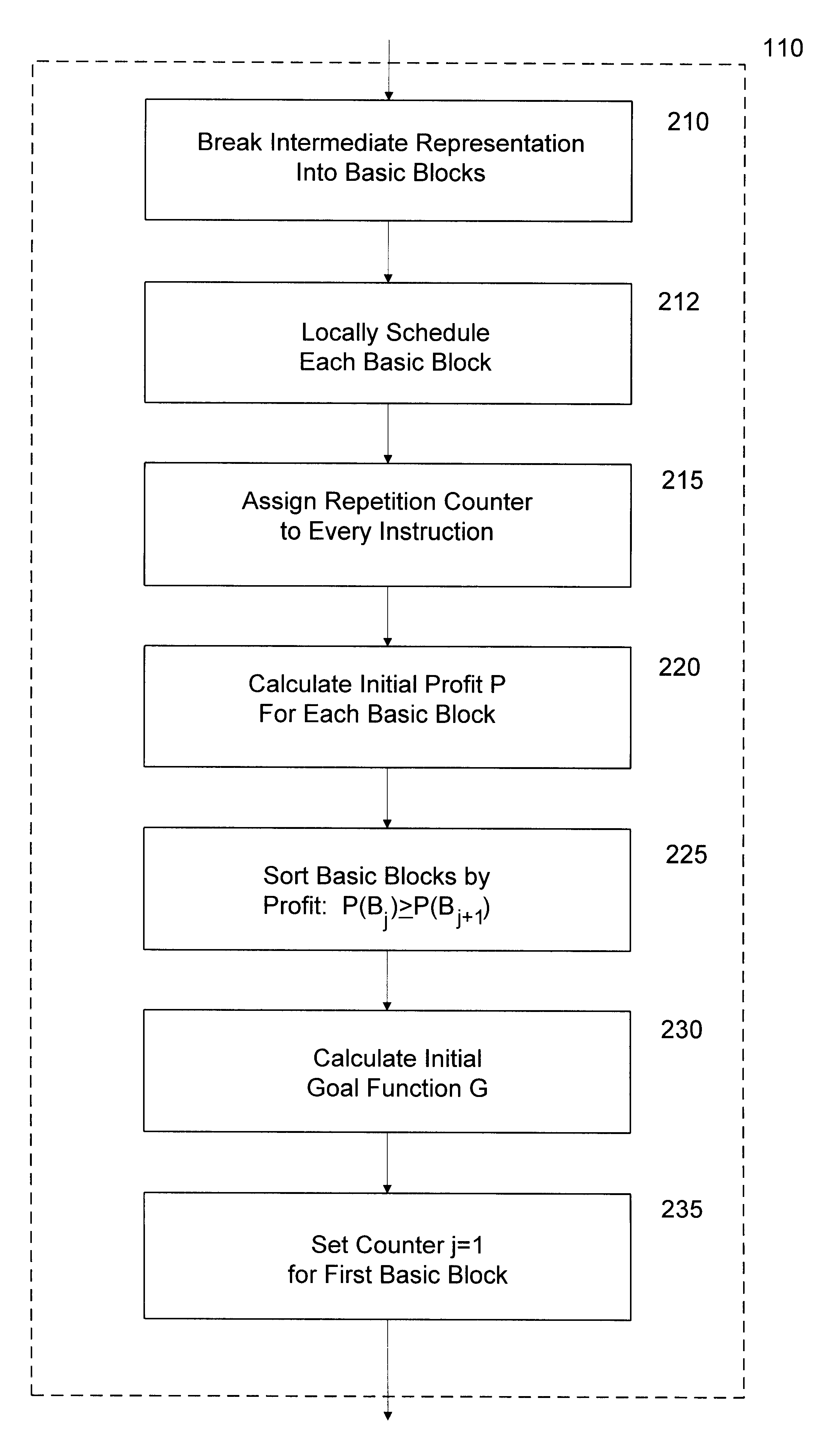
A method and apparatus for generating an optimized intermediate representation of source code for a computer program are described. An initial intermediate representation is extracted from the source code by organizing it as a plurality of basic blocks that each contain at least one program instruction ordered according to respective estimated profit values. A goal function that measures the degree of optimization of the program is calculated in accordance with its intermediate representation. The effect on the goal function of modifying the intermediate representation by moving an instruction from one of the basic blocks to each of its predecessors is tested iteratively and adopting the modified intermediate representation if it causes a reduction in the goal function.
Owner:ELBRUS INT
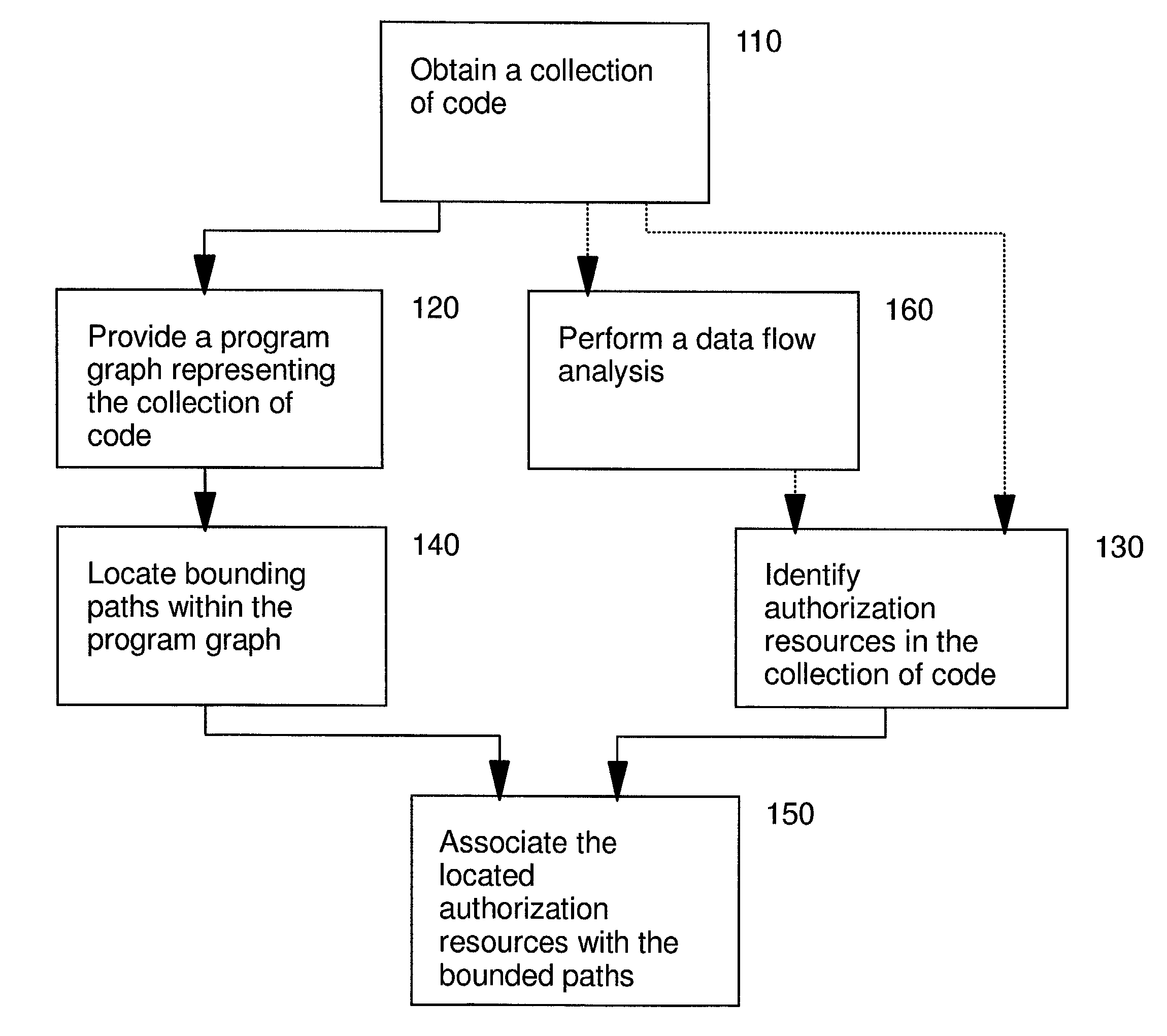
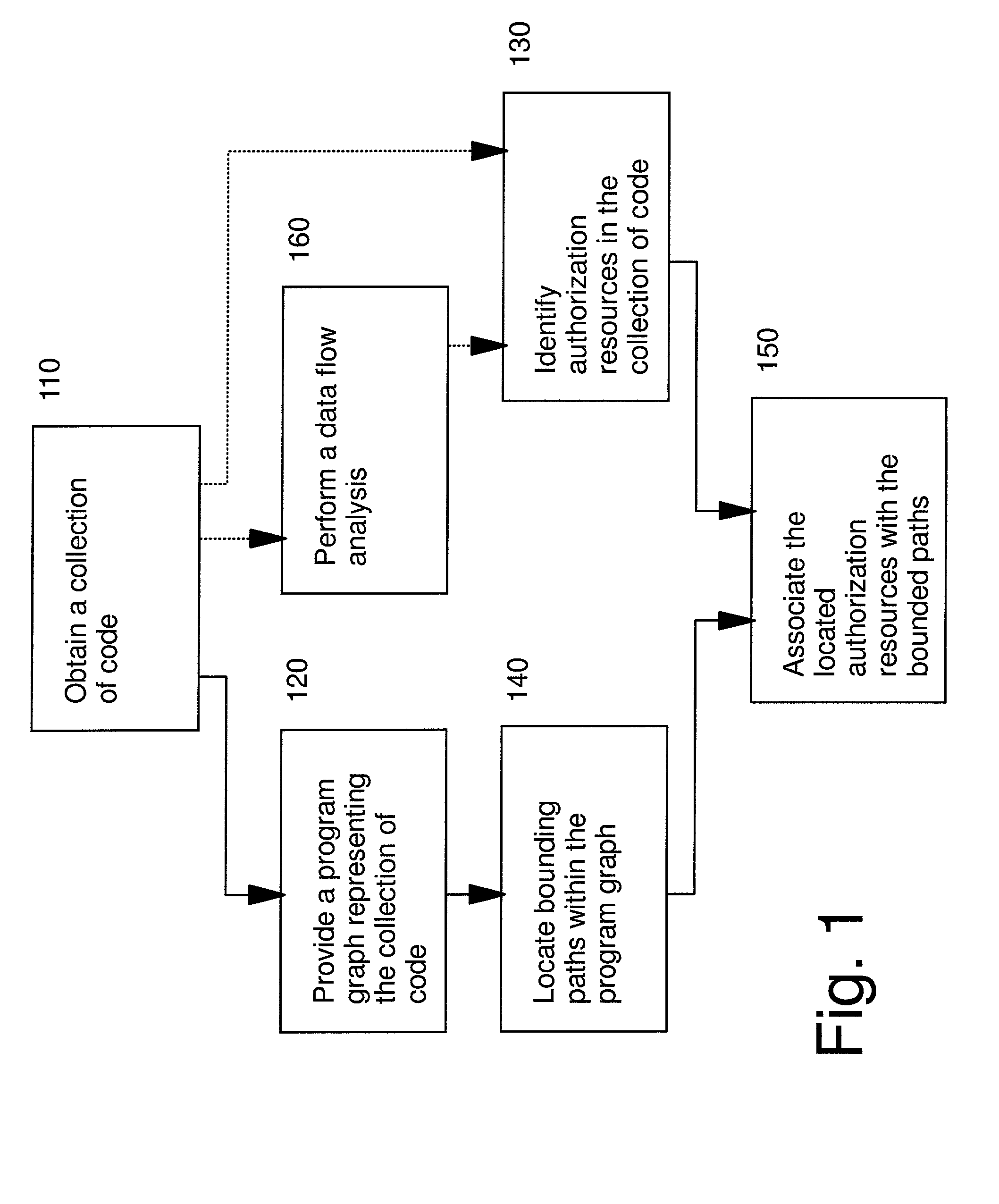
Automated program resource identification and association
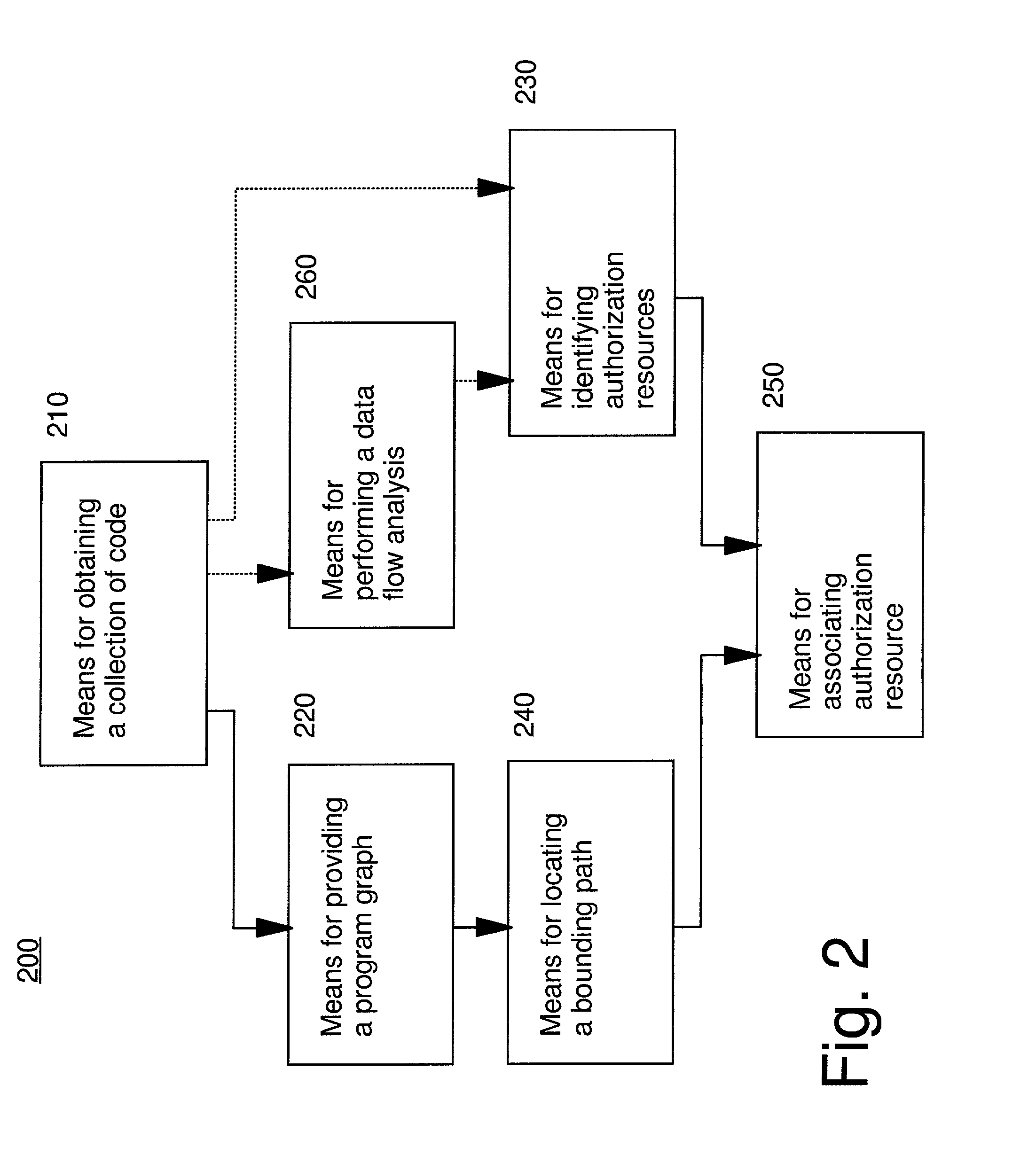
This invention provides methods and apparatus for determining a set of authorization usage for collection of code. By using a program graph, the present invention identifies the code within in bounded paths in the program graph that use authorization. The level of precision is able to identify authorization usage to the level of basic blocks, methods, classes or other collections of code. By using the analysis technique described in this invention, we can determine the authorizations needed by collections code, including Java applets, servlets, and Enterprise JavaBeans. By using the present invention, it is possible, prior to loading the mobile code, to prompt the administrator or end-user to authorize or deny the code access to restricted the resources, or determine whether authorization testing will be required.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com